Patents
Literature
239 results about "Distributed security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
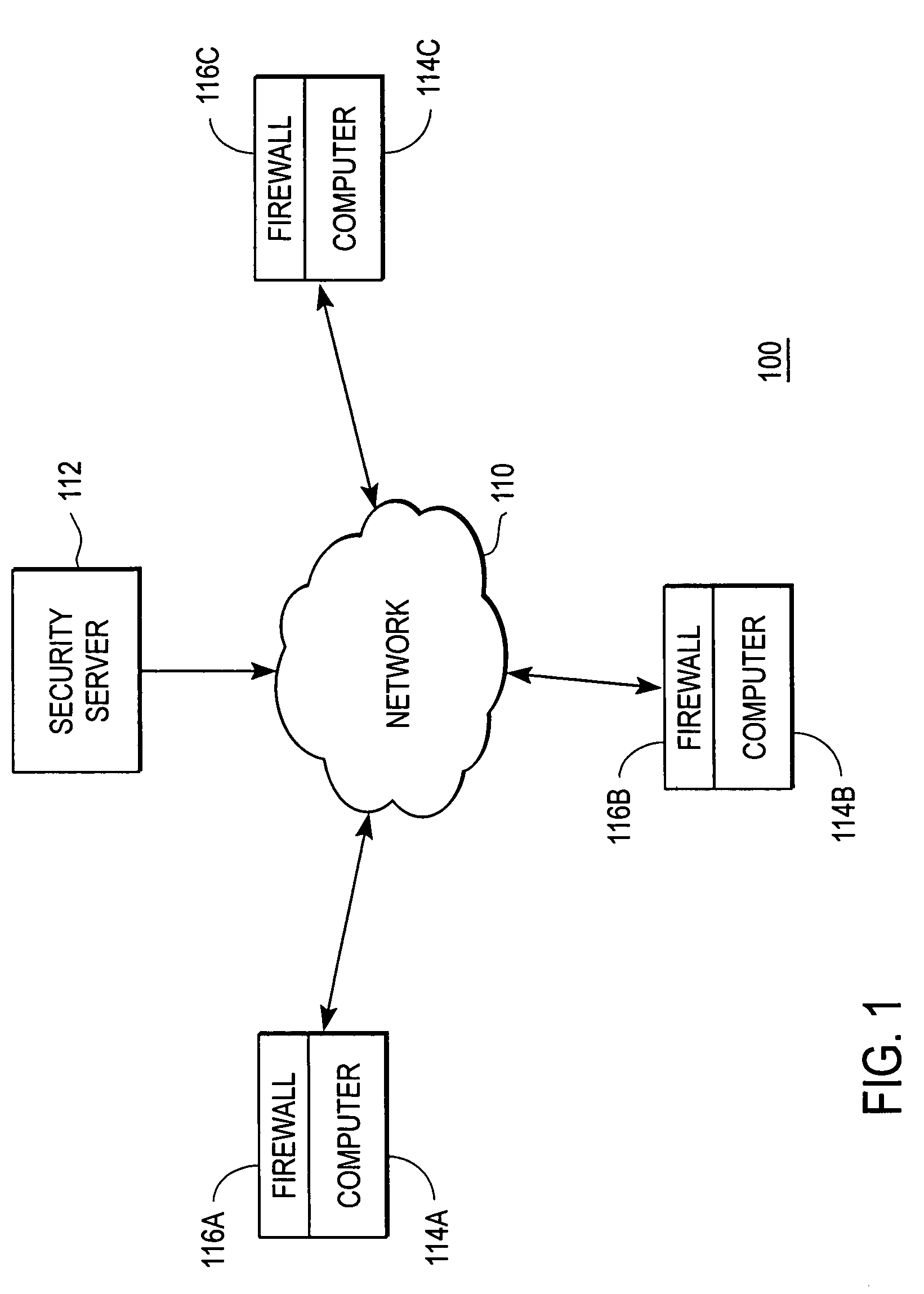
Distributed Security, Inc. is a private security company. They are the creators of distributed security networks that enable enterprises to develop Distributed Security Bases and operate private security forces capable of defending immediate community assets.
Systems and methods for mobile application security classification and enforcement
ActiveUS20110167474A1Avoid forwardingMemory loss protectionError detection/correctionUser deviceThe Internet
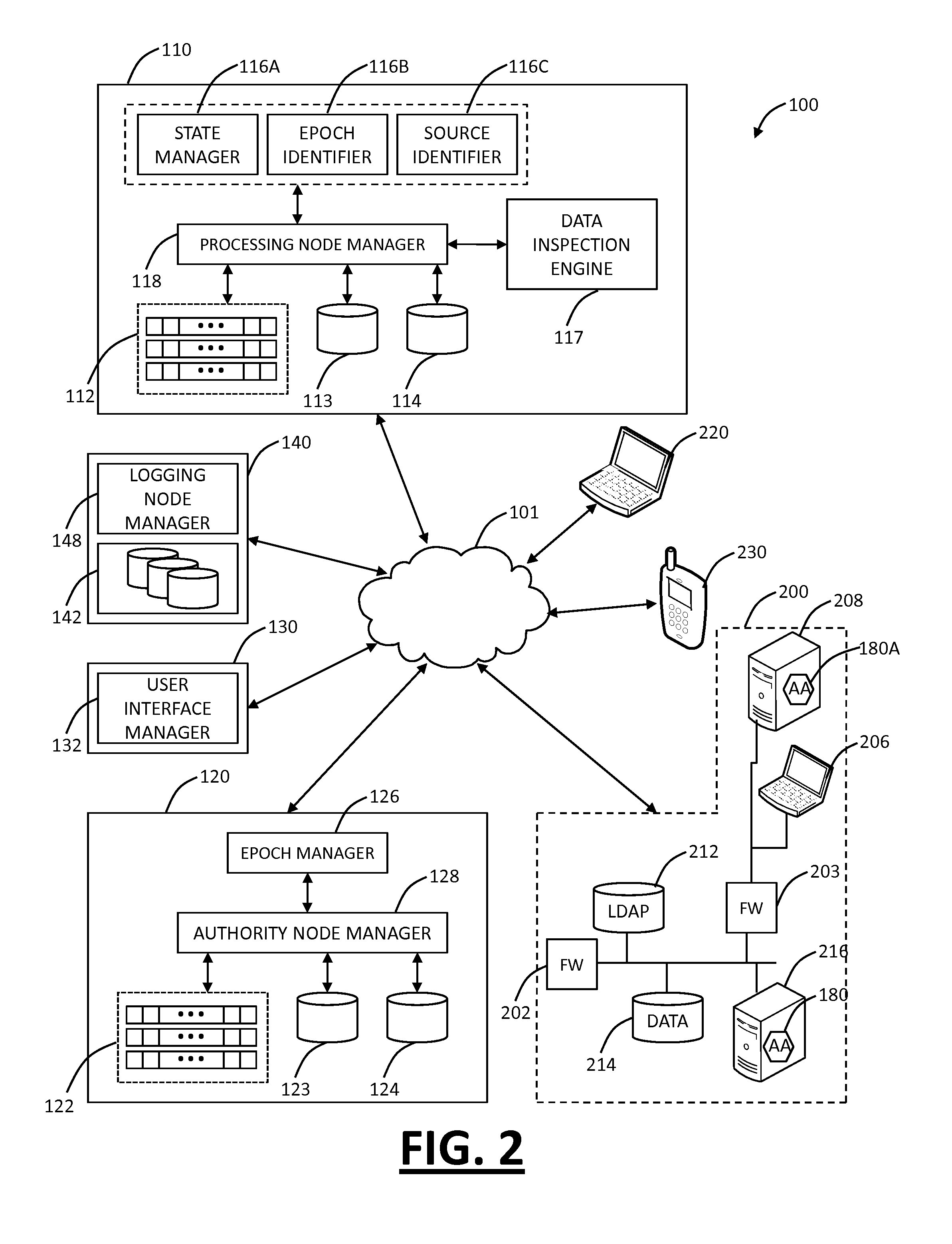
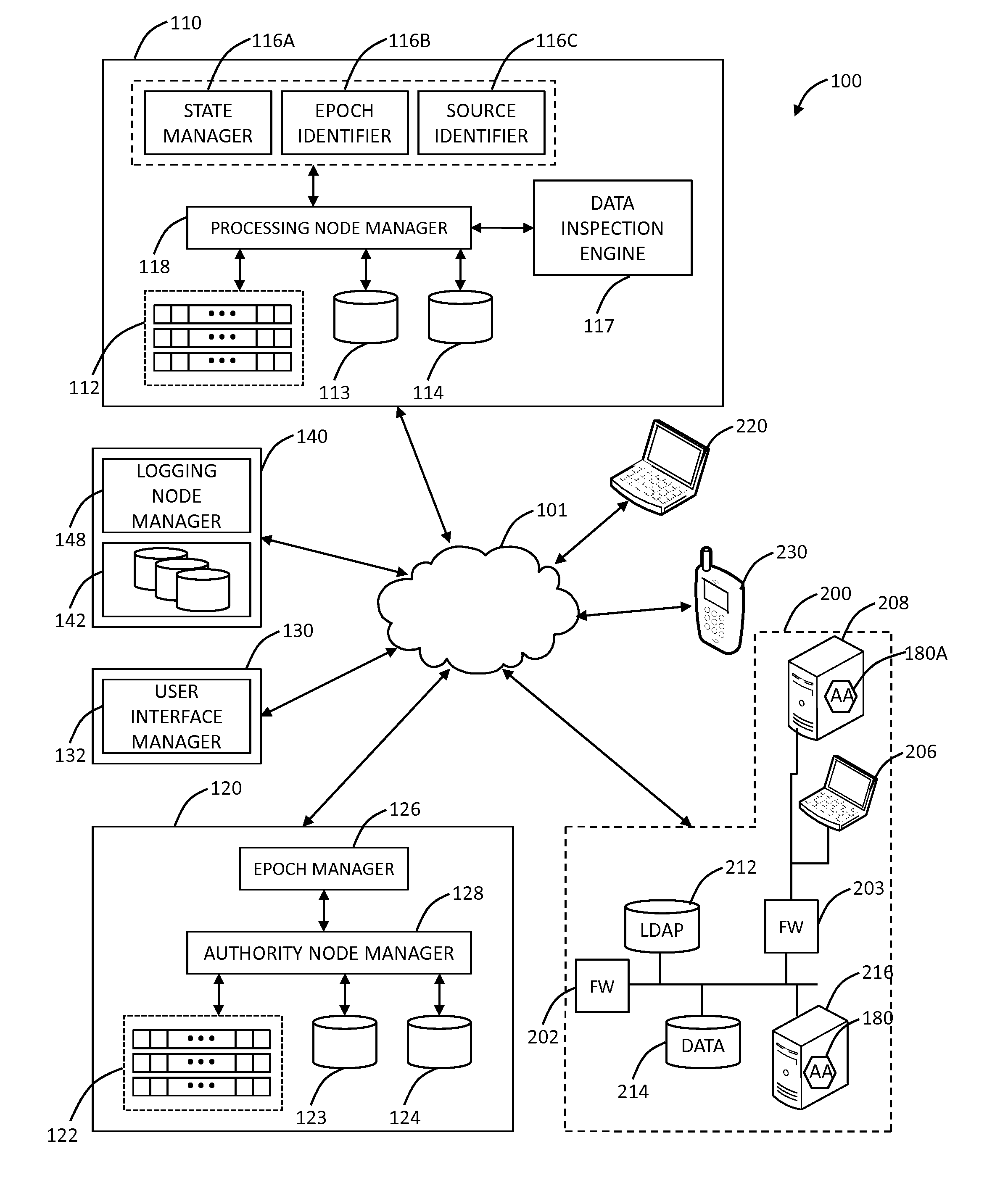
The present disclosure provides systems and methods for mobile application security classification and enforcement. In particular, the present invention includes a method, a mobile device, and a distributed security system (e.g., a “cloud”) that is utilized to enforce security on mobile devices communicatively coupled to external networks (i.e., the Internet). Advantageously, the present invention is platform independent allowing it to operate with any current or emerging mobile device. Specifically, preventing malicious applications from running on an end user's mobile device is challenging with potentially millions of applications and billions of user devices; the only effective way to enforce application security is through the network that applications use to communicate.
Owner:ZSCALER INC
Systems and methods for mobile application security classification and enforcement
The present disclosure provides systems and methods for mobile application security classification and enforcement. In particular, the present invention includes a method, a mobile device, and a distributed security system (e.g., a “cloud”) that is utilized to enforce security on mobile devices communicatively coupled to external networks (i.e., the Internet). Advantageously, the present invention is platform independent allowing it to operate with any current or emerging mobile device. Specifically, preventing malicious applications from running on an end user's mobile device is challenging with potentially millions of applications and billions of user devices; the only effective way to enforce application security is through the network that applications use to communicate.
Owner:ZSCALER INC
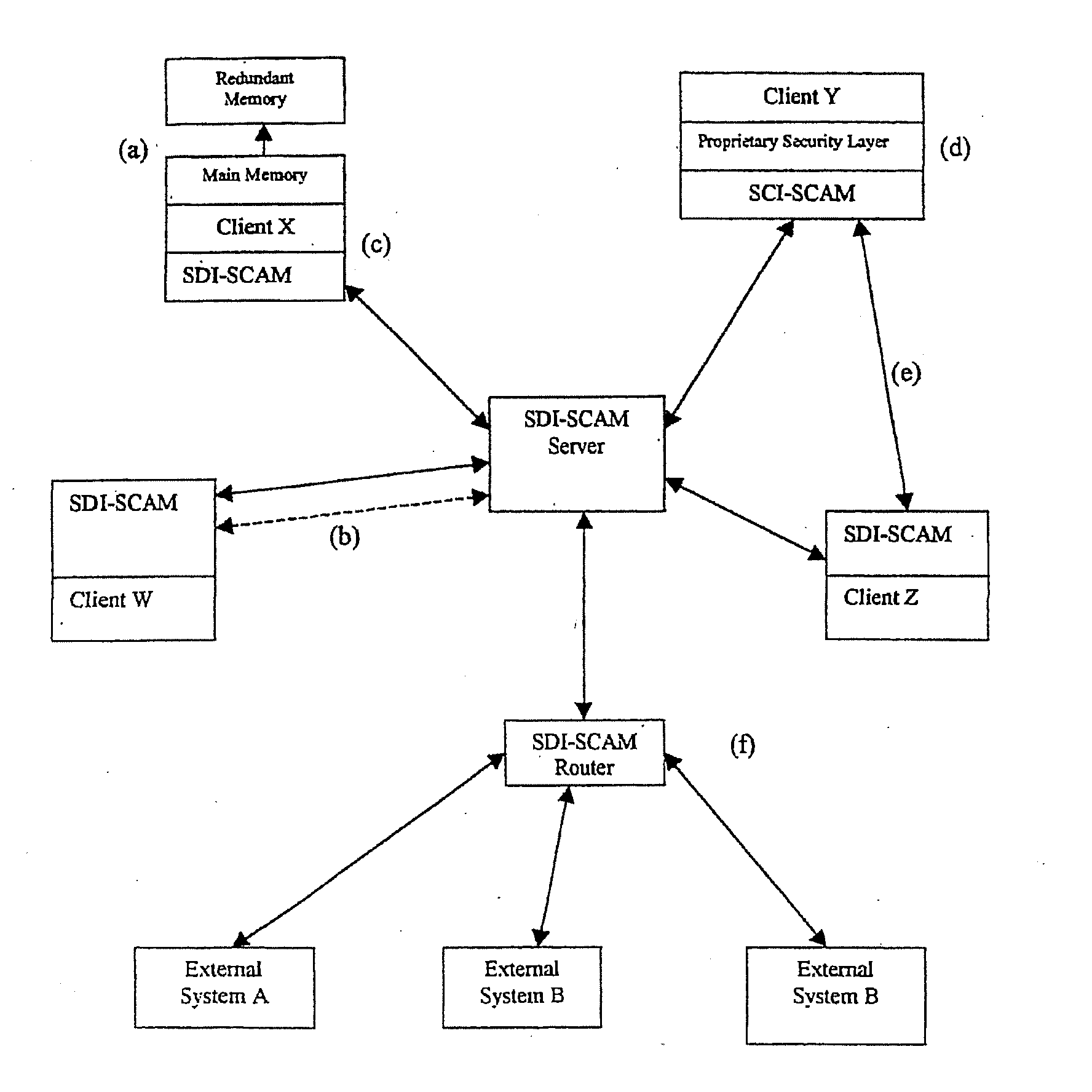
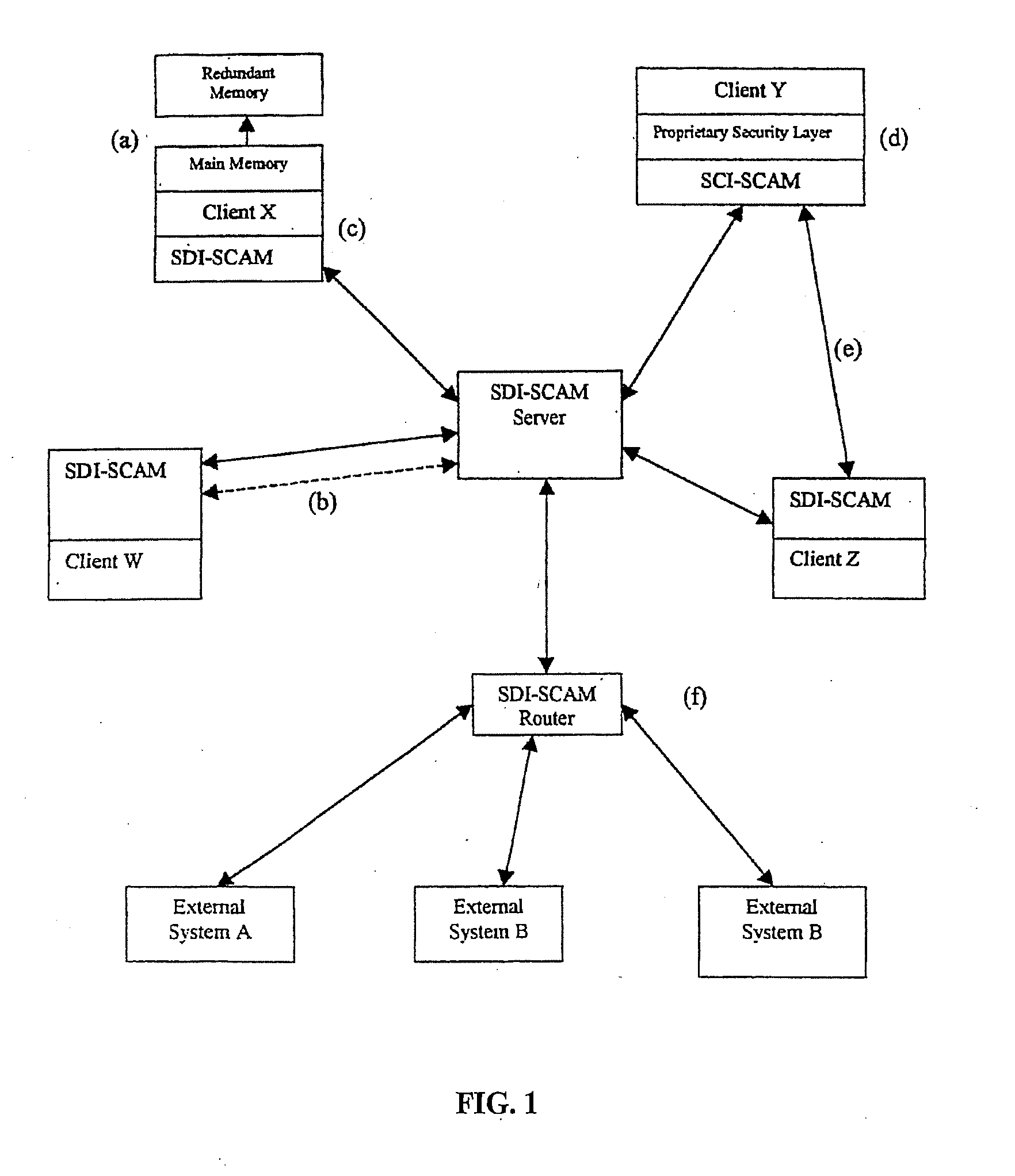
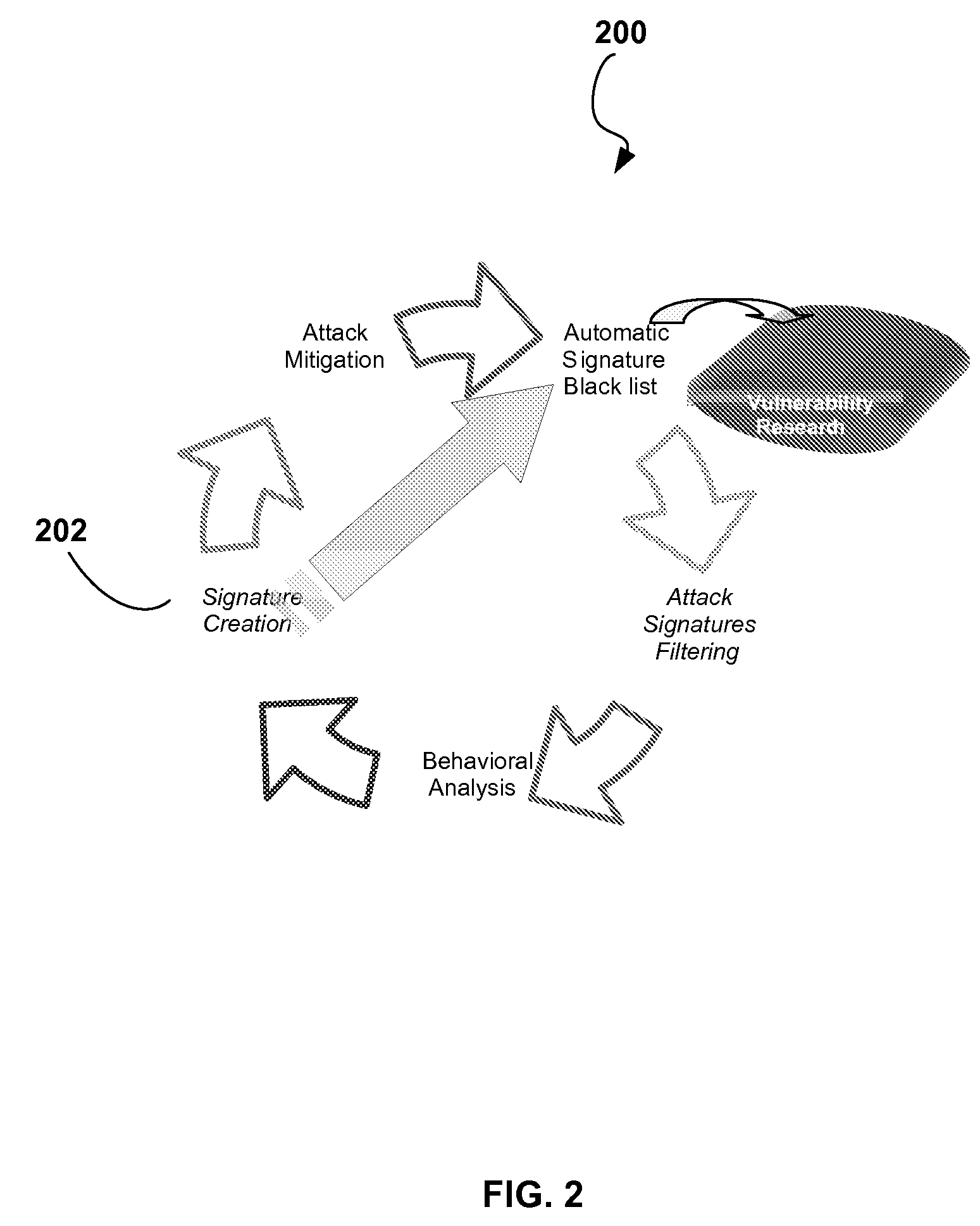
Distributed agent based model for security monitoring and response
ActiveUS20140237599A1Quick checkHigh and uniform level of securityMemory loss protectionError detection/correctionCountermeasureAgent-based model
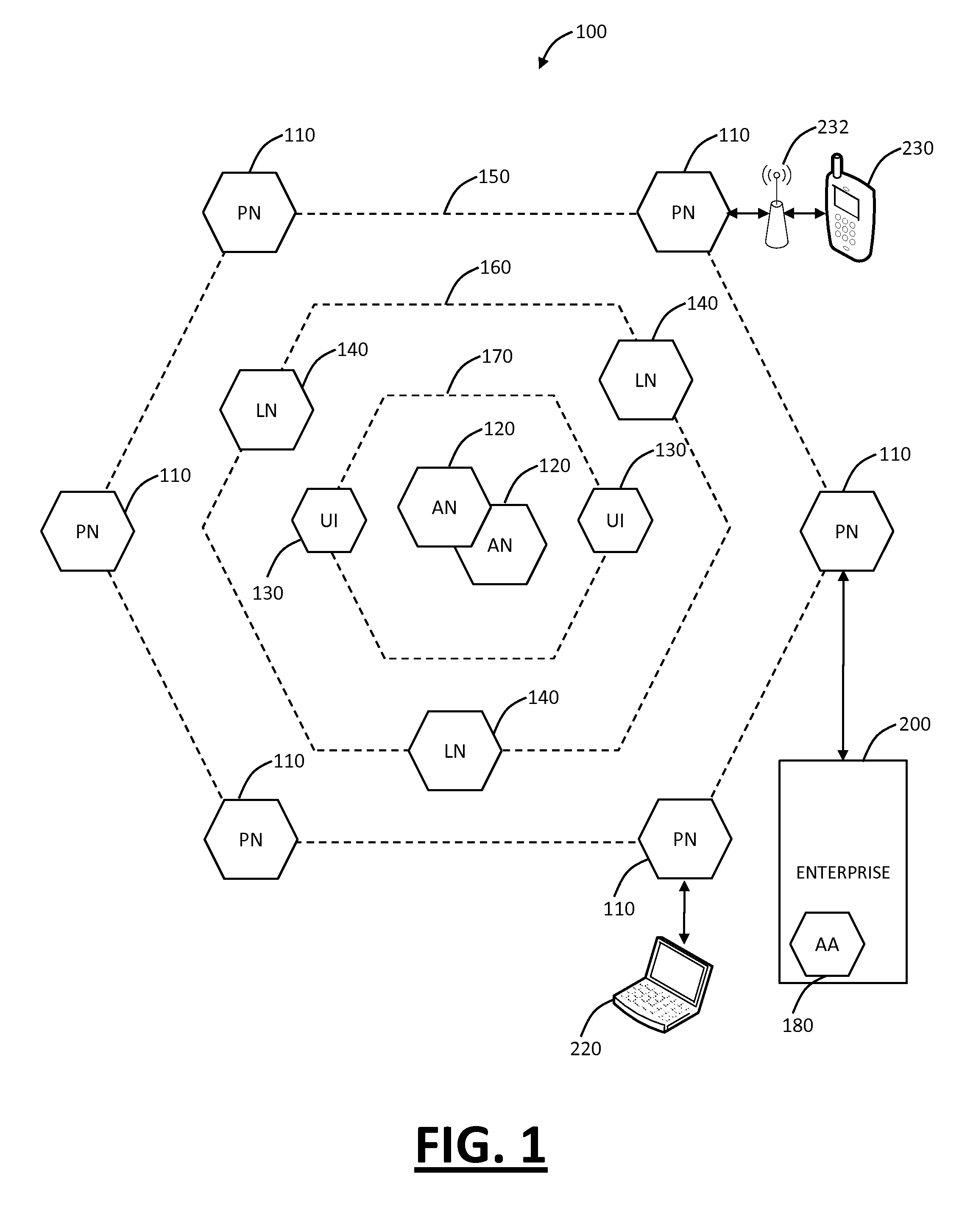
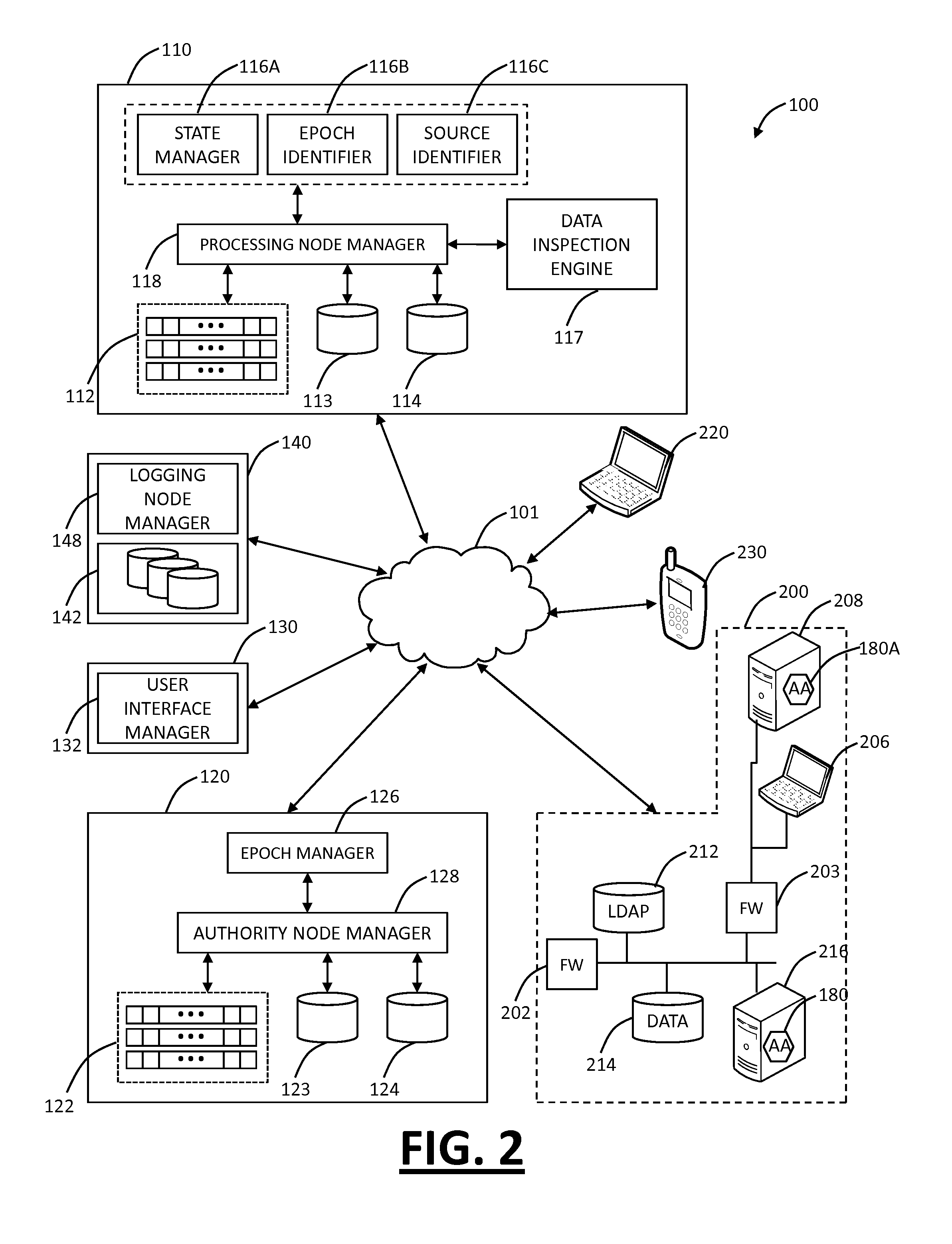
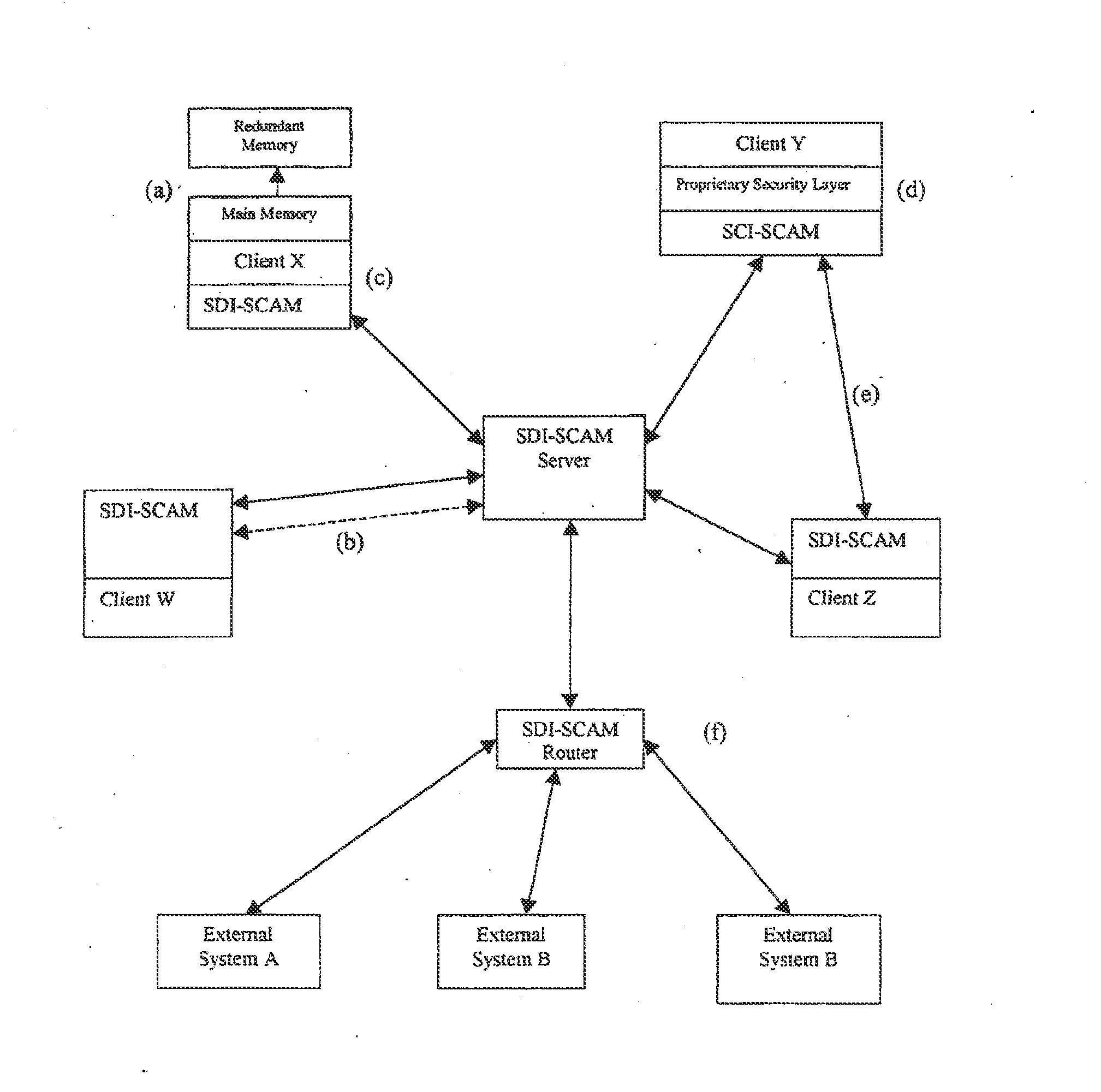
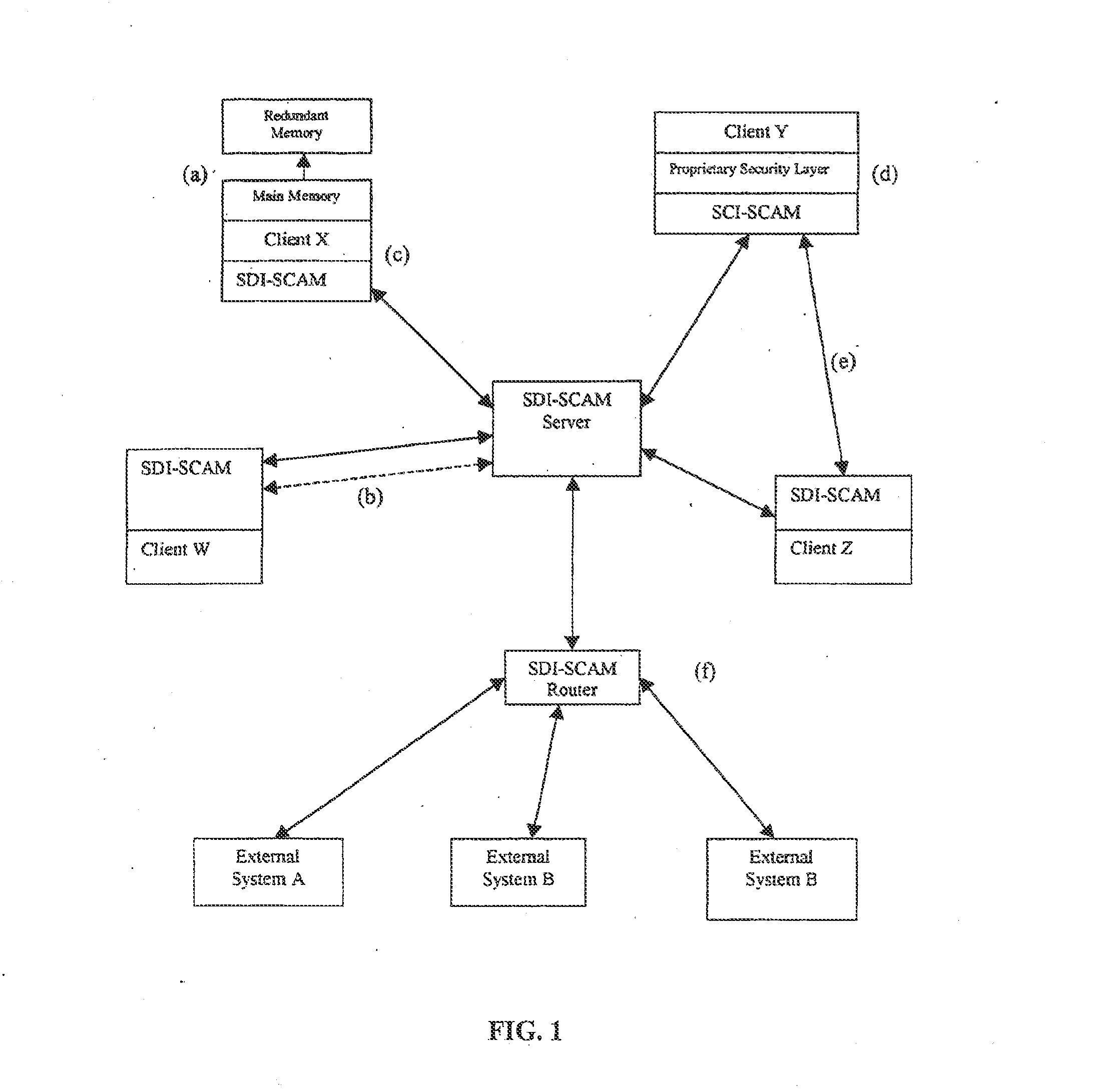
An architecture is provided for a widely distributed security system (SDI-SCAM) that protects computers at individual client locations, but which constantly pools and analyzes information gathered from machines across a network in order to quickly detect patterns consistent with intrusion or attack, singular or coordinated. When a novel method of attack has been detected, the system distributes warnings and potential countermeasures to each individual machine on the network. Such a warning may potentially include a probability distribution of the likelihood of an intrusion or attack as well as the relative probabilistic likelihood that such potential intrusion possesses certain characteristics or typologies or even strategic objectives in order to best recommend and / or distribute to each machine the most befitting countermeasure(s) given all presently known particular data and associated predicted probabilistic information regarding the prospective intrusion or attack. If any systems are adversely affected, methods for repairing the damage are shared and redistributed throughout the network.
Owner:INVENTSHIP LLC
Security appliances
InactiveUS20070192867A1Memory loss protectionError detection/correctionInternet privacySystems management
A security micro-appliance provides dynamic, reconfigurable threat protection. The micro-appliance may be deployed as a standalone system, or as a component in a distributed security system management from a central administrative location. In another aspect, a security appliance or micro-appliance employs RSS feeds and XML-based tests, alerts, and the like for monitoring and dynamic reconfiguration.
Owner:NETCLARITY
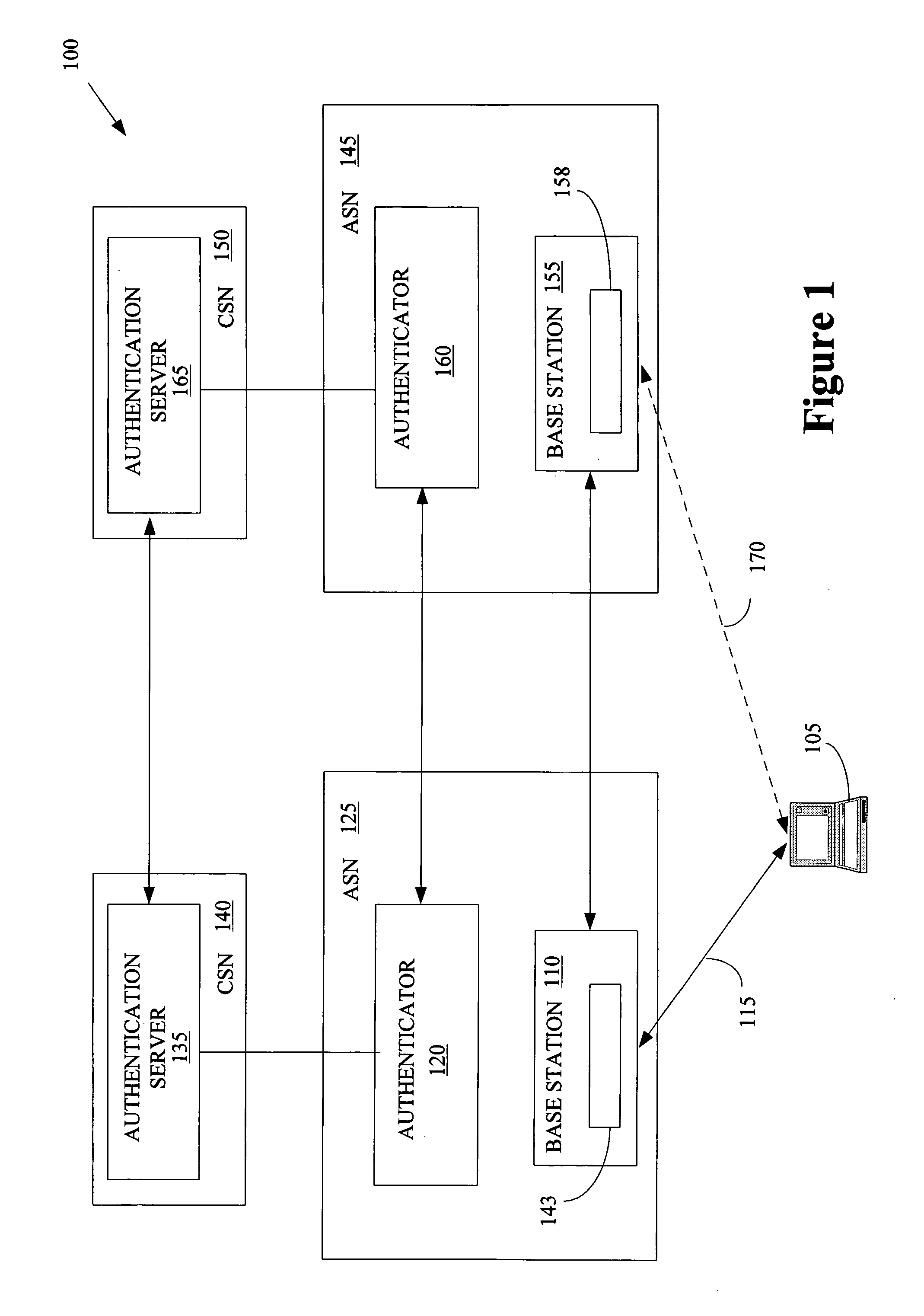
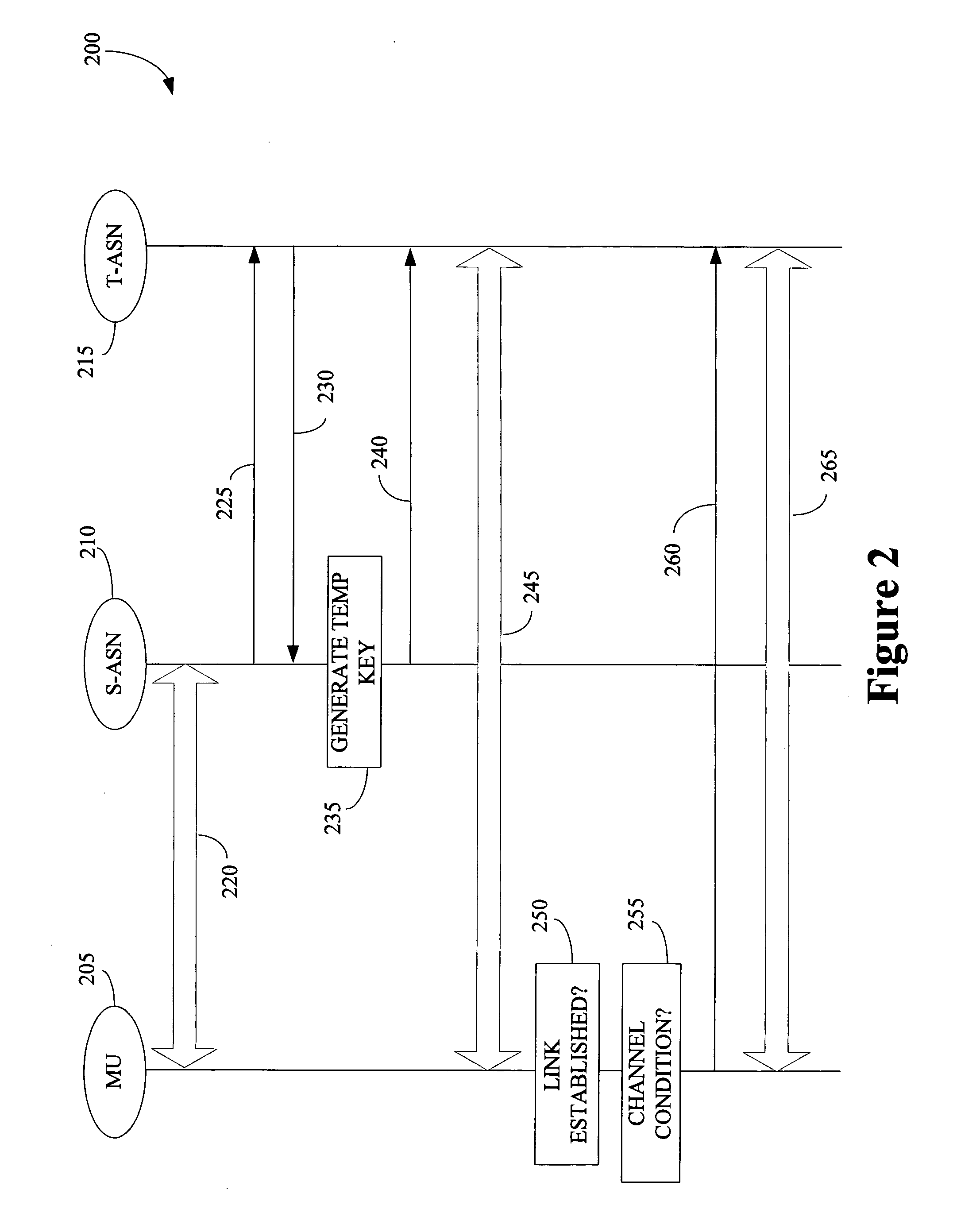
Method for distributing security keys during hand-off in a wireless communication system
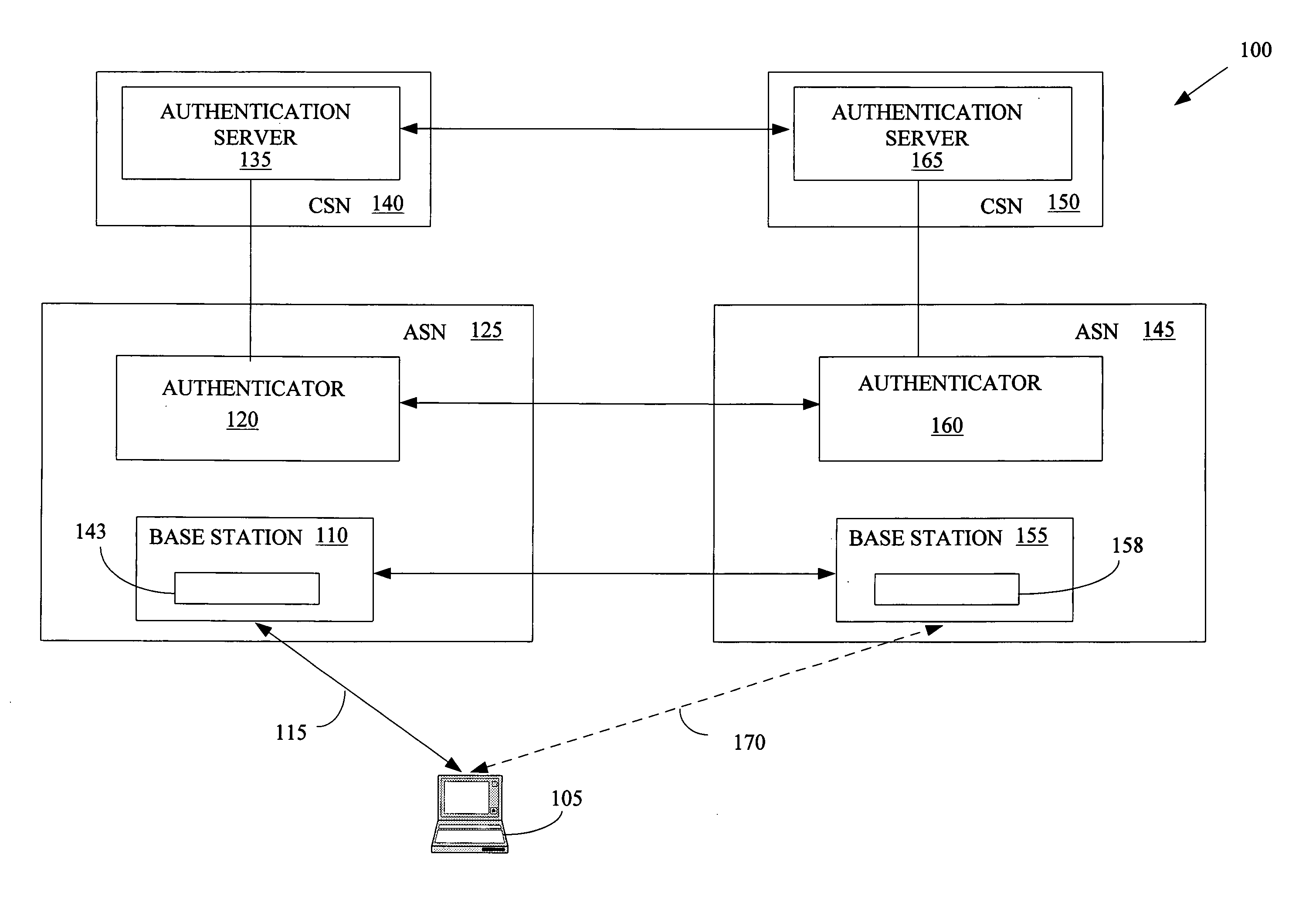
ActiveUS20070003062A1Well formedKey distribution for secure communicationUser identity/authority verificationTelecommunications linkCommunications system
The present invention provides a method of wireless communication involving at least one first base station associated with a first access serving network and at least one second base station associated with a second access serving network is provided. The method may include generating a first key associated with the first access serving network and the second base station, receiving information indicating that the first key is temporary, and establishing a communication link with the second base station using the first key.
Owner:NOKIA TECHNOLOGLES OY
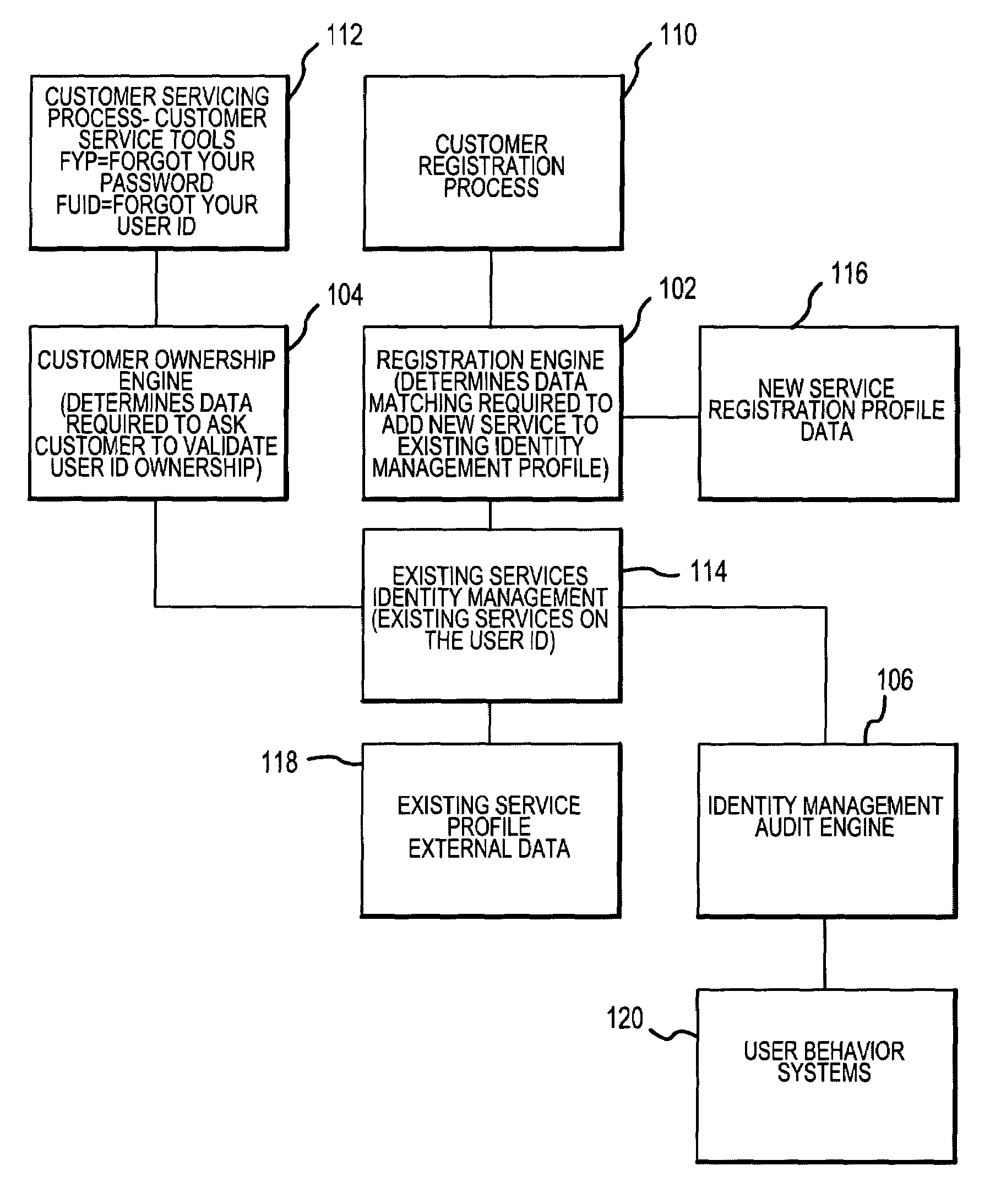
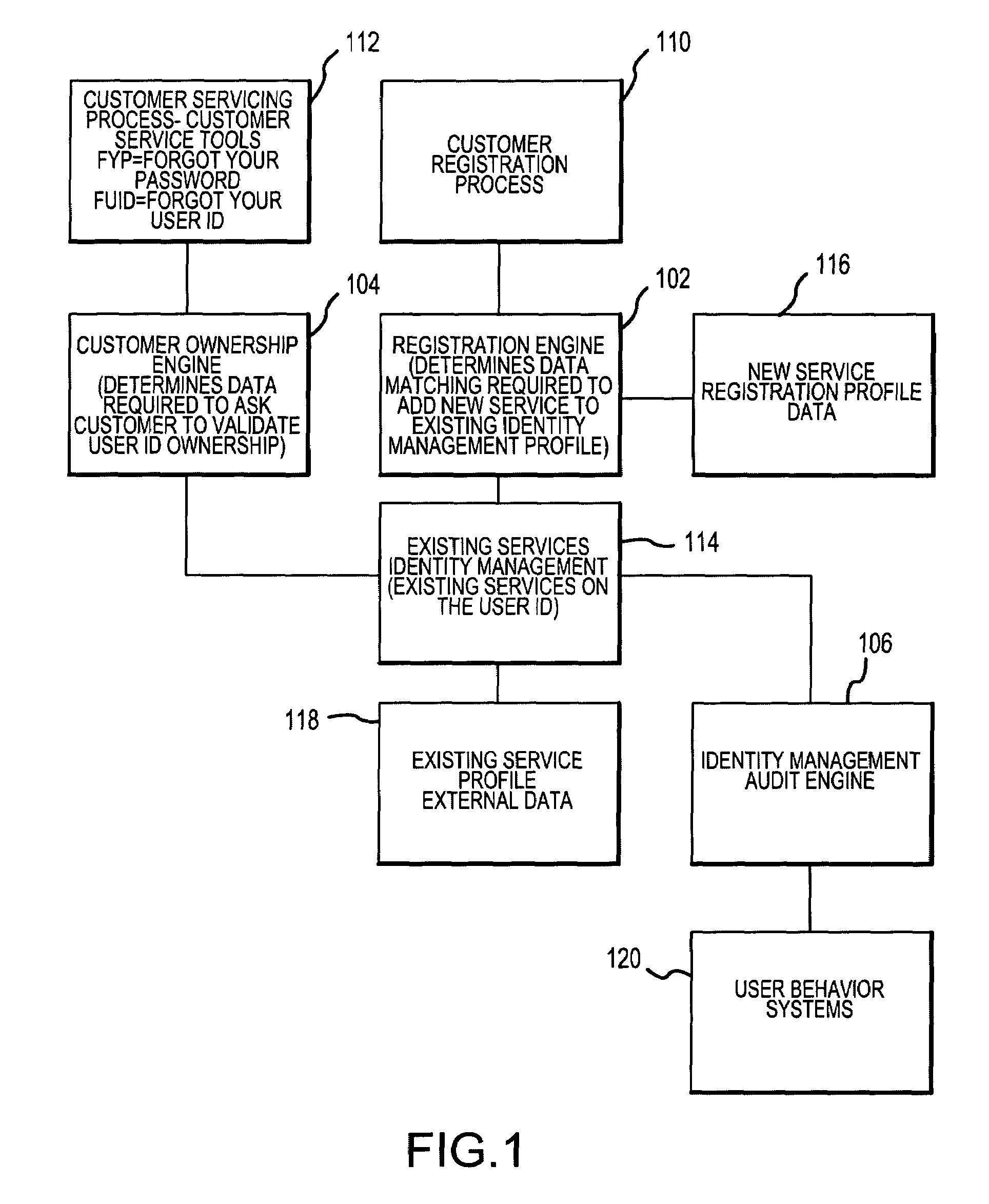
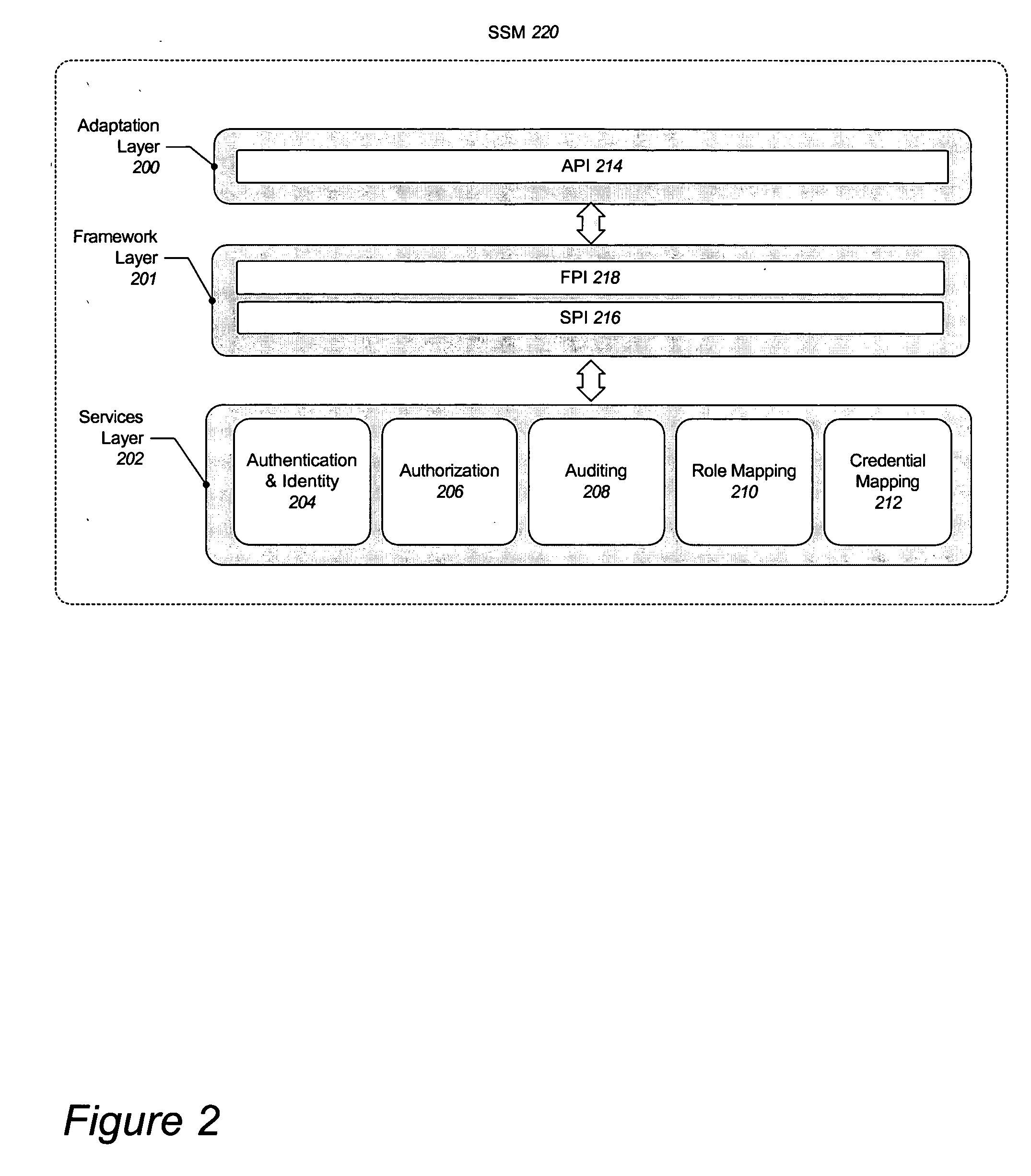
Method and system for implementing and managing an enterprise identity management for distributed security
InactiveUS7143095B2FinanceMultiple digital computer combinationsPrivileged identity managementComputerized system
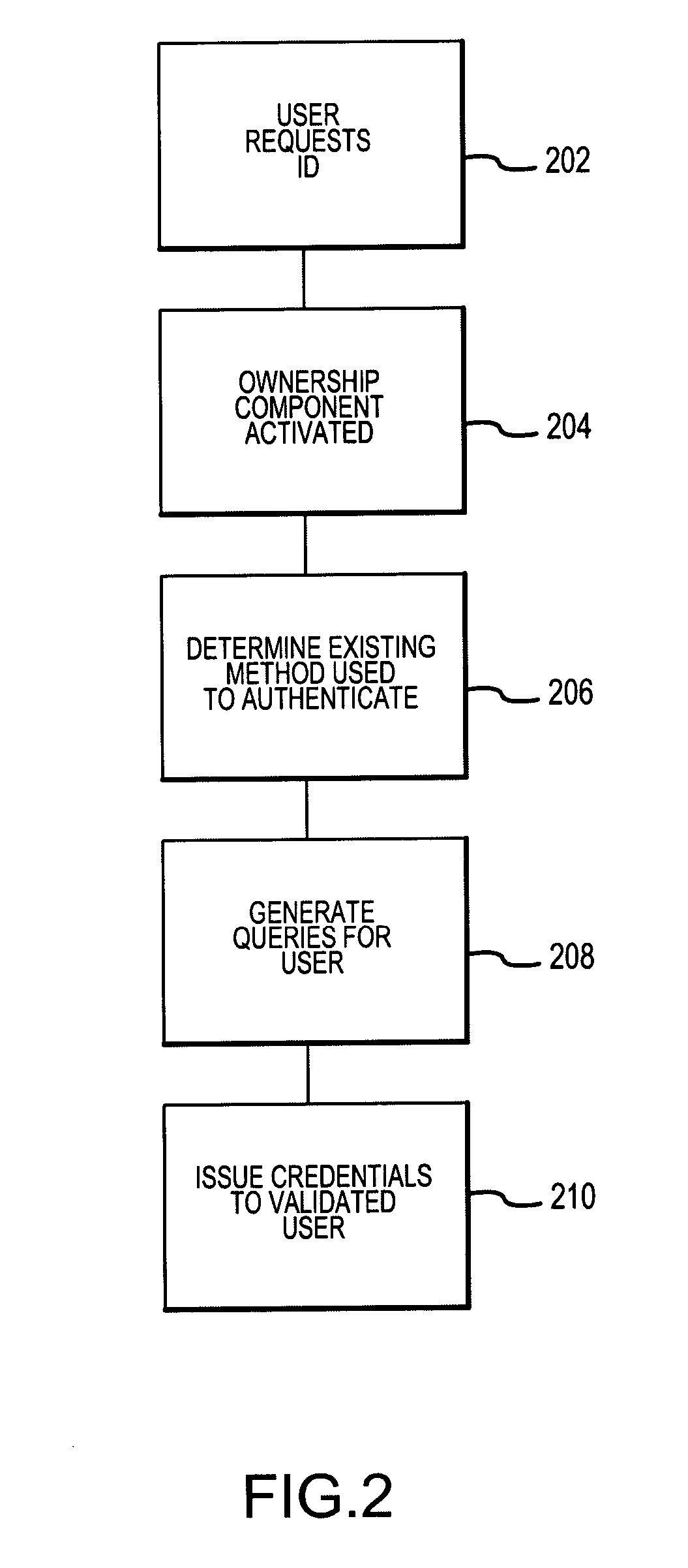
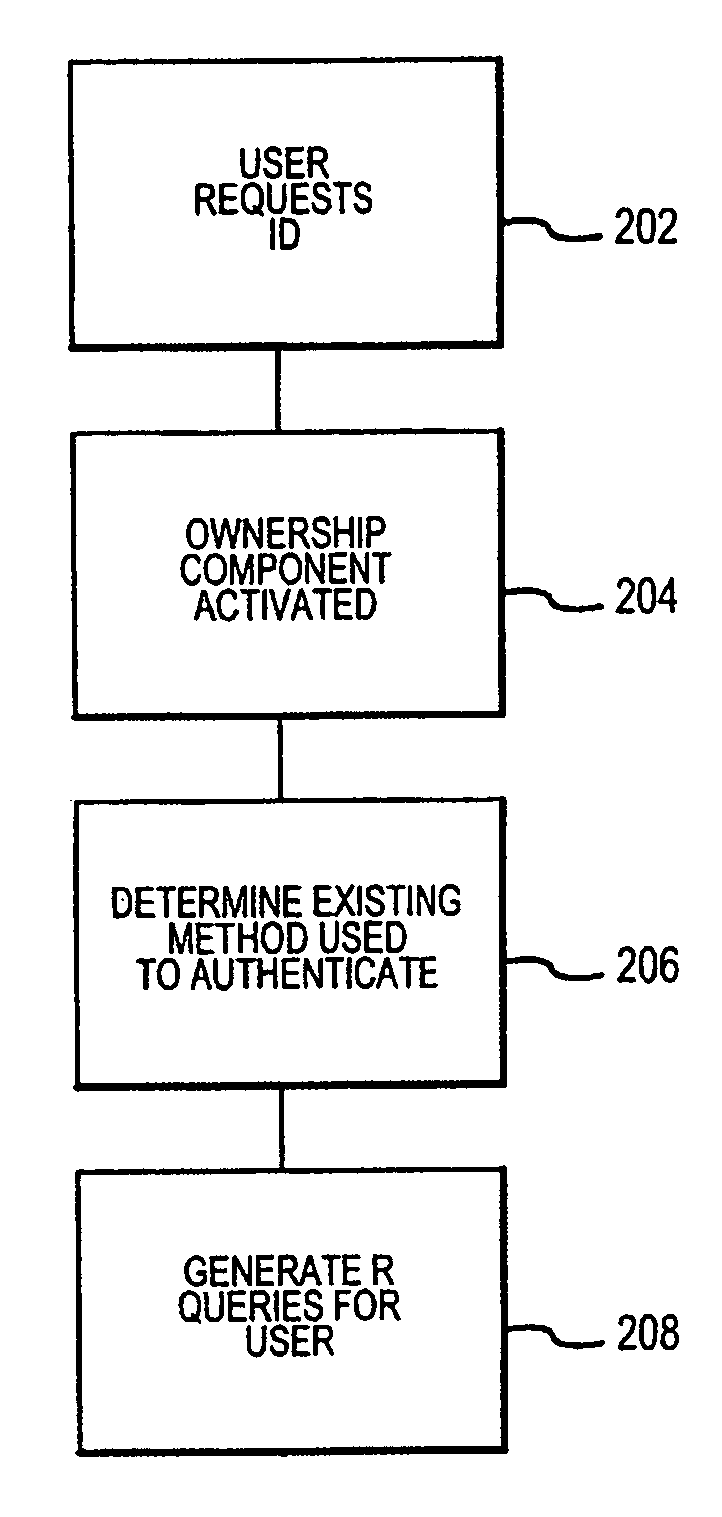
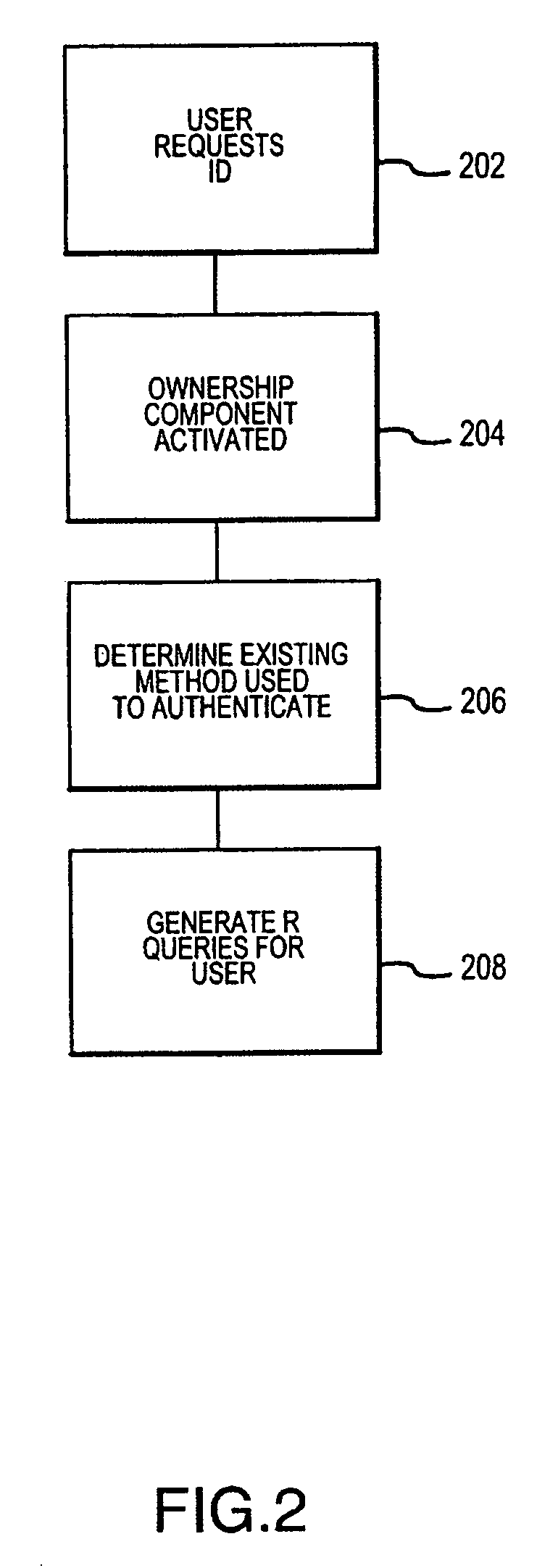
An Enterprise Identity Management system includes a registration component, an ownership component, and an audit component. The registration component is configured to associate a user ID with specific accounts that are accessible via a computer system. The ownership component is configured to verify the ownership of the accounts. The audit component is configured to perform periodic checks to ensure the validity of the association between the user ID and the ownership of the accounts.
Owner:LIBERTY PEAK VENTURES LLC
Framework for automated dissemination of security metadata for distributed trust establishment
ActiveUS20080289019A1Quickly and securely exchangedImprove interoperabilityDigital data processing detailsUser identity/authority verificationDistributed securityDissemination
Methods, systems, and machine-readable media for disseminating security metadata from one distributed entity to another in an automated fashion are disclosed. According to one embodiment of the present invention, a computer-implemented method for distributing security metadata comprises receiving at a first service a request for security metadata, the request being received from a process associated with a second service. The method further comprises generating an identifier and security metadata for the second service, the identifier and the security metadata being unique to the second service, and storing the identifier and the security metadata in a first memory accessible to the first service. The identifier and the security metadata are then transmitted to the process associated with the second service and stored in a second memory. The second service is configured to access the security metadata stored in the second memory to encrypt a first communication and decrypt a second communication.
Owner:ORACLE INT CORP
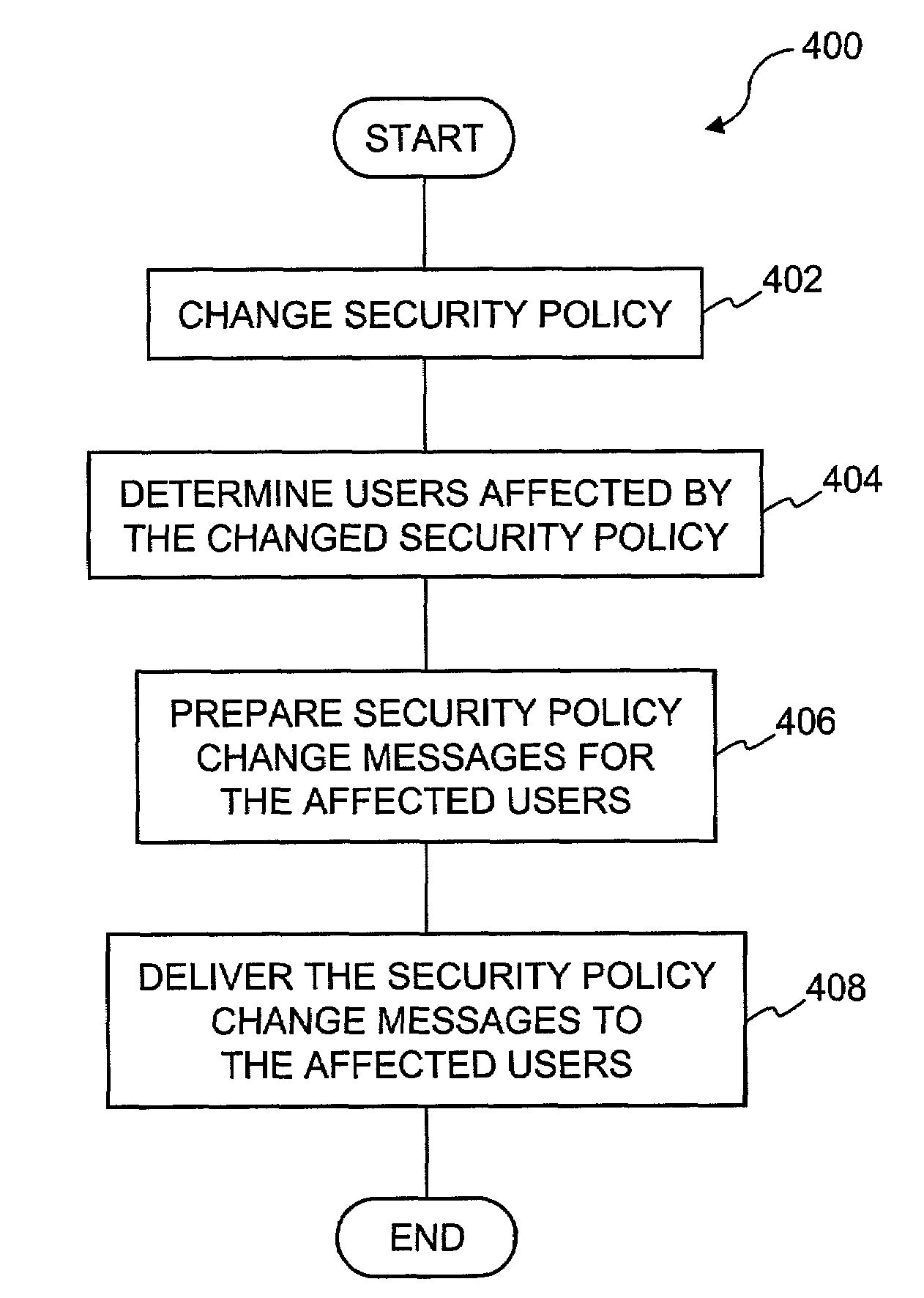
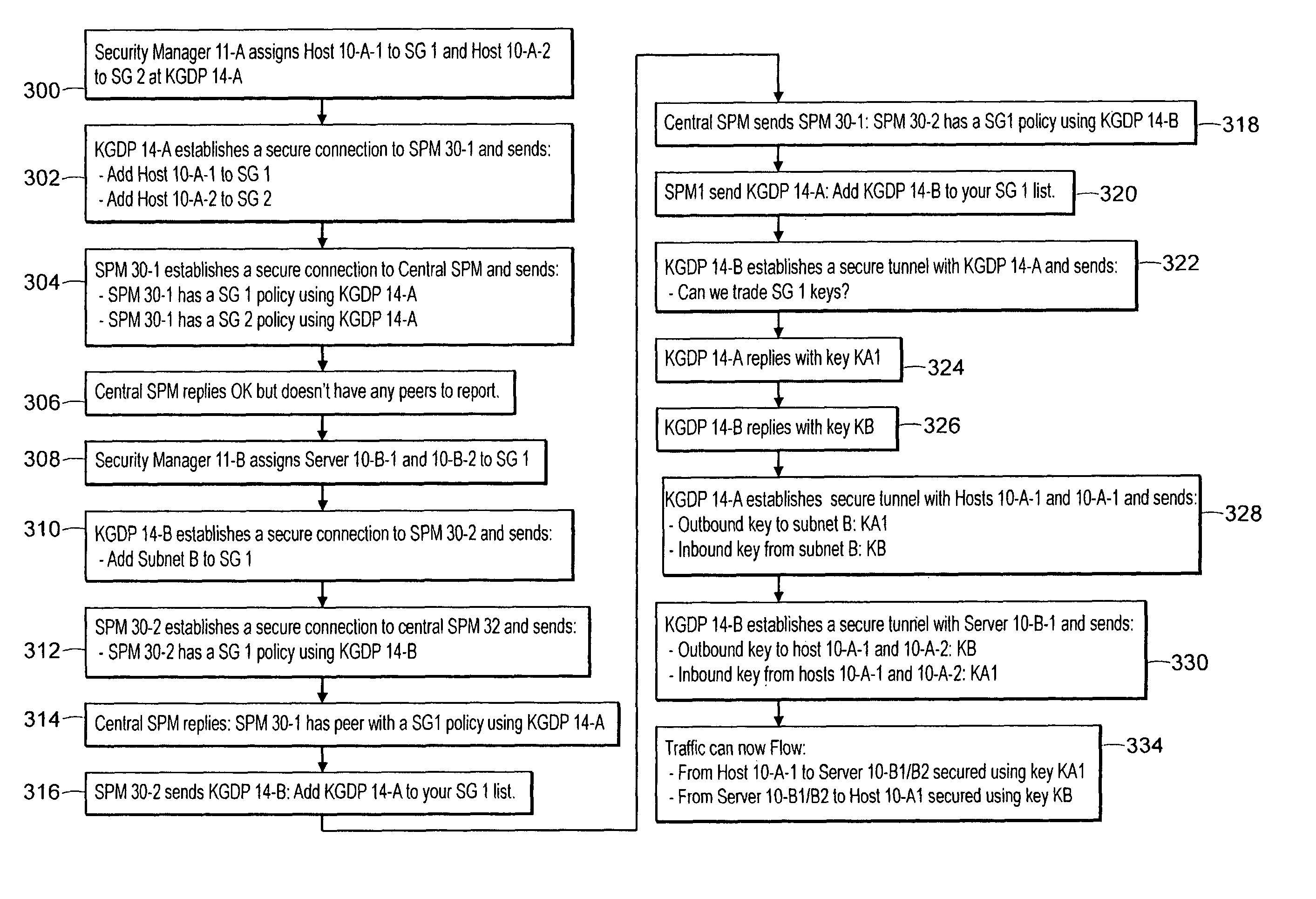
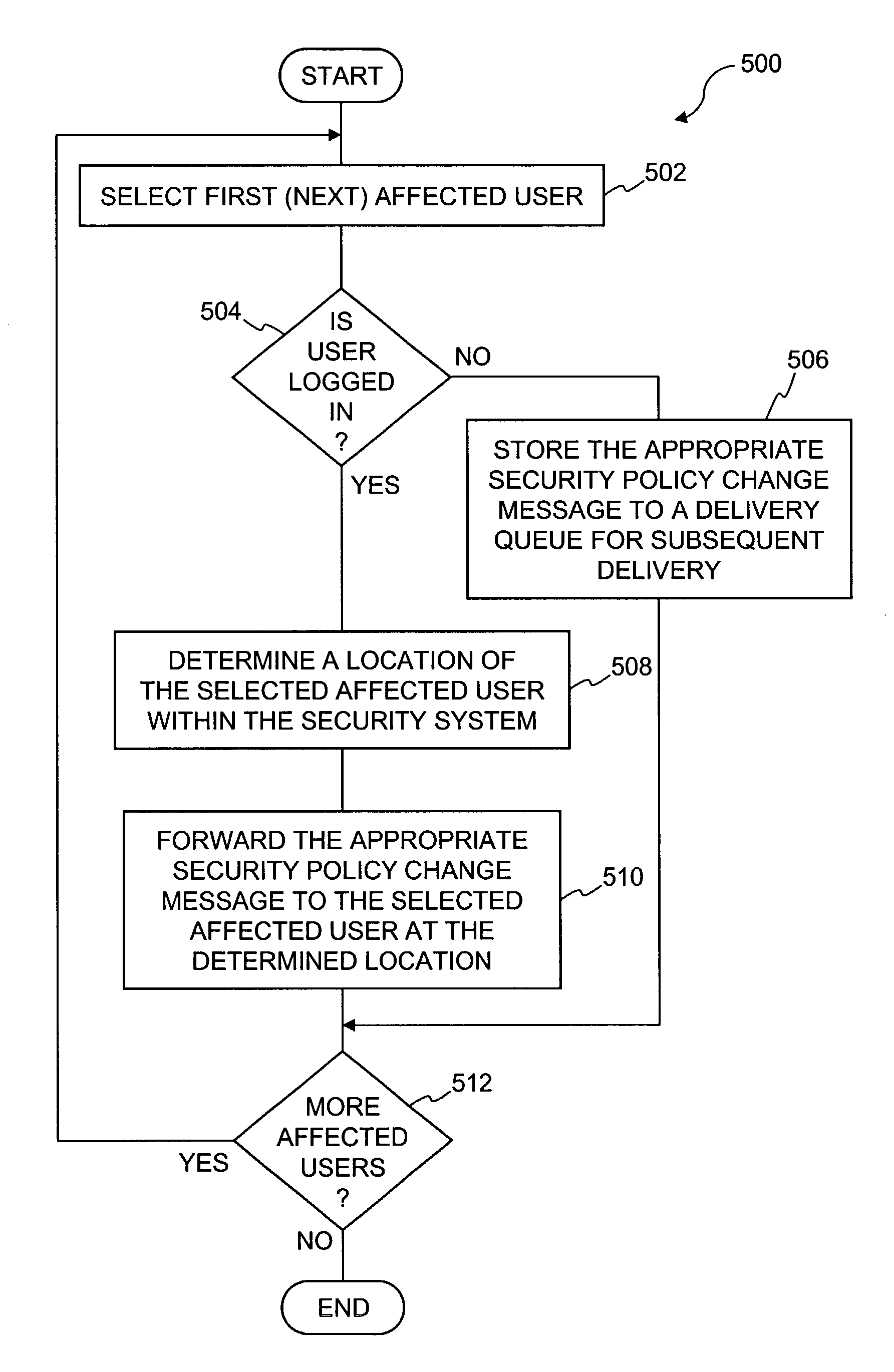
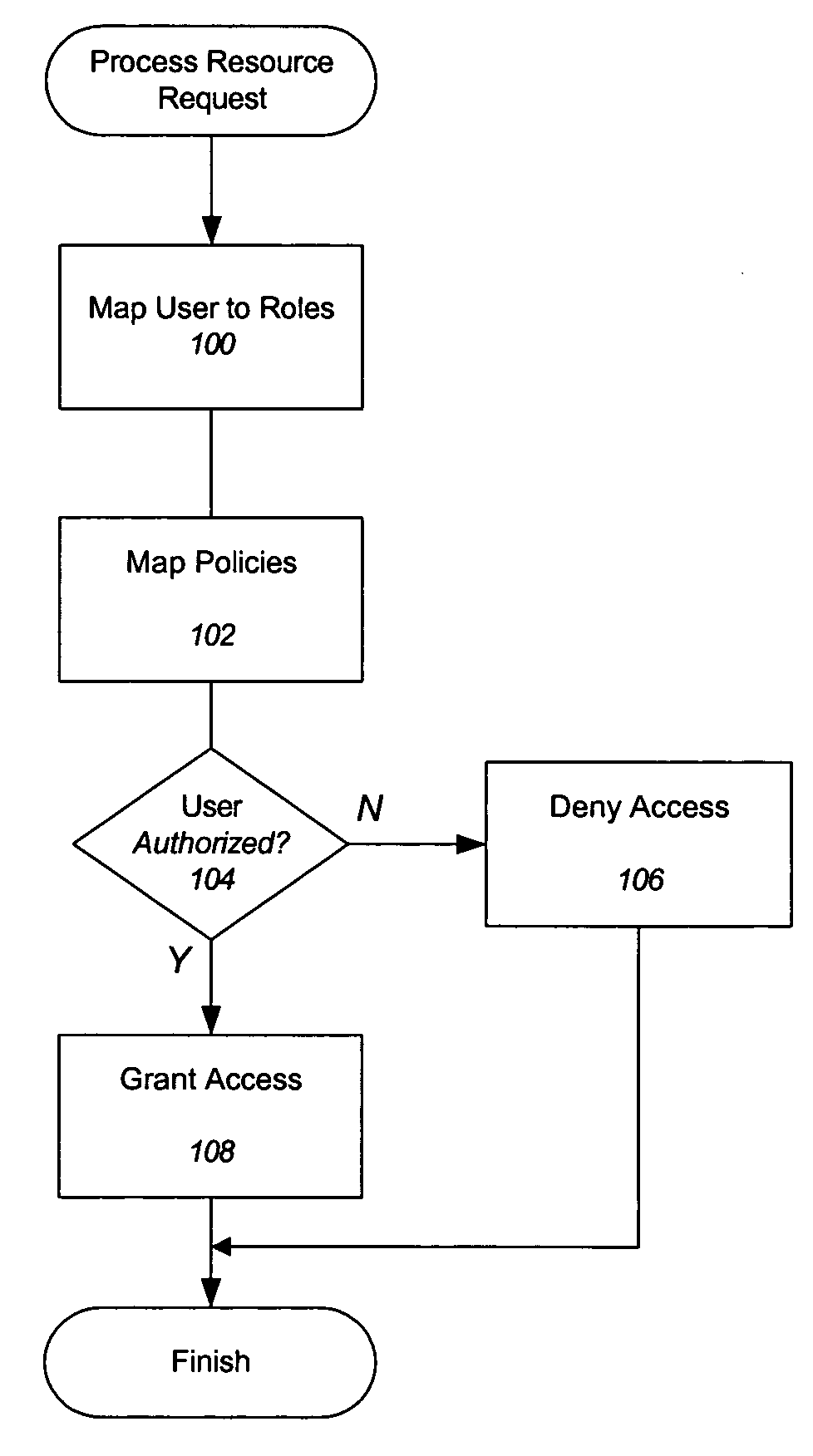
Guaranteed delivery of changes to security policies in a distributed system
ActiveUS7478418B2Digital data processing detailsComputer security arrangementsDistributed securitySecurity policy
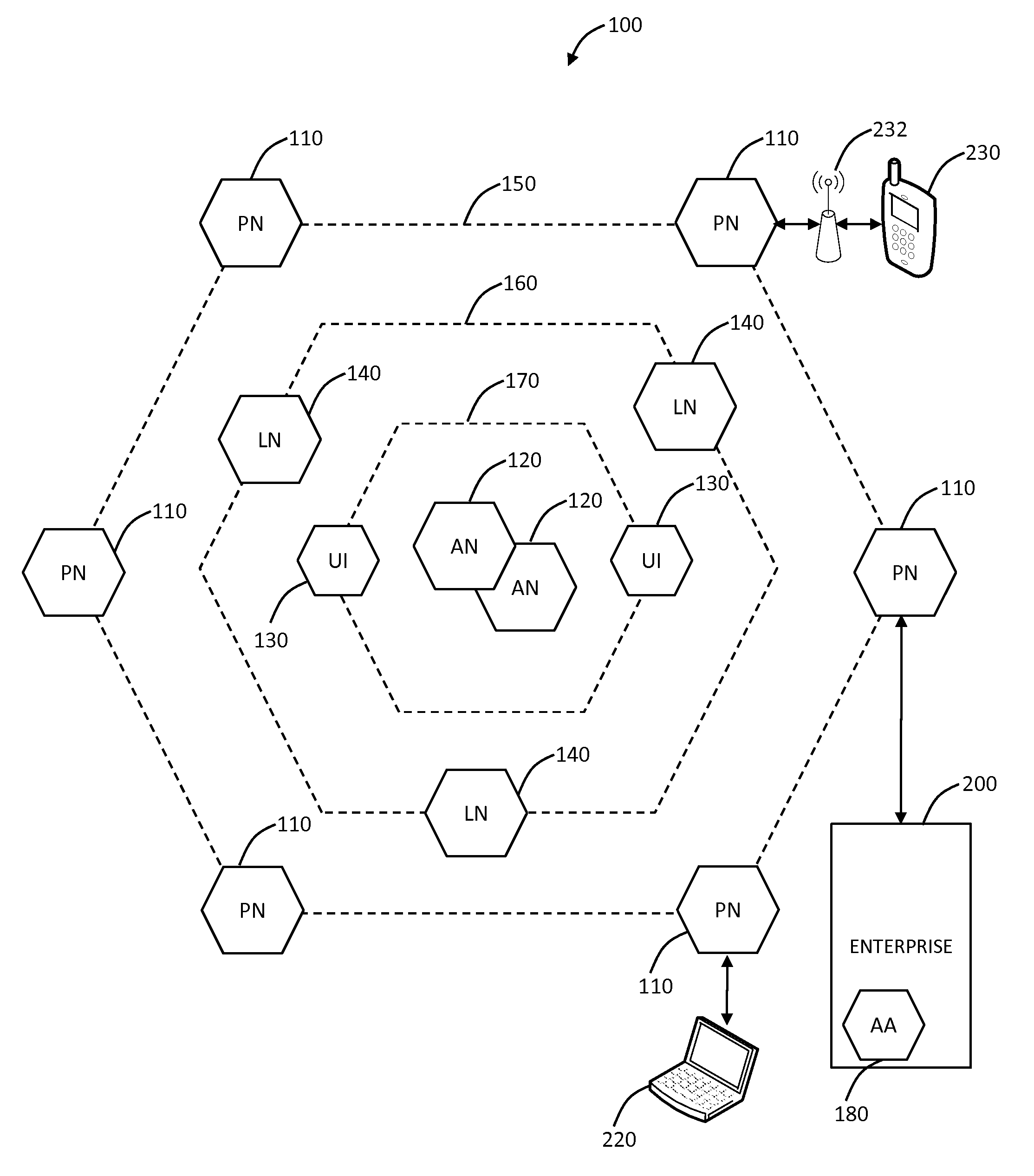
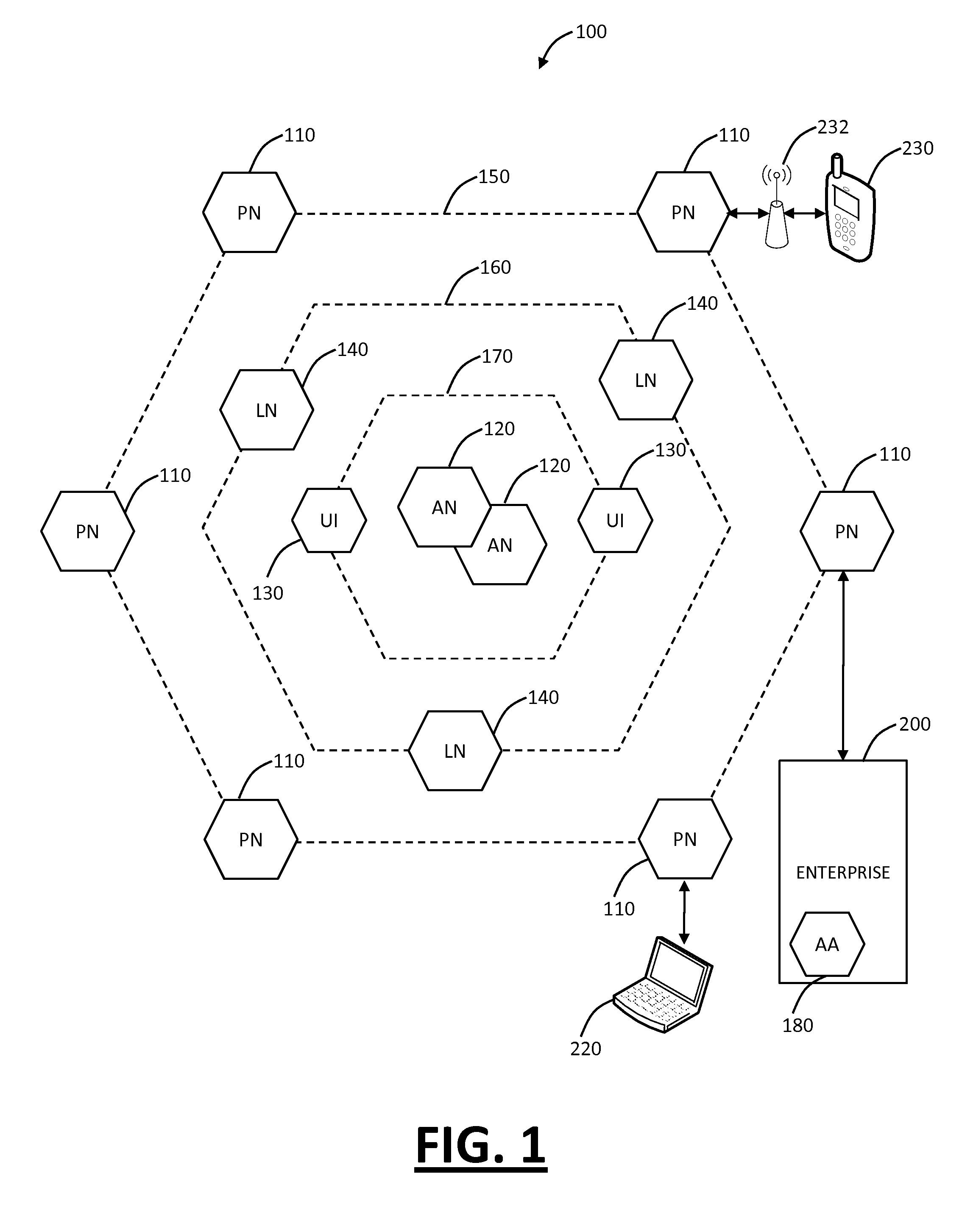
Improved approaches for communicating changes to security policies (or rules) in a distributed security system are disclosed. Depending on the status of an affected user in the system, the changes can be delivered to the user if the user is logged in the system or effectuated in a state message in a local server and the state message is delivered to the user next time the user is logged in the system. If a local server is not operative at the time that a change request is received for a user of the local server, the change request is redirected to another local server. The user is directed to the another local server to affect the change request. As a result, various changes are guaranteed to be delivered to the affected users without compromising the network efficiency.
Owner:INTELLECTUAL VENTURES I LLC
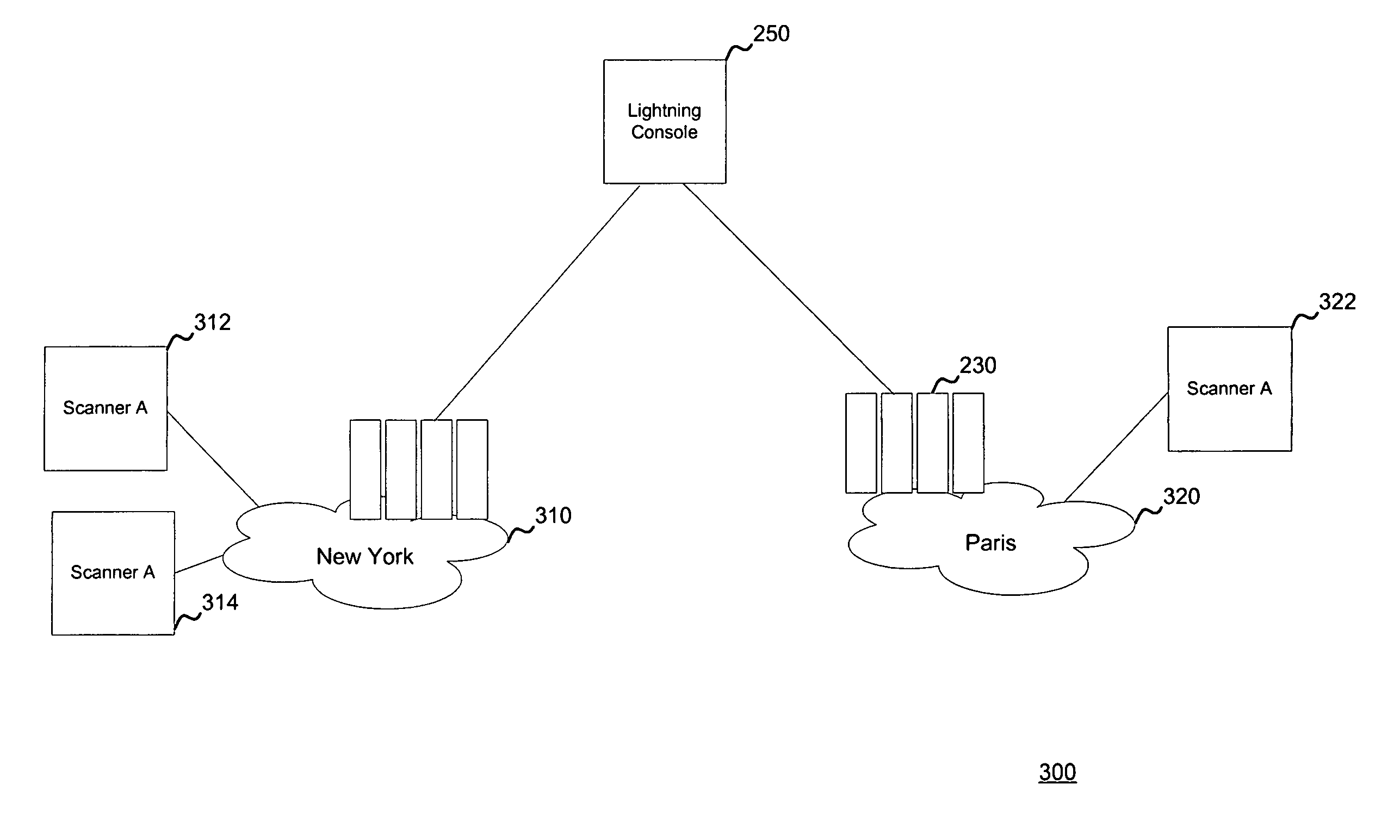
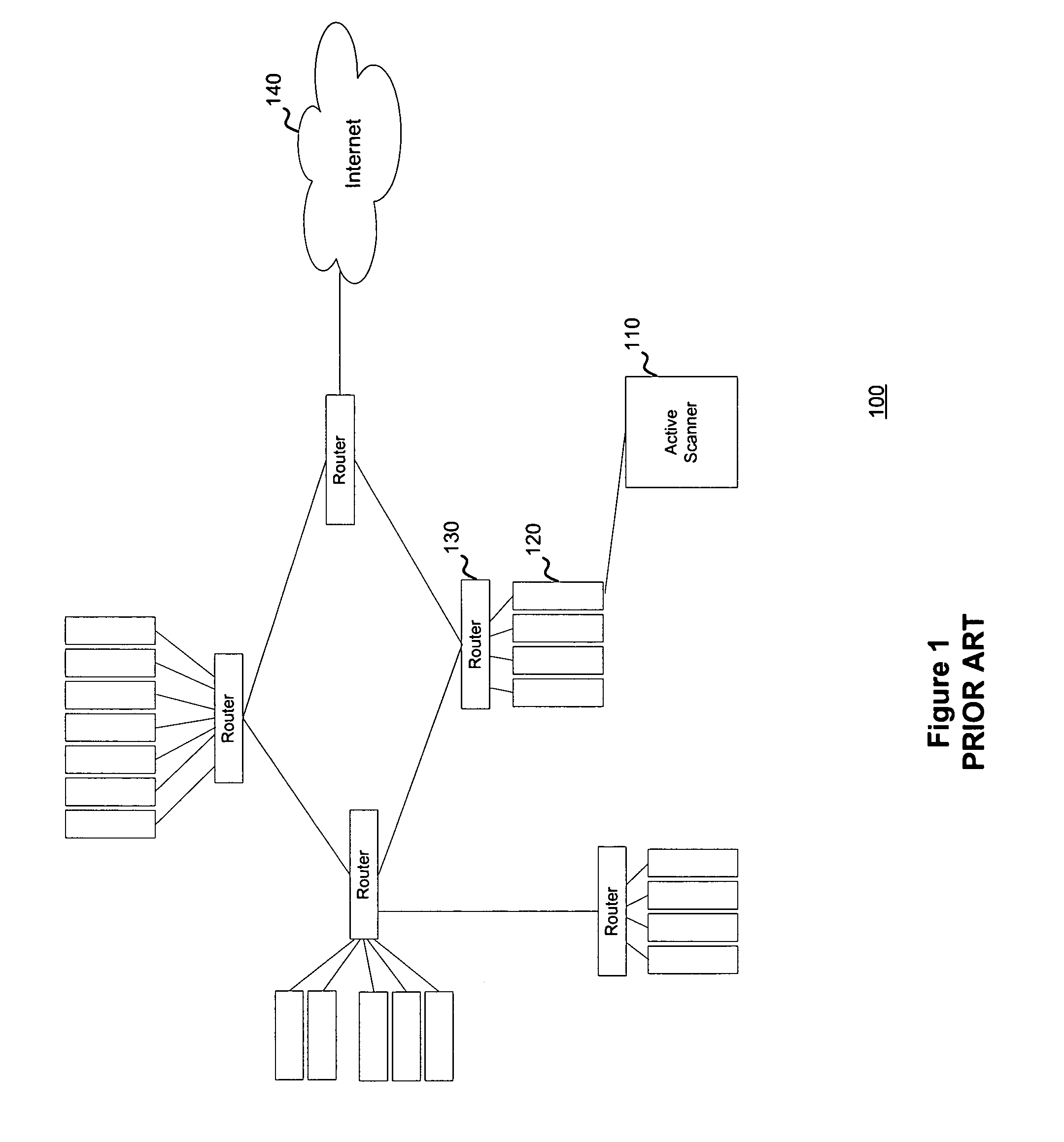
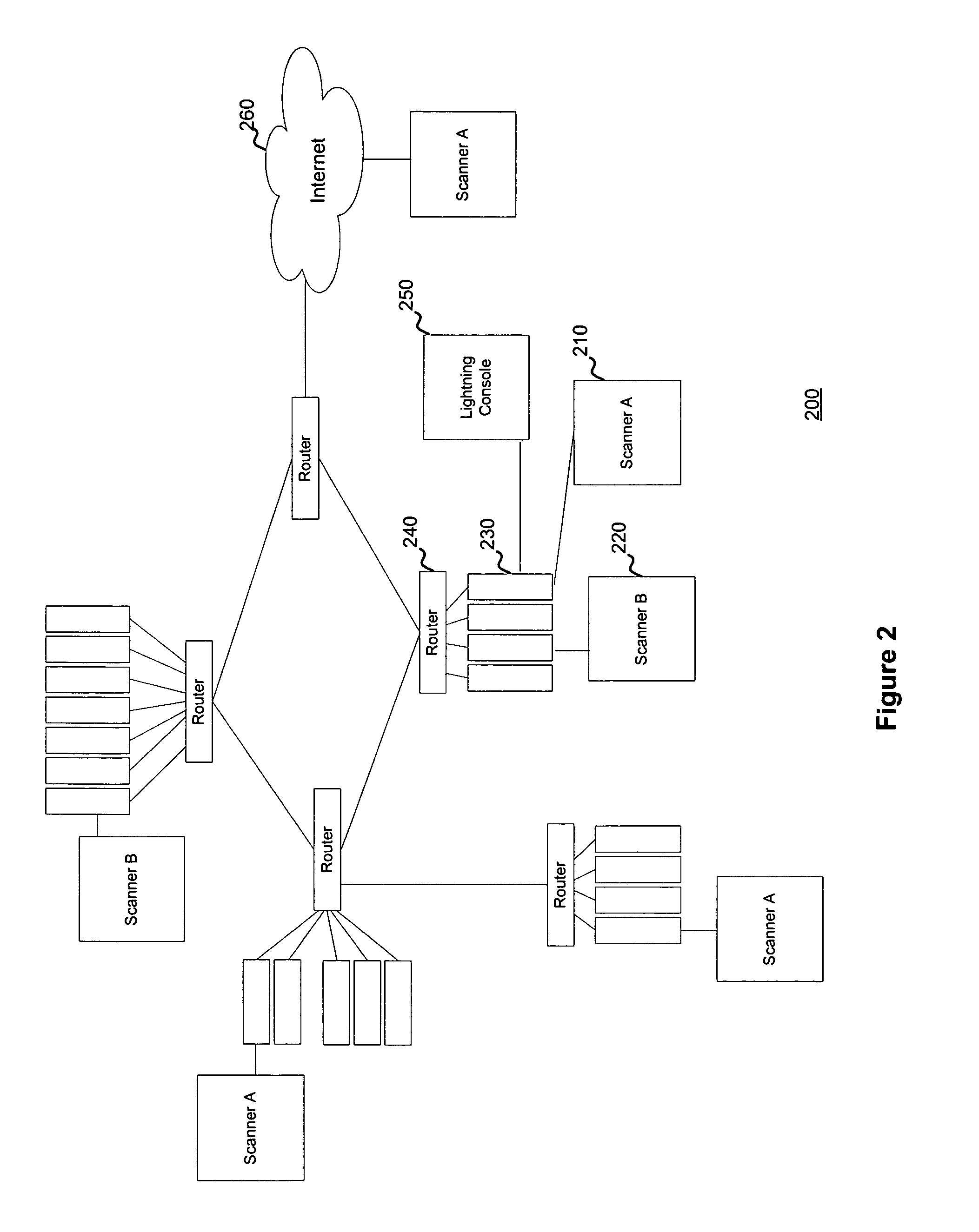
System and method for managing network vulnerability analysis systems
ActiveUS7926113B1Memory loss protectionError detection/correctionSystems managementDistributed security
Systems and methods to manage multiple vulnerability scanners distributed across one or more networks using a distributed security management system, herein called a Lightning Console. By distributing multiple scanners across a network, the work load of each scanner may be reduced to significantly reduce the impact on the network routing and switching infrastructure. In addition, scanners may be placed directly behind firewalls for more thorough scanning. Further, scanners may be placed closer to their scanned networks. By placing vulnerability scanners closer, the actual scanning traffic does not cross the core network switch and routing fabric, thereby avoiding potential network outages due to scanning activity. In addition, the closer distance of the scanners to the scanned targets speeds scan times by reducing the distance that the packets must traverse.
Owner:TENABLE INC
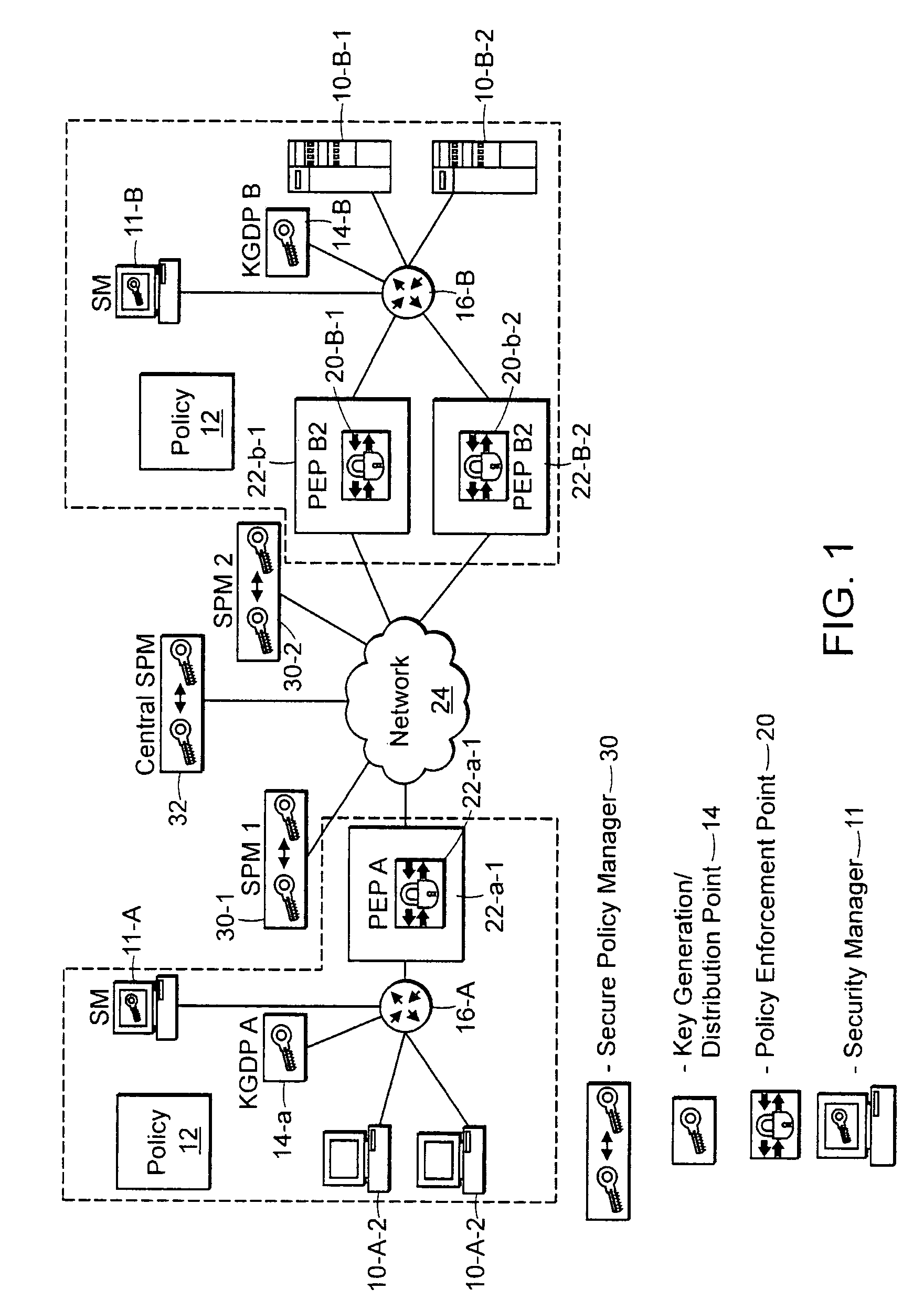
Securing network traffic by distributing policies in a hierarchy over secure tunnels
A technique for securing message traffic in a data network using a protocol such as IPsec, and more particularly various methods for distributing security policies among peer entities in a network while minimizing the passing and storage of detailed policy or key information except at the lowest levels of a hierarchy.
Owner:CIPHEROPTICS
Data processing system for the selective distribution of assets between different portfolios
InactiveUS6029148AHigh degreeFull legal independenceFinanceSpecial data processing applicationsData processing systemDistributed security
Owner:FASTNET RESOURCES
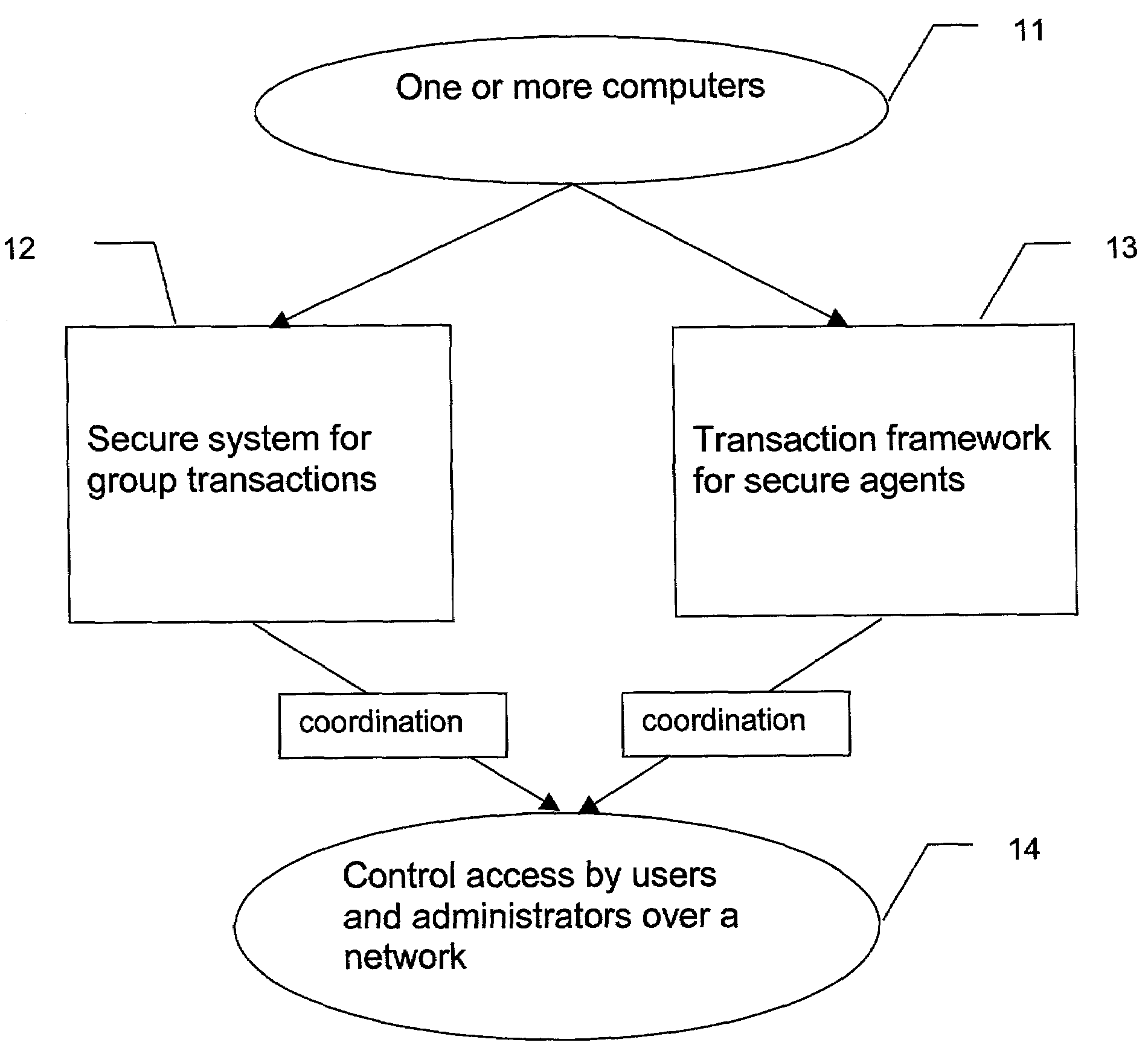
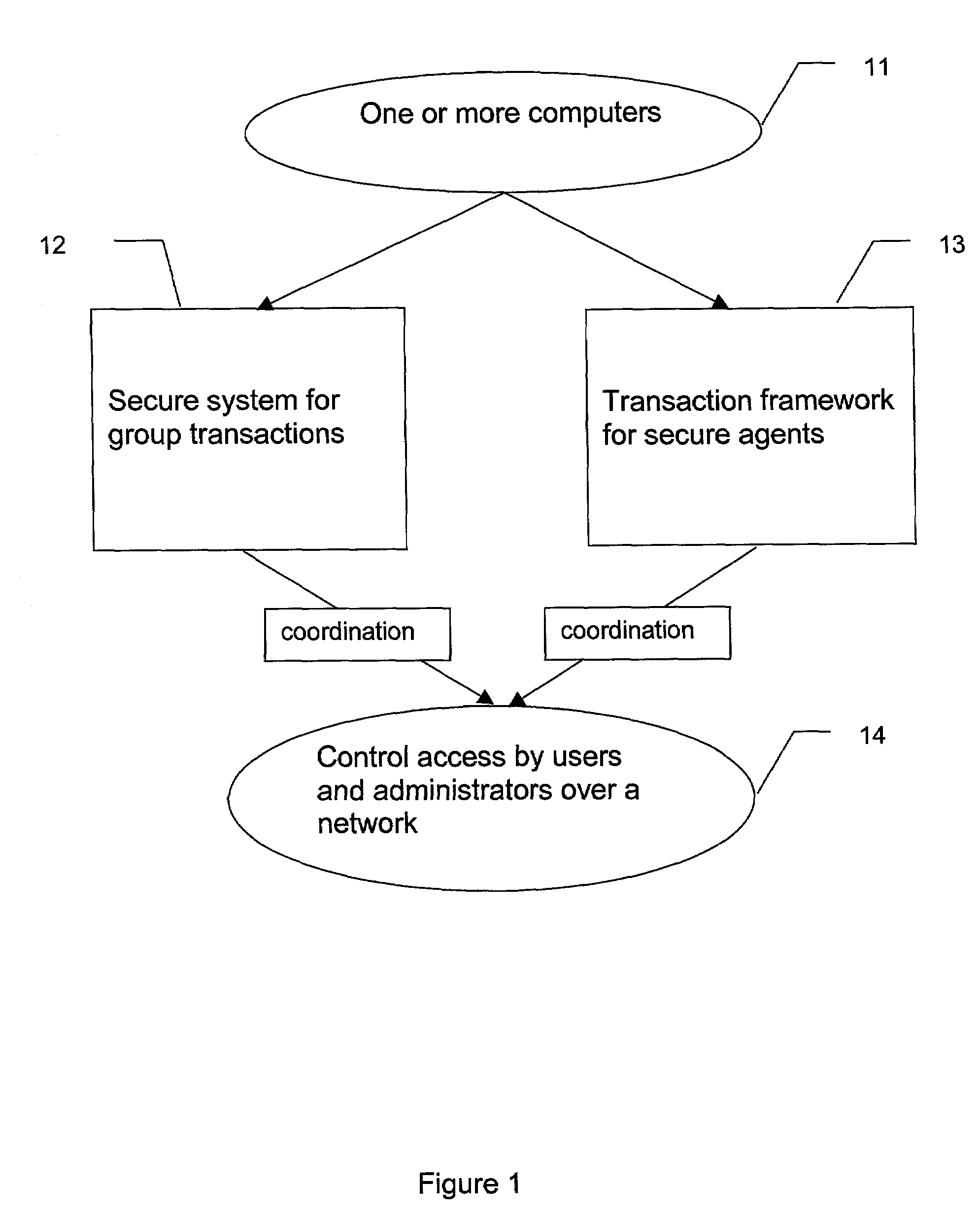
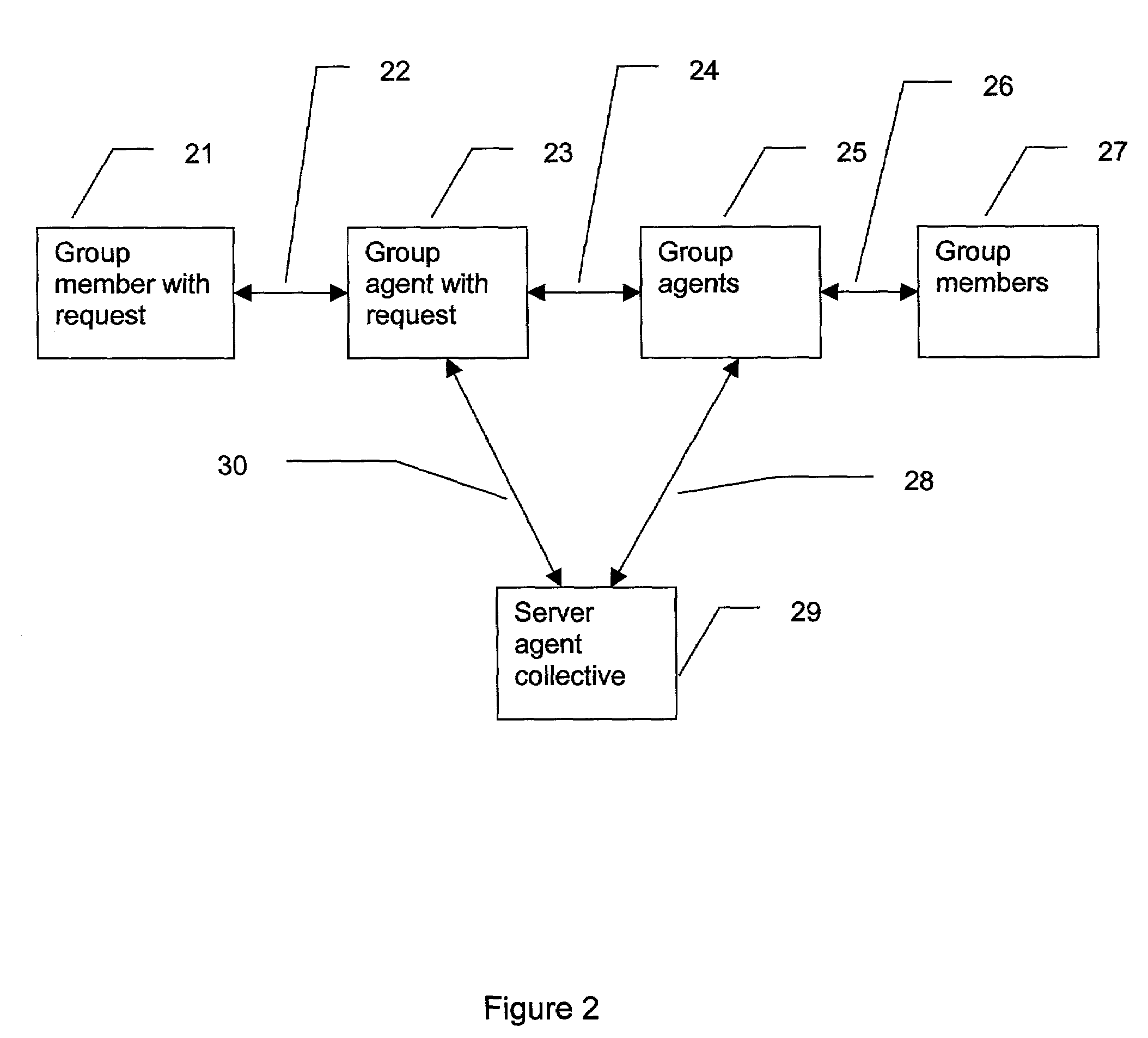
System and method for secure group transactions
ActiveUS7036146B1Digital data processing detailsUnauthorized memory use protectionDistributed securityWeb environment
A method and a secure system, processing on one or more computers, provides a way to control a group transaction. The invention uses group consensus access control and multiple distributed secure agents in a network environment. Each secure agent can organize with the other secure agents to form a secure distributed agent collective.
Owner:NAT TECH & ENG SOLUTIONS OF SANDIA LLC
Method and system for implementing changes to security policies in a distributed security system
ActiveUS7565683B1User identity/authority verificationComputer security arrangementsParallel computingEngineering
Improved approaches for effectuating changes to security policies in a distributed security system are disclosed. The changes to security policies are distributed to those users (e.g., user and / or computers) in the security system that are affected. The distribution of such changes to security policies can be deferred for those affected users that are not activated (e.g., logged-in or on-line) with the security system.
Owner:INTELLECTUAL VENTURES I LLC
Securing network traffic by distributing policies in a hierarchy over secure tunnels
A technique for securing message traffic in a data network using a protocol such as IPsec, and more particularly various methods for distributing security policies among peer entities in a network while minimizing the passing and storage of detailed policy or key information except at the lowest levels of a hierarchy.
Owner:CIPHEROPTICS
Using Private Threat Intelligence in Public Cloud
ActiveUS20170272469A1Preserving data integrityPreserving securityComputer security arrangementsTransmissionUser deviceQuery string
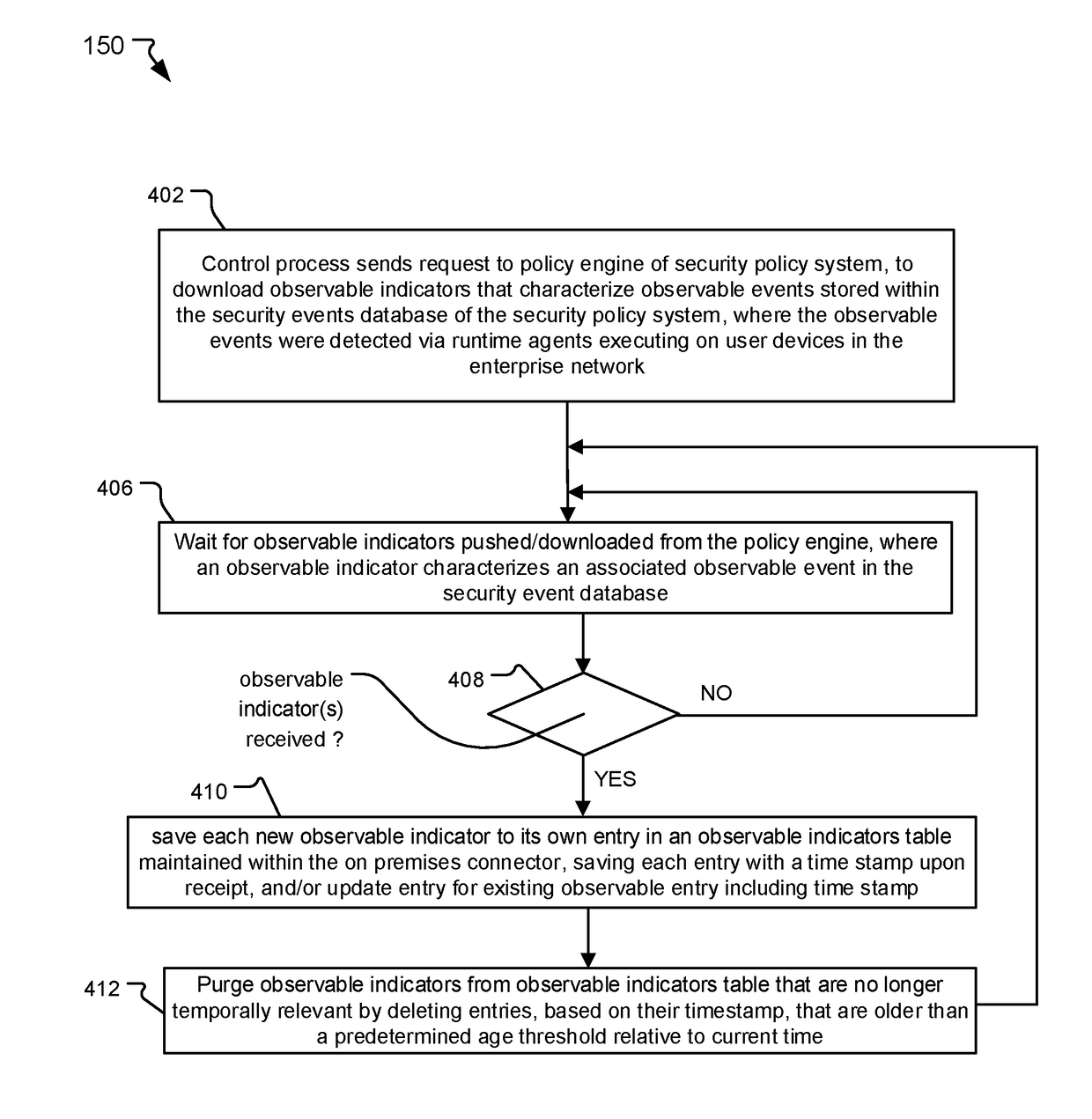
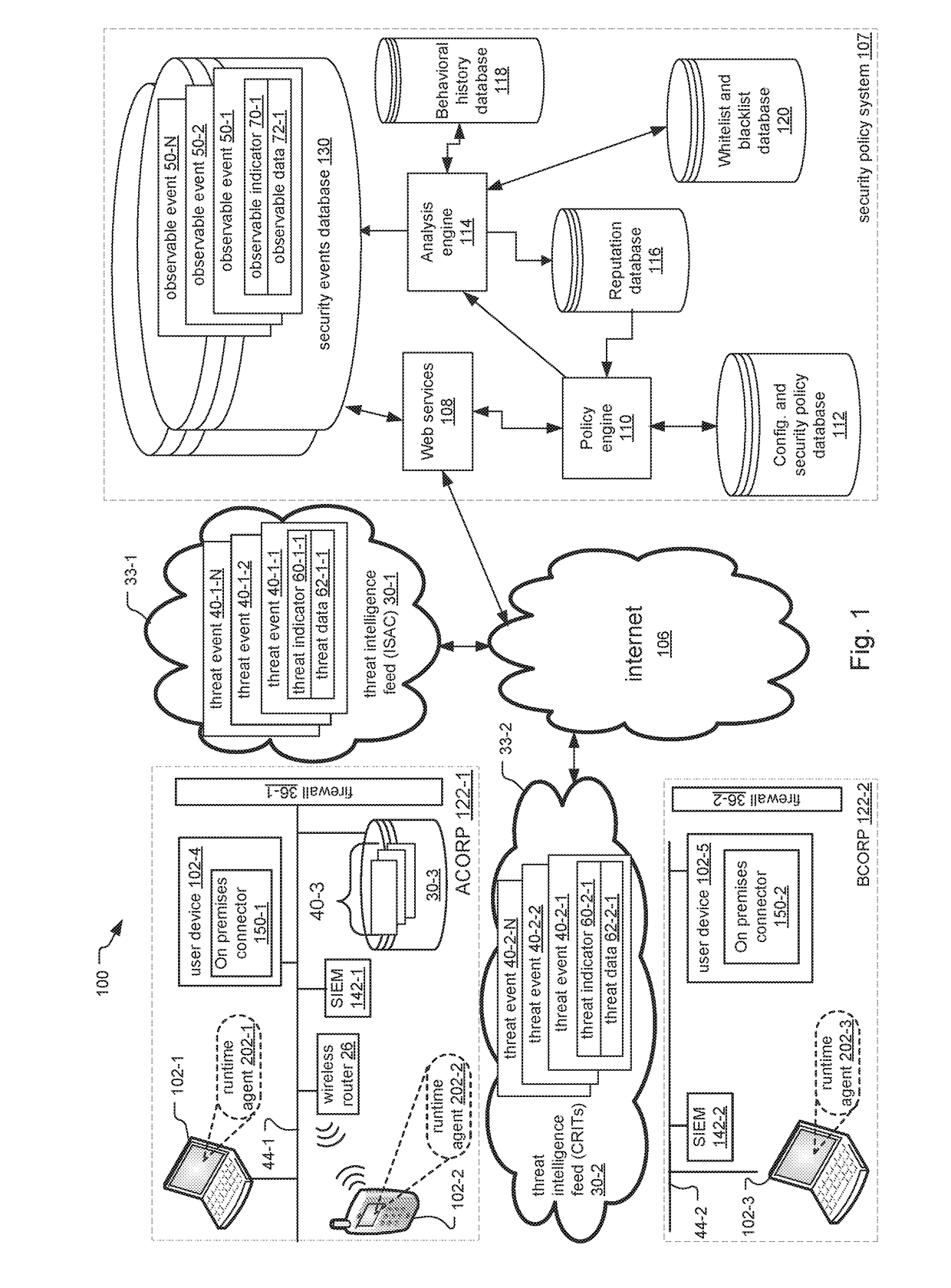
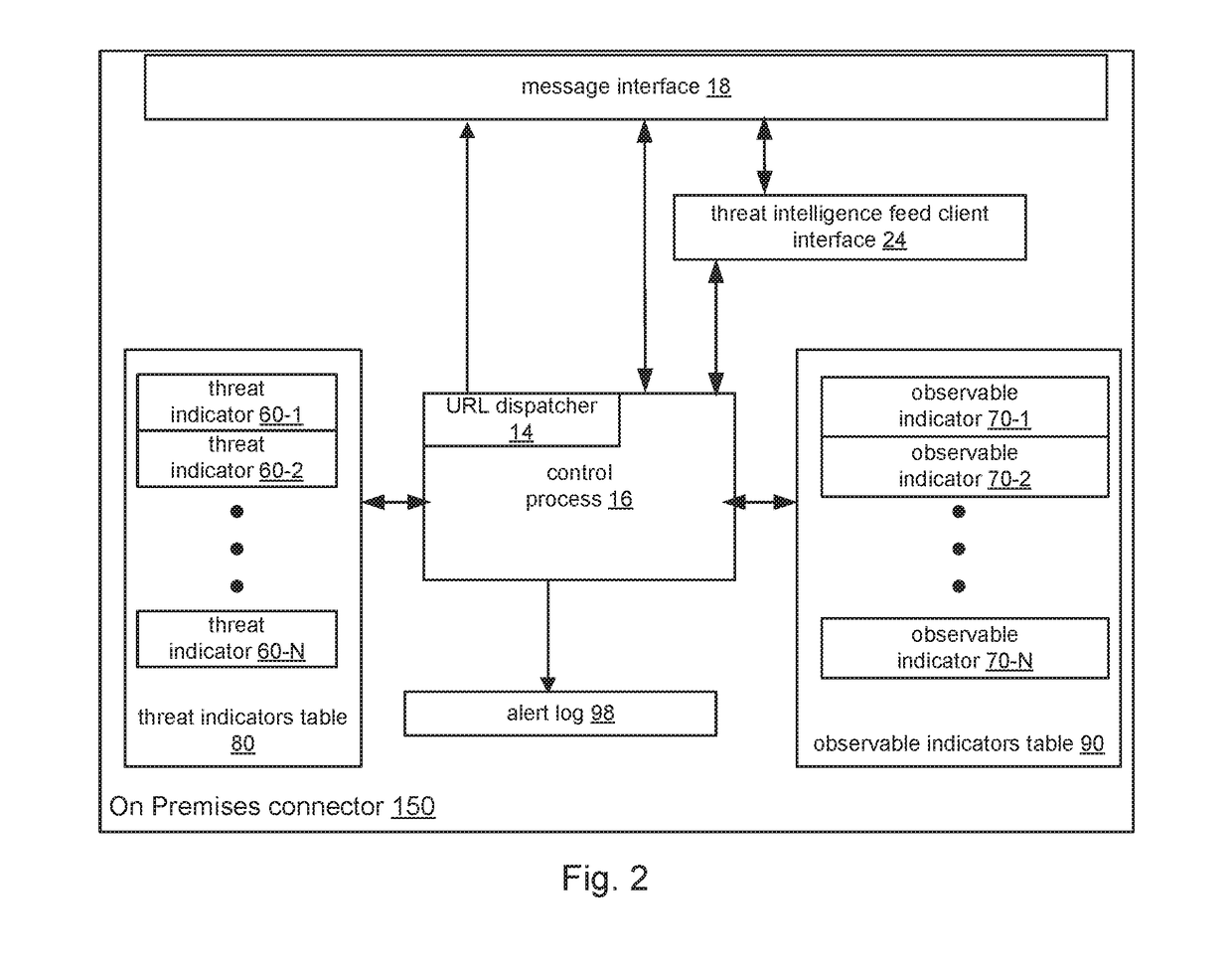
A distributed security system and method are disclosed that enable access to known threat events from threat intelligence feeds when the system includes public cloud components. A cloud-based security policy system stores observable events for security incidents detected by and sent from user devices within an enterprise network. The observable events include observable indicators for characterizing the observable events. The threat events within the feeds include threat indicators for characterizing the threat events. An on-premises connector within the enterprise network downloads the observable indicators from the security policy system and the threat indicators from the feeds. In response to determining that any observable indicators match any threat indicators, the on-premises connector provides access to the threat events and / or the observable events having the matching indicators. In one example, the on-premises connector generates opaque query strings for users on user devices to access the threat events / observable events having the matching indicators.
Owner:CARBON BLACK
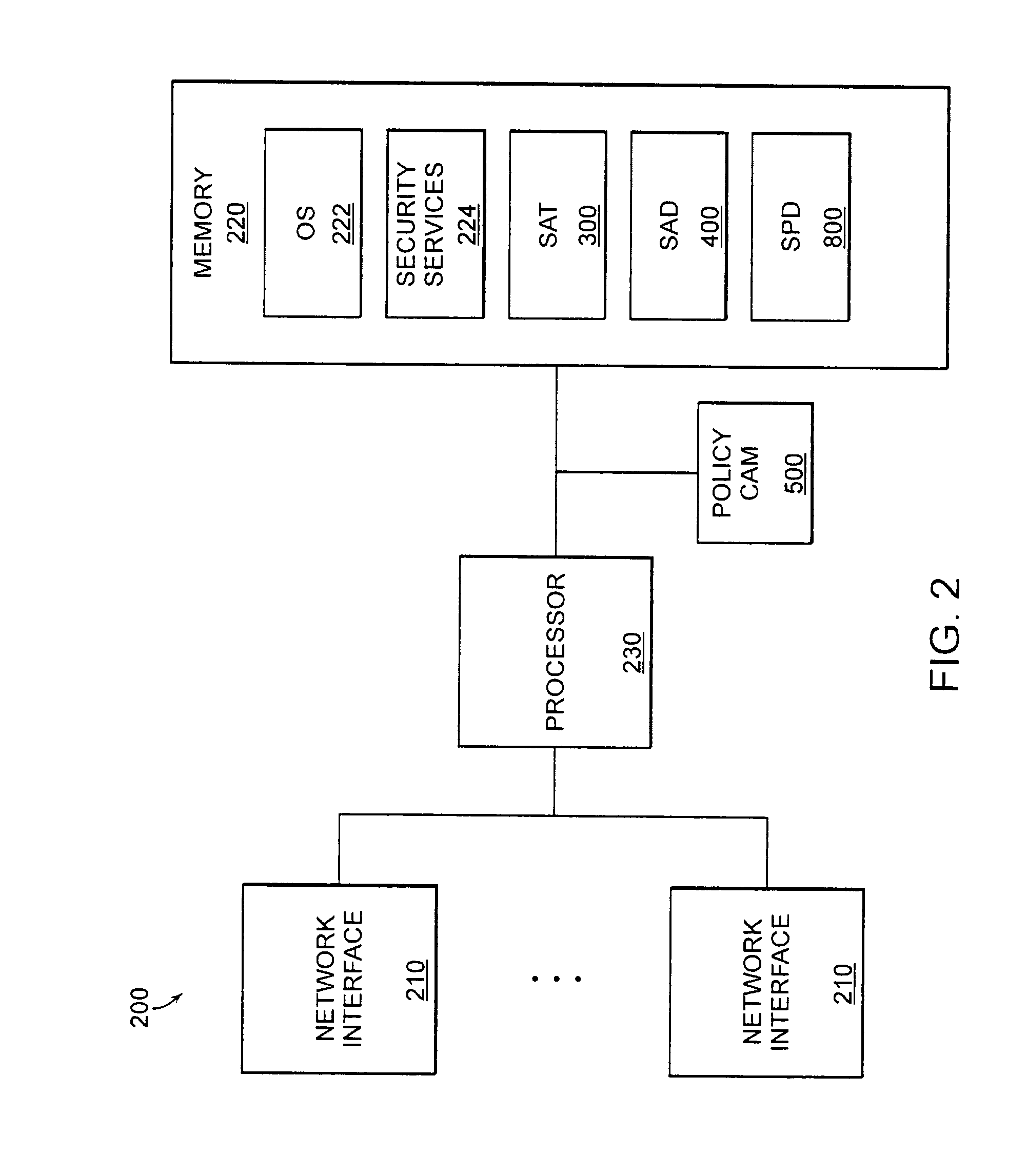
Dynamically configurable distributed security system
InactiveUS20050081055A1Digital data processing detailsDigital computer detailsResource basedDistributed security
A system and method for a dynamically configurable security system, comprising, a security service module capable of dynamically instantiating one or more plugin security provider modules, the one or more security provider modules are coupled to the security service module wherein the one or more security provider modules are capable of responding dynamically to changes in configuration information, wherein the security service module is capable of receiving one or more security information updates, and wherein the security service module is capable of controlling access to one or more resources based on the one or more security information updates.
Owner:BEA SYST INC
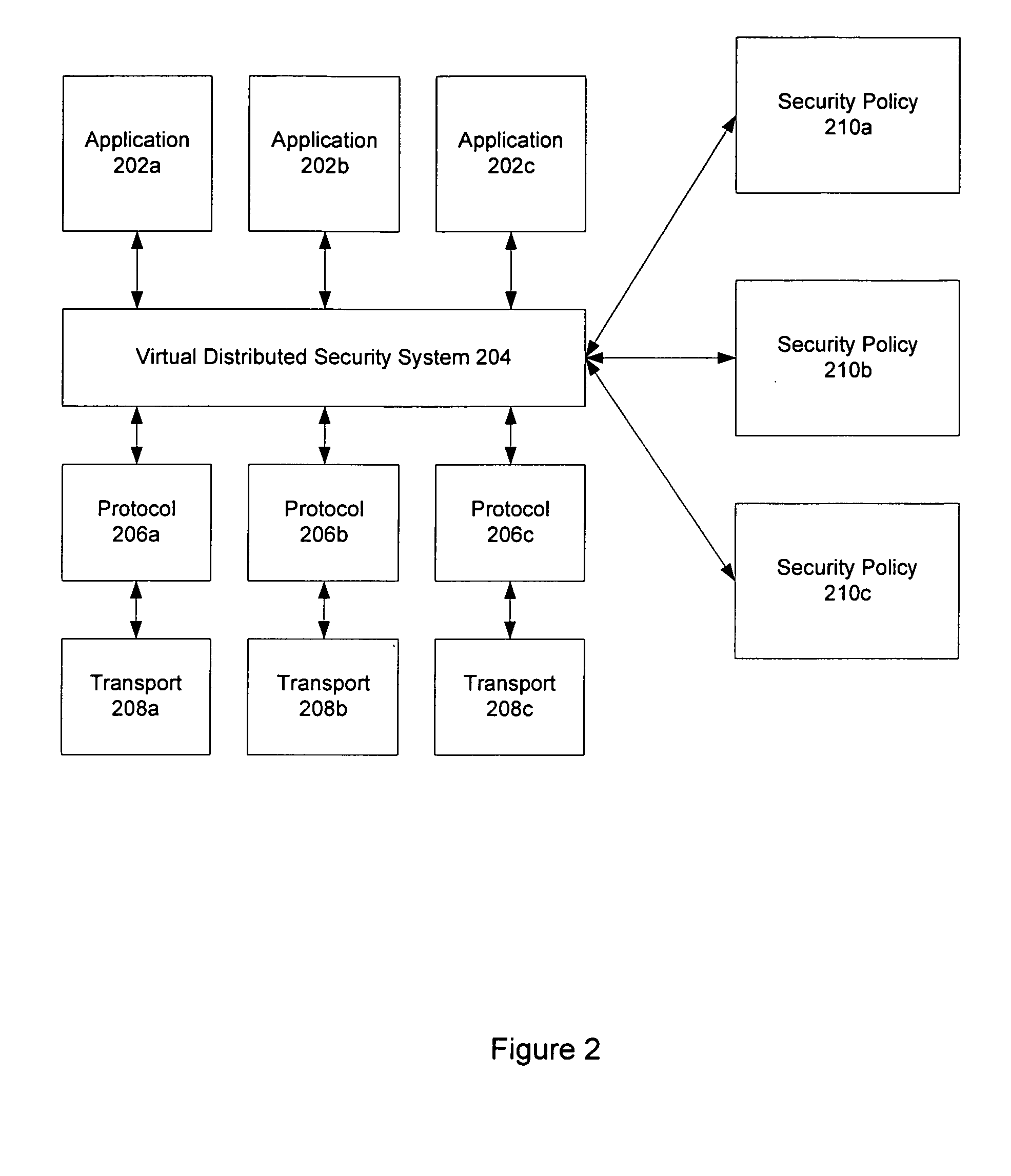
Virtual distributed security system
ActiveUS20060041929A1Increase flexibilityImprove scalabilityUnauthorized memory use protectionDigital data protectionDistributed securitySecurity policy
A distributed security system is provided. The distributed security system uses a security policy that is written in a policy language that is transport and security protocol independent as well as independent of cryptographic technologies. This security policy can be expressed using the language to create different security components allowing for greater scalability and flexibility. By abstracting underlying protocols and technologies, multiple environments and platforms can be supported.
Owner:MICROSOFT TECH LICENSING LLC
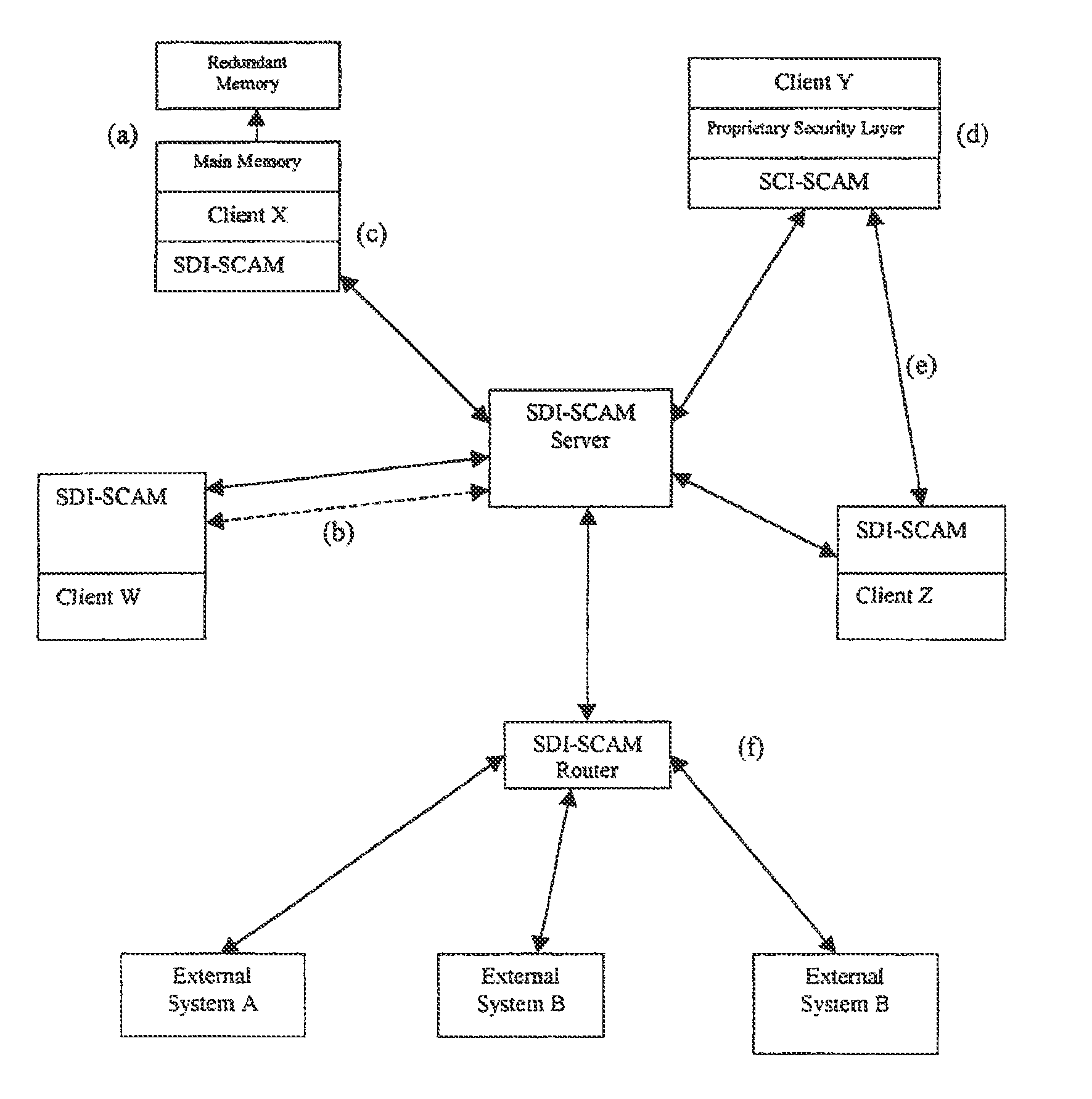
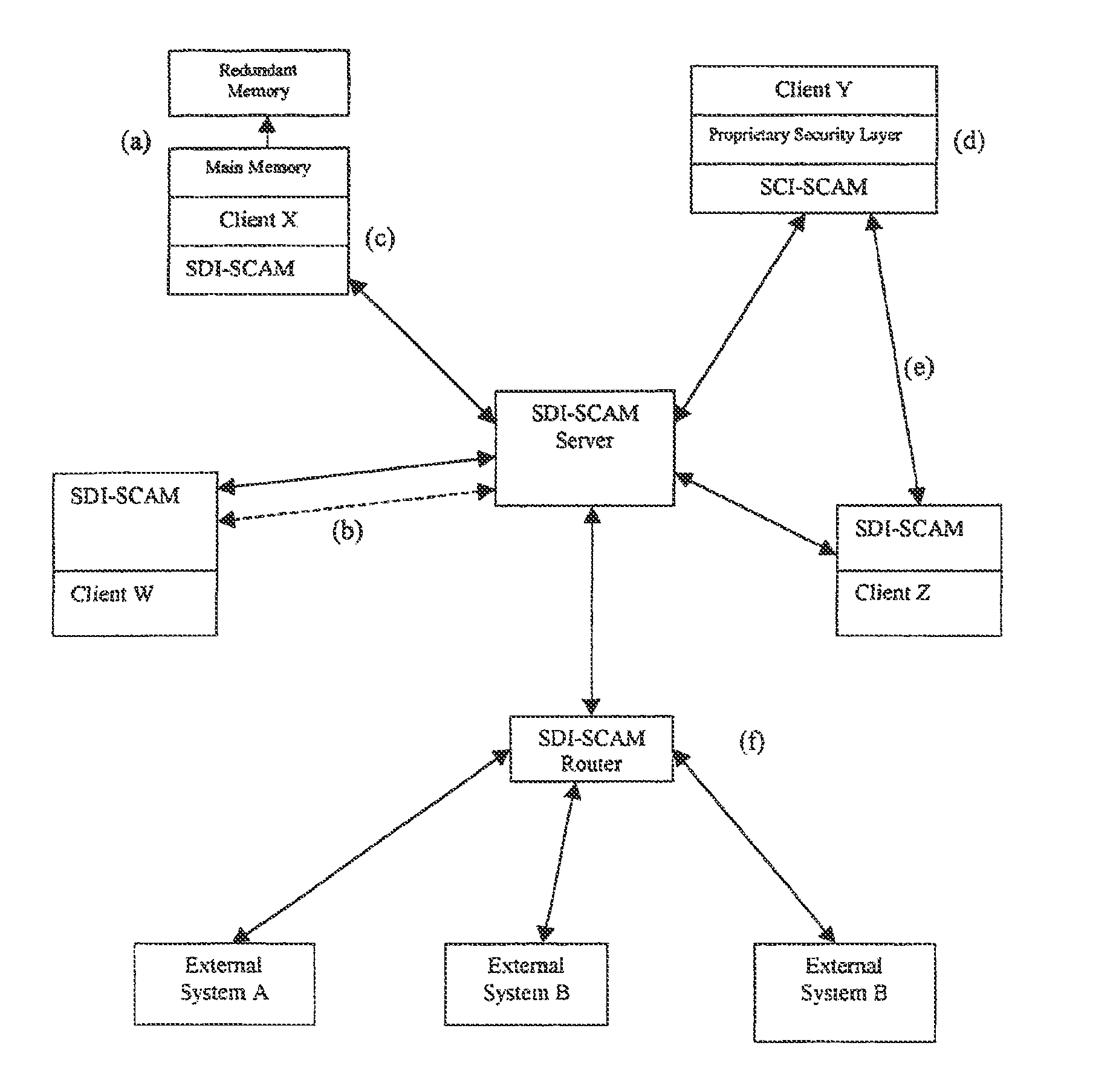
System and method for a distributed application of a network security system (SDI-SCAM)
InactiveUS20130091573A1Memory loss protectionError detection/correctionCountermeasureRelative probability
A widely distributed security system (SDI-SCAM) that protects computers at individual client locations, but which constantly pools and analyzes information gathered from machines across a network in order to quickly detect patterns consistent with intrusion or attack, singular or coordinated. When a novel method of attack has been detected, the system distributes warnings and potential countermeasures to each individual machine on the network. Such a warning may potentially consist of a probability distribution of the likelihood of an intrusion or attack as well as the relative probabilistic likelihood that such potential intrusion possesses certain characteristics or typologies or even strategic objectives in order to best recommend and / or distribute to each machine the most befitting countermeasure(s) given all presently known particular data and associated predicted probabilistic information regarding the prospective intrusion or attack. If any systems are adversely affected, methods for repairing the damage are shared and redistributed throughout the network.
Owner:INVENTSHIP LLC
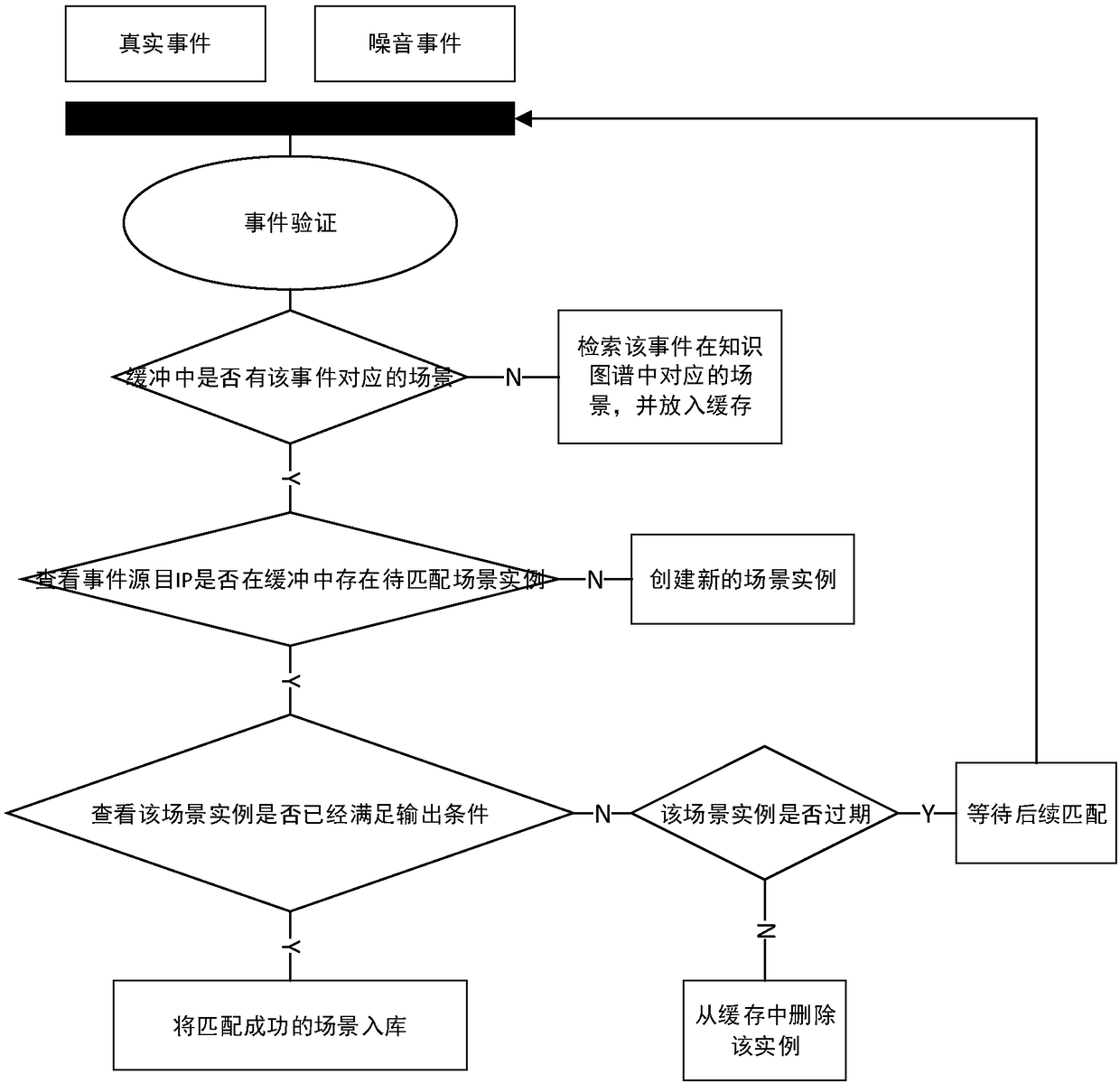
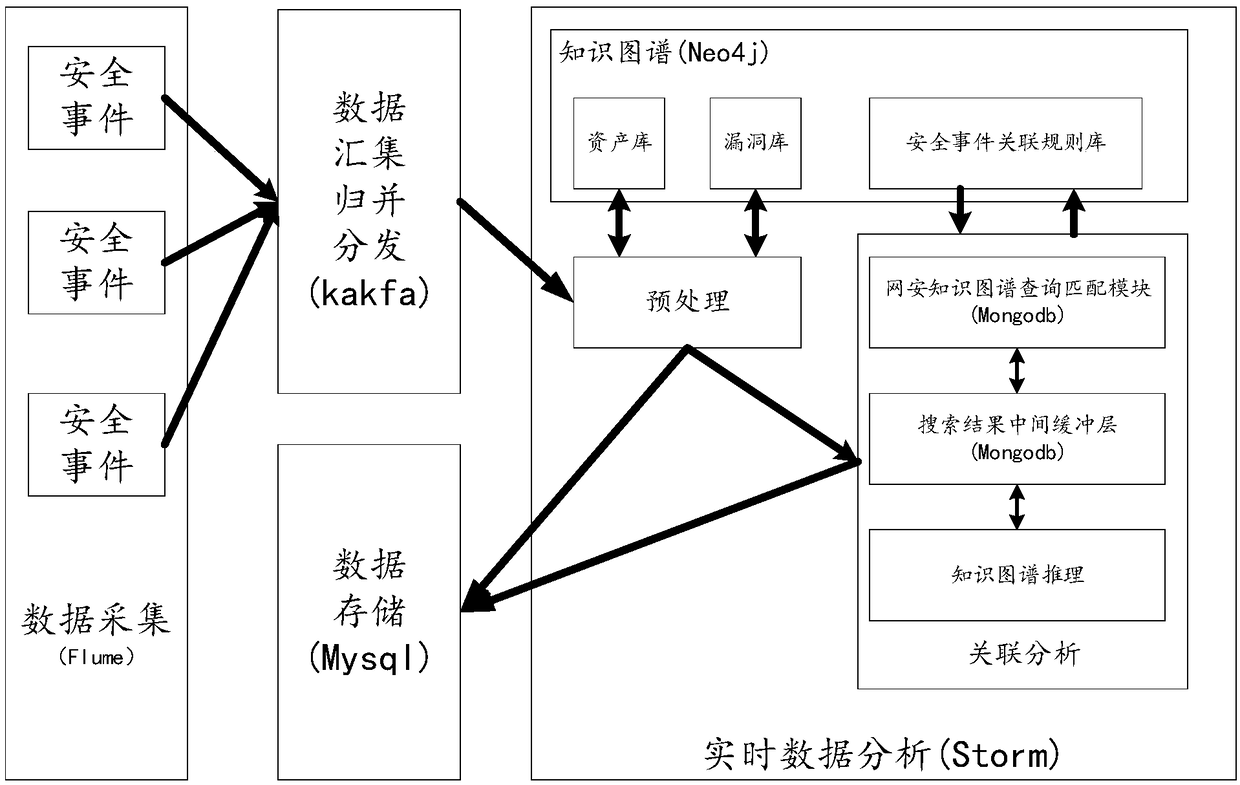
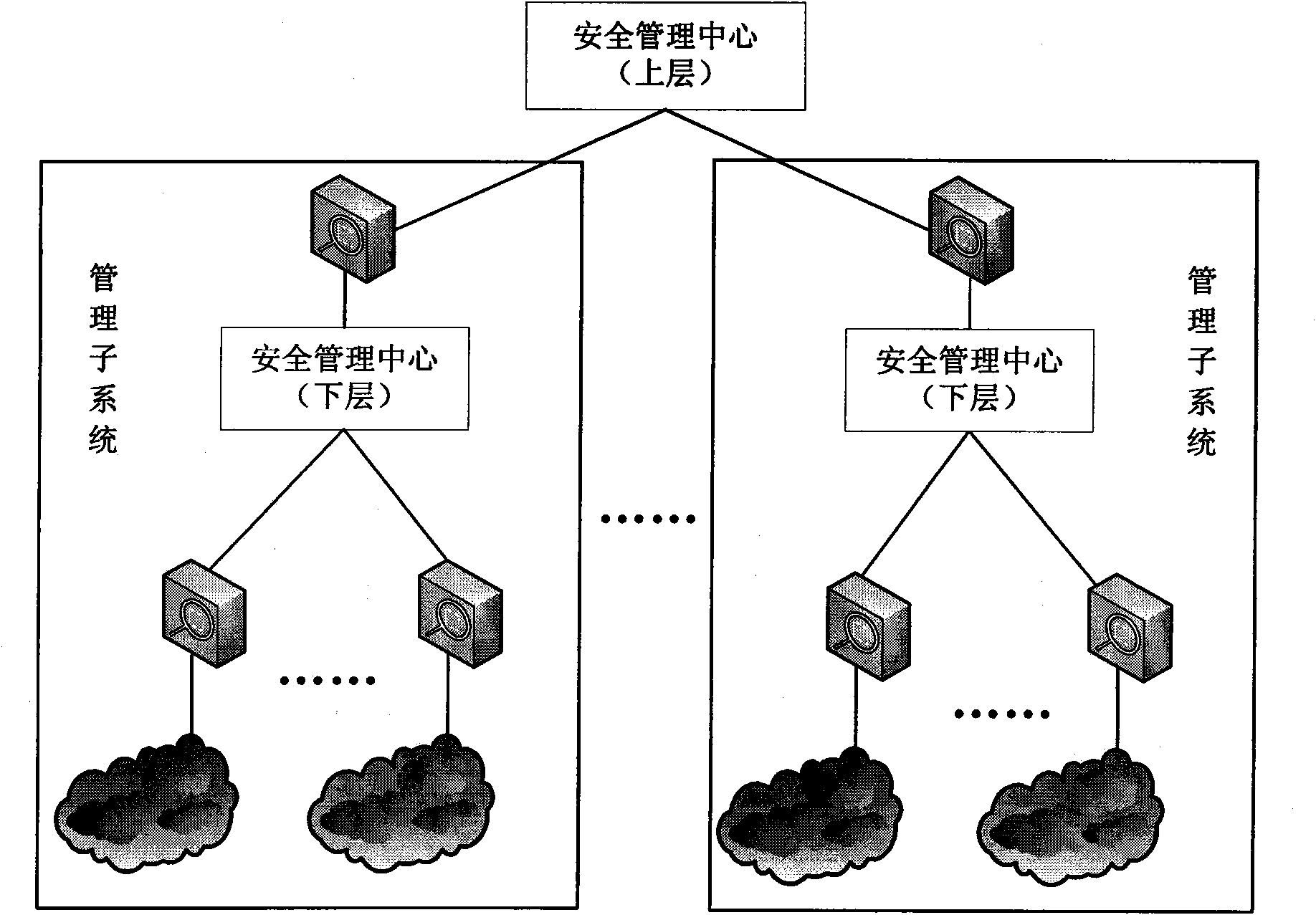
Distributed security event associated analysis method based on knowledge graph
ActiveCN108270785ASpeed up federated searchesRealize the designData switching networksBasic dimensionData platform
The invention discloses a distributed network security event associated analysis method based on a knowledge graph. The method specifically comprises the following steps of 1, building a network security knowledge graph comprising five dimensions such as the basic dimension, the loophole dimension, the threat dimension, the alarm event dimension and the attack rule dimension; 2, designing a security event implementation associated analysis algorithm based on the knowledge graph built in the step 1; and 3, building a real-time big data analysis platform, applying the associated analysis algorithm designed in the step 2 to the built big data platform, and thus achieving a distributed associated analysis system. According to the method provided by the invention, related technologies of current big data process are fully used for dealing with the large data volume, the associated analysis algorithm is parallelized, and the design of the distributed associated analysis algorithm based on the knowledge graph is achieved.
Owner:NAT UNIV OF DEFENSE TECH +1
System and method for managing security of general network
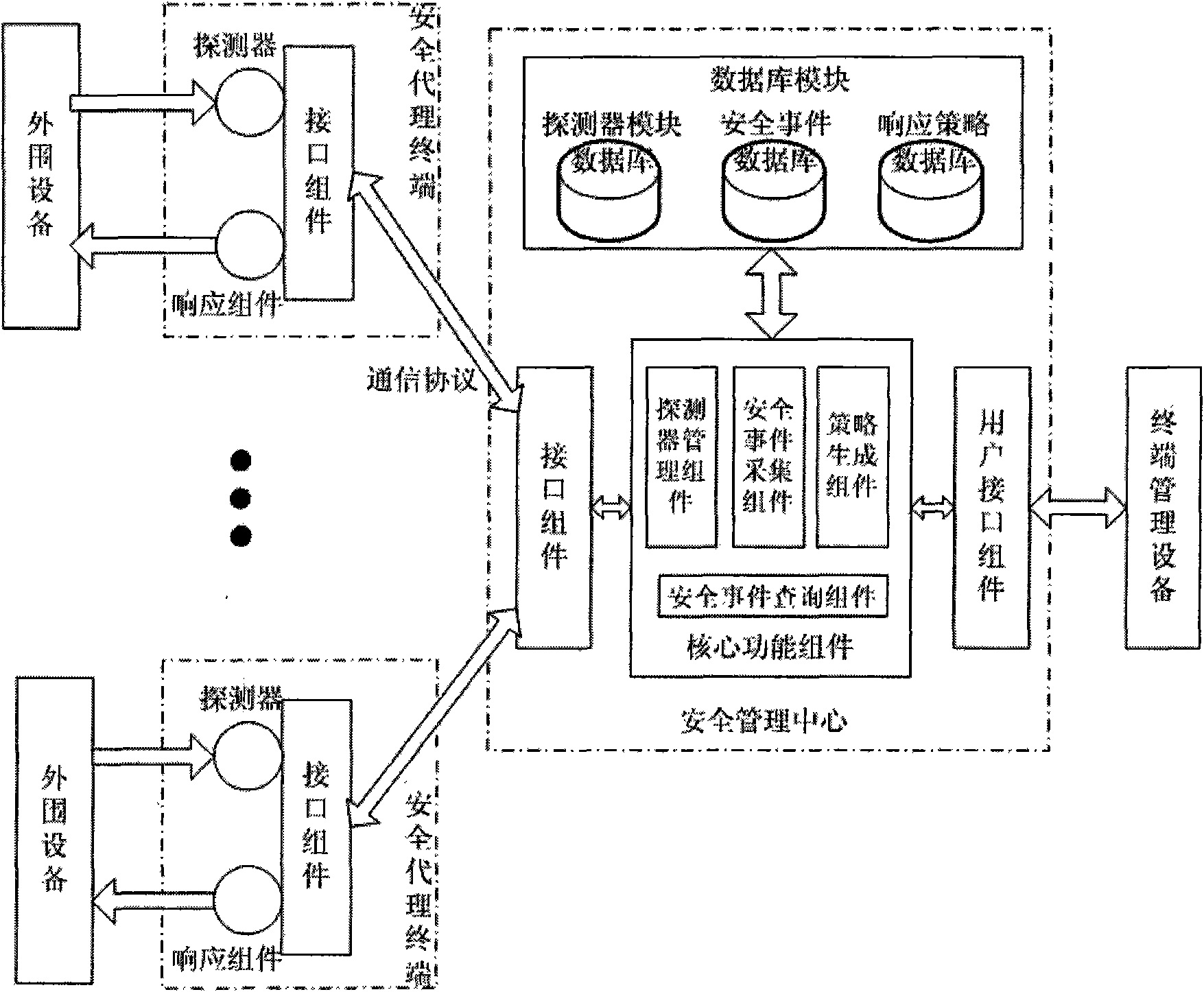
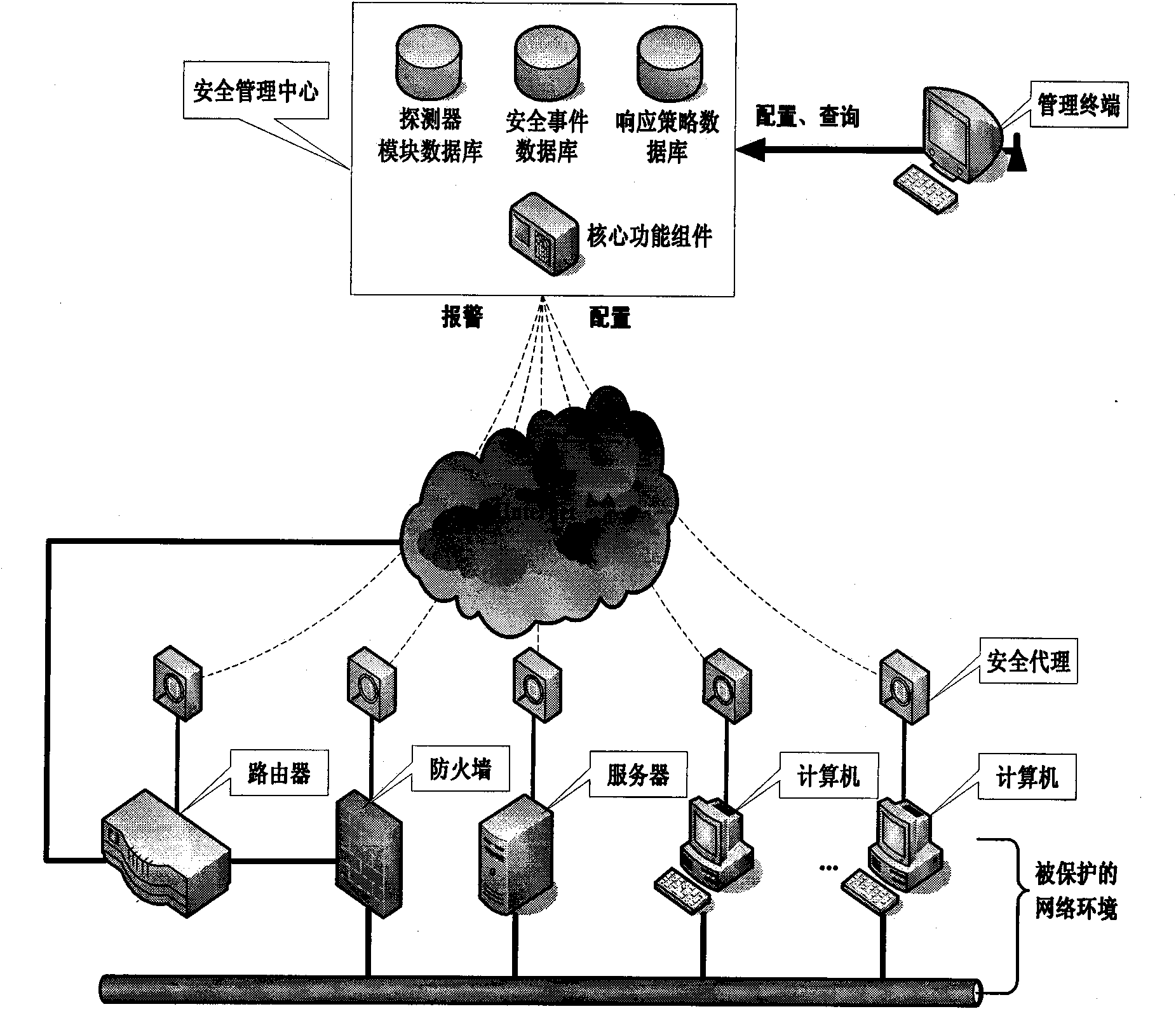
InactiveCN101582883AImprove general performanceIncrease opennessData switching networksDistributed securityProtection system
The invention discloses a system and a method for managing security of a general network, and mainly overcomes the defects of poor openness and expansibility and weak functional completeness existing in the prior network security management system. The system mainly comprises peripheral equipment, a security agent terminal, a security management center and terminal management equipment, wherein the security management center applies security technology of network access control, intrusion detection, virus detection and vulnerability management to the security agent terminal through an interface component, a data base module and a user interface component; and under the unified management and control, all security technology is mutually complemented and matched to detect and control network behaviors, so that a distributed security protection system structure in which security strategies are under central management and the security detection is separately distributed is formed. The system and the method have the advantages of flexible configuration, easy expansion, good openness, support of the different level management, and suitability for the security management and protection of the computer network in governments, colleges and universities, and large- and medium-sized enterprises.
Owner:XIDIAN UNIV
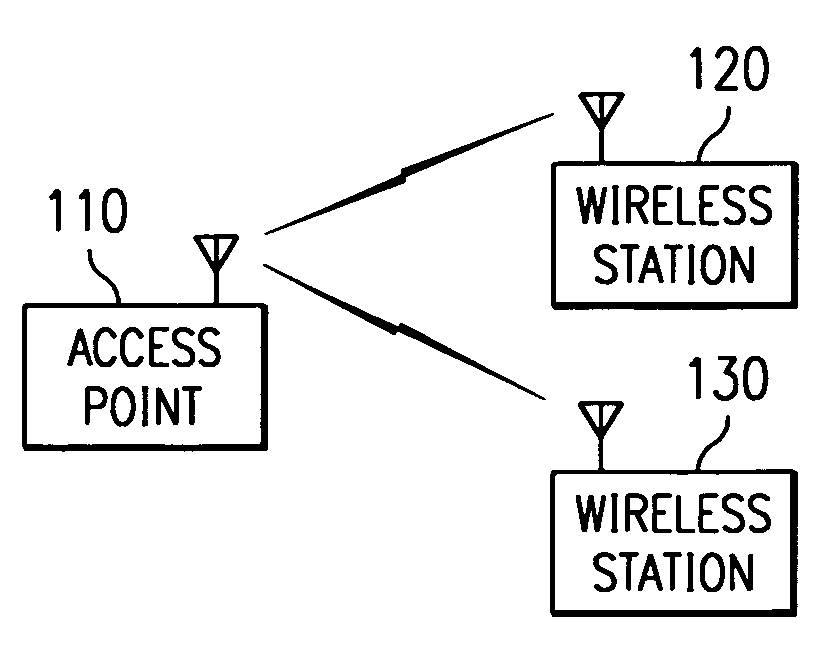
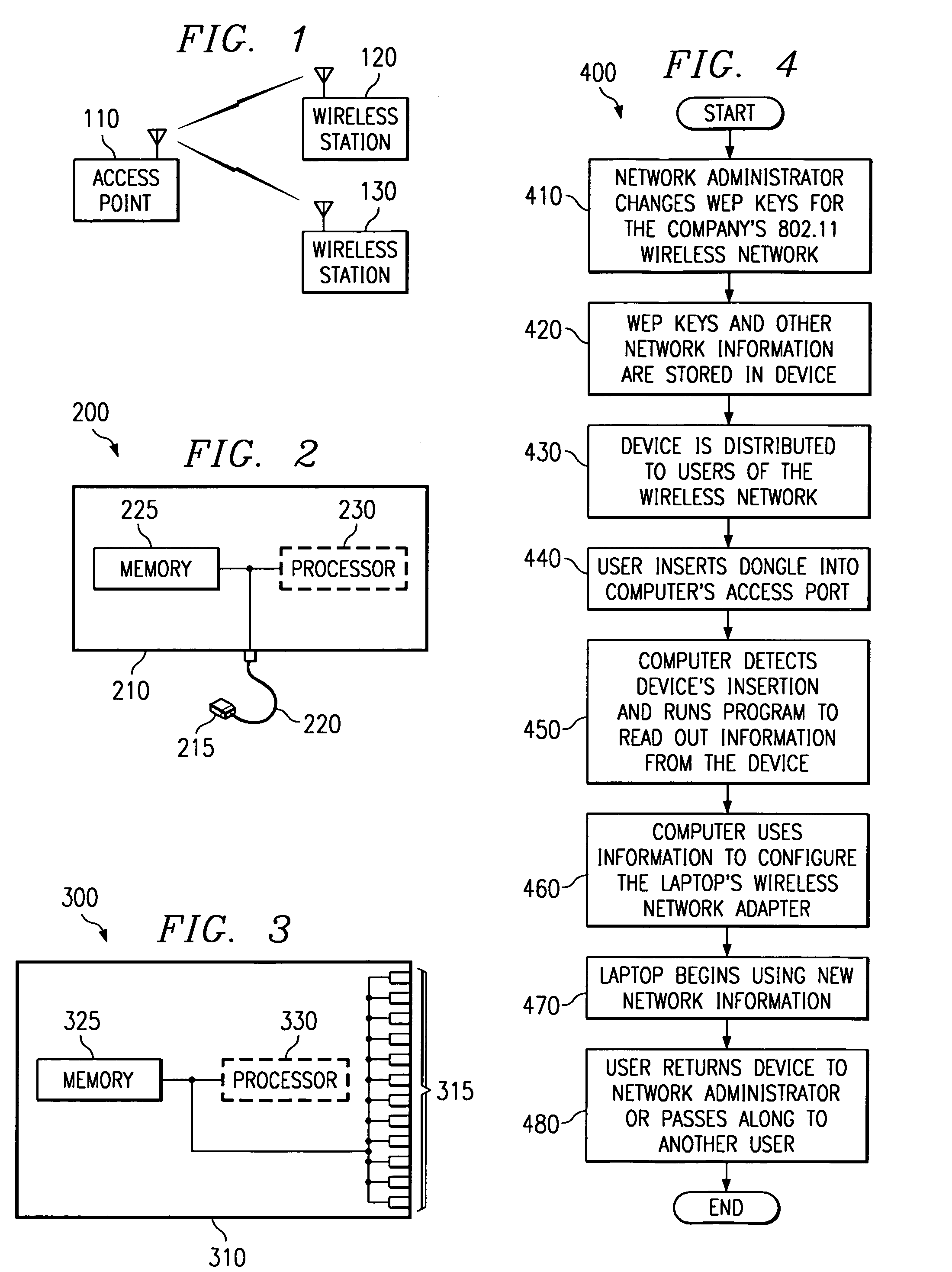
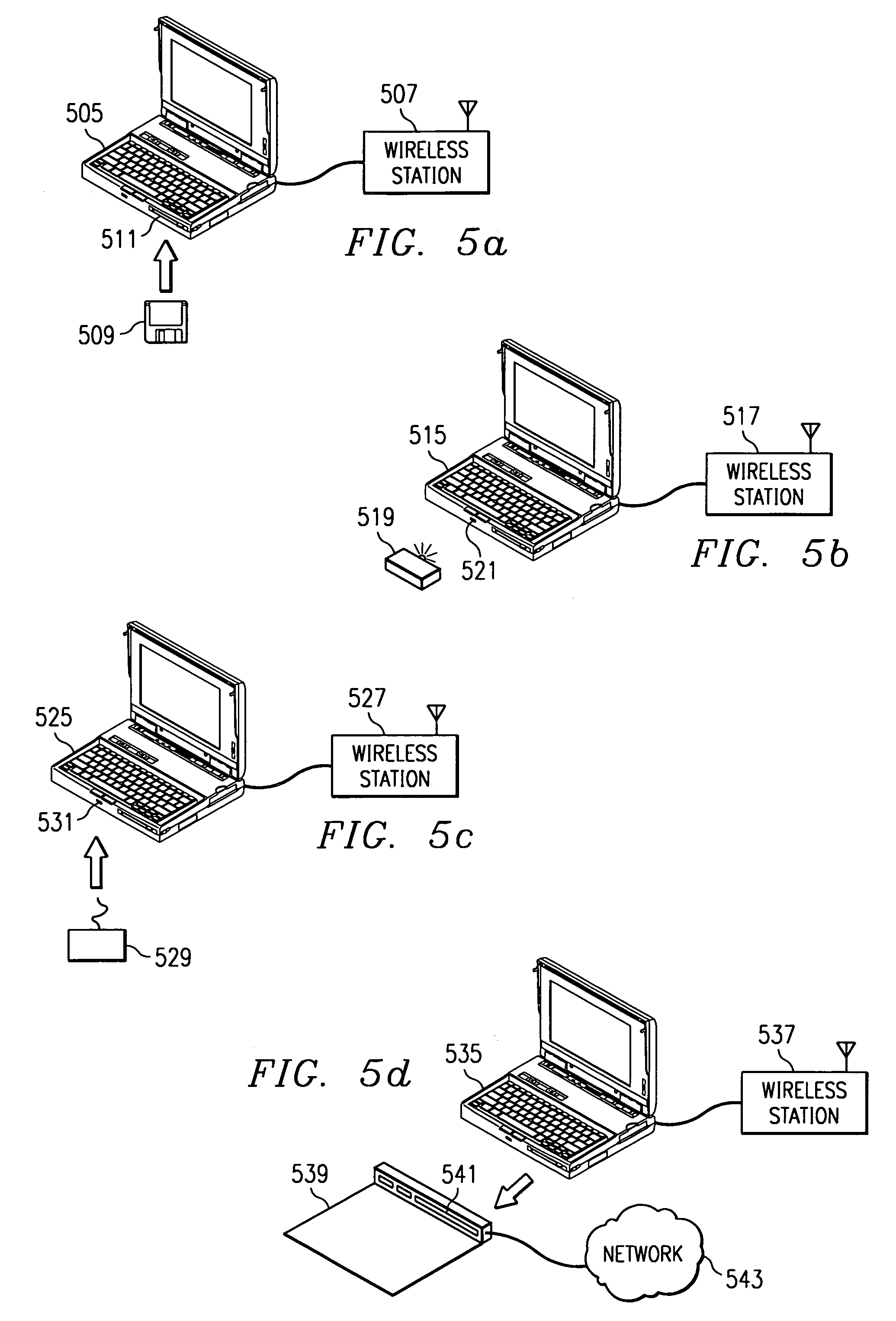
Method for physically updating configuration information for devices in a wireless network
ActiveUS7321784B2Slow changeReduce chanceNetwork traffic/resource managementNetwork topologiesSecure communicationComputer hardware
A method for providing configuration information for use in installing a new wireless station to a wireless network that minimizes errors is presented. The configuration information is distributed by storing the configuration information onto a device with a memory and then distributing the device to the users interested in installing new wireless stations. The device is attached to a computer to which the wireless station is coupled, initiating a transfer of the configuration information. The computer uses the configuration information to configure the wireless station. The method also provides a way to limit access to the configuration information through the use of encryption and limiting the number of times the configuration information is retrieved. The method is also an effective way to distribute security keys for encryption systems whose purpose is to secure communications in a wireless network.
Owner:TEXAS INSTR INC
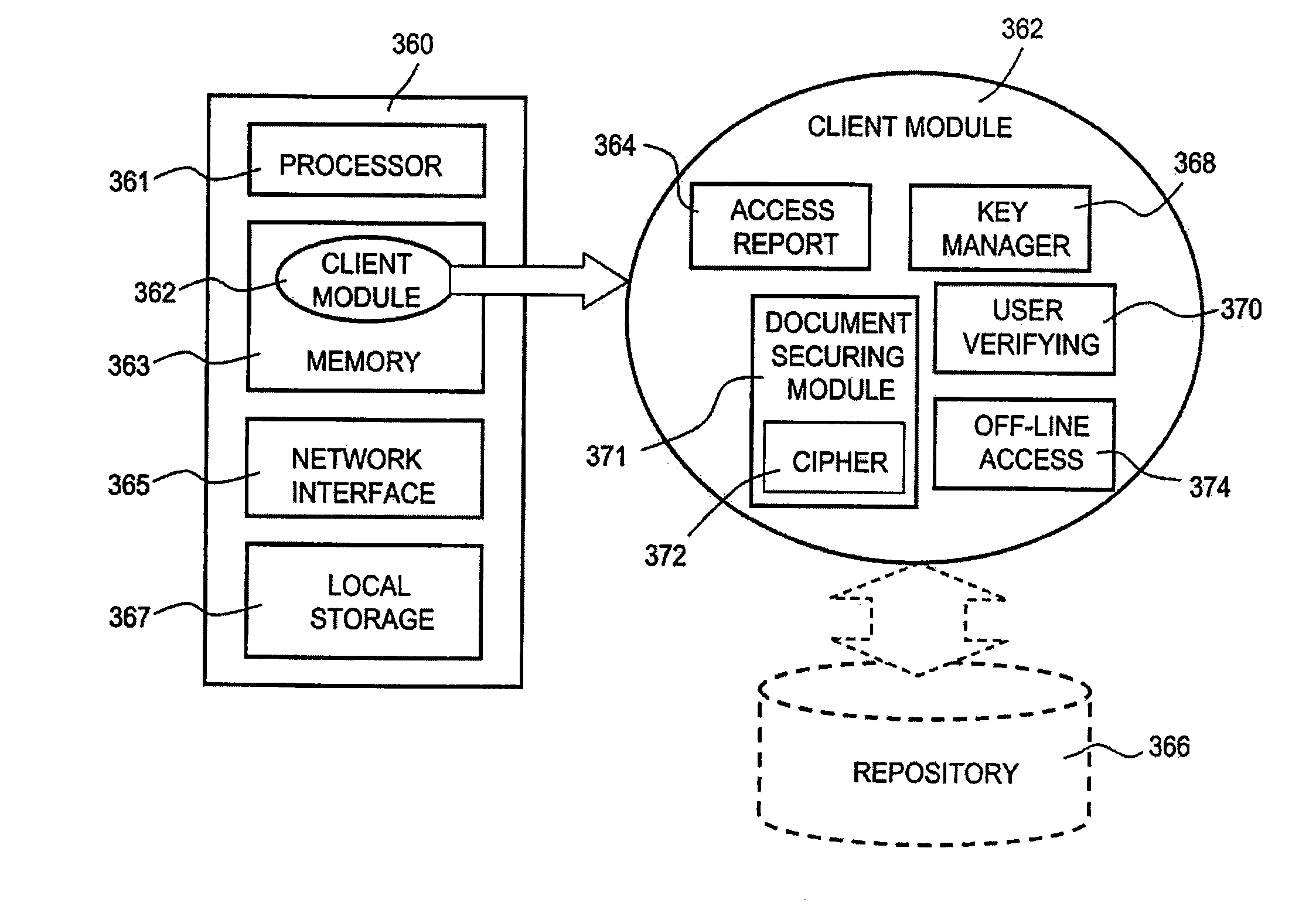
Multi-level cryptographic transformations for securing digital assets
ActiveUS7930756B1Digital data processing detailsUnauthorized memory use protectionStructure of Management InformationDistributed security
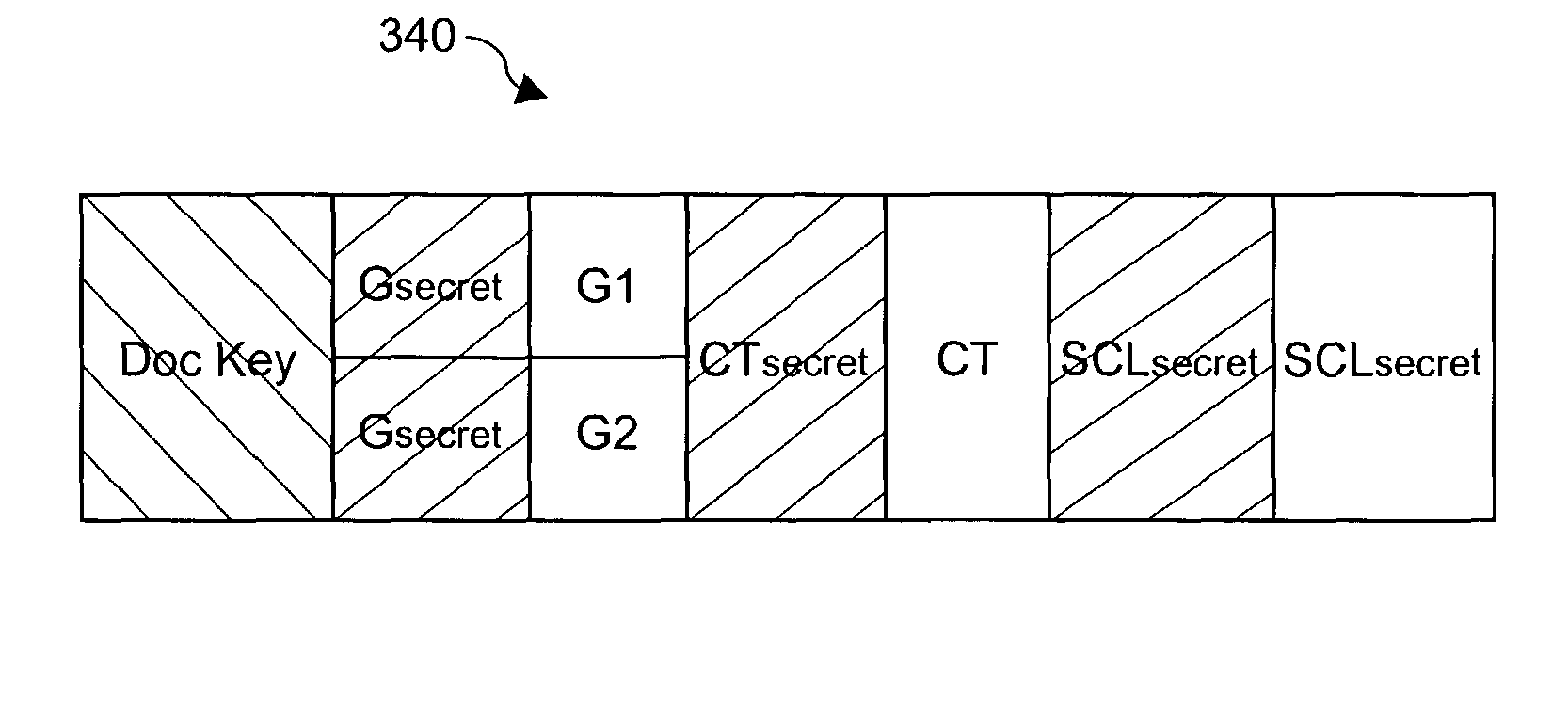
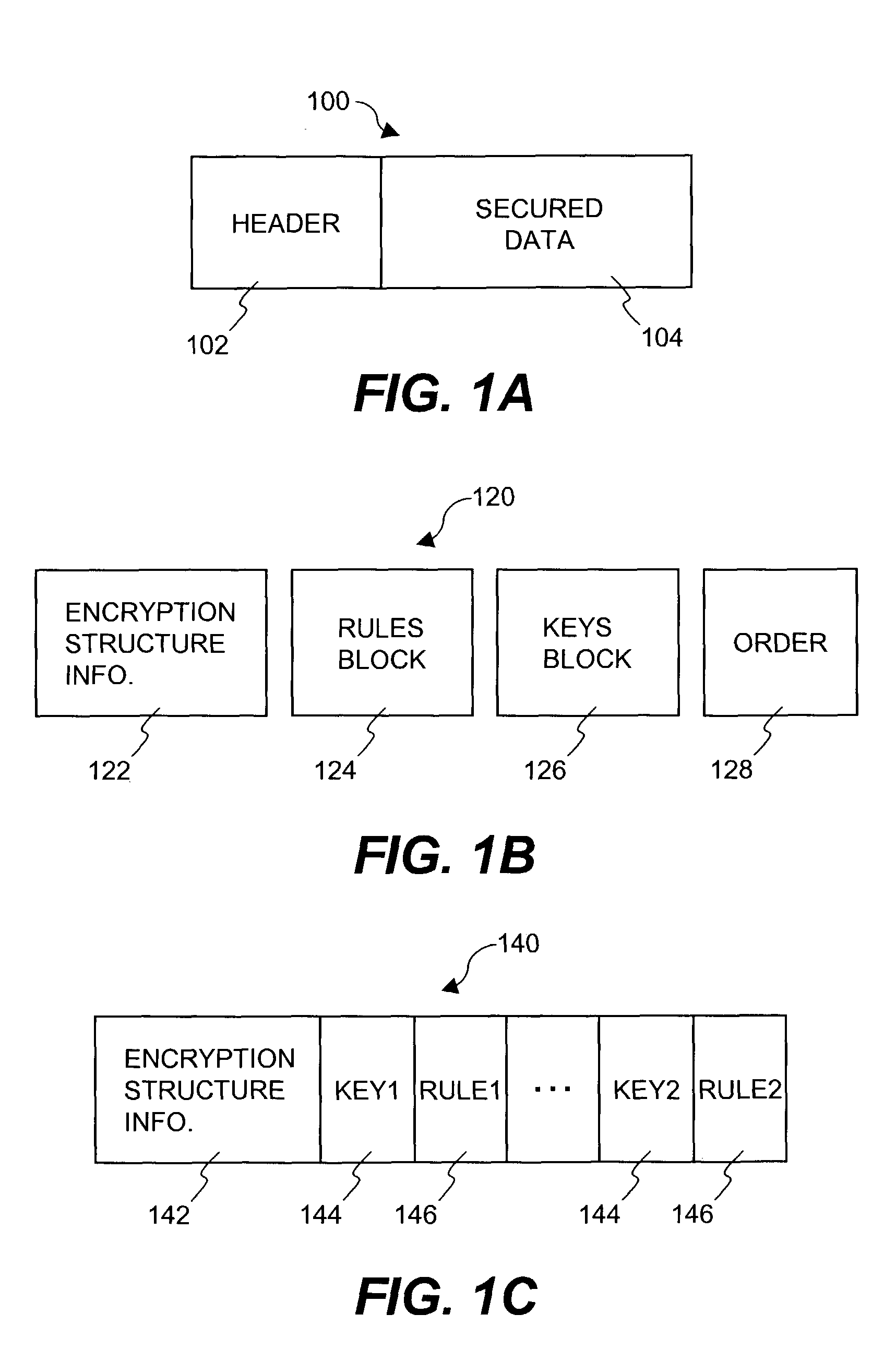
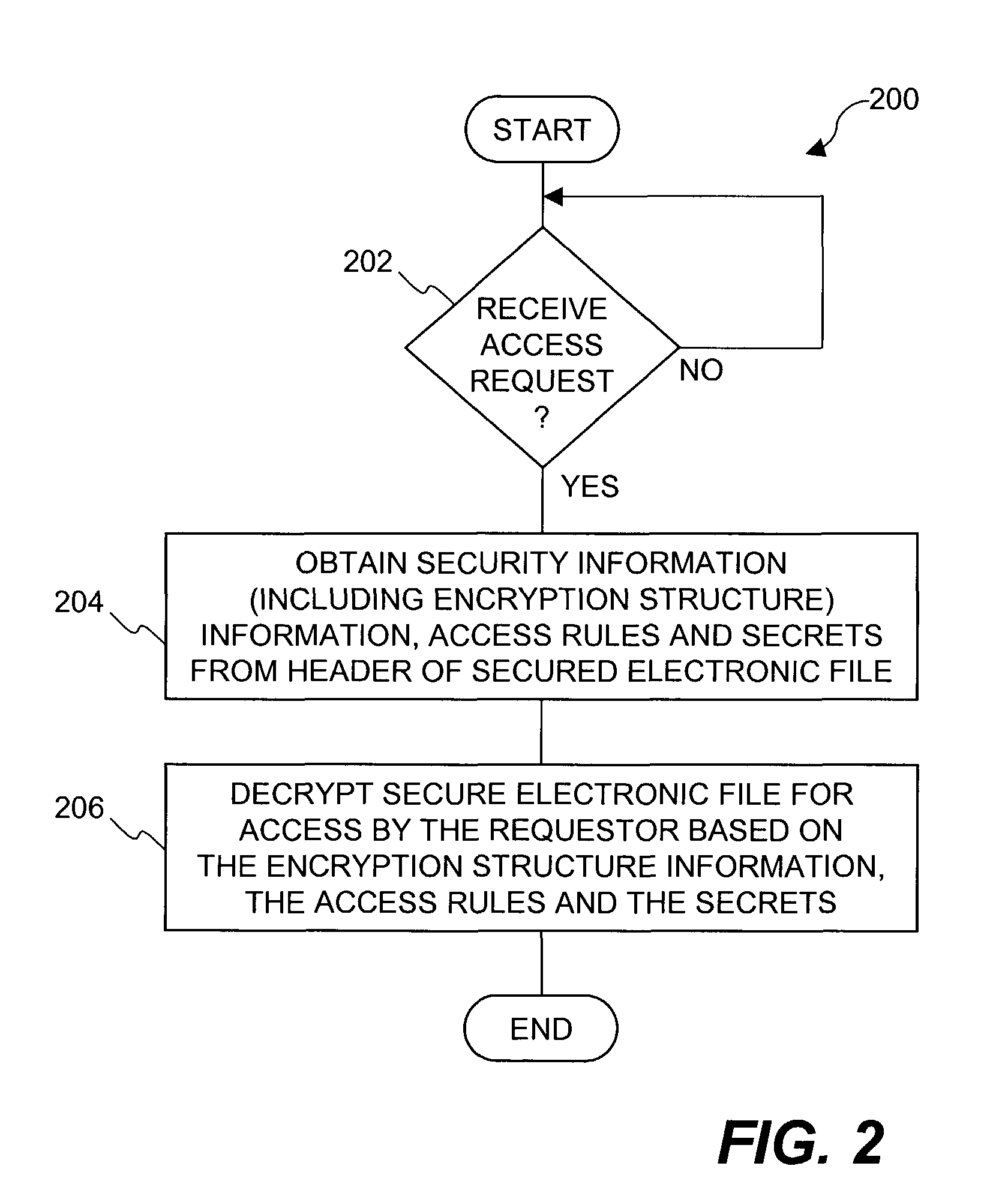
Enhanced multi-level cryptographic transformations that secure electronic files are disclosed. The secured electronic files contain not only secured data but also security information. The security information includes cryptographic structure information, access rules and secrets (e.g., keys). The cryptographic structure information explains the multi-level cryptographic transformations associated with securing or unsecuring the electronic files. The access rules and the secrets are used by the cryptographic transformations to secure the electronic files. Since the secured electronic files contain the cryptographic structure information, the particular cryptographic transformations (including their sequencing) can vary with each electronic file, if so desired. Typically, the secured electronic files are secured and managed by a file security system, such as a distributed security system.
Owner:INTELLECTUAL VENTURES I LLC
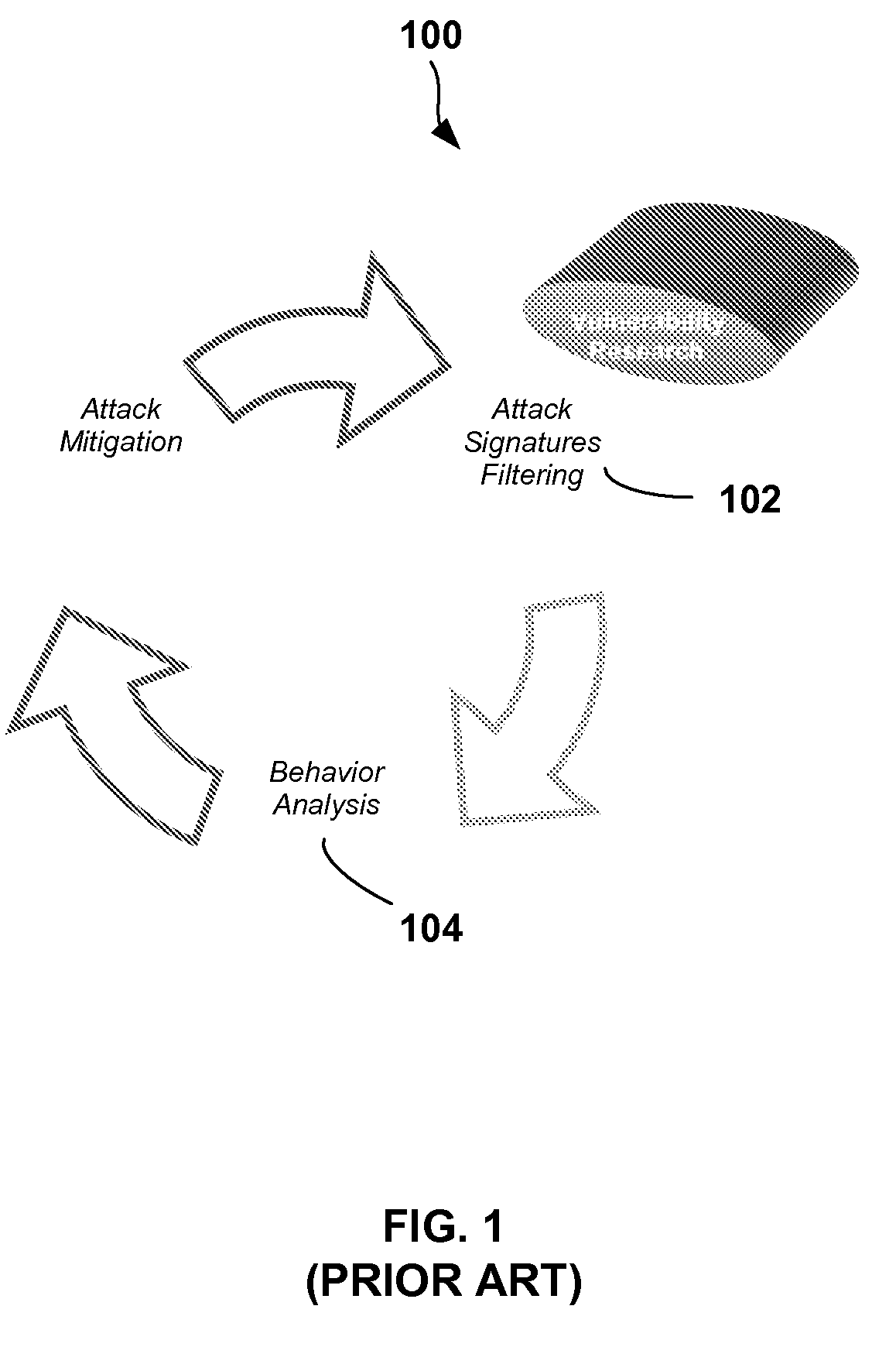
Automatic Signature Propagation Network
ActiveUS20080086772A1Reduces blocking response timeExpand the scope of protectionMemory loss protectionError detection/correctionDigital signatureDistributed security
A distributed security system wherein intelligent security agents (i.e., agent devices) share security incident information between themselves via a controller. An adaptive security decision making involving network worms (non-SMTP worms) and DoS floods attacks is also described; wherein the Worms and DoS flood digital signatures are generated to assist in intrusion prevention process.
Owner:RADWARE
Distributed agent based model for security monitoring and response
An architecture is provided for a widely distributed security system (SDI-SCAM) that protects computers at individual client locations, but which constantly pools and analyzes information gathered from machines across a network in order to quickly detect patterns consistent with intrusion or attack, singular or coordinated. When a novel method of attack has been detected, the system distributes warnings and potential countermeasures to each individual machine on the network. Such a warning may potentially include a probability distribution of the likelihood of an intrusion or attack as well as the relative probabilistic likelihood that such potential intrusion possesses certain characteristics or typologies or even strategic objectives in order to best recommend and / or distribute to each machine the most befitting countermeasure(s) given all presently known particular data and associated predicted probabilistic information regarding the prospective intrusion or attack. If any systems are adversely affected, methods for repairing the damage are shared and redistributed throughout the network.
Owner:INVENTSHIP LLC
Method and system for implementing and managing an enterprise identity management for distributed security in a computer system
InactiveUS7660795B2FinanceDigital data processing detailsComputerized systemEnterprise data management
A method and system for facilitating the management of user identities includes an ownership component, a registration component, and a servicing component. When a user first desires to access a system using the present invention, the registration component verifies the user's ownership of the underlying account by asking a variety of questions. Thereafter, when a user desires to service his account, the user may be re-queried to determine if he is attempting to access the correct information. An authentication and access component provides the functionality to access a system of the present invention. An audit component can be configured to periodically monitor the various accounts to ensure a continued linking between users and accounts.
Owner:LIBERTY PEAK VENTURES LLC +2
Content delivery network protection from malware and data leakage
Content Delivery Network (CDN) protection systems and methods, performed by a cloud node in a distributed security system include receiving traffic between one or more origin servers and the CDN; monitoring the traffic based on policy; detecting one or more of malware and data leakage in the traffic based on the policy; and blocking the traffic responsive to the detecting the one or more of the malware and the data leakage in the traffic, prior to the traffic entering the CDN.
Owner:ZSCALER INC
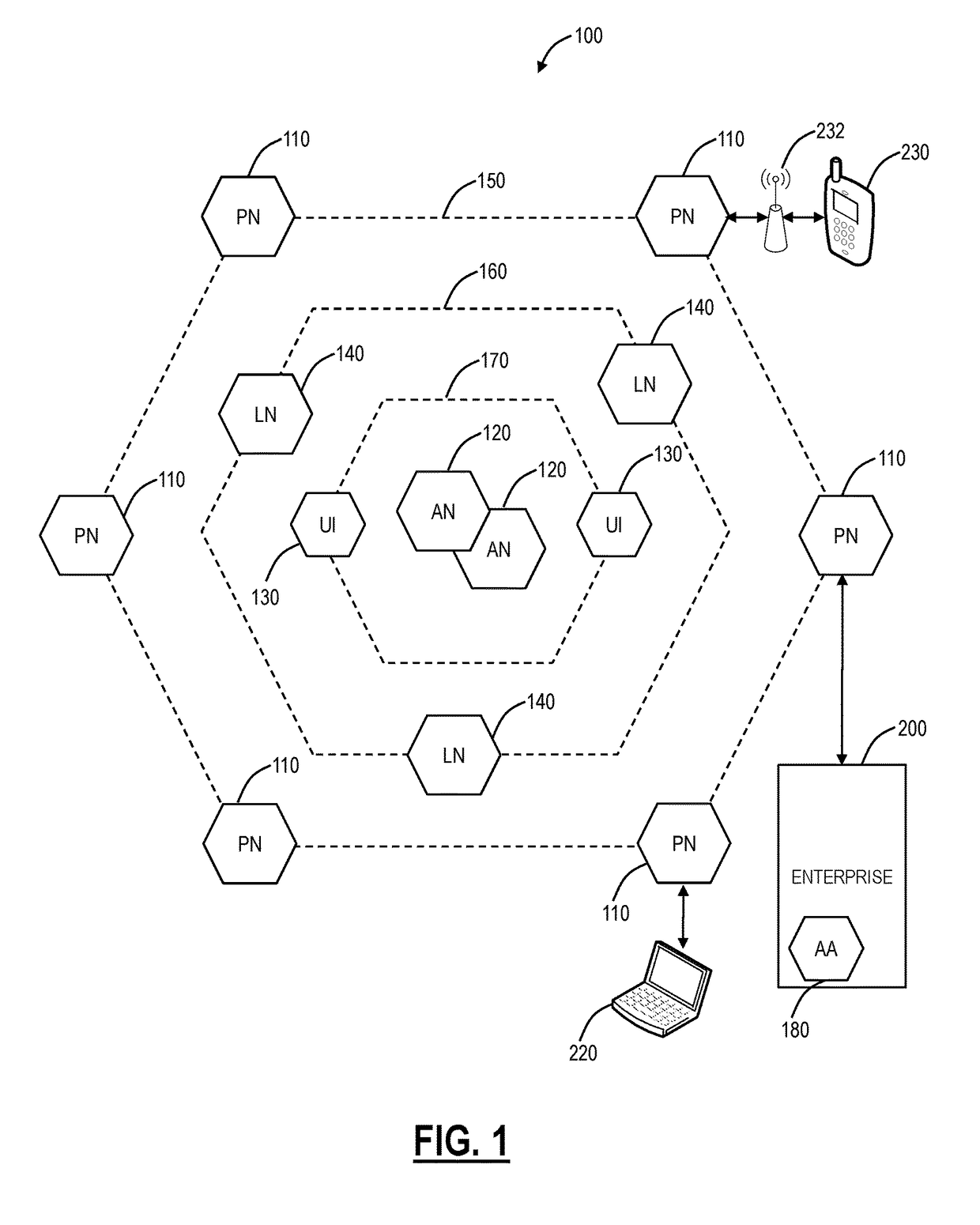
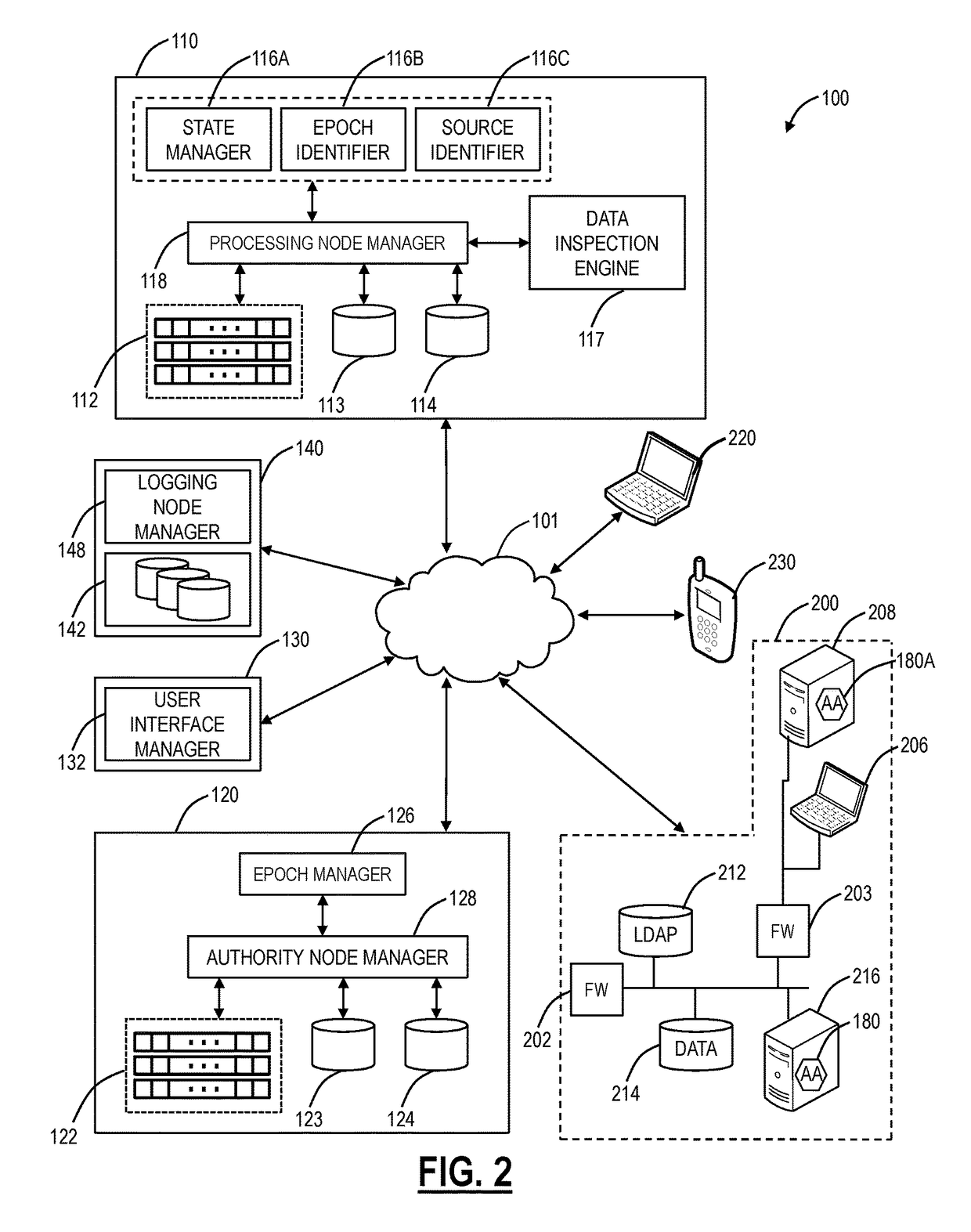
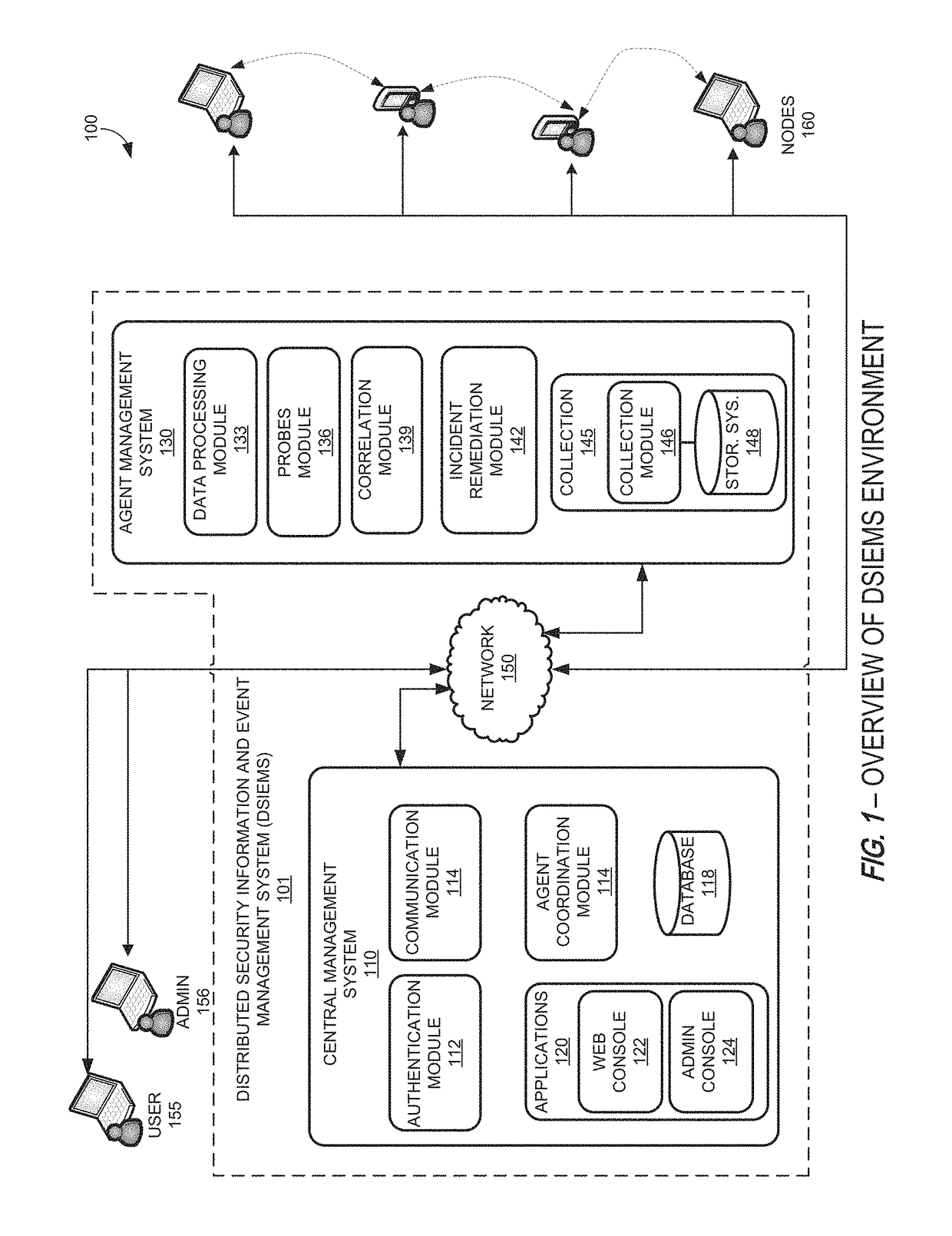
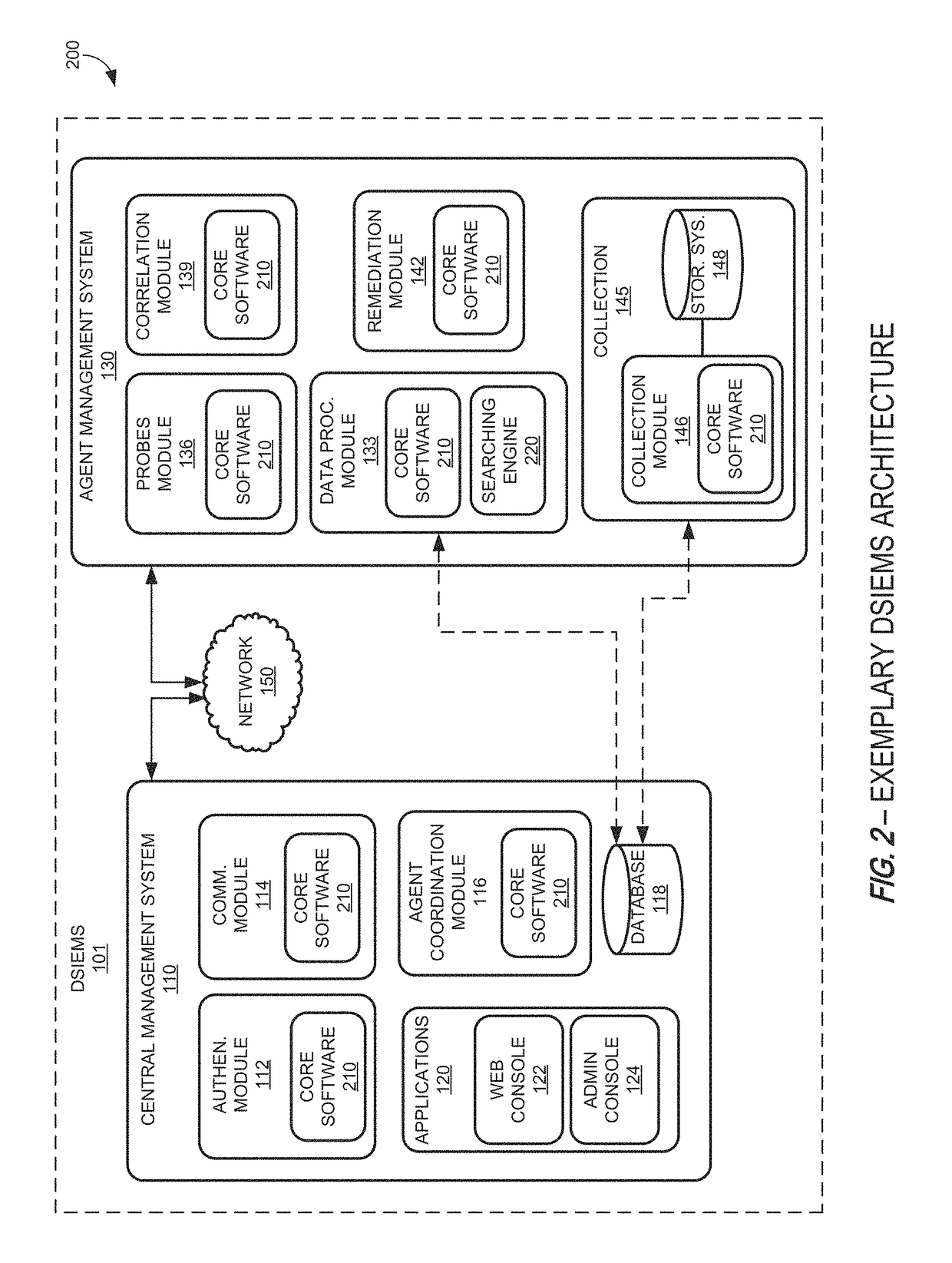
Systems and methods for providing a security information and event management system in a distributed architecture
ActiveUS9813449B1Quick installationEnables flexibilityTransmissionProgram/content distribution protectionSecurity information and event managementData access
A Distributed Security Information and Event Management System (DSIEMS) is a scalable, intelligent, security and fraud management platform that proactively collects information from a network's computer systems, applications, users, and external intelligence data feeds, and aggregates the information into a centralized repository where the information can then be analyzed and quickly acted upon when necessary. Further, according to one aspect, a DSIEMS analyzes aggregated information to discern patterns of potential attack, inappropriate data movement, and fraud from normal and legitimate network activity, account activity, user activity, and data access. According to one embodiment, aspects of the present disclosure are implemented in a distributed architecture. In particular, aspects of the present DSIEMS utilize an agent-based architecture in which intelligent software agents are deployed on each node (e.g., endpoint computing device) within the system.
Owner:LOOKWISE SL
Method and System for Implementing Changes to Security Policies in a Distributed Security System
InactiveUS20090254972A1Digital data processing detailsAnalogue secracy/subscription systemsImproved methodDistributed security
Improved approaches for effectuating changes to security policies in a distributed security system are disclosed. The changes to security policies are distributed to those users (e.g., user and / or computers) in the security system that are affected. The distribution of such changes to security policies can be deferred for those affected users that are not activated (e.g., logged-in or on-line) with the security system.
Owner:INTELLECTUAL VENTURES I LLC
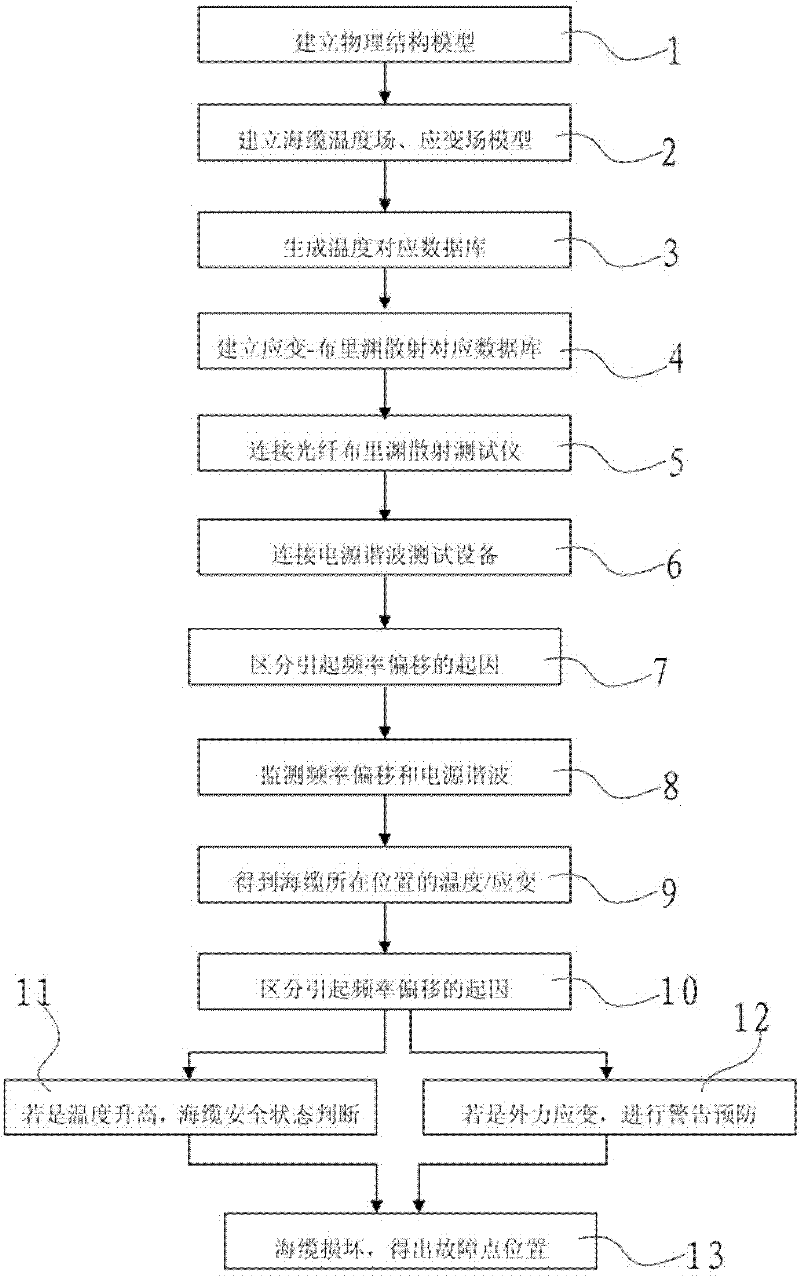
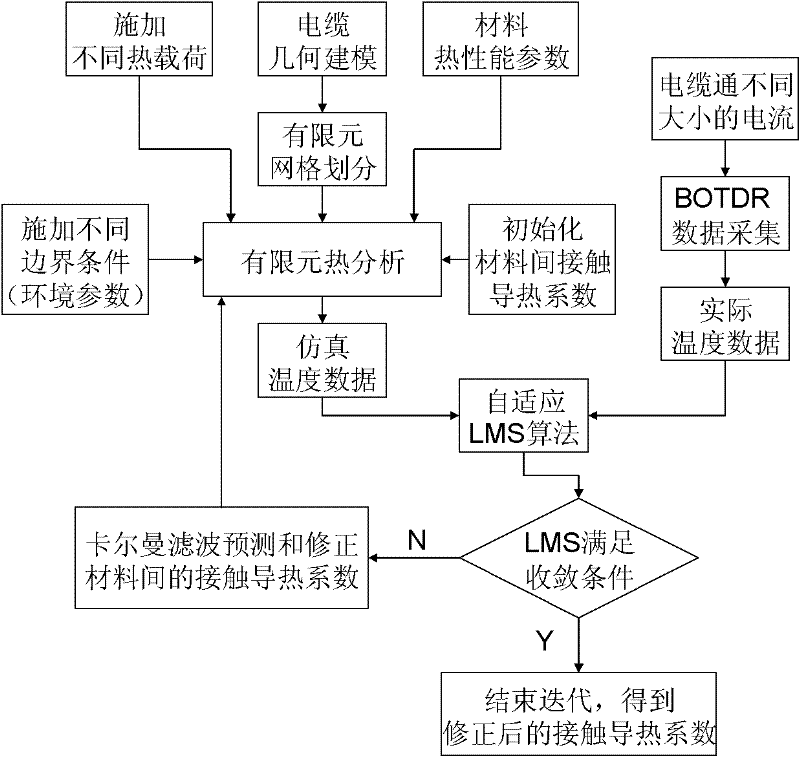
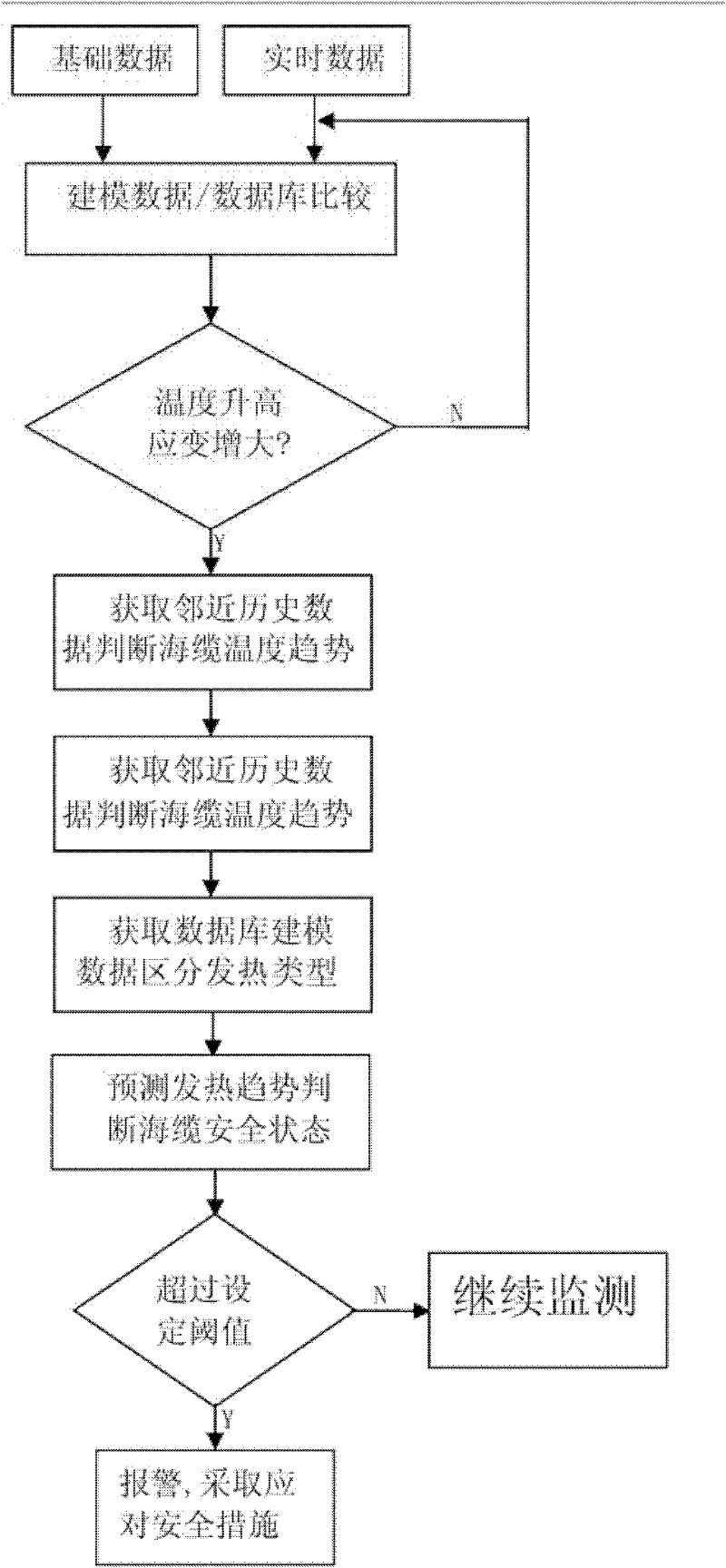
Temperature rise strain monitoring and alarming and fault analysis method for composite submarine cable
The invention discloses a temperature rise strain monitoring and alarming and fault analysis method for a composite submarine cable. The method comprises the following steps of: performing real-time temperature stress sensing on the composite submarine cable by utilizing abundant single mode fibers in a submarine cable, and evaluating the safety state of the composite submarine cable according to a power supply harmonic test parameter to realize real-time monitoring of the composite submarine cable. According to the method disclosed by the invention, real-time distributive safety monitoring and alarming can be performed on the composite submarine cable, and the safety sate of the composite submarine cable is judged according to the monitored power grid quality parameter, communication optical fiber excited brillouin reflection frequency offset and calibration data; and the fault analysis is performed on the composite submarine cable having a fault to find out the main reason of the fault.
Owner:SHANGHAI MARITIME UNIVERSITY +2
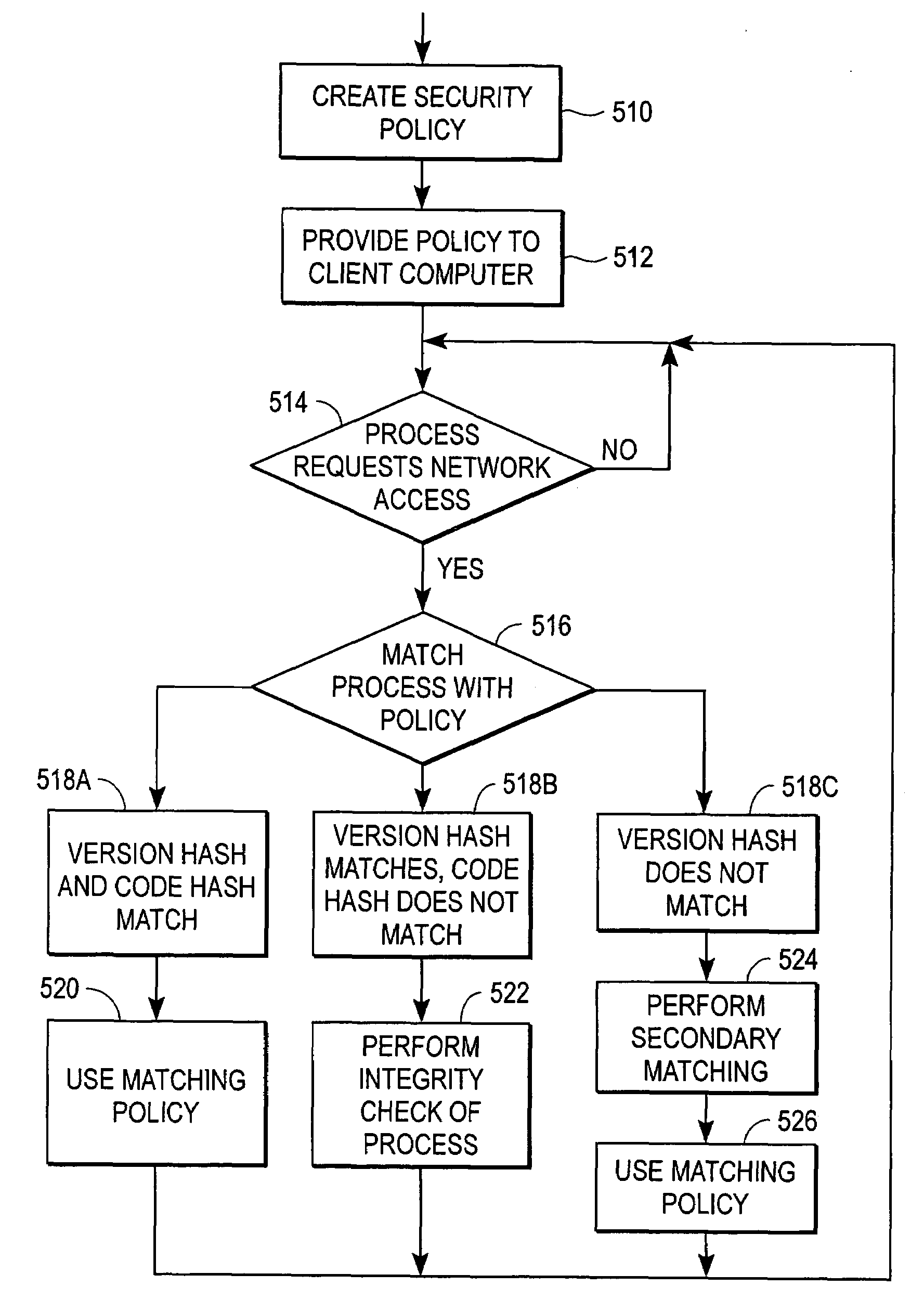
Forward application compatible firewall
A security server distributes security polices to the client computers. Each security policy includes an identifier identifying the process to which the policy pertains, and security rules for use with that process. The identifier includes a version hash and a code hash. The version hash of a process is likely to remain unchanged if the process is modified by a legitimate agent, such as by a software update. The code hash of a process is likely to change if the process is modified by a malicious agent. When a process executing on the client computer requests access to a resource, the client computer generates a version hash of the process and uses it to identify the security policy pertaining to the process. If the version hash matches a version hash in a security policy, but the code hash does not match, the client computer declares the process potentially malicious.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com