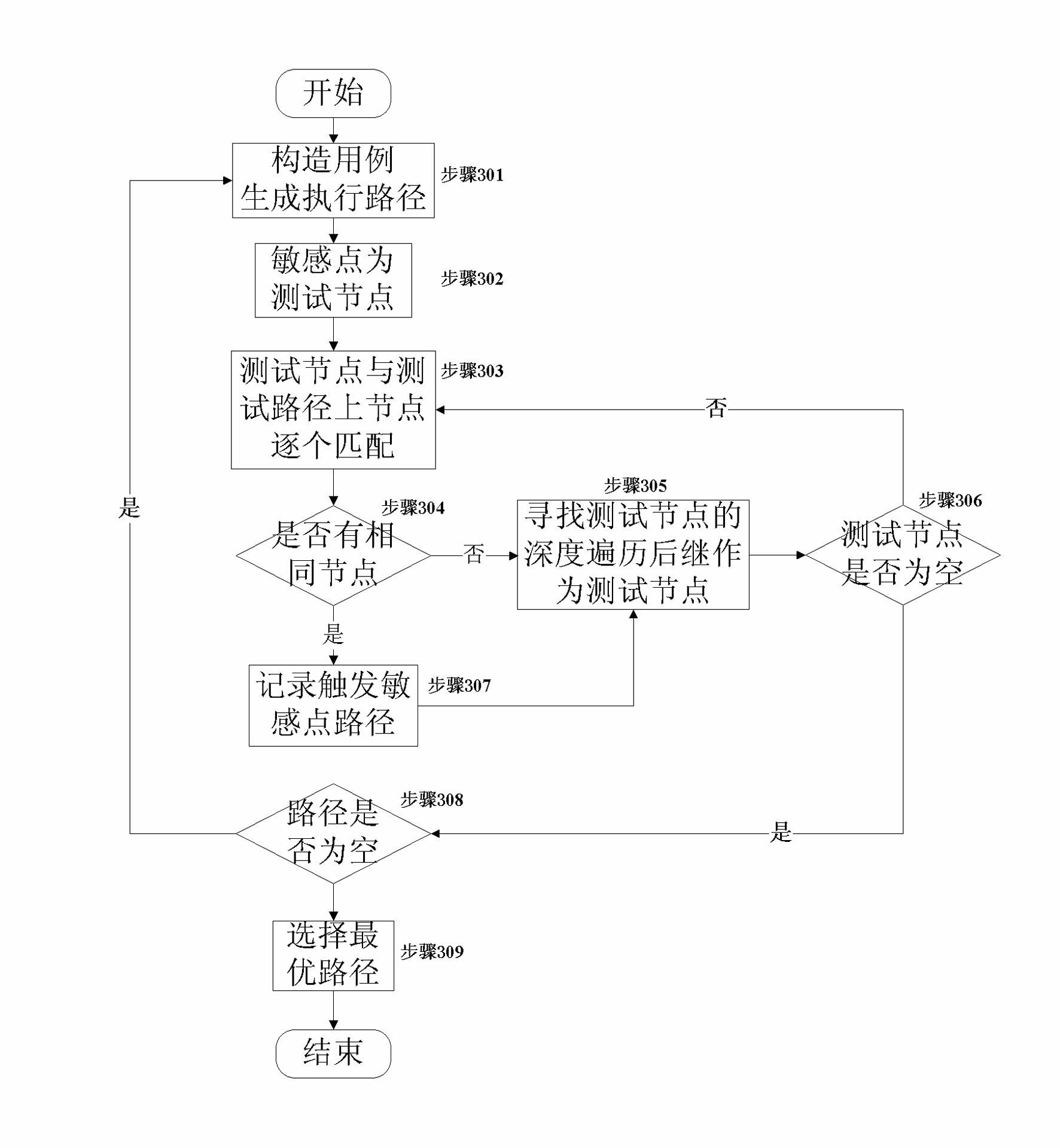
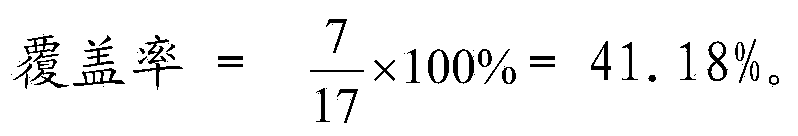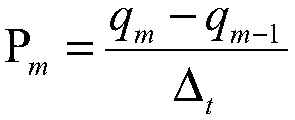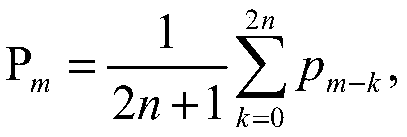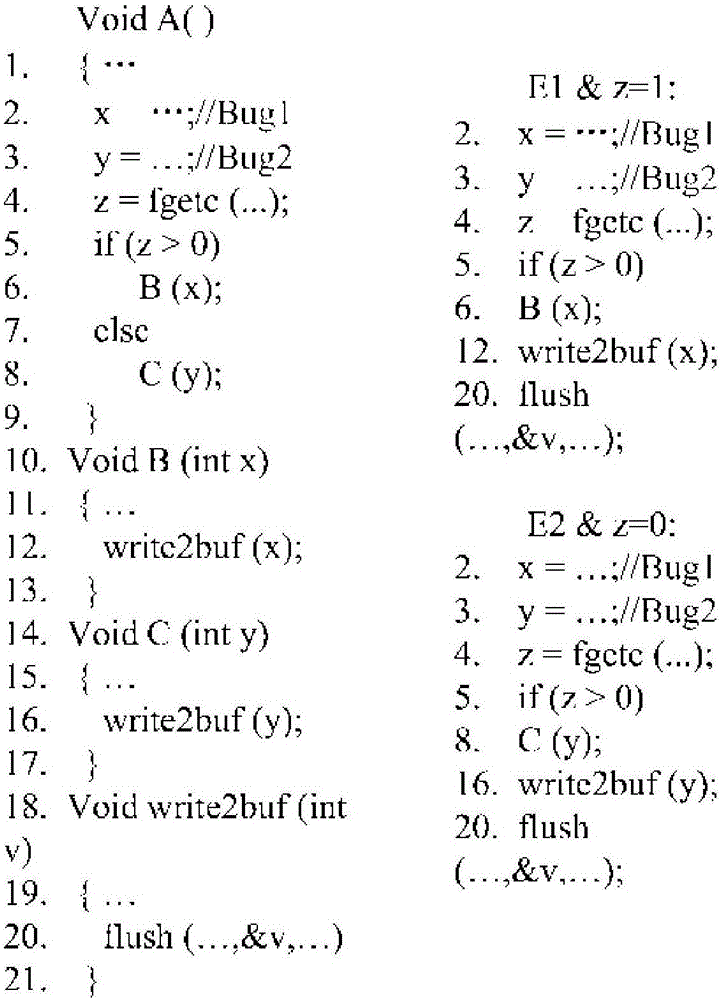Patents
Literature
112 results about "Path coverage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Path coverage refers to designing test cases such that all linearly independent paths in the program are executed at least once. A linearly independent path can be defined in terms of what’s called a control flow graph of an application. Great.
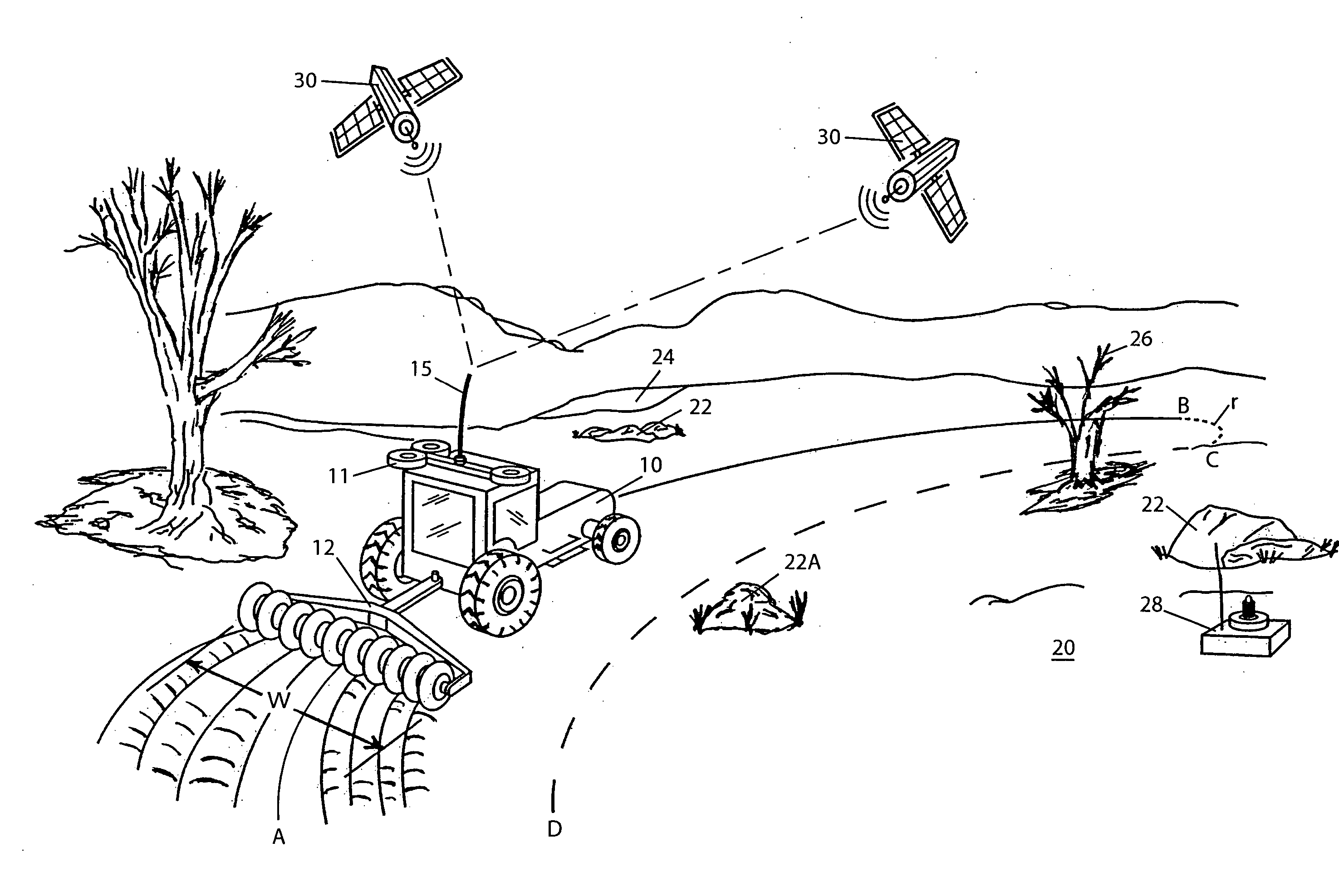
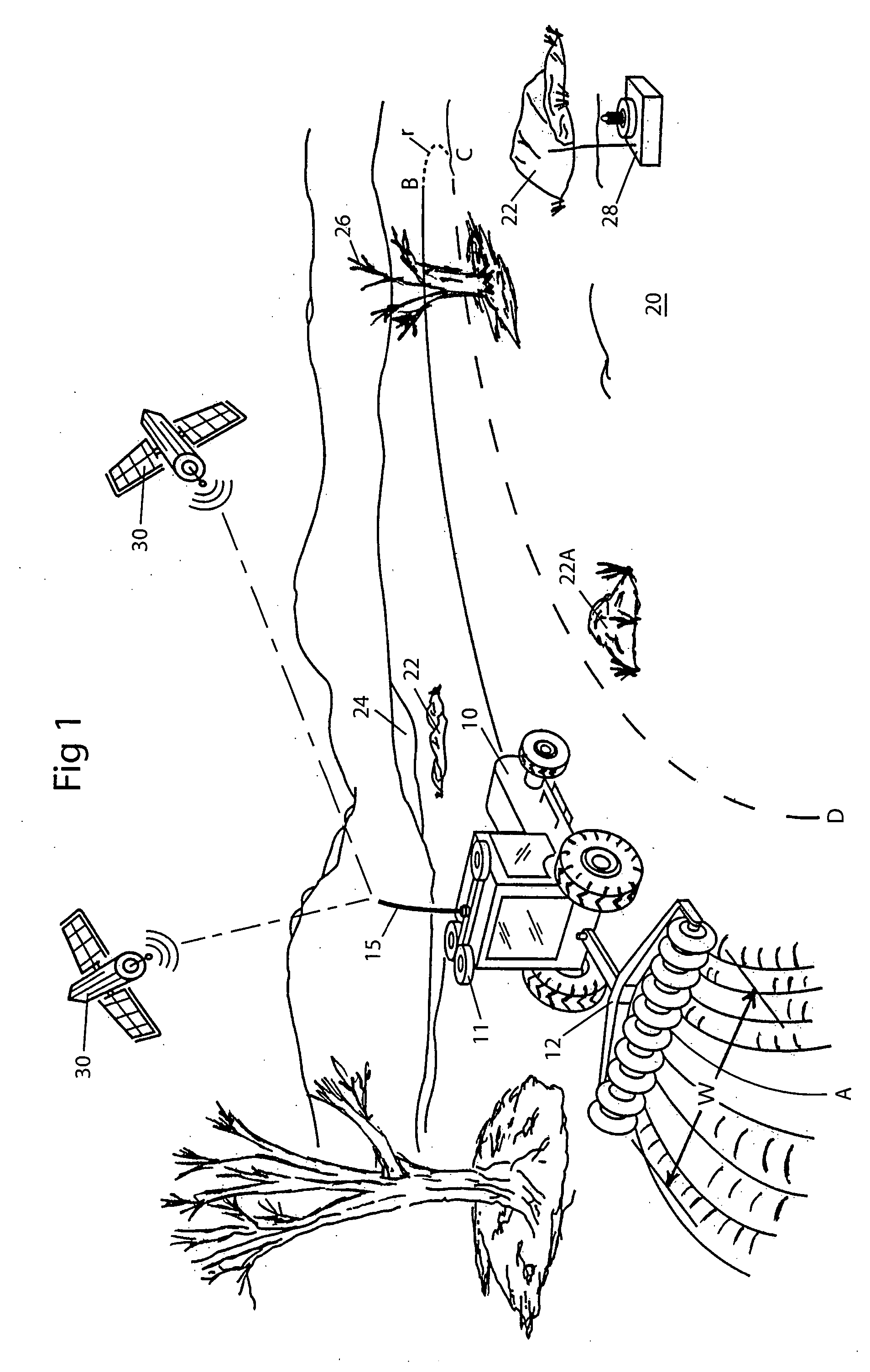
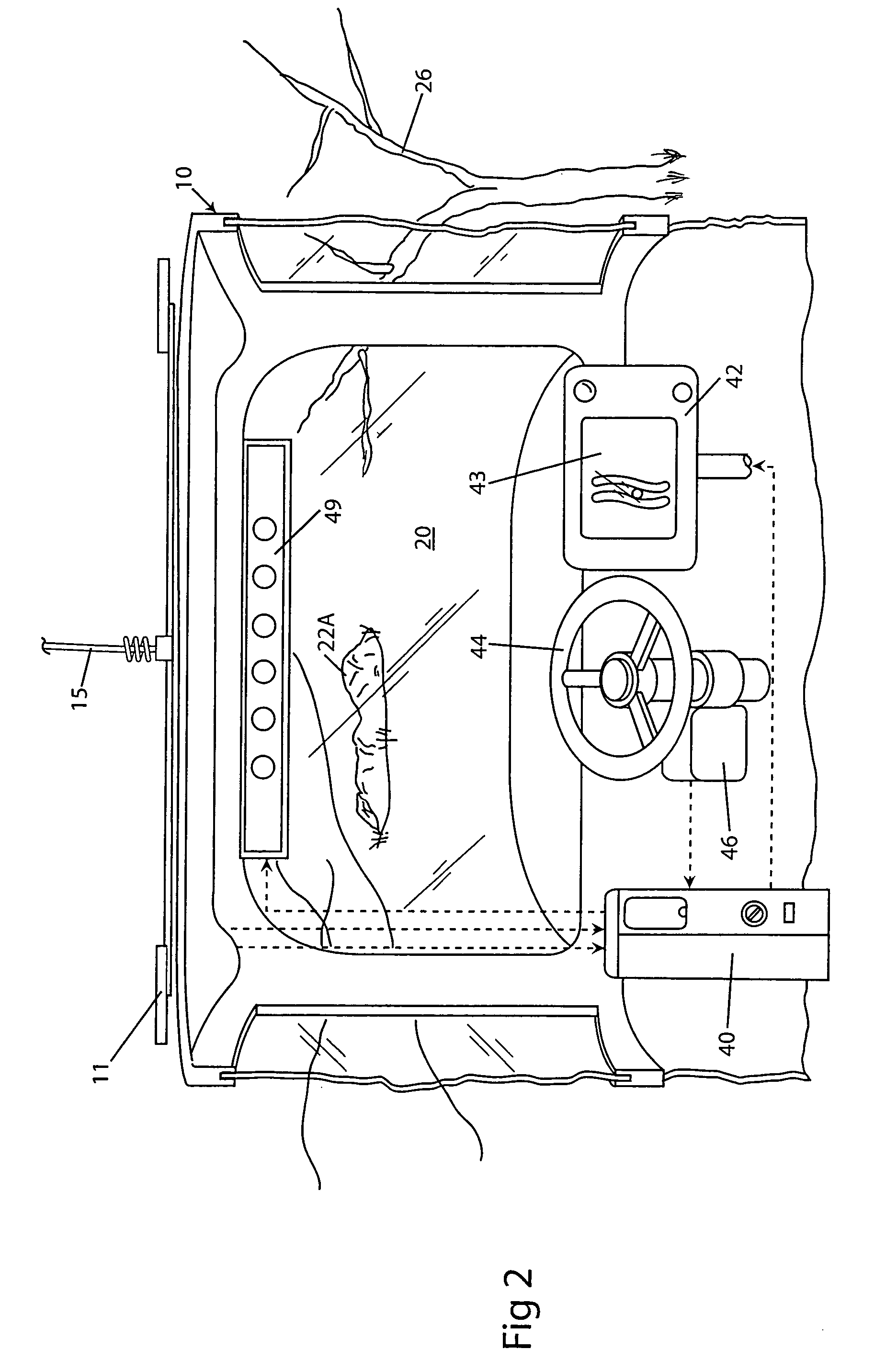
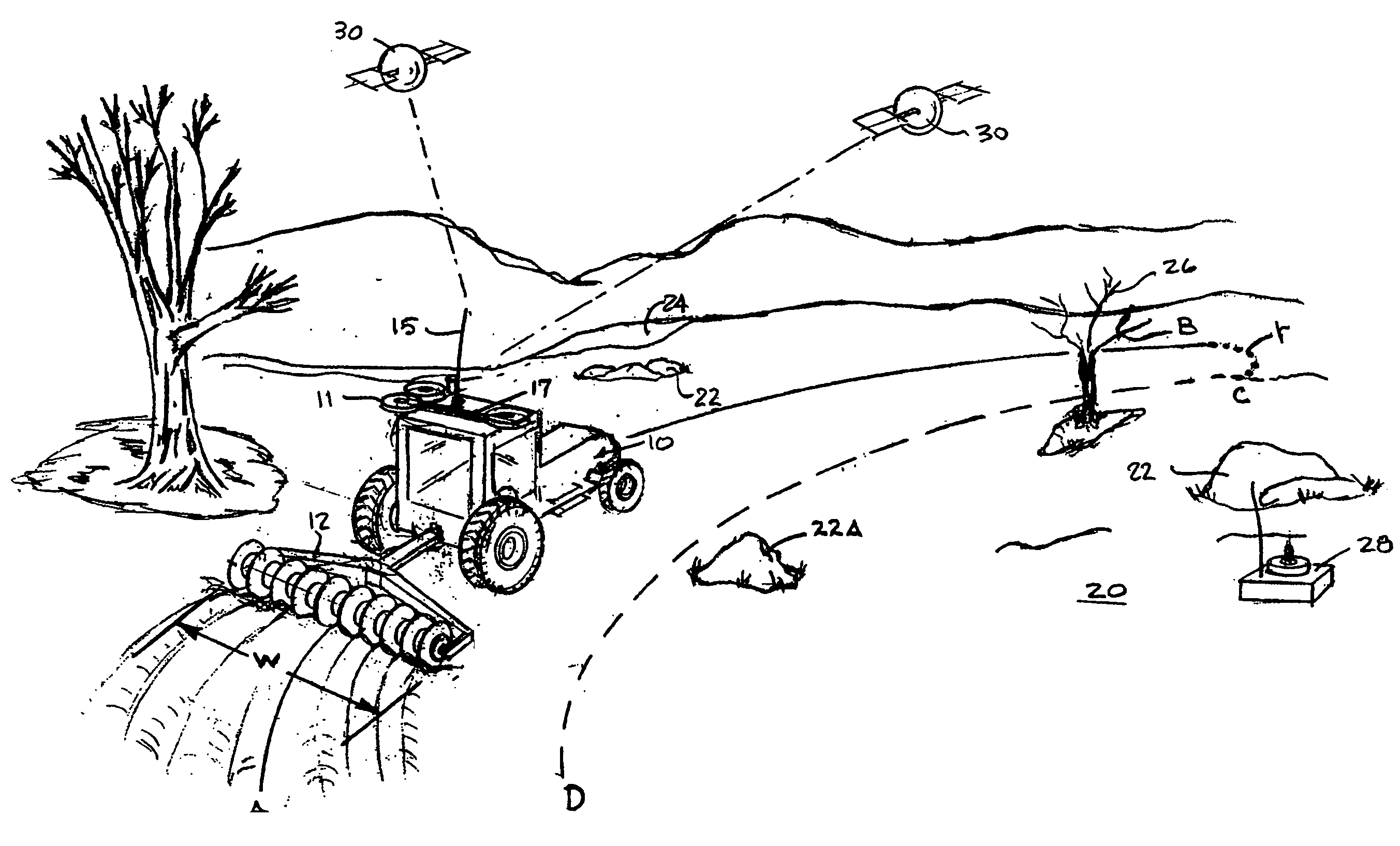
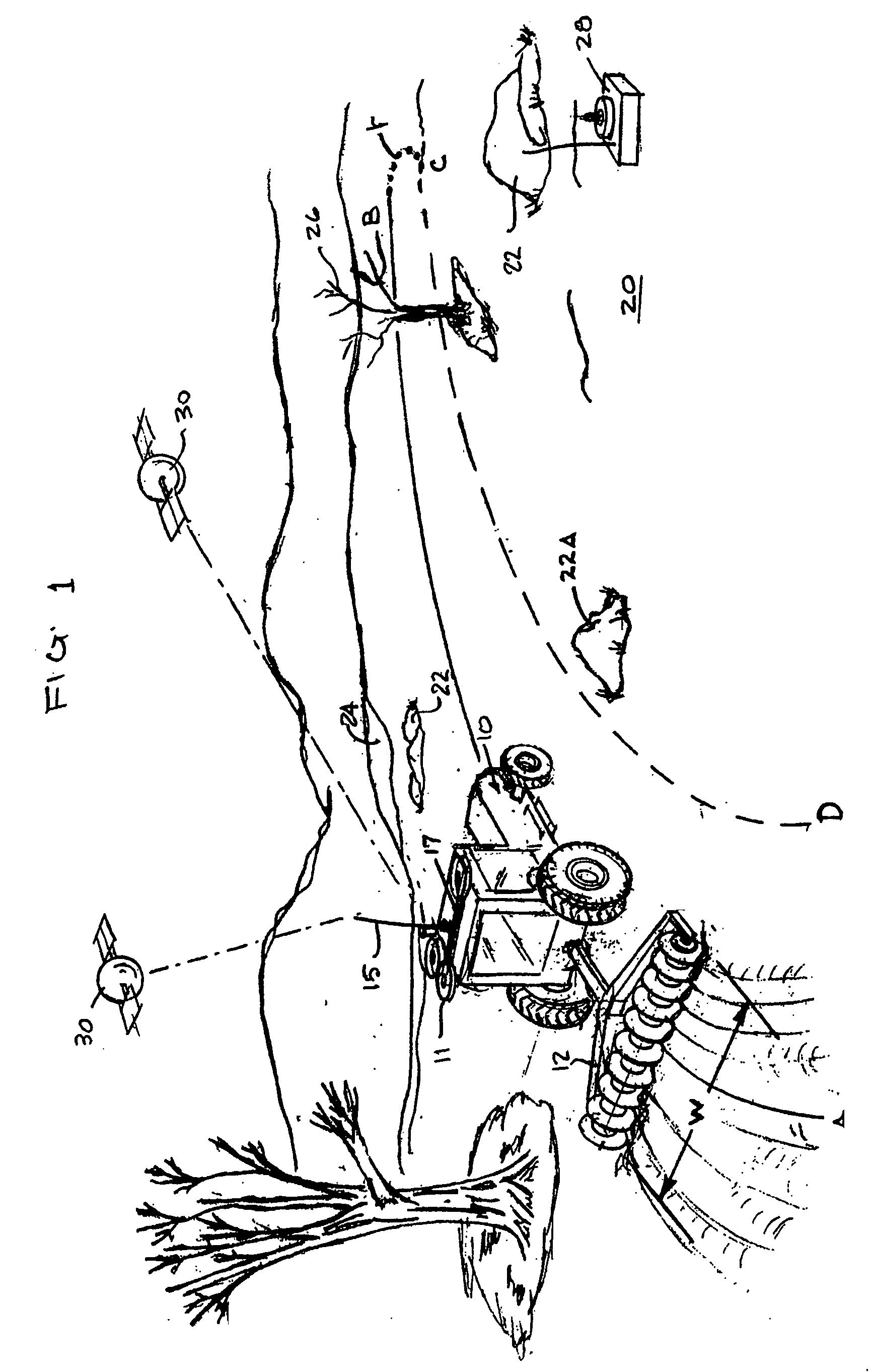
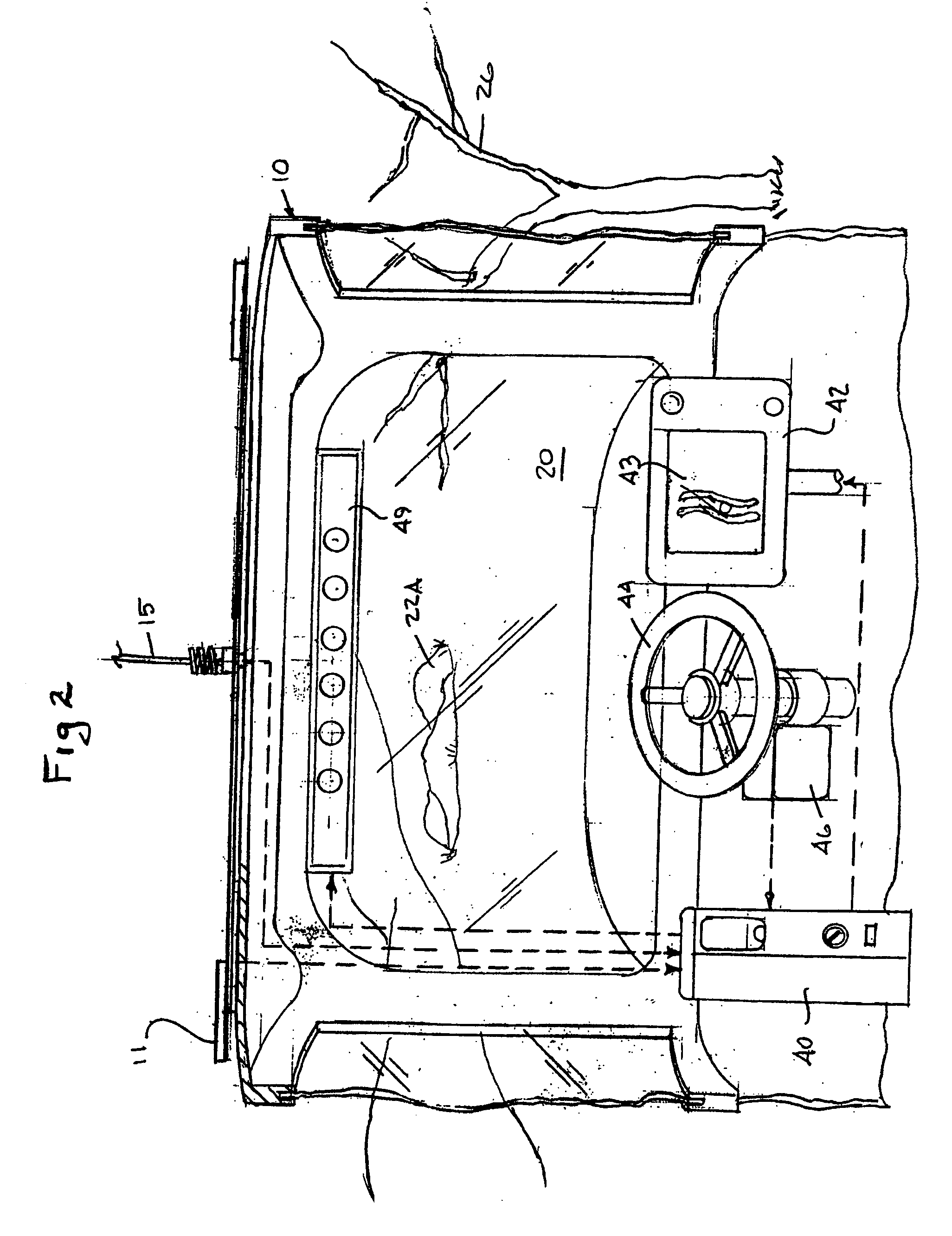
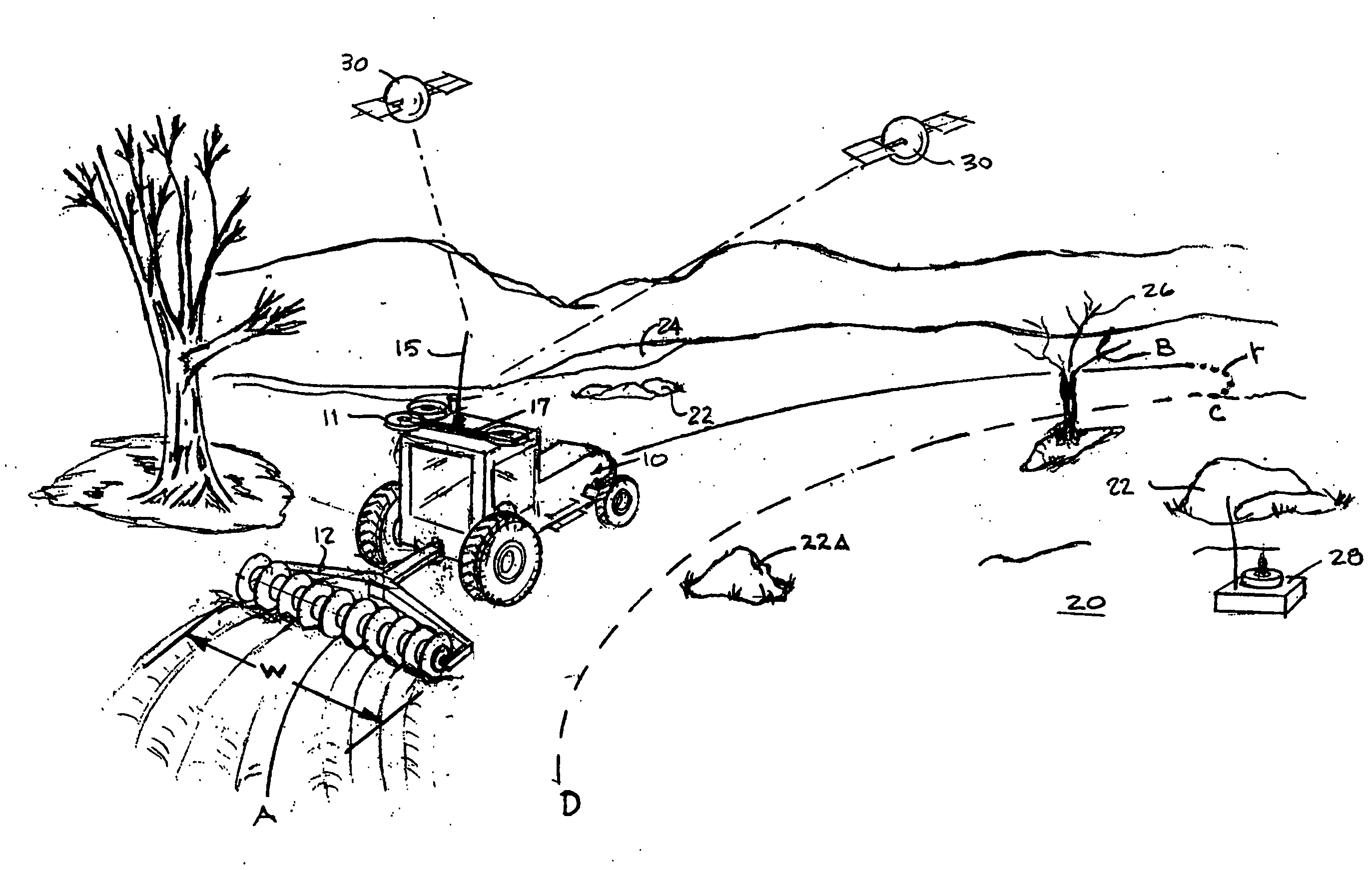
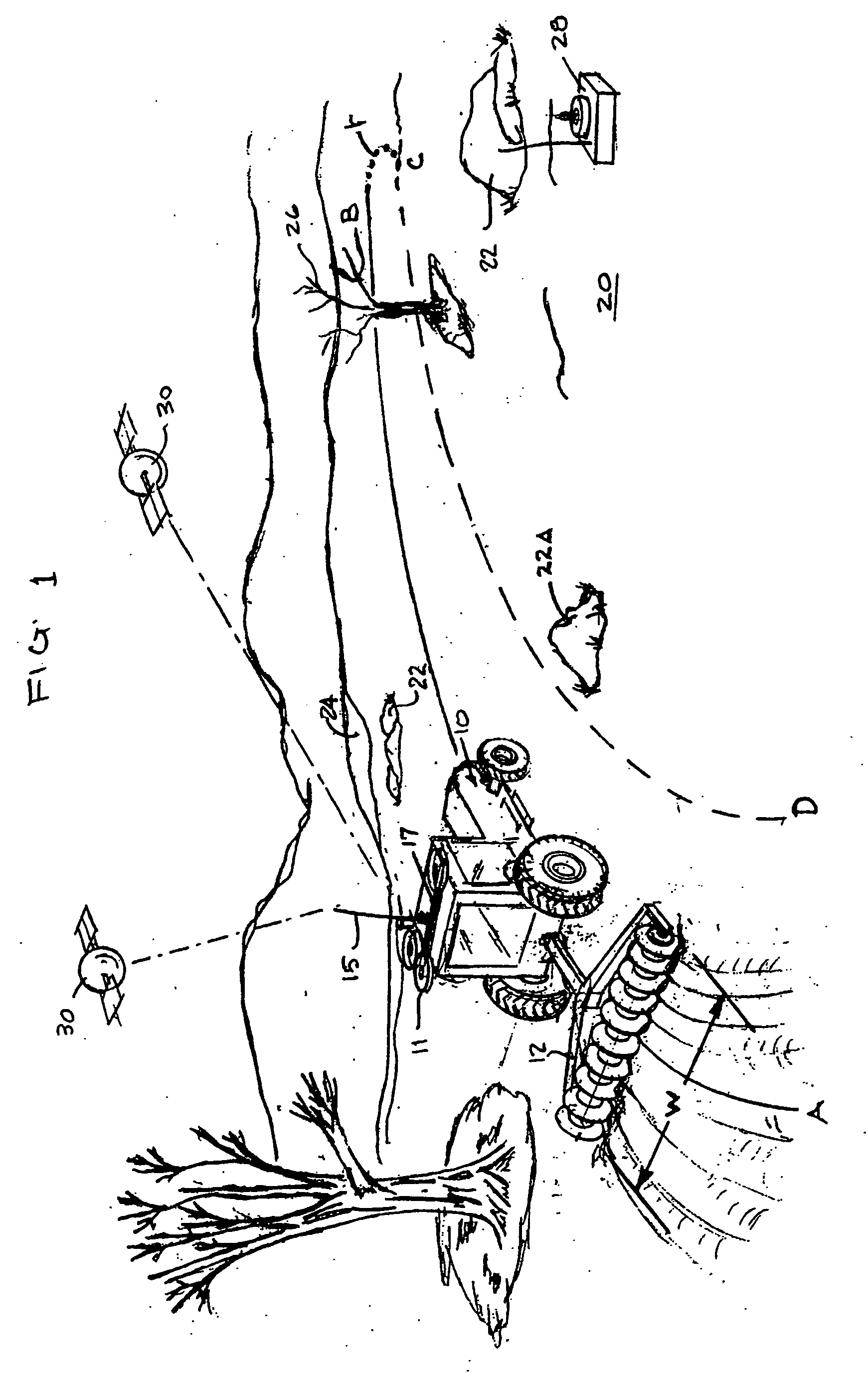
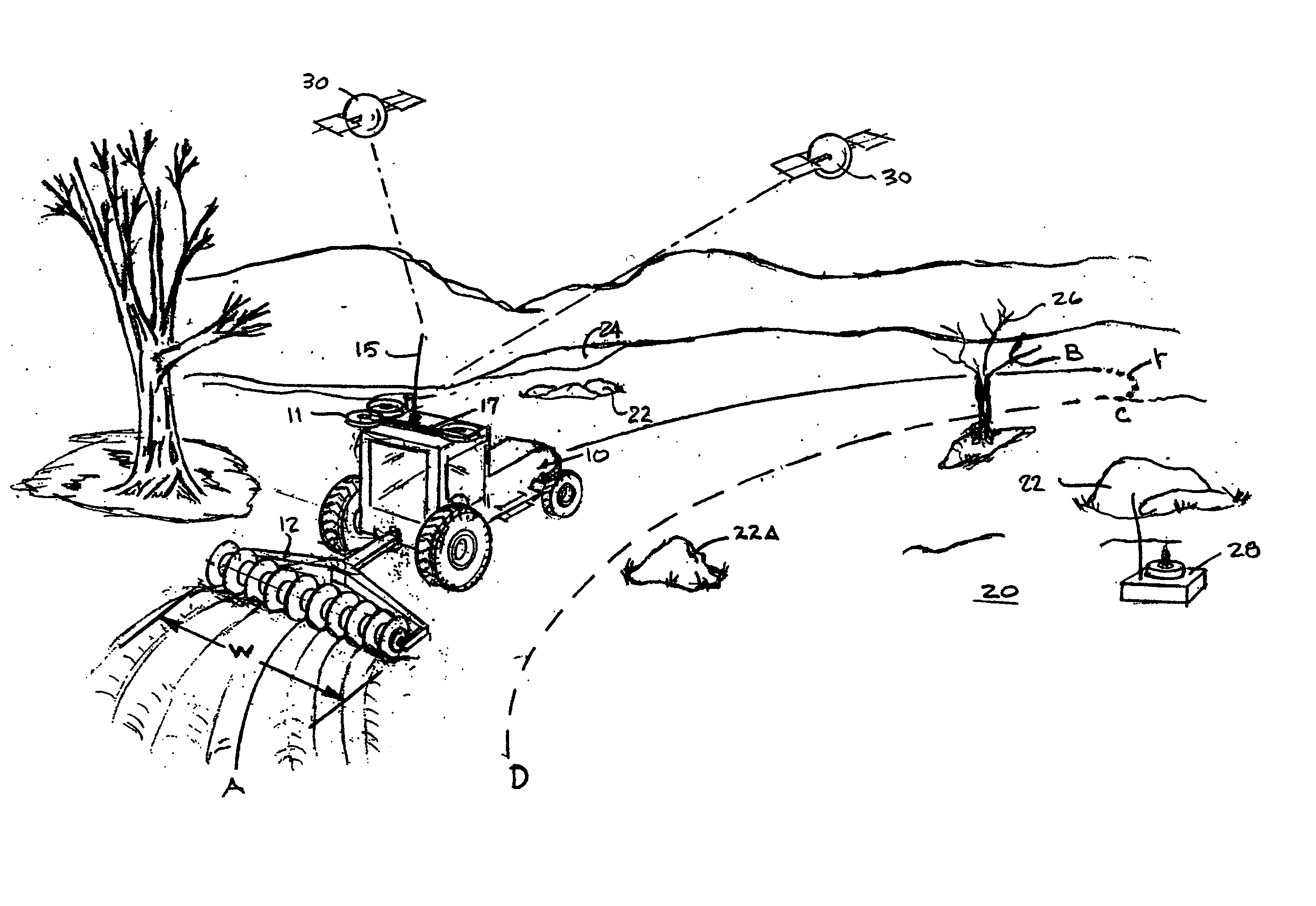
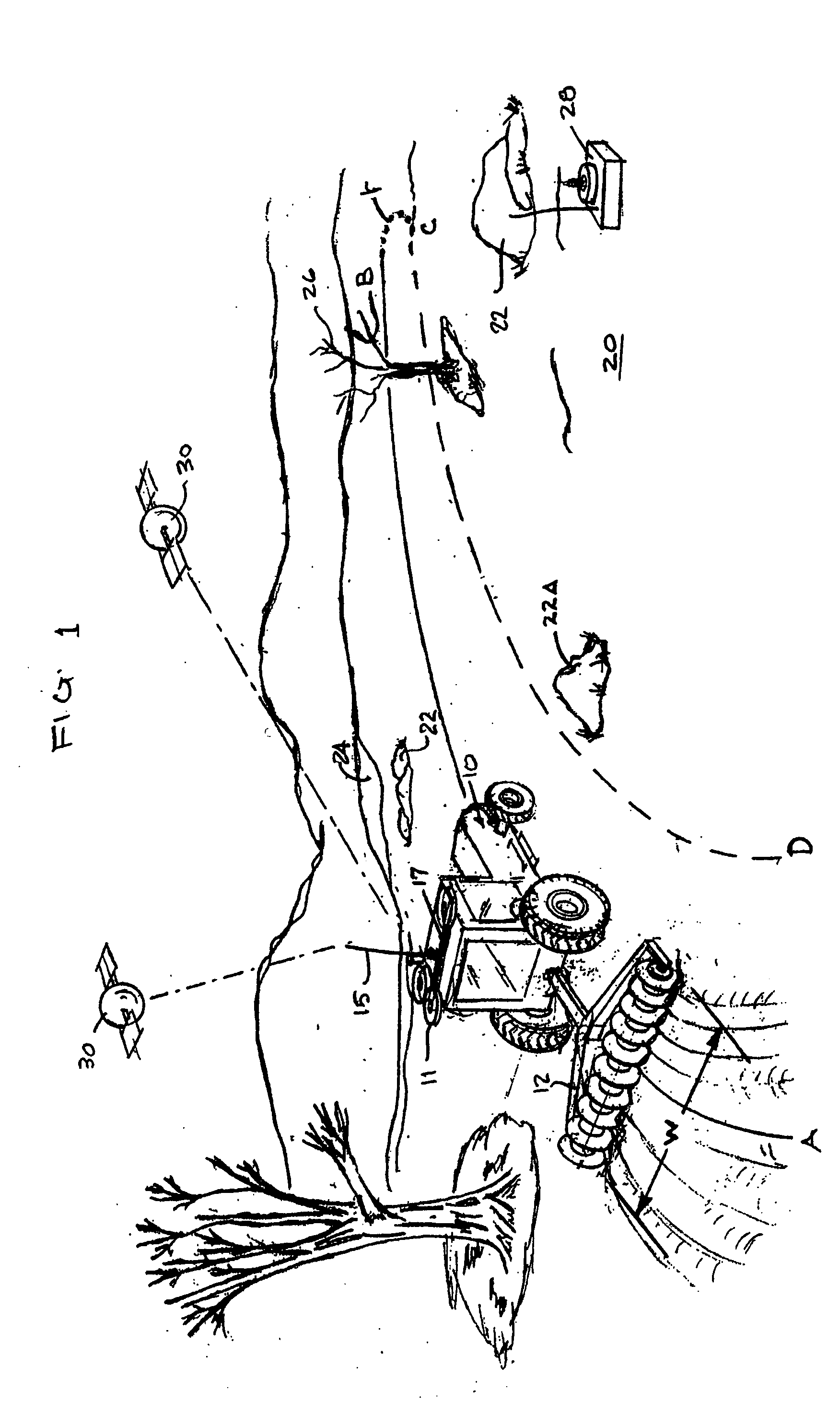
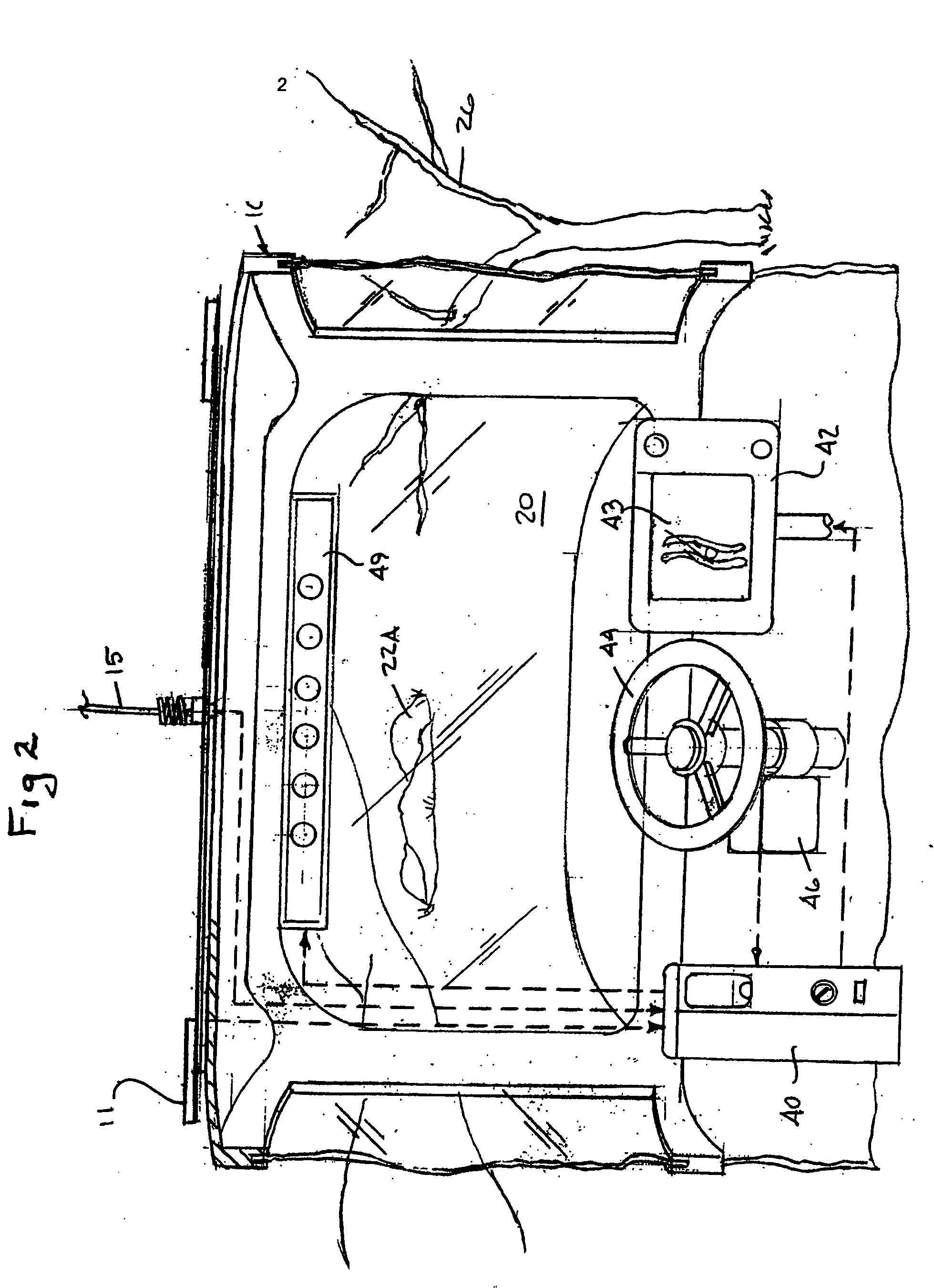
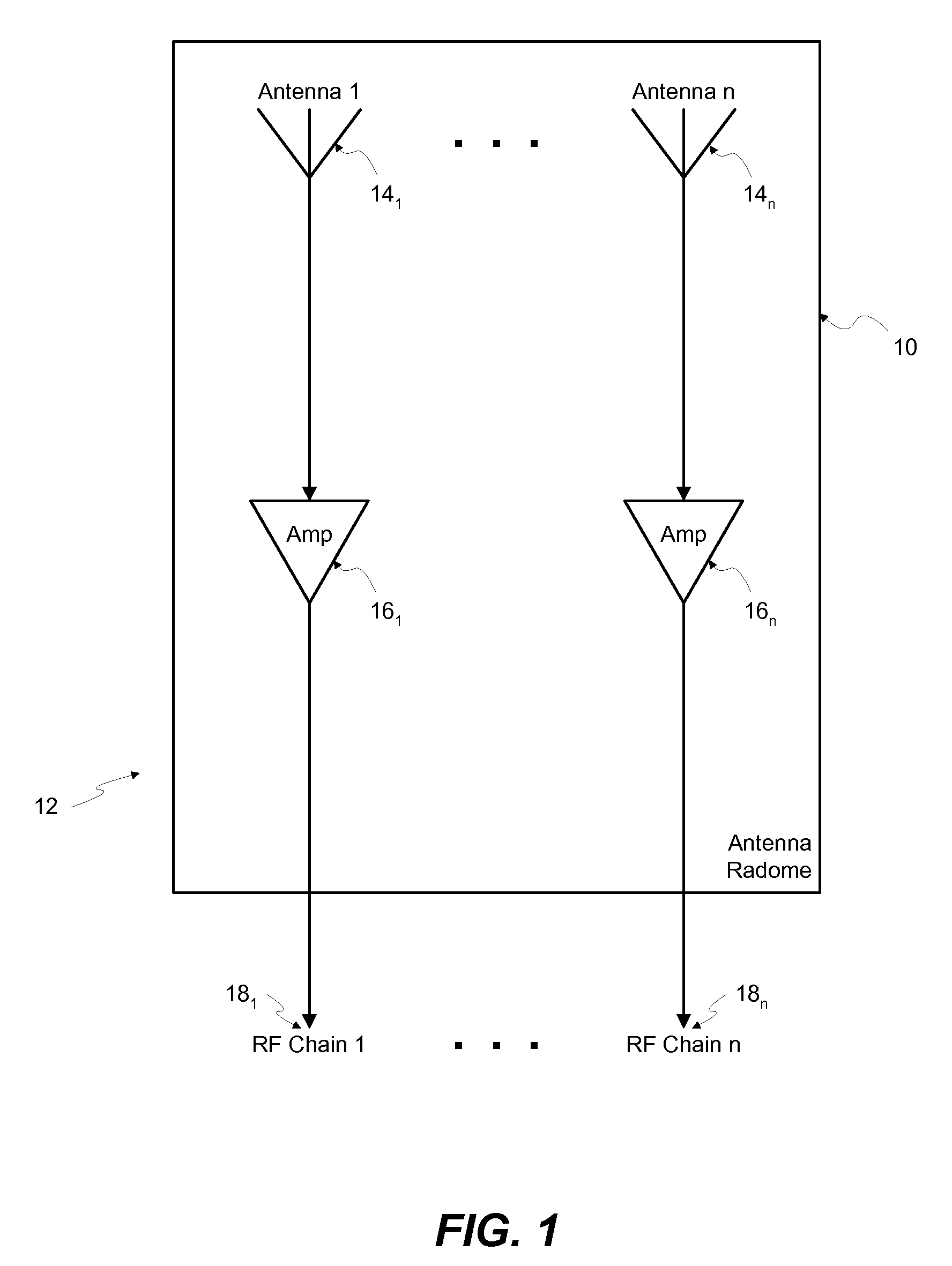
System and method for interactive selection of agricultural vehicle guide paths with varying curvature along their length
ActiveUS20060178825A1Improve accuracyInstruments for road network navigationRoad vehicles traffic controlGraphicsGraphical user interface
A system and method provide for precision guiding of agricultural vehicles along a series of adjacent paths to form rows for cultivating a field. In one aspect of the invention the vehicle is moved along a first path while receiving positioning information from a navigational system (e.g., RTK GPS). This positioning information is stored in a processor and is used by the processor to compute a second path adjacent to said first path by calculating piecewise perpendicular offsets from the first path at multiple locations along the first path. The process is repeated to compute a third and subsequent paths so as to cover the field. Because of the offset process, the field may be covered with paths that have varying curvature along their length, while providing substantially no gaps or overlaps in the coverage of the field. In another aspect of the invention, the system may propose alternative paths and the user can intervene by steering the vehicle or using a graphical user interface to select among the alternative paths. A still further aspect of the invention allows for the recording of the paths that provide coverage of a field in the form of a template. This template can then be used to cause the vehicle to automatically steer along a previously calculated path in subsequent operations on the field, and in subsequent years.
Owner:NOVARIANT
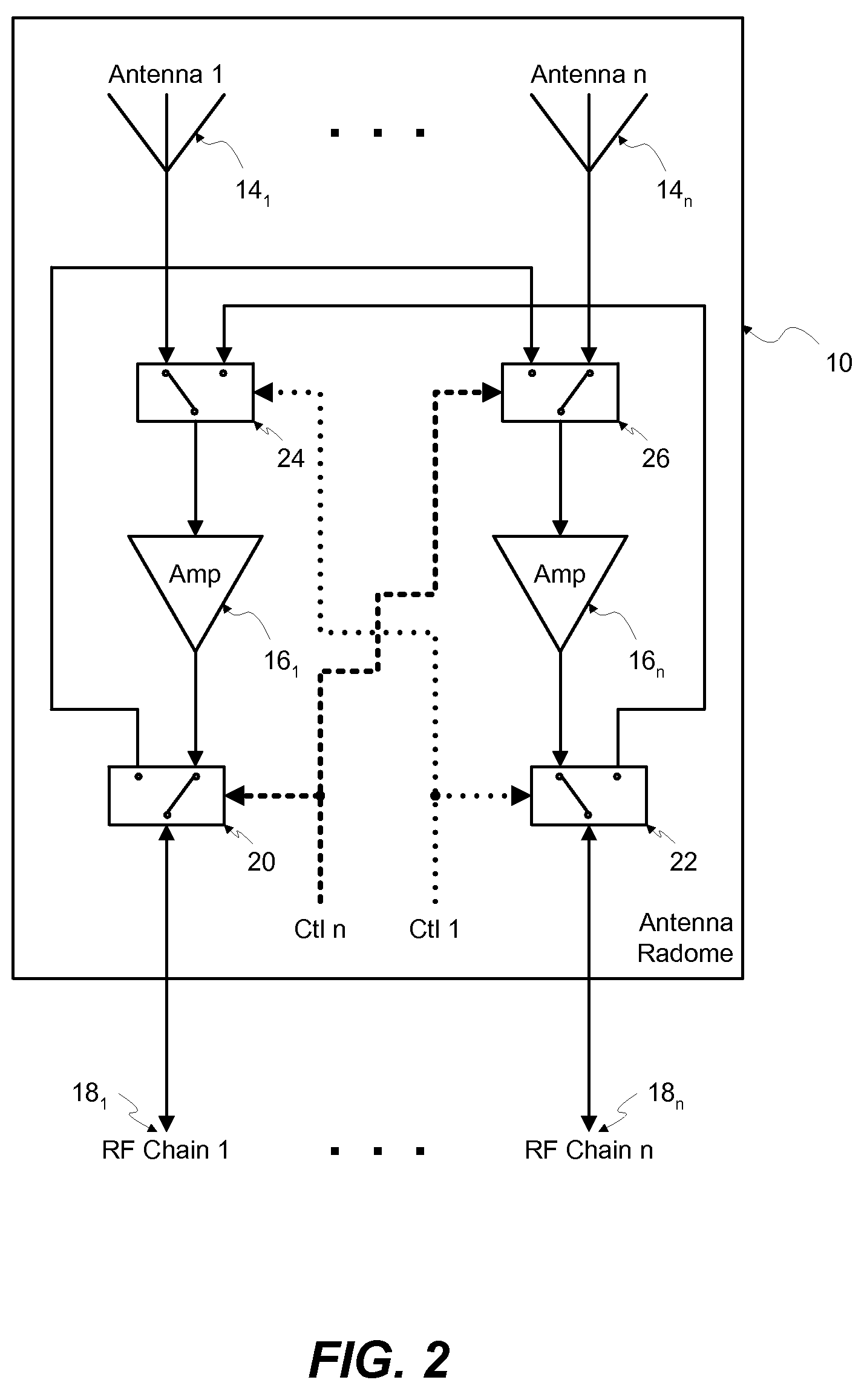
System and method for interactive selection of agricultural vehicle guide paths through a graphical user interface other than moving the vehicle
ActiveUS20060175541A1Improve accuracyMaterial analysis by optical meansCounting objects on conveyorsMobile vehicleGraphics
A system and method provide for precision guiding of agricultural vehicles along a series of adjacent paths to form rows for cultivating a field. In one aspect of the invention the vehicle is moved along a first path while receiving positioning information from a navigational system (e.g., RTK GPS). This positioning information is stored in a processor and is used by the processor to compute a second path adjacent to said first path by calculating piecewise perpendicular offsets from the first path at multiple locations along the first path. The process is repeated to compute a third and subsequent paths so as to cover the field. Because of the offset process, the field may be covered with paths that have varying curvature along their length, while providing substantially no gaps or overlaps in the coverage of the field. In another aspect of the invention, the system may propose alternative paths and the user can intervene by steering the vehicle or using a graphical user interface to select among the alternative paths. A still further aspect of the invention allows for the recording of the paths that provide coverage of a field in the form of a template. This template can then be used to cause the vehicle to automatically steer along a previously calculated path in subsequent operations on the field, and in subsequent years.
Owner:NOVARIANT
System and method for guiding an agricultural vehicle through a recorded template of guide paths
InactiveUS20060178820A1Improve accuracyInstruments for road network navigationAnalogue computers for trafficGraphicsGraphical user interface
A system and method provide for precision guiding of agricultural vehicles along a series of adjacent paths to form rows for cultivating a field. In one aspect of the invention the vehicle is moved along a first path while receiving positioning information from a navigational system (e.g., RTK GPS). This positioning information is stored in a processor and is used by the processor to compute a second path adjacent to said first path by calculating piecewise perpendicular offsets from the first path at multiple locations along the first path. The process is repeated to compute a third and subsequent paths so as to cover the field. Because of the offset process, the field may be covered with paths that have varying curvature along their length, while providing substantially no gaps or overlaps in the coverage of the field. In another aspect of the invention, the system may propose alternative paths and the user can intervene by steering the vehicle or using a graphical user interface to select among the alternative paths. A still further aspect of the invention allows for the recording of the paths that provide coverage of a field in the form of a template. This template can then be used to cause the vehicle to automatically steer along a previously calculated path in subsequent operations on the field, and in subsequent years.
Owner:NOVARIANT
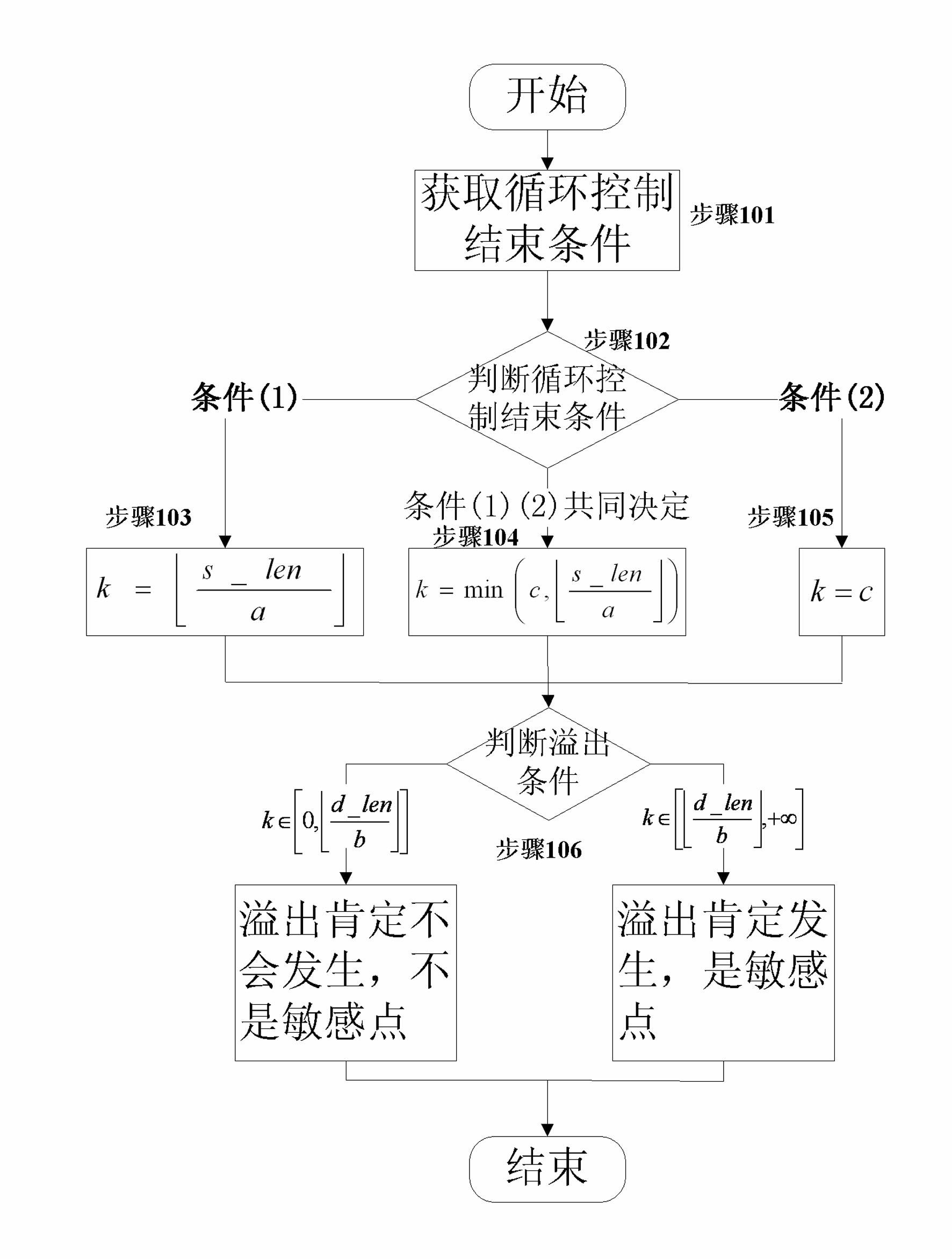
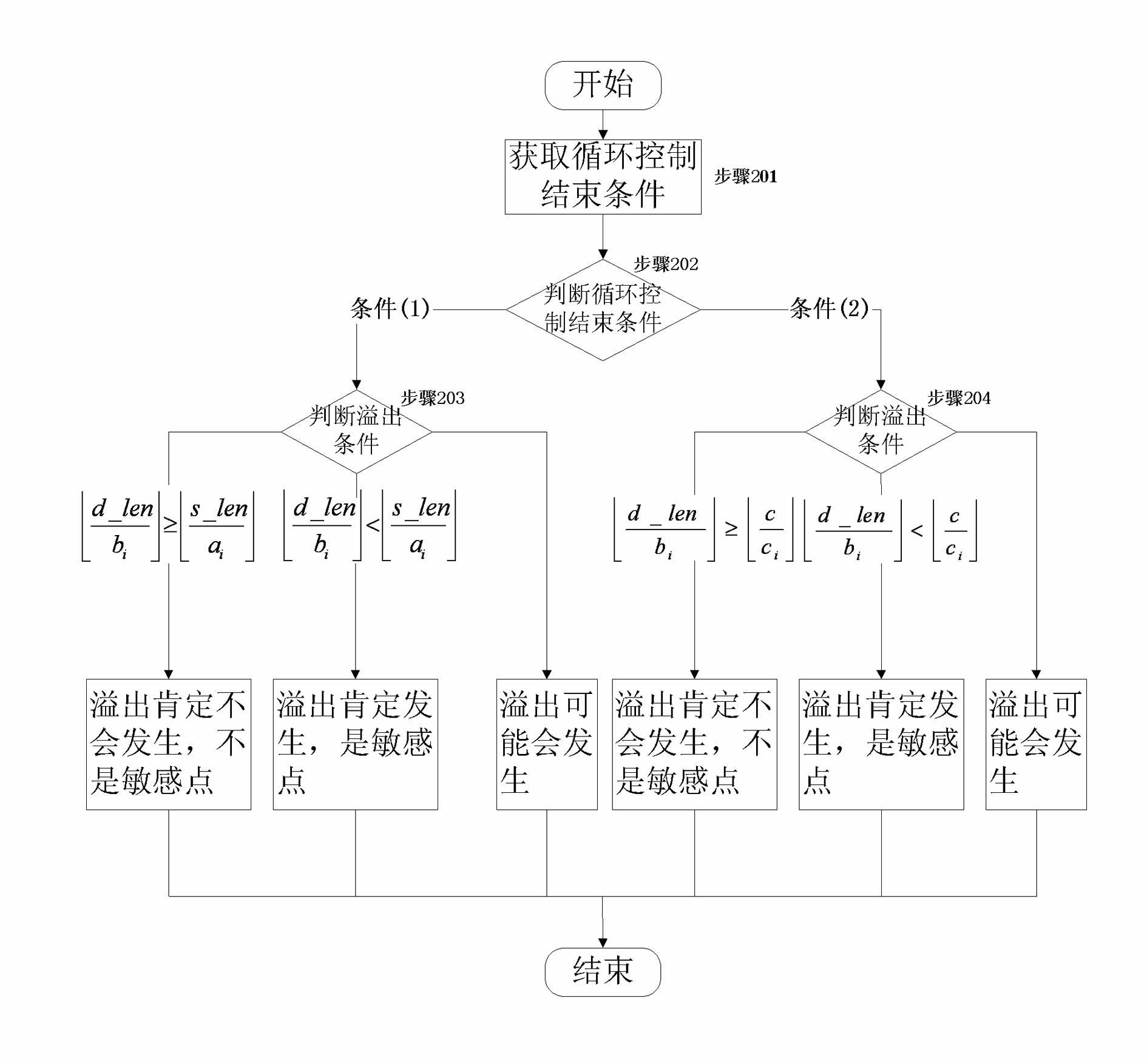
Detector for binary-code buffer-zone overflow bugs, and detection method thereof
InactiveCN101714118AGuaranteed feasibilityGuaranteed accuracyMultiprogramming arrangementsSoftware testing/debuggingBuffer overflowSource code
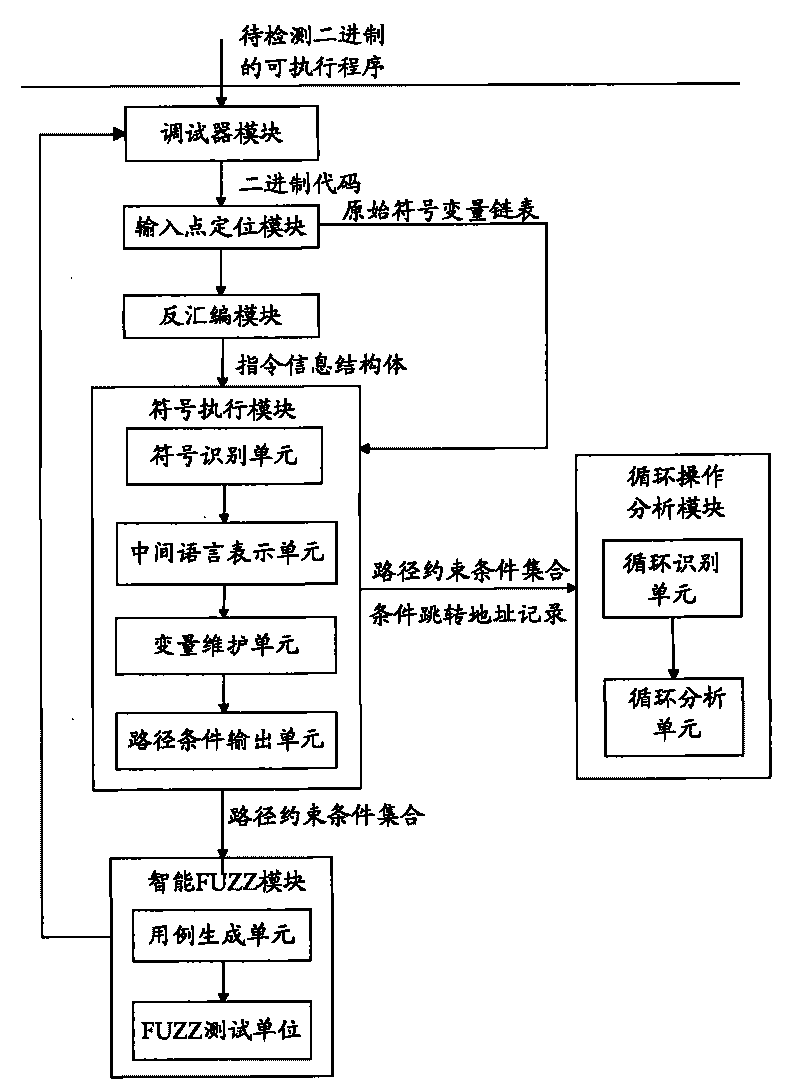
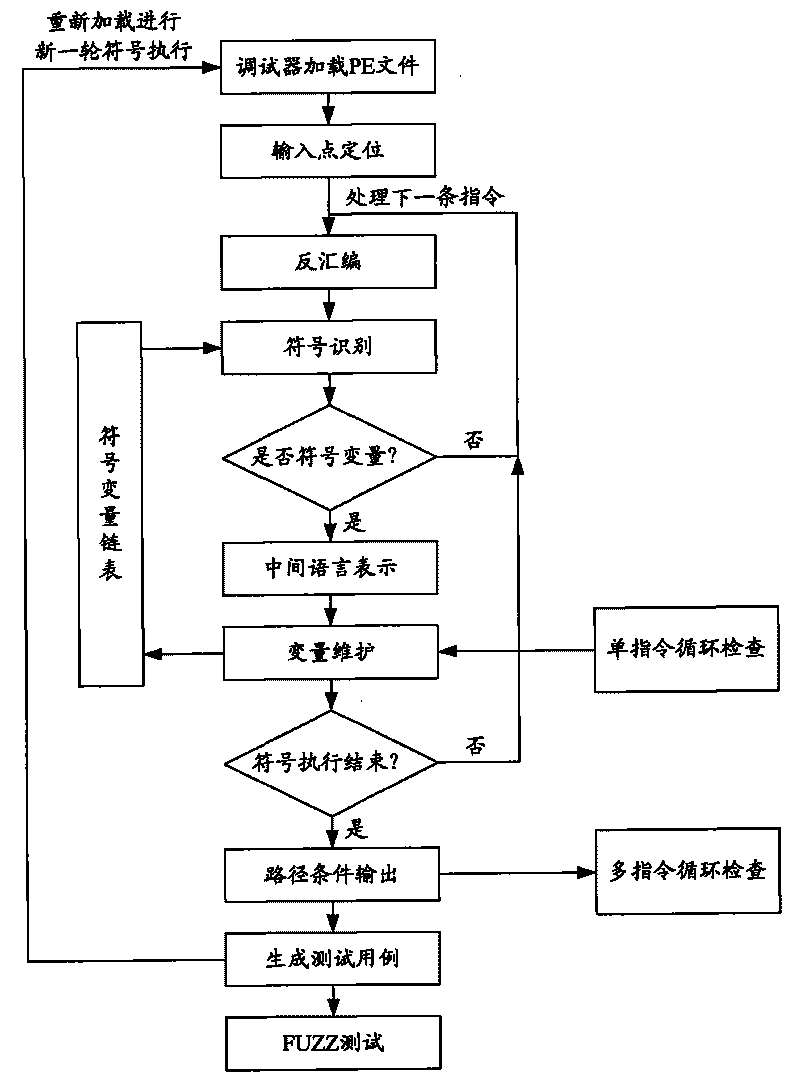
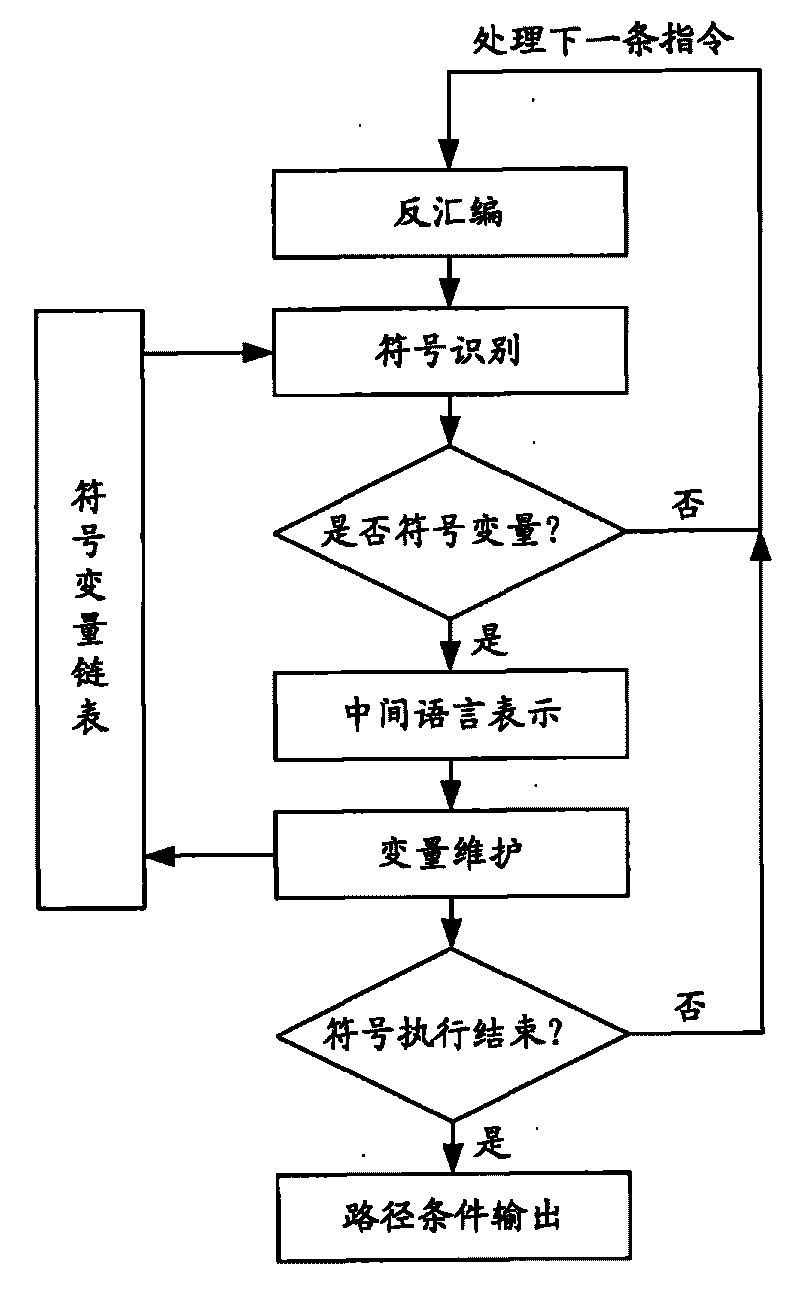
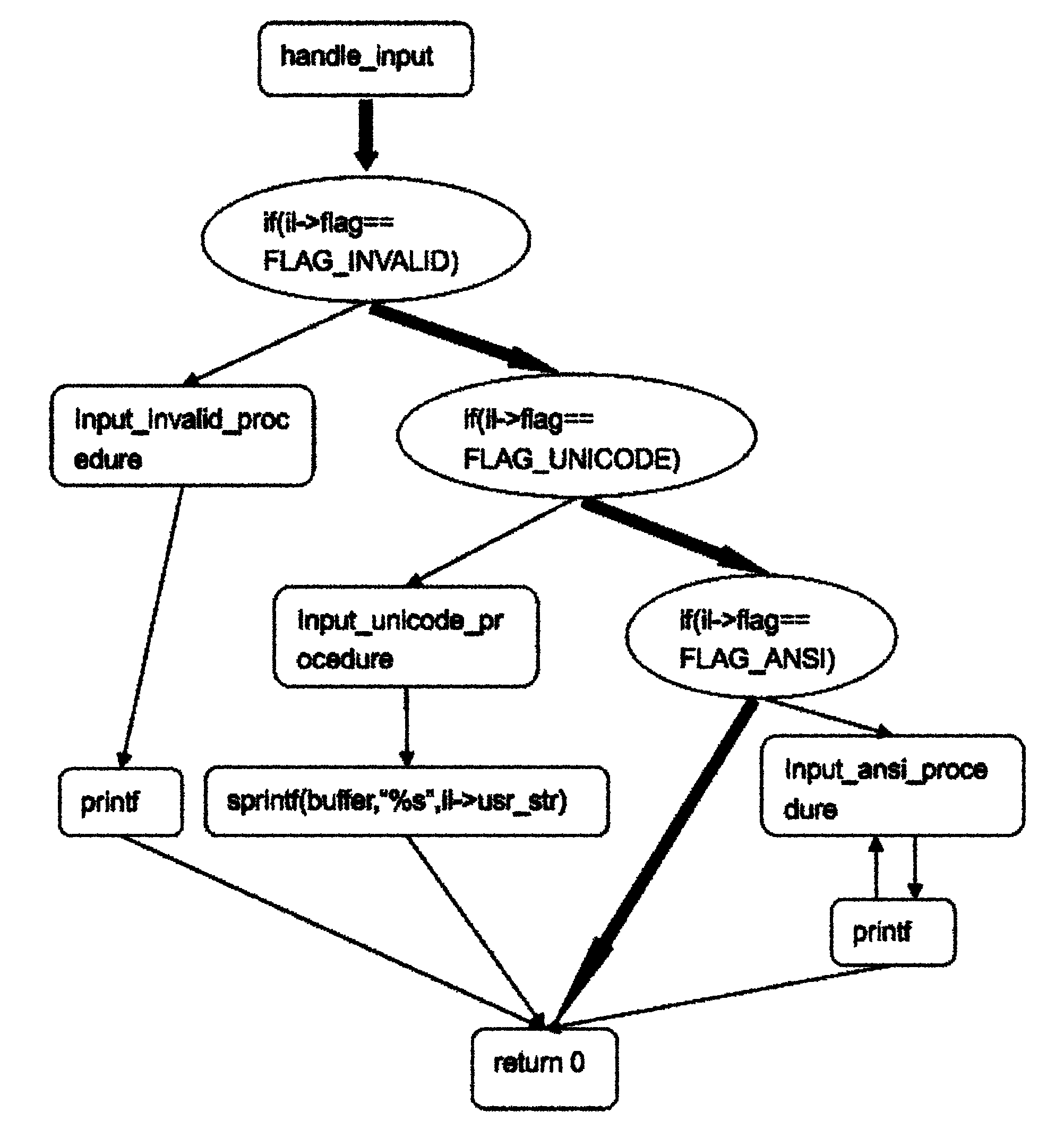
The invention provides a detector for binary-code buffer-zone overflow bugs, and a detection method thereof. The detector comprises six functional modules, namely a debugger module, an input point positioning module, a disassembling module, a symbolic execution module, a loop operation analysis module and an intelligent FUZZ test module. Differing from static symbolic execution, the detection method dynamically loads programs through the self-developed debugger module to synchronously performing symbolic execution and single-step practical execution, and then applies a model to solve each difficulty in binary code analysis so as to test path coverage and detect overflow bugs in accordance with all executable programs of PE format under a Windows platform. The detection can also provide propagation paths of input data and other important information related to bug formation cause while positioning the bugs, only analyzes the selves of the executable programs, needs no source codes, is unrelated to the species of source codes and development tools, and is extensive in applicable occasions, so the detection method has good prospects for popularization and application.
Owner:BEIJING UNIV OF POSTS & TELECOMM
System and method for propagating agricultural vehicle guidance paths that have varying curvature along their length
InactiveUS20060178823A1Instruments for road network navigationRoad vehicles traffic controlGraphicsGraphical user interface
A system and method provide for precision guiding of agricultural vehicles along a series of adjacent paths to form rows for cultivating a field. In one aspect of the invention the vehicle is moved along a first path while receiving positioning information from a navigational system (e.g., RTK GPS). This positioning information is stored in a processor and is used by the processor to compute a second path adjacent to said first path by calculating piecewise perpendicular offsets from the first path at multiple locations along the first path. The process is repeated to compute a third and subsequent paths so as to cover the field. Because of the offset process, the field may be covered with paths that have varying curvature along their length, while providing substantially no gaps or overlaps in the coverage of the field. In another aspect of the invention, the system may propose alternative paths and the user can intervene by steering the vehicle or using a graphical user interface to select among the alternative paths. A still further aspect of the invention allows for the recording of the paths that provide coverage of a field in the form of a template. This template can then be used to cause the vehicle to automatically steer along a previously calculated path in subsequent operations on the field, and in subsequent years.
Owner:NOVARIANT
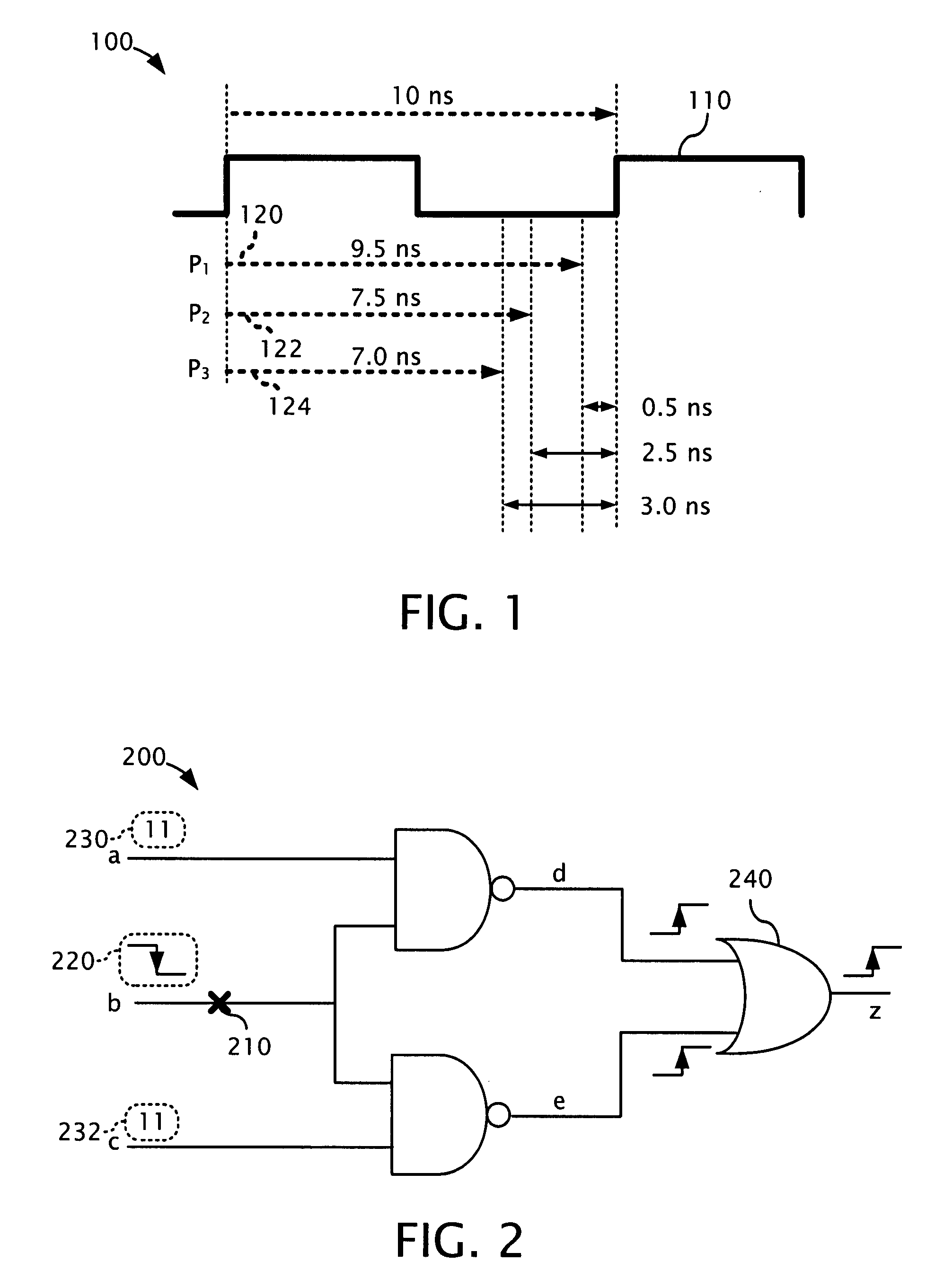
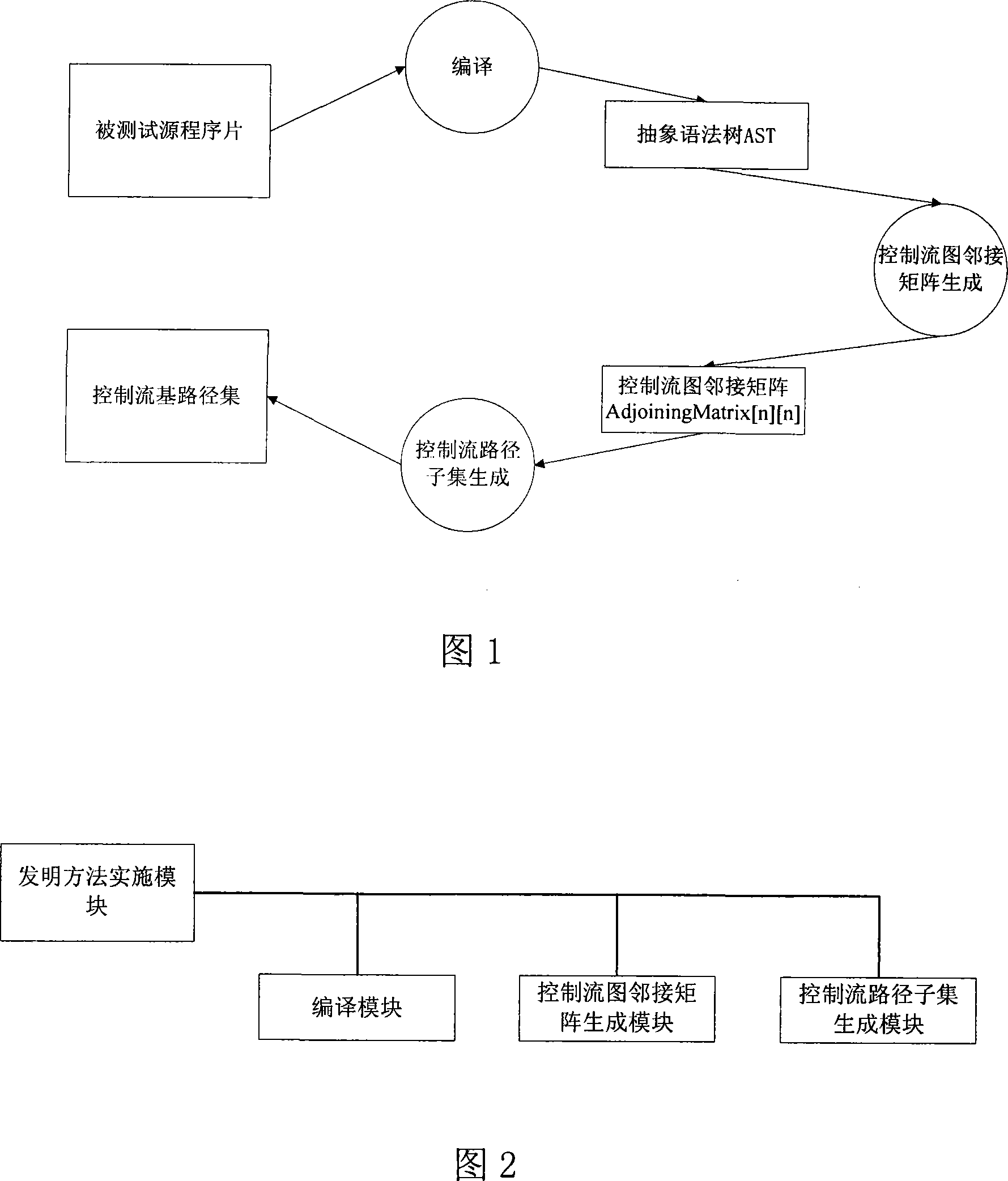
Timing-aware test generation and fault simulation
ActiveUS20070288822A1Quality improvementExpand coverageElectronic circuit testingError detection/correctionTime informationRandom method
Disclosed herein are exemplary methods, apparatus, and systems for performing timing-aware automatic test pattern generation (ATPG) that can be used, for example, to improve the quality of a test set generated for detecting delay defects or holding time defects. In certain embodiments, timing information derived from various sources (e.g. from Standard Delay Format (SDF) files) is integrated into an ATPG tool. The timing information can be used to guide the test generator to detect the faults through certain paths (e.g., paths having a selected length, or range of lengths, such as the longest or shortest paths). To avoid propagating the faults through similar paths repeatedly, a weighted random method can be used to improve the path coverage during test generation. Experimental results show that significant test quality improvement can be achieved when applying embodiments of timing-aware ATPG to industrial designs.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
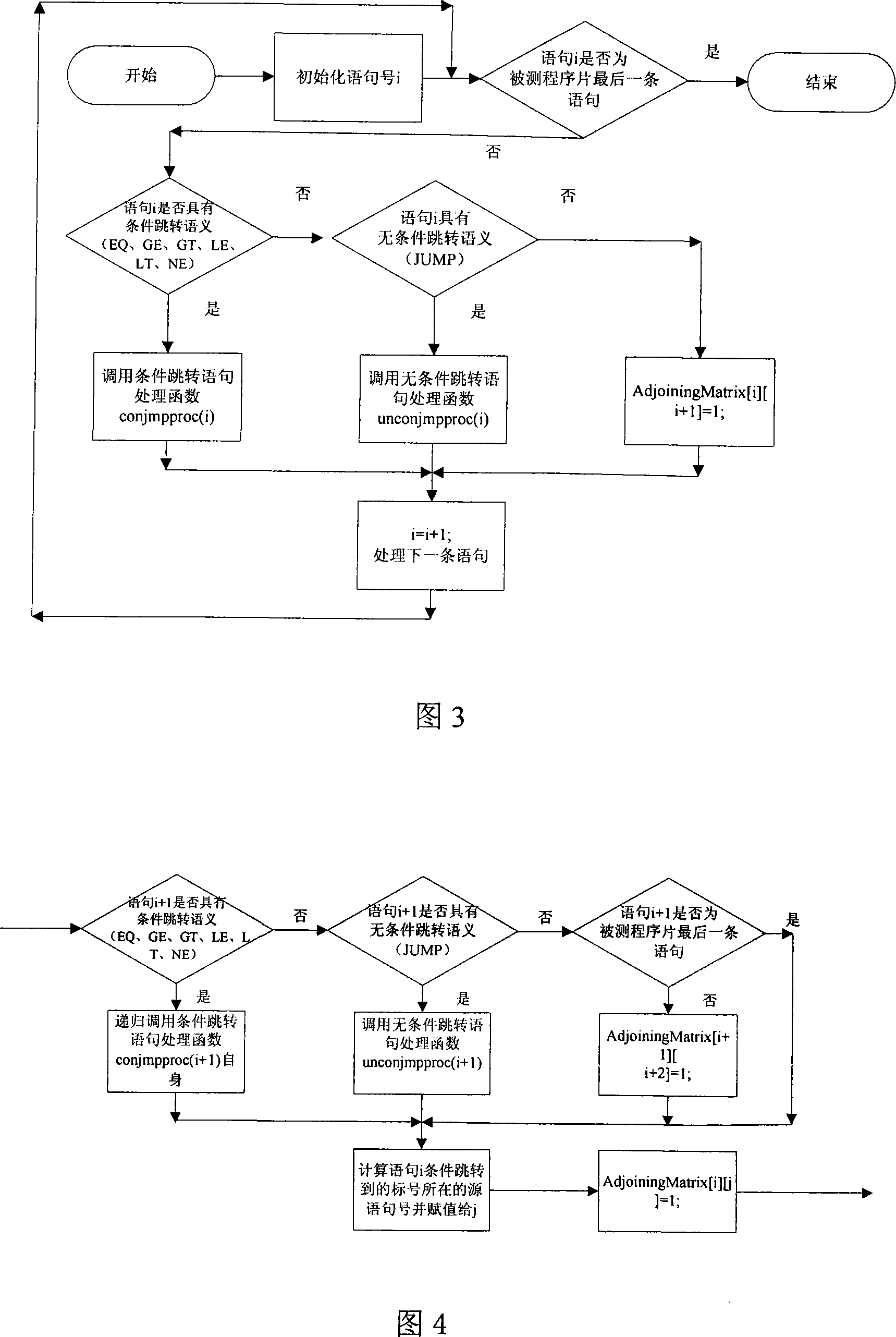
Test program control stream path set creation method based on base path
InactiveCN101216803ASolve the completeness problemSolving automation problemsSoftware testing/debuggingPath generationProgram testing
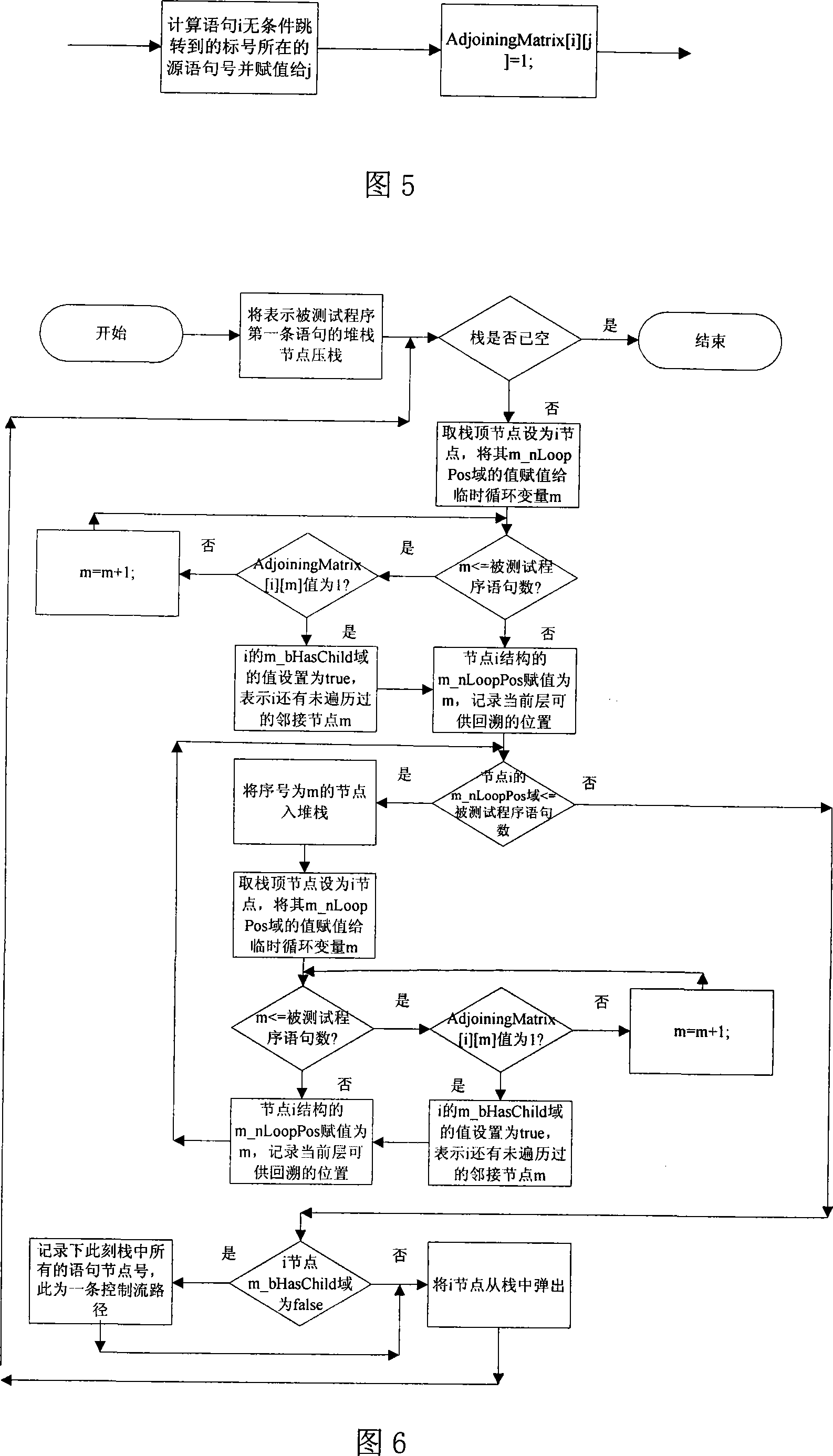
The invention pertains to a path testing in a program testing. The concept of a program control flow base path is defined through bringing in the concept of base in mathematics, a data structure showing a program structure of a source program slice is obtained by using a compiler module first; then through traversing the data structure, a control flow path generating algorithm is utilized to generate a subset compiler module of a program control flow path which is based on a base path to interpret the semanteme on a tested source program, an abstract syntax tree structure showing the structural information of the tested program control flow is output. An adjacency matrix of a control flow graph generates a module ergodicity abstract syntax tree structure, and generates the adjacency matrix representation of a program flow chart. A control flow path subset generating module acquires the control flow information of the tested program through traversing the adjacency matrix, traverses the adjacency matrix by adopting a depth-first multiple backtracking method, and processes sentence nodes, thus a program control flow path subset based on the base path is generated. The method has the outstanding advantages in generating results and flows, and can be widely used in the engineering practice of a path cover testing in a software structure testing.
Owner:SICHUAN UNIV
Coverage rate dynamic tracking method and device based on function call paths
InactiveCN103473171AEasy to implementGuaranteed accuracySoftware testing/debuggingData streamParallel computing
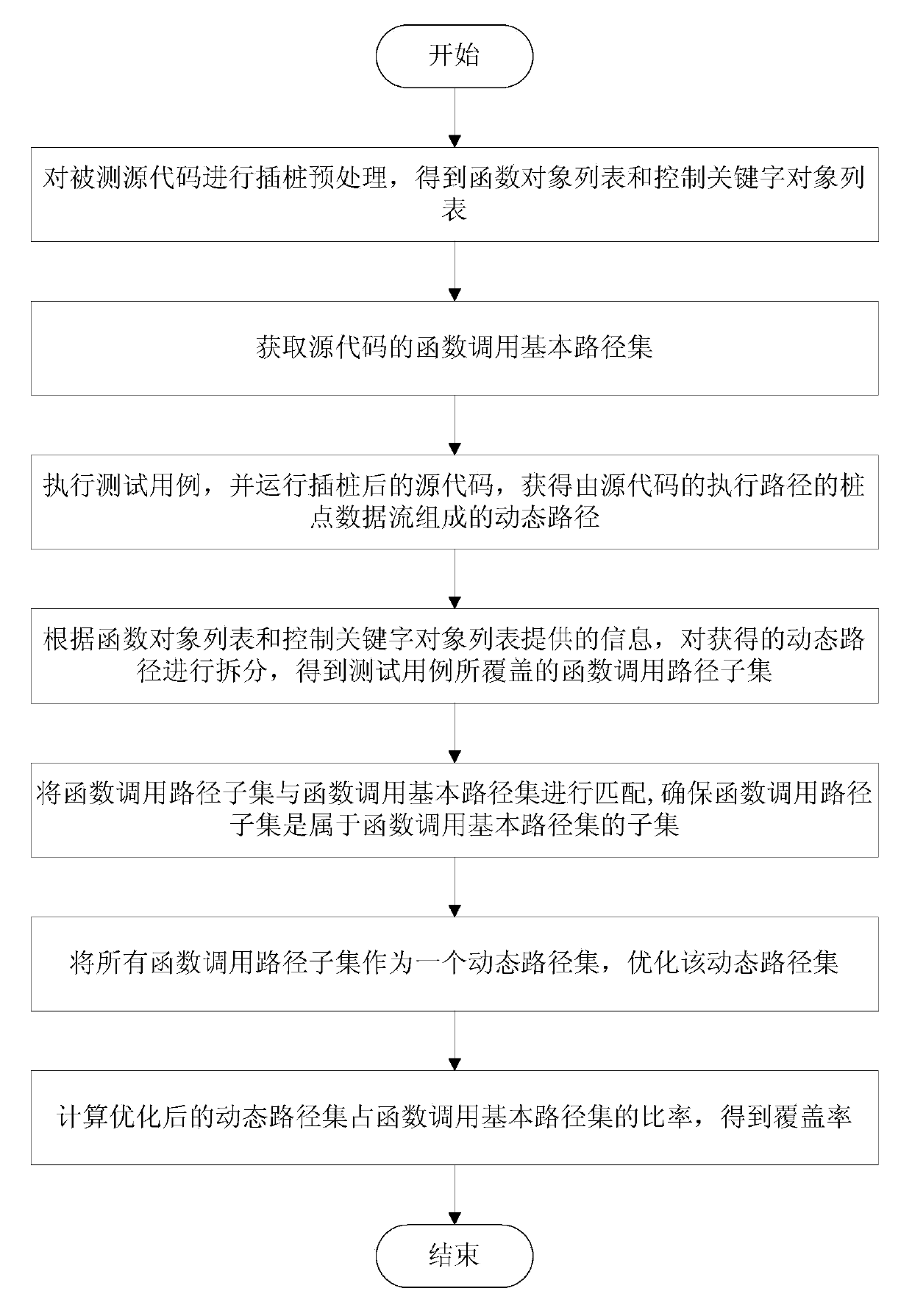
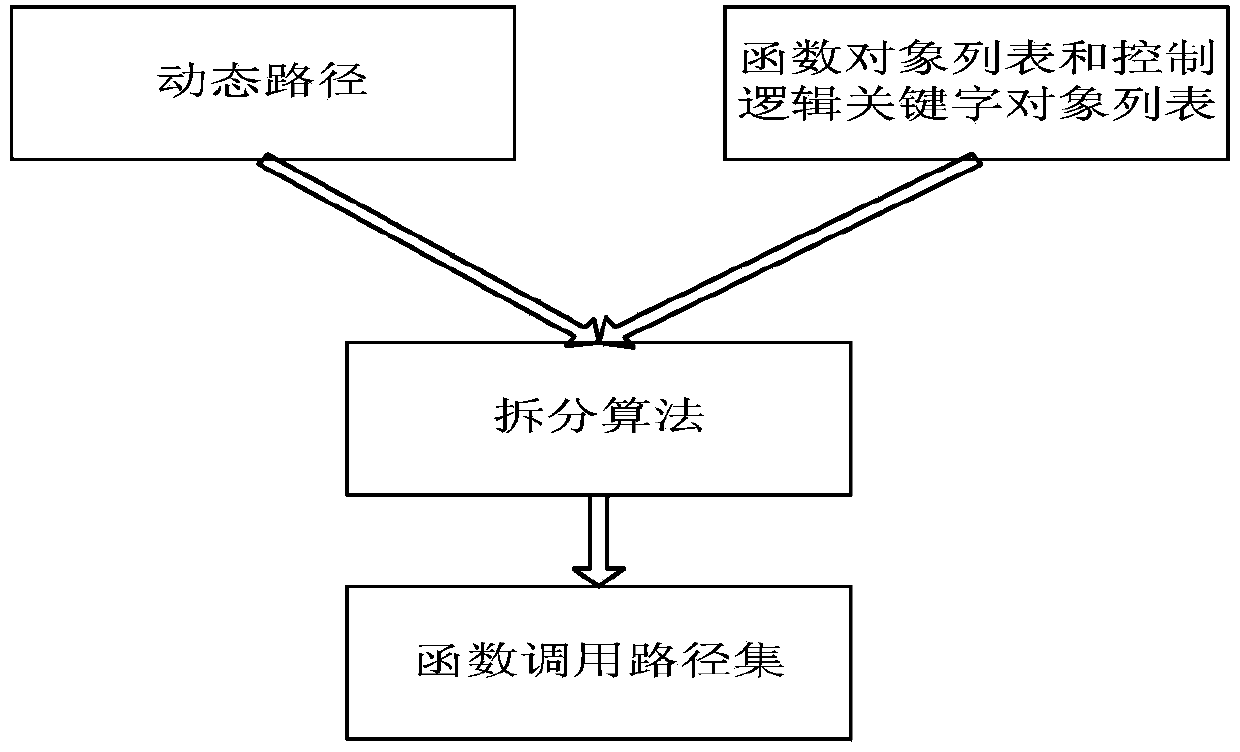
The invention relates to a coverage rate dynamic tracking method and device based on function call paths. The method includes: performing pile insertion pretreatment on a to-be-tested source code to obtain a function object list and a control keyword object list; obtaining a basic function call path set of the source code; executing a test case, and operating the source code with pile insertion to obtain a dynamic path formed by pile point data streams of the execution path of the source code; separating the dynamic path to obtain function call path subsets covered by the test case; matching the function call path subsets with the basic function call path set; using all the function call path subsets as a dynamic path set, and optimizing the dynamic path set; calculating the rate of the optimized dynamic path set accounting for the basic function call path set so as to obtain the coverage rate. The method has the advantages that path coverage particle size is expanded from statement to function, and the problem that traditional path coverage is huge, and each path cannot be tested completely.
Owner:BEIJING INFORMATION SCI & TECH UNIV +1
System for detecting software bug triggered during practical running of computer program
InactiveCN101968766AOvercoming the disadvantage of low analysis coverageIncrease vulnerabilitySoftware testing/debuggingSoftware bugDynamic program analysis
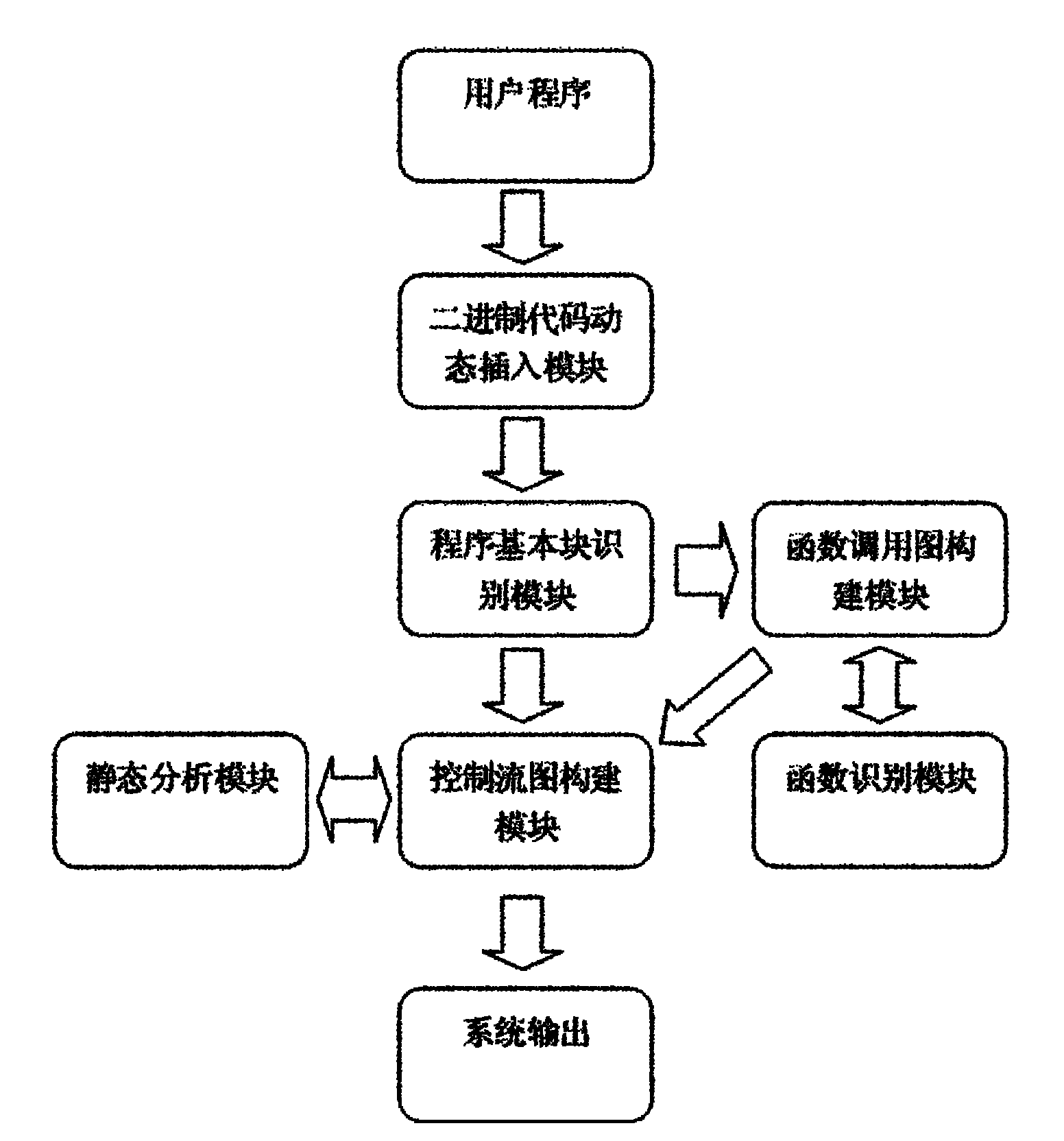
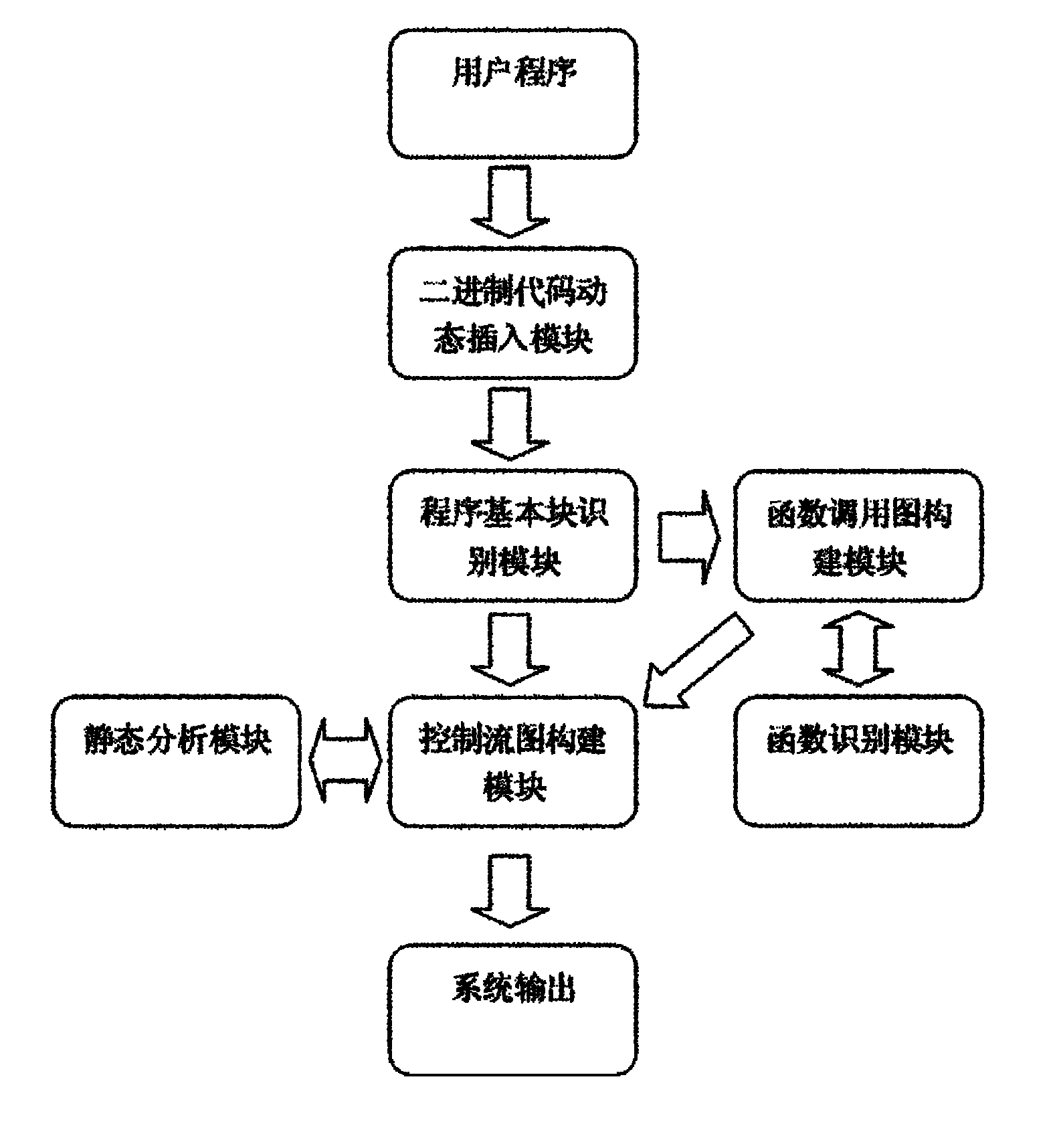
The invention relates to a system for detecting a software bug triggered during practical running of a computer program in the technical field of computers. The system comprises a binary code dynamic inserting module, a program basic block recognizing module, a function call graph constructing module, a control flow graph constructing module, a function recognizing module and a static analysis module. By combining two technologies of dynamic program analysis and static analysis path complementation, the invention not only can detect the bugs which can be triggered during the practical running of the program but also can reach higher program path coverage rate, carry out bug detects on the path which is not covered in the dynamic analysis process, improve the success rate of bug detection and reduce the false rate of the bugs. Meanwhile, the static analysis path complementation technology only analyzes a path which is not executed in dynamic analysis instead of all program paths, thereby greatly reducing the cost on time and system resources.
Owner:SHANGHAI JIAO TONG UNIV
Distributed built-in test and performance monitoring system for electronic surveillance
InactiveUS7683842B1Precise maintenanceAccurate performanceReceivers monitoringSpatial transmit diversityCritical positionDistributed testing
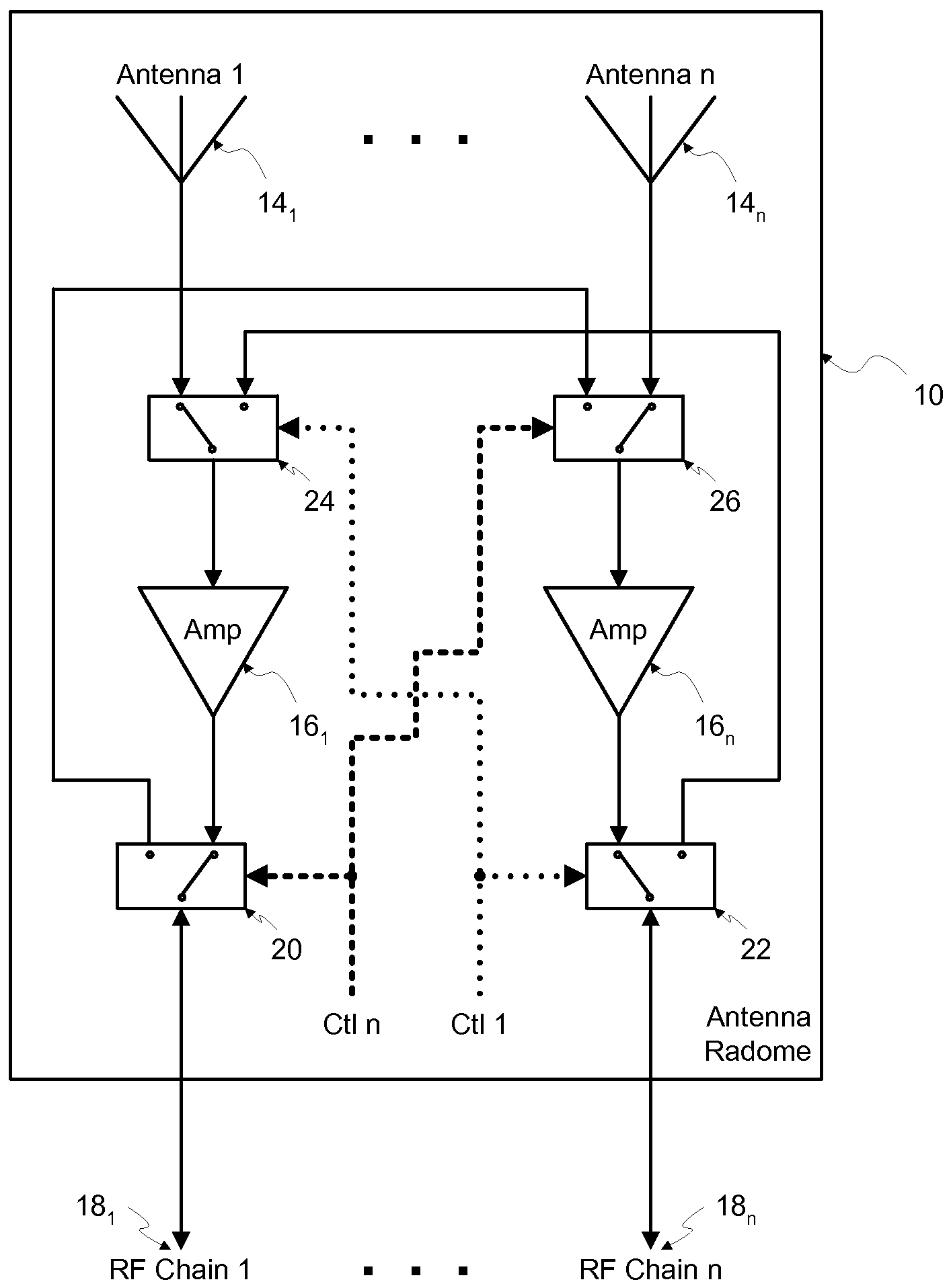
A distributed test system for implementing enhanced BIT (Built-In-Test) within an ESM (Electronic Surveillance Monitoring) or RF receiver system. The distributed test system includes a system processor, a programmable RF source element or other comparable test signal generating arrangement, and switched path coupled elements and various measurement elements, each embedded at strategic locations within the ESM system so as to effect maximum path coverage and test benefit.
Owner:ADVANCED TESTING TECH
Dynamic and static combined software security test method
InactiveCN102360334AIncreased security testing productivitySolve the path space explosion problemSoftware testing/debuggingCall graphBasic block
The invention relates to a computer software security test method, and in particular relates to a dynamic and static combined software security test method. The test method comprises the following steps: firstly carrying out disassembly and intermediate language transformation on an executable program so as to generate a function call graph (CG) and a control flow graph (CFG) of a file; finding out a vulnerable point of a system by means of static analysis of the function CG, and constructing a test case generation execution path by virtue of a dynamic analysis method; searching a called function based on the function CG, finding out a specific path for triggering the vulnerable point on a first-grade basic block according to the CFG if the function is located on the generated execution path, and then ending the loophole mining process corresponding to the sensitive point; and if the path can not be found, reconfiguring the test case generation execution path and then searching the called function in a cyclic manner. The dynamic and static combined software security test method has the advantages of better solving the problem of path state space blast caused by single Fuzz dynamic test, and greatly improving the path coverage hit rate and the software test analysis efficiency.
Owner:THE PLA INFORMATION ENG UNIV
Cleaning mode for robot cleaner
ActiveCN104757909AAvoid mindless cleaningReduce cleaning efficiencyMachine detailsFloor sweeping machinesWorking environmentVolumetric Mass Density
The invention discloses a cleaning mode for a robot cleaner. For the robot cleaner, the cleaning mode sequentially includes the following steps: a, the robot cleaner enters into an operating region to roughly detect work environment and to confirm to enter an empty area; b, the robot cleaner is totally covered for cleaning in the empty area; when the robot cleaner is totally covered for cleaning, the path coverage density is more than that caused due to rough detection of the robot cleaner; c, the robot cleaner quits the cleaning mode after meeting preset system conditions. According to the cleaning mode, the increased cleaning time and the reduced cleaning efficiency are avoided when the robot cleaner blindly and repeatedly cleans in an unknown area.
Owner:SHENZHEN SILVER STAR INTELLIGENT TECH CO LTD
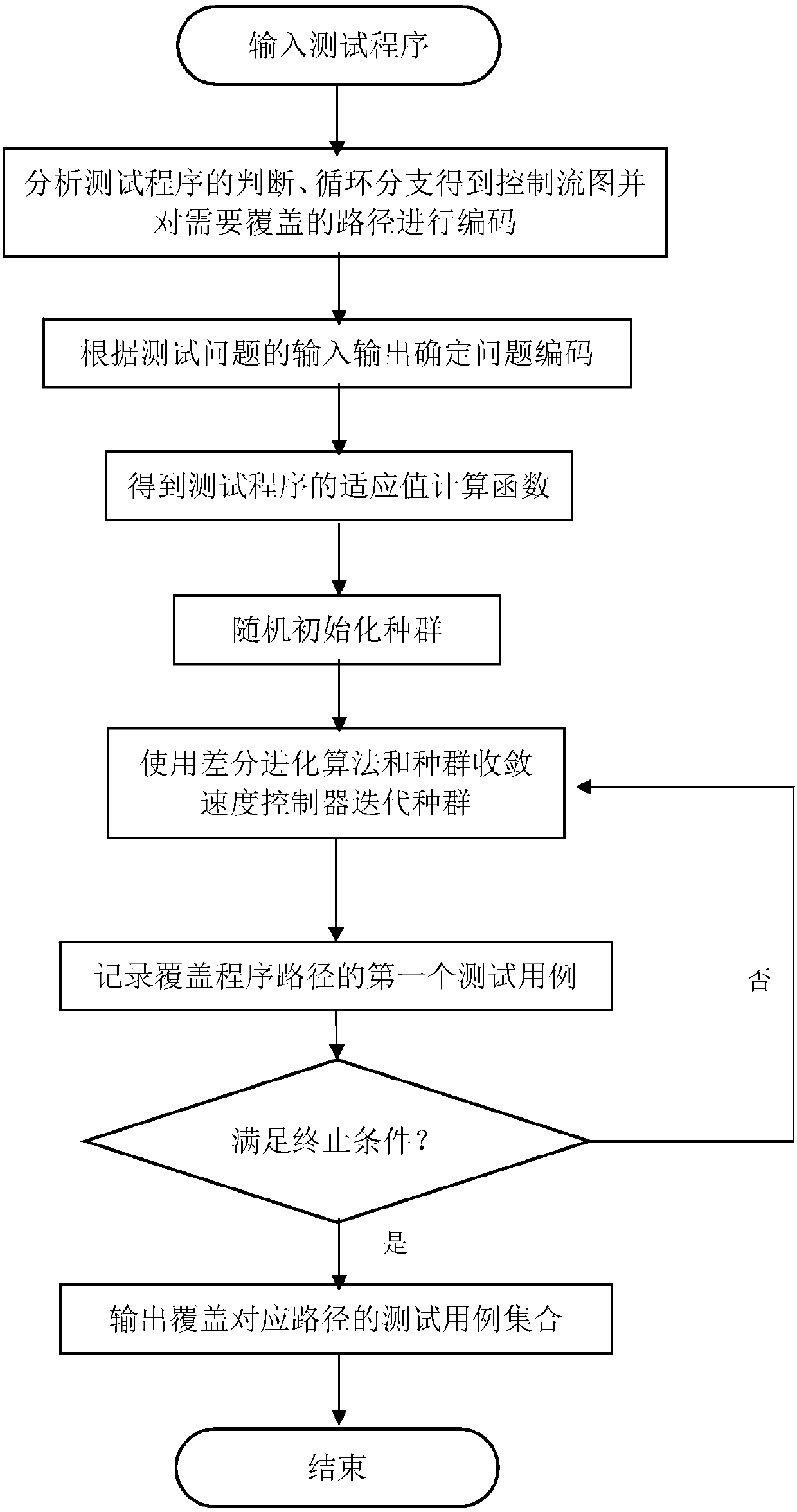
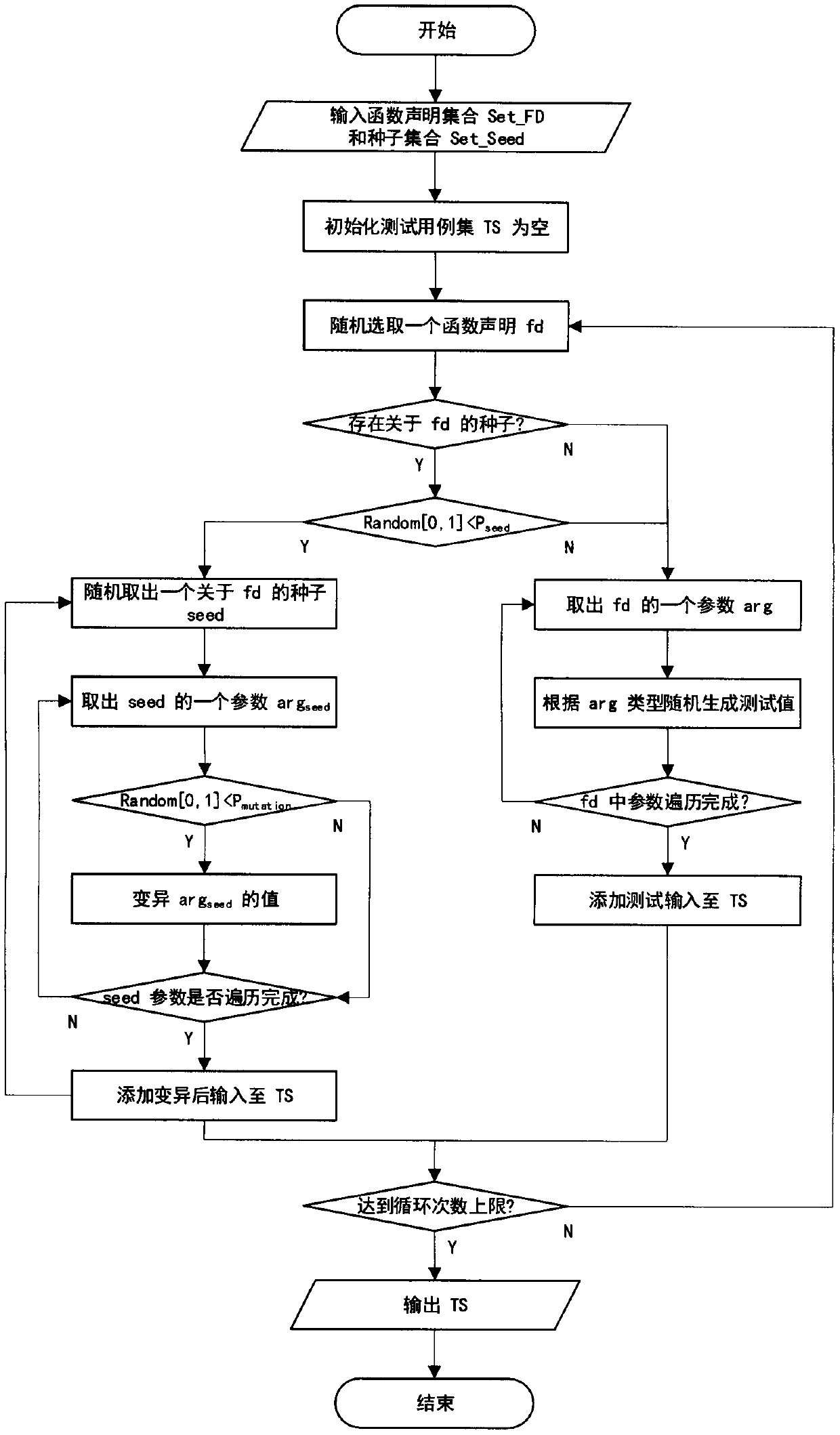
Path coverage software test-based automatic test case generation method
ActiveCN107590073AImprove the ability to solveStrong error correction abilitySoftware testing/debuggingProgramming languageWorking environment
The invention provides a path coverage software test-based automatic test case generation method. The method comprises the following steps of: analyzing a code of a tested program to obtain a controlflow graph (CFG) of the program and a path of the program; obtaining and calculating a fitness function of a group of corresponding test cases according to the control flow graph obtained in the laststep and a branch distance-based method; carrying out iterative updating on a randomly initialized population by using the fitness function through a differential evolution algorithm and a convergencespeed controller; and recording the first test case of paths corresponding to a coverage program until the test cases of all the paths are obtained or the iteration frequency of the algorithm exceedsa limit, and outputting a test case set of the paths corresponding to the coverage program. The method is capable of effectively utilizing the tested program to cover heuristic information of the test cases on the basis of the paths, and can be applied to practical software test work environment.
Owner:微科智检(佛山市)科技有限公司
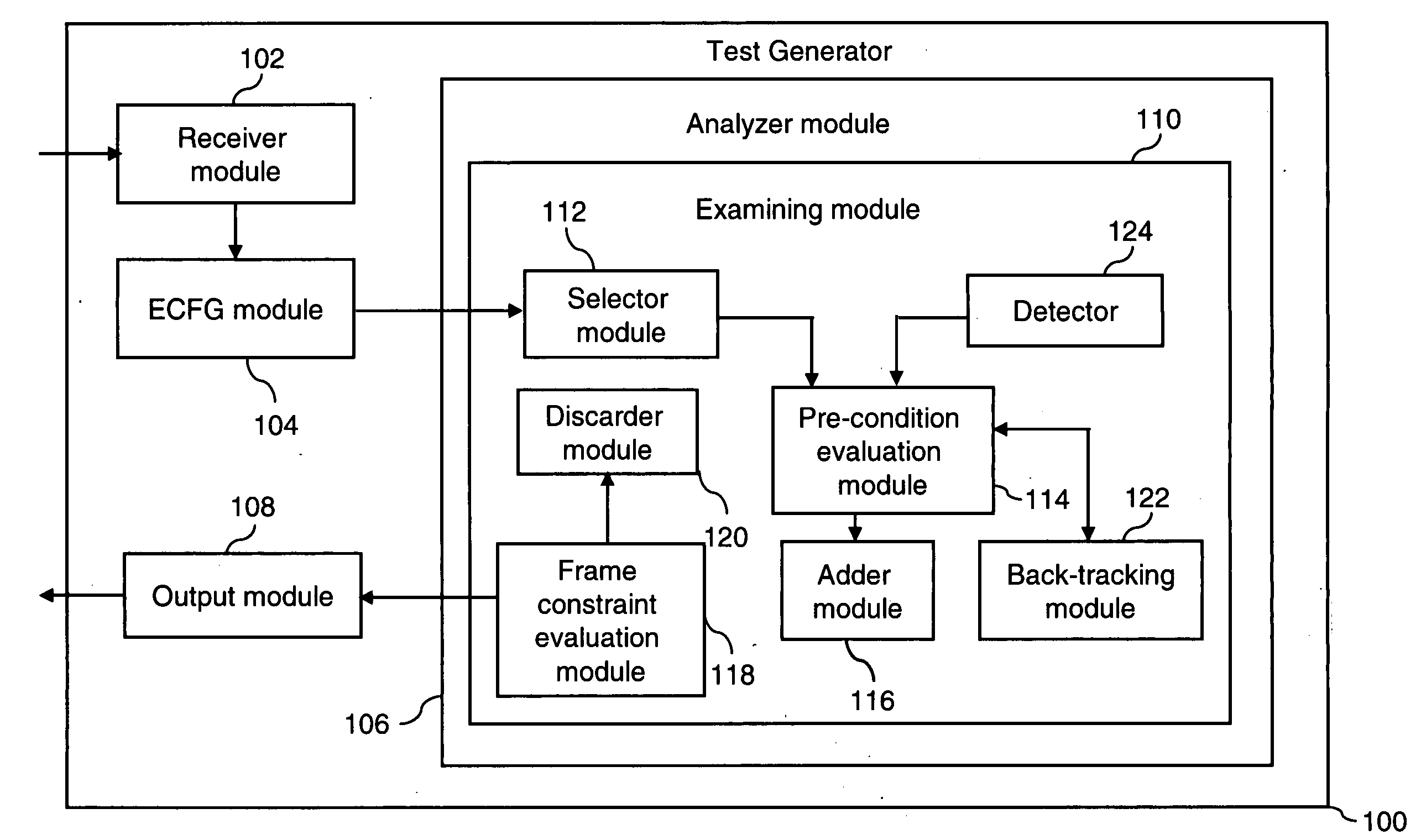
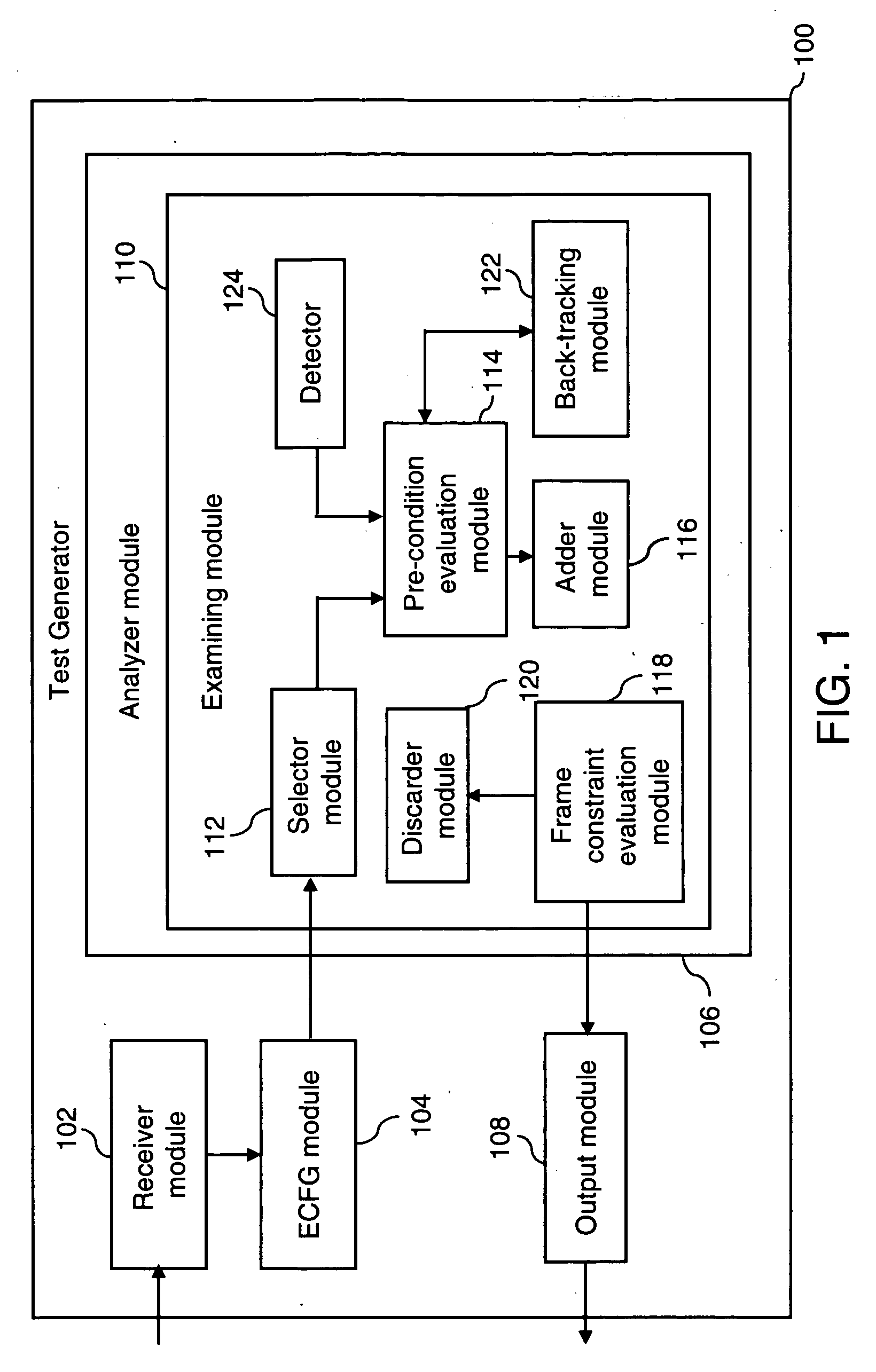
Path coverage criterion in specification-based testing based on an extended context-free grammar-based test specification model and a new test generation algorithm
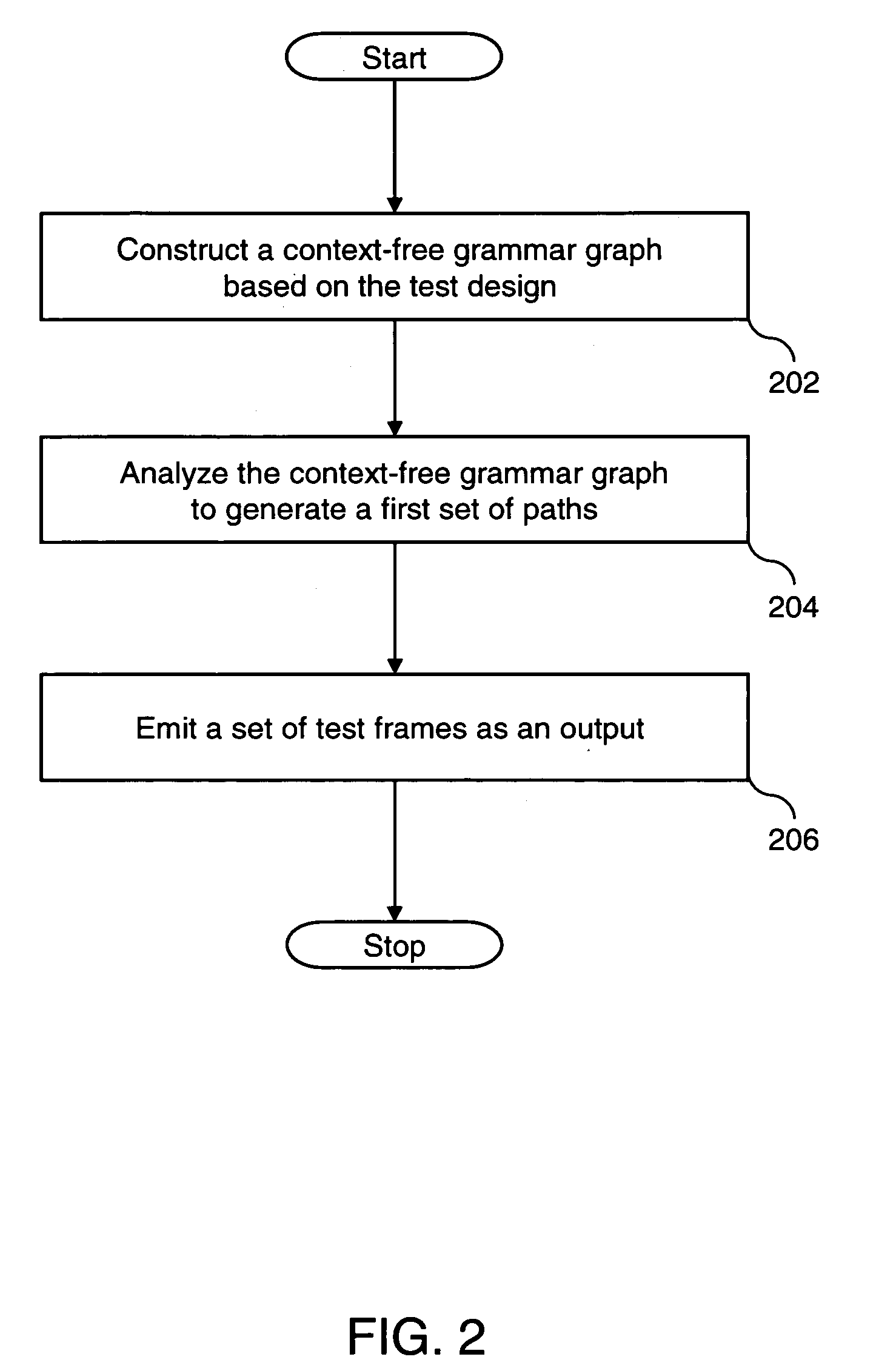
InactiveUS20060214948A1Reduces frequent back-trackingError detection/correctionCathode-ray tube indicatorsTest designTest specification
A system and method for generating test frames in specification-based testing by using a path-coverage criterion is provided. The method includes receiving a test design as an input, and constructing a context-free grammar graph, based on the test design. The method further includes analyzing the context-free grammar graph to generate a first set of paths, and emitting a set of test frames as an output, based on the first set of paths.
Owner:SIEMENS INFORMATION SYSTEMS LTD
Genetic algorithm optimization-based software test data generation method
ActiveCN108509335AFast convergenceSave time and costSoftware testing/debuggingArtificial lifeAlgorithmTest data generation
The invention discloses a genetic algorithm optimization-based software test data generation method, and belongs to the field of software testing. The method comprises the steps of performing static analysis on a current tested program to obtain a branch path coverage matrix; by considering the influence of layer proximity, branch distances and branch weights, designing a proper fitness function;in combination with an elite thought, improving a direction and a probability in a genetic operator of a genetic algorithm; selecting an initial population; replacing part of the initial population with a population comprising heuristic information and obtained by the coverage matrix; equally dividing the population; performing parallel genetic algorithm operation by using the improved fitness function and genetic operator; and selecting out optimal software test data meeting the conditions. The convergence speed of the genetic algorithm is increased while the algorithm is prevented from falling into local optimum, and the time cost of software test data generation is reduced.
Owner:HANGZHOU HUICUI INTELLIGENT TECH CO LTD
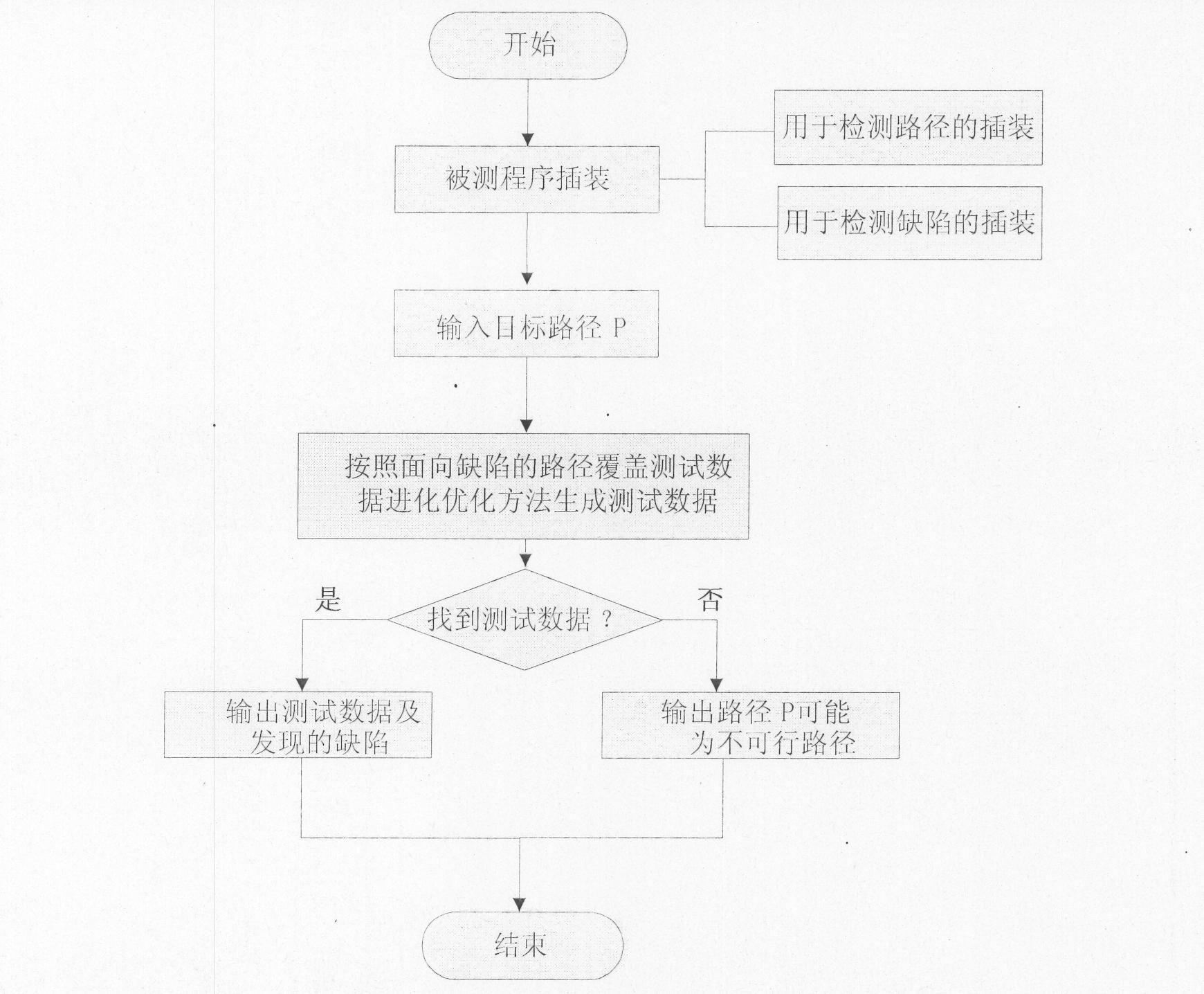
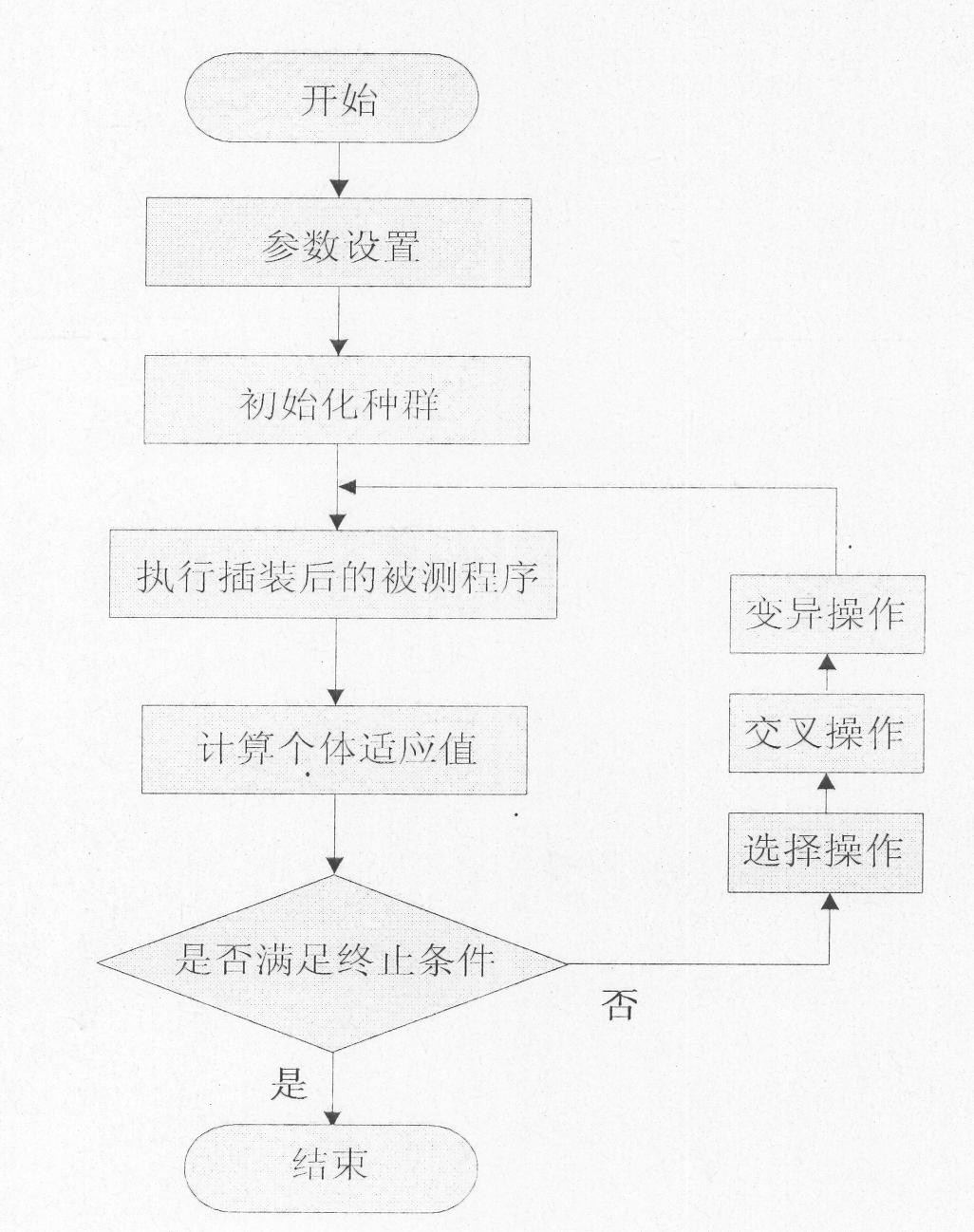
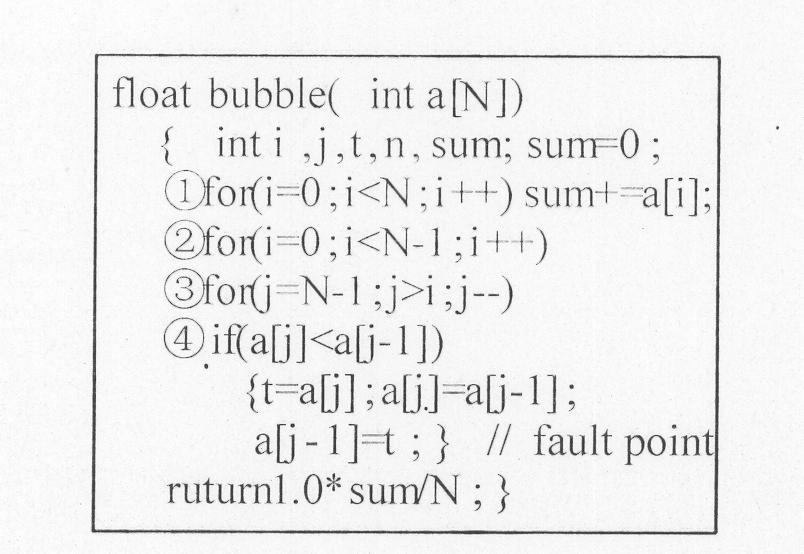
Method for evolving and generating path coverage test data facing defects
InactiveCN102141958AImprove efficiencyQuality improvementSoftware testing/debuggingSmall probabilityMathematical model
The invention discloses a method for evolving and generating path coverage test data facing defects, which aims to expose the defects in a target path as much as possible from the generated test data so as to effectively enhance the quality of the test data. The method comprises the following steps of: firstly, establishing a math model for generating the path coverage test data facing the defects by using a path, in which the largest number of defects are found during tested procedure execution by the test data and the danger level of the defects is highest, as a target under the condition of a restraint that the test data must pass through the target path; and secondly, designing a restraining method for optimizing a plurality of targets so as to solve the problem, and evolving and generating the through target path by using a genetic algorithm, and effectively exposing the test data of the defects at the same time. By the method, the problem that the test data generated by the conventional method can only just pass through the target path instead of effectively exposing the defects in the target path, in particular some small-probability defects, can be solved; and the method can be used for generating the test data for a white box test or a regression test, so the efficiency of the software test can be improved greatly.
Owner:CHINA UNIV OF MINING & TECH
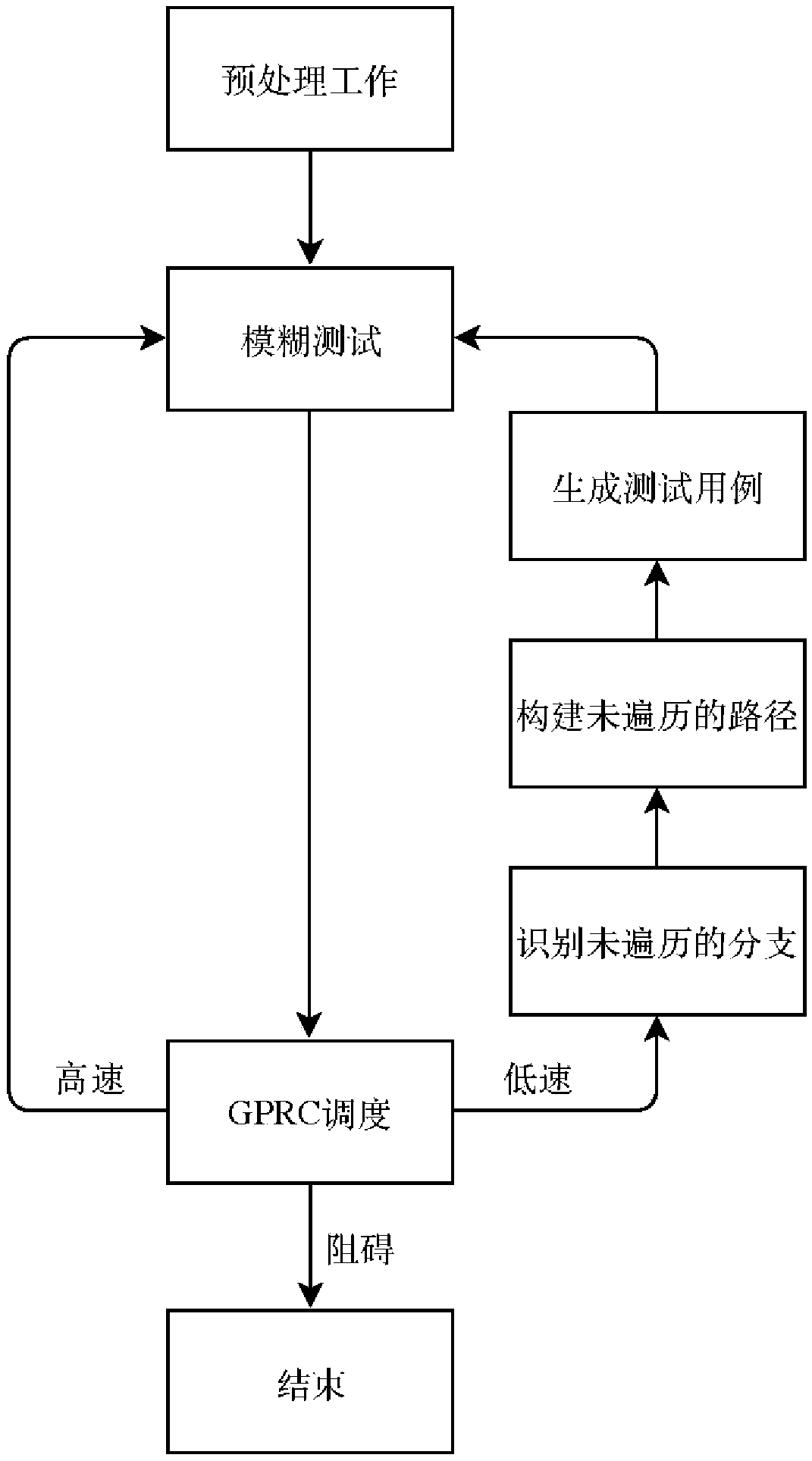
Method for improving software fuzzy testing efficiency in combination with symbol execution
ActiveCN108845944AAvoid blindnessAvoid problems such as low code coverageSoftware testing/debuggingTest efficiencyFalse alarm
The invention discloses a method for improving software fuzzy testing efficiency in combination with symbol execution. The method comprises the steps of S1, preprocessing a target program to obtain information of the target program; S2, inputting a fuzzy tester into the target program to generate a test case, and detecting whether the program is abnormal or not; S3, constructing scheduling parameters based on a path coverage rate, calculating the scheduling parameters in a fuzzy testing process, judging a state of the fuzzy tester, if the fuzzy tester is in a low-speed state, going to the stepS4, if the tester is in a high-speed state, returning to the step S2, and if the tester is in a halt state, exiting from the testing; and S4, identifying branches which are not traversed in the fuzzytesting process, constructing a non-traversed program path, generating an effective test case by using a symbol execution method to stimulate the fuzzy tester to be in the high-speed state, and if the effective test case cannot be generated and the tester is in the halt state, exiting from the testing. The method has the advantages of simple implementation principle, good vulnerability mining performance, high efficiency, low false alarm rate, flexible and reliable use, and the like.
Owner:NAT UNIV OF DEFENSE TECH
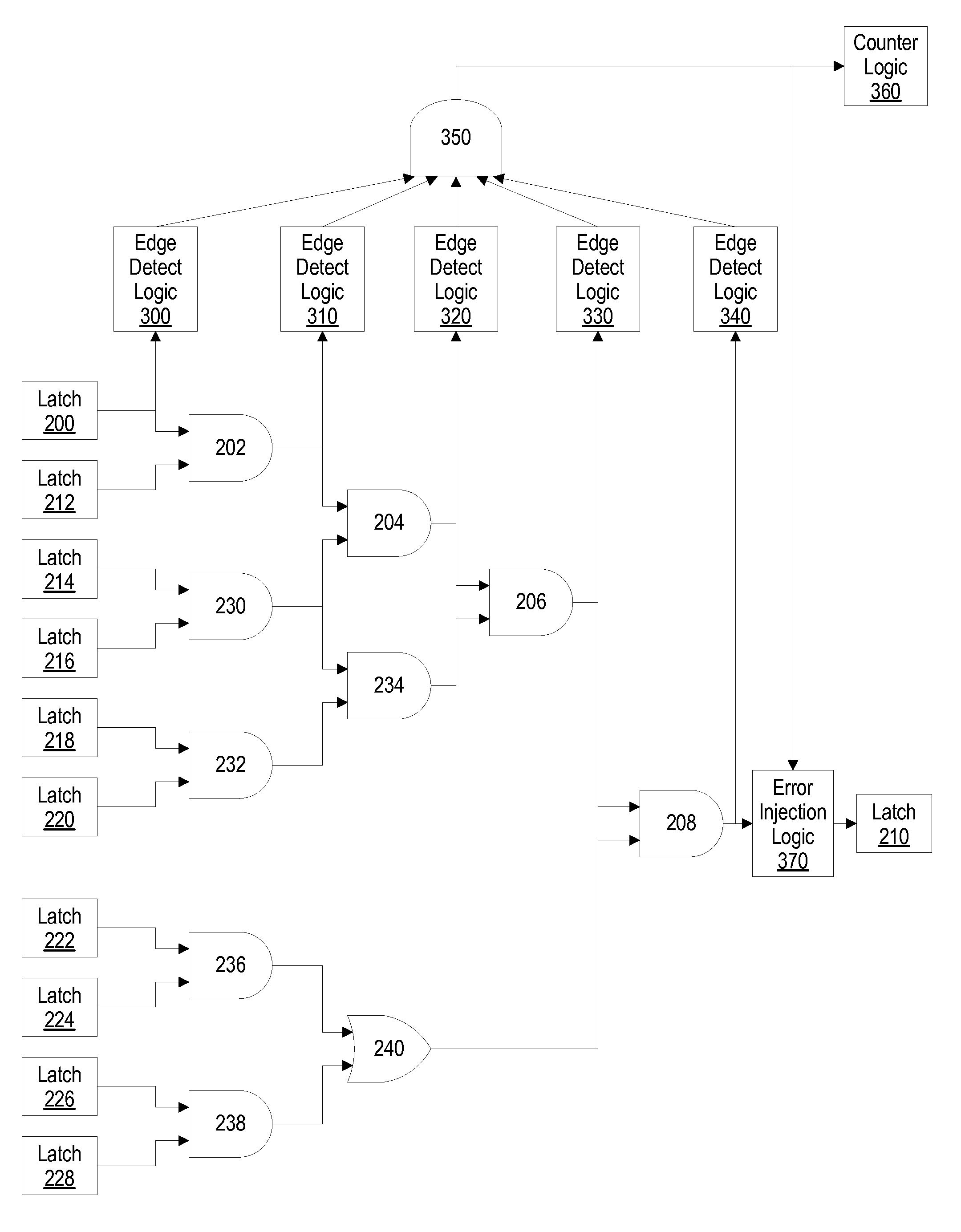
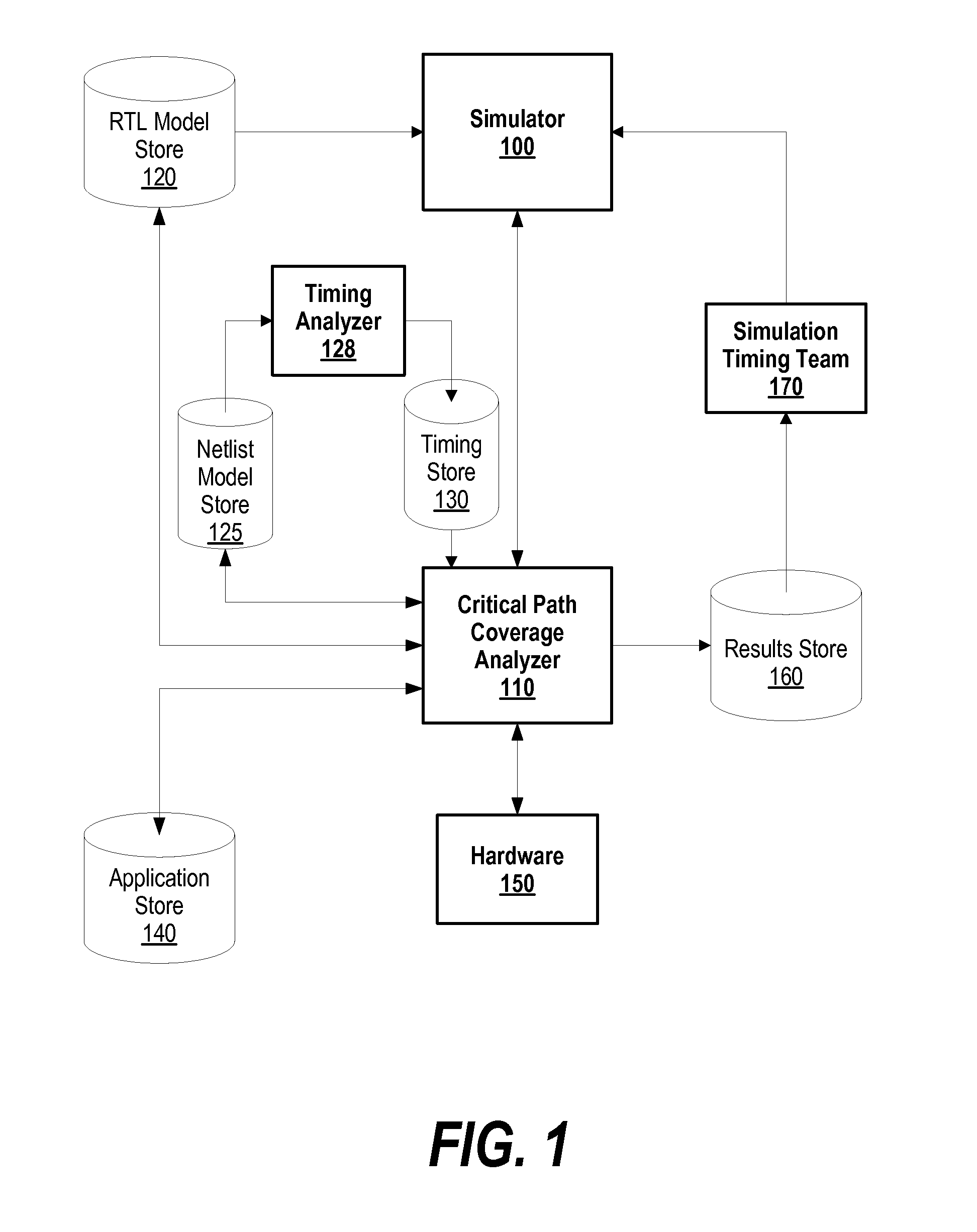
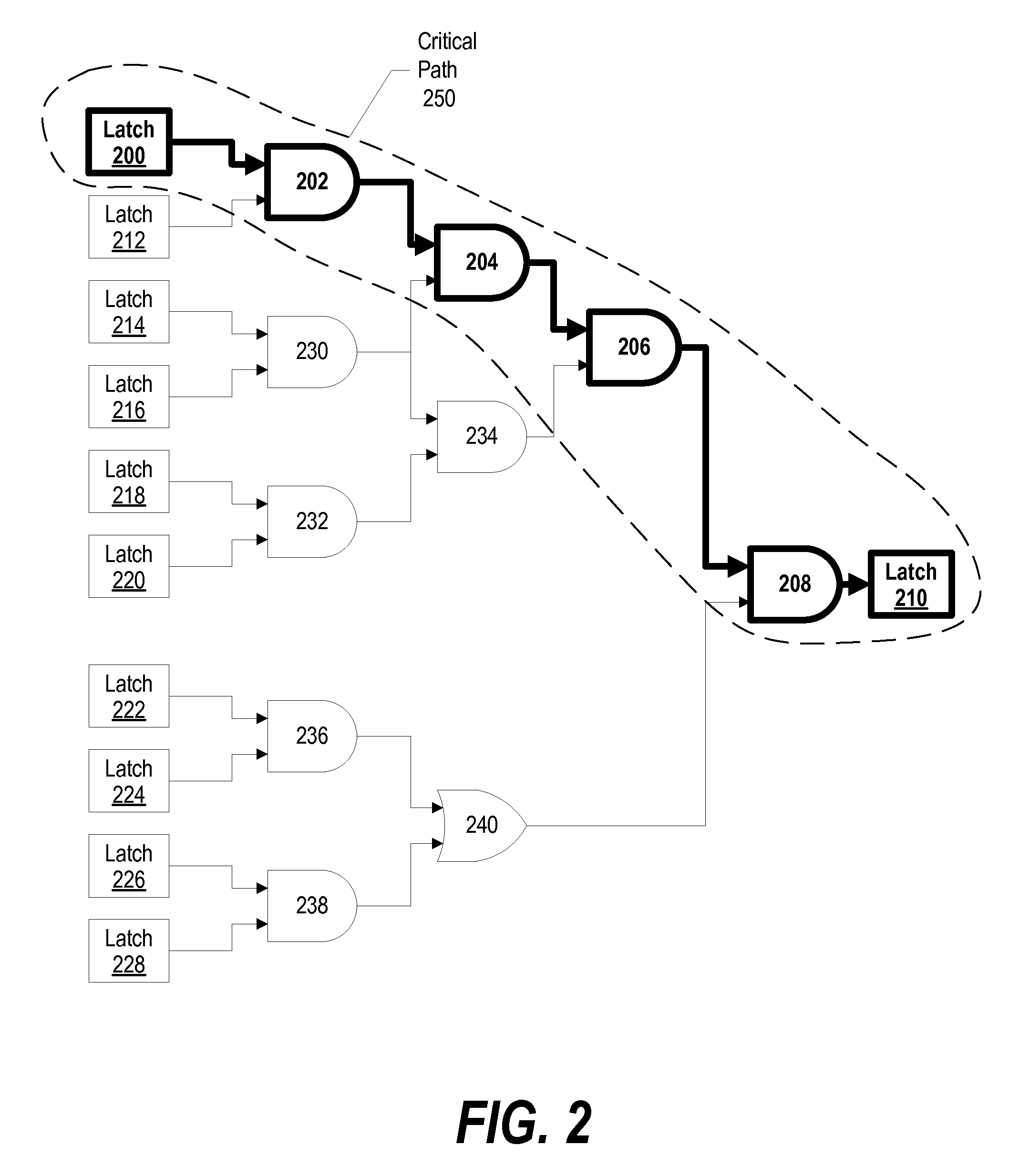
System and Method of Automating the Addition of RTL Based Critical Timing Path Counters to Verify Critical Path Coverage of Post-Silicon Software Validation Tools
ActiveUS20090112557A1Improve accuracyComputer aided designSpecial data processing applicationsVisibilityCritical path method
A system and method for modifying a simulation model and optimizing an application program to produce valid hardware-identified operating conditions that are matched with simulator-identified operating conditions in order to modify a simulator accordingly is presented. A critical path coverage analyzer includes critical path measurement logic into a simulation model that injects errors into the critical path and provides visibility into the number of times that an application program exercises the critical path. The critical path coverage analyzer uses the critical path measurement logic to optimize an application program to adequately exercise and test the critical paths. Once optimized, the critical path coverage analyzer runs the optimized application program on a hardware device to produce hardware-identified operating conditions. The hardware-identified operating conditions are matched against simulator-identified operating conditions. When discrepancies exist, the simulator is modified accordingly to match the hardware-identified operating conditions.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
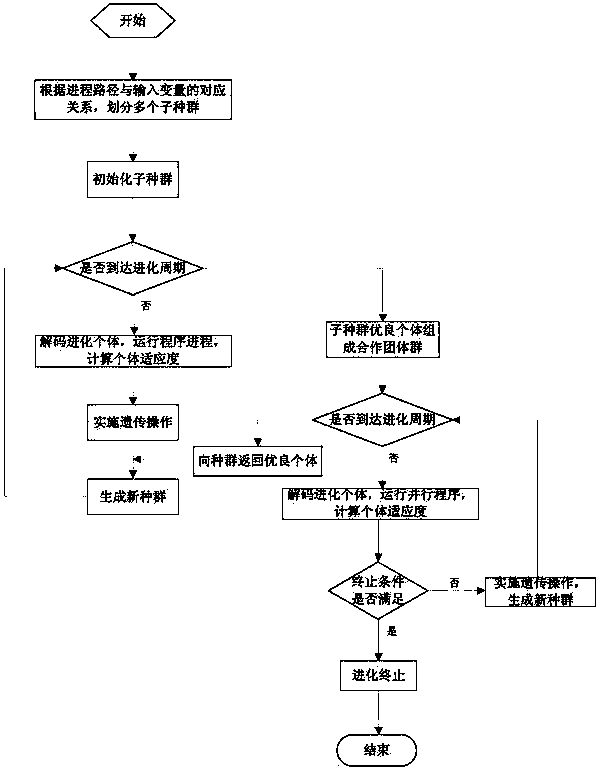
Method for generating test data covering parallel program paths based on coevolution
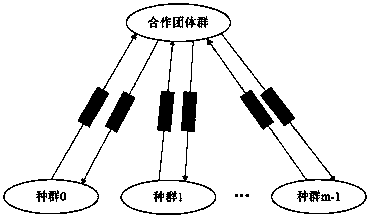
InactiveCN103902457AGenerate efficientlyGenetic modelsSoftware testing/debuggingMathematical modelTheoretical computer science
The invention provides a method for generating test data covering parallel program paths based on coevolution, and aims to provide a method for automatically and efficiently generating test data covering parallel program objective paths. The method includes the following specific steps that firstly, a mathematical model of a test data generation problem is built, and a problem for generating the test data covering the parallel program paths is modeled into a single-object optimization problem; secondly, a coevolution genetic algorithm is designed to solve the model. According to the method, groups are divided into a plurality of sub groups and a cooperative team group according to the correlation of course paths and program input components. Each sub group is used for independently optimizing a part of input components relevant to one certain course path. After the sub groups are evolved into a certain period, excellent individuals of the sub groups are combined to form an initial individual of the cooperative team group so as to be used for optimizing complete program input. After the cooperative group is evolved into a certain period, the excellent individuals are returned to the sub groups. Through alternate coevolution of the cooperative team group and the sub groups, the expected test data are generated.
Owner:CHINA UNIV OF MINING & TECH
Unit test method which is automatically generated based on a path coverage test case
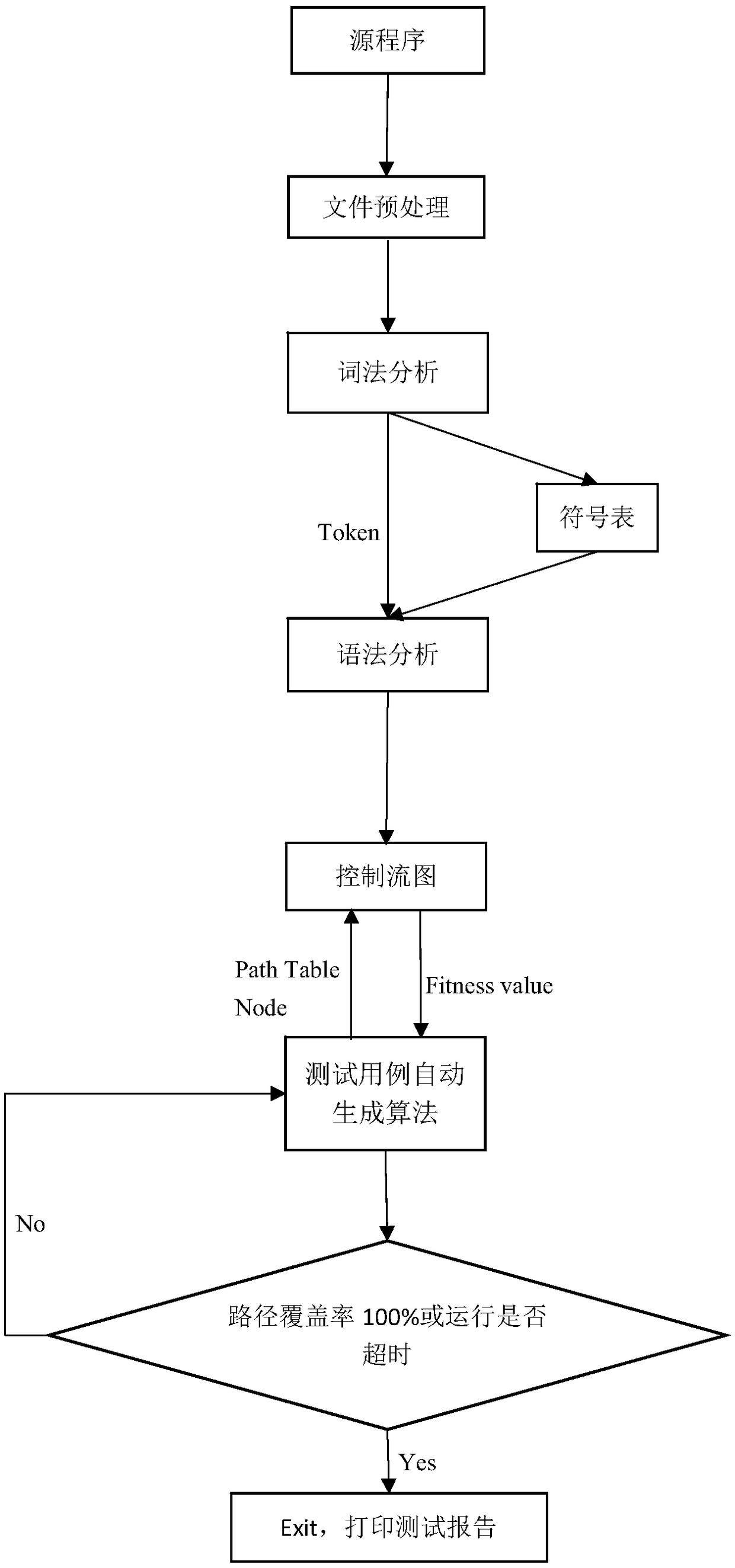
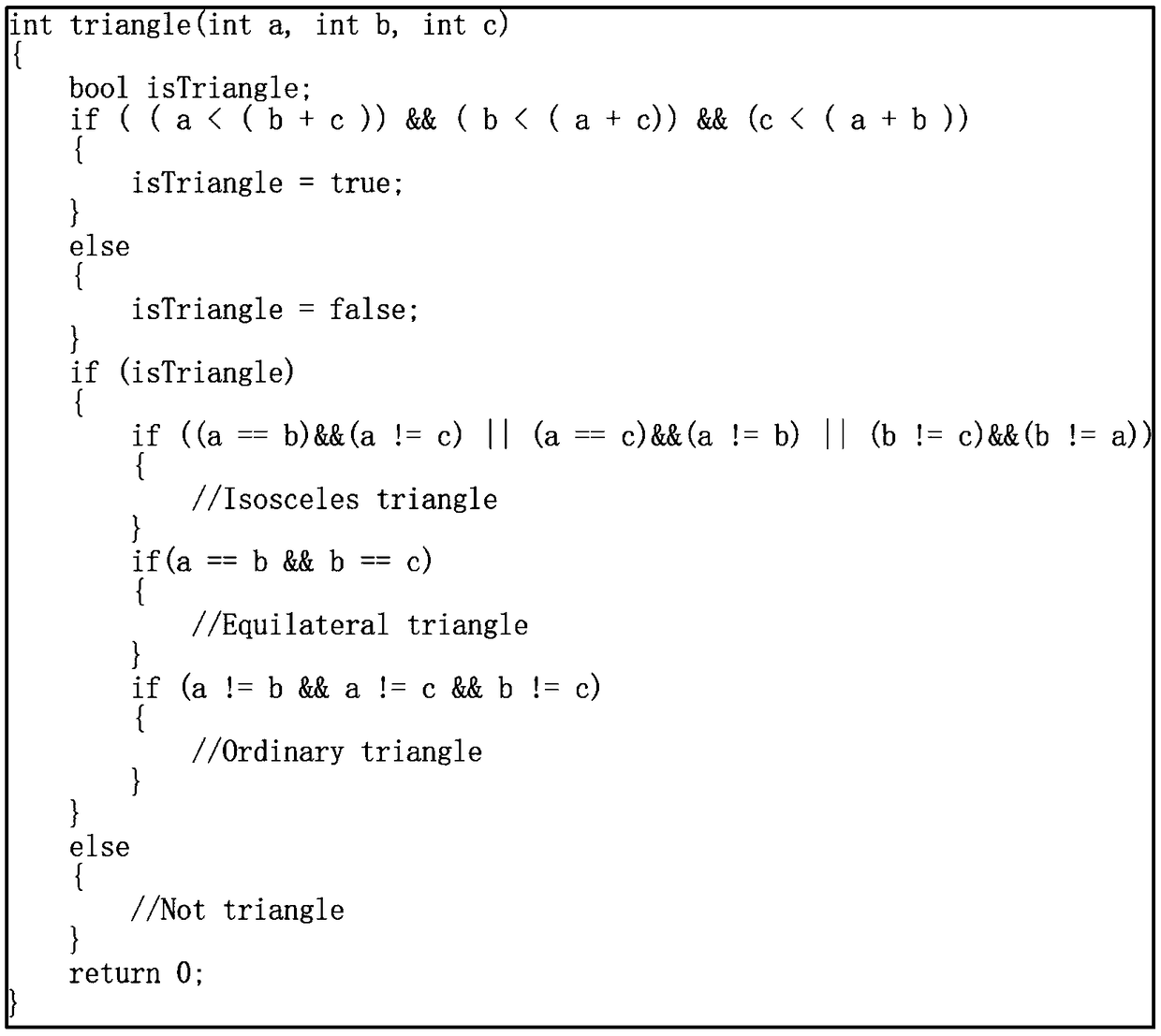
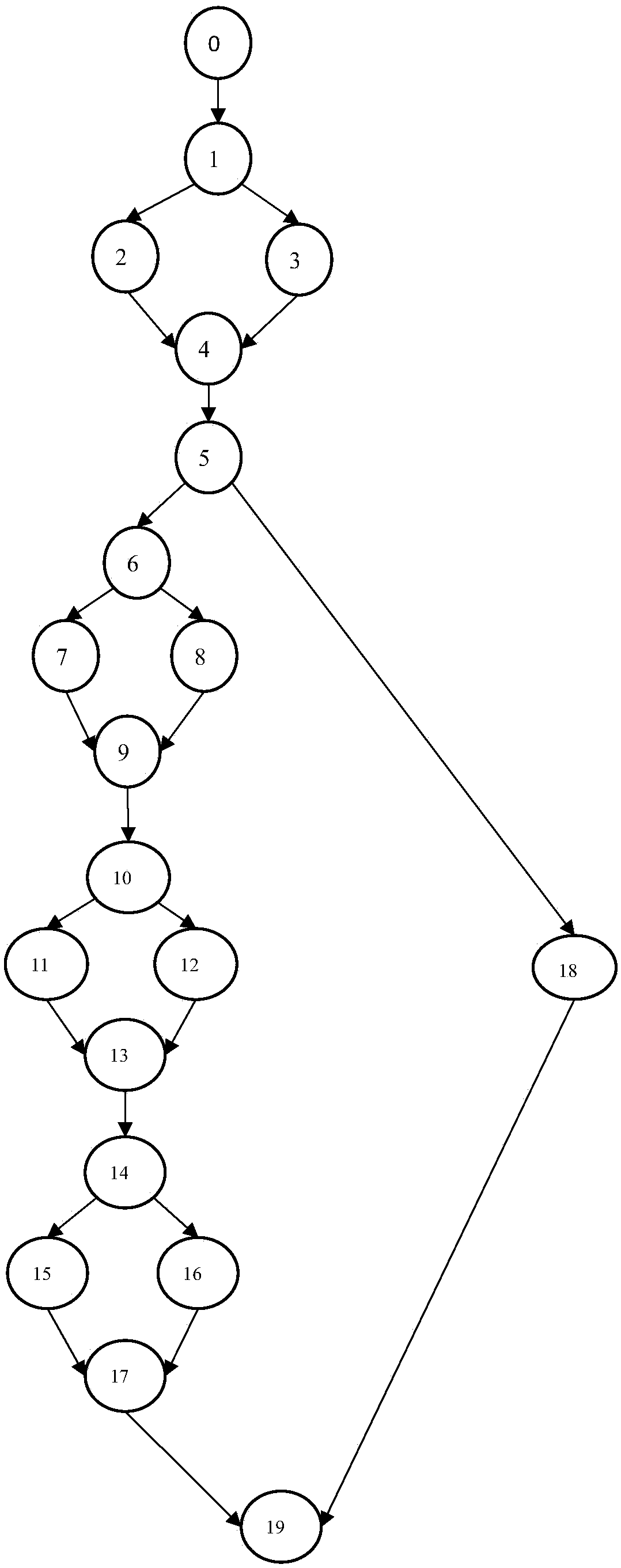
ActiveCN108710575AImprove test efficiencyEasy to completeSoftware testing/debuggingControl flowLexical analysis
The invention provides a unit test method which is automatically generated based on a path coverage test case. Firstly, a lexical analysis and a syntax analysis are carried out on a code of a programto be tested, and then a control flow diagram of the program is obtained. After obtaining the control flow graph, the node table is generated according to the known number of nodes. Based on the automatically generated test cases, the execution of executable codes in the nodes is driven in the generated control flow diagram, at the same time, according to the execution result of executable codes,the fitness value is calculated and obtained, and the child nodes are selected to continue to repeat the process until the termination node in the graph is found, and finally, the path marker and thefitness value corresponding to the path marker are generated. Then the automatic test case generation algorithm is run, which automatically generates test cases according to the fitness value returneduntil the path is completely covered or exits when the set run time expires. The invention is suitable for software testing, and can be applied to actual software testing working environment throughexperimental verification.
Owner:SOUTH CHINA UNIV OF TECH +1
Smart contract testing method based on path coverage sufficiency criterion
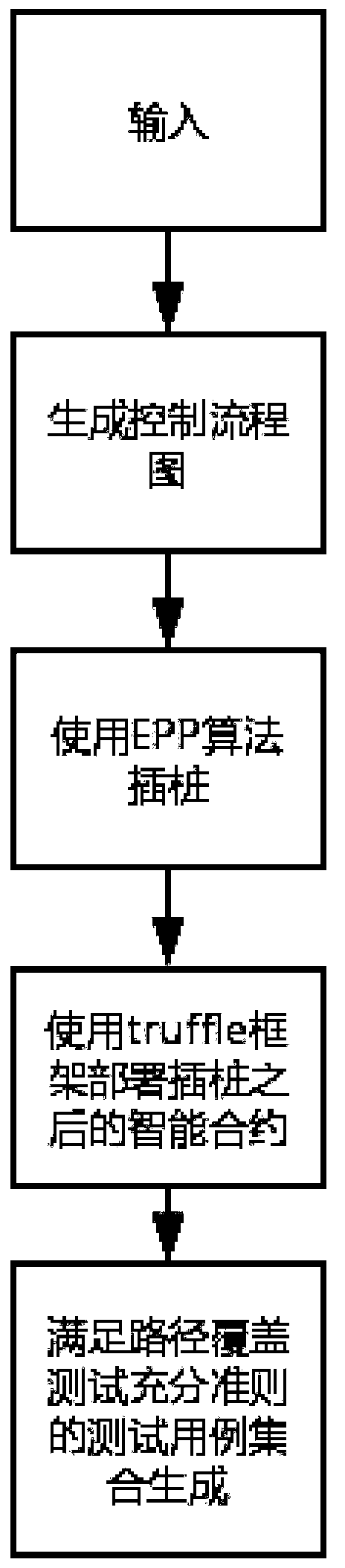
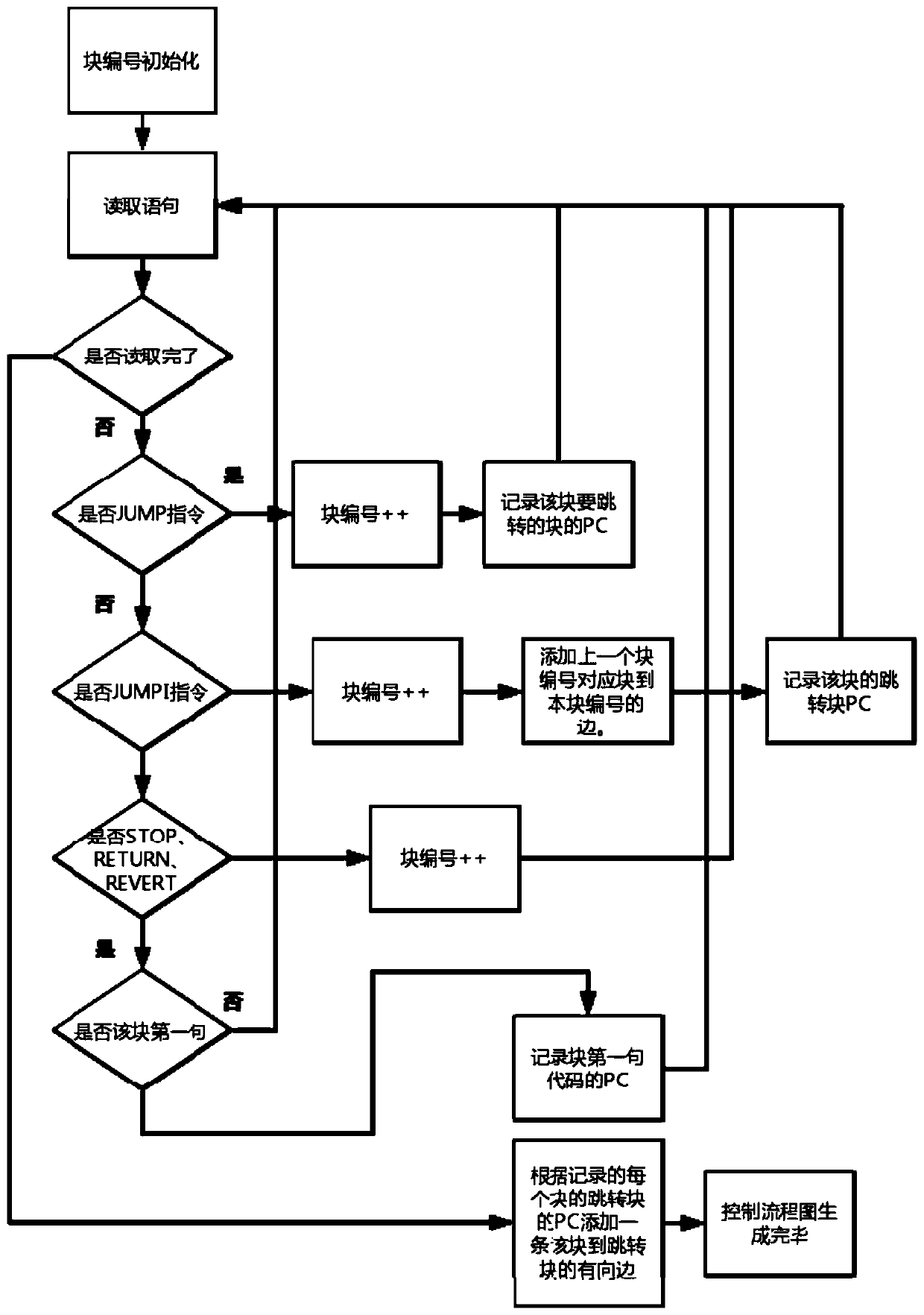
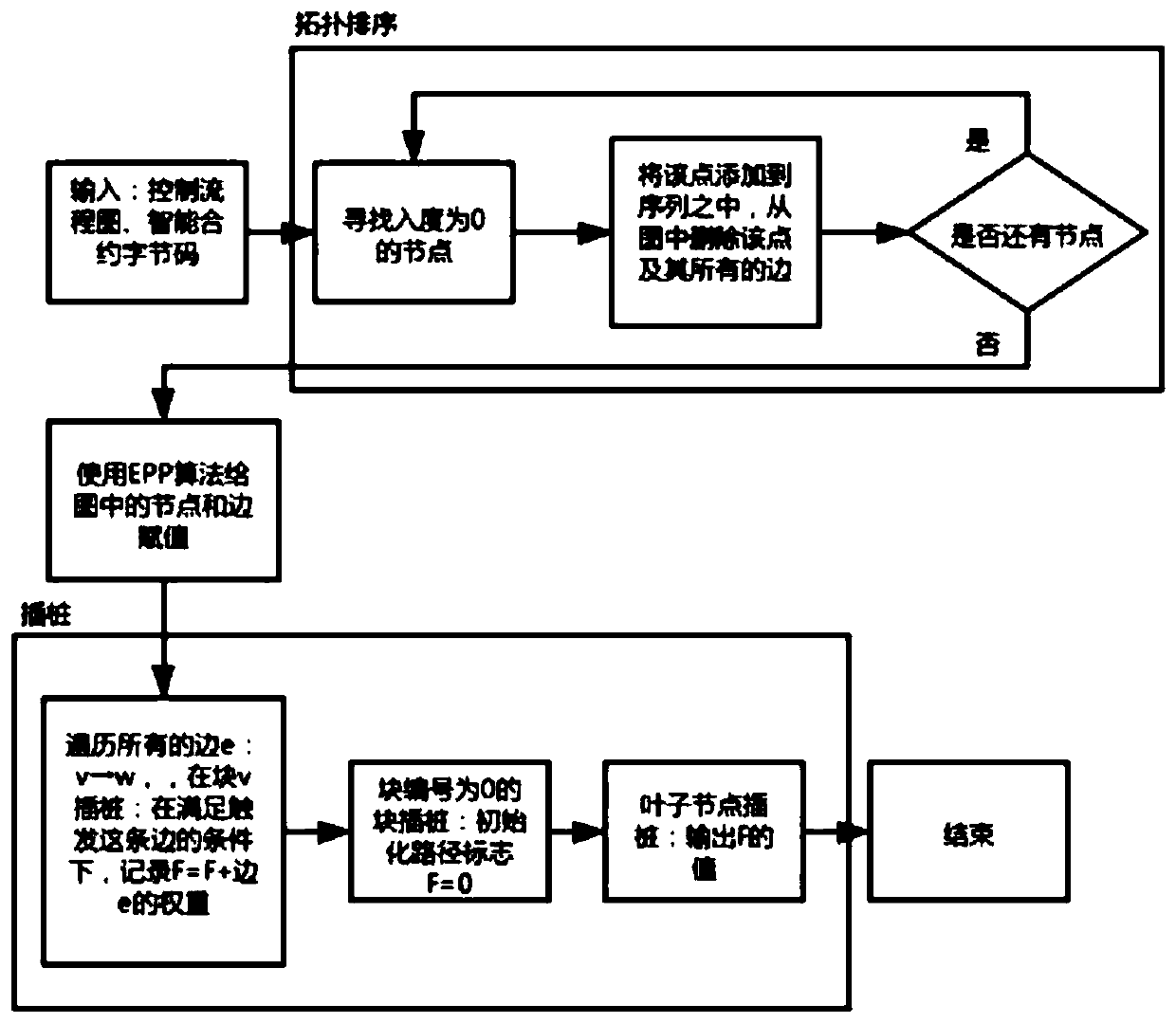
ActiveCN110046089AExpose errorsImprove the effectiveness of vulnerability detectionFinanceSoftware testing/debuggingControl flowGuideline
The invention discloses a smart contract test method based on a path coverage sufficiency criterion. The method comprises the following steps: step 1, inputting byte codes of a smart contract and ABIsof the smart contract; step 2, generating a control flow chart according to the byte code; step 3, using an EPP algorithm for analyzing the control flow chart, finding out blocks needing instrumentation, and conducting instrumentation; step 4, deploying the instrumented smart contract on the trace; and step 5, generating a test case set meeting requirements according to a path coverage test sufficiency criterion. Compared with other technologies for analyzing the source code, the byte code of the smart contract is analyzed, and the method is more efficient. According to the method, the test case is automatically generated for the smart contract, whether the sufficient test case set is generated or not is judged according to the adequacy criterion of path coverage, errors possibly existingin the smart contract code are fully exposed as much as possible, the vulnerability detection effect is improved, and the labor cost is reduced.
Owner:SOUTH CHINA NORMAL UNIVERSITY +1
Program source code judgment system and method based on B/S framework
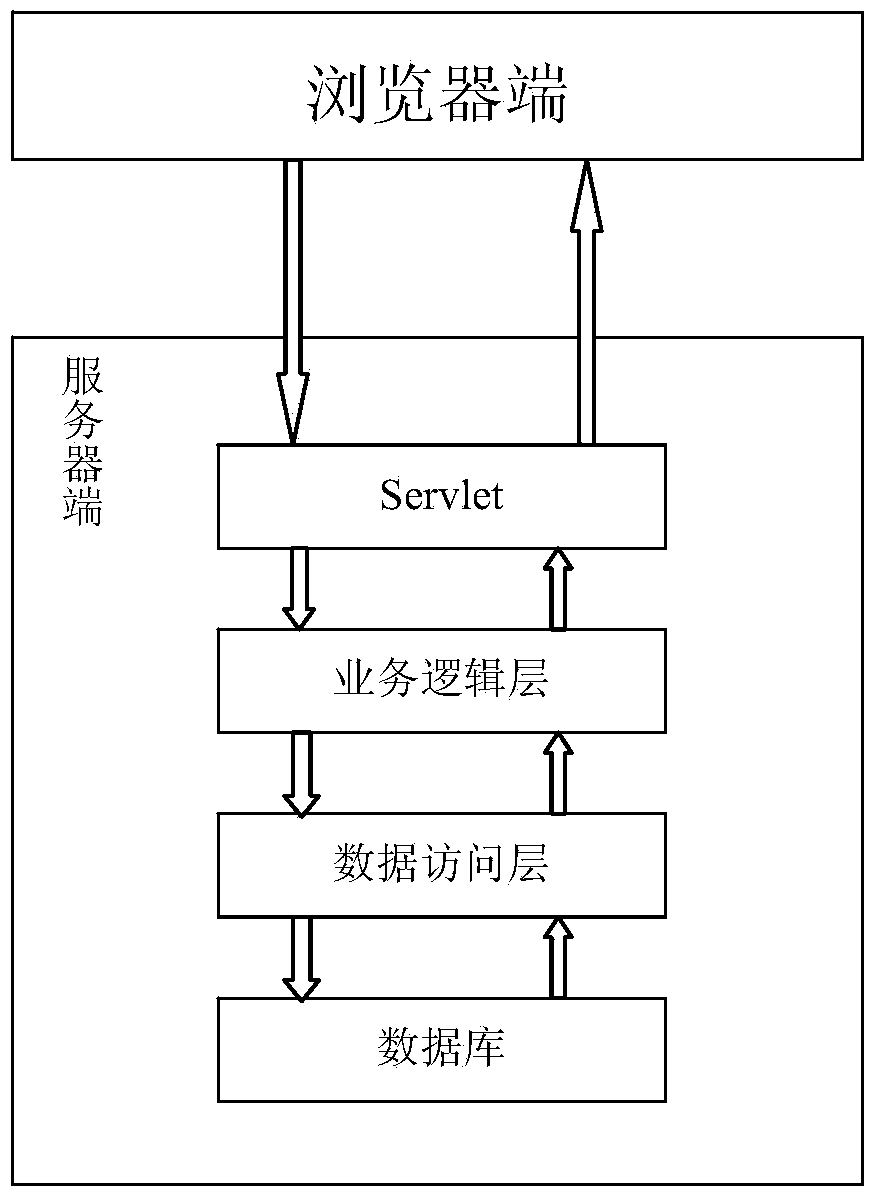
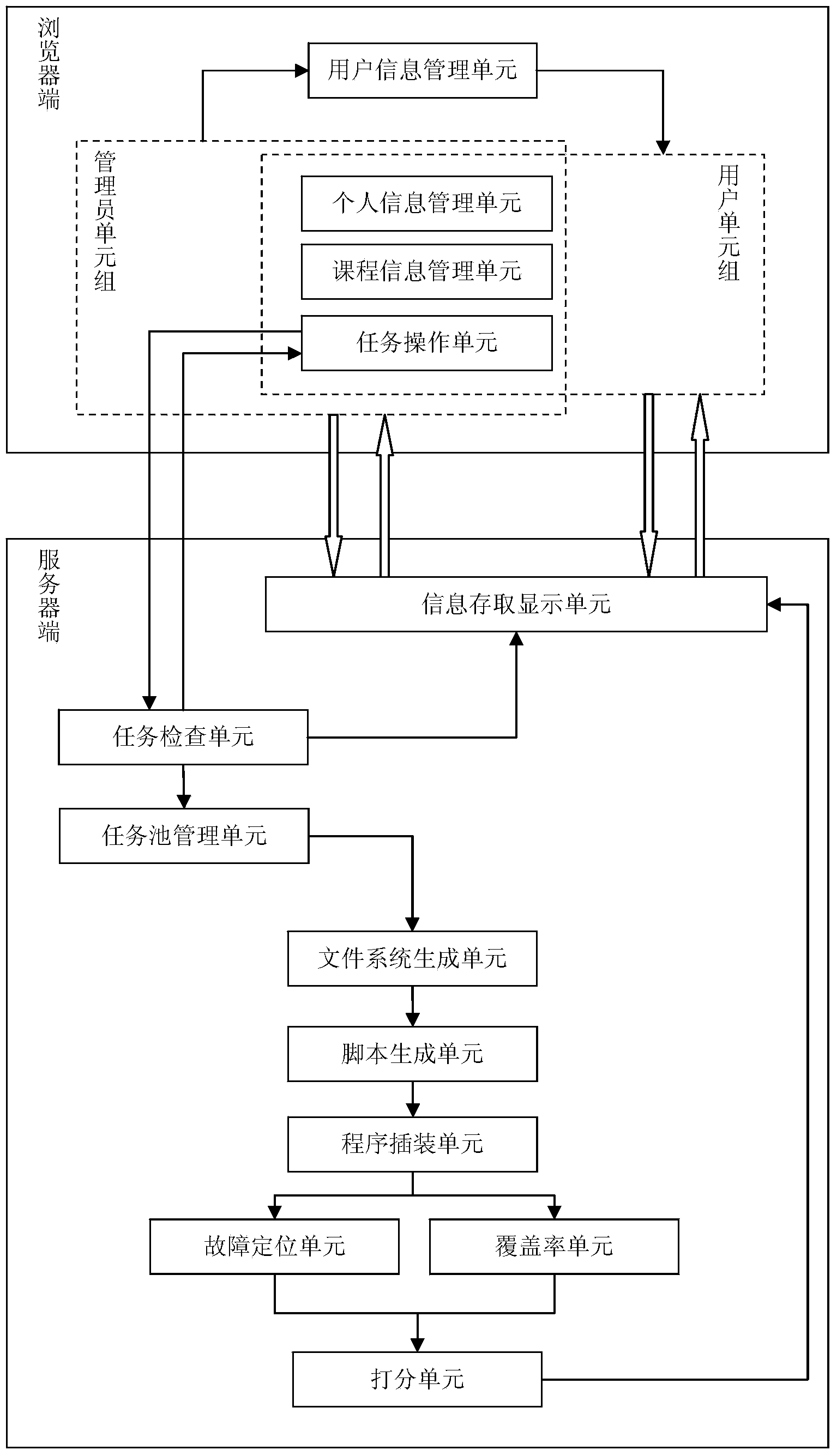
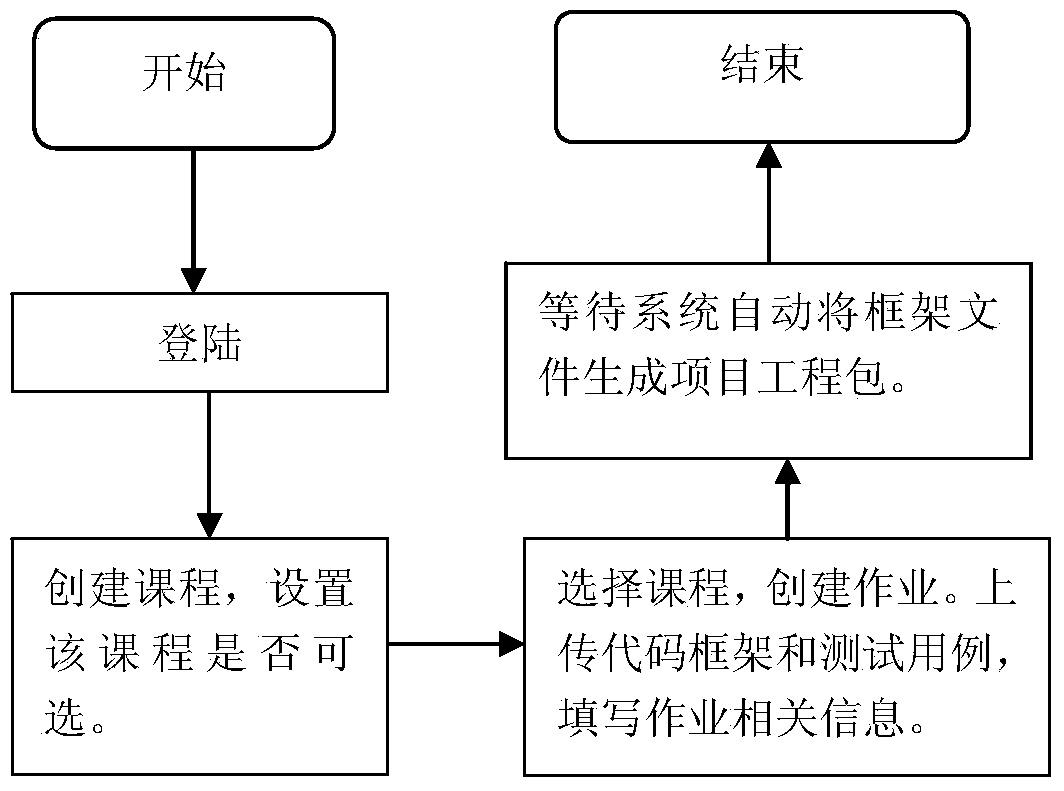
InactiveCN104077227AEasy to operateEasy to useSoftware testing/debuggingSpecific program execution arrangementsManagement unitFile system
The invention discloses a program source code judgment system and method based on a B / S framework. The system comprises a browser side and a server side. In the server side, a task pool management unit conducts detection after obtaining task submission information, a file system generation unit generates a file system and a catalogue which correspond to a task and copies a program to be detected to the generated catalogue, a script generation unit generates a script file according to the instruction required for executing the program to be detected while the program to be detected is installed in a plug-in mode and run through a program plug-in unit, execution paths and test case information of all test case are generated, a fault positioning unit runs generated path coverage information and conducts fault positioning according to the test cases, the equivocation of statements is calculated, and the statements are ranked according to the degrees of the equivocation, and a coverage rate unit conducts statistics on the program coverage information; a grading unit completes grading according to the grading standards; information of the statement equivocation, the information of the coverage rate and information of the task grade are fed back to the browser side through an information access and display unit, a result report is generated, and the judgment result is displayed. The method and the system have the advantages of being easy to operate and convenient to use.
Owner:DALIAN MARITIME UNIVERSITY
Path coverage monitoring method for wireless multimedia sensor network
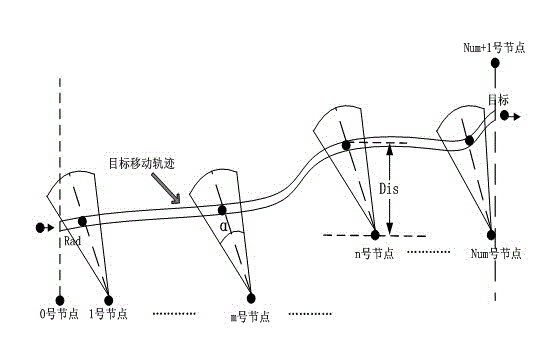
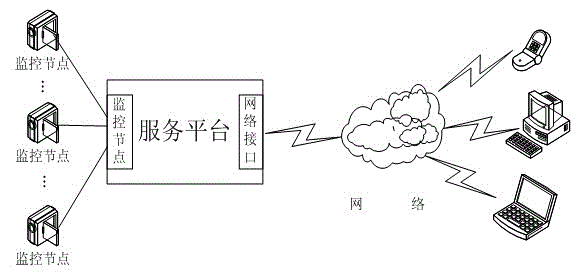
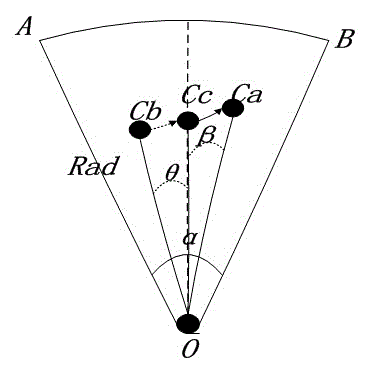
ActiveCN103188707AEasy to analyzeReduce engagementNetwork topologiesHigh level techniquesVideo sensorsNode deployment
The invention provides a path coverage monitoring method for a wireless multimedia sensor network. A few of multimedia sensor nodes are arranged on certain key paths, and an interested object can be found in time by utilizing the cooperation of the plurality of nodes of the sensor network when the interested object appears, sleeping nodes near a moving object predication track are awakened to take part in a tracking process, so that the energy consumption of the network is considered, and meanwhile, a moving object is fully monitored. By utilizing the adjustability of the direction of the nodes in a video sensor network, the number of the nodes of a node deployment sensor is reduced, and meanwhile, a monitoring effect can be enhanced, and the energy can be saved.
Owner:NANJING UNIV OF POSTS & TELECOMM
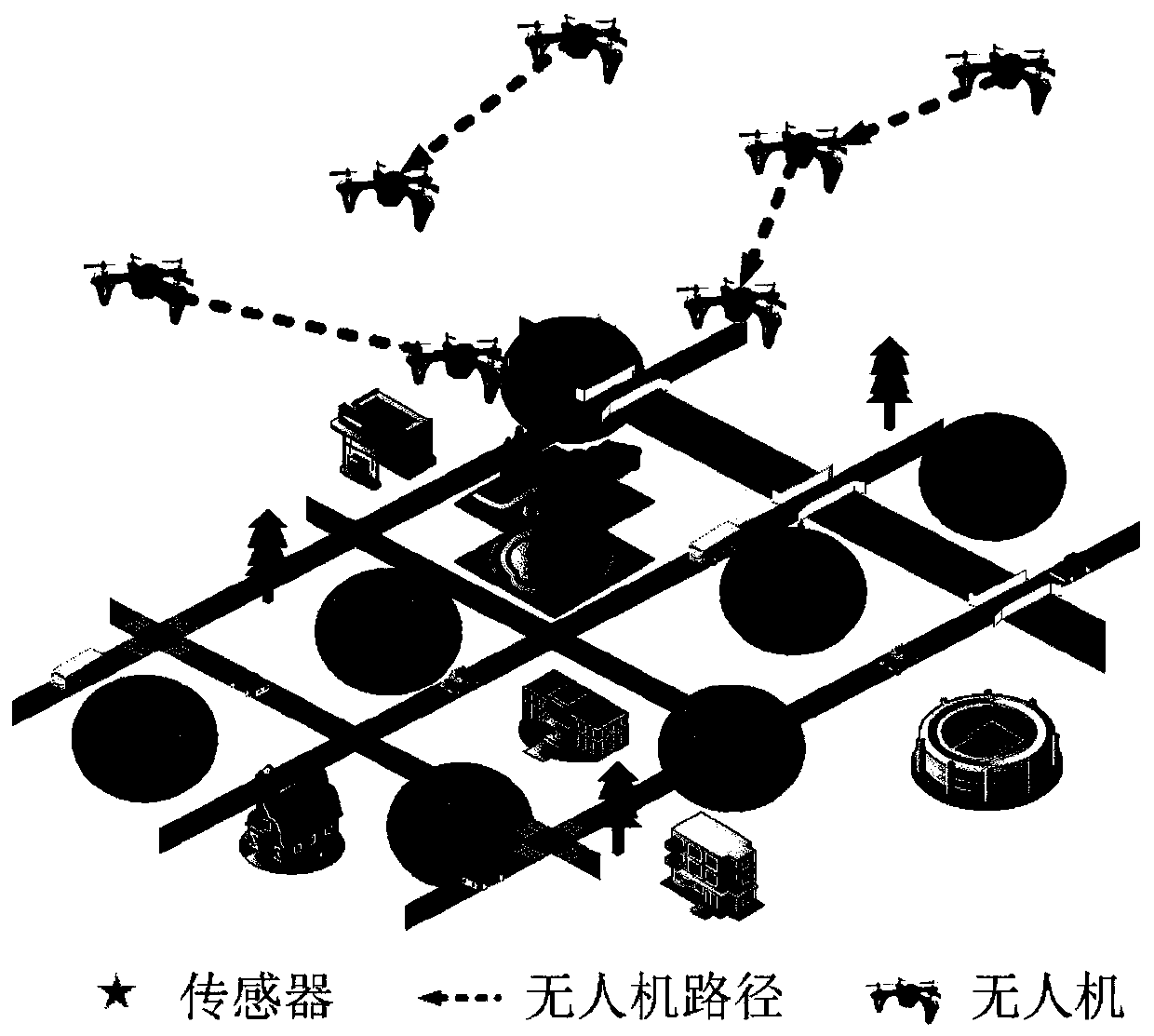
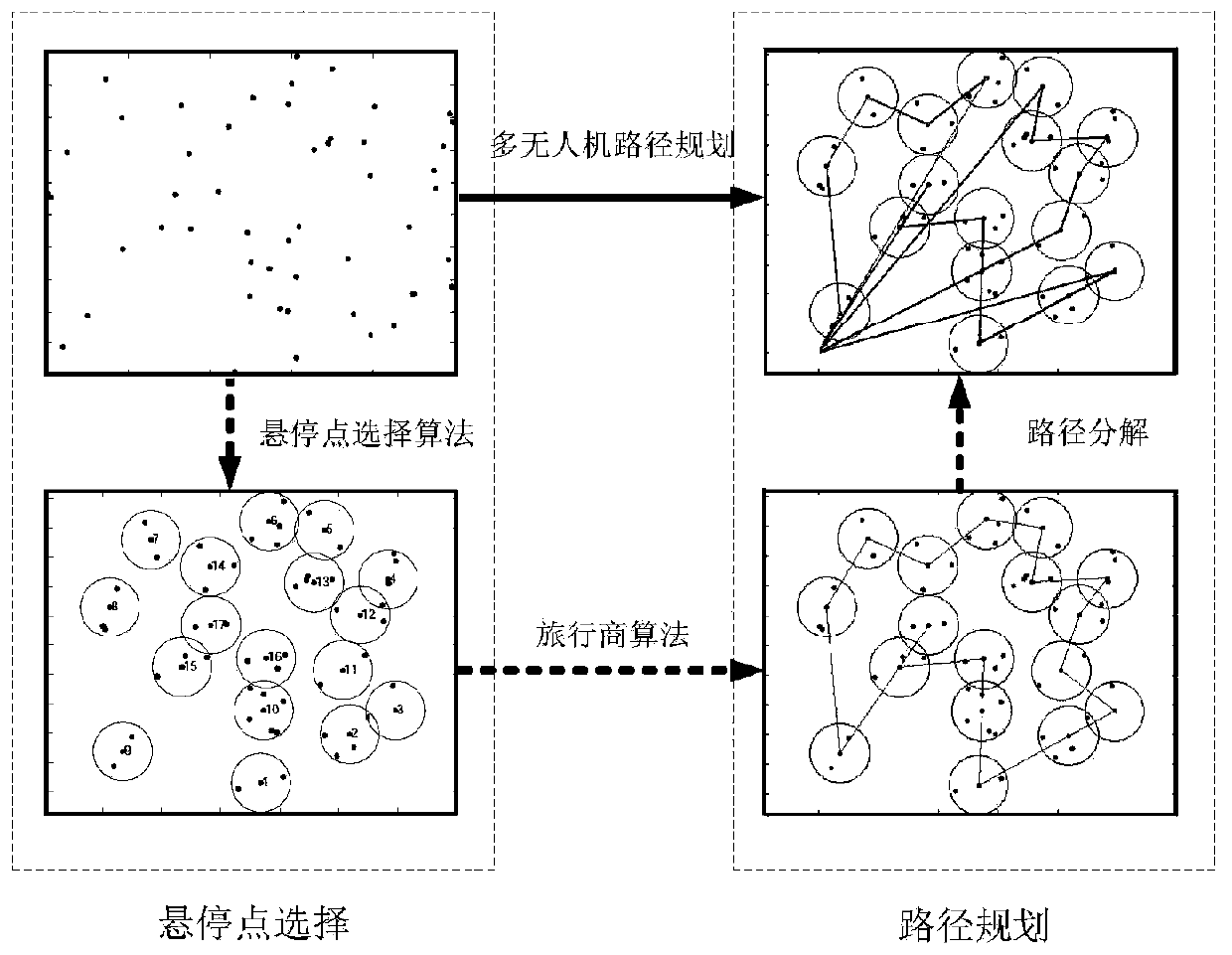
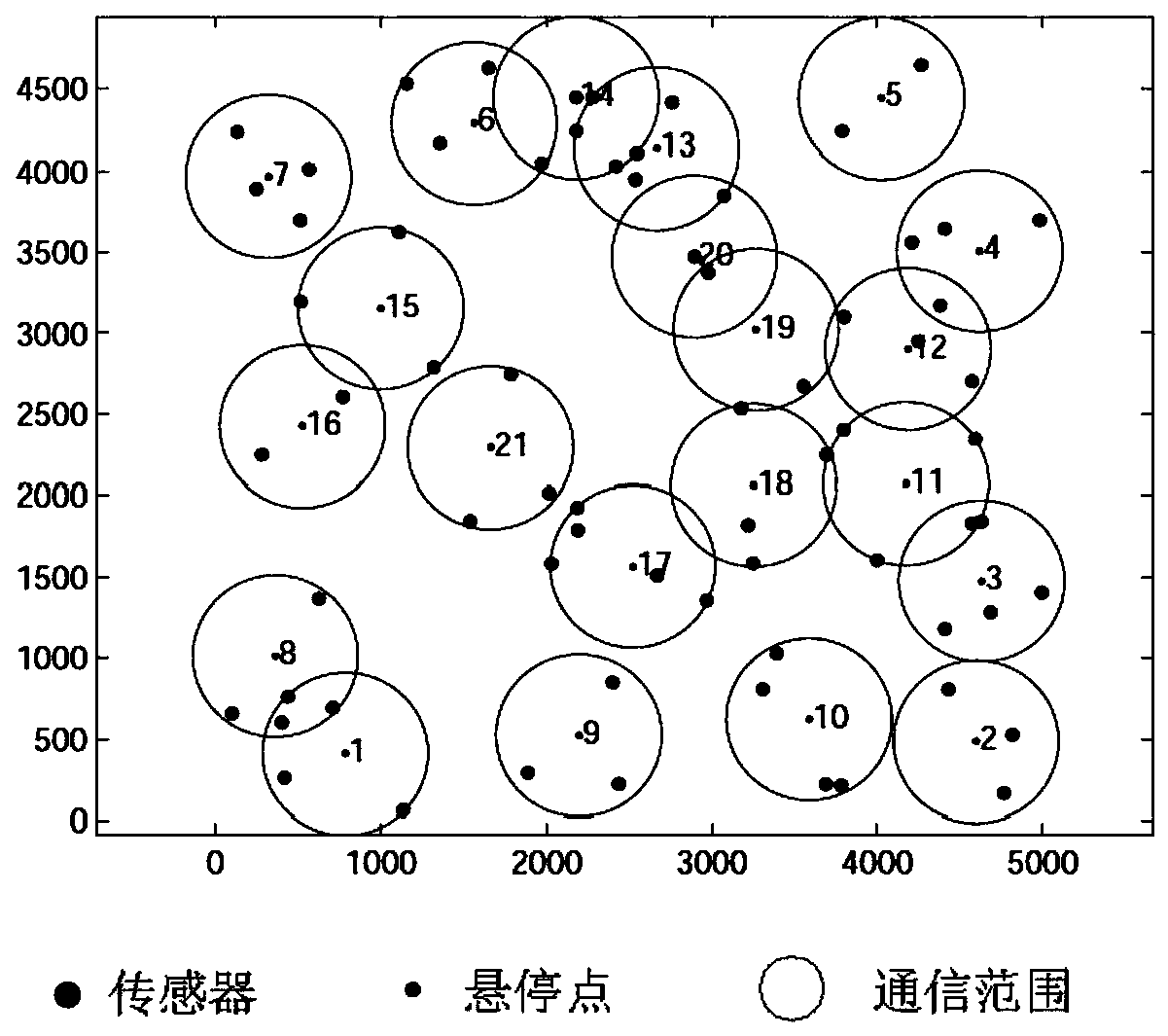
Multi-drone path planning method based on minimization of mission completion time
ActiveCN110426039AIncrease speedGuaranteed completion efficiencyNavigational calculation instrumentsCompletion timeTask completion
The invention discloses a multi-drone path planning method based on minimization of mission completion time, and the method realizes the purpose of the minimization of mission completion time of the drone with the longest time through path planning for K drones on the premise of considering the quality of information collection, in particular comprising the following steps of determining hover points of the drones in the process of information collection tasks according to base station coverage principle and the set requirements of the information collection tasks; assigning the information collection tasks and planning the trajectory of each drone by using the minimum-maximum path coverage algorithm according to the positions of the hover points; considering the situation of the drones collecting information during flight based on the planned trajectories of the drones, and performing optimal distribution on the flight time and information collection time. The method provided by the invention plans trajectories of the drones by using the algorithm of fairness principle, and minimizes the completion time of the tasks so as to ensure the completion efficiency of the information collection tasks.
Owner:ARMY ENG UNIV OF PLA
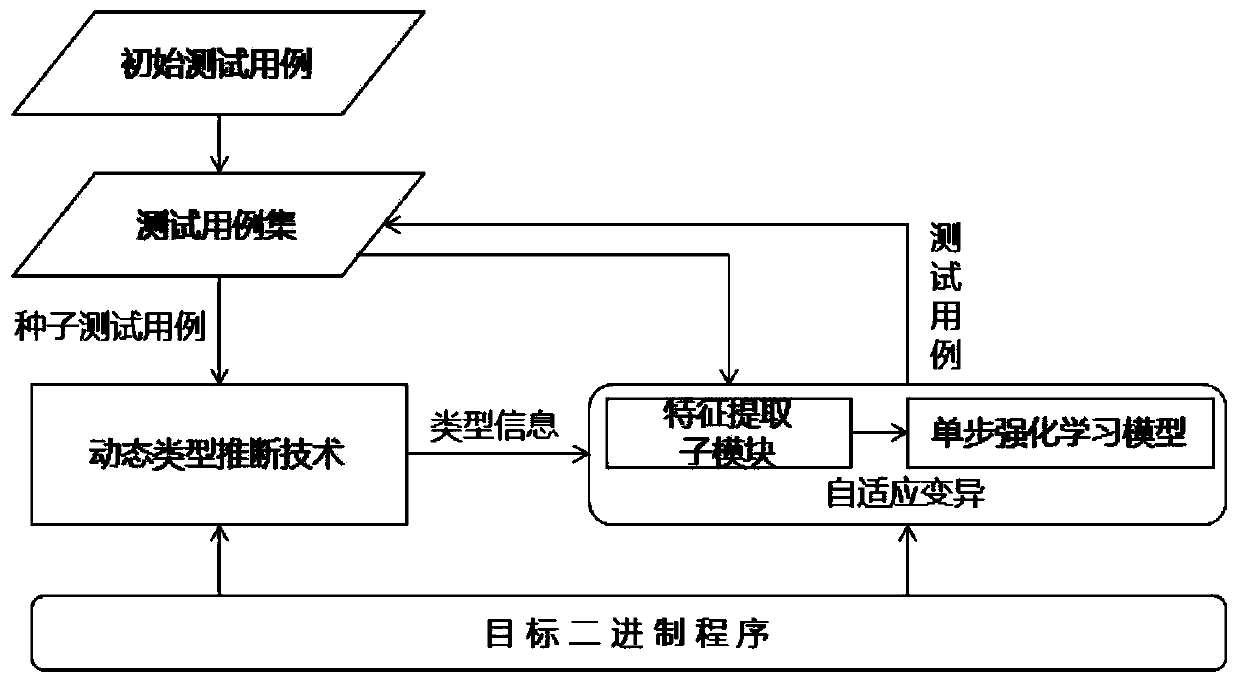
Fuzzy test case adaptive variation method and device based on reinforcement learning
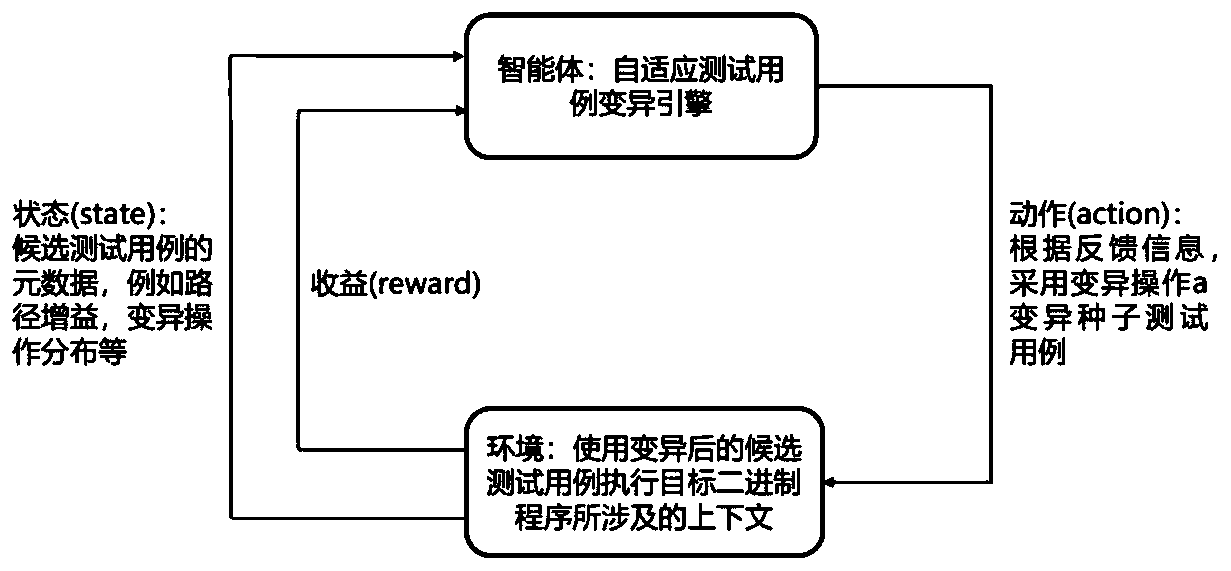
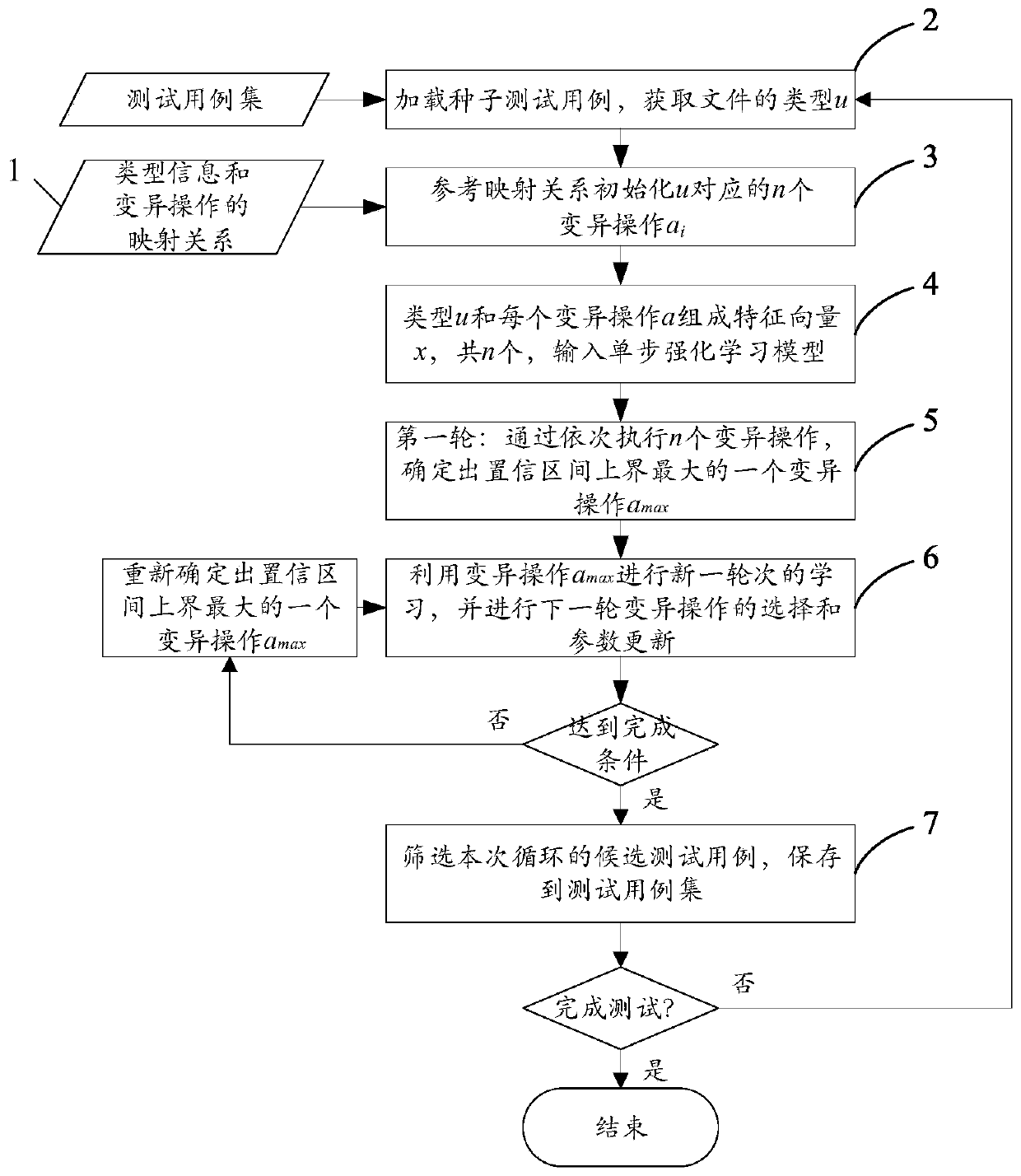
ActiveCN110175120AHigh degree of intelligenceImprove path coverageSoftware testing/debuggingAdaptive learningState variation
The invention discloses a fuzzy test case adaptive variation method and device based on reinforcement learning, and the method comprises the steps of selecting a variation operation group corresponding to a to-be-mutated test case type to carry out the learning of adaptive variation, thereby selecting a variation strategy in a targeted manner, and achieving the variation operation with a finer granularity. According to the present invention, the type information and the variation operation are further adopted to form the context information to be input into a single-step reinforcement learningmodel, the single-step reinforcement learning model converts the selection problems of different variation operations into the selection of different rocker arms in a multi-arm gambling machine problem, and the context-related confidence interval upper bound algorithm LLUCB is used for learning the adaptive variation operation, so that the adaptive learning of the variation operation under different types of scenes is realized, the variation operation capable of obtaining a higher path coverage rate is used for carrying out test case variation, and the efficiency and the quality of the fuzzytest adaptive variation are improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
A fuzzy test case generation method and system based on genetic variation
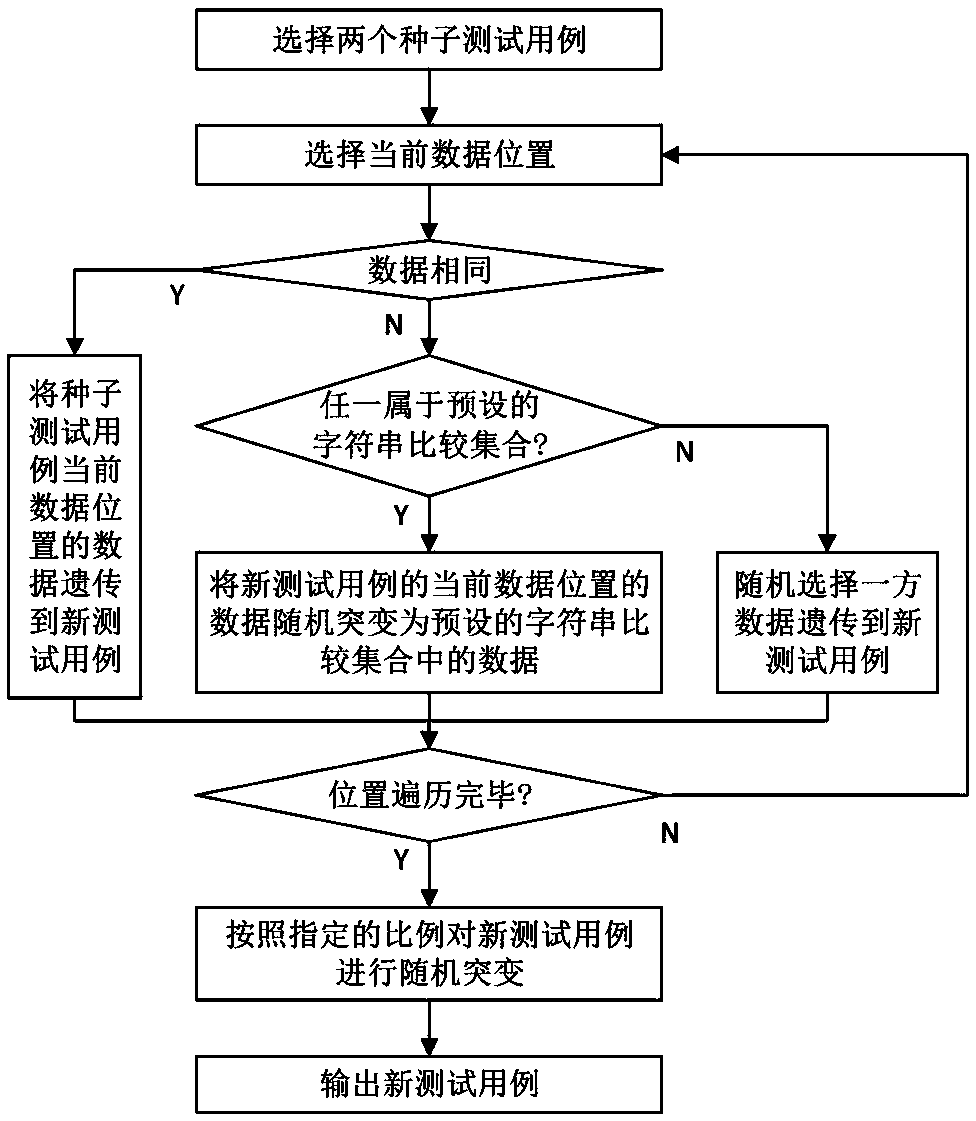
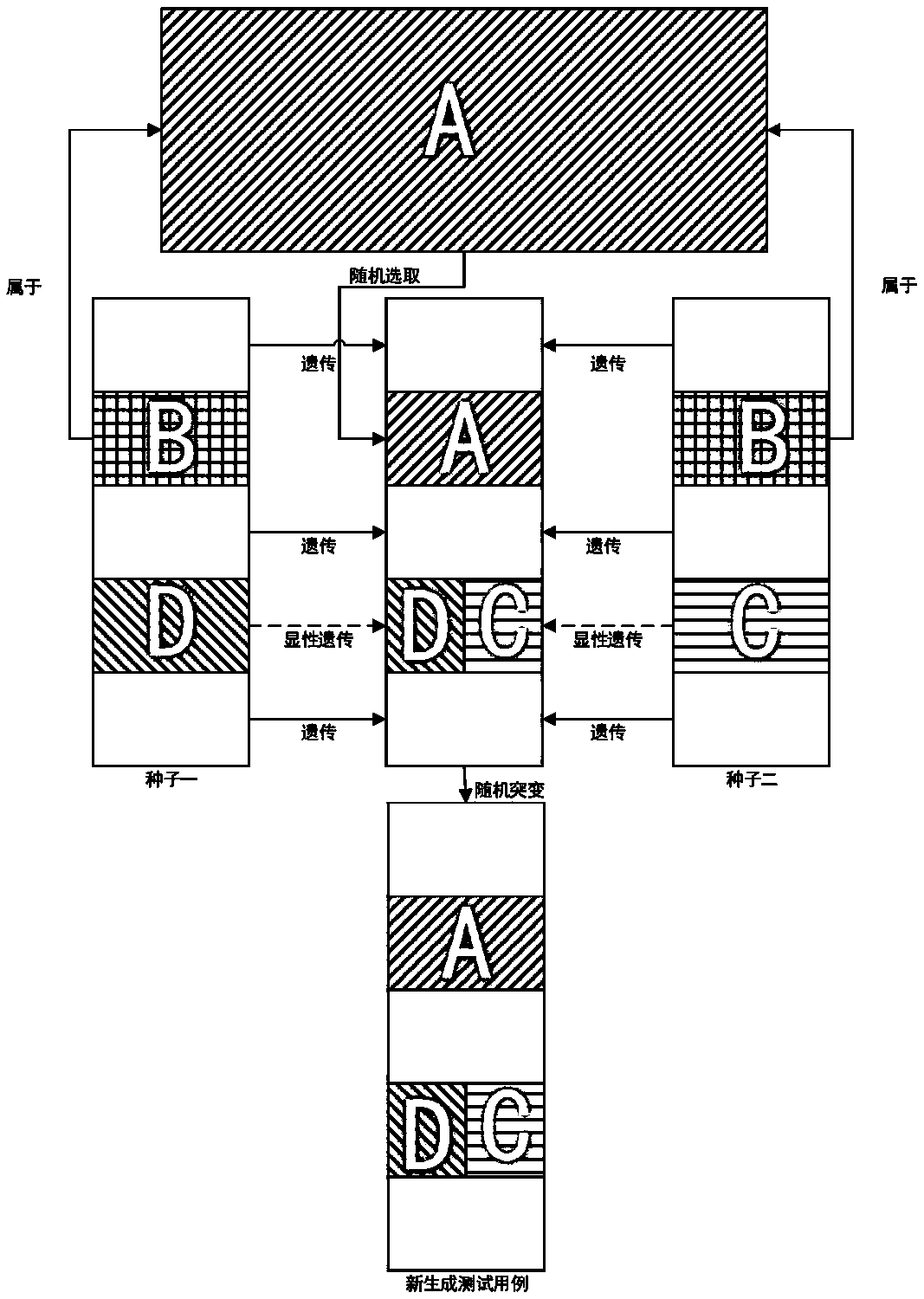
ActiveCN109597767AIncrease coverageSoftware testing/debuggingGenetic algorithmsVariation (Genetics)Test case
The invention discloses a fuzzy test case generation method and system based on genetic variation. The method comprises the following steps: selecting two seed test cases, aiming at a data position ofa new test case, if the two seed data are the same, inheriting the data to the current data position of the new test case; and if the two pieces of seed data are different and belong to any characterstring comparison set for static analysis and extraction of the target binary file, randomly mutating the data into data in the preset character string comparison set, or else randomly selecting thedata of one seed to be inherited to the current data position of the new test case. According to the invention, respective advantages of the test case generation method based on generation and the test case generation method based on variation are inherited; and meanwhile, the corresponding defects are avoided, the core code of the large-scale fuzzing target program without manual operation can berealized, and the method has the advantages that the generation of the test case has higher possibility, the path coverage rate is increased, and the collapse is easy to trigger.
Owner:NAT UNIV OF DEFENSE TECH
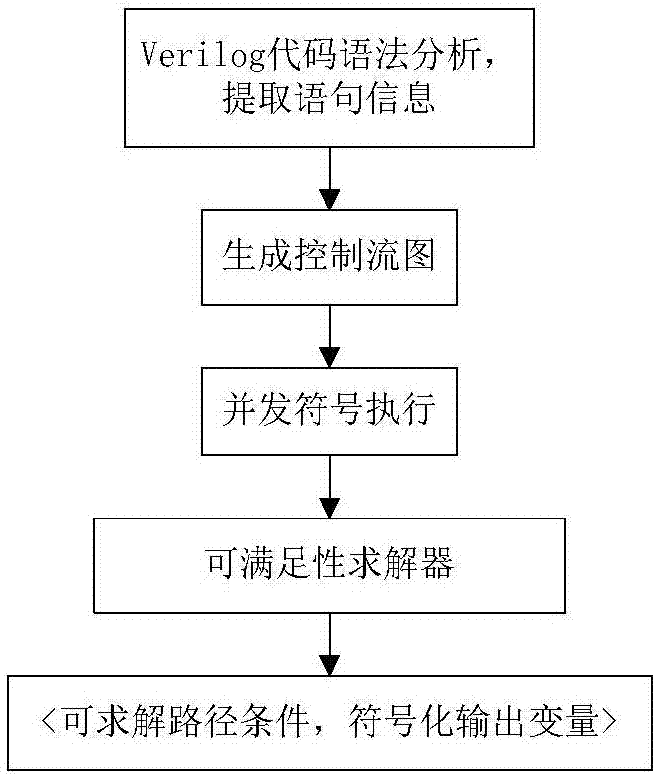
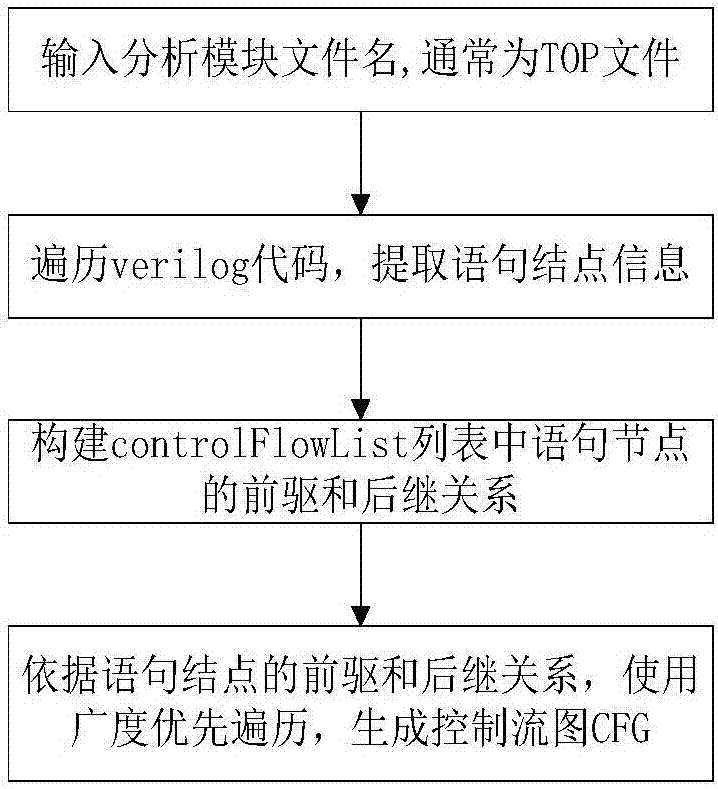
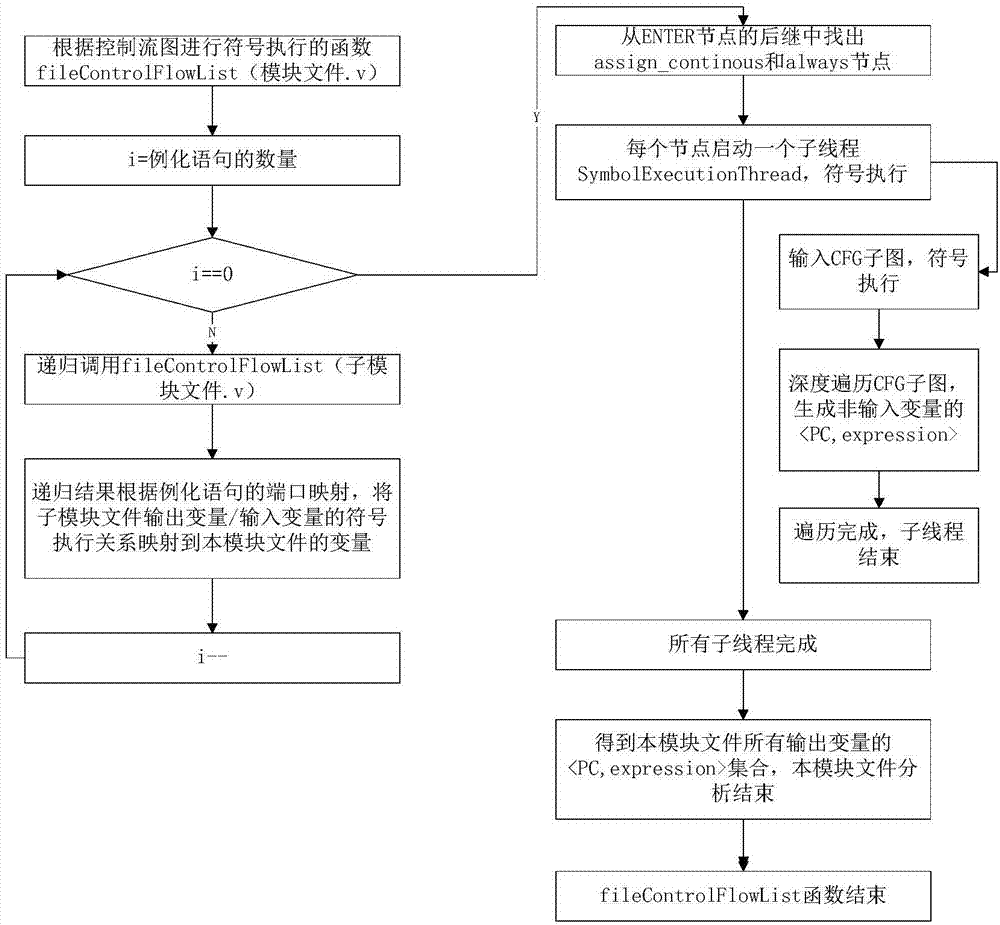
Method for generating RTL hardware Trojan test vectors
The invention discloses a method for generating RTL hardware Trojan test vectors. The method mainly includes generation of a control flow chart, concurrent symbol execution, and satisfiability solving and generation of test vectors. The method provided by the invention adopts a method of statically analyzing Veri log codes, and adopts a multi-thread concurrency technology to realize concurrent symbol execution of the Veri log codes, thereby achieving the purpose of rapidly generating test vectors with a high path coverage rate.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
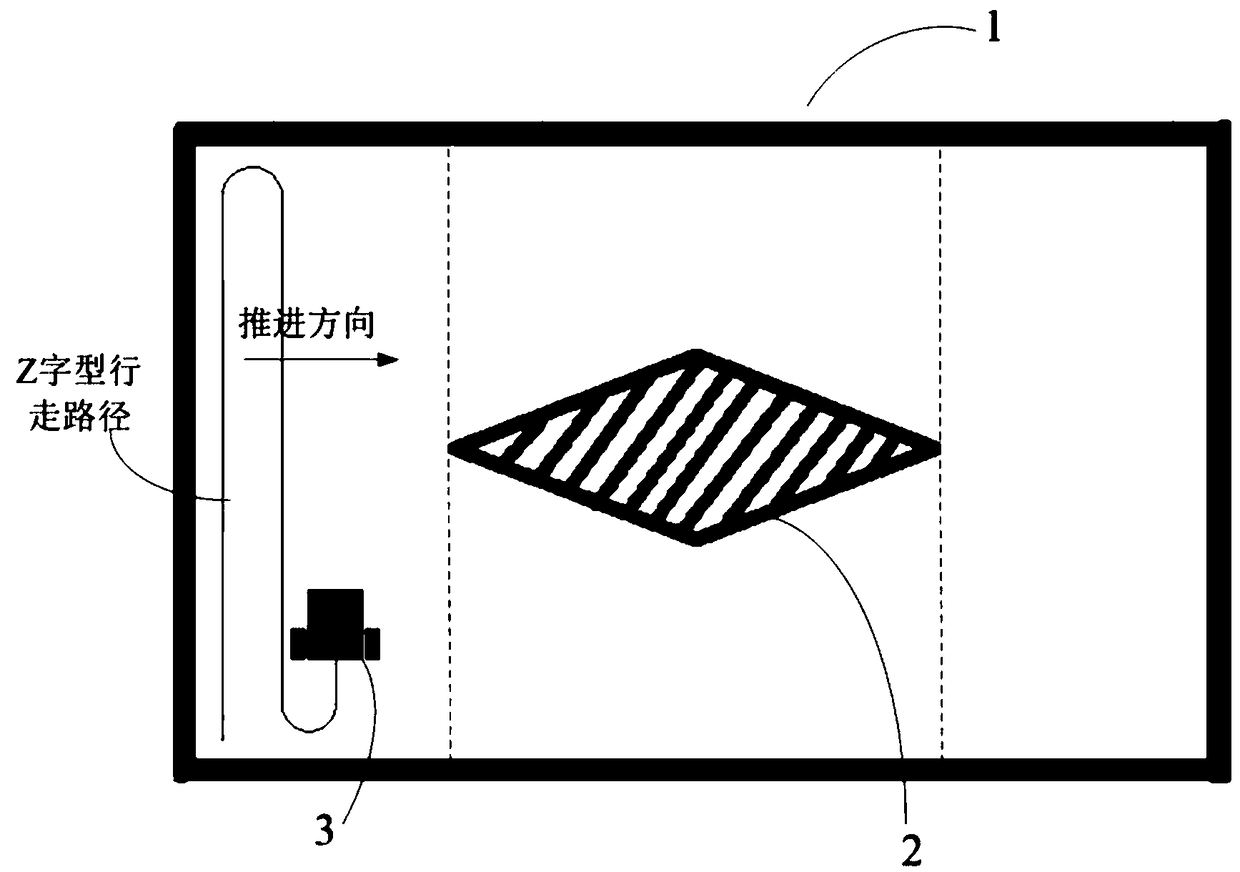
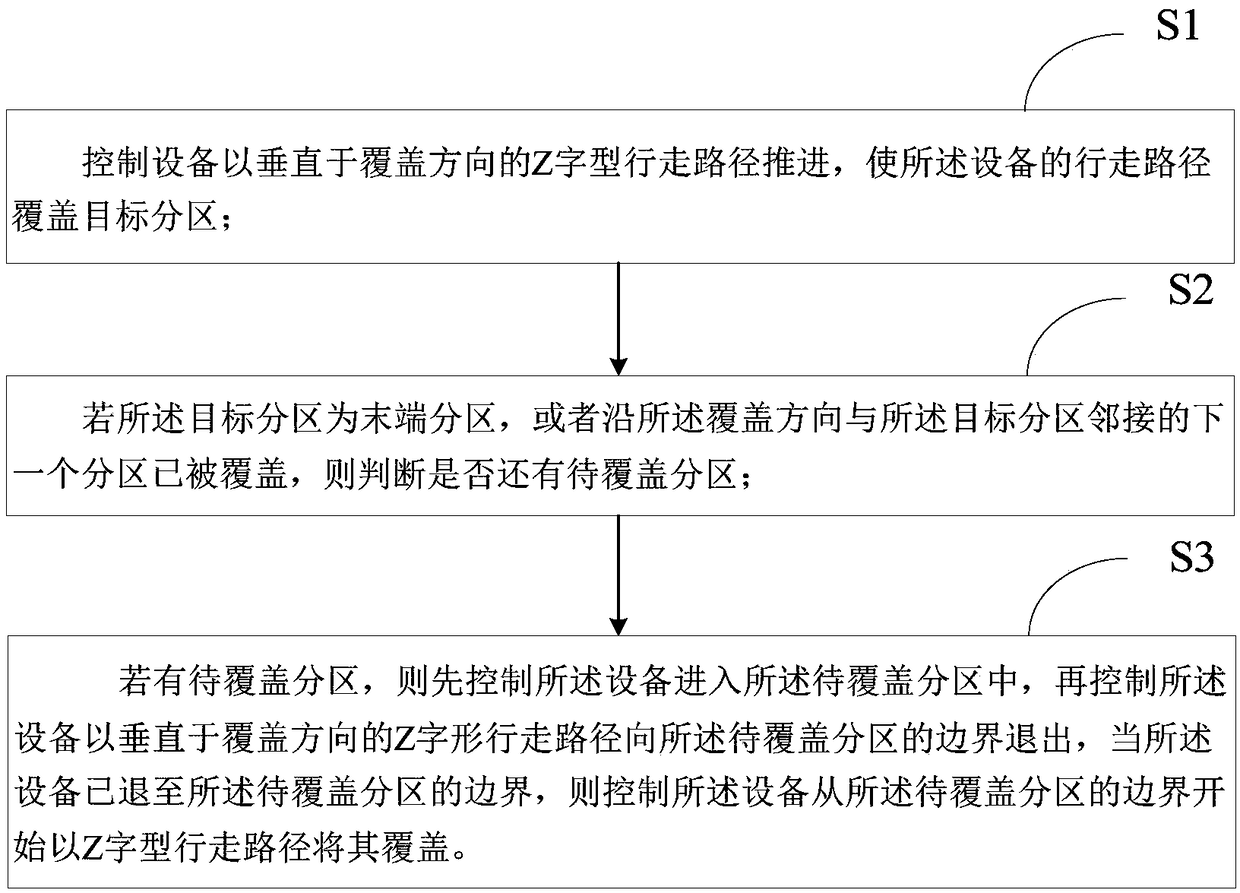
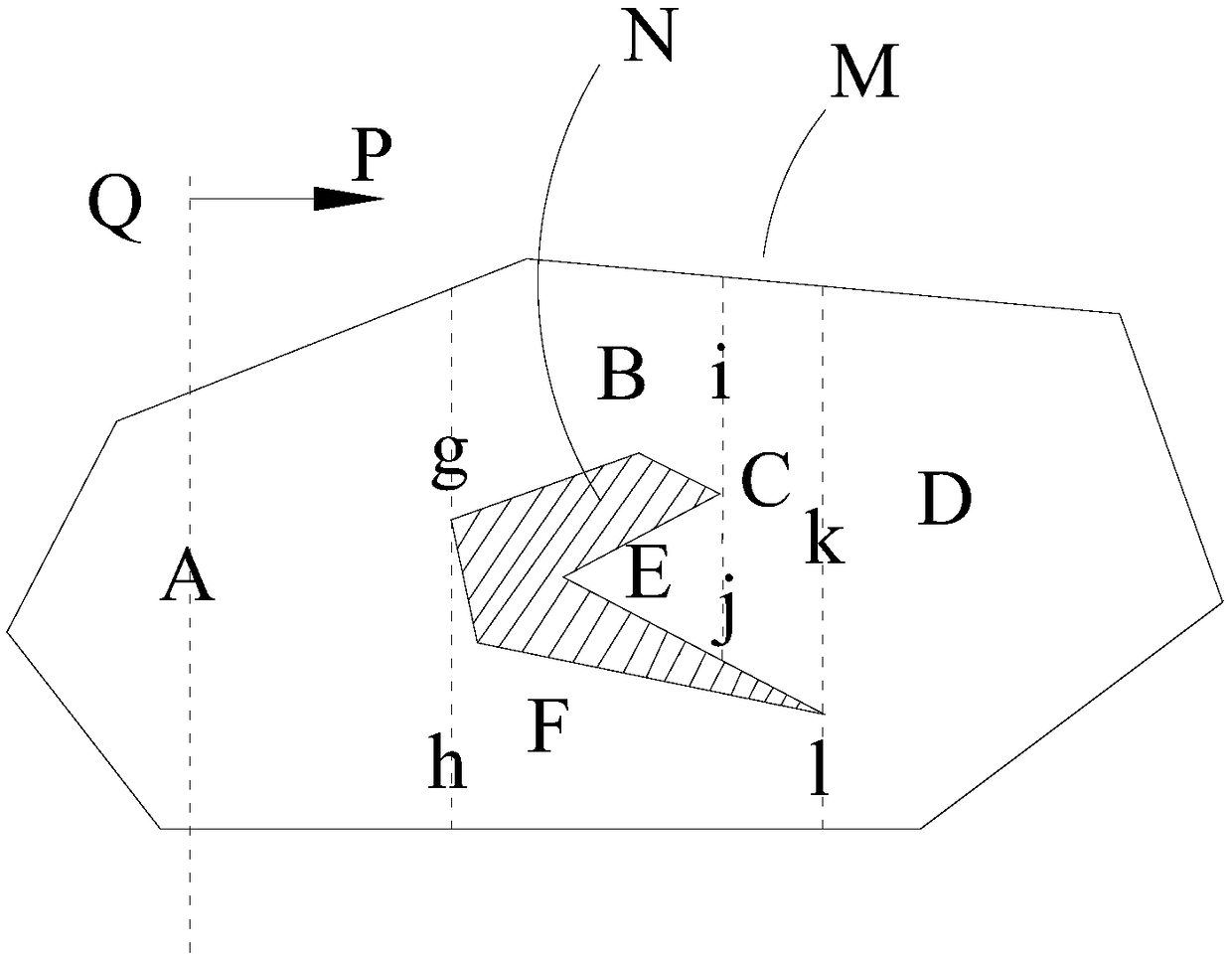
Coverage path planning method, device, equipment, computer device and storage medium
ActiveCN108663063AImprove efficiencyLower requirementInstruments for road network navigationVehicle position/course/altitude controlBoustrophedonComputer science
The invention is applicable to the field of path planning, and provides a coverage path planning method, device, equipment, computer device and storage medium. The method is applied to a scene in which a work region is partitioned by a boustrophedon decomposition method, and comprises the following steps: controlling the equipment to propel in a Z-shaped walking path perpendicular to a coverage direction so that the walking path of the equipment covers a target subregion; if the target subregion is an end subregion or a next subregion adjacent to the target region in the coverage direction iscovered, judging whether a subregion to be covered exists; if so, firstly controlling the equipment to enter the subregion to be covered, and then controlling the equipment to retreat toward a boundary of the subregion to be covered in the Z-shaped walking path perpendicular to the coverage direction; and when the equipment retreats to the boundary of the subregion to be covered, controlling the equipment to cover the subregion to be covered in the Z-shaped walking path by starting from the boundary of the subregion to be covered. According to the invention, the coverage path can be planned without precise positioning so that the cost is greatly reduced, and the efficiency of coverage operation is relatively high.
Owner:宁波拓邦智能控制有限公司
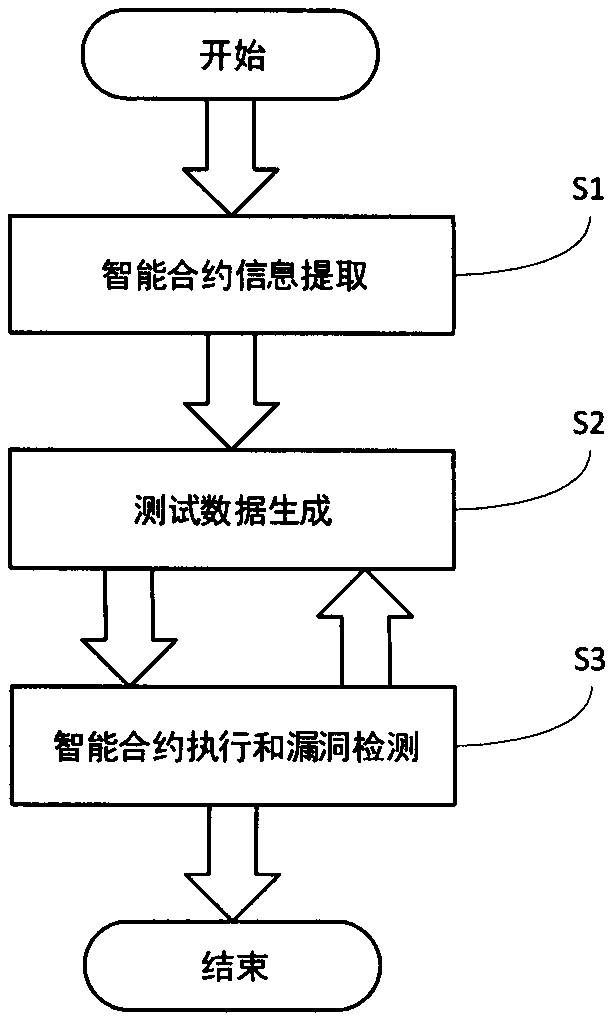
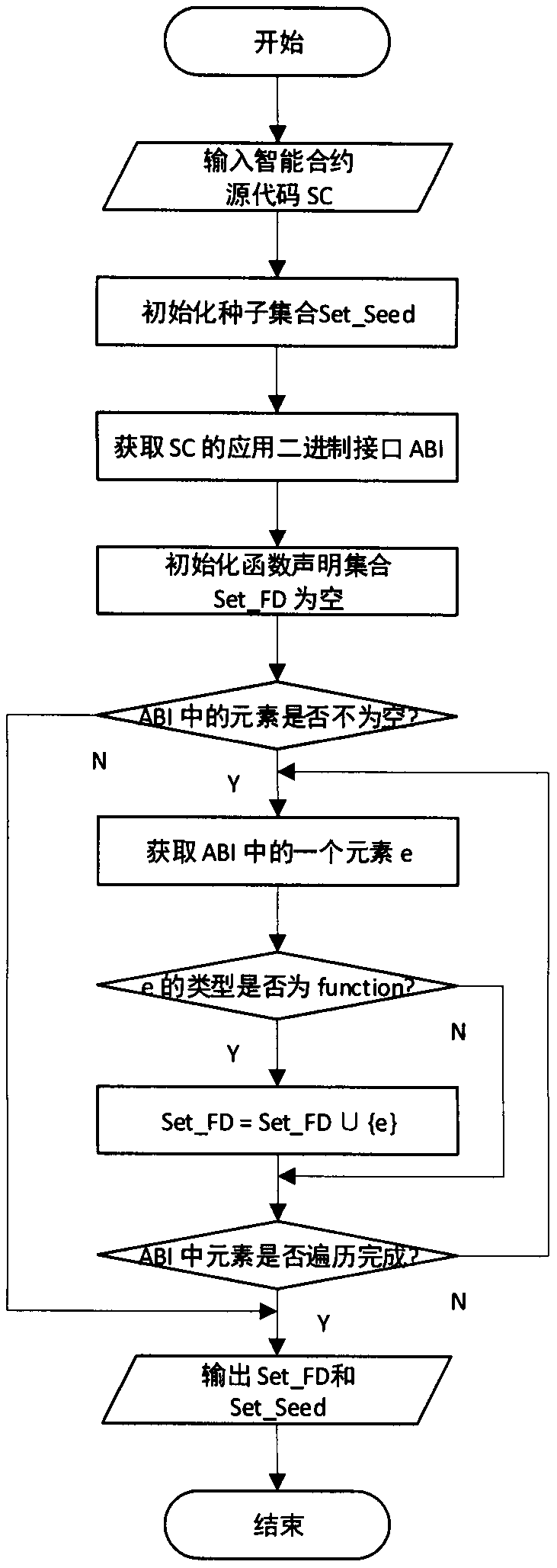
Intelligent contract security test method based on variation fuzz
The invention provides an intelligent contract security test method based on variation fuzz. The method comprises: taking a source code of a smart contract as an input, obtaining an ABI (Application Binary Interface) of the smart contract, finding out elements of function types from the ABI, and extracting function declarations of the elements; on the basis, further generating test data: if the tested function has no seed, randomly generating the test data, otherwise, generating the test data with a certain probability based on seed variation; and then, executing the intelligent contract on the private chain by using the test data, further carrying out vulnerability detection, updating the seeds, and returning to the test input generation step again, and repeating the steps until a presettest termination condition (the termination condition can be test time, path coverage rate and the like) is reached. Through the method, a tester can check whether the smart contract has a security problem or not in a short time, and can refer to input to reproduce the problem.
Owner:NANJING UNIV
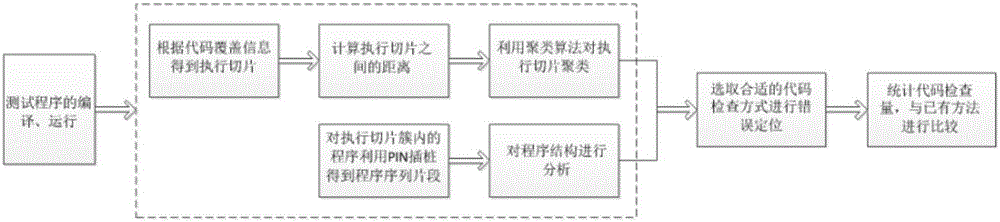
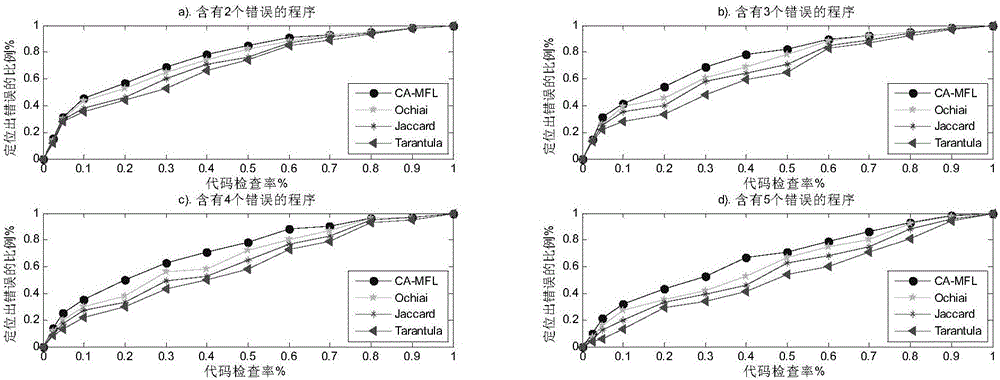
Error locating method based on program failure clustering analysis
ActiveCN106598850AAvoid the problem of low efficiency of false positioningSoftware testing/debuggingFailure causesBasic block
The invention provides an error locating method based on program failure clustering analysis. A failure caused by the same error has similarity trigger. The method comprises the following steps of firstly, obtaining execution slices for each failure test and computing a distance between the execution slices according to a Jaccard distance formula; secondly, carrying out clustering on program failure execution slides according to a K-Means clustering algorithm to obtain a failure execution slice cluster; thirdly, obtaining a program status sequence chart of the failure execution slices according to a runtime program status division method of a jump instruction; fourthly, respectively establishing execution path coverage vectors in basic blocks / rows and a coverage matrix according to the function nest call frequency in the program status sequence chart; and lastly, respectively computing suspiciousness degree of each basic block / row and sorting in a descending order, solving a frequent set in basic blocks / rows and checking whether each basic block / row contains errors in sequence according to the suspiciousness degree of the basic blocks / rows and the corresponding frequent set.
Owner:ZHEJIANG SCI-TECH UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com