Method for detecting SQL (structured query language) injection vulnerability
A vulnerability detection and injection point technology, applied in the field of network information security, can solve the problem that SQL injection is difficult to guarantee no false positives, etc., and achieve the effect of improving accuracy and reducing false alarm rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The preferred embodiments of the present invention will be specifically described below in conjunction with the accompanying drawings.
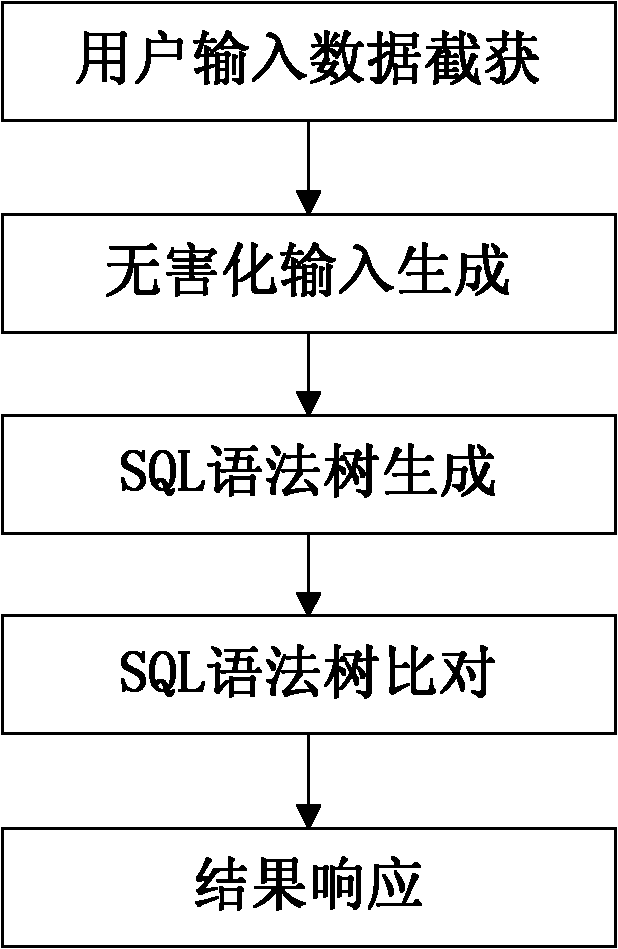
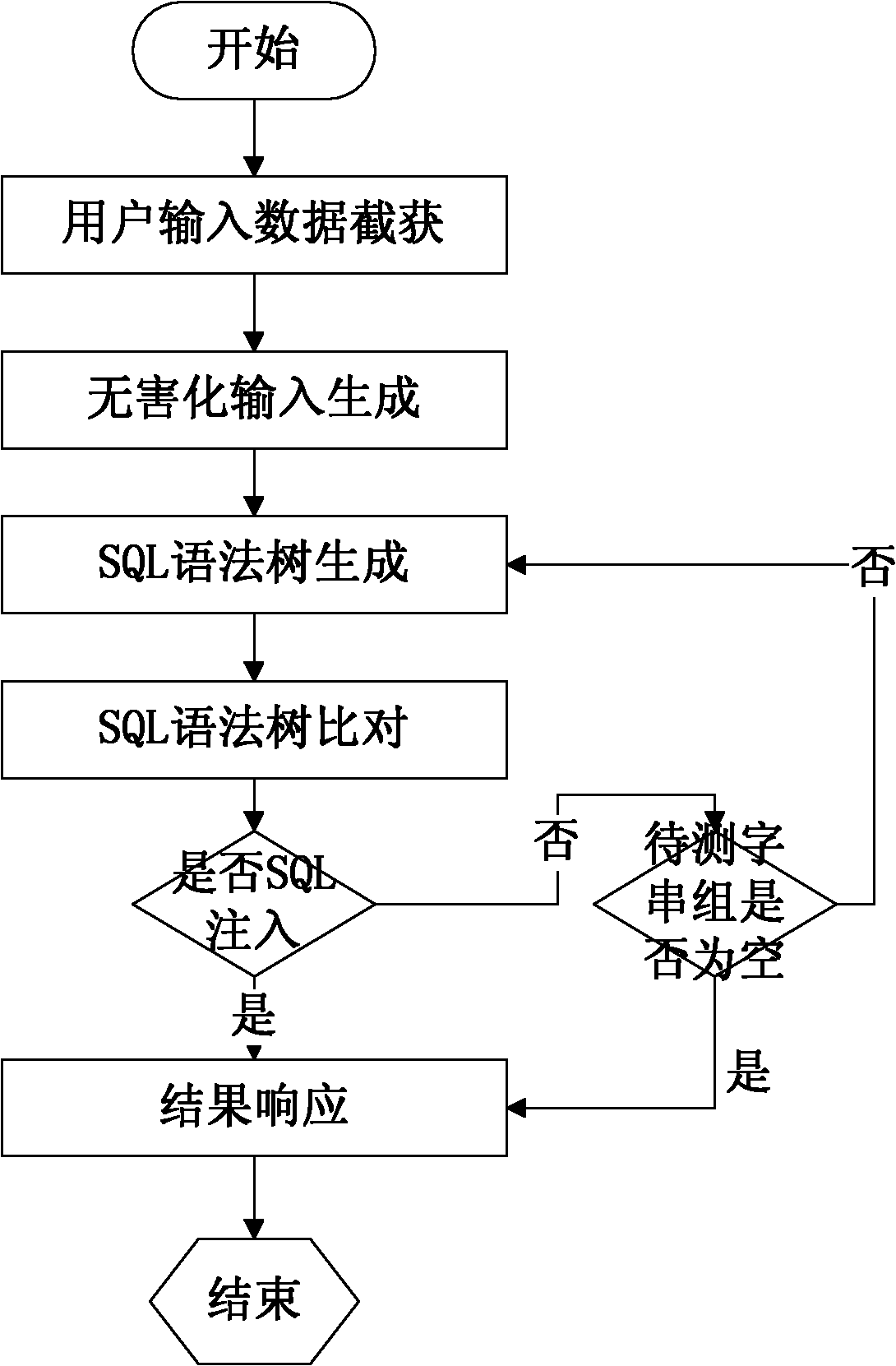
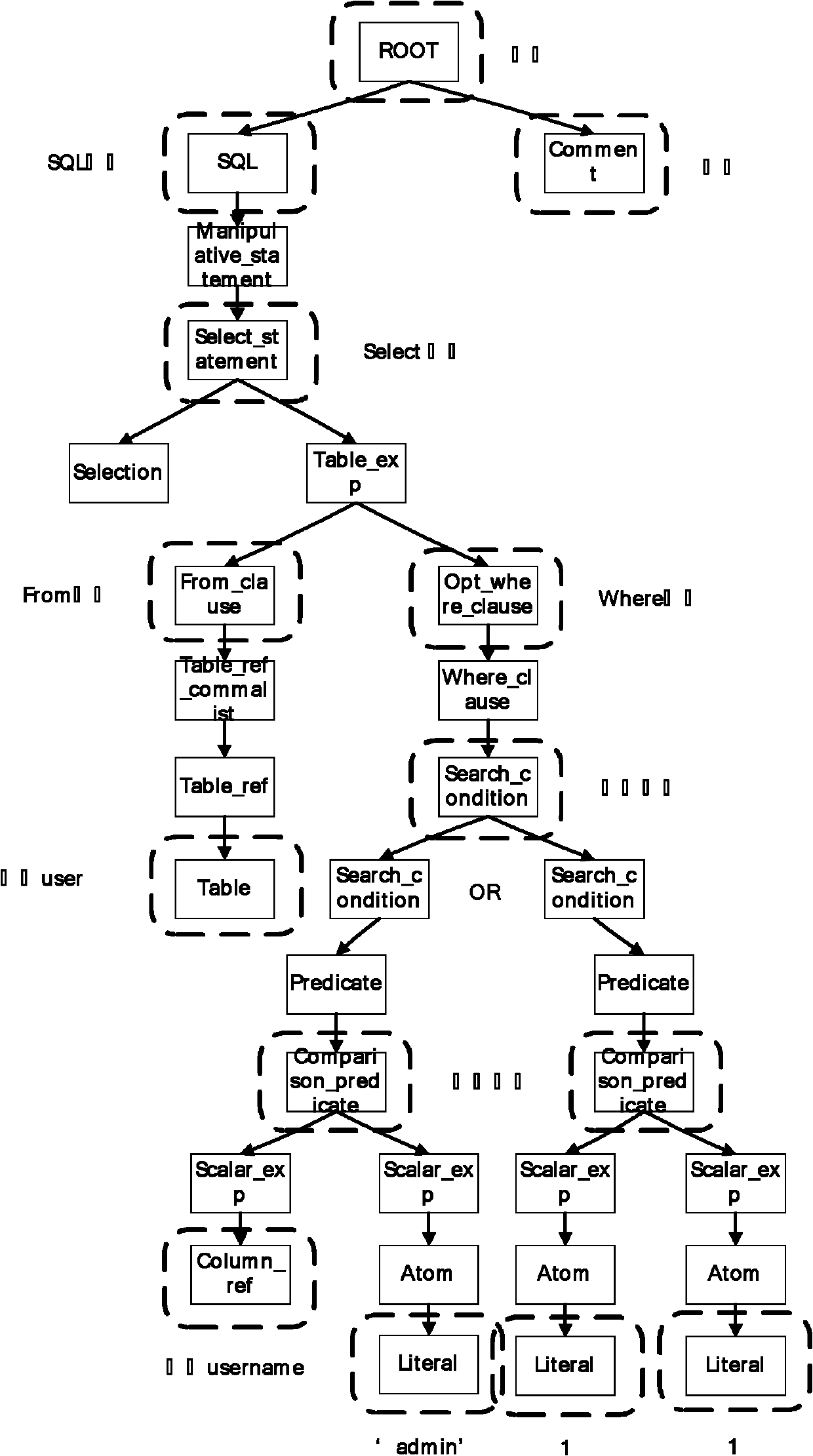
[0051] This embodiment specifically implements a SQL injection vulnerability detection method described in the present invention, comprising the following steps:
[0052] 1. User input data interception:
[0053] In the step of intercepting user input data, how to completely obtain the parameters that the user may submit to the application program while ignoring the data irrelevant to the database is the key to the subsequent detection work.
[0054] In this embodiment, two methods are provided to obtain input data:
[0055] 1. A standard web application always needs to be accessed through a server (or the application itself is a server), and the most common and popular web server always provides us with a set of interfaces to reproduce the data submitted by users. Processing, that is, the core component of the WEB server, can be und...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com