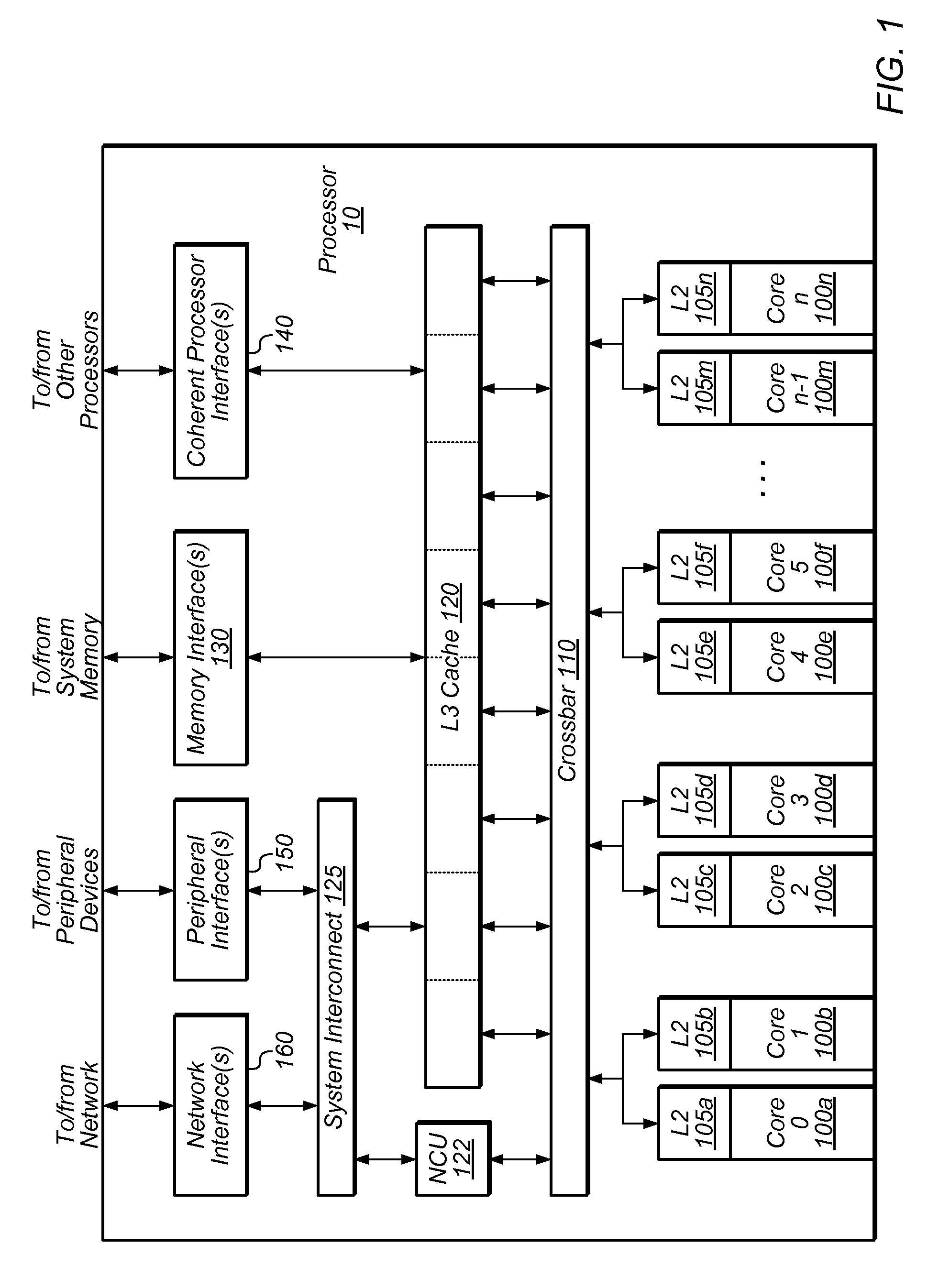
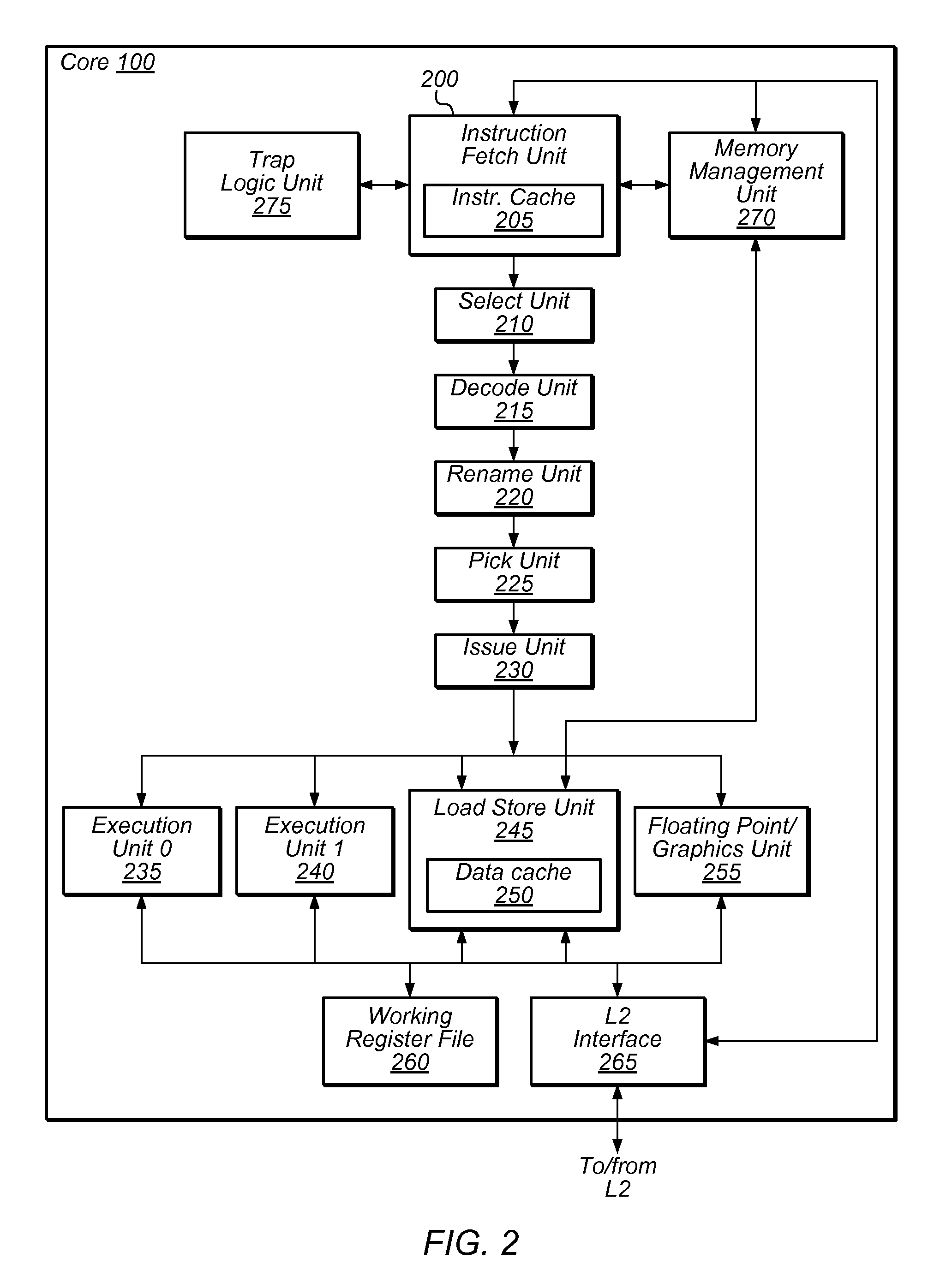
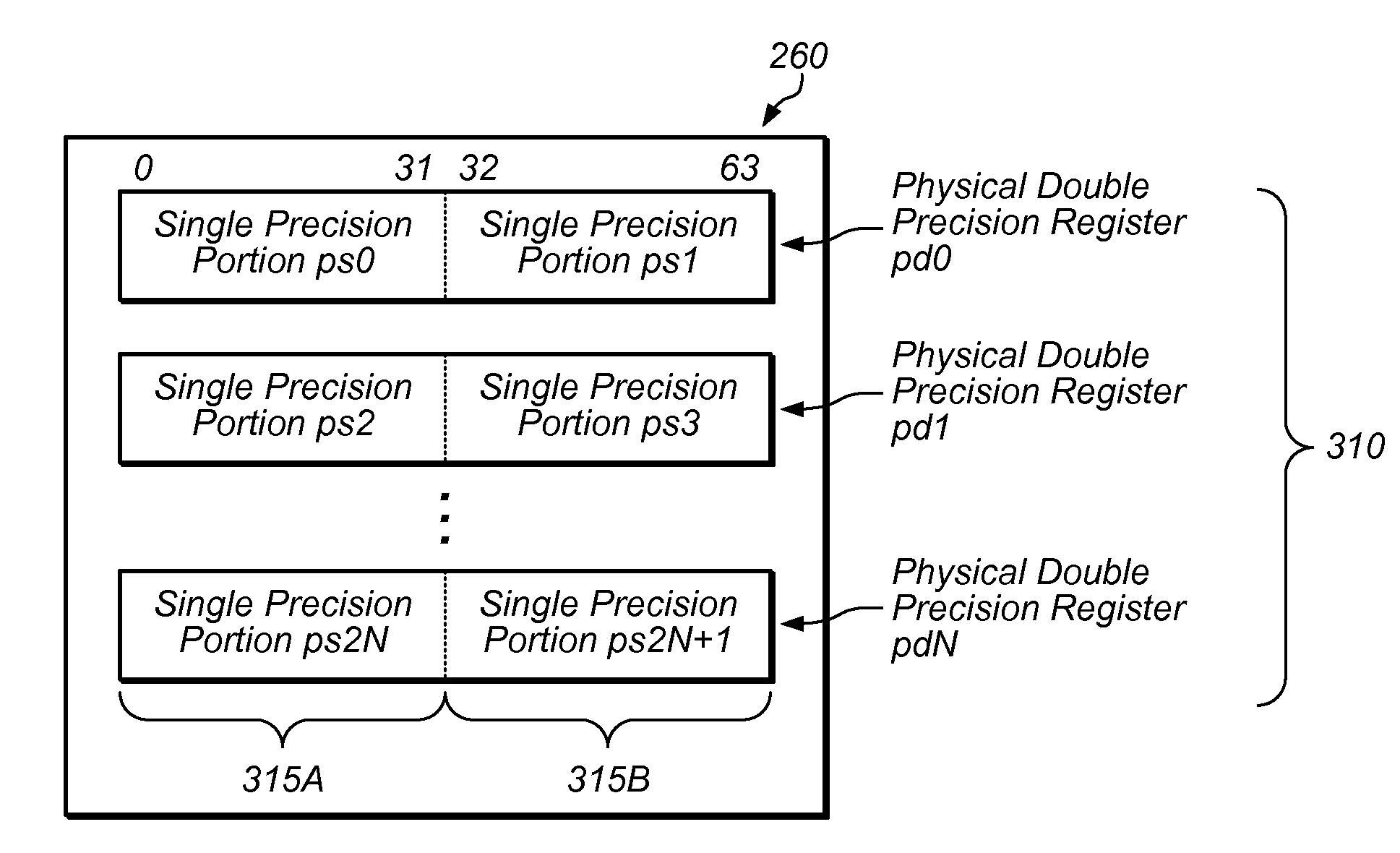
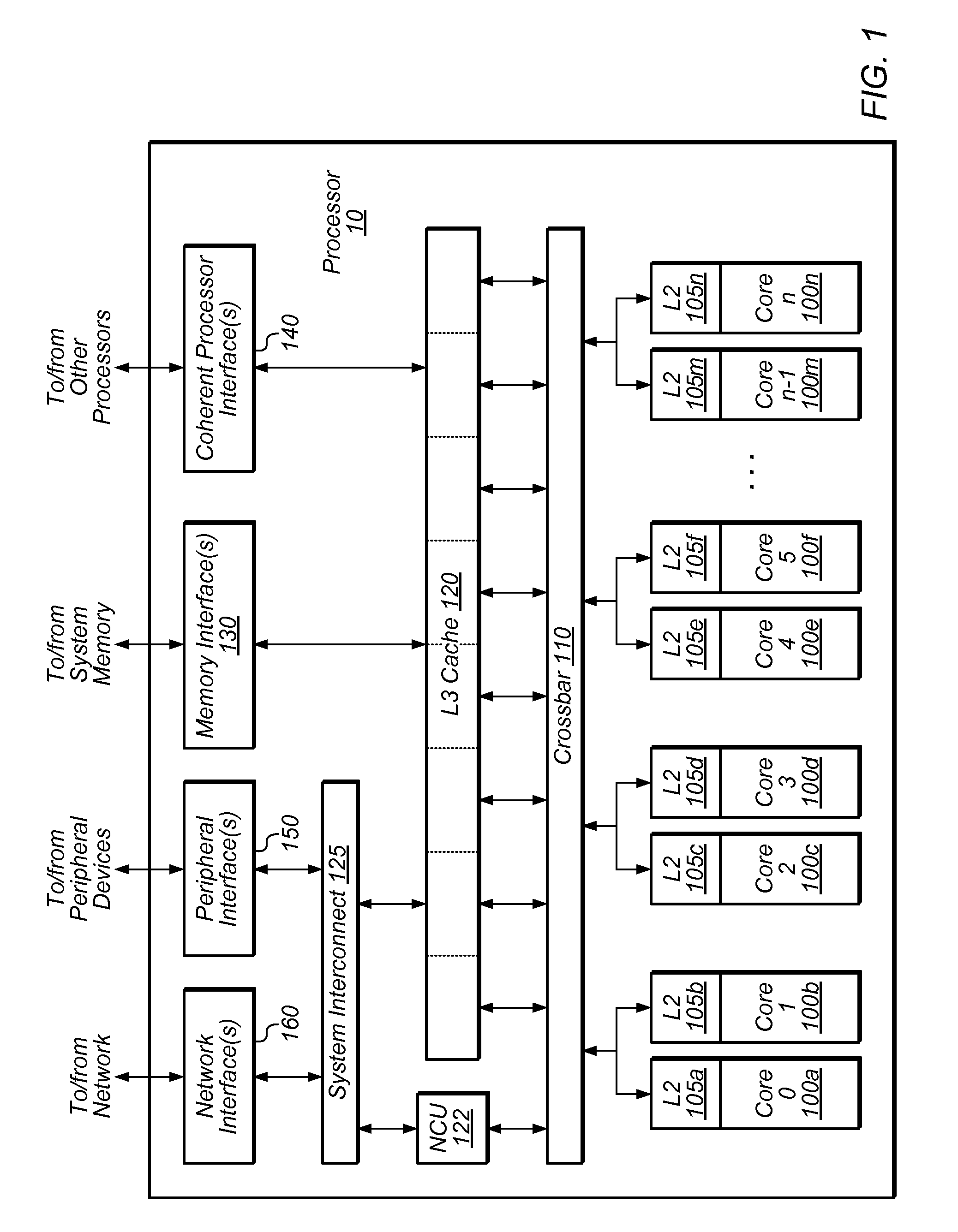
Patents
Literature
68 results about "Rename" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, rename refers to the altering of a name of a file. This can be done manually by using a shell command such as ren or mv, or by using batch renaming software that can automate the renaming process.
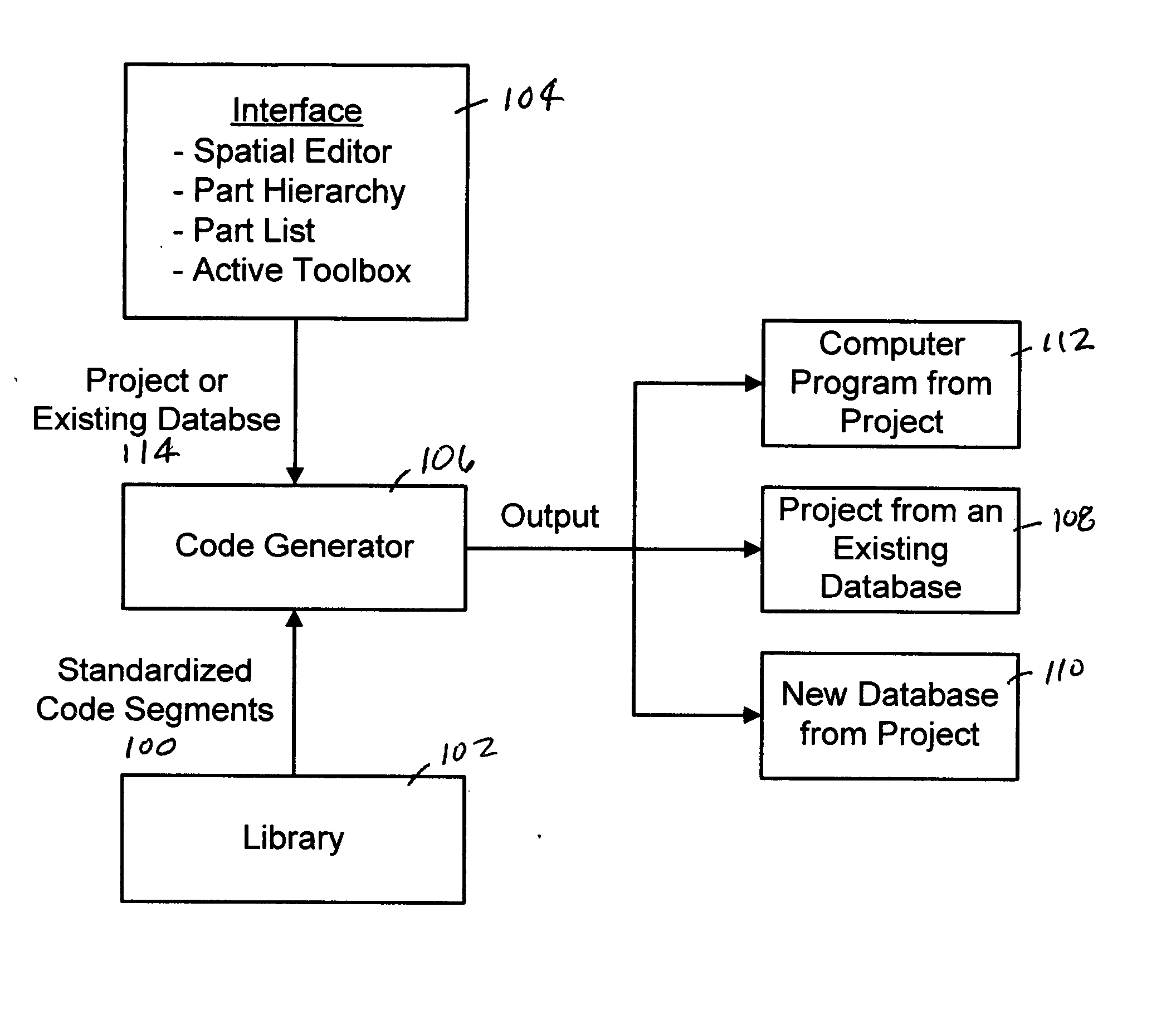
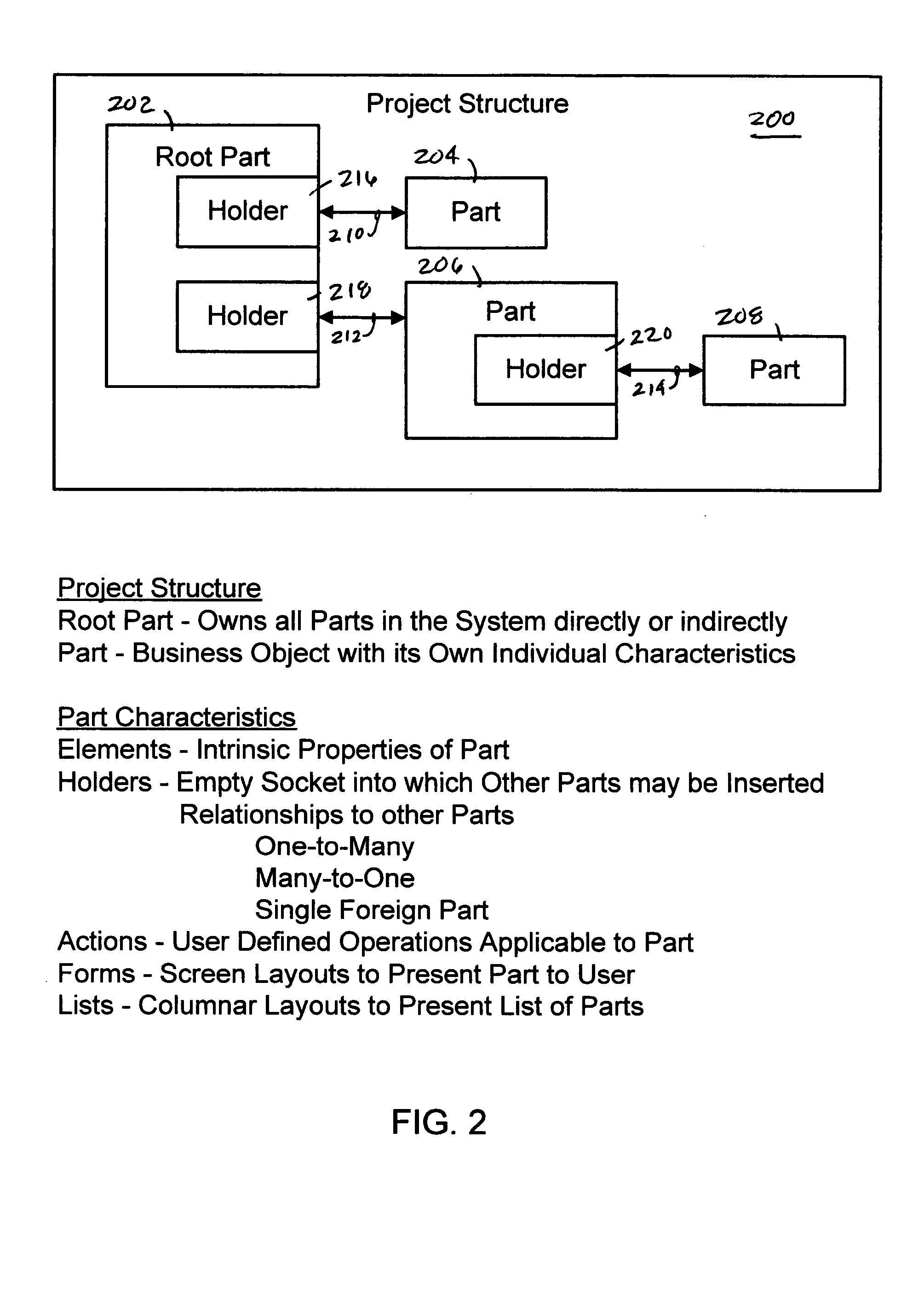
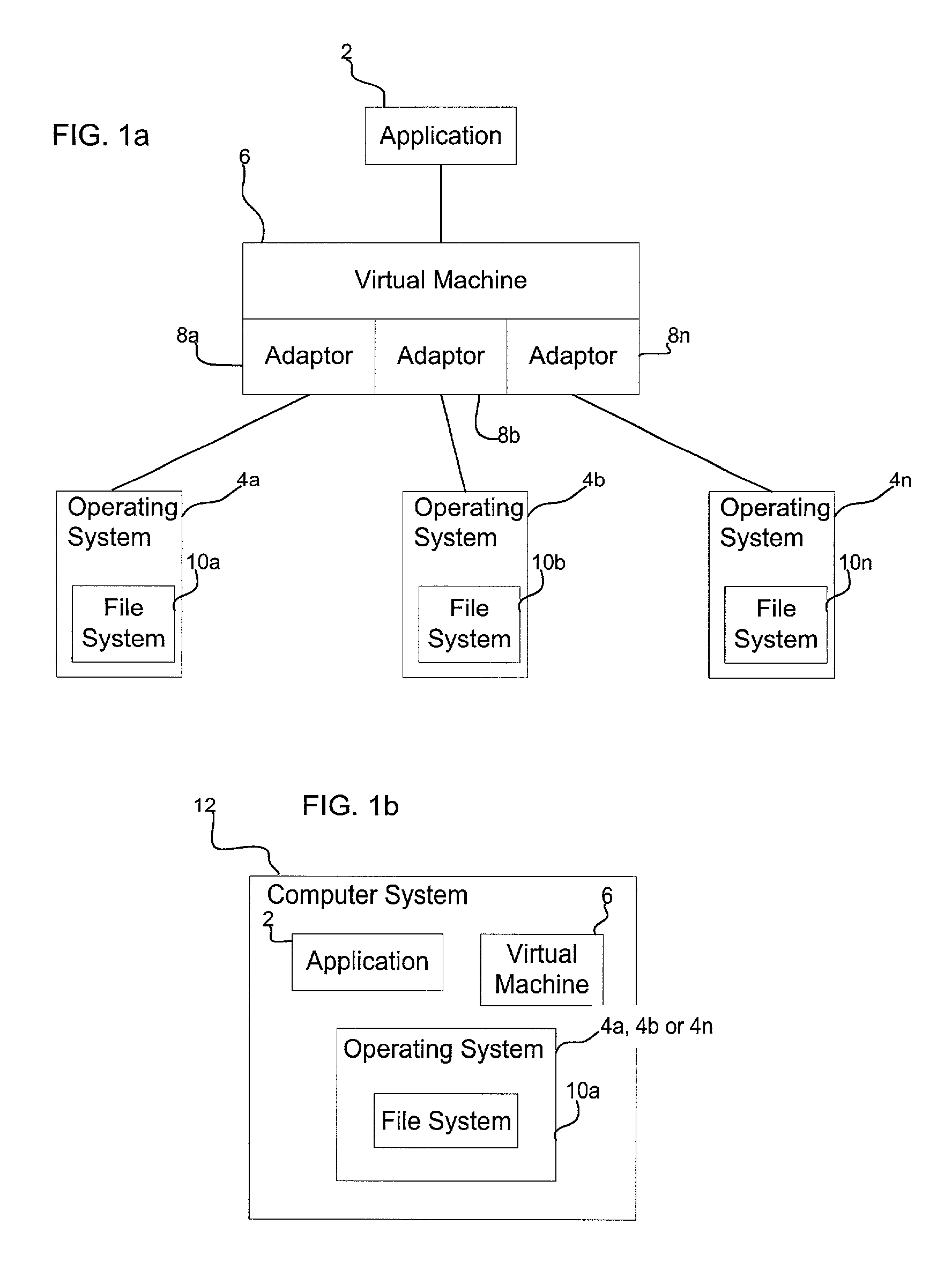
System, method and apparatus for developing software
InactiveUS20050065970A1Inexpensive and easy to useAccelerates software developmentDigital data processing detailsVisual/graphical programmingCode segmentStandardization
The present invention provides a system, method and apparatus for developing software that includes a set of standardized code segments, an interface for defining a structure of a project and a code generator communicably coupled to the set of standardized code segments and the interface that can create a computer program from the project. The present invention also generates a new computer program by (a) creating and renaming a root part for a project having a structure, (b) adding and renaming one or more holders to the renamed root part, (c) adding and renaming a part to one or more of the renamed holders, (d) adding and renaming one or more holders to the renamed parts, (e) creating one or more elements for each renamed part, (f) repeating steps (c), (d) and (e) as needed to complete the structure, and (g) generating the new computer program from the project.
Owner:KING ANTHONY GRAHAM +2
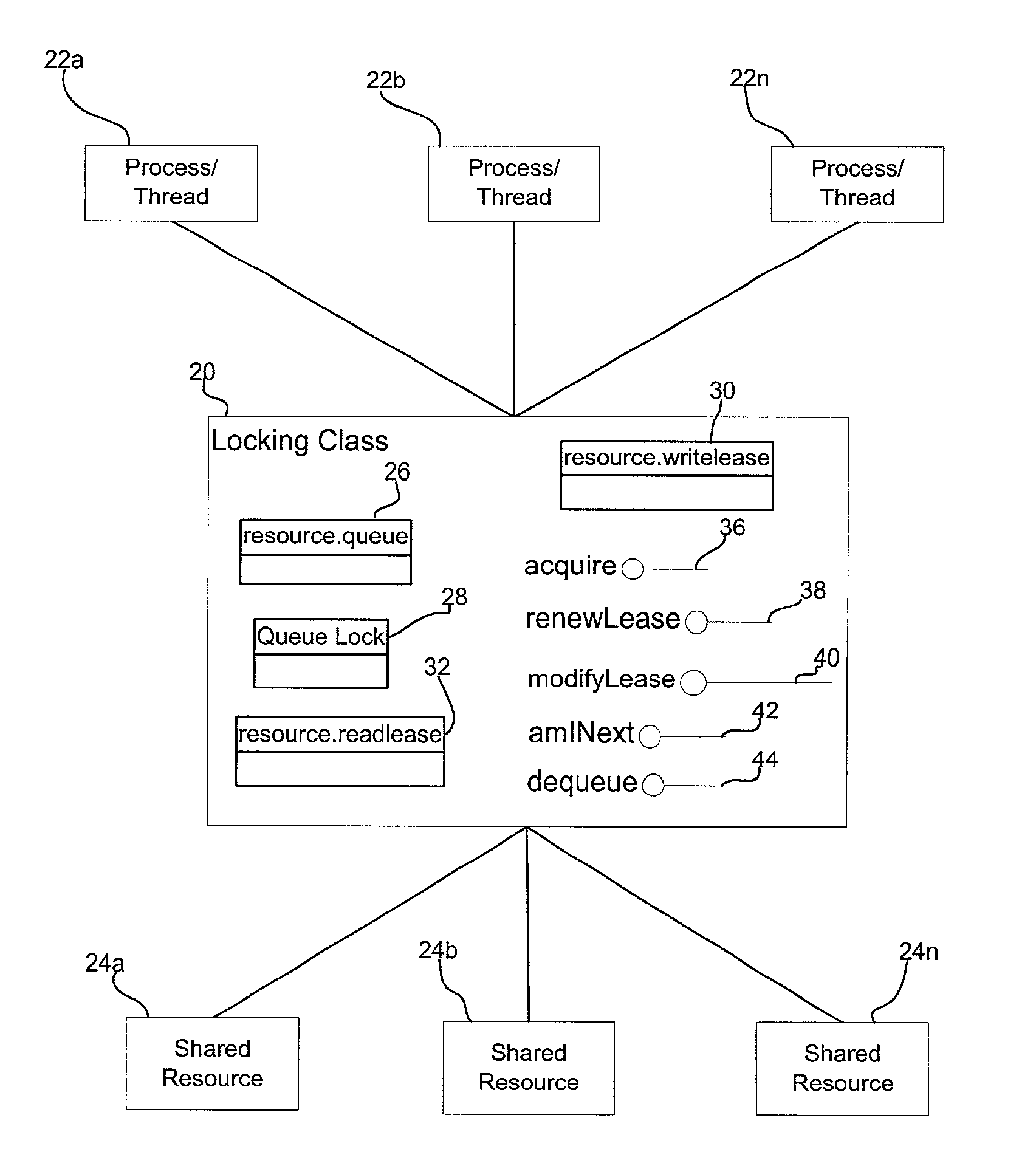
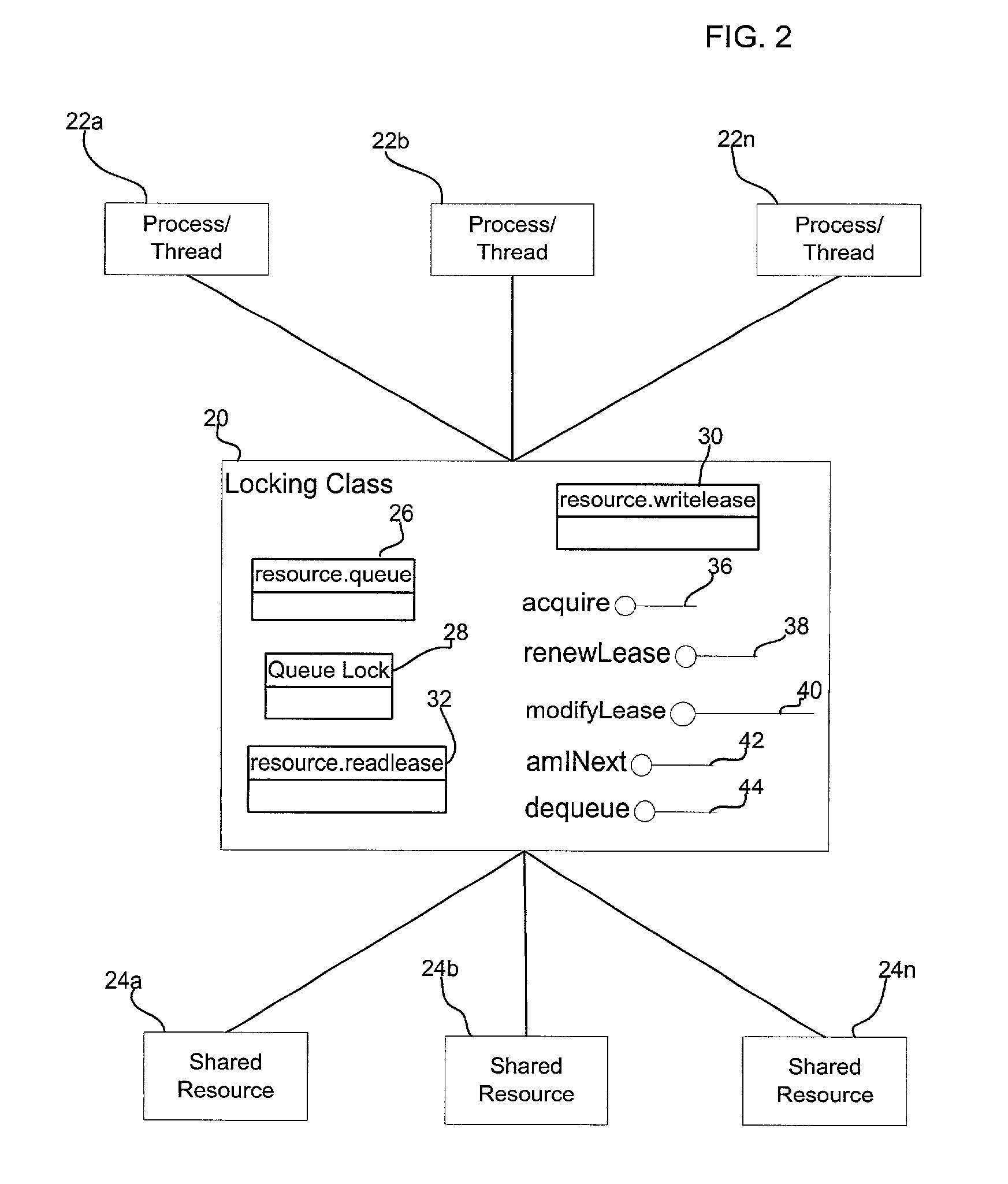
Method, system, program, and data structure for implementing a locking mechanism for a shared resource
ActiveUS7107267B2Data processing applicationsProgram synchronisationLocking mechanismShared resource
Provided are a method, system, program, and data structure for implementing a locking mechanism to control access to a shared resource. A request is received to access the shared resource. A determination is made of whether a first file has a first name. The first file is renamed to a second name if the first file has the first name. A second file is updated to indicate the received request in a queue of requests to the shared resource if the first file is renamed to the second name. An ordering of the requests in the queue is used to determine whether access to the shared resource is granted to the request. The first file is renamed to the first name after the second file is updated.
Owner:ORACLE INT CORP
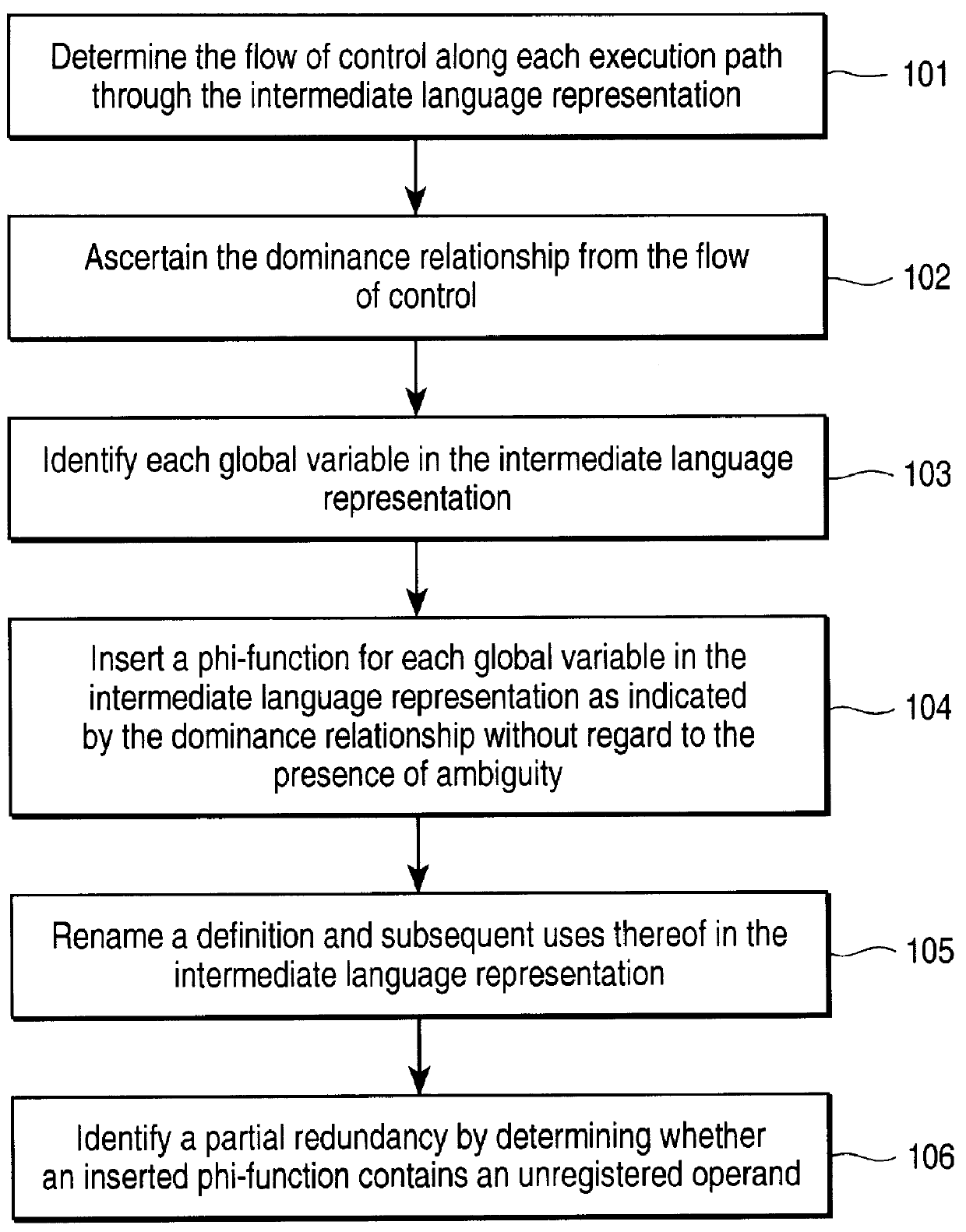
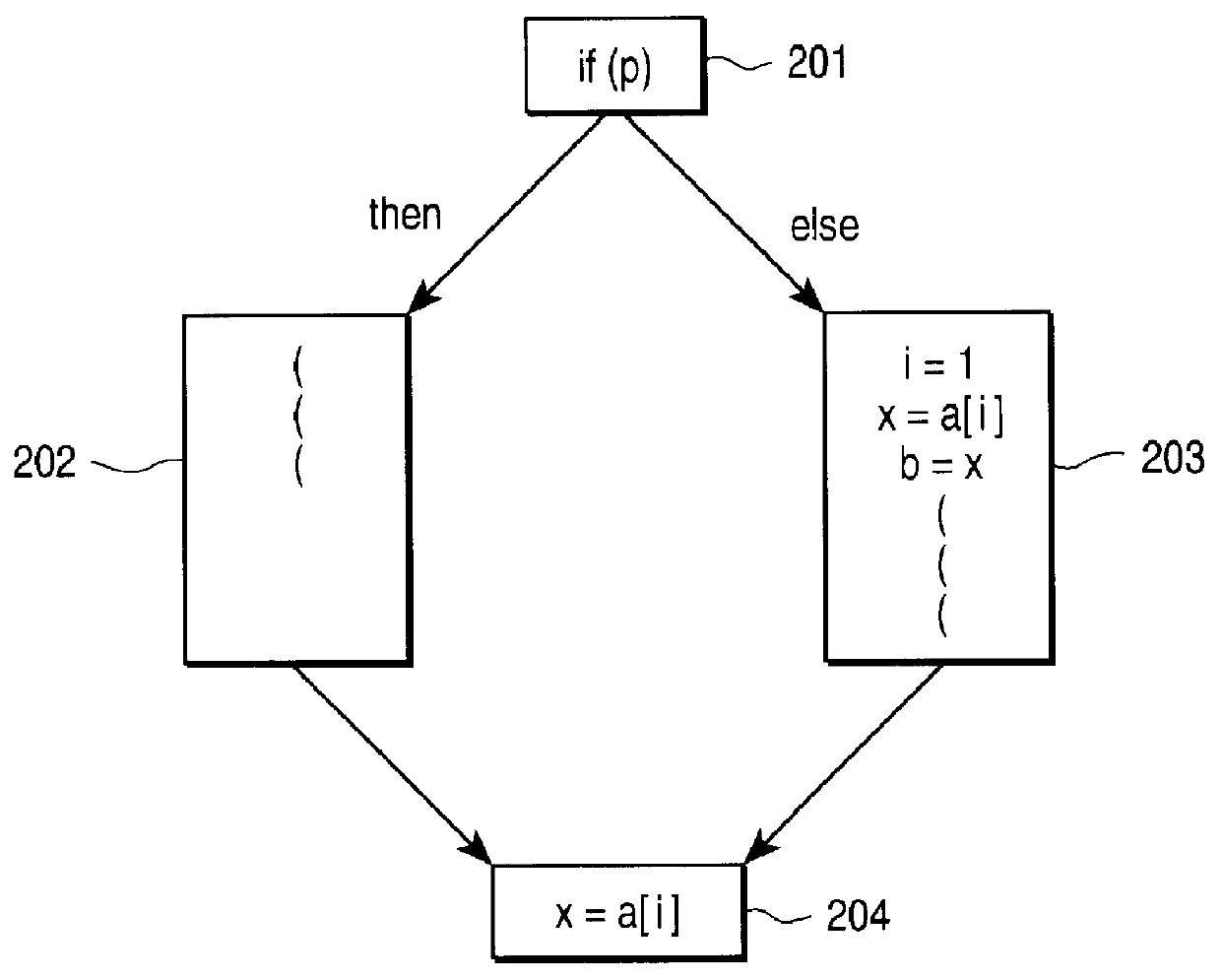
Method for identifying partial redundancies in a new processor architecture
The invention, in one embodiment, is a method for compiling at least a portion of a computer program. The method includes (a) inserting a phi-function for a global variable reaching a join point in the intermediate language representation subsequent to the join point without regard to the presence of ambiguity; (b) renaming a definition and any subsequent use of the definition in the intermediate language representation; and (c) identifying a partially redundant load by determining whether any of the operands of the inserted phi-function have not been renamed.
Owner:INTEL CORP
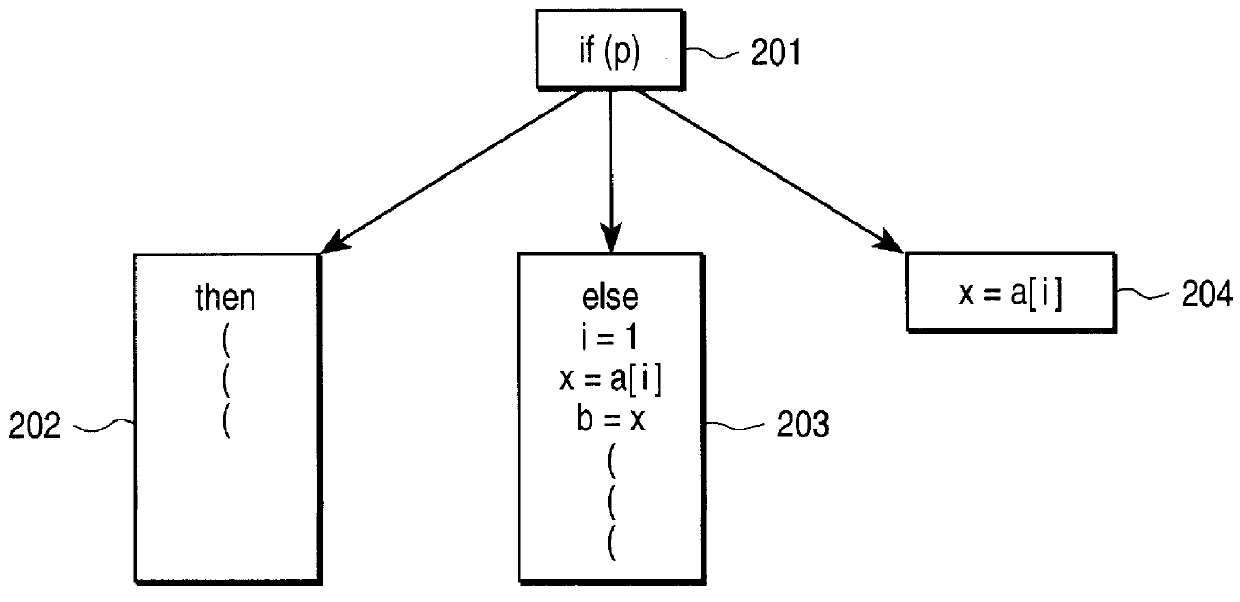
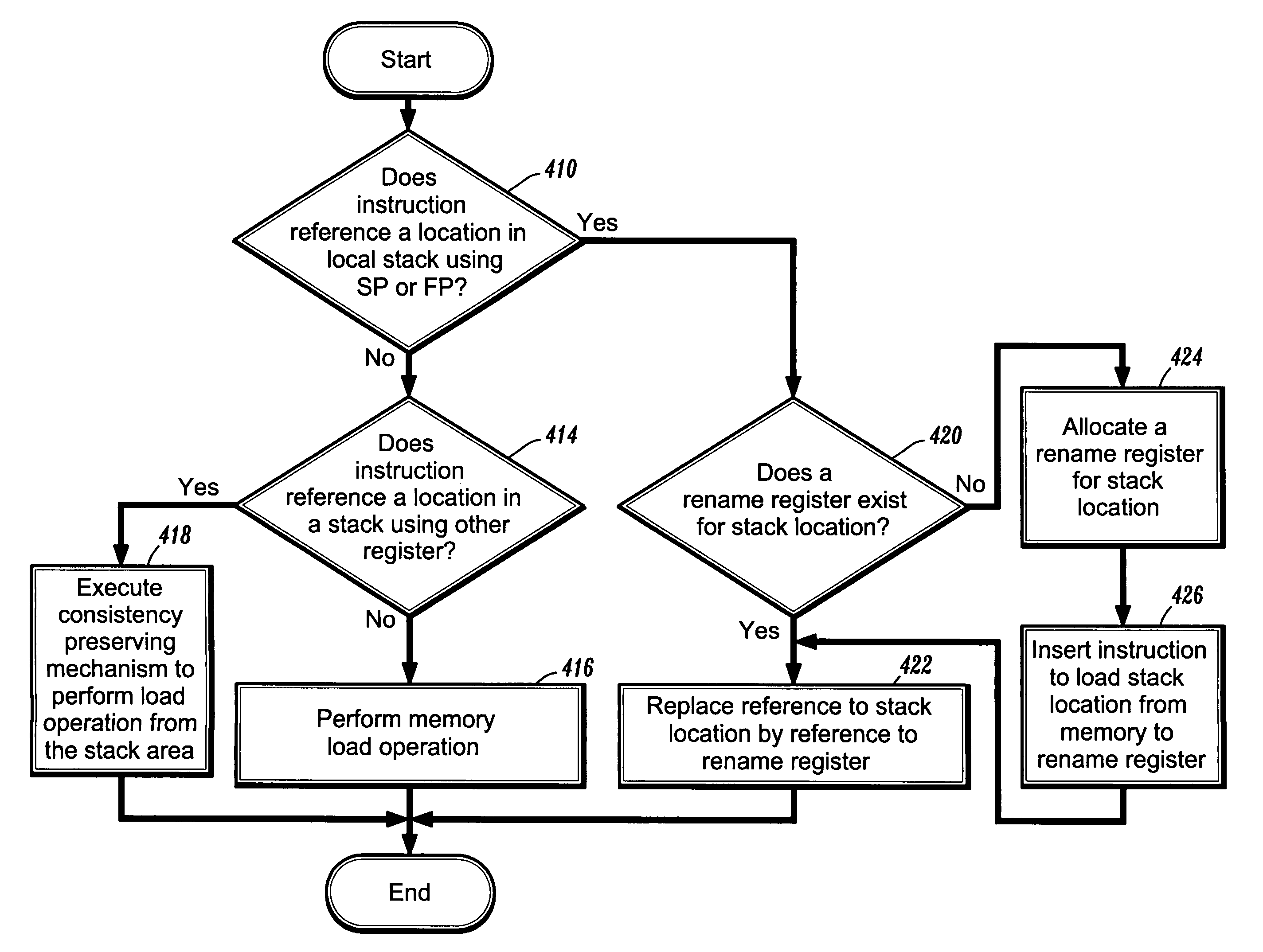
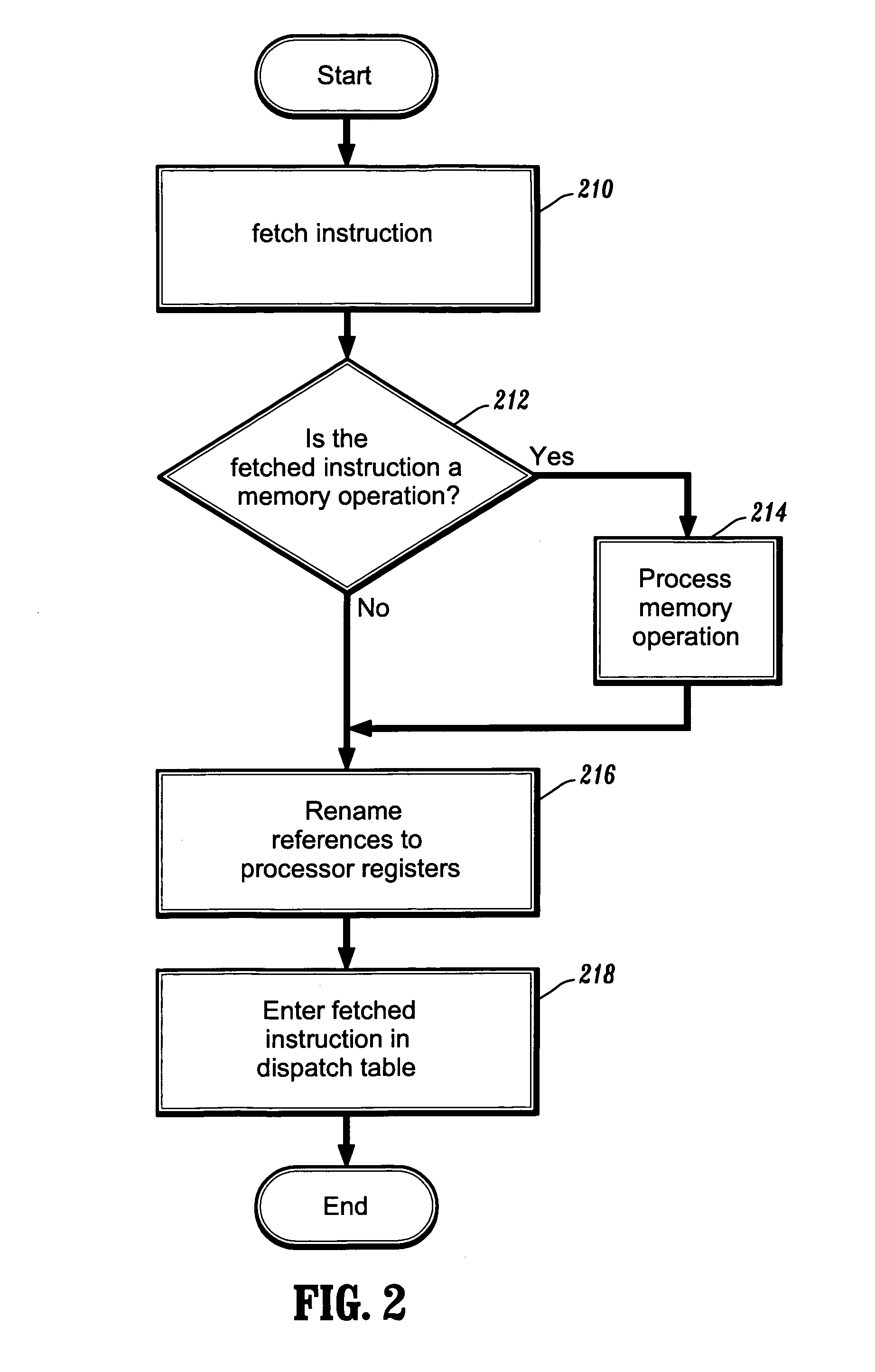
Methods for renaming stack references to processor registers
InactiveUS7085914B1Memory adressing/allocation/relocationDigital computer detailsAccess methodProcessor register
According to one aspect of the invention, there is provided a method for renaming memory references to stack locations in a computer processing system. The method includes the steps of detecting stack references that use architecturally defined stack access methods, and replacing the stack references with references to processor-internal registers. The architecturally defined stack access methods include memory accesses that use one of a stack pointer, a frame pointer, and an argument pointer. Moreover, the architecturally defined stack access methods include push, pop, and other stack manipulation operations.
Owner:LINKEDIN
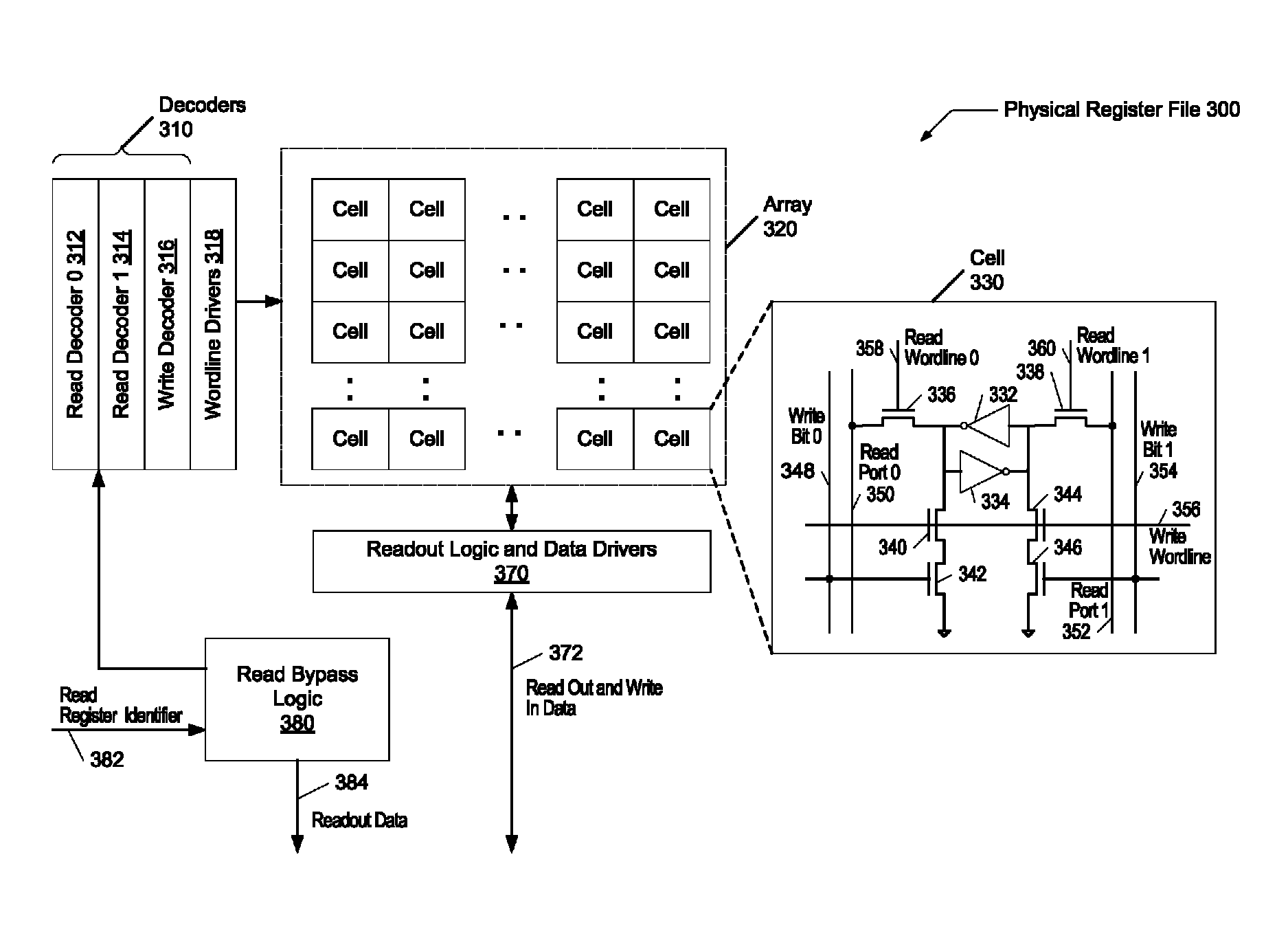
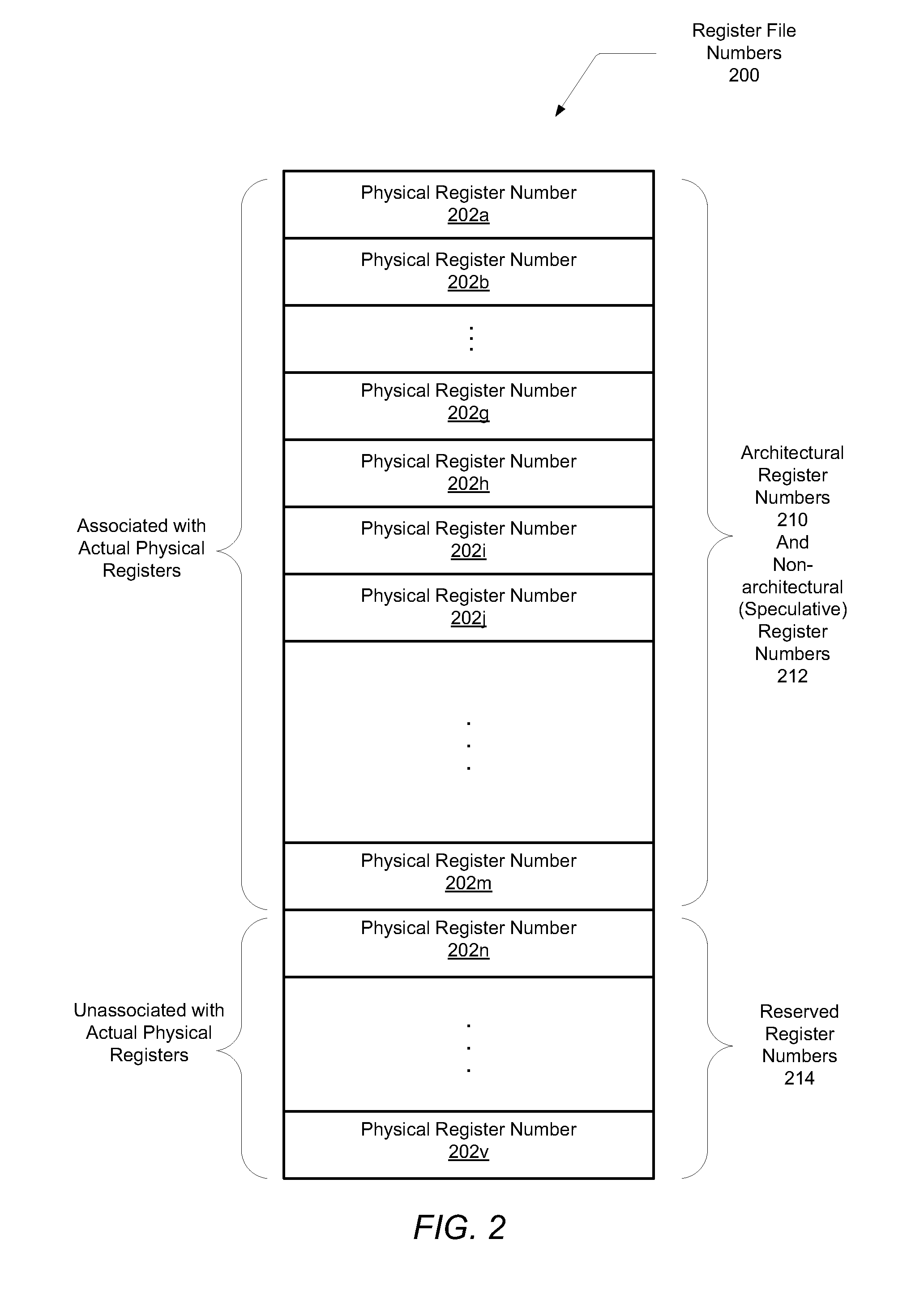
Method And Apparatus For Register Renaming Using Multiple Physical Register Files And Avoiding Associative Search
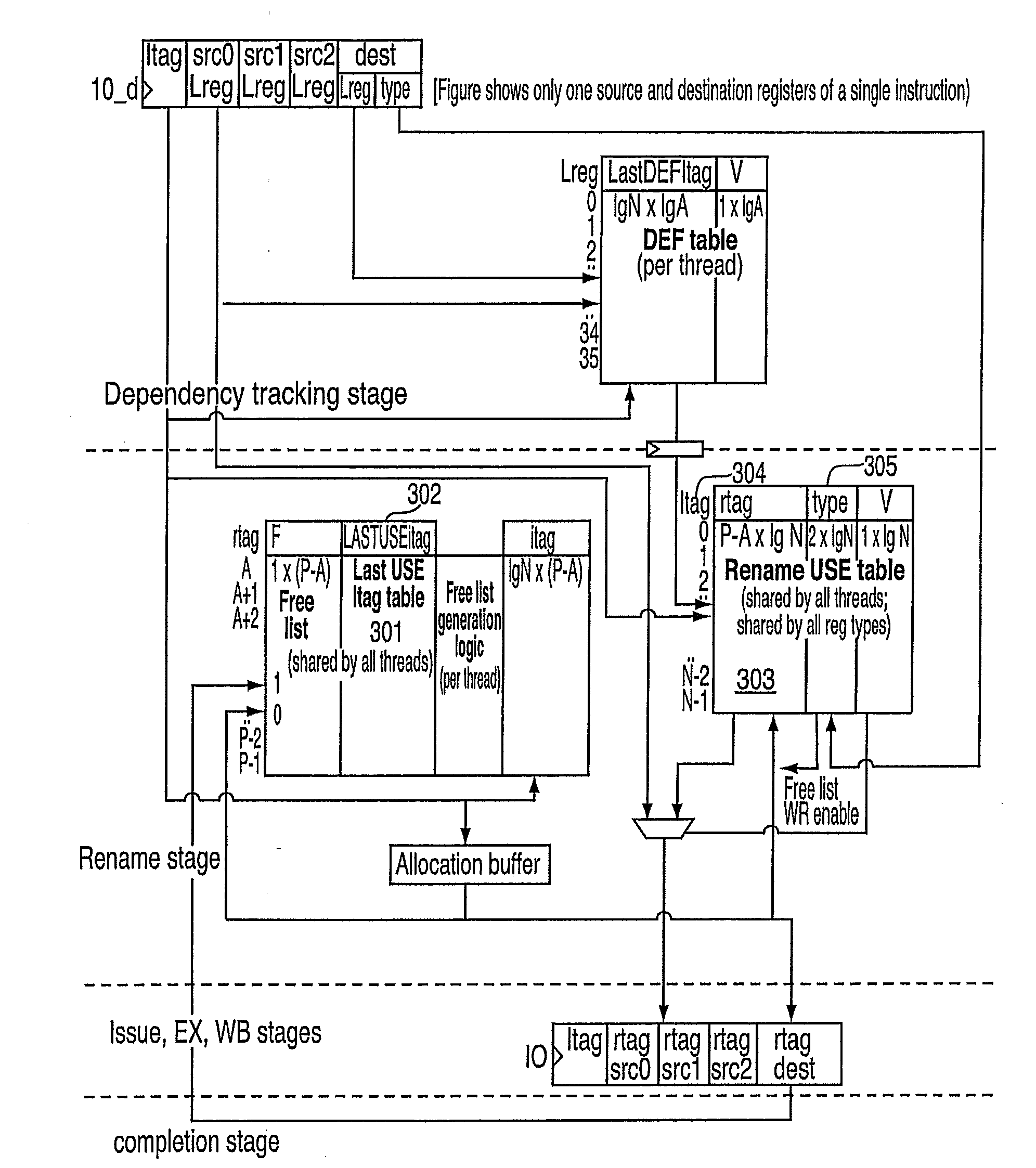
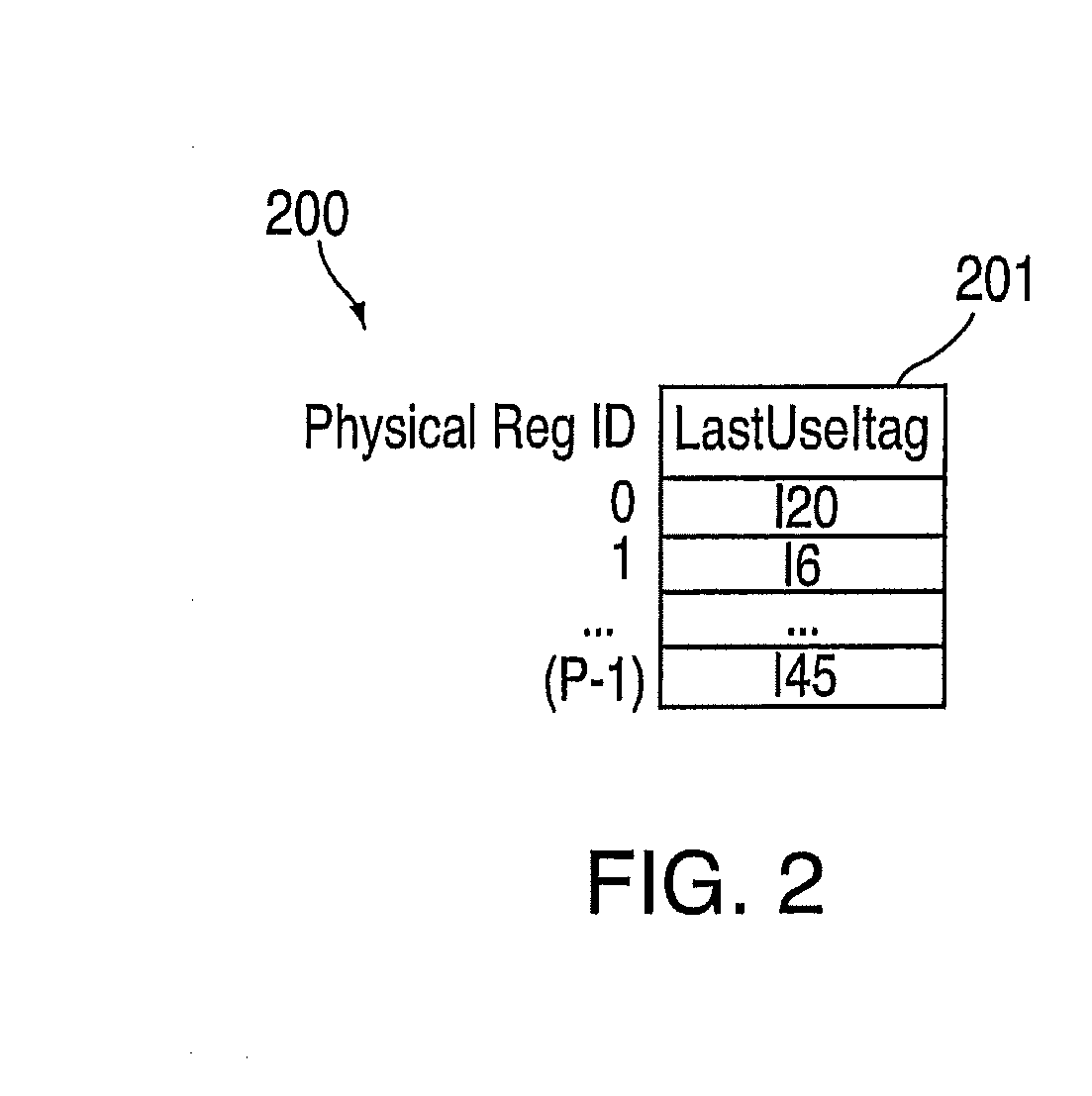
A method for implementing a register renaming scheme for a digital data processor using a plurality of physical register files for supporting out-of-order execution of a plurality of instructions from one or more threads, the method comprising: using a DEF table to store the instruction dependencies between the plurality of instructions using the instruction tags, the DEF table being indexed by a logical register name and including one entry per logical register; using a rename USE table indexed by the instruction tags to store logical-to-physical register mapping information shared by multiple sets of different types of non-architected copies of logical registers used by multiple threads; using a last USE table to transfer data of the multiple sets of different types of non-architected copies of logical registers into the first set of architected registered files, the last USE table being indexed by a physical register name in the second set of rename registered files; and performing the register renaming scheme at the instruction dispatch or wake-up / issue time.
Owner:INT BUSINESS MASCH CORP
Logical map table for detecting dependency conditions
ActiveUS20100274993A1Detection can be executedDigital computer detailsSpecific program execution arrangementsContent-addressable storageProgramming language
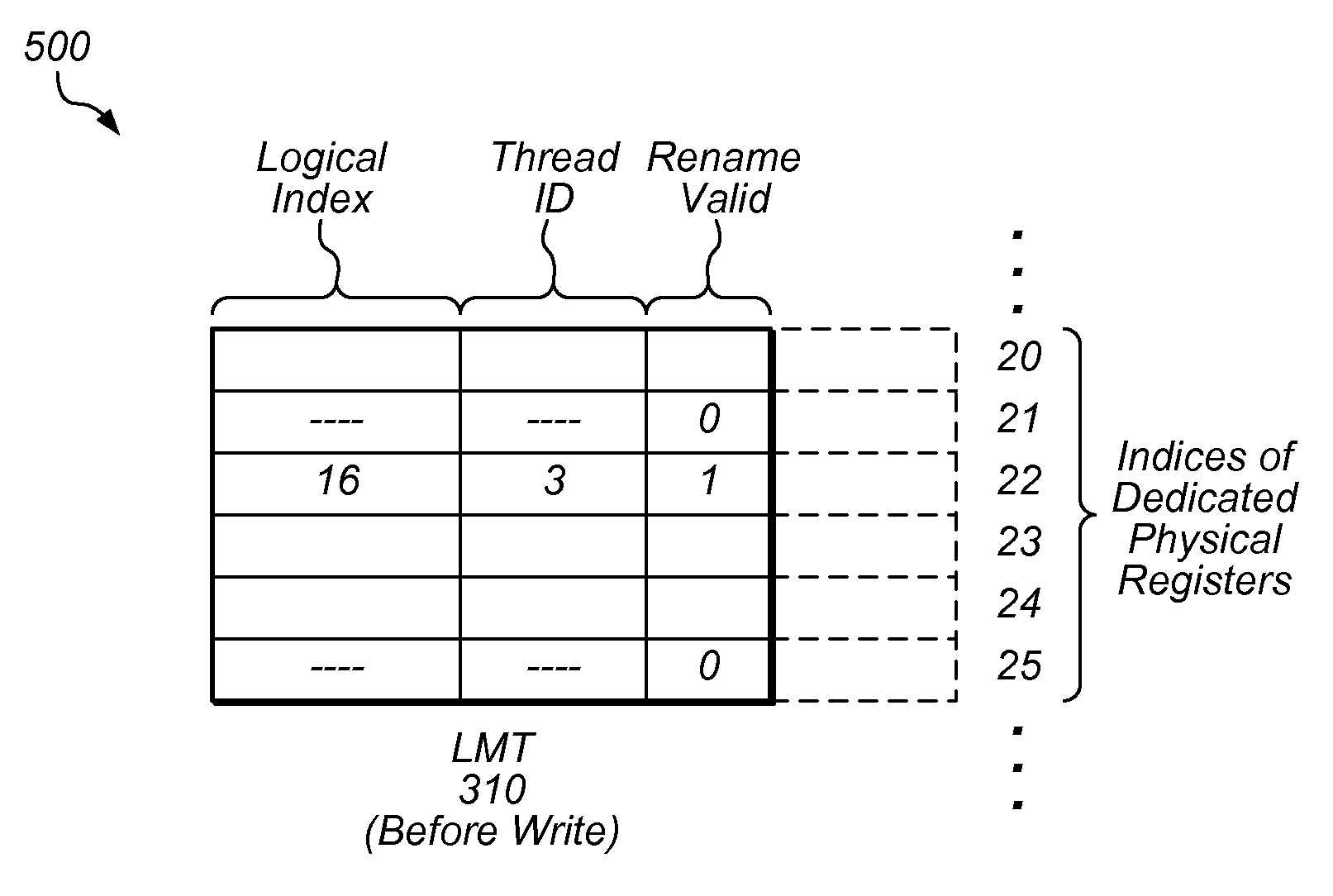
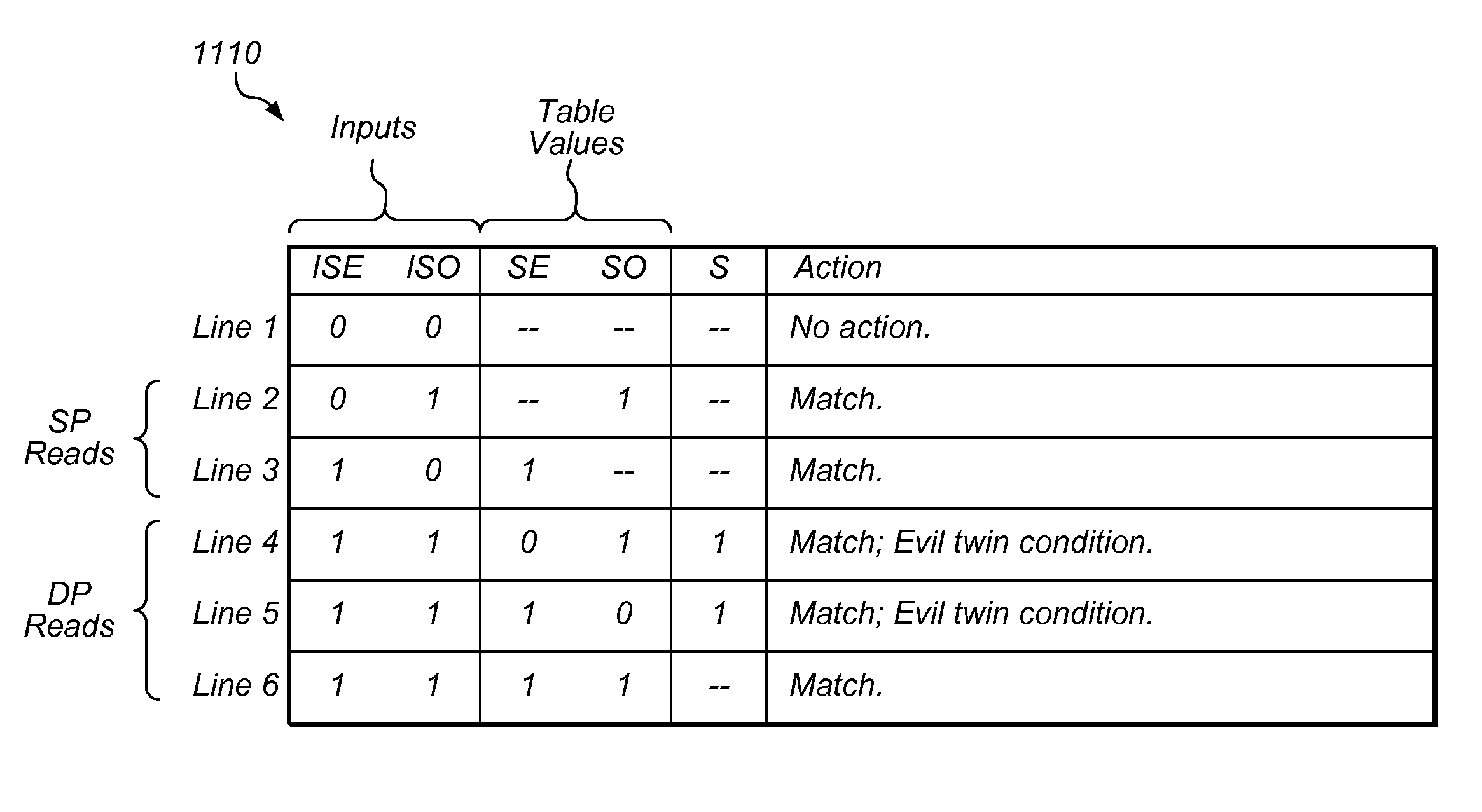
Techniques and structures are described which allow the detection of certain dependency conditions, including evil twin conditions, during the execution of computer instructions. Information used to detect dependencies may be stored in a logical map table, which may include a content-addressable memory. The logical map table may maintain a logical register to physical register mapping, including entries dedicated to physical registers available as rename registers. In one embodiment, each entry in the logical map table includes a first value usable to indicate whether only a portion of the physical register is valid and whether the physical register includes the most recent update to the logical register being renamed. Use of this first value may allow precise detection of dependency conditions, including evil twin conditions, upon an instruction reading from at least two portions of a logical register having an entry in the logical map table whose first value is set.
Owner:ORACLE INT CORP
Apparatus and method for handling dependency conditions
Owner:ORACLE INT CORP
General register renaming method and microprocessor possessing general register renaming
A unified register rename mechanism for targets of different instruction types is provided in a microprocessor. The universal rename mechanism renames destinations of different instruction types using a single rename structure. Thus, an instruction that is updating a floating point register (FPR) can be renamed along with an instruction that is updating a general purpose register (GPR) or vector multimedia extensions (VMX) instructions register (VR) using the same rename structure because the number of architected states for GPR is the same as the number of architected states for FPR and VR. Each destination tag (DTAG) is assigned to one destination. A floating point instruction may be assigned to a DTAG, and then a fixed point instruction may be assigned to the next DTAG and so forth. With a universal rename mechanism, significant silicon and power can be saved by having only one rename structure for all instruction types.
Owner:INT BUSINESS MASCH CORP
Electronics assembly engineering system employing naming and manipulation functions for user defined data structures in a data system using transaction service
InactiveUS6865583B2Data processing applicationsNatural language data processingSearch data structureArray data structure
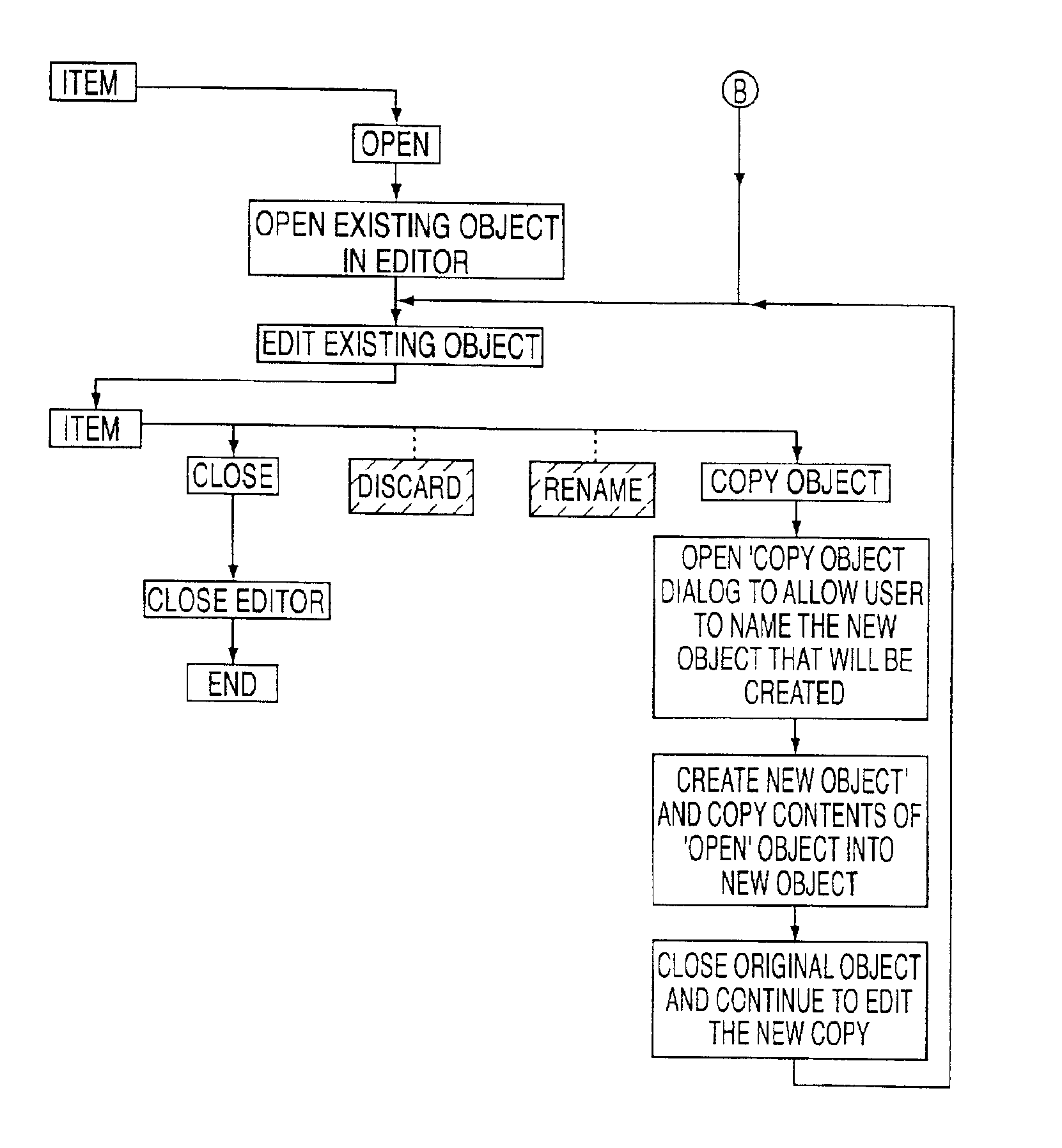
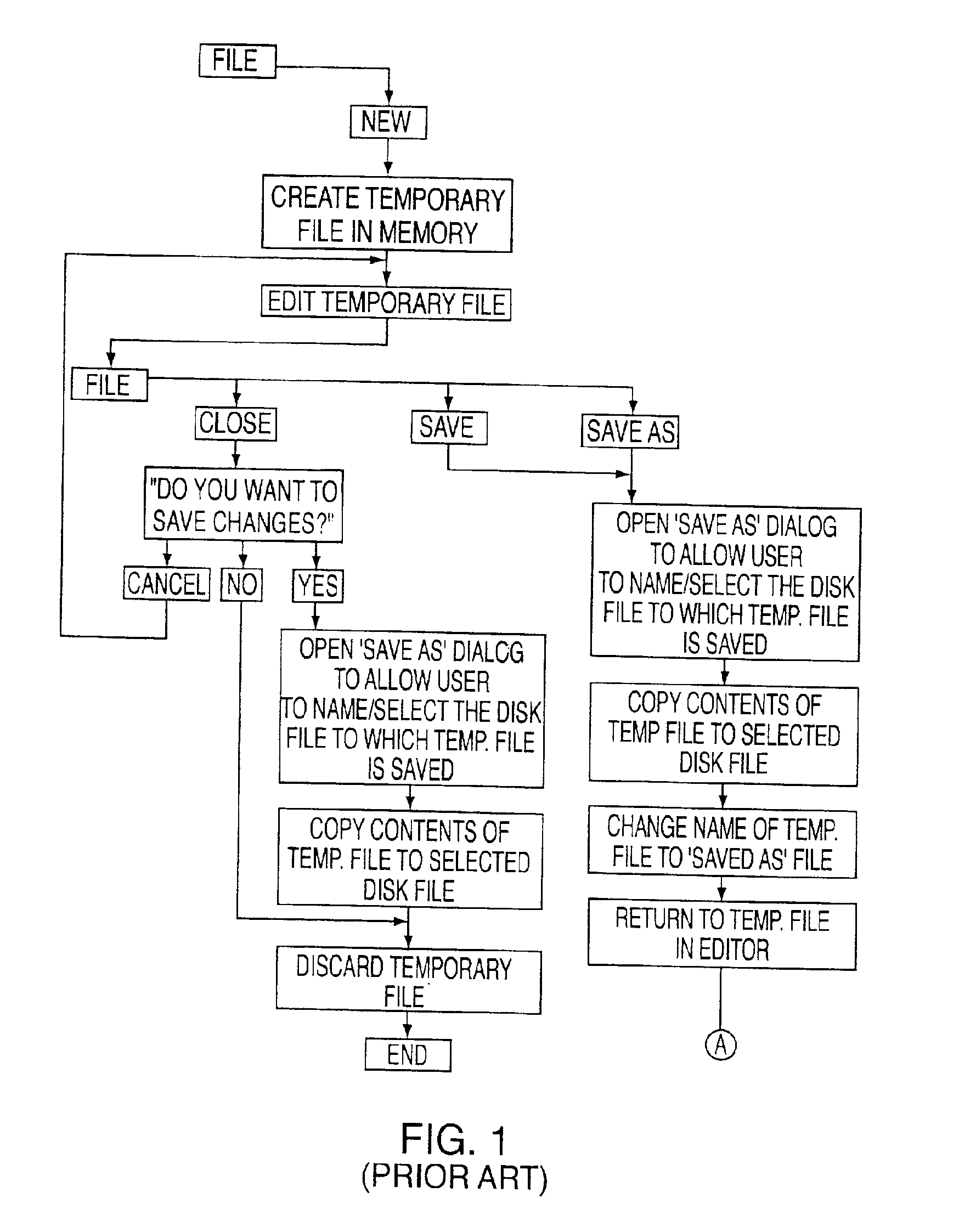
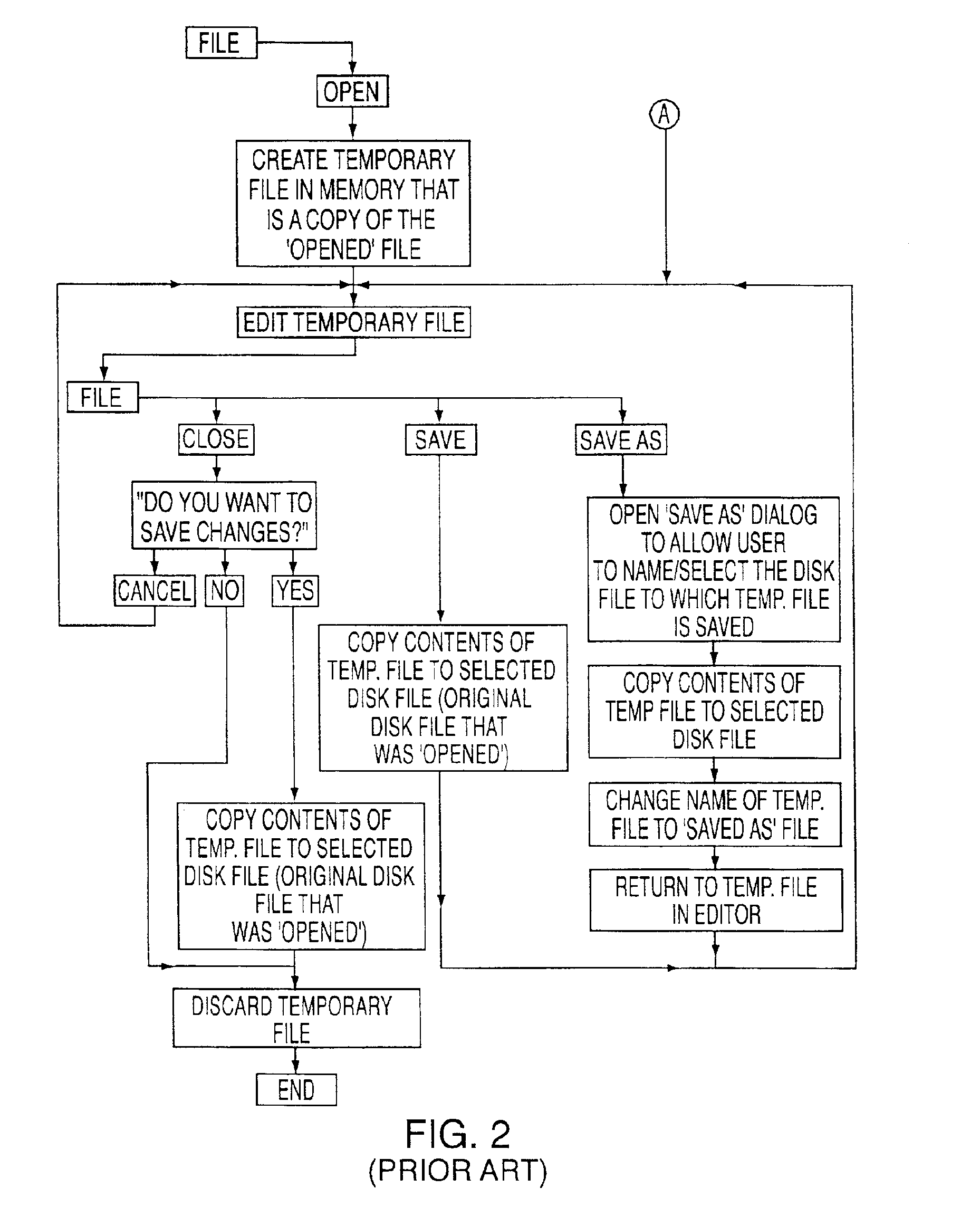
The present invention provides novel naming and manipulation functions for user defined data structures in a data system using transaction service. In particular, in an electronics assembly engineering system having a computer subsystem in which user-defined data structures accessible to editor software have referential integrity and in which user modifications to the data structures during editing are made directly to the data structures rather than indirectly by way of a temporary file, the invention provides a method for permitting naming and manipulation of the data structures. The method includes the steps of (i) providing close, discard and rename functions for the data structures in the case where a newly-created data structure is being edited; (ii) providing close and copy functions for the data structures if an existing data structure is being edited; and (iii) excluding a save-as function for the data structures.
Owner:SIEMENS ELECTRONICS ASSEMBLY SYST LLC +1
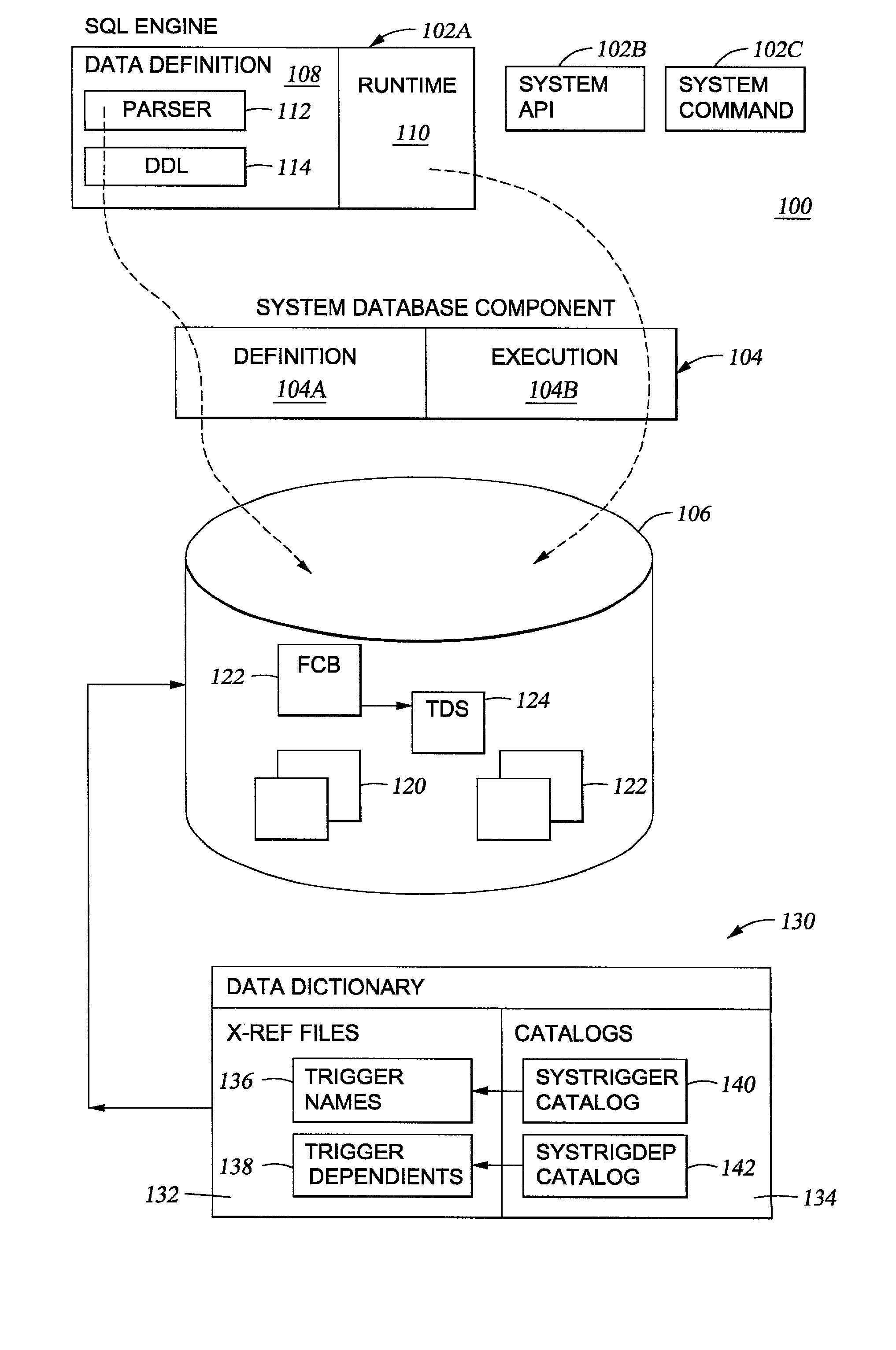
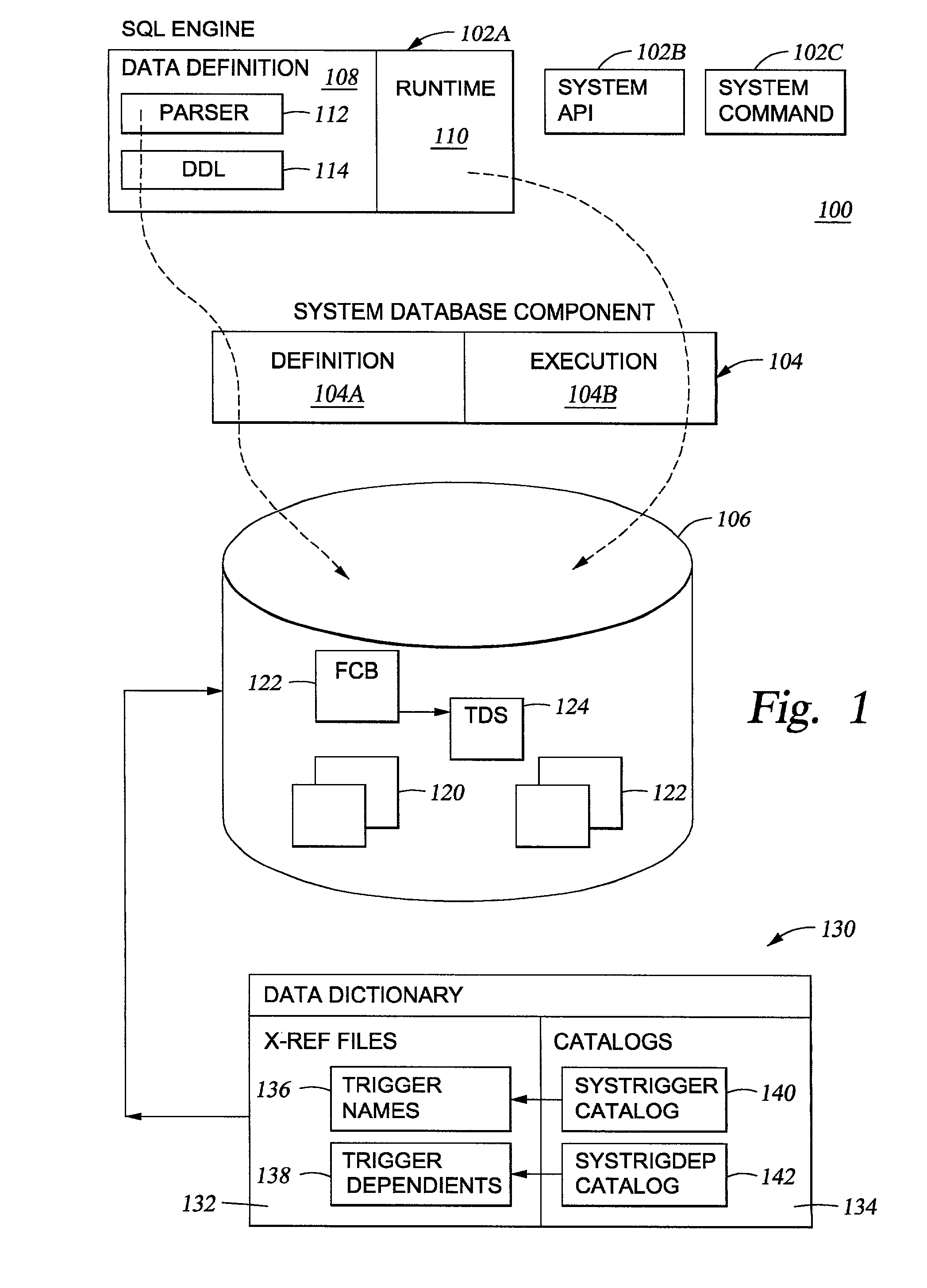
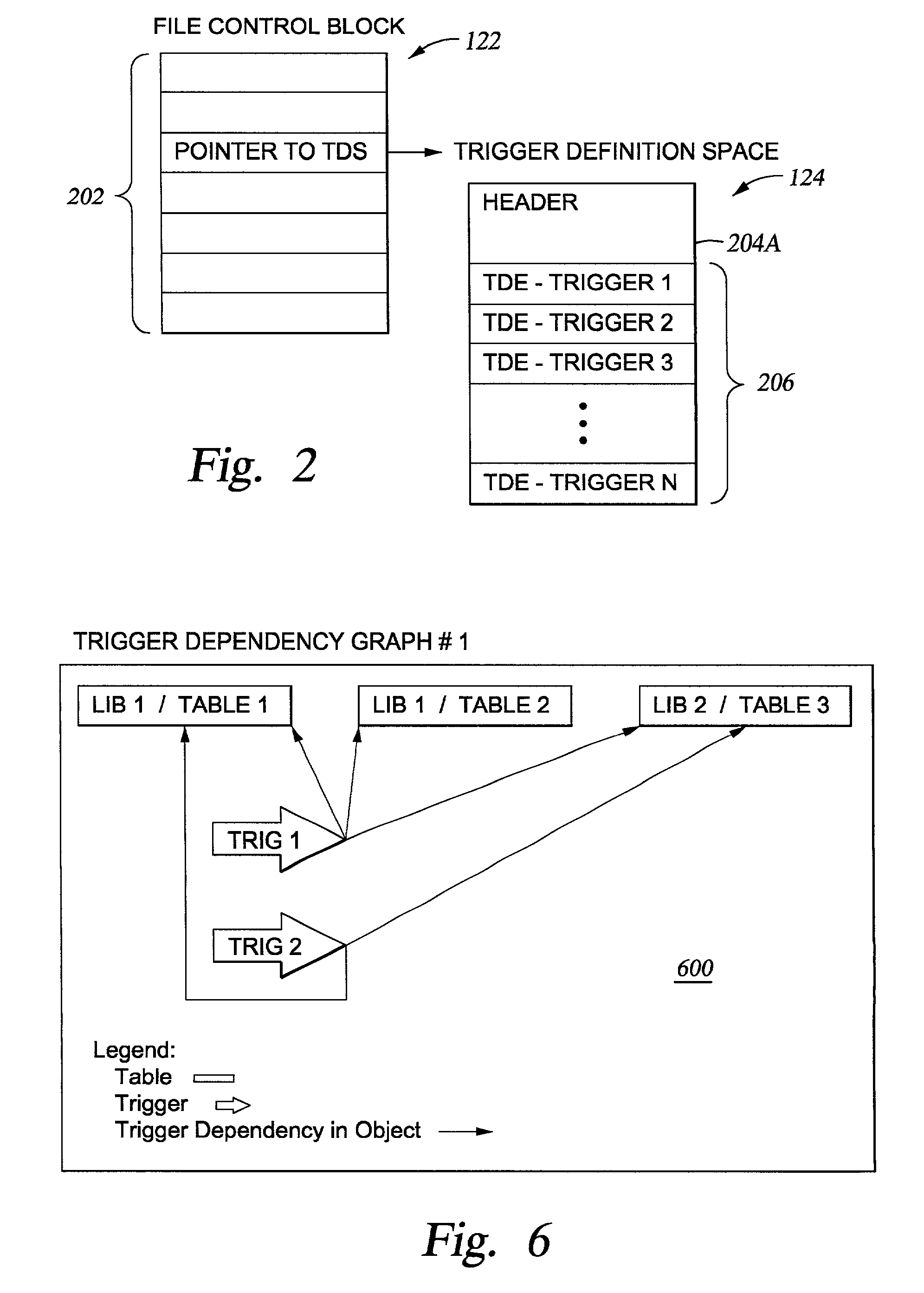
Dependent object processing for triggers
InactiveUS20020184207A1Data processing applicationsDigital data information retrievalComputer scienceManagement system
Methods, systems and articles of manufacture are provided for setting a state of triggers between operative and inoperative. In an operative state the trigger may be called during triggering I / O operations such as Insert, Update and Delete. The inoperative state indicates that the system has detected a condition requiring user intervention. In a particular embodiment, a database management system (DBMS) will analyze the function being performed on a table (such as a rename of the table) and with dependent object data, the DBMS will determine if the trigger is self-referencing. If so, the trigger made inoperative. Making the trigger inoperative and requiring user intervention prevents the system from potentially producing undesired results. In another embodiment, a determination of dependency is made upon receiving a database command to affect an object. According to the type of command, the object and its dependents are either affected or unaffected.
Owner:IBM CORP
Method of automatically correcting broken links to files stored on a computer
InactiveUS20030004978A1Data processing applicationsError detection/correctionComputer data storageData memory
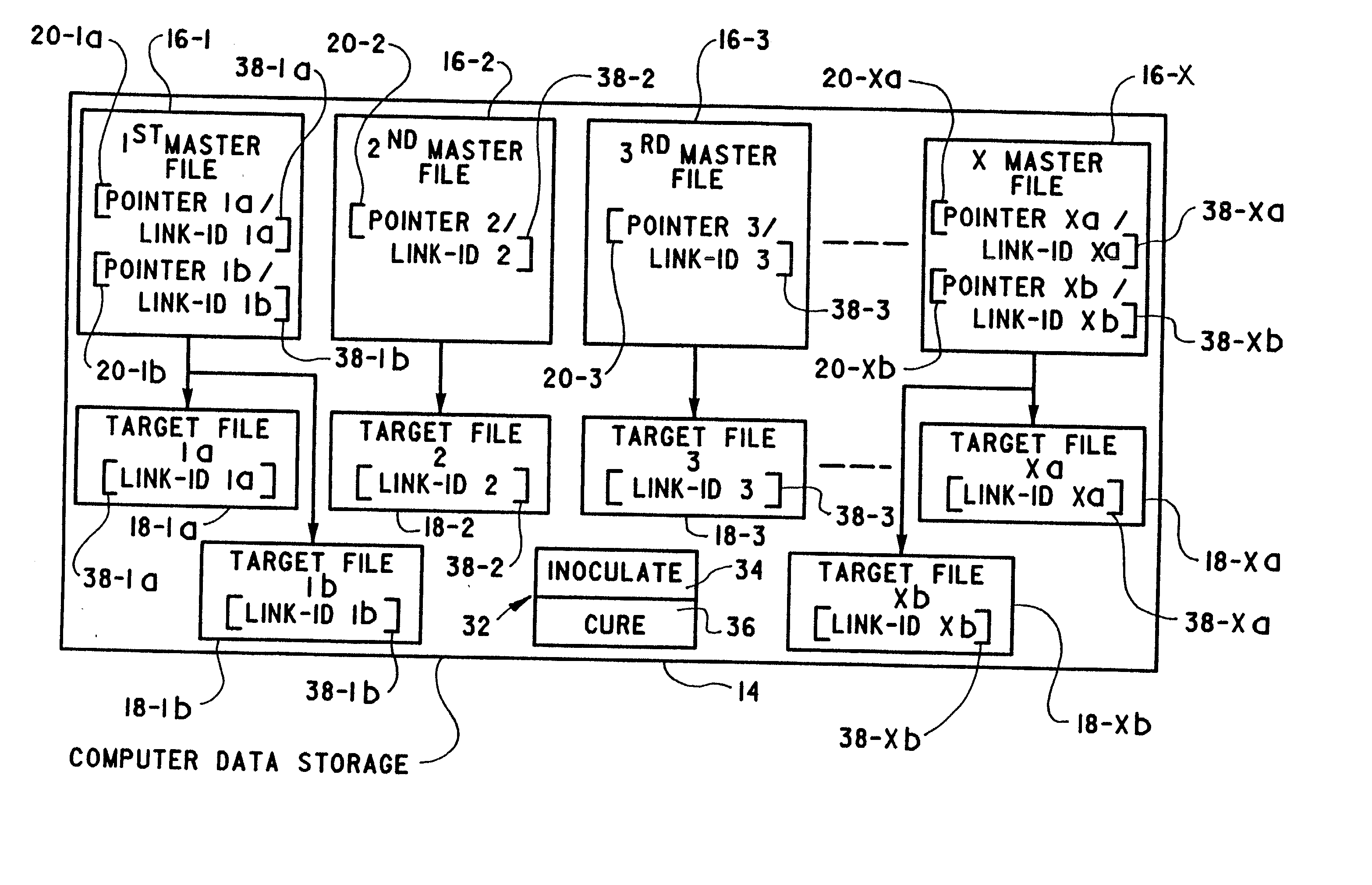
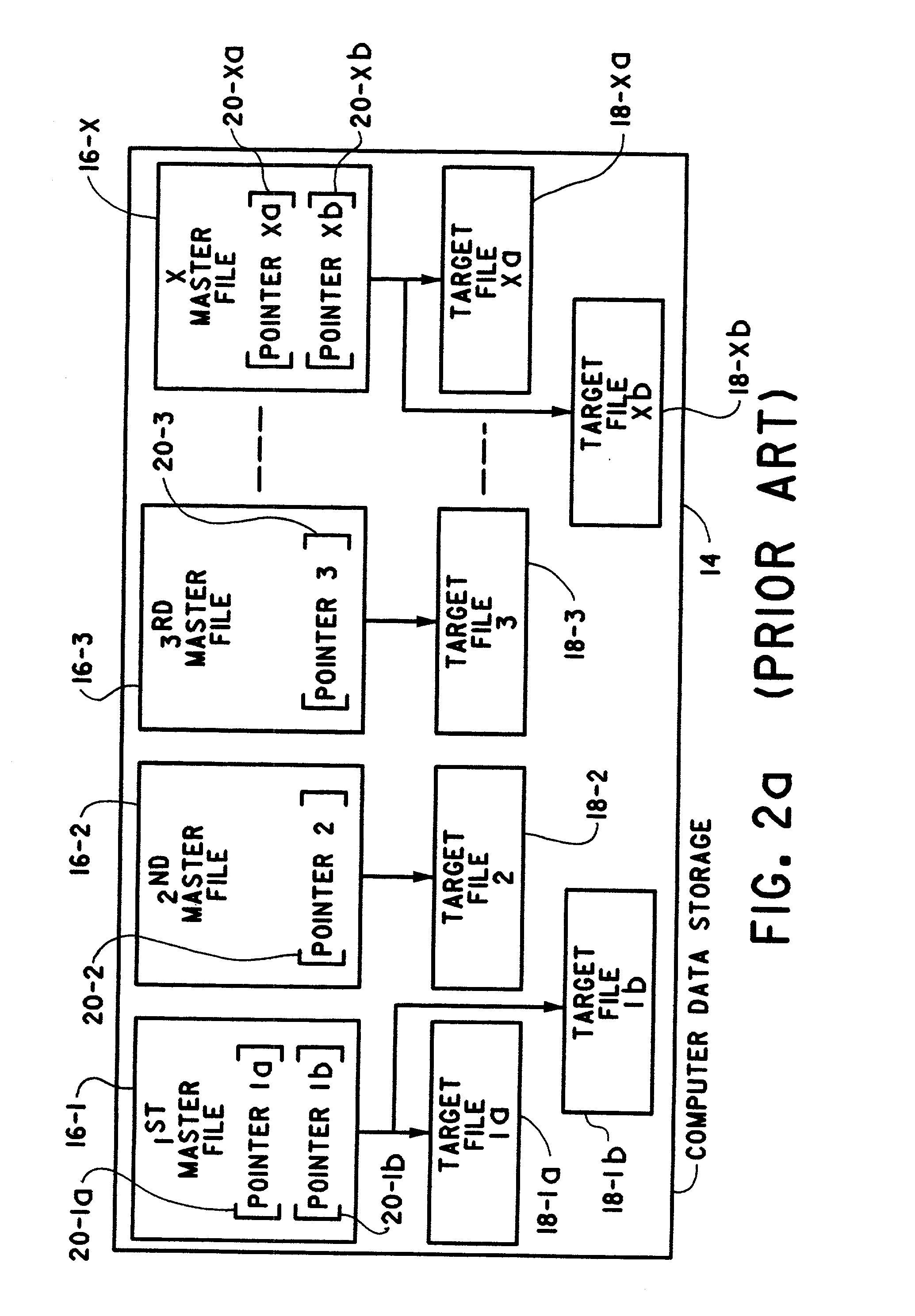
A method of correcting broken software links includes providing a computer data storage having target files and master files. Each master file includes a pointer to a storage location where at least one target file called by the master file resides. A link-id is determined for each target file and is stored in each master file configured to call the target file. The target file is then either renamed or moved so that each master file configured to call the target file cannot locate it from the pointer data. The target file is then located on the computer data storage based on a match between the link-id for the target file and the link-id stored in the calling master file. The data comprising the pointer of the master file is then updated whereupon it can locate the target file on the computer data storage.
Owner:AXIOM SERVICES
Logical map table for detecting dependency conditions between instructions having varying width operand values
Owner:ORACLE INT CORP
Simultaneous finish of stores and dependent loads
ActiveUS20140325188A1Reducing a pipeline stallDigital computer detailsMemory systemsLoad instructionParallel computing
A method for reducing a pipeline stall in a multi-pipelined processor includes finding a store instruction having a same target address as a load instruction and having a store value of the store instruction not yet written according to the store instruction, when the store instruction is being concurrently processed in a different pipeline than the load instruction and the store instruction occurs before the load instruction in a program order. The method also includes associating a target rename register of the load instruction as well as the load instruction with the store instruction, responsive to the finding step. The method further includes writing the store value of the store instruction to the target rename register of the load instruction and finishing the load instruction without reissuing the load instruction, responsive to writing the store value of the store instruction according to the store instruction to finish the store instruction.
Owner:GLOBALFOUNDRIES US INC
Processor efficiency by combining working and architectural register files
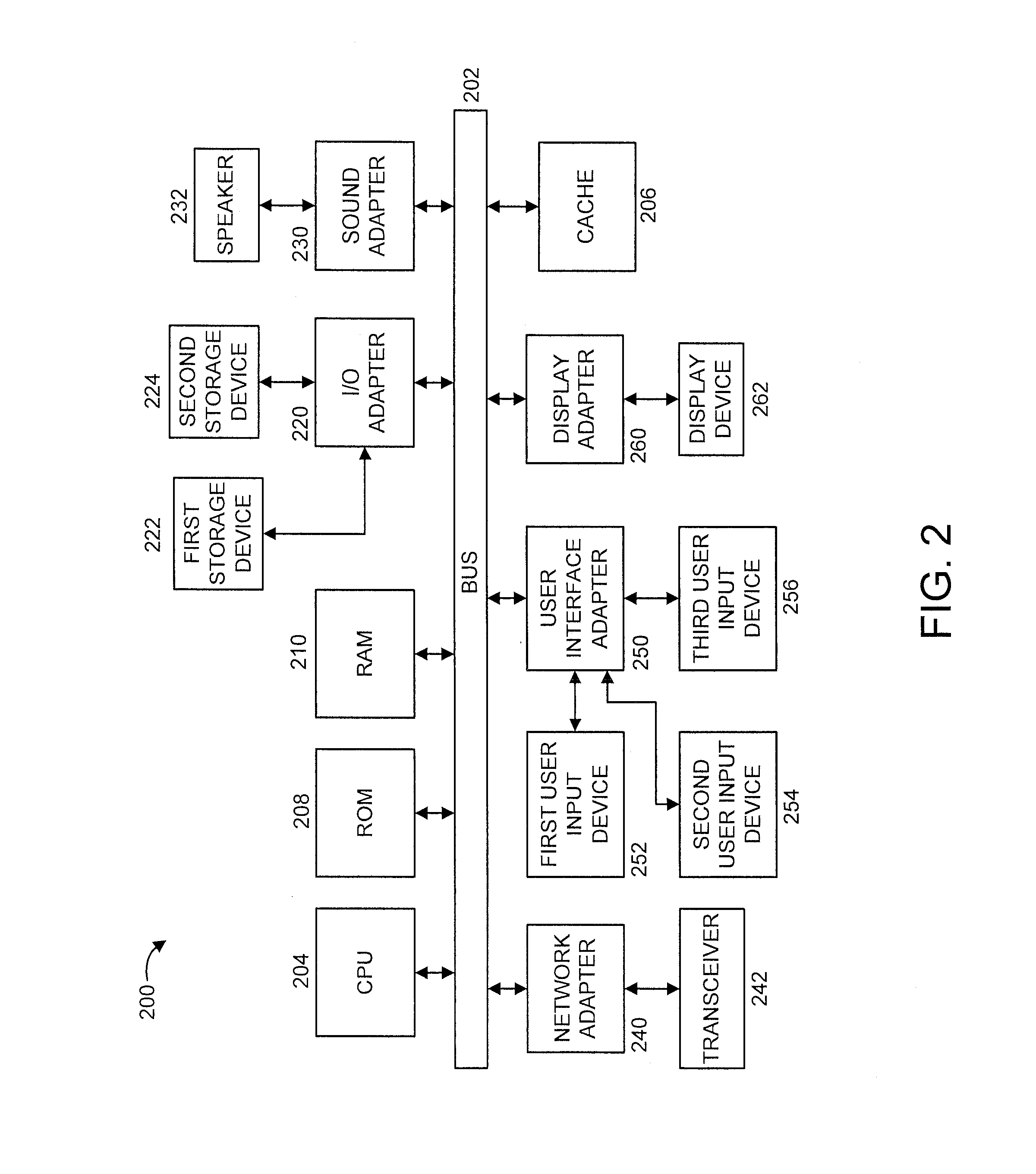
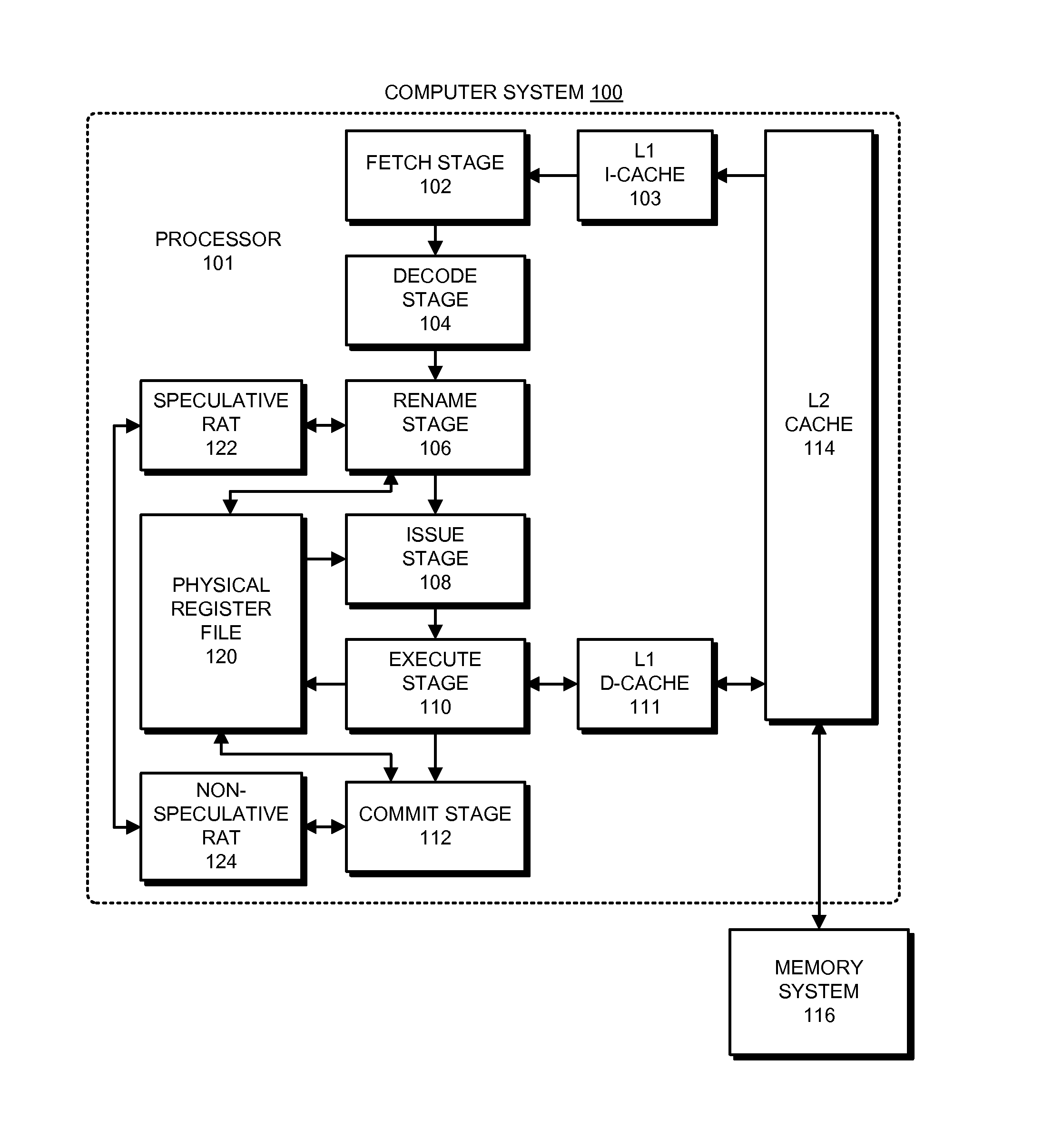
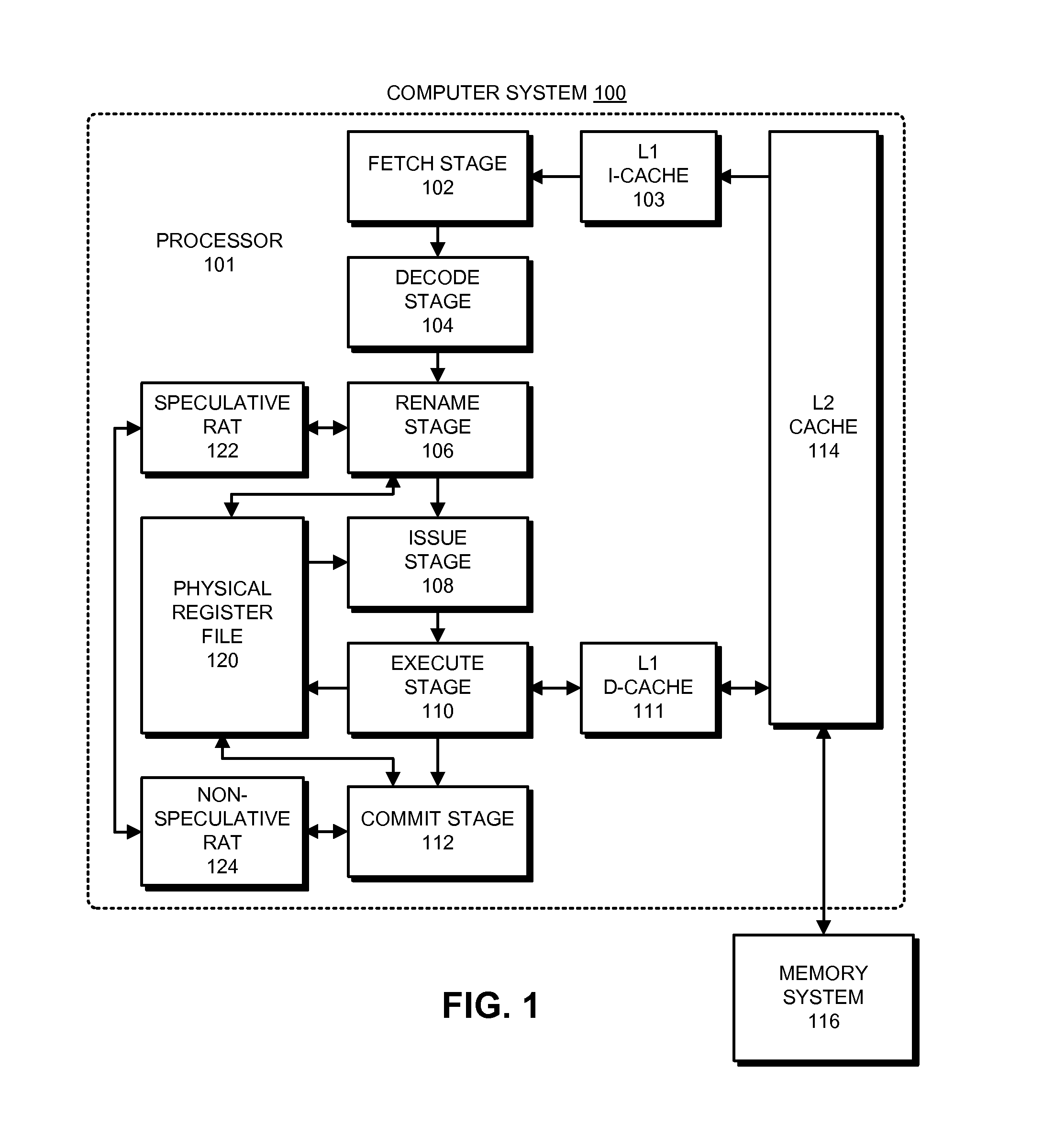
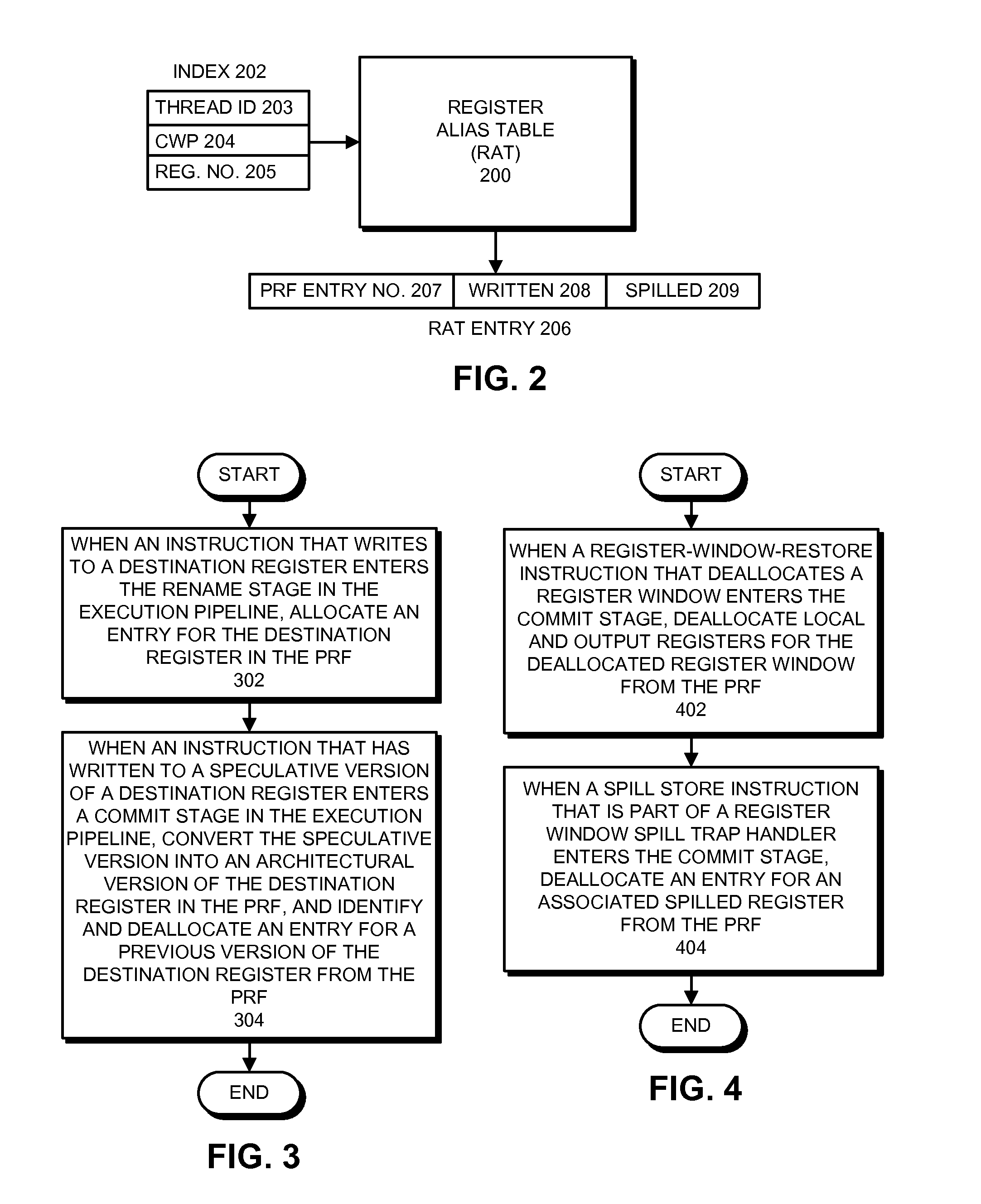
ActiveUS20150242209A1Efficient storageRegister arrangementsDigital computer detailsEngineeringRename
A processor includes an execution pipeline configured to execute instructions for threads, wherein the architectural state of a thread includes a set of register windows for the thread. The processor also includes a physical register file (PRF) containing both speculative and architectural versions of registers for each thread. When an instruction that writes to a destination register enters a rename stage, the rename stage allocates an entry for the destination register in the PRF. When an instruction that has written to a speculative version of a destination register enters a commit stage, the commit stage converts the speculative version into an architectural version. It also deallocates an entry for a previous version of the destination register from the PRF. When a register-window-restore instruction that deallocates a register window enters the commit stage, the commit stage deallocates local and output registers for the deallocated register window from the PRF.
Owner:ORACLE INT CORP
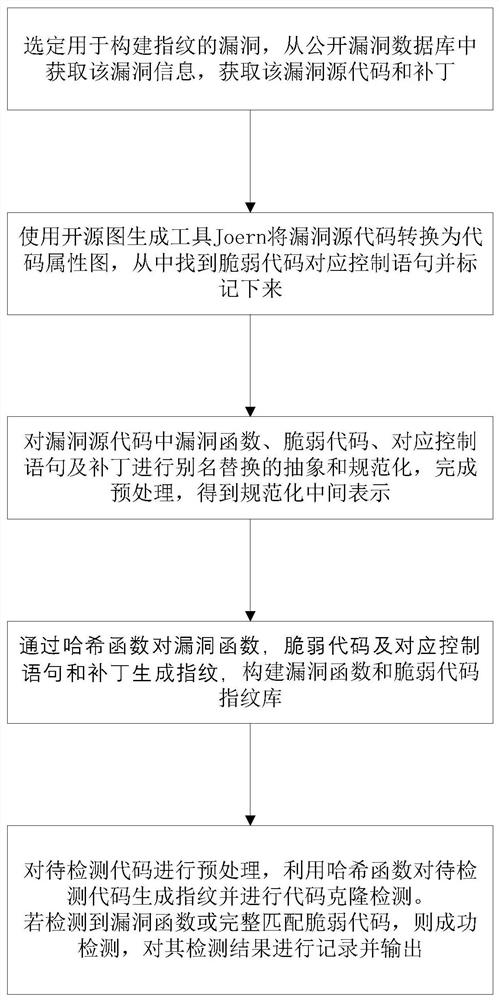
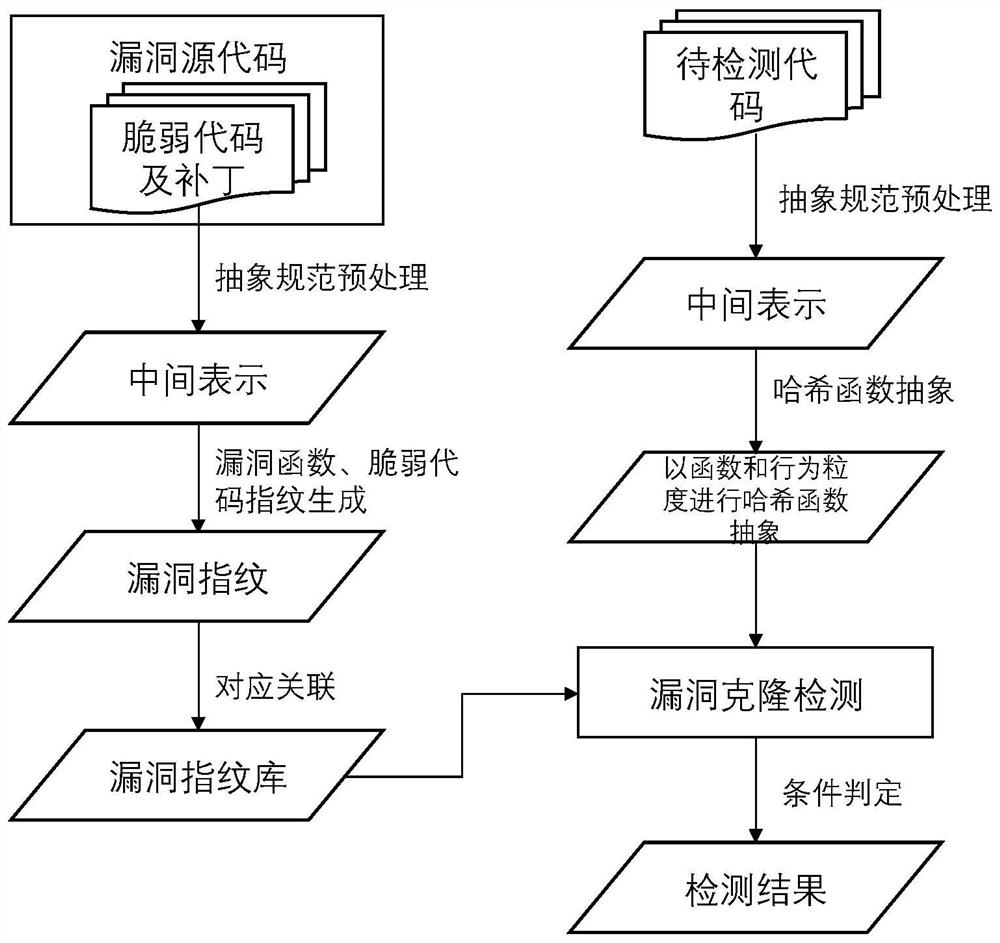
Vulnerability code clone detection method based on context semantics and patch verification
ActiveCN112651028AImprove detection efficiencyEasy to detectPlatform integrity maintainanceCode compilationAlgorithmRename
The invention discloses a vulnerability code clone detection method based on context semantics and patch verification, and solves the problem that an existing vulnerability code clone detection method cannot obtain vulnerability context and patch repair. The method comprises the steps of obtaining vulnerability data; marking vulnerability code control statements; performing abstract normalization preprocessing on vulnerability source codes and patches; constructing a vulnerability function and a vulnerability vulnerability code fingerprint library; cloning and detecting a to-be-detected code; and judging a detection result and outputting the detection result to finish vulnerability clone detection of the software. Based on the code fingerprint, the problem of low accuracy of a high-level abstract technology is avoided; according to the method, the influence of renaming on the detection accuracy is eliminated for the code abstract preprocessing operation; the context relationship and the patch are verified, so that the false alarm rate is reduced; besides, fragile code, control statement and patch detection is carried out on the to-be-detected code, so that the application scene is expanded and the missing report rate is reduced. The method is used for detecting bugs caused by code cloning in software.
Owner:陕西阡陌通达科技有限公司
Method to protect software against unwanted use with a “renaming” principle
ActiveUS7343494B2Unauthorized memory use protectionHardware monitoringData processing systemOrder form
The invention concerns a process to protect a vulnerable software working on a data processing system against its unauthorized usage using a processing and memorizing unit. The process comprises defining: 1) a set of dependent functions whose dependent functions are liable to be executed in a processing and memorizing unit 2) a set of triggering commands, said triggering commands being liable to be executed in the data processing system and to trigger the execution in a processing and memorizing unit, of the dependent functions 3) for each triggering command, an order 4) a method of renaming of the orders 5) restoring means designed to be implemented in a processing and memorizing unit during a usage phase, and enabling to restore the dependent function to execute, from the renamed order.
Owner:VALIDY NET
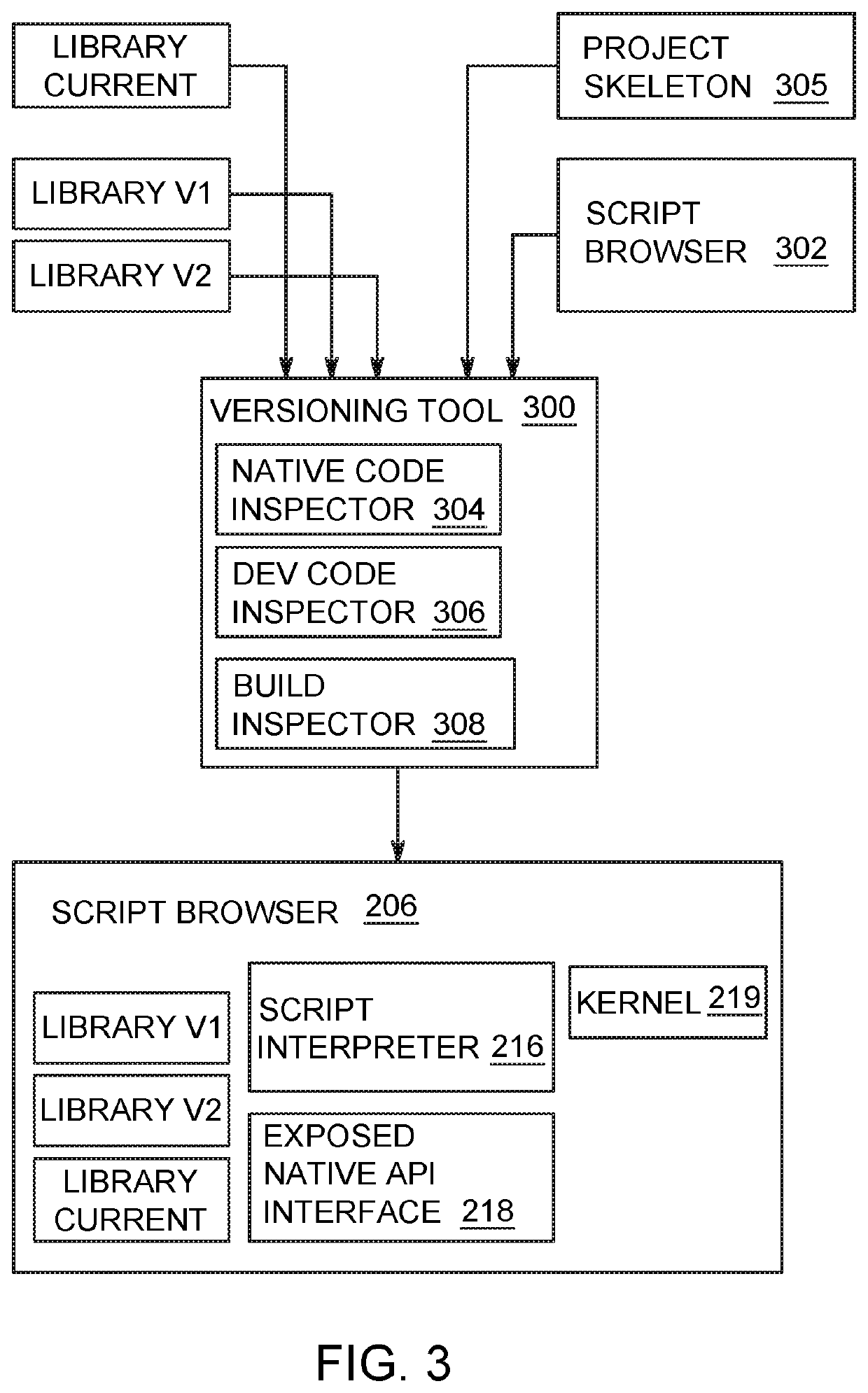
Method and apparatus for loading multiple differing versions of a native library into a native environment
A method for modifying a native runtime environment comprising modifying symbols in the least one of a compiled executable or byte-code of each of a plurality of library versions, modifying references to the symbols in development code associated with the at least one of the compiled executable or byte-code, building the development code into a plurality of versioned library packages, renaming identifiers in each of the versioned library packages and modify an application build for the native runtime environment to reference each of the versioned library packages according to their renamed identifiers.
Owner:650 IND INC
OLAP pre-computation engine optimization method based on object storage and application
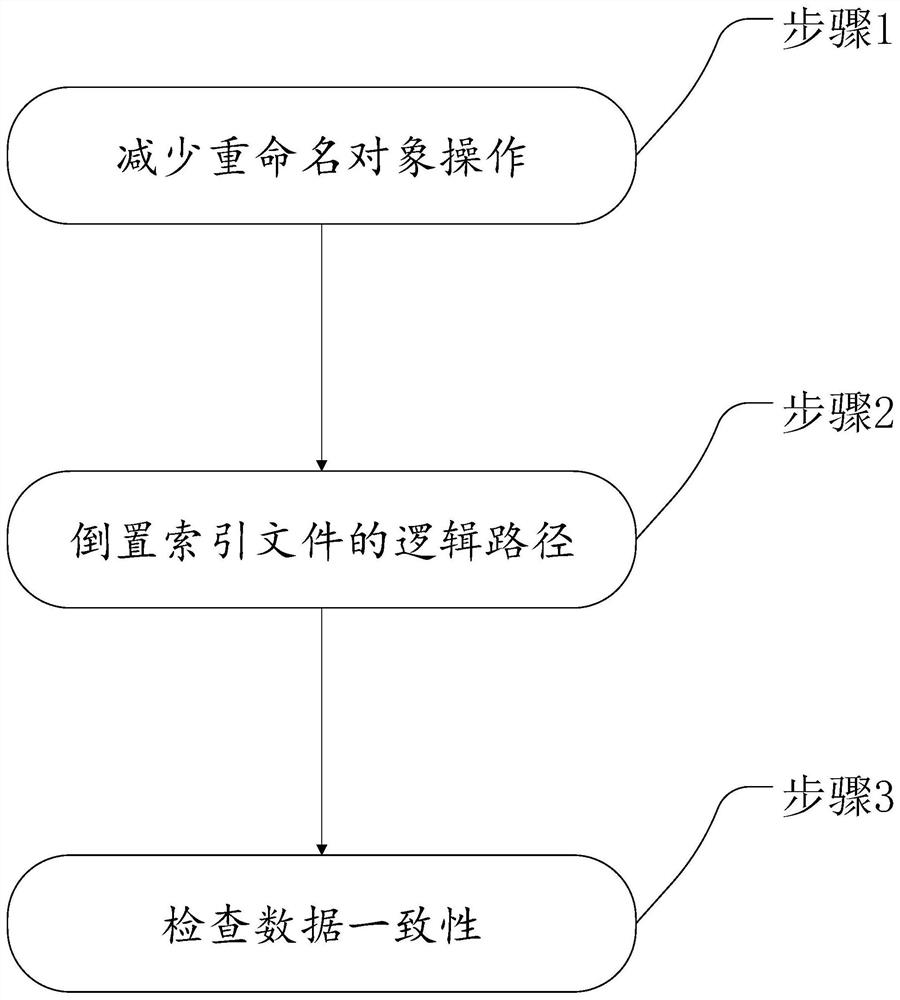
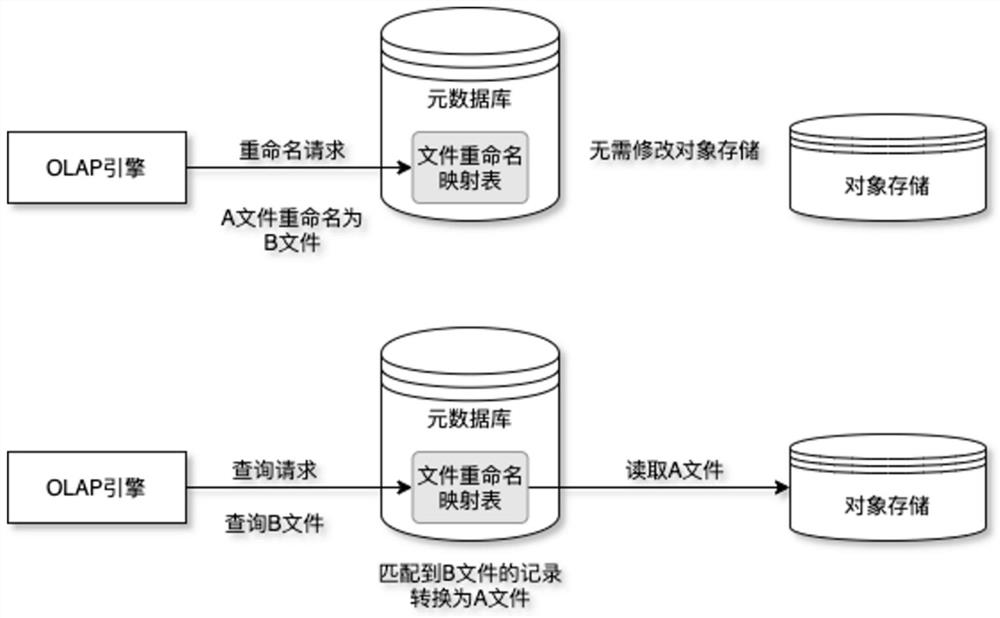
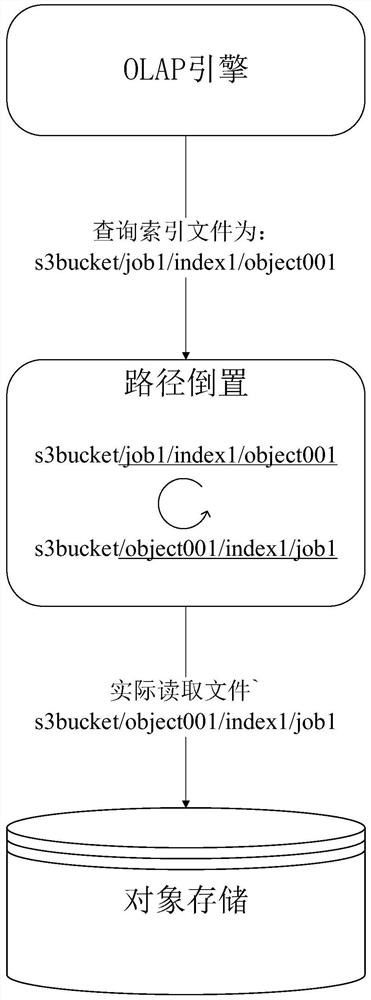
ActiveCN112597114AImprove reading and writingImprove execution efficiencyFile access structuresProgram controlPathPingRename
The invention provides an OLAP pre-computation engine optimization method based on object storage and application. Three optimization directions are provided, namely, the logic paths of renaming object operation reduction, data consistency check and inverted index file inversion are provided. Through a file mapping table added to the metadata layer, a mapping relationship between files before andafter renaming is matched, and renaming operation on the bottom layer of the file system is reduced; and a logic path of a partition directory hierarchical structure of the file is inverted to correspond to a prefix of the file in the object storage, thereby realizing quick query and reading of the object storage, adding logic verification to reading operation, deleting operation and writing operation, and checking data consistency. According to the method, the read-write mode of the OLAP engine in the object storage using process is optimized, the execution efficiency of the engine is improved, response to the analysis requirement of an upper-layer report system is accelerated, and based on the method, an efficient OLAP calculation query execution engine can be constructed, the construction efficiency is improved, and query is accelerated.
Owner:KUYUN SHANGHAI INFORMATION TECH CO LTD
Assembly program control flow path detection method and device
The invention belongs to the technical field of computer program analysis and software testing and discloses an assembly program control flow path detection method. The method comprises the followingsteps of detecting and deleting annotations of code segments in an assembly program, and renaming an integer register; obtaining a control flow graph CFG of the assembly program through the auxiliarytable AT and the control flow original data CRD; inserting a path label into the head of the instruction sequence of the basic block BBN to generate new control flow original data CRD; recombining thenew control flow original data CRD to obtain a new assembly program with a path label; compiling the new assembly program with the path label and the probe program into an executable file, and generating a result file; and reading the generated result file, and performing statistics according to paths to obtain passing rates of different paths. According to the detection method, the control flowinformation of the assembly program can be rapidly and accurately obtained, then the dynamic information such as path coverage testing is obtained, and the detection method has advantages of being light in weight, high in pertinence, easy to modify and maintain and the like.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Method and system for renaming resource files of Android engineering project in batches,equipment and medium
PendingCN113157651AImprove reliabilityImprove stabilityFile/folder operationsSpecial data processing applicationsBatch renamingRename
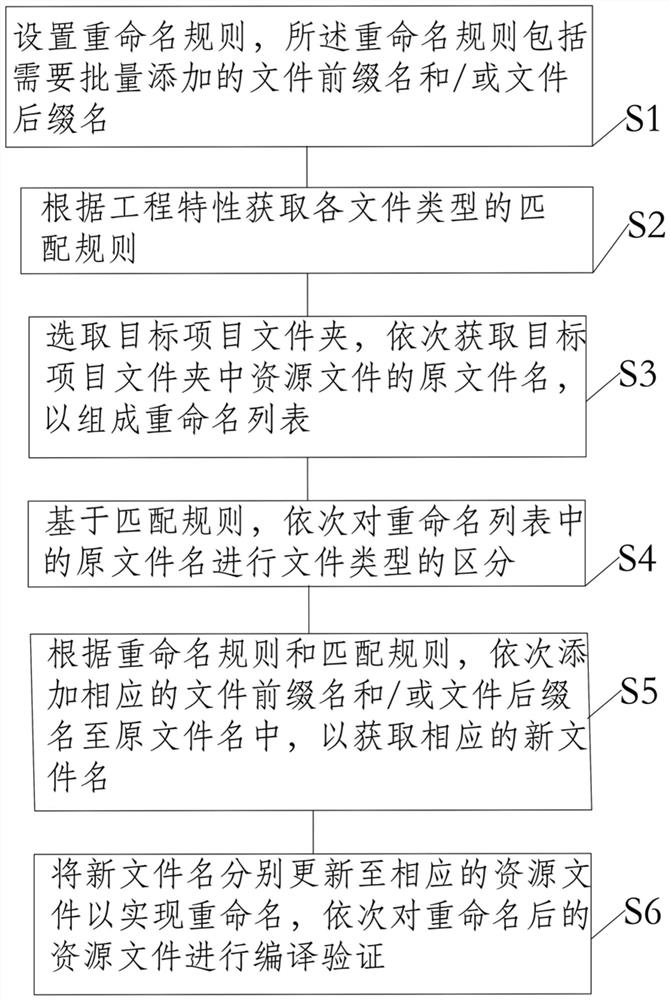
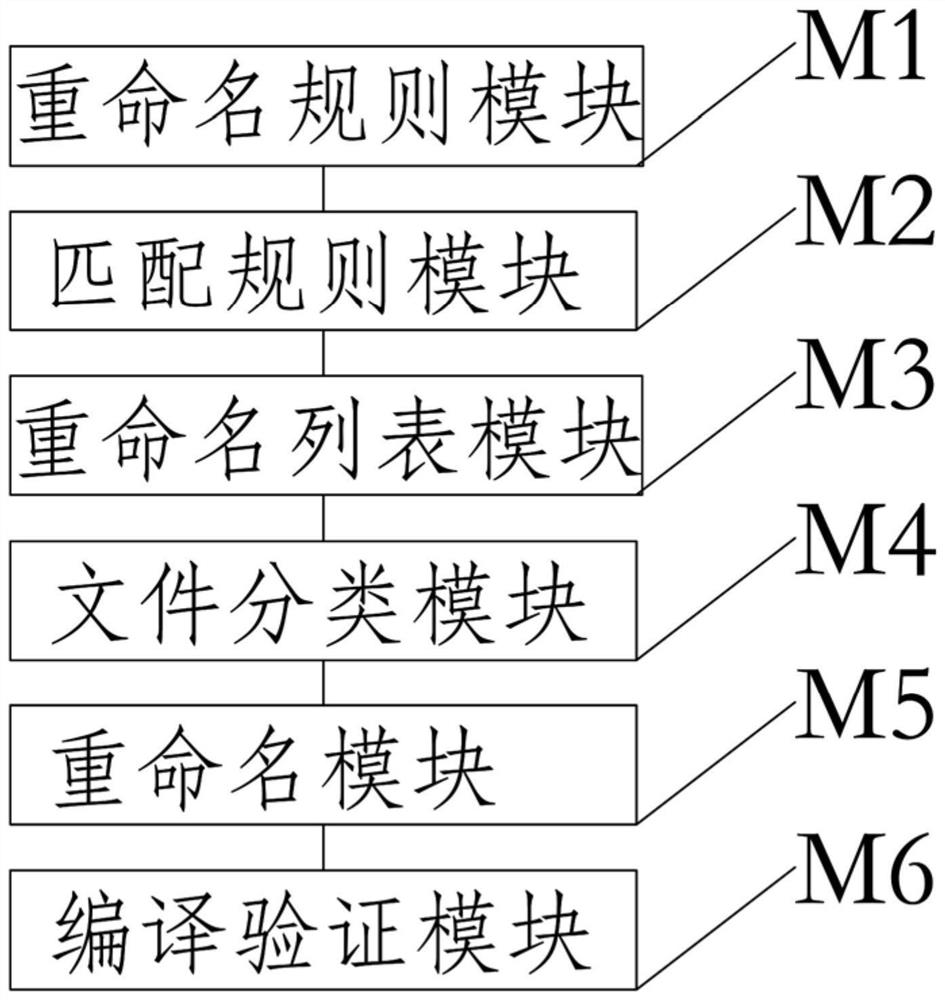
The invention discloses a method and system for renaming resource files of an Android engineering project in batches, equipment and a medium, and the method comprises the following steps: setting a renaming rule which comprises file prefixes and / or file suffixes needing to be added in batches; obtaining a matching rule of each file type according to the engineering characteristics; selecting a target project folder, and sequentially obtaining original file names of resource files in the target project folder to form a renaming list; on the basis of a matching rule, performing file type distinguishing on the original file names in the renaming list in sequence; according to a renaming rule and a matching rule, sequentially adding corresponding file prefix names and / or file suffix names into the original file names to obtain corresponding new file names; and respectively updating the new file names to the corresponding resource files to realize renaming, and sequentially compiling and verifying the renamed resource files. According to the method, batch renaming of the resource files in the development process of the Android system can be achieved.
Owner:广州宸祺出行科技有限公司
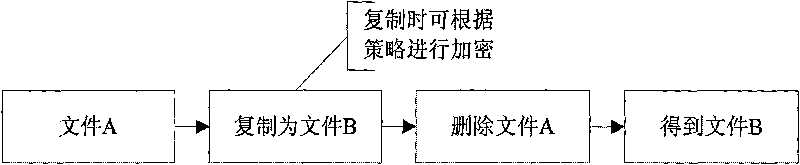
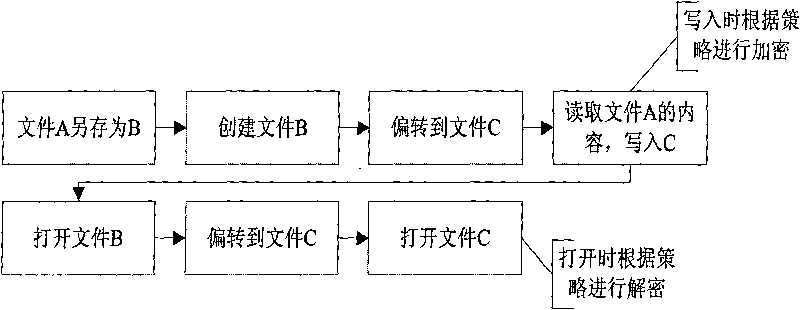
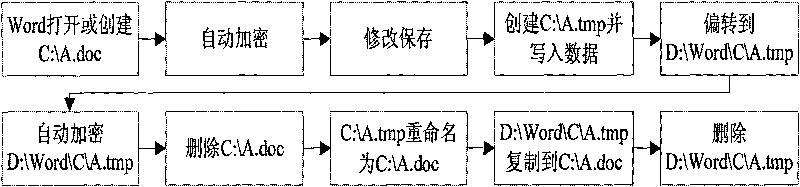
File encryption method combined with access deflection
InactiveCN101763474ASolve the problem of complex policy configurationNo risk of disclosureDigital data protectionComputer hardwareRename
The invention discloses a file encryption method combined with access deflection, which is applied in information safety field. The method uses an access deflection module converts file rename into a combination of duplication and deletion operation, and deflects operations like simultaneous open and establishment. The problem of complex strategy allocation caused by rename can be solved when the access deflection module is coordinately used with a transparent encryption module; and when a user performs the operation of Save Copy As which is possible to result in divulging secrets, the invention can automatically deflect and encrypt, thus avoiding the possibility of divulging secretes. The invention has the advantages of simple strategy, wide application range and the like.
Owner:深圳市虹安信息技术有限公司
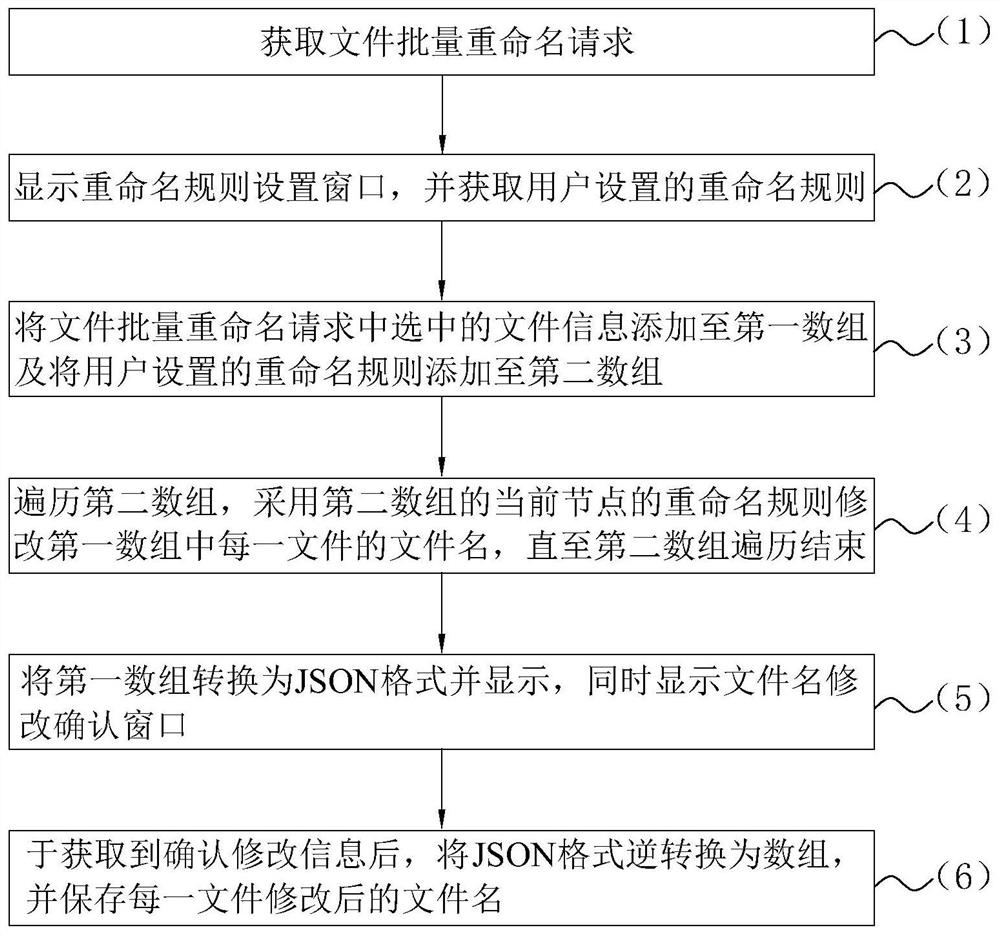
File batch renaming method, electronic equipment and computer readable storage medium
PendingCN111813747AEasy to operateFile/folder operationsSpecial data processing applicationsBatch renamingRename
The invention discloses a file batch renaming method. The method comprises the following steps: (1) obtaining a file batch renaming request; (2) displaying a renaming rule setting window; (3) adding file information selected in the file batch renaming request to a first array and adding a renaming rule set by a user to a second array; (4) traversing the second array, and modifying the file name ofeach file in the first array by adopting a renaming rule of the current node of the second array until the second array is traversed; (5) converting the first array into a JSON format and displayingthe first array, and displaying a file name modification confirmation window at the same time; and (6) after modification confirmation information is obtained, reversely converting the JSON format into an array, and storing the modified file name of each file. According to the method and the device, batch renaming of the files is realized by adopting multiple renaming rules, and the user operationis simple. In addition, the invention further discloses electronic equipment and a computer readable storage medium.
Owner:GUANGDONG 115 TECH
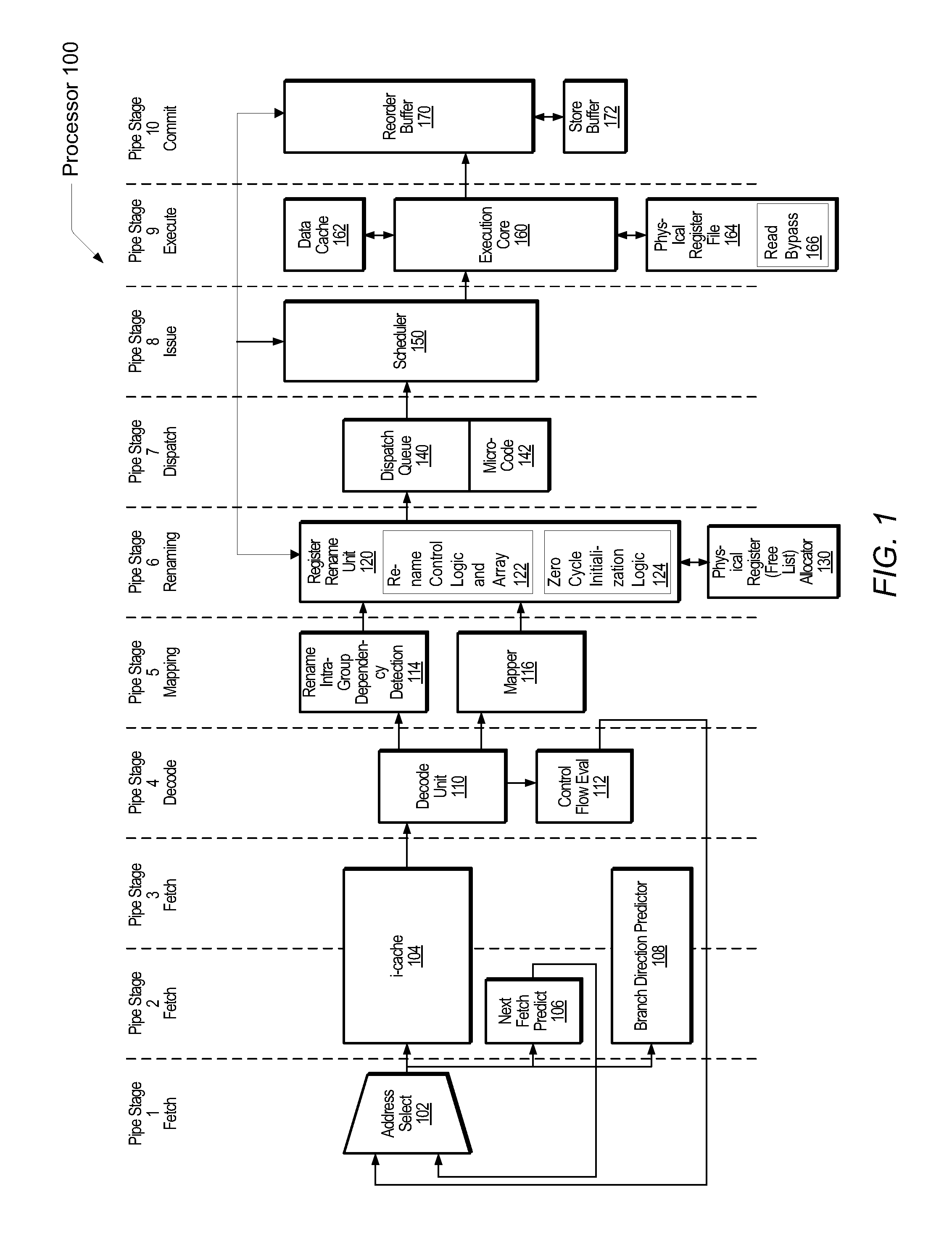
Optimizing register initialization operations
ActiveUS9430243B2Efficiently reducing latencyDigital data processing detailsConcurrent instruction executionComputer architectureRename
A system and method for efficiently reducing the latency of initializing registers. A register rename unit within a processor determines whether prior to an execution pipeline stage it is known a decoded given instruction writes a particular numerical value in a destination operand. An example is a move immediate instruction that writes a value of 0 in its destination operand. Other examples may also qualify. If the determination is made, a given physical register identifier is assigned to the destination operand, wherein the given physical register identifier is associated with the particular numerical value, but it is not associated with an actual physical register in a physical register file. The given instruction is marked to prevent it from proceeding to an execution pipeline stage. When the given physical register identifier is used to read the physical register file, no actual physical register is accessed.
Owner:APPLE INC
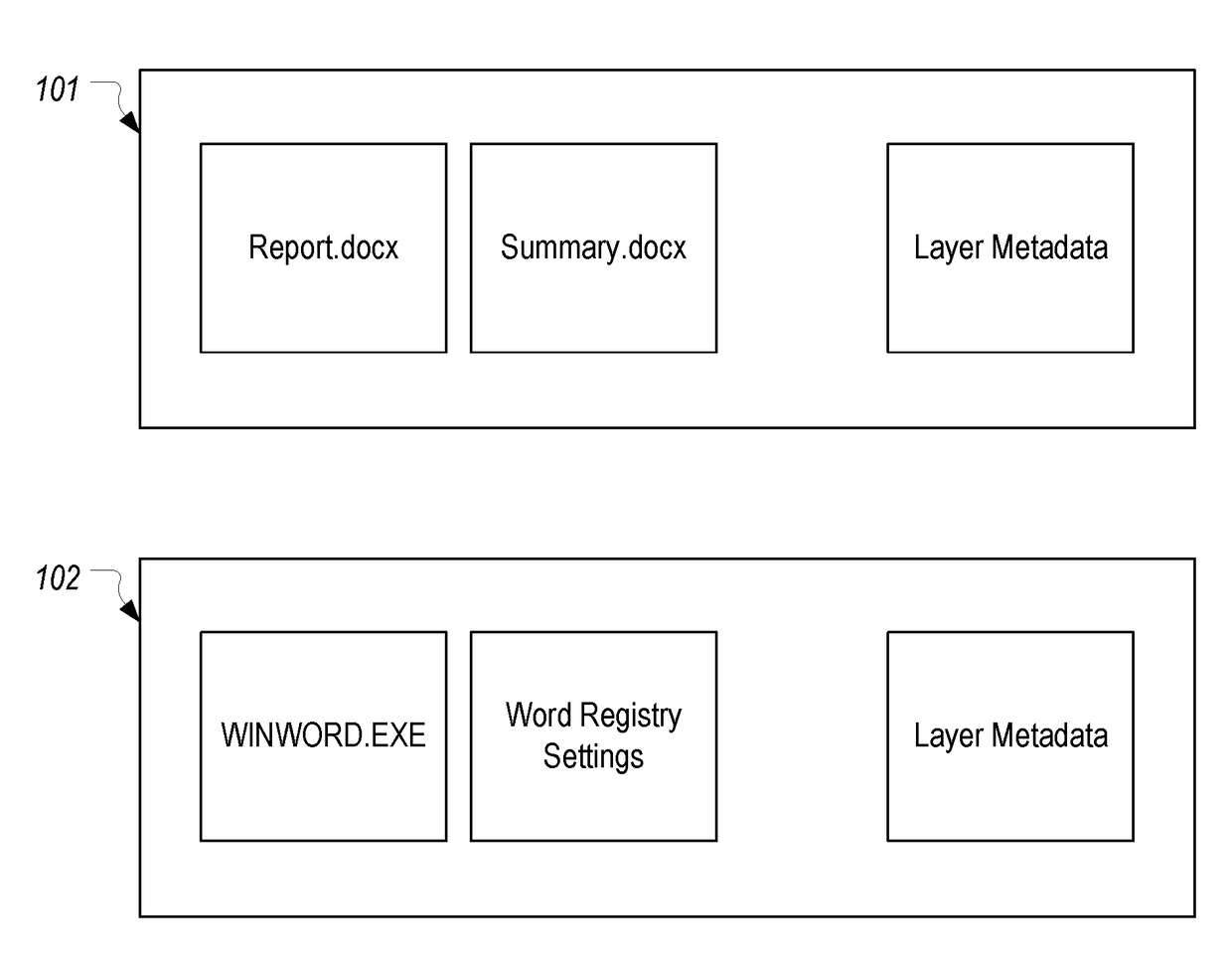
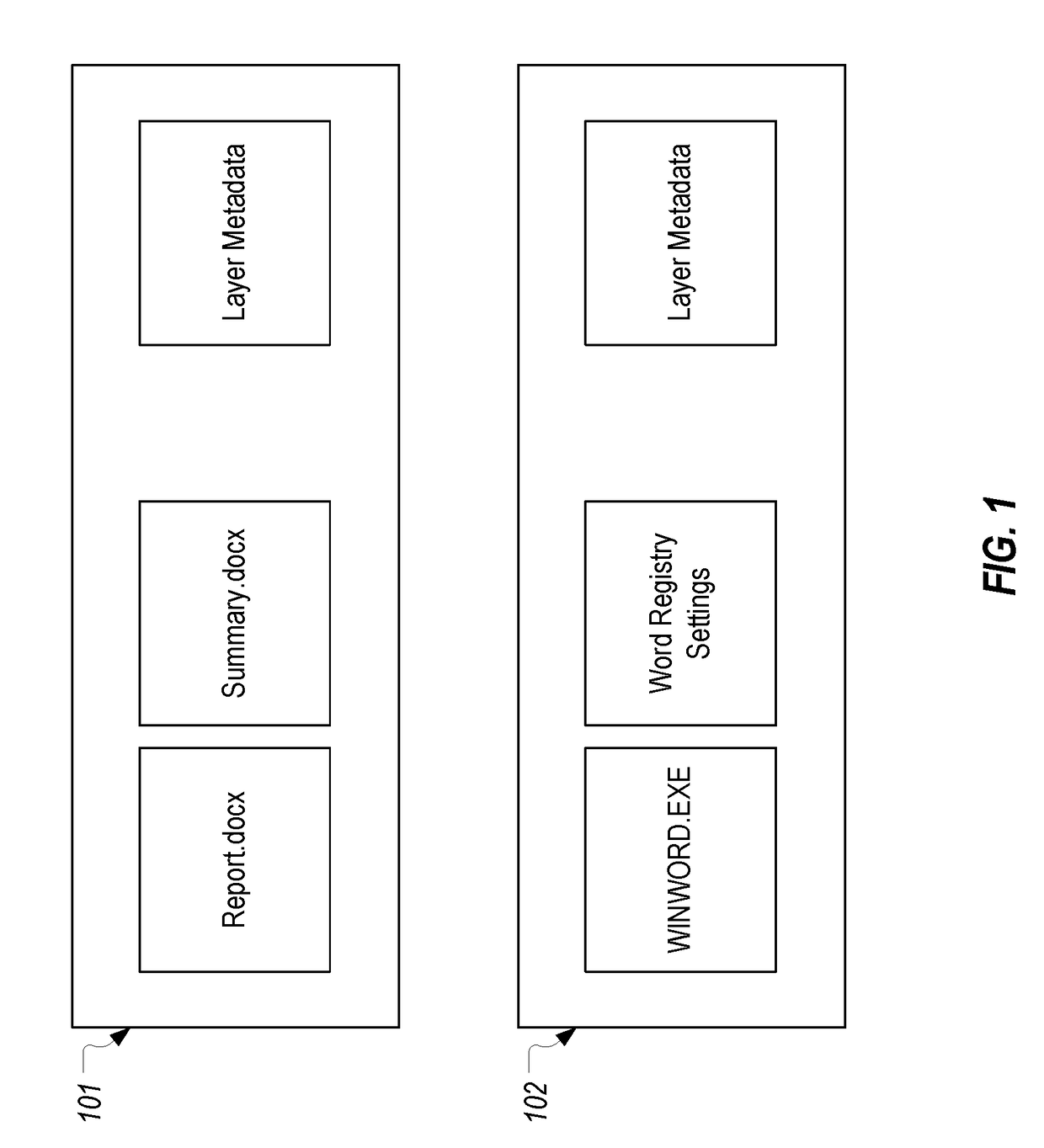
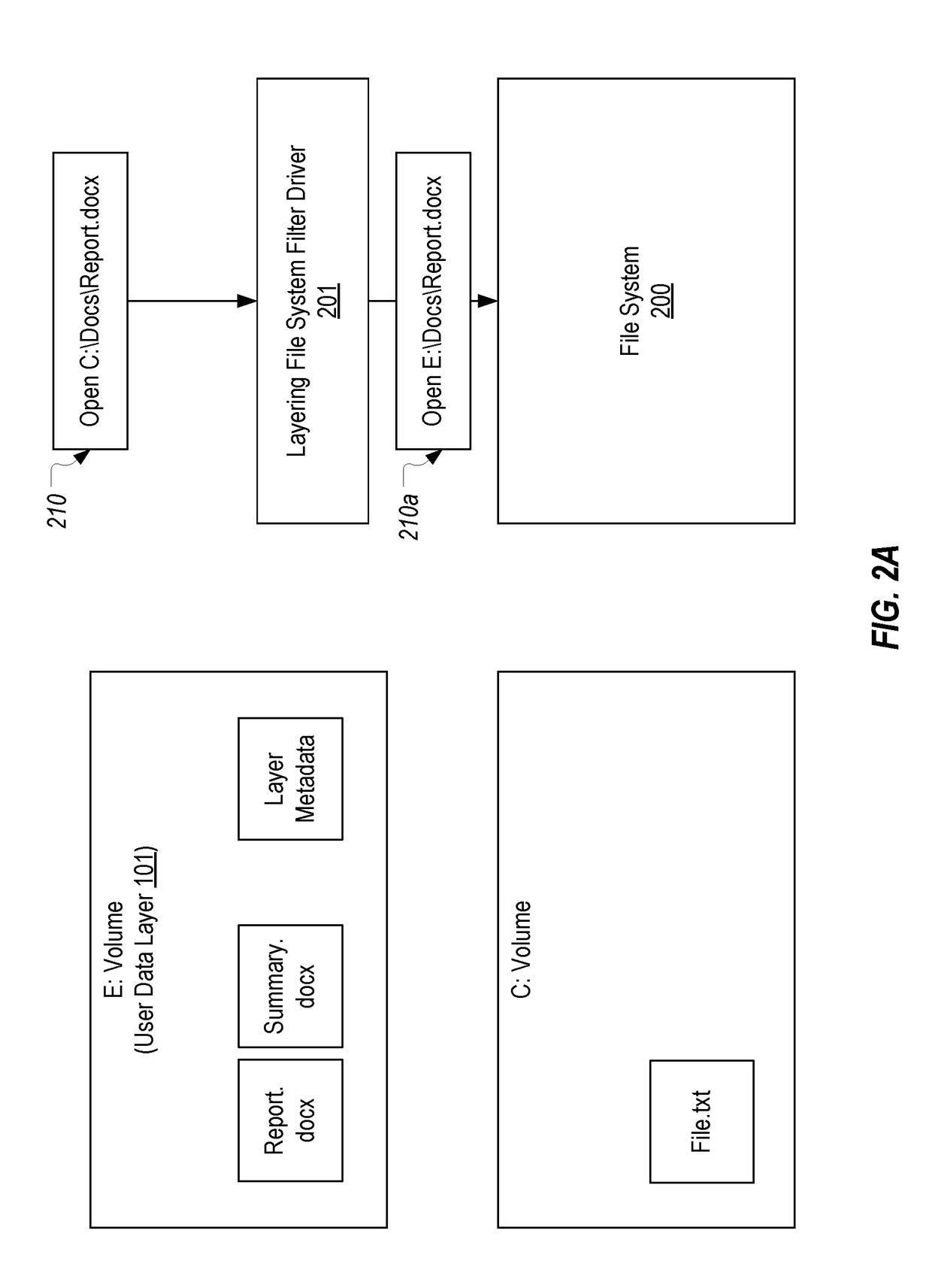
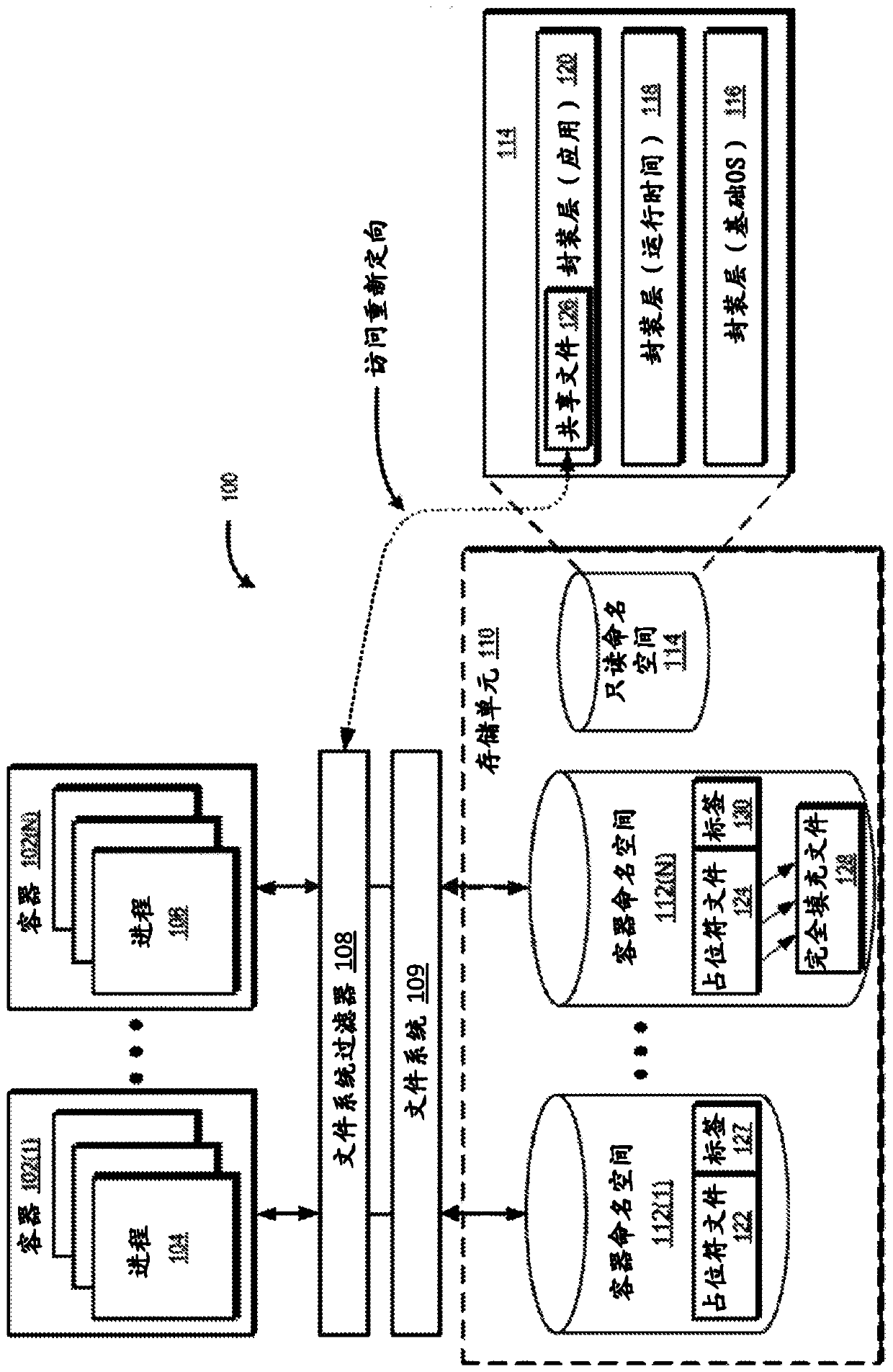
Renaming a directory that resides on a layered volume
ActiveUS20170315999A1Digital data information retrievalSpecial data processing applicationsOperational systemHooking
A directory that resides on a layered volume can be renamed A hooking module can be employed to intercept rename requests. The hooking module can query a layering file system filter driver to determine the volume of the source and target of the rename request. If the source and target are on different volumes, thereby indicating that the source is a directory of a layered volume, the hooking module can append a signature to the target which identifies the actual volume of the source. The modified rename request can then be passed to the operating system which will perform its normal operations including verifying that the source and target are on the same volume. During this verification, the layering file system filter driver can detect the appended signature in the target and can inform the operating system that the target is on the volume identified in the signature.
Owner:DELL MARKETING CORP
Instruction processing method and device
PendingCN111857815AImprove emptying efficiencyReduce in quantityMachine execution arrangementsComputer architectureRename
The invention provides an instruction processing method and device. The instruction processing method comprises the following steps: renaming a branch instruction needing to be lifted in a first program and a write variable in a dependent instruction of the branch instruction, so that the write variable has a globally unique variable name; and obtaining a first instruction sequence according to the branch instruction and the dependency instruction after the write variable is renamed. According to the technical scheme provided by the invention, the read-write problem caused by write variables with the same name in a branch conversion technology can be solved.
Owner:HUAWEI TECH CO LTD
Multi-layer merge in a storage virtualization system
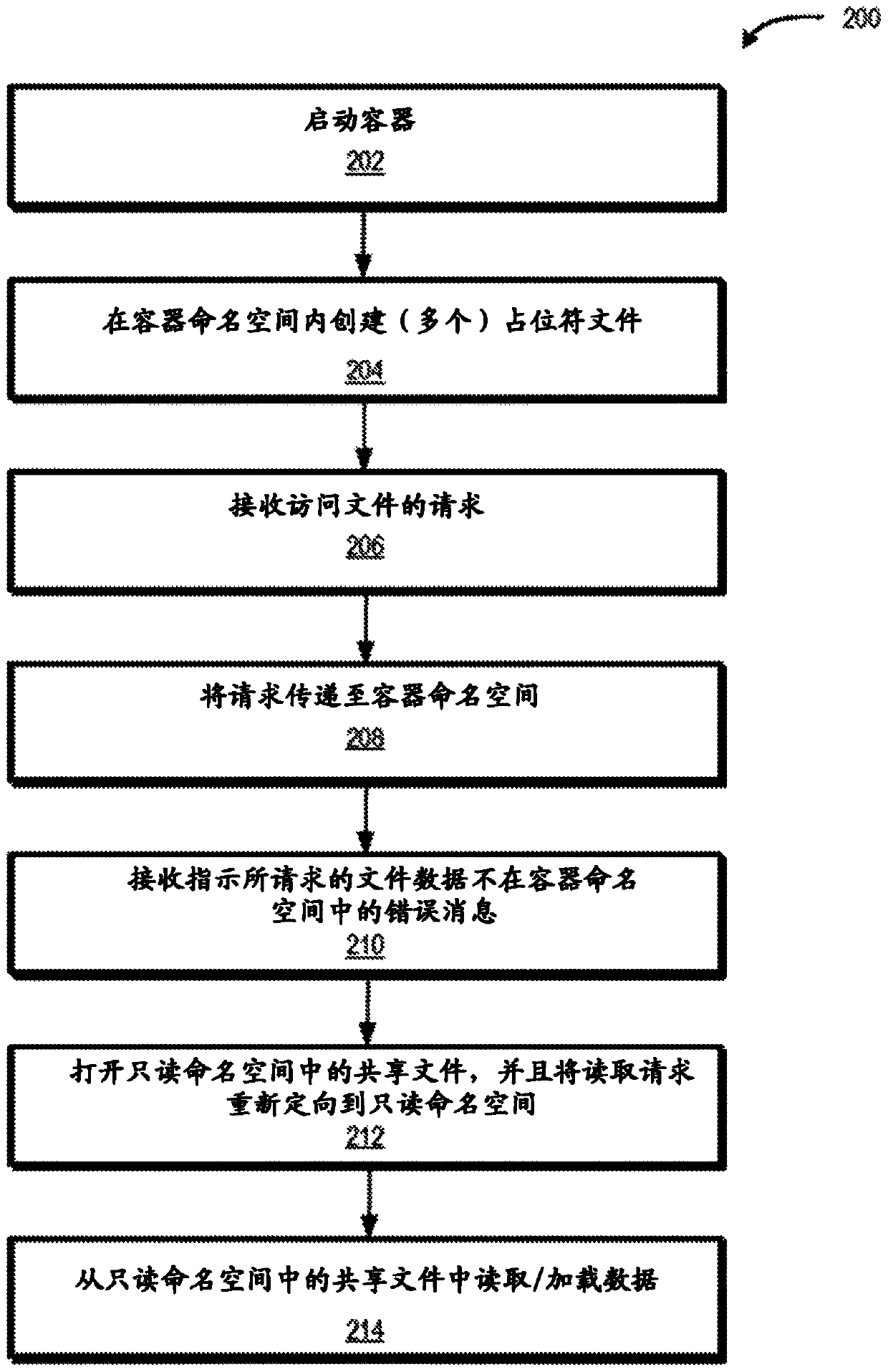
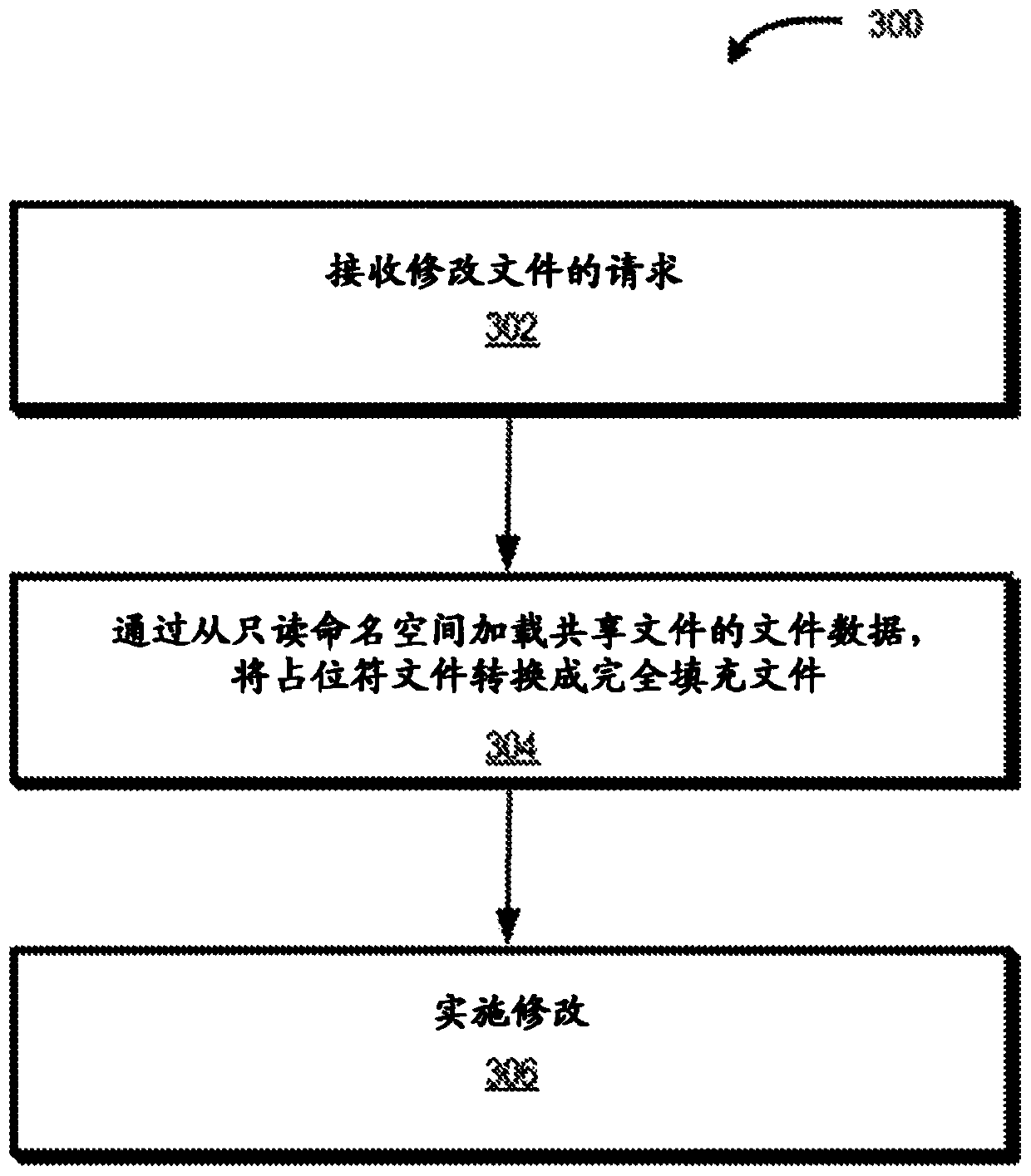
The state of a file may be a combination of local state, typically small (e.g., a placeholder file), and some external source state such as that maintained in a read-only namespace managed by a cloudprovider or by another local file system, typically large. A file system component responsible for overlaying (i.e., merging) the partial local state and the external source state into a single file system view that can be used by an application of a container as if the full state exists locally. Overlays that comprise the file system state may be referred to as 'layers'. A tombstone mechanism maybe provided to record delete or rename modifications in the top layer.
Owner:MICROSOFT TECH LICENSING LLC
A Java program anti-obfuscation method and terminal
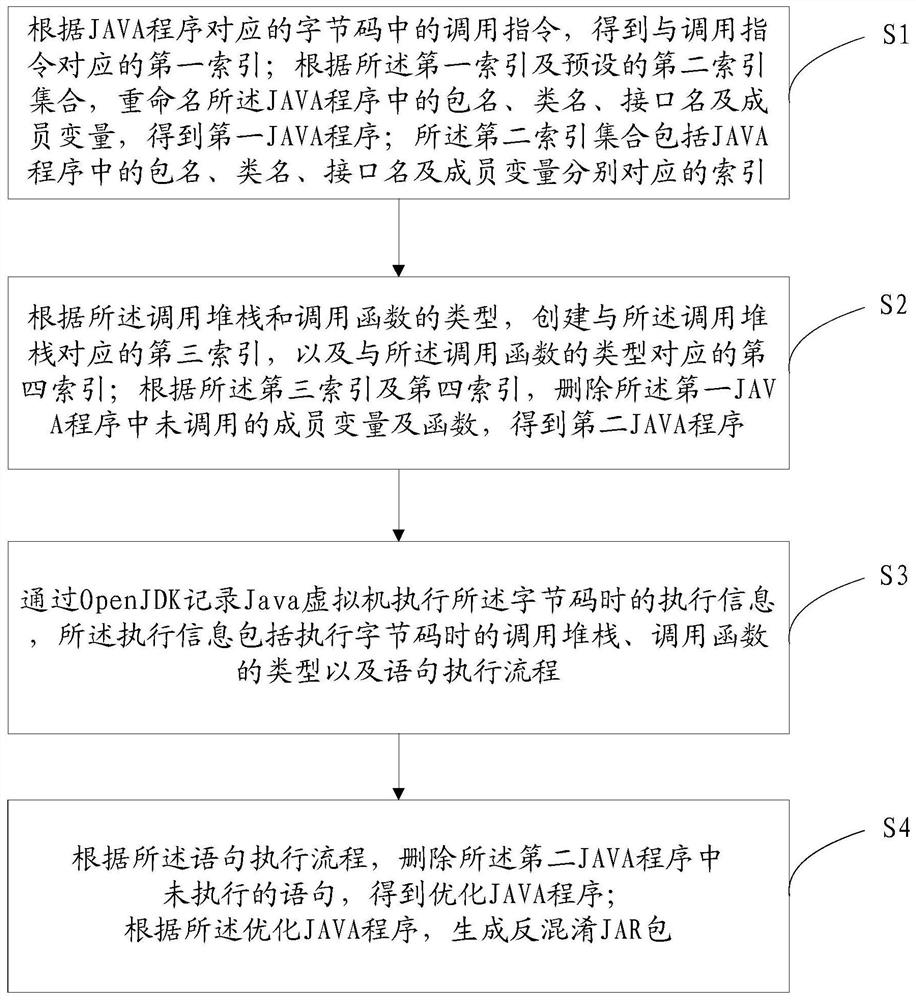
ActiveCN108153518BFix bugsLow costDecompilation/disassemblySoftware designReverse analysisMember variable
The present invention provides a JAVA program anti-obfuscation method and terminal, renaming the package name, class name, interface name and member variables in the JAVA program according to the first index and the preset second index set, to obtain The first JAVA program, and record the execution information when the Java virtual machine executes the bytecode through OpenJDK, delete the member variables and functions not called by the first JAVA program, obtain the second JAVA program, and execute according to the statement in the execution information Flow process, delete the unexecuted statement in the second JAVA program, obtain optimized JAVA program; The present invention solves in the Jar package that has confused originally, and the package name, class name, method in its JAVA program are replaced with no Any meaningful name will cause a lot of confusion when viewed in reverse analysis, resulting in a very time-consuming problem in the reverse analysis process.
Owner:XIAMEN MEIYA PICO INFORMATION
Security reinforcement method and device based on programming language library
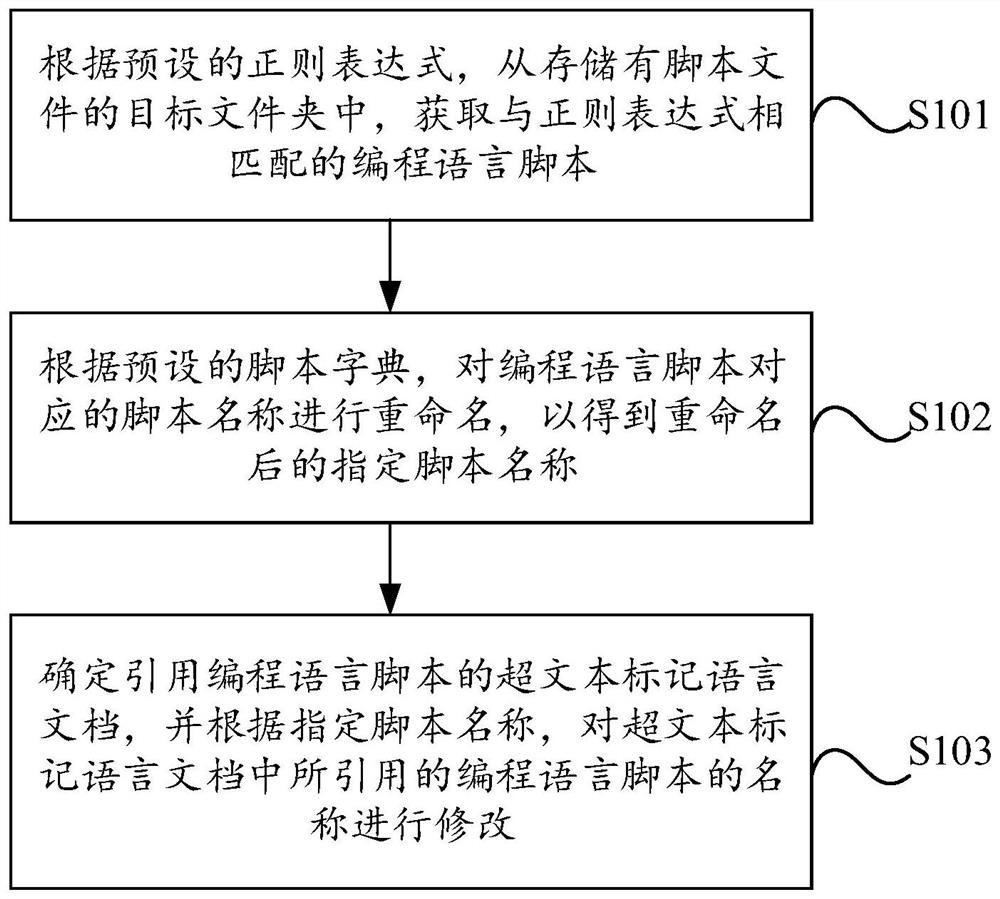
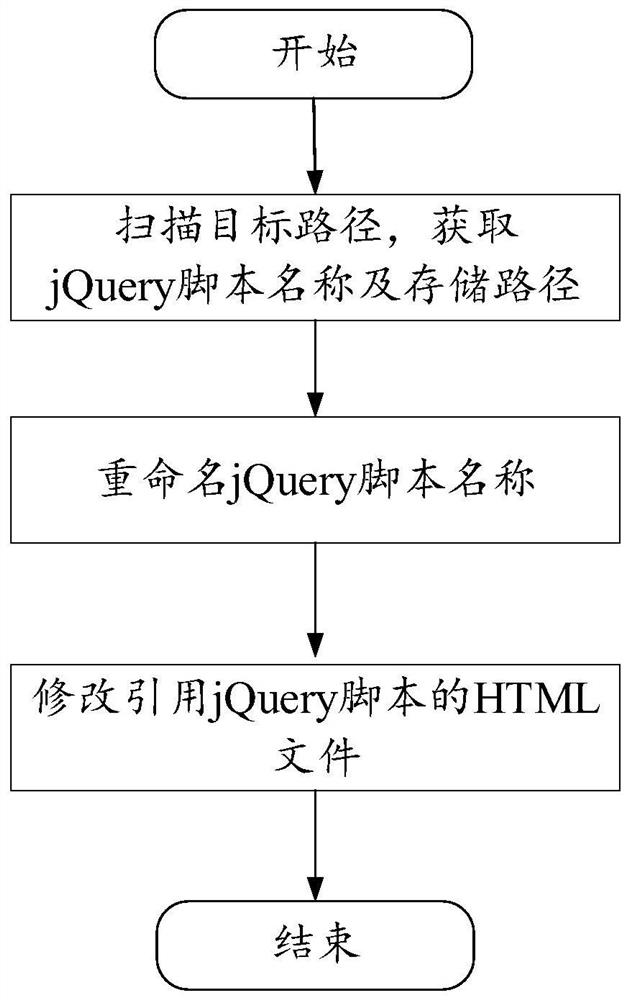
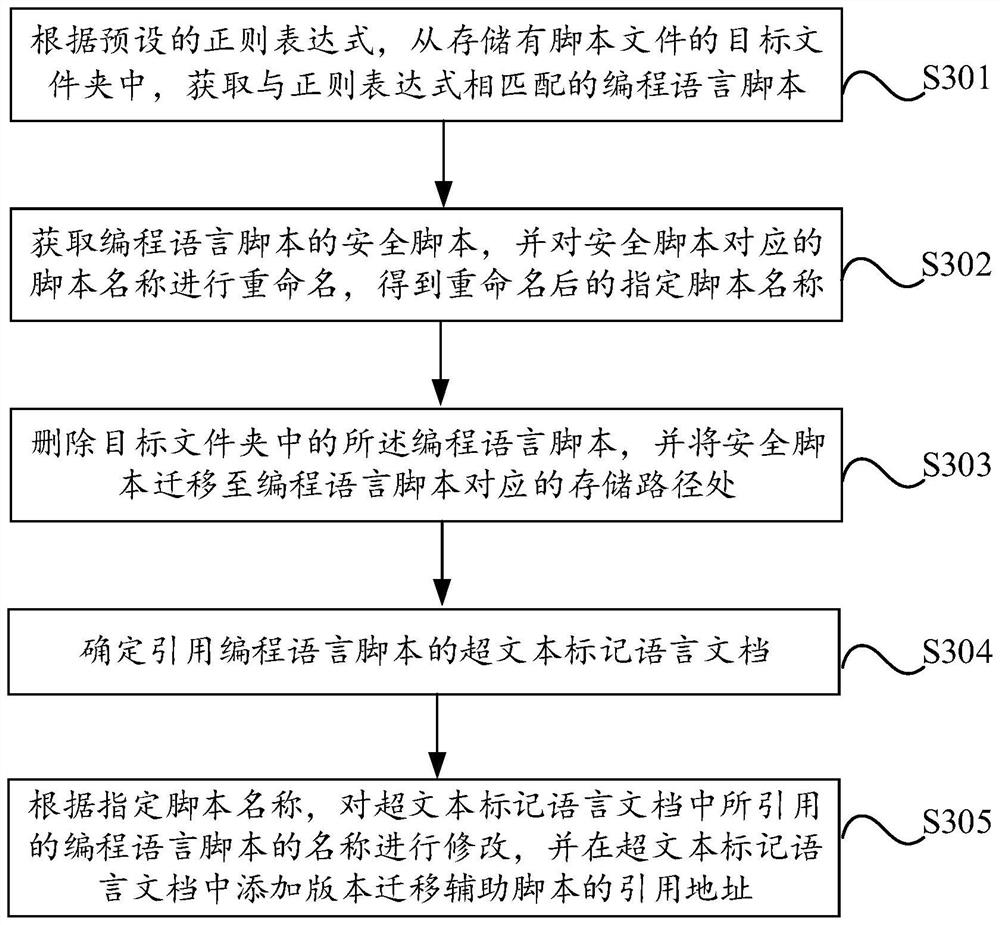
PendingCN114528556AImplement security hardeningImprove stabilityVersion controlPlatform integrity maintainanceRenameSoftware engineering
The invention discloses a security reinforcement method and device based on a programming language library, and aims to solve the technical problem that a site administrator usually adopts a manual mode to perform security reinforcement on a site at present, and the situation of missing replacement and change is easy to occur. The method comprises the following steps: according to a preset regular expression, obtaining a programming language script matched with the regular expression from a target folder in which a script file is stored; according to a preset script dictionary, renaming a script name corresponding to the programming language script to obtain a renamed specified script name; and determining a hypertext markup language document referencing the programming language script, and modifying the name of the programming language script referenced in the hypertext markup language document according to the specified script name.
Owner:SHANDONG INSPUR GENESOFT INFORMATION TECH CO LTD
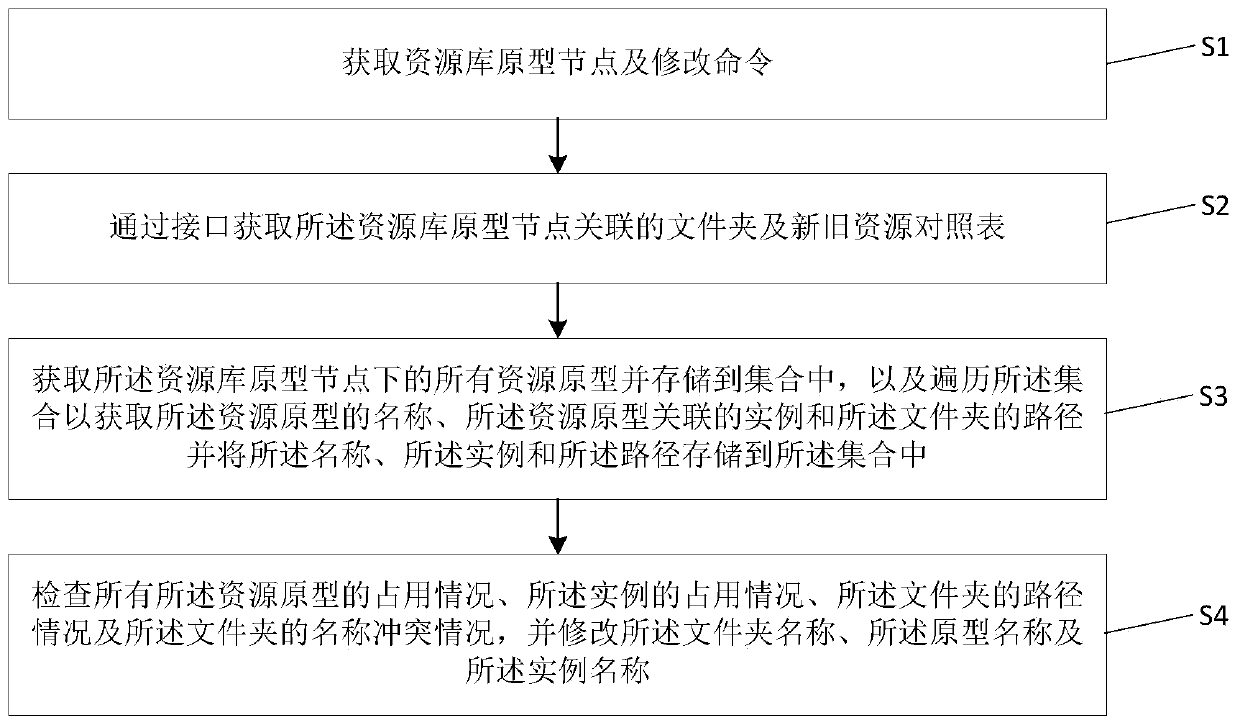
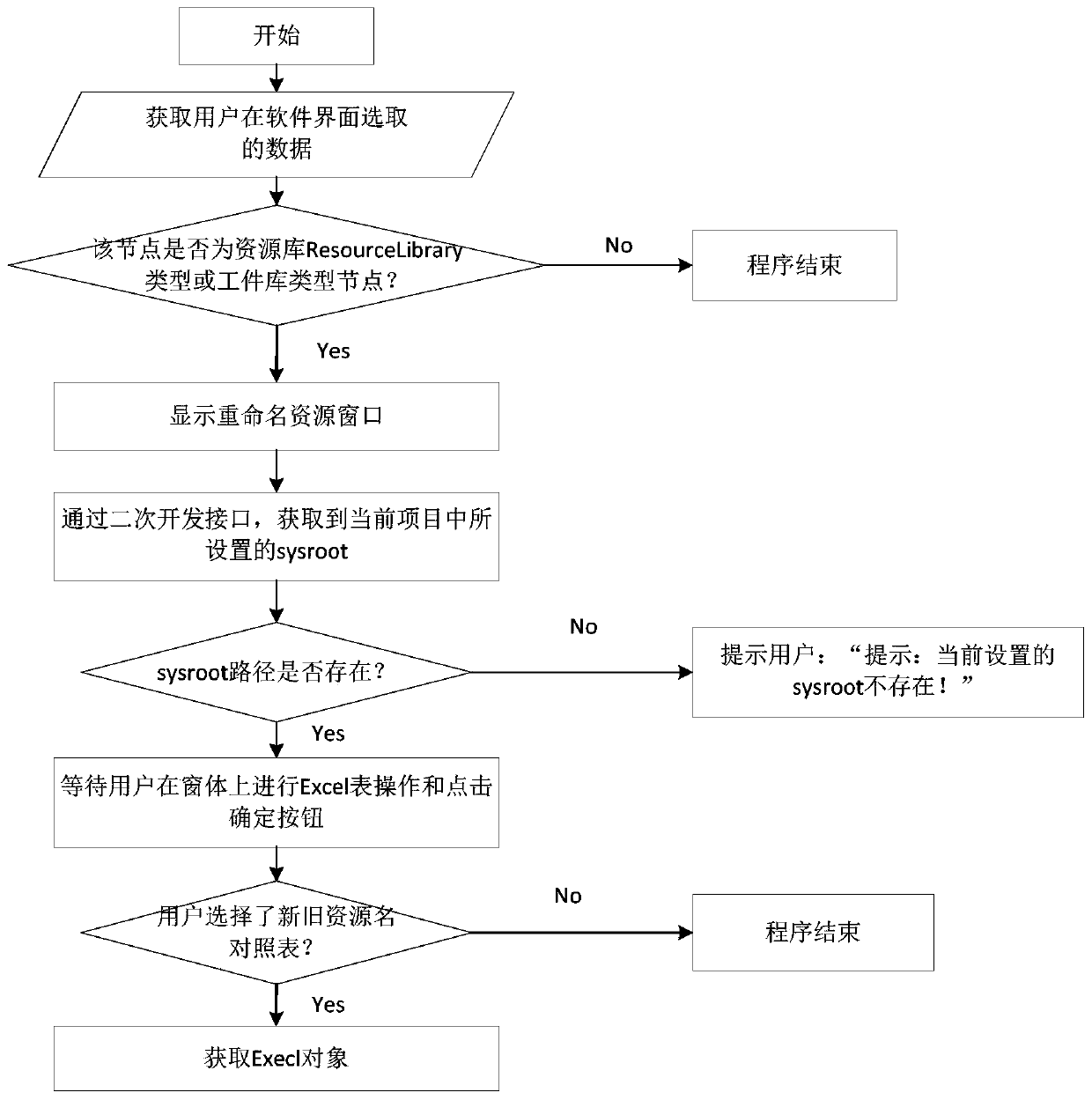
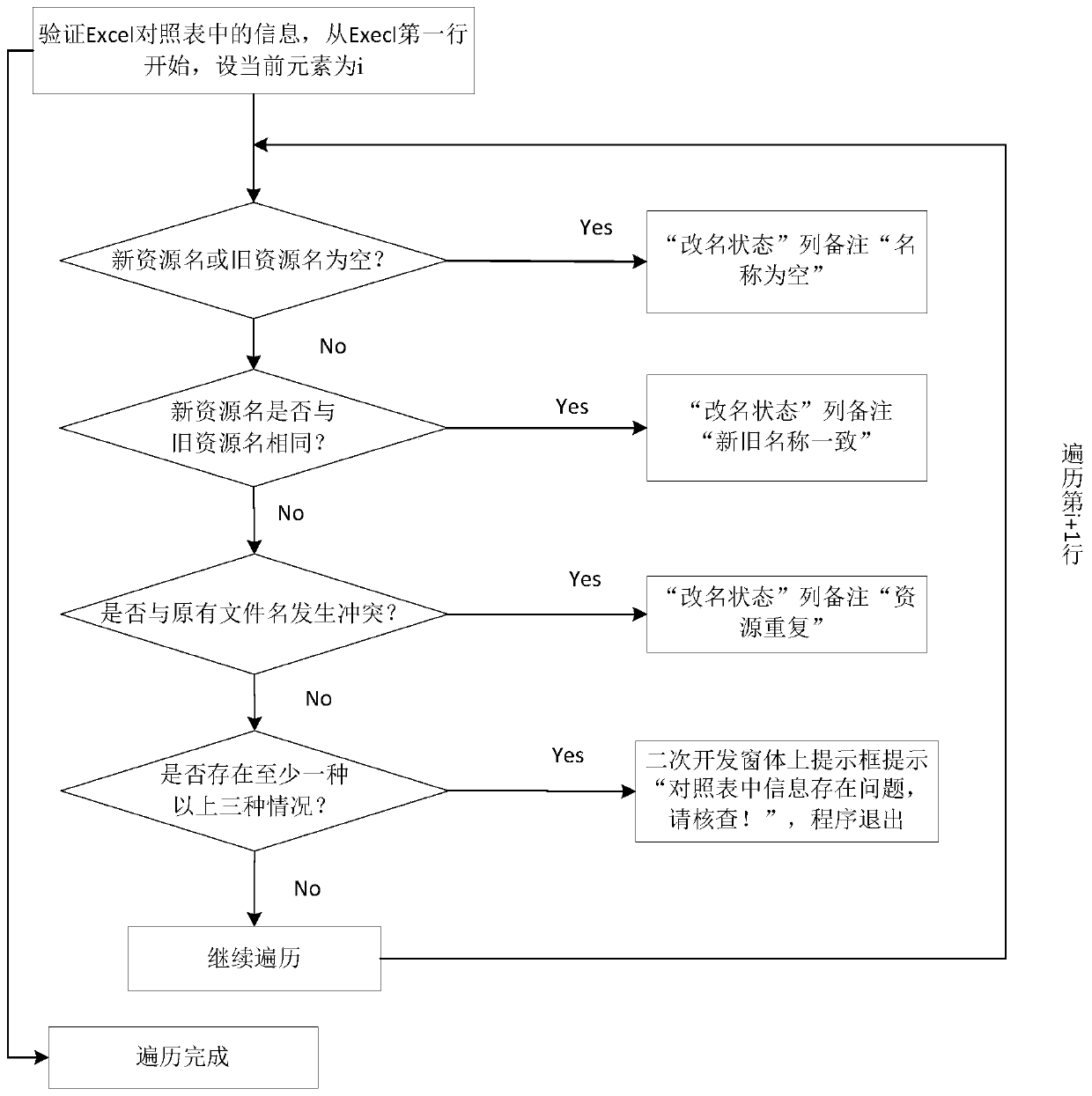
Prototype, instance and folder renaming method and storage medium
ActiveCN110968558AImplement renamingHigh speedFile/folder operationsSpecial data processing applicationsPathPingRename
The invention discloses a prototype, instance and folder renaming method and system and a storage medium. The method comprises the steps of acquiring resource library prototype nodes and modificationcommands; obtaining folders associated with the prototype nodes of the resource library and a new and old resource comparison table through an interface; acquiring all resource prototypes under a resource library prototype node, storing the resource prototypes into a set, traversing the set to acquire names of the resource prototypes, instances associated with the resource prototypes and paths offolders, and storing the names, the instances and the paths into the set; and checking occupation conditions of all resource prototypes, occupation conditions of instances, path conditions of foldersand name conflict conditions of folders, and modifying folder names, prototype names and instance names. The resource prototypes in the Process Design resource library and the resource instances and folders associated with the resource prototypes can be quickly renamed in batches, and the accuracy is high. The invention can be widely applied to the field of computer simulation.
Owner:GUANGZHOU MINO AUTOMOTIVE EQUIP CO LTD
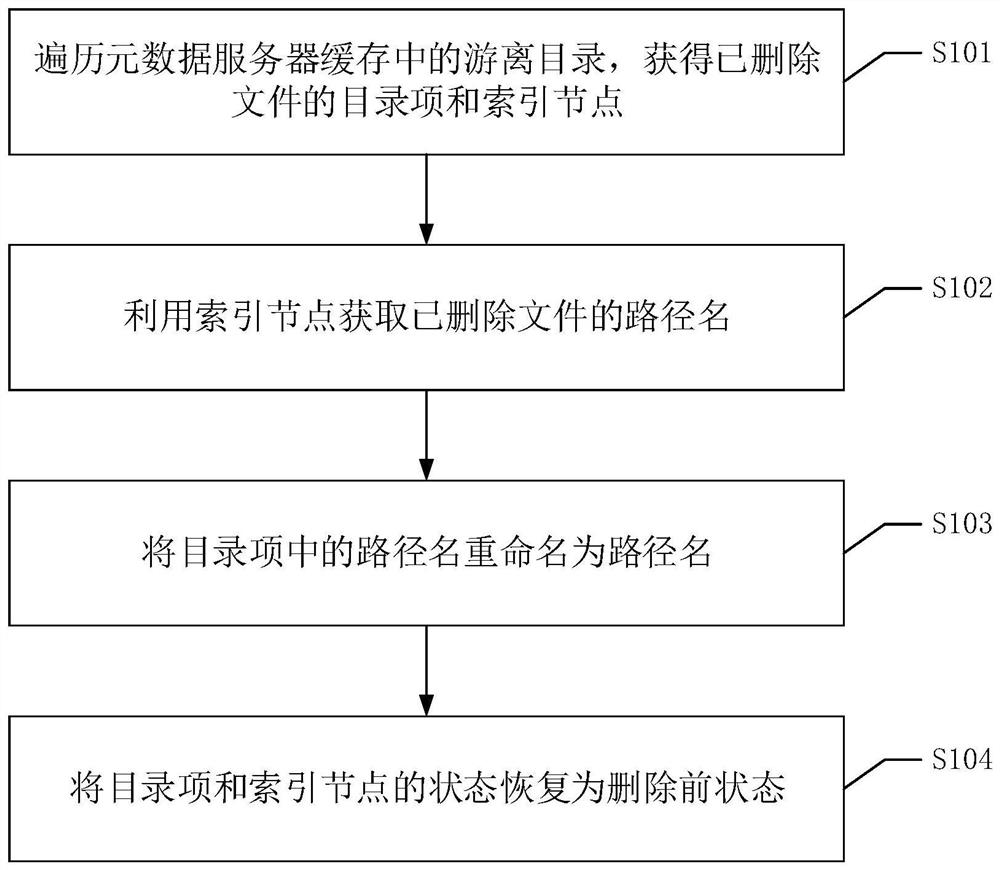
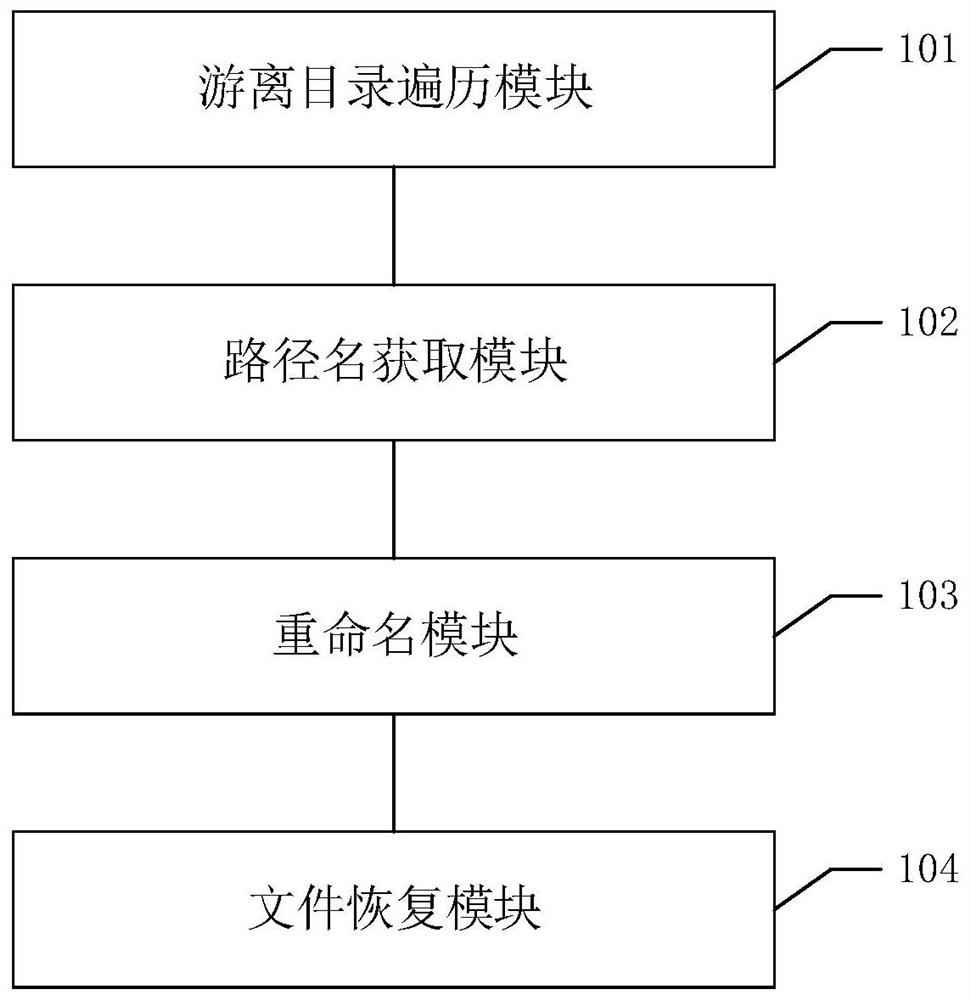
A deleted file recovery method, device, equipment and readable storage medium
The invention discloses a deleted file recovery method, device, equipment and readable storage medium. The method comprises the following steps: traversing the free directory in the cache of the metadata server to obtain the directory entry and the index node of the deleted file; using the index The node gets the pathname of the deleted file; renames the pathname in the directory entry to the pathname; restores the state of the directory entry and inode to the state before deletion. With this method, the deleted files in the Unix / Linux system can be recovered, and the data content of the deleted files can be continued to be accessed.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com