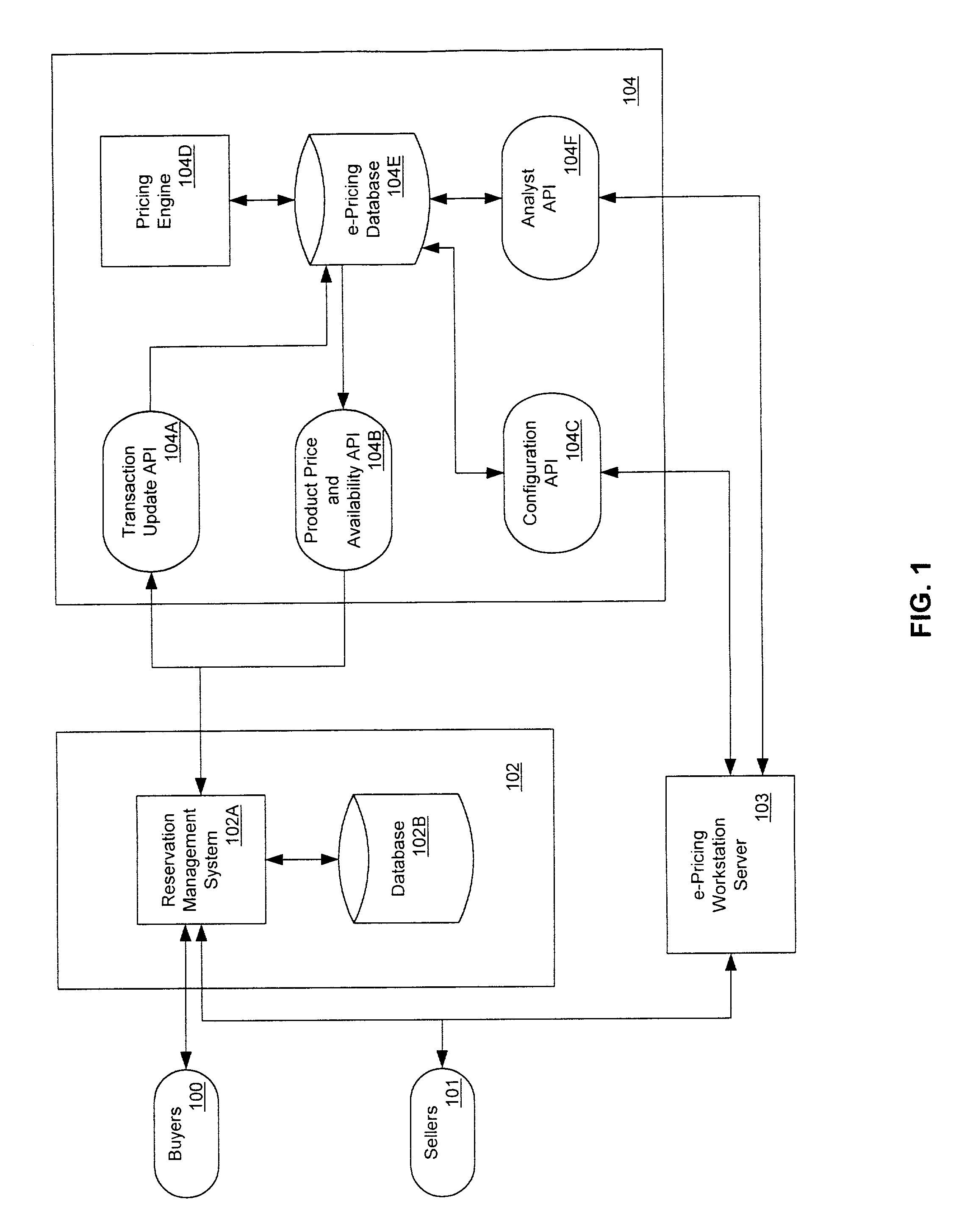
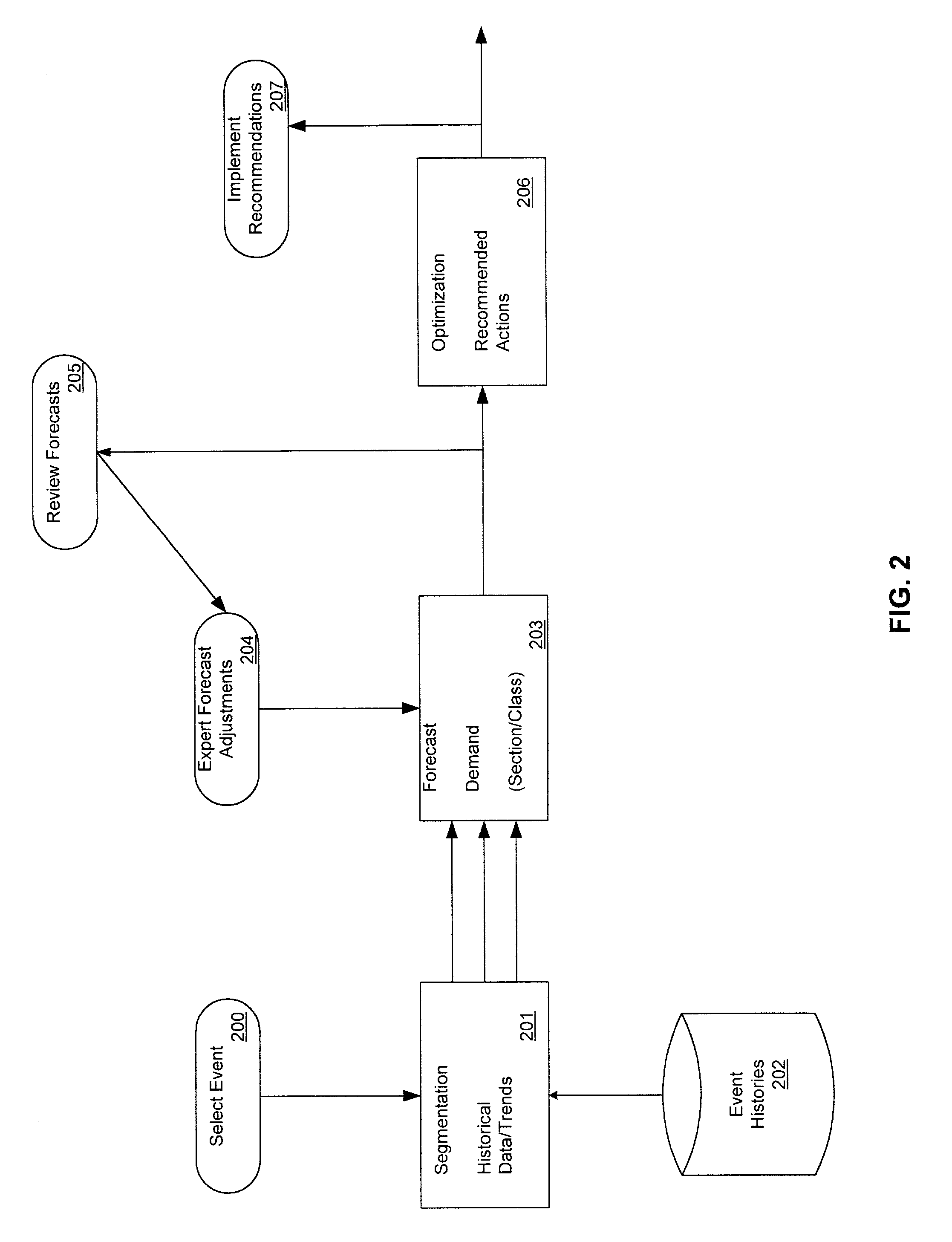
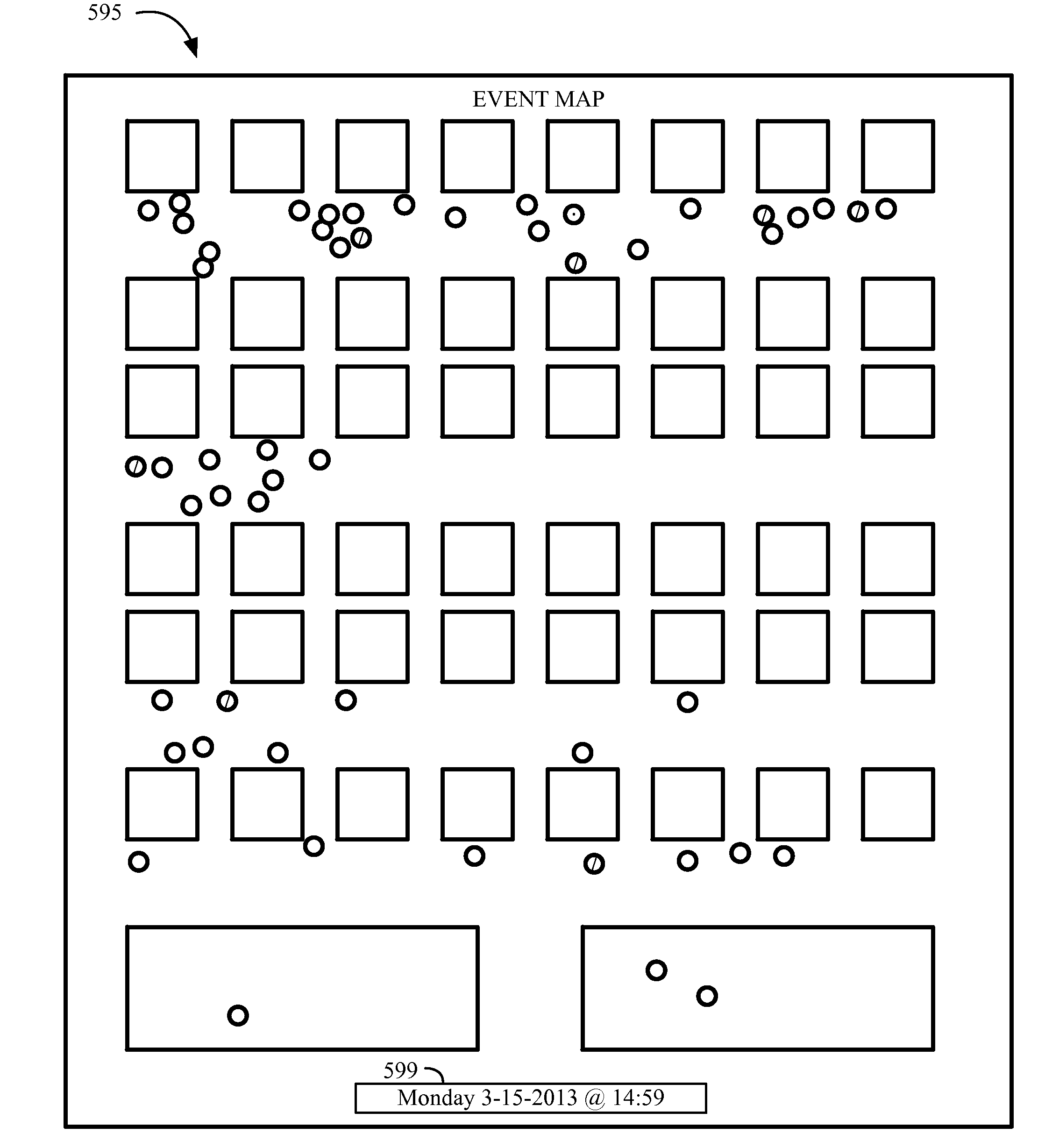
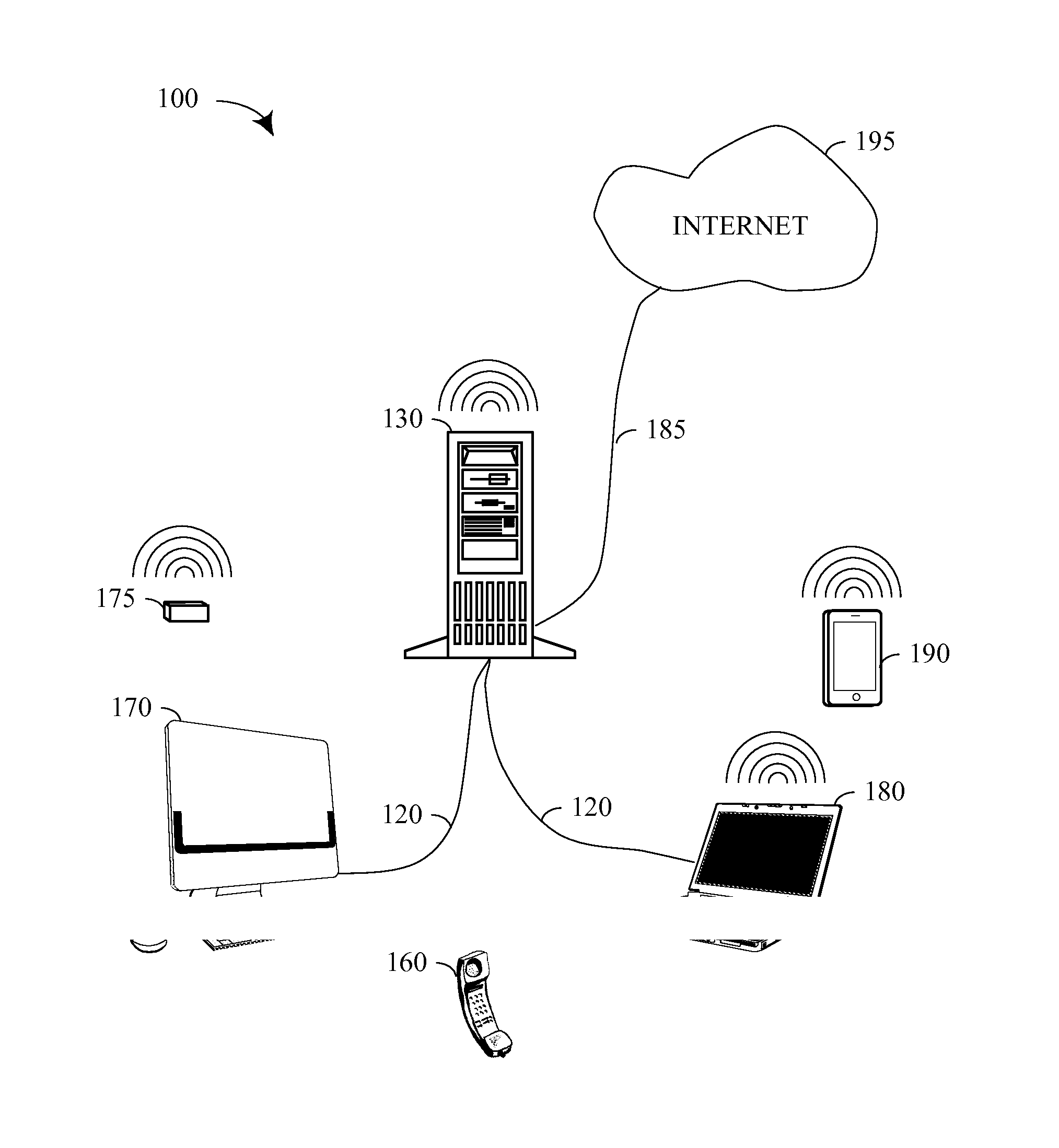
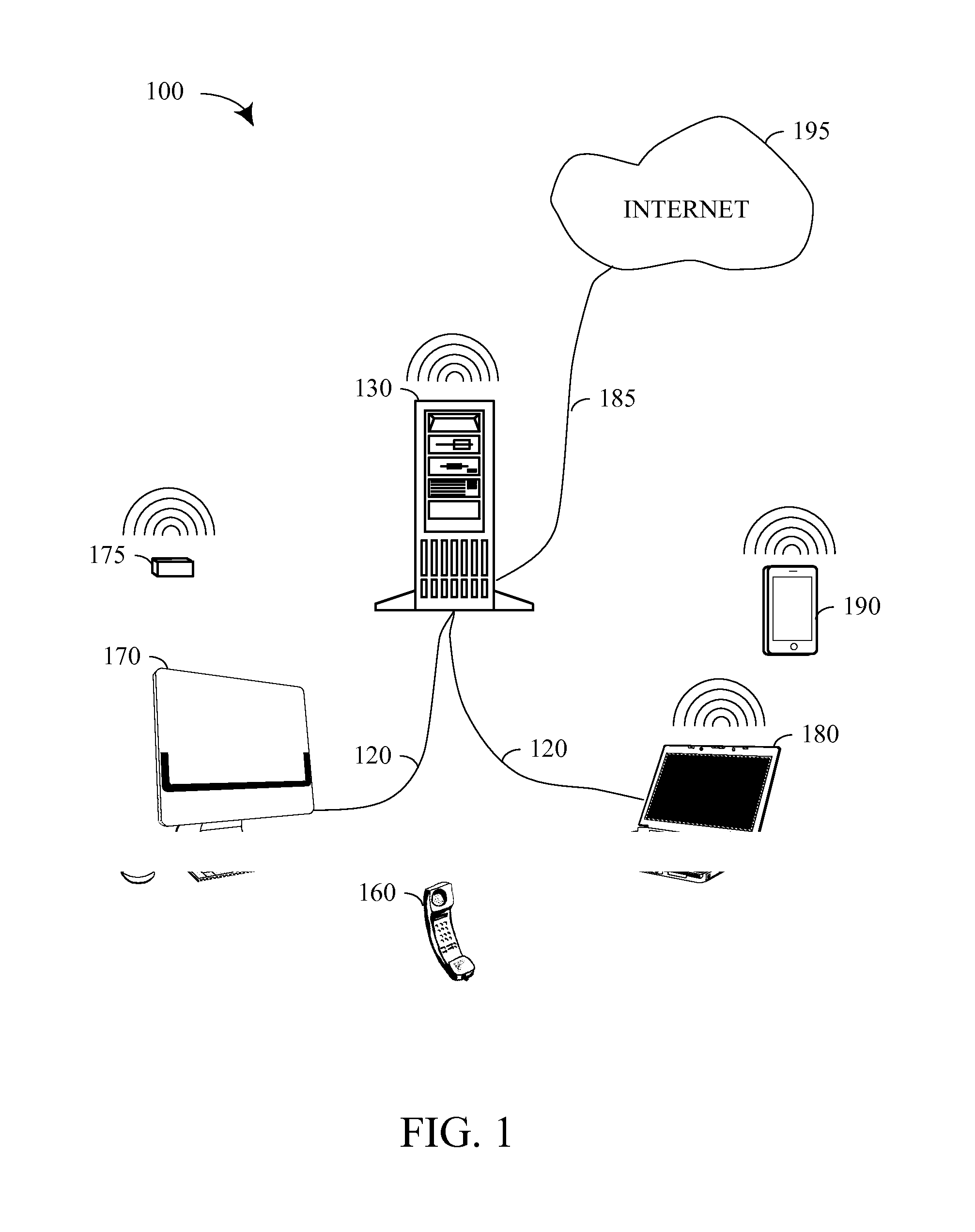
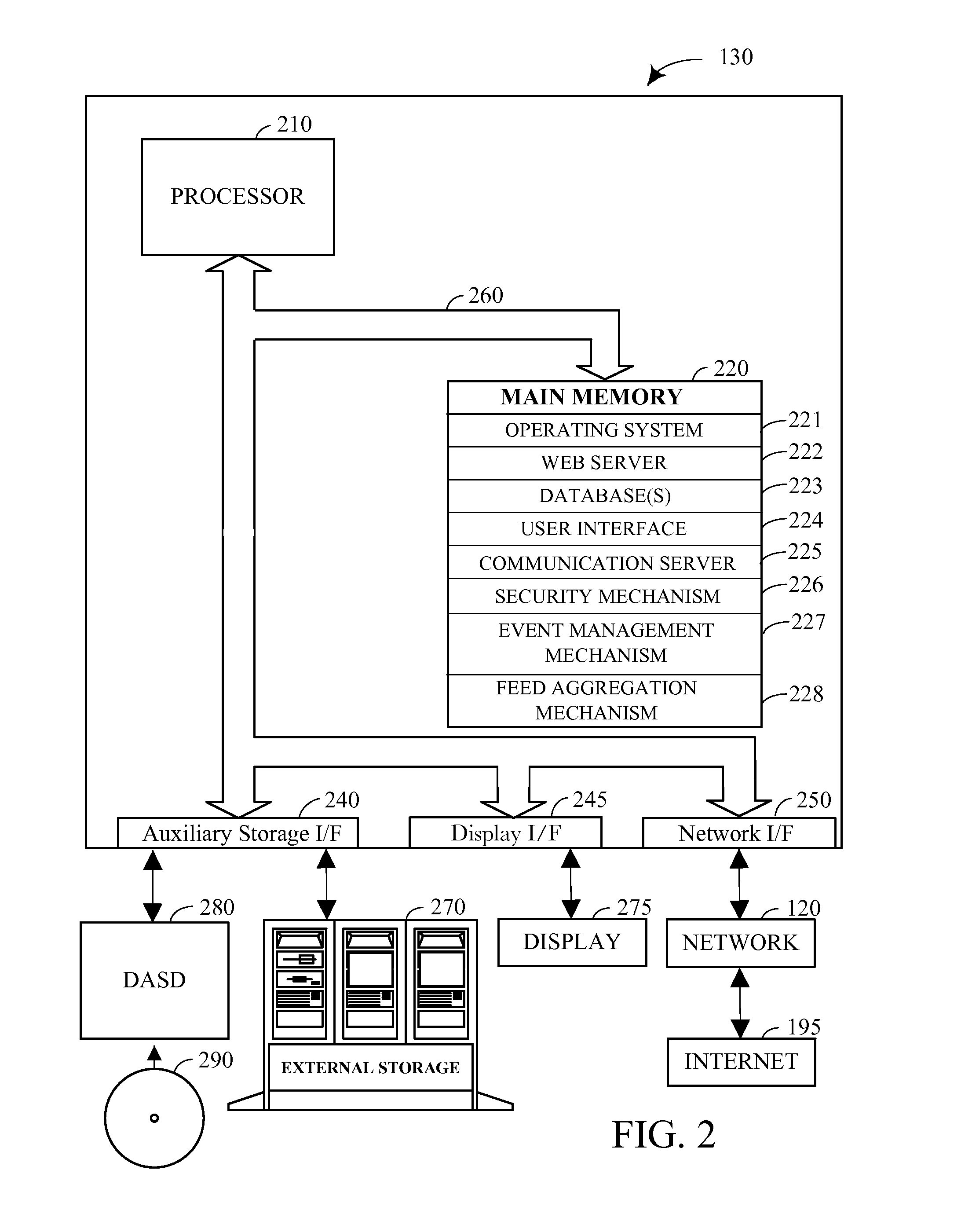
Patents
Literature
725 results about "Event management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Event management is the application of project management to the creation and development of large-scale events such as festivals, conferences, ceremonies, weddings, formal parties, concerts, or conventions.It involves studying the brand, identifying its target audience, devising the event concept, and coordinating the technical aspects before actually launching the event.
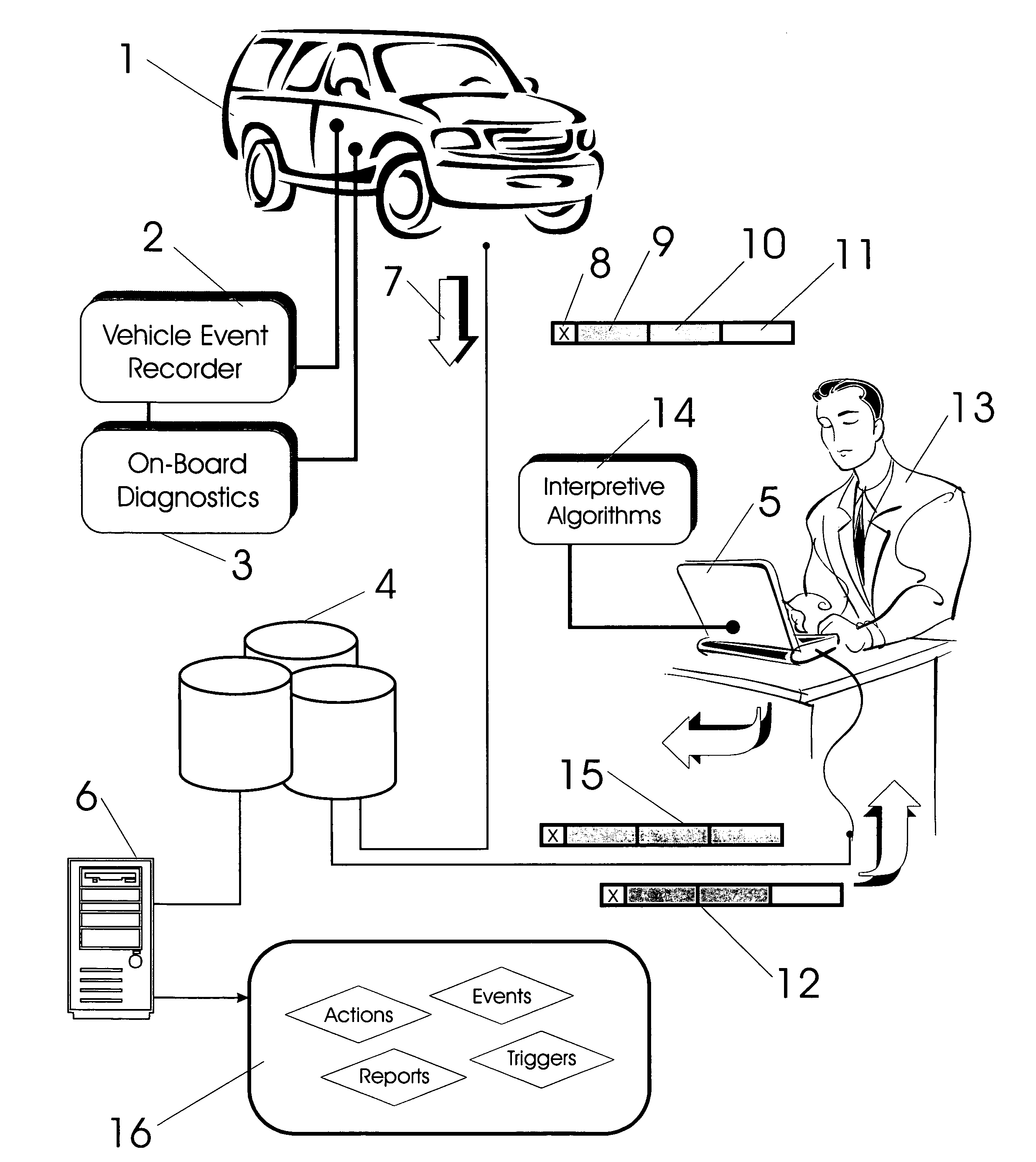
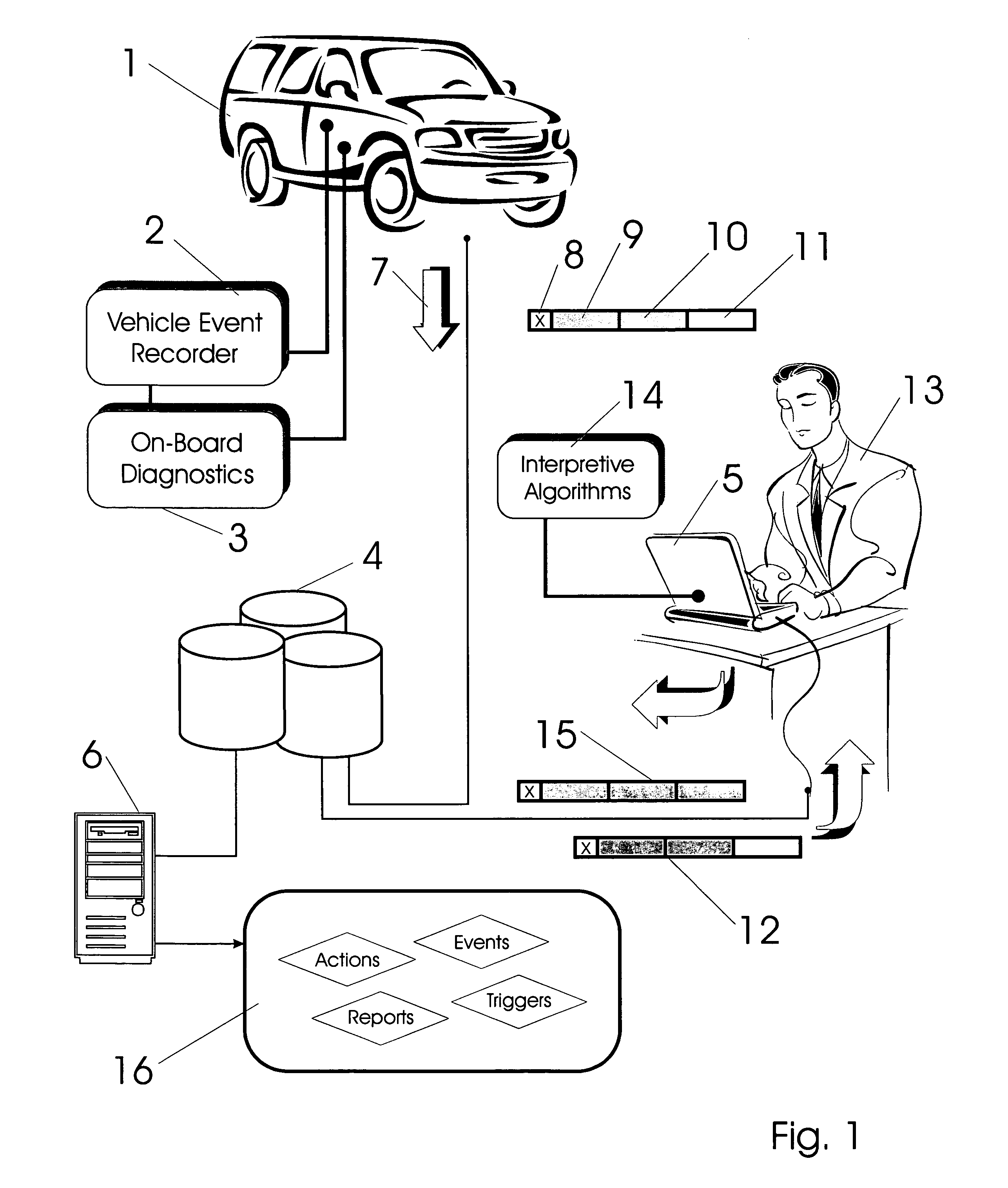
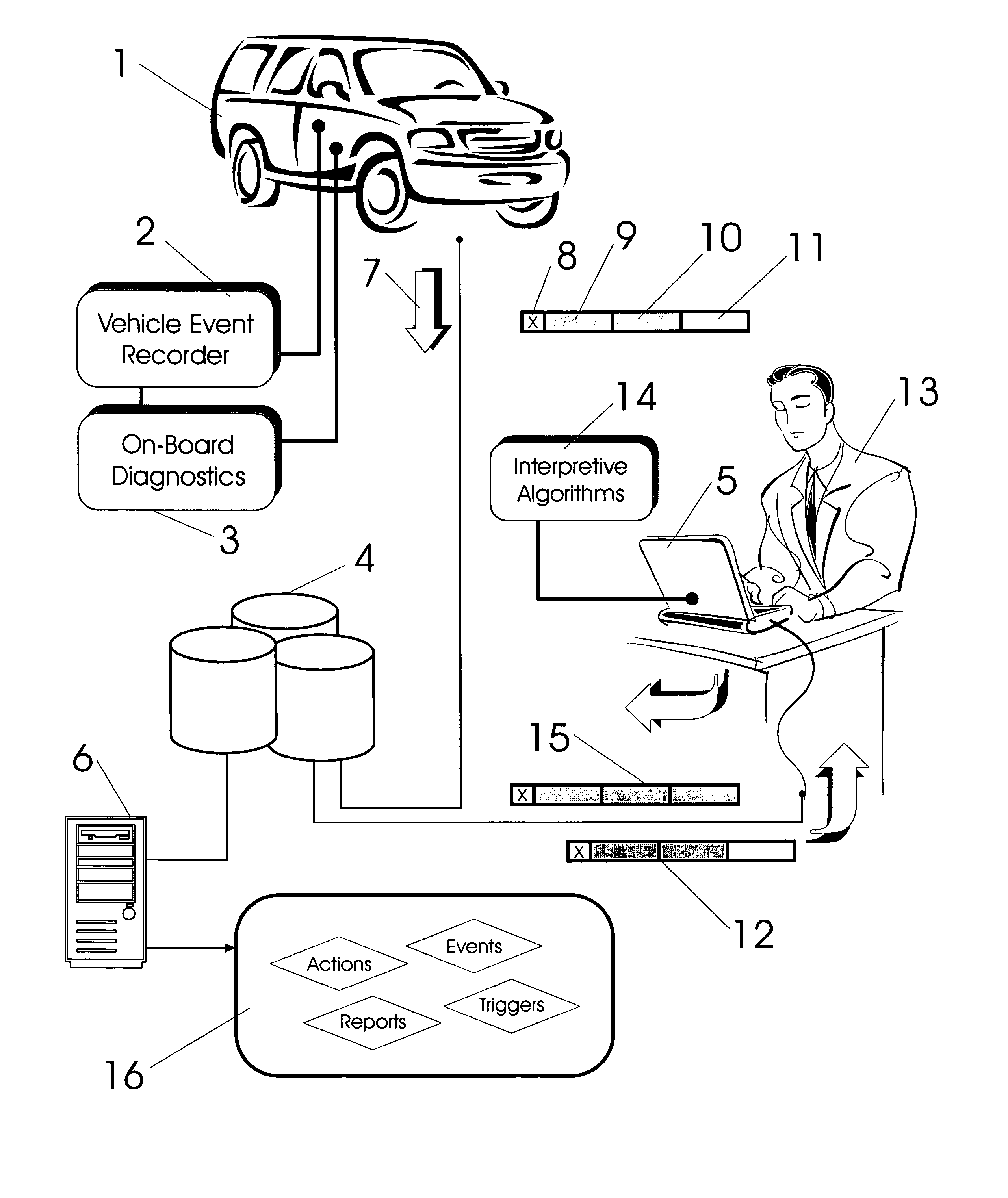
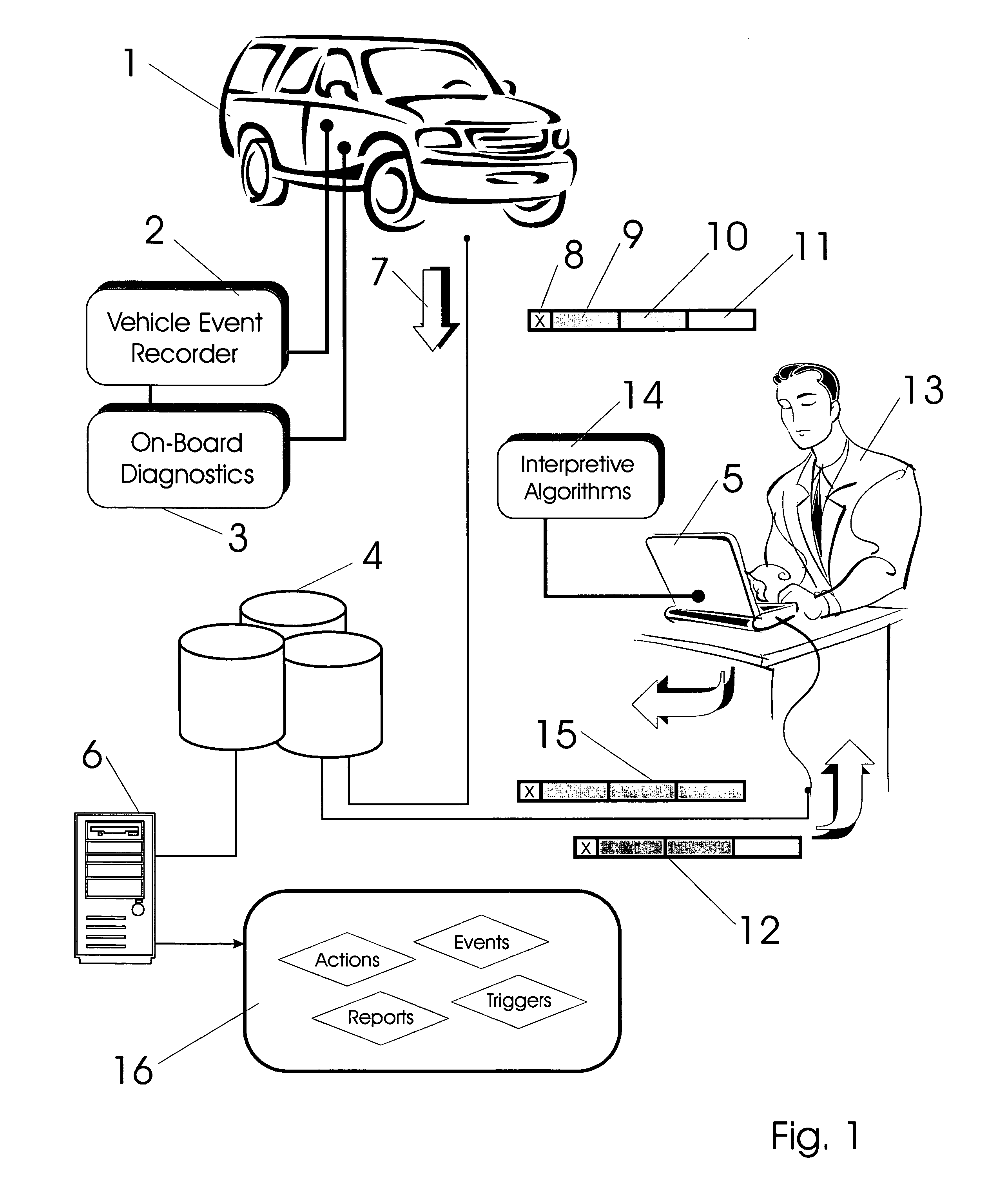
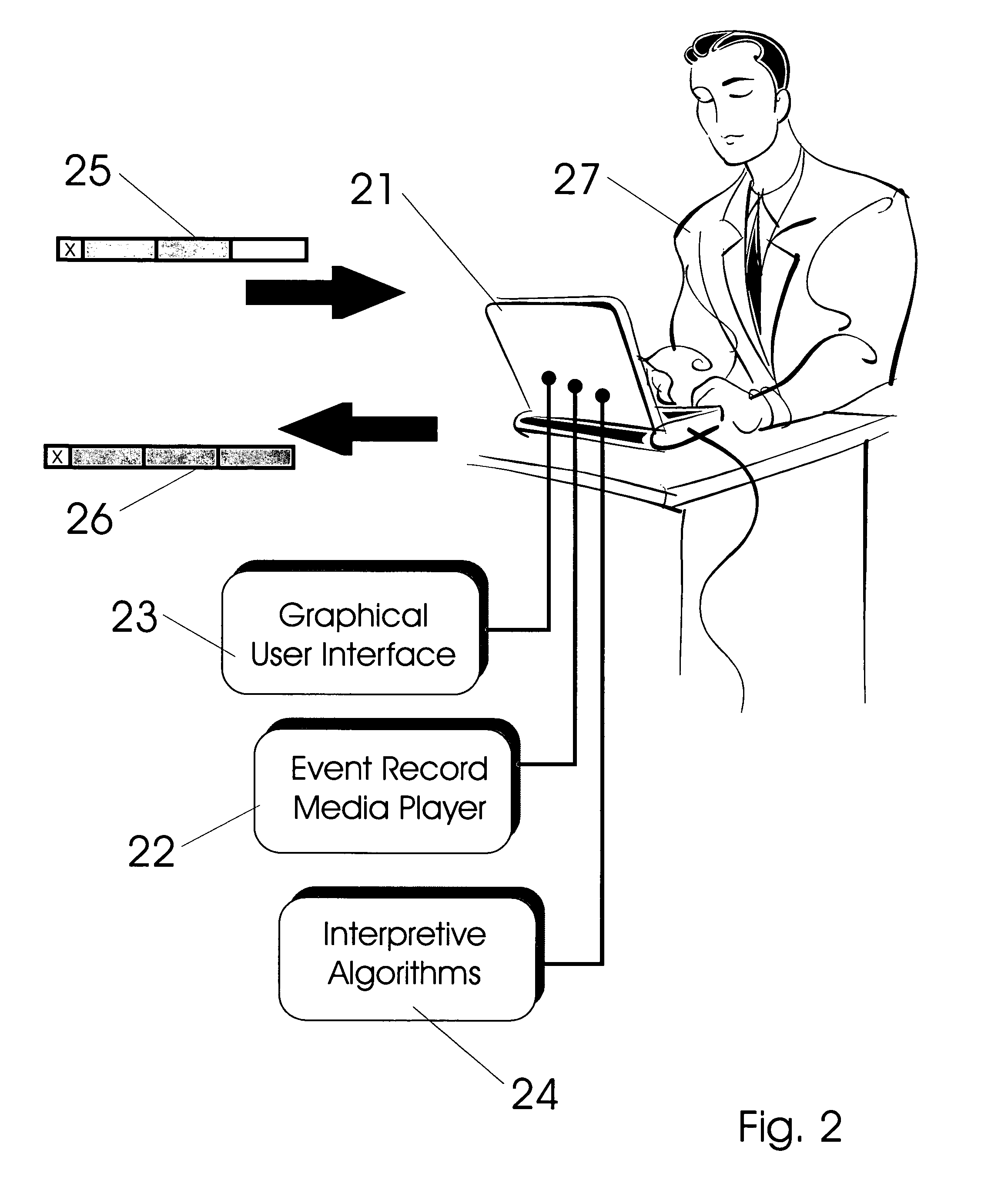
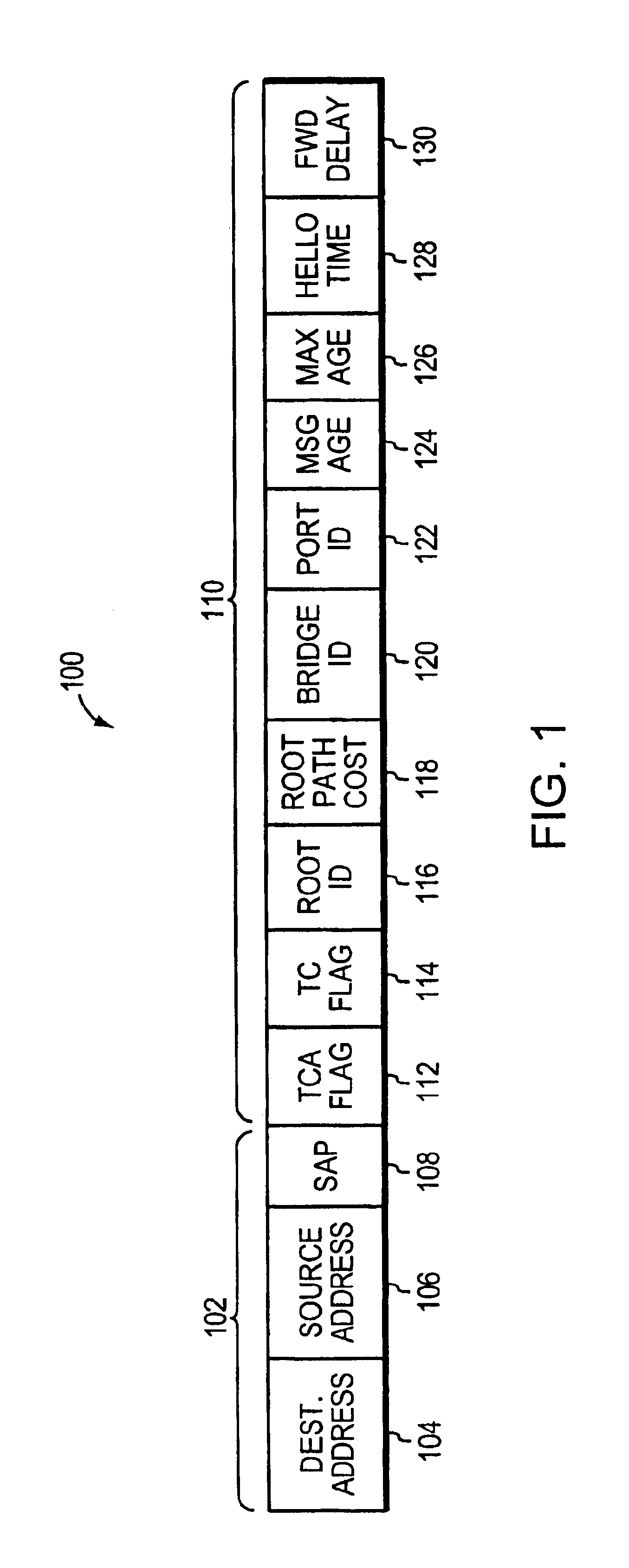
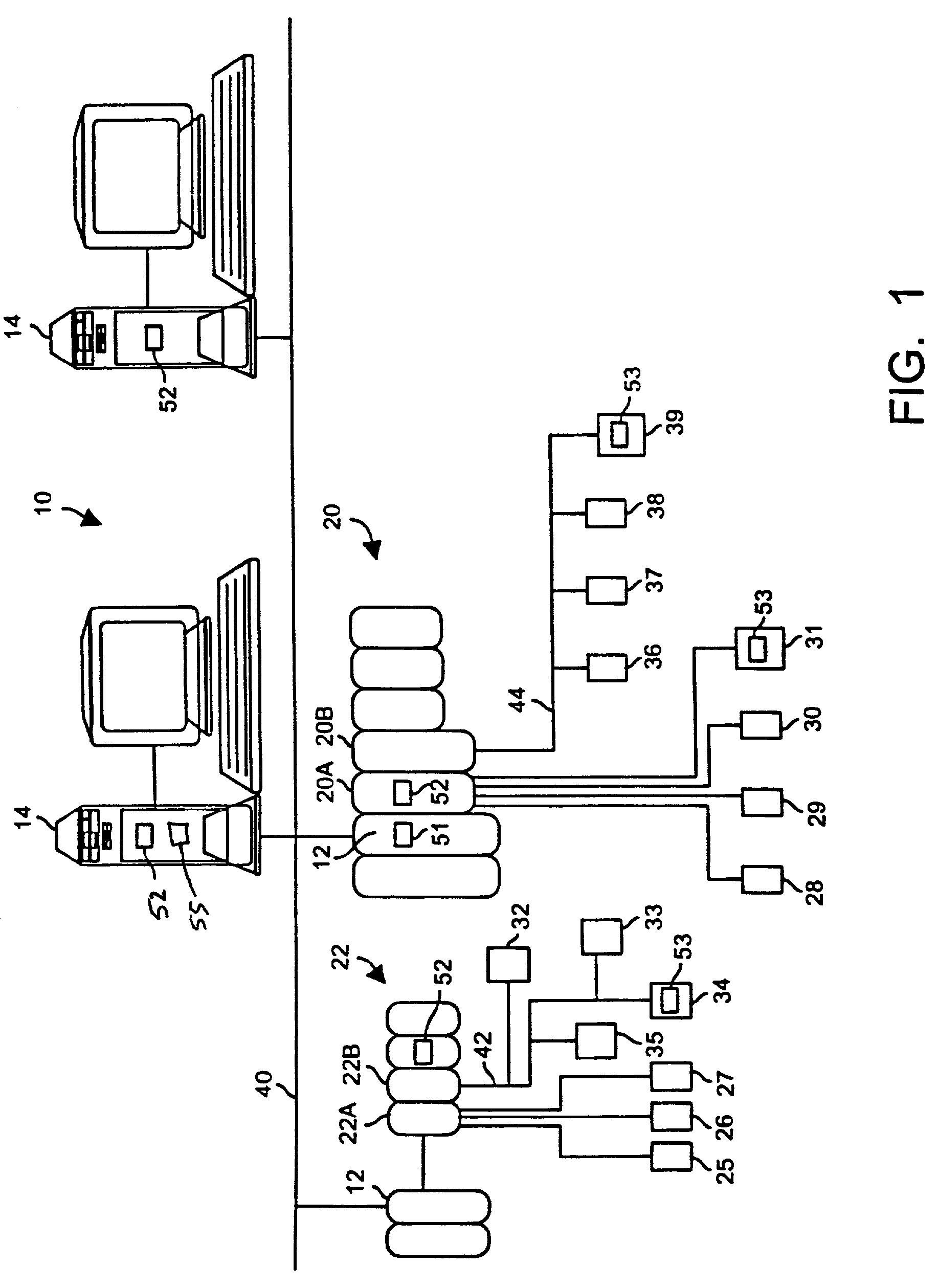
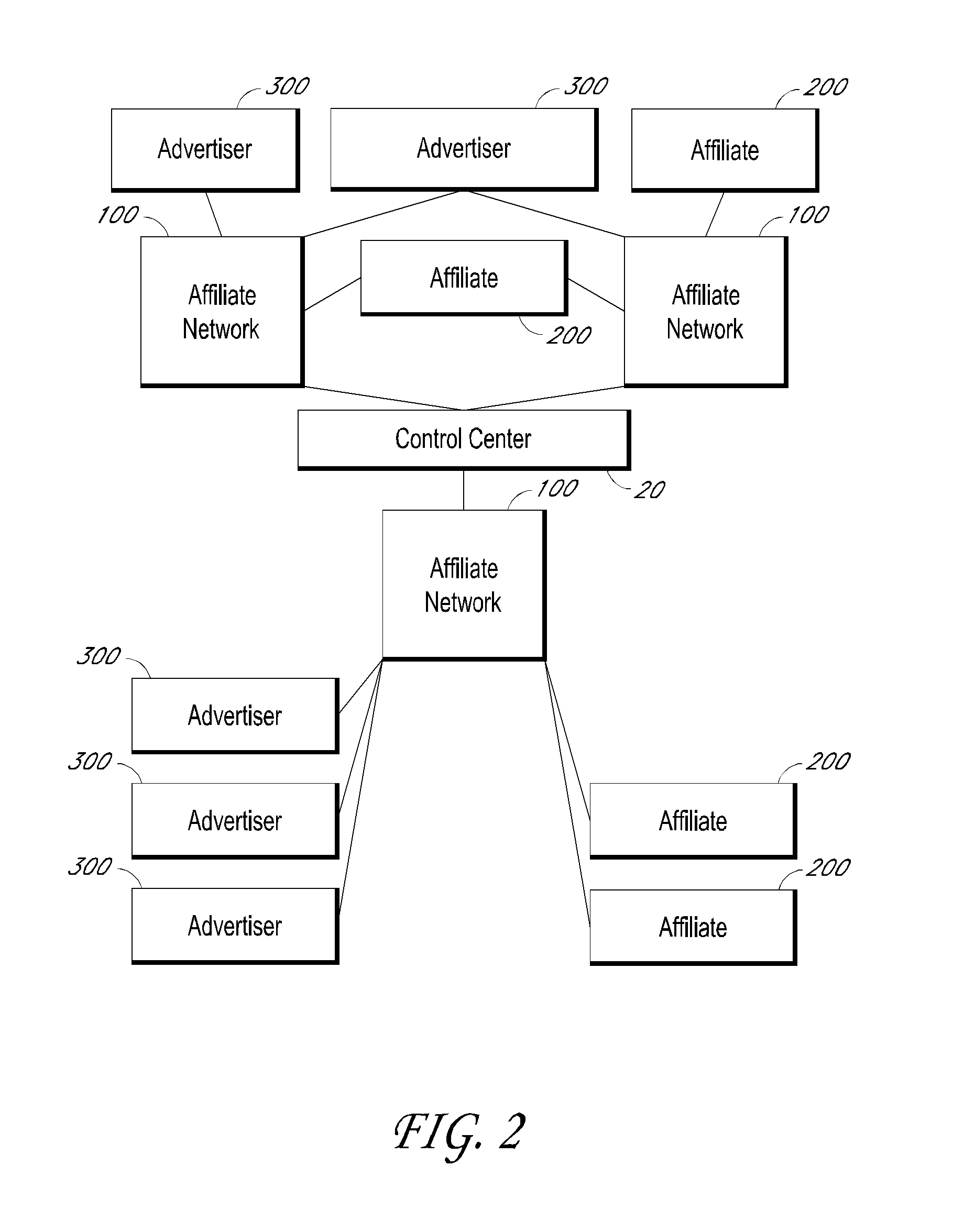
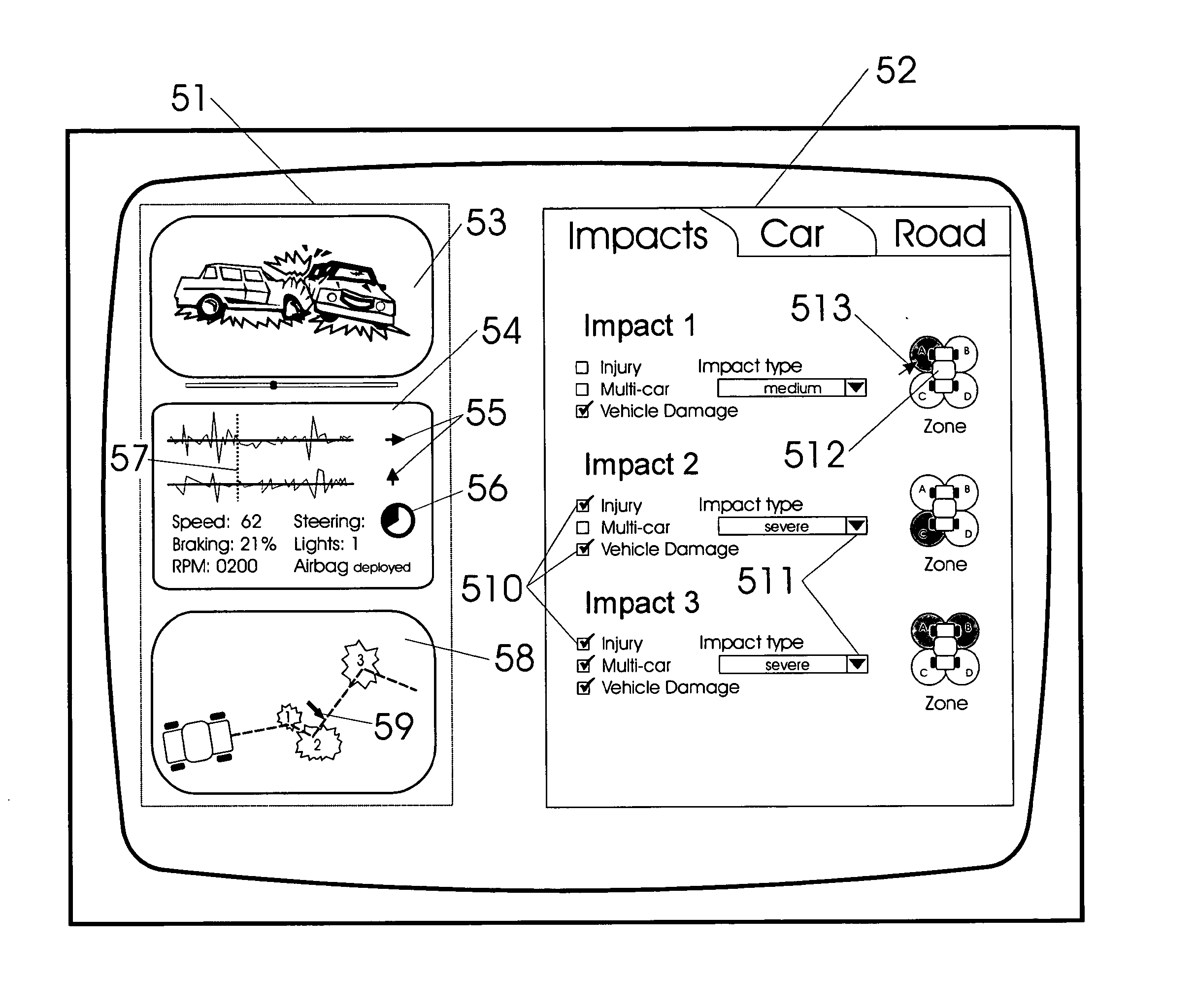
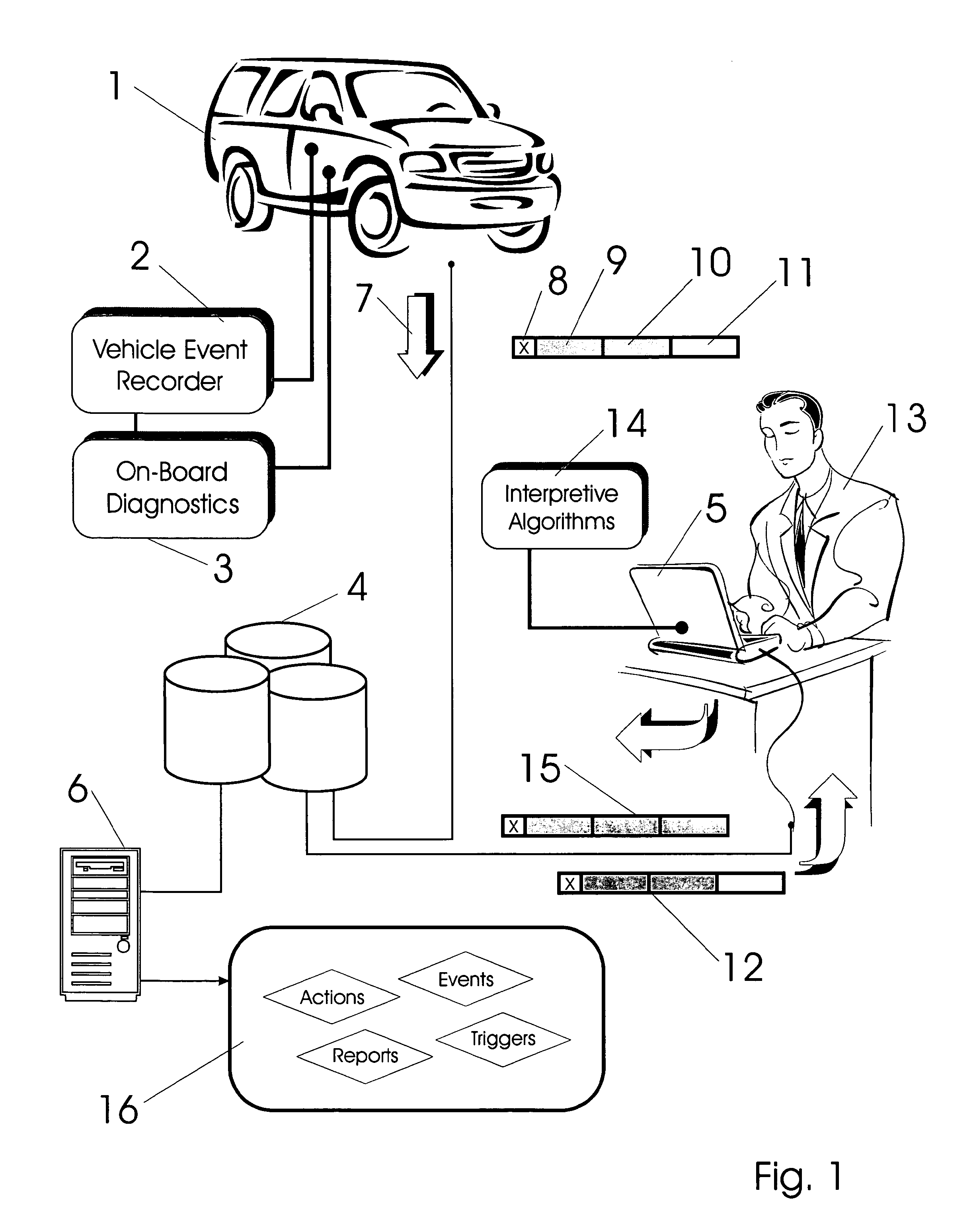
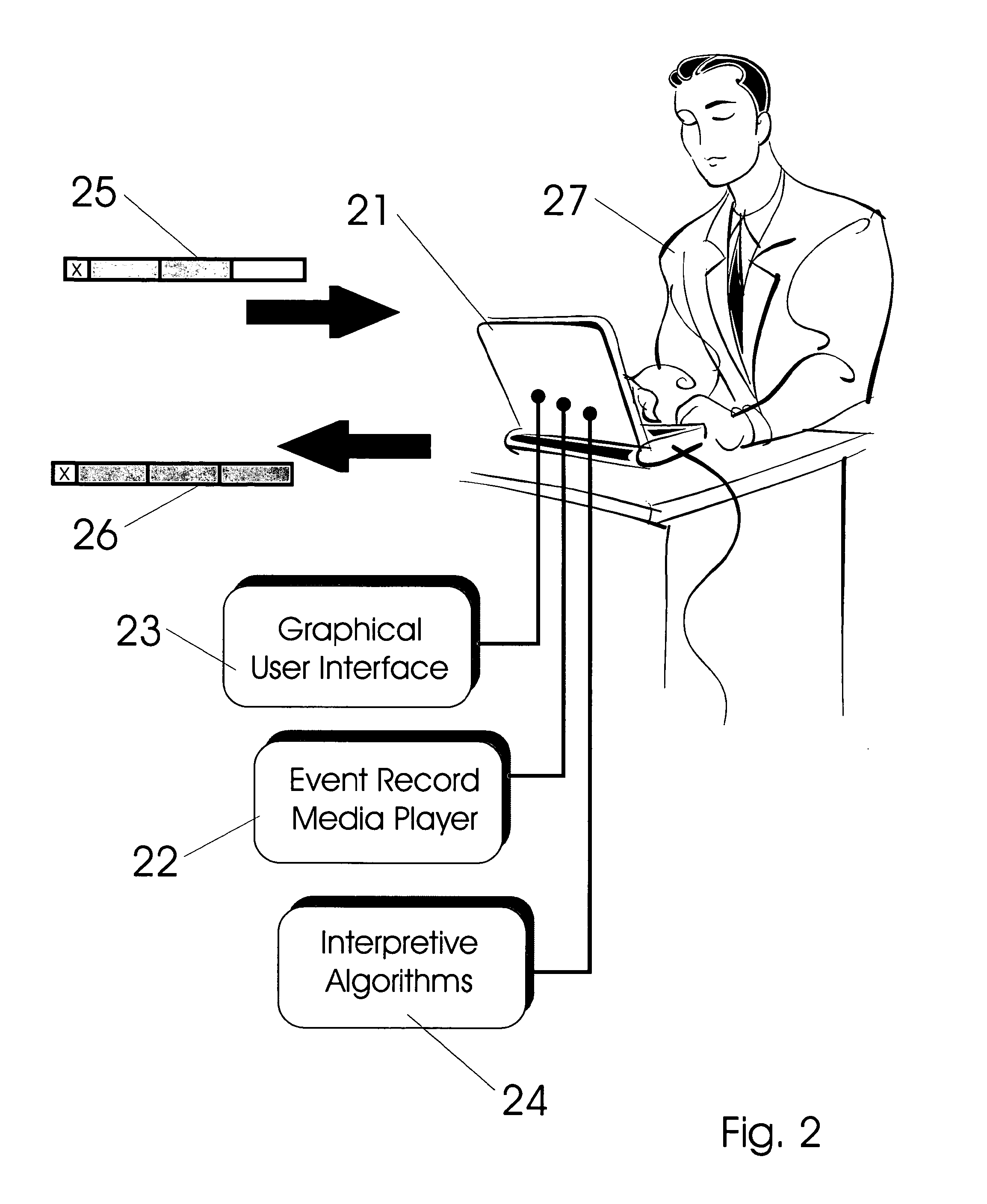
Vehicle exception event management systems
ActiveUS20080111666A1Easy to operateHeat generationRegistering/indicating working of vehiclesOptical signallingMobile vehicleNetwork connection
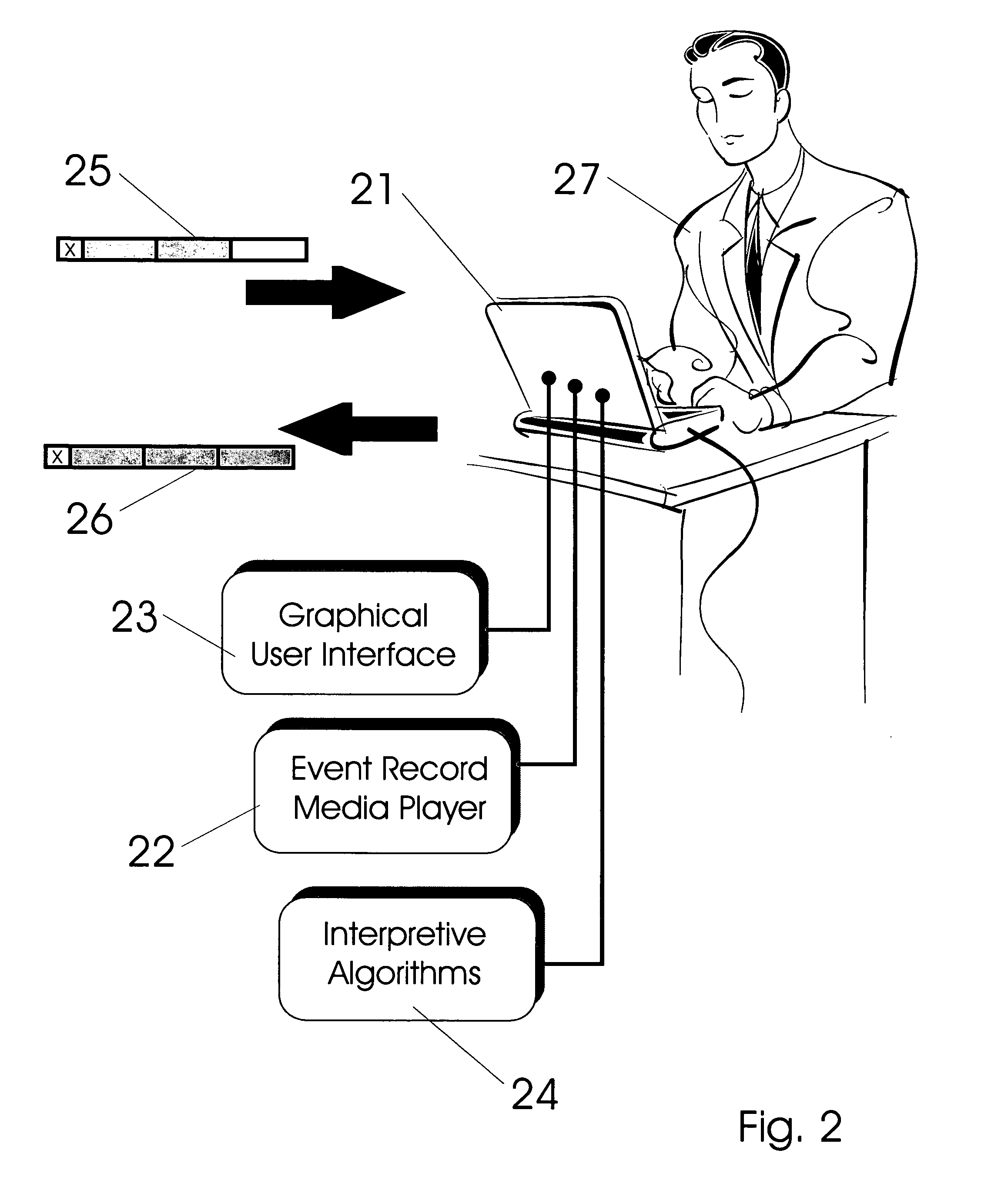
Exception event recorders and analysis systems include: vehicle mounted sensors arranged as a vehicle event recorder to capture both discrete and non-discrete data; a discretization facility; a database; and an analysis server all coupled together as a computer network. Motor vehicles with video cameras and onboard diagnostic systems capture data when the vehicle is involved in a crash or other anomaly (an ‘event’). In station where interpretation of non-discrete data is rendered, i.e. a discretization facility, captured data is used as a basis for production of supplemental discrete data to further characterize the event. Such interpreted data is joined to captured data and inserted into a database in a structure which is searchable and which supports logical or mathematical analysis by automated machines. A coupled analysis server is arranged to test stored data for prescribed conditions and upon finding such, to initiate further actions appropriate for the detected condition.
Owner:SMARTDRIVE SYSTEMS
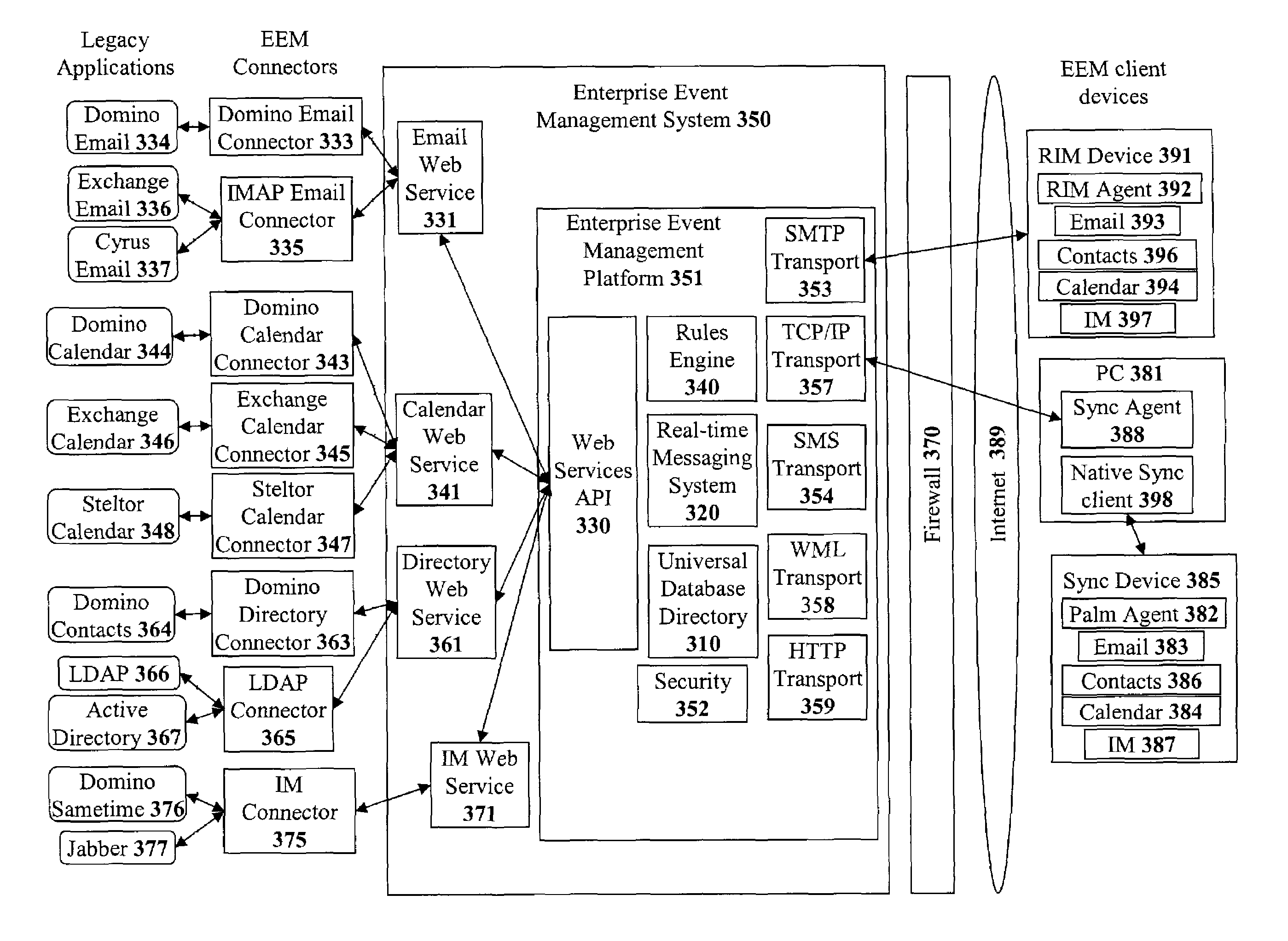
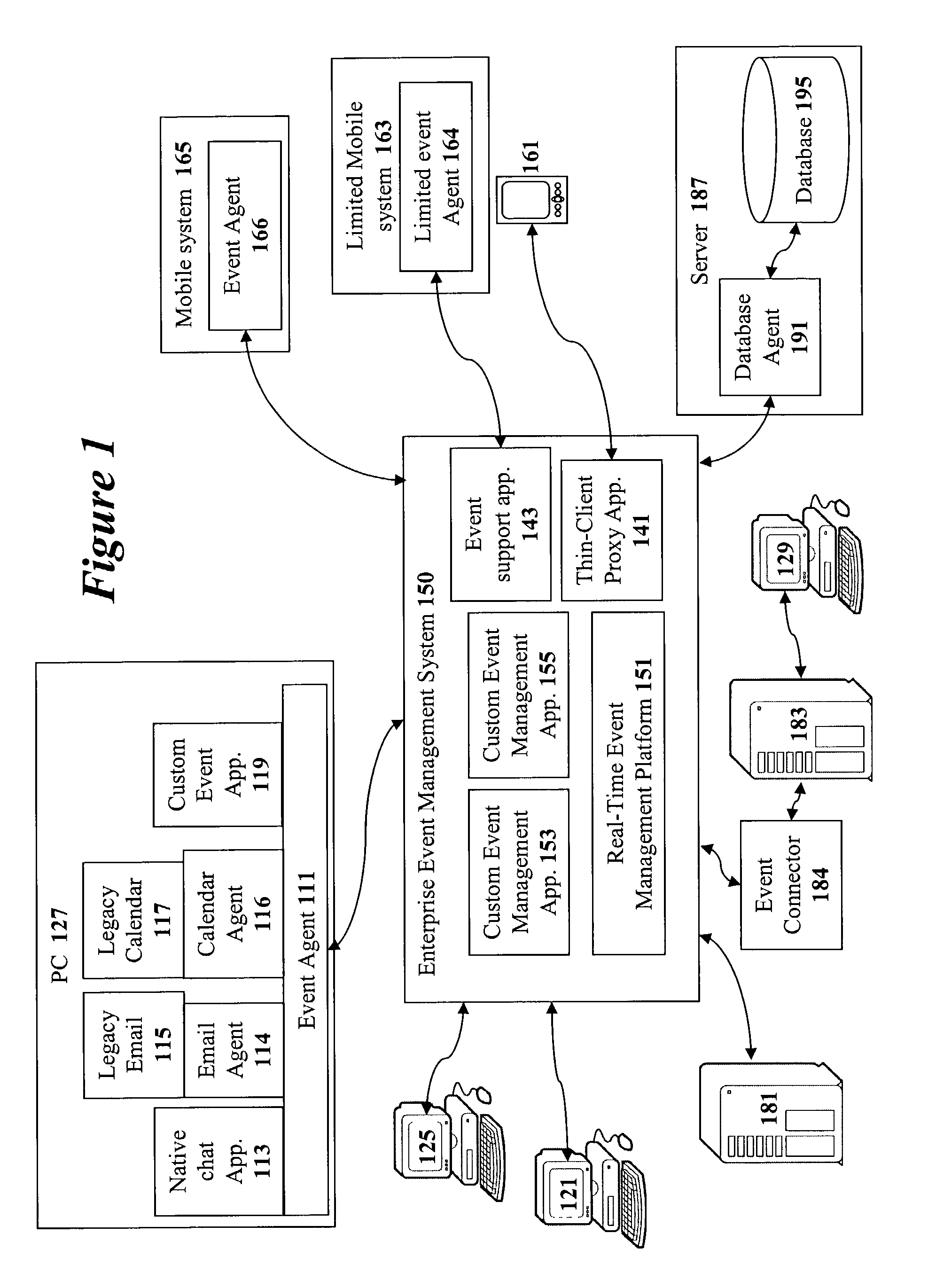
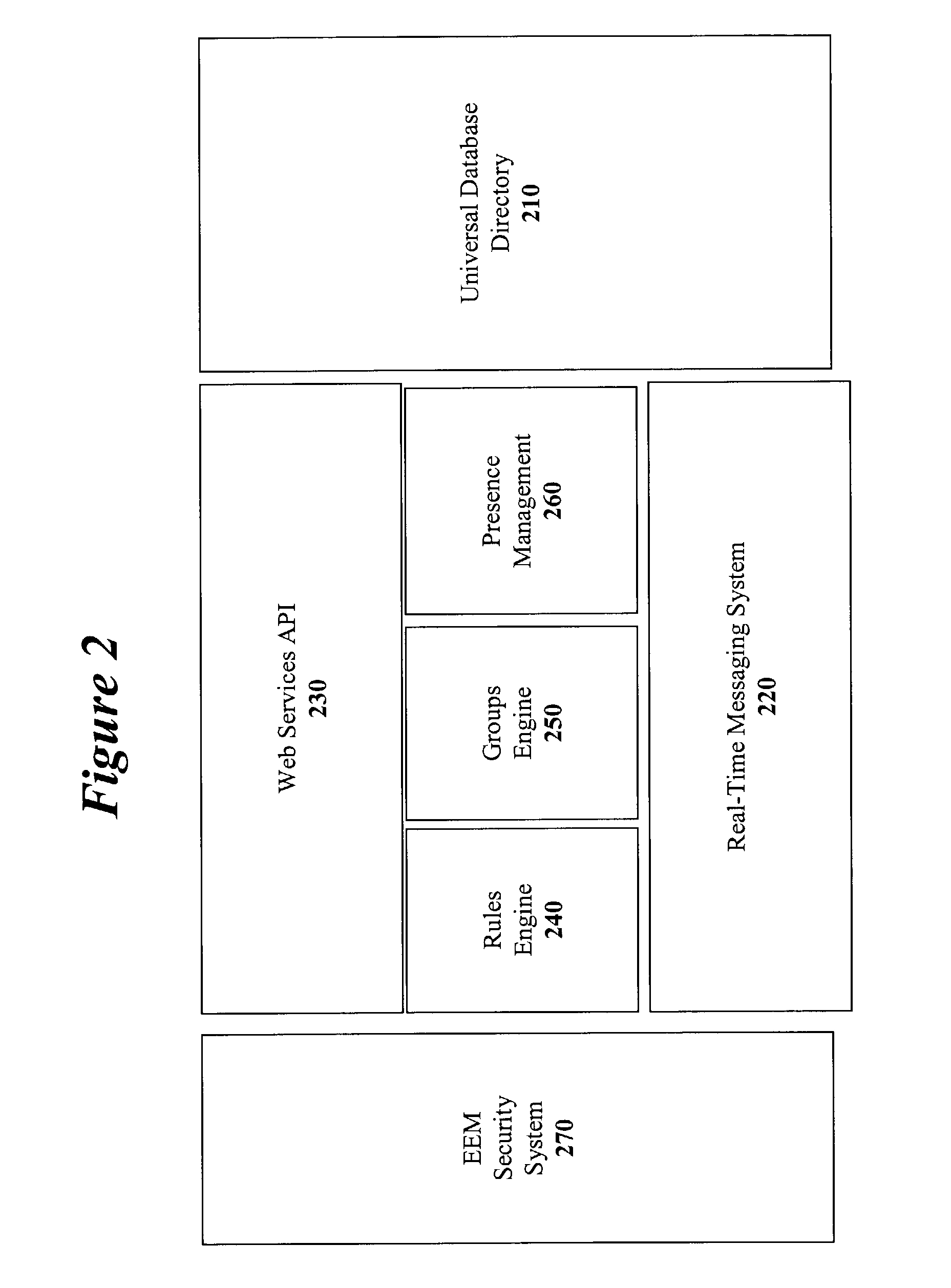
Method and apparatus for implementing a real-time event management platform
ActiveUS7454459B1Multiple digital computer combinationsOffice automationExtensible markupDocumentation
A method and apparatus for implementing a real-time enterprise event management system is disclosed. The enterprise event management (EEM) system couples together various “event aware” computing resources that publish and subscribe to “events” that provide information about the state computing resources. All of the events are represented as eXtensible Mark-up Language (XML) documents. Chains of related events are known as “event streams”. In the real-time event management platform, the event streams are available to all other event-aware computing resources operating in the shared event driven environment. The three main components are a real-time messaging system or handing event messages, a rules engine for allowing specific event message handing rules to be created, and a enterprise directory schema for providing a comprehensive directory of all the available resources and the means in which the resources may be accessed.
Owner:MALIKIE INNOVATIONS LTD
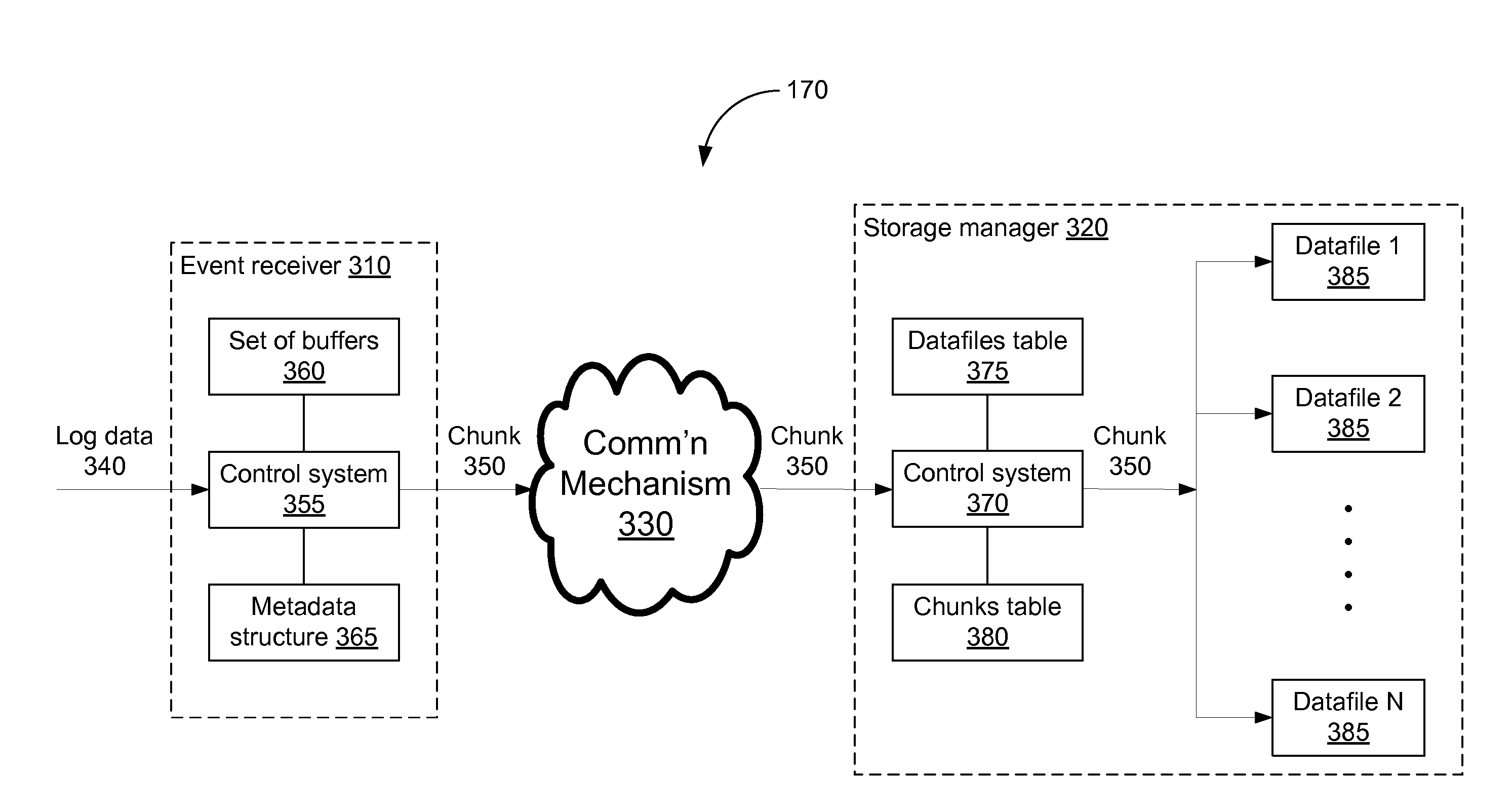
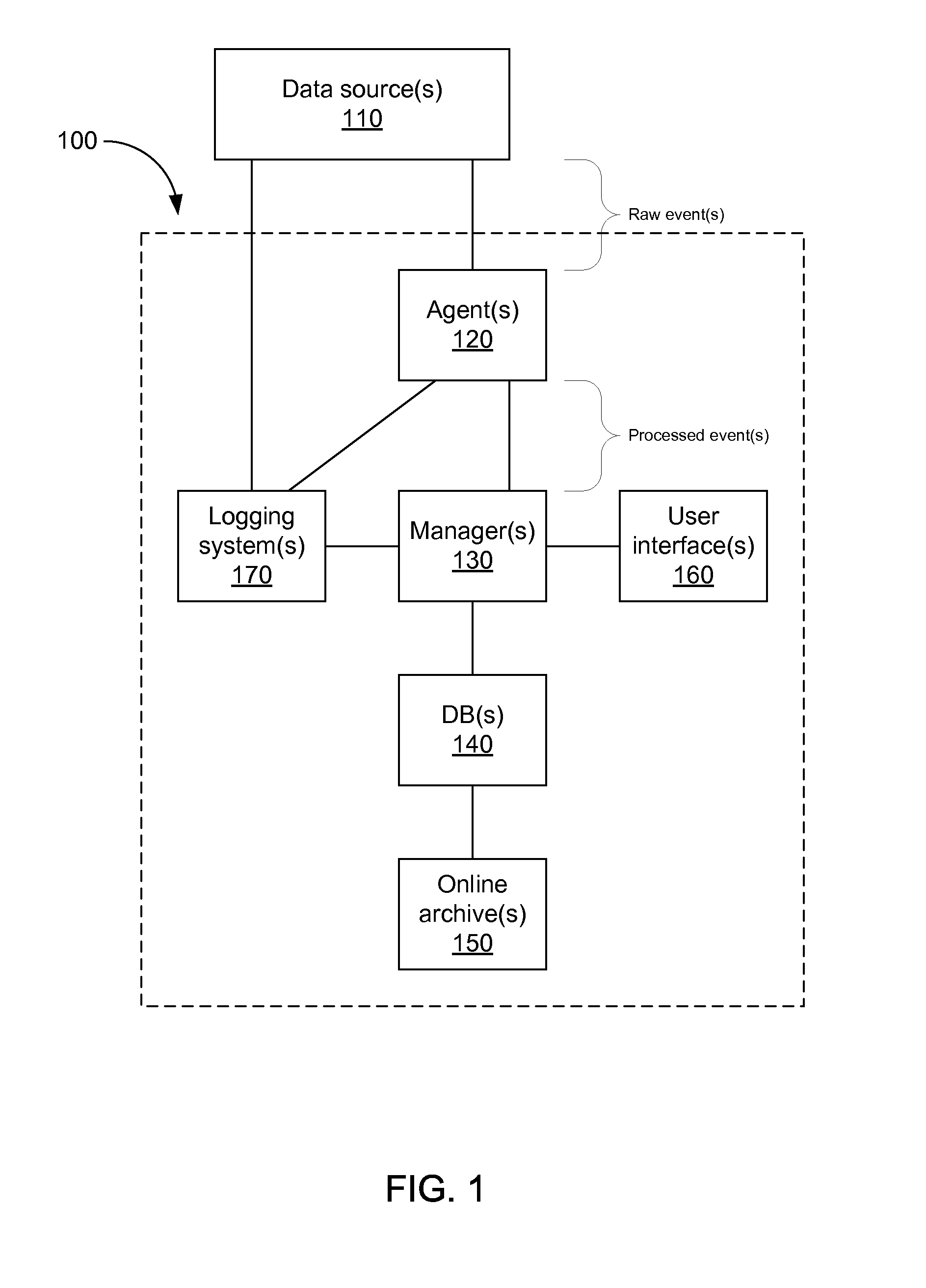
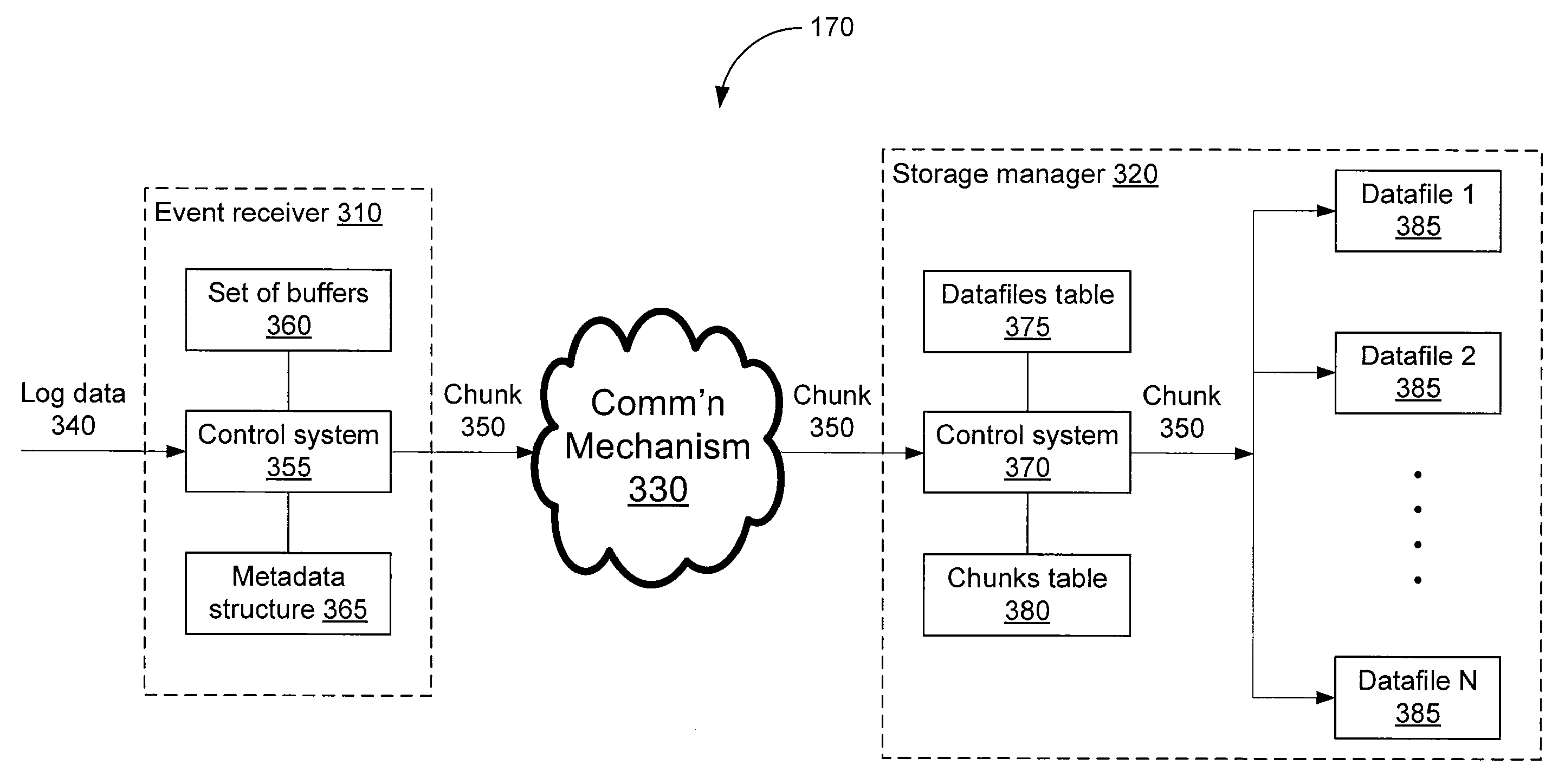
Storing log data efficiently while supporting querying
A logging system includes an event receiver and a storage manager. The receiver receives log data, processes it, and outputs a column-based data “chunk.” The manager receives and stores chunks. The receiver includes buffers that store events and a metadata structure that stores metadata about the contents of the buffers. Each buffer is associated with a particular event field and includes values from that field from one or more events. The metadata includes, for each “field of interest,” a minimum value and a maximum value that reflect the range of values of that field over all of the events in the buffers. A chunk is generated for each buffer and includes the metadata structure and a compressed version of the buffer contents. The metadata structure acts as a search index when querying event data. The logging system can be used in conjunction with a security information / event management (SIEM) system.
Owner:MICRO FOCUS LLC
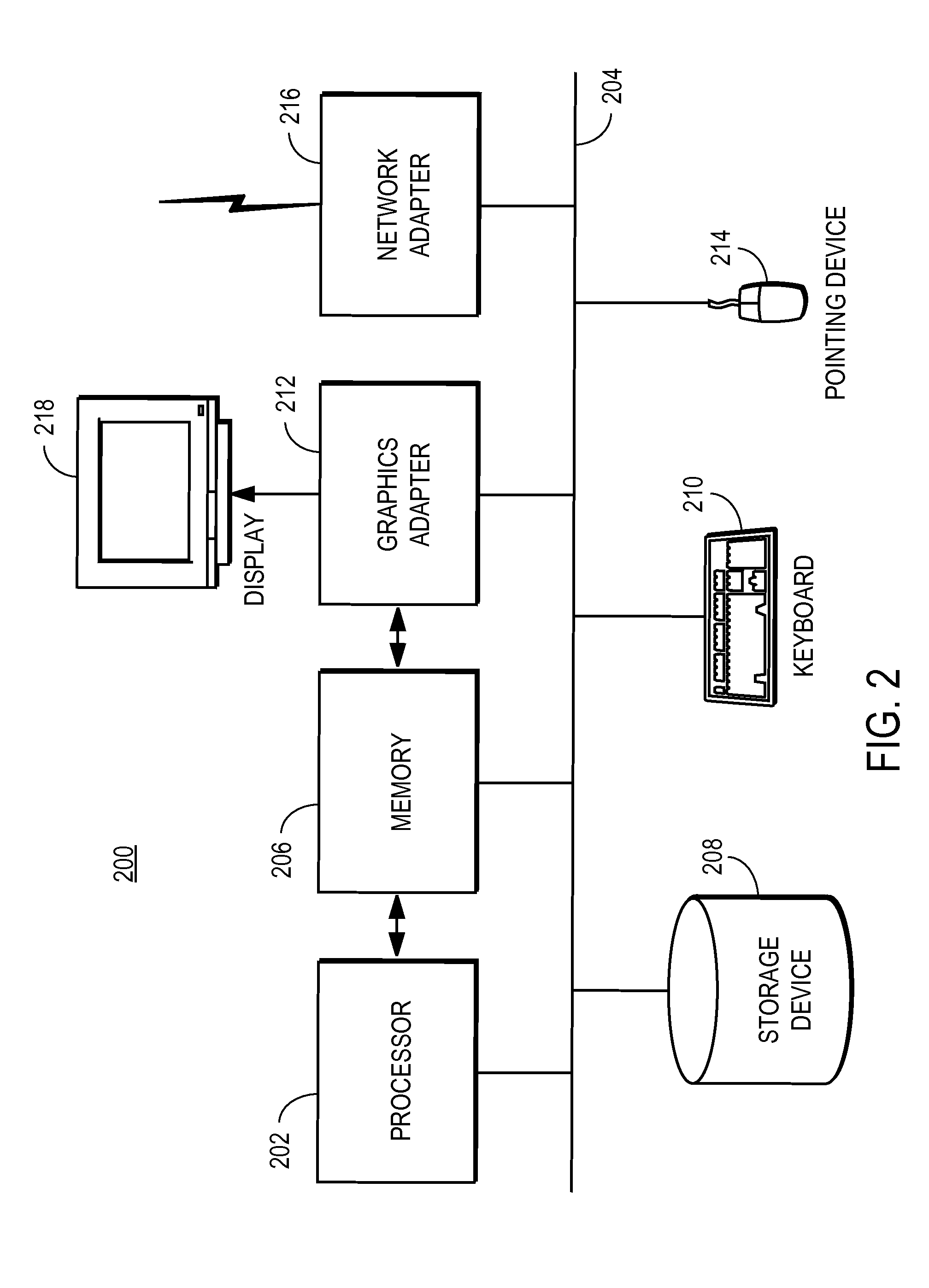
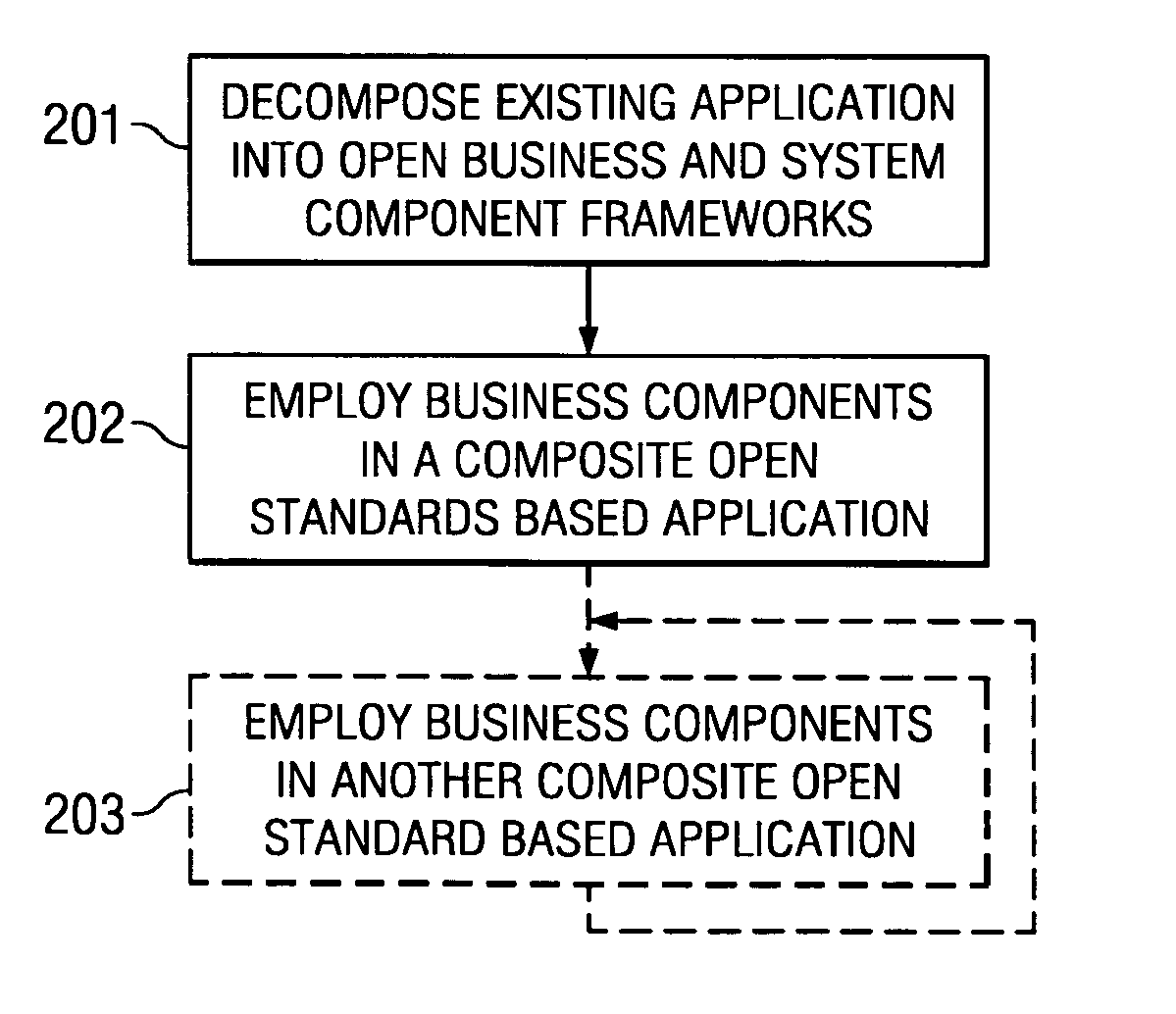
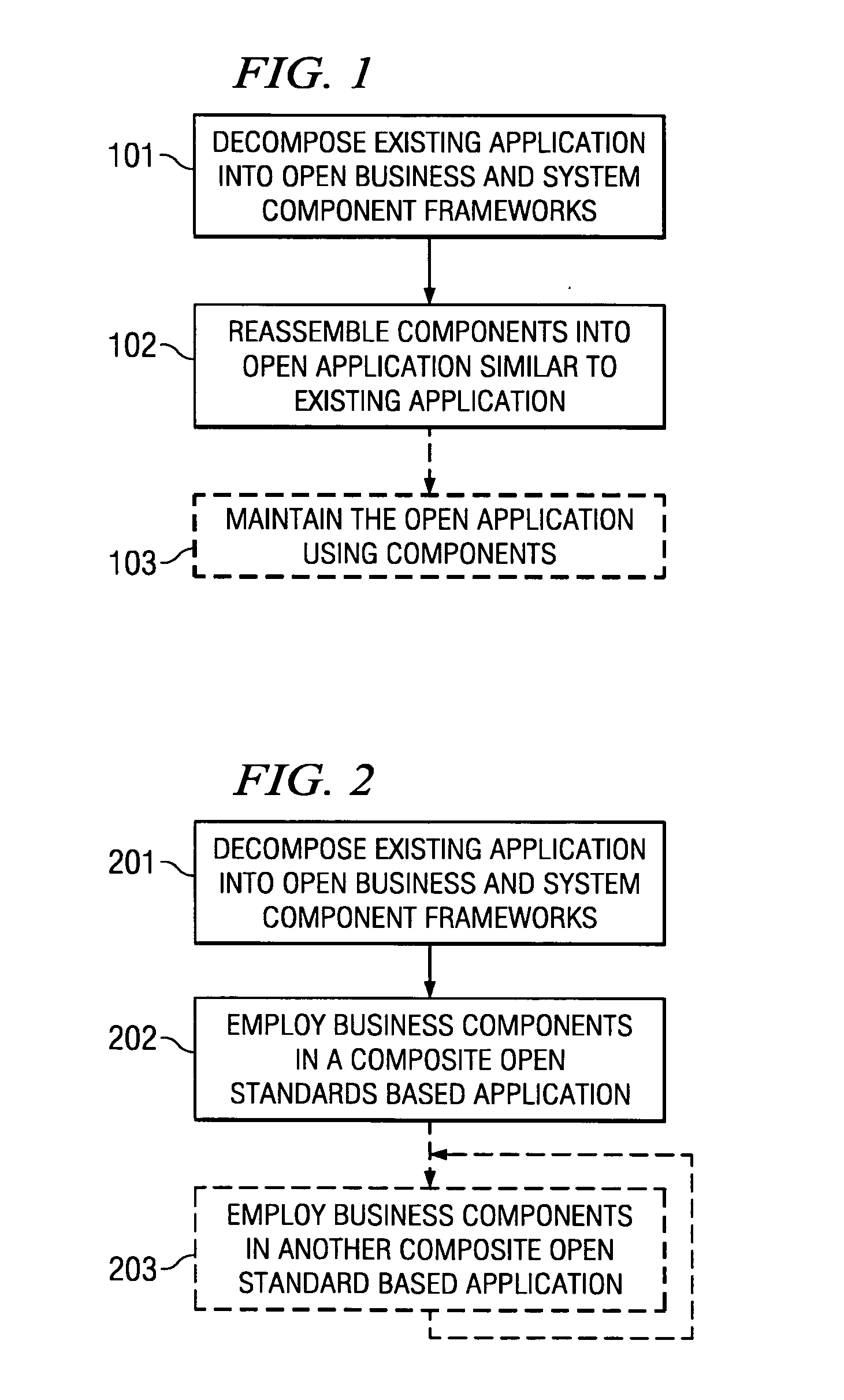
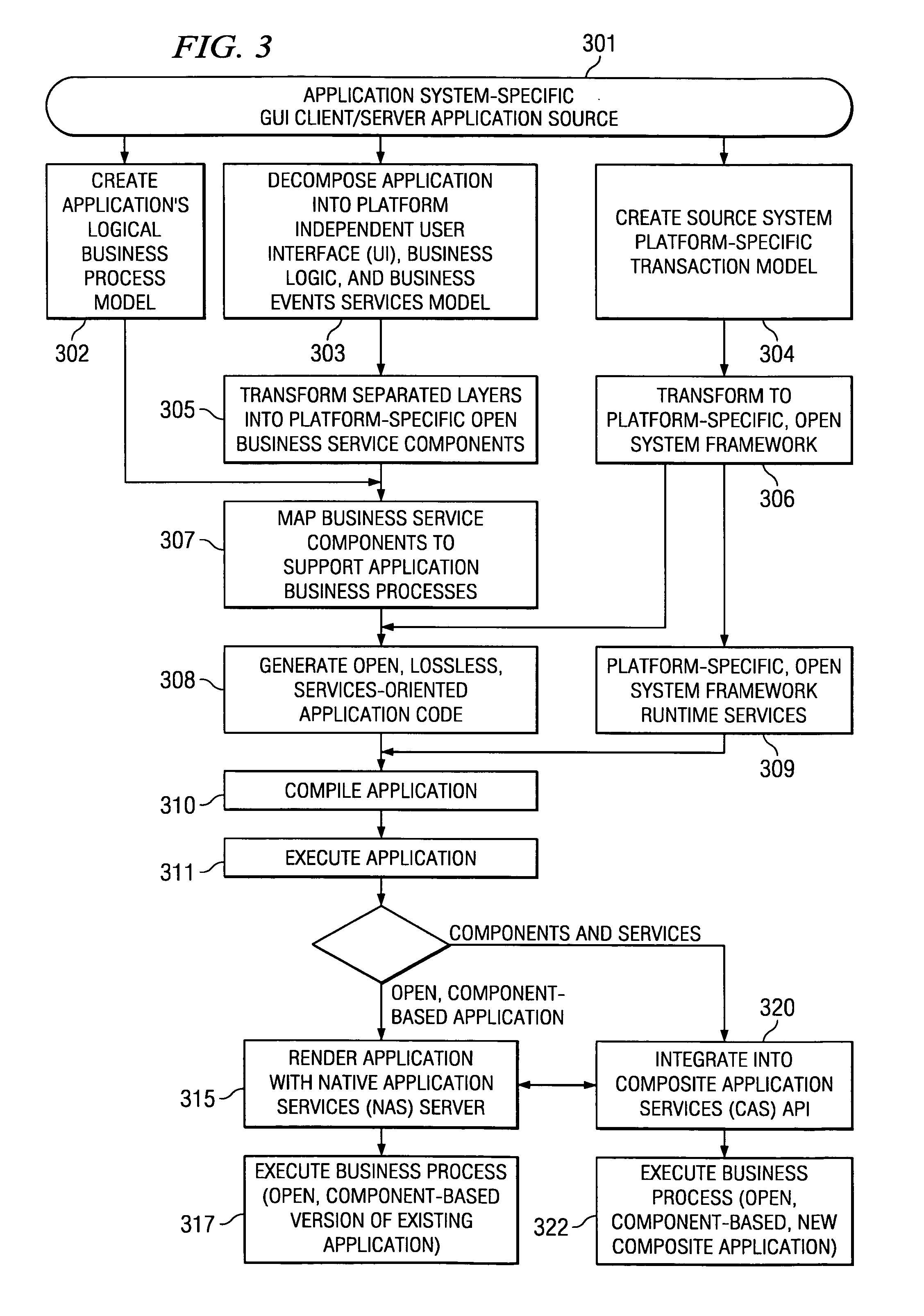
Systems and methods for modeling and generating reusable application component frameworks, and automated assembly of service-oriented applications from existing applications
InactiveUS20050144226A1Effective and meaningful supportLower barrierSoftware maintainance/managementMultiple digital computer combinationsService oriented applicationsBusiness process
Embodiments of systems and methods model and generate open reusable, business components for Service Oriented Architectures (SOAs) from existing client / server applications. Applications are decomposed into business component frameworks with separate user interface, business logic, and event management layers to enable service-oriented development of new enterprise applications. Such layers are re-assembled through an open standards-based, Native Application Services (NAS) to render similar or near identical transactional functionality within a new application on an open platform, without breaking former production code, and without requiring a change in an end-user's business processes and / or user experience. In addition, the same separated layers may form re-usable business components at any desired level of granularity for re-use in external composite applications through industry-standard interfaces, regardless of usage, context, or complexity in the former Client / Server application.
Owner:SAP AG
Storing log data efficiently while supporting querying to assist in computer network security
ActiveUS20080162592A1Data processing applicationsError detection/correctionSystem of recordEvent management
A logging system includes an event receiver and a storage manager. The receiver receives log data, processes it, and outputs a data “chunk.” The manager receives data chunks and stores them so that they can be queried. The receiver includes buffers that store events and a metadata structure that stores metadata about the contents of the buffers. The metadata includes a unique identifier associated with the receiver, the number of events in the buffers, and, for each “field of interest,” a minimum value and a maximum value that reflect the range of values of that field over all of the events in the buffers. A chunk includes the metadata structure and a compressed version of the contents of the buffers. The metadata structure acts as a search index when querying event data. The logging system can be used in conjunction with a security information / event management (SIEM) system.
Owner:MICRO FOCUS LLC
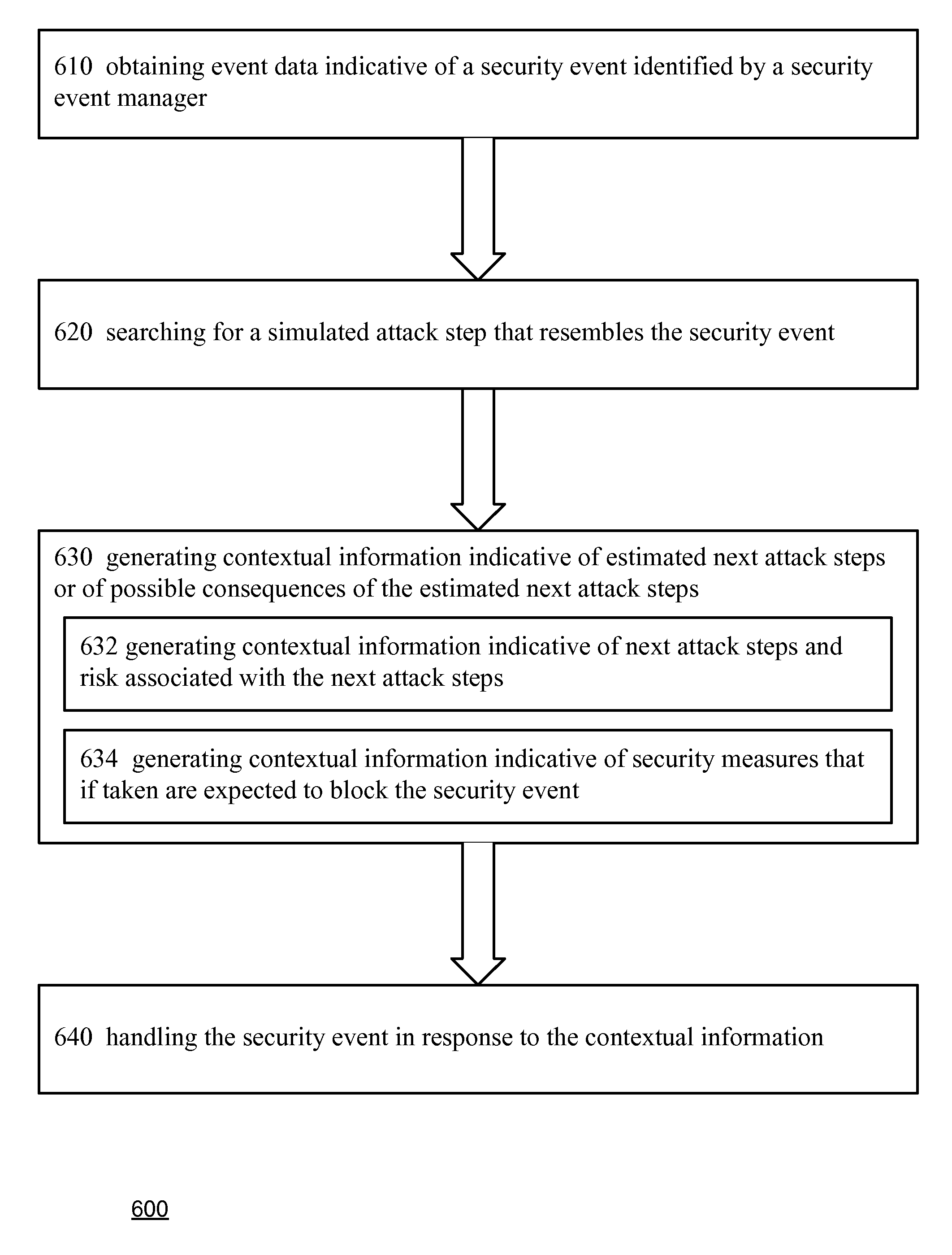
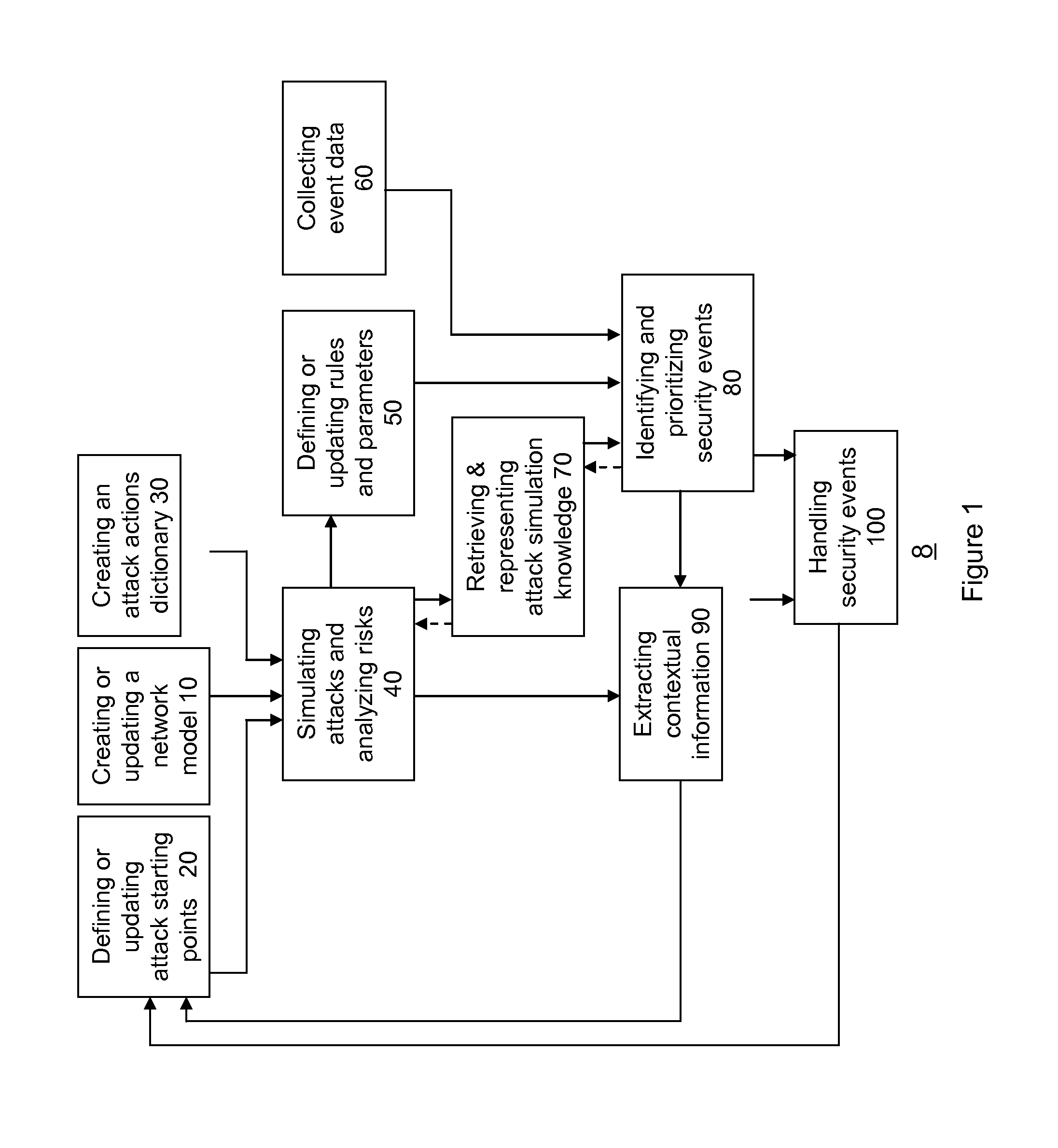
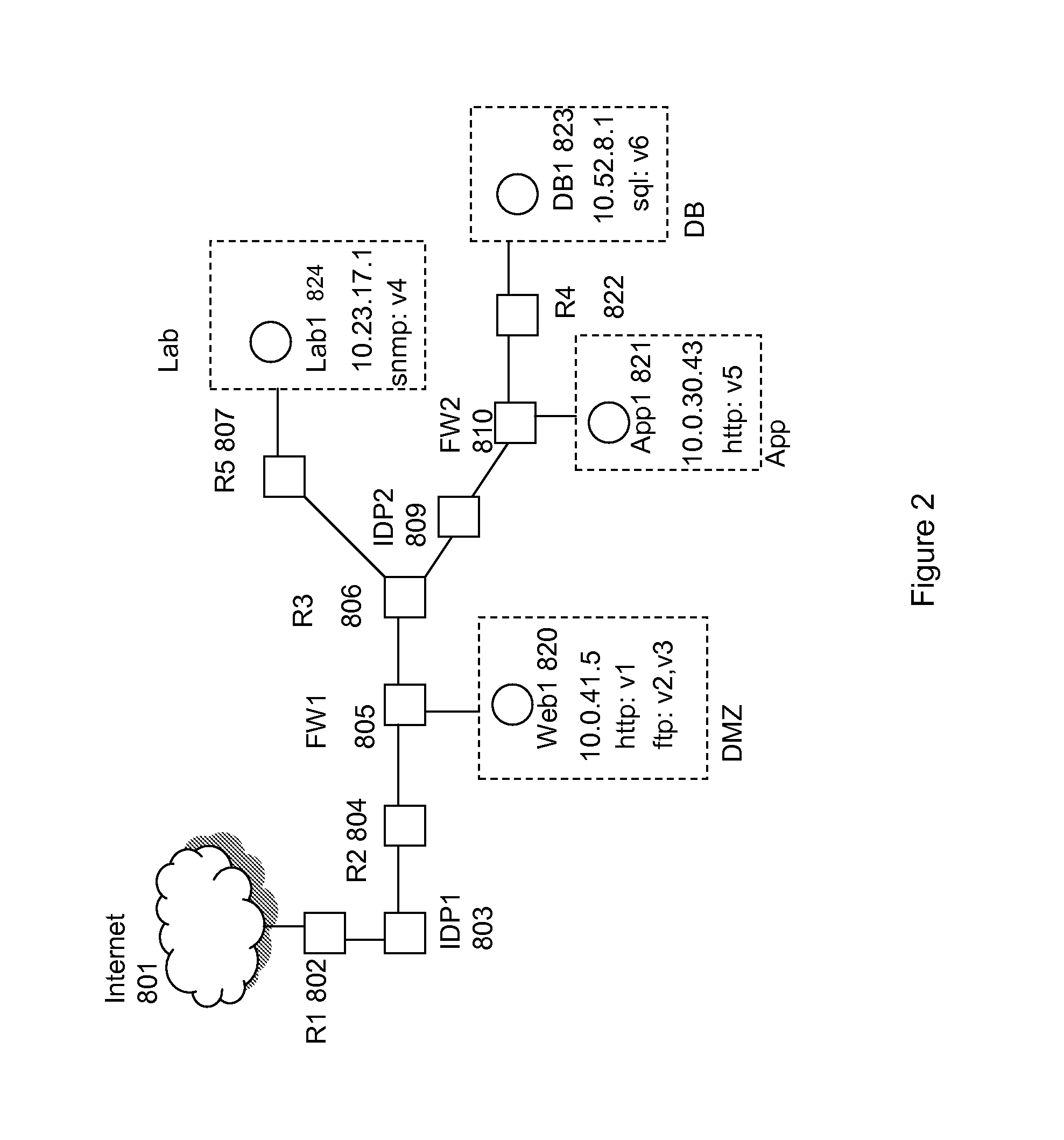
Method for simulation aided security event management
A method for simulation aided security event management, the method includes: generating attack simulation information that comprises multiple simulation data items of at least one data item type out of vulnerability instances data items, attack step data items and attack simulation scope data items; wherein the generating of attack simulation information is responsive to a network model, at least one attack starting point and attack action information; identifying security events in response to a correlation between simulation data items and event data; and prioritizing identified security events.
Owner:SKYBOX SECURITY
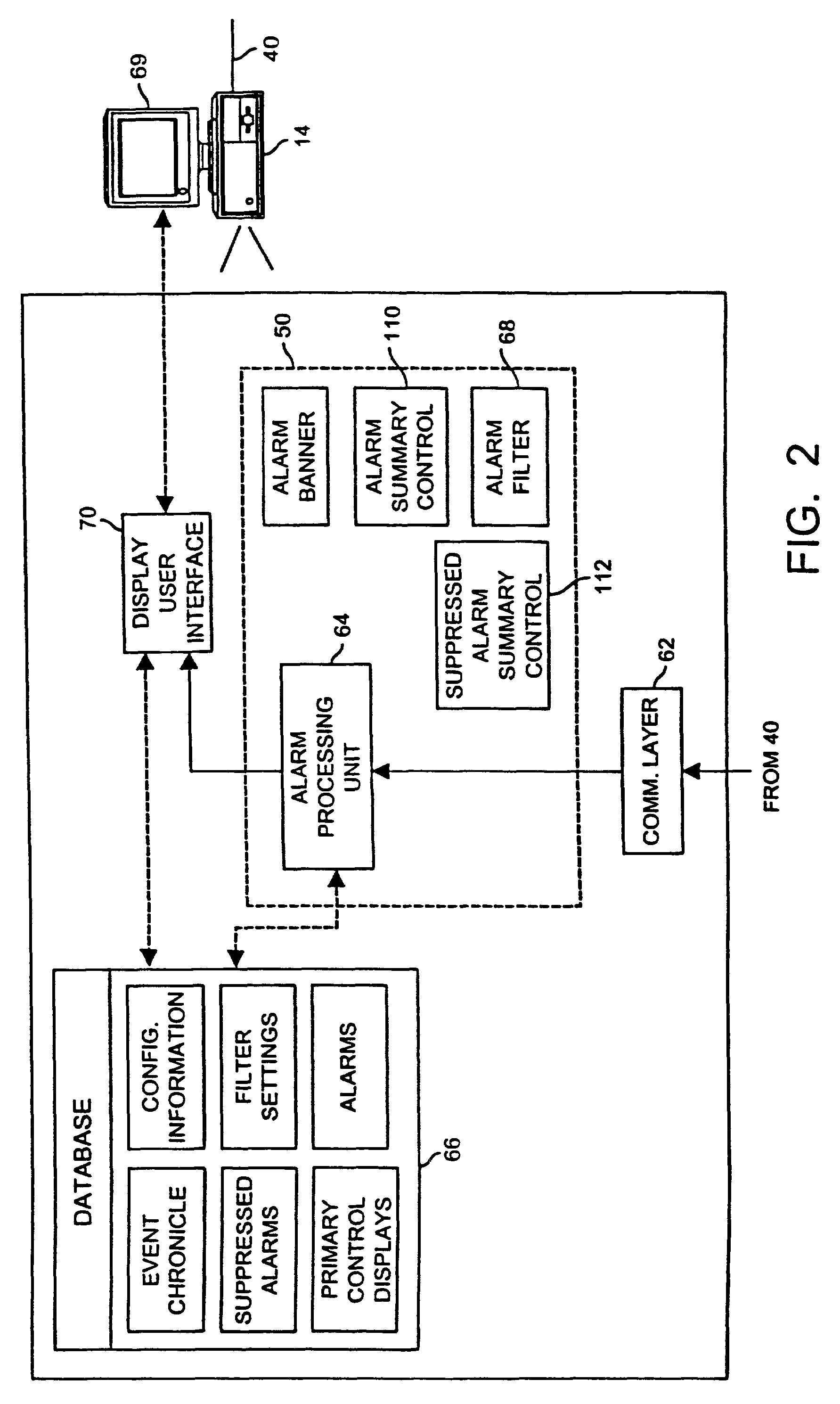
Event manager for use in a facilities monitoring system having network-level and protocol-neutral communication with a physical device
InactiveUS20060136558A1Multiple digital computer combinationsNetwork connectionsBuilding automationEvent management
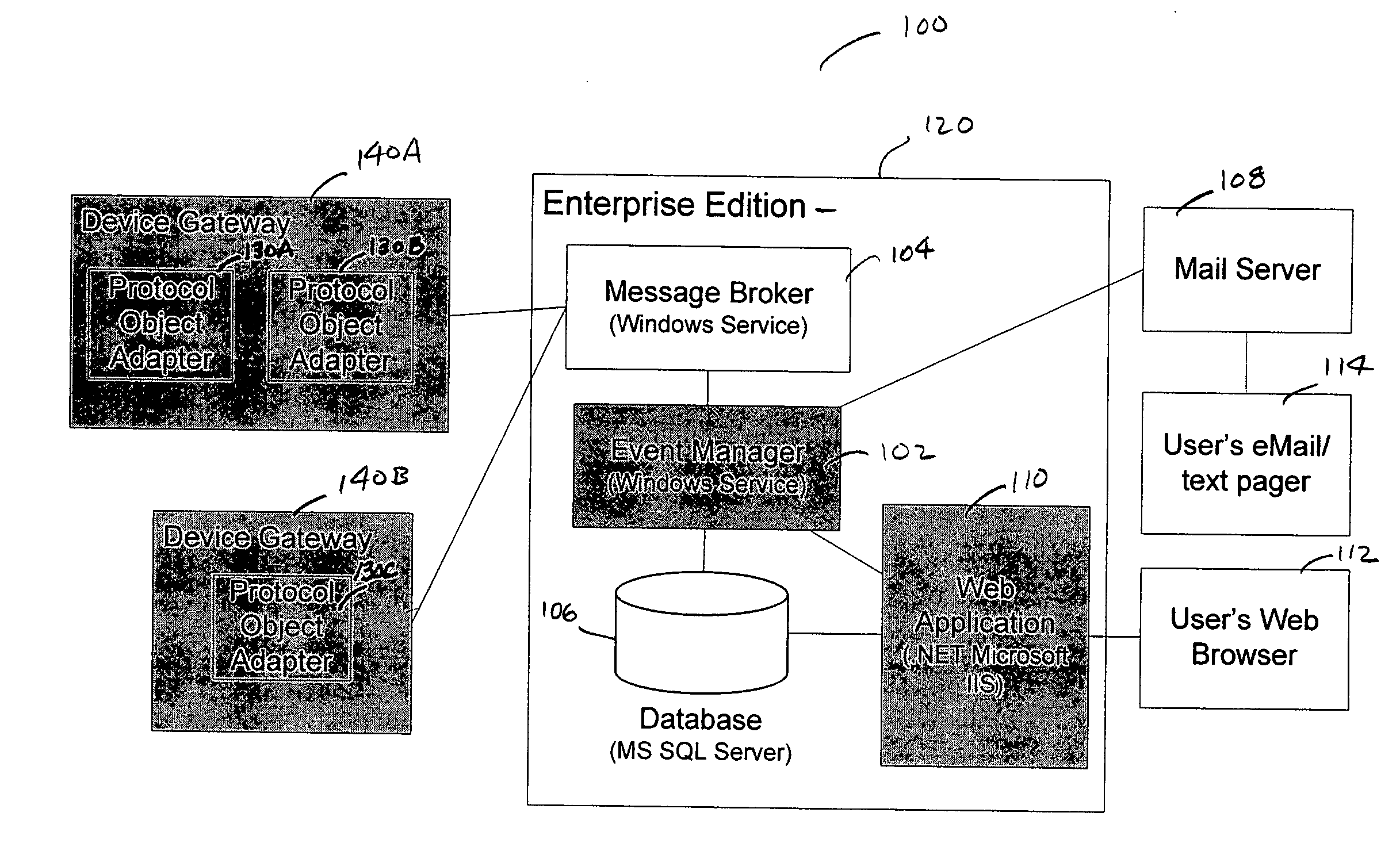
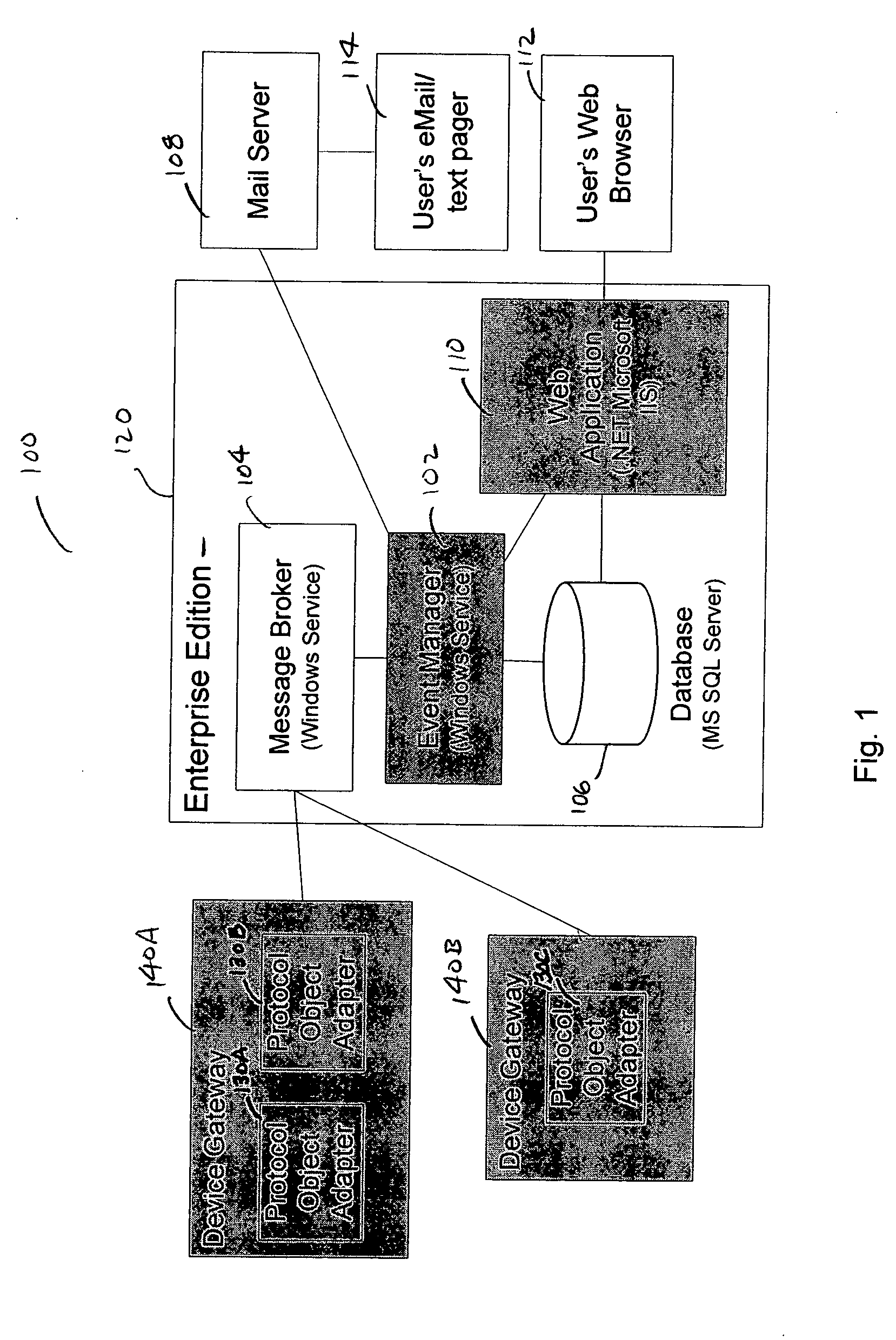
A method and a system for the off site monitoring / diagnostics, command / control, alarm / event management, historical / trend analysis, and configuration / administration of building automation systems through an event manager for use in a facilities monitoring system having network-level and protocol-neutral communication with a physical device. The method includes managing a non internet protocol-based physical device, including coupling a device gateway with the physical device, wherein the device gateway is configured to expose the physical device as a networked device on a server. The method also includes receiving event information from the coupled physical device, wherein the event information includes an event and a device identifier; responsive to a determination that the event information includes an actionable event, processing the event, the device identifier, and the actionable event to determine a responsible process; and notifying the responsible process of the event.
Owner:MODIUS
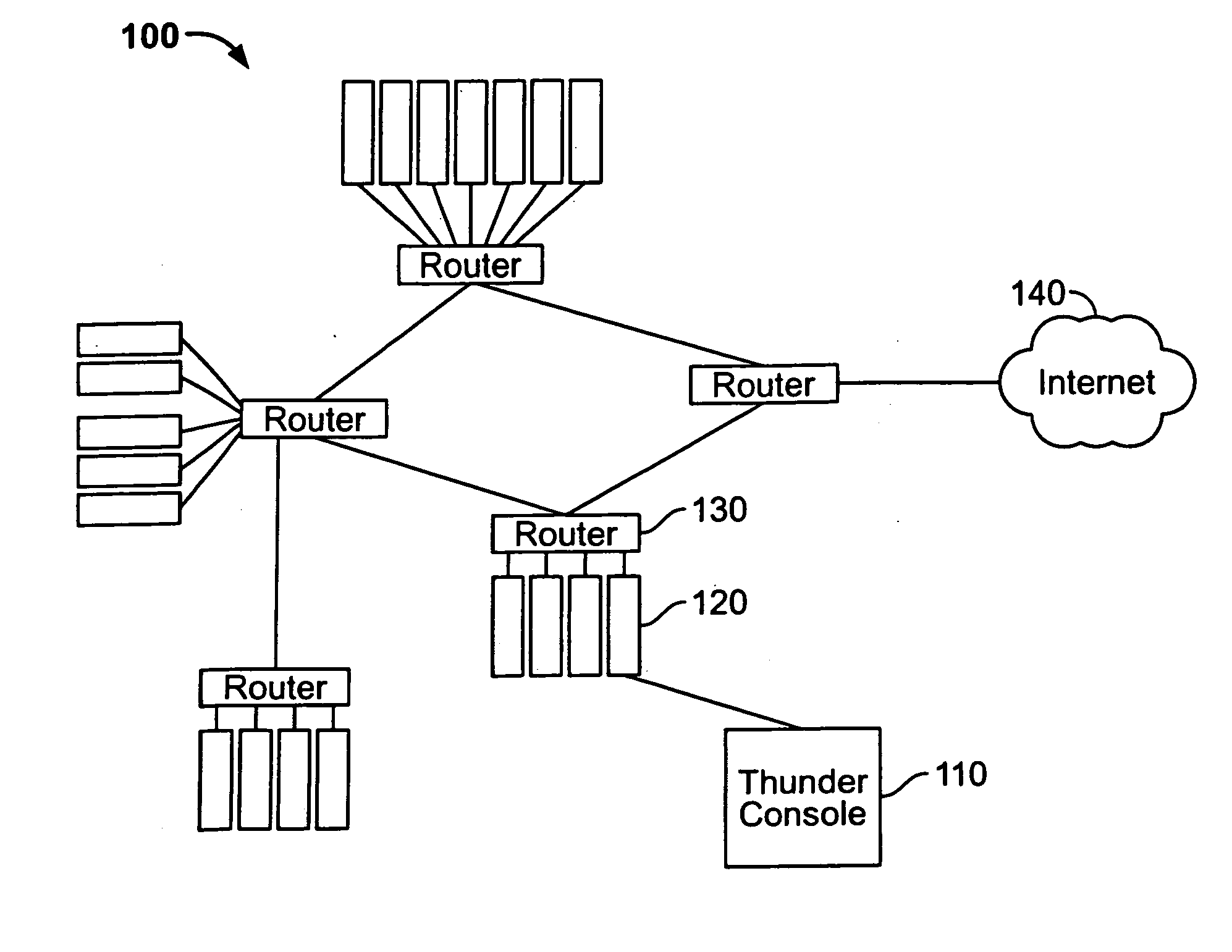
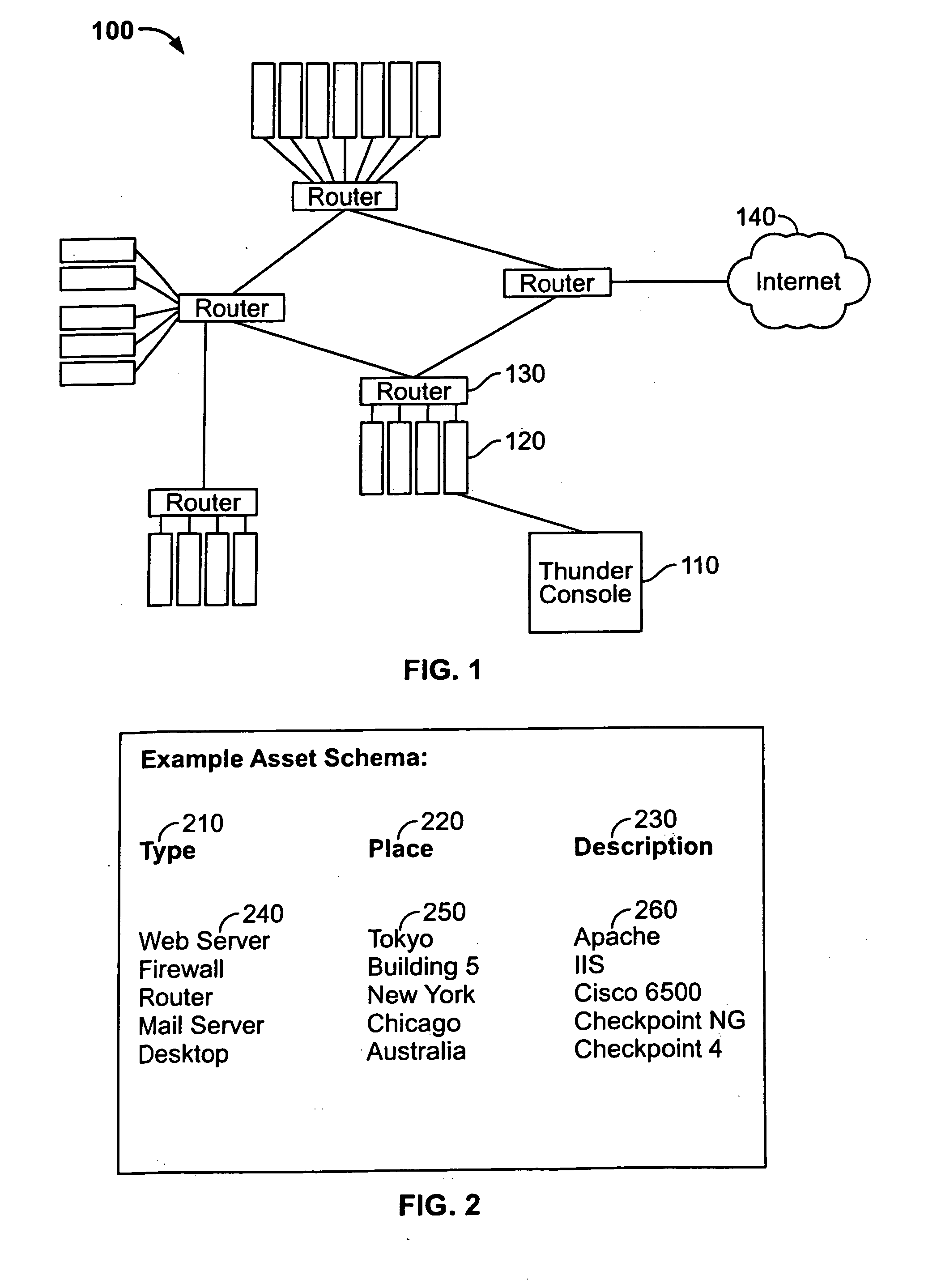
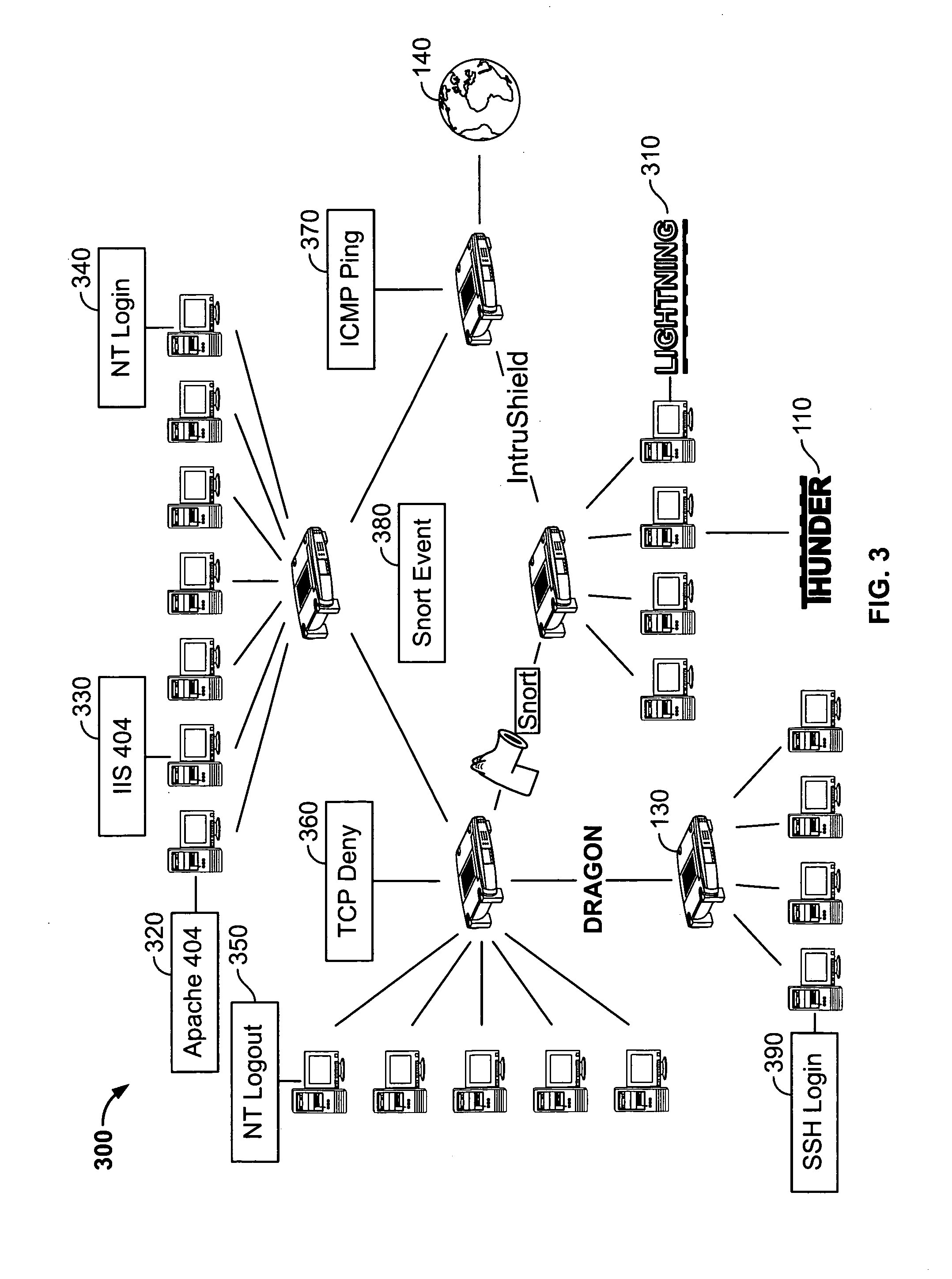
System and method for managing events
Systems and methods to manage logs from log sources distributed across one or more networks using a log event management system, herein called a Thunder console. The Thunder console is a log aggregator that allows networks to deploy servers which collect, normalize, and analyze a large number of log events. These logs can be stored for a specific period of time. Alerts can be generated to communicate information regarding the log events.
Owner:TENABLE INC
Vehicle exception event management systems
ActiveUS8868288B2Easy to operateHeat generationVehicle testingRegistering/indicating working of vehiclesStructure of Management InformationDiscretization
Exception event recorders and analysis systems include: vehicle mounted sensors arranged as a vehicle event recorder to capture both discrete and non-discrete data; a discretization facility; a database; and an analysis server all coupled together as a computer network. Motor vehicles with video cameras and onboard diagnostic systems capture data when the vehicle is involved in a crash or other anomaly (an ‘event’). In station where interpretation of non-discrete data is rendered, i.e. a discretization facility, captured data is used as a basis for production of supplemental discrete data to further characterize the event. Such interpreted data is joined to captured data and inserted into a database in a structure which is searchable and which supports logical or mathematical analysis by automated machines. A coupled analysis server is arranged to test stored data for prescribed conditions and upon finding such, to initiate further actions appropriate for the detected condition.
Owner:SMARTDRIVE SYSTEMS
Event revenue management system
Owner:JDA SOFTWARE GROUP
System and method for enhanced event participation
ActiveUS20130282421A1Effectively and efficiently createQuickly and easily identifyOffice automationTransmissionComputer scienceEvent management
The various implementations of the present invention are provided as a computer-based system for enhanced communications and event management that focuses on customization of the event attendee experience. Each event attendee is provided with the tools necessary to effectively and efficiently create an event experience that most closely matches their goals and objectives. For example, a variety of dynamic event activity maps provide event attendees with the ability to quickly and easily identify and locate the most interesting and pertinent seminars, classes, speakers, vendors, exhibitors, etc. Additionally, event attendees can update and control their event schedule, customize communications that are sent and received, set up meetings with other event attendees, and receive updates about event activities and schedules. Vendors, exhibitors, and event organizers are provided with a series of tools, including “gamification” tools, that will allow them engage event attendees in event activities to increase attendee participation.
Owner:PARLANT TECH
Distributed and interactive database architecture for parallel and asynchronous data processing of complex data and for real-time query processing
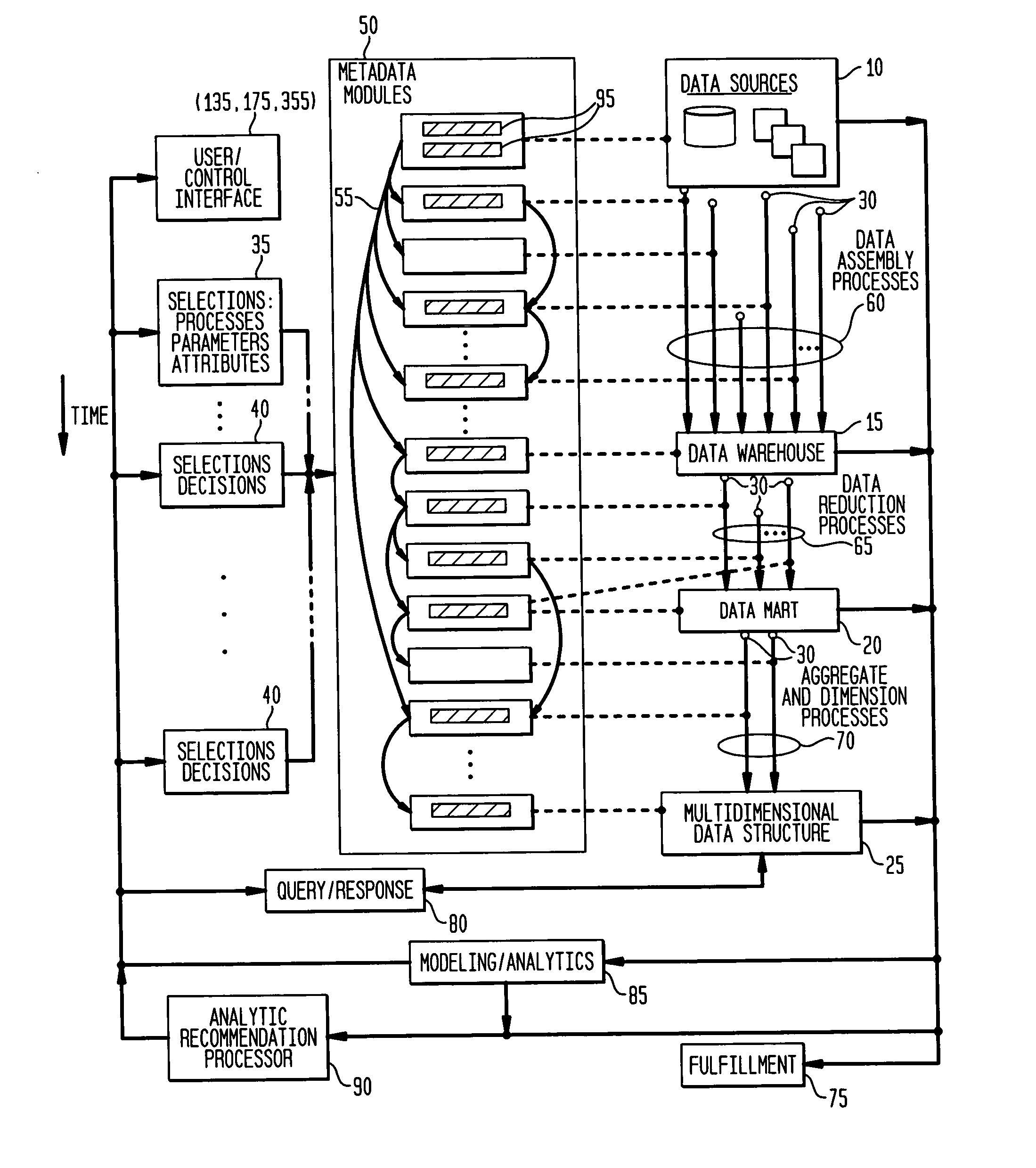
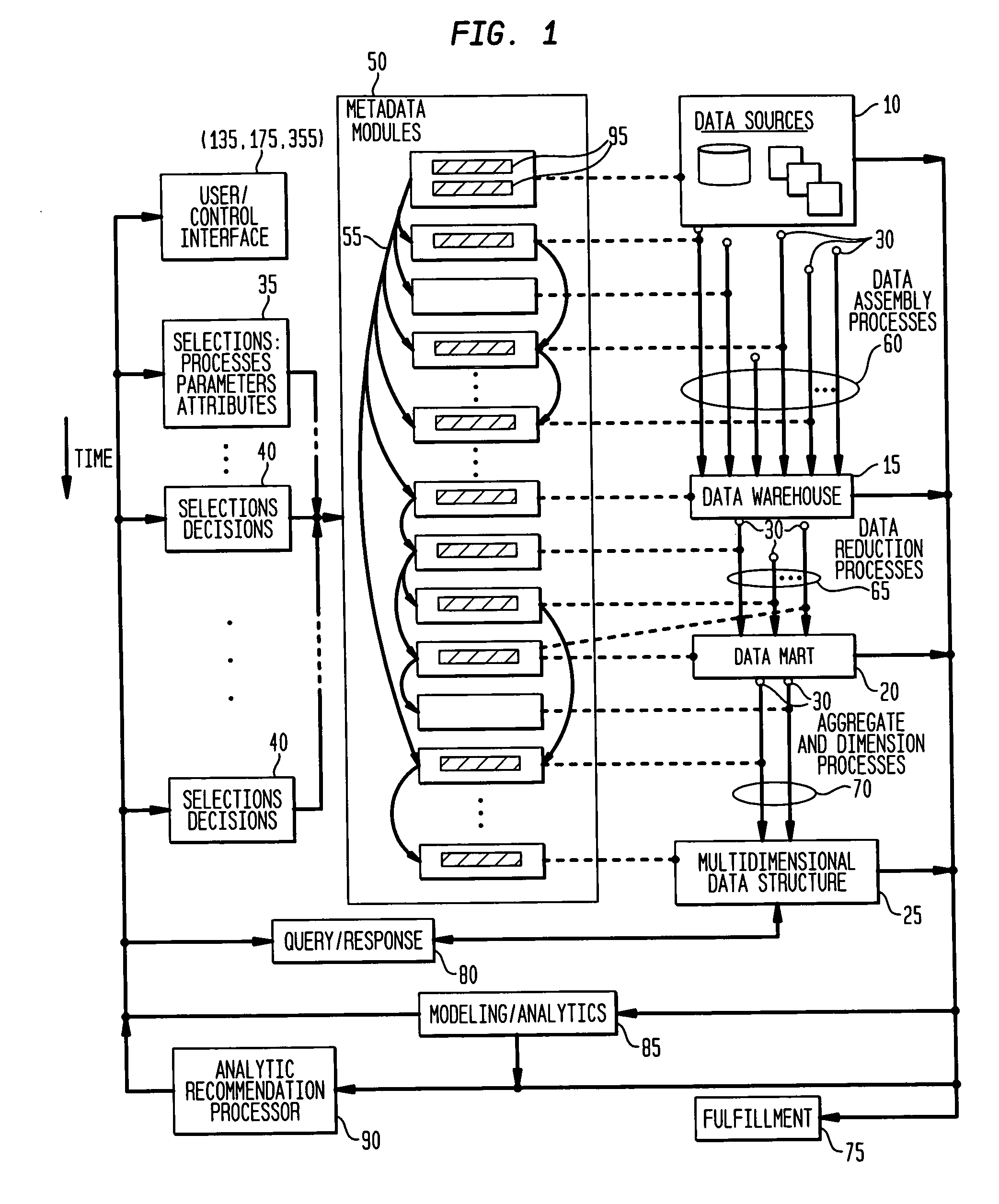
ActiveUS20060271568A1Effective and valuable decouplingIncrease speedDigital data processing detailsOffice automationMultidimensional dataData store
The various embodiments of the invention provide a data processing system and method, for applications such as marketing campaign management, speech recognition and signal processing. An exemplary system embodiment includes a first data repository adapted to store a plurality of entity and attribute data; a second data repository adapted to store a plurality of entity linkage data; a metadata data repository adapted to store a plurality of metadata modules, with a first metadata module having a plurality of selectable parameters, received through a control interface, and having a plurality of metadata linkages to a first subset of metadata modules; and a multidimensional data structure. The control interface may modify the plurality of selectable parameters in response to received control information. A plurality of processing nodes are adapted to use the plurality of selectable parameters to assemble a first plurality of data from the first and second data repositories and from input data, to reduce the first plurality of data to form a second plurality of data, and to aggregate and dimension the second plurality of data for storage in the multidimensional data structure.
Owner:EXPERIAN MARKETING SOLUTIONS
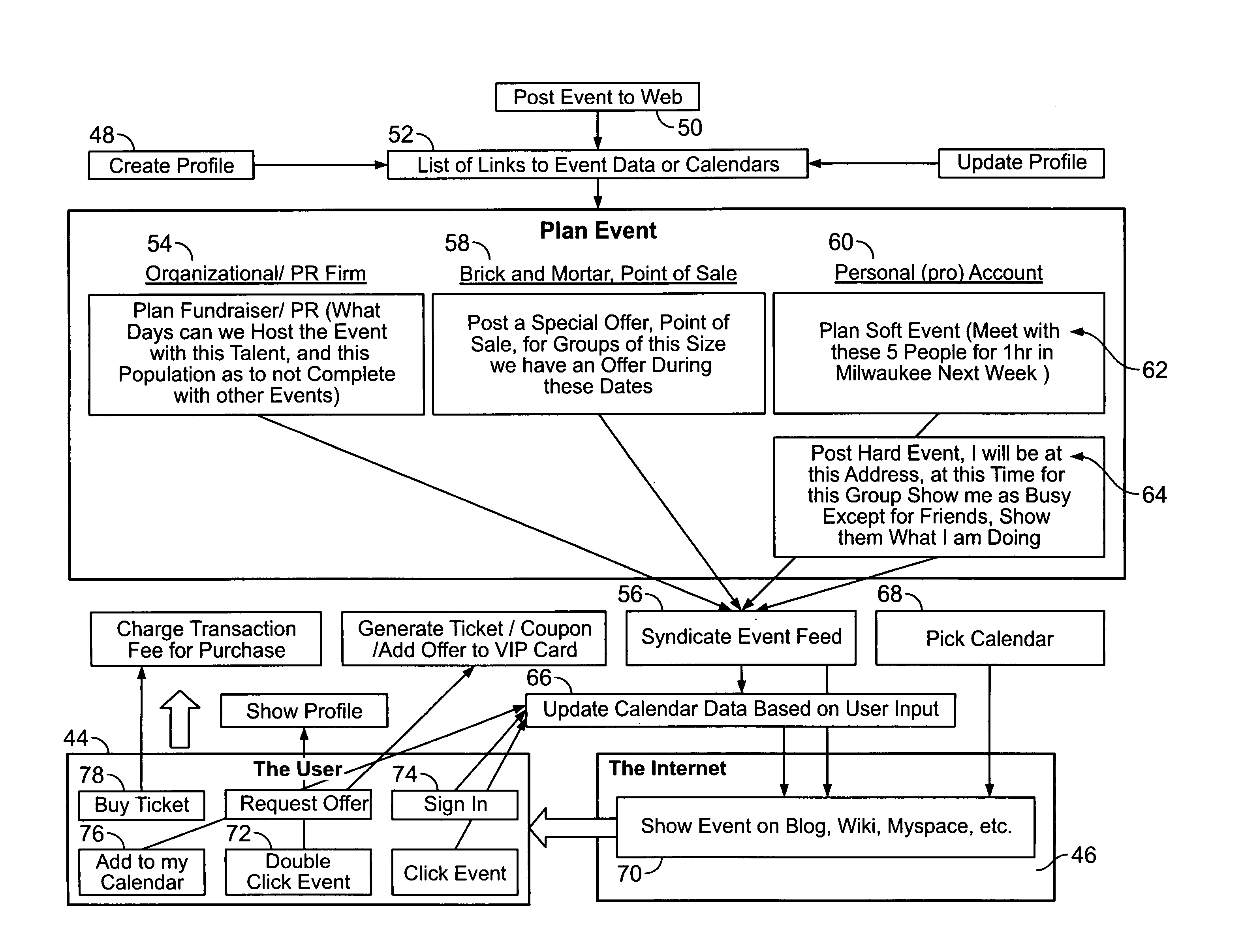
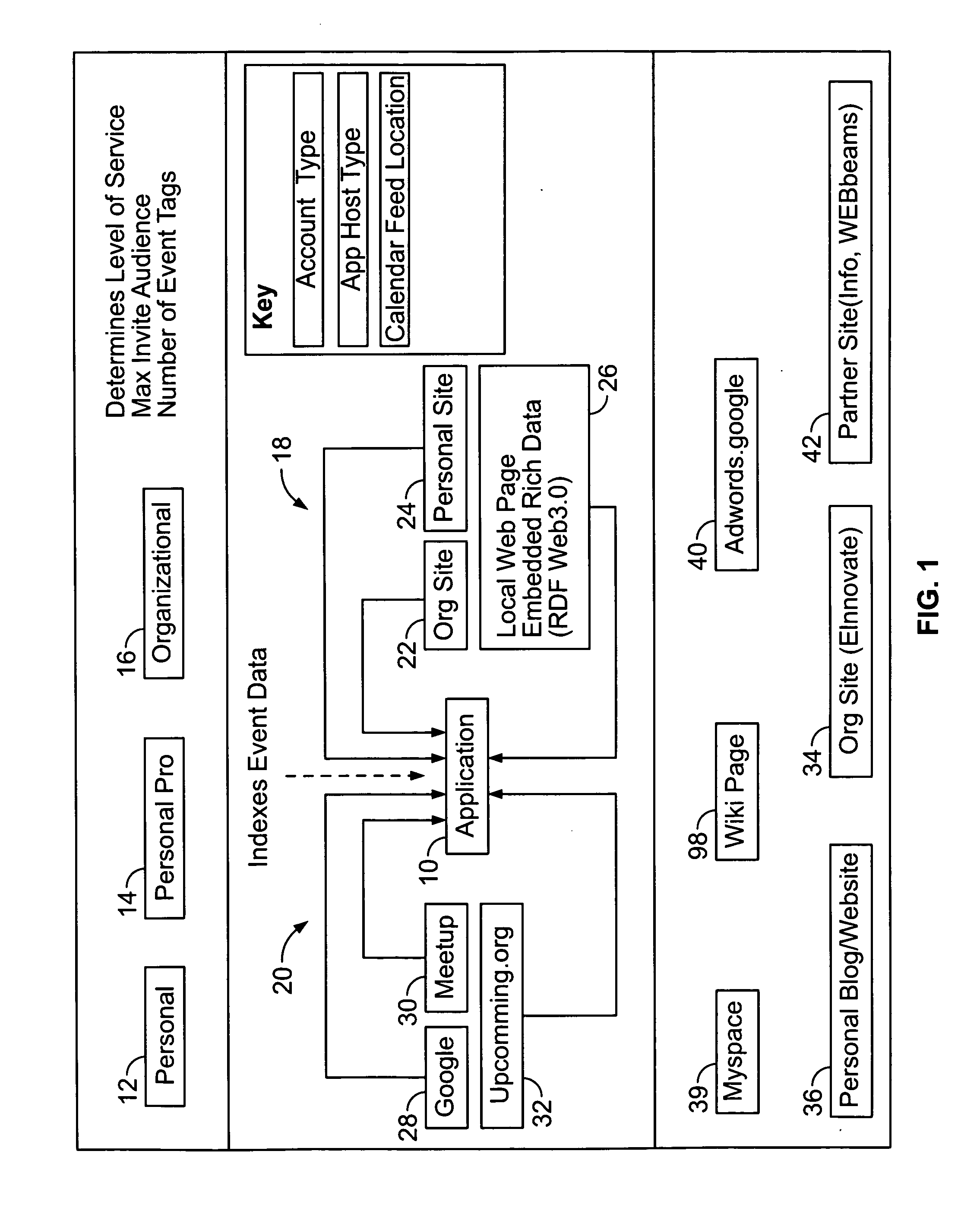
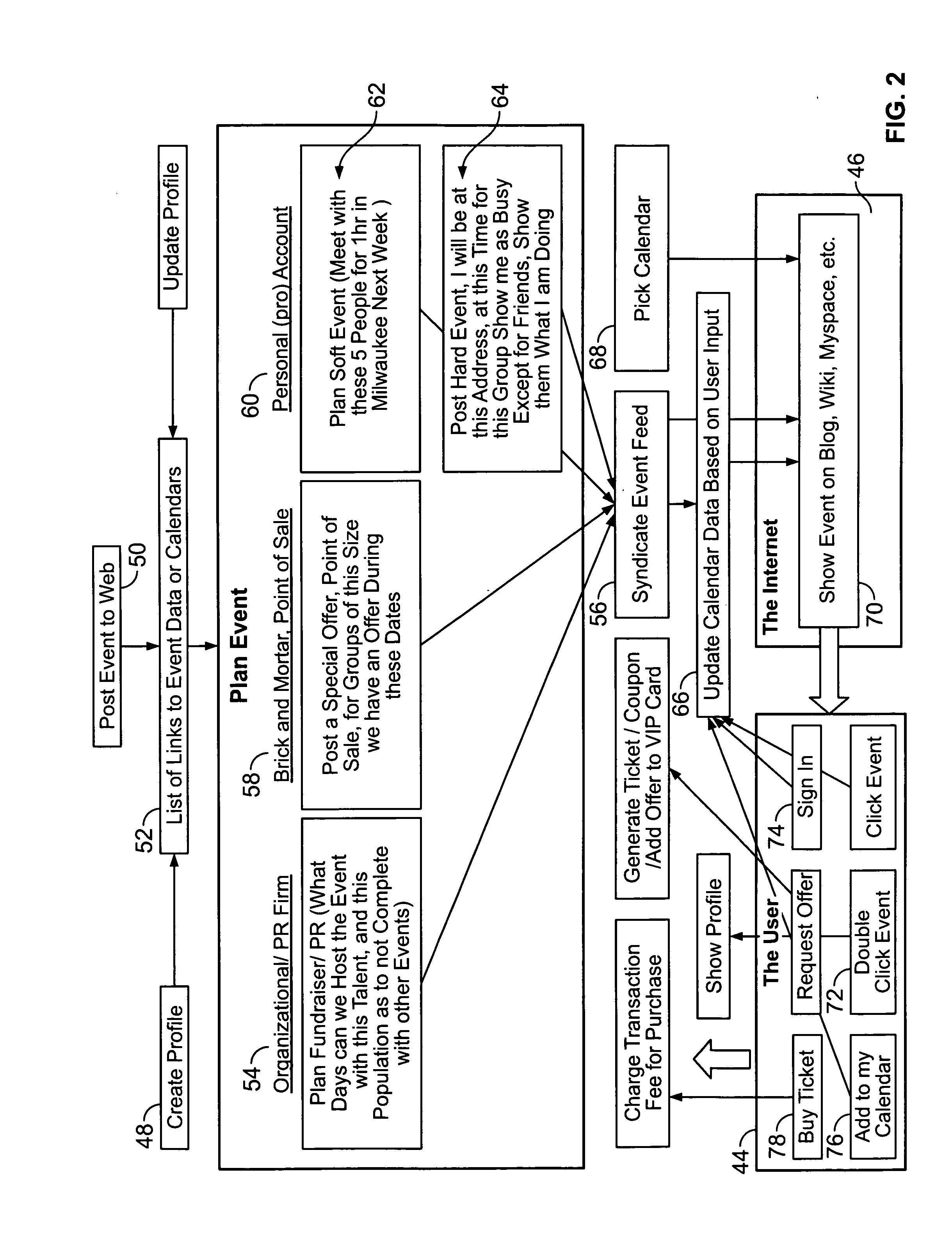
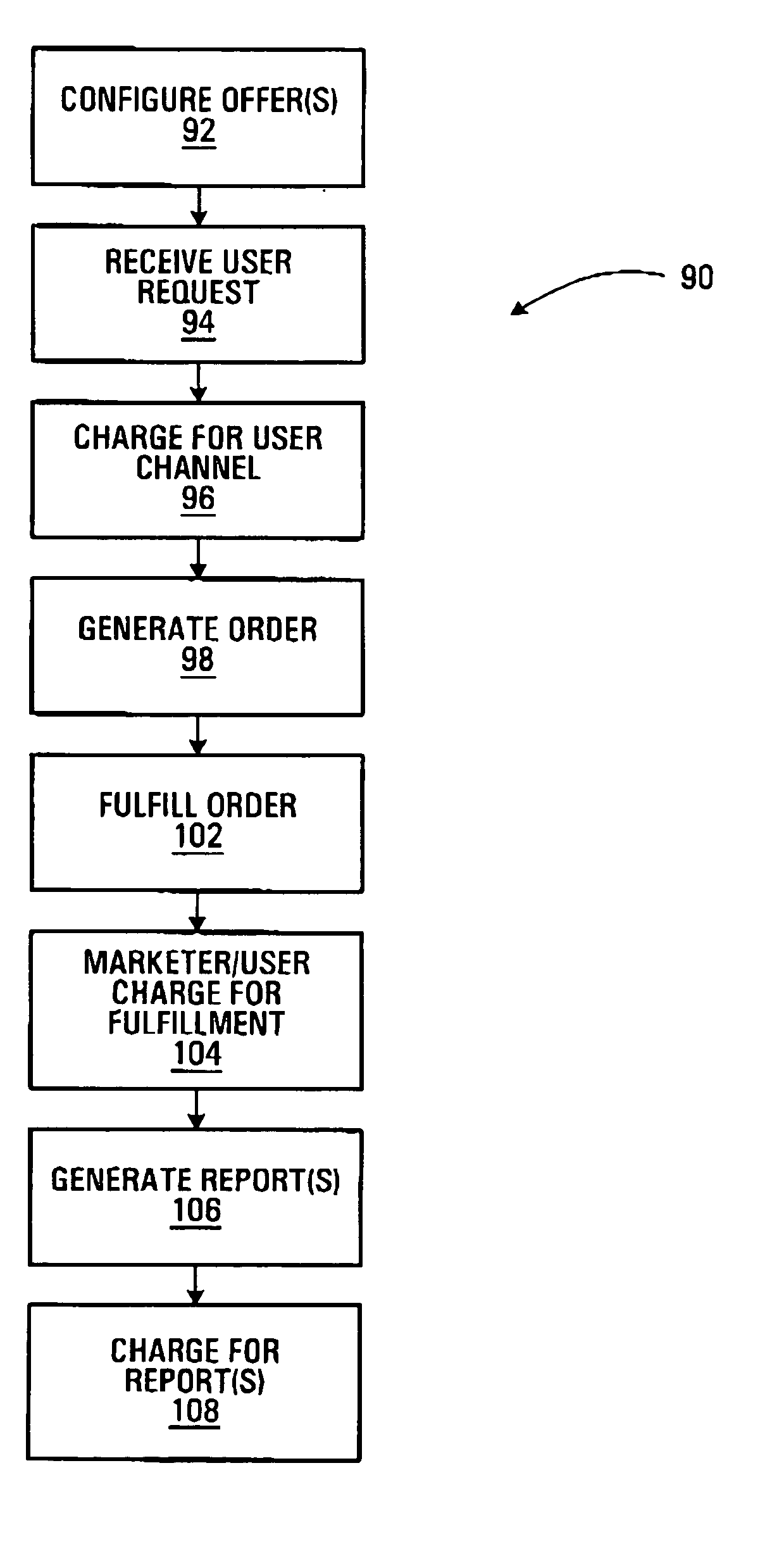
Event management system and method with calendar interface
A system and method for managing, advertising, and promoting events. Event information is collected from users and the Internet and stored in one or more databases on one or more servers. The event information is organized in the one or more databases according to various attributes and may be selectively displayed on one or more styles of calendar display interfaces, which may be in the form of a web page. The system monitors user interaction with the calendar display interfaces to charge and credit event advertisers, event promoters, and managers of event calendars.
Owner:KRUGER JUSTIN DAVID +2
Systems and methods of managing marketing campaigns
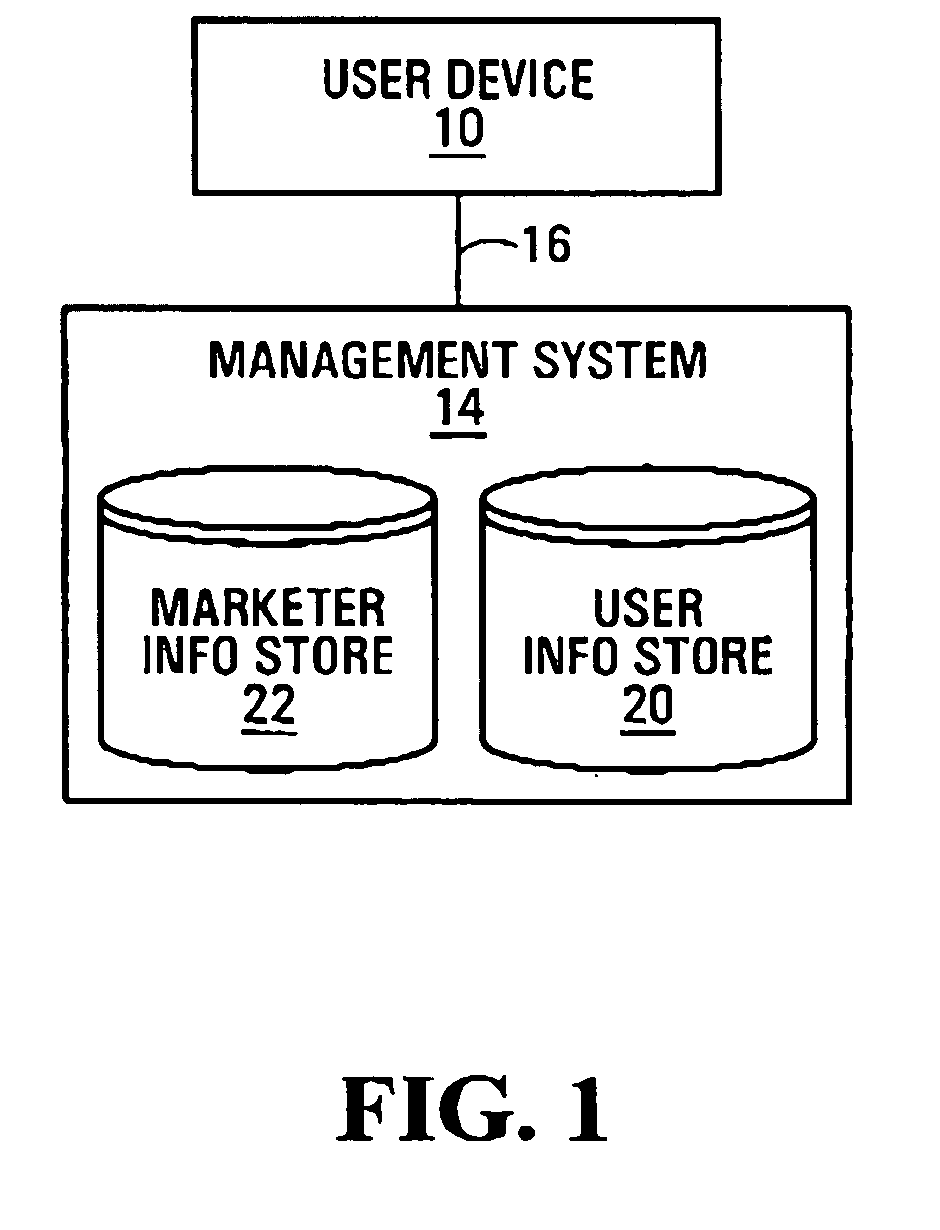
InactiveUS20050125291A1Special service provision for substationUser identity/authority verificationService provisionOrder form
Systems and methods relating to management of marketing campaigns are provided. Requests from users are matched to stored offers relating to available marketing materials to generate an order for each request. Orders may be fulfilled by delivering the marketing materials to the user, for example. The matching of requests to offers may be based on information in the requests, user information associated with users from which the requests are received, offer rules associated with the stored offers, or any combination thereof. Some embodiments provide for user registration with a marketing campaign management system which exploits user information which is available from an external source, such as a service provider system which provides a service for which the user has previously registered or a system which provides a reverse lookup function.
Owner:CANADA POST
Event revenue management system
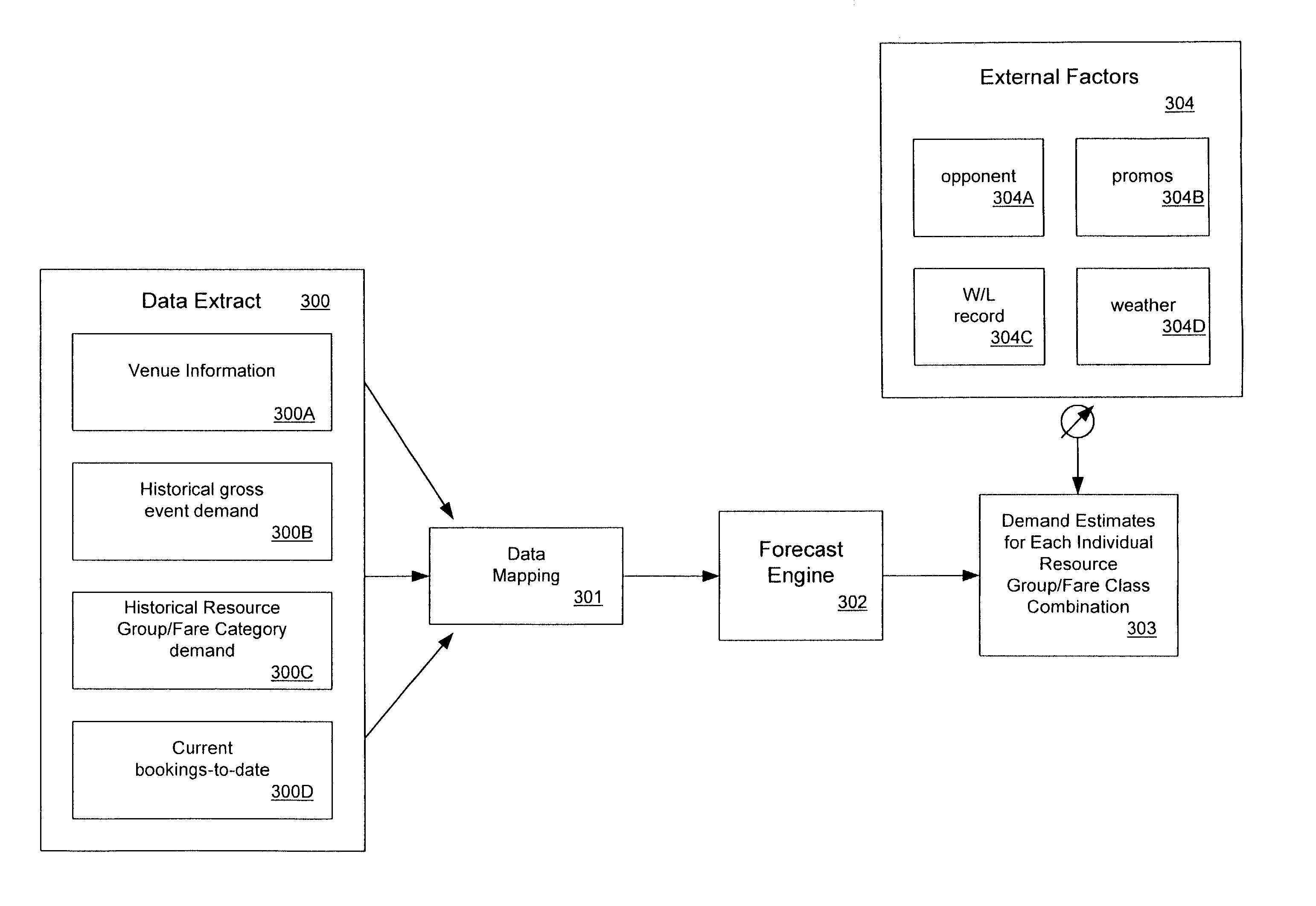
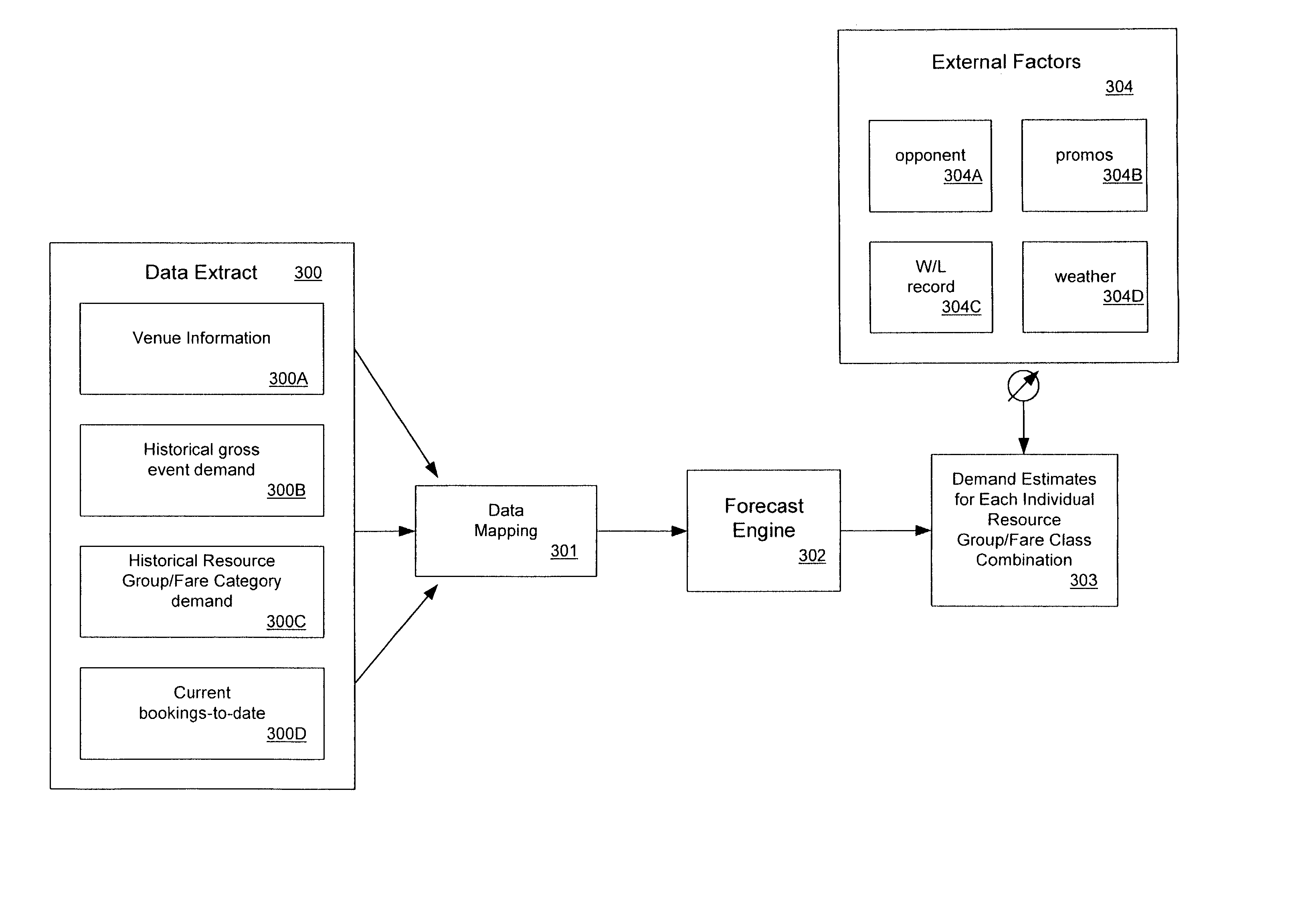
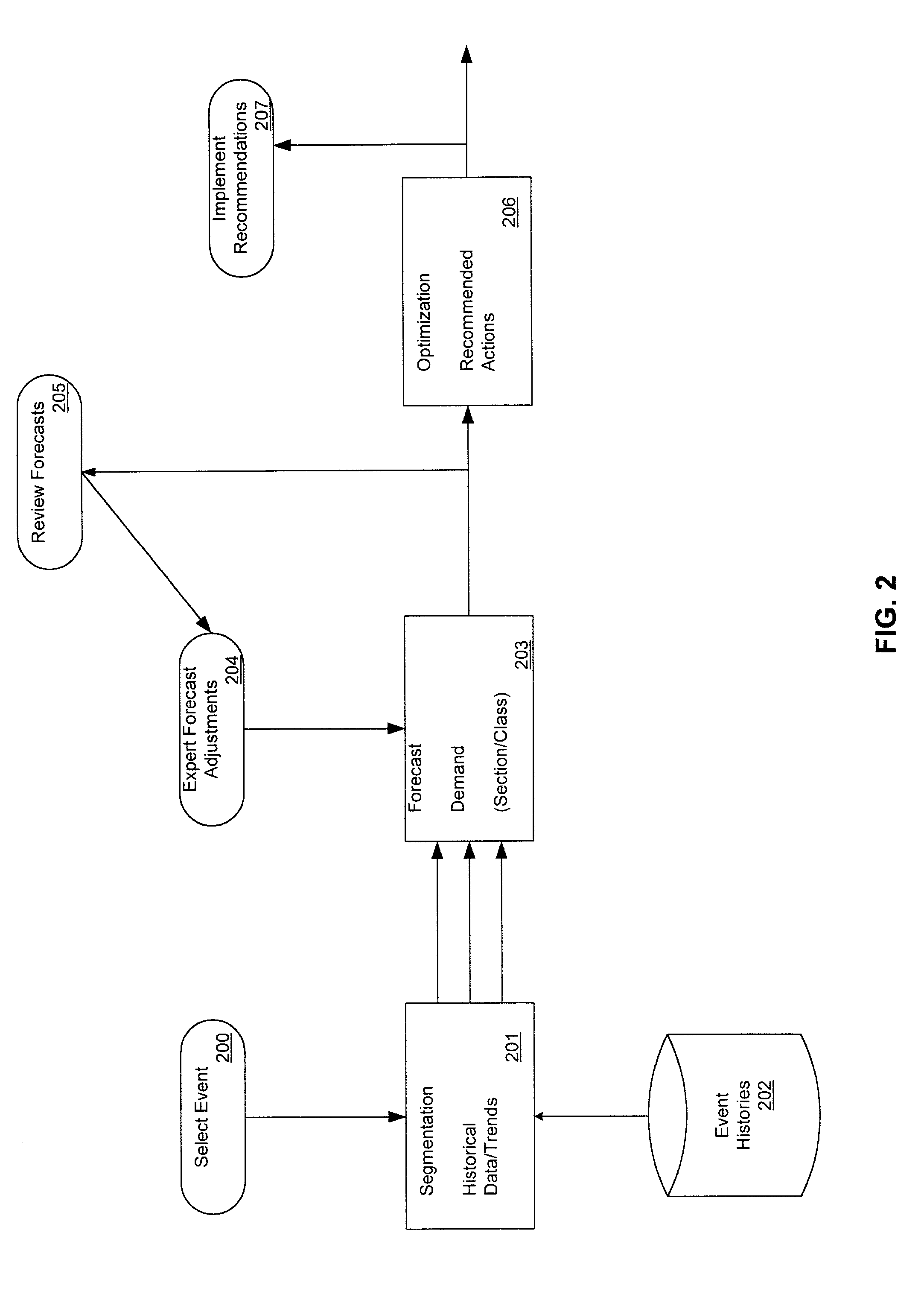
InactiveUS20020120492A1Huge profitsRealize SegmentationMarket predictionsResourcesBusiness forecastingData mining
The present invention provides an event revenue management system that calculates event pricing to manage revenue and to maximize profit from the event. In particular, the system uses event parameters, including timing, resource, and discount categories, and initializes forecasting parameters. The system aggregates historical data using the forecasting parameters to generate initial forecast statistics, taking into account the event parameters. It then forecasts demand by updating the initial forecast statistics based on current data and optimizes pricing and availability of the event based on the forecasted demand.
Owner:JDA SOFTWARE GROUP
Event management apparatus, systems, and methods
ActiveUS20130055145A1Programme controlTesting/monitoring control systemsOperational systemComputerized system
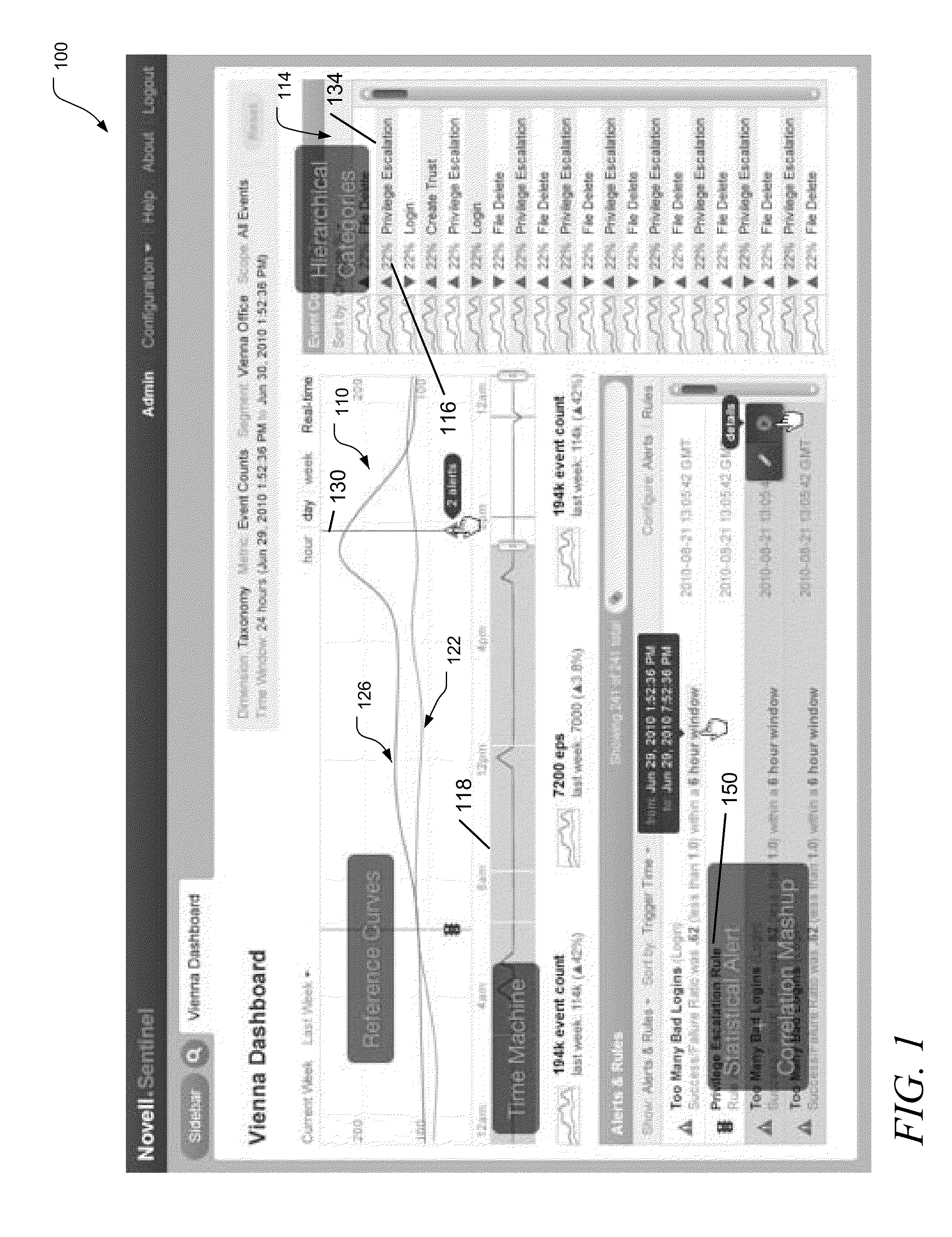
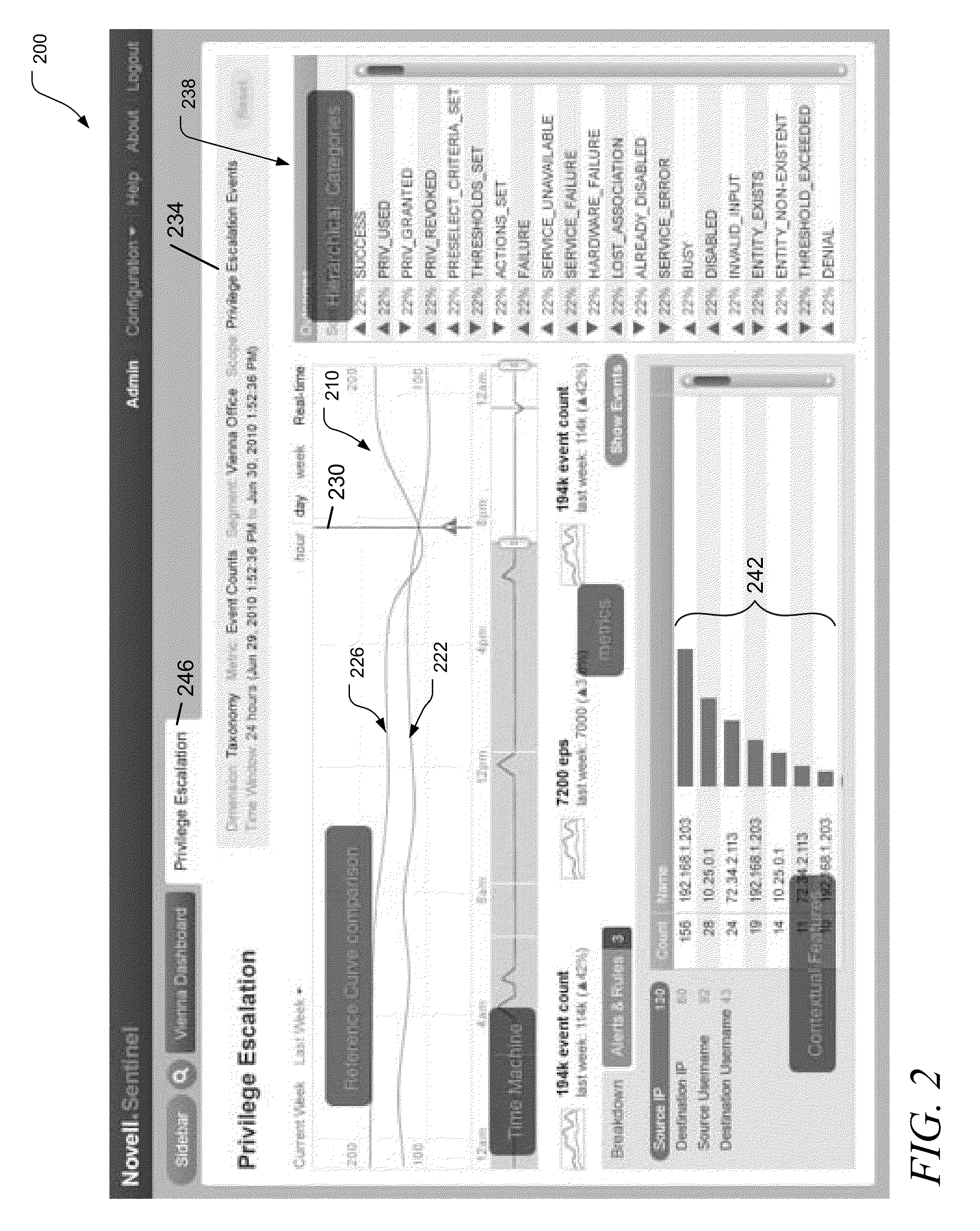
Apparatus, systems, and methods may operate to generate a reference statistical model of an operating system, such as a computer system, and display the reference statistical model as a hierarchical, segmented time series event stream graph, along with a graph representing current behavior of the system. The event stream graph may be derived from one or more streams of security events. Additional operations may include receiving requests to display further detail respecting discrepancies between the reference statistical model and the current behavior. Other apparatus, systems, and methods are disclosed.
Owner:MICRO FOCUS SOFTWARE INC
Restartable spanning tree for high availability network systems
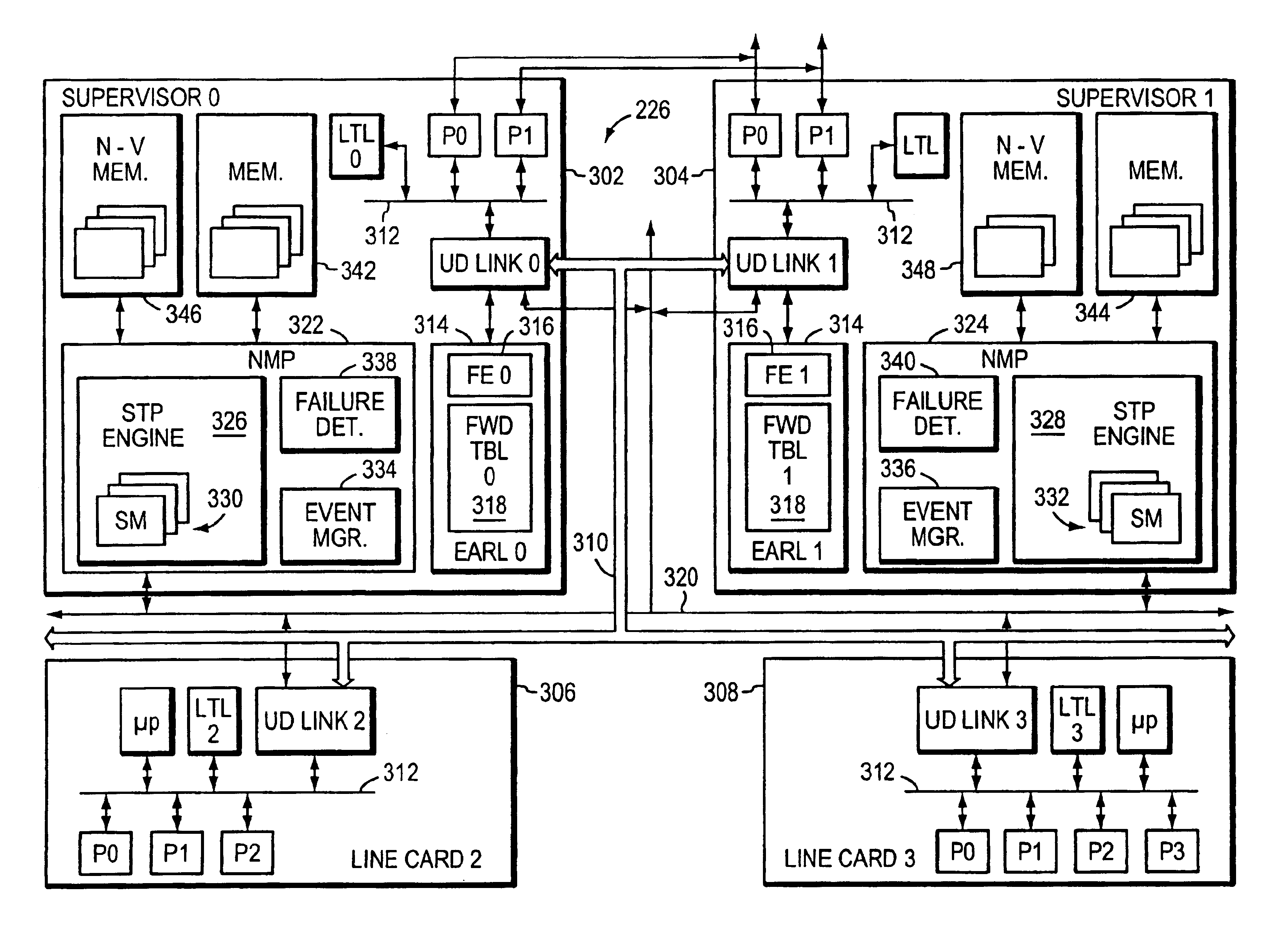
InactiveUS6898189B1Avoiding significant network disruptionQuick fixError preventionTransmission systemsHigh availabilitySupervisor review
A method and apparatus for continuing the operation of a spanning tree protocol at a network device despite crashes or failures at that device. A supervisor card contained in the network device is designated an active supervisor, while all other supervisor cards are designated standby supervisors. The active supervisor runs the spanning tree protocol, and informs the standby supervisors of the states of ports, but not of the identity of the root or designated bridges. When a crash or failure occurs at the active supervisor, one of the standby supervisors is immediately designated to be the new active supervisor. The newly active supervisor reviews the port state, and queries the line cards to determine whether that port state information is still valid. The newly active supervisor adopts the valid port state information, leaving those ports in their current spanning tree port state.
Owner:CISCO TECH INC
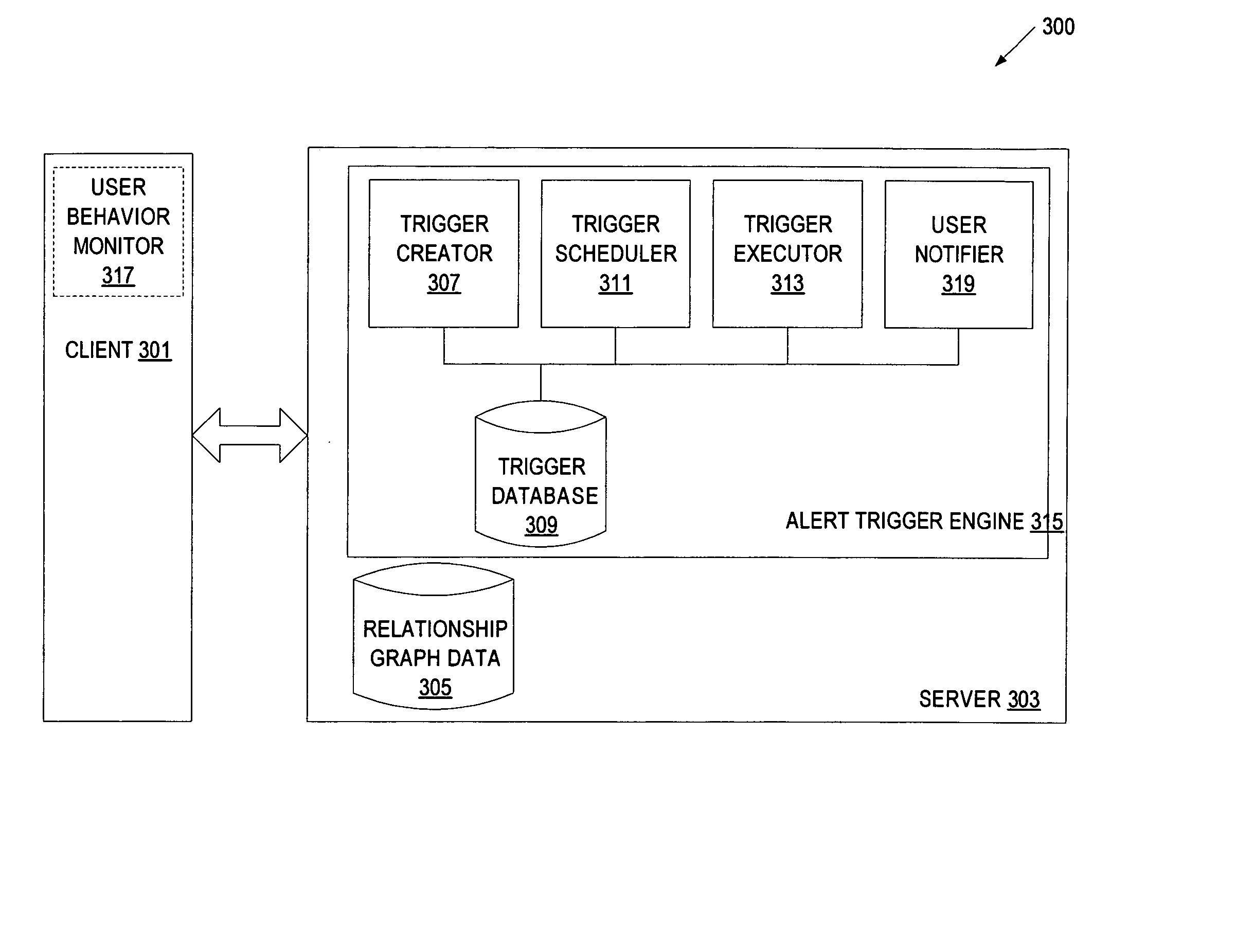
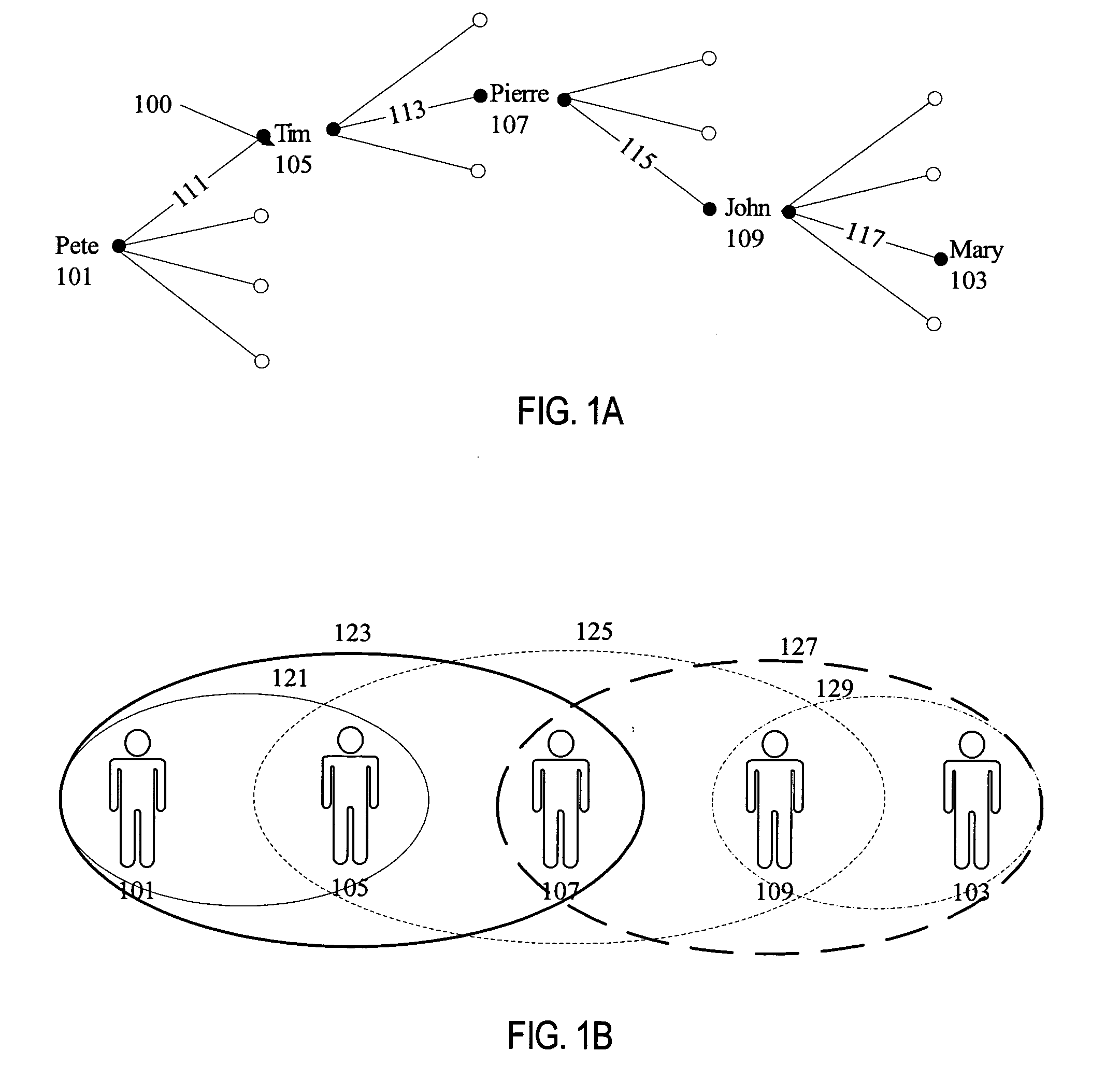
Alert triggers and event management in a relationship system
InactiveUS20050283753A1Digital data information retrievalDigital computer detailsRelational systemData mining
A method and apparatus to manage alert triggers in a relationship system are disclosed. In one embodiment, the method includes maintaining a set of alert triggers that define operations for detecting changes pertaining to elements of a relationship graph. The elements of the relationship graph include nodes representing entities and edges representing relationships between entities. The method further includes performing the operations defined by the set of alert triggers, and providing an alert to one or more users when any of the defined operations satisfy an alert condition associated with a corresponding alert trigger.
Owner:SPOKE SOFTWARE
Systems and methods for rule based inclusion of pixel retargeting in campaign management
InactiveUS20120054143A1Suitable for developmentKnowledge representationCommerceFlexible MechanismsData mining
The present solution provides a configurable, dynamic and flexible mechanism to define and use pixel rules to identity and select campaigns for the user based on the user's pixel history as well as other behavior data. The pixel rules can be configured to identify one or more mandatory pixels that have to be present or tracked for the user in order to include or exclude a campaign in a campaign selection process. The pixel rules can be configured to identify weighted pixels that have to be present or tracked for the user in order to include or exclude a campaign in a campaign selection process. The pixel rules may identify any combination of mandatory and weighted pixel rules. These pixel rules may be configured via a user interface of a development tool and during run-time campaign management applied to the user pixel history to select and deliver campaigns.
Owner:VIBRANT MEDIA
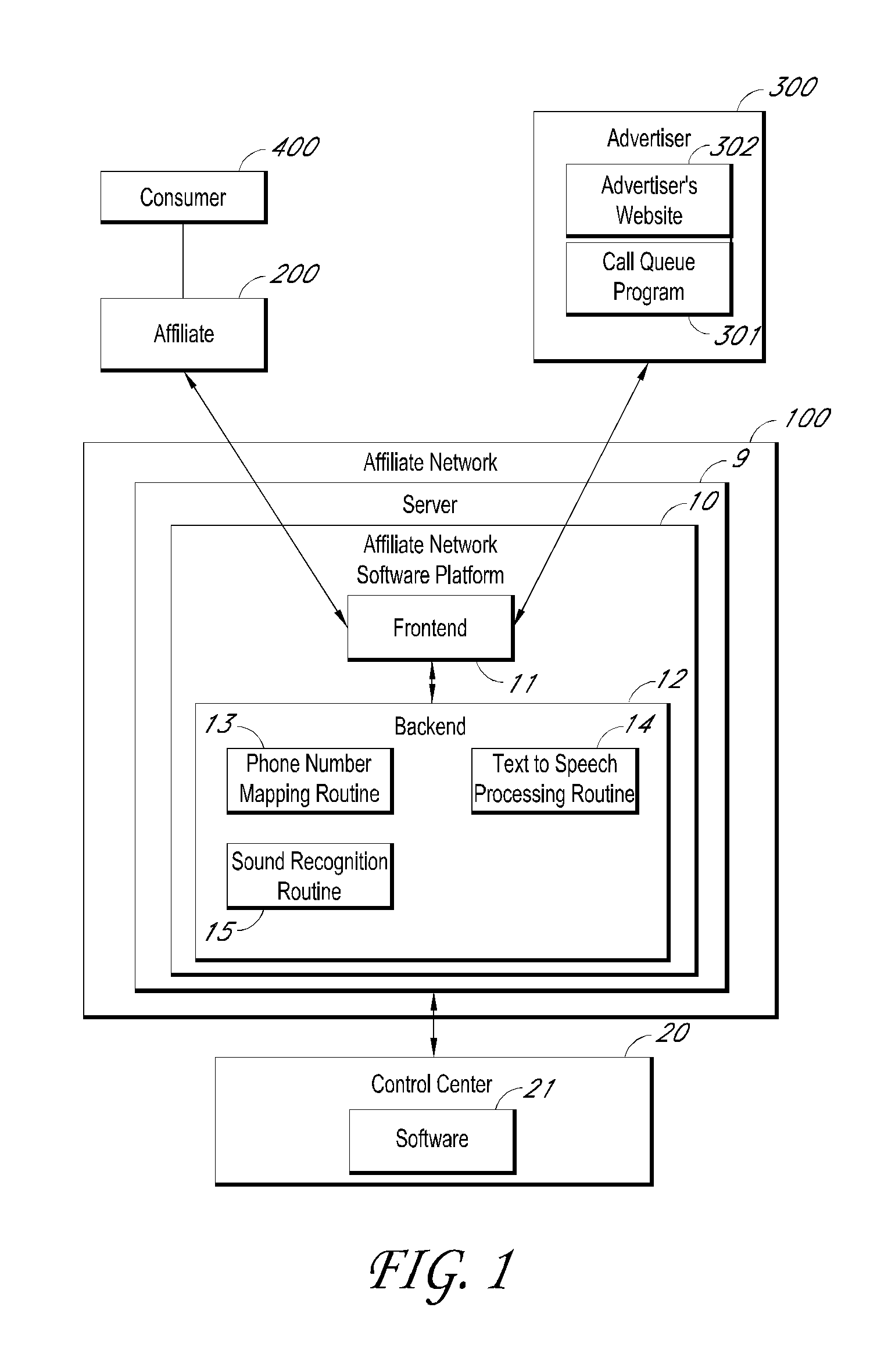
Web-Based Interactive Meeting Event Facility
InactiveUS20110289142A1Multiple digital computer combinationsOffice automationLibrary scienceEvent management
A computer implemented method for organizing a network of affiliated live events, the method comprising: providing an event management resource to a promoter through a web-based meeting event facility, wherein the event management resource enables the promoter to initiate and manage a grouping of a plurality of affiliated in-person gatherings as live events in an event container controlled by the promoter, and where at least one such live event is allowed to be controlled at least in part by a leader associated with such live event in the event container subject to event criteria set by the promoter.
Owner:MEETUP
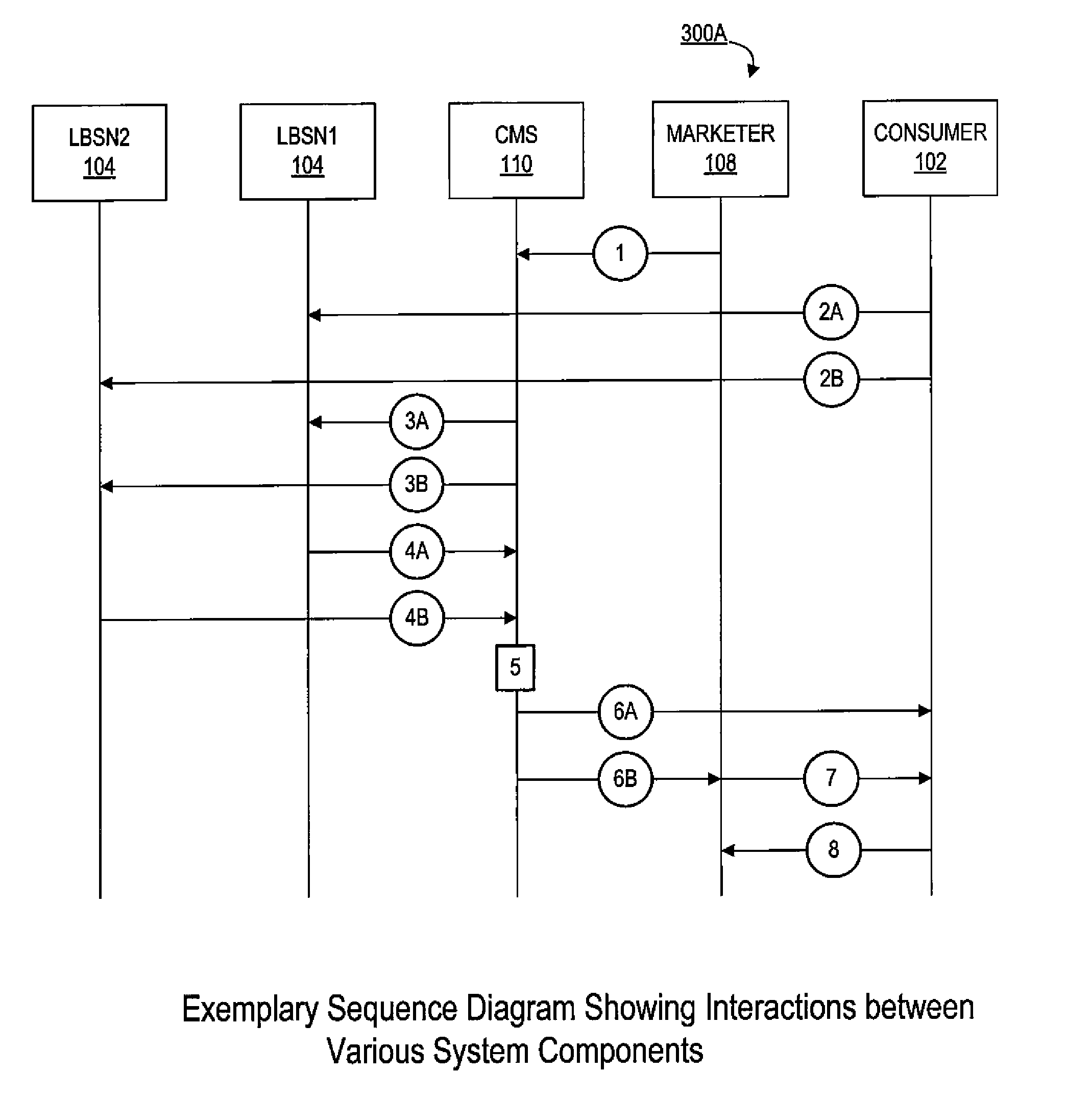
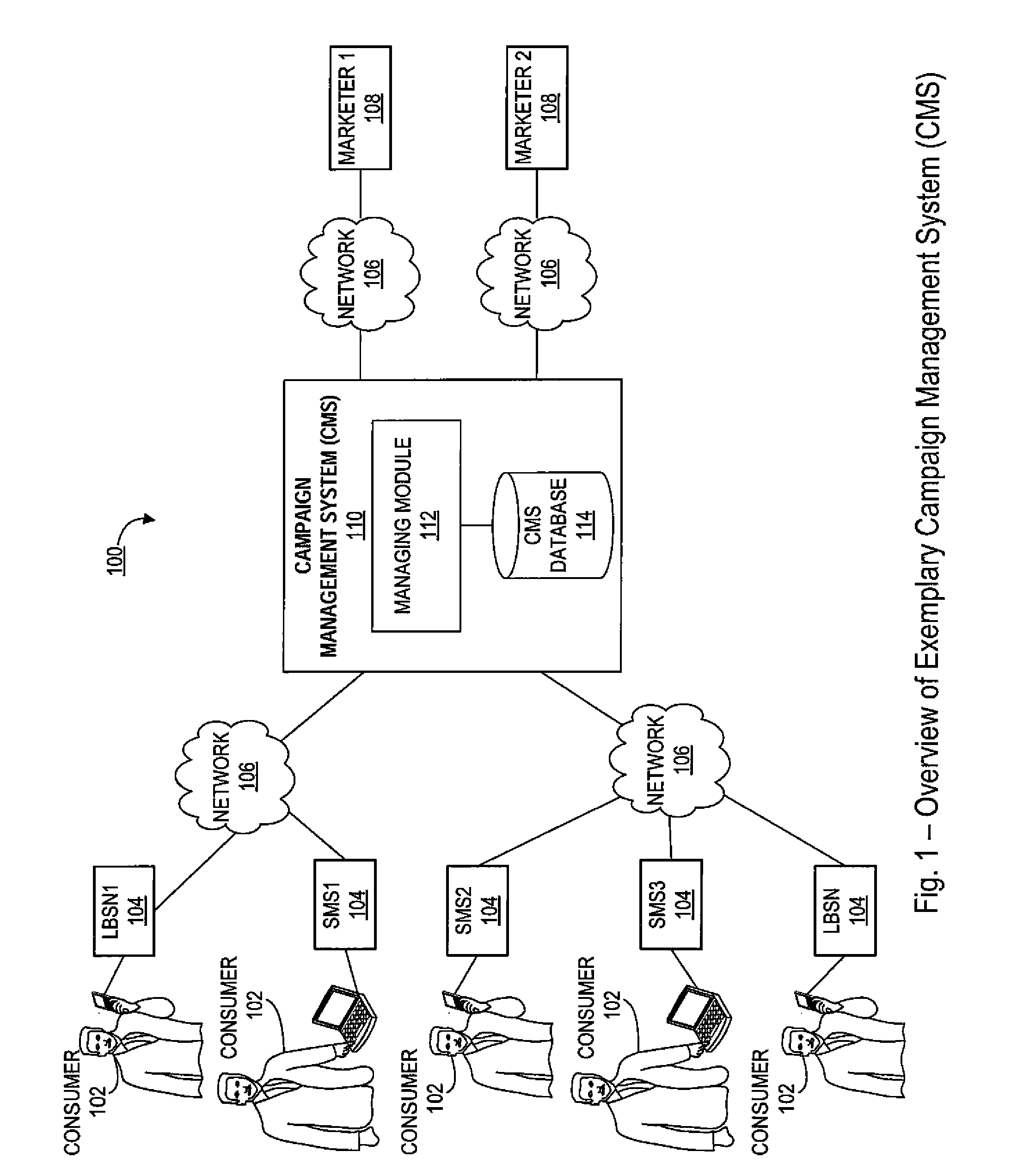
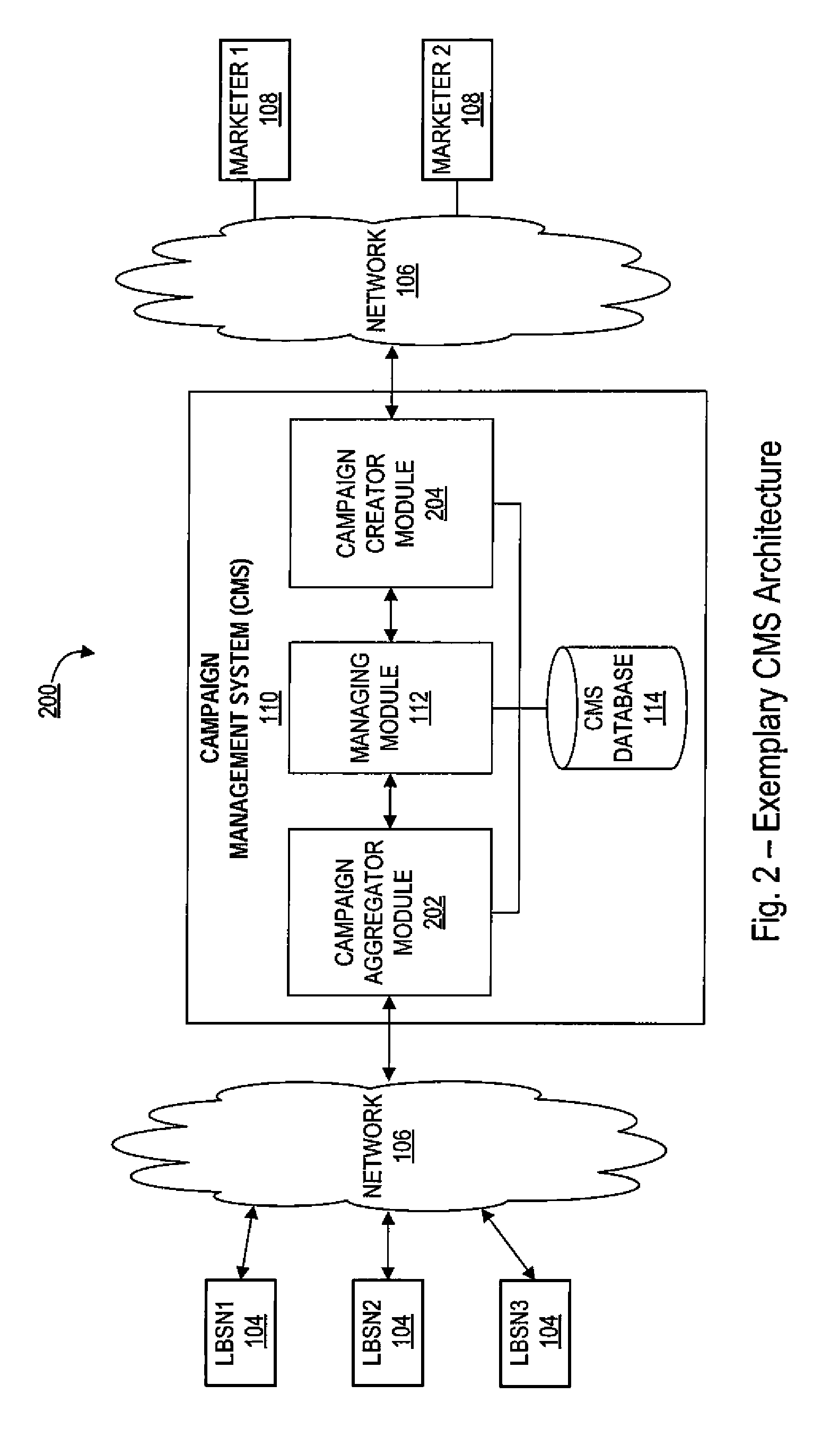
Systems and methods for delivering targeted content to a consumer's mobile device based on the consumer's physical location and social media memberships
Systems and methods for creation, management and delivery of targeted marketing campaigns to a consumer based on a consumer's social check-in activity as identified by a consumer on one or more location based social networks. In one embodiment, a campaign management system receives information relating to a consumer's social check-in activity from various (heterogeneous) location based social networks in a wide variety of formats, and further normalizes such disparate information received into a standardized format. According to an aspect, the system processes the normalized information in conjunction with pre-stored marketing campaigns created by marketers for purposes of identifying consumers who satisfy one or more conditions specific to the pre-stored marketing campaigns. Campaign-related information corresponding to the pre-stored marketing campaigns generally comprise various promotional offers, discounts, coupons, etc., which are delivered to the identified consumers, who initiate some kind of action thereby fulfilling the marketing campaign.
Owner:ORACLE INT CORP
System and method for enhanced event participation
InactiveUS20140358632A1Effectively and efficiently createQuickly and easily identifyReservationsHybrid transportComputer scienceEvent management
The various implementations of the present invention are provided as a computer-based system for enhanced communications and event management that focuses on customization of the event attendee experience. Each event attendee is provided with the tools necessary to effectively and efficiently create an event experience that most closely matches their goals and objectives. For example, a variety of dynamic event activity maps provide event attendees with the ability to quickly and easily identify and locate the most interesting and pertinent seminars, classes, speakers, vendors, exhibitors, etc. Additionally, event attendees can update and control their event schedule, customize communications that are sent and received, set up meetings with other event attendees, and receive updates about event activities and schedules. Vendors, exhibitors, and event organizers are provided with a series of tools, including “gamification” tools, that will allow them engage event attendees in event activities to increase attendee participation.
Owner:PARLANT TECH
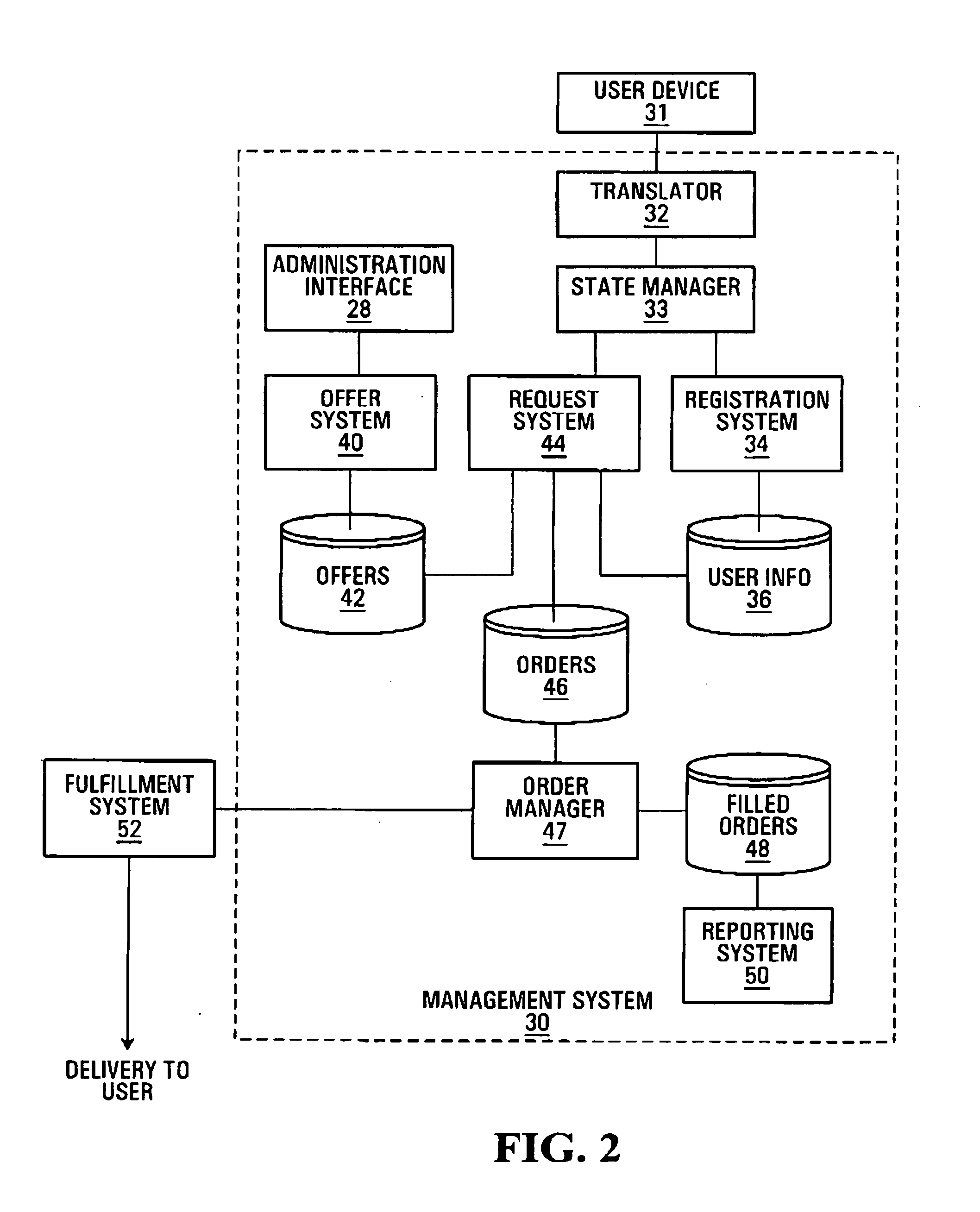
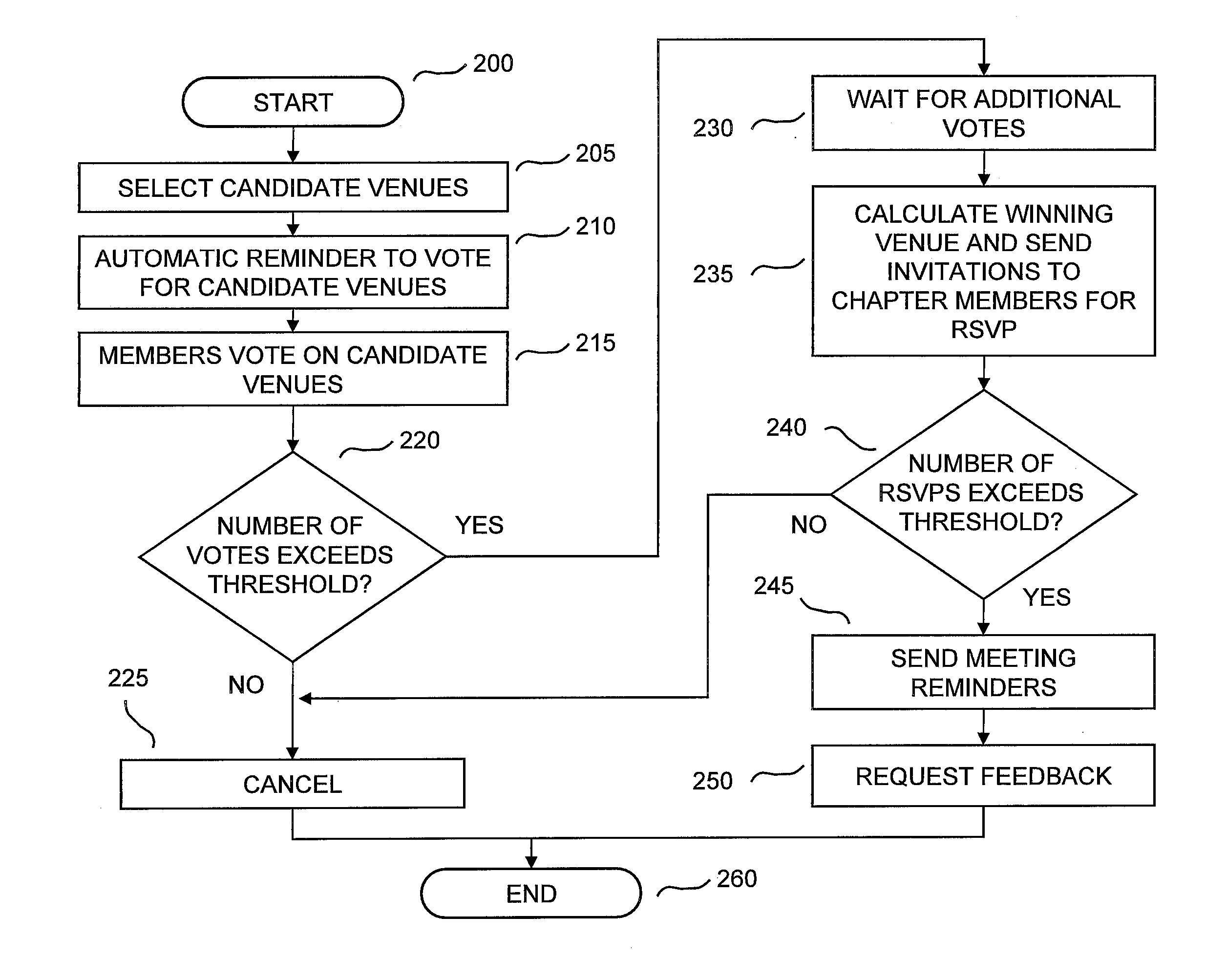
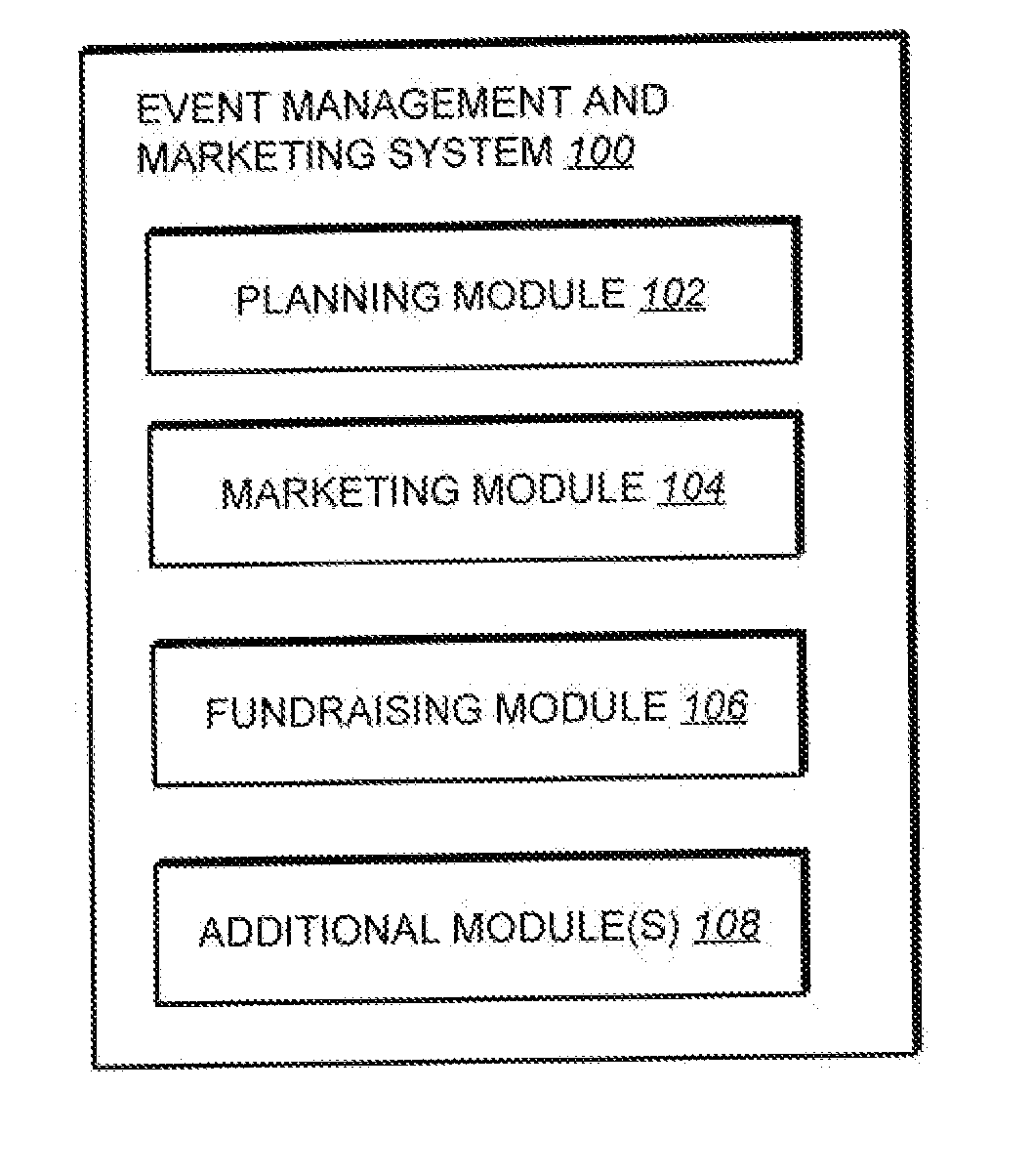
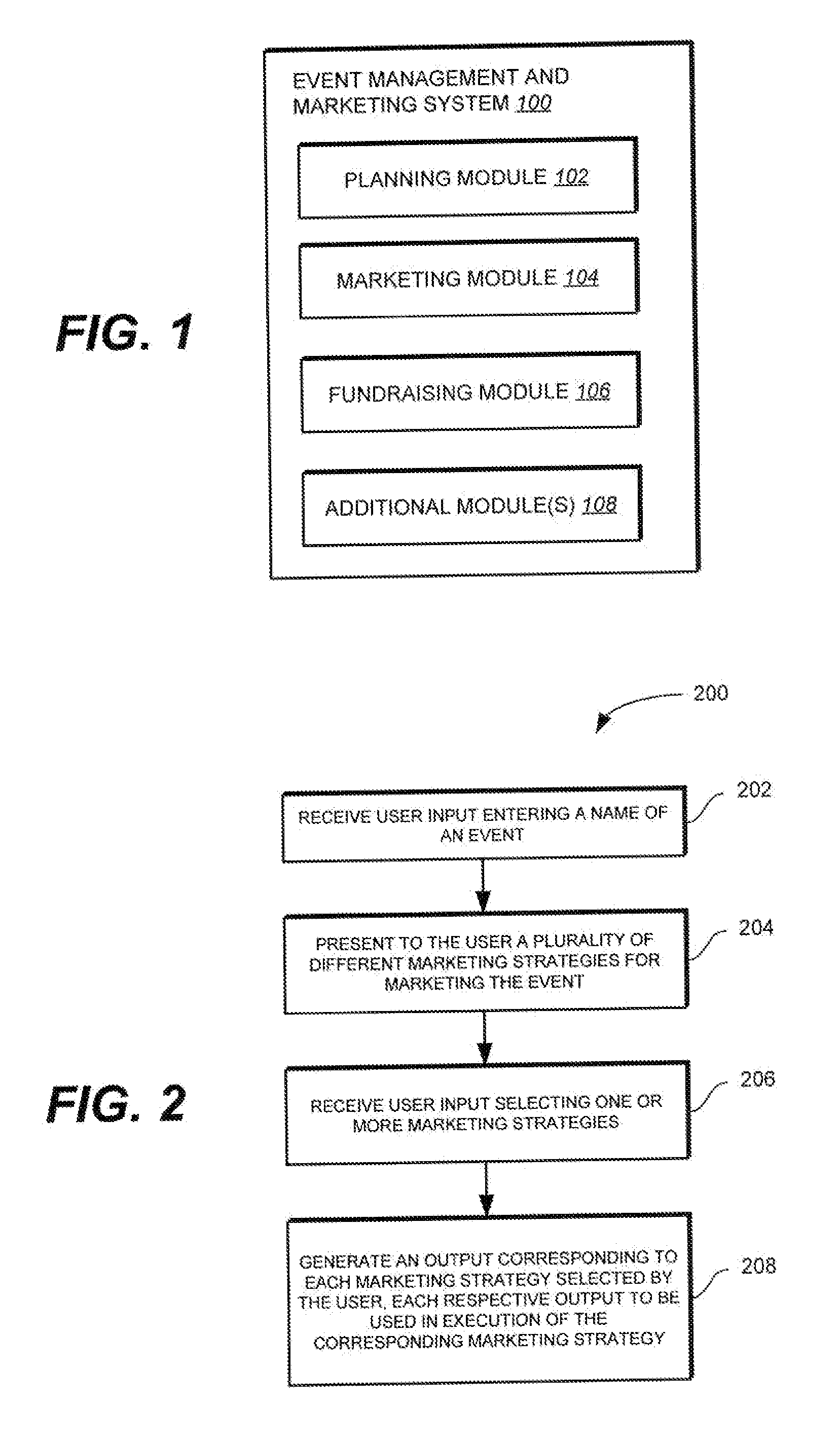
Event Management and Marketing System
An event management and marketing system is provided. In one implementation, the event management and marketing system includes a planning module to receive user input entering a name of an event, and a marketing module to present to the user a plurality of different marketing strategies for marketing the event; receive user input selecting one or more of the of different marketing strategies; and generate an output corresponding to each marketing strategy selected by the user, each respective output to be used in execution of the corresponding marketing strategy.
Owner:LYNCH KEVIN MAURICE
Game processing server apparatus and game processing server system
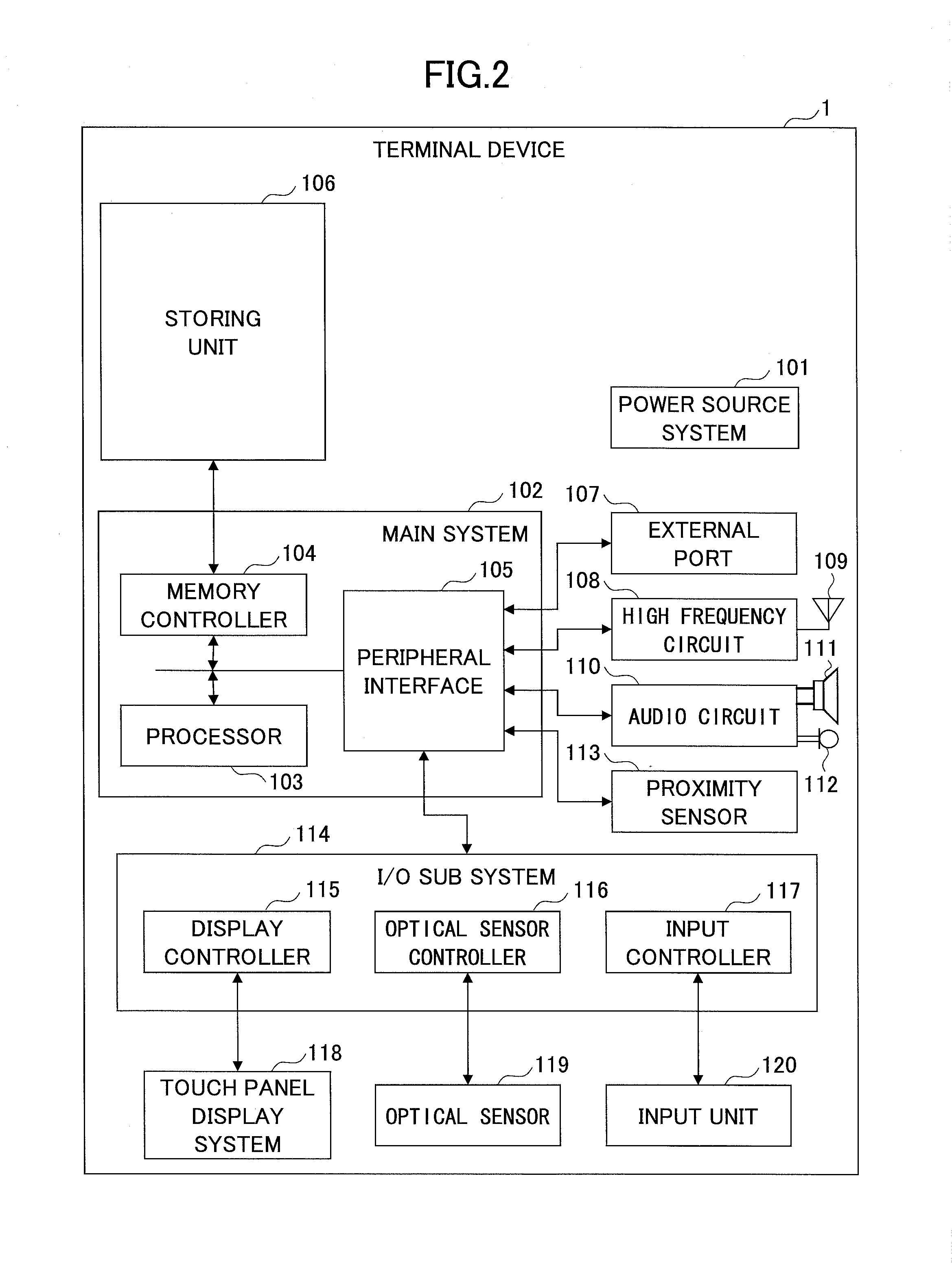
InactiveUS20140073436A1Increasing adventurousnessNot tedious feeling in playingVideo gamesSpecial data processing applicationsManagement unitTerminal equipment
A game processing server apparatus, to which plural terminal devices each being operated by a player are connected via a network, configured to provide a game service to the plural terminal devices, includes a player management unit which manages an association of a target player with other plural players; and an event management unit which controls a generation of a predetermined event, manages an event generation status for each of the target player and the players associated with the target player, determines whether a specific event is already generated for the target player and the players associated with the target player by referring to the event generation status for each of the target player and the players associated with the target player, determines, based on the determined result, an event to be generated for the target player.
Owner:DENA CO LTD
Systems and methods for performing or creating simulated phishing attacks and phishing attack campaigns
ActiveUS20170251009A1Risk minimizationMalicious action is preventedTransmissionElectronic mailData library
A method for establishing a campaign for a simulated phishing attack includes receiving, via a campaign manager, specification of a plurality of parameters for a campaign including at least an identifier of a campaign and identification of users to which to send the campaign, establishing, via the campaign manager, a type of exploit for the campaign and one or more types of data to collect via the type of exploit, storing, by the campaign manager, the campaign comprising the plurality of parameters, and identifying, by a simulation server, the campaign stored in the database to create a simulated phishing email, to be sent to email accounts of the users, using the plurality of parameters of the campaign, wherein the simulated phishing email is to be created to have a link to a landing page comprising the type of exploit and configured to collect the one or more types of data.
Owner:KNOWBE4 INC
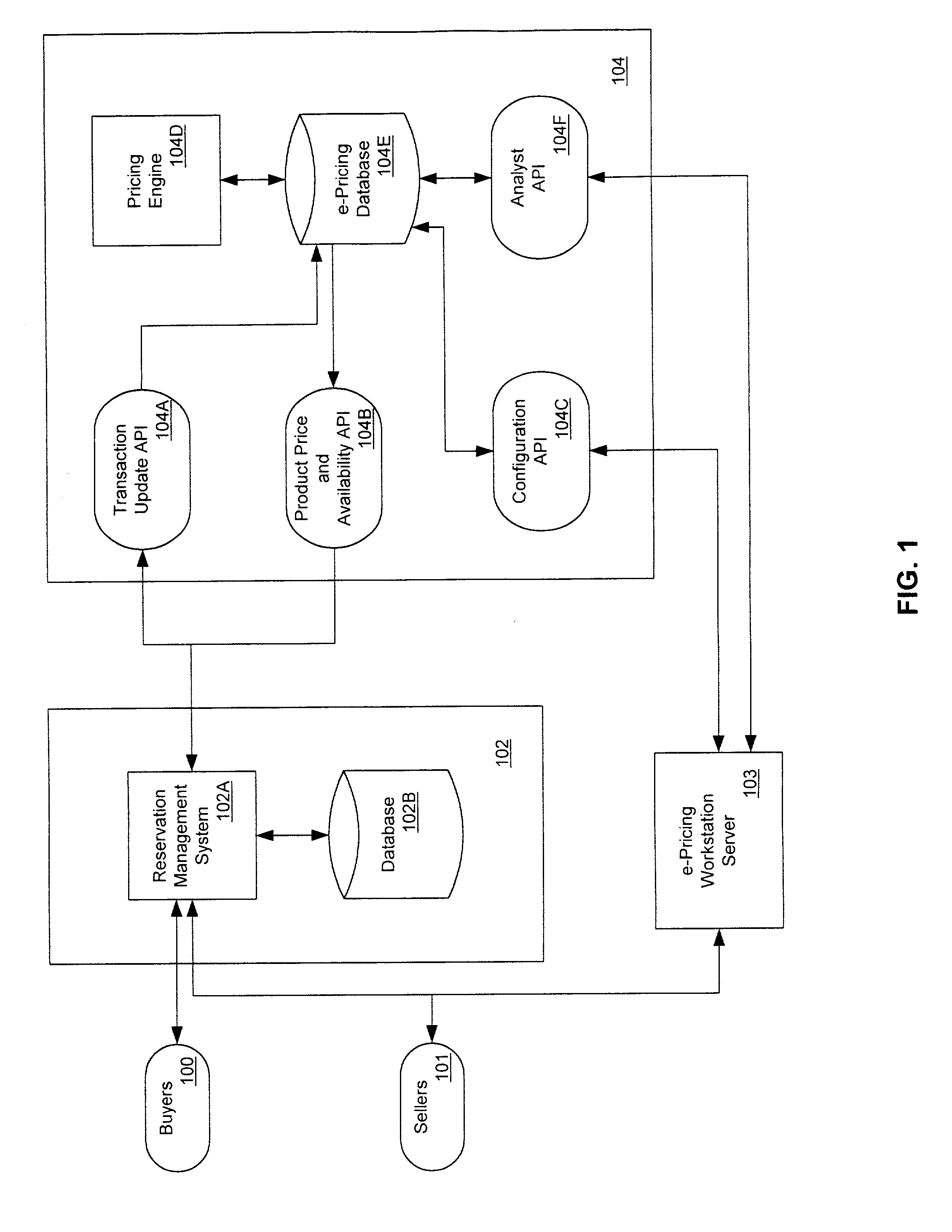
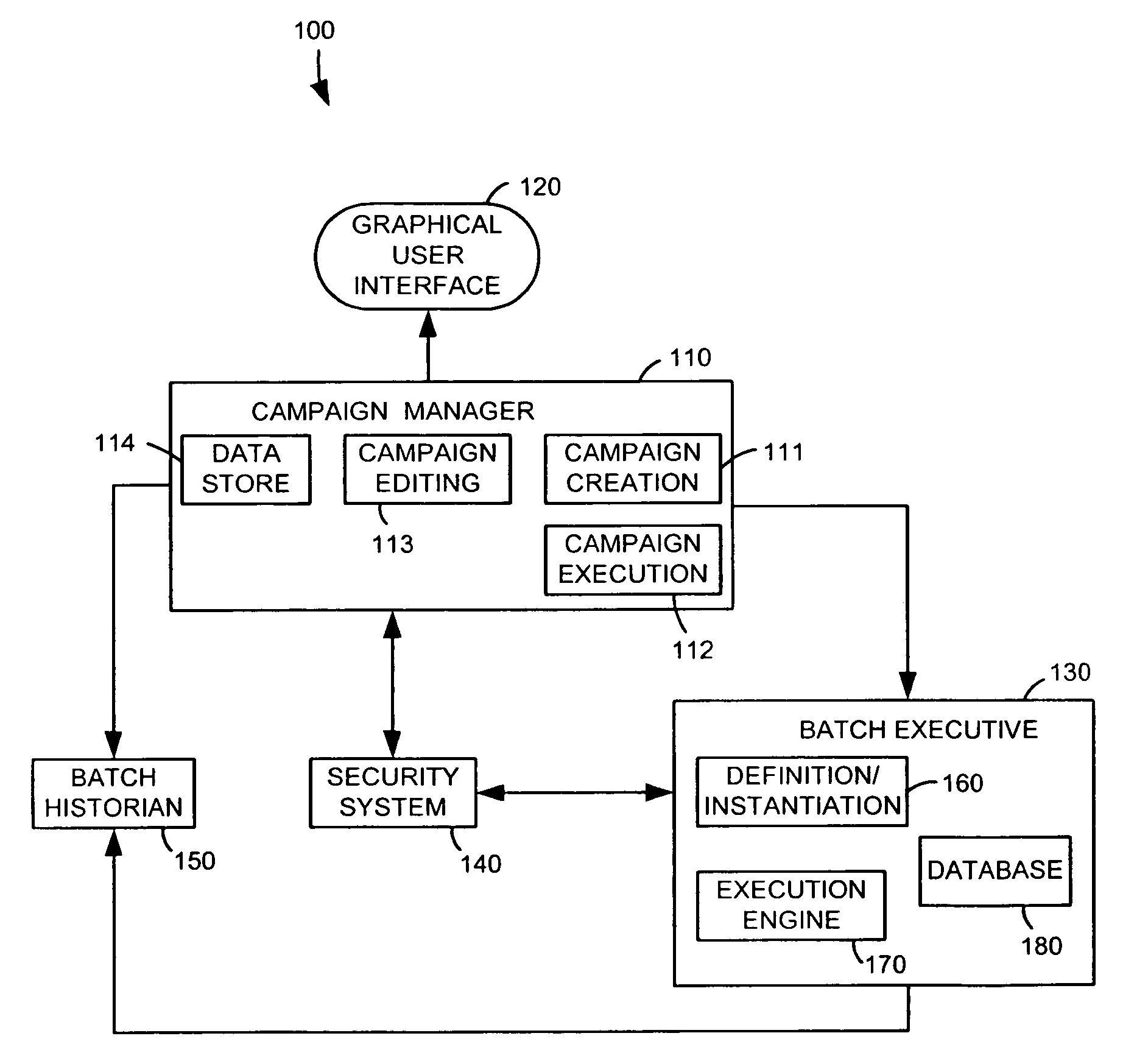
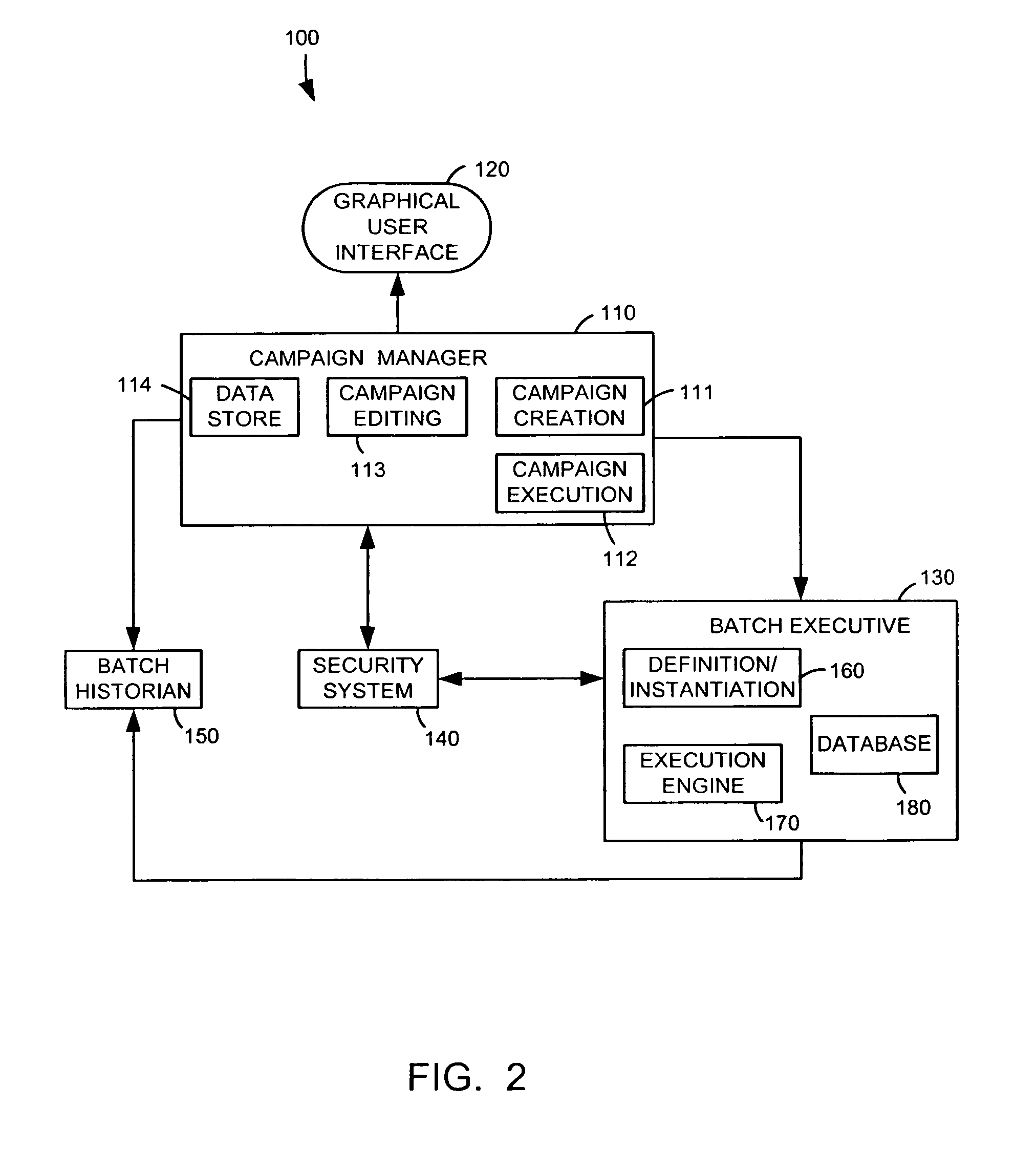
Campaign management for batch processes
A campaign management technique for batch processes enables a process control system user to flexibly create, edit and execute batch process campaigns. The campaign management technique uses a campaign management function that sends messages requesting batch information to a batch executive function. The batch executive function extracts the requested batch information from a database and sends responsive messages containing the requested batch information to the campaign management function. The campaign management function displays the requested batch information to a user via a graphical display and enables the user to select batch information to be included within a batch process campaign. The user can create a campaign having multiple types of batches, which can include special startup and cleanup batches. The campaign management function releases batches of a campaign for execution by the batch executive function according to a user-specified batch execution mode, which may queue a ready batch in the batch executive function prior to the completion of a currently executing batch. A user can add batches to a campaign and / or can modify or delete unreleased batches of a currently executing campaign. Additionally, the campaign management function is tightly integrated with a data historian function and a security function and automatically sends campaign execution messages to the data historian and uses the security function to control user access to the campaign management function.
Owner:FISHER-ROSEMOUNT SYST INC
Integrated device alerts in a process control system
InactiveUS8044793B2Electric testing/monitoringElectric/electromagnetic visible signallingControl systemManagement system
An events management system coordinates the exchange of device alert or alarm information between an asset management system and one or more business systems within a process control system or plant. The events management system receives device alerts from the asset management system and uses a rules-engine and one or more state machines to send notifications containing device alert information to one of more of the business systems.
Owner:FISHER-ROSEMOUNT SYST INC
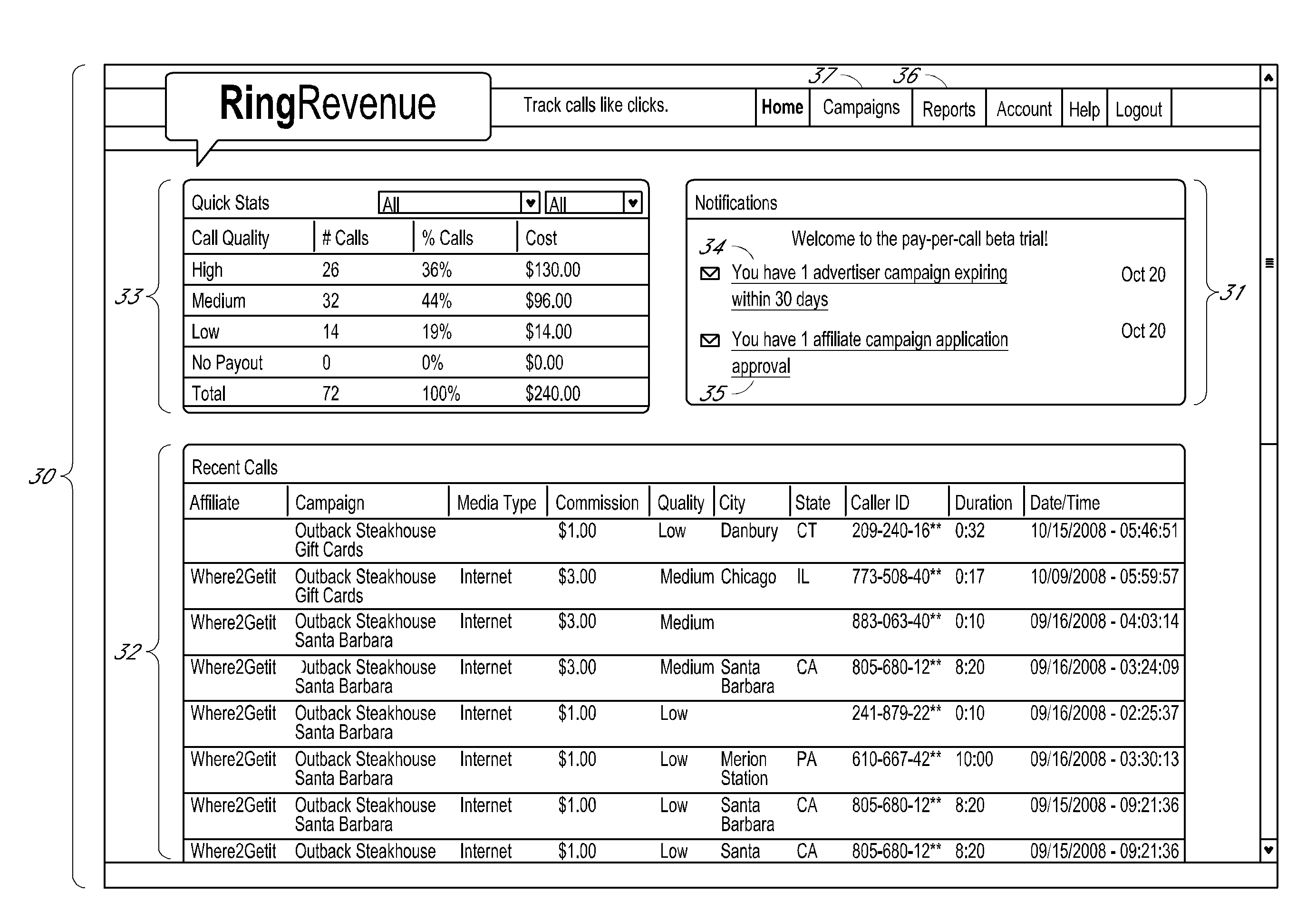
Methods and systems for data transfer and campaign management
ActiveUS20160173693A1Quickly and easily enter into and monitorAdvertisementsSpecial service for subscribersEntity identifierQuality rating
An online and offline communication processing and tracking using data processing and data / voice networks is described. A phone address from a phone address number pool is automatically assigned to a first entity. A call quality rating is determined and recorded. A call from a caller directed to the phone address is received at a call bridging system coupled to at least one network, wherein the call is associated with call signaling information. Based at least in part on the call quality associated with the caller call, the caller call is assigned to a first location in a call queue. An outbound call is generated from the call bridging system and the inbound and the outbound calls are bridged. One or more parameters of the bridged call are compared to the call quality rating. An indication is recorded regarding the successful bridging of the calls in association with an entity identifier.
Owner:INVOCA
Vehicle Exception Event Management Systems
ActiveUS20150035665A1Easy to operateHeat generationRegistering/indicating working of vehiclesOptical signallingMobile vehicleNetwork connection
Exception event recorders and analysis systems include: vehicle mounted sensors arranged as a vehicle event recorder to capture both discrete and non-discrete data; a discretization facility; a database; and an analysis server all coupled together as a computer network. Motor vehicles with video cameras and onboard diagnostic systems capture data when the vehicle is involved in a crash or other anomaly (an ‘event’). In station where interpretation of non-discrete data is rendered, i.e. a discretization facility, captured data is used as a basis for production of supplemental discrete data to further characterize the event. Such interpreted data is joined to captured data and inserted into a database in a structure which is searchable and which supports logical or mathematical analysis by automated machines. A coupled analysis server is arranged to test stored data for prescribed conditions and upon finding such, to initiate further actions appropriate for the detected condition.
Owner:SMARTDRIVE SYSTEMS
Systems and methods for performing or creating simulated phishing attacks and phishing attack campaigns
ActiveUS9894092B2Expose a lack of vigilance and/or know-howRisk minimizationTransmissionElectronic mailData library
A method for establishing a campaign for a simulated phishing attack includes receiving, via a campaign manager, specification of a plurality of parameters for a campaign including at least an identifier of a campaign and identification of users to which to send the campaign, establishing, via the campaign manager, a type of exploit for the campaign and one or more types of data to collect via the type of exploit, storing, by the campaign manager, the campaign comprising the plurality of parameters, and identifying, by a simulation server, the campaign stored in the database to create a simulated phishing email, to be sent to email accounts of the users, using the plurality of parameters of the campaign, wherein the simulated phishing email is to be created to have a link to a landing page comprising the type of exploit and configured to collect the one or more types of data.
Owner:KNOWBE4 INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com