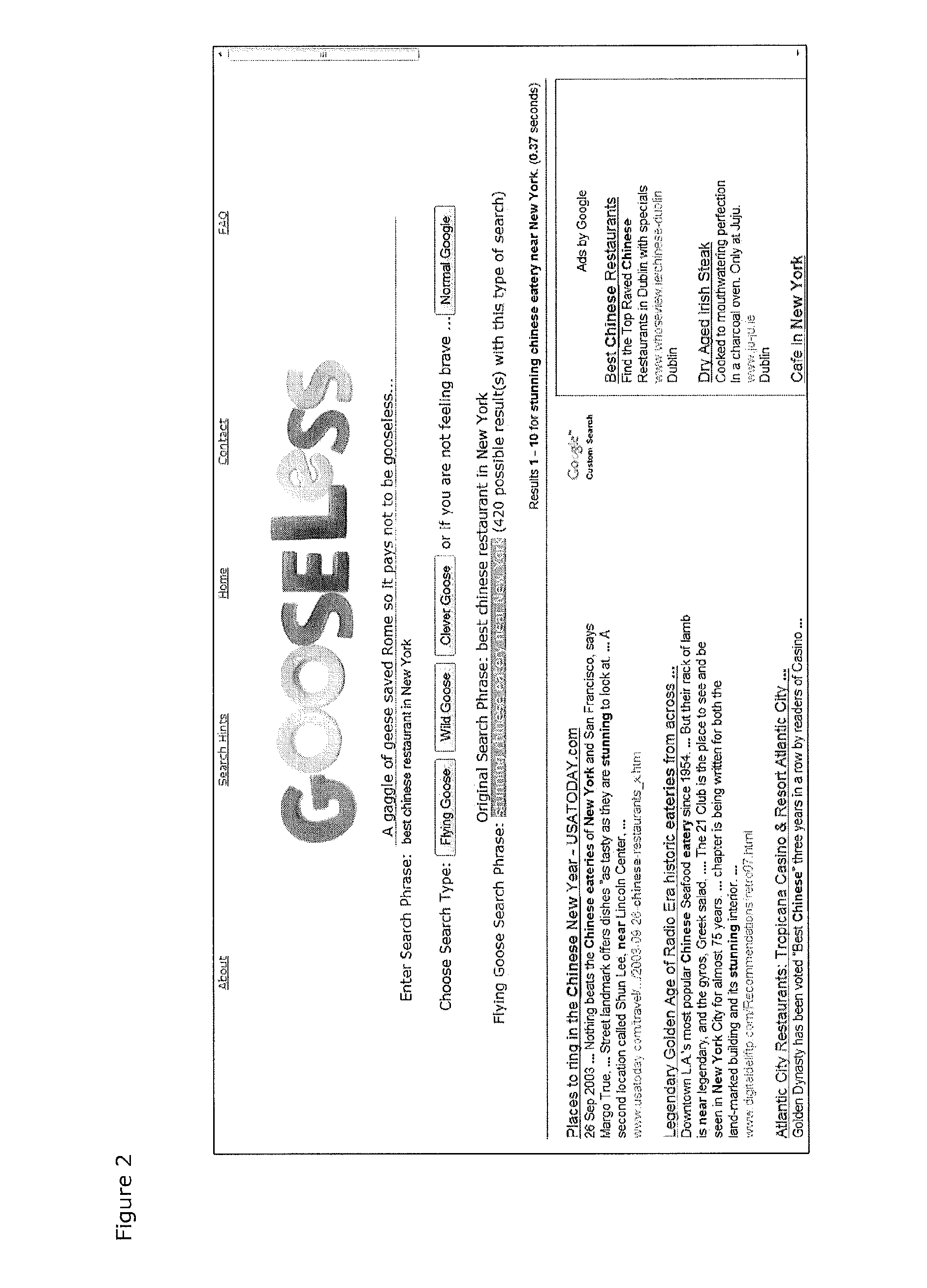
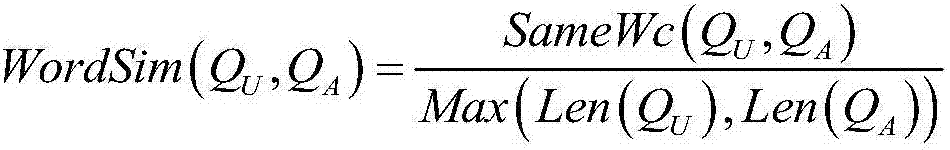Patents
Literature
471 results about "Lexical analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
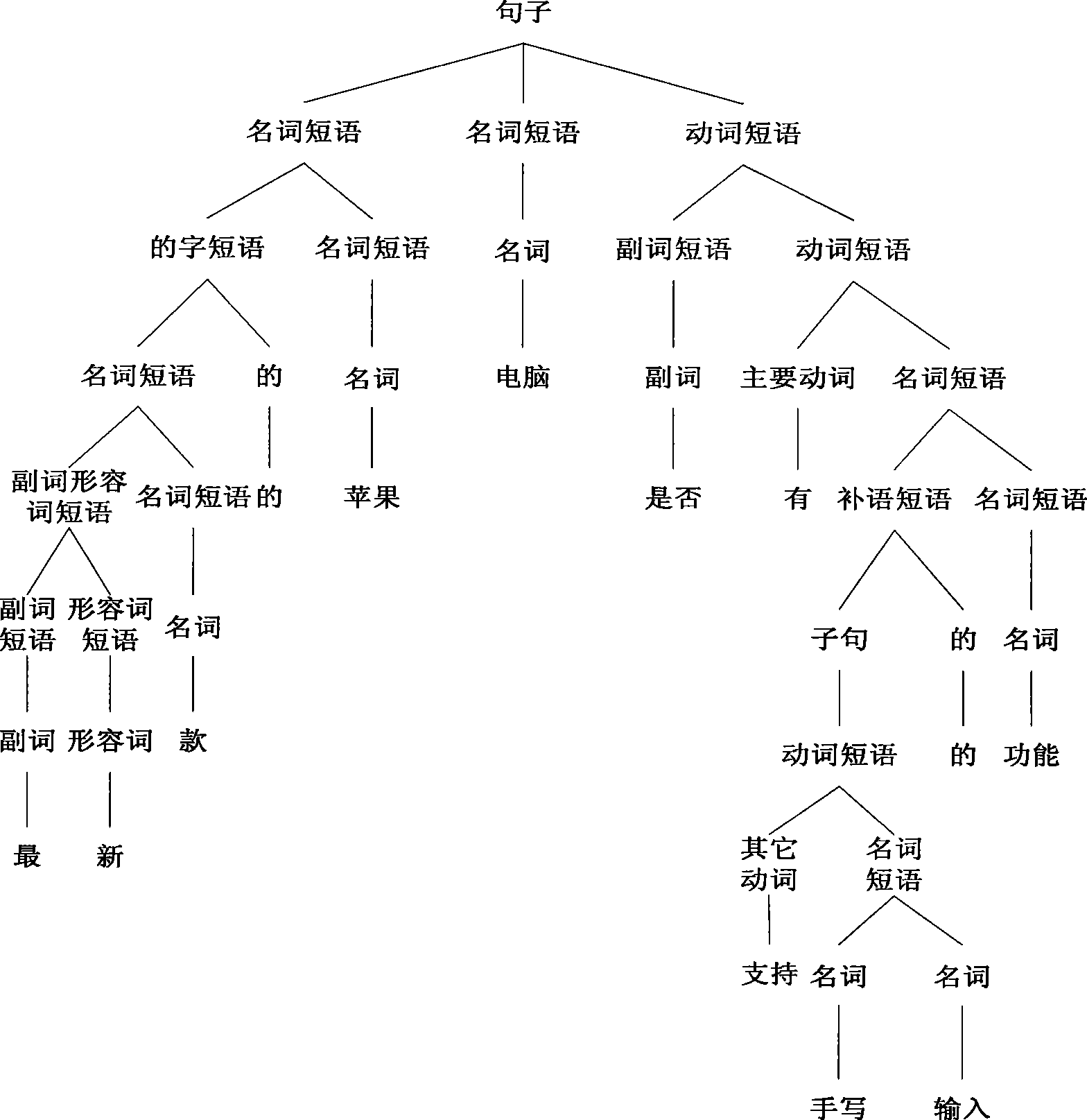
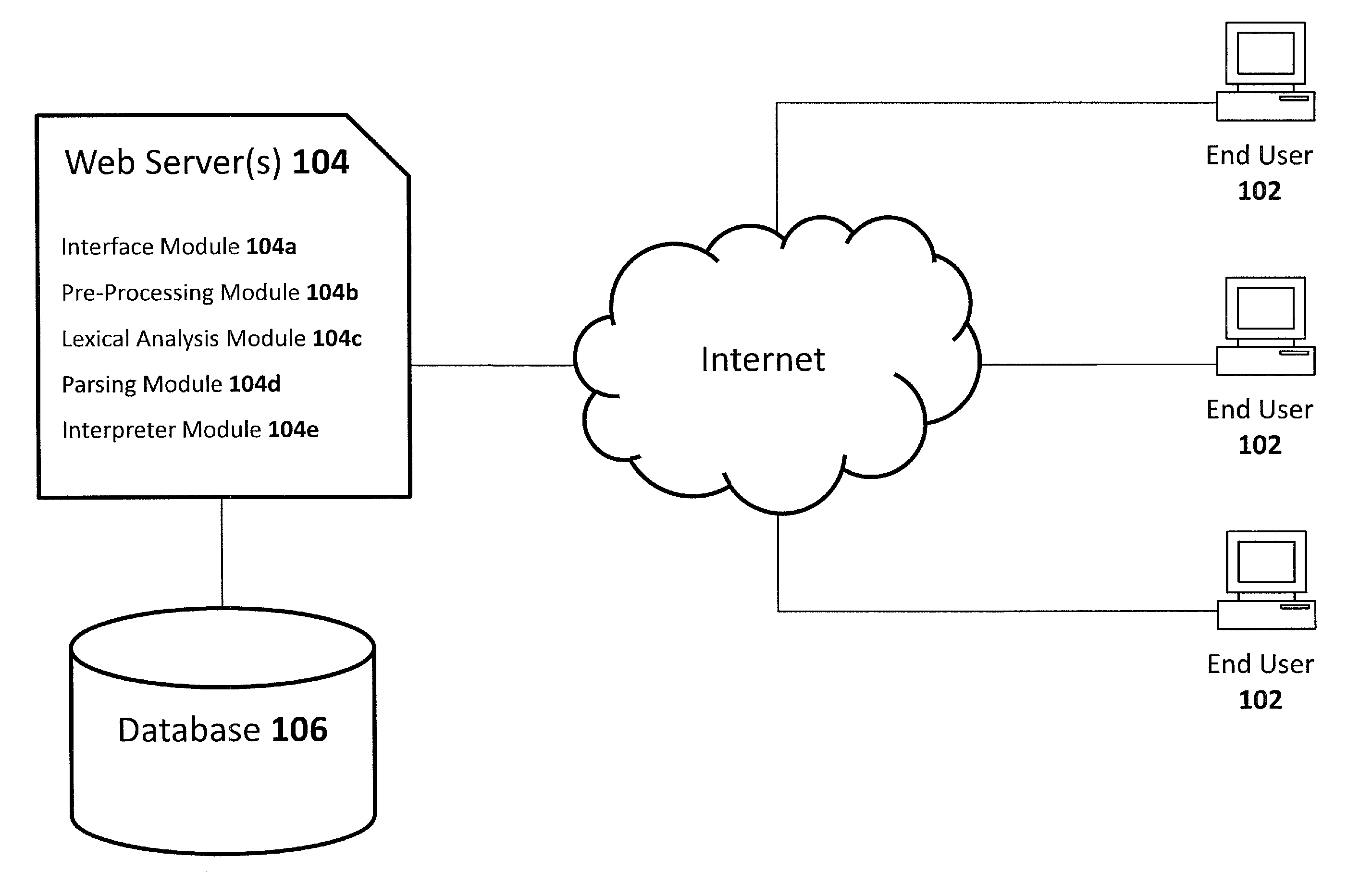
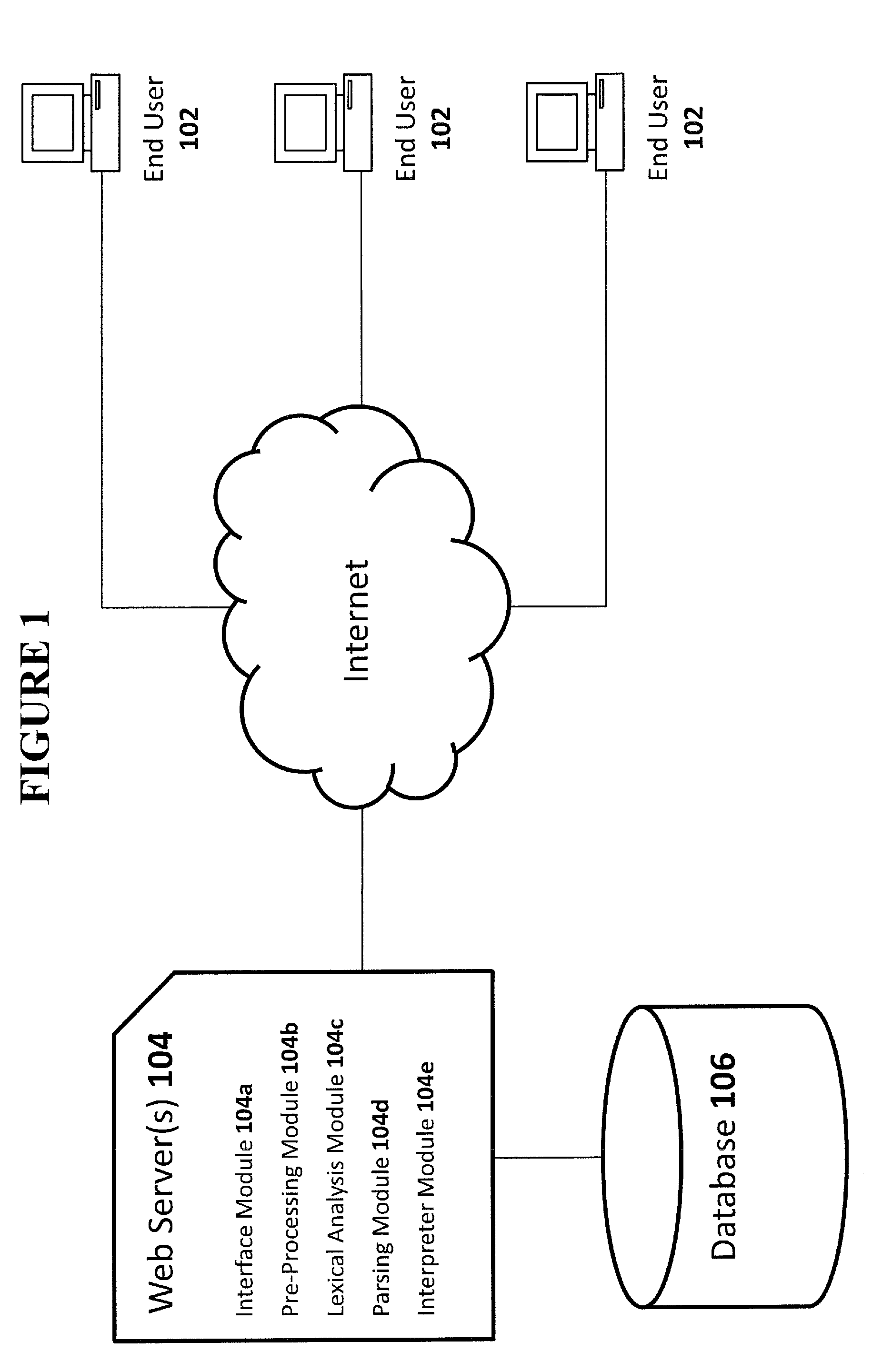
In computer science, lexical analysis, lexing or tokenization is the process of converting a sequence of characters (such as in a computer program or web page) into a sequence of tokens (strings with an assigned and thus identified meaning). A program that performs lexical analysis may be termed a lexer, tokenizer, or scanner, though scanner is also a term for the first stage of a lexer. A lexer is generally combined with a parser, which together analyze the syntax of programming languages, web pages, and so forth.
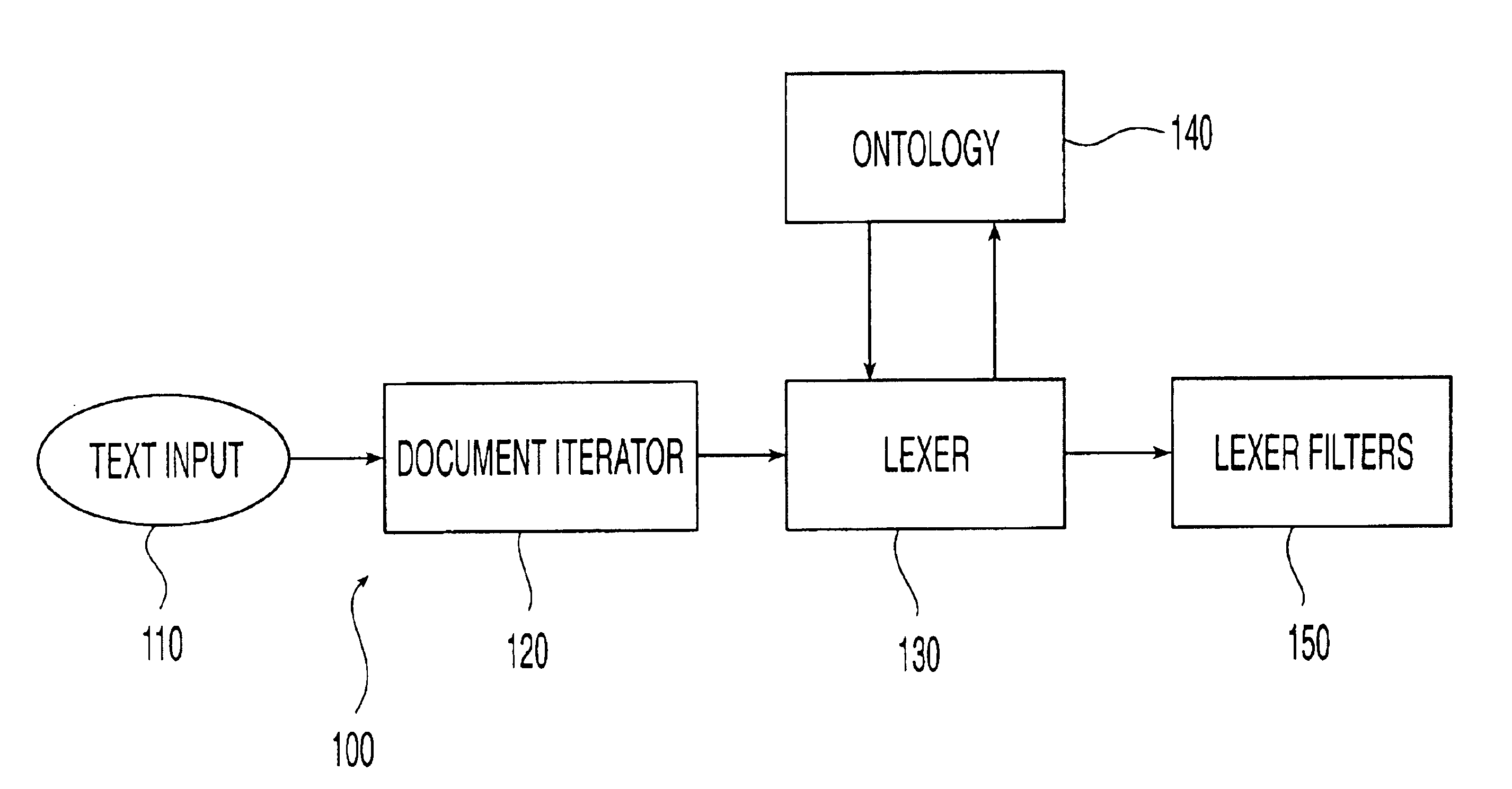
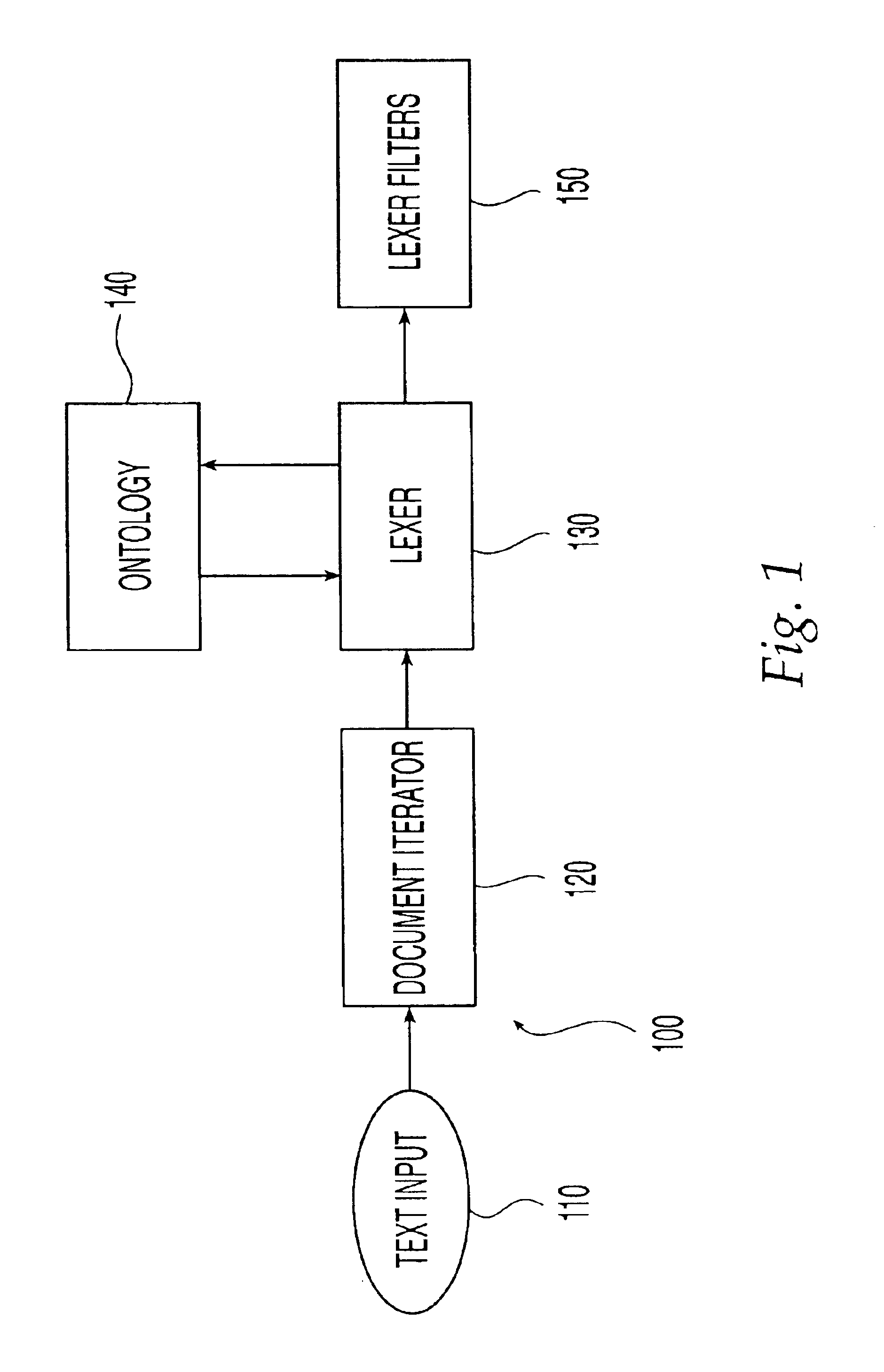
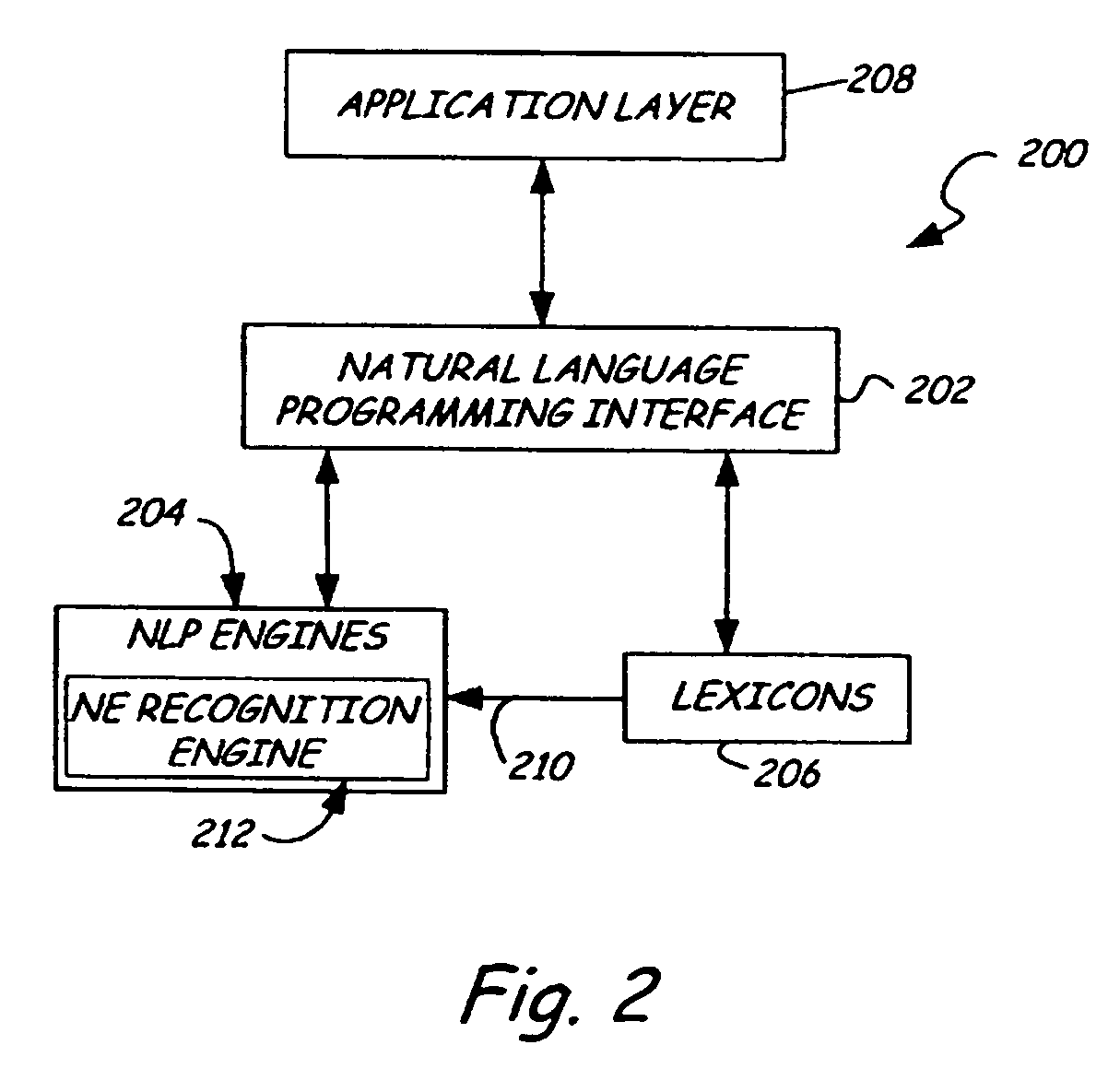
Ontology-based parser for natural language processing
ActiveUS7027974B1Maximum speedData processing applicationsNatural language data processingPart of speechNatural language programming
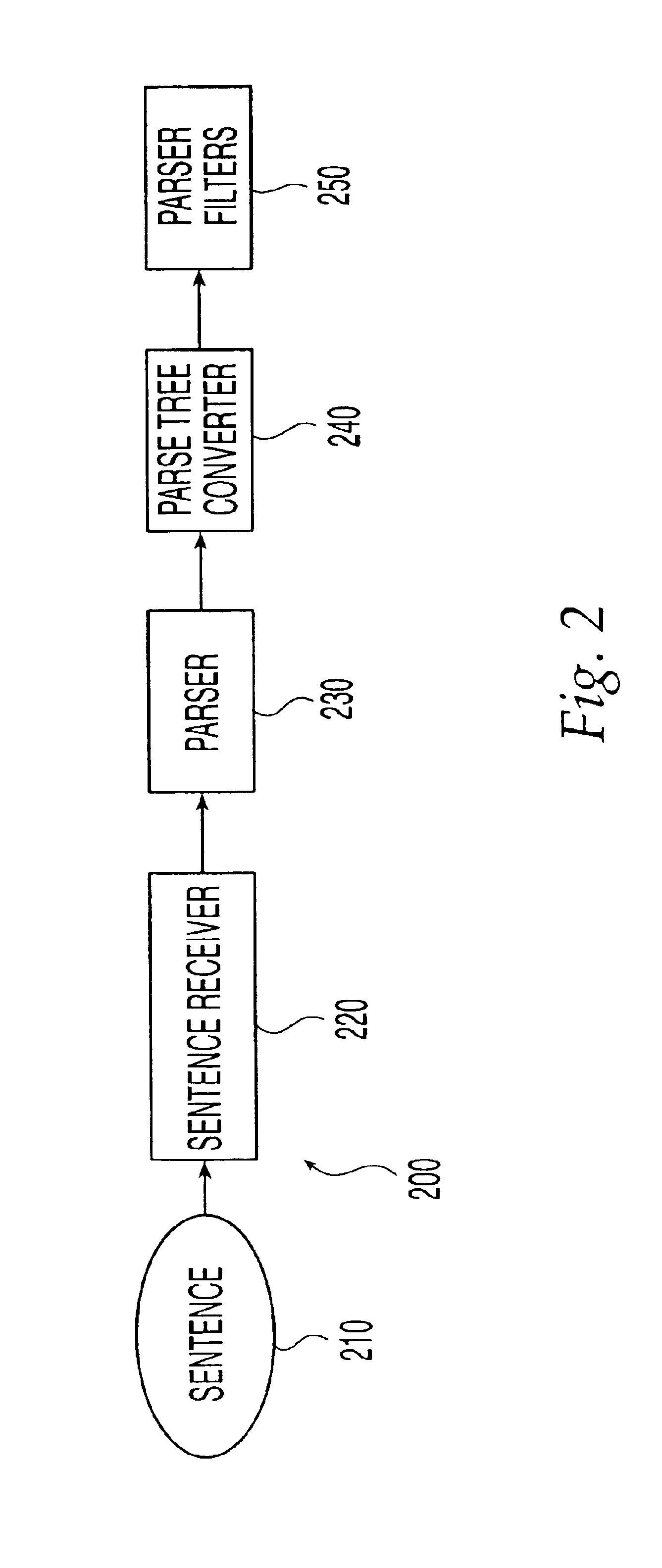
An ontology-based parser incorporates both a system and method for converting natural-language text into predicate-argument format that can be easily used by a variety of applications, including search engines, summarization applications, categorization applications, and word processors. The ontology-based parser contains functional components for receiving documents in a plurality of formats, tokenizing them into instances of concepts from an ontology, and assembling the resulting concepts into predicates. The ontological parser has two major functional elements, a sentence lexer and a parser. The sentence lexer takes a sentence and converts it into a sequence of ontological entities that are tagged with part-of-speech information. The parser converts the sequence of ontological entities into predicate structures using a two-stage process that analyzes the grammatical structure of the sentence, and then applies rules to it that bind arguments into predicates.
Owner:LEIDOS
Enquiry statement analytical method and system for information retrieval
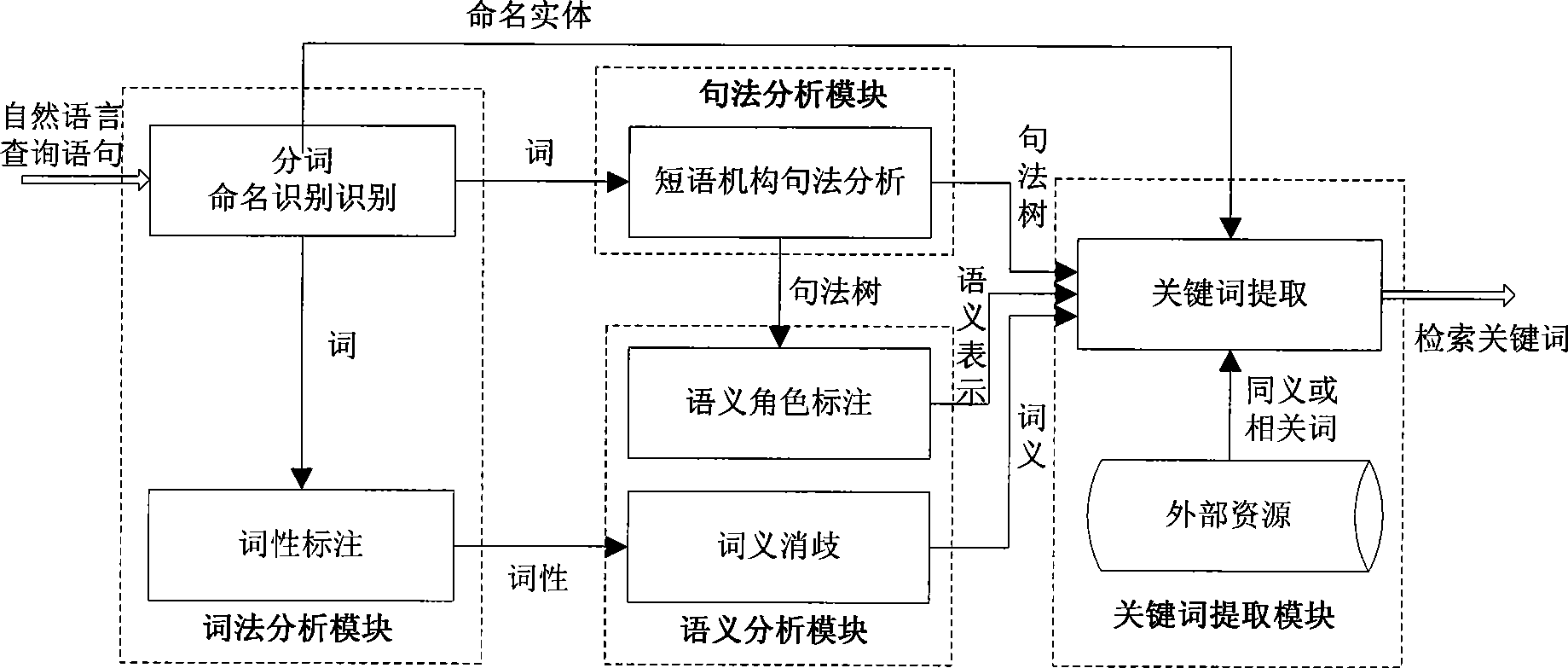
InactiveCN101510221ASearch results are accurateExact matchNatural language data processingSpecial data processing applicationsNamed-entity recognitionLexical analysis
The invention discloses a query sentence analyzing method based on understanding of natural languages and a system thereof, and belongs to the technical field of information retrieval. The query sentence analyzing method comprises the following steps: (1) automatic segmenting, named entity identification and part-of-speech tagging of an input Chinese query sentence are implemented; (2) syntax structure of the segmented sentence is analyzed so as to obtain a syntax structural tree, and meaning of each word is determined according to the sentence after the part-of-speech tagging; (3) according to the syntax structure and the meaning of each word, semantic roles of predicates in the sentence are tagged; and (4) according to the analyzed result of the sentence from the levels of syntactics, syntax and semantics, keywords are expanded and the keywords that can reflect user information retrieval requirements are extracted. The query sentence analyzing system of the invention comprises a syntactic analyzing module, a syntax analyzing module, a semantic analyzing module and a keyword extracting module. The query sentence analyzing method and system can greatly improve the accuracy of query results and provide desired query results for users.
Owner:PEKING UNIV
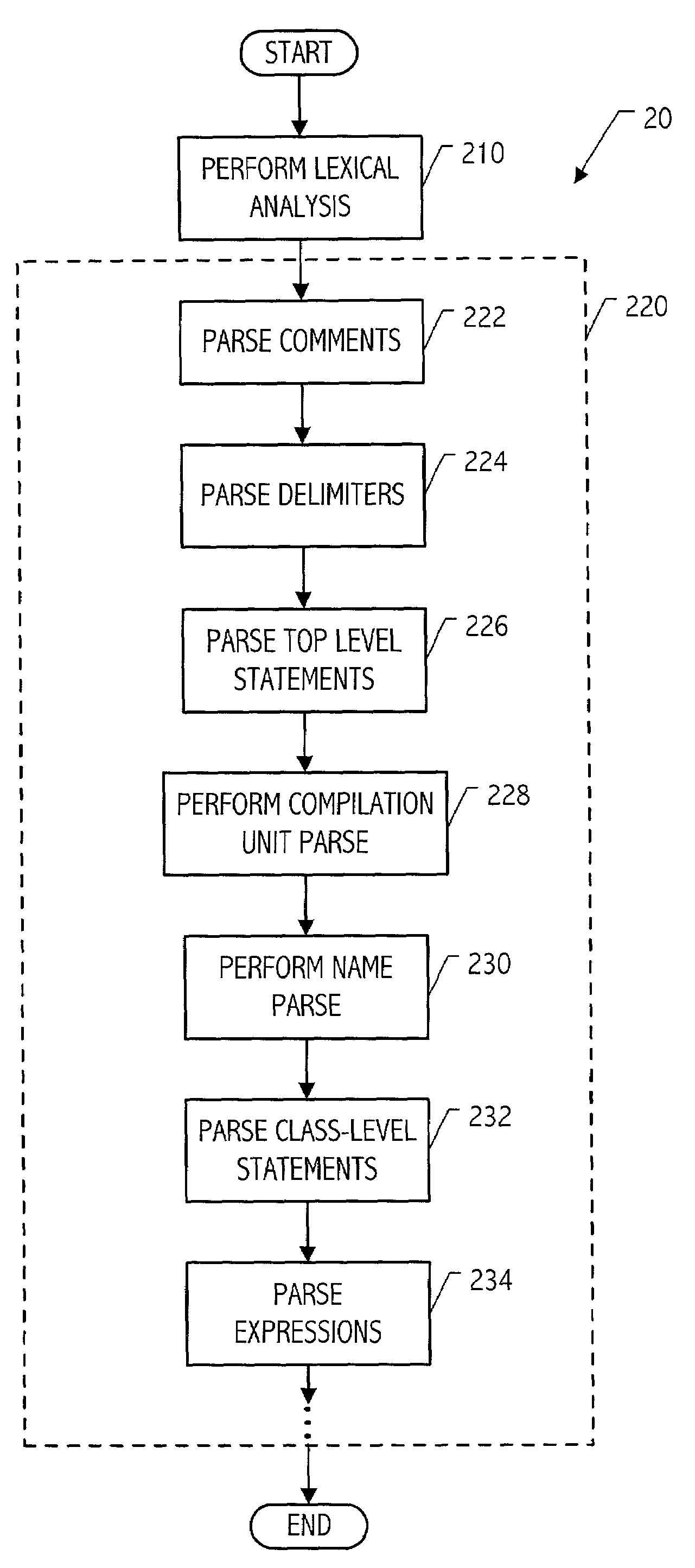
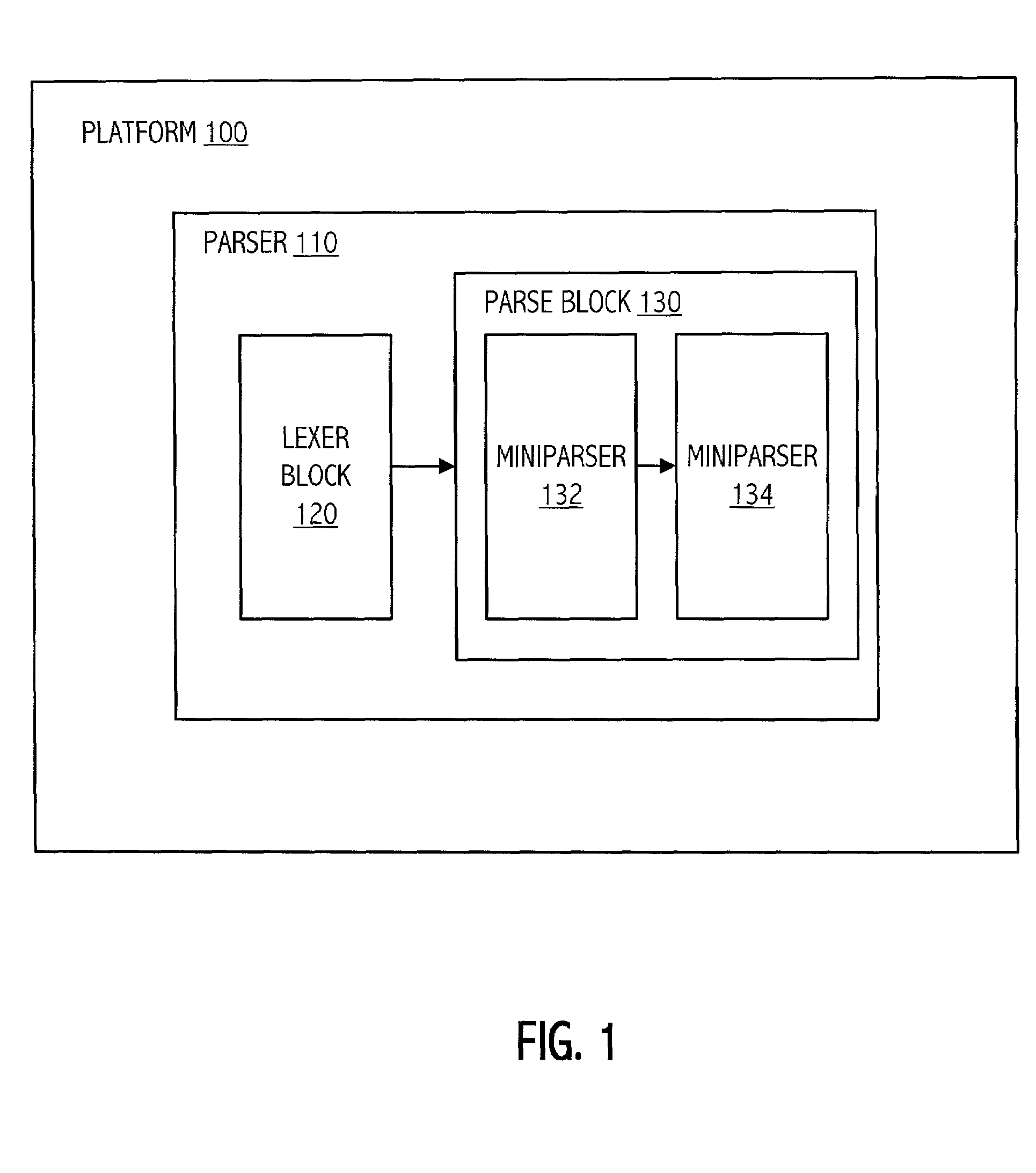
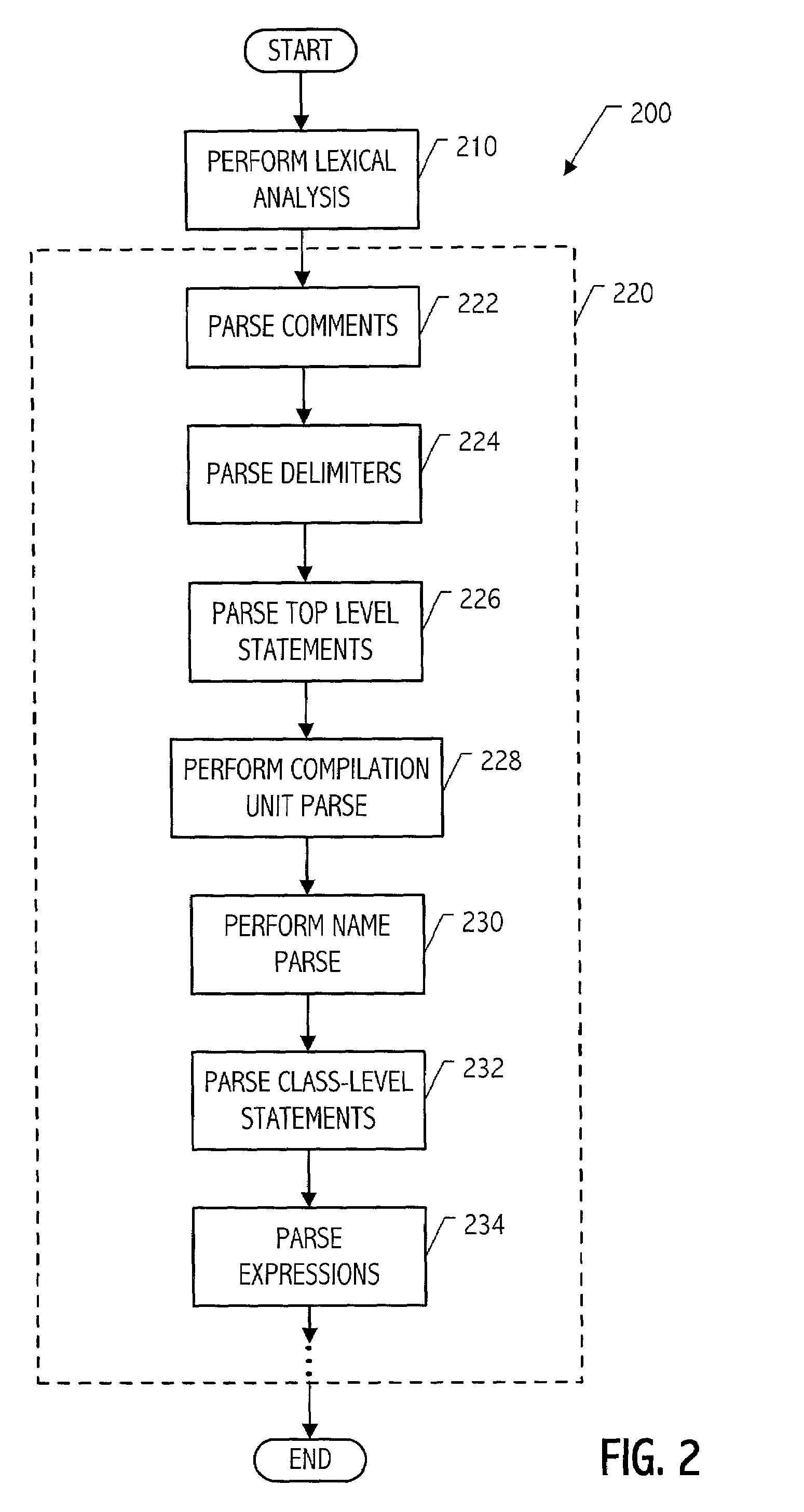
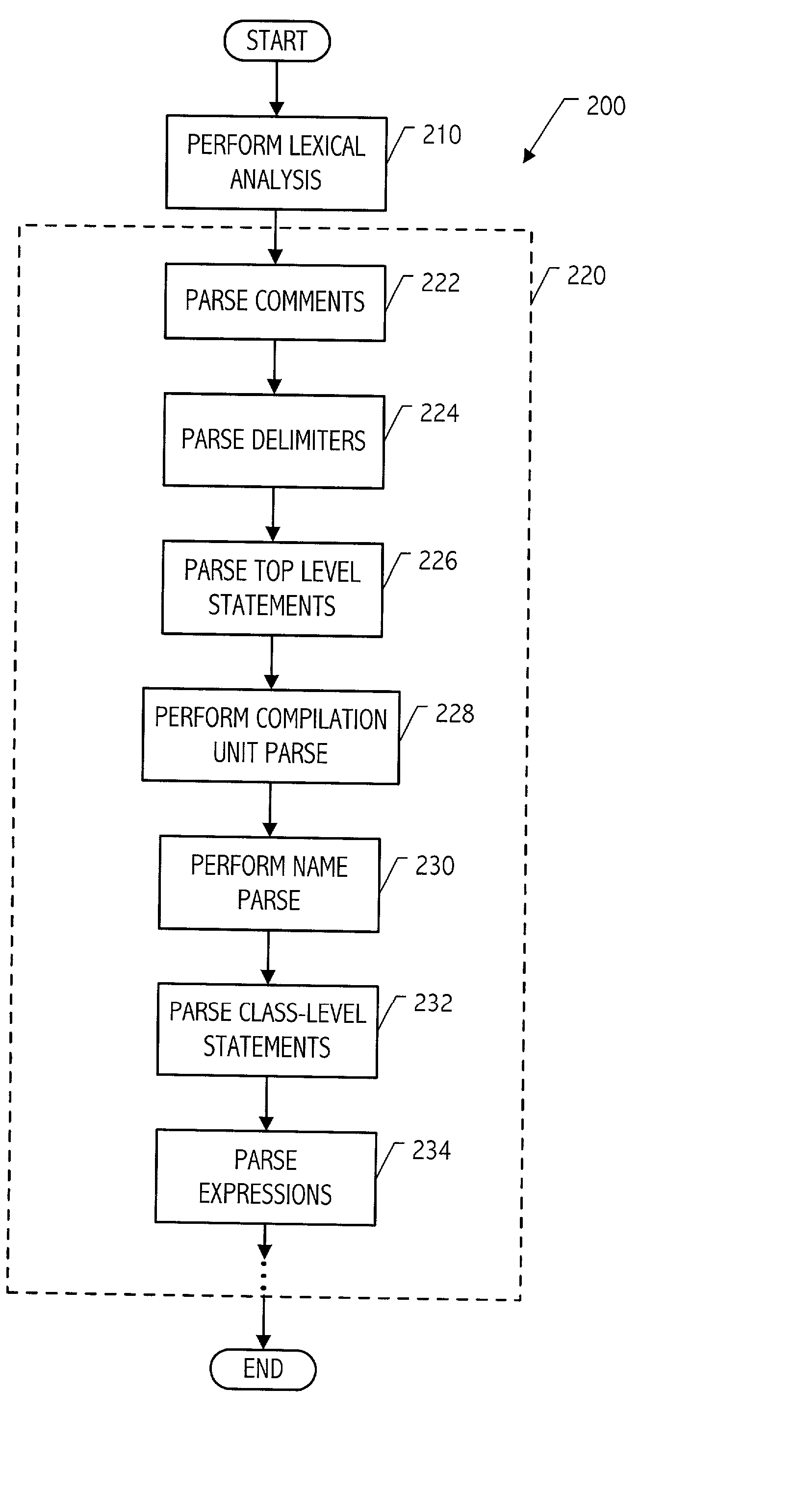
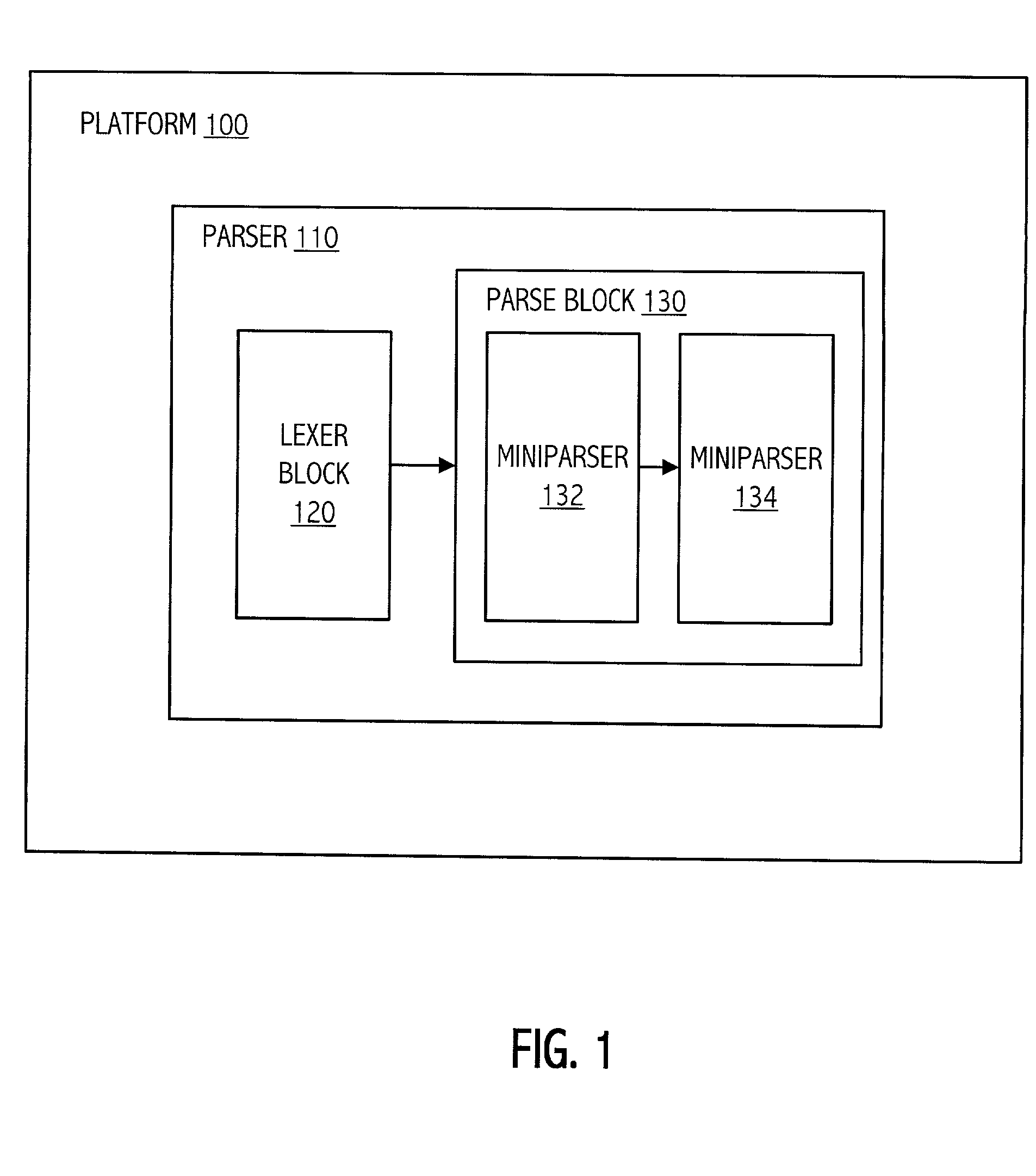
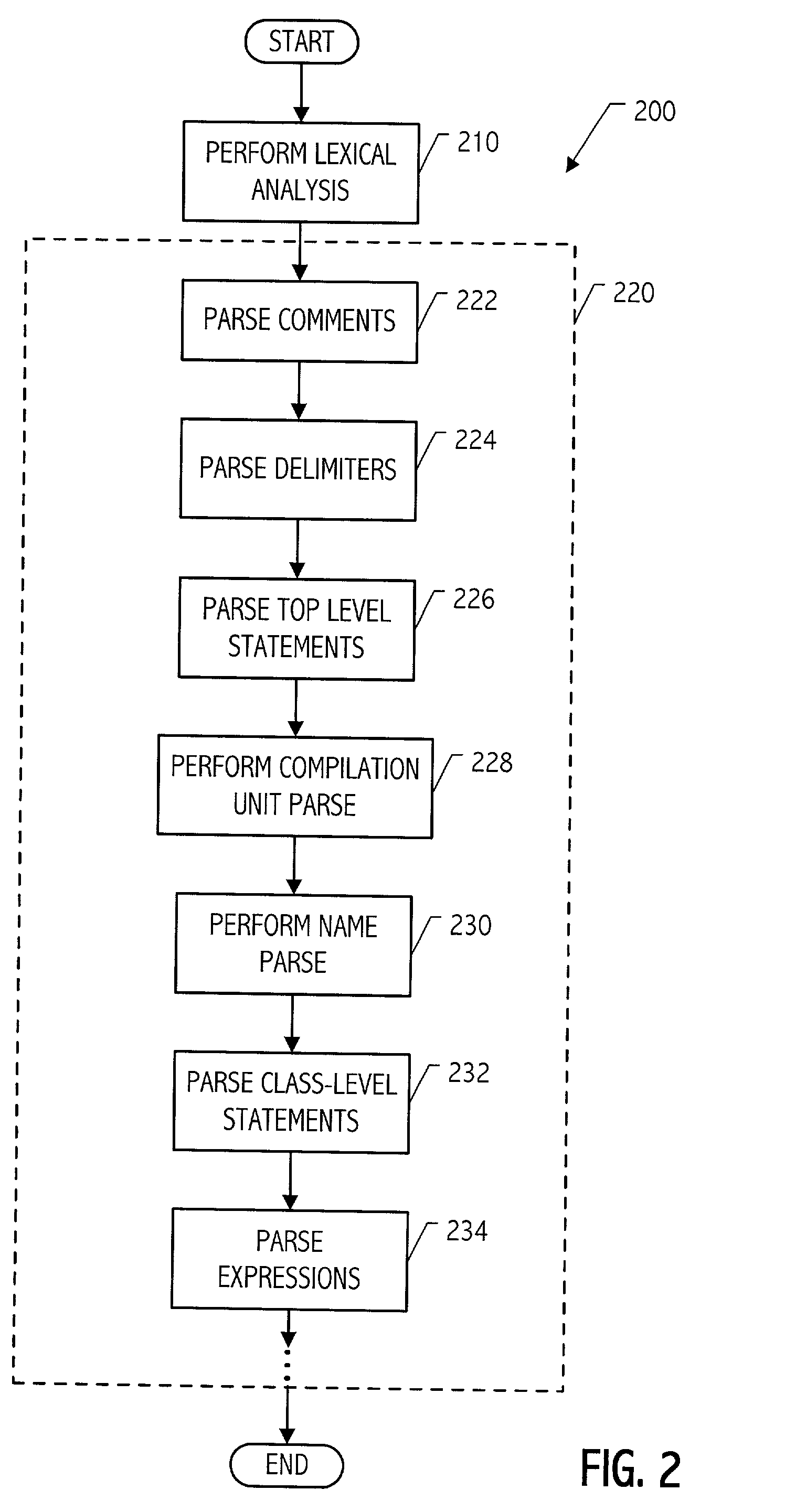
Modular parser architecture with mini parsers
InactiveUS7089541B2Software engineeringSpecific program execution arrangementsMicrocomputerLexical analysis
A modular parser architecture and methods related thereto make use of a number of miniparsers. Each miniparser is capable of receiving input and generating an output dependent thereon. In one embodiment, a lexer or a miniparser capable of lexical analysis receives certain code and provides an abstract syntax tree. Each miniparser performs operations on a set of syntactical constructs to produce a corresponding output syntax tree, which in turn may become an input syntax tree for a next miniparser which may operate on a different set of syntactical constructs.
Owner:ORACLE INT CORP
Test method and system based on software defect mode
InactiveCN101286132AReduce false positivesImprove test accuracySoftware testing/debuggingControl flowPresent method
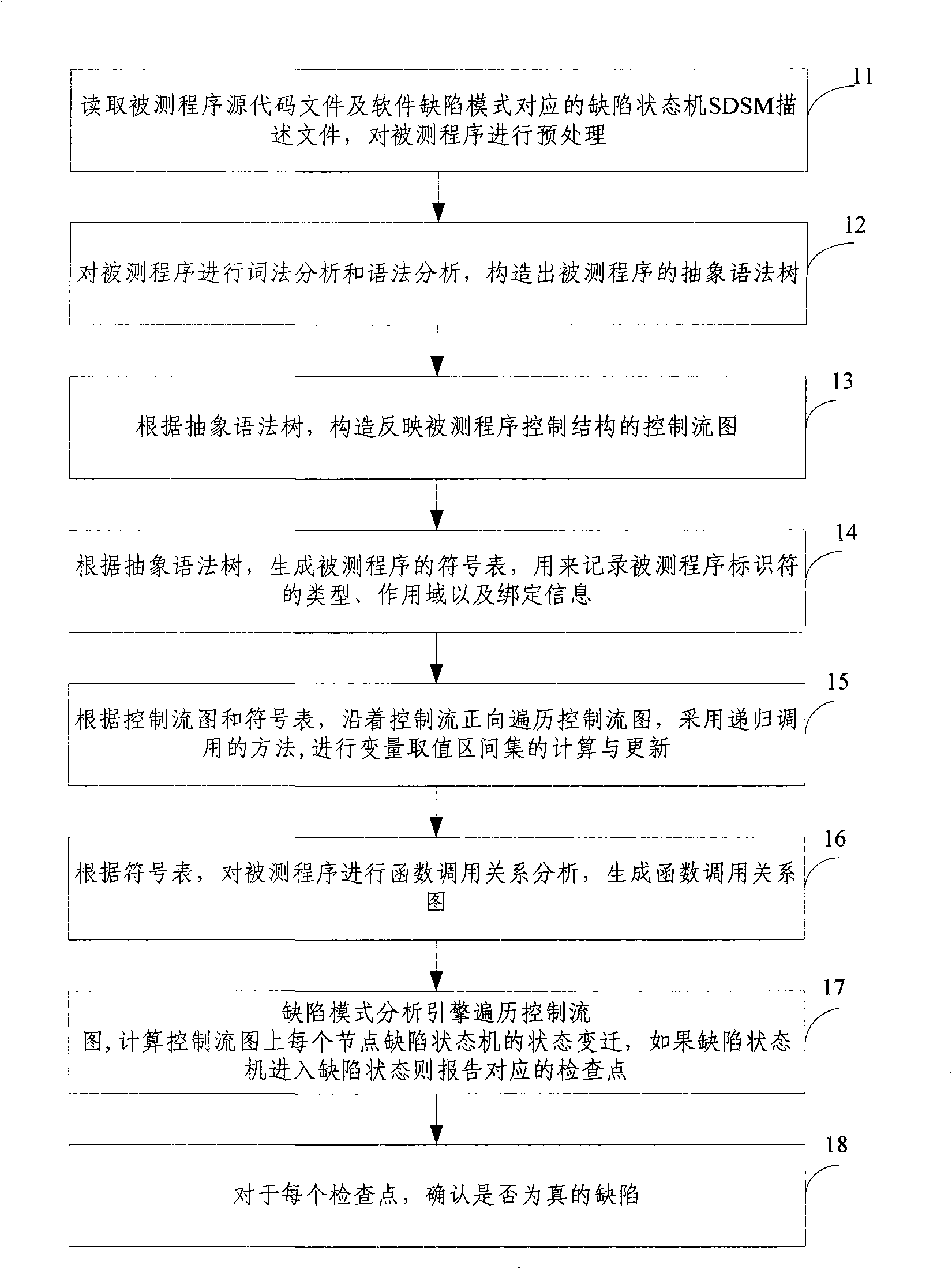
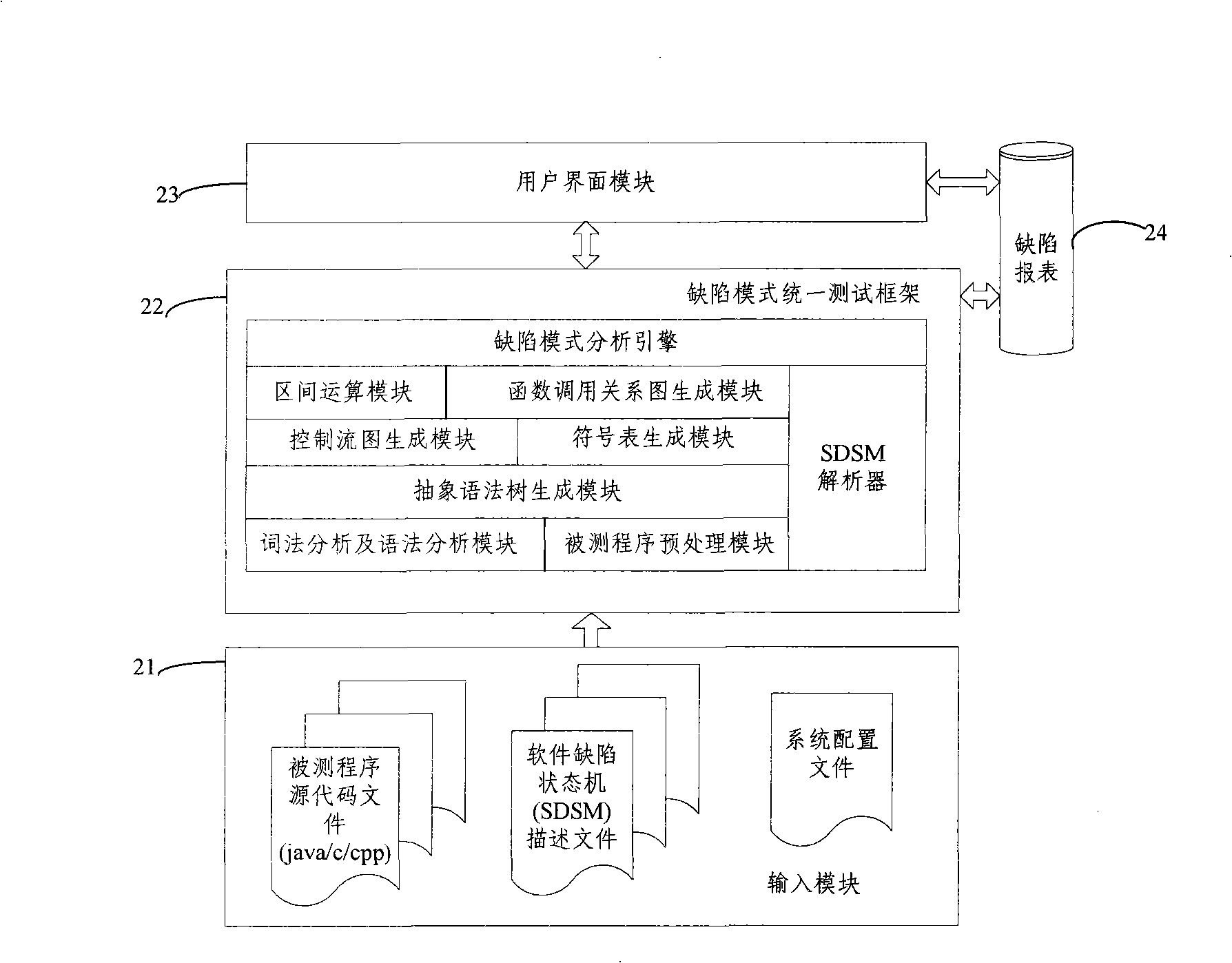
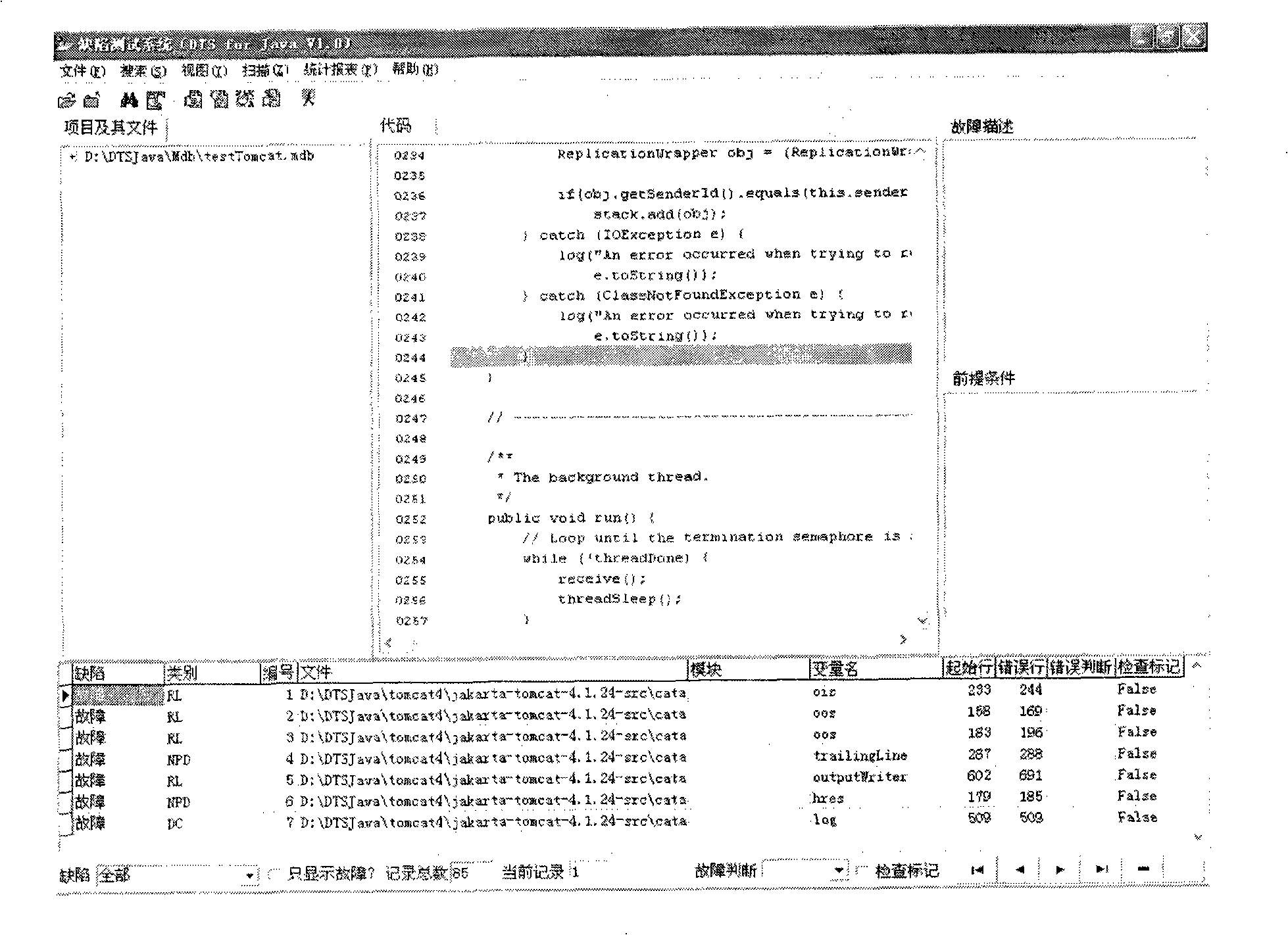
The invention discloses a testing method based on software defect mode, comprising the steps of: reading source code files of programs to be tested and SDSM description file of a defect state machine, carrying out pre-processing of the programs to be tested, analyzing the SDSM description file; carrying out lexical analysis and grammar analysis of the programs to be tested and constructing abstract syntax tree; generating a control flow graph and a symbol table according to the abstract syntax tree and carrying out the calculating and updating of variable value interval sets according to the control flow graph and the symbol table; carrying out function invoking relation analysis of the programs to be tested and generating a function invoking relation graph; searching the control flow graph by taking the function as unit according to the function invoking relation graph, calculating the state migration of each node defect state machine on the control flow graph, and reporting corresponding checking point when the defect state machine enters the defect state. The invention also discloses a testing system based on software defect mode, which comprises an input module, a defect mode uniformity testing frame and a user interface module and completes the uniform test on the programs to be tested.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Software test case automatic generating method and system
InactiveCN101436128AImprove efficiencyHigh degree of automationSoftware testing/debuggingSpecific program execution arrangementsControl flowLexical analysis
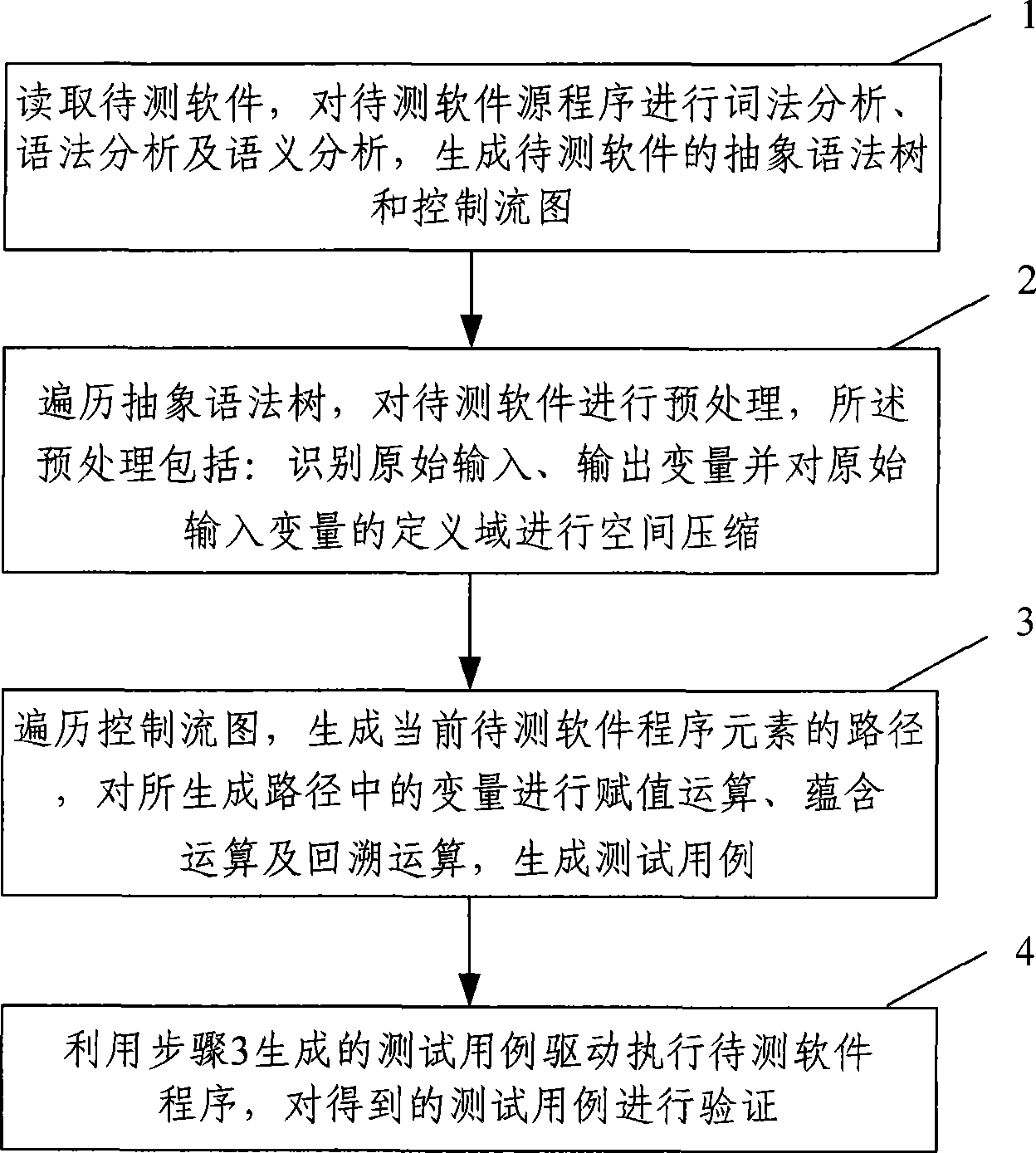
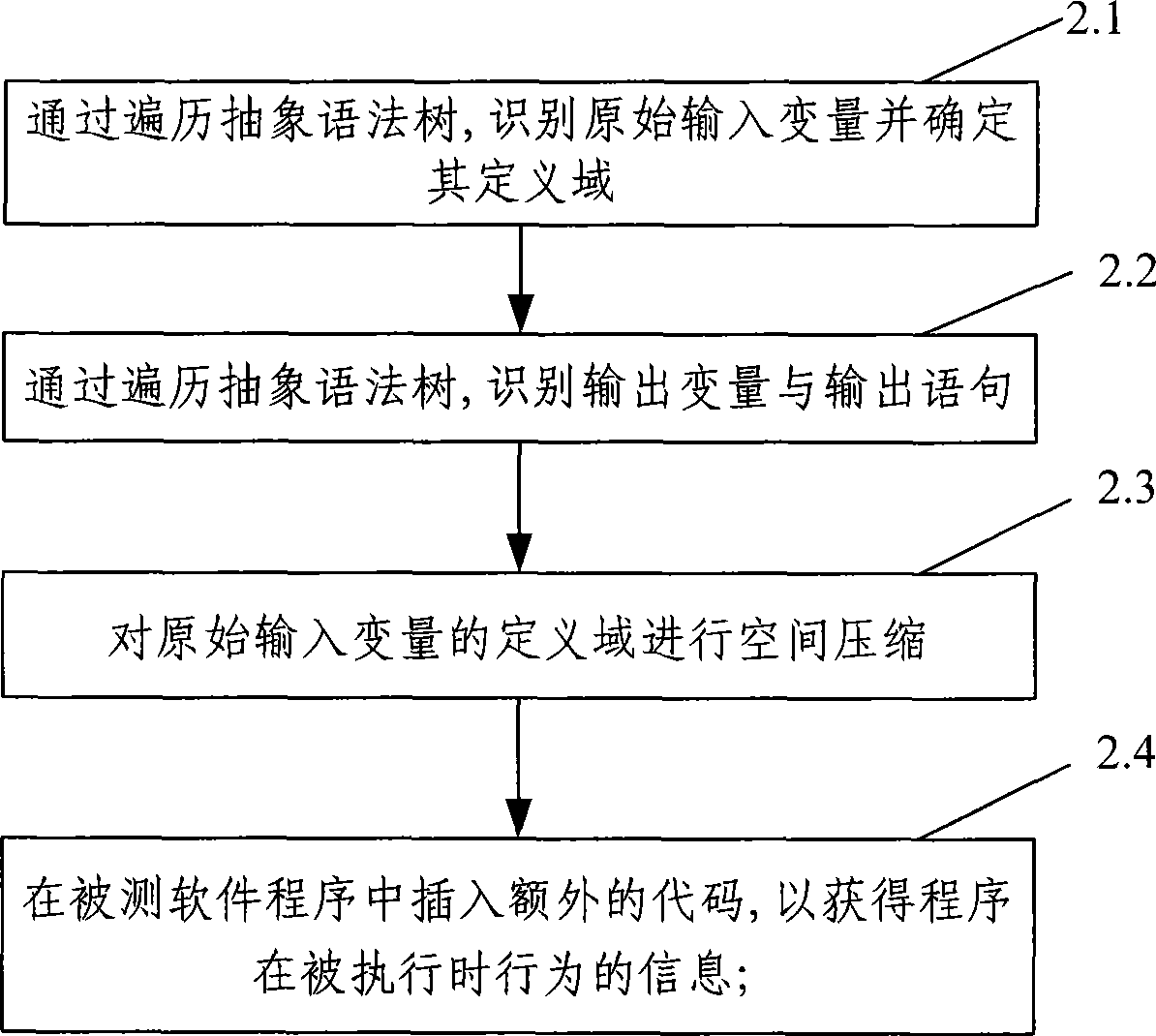
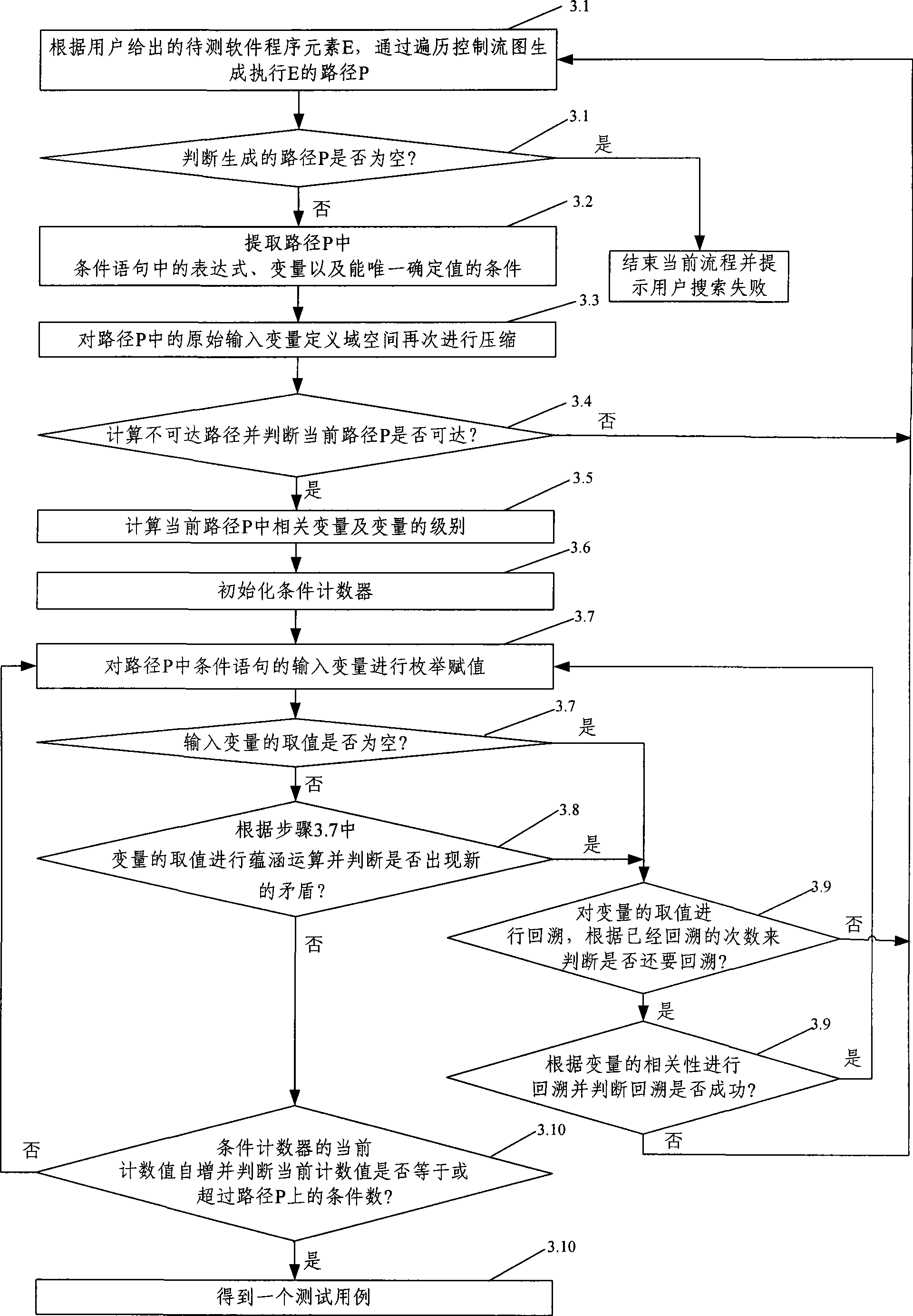
The invention provides a method for automatically generating software test cases. The method comprises the following steps of: A. reading to-be-tested software, carrying out lexical analysis, syntax analysis and semantic analysis on a source program of the to-be-tested software and generating an abstract syntax tree and a control flow graph of the to-be-tested software; B. preprocessing the source program of the to-be-tested software by traversing the generated abstract syntax tree, identifying initial input-output variables and compressing the space of a definition domain of the initial input variables; and C. generating a path of program elements of the current to-be-tested software by traversing the control flow graph, carrying out assignment operation, implication operation and backtracking operation on the variables in the path, and generating the test cases. The invention also provides a system for automatically generating software test cases. The method and the system for automatically generating the software test cases can accurately and automatically generate the test cases according to the given program elements of the to-be-tested software and verify the generated test cases, thereby improving the accuracy, efficiency and automation degree of the test cases.
Owner:BEIJING UNIV OF POSTS & TELECOMM
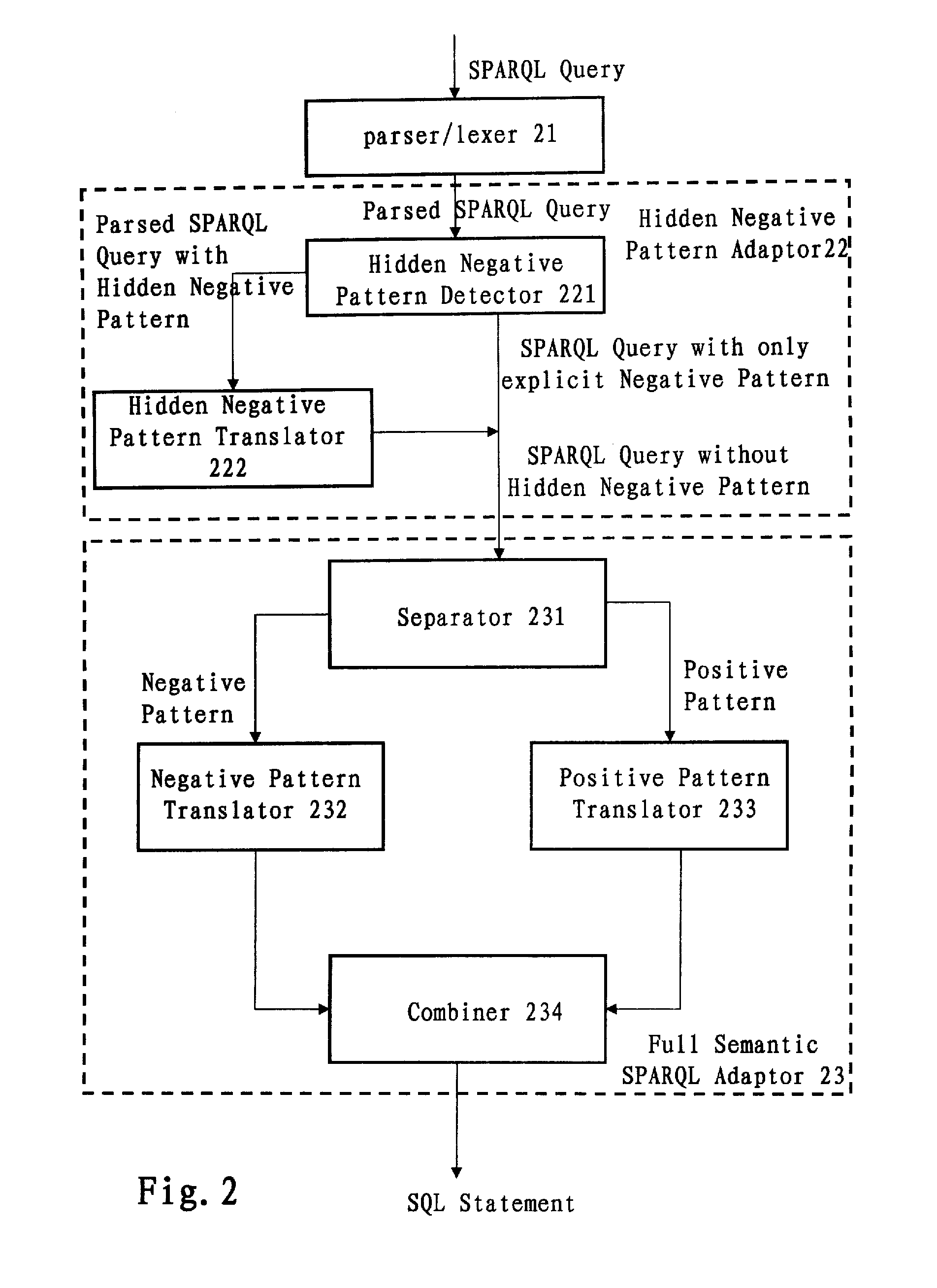
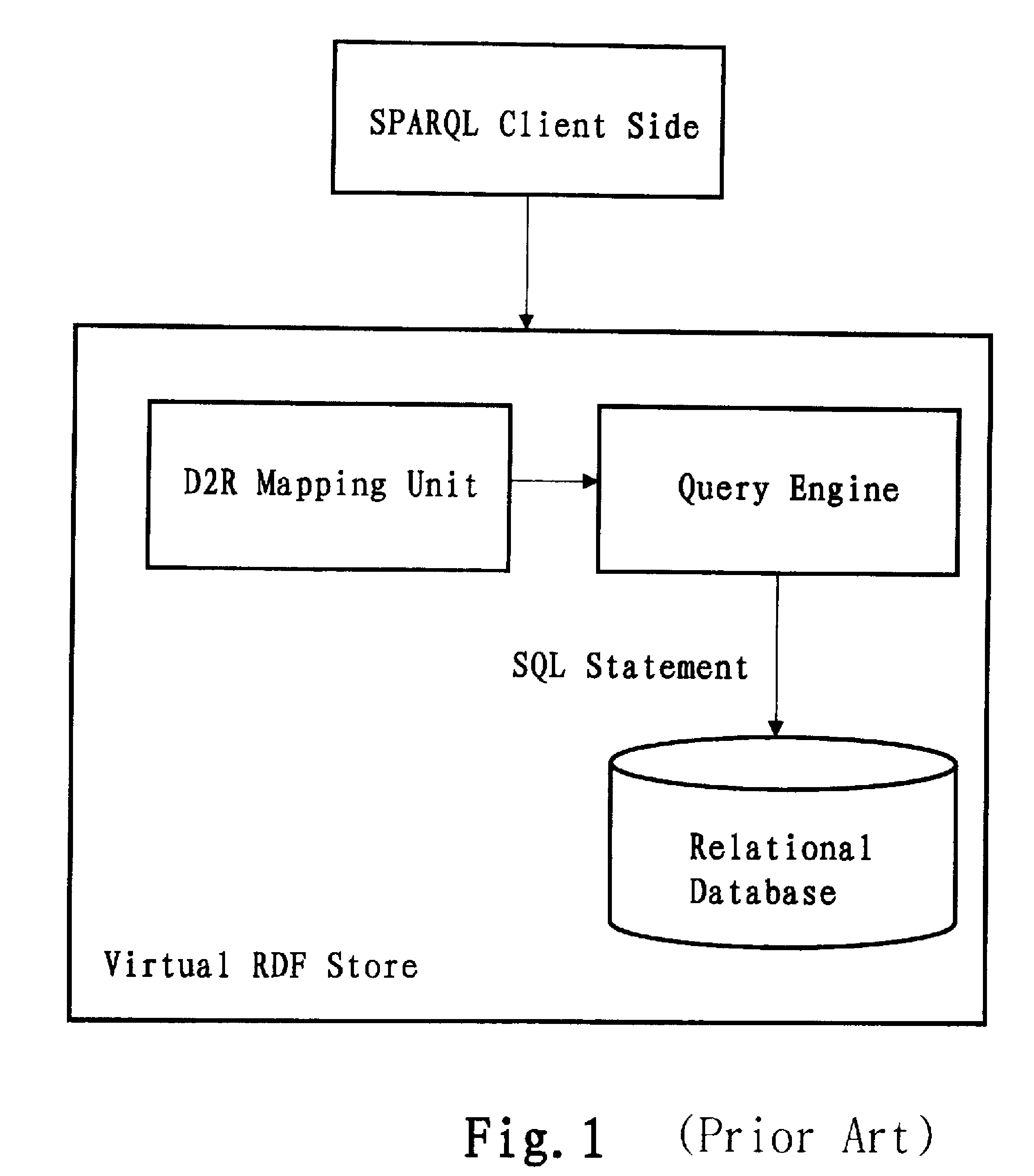
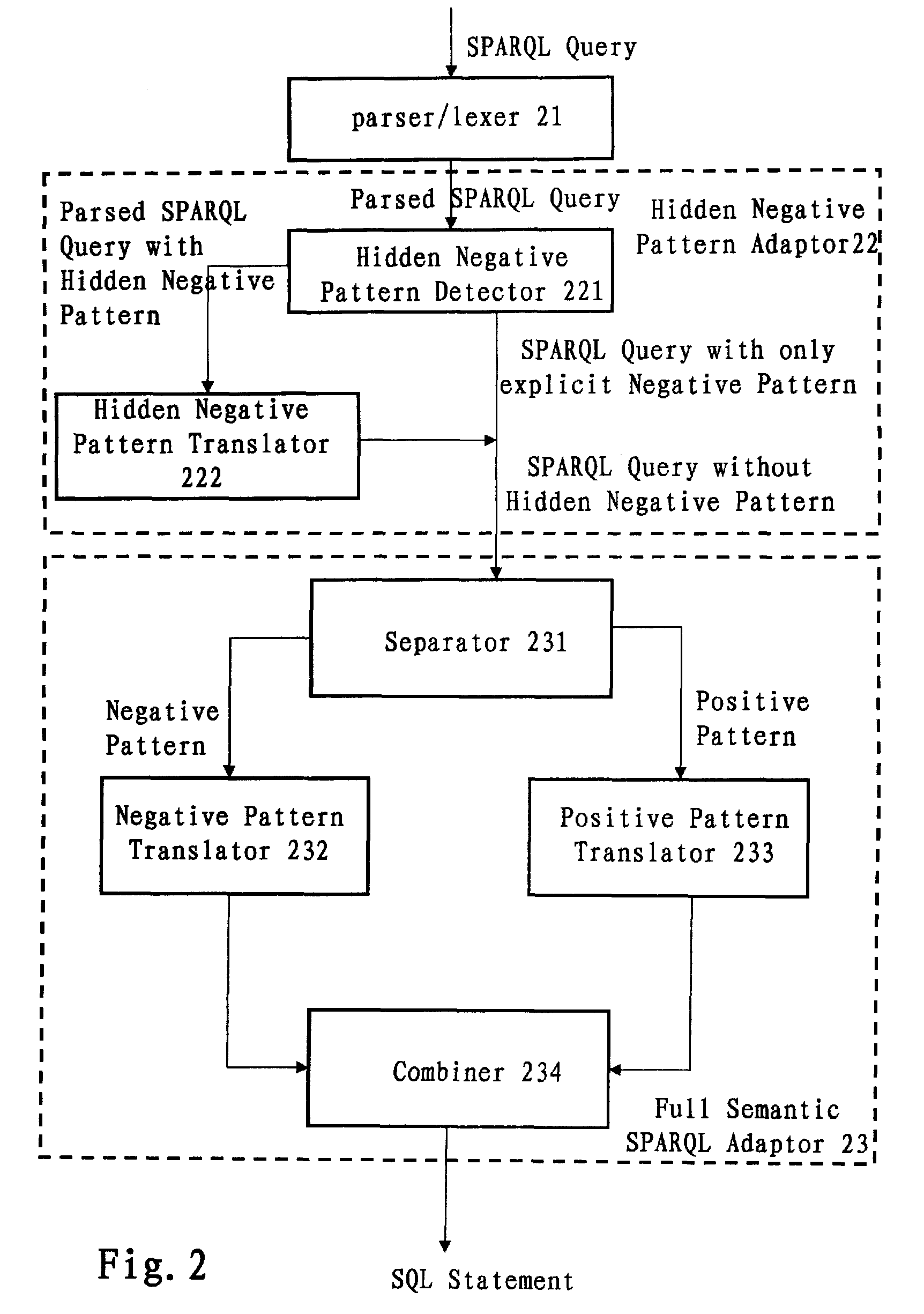
Translation system and method for sparql queries
InactiveUS20100250577A1Efficiently translatedDigital data information retrievalDigital data processing detailsLexical analysisPattern detection
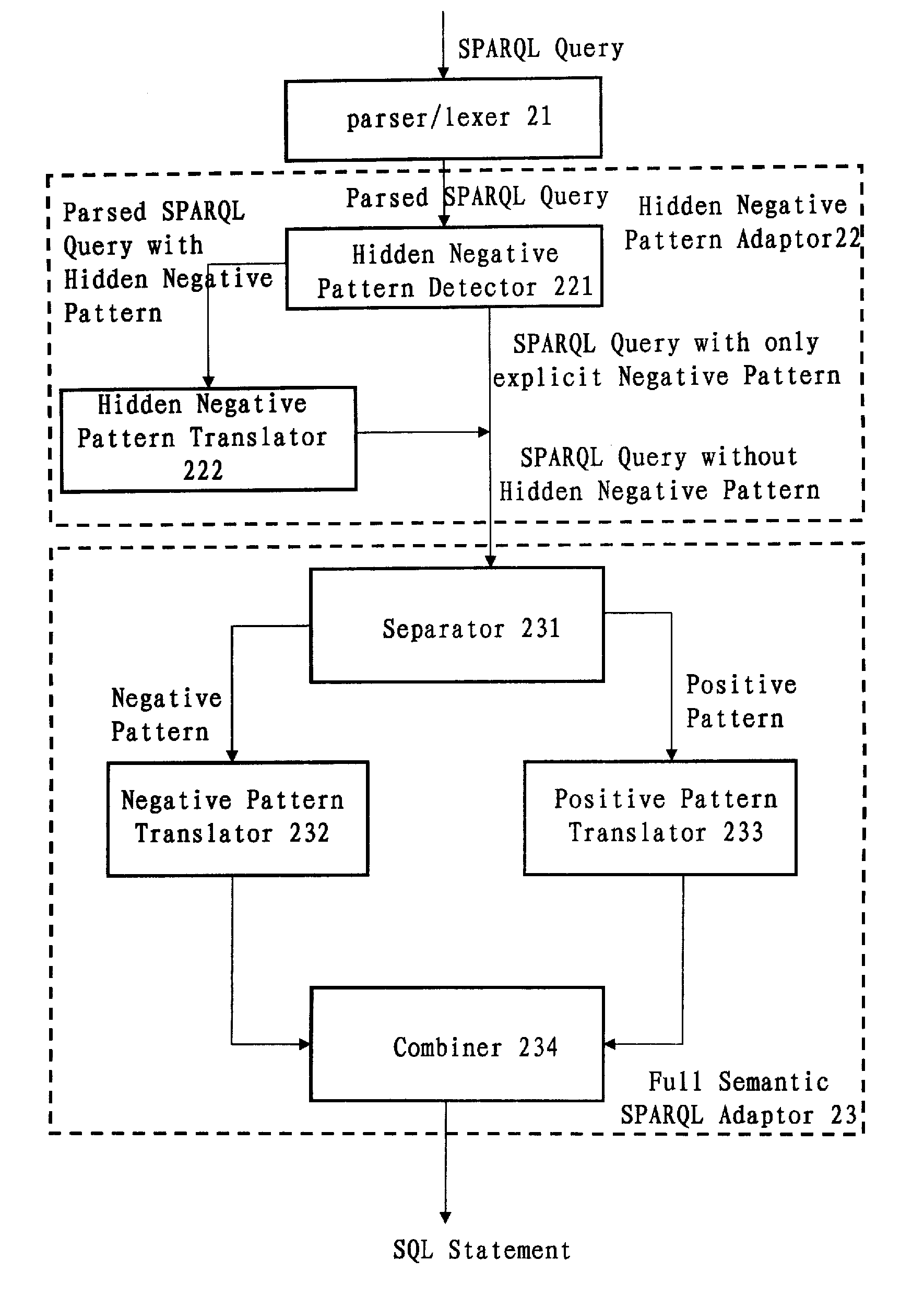
A computer-implemented system and method for translating a SPARQL query. The system includes: a parser / lexer for parsing the SPARQL query; a hidden negative pattern detector for detecting a hidden negative pattern in the parsed SPARQL query; a hidden negative pattern translator for translating the detected hidden negative pattern into an explicit negative pattern; a separator for separating the explicit negative pattern from a positive pattern in the parsed SPARQL query; a negative pattern translator for translating the explicit negative pattern into a negative portion of an SQL statement; a positive pattern translator for translating the positive pattern into a positive portion of the SQL statement; and an SQL statement combiner for combining the negative portion of the SQL statement with the positive portion of the SQL statement.
Owner:IBM CORP
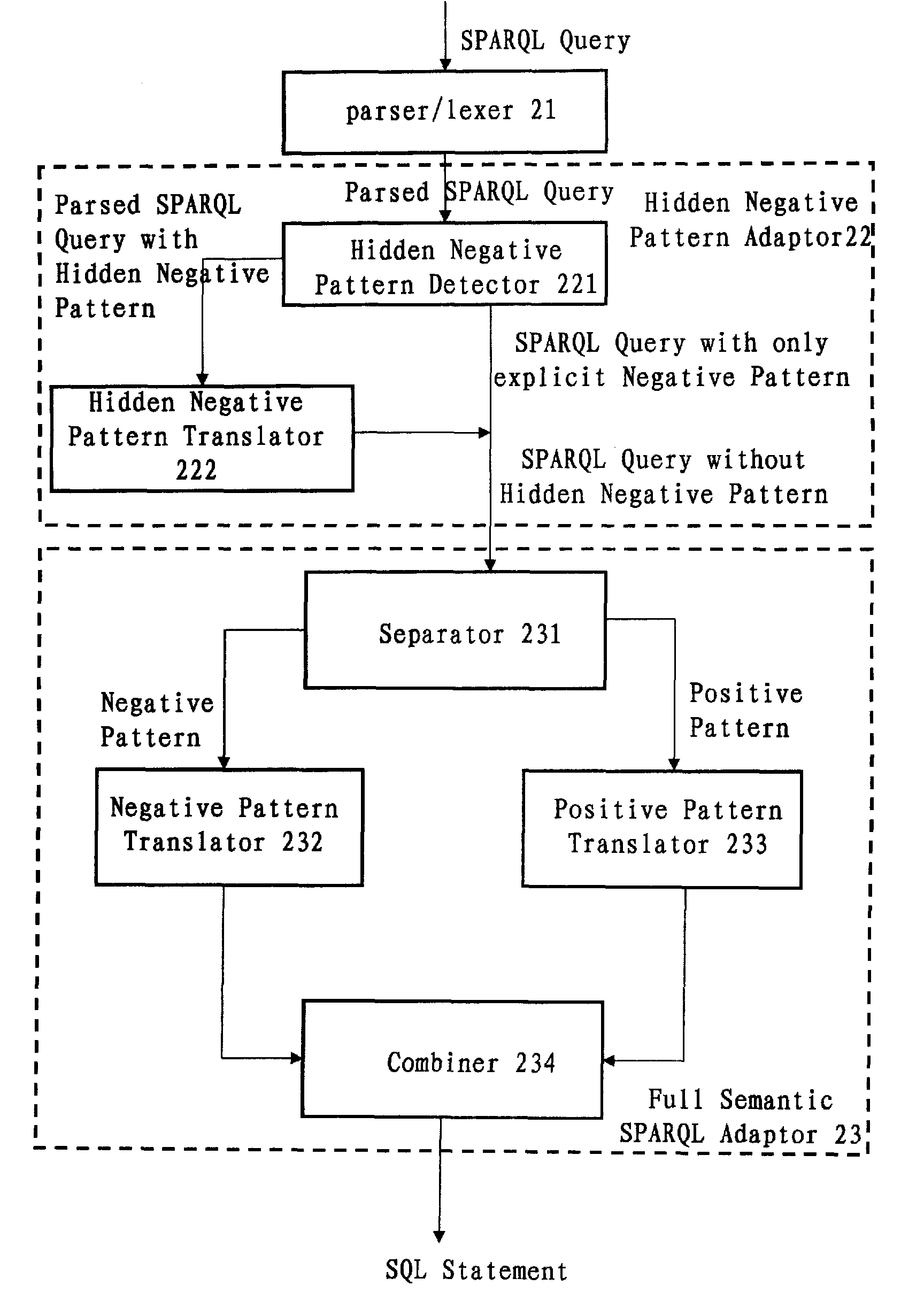
Translation system and method for SPARQL queries
InactiveUS8275784B2Efficiently translatedDigital data information retrievalDigital data processing detailsLexical analysisTheoretical computer science
A computer-implemented system and method for translating a SPARQL query. The system includes: a parser / lexer for parsing the SPARQL query; a hidden negative pattern detector for detecting a hidden negative pattern in the parsed SPARQL query; a hidden negative pattern translator for translating the detected hidden negative pattern into an explicit negative pattern; a separator for separating the explicit negative pattern from a positive pattern in the parsed SPARQL query; a negative pattern translator for translating the explicit negative pattern into a negative portion of an SQL statement; a positive pattern translator for translating the positive pattern into a positive portion of the SQL statement; and an SQL statement combiner for combining the negative portion of the SQL statement with the positive portion of the SQL statement.
Owner:IBM CORP
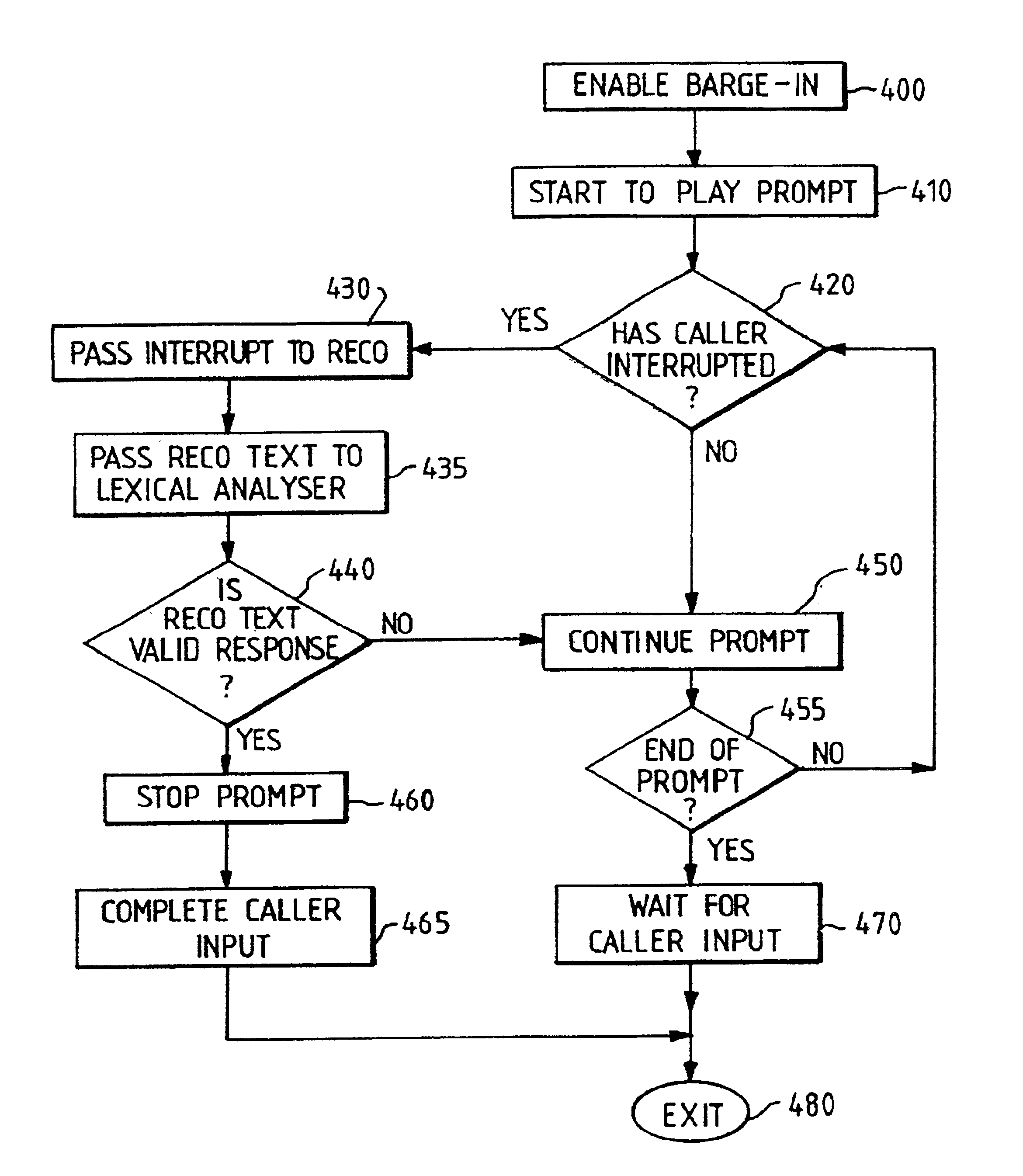
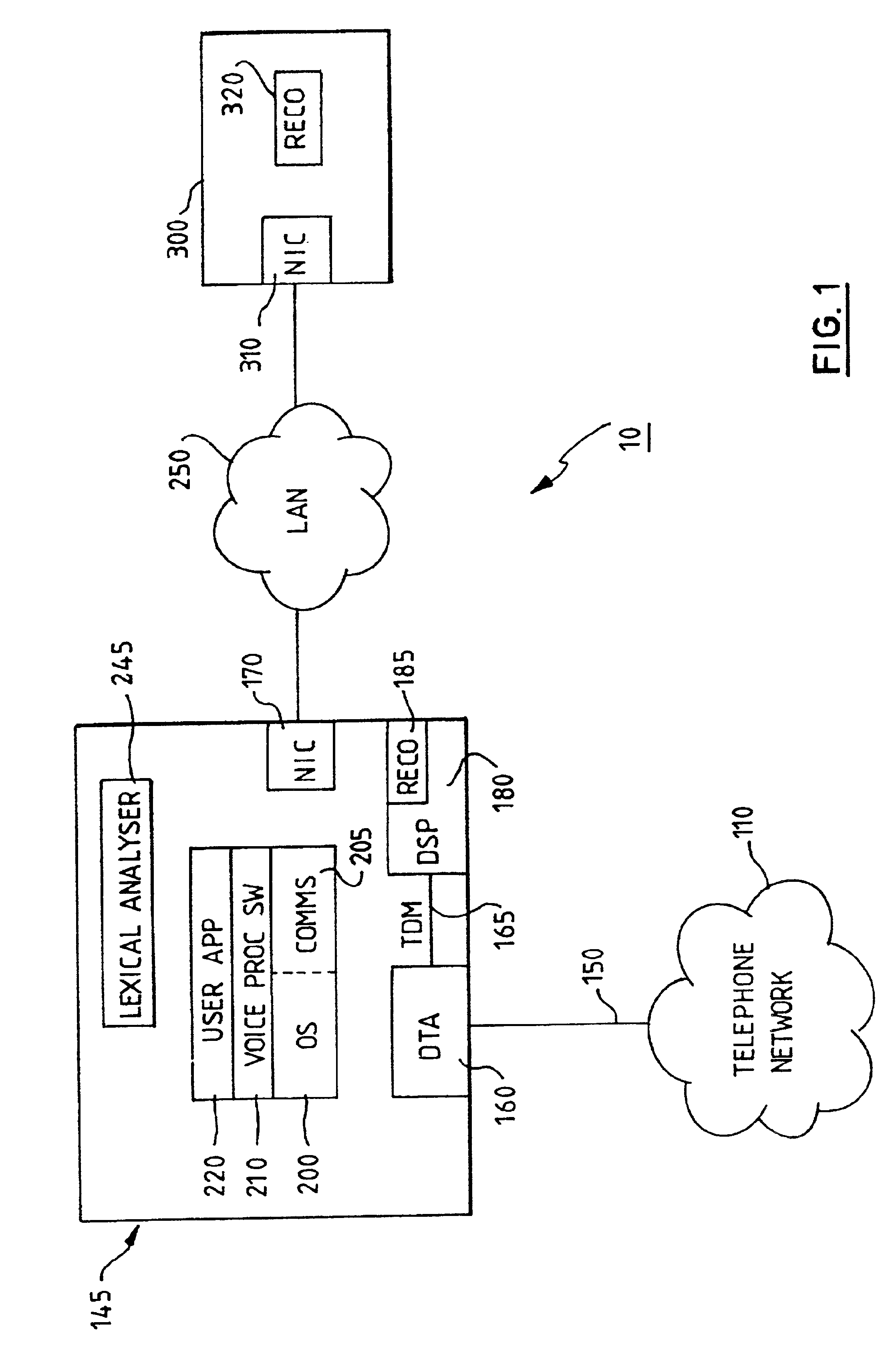
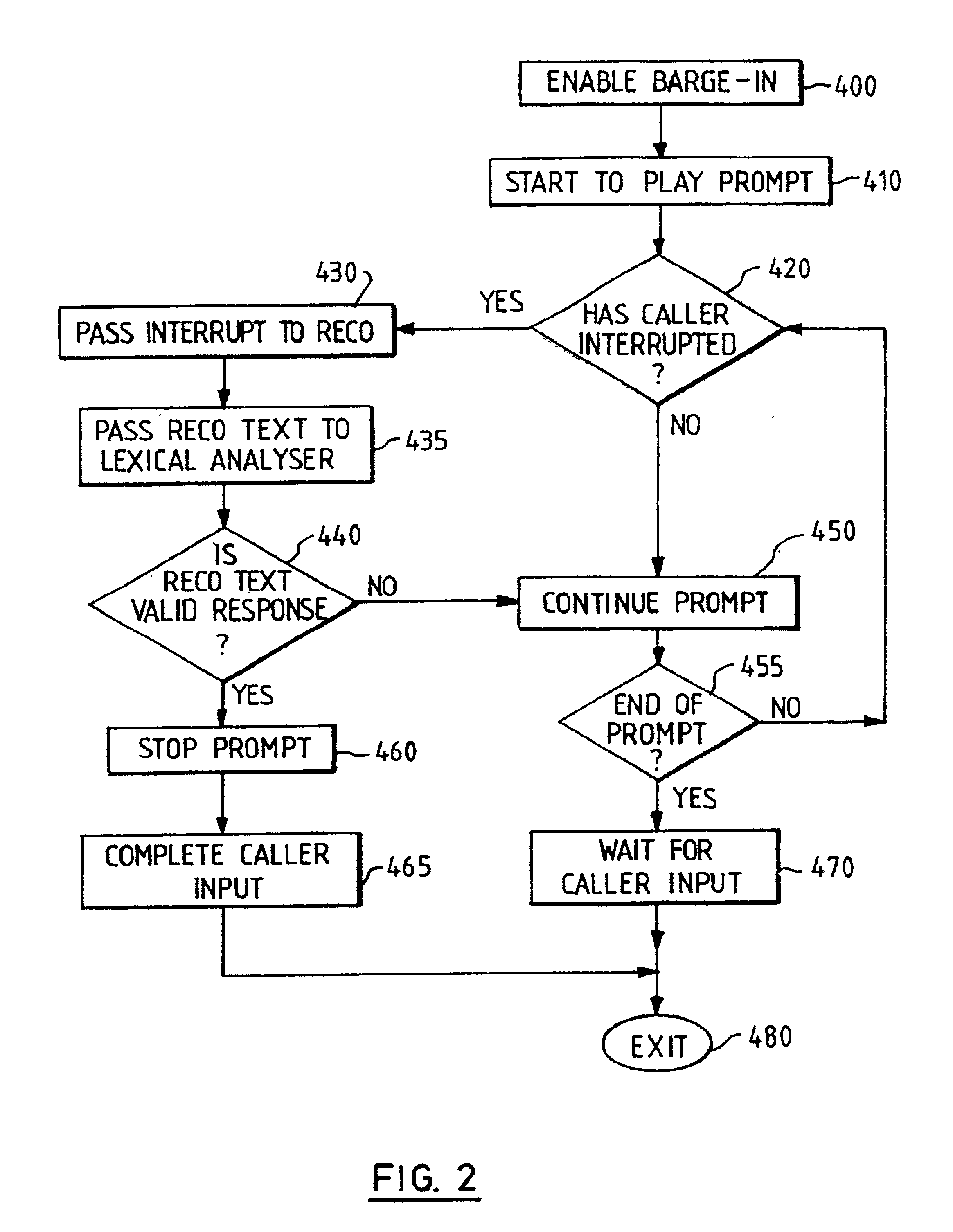
Speech recognition system with barge-in capability
InactiveUS6882973B1Automatic call-answering/message-recording/conversation-recordingSpeech recognitionLexical analysisMultiple criteria
A voice processing system includes a speech recognition facility with barge-in. The system plays out a prompt to a caller, who starts to provide their spoken response while the prompt is still being played out. The system performs speech recognition on this response to determine a corresponding text, which is then subjected to lexical analysis. This tests whether the text satisfies one or more conditions, for example, including one or more words from a predefined set of task words. If this is found to be the case, the playing out of the prompt is terminated (i.e. barge-in is effected); otherwise, the playing out of the prompt is continued, essentially as if the caller bad not interrupted.
Owner:LENOVO (SINGAPORE) PTE LTD
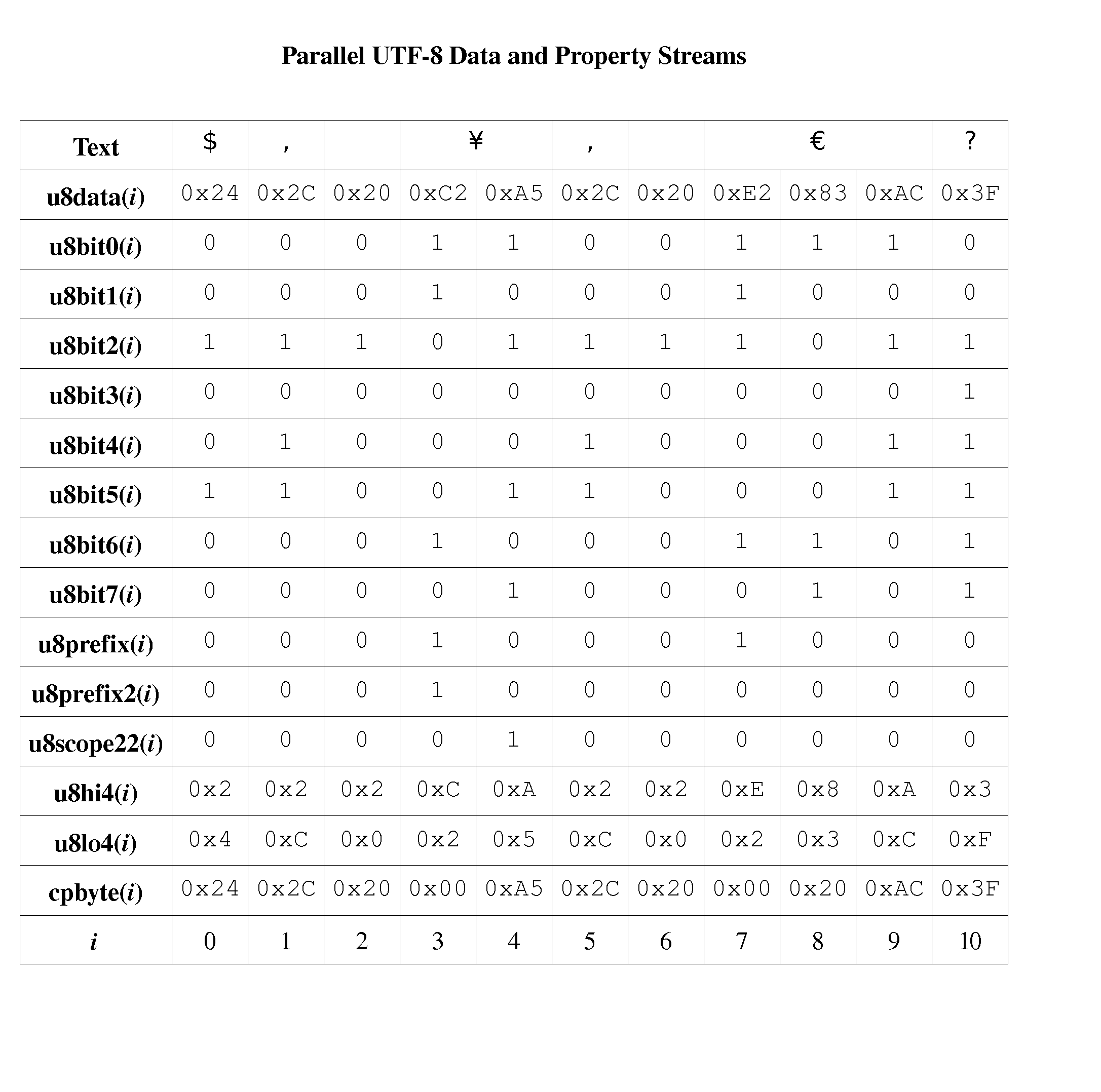
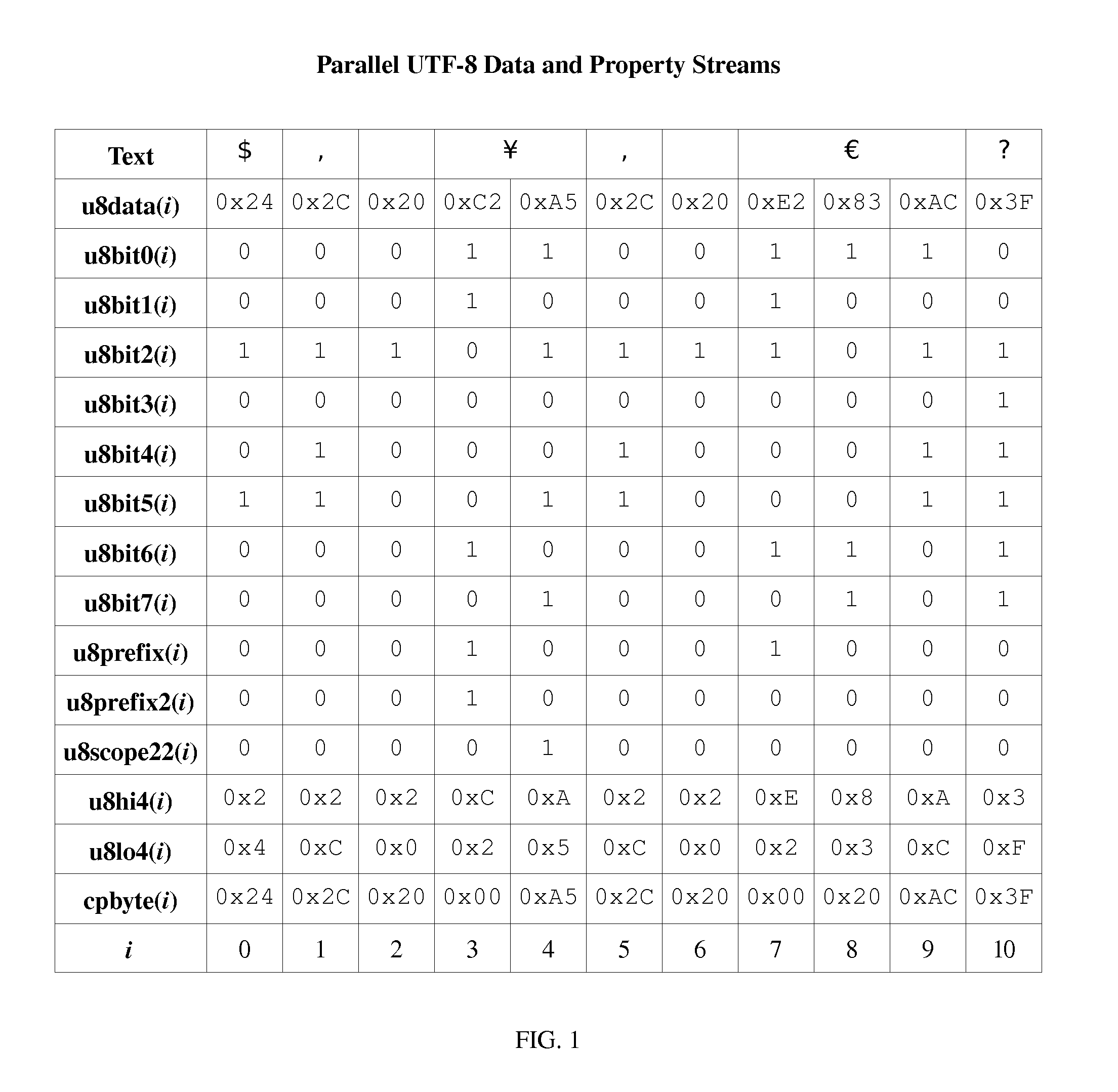
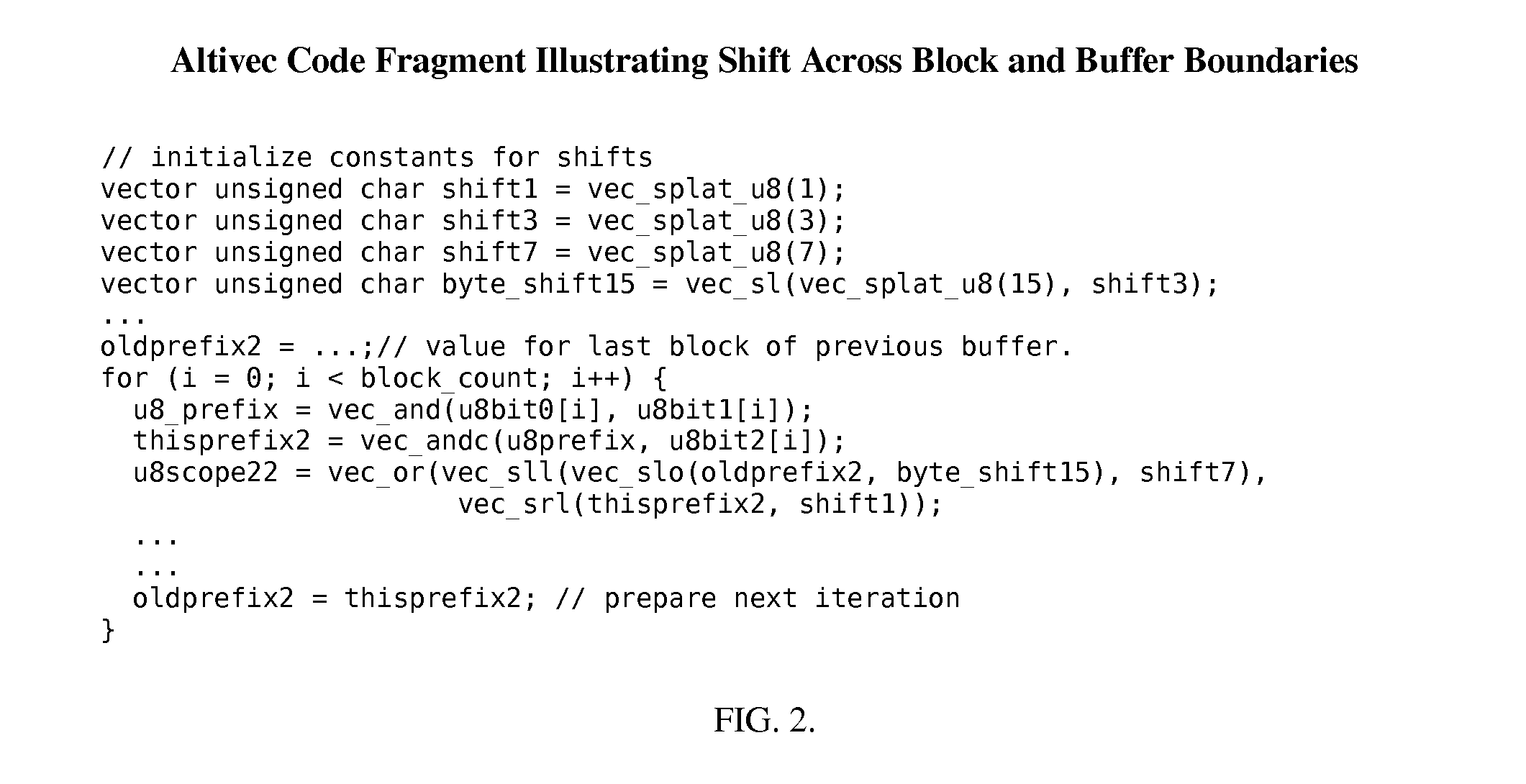
Method and Apparatus for Lexical Analysis Using Parallel Bit Streams
InactiveUS20080030383A1Individual digits conversionSemi-structured data queryingLexical analysisLexical item
One embodiment of the present invention is a method for lexical analysis of a character stream including: (a) generating one or more parallel property bit streams in response to the character stream; (b) generating one or more lexical item streams in response to the one or more parallel property bit streams; and (c) generating one or more token streams in response to the one or more lexical item streams.
Owner:INT CHARACTERS INC
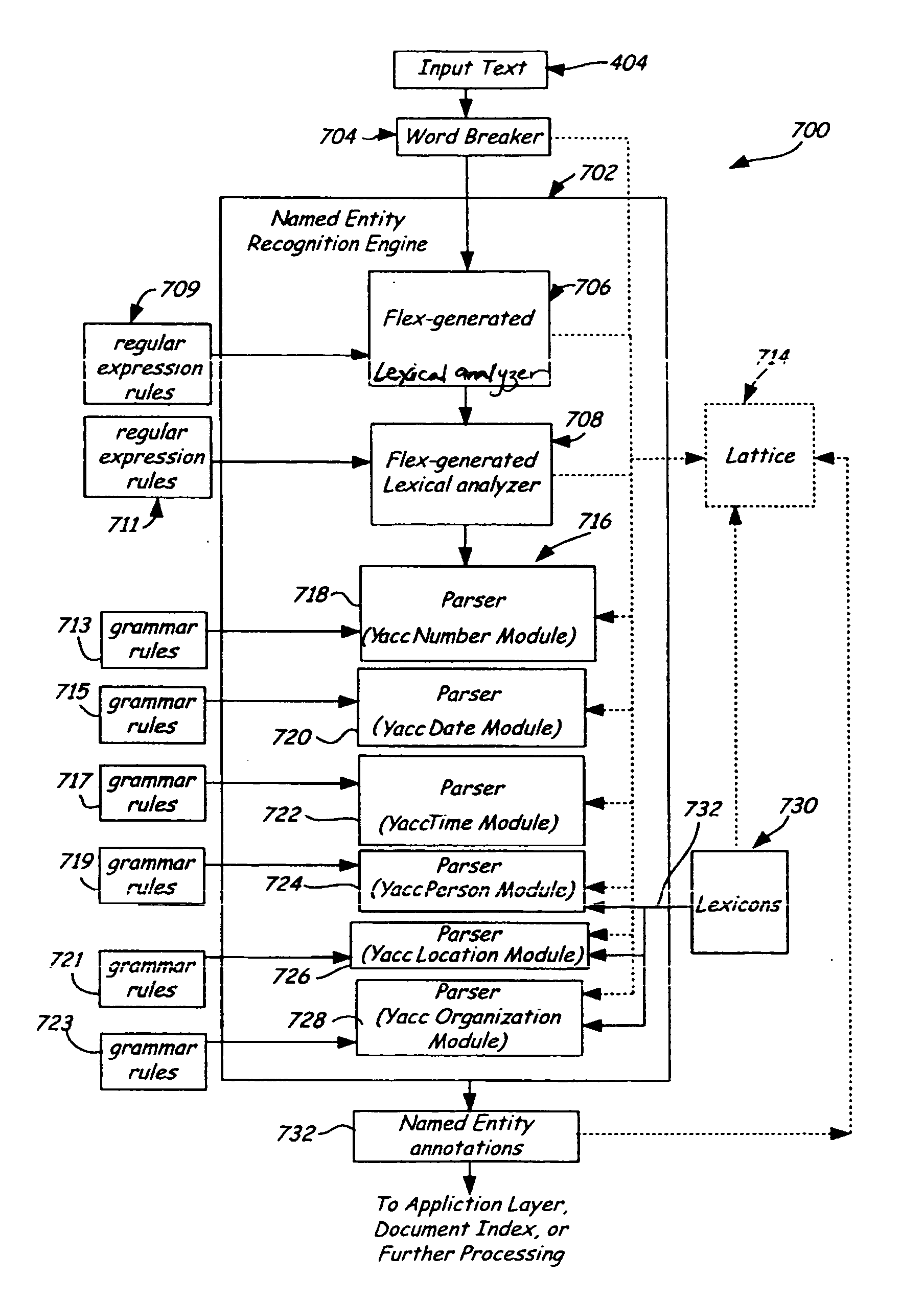
Creating a document index from a flex- and Yacc-generated named entity recognizer
InactiveUS20060047691A1Natural language data processingSpecial data processing applicationsLexical analysisNamed-entity recognition
Methods of constructing a document index including named entity information generated by at least one tool associated with parsing computer programs are presented. The methods include using a lexical analyzer generator, e.g. Flex, and / or a parser generator, e.g. Yacc, to generate named entity recognizers. The named entity recognizers are used to identify named entities in documents, in particular, very large document sets such as web pages available on the Internet. The identified named entities are stored as named entity annotations in the document index. Also, methods of performing searches using the document index are presented. The searches are performed based on queries that can be received on an application programming interface (API). Relevant documents are obtained using the named entity annotations, which can be returned across the API. Also presented are associated computer readable media.
Owner:MICROSOFT TECH LICENSING LLC
Complementary Character Encoding for Preventing Input Injection in Web Applications
InactiveUS20110252475A1Reduce overheadPreventing executionMemory loss protectionError detection/correctionSQL injectionLexical analysis
Method to prevent the effect of web application injection attacks, such as SQL injection and cross-site scripting (XSS), which are major threats to the security of the Internet. Method using complementary character coding, a new approach to character level dynamic tainting, which allows efficient and precise taint propagation across the boundaries of server components, and also between servers and clients over HTTP. In this approach, each character has two encodings, which can be used to distinguish trusted and untrusted data. Small modifications to the lexical analyzers in components such as the application code interpreter, the database management system, and (optionally) the web browser allow them to become complement aware components, capable of using this alternative character coding scheme to enforce security policies aimed at preventing injection attacks, while continuing to function normally in other respects. This approach overcomes some weaknesses of previous dynamic tainting approaches by offering a precise protection against persistent cross-site scripting attacks, as taint information is maintained when data is passed to a database and later retrieved by the application program. The technique is effective on a group of vulnerable benchmarks and has low overhead.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
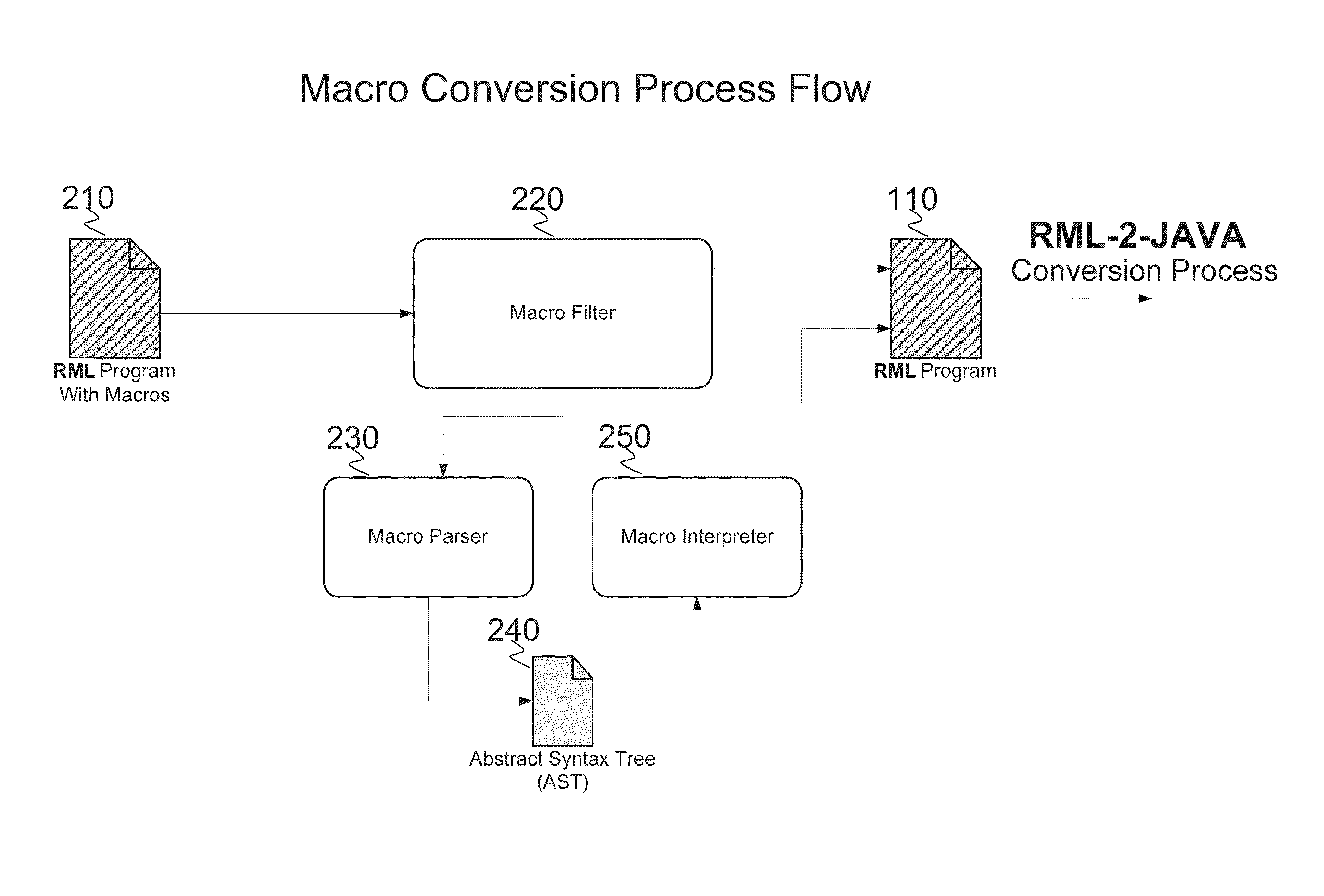
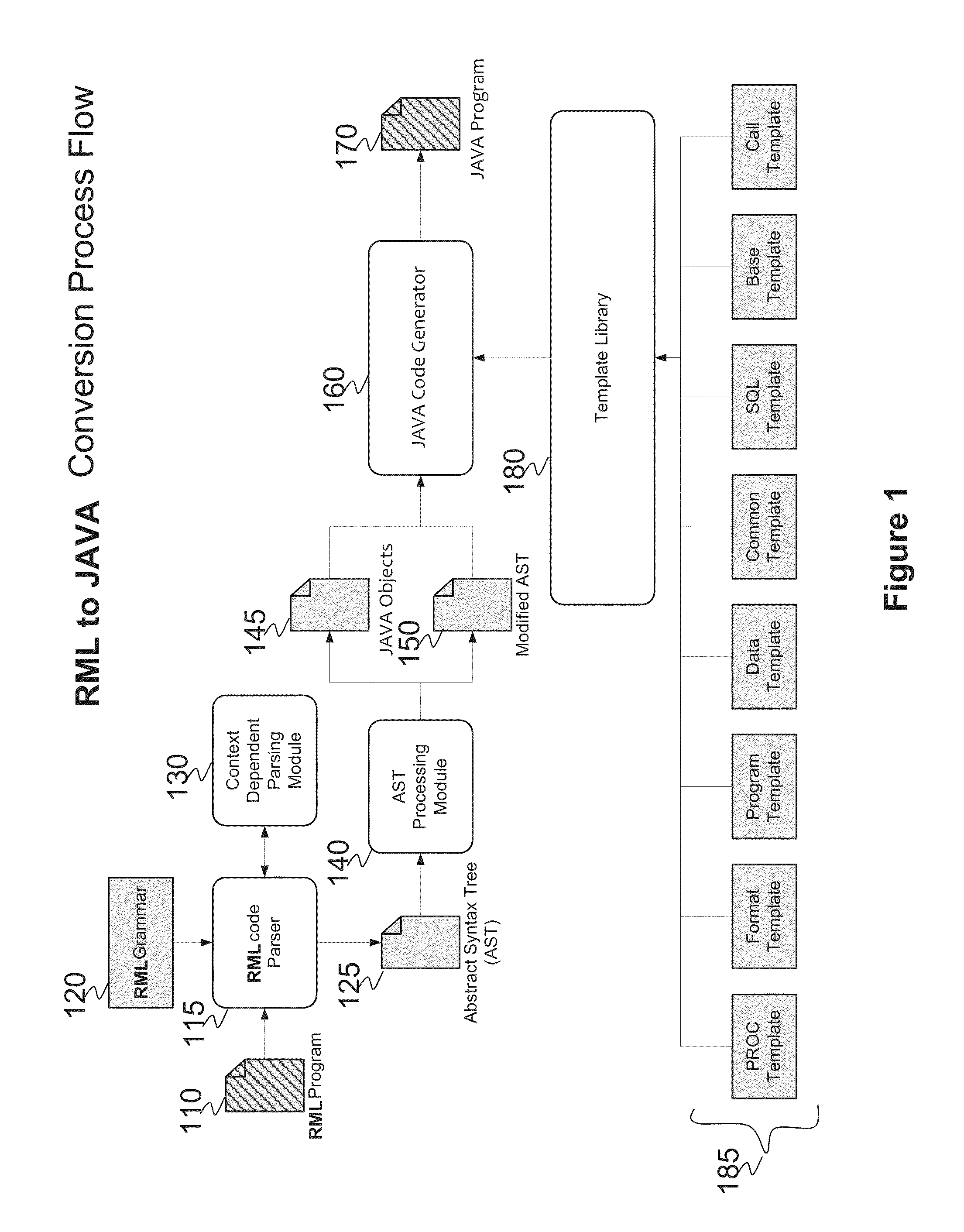
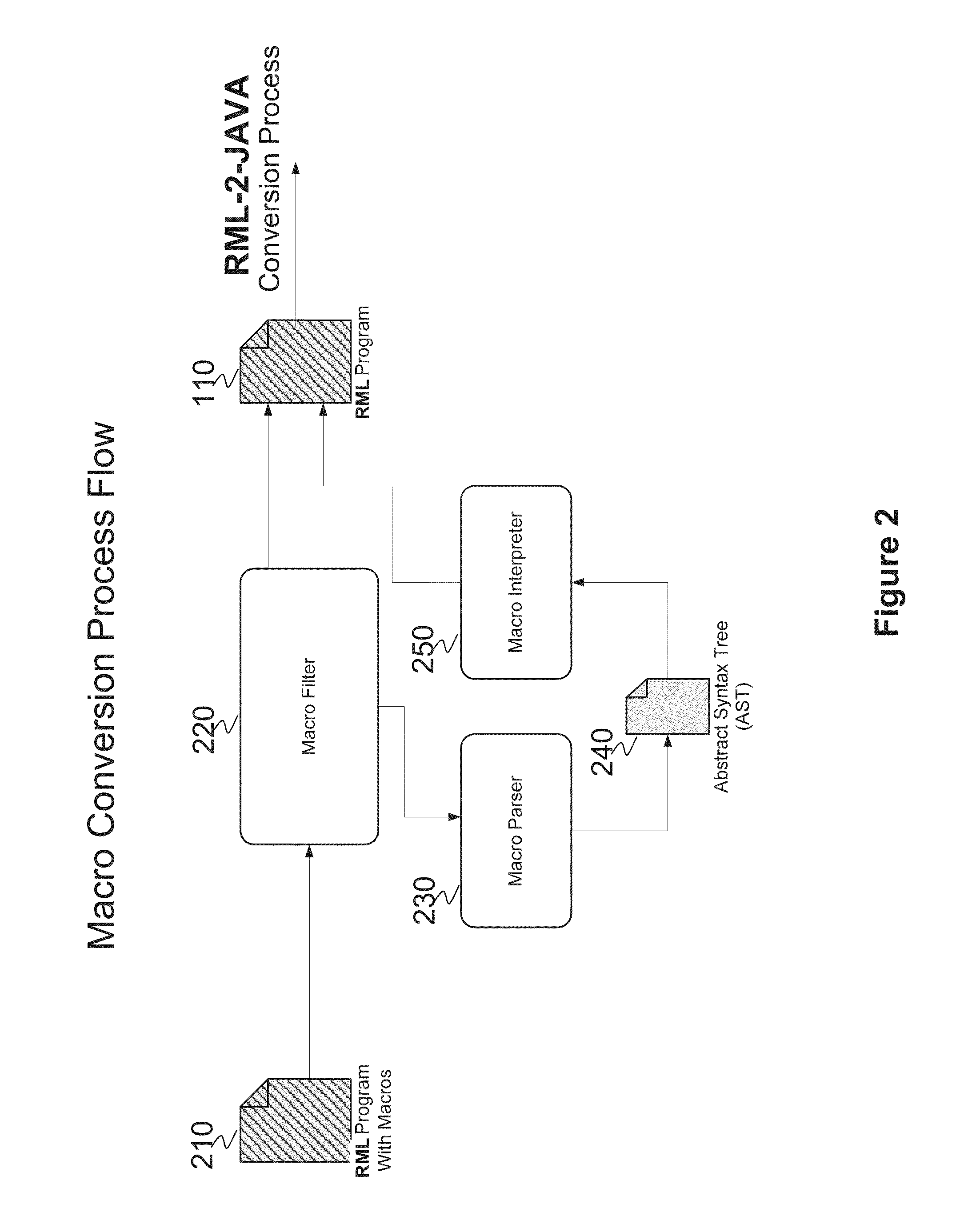
System and method for converting base SAS runtime macro language scripts to JAVA target language
ActiveUS8453126B1Overcome incidenceOvercome the impactProgram controlMemory systemsControl flowLexical analysis
A system and method for automated conversion of a SAS runtime macro language (RML) program to a target language program such as JAVA. RML macros are identified and converted for inclusion in the RML program. A lexer is applied to generate a stream of tokens, including a token type for ambiguous tokens. A context dependent parsing module, including a token filter to resolve ambiguous tokens, assists the parser in generating an abstract syntax tree (AST), which is modified to express RML specific control flow constructs with target language program elements. The elements of the modified AST are replaced with target language templates from a library, with template parameters filled from the corresponding AST element. A run time library is provided for execution of the target language program.
Owner:DULLES RES
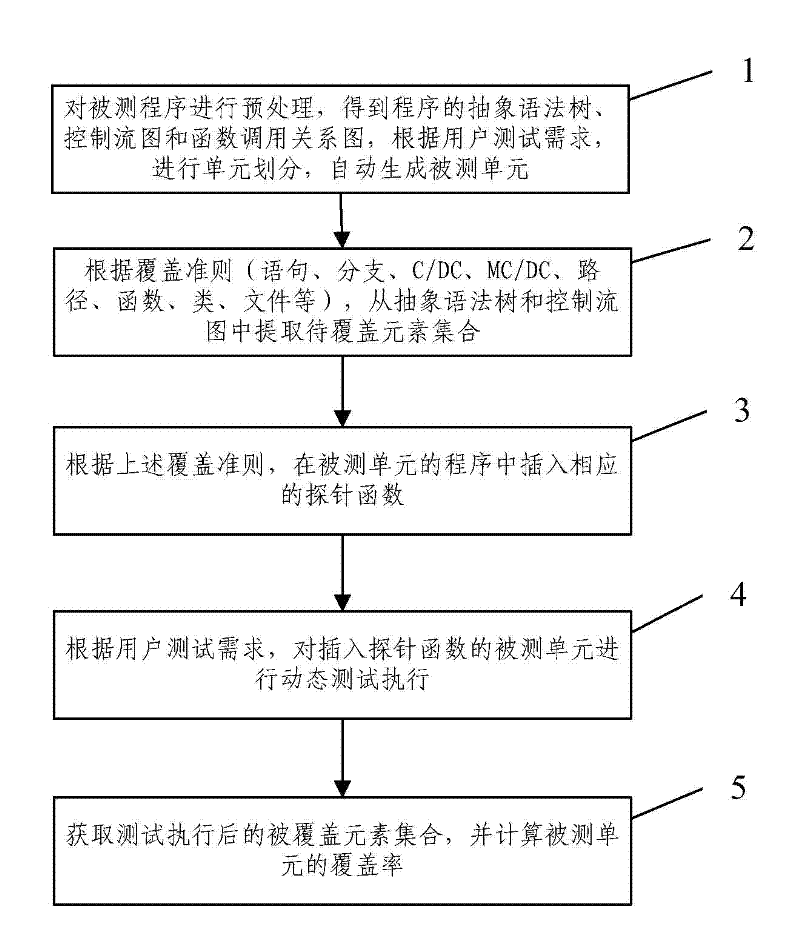
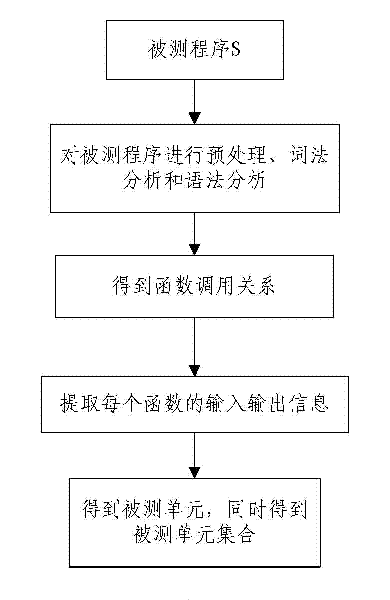
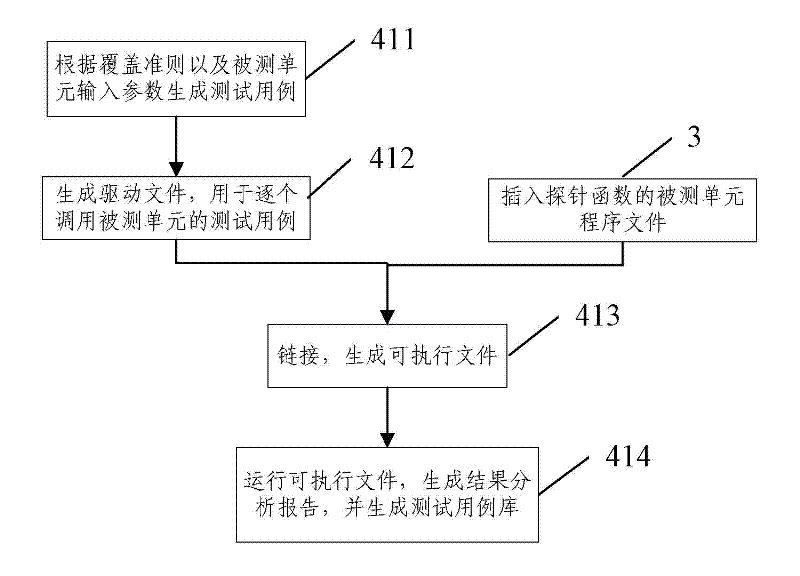
Method for determining software test process sufficiency based on coverage rate quantitative indicators
InactiveCN102419728AImprove efficiencyImprove accuracySoftware testing/debuggingAlgorithmLexical analysis
The invention provides a method for determining software test process sufficiency based on coverage rate quantitative indicators. The method comprises the following steps of: A, performing precompilation, lexical analysis and syntax analysis on a tested program to acquire the calling relationship diagram of the abstract syntax tree, the control flow graph and the function of the program, and automatically generating a tested unit according to the test requirement of a user; B, extracting a corresponding element set to be covered in the tested unit from the abstract syntax tree and the control flow graph according to a coverage criterion; C, inserting a corresponding probe function into the program of the tested unit according to the coverage criterion; D, dynamically testing the tested unit into which the probe function is inserted by selecting a system automatic executing mode or a user manual executing mode according to the test requirement of the user; and E, acquiring the covered element set of the tested unit according to the returned information of dynamic test execution, and calculating the coverage rate of the tested unit. By the method, the efficiency and the accuracy of a software evaluation test can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
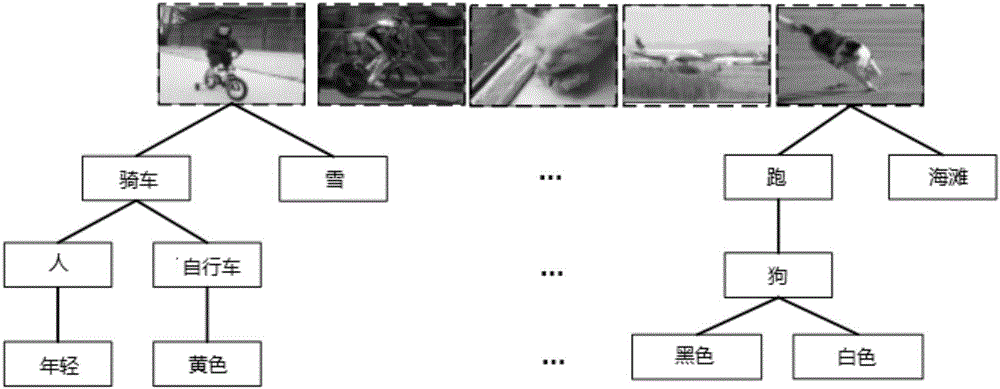
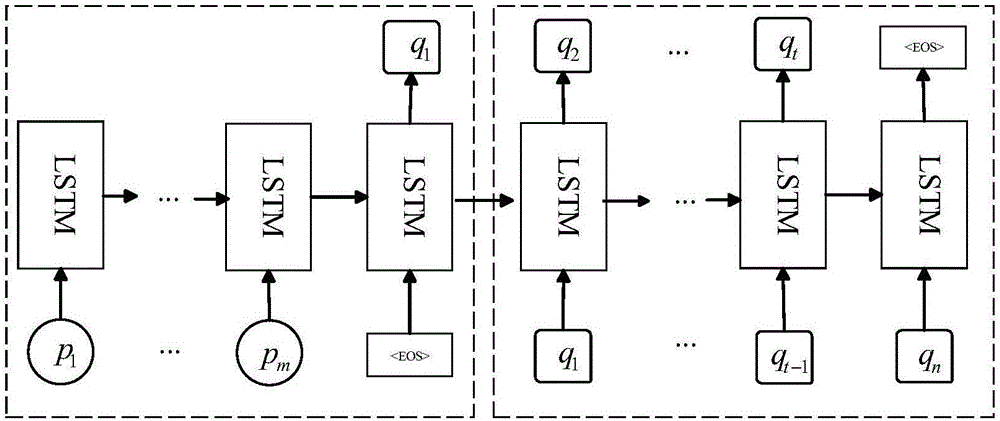
Generation method of image description from structured text
ActiveCN106503055AActive implementation of technical effectsGood varietyStill image data indexingSpecial data processing applicationsLexical analysisThe Internet
The invention discloses a generation method of an image description from a structured text. The generation method comprises the steps of downloading pictures from the internet to form a picture training set; conducting morphological analysis on descriptions which correspond to the pictures in the picture training set to form the structured text; using an existing neural network model to extract convolution neural network characteristics of the pictures in the training set, and using <, picture characteristics and structured text < as inputs to form a multitasking recognition model; using the structured text extracted from the training set and a description which corresponds to the structured text as inputs of a recurrent neural network, and conducting training to obtain a parameter of a recurrent neural network model; inputting the convolution neural network characteristics of an image ready to be described, and obtaining a predicted structured text through the multitasking recognition model; inputting the predicted structured text, and obtaining the image description through the recurrent neural network model. Compared with the prior art, a better image description effect, accuracy and sentence variety can be generated through the method, and the generation method of the image description from the structured text can be effectively popularized in an application of image retrieval.
Owner:哈尔滨米兜科技有限公司
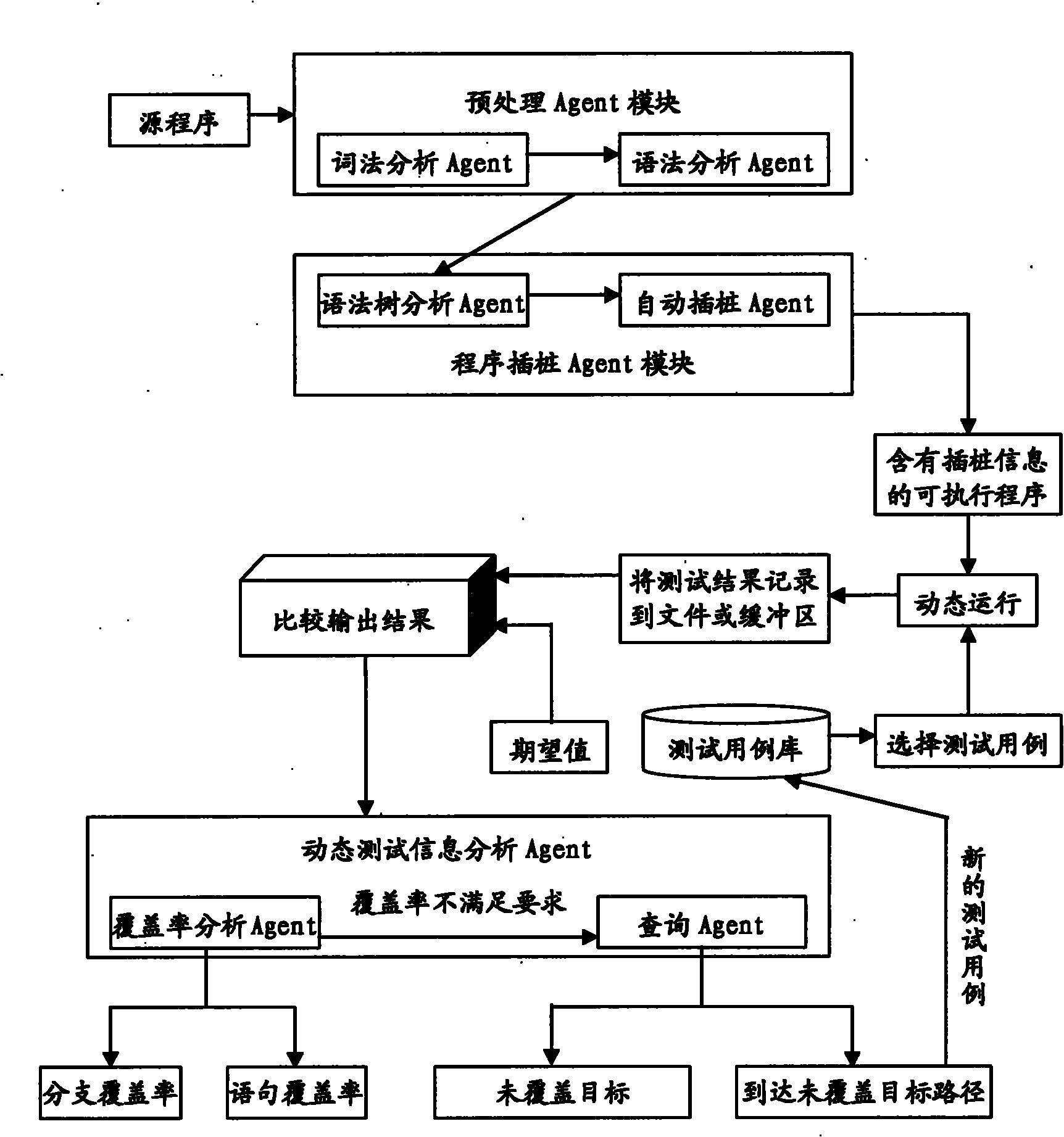
Embedded software intelligent testing method based on Agent
InactiveCN101833500AReduce interventionImprove automated testing efficiencySoftware testing/debuggingOperational systemInformation analysis
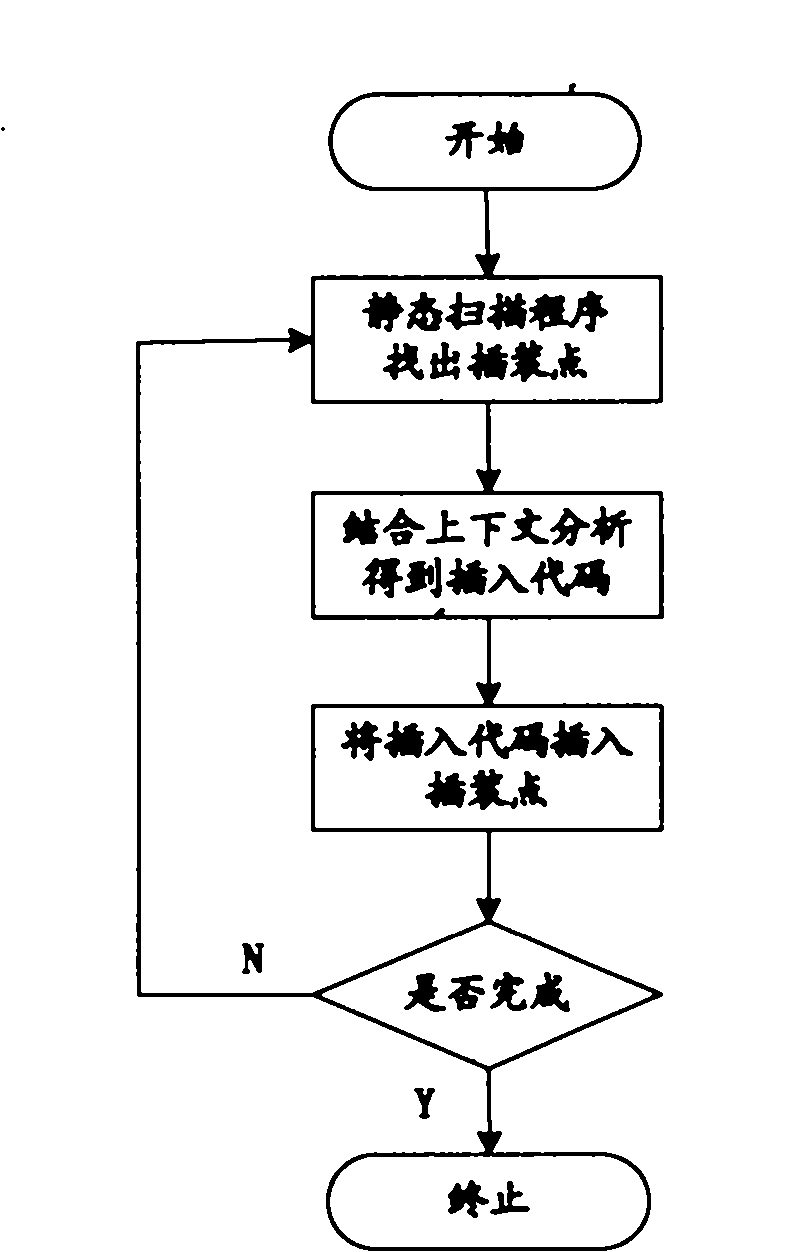
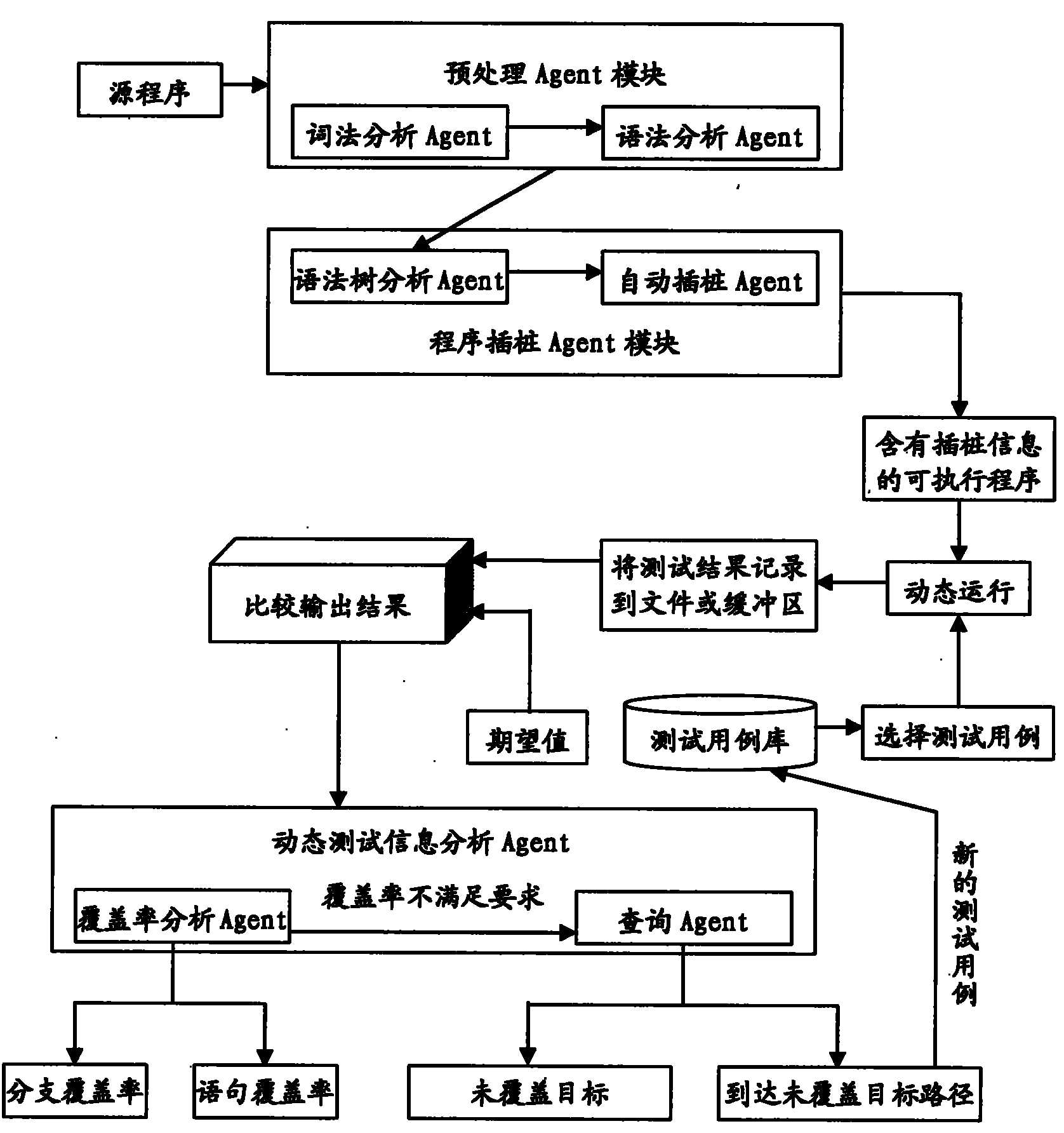
The invention relates to an embedded software intelligent testing method based on Agent, which is an improved software testing method using a Linux system as an embedded operation system core, mainly comprising three Agent modules: a pre-processing Agent module, a program instrumentation Agent module and a dynamic test information analysis Agent module. The pre-processing Agent module comprises a lexical analysis Agent and a grammar analysis Agent that are used for generating a grammar tree structure of a source program; the program instrumentation Agent module comprises a grammar tree analysis Agent and an automatic instrumentation Agent that are mainly used for analyzing the grammar tree, finding out the key point of the source program, and automatically inserting probe functions in the source program so as to acquire the dynamic information during the operation of the program; and the dynamic test information analysis Agent module comprises a cover ratio analysis Agent and an inquiry Agent that are mainly used for testing the sentence and the branch cover ratio of the source program, and automatically inquiring the relevant conditions of the uncovered target in the source program when the cover ratio cannot satisfy the requirements. The invention can be applied to different programs simply and conveniently, thereby greatly improving the efficiency of the software automation test with strong commonality.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Information processing method and device for realizing intelligent question answering
InactiveCN107273350AImprove experienceImprove targetingSemantic analysisSpecial data processing applicationsInformation processingNatural language understanding
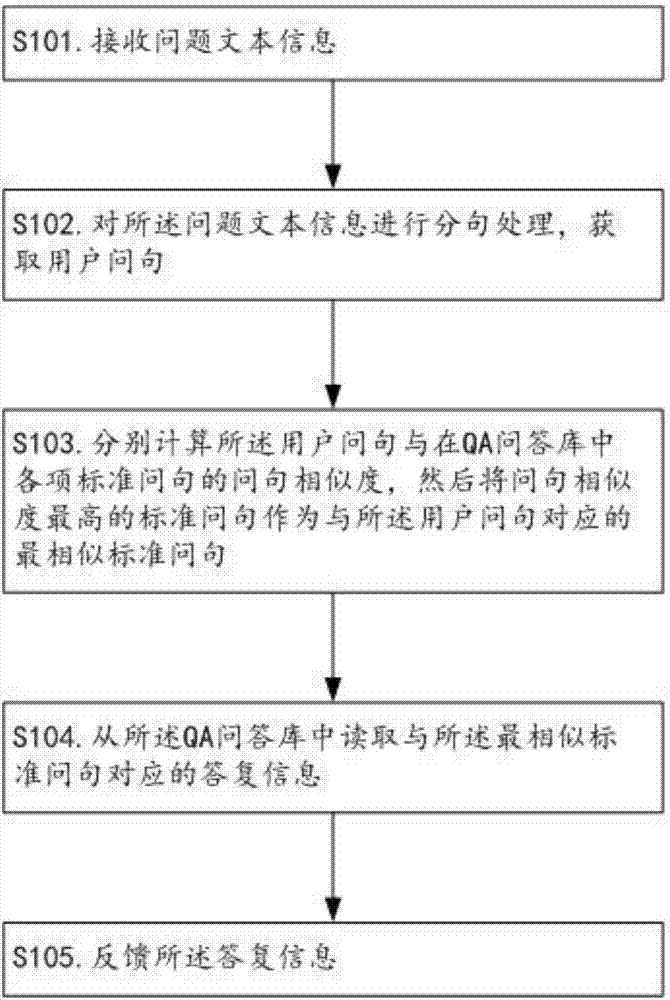
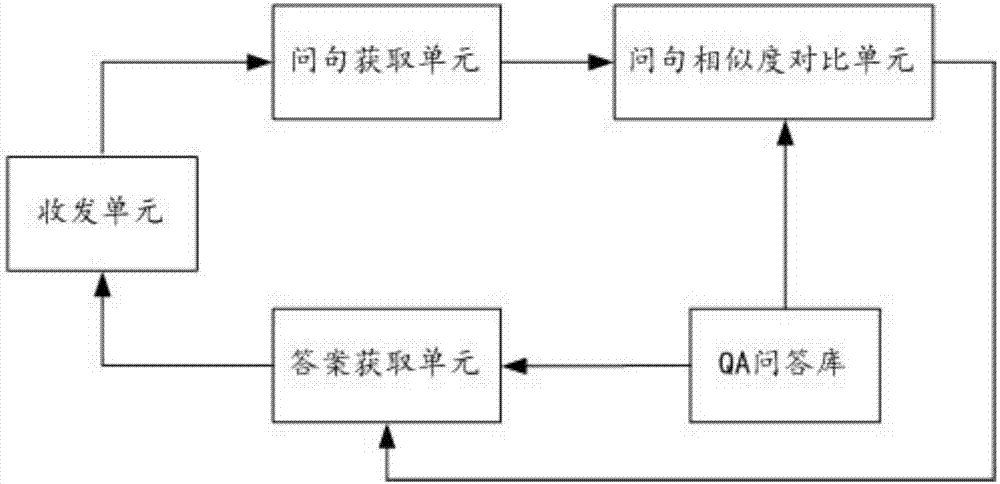
The invention relates to the technical field of man-machine interaction, and discloses an information processing method and device for realizing intelligent question answering. The information processing method comprises the following steps of: carrying out sentence segmentation on question text information to obtain a user question; and searching a standard question most similar to the user question and corresponding answer information from a QA library on the basis of a question similarity. Compared with the existing keyword retrieval-based question answering method, the method disclosed by the invention does not need to require the users to have keyword decomposition ability, is automatic in the whole process and is capable of greatly enhancing the user experience and improving the search effect and the pertinence and effectiveness of answers. Meanwhile, through fusing natural language understanding technologies such as sentence model analysis, lexical analysis and lexical meaning extension, and carrying out comprehensive calculation on multi-dimensional similarity, the method is capable of improving the correctness of a final sentence similarity in a Chinese automatic question answering process, and enabling a Chinese intelligent question answering system to be possible.
Owner:JIANGMEN POWER SUPPLY BUREAU OF GUANGDONG POWER GRID
Modular parser architecture
ActiveUS20030106049A1Software engineeringSpecific program execution arrangementsMicrocomputerLexical analysis
A modular parser architecture and methods related thereto make use of a number of miniparsers. Each miniparser is capable of receiving input and generating an output dependent thereon. In one embodiment, a lexer or a miniparser capable of lexical analysis receives certain code and provides an abstract syntax tree. Each miniparser performs operations on a set of syntactical constructs to produce a corresponding output syntax tree, which in turn may become an input syntax tree for a next miniparser which may operate on a different set of syntactical constructs.
Owner:ORACLE INT CORP
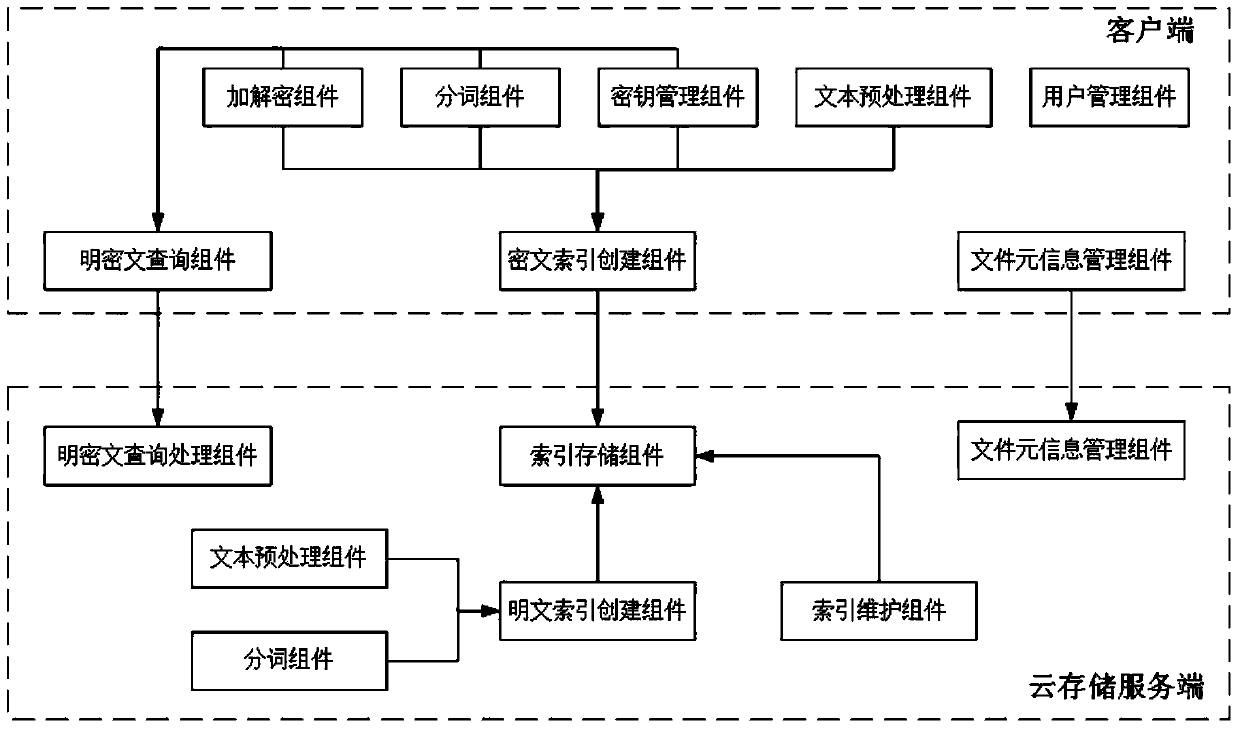
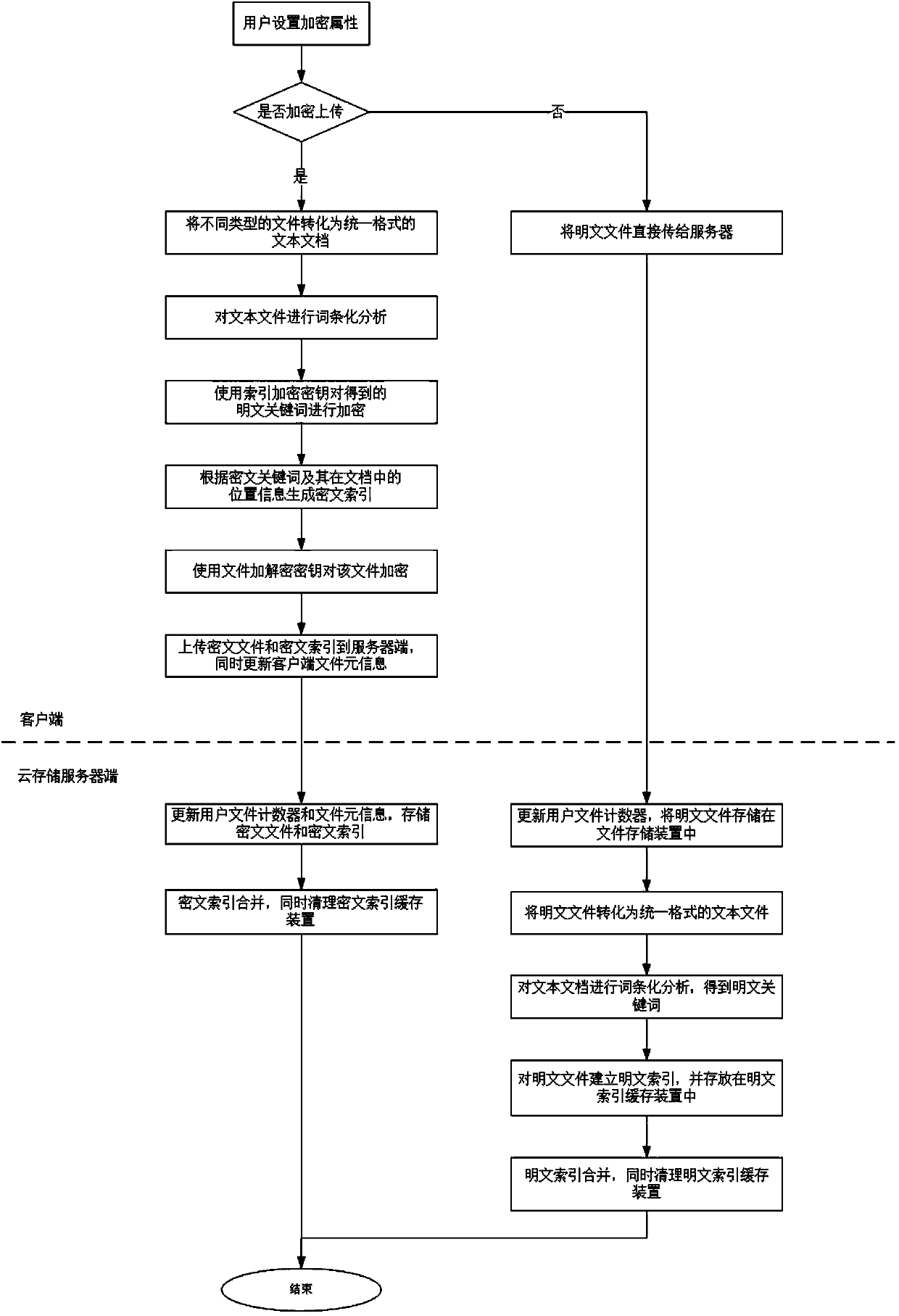
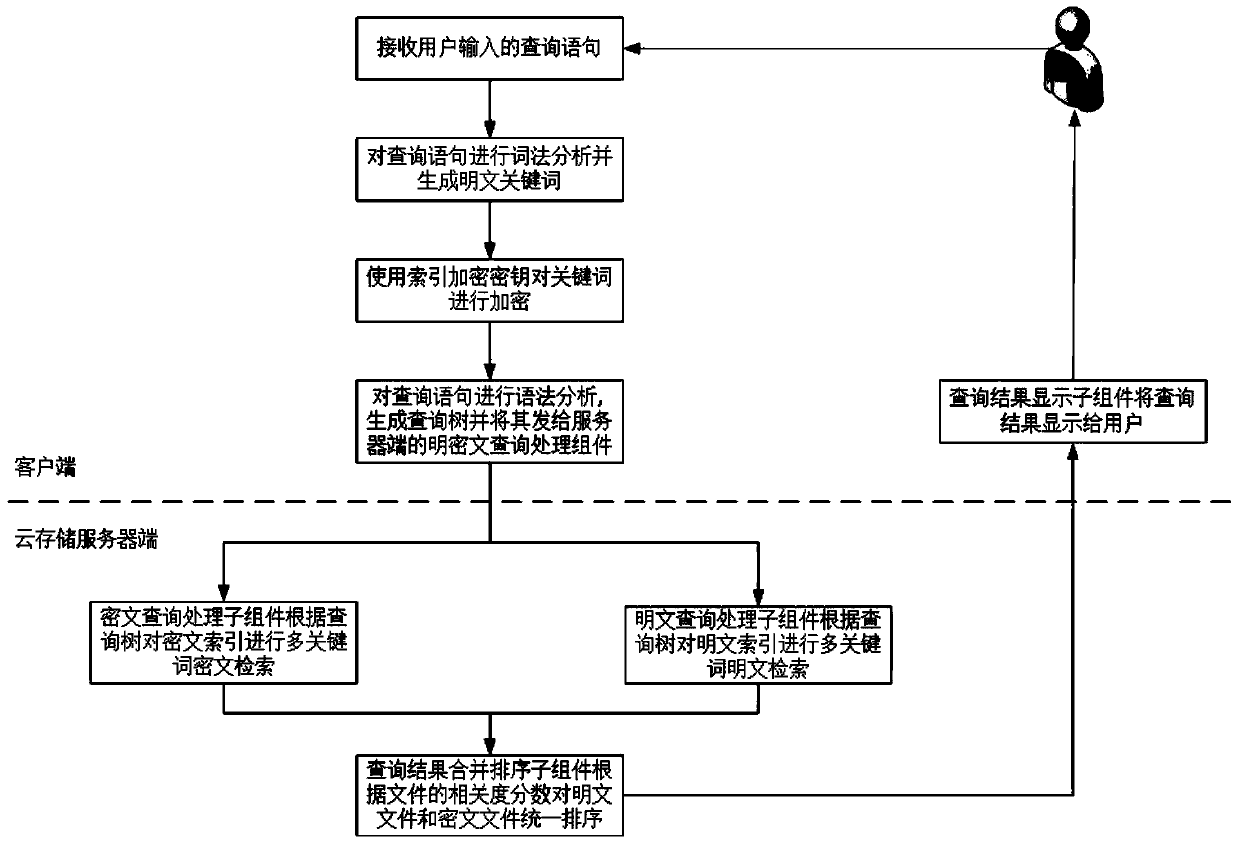
Multi-keyword plaintext and ciphertext retrieving method and device oriented to cloud storage
InactiveCN103593476AFix bugsAddress riskKey distribution for secure communicationComputer security arrangementsPlaintextComputer hardware
The invention relates to a multi-keyword plaintext and ciphertext retrieving method and device oriented to cloud storage and relates to the field of information safety. The method includes the following steps that firstly, a client terminal performs lexical analysis according to inquiry statements and generates plaintext keywords; secondly, a corresponding user index encryption key is obtained according to a main key bound with the identity of a user, and the plaintext keywords are encrypted with the encryption algorithm of the index encryption key, and ciphertext keywords are generated; thirdly, multi-keyword ciphertext retrieving is performed on a ciphertext index in a cloud storage server according to an inquire tree generated by the client terminal, and retrieved data element information and retrieved relevancy scores undergo inquiry result merging and sequencing; fifthly, inquiry result merging and sequencing are performed in the cloud storage server with the same method; sixthly, a unified sequence result is sent to the client terminal, and an inquiry result is displayed to the user. According to the multi-keyword plaintext and ciphertext retrieving method and device oriented to the cloud storage, a key management scheme which is higher in safety degree is provided, plaintext and ciphertext united retrieving can be supported and multi-keyword retrieving can be provided.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Method and system for implementing online advertisement
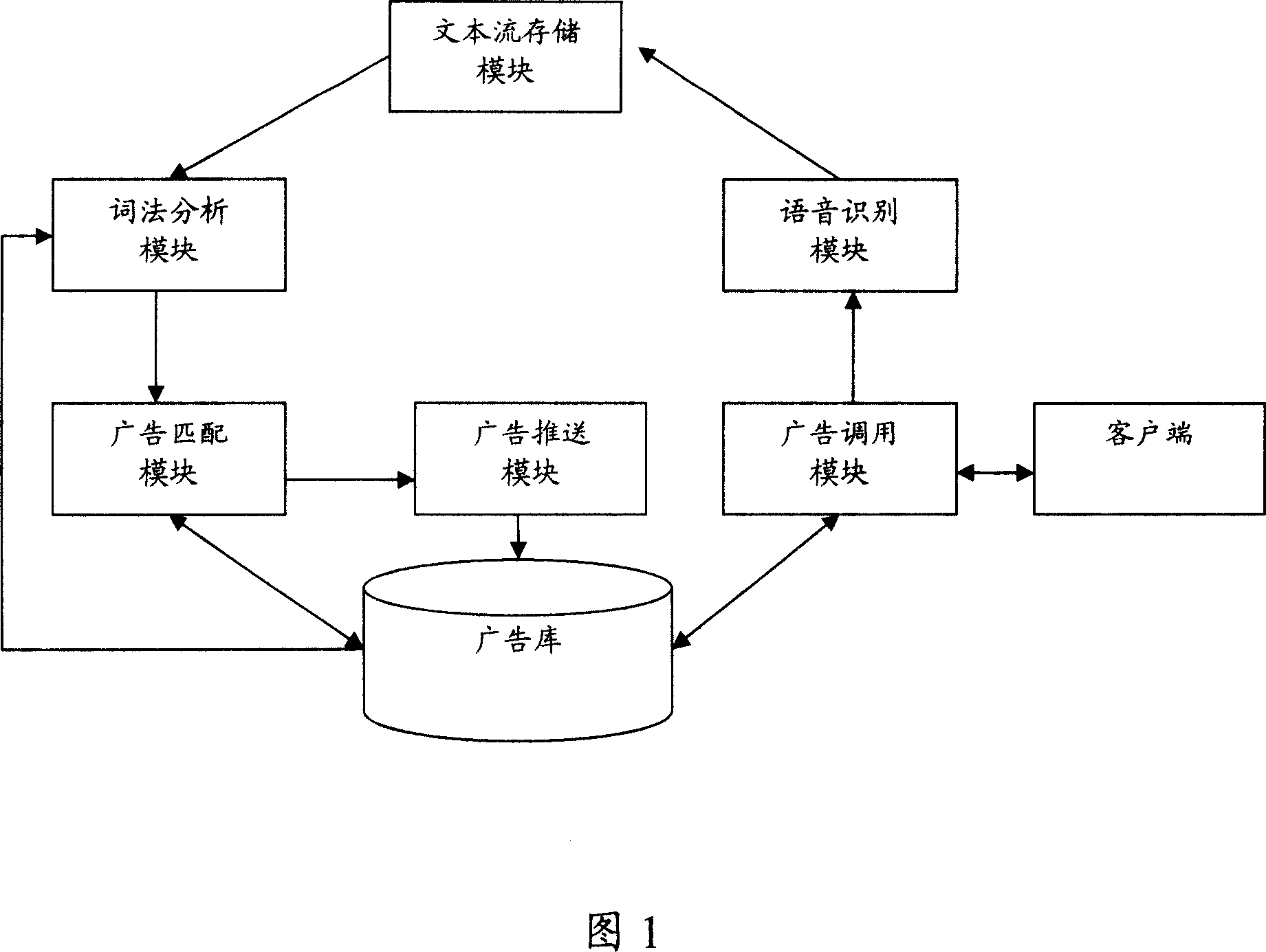
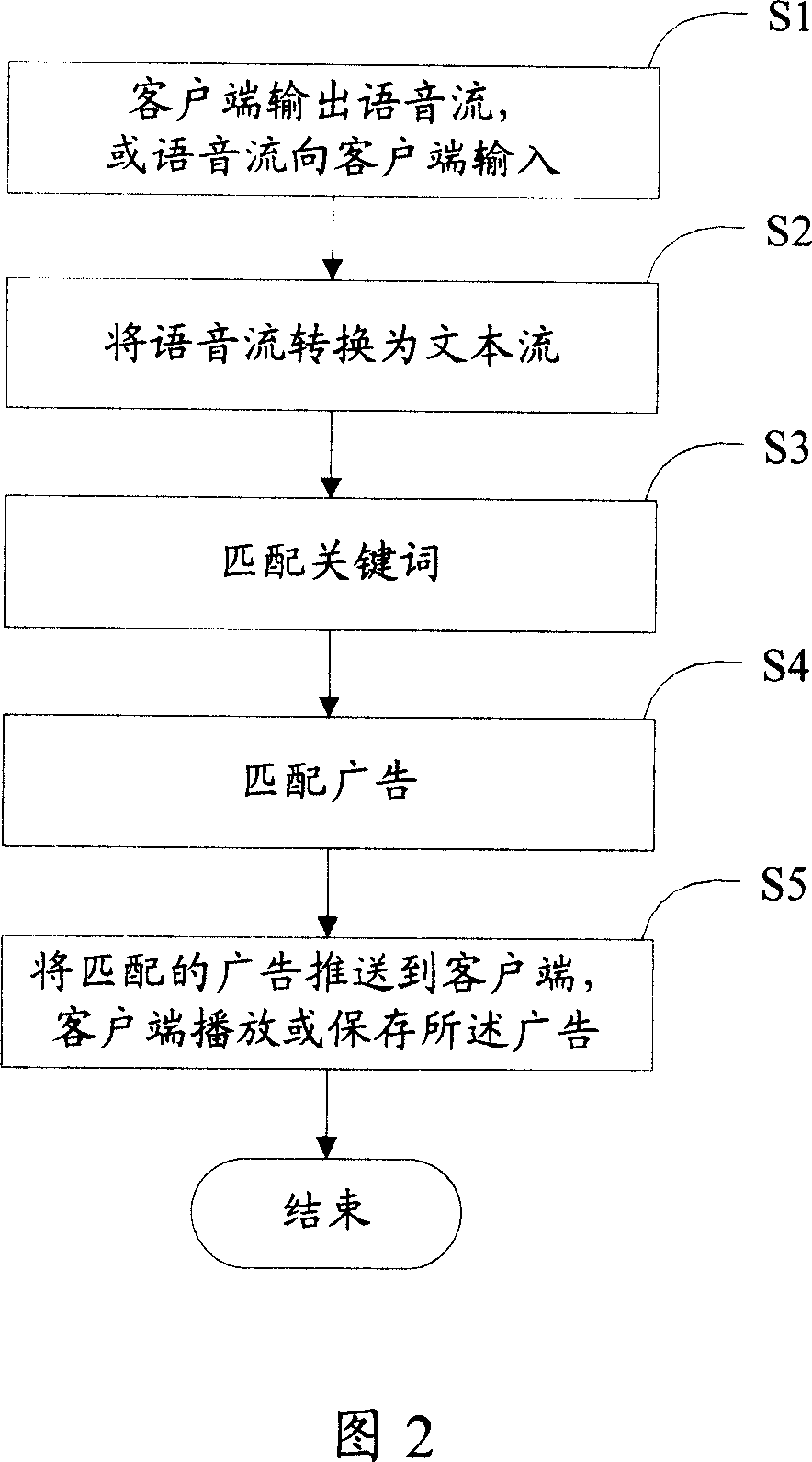
InactiveCN101034455AAvoid advertising harassmentAdvertisements are effectiveSpecial service provision for substationMarketingBasementLexical analysis
This invention opens a method and system of realization of the online advertising,it aims to solve the problem that the network side can not in accordance with the contents of voice to push the advertising issue for the client. The invention includes: A. voice flow through the client side will be transformed into text flow; B. through keyword matching, matching advertising for the described text flow; C. network side will be pushed matching advertisements to the client side for users to browse. This invention system includes: advertising calling module, advertising basement, lexical analysis module, advertising matching module, advertising push module; Aboved system also includes: speech recognition module, whish is used for voice flow gained by advertising calling module transforming into text flow; text flow memory modules for use in storage of text flow of language recognition module output, to prepare for lexical analysis module called. Through the implementation of the invention, we may push corresponding advertising to the client side, basing on the contents of the voice flow between clients altenantly.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and device for detecting security flaws of source files
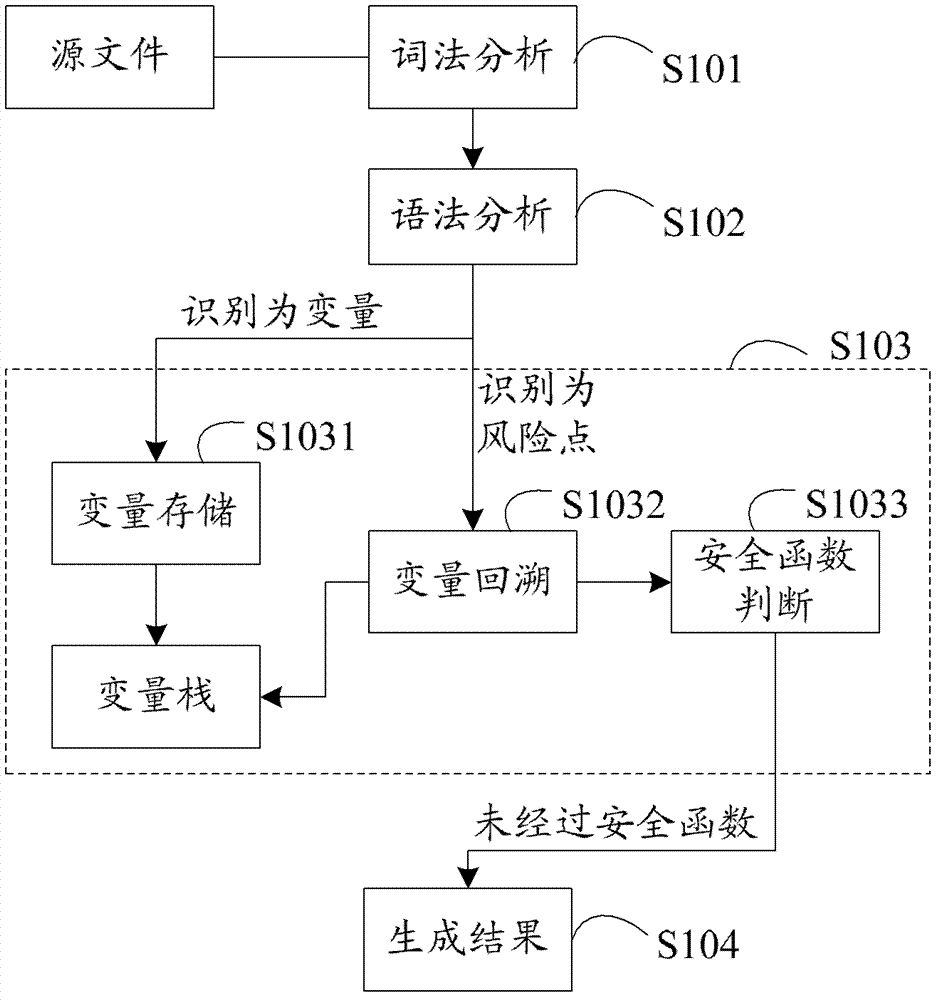
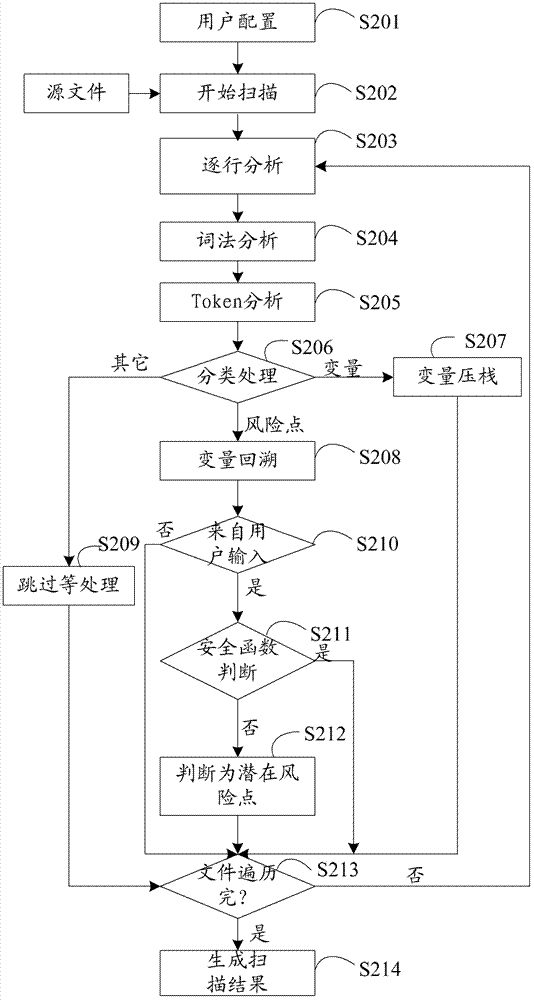
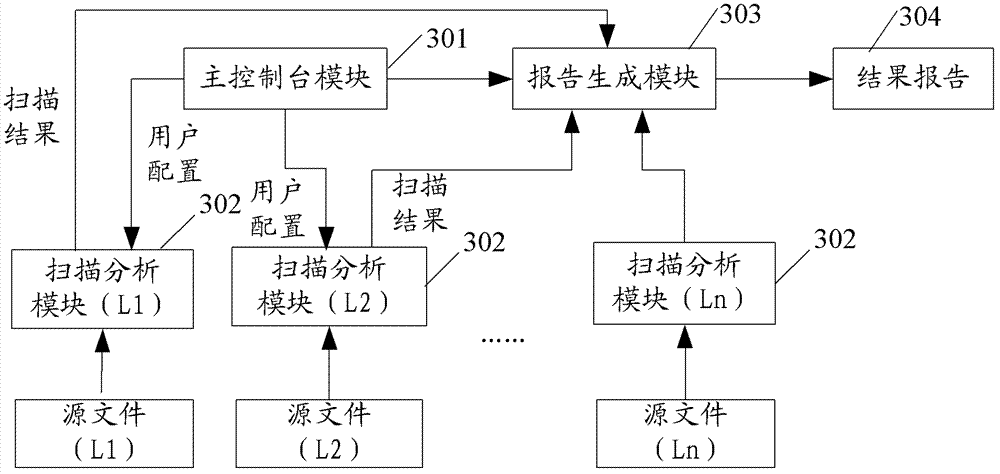
ActiveCN102955914ASave resourcesImprove scanning efficiencyPlatform integrity maintainanceIdentifying VariableLexical analysis
The invention provides a method and a device for detecting security flaws of source files. The method includes scanning the source files one by one and executing steps on the scanned source files including subjecting the source files to lexical analysis and grammatical analysis, performing variable identification operation and risk point identification operation in the process of the lexical analysis, wherein the variable identification operation includes identifying variables and storing identified variables; the risk point identification operation includes identifying risk points, backtracking the stored variables by means of parameters of the risk points which are identified, and if the parameters of the risk points can be backtracked to an importable point, considering the risk point is potential risk points to cause security flaws when without security function processing in the process of backtracking. Compared with the prior art, the method for detecting security flaws of the source files has no need to build up an abstract syntax tree, processing procedures are simplified, resources of a testing system are saved, and code scanning efficiency is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Method and system for interactive generation of presentations
InactiveUS20110264705A1Input/output for user-computer interactionDigital data information retrievalOperational systemLexical analysis
Embodiments disclosed include computerized methods and systems for creating slideshow presentations using an outline based programming language. The outline based input is normalized, thereby permitting receipt of the input from devices using different operating systems. A lexical analysis is performed on the input to compile a set of tokens and a hierarchical data structure is created from the set of tokens. A slideshow presentation is created from the hierarchical data structure.
Owner:DIAMOND BRANDON
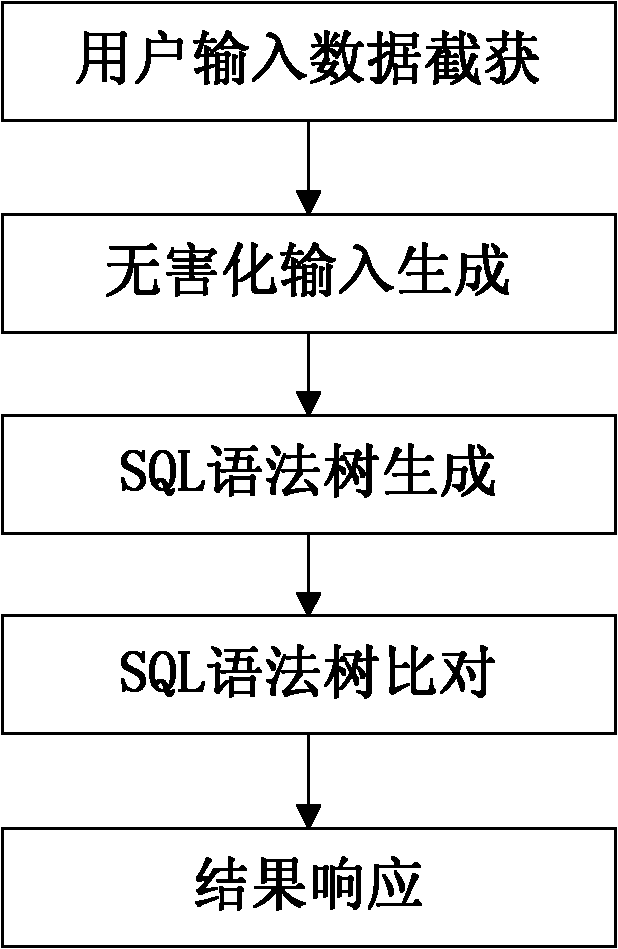
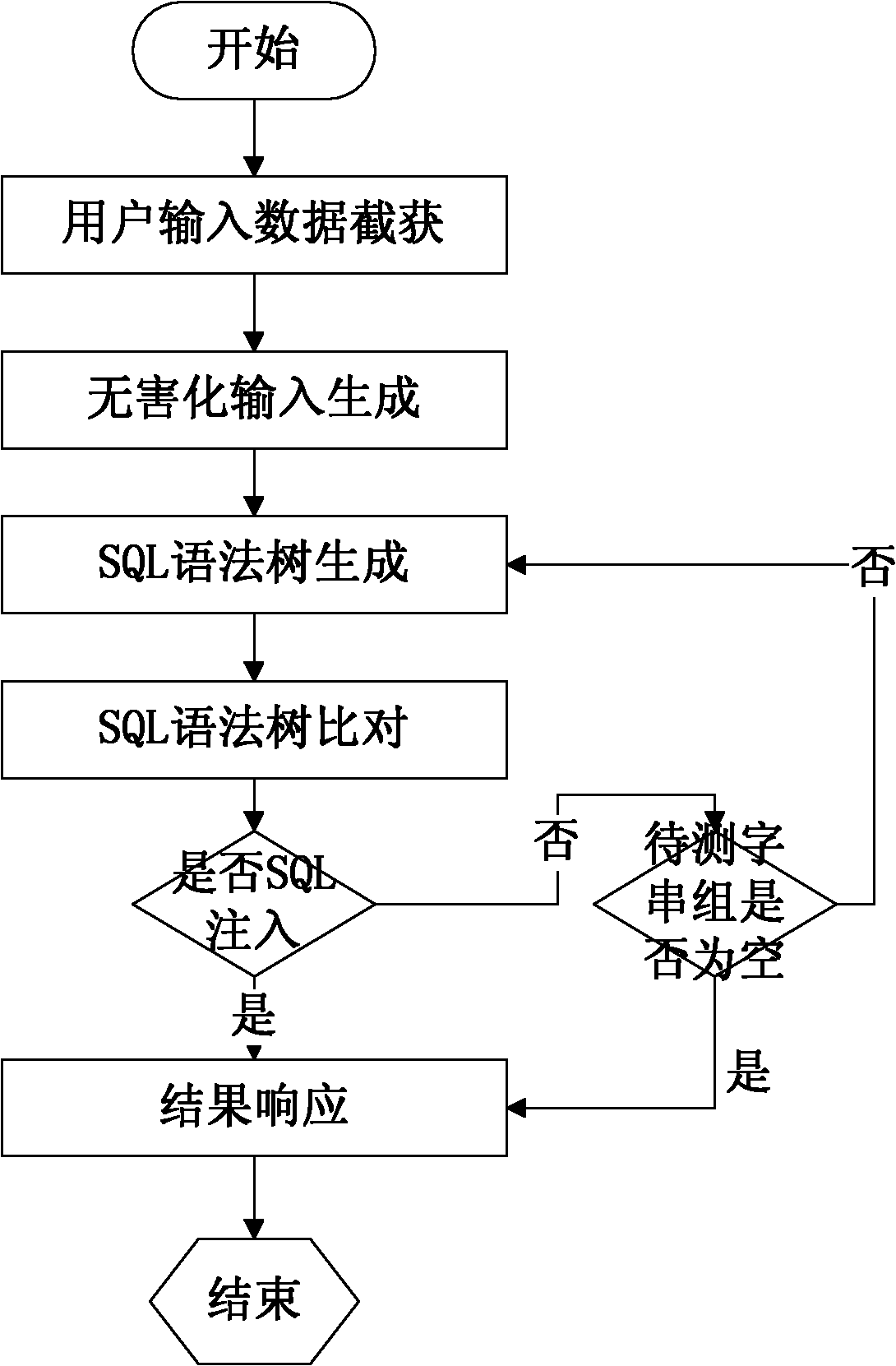
Method for detecting SQL (structured query language) injection vulnerability
InactiveCN102185930AReduce false alarm rateImprove accuracyTransmissionSpecial data processing applicationsUser inputSQL injection
The invention relates to a method for detecting SQL (structured query language) injection vulnerability, comprising the following steps: 1, capturing user input data; 2, generating harmless input; 3, carrying out SQL lexical analysis and syntactic analysis to generate SQL syntax trees, wherein the SQL syntax trees comprise a syntax tree based on user input word strings and a syntax tree based on harmless word strings; 4, comparing the two SQL syntax trees, and if the two SQL syntax trees are same, considering a group of testing word strings to pass a test; and 5, responding the result, if a user attempting to carry out SQL injection is found out, blocking an HTTP (hyper text transport protocol) package, and otherwise, releasing the HTTP package. In the method, analyzed objects are input by the user directly or indirectly, thus maximally restoring the real intentions of the user and reducing the rate of false alarm; and meanwhile, based on the analysis of the SQL syntax trees, the SQL injection can be blocked fundamentally, thereby improving the accuracy rate of the detection.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
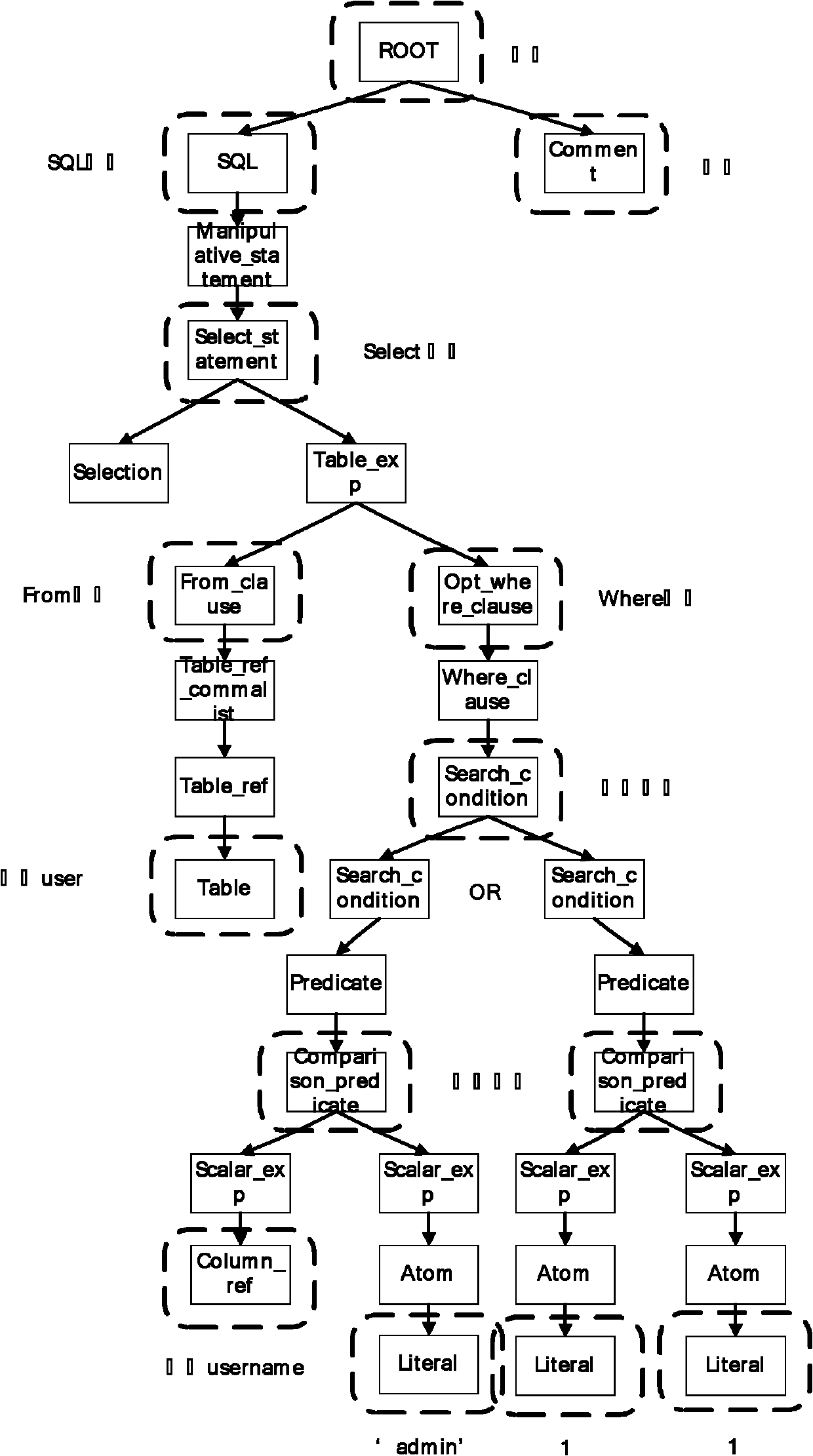
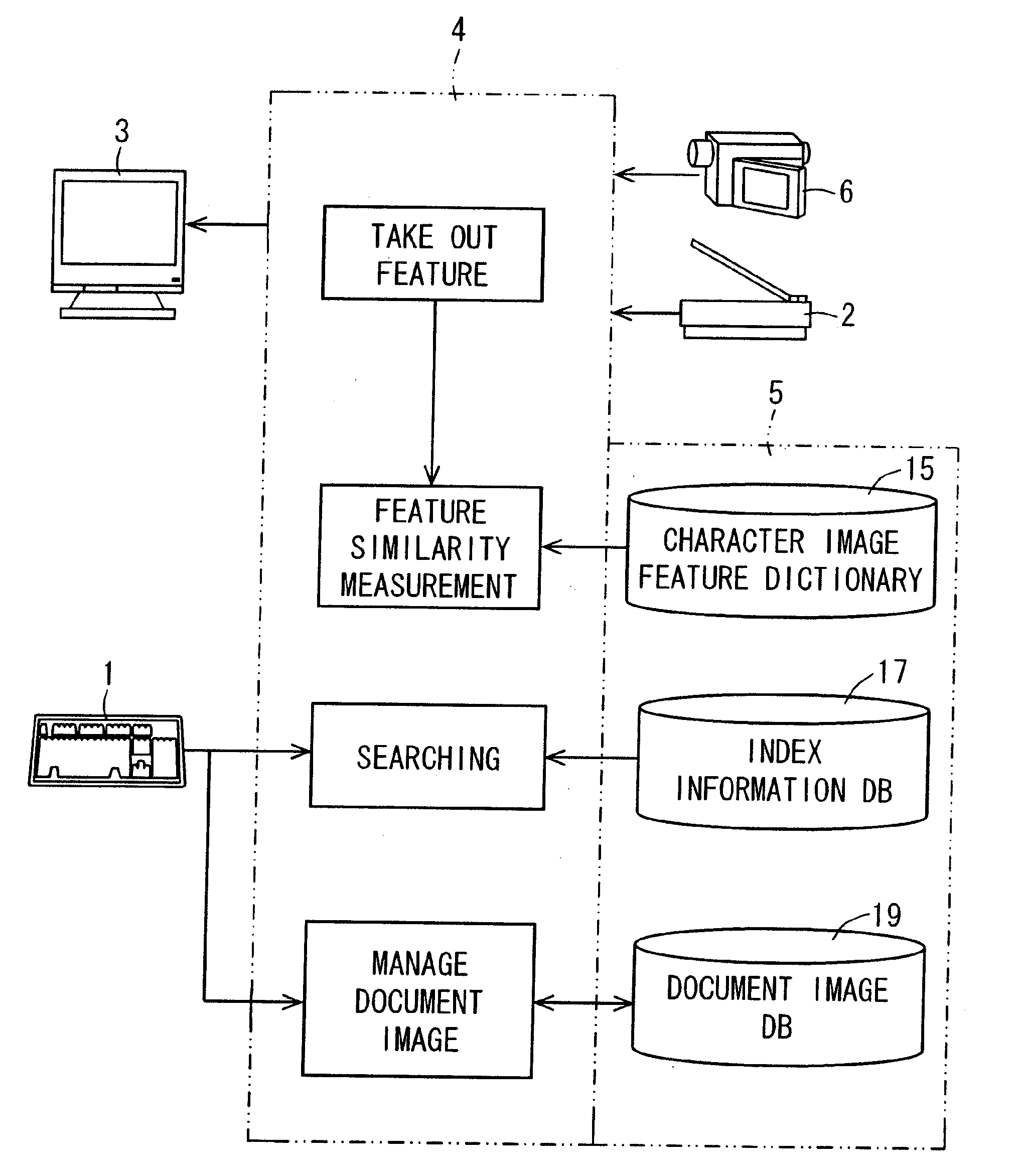
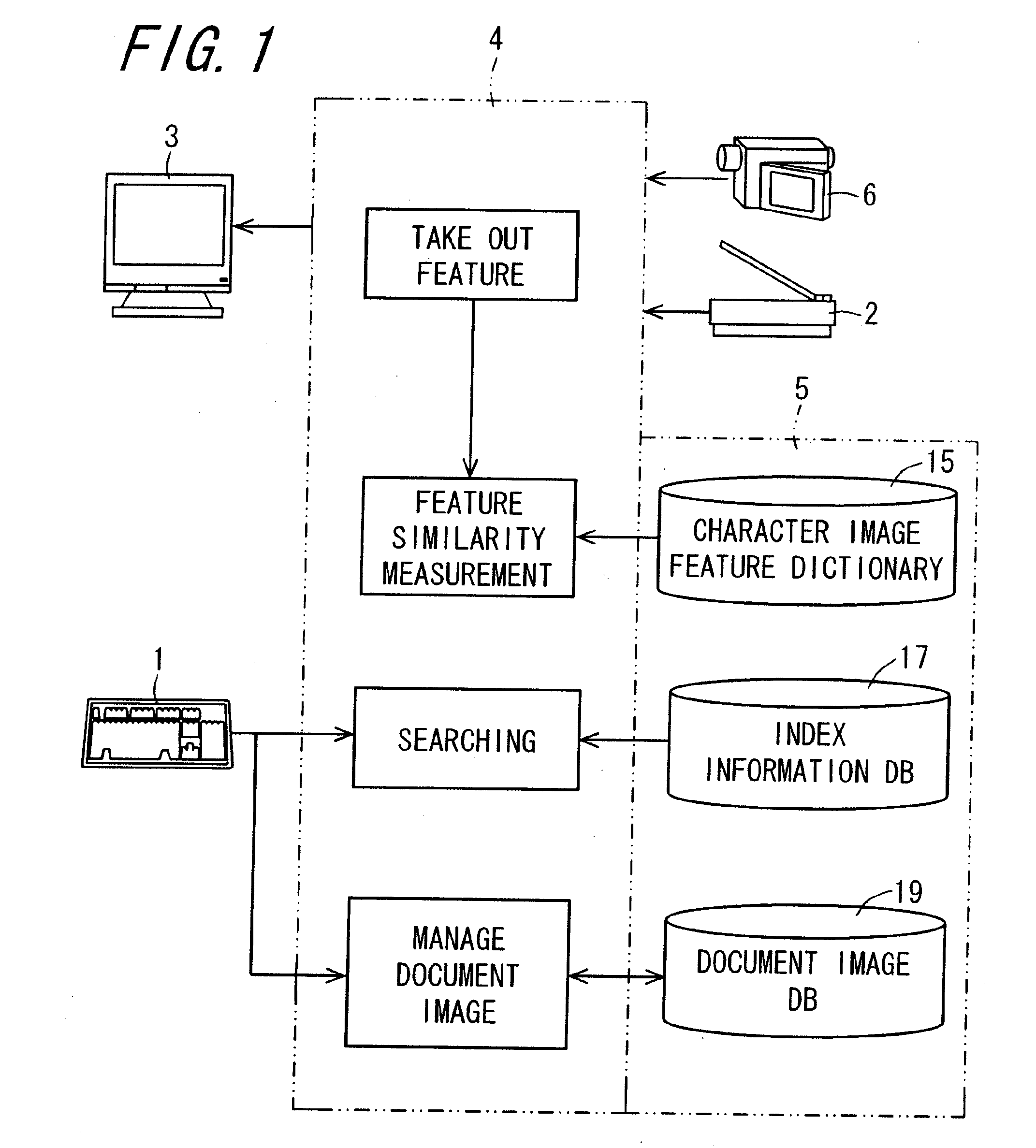
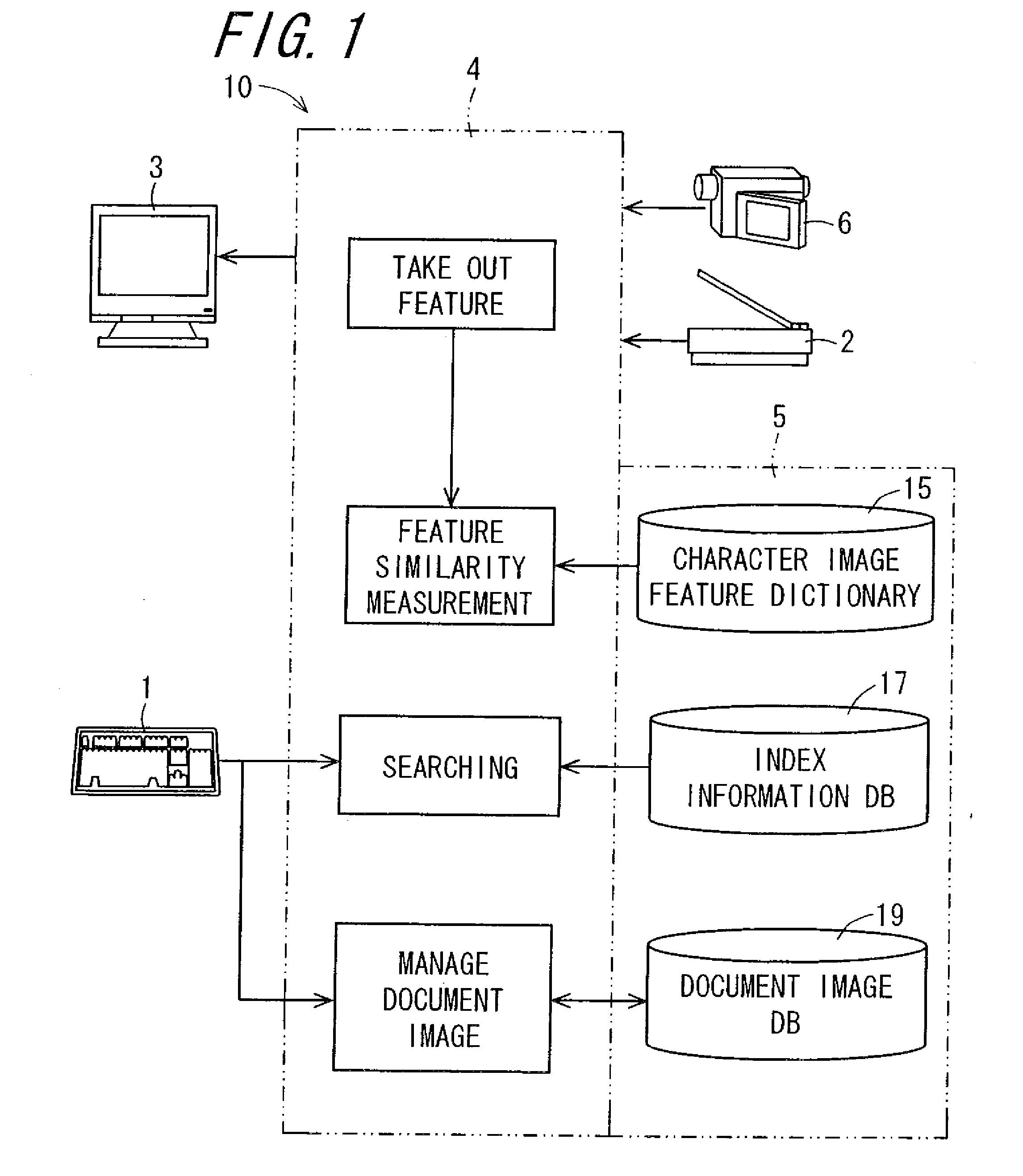
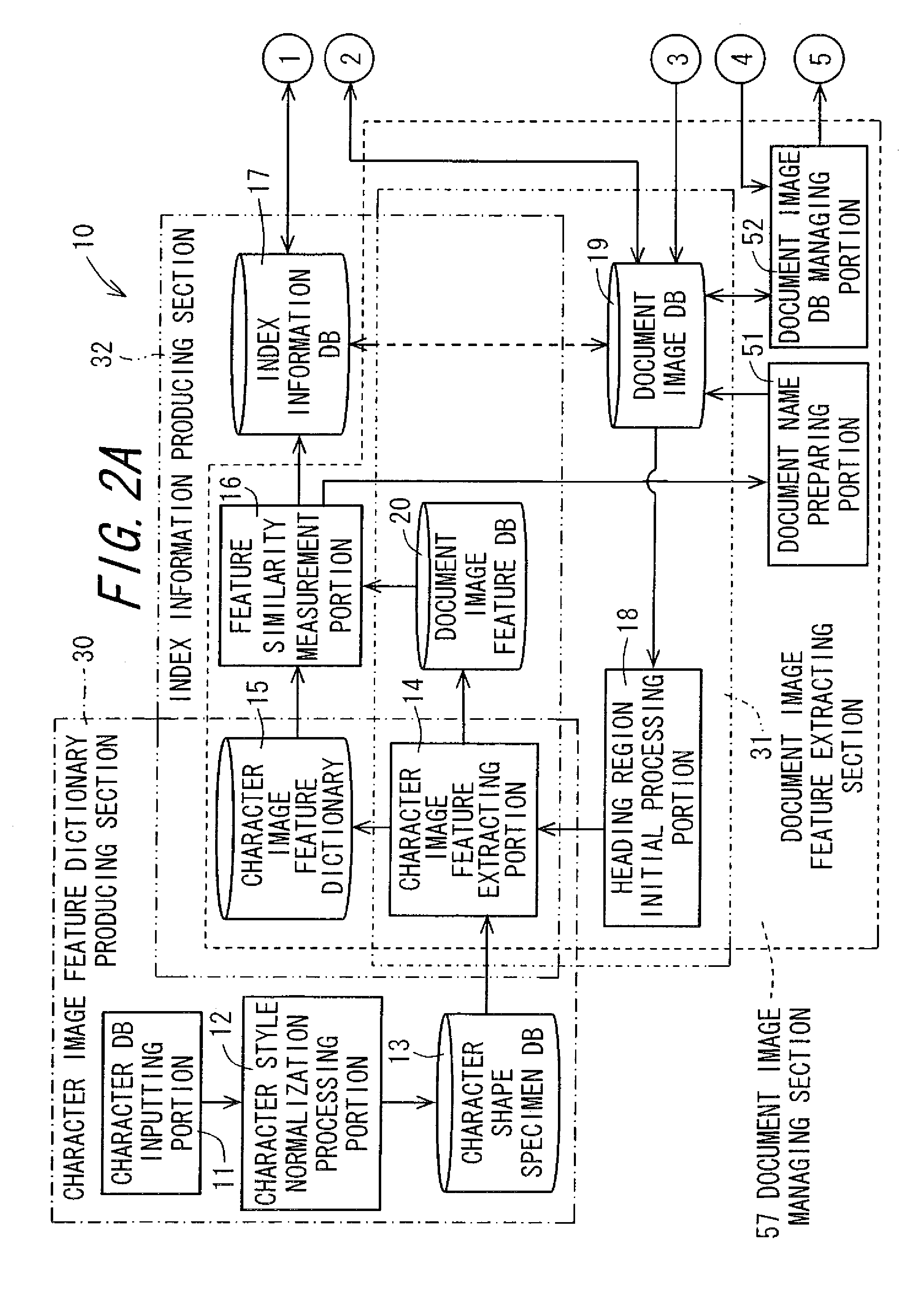
Document image processing apparatus, document image processing method, document image processing program, and recording medium on which document image processing program is recorded
ActiveUS20090028446A1High precision searchHigh precisionDigital data information retrievalSpecial data processing applicationsPattern recognitionLexical analysis
An image of a character string composed of M pieces of characters is clipped from a document image, and the image is divided into separate characters. Image features of each character image are extracted. Based on the image features, N (N>1, integer) pieces of character images in descending order of degree of similarity are selected as candidate characters, from a character image feature dictionary which stores the image features of character image in units of character, and a first index matrix of M×N cells is prepared. A candidate character string composed of a plurality of candidate characters constituting a first column of the first index matrix, is subjected to a lexical analysis according to a language model, and whereby a second index matrix having a character string which makes sense is prepared. In the language model, statistics are taken and then, the lexical analysis is performed.
Owner:SHARP KK
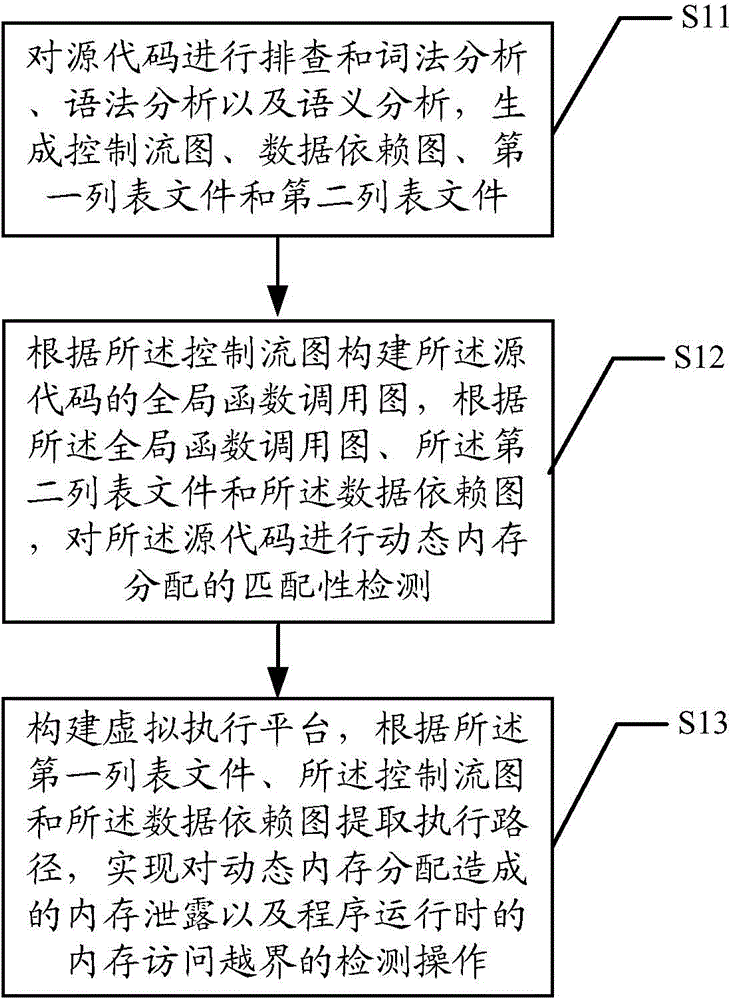
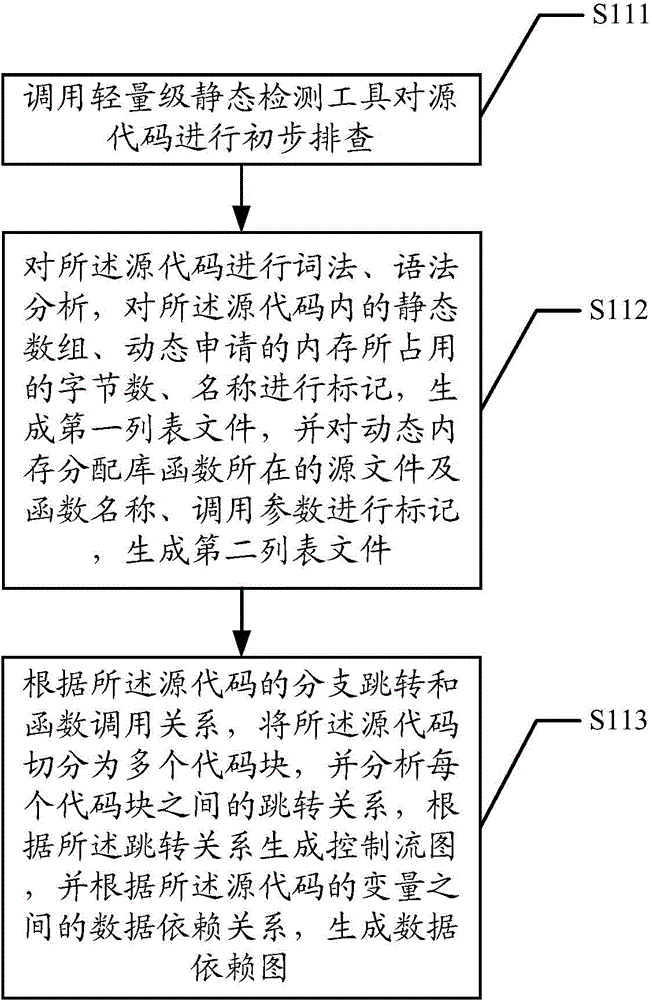
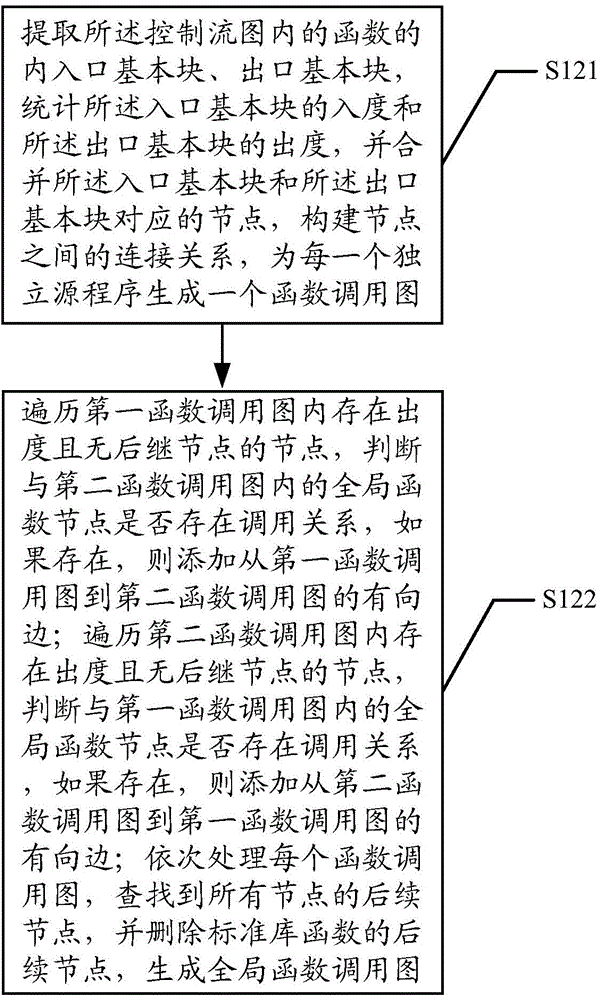
Memory access abnormity detecting method and memory access abnormity detecting device
ActiveCN104636256AImplement detection operationsRealize the detection operation of memory access out of boundsSoftware testing/debuggingPlatform integrity maintainanceData dependency graphLexical analysis
The invention discloses a memory access abnormity detecting method and a memory access abnormity detecting device. The memory access abnormity detecting method comprises the following steps of checking source codes and analyzing the morphology, the grammar and the semanteme of the source codes to generate a control flow diagram, a data dependence diagram, a first list file and a second list file; establishing a global function invocation diagram of the source codes according to the control flow diagram; performing matching detection on dynamic memory allocation of the source codes according to the global function invocation diagram, the second list file and the data dependence diagram; and establishing a virtual executing platform; and extracting an executing path according to the first list file, the control flow diagram and the data dependence diagram so as to detect memory leakage caused by dynamic memory allocation and memory access violation during running of a program. Memory access abnormity in the source codes can be sufficiently dug by analyzing the first list file, the second list file, the control flow diagram, the data dependence diagram and the global function invocation diagram, establishing the virtual executing platform and extracting the executing path, and the memory access abnormity can be detected efficiently.
Owner:AGRICULTURAL BANK OF CHINA
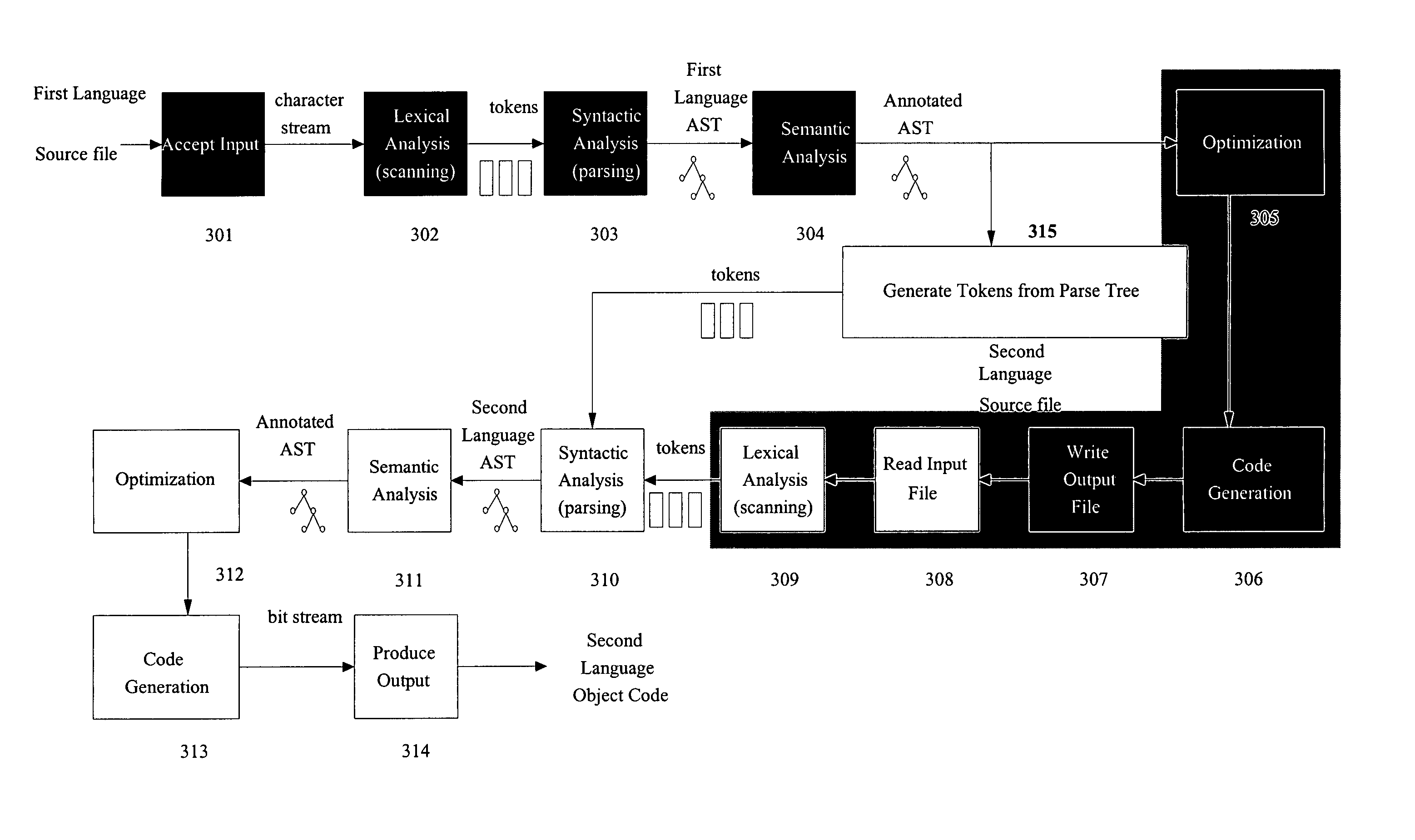
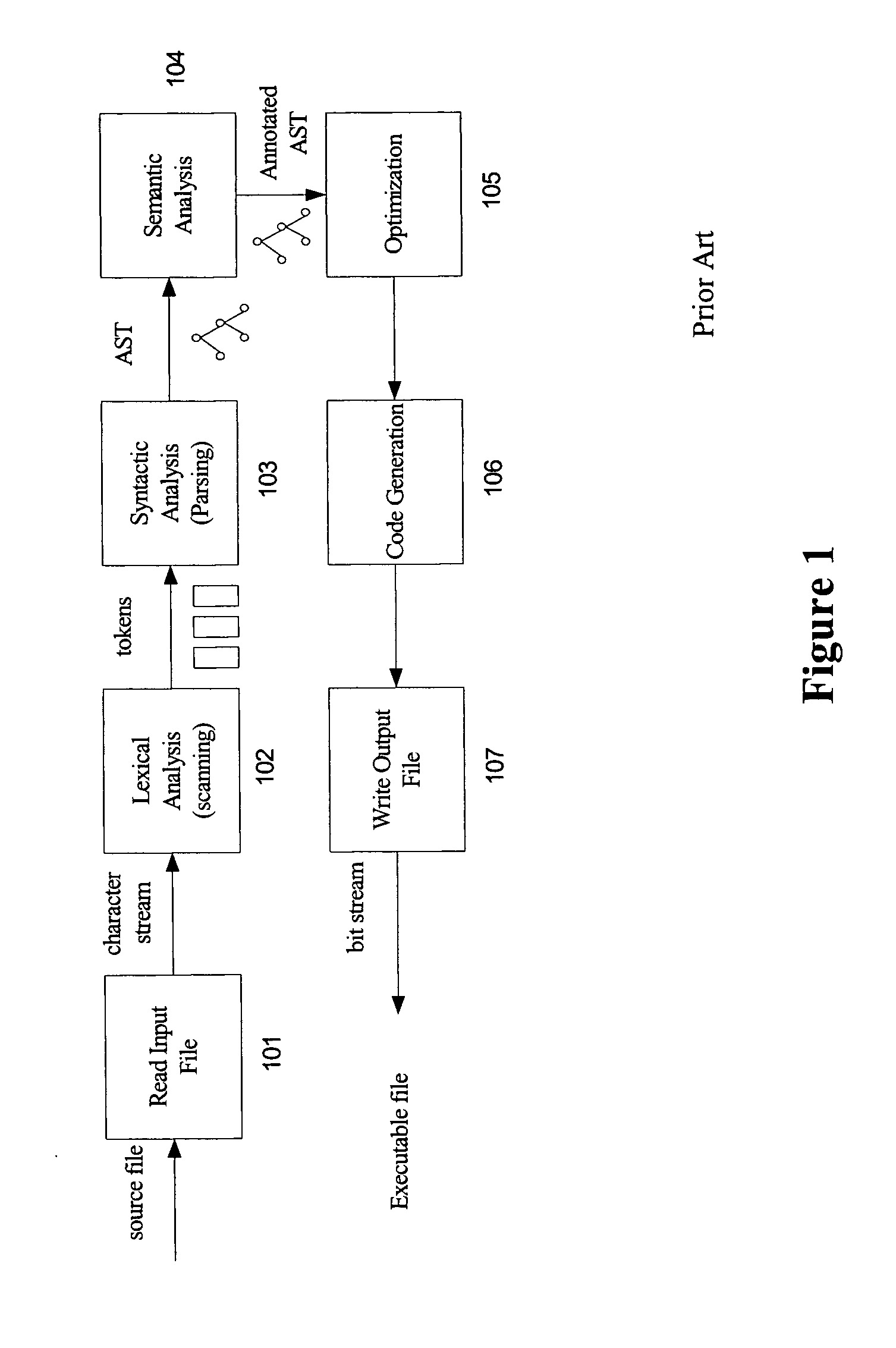
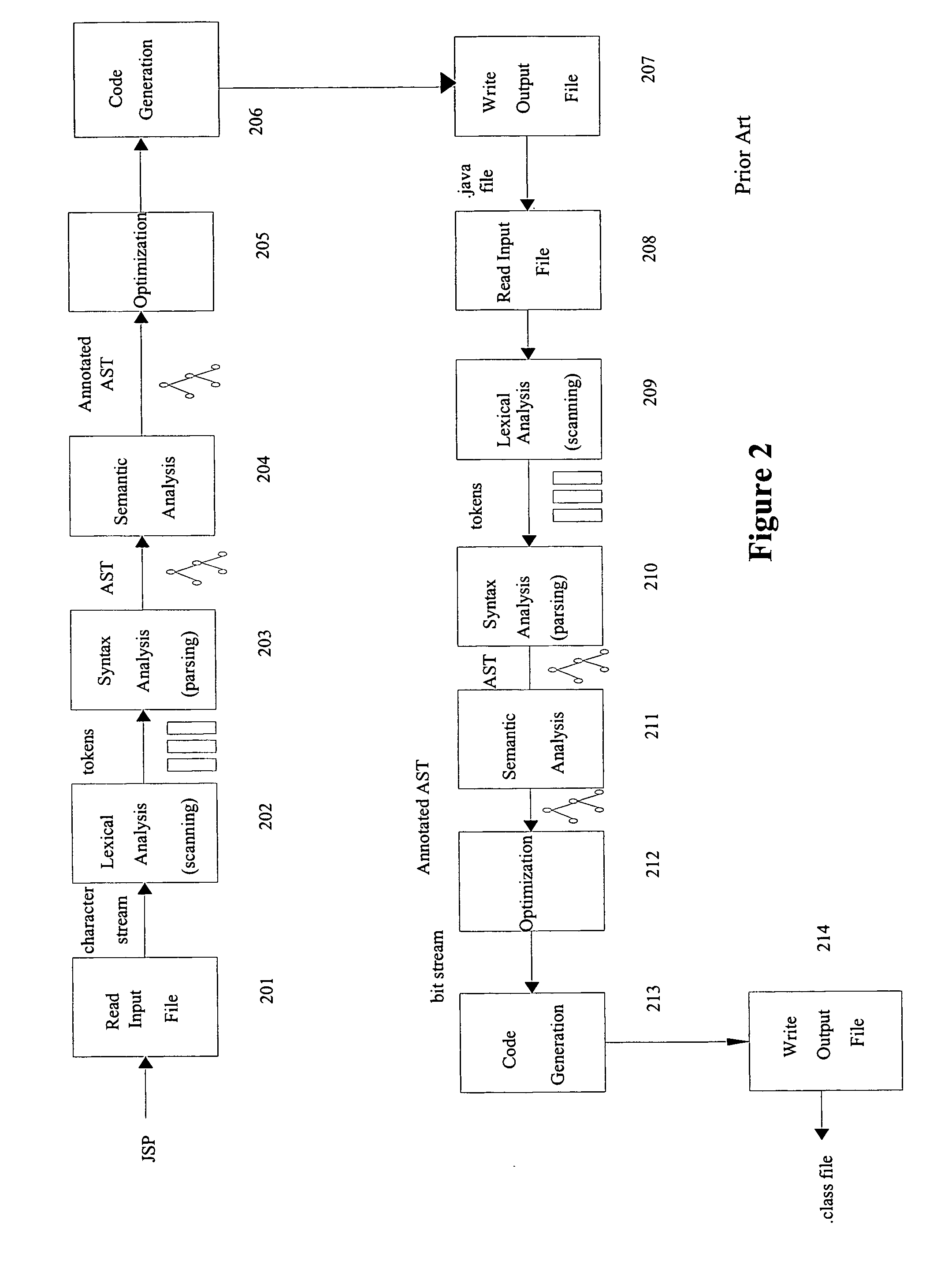
Method and system for translating programming languages
The present invention enable the language translation process involving more than one compilers to be completed entirely in memory, making it faster and more efficient. Two approaches can be adopted: the first approach employs a transformation component capable of generating a token stream from the parsed representation produced by the first compiler and providing it to the parser of the second compiler, skipping the “Optimization”, “Code Generation”, and “Write Output File” phases of the first compiler and the “Read Input File” and “Lexical Analysis” phases of the second compiler; The second approach passes the bit stream produced by the code generator of the first compiler directly to the lexical analyzer of the second compiler instead of writing the bit stream to disk and then reading it back from the disk, eliminating the “Write Output File” phase of the first compiler and the “Read Input File” phase of the second compiler. Both approaches are not limited to any particular source language or target language. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:ORACLE INT CORP
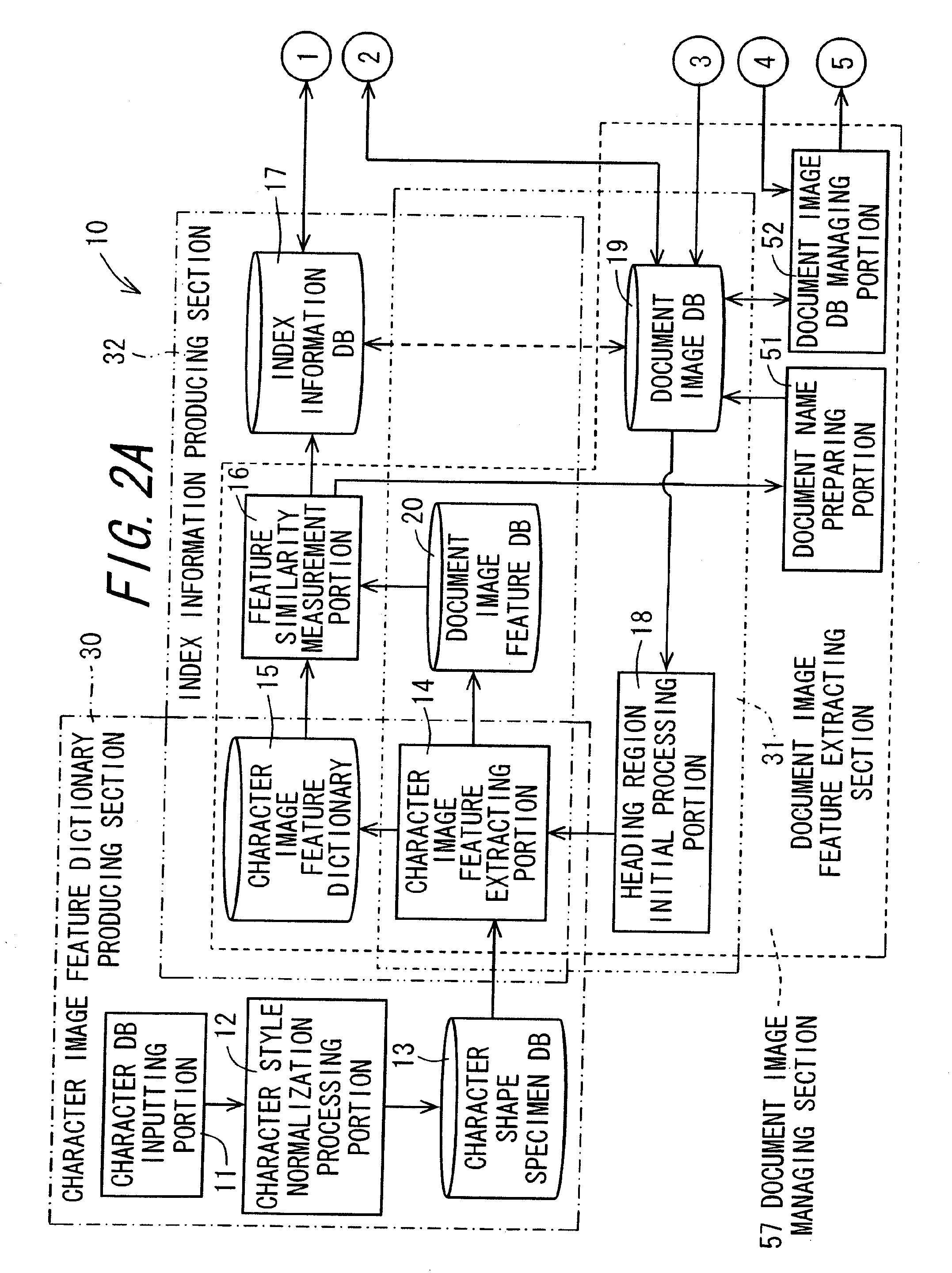
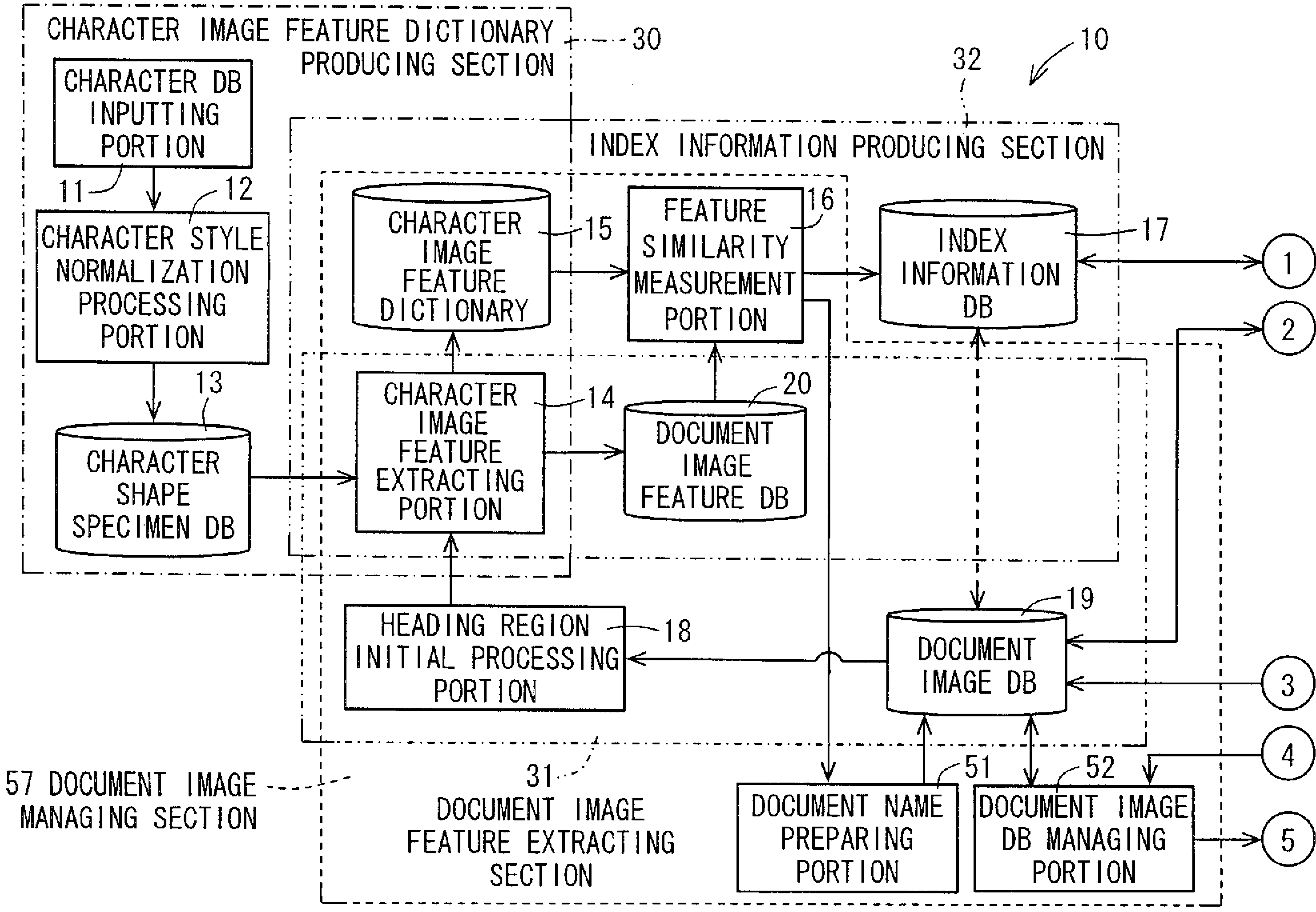
Character image feature dictionary preparation apparatus, document image processing apparatus having the same, character image feature dictionary preparation program, recording medium on which character image feature dictionary preparation program is recorded, document image processing program, and recording medium on which document image processing program is recorded
ActiveUS20090028445A1High precisionDigital data information retrievalSpecial data processing applicationsPattern recognitionLexical analysis
An image of a character string composed of M pieces of characters is clipped from a document image, and the image is divided character by character, and image features of each character image are extracted. On the basis of the image features, N (N>1, integer) pieces of character images in descending order of degree of similarity are selected as candidate characters from a character image feature dictionary which stores the image features of character image in units of character, and the first index matrix of M×N cells is prepared. A candidate character string composed of a plurality of candidate characters constituting the first column of the first index matrix, is subjected to a lexical analysis according to a predetermined language model, whereby a second index matrix adjusted into a character string which makes sense is prepared to he utilized for searching.
Owner:SHARP KK
Intelligent questioning-answering method, terminal and storage medium
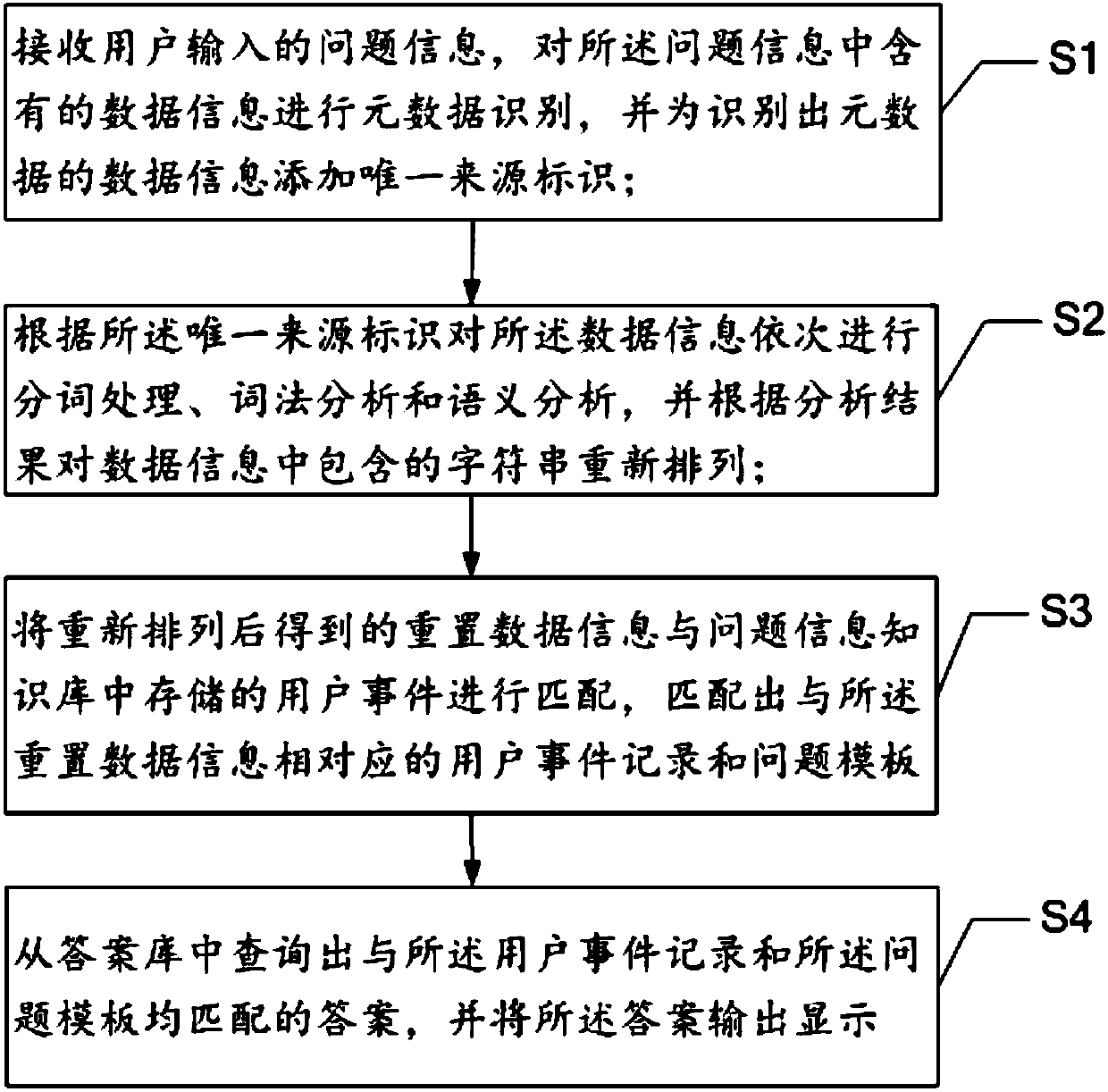
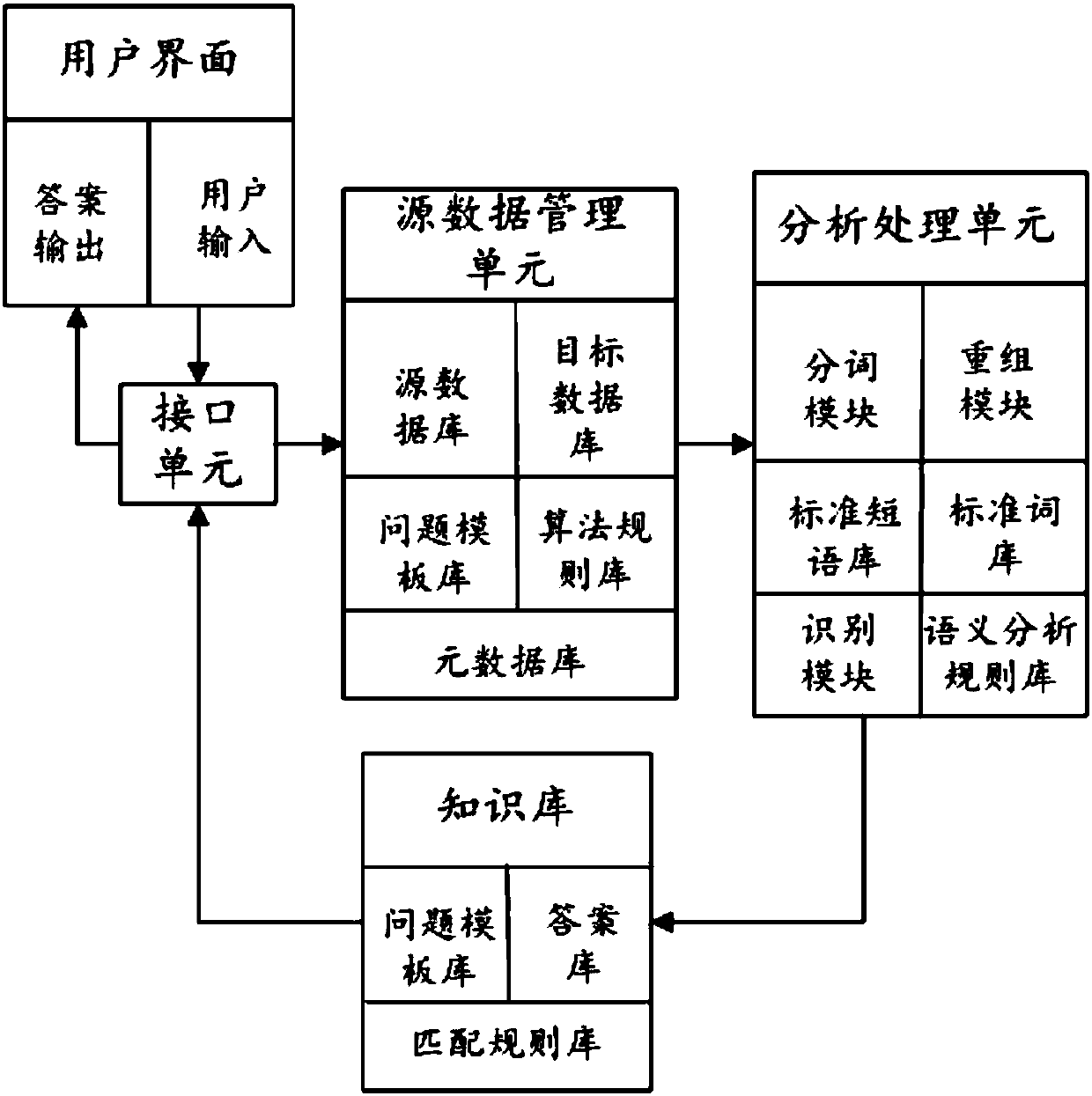
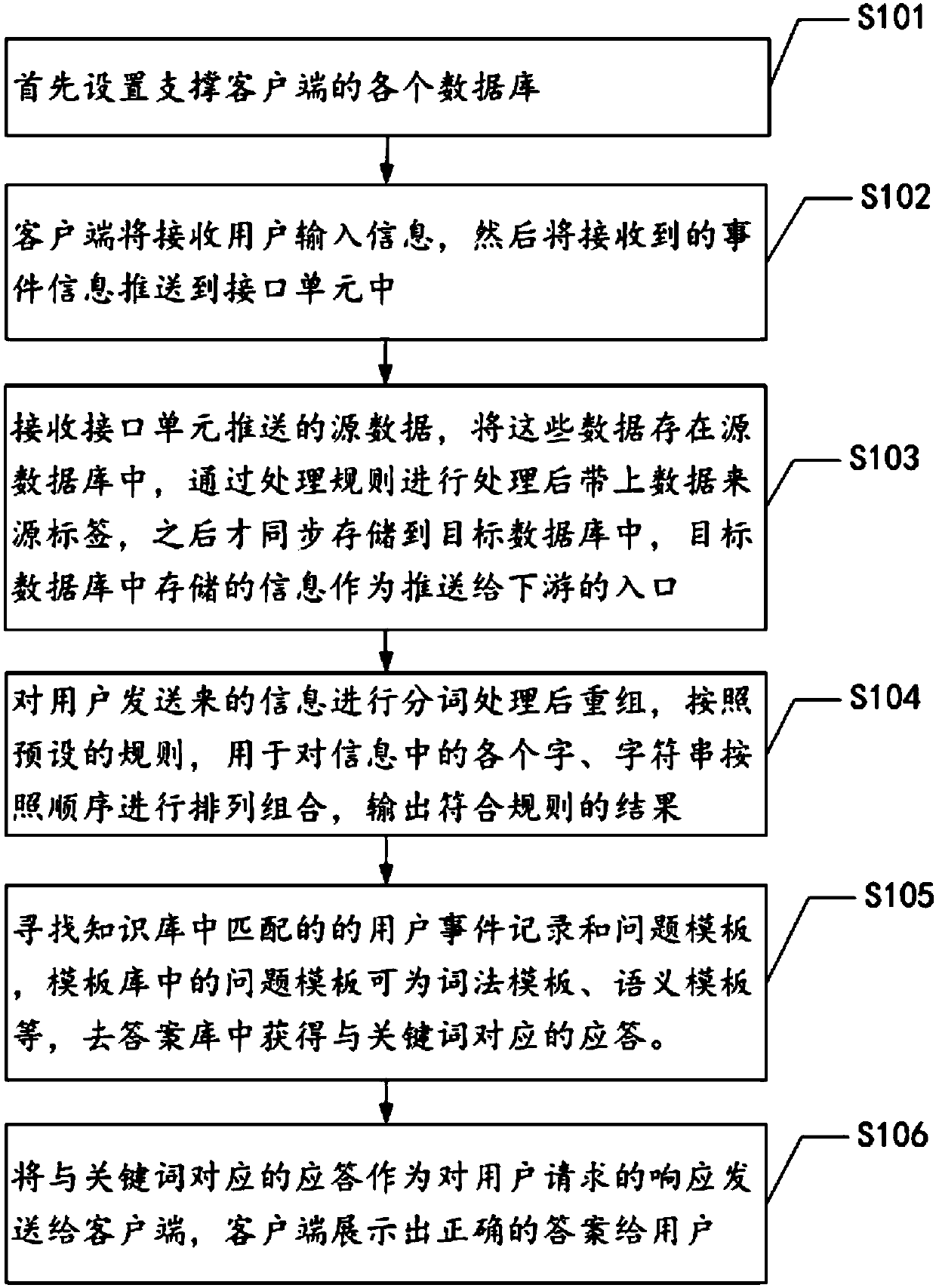
InactiveCN107766511AEasy to useAutomatic and timely feedbackSemantic analysisSpecial data processing applicationsData informationLexical analysis
The invention provides an intelligent questioning-answering method, a terminal and a storage medium. According to the method, metadata recognition is performed on data information contained in user question information, word segmentation processing, lexical analysis and semantic analysis are sequentially performed on the data information, strings contained in the data information are rearranged according to analysis results, the reset data information obtained after rearrangement is matched with user events stored in a question information knowledge base, a user event record and a question template corresponding to the reset data information are obtained through matching, an answer matched with both the user event record and the question template is queried from an answer base, and the answer is output and displayed. Through the method, source processing is performed on data input by a user, the corresponding answer is acquired according to a unique identifier and the question template, therefore, the more accurate question answer can be acquired, working efficiency is improved, and waiting time of the user is shortened.
Owner:深圳市前海众兴科研有限公司
Function call graph key node recognition and identification method based on complex network analysis
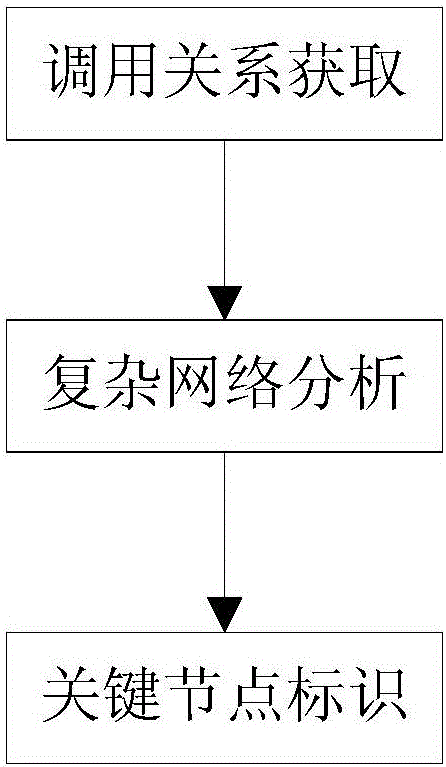
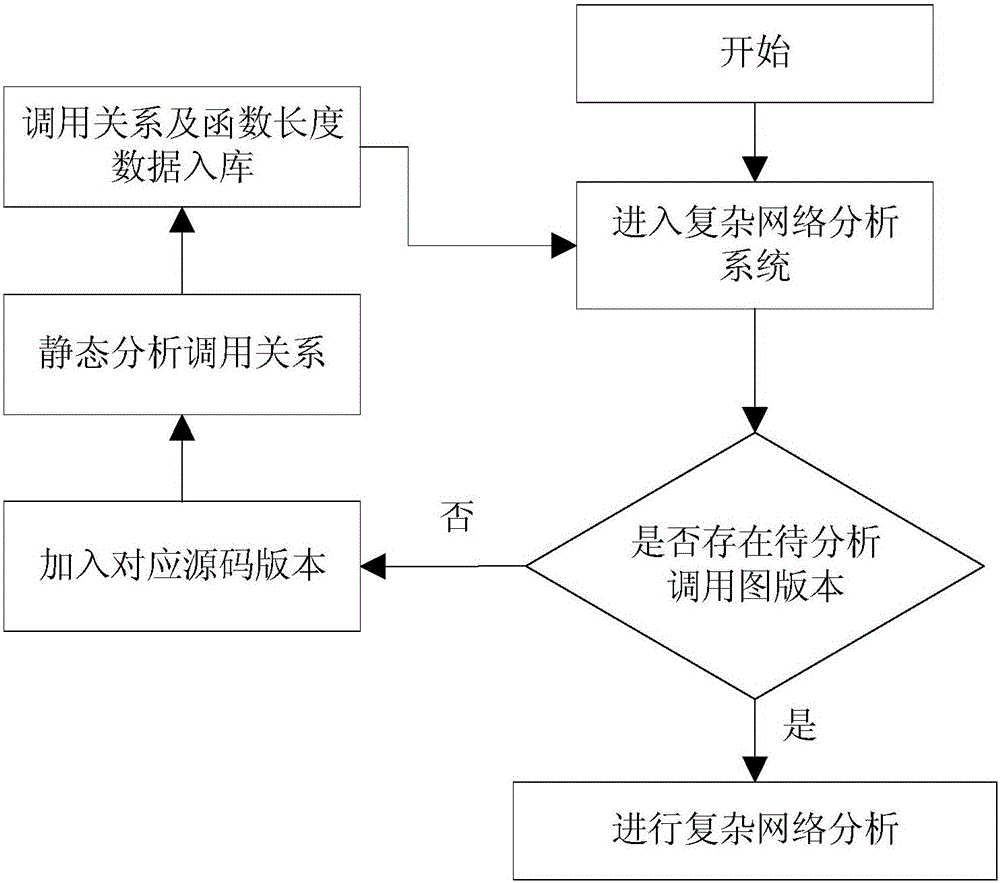
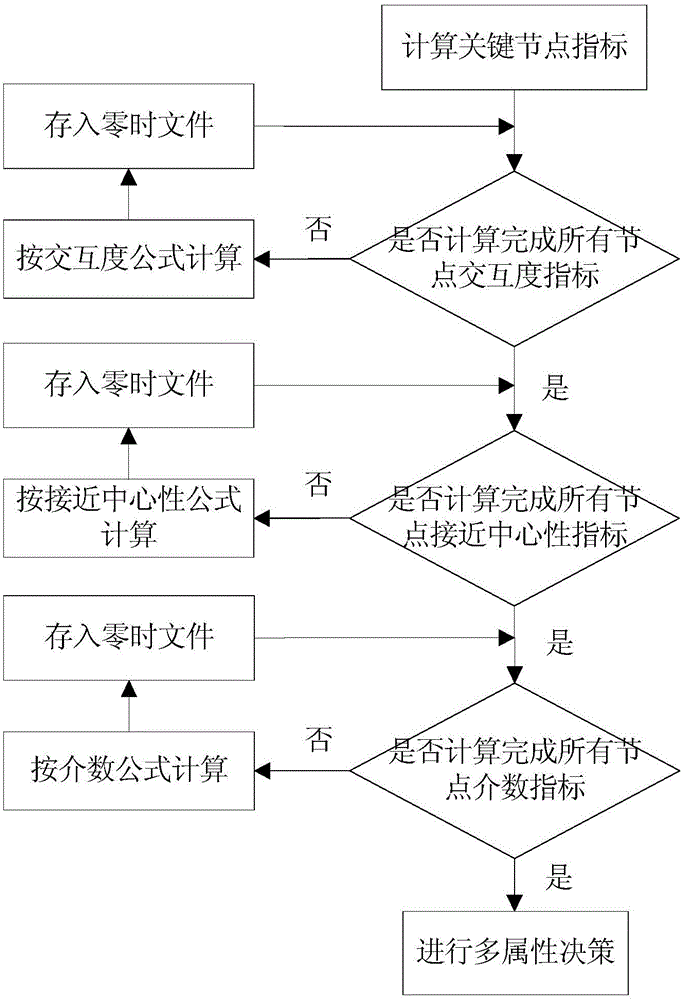
ActiveCN106020950AImprove work efficiencyProgram initiation/switchingInterprogram communicationComplex network analysisLexical analysis
The invention relates to a function call graph key node recognition and identification method based on complex network analysis. The method comprises the steps of carrying out lexical analysis, grammatical analysis and control stream analysis through a sound code static analysis technology, thereby obtaining source code call relationship data and function length data, and storing all data in a database in a classification mode; generating a call graph according to the obtained data, calculating node indexes of the call graph by employing a complex network analysis method, wherein the indexes comprise interaction degree, closeness centrality, node betweenness and function length, and calculating node key degree by employing a multi-attribute decision-making method; and through combination of user demands and state data stored in the database, calculating a key node rank and corresponding grey proportion data by employing the obtained node key degree data of the function call graph, and carrying out visual display. According to the method, the key nodes in the complex call relationship graph can be recognized and identified rapidly, and the working efficiency is remarkably improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Linguistically enhanced search engine and meta-search engine
InactiveUS20110173174A1More focused search resultThe result is moreWeb data indexingDigital data processing detailsLexical analysisHuman search engine
A search enhancement system (whether linked through an API to a search engine or integral to a search engine) creates a series of different narrow searches through the selective use of synonyms, hyponyms for a narrower search, hypernyms for a broader search, and antonyms for a reverse search. Lexical analysis can also be used to create alternative narrow searches. This allows a user to explore different nuances of meaning in an original search phrase until the user finds what he or she wants, while keeping individual searches narrow, thus leading to more focused search results.
Owner:FLITCROFT INVESTMENTS
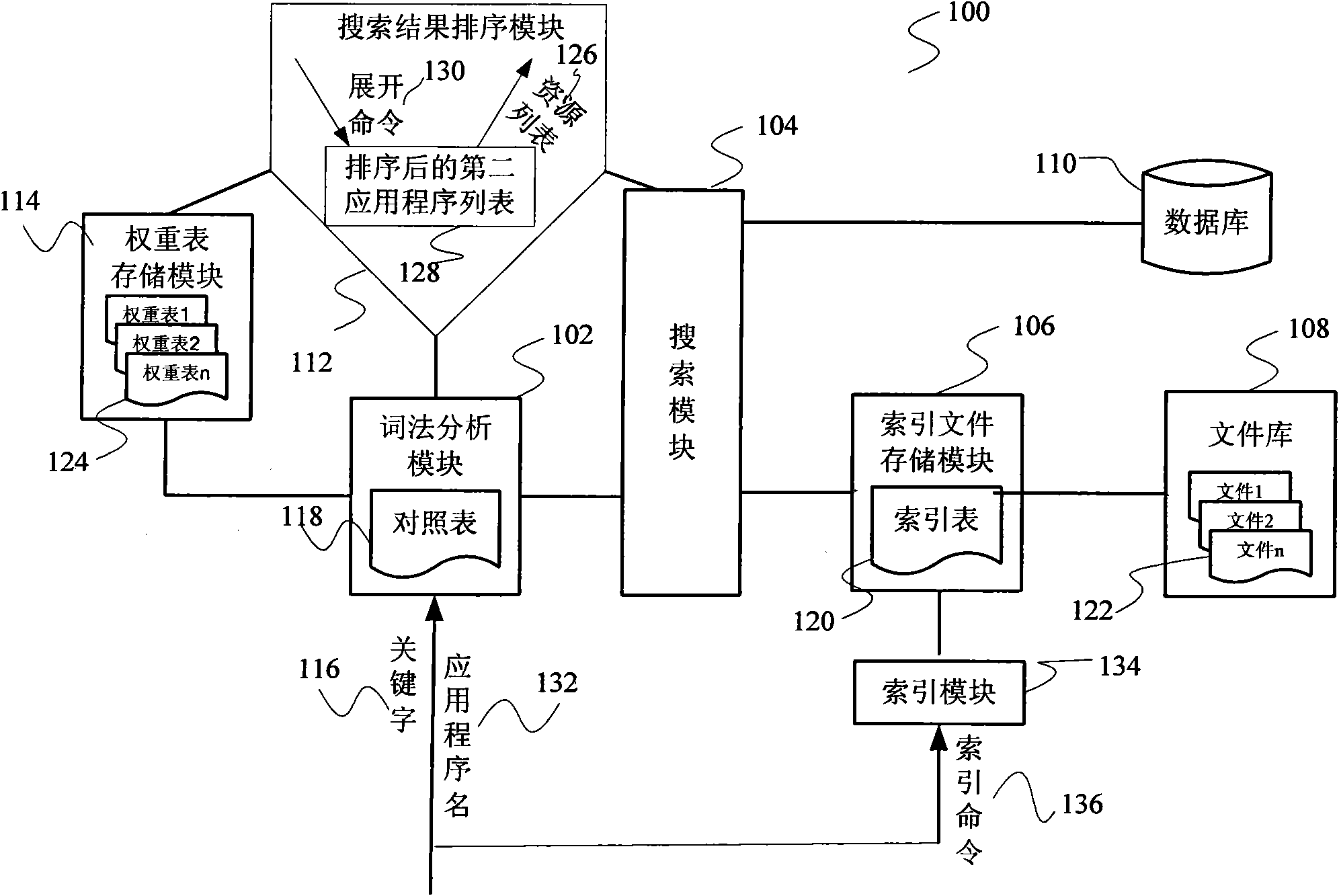
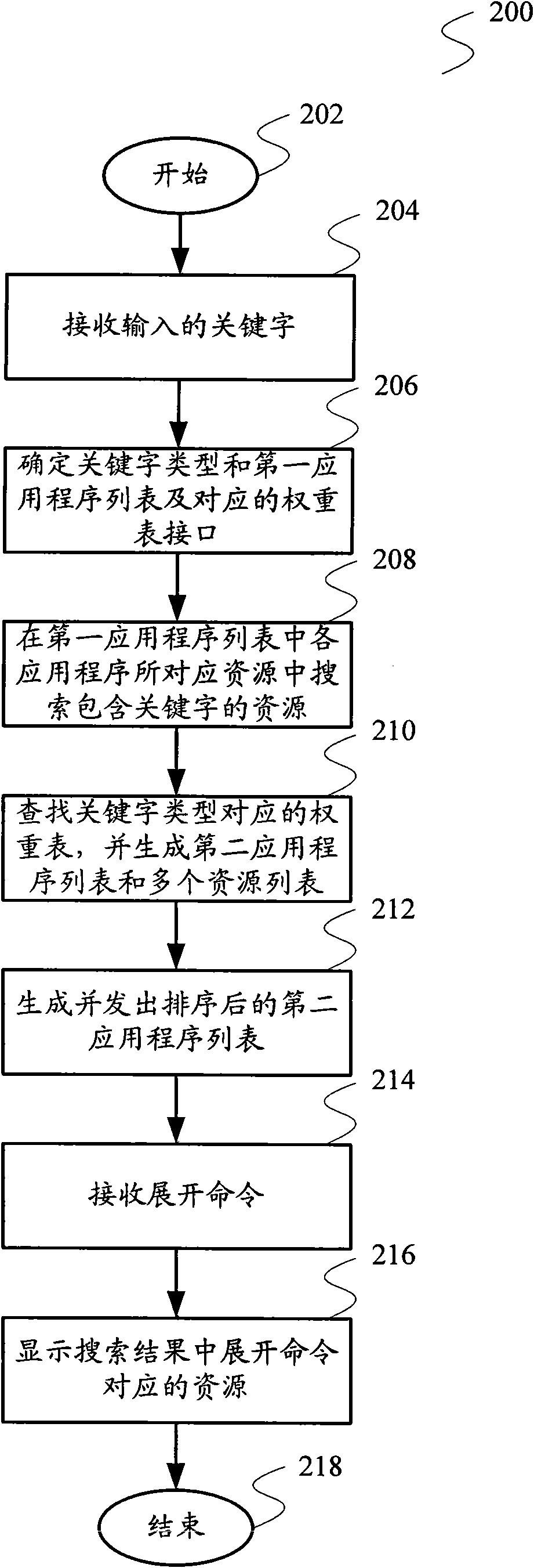
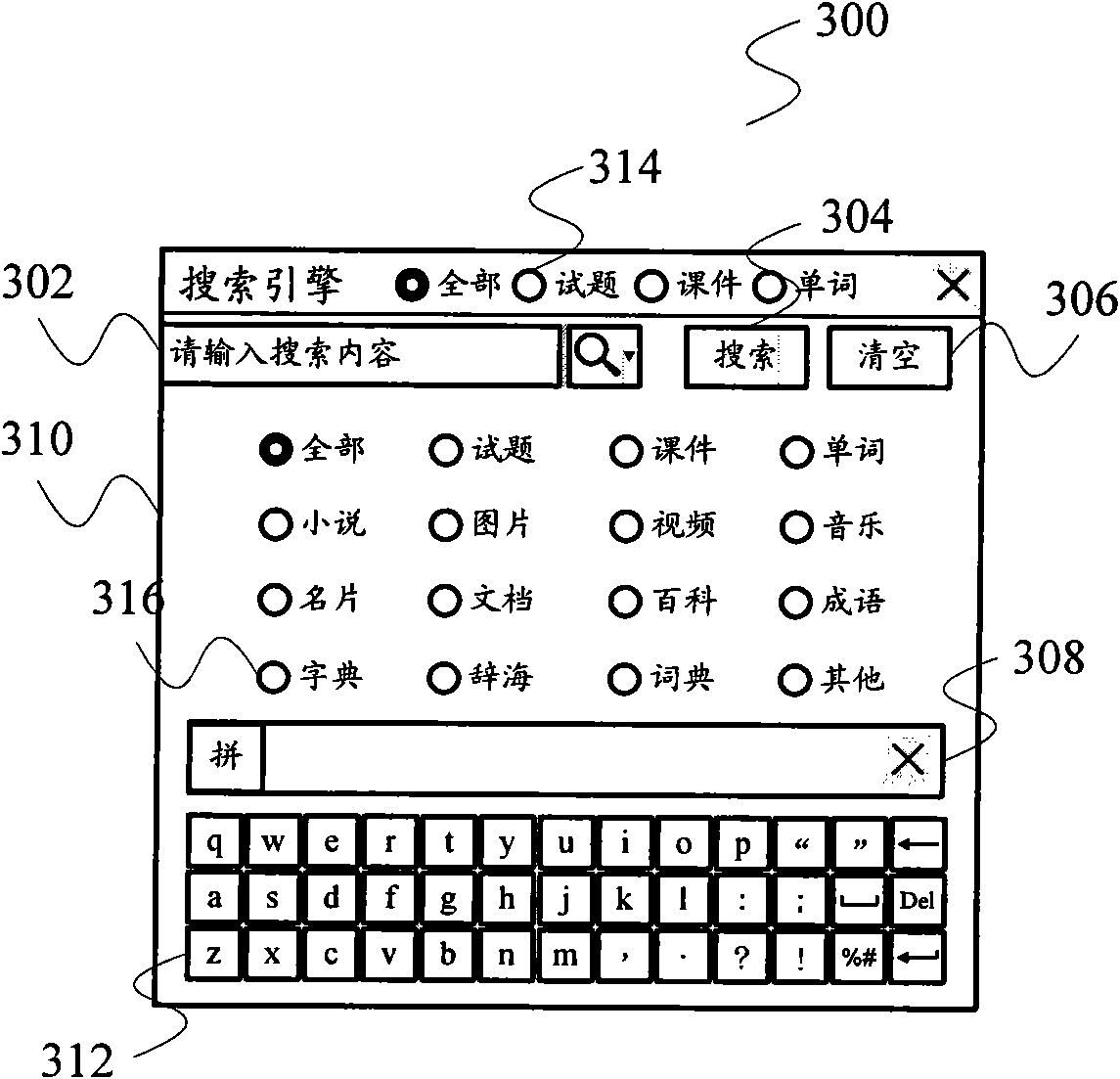
Search engine used in personal hand-held equipment and resource search method
InactiveCN101566984AReduce in quantityImprove hit rateSpecial data processing applicationsResource poolLexical analysis
The invention relates to a search technology and provides a search engine used in personal hand-held equipment and a resource search method to solve the defects, such as inconvenient lookup of page turning caused by excessive search results, and the like. The search engine comprises a lexical analysis module, a search module and a search result sequencing module, wherein the lexical analysis module receives key words, confirms to the type of the key words and sends out the key words, the search module searches a resource containing the key words in a resource pool and generates and sends out search results containing the found-out resource and the applying program name corresponding to the resource; and the search result sequencing module receives the types of the key words and invokes the corresponding weight table. The search results are received and sequenced to generate a first-stage resource list, the weighting corresponding to every applying program in a second applying program list is looked up in the weight table, the second applying program list is sequenced according to the weight, and the sequenced second applying program list is outputted. The invention also provides a resource search method. The search range can be further reduced by carrying out the lexical analysis of the key words to greatly reduce the quantity of the search results.
Owner:SHENZHEN YOUXUETIANXIA EDUCATION DEV CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com