Patents
Literature
207 results about "Undo" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
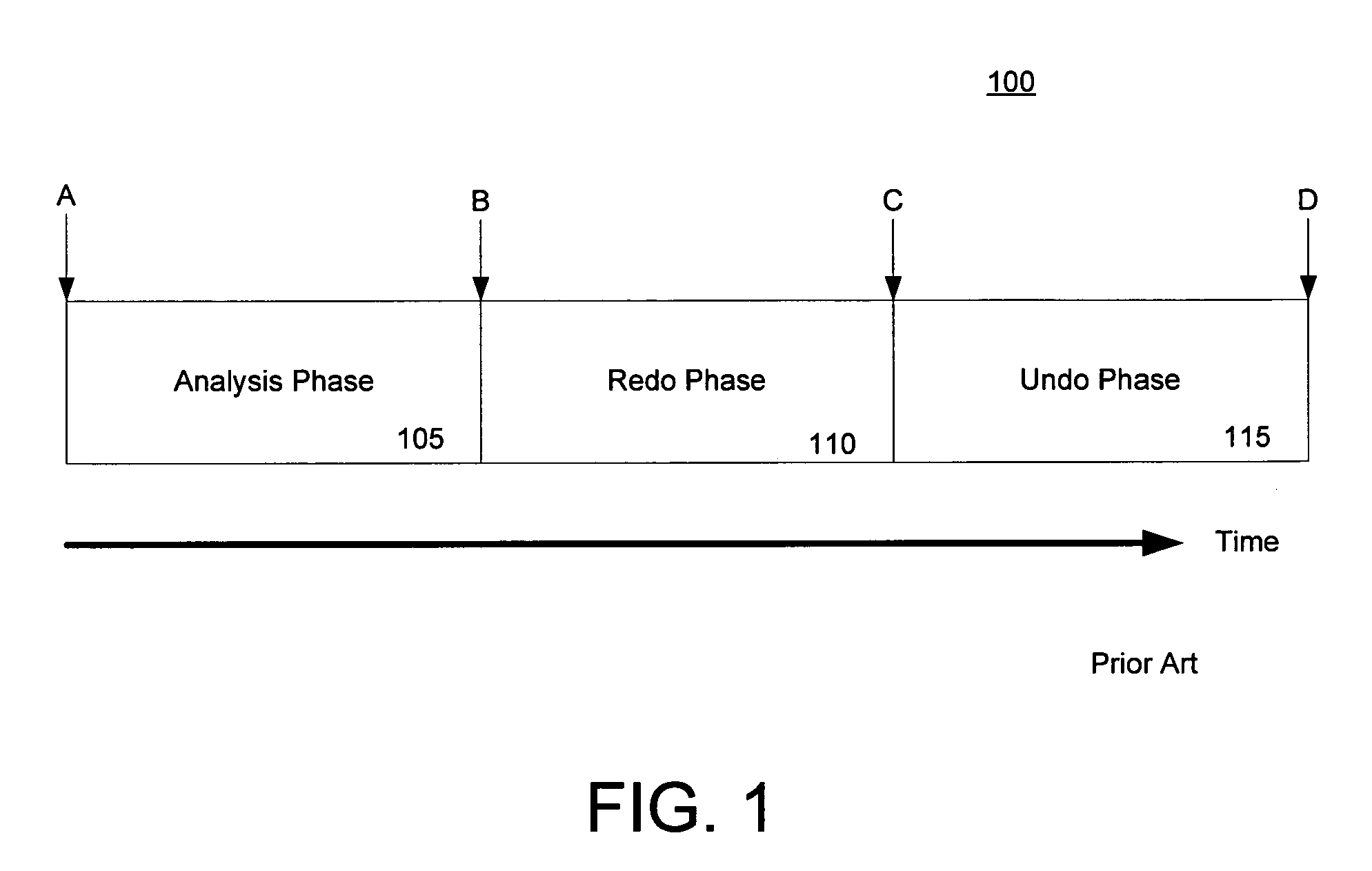
Undo is an interaction technique which is implemented in many computer programs. It erases the last change done to the document, reverting it to an older state. In some more advanced programs, such as graphic processing, undo will negate the last command done to the file being edited. With the possibility of undo, users can explore and work with without fear of making mistakes, because they can easily be undone.
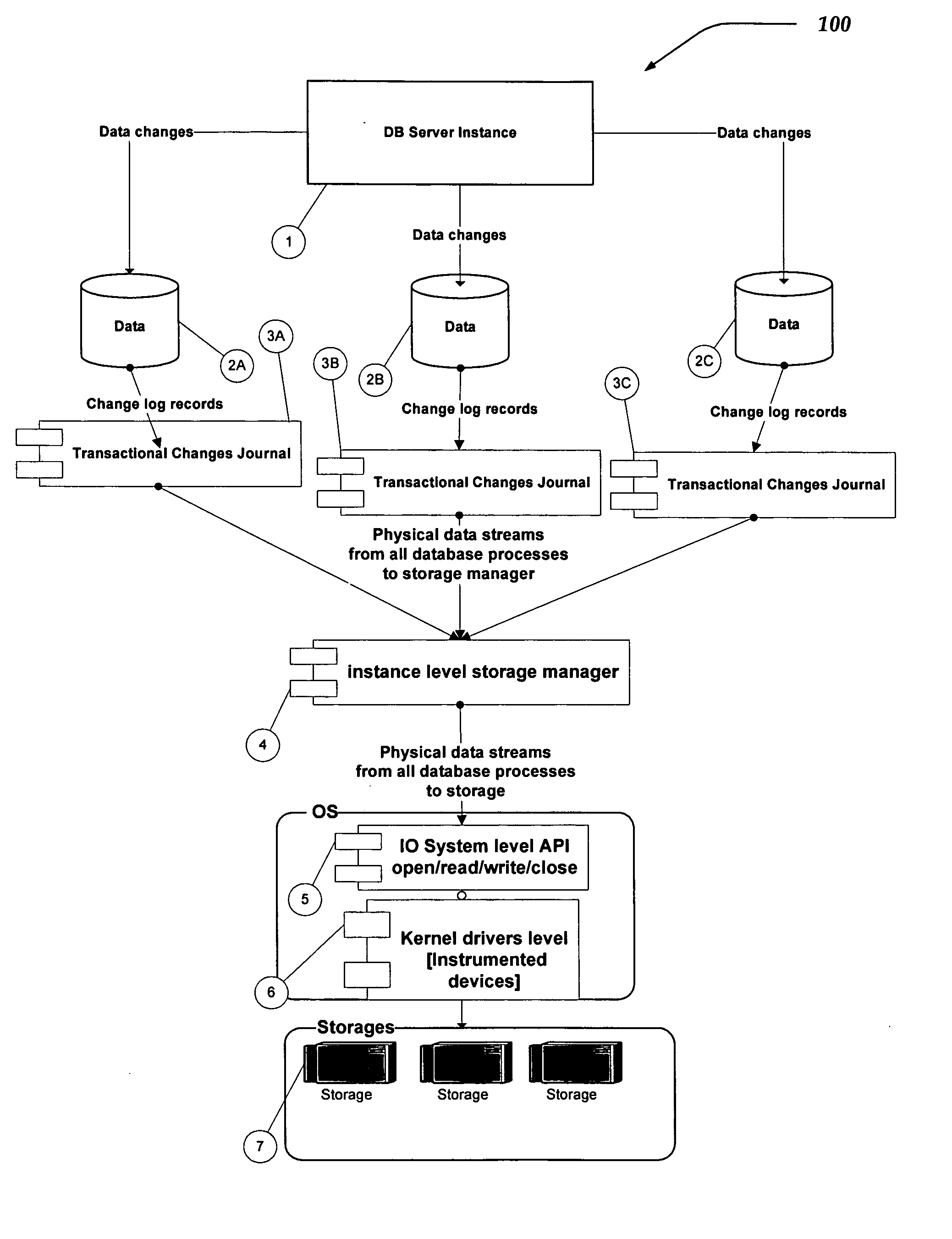
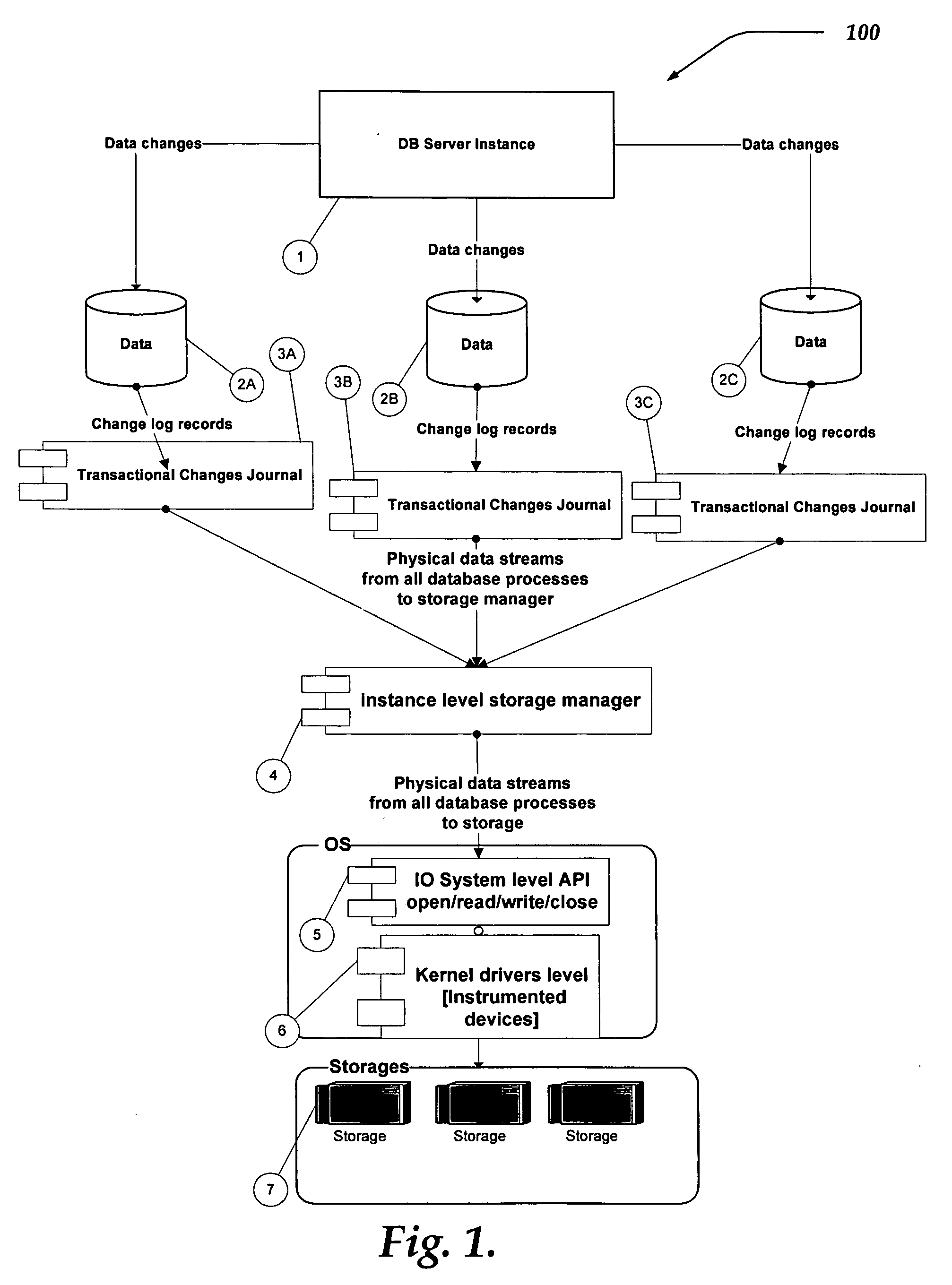
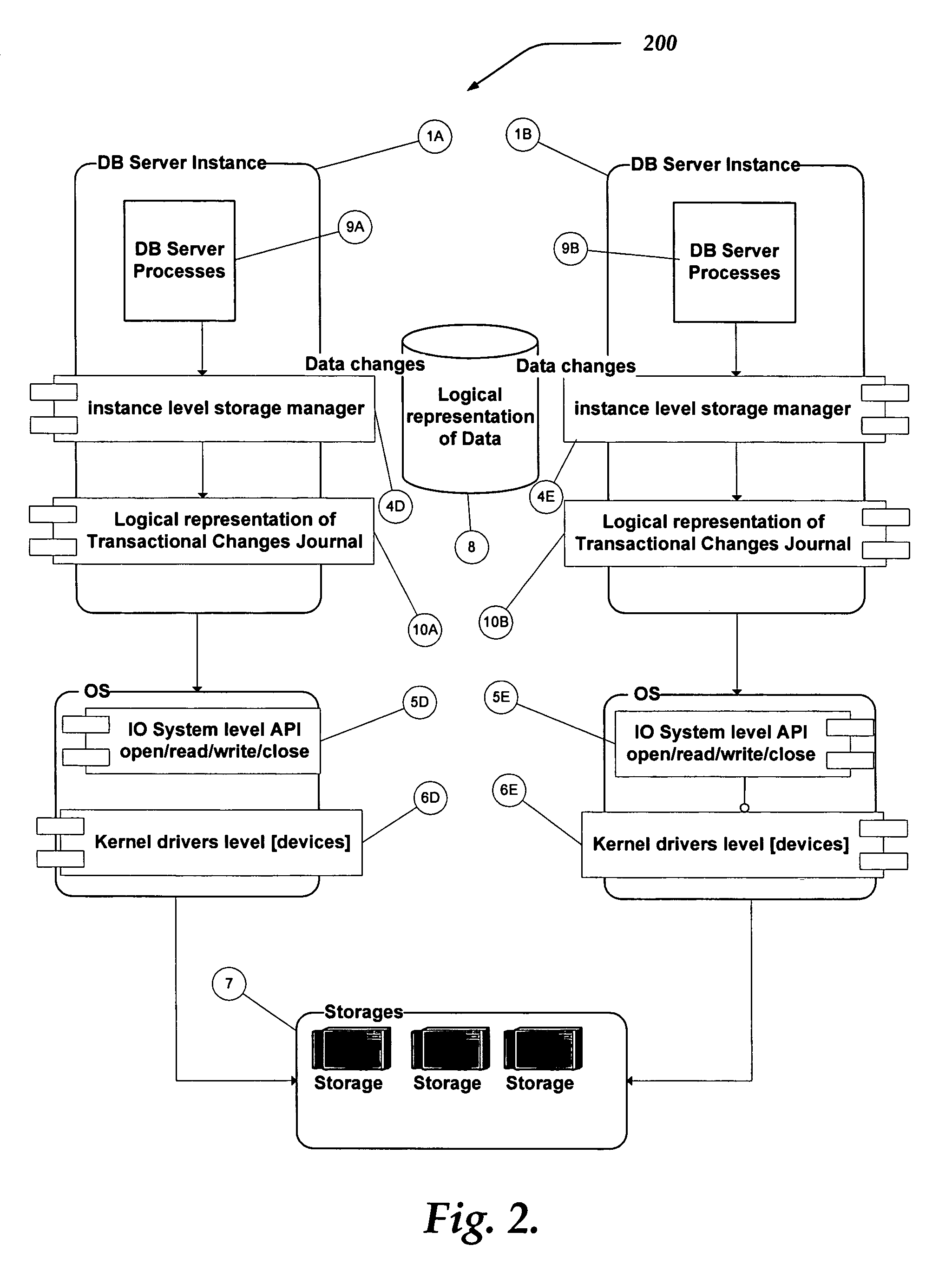
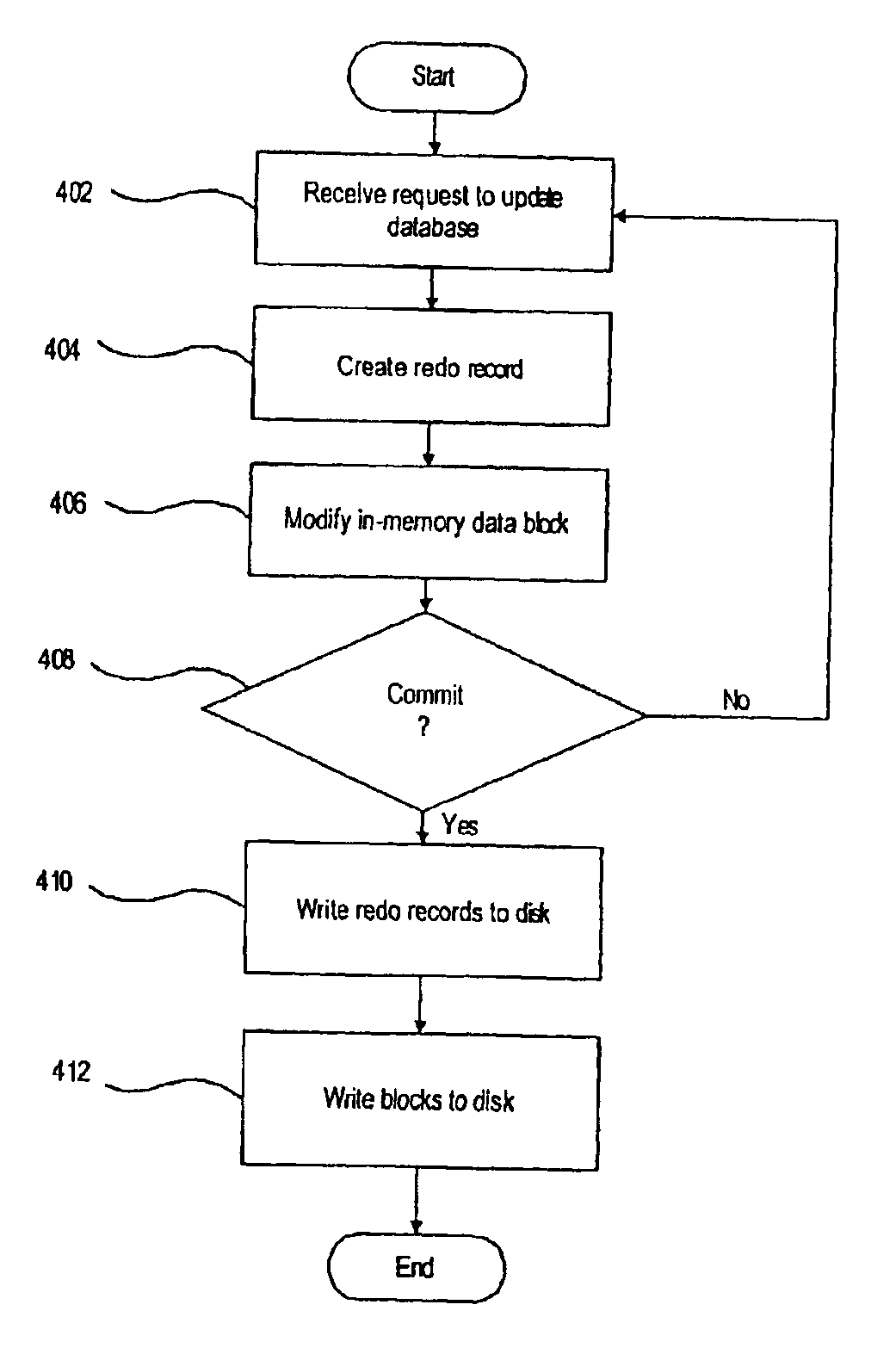
System and method for database replication by interception of in memory transactional change records
InactiveUS20060047713A1Database distribution/replicationSpecial data processing applicationsTerm memorySource level
A system and method are directed towards providing a database replication technique using interception in memory of the transaction change data records. The invention employs Input / Output instrumentation to capture and split out the in memory transaction change journal records. Captured memory blocks are sent to a parser, which concatenates the records into a single record, and creates a redo / undo vector that can be converted to original DML / DDL statements. Source level transformations can be applied to the vectors, which are then sent to a post agent on the same or a different computing device. The post agents may perform destination level transformations, and generate DML / DDL statements to be executed by the corresponding destination RDBMS instance. Post agents may also perform conflict detection and resolution during DML / DDL statement executions. Transaction consistency is supported by performing commits / rollback on the destination after receiving the redo / undo vector representing a commit / rollback on the source.
Owner:WISDOMFORCE TECH
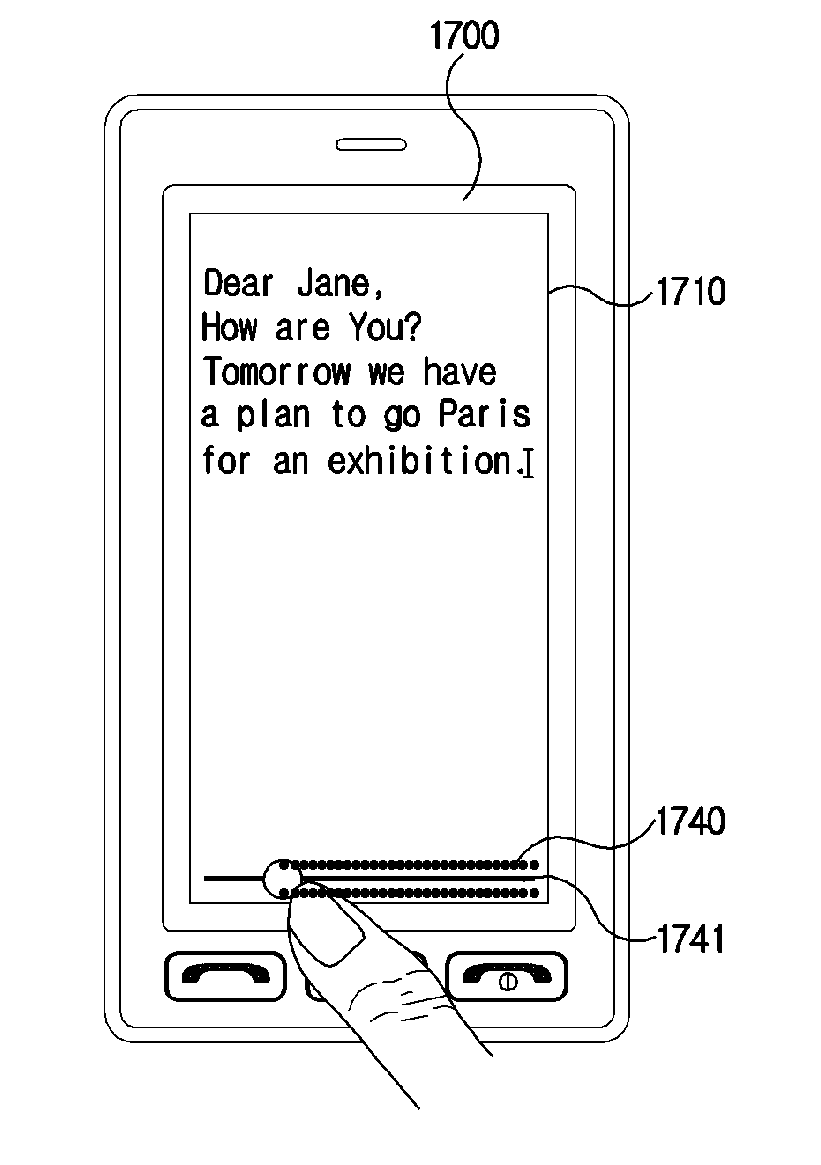
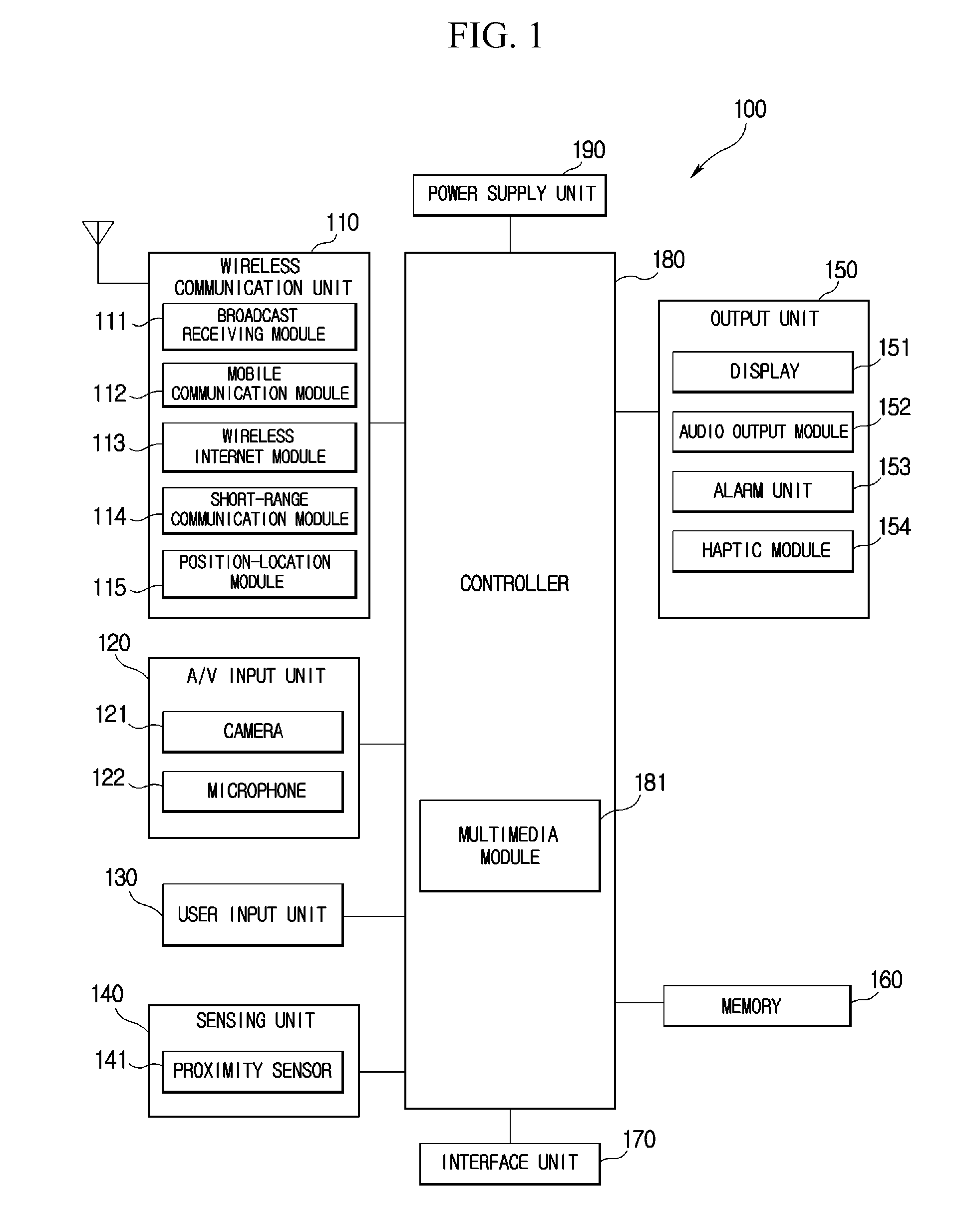
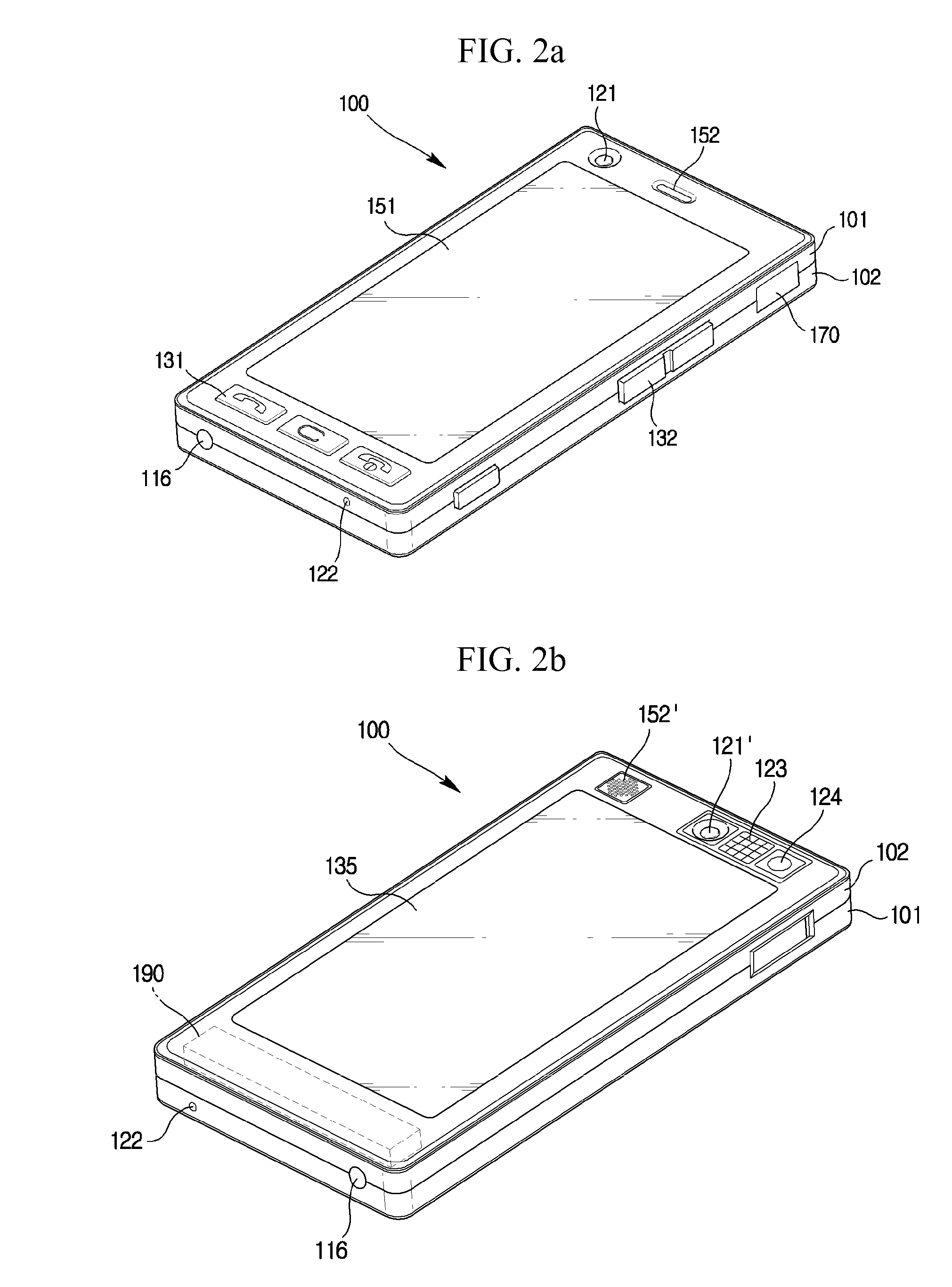
Method for editing data in mobile terminal and mobile terminal using the same
A method for editing data in a mobile terminal configured to conveniently change a symbol and a mobile terminal using the method for editing data are disclosed, wherein the method includes displaying an inputted data on a touch screen, displaying on the touch screen a progress bar including a handler if a progress bar display signal is inputted, generating an undo signal or a redo signal based on a drag direction by touching the handler, and deleting the data in response to the undo signal, or reinstate the data in response to the redo signal.
Owner:LG ELECTRONICS INC
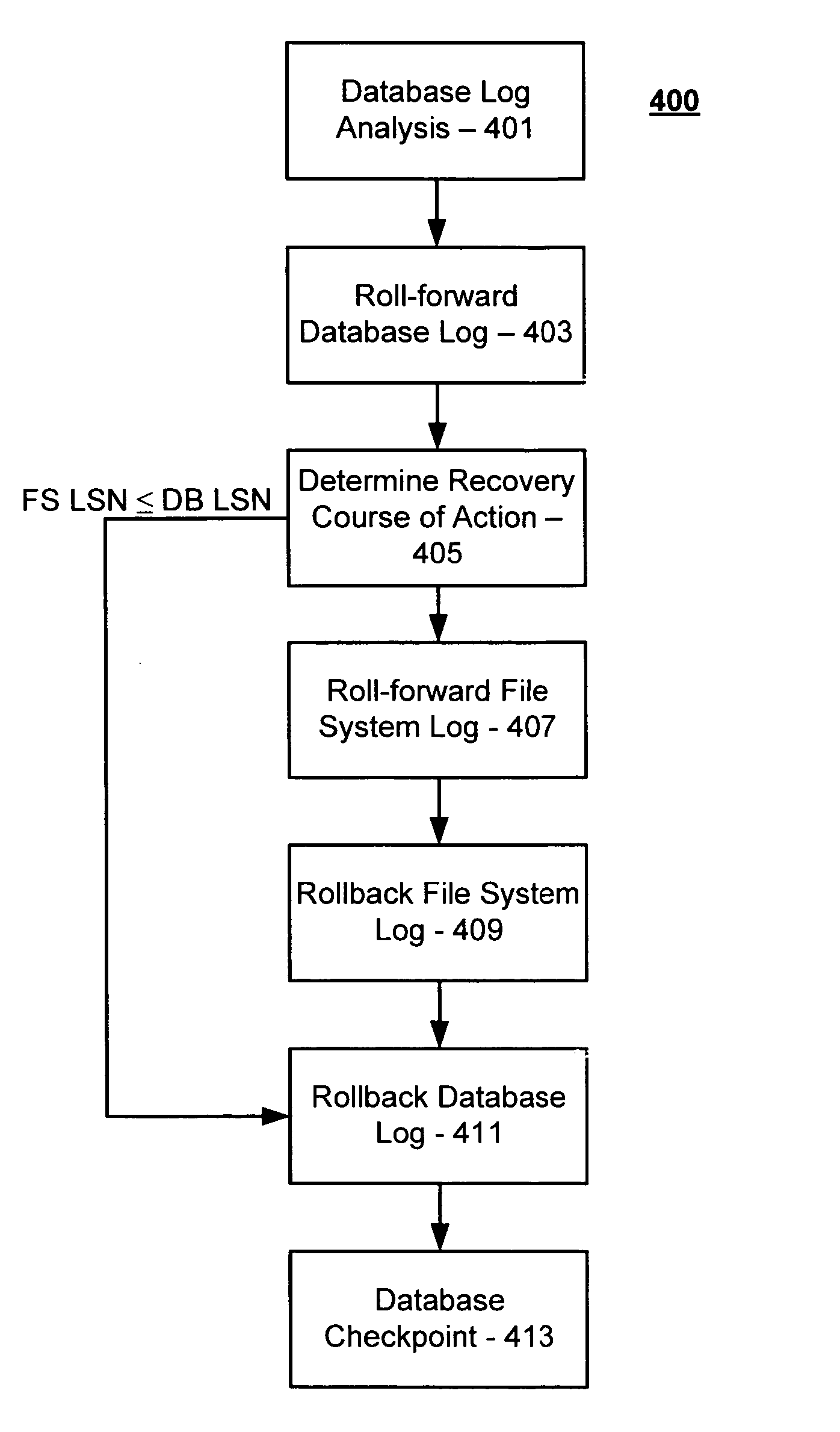
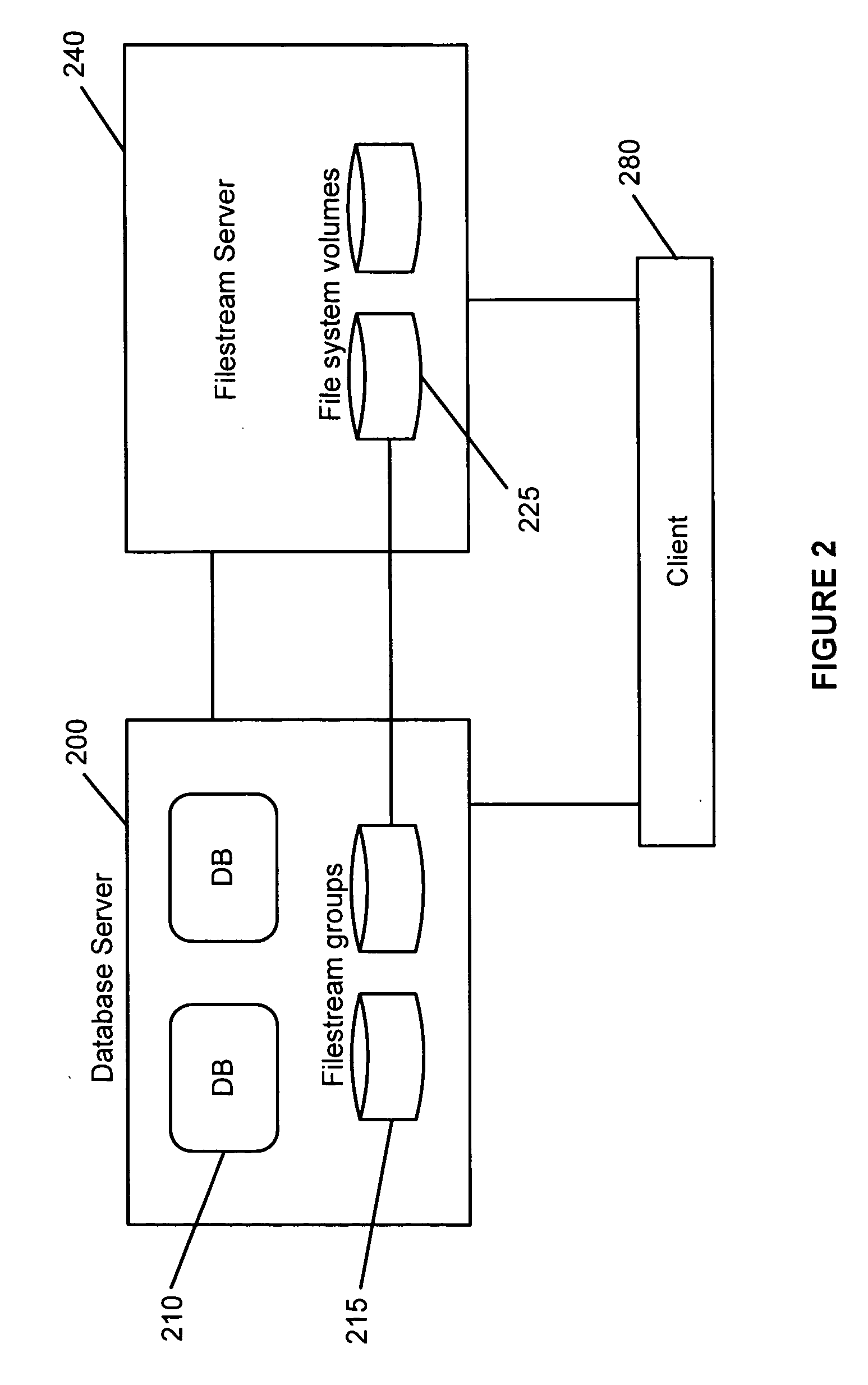
Maintenance of link level consistency between database and file system
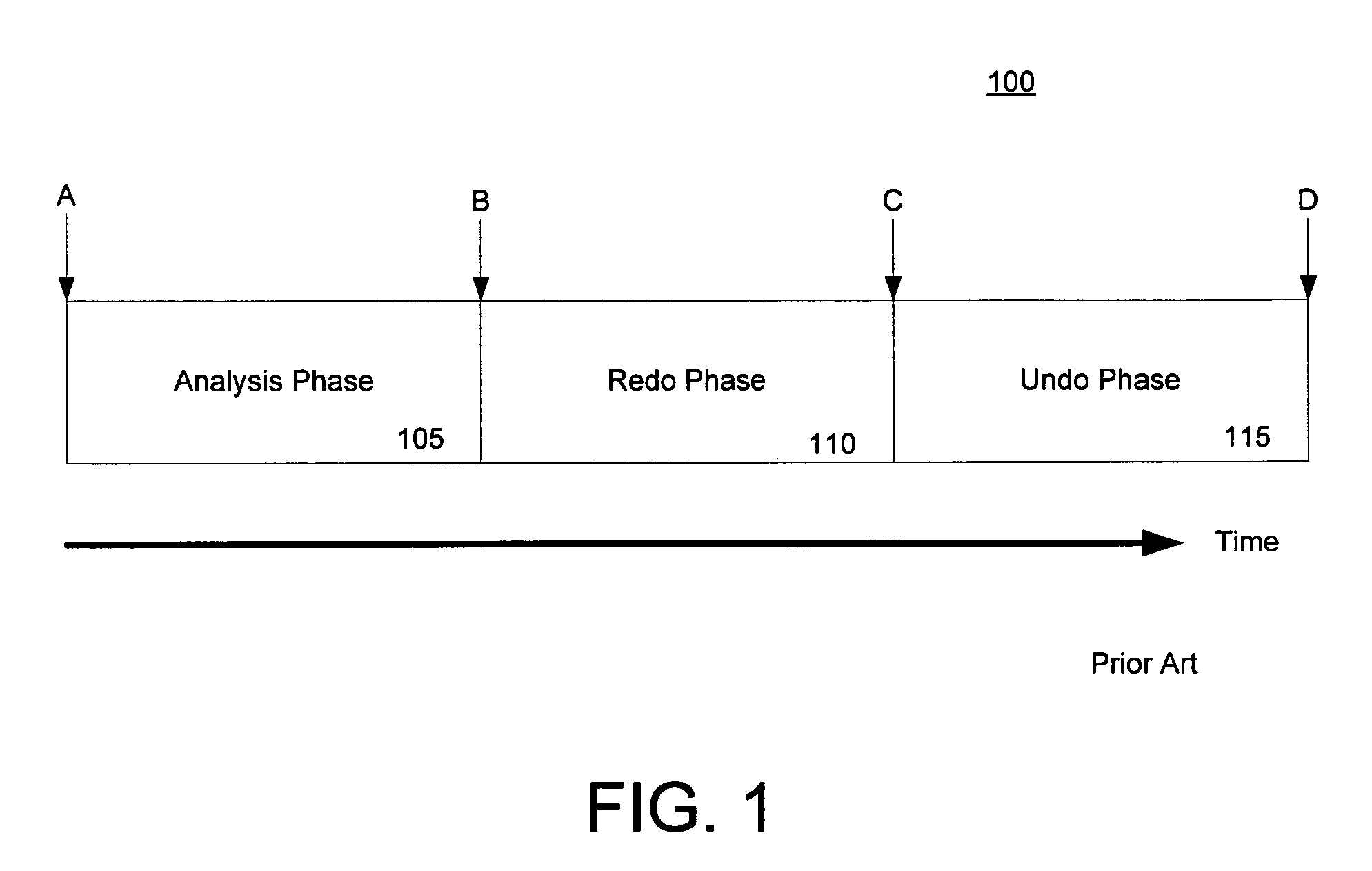
Methods and computer-readable media for maintaining transactional link-level consistency between a database and a file system. A file system change is logged in a record of a database log and a file corresponding to the file system change is created in a file system folder. During a restart recovery process, an analysis operation and a conditional redo operation are performed based on the database log, and a conditional redo operation and an undo operation are performed based on the files in the file system folder. An undo operation is then performed based on the database log.
Owner:MICROSOFT TECH LICENSING LLC
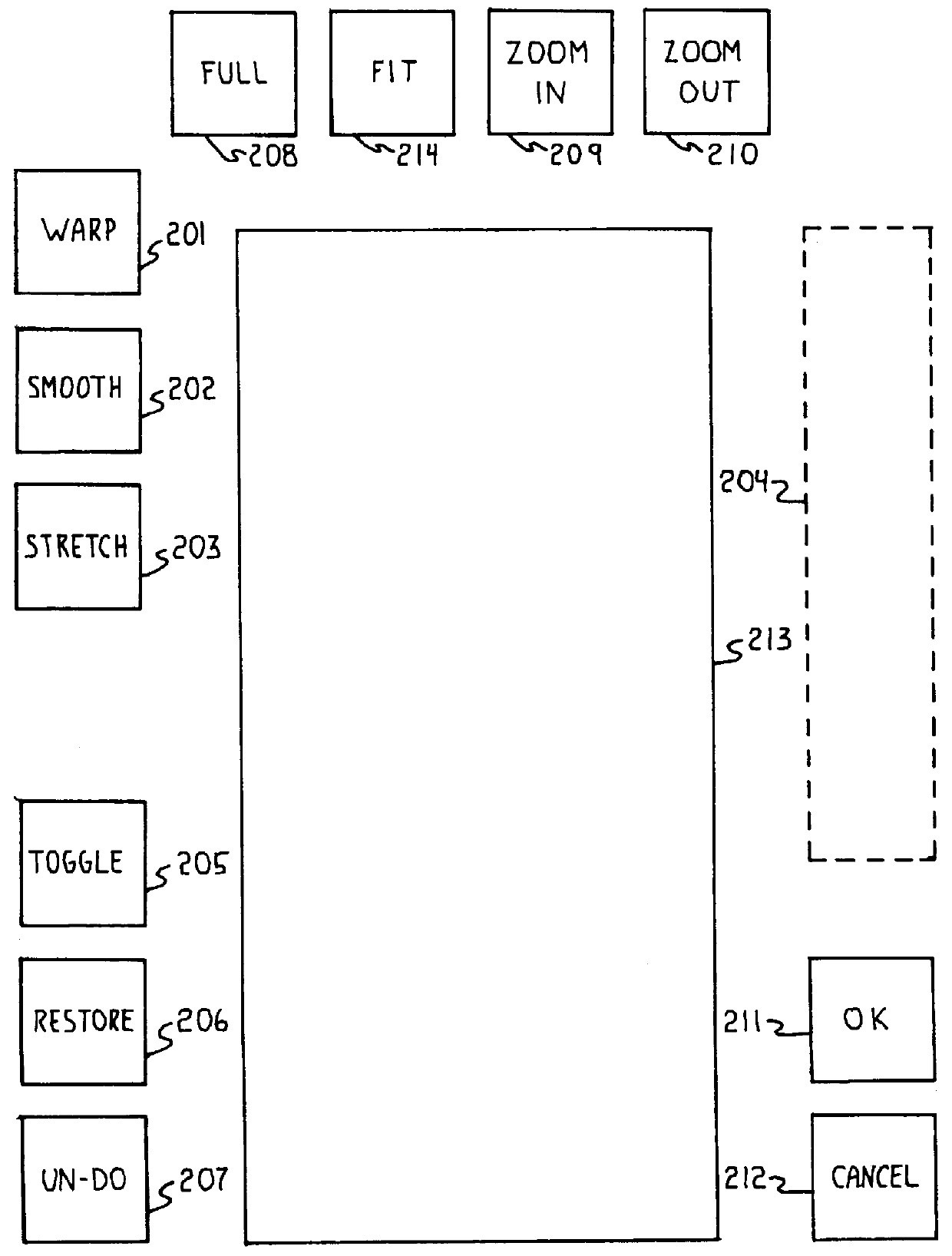
Apparatus for modifying graphic images
InactiveUS6084598AIncrease speedConsistent qualityDrawing from basic elementsGeometric image transformationChange managementShape change
A computer system modifies digital images of the human form as well as other objects. The computer system provides intuitive means for accessing warp, smooth, stretch, copy, and paste tools for image modification; undo, toggle and restore tools for change management; and zoom, fit, and full tools for image display sizing. The computer system is controlled by a program that uses a combination of novel approaches to make image manipulation fast and easy. Buttons are displayed only when they are actually available for use, based on the current system operating mode. The image sizing tools enable an image size change to accomodate the tool size without a required change to the cursor state or to the edit mode state. When regions are defined by the user, the cursor shape changes to indicate whether the cursor is located inside a region, outside the region, and on the region bounding box; allowing a user to perform different operations depending upon cursor location rather than depending upon, and requiring, user executed button pushing as a specific operation. The computer system uses display contexts and bitmap masks that enhance operation speed. Operations are always performed on the full image resolution rather than a displayed image resolution.
Owner:CHEKERYLLA JAMES
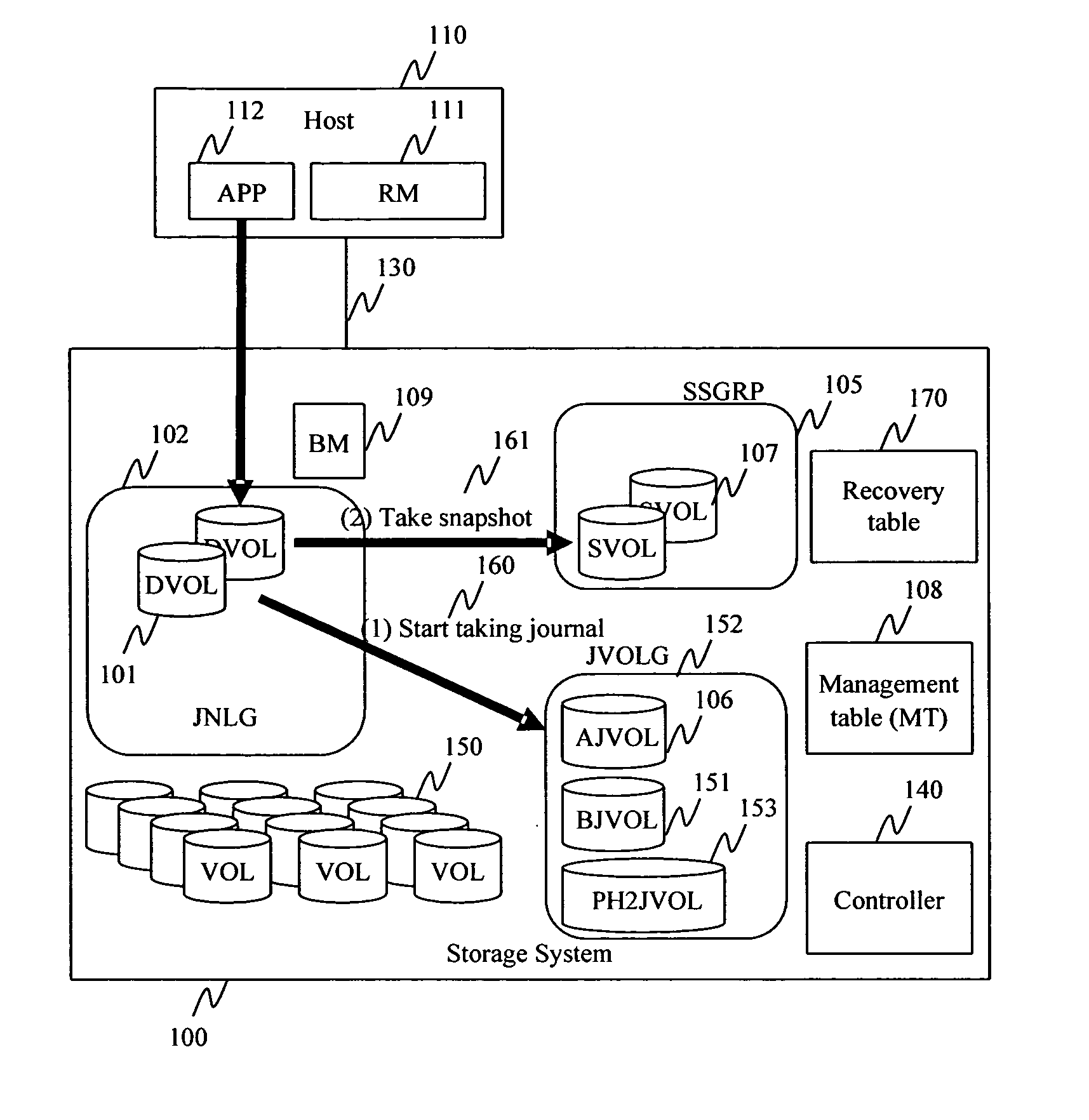
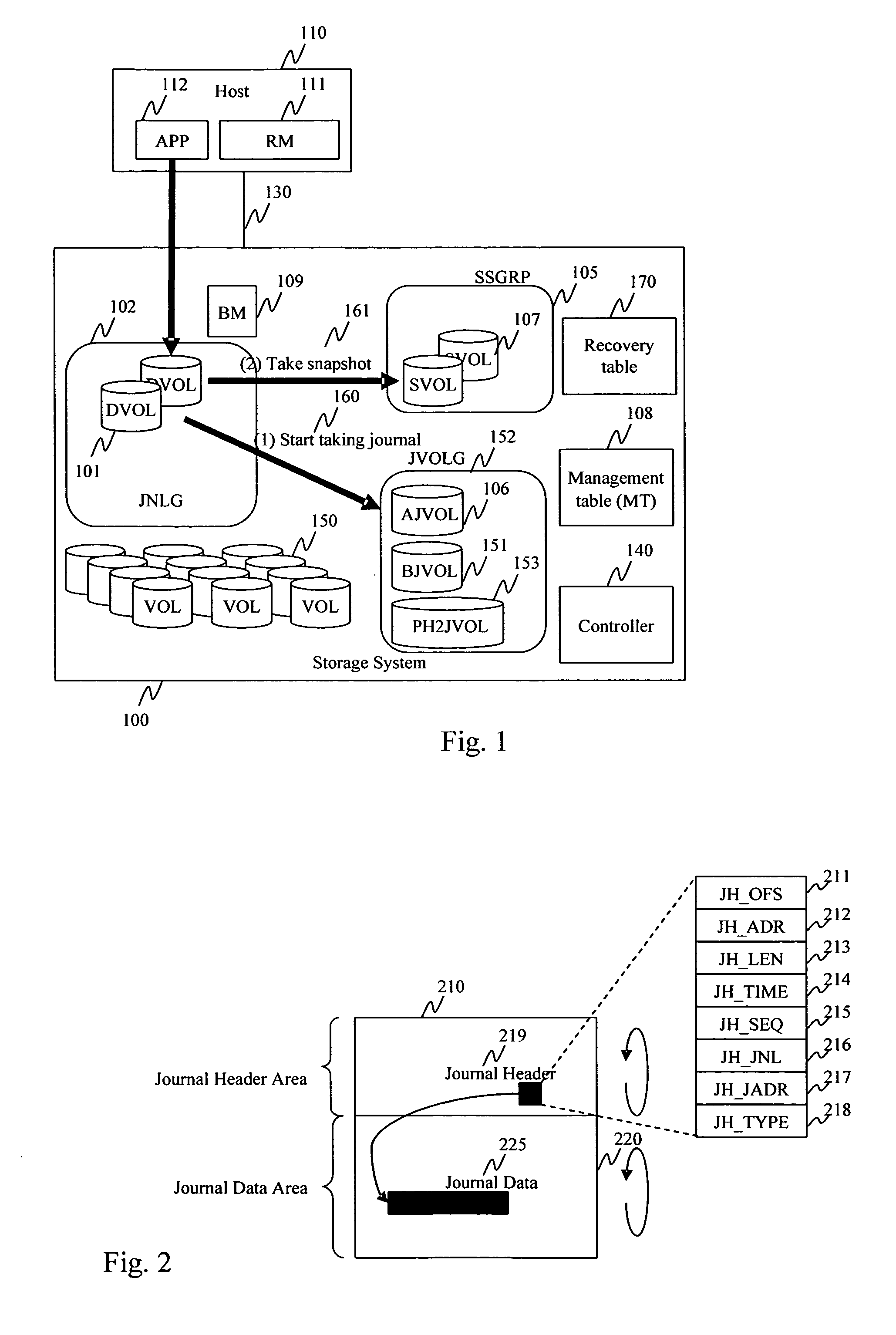
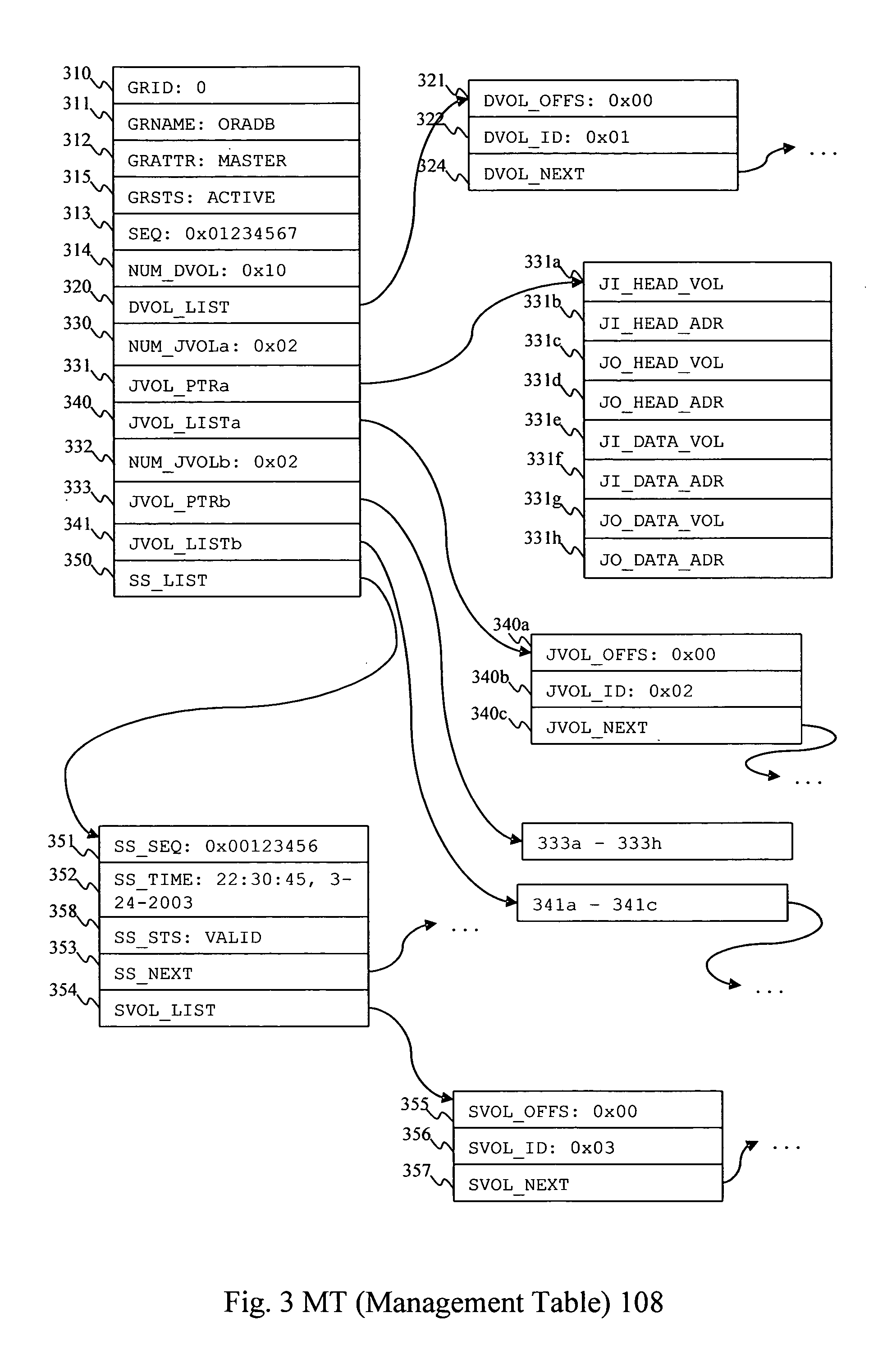
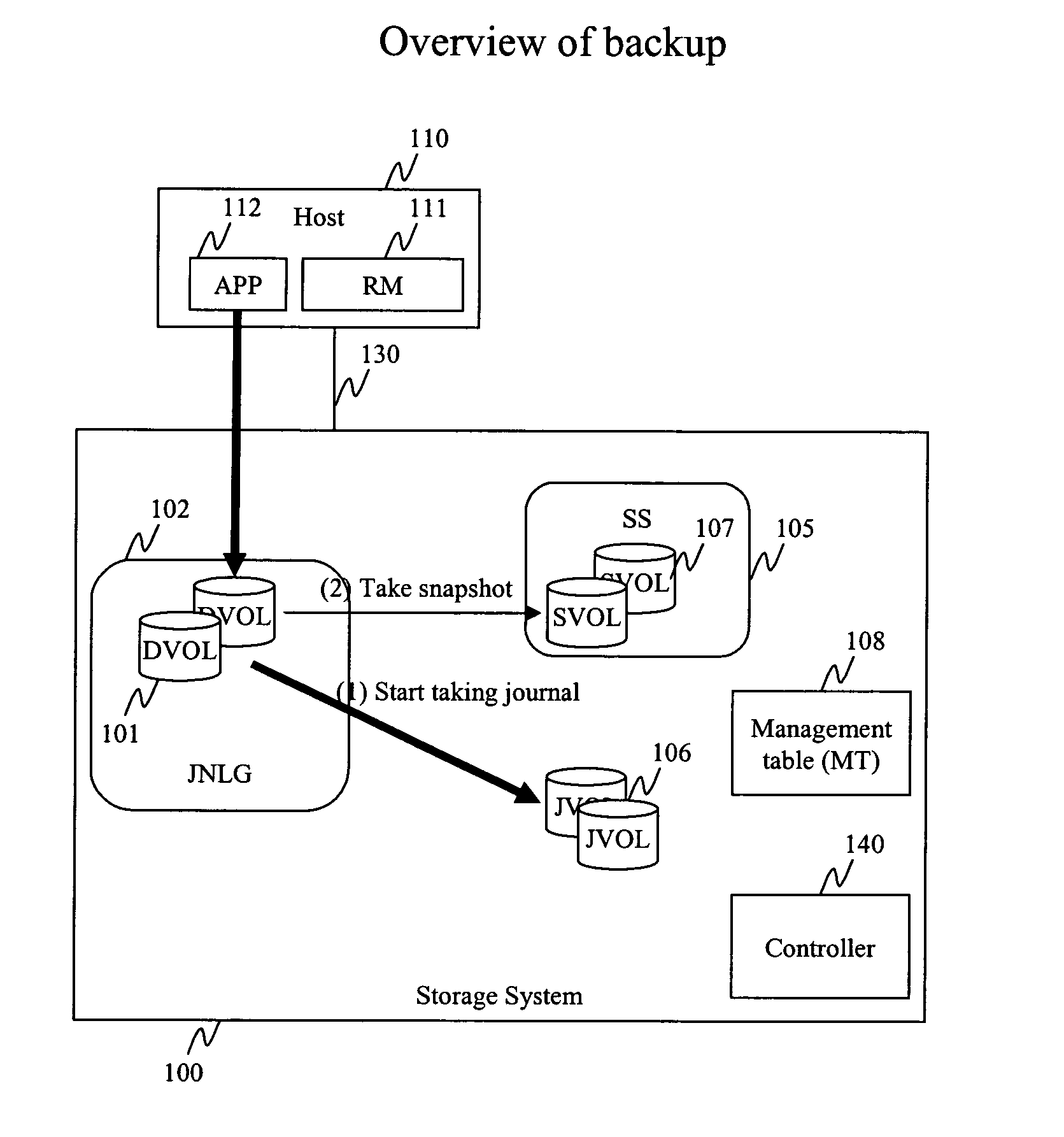
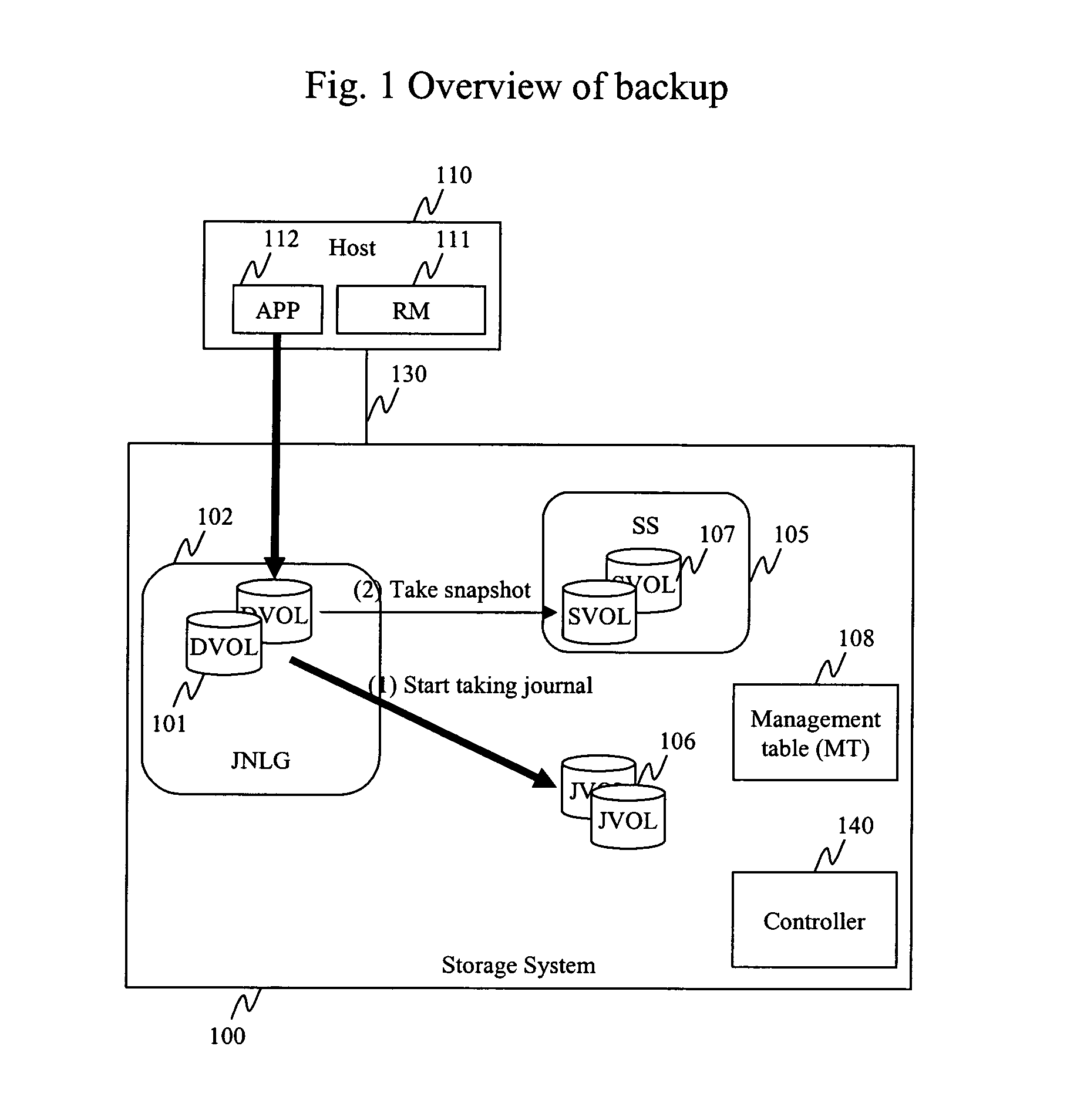
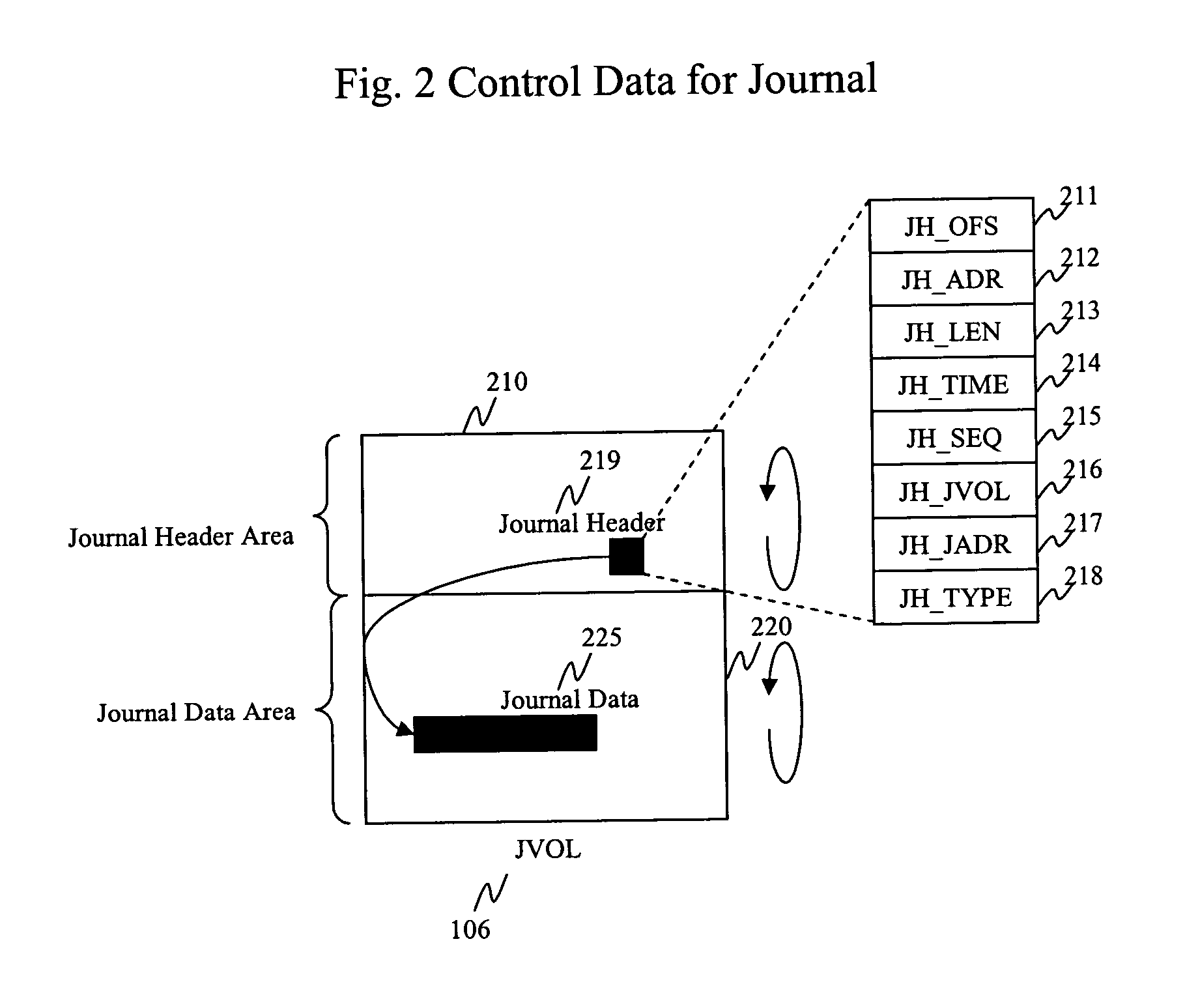
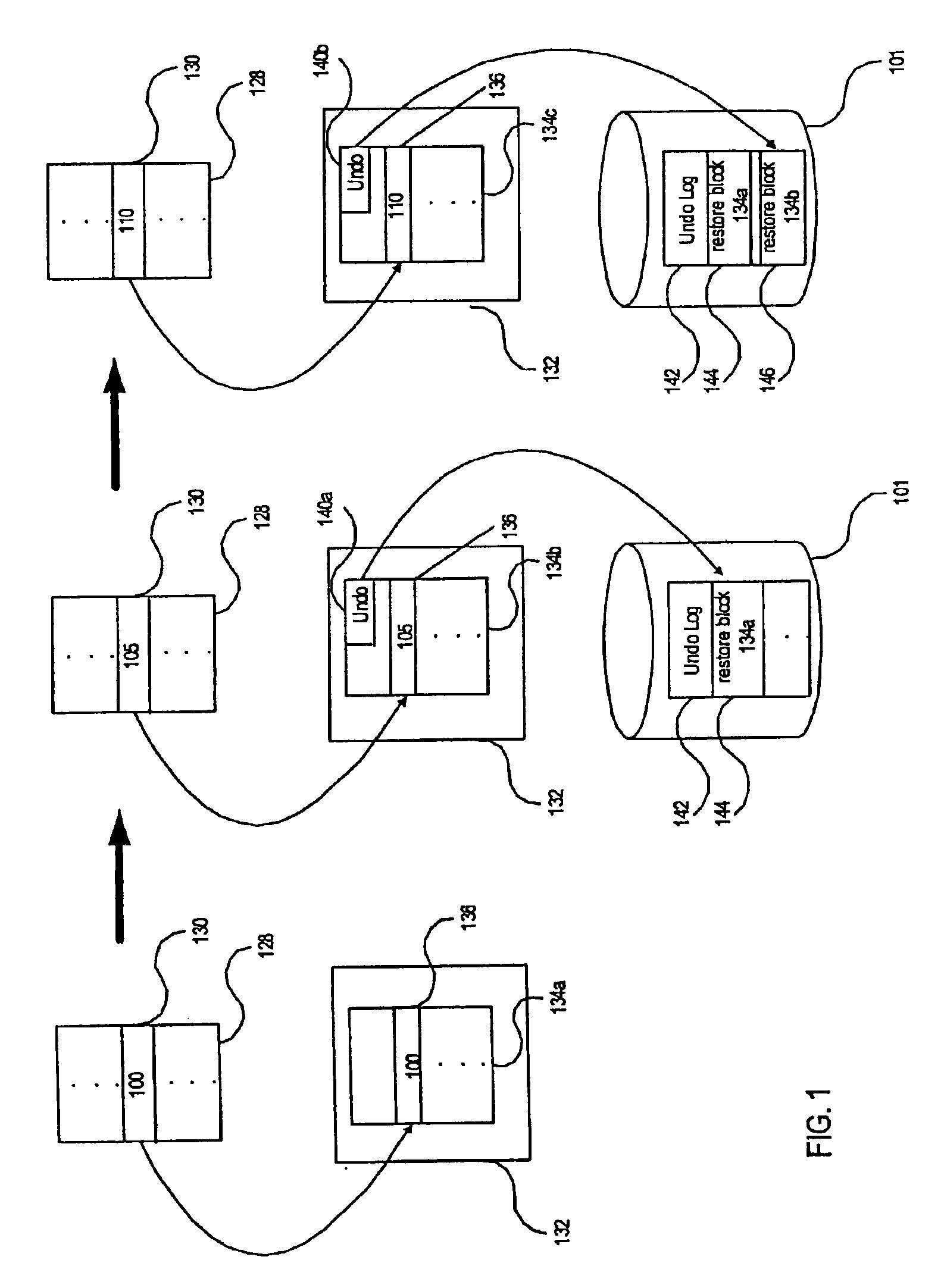
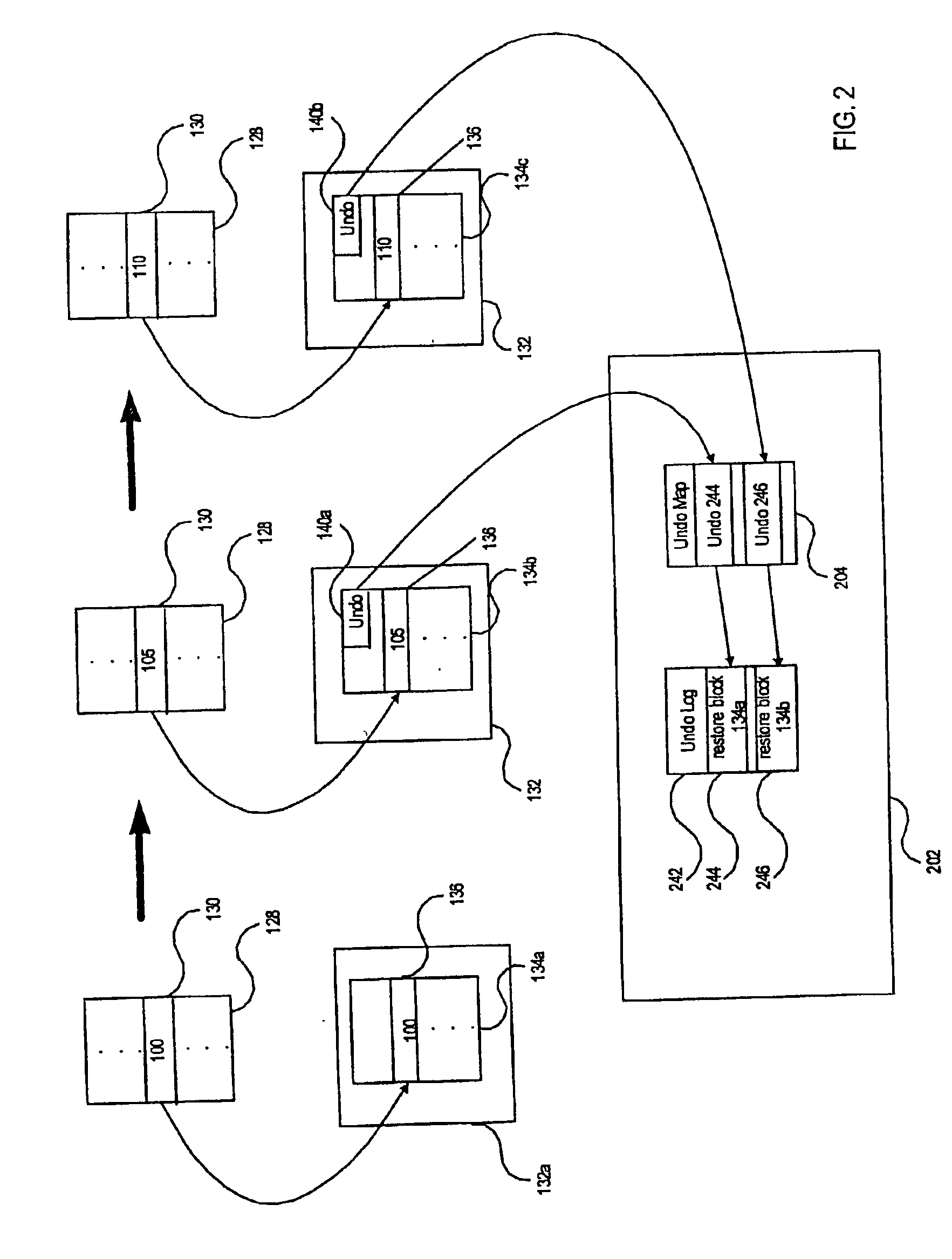
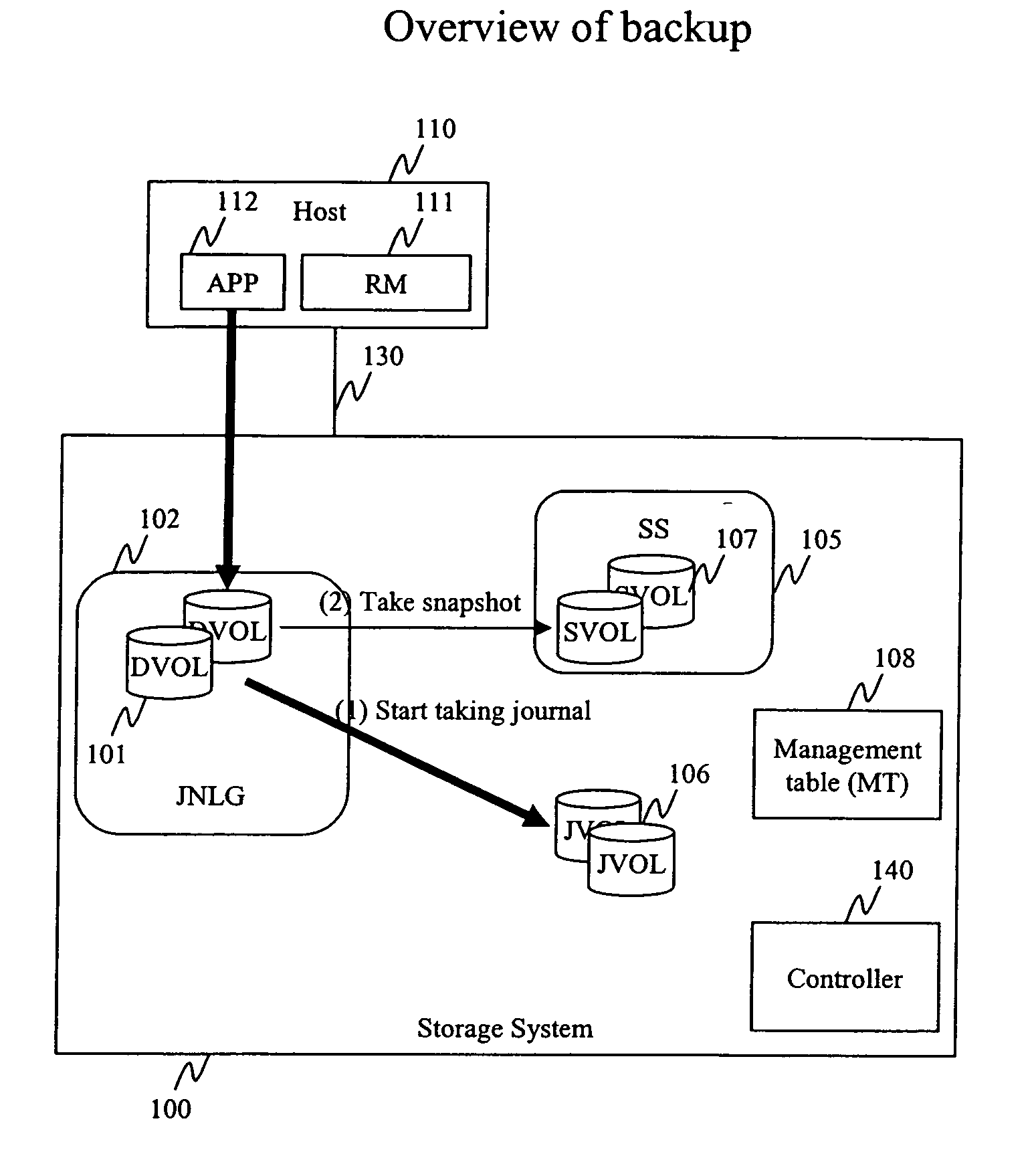
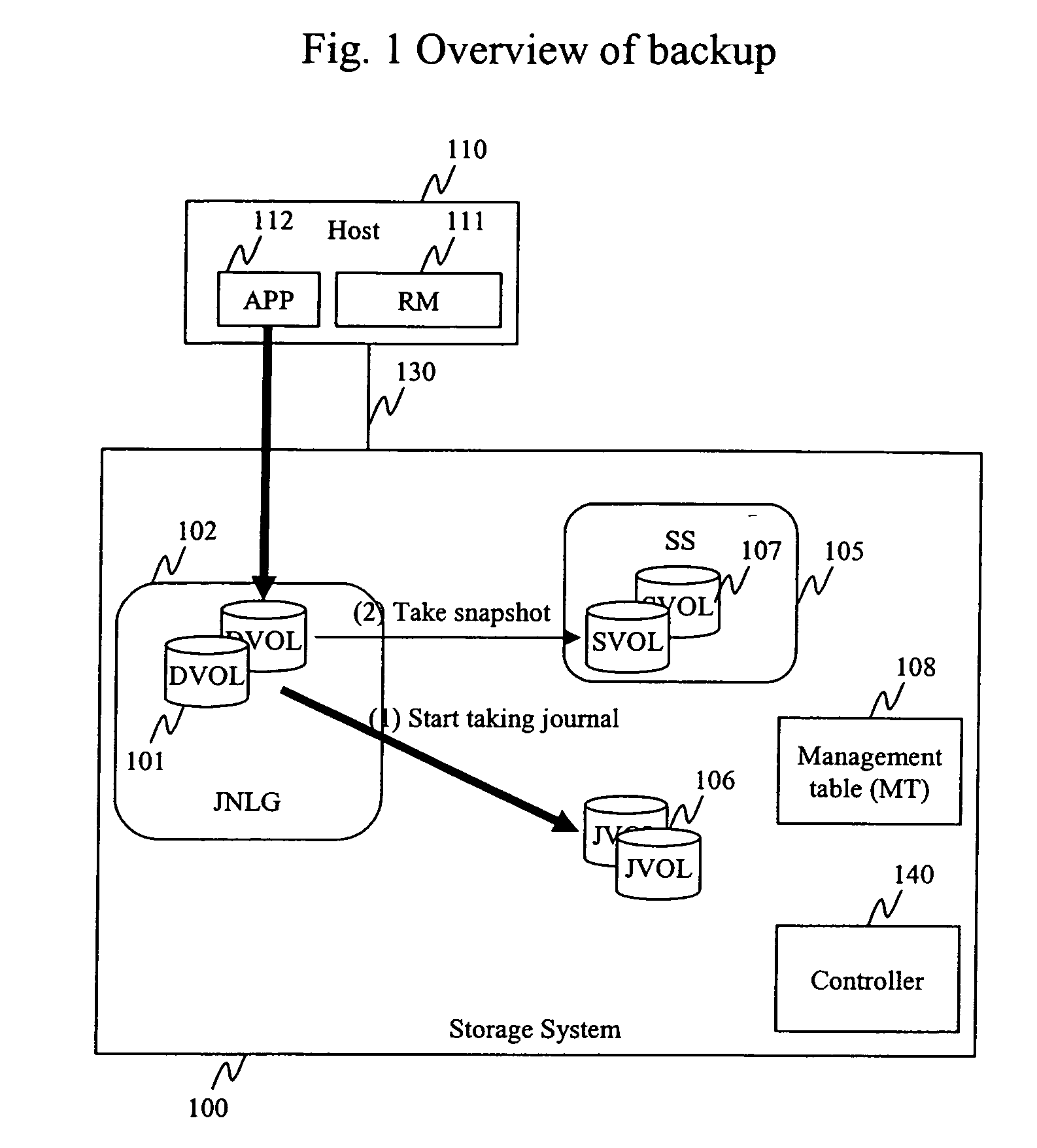
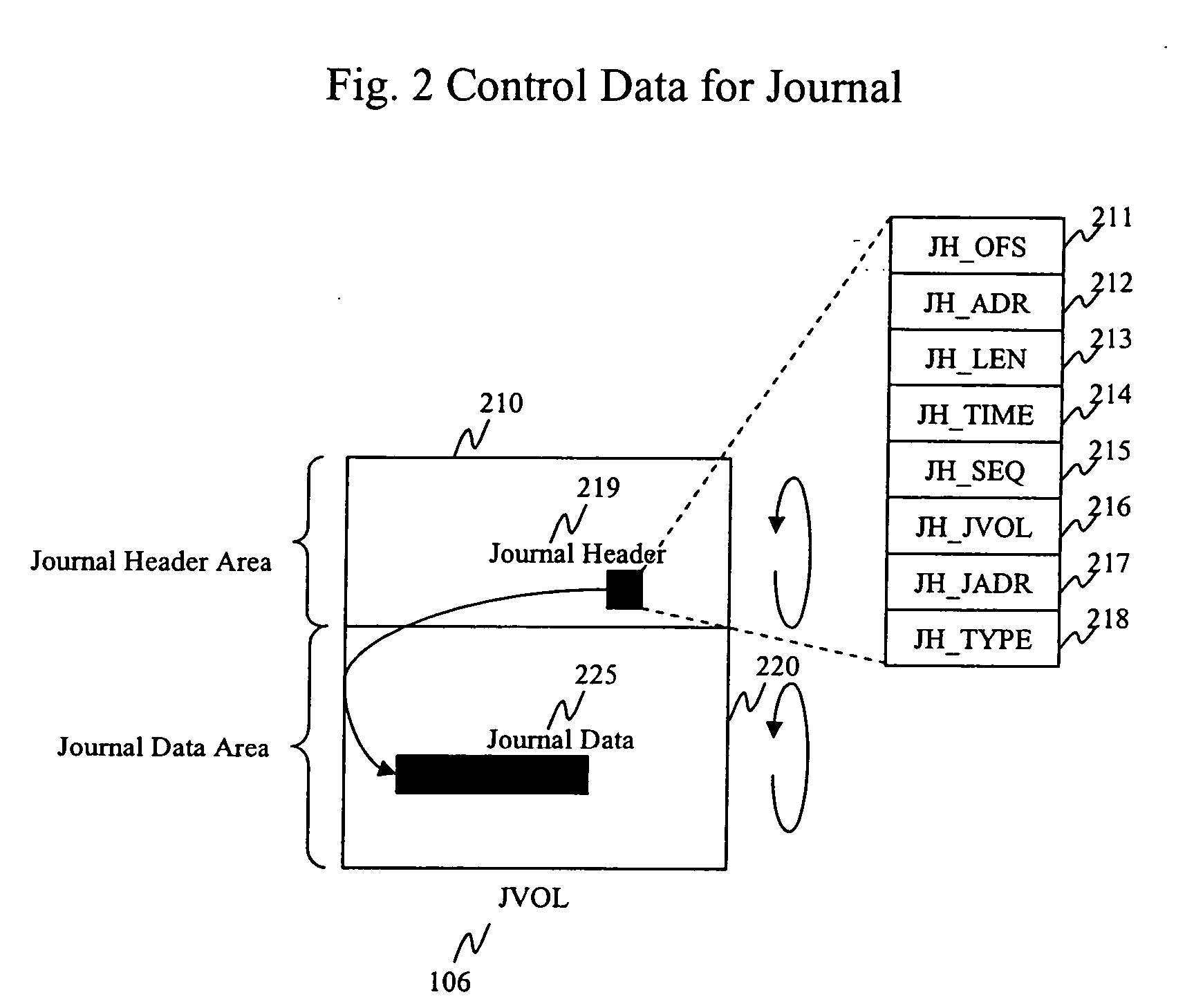
Method and apparatus for data recovery system using storage based journaling
InactiveUS20050028022A1Data processing applicationsError detection/correctionSystem maintenanceDatabase
A storage system maintains a journal and a snapshot of one or more data volumes. Two journal entry types are maintained, an AFTER journal entry and a BEFORE journal entry. Two modes of data recovery are provided: “fast” recovery and “undo-able” recovery. A combination of both recovery modes allows the user to quickly recover a targeted data state.
Owner:HITACHI LTD
Method and apparatus for data recovery using storage based journaling
InactiveUS20050015416A1Resume normal operationError detection/correctionMemory systemsSystem maintenanceComputer science
A storage system maintains a journal and a snapshot of one or more data volumes. Two journal entry types are maintained, an AFTER journal entry and a BEFORE journal entry. Two modes of data recovery are provided: “fast” recovery and “undo-able” recovery. A combination of both recovery modes allows the user to quickly recover a targeted data state.
Owner:HITACHI LTD
Method and system for harmonization of variants of a sequential file
InactiveUS20080313243A1Digital data processing detailsNatural language data processingComputational scienceVisibility
A set of versions of a file, with one chosen as baseline version, is displayed as a single flow of material where all agree with the baseline and in separate difference columns where they do not. A current version may be edited either directly or by adoption of material from different versions, which may be toggled in and out of visibility. Sequential undo (step-wise or by a slider) can be localized to chosen subsets of the current version, and any chosen subset can be restored as a unit to an earlier state.
Owner:PADO DEPLOYMENT
Method and mechanism for batch processing transaction logging records
InactiveUS6976022B2Data processing applicationsDigital data information retrievalBatch processingTransaction log
Owner:ORACLE INT CORP
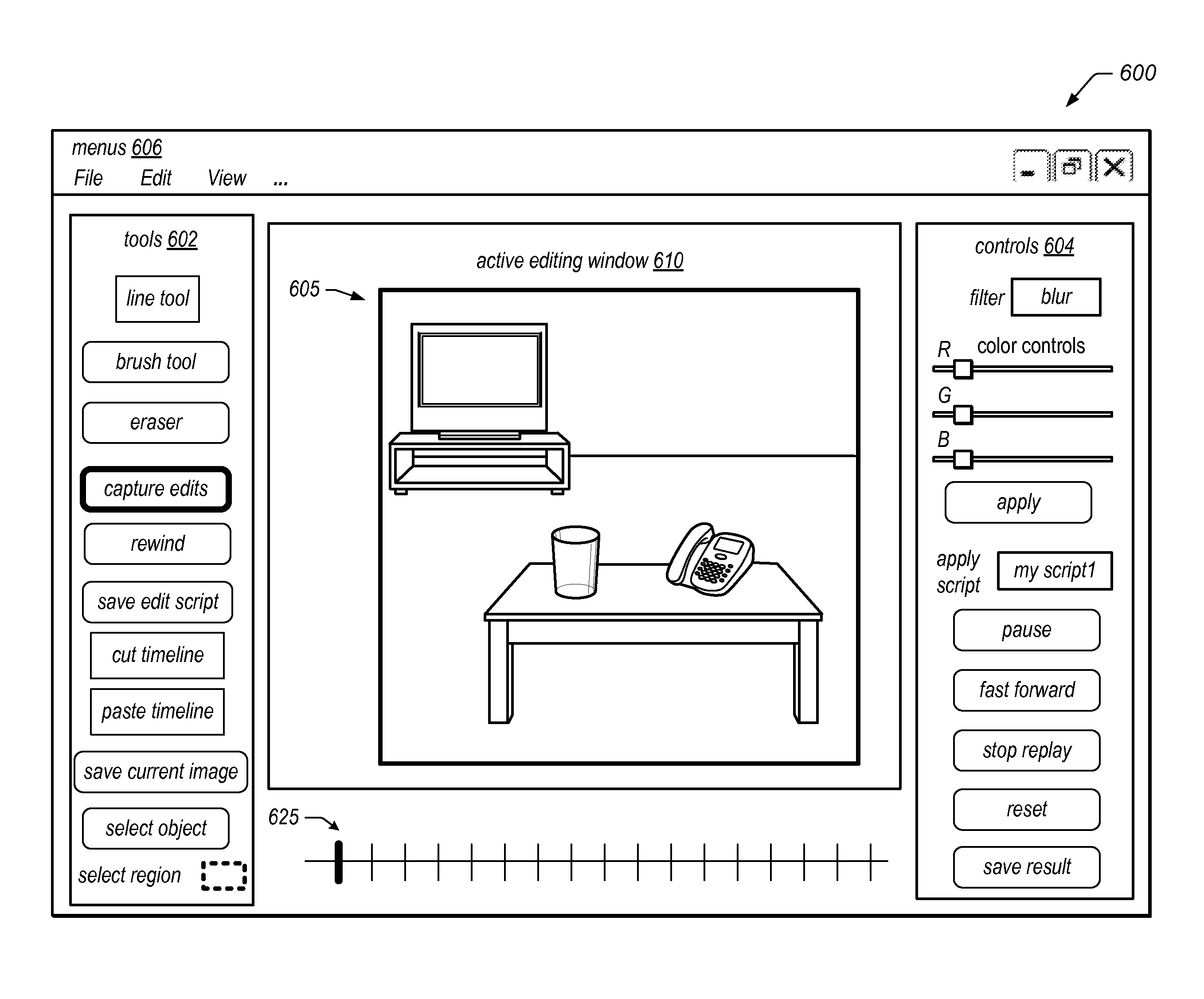
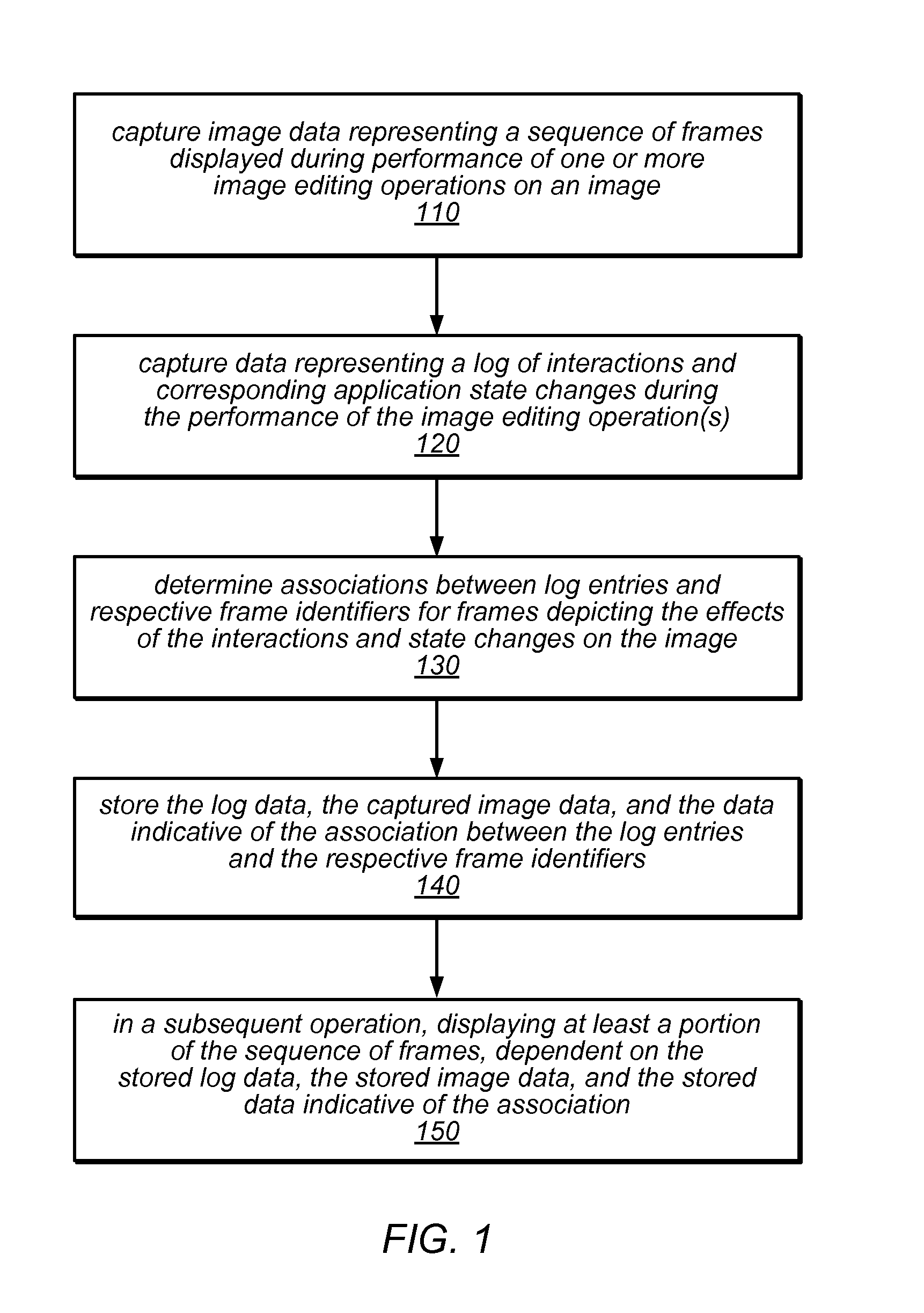
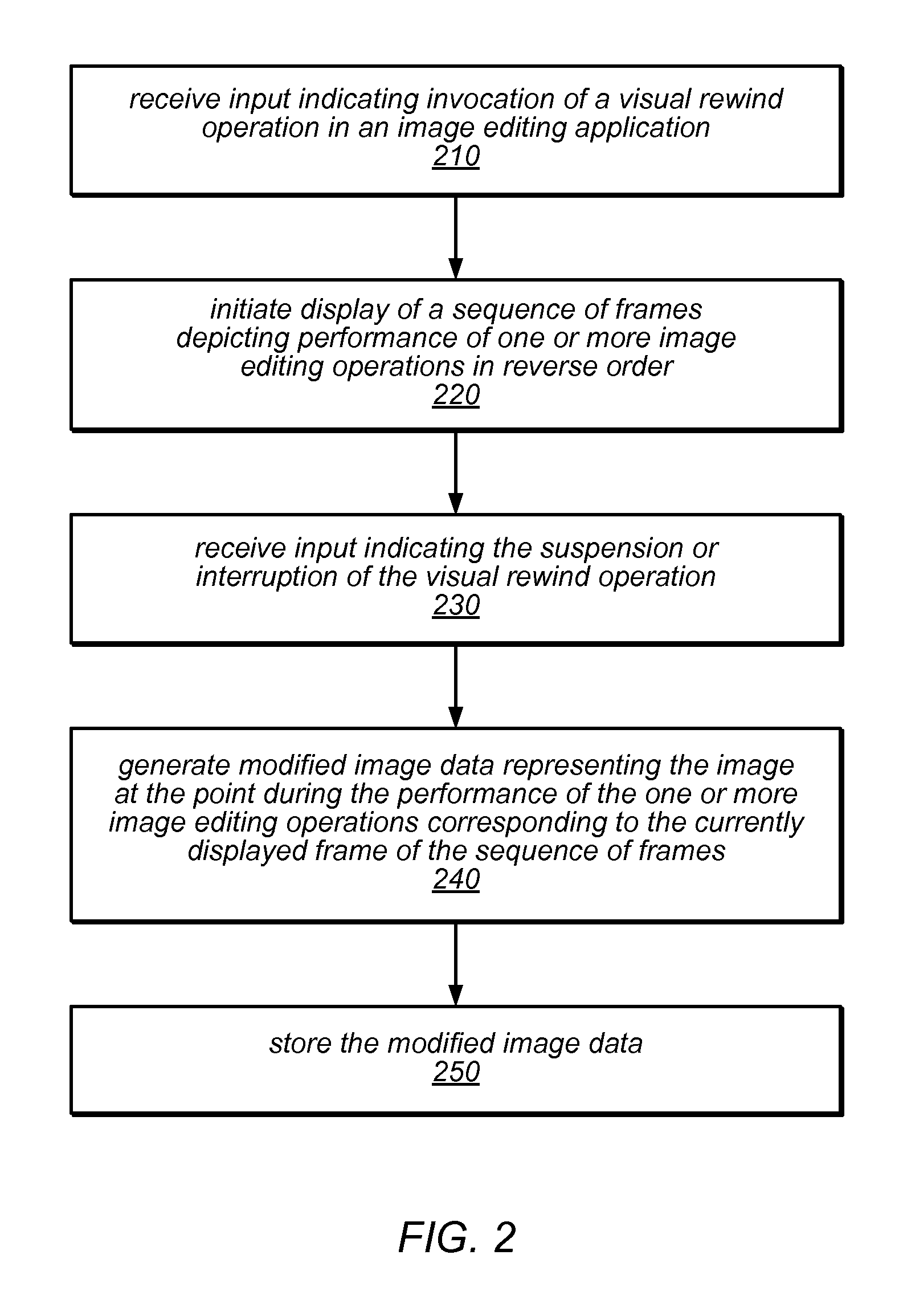
System and Method for Image Editing Using Visual Rewind Operation
ActiveUS20130120439A1Reduce the impactReduce impactElectronic editing digitised analogue information signalsCharacter and pattern recognitionGraphicsReverse order
Systems, methods, and computer-readable storage media for performing a visual rewind operation in an image editing application may include capturing, compressing, and storing image data and interaction logs and correlations between them. The stored information may be used in a visual rewind operation, during which a sequence of frames (e.g., an animation) depicting changes in an image during image editing operations is displayed in reverse order. In response to navigating to a point in the animation, data representing the image state at that point may be reconstructed from the stored data and stored as a modified image or a variation thereof. The methods may be employed in an image editing application to provide a partial undo operation, image editing variation previewing, and / or visually-driven editing script creation. The methods may be implemented as stand-alone applications or as program instructions implementing components of a graphics application, executable by a CPU and / or GPU.
Owner:ADOBE INC
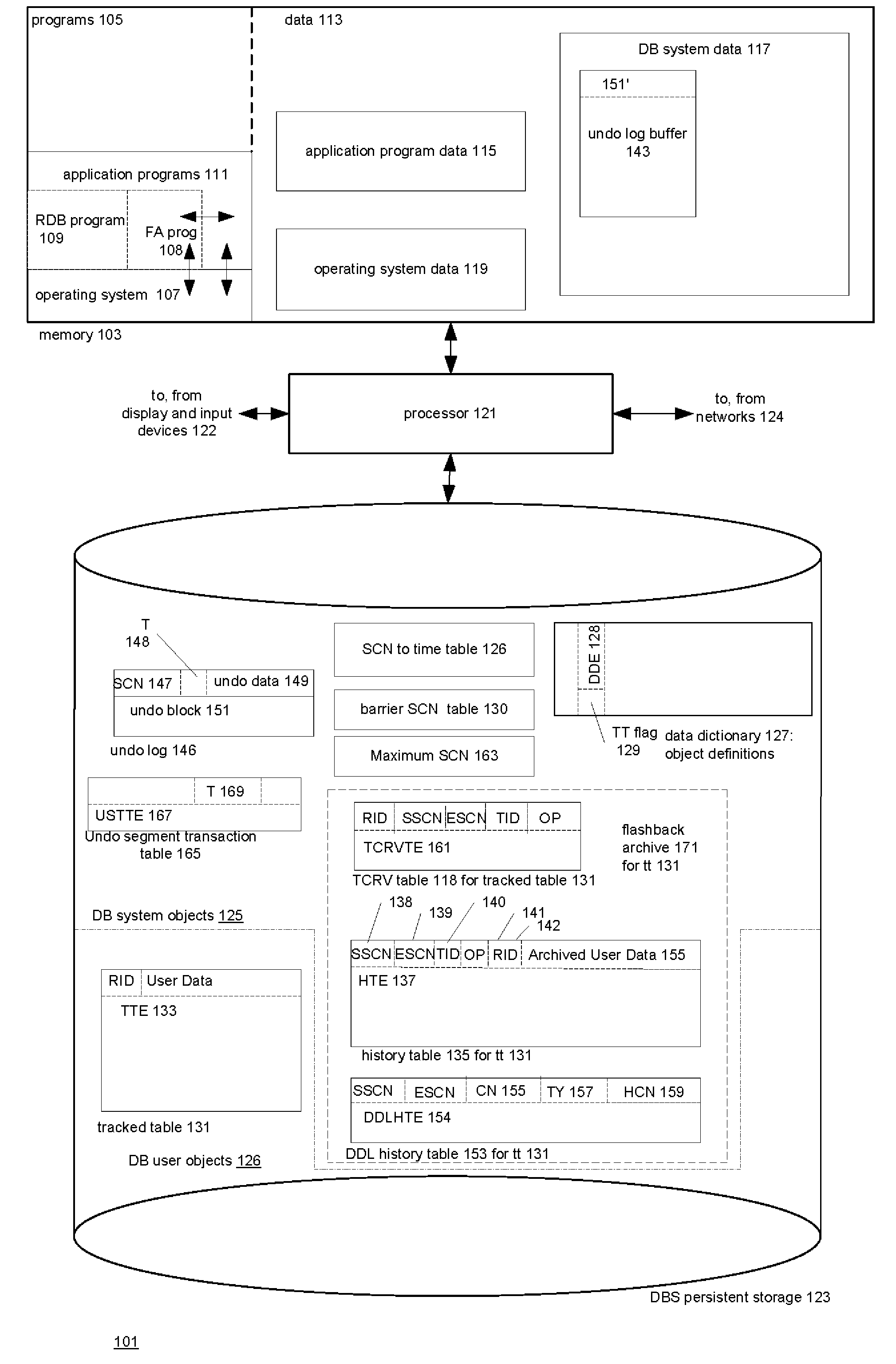
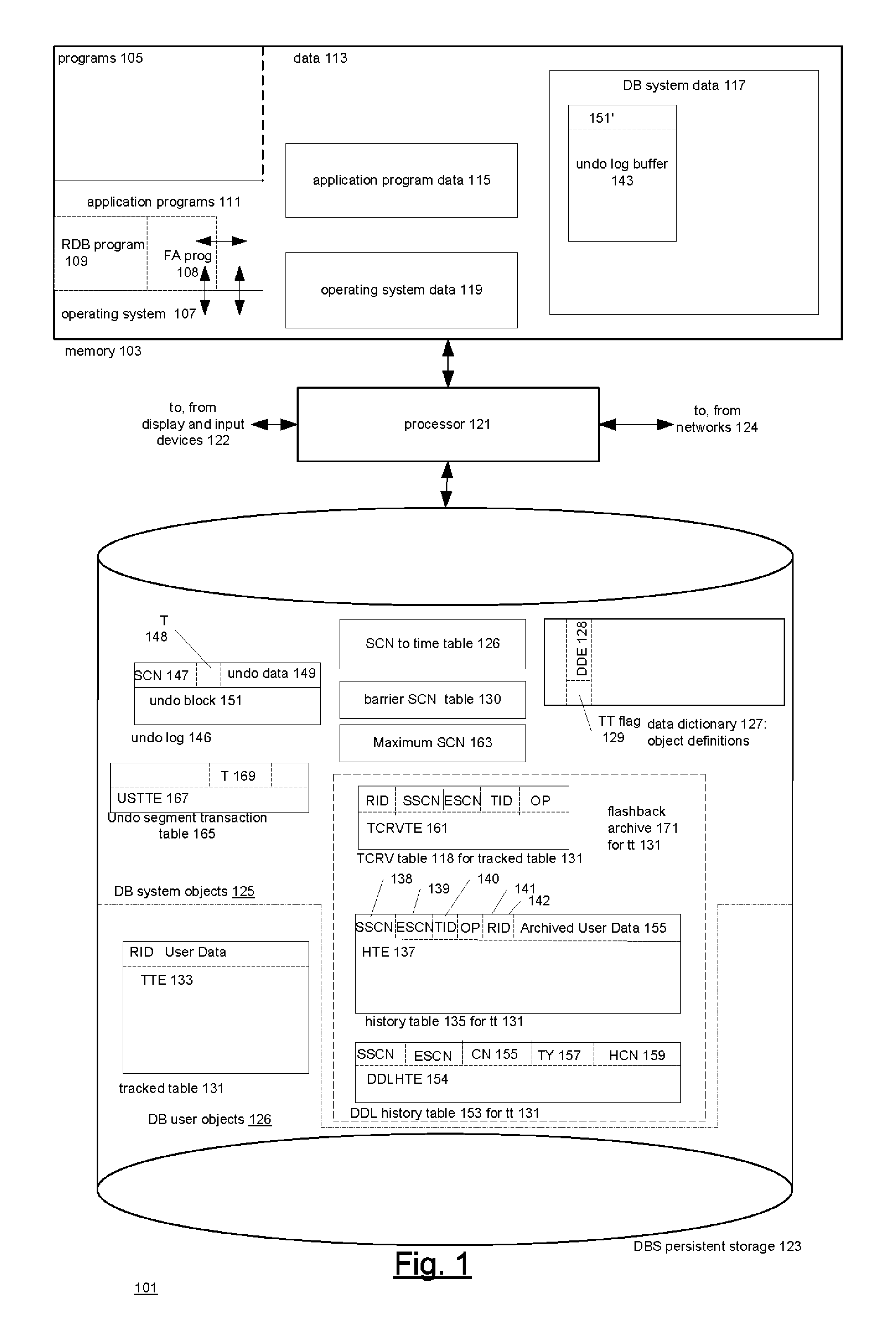
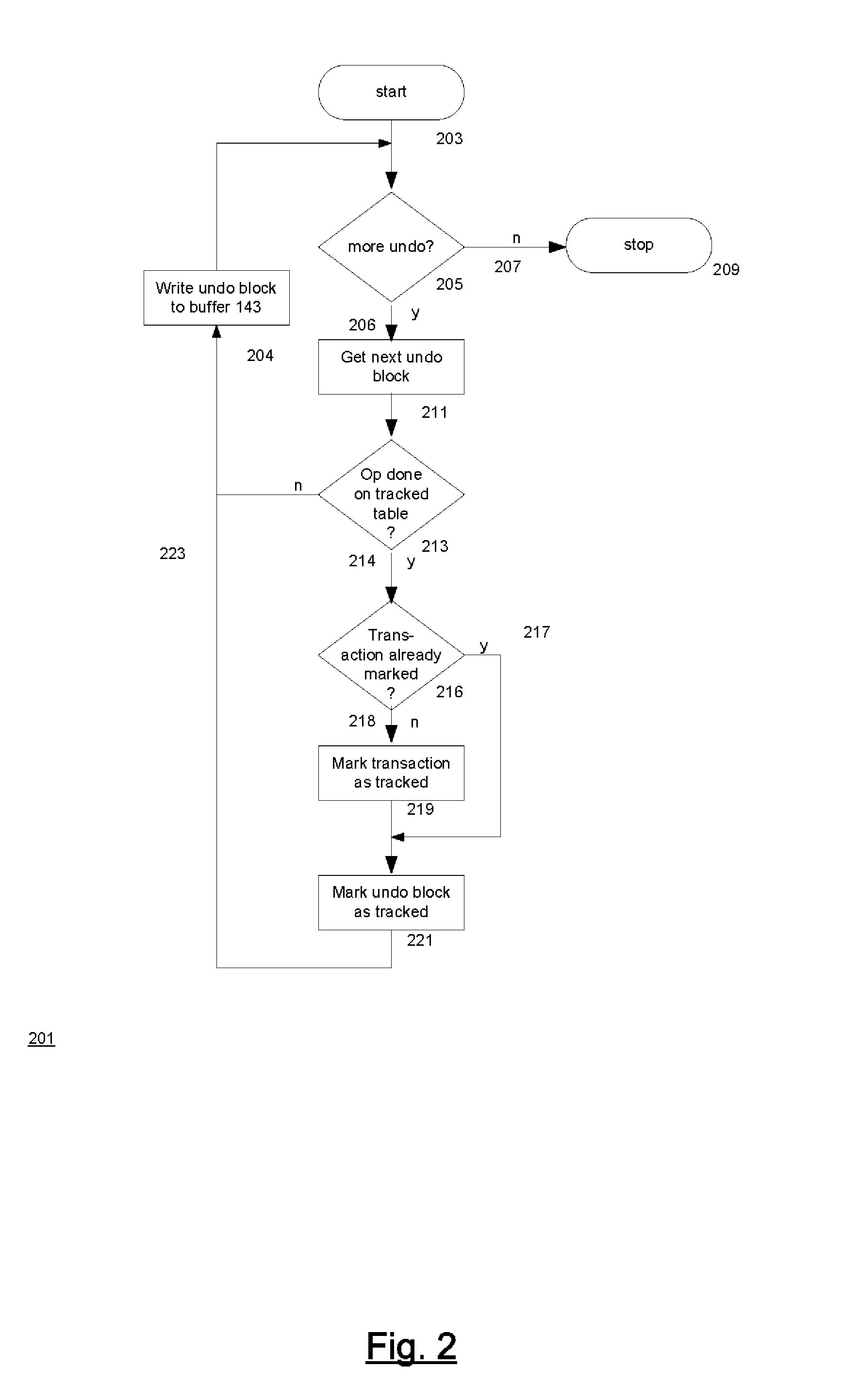
Techniques for automatically tracking and archiving transactional data changes
ActiveUS20080098045A1Error detection/correctionDigital data processing detailsBackground processManagement system
A technique for making versions of rows of a user-defined tracked table temporally queryable. The database management system of the technique permits temporal queries of user-defined tables. The queries return versions of rows in the user-defined table that are currently in an undo log maintained by the database system. Associated with the tracked table are a system history table which contains versions of the rows and temporal metadata indicating when the versions were in the tracked table and a system form history table which contains versions of the form of the tracked table and metadata indicating when the tracked table had the form. These tables are created and maintained by a background process in the database management system. A temporal query on the tracked table combines results from the undo log with results from the system history table. The results' form is determined by the system form history table.
Owner:ORACLE INT CORP
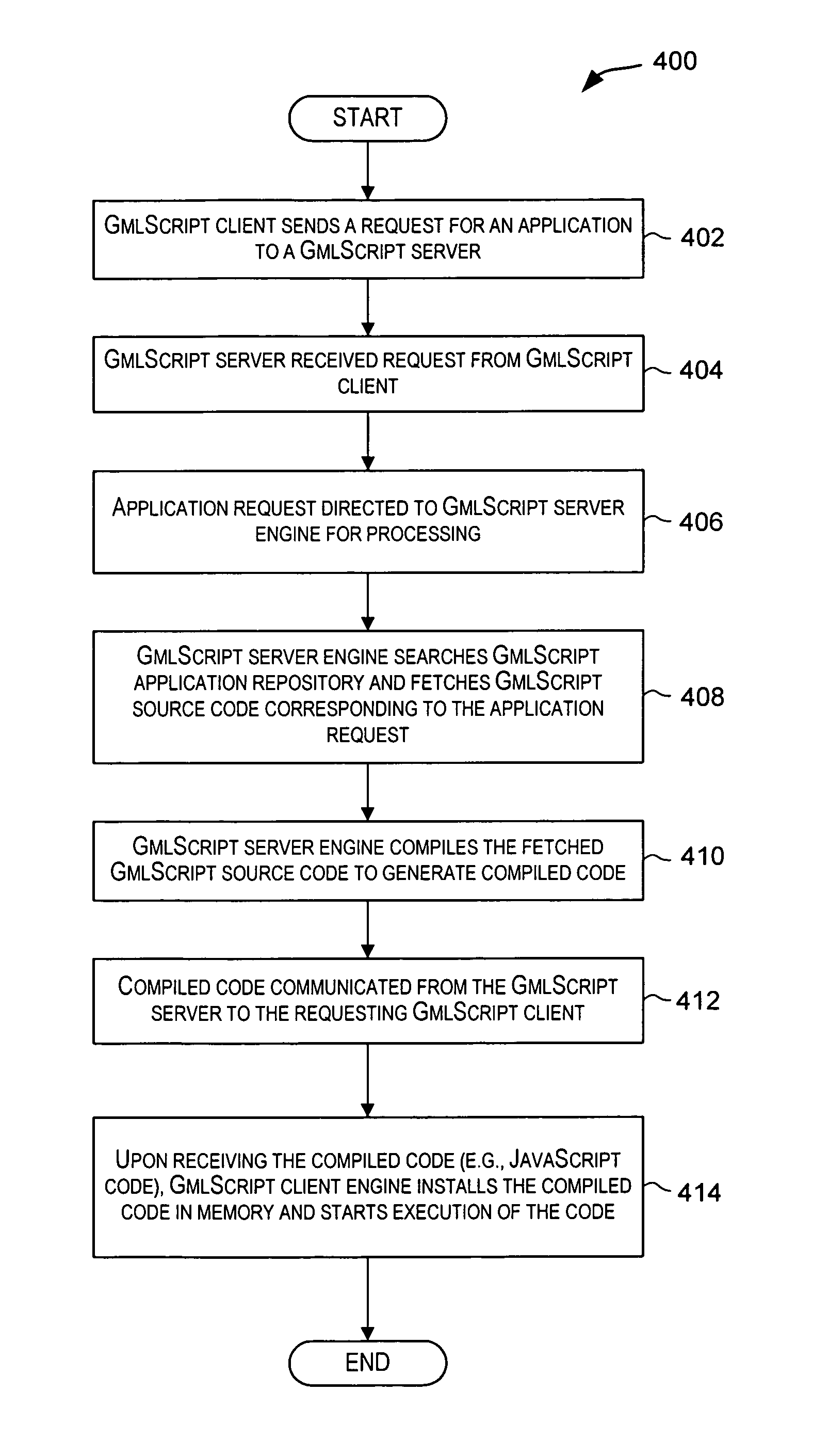
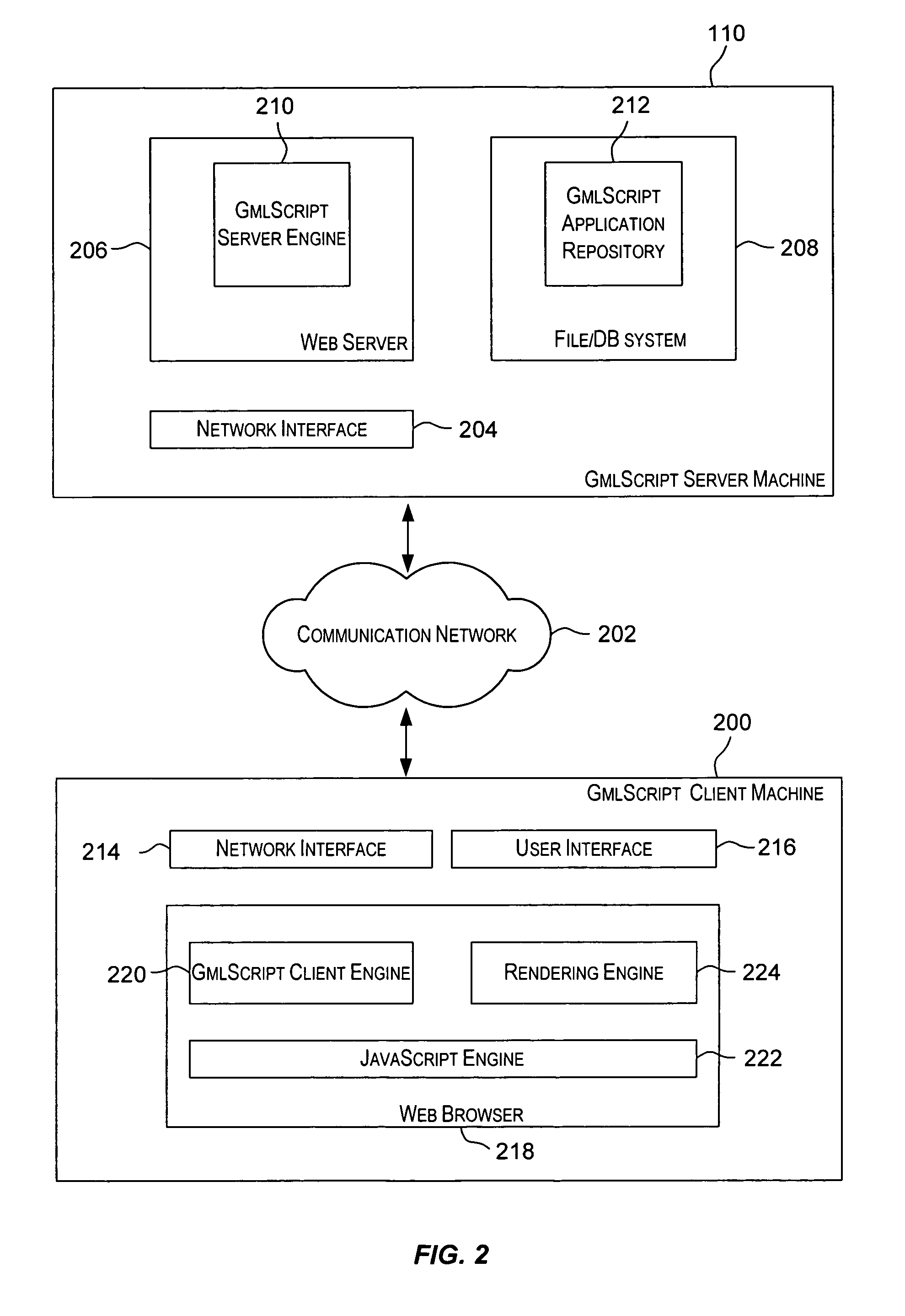
Programming language techniques for client-side development and execution
ActiveUS7971194B1Promote application developmentSoftware designRequirement analysisSoftware engineeringComponent (UML)
Techniques that facilitate development of applications that may be executed by a client program. The client program may be a modeling framework that may be hosted by a browser or other client-side program. A programming language (referred to as “GmlScript”) is provided for developing the applications. In one embodiment, the programming language provides various features such as object-oriented programming, client-side scripting, self-contained components, aspect-oriented programming, namespaces and self-contained components (kits), classes, methods, and properties, prototypes for multiple inheritance, events and listeners for implementing dynamics and constraints, transactions for ensuring model consistency and for undo / redo operations, objects persistency, dynamic loading, introspection, self documentation, preprocessing pragmas, and other features.
Owner:SAP PORTALS ISRAEL
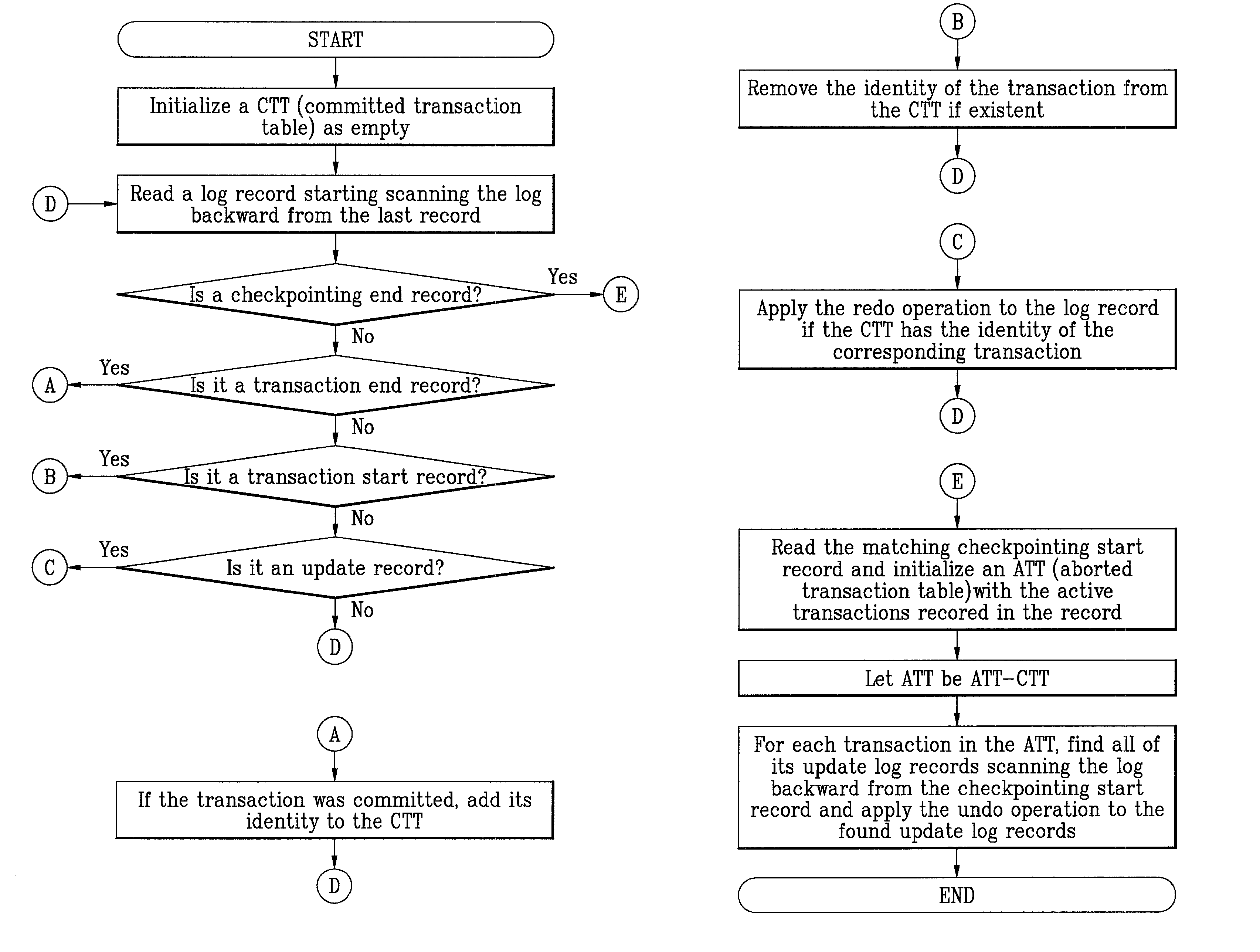
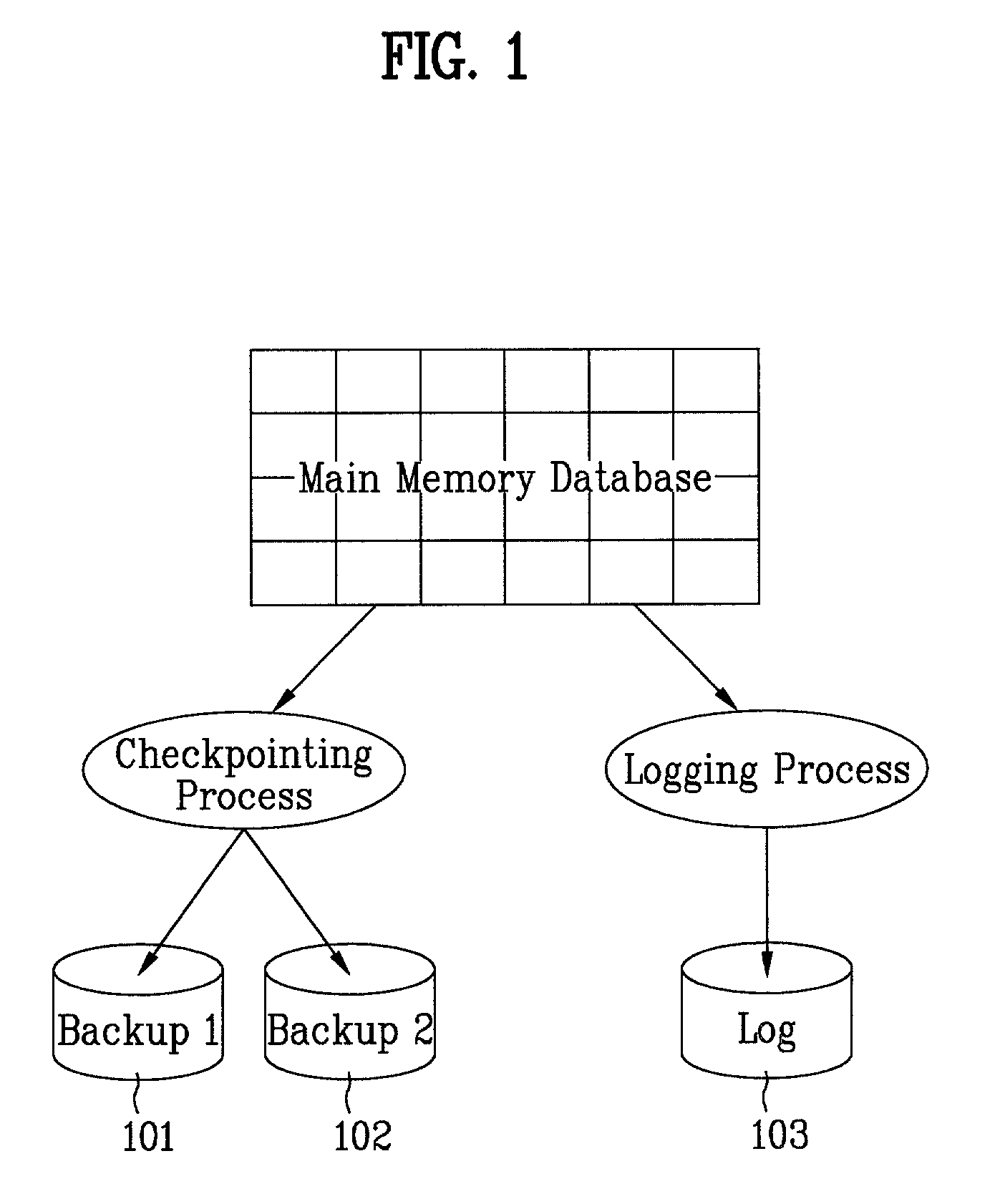
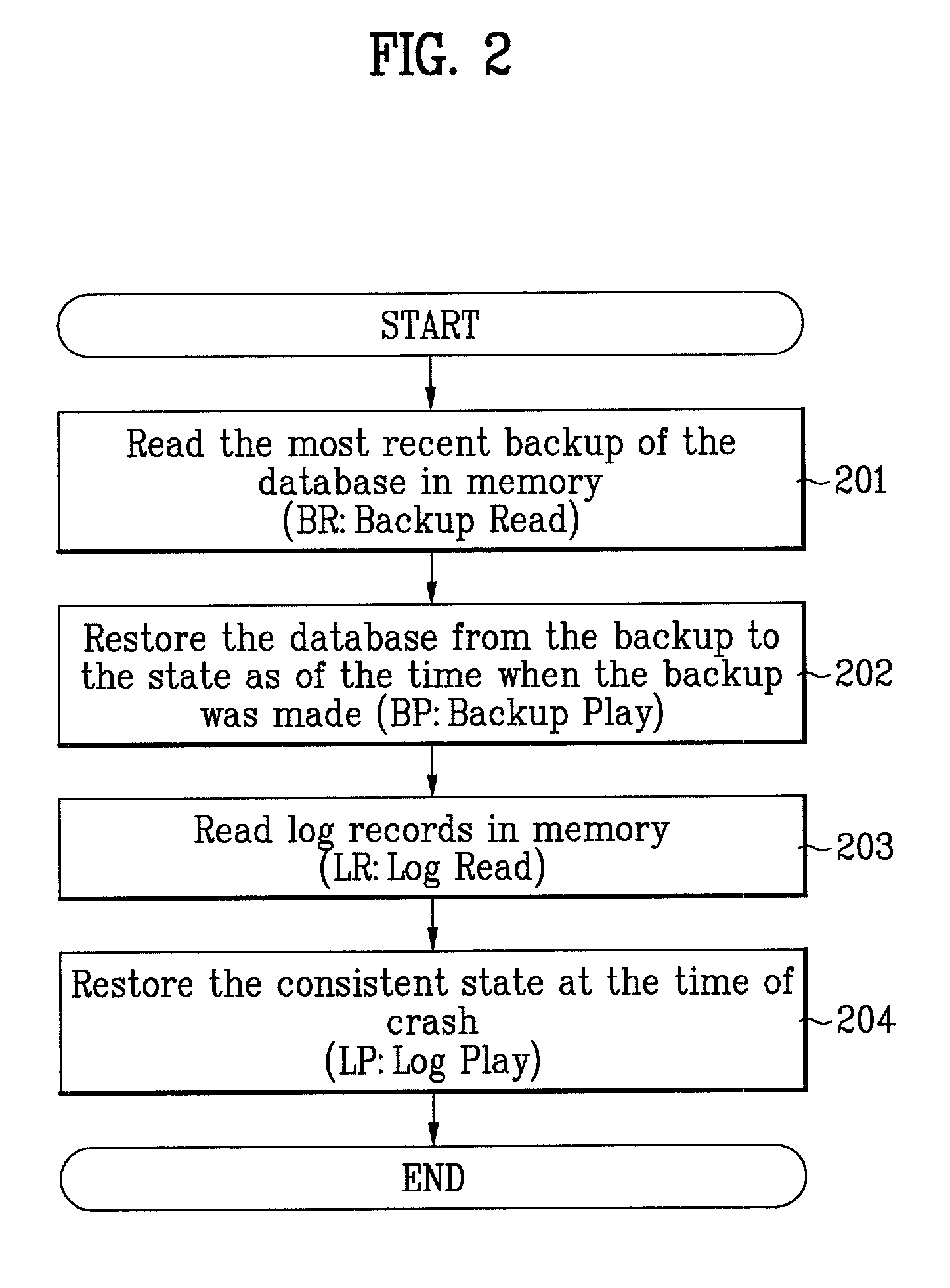
Method and system for highly-parallel logging and recovery operation in main-memory transaction processing systems
InactiveUS7065537B2Data processing applicationsDigital data processing detailsExclusive orTransaction processing system
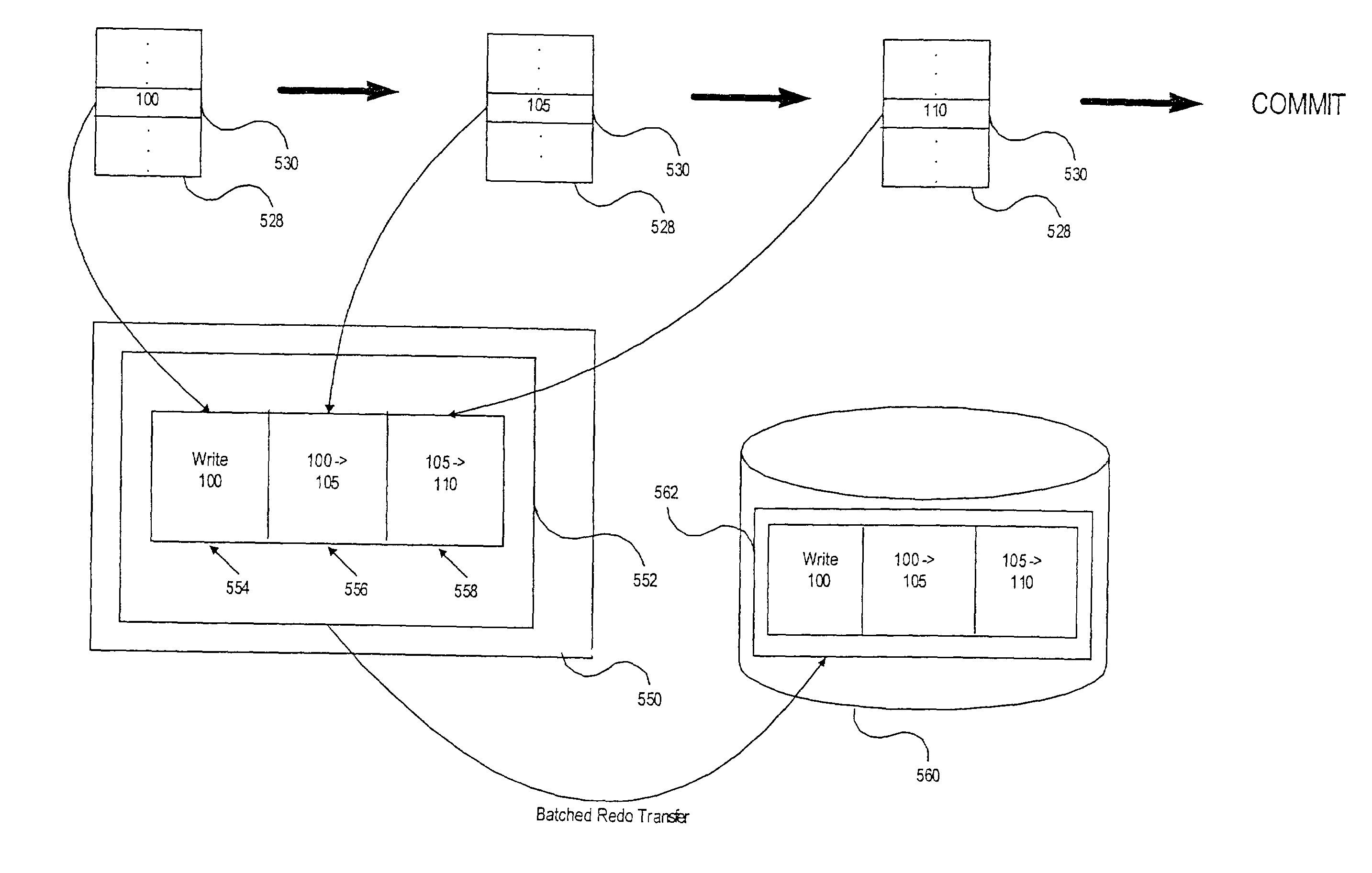
An efficient logging method and system is disclosed that can be used to recover from a failure in a transaction system. It is based on a differential logging scheme that allows commutative and associative recovery operations. The method includes the steps of taking a before-image of the primary database in main memory before an update to the primary database; taking an after-image of the primary database after the update; generating a differential log by applying bit-wise exclusive-OR (XOR) between the before-image and the after-image; and performing either a redo or undo operation by applying XOR between said one or more logs and the before-image. Since XOR operations are commutative and associative, correct recovery is possible regardless of the creation sequence of log records. The present invention improves the performance of a logging system by reducing the size of log records and by allowing parallel execution of recovery operations.
Owner:TRANSACT & MEMORY
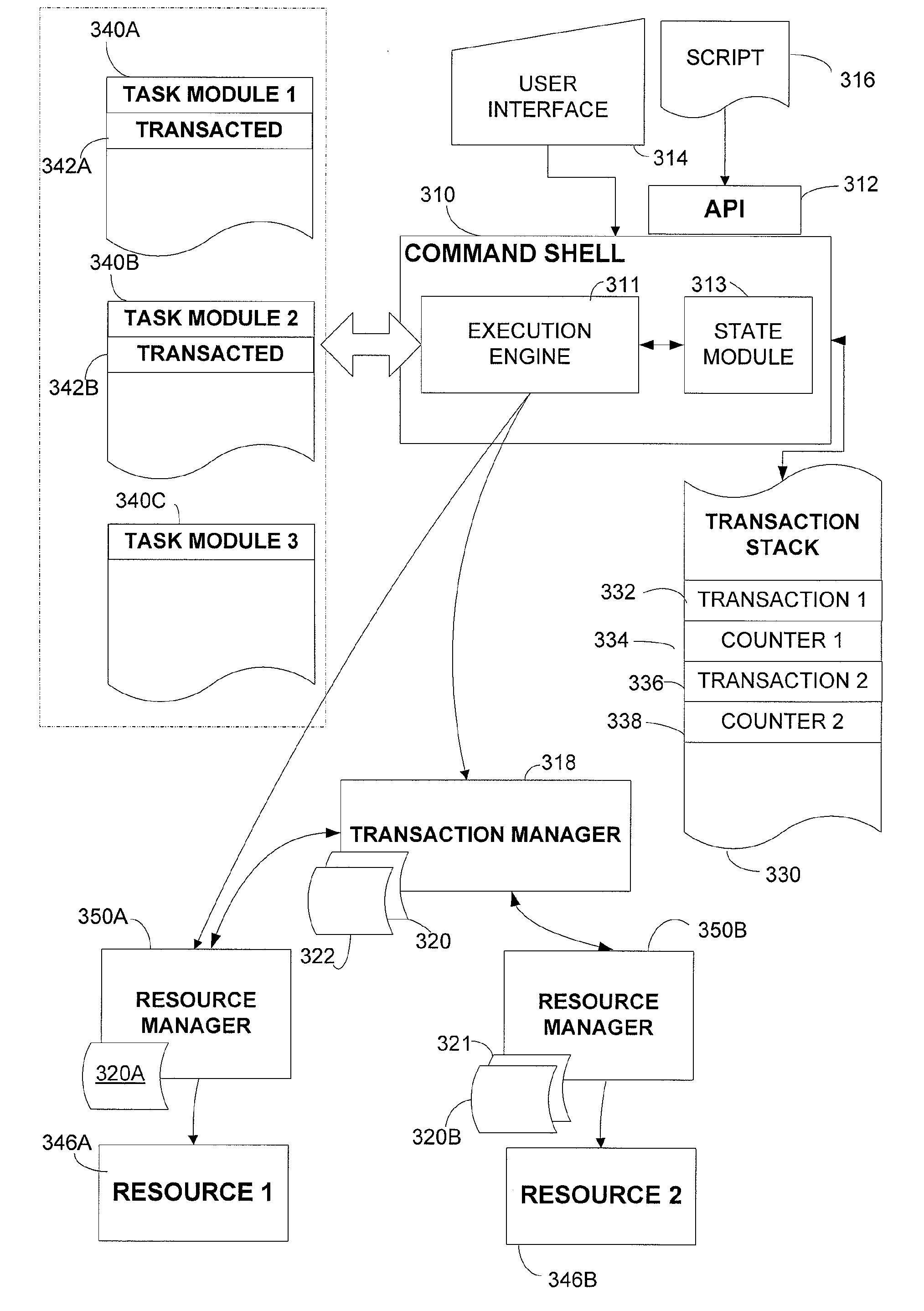
Command line transactions
InactiveUS20090260011A1Maximum flexibilityMemory systemsTransaction processingResource managementTransaction processing
A computer system with a command shell that supports execution of commands within transactions. The command shell responds to commands that start, complete or undo transactions. To support transactions, the command shell may maintain and provide transaction state information. The command shell may interact with a transaction manager that interfaces with resource managers that process transacted instructions within transacted task modules to commit or roll back transacted instructions from those task modules based on transaction state information maintained by the shell. Parameters associated with commands can control behavior in association with transaction process, including supporting nesting transactions and non-nested transactions and bypassing transacted processing in some instances of a command.
Owner:MICROSOFT TECH LICENSING LLC
Multi-level undo of main-memory and volatile resources
ActiveUS7234076B2Error detection/correctionDigital data processing detailsTransaction logManagement system
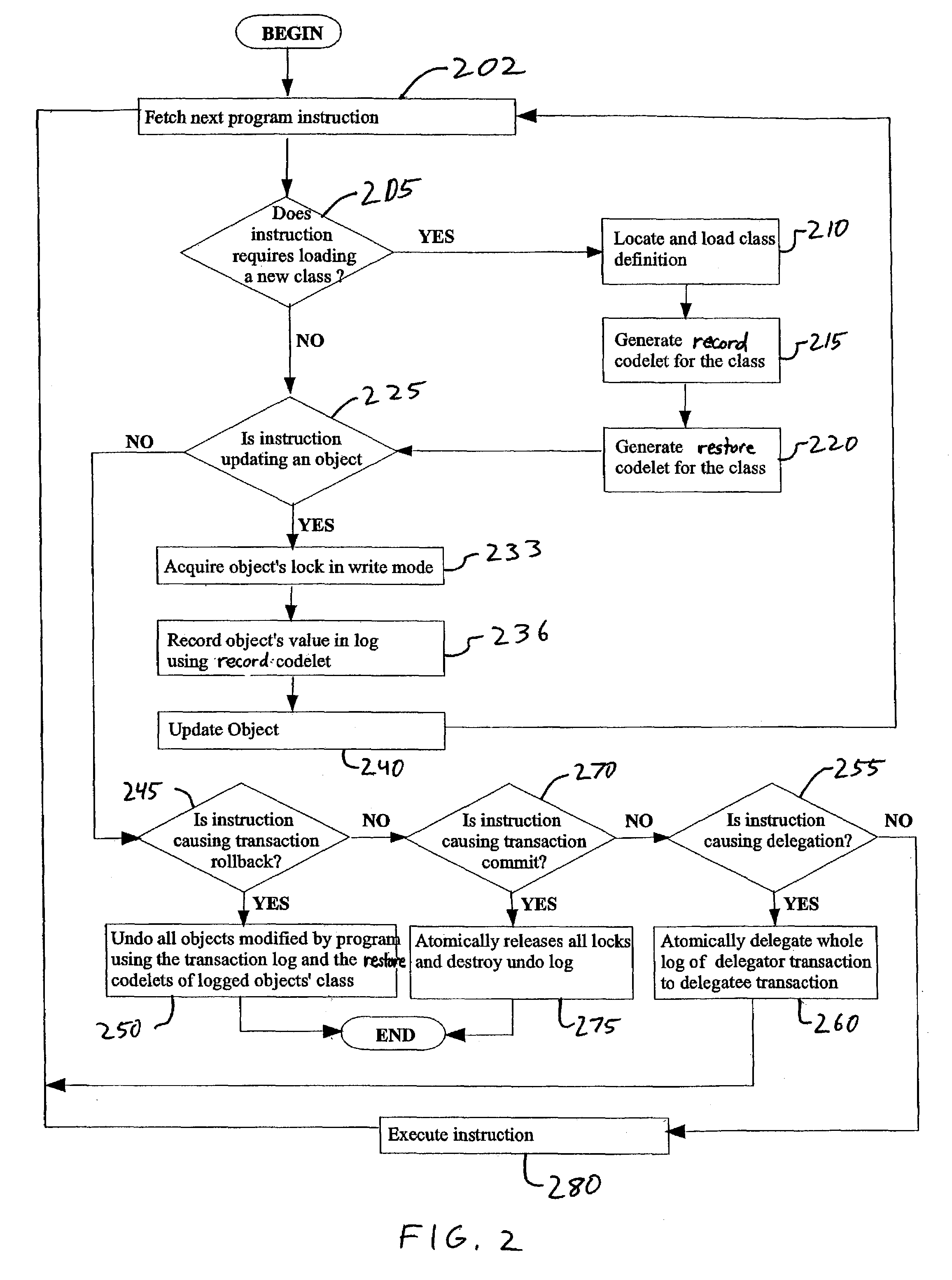
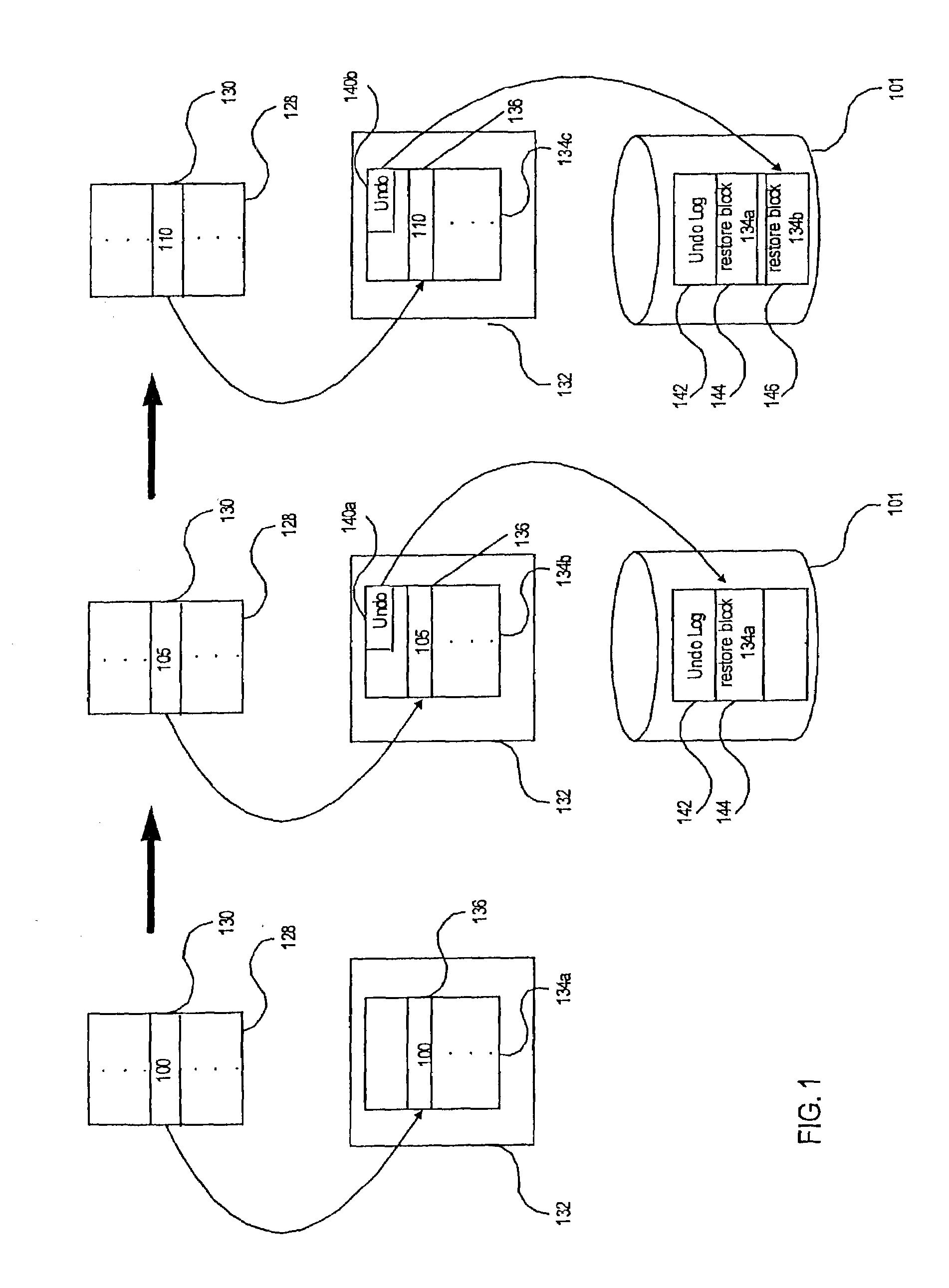
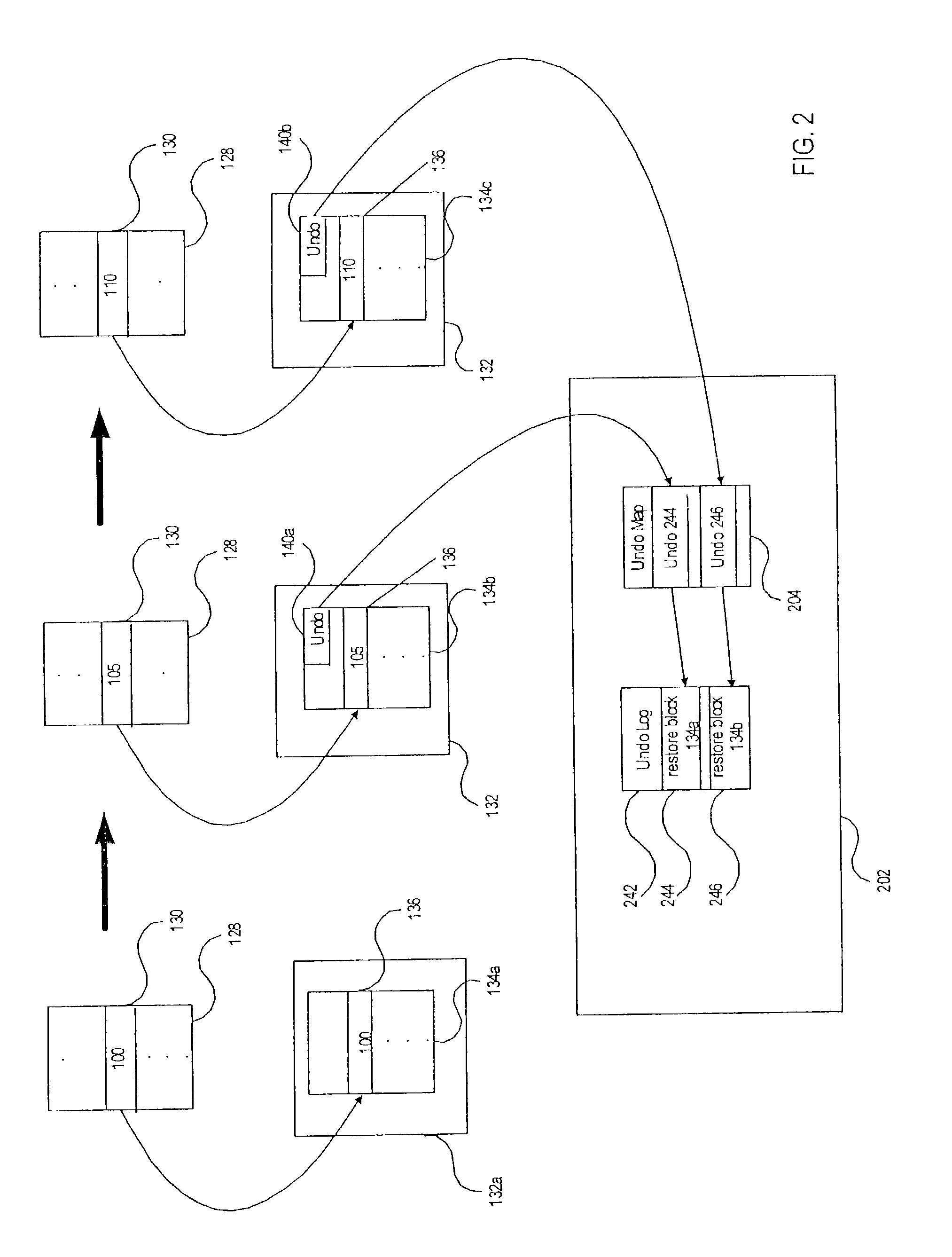
System resources (e.g., objects or other resources) are managed to provide multiple levels of undo and / or support for delegation of updates on main-memory resident objects accessible by concurrent transactions. For example, a log associated with each transaction stores information regarding an update to an object when the object is locked in an update mode (e.g., a write mode) by the transaction. The transaction can be rolled back by restoring information from the log of the transaction to the object. If the transaction commits, then the log may be destroyed. If the transaction delegates to another transaction, the log of the transaction is also delegated. A record codelet can be automatically generated to perform the storing of information in the log, and a restore codelet can be automatically generated to undo updates by restoring information from the log to the updated objects. The codelets may be specific to each class of objects. Lock state information is used to identify undo information age so that the undo information may be stored in the log without regard to order, thereby enhancing the speed of the recording process.
Owner:ORACLE INT CORP
Failure recovery and error correction techniques for data loading in information warehouses
InactiveUS20080307255A1Error detection/correctionSpecial data processing applicationsComputer hardwareCorrection technique
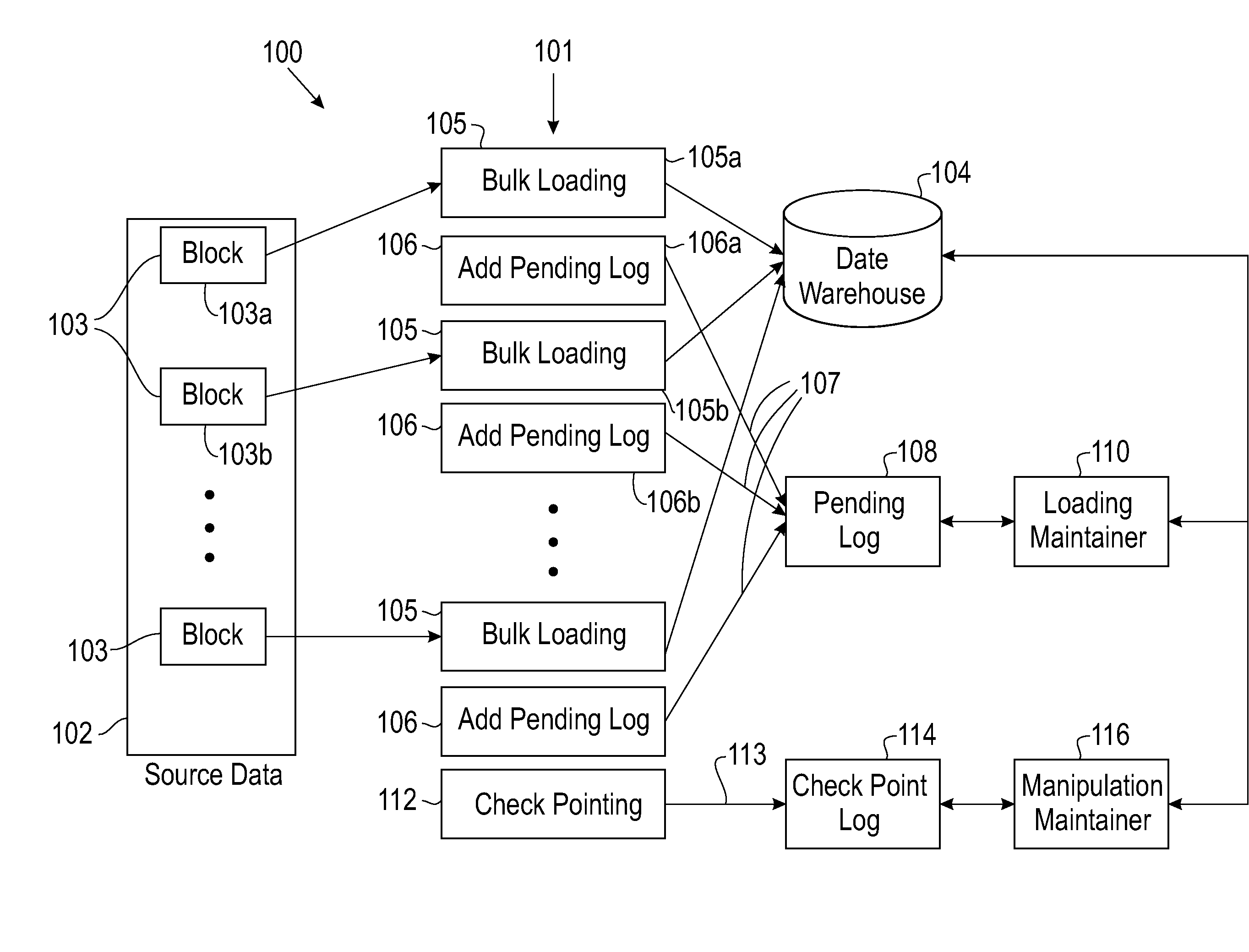
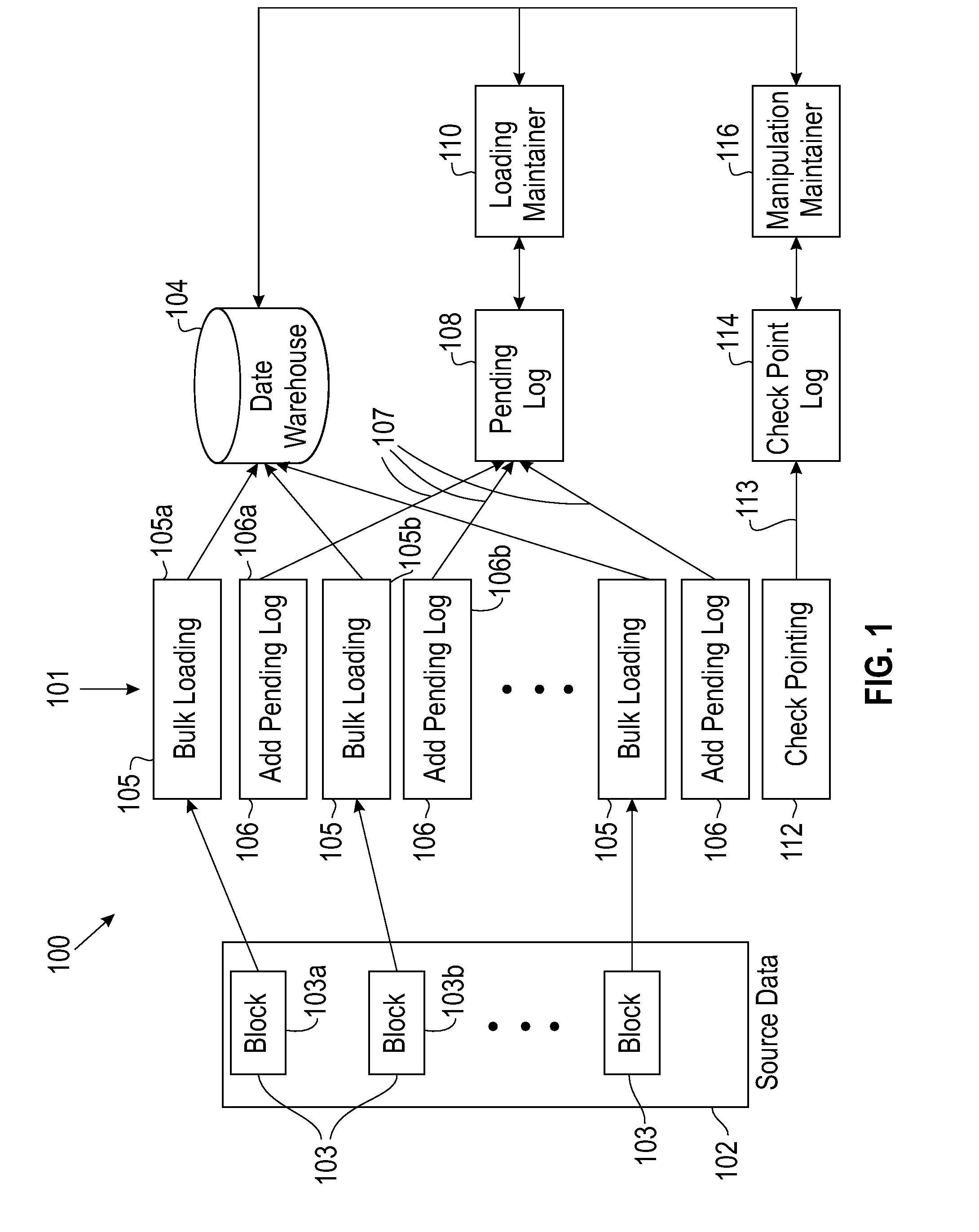
A method of data loading for large information warehouses includes performing checkpointing concurrently with data loading into an information warehouse, the checkpointing ensuring consistency among multiple tables; and recovering from a failure in the data loading using the checkpointing. A method is also disclosed for performing versioning concurrently with data loading into an information warehouse. The versioning method enables processing undo and redo operations of the data loading between a later version and a previous version. Data load failure recovery is performed without starting a data load from the beginning but rather from a latest checkpoint for data loading at an information warehouse level using a checkpoint process characterized by a state transition diagram having a multiplicity of states; and tracking state transitions among the states using a system state table.
Owner:IBM CORP
Dynamic partitioning of a reusable resource
InactiveUS7047386B1Data processing applicationsDigital data information retrievalComputerized systemManaging change
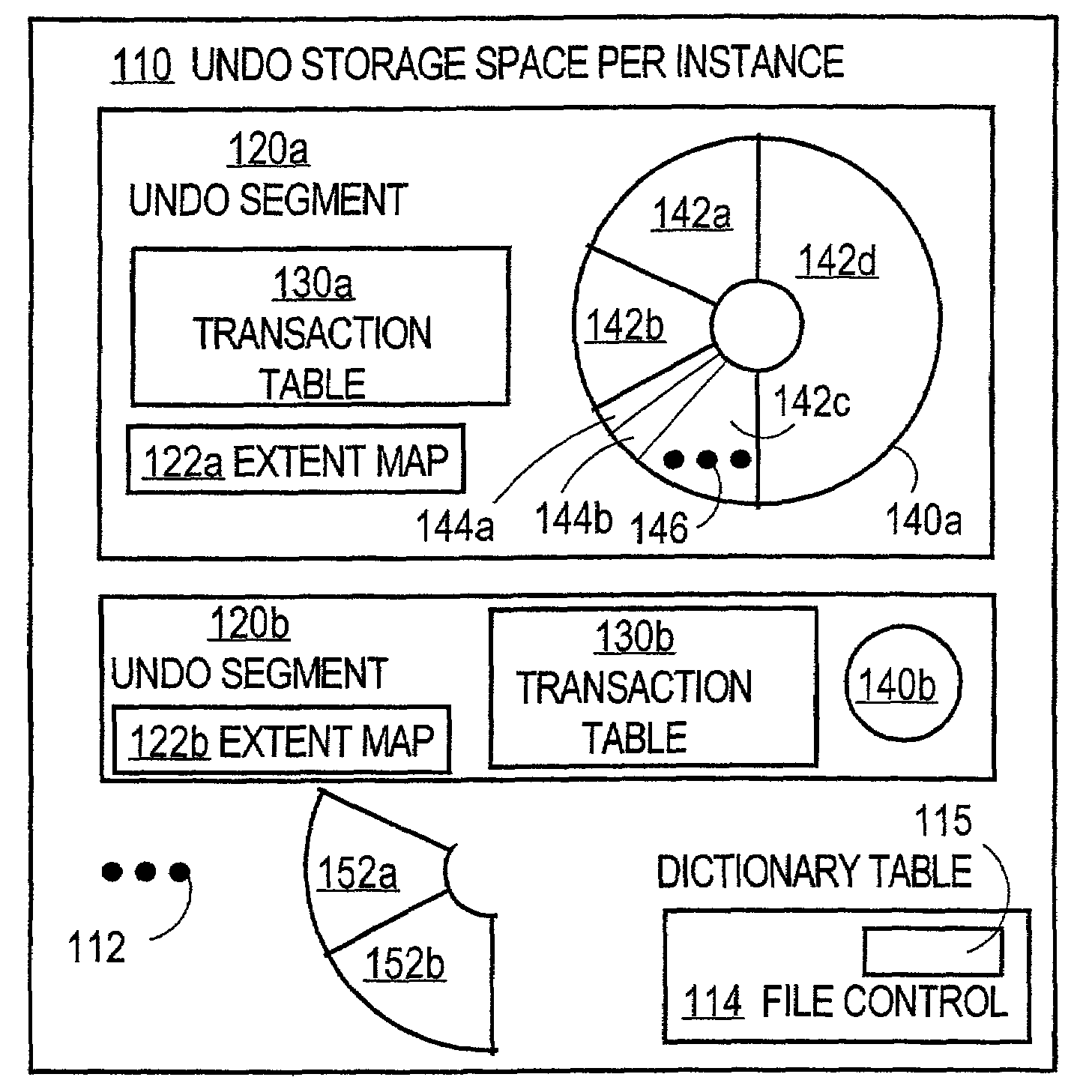
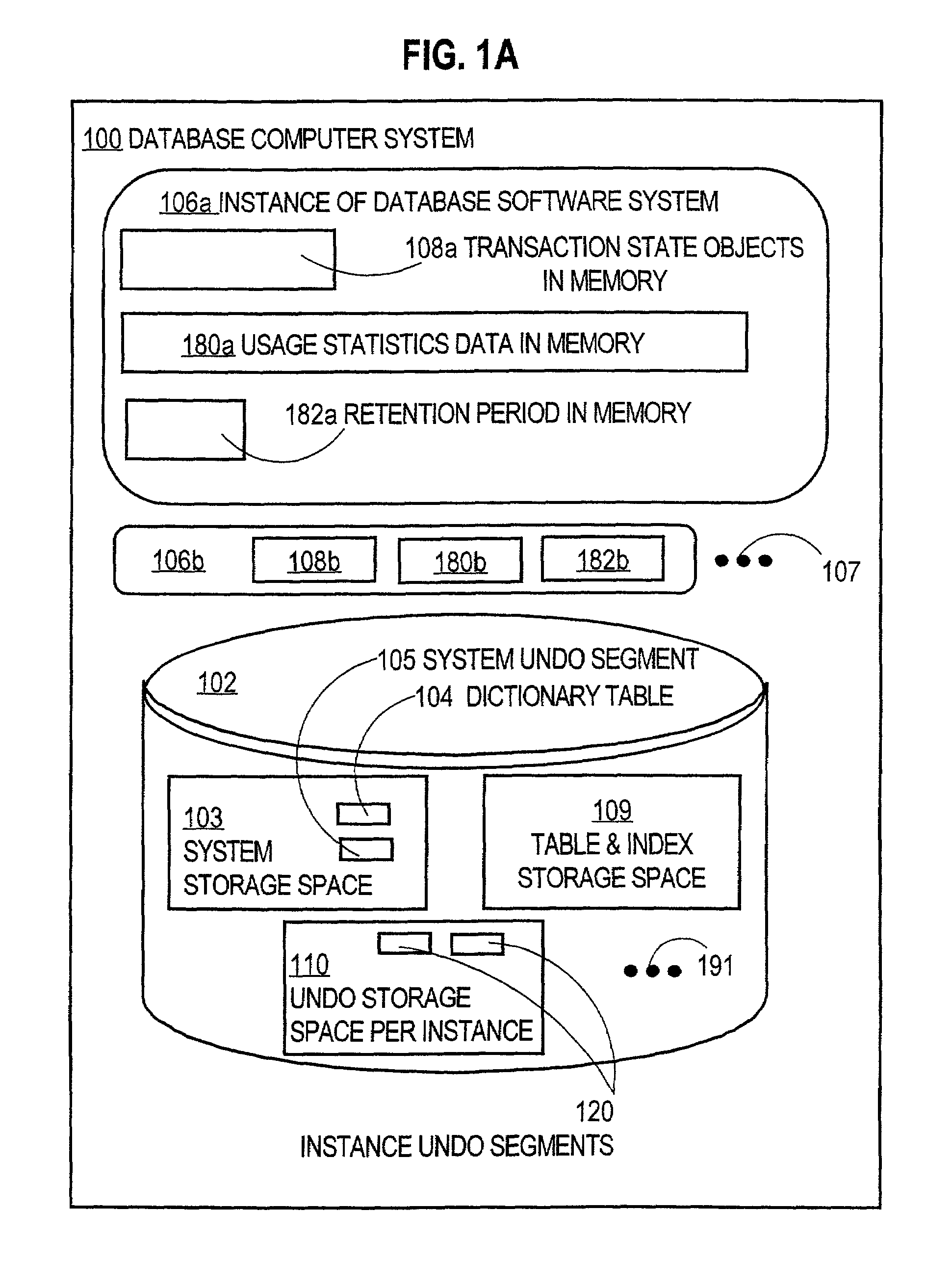
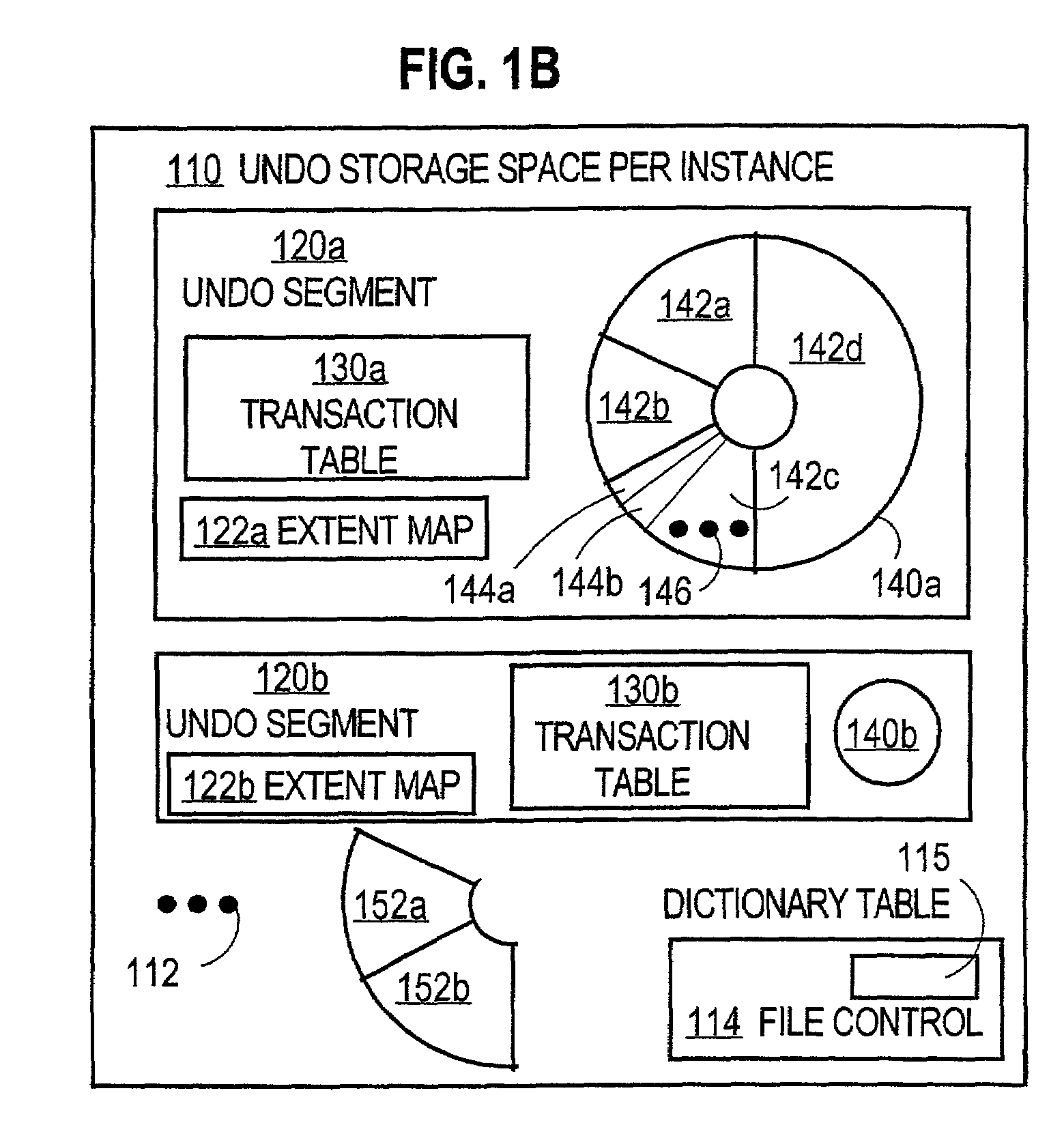
Techniques for managing changes in a computer system include storing, in a storage space, undo information for removing changes that are being made by entities. The undo information for each entity is stored in a segment of multiple segments within the storage space. Usage of the storage space by the entities is monitored. The number of segments in the plurality of segments or the sizes of the plurality of segments or both are adjusted automatically based on the usage. These techniques allow a resource to be recycled and allocated for new uses by other entities in a computer system dynamically based on usage. These techniques do not burden a human administrator with partitioning the resource and then penalize the administrator and users by generating errors when the partitions do not match usage.
Owner:ORACLE INT CORP
Keyboard with improved function and editing sections
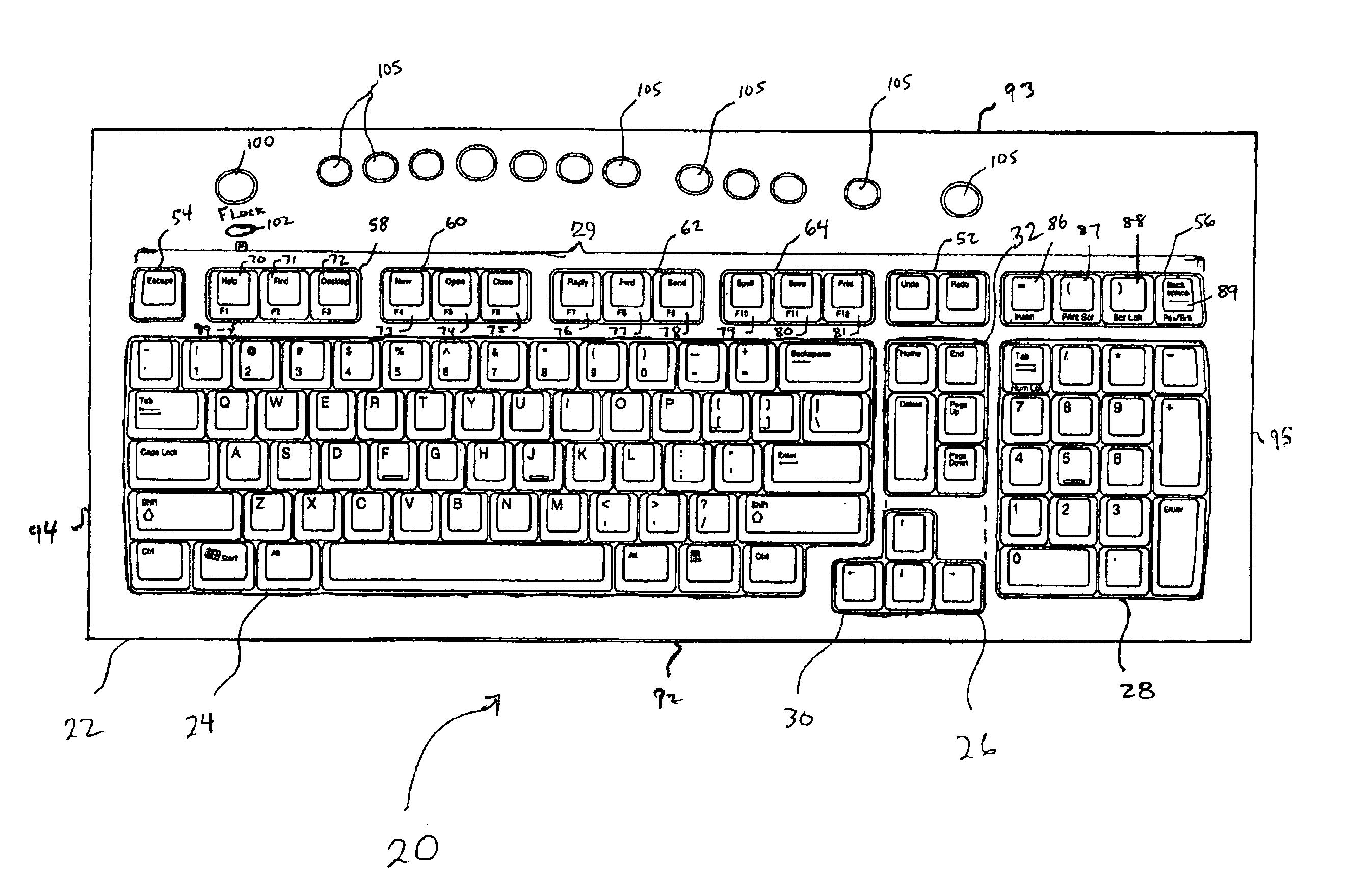
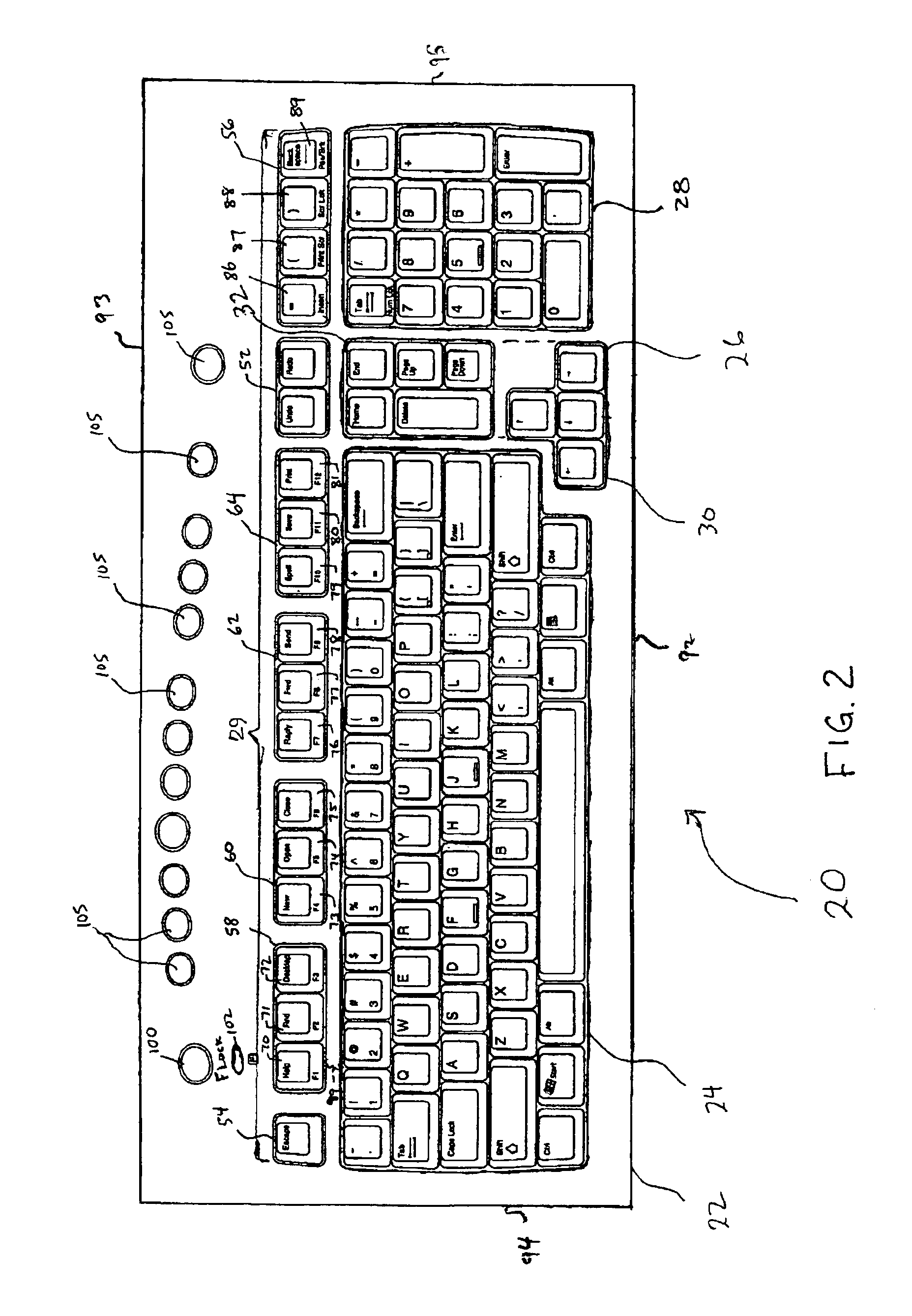
InactiveUS6910818B2Input/output for user-computer interactionCathode-ray tube indicatorsGraphicsGraphical tools
A keyboard having an improved function key section and an improved editing section. A row of keys is located behind the alphanumeric section. The row of keys includes individual predefined command keys. The groupings of the predefined command keys may be made based on the functionality of the keys, their use on common applications or programs, and / or other by other grouping techniques. Further, the keys within each group may be ordered based on chronological order of use, frequency of use, or by a correlation to a graphical toolbar. Each of at least two adjacent groupings of keys behind the alphanumeric region consists of exactly three keys, and each of at least three adjacent key groupings in the entire row consists of exactly three keys. The keys are each capable of functioning as predetermined command keys in a first mode and standard function keys in a second mode. A Function Lock key may be used to convert these keys from their use in one mode as their predefined command keys to another mode where they become standard function keys. These keys are preferably primarily labeled as their command keys and secondarily labeled as standard function keys. The editing section includes a first key cluster having a plurality of keys forming a two dimensional array of cells. At least one key occupies a single cell and a Delete key occupies at least two cells. A key cluster is located behind and spaced from the editing section, and consists of an Undo key and a Redo key.
Owner:MICROSOFT TECH LICENSING LLC
Unified virtual machine and data storage snapshots
ActiveUS9015121B1Digital data information retrievalDigital data processing detailsVirtual machineUndo
The system described herein provides for unifying the streams of I / O, external VM snapshot triggers and VM internal operations into one in connection with providing for snapshotting of both the data storage of a storage system and one or more associated VMs over time. The system described herein thereby allows recording undo and redo journals for all the streams substantially simultaneously. The system described herein unifies snapshots for data storage and all associated VMs in response to one or more triggers. A tag of the unified snapshots may therefore automatically refer to a point-in-time of both the VM and array data.
Owner:EMC IP HLDG CO LLC
Method and mechanism for implementing in-memory transaction logging records
ActiveUS6981004B2Data processing applicationsSpecial data processing applicationsTransaction logDatabase
Owner:ORACLE INT CORP
Method and apparatus for data recovery using storage based journaling
ActiveUS20060149798A1Digital data processing detailsError detection/correctionSystem maintenanceDatabase
A storage system maintains a journal and a snapshot of one or more data volumes. Two journal entry types are maintained, an AFTER journal entry and a BEFORE journal entry. Two modes of data recovery are provided: “fast” recovery and “undo-able” recovery. A combination of both recovery modes allows the user to quickly recover a targeted data state.
Owner:HITACHI LTD
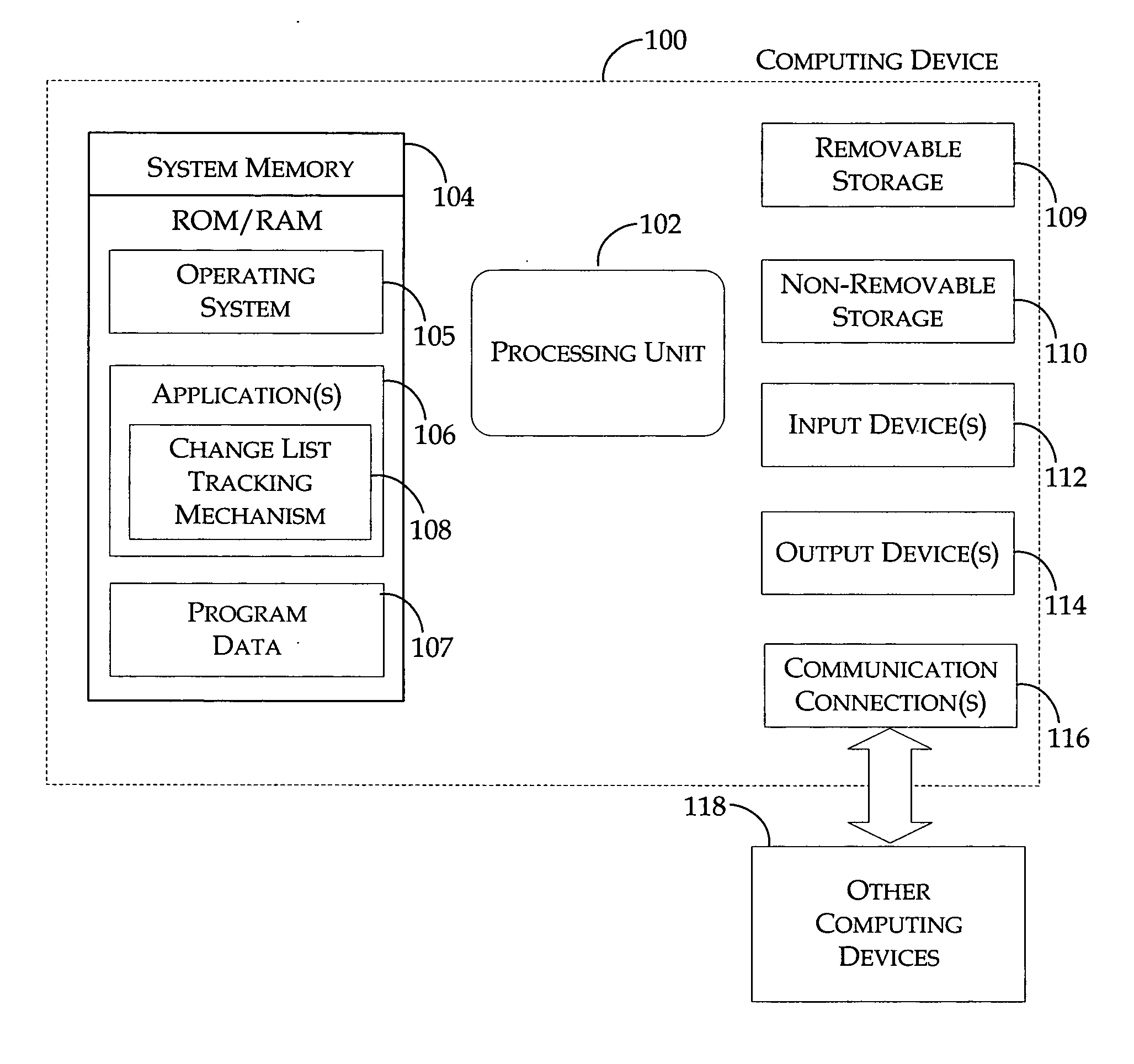
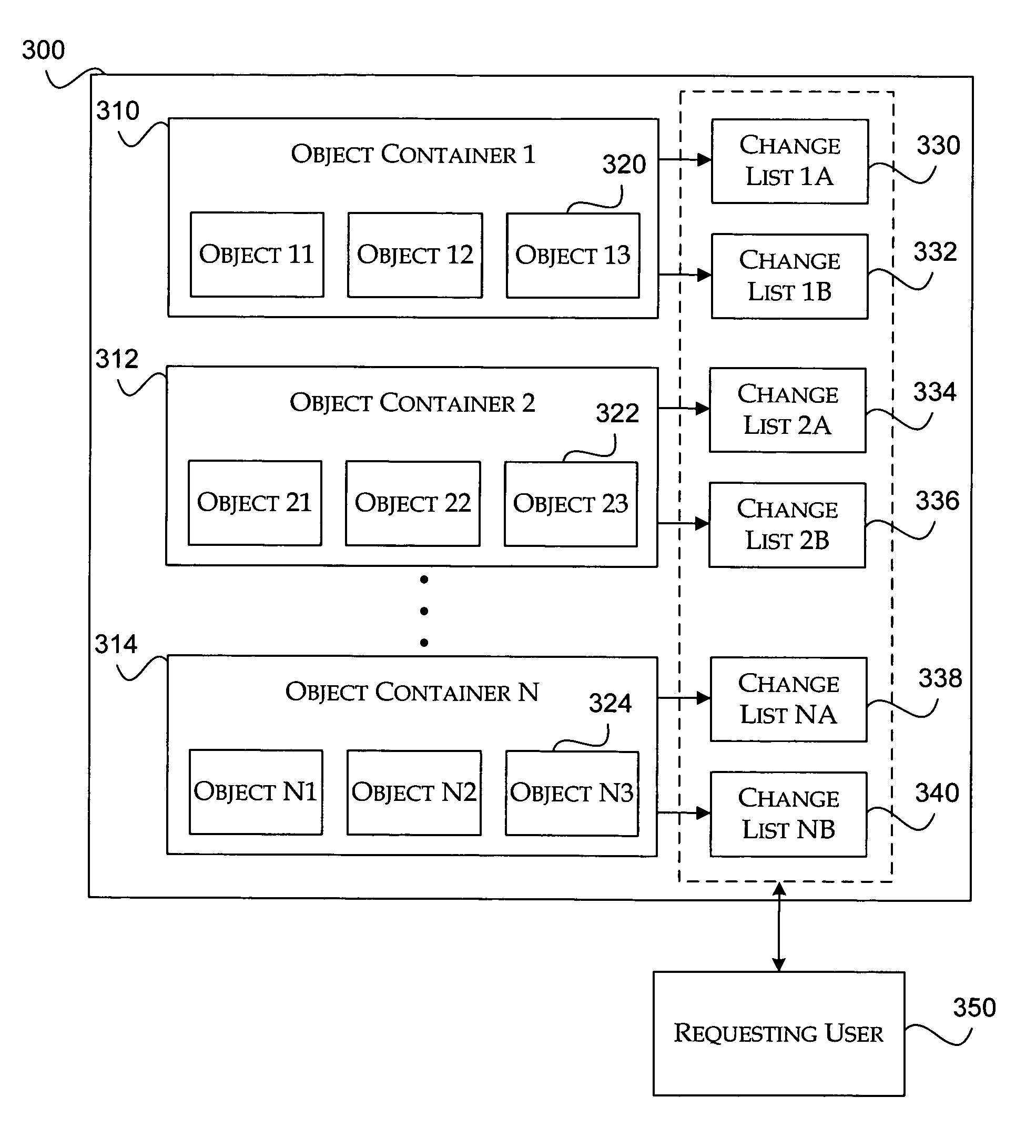
Method and system for tracking changes in a document
InactiveUS20060136510A1Digital data processing detailsNatural language data processingProperty valueApplication software
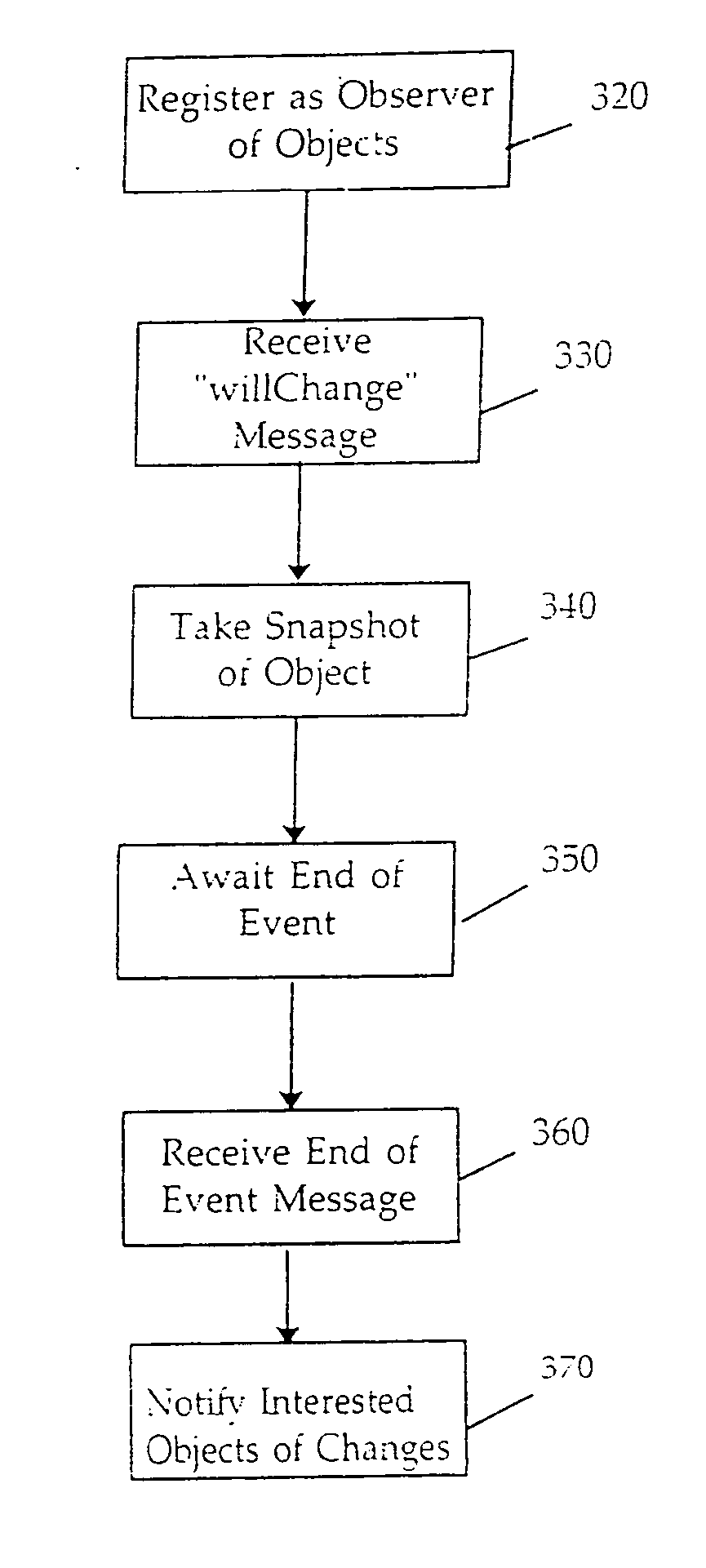
A change list tracking mechanism supports features that require a record of values that have been modified in a document of a project management software application. Examples of the features supported include multiple undo, report generation, and audit logging. The change list tracking mechanism includes object containers and change lists. Each object container includes objects that are associated with properties of the document. A user who wants to be notified of specific modifications creates the change list to track modifications made to a specific object property in a particular object container. A property value identified in the change list may be modified by any user that accesses the document. The corresponding object container provides information about the modification to the change list. The user is identified and notified of the modification.
Owner:MICROSOFT TECH LICENSING LLC
Inheritance based network management
ActiveUS20060212924A1Special data processing applicationsSecuring communicationComputer hardwareControl system
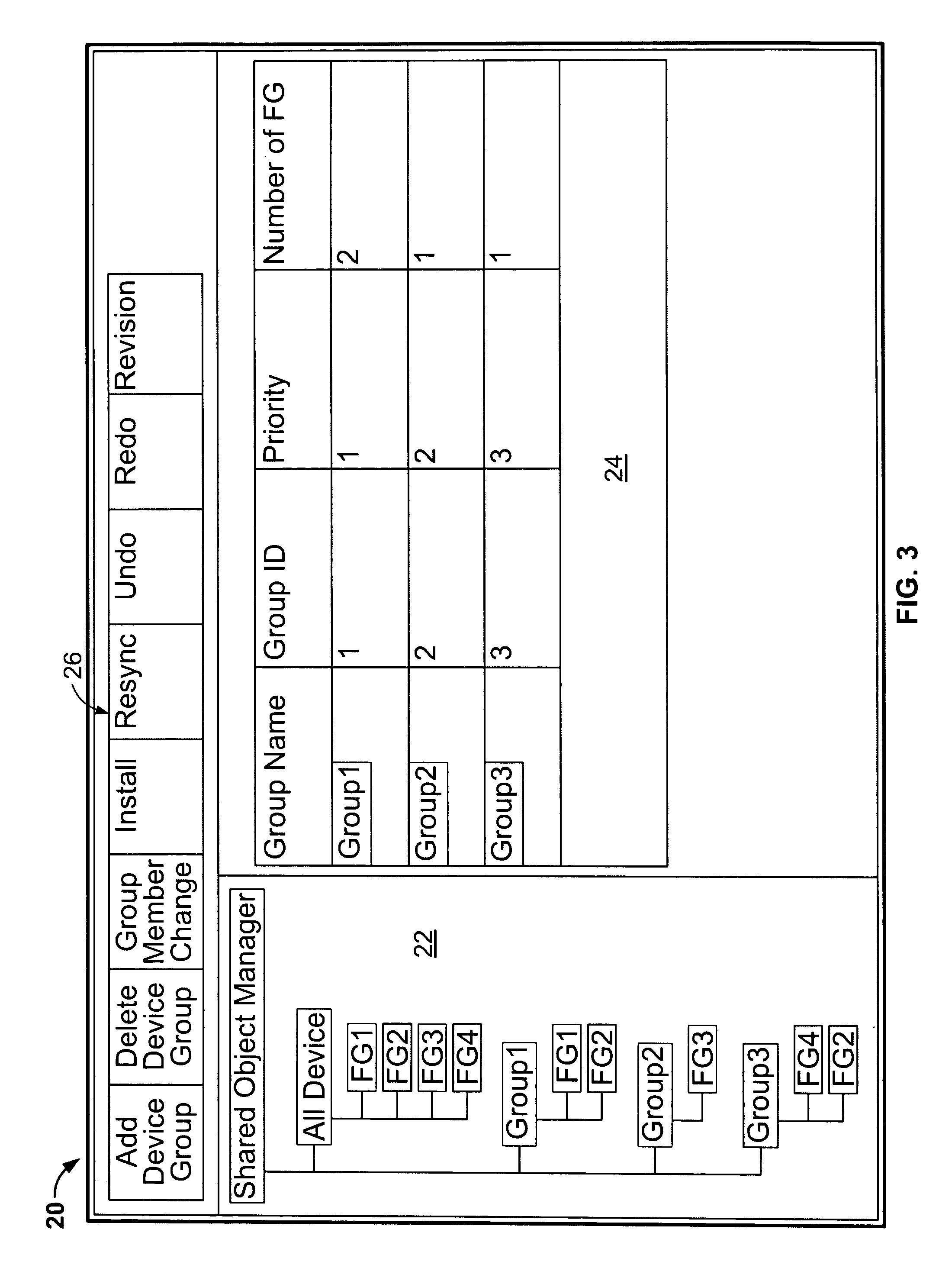
The present invention teaches a methodology for provisioning and managing a network having many network devices. In certain embodiments, groups of member devices are created each having a group policy configuration inherited by member devices. A variety of rules regarding prioritization, versioning, system snapshot, redo and undo are also taught. This embodiment is useful when the network devices can be partitioned into groups of similar type devices for similar applications. Similar physical attributes can also be mappend into identical virtual attributes, enabling policy configurations to be applied to varying devices and physical attribute configurations can be resolved upon device installation.
Owner:FORTINET
Object graph editing context and methods of use
InactiveUS20060271586A1Data processing applicationsDigital data processing detailsGraphicsManaging change
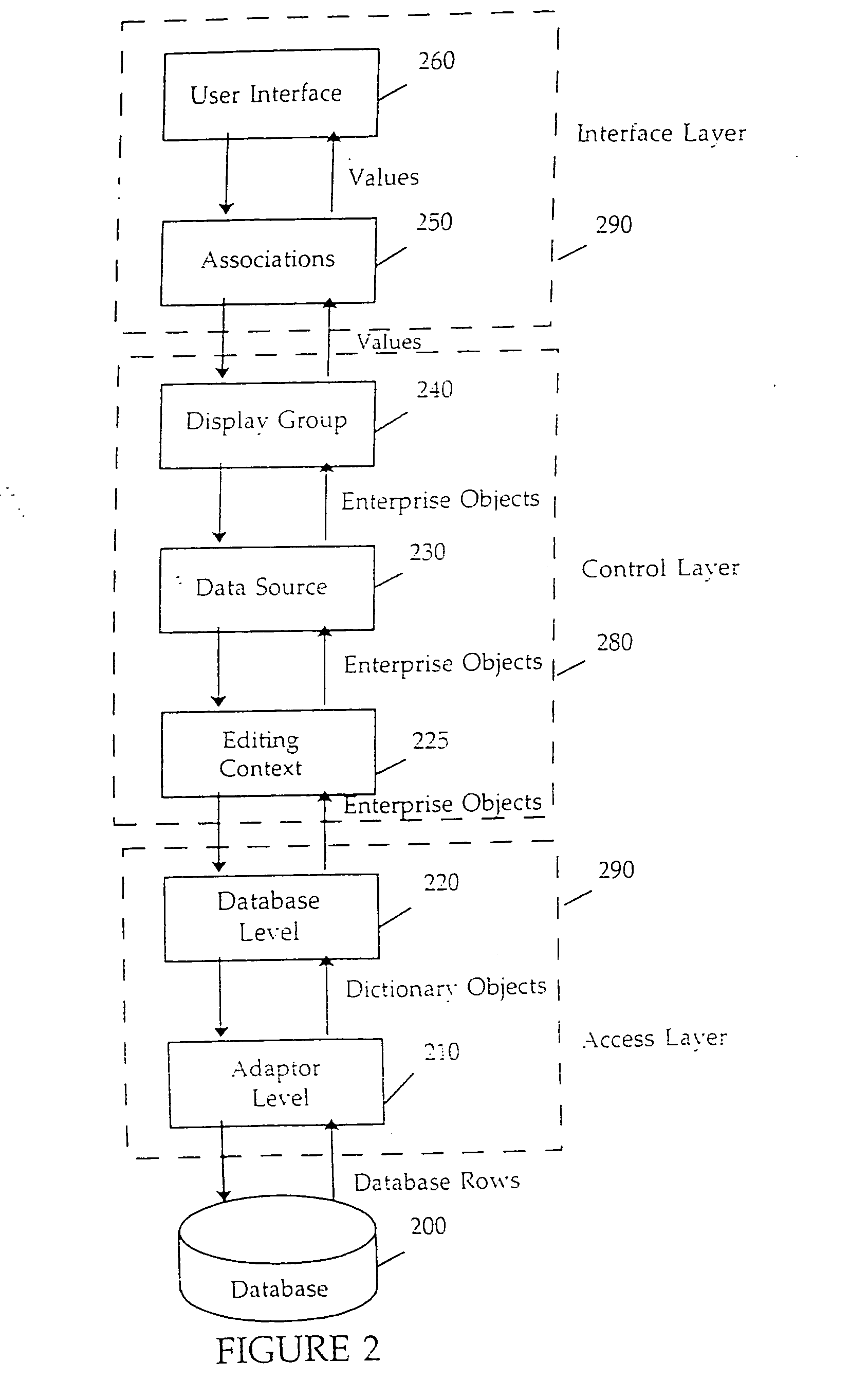
The present invention comprises a novel system for managing changes to a graph of data bearing objects. In one embodiment, an object graph manager object referred to as an editing context is used to identify changes made to data bearing enterprise objects and to notify other interested objects when changes occur. As a result, data bearing objects need not themselves contain code necessary for monitoring changes. In another embodiment of the invention, the editing context is used to provide event-based “undo” capabilities. In another embodiment of the invention, each enterprise object has a primary key that is used to maintain the identification between an enterprise object instance and a corresponding database row. In another embodiment of the invention, multiple levels of editing contexts are used to provide multiple isolated object graphs, each of which allows independent manipulation of the underlying data bearing objects.
Owner:NEXT
Method and system for tracking changes in a document
InactiveUS7788237B2Digital data processing detailsNatural language data processingProperty valueApplication software
A change list tracking mechanism supports features that require a record of values that have been modified in a document of a project management software application. Examples of the features supported include multiple undo, report generation, and audit logging. The change list tracking mechanism includes object containers and change lists. Each object container includes objects that are associated with properties of the document. A user who wants to be notified of specific modifications creates the change list to track modifications made to a specific object property in a particular object container. A property value identified in the change list may be modified by any user that accesses the document. The corresponding object container provides information about the modification to the change list. The user is identified and notified of the modification.
Owner:MICROSOFT TECH LICENSING LLC
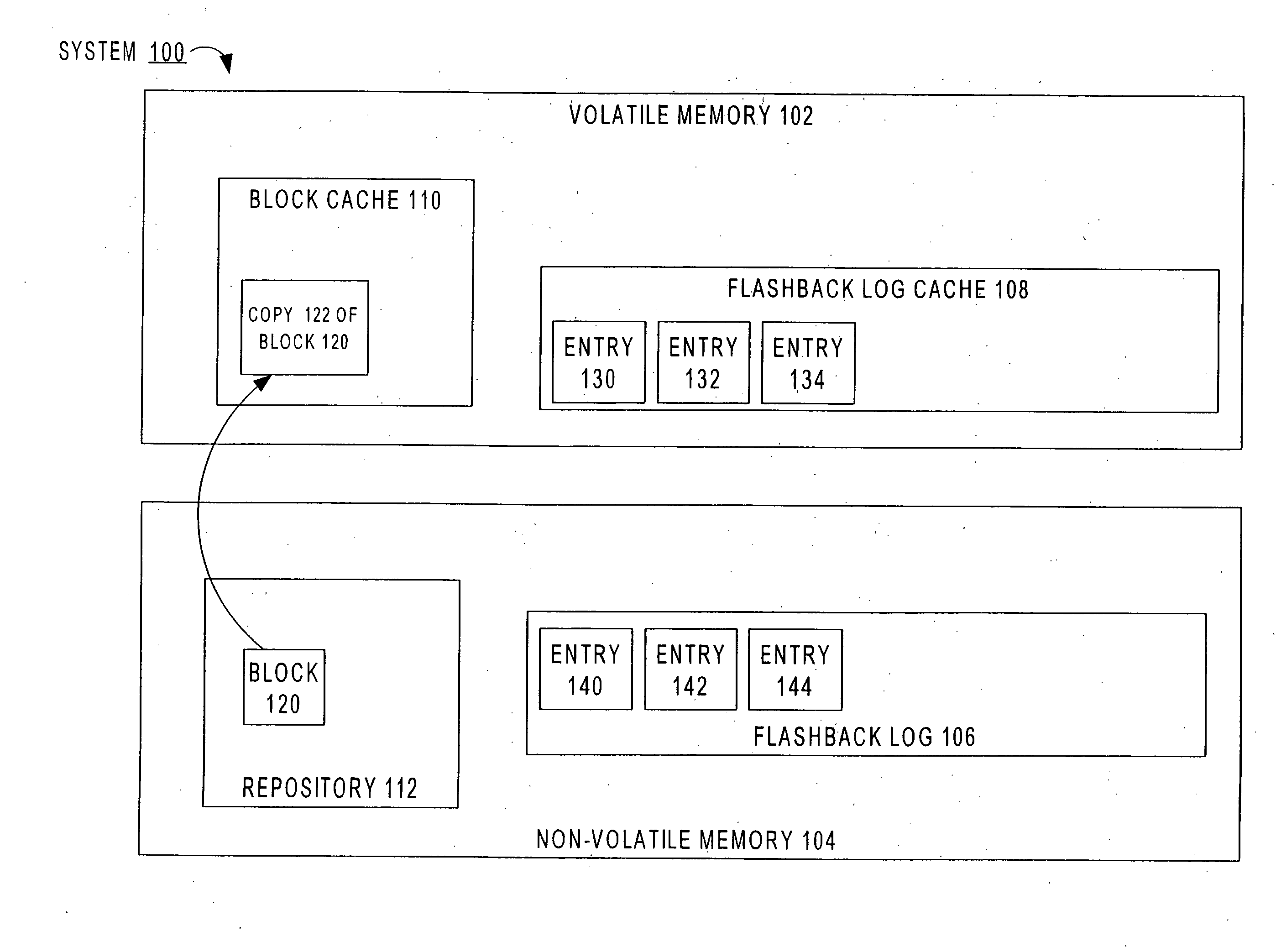
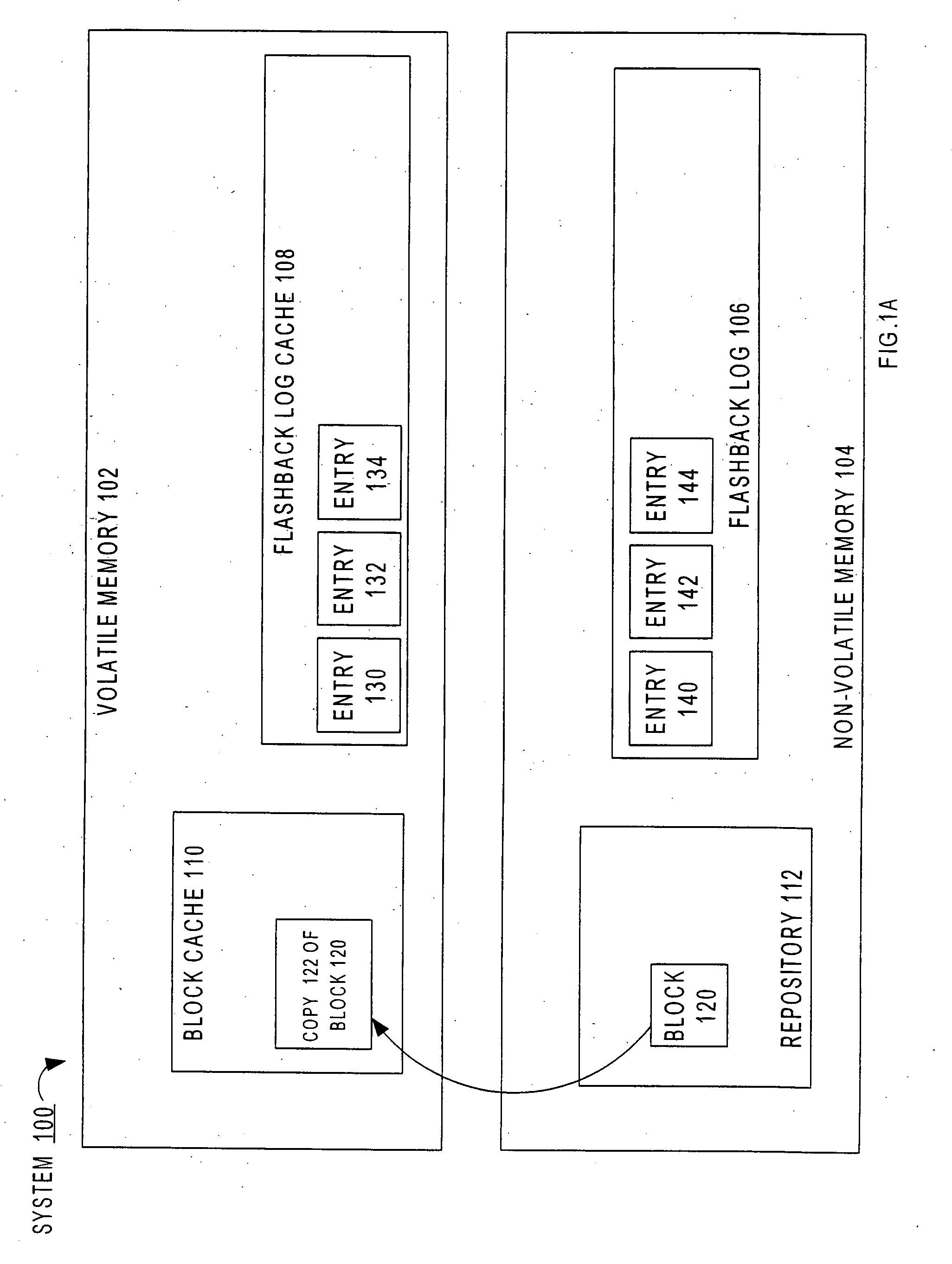
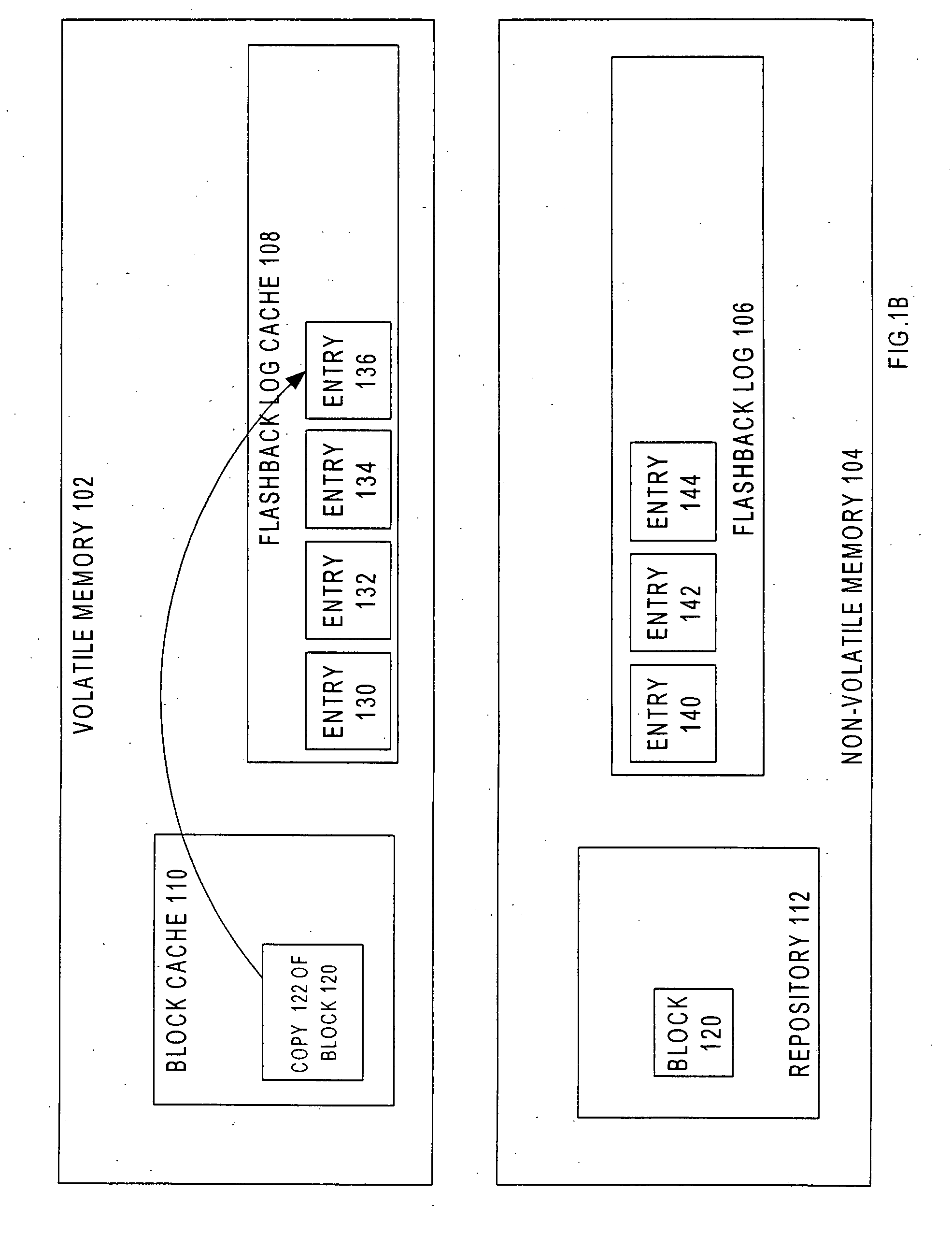
Flashback database
ActiveUS20070244918A1Data processing applicationsRedundant operation error correctionData miningSpecific time
Techniques are described herein for returning a repository to a prior state. The repository may be, for example a database, and the prior state may be, for example the consistent state that the database had at a particular point in time in the past. When a operator-caused error has been introduced to the database by changes made by an already-committed transaction, the techniques described herein may be used to recover from the error by returning the database to a point in time prior to the commit time of the transaction that introduced the error. The techniques involve the generation of “physical undo” information, and the use of the physical undo information in conjunction with physiological undo and physiological redo to efficiently return a repository to the prior state.
Owner:ORACLE INT CORP
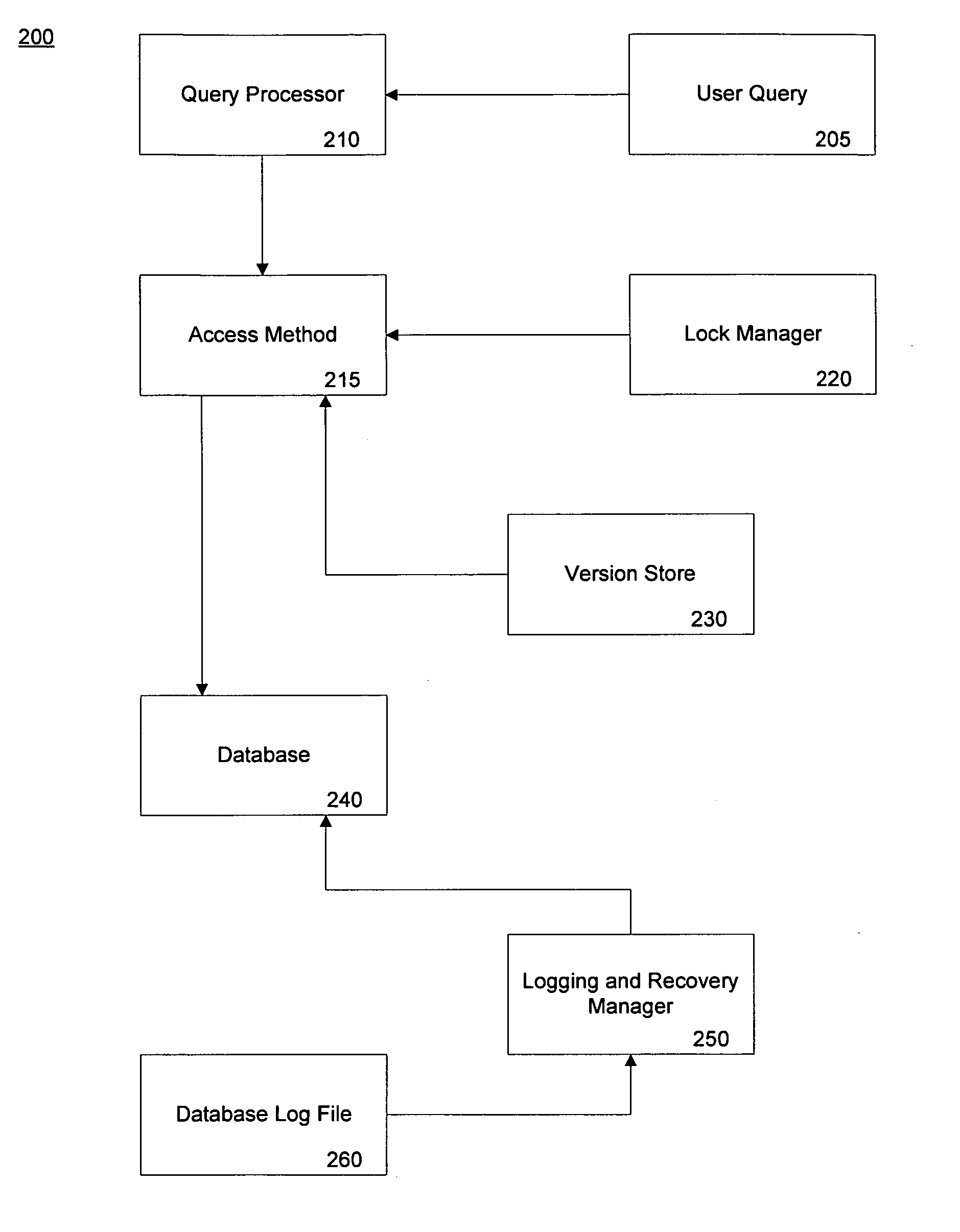
System and method for a snapshot query during database recovery
InactiveUS20050216462A1Data processing applicationsDigital data information retrievalFailoverRollback Operation
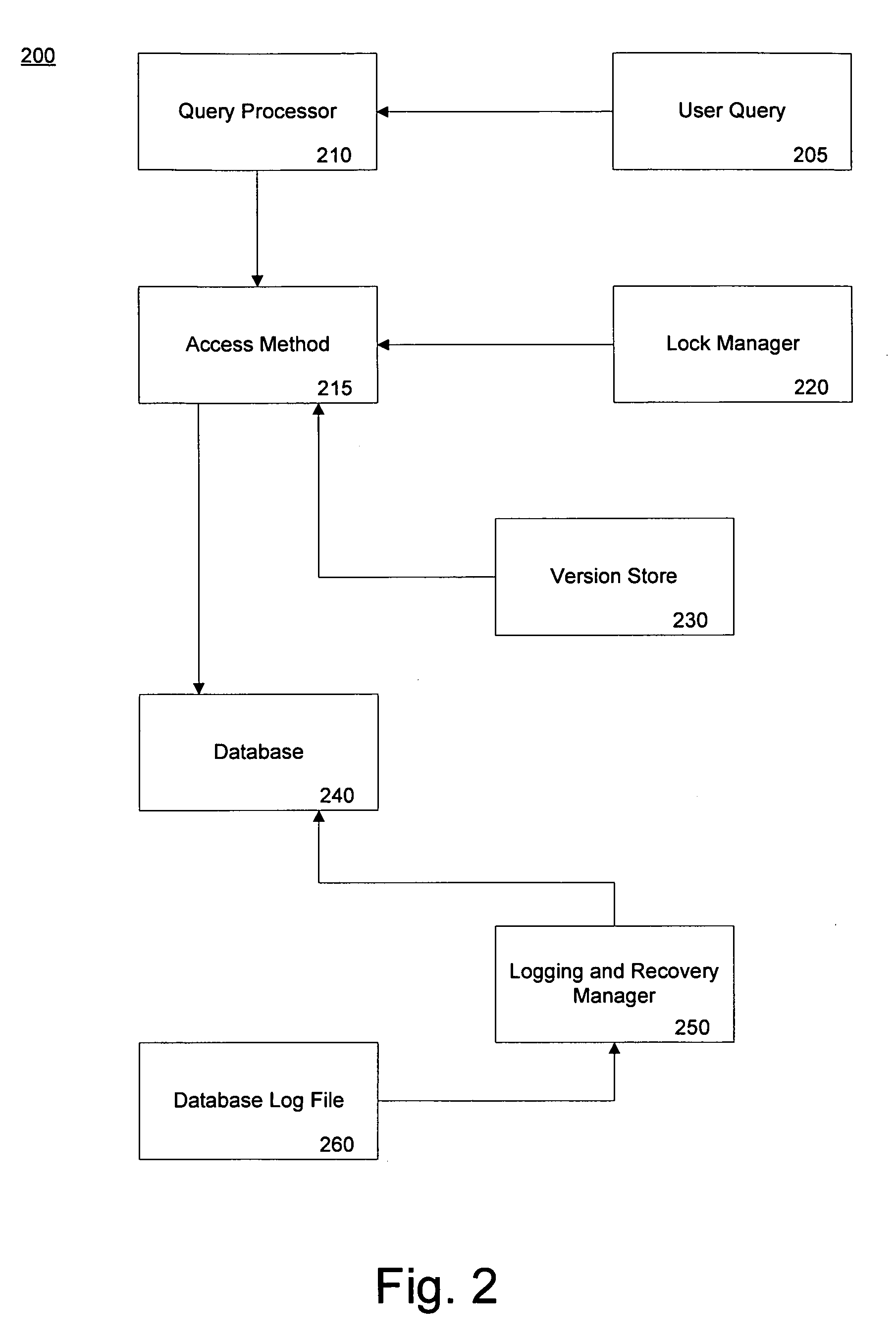
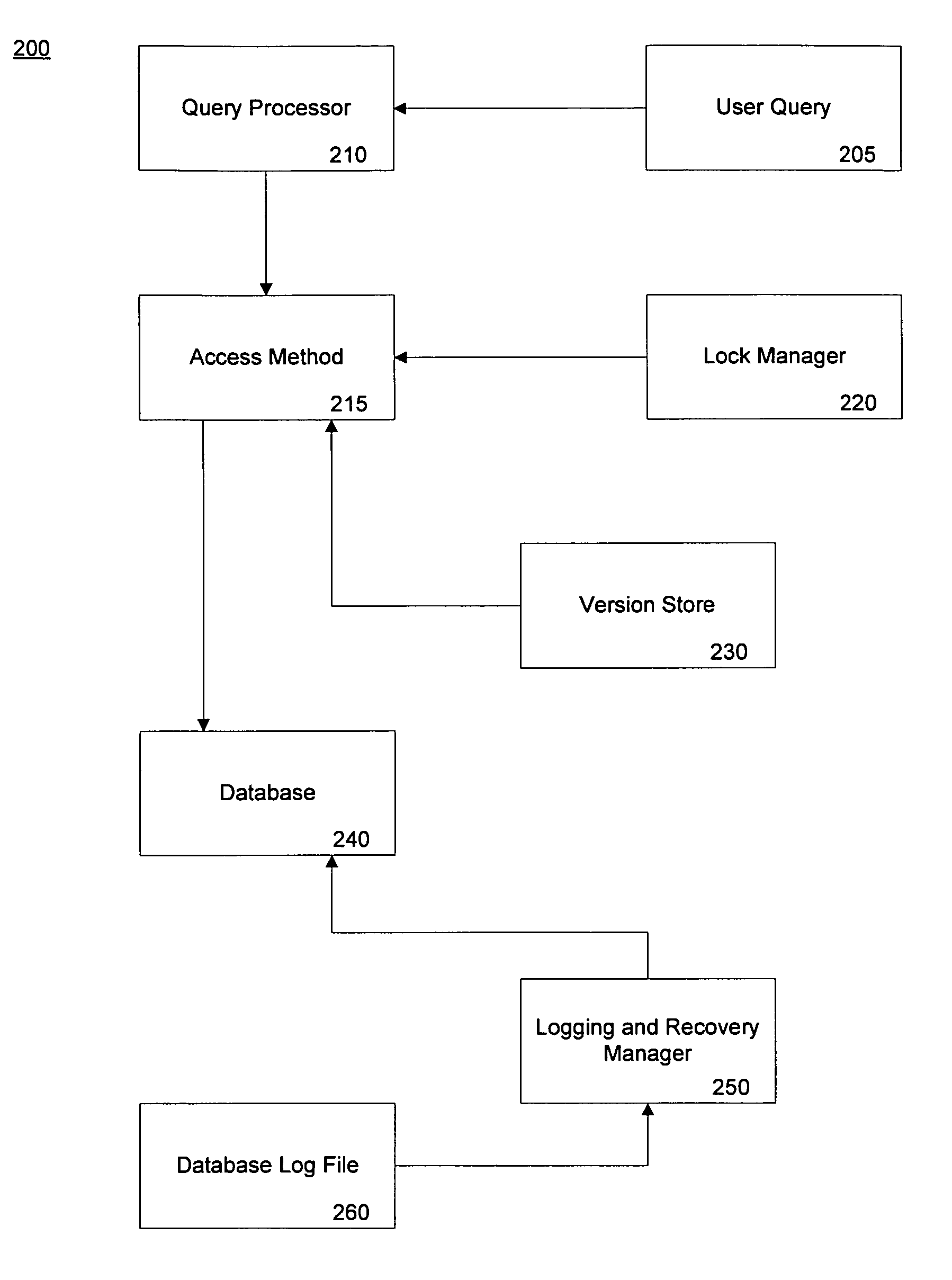
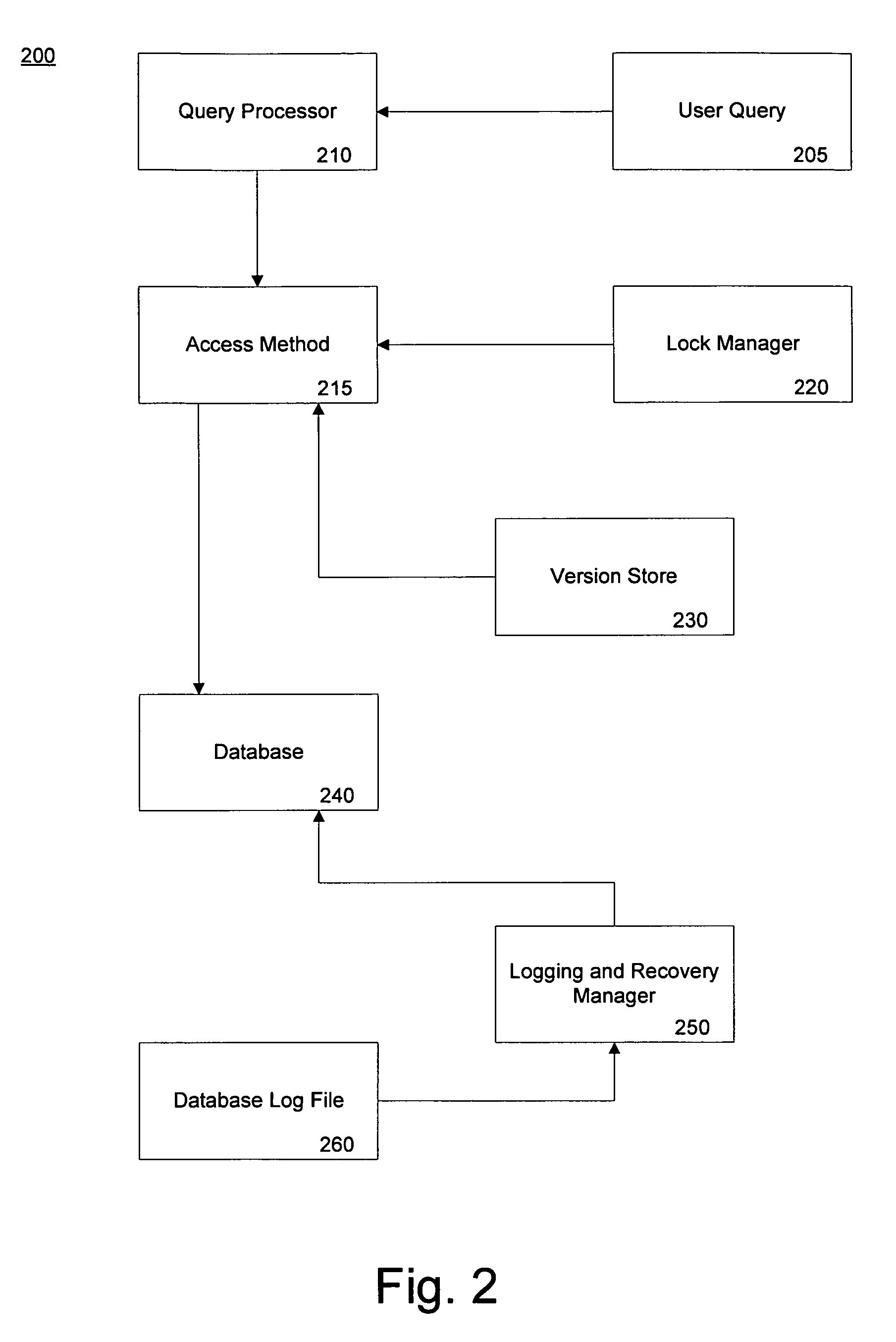
A method of performing a snapshot query in a database undergoing recovery allows access to the database during rollback or undo operations. The method includes allowing the query to detect whether a redo lock is present on a data item and if so, waiting until subsequent rollback operations release the lock. If another user has placed an exclusive lock on a data item of the database, the query may continue by reading a version of the data item form the version store. In an embodiment where a mirror database is used for recovery, the constant redo operations have an associated version store. Upon failover to the mirror database, queries may begin during the undo phase of recovery by allowing a query to read the version store of redo operations.
Owner:MICROSOFT TECH LICENSING LLC
System and method for a snapshot query during database recovery
InactiveUS7146386B2Data processing applicationsDigital data information retrievalFailoverRollback Operation
A method of performing a snapshot query in a database undergoing recovery allows access to the database during rollback or undo operations. The method includes allowing the query to detect whether a redo lock is present on a data item and if so, waiting until subsequent rollback operations release the lock. If another user has placed an exclusive lock on a data item of the database, the query may continue by reading a version of the data item form the version store. In an embodiment where a mirror database is used for recovery, the constant redo operations have an associated version store. Upon failover to the mirror database, queries may begin during the undo phase of recovery by allowing a query to read the version store of redo operations.
Owner:MICROSOFT TECH LICENSING LLC
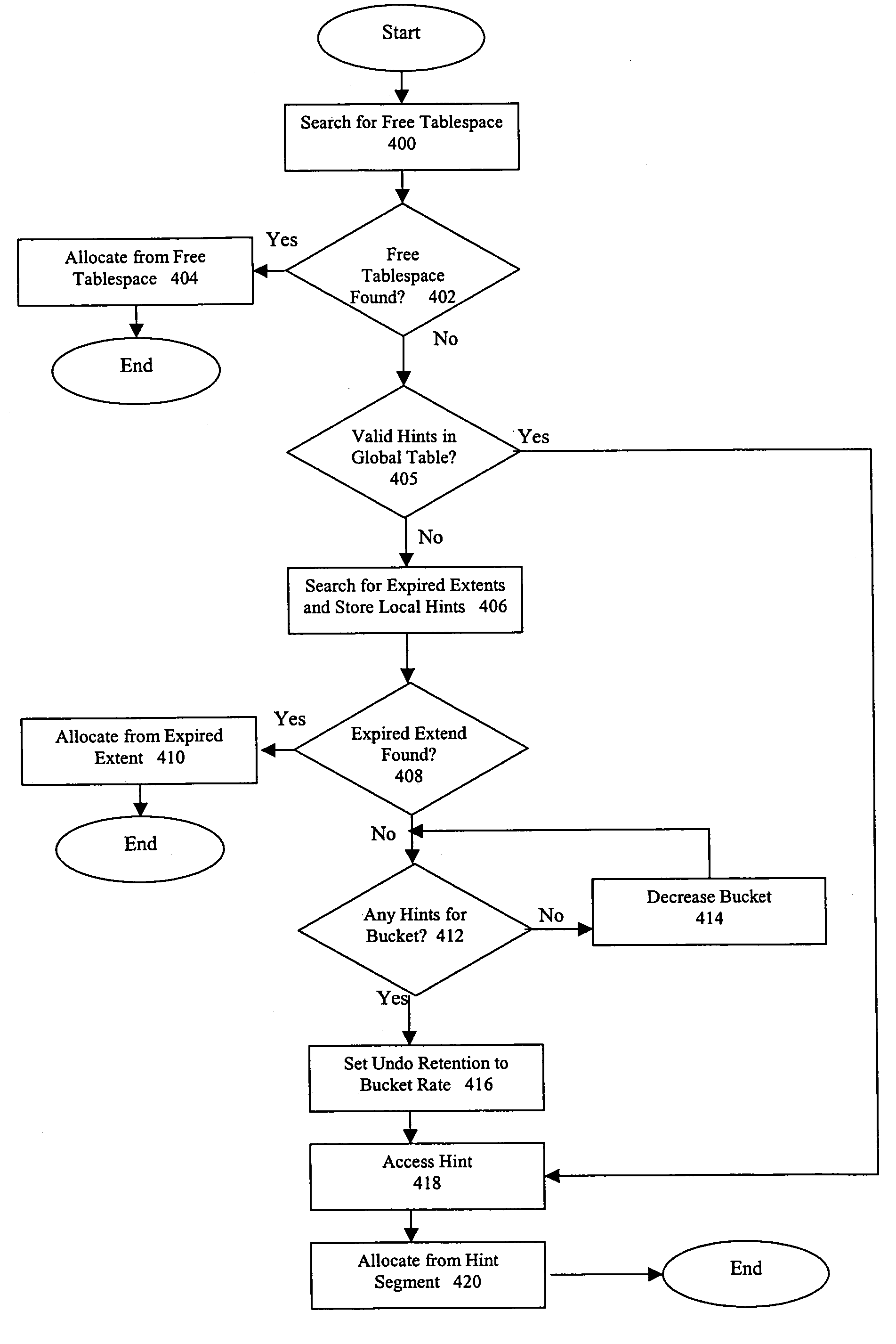
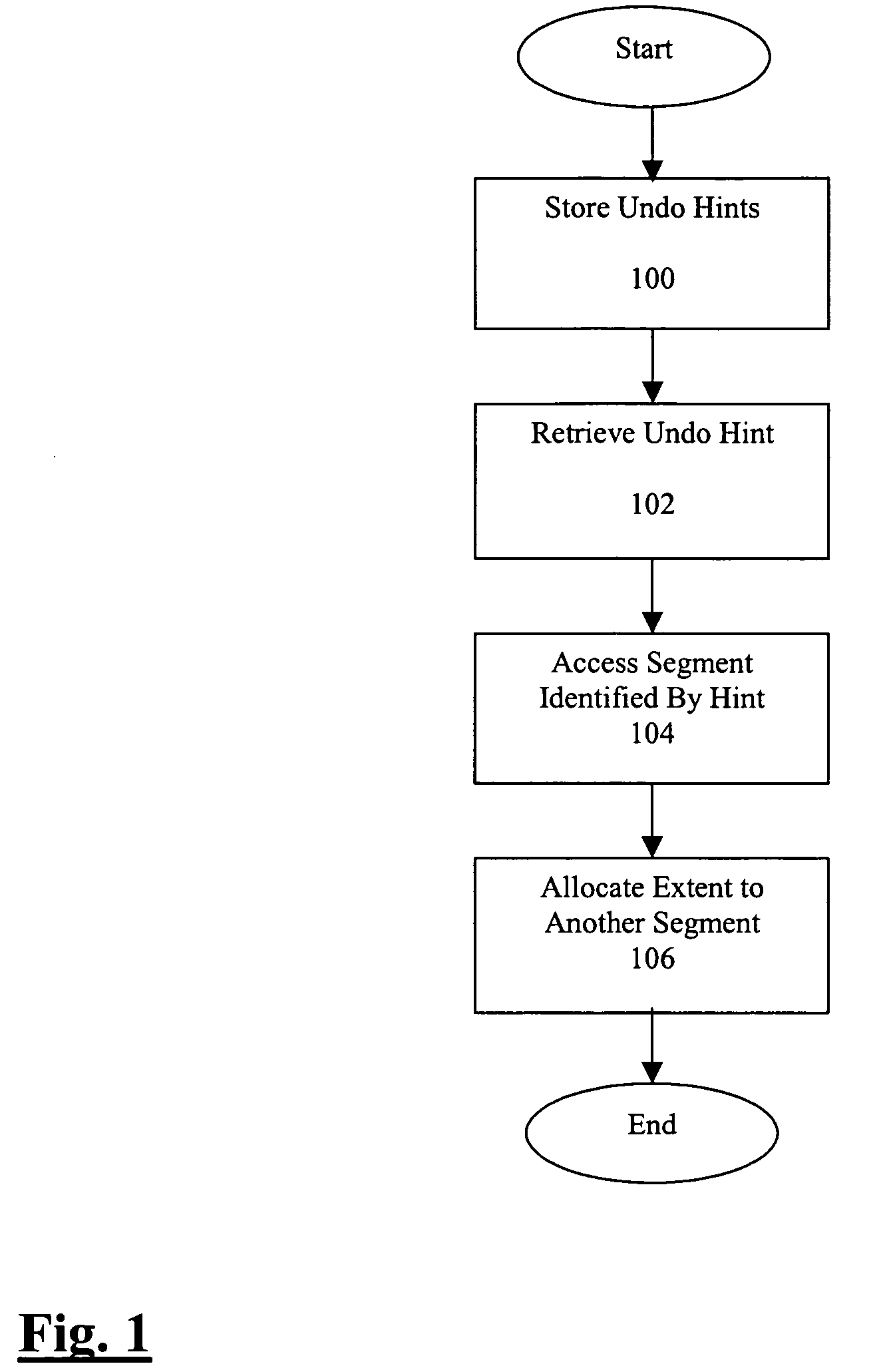
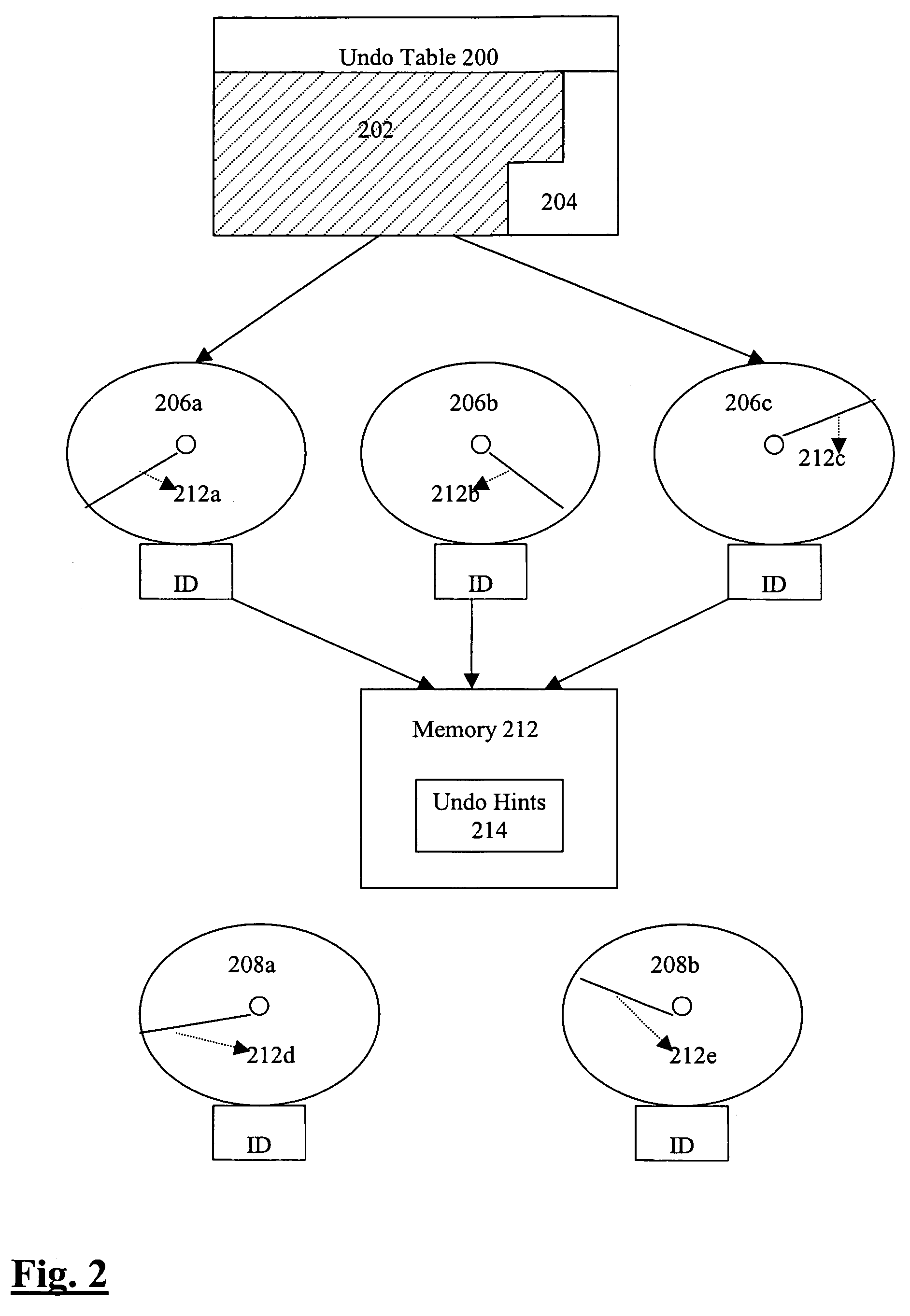
Undo hints to speed up segment extension and tuning of undo retention
ActiveUS7801932B2Digital data information retrievalData processing applicationsRetention timeEngineering
Methods and systems for using undo hints to speed up segment extension are disclosed. While a process is searching other segments to find available space, the process collects undo hints that describe when space in a segment might become available. These undo hints are placed in a table of undo hints. When a process is not able to find available space, it may consult the table of undo hints to determine how much to decrease the undo retention. After the undo retention is decreased, the process may again consult the table of undo hints to find a segment that likely contains available space now that the undo retention time has been reduced.
Owner:ORACLE INT CORP
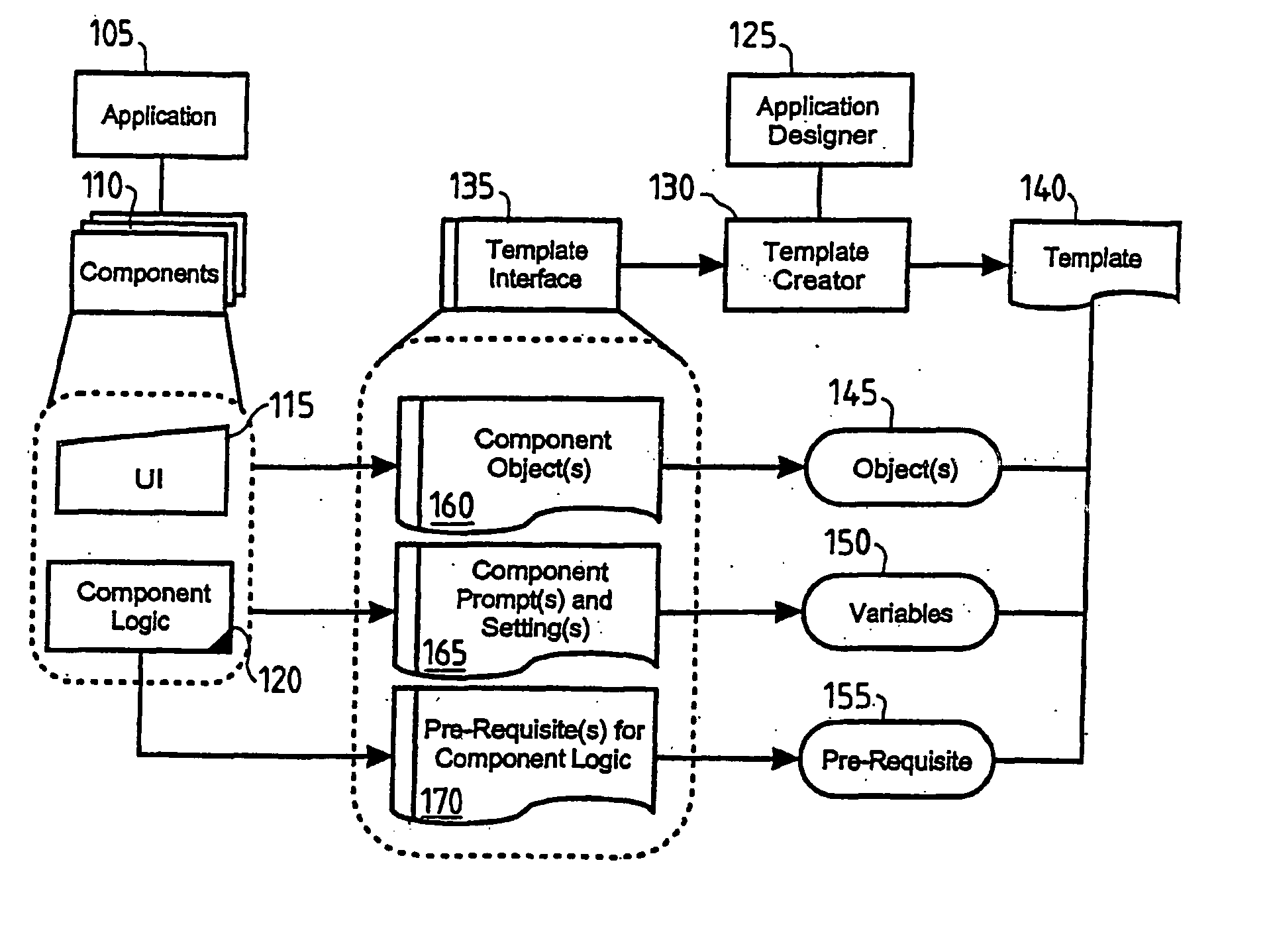
Method and system for updating application design
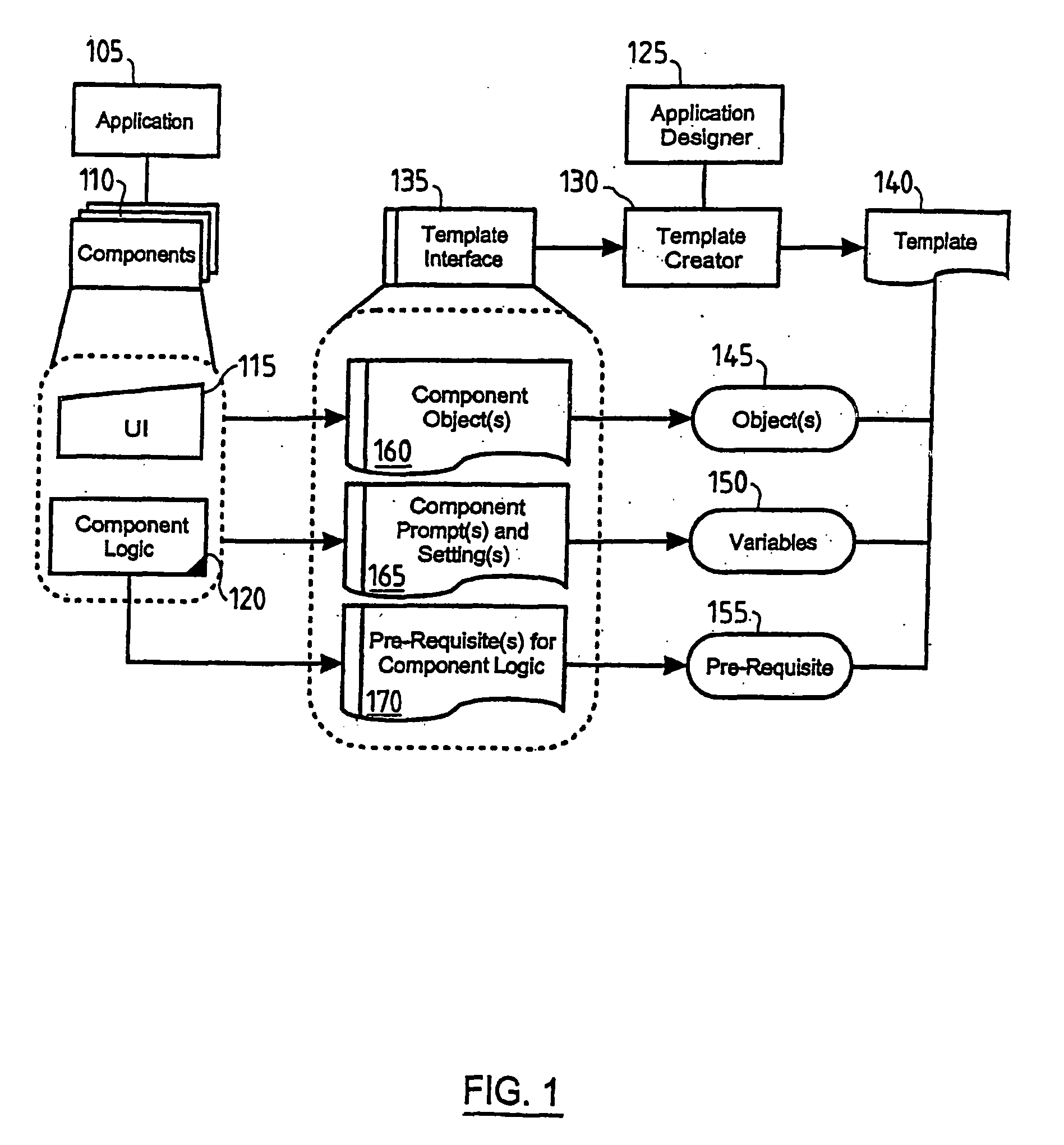
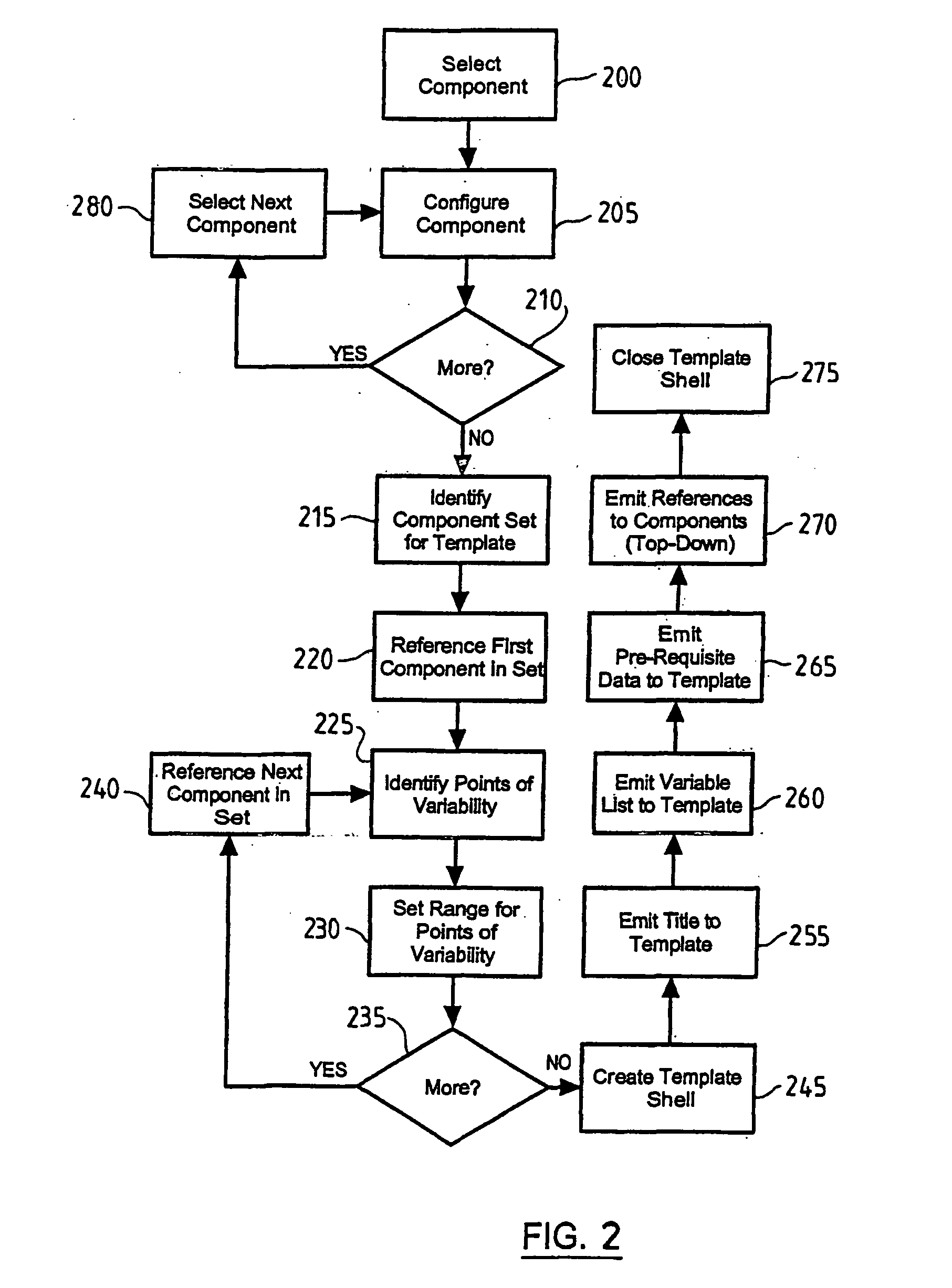
InactiveUS20060150178A1Facilitates ‘ undoing ’Facilitates rollbackVersion controlSpecific program execution arrangementsComputer architectureApplication software
A method and system for updating templated application design, which facilitates the later ‘undoing’ of the design update is provided. The method intercepts all design update requests and automatically creates and stores a description of the pre-update version of the application. When a developer intends to apply an update to a design of an application, the application is first asked to provide a description of itself, e.g. a template. If the application comprises a plurality of components, each application component provides a description. Thus a point-in-time design description of the application is created. This is stored and can later be used for an undo method or even multi-level rollback, as required.
Owner:IBM CORP
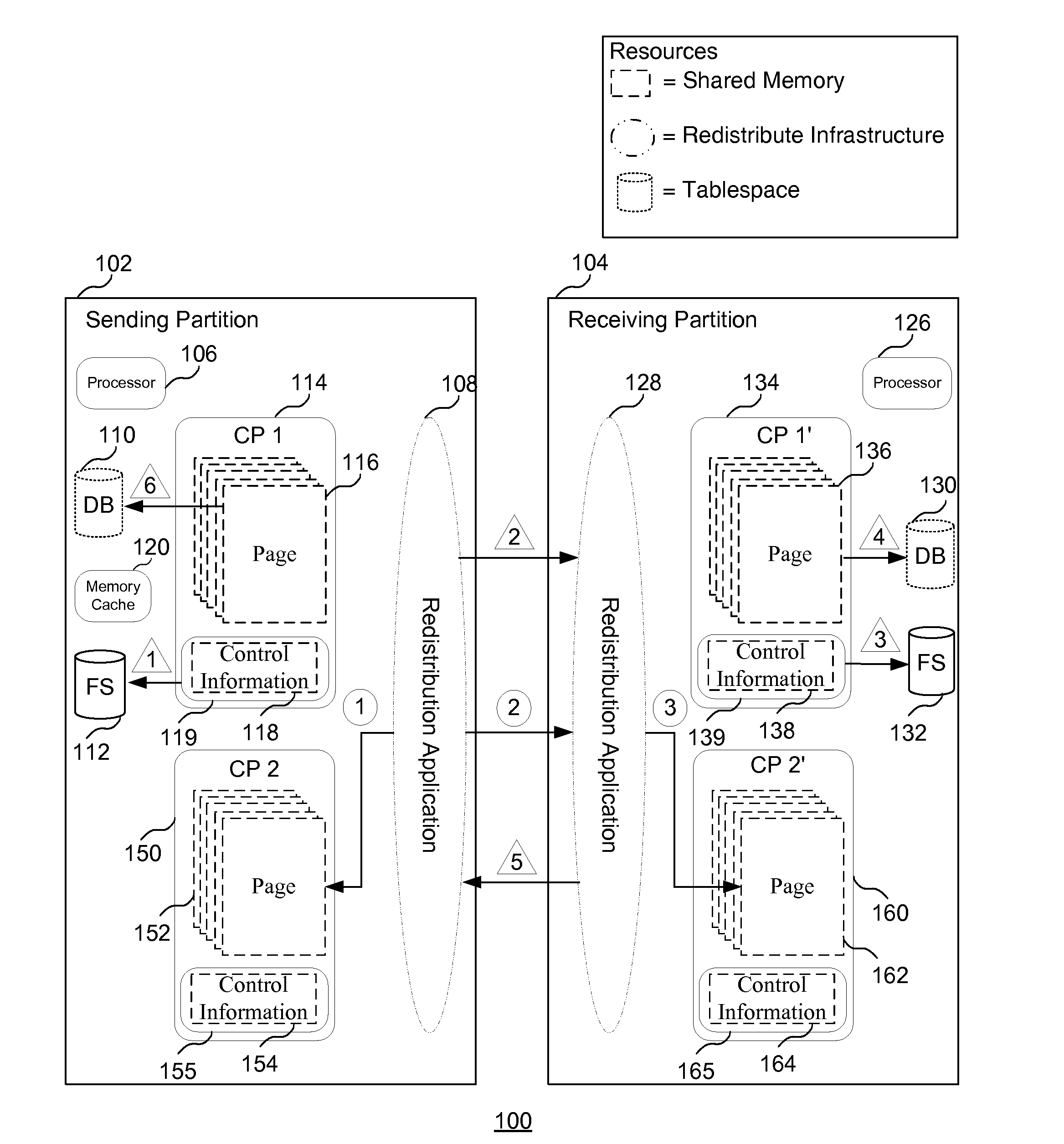
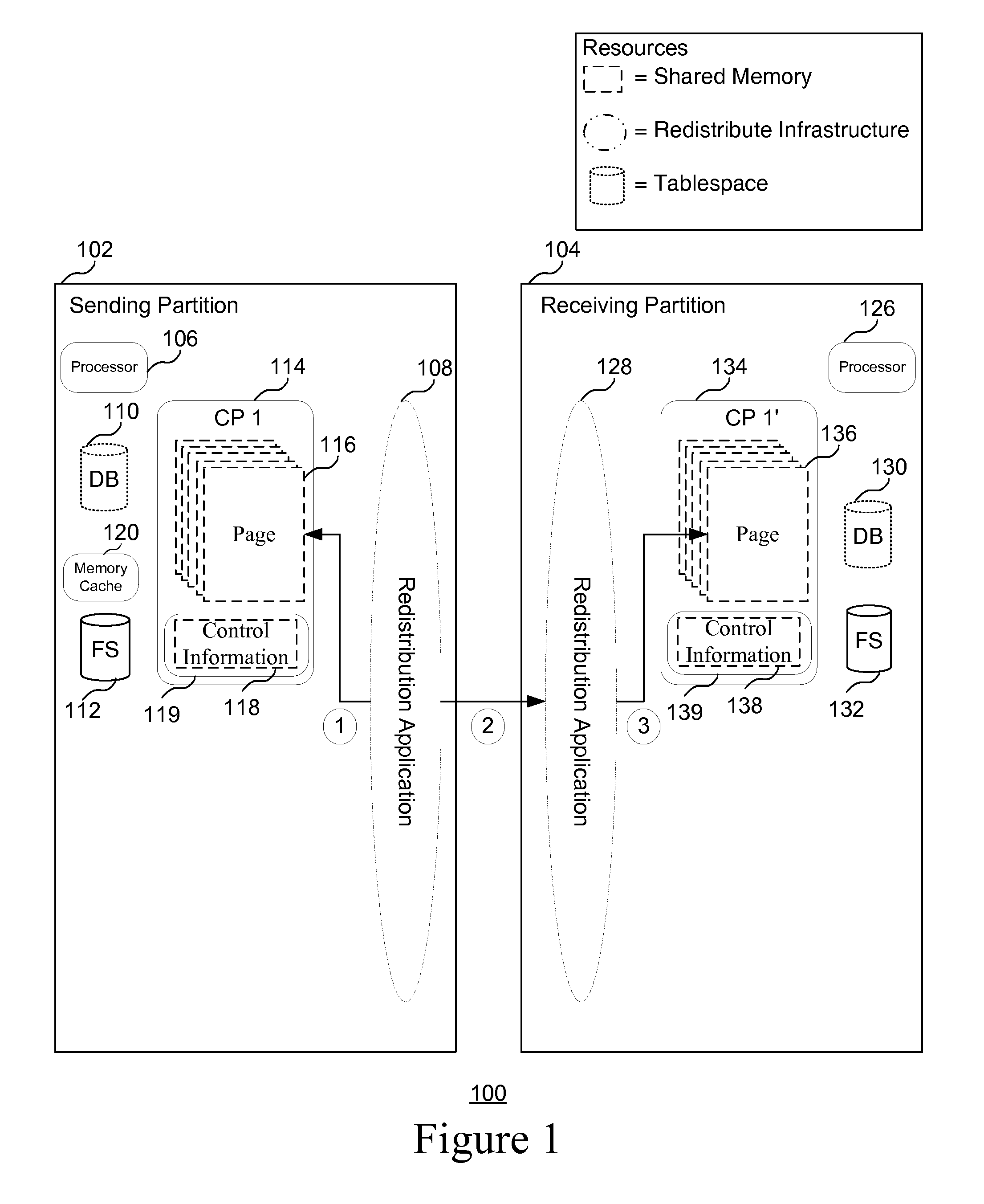
Efficient undo-processing during data redistribution
InactiveUS20100125555A1Minimize controlDigital data processing detailsDatabase distribution/replicationDocument IdentifierDatabase
A method and system for facilitating an undo operation. In one embodiment, the method includes generating a plurality of control files, where each of the control files is associated with a batch of data that is received from a sending partition during a redistribution process, and where each control file includes a list of pages and corresponding ranges of rows of data that have been appended to the pages. The method also includes writing the control files to a persistent memory for each control file where all of the associated rows of the respective consistency point have been appended to pages and written to a persistent memory. The method also includes, in response to an interruption in the redistribution process, identifying pages and rows to be deleted during an undo operation based on the plurality of control files.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com