Patents
Literature
39results about How to "Maintain data consistency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
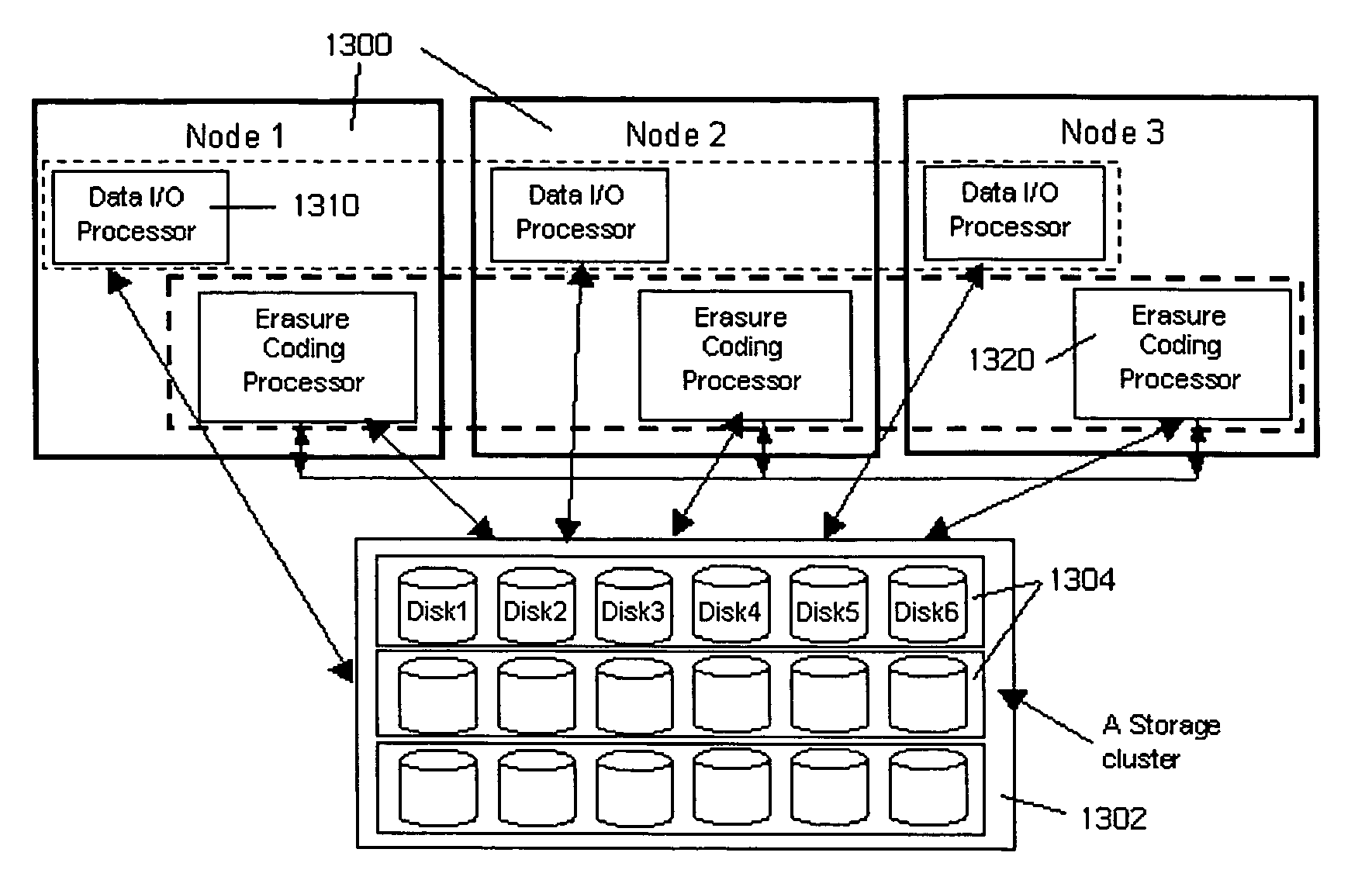
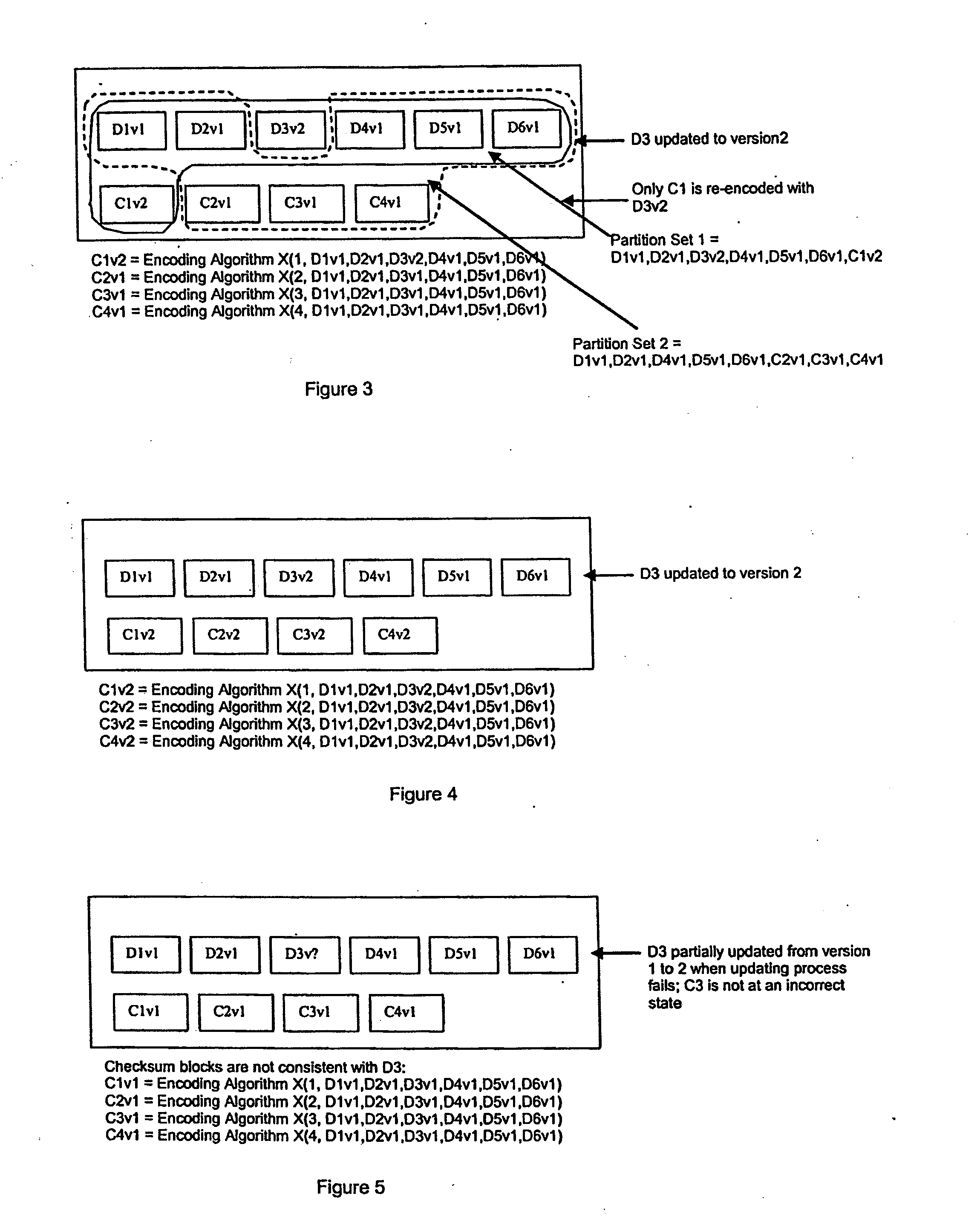
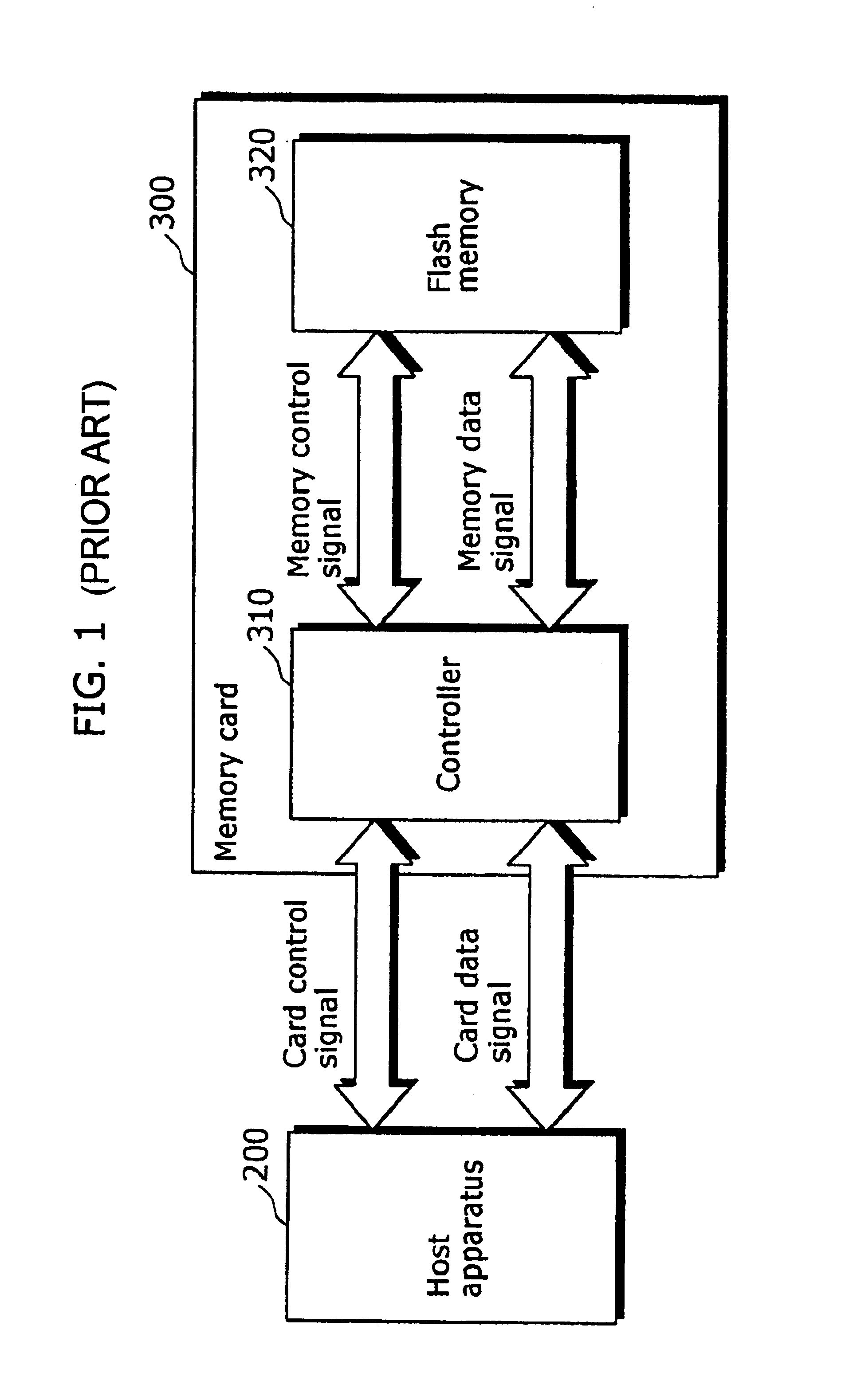
Method for lock-free clustered erasure coding and recovery of data across a plurality of data stores in a network
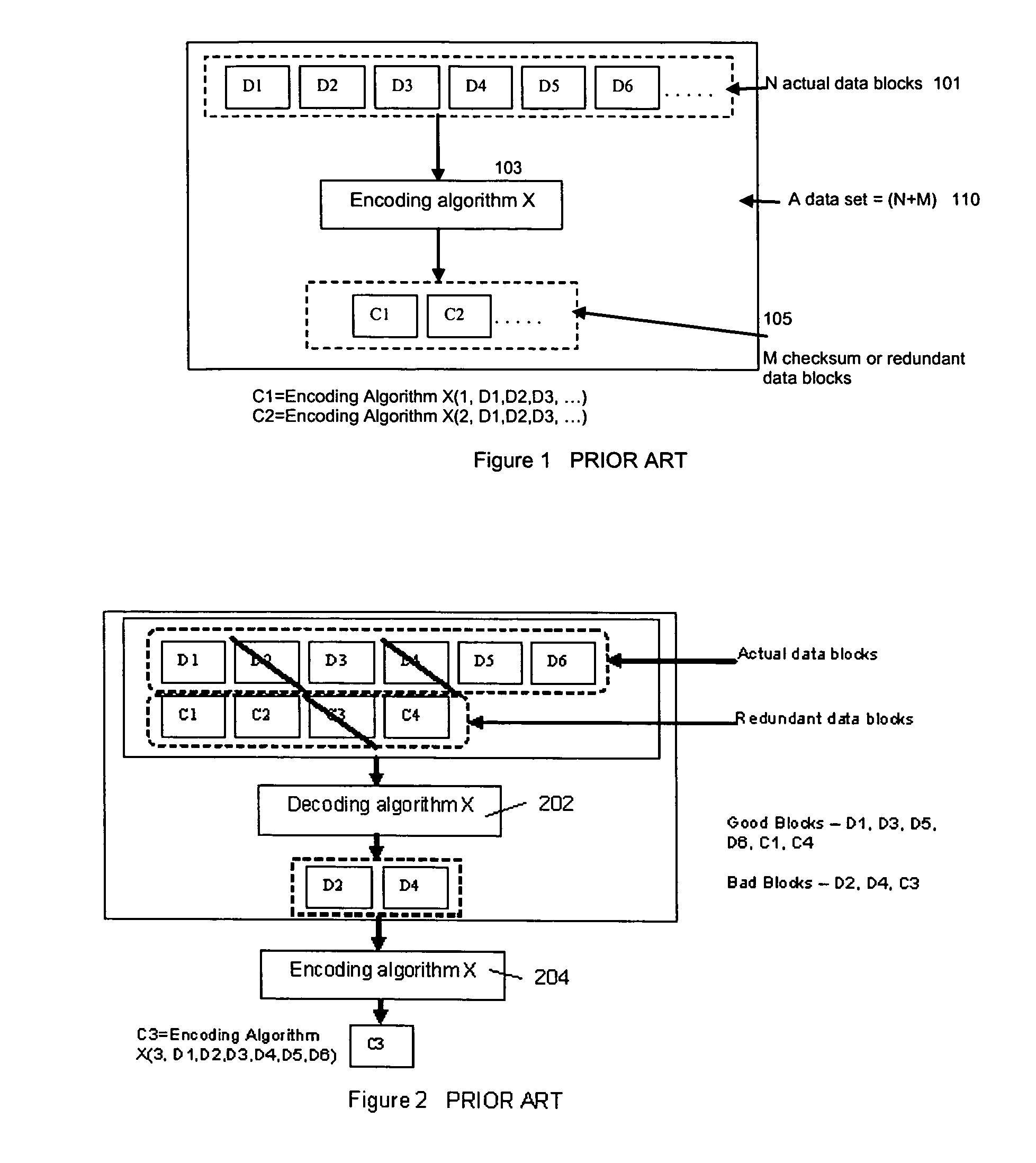
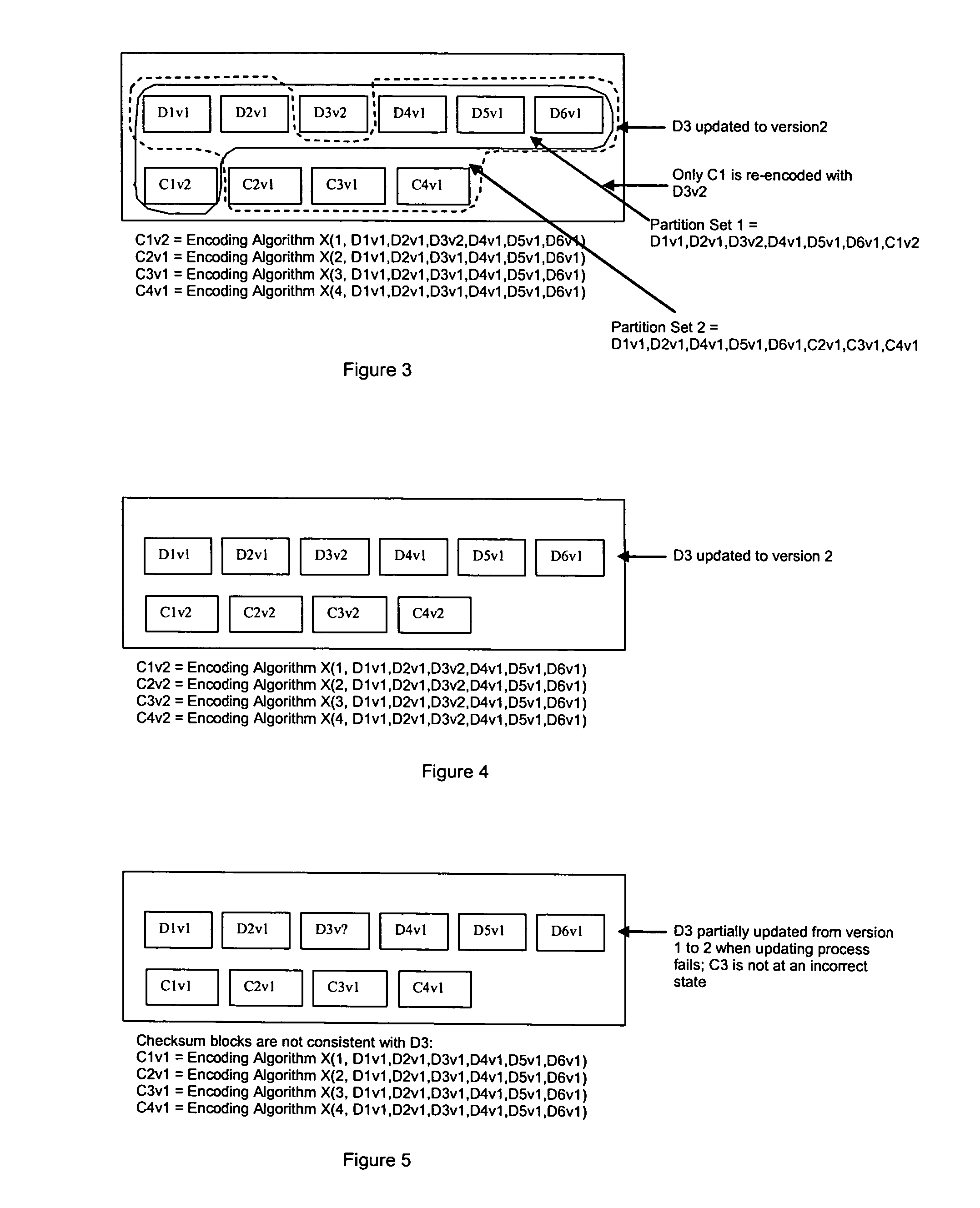
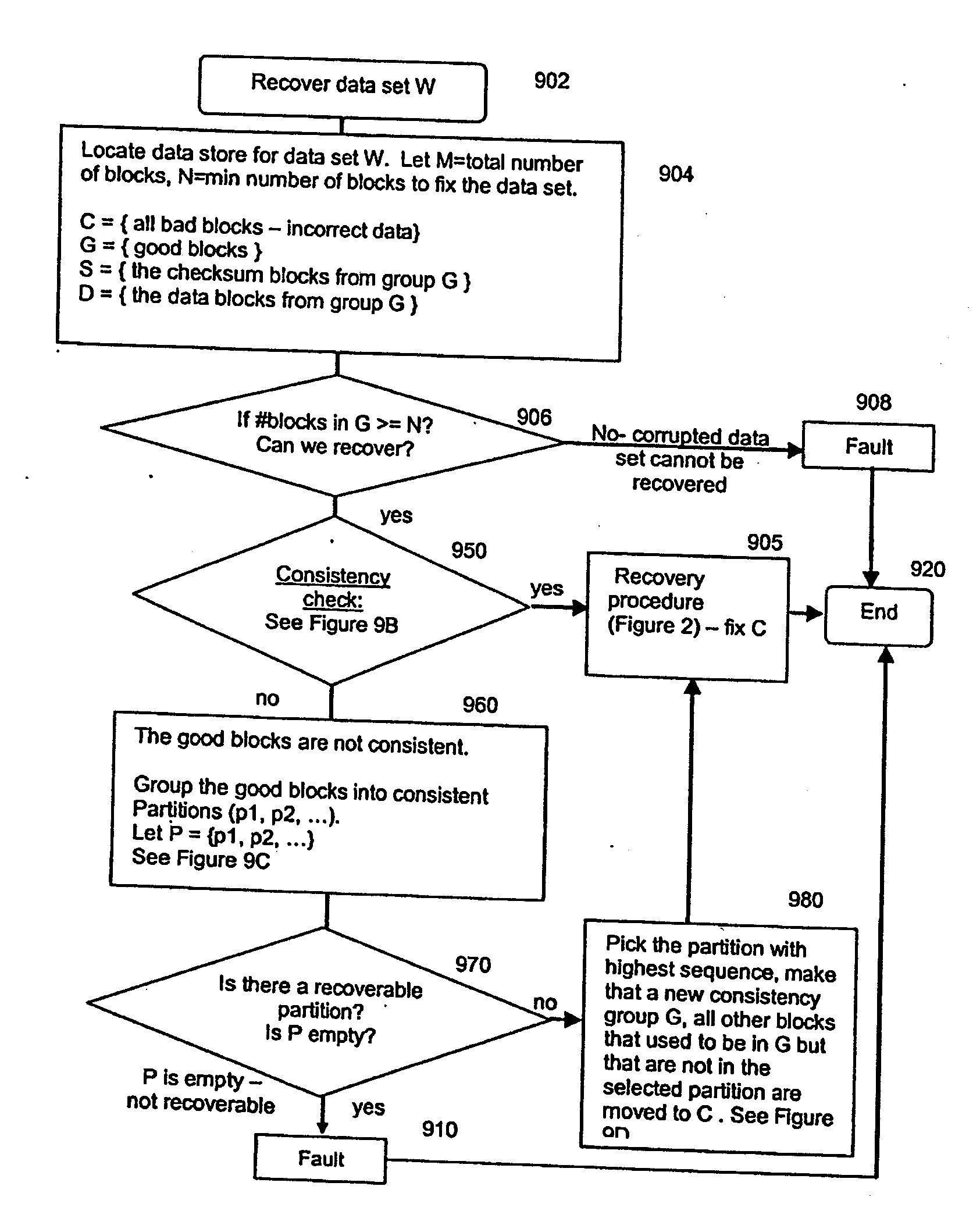
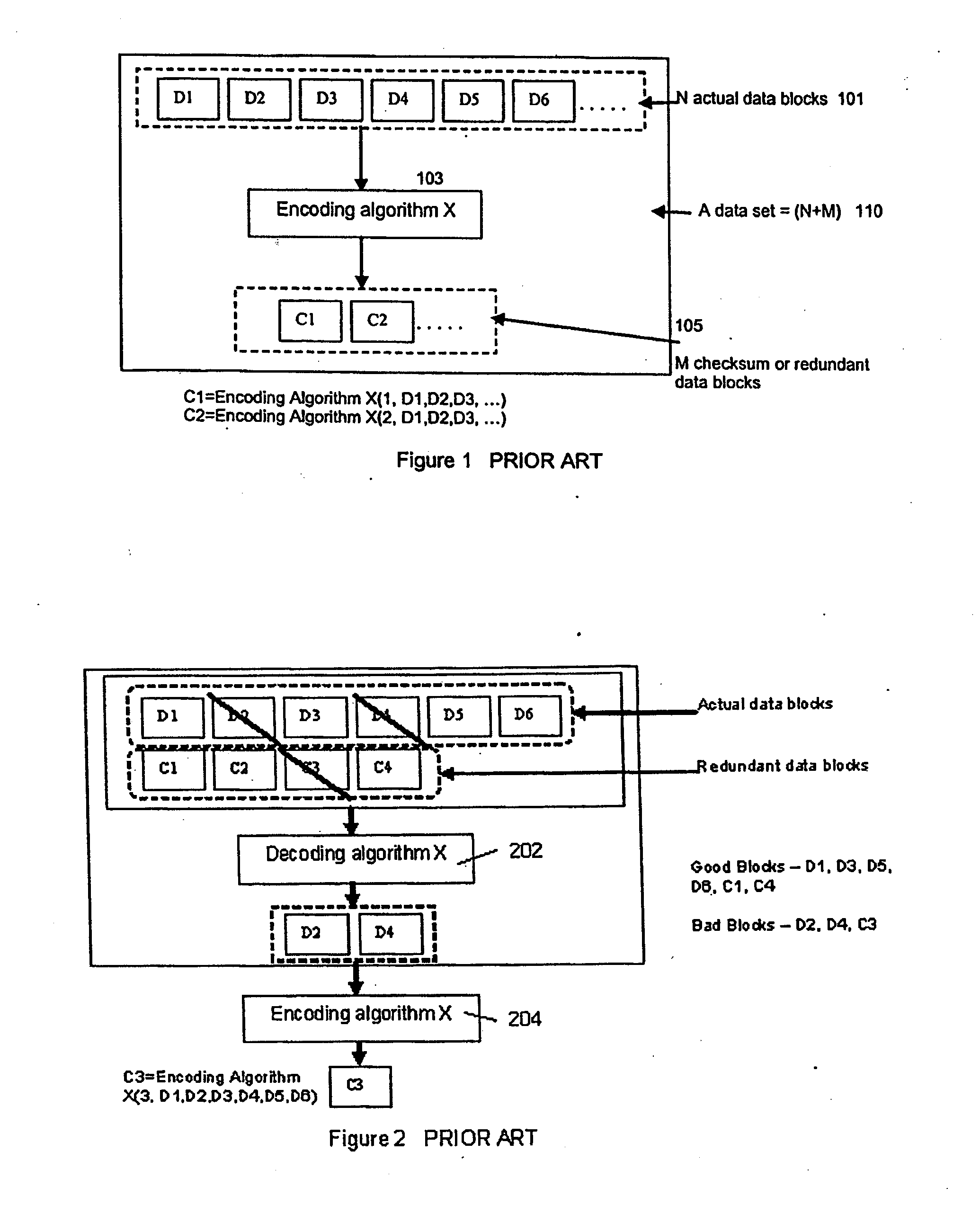
ActiveUS7681105B1Maintain data consistencyEffective applicationError detection/correctionCode conversionData storingData store
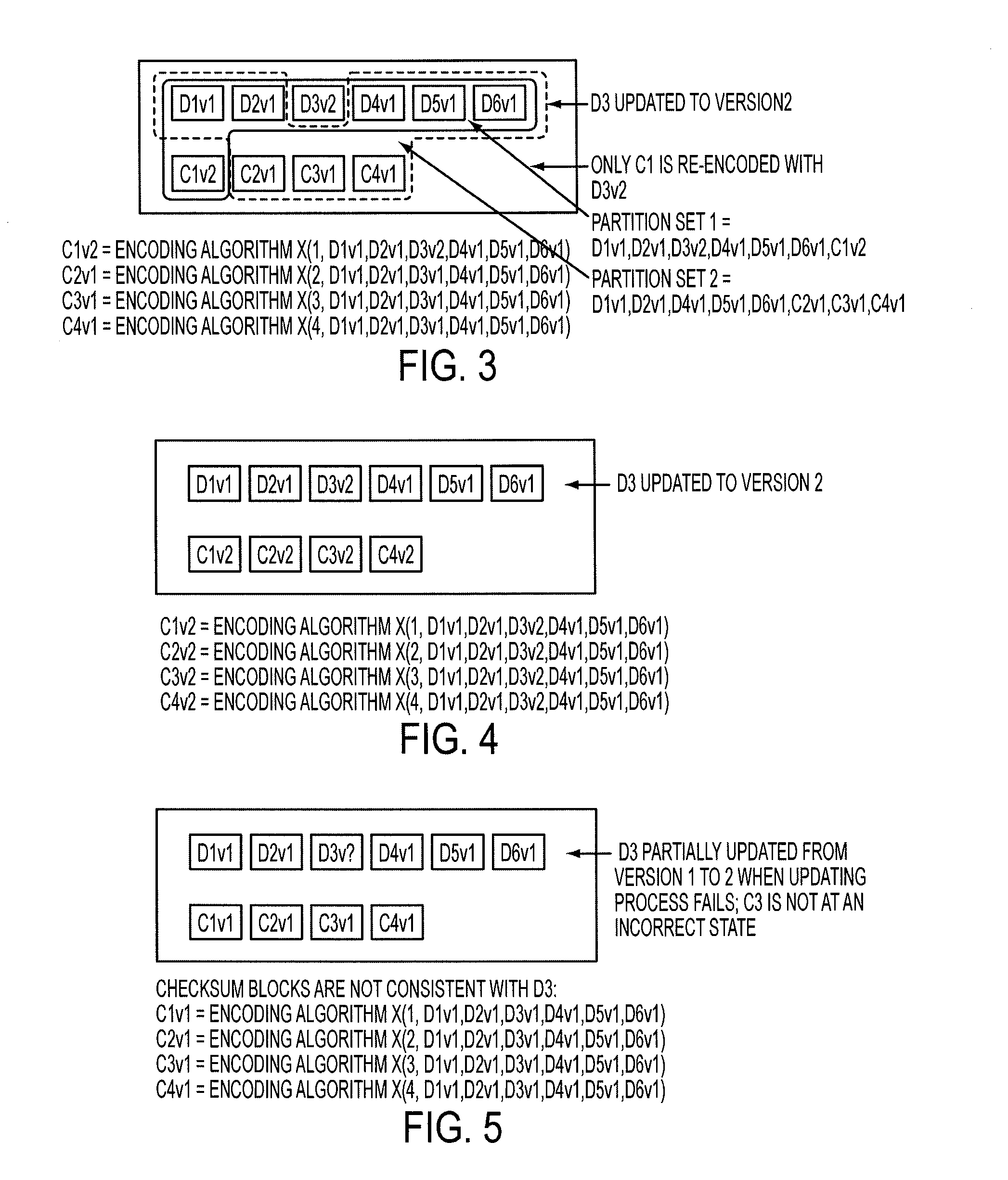
The present invention provides a distributed clustering method to allow multiple active instances of consistency management processes that apply the same encoding scheme to be cooperative and function collectively. The techniques described herein facilitate an efficient method to apply an erasure encoding and decoding scheme across dispersed data stores that receive constant updates. The technique can be applied on many forms of distributed persistent data stores to provide failure resiliency and to maintain data consistency and correctness.
Owner:QUEST SOFTWARE INC
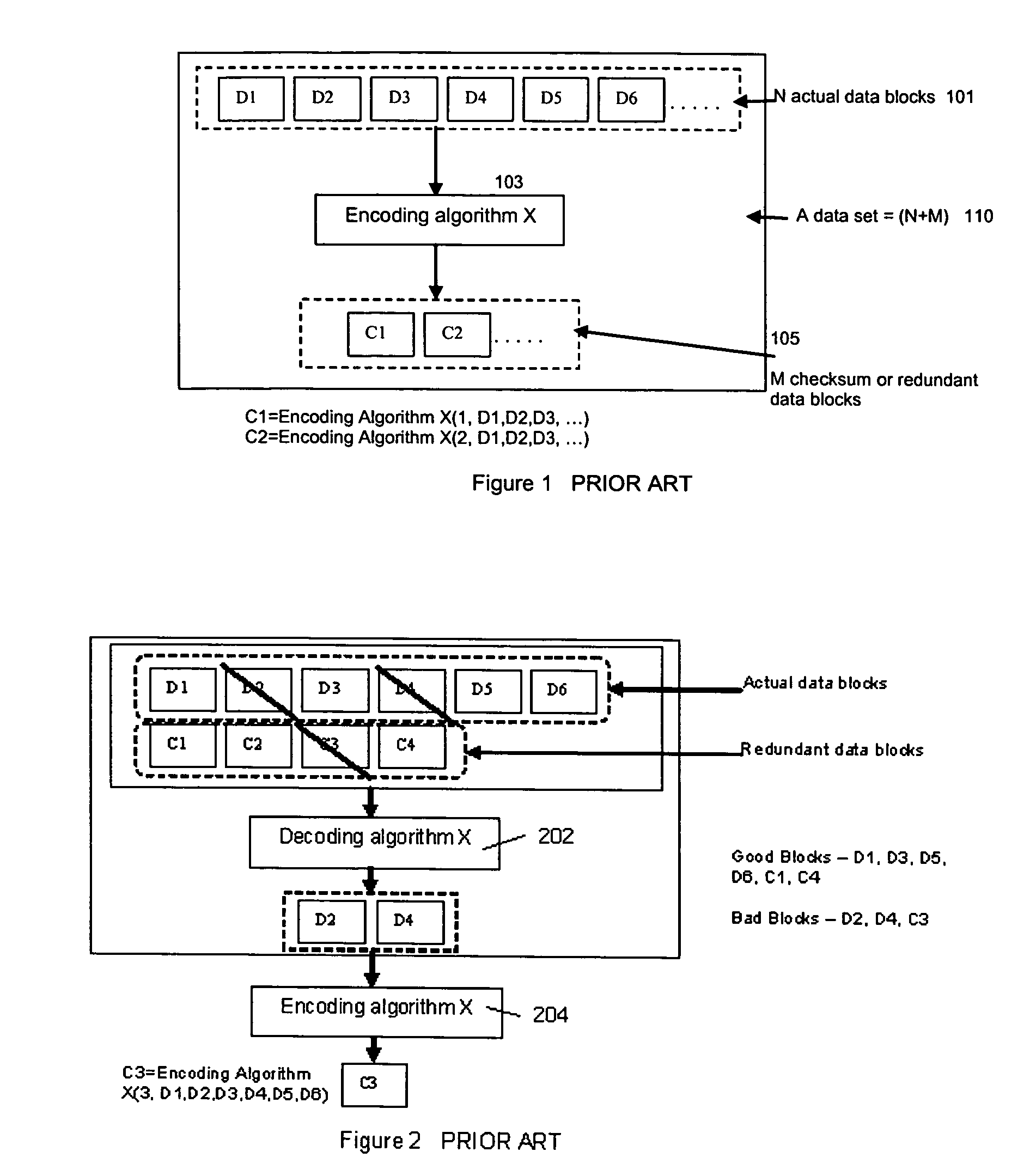
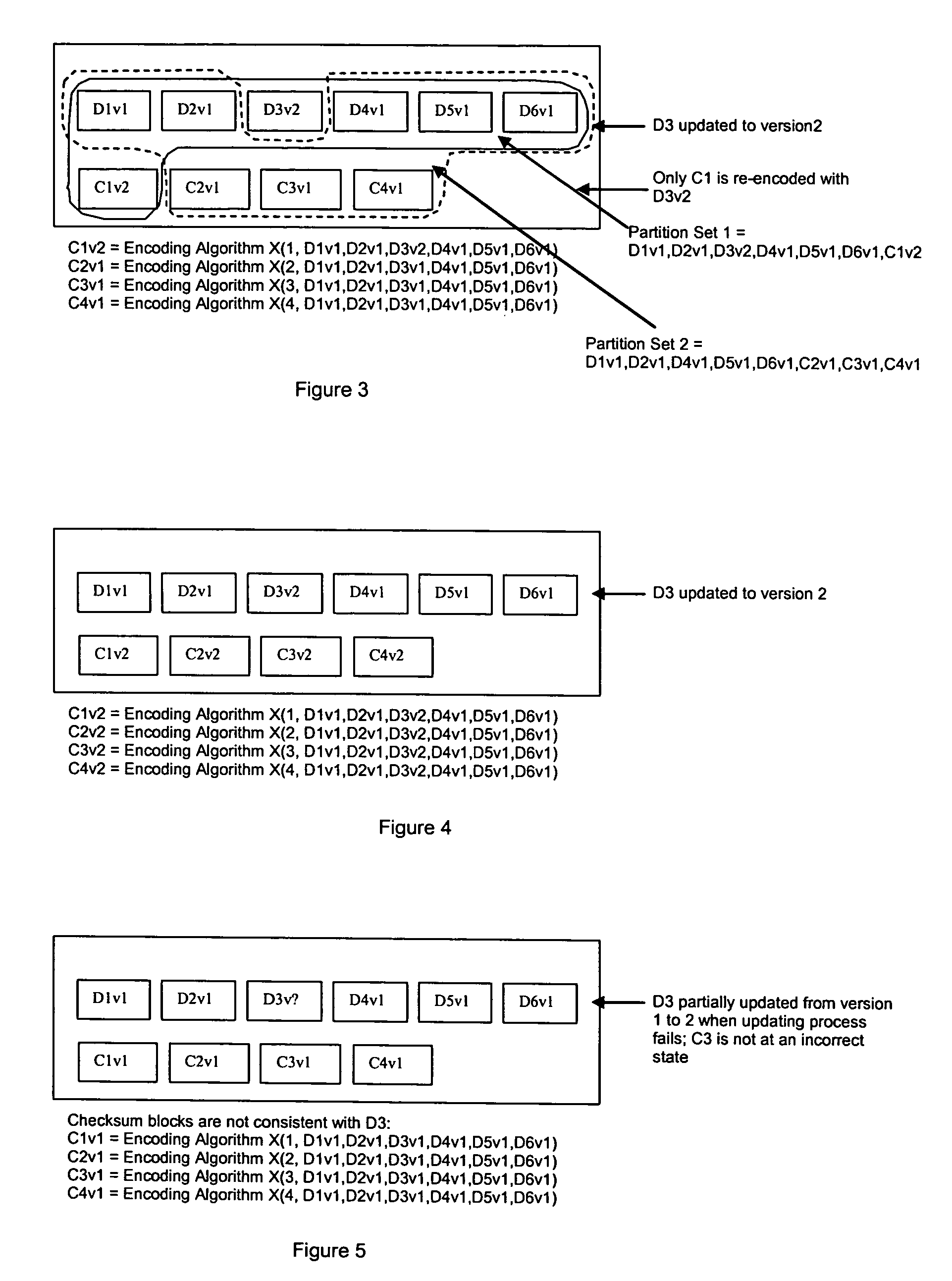
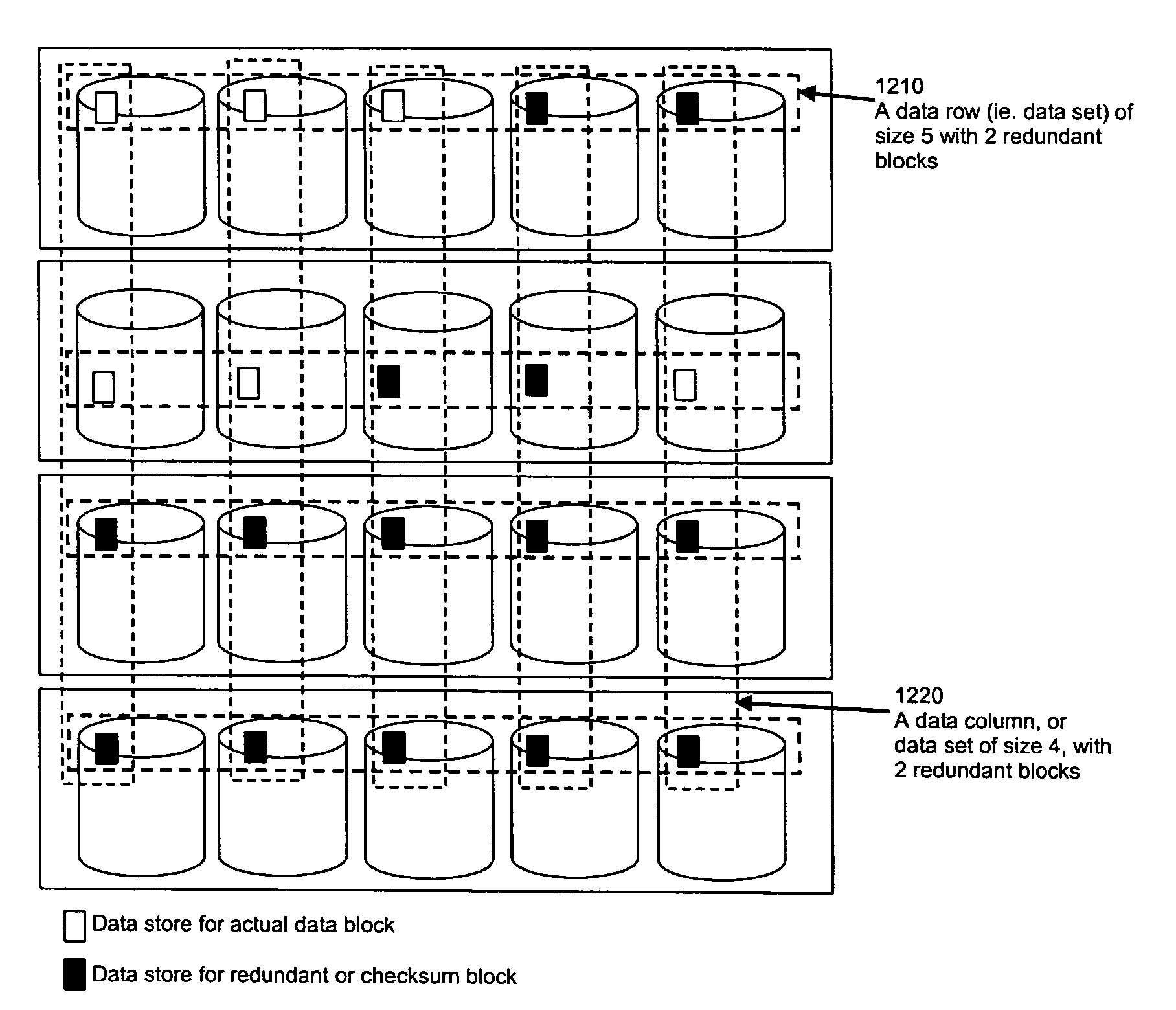
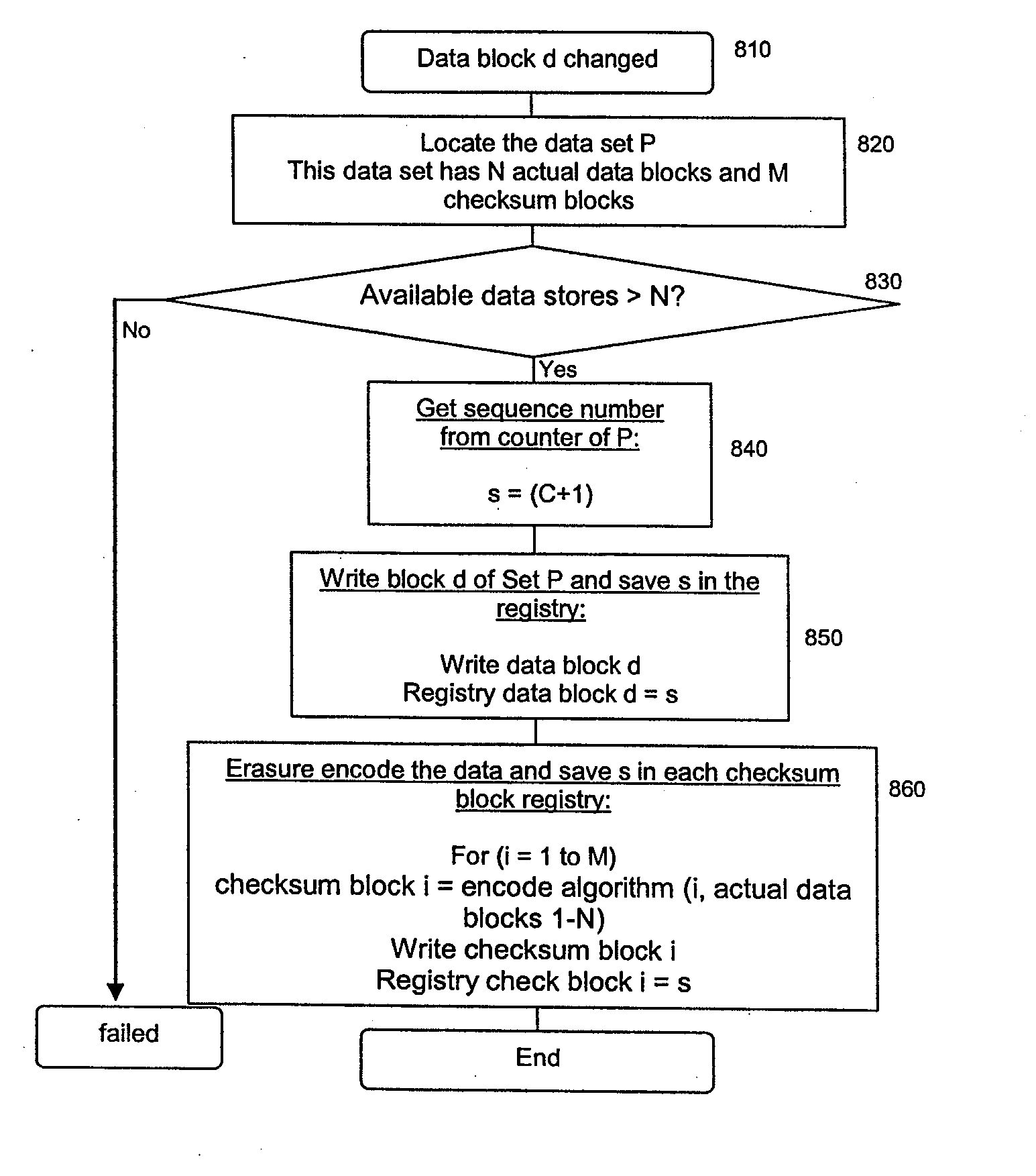
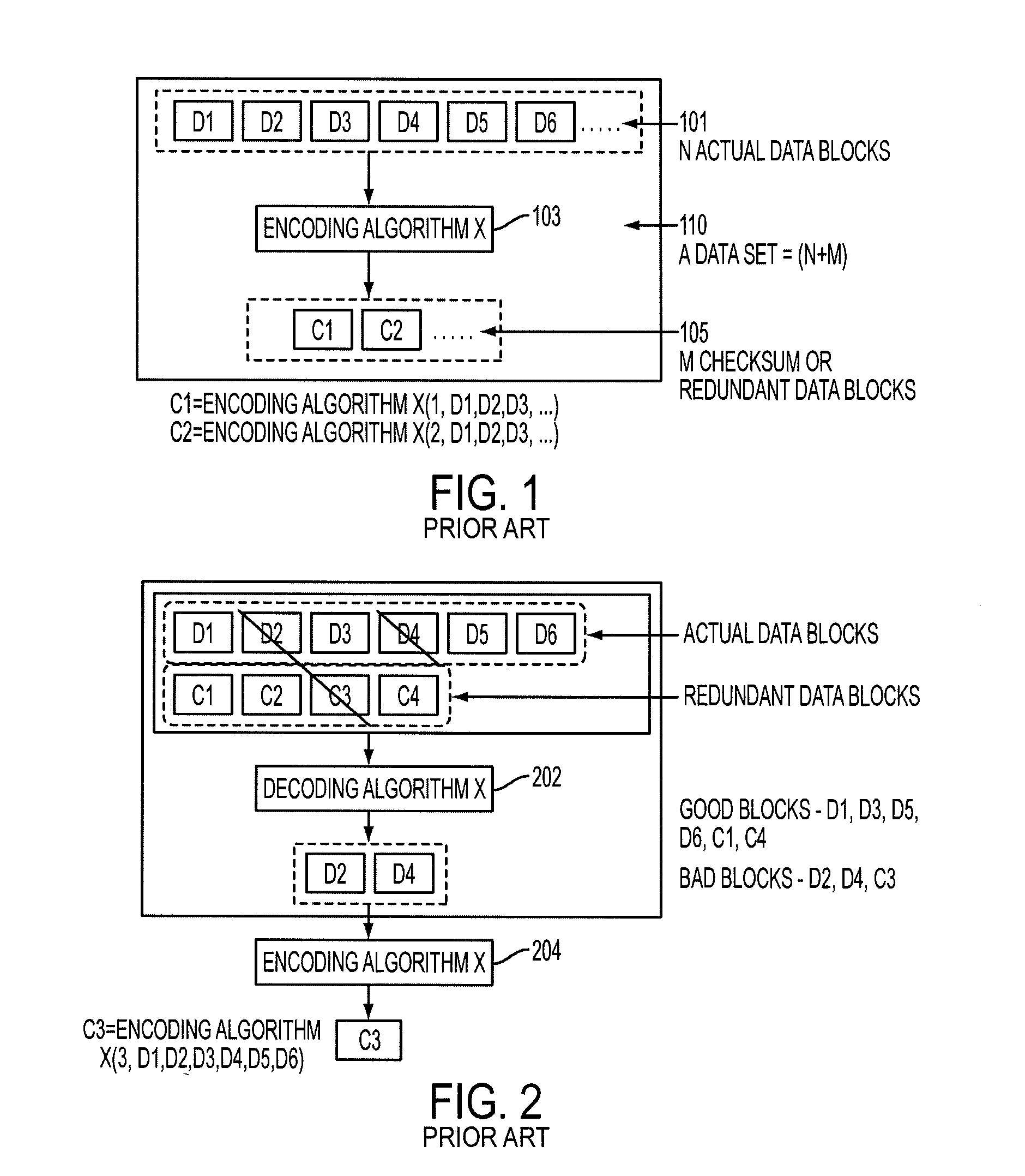
Method for erasure coding data across a plurality of data stores in a network
ActiveUS7681104B1Maintain data consistencyEffective applicationError preventionCode conversionData setTheoretical computer science
An efficient method to apply an erasure encoding and decoding scheme across dispersed data stores that receive constant updates. A data store is a persistent memory for storing a data block. Such data stores include, without limitation, a group of disks, a group of disk arrays, or the like. An encoding process applies a sequencing method to assign a sequence number to each data and checksum block as they are modified and updated onto their data stores. The method preferably uses the sequence number to identify data set consistency. The sequencing method allows for self-healing of each individual data store, and it maintains data consistency and correctness within a data block and among a group of data blocks. The inventive technique can be applied on many forms of distributed persistent data stores to provide failure resiliency and to maintain data consistency and correctness.
Owner:QUEST SOFTWARE INC
Method for lock-free clustered erasure coding and recovery of data across a plurality of data stores in a network
ActiveUS20100162076A1Maintain data consistencyEfficient methodCode conversionCyclic codesData storingData store
The present invention provides a distributed clustering method to allow multiple active instances of consistency management processes that apply the same encoding scheme to be cooperative and function collectively. The techniques described herein facilitate an efficient method to apply an erasure encoding and decoding scheme across dispersed data stores that receive constant updates. The technique can be applied on many forms of distributed persistent data stores to provide failure resiliency and to maintain data consistency and correctness.
Owner:QUEST SOFTWARE INC
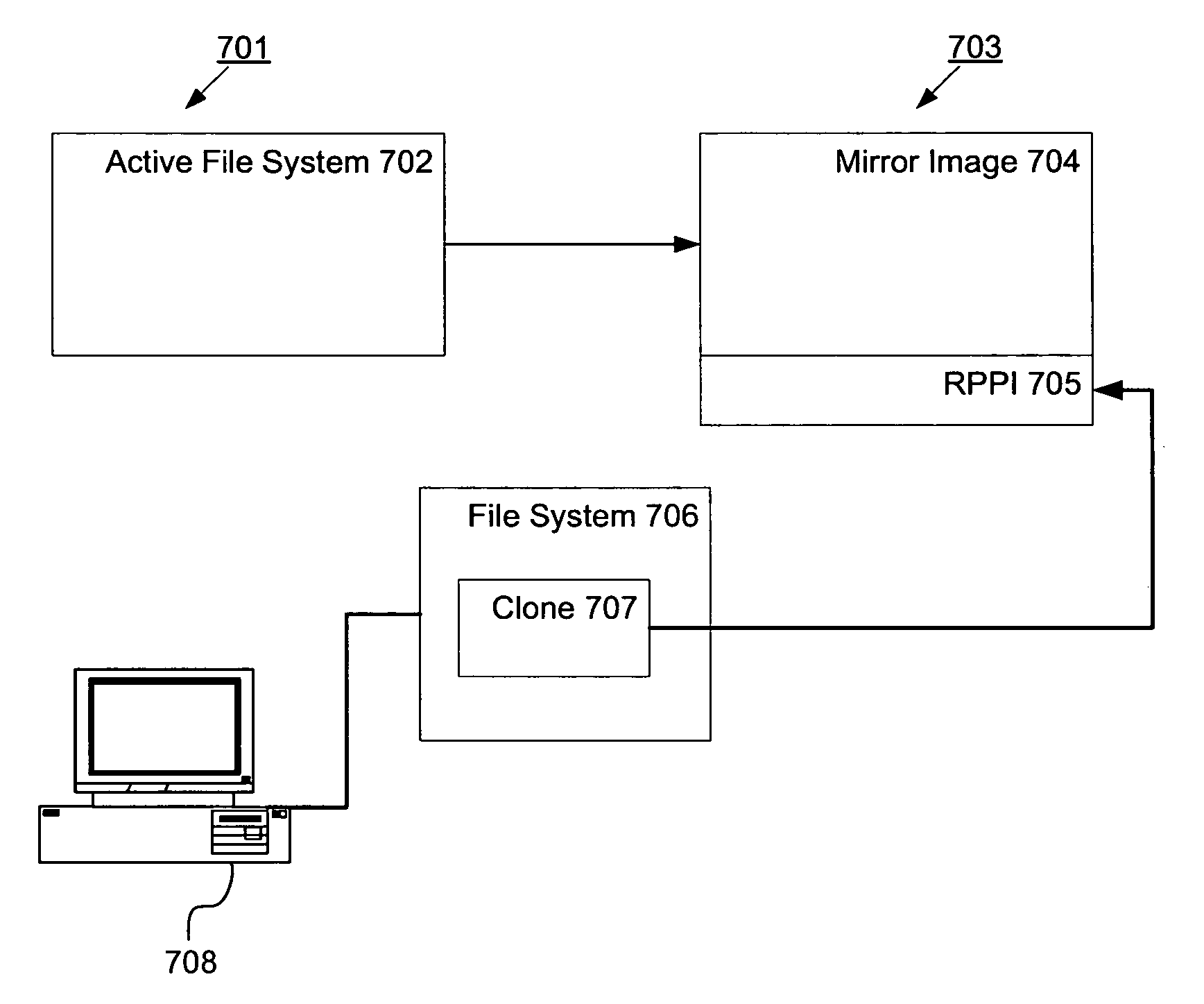
Method and system to make a read-only file system appear to be writeable
ActiveUS7587563B1Maintain data consistencyError detection/correctionSpecial data processing applicationsFile systemData set
A writeable clone of a read-only dataset, e.g., an RPPI of a file system, a mirror file system, etc., is created to make the read-only dataset appear from a client's perspective to be modifiable / writeable, yet without actually modifying the read-only dataset itself. Any change attempted to be made on the read-only dataset is stored in the writeable clone. In one embodiment, the clone shares data blocks with the read-only dataset.
Owner:NETWORK APPLIANCE INC
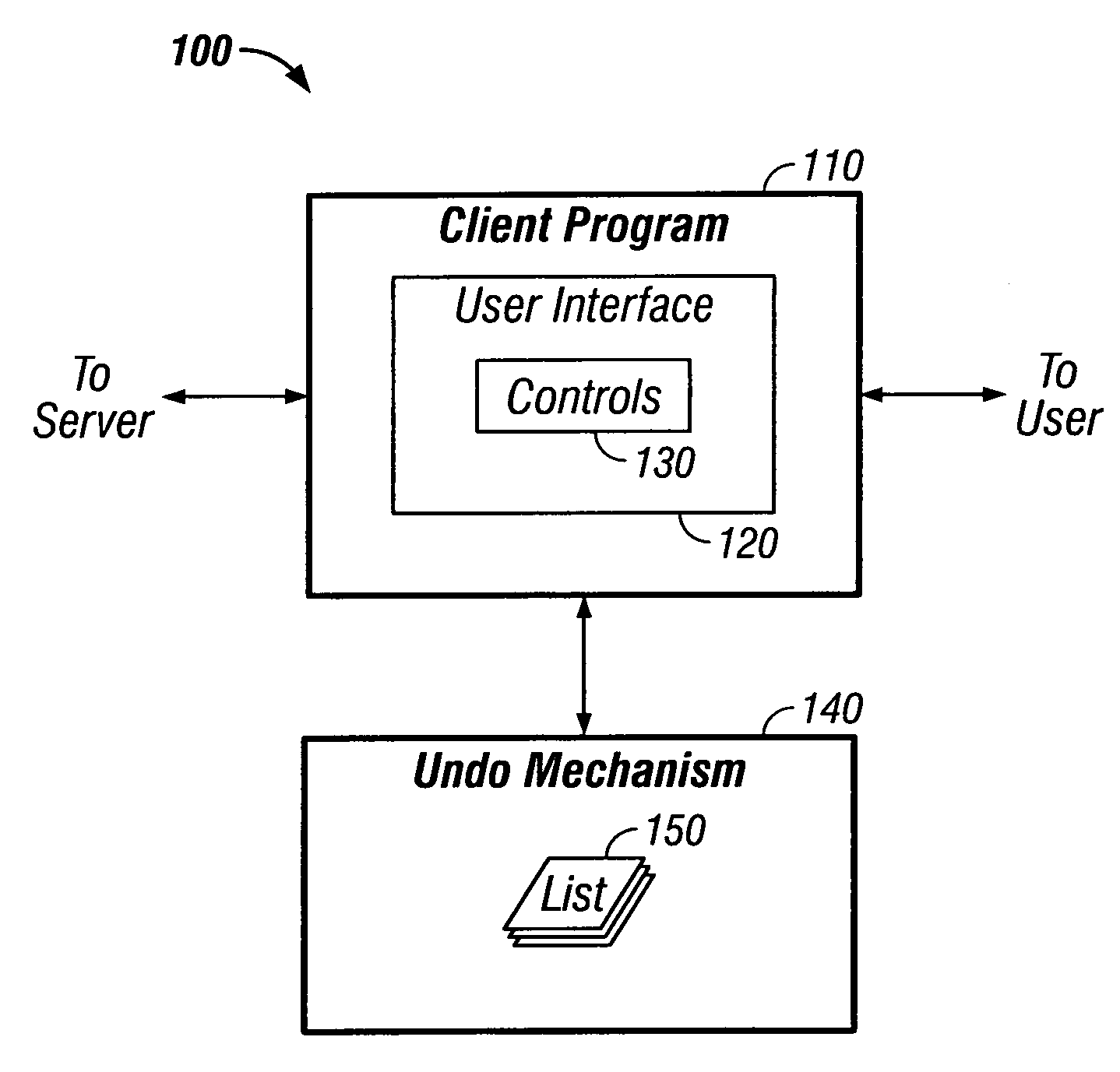
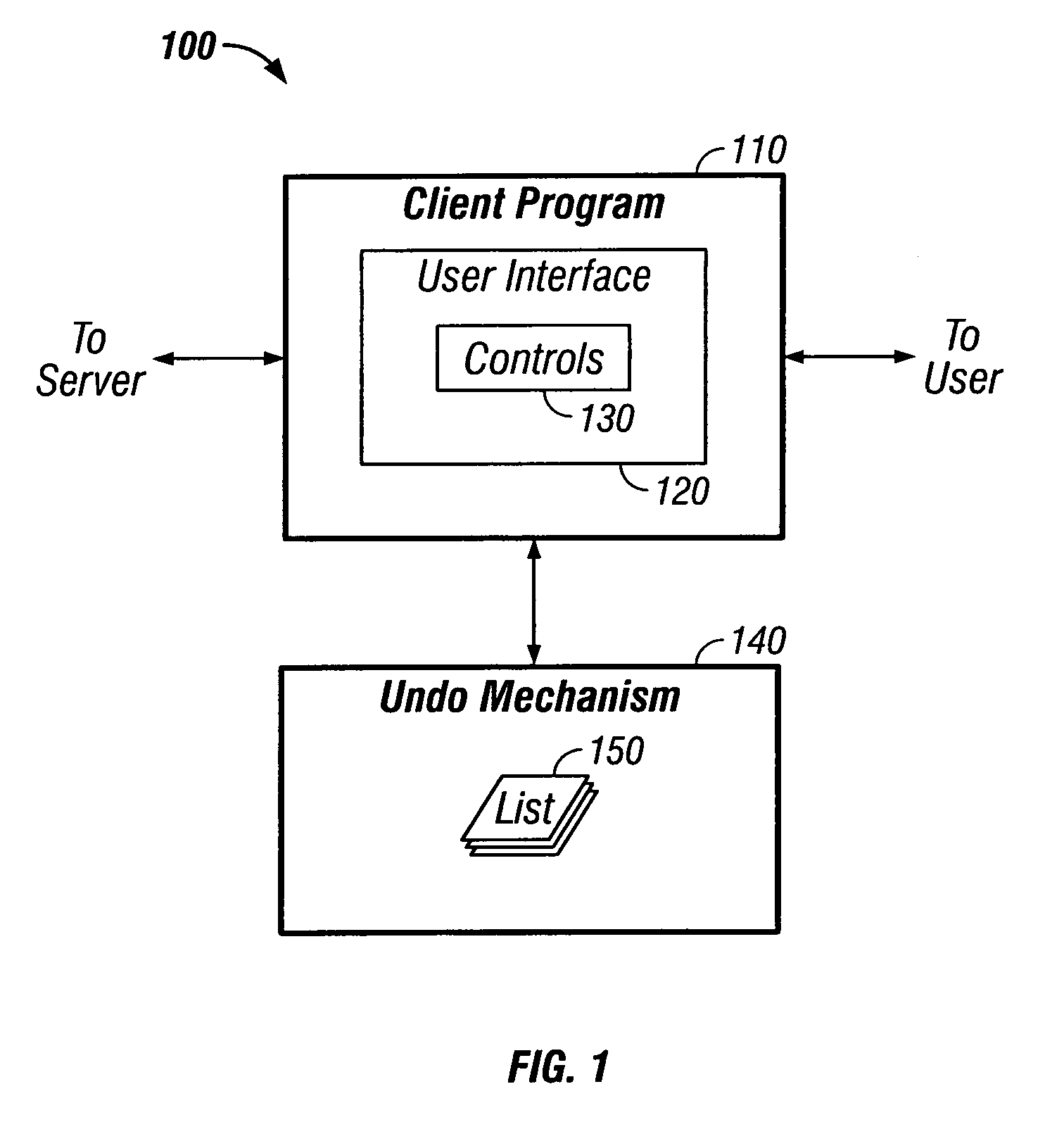
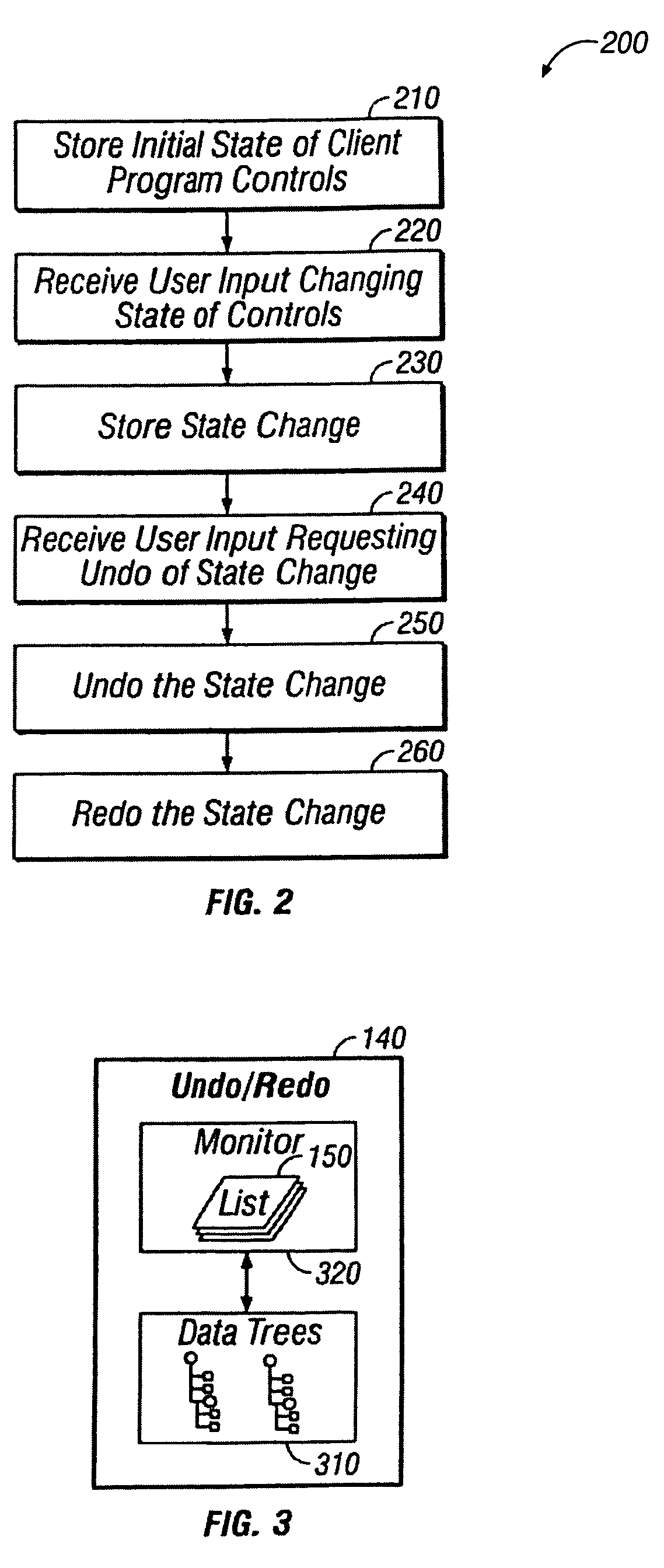
Undoing user actions in a client program
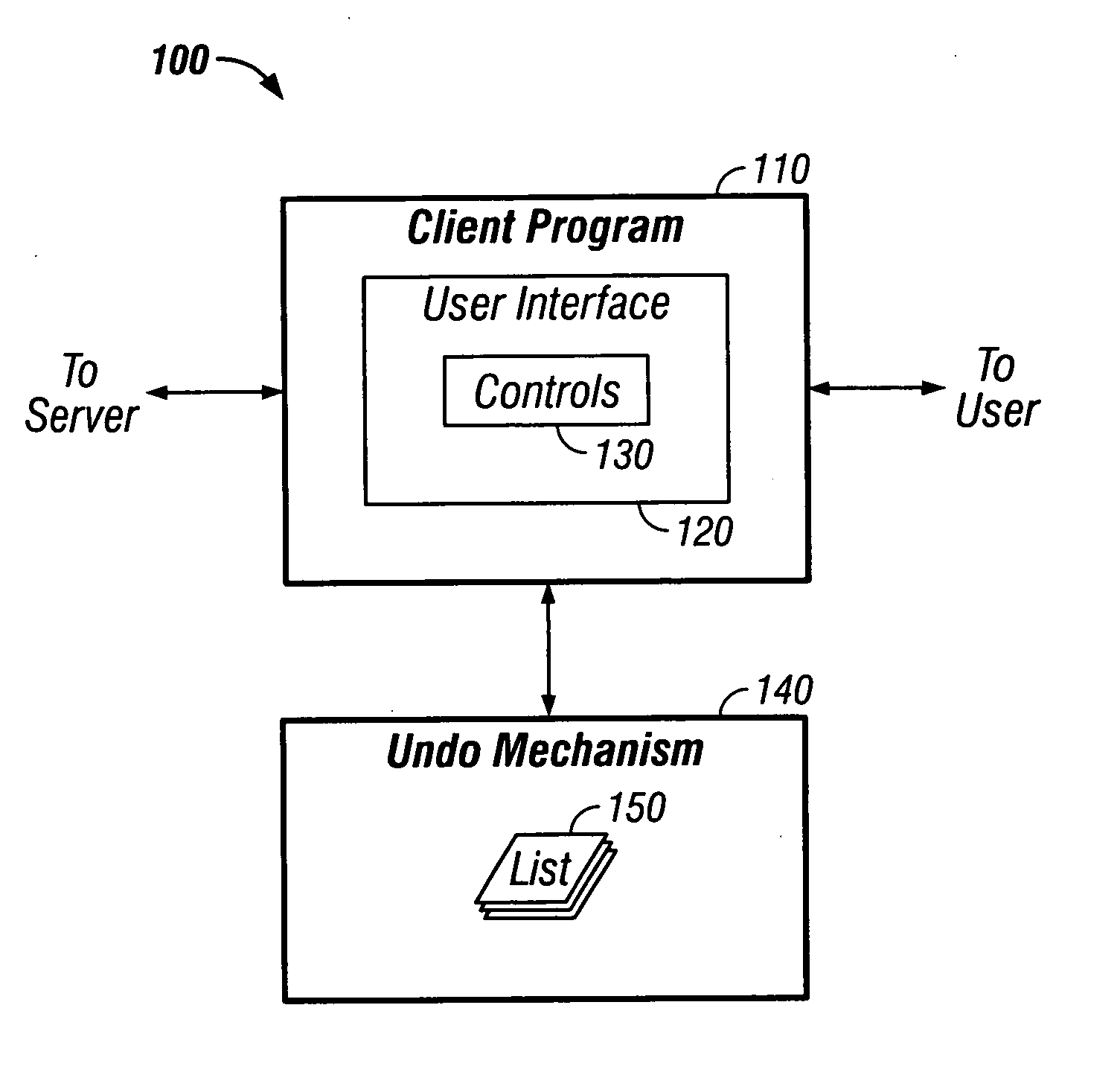
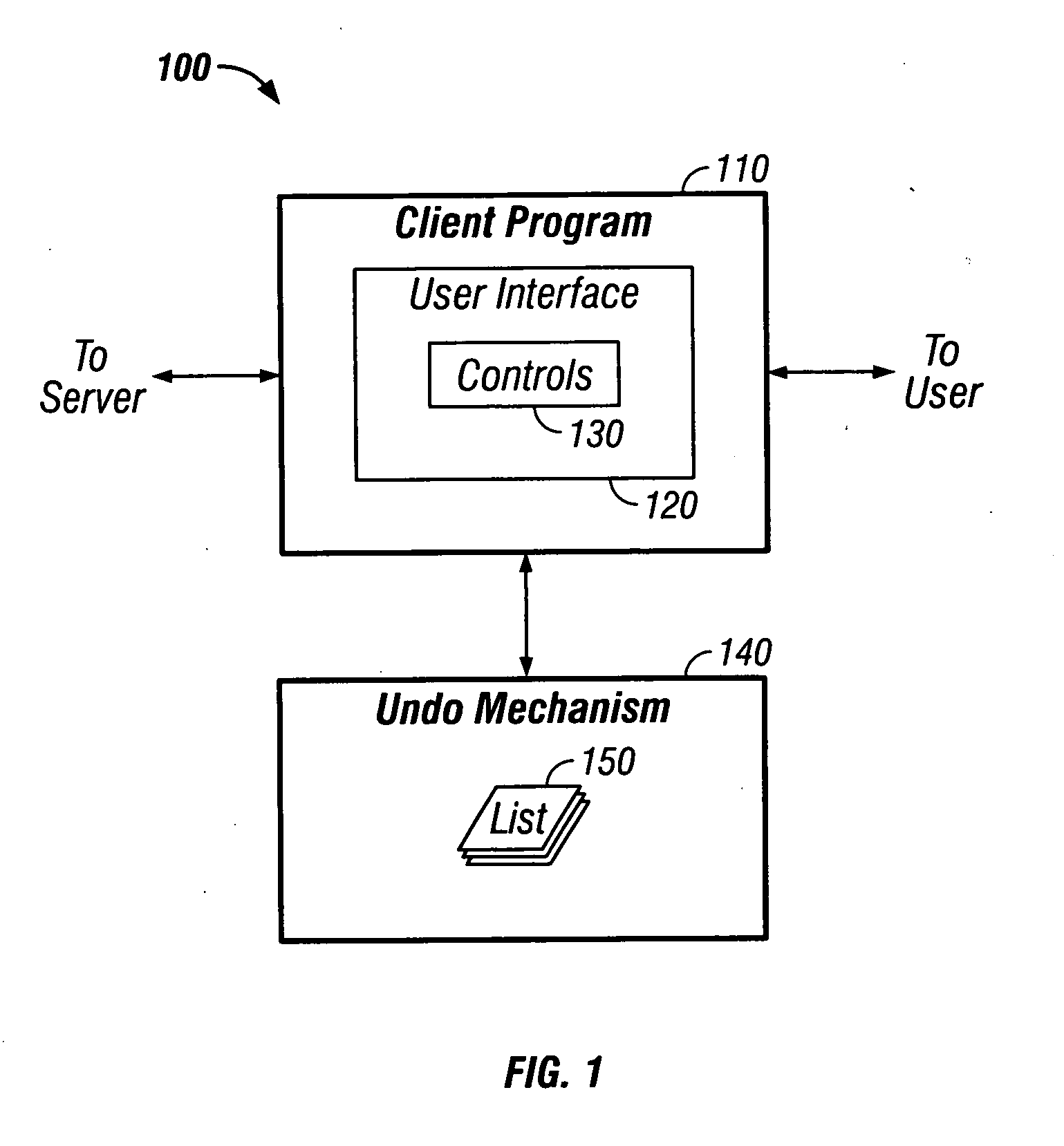
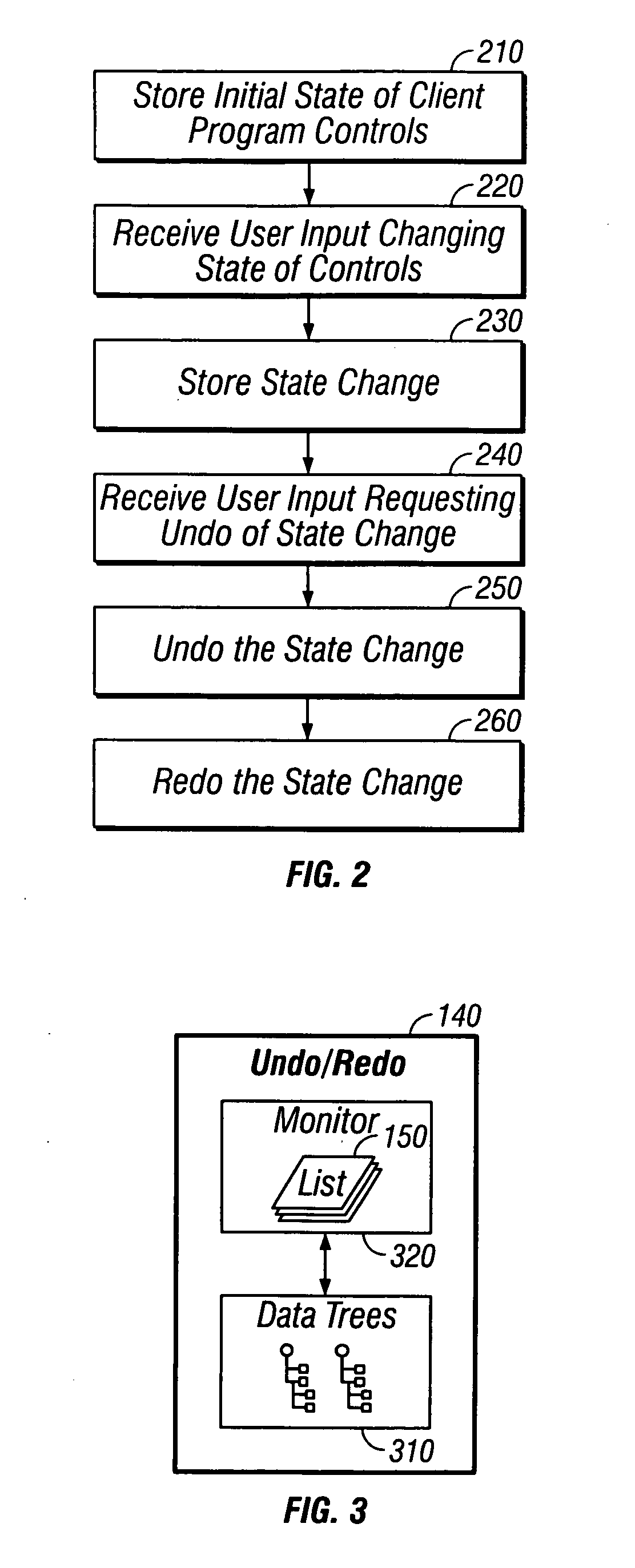
ActiveUS20050081105A1Maintain data consistencyError detection/correctionExecution for user interfacesClient-sideComputer program
Methods and apparatus, including computer program products, implementing techniques for undoing user actions in a client program. The techniques include displaying a user interface in a client program, the user interface having a plurality of controls, the plurality of controls including multiple types of controls, each control having a state; for each control in the plurality of controls, storing the state of the control as a first state for the control; receiving user input comprising a change to the state of a control in the plurality of controls; updating the state of the control based on the user input; storing the updated state of the control as a second state for the control; receiving user input comprising a request to undo the change; and restoring the state of the control to reflect the first state for the control.
Owner:SAP AG
Robust Data Replication
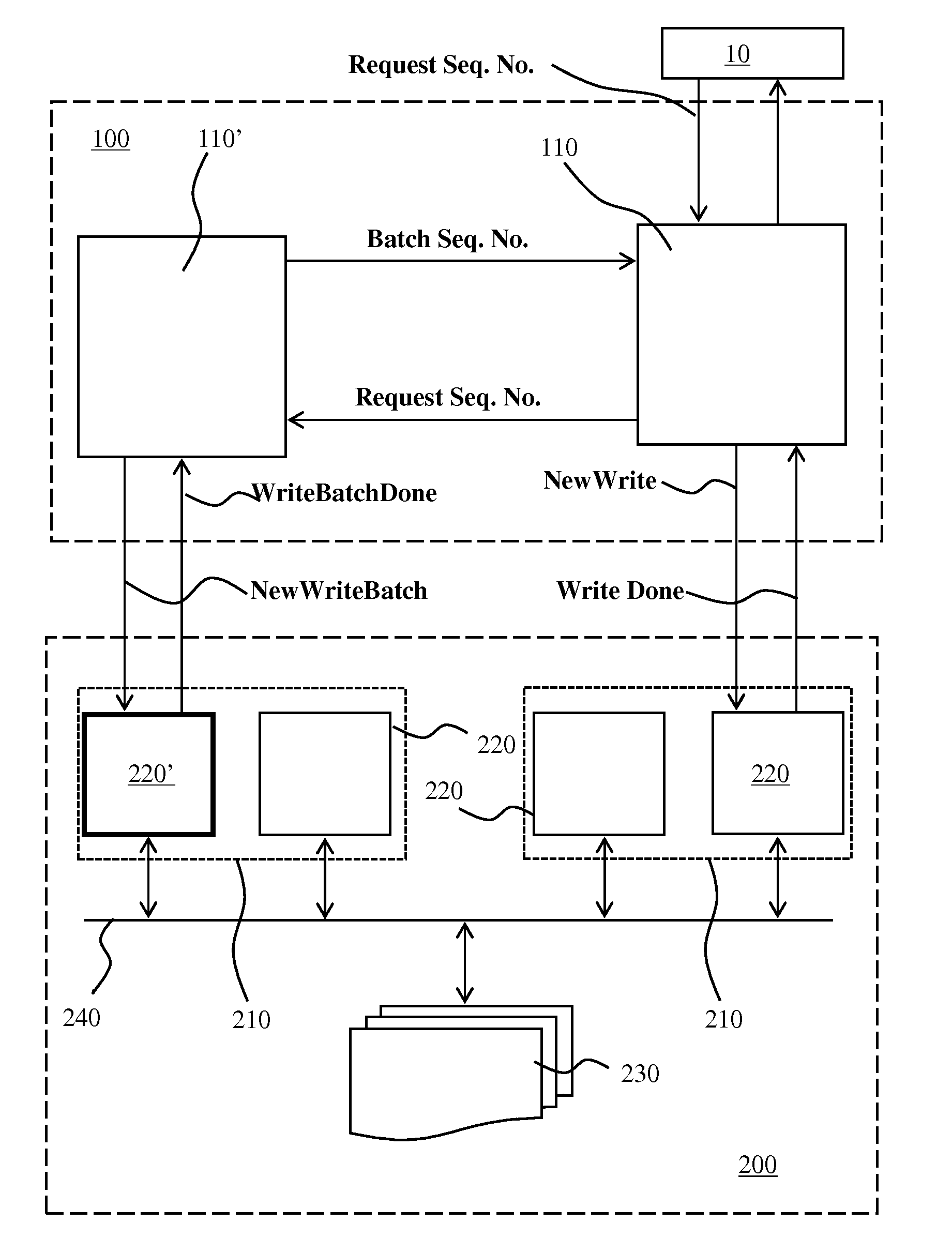
ActiveUS20150106549A1Maintain data consistencyEnsure data consistencyInput/output to record carriersRedundant operation error correctionBatch processingData store
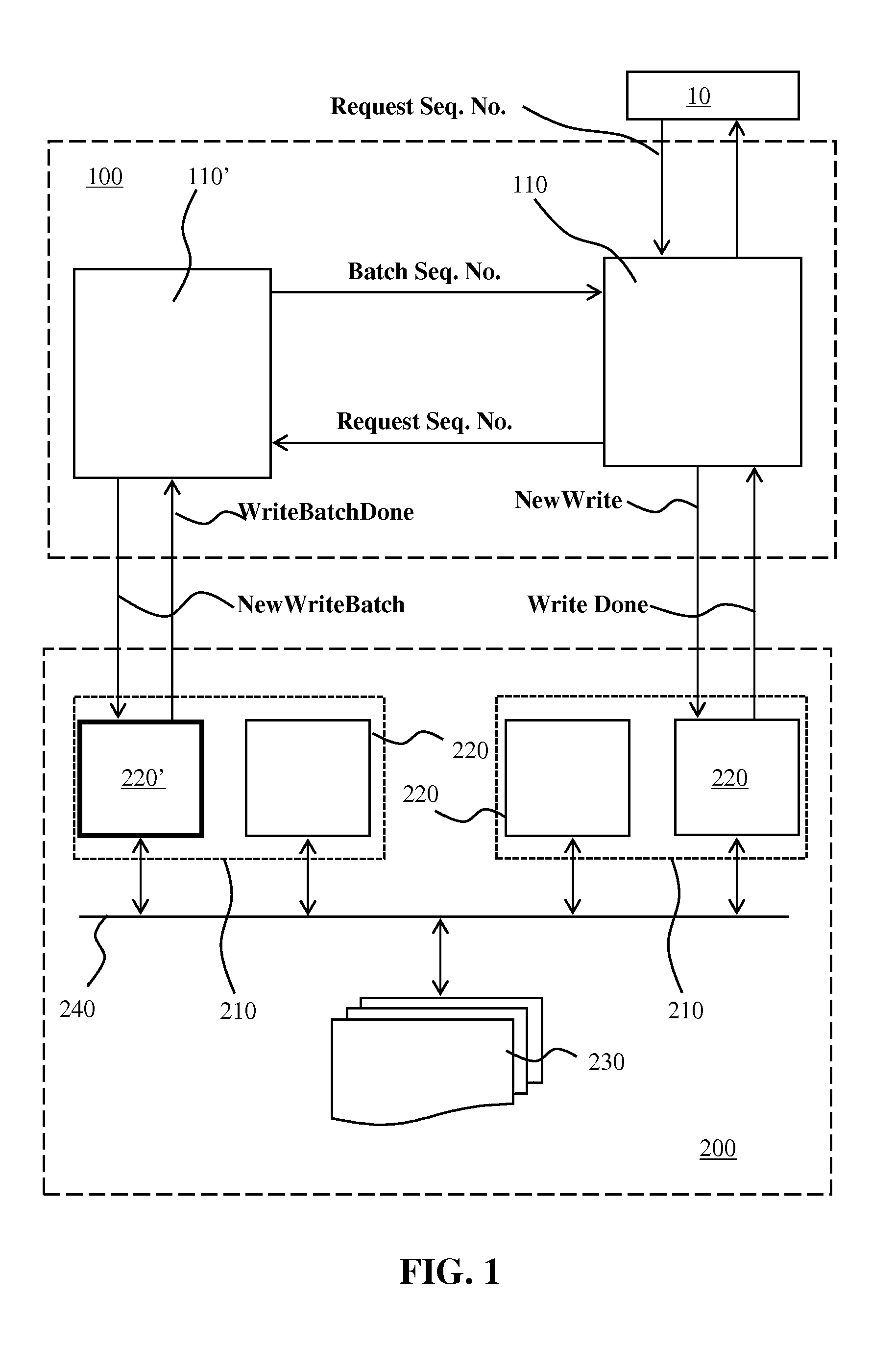
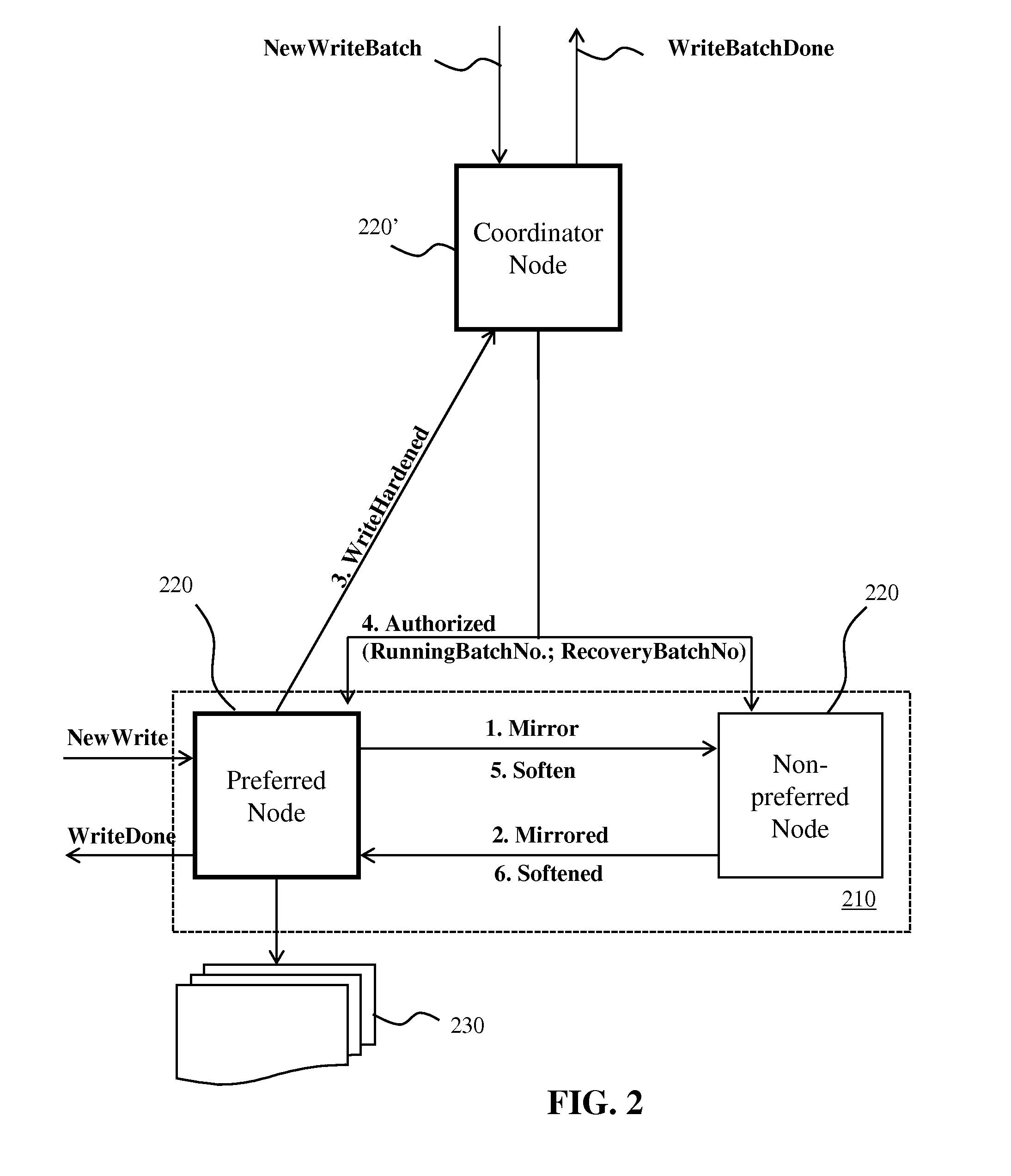
Disclosed is a system for replicating data. The system may comprise a plurality of nodes preferably organised in groups with one of the nodes acting as a coordinator node. The nodes are configured to receive write requests from an external server and to apply these write requests to a data storage source of the data storage system. The write requests typically belong to a batch of independent write actions identified by a batch sequence number. Each node stores the write request in non-volatile memory with the coordinator node monitoring which batches are secured in their entirety in non-volatile memory. The coordinator node authorises all other nodes to sequentially replicate the write requests in their non-volatile memory to the data storage source for all writes up to the highest batch sequence number for which all writes have been secured in non-volatile memory.
Owner:GLOBALFOUNDRIES US INC
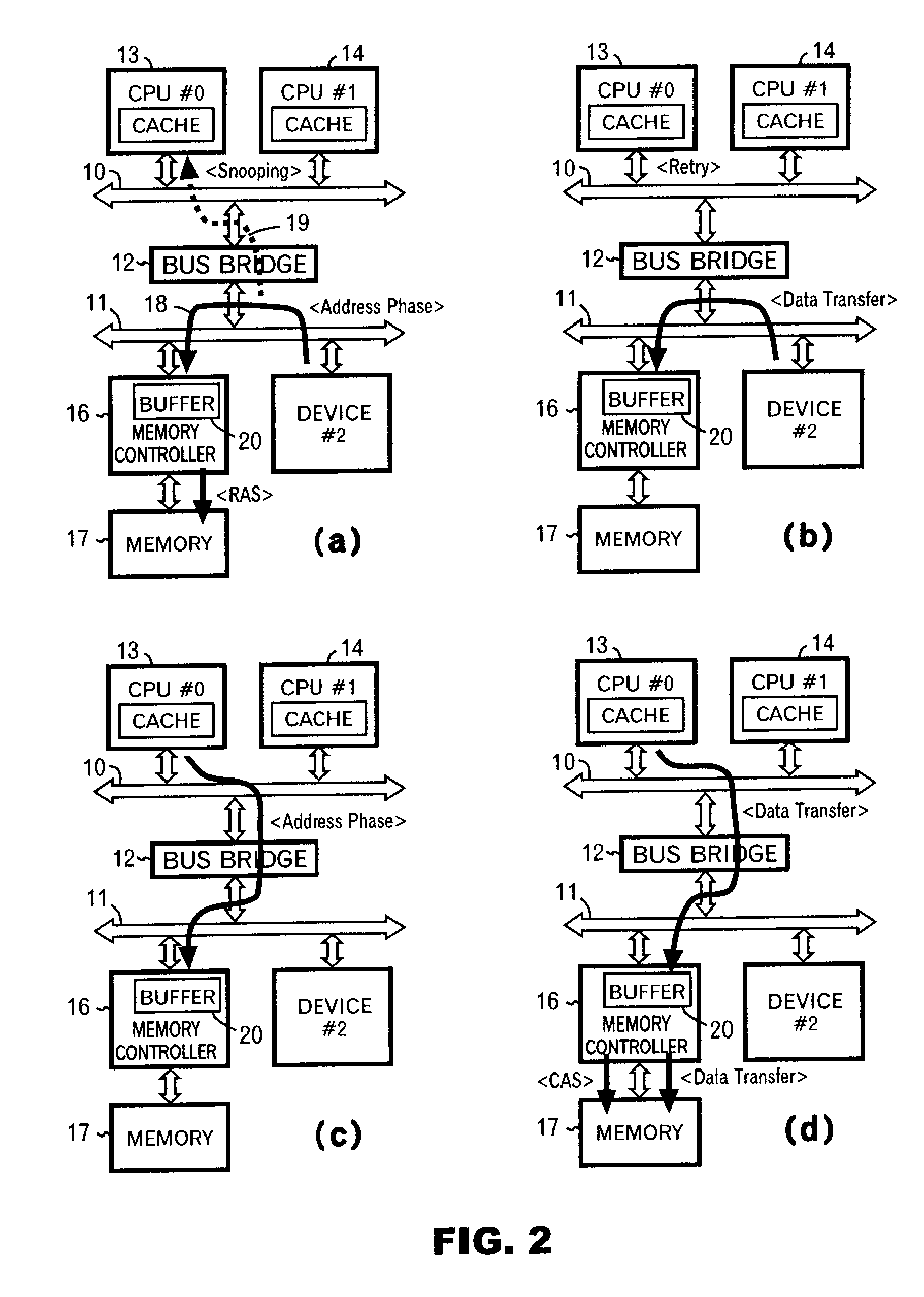
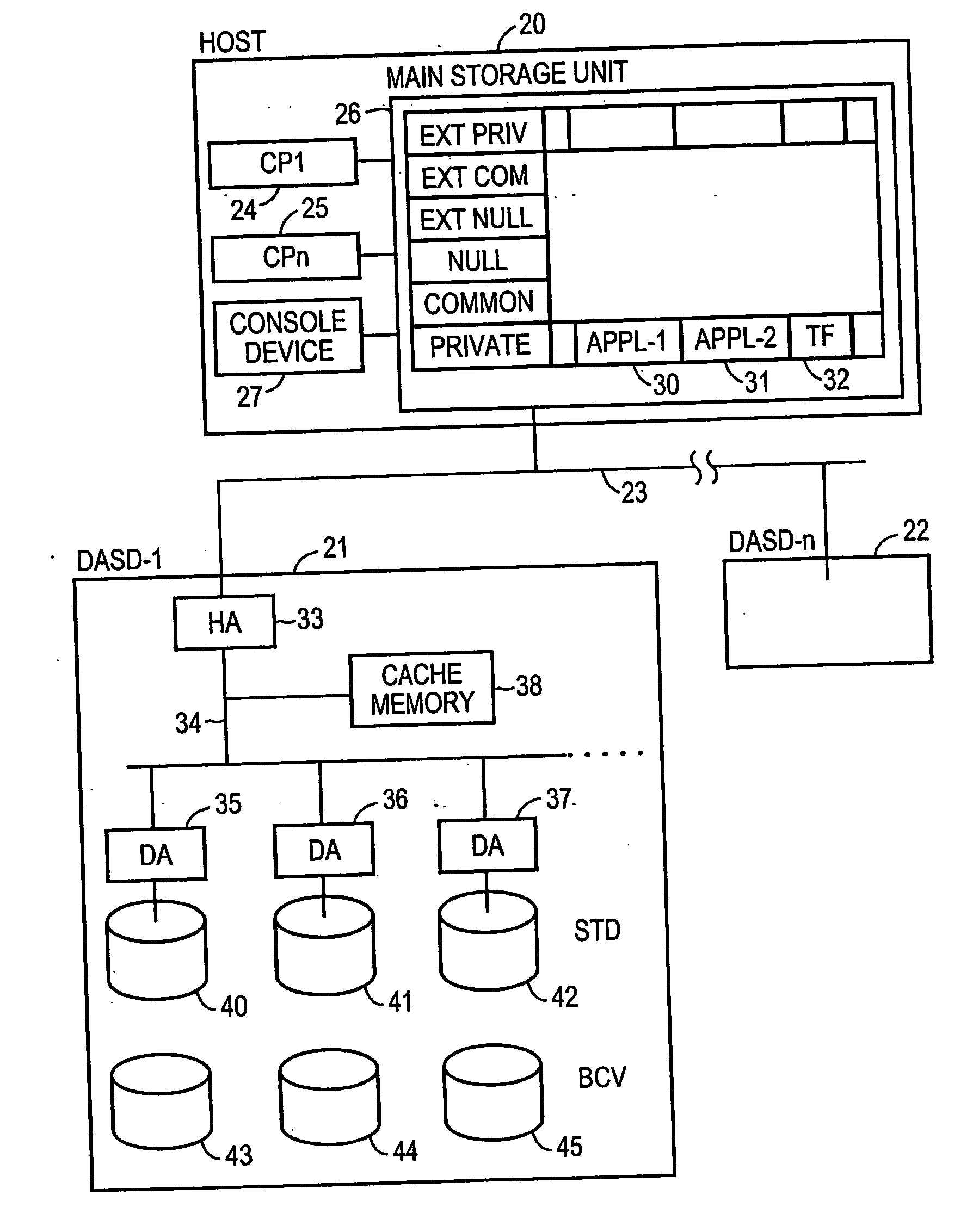
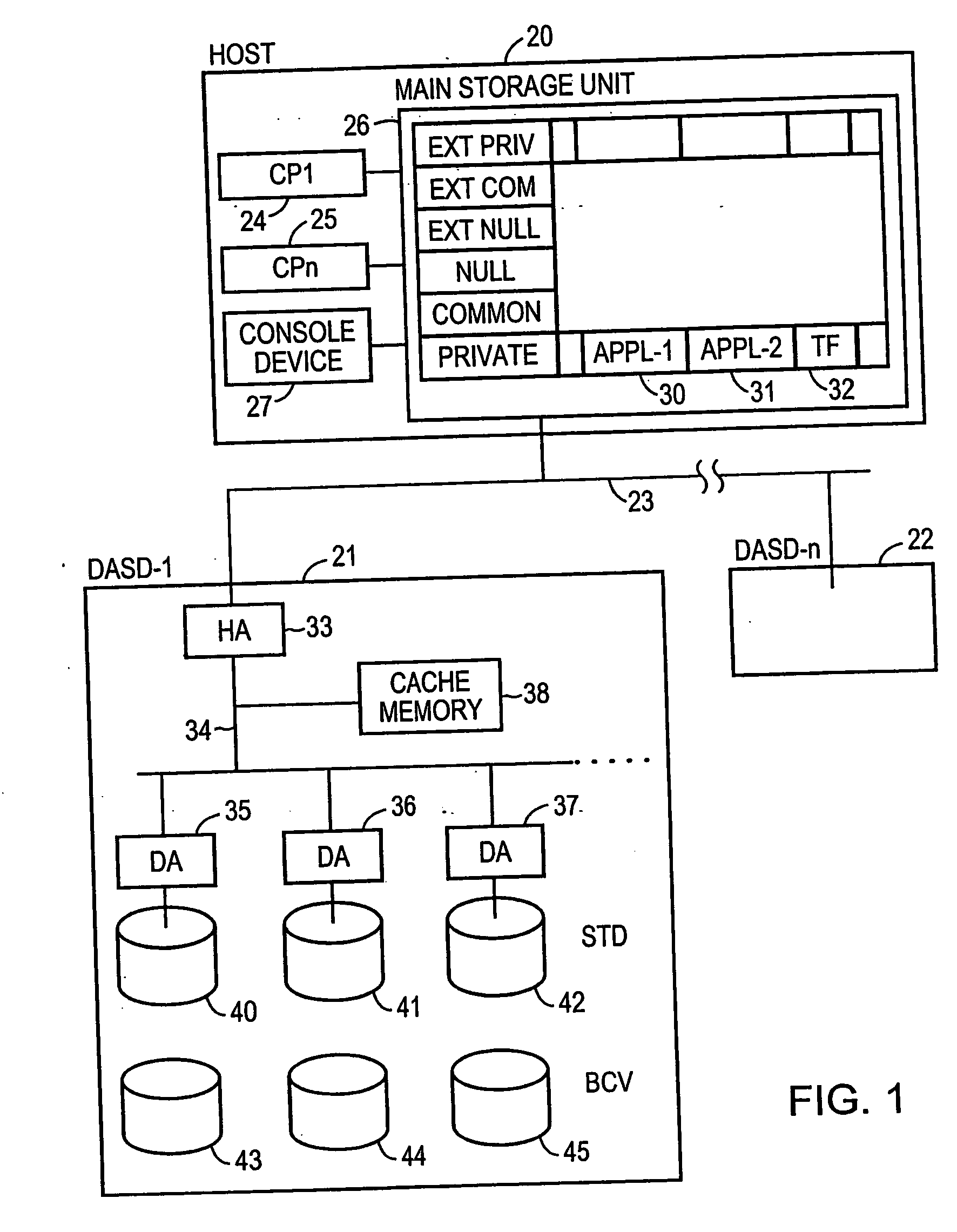
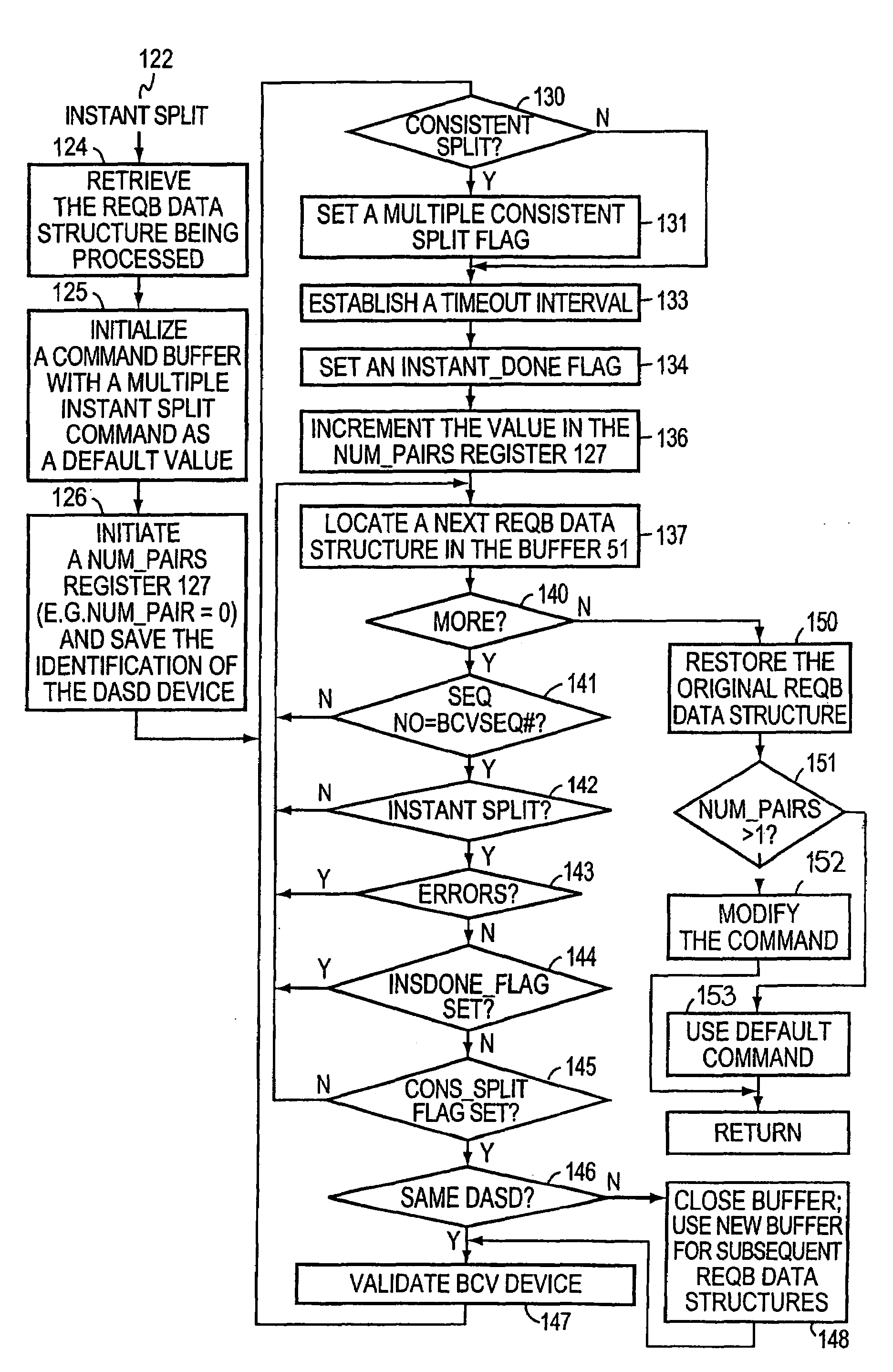
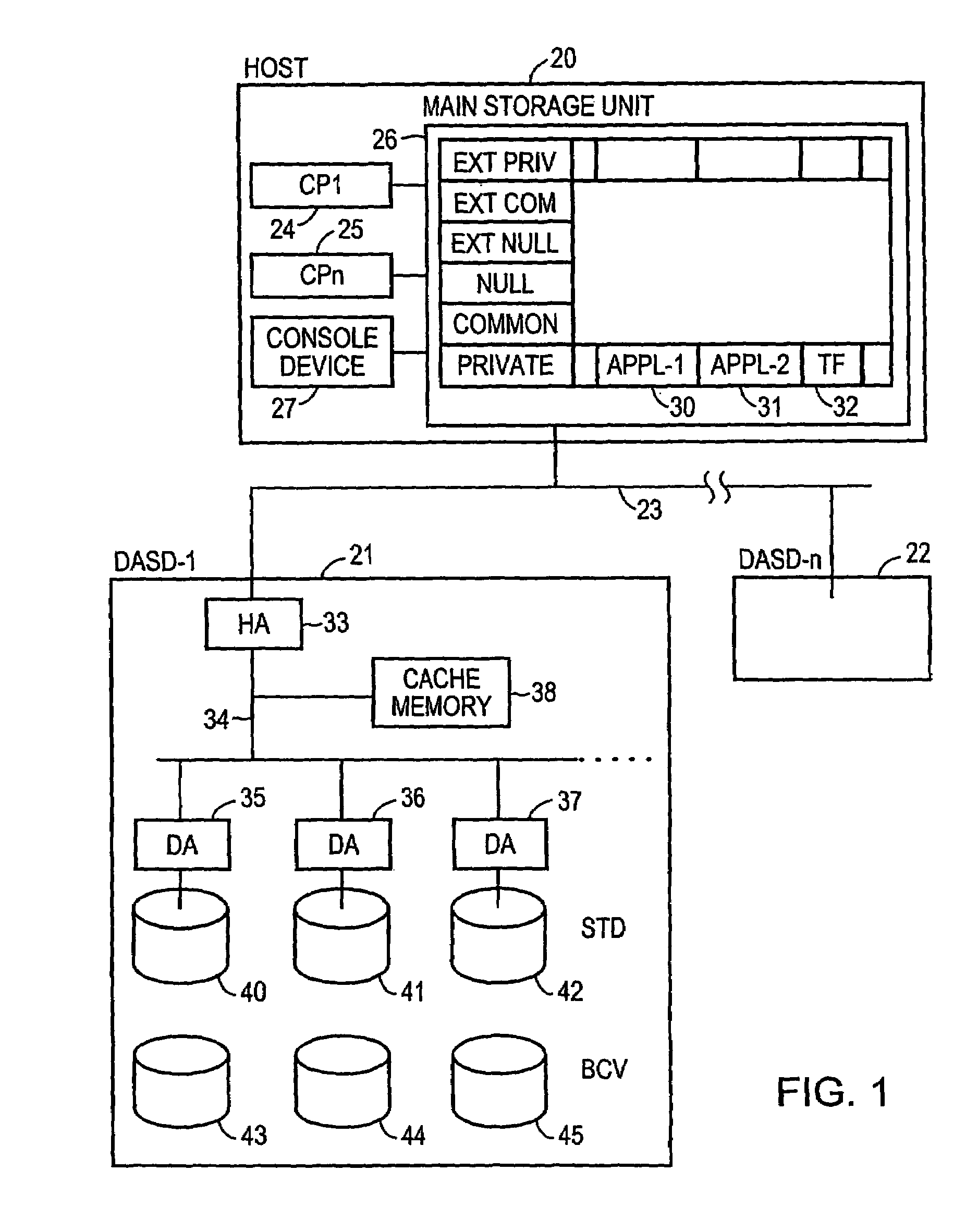
Method and apparatus for enabling consistent ancillary disk array storage device operations with respect to a main application
InactiveUS6754682B1Maintain data consistencyInput/output to record carriersData processing applicationsData processing systemData set
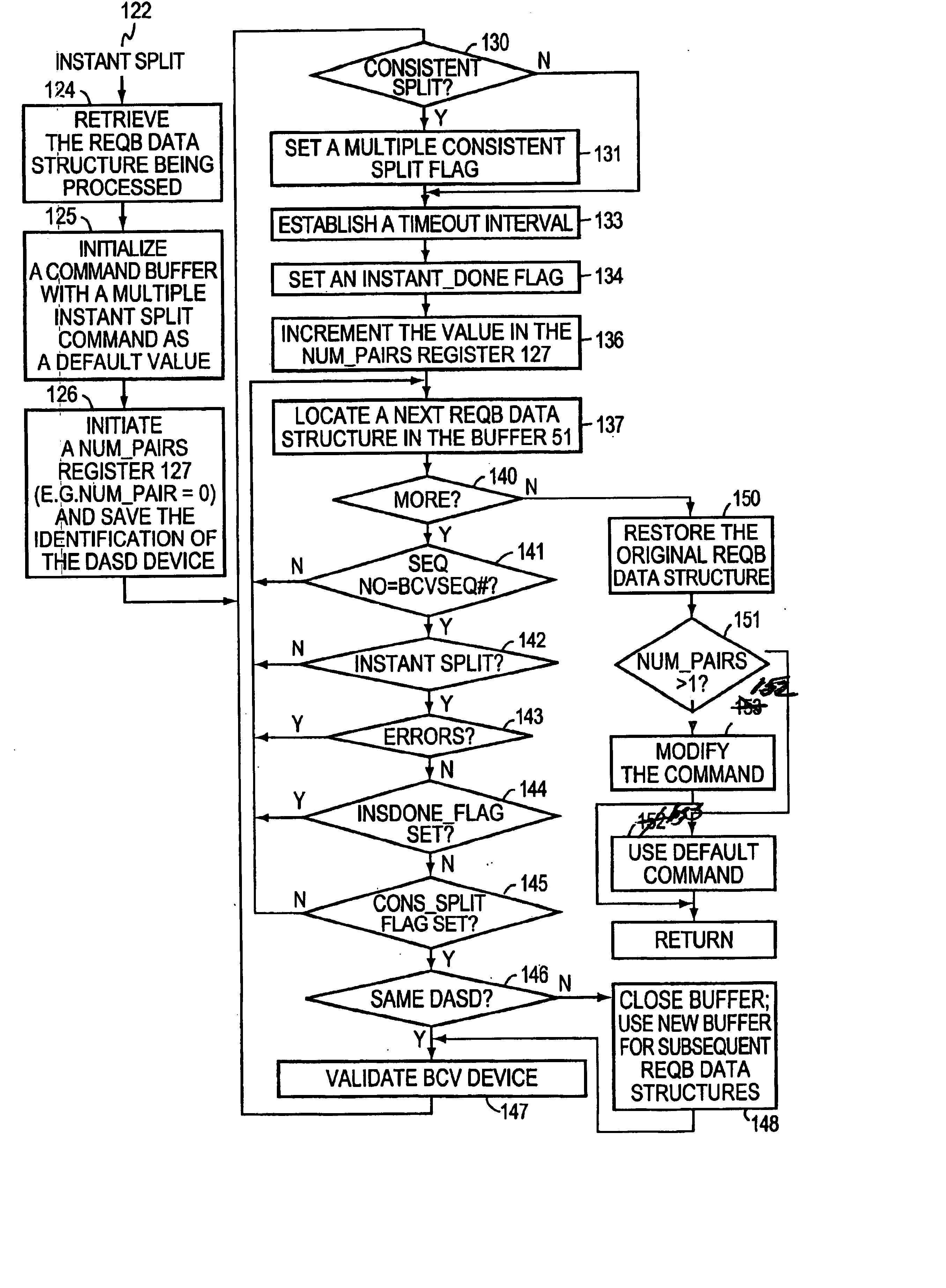
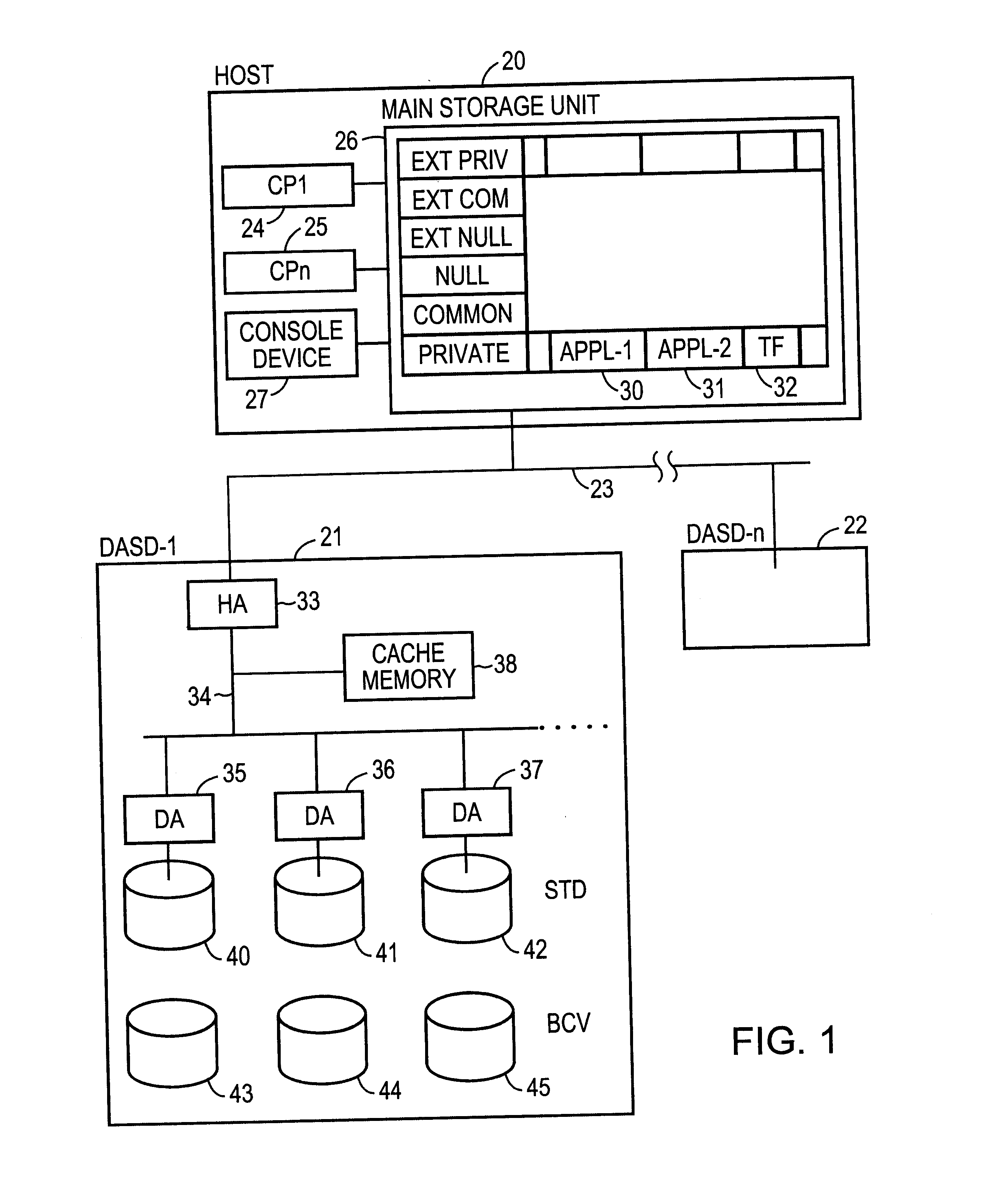
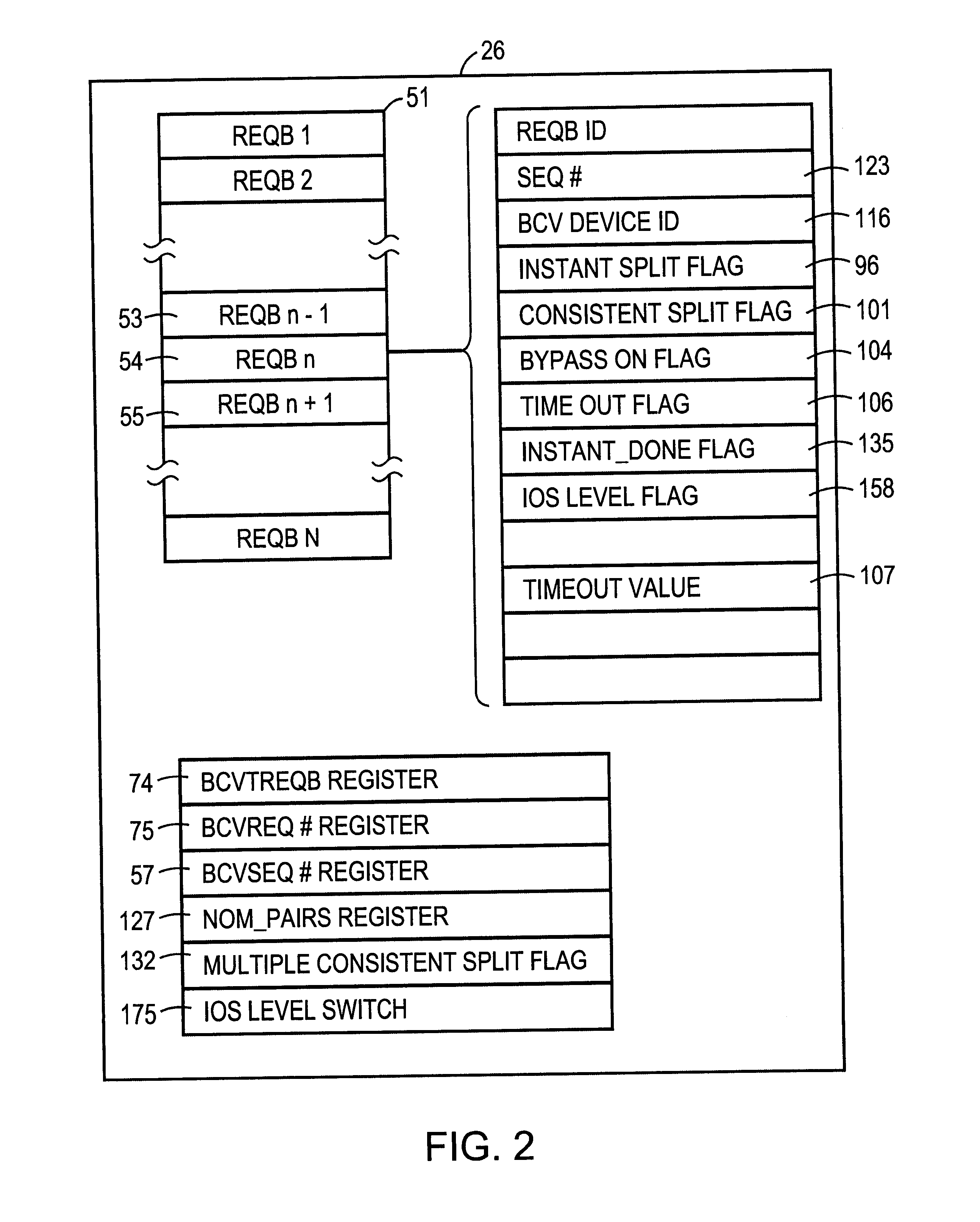
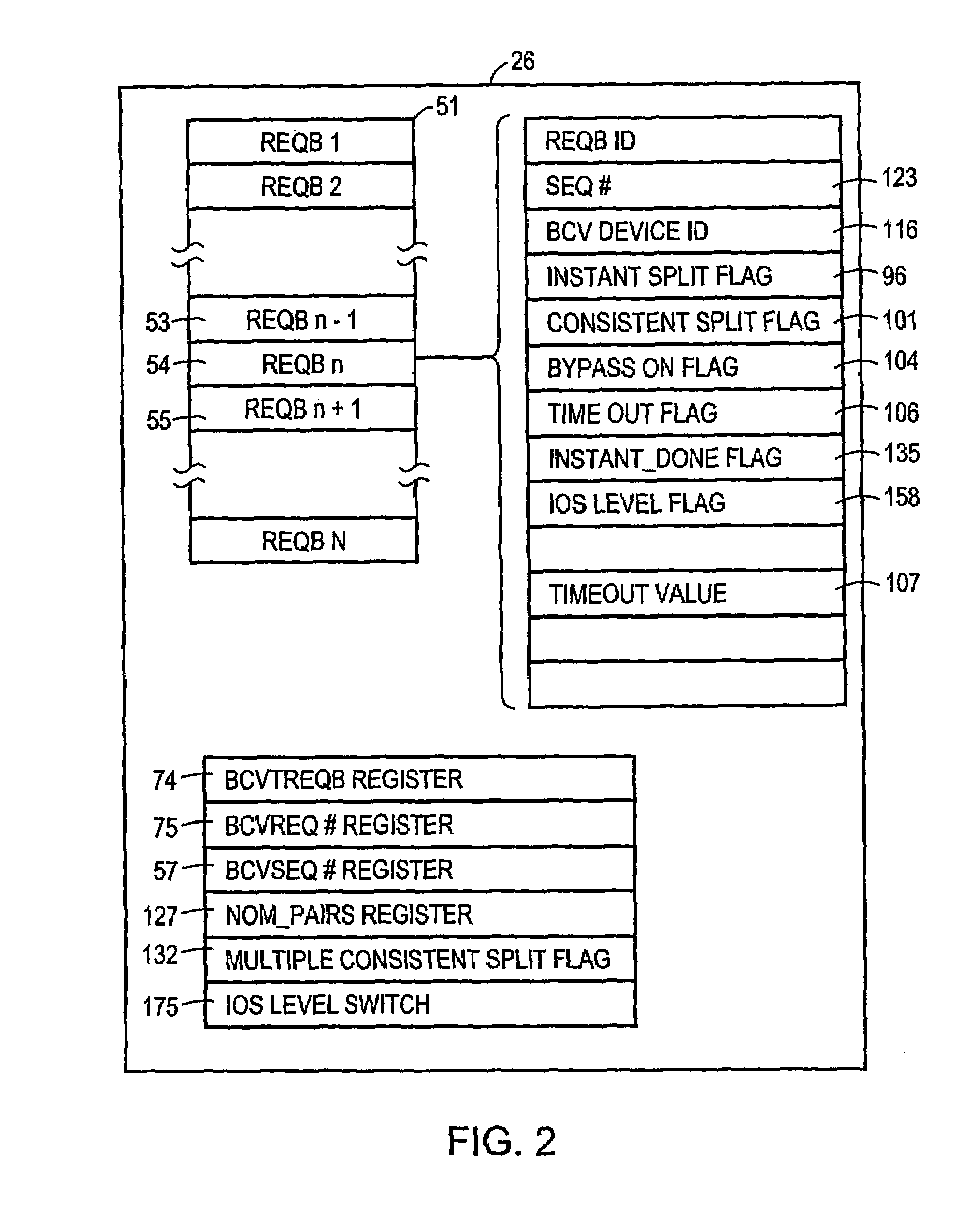
A method and apparatus for enhancing data recovery in data processing systems in which applications span multiple logical devices. A data processing system includes multiple standard devices for storing data and corresponding BCV devices for, in one mode, operating as mirrors of those standard devices. If certain of those BCV devices are associated with the same data set, a CONSISTENT SPLIT operation controls the way in which each of these BCV devices is detached from its corresponding standard device and made available to another application. Each command to an application for controlling the BCV devices is translated into one or more request data structures that identify the BCV devices as being involved in a consistent split operation and that establishes a system lock out for those particular devices during which those devices are split from their respective devices in a consistent manner.
Owner:EMC IP HLDG CO LLC
Table format customizable Excel table analysis method
InactiveCN103150380ARealize business needsMaintain accuracySpecial data processing applicationsTransaction managementWeb service
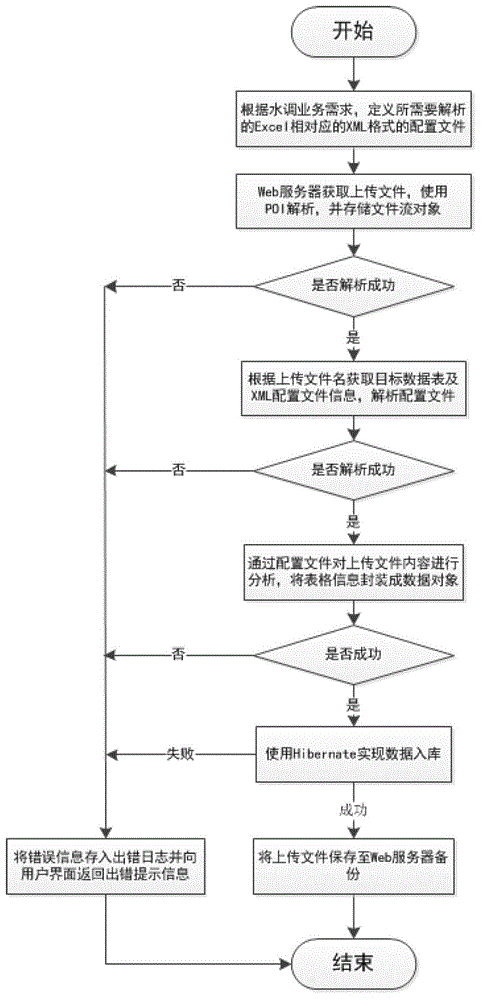
The invention discloses a table format customizable Excel table analysis method which comprises the steps of defining an XML (Extensive Makeup Language) format configuration file corresponding to an Excel table to be resolved according to water diversion business requirements, uploading an Excel file to a Web server through a browser, resolving the file, obtaining a target data sheet of the file and information of the corresponding XML configuration file according to a filename of the uploaded file, resolving the configuration file, analyzing contents of the uploaded file through the information of the configuration file, packaging the information to be warehoused into a data object, warehousing data with Hibernate, and uploading a file backup to the server. According to the method, general resolution of complicated Excel is realized through the configurable file, the method is particularly applicable to processing river basin water diversion business tables, and a precise error information prompt mechanism and a transaction management mechanism ensures accuracy and consistency of the data of a database.
Owner:HOHAI UNIV
Cache memory system and control method of the cache memory system
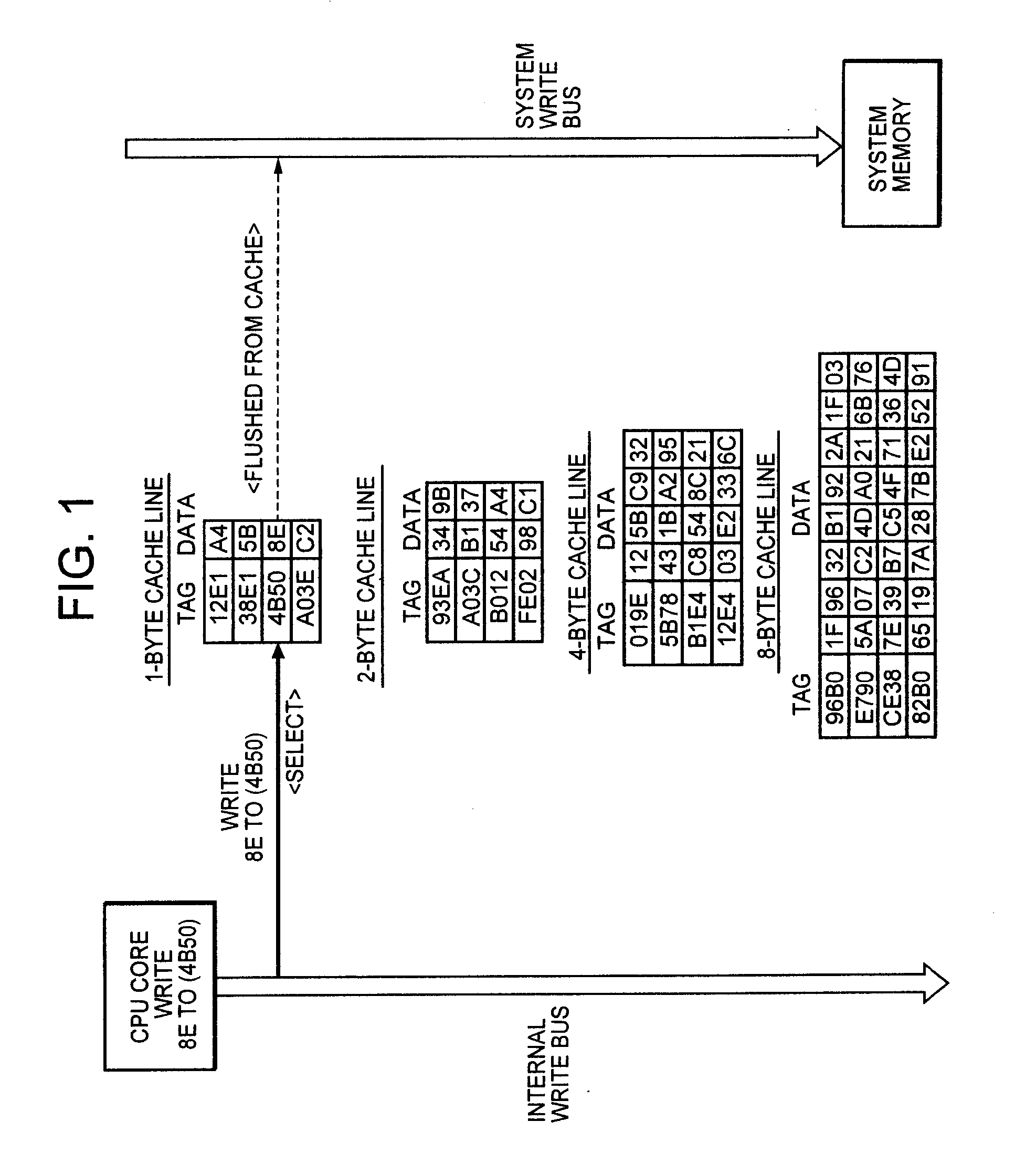
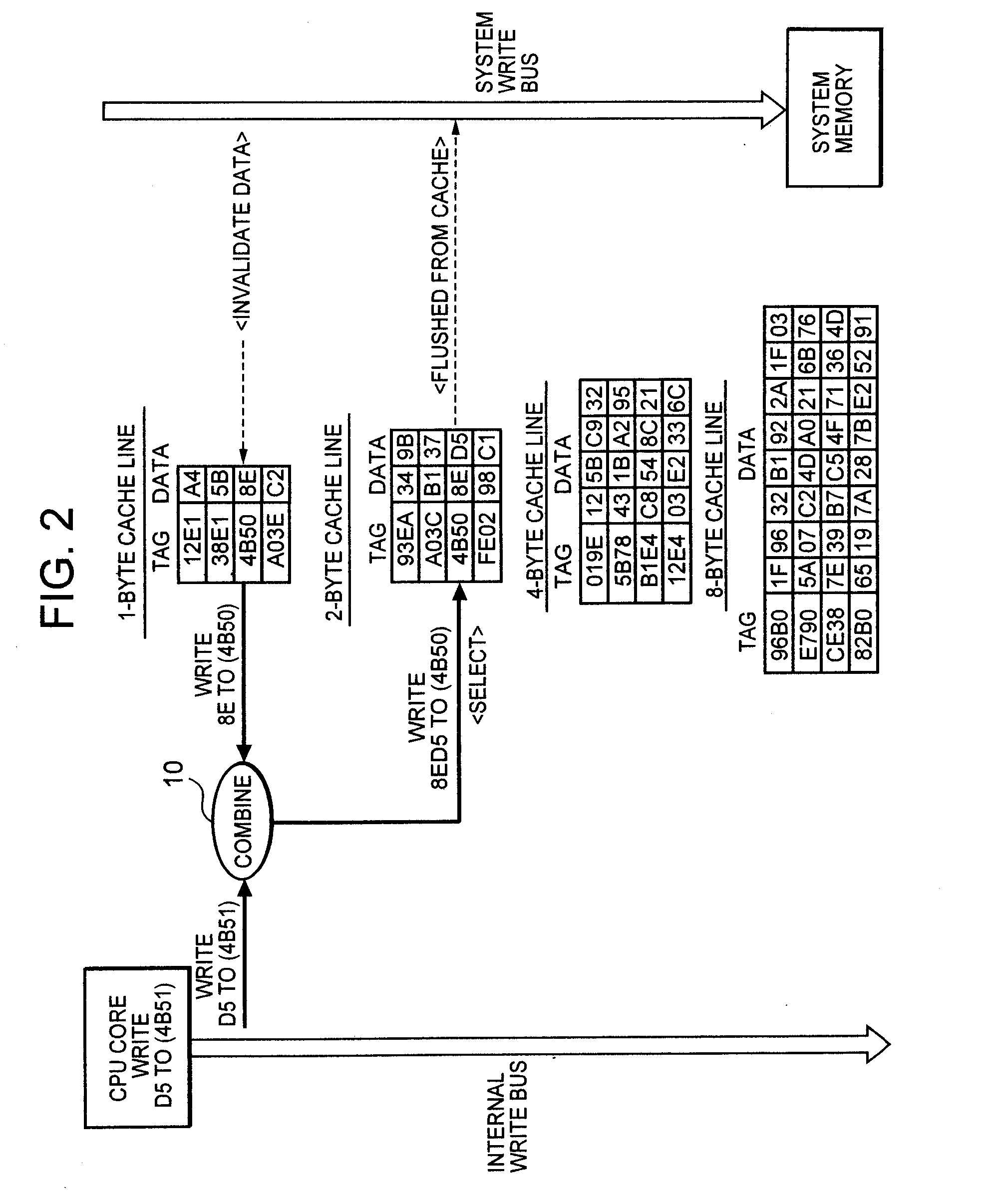
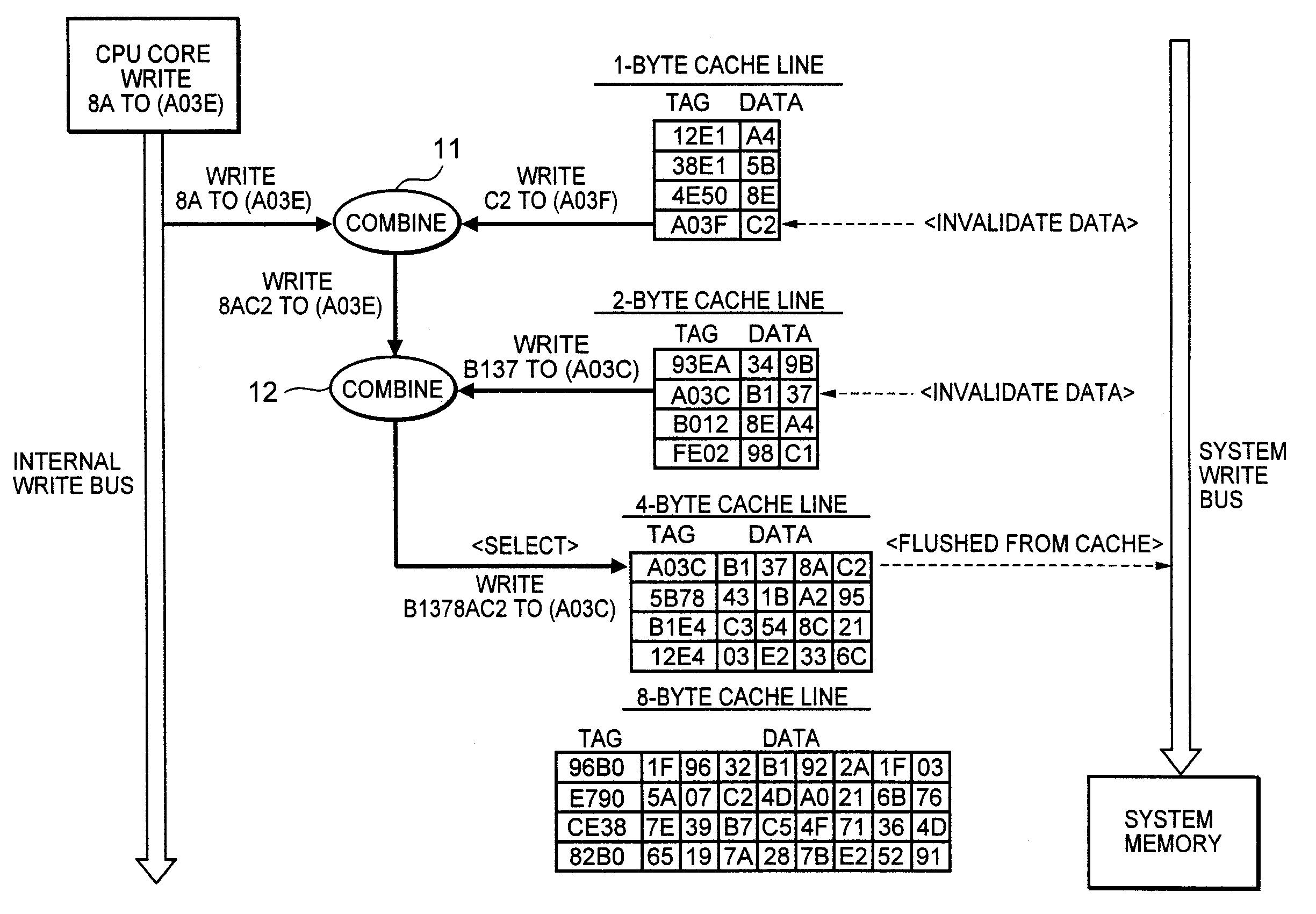
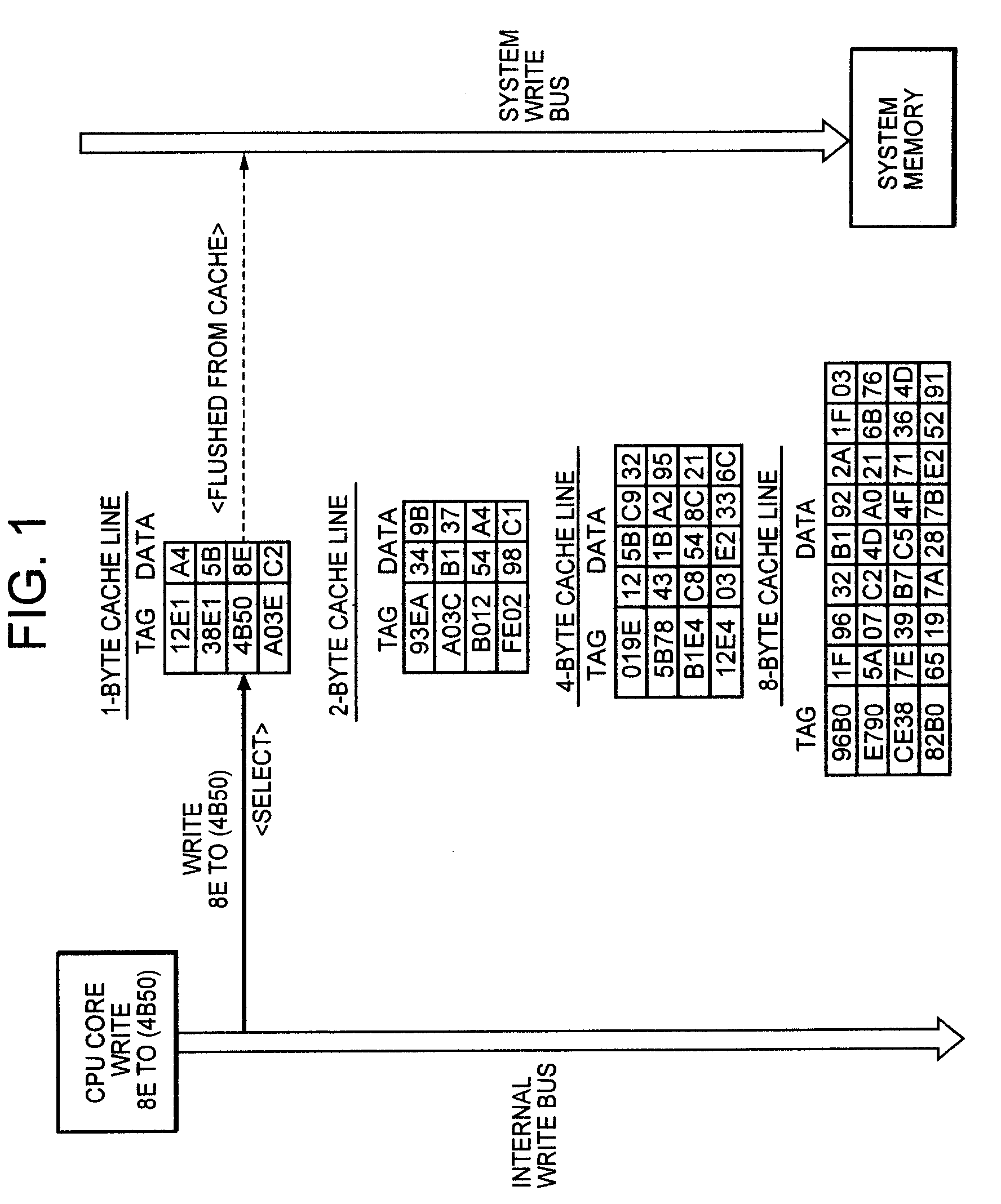
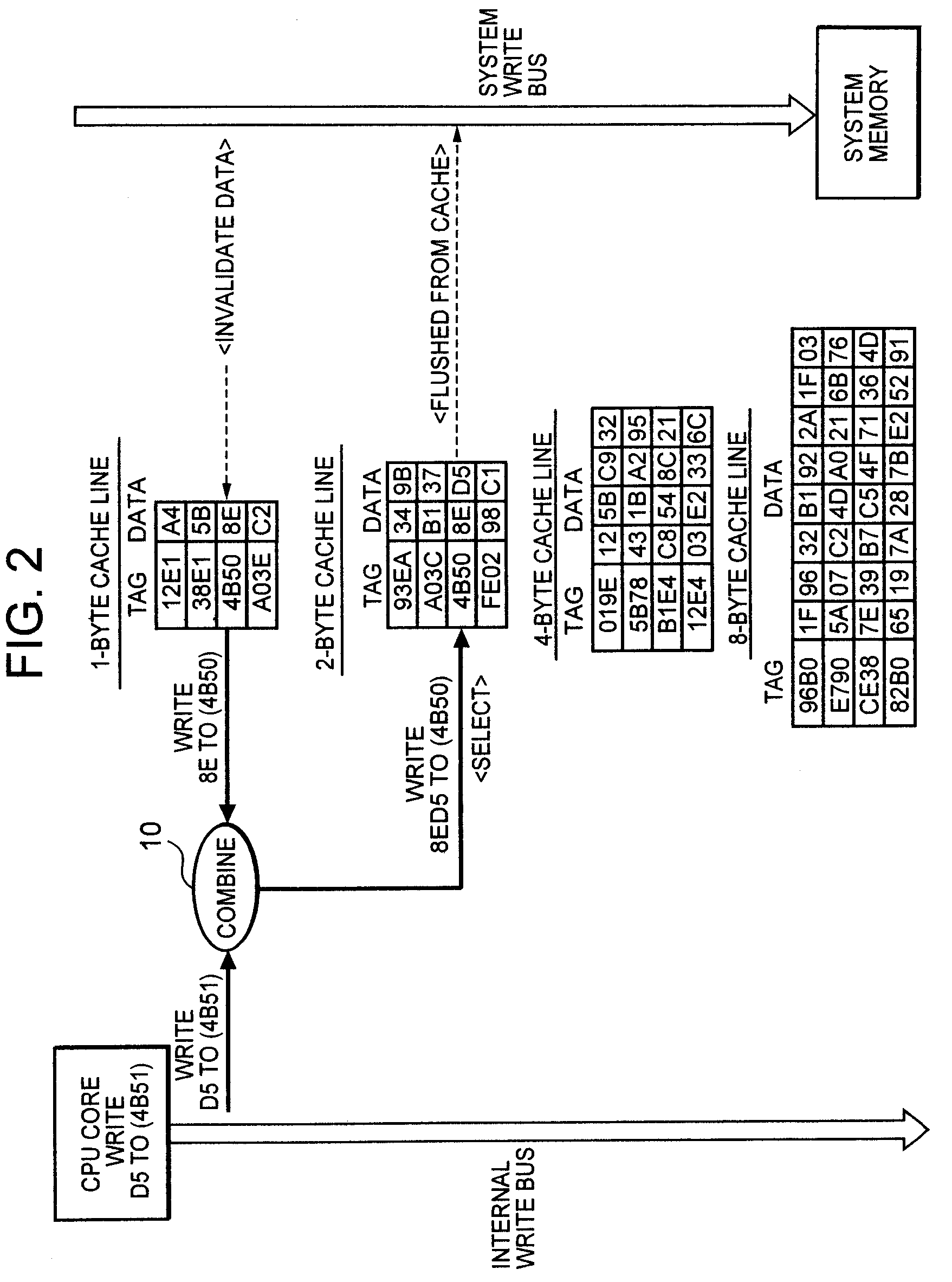
InactiveUS20060059309A1Reduce in quantityImprove data processing speedMemory systemsParallel computingTerm memory
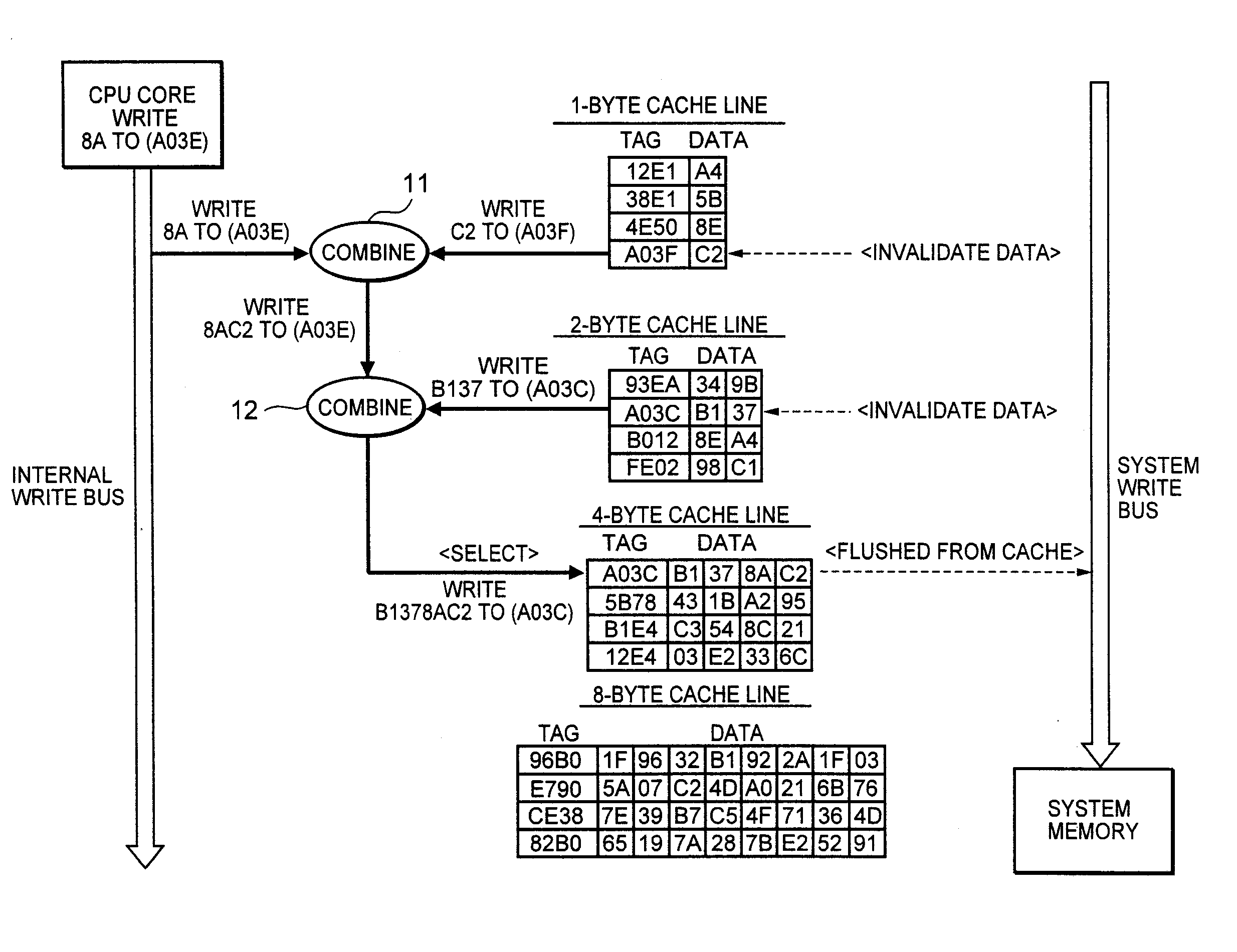
To improve the efficiency of access to a system memory associated with changes (writes) to cache data, a cache line having the same memory size as write data is selected and the write data is written into the selected cache line, thereby reducing the number of accesses to the system memory to cache data from the system memory associated with partial replacement of cache lines. Further, valid data at an address contiguous with the address of the write data is combined with the write data, and written into a cache line having the same size as the combined data, thereby reducing the number of accesses to the system memory to flush data from the cache associated with writes to the cache.
Owner:IBM CORP
Cache memory system and control method of the cache memory system
InactiveUS7493445B2Improve efficiencyReduce frequencyMemory systemsParallel computingData combination
To improve the efficiency of access to a system memory associated with changes (writes) to cache data, a cache line having the same memory size as write data is selected and the write data is written into the selected cache line, thereby reducing the number of accesses to the system memory to cache data from the system memory associated with partial replacement of cache lines. Further, valid data at an address contiguous with the address of the write data is combined with the write data, and written into a cache line having the same size as the combined data, thereby reducing the number of accesses to the system memory to flush data from the cache associated with writes to the cache.
Owner:INT BUSINESS MASCH CORP
Mechanisms for merging index structures in molap while preserving query consistency
ActiveUS20170011082A1Improved OLAP query performanceLess complex processingMulti-dimensional databasesSpecial data processing applicationsMOLAPSubject matter
Novel methods are described herein to provide an OLAP database system that performs lock-less bulk insertion while maintaining high query performance and minimizing additional storage requirements. Aspects of the claimed subject matter include novel methods for merging two index structures while maintaining query consistency without the use of a versioning scheme by using copies of vertical segments of an index tree page; a method to prepare and merge two index structures that operates within storage constraints; and a method to execute queries concurrently while index maintenance is in progress while still producing consistent results. According to an aspect of the present disclosure, a flexible index merge mechanism is provided that merges data from incremental indices to a primary data index in three phases: a load phase, a copy phase, and a replace phase.
Owner:FUTUREWEI TECH INC
Undoing user actions in a client program
ActiveUS7818718B2Maintain data consistencyError detection/correctionExecution for user interfacesUser inputSoftware engineering
Methods and apparatus, including computer program products, implementing techniques for undoing user actions in a client program. The techniques include displaying a user interface in a client program, the user interface having a plurality of controls, the plurality of controls including multiple types of controls, each control having a state; for each control in the plurality of controls, storing the state of the control as a first state for the control; receiving user input comprising a change to the state of a control in the plurality of controls; updating the state of the control based on the user input; storing the updated state of the control as a second state for the control; receiving user input comprising a request to undo the change; and restoring the state of the control to reflect the first state for the control.
Owner:SAP AG
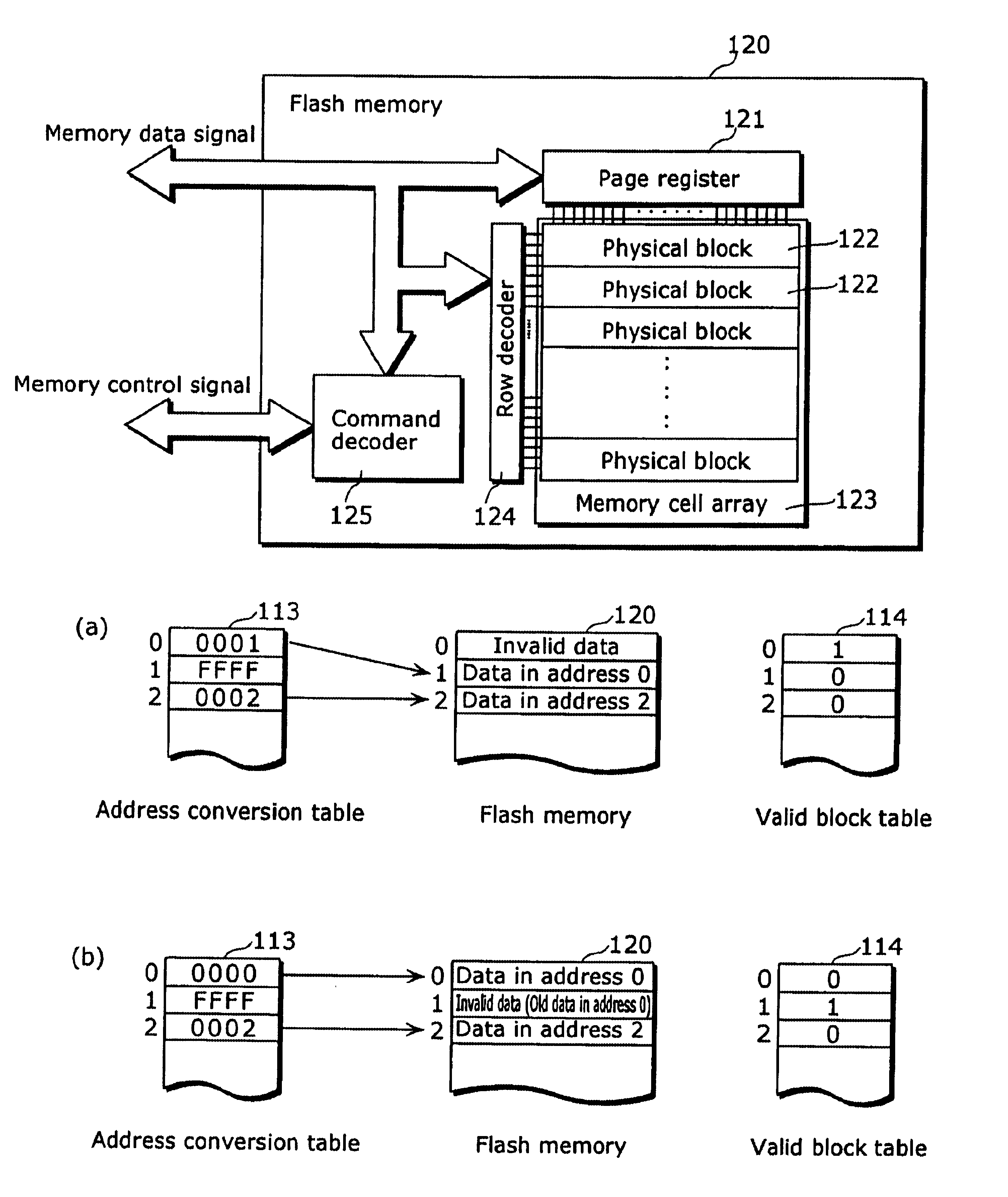
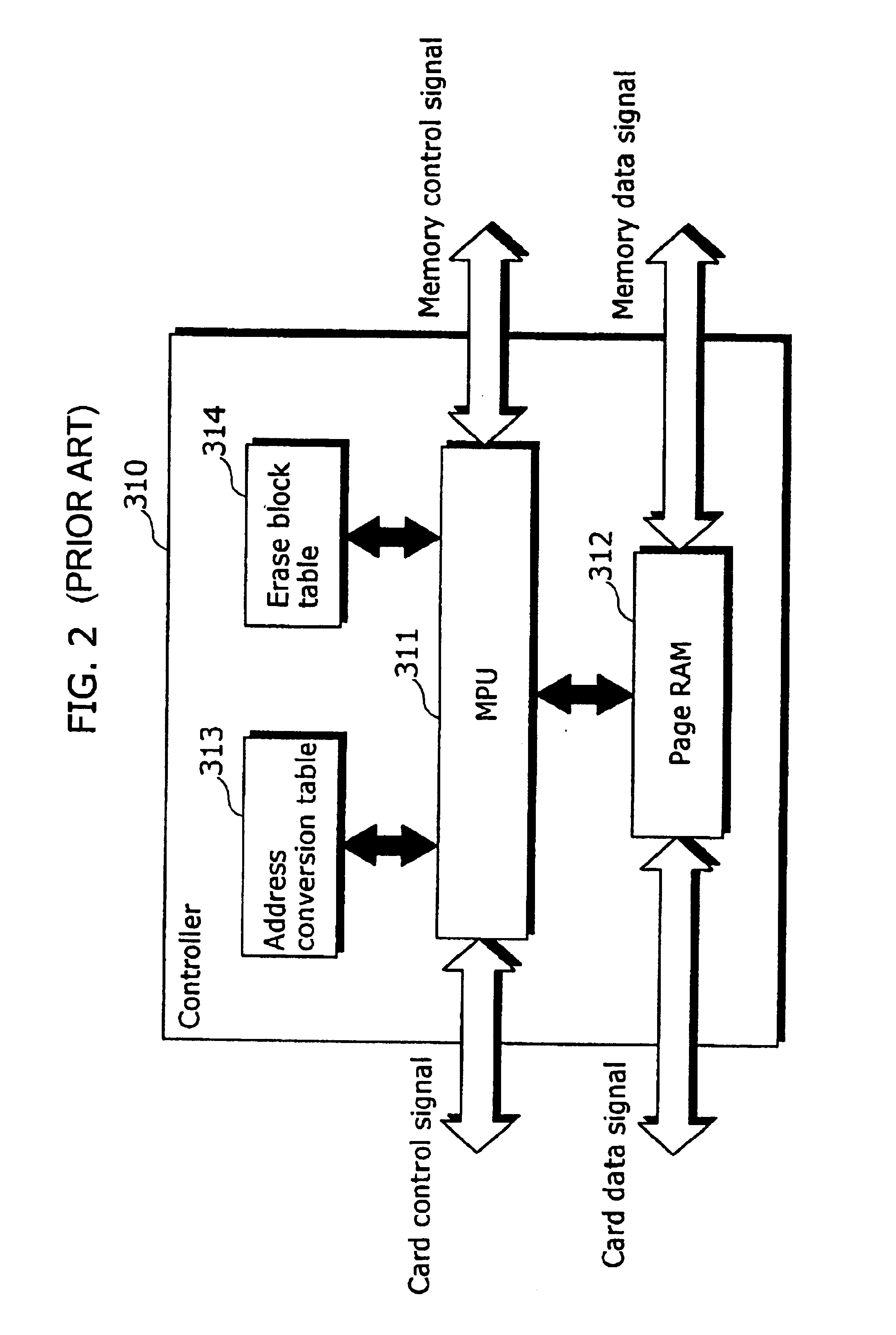
Non-volatile storage device and control method thereof
InactiveUS6944060B2Solve large capacityMaintain data consistencyMemory adressing/allocation/relocationRead-only memoriesProcessor registerMemory cards
A memory card (100) is comprised of: a flash memory (120) that includes a plurality of physical blocks (122) made up of a plurality of pages for storing data and a page register (121) that holds data to be written to a page; and a controller (110) that specifies and erases an invalid physical block with reference to a valid block table (114) indicating whether valid data is stored in each of the physical blocks (122), when data is written, and that transfers, at the same time, the data to be written to the page register (121) while carrying out said erasure.
Owner:PANASONIC CORP
Method for erasure coding data across a plurality of data stores in a network
InactiveUS20100162044A1Maintain data consistencySimple and efficientError preventionCode conversionSelf-healingData set
An efficient method to apply an erasure encoding and decoding scheme across dispersed data stores that receive constant updates. A data store is a persistent memory for storing a data block. Such data stores include, without limitation, a group of disks, a group of disk arrays, or the like. An encoding process applies a sequencing method to assign a sequence number to each data and checksum block as they are modified and updated onto their data stores. The method preferably uses the sequence number to identify data set consistency. The sequencing method allows for self-healing of each individual data store, and it maintains data consistency and correctness within a data block and among a group of data blocks. The inventive technique can be applied on many forms of distributed persistent data stores to provide failure resiliency and to maintain data consistency and correctness.
Owner:QUEST SOFTWARE INC
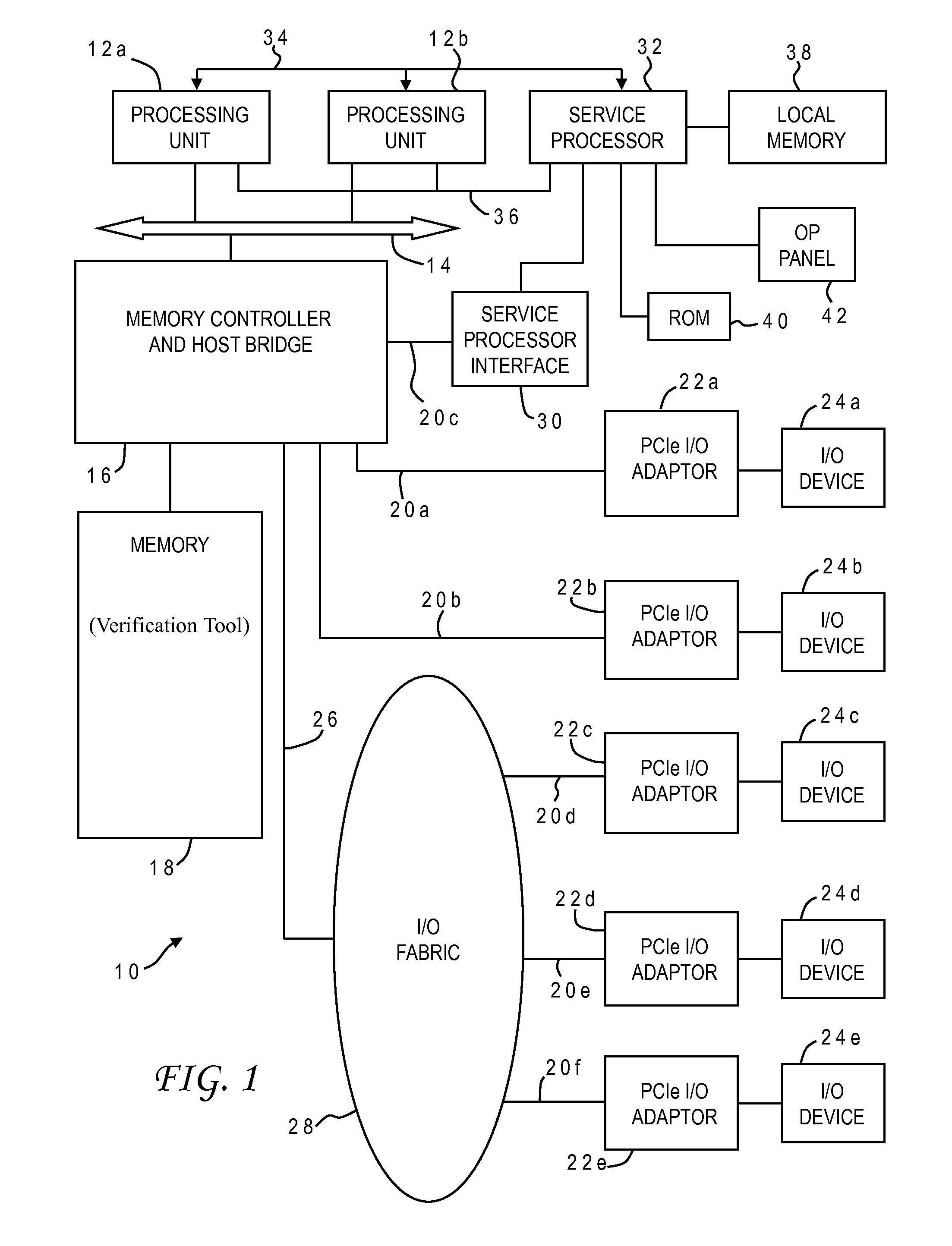
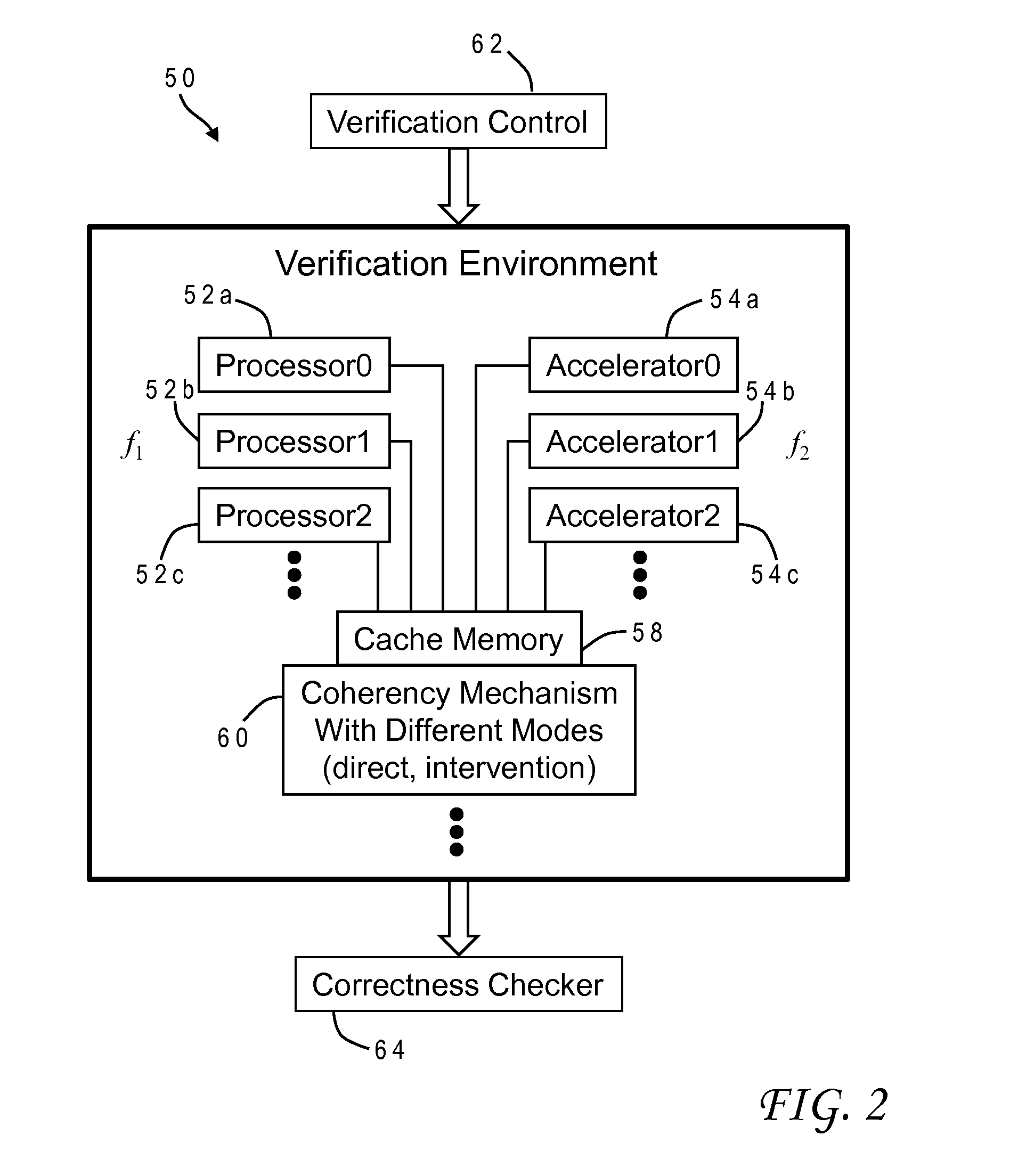
Efficient validation of coherency between processor cores and accelerators in computer systems
ActiveUS20140237194A1Maintain data consistencyVerify correctnessMemory adressing/allocation/relocationComputer system designAs Directed
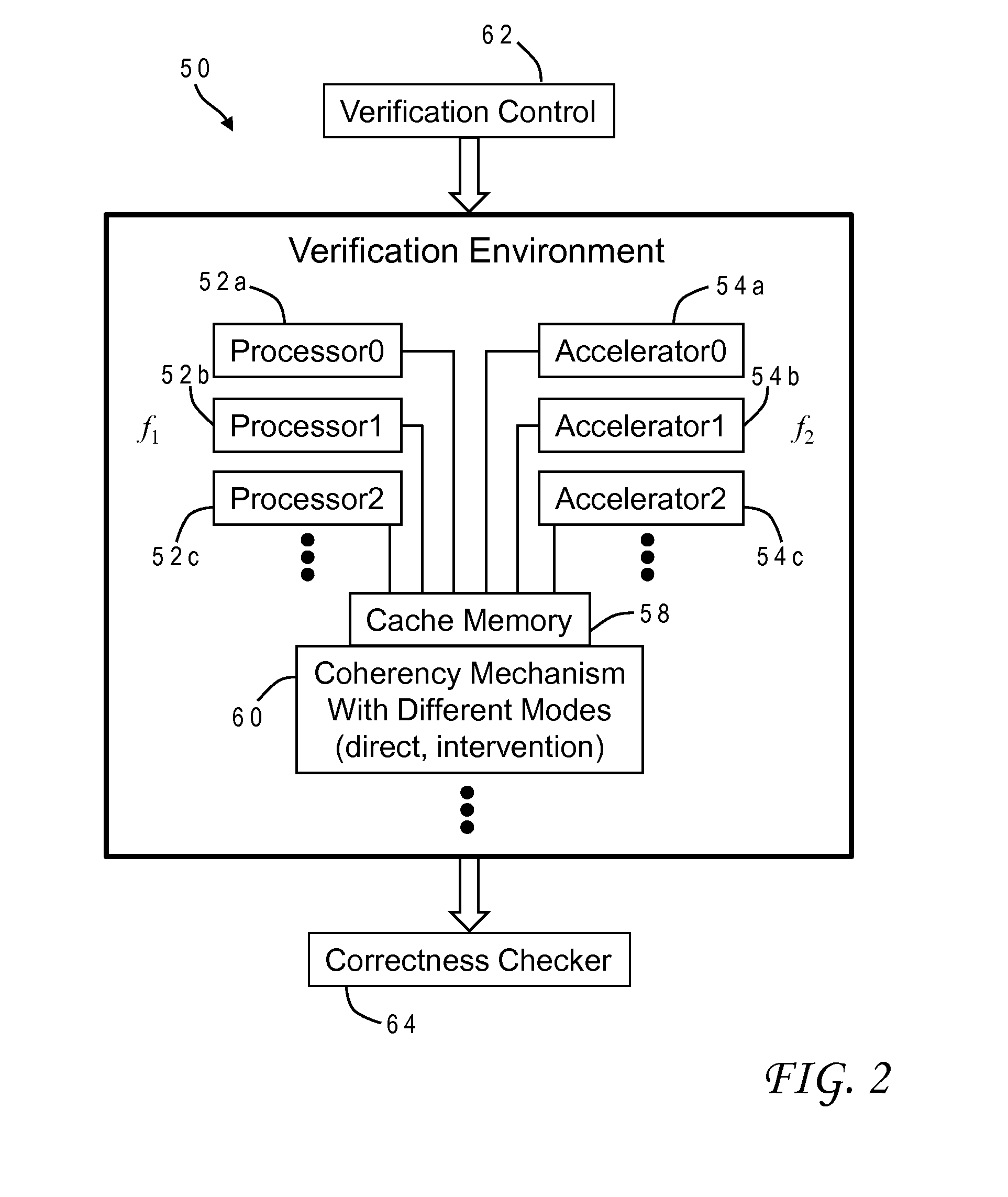
A method of testing cache coherency in a computer system design allocates different portions of a single cache line for use by accelerators and processors. The different portions of the cache line can have different sizes, and the processors and accelerators can operate in the simulation at different frequencies. The verification system can control execution of the instructions to invoke different modes of the coherency mechanism such as direct memory access or cache intervention. The invention provides a further opportunity to test any accelerator having an original function and an inverse function by allocating cache lines to generate an original function output, allocating cache lines to generate an inverse function output based on the original function output, and verifying correctness of the original and inverse functions by comparing the inverse function output to the original function input.
Owner:GLOBALFOUNDRIES US INC
Cache memory and method of controlling the same
InactiveUS20100106910A1Maintain data consistencyEfficient processingMemory adressing/allocation/relocationData memoryParallel computing
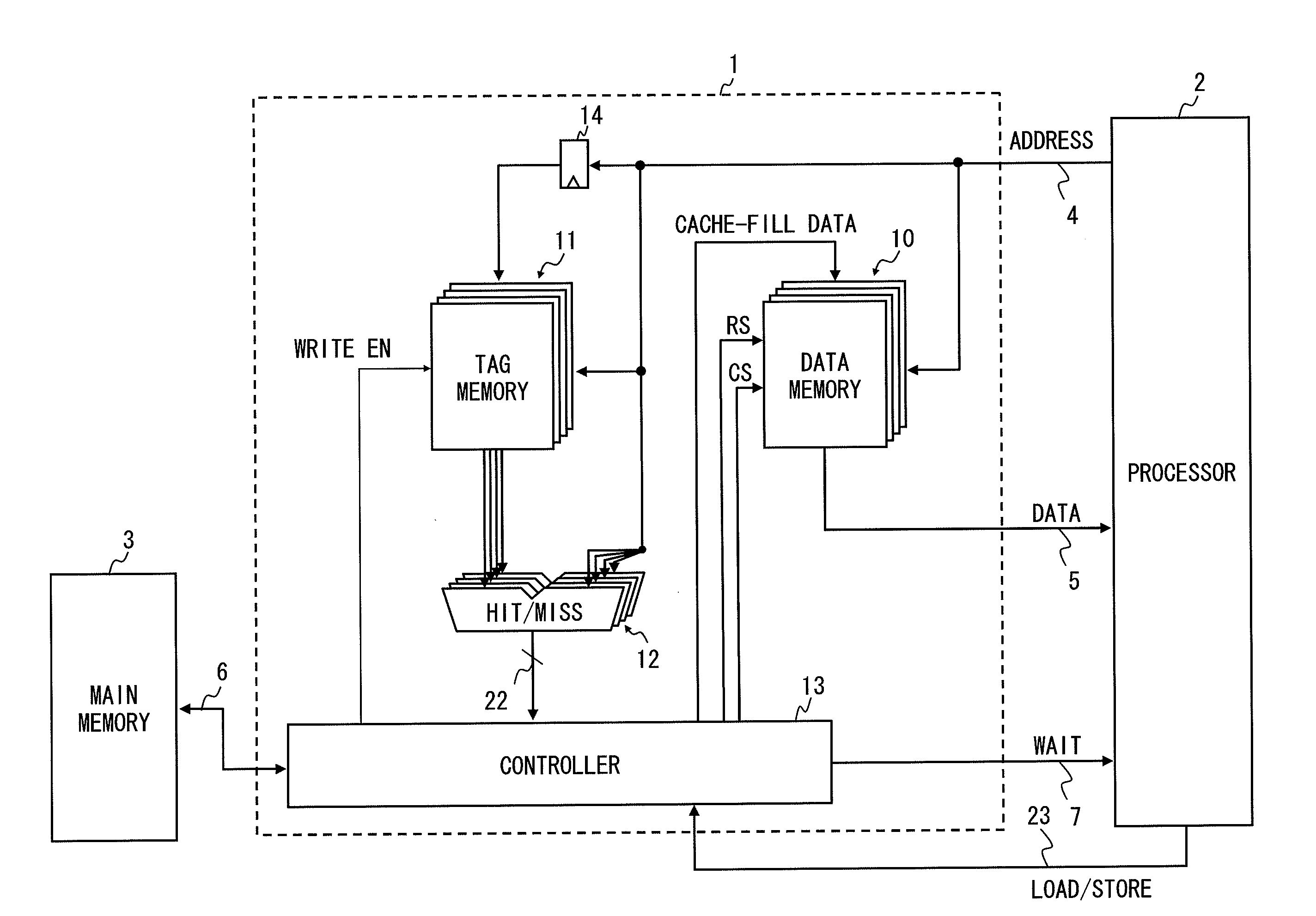
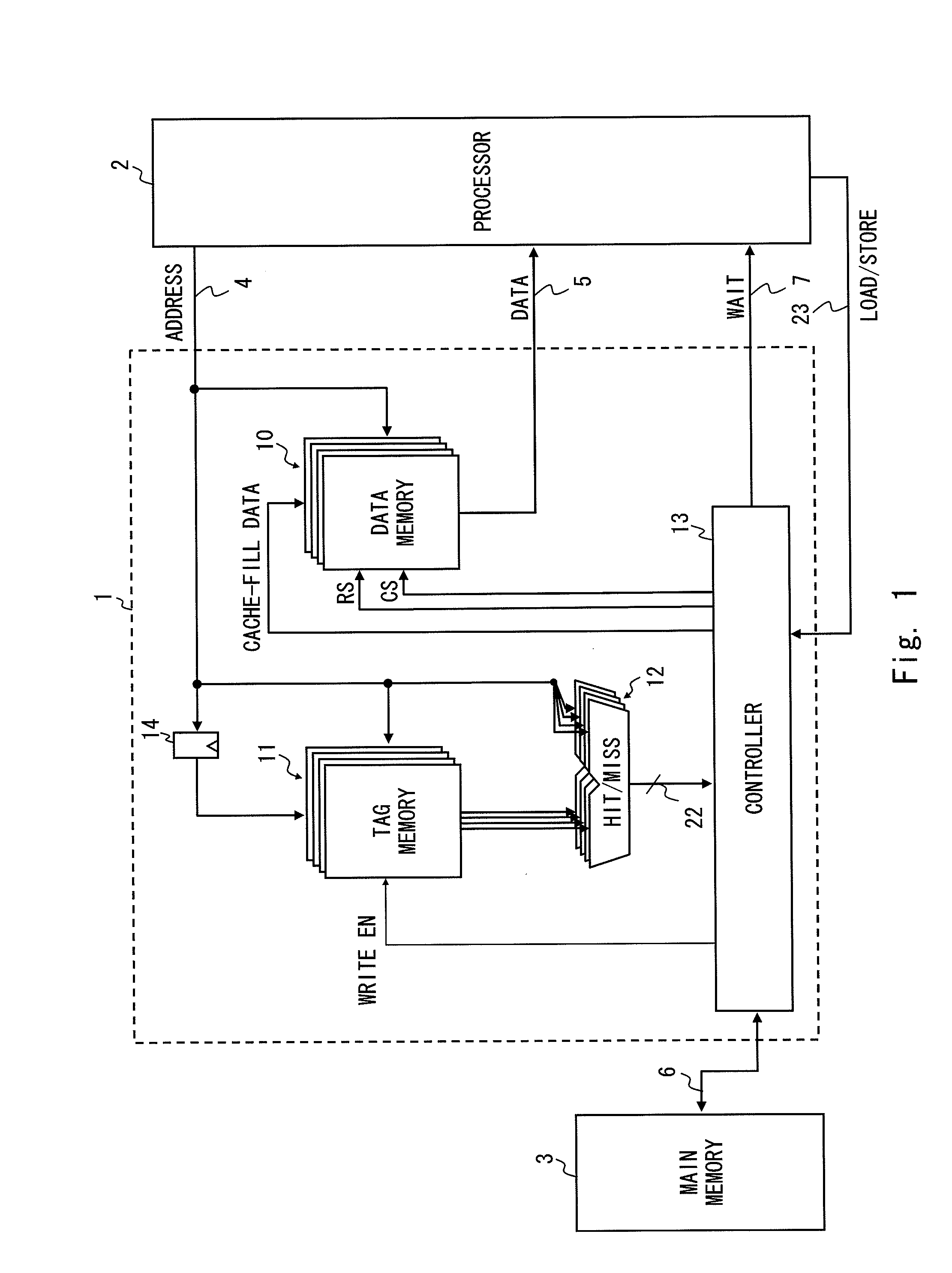
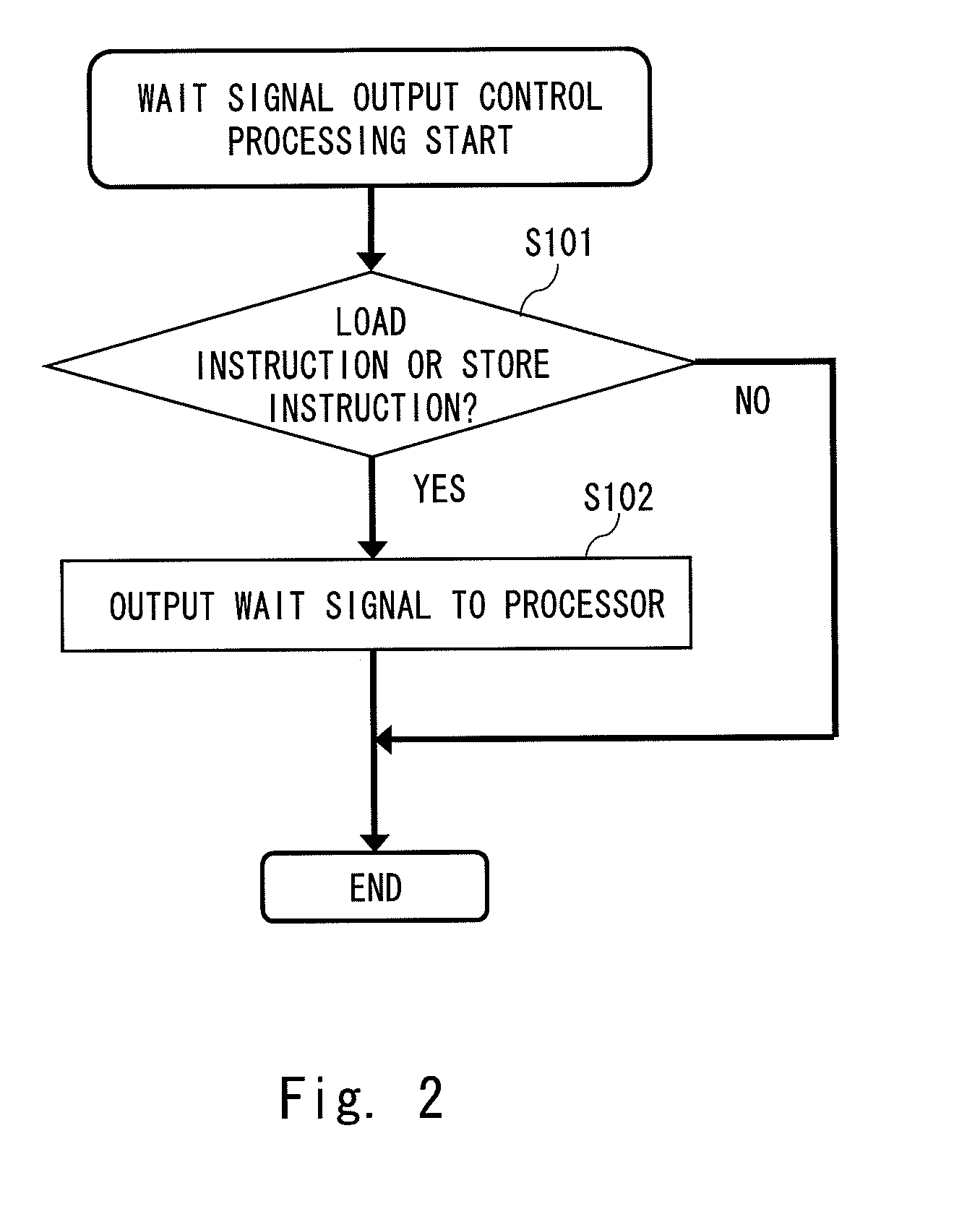
It is an object of the present invention to reduce output of a WAIT signal to maintain data consistency to effectively process subsequent memory access when there is no subsequent memory access in case of miss hit in a cache memory having a multi-stage pipeline structure. A cache memory according to the present invention performs update processing of a tag memory and a data memory and decides whether or not there is a subsequent memory access upon decision by a hit decision unit that an input address is a miss hit. Upon decision that there is a subsequent memory access, a controller outputs a WAIT signal to generate a pipeline stall for the pipeline processing of the processor to the processor, while the controller does not output a WAIT signal upon decision that there is no subsequent memory access.
Owner:RENESAS ELECTRONICS CORP
Efficient validation of coherency between processor cores and accelerators in computer systems
InactiveUS20140236561A1Maintain data consistencyVerify correctnessMemory adressing/allocation/relocationDesign optimisation/simulationComputer system designAs Directed
A method of testing cache coherency in a computer system design allocates different portions of a single cache line for use by accelerators and processors. The different portions of the cache line can have different sizes, and the processors and accelerators can operate in the simulation at different frequencies. The verification system can control execution of the instructions to invoke different modes of the coherency mechanism such as direct memory access or cache intervention. The invention provides a further opportunity to test any accelerator having an original function and an inverse function by allocating cache lines to generate an original function output, allocating cache lines to generate an inverse function output based on the original function output, and verifying correctness of the original and inverse functions by comparing the inverse function output to the original function input.
Owner:GLOBALFOUNDRIES INC
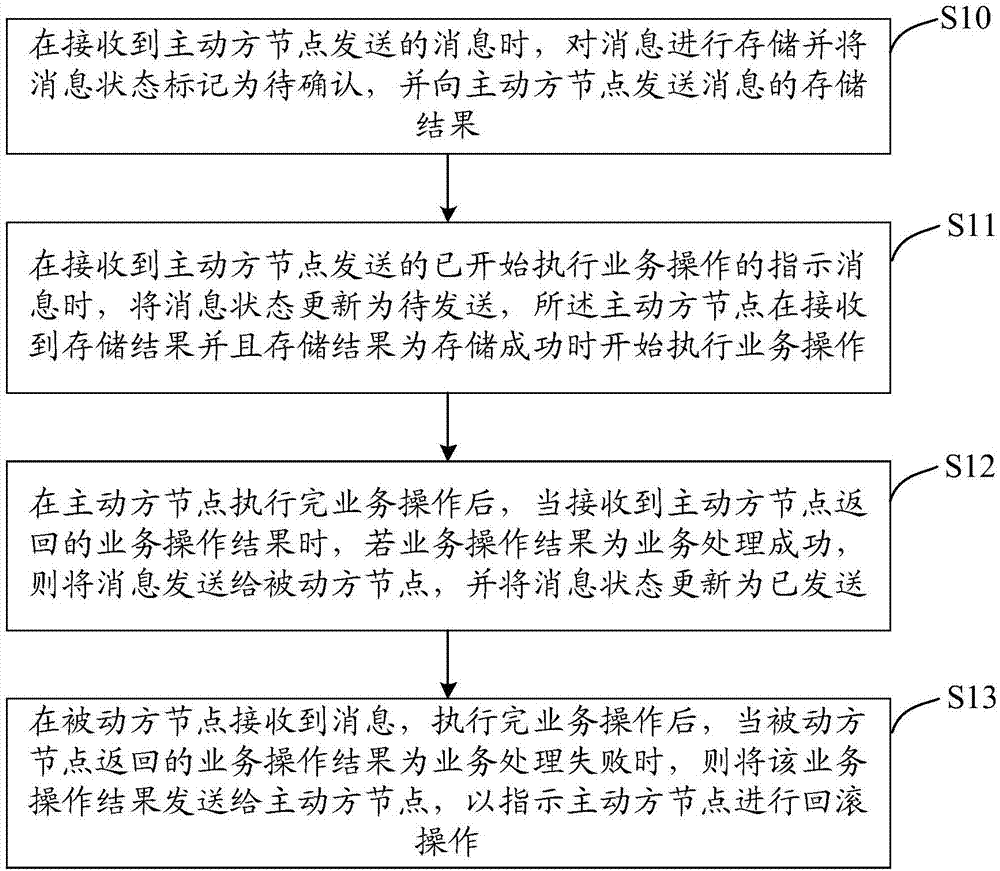
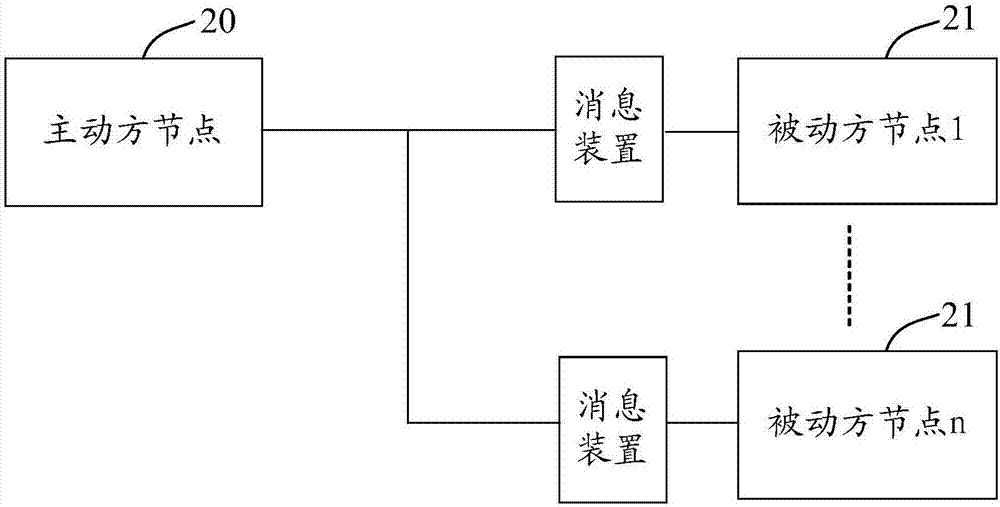
Distributed system transaction management method and device
InactiveCN107332906AMaintain data consistencyImprove processing efficiencyTransmissionSpecial data processing applicationsRollback OperationDistributed computing
The invention discloses a distributed system transaction management method and device. The method comprises the steps of: when a message sent by an active party node is received, carrying out storage on the message, marking a message state as a to-be-confirmed state, and sending a storage result of the message to the active party node; when an indication message sent by the active party node and used for indicating that a service operation is executed is received, updating the message state into a to-be-sent state; after the active party node executes the service operation, when a service operation result returned by the active party node is received, if the service operation result is that a service is successfully processed, sending the message to a passive party node, and updating the message state into a sent state; and after the passive party node executes the service operation, when a service operation result returned by the passive party node is that the service is failed in processing, sending the service operation result to the active party node and indicating the active party node to carry out a rolling-back operation. The method and the device which are disclosed by the invention achieve an effect of keeping consistency of data between the active party node and the passive party node.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Systems and methods for consensus protocol selection based on delay analysis
InactiveUS20160150060A1Maintain data consistencyDigital computer detailsTransmissionDelay analysisData consistency
A method for selecting a consensus protocol comprises separating a consensus protocol into one or more communication steps, wherein the consensus protocol is useable to substantially maintain data consistency between nodes in a distributed computing system, and wherein a communication step comprises a message transfer, attributable to the consensus protocol, in the distributed computing system, and computing an estimated protocol-level delay based on one or more attributes associated with the separated communication steps of the consensus protocol.
Owner:IBM CORP
Method for restarting control nodes in automatic switching optical network
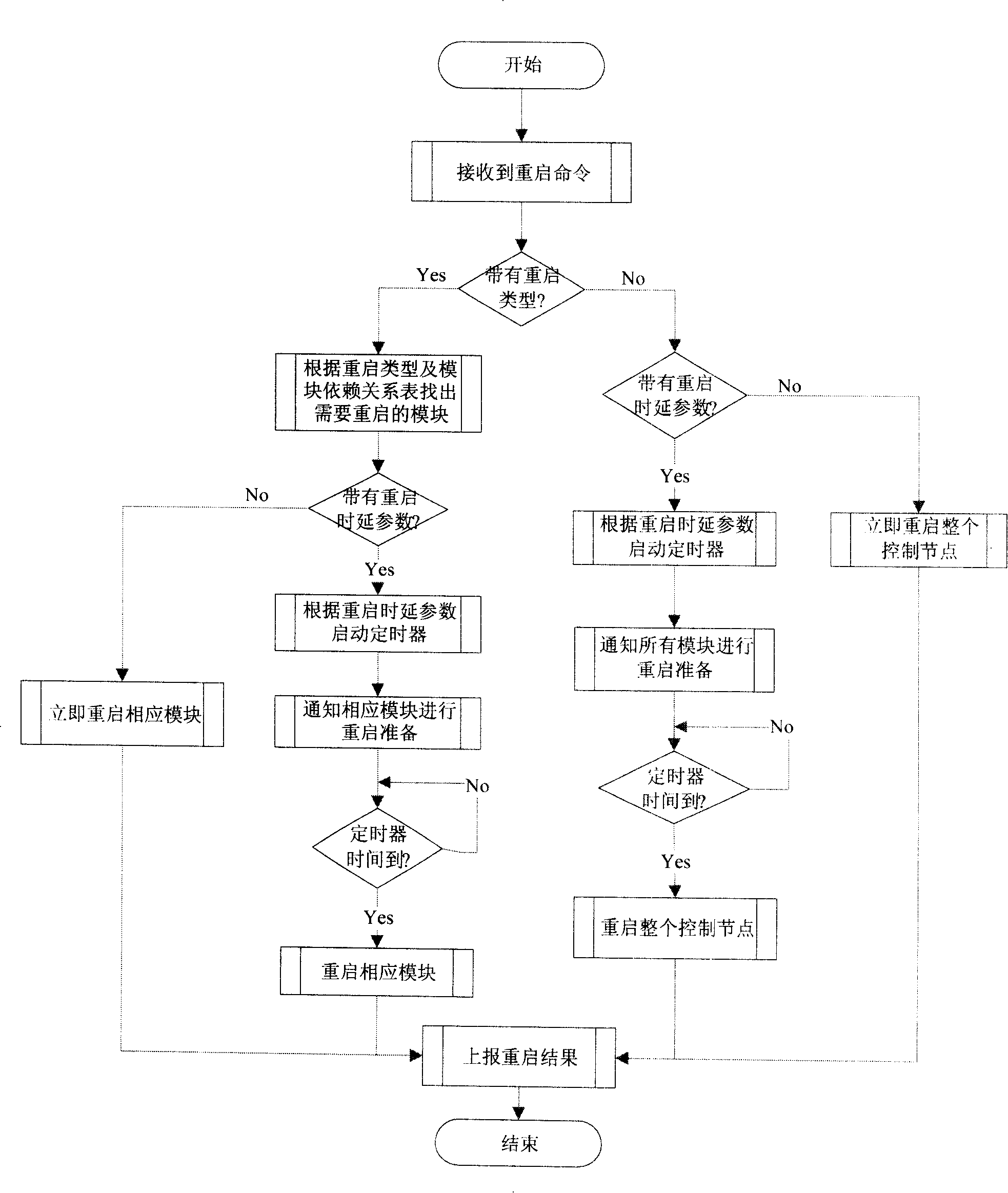
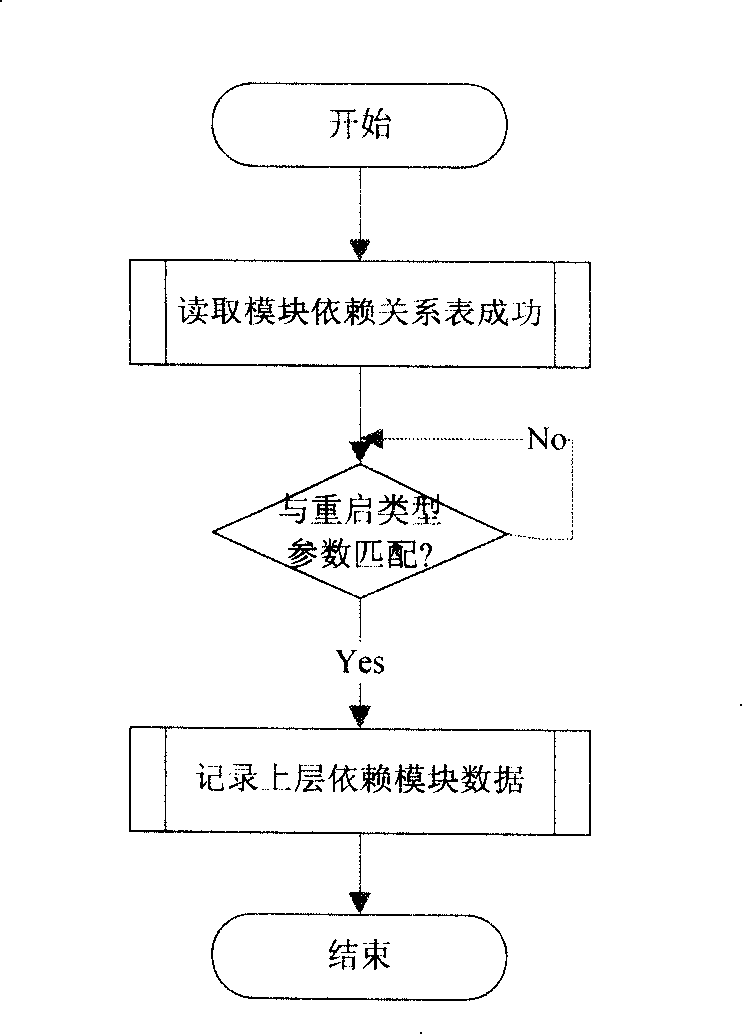
InactiveCN101212340ADoes not affect functionalityCushion the shockMultiplex system selection arrangementsData switching networksTime delaysAutomatically switched optical network
The invention discloses a method for restarting a control node in an automatic switching optical network, which comprises the following processes: a restarting order is received by the control node and a restarting parameter in the restarting order is detected; the whole control node is restarted if a restarting type is not obtained in the restarting parameter; relevant modules and upper layer modules are restarted according to the restarting type and a module depending relationship table if the restarting type is contained in the restarting parameter. A time delay parameter can also be contained in the restarting parameter for preparing restarting. The invention solves the problem of too much impact on the system when the whole node is restarted in the condition that only parts of the modules (protocols) are necessary to be restarted. And the invention preferably maintains the data consistency of the control node.
Owner:ZTE CORP
Memory system and method for controlling the same, and method for maintaining data coherency
InactiveUS20070186051A1Improve memory access efficiencyMaintain data consistencyMemory systemsData memoryTerm memory
Owner:IBM CORP
Method and apparatus for enabling consistent ancillary disk array storage device operations with respect to a main application
InactiveUS20040193944A1Maintain data consistencyData processing applicationsInput/output to record carriersData processing systemData set
A method and apparatus for enhancing data recovery in data processing systems in which applications span multiple logical devices. A data processing system includes multiple standard devices for storing data and corresponding BCV devices for, in one mode, operating as mirrors of those standard devices. If certain of those BCV devices are associated with the same data set, a CONSISTENT SPLIT operation controls the way in which each of these BCV devices is detached from its corresponding standard device and made available to another application. Each command to an application for controlling the BCV devices is translated into one or more request data structures that identify the BCV devices as being involved in a consistent split operation and that establishes a system lock out for those particular devices during which those devices are split from their respective devices in a consistent manner.
Owner:EMC IP HLDG CO LLC
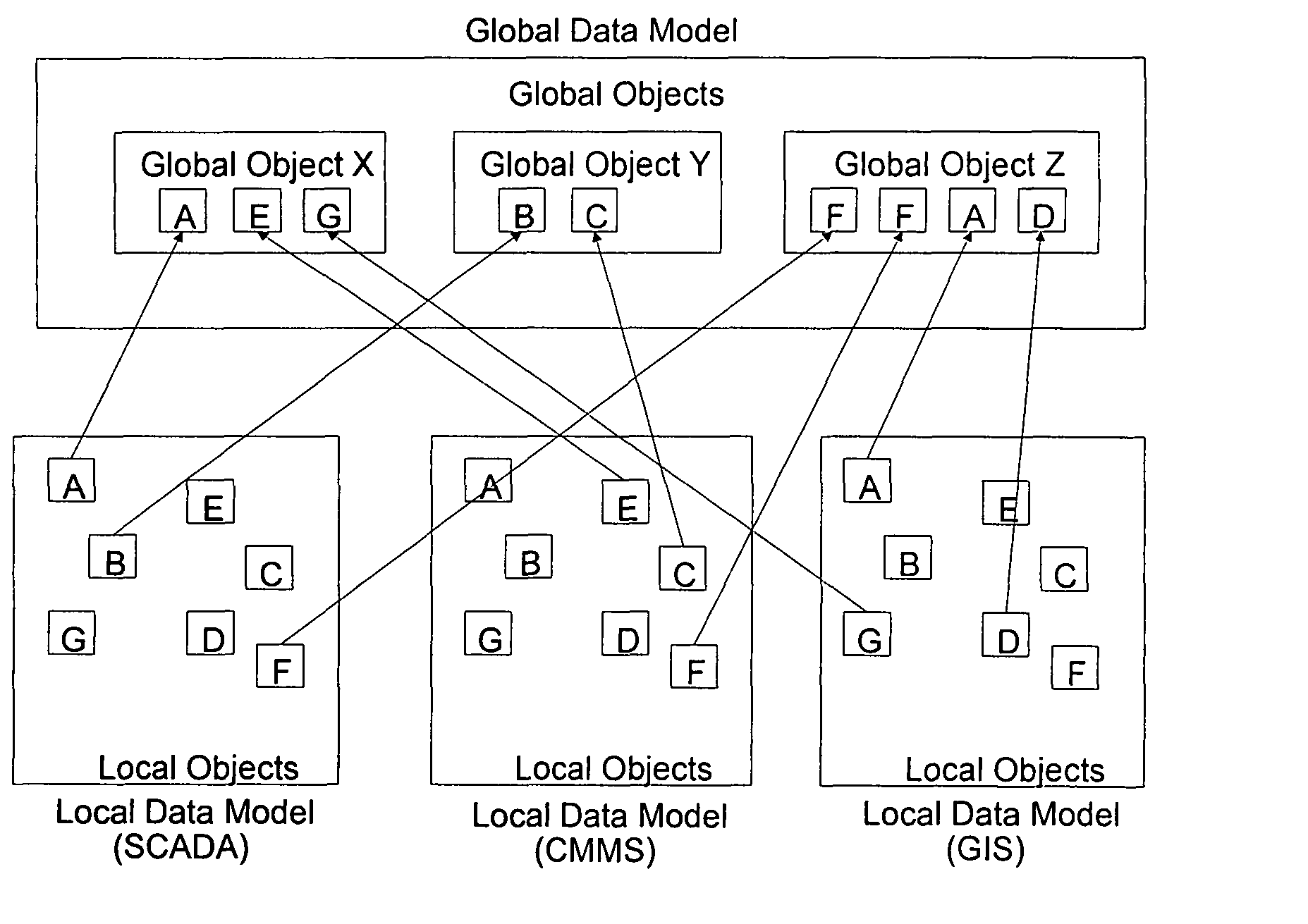
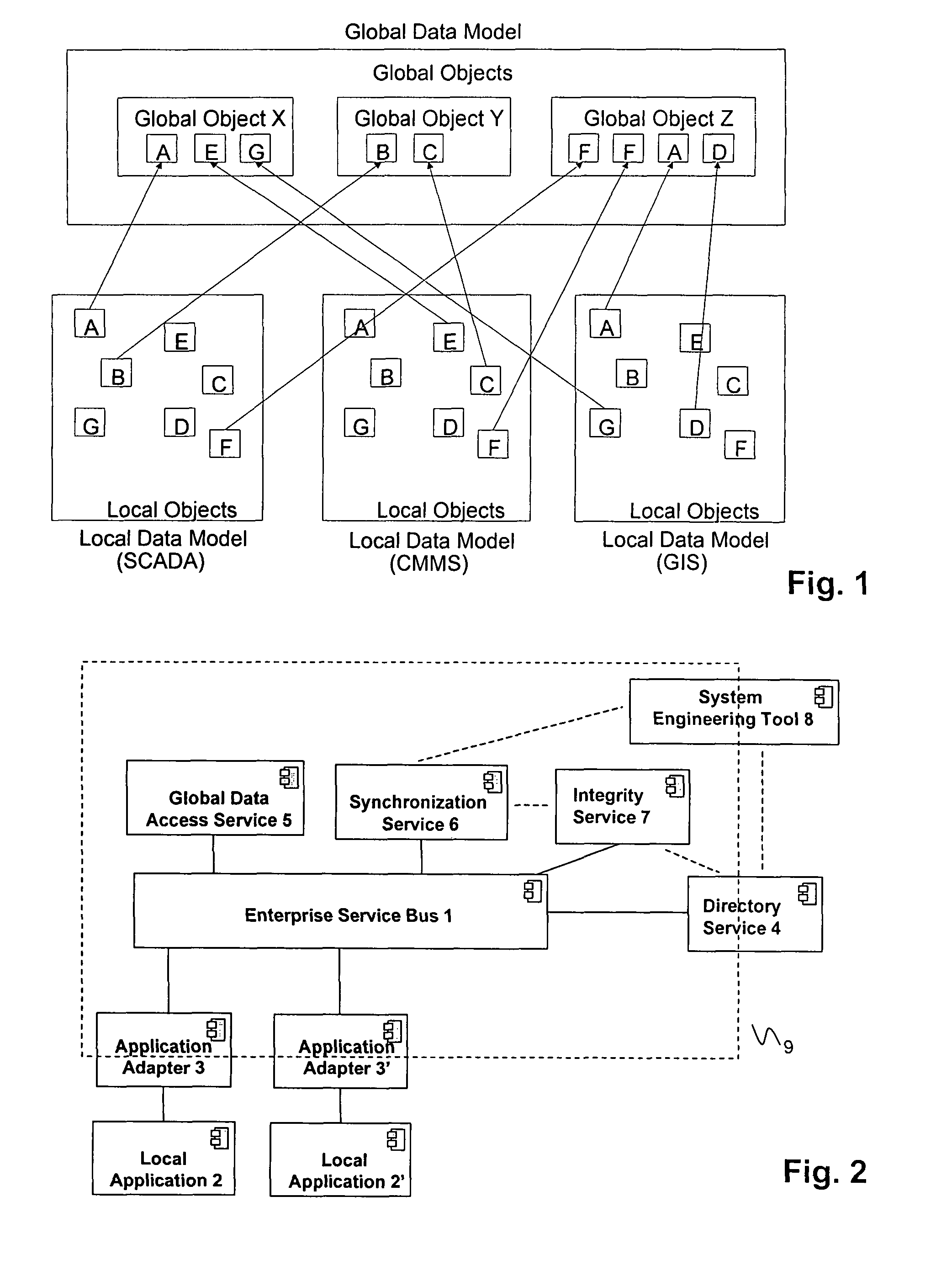
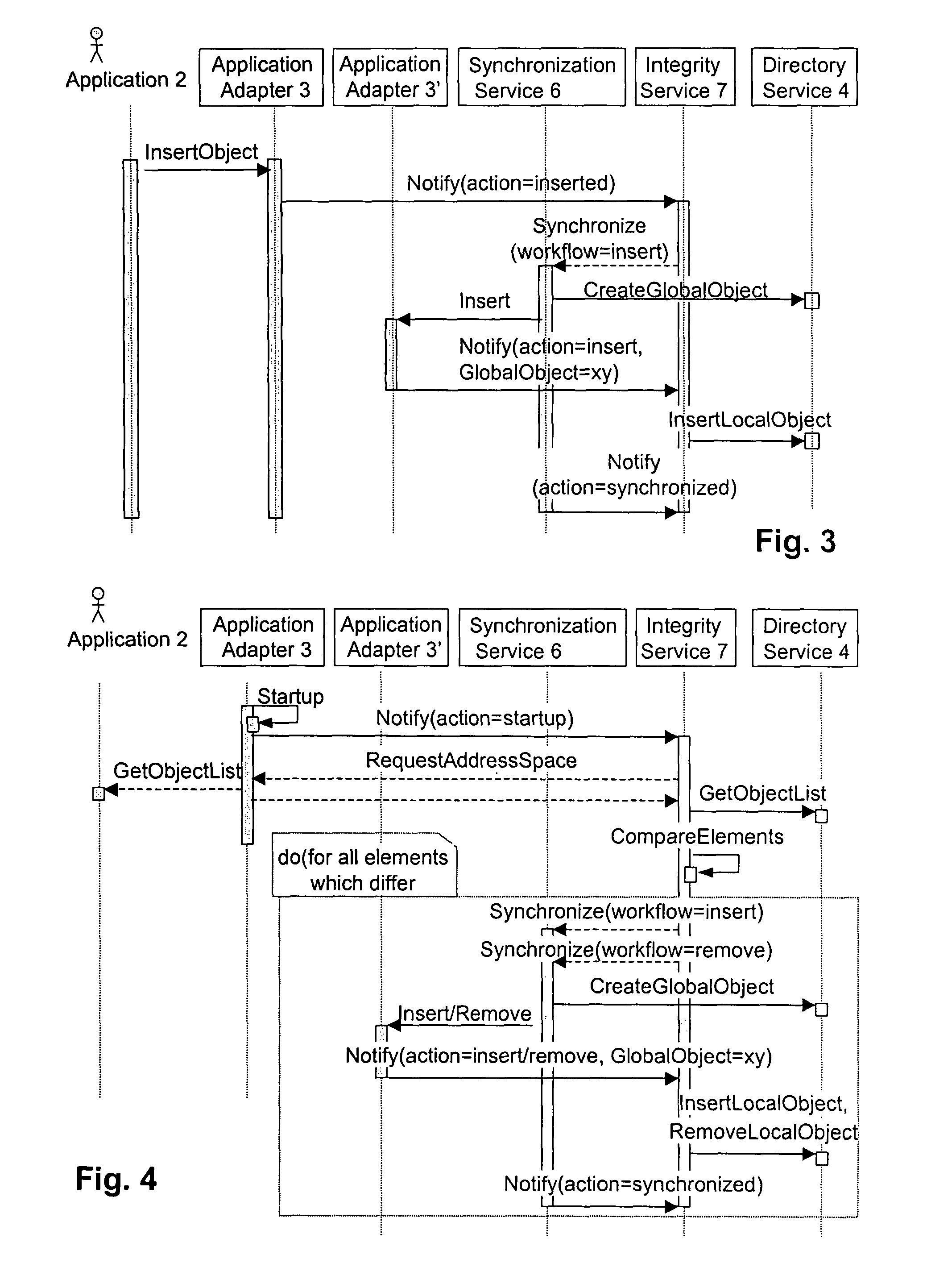
Maintaining data consistency between integrated applications
ActiveUS7958092B2Improve interoperabilityFaster and cheap synchronization and consistency maintenanceProgram synchronisationDigital data processing detailsGlobal address spaceApplication software
The present disclosure facilitates the interoperability between different local applications. Related local data objects are referenced via global objects or reference containers within a global data model or a global address space of an integration solution. The present disclosure assumes that the integration solution is per default in a consistent state, e.g., an engineered or initially configured global address space is regarded as consistent, and all software components that operate within this space assume that the information they access is valid and likewise consistent. The local applications are the only components that can interact with the global address space and introduce invalidations, they are continuously monitored for changes. Invalidation and subsequent synchronization or restoration of consistency is performed upon a particular triggering event related to a change in a local application object (such as an insertion or removal of an object or a modification of an attribute thereof) or related to a changing application or adapter status (component shutdown / startup).
Owner:HITACHI ENERGY LTD
Method and device for determining data table association relationship
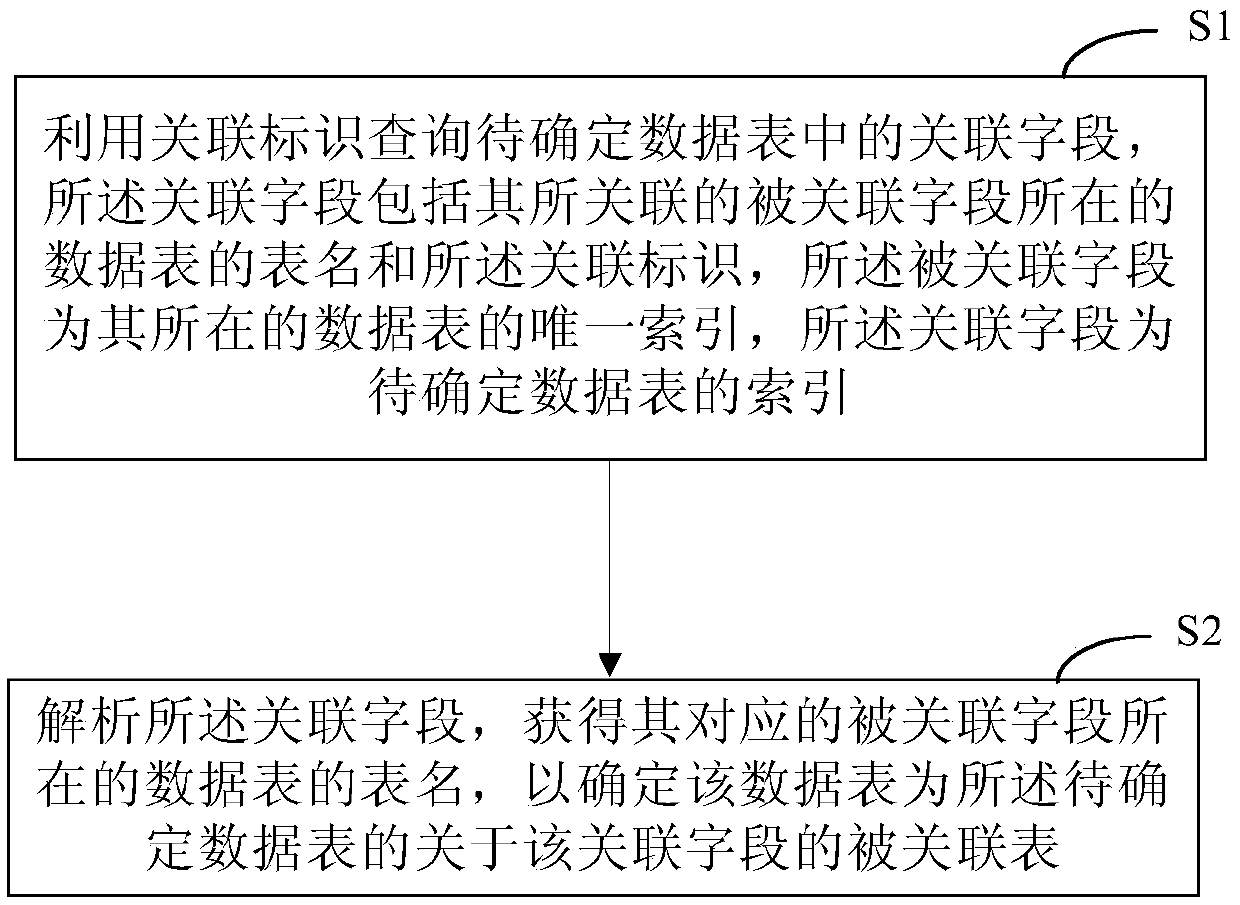
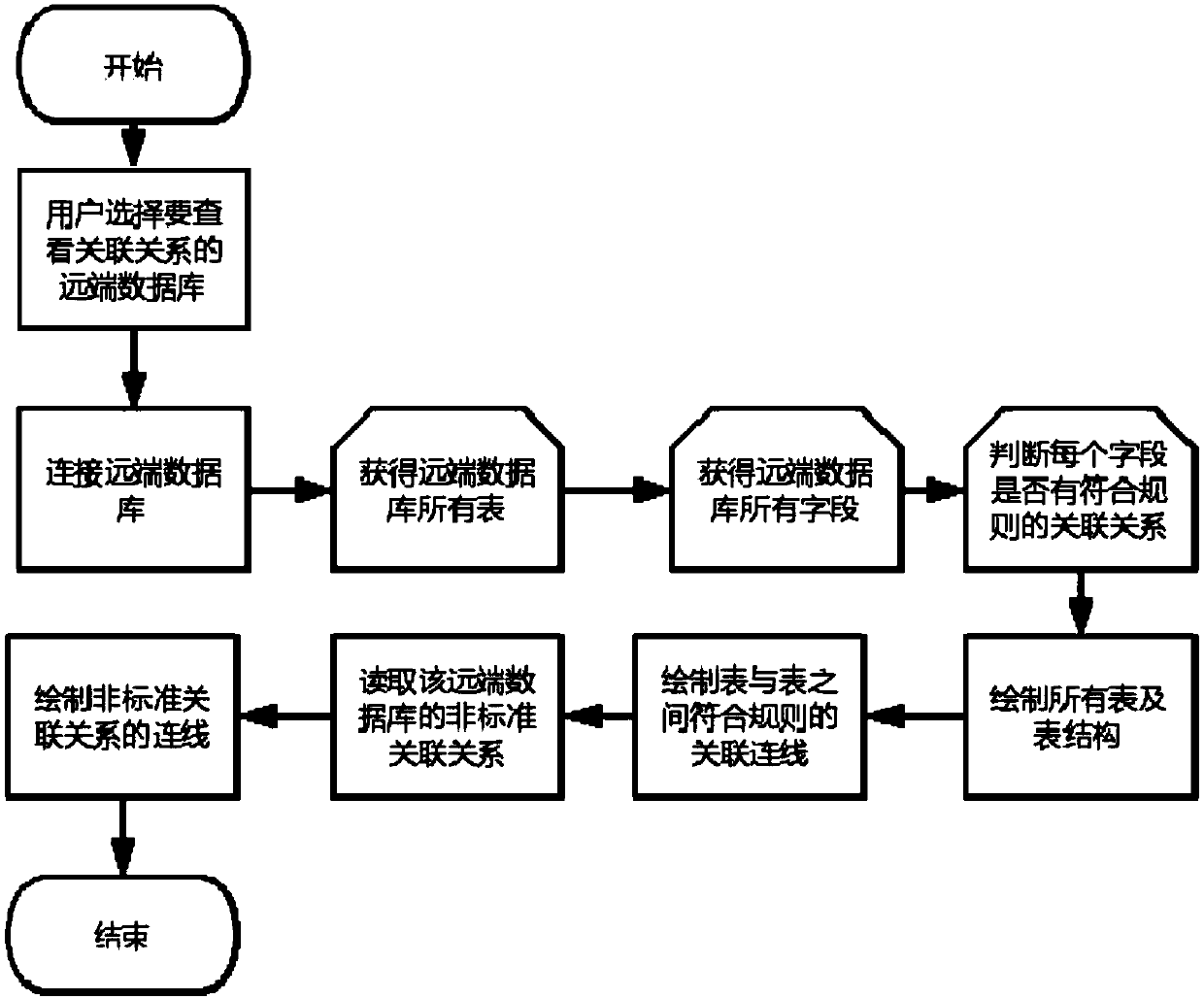
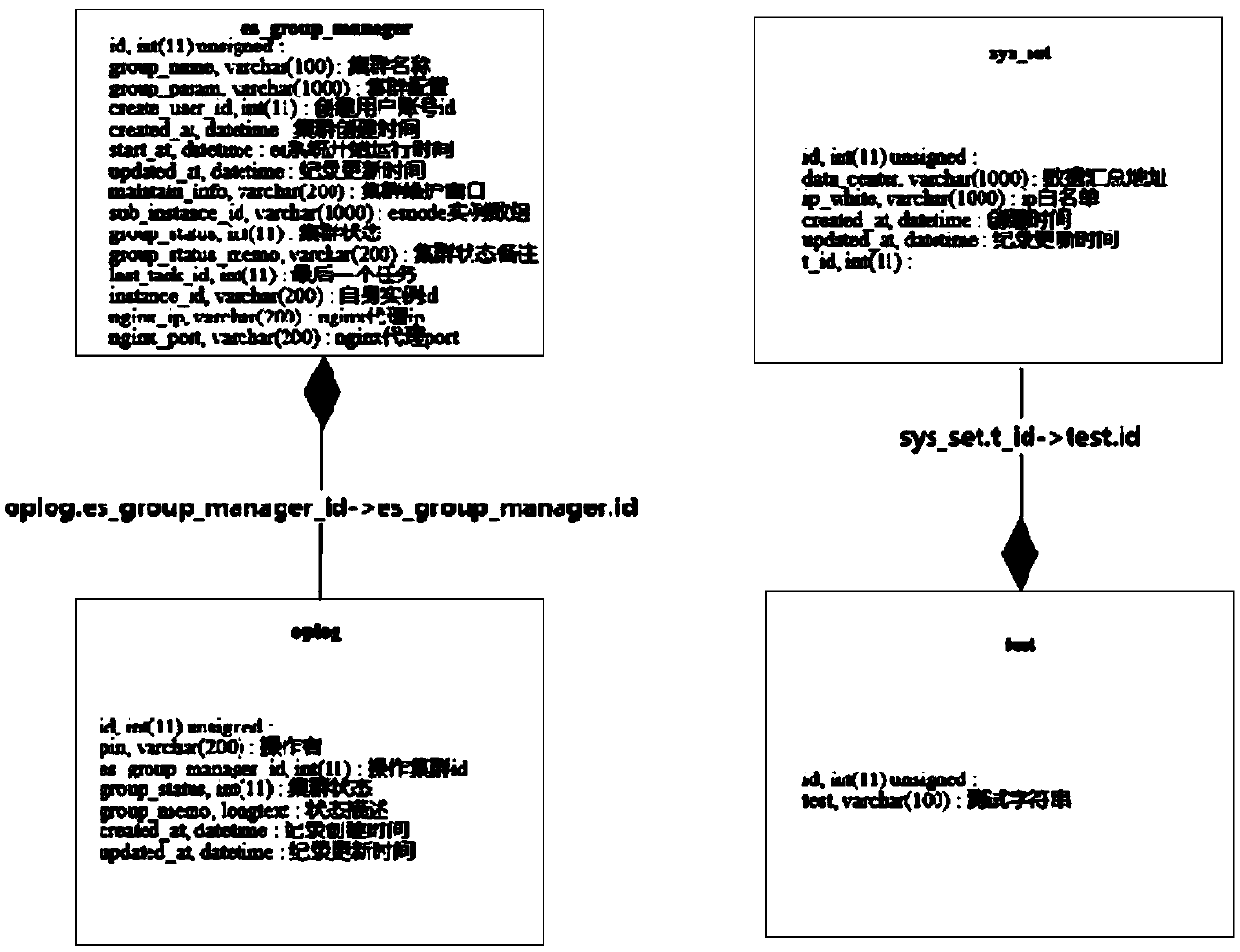
PendingCN111309721ASimplify change operationsImprove application flexibilityDatabase updatingDatabase indexingEngineeringData mining
The invention discloses a method and device for determining a data table association relationship, and relates to the technical field of computers. One specific embodiment of the method comprises thefollowing steps: S1, querying an associated field in a to-be-determined data table by utilizing an associated identifier, the associated field comprising a table name of the data table where an associated field associated with the associated field is located and the associated identifier, the associated field being a unique index of the data table where the associated field is located, and the associated field being an index of the to-be-determined data table; and S2, analyzing the associated fields, and obtaining the table names of the data tables where the associated fields corresponding tothe associated fields are located, so as to determine that the data tables are associated tables about the associated fields of the to-be-determined data tables. According to the embodiment, the change operation of the associated data table can be simplified, the application flexibility of the associated data table is improved, and meanwhile, the data consistency and integrity of the associated data table can be kept.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
File-based method for communication between virtual machine and host machine
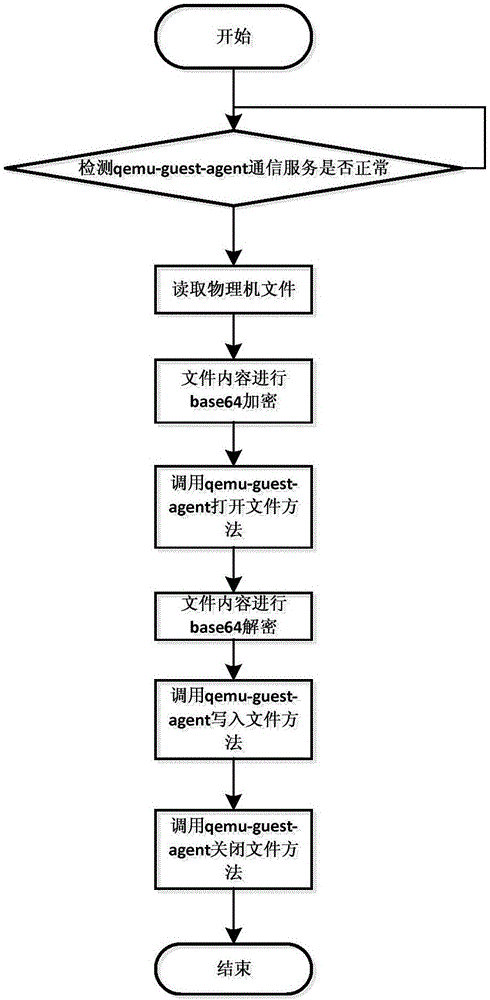
InactiveCN106453616AMaintain integrityMaintain data consistencyProgram loading/initiatingTransmissionCloud computingWeb technology
The invention relates to the field of cloud computing and network technologies, especially to a file-based method for communication between a virtual machine and a host machine. Serial channel communication between a virtual machine and a physical machine is kept by using a qemu-guest-agent tool and a file content is encrypted to prevent coding during the communication process; a writable file path in the virtual machine is opened by using the qemu-guest-agent tool; and then the encrypted content is decrypted and then the decrypted content is written into the file, thereby realizing communication between the physical machine and the virtual machine in a file manner. According to the method provided by the invention, a cloud platform can update the file inside the virtual machine, thereby keeping function completeness and data consistency of the virtual machine; and thus the internal environment of the virtual machine owned by the client can be updated without the need to transfer any service, thereby enhancing the user experience.
Owner:G CLOUD TECH
Method for creating avatars for protecting sensitive data
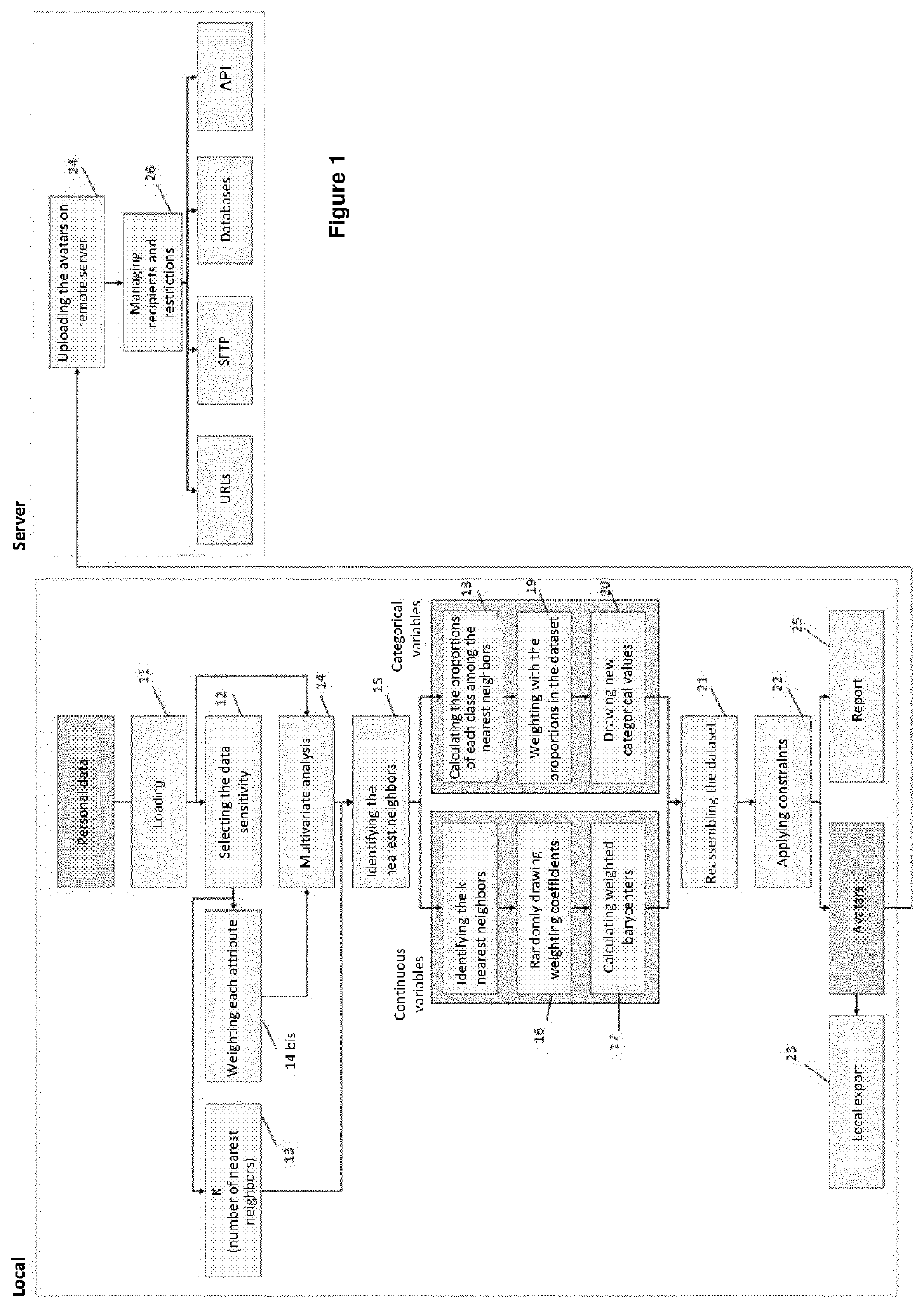
PendingUS20220067202A1Improve protectionMaintain data consistencyDigital data protectionNear neighborData mining
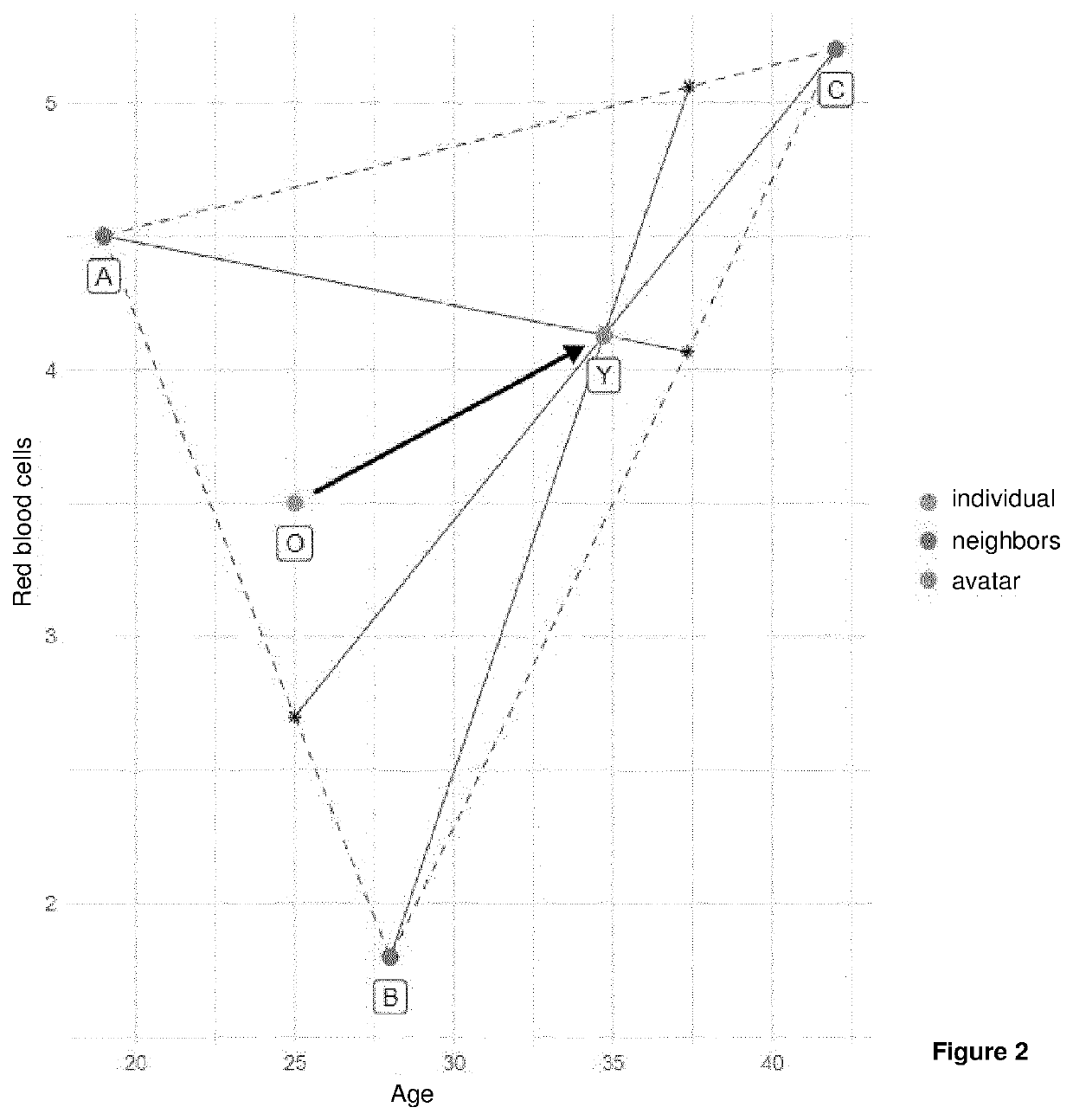
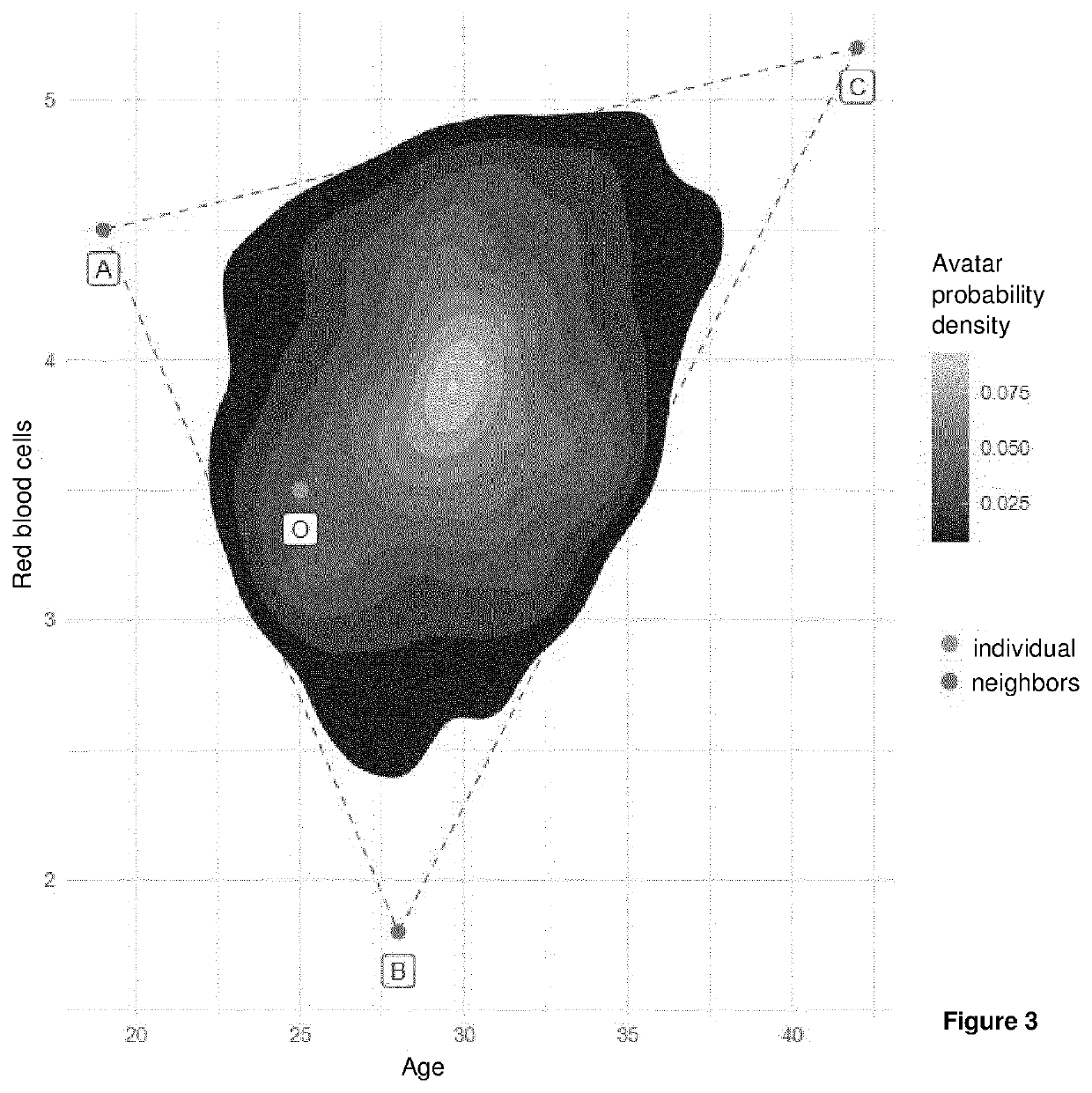
The present invention relates to a method for creating avatars from an initial sensitive data set stored in a database of a computer system, the initial data comprising attributes relating to a plurality of individuals, the method comprising: a) choosing a number {k} of nearest neighbors to be used from all the individuals in the initial data set, b) identifying, for attributes relating to a given individual, the k nearest neighbors from among the other individuals in the data set, c) generating, for at least one attribute relating to said individual, a new attribute value from quantities which are characteristic of the attribute in the identified k nearest neighbors and weighted by a coefficient, and d) creating avatar data comprising the new attribute value(s), so as to ensure the sensitive data relating to the individual are non-identifiable.
Owner:BIG DATA SANTE
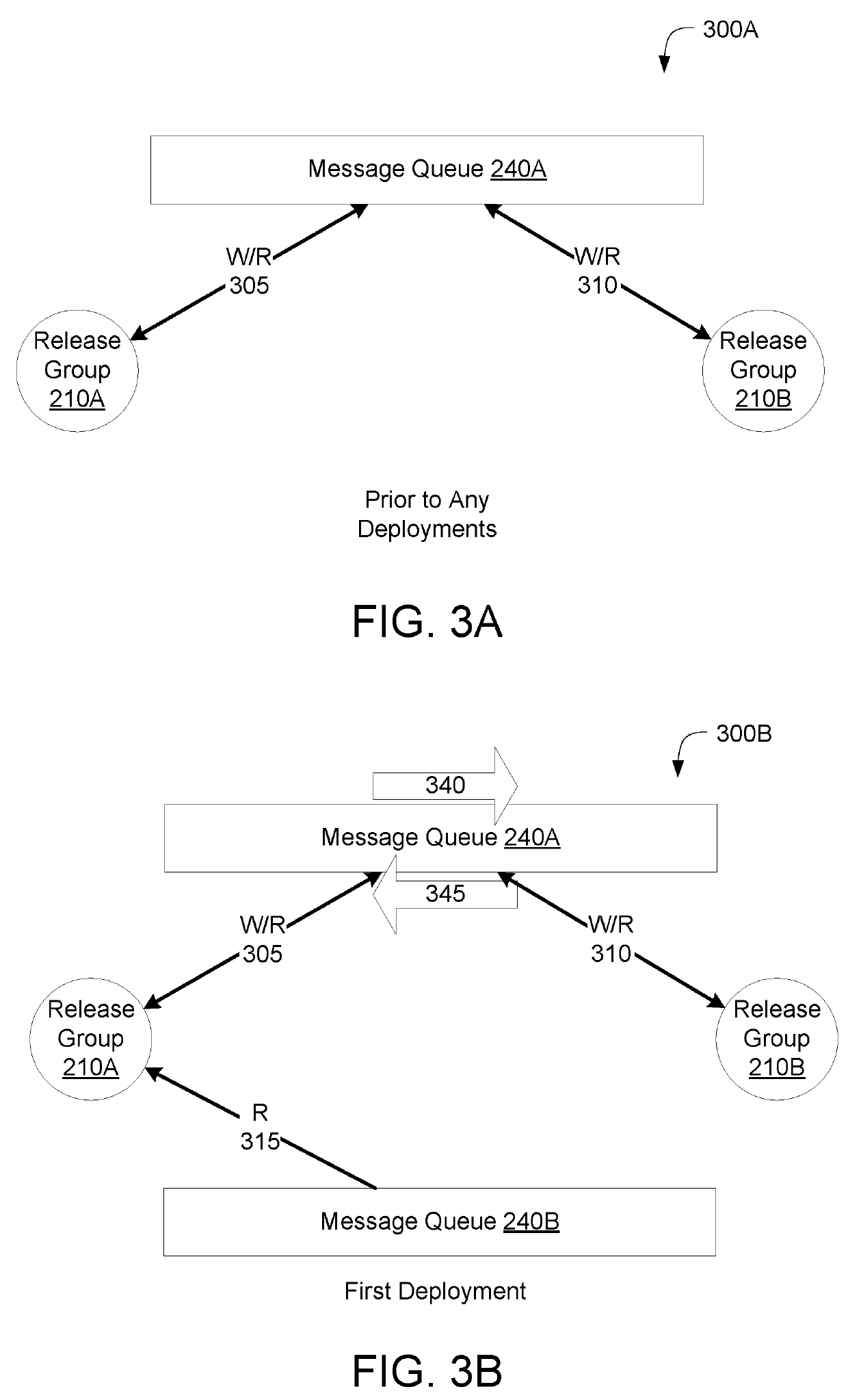
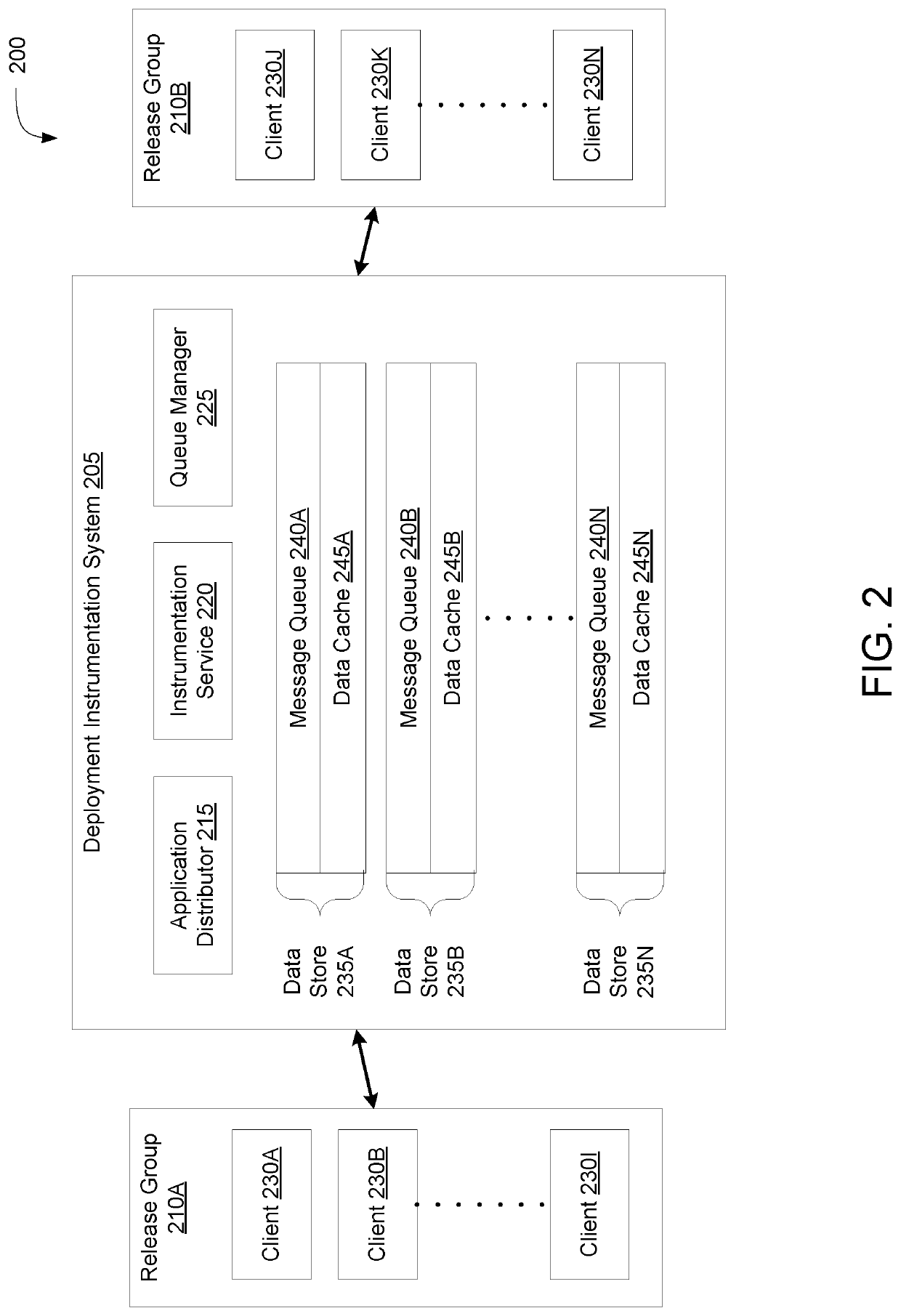
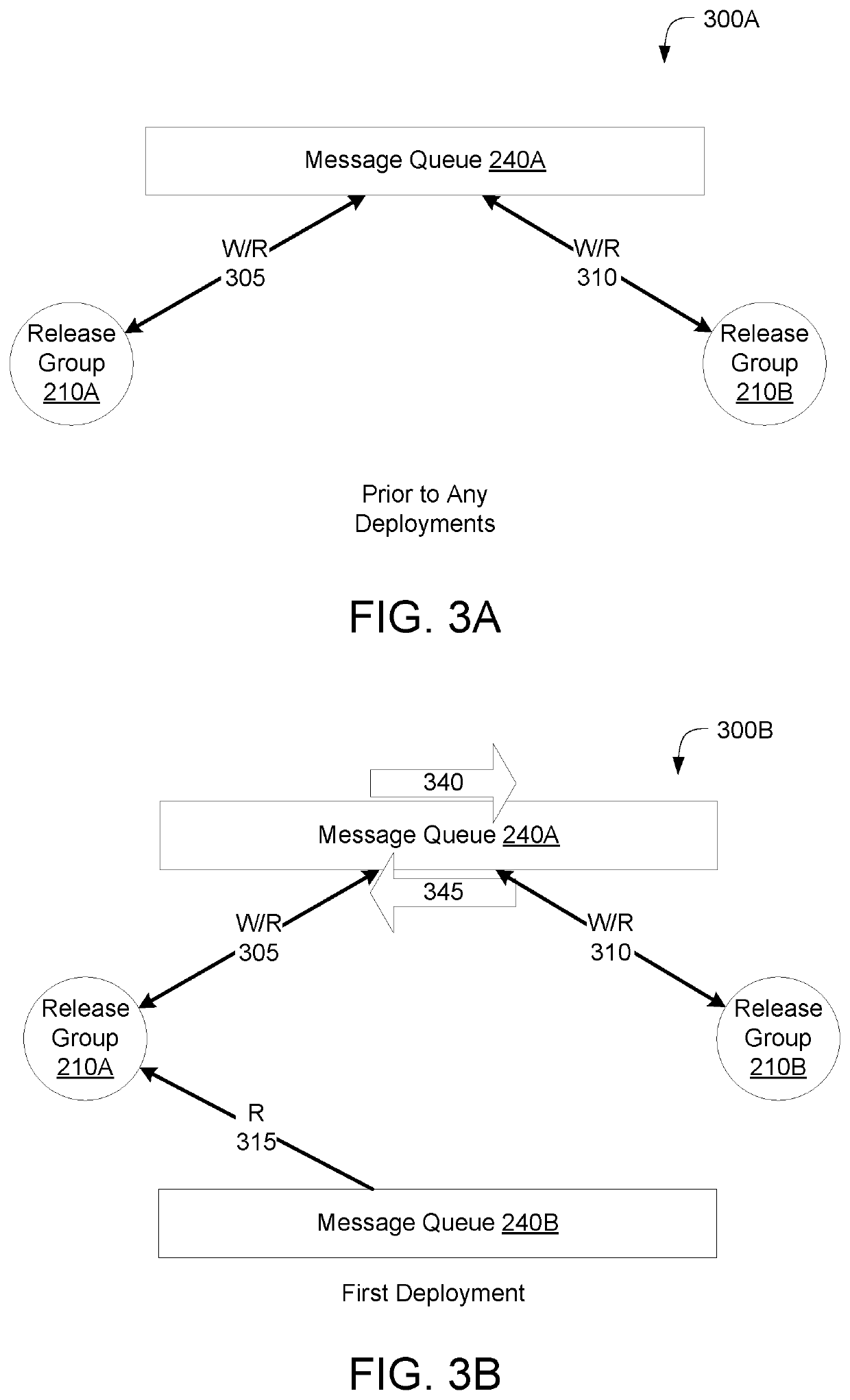
Message queue migration on a/b release environments
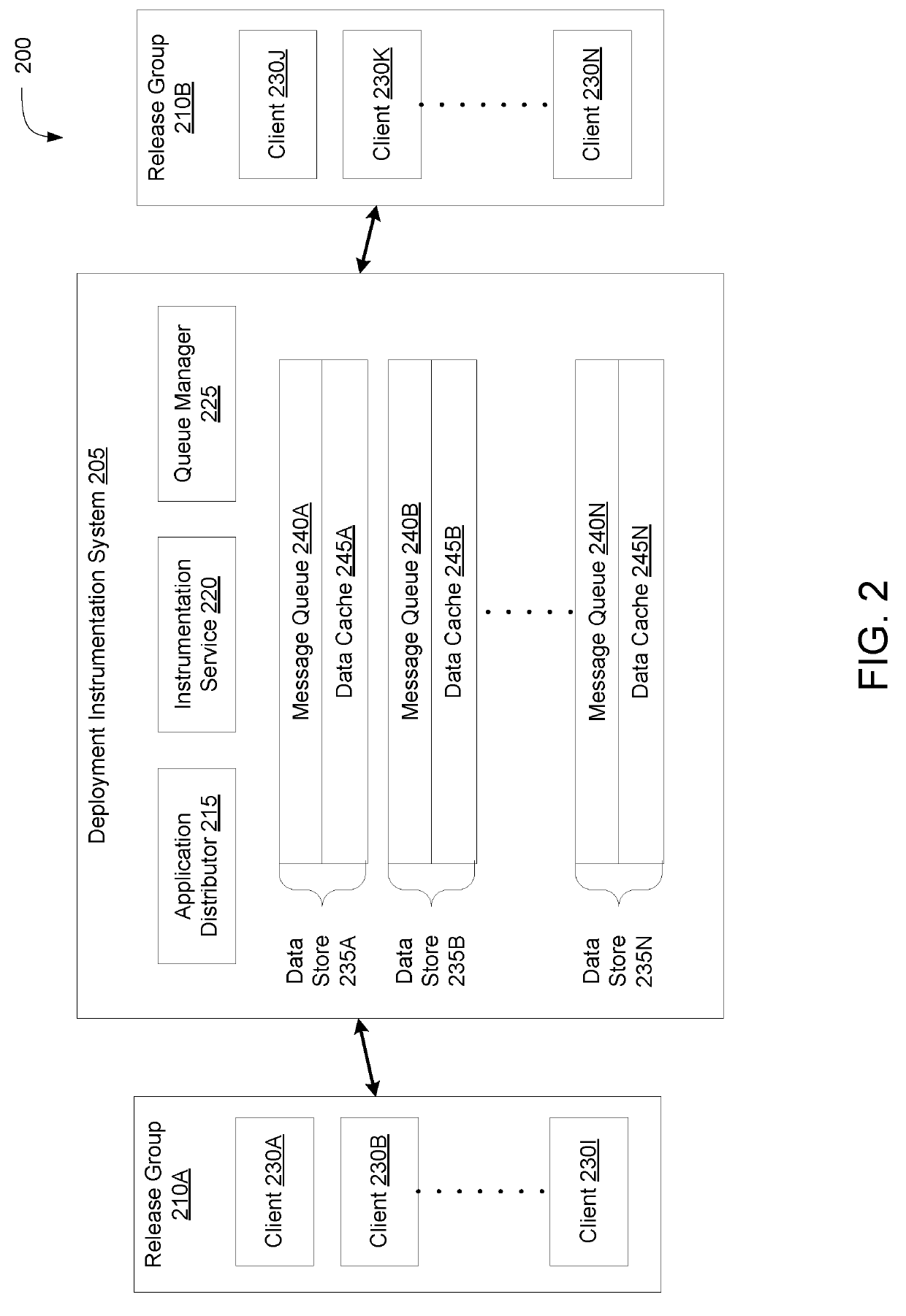
ActiveUS20190245739A1Maintain data consistencyData switching networksMessage queueDistributed computing
Described embodiments provide systems and methods of maintaining message queues during deployments of application updates. A queue manager may maintain a first message queue including a first channel for messages between a first release and a second release. The first release and the second release may write to and read from the first message queue. The queue manager may establish, responsive to deployments, a second message queue including a second channel for messages between the first release and the second release. The queue manager may transfer, from the first message queue to the second message queue, the first channel. The first release and the second release may cease to write to and read from the first message queue.
Owner:CITRIX SYST INC
Message queue migration on A/B release environments
ActiveUS10637730B2Maintain data consistencyDigital computer detailsData switching networksMessage queueEngineering
Described embodiments provide systems and methods of maintaining message queues during deployments of application updates. A queue manager may maintain a first message queue including a first channel for messages between a first release and a second release. The first release and the second release may write to and read from the first message queue. The queue manager may establish, responsive to deployments, a second message queue including a second channel for messages between the first release and the second release. The queue manager may transfer, from the first message queue to the second message queue, the first channel. The first release and the second release may cease to write to and read from the first message queue.
Owner:CITRIX SYST INC
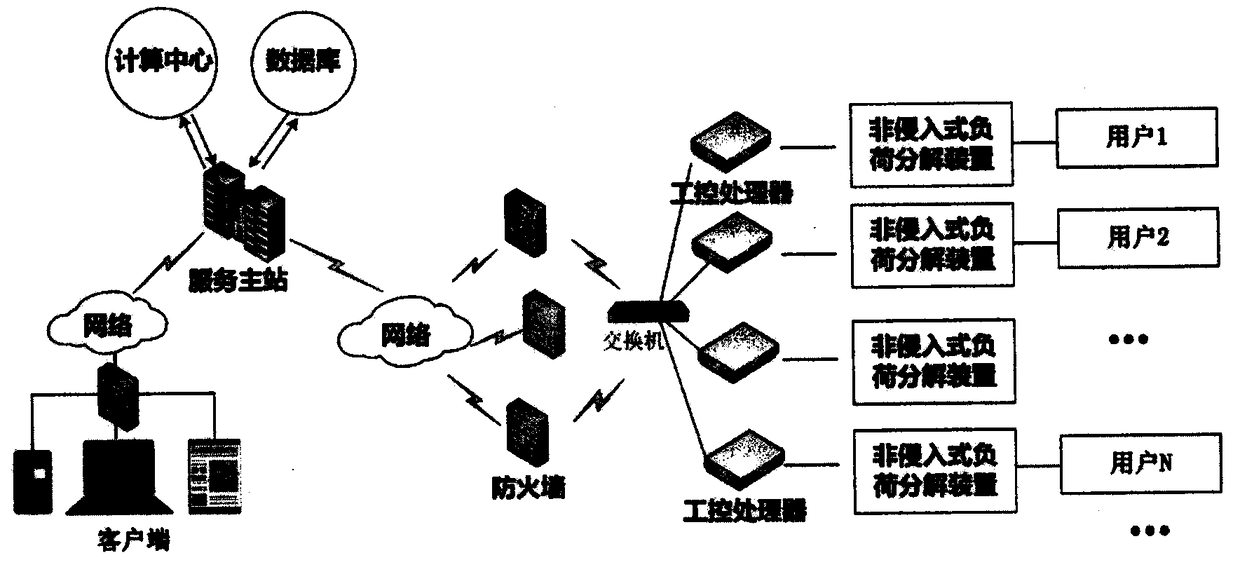
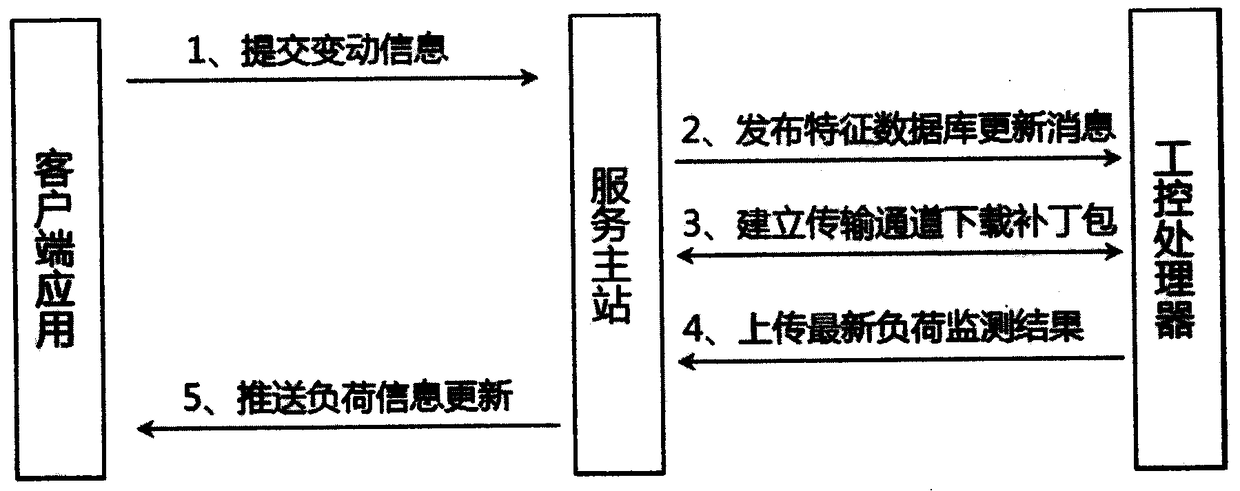
Non-intrusive monitoring-oriented online load feature database maintenance method
InactiveCN108733661ASolve the problem of online real-time updateMaintain scalabilityTransmissionSpecial data processing applicationsExtensibilityMaster station
The invention provides a non-intrusive monitoring-oriented online load feature database maintenance method. According to the method, a service master station is taken as a central link, an interactionbridge between a client side and a monitoring side is set up, and the online real-time updating and maintenance problem of a non-intrusive monitoring load feature database is solved. A user can timely feed back addition of new load equipment to the service master station through a client side application, so the data consistency and expandability between a power utilization side and the monitoring side is maintained, the monitoring side can effectively identify various internal load types of the user, the powerful support for the user side load type identification accuracy is provided, the user is helped to optimize the power utilization, and the interaction management at the user side is prompted.
Owner:深圳点亮新能源技术有限公司
Method and apparatus for enabling consistent ancillary disk array storage device operations with respect to a main application
InactiveUS7281157B2Maintain data consistencyInput/output to record carriersData processing applicationsData processing systemData set
A method and apparatus for enhancing data recovery in data processing systems in which applications span multiple logical devices. A data processing system includes multiple standard devices for storing data and corresponding BCV devices for, in one mode, operating as mirrors of those standard devices. If certain of those BCV devices are associated with the same data set, a CONSISTENT SPLIT operation controls the way in which each of these BCV devices is detached from its corresponding standard device and made available to another application. Each command to an application for controlling the BCV devices is translated into one or more request data structures that identify the BCV devices as being involved in a consistent split operation and that establishes a system lock out for those particular devices during which those devices are split from their respective devices in a consistent manner.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com