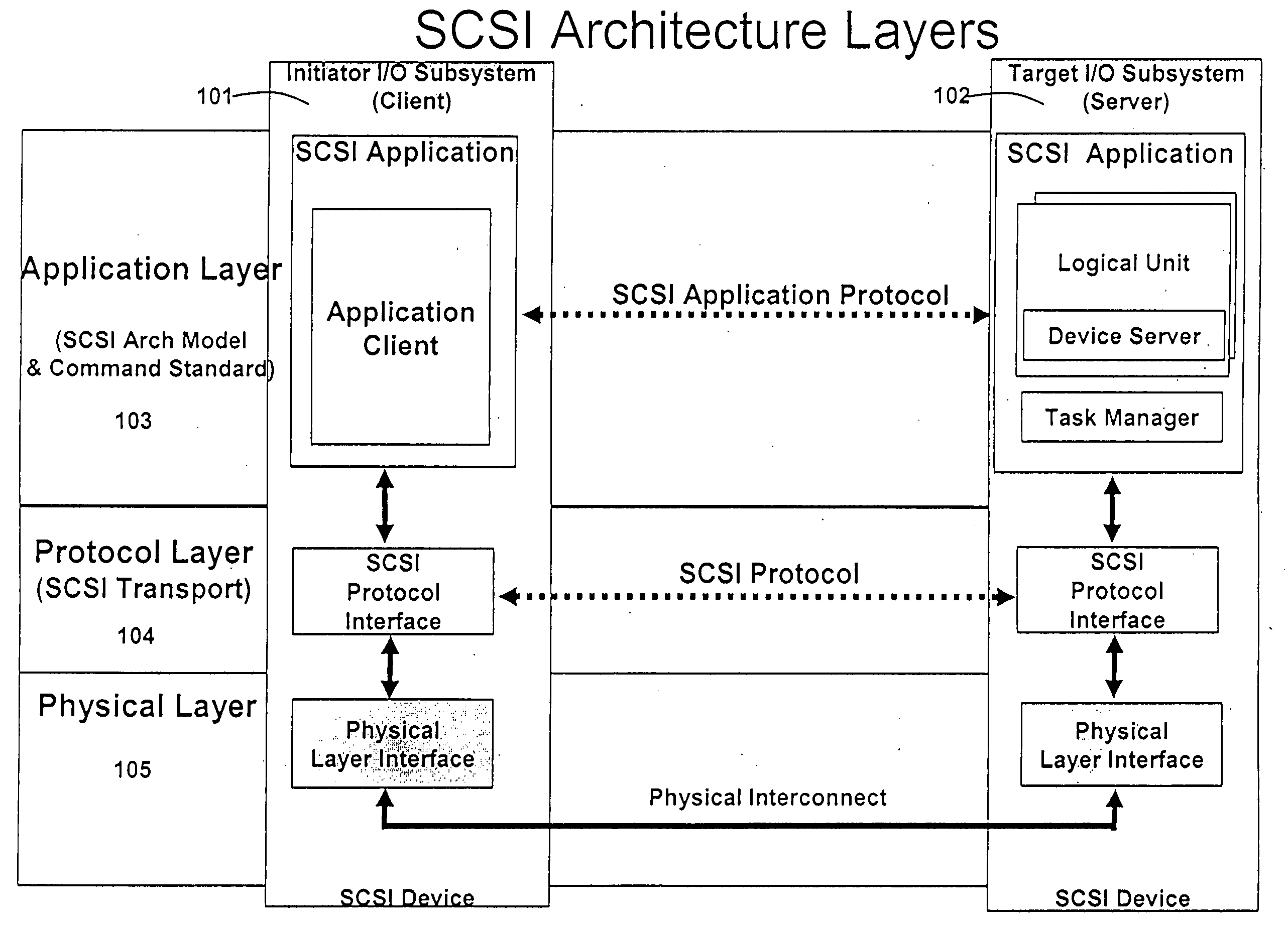
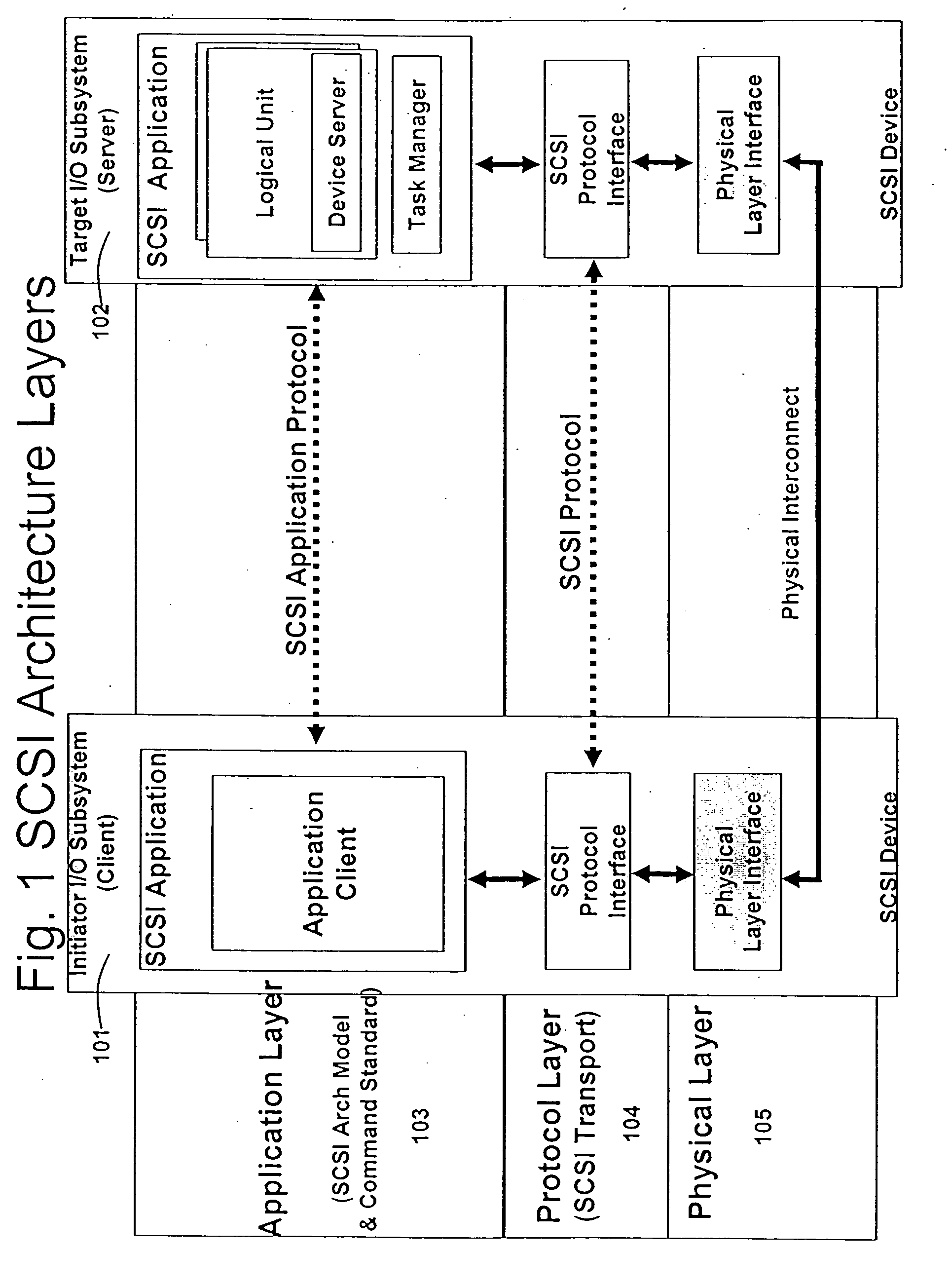
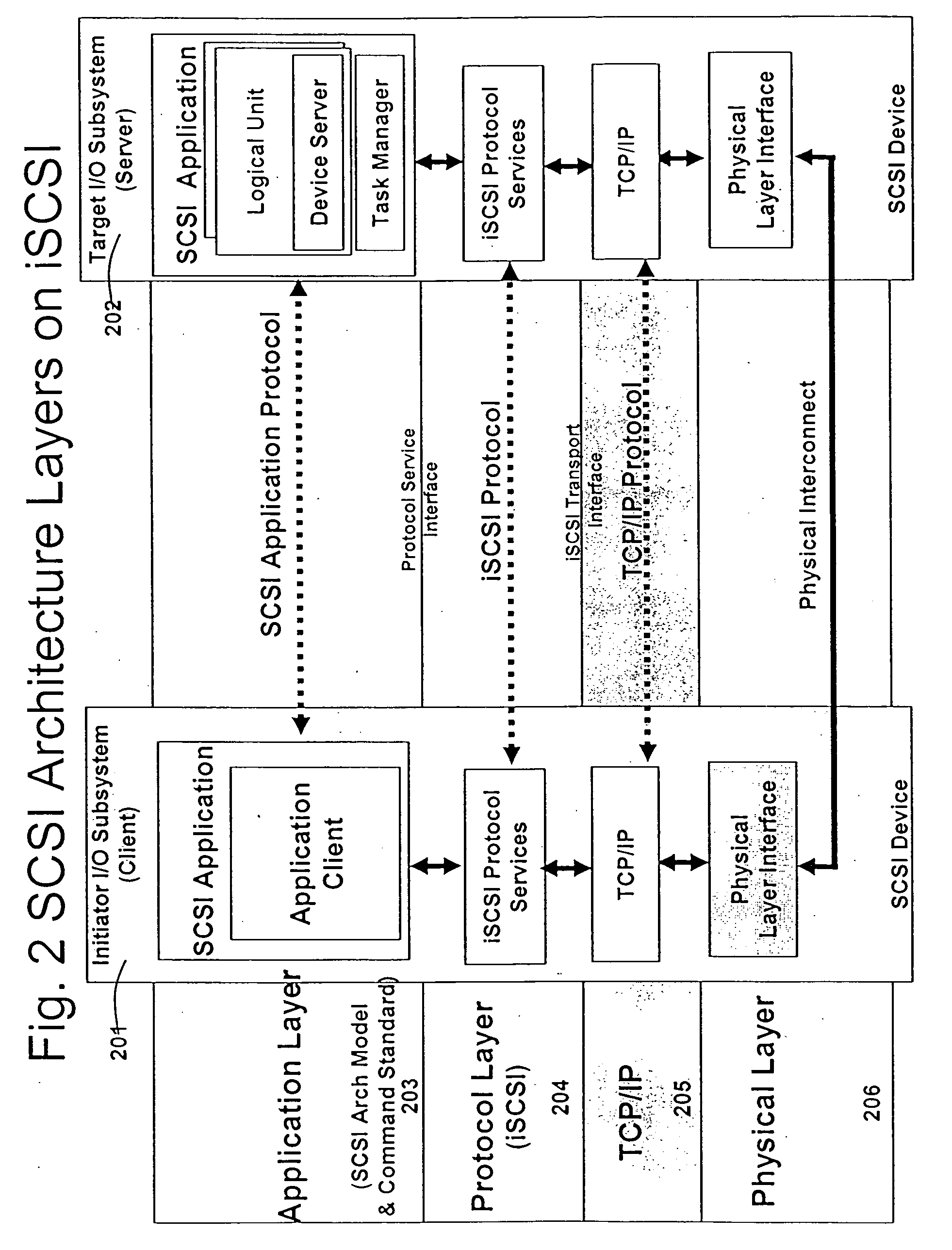
Patents
Literature
122 results about "Adaptive security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Adaptive security is an approach to safeguarding systems and data by recognizing threat-related behaviors rather than the files and code used by virus definitions. The essence of the approach is the ability to adapt and respond to a complex and constantly changing environment.
Runtime adaptable security processor
InactiveUS20050108518A1Improve performanceReduce overheadSecuring communicationInternal memoryPacket scheduling
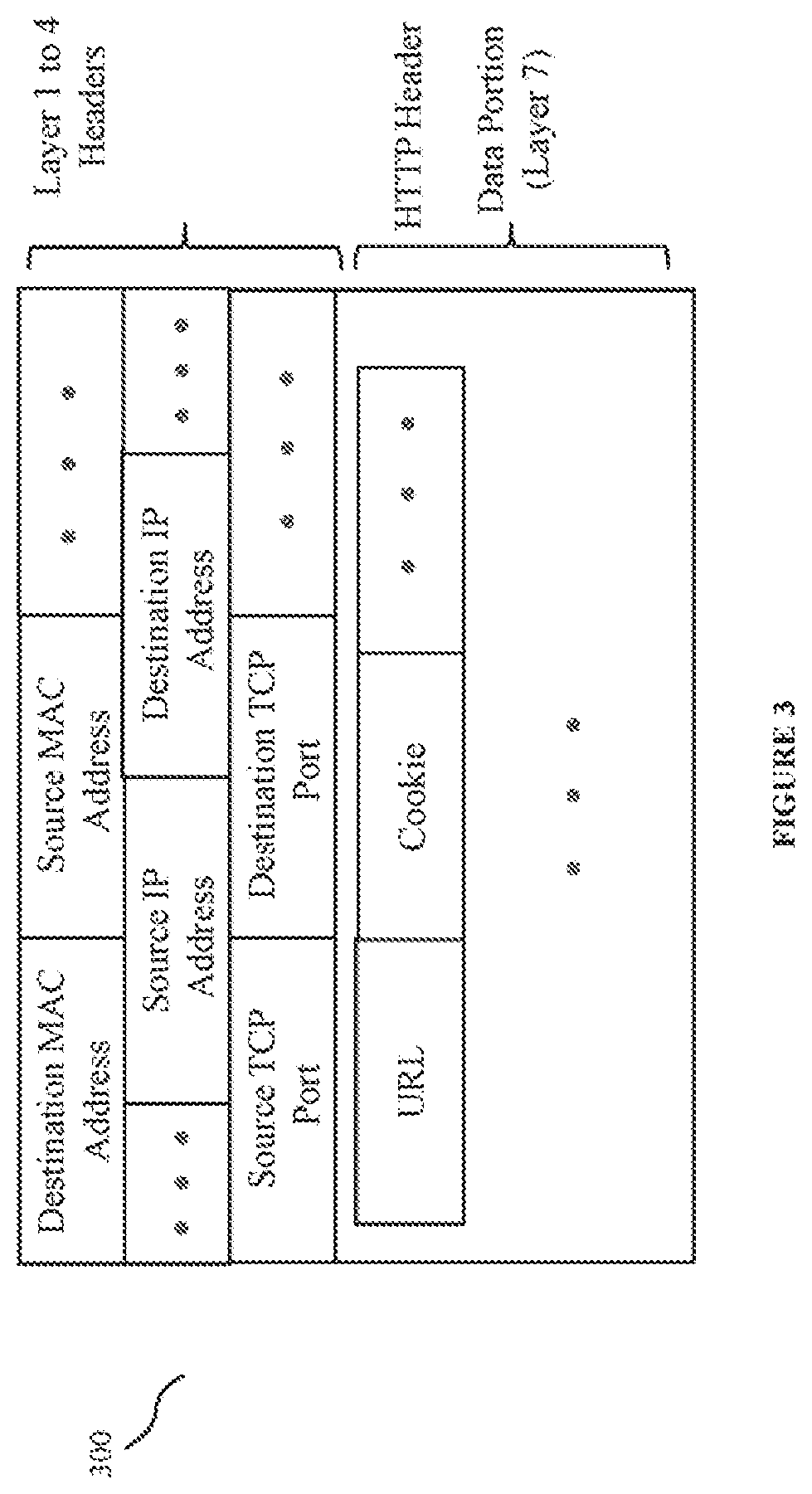
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
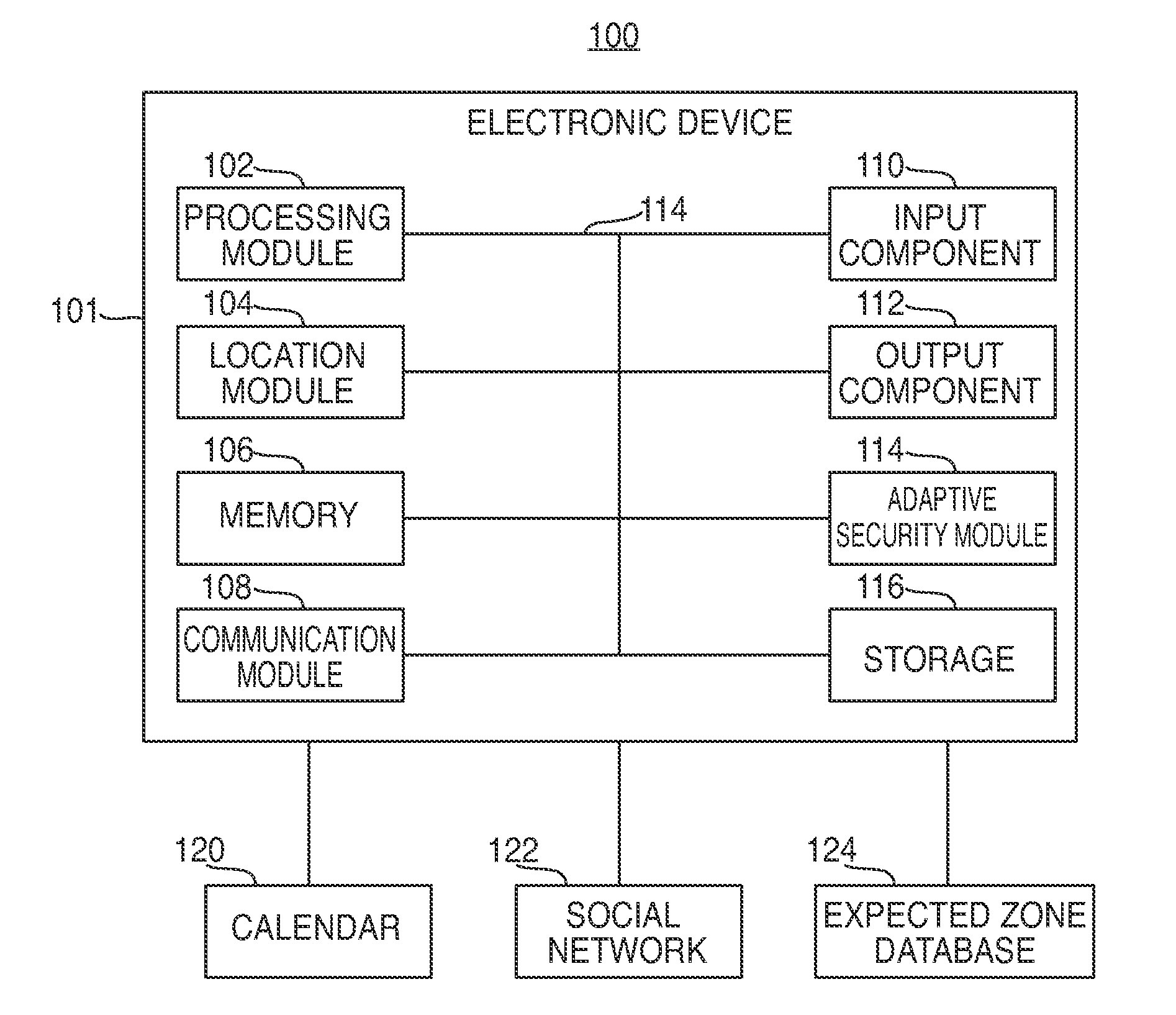
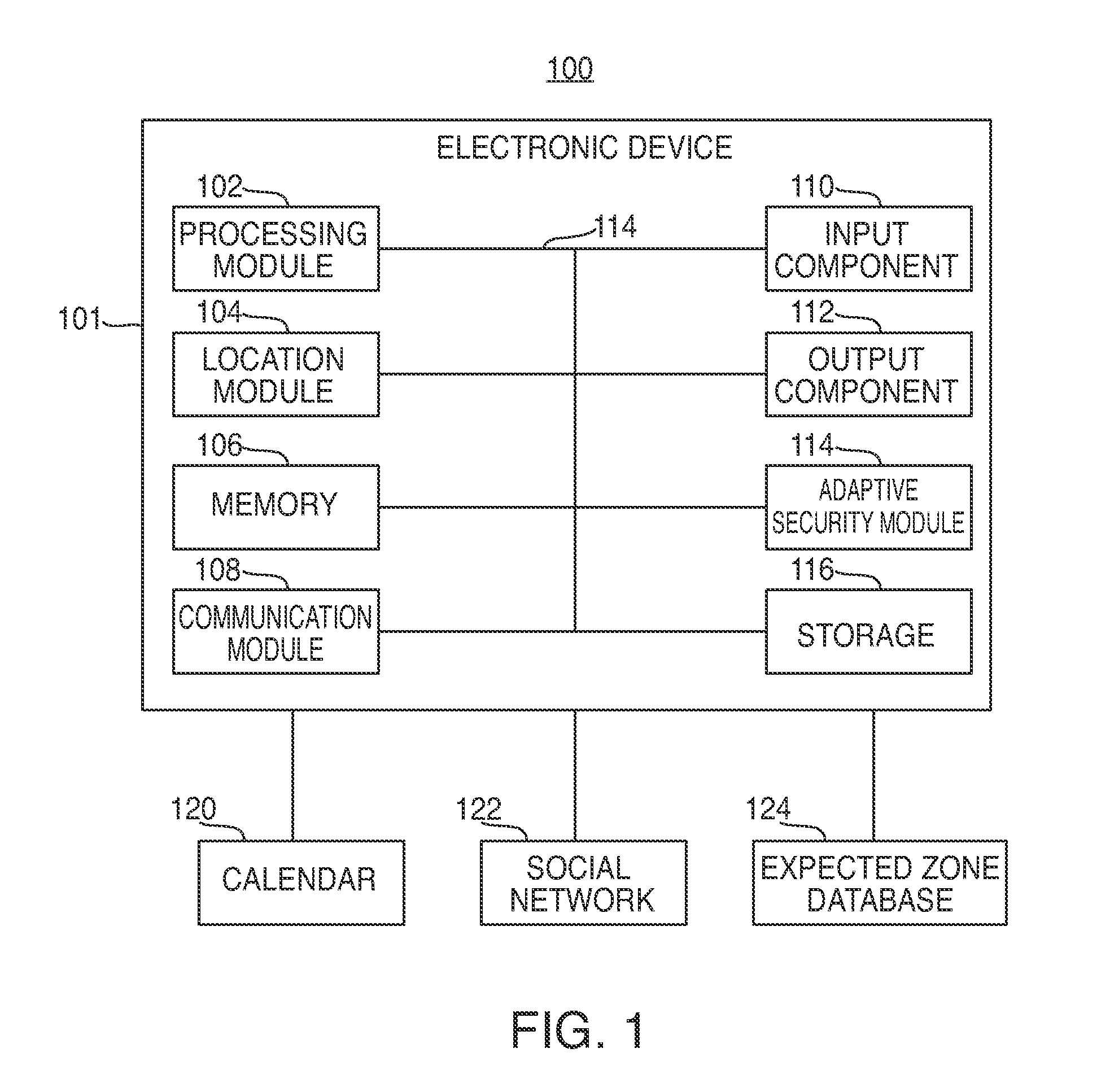
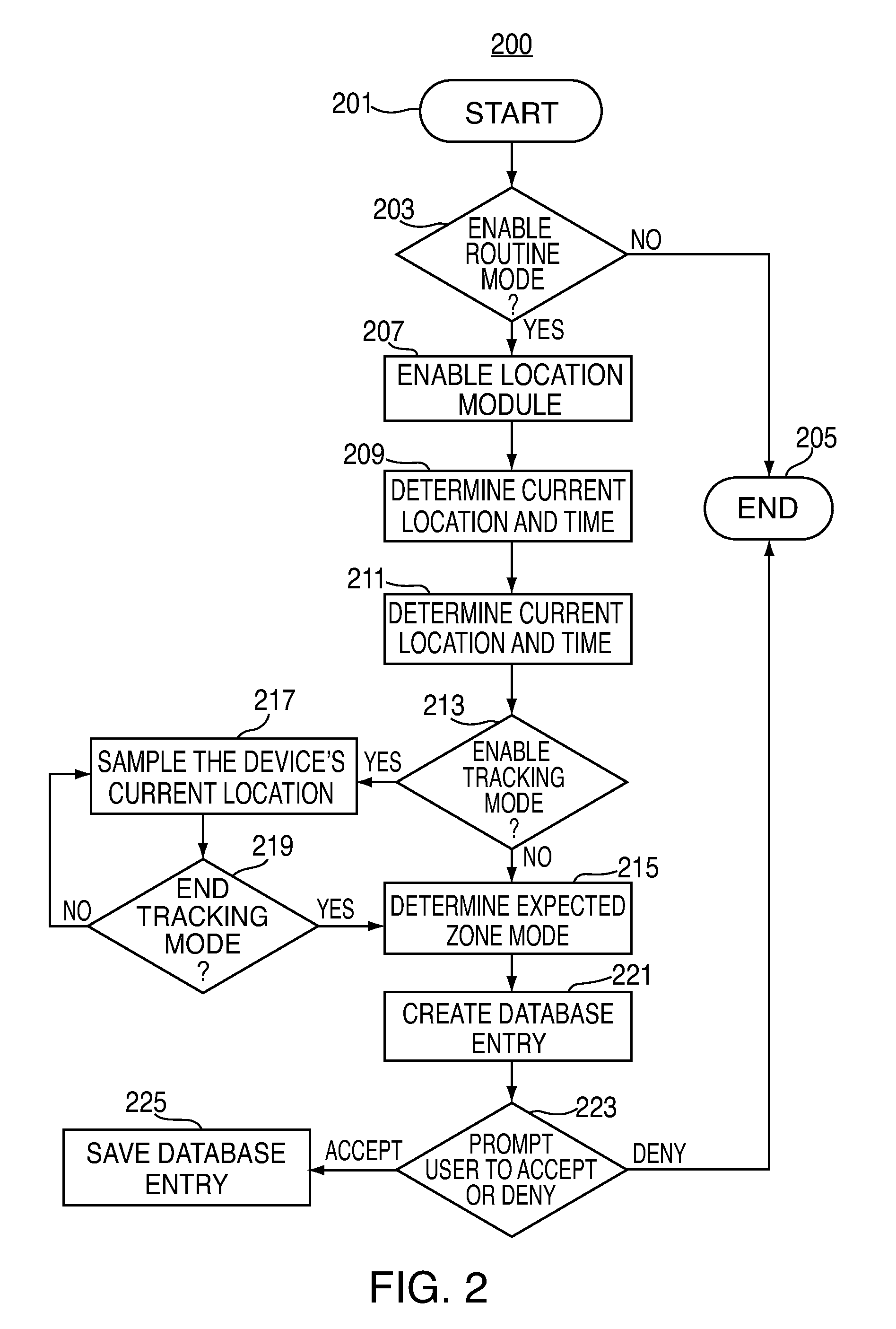
Electronic devices having adaptive security profiles and methods for selecting the same
ActiveUS20120284779A1Digital data processing detailsUser identity/authority verificationAdaptive securitySelf adaptive
Adaptive security profiles are supported on an electronic device. One or more security profiles may be automatically or selectively applied to the device based on the device's location and one or more geographic zone definitions. The security profiles may be used to determine the level of authentication or number of invalid authentication attempts for a particular feature or application or set of features or applications.
Owner:APPLE INC
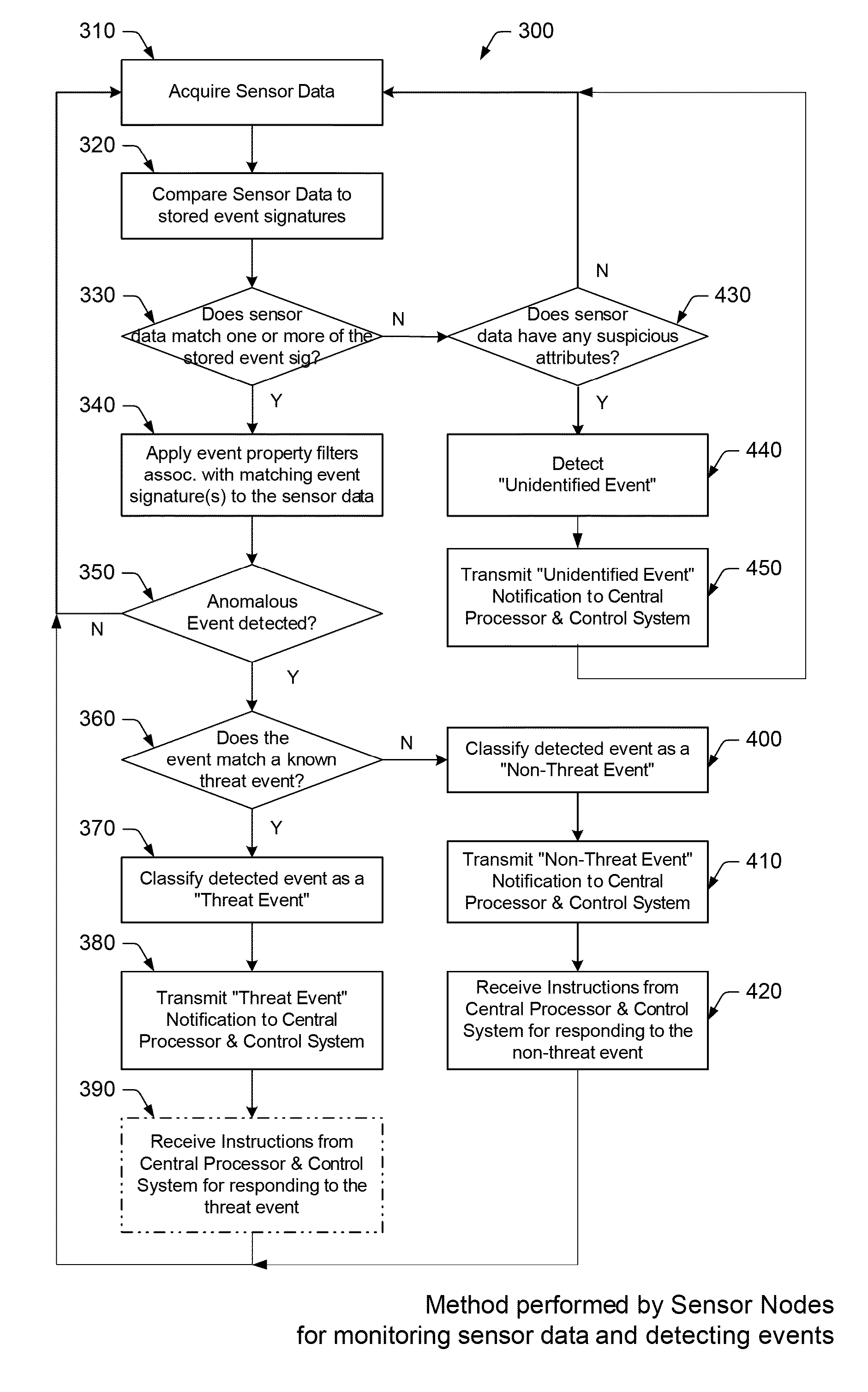
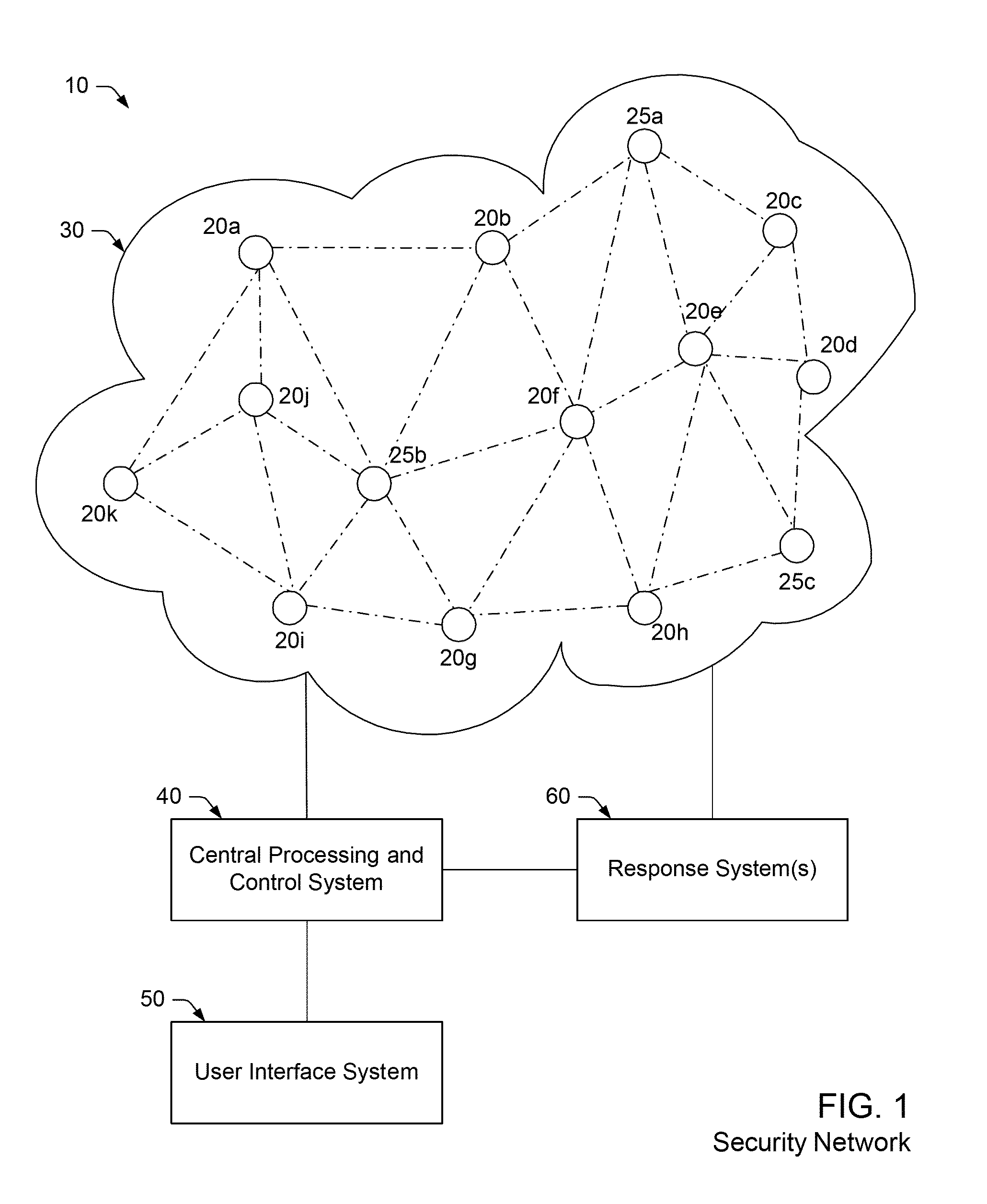
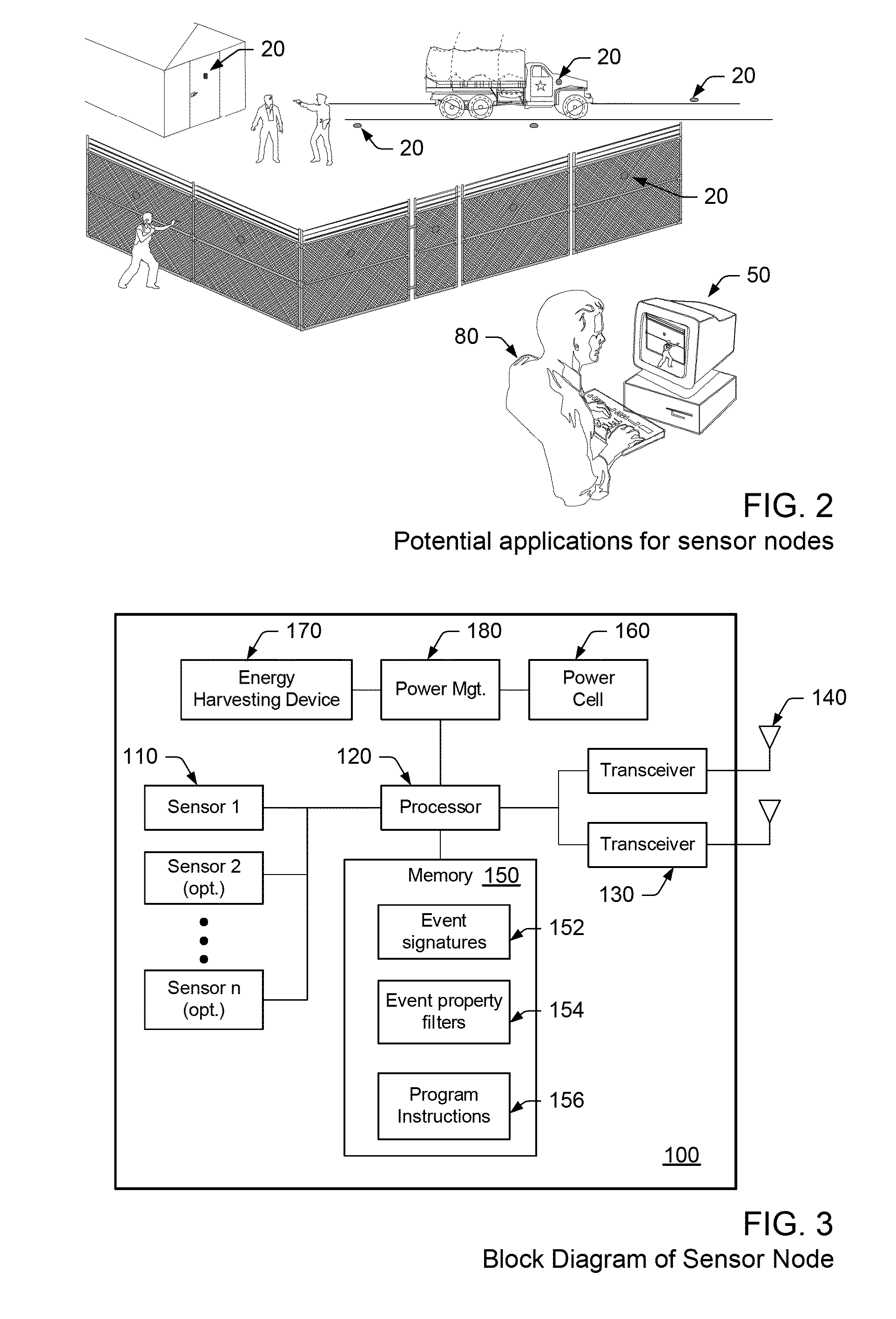
Adaptive security network, sensor node and method for detecting anomalous events in a security network
An adaptive security network, sensor node and methods for detecting and responding to anomalous events in a security network are provided herein. In general, the adaptive security network comprises a plurality of sensor nodes interconnected to form a communication network, wherein each sensor node is configured for detecting an anomalous event occurring within a vicinity of the sensor node and for identifying the detected anomalous event as a specific threat-event, a specific non-threat event or an unidentified event. In addition, the adaptive security network comprises a central processing and control system coupled to the plurality of sensor nodes for receiving an event notification message from at least one of the sensor nodes indicating an identity of an anomalous event detected by the at least one sensor node. Upon receiving the event notification message, the central processing and control system is configured for confirming the identity of the anomalous event provided by the at least one sensor node and for responding to the anomalous event once the identity is confirmed.
Owner:SOLIO SECURITY
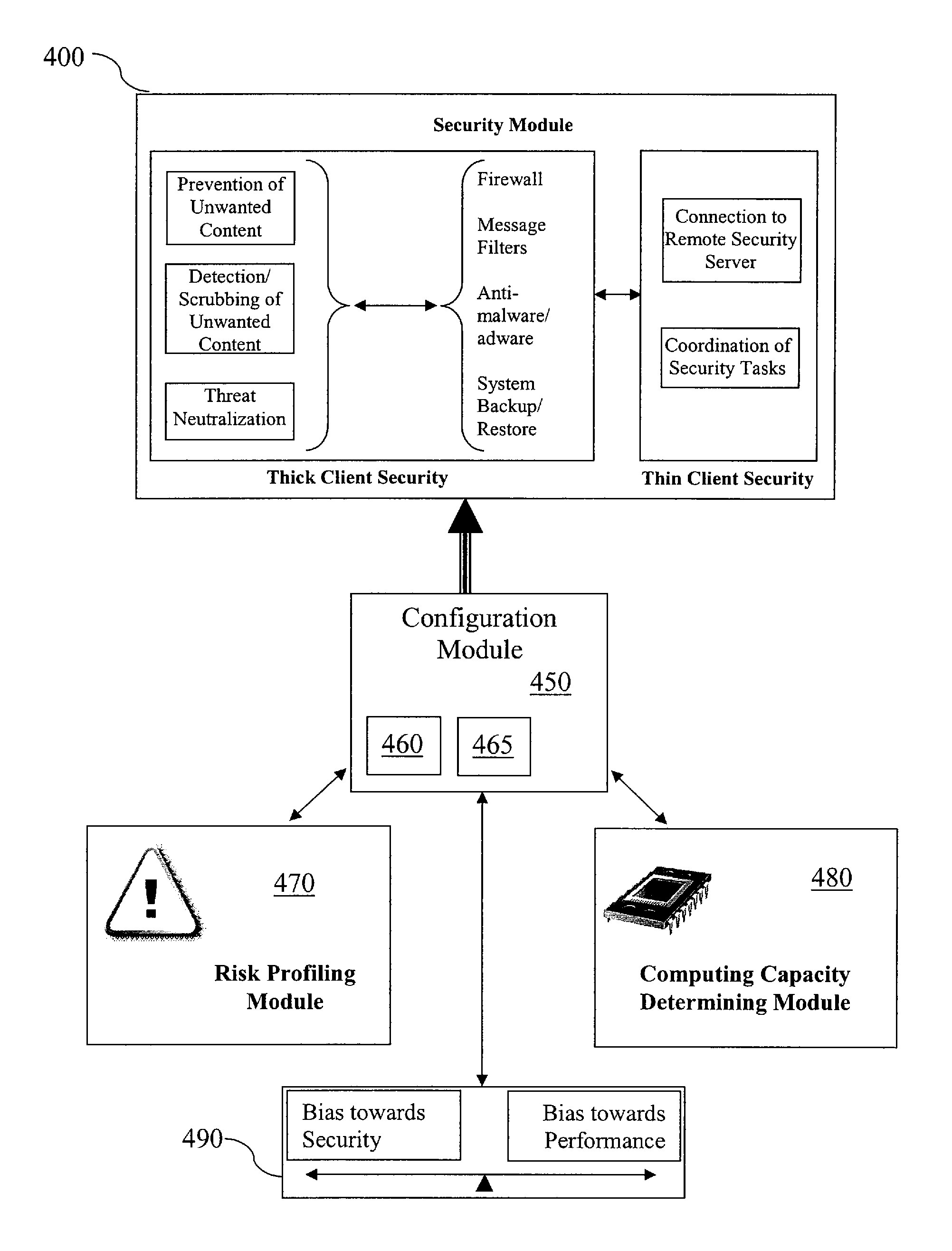
Adaptive security for information devices
ActiveUS7584508B1Improve usabilityReduce loadMemory loss protectionError detection/correctionRisk profilingInformation device
An information device includes a dynamically configurable security module in which operational settings are automatically and dynamically configured based on risk profile or computing capacity information, or both.
Owner:AO KASPERSKY LAB
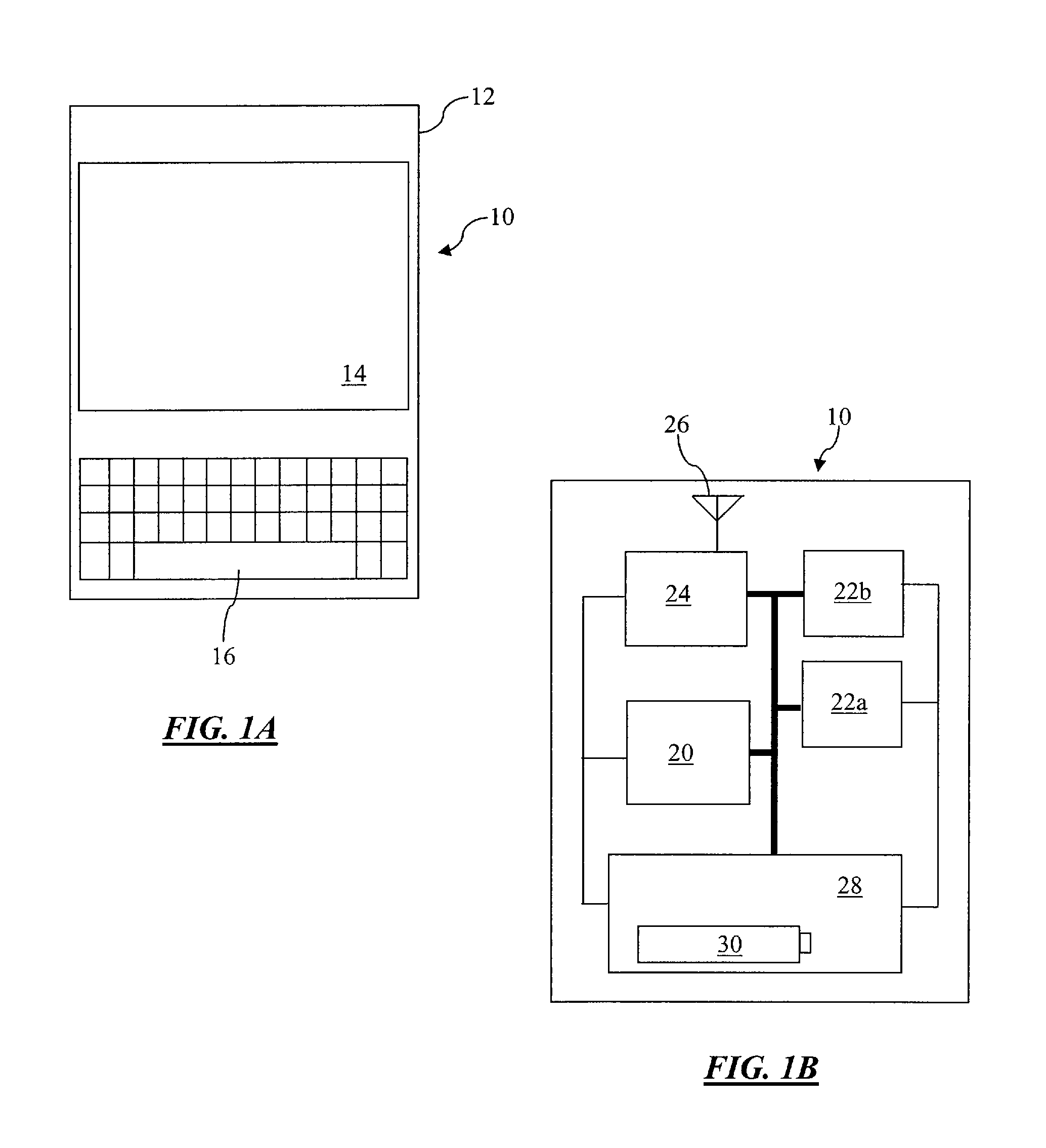
Adaptive security for portable information devices
ActiveUS7607174B1Facilitates selectively providing security serviceMemory loss protectionError detection/correctionInformation deviceClient-side
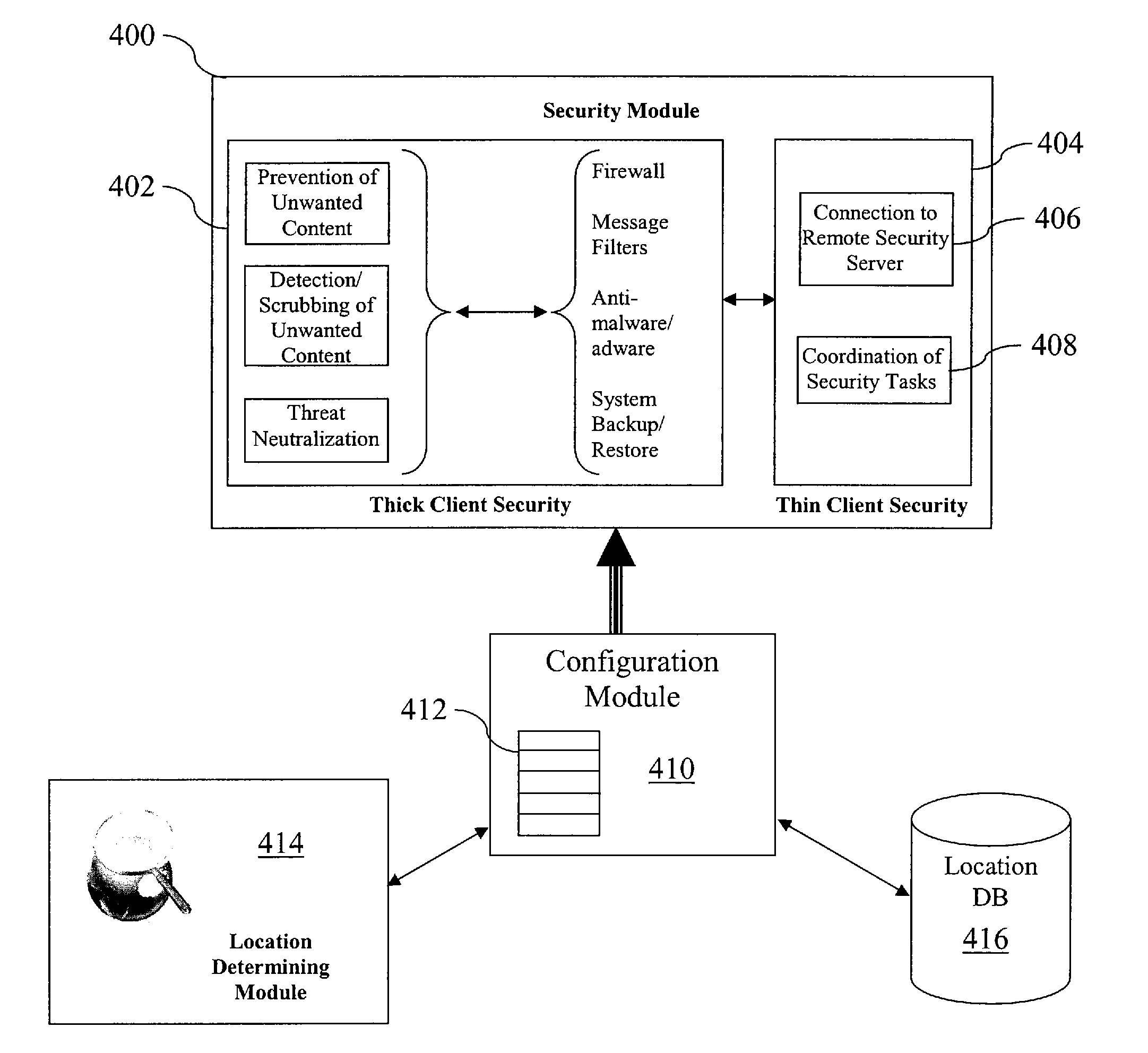
A portable information device includes a dynamically configurable security arrangement in which operational settings are automatically and dynamically configured for either thick client or thin client protection schemes based at least in part on the current location of the device.
Owner:AO KASPERSKY LAB
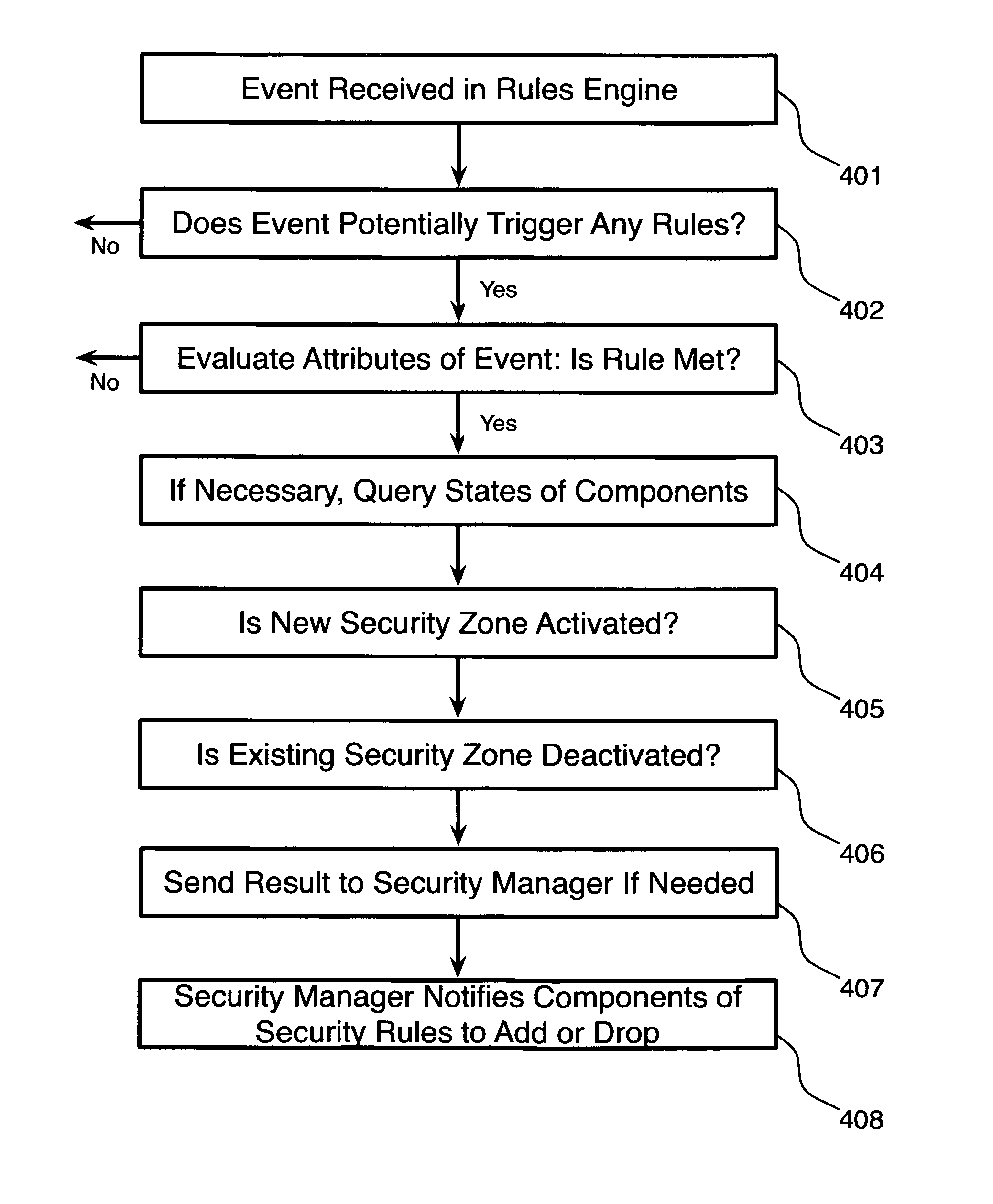
System and method for implementing adaptive security zones
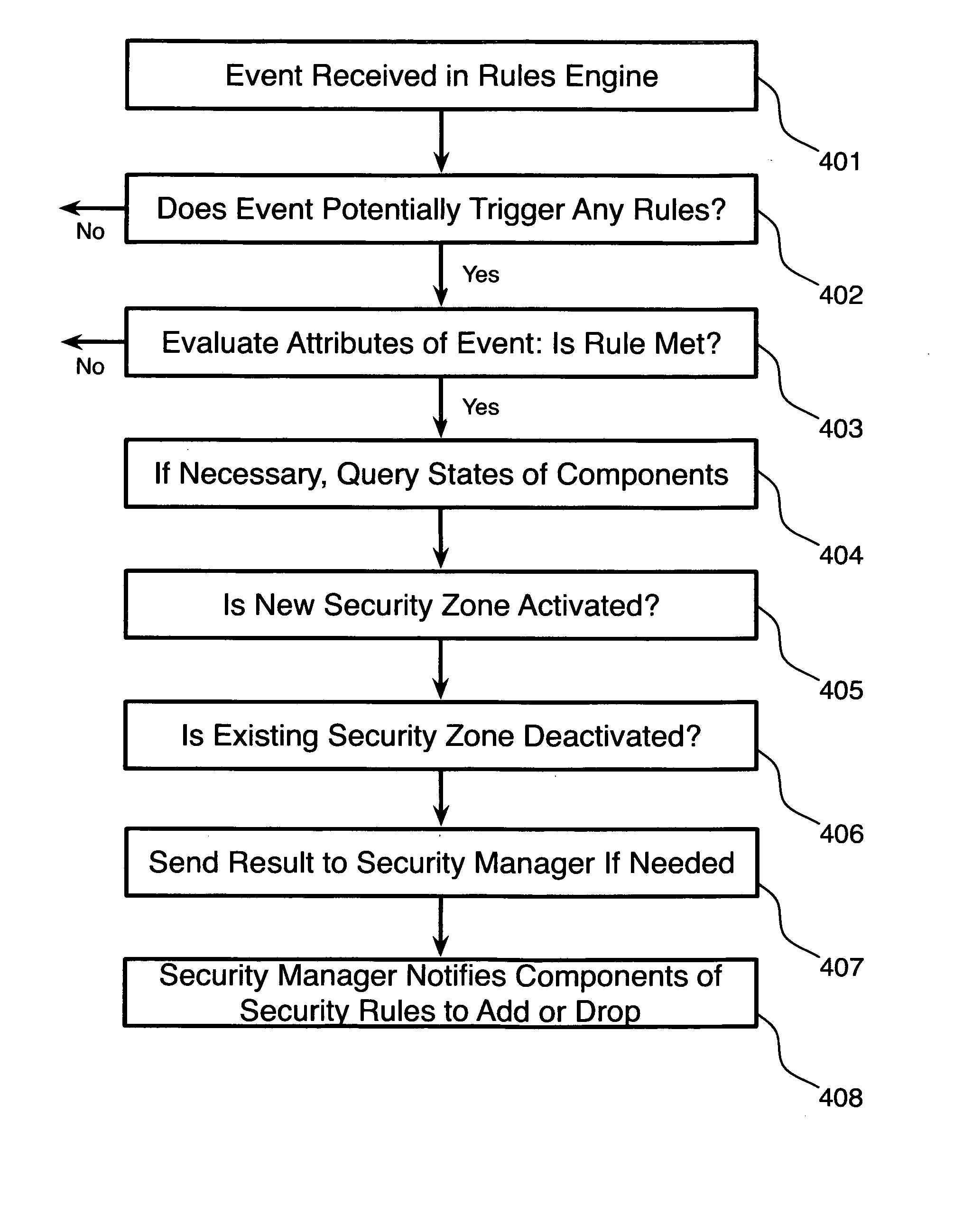
A system for managing adaptive security zones in complex business operations, comprising a rules engine adapted to receive events from a plurality of event sources and a security manager coupled to the rules engine via a data network, wherein upon receiving an event, the rules engine determines what rules, if any, are triggered by the event and, upon triggering a rule, the rules engine determines if the rule pertains to security and, if so, sends a notification message to the security manager informing it of the triggered event, and wherein the security manager, on receiving a notification message from the rules engine, automatically establishes a new security zone based at least in part on the contents of the notification message, is disclosed
Owner:SERENOVA LLC
Runtime adaptable security processor
InactiveUS20120117610A1Sharply reduces TCP/IP protocol stack overheadImprove performanceComputer security arrangementsSpecial data processing applicationsInternal memoryApplication software
A runtime adaptable security processor is disclosed. The processor architecture provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. A scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer.
Owner:MEMORY ACCESS TECH LLC
Adaptive data security systems and methods
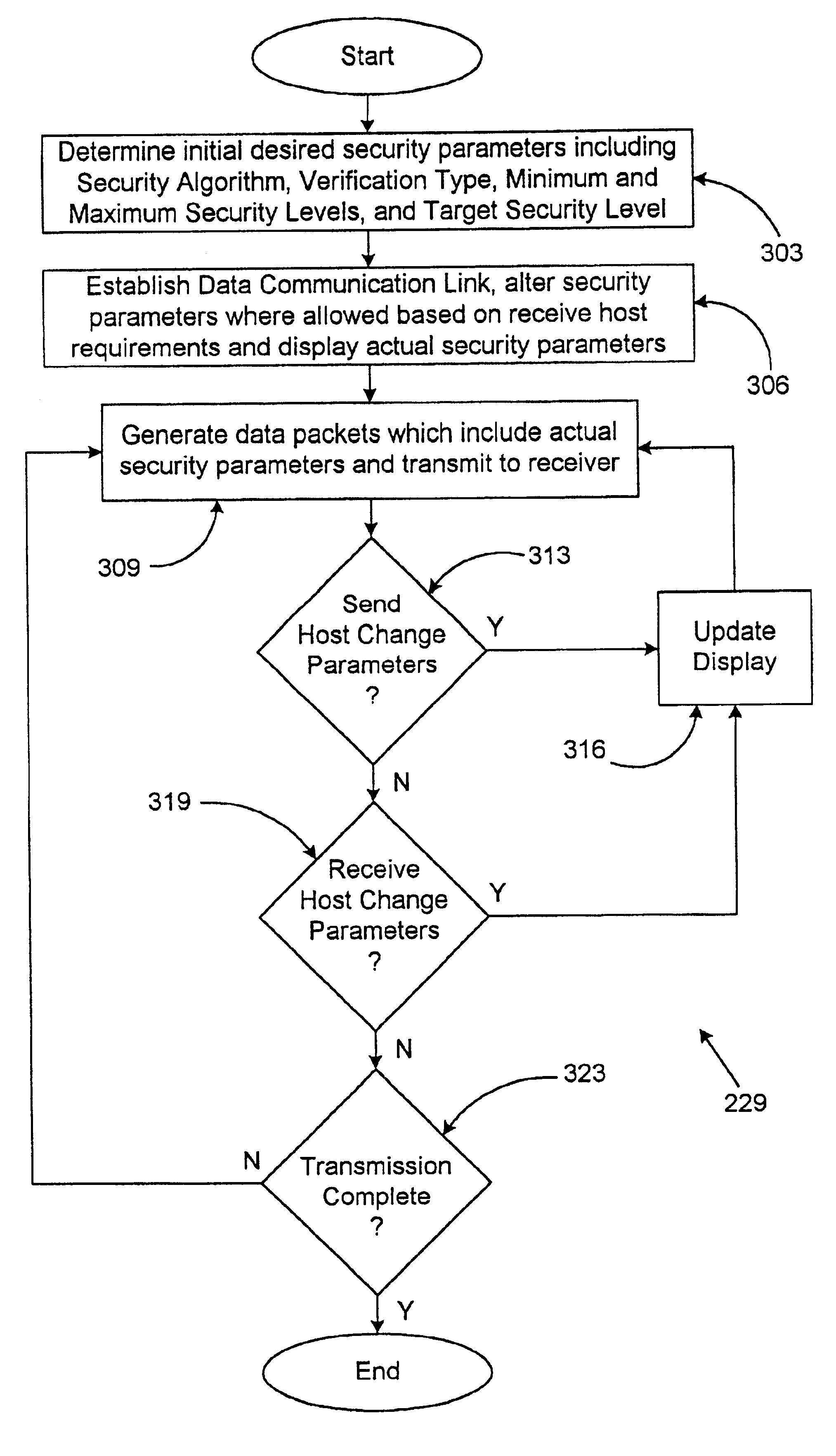
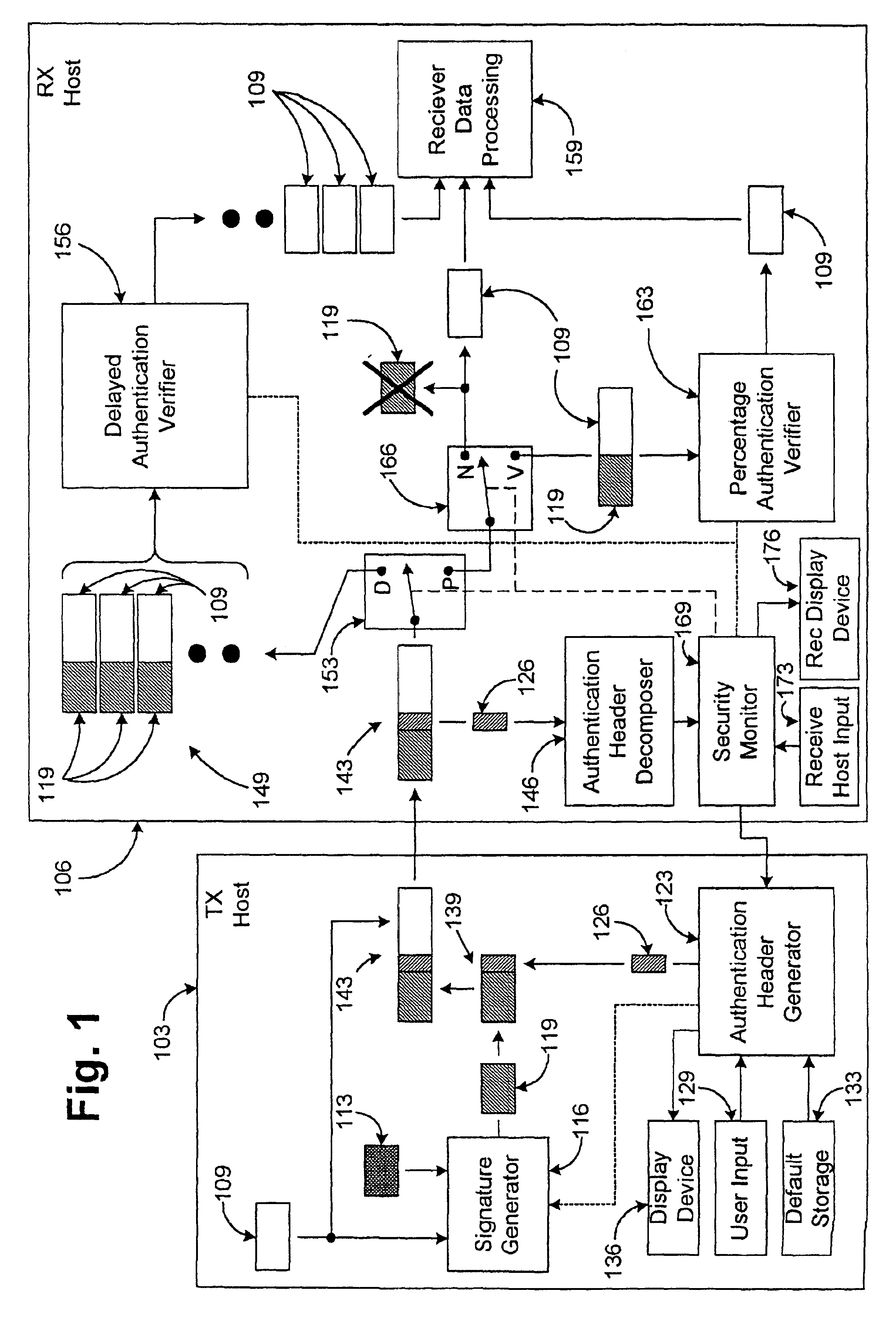
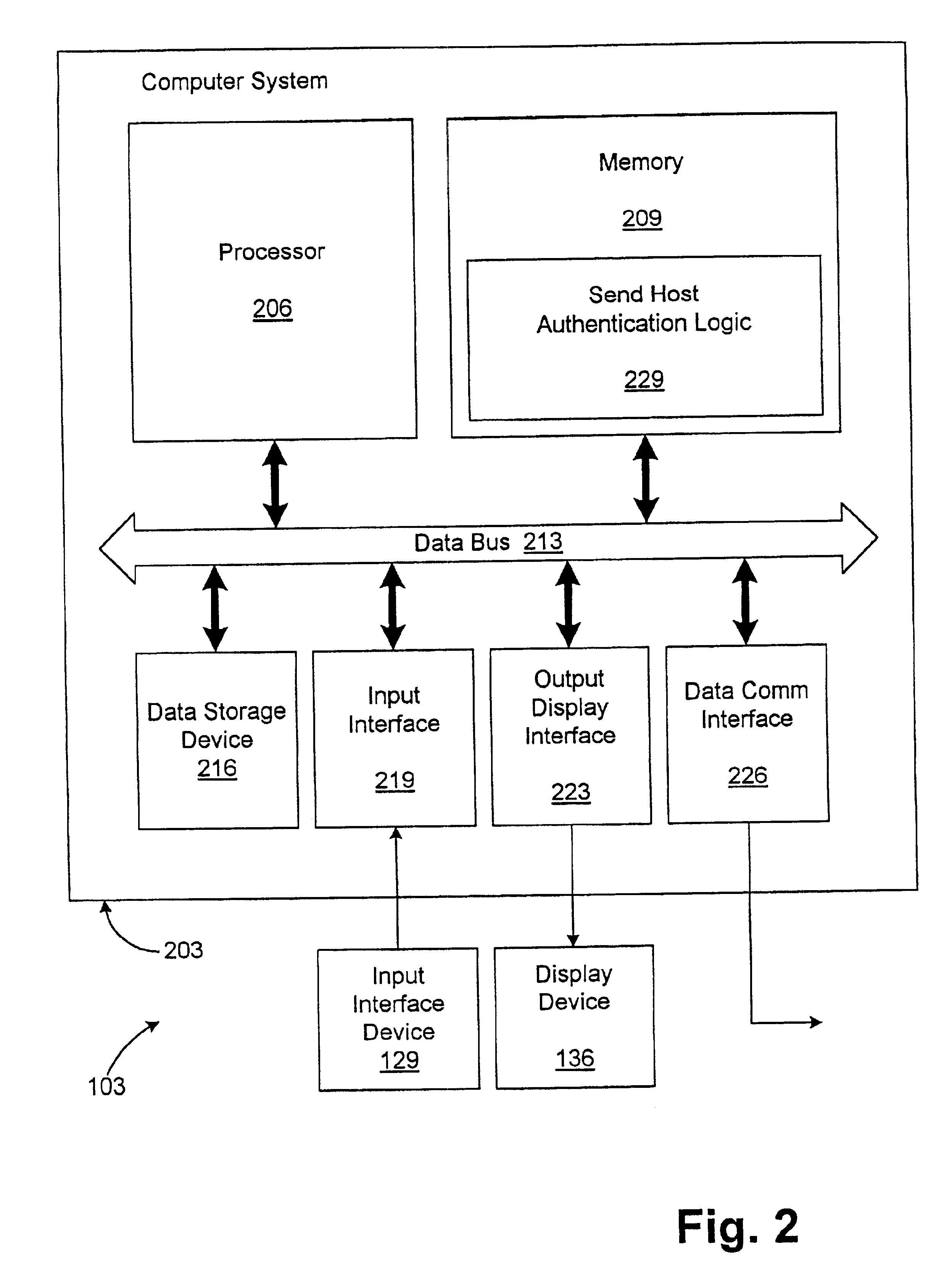
The present disclosure relates to a method for communicating and applying adaptive security to a data stream comprising a plurality of data packets. The method comprises the steps of identifying a desired security level range and a desired actual security level which falls within the desired security level range. The availability of a number of security processor operations at the host is determined so that, if needed, computing resources at the host can be reallocated to ensure that the data stream can be verified at the desired actual security level. If there are not sufficient resources available for reallocation at the host, communication resources can be reallocated, for example by changing the bandwidth of the data stream or another incoming data stream. With this method, the actual security level will be kept within the desired security level range.
Owner:GEORGIA TECH RES CORP
Connected vehicles adaptive security signing and verification methodology and node filtering
ActiveUS20160036558A1Road vehicles traffic controlParticular environment based servicesValidation methodsNoise level
We introduce a connected vehicles adaptive security signing and verification methodology. We also introduce an adaptive node filtering at receiver, using noise levels and received signal strength. This invention addresses two important pillars in connected vehicle technology and autonomous cars: The first one is related to the security 1609.2 format and its main two functions: signing and verification. The second one explains how the noise level and signal strength can be used to filter undesired connected nodes. In this presentation, we provide various examples and variations on these topics.
Owner:HARMAN INT IND INC
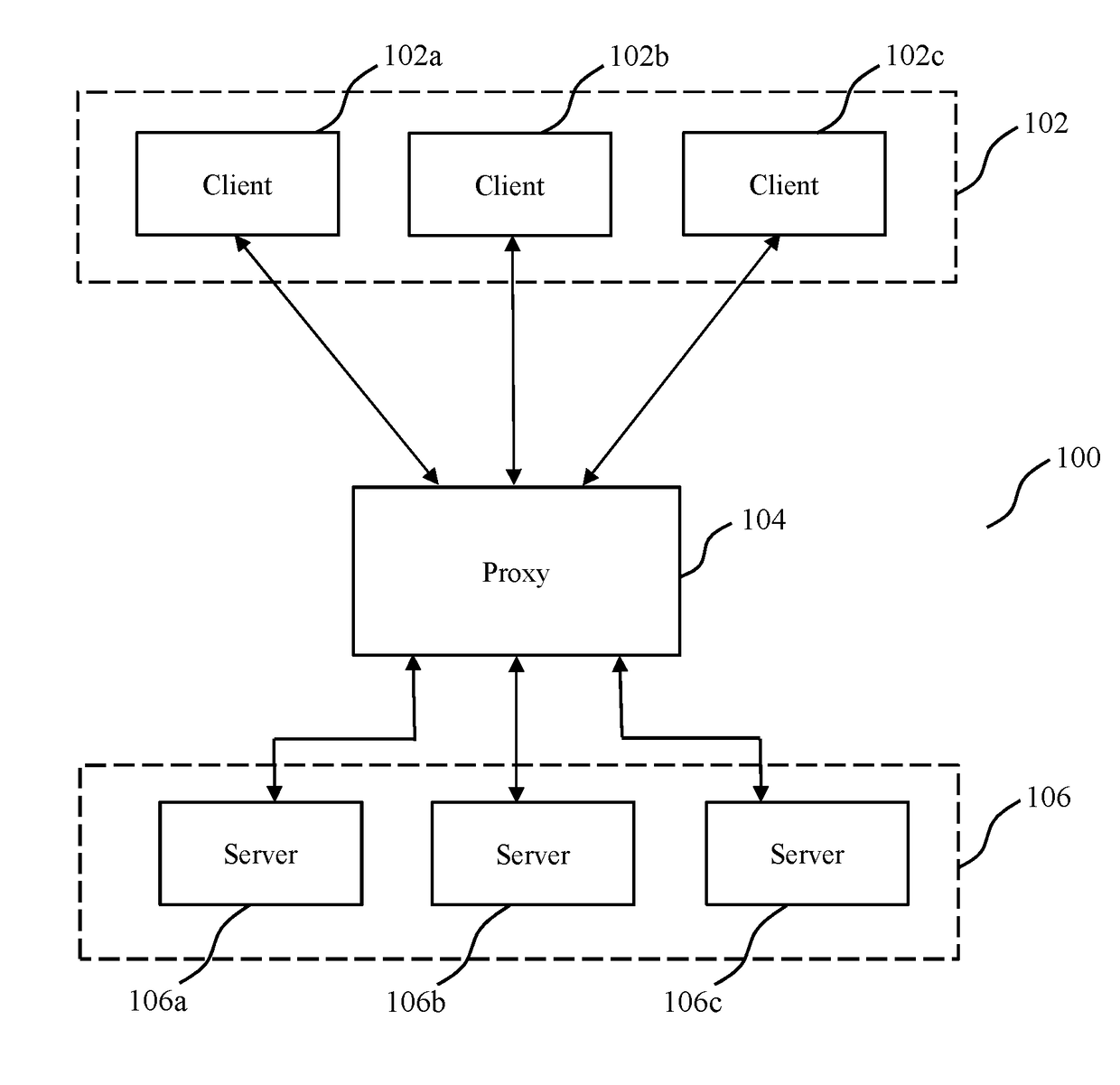
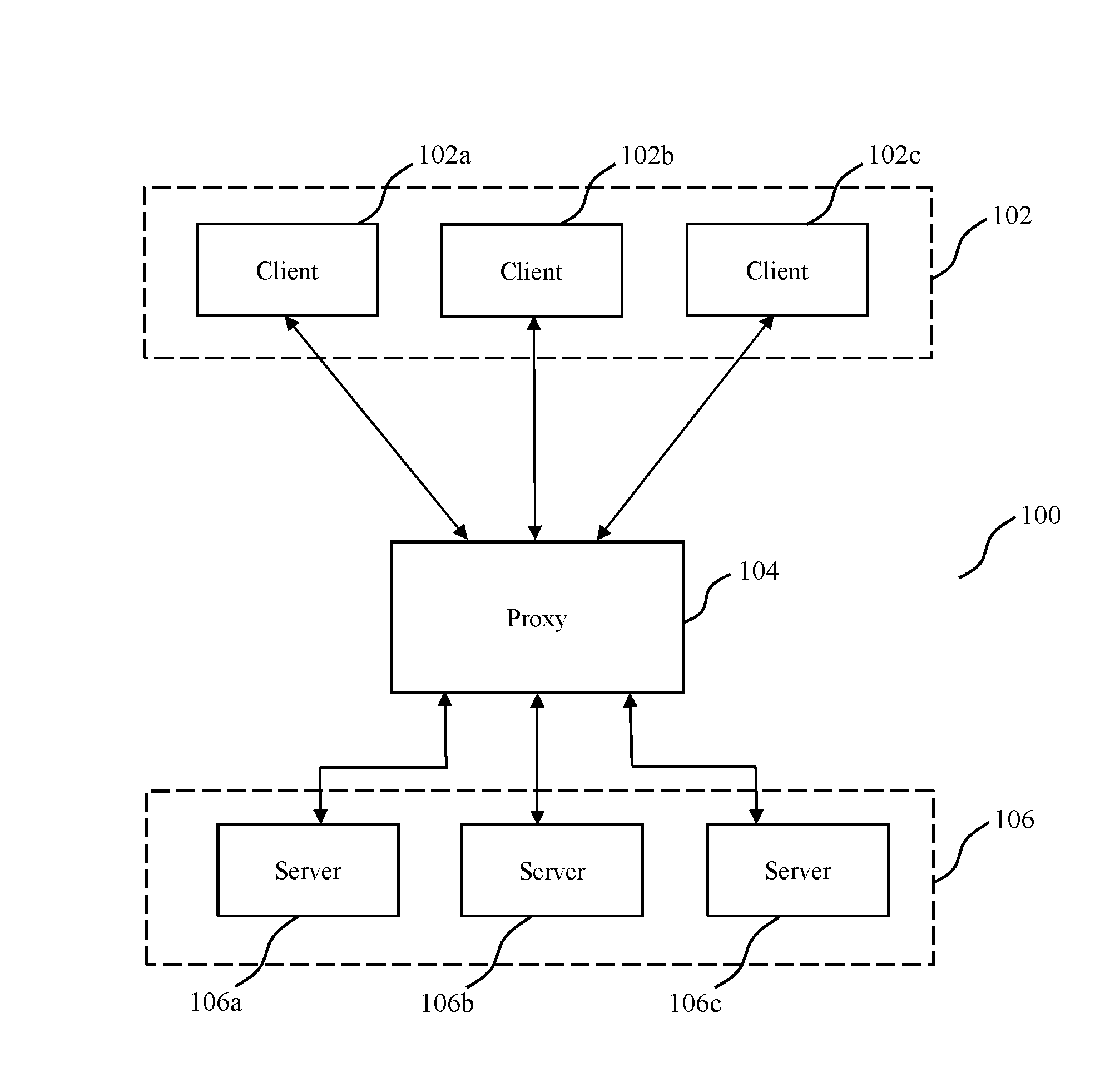
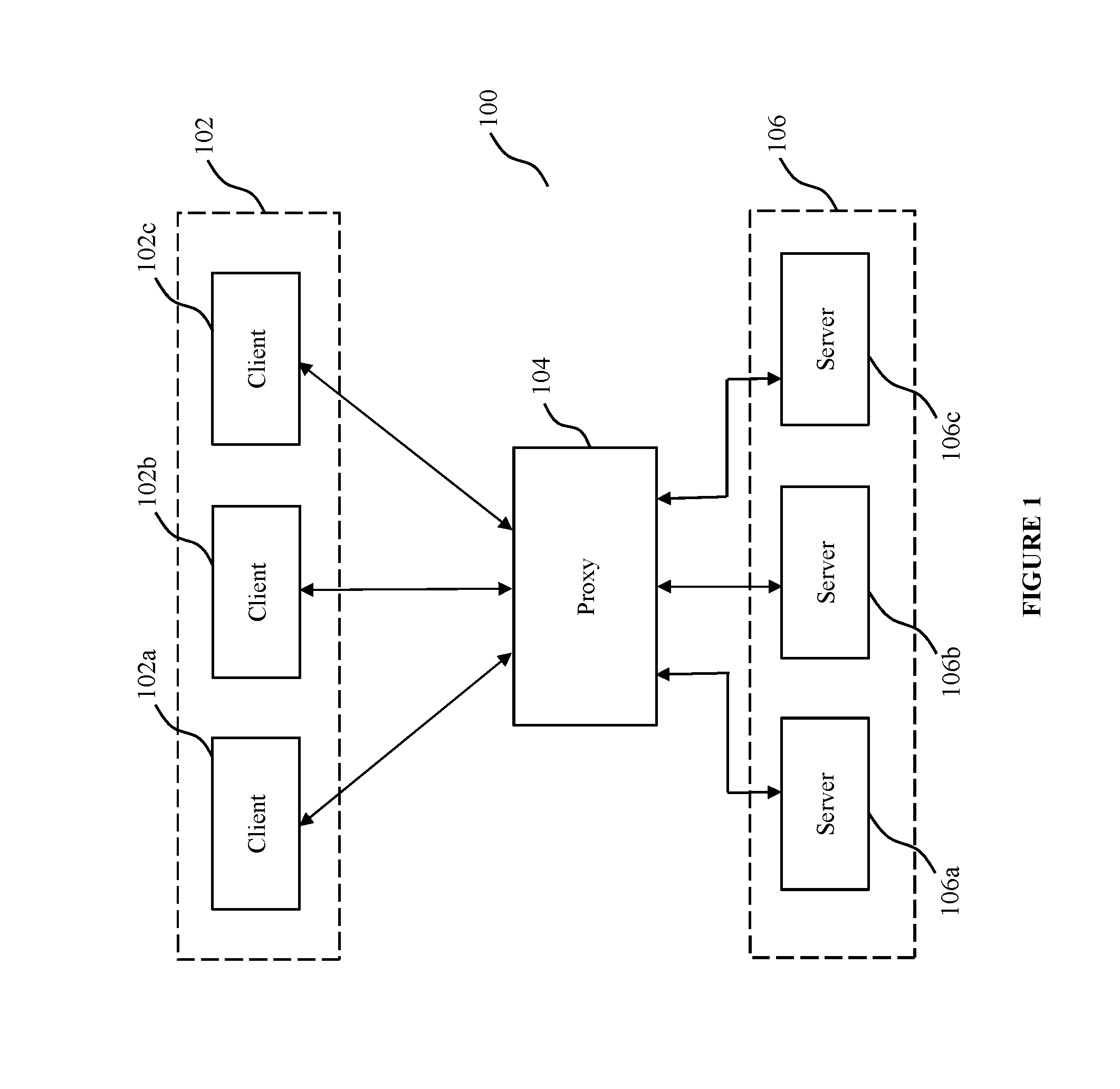
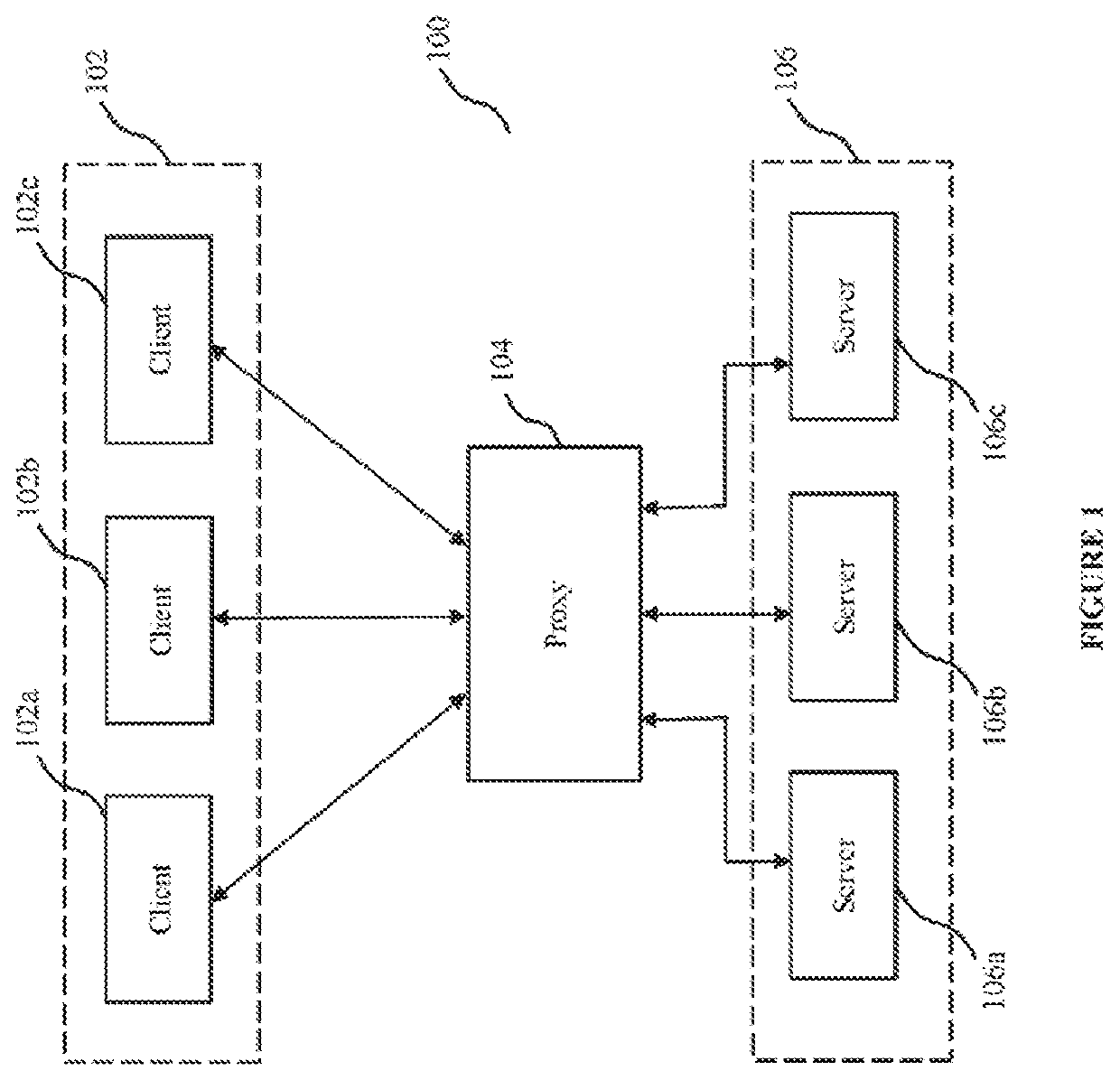
Methods and systems for api proxy based adaptive security
ActiveUS20180337891A1Promote resultsEasy to identifyInterprogram communicationData switching networksRouting decisionSelf adaptive
The invention concerns API proxy based adaptive security. The invention implements adaptive security for API servers, while avoiding data bottlenecks and maintaining client experience. The invention provides methods and configurations for API security that may be employed at proxies for implementing routing decisions involving client messages received at said proxies. The invention also involves generating or collecting at proxies, log information that captures data corresponding to received client messages and responses from API servers—which log information correlates communications between clients, proxies and backend API servers, and includes data relevant for purposes generating API metrics and identifying anomalies and / or indicators of compromise. The invention yet further provides security server clusters configured for generating API metrics and / or identify anomalies or indicators of compromise—which may be used by proxies to terminate existing connections and block subsequent requests or messages from clients associated with the identified anomalies or indicators of compromise.
Owner:PING IDENTITY
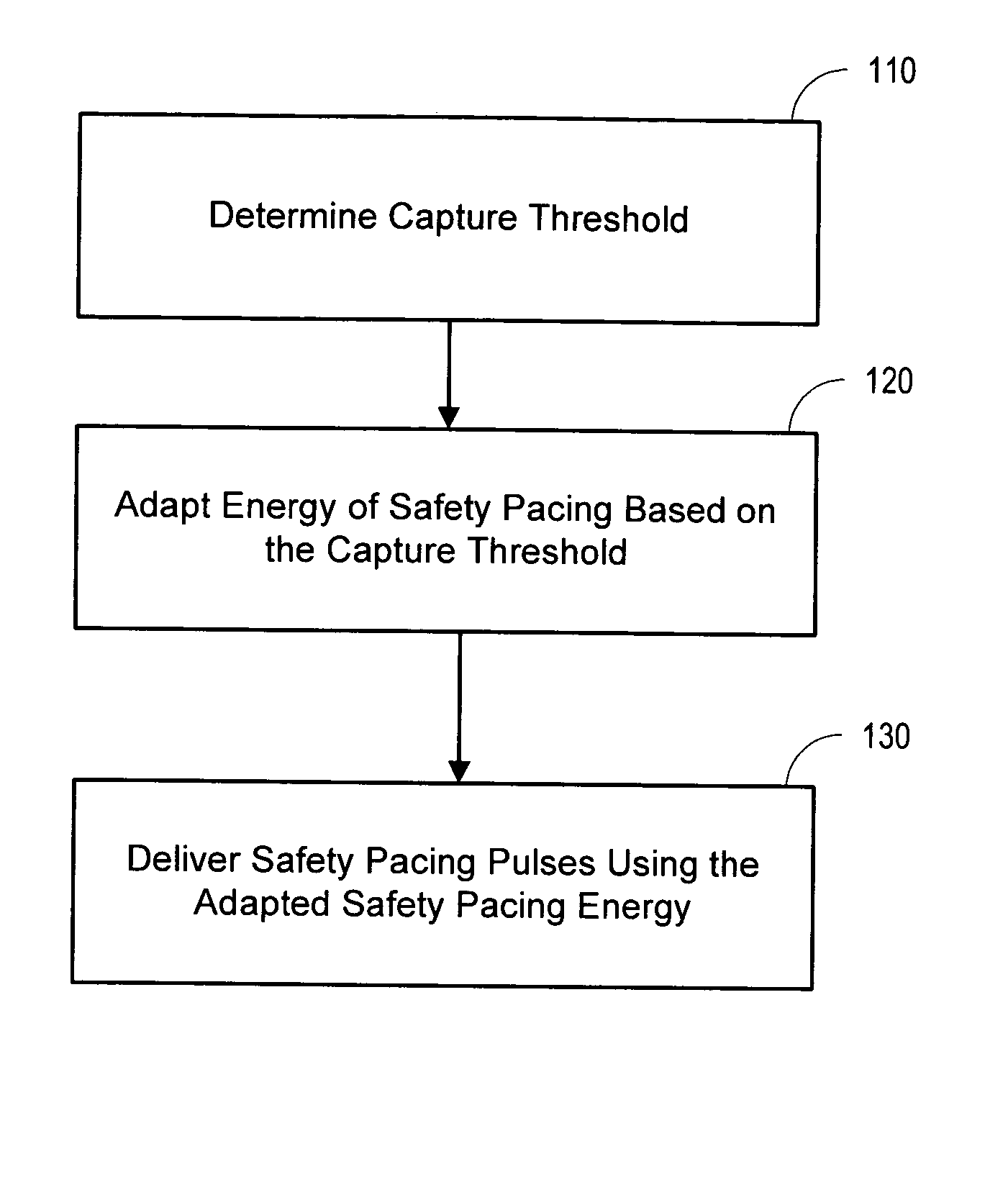
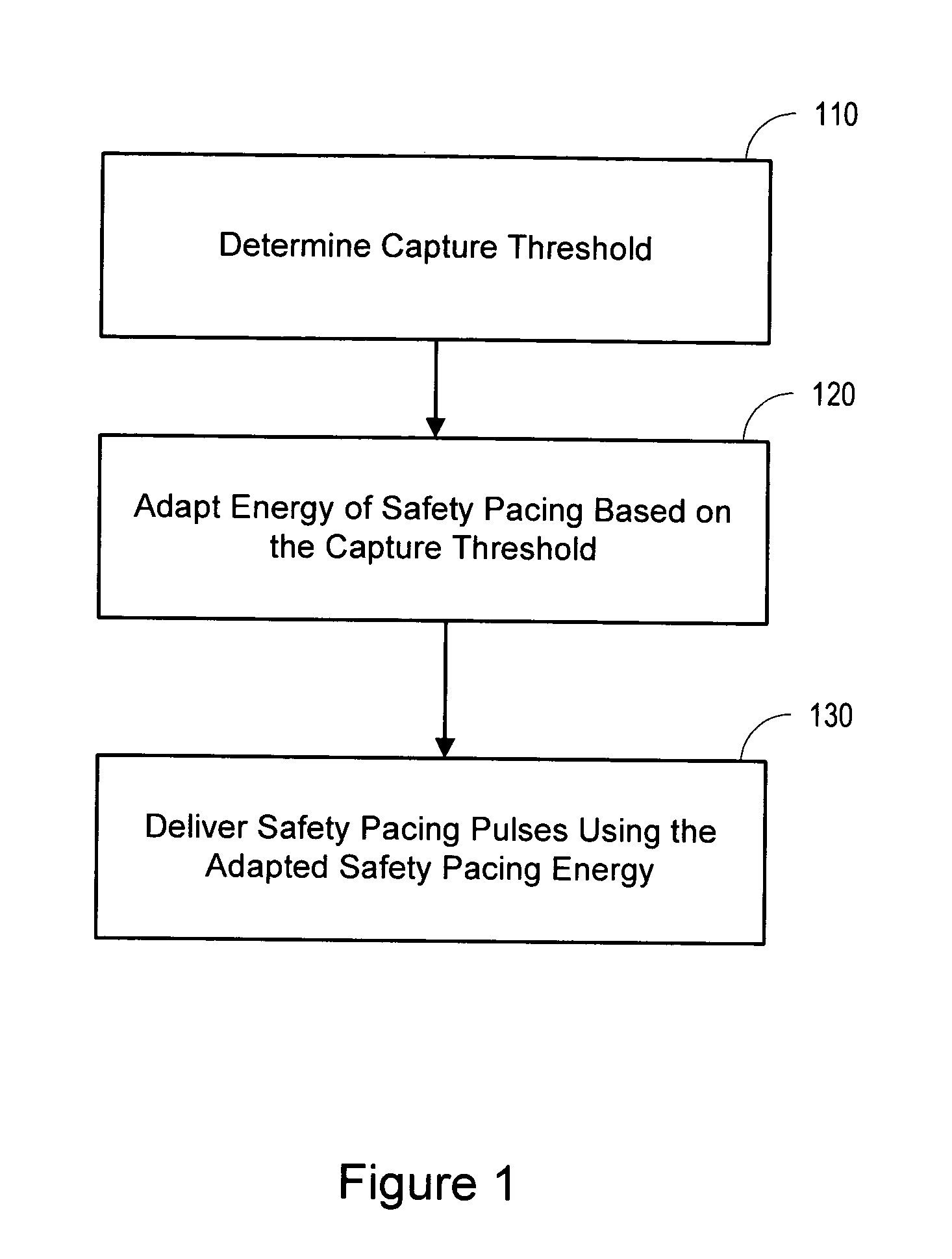
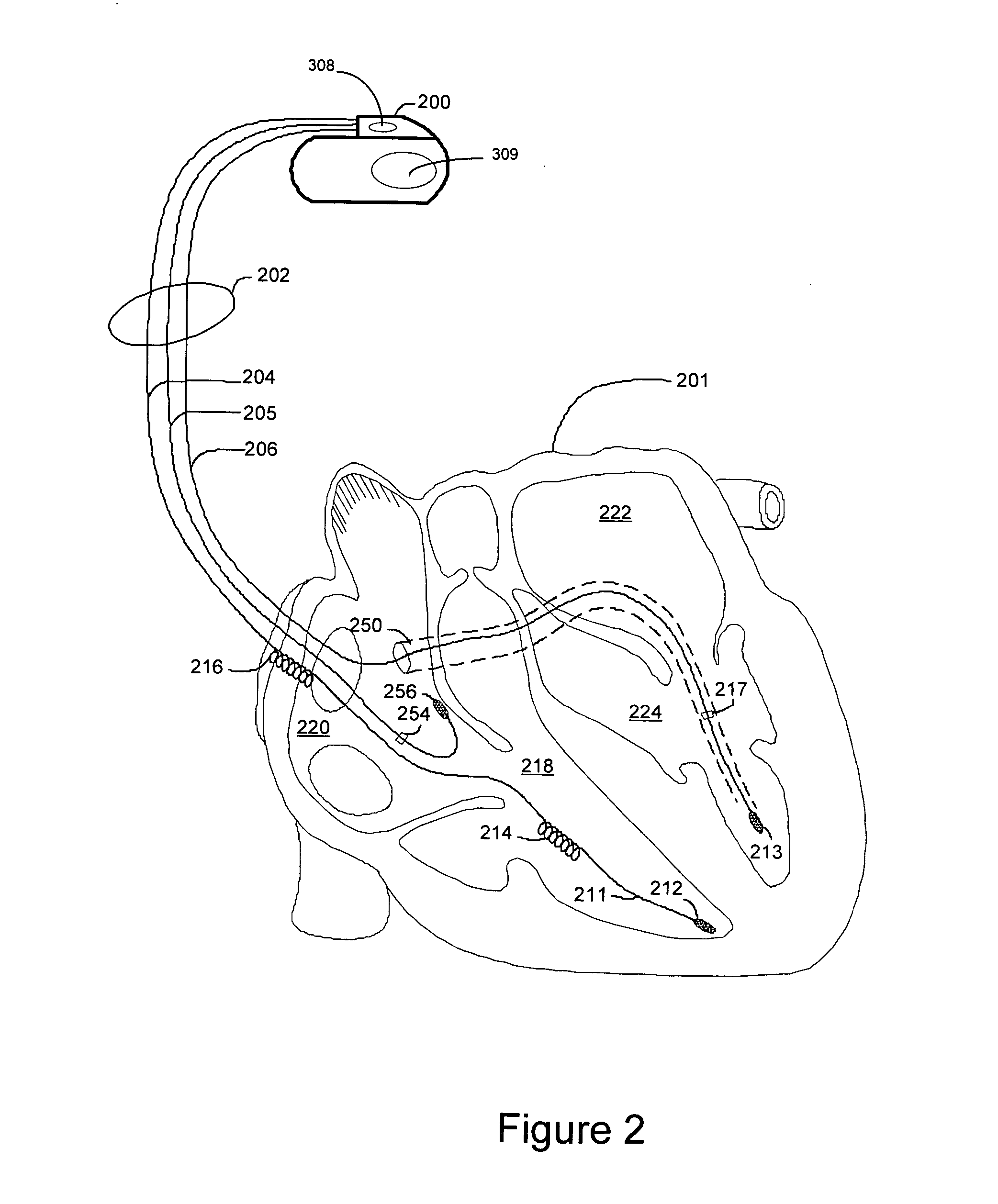
Adaptive safety pacing
Methods and systems involve adjusting an energy used for safety pacing based on the capture threshold. The safety pacing energy may be adjusted prior to a capture threshold test. During the capture threshold test, backup safety paces are delivered using the adjusted pacing energy. Following suspension of automatic capture verification, the device may enter a suspension mode. During the suspension mode, safety pacing pulses are delivered using a pacing energy adjusted based on capture threshold.
Owner:CARDIAC PACEMAKERS INC
Methods and systems for api proxy based adaptive security
ActiveUS20170012941A1Promote resultsEasy to identifyInterprogram communicationData switching networksRouting decisionSelf adaptive
The invention concerns API proxy based adaptive security. The invention implements adaptive security for API servers, while avoiding data bottlenecks and maintaining client experience. The invention provides methods and configurations for API security that may be employed at proxies for implementing routing decisions involving client messages received at said proxies. The invention also involves generating or collecting at proxies, log information that captures data corresponding to received client messages and responses from API servers—which log information correlates communications between clients, proxies and backend API servers, and includes data relevant for purposes generating API metrics and identifying anomalies and / or indicators of compromise. The invention yet further provides security server clusters configured for generating API metrics and / or identify anomalies or indicators of compromise—which may be used by proxies to terminate existing connections and block subsequent requests or messages from clients associated with the identified anomalies or indicators of compromise.
Owner:PING IDENTITY
Self discovering adaptive security system and method
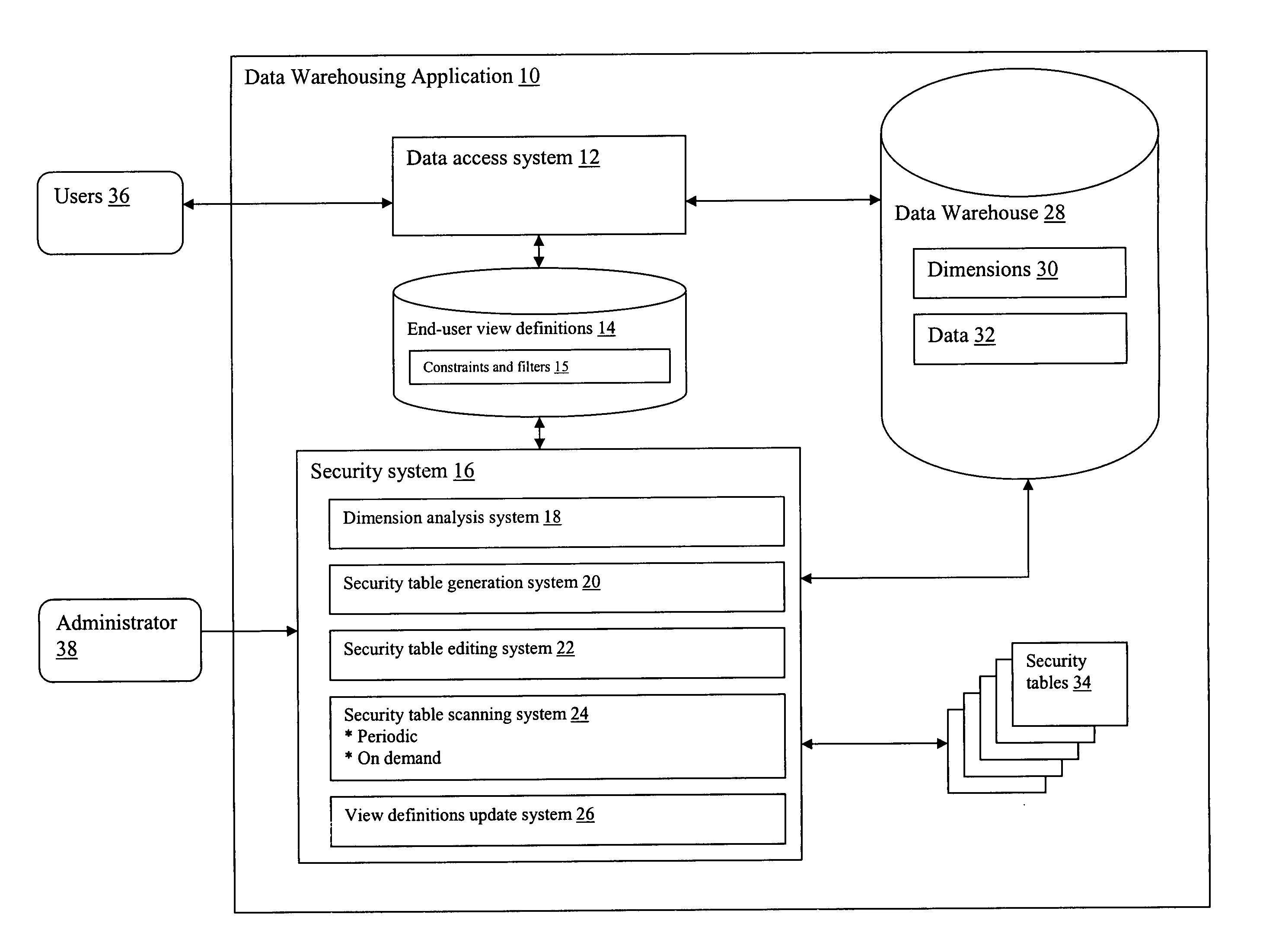
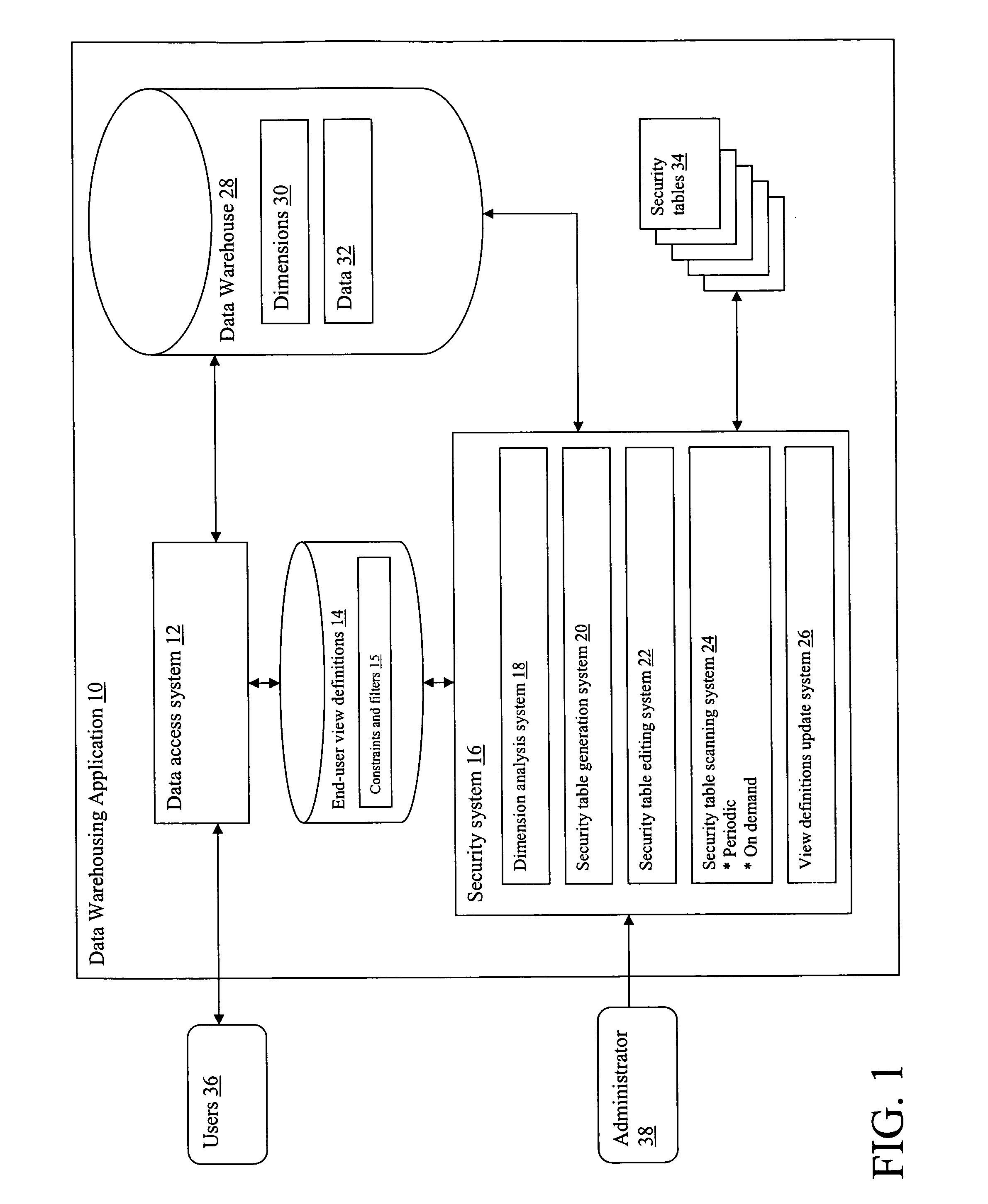
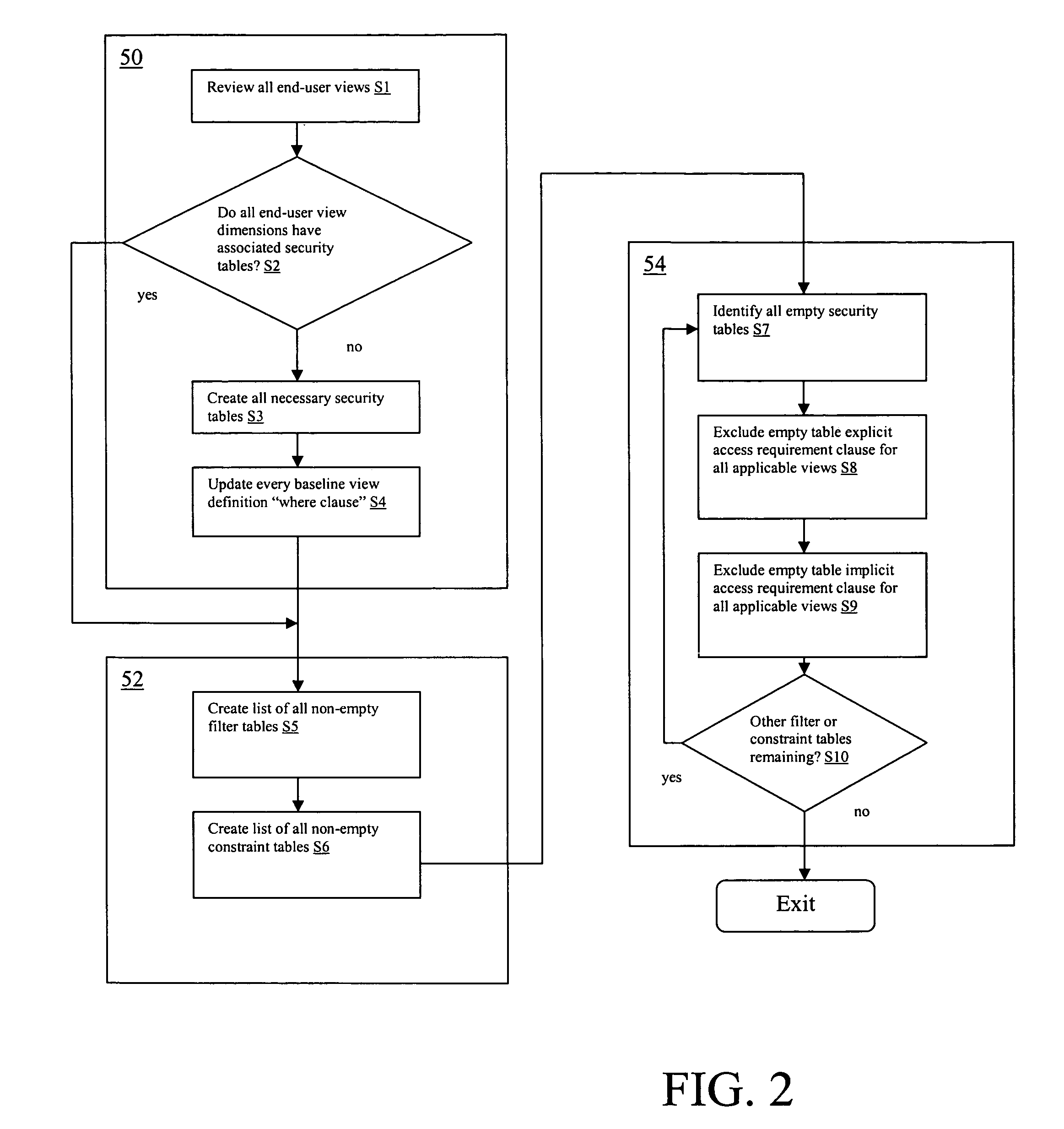
ActiveUS20070027871A1Simpler and flexibleImprove approachDigital data processing detailsAnalogue secracy/subscription systemsData warehouseFull table scan
A system and method for providing security to a data warehousing application. A system is described having: a dimension analysis system that identifies dimensions defined for viewing data in a data warehouse; a security table generation system for automatically generating security tables for identified dimensions; a security tables scanning system for analyzing inputs within the security tables; and an end-user view definitions update system for updating the data warehouse based on inputs in the security tables.
Owner:TWITTER INC
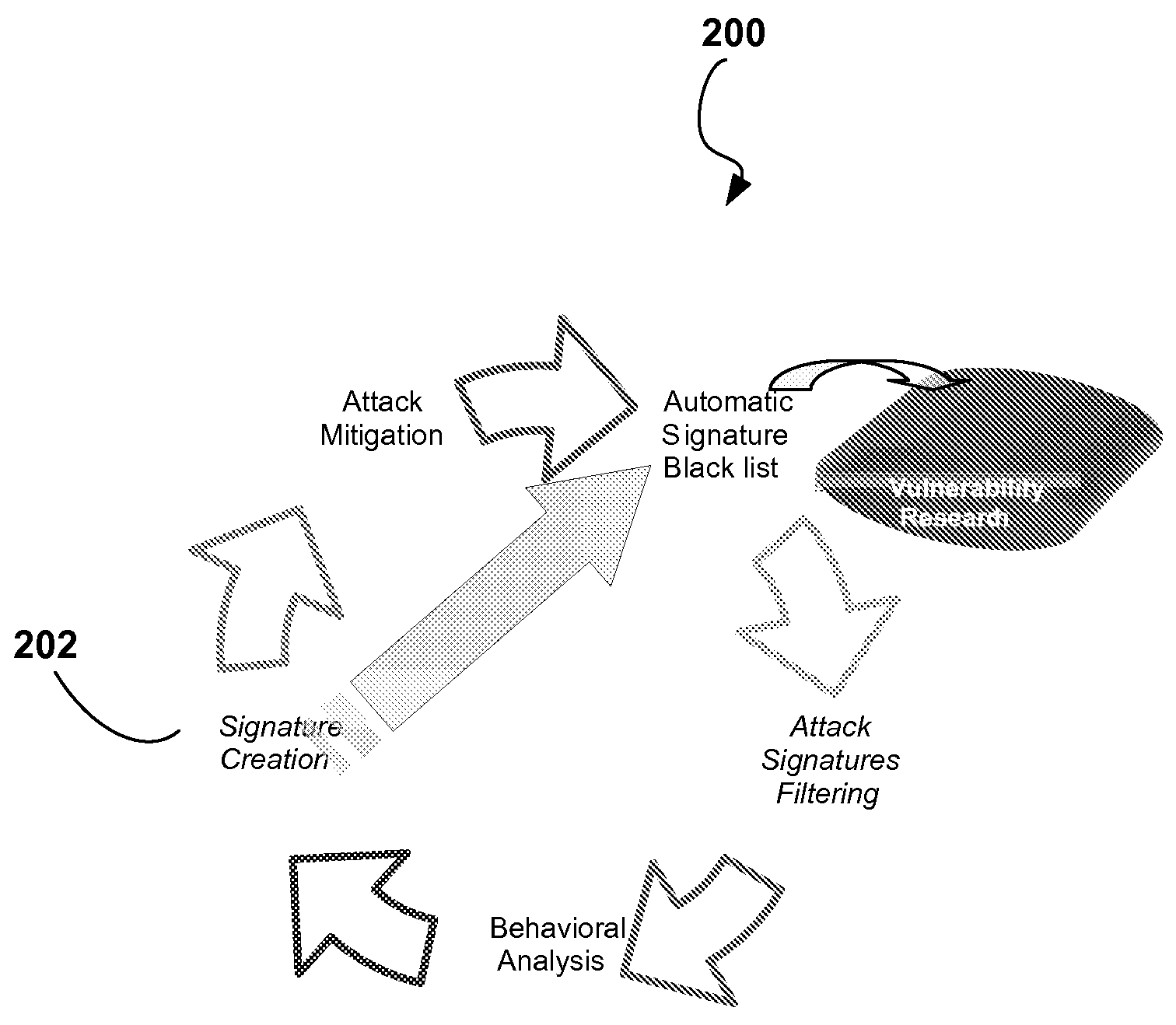
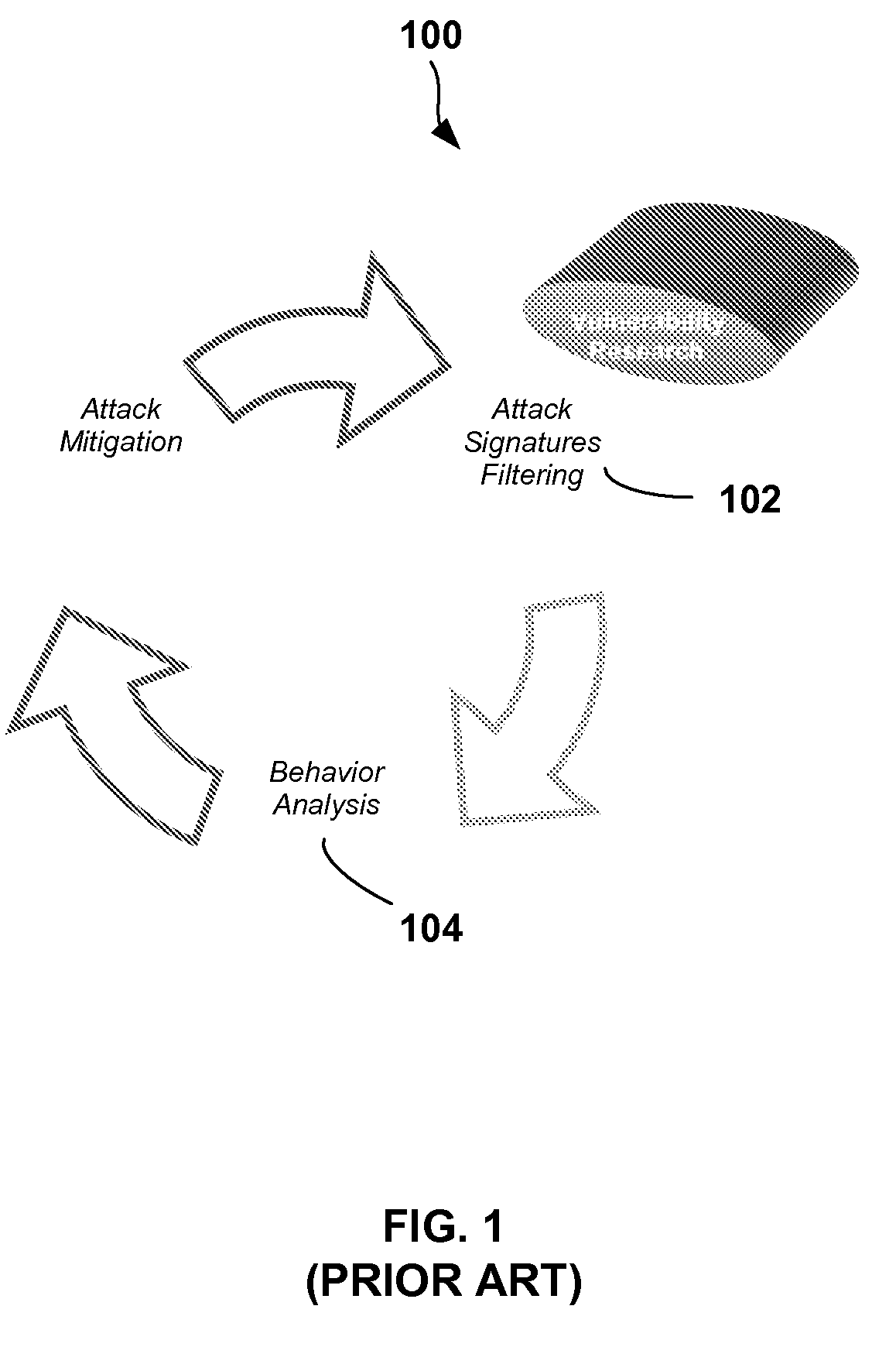
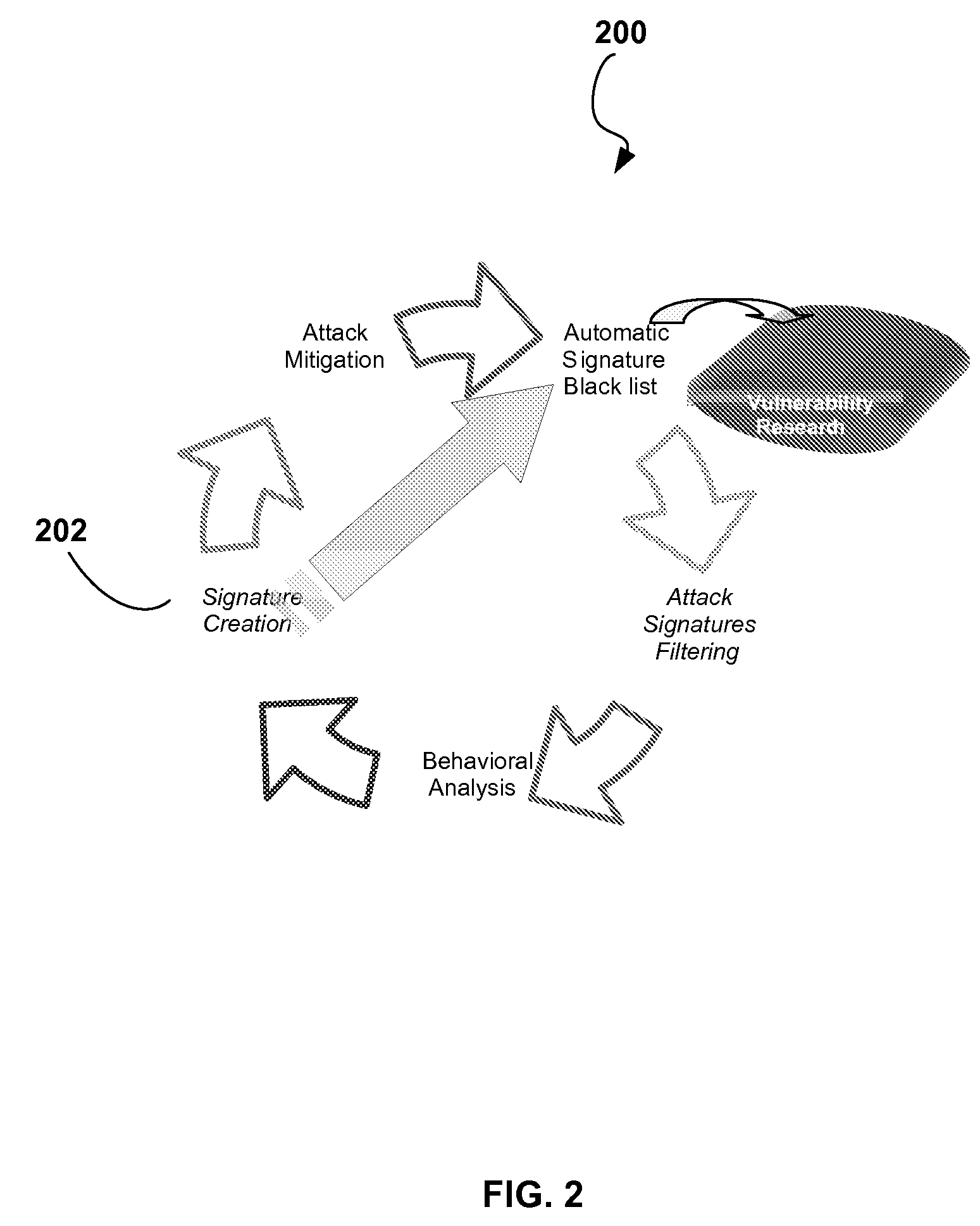
Automatic Signature Propagation Network
ActiveUS20080086772A1Reduces blocking response timeExpand the scope of protectionMemory loss protectionError detection/correctionDigital signatureDistributed security
A distributed security system wherein intelligent security agents (i.e., agent devices) share security incident information between themselves via a controller. An adaptive security decision making involving network worms (non-SMTP worms) and DoS floods attacks is also described; wherein the Worms and DoS flood digital signatures are generated to assist in intrusion prevention process.
Owner:RADWARE
Methods and systems for data traffic based adaptive security
The present disclosure relates to traffic monitoring through one or more access control servers configured configured for (i) routing server resource request messages to resource server(s), (ii) extracting information identifying a target server resource from data packets corresponding to one or more received server resource request messages, and (iii) selectively transmitting the received server resource request message to a resource server. The security server(s) is configured to receive a server resource request message data extracted from a server resource request message and initiate a first security response, wherein the initiated first security response is dependent on analysis of the server resource request message data. Responsive to identifying an indicator of compromise or that an originating terminal corresponding to the server resource request is identified within a blacklist, the first security response comprises non-transmission of at least one server resource request message by the access control server to a resource server.
Owner:PING IDENTITY
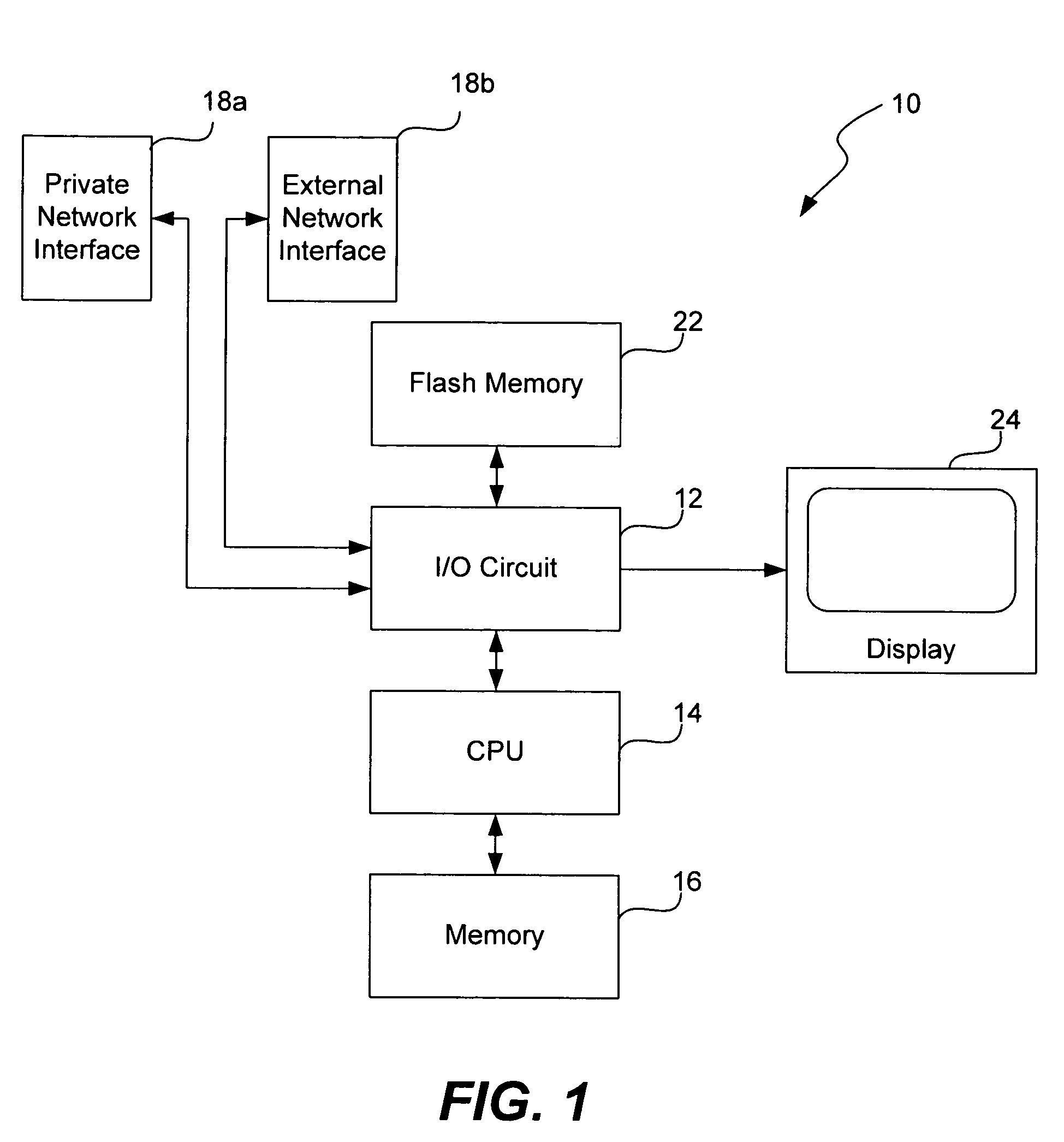
Pre-boot authentication system
InactiveUS7000249B2Volume/mass flow measurementDigital computer detailsPre-boot authenticationComputer module
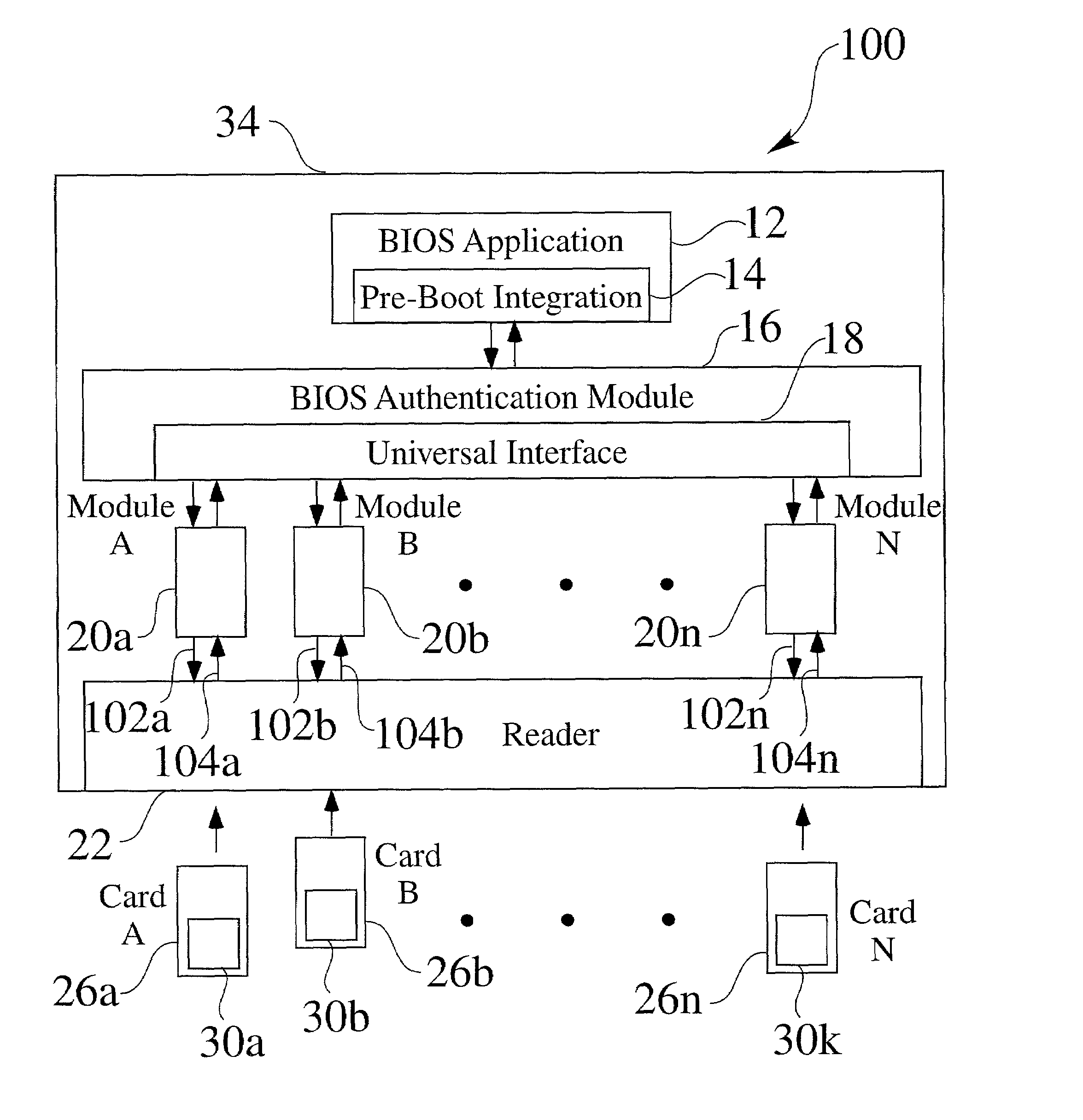
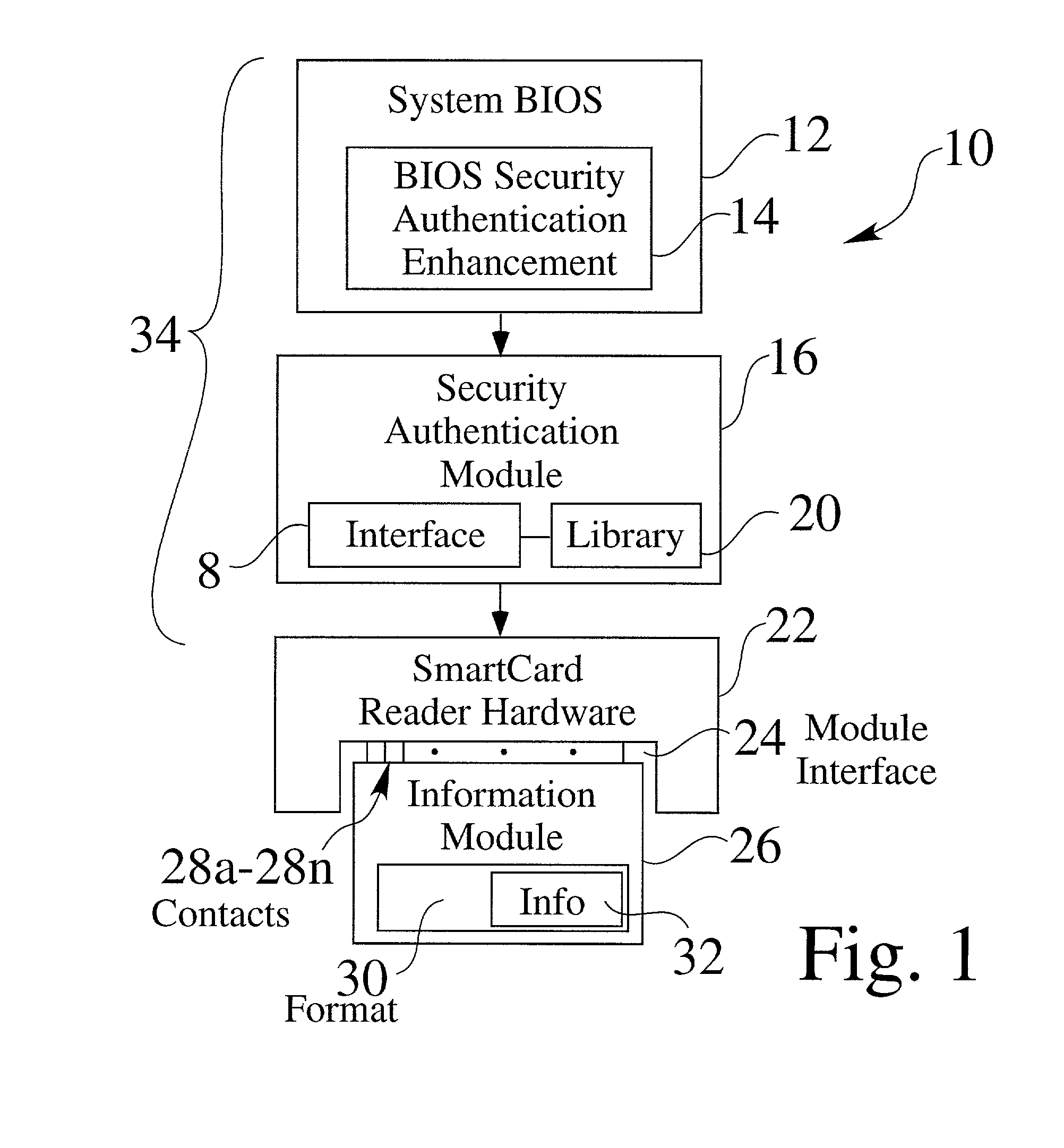
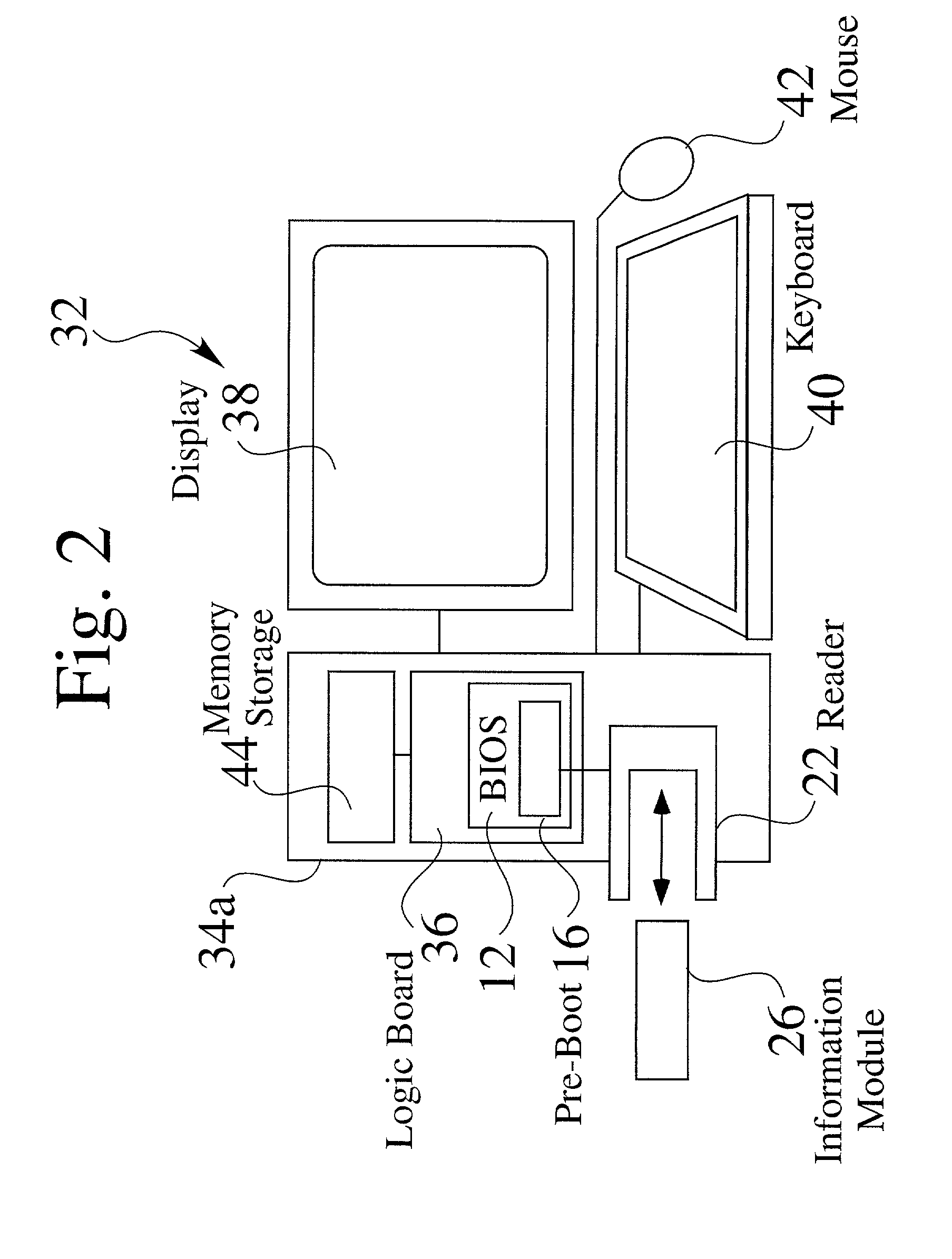
Systems are provided for the enhancement of the system BIOS for microprocessor-based devices. Before the end of a BIOS start-up procedure, the BIOS operation is diverted to a BIOS security authentication system which may be a portion of an enhanced system BIOS. The BIOS security authentication system establishes communication with an information module, if the information module is present. The information module is typically a removable or installable card, which may be unique to one or more users. Based upon an information exchange between the security authentication module and the information module, the security authentication module controllably allows or prevents the system BIOS start-up procedure to resume and finish. In a preferred embodiment, the security authentication module is used as a pre-boot authentication system, to prevent a microprocessor-based device from booting up, unless a valid authorized information module is present. In other preferred embodiments, an adaptive security authentication module interface is provided, to allow information exchange with a variety of information modules having one or more information formats. In alternate embodiments, information from the information exchange may be transferred to the main system BIOS (such as to provide system functions to the BIOS, or to provide identity information of the user, based upon the information module).
Owner:MAISHI ELECTRONICS (SHANGHAI) LTD
Mobile AD Hoc network self-adapting secure routing method based on reliability
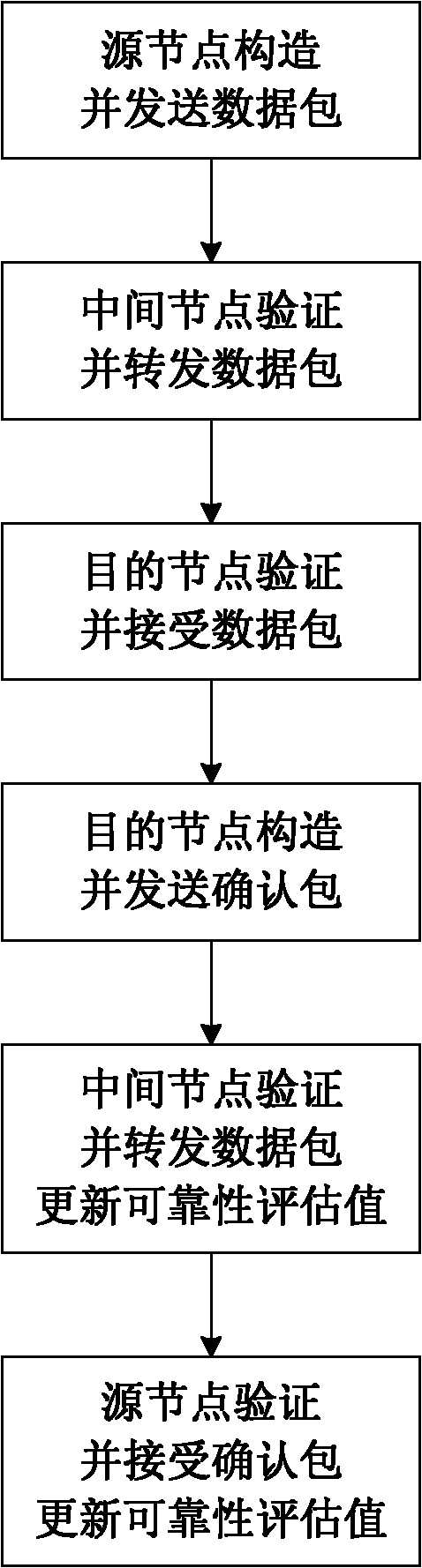
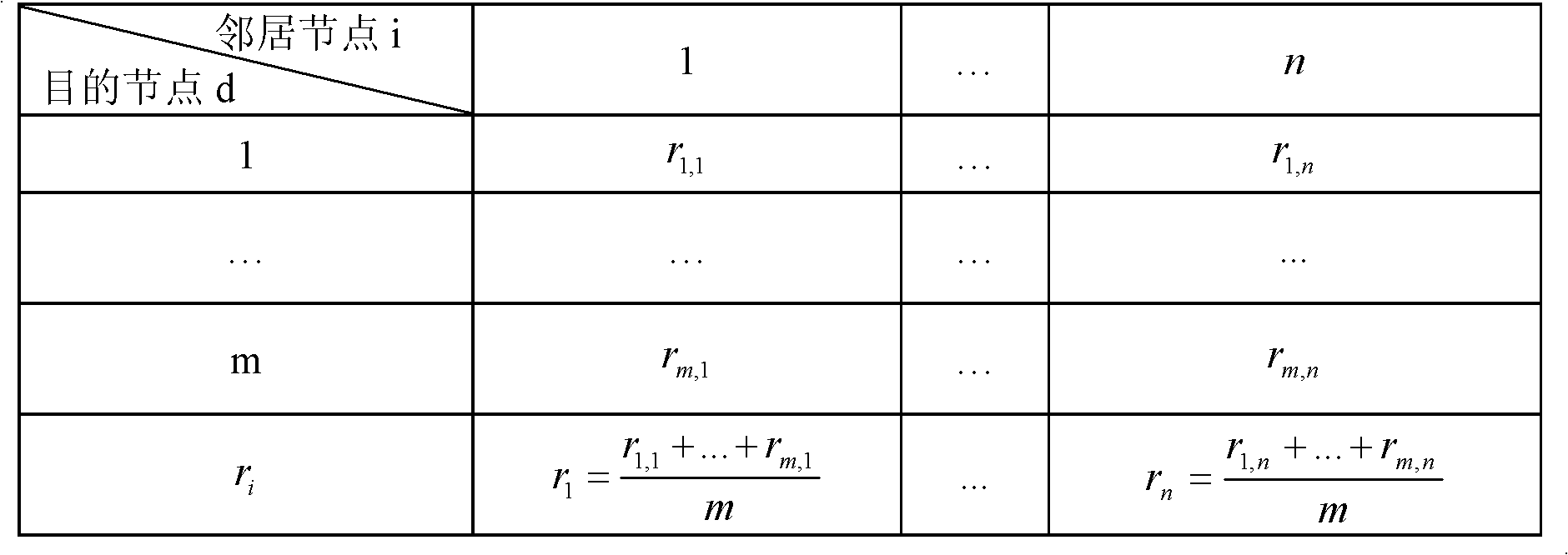
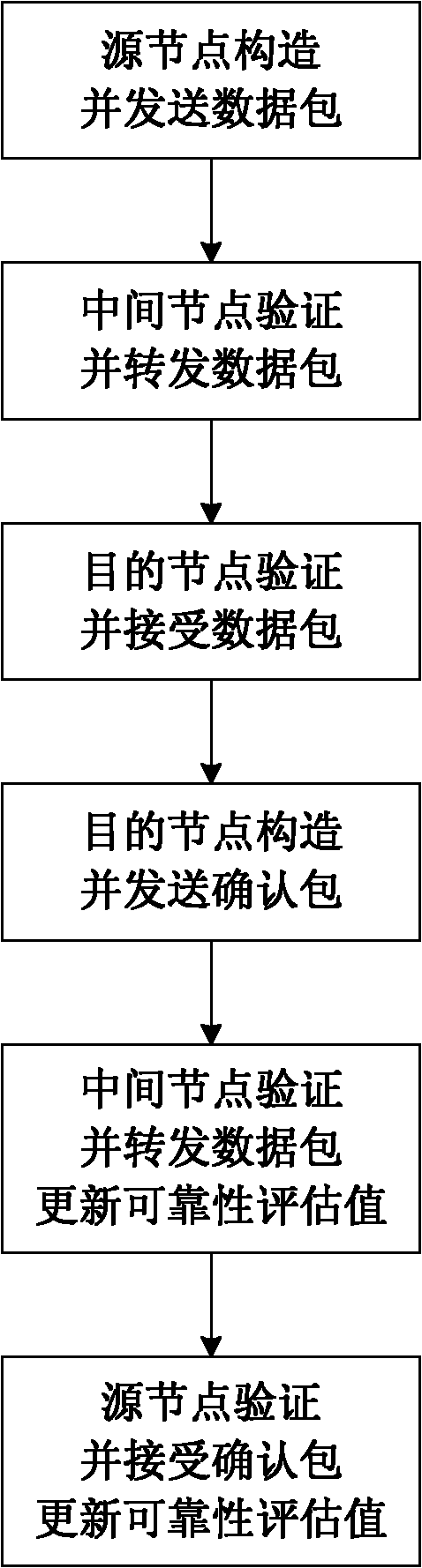
ActiveCN102158864AGuaranteed validityIntegrity guaranteedNetwork topologiesSecurity arrangementRouting decisionNetwork size
The invention discloses a mobile AD Hoc network self-adapting secure routing method based on reliability. The method comprises the following four major steps: step I, a source node transmits data packets; step II, an intermediate node forwards the data packets; step III, a destination node receives the data packets; and step IV, the data packets are transmitted and confirmed and reliability is updated. The method integrates route discovery and data transmission into a whole process, each node evaluates the reliability of adjacent nodes reaching the destination node through a response feedbackmechanism, and independently makes a route decision according to reliability evaluation level, so that unreliable nodes are avoided and a reliable path is selected from a plurality of alternative paths, the method solves secure and reliable data transmission and symmetrical secret key transmission while solving secure routing discovery problem, and improves the security and the adaptability of the network. Compared with an existing AD Hoc network routing method, the method can resist attack to a greater extent on the basis that higher expense is not needed, still has good restorability when anetwork size is changed, nodes rapidly moves and even attack in a large scope exists and error of nodes exists, and is applicable to large-scale network with rapidly moving nodes. The method has a higher practical value and a wide application prospect in the technical field of mobile AD Hoc network security.
Owner:BEIHANG UNIV
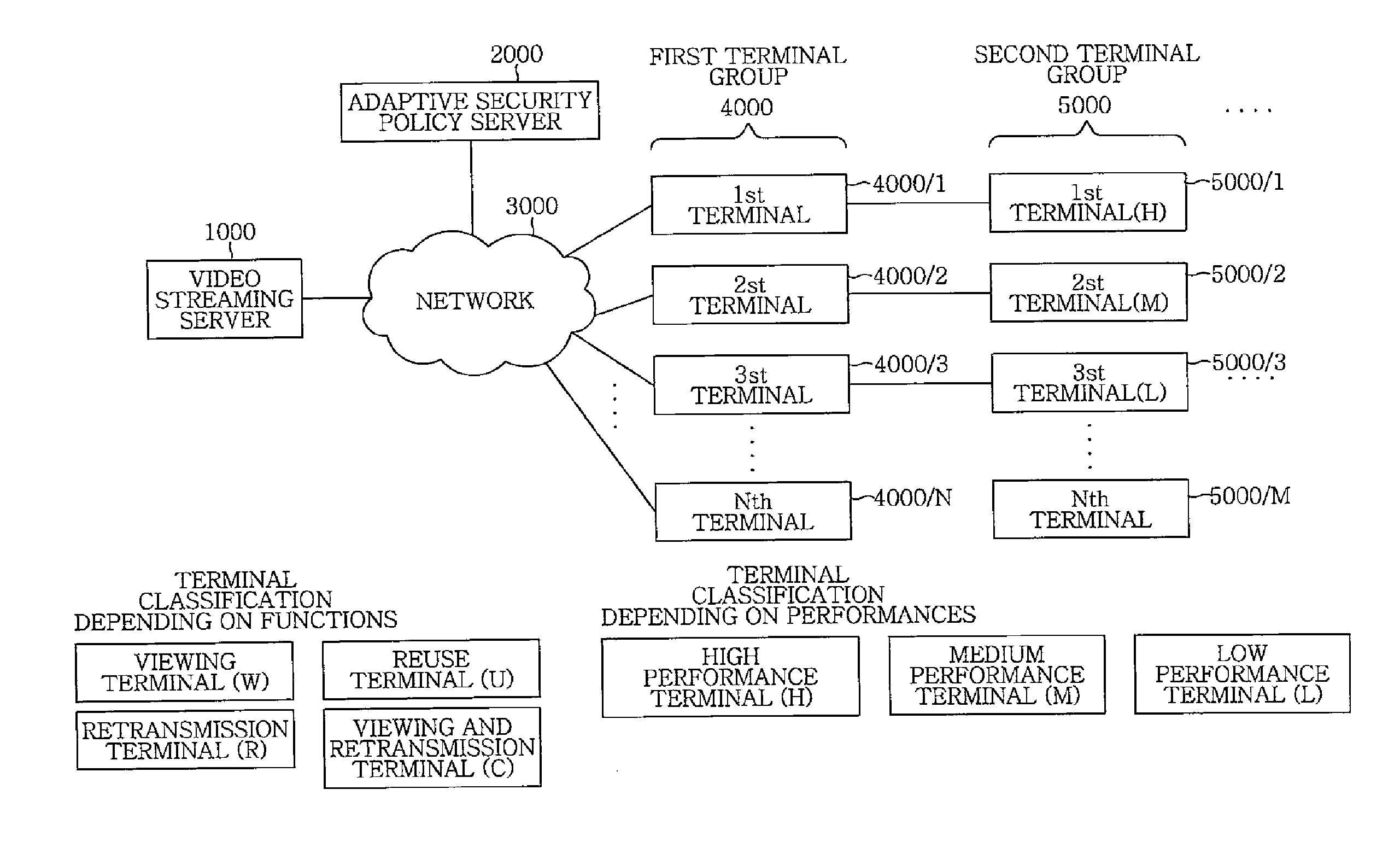
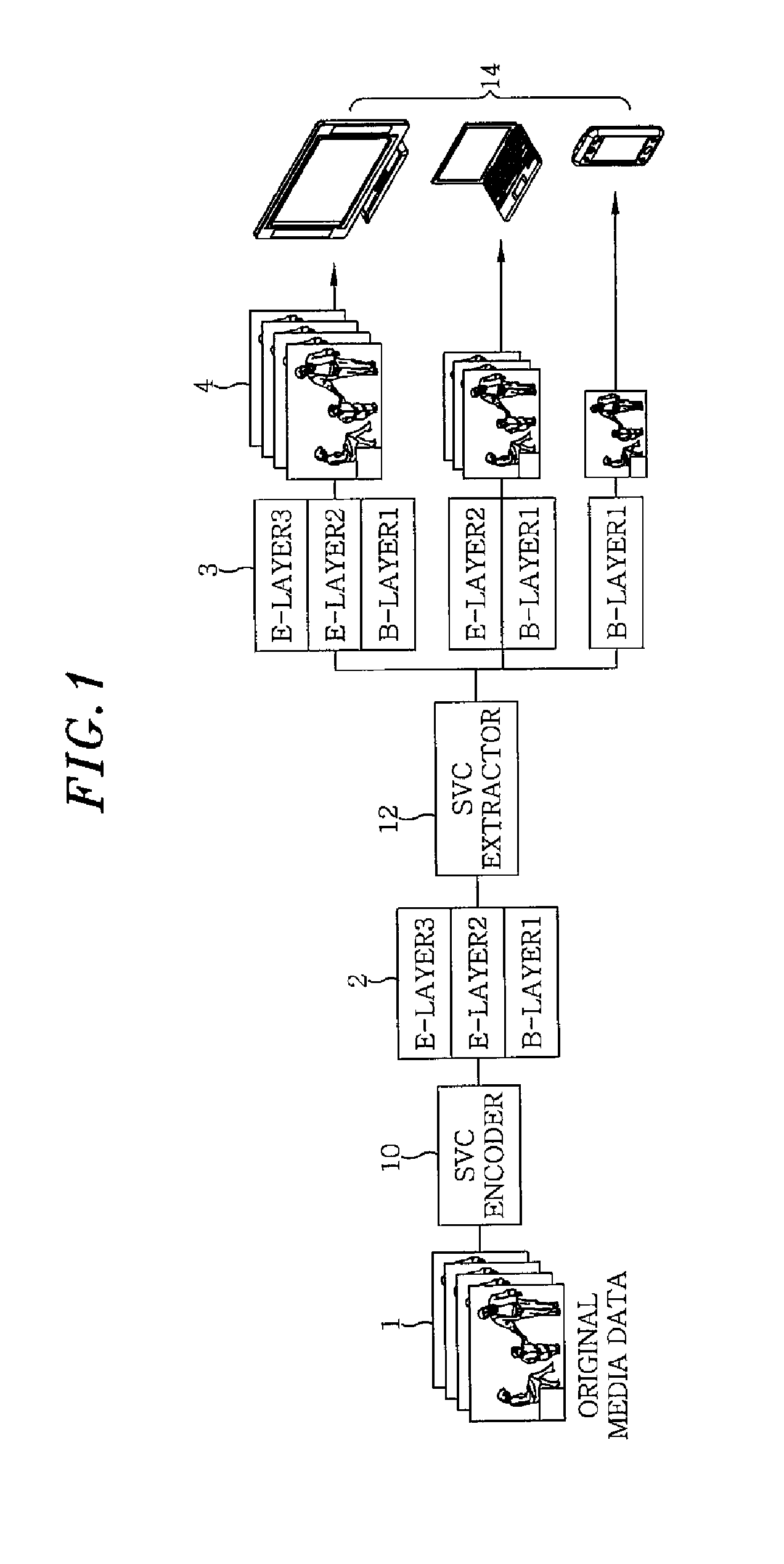
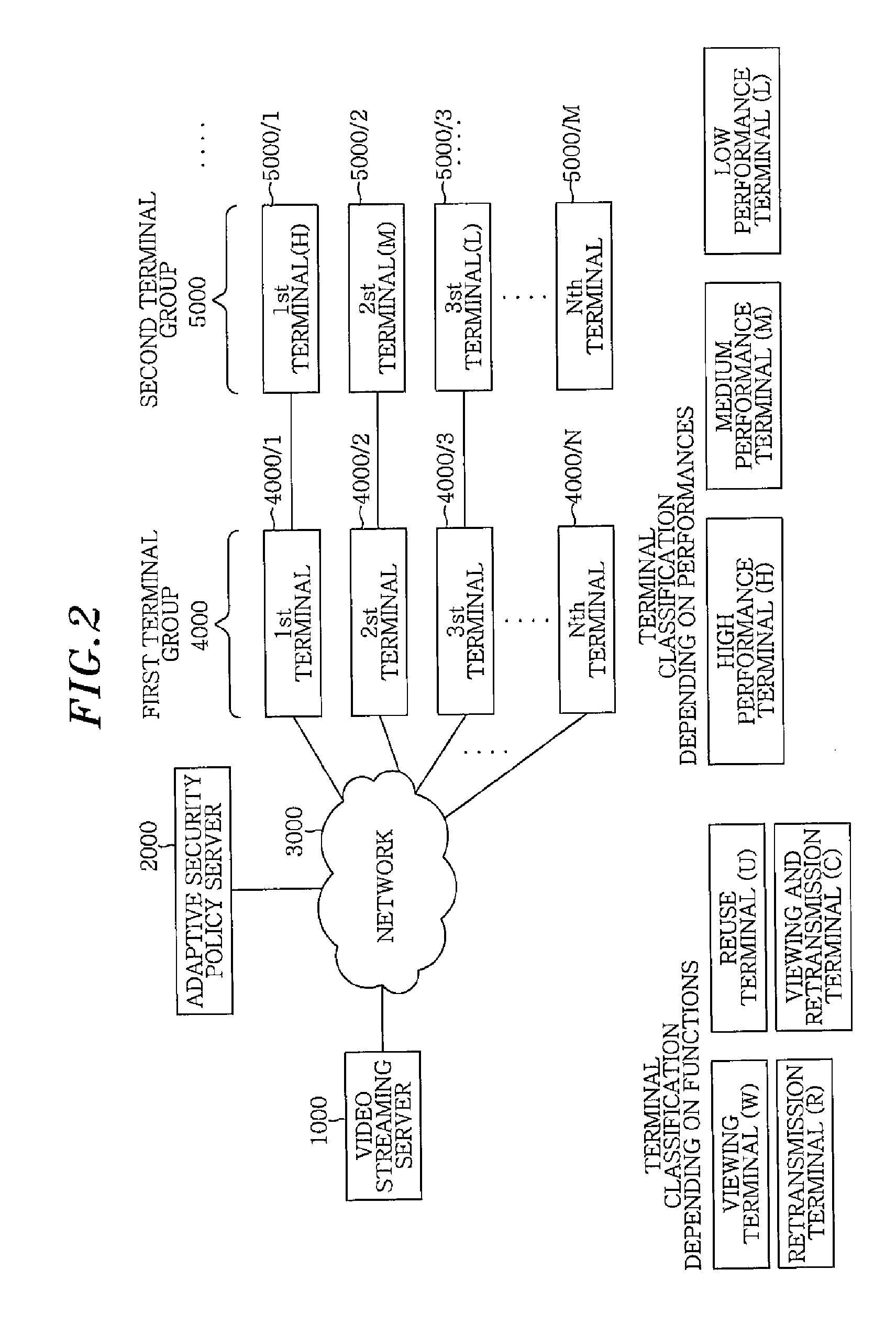
Adaptive security policy based scalable video service apparatus and method
ActiveUS20110145560A1Reliable and safe serviceSimple technologyKey distribution for secure communicationMultiple digital computer combinationsStreaming dataService profile
An adaptive security policy based scalable video service apparatus includes a video streaming server, an adaptive security policy server and a terminal. The video streaming server receives a service demand via a network and generates an encrypted streaming data. The adaptive security policy server analyzes a media structure and the service demand, by using a service profile received from the video streaming server, so as to generate a security policy description. The terminal generates and transmits the service demand to the video streaming server or the adaptive security server, obtains the encrypted streaming data from the video streaming server and decrypts the encrypted streaming data for playback, storing and retransmission.
Owner:ELECTRONICS & TELECOMM RES INST
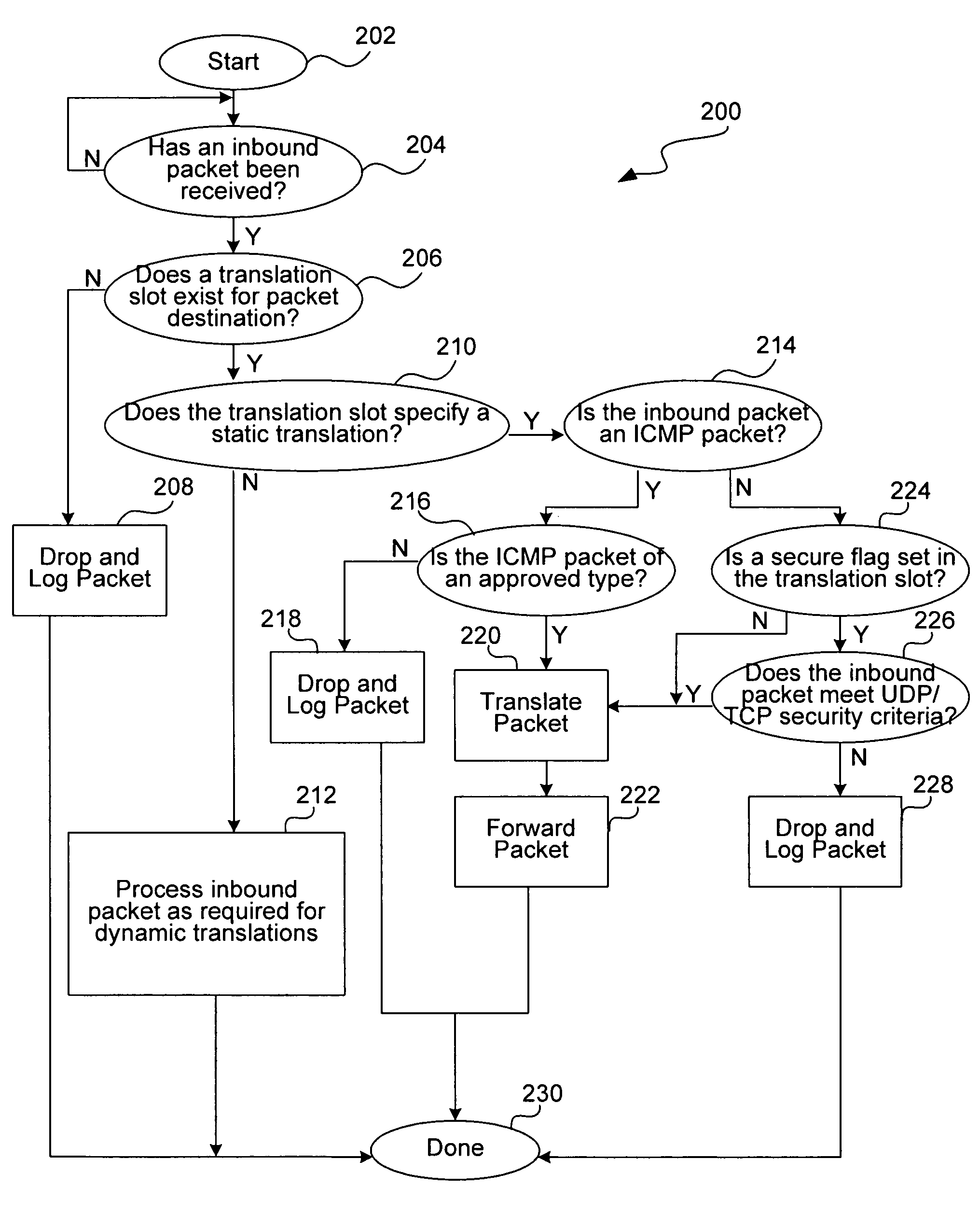
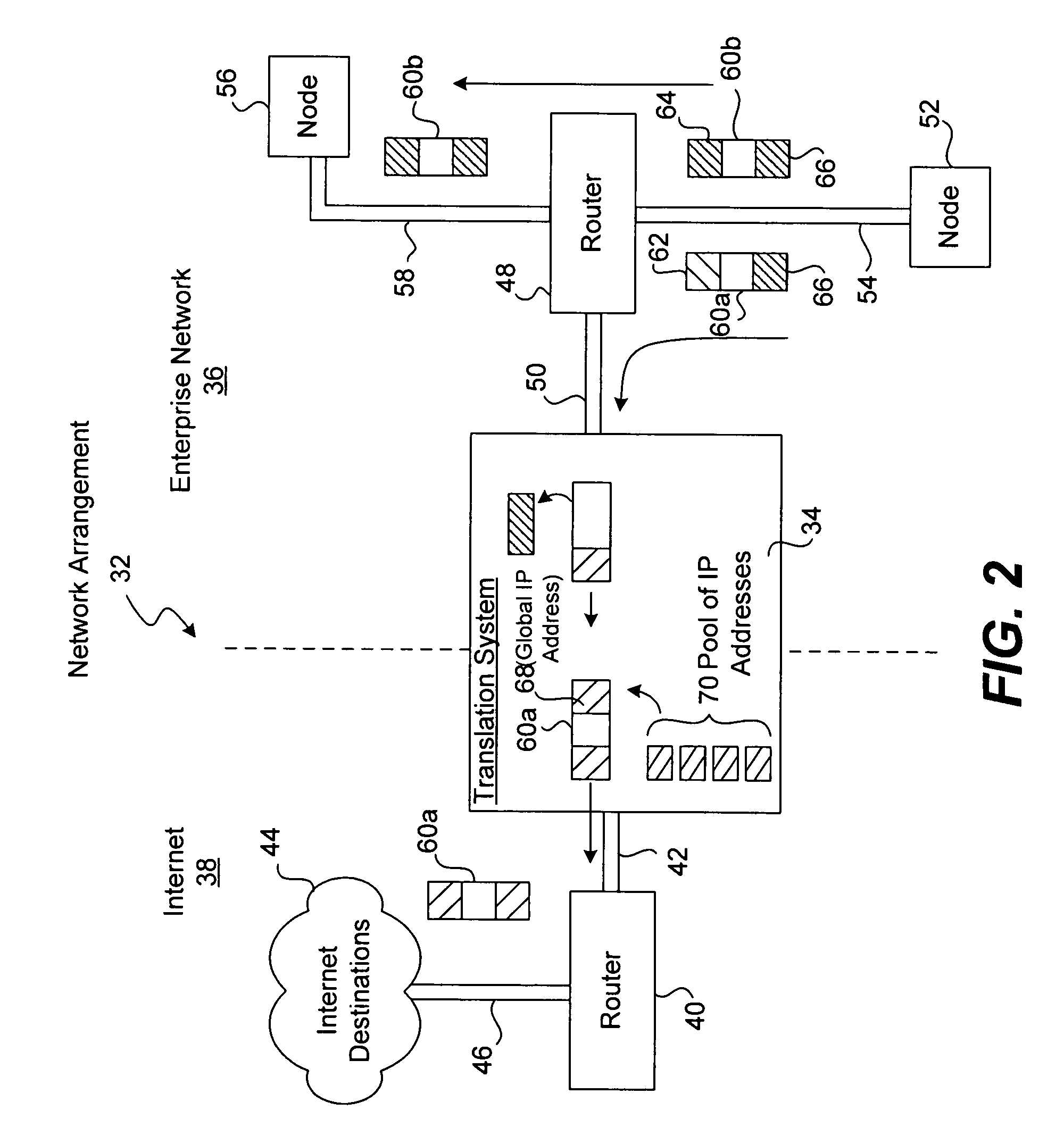
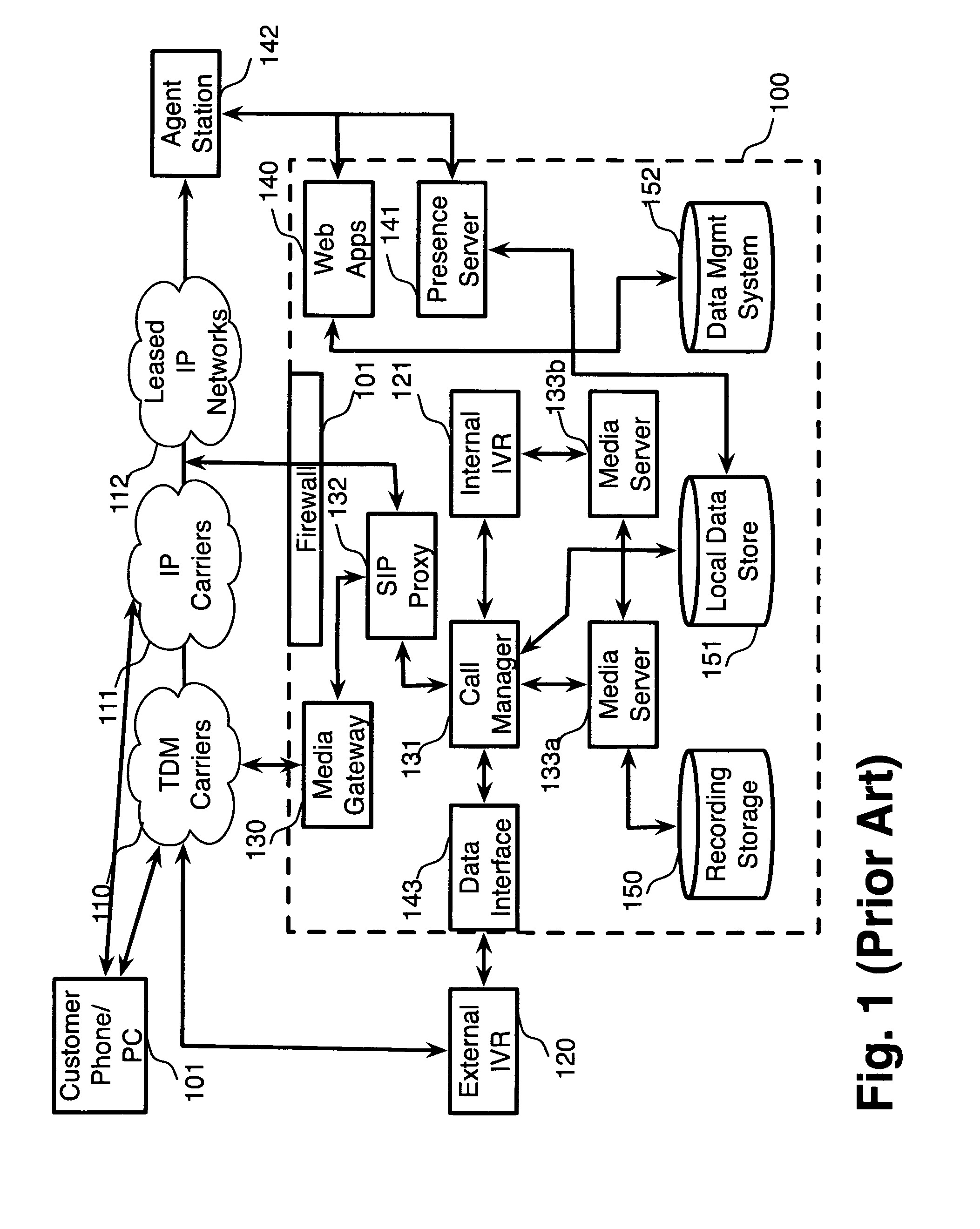
Security system for network address translation systems
InactiveUS7583668B1Data switching by path configurationMultiple digital computer combinationsIp addressThe Internet
A system and method are disclosed for providing perform network address translation of network layer addresses of packets exchanged between nodes on a local network and nodes outside the local network. This allows local hosts in an enterprise network to share global IP addresses from a limited pool of such addresses available to the enterprise. The translation may be accomplished by replacing the source address in headers on packets destined for the Internet and by replacing destination address in headers on packets entering the local enterprise network from the Internet. Packets arriving from the Internet are screened by an adaptive security algorithm. According to this algorithm, packets are dropped and logged unless they are deemed nonthreatening.
Owner:CISCO TECH INC
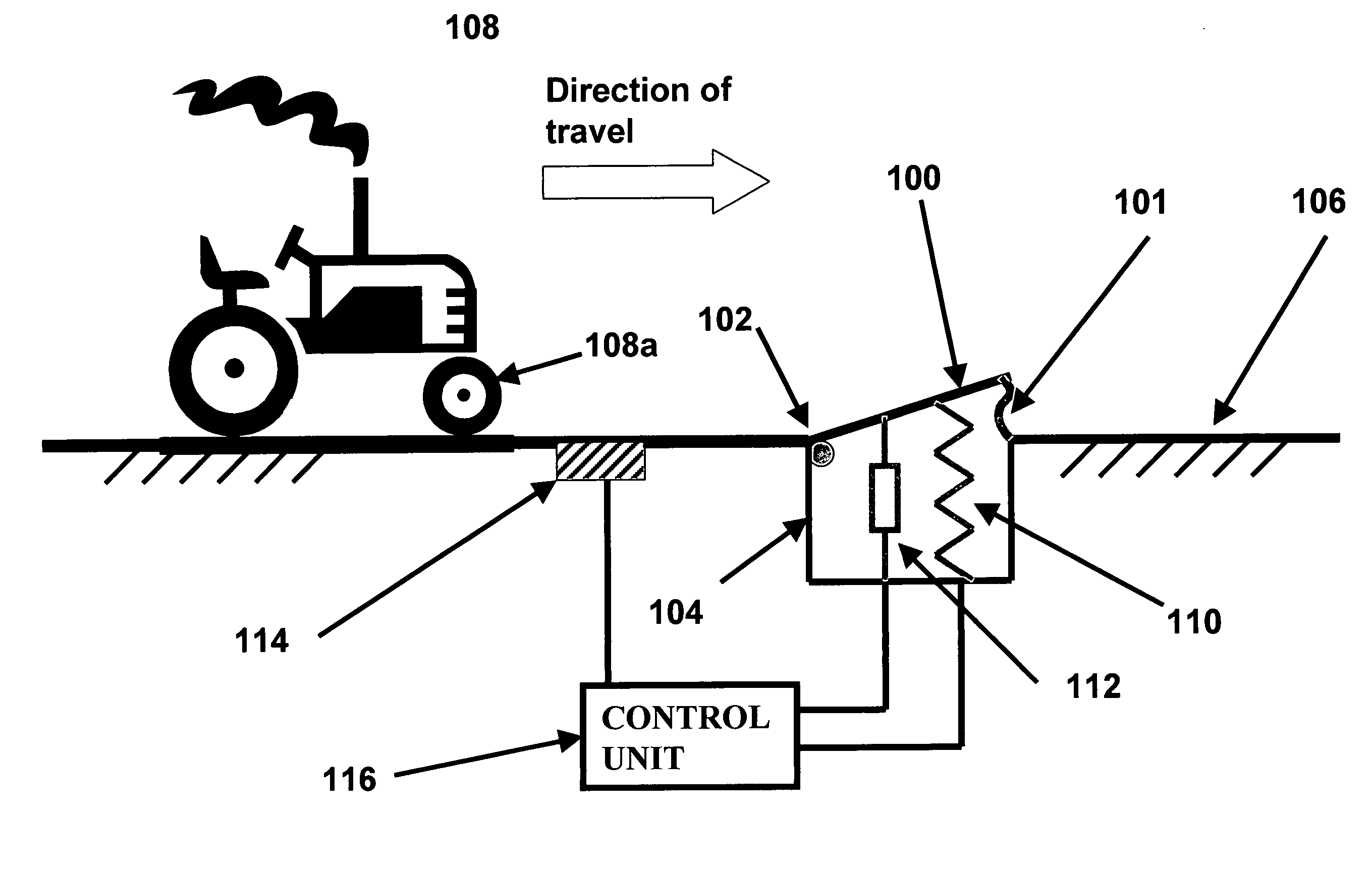
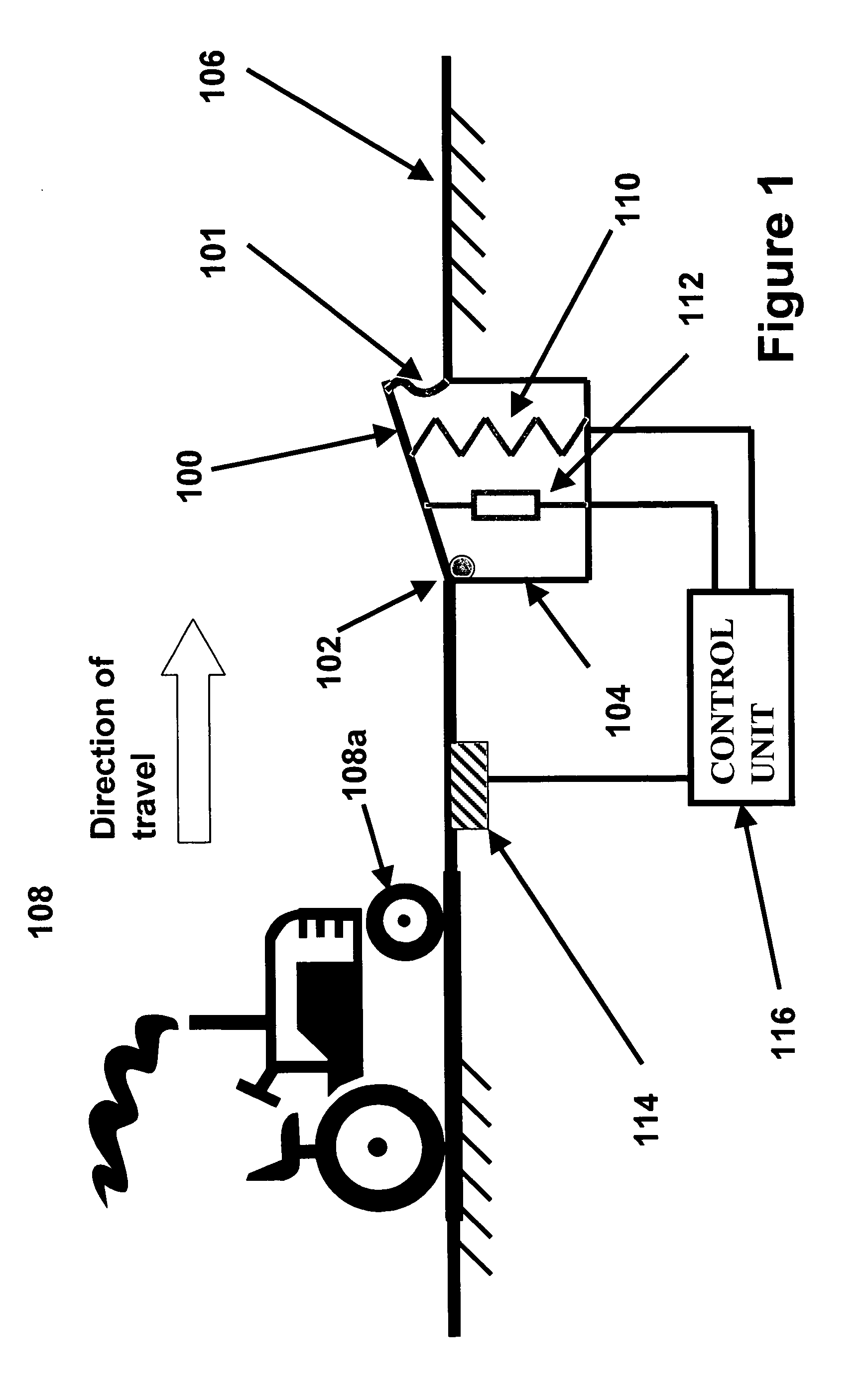
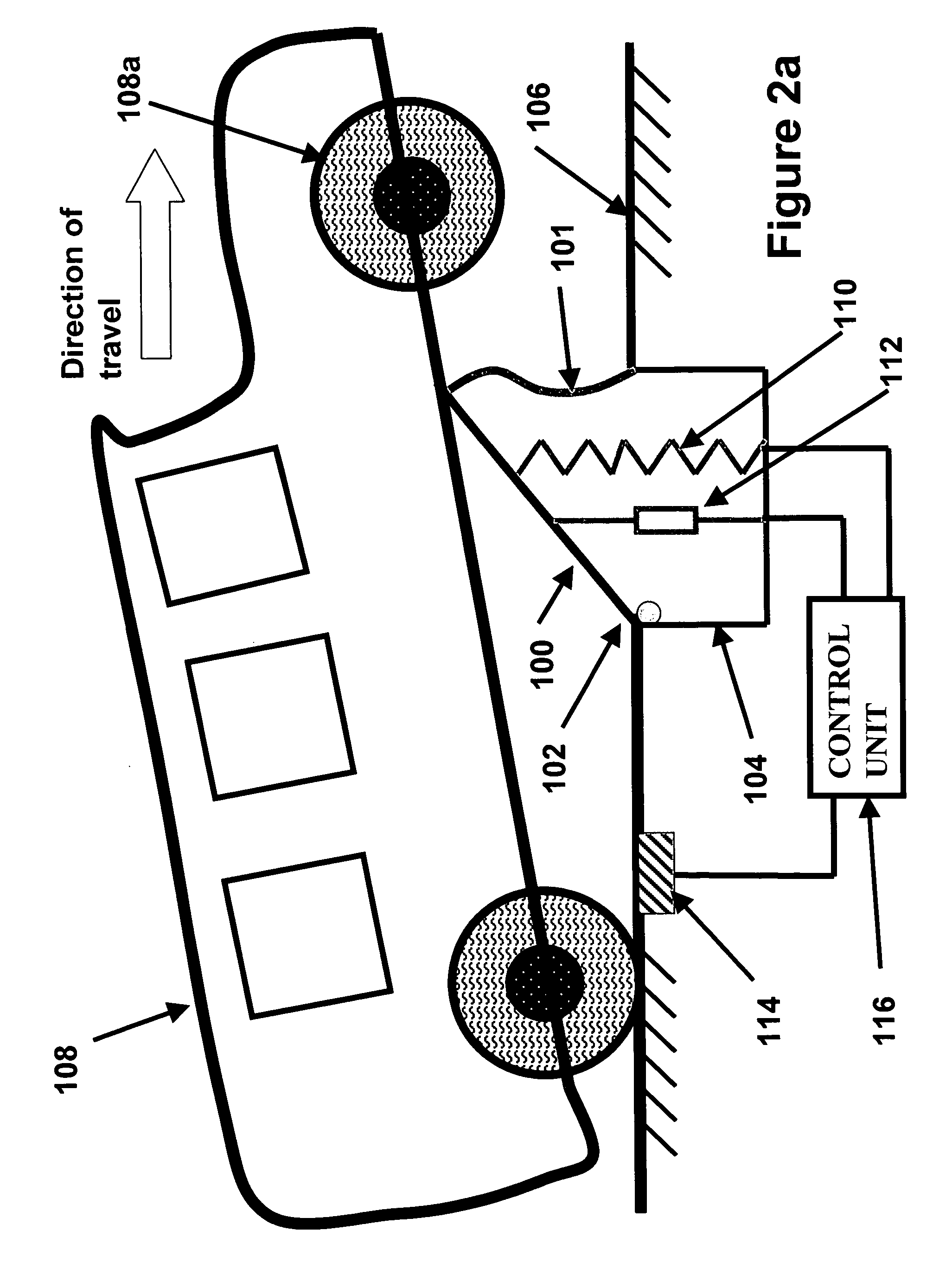
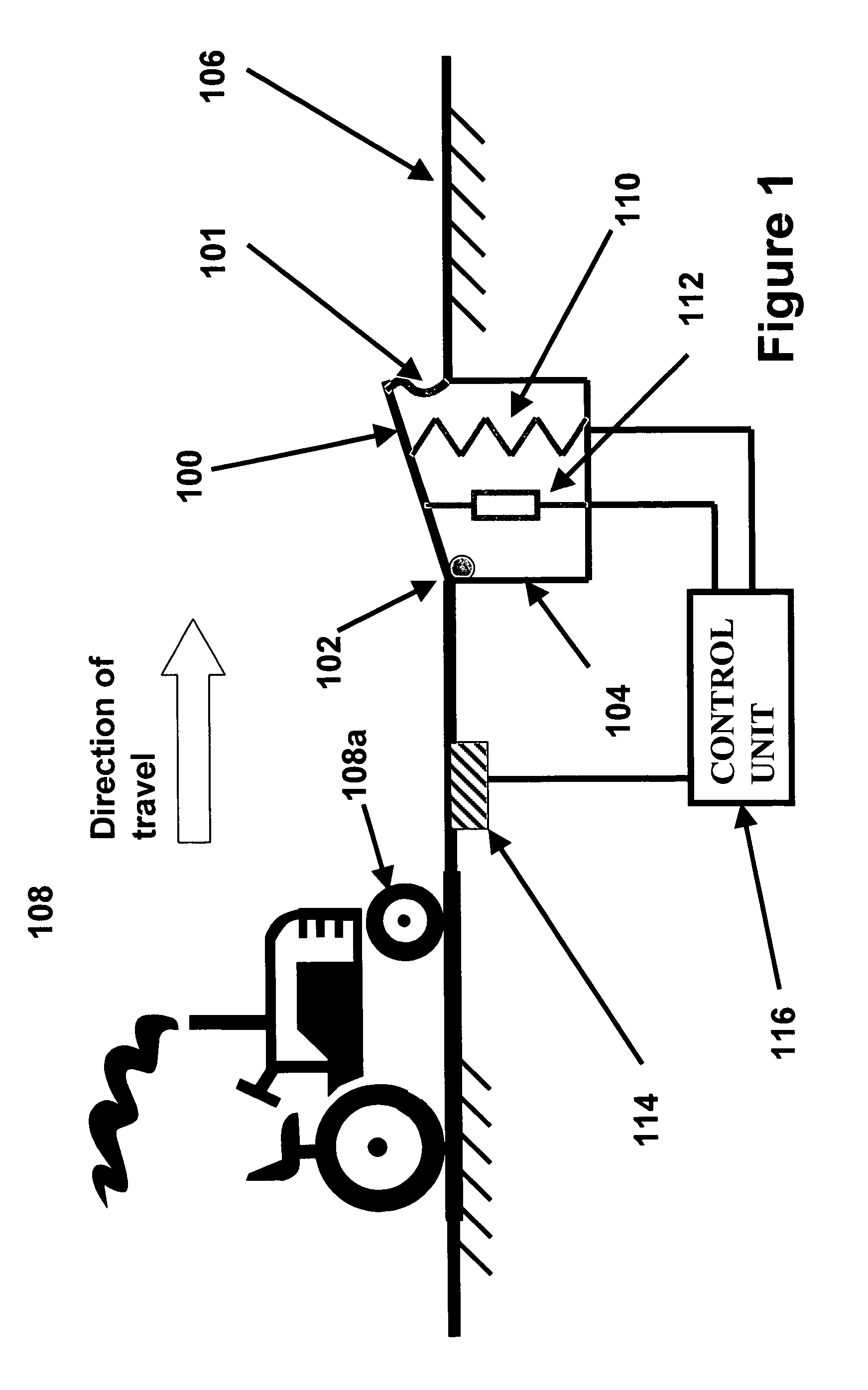
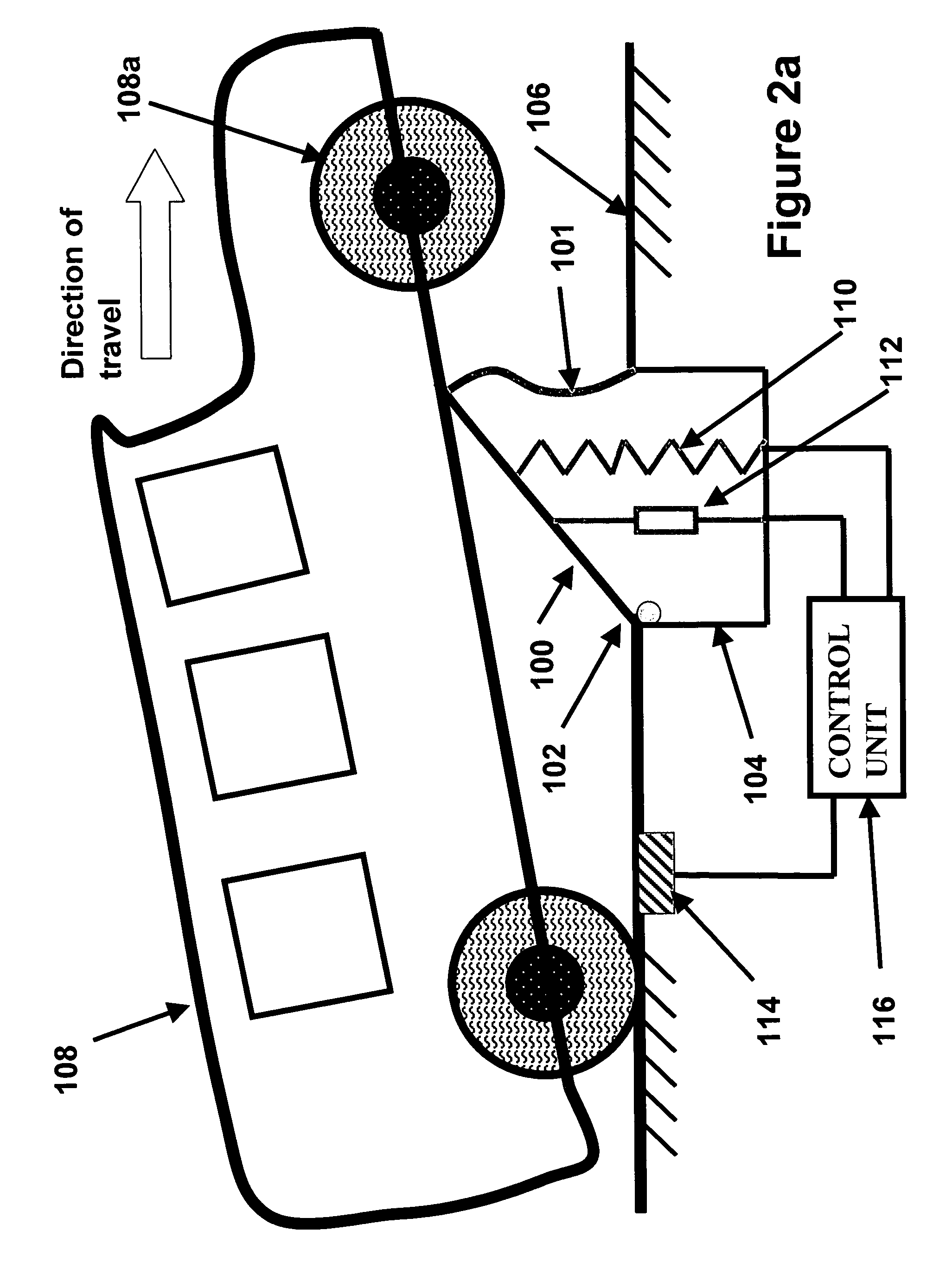
Adaptive security and protective barriers and traffic control speed bumps
InactiveUS20050201827A1Few personnelHigh initial costTraffic signalsEmbedding padsSpeed bumpEngineering
Owner:OMNITEK PARTNERS LLC
Systems and Methods for Runtime Adaptive Security to Protect Variable Assets
ActiveUS20140090071A1Reduce security risksImprove overall utilizationMemory loss protectionError detection/correctionApplication softwareSecurity question
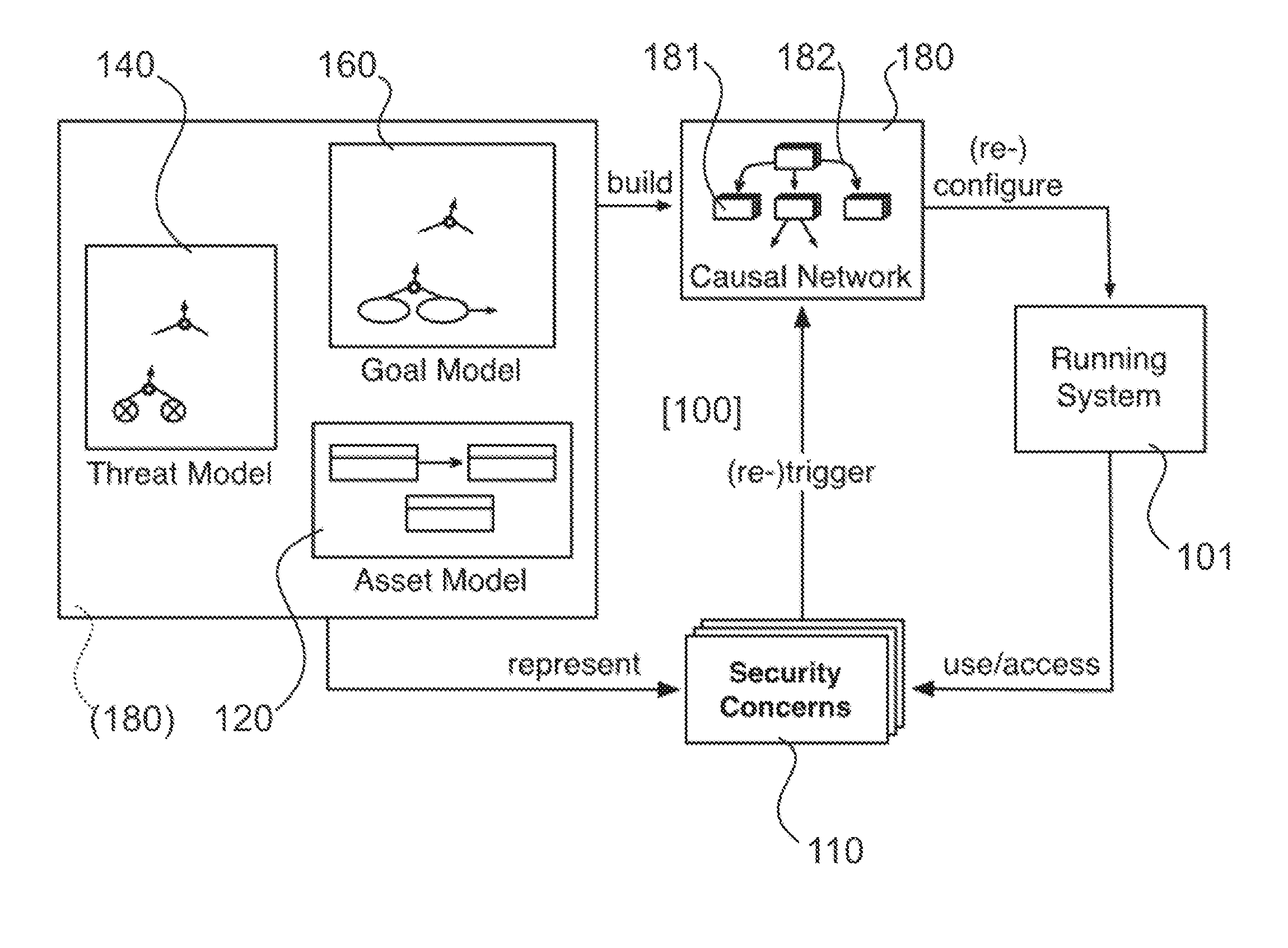
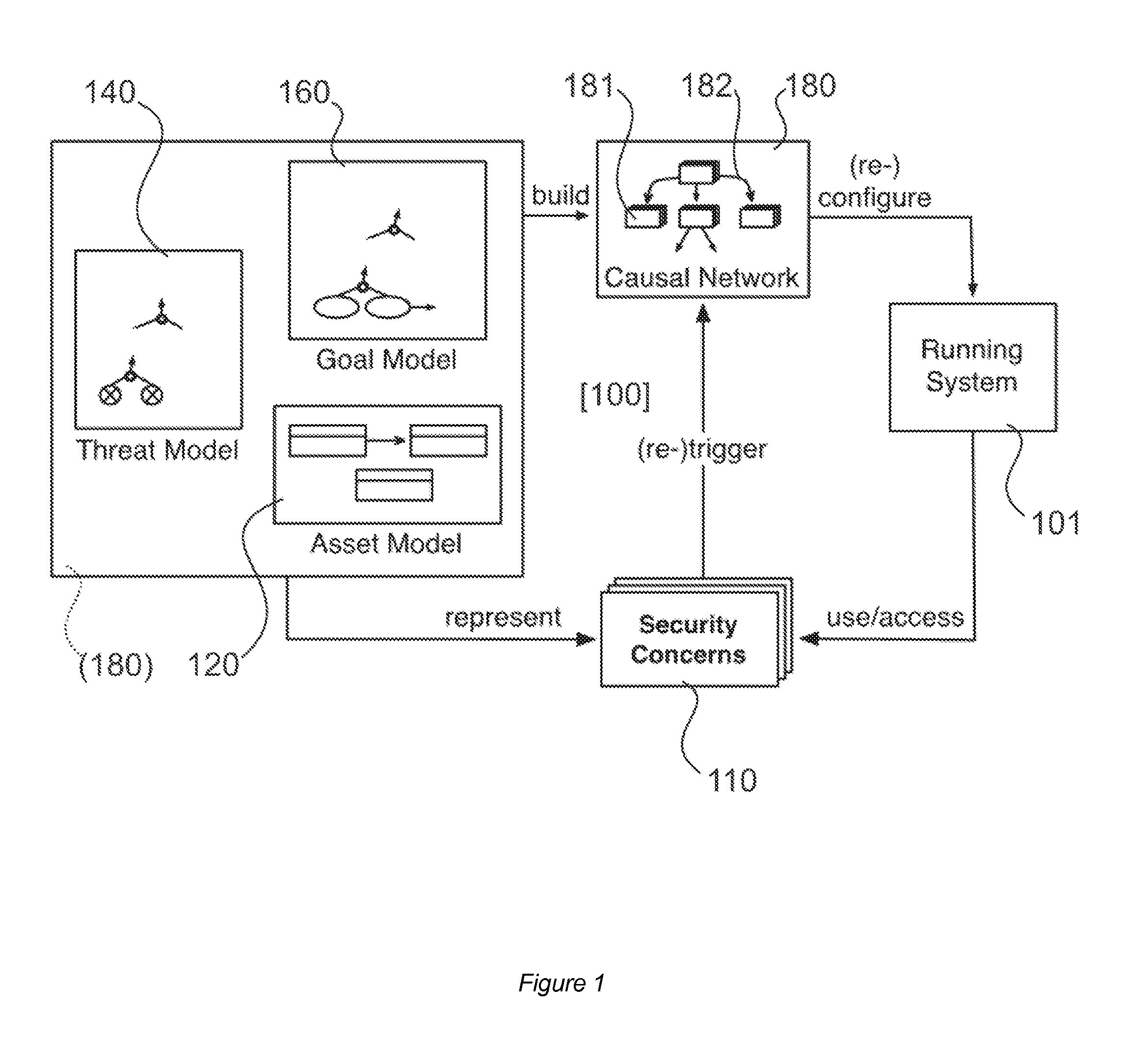
A method of adapting a security configuration of a data processing application at runtime, and a system, together with its computing architecture, are disclosed. The system stores a causal network comprising a plurality of nodes and a plurality of incoming and outgoing causal links associated therewith, wherein each node of the causal network is associated with a security concern or a requirement that can be affected by any configuration of the security controls. The current value of assets nodes, as well as those of the security concerns that can be affected by monitored contextual factors, are updated. The control nodes corresponding to the security controls is updated according to the security configuration whose utility is evaluated by the causal network. The node corresponding to the at least one variable is updated with the determined current value, which is propagated through the causal network through the causal links associated with the updated node. The security configuration with the highest utility is selected and replaces the actual configuration by activating and / or deactivating the security functions corresponding to security control nodes enabled / disabled in the selected security configuration.
Owner:UNIVERSITY OF LIMERICK
Adaptive security and protective barriers and traffic control speed bumps
InactiveUS7114873B2Reduce operating costsOperational securityTraffic signalsEmbedding padsSpeed bumpEngineering
Owner:OMNITEK PARTNERS LLC
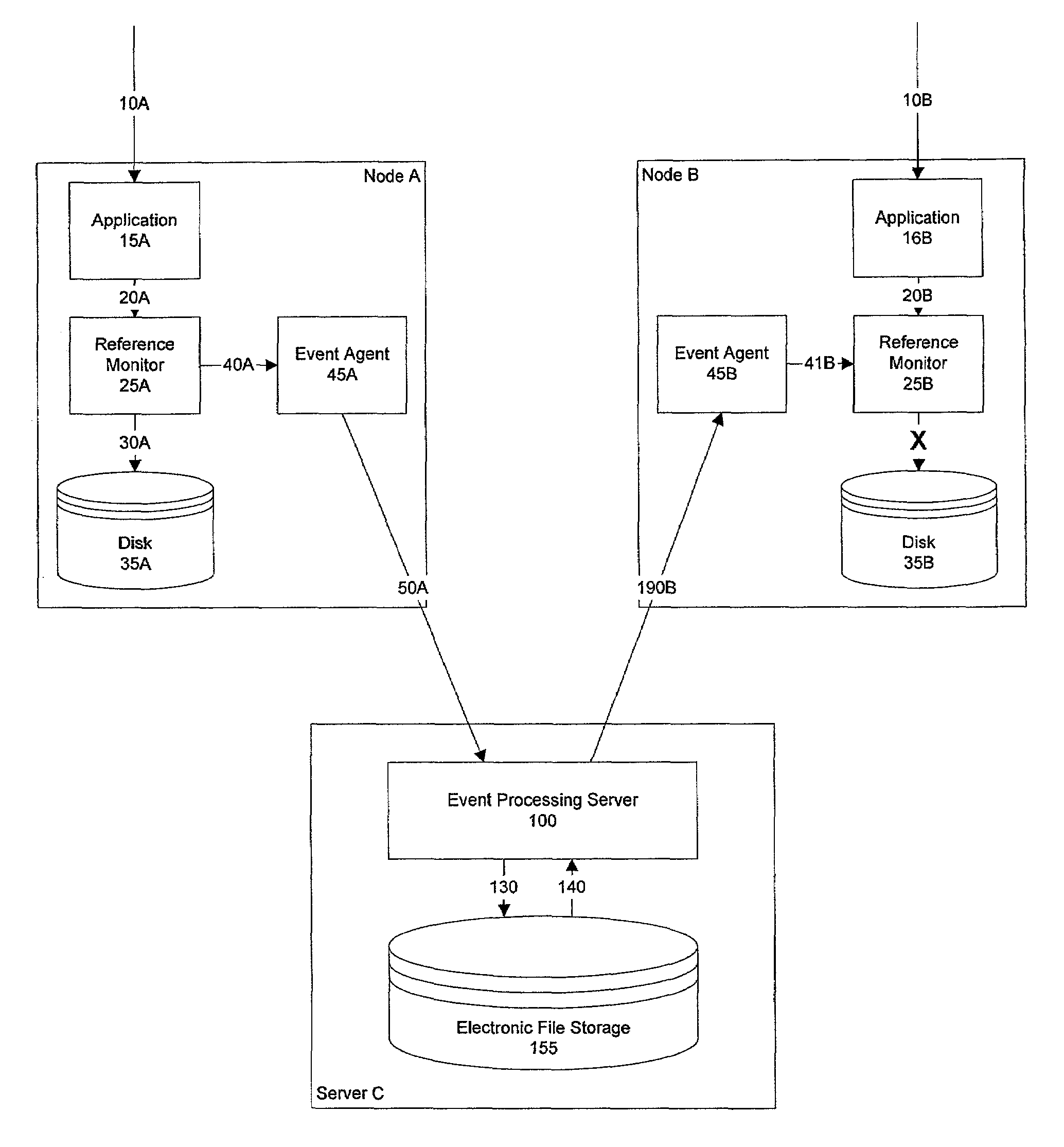
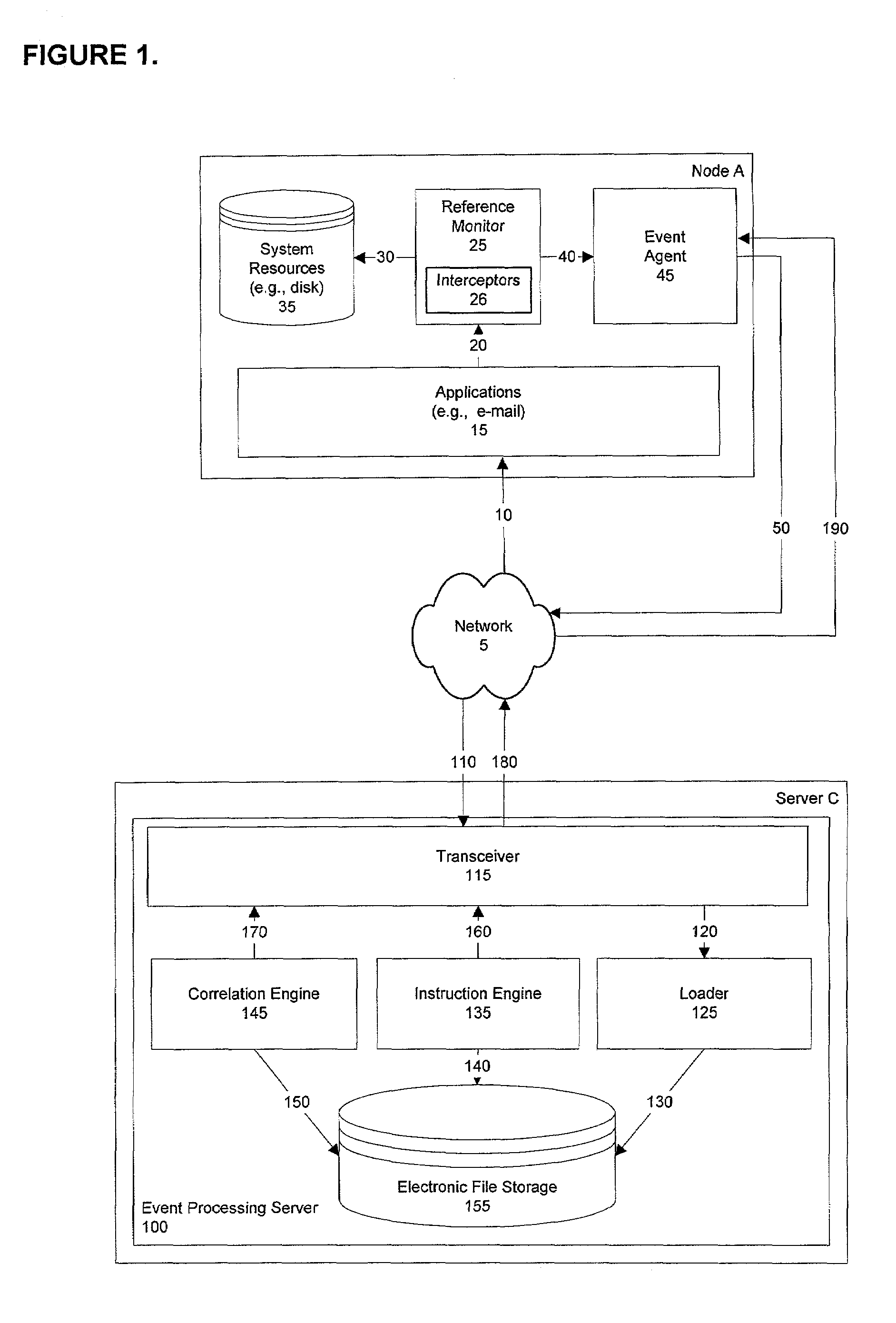
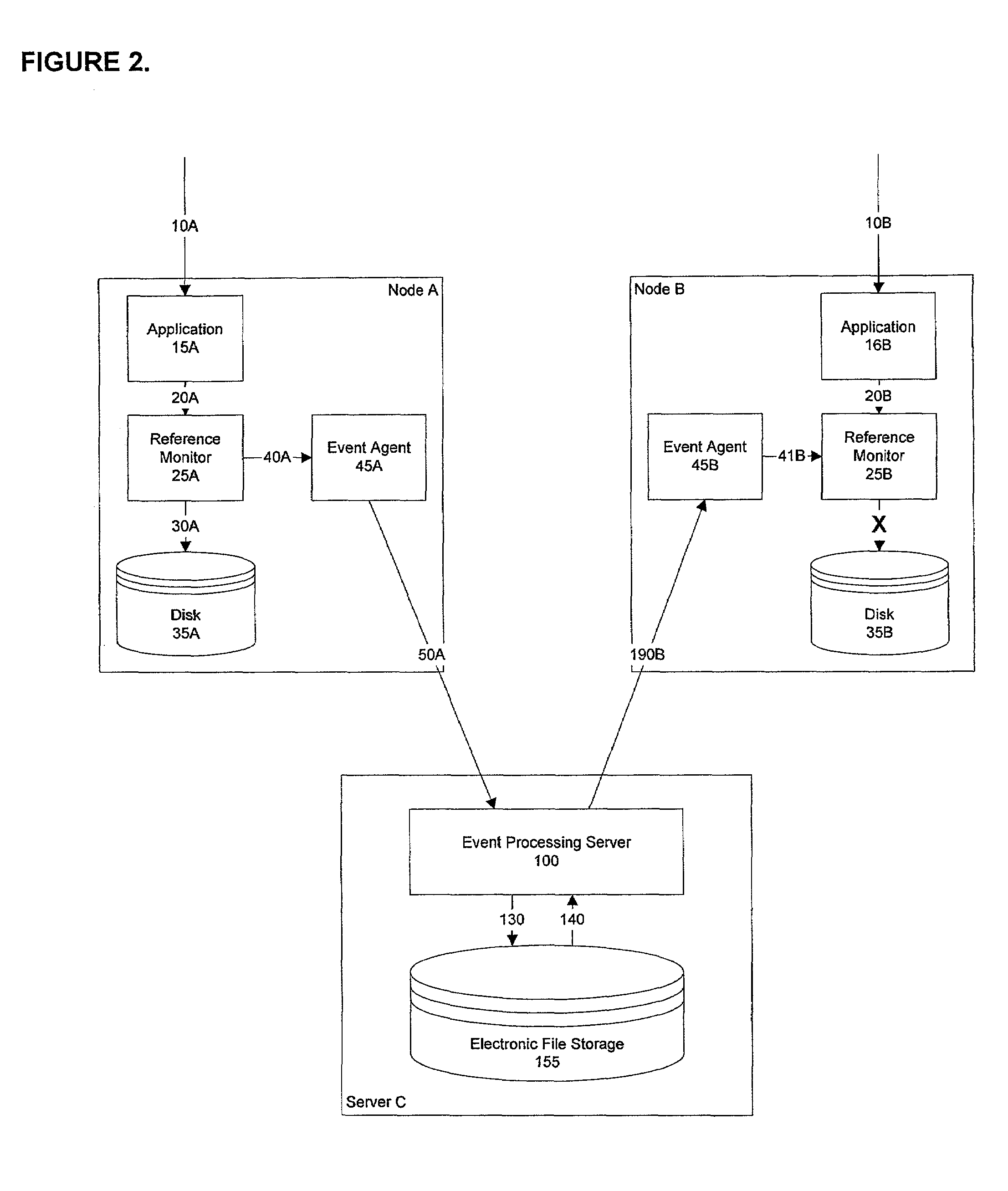
Stateful distributed event processing and adaptive security
ActiveUS7594267B2No human intervention requiredMemory loss protectionError detection/correctionComplex event processingComputerized system
The invention provides method and apparatus for maintaining a networked computer system including first and second nodes and an event processing server, the method comprising the first and second nodes detecting changes in state, the event processing server receiving notification of the changes in state from the first and second nodes, the event processing server correlating changes in state detected in the first and second nodes, and the event processing server executing a maintenance decision which affects the first and second nodes. The detecting, transmitting, correlating, and executing occurs without human intervention.
Owner:CISCO TECH INC
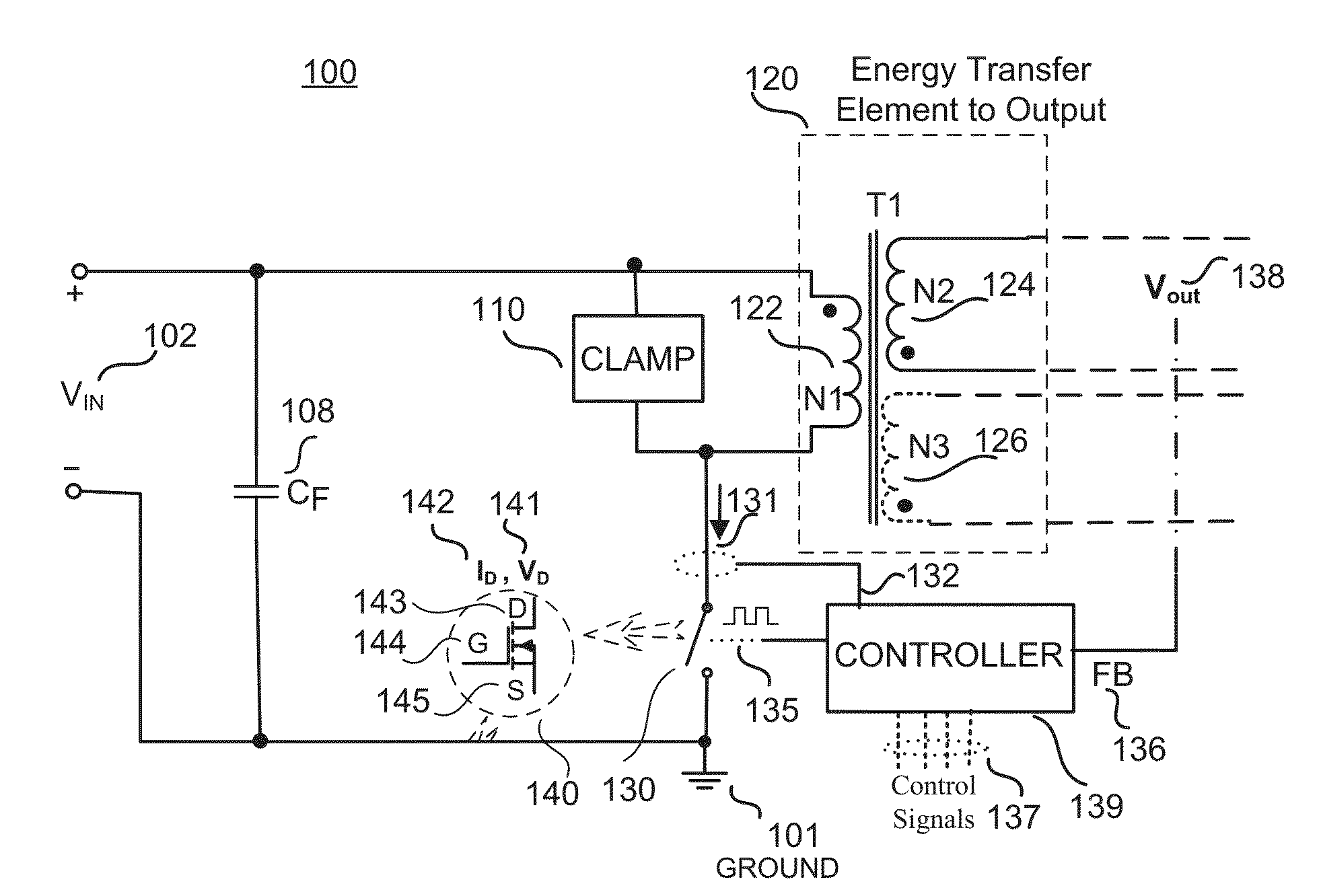
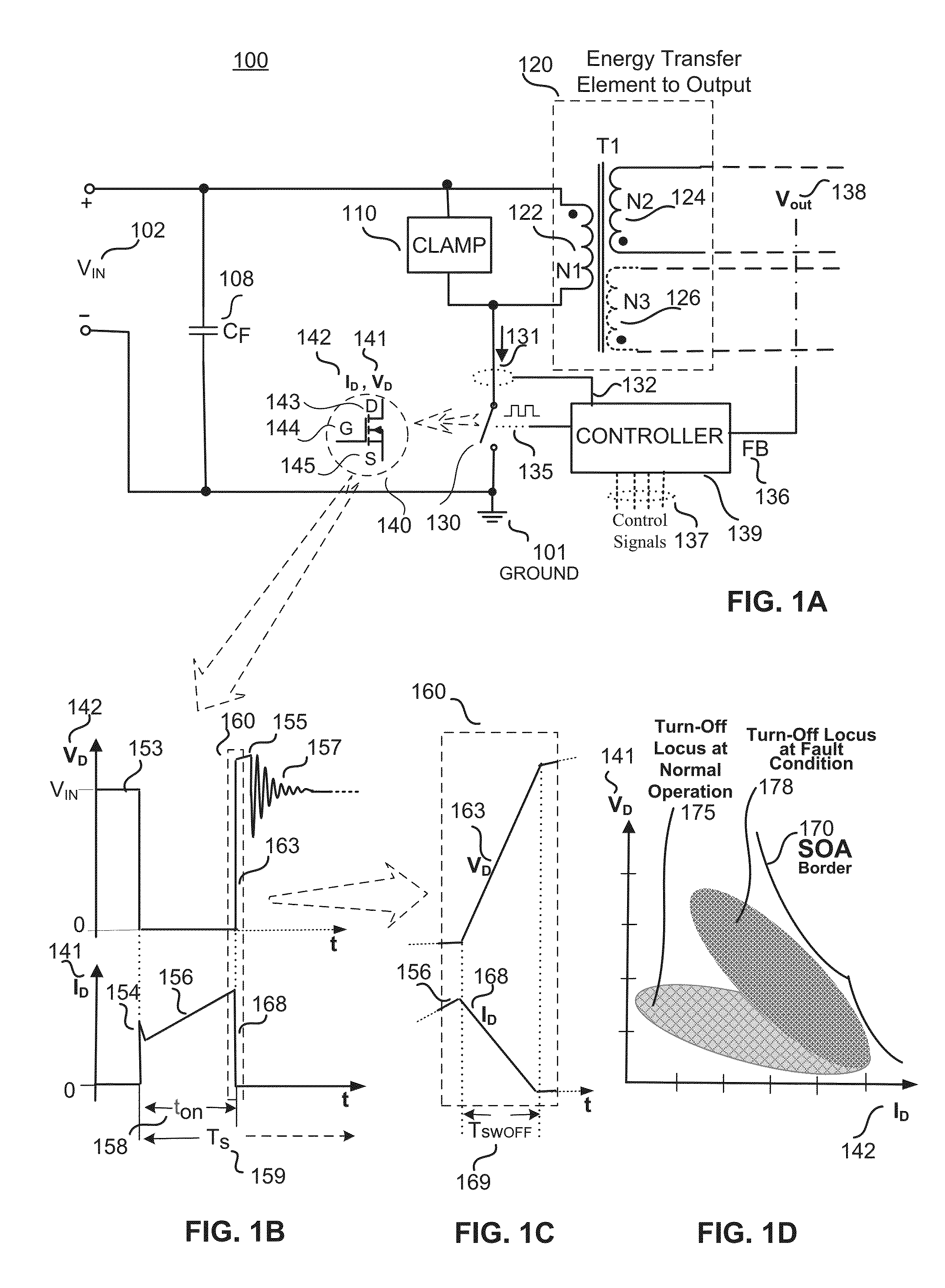
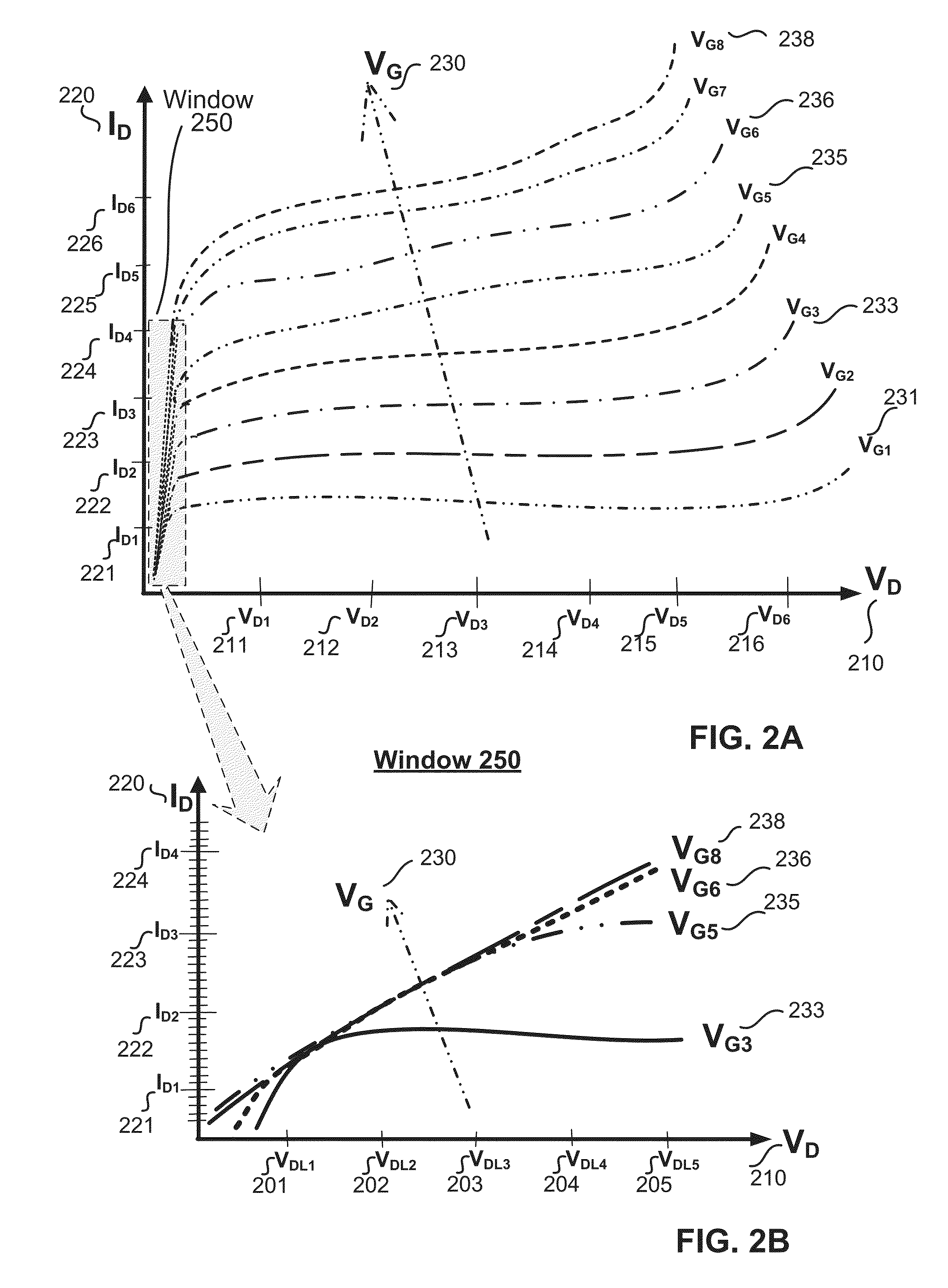
Mosfet driver with pulse timing pattern fault detection and adaptive safe operating area mode of operation
A Safe Operating Area (SOA) adaptive gate driver for a switch mode power converter is disclosed. In response to a detection of a fault condition, the SOA adaptive gate driver may limit the peak current in a power transistor (e.g., power MOSFET) of the power converter by limiting the voltage applied to the gate of the power MOSFET or by limiting the current injected into the gate of the power MOSFET. The limited gate voltage or current may increase the margin between an SOA border and the turn-off locus of the drain voltage and current (VD and ID) to ensure safe operation of the switch mode power converter during the fault condition.
Owner:POWER INTEGRATIONS INC
Method and apparatus for wireless security enhancement using multiple attributes monitoring, continuous and interleaved authentication, and system adaptation
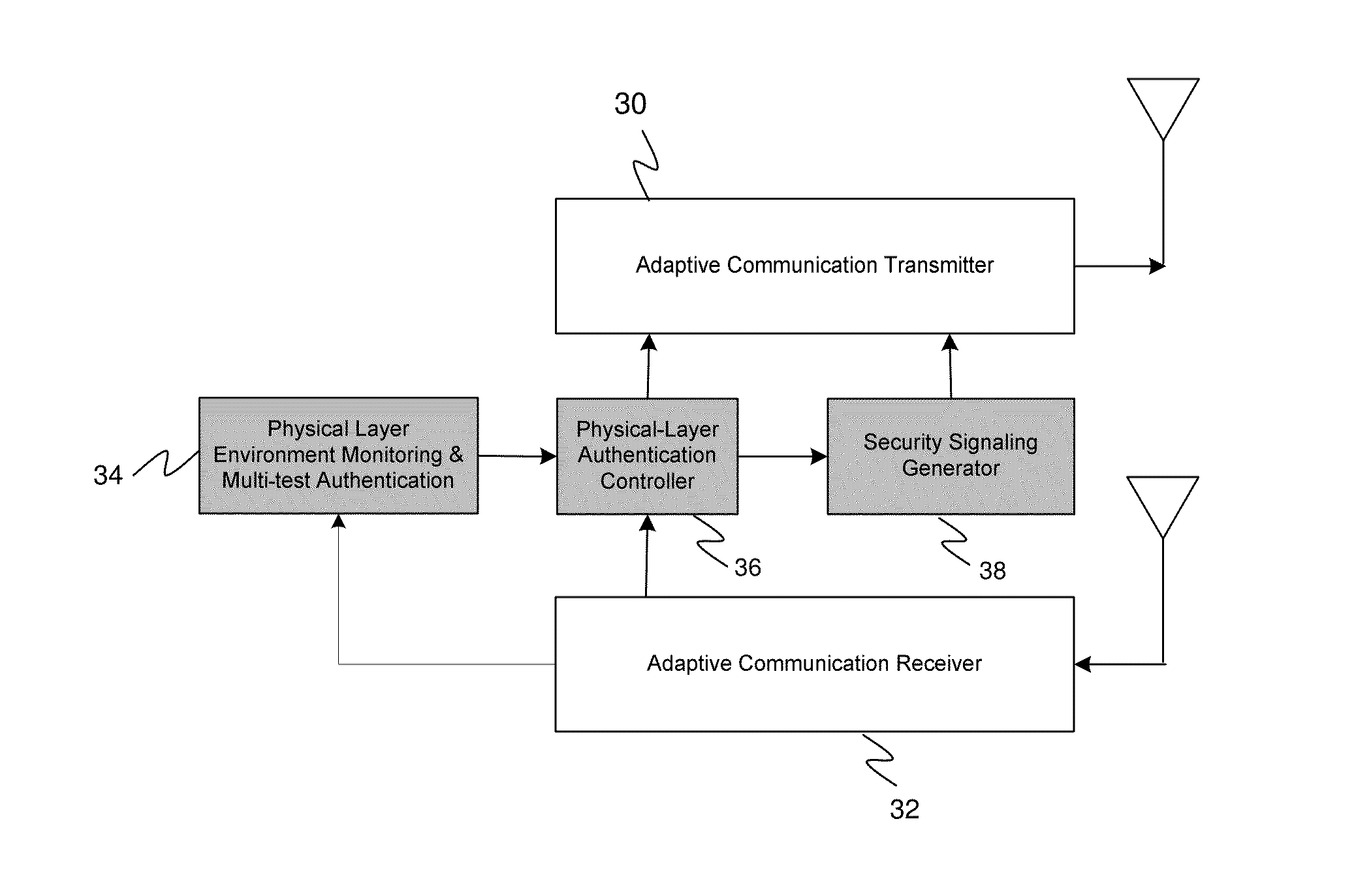
ActiveUS20140040985A1Improve securityDigital data processing detailsMultiple digital computer combinationsTransceiverMultiple attribute
The present invention is an adaptive secure wireless communications system and method. Generally, the present invention may be operable to address challenges and threats to a secure communication session. The secure wireless communication system of the present invention may operate one or more of the following: multiple physical-layer attributes monitoring; multiple parameter confidence testing related to transceiver (Tx-Rx) specific environment and transmitter receiver hardware characteristics; continuous and interleaved authentication; and security enhancement using dynamic adaptation of the transmission system parameters based concurrent and / or conjugated transmission of data-carrying signal and security control information. The real-time physical-layer related monitoring and interaction between transmitter and receiver, using Tx-Rx related physical environment, of the present invention may effectively reduce many wireless security threats including interception and spoofing.
Owner:WANG XIANBIN
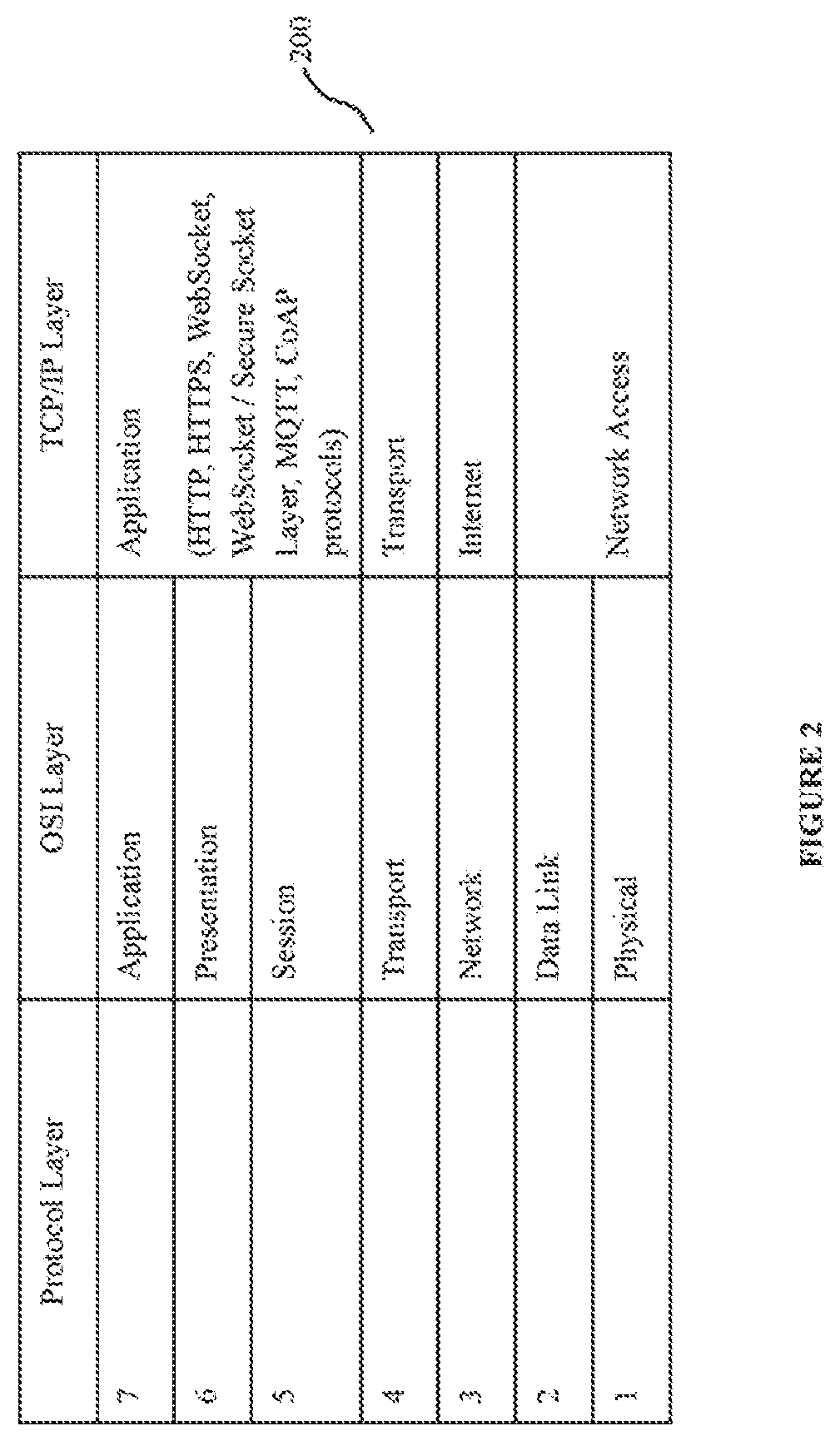
Framework for packet processing for secure v2v applications on resource-constrained platforms
ActiveUS20140002276A1Guaranteed trackRoad vehicles traffic controlParticular environment based servicesKinematicsApplication software
A packet processing framework is provided for a vehicle-to-vehicle communication packet processing system. The framework includes a neighborhood vehicle tracking module for tracking neighboring vehicles relative to a host vehicle. The neighborhood vehicle tracking module assigns a priority level of neighboring vehicles relative to a host vehicle. An adaptive security processing module regulates messages streamed to the neighboring vehicle tracker module that are in accordance with the priorities set forth by the neighborhood vehicle tracking module. The adaptive security processing module selects security modes and schedules messages streamed to the neighborhood vehicle tracking module as a function of priorities set forth by the neighborhood vehicle tracking module, a communication reliability of the transmitting neighboring vehicle, and a likelihood that a message from the neighboring vehicle is genuine as determined by the adaptive security processing module. The neighborhood vehicle tracking module outputs processed kinematics and alert information to at least one vehicle-to-vehicle application.
Owner:GM GLOBAL TECH OPERATIONS LLC
System and method for implementing adaptive security zones
Owner:SERENOVA LLC
Method and system for adaptive security in cloud-based services
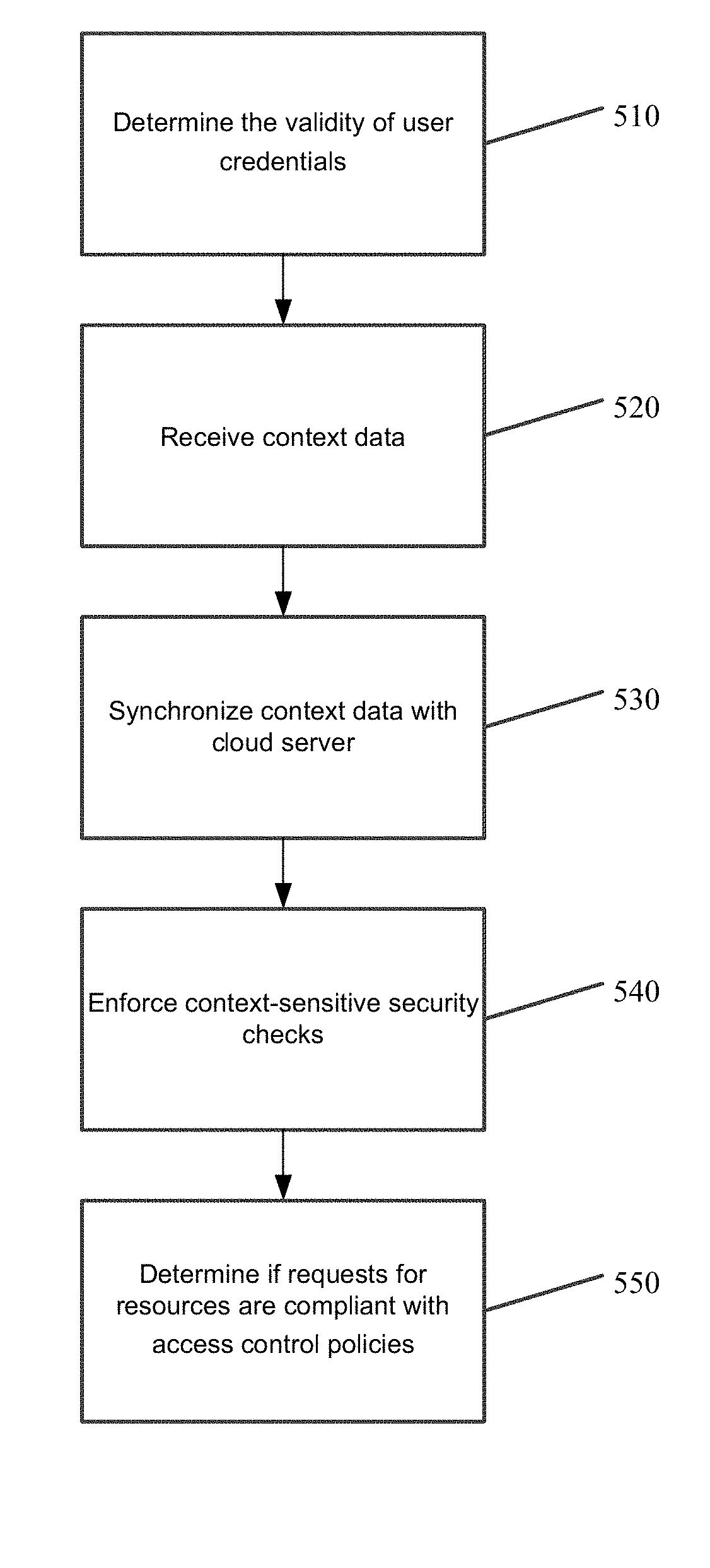
ActiveUS20180114015A1Digital data authenticationPlatform integrity maintainanceUser deviceInternet privacy
Certain embodiments may generally relate to controlling access to data held in the cloud. A method for controlling access to data held in the cloud may include determining, at a cloud server, the validity of user credentials received from a user device. The method may also include receiving context data related to the user device based on the validity of the user credentials. The method may further include synchronizing the context data with the cloud server. In addition, the method may include enforcing context-sensitive security checks on requests made by the user for resources based on the sensor data collected by the user device.
Owner:QATAR UNIVERSITY
Method for preventing surge in a dynamic compressor using adaptive preventer control system and adaptive safety margin
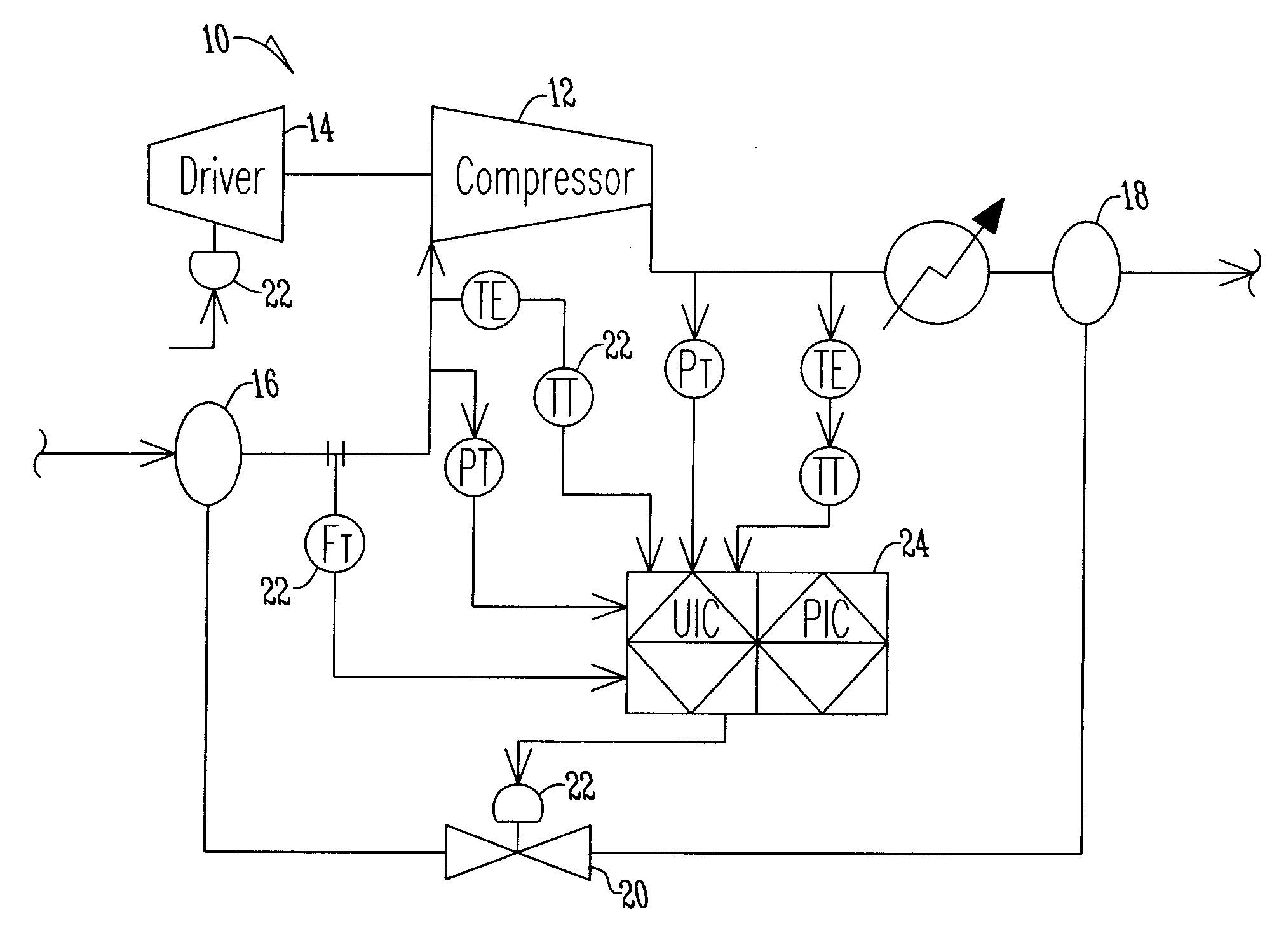
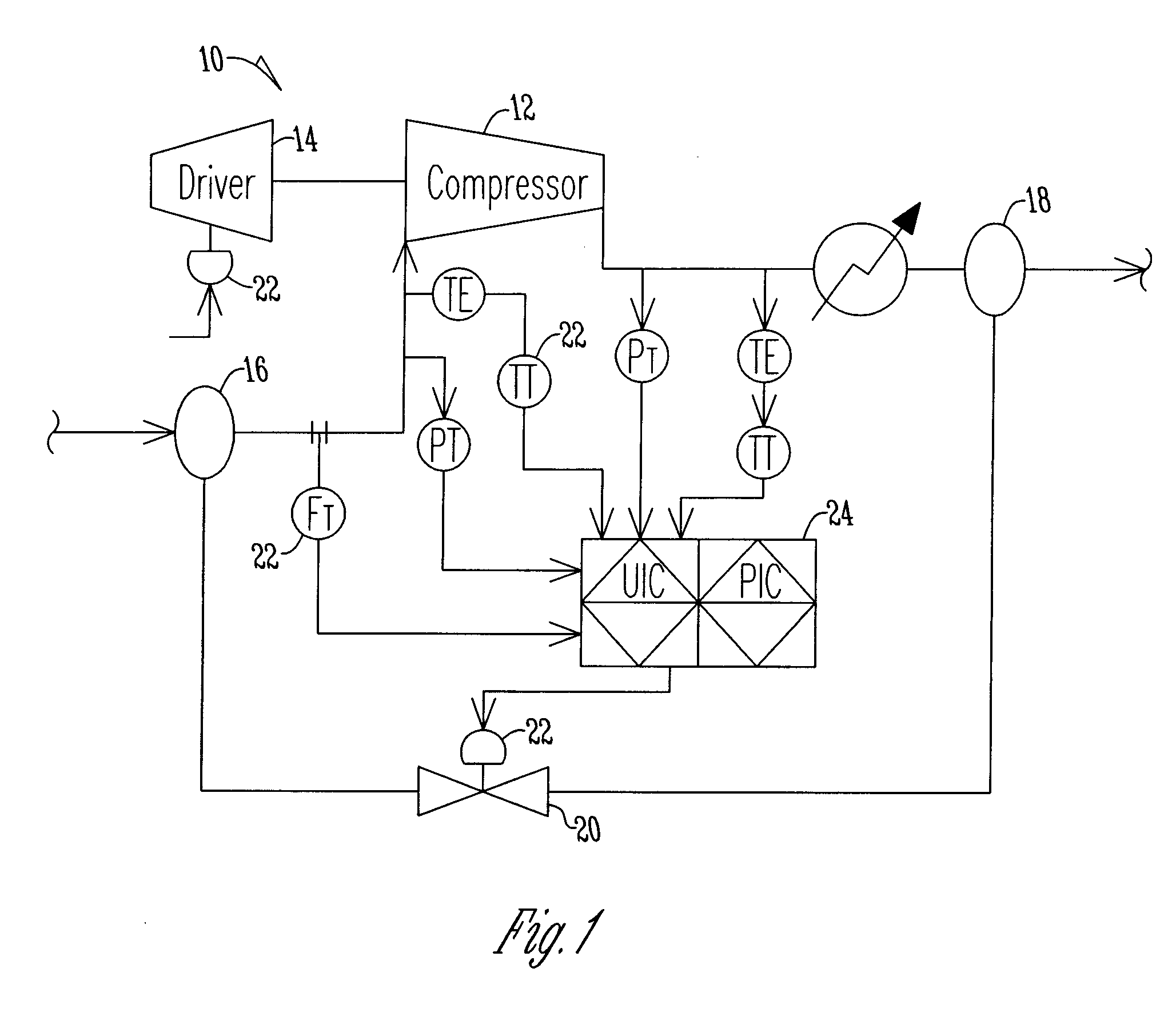
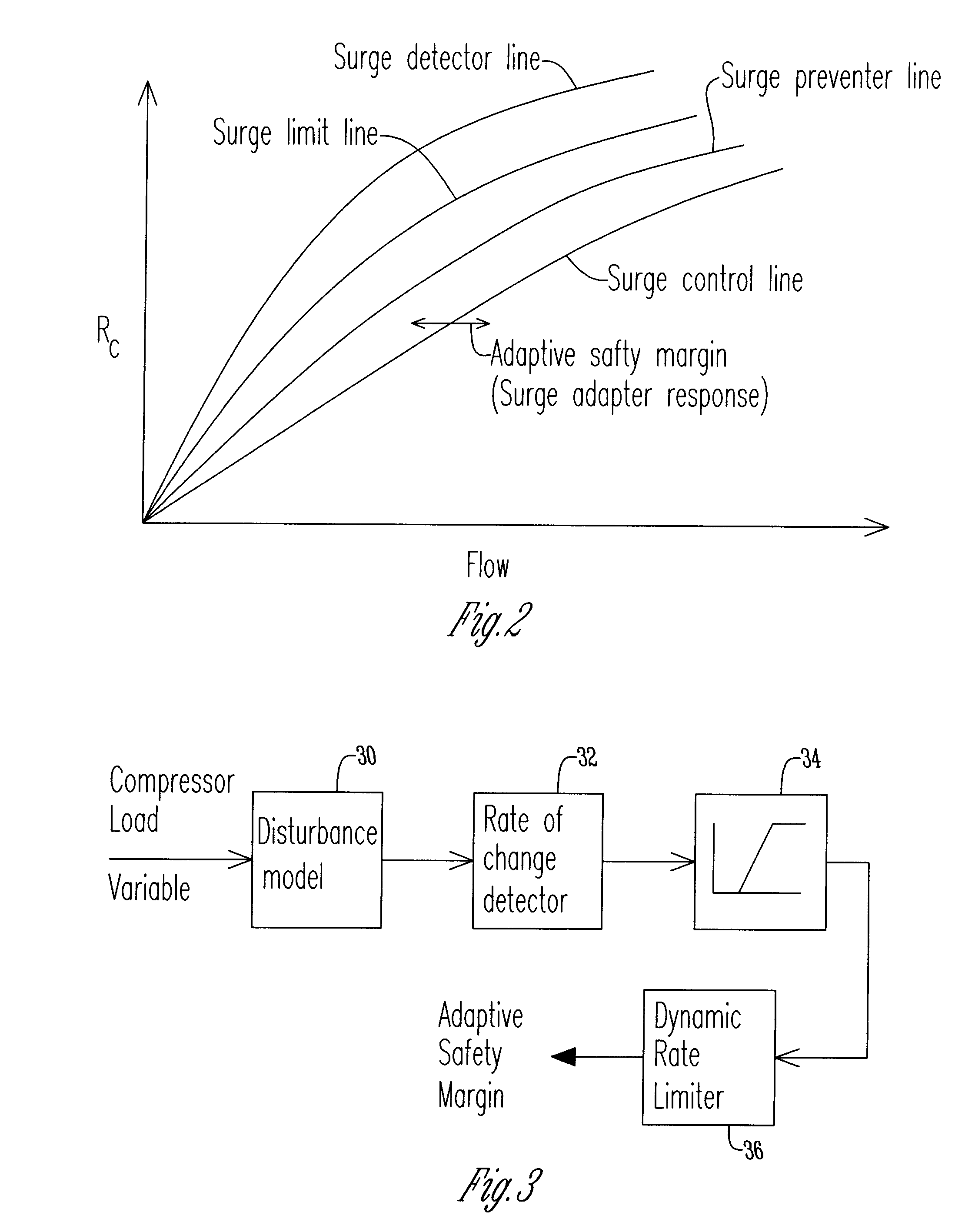
ActiveUS20120183385A1Pump controlNon-positive displacement fluid enginesTraffic capacityRate limiting
A method of preventing surge in a dynamic compressor is disclosed. The method includes providing an anti-surge valve having an adjustable opening for increasing the flow through a dynamic compressor. The next step is sensing process conditions in the dynamic control to determine a compressor load variable. A control system estimates a process disturbance model using the compressor load variable. The control system then adjusts a safety margin using a rate limited response and initiates a closed loop response using process feedback based on the process disturbance model. The control system adjusts the opening of the anti-surge valve according to the safety margin and closed loop response.
Owner:ENERGY CONTROL TECH
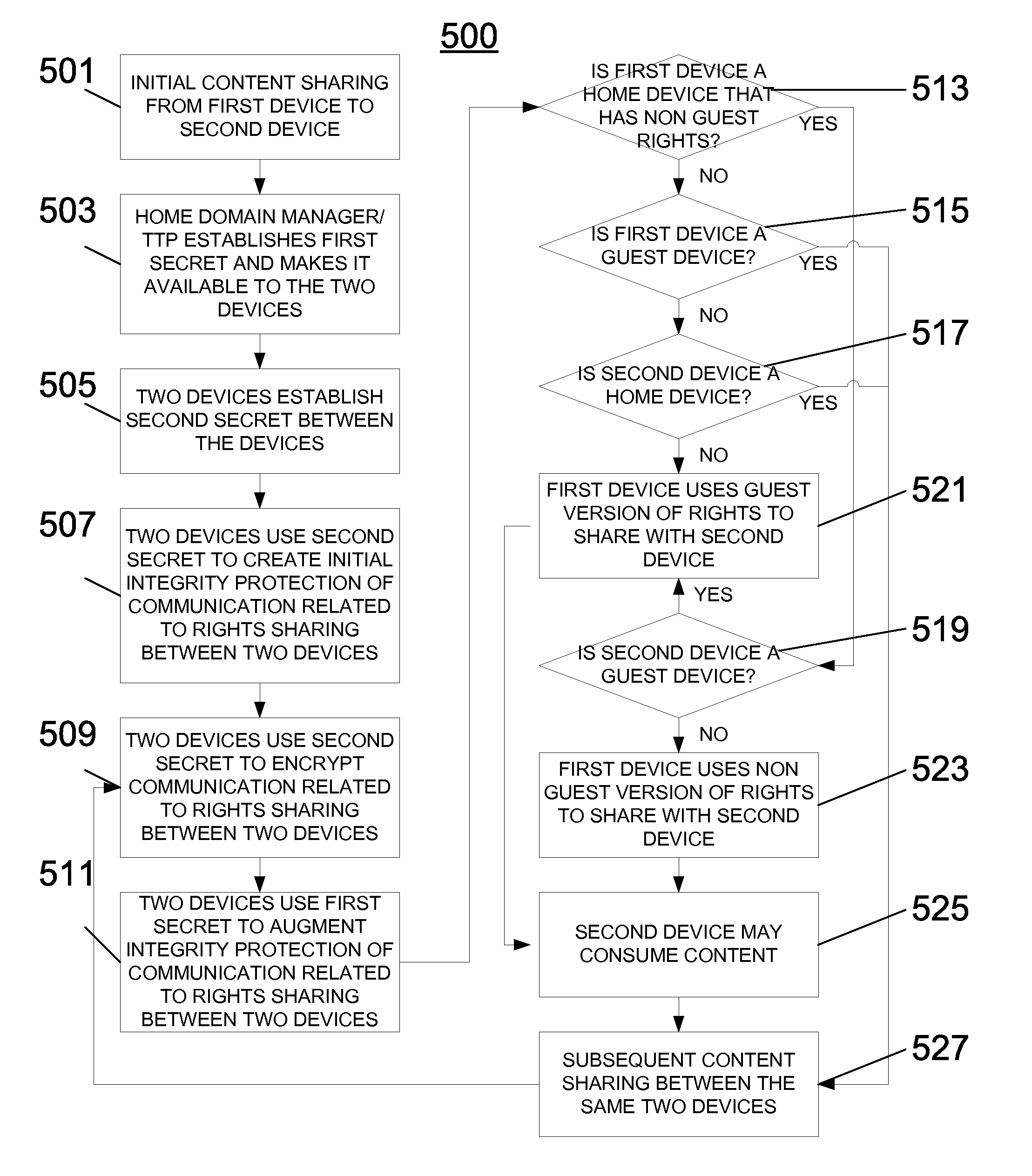
Adaptive secure authenticated channels for direct sharing of protected content between devices
InactiveUS20090180621A1Key distribution for secure communicationProgram/content distribution protectionComputer hardwareTrusted third party
A method for a communication device for establishing a secure authenticated channel using multiple shared keys traded with another device is described. A first shared key common to a home domain is received from a non-device entity, such as a domain manager or a trusted third party. Also, a second shared key is established with the other device. An initial integrity protection of communication relating to rights sharing between the communication device and the other device is then created using the second shared key. The integrity protection of communication relating to rights sharing between the communication device and the other device is thereafter augmented using the first shared key.
Owner:MOTOROLA MOBILITY LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com