Patents
Literature
60 results about "Relational system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
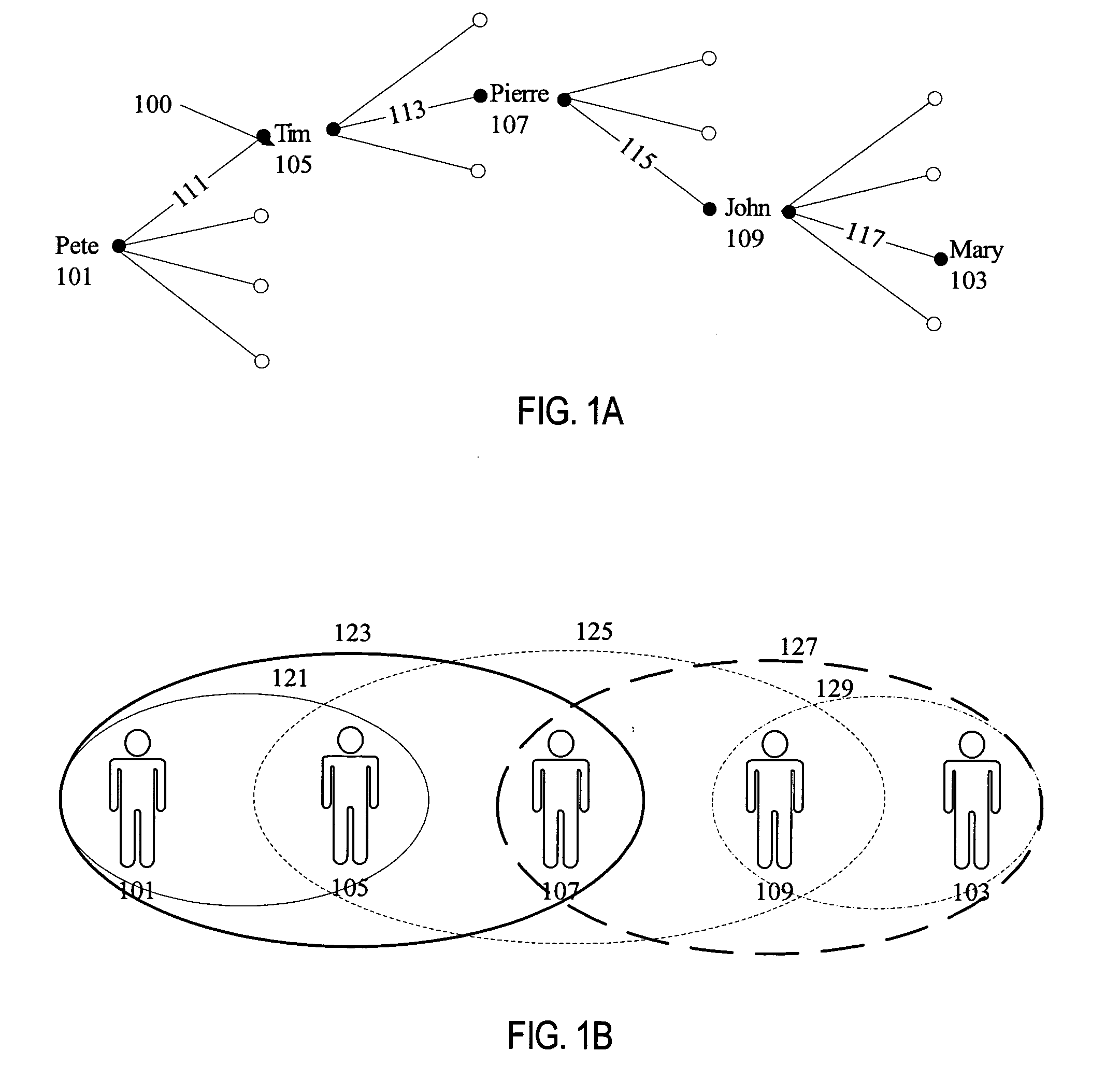
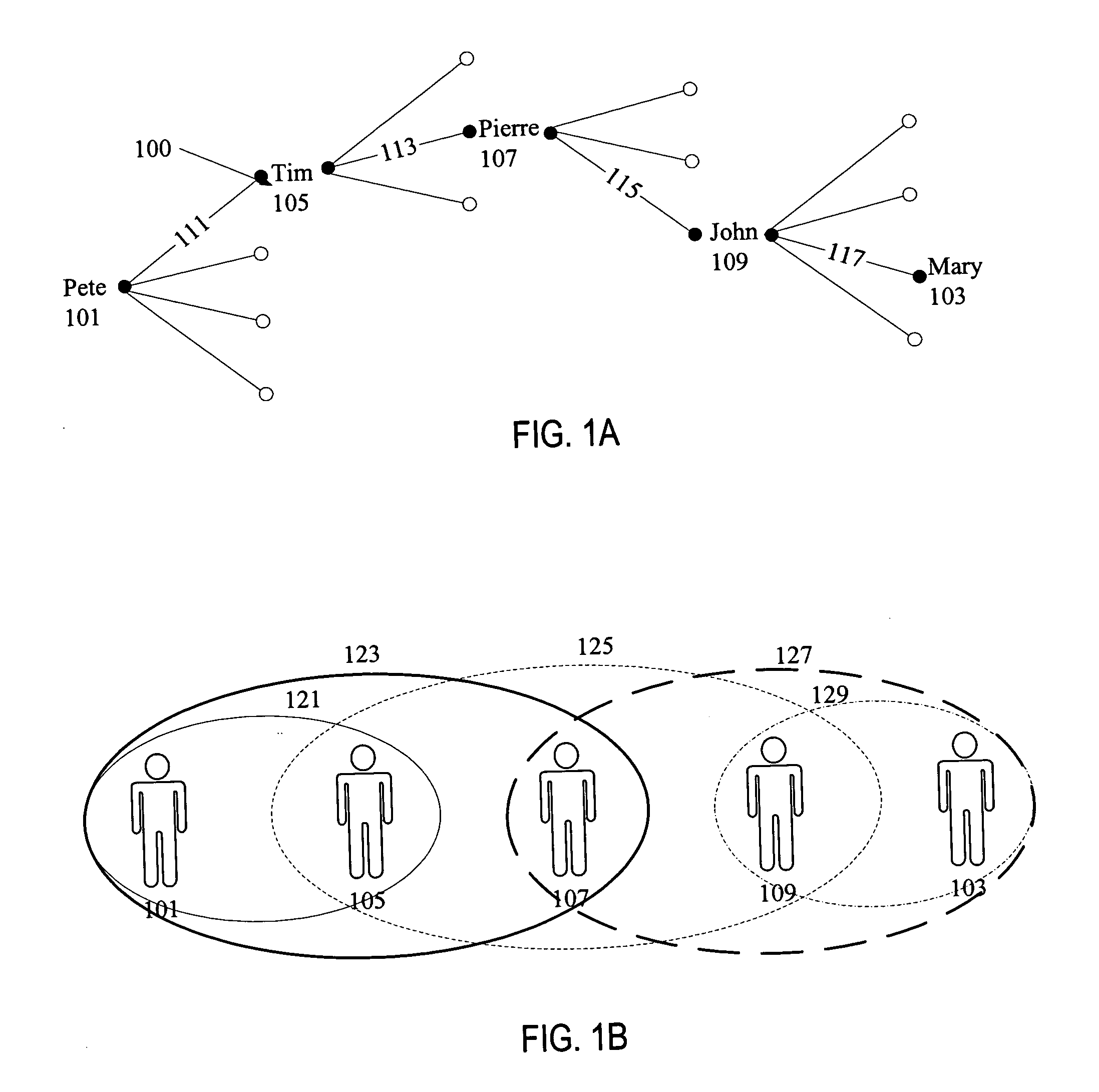
A relational database is a database model that stores data in tables. The vast majority of databases used in modern applications are relational, so the terms "database" and "relational database" are often used synonymously. Likewise, most database management systems (DBMSes) are relational database management systems (RDBMSes).
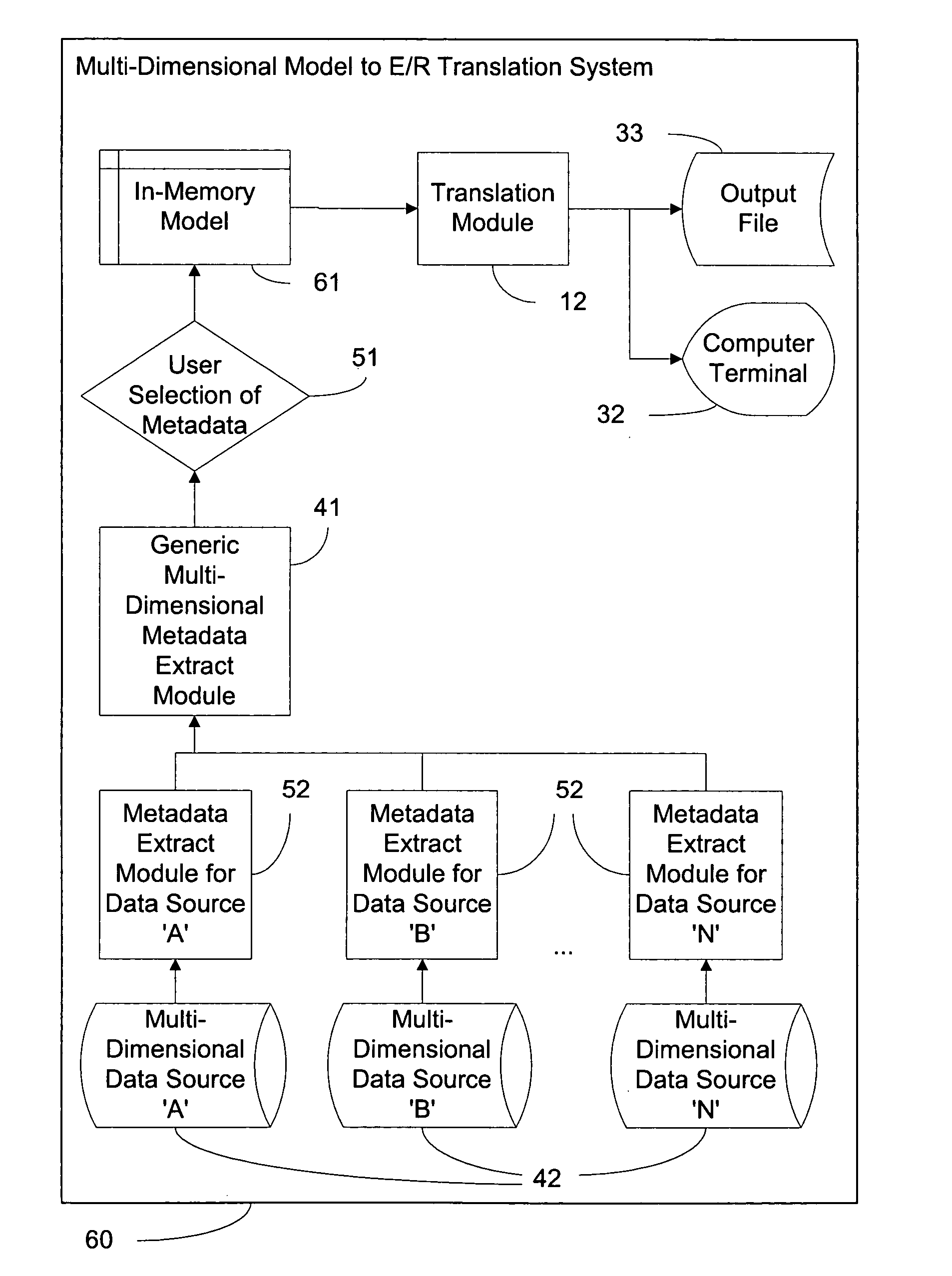
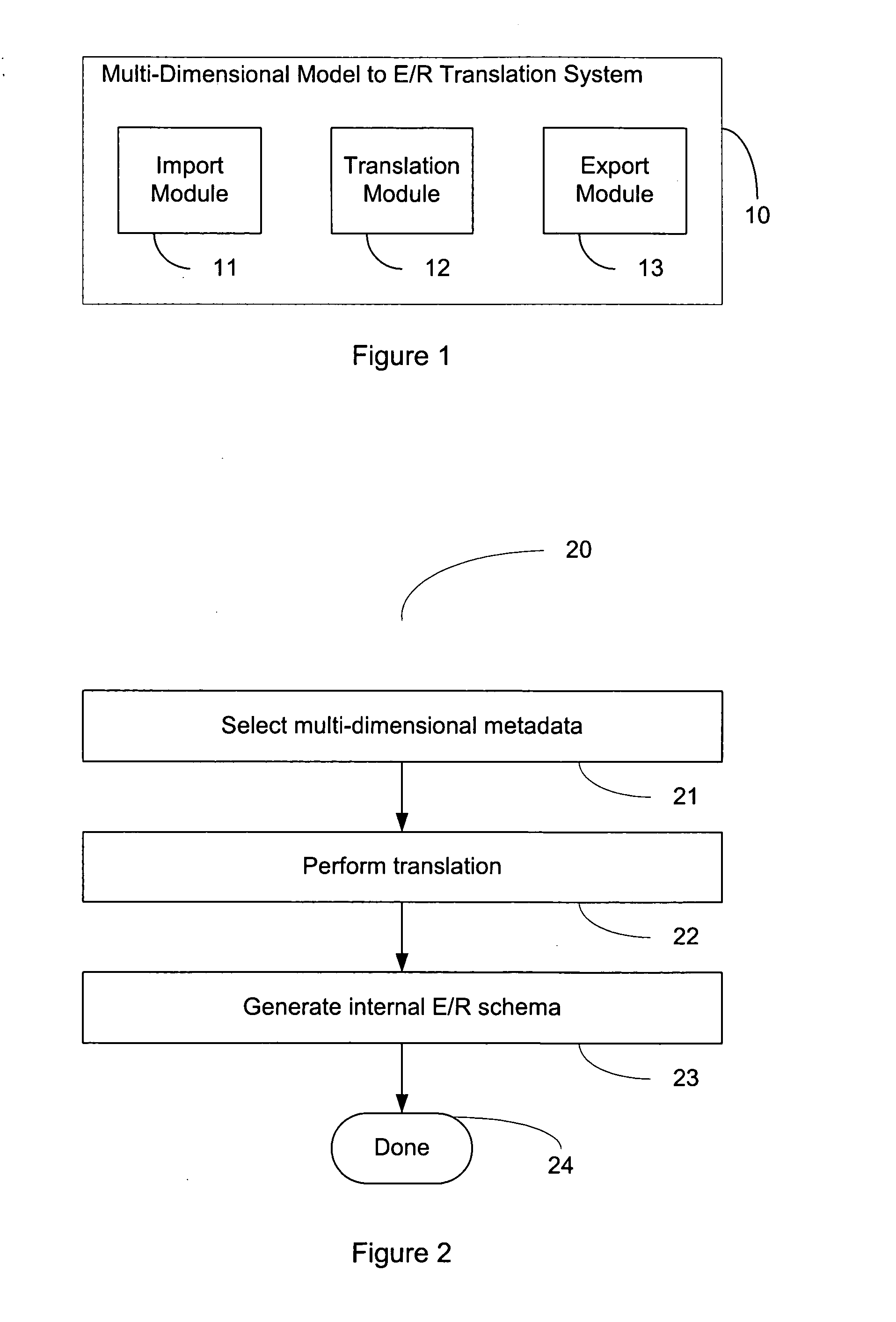
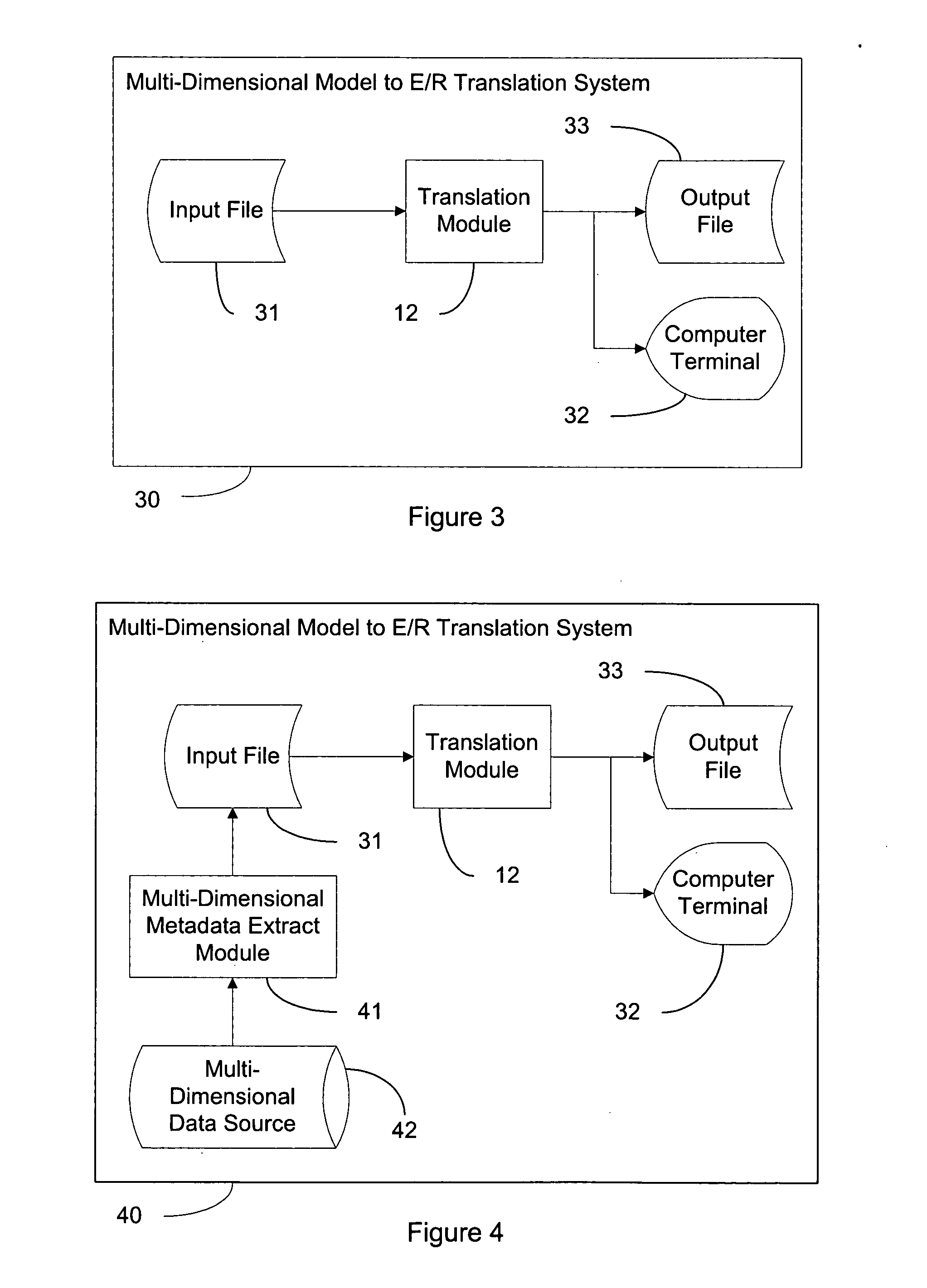
System and method of modelling of a multi-dimensional data source in an entity-relationship model
InactiveUS20050010550A1Easy to createDigital data processing detailsMulti-dimensional databasesRelational systemData source
An entity-relationship modelling system for modelling a multi-dimensional data source in an entity-relationship model is provided. The entity-relationship system comprises an import module for performing translations on multi-dimensional data, a translation module for translating multi-dimensional data into an entity-relationship schema, and a repository for storing the entity-relationship schema.
Owner:IBM CORP
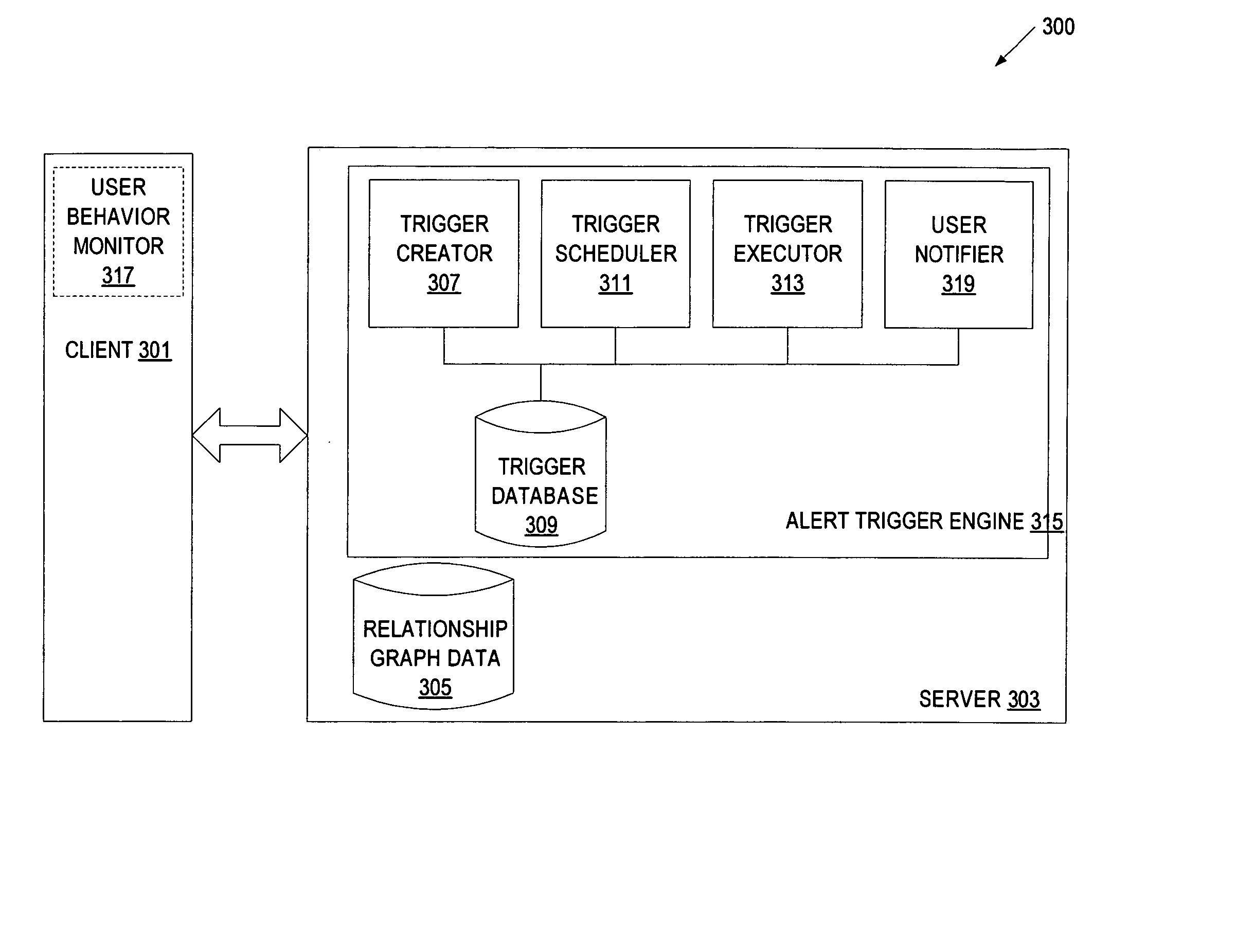
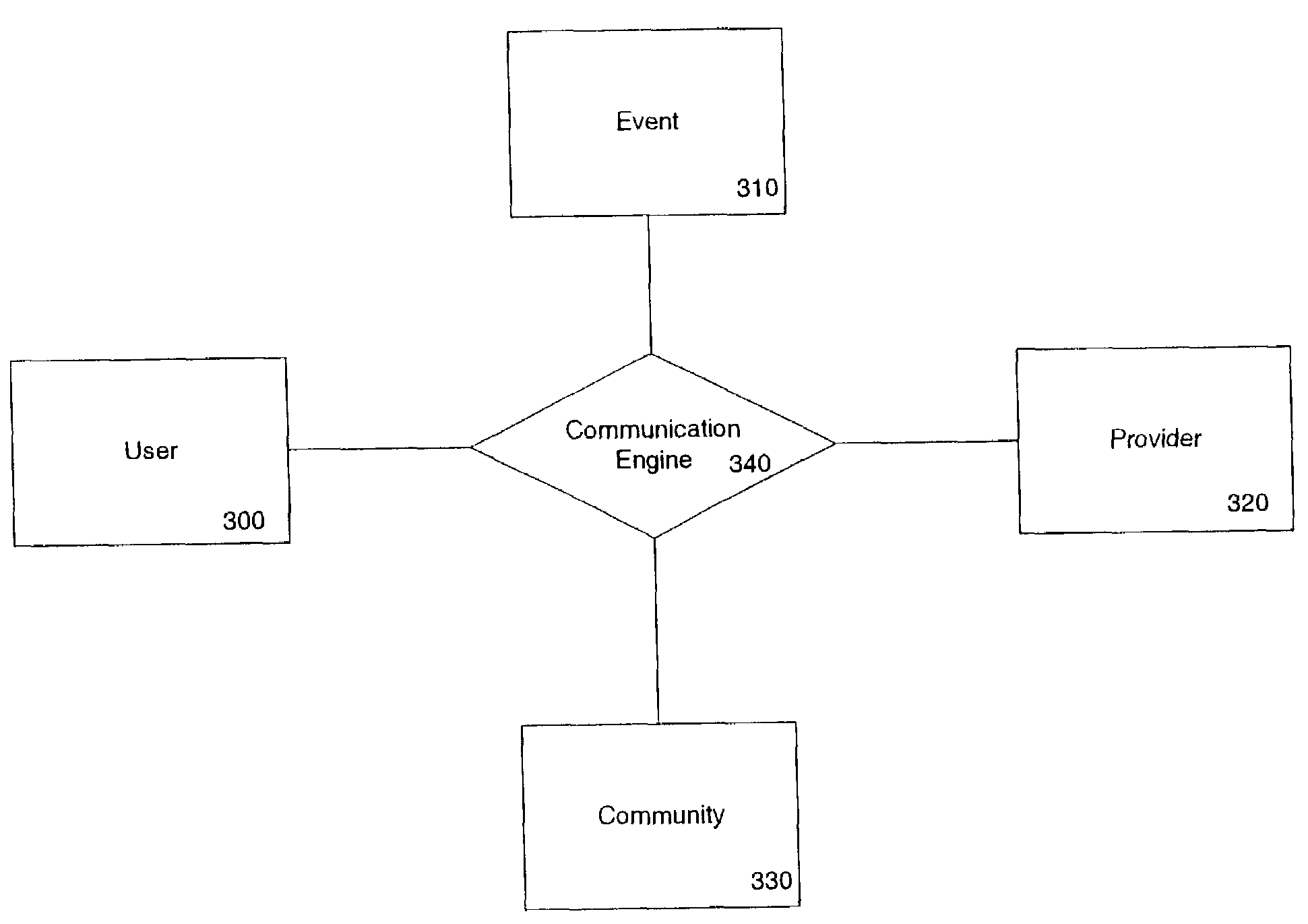
Alert triggers and event management in a relationship system
InactiveUS20050283753A1Digital data information retrievalDigital computer detailsRelational systemData mining
A method and apparatus to manage alert triggers in a relationship system are disclosed. In one embodiment, the method includes maintaining a set of alert triggers that define operations for detecting changes pertaining to elements of a relationship graph. The elements of the relationship graph include nodes representing entities and edges representing relationships between entities. The method further includes performing the operations defined by the set of alert triggers, and providing an alert to one or more users when any of the defined operations satisfy an alert condition associated with a corresponding alert trigger.
Owner:SPOKE SOFTWARE
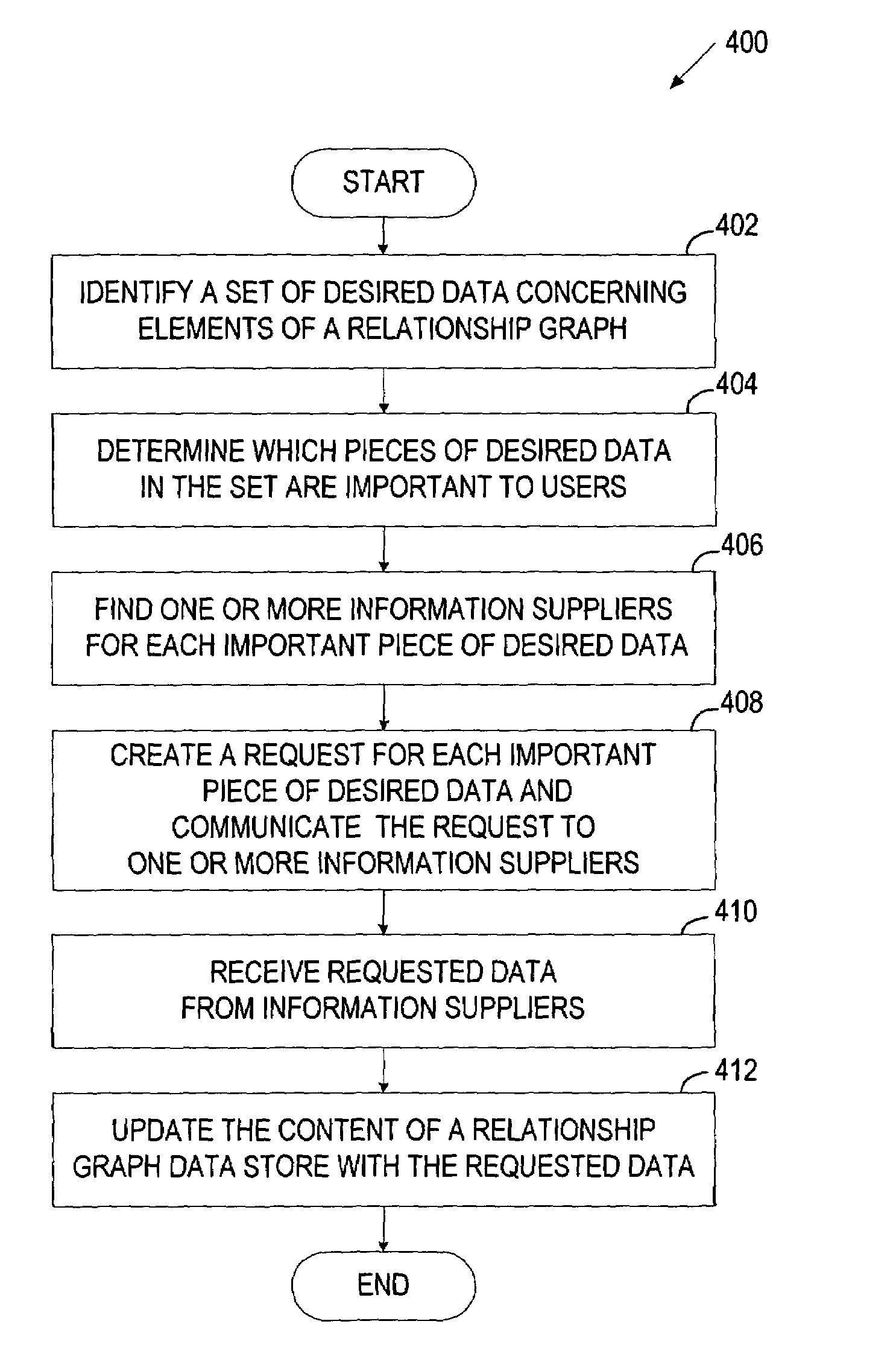
Periodic update of data in a relationship system
InactiveUS20060031203A1Digital data information retrievalOffice automationRelational systemData mining
A method and system for periodically updating data in a relationship system are disclosed. In one embodiment, the method includes identifying a set of desired data concerning elements of a relationship graph. The elements of the relationship graph include nodes representing entities and edges representing relationships between entities. The method further includes determining which pieces of the desired data are important to users and finding one or more information suppliers for each important piece of the desired data.
Owner:SPOKE SOFTWARE
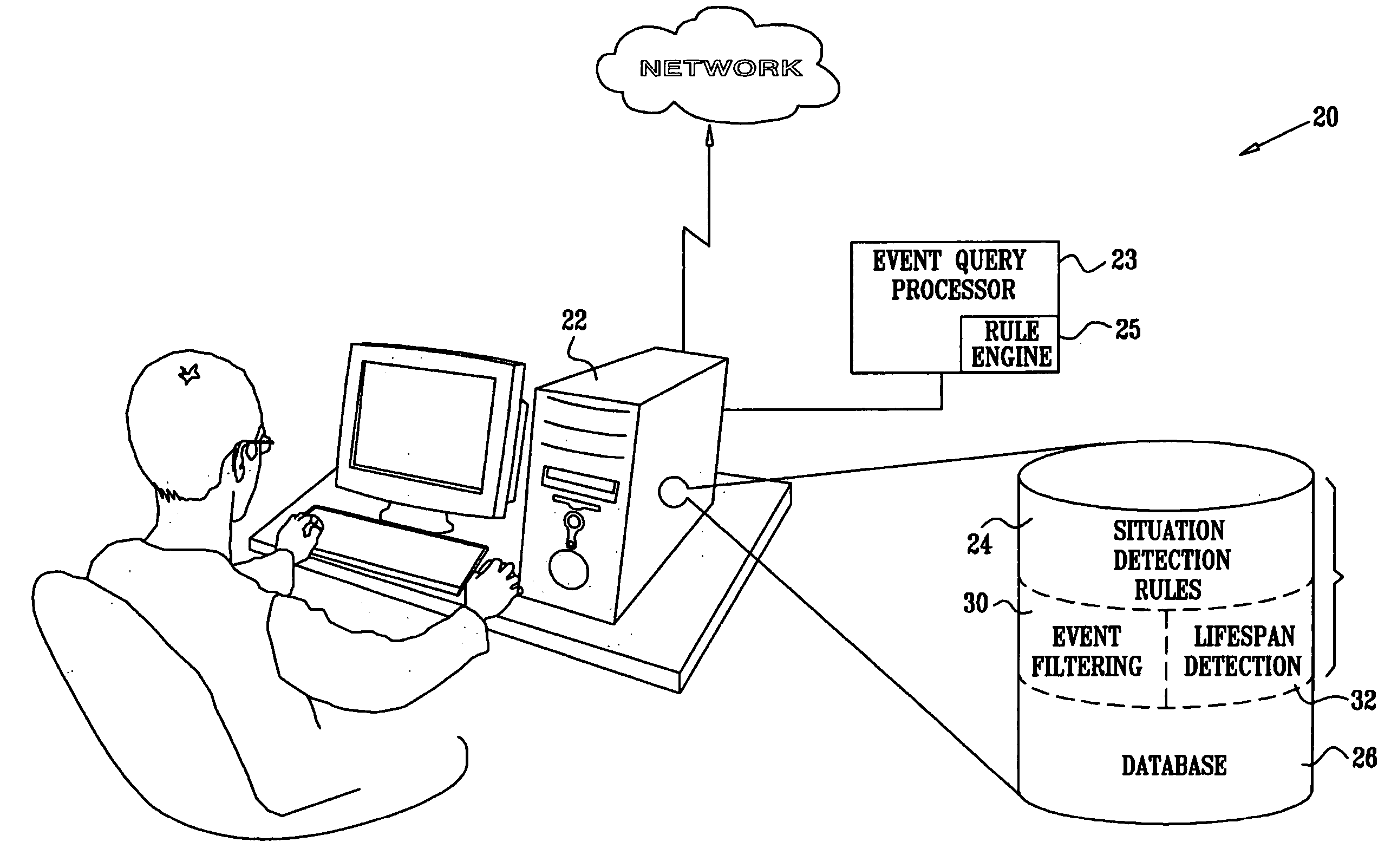
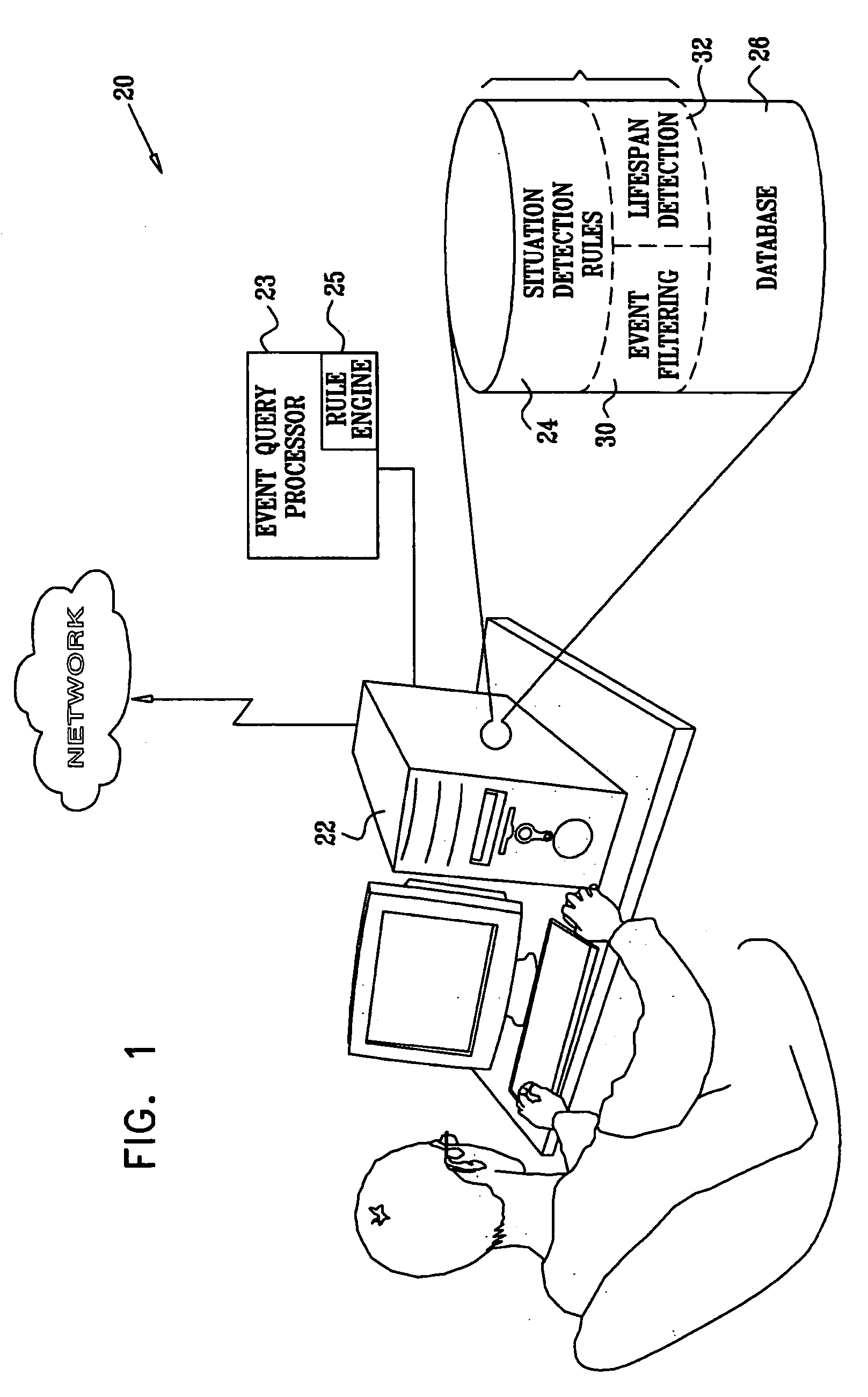
Complex event discovery in event databases
InactiveUS20060155719A1Improve abilitiesIncrease capacityDigital data processing detailsDatabase modelsRelational systemEvent data
Situation detection systems and methods are provided, in which the capabilities of standard event stores and relational systems are enhanced by augmented event-oriented algebraic operators. Rules involving the event-oriented operators are combined with conventional relational algebraic techniques, and applied to an event database in order to detect more complex patterns, indicative of composite events or situations.
Owner:IBM CORP
Choice-based relationship system (CRS)
A method and apparatus for building relationship opportunities for event participants with similar interests before, during and after the event are disclosed. The method includes creating a profile of a first user registered for an event, the profile includes terms indicative of preferences and characteristics of the first user. The method also includes receiving an inquiry from the first user for at least one match based on at least one keyword and providing a list of matches to the user in response to the inquiry, wherein the match is a second user sharing similar interests with the first user.
Owner:XENOGENIC DEV LLC
Periodic update of data in a relationship system
InactiveUS7373389B2Digital data information retrievalMultiple digital computer combinationsRelational systemData mining
A method and system for periodically updating data in a relationship system are disclosed. In one embodiment, the method includes identifying a set of desired data concerning elements of a relationship graph. The elements of the relationship graph include nodes representing entities and edges representing relationships between entities. The method further includes determining which pieces of the desired data are important to users and finding one or more information suppliers for each important piece of the desired data.
Owner:SPOKE SOFTWARE
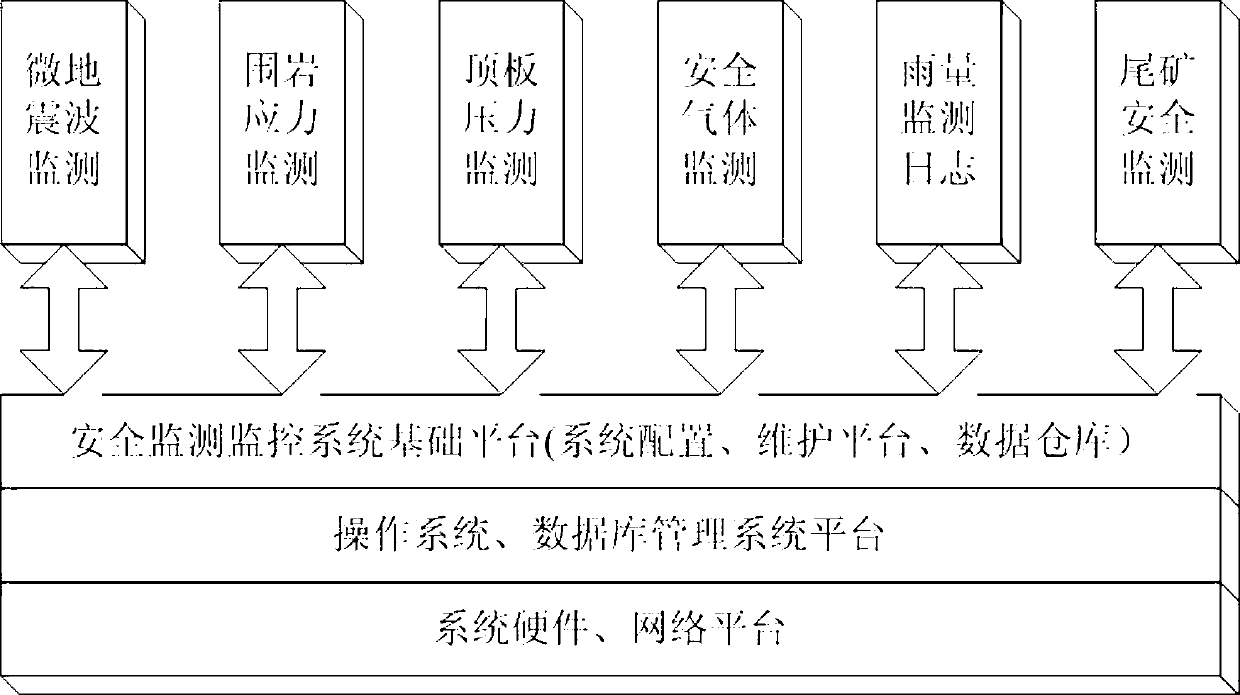
Digital mine safety monitoring and inspecting system
InactiveCN102999873AReduce outputSafe and efficient productionData processing applicationsInformation processingRelational system
The invention provides a digital mine safety monitoring and inspecting system which sequentially comprises four layers, namely a system hardware and network platform, an operation system and database management system platform, a safety monitoring and inspecting system base platform and a safety monitoring and inspecting system software platform, wherein in the four layers, the lower layer provides service for the upper layer and provides interactive connectors. The digital mine safety monitoring and inspecting system is integrally constructed on the hardware platform and network platform, and interaction between the digital mine safety monitoring and inspecting system and a bottom layer hardware facility and a monitoring and inspecting system is achieved through an operation system and a database management system, the interactive information is processed and stored in the safety monitoring and inspecting system base platform in distributing mode, and the safety monitoring and inspecting system software platform at the highest layer achieves scanning and processing on the interactive information through different functional subsystems and issues control information to the operation system and database management system platform through the safety monitoring and inspecting system base platform. The digital mine safety monitoring and inspecting system has the advantages of being capable of achieving safety monitoring, safety alarm and safety control on mines.
Owner:SHANDONG GOLD GROUP
Apparatus and method for deletion of objects from an object-relational system in a customizable and database independent manner
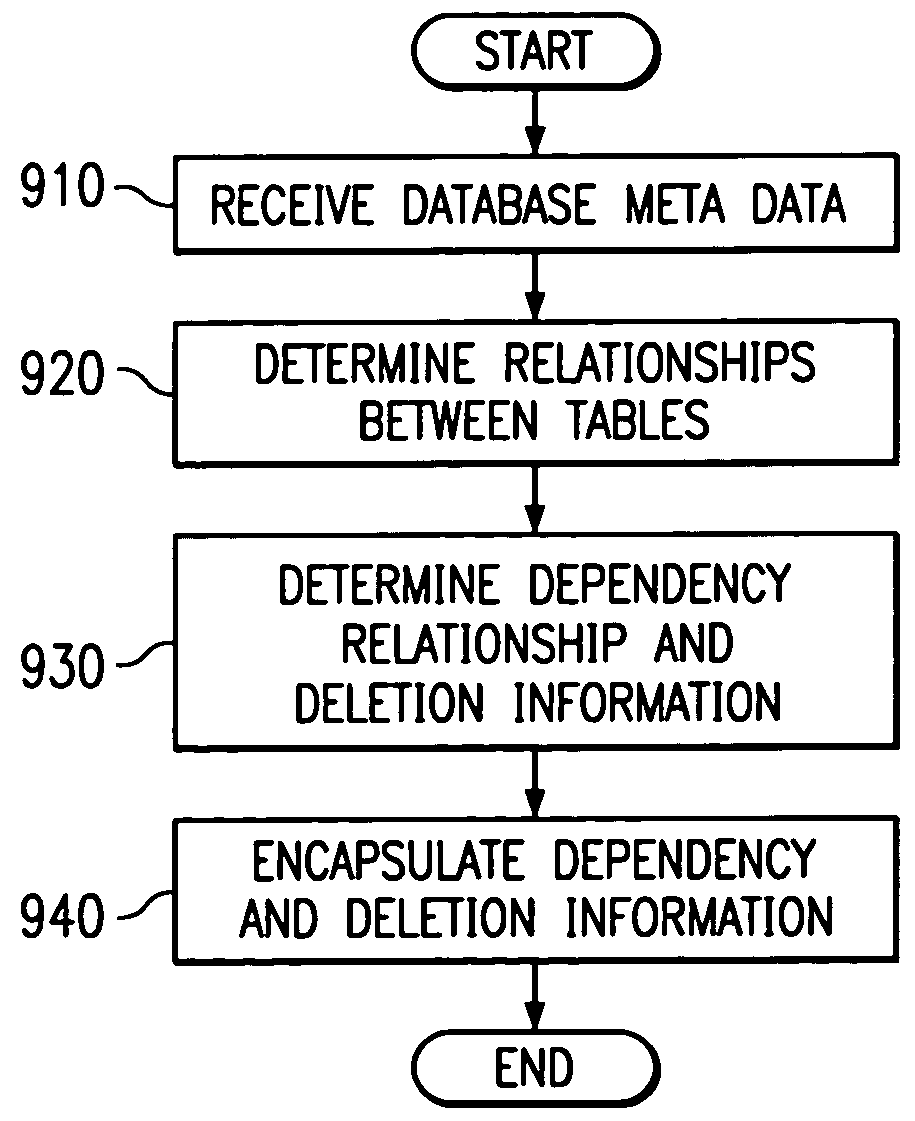
InactiveUS7143108B1Data processing applicationsRelational databasesRelational systemDependency structure
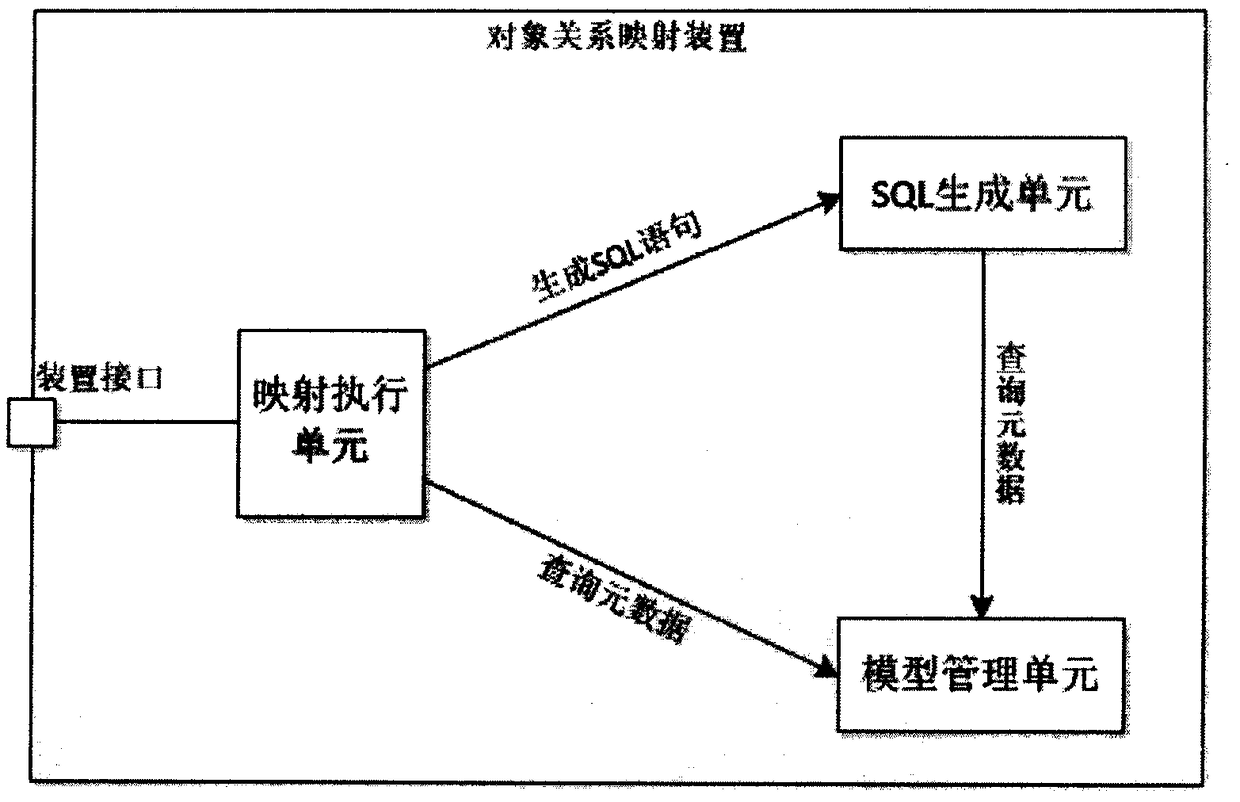
An apparatus and method for deleting objects from an object-relational system in a customizable and database independent manner. The apparatus and method provide a customizable and database independent mechanism for the deletion of object data from a relational database. The method implemented by the apparatus determines the dependency structure of a relational database using database metadata. The dependency structure is then utilized to determine the type of deletion to be performed on data representations of the object and its related objects, i.e., parent or child objects. The deletion actions include cascade deletion and nullify columns deletion. Appropriate SQL statements are then automatically generated at run-time to perform the deletion of the object data from the relational database.
Owner:LINKEDIN
Systems and method for improving investment performance
InactiveUS20060080199A1Eliminate orAmeliorate possible economic conflict of interestFinancePayment architectureProgram planningEngineering
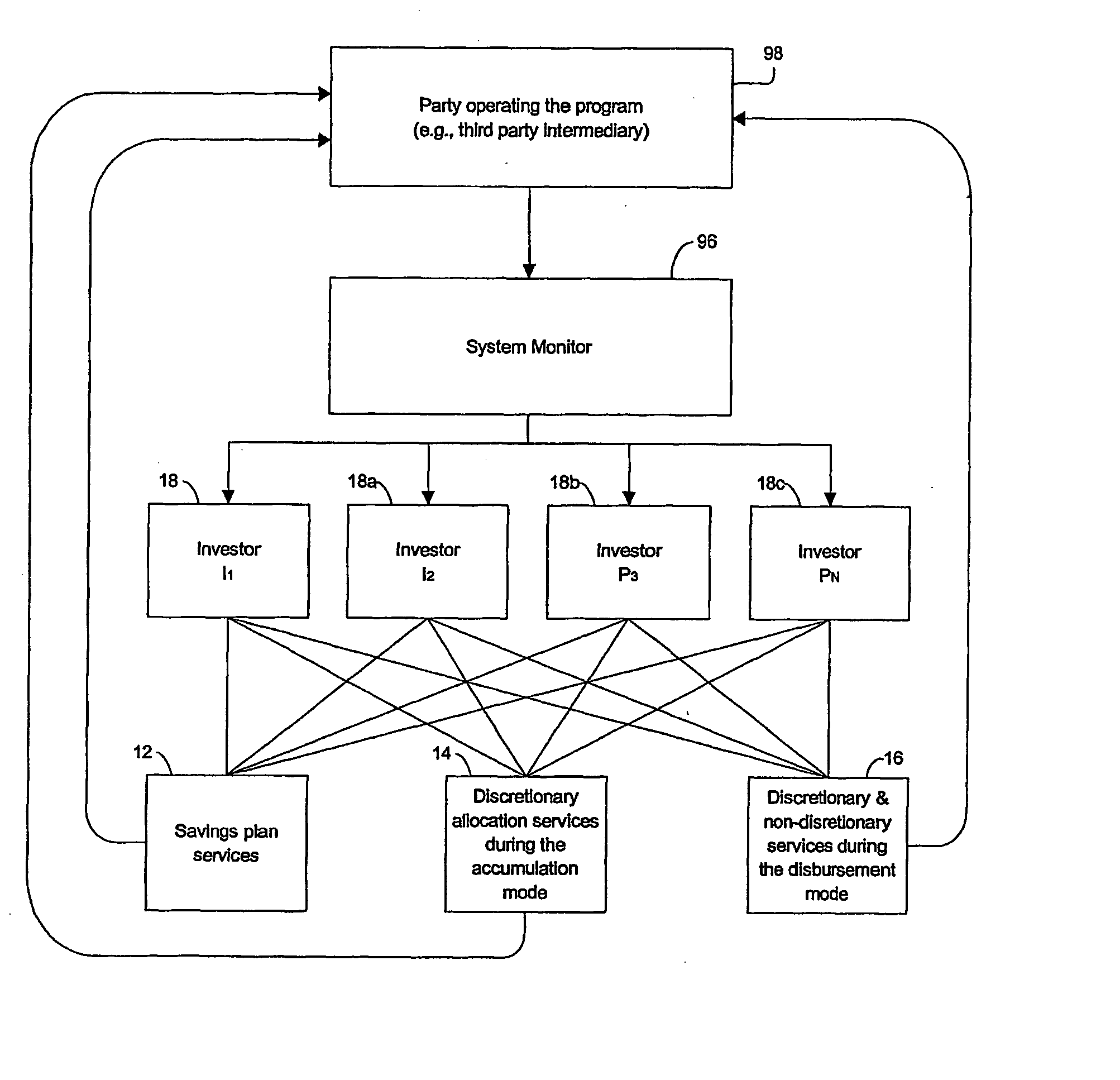
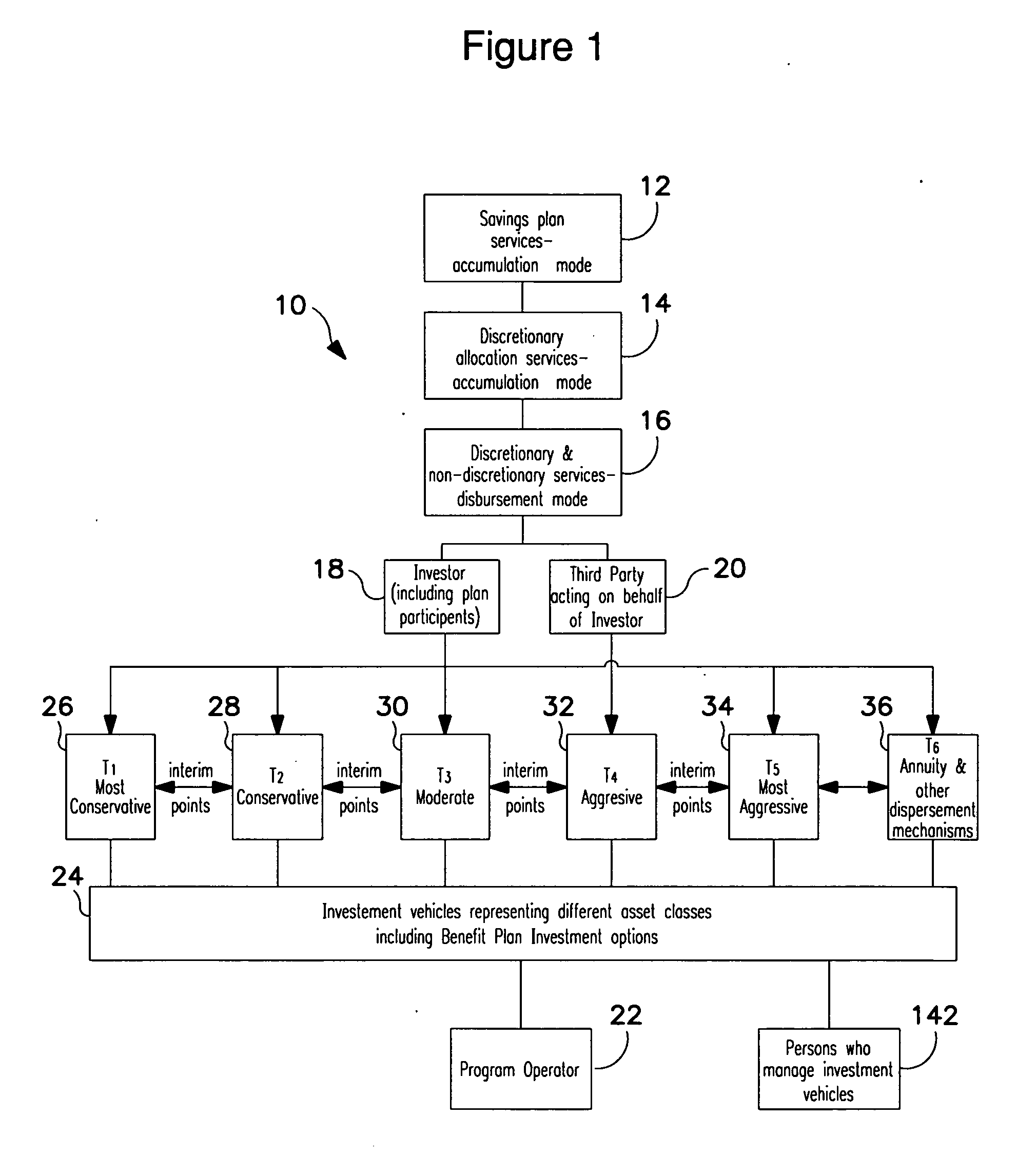
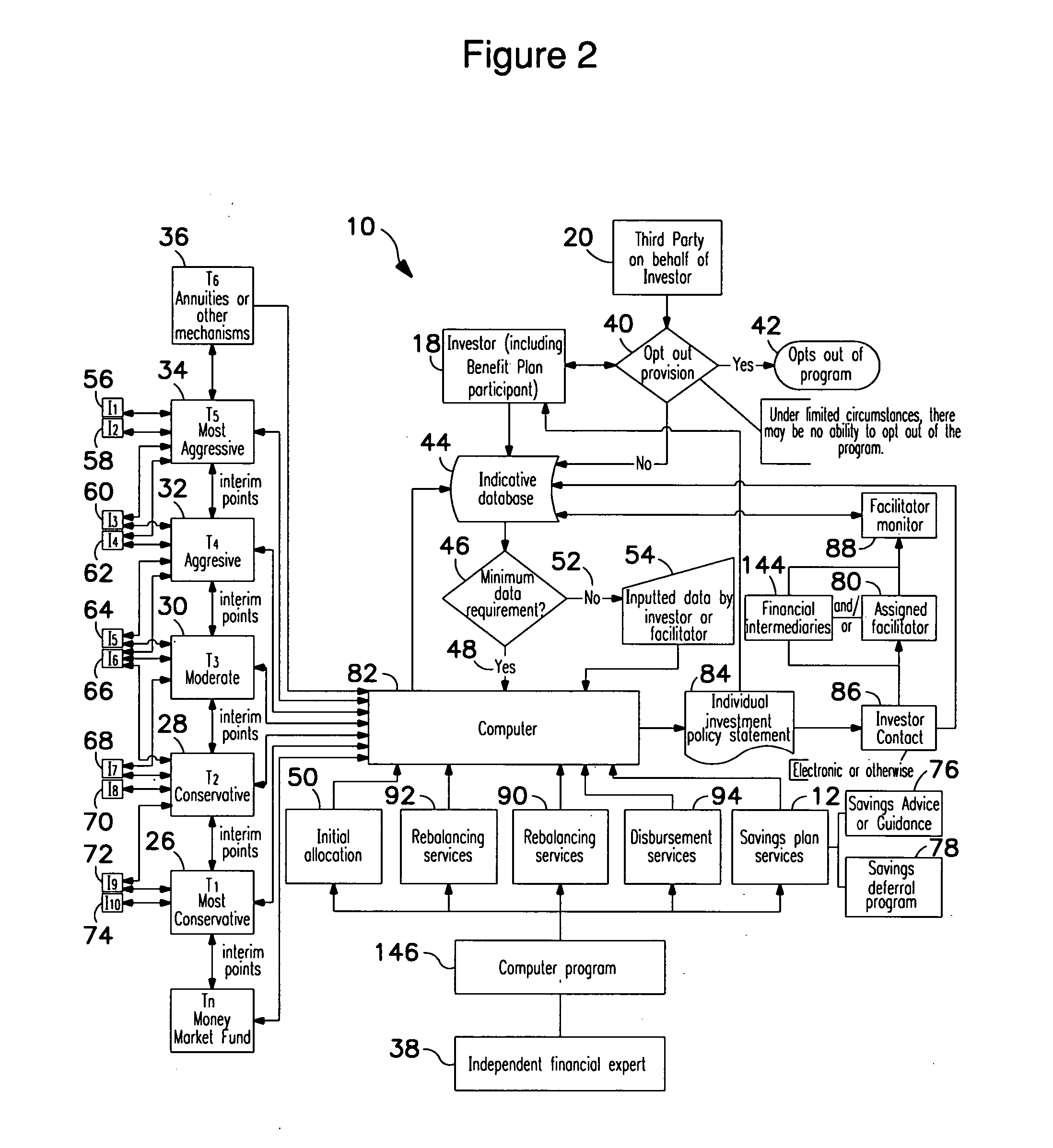
Methods for a data processor implemented system monitor for enabling persons to turn over the allocation of their investment assets, and / or receive assistance concerning how to receive disbursements from investments, in a manner that is free from or ameliorates the traditional conflicts of interest in previous systems. The systems and methods are adapted to ameliorate the tension between other functions where the compensation may be affected by asset allocation. The systems and methods collect, monitor, and direct information from persons who hold indicative data, e.g., employers, to provide professional asset allocation services, including automatic allocation, rebalancing, and reallocation of investment assets, on a regular basis; as well as assistance in determining how much to save or how to receive disbursements in a manner that ameliorates conflicts of interest, which, in the case of employee benefit plans, is consistent with the regulatory restraints of ERISA.
Owner:TARBOX INTPROP LLC
Data processing system and method for detecting mandatory relations violation in a relational database
InactiveUSRE40235E1Increase speedEasily expandableData processing applicationsDigital data processing detailsRelational systemRelational database
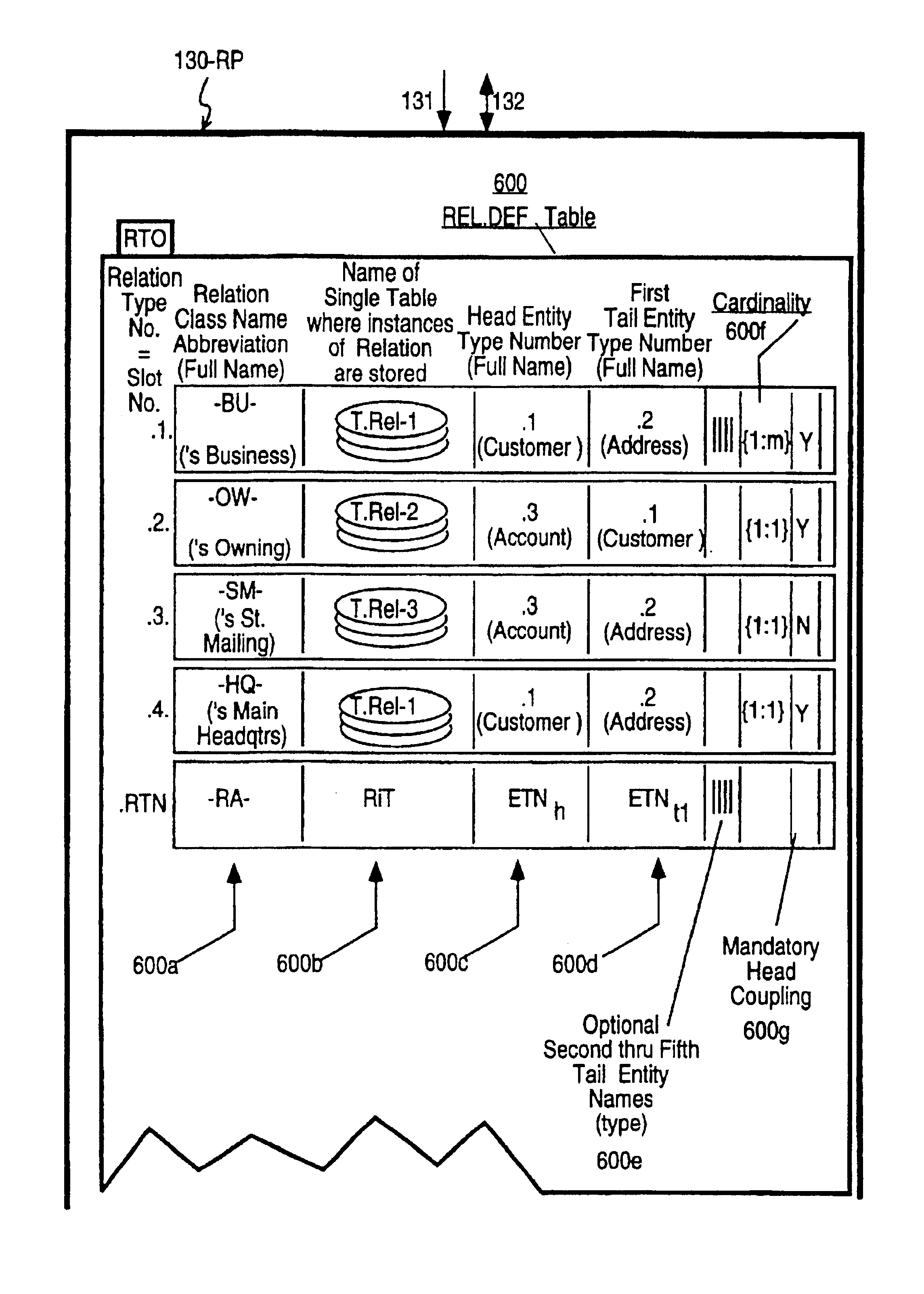
Machine automated techniques are described for a method of data processing called Relationships Processing. A computing system is disclosed which provides for the high speed recording and extraction of data objects (entities) and for the development of data representing a queried relationship between the entities. Furthermore, methods and systems are disclosed to detect mandatory relations violation between entities by examining whether certain relations exist. The system is expandable to handle the relatively voluminous data bases of large commercial data repositories. A user defines a set of entities and allowed relationships between the entities. The user can expand this set of allowed entities and relationships at any time during the life of the system without reprogramming or compiling of computer program code or disrupting concurrent operational use of the system. Large systems can now be built that are no longer limited to the scope of design requirements known during initial system development. For a given set of defined relationships the system allows the user to perform complex inquiries (again without programming at the code level) that would normally require multiple nested inquiries to be coded programmatically and would not achieve the performance levels of the Relationships Processor.
Owner:FINANCIAL SYST TECH
Ranking Enterprise Search Results Based on Relationships Between Users
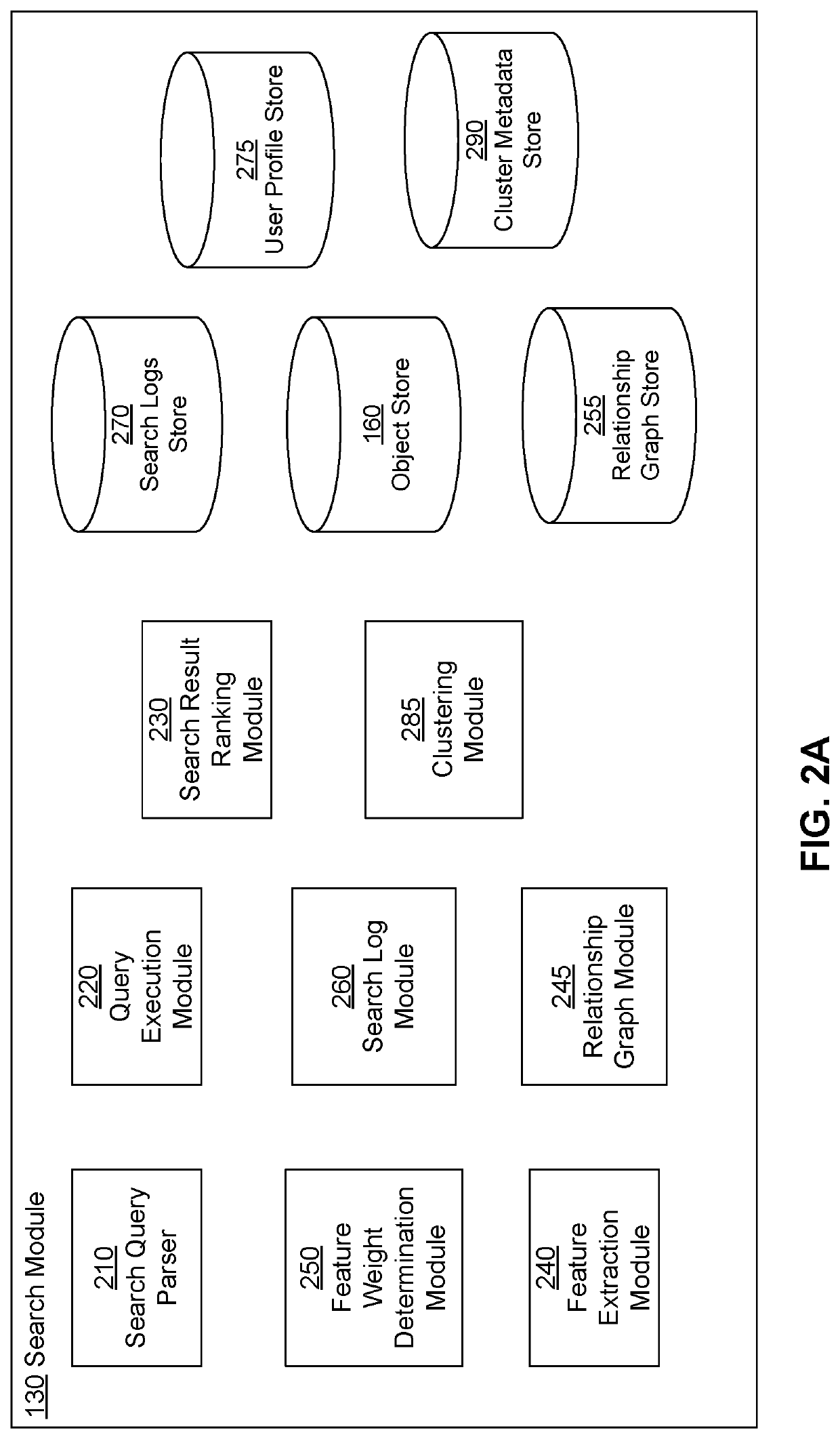
PendingUS20200097560A1Relational databasesSpecial data processing applicationsRelational systemEntity type
A system stores records of different entity types and processes search queries to determine search results comprising records that match the search query. The system receives a search query comprising search keywords from a source user. The system identifies a target user based on a search keyword received in the search query. The system determines a relationship between the source user and the target user. The system determines a relationship strength score for the relationship between the source user and the target user and ranks the search results based on the relationship strength score. The system provides the search results to the source user.
Owner:SALESFORCE COM INC
Remote payment account relational system and method for retail devices
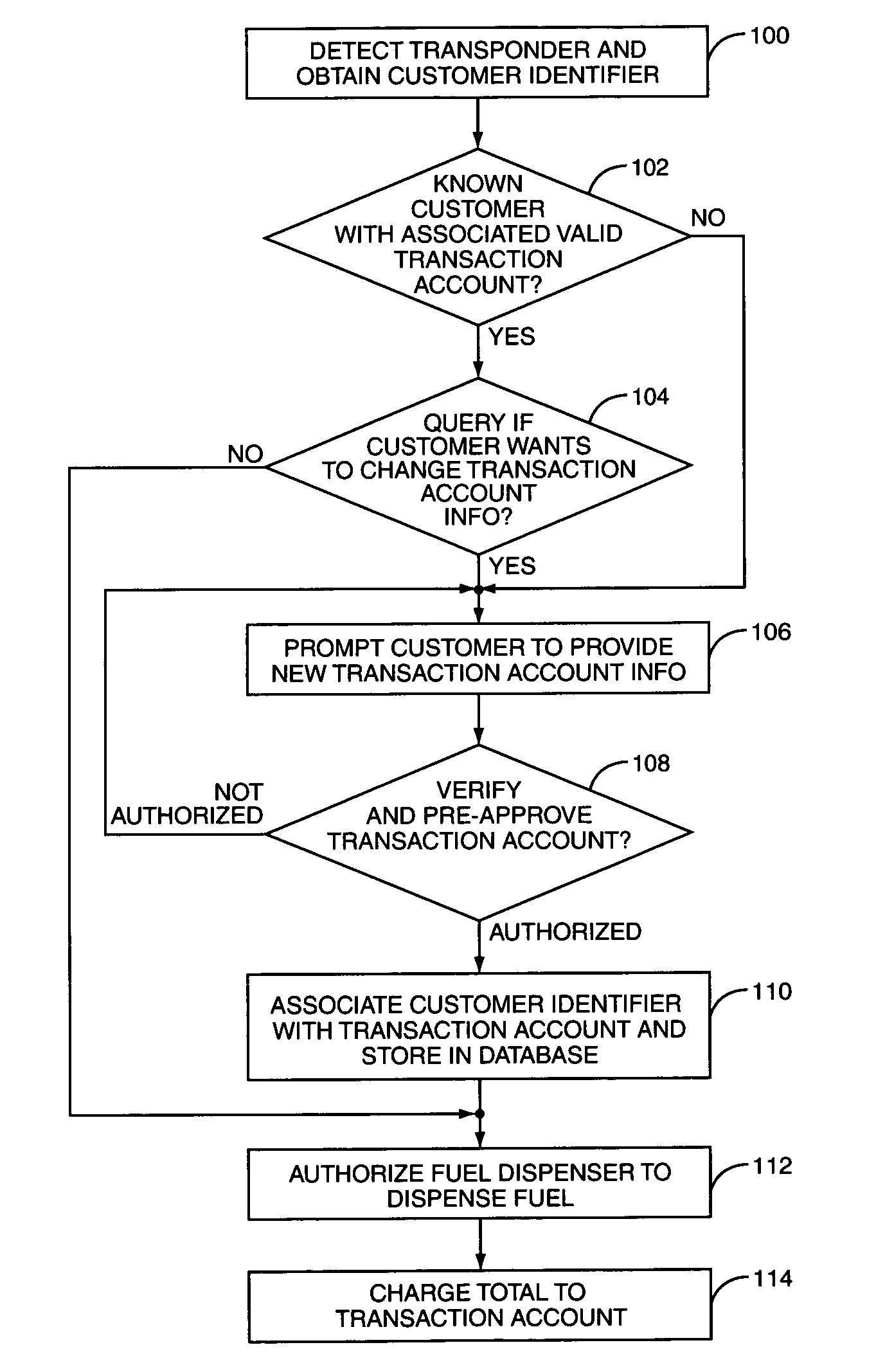
A retail transactions station capable of identifying a customer, retrieving transaction account information associated with the customer, and charging the customer's purchases to the transaction account is operative to receive new transaction account information from the customer at the retail transactions station, verify the transaction account, and associate the new transaction account with the customer for pending and future purchases. In one embodiment, with the retail transactions station identifies the customer via an RFID interrogator at the retail transactions station and a corresponding RFID transponder in the customer's possession. New transaction account information is obtained via a magnetic stripe card reader at the retail transactions station. In another embodiment, the retail transactions station comprises a fuel dispenser. In another embodiment, a system comprises a retail transactions station operative to identify a customer and receive transaction account information, a database containing customer identifiers and associated valid transaction accounts, and a controller operative to control the database and to perform financial transaction processing across a network.
Owner:GILBARCO
Contact relationship systems and methods
Owner:APEX COVANTAGE
Operators for accessing hierarchical data in a relational system
ActiveUS7028037B1Efficient managementData processing applicationsDigital data processing detailsRelational systemData storing
Techniques and systems are provided for efficiently managing hierarchical relational data stored in object-relational database system by extending the syntax of the database language supported by the database system (e.g. SQL) to incorporate several new “hierarchical” operators. These operators are evaluated based on the hierarchical relationship defined for hierarchical relational data. The operators maybe incorporated in SQL queries along with relational operators.
Owner:ORACLE INT CORP
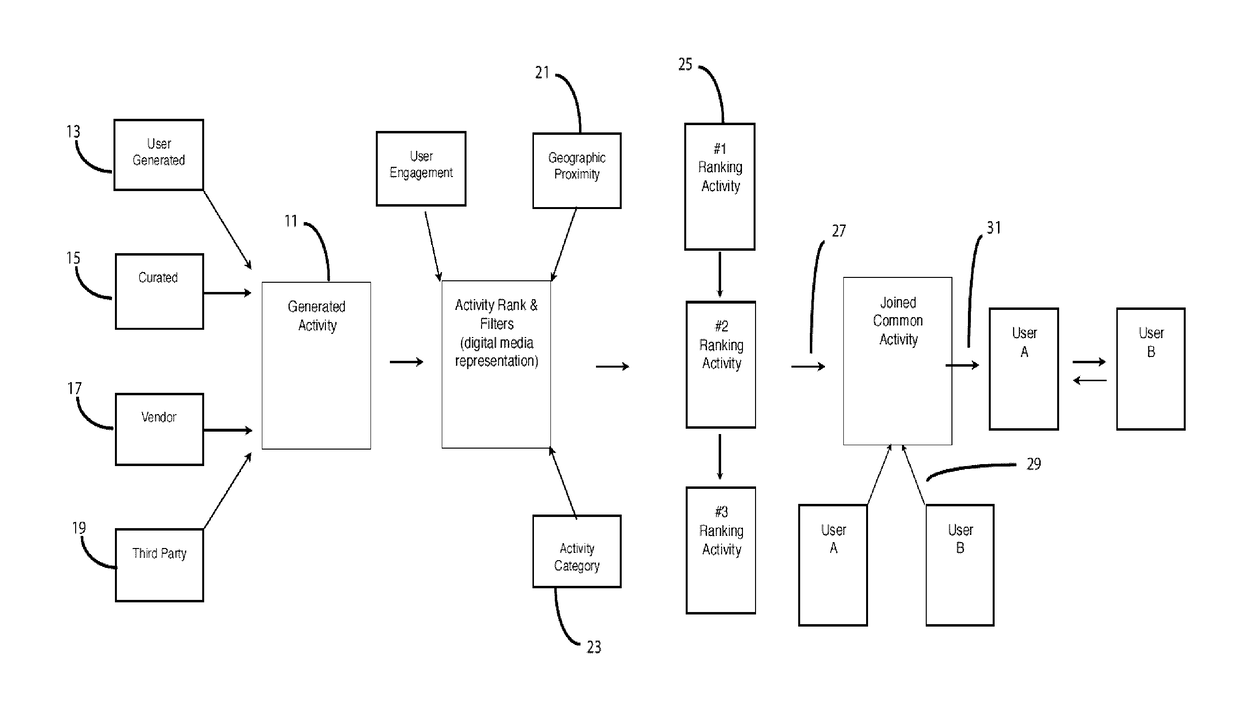
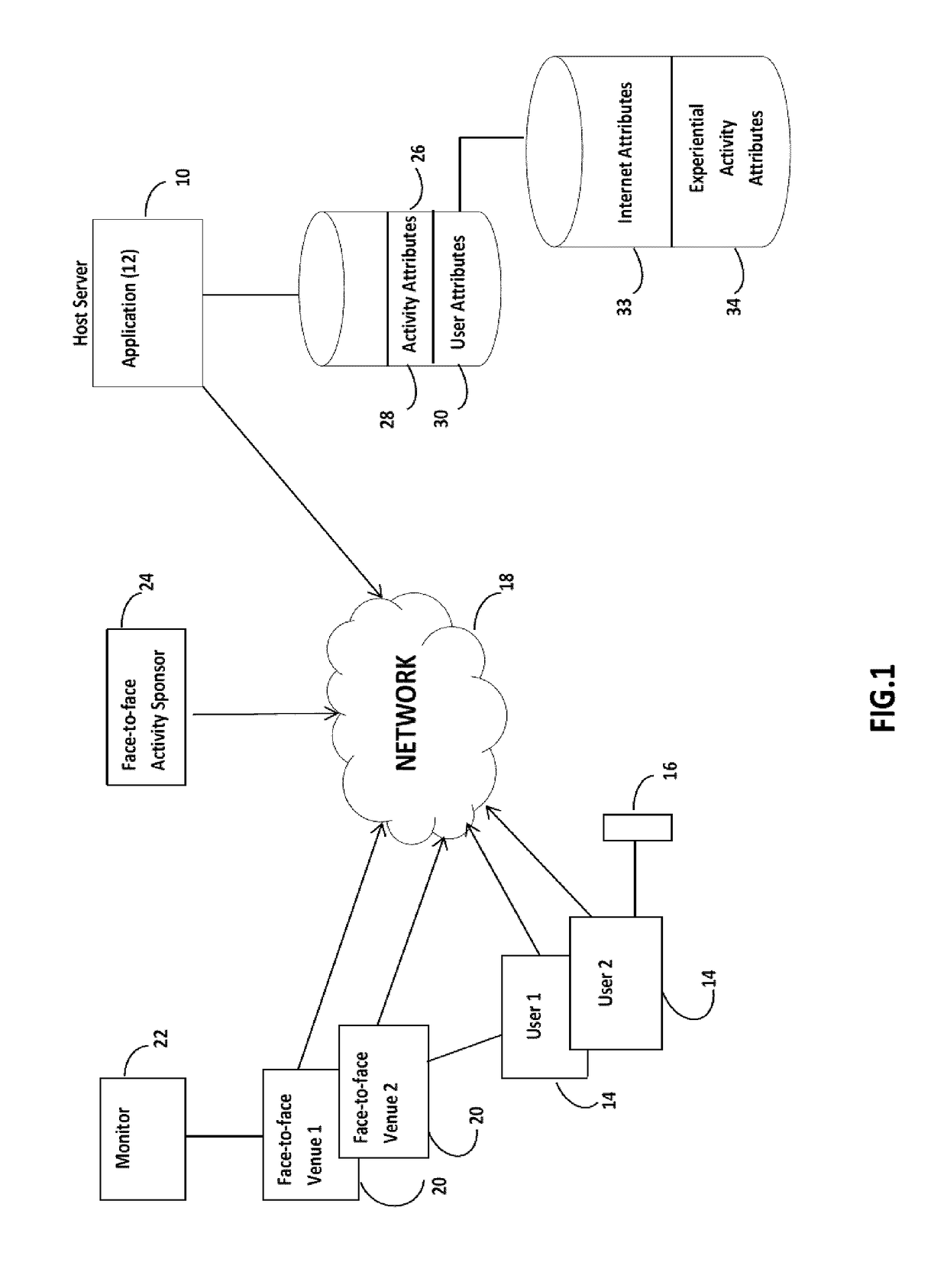
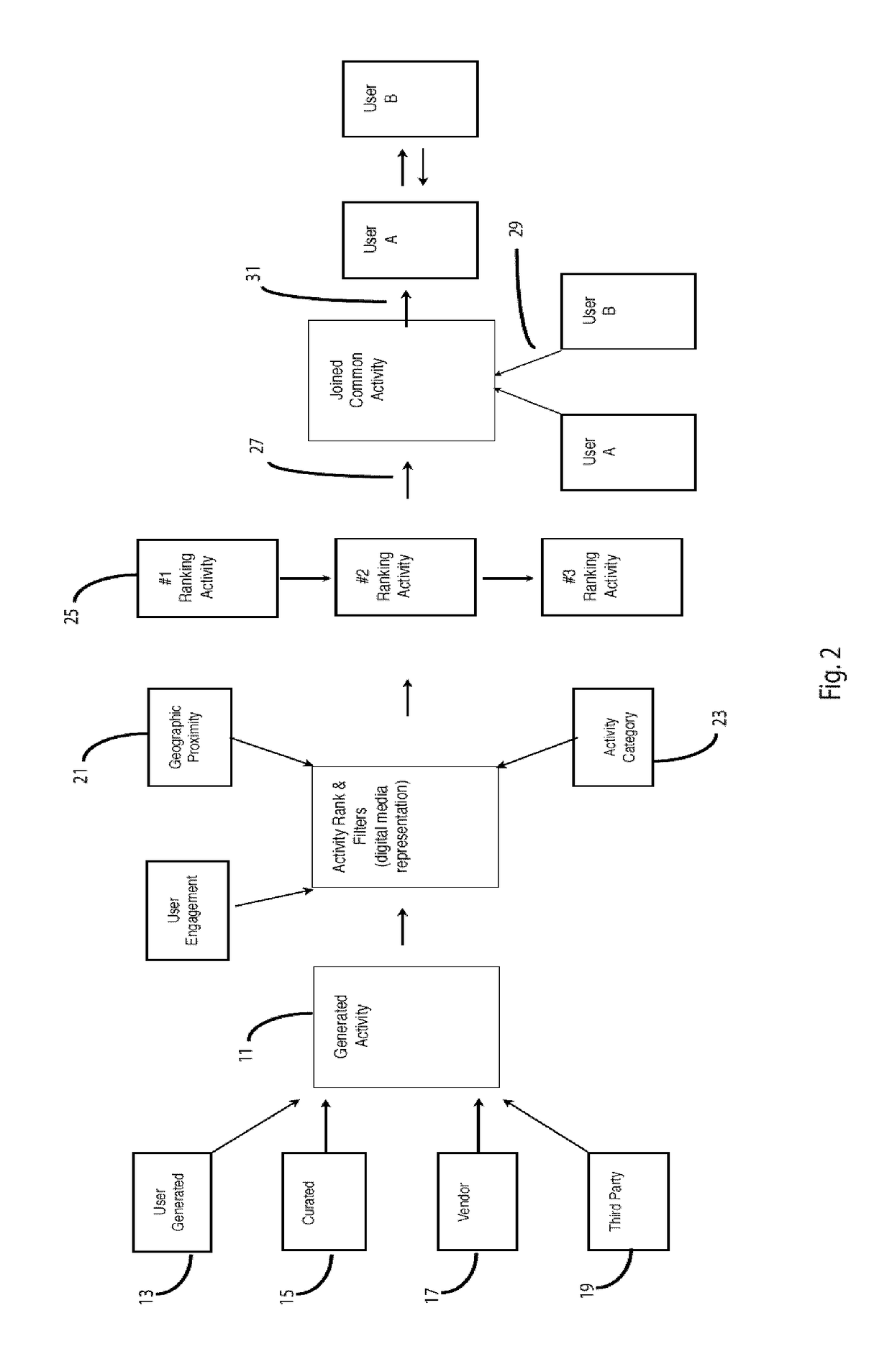
An Activity-Centric System And Method For Relationship Matching
An online dating and relationship system relies on common interests in, and arranging for, specific face-to-face in-person activities. Potential activities are ranked by an activity ranking engine drawing on activity-related attributes of the users and of the activities. Mutual selection of an in-person activity enables the users to vet potential matches and to proceed to engage in the activity together. The ranking and match engines may take into account intrinsic user and activity attributes as well as activity-related attributes derived from the behavior of the users in relation to the activities.
Owner:SUPERDATE NETWORKS INC
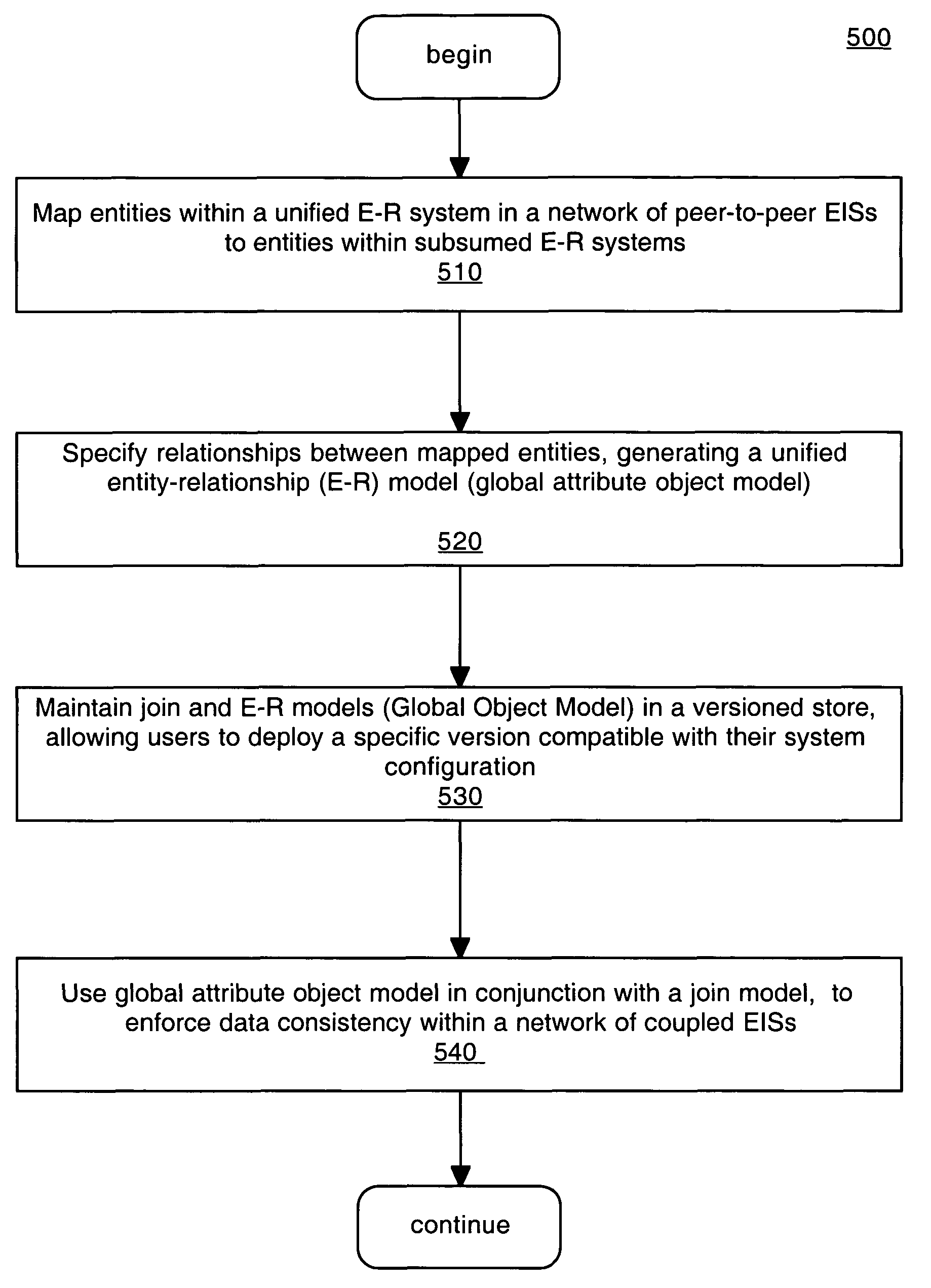
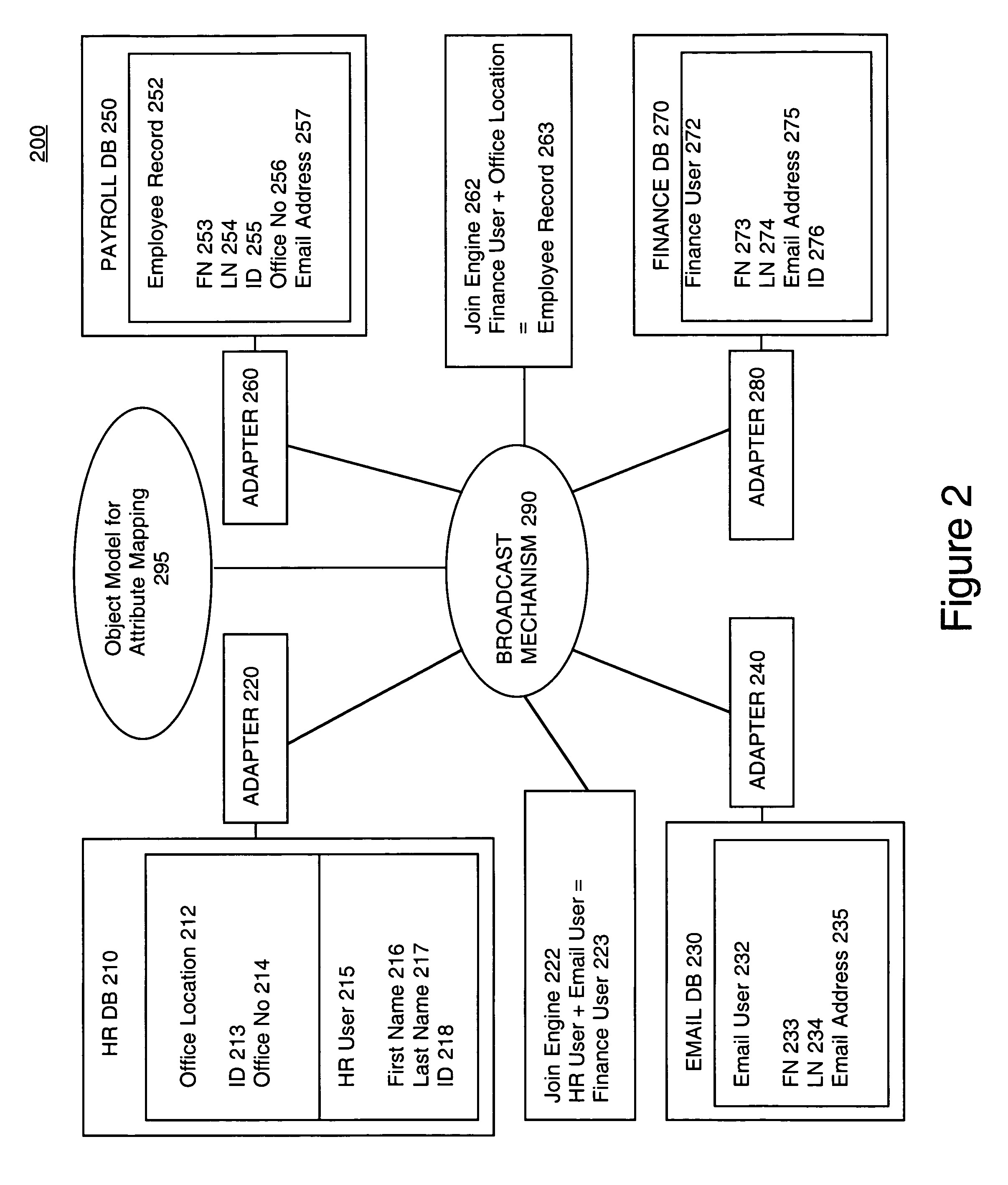
Global attribute mapping data in an enterprise information system
ActiveUS7822708B1Maintain data consistencyDigital data processing detailsRelational databasesRelational systemEnterprise integration
Methods and systems for identifying and maintaining relationships in a network of peer-to-peer enterprise information systems that include a unified entity-relationship system that has a number of entities, each of which has a number of attributes. Subsumed entity-relationship systems are coupled to the unified entity-relationship system, and the entities of the unified entity-relationship system are mapped to one another and to entities and attributes of entities of the subsumed entity-relationship systems. A join engine is coupled to the unified entity-relationship system for performing joins and splits to form related entities and an object model that is coupled to the join engine is available globally throughout the network. The object model contains the mapped relationships and is deployed in conjunction with a join model, the join model specifying transformations and queries required for forming an entity from a set of related entities.
Owner:ORACLE INT CORP
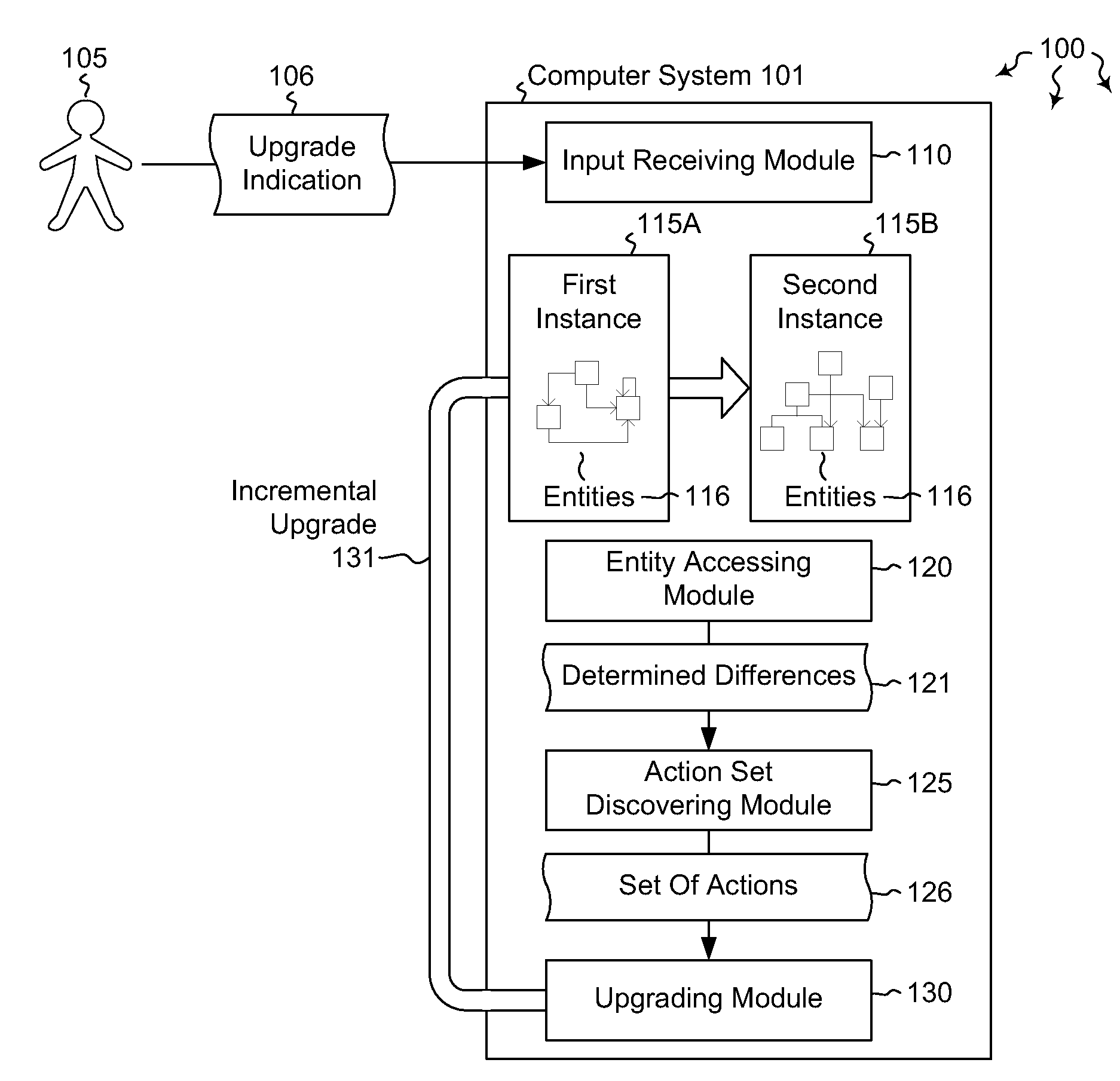
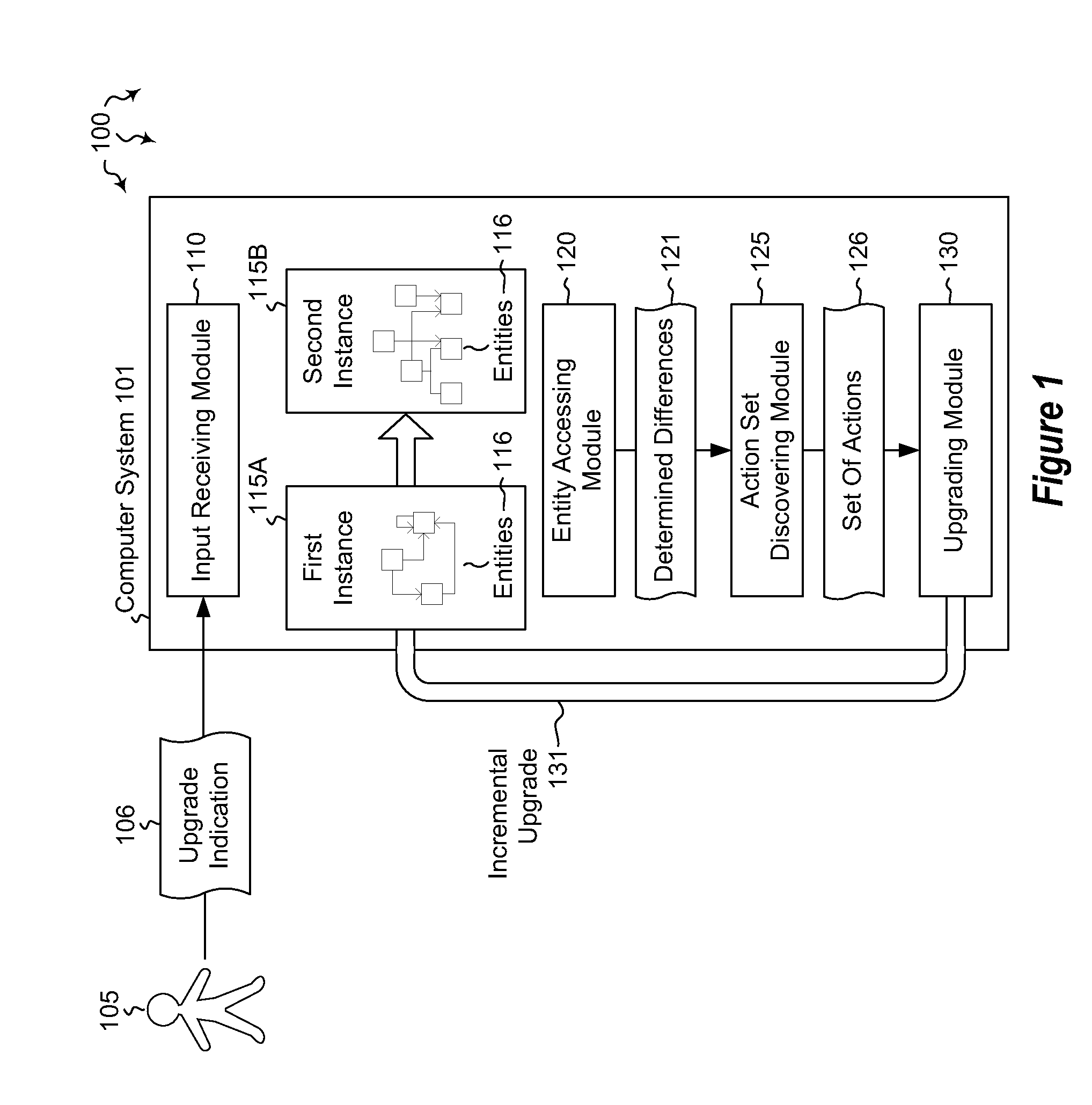
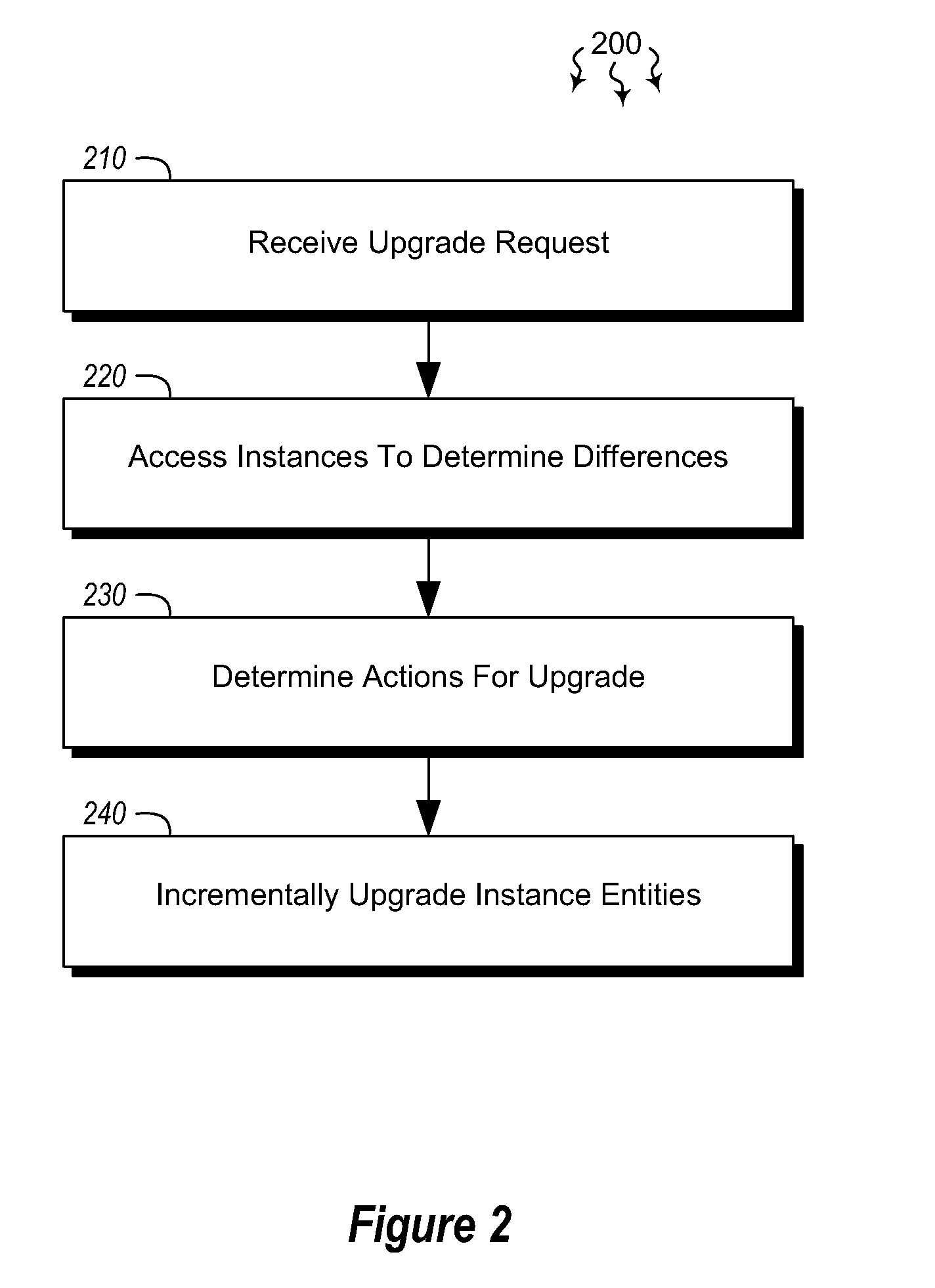
Incremental upgrade of entity-relationship systems
InactiveUS20120272225A1Well formedRelational databasesSpecial data processing applicationsRelational systemSoftware engineering
Embodiments are directed to incrementally upgrading an entity-relationship system. In an embodiment, a computer system receives an indication that one instance including its own specified set of entities is to be upgraded to a second instance including a different specified set of entities. The computer system accesses the two instances to determine the differences between the entities of each instance. The computer system then discovers, based on the determined differences between the two instances, a set of actions that, when executed, change the entities of the first instance to the entities of the second instance. The set of actions is ordered such that processing order constraints are respected. The computer system then incrementally upgrades the entities of the first instance to the entities of the second instance by processing the determined set of actions in the appropriate, constraint-aware order.
Owner:MICROSOFT TECH LICENSING LLC
Object relationship mapping method and device based on object data model
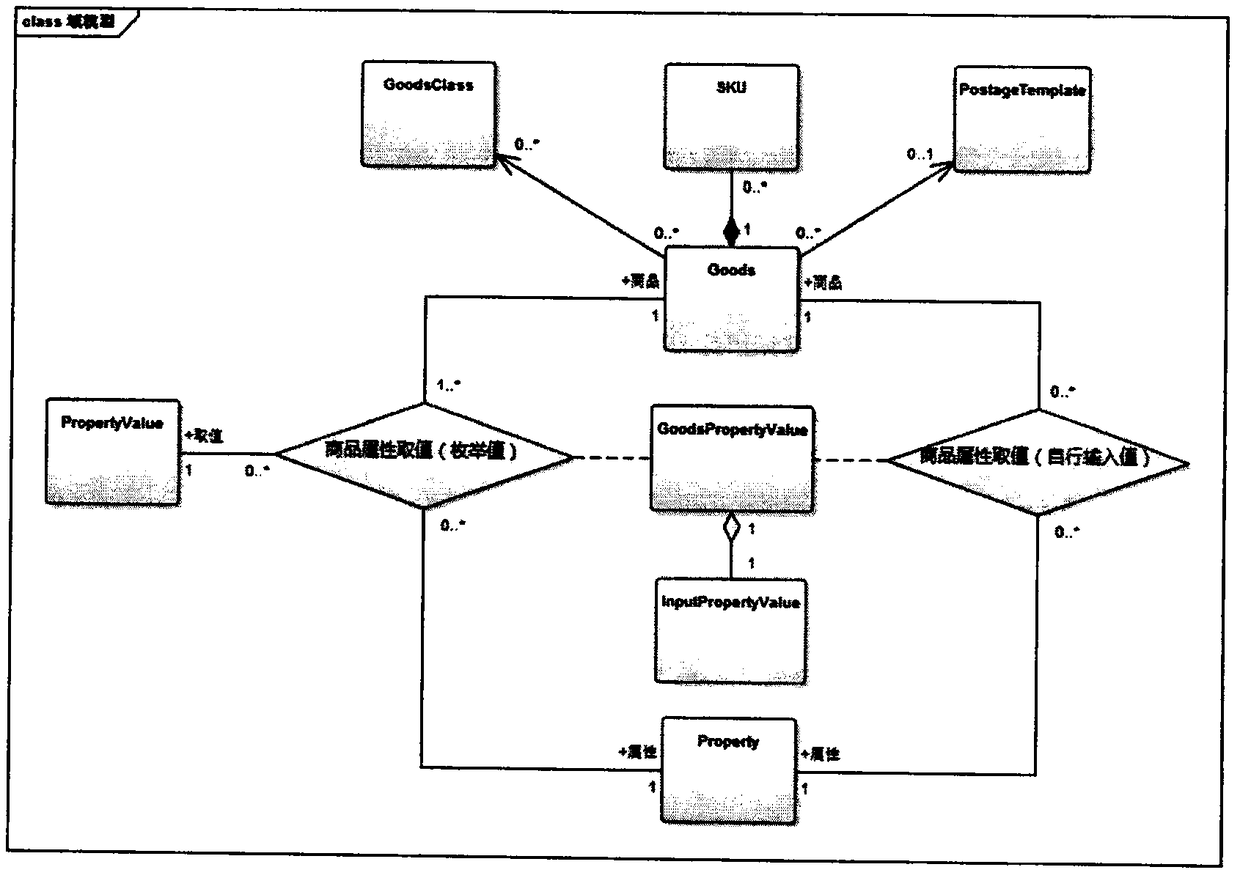
InactiveCN108984541AImprove versatilitySupport multi-party complex associationSpecial data processing applicationsRelational systemObject based
The invention belongs to the technical field of computes and discloses an object relationship mapping method and device based on an object data model. The method is based on a metadata system for describing an object system and a mapping rule between the object system and a relational system, and the method comprises a step of constructing an object system formal model and naming the model the object data model, a step of storing an object to a relation storage system, a step of inquiring the object from the relation storage system, a step of creating an associated end object, and a step of loading an associated reference object. According to the method of the invention, by constructing the object data model and performing object relation mapping based on the object data model, the versatility of an ORM program can be expanded, and a multi-party complex association is supported.
Owner:陈瑞
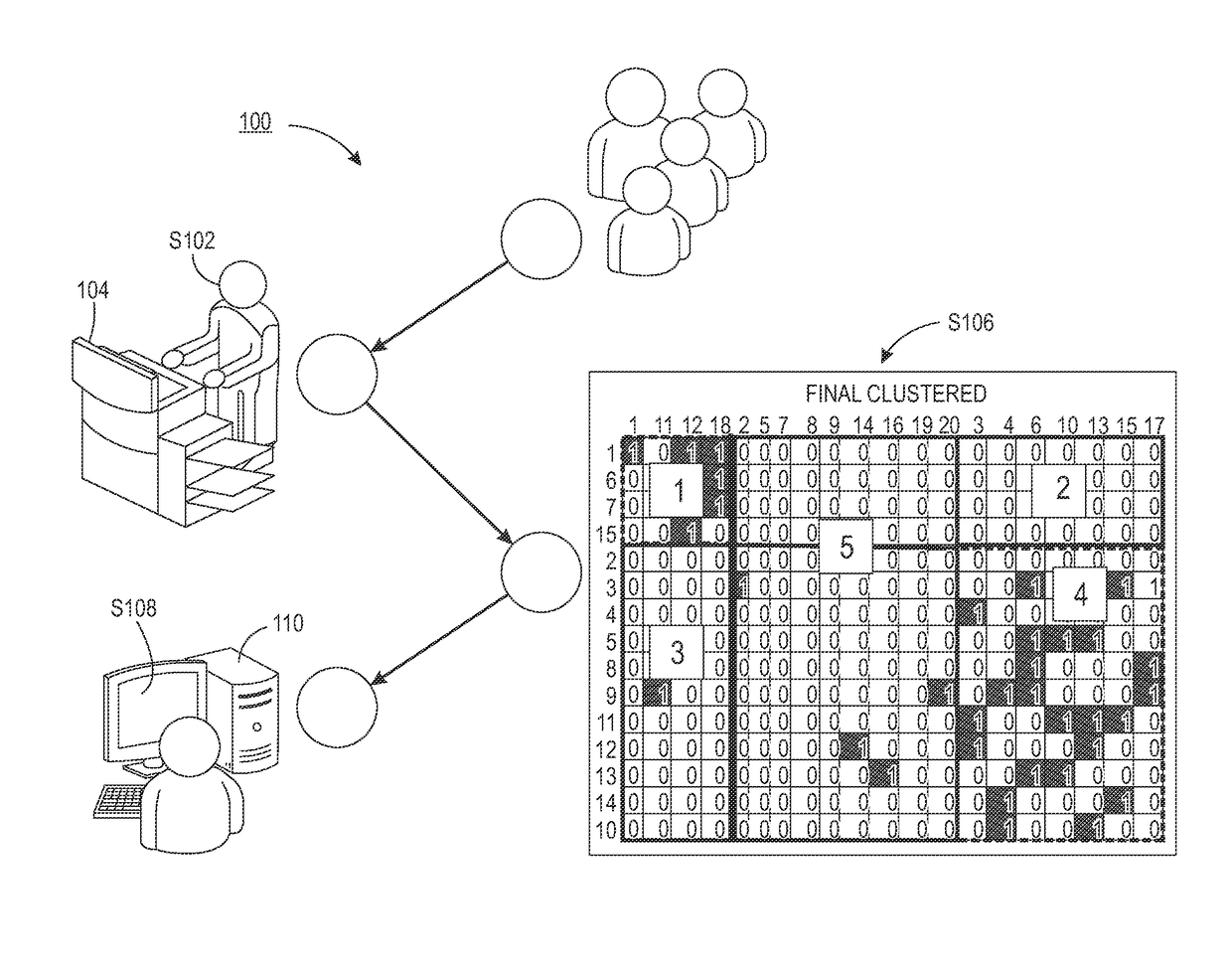
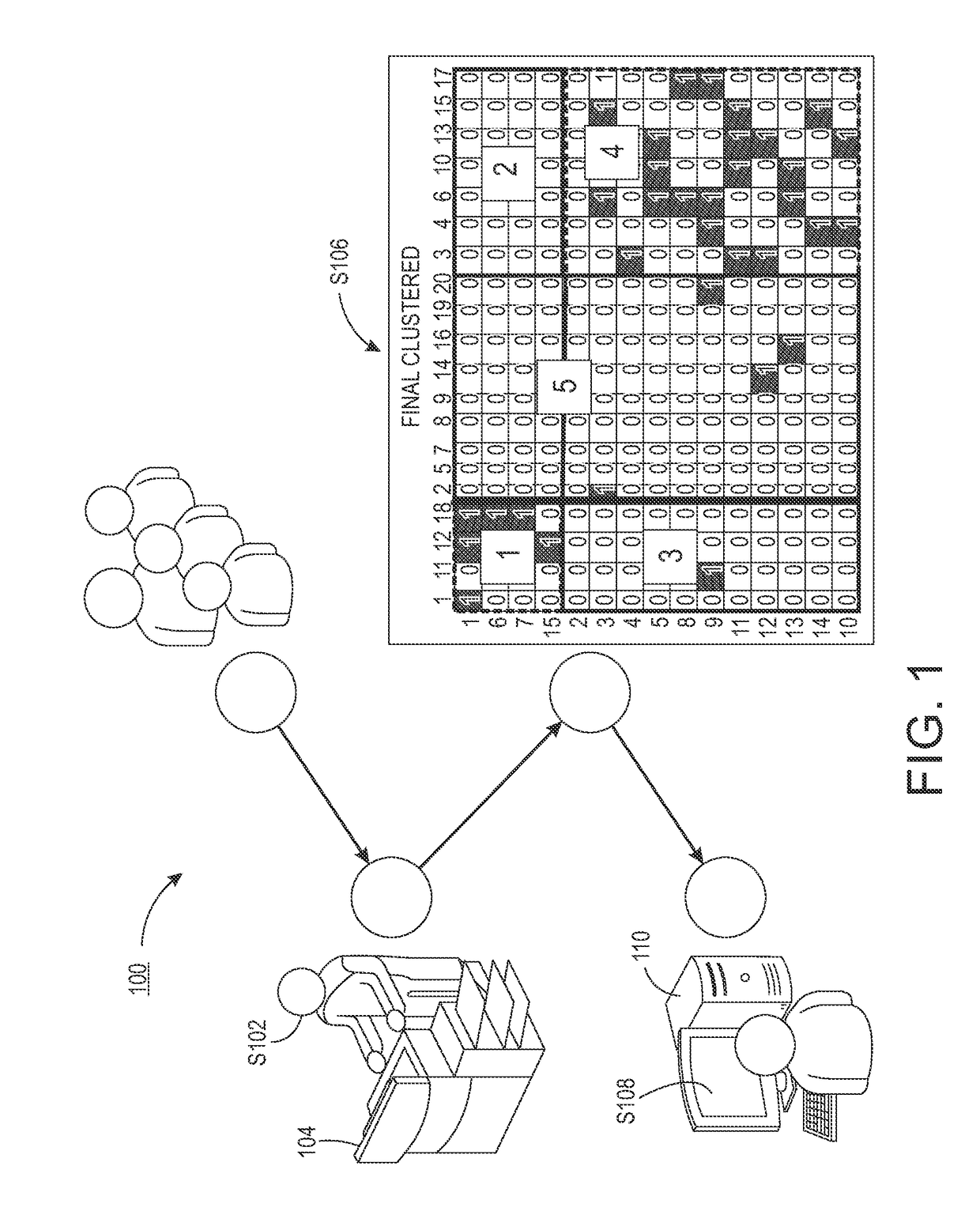
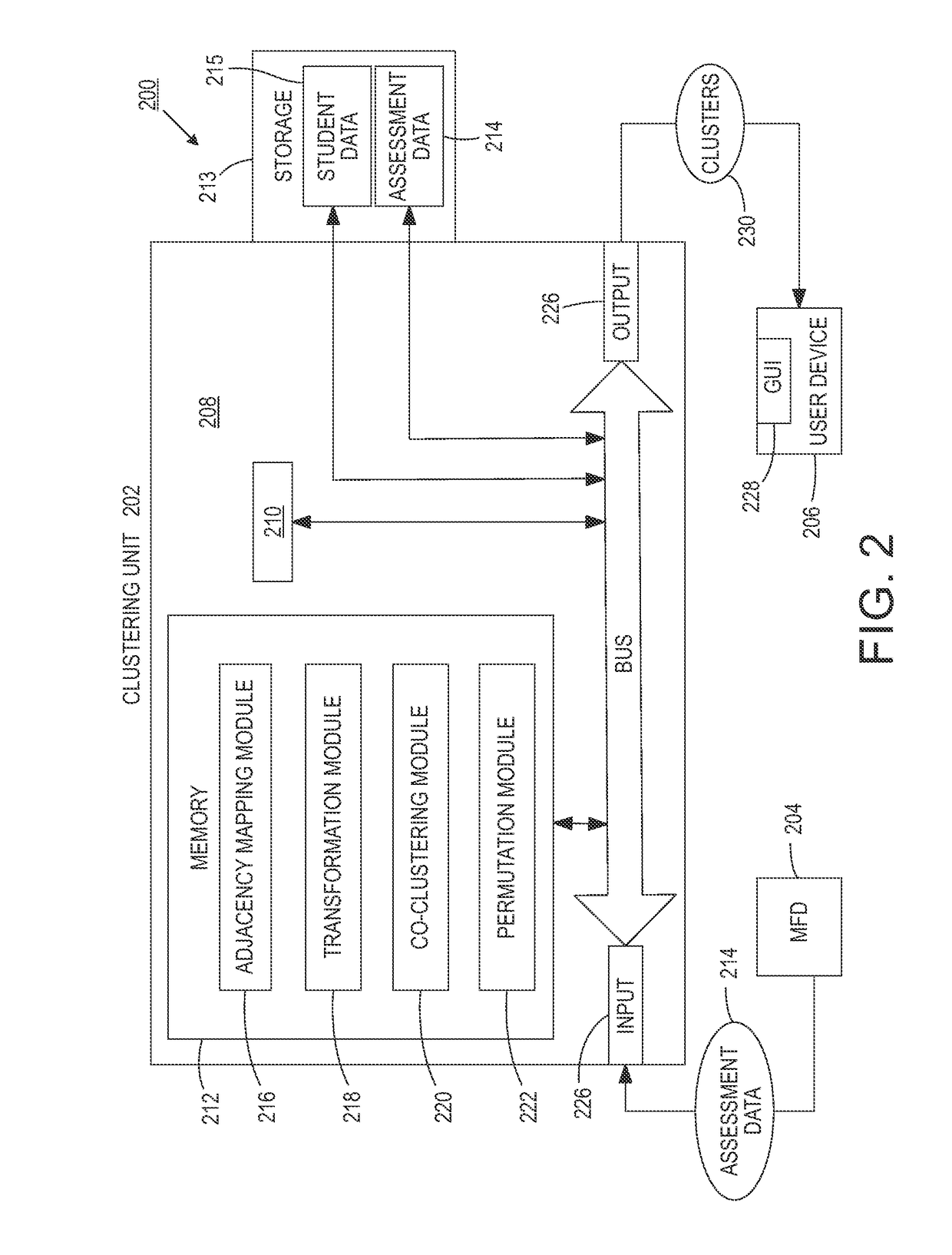
Latent student clustering using a hierarchical block clustering method
The present disclosure relates to a system for verifying homogeneity in clusters and comprises a processor and a non-transitory computer readable memory storing instructions that are executable by the processor. The system creates at least one adjacency matrix representing a relationship between rows and columns of a table. The system applies an algorithm to the table to identify a first set of clusters. For each identified cluster, the system compares a computed dispersion value to a predetermined threshold. The cluster is associated as being homogeneous if the threshold is not met and not homogeneous if the threshold is met. The system reapplies the algorithm to the set of non-homogenous clusters within the data set and repeats the thresholding processes until each cluster resulting from the data set is homogeneous. Upon reaching the desired homogeneity for each cluster, the system recombines the clusters sequentially while keeping the each identified cluster together.
Owner:CONDUENT BUSINESS SERVICES LLC
Line topology checking method and system based on power failure information big data analysis
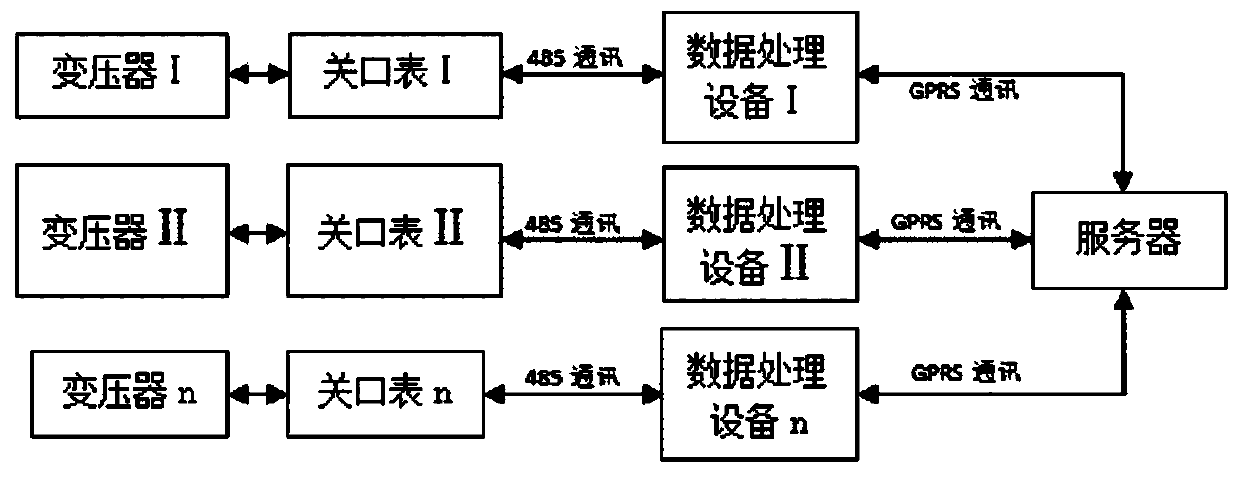
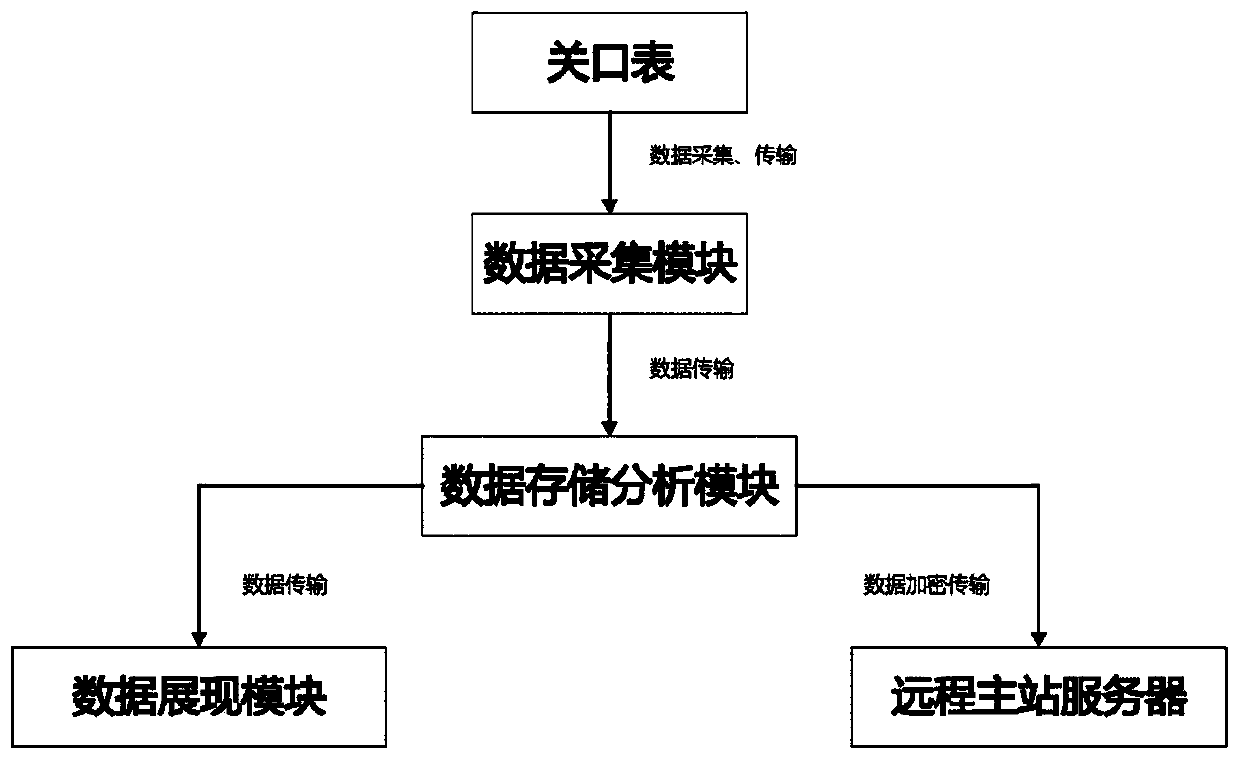
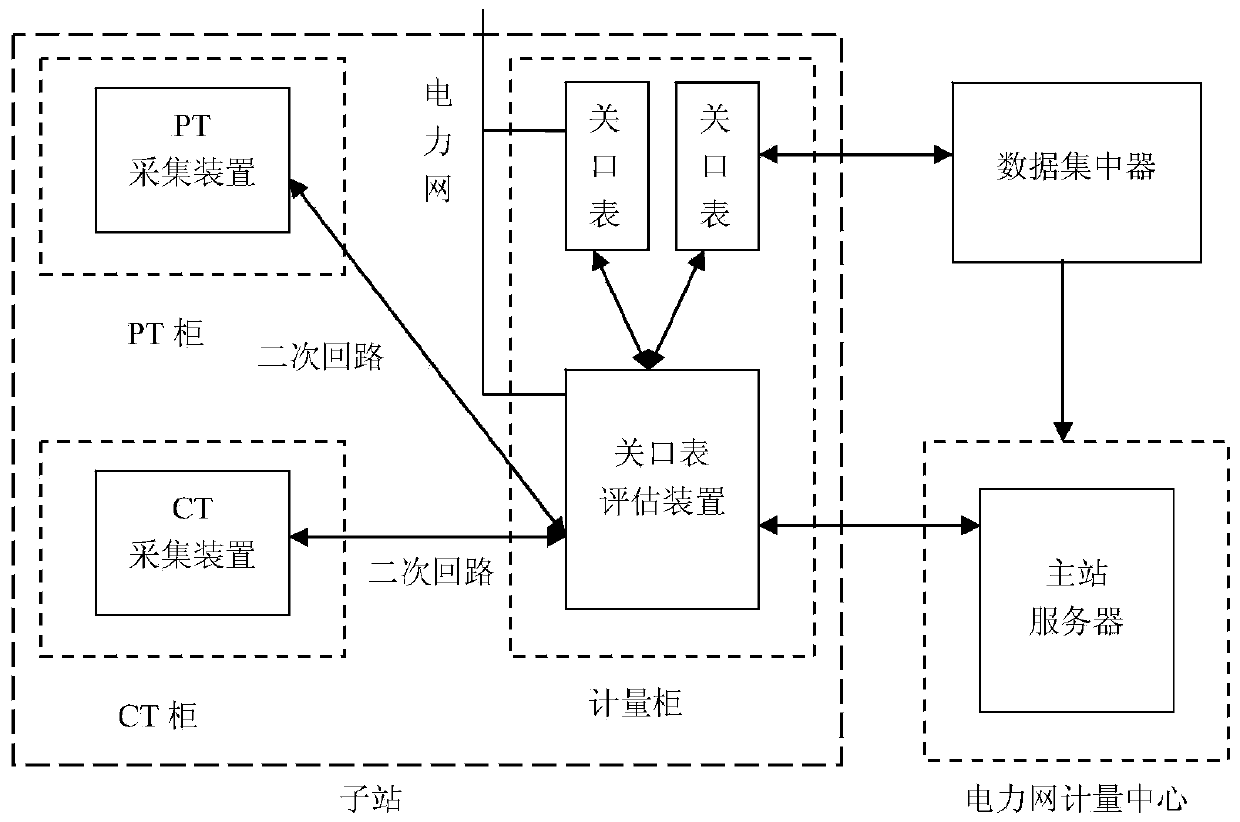
PendingCN110928866AImprove calculation accuracyImprove accuracyData miningResourcesRelational systemData information
The invention discloses a line topology checking method and system based on power failure information big data analysis. The line topology checking method comprises the steps: S1, acquiring power failure information of a gateway meter installed on a transformer; S2, performing logic analysis on the power failure information, and filtering redundant data information and interference data; and S3, analyzing, processing and mining the filtered power failure information by adopting a big data mining method, finding out an abnormal line change relationship, and rectifying the line change relationship. The line topology checking system comprises a gateway meter, data processing equipment and a server, wherein the gateway meter collects and records various parameters of the transformer; the dataprocessing equipment comprehensively collects data in the gateway meter in a power failure time period and transmits the data to the server; and the server analyzes the data and stores the data into adatabase. Technical guidance is provided for carrying out line change relationship field investigation, and technical support is provided for lean marketing management.
Owner:STATE GRID TIANJIN ELECTRIC POWER +2
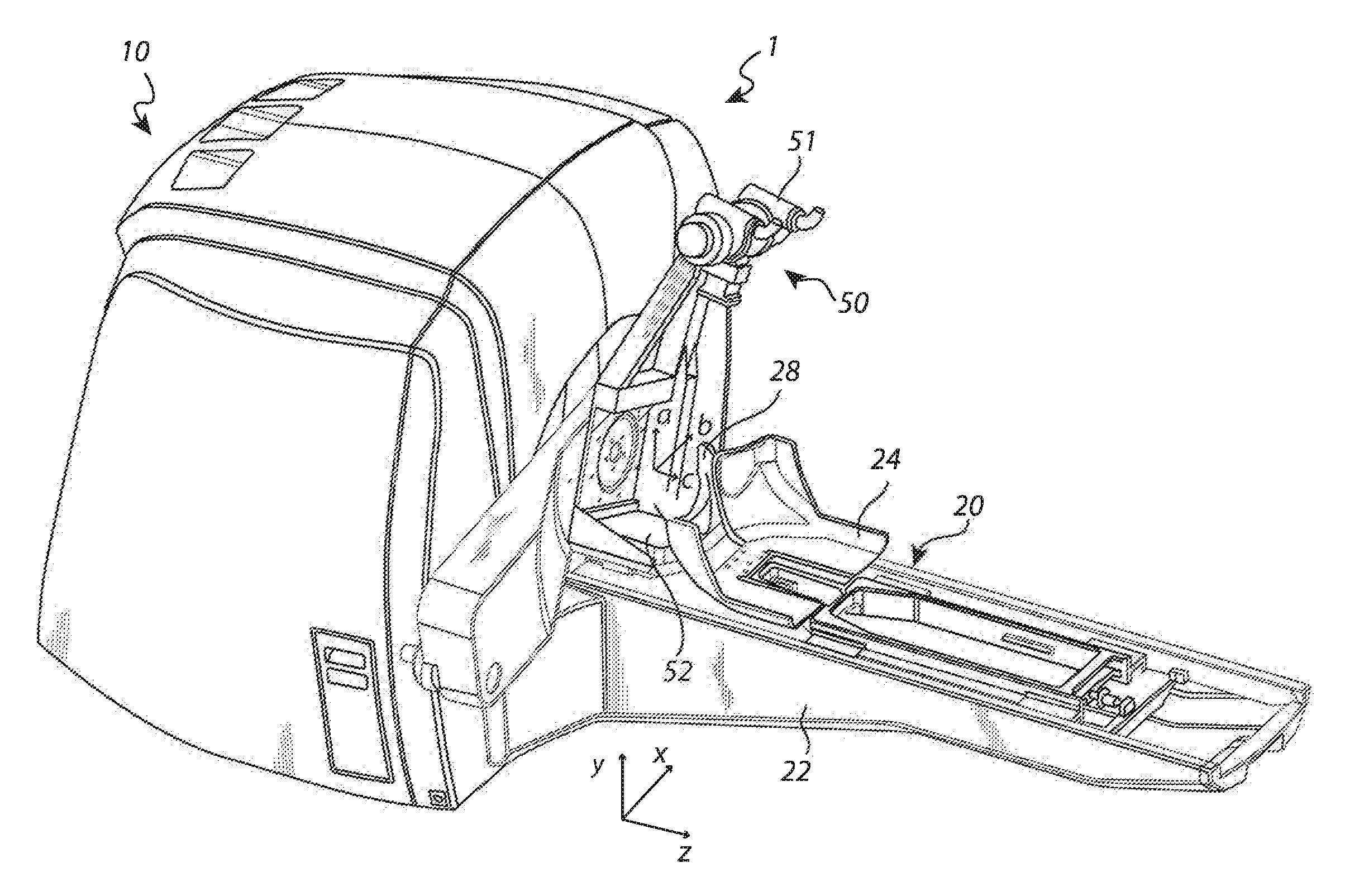
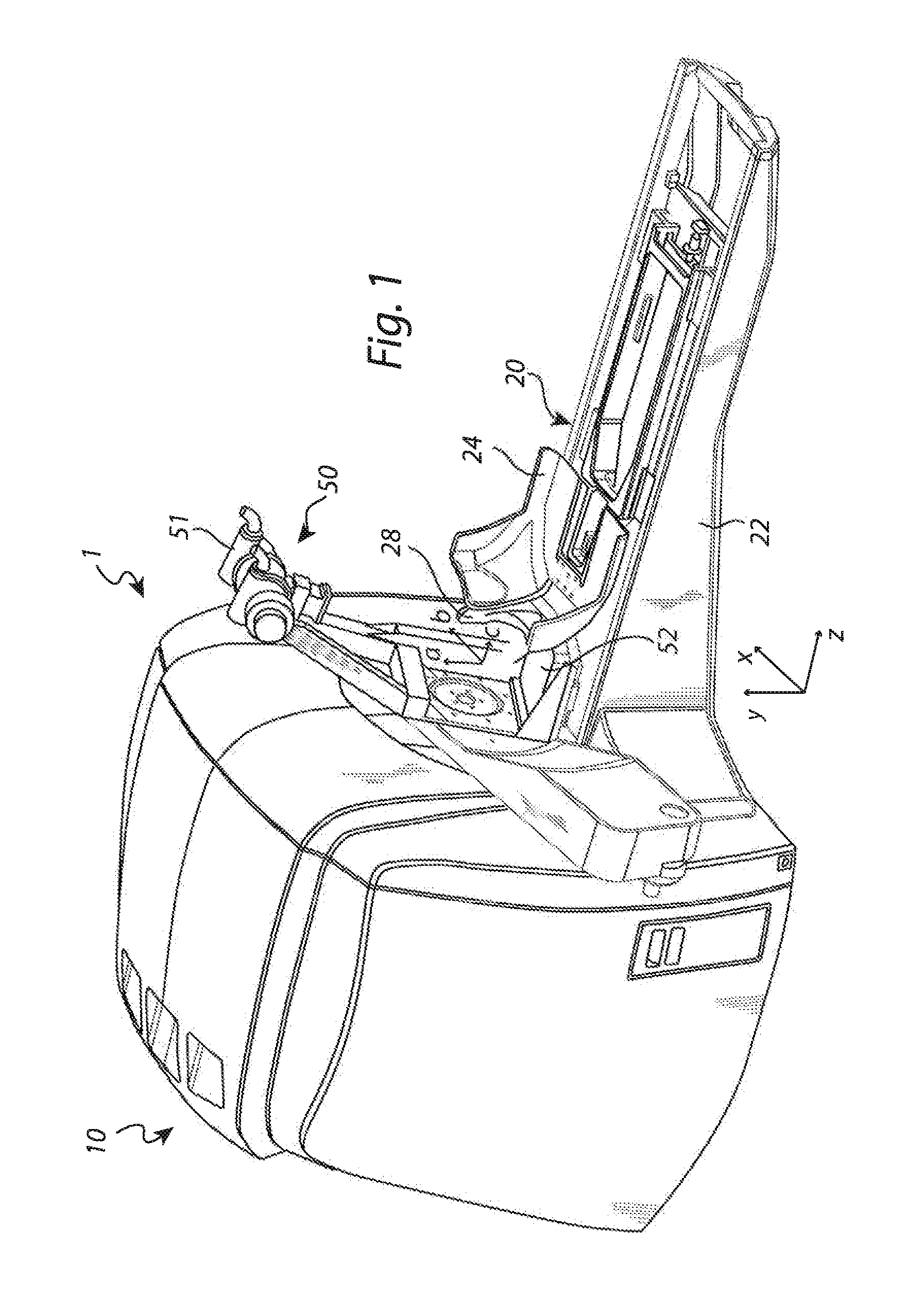
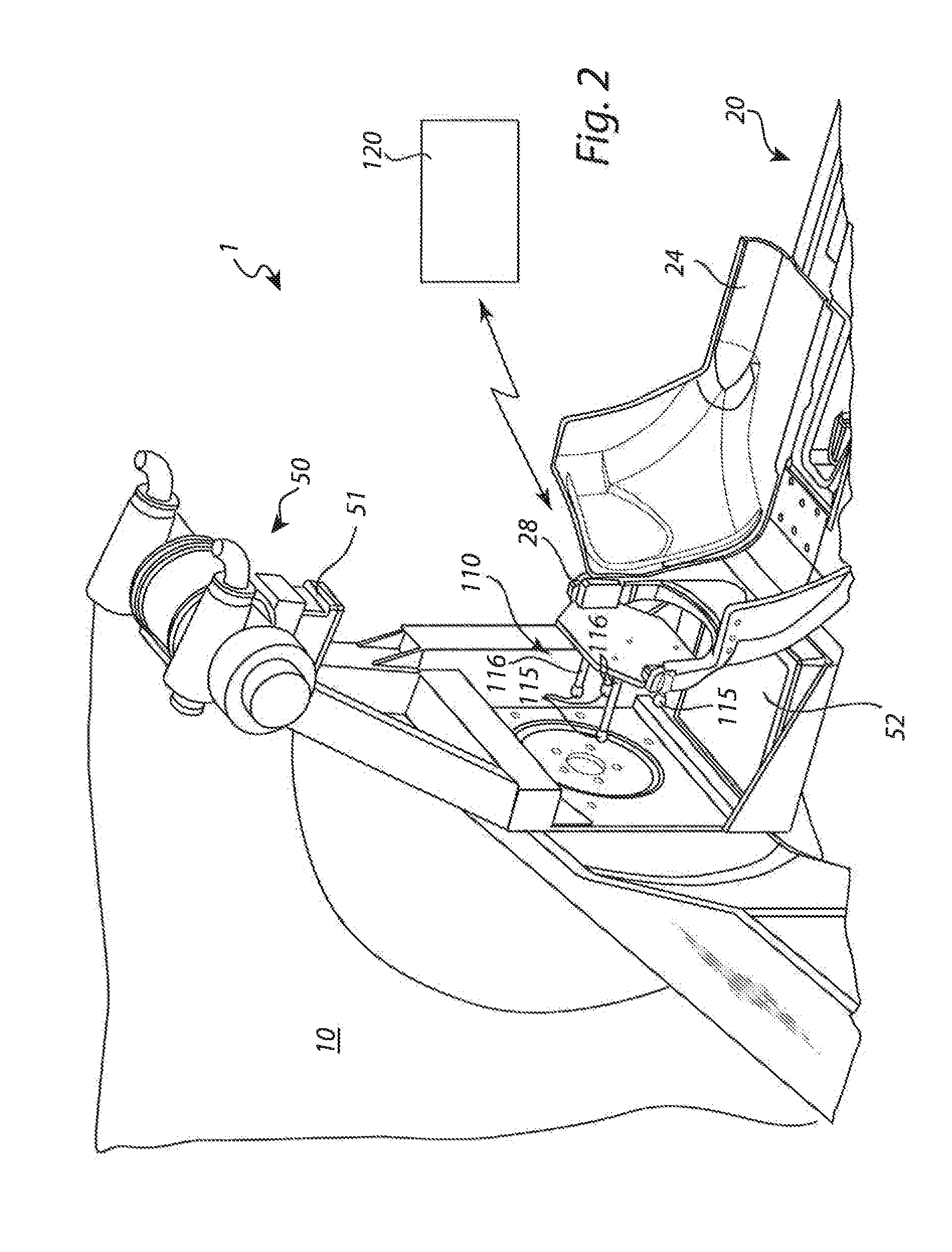
Method for calibration and qa
InactiveUS20140046601A1Large deviationLarge positioningMechanical/radiation/invasive therapiesLocal control/monitoringRelational systemRadiotherapy unit
The present invention relates to the field of radiation therapy. In particular, the invention concerns a method of calibrating a positioning system in a radiation therapy system comprising a radiation therapy unit having a fixed radiation focus point. The method comprises the steps of: —releasably attaching a calibration tool to the fixation arrangement; —performing an image scanning procedure with the imaging system; —determining a position of the calibration tool in a coordinate system related to the imaging system; and —calculating a position difference between the determined position of the calibration tool in the coordinate system related to the imaging system and a position of the calibration tool in the stereotactic fixation unit coordinate system, thereby determining a relationship between the coordinate system related to the imaging system and the position of the calibration tool in the stereotactic fixation unit coordinate system.
Owner:ELEKTA AB
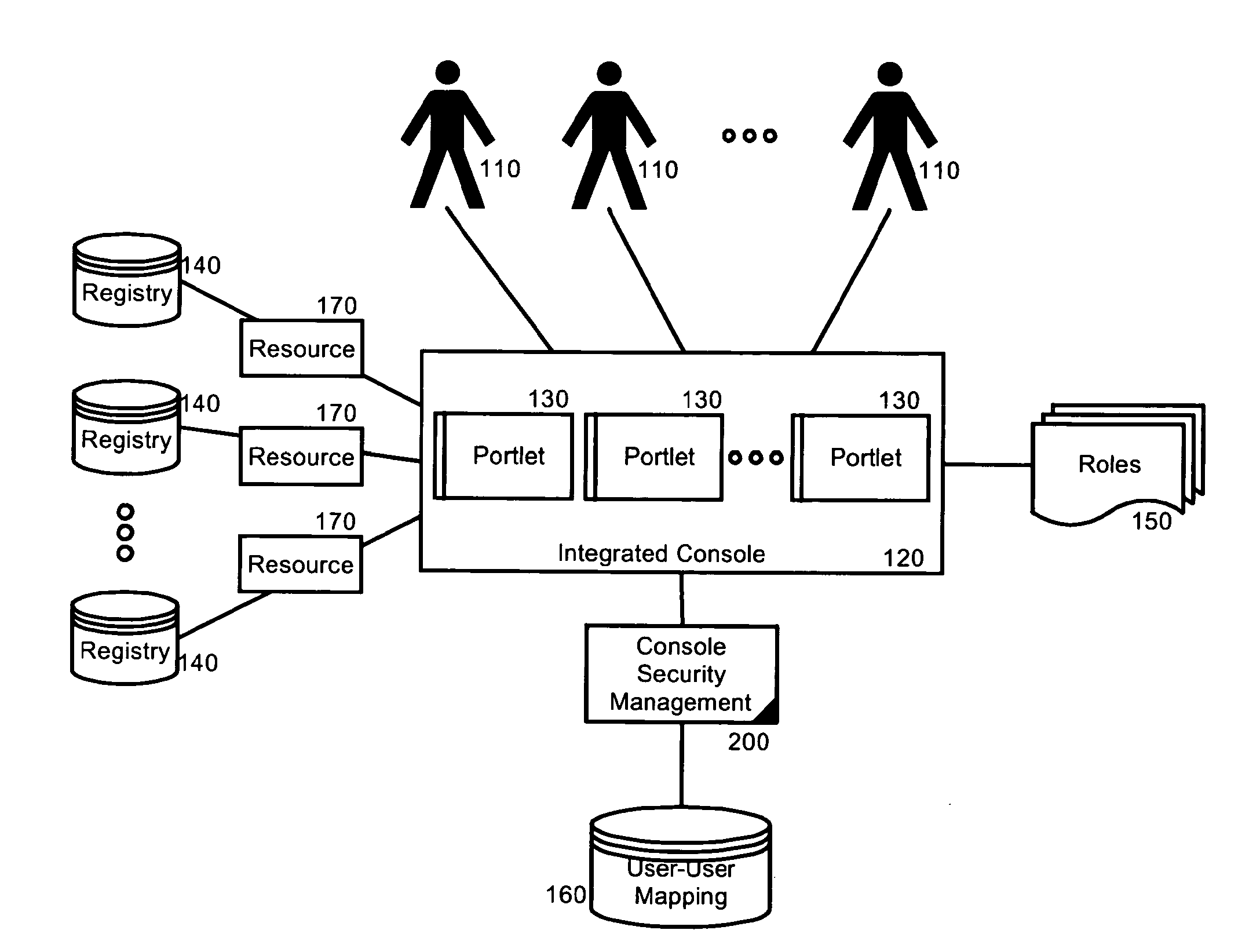
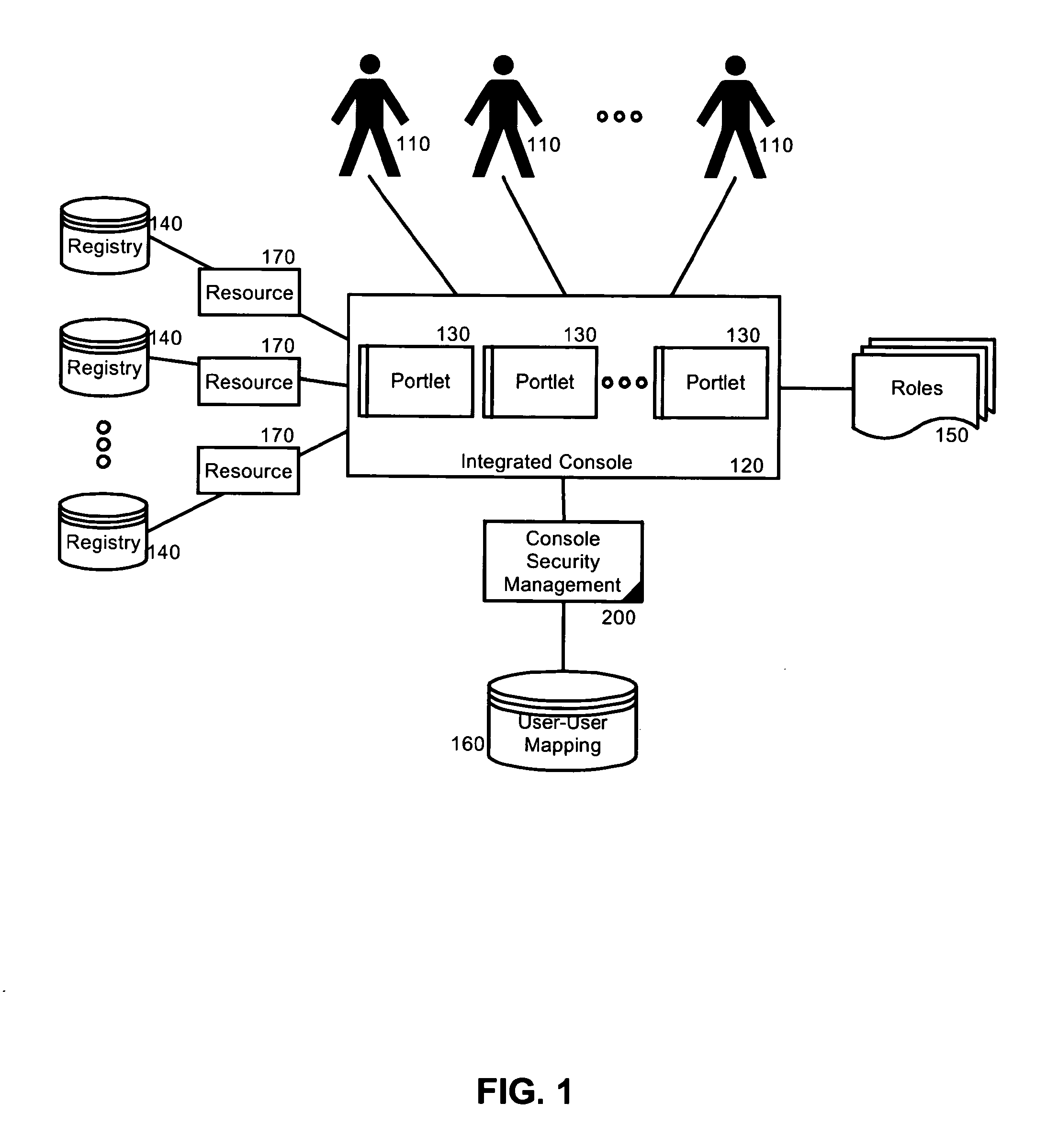
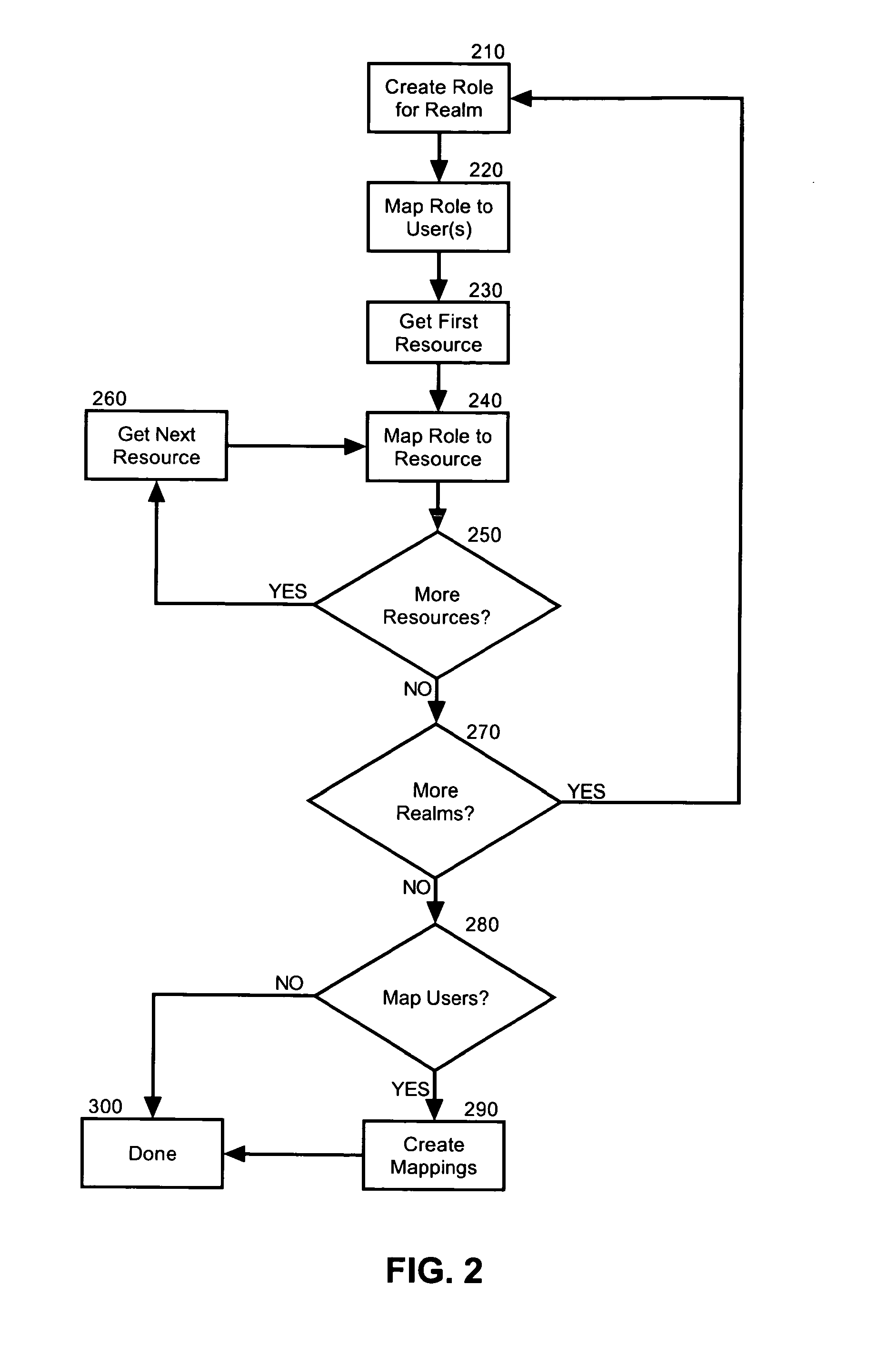
Security management for an integrated console for applications associated with multiple user registries
ActiveUS20120210419A1Digital data processing detailsUnauthorized memory use protectionRelational systemApplication software
A system for security management for applications associated with multiple user registries can include an integrated console configured to host a one or more applications or resource objects in corresponding realms. The system also can include one or more roles mapped to different ones of the resource objects and also to different users permitted to access the integrated console. The system yet further can include a user relationship system having associations with multiple different ones of the roles. Finally, the system can include console security management logic programmed to manage authentication for the users using realm of the resource object while not requiring a separate user registry for the integrated console.
Owner:INT BUSINESS MASCH CORP
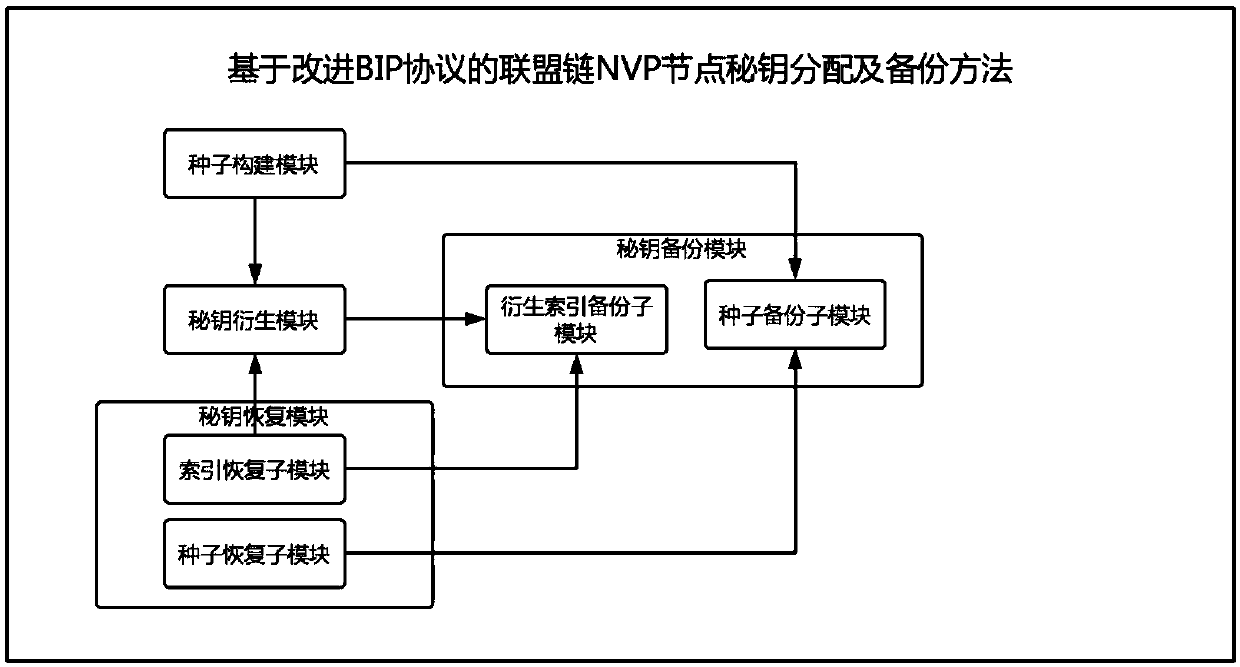
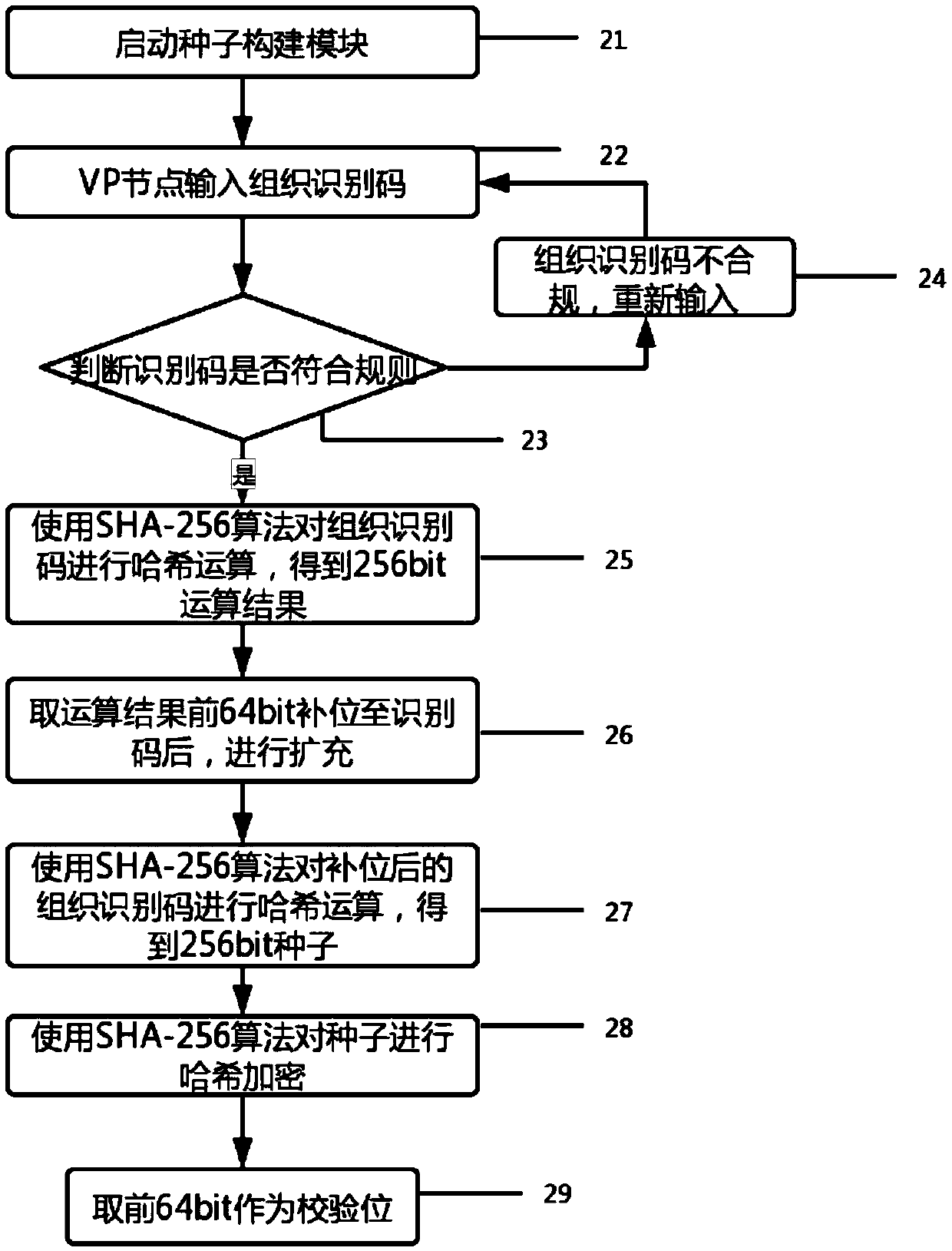
Alliance chain node secret-key distribution and backup system by improved BIP protocol
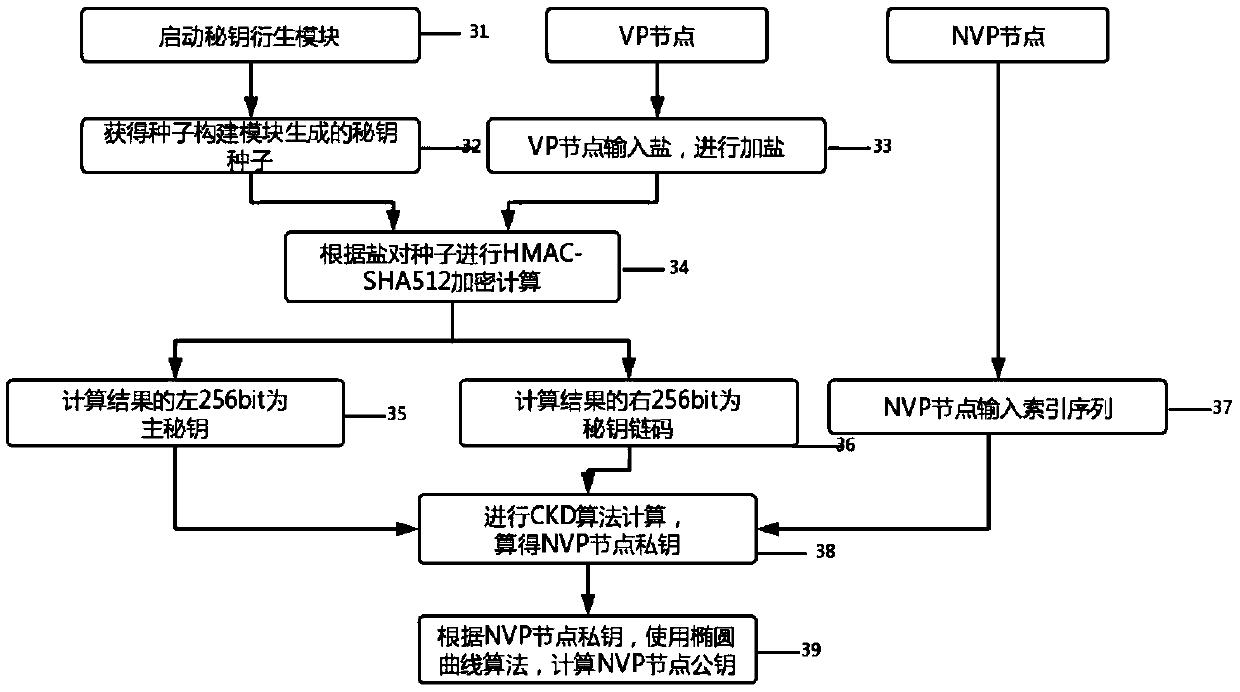
ActiveCN109547218AImprove management efficiencyImprove operational efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesRelational systemKey distribution
The invention relates to an alliance chain node secret-key distribution and backup system by an improved BIP protocol. The method comprises four parts including a seed construction module, a secret-key derivative module, a secret-key backup module and a secret-key recovery module, wherein the seed construction module is used for generating a secret-key seed organized in an alliance chain network;the secret-key derivative module is used for calculating an NVP node secret-key pair by using the secret-key seed, and comprises two parts including NVP node secret-key derivation and NVP public-key calculation; the secret-key backup module is used for backing up the secret-key seed and an index sequence input by an NVP node in the secret-key derivative module, and comprises a seed backup module and a derivative index backup module; and the secret-key recovery module is used for recovering the secret key of the NVP node after the secret key of the NVP node is lost, and comprises three parts including a seed recovery sub-module, an index recovery sub-module and a secret-key recovery sub-module. The invention creates a safe and reliable secret-key relationship system, which can safely generate seeds and store backup; and multi-secret-key extension is supported.
Owner:BEIJING UNIV OF TECH
Object mapping and conversion system
A system for mapping, converting, pruning, flattening, and persisting data amongst object-oriented systems and relational systems. Object class definitions and JSON objects define an object-oriented system and a relational database defines a relational system. An Object Relational Mapping (ORM) system exchanges data between an object-oriented system and a relational system. An ORM system includes an ORM Grammar, an ORM Specification, an ORM Data Structure, and an OR Mapping Unit. Data transfer can be achieved amongst relational and non-relational systems. An Object Conversion System (OCS) system exchanges data between one or more object-oriented systems. An OCS system includes an OCS Grammar, an OCS Specification, an OCS Data Structure, and an Object Conversion Unit. The ORM and OCS Specifications may use virtual attributes including path expressions. A path expression includes a chain of attribute names to specify a nested attribute in an object graph. Objects may be augmented with extra attributes during mapping or conversion. An OCS system can be used as an automatic object conversion machine. Multiple OCS systems may provide an Object Conversion Exchange service.
Owner:SOFTWARE TREE LLC
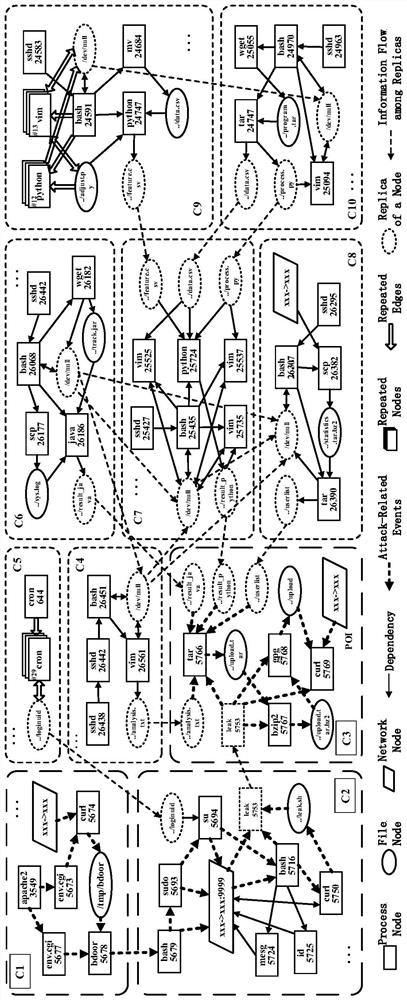
Summary graph generation method of system log dependency graph for attack investigation and restoration
PendingCN114637892AReduce sizeEasy to viewOther databases indexingSpecial data processing applicationsRelational systemAlgorithm
The invention provides a summary graph generation method of a system log dependency graph for attack investigation and restoration, comprising: determining a system entity dependency graph of an attack event to be investigated and restored, the dependency graph comprising system entity nodes associated with the attack event and a call relationship between the system entity nodes; the system entity nodes comprise process nodes and resource nodes; executing hierarchical random walk on process nodes in the dependency graph, and determining behavior representation of the process nodes; clustering the process nodes based on the behavior representation, and dividing the dependency graph into at least one first sub-graph based on a clustering result; compressing each first sub-graph to obtain at least one second sub-graph; generating a summary corresponding to each second sub-graph, and obtaining a summary graph corresponding to the dependency graph. According to the method, the dependency graph is divided into the sub-graphs, and the simple summary is provided for each sub-graph to generate the summary graph, so that the summary of related system activities and the summary information of the sub-graphs related to attacks can be conveniently checked.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Trusted product transaction system realizing method and realizing system
InactiveCN105844484ASave the cost of counterfeitingResolve trust issuesCustomer relationshipRelational systemE-commerce
The present invention relates to the field of electronic commerce, and provides a reliable product transaction system realization method and realization system, and establishes a user-based user relationship system based on trusted acquaintances in the real society to control product transactions or product promotion levels, without restrictions Products with trustworthy qualifications continue to trade, restrict products that do not have trustworthy qualifications from continuing to recommend, prevent products from being traded or advertised at the level of untrustworthy users, and check products at all levels through trusted acquaintances in the real society, and trade products Or product promotion is always controlled within the trustworthy range, effectively solving the trust problem, so that users can shop online with confidence; and because users in the trusted user level are acquaintances in the real world, it is easy to form a community of interests, and the system can explore the community of interests. Allow users within the trusted hierarchy to benefit.
Owner:郭英
Contact relationship systems and methods
Owner:APEX COVANTAGE
System and method for a real-time egocentric collaborative filter on large datasets
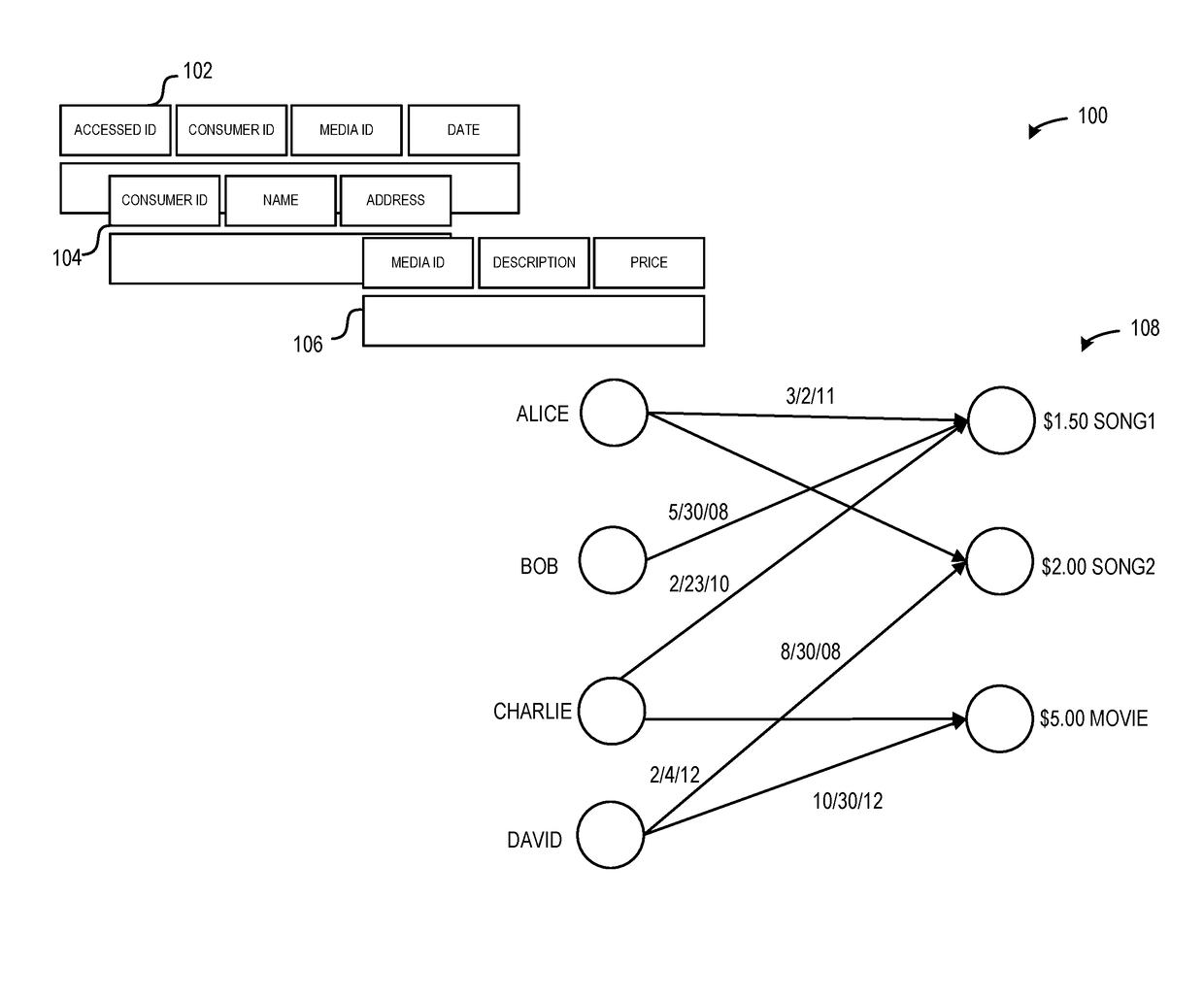
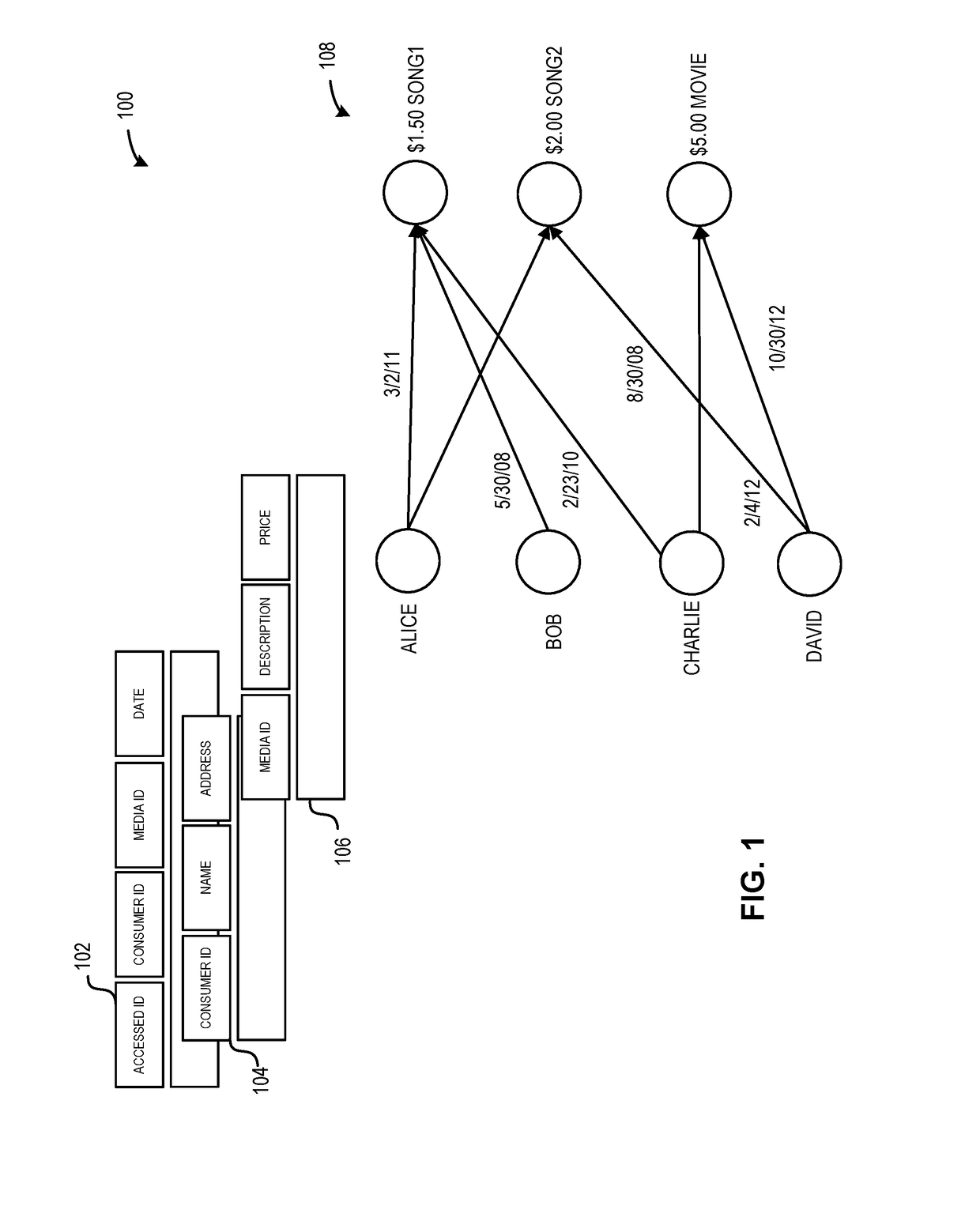
One embodiment of the present invention provides a system for generating a product recommendation. During operation, the system obtains data indicating vertices and edges of a graph. The vertices represent consumers and products and an edge represents an access relationship. The system may receive a query indicating an ego for determining a product recommendation. The system may then traverse the graph from a vertex representing the ego through a plurality of edges to a plurality of vertices representing products. The system may traverse the graph from the plurality of vertices representing products to a plurality of vertices representing other consumers. The system may then traverse the graph from the plurality of vertices representing other consumers to a plurality of vertices representing other products. The system may generate a recommendation that based on the plurality of vertices representing other products.
Owner:XEROX CORP
Image processing apparatus, image processing method, and storage medium
ActiveUS20190260976A1Static indicating devicesPicture reproducers using projection devicesImaging processingRelational system
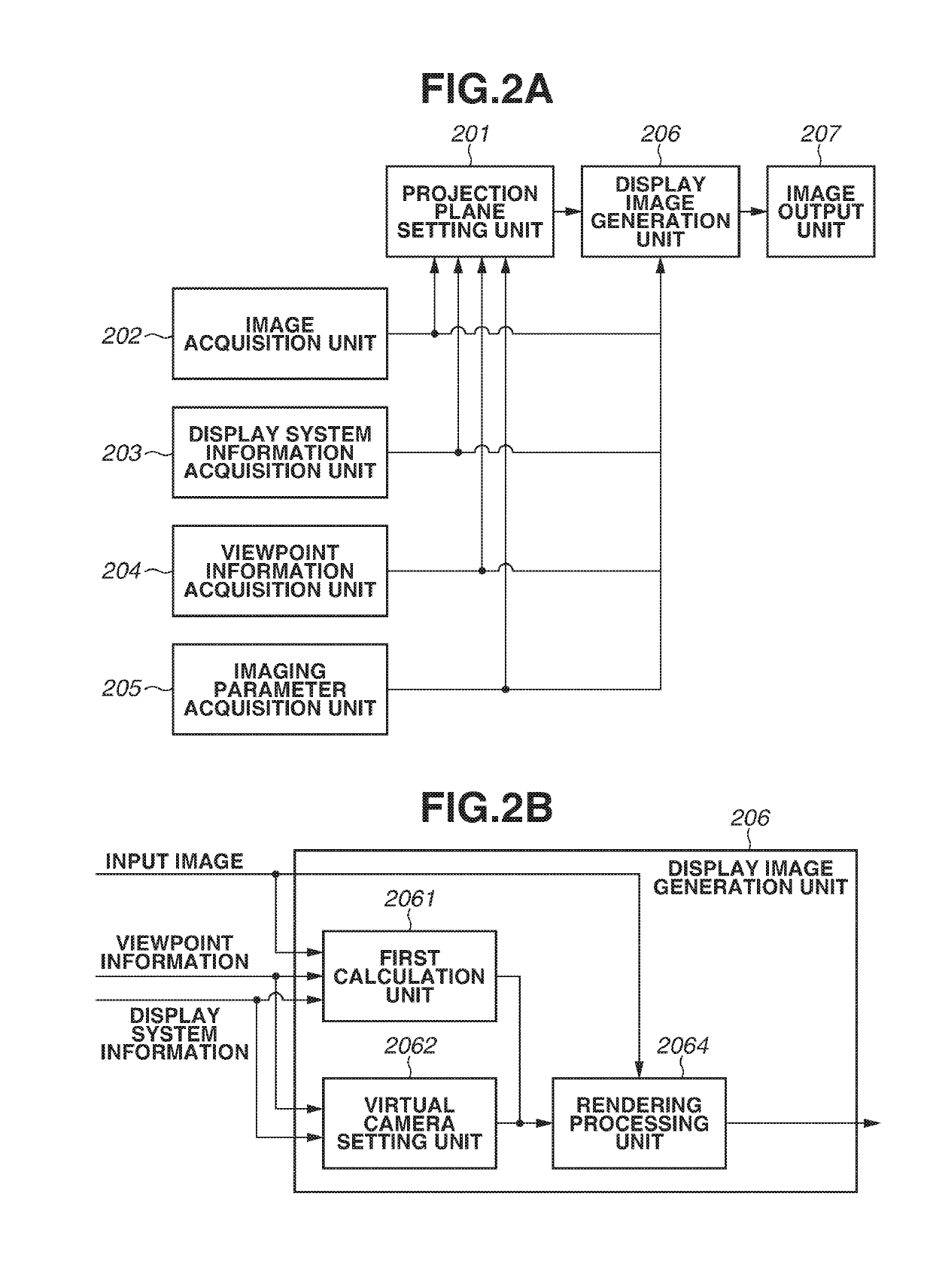
An image processing apparatus includes a first acquisition unit configured to acquire an imaging angle of view at which an input image is captured, a second acquisition unit configured to acquire display system information indicating, in a display system including a display portion, a display angle, which is a visual angle at which the display portion is viewed from a viewpoint position, and a generation unit configured to, using a correspondence relationship between a projection plane and the display portion in a virtual space based on the imaging angle of view and the display system information, generate a display image to be displayed on the display portion.
Owner:CANON KK
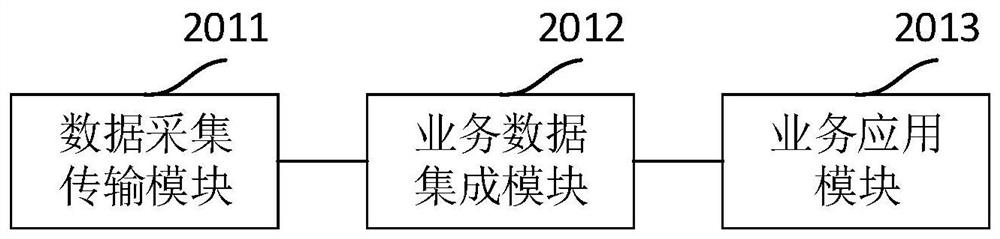
Production line edge terminal and production line management system
InactiveCN111880487AImprove management efficiencyAchieve integrationTotal factory controlProgramme total factory controlRelational systemIndustrial equipment
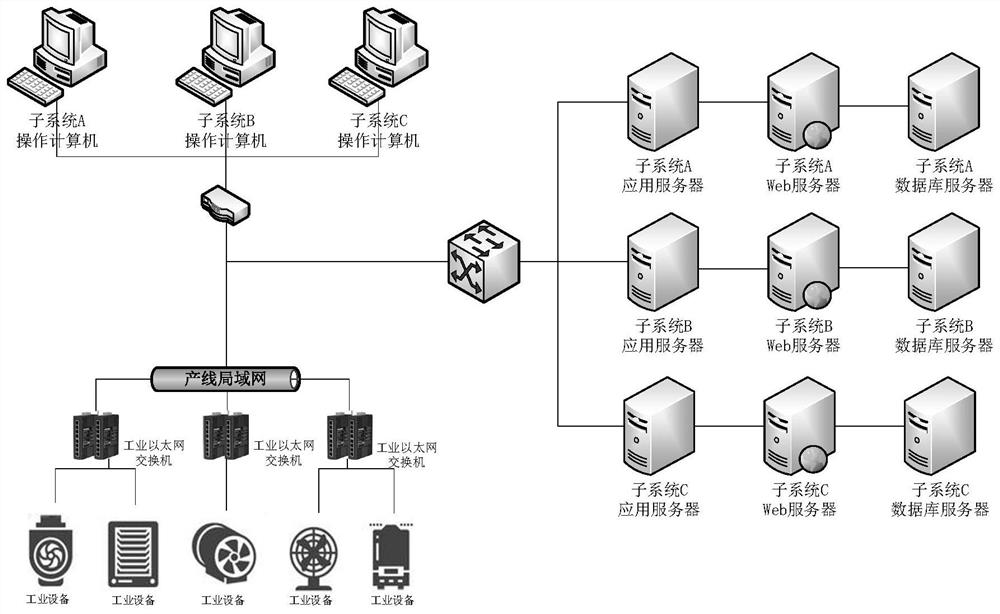
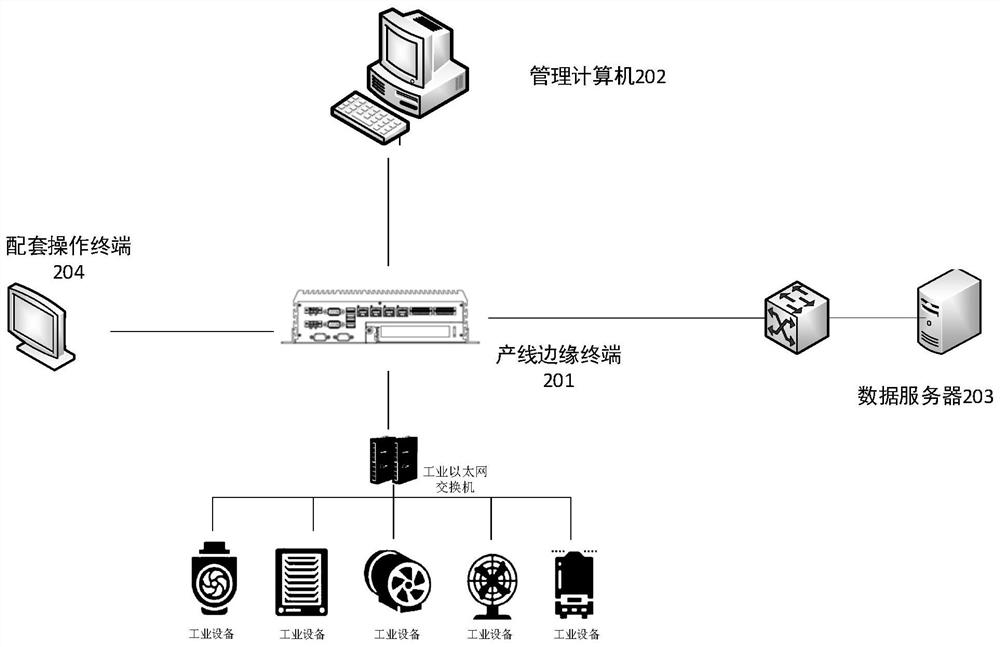
The invention discloses a production line edge terminal and a production line management system. The production line edge terminal is provided with a plurality of communication interfaces, the terminal is connected with a management computer and a plurality of industrial devices, and the communication interfaces supported by the plurality of industrial devices are the same or different. The terminal comprises: a data acquisition and transmission module, which is used for acquiring data from the plurality of industrial devices and carrying out data transmission with the management computer; thebusiness data integration module which is used for preprocessing the acquired data according to different business requirements; and the service application module which is used for analyzing and managing the preprocessed data according to different service requirements. The system comprises the production line edge terminal, a management computer and a data server. According to the scheme, a production line relation system is simplified, integration and upgrading of software and hardware are achieved, the production line management efficiency is improved, and the management cost is reduced.
Owner:中工互联(北京)科技集团有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com