Patents
Literature
174 results about "Code injection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Code injection is the exploitation of a computer bug that is caused by processing invalid data. Injection is used by an attacker to introduce (or "inject") code into a vulnerable computer program and change the course of execution. The result of successful code injection can be disastrous, for example by allowing computer worms to propagate.
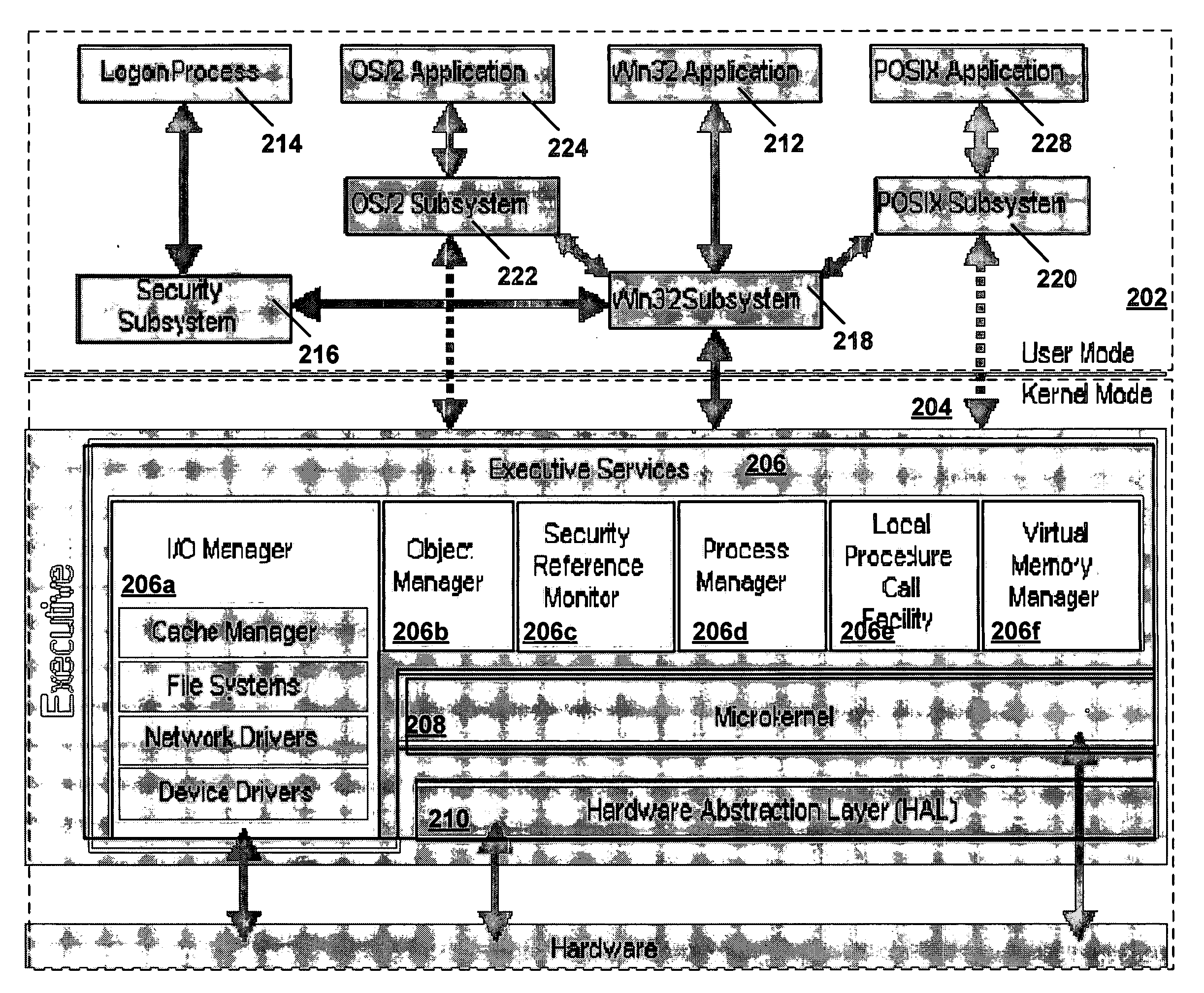
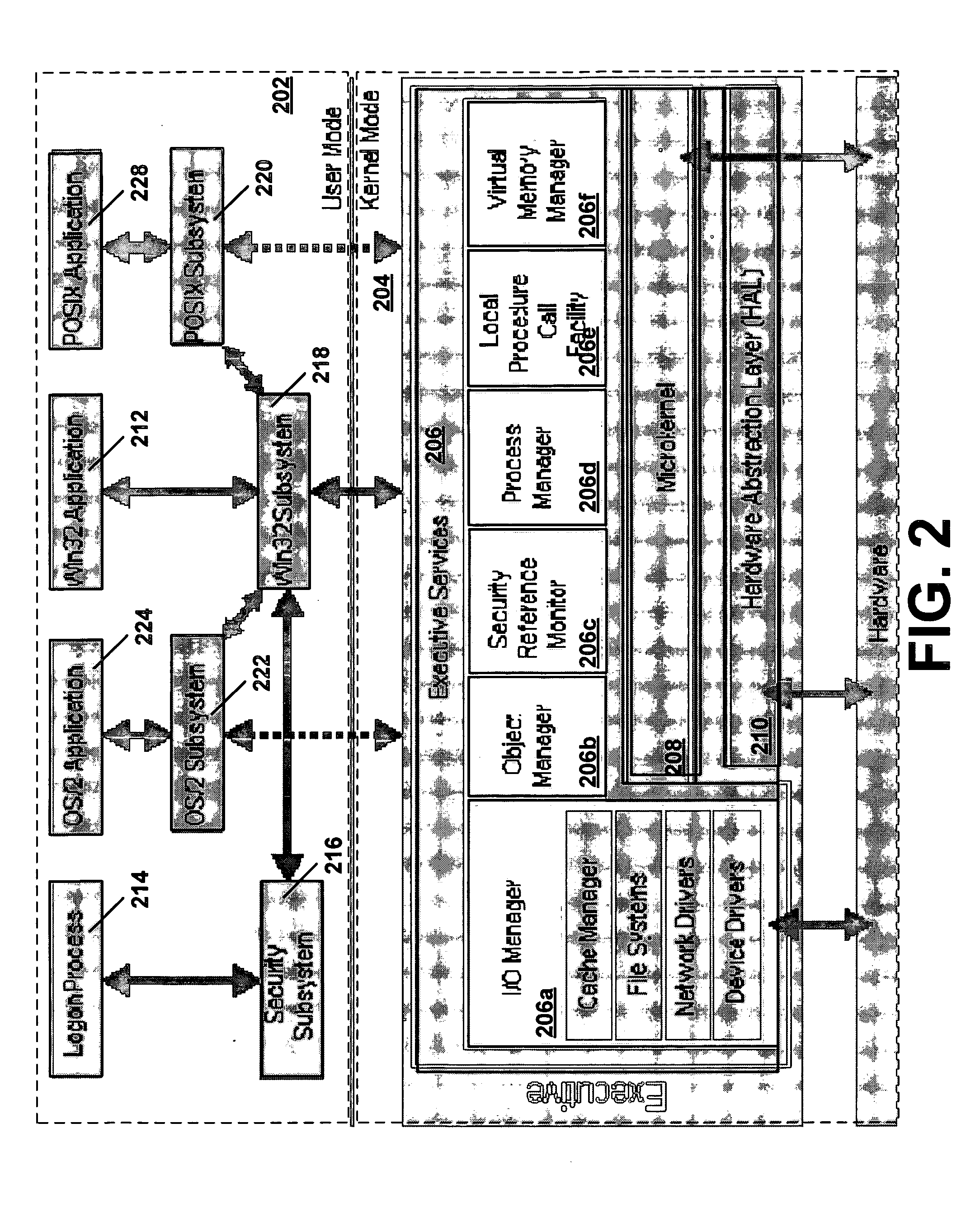
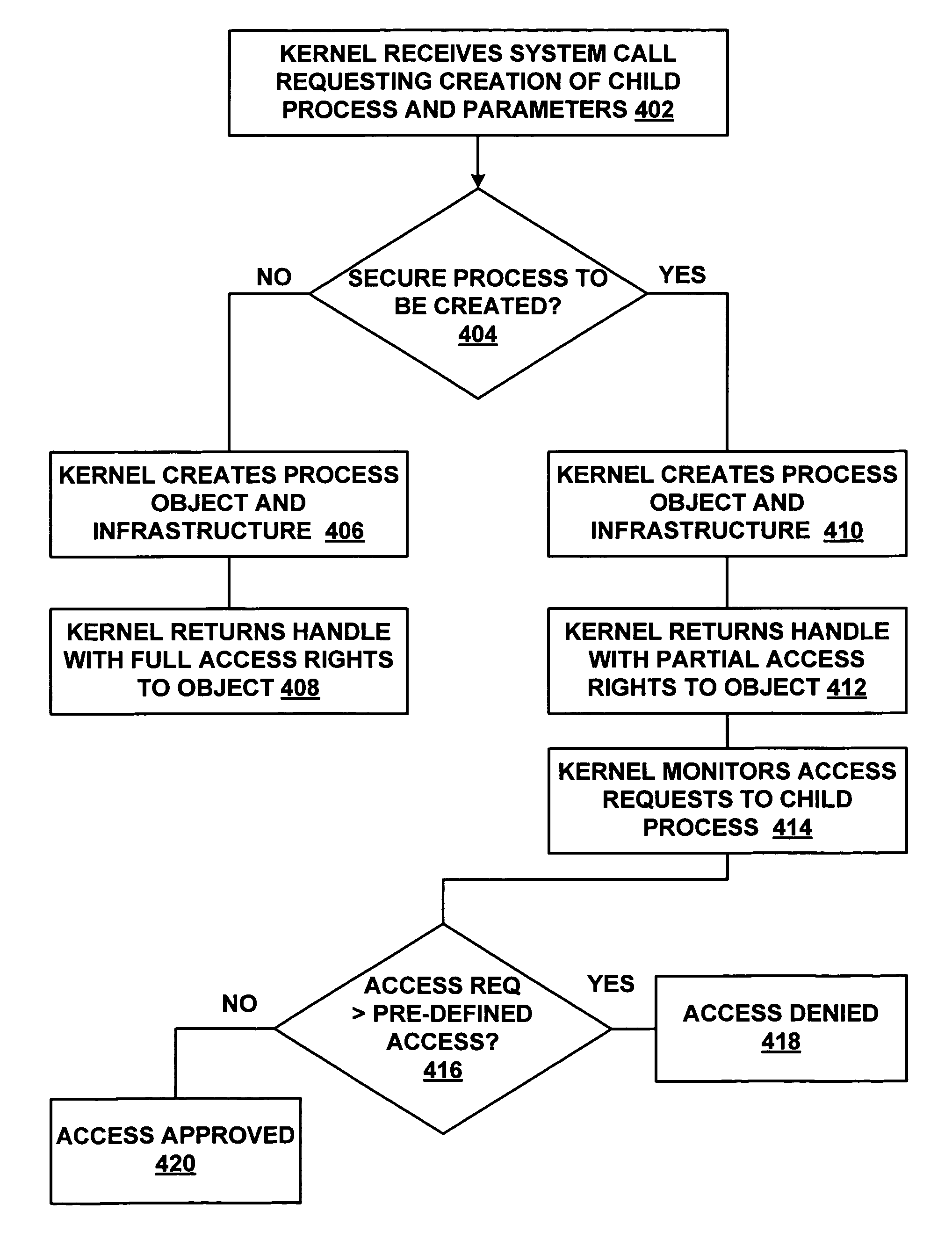
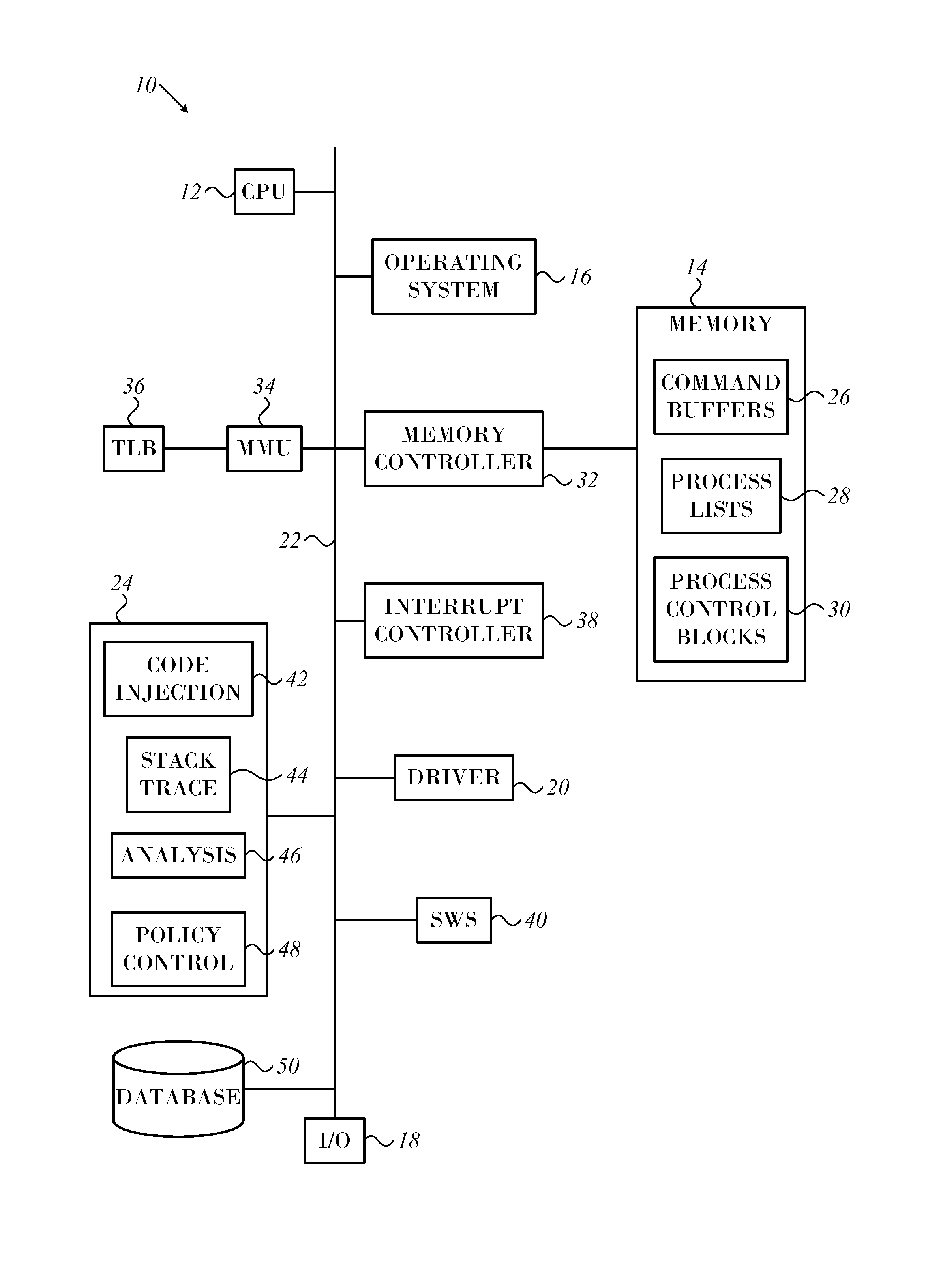
Creating secure process objects
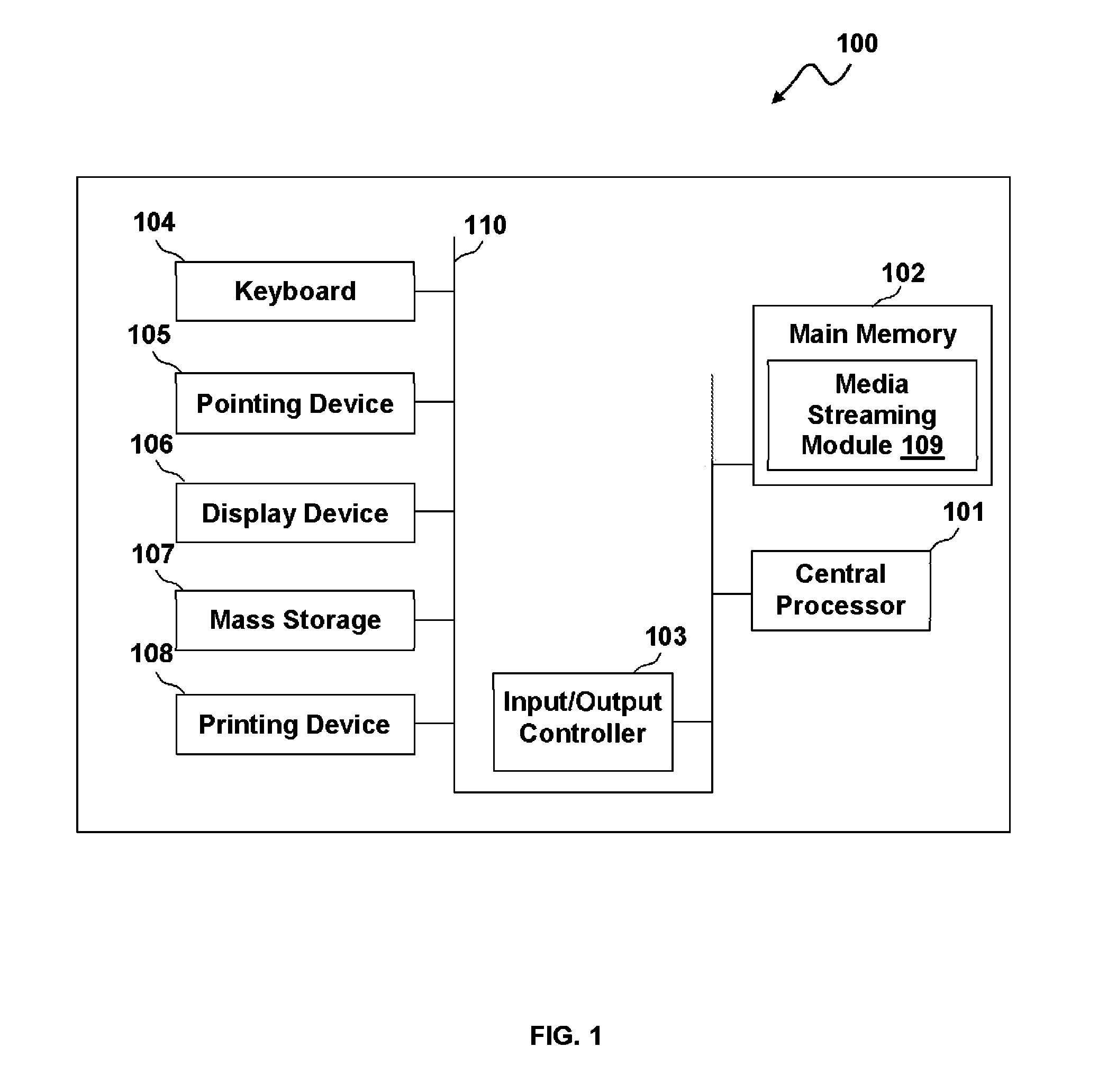
InactiveUS20060259487A1Precise processingReduce in quantityDigital data processing detailsAnalogue secracy/subscription systemsVirtual memoryInit
A secure process may be created which does not allow code to be injected into it, does not allow modification of its memory or inspection of its memory. The resources protected in a secure process include all the internal state and threads running in the secure process. Once a secure process is created, the secure process is protected from access by non-secure processes. Process creation occurs atomically in kernel mode. Creating the infrastructure of a process in kernel mode enables security features to be applied that are difficult or impossible to apply in user mode. By moving setup actions previously occurring in user mode (such as creating the initial thread, allocating the stack, initialization of the parameter block, environment block and context record) into kernel mode, the need of the caller for full access rights to the created process is removed. Instead, enough state is passed from the caller to the kernel with the first system call so that the kernel is able to perform the actions previously performed using a number of calls back and forth between caller and kernel. When the kernel returns the handle to the set-up process, some of the access rights accompanying the handle are not returned. Specifically, those access rights that enable the caller to inject threads, read / write virtual memory, and interrogate or modify state of the threads of the process are not returned to the caller.
Owner:MICROSOFT TECH LICENSING LLC
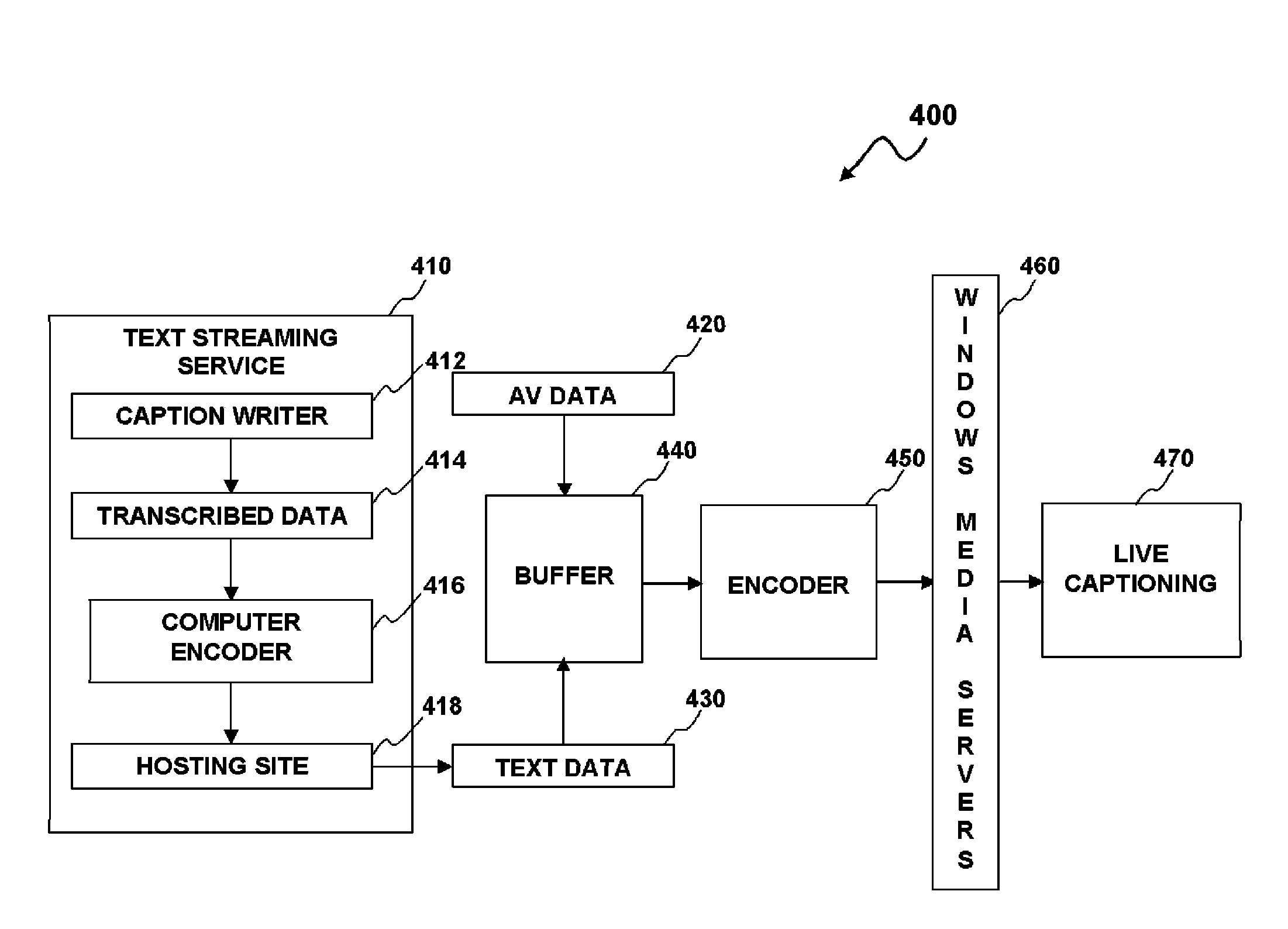
Real-time dynamic and synchronized captioning system and method for use in the streaming of multimedia data
ActiveUS20090307267A1Adjustable speedFacilitate profile buildingDigital data processing detailsPicture reproducers using cathode ray tubesGraphicsGraphical user interface
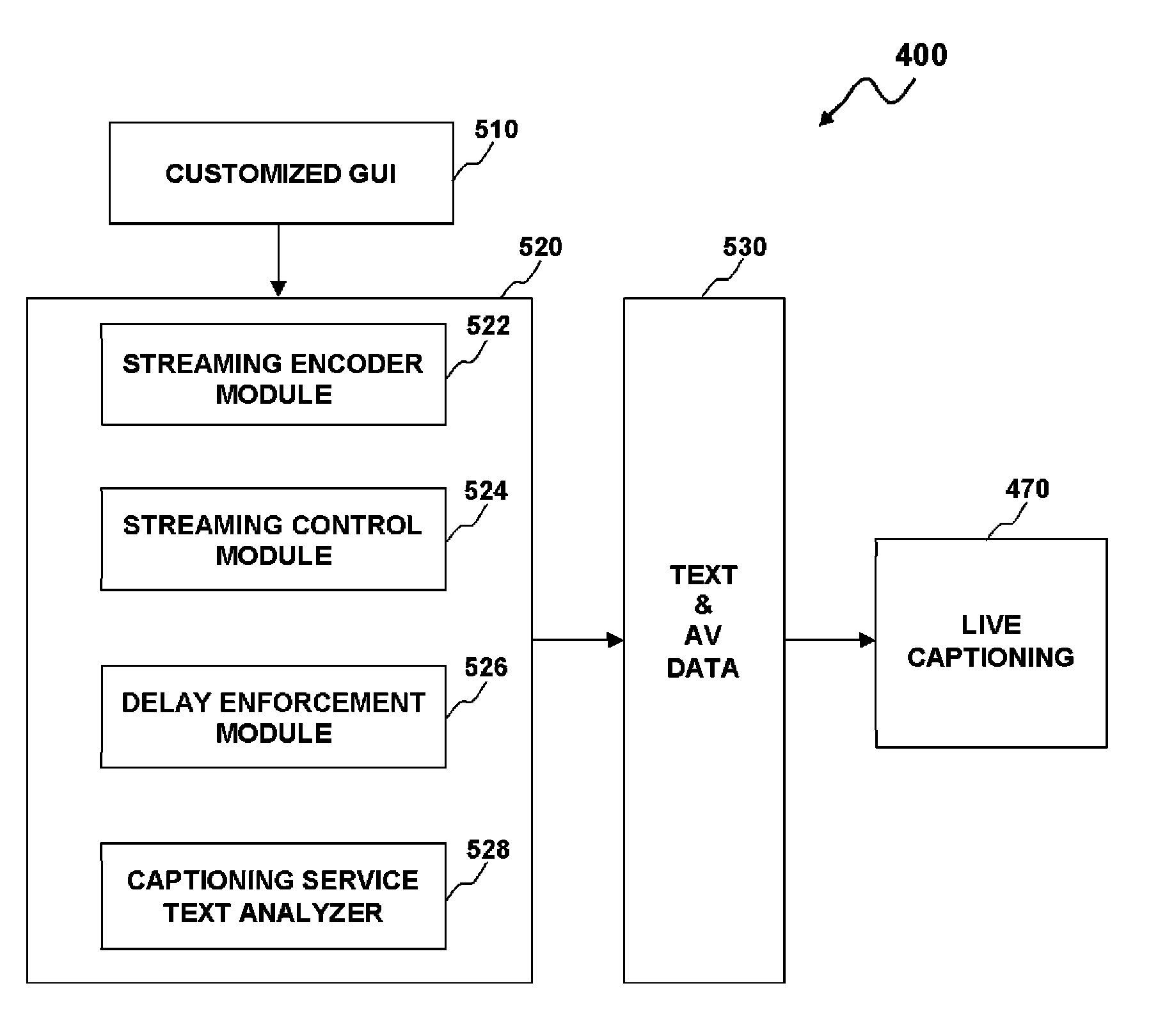
A dynamic and synchronized real-time captioning system and method for streaming media. A streaming encoder module can provide a code injection to marry textual data and audio / video (AV) data in order to form a text and / or audio stream. A streaming control module can allow an end-user to specify font format utilized to embed into an AV stream. A delay enhancement tool can be adapted to adjust speed of the text and / or audio stream, which allows the end-user to receive the text and / or audio stream at a proper speed. A customized graphical user interface (CGUI) can be adapted to assist with streaming administration to provide an encoding option, caption source location, delay control and slide control. Therefore, the captioning system can be able to synchronize and deliver the textual data and the AV data for live media streaming at an end-user's system.
Owner:KYNDRYL INC
Flexible and extensible java bytecode instrumentation system
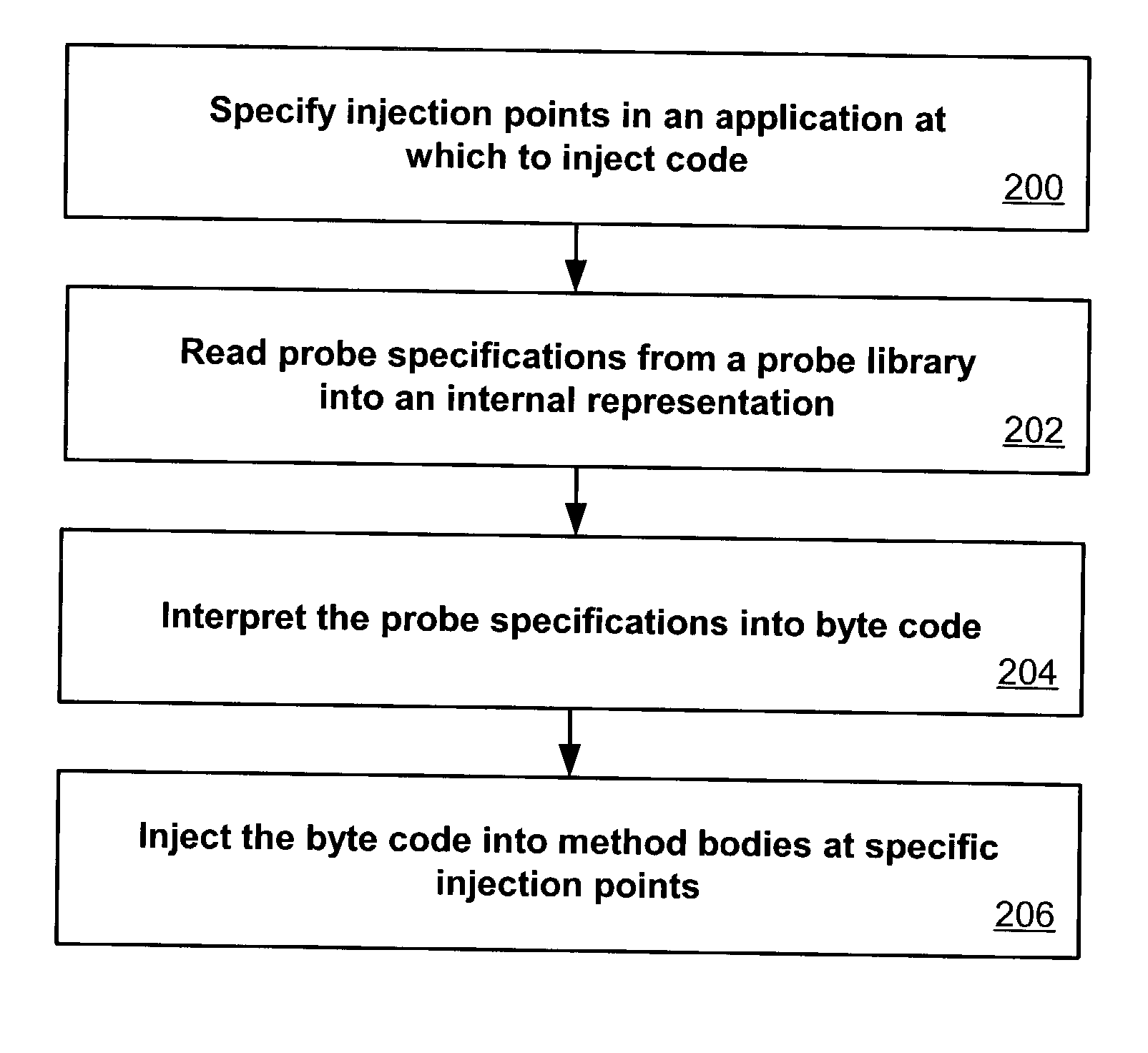
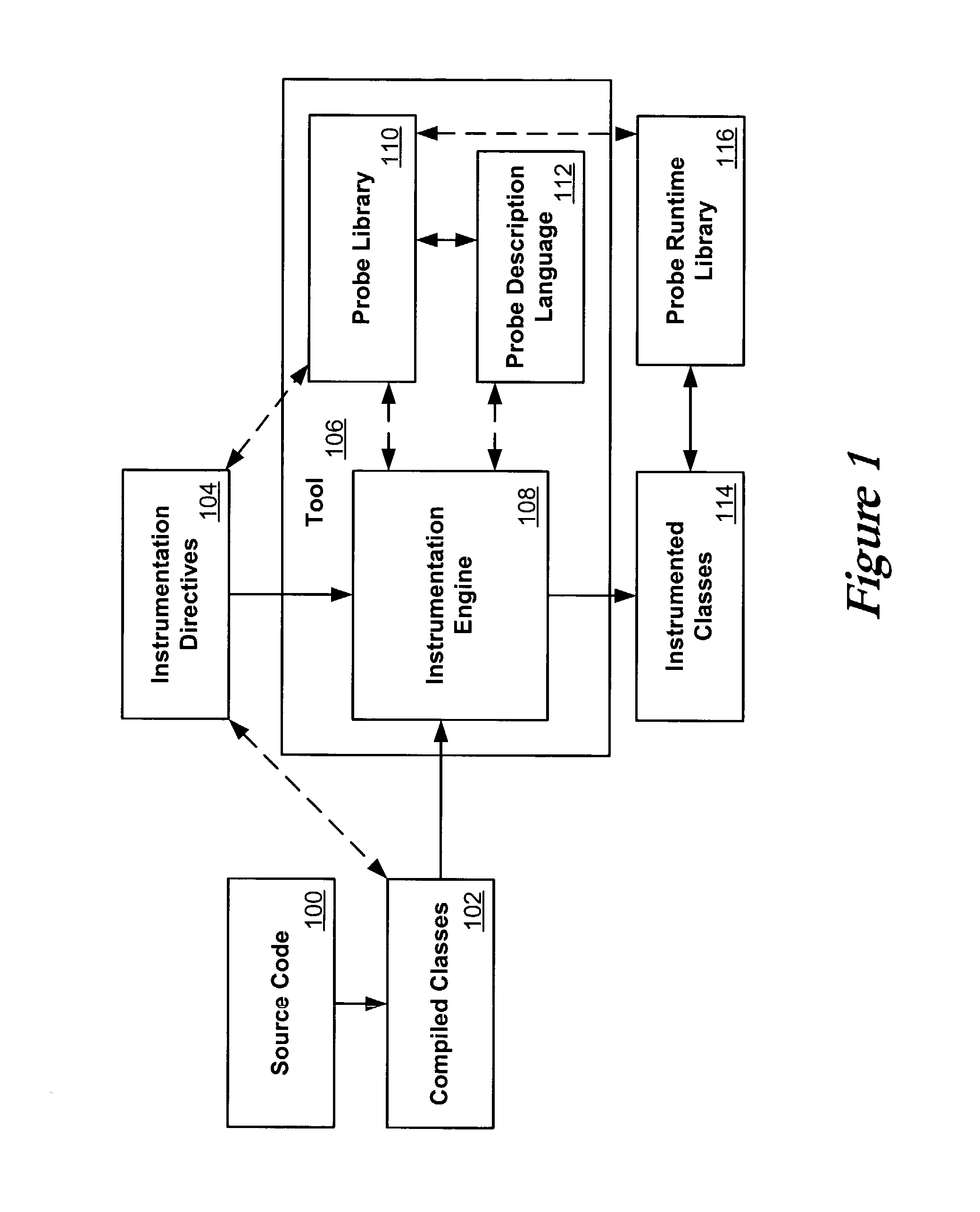
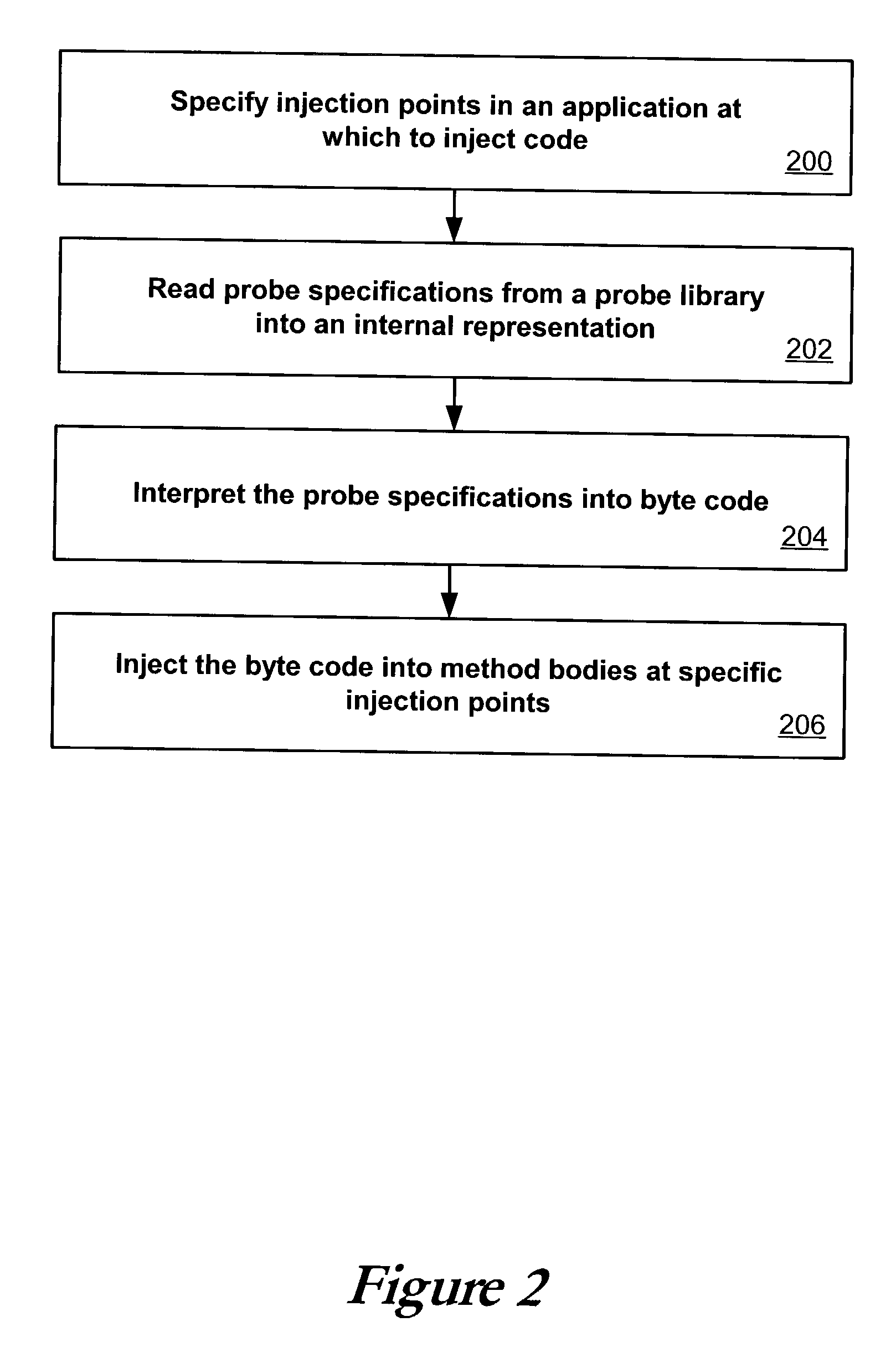
ActiveUS20030149960A1Error detection/correctionDigital computer detailsInjection pointCode injection
Code can be injected into a compiled application through the use of probes comprised of instrumentation code. Probes can be implemented in a custom high level language that hides low level instruction details. A directive file contains instructions on injecting a probe into a compiled application. An instrumentation engine reads these instructions and injects the probe into the compiled application at the appropriate injection points. Multiple probes can be used, and can be stored in a probe library. Each probe can inject code into the application at, for example, a package, class, method, or line of the compiled application. Calls can also be made to external runtime libraries. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
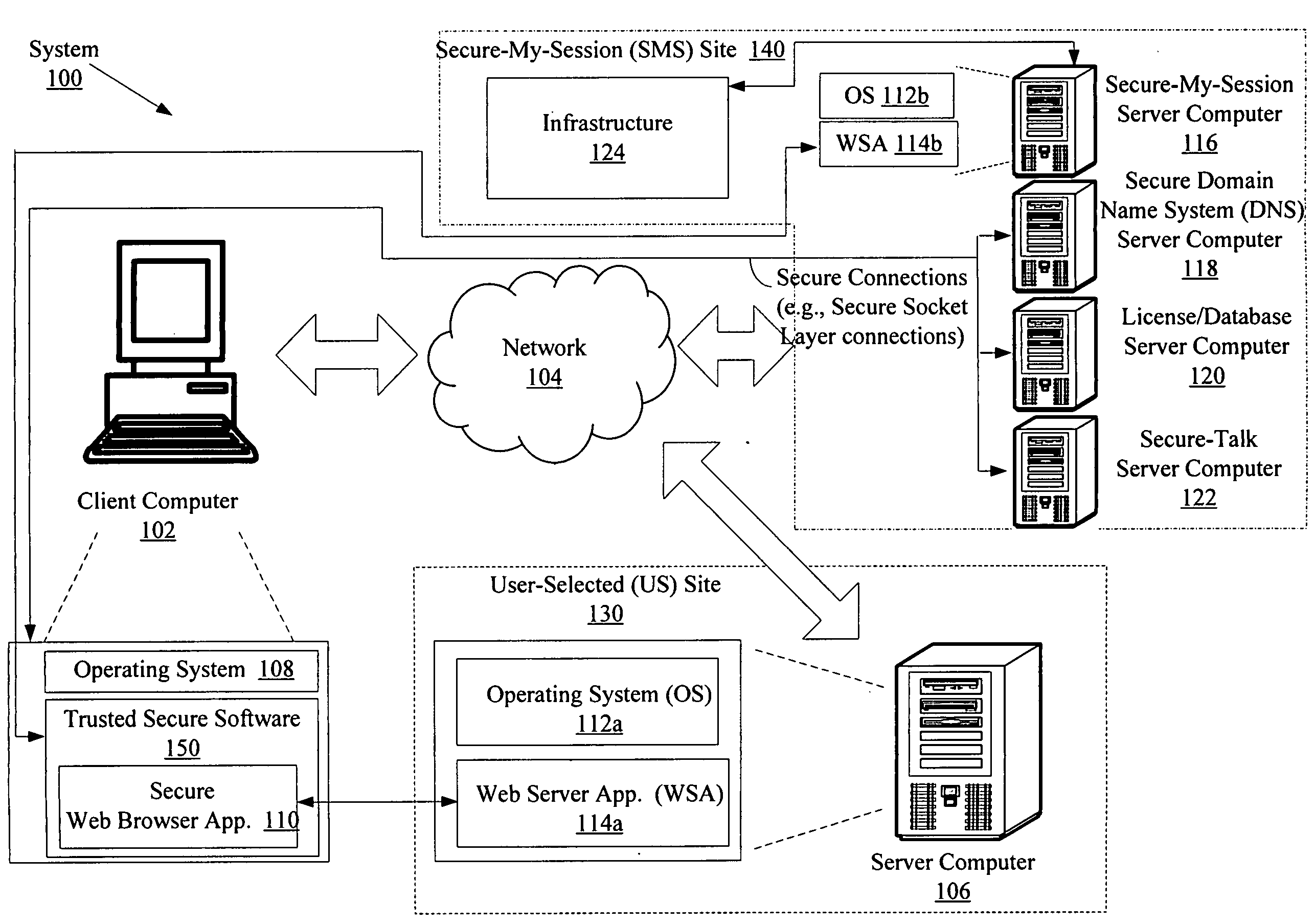
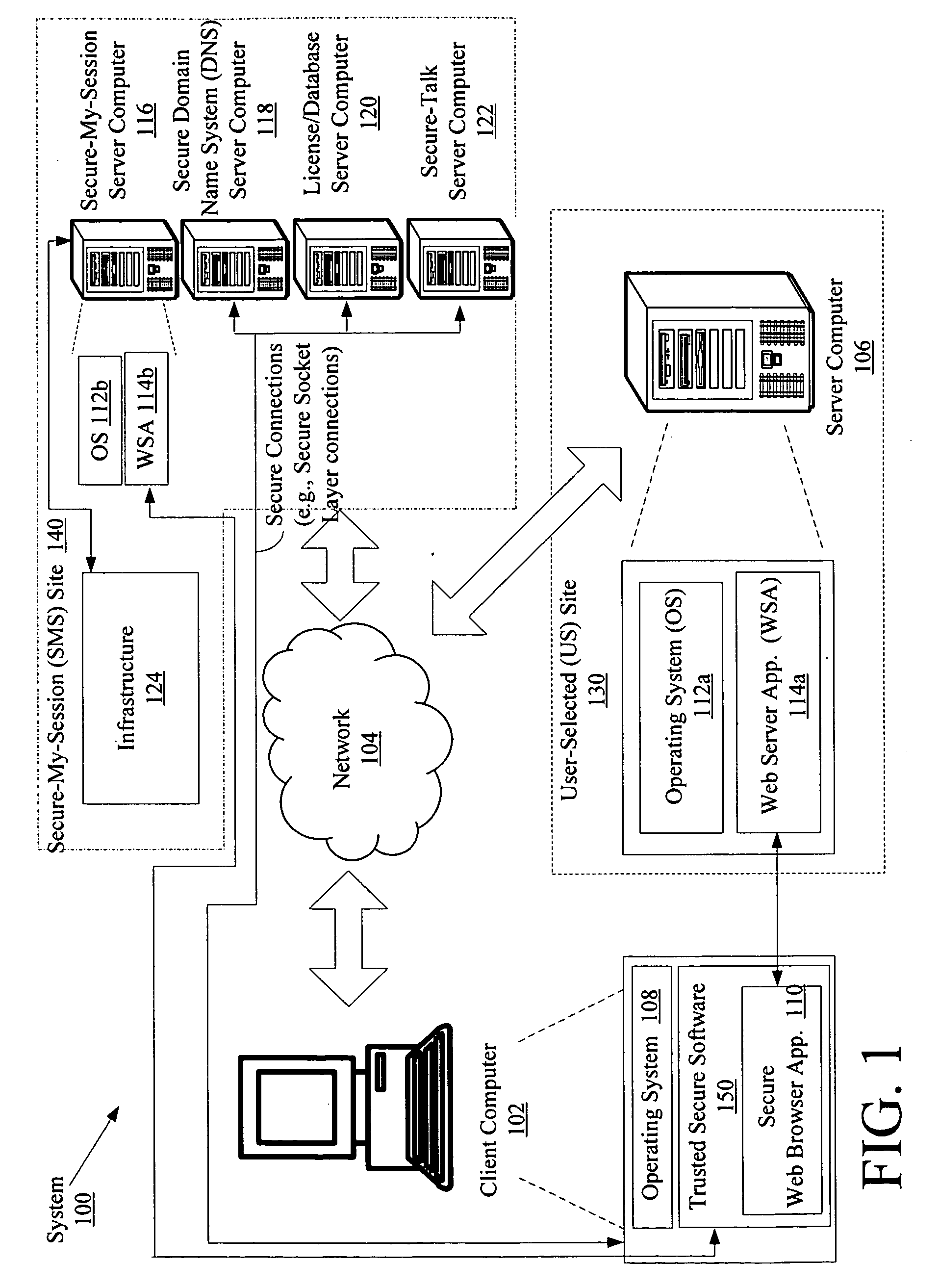
System and method for protecting data accessed through a network connection
ActiveUS20090187763A1Facilitates secure communicationFacilitate gathering of informationPlatform integrity maintainanceSecuring communicationInternal memoryTelecommunications link
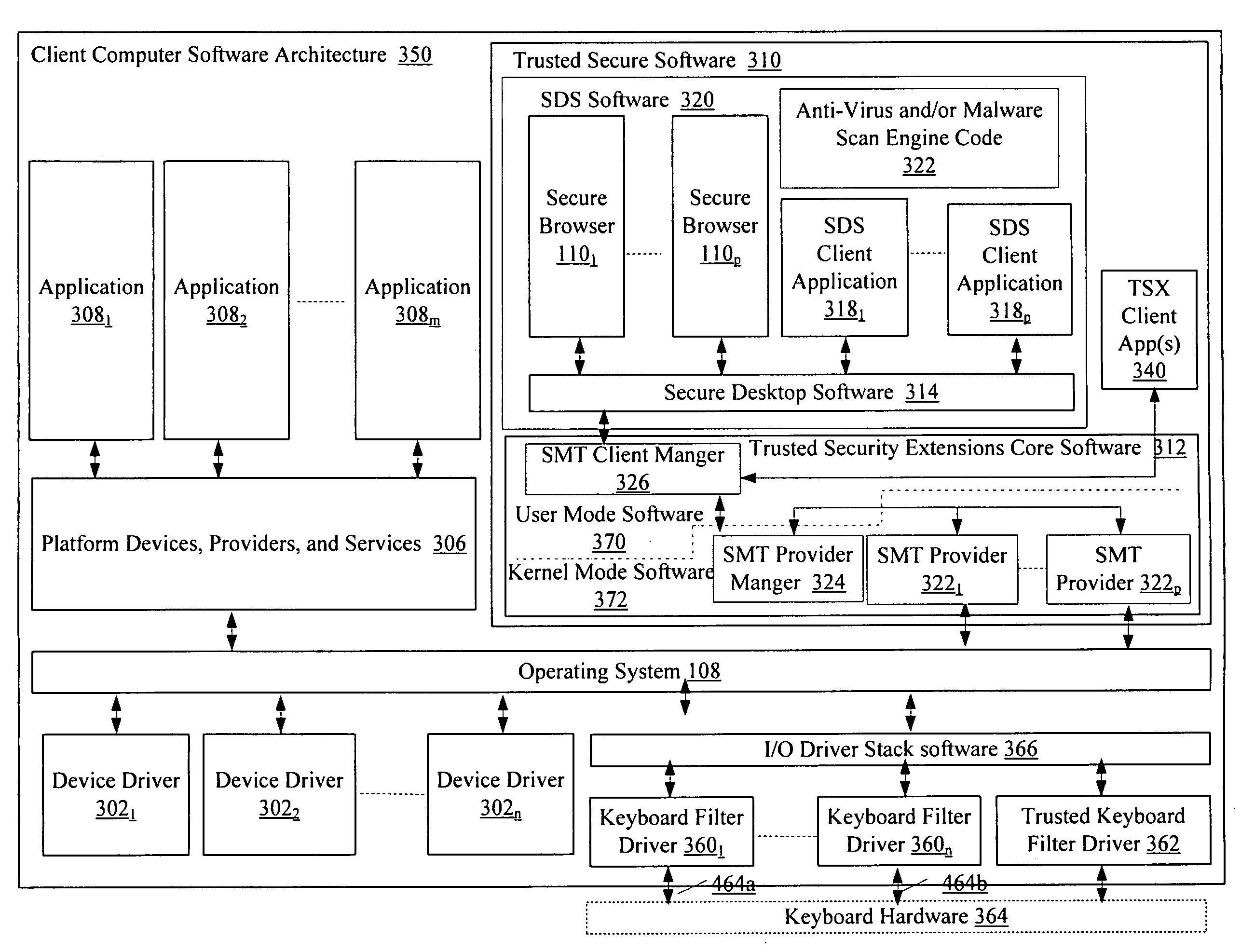
Systems (100) and methods (400) for protecting data accessed through a network connection. The methods involve transferring security software (150) from an external memory device of a client computer (102) to an internal memory device of the client computer. The security software is operative to protect data communicated to and from the client computer via communication links. The security software is also operative to provide a web browser (1101, 1102, . . . , 110p) which executes in user mode on a trusted secured desktop (904) configured to run simultaneously with an unsecured desktop (902) of the client computer. The security software is further operative to provide a security service to the web browser. The security service includes at least one service selected from the group consisting of a keylogger prevention service, a code injection prevention service, and a screen scraper protection service.
Owner:WONTOK
Continuous run-time validation of program execution: a practical approach
ActiveUS20140082327A1Easy to modifyGuaranteed CompatibilityError detection/correctionDigital computer detailsControl flowReal time validation
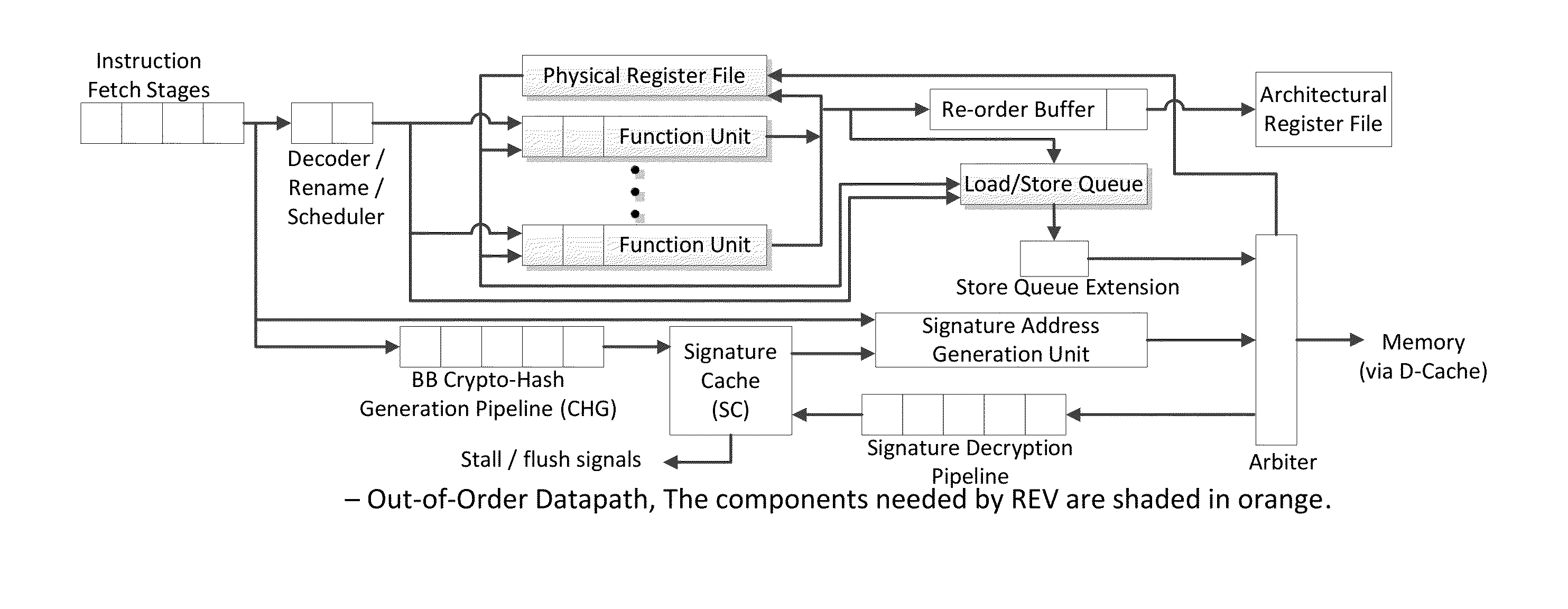
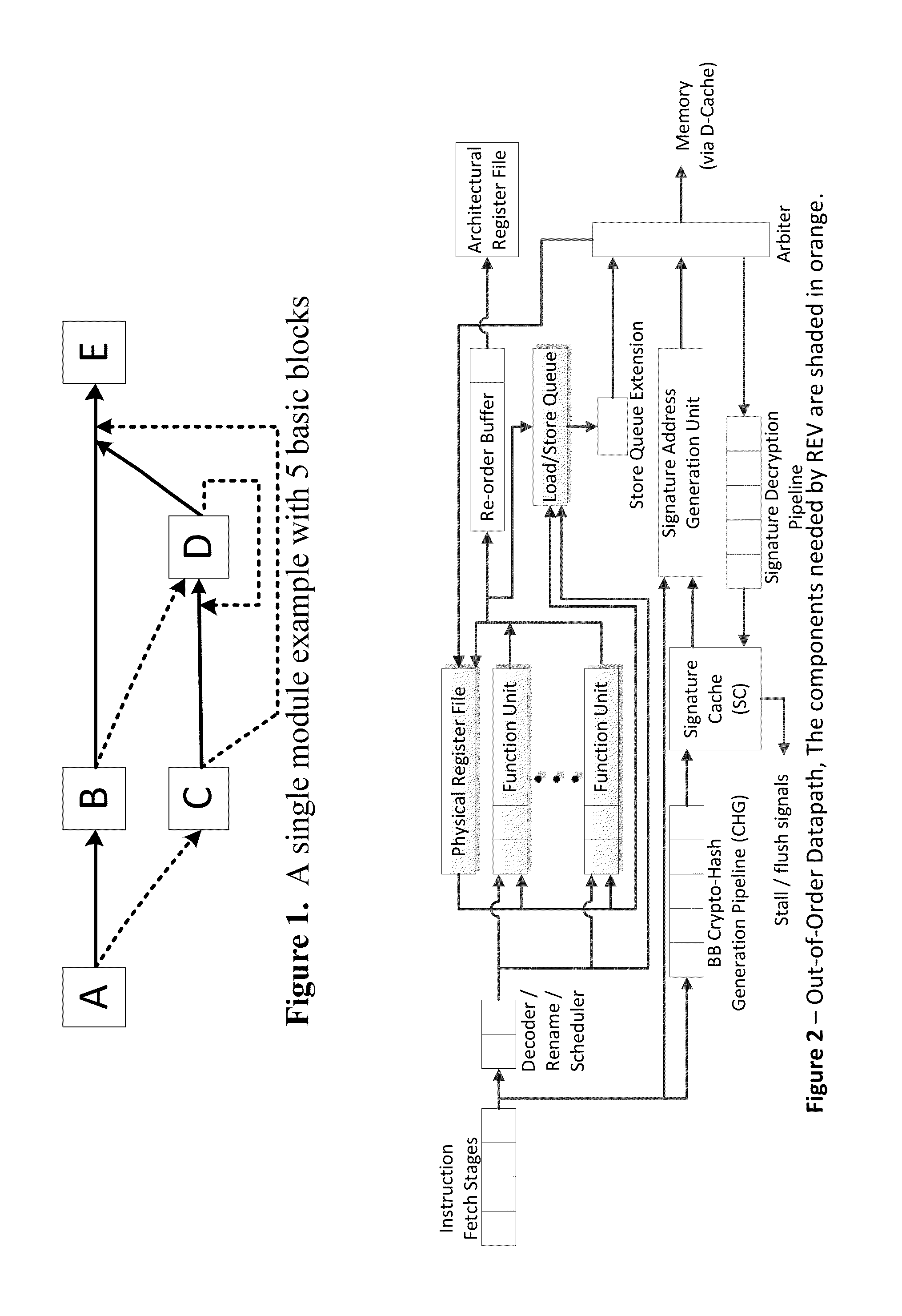
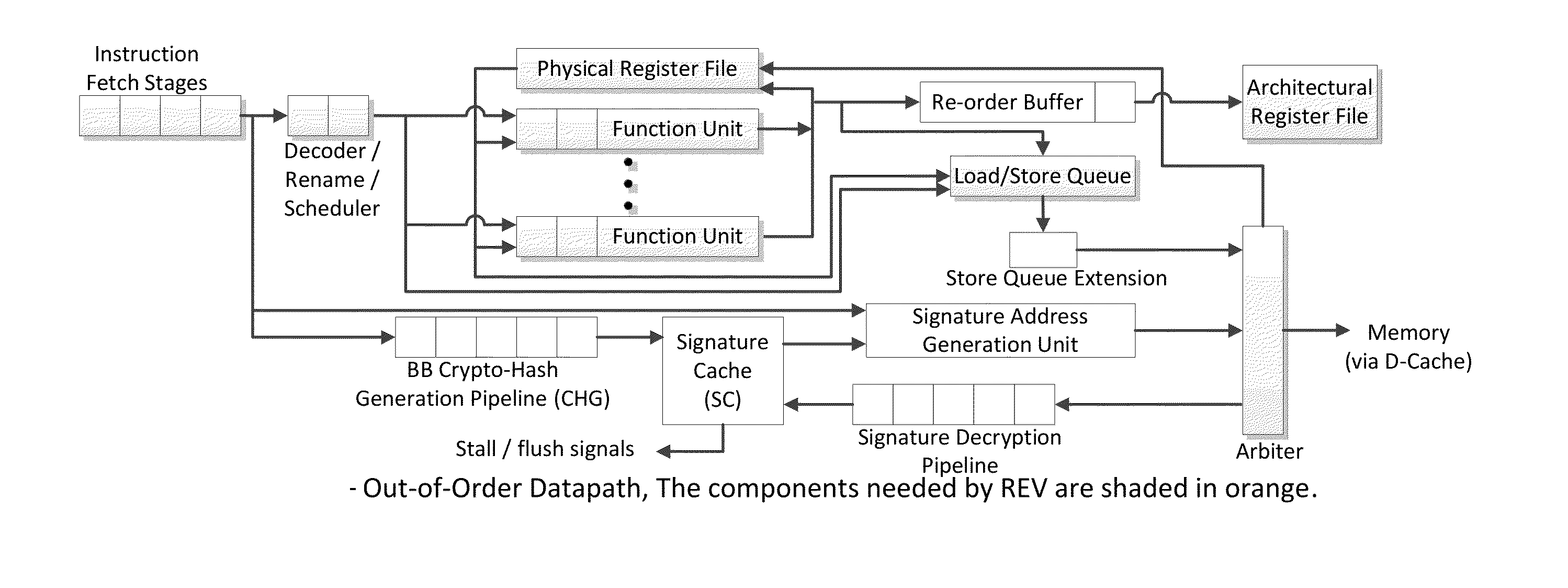
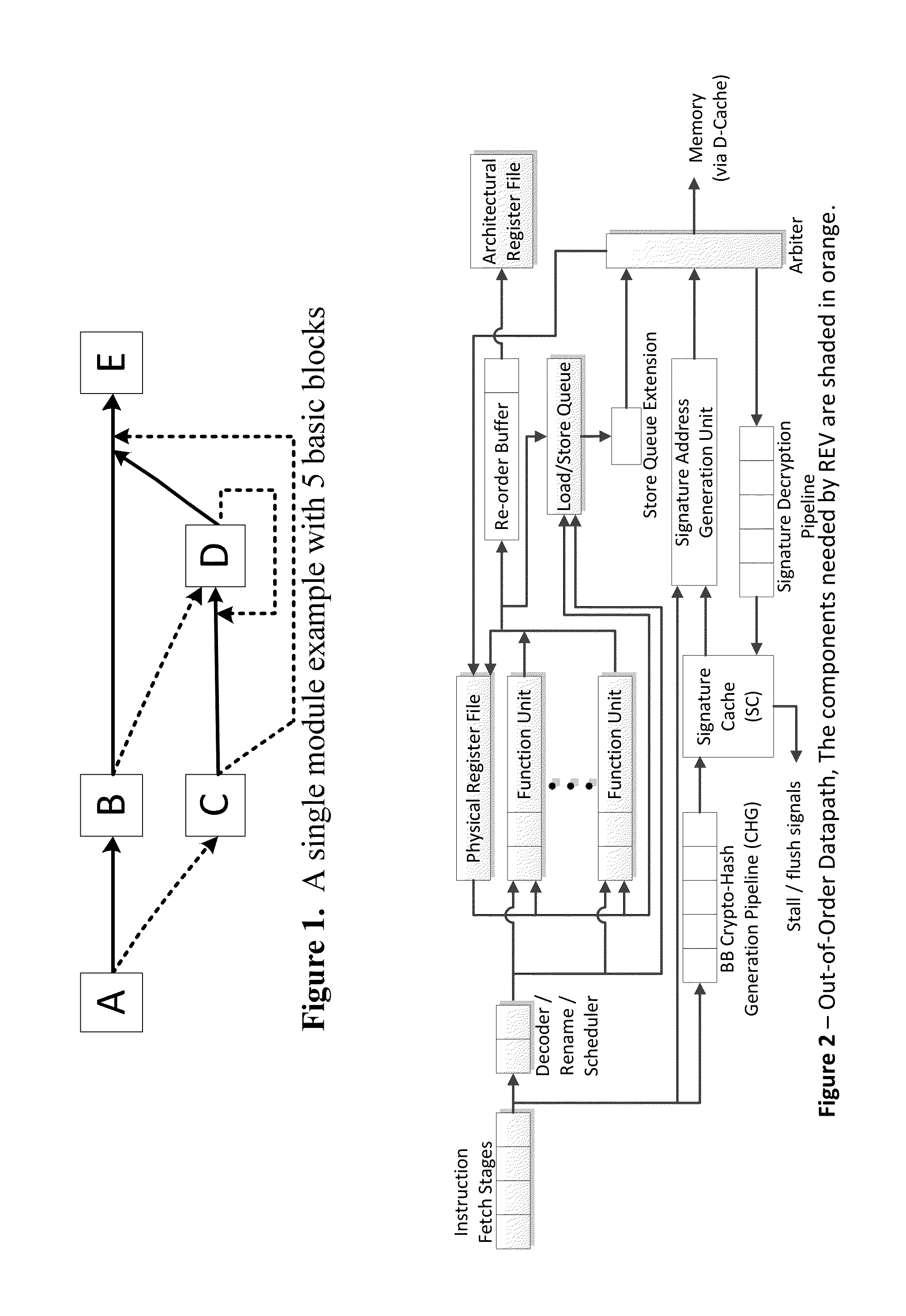
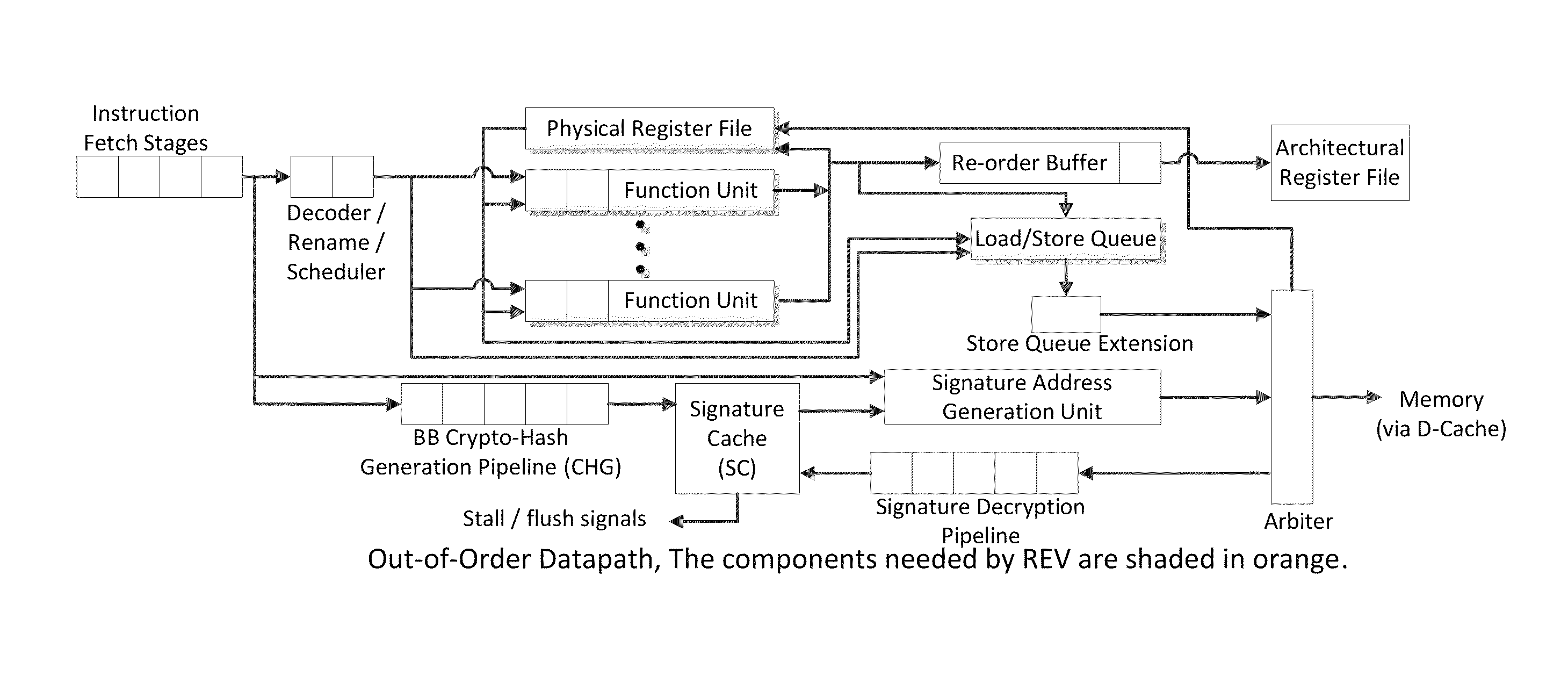
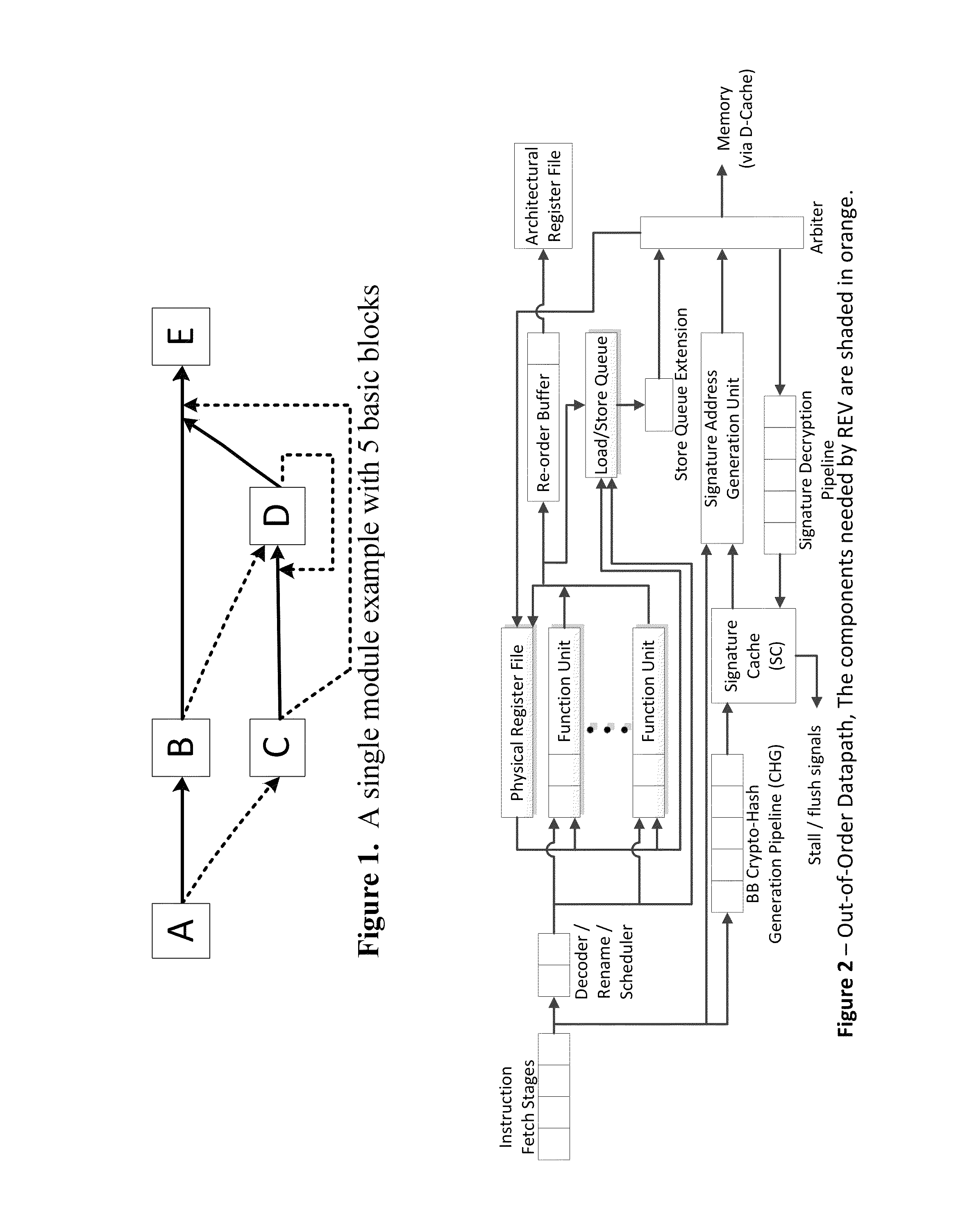
Trustworthy systems require that code be validated as genuine. Most systems implement this requirement prior to execution by matching a cryptographic hash of the binary file against a reference hash value, leaving the code vulnerable to run time compromises, such as code injection, return and jump-oriented programming, and illegal linking of the code to compromised library functions. The Run-time Execution Validator (REV) validates, as the program executes, the control flow path and instructions executed along the control flow path. REV uses a signature cache integrated into the processor pipeline to perform live validation of executions, at basic block boundaries, and ensures that changes to the program state are not made by the instructions within a basic block until the control flow path into the basic block and the instructions within the basic block are both validated.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
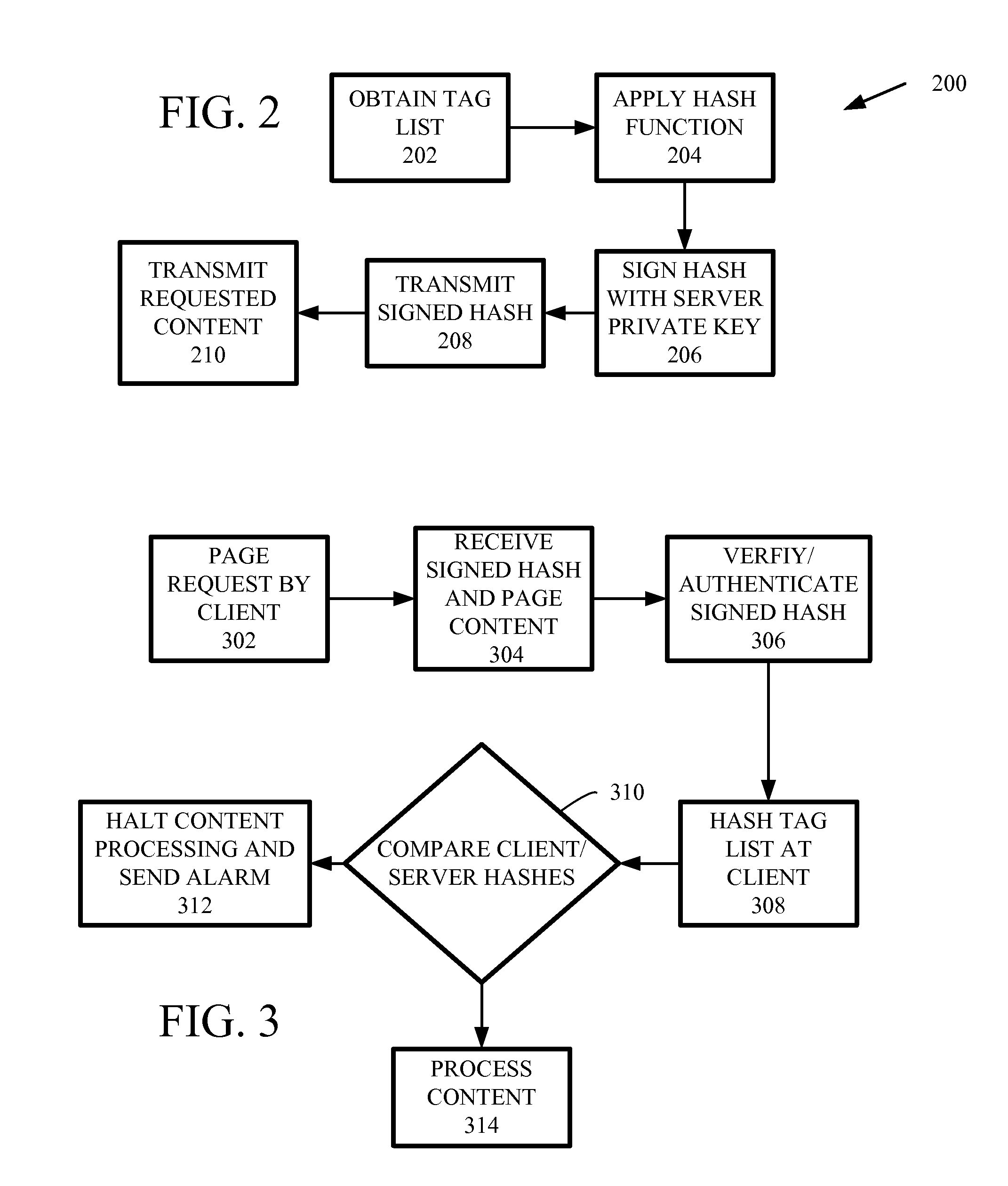
Detecting code injections through cryptographic methods
ActiveUS20120255027A1Digital data processing detailsAnalogue secracy/subscription systemsComputer hardwareCode injection
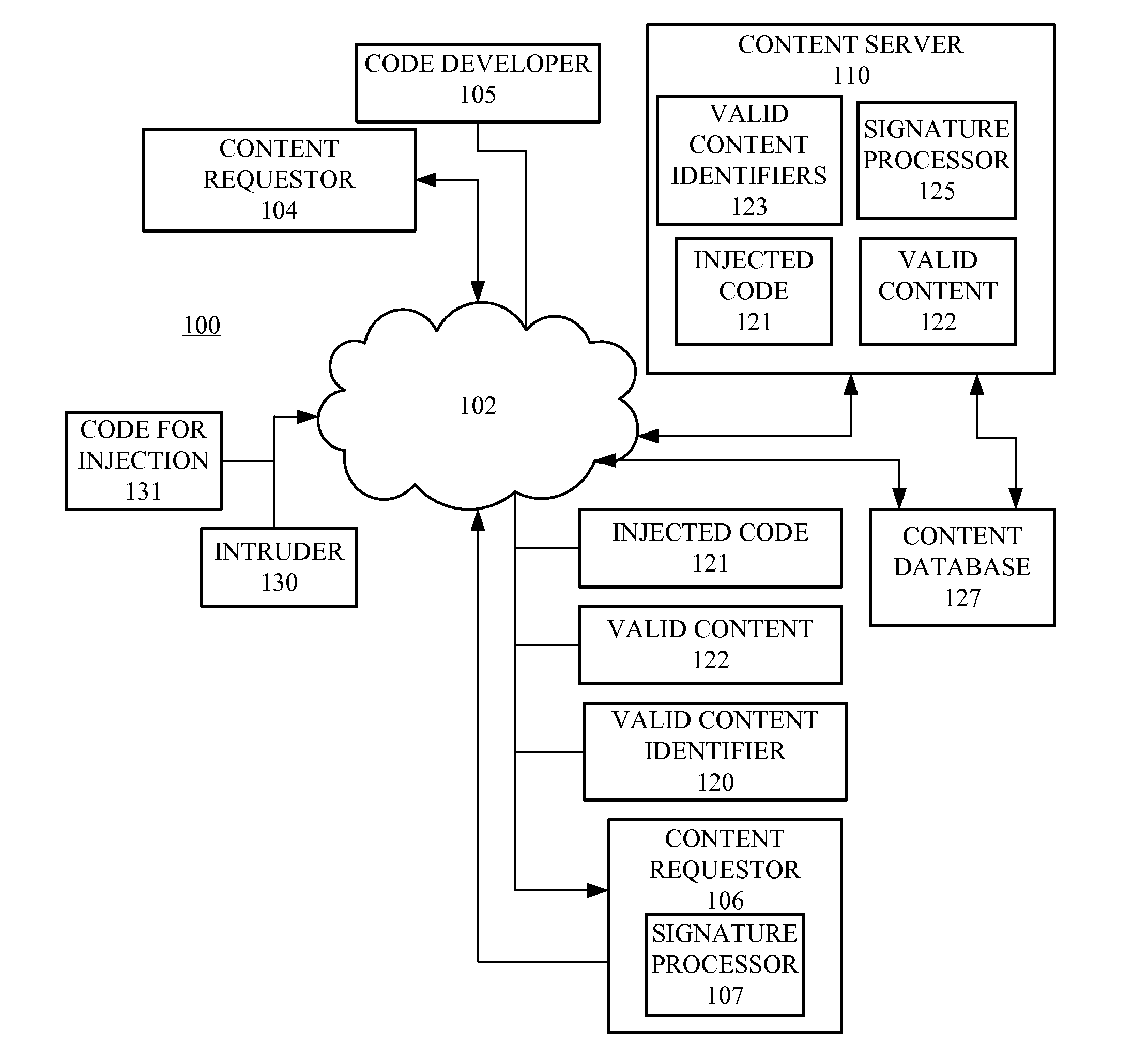
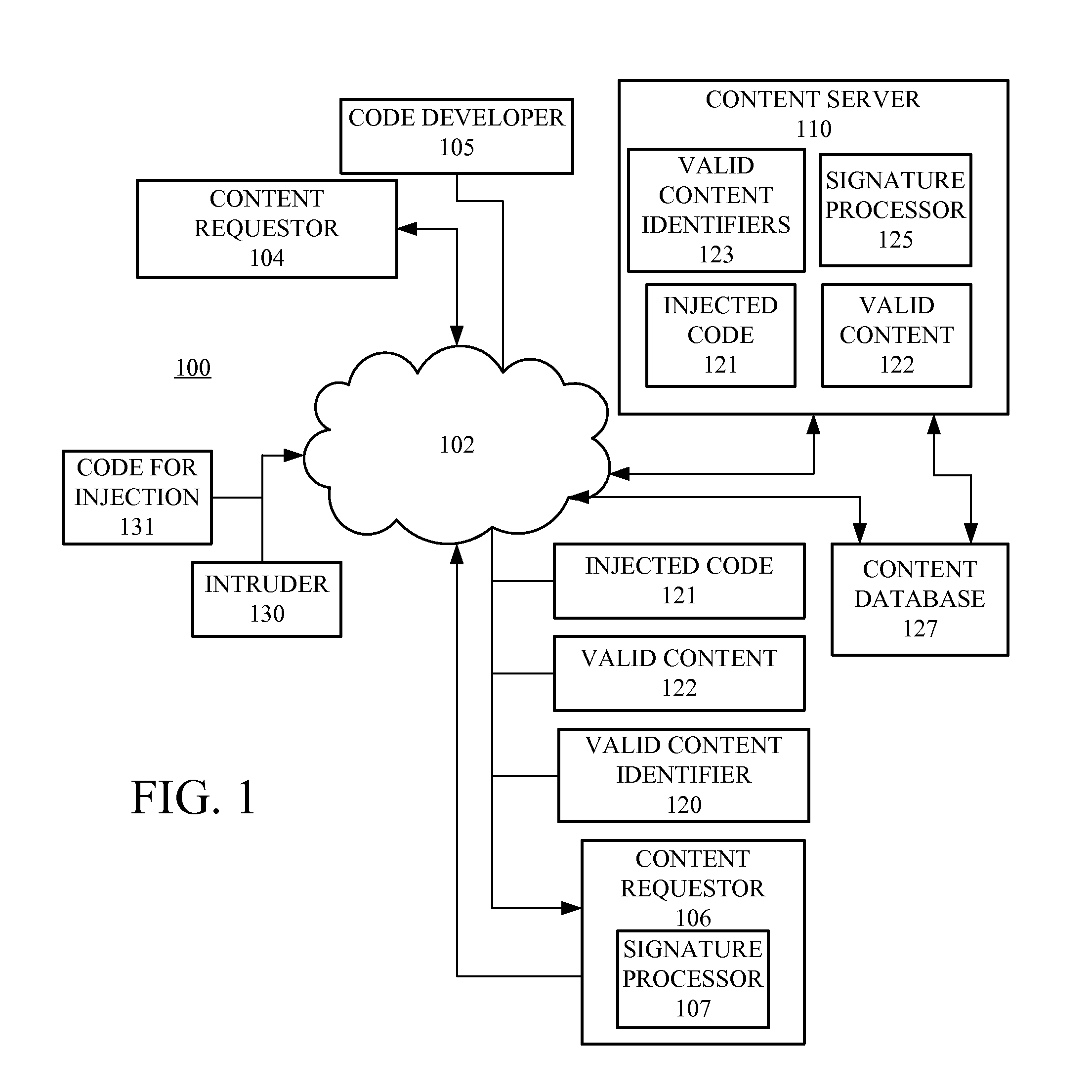
Code injection is detected based on code digests associated with hashes of selected portions of content supplied to clients by a server. A client receives the content and generates a corresponding code digest, and based upon a comparison with the code digest received from the server, determines if the received content has been corrupted. The code digest can be signed or supplied with a digital certification for verification that the code digest originated from the server providing the content.
Owner:INFOSYS LTD
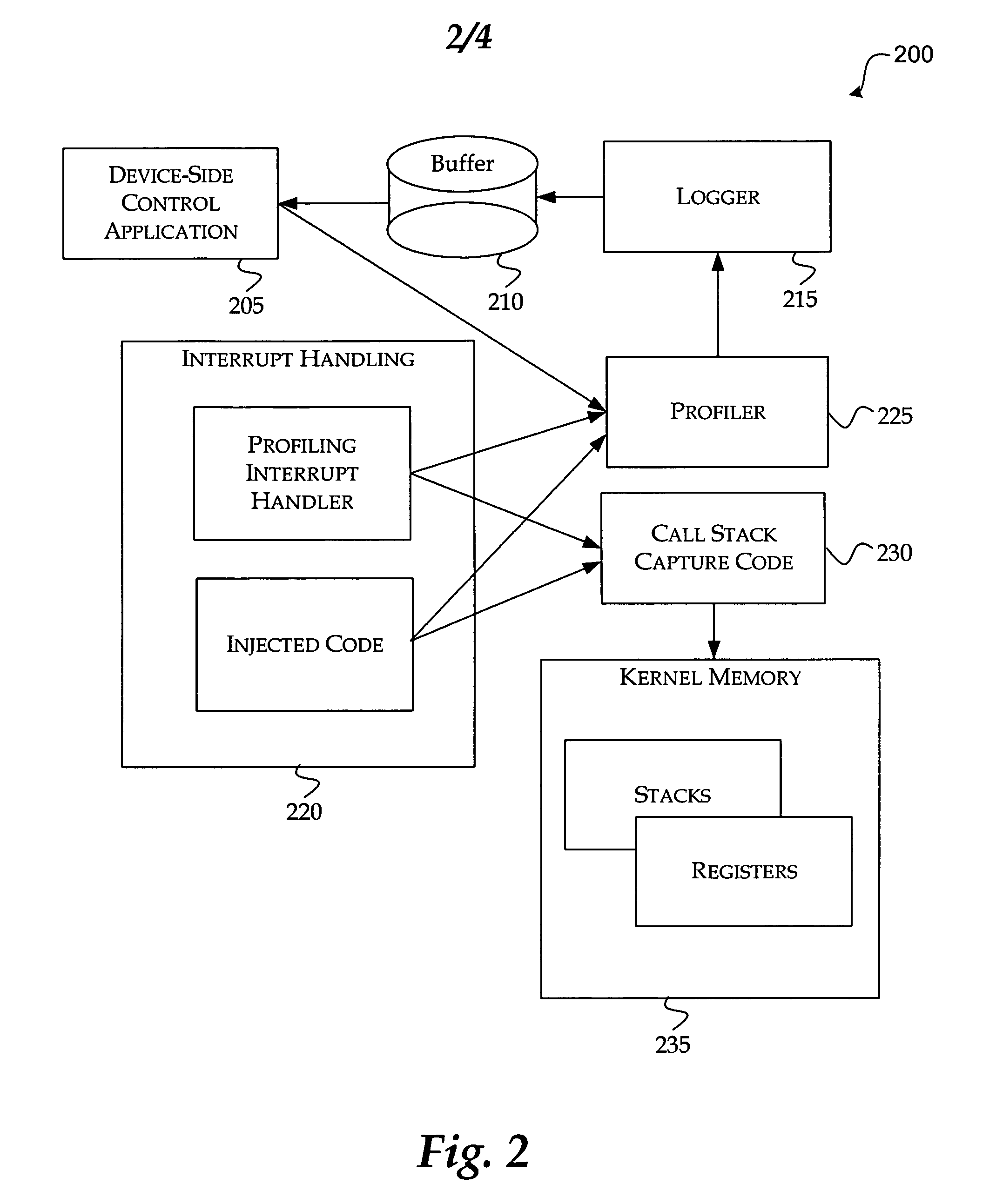
Call stack capture in an interrupt driven architecture
InactiveUS20060059486A1Simplify workError detection/correctionMultiprogramming arrangementsCall stackCpu architecture
The present invention provides a method and system for capturing the call stack of a currently-running thread at the time a profiler interrupt occurs. The thread context of the thread is determined before a full push of the thread context is performed by the CPU architecture. The hardware state at the time of the interrupt is used to aid in determining which portions of memory to search for portions of the thread context. Based on the hardware state and the software state of the thread at the time of the interrupt the thread context is captured. Code may also be injected into a thread to capture a thread's call stack. The state of the thread is altered to induce the thread to invoke the kernel's call stack API itself, using its own context.
Owner:MICROSOFT TECH LICENSING LLC
Webpagehanging trojan detecting and protecting method and system as well as method for extracting corresponding code
InactiveCN102546576AImprove the performance of Trojan detectionEasy to controlData switching networksAnomaly detectionCode injection
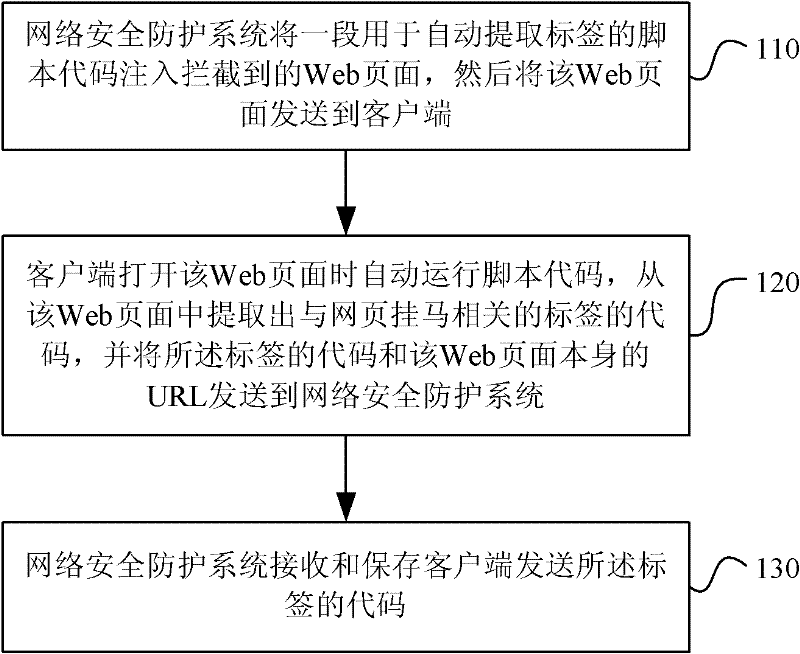
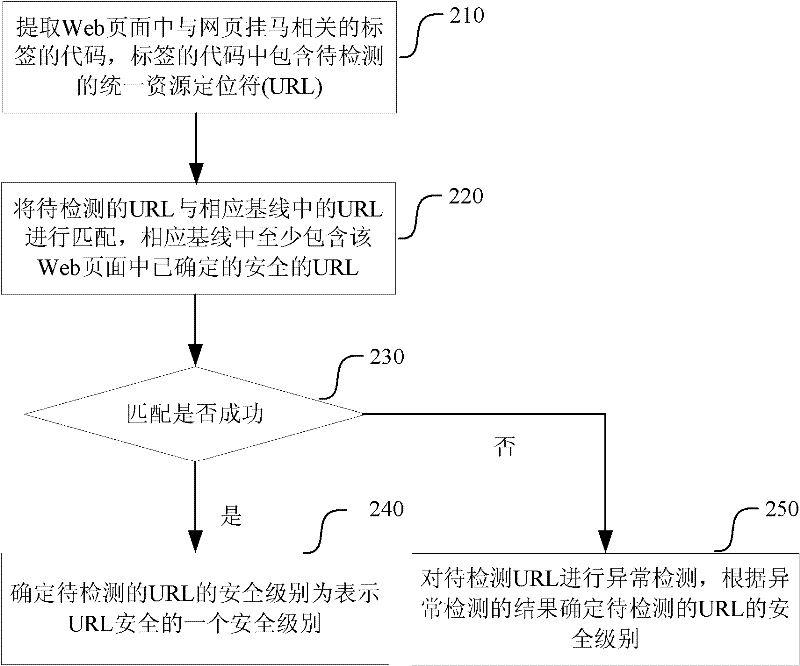
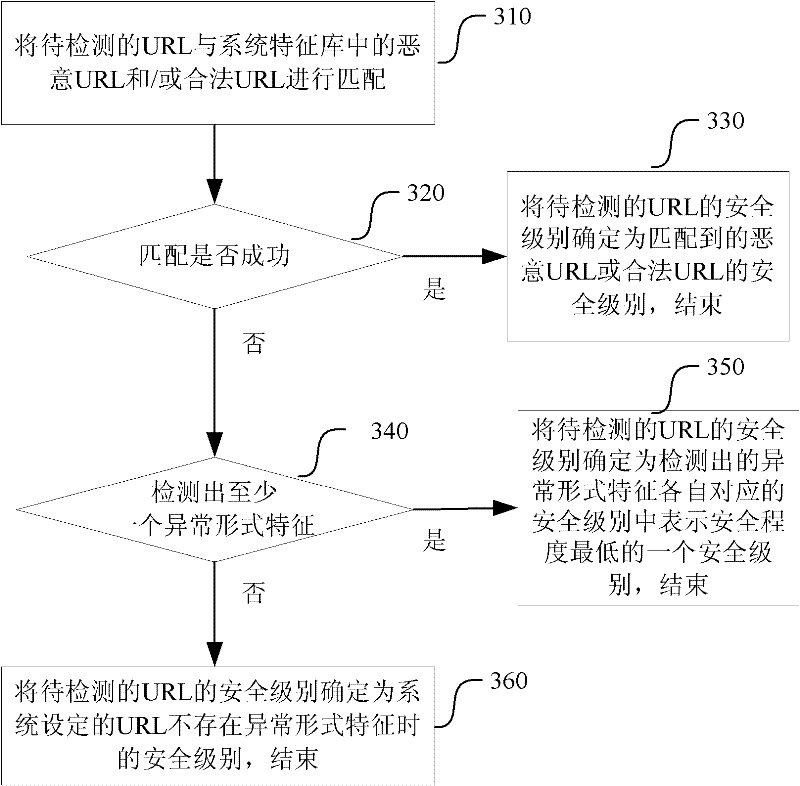
The invention relates to a webpagehanging trojan detecting and protecting method and a webpagehanging trojan detecting and protecting system, as well as a method for extracting a corresponding code. The system injects a section of script code for automatically extracting a tag into an intercepted Web page and sends the Web page to a client side; the client side runs the script code, extracts the code of the tag related to the webpage hanging horse, and sends the code and a URL (Uniform Resource Locator) of the Web page to the system; and the system can match a URL to be detected with a safe URL in a corresponding baseline, if match is failed, abnormal detection is carried out on the URL to be detected, so that the security level is confirmed. The webpagehanging trojan detecting and protecting method and the webpagehanging trojan detecting and protecting system as well as the method for extracting the corresponding code have small dependence on the environment, failure in report can be reduced, and the code of the tag can be effectively extracted.
Owner:BEIJING VENUS INFORMATION TECH +1
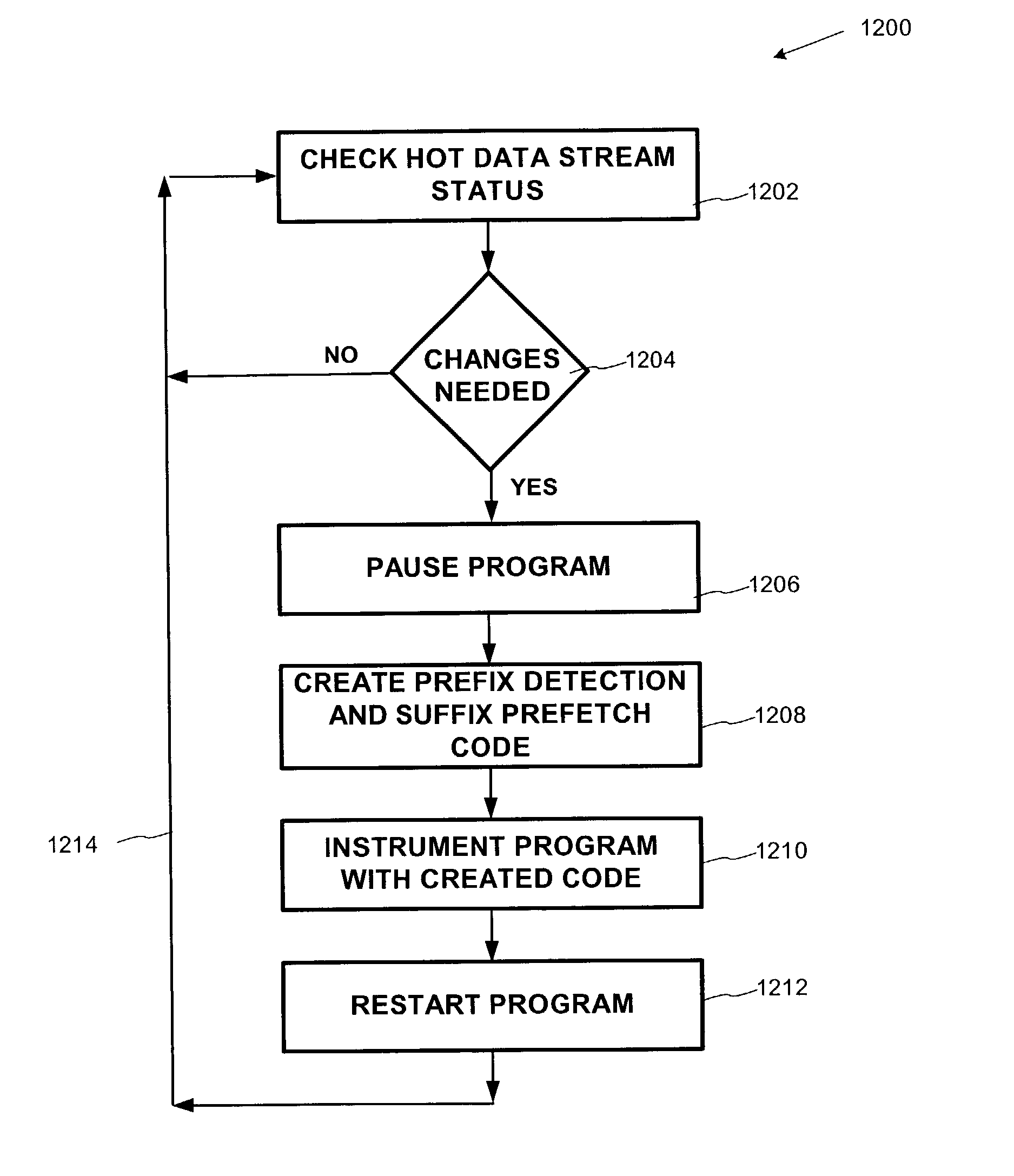
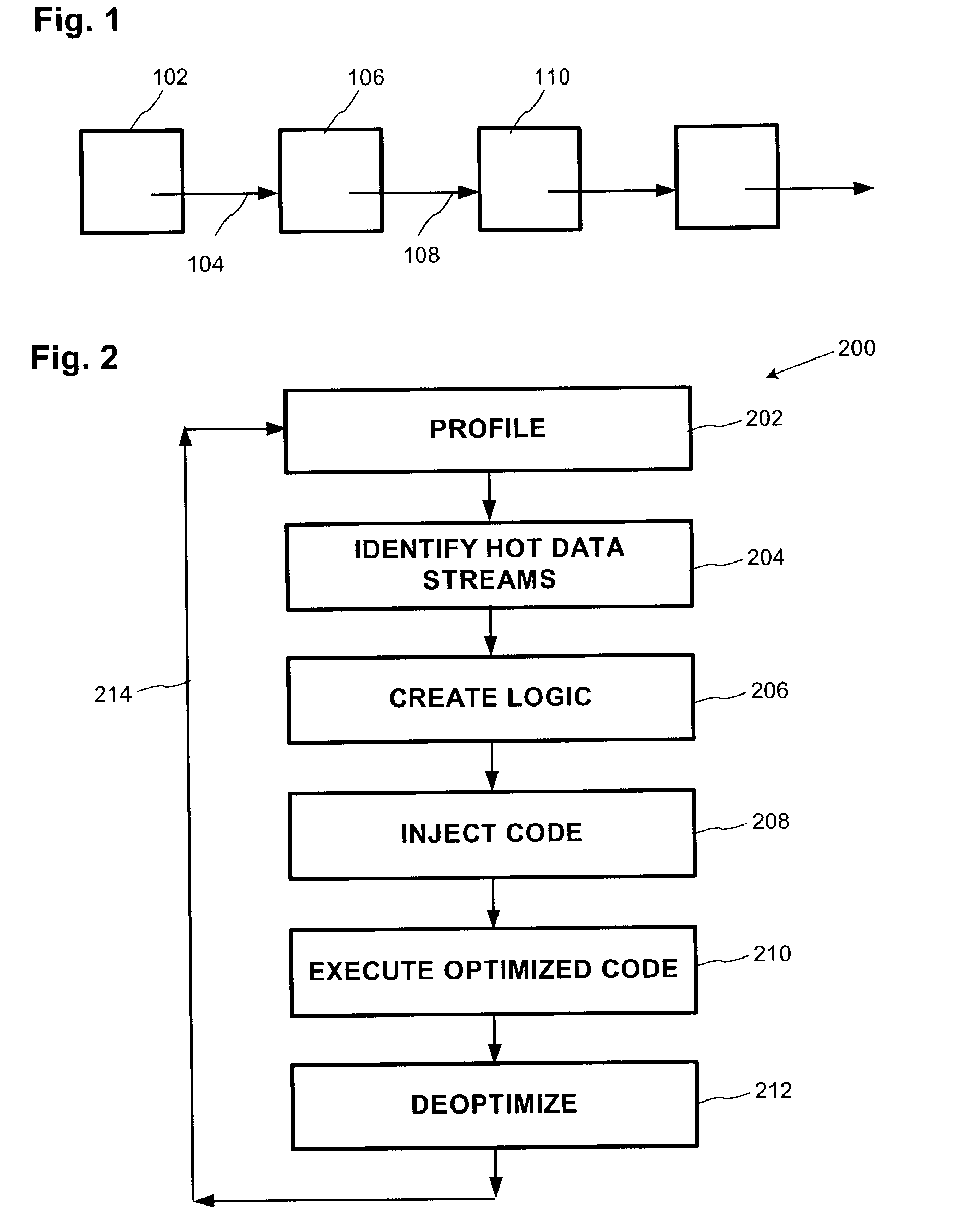
Dynamic prefetching of hot data streams
InactiveUS7058936B2Software engineeringSpecific program execution arrangementsData streamCode injection
A method and system for creating and injecting code into a running program that identifies a hot data stream, and prefetching data elements in the stream so they are available when needed by the processor. The injected code identifies the first few elements in a hot data stream (i.e. the prefix), and prefetches the balance of the elements in the stream (i.e., the suffix). Since the hot data stream identification code and prefetch code is injected at run time, pointer related time-dependencies inherent in earlier prefetch systems are eliminated. A global deterministic finite state machine (DFSM) is used to help create conceptual logic used to generate the code injected into the program for prefix detection.
Owner:MICROSOFT TECH LICENSING LLC
Creating secure process objects
InactiveUS7665143B2Precise processingReduce in quantityDigital data processing detailsAnalogue secracy/subscription systemsCode injectionComputer security
A secure process may be created which does not allow code to be injected into it, does not allow modification of its memory or inspection of its memory. The resources protected in a secure process include all the internal state and threads running in the secure process. Once a secure process is created, the secure process is protected from access by non-secure processes. Process creation occurs atomically in kernel mode. Creating the infrastructure of a process in kernel mode enables security features to be applied that are difficult or impossible to apply in user mode. By moving setup actions previously occurring in user mode such as creating the initial thread, allocating the stack, initialization of the parameter block, environment block and context record into kernel mode, the need of the caller for full access fights to the created process is removed.
Owner:MICROSOFT TECH LICENSING LLC
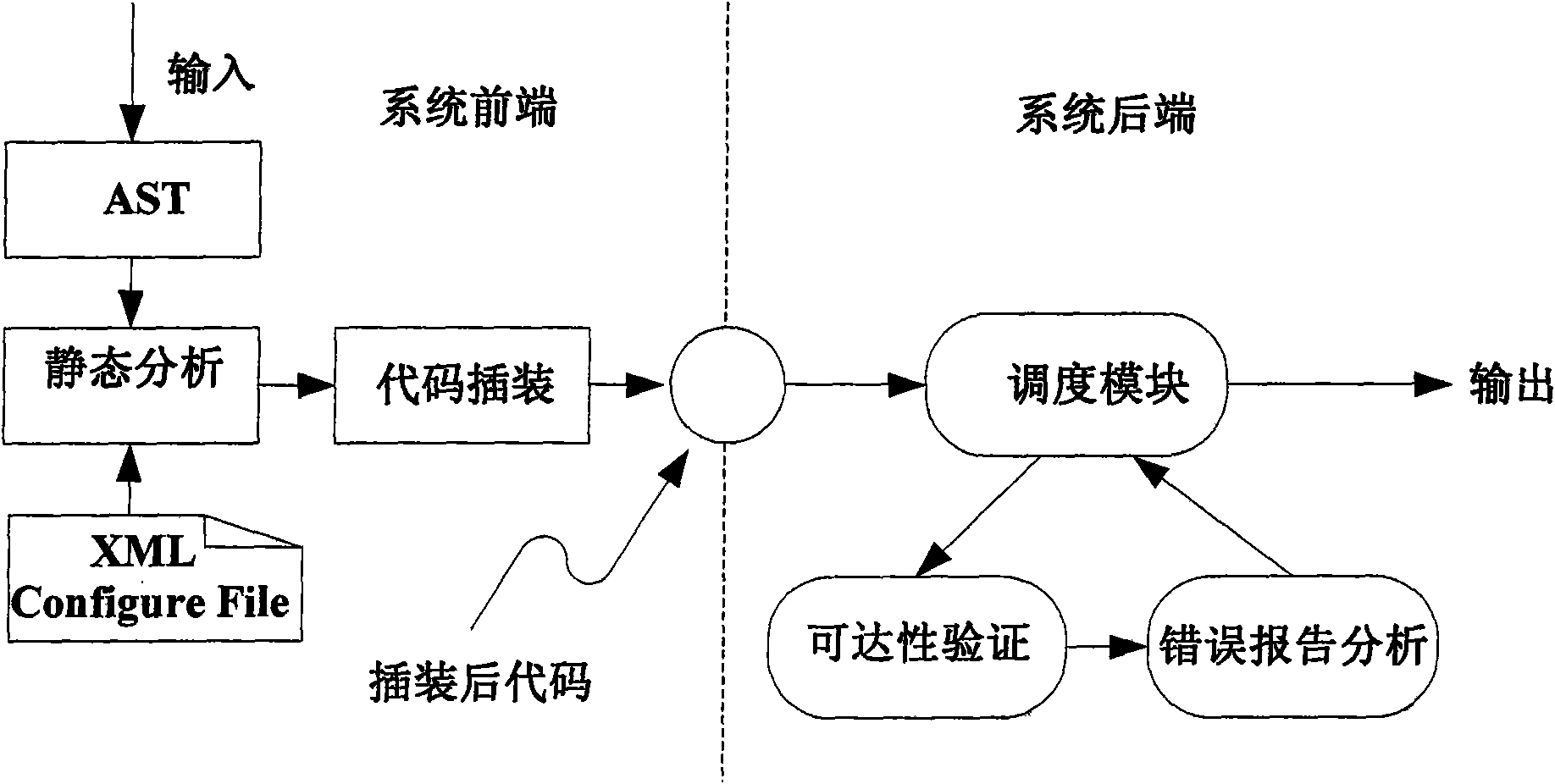
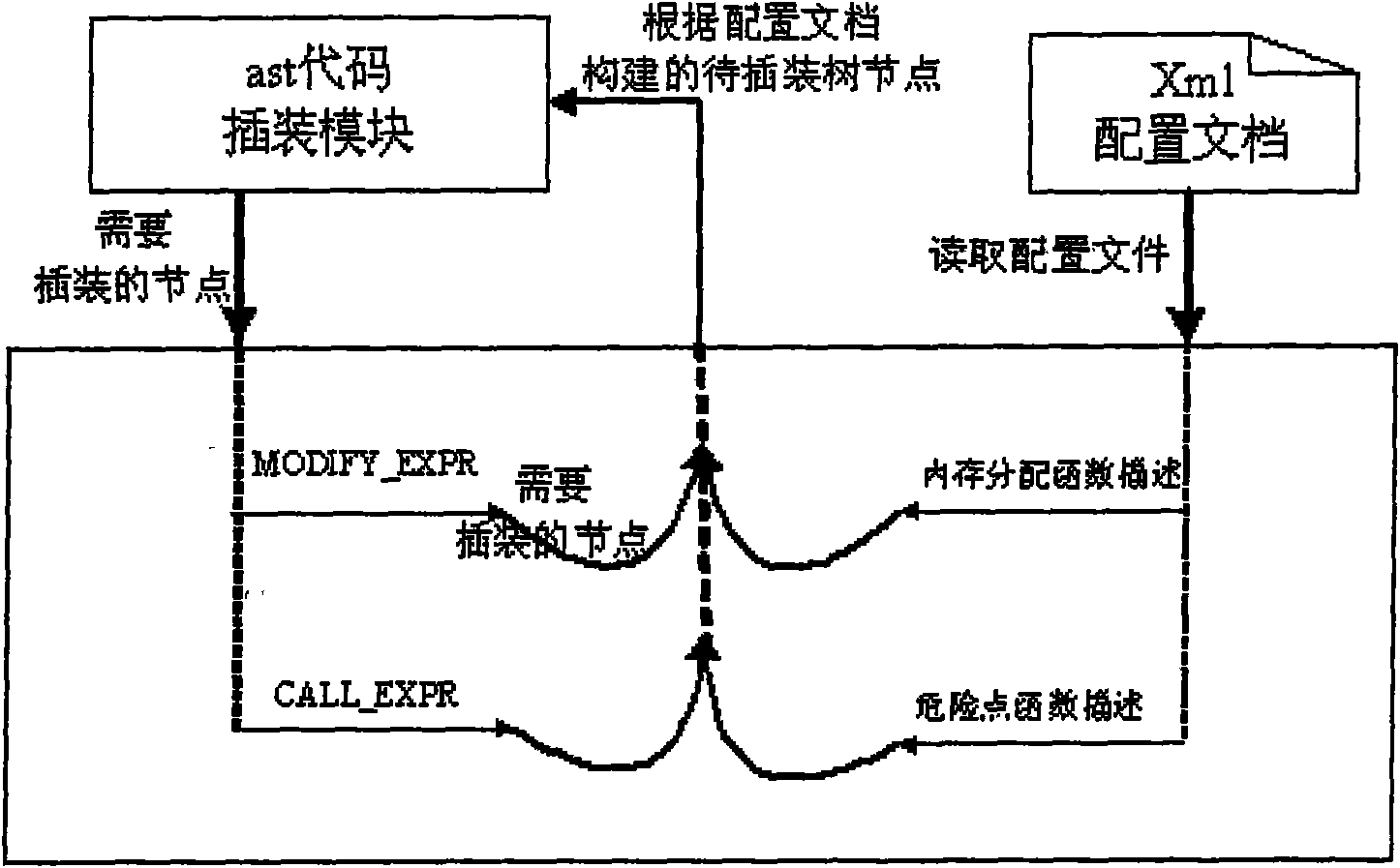
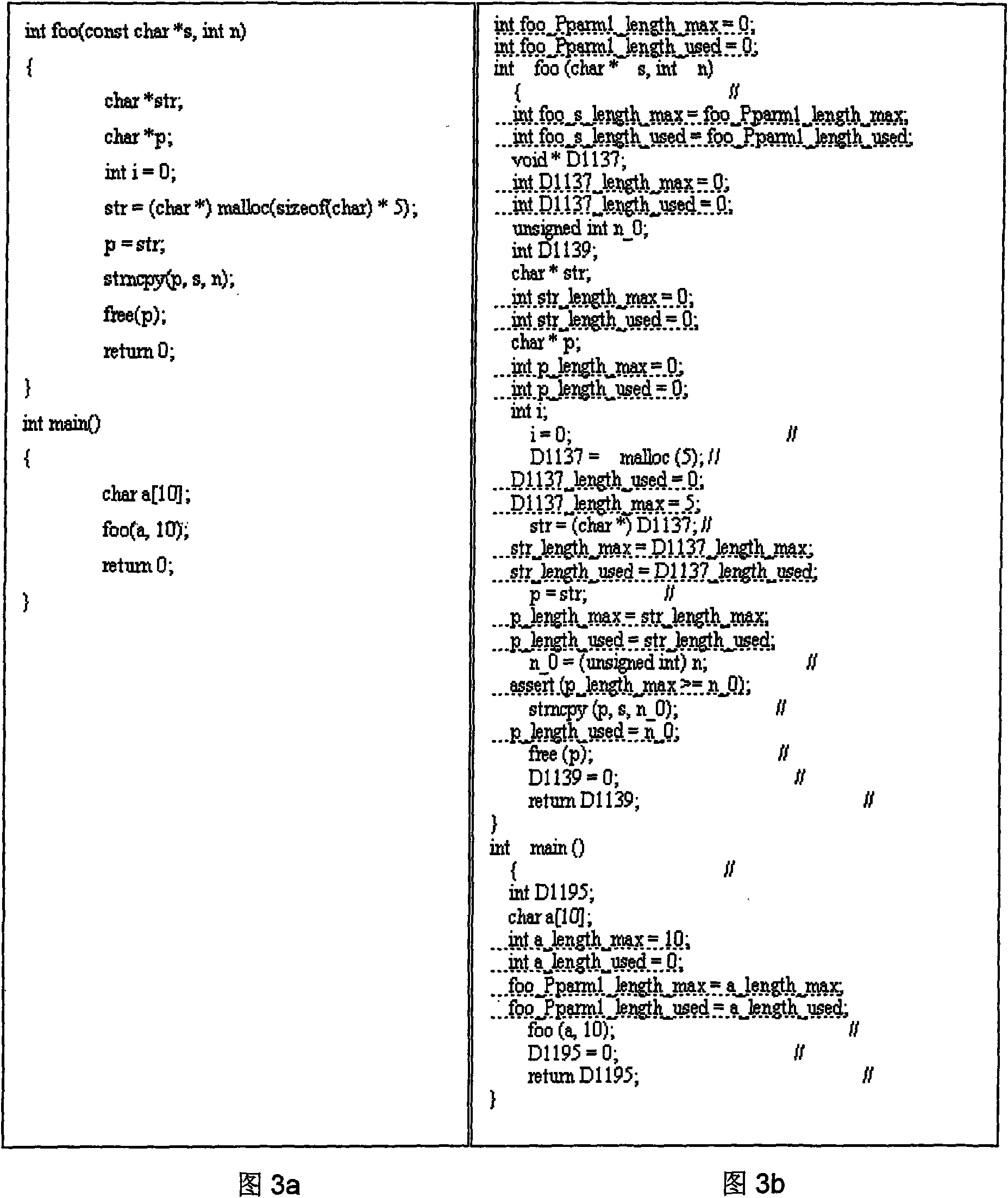
Method for detecting code security hole based on constraint analysis and model checking
The invention relates to a method for detecting a code security hole based on constraint analysis and model checking, which can extract the source code of a C program in a constraint way and detect the security hole of the program with the model checking. The main content comprises the following steps: buffer attribute information which is involved in the source code of the C program is extracted with a constraint analysis technology; the corresponding ASSERT sentence information of attribute generation, attribute transmission and attribute constraint is inserted into variable declaration, variable assignment and function call site with the buffer attribute information; the inserted code can be taken as the input of the model checking to judge whether the program is accessible, find whether the dangerous points in the program really has an accessible path and finally find the security hole in the source code. Currently, independent model checking can not detect the security hole of the buffer and the like, the method combines the static detecting technology of the constraint analysis with the model detecting technology to realize the detection of the security hole of the buffer overflow and the like, wherein, the detecting precision of the method is higher than that of the general static detecting technology. By extracting the other dangerous function information of the source code, corresponding inserting process is carried out. The invention also can detect the security holes such as formative character string, code injection, privilege escalation, etc.
Owner:BEIHANG UNIV
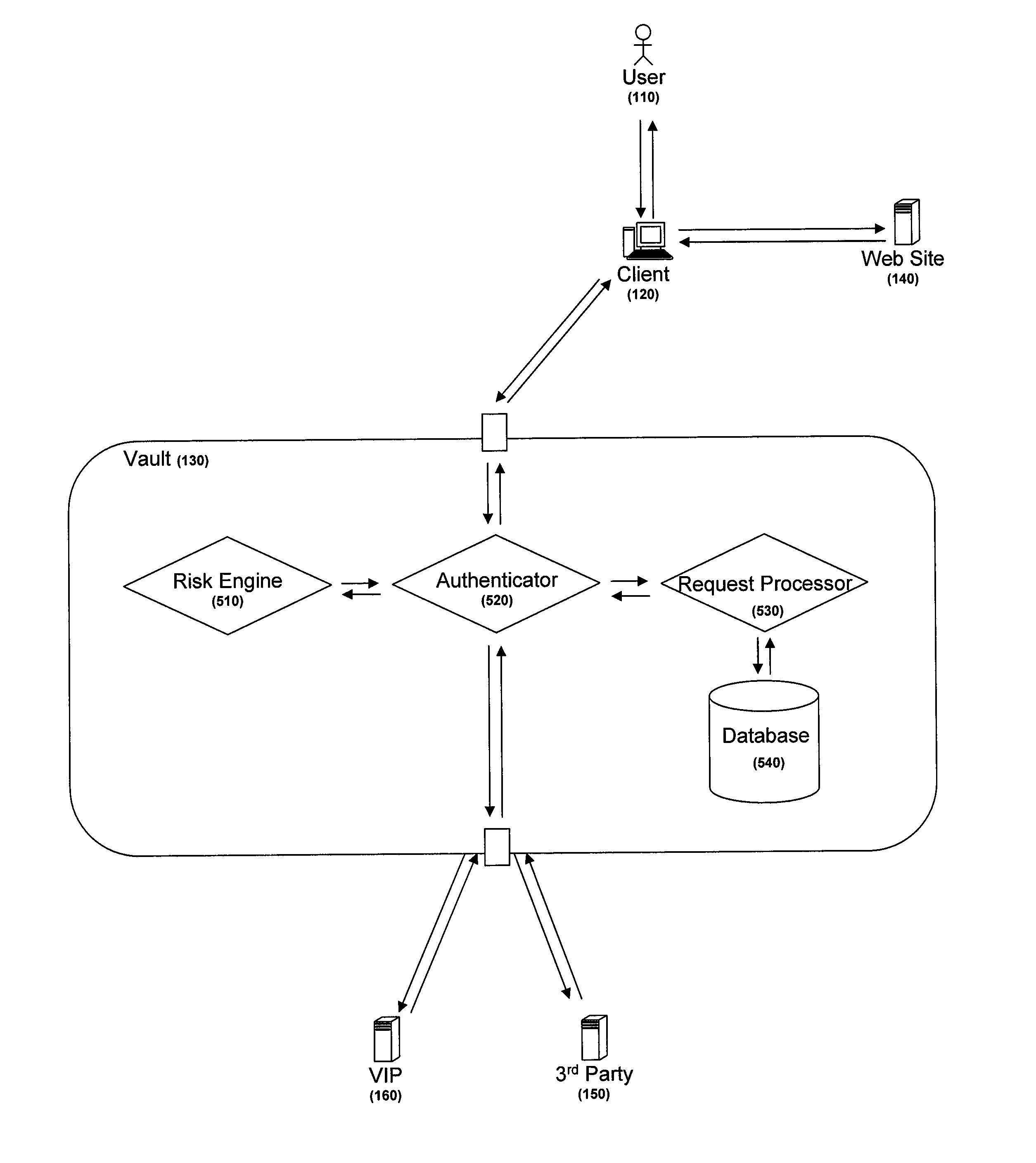
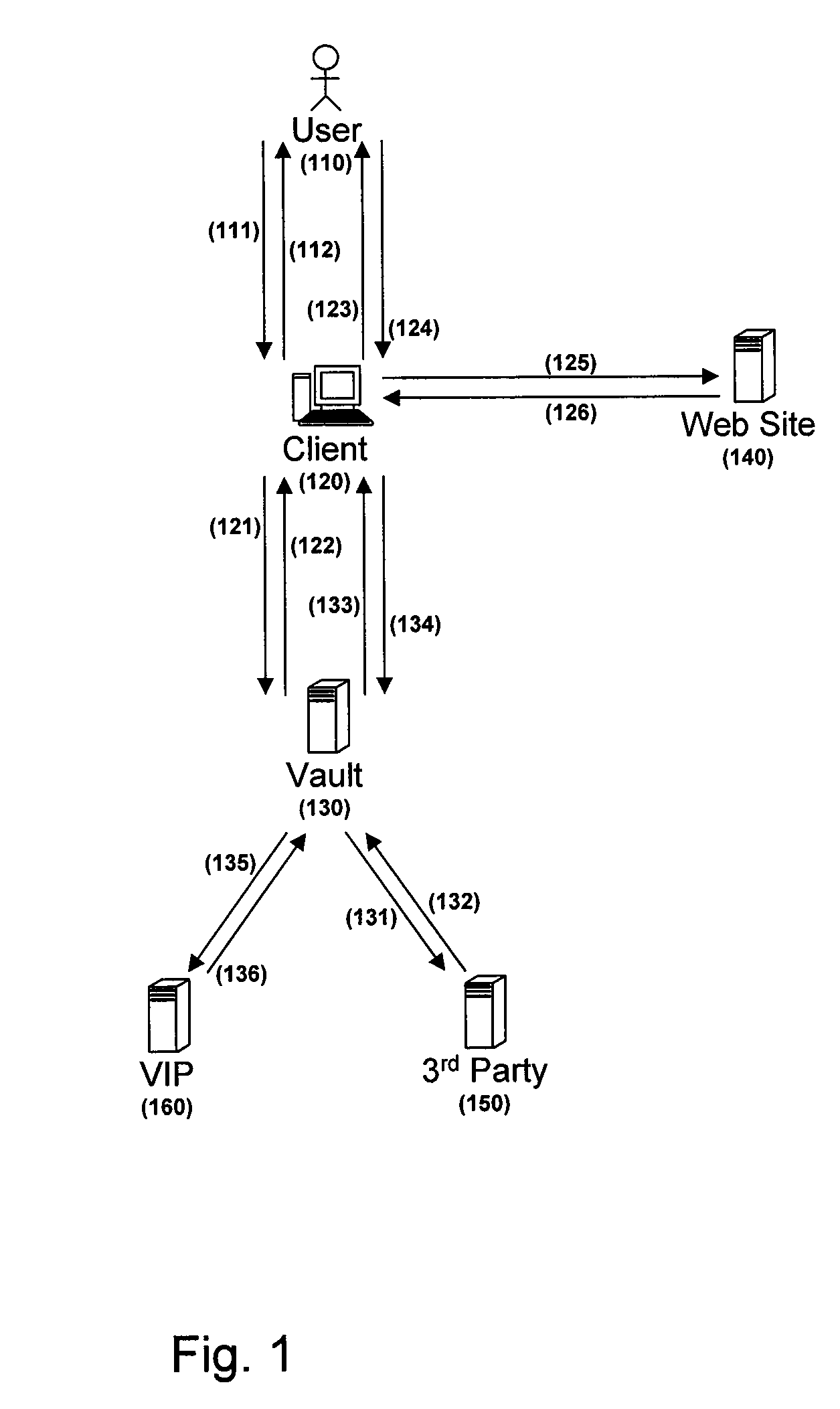
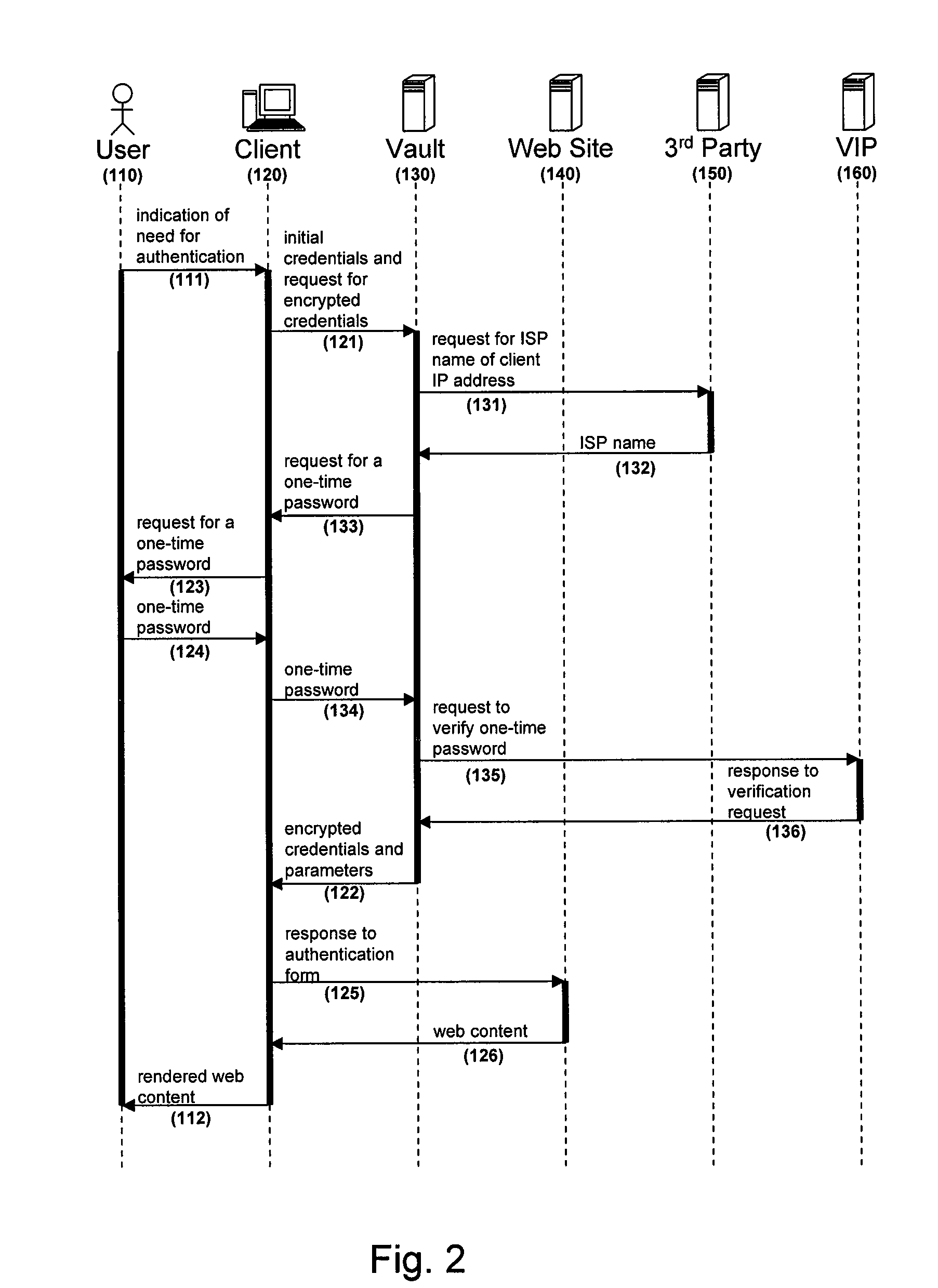
Credential management system and method
ActiveUS8438382B2Reduce riskVolume/mass flow measurementUser identity/authority verificationThird partyCode injection
A centralized credential management system includes website credentials that are stored at a vault. The website credentials are encrypted based upon a key not available to the vault and are for authenticating a user to a third party website. Through a client, a user authenticates to the vault and retrieves the encrypted website credentials and parameters and code for properly injecting the credentials into a website authentication form. The website credentials are decrypted at the client and injected into the authentication form using the parameters and code.
Owner:SYMANTEC CORP
Method and system for advanced messaging
ActiveUS20070162598A1Eliminate the problemDigital computer detailsMarketingThe InternetCode injection
An implementation of the inventive concept enables an outside entity to alter user's internet experience on a system-wide level. Specifically, inventive system enables a merchant, a distributor or any other entity to send contextually-relevant messages directly to the user's computer. Upon the receipt of the messages by the controller application residing on the user's computer, the messages are shown to the user by being incorporated into representation of various resources viewed by the user. For example, the received messages are incorporated into web pages viewed by the user by means of code injection. This way, the merchant, distributor or any other entity may provide targeted advertising to the user in a contextually relevant manner. Specifically, the controller application residing on the user's computer may detect requests for specific resources issued by the user in accordance with a predetermined criteria and incorporate the aforesaid received messages into those selected resources.
Owner:AURA SUB LLC
Continuous run-time validation of program execution: a practical approach
ActiveUS20140082329A1Easy to modifyGuaranteed CompatibilityError detection/correctionDigital computer detailsControl flowReal time validation
Trustworthy systems require that code be validated as genuine. Most systems implement this requirement prior to execution by matching a cryptographic hash of the binary file against a reference hash value, leaving the code vulnerable to run time compromises, such as code injection, return and jump-oriented programming, and illegal linking of the code to compromised library functions. The Run-time Execution Validator (REV) validates, as the program executes, the control flow path and instructions executed along the control flow path. REV uses a signature cache integrated into the processor pipeline to perform live validation of executions, at basic block boundaries, and ensures that changes to the program state are not made by the instructions within a basic block until the control flow path into the basic block and the instructions within the basic block are both validated.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Systems and methods for managing loading priority or sequencing of fragments of a web object
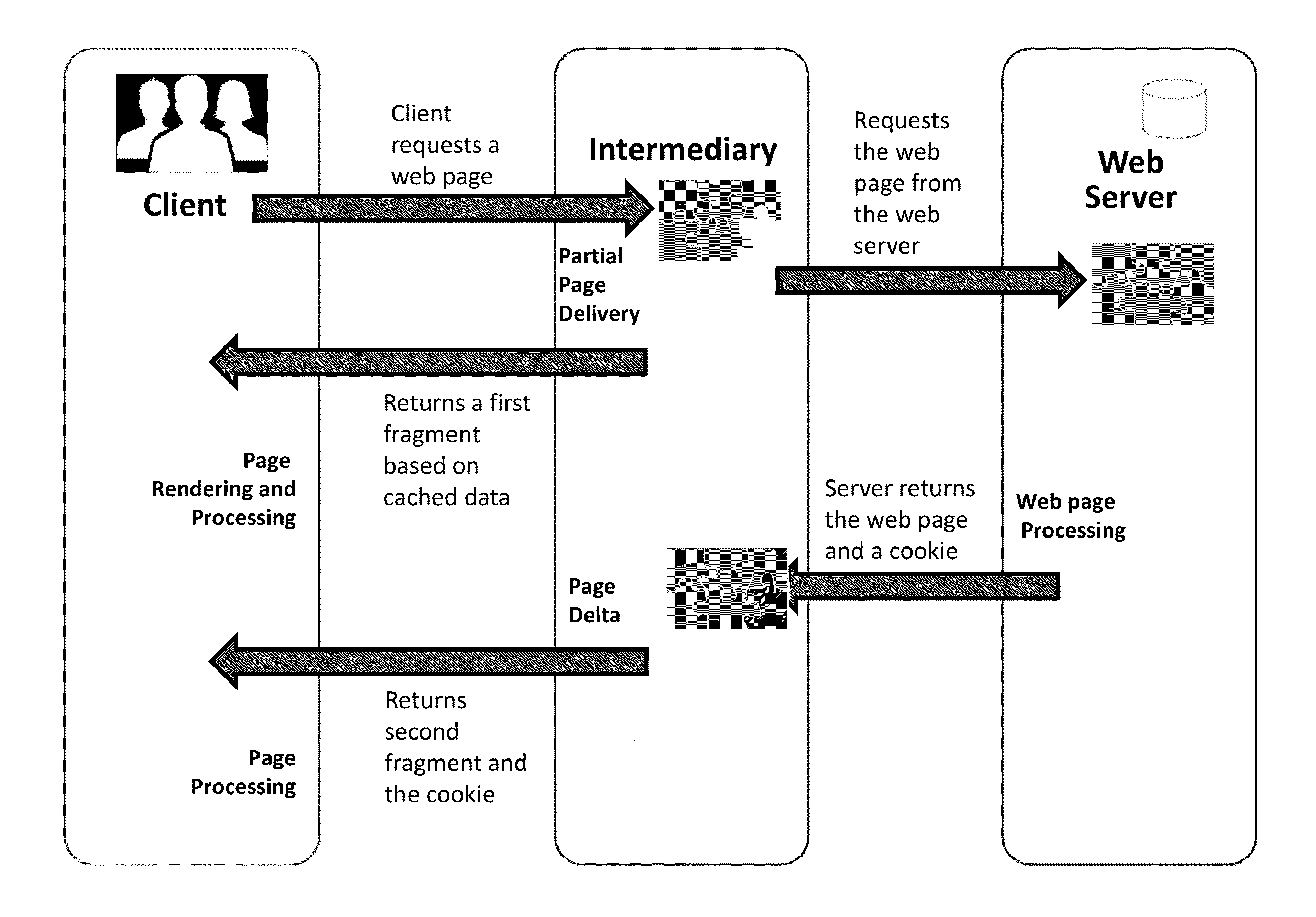
ActiveUS9282145B2Improve experienceImprove performanceDigital data information retrievalInterprogram communicationCode injectionDatabase
This disclosure is directed to methods and systems for managing rendering of a web page in a browser. A client operated by a user may execute code within a first fragment of a web page as the first fragment is presented to the user. The code may be injected into the first fragment by an intermediary between the client and a server of the web page. The intermediary may have split the web page into the first fragment and a plurality of fragments, and may have modified a default rendering characteristic for each of the plurality of fragments. Each of the modified rendering characteristic may include a trigger and action for rendering of a corresponding fragment. The executing code may dynamically detect a trigger for rendering of a second fragment from the plurality of fragments. The executing code may initiate a corresponding action for rendering of the second fragment.
Owner:YOTTAA
Plug-in-based building method and system for Web application, and server
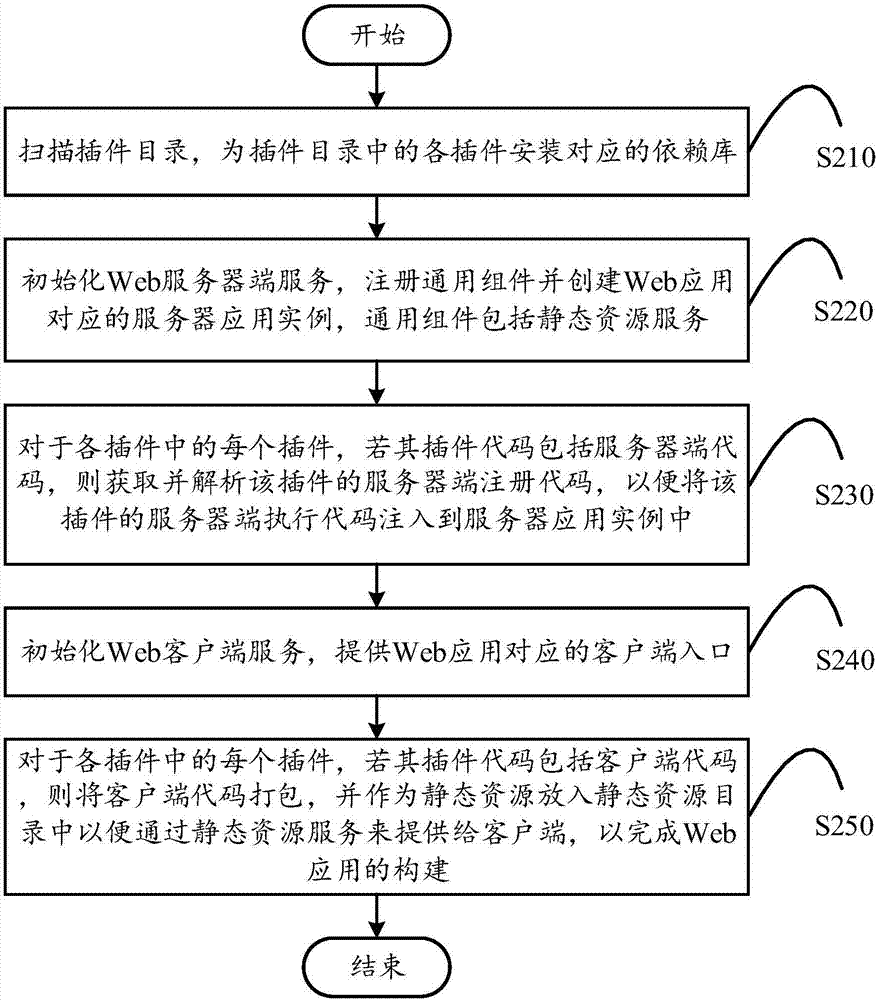
ActiveCN107291458AImprove usabilityImprove compatibilitySoftware designSpecific program execution arrangementsWeb applicationWeb service
The invention discloses a plug-in-based building method and system for a Web application. The method comprises the steps of scanning a plug-in directory and installing a corresponding dependency library for each plug-in in the plug-in directory; initializing a Web server service, registering a generic component and creating a server application instance corresponding to a Web application, wherein the generic component comprises a static resource service; for each plug-in in the plug-ins, if plug-in codes of the plug-in include server codes, obtaining and analyzing the server registration code of the plug-in, thereby injecting the server execution code of the plug-in into the server application instance; initializing a Web client service and providing a client entry corresponding to the Web application; and for each plug-in in the plug-ins, if the plug-in codes of the plug-in include client codes, packaging the client codes and putting the client codes as static resources into a static resource directory, thereby providing the client codes for a client through a static resource service to finish the building of the Web application.
Owner:BEIJING KNOWNSEC INFORMATION TECH
Method for monitoring application program based on window platform
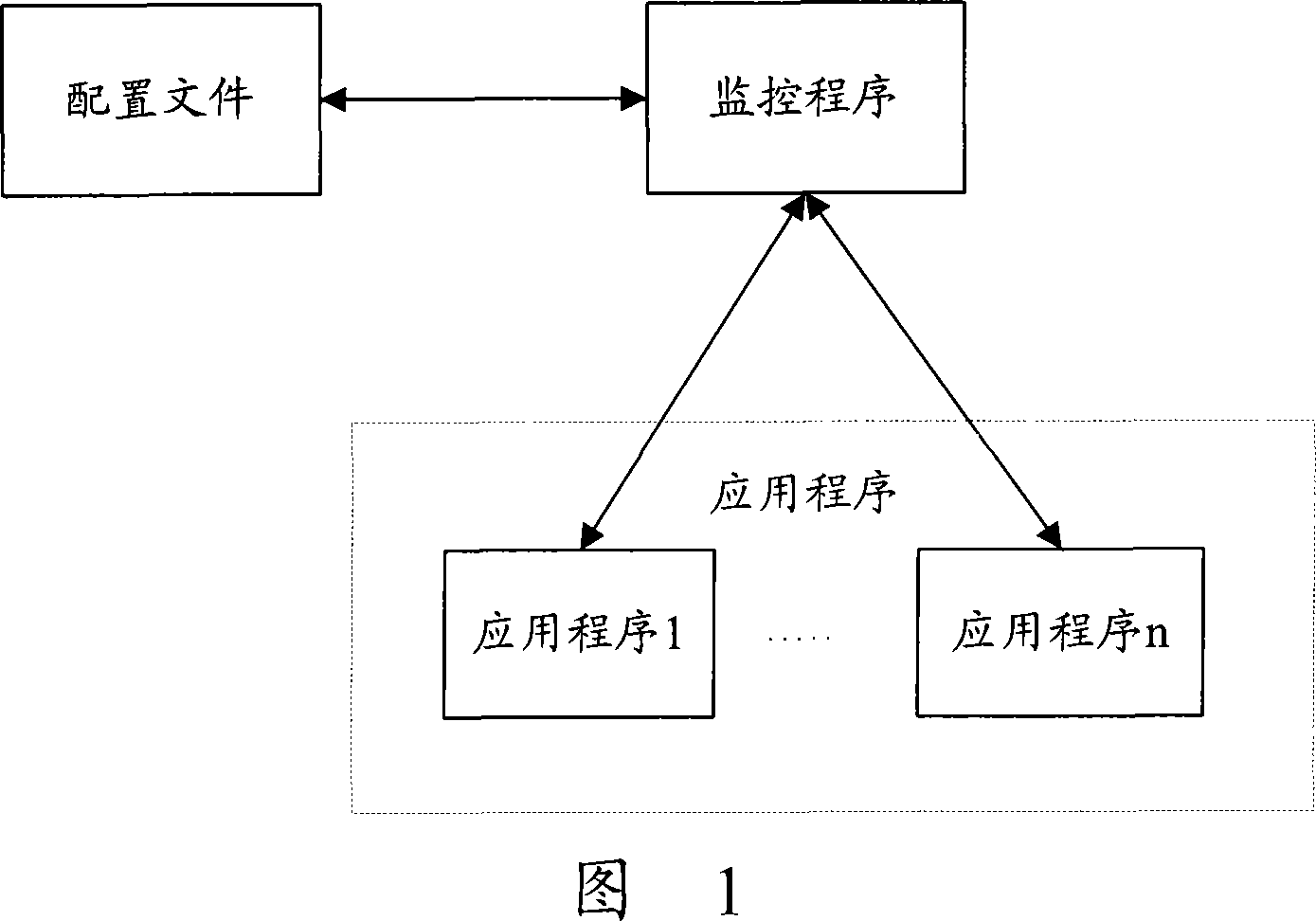
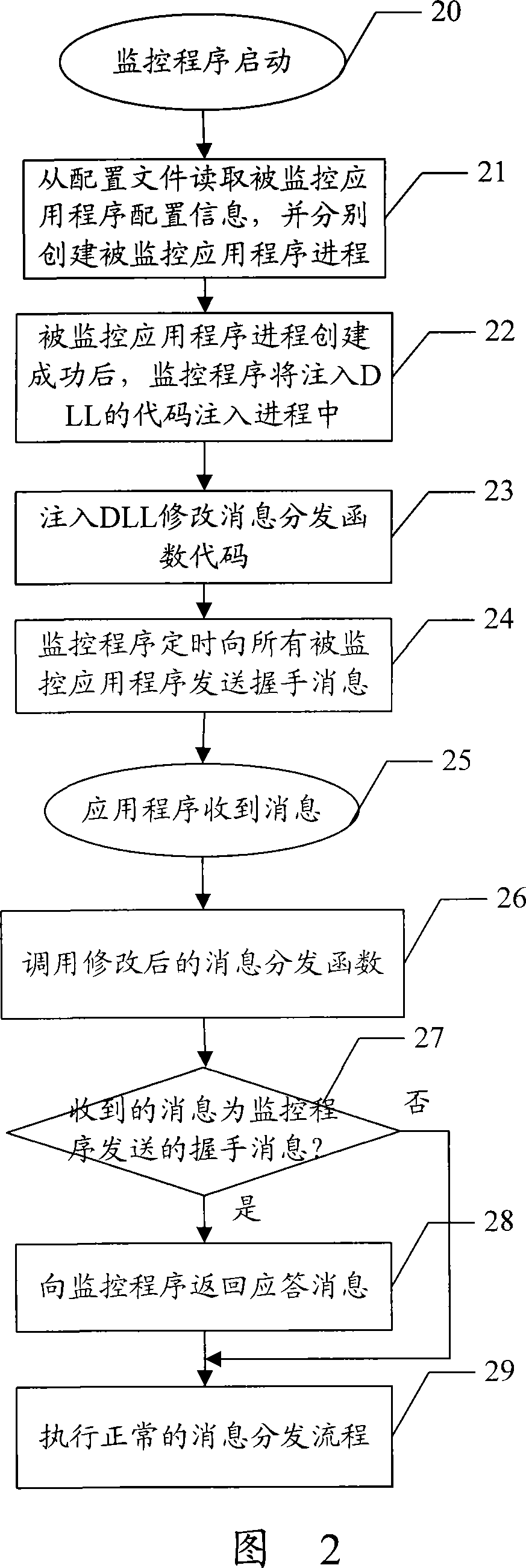
InactiveCN101227630AImprove scalabilityAccurate real-time monitoringSupervisory/monitoring/testing arrangementsData switching networksCode injectionApplication software
The invention discloses an application program monitoring process based on a window platform, which comprises the following steps respectively establishing a process of the application program which is monitored after the starting of the monitor program, wherein the monitor program inputs the code which belongs to a dynamic link library (DLL), inputting a message distribution function code in a modification process of DLL, sending handshaking messages to all the monitored programs by the monitor program on a scheduled time, transferring modified message distribution function by the monitored programs the after receiving the message, sanding a return answer message to the monitor program after the message distribution function ascertains the massage is the handshaking message which is sent by the monitor program. The monitoring method of the invention adopts the DLL inputting mode to modify the code of the system information distribution function, which enables the system information distribution function to capture and answer the handshaking message from the monitor program without adding code combined monitoring in application programs, and has the advantages of good scalability and can realize a accurate real-time monitor.
Owner:ZTE CORP
Mitigating malware code injections using stack unwinding
InactiveUS20160232347A1Prevent destructive behaviorLess vulnerablePlatform integrity maintainanceCode injectionSystem call
Malware in a computer is found by detecting a sequence of function calls in a memory space of a process executing on a computer, tracing the process stack to locate members of the sequence in a database of non-malicious function calls, failing to locate the sequence in the database, and responding to the failure by a combination of logging the failure, alerting an operator and terminating, blocking or otherwise disabling the process or a system call initiated by the process.
Owner:PALO ALTO NETWORKS INC
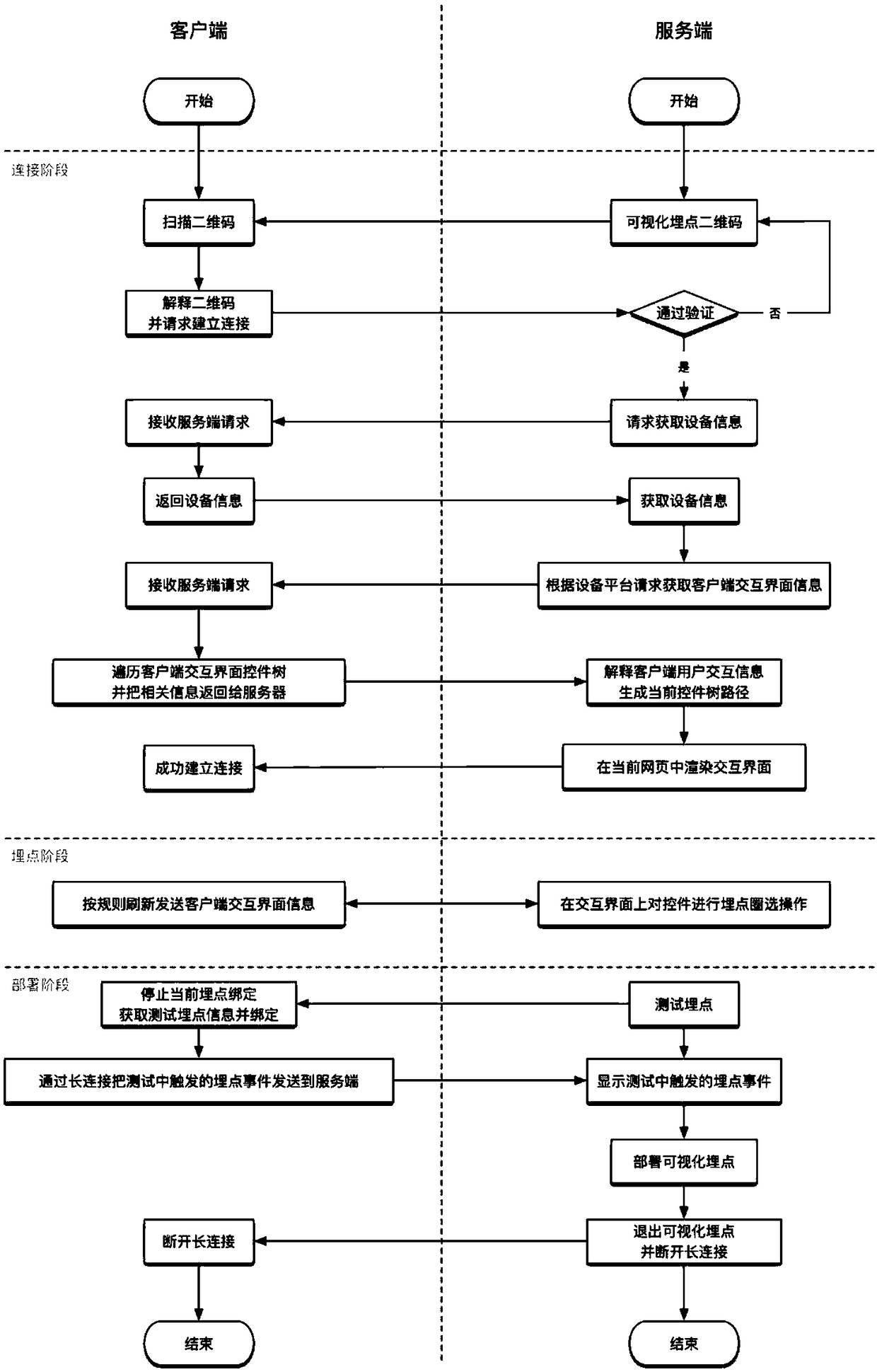
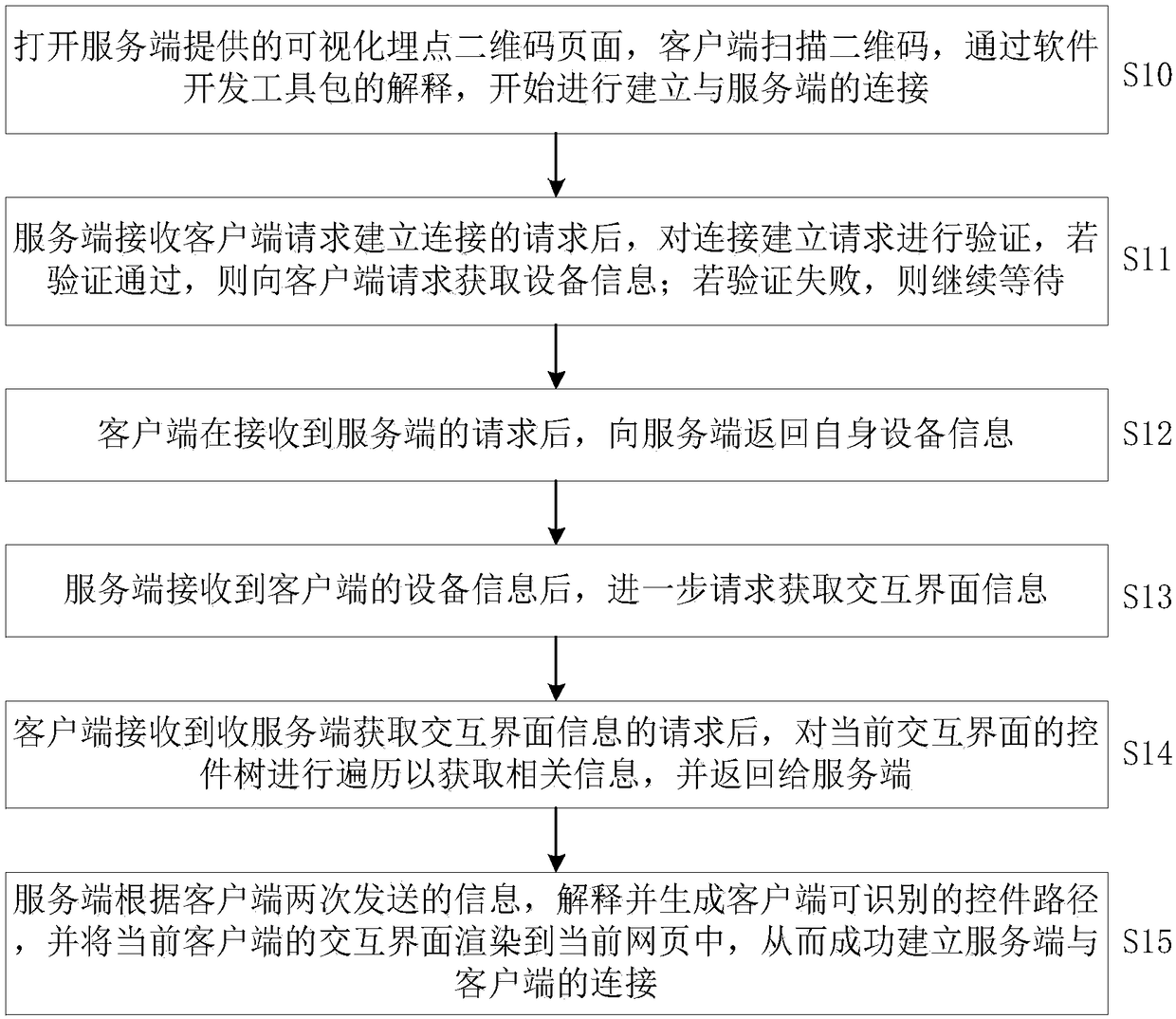
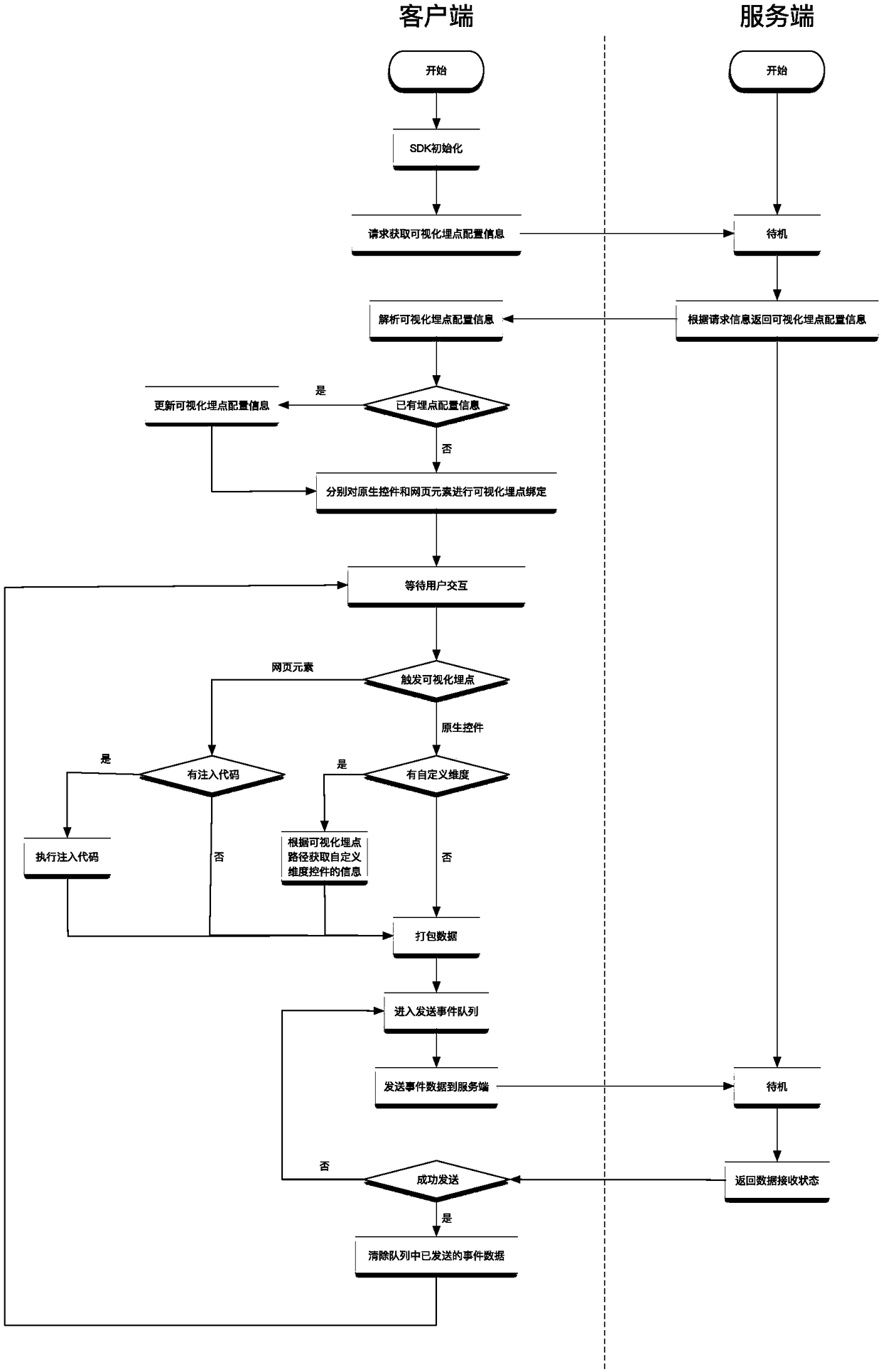
Visual point burying method for cross-platform mobile terminal
ActiveCN108304176AAdded custom dimension function for buried pointsSoftware testing/debuggingVisual/graphical programmingControl subjectsRelevant information
The invention discloses a visual point burying method for a cross-platform mobile terminal. The method comprises the steps that control tree related information sent to a current interactive interfaceof a server is refreshed after a client establishes a connection with the server; the server synchronously updates a rendering interface according to the received information, and a user performs visual point burying selection operation on a control in the server; a binding condition of the control is tested, the server sends point burying information to the client, and the client confirms the control specified in the obtained point burying information and performs binding; the test of the bound control is triggered in the client, event information of the control is triggered and sent to theserver, and after the test is passed, the server performs deployment operation on the control subjected to point burying and selection. A point burying dimension self-definition function is added; thesupport of point burying of HTML elements is added; the interactive interface control is universally used for various self-defined client interactive interfaces; and for the webpage control, a visualcode injection point burying function and a similar element point burying function are supported.
Owner:广东数果科技有限公司
Real-time dynamic and synchronized captioning system and method for use in the streaming of multimedia data
ActiveUS7991801B2Adjustable speedEasy constructionDigital data processing detailsPicture reproducers using cathode ray tubesGraphicsGraphical user interface
A dynamic and synchronized real-time captioning system and method for streaming media. A streaming encoder module can provide a code injection to marry textual data and audio / video (AV) data in order to form a text and / or audio stream. A streaming control module can allow an end-user to specify font format utilized to embed into an AV stream. A delay enhancement tool can be adapted to adjust speed of the text and / or audio stream, which allows the end-user to receive the text and / or audio stream at a proper speed. A customized graphical user interface (CGUI) can be adapted to assist with streaming administration to provide an encoding option, caption source location, delay control and slide control. Therefore, the captioning system can be able to synchronize and deliver the textual data and the AV data for live media streaming at an end-user's system.
Owner:KYNDRYL INC
Coded mass spectroscopy methods, devices, systems and computer program products
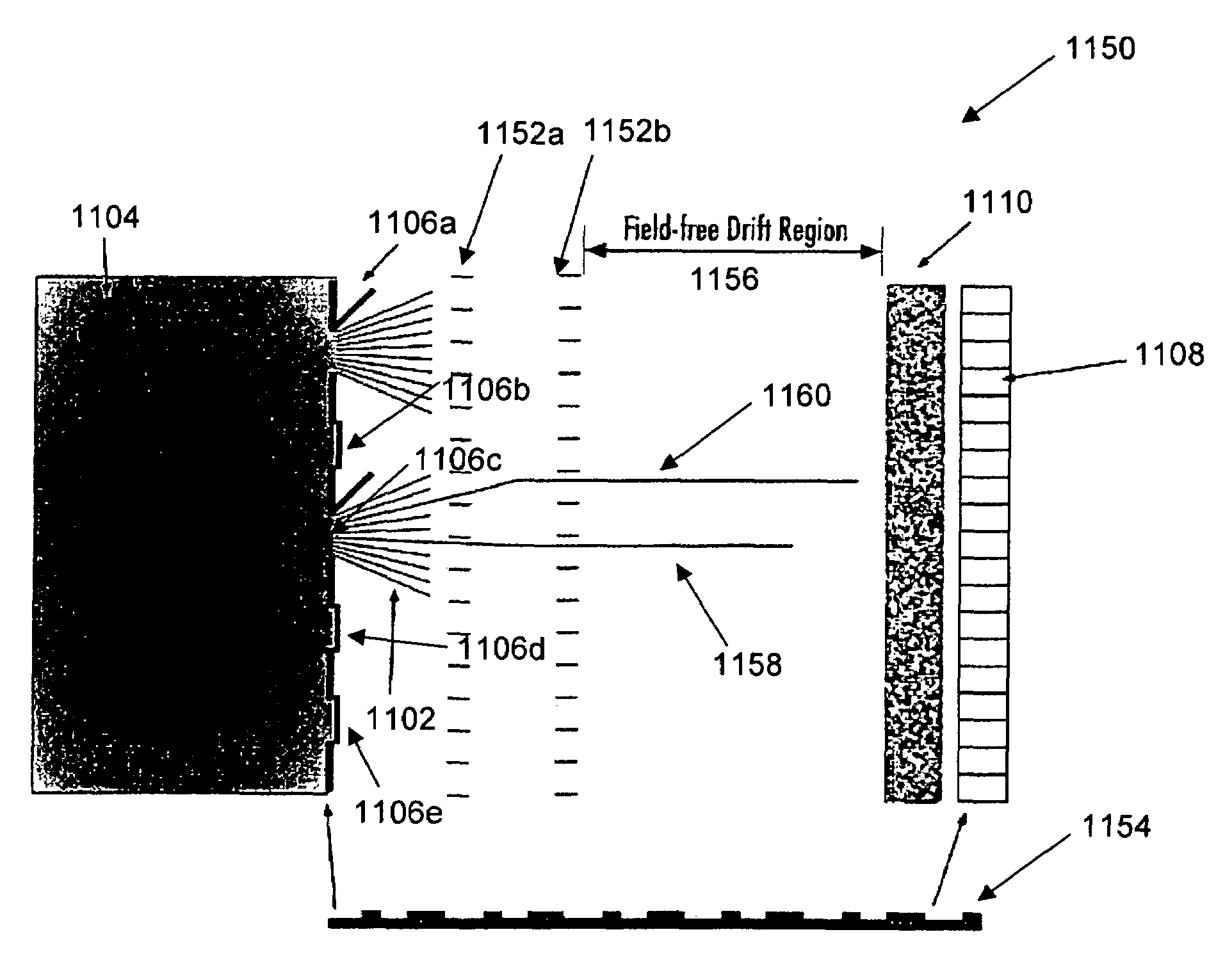
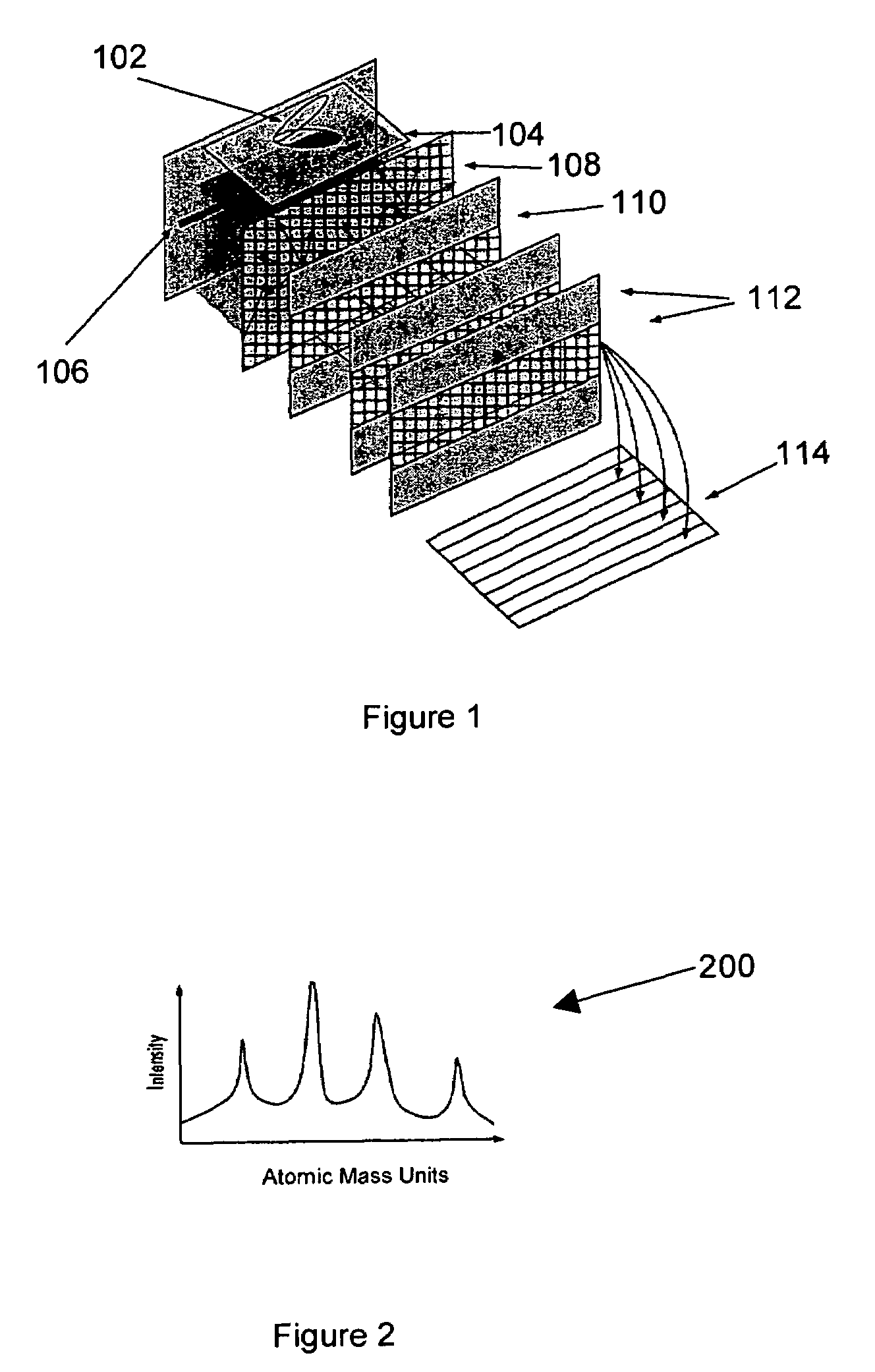
ActiveUS7399957B2Large sampling volumeShorten the timeTime-of-flight spectrometersParticle spectrometer methodsImage resolutionCode injection
Owner:DUKE UNIV
Browser page display method and device as well as browser and terminal
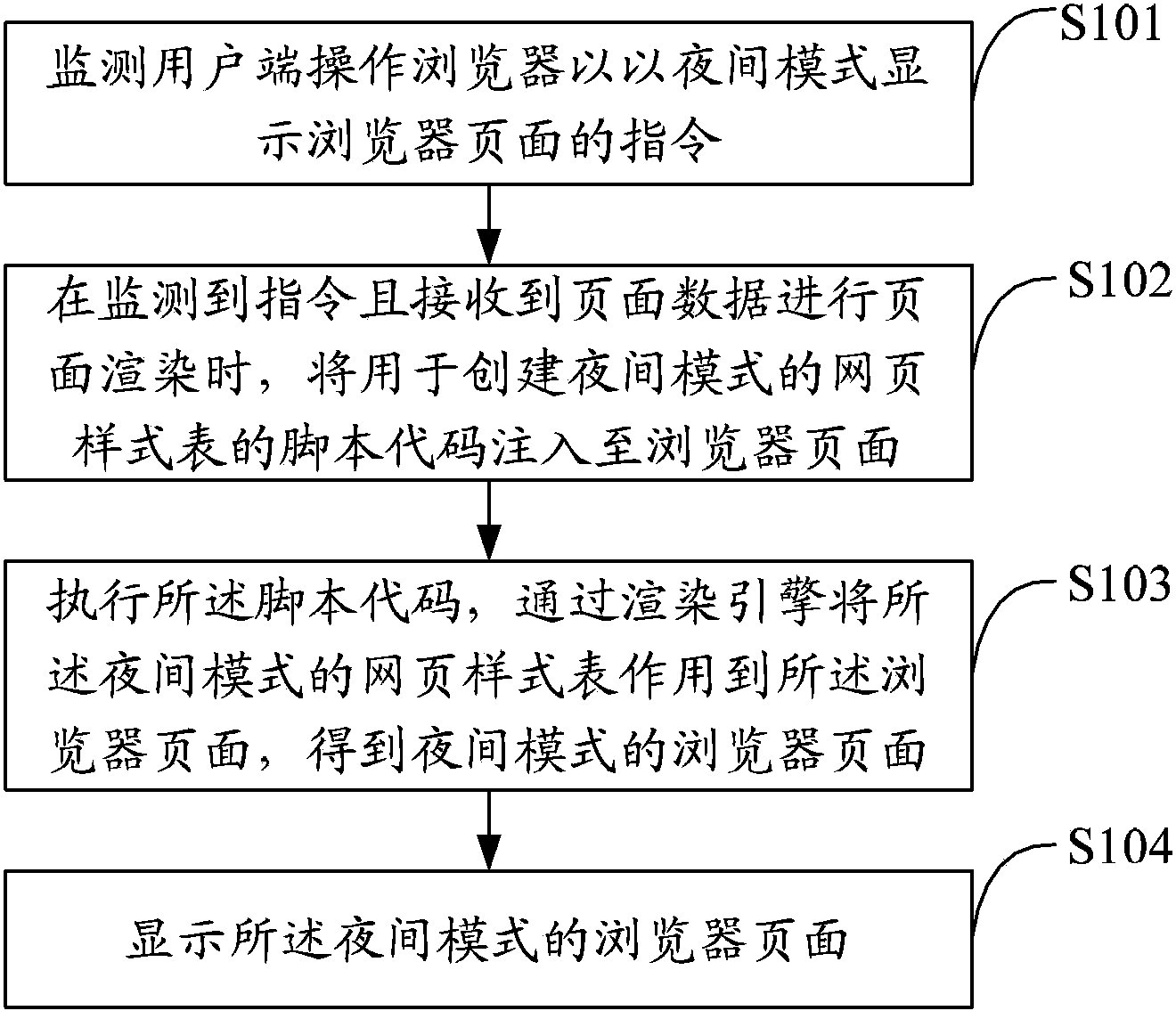
InactiveCN104346403AAvoid display blurSpecific program execution arrangementsSpecial data processing applicationsDisplay deviceCode injection
The invention relates to a browser page display method and a browser page display device as well as a browser and a terminal. The method comprises the following steps: monitoring an instruction of displaying a browser page by a client operation browser via a night mode; when receiving page data and carrying out page rendering after monitoring the instruction, injecting a script code which is used for creating a web page style sheet in night mode into the browser page; executing the script code and acting the web page style sheet in night mode to the browser page through a rendering engine so as to obtain browser page in night mode; displaying the browser page in night mode. Through injecting the script code for dynamically creating the night web page style sheet to the original page and executing the script code to render the browser page into night effect, the problem of blurry page display caused by adding a shade in the prior art is avoided and the night-mode page display effect of the terminal browser is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Trusted secure desktop
Systems and methods for simultaneously protecting software components (150) installed on a computer system (102) against malware. The methods involve executing a first end user application (3181, 3182, . . . , 318p) to the computer system (102) which execute in user mode on a trusted secure desktop (904). The trusted secure desktop is configured to run simultaneously with an unsecure desktop (902). The methods also involve performing a security service operation to protect the first end user application against malware. The security service operations include a keylogger prevention service operation, a code injection prevention service operation, a screen scraper protection service operation, a process termination prevention service operation, or a Domain Name System service operation.
Owner:WONTOK
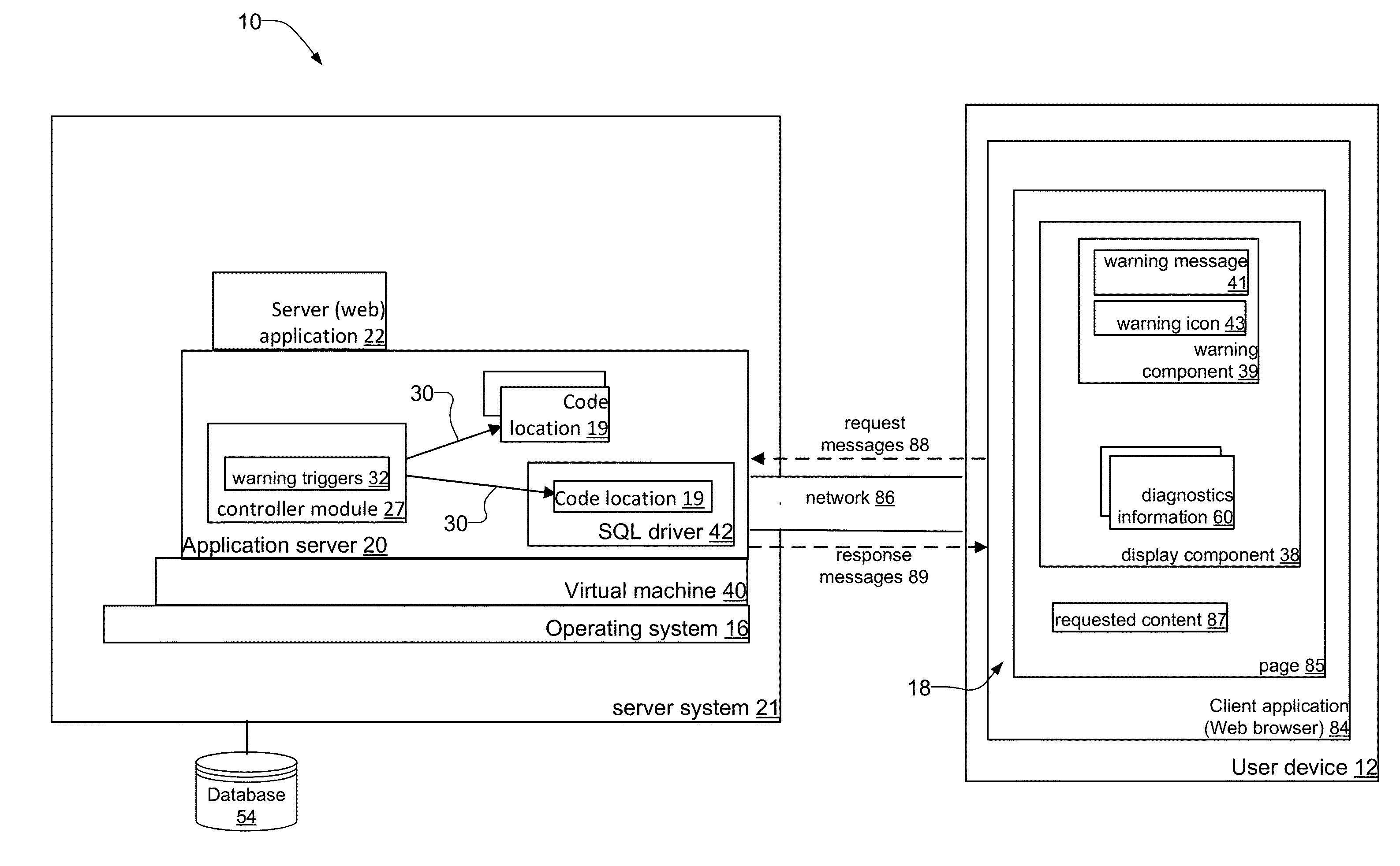
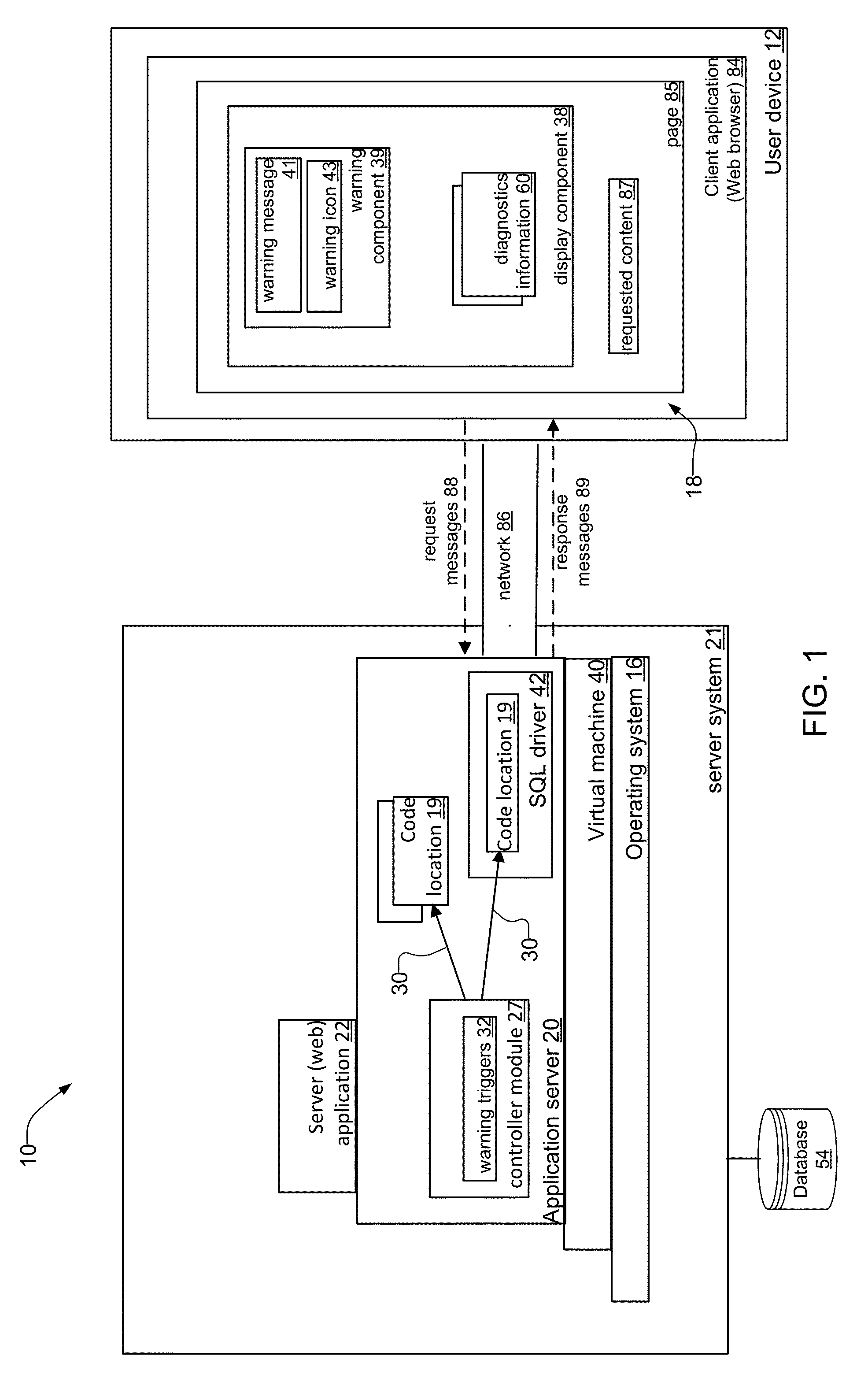
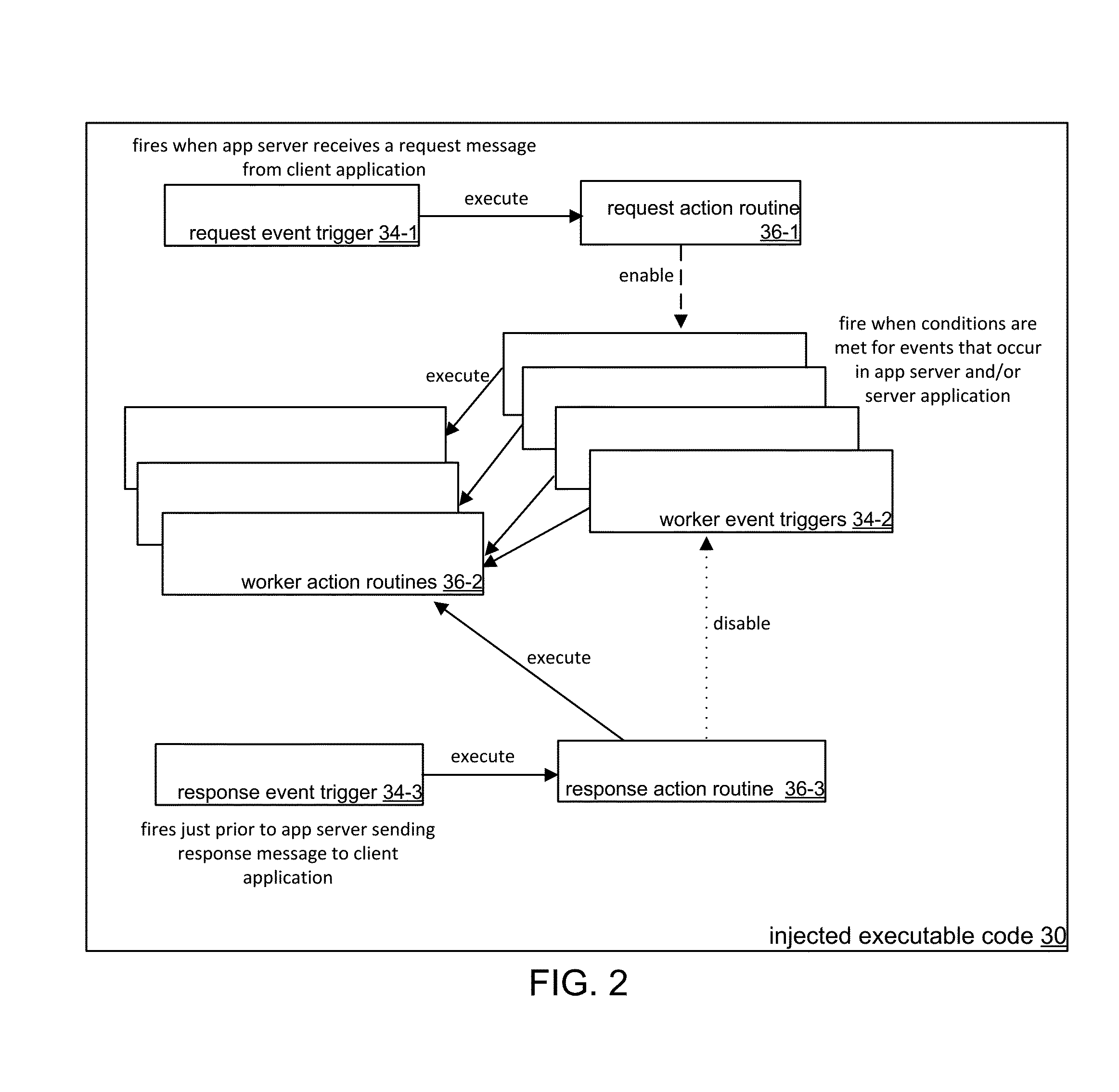
System and Method for Providing Runtime Diagnostics of Executing Applications
ActiveUS20150220421A1Improve abilitiesEnhanced informationHardware monitoringSoftware testing/debuggingCall stackUser device
A system and method that provides runtime diagnostics information of server applications executing on application servers of a server system. At class load time, the system injects executable software code that creates and displays the diagnostics information without necessarily having to stop and restart the executing server application. In response to user applications on user devices sending request messages for content from the server application, the system injects executable code into the application server that collects the diagnostics information, produces display components, and includes the diagnostics information within the display components. The server application then includes the display components and the requested content in response messages sent to the user devices. Preferably, the diagnostics information is presented in the same display context on the user device as the requested content, such as pages within a web browser. In examples, the diagnostics information includes enhanced call stack trace and memory profilers.
Owner:ZEROTURNAROUND
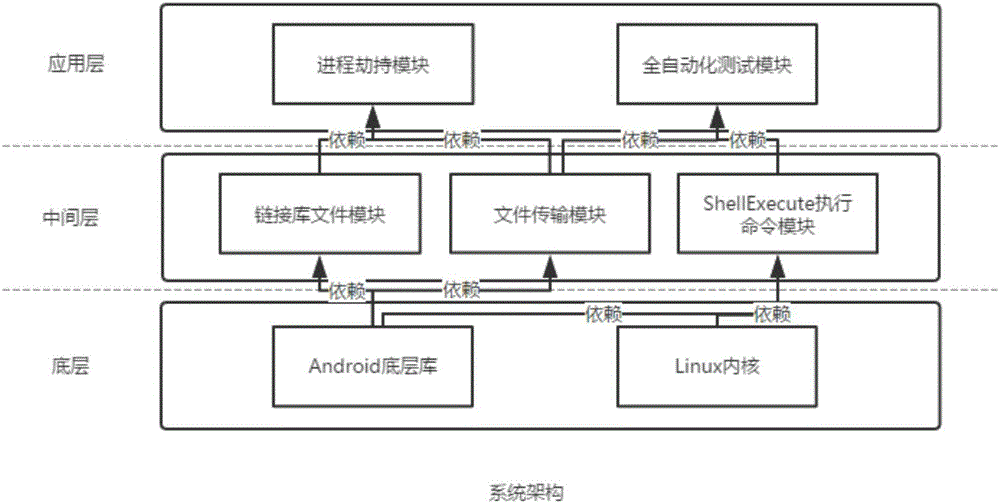
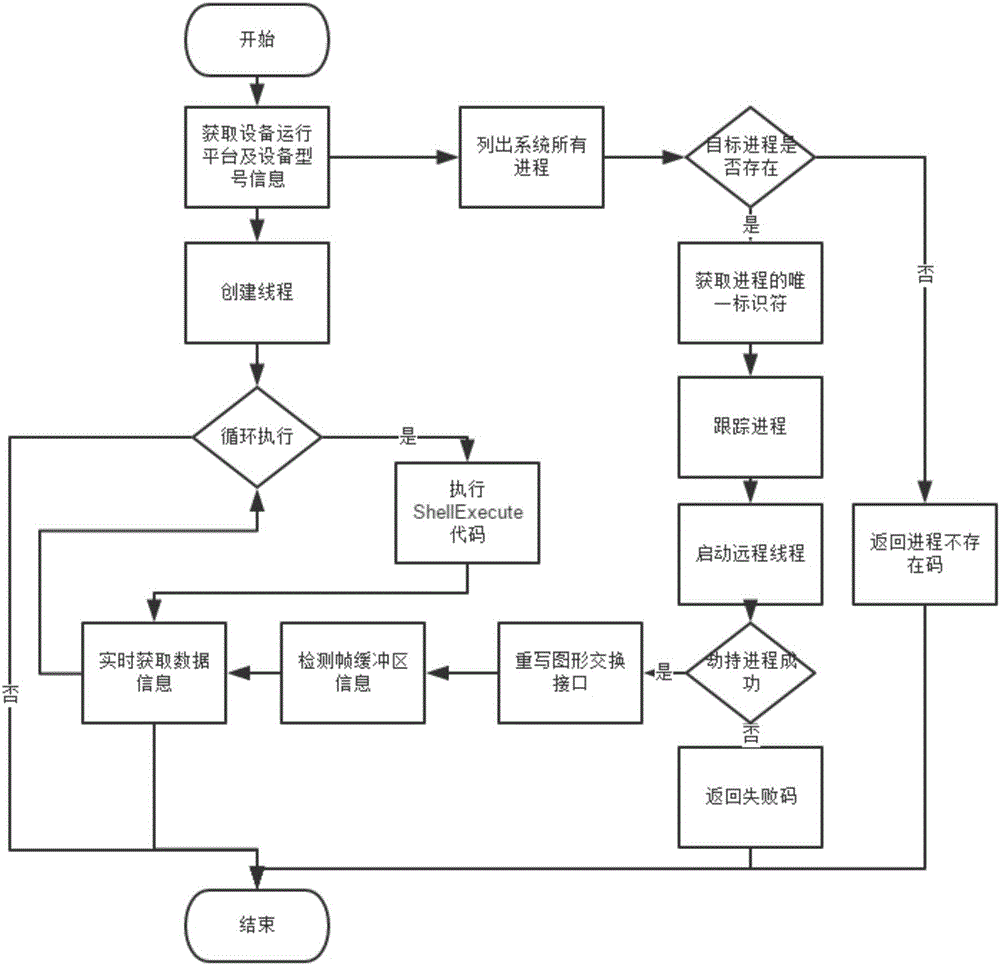
System and method for mobile terminal application testing based on code injection
ActiveCN106055469AImprove adaptabilityEasy to operateSoftware testing/debuggingGraphicsUnique identifier
The invention discloses a system and method for mobile terminal application testing based on code injection. The system comprises a process hijacking module and a full-automatic testing module, wherein the process hijacking module detects a system process, a unique identifier of the process is acquired and the process is hijacked if the process exists, a code used to acquire process information is injected and can be used to detect and acquire running information of the process in real time if hijacking is successful, a failure code is returned if the hijacking fails, and a process inexistence code is returned if the process does not exist; and the full-automatic testing module executes a cycle to acquire information of frame drawing time in graphic drawing. The system and the method disclosed by the invention are characterized in that automatic testing and analysis are carried out to graphic running fluency during application running; testing efficiency is increased; source codes of an application do not need to be modified; the method is applicable to mobile Android equipment with diversified screen sizes; and an automatic testing platform and a developer can test the application much more conveniently.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Continuous run-time validation of program execution: a practical approach
ActiveUS9063721B2Easy to integrateTolerable performance overheadConcurrent instruction executionInternal/peripheral component protectionPre validationControl flow
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Method, system, server and client side for displaying and operating 3D (Three-Dimensional) game
InactiveCN102355489ABroaden your audienceEasy to implementTransmissionSpecial data processing applicationsDirectXUser input
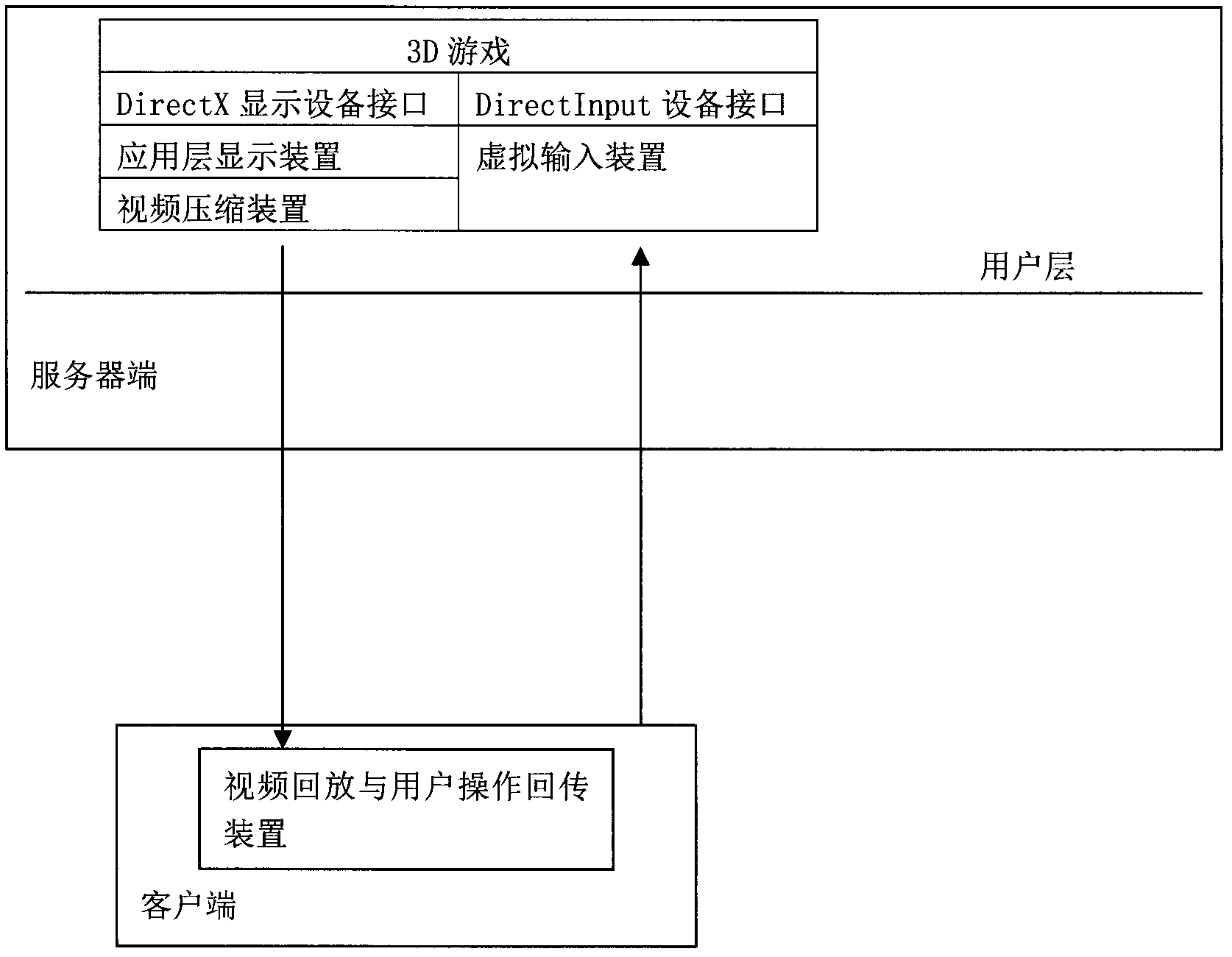
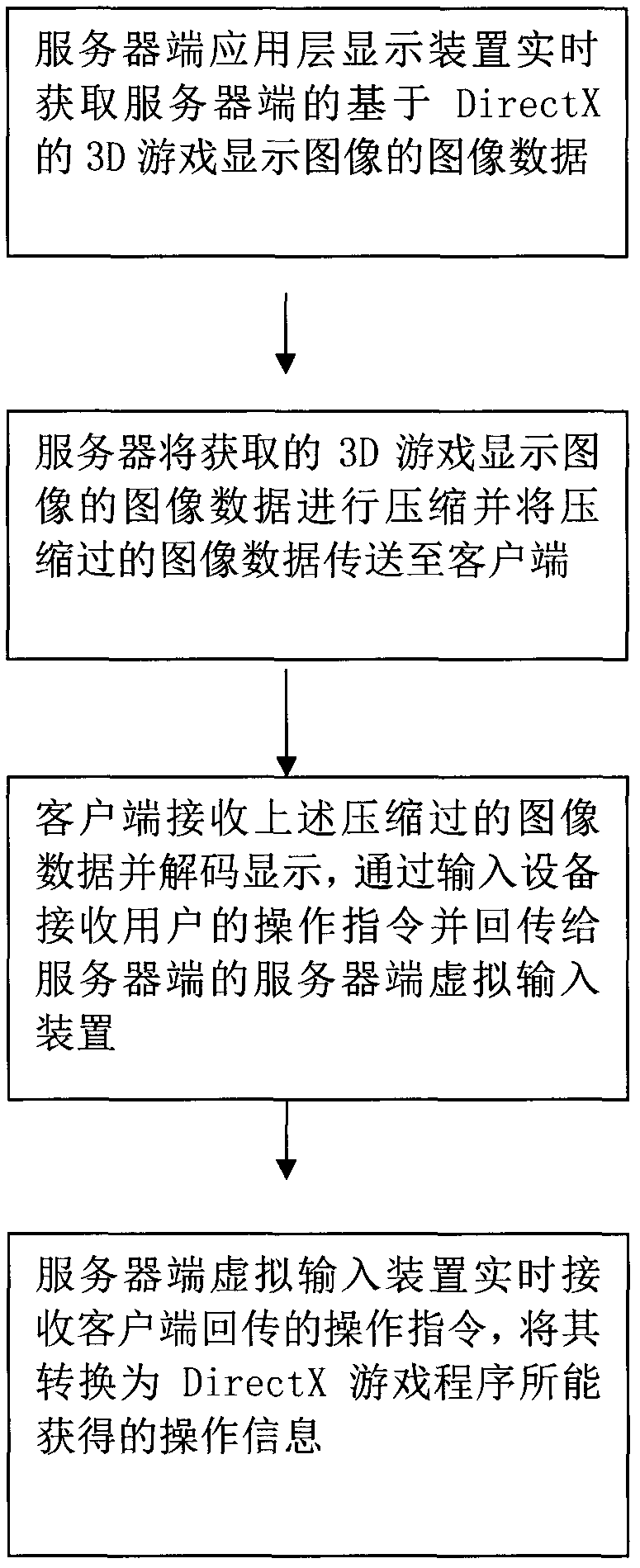
The invention provides a method, system, server and client side for remotely displaying and operating a 3D (Three-Dimensional) game. The method comprises the following steps of: 1, acquiring image data of a DirectX-based 3D game display image of a server side by a server-side application layer display device in real time; 2, compressing the acquired image data of the 3D game display image by the server and transmitting the compressed image data to the client side; 3, receiving, decoding and displaying the compressed image data by the client side, receiving an operation instruction of a user by input equipment and passing the operation instruction back to a server-side virtual input device at the server side; and 4, receiving the operation instruction passed back by the client side by the server-side virtual input device in real time, and converting the operation instruction into operation information capable of being acquired by a DirectX game program. According to the method and system provided by the invention, the image data of the 3D game are acquired in real time in a user-layer code injection manner on the premise of not modifying the original game; and the user input passed back by the client side is provided to the game in the user-layer code injection manner on the premise of not modifying the original game.
Owner:焦秀琴
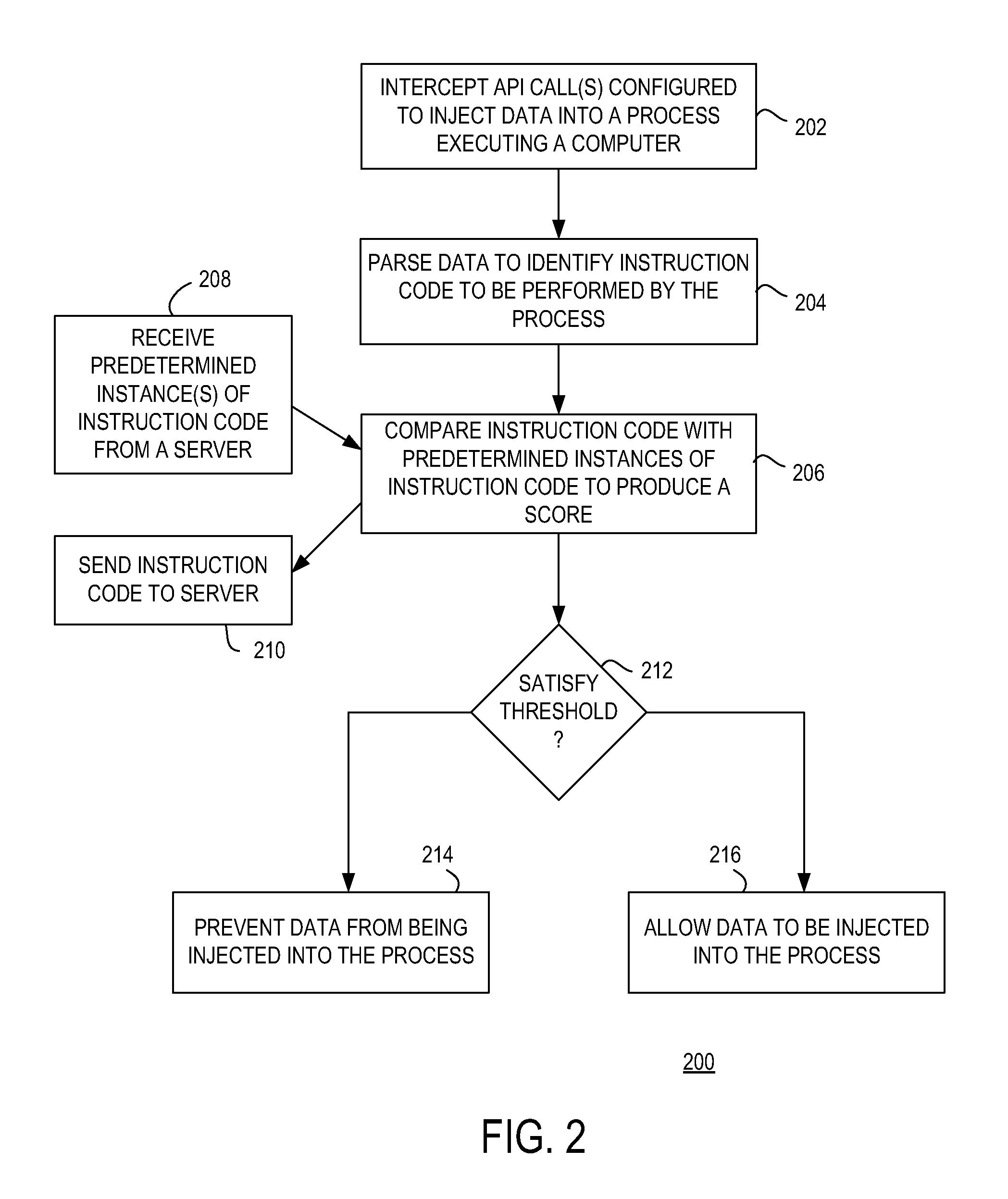
Method and apparatus for monitoring code injection into a process executing on a computer
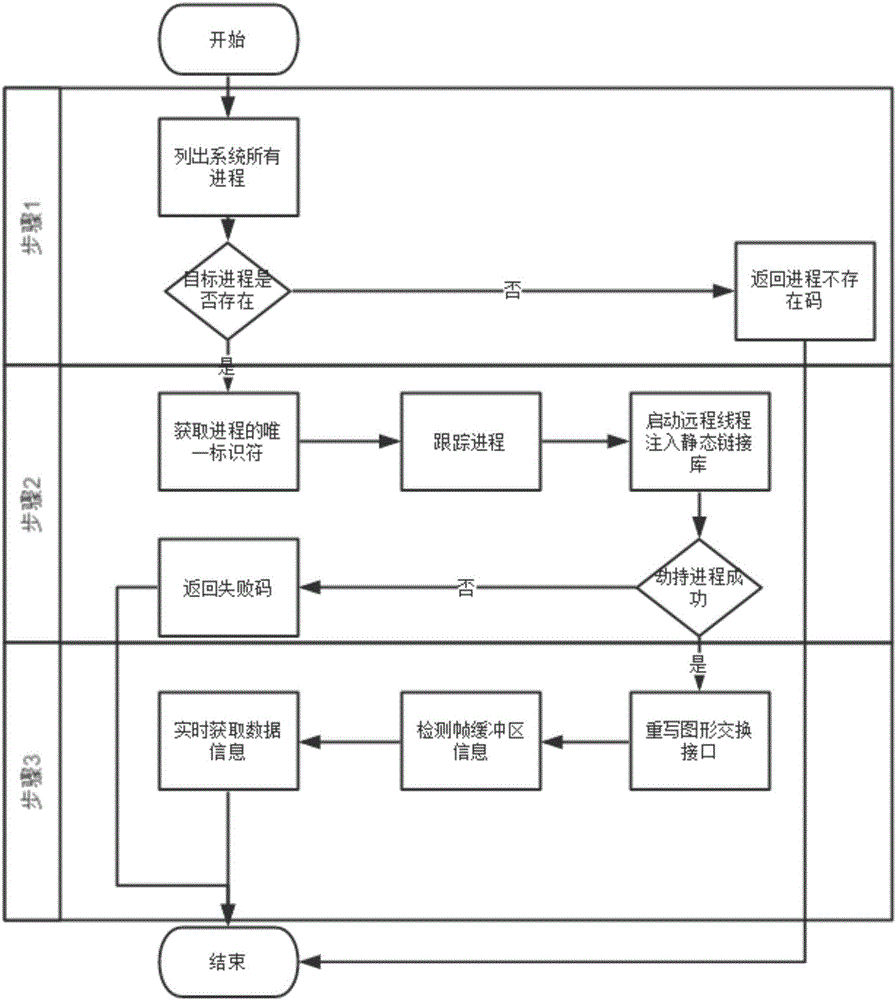
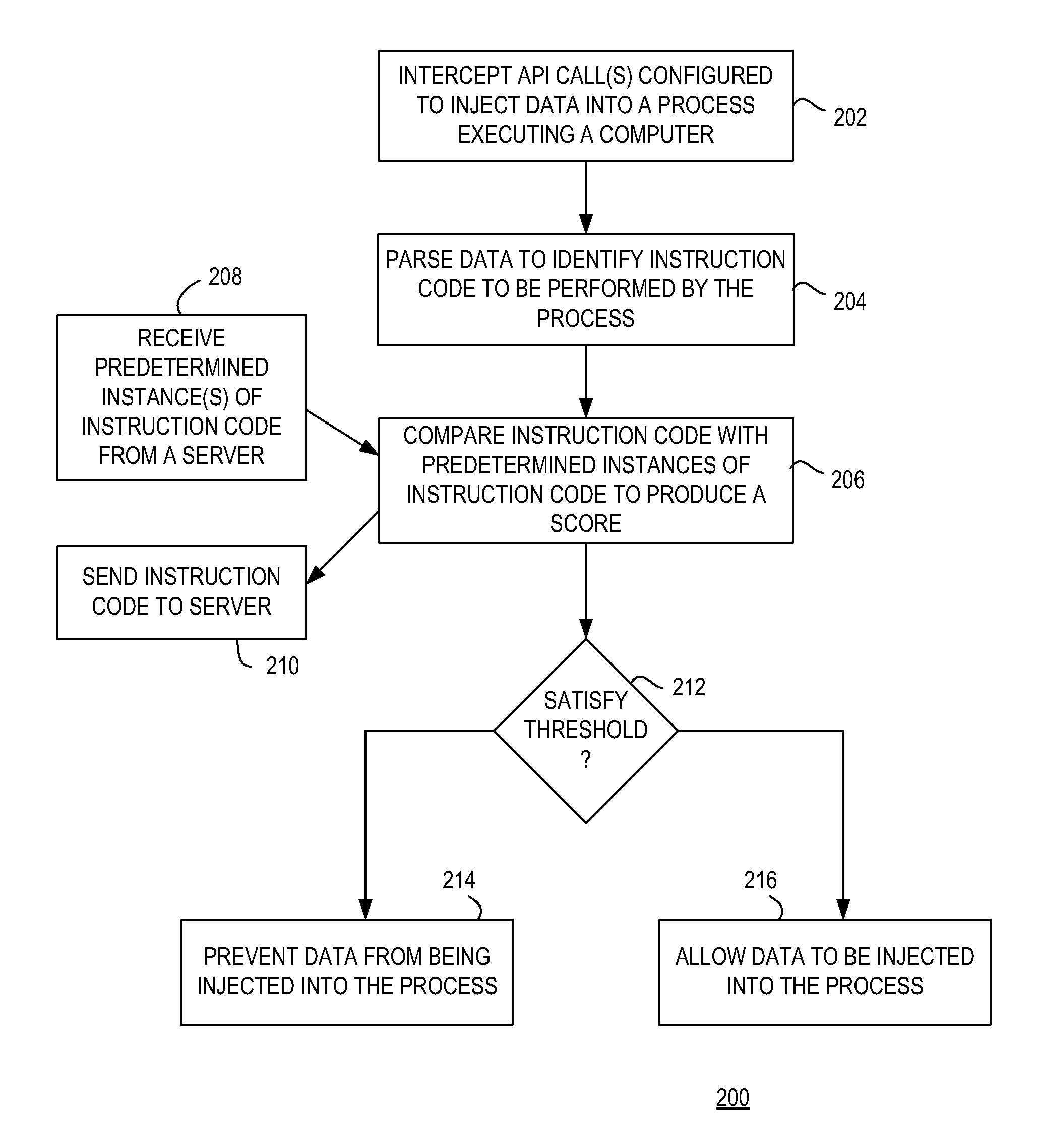
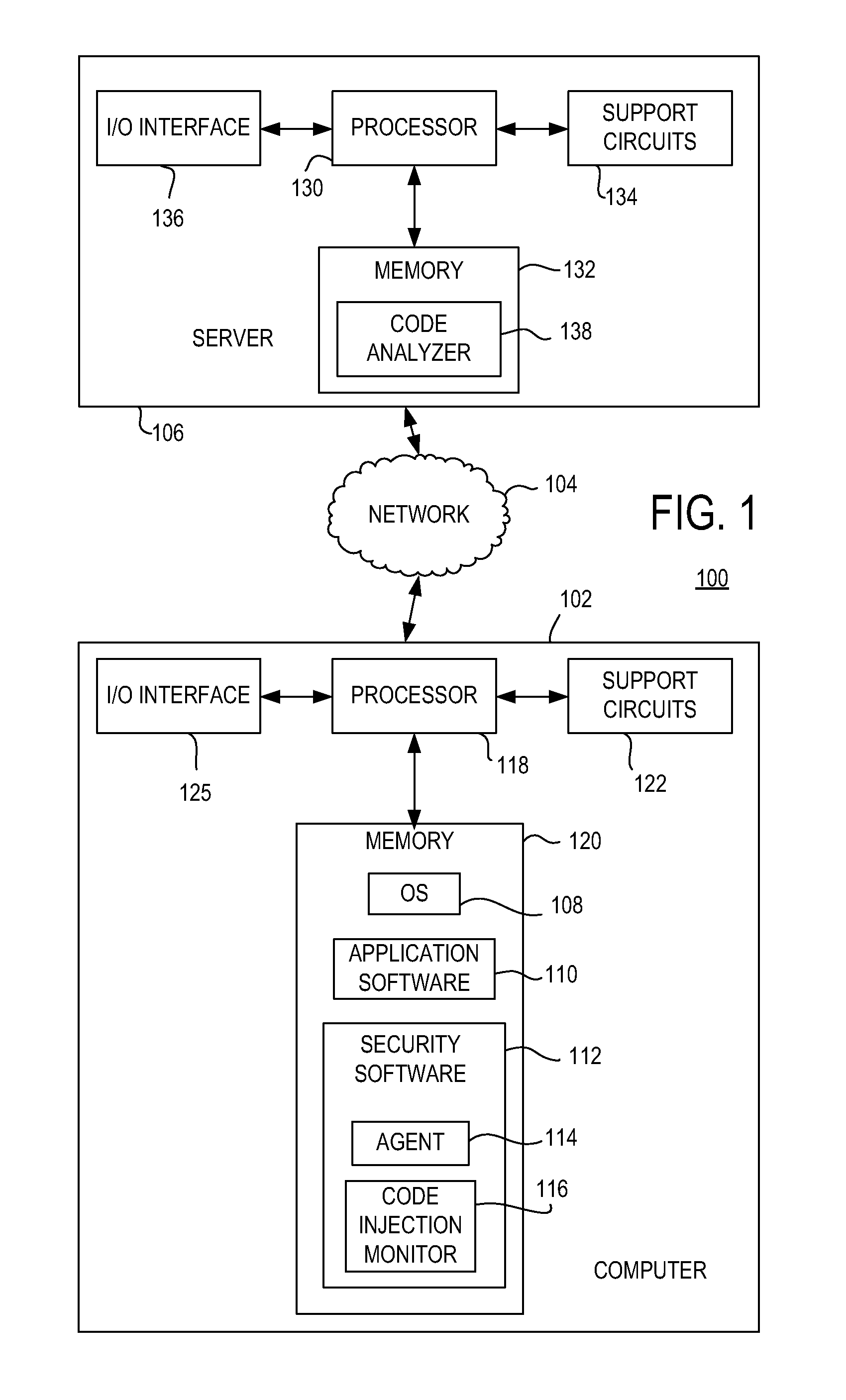
ActiveUS8612995B1Reduce processing stepsMemory loss protectionError detection/correctionApplication programming interfaceCode injection
Method, apparatus, and computer readable medium for monitoring code injection in a computer is described. In some examples, at least one application programming interface (API) call configured to inject data into a process executing on the computer is intercepted. The data is parsed to identify instruction code to be performed by the process. The instruction code is compared with instances of predetermined instruction code to produce a score for the instruction code. The data is prevented from being injected into the process in response to the score satisfying a threshold score. The data may be allowed to be injected into the process in response to the score not satisfying the threshold score.
Owner:CA TECH INC
Coded mass spectroscopy methods, devices, systems and computer program products
ActiveUS20070080290A1Increase productionReduce in quantityTime-of-flight spectrometersParticle spectrometer methodsImage resolutionMass Spectrometry-Mass Spectrometry
A coded mass spectrometer incorporates a spatial or temporal code to reduce the resolution / sensitivity dichotomy inherent in mass spectrometry. The code is used to code one or more portions of a mass spectrometer. Coding patterns, such as Hadamard codes, Walsh codes, and perfect code sequences can be used. The coding can be spatial, for example, by using an aperture mask and / or temporal, for example, by coded injection of ions for analysis.
Owner:DUKE UNIV
Code injection based privacy information protection method
InactiveCN105653979AEasy Deep OptimizationUniversalDigital data protectionFrame basedInternet privacy
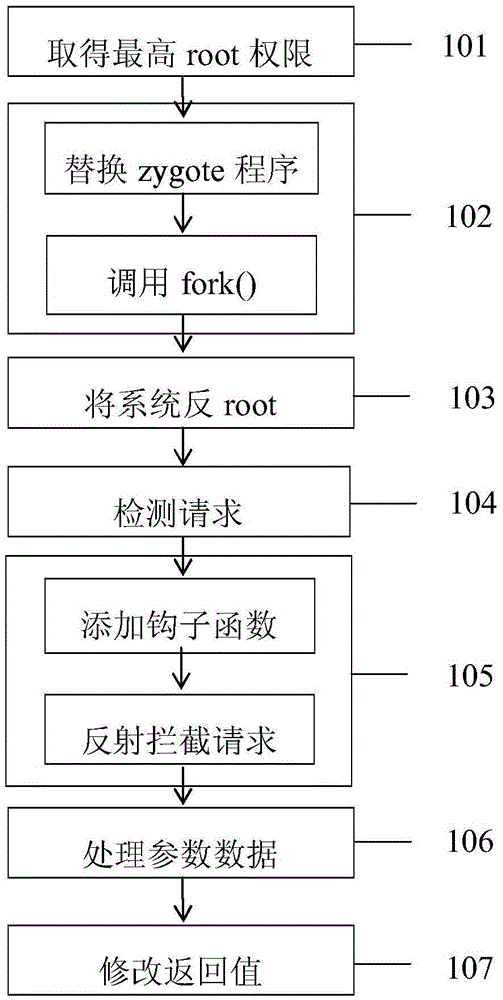
The present invention provides a code injection based privacy information protection method. The method comprises the following steps: (1) obtaining the highest root privilege of an Android system; (2) replacing a zygote program of the Android system by means of a file manager, and adding a new process by calling a fork() function by a system; (3) un-rooting the system; (4) detecting a specific request proposed by an application; (5) intercepting the request in the manner of reflection, and adding an Xposed frame based hook function for a specific permission access when a program that needs to be spoofed in the request is started; (6) when an application runs, processing read parameter data before access of a privacy function; and (7) modifying and spoofing an acquired reality return value after the function ends, so as to achieve the purpose of privacy information protection. The method provided by the present invention is excellent in applicability, convenient for operation and excellent in reliability.
Owner:ENJOYOR COMPANY LIMITED
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com