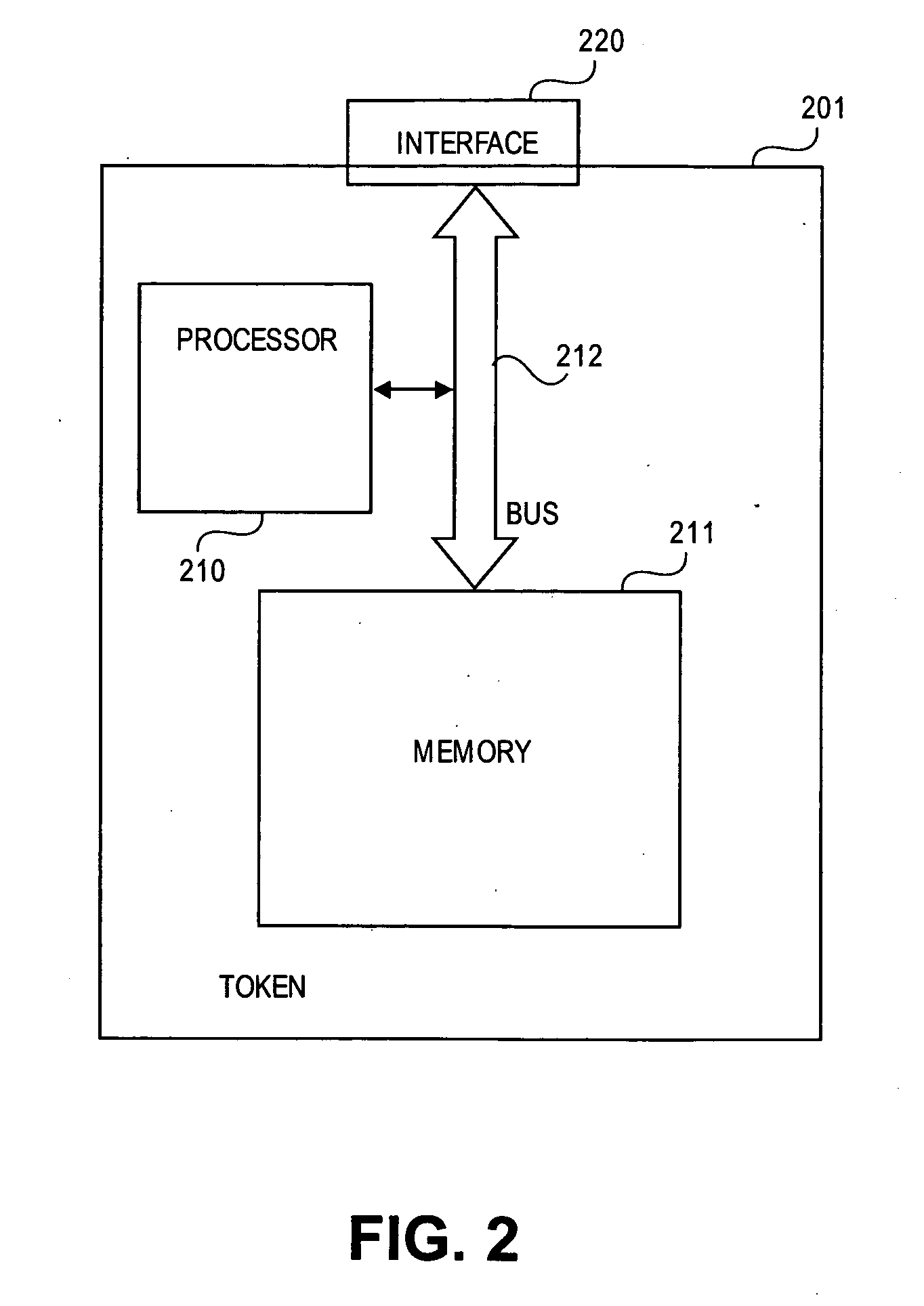
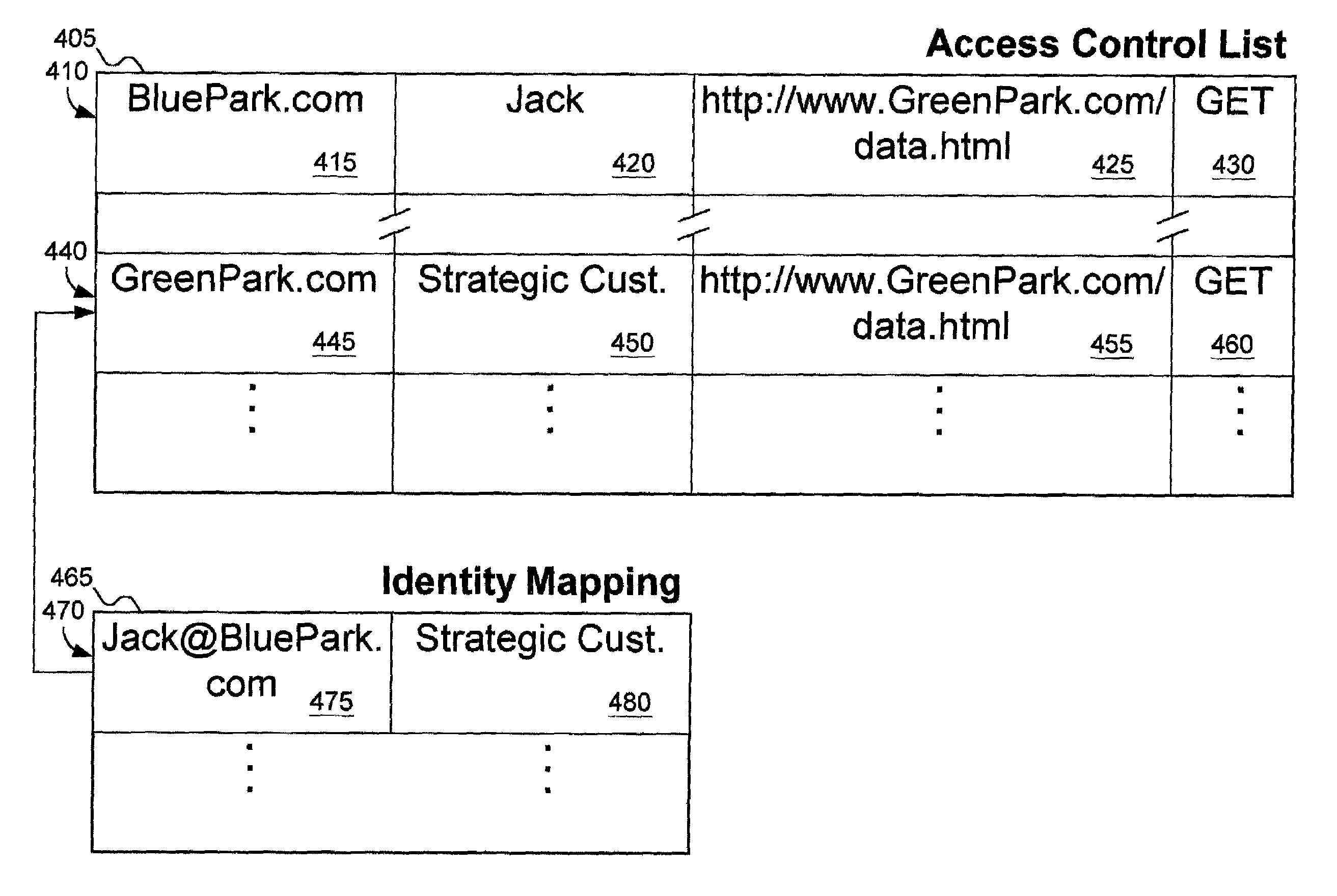
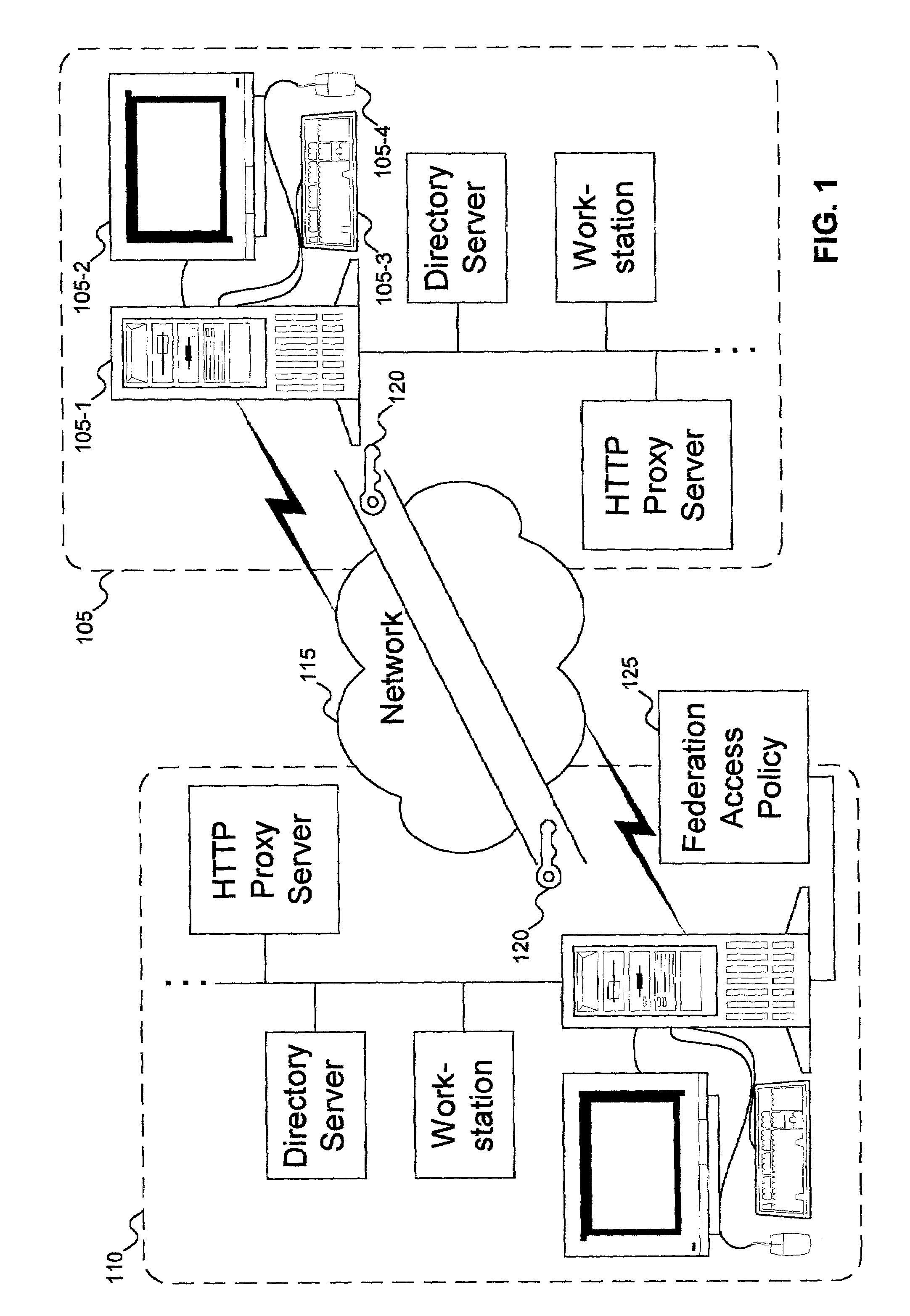
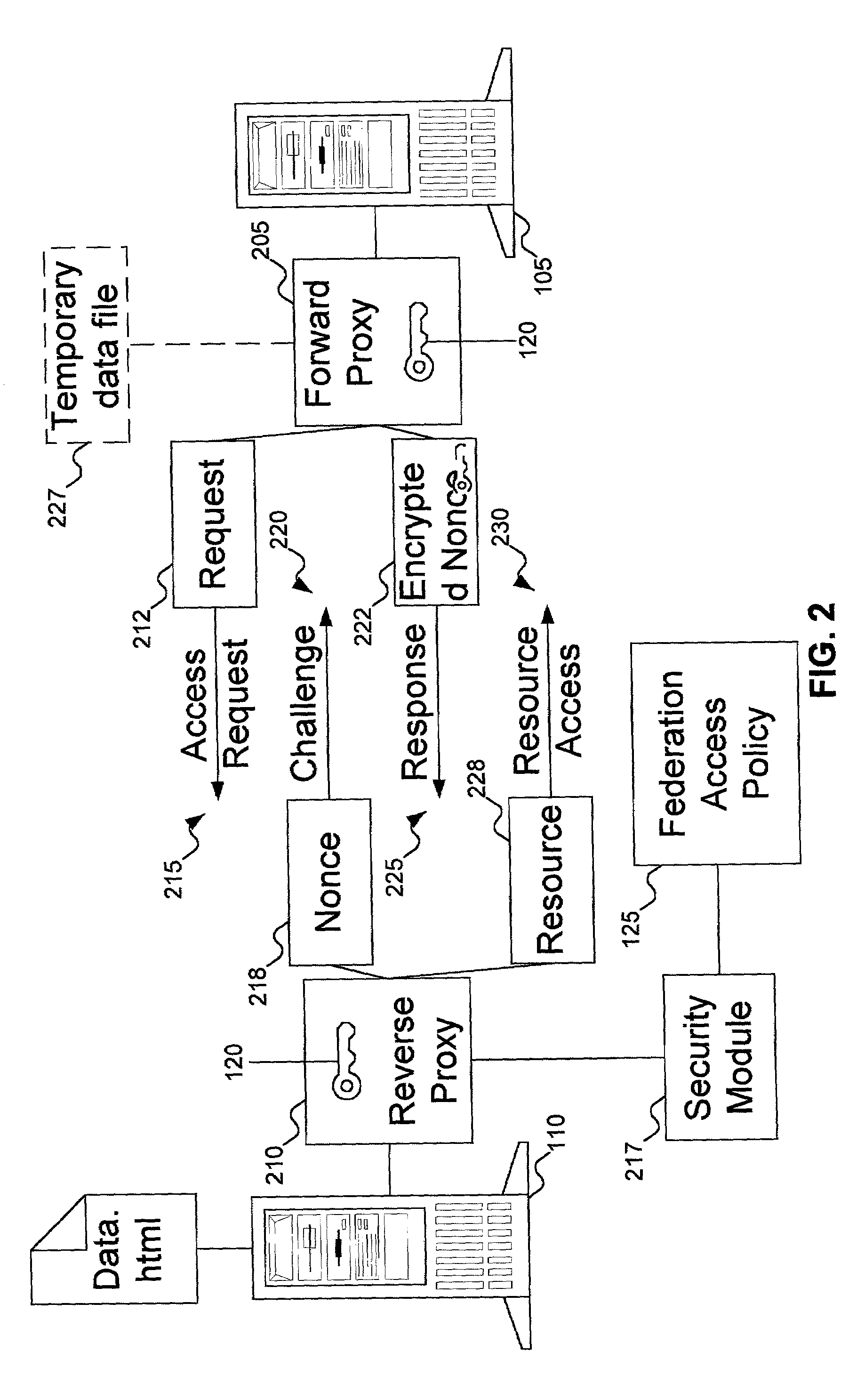
Patents
Literature
1102 results about "Security service" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security service is a service, provided by a layer of communicating open systems, which ensures adequate security of the systems or of data transfers as defined by ITU-T X.800 Recommendation. X.800 and ISO 7498-2 (Information processing systems – Open systems interconnection – Basic Reference Model – Part 2: Security architecture) are technically aligned.
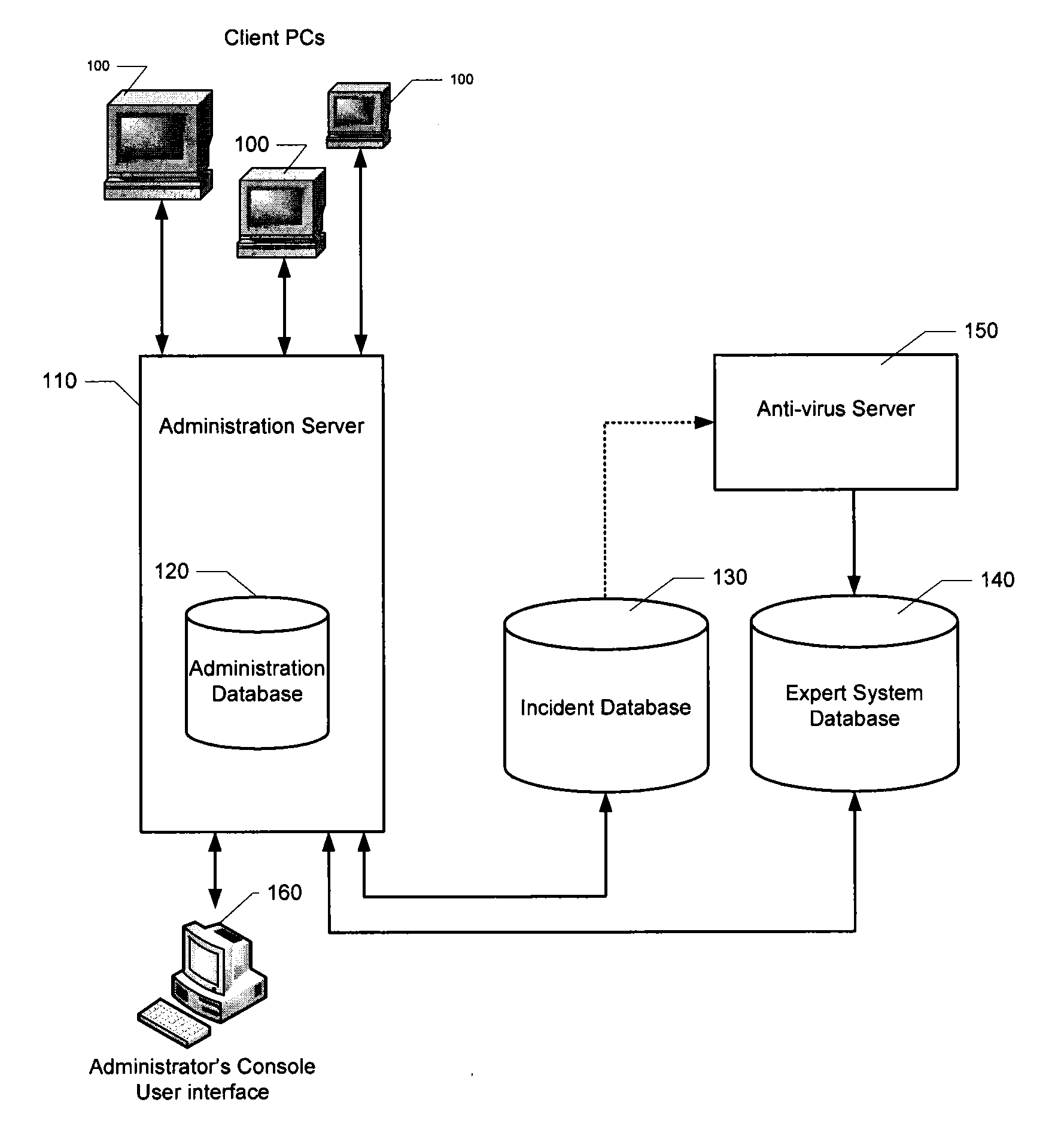
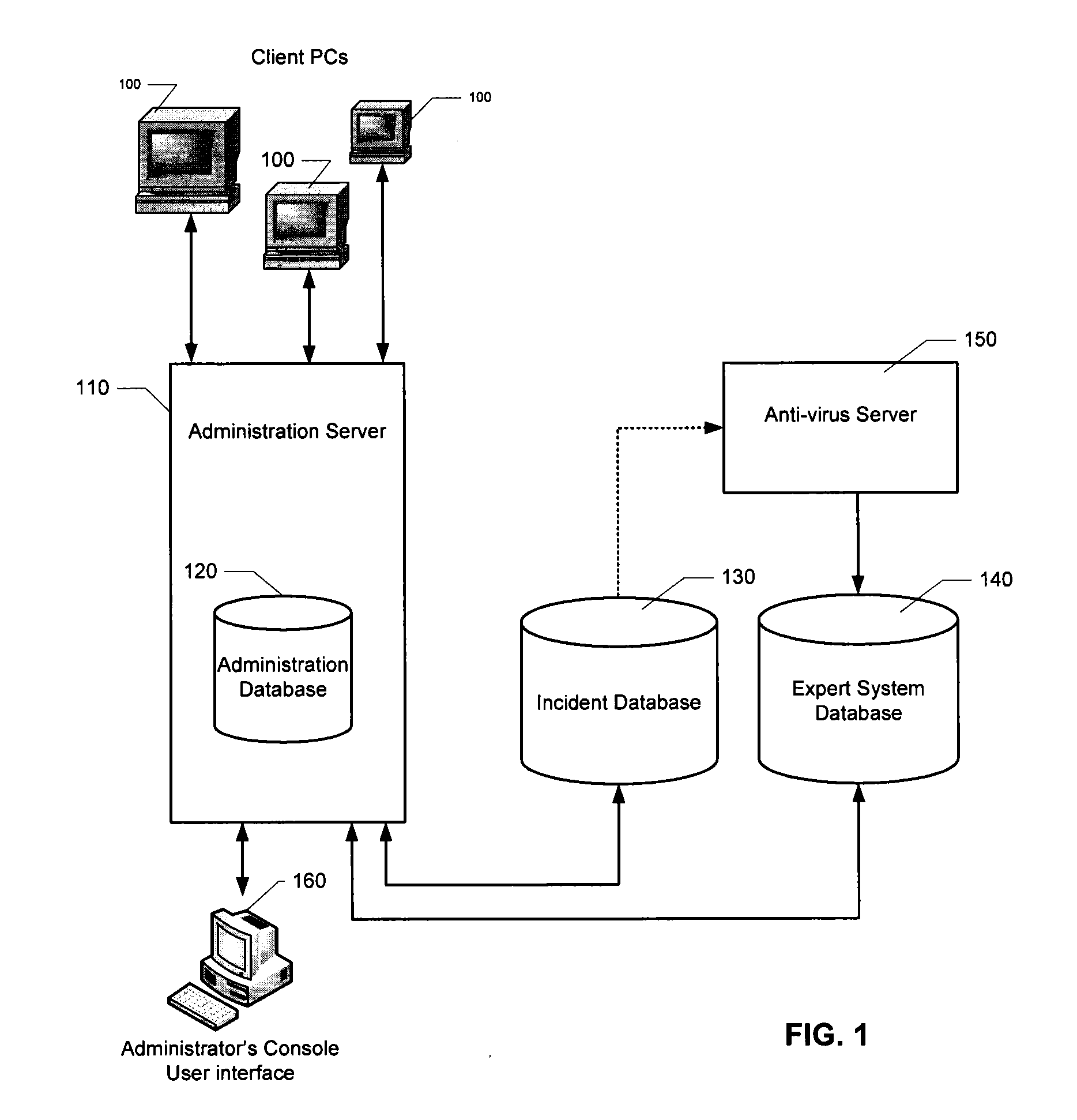
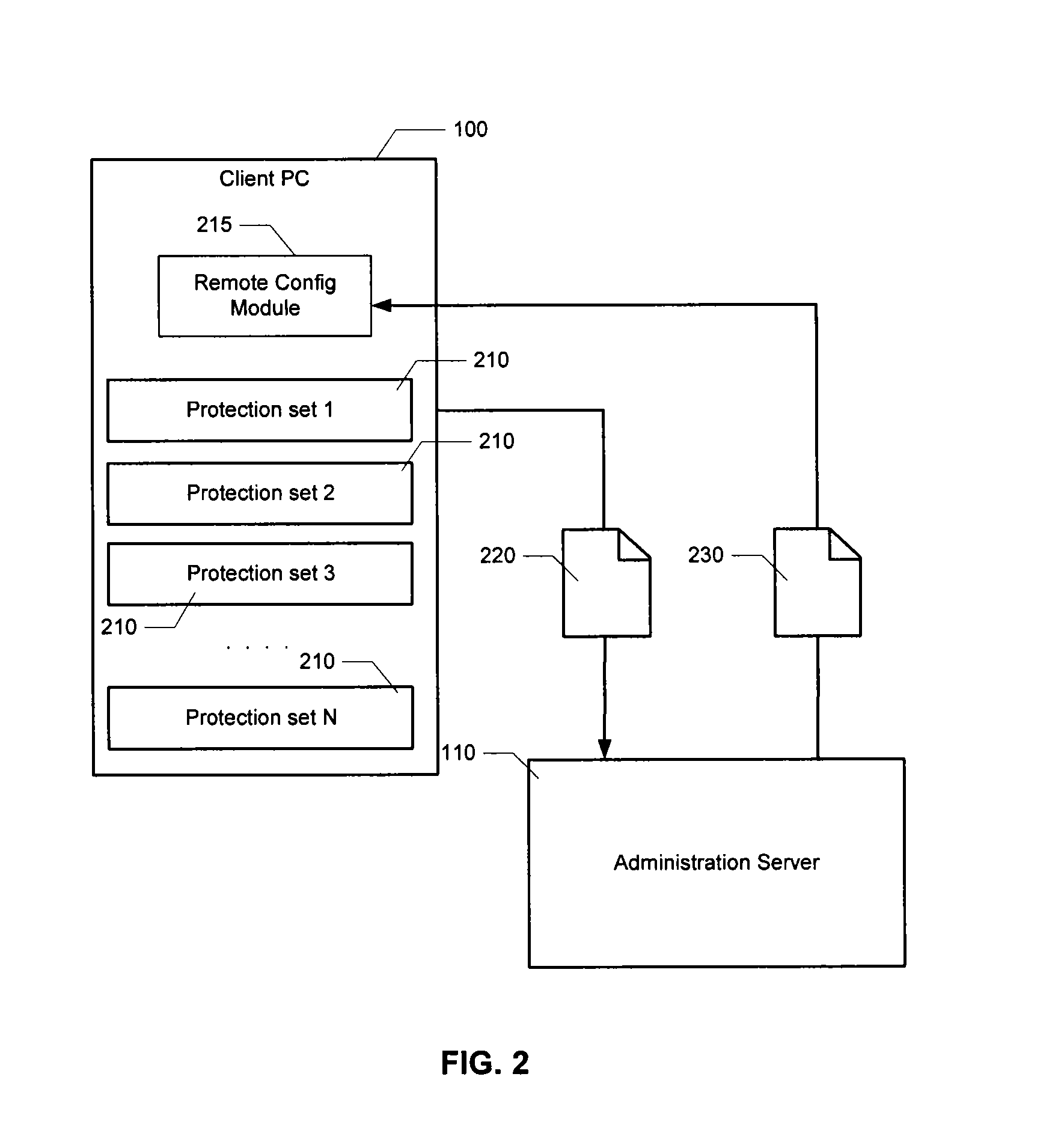
HTTP distributed remote user authentication system
InactiveUS6092196AExemption stepsAvoid necessityDigital data processing detailsUser identity/authority verificationUser authenticationUser identifier
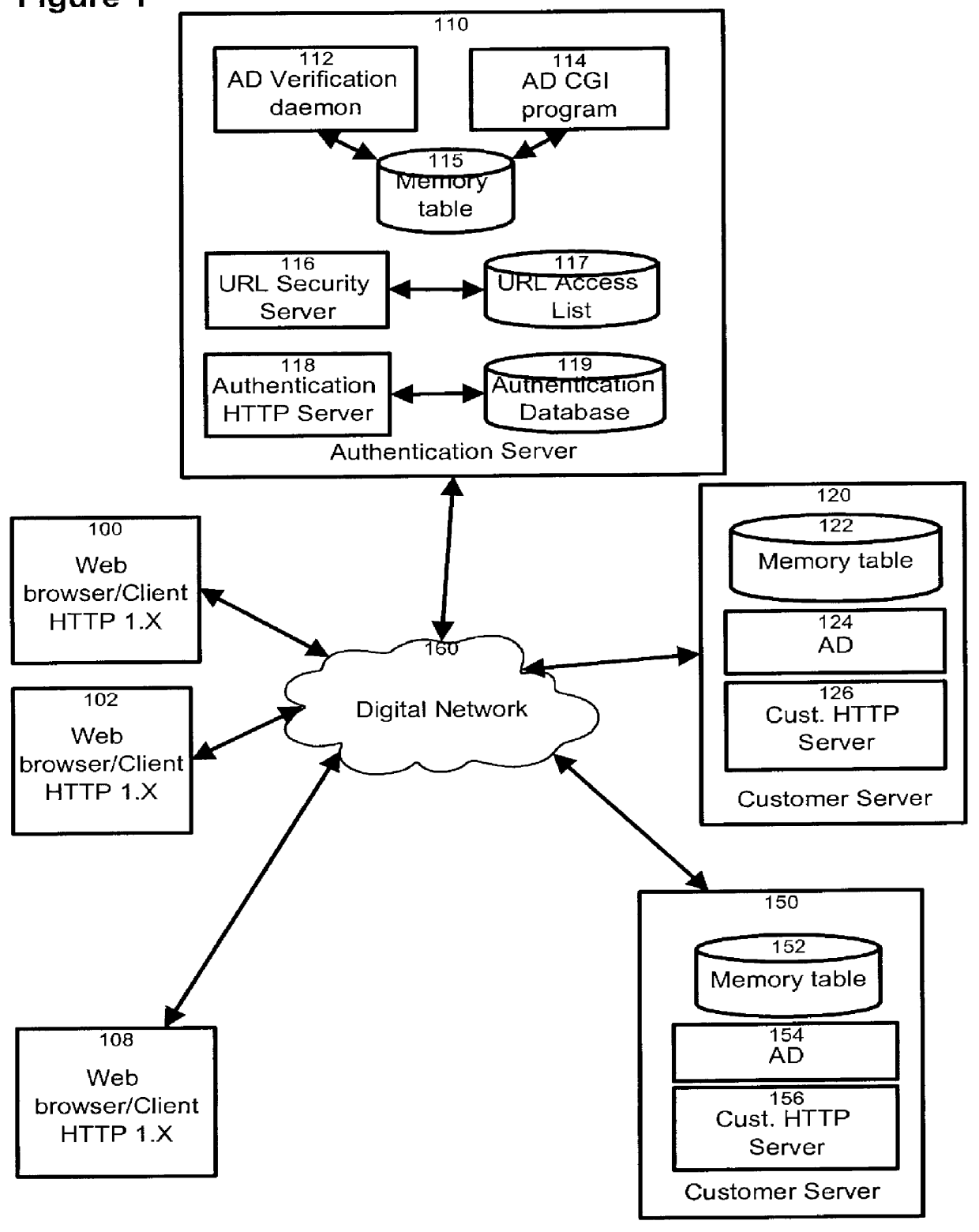
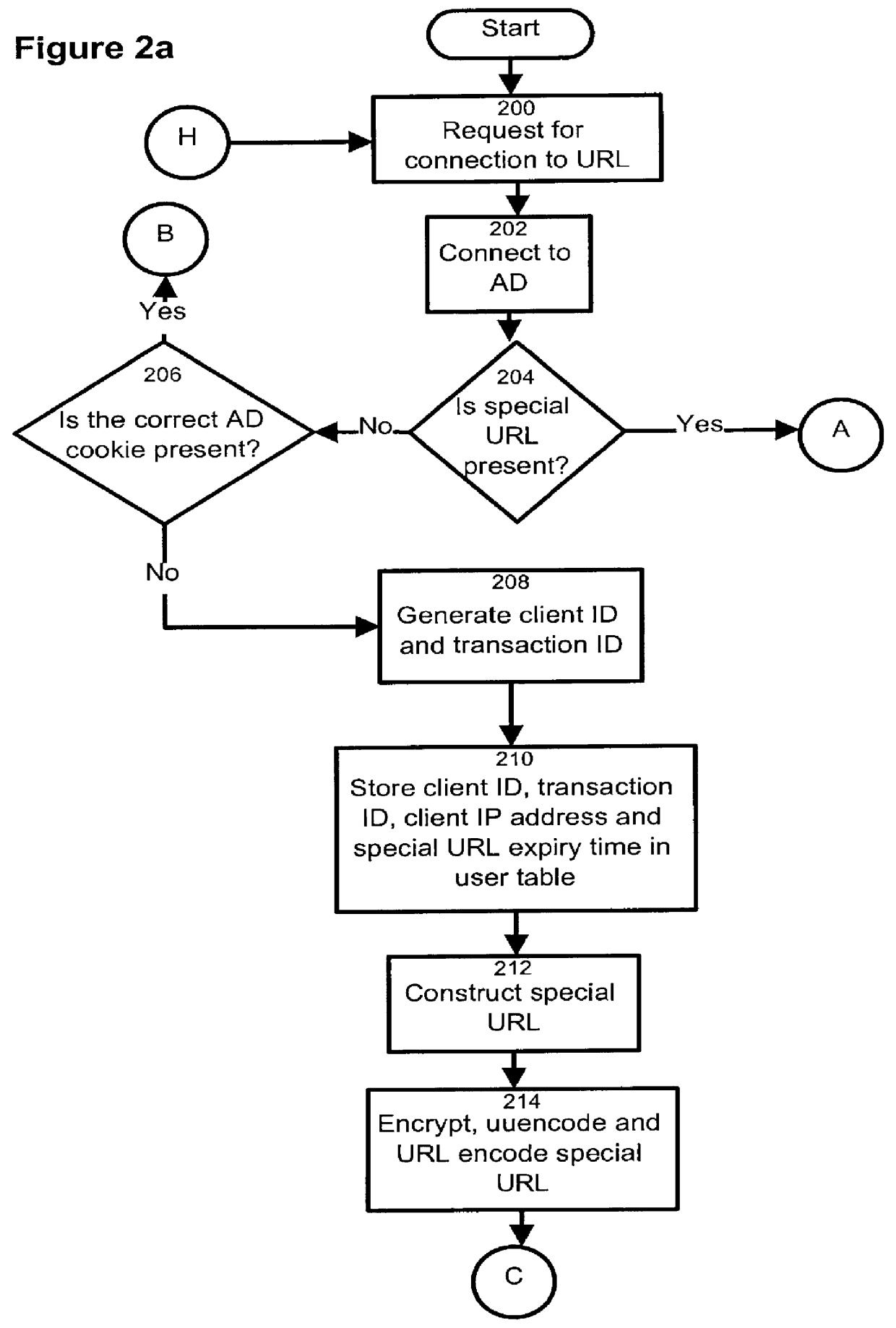
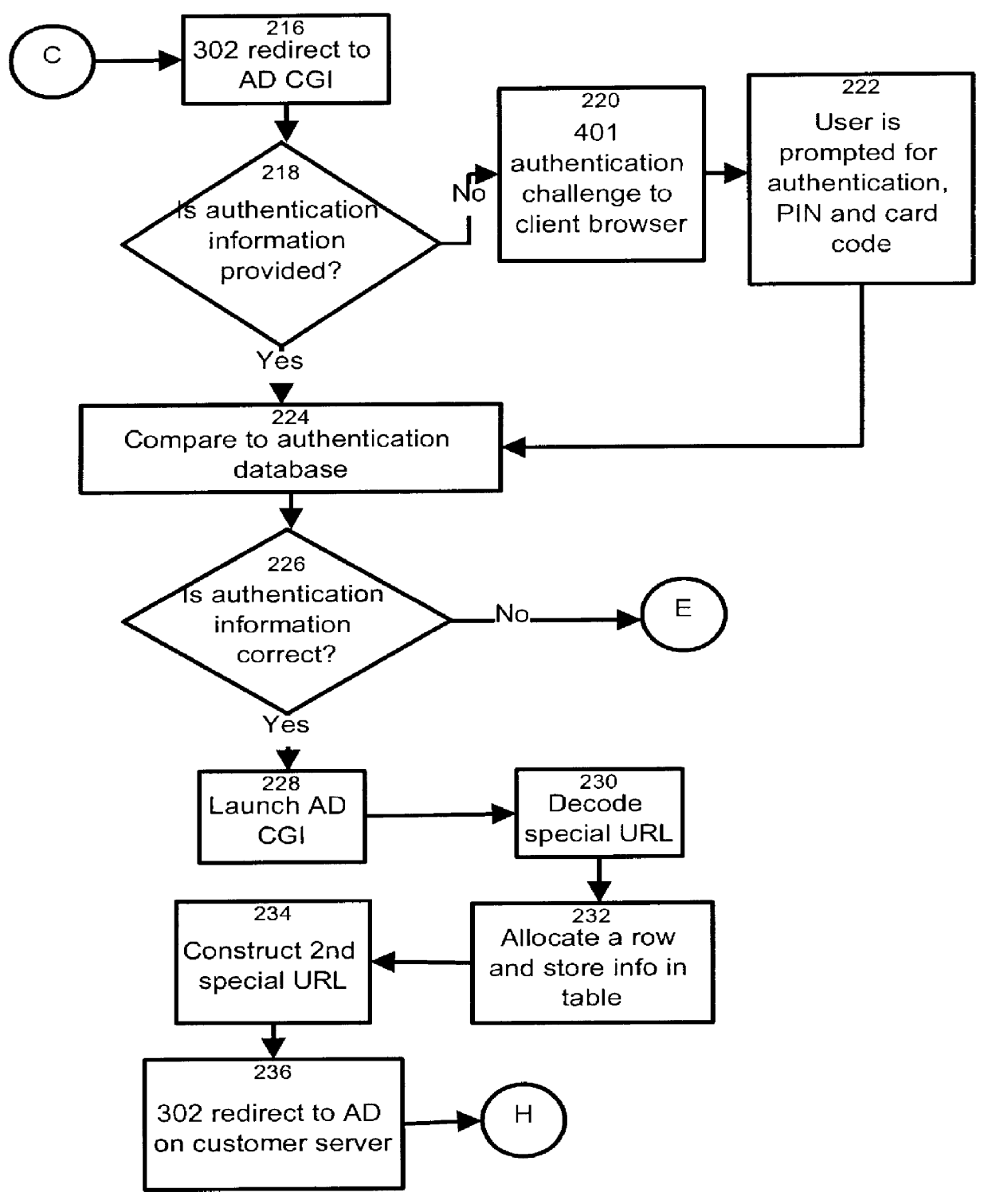
The present invention relates to the field of data and computer network security. Data and computer network security is of the utmost importance to most organizations that possess such networks. One of the difficulties that users and managers of these networks face is that the users have to provide a user ID and password every time they wish to access one of the organization's secured HTTP servers or URLs. This creates a problem for users and managers since lists of numerous user IDs and passwords need to be maintained and therefore can easily be lost or their confidentiality compromised. This invention addresses these problems by providing a transparent, scalable, single point of authentication for remote users across any number of HTTP servers anywhere on a data network, such as an Intranet, using any user ID and password scheme implemented by a main authentication HTTP server.
Owner:RPX CLEARINGHOUSE
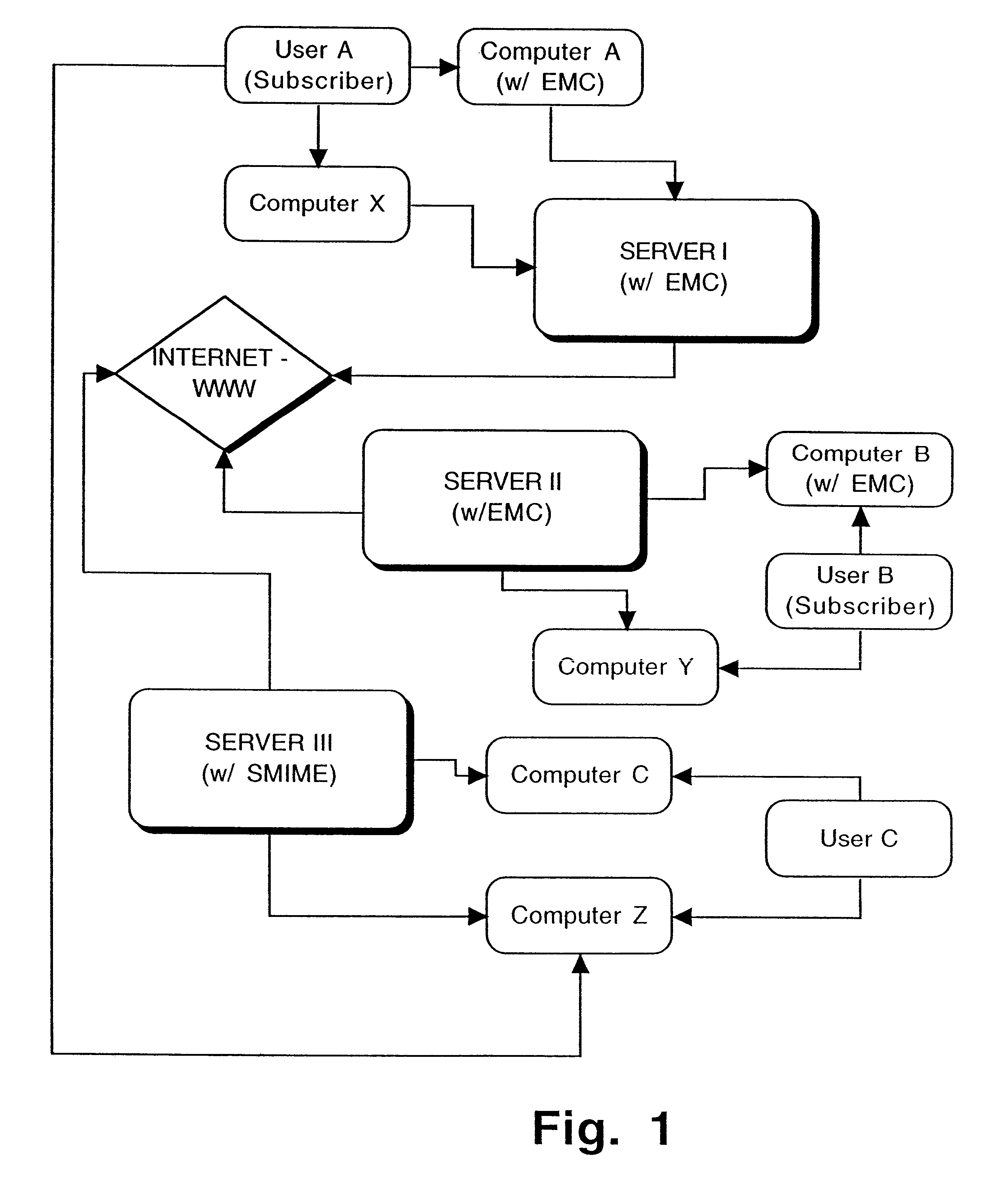
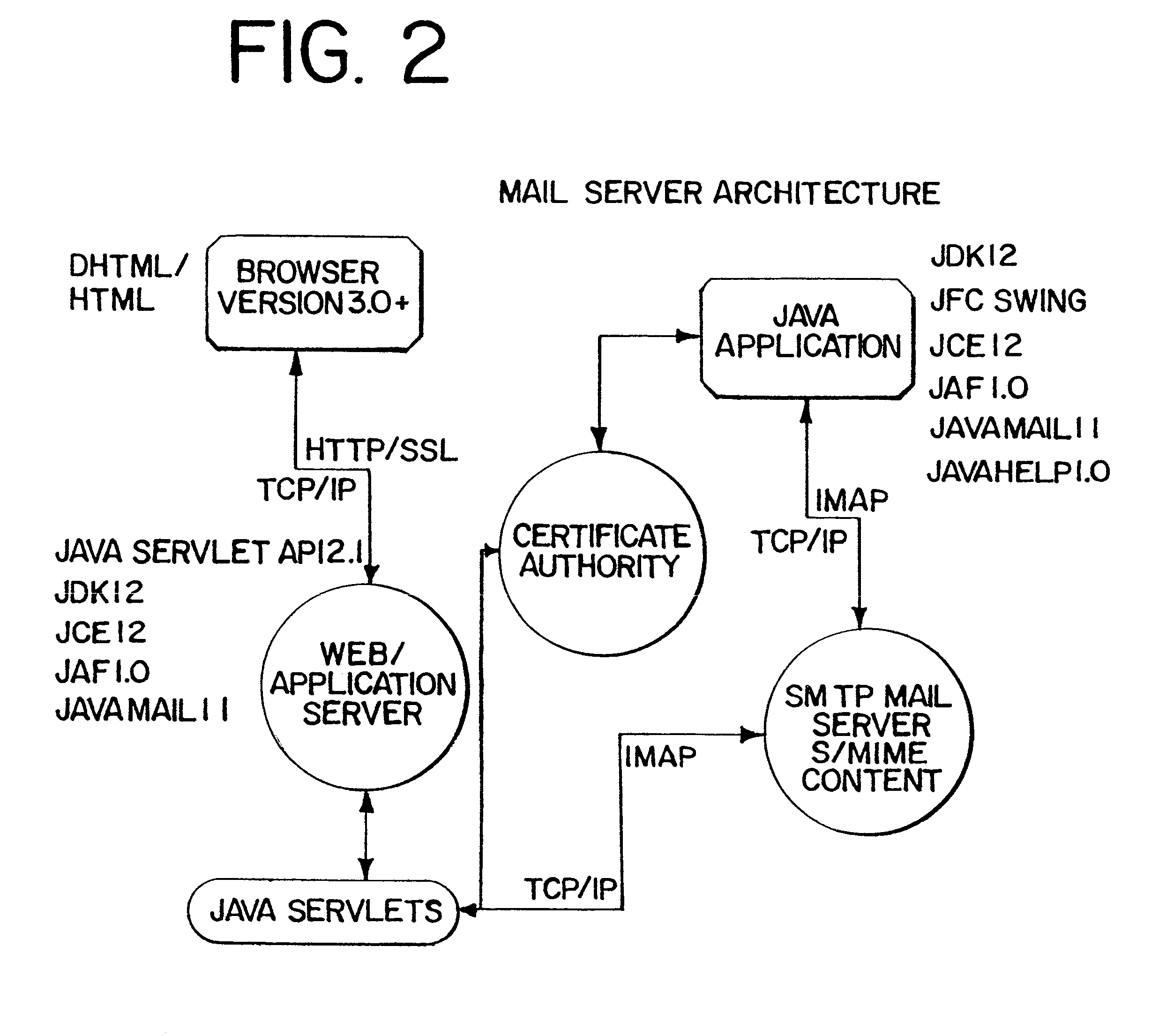
Interoperable full-featured web-based and client-side e-mail system
InactiveUS6356937B1More secure log-inMultiple digital computer combinationsOffice automationApplication softwareProprietary software
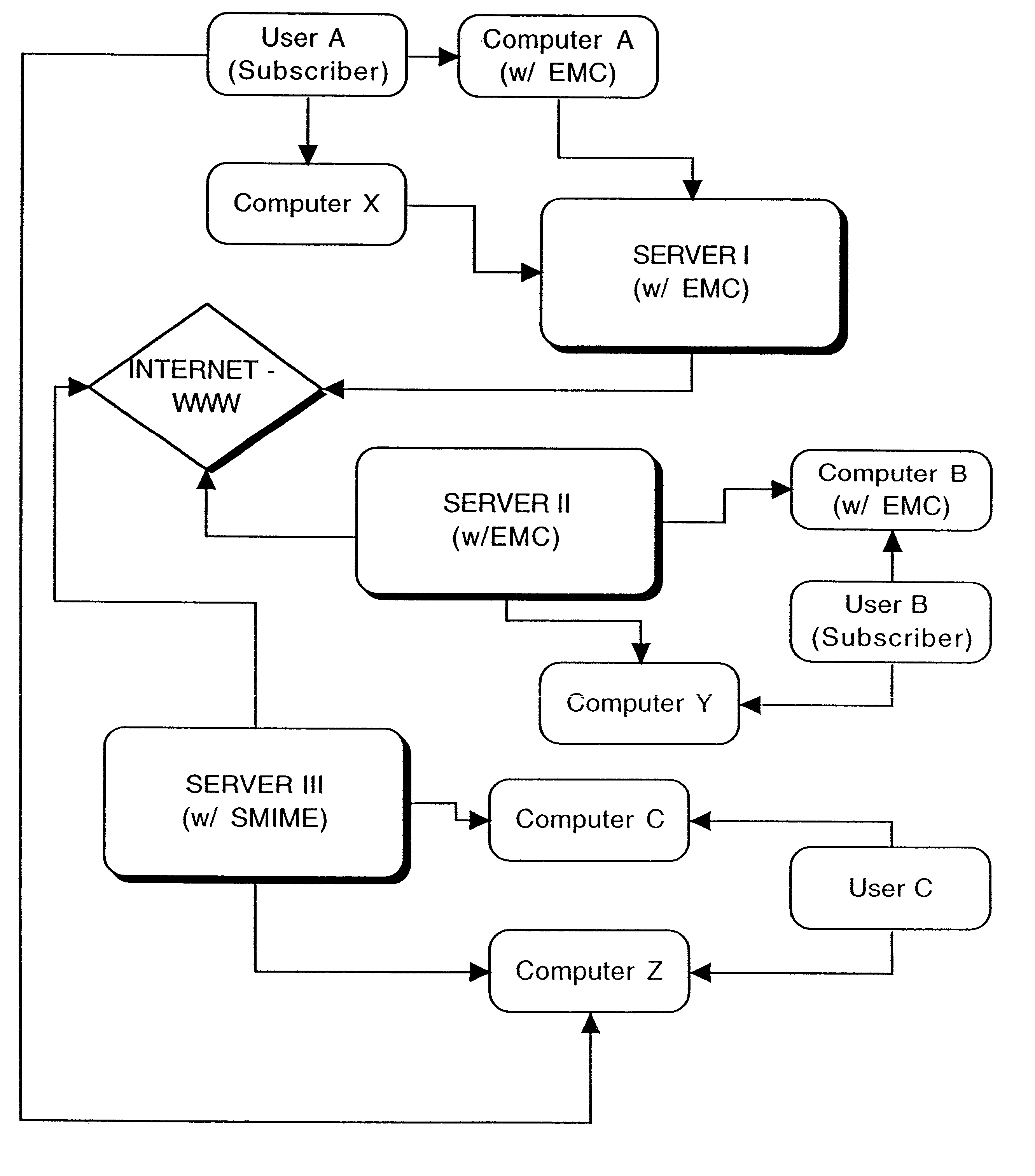
A full-featured e-mail system is used in both Internet-based and client-side (personal computer) forms. In each form, either basic e-mail service is provided to system subscribers or a secure, premium service with authentication, concealment, integrity, and non-repudiation functions for electronic messaging services is provided. In either form and at either level of service, subscribers can work off-line on their own computers with proprietary software loaded or, alternatively, on-line on any computer with an Internet connection. The system is interoperable, to preserve security, with all S / MIME compliant software applications, even for those users not subscribing to a service implementing the disclosed system. Digital certificates can be provided as a security service of the disclosed system, rather than requiring a second source with separate verification procedures. As additional optional features, the subscriber can control compression of outgoing attachment files, rather than having that function absent or operate in some automatic way. Decompression of such file attachments when received occurs automatically for subscribers, without having to invoke a different program or system. Interactive help features, book hierarchy uniformity for messages, accounts, certificates, virus warnings, and dual naming capability are also provided and available to subscribers in both the Web-based and the client-side application forms disclosed herein, and in both basic and premium service levels.
Owner:MEC MANAGEMENT LLC
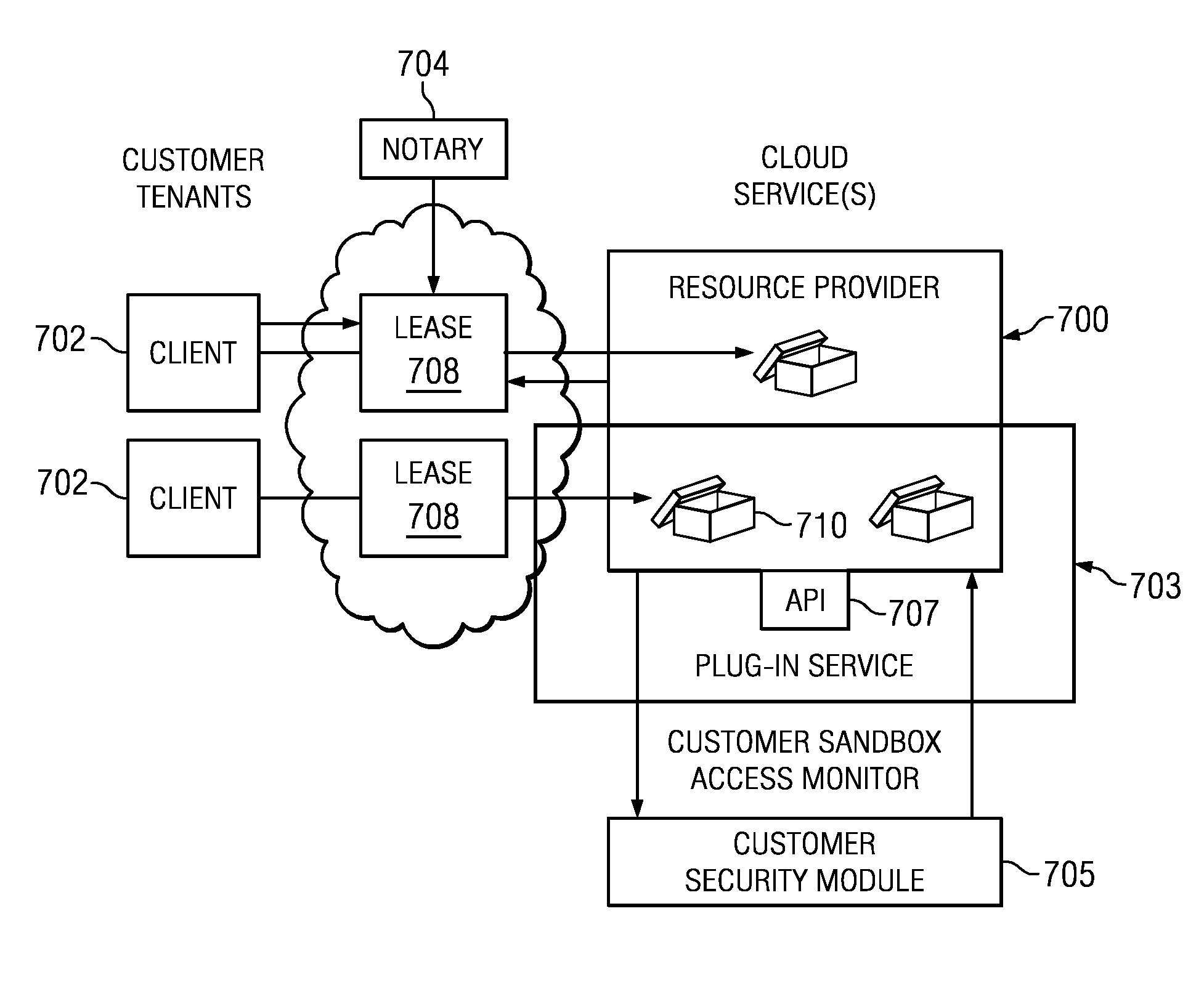
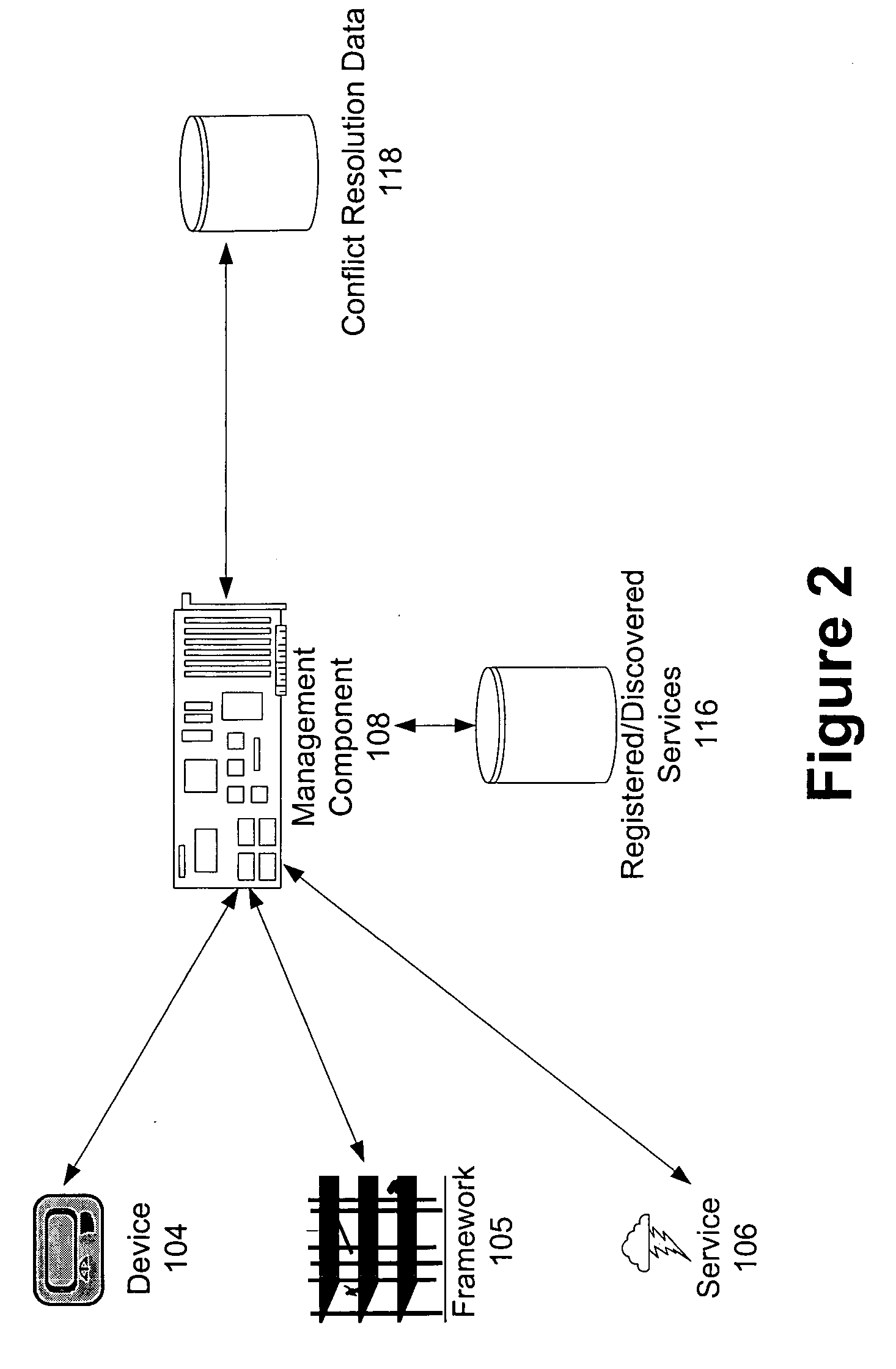
Authentication and authorization methods for cloud computing security
ActiveUS8769622B2Retain controlKey distribution for secure communicationDigital data processing detailsResource poolThird party
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
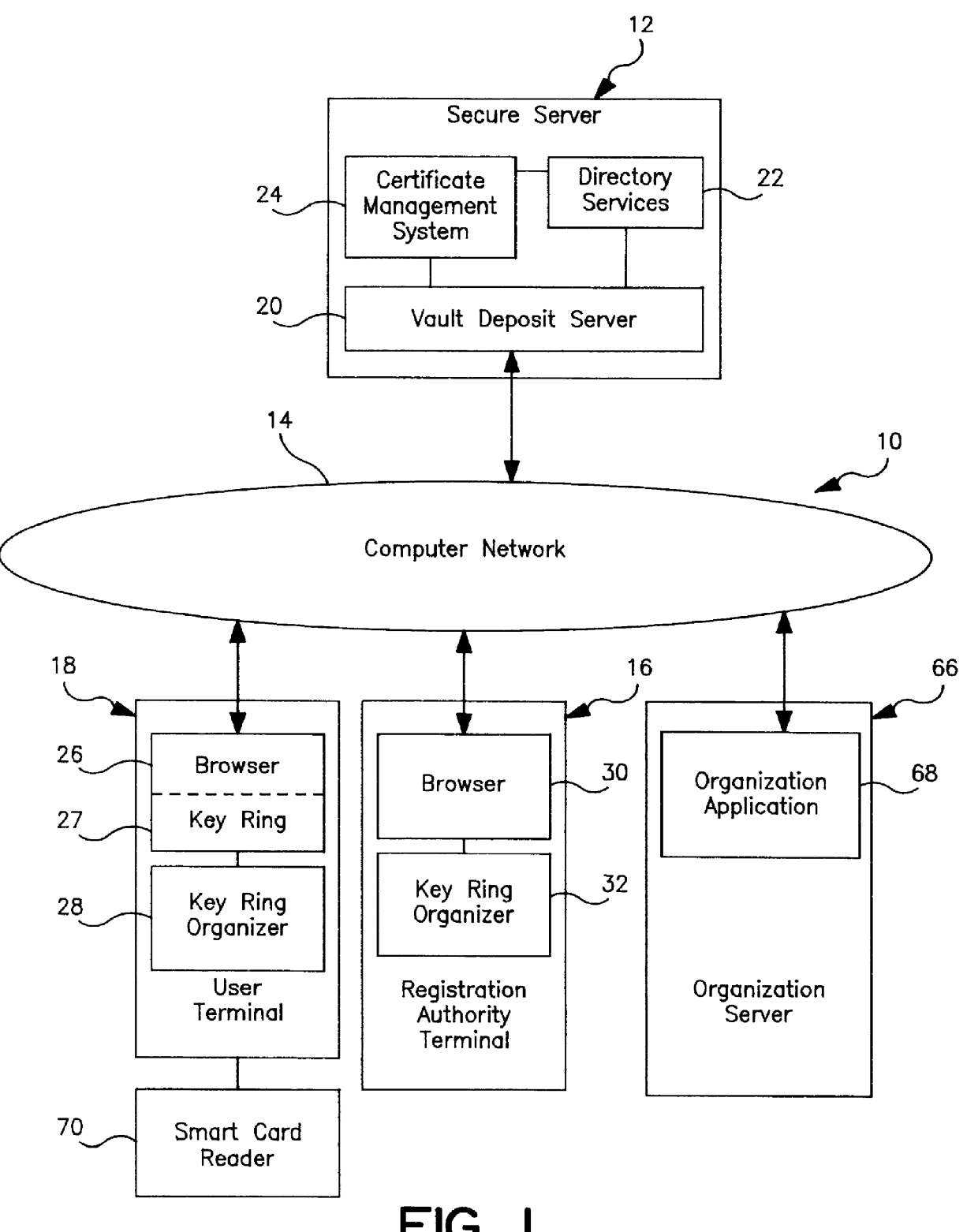
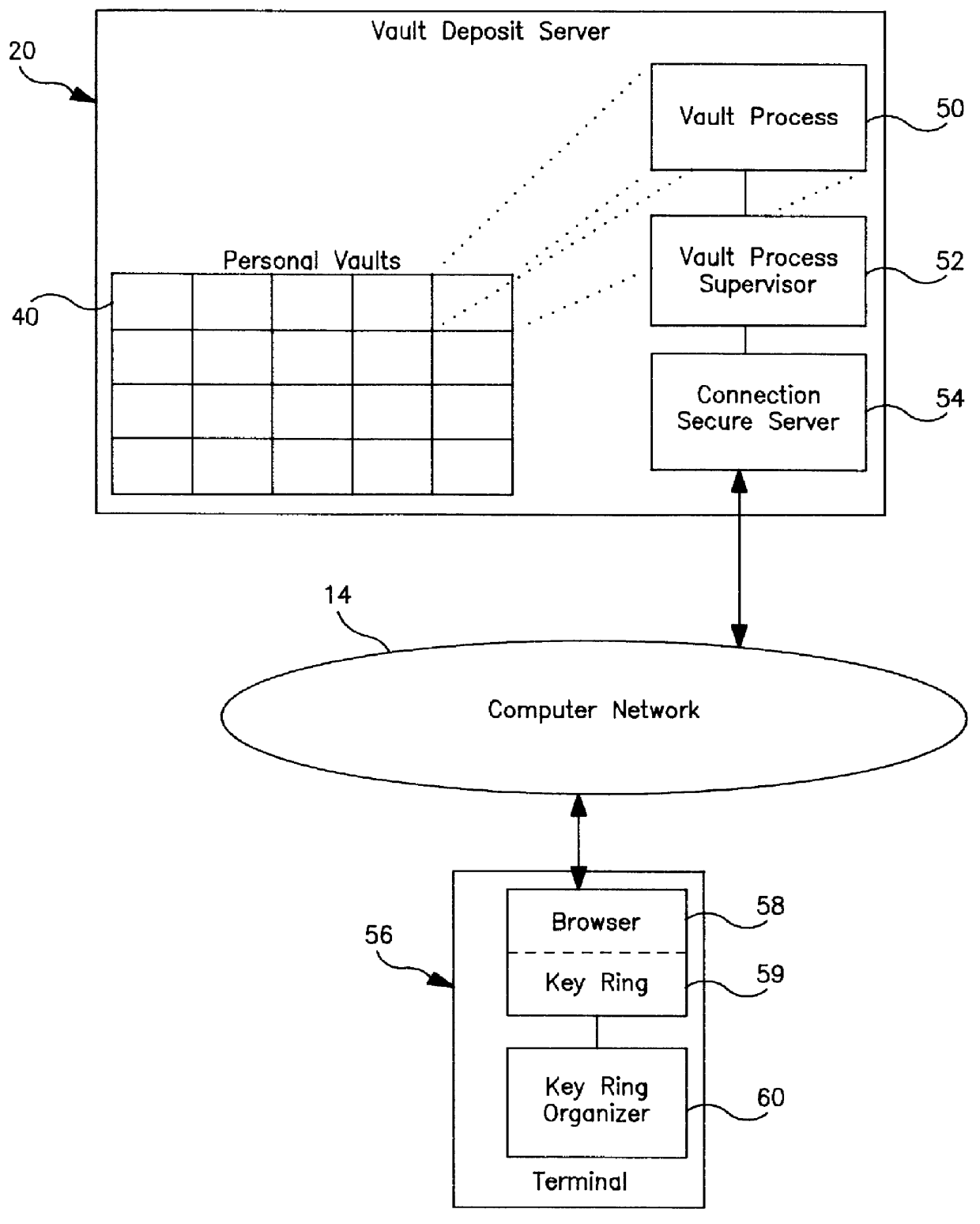
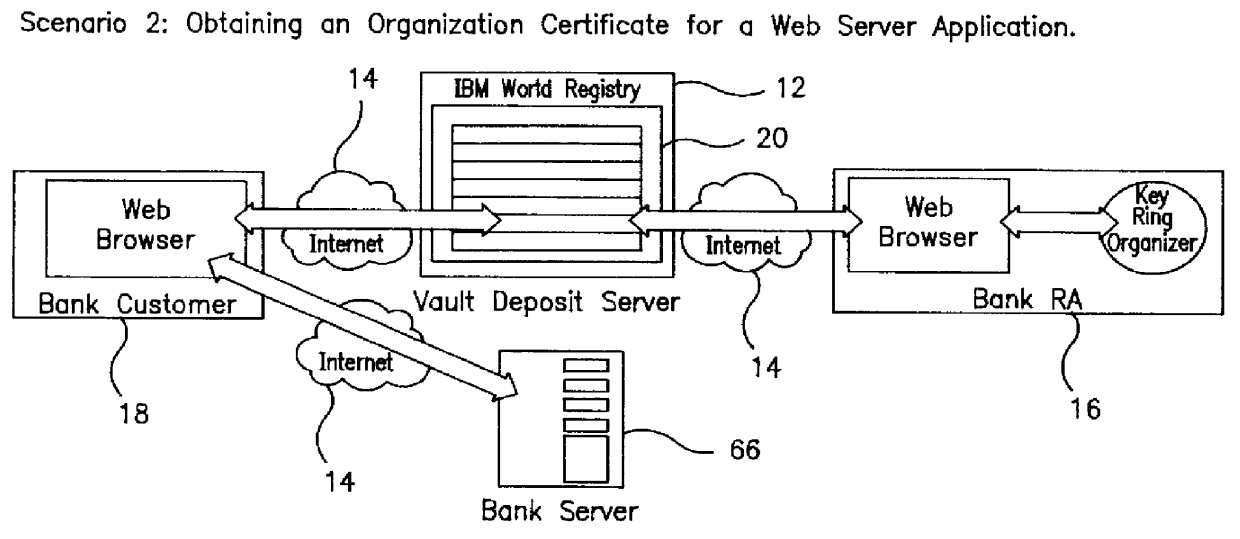
Secure server and method of operation for a distributed information system
InactiveUS6105131AKey distribution for secure communicationDigital data processing detailsComputer terminalInformation system
A secure server in a secure distributed information system isolates interaction from terminals to specific personal vaults including and to only those personal vaults, creating a "virtual logon". The secure server includes a secure connection server coupled to the system and to a vault deposit server having personal vaults in which user specific vault processes execute on dedicated encrypted data, after authentication of the user by a vault supervisor. The supervisor forwards vault process results to the user through the browser.
Owner:IBM CORP
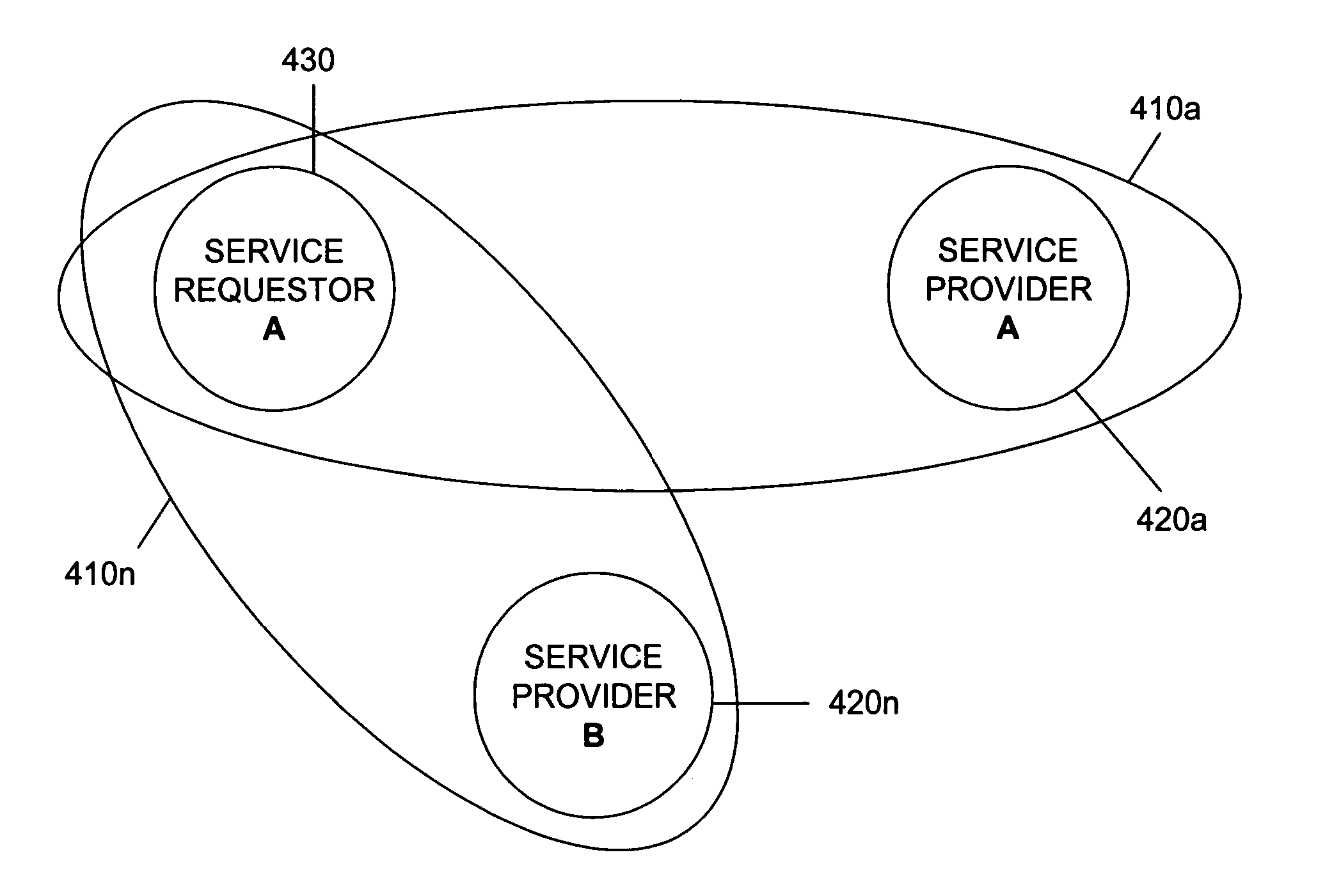
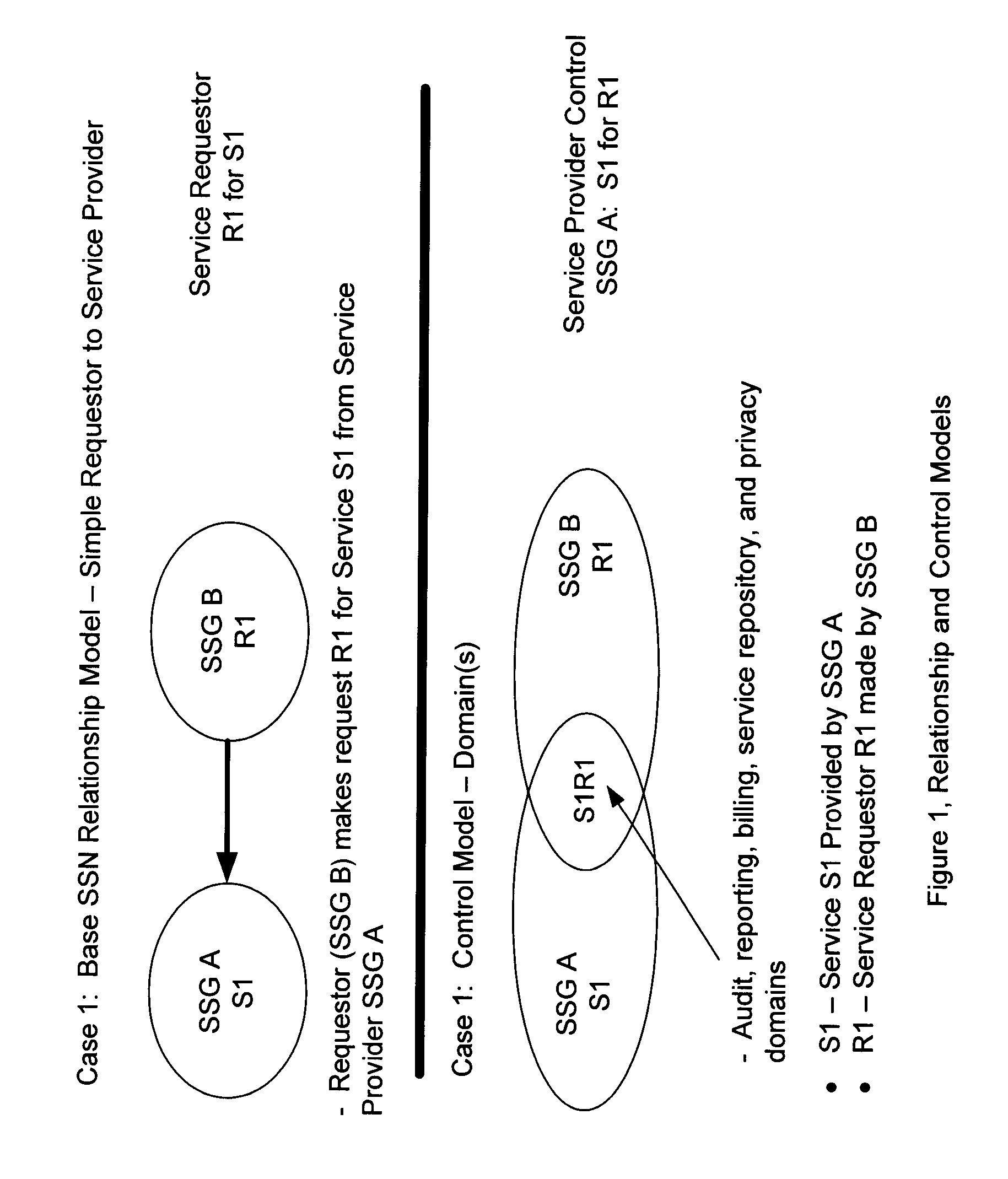
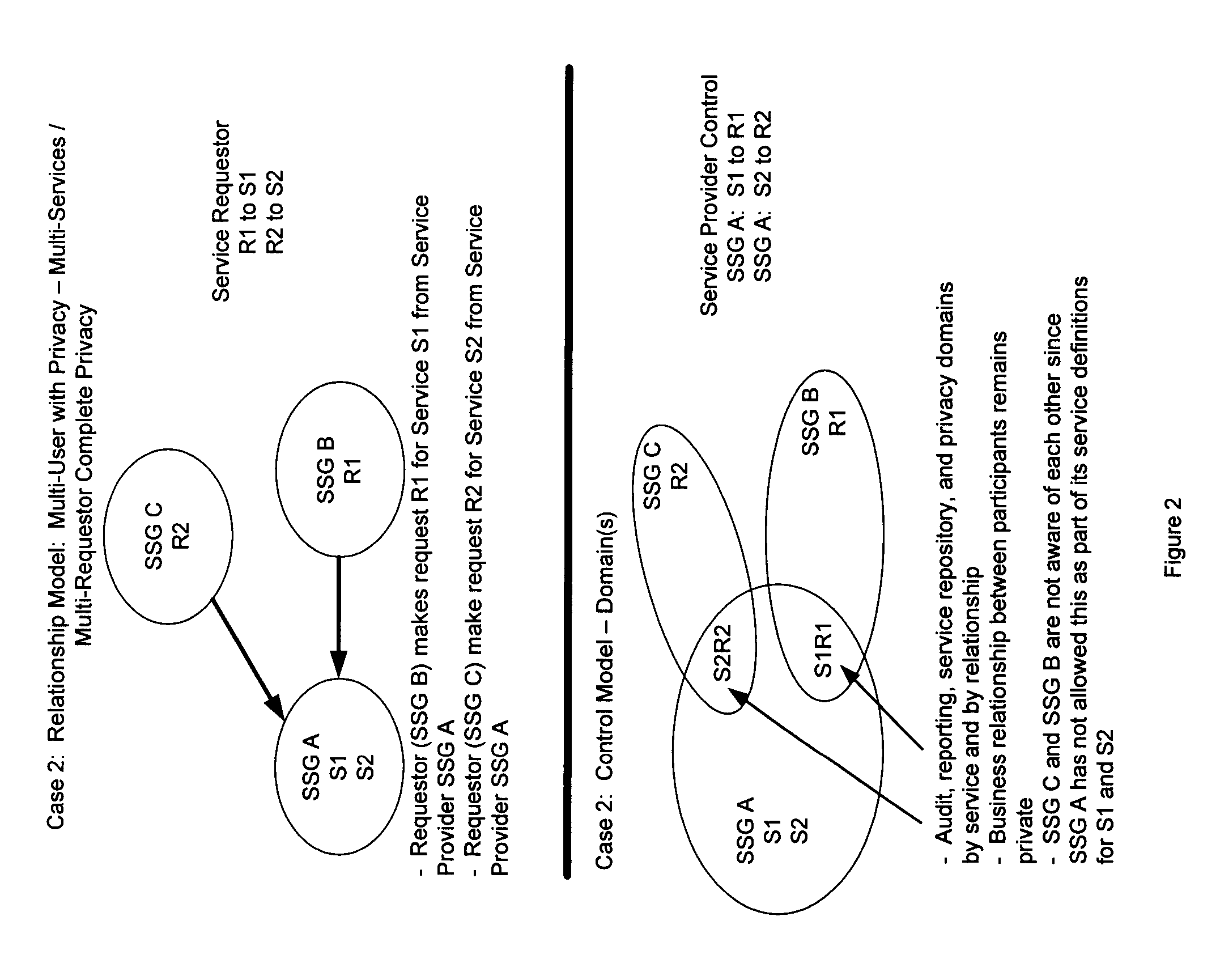
Secure service network and user gateway
ActiveUS20060107036A1Limited in functionally and participant reach and flexibilityLow costFinanceBilling/invoicingEngineeringPeer-to-peer
A secure service network (SSN) comprising an IP network infrastructure wherein the access of one participant to another participant in the network is controlled by a secure service gateway (SSG) in which a point of origination universal identifier (PoUID) represents a unique identifier for the participant within a participant's internal network domain and the interconnection of the SSGs within the SSN as a precondition of access creates a bilaterally secure peer to peer service connection. Participants in the network are service providers, service requesters, or both. A global secure service gateway (GSSG) may be interconnected in the SSN to provide a central access authority and management services.
Owner:WMR E PIN
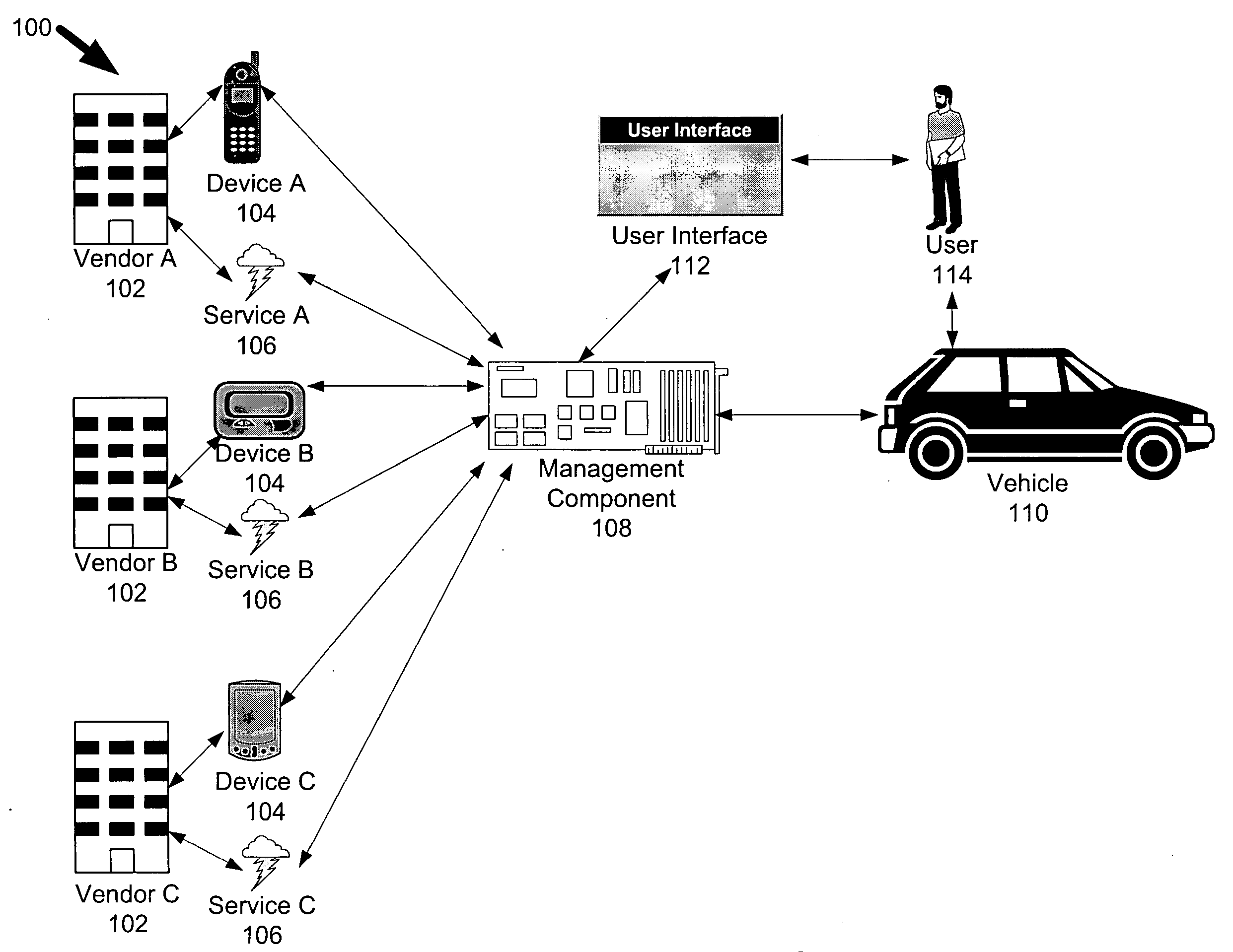
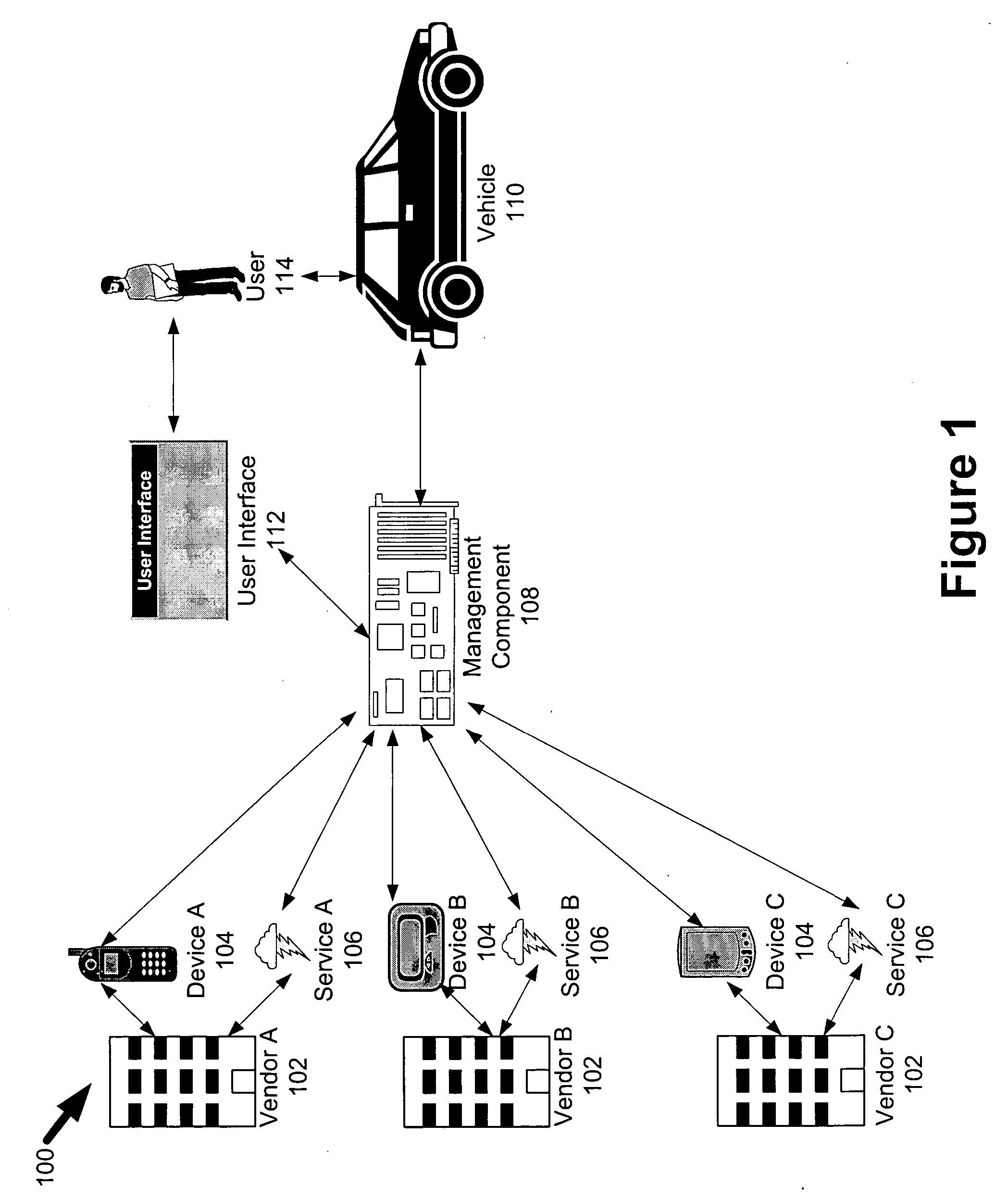
Vehicle services manager
InactiveUS20050283284A1Vehicle testingInstruments for road network navigationSatellite radioWeb site
Services for a vehicle or fleet of vehicles can be ordered, renewed, modified, managed, configured, and / or cancelled through a common interface. Services may be managed remotely from outside the vehicle as well as from within the vehicle. For example, the driver of a vehicle could access a secure web site from their home computer to subscribe for satellite radio services, cancel a subscription for global positioning information, renew a contract for broadband Internet access in the vehicle, and modify a relationship for remote vehicle security services. Each service that is registered with the system can possess a different status. Such functionality allows devices necessary for various services to be pre-installed in the vehicle. The service management system can also store user profiles that reflect user preferences and patterns of behavior with respect to how the services are performed and configured.
Owner:YAZAKI NORTH AMERICA
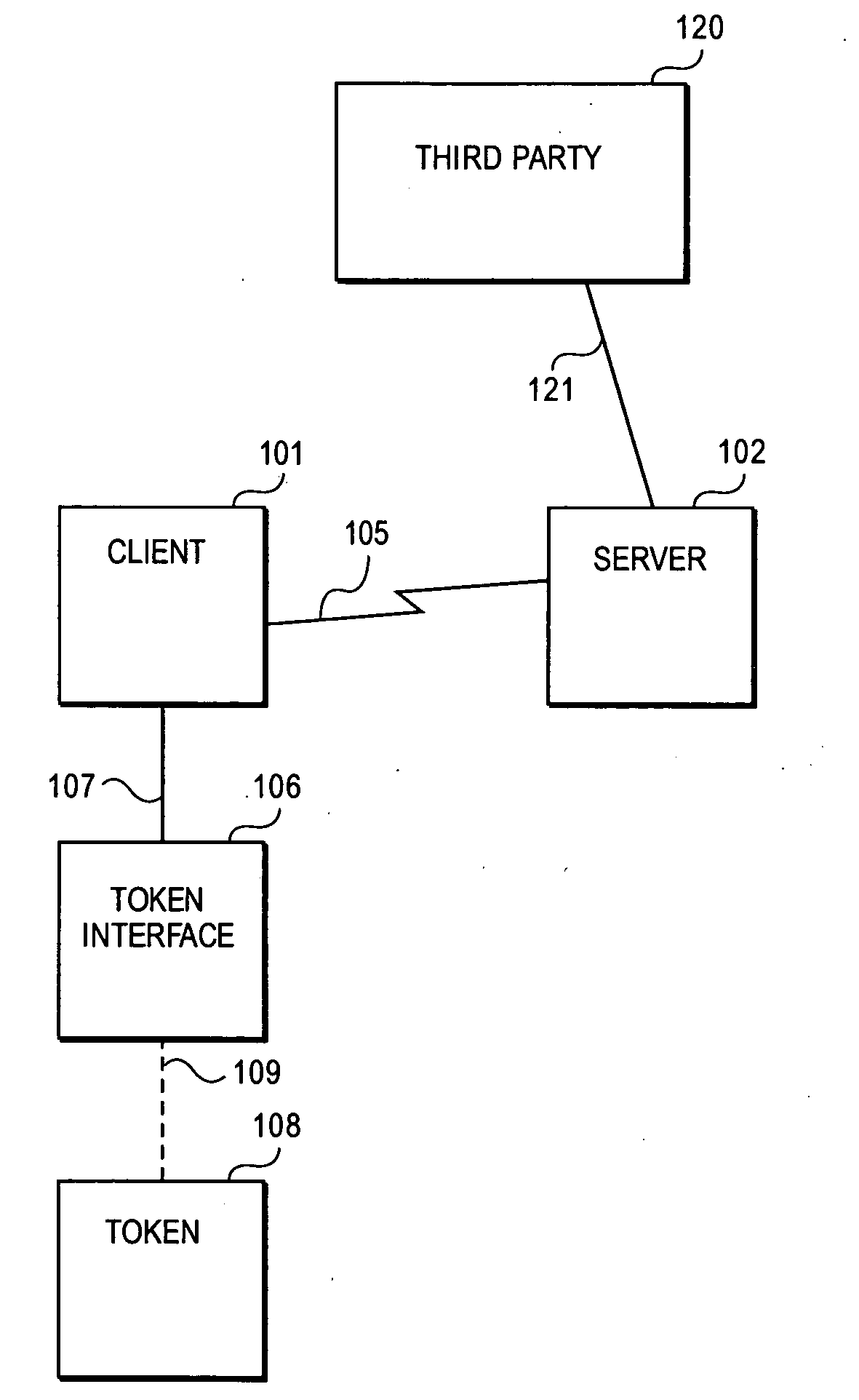
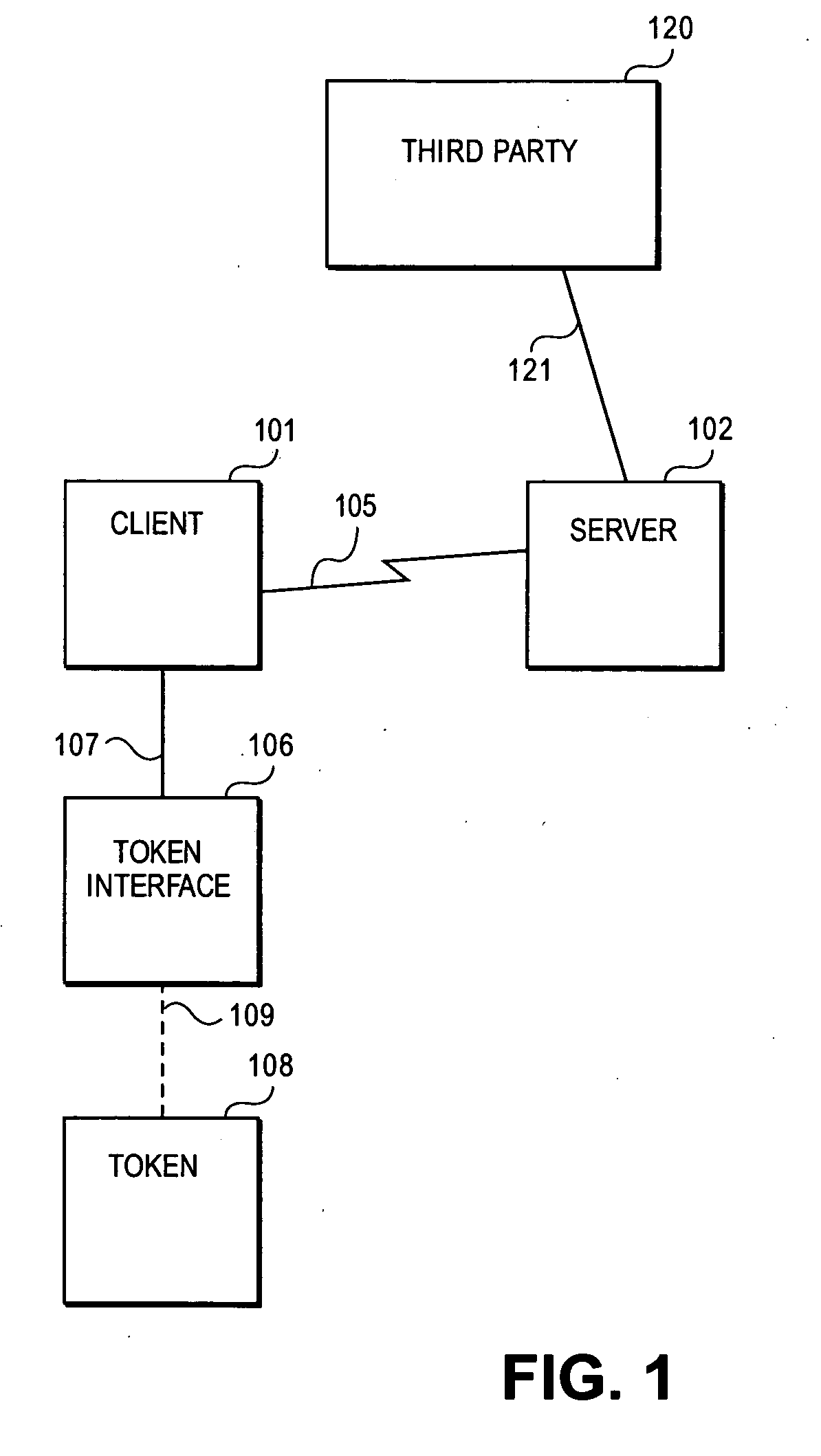
Methods and systems for remote password reset using an authentication credential managed by a third party
ActiveUS20080046982A1Digital data processing detailsUser identity/authority verificationThird partyPassword
Embodiments of the present invention provide a secure remote password reset capability. In some embodiments, an exemplary method provides a remote reset of a password associated with a token in a computer system having a security server. A token-based authentication process is activated by connecting the token to the security server. A server-based authentication process is initiated in the security server by activating a password reset process in a security client. The server-based authentication process communicates with the token-based authentication process over a secure channel. An authentication credential is managed by a third party agent that supplies a query and the authentication credential as a correct response to the query to the security server. A prompt provided by the password reset process collects the authentication credential and a new password. After the authentication credential is validated mutually authentication is performed between the security server and the token. The token is updated with the new password based on a successful result of the mutual authentication.
Owner:RED HAT
Cross domain authentication and security services using proxies for HTTP access
ActiveUS7370351B1Digital data processing detailsUser identity/authority verificationInternet privacyAuthentication
Owner:EMC IP HLDG CO LLC
Secure, real-time application execution control system and methods
InactiveUS20050182958A1Securely identifyingKey distribution for secure communicationMemory loss protectionControl systemExecution control
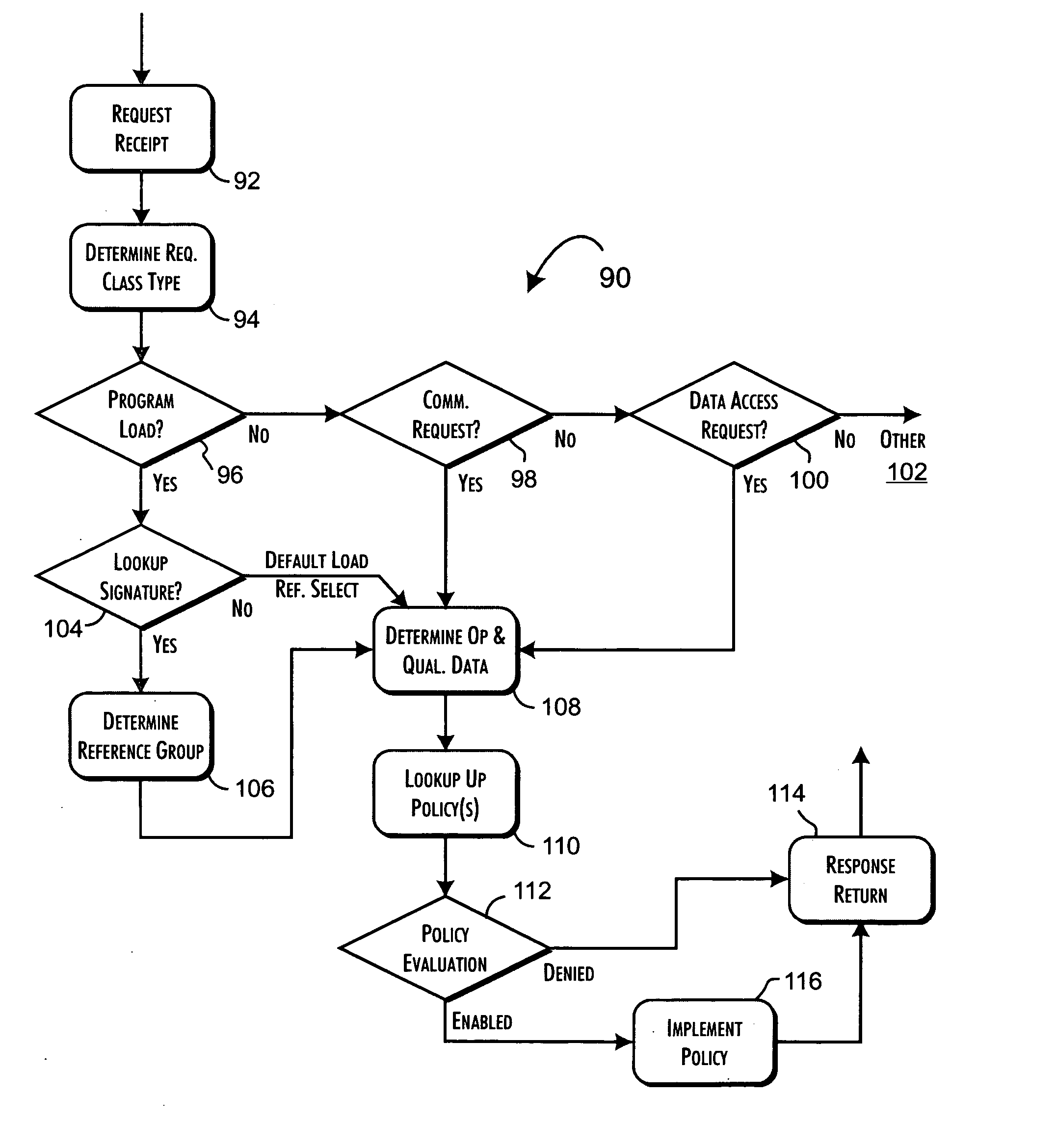
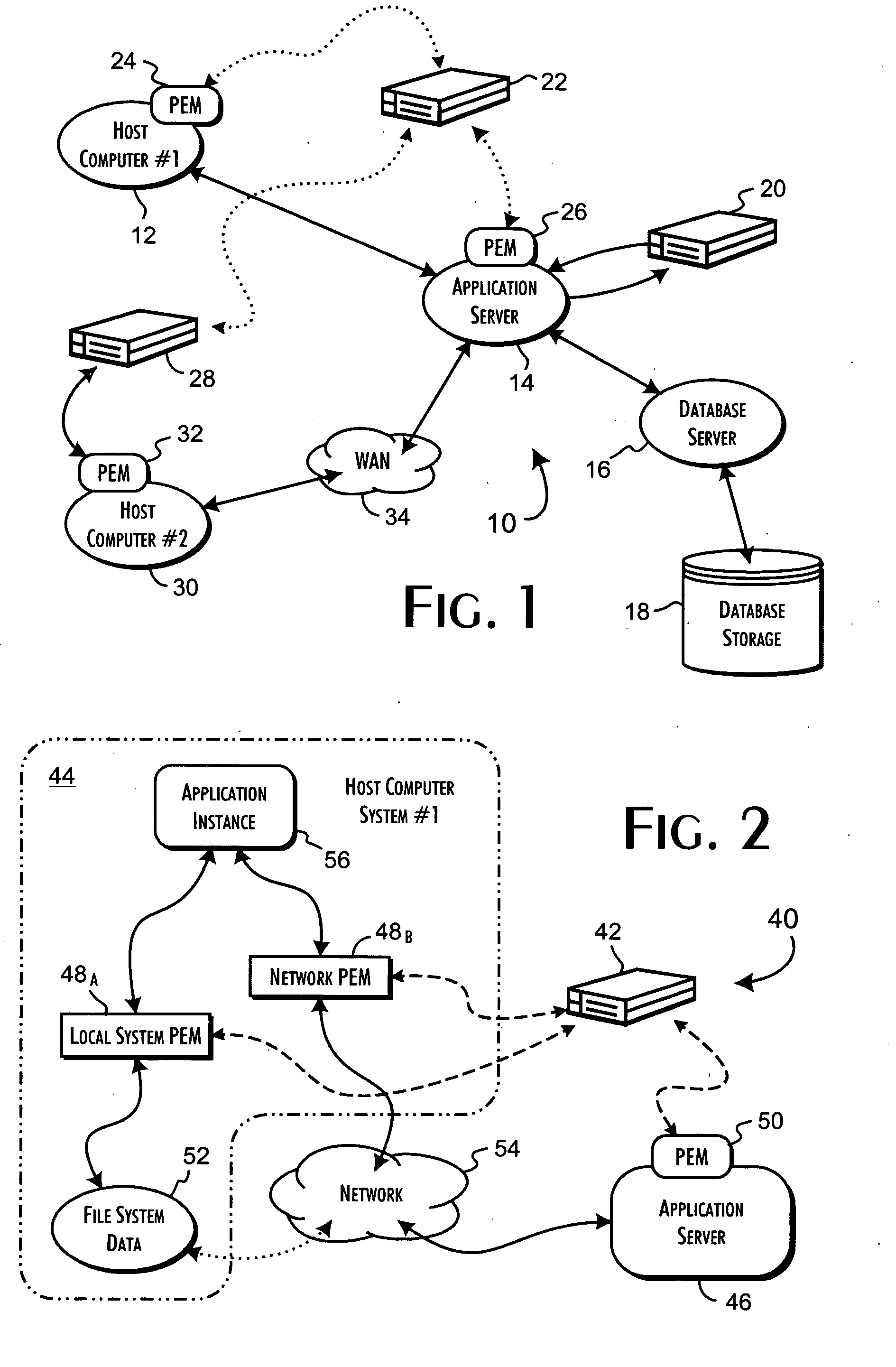
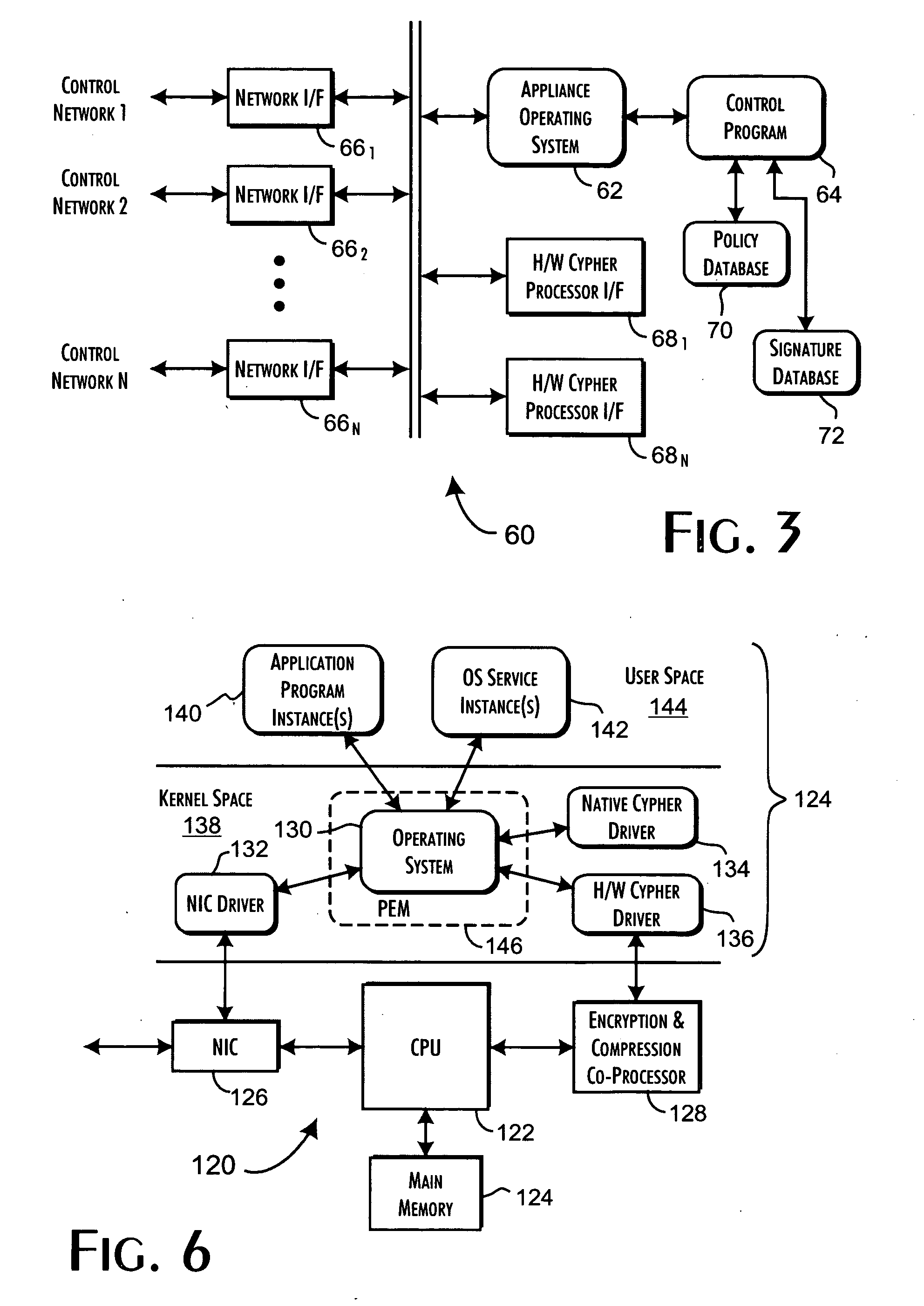
A security server qualifies the execution of programs for networked host computer systems using a database storing pre-qualified program signatures and defined policy rules associating execution permission qualifiers with execution control values. The server executes a control program in response to execution requests received via a communications network interface from identifiable hosts, wherein a predetermined execution request received from a predetermined host computer system includes an identification of a program load request, request context related data, and a secure program signature. The control program determines an execution control value based on an evaluation of the execution request relative to the pre-qualified program signatures and defined policy rules. The execution control value is then returned to the predetermined host computer system to securely qualify the execution of the program identified from the program load request.
Owner:PHAM DUC +3
Methods and systems for detecting and preventing network connection compromise
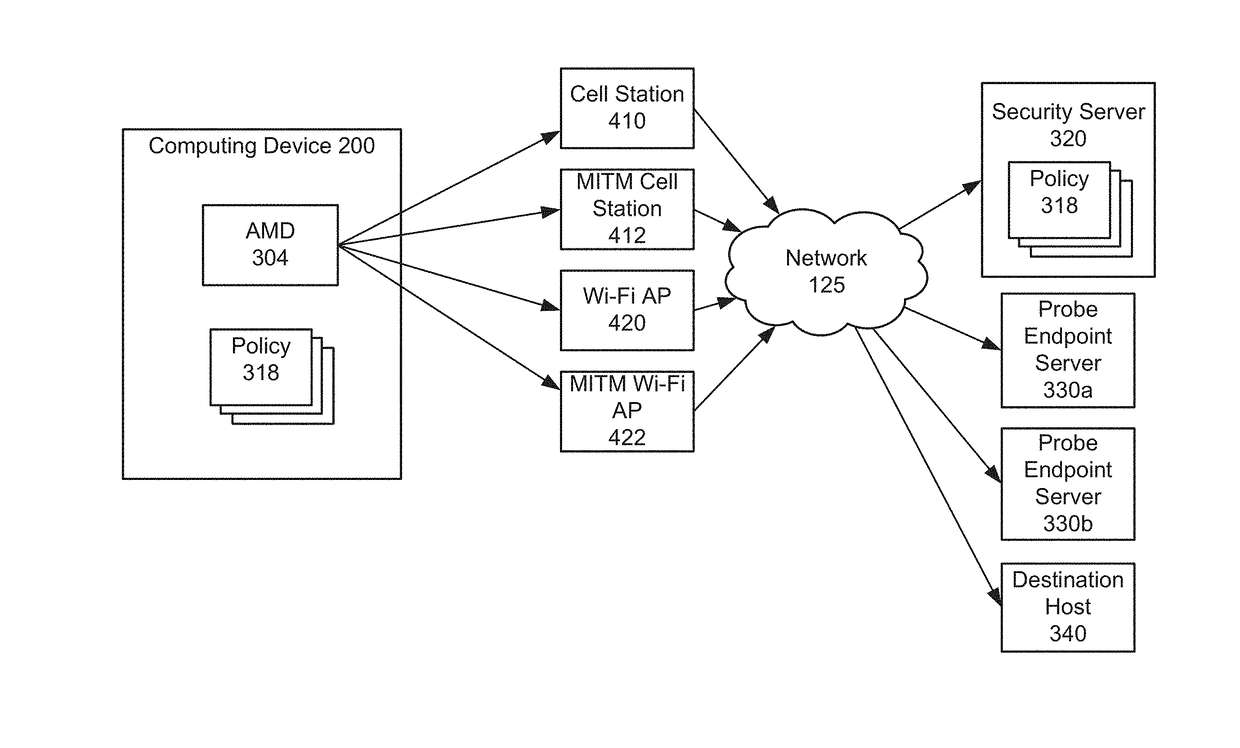
ActiveUS20170346853A1Ensure safetyCompromise safetyPlatform integrity maintainanceData switching networksNetwork connectionMan-in-the-middle attack
The security of network connections on a computing device is protected by detecting and preventing compromise of the network connections, including man-in-the-middle (MITM) attacks. Active probing and other methods are used to detect the attacks. Responses to detection include one or more of displaying a warning to a user of the computing device, providing an option to disconnect the network connection, blocking the network connection, switching to a different network connection, applying a policy, and sending anomaly information to a security server.
Owner:LOOKOUT MOBILE SECURITY
Blockchain identity safe and authentication system
InactiveUS20200026834A1Reduce needKey distribution for secure communicationEncryption apparatus with shift registers/memoriesThird partyInternet privacy
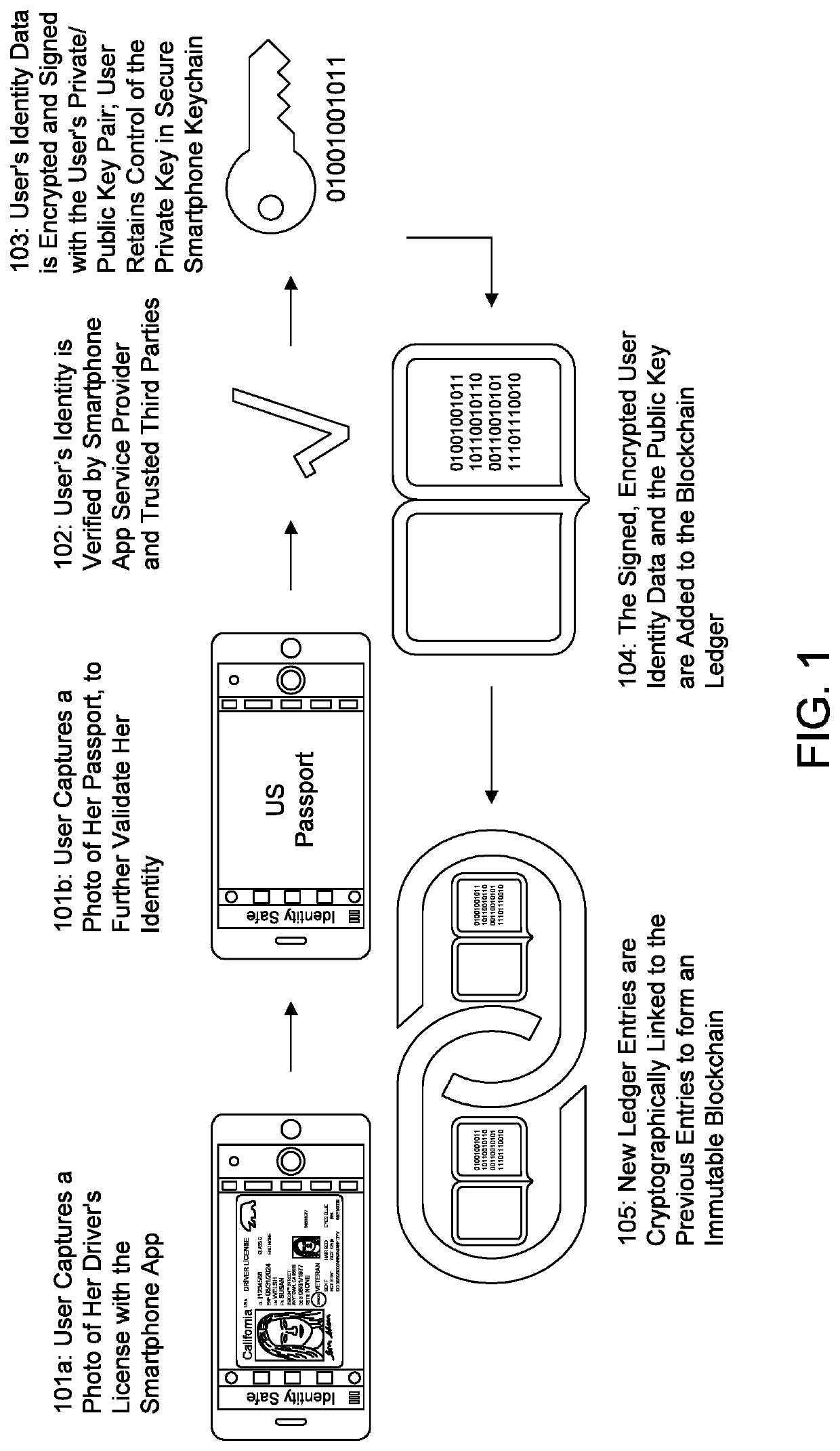
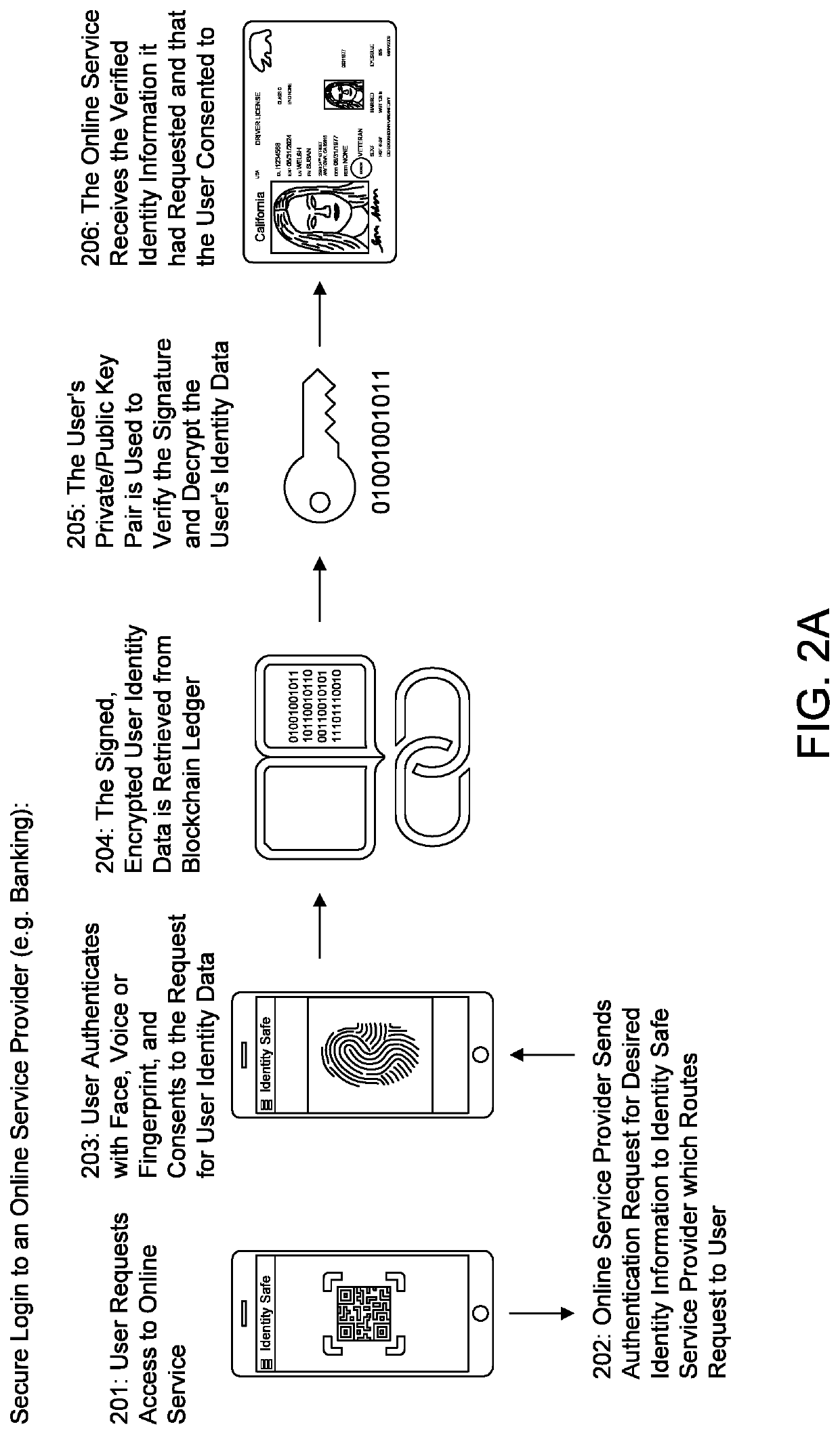
The present invention relates to a system and corresponding method for creating an identity safe in which a user's identity and other data (such as payment data) is securely stored. An identity safe service provider receives from the user's device (e.g., smartphone) at least two forms of the user's identity (e.g., driver's license and passport). The identity safe and third party service providers verify the user's identity data. The identity safe service provider generates a public key and a private key associated with the user, the private key being sent to and retained by the user's secure smartphone keychain. The identity safe service provider encrypts and signs the verified user identity data with the private / public key pair, and adds that data to a blockchain ledger as a new entry. The new entry is cryptographically linked to a prior entry on the blockchain ledger to form the identity safe, which is immutable and incorruptible. An online service provider may subsequently verify the signature and decrypt the user's identity data with the user's private / public key pair to authenticate the user.
Owner:ONE KOSMOS INC
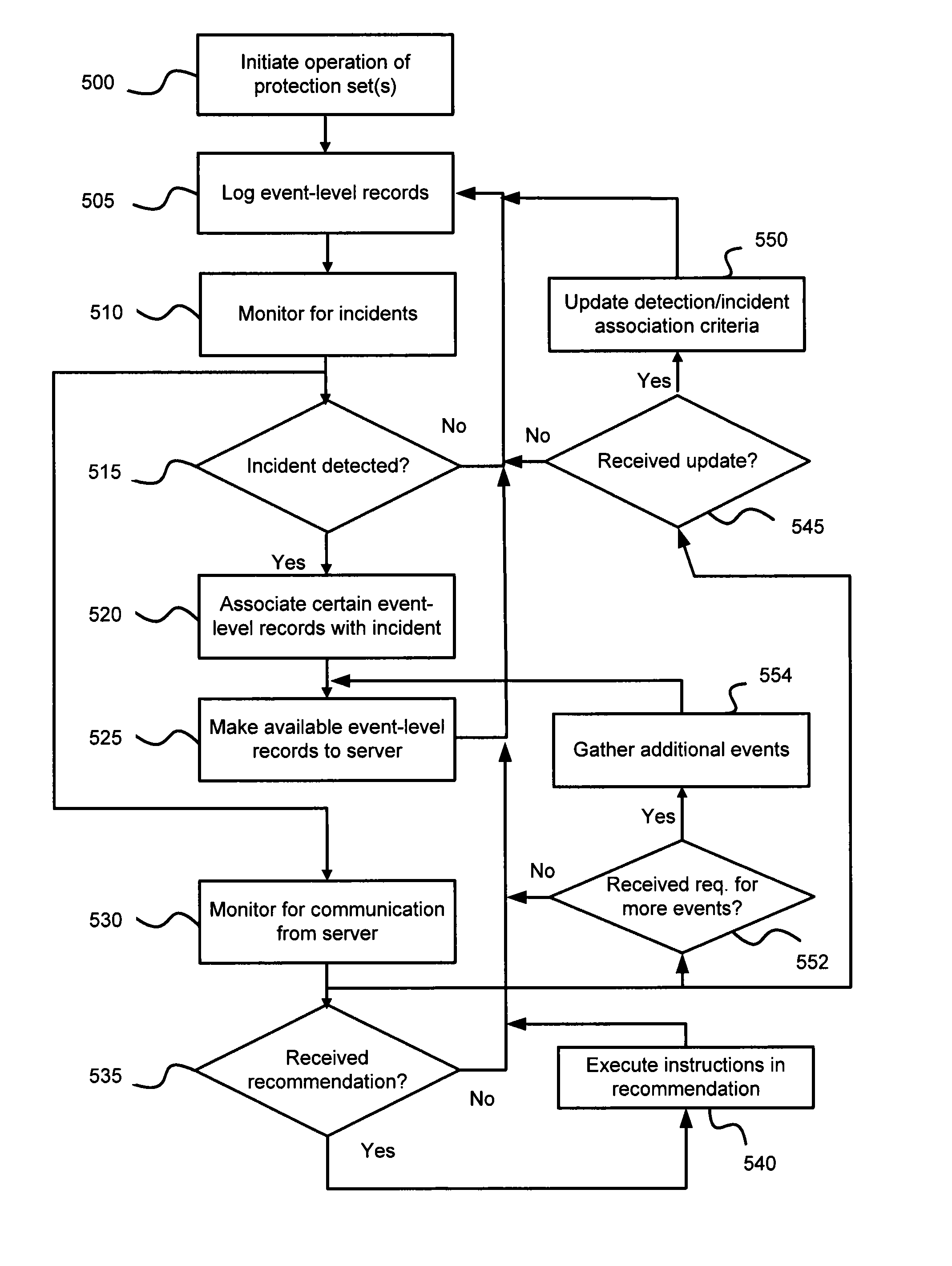
Automatic analysis of security related incidents in computer networks
ActiveUS8776241B2Shorten the timePrevent relapseMemory loss protectionError detection/correctionEvent levelRelevant information
Owner:AO KASPERSKY LAB
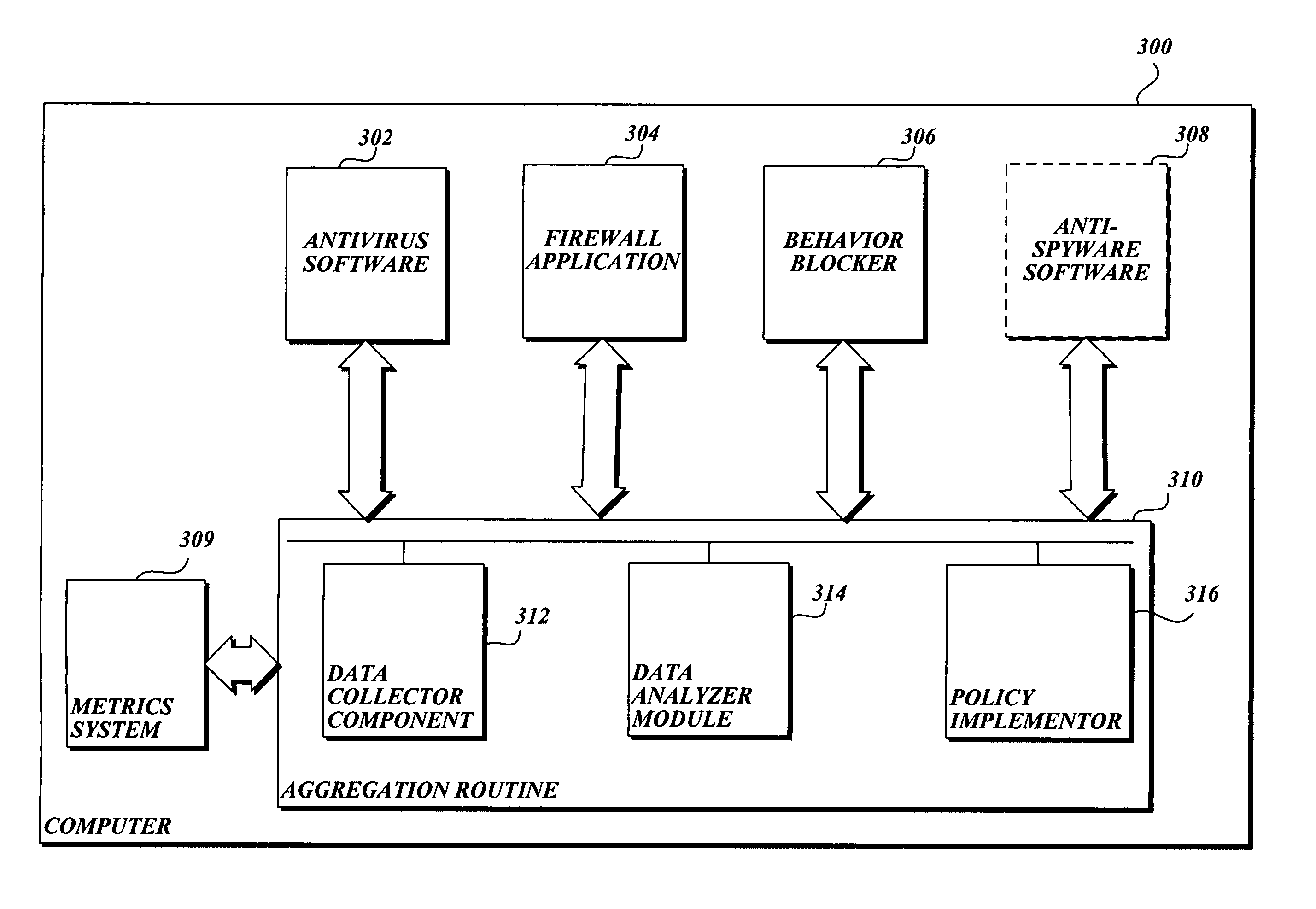
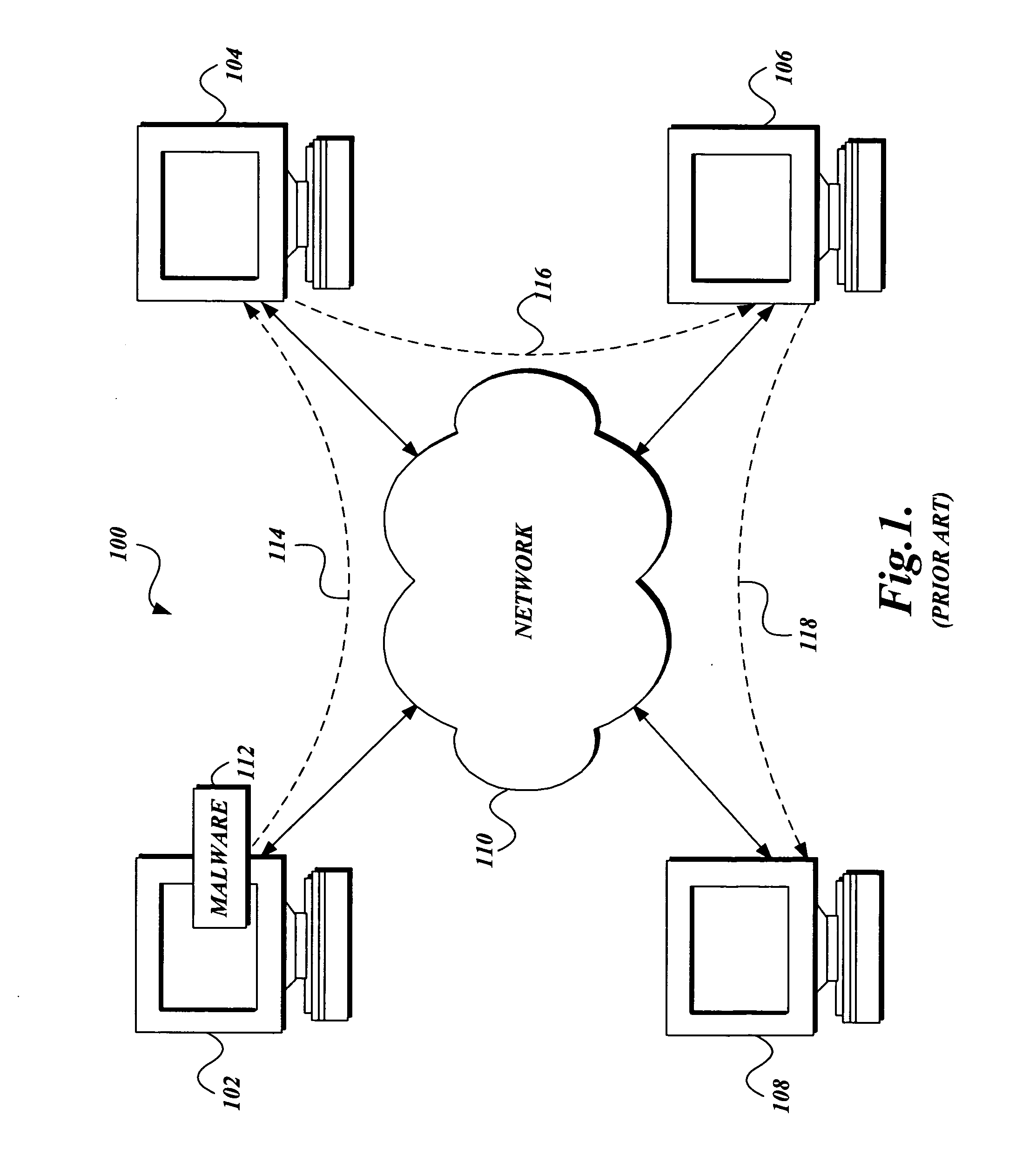
Aggregating the knowledge base of computer systems to proactively protect a computer from malware
In accordance with the present invention, a system, method, and computer-readable medium for aggregating the knowledge base of a plurality of security services or other event collection systems to protect a computer from malware is provided. One aspect of the present invention is a method that proactively protects a computer from malware. More specifically, the method comprises: using anti-malware services or other event collection systems to observe suspicious events that are potentially indicative of malware; determining if the suspicious events satisfy a predetermined threshold; and if the suspicious events satisfy the predetermined threshold, implementing a restrictive security policy designed to prevent the spread of malware.
Owner:MICROSOFT TECH LICENSING LLC
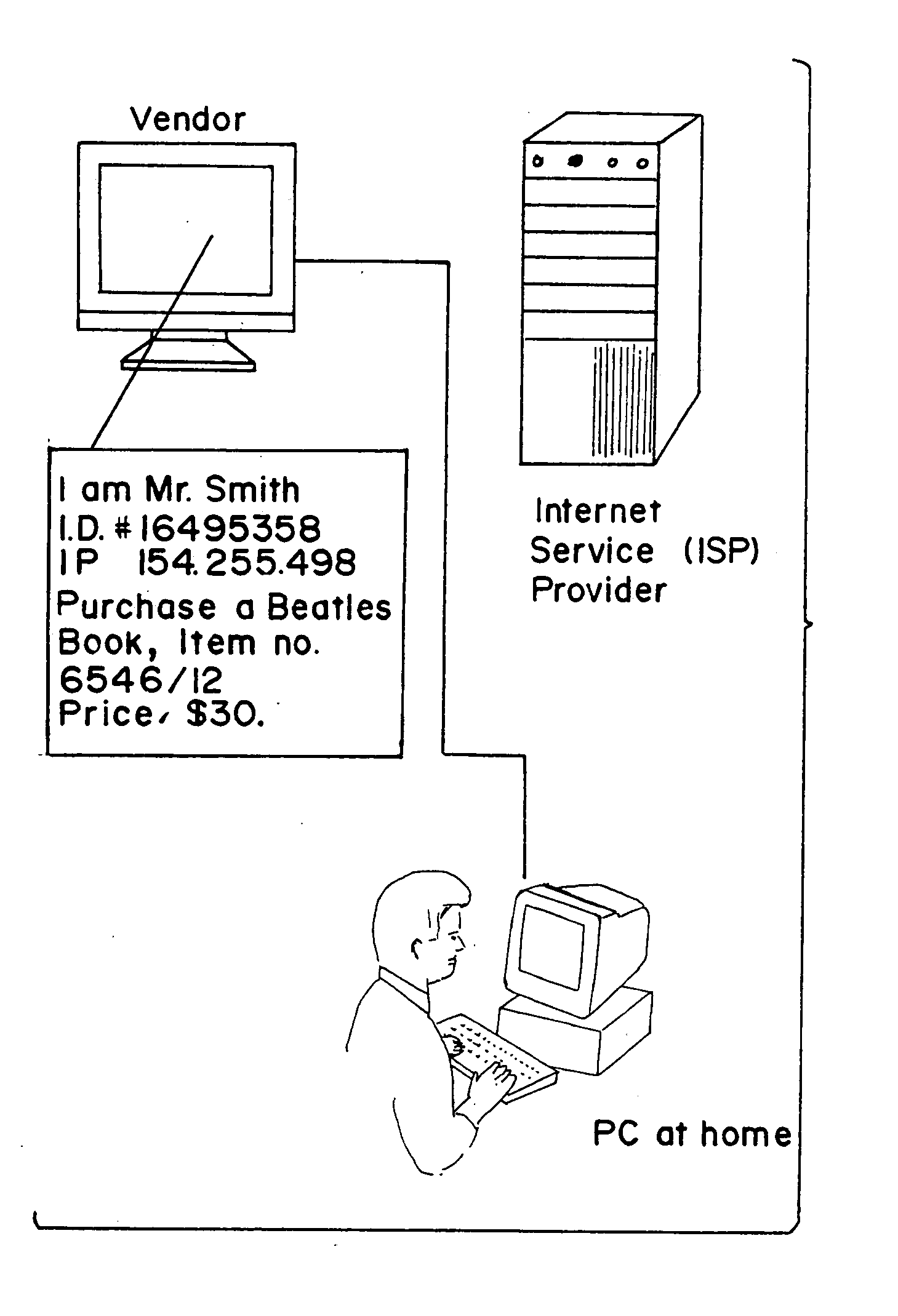
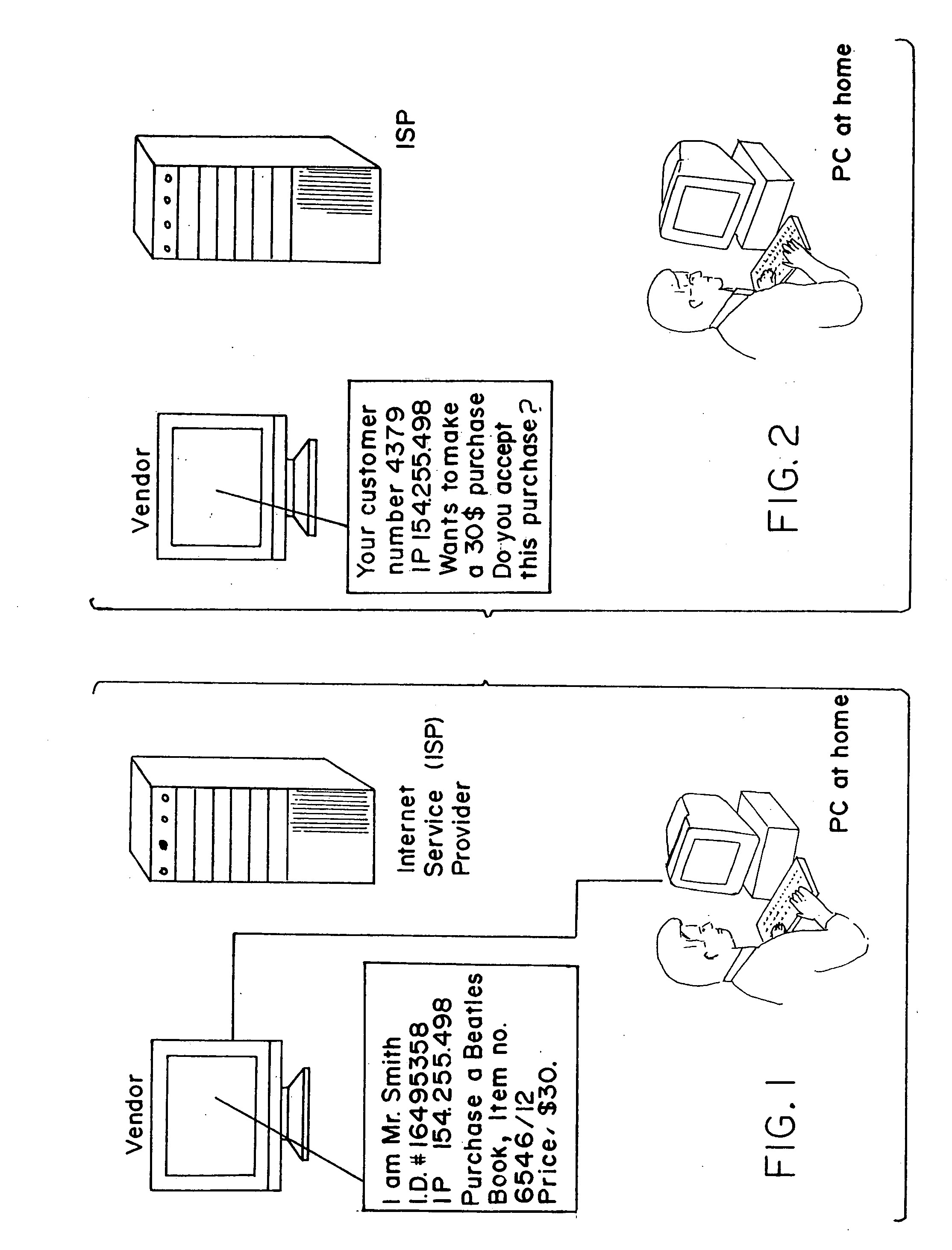
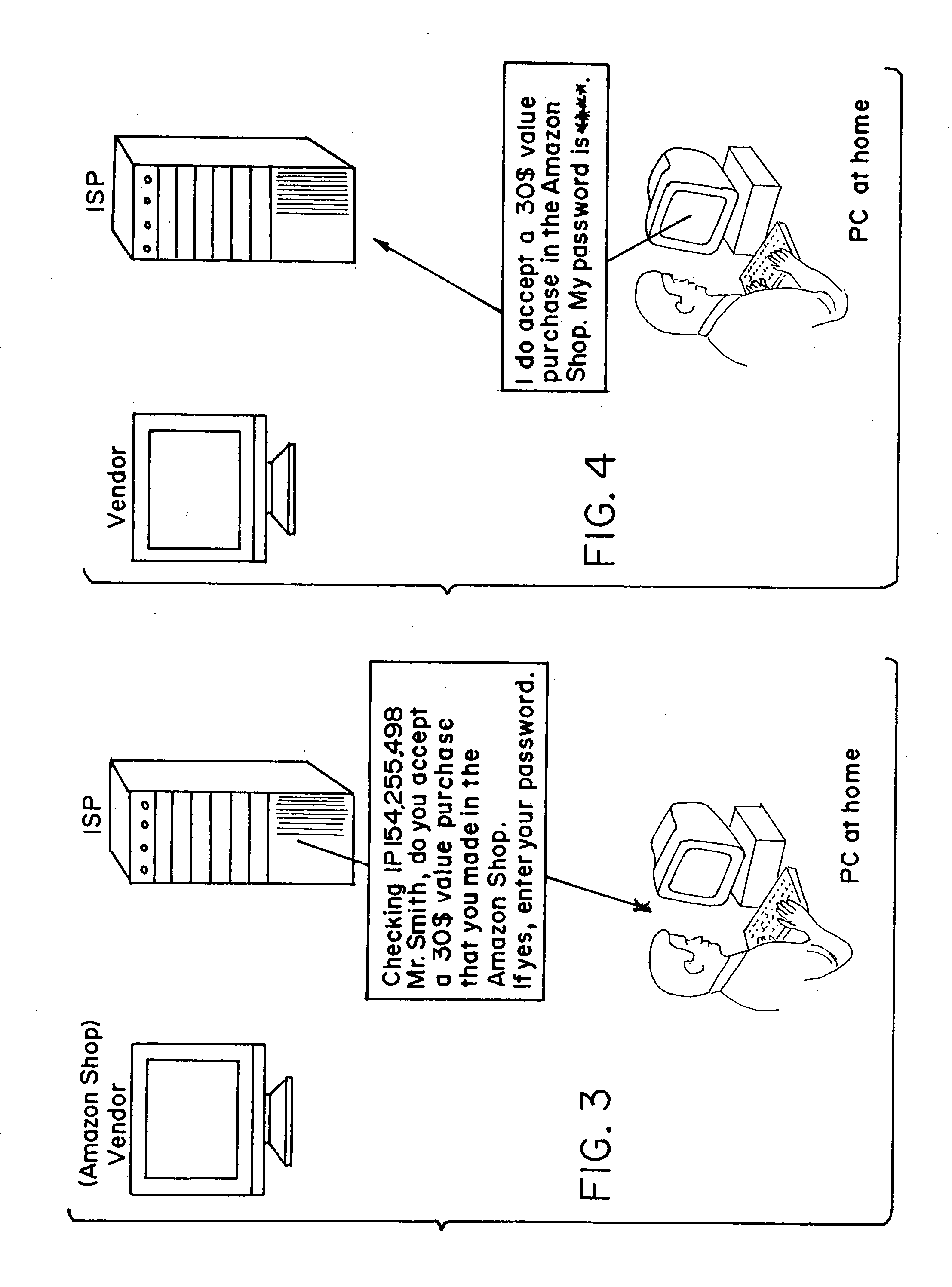
System and method for secure network purchasing
InactiveUS20040117321A1Risk minimizationConfidenceDigital data authenticationBuying/selling/leasing transactionsSecure Electronic TransactionMethod selection
There is disclosed a method for performing secure electronic transactions on a computer network, the network comprising a buyer's computer, a vendor server, a creditor server and a security server. The buyer's computer has a fingerprint file stored in the memory thereof. The method includes the steps of: i) the buyer computer requesting to purchase merchandise to the vendor server, the purchase request including said buyer computer's IP address; ii) the buyer computer selecting a predetermined form of secured payment method; iii) the payment method selection causing the vendor server to transmit to the security server a request for confirmation of the buyer computer's identity at the buyer computer's IP address; iv) the confirmation request causing the security server to send a retrieval request to the IP address, the retrieval request including a retrieval program for detecting and retrieving the buyer's computer's fingerprint file, and the retrieval request further comprising a response request asking for confirmation of the purchase request; whereby a positive response from the buyer's computer to the security server accompanied by the fingerprint file causes the security server to confirm the buyer computer's identity to the vendor server and to approve the purchase.
Owner:IPASS
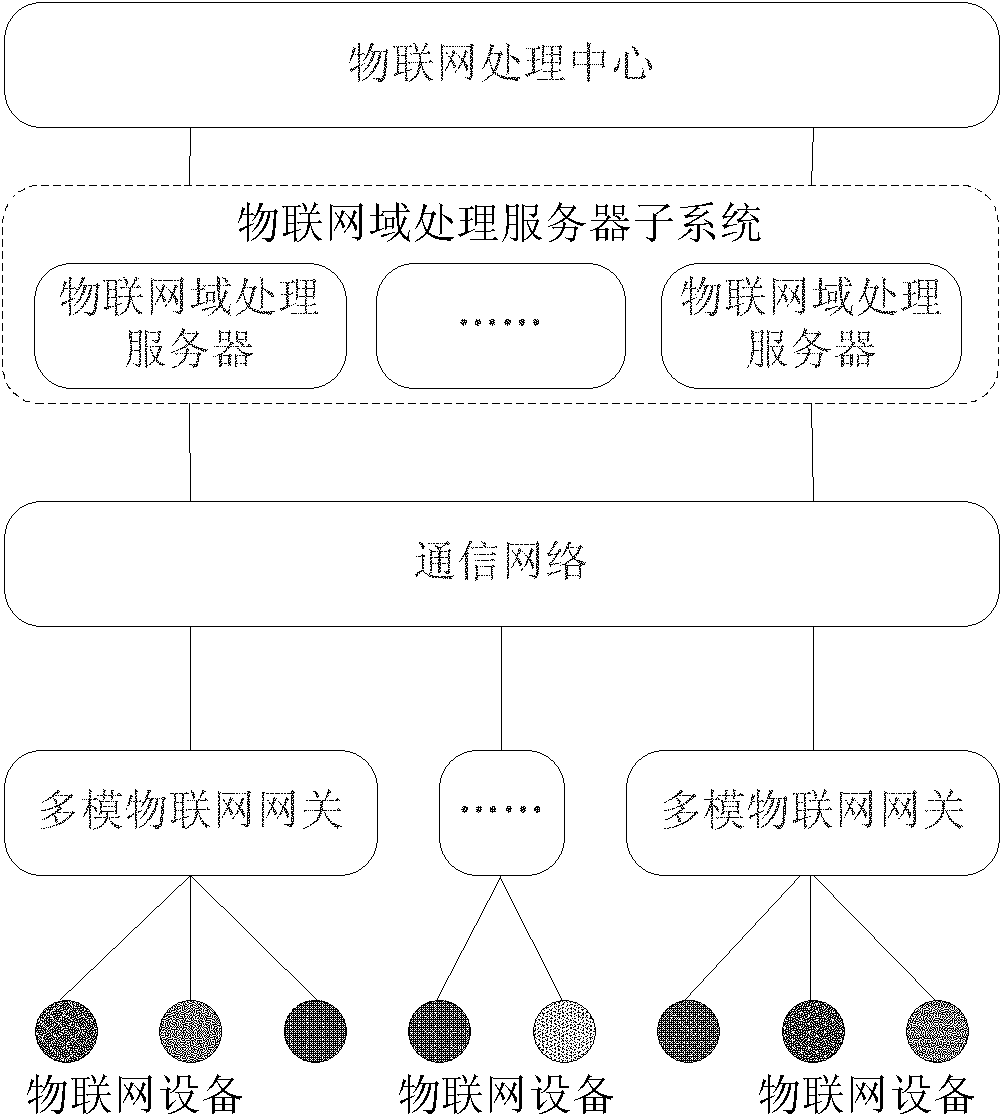
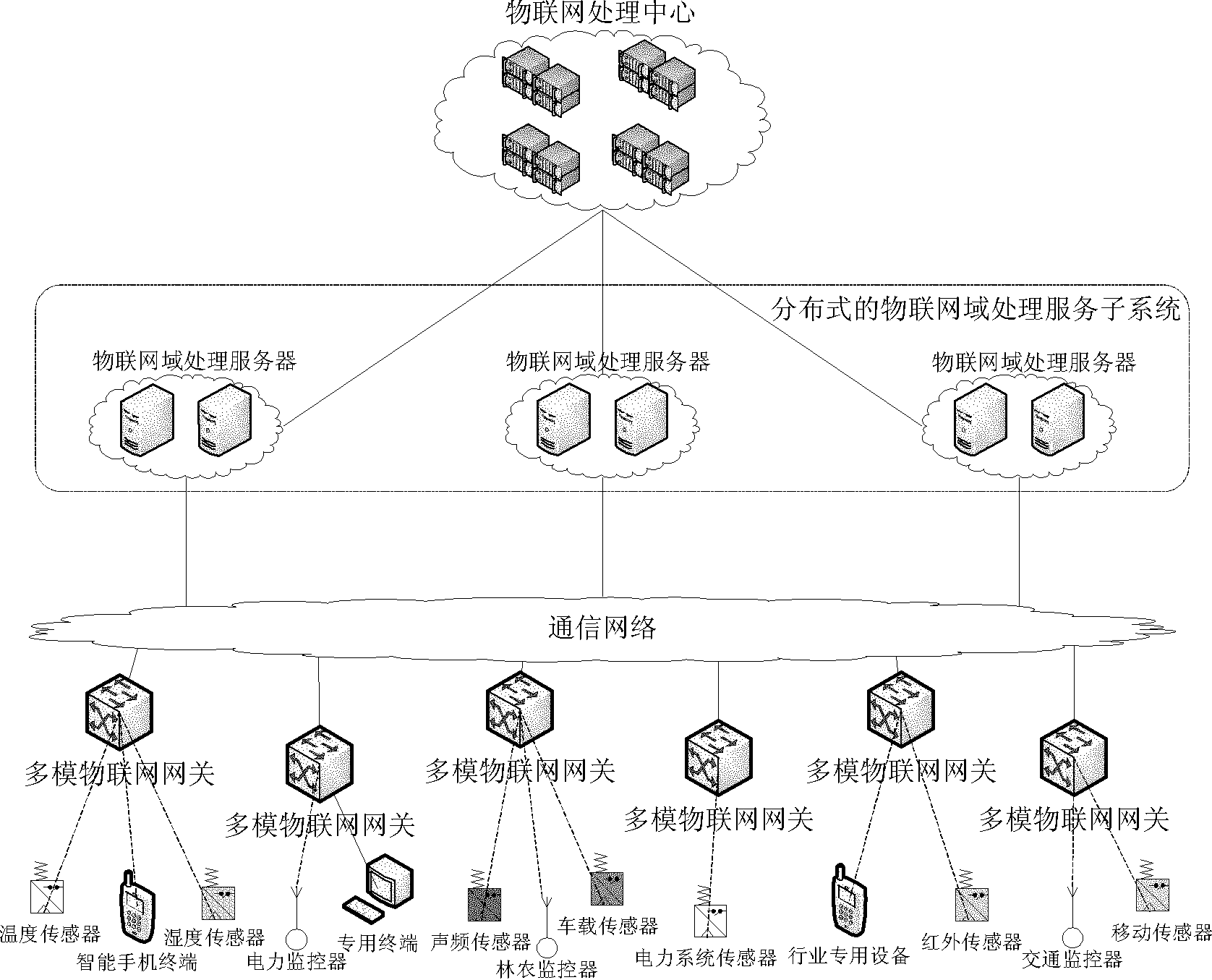
Network system of Internet of things and data processing method thereof
InactiveCN102025577ARelieve pressureIncrease profitData switching by path configurationMobile application execution environmentsIot gatewayThe Internet
The invention discloses a network system of Internet of things and a data processing method thereof, mainly solving the problems of unavailable heterogeneous network integrated access, difficult resource sharing and poor security control of the existing network of Internet of things. The network system mainly comprises an Internet of things processing center, a distributed Internet of things domain processing and servicing subsystem, a multimode Internet of things gateway, and Internet of things devices. The Internet of things processing center provides service and a development platform for the public, the distributed Internet of things domain processing and servicing subsystem assists the Internet of things processing center to provide the service for the user, the multimode Internet of things gateway provides the protocol conversion and the security service, and the Internet of things devices are used to receive and transmit the Internet of things data or to execute instruction, and perform the inter-domain processing or the intra-domain processing on the network data according to different services when processing the network data in the network system of Internet of things. According to the invention, the problem of heterogeneous network integrated access is solved, the resource sharing rate of the Internet of things is enhanced, and the security control of the Internet of things information is strengthened, therefore, the system and the method can be used in designing and building of the Internet of things network.
Owner:XIDIAN UNIV
Security server system
InactiveUS7325127B2Raise security concernsHigh degreeData switching networksSecuring communicationKey serverMessage Title
A security server system and method permitting participants acting as the source or destinations for a message or a conversation with multiple messages to securely communicate the messages. The messages have a message header and a message content. A message router connects the participants via a network and delivers the message between the participants based on the message header. A key server creates, stores, and releases conversation keys that the participants use to protect the message content of the message.
Owner:PROOFPOINT INC
Authentication and tracking system
ActiveUS20050097054A1Digital data processing detailsAnalogue secracy/subscription systemsComputer hardwareInformation transfer
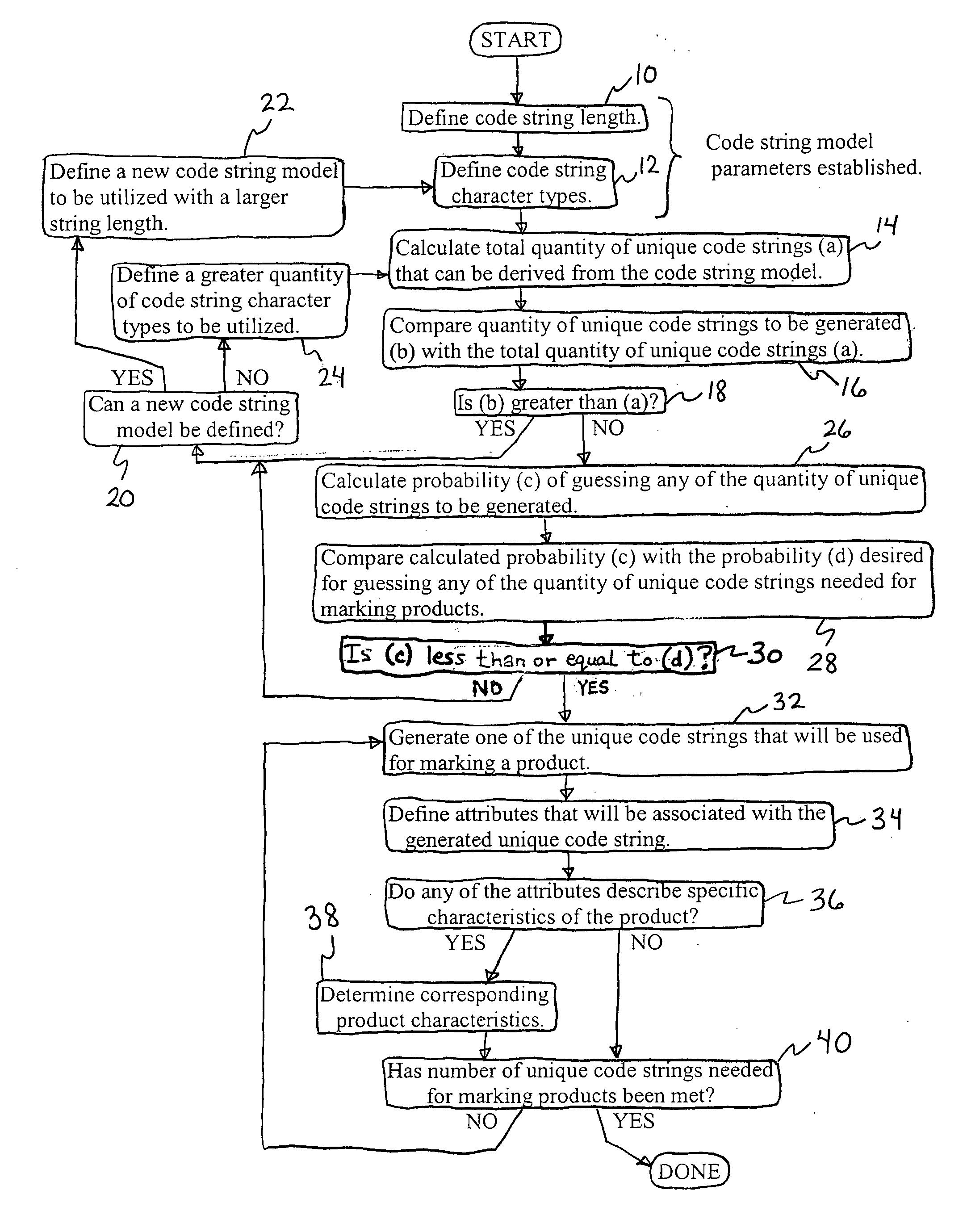
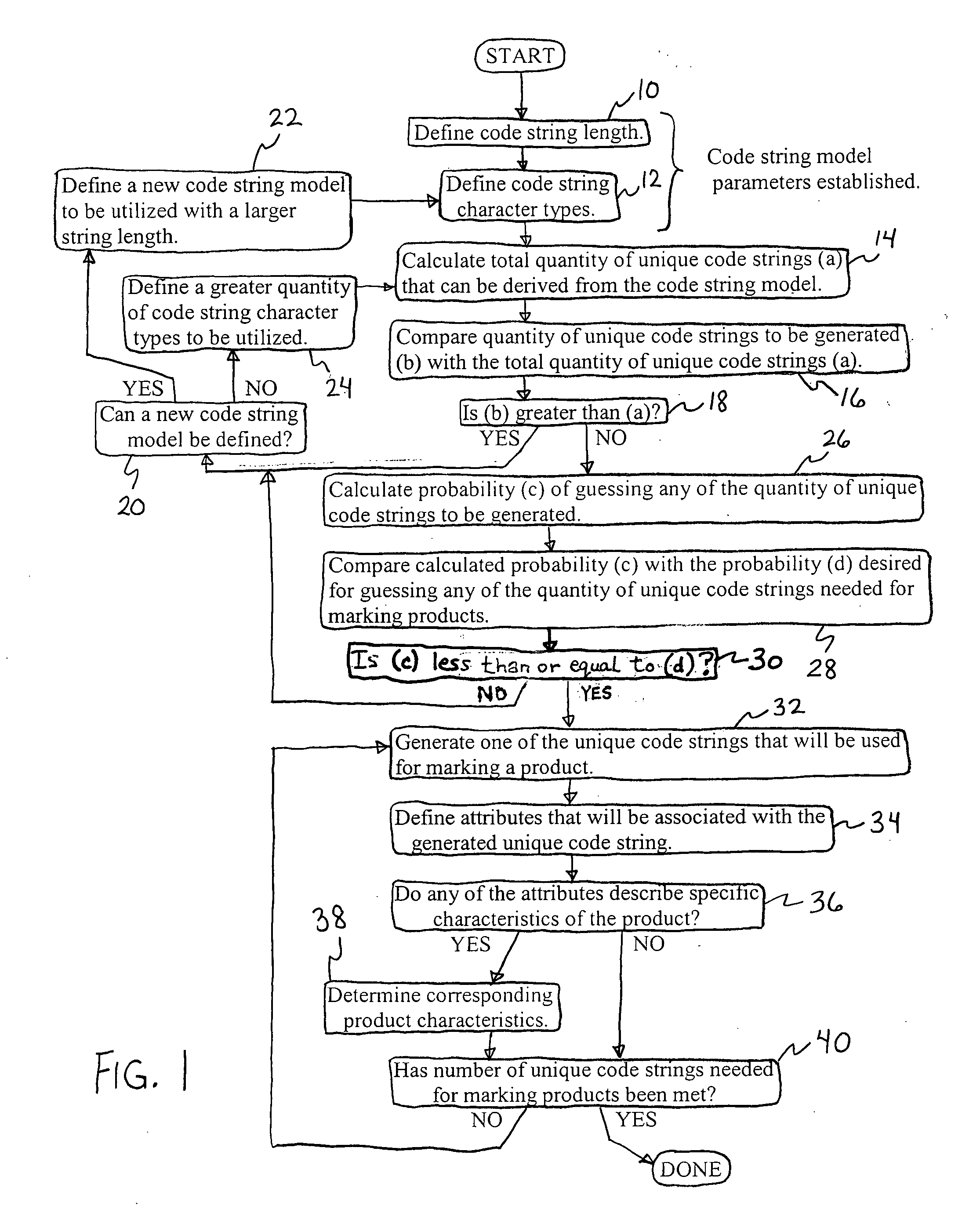
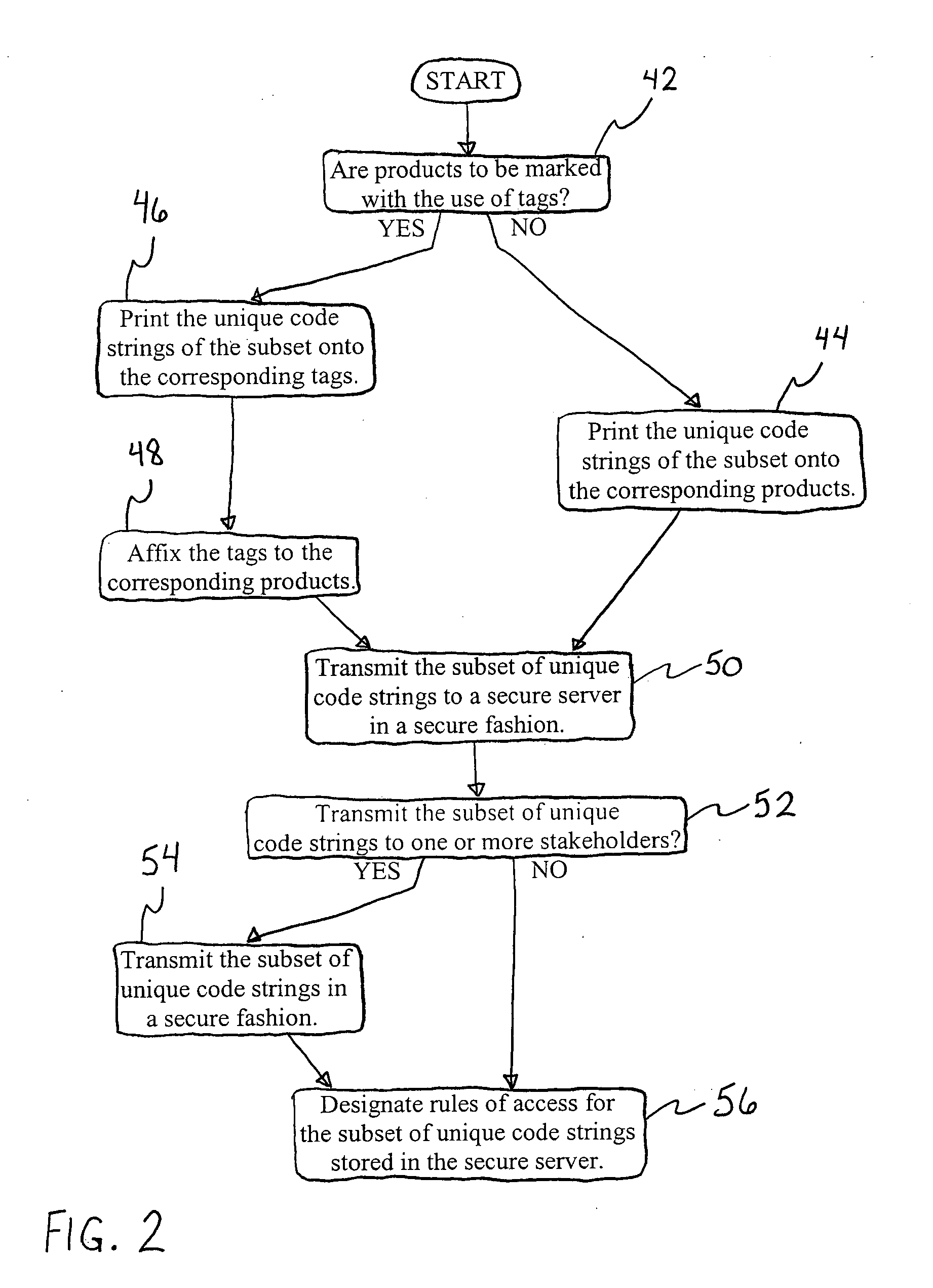
A subset of unique codes are generated from a set of codes. The subset of codes are stored in a database on a secure server and each of the codes is marked on a corresponding instantiation of the product. The marked instantiations are distributed. During their distribution, the marked instantiations are verified for authenticity and for routing. This verification is performed by reading or scanning the codes on the instantiations, and transmitting that information to the secure server for comparison against the codes and other information located in the database contained therein.
Owner:THE MEYERS PRINTING
System and method for authentication in a mobile communications system
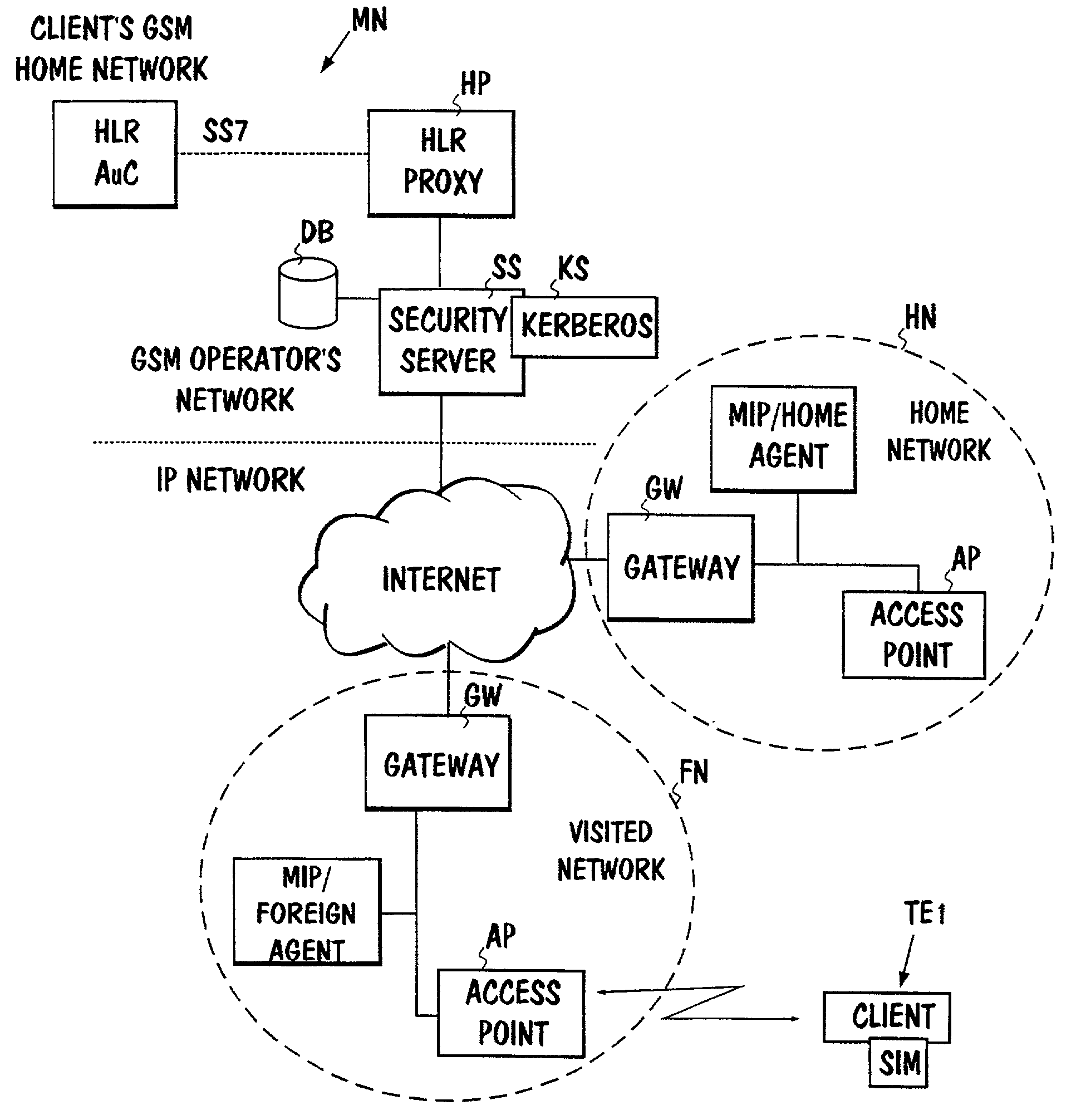
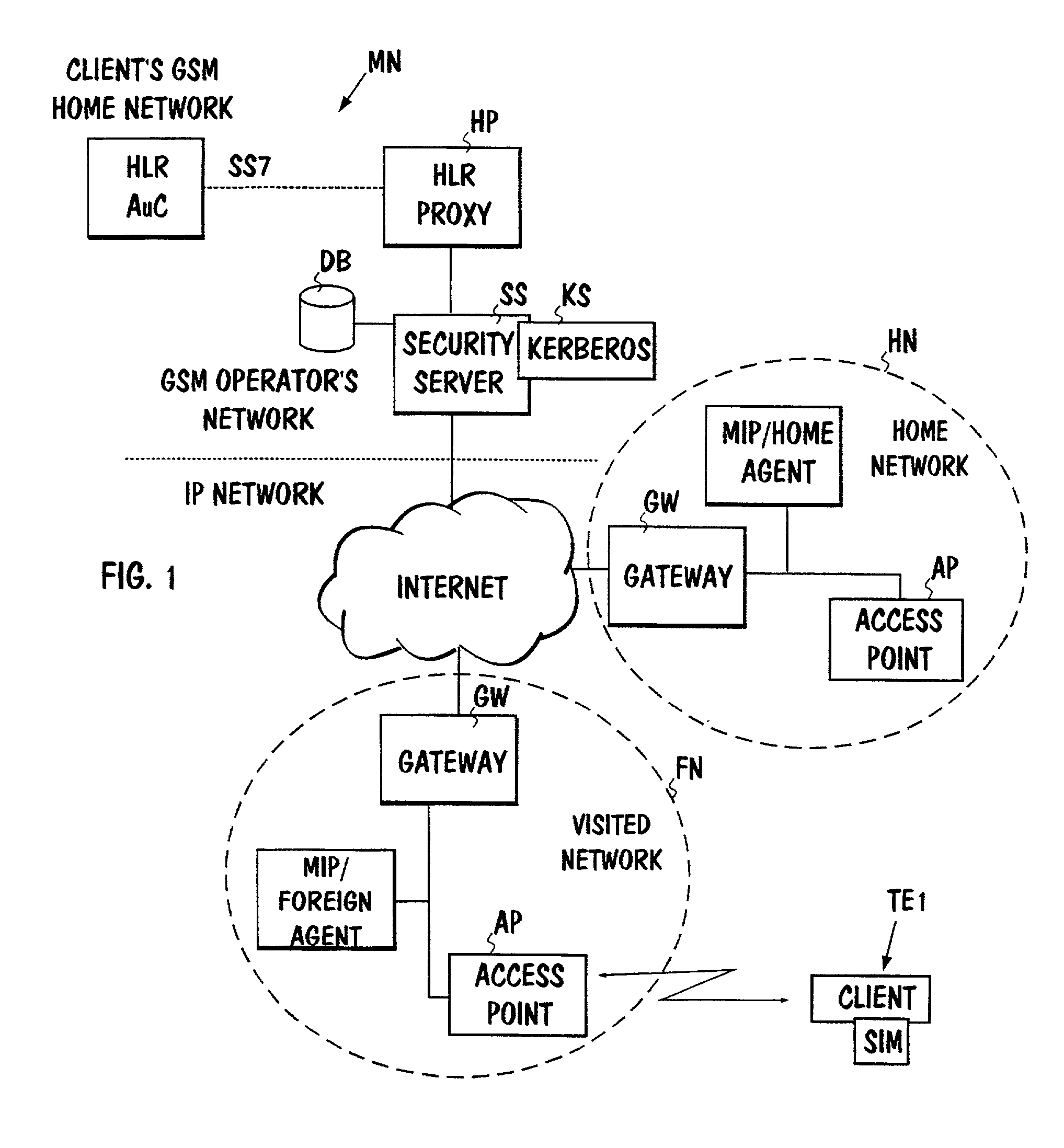
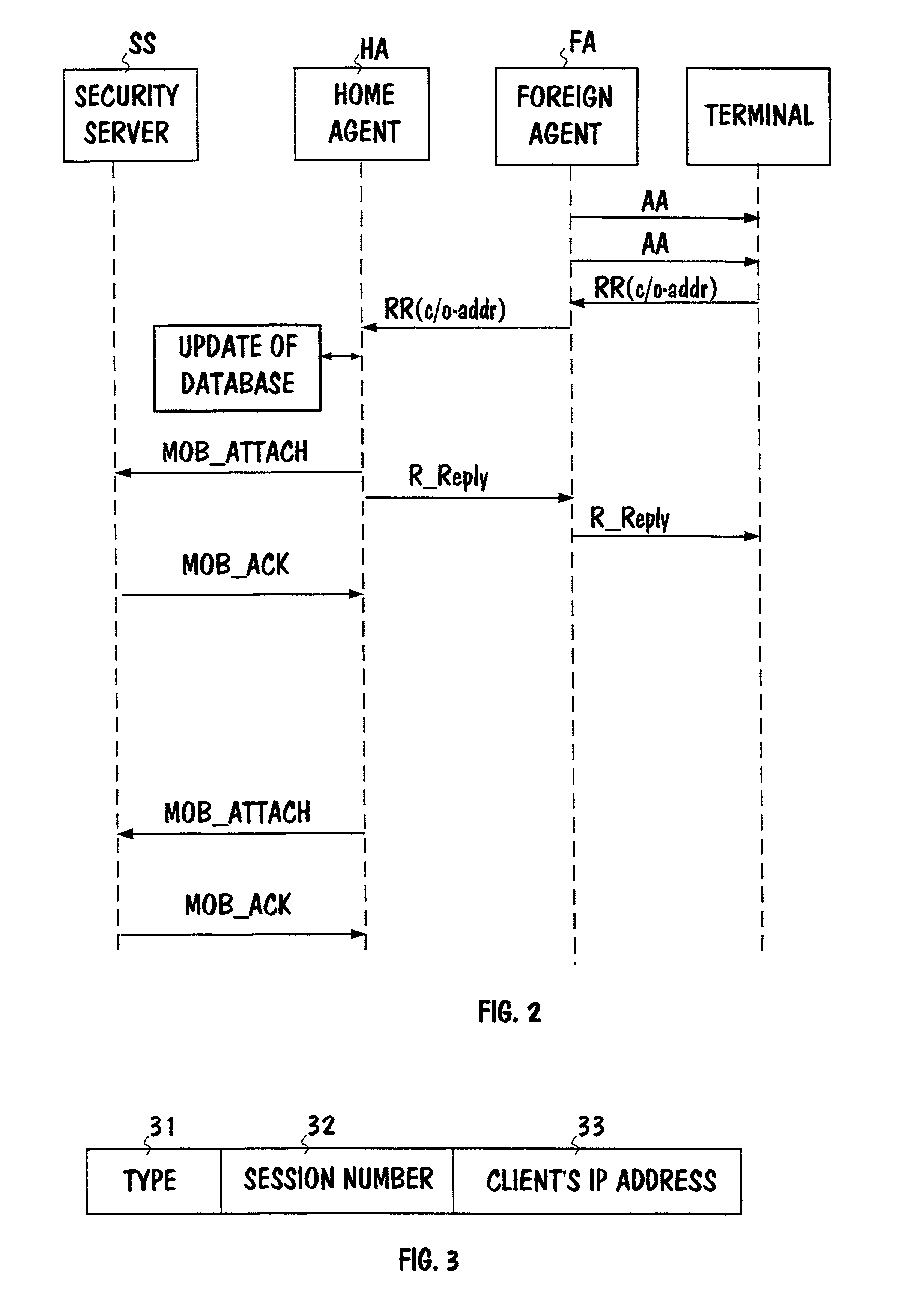
InactiveUS7003282B1Simply and smoothly authenticatedEasily and smoothly authenticatedUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemTelecommunications network
The invention concerns authentication to be performed in a telecommunications network, especially in an IP network. To allow a simple and smooth authentication of users of IP networks in a geographically large area, the IP network's terminal (TE1) uses a subscriber identity module (SIM) as used in a separate mobile communications system (MN), whereby a response may be determined from the challenge given to the identity module as input. The IP network also includes a special security server (SS), to which a message about a new user is transmitted when a subscriber attaches to the IP network. The subscriber's authentication information containing at least a challenge and a response is fetched from the said mobile communications system to the IP network and authentication is carried out based on the authentication information obtained from the mobile communications system by transmitting the said challenge through the IP network to the terminal, by generating a response from the challenge in the terminal's identity module and by comparing the response with the response received from the mobile communications system. Such a database (DB) may also be used in the system, wherein subscriber-specific authentication information is stored in advance, whereby the information in question need not be fetched from the mobile communications system when a subscriber attaches to the network.
Owner:NOKIA TECHNOLOGLES OY
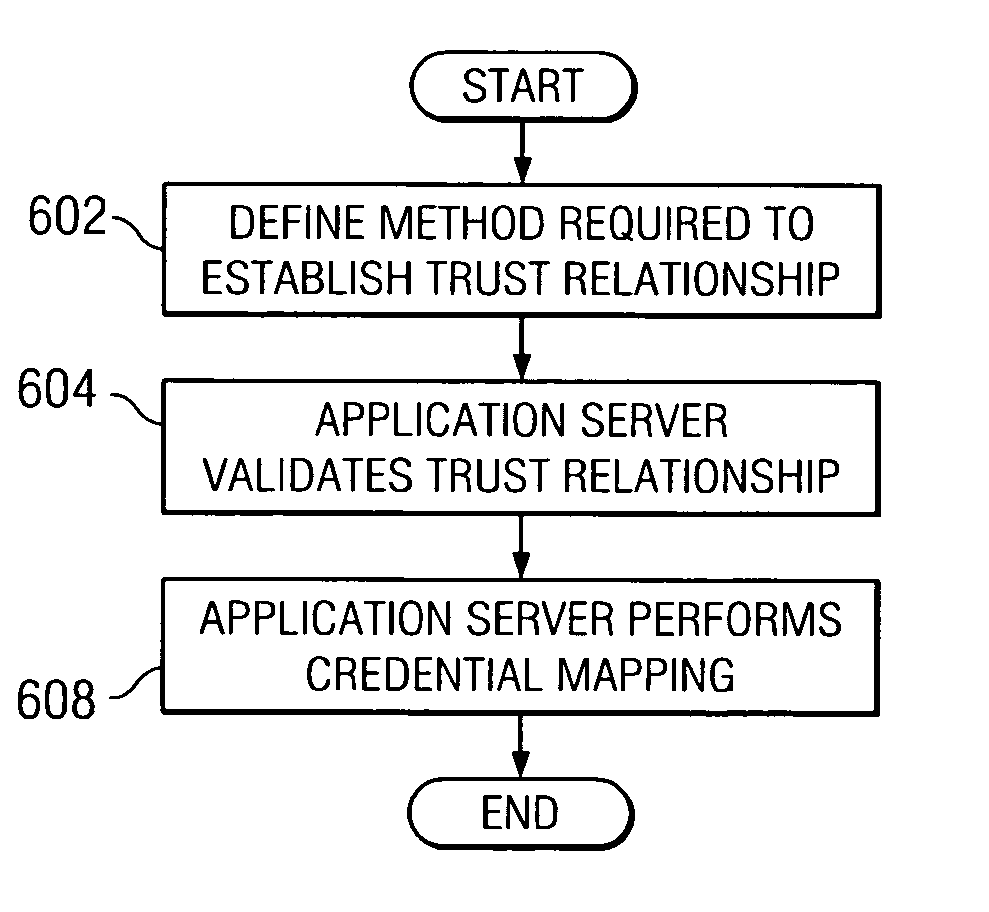
Declarative trust model between reverse proxy server and websphere application server
A method and system for providing a declarative trust association model that formalizes the way trust is established and requires corresponding authentication information to be presented in a standard format. Consequently, the application server may provide a guaranteed level of protection. The mechanism of the present invention provides a framework that allows an application server to enforce a trust evaluation and allows reverse proxy security server to assert a client's security identity, as well as other client security credential information. A known trust association interceptor model is extended to allow the reverse proxy security server to assert the authenticated user's security attributes. Such security attributes include, for example, group information, authentication strength, and location (i.e., where does the user enter the request, intranet vs. internet, IP address, etc.,). The security attributes can be used in making authorization decisions.
Owner:IBM CORP
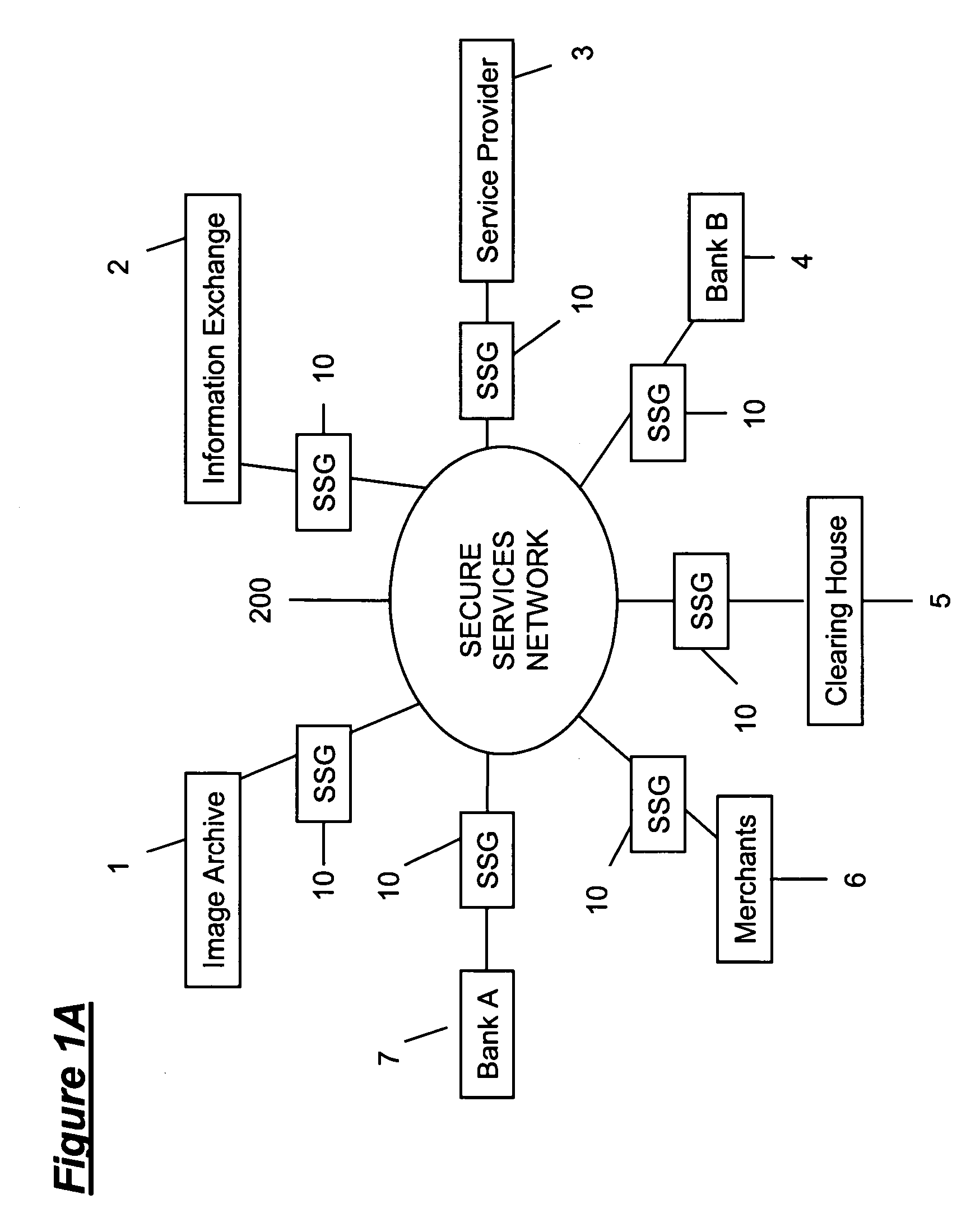
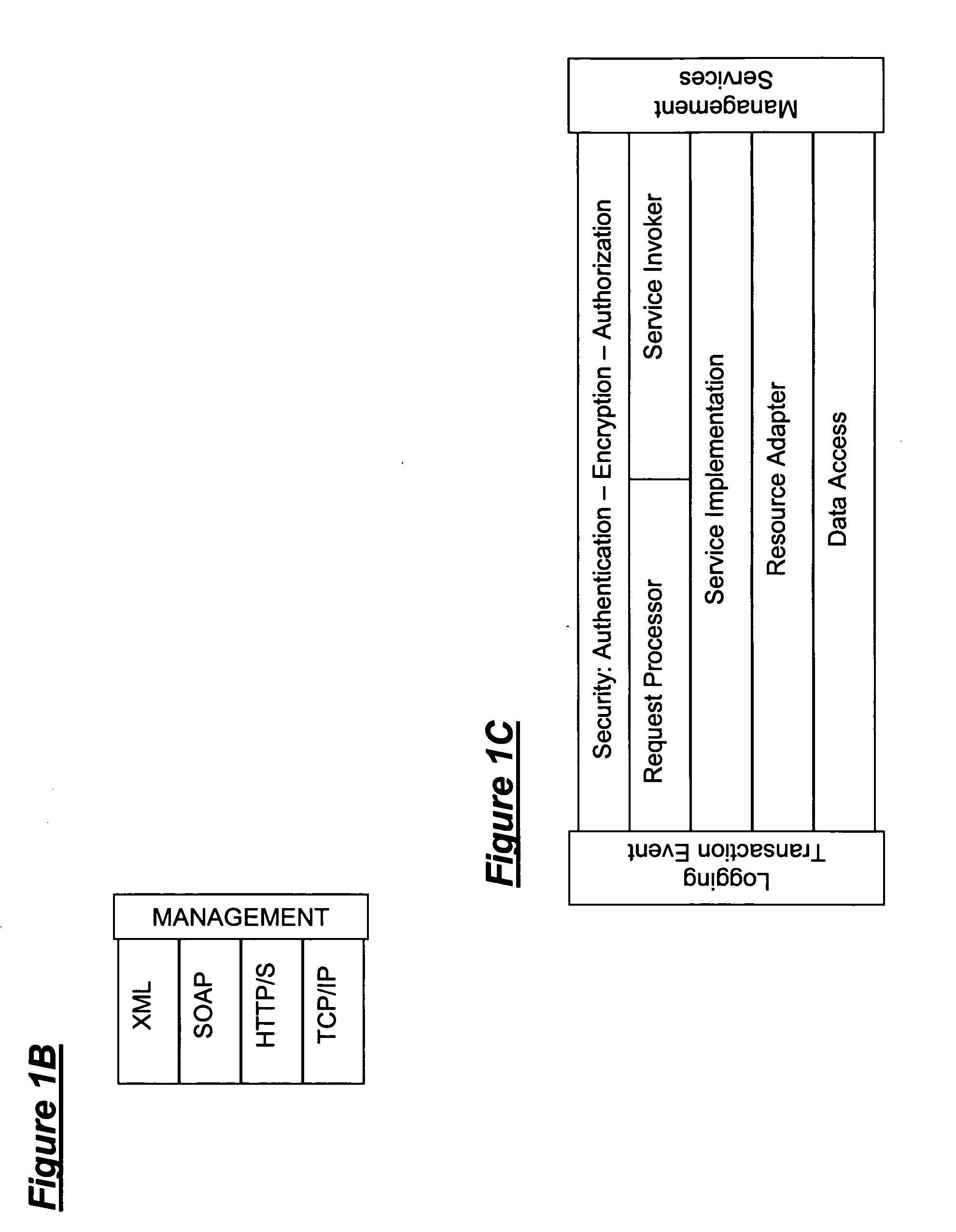
A Secure Virtual Network Layer and Virtual Network Manager that Establishes a Comprehensive Business Reporting and Security Infrastructure as an Integral Part of the Network
InactiveUS20060248205A1Increase valueMaintenance safetyMultiple digital computer combinationsTransmissionWeb serviceVirtual network topology
A Secure Service Network (SSN) in which at least two participants having a relationship are connected to a physical network by way of Secure Service Gateways and share information defined by one or more Service Definitions allowing for the creation of a secure Virtual Service Connection (VSC) between the participants in which the VSC is specific to the activity being performed and the participants provisioned for that activity. SSN enables the creation of a secure virtual network topology on any network transport that allows participants to exchange documents and transact business over the network real time, where all activity inherits a business and security infrastructure that is independent and in addition to the applications, devices, web services, users using the network.
Owner:RANDLE WILLIAM M +1
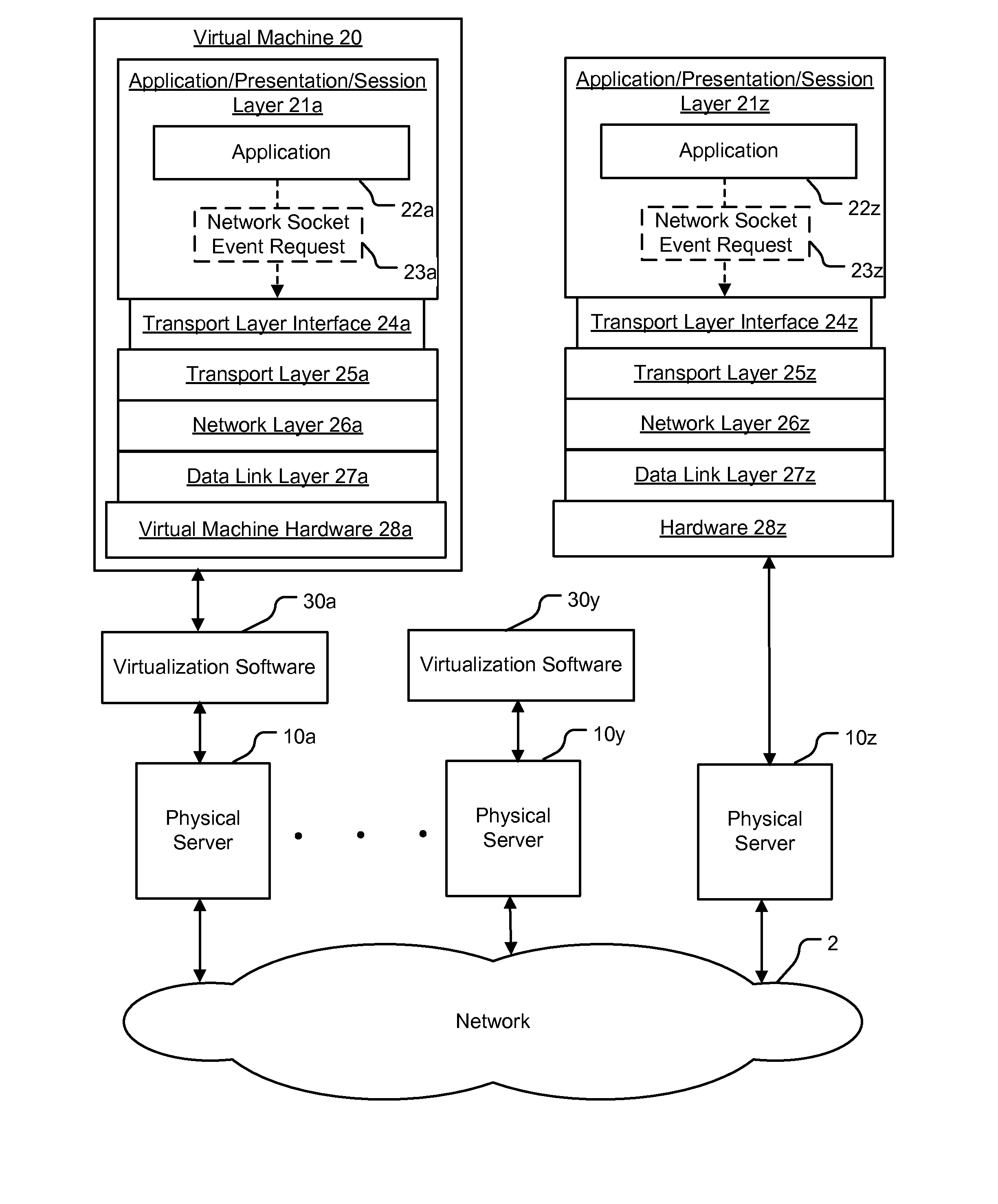
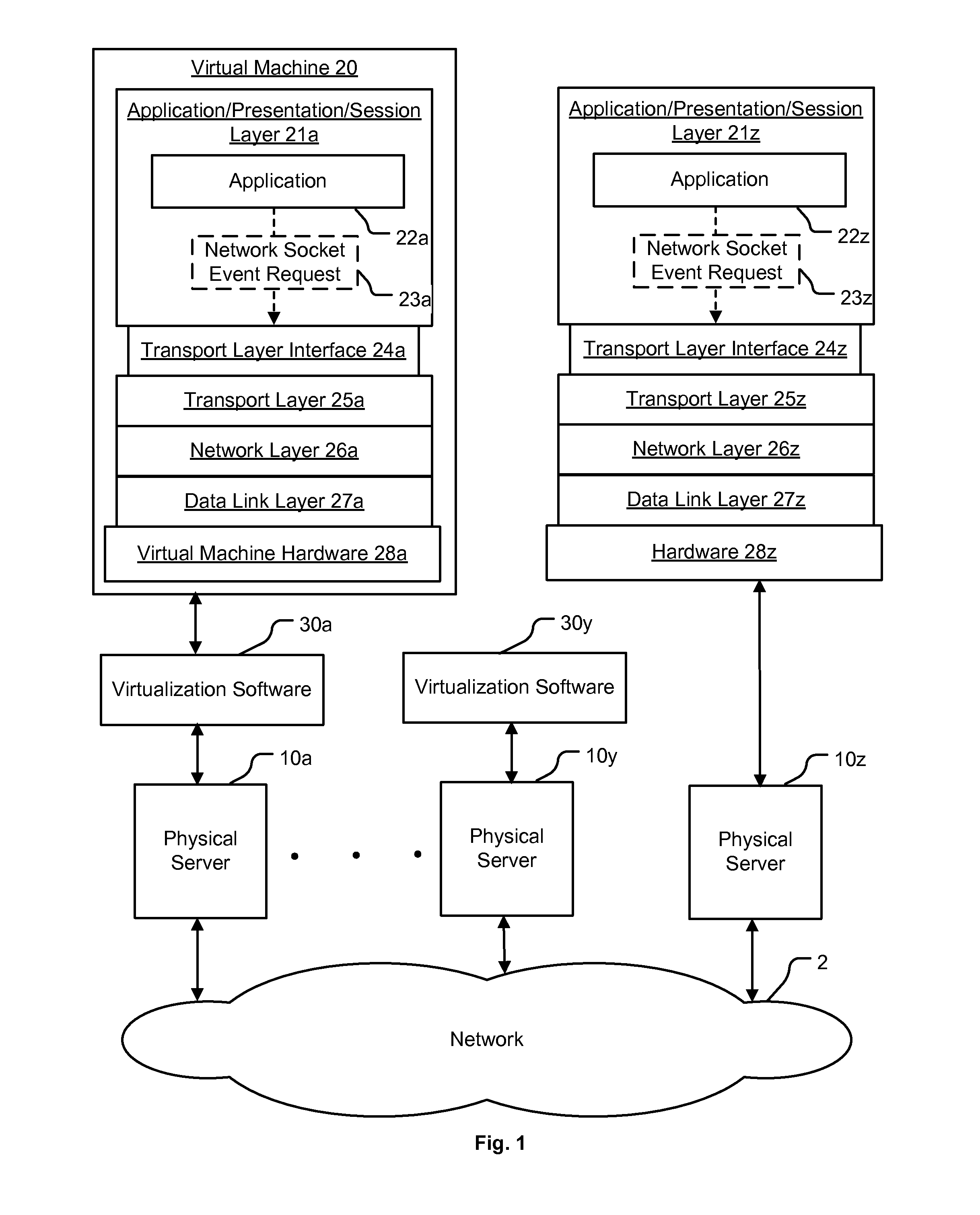
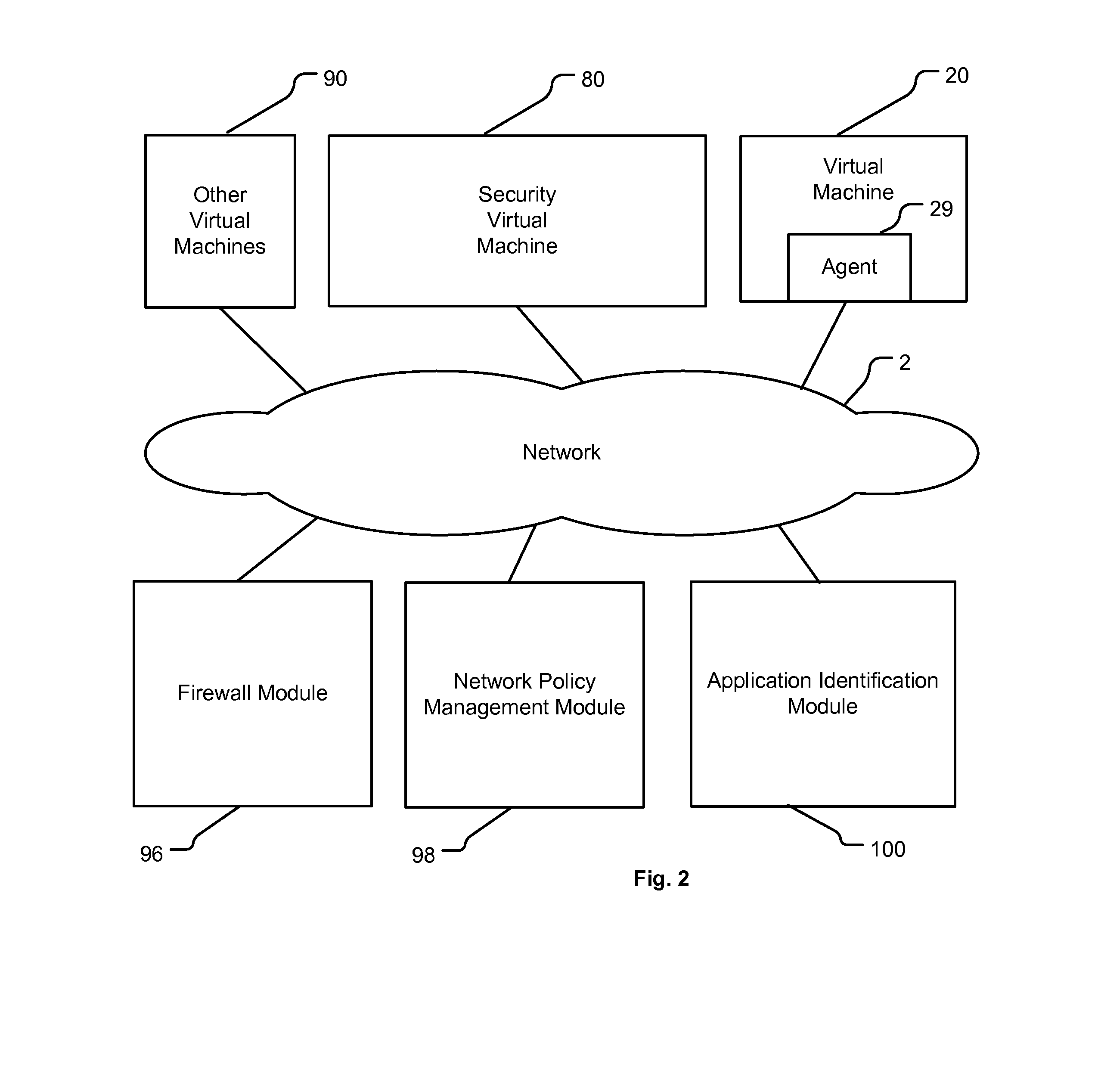
Method and apparatus for application awareness in a network
A method for enforcing a network policy is described herein. In the method, a network socket event request from an application executing in a first context is intercepted by an agent prior to the request reaching a transport layer in the first context. A context refers to virtualization software, a physical computer, or a combination of virtualization software and physical computer. In response to the interception of the request, the agent requests a decision on whether to allow or deny the network socket event request to be communicated to a security server executing in a second context that is distinct from the first context. The request for a decision includes an identification of the application. The agent then receives from the security server either an allowance or a denial of the network socket event request, the allowance or denial being based at least in part on the identification of the application and a security policy. The agent blocks the network socket event from reaching the transport layer when the denial is received from the security server. In one embodiment, the method is implemented using a machine readable medium embodying software instructions executable by a computer.
Owner:VMWARE INC
Method and apparatus for a service provider to provide secure services to a user
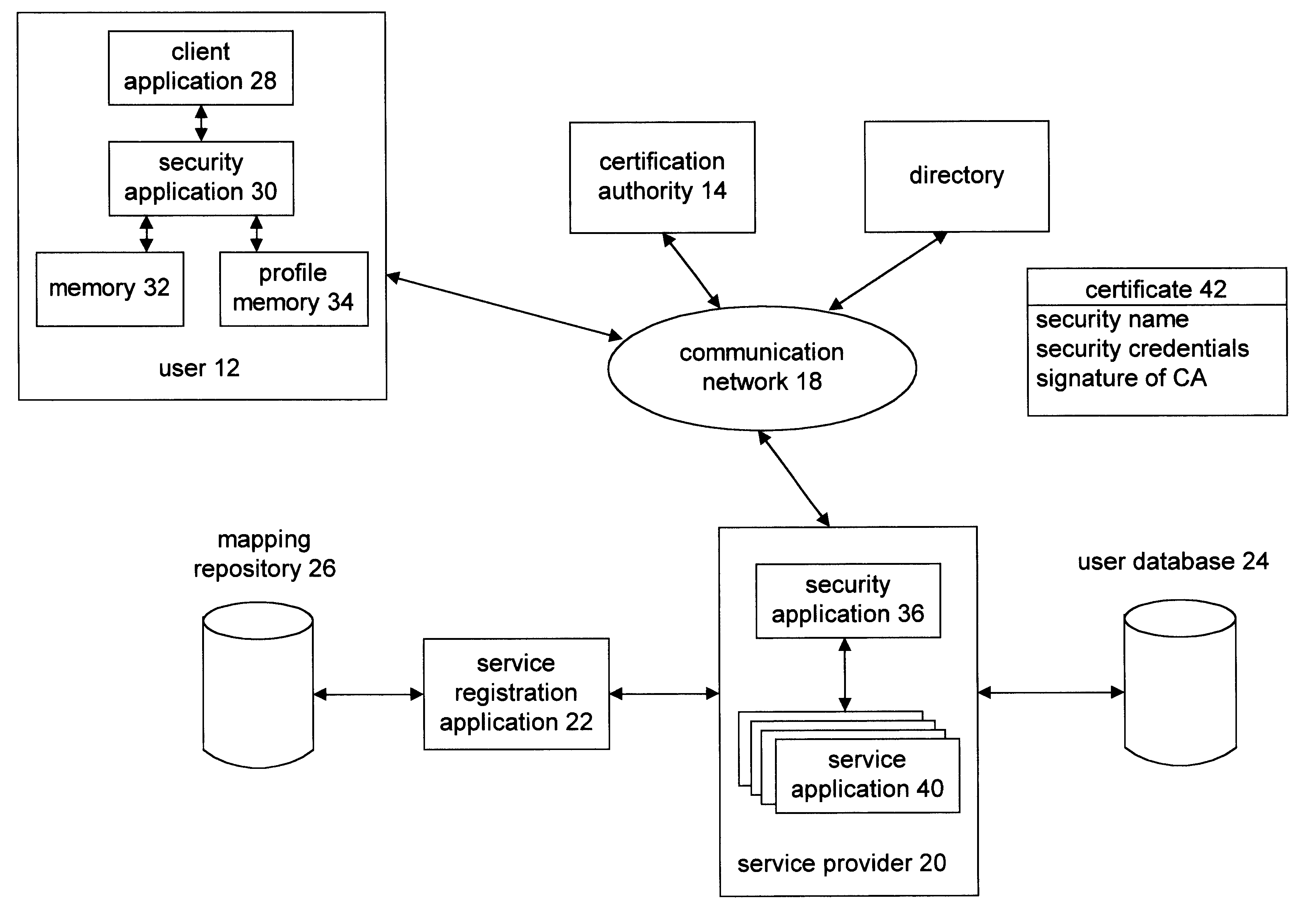
InactiveUS6934838B1User identity/authority verificationComputer security arrangementsPayment service providerService provisioning
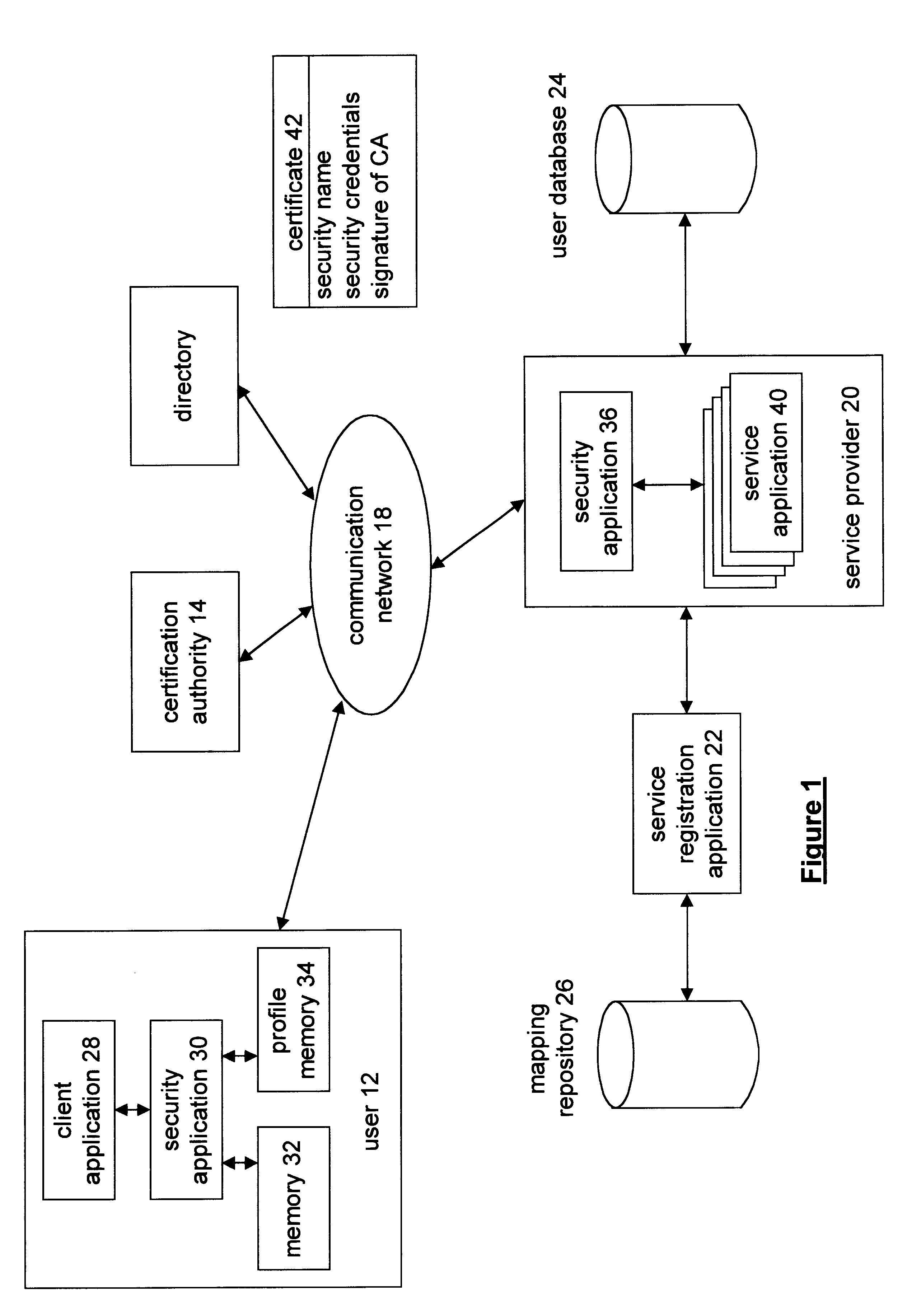
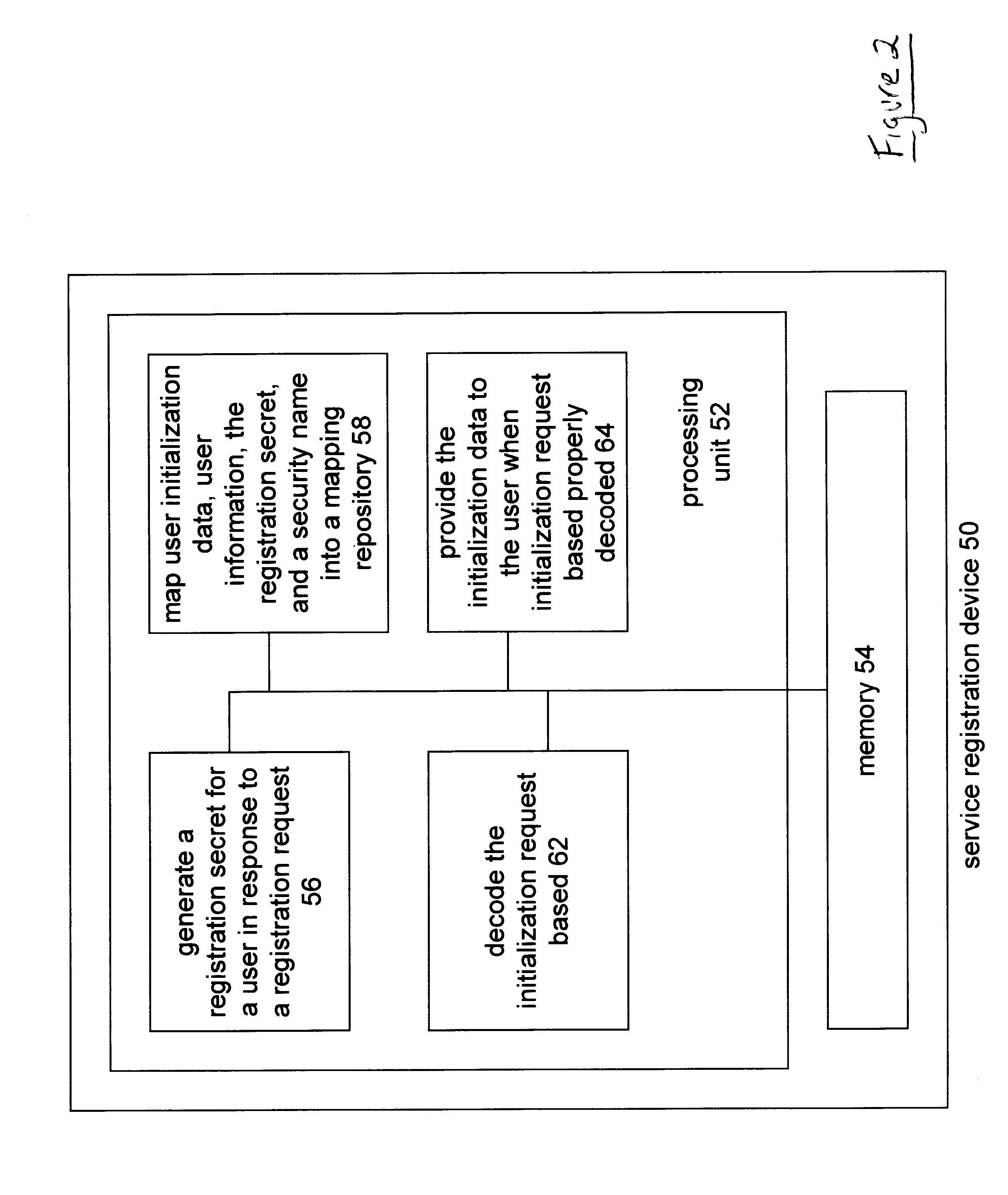
A method and apparatus for establishing security credentials for a user to access and subsequently use in secure on-line transactions begins when a service provider generates a registration secret for a user in response to a registration request. The registration request identifies user information of a particular user. Before a registration request can be provided to the service provider, the user must establish a relationship with the service provider. Having generated the registration secret, the service provider stores a user identifying secret, which includes the initialization data, the user information, the registration secret, and / or a security name in a mapping repository. The service provider provides the registration secret to the user in a trustworthy manner. Sometime thereafter, the user provides an on-line initialization request for the initialization data, where the initialization request is encoded based on at least a part of the user identifying secret. Upon receiving the request, the service provider decodes the request and subsequently provides the initialization data to the user. The user then utilizes the initialization data to obtain security credentials. Once the user has obtained the security credentials, it utilizes them for on-line transactions with the service provider.
Owner:ENTRUST
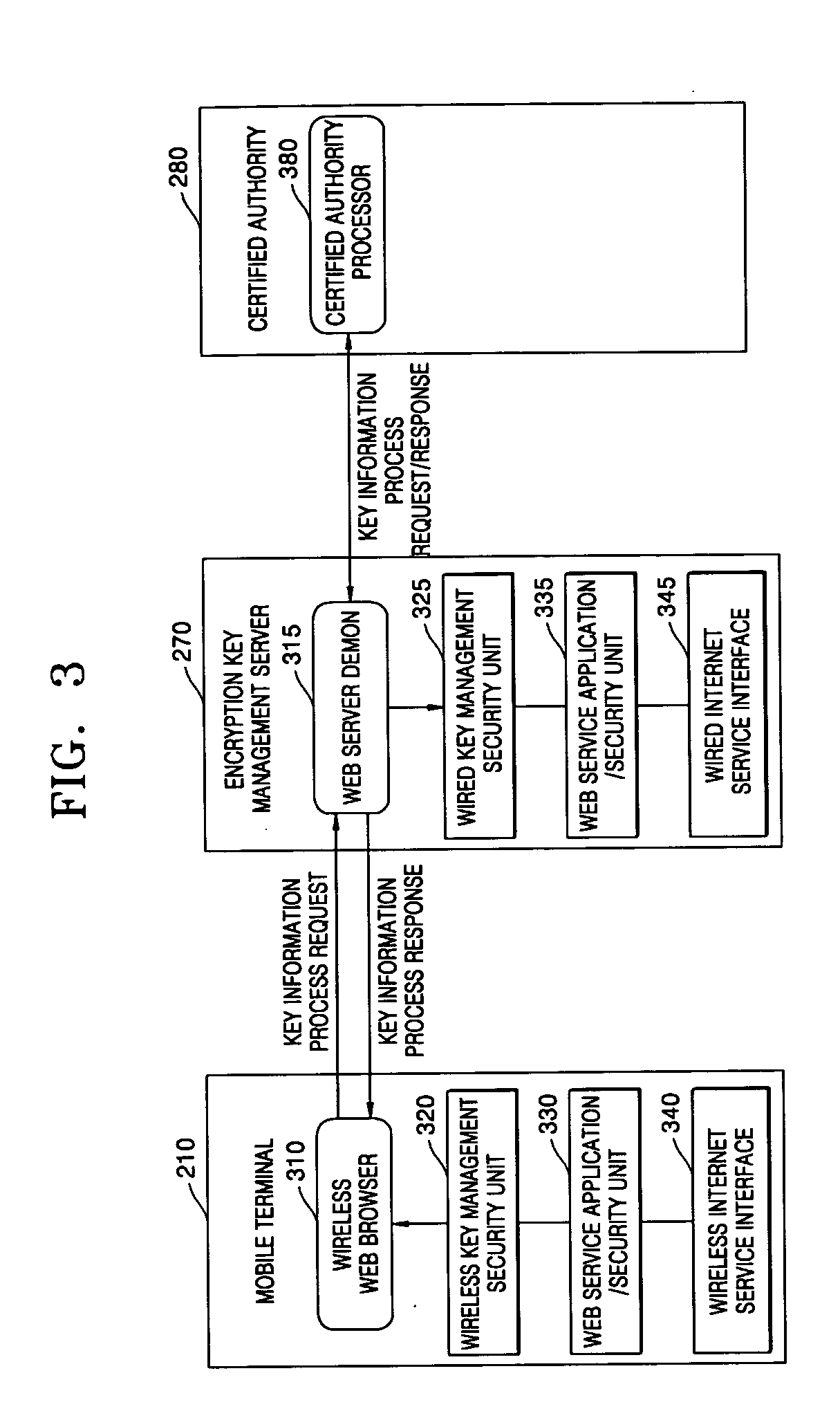
System and method of managing encryption key management system for mobile terminals
InactiveUS20050144439A1Reduce hardware loadKey distribution for secure communicationMultiple keys/algorithms usageTransfer operationManagement system
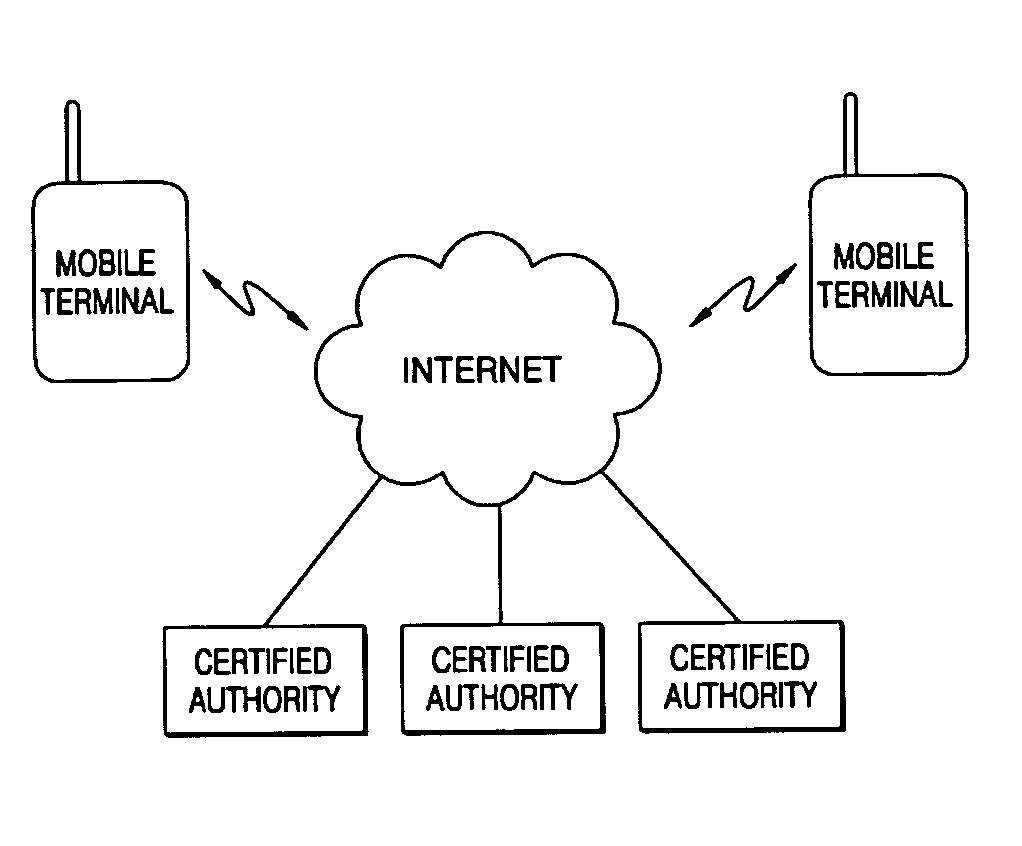
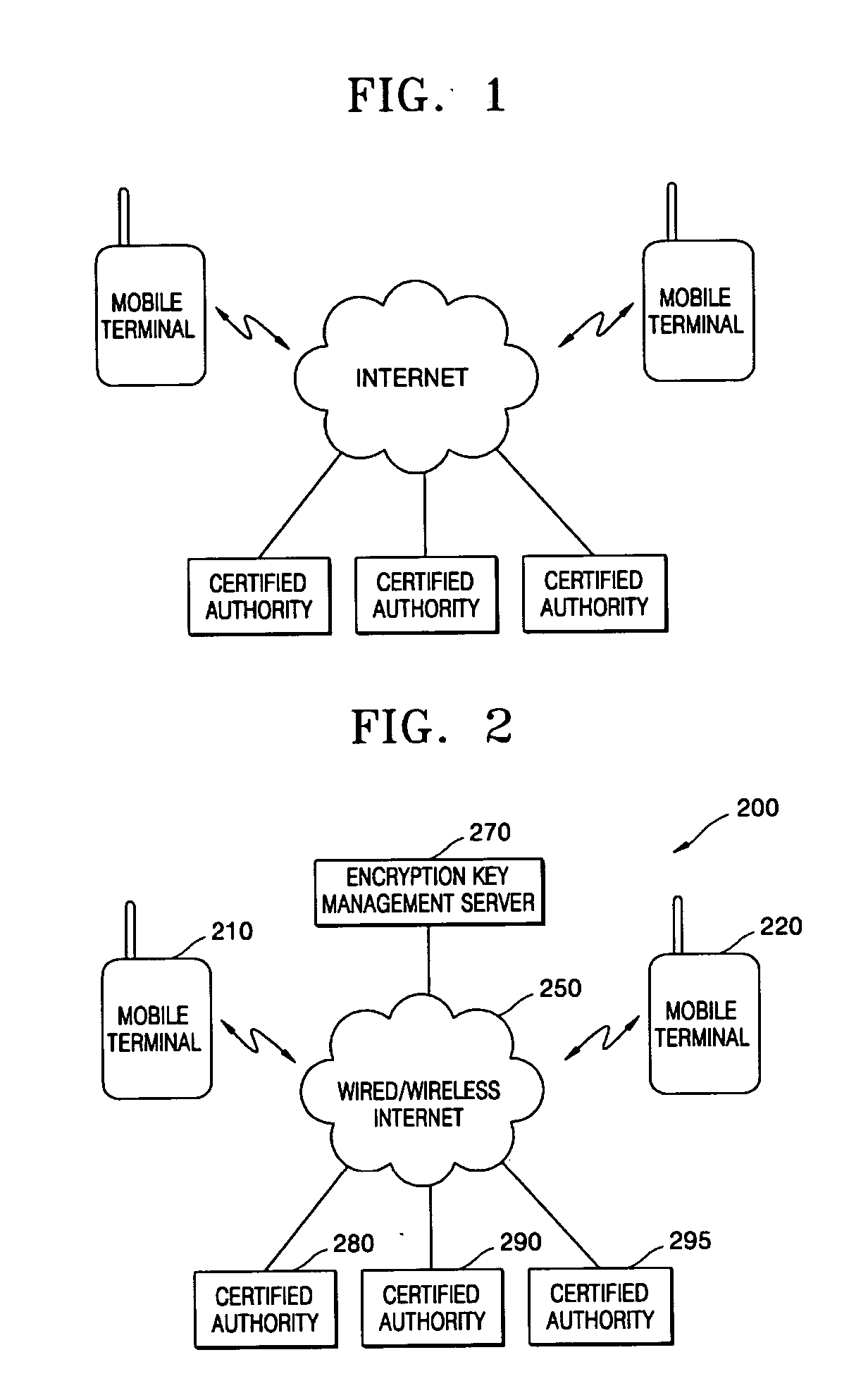
An encryption key management method for mobile terminals for providing at least one mobile terminal which is connected to a network to use services with an encryption key required for issuing a certificate which is needed for the services and managed by a certification authority by using an encryption key management server is provided. The method includes operations of: a registration requesting operation where the mobile terminal generates an encryption key registration request; an encryption key managing operation where the encryption key management server generates and manages the encryption key in response to the encryption key registration request; a transferring operation of sending the generated encryption key to the mobile terminal; and a security service providing operation of receiving the certificate managed by the certification authority and providing selective security services specific to the content of the services provided to the mobile terminal. The method can relieve the hardware load of mobile terminals while providing a security service using various conventional certification authorities.
Owner:ELECTRONICS & TELECOMM RES INST
Key management using quasi out of band authentication architecture
ActiveUS8713325B2Key distribution for secure communicationDigital data processing detailsSecure communicationKey (cryptography)
Owner:PAYFONE
Automatic analysis of security related incidents in computer networks
ActiveUS20130055399A1Reduce time spent on investigatingEasy to detectMemory loss protectionError detection/correctionEvent levelChain of events
Solutions for responding to security-related incidents in a computer network, including a security server, and a client-side arrangement. The security server includes an event collection module communicatively coupled to the computer network, an event analysis module operatively coupled to the event collection module, and a solution module operatively coupled to the event analysis module. The event collection module is configured to obtain incident-related information that includes event-level information from at least one client computer of the plurality of client computers, the incident-related information being associated with at least a first incident which was detected by that at least one client computer and provided to the event collection module in response to that detection. The event analysis module is configured to reconstruct at least one chain of events causally related to the first incident and indicative of a root cause of the first incident based on the incident-related information. The solution module is configured to formulate at least one recommendation for use by the at least one client computer, the at least one recommendation being based on the at least one chain of events, and including corrective / preventive action particularized for responding to the first incident.
Owner:AO KASPERSKY LAB
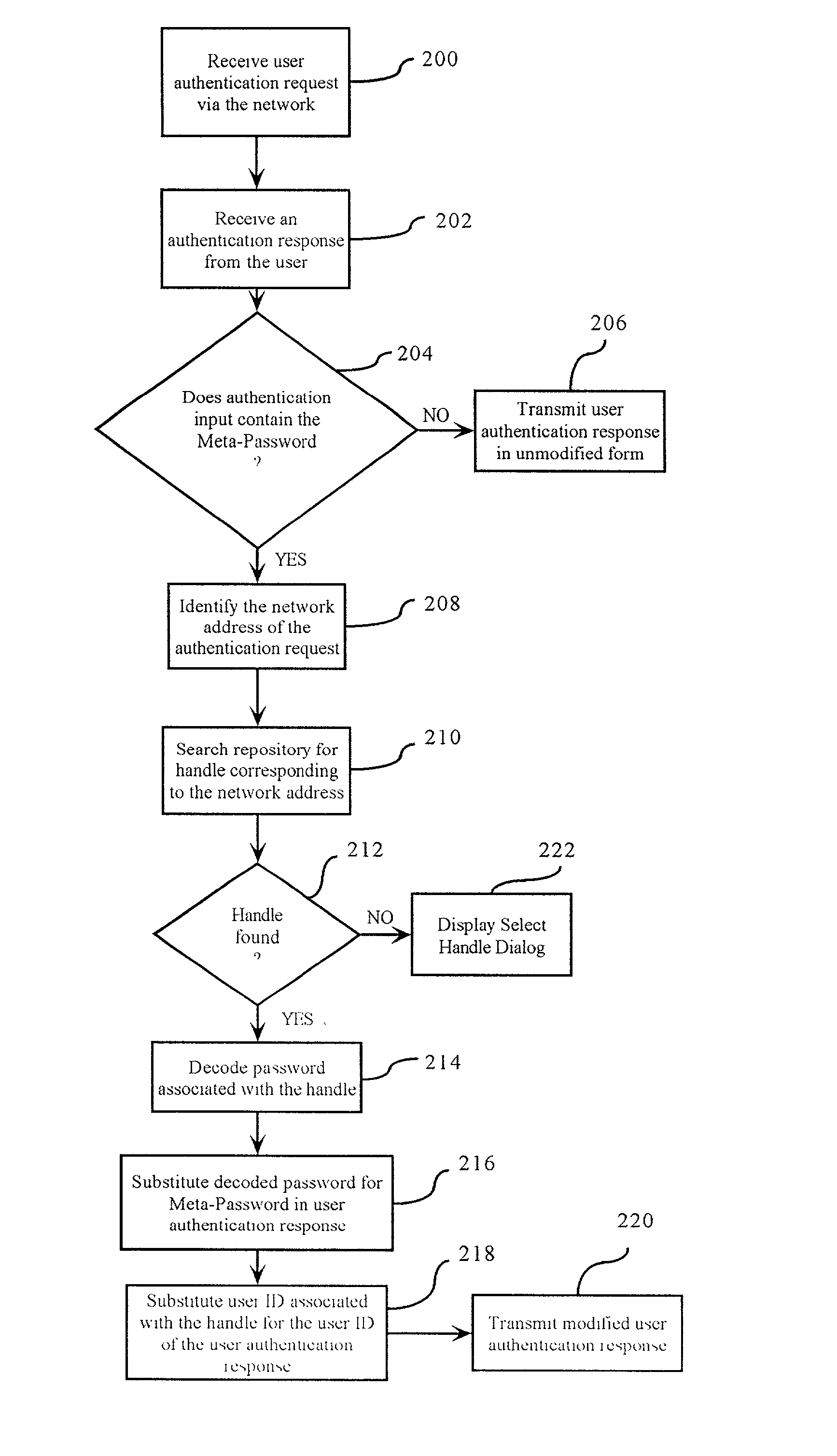
User authorization management system using a meta-password and method for same
InactiveUS7103912B2Reduce security impactDigital data processing detailsError detection/correctionEngineeringUser authentication
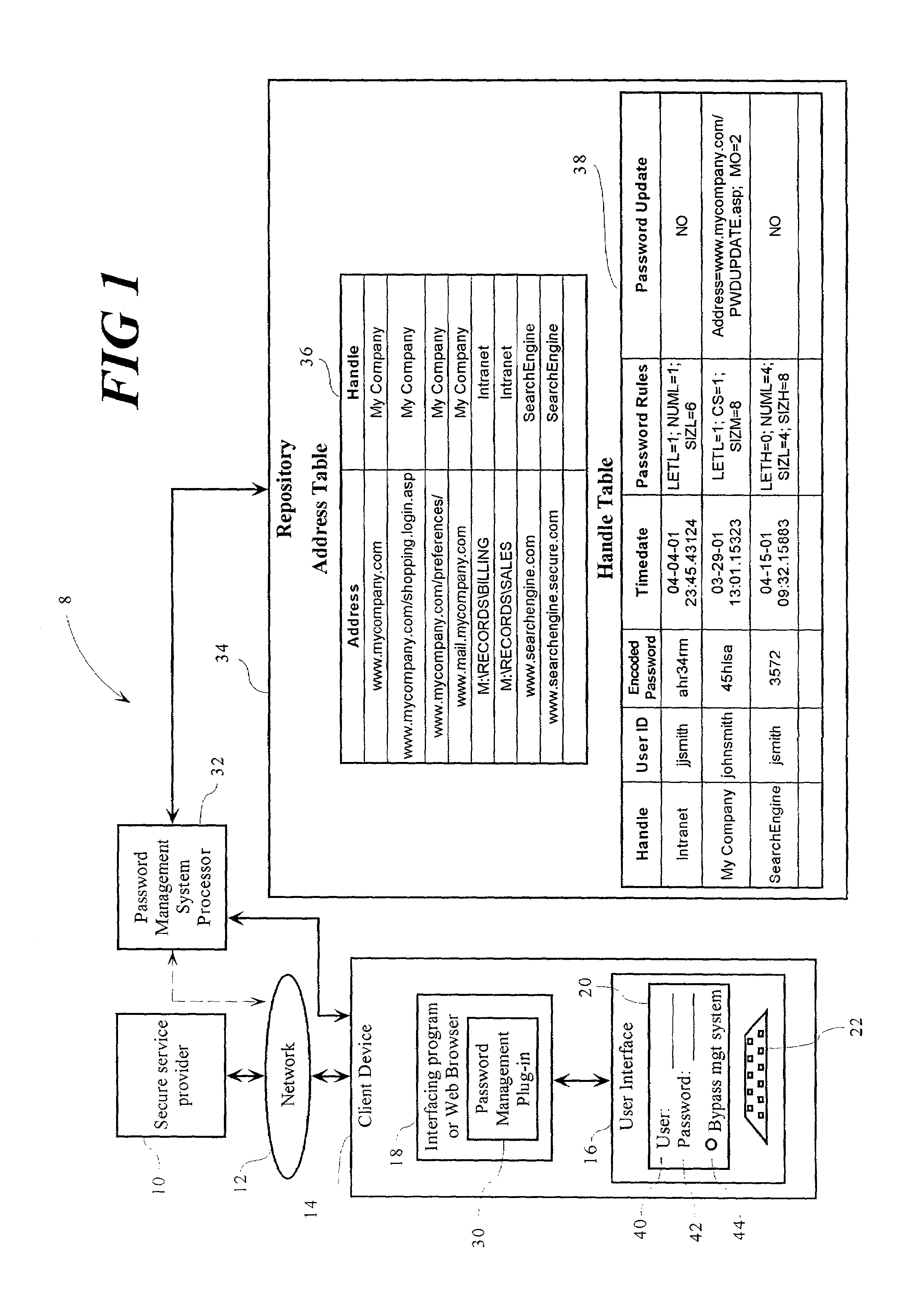
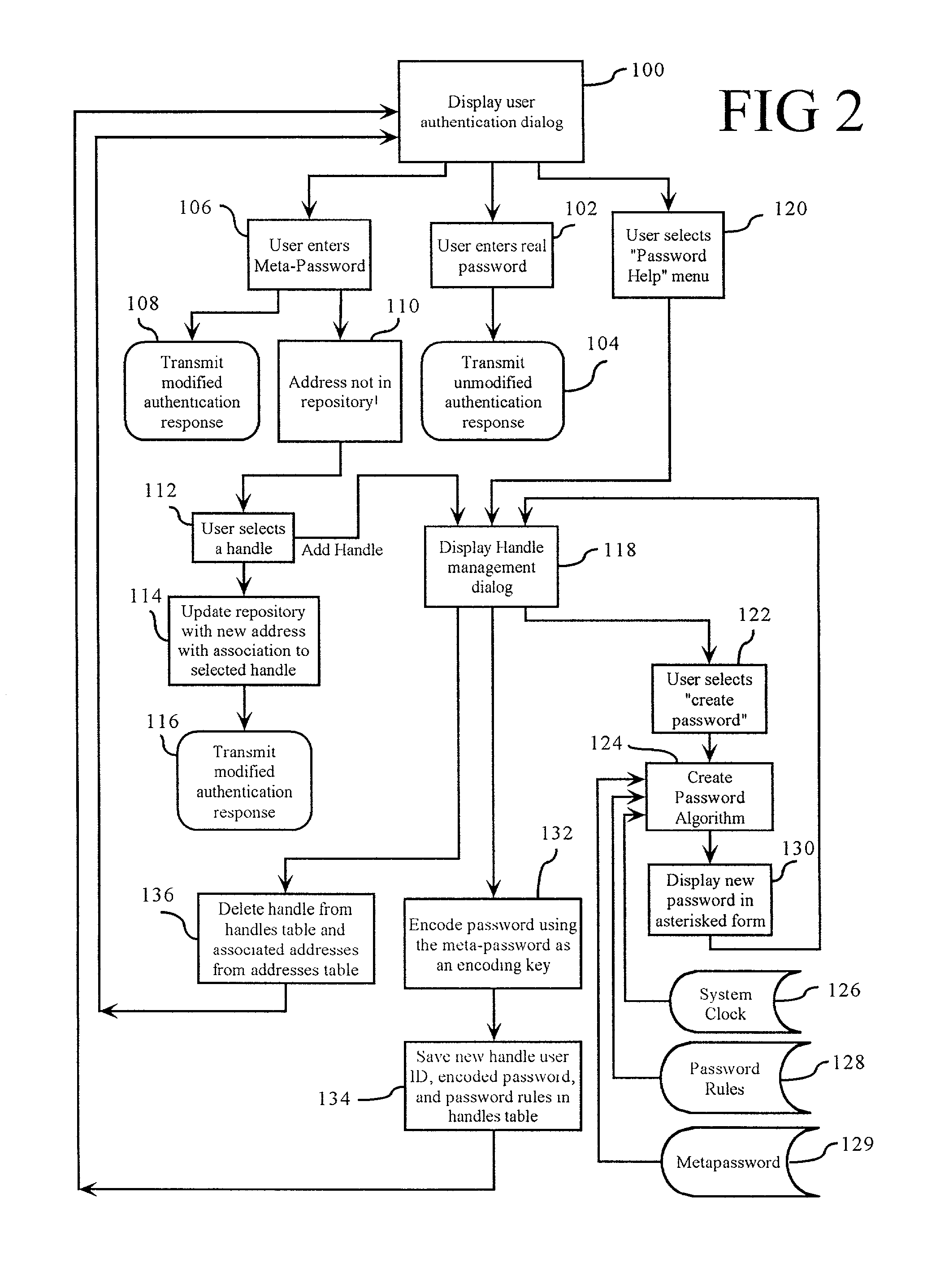
A user authentication information management method receives a meta-password from a user. A repository (34) lists network addresses (36) and associated handles (38), each handle having an associated encoded password. An authentication response from the user is intercepted. A modified authentication response is generated by identifying a network address to which the response is directed (208), searching for the identified network address (210) in the repository (34), identifying a handle (212) corresponding to the address based on the searching (210), decoding the password associated with the handle using the meta-password as a decoding key (214), and substituting the decoded password for the meta-password in the authentication response (216). The method also generates pseudo-random passwords (124) consistent with password rules (128). The repository (34) can reside on a client device (14), a proxy server, a local area network, or a security server having an Internet protocol (IP) address. The repository (34) can also be disposed at a database service.
Owner:IBM CORP
Methods and systems for api proxy based adaptive security
ActiveUS20170012941A1Promote resultsEasy to identifyInterprogram communicationData switching networksRouting decisionSelf adaptive
The invention concerns API proxy based adaptive security. The invention implements adaptive security for API servers, while avoiding data bottlenecks and maintaining client experience. The invention provides methods and configurations for API security that may be employed at proxies for implementing routing decisions involving client messages received at said proxies. The invention also involves generating or collecting at proxies, log information that captures data corresponding to received client messages and responses from API servers—which log information correlates communications between clients, proxies and backend API servers, and includes data relevant for purposes generating API metrics and identifying anomalies and / or indicators of compromise. The invention yet further provides security server clusters configured for generating API metrics and / or identify anomalies or indicators of compromise—which may be used by proxies to terminate existing connections and block subsequent requests or messages from clients associated with the identified anomalies or indicators of compromise.
Owner:PING IDENTITY
Methods and systems for secure key entry via communication networks
InactiveUS20100024022A1Digital data processing detailsUser identity/authority verificationInternet privacyEngineering
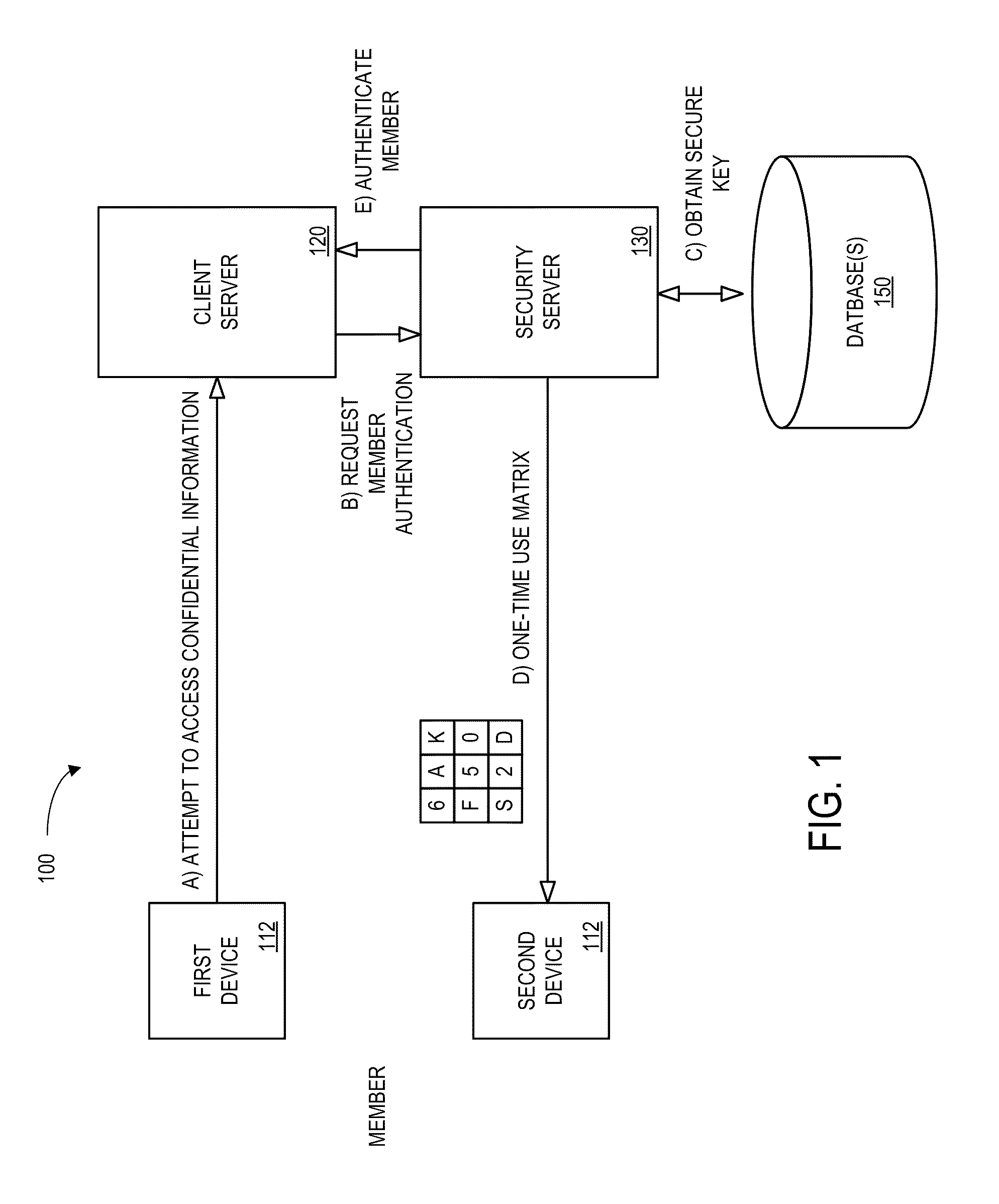
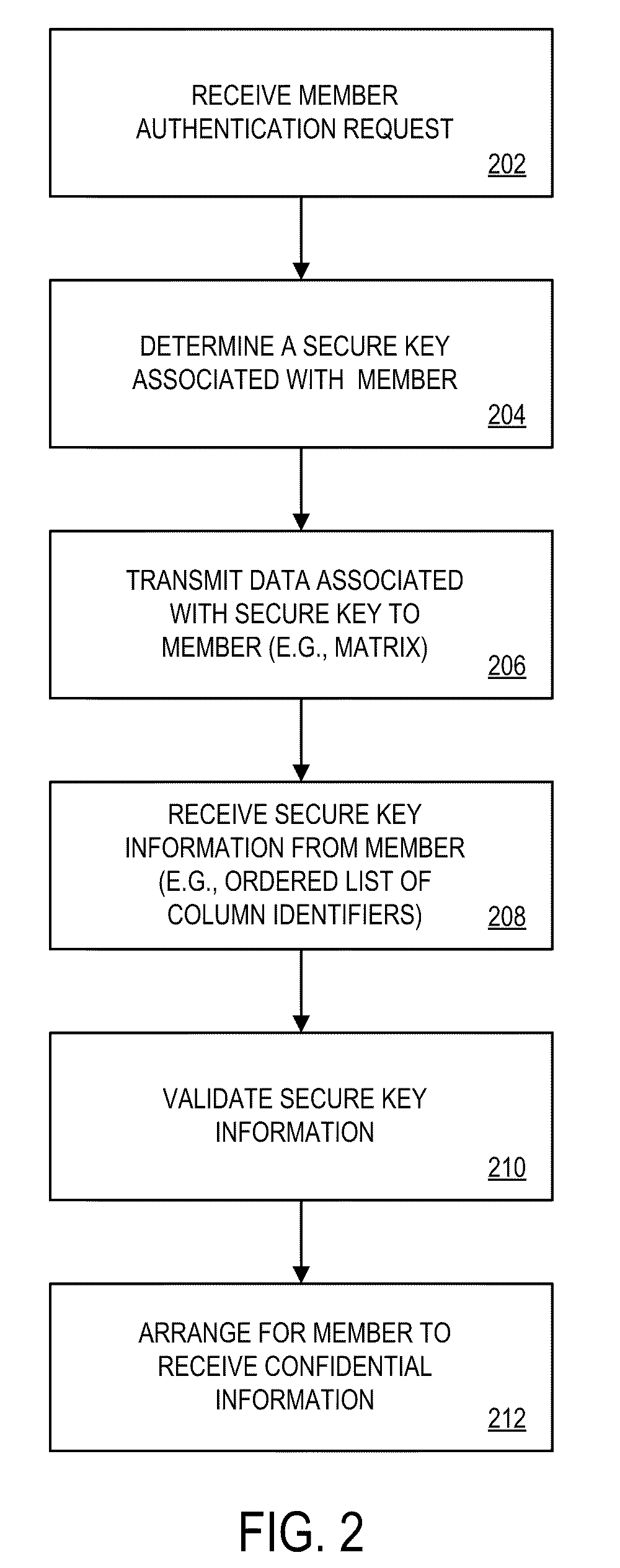
According to some embodiments, a member authentication request is received at a security server from a client server. The member authentication request may be associated with, for example, a member attempting to access confidential information from the client server. A secure key associated with the member may be determined and data associated with that key may be transmitted to the member (e.g., via his or her wireless device or computer). Secure key information may be received from the member and validated. Based on the validated secure key information, it may be arranged for the member to receive the confidential information from the client server.
Owner:NEXT ACCESS TECH
Method for secure user and site authentication
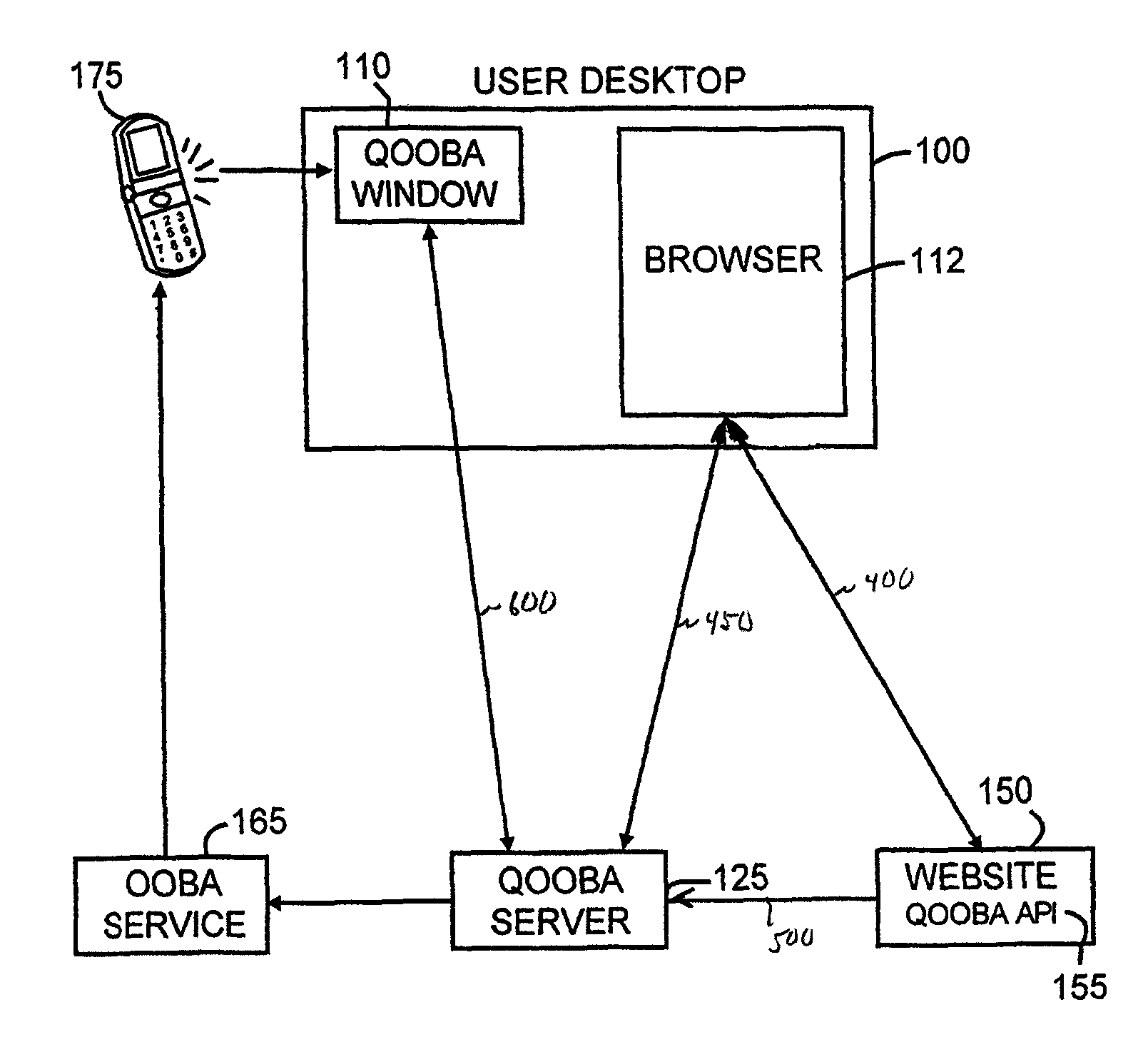
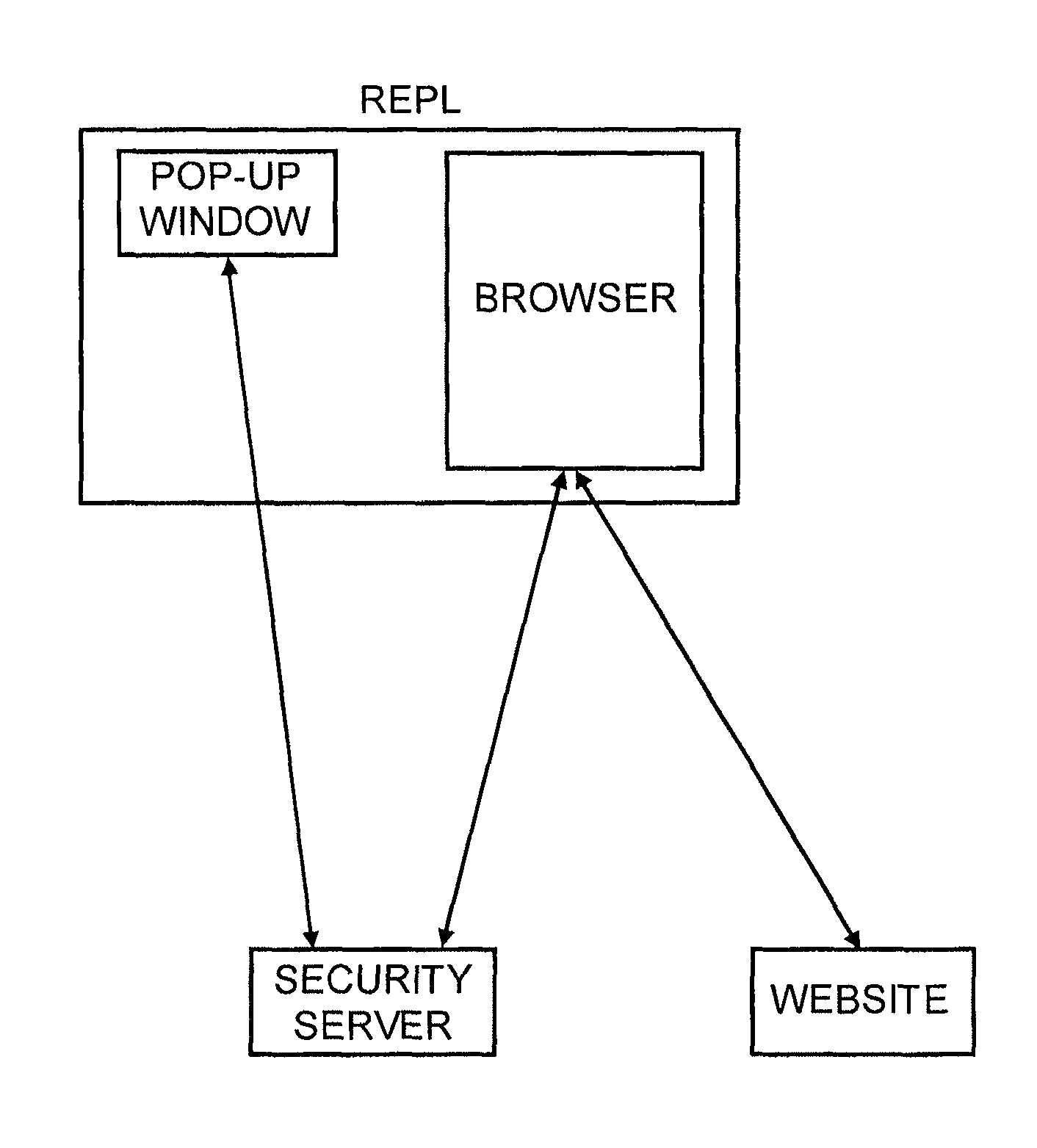
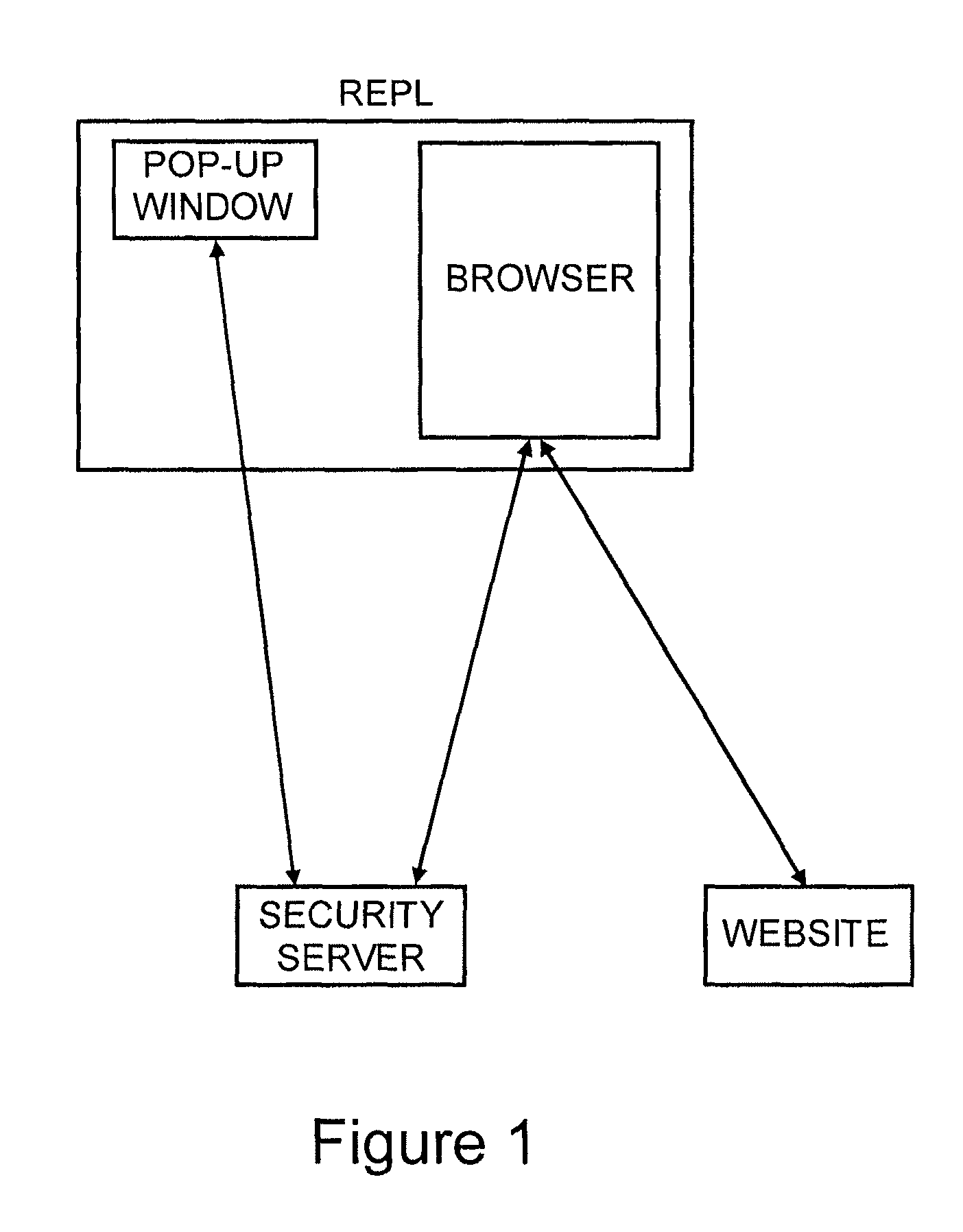
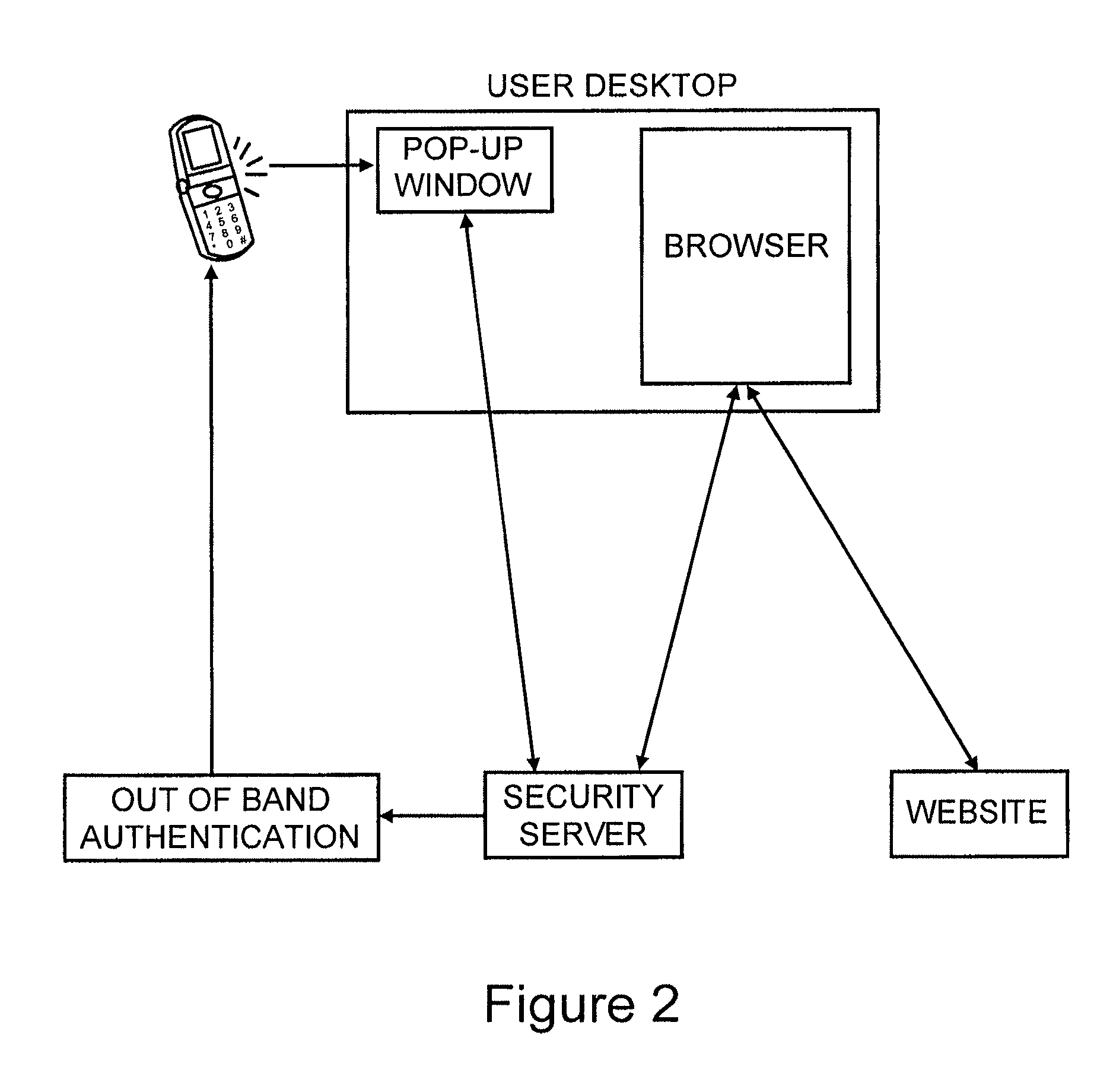
ActiveUS8549601B2Not easily defeatedImprove securityDigital data processing detailsMultiple digital computer combinationsUser authenticationOne-time password
User authentication is achieved by creating a window on the user's PC that is in communication with a security server, where this communication channel is separate from the communication channel between the user's browser and whichever web site they are at. A legitimate web site embeds code in the web page which communicates to the security server from the user's desktop. The security server signals both the web page on the user's browser and the window to which it has a separate channel. If user authentication is requested by the web site, the security server computes a one time password based on a secret which it shares with the web site, but not with the user, and which is not associated with any particular user, and the web site can re-compute the one time password to authenticate the user.
Owner:PAYFONE
Method and device for uplink power control
ActiveUS20200037260A1Efficient power controlEfficient method of controlPower managementModulated-carrier systemsCommunications systemControl channel
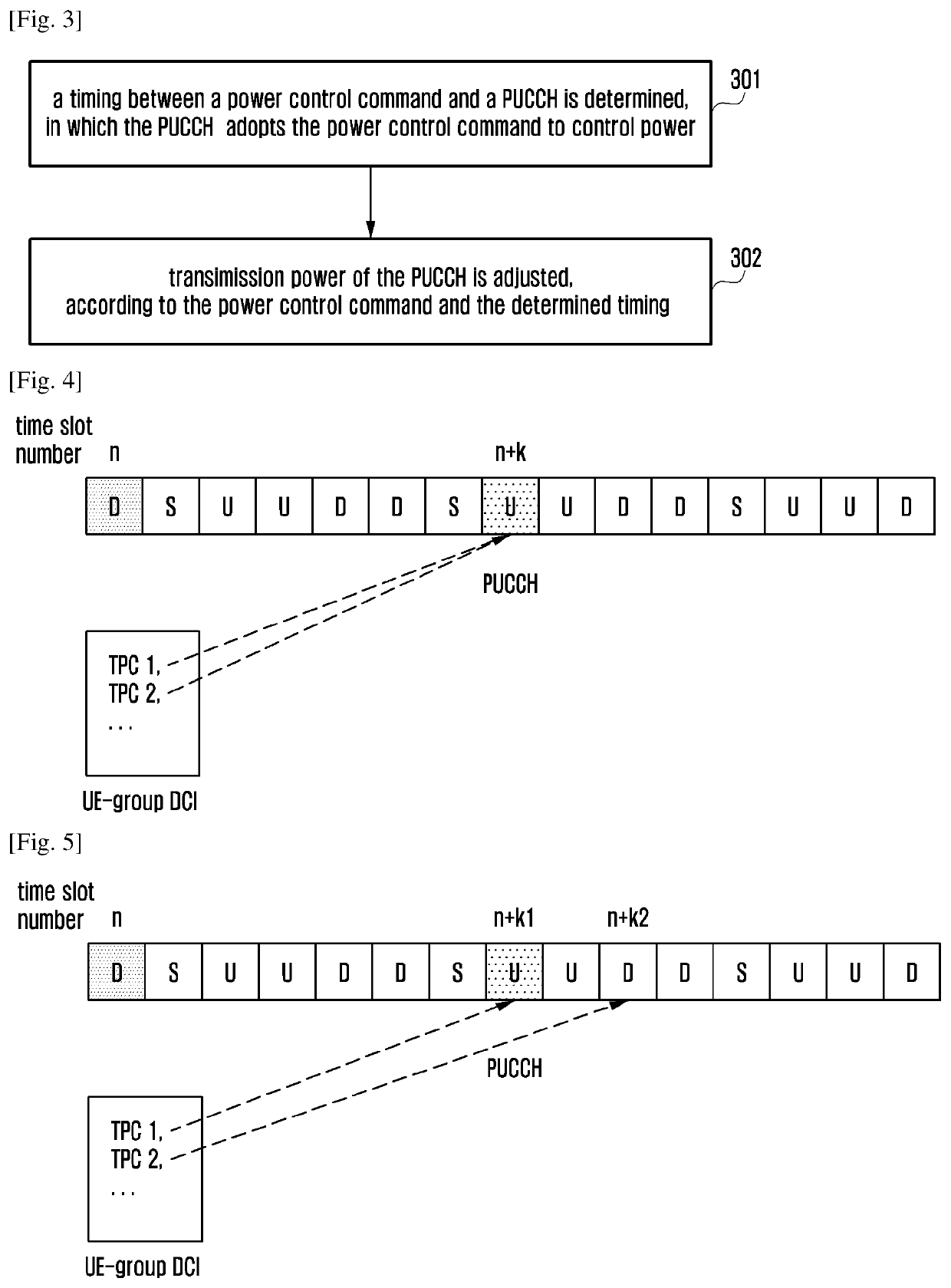
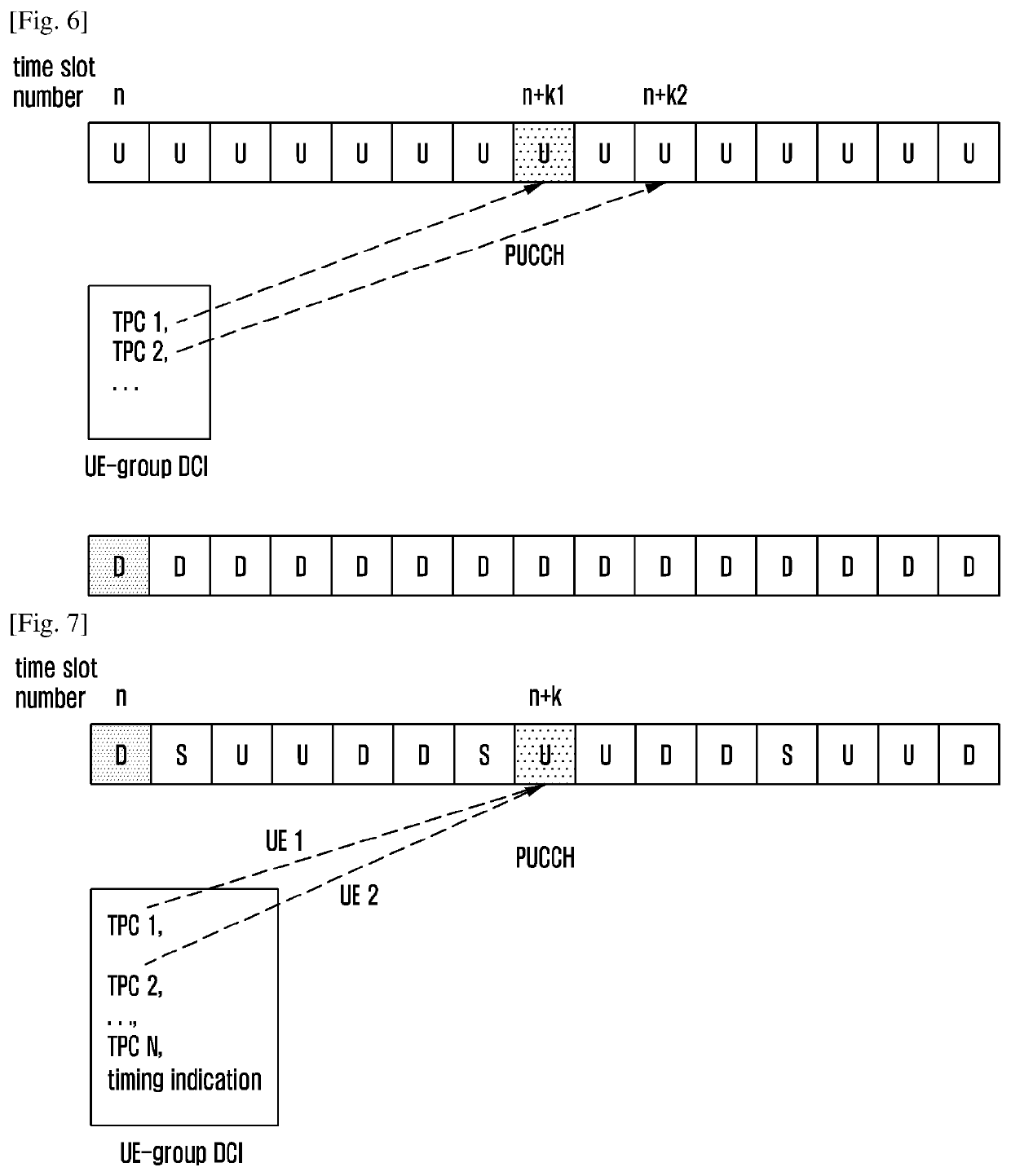
The present disclosure relates to a communication method and system for converging a 5th-Generation (5G) communication system for supporting higher data rates beyond a 4th-Generation (4G) system with a technology for Internet of Things (IoT). The present disclosure may be applied to intelligent services based on the 5G communication technology and the IoT-related technology, such as smart home, smart building, smart city, smart car, connected car, health care, digital education, smart retail, security and safety services. The present disclosure provides a method for uplink power control, which is applied to a User Equipment (UE), and the method includes: determining a timing between a power control command and a Physical Uplink Control Channel (PUCCH), which adopts the power control command to control power. The present disclosure also provides a corresponding device.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com