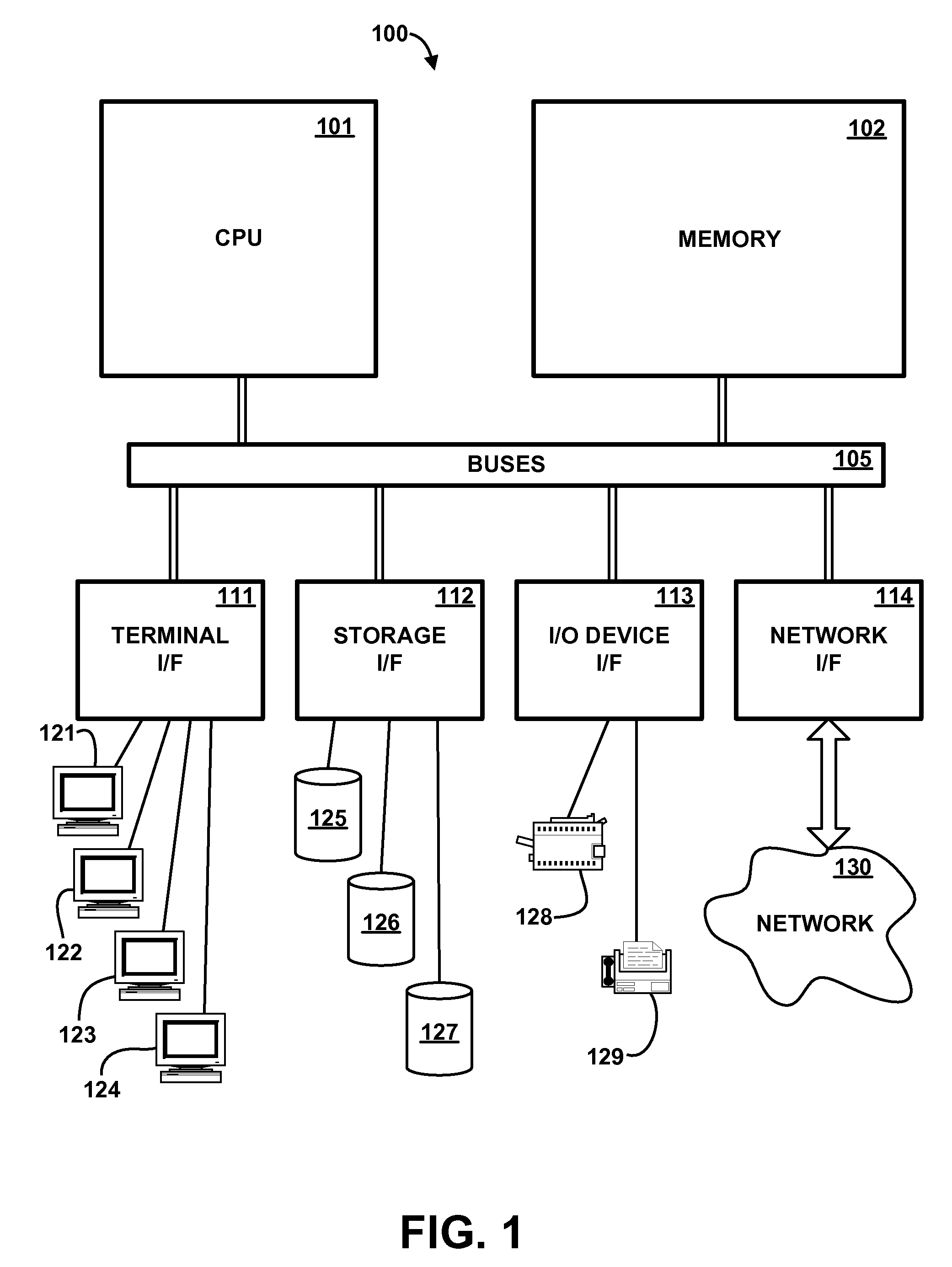
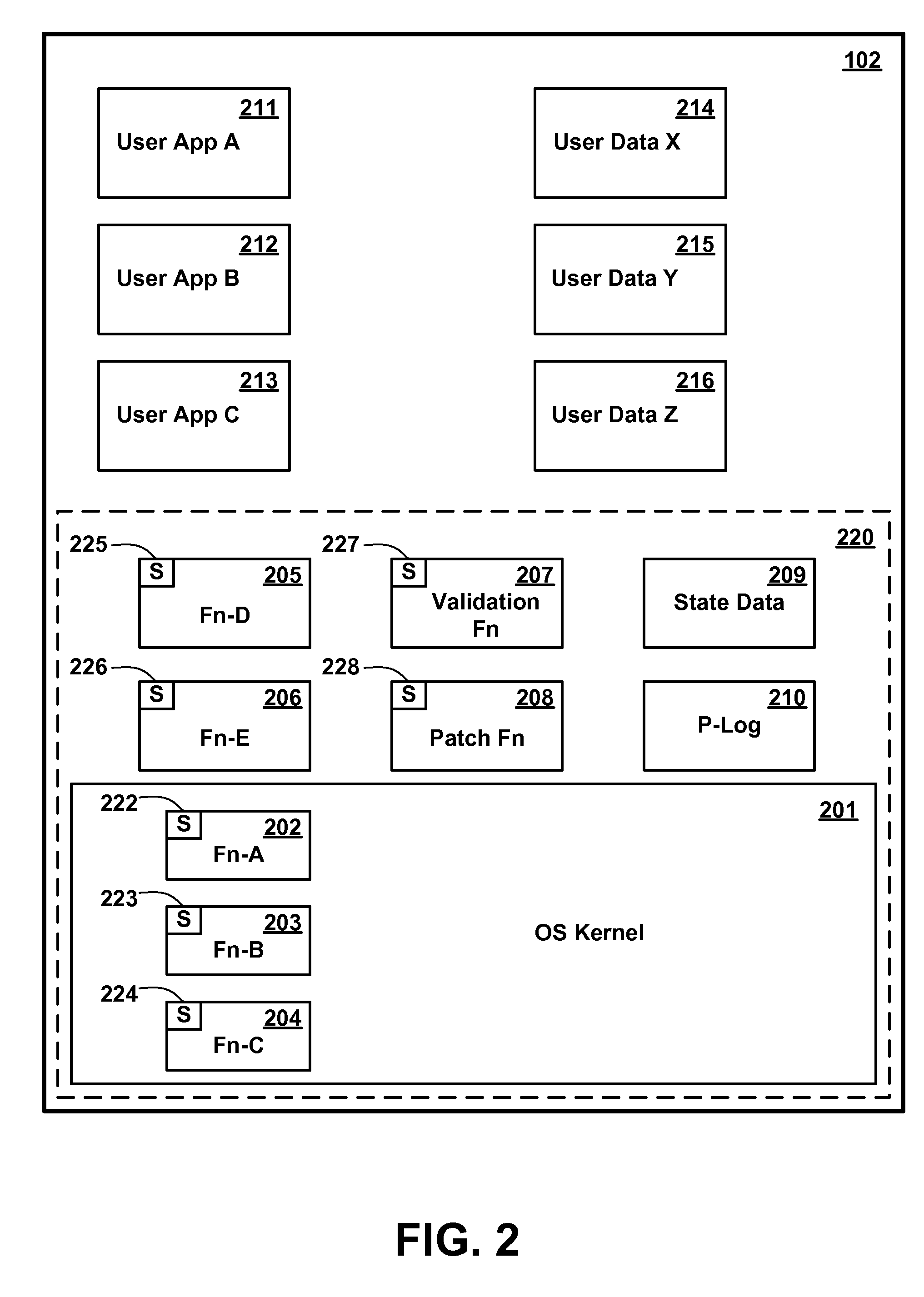
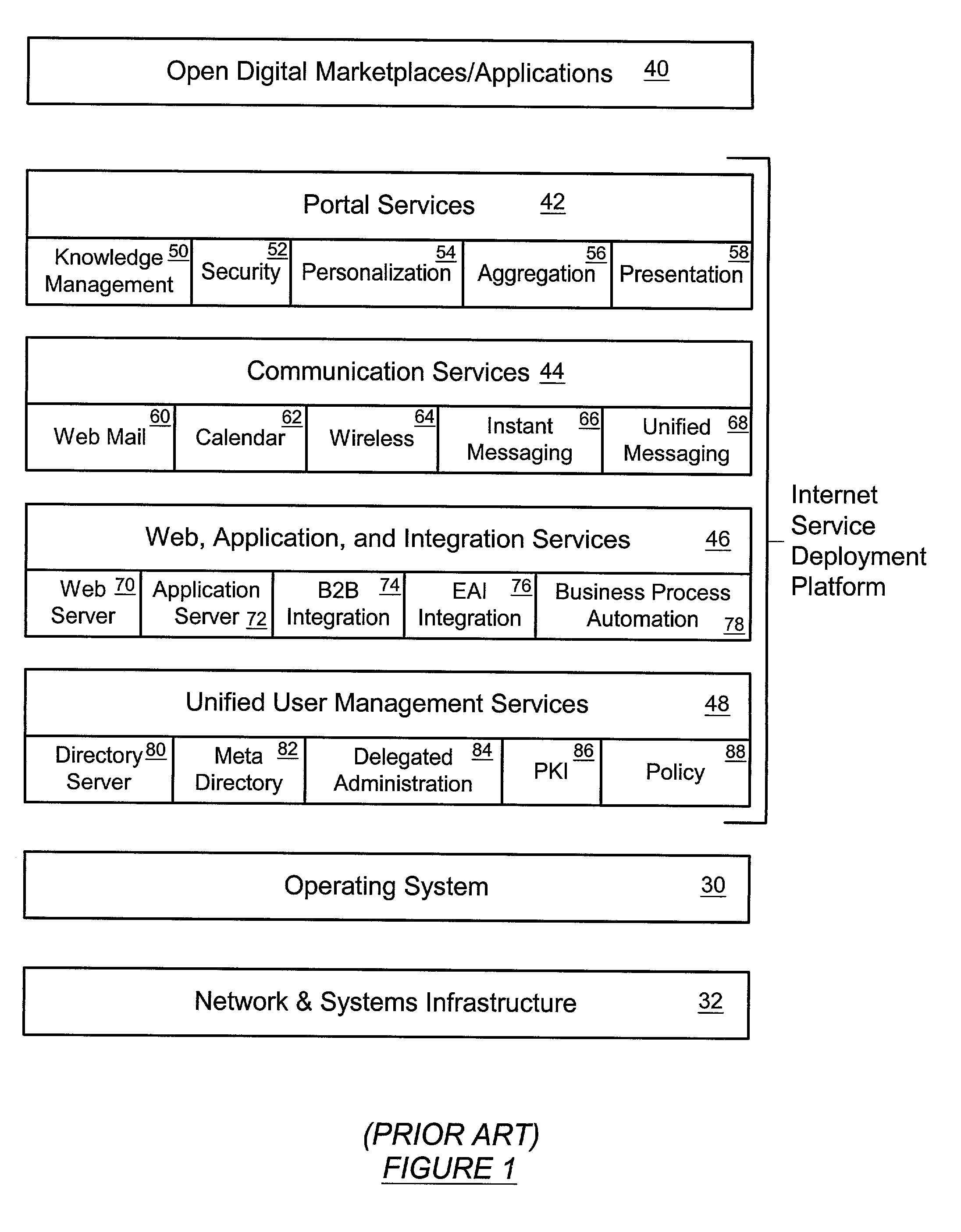
Patents
Literature
85 results about "Changelog" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
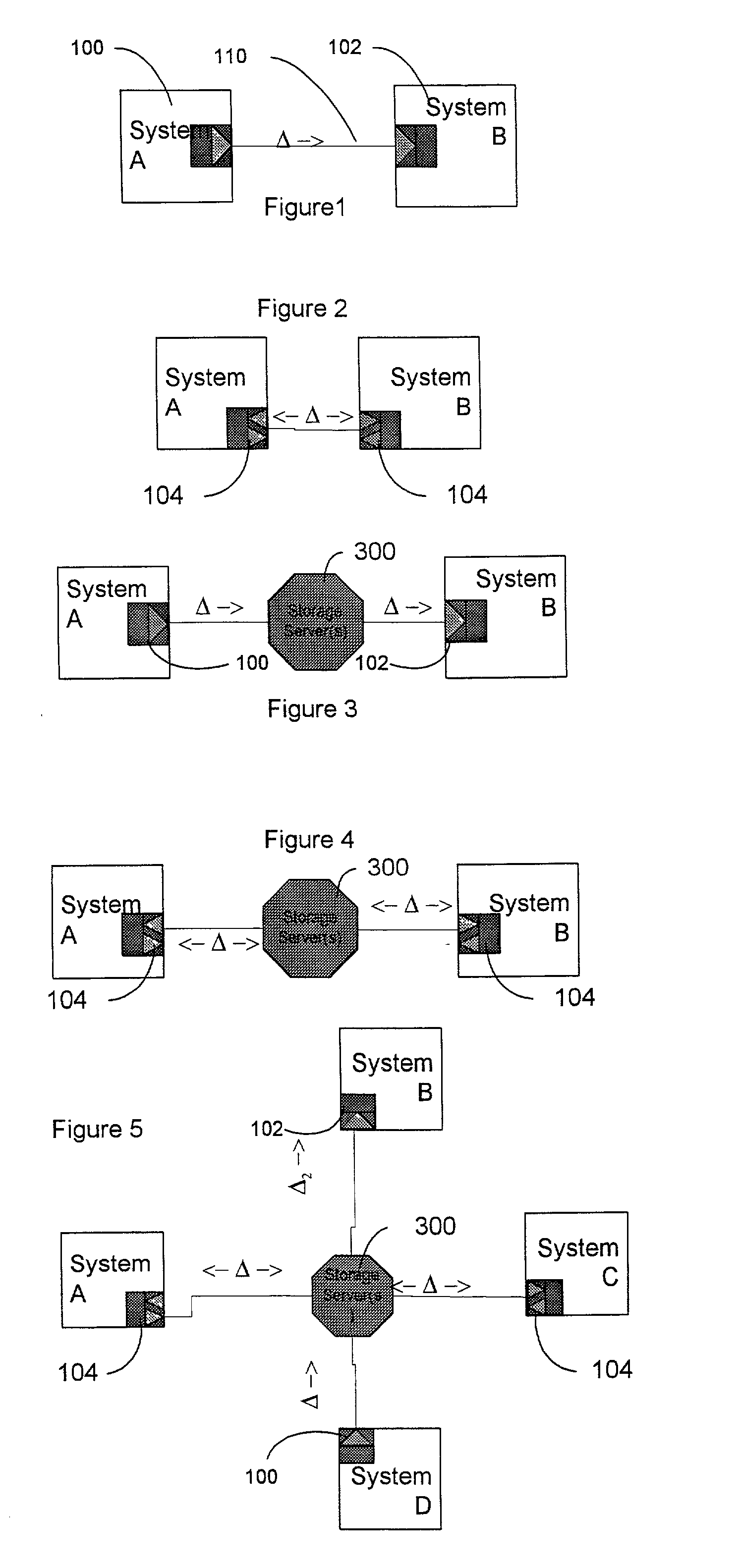
A changelog is a log or record of all notable changes made to a project. The project is often a website or software project, and the changelog usually includes records of changes such as bug fixes, new features, etc. Some open source projects include a changelog as one of the top level files in their distribution.
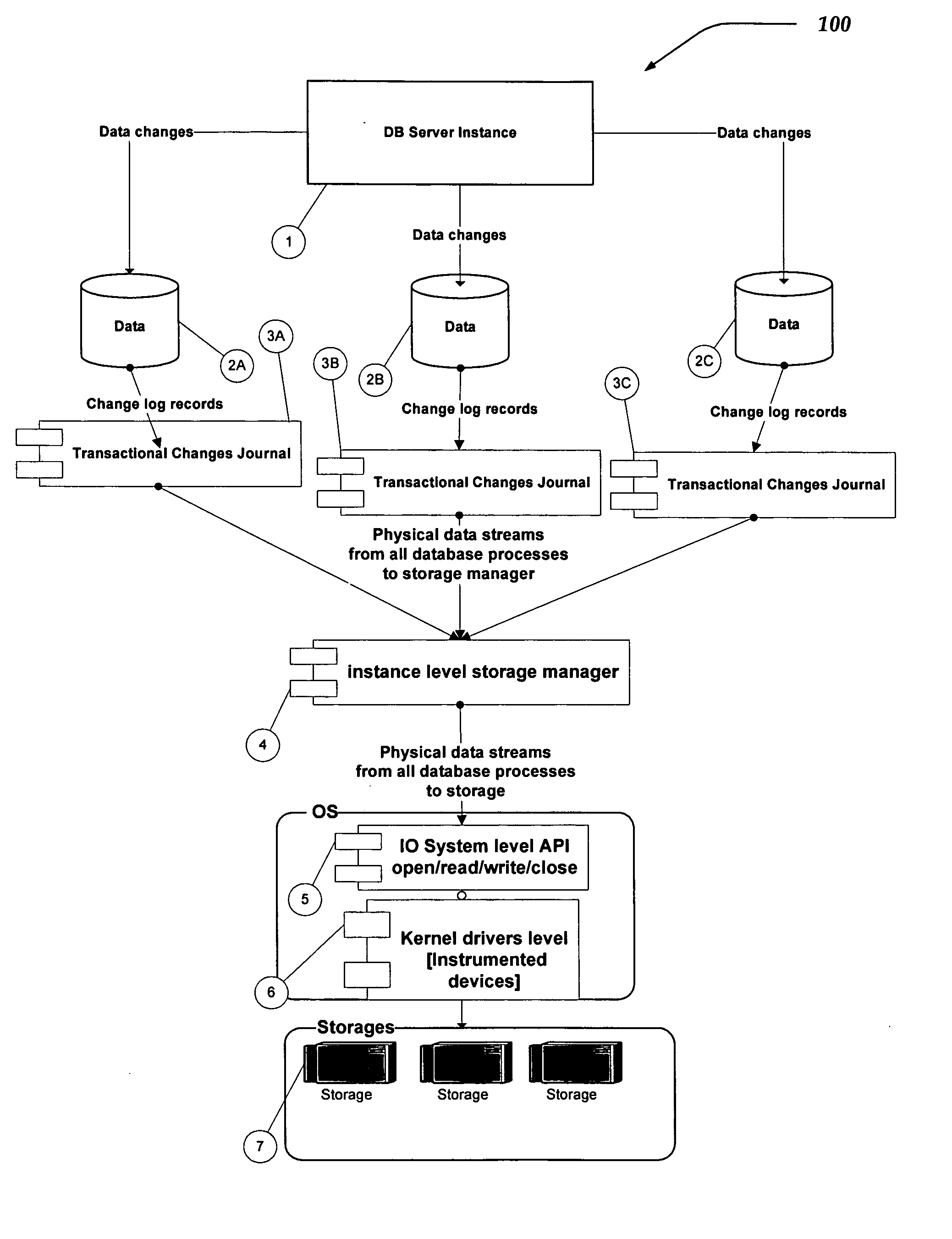
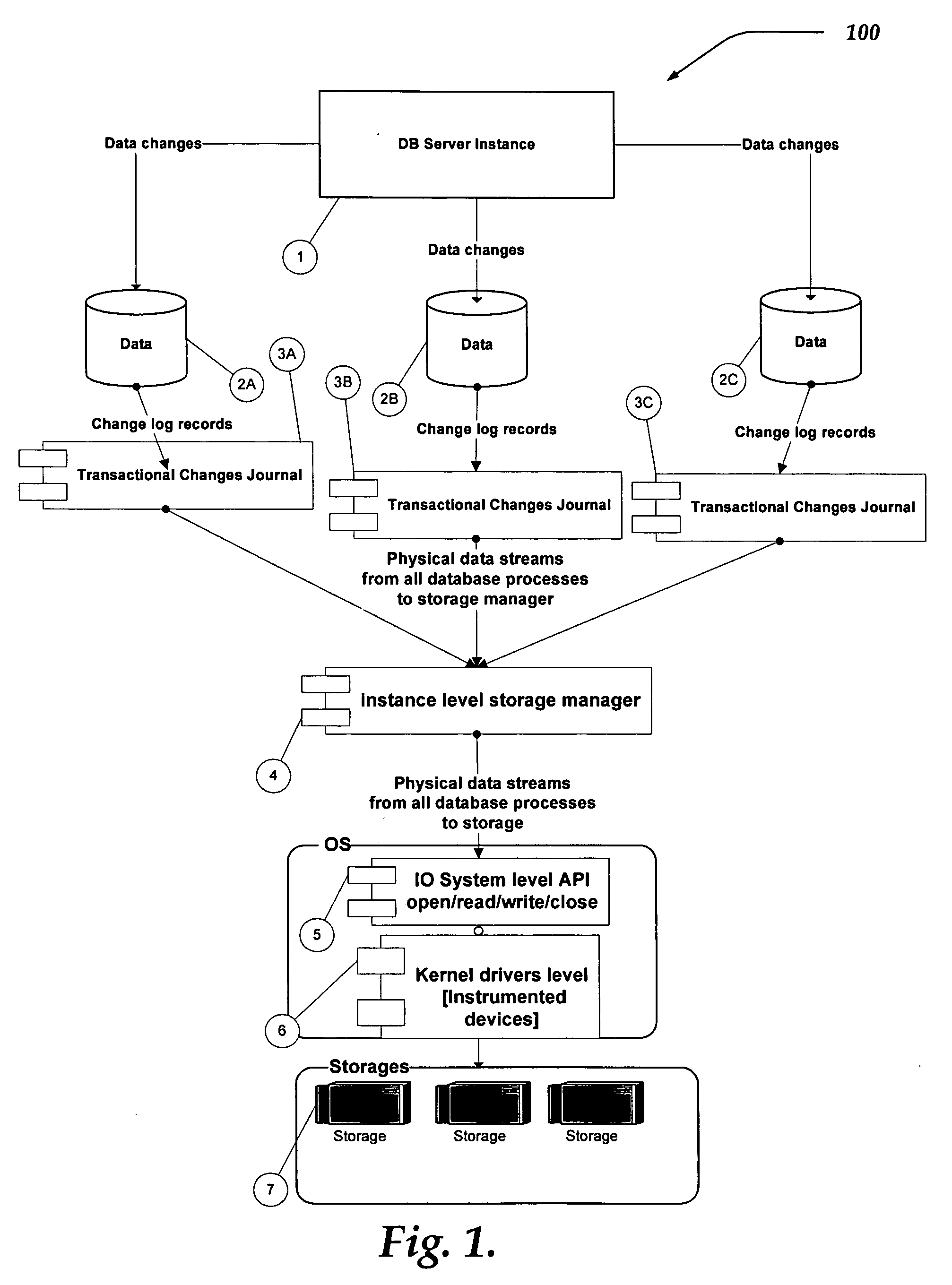
System and method for database replication by interception of in memory transactional change records
InactiveUS20060047713A1Database distribution/replicationSpecial data processing applicationsTerm memorySource level
A system and method are directed towards providing a database replication technique using interception in memory of the transaction change data records. The invention employs Input / Output instrumentation to capture and split out the in memory transaction change journal records. Captured memory blocks are sent to a parser, which concatenates the records into a single record, and creates a redo / undo vector that can be converted to original DML / DDL statements. Source level transformations can be applied to the vectors, which are then sent to a post agent on the same or a different computing device. The post agents may perform destination level transformations, and generate DML / DDL statements to be executed by the corresponding destination RDBMS instance. Post agents may also perform conflict detection and resolution during DML / DDL statement executions. Transaction consistency is supported by performing commits / rollback on the destination after receiving the redo / undo vector representing a commit / rollback on the source.
Owner:WISDOMFORCE TECH
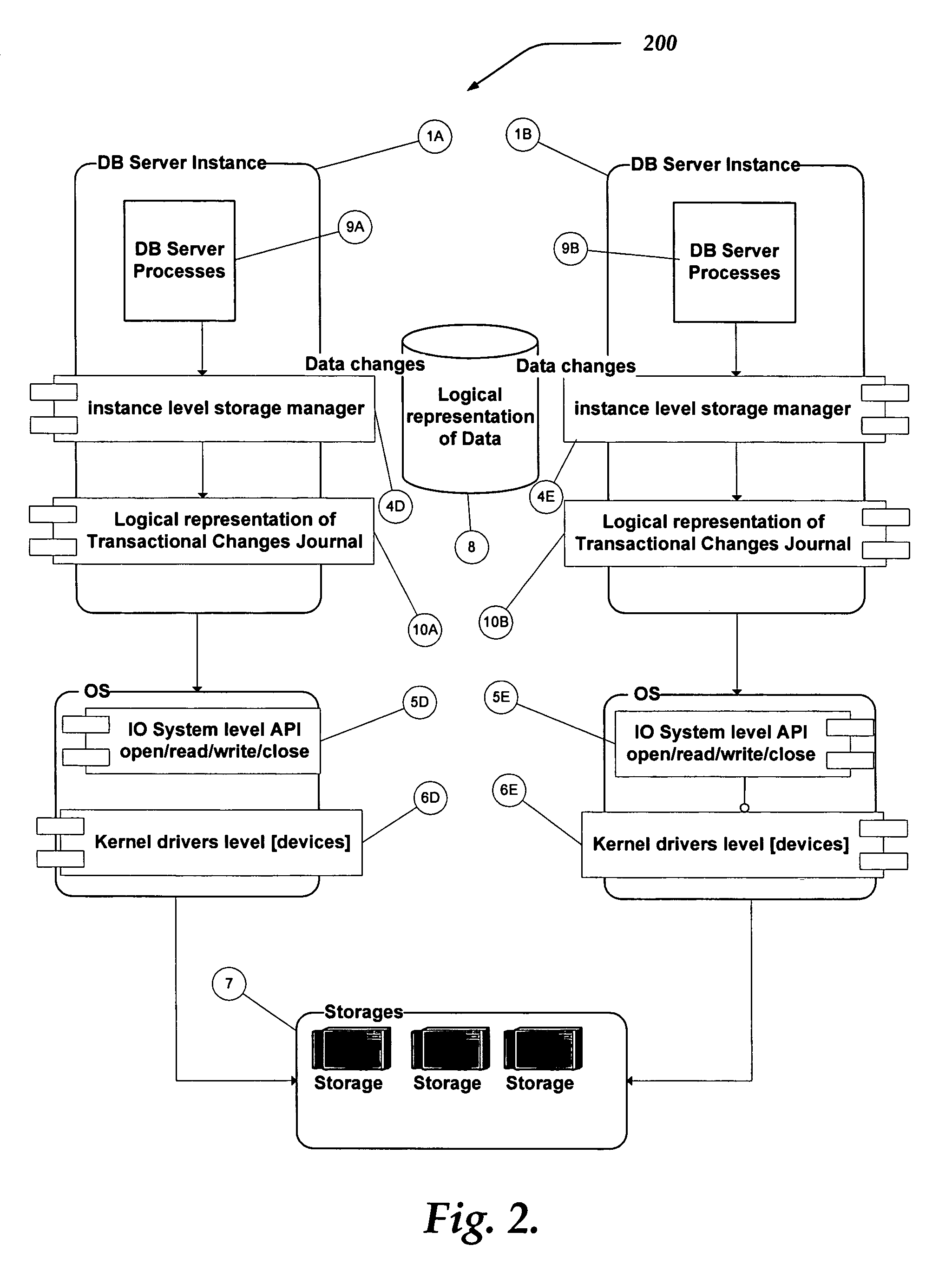
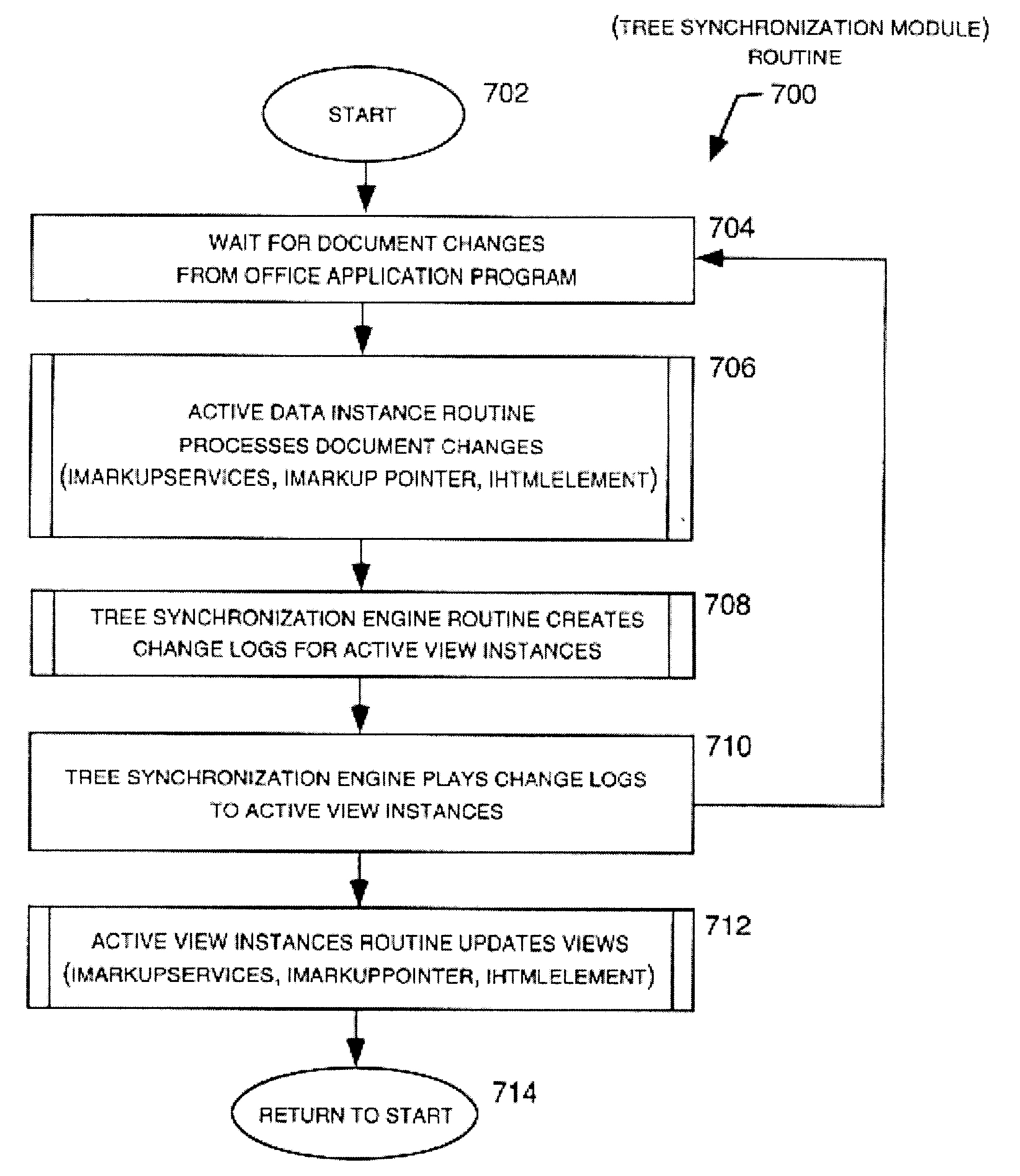
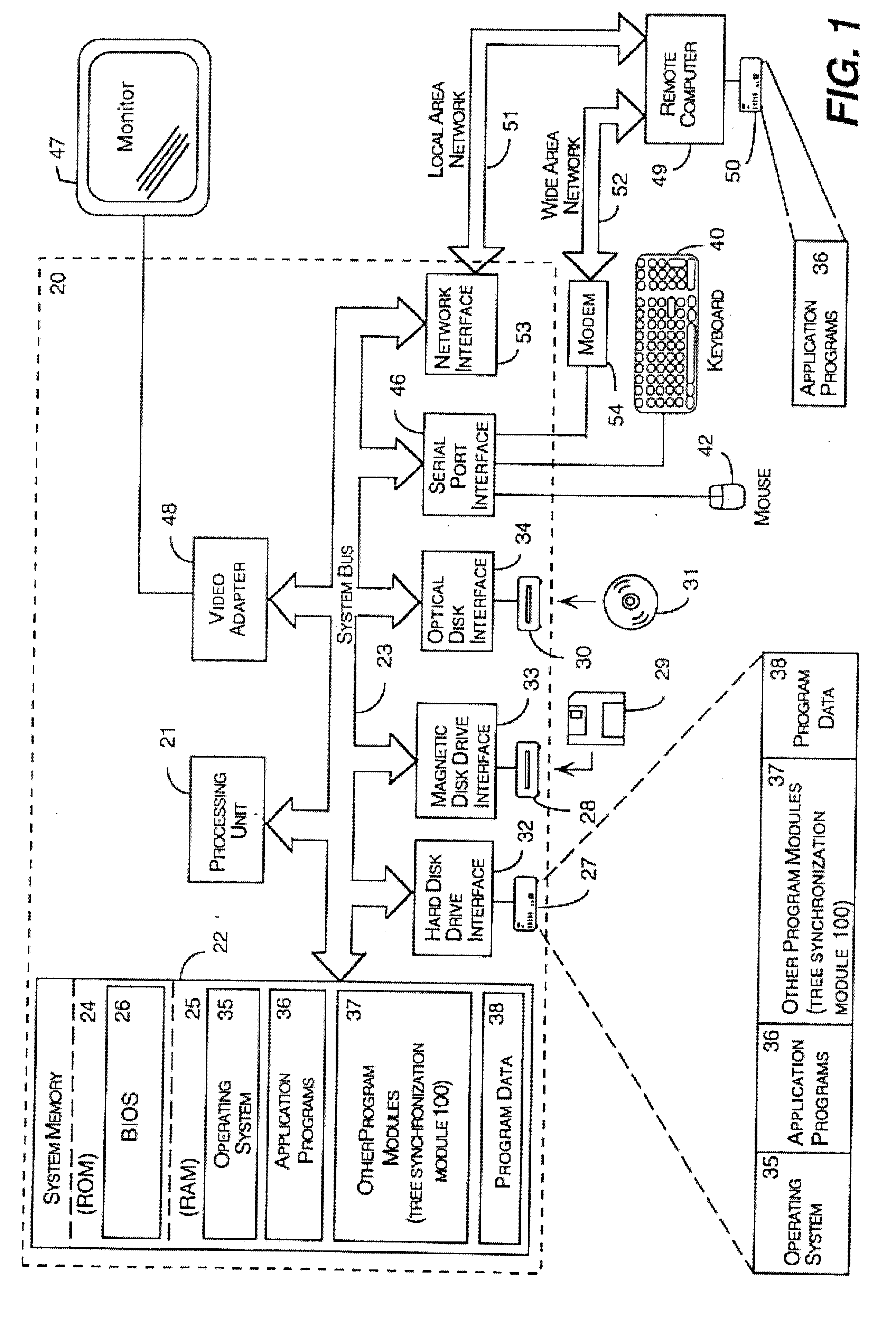
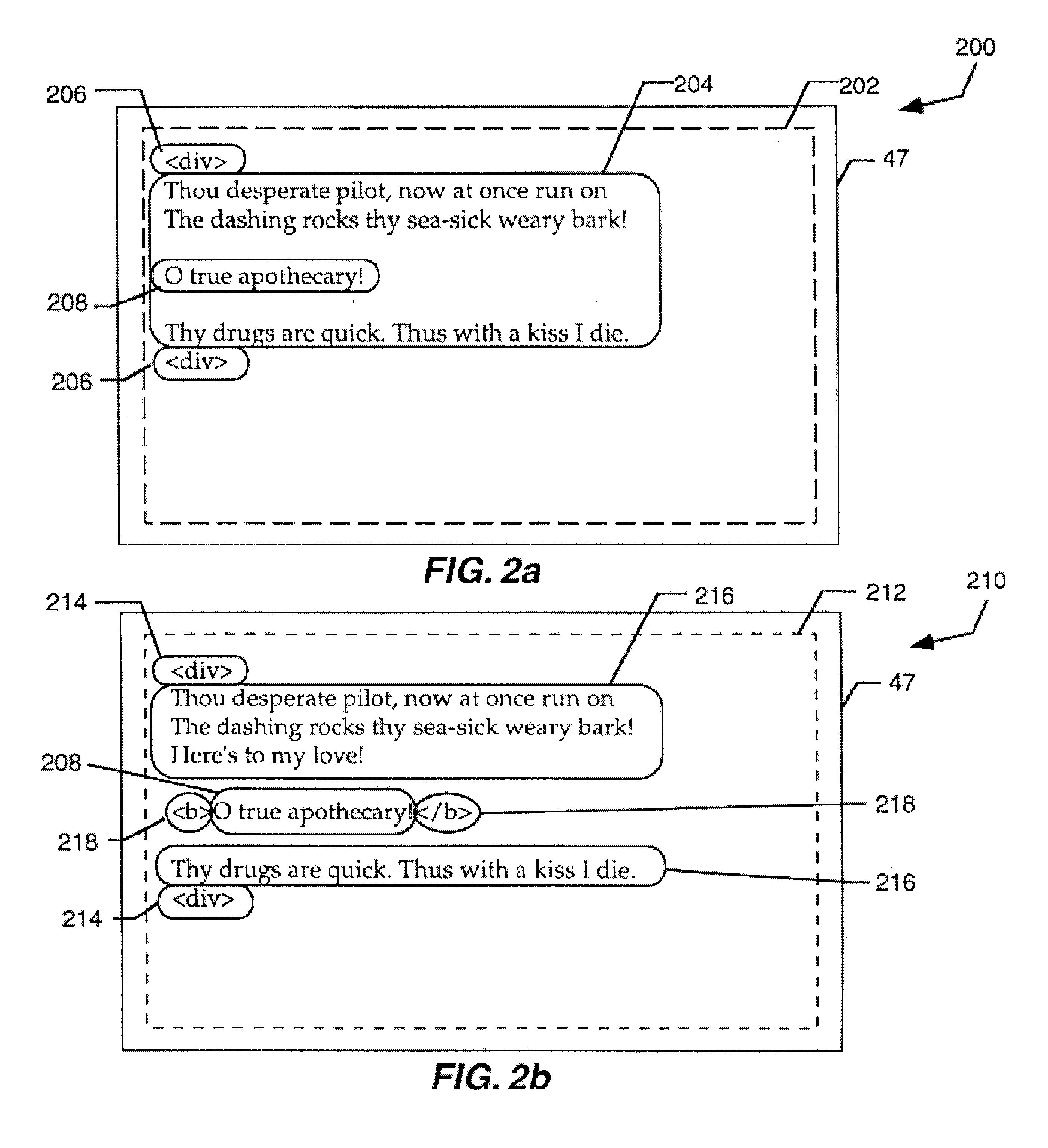
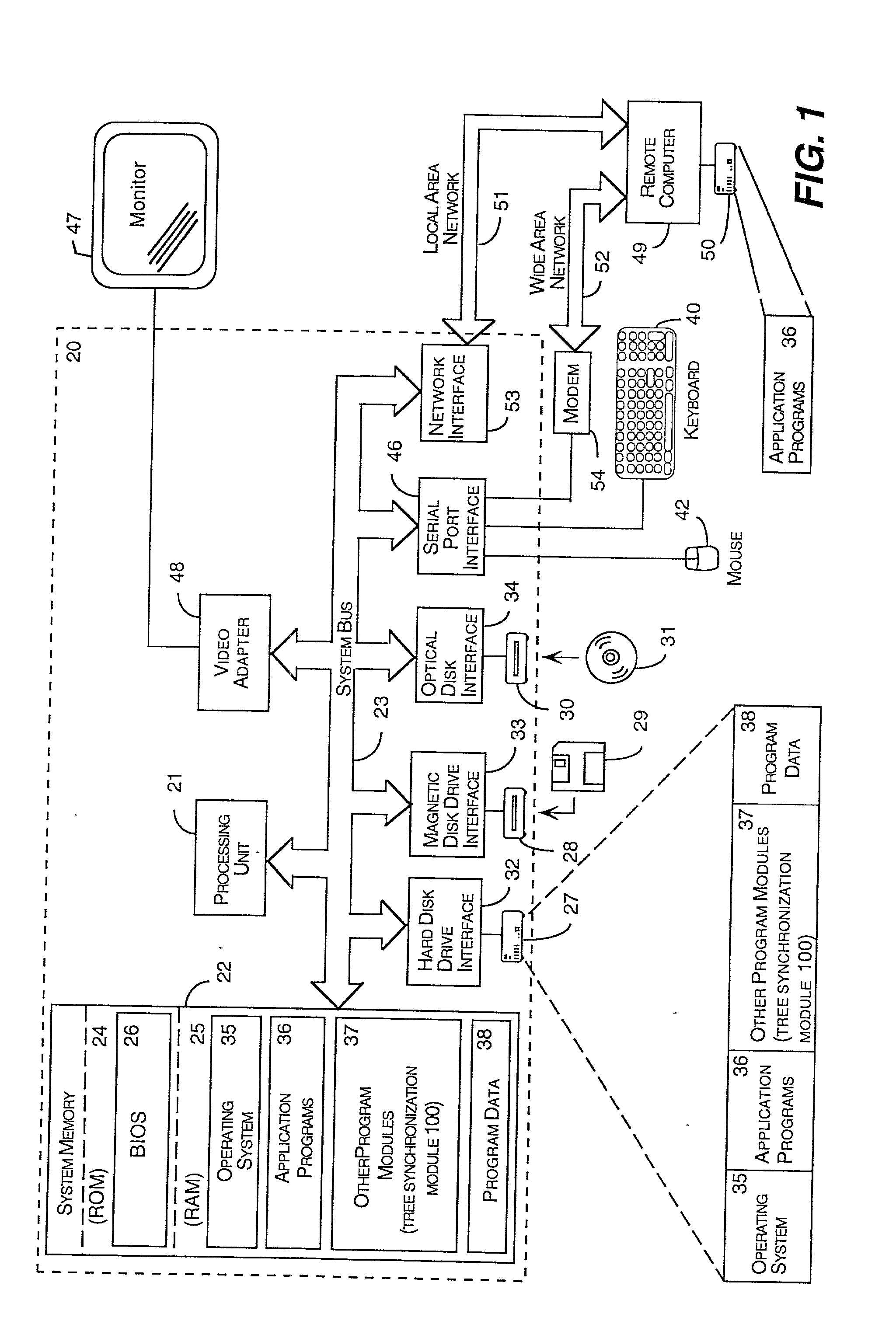
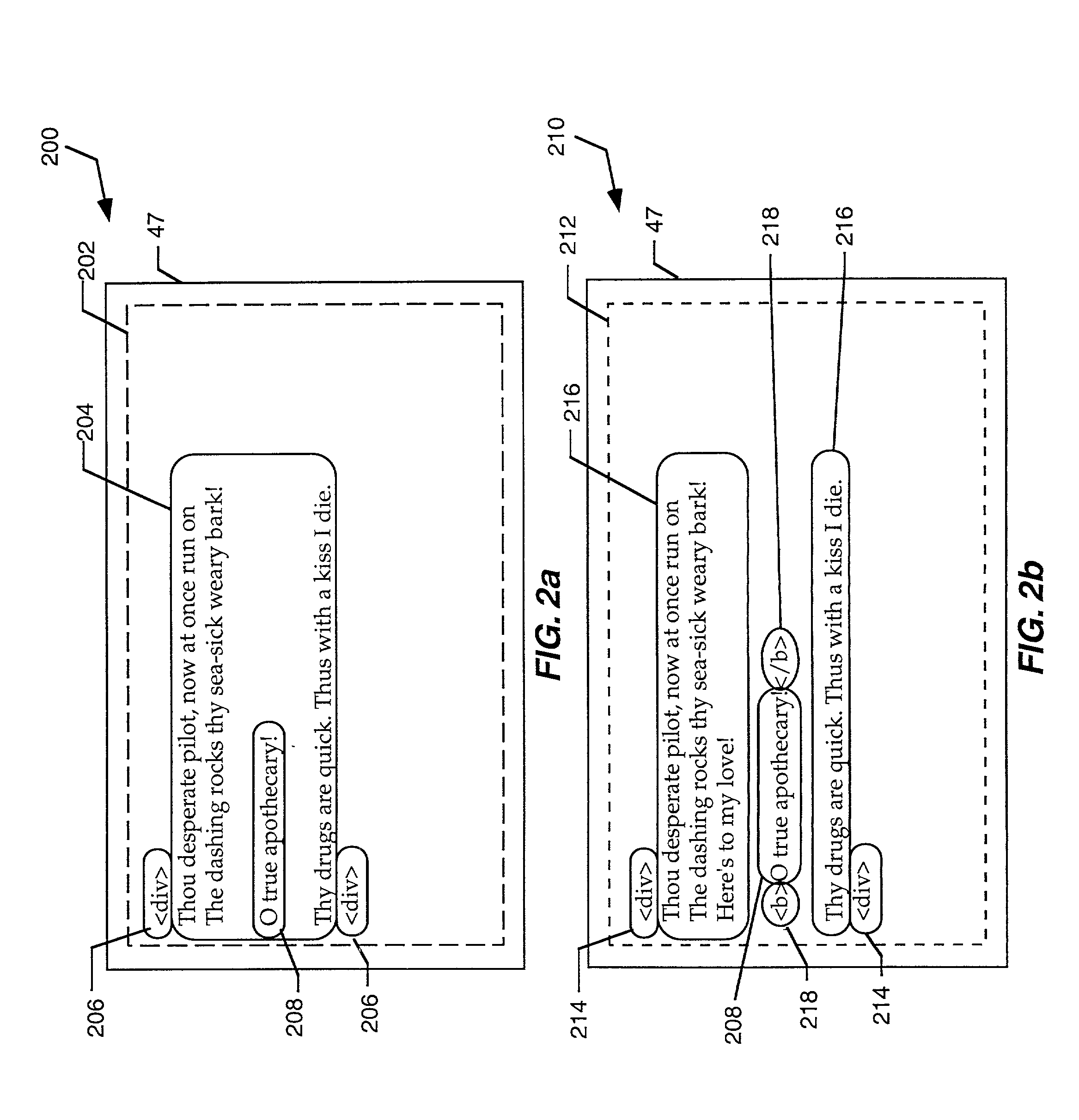
HTML/XML tree synchronization
InactiveUS6681370B2Lower performance requirementsImprove synchronicityData processing applicationsNatural language data processingApplication softwareDocument tree
The HTML / XML tree synchronization module synchronizes a document with a view or multiple views, after a change has been made to the document. First, the tree synchronization module receives a document change from an application program. An update processor converts the tree data of the document to a character string, and receives document change information from one or more application program interfaces. The update processor utilizes the document change information to update the document tree data character string. The document change information is then sent to one or more application program interfaces to determine the scope and content of the document views. A log generator receives the view change information, and creates record logs for each changed document view. These logs are played by a log player to each view, and each view data tree is updated with the view changes contained in the change logs. The tree synchronization module sends the subsequent view changes to the application program to update the display views.
Owner:MICROSOFT TECH LICENSING LLC
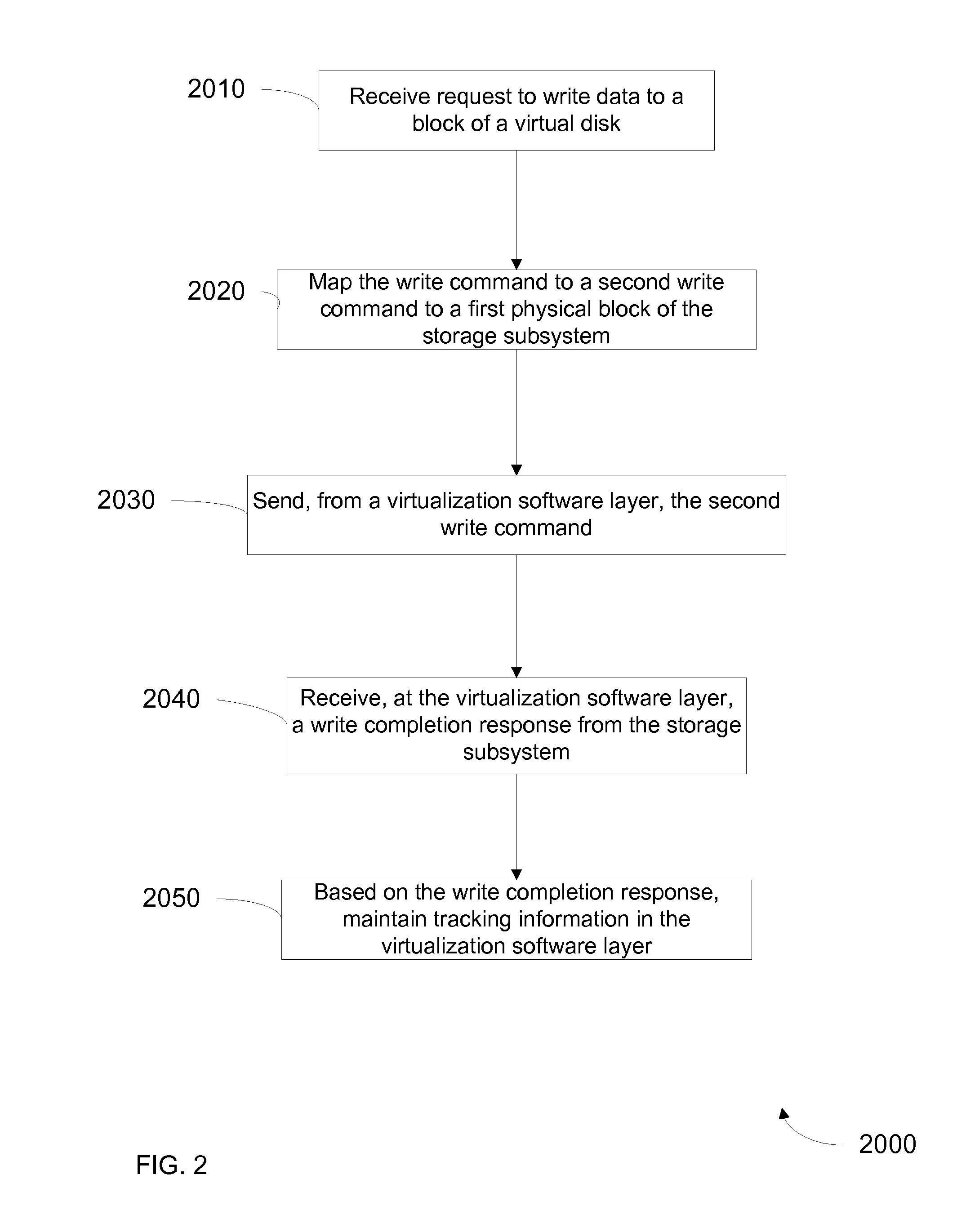
Method for tracking changes in virtual disks
ActiveUS20100228913A1Reduce the impactMore efficientMemory loss protectionError detection/correctionVirtualizationGranularity
Systems and methods for tracking changes and performing backups to a storage device are provided. For virtual disks of a virtual machine, changes are tracked from outside the virtual machine in the kernel of a virtualization layer. The changes can be tracked in a lightweight fashion with a bitmap, with a finer granularity stored and tracked at intermittent intervals in persistent storage. Multiple backup applications can be allowed to accurately and efficiently backup a storage device. Each backup application can determine which block of the storage device has been updated since the last backup of a respective application. This change log is efficiently stored as a counter value for each block, where the counter is incremented when a backup is performed. The change log can be maintained with little impact on I / O by using a coarse bitmap to update the finer grained change log.
Owner:VMWARE INC
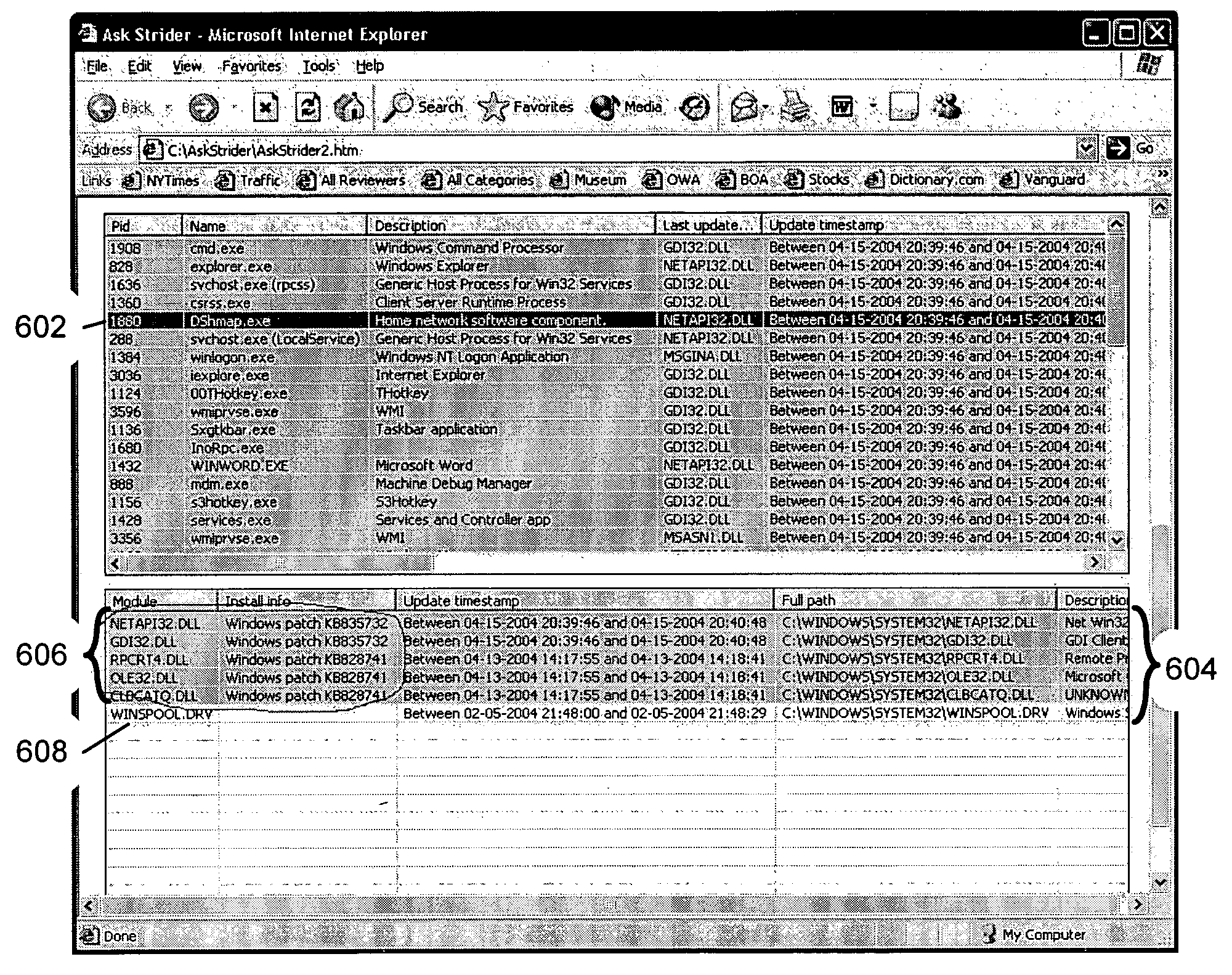
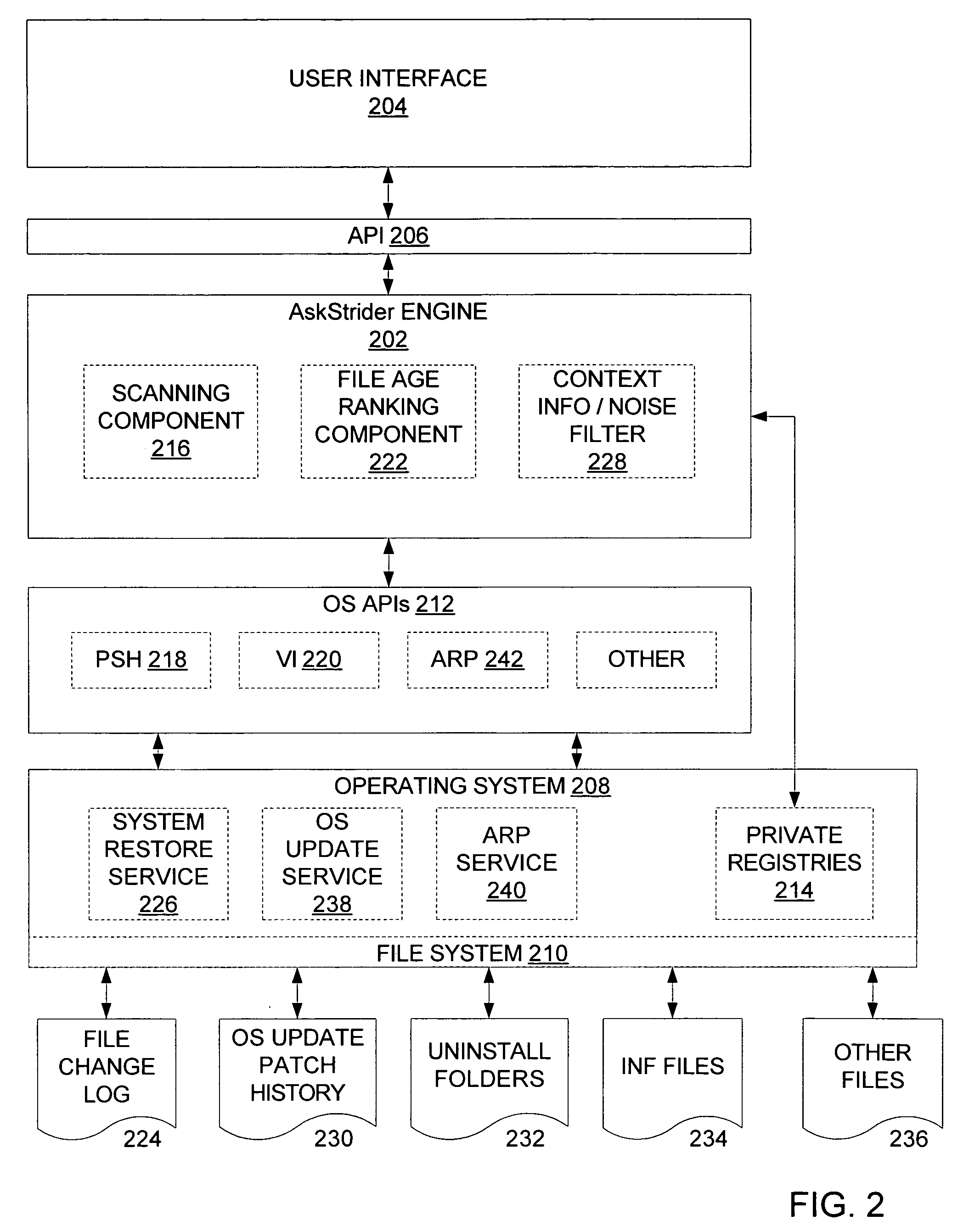
Changed file identification, software conflict resolution and unwanted file removal
InactiveUS20050155031A1Memory loss protectionUnauthorized memory use protectionData miningProcess information
As computer programs grow more complex, extensible, and connected, it becomes increasingly difficult for users to understand what has changed on their machines and what impact those changes have. An embodiment of the invention is described via a software tool, called AskStrider, that answers those questions by correlating volatile process information with persistent-state context information and change history. AskStrider scans a system for active components, matches them against a change log to identify recently updated and hence more interesting state, and searches for context information to help users understand the changes. Several real-world cases are provided to demonstrate the effectiveness of using AskStrider to quickly identify the presence of unwanted software, to determine if a software patch is potentially breaking an application, and to detect lingering components left over from an unclean uninstallation.
Owner:MICROSOFT TECH LICENSING LLC
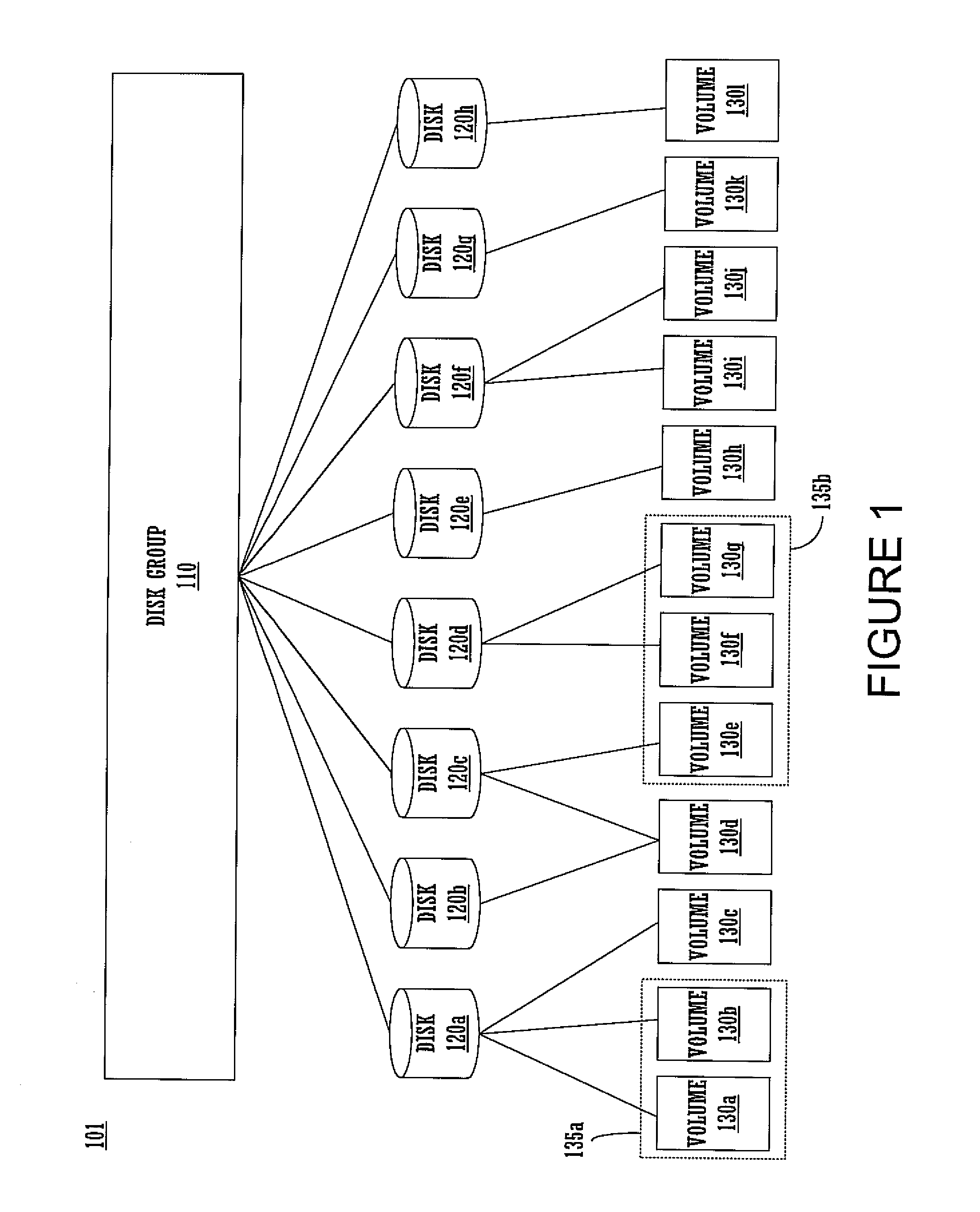
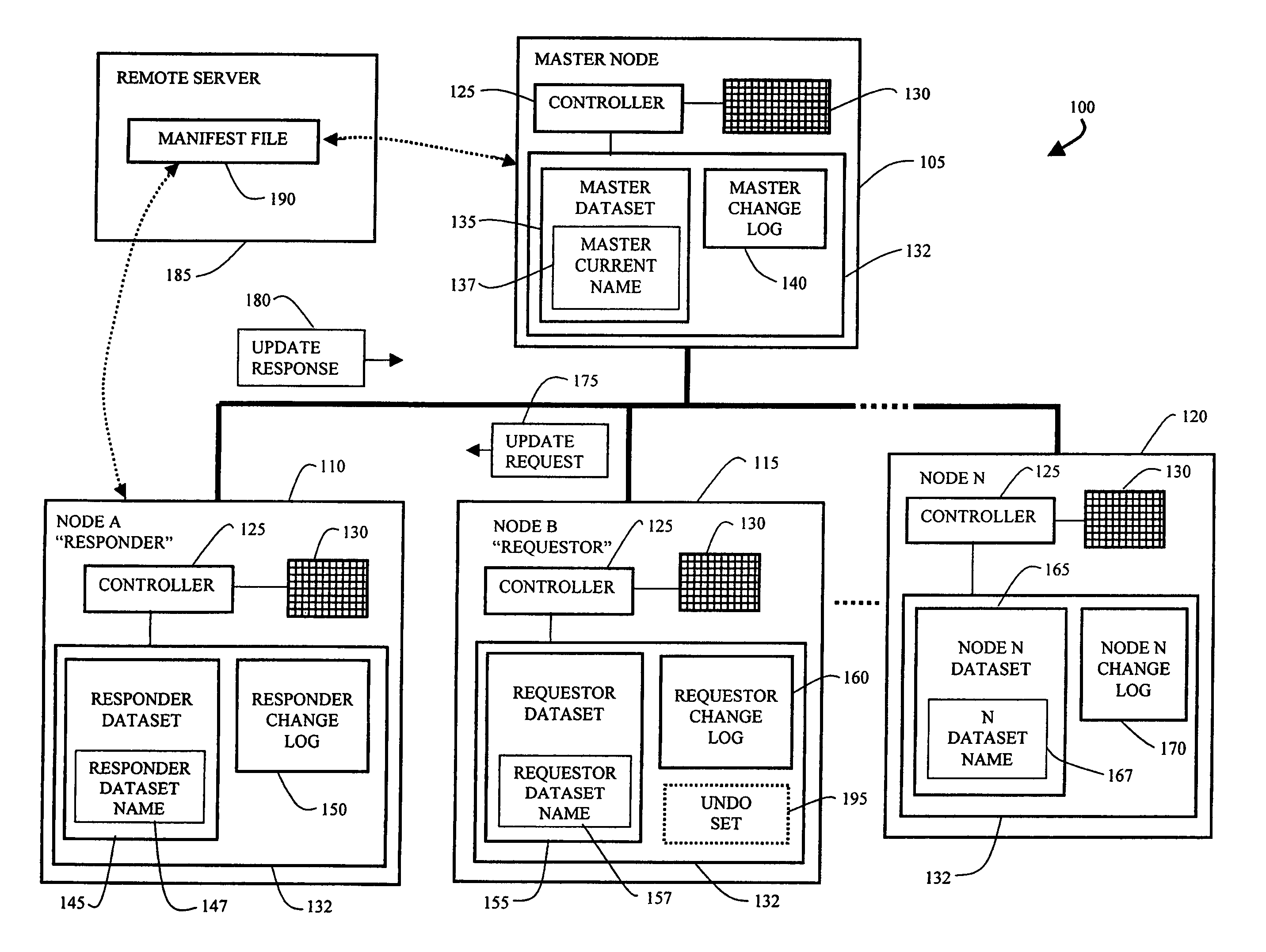
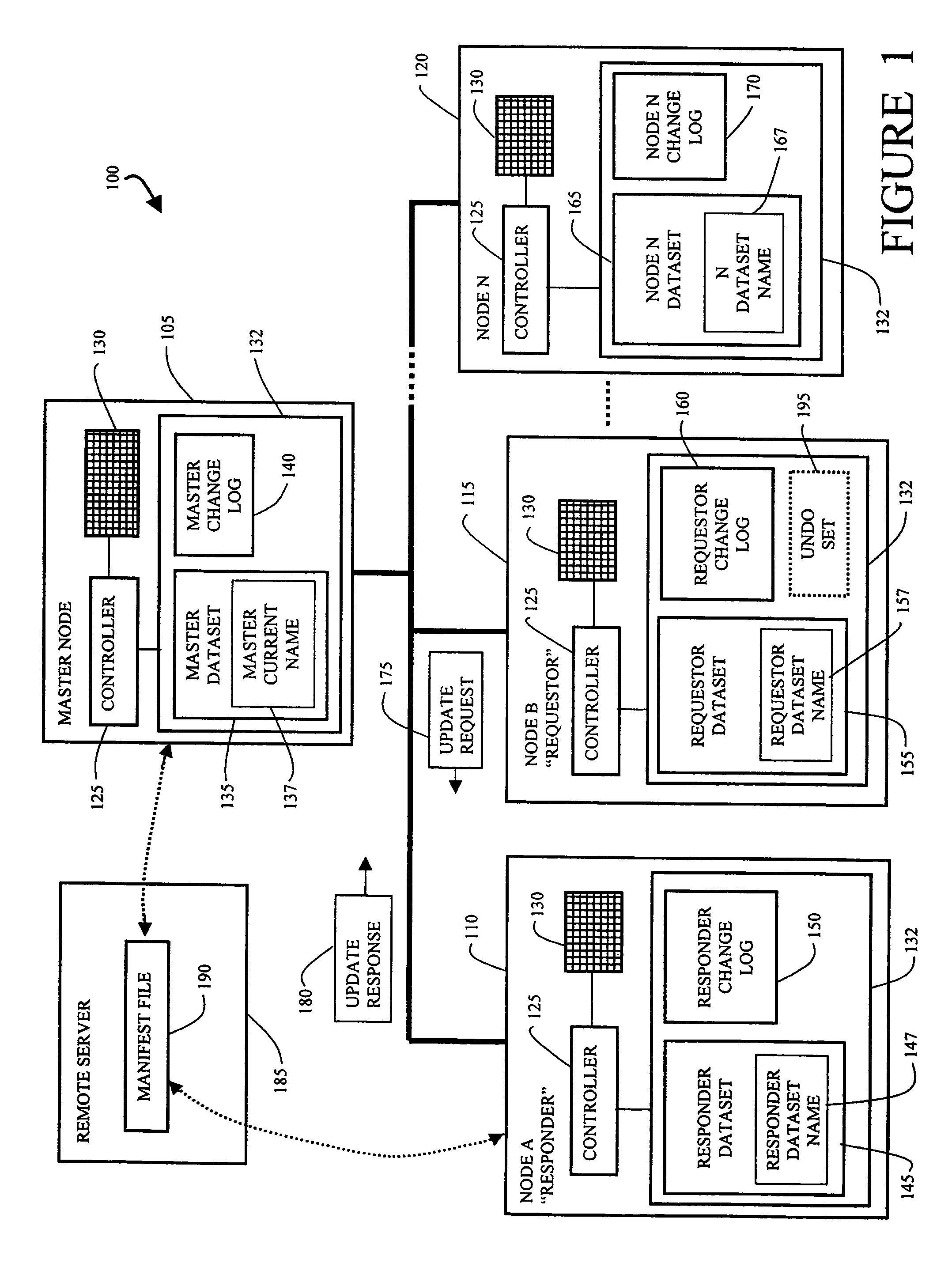
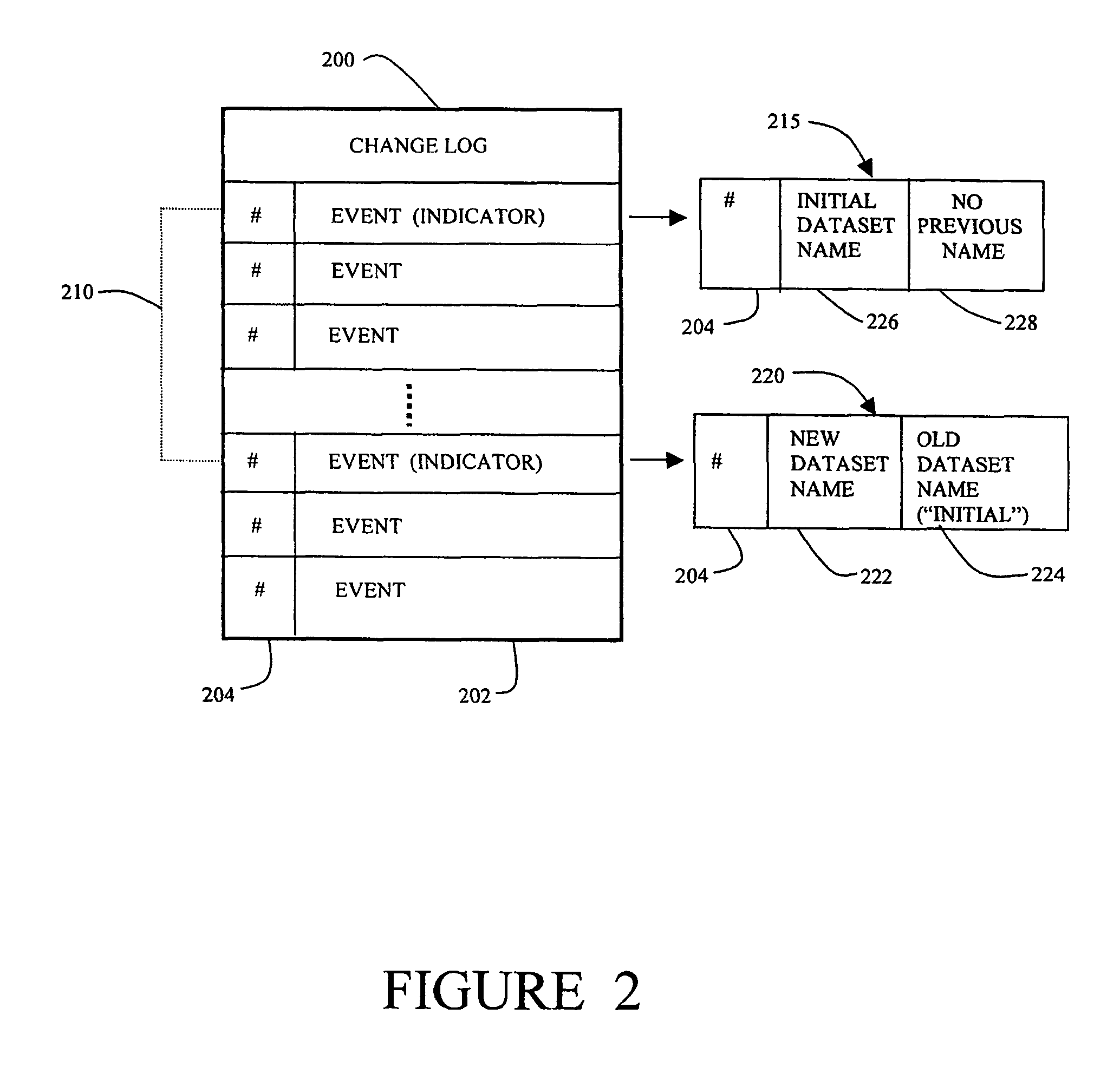
Method and apparatus for efficient propagation of large datasets under failure conditions
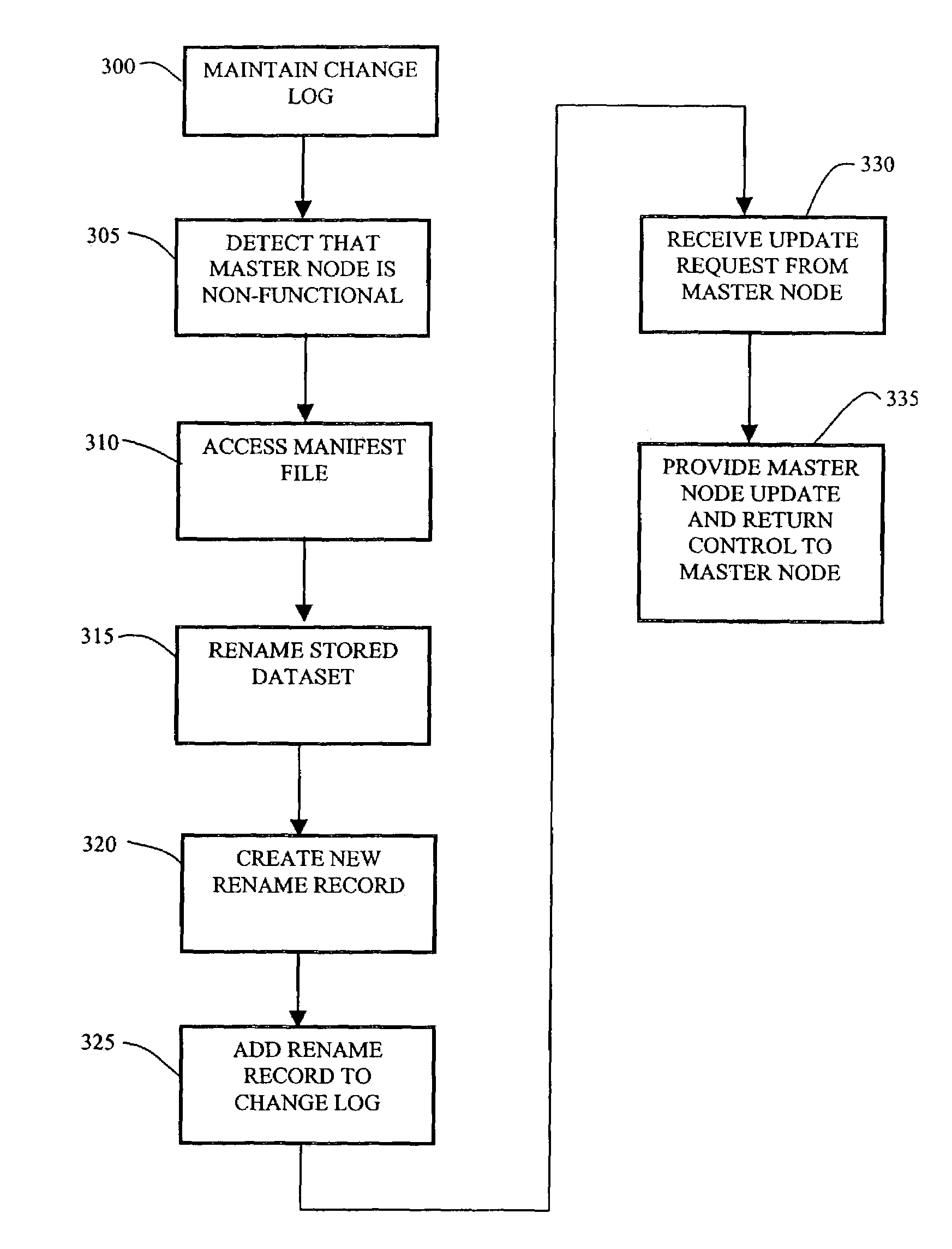
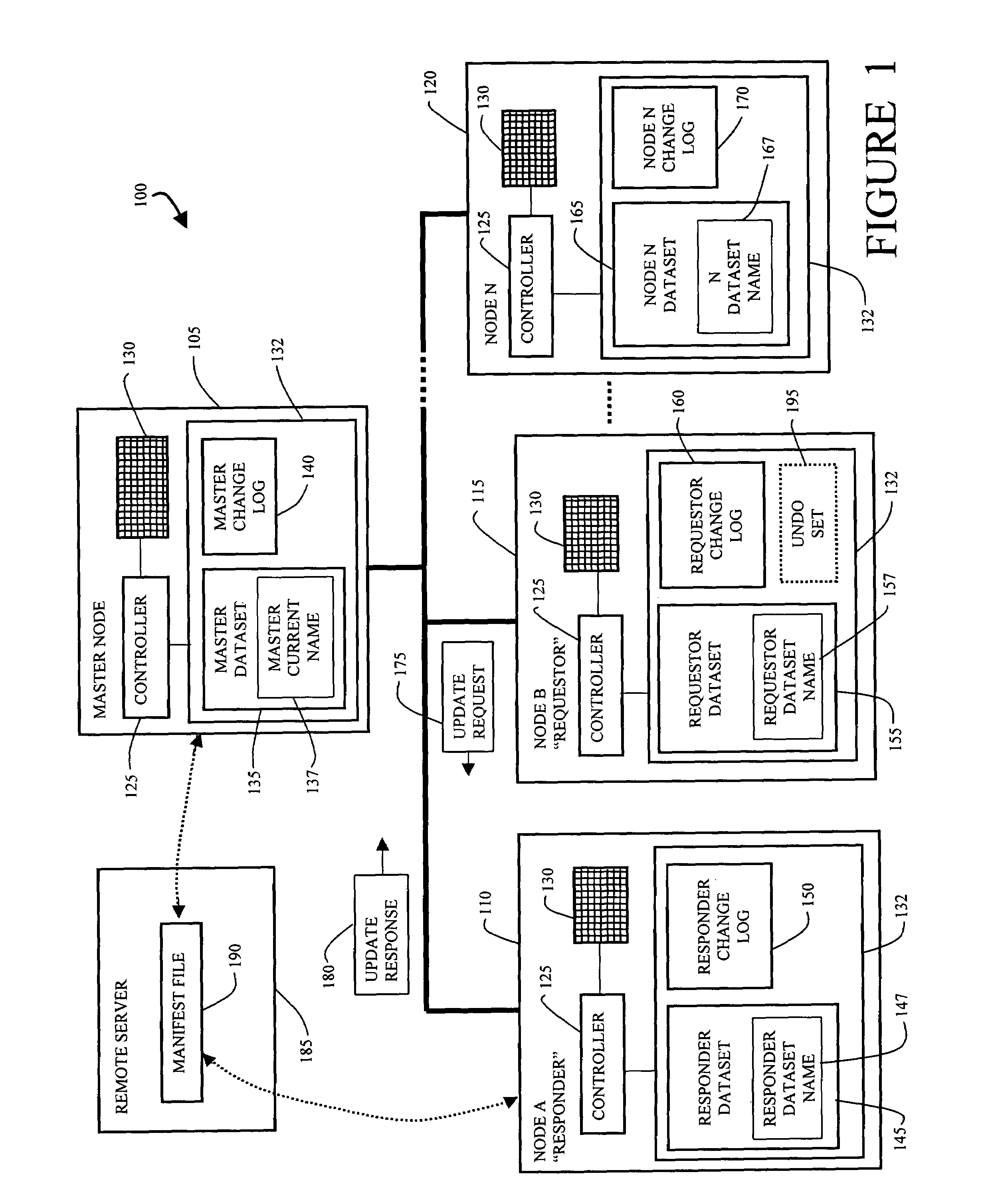
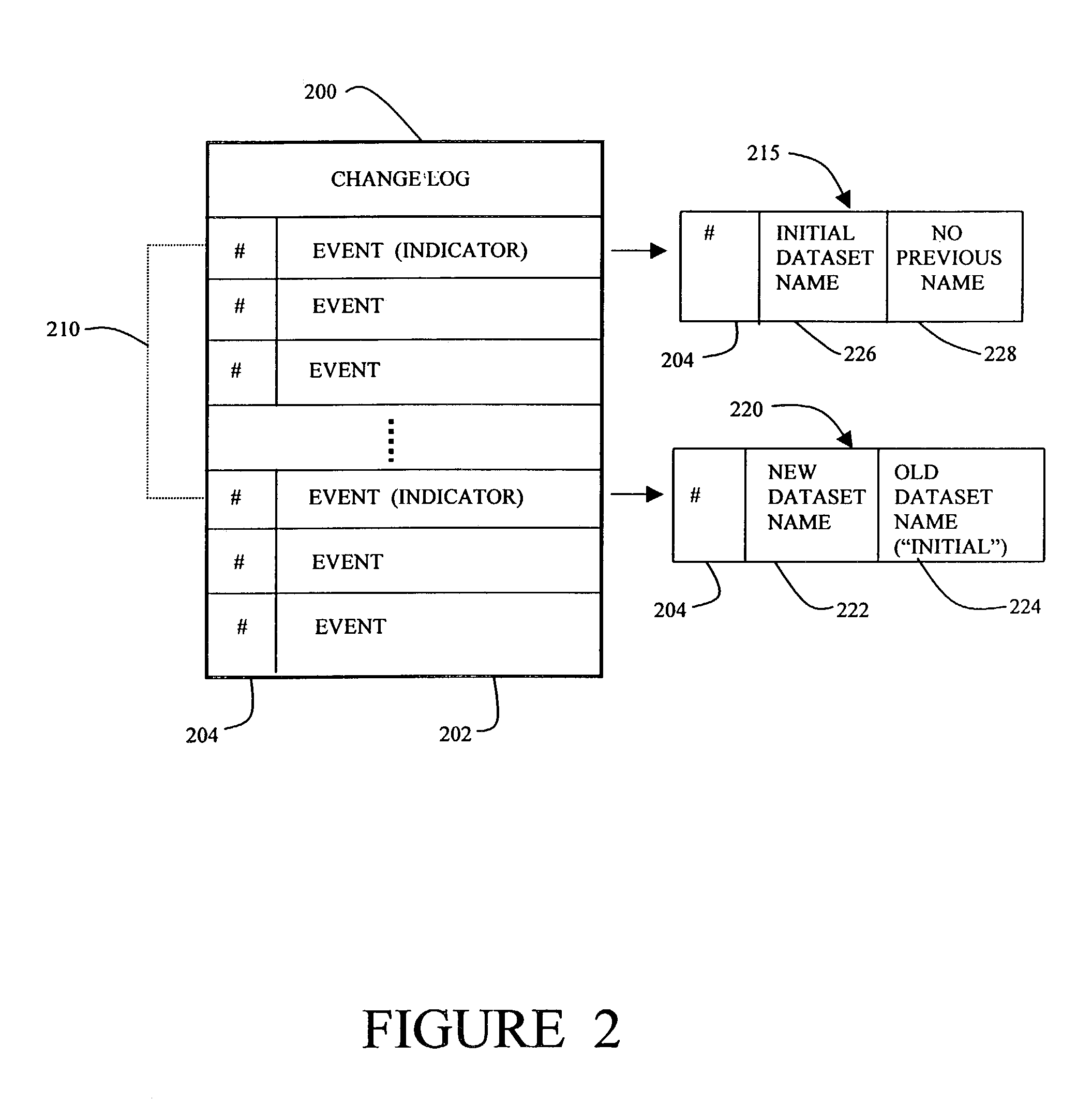
InactiveUS7158985B1Efficiently and accurately propagating dataset changes among nodesEffective maintenanceData processing applicationsDigital data processing detailsData setDistributed computing
A network of nodes caches replicated datasets in which dataset changes are efficiently propagated as a set of changes even under failure conditions. A master node and a plurality of subordinate nodes in the network each maintain a copy of the dataset and a change log storing change events in the dataset in that node. The change log further includes a rename chain having a plurality of linked rename records created in response to a new master gaining control of the dataset. The master node computes and propagates dataset changes to the subordinate nodes as a set of change events. If the master node fails, one of the subordinate nodes becomes temporary master and continues to propagate dataset changes using its dataset and its change log in response to update requests from other nodes where the update request contains information from the change log of the requestor node.
Owner:CISCO TECH INC
Data package including synchronization data
InactiveUS20020010807A1Digital data information retrievalData processing applicationsNetwork packetData source
A difference information receiver, a difference information transmitter and a difference information synchronizer which cooperate in a system or device to update data in the device with data received from other systems, or provide data for other systems to use in updating themselves are disclosed. A difference receiver in a device having at least one application data destination having a format includes a difference engine receiving difference information associated with a change to said at least one application data destination; and an application interface, applying said difference information to said at least one data destination. A method for updating data files in a system is also disclosed. The method may include the steps of: receiving difference information for a subset of said data files; and applying said difference information to said subset of said data files. In particular said step of receiving may comprise: receiving a change log detailing changes to data files on another system; and applying said changes to a data store containing data identical to said data files to generate changed data. A difference transmitter comprises an application in a system having a data source in a source format. The application may include an application interface, extracting data from said data source; and a difference engine receiving said data and outputting difference information associated with changes to said data source. A method for updating a data source in a system is also disclosed. The method may include the steps of extracting difference information from at least a subset of said data source; and outputting difference information for at least the subset of said data source. The step of extracting may comprise determining whether changes have been made to the subset of data source in the system; and generating a change log detailing changes to the subset of data source on another system. A difference synchronizer includes an extraction routine for extracting a first set of difference information resulting from changes to the data files; a differencing transmitter for transmitting said first set of difference information to an output; a differencing receiver for receiving a second set of difference information from an input; and a reconstruction routine for applying the second set of difference information to the data files. In a particular embodiment, the invention comprises a device engine including an application object; an application object store; and a delta module.
Owner:SYNCHRONOSS TECH
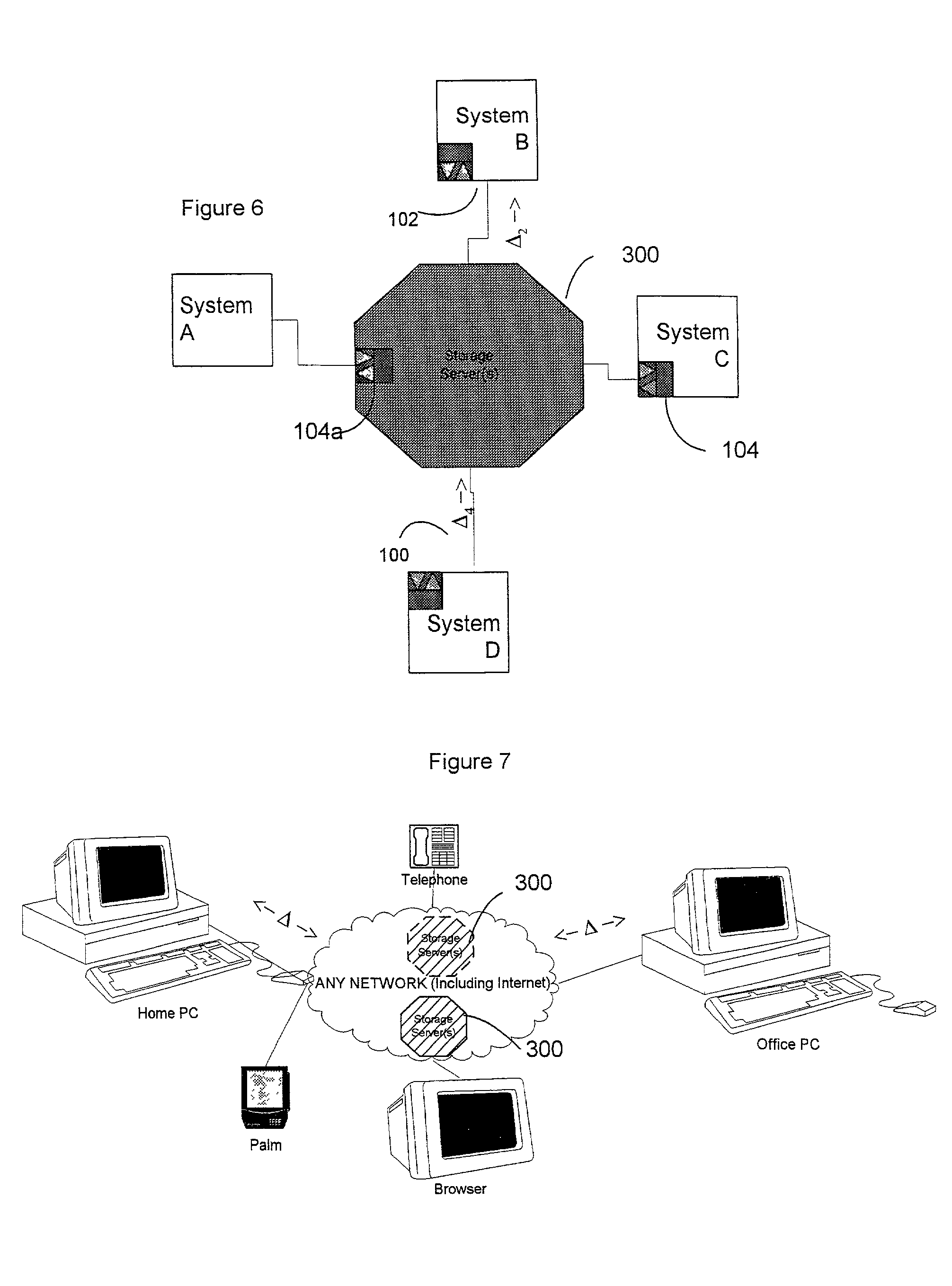
Method of automatically replicating data objects between a mobile device and a server
ActiveUS20060171523A1Best useEfficient use ofMetering/charging/biilling arrangementsDigital data processing detailsControl dataMobile device
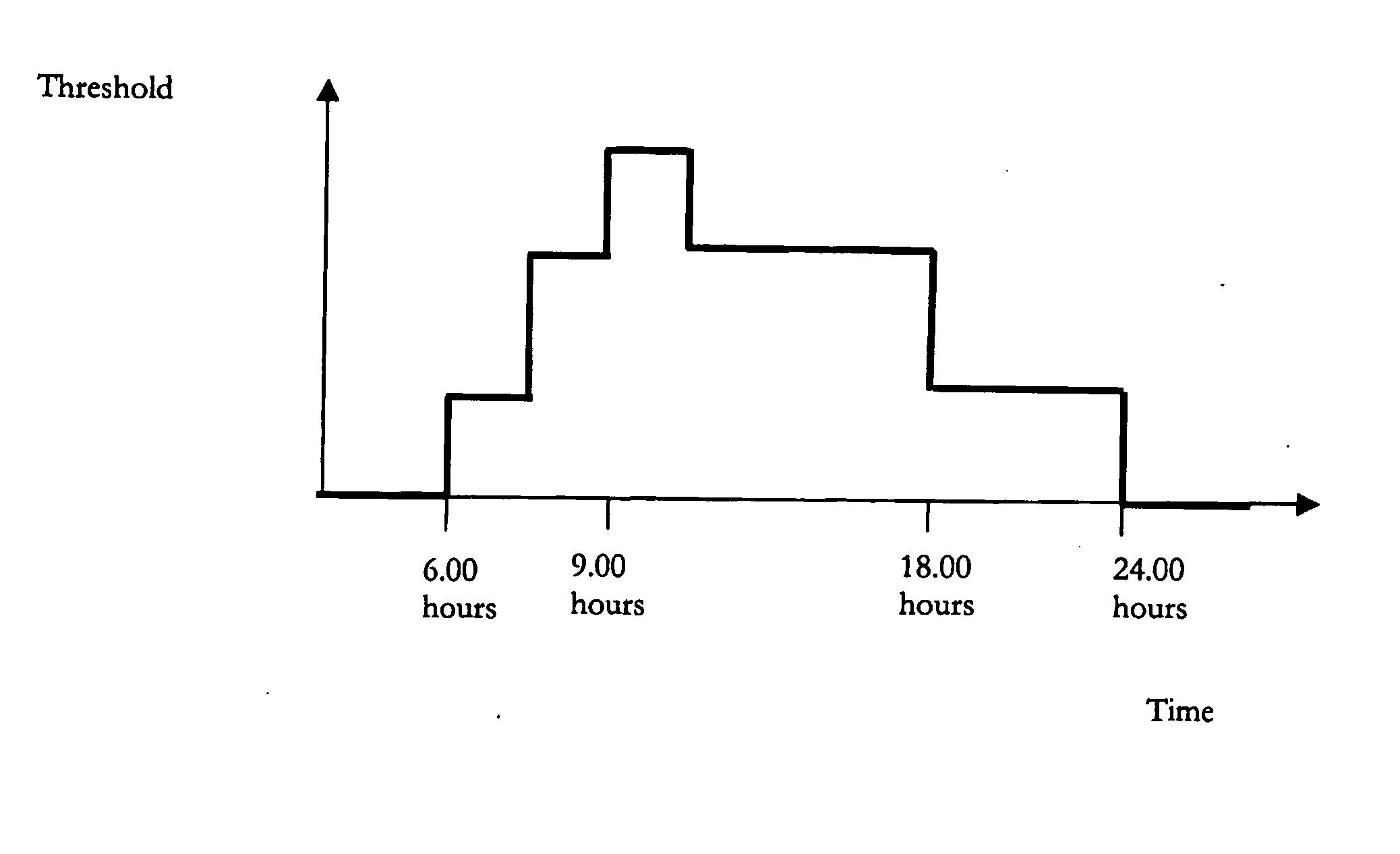
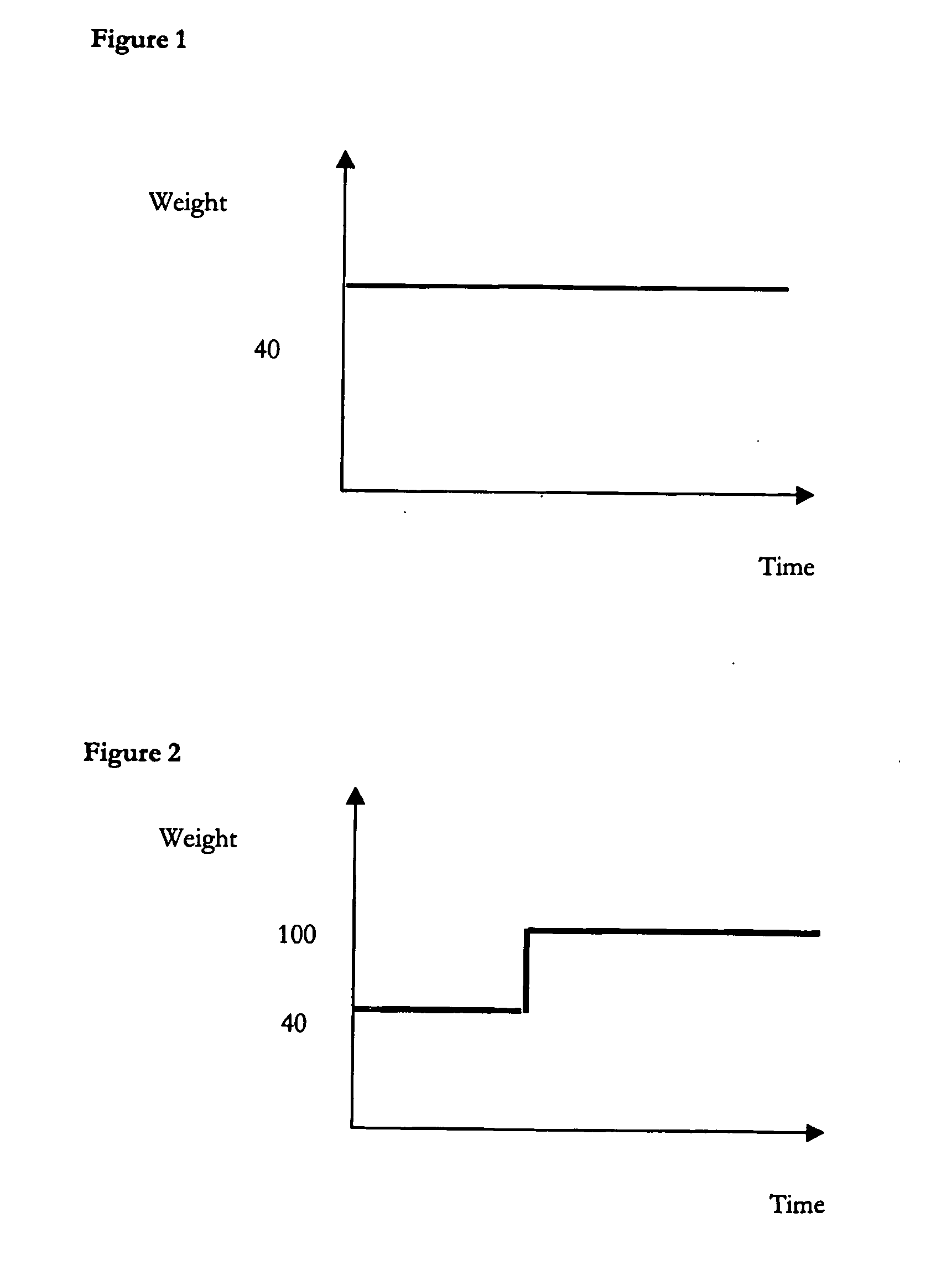
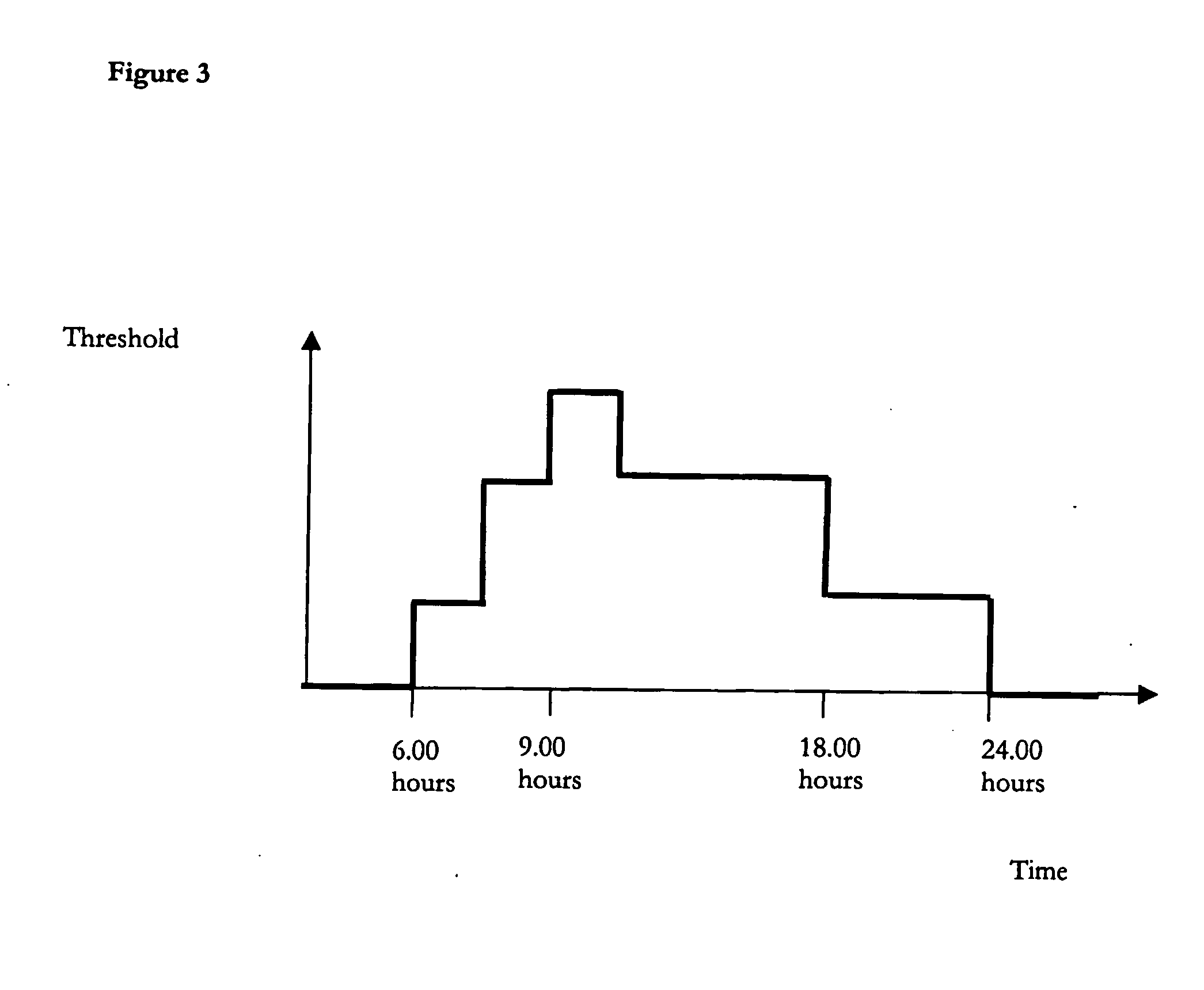
Network operators can control how data replication services use available bandwidth, in order to make the most efficient usage of that bandwidth, using parameters applied to a data object to be replicated. The parameters may be both time dependent and also relate to how urgently that object needs to be replicated. A change log lists all objects at the device and / or server to be replicated and the parameters then comprise a weight associated with each object that defines how urgently that object needs to be replicated; the weight of each object is then locally compared to a threshold at a given time and the outcome of the comparison determines whether the object is sent for replication or not at that time. This combination of weight and threshold gives a flexible way to control the timing of data replication and hence make the best use of bandwidth.
Owner:SONY DEUT GMBH +1
Binary data synchronization engine
InactiveUS20020040369A1Data processing applicationsDigital data information retrievalData synchronizationData source
A difference information receiver, a difference information transmitter and a difference information synchronizer which cooperate in a system or device to update data in the device with data received from other systems, or provide data for other systems to use in updating themselves are disclosed. A difference receiver in a device having at least one application data destination having a format includes a difference engine receiving difference information associated with a change to said at least one application data destination; and an application interface, applying said difference information to said at least one data destination. A method for updating data files in a system is also disclosed. The method may include the steps of: receiving difference information for a subset of said data files; and applying said difference information to said subset of said data files. In particular said step of receiving may comprise: receiving a change log detailing changes to data files on another system; and applying said changes to a data store containing data identical to said data files to generate changed data. A difference transmitter comprises an application in a system having a data source in a source format. The application may include an application interface, extracting data from said data source; and a difference engine receiving said data and outputting difference information associated with changes to said data source. A method for updating a data source in a system is also disclosed. The method may include the steps of extracting difference information from at least a subset of said data source; and outputting difference information for at least the subset of said data source. The step of extracting may comprise determining whether changes have been made to the subset of data source in the system; and generating a change log detailing changes to the subset of data source on another system. A difference synchronizer includes an extraction routine for extracting a first set of difference information resulting from changes to the data files; a differencing transmitter for transmitting said first set of difference information to an output; a differencing receiver for receiving a second set of difference information from an input; and a reconstruction routine for applying the second set of difference information to the data files. In a particular embodiment, the invention comprises a device engine including an application object; an application object store; and a delta module.
Owner:SYNCHRONOSS TECH
Method of replicating data between computing devices
InactiveUS20050021571A1Minimizes bandwidth requirementSave considerable memory spaceEnergy efficient ICTDatabase distribution/replicationWireless computingElectronic mail
Resource constrained wireless computing devices (e.g. mobile telephones) are given a replication capability for database records (e.g. to enable backing up contacts, e-mails, photographs etc. onto a remote server). This operates without undue processing burden, using low bandwidth unreliable wireless connections. This is achieved by not including a time stamp in each database record, but instead time stamping only a change log record; this approach saves considerable memory space on the wireless device since there is no need to time stamp every database record, as is usually done in the prior art. The change log defines what data is to be replicated; it alone has to be sent to a main server which hosts a master copy of the database and hence has to be kept up to date. Because the change log is compact, far less data has to be sent for data replication purposes—typically only the field which has changed, how it was be changed and when it was changed on the wireless computing device. Prior art systems typically send an entire record, even though that will contain data that has not changed.
Owner:COGNIMA
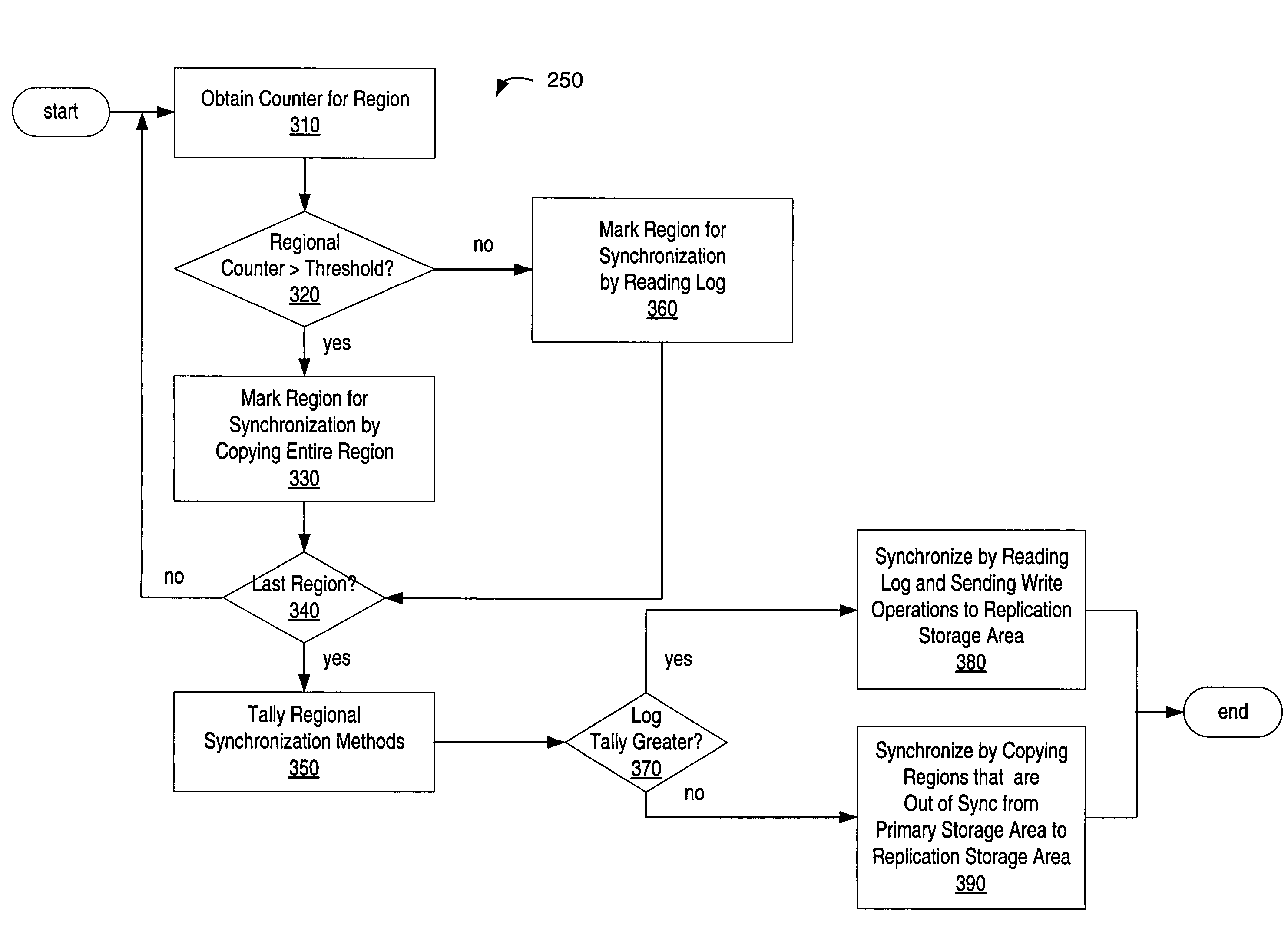
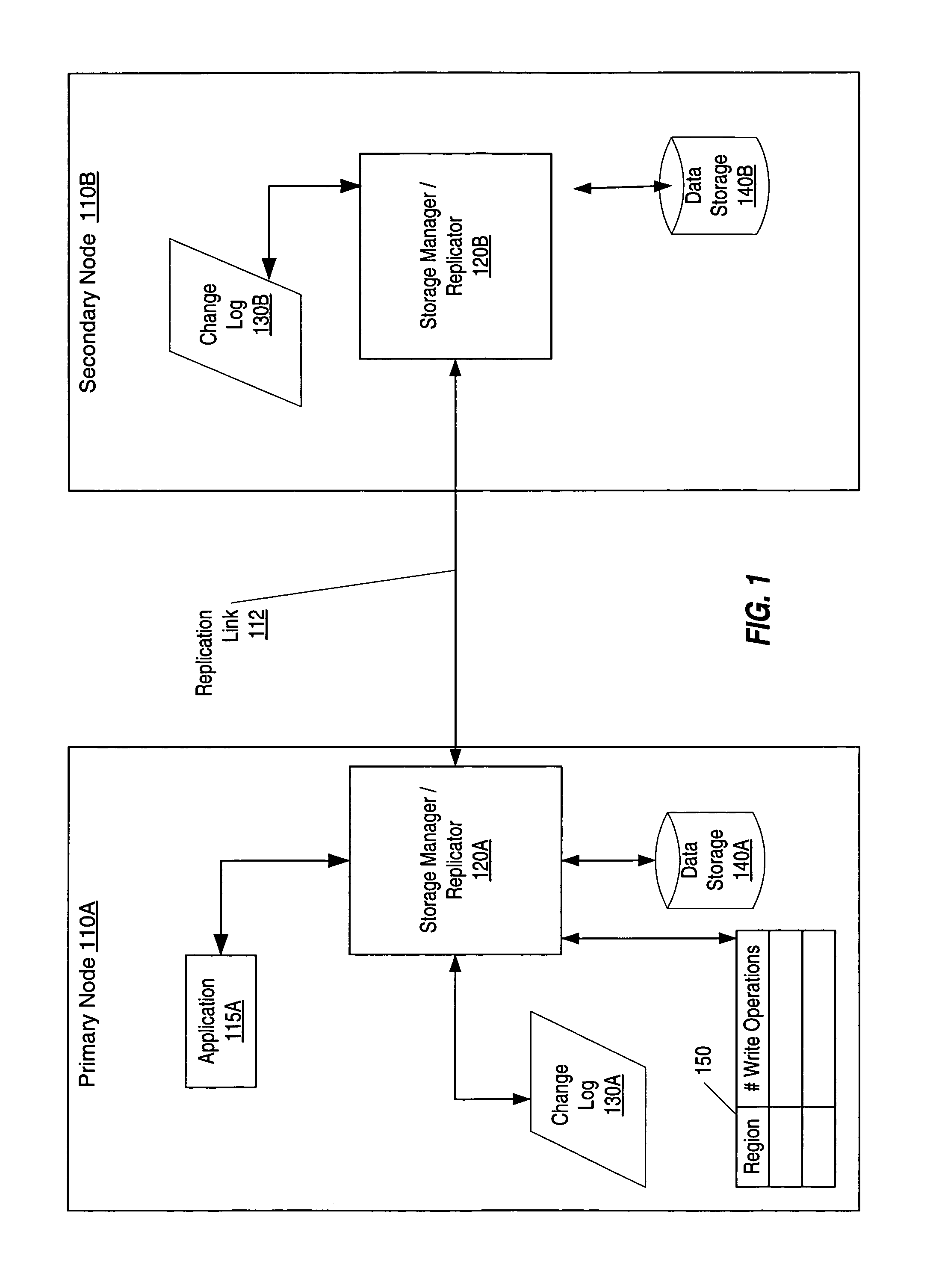
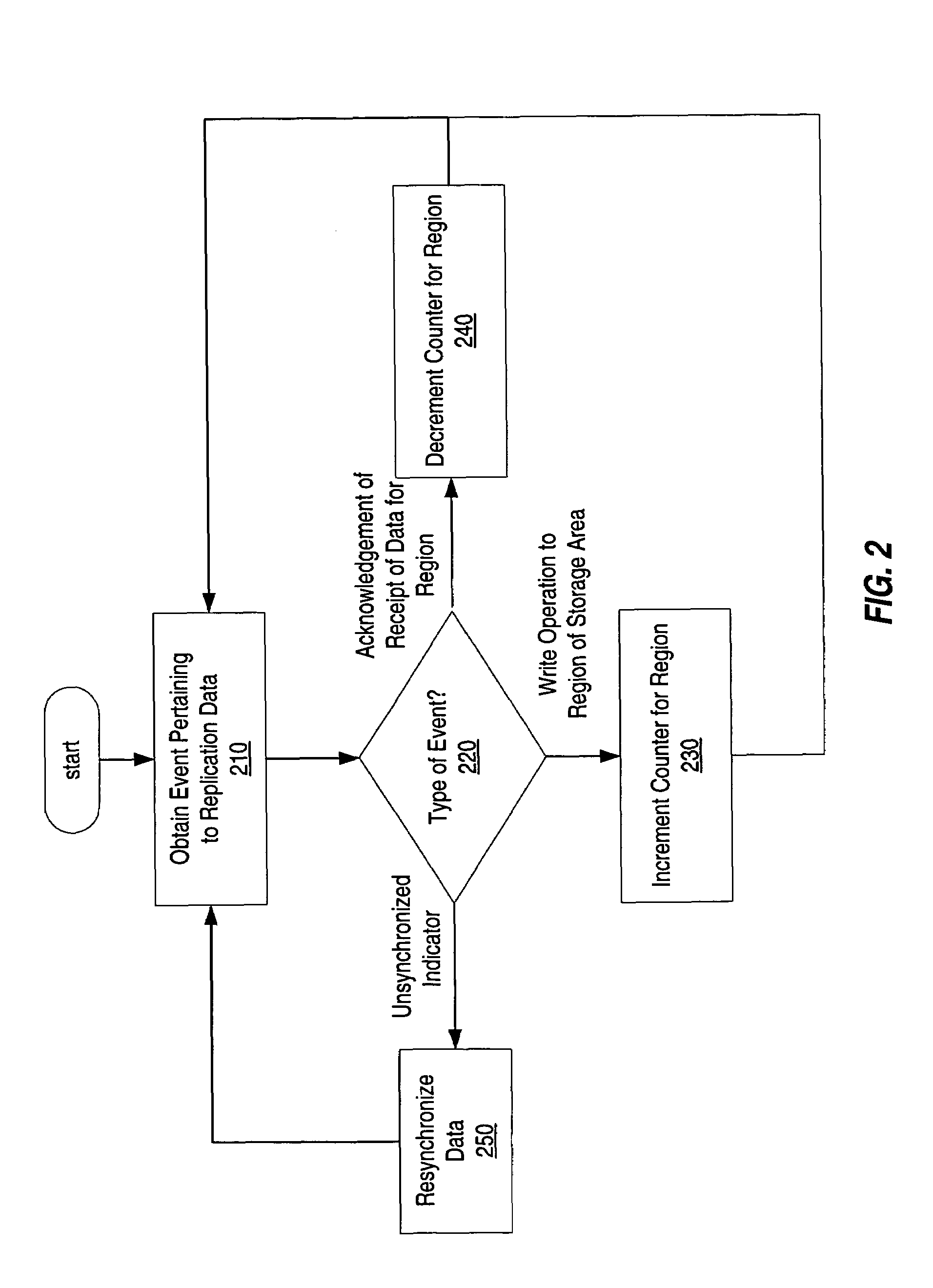
Maintaining spatial locality of write operations
ActiveUS7461230B1Data efficientEasy to operateError detection/correctionMemory systemsComputerized systemAncillary data
A method, system, computer system, and computer-readable medium that identify the number of times areas of storage are updated and use that information to synchronize primary and secondary storage areas. The invention enables quick resumption of operations upon a discovery that primary and secondary data have become unsynchronized. Regions of storage that are unsynchronized can be identified quickly without the need to read the change log. In addition, data are copied efficiently, with minimal or no duplication of effort or data. Faster and more reliable storage can be allocated for storing regions of data that are “hot spots,” thereby making better use of existing storage resources and budgets.
Owner:SYMANTEC OPERATING CORP
Html/xml tree synchronization
InactiveUS20030028561A1Lower performance requirementsImprove synchronicityData processing applicationsDigital computer detailsApplication softwareDocument tree
The HTML / XML tree synchronization module synchronizes a document with a view or multiple views, after a change has been made to the document. First, the tree synchronization module receives a document change from an application program. An update processor converts the tree data of the document to a character string, and receives document change information from one or more application program interfaces. The update processor utilizes the document change information to update the document tree data character string. The document change information is then sent to one or more application program interfaces to determine the scope and content of the document views. A log generator receives the view change information, and creates record logs for each changed document view. These logs are played by a log player to each view, and each view data tree is updated with the view changes contained in the change logs. The tree synchronization module sends the subsequent view changes to the application program to update the display views.
Owner:MICROSOFT TECH LICENSING LLC
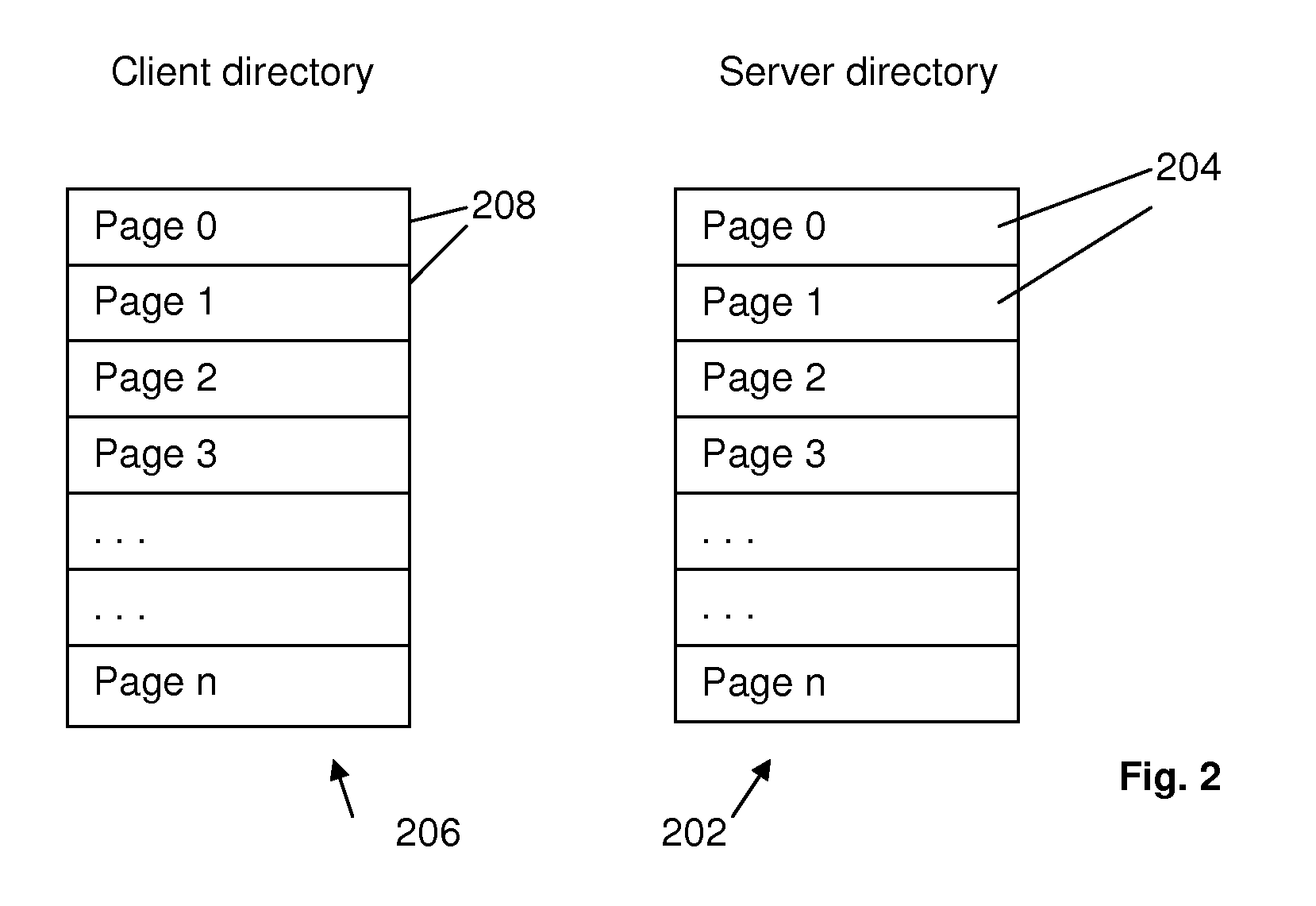
Method, Apparatus and Computer Program Product for Maintaining File System Client Directory Caches with Parallel Directory Writes
InactiveUS20100174690A1Avoid spreadingShort response timeDigital data information retrievalDigital data processing detailsDistributed File SystemFile system
A cached version of a file system directory is synchronized with a server version of the directory in a distributed file system. Both a server and a client specify version numbers for their directory versions. On receiving a request from the client specifying a directory update, the server updates its version, increments its version number, and transmits a reply to the client containing a change log with the incremented version number. Upon receiving the reply, the client compares the received version number with that of its cached version. If the version number matches that of the next expected update, the client applies the updates to its cached version and increments its version number. Otherwise, it adds the received change log to a change log queue for the directory without incrementing the last applied version. Mechanisms are provided for handling parallel read and update requests without awaiting replies from the server.
Owner:IBM CORP
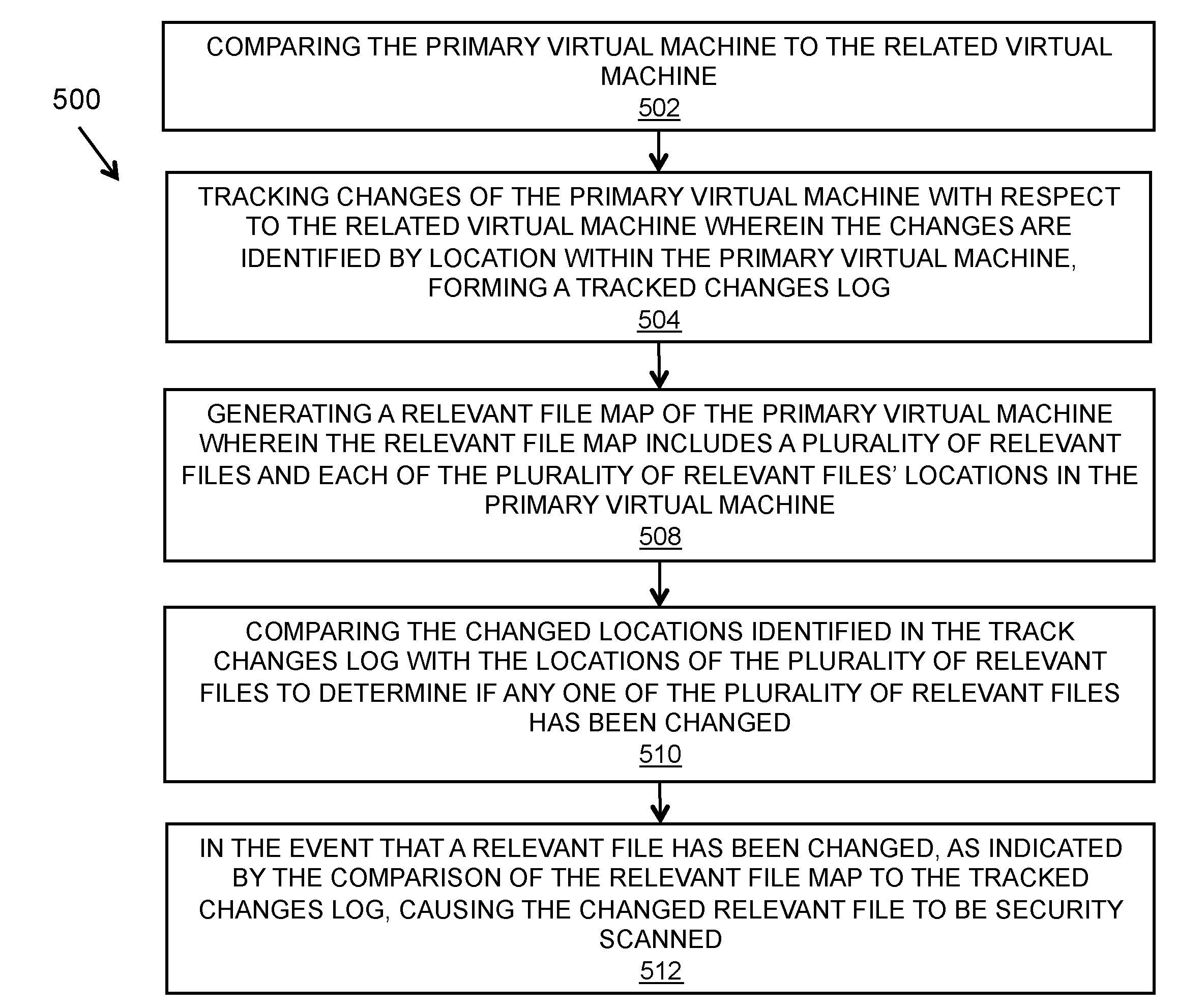
System and method of whitelisting parent virtual images
ActiveUS20120066762A1Convenient ArrangementLower requirementMemory loss protectionError detection/correctionChangelogWhitelist
In embodiments of the present invention improved capabilities are described for virtual machine scan optimization. In response to a change in the primary virtual machine, the virtual machine scan optimization may involve comparing the primary virtual machine to the related virtual machine and tracking changes of the primary virtual machine with respect to the related virtual machine wherein the changes are identified by location within the primary virtual machine; forming a tracked changes log; generating a relevant file map of the primary virtual machine wherein the relevant file map includes a plurality of relevant files and each of the plurality of relevant files' locations in the primary virtual machine; comparing the changed locations identified in the track changes log with the locations of the plurality of relevant files to determine if any one of the plurality of relevant files has been changed; and in the event that a relevant file has been changed, as indicated by the comparison of the relevant file map to the tracked changes log, causing the changed relevant file to be security scanned.
Owner:SOPHOS
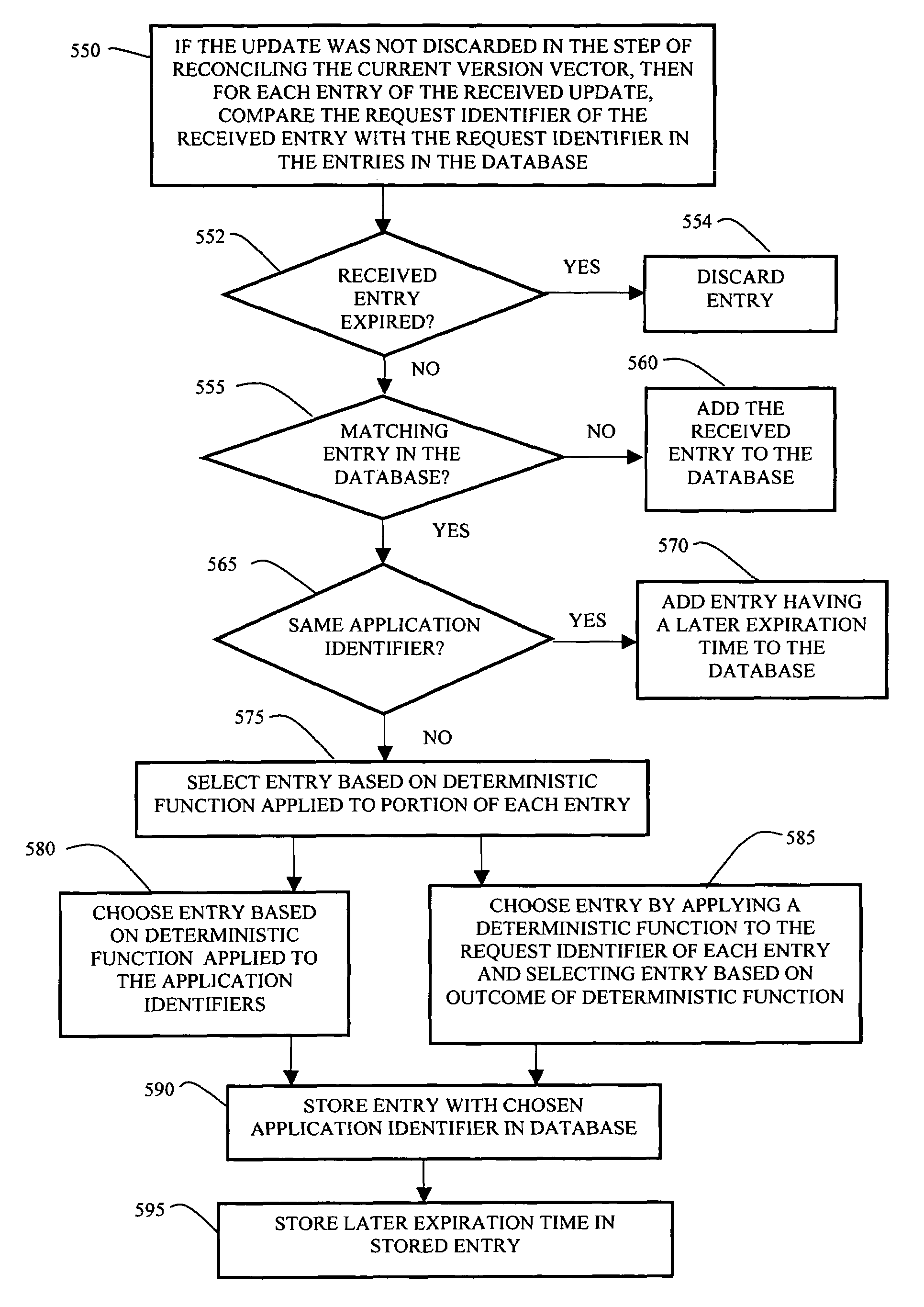
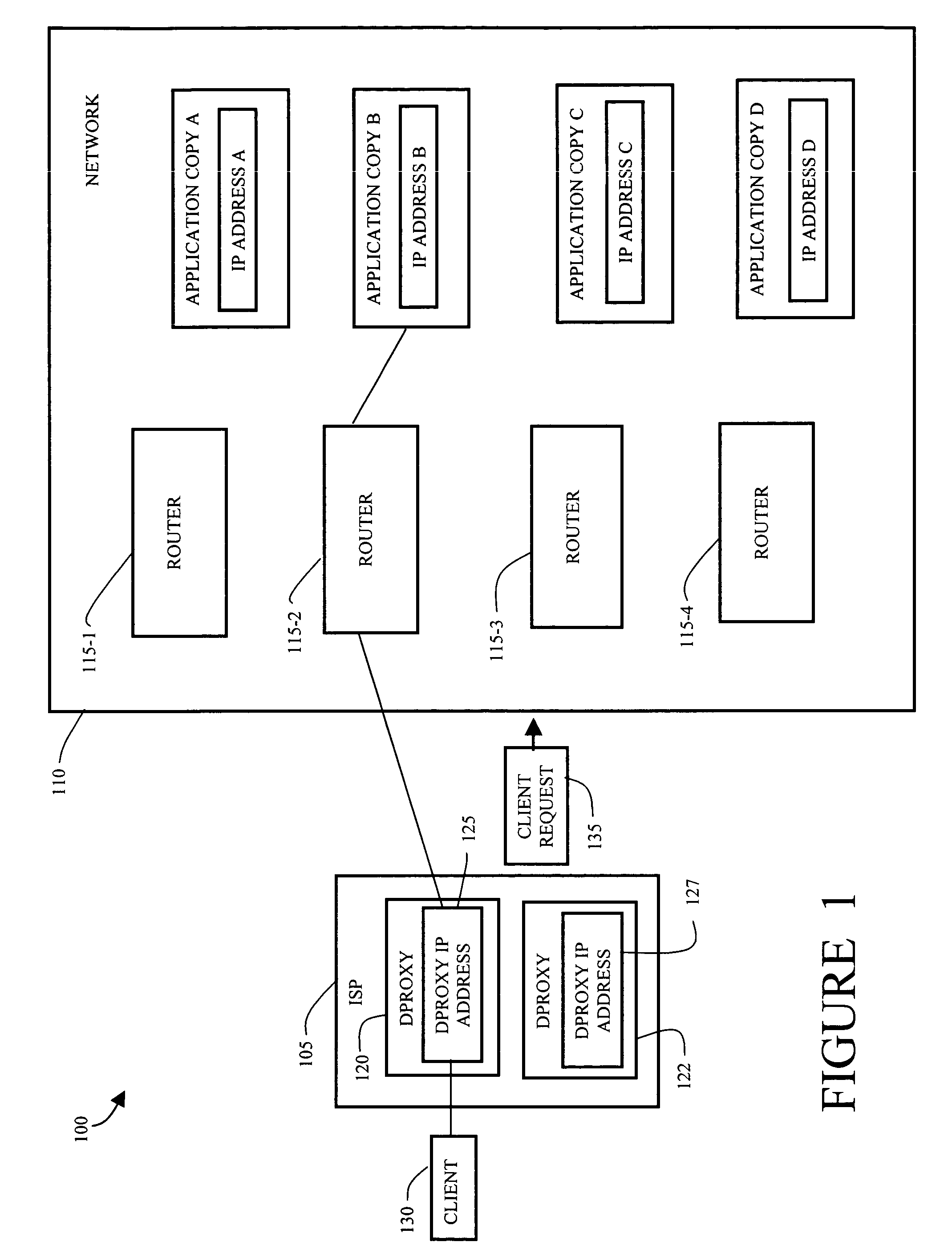
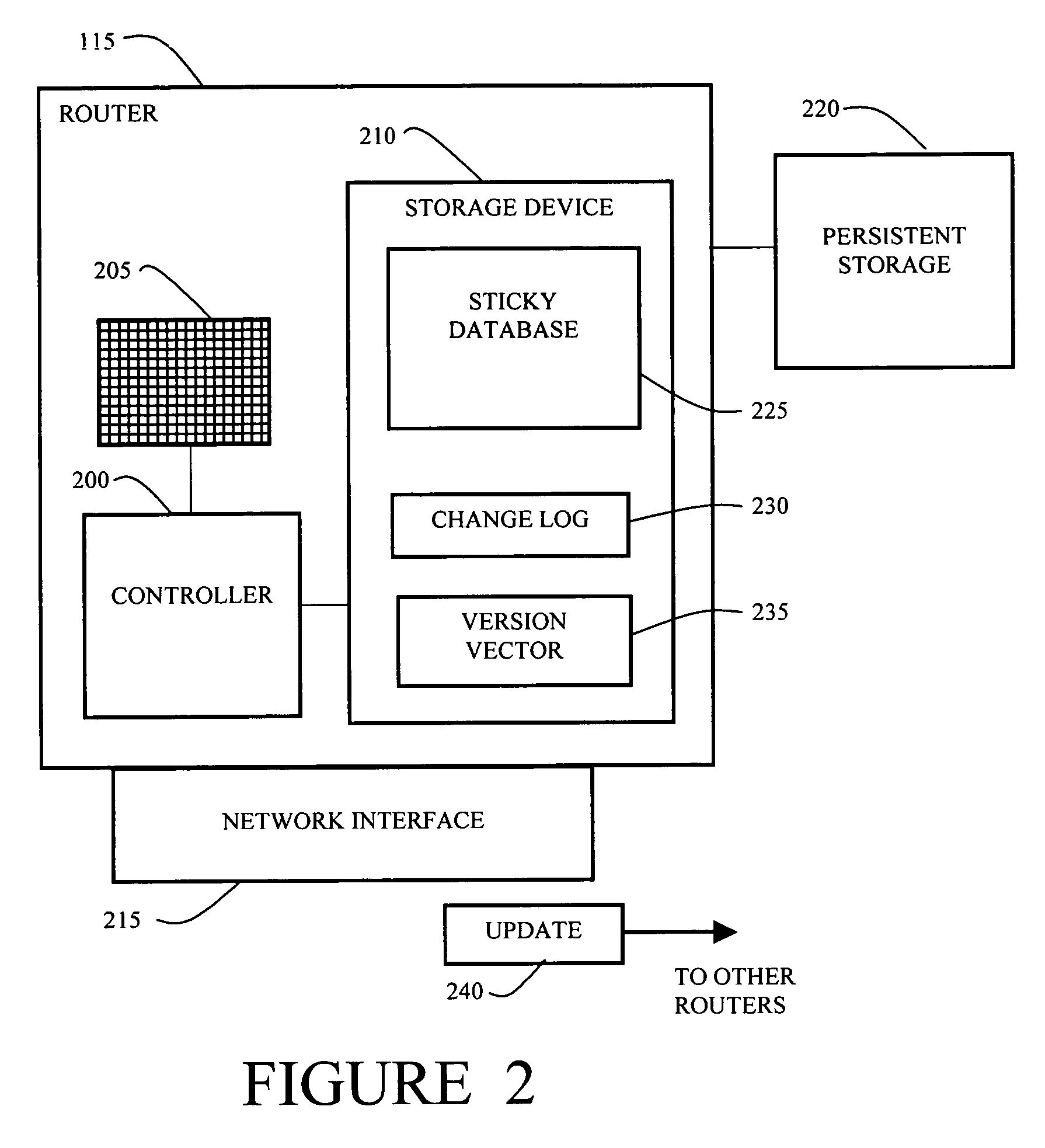
Method and apparatus for providing sticky bindings using version vectors
InactiveUS7610387B1Promote recoveryImprove performanceDatabase queryingTime-division multiplexClient-sideComputer science
In a network having a plurality of routers and also an application running at a plurality of replicas, a system for maintaining a client session between a client and a particular replica includes providing a database of bindings of client request identifiers to replicas. The system further includes a change log of changes made to the database where each entry has an event number. A version vector associated with the database and the change log holds a most recent event number for each router in the network. The system receives updates of change events made at the routers in the network and reconciles the updates with the database and current version vector. The system has data to maintain a client session between the client and the particular replica through repeated requests. Also the system and routers share data so that the client session can be maintained no matter which router handles subsequent client requests.
Owner:CISCO TECH INC
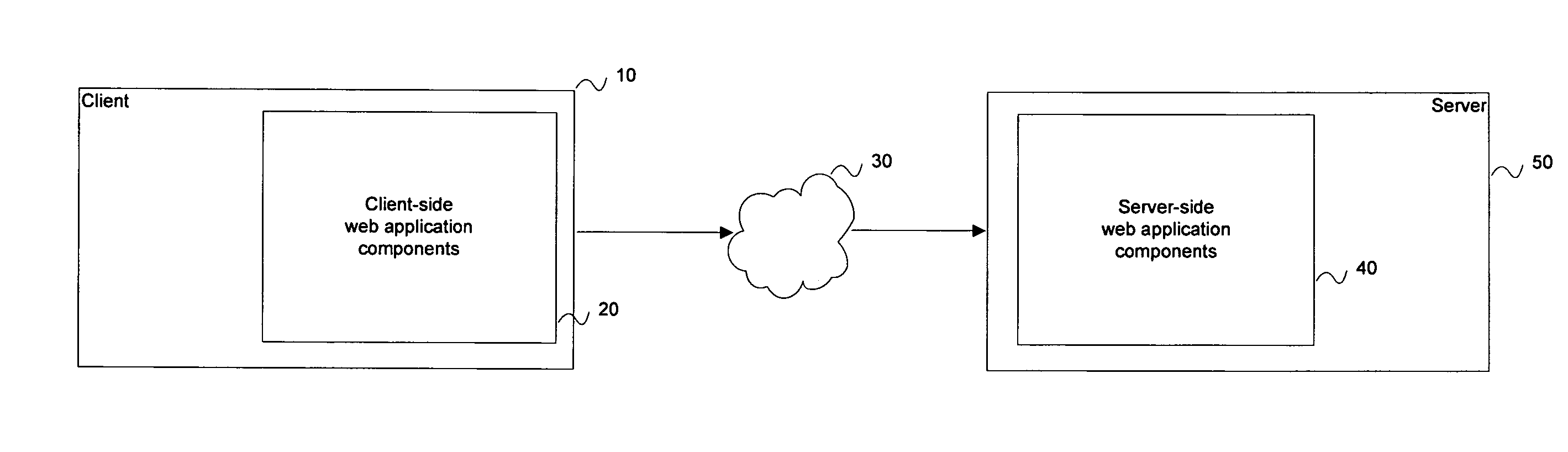
Asynchronous client to server updates
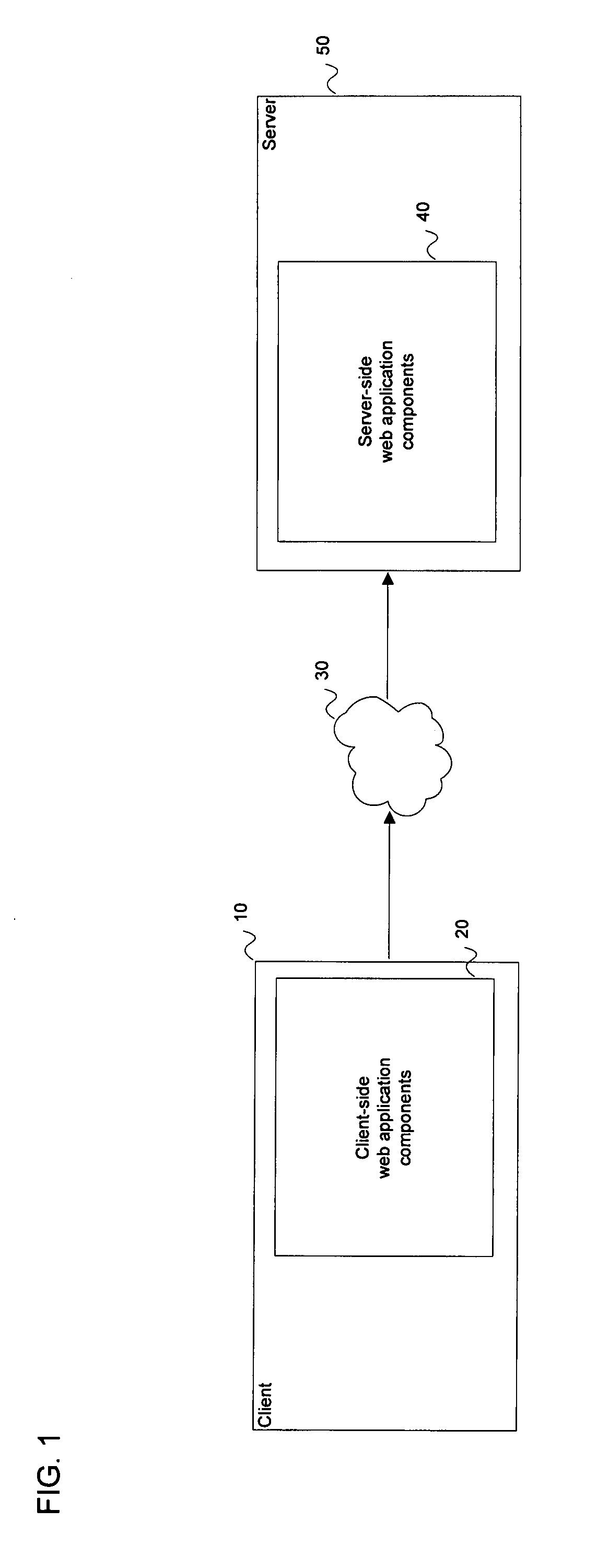
ActiveUS20090119302A1Improve responsivenessReduce the amount requiredWebsite content managementSpecial data processing applicationsWeb applicationApplication software
Methods and apparatus are provided which enable client-server communication during the execution of a web application to be batched, so as to manage the processing load on server-side components of the web application and the transmission load on the network(s) coupling the client and server. In some embodiments, client-side components of the web application are operable to capture processing events in a change log on the client, and transmit at least a subset of the entries in the change log to the server upon the occurrence of a predetermined event, such as a passage of time since a previous transmission.
Owner:MICROSOFT TECH LICENSING LLC
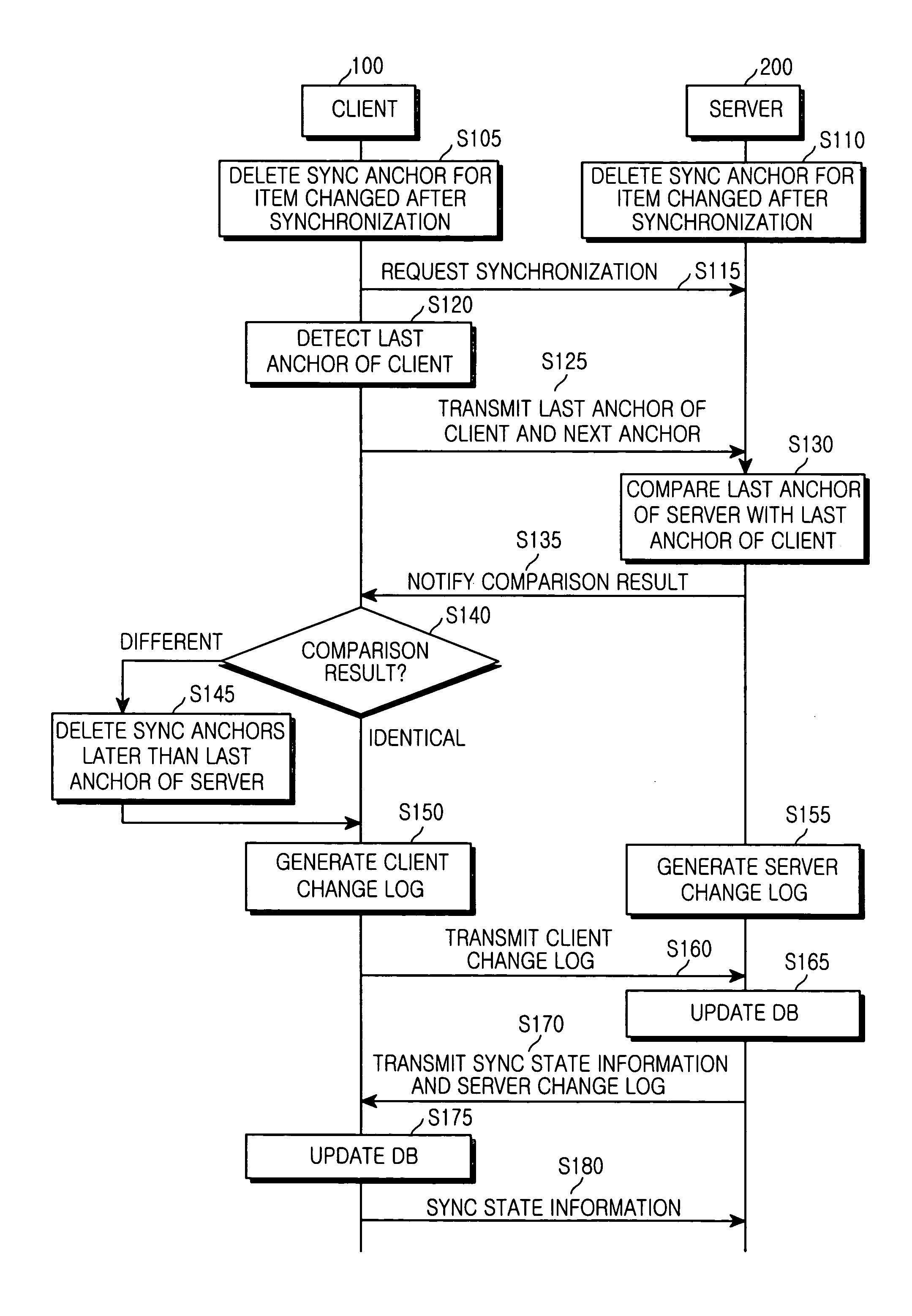
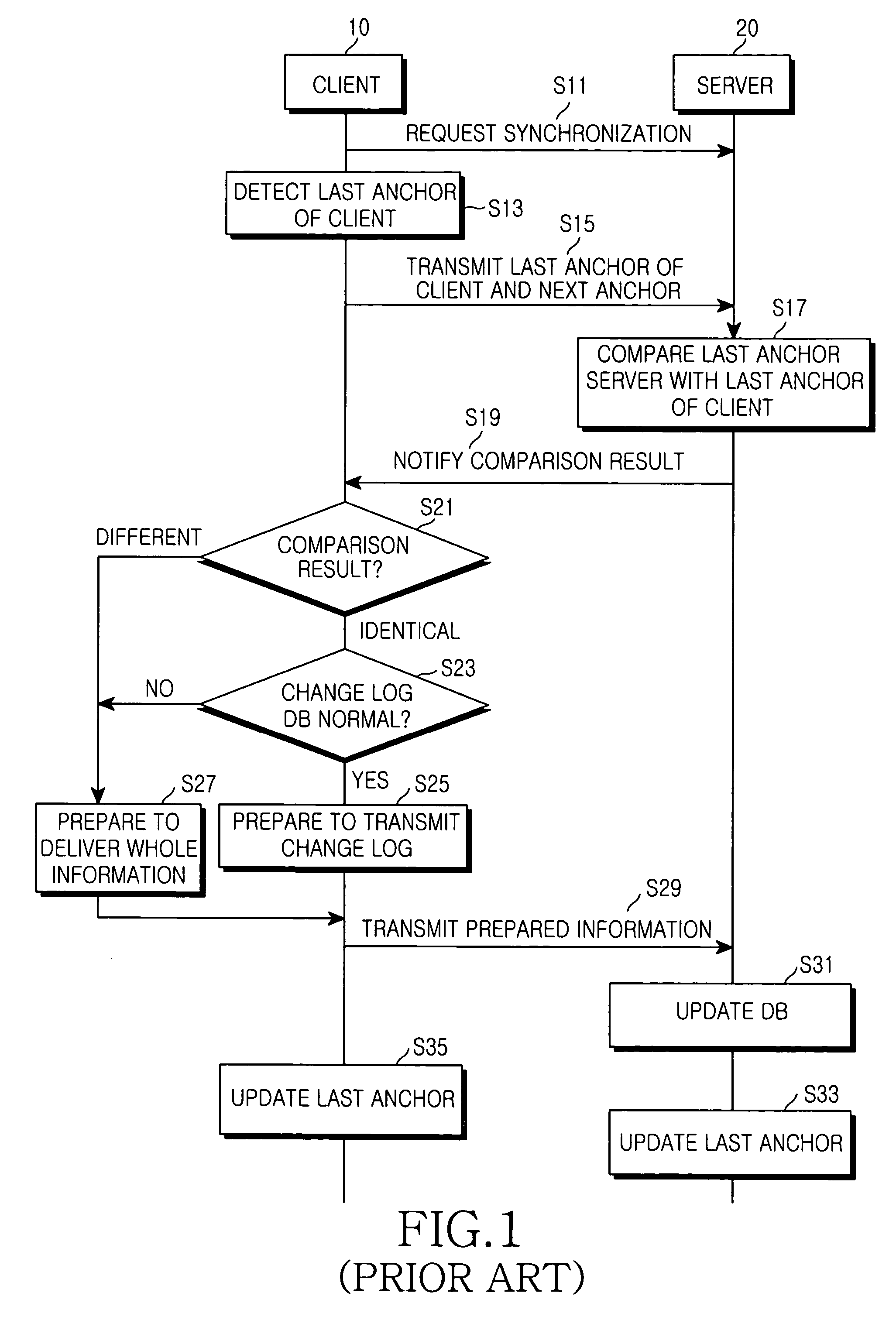
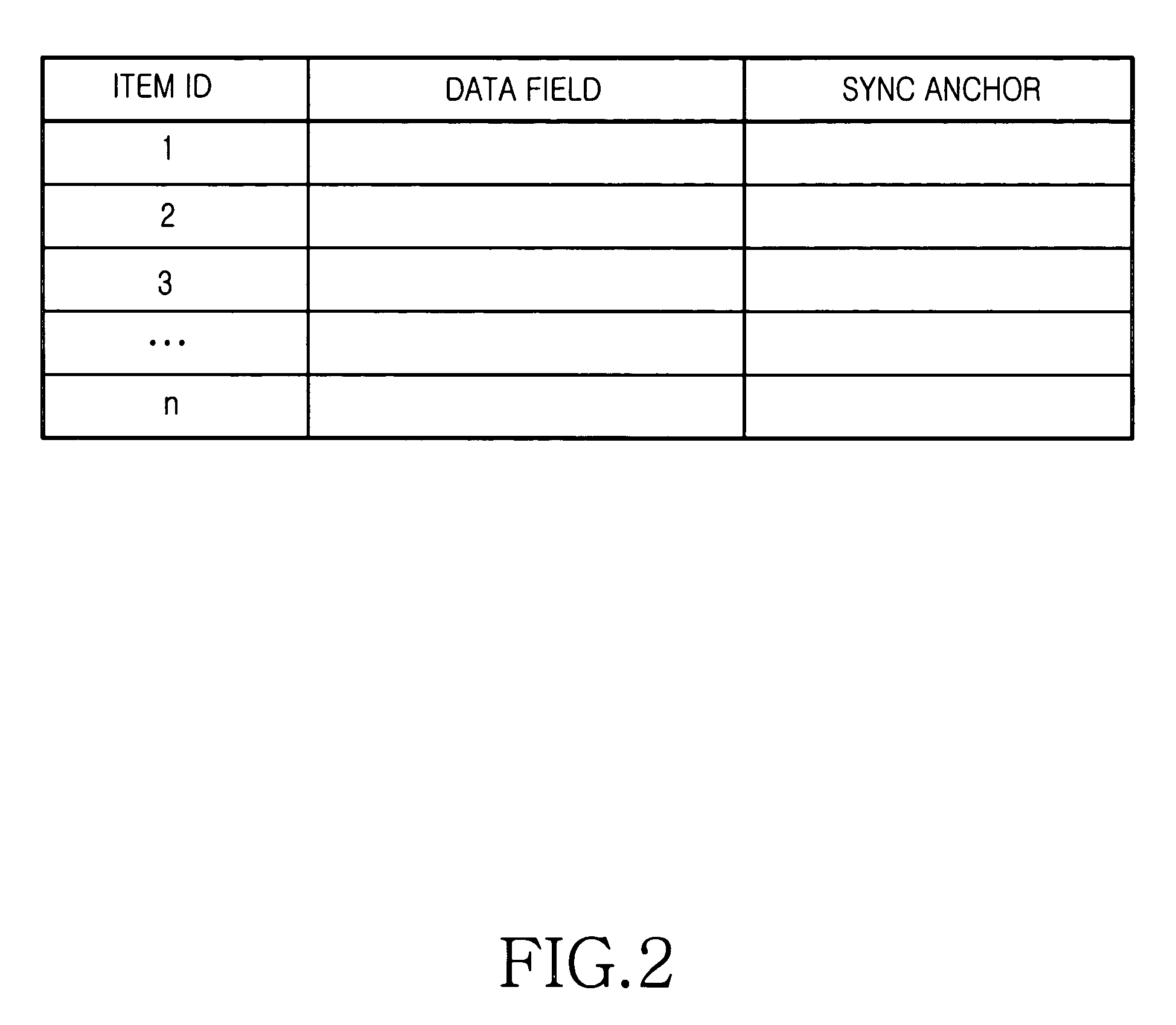
System and method of synchronizing data between a server and a client
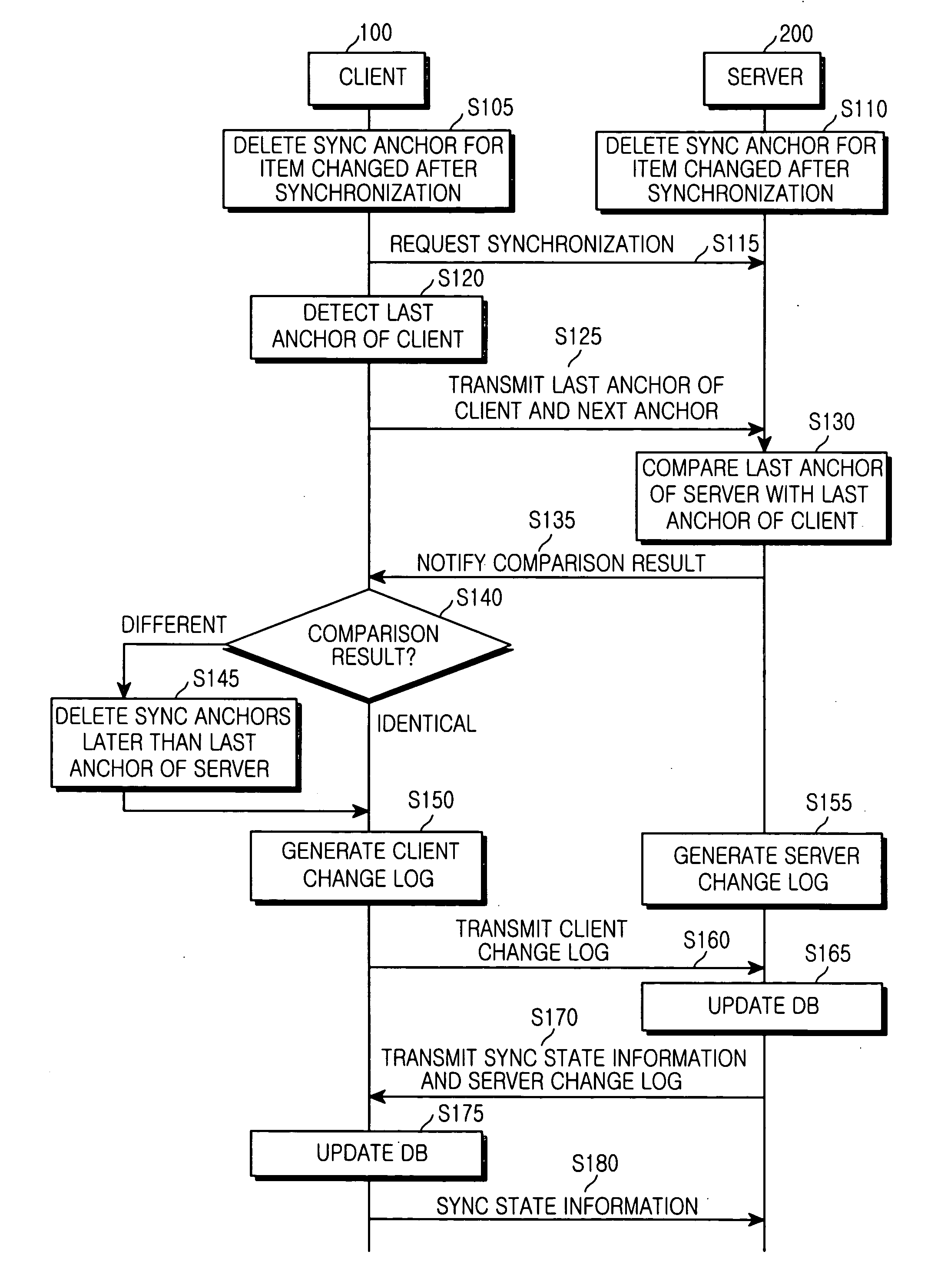
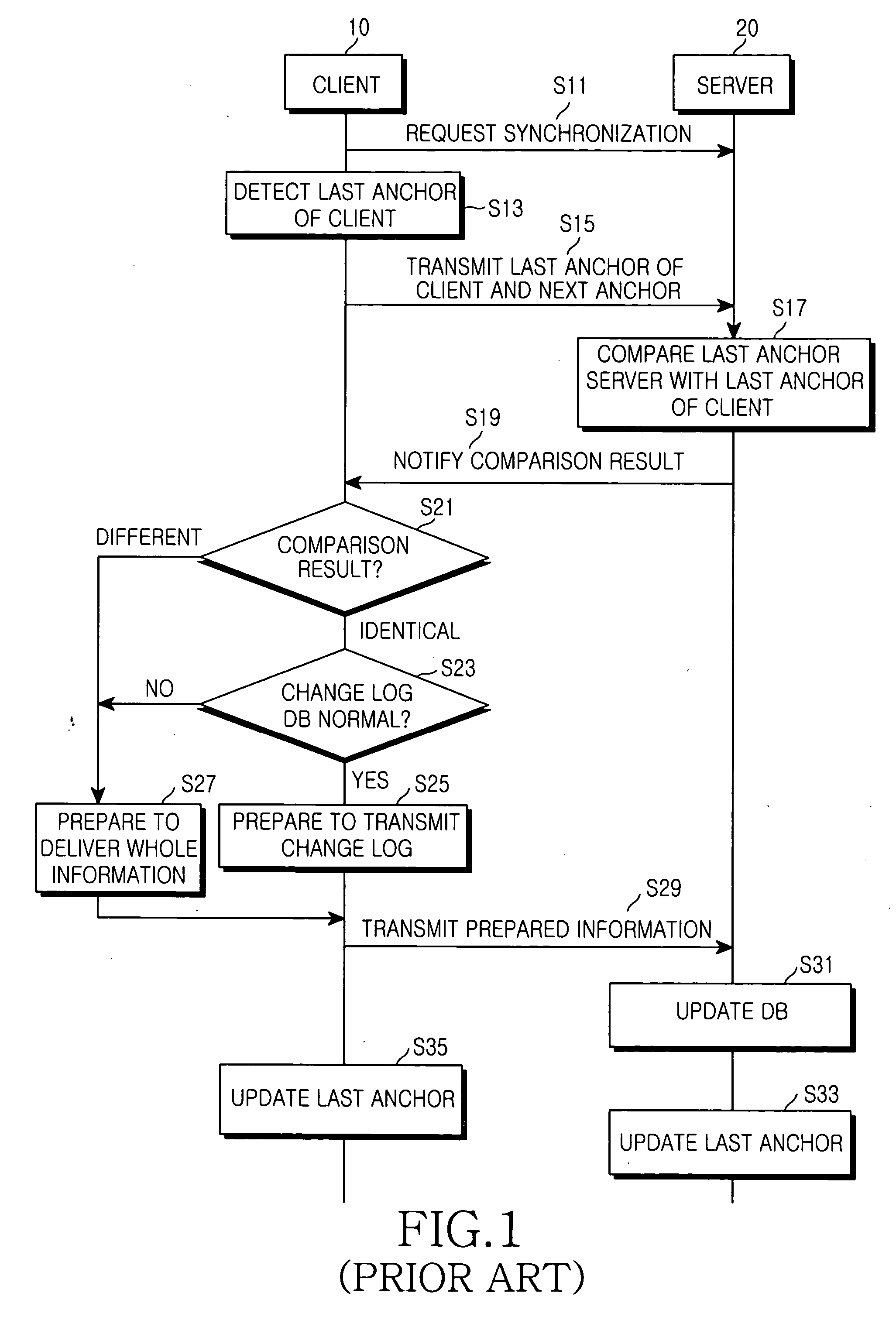
ActiveUS20050198084A1Reduce sync delayIncrease speedDigital data processing detailsMultiple digital computer combinationsData synchronizationClient-side
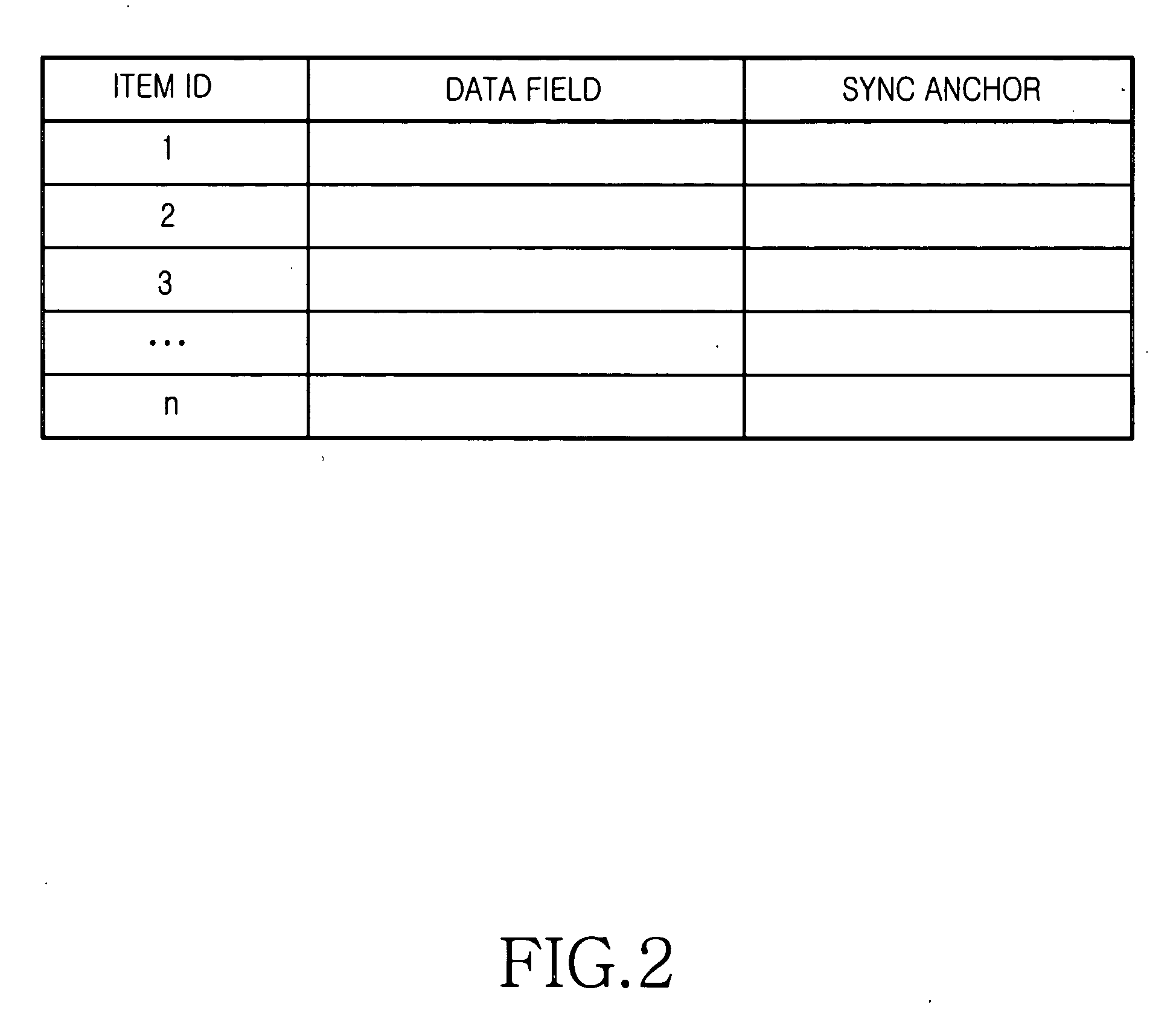
A data synchronizing method between a server and a client is provided. The server and the client manage database changed after a previous synchronization of data shared by them. The database includes a sync anchor field for each data item. When a sync session is initiated upon request of the client, a last anchor is detected from the database stored in the client and a last anchor from the database stored in the server. The last anchor of the client is compared with the last anchor of the server. A client change log and a server change log are generated according to a comparison result based on a database change that occurred after the last anchor of client or server when the last anchor of the client is identical to the last anchor of the server. The databases are updated according to the client change log and the server change log.
Owner:SAMSUNG ELECTRONICS CO LTD
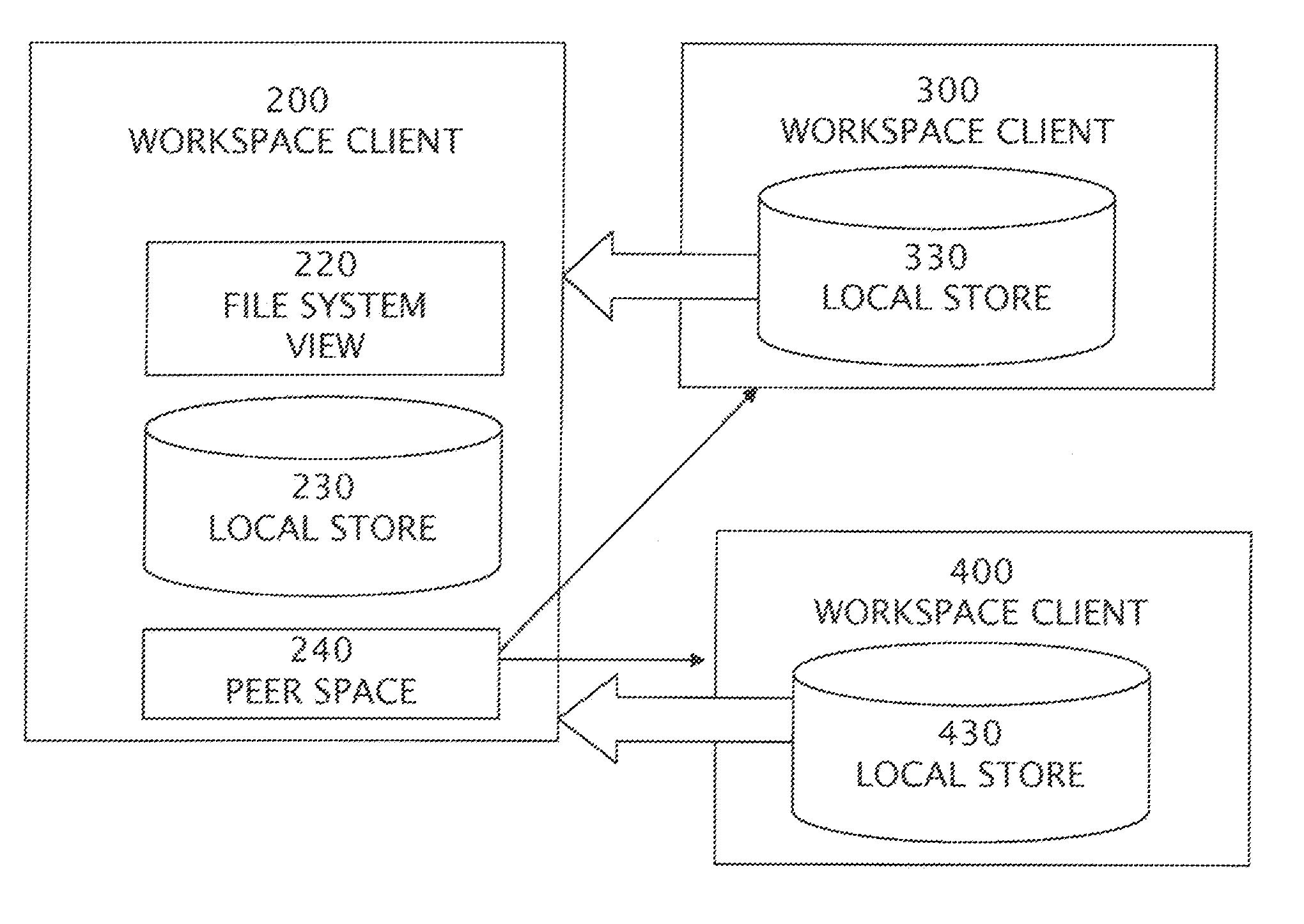
Coherent File State Maintained Among Confederated Repositories By Distributed Workspace Apparatuses Backed Up By a File State Ledgerdemain Store
InactiveUS20140222758A1Digital data processing detailsFile access structuresDocument StatusFile system
Each one of many networked user workstation apparatuses may commit a file into the variant controlled file system by storing a version tracking record for each change log and content point for each block of the file into its local file system view store, and transmitting a version tracking record to a network attached file state ledgerdemain store. Each user workstation displays a file system view of every variant of every file in the file system for selection. When required, the workstation applies change logs to content points according to first a local file system view store for a version tracking record, then requesting and comparing version tracking records from confederated repositories at other user workstation apparatuses, and if unsatisfied, obtains a version tracking record from a network attached file state ledgerdemain store.
Owner:IC MANAGE
Systems and methods for generating a change log for files in a managed network
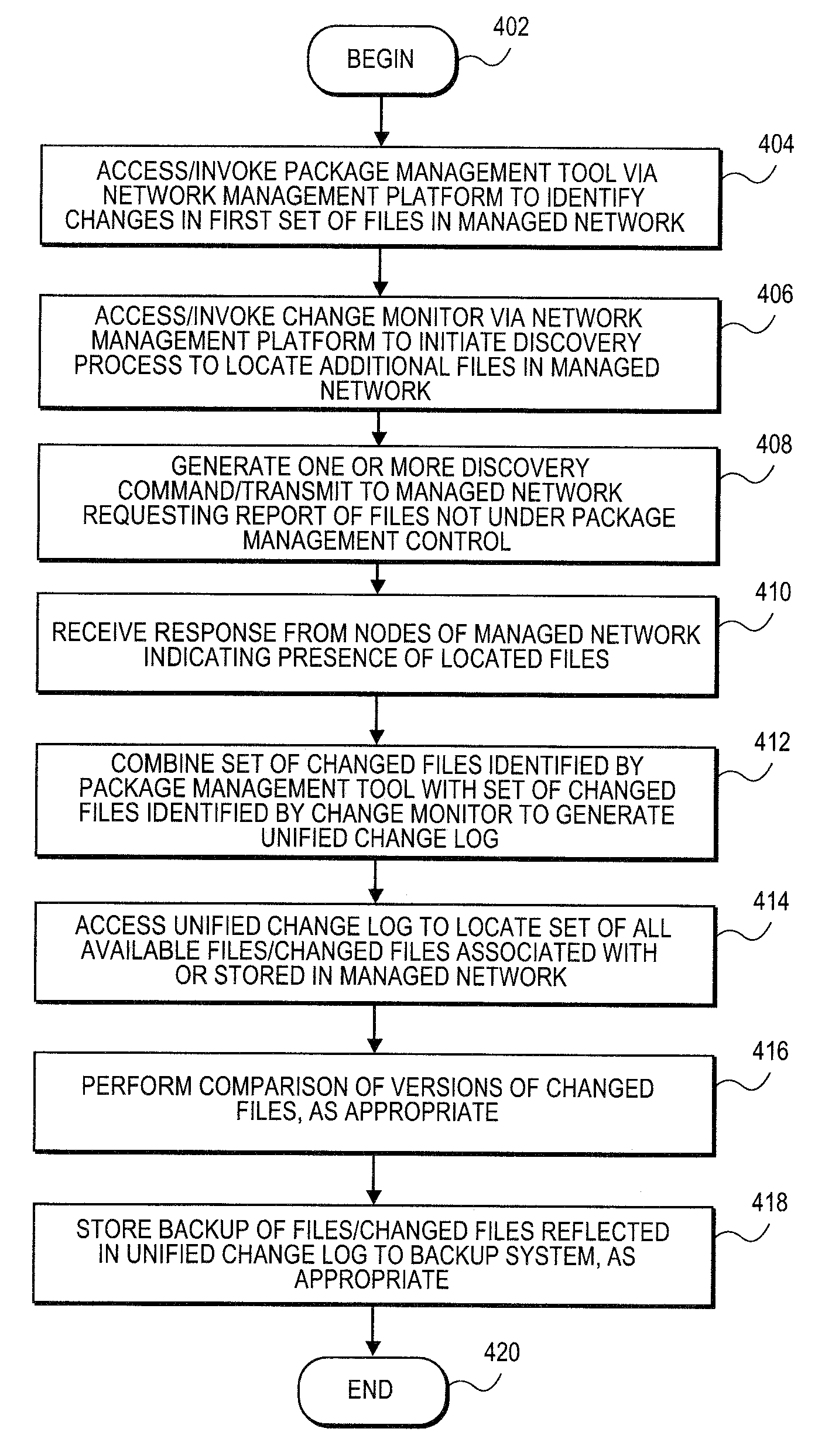
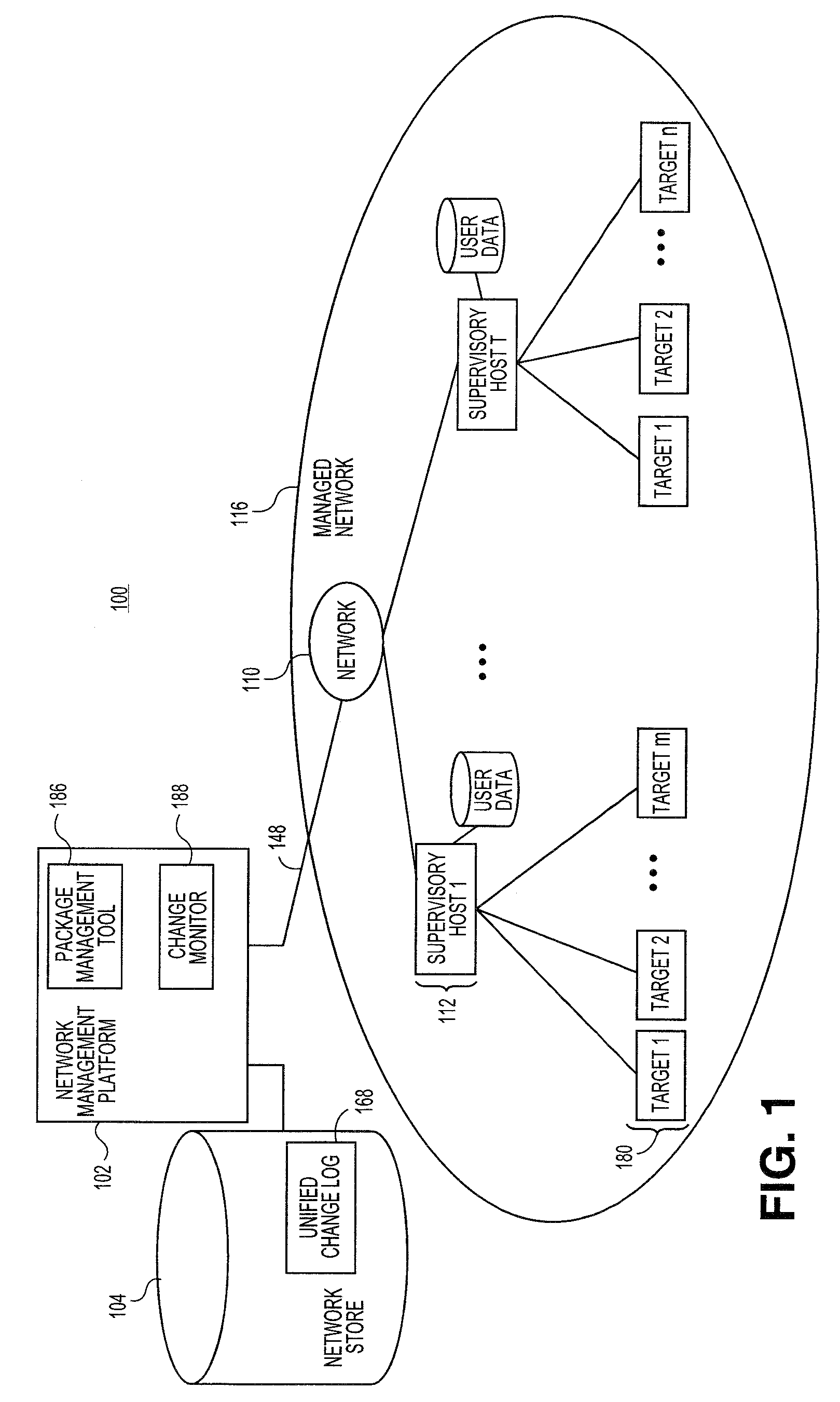
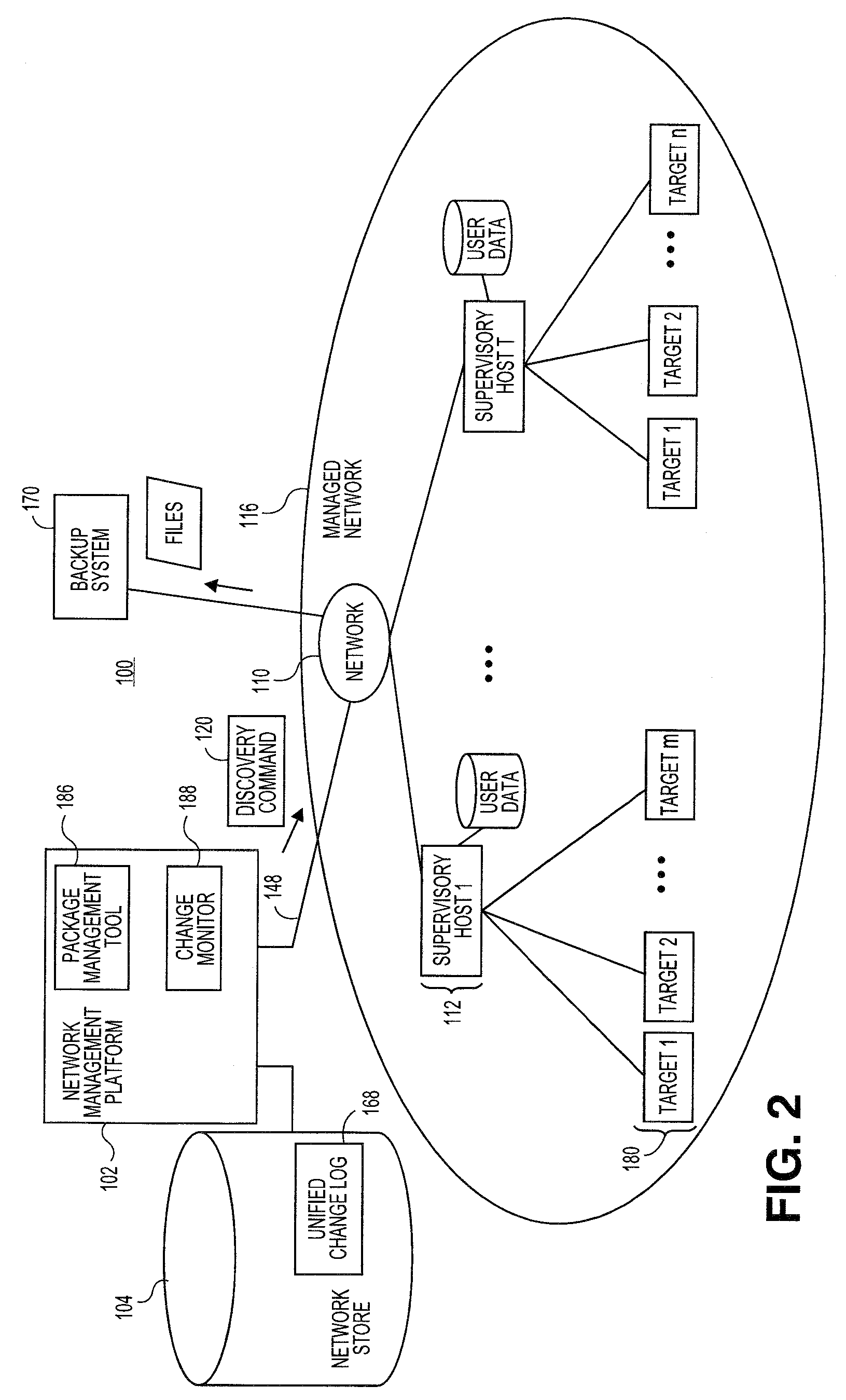
ActiveUS20100223274A1Digital data information retrievalMemory loss protectionManagement toolPackage management
Embodiments relate to systems and methods for generating a change log for files in managed network. A set of managed machines, such as personal computers or servers, can be managed by a network management platform communicating with the machines via a secure channel. The network management platform can employ a package management tool to manage files stored or hosted in the managed network. The network management platform can further employ a change monitor or other logic to locate additional files located in the managed network but that may not be under the control of or registered to the package management tool. A systems administrator or other user can invoke both the package management tool and the change monitor logic to initiate a discovery process and locate all available files associated with the network, and generate a unified change log recording all available files and / or their changes.
Owner:RED HAT
Method for quickly identifying data residing on a volume in a multivolume file system
ActiveUS20110106862A1Quick fixDigital data information retrievalSpecial data processing applicationsFile systemChangelog
A method for quickly identifying data residing on a volume in a multivolume file system. The method includes generating a file location map, the file location map containing a list of the locations of files that occupy space on each of a plurality of volumes of the file system. The file system comprises least a first volume and a second volume. The file location map is updated in accordance with changes in a file change log for the file system. Data residing on the first volume of the file system is identified by scanning the file location map.
Owner:VERITAS TECH
Method and apparatus for efficient propagation of large datasets under failure conditions
InactiveUS7853565B1Efficiently and accurately propagating dataset changes among nodesEffective maintenanceData processing applicationsError detection/correctionData setDistributed computing
A network of nodes caches replicated datasets in which dataset changes are efficiently propagated as a set of changes even under failure conditions. A master node and a plurality of subordinate nodes in the network each maintain a copy of the dataset and a change log storing change events in the dataset in that node. The change log further includes a rename chain having a plurality of linked rename records created in response to a new master gaining control of the dataset. The master node computes and propagates dataset changes to the subordinate nodes as a set of change events. If the master node fails, one of the subordinate nodes becomes temporary master and continues to propagate dataset changes using its dataset and its change log in response to update requests from other nodes where the update request contains information from the change log of the requestor node.
Owner:CISCO TECH INC
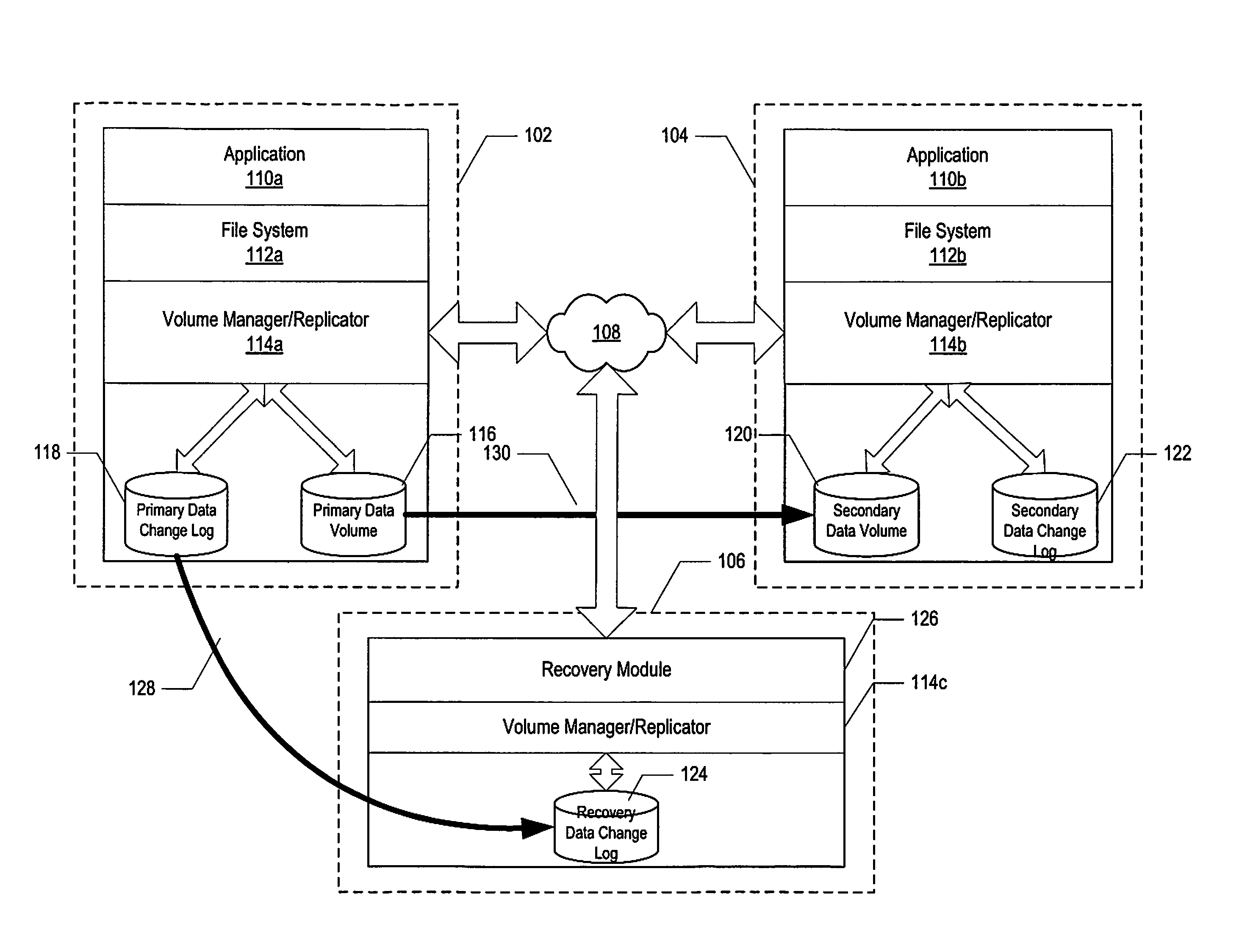
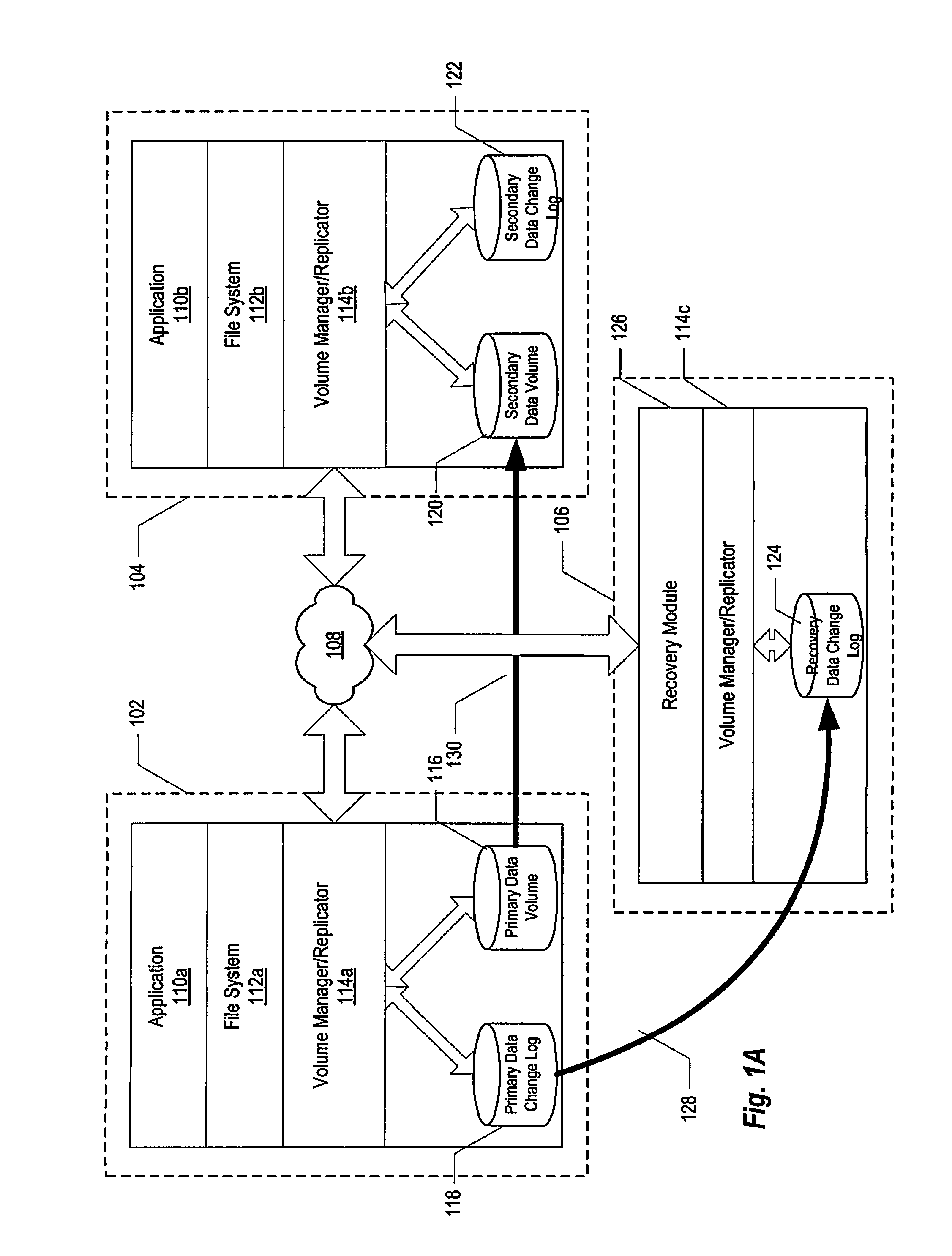
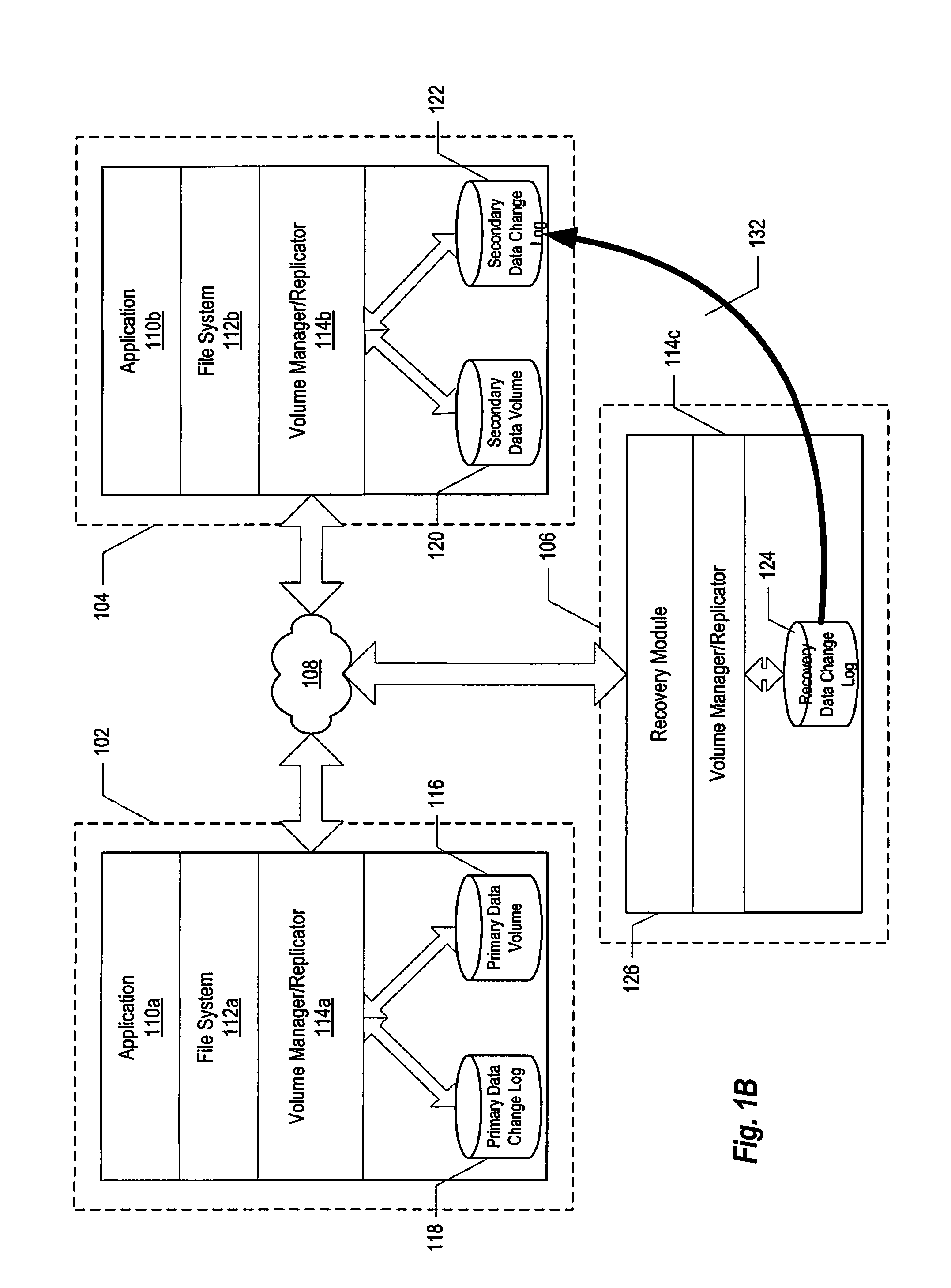
Method and system of replicating data using a recovery data change log
InactiveUS7457830B1Quickly and reliably replicateReducing replication costError detection/correctionMemory systemsData miningComputer science
A method and system of replicating data using a recovery data change log. According to one embodiment a method is provided in which a copy of a data change log at a primary node is maintained at a data recovery node, the data change log being associated with a primary data volume of the primary node, a failure of the primary data volume is detected, and a secondary data volume of a secondary node is updated using the copy of the data change log in response to the detection.
Owner:SYMANTEC OPERATING CORP
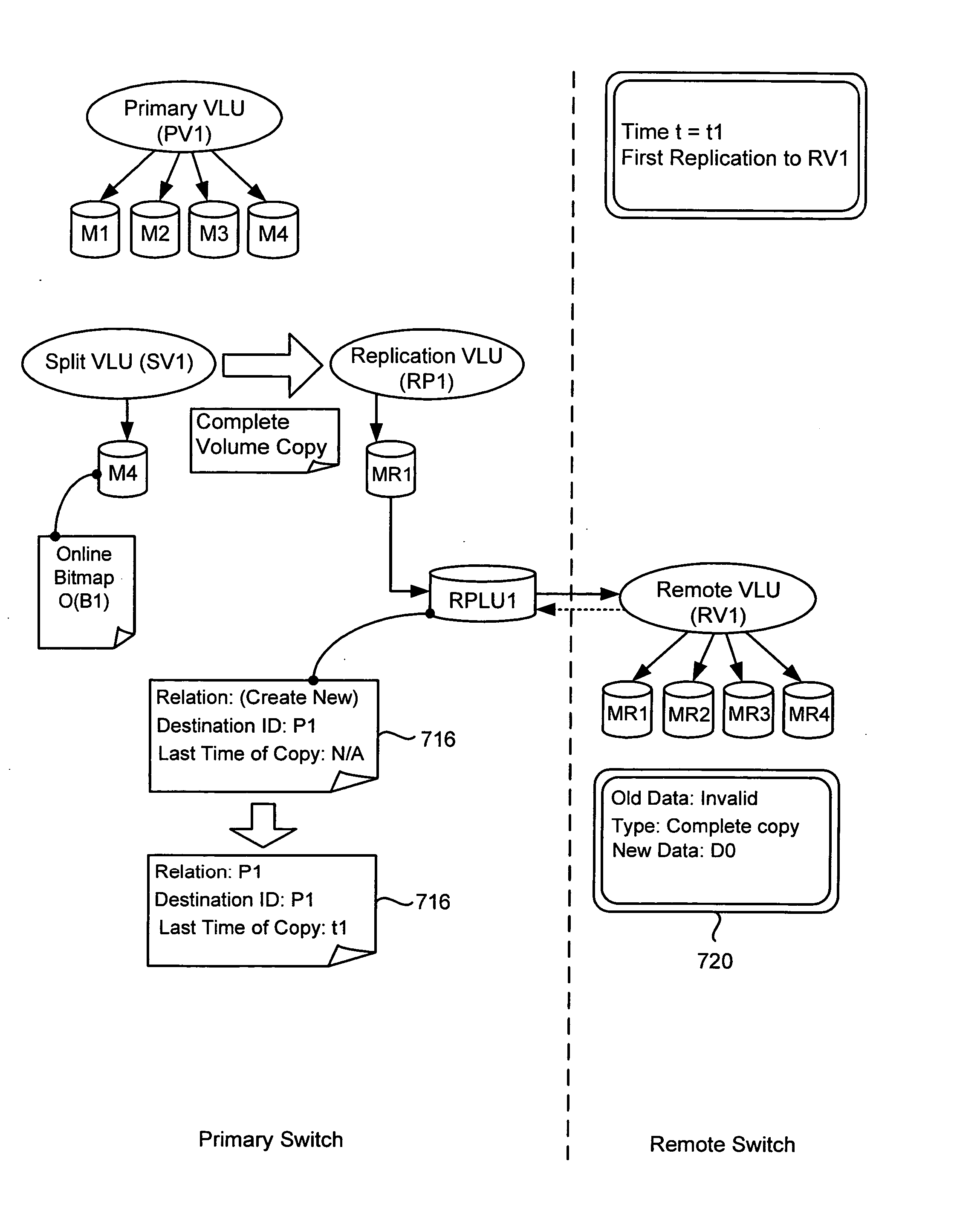
Storage switch asynchronous replication
ActiveUS20060047928A1Improve availabilityHigh data reliabilityMemory loss protectionError detection/correctionLogic cellAsynchronous replication
Owner:EMC IP HLDG CO LLC
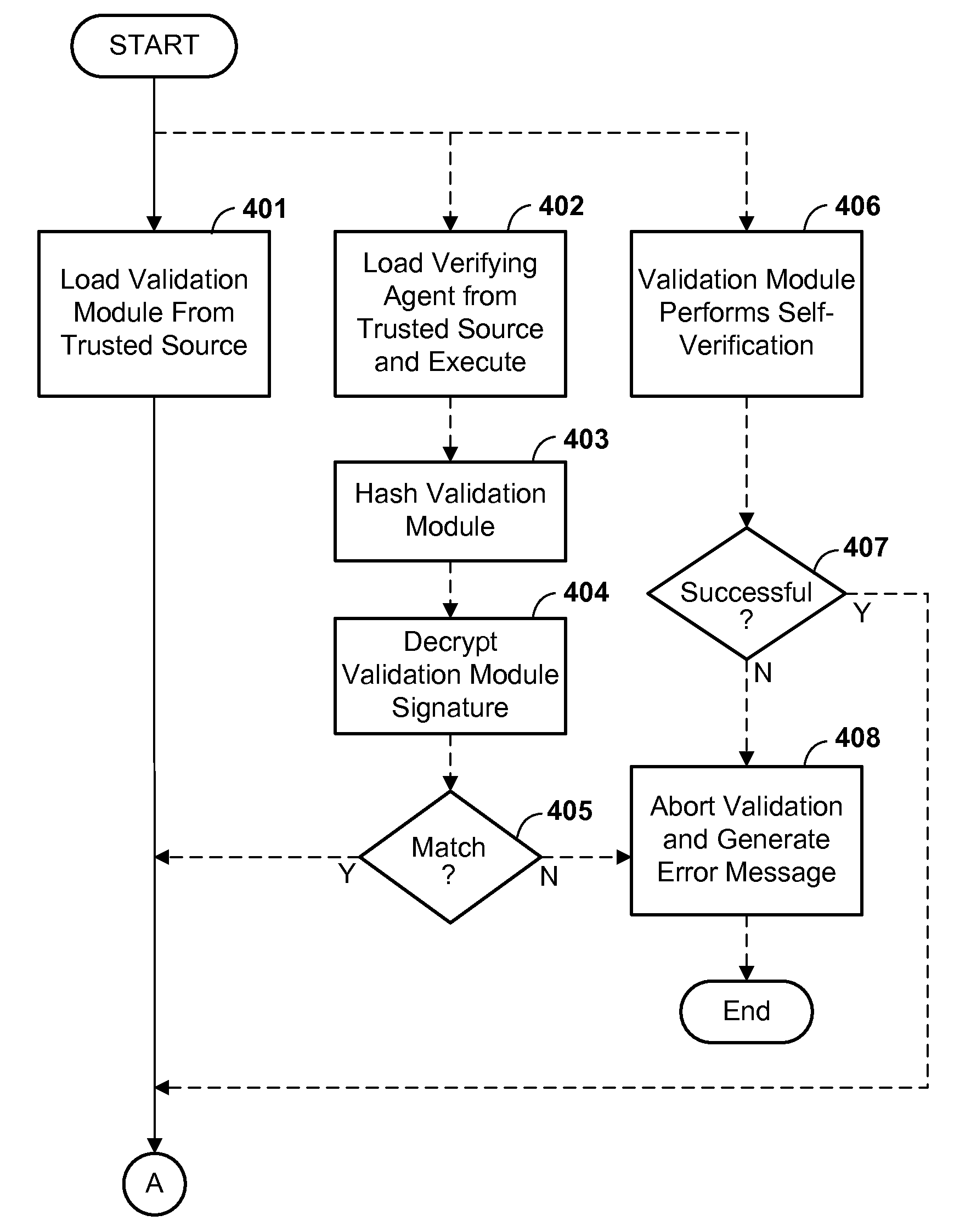
Method and Apparatus for Verifying Integrity of Computer System Vital Data Components
InactiveUS20090049309A1Difficult can be safeReduce security risksUnauthorized memory use protectionHardware monitoringData validationDigital signature
Vital data components of a computer system are protected by a mechanism for detecting unauthorized alteration, preferably in the form of digital signatures to detect unauthorized alteration. A vital data validation mechanism is provided to verify that vital data modules have not been tampered with. The vital data validation mechanism verifies the current state of each vital data module, preferably by decrypting the digital signature. The validation mechanism also checks an alteration log to verify that no alterations have been made to the corresponding memory locations. The second verification is intended to detect whether a vital data module has been altered temporarily, and then restored to its initial state.
Owner:IBM CORP
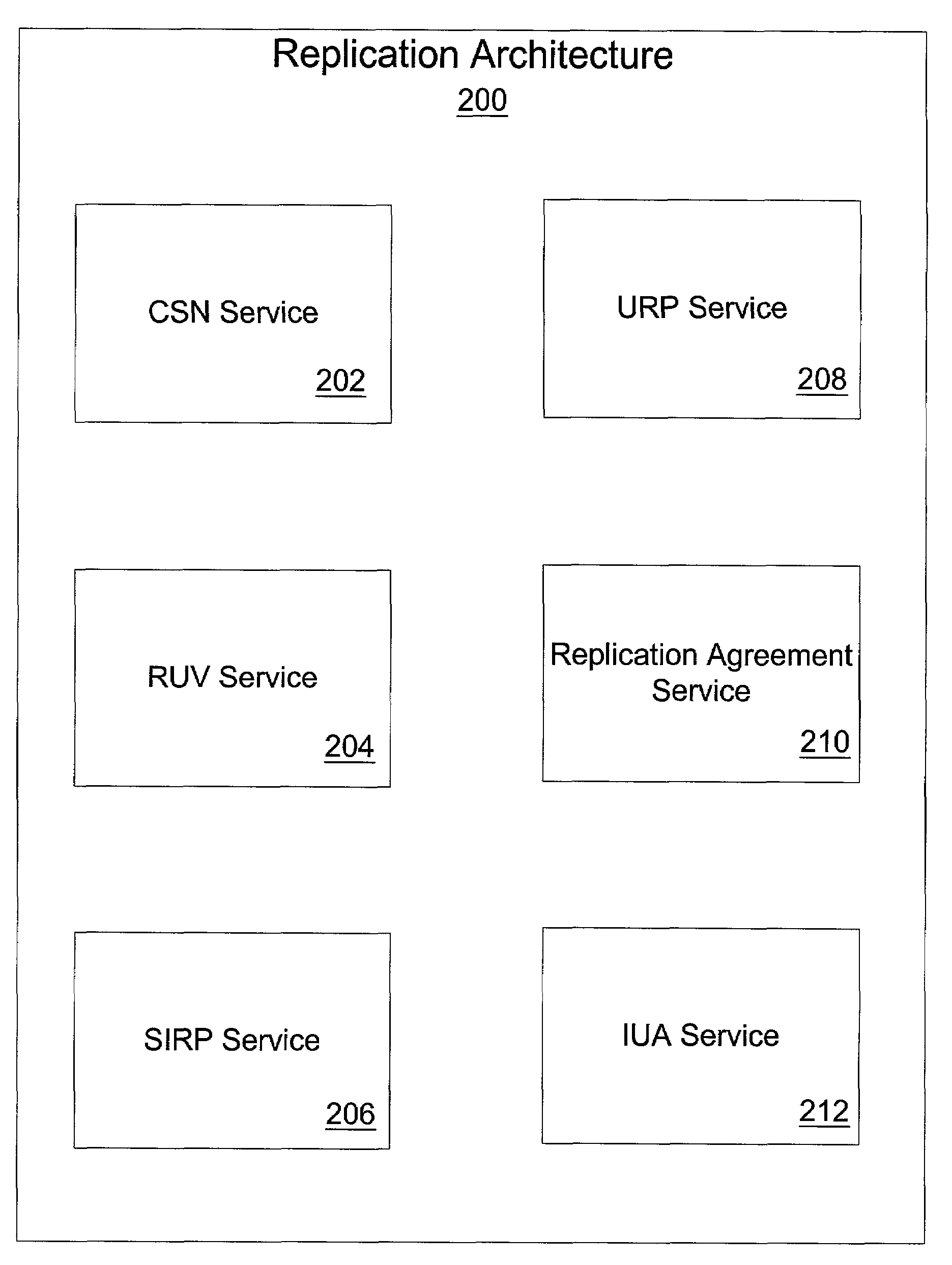
Replication architecture for a directory server
InactiveUS6973463B2Data processing applicationsSpecial data processing applicationsServer replicationDistributed computing
A directory server includes a supplier server, a consumer server in communication with the supplier server, a plurality of pluggable services that manage replication of data contained within the directory server from the supplier server to the consumer server, and a change log maintained on the consumer server of data replicated to the consumer server. The replication of data is managed by the plurality of pluggable services using the change log.
Owner:ORACLE INT CORP
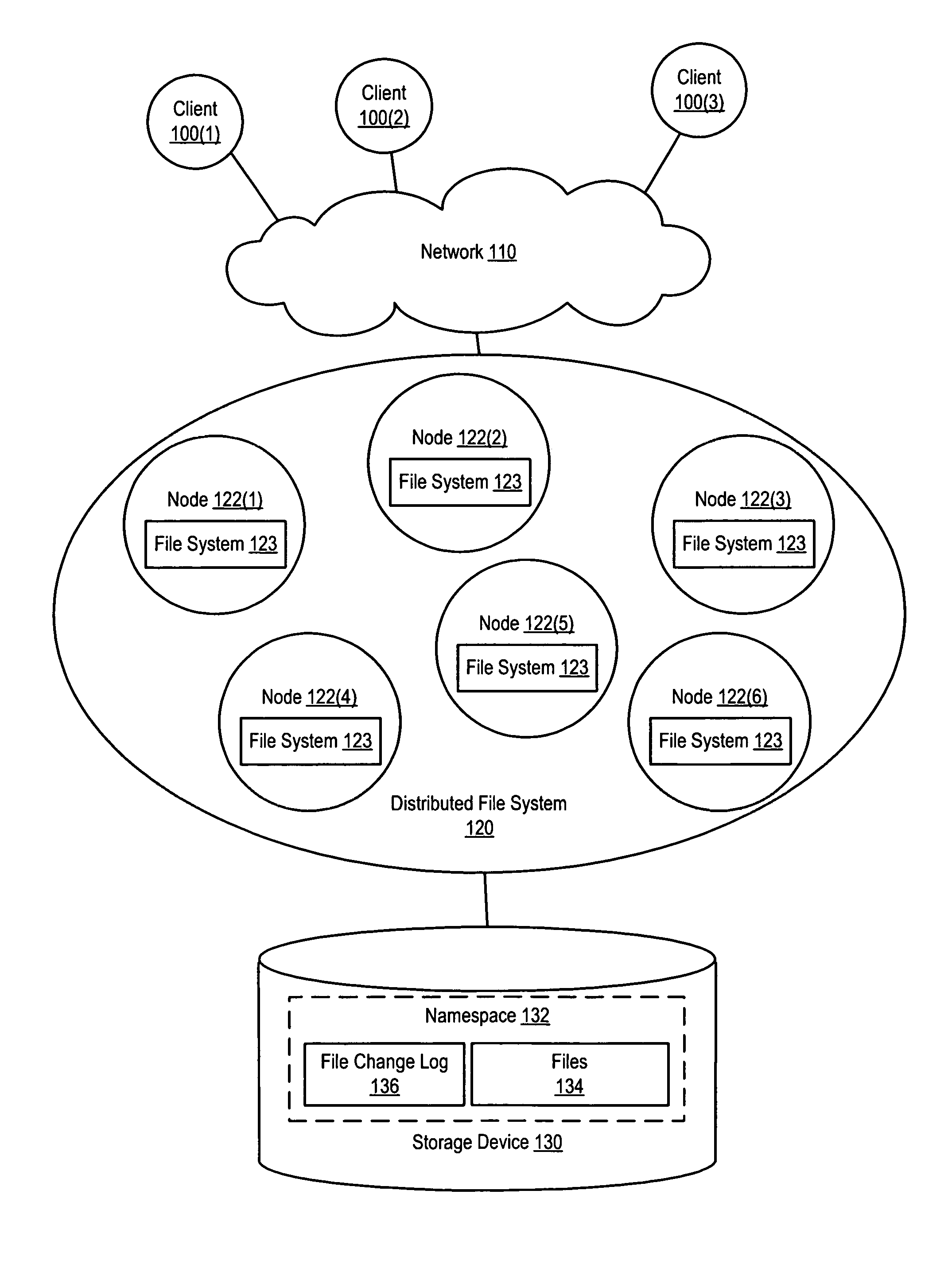
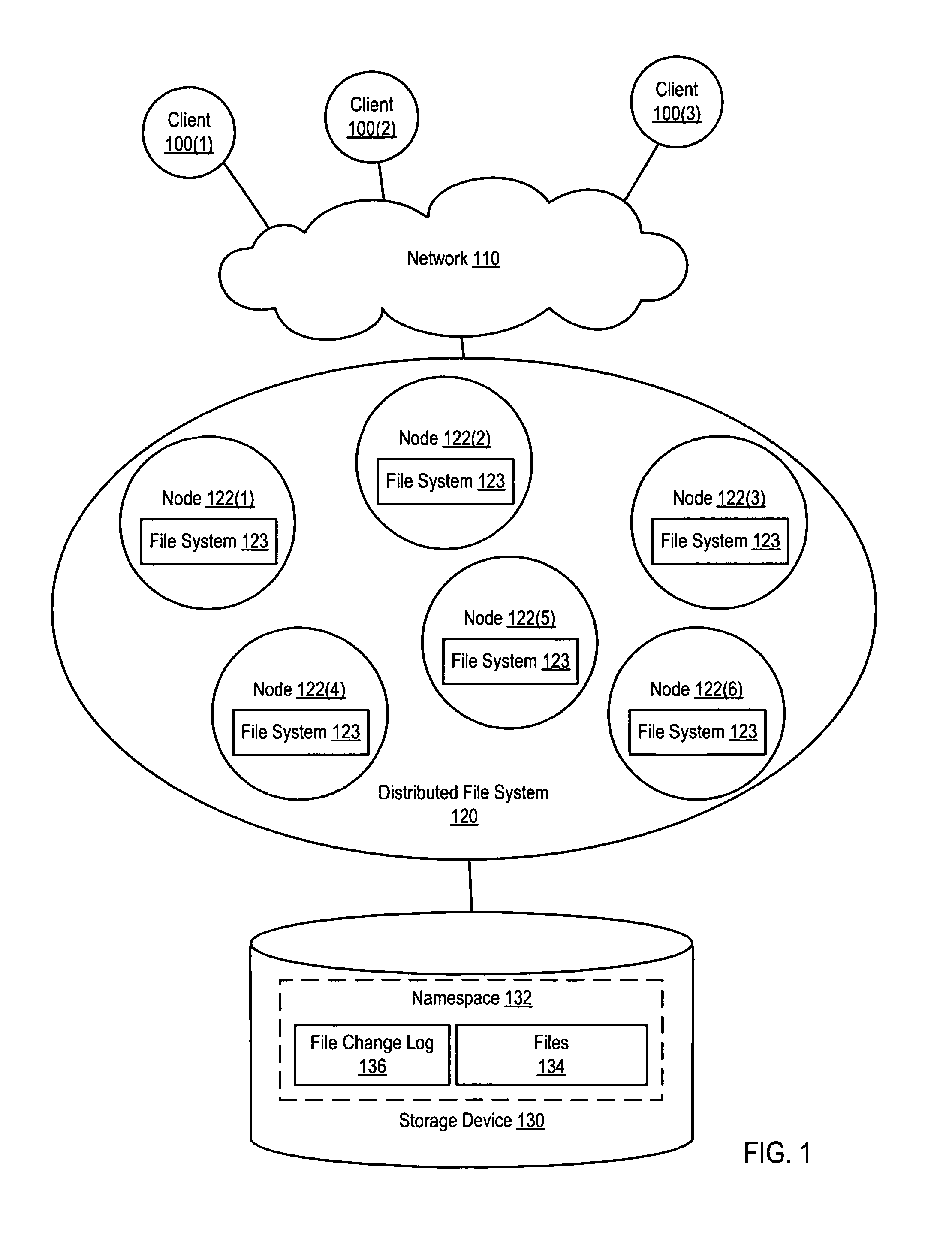
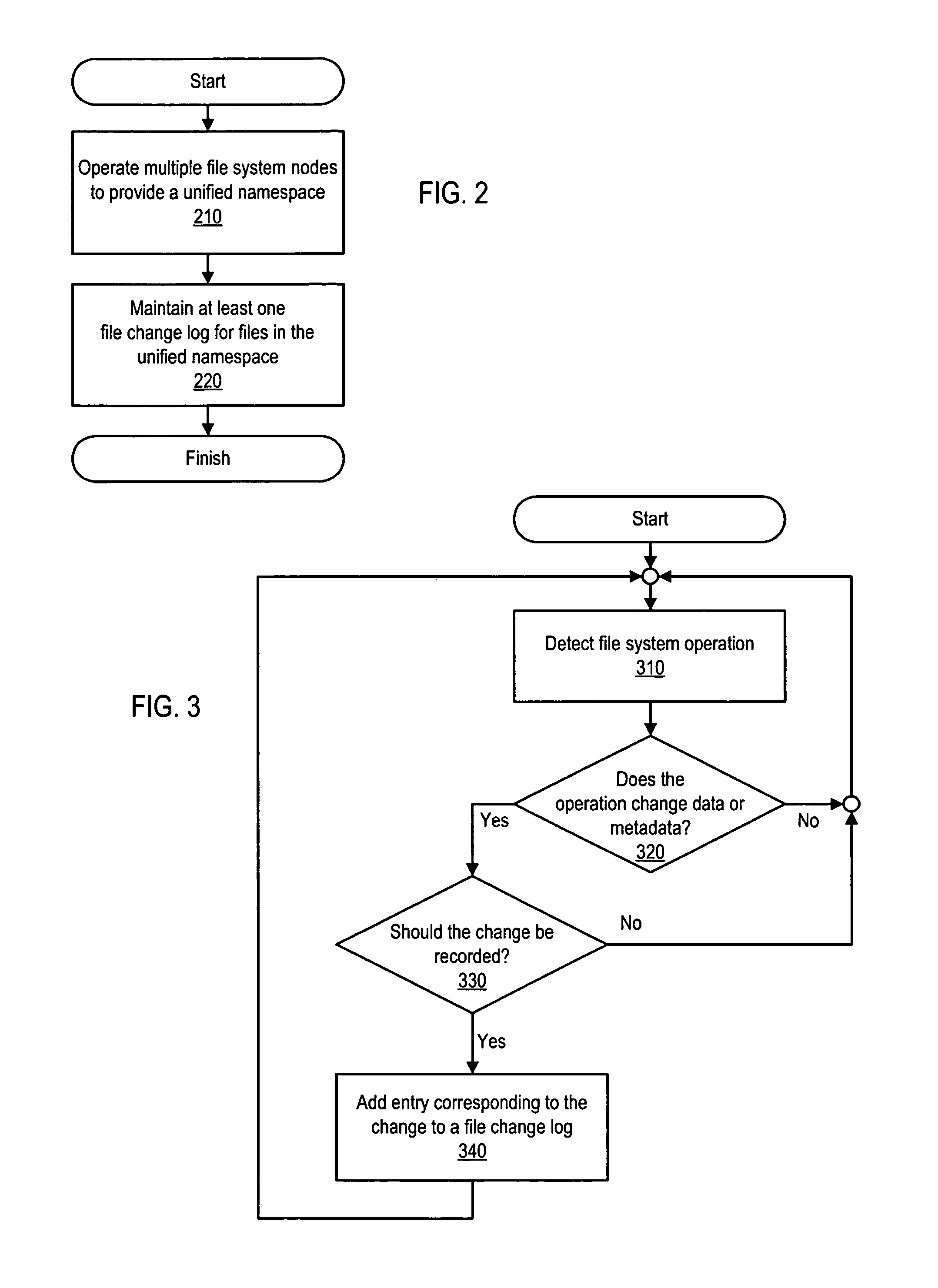
System and method for maintaining a file change log within a distributed file system
ActiveUS9367579B1Digital data information retrievalSpecial data processing applicationsDistributed File SystemFile system
Various methods and systems for implementing a file change log in a distributed file system are disclosed. In one embodiment, a method involves operating a distributed file system that presents a namespace and maintaining a file change log for the namespace. Operating the distributed file system involves executing an instance of a file system on each of several nodes. Maintaining the file change log can involve maintaining a single file change log for the namespace. Updates to the single file change log can be handled by a primary node or controlled using a locking mechanism. Alternatively, several private file change logs (e.g., one per node) can be maintained, and these private file change logs can be merged into a single file change log (e.g., by a primary node).
Owner:SYMANTEC OPERATING CORP
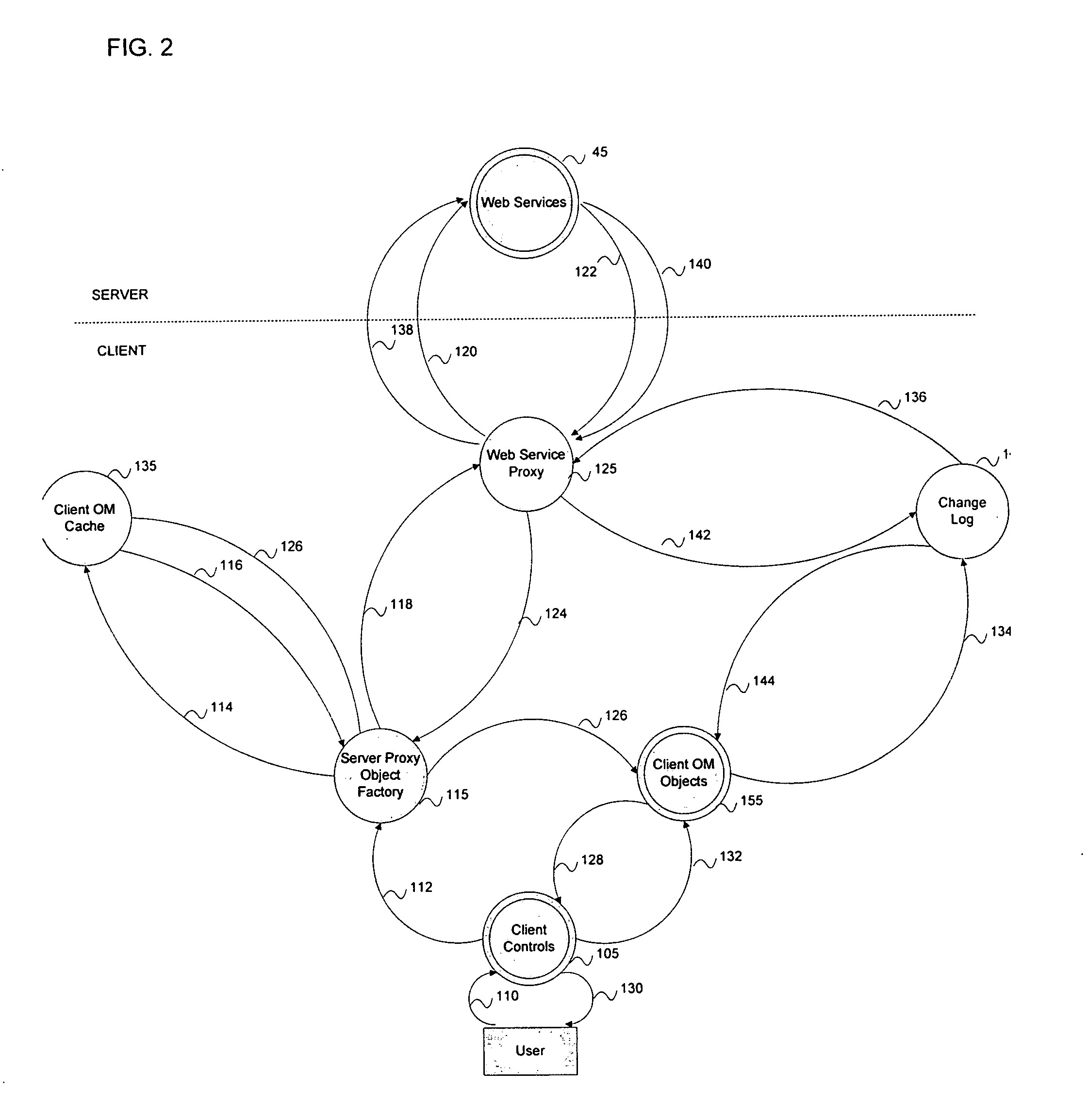
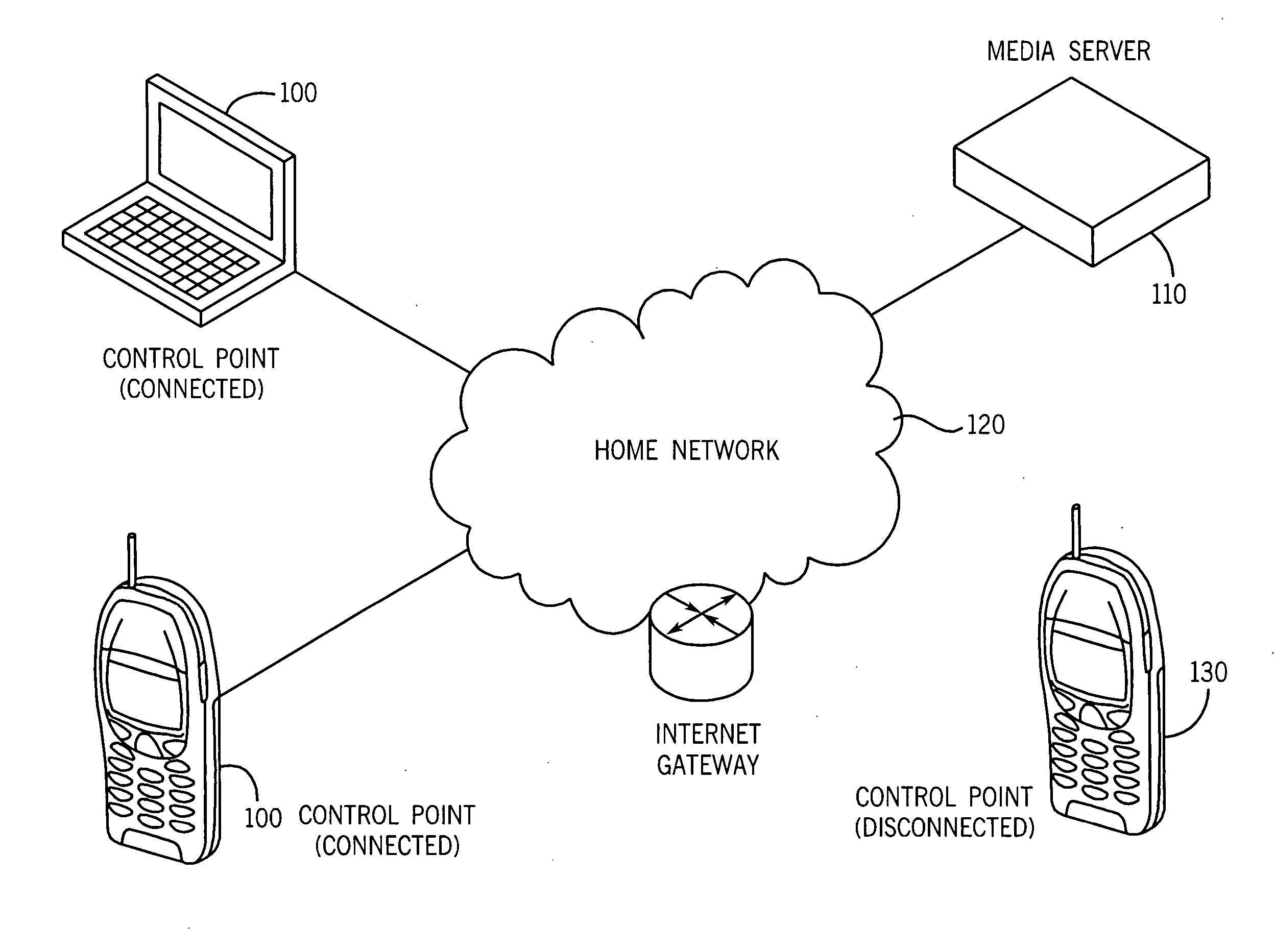
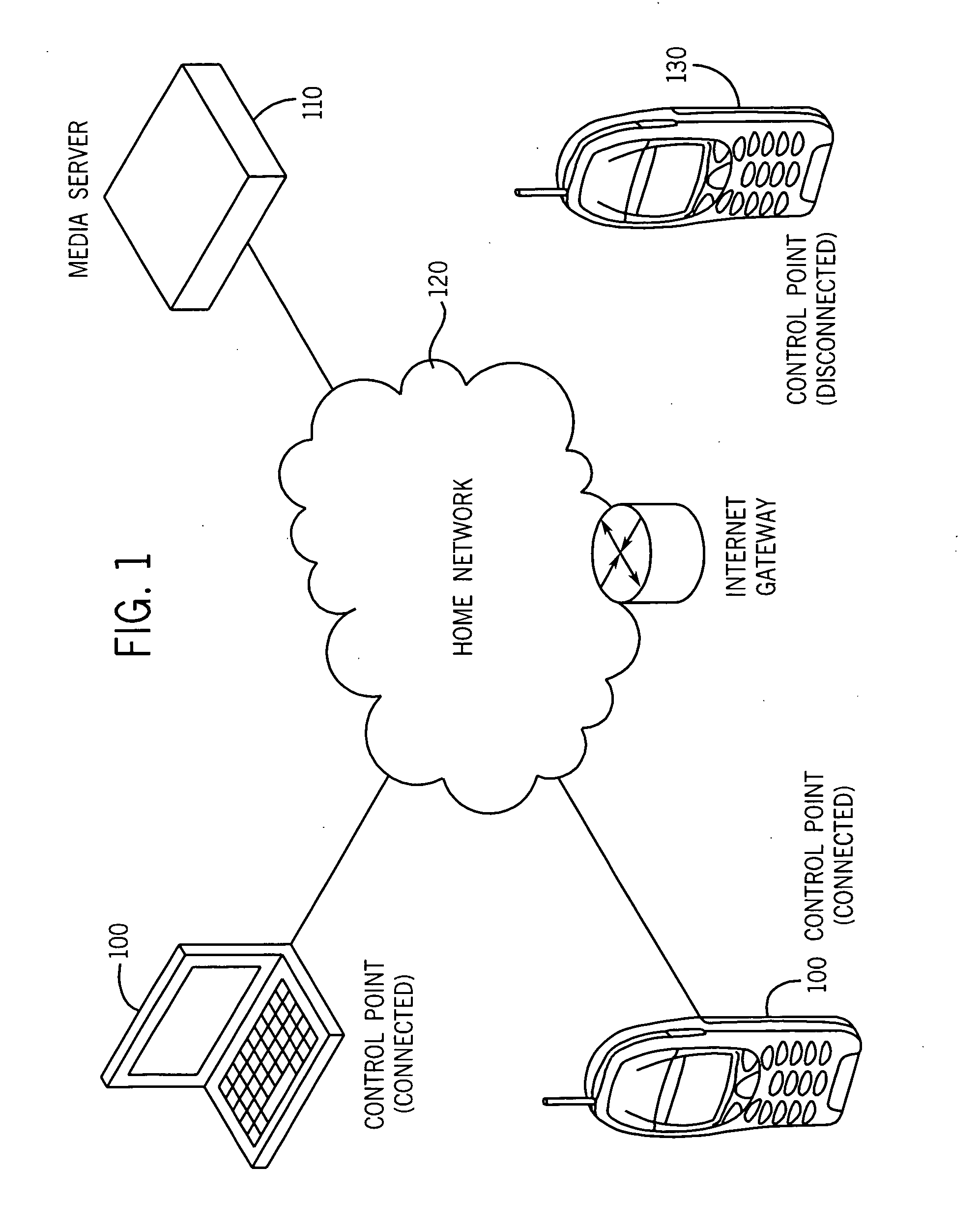
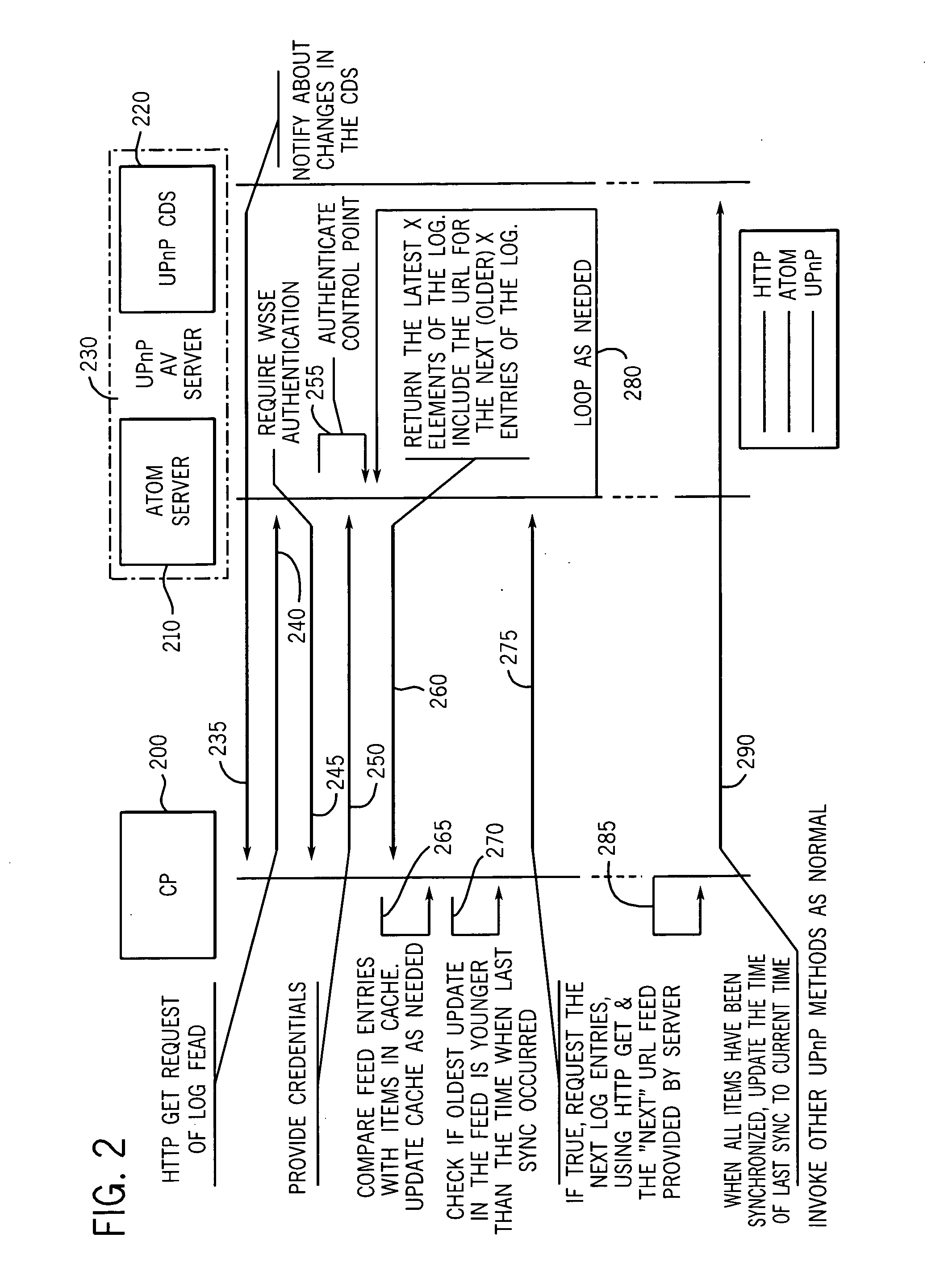
System and method for using web syndication feeds as a change log for synchronization in a UPnP audio/video environment
InactiveUS20070226312A1Simple in natureEasy to implementMultiple digital computer combinationsElectric digital data processingAudio frequencyComputer science
The use of ATOM / RSS feeds as a change log for web syndication. According to the present invention, whenever the SystemUpdateID changes, the CDS logs the change as a new entry in the ATOM feed. The SystemUpdateID is checked by a control point whenever it joins the network. If the SystemUpdateID is different, the control point promptly fetches the log, thereby eliminating the need to browse the entire CDS. When all of the items have been synchronized, the control point updates the time of last synchronization to reflect the current time. The control point then invokes other UPnP methods as necessary or desired.
Owner:NOKIA CORP
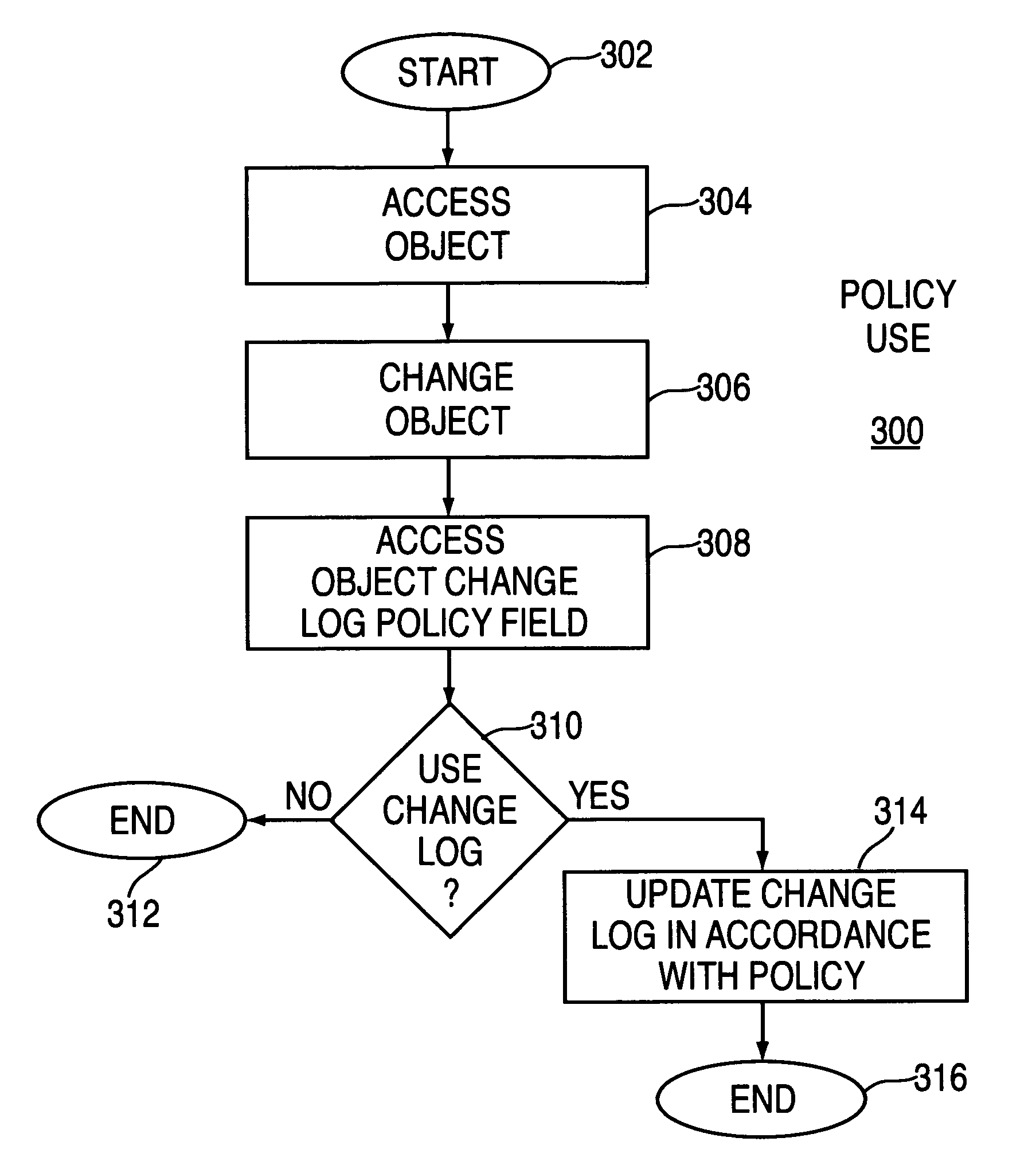
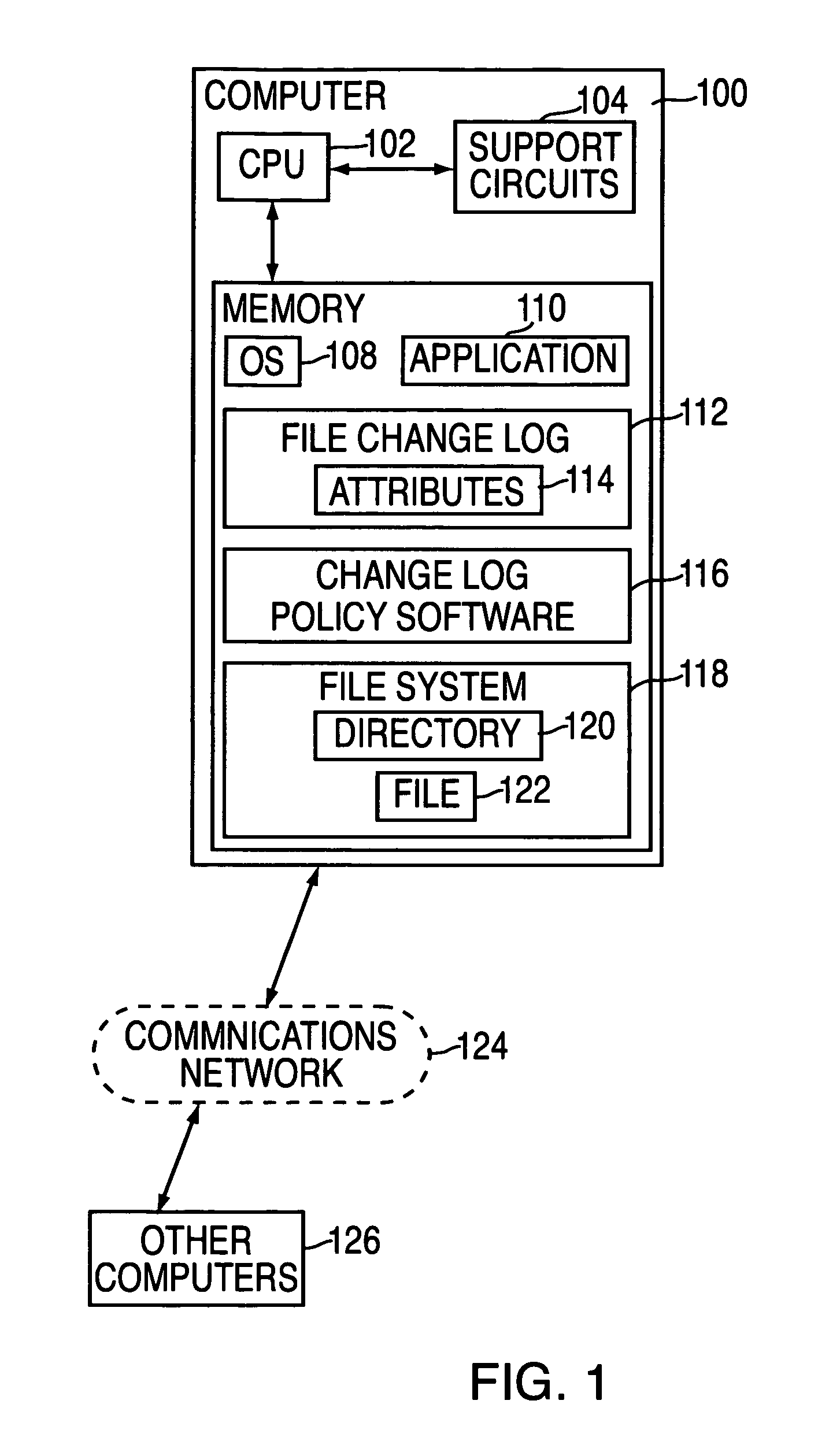
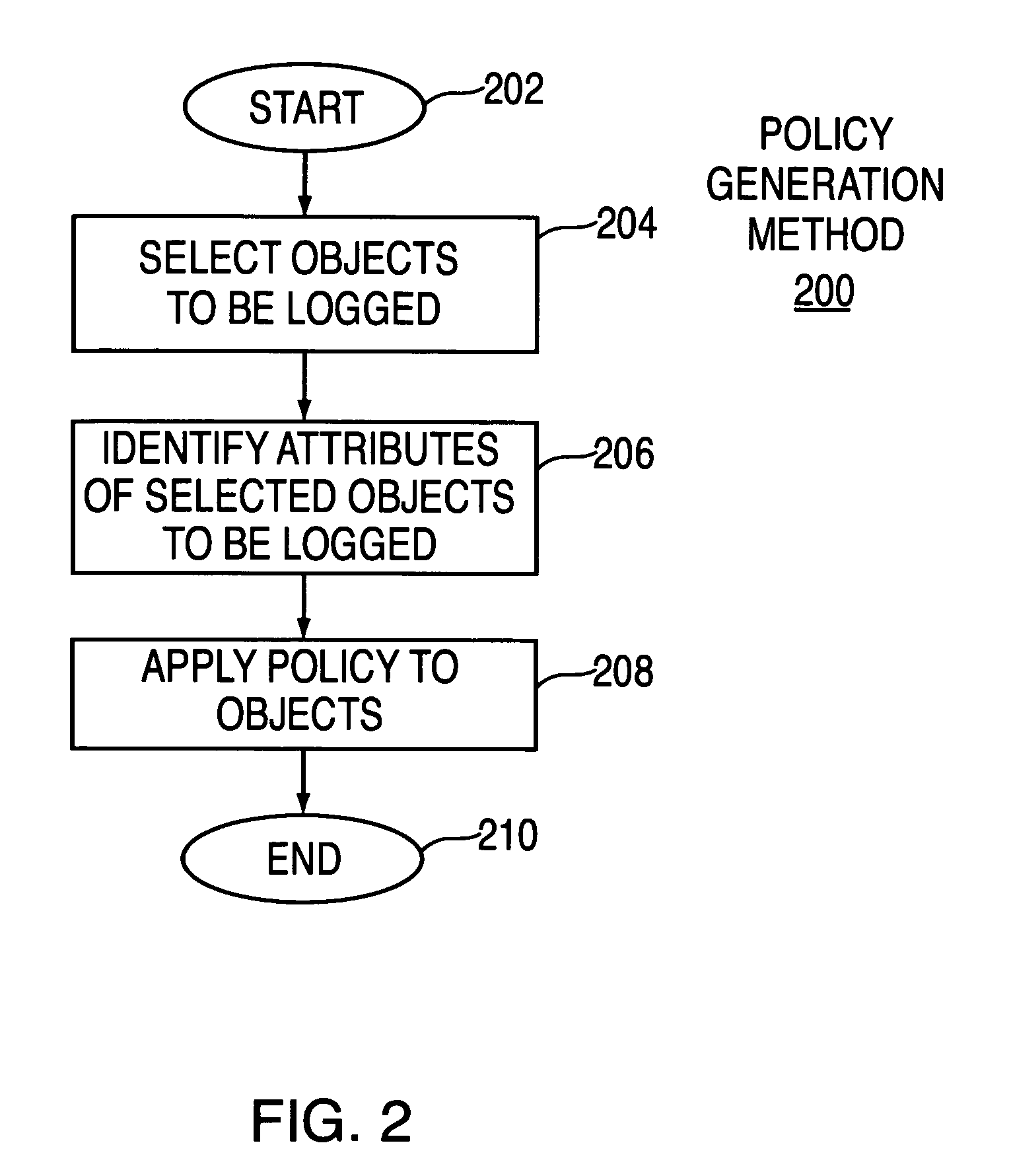
Method and apparatus for creating and using a policy-based access/change log
InactiveUS7636736B1Digital data information retrievalSpecial data processing applicationsFile systemChangelog
A method and apparatus for creating and using a policy-based file access / change log. Using the policy-based techniques, specific objects within the file system are selected for logging within an access / change log. These selected objects are then processed to identify attributes of the selected objects that are to be logged such that a policy is created regarding the objects to be logged and the attributes of those objects. Lastly, the policy is applied to the object either by having a separate object (file) created that is related to the object to be logged that identifies the policy for logging, or by attaching certain attributes directly to the object such that access to the object identifies the logging policy for that object. When an object that uses policy-based logging is changed, the object access / change log policy is utilized to log only the information that is identified in the policy. In this manner, the amount of information that is logged is controlled by the logging policy, limiting the size of the access / change log.
Owner:SYMANTEC OPERATING CORP
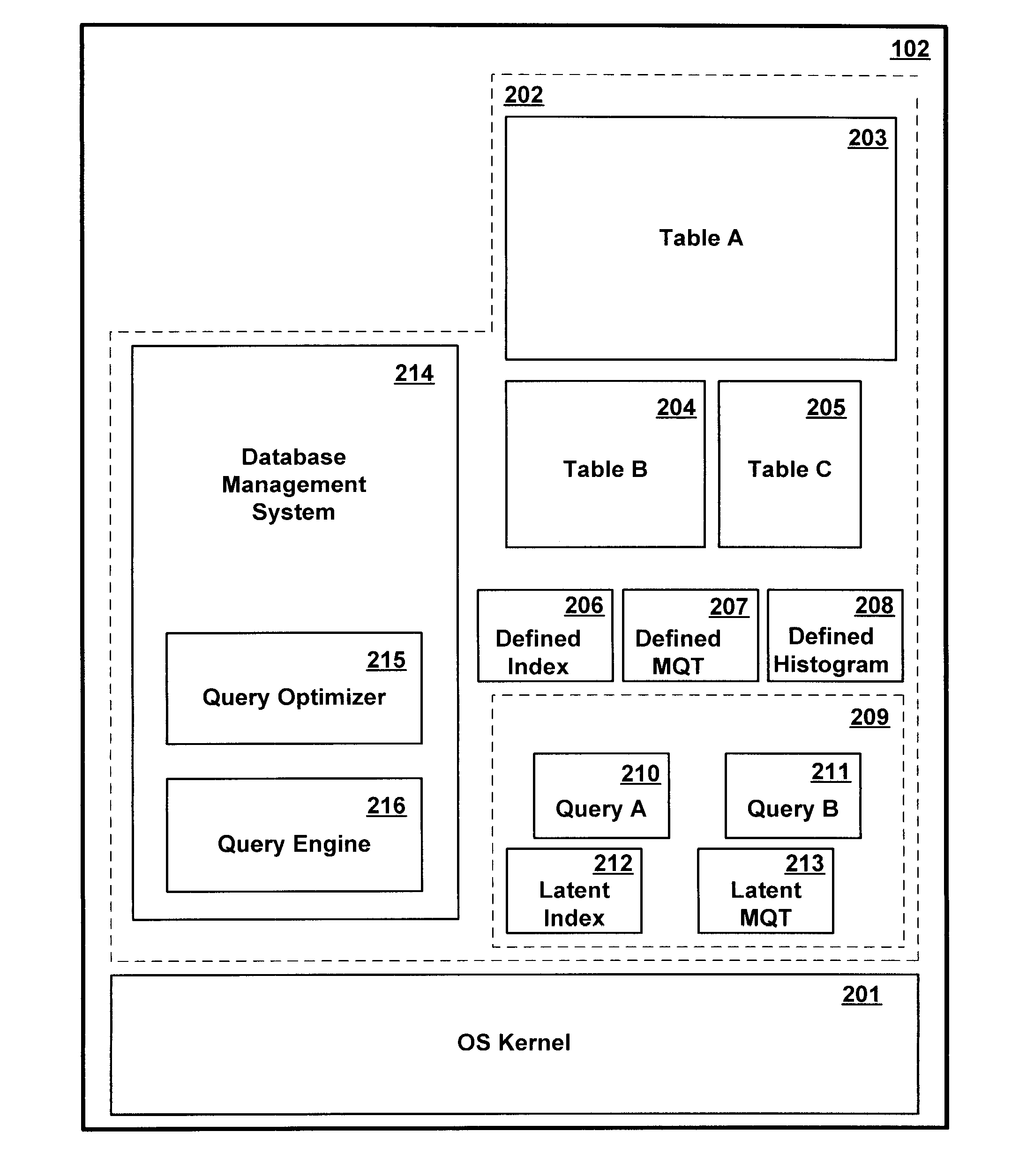
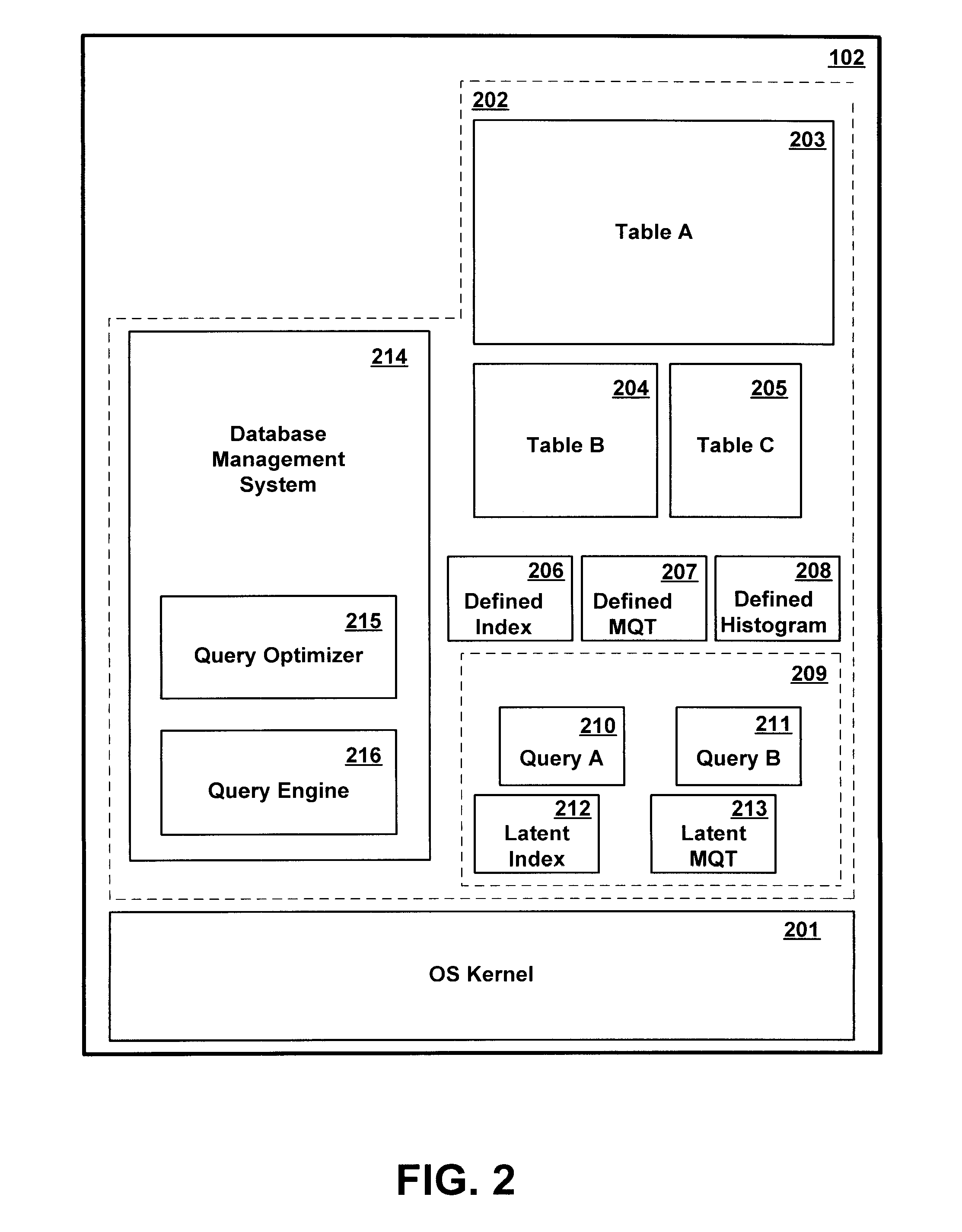
Method and Apparatus for Autonomically Maintaining Latent Auxiliary Database Structures for Use in Executing Database Queries
InactiveUS20070250517A1Digital data processing detailsSpecial data processing applicationsDatabase queryLatent structure
A latent auxiliary database structure constructed for executing a query is automatically saved for reuse in subsequent query execution instances. The latent auxiliary database structure is not maintained concurrently with changes to records in the database tables. If a query execution strategy is subsequently invoked which uses the latent auxiliary database structure, a determination is made dynamically whether to update the previously saved latent structure from database changes recorded in one or more change logs, or to rebuild the latent structure from scratch. Where the cost of updating from the change log is deemed less than the cost of a rebuild from scratch, the previously saved latent structure is updated from the log.
Owner:IBM CORP
System and method of synchronizing data between a server and a client
ActiveUS7792790B2Reduce sync delayIncrease speedDigital data processing detailsHybrid transportData synchronizationClient-side
A data synchronizing method between a server and a client is provided. The server and the client manage database changed after a previous synchronization of data shared by them. The database includes a sync anchor field for each data item. When a sync session is initiated upon request of the client, a last anchor is detected from the database stored in the client and a last anchor from the database stored in the server. The last anchor of the client is compared with the last anchor of the server. A client change log and a server change log are generated according to a comparison result based on a database change that occurred after the last anchor of client or server when the last anchor of the client is identical to the last anchor of the server. The databases are updated according to the client change log and the server change log.
Owner:SAMSUNG ELECTRONICS CO LTD
Embedded change logging for data synchronization
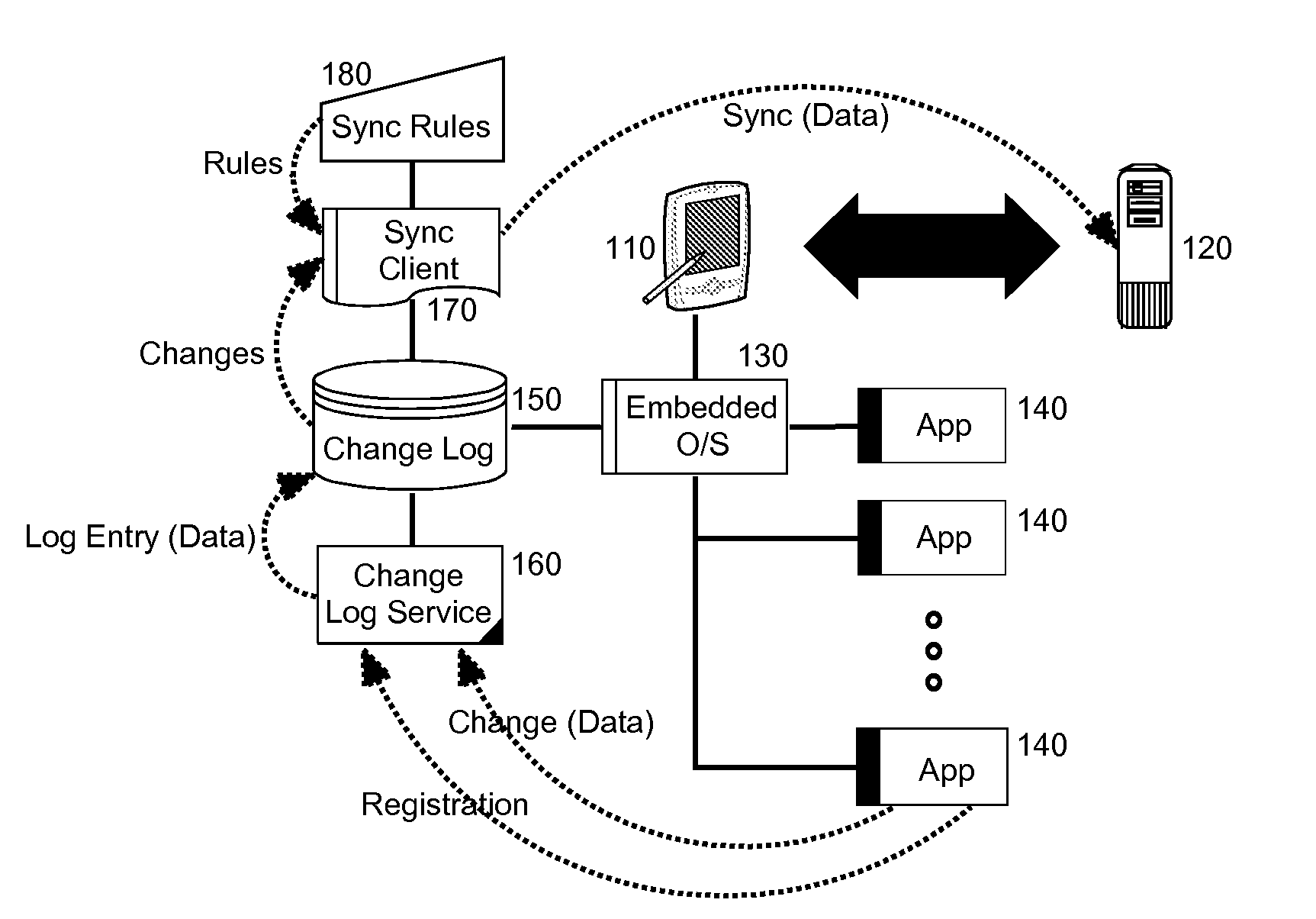
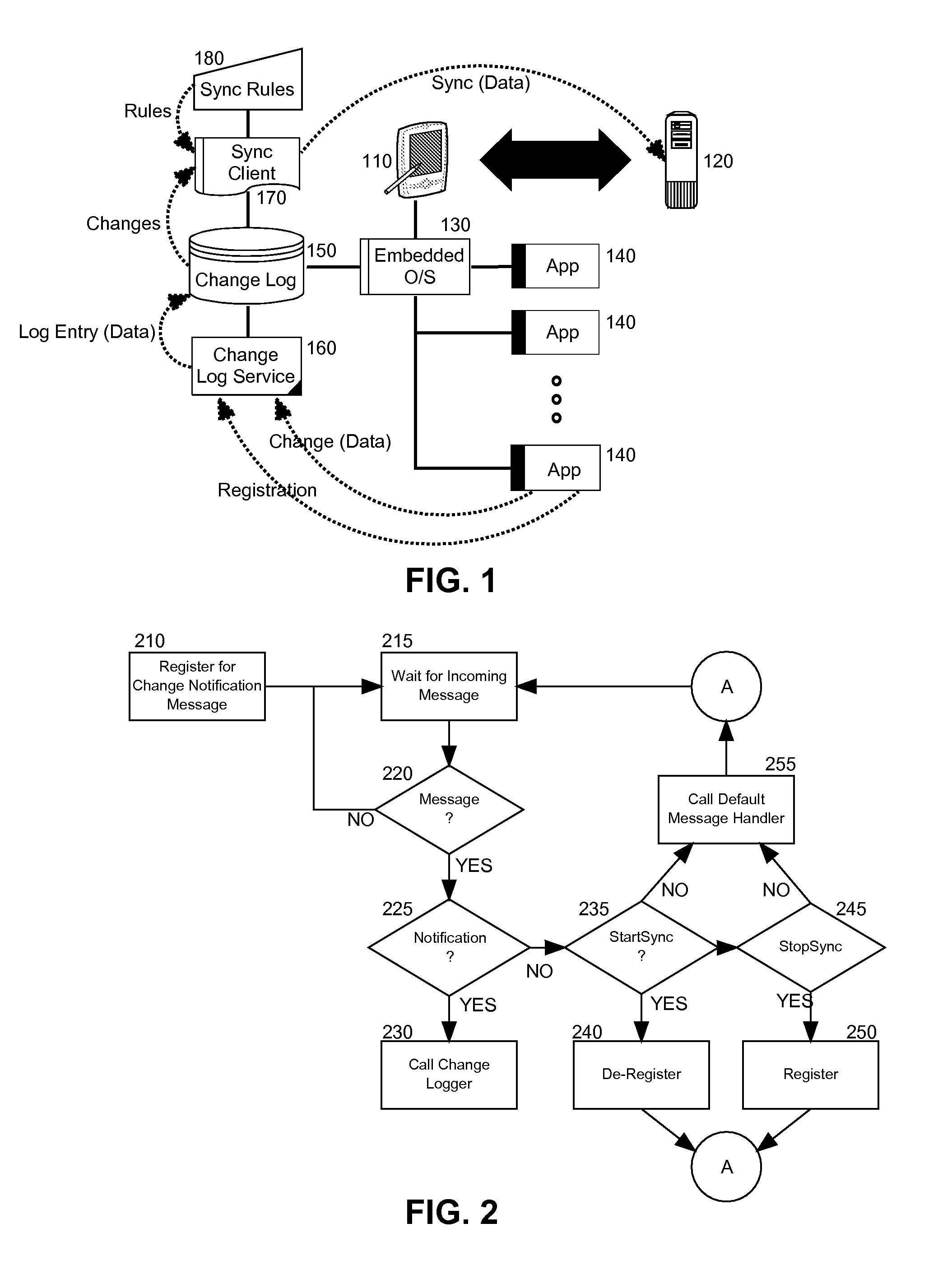
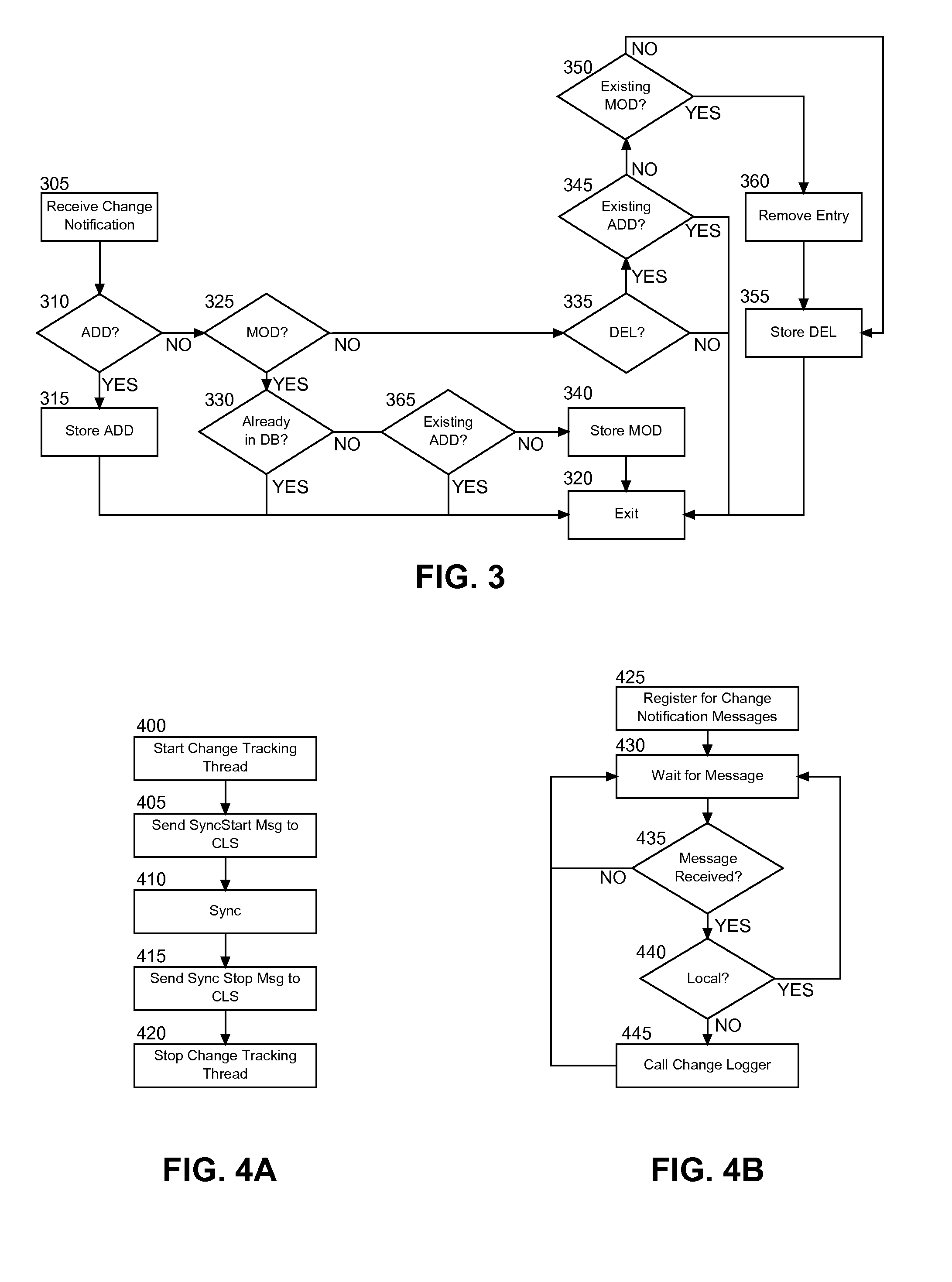
InactiveUS20100023533A1Digital data processing detailsDatabase distribution/replicationClient-sideChangelog
Embodiments of the present invention provide for embedded change logging for data synchronization. In an embodiment of the invention, an embedded change logging data processing system can include a change embedded database (EDB) disposed in a pervasive device. The EDB can store entries for notified changes in data for multiple different end-user applications in the pervasive device. The system also can include a change log service (CLS) disposed in the pervasive device and coupled to the EDB. The CLS can include program code enabled to register with multiple different end-user applications in the pervasive device to receive notifications of changes, and to write entries to the EDB responsive to the notifications. Finally, the system can include a synchronization client disposed in the pervasive device separately from the CLS. The synchronization client can include program code enabled to directly access the EDB to perform data synchronization with a remote host.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com