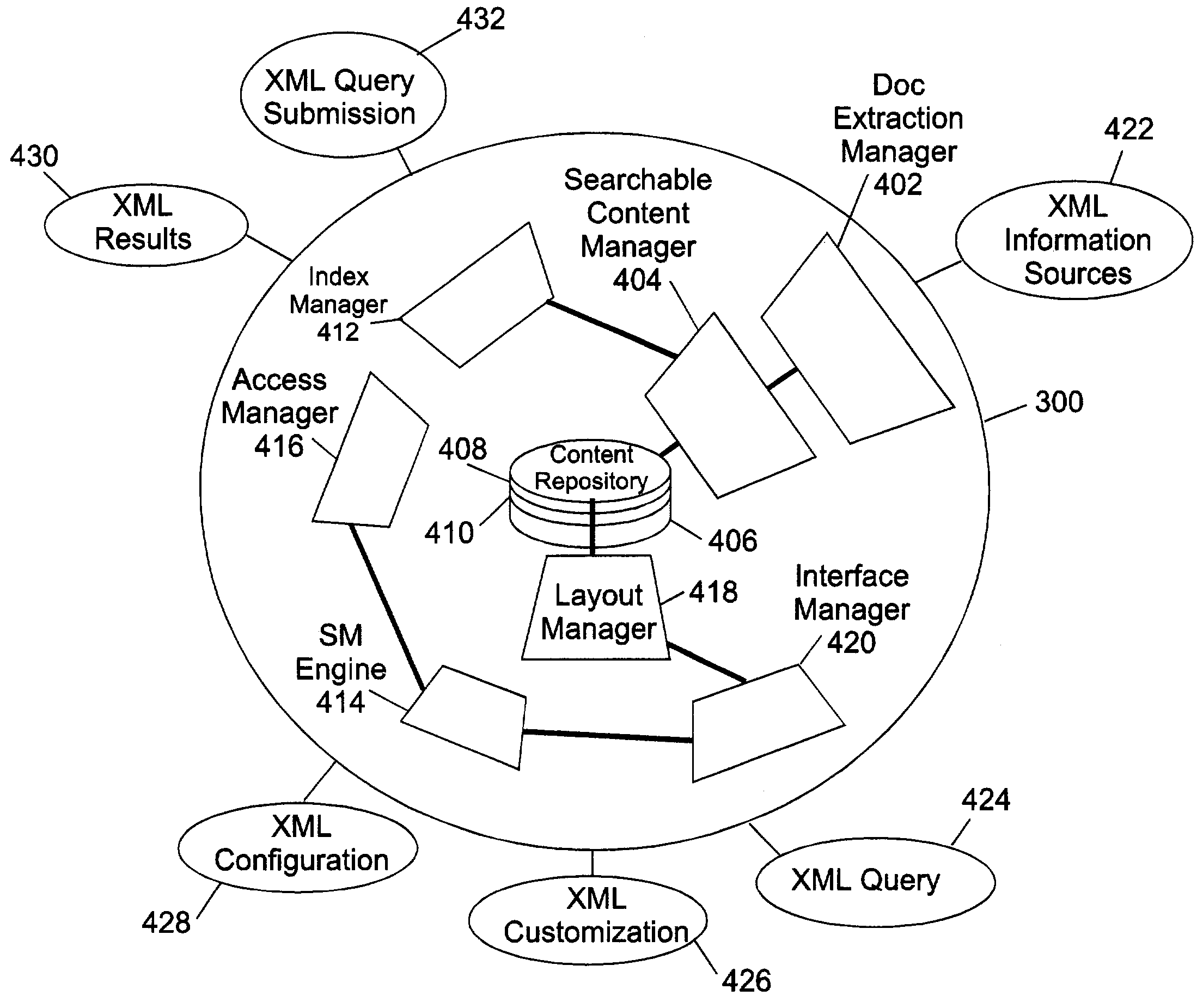
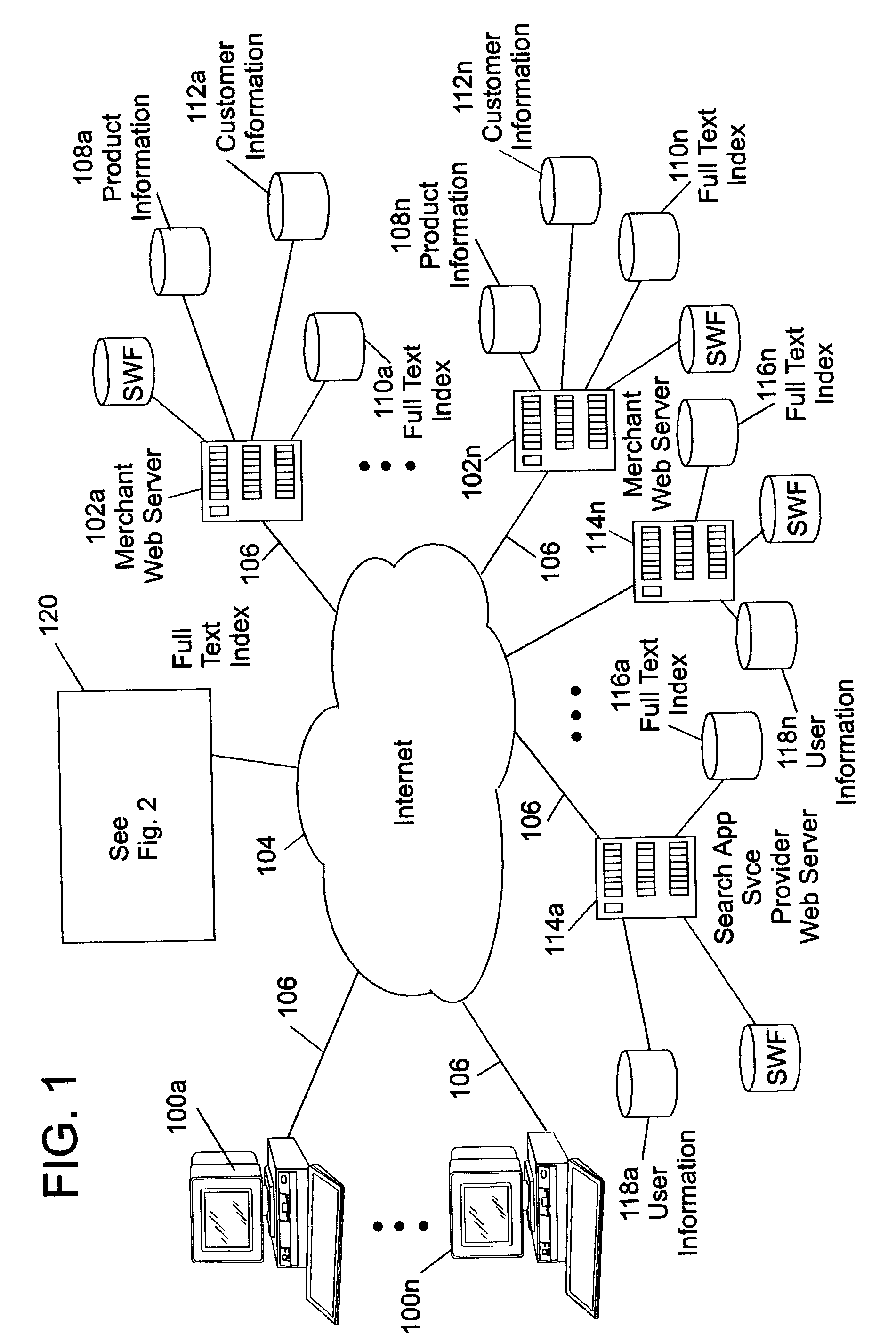
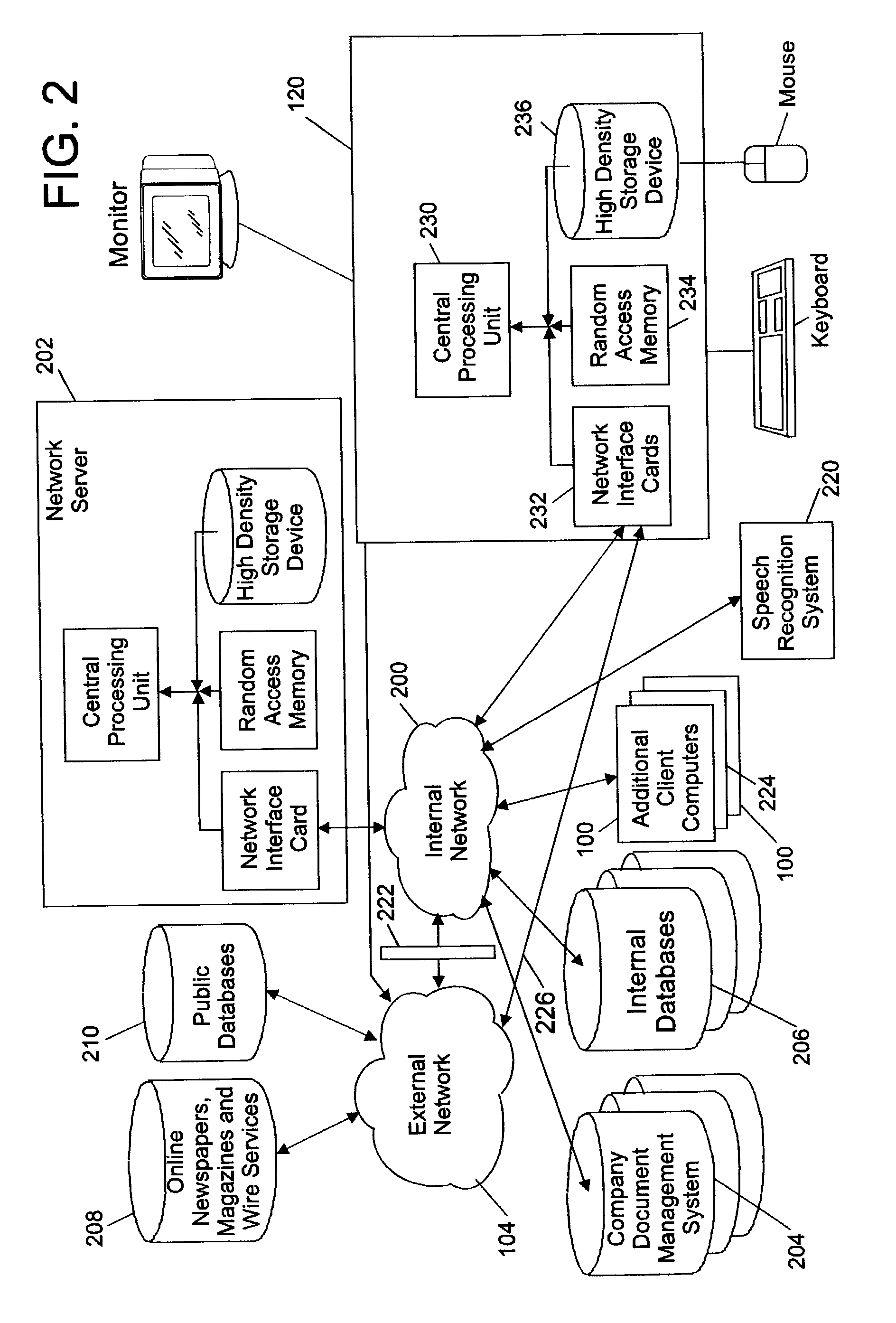
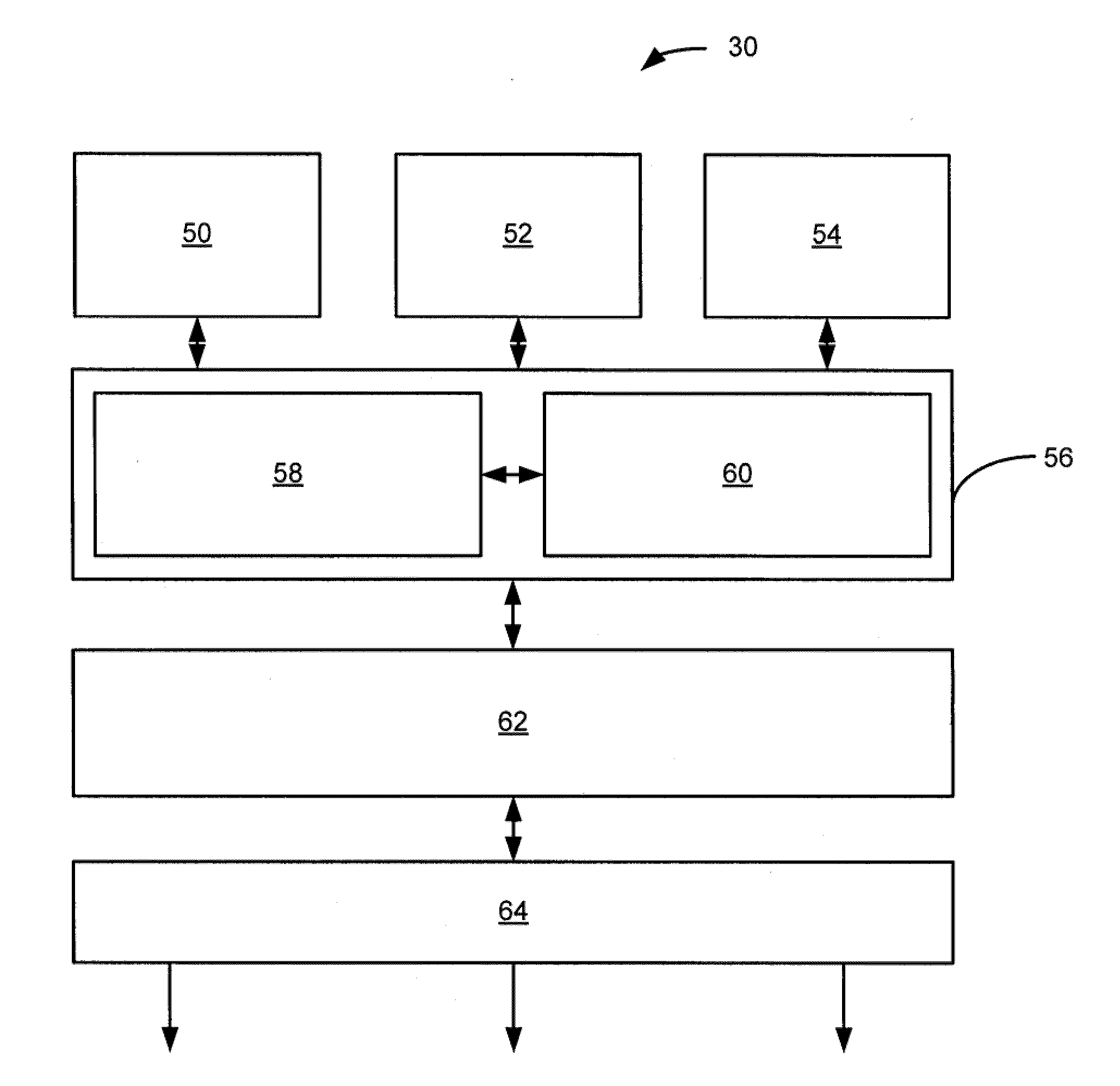
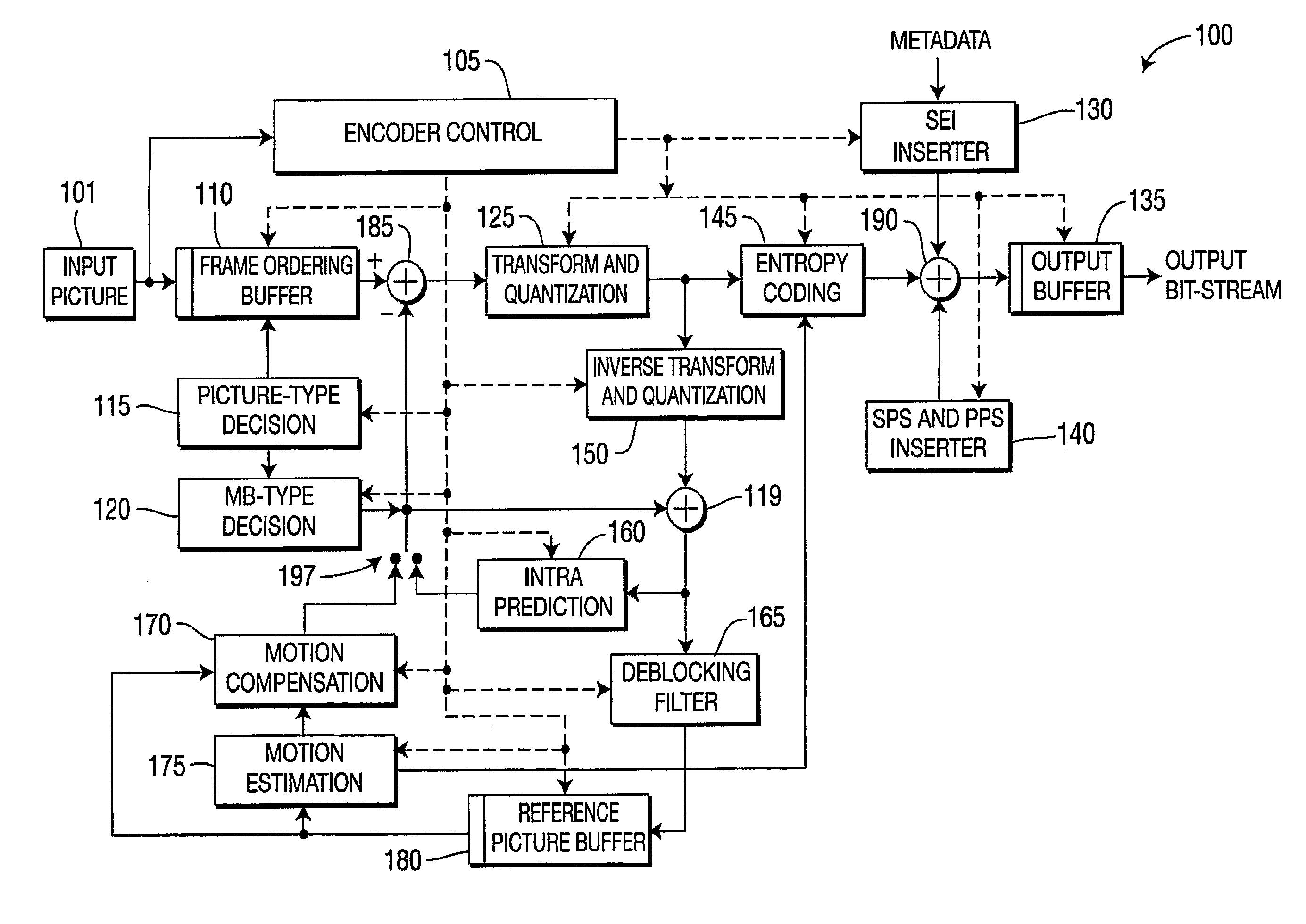
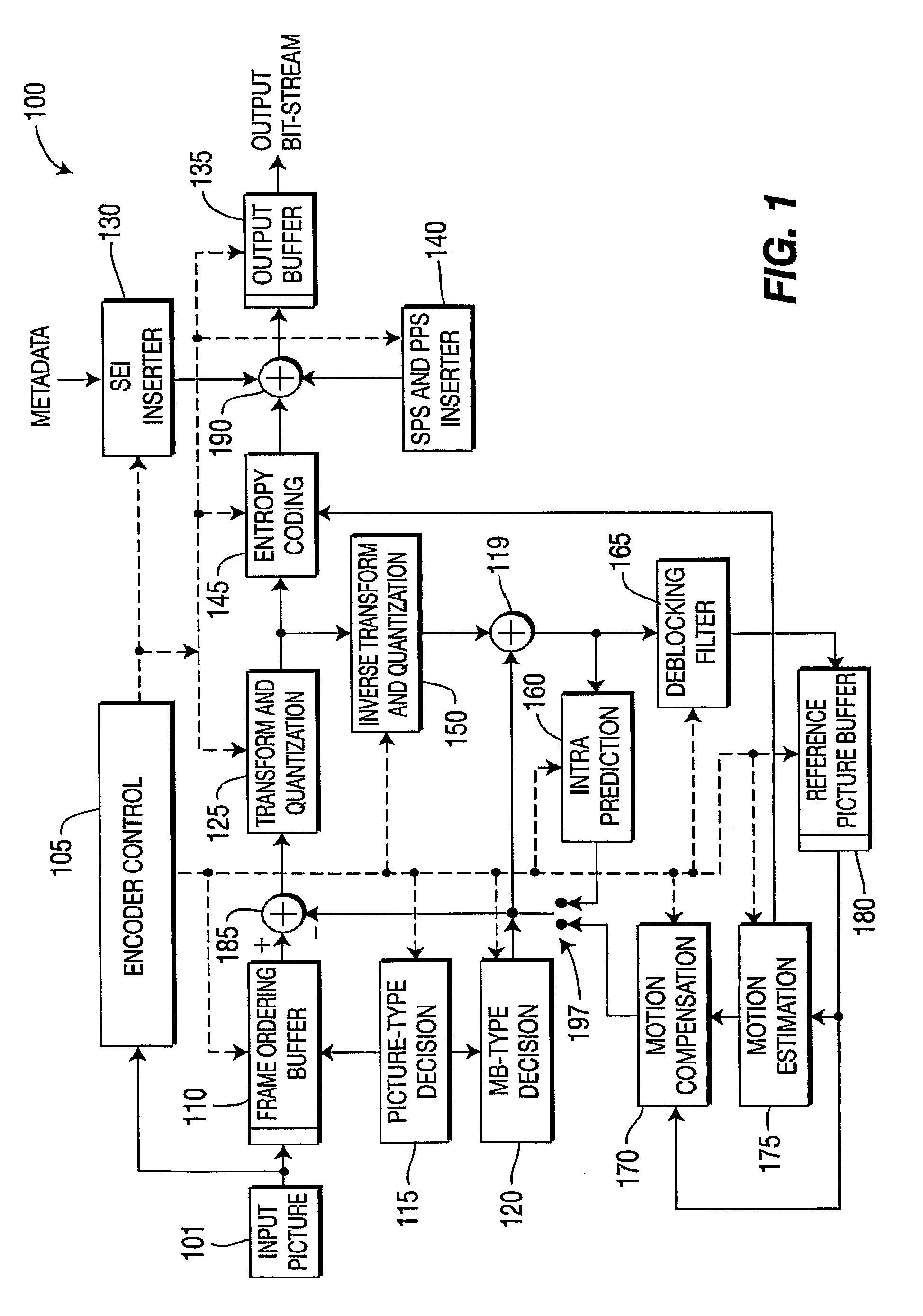
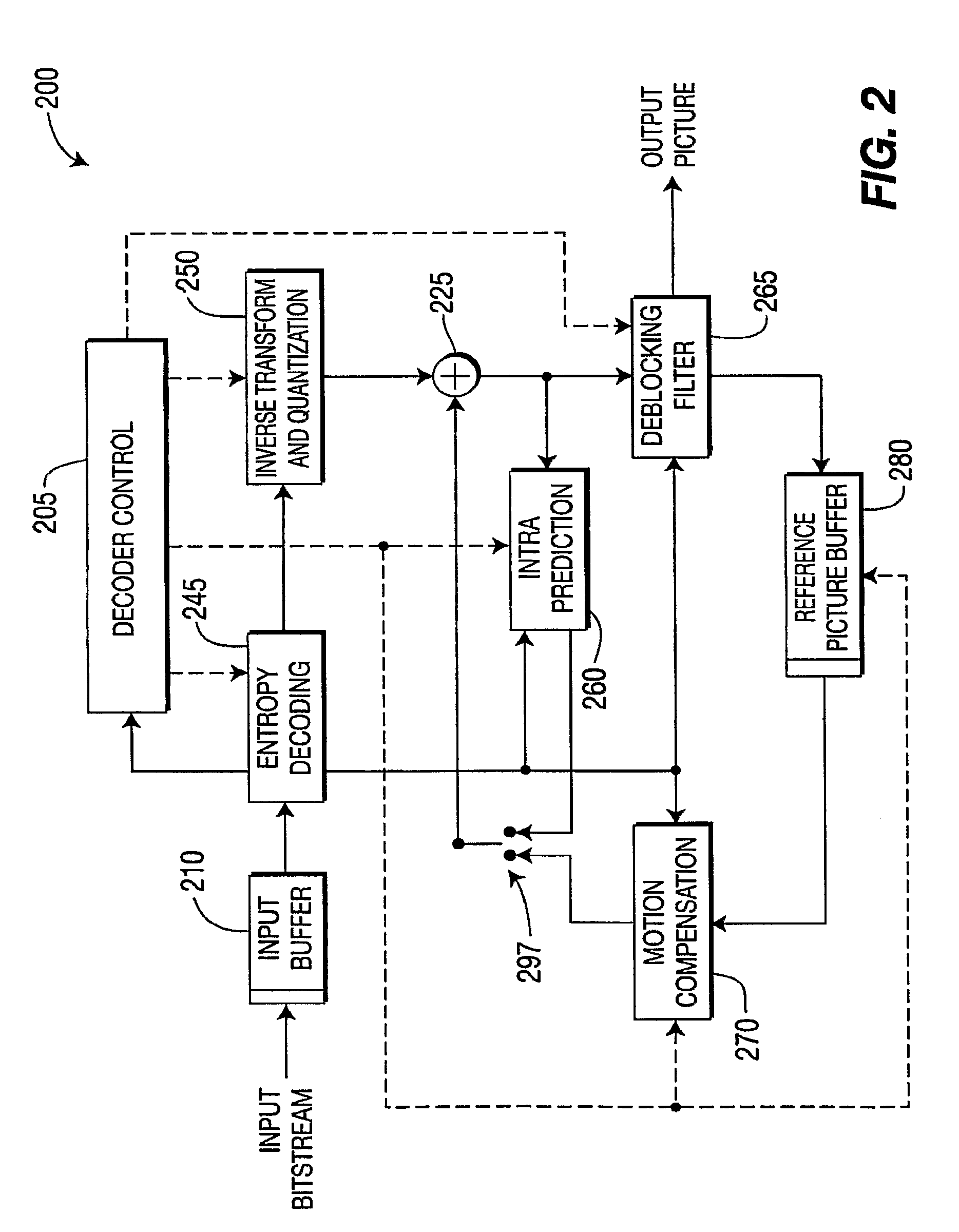
Patents
Literature
1347 results about "Tree based" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Personalized navigation trees
InactiveUS6393427B1Minimize the numberData processing applicationsDigital data processing detailsPersonalizationUsability
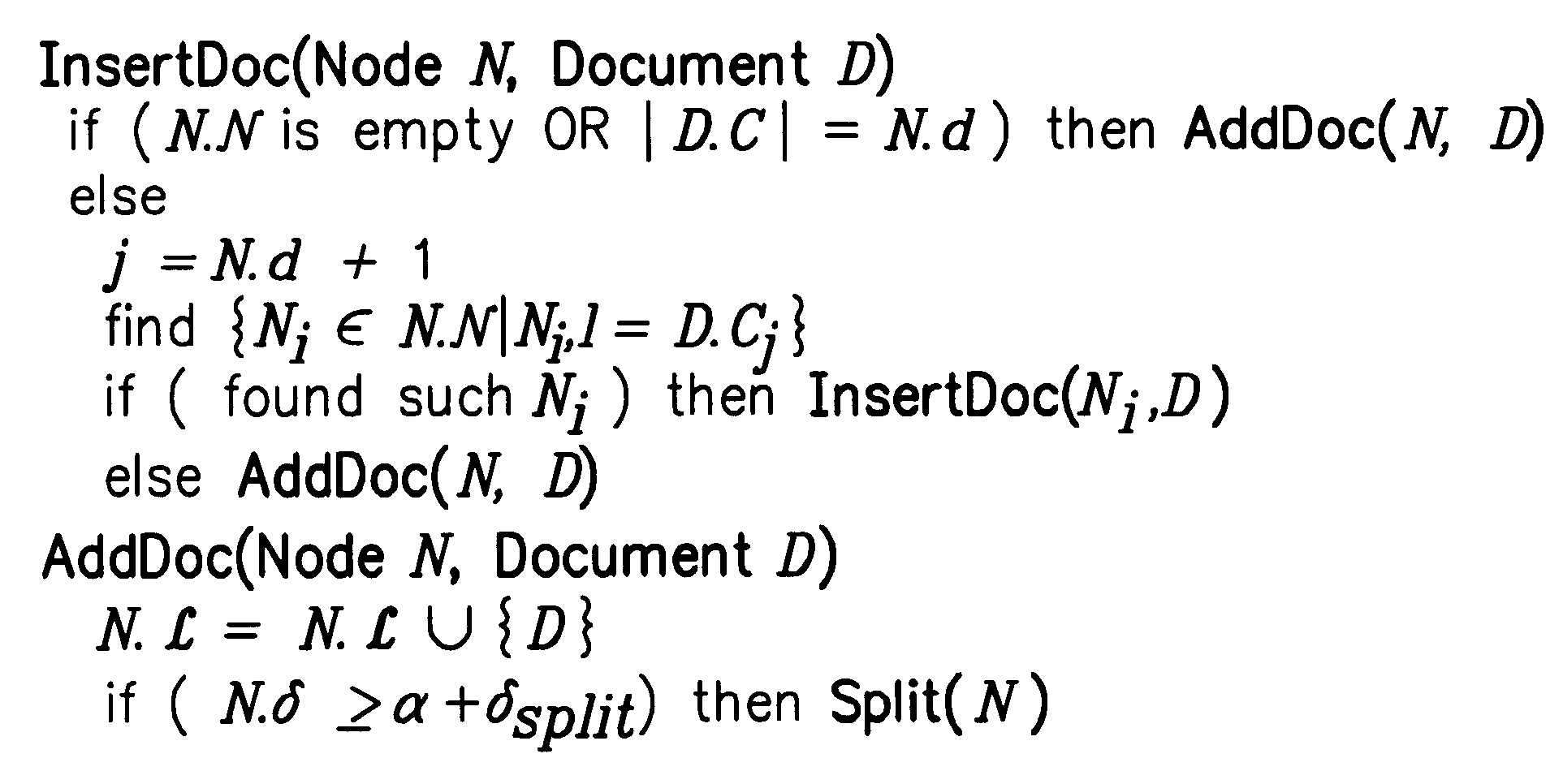
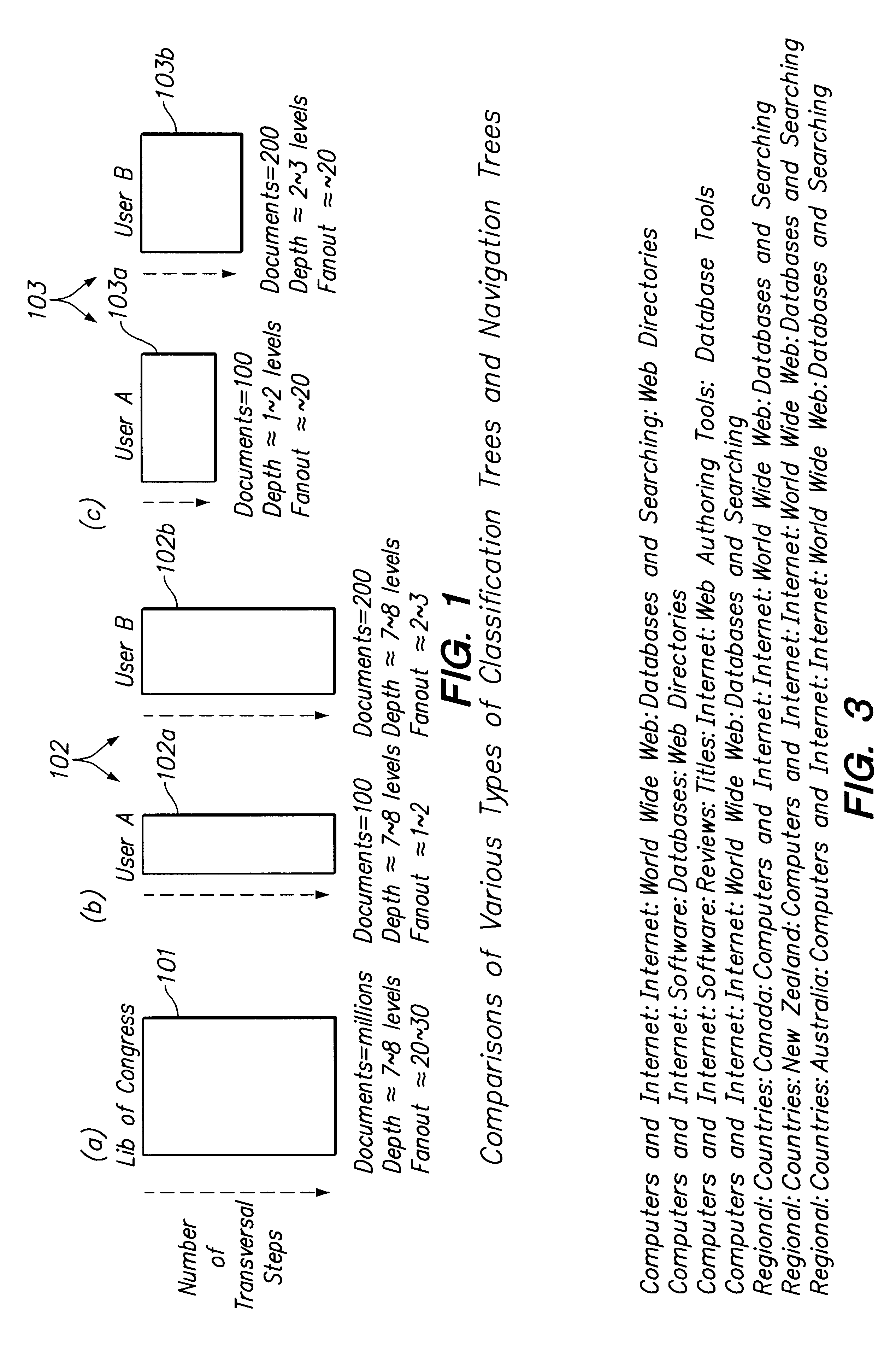
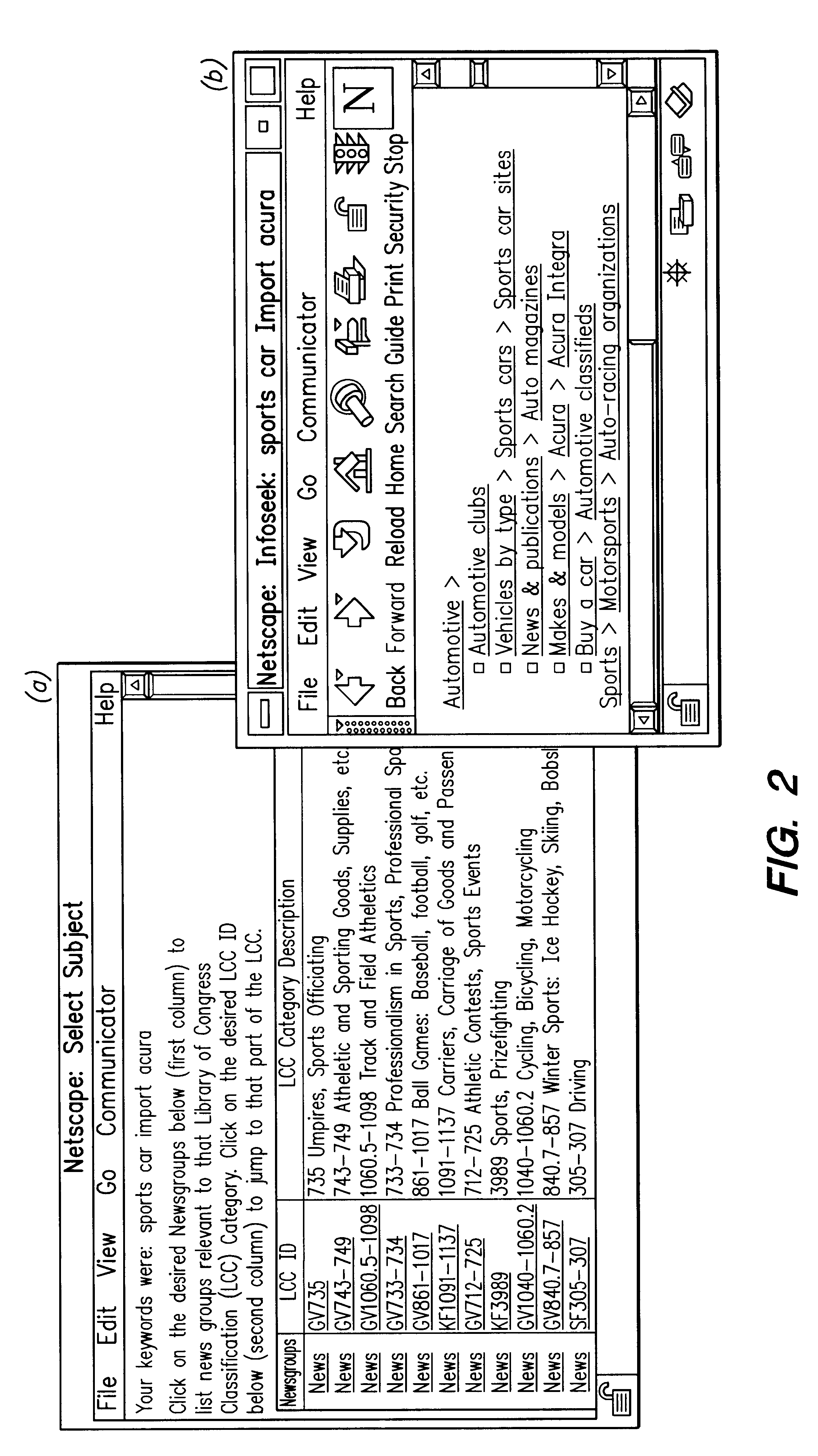
A method for constructing and maintaining a navigation tree based on external document classifiers is provided. In one embodiment, based on the returned category labels from the classifiers, a navigation tree is constructed by taking usability and user preferences into consideration. Control parameters and algorithms are provided for inserting into and deleting documents from the navigation tree, and for splitting and merging nodes of the navigation tree, are provided.
Owner:NEC CORP
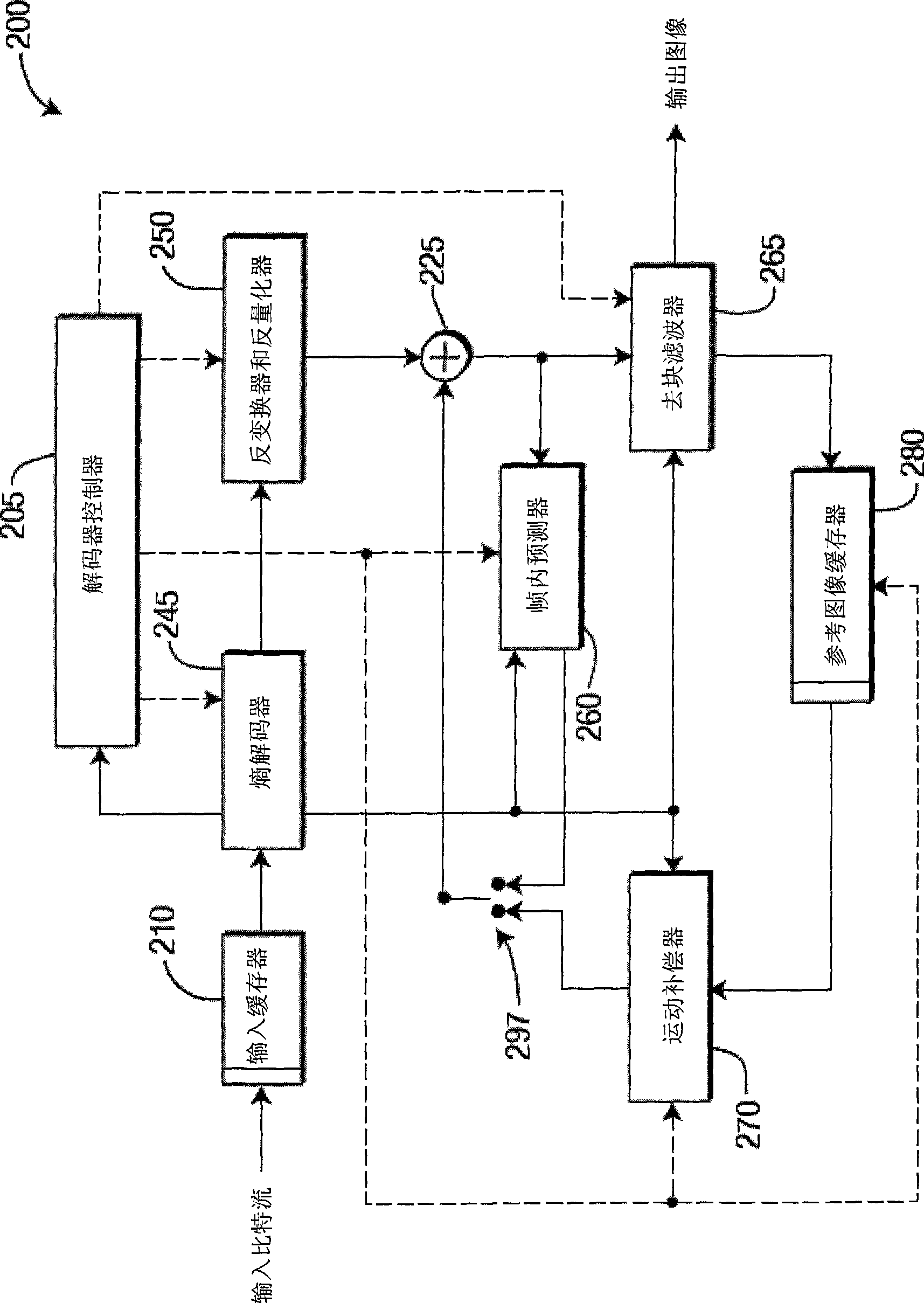
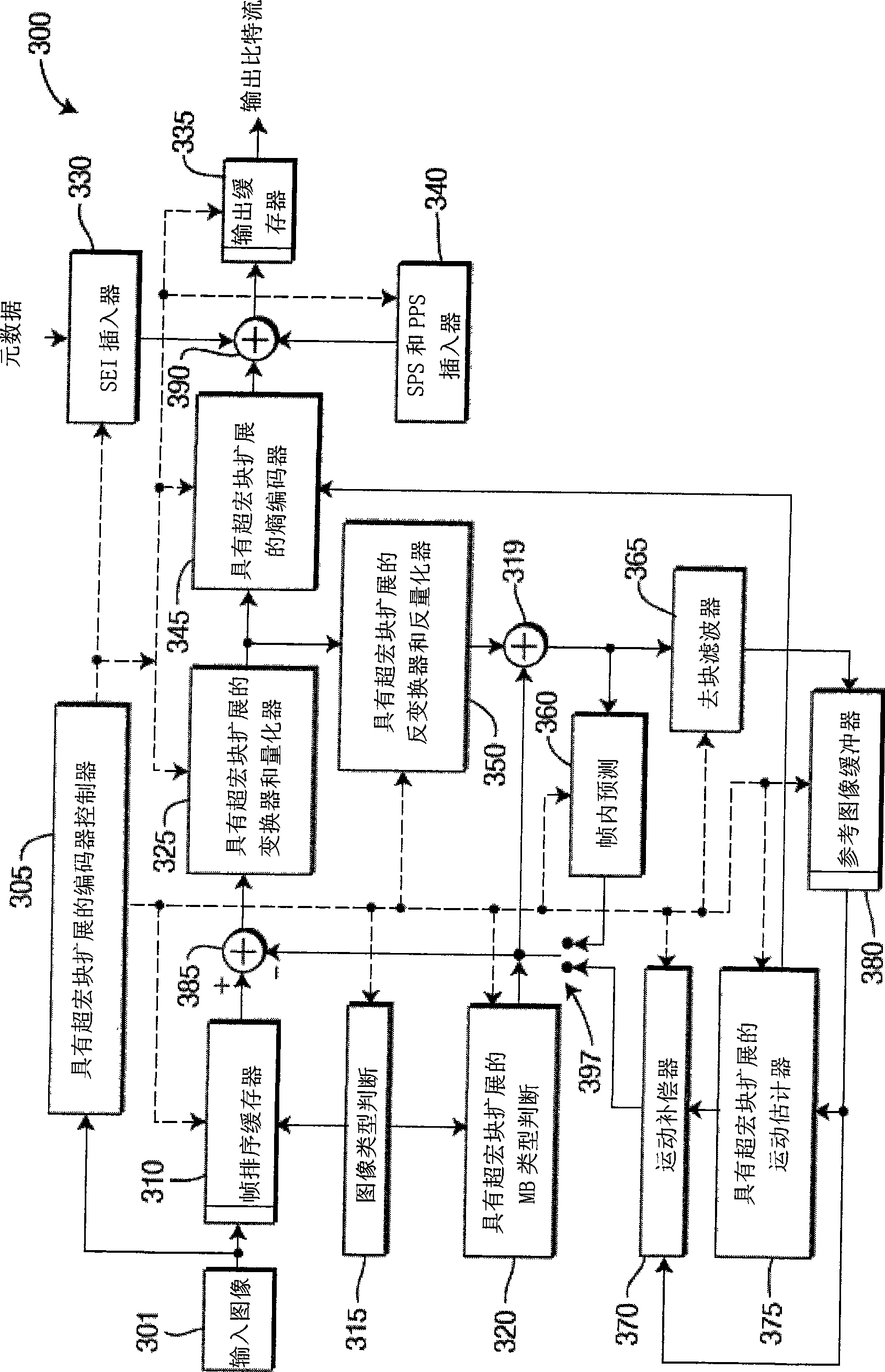
Methods and apparatus for reduced resolution partitioning
ActiveCN101507280APulse modulation television signal transmissionDigital video signal modificationImage resolutionTheoretical computer science
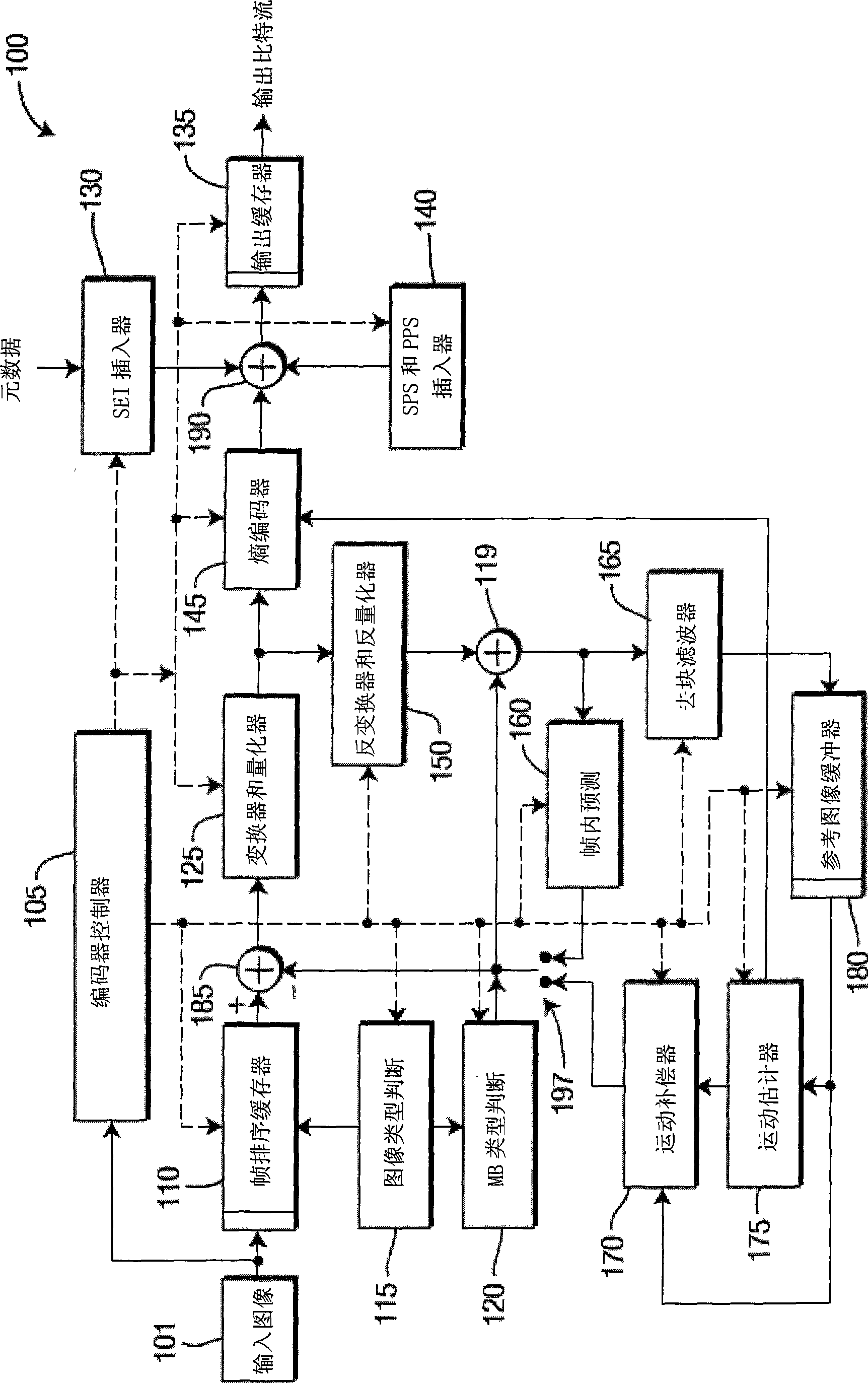
There are provided methods and apparatus for reduced resolution partitioning. An apparatus includes an encoder (300) for encoding video data using adaptive tree-based frame partitioning, wherein partitions are obtained from a combination of top-down tree partitioning and bottom-up tree joining.
Owner:INTERDIGITAL VC HLDG INC
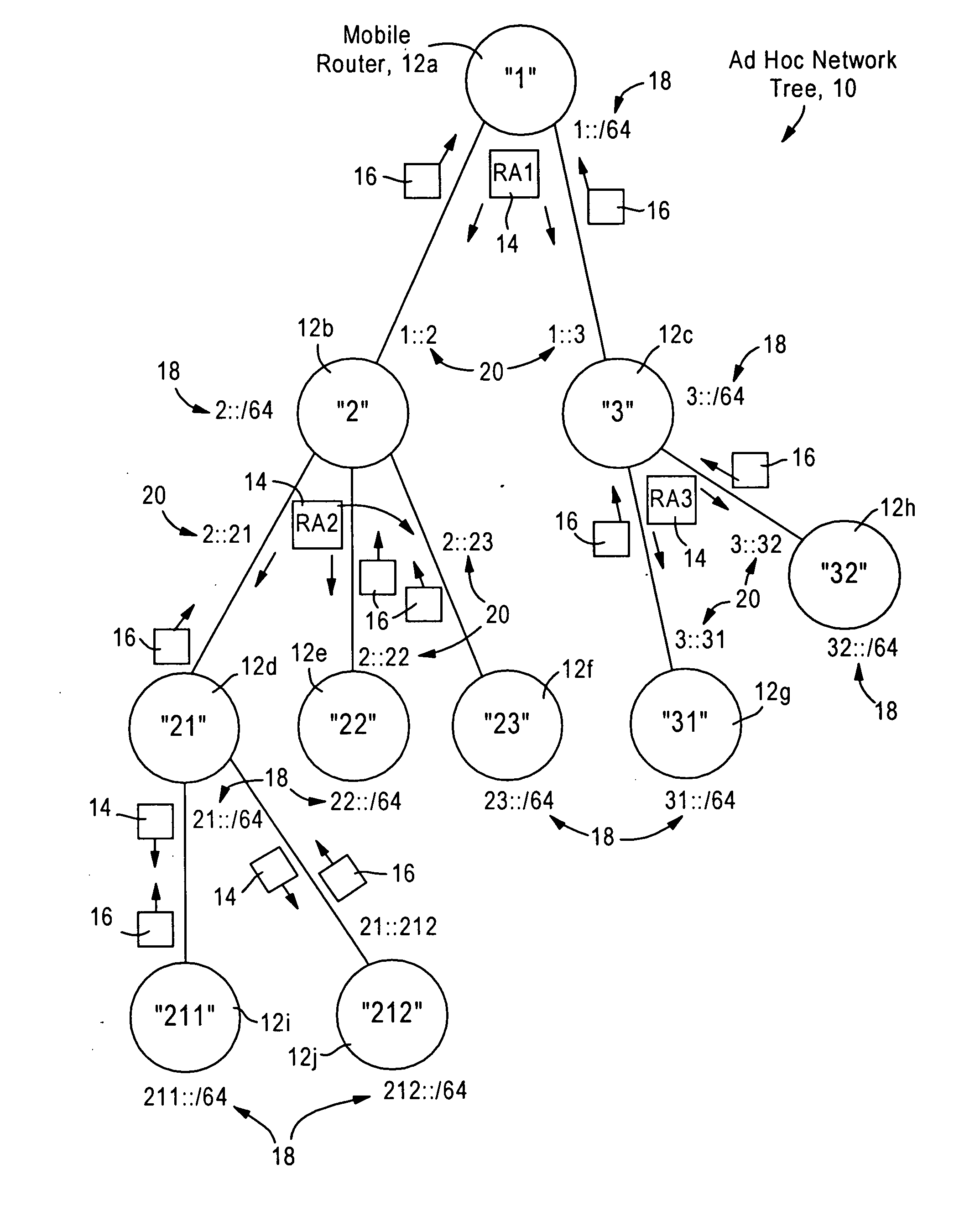
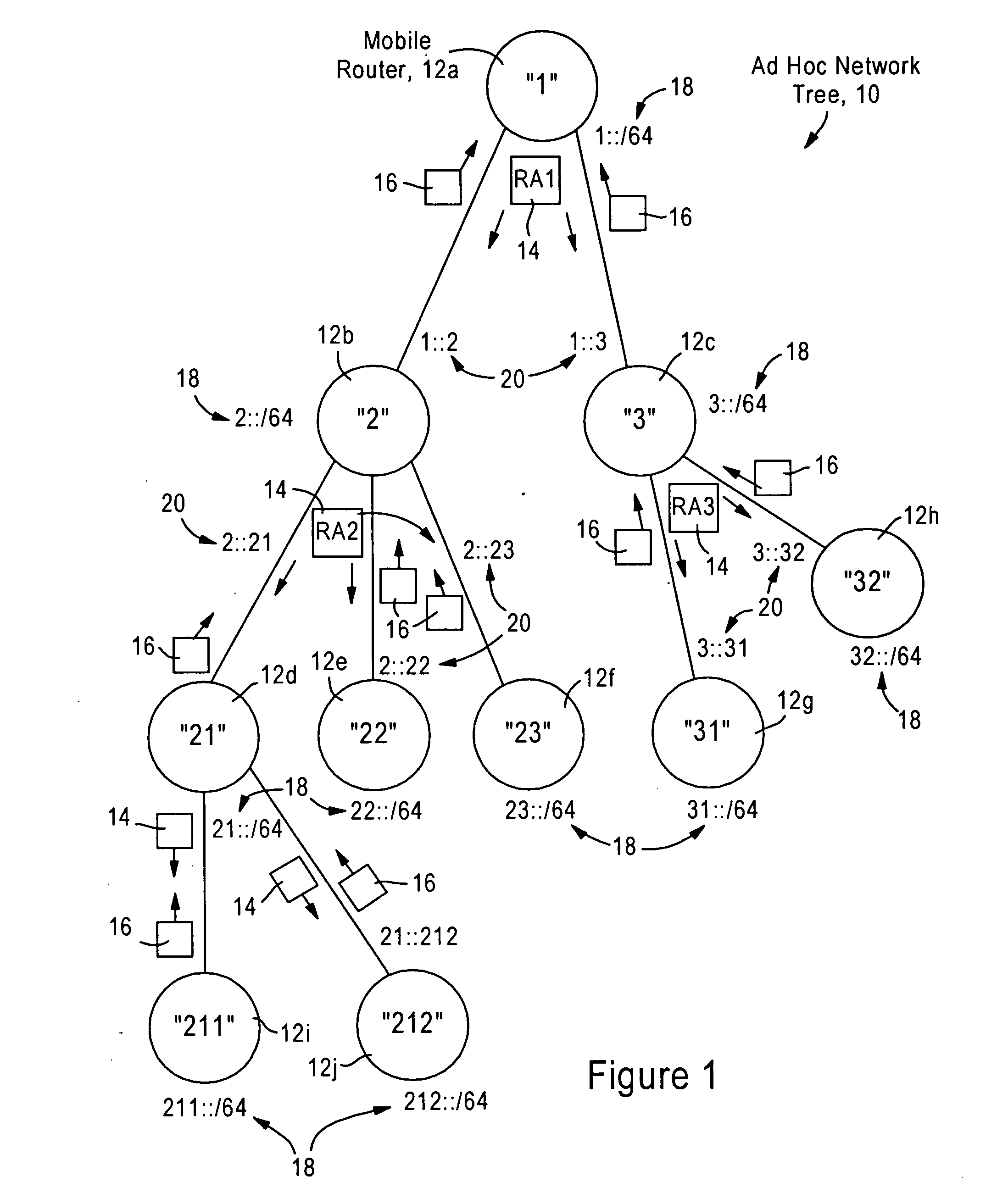
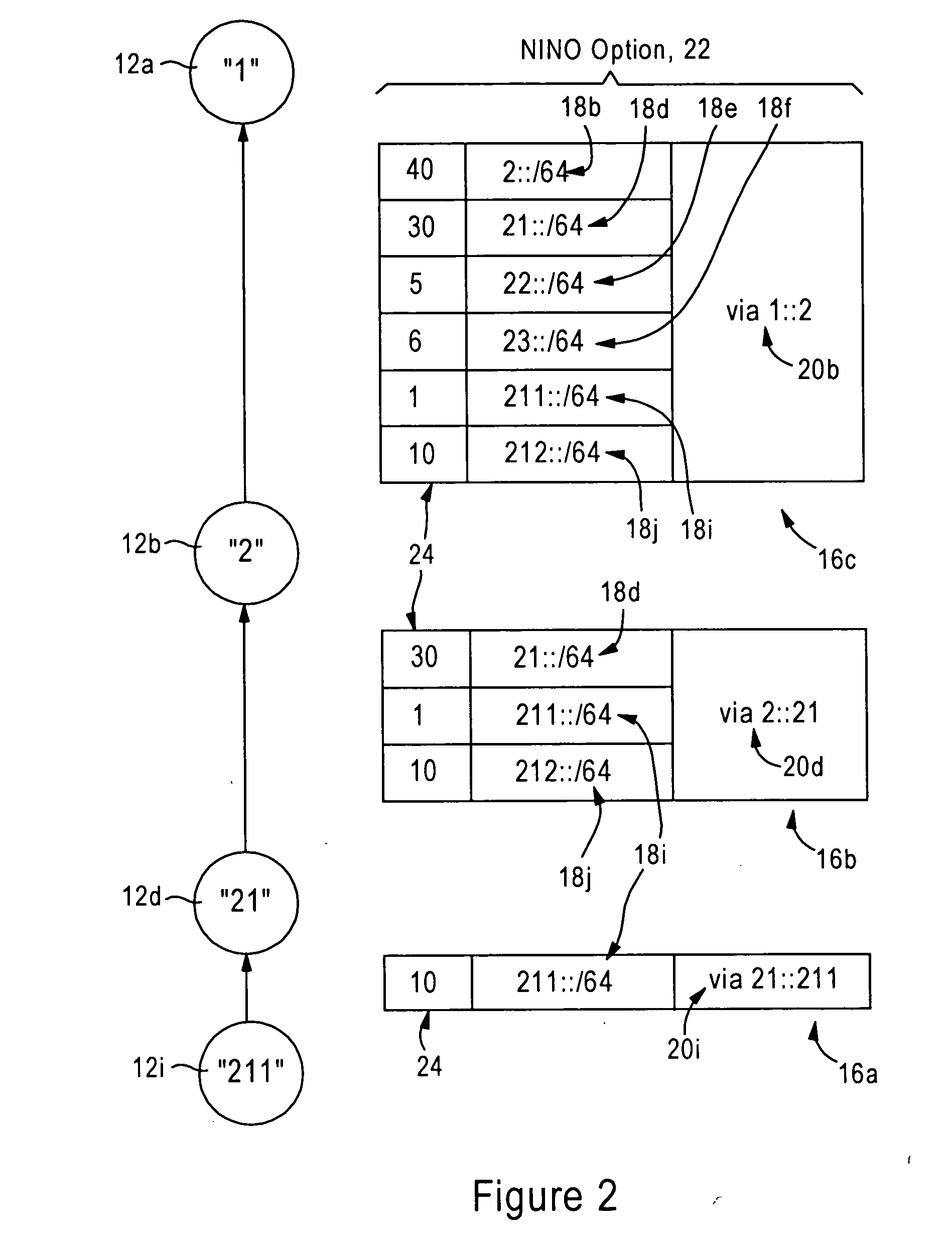
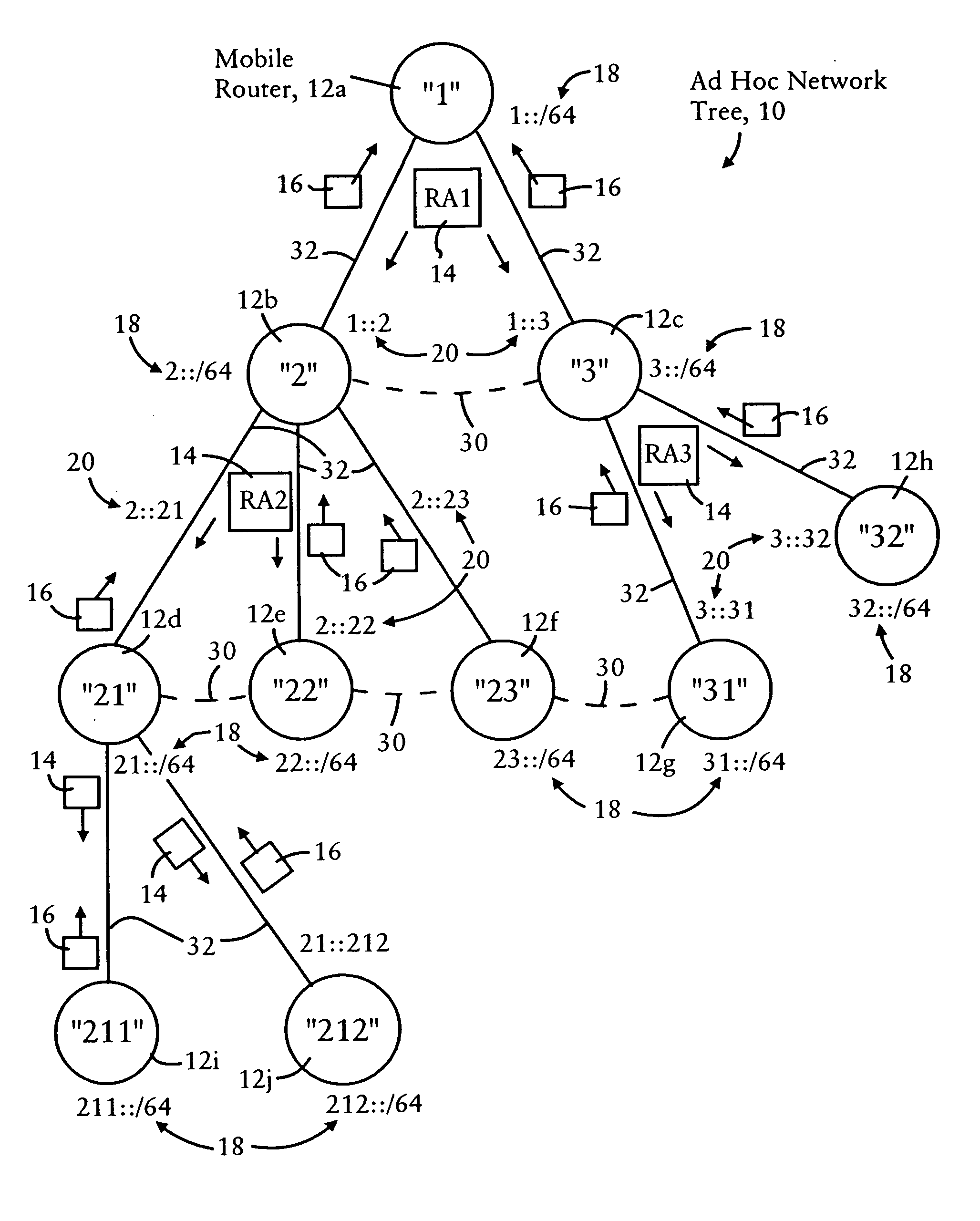
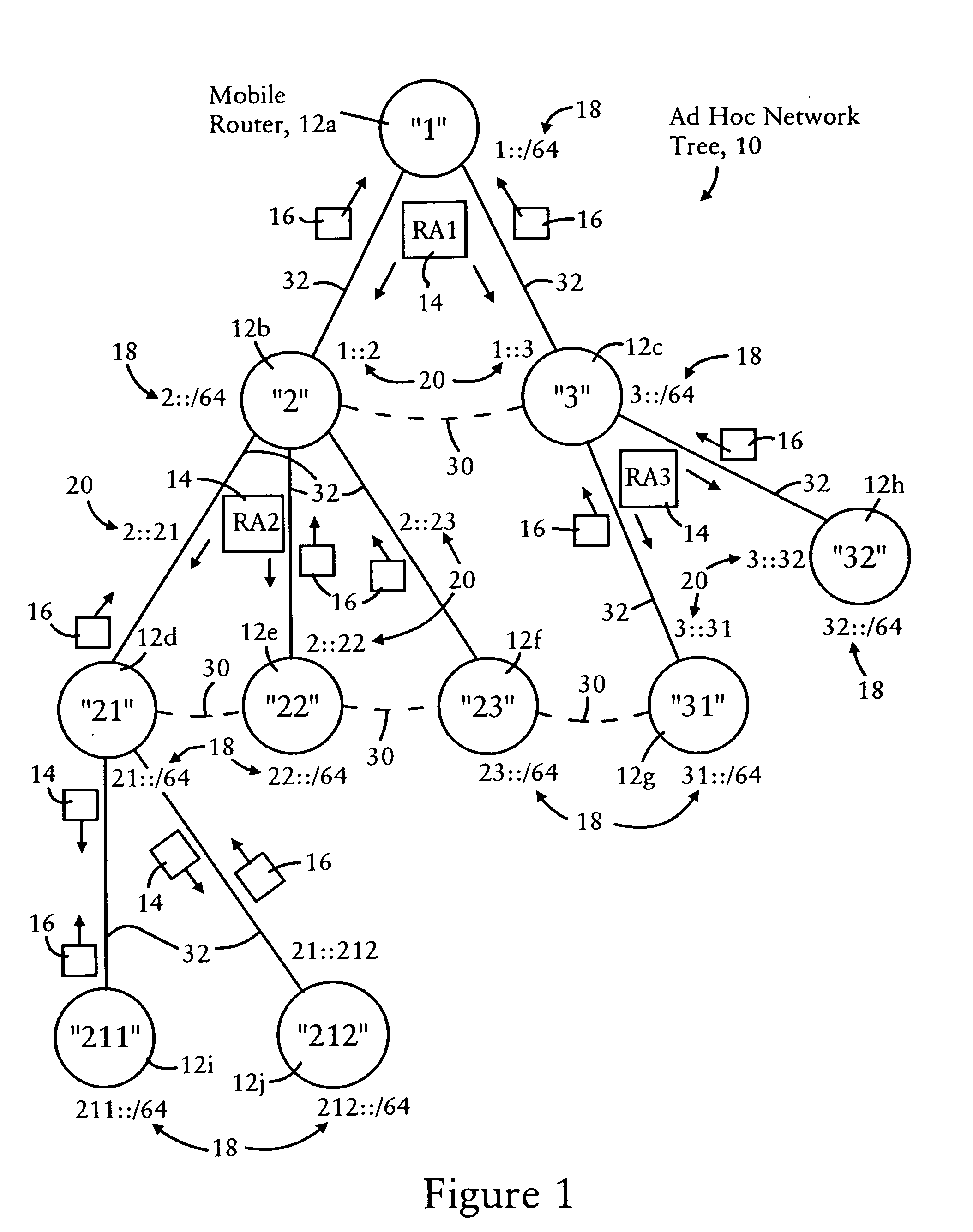
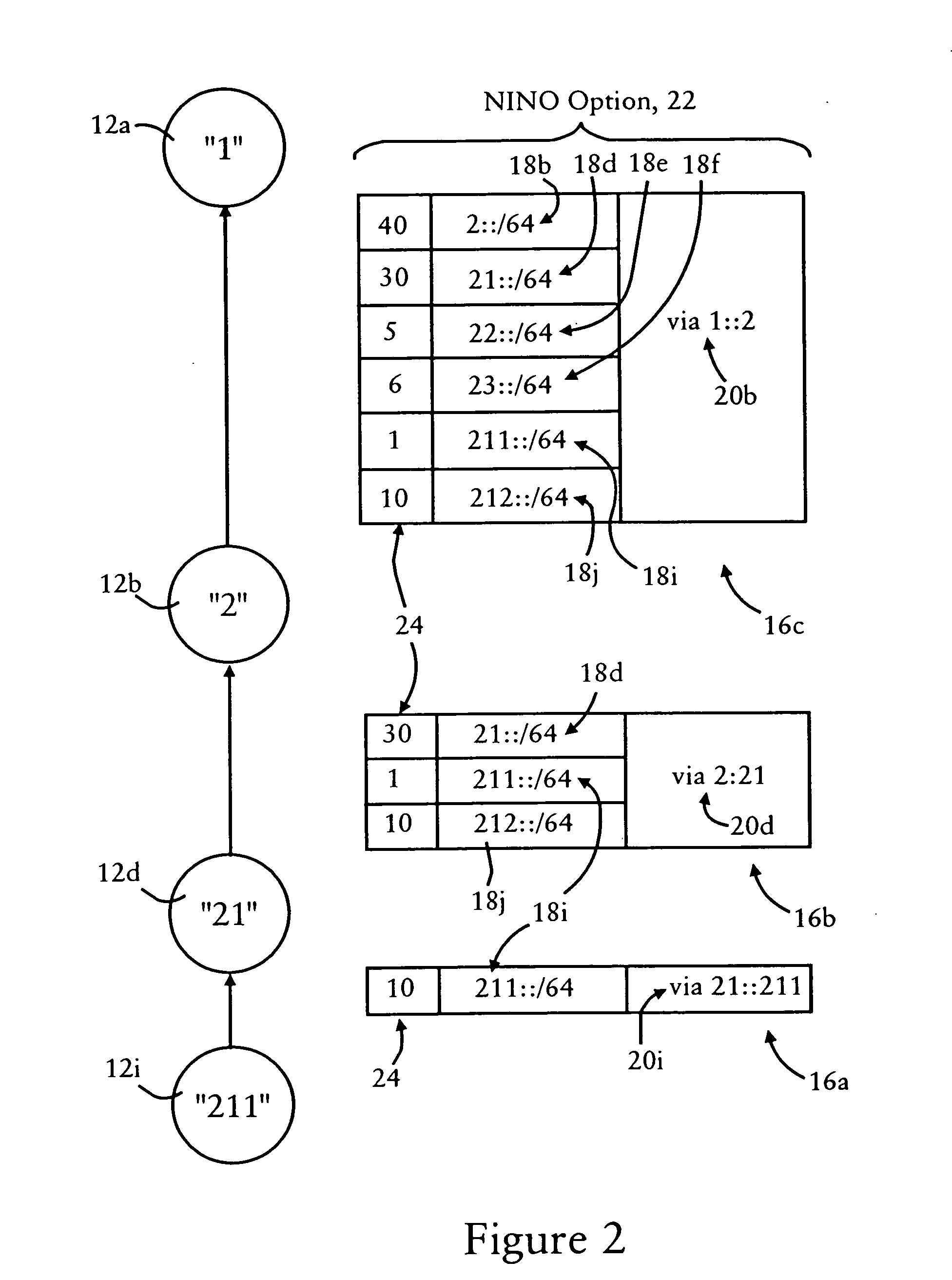
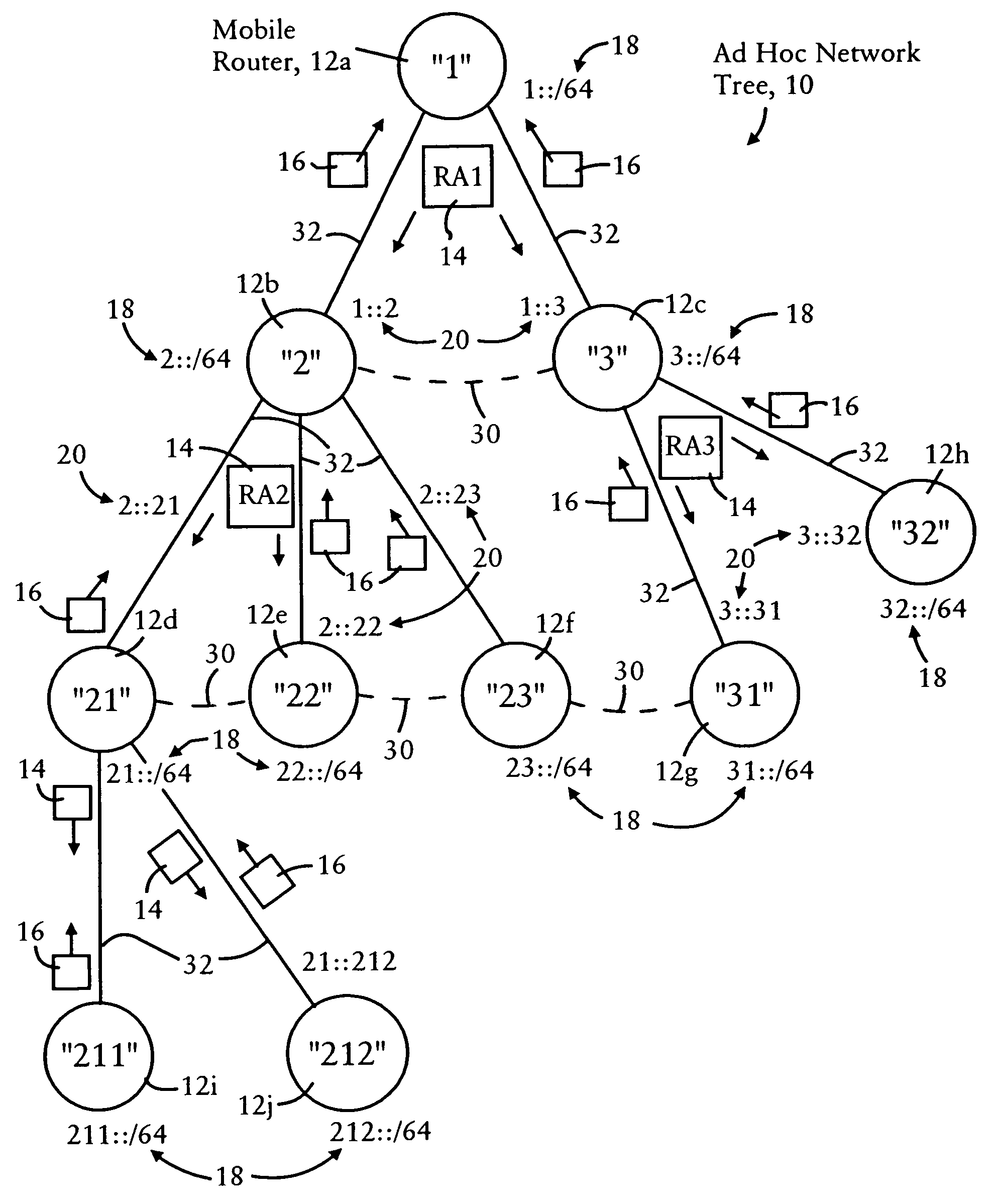
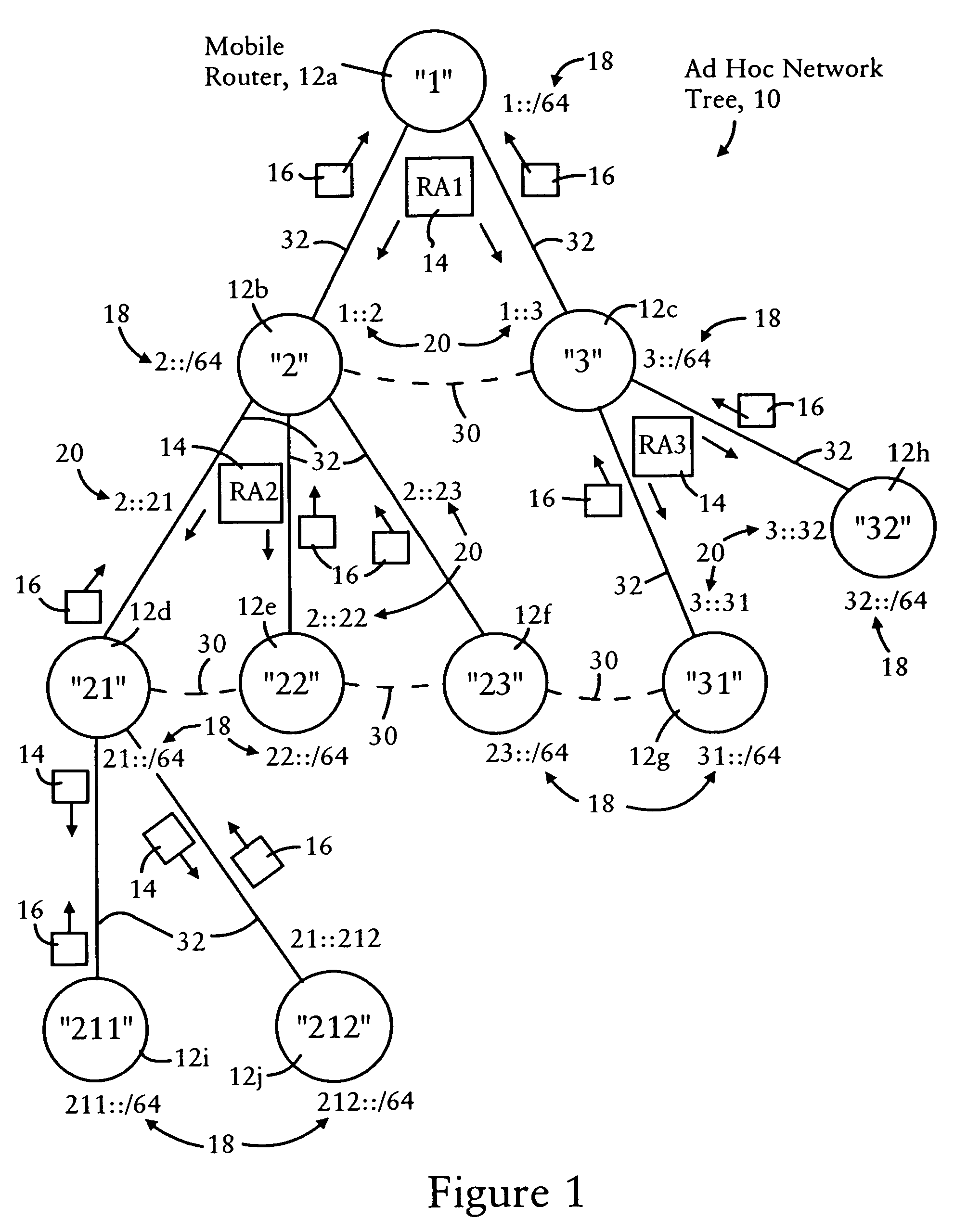
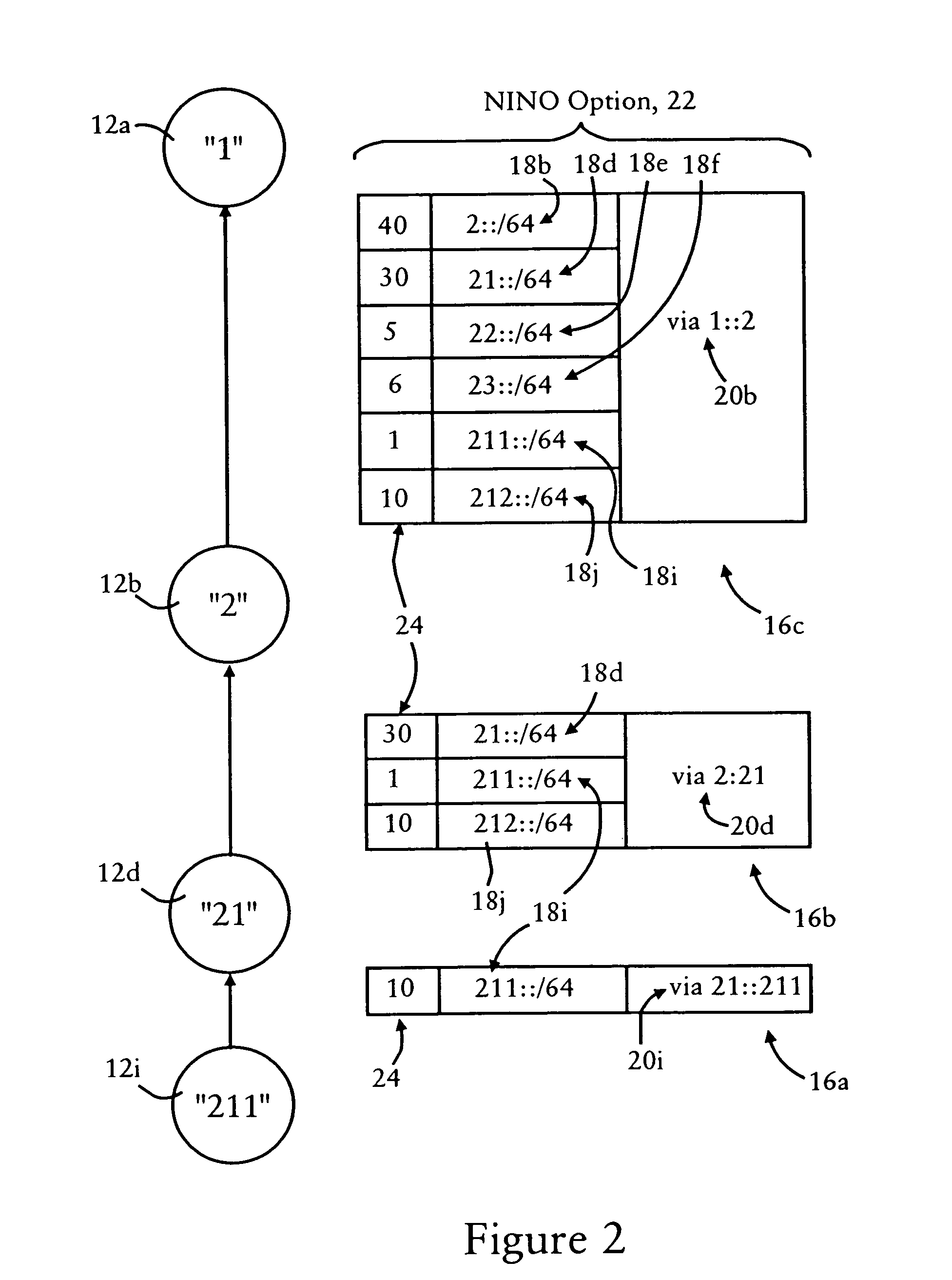
Arrangement for providing network prefix information from attached mobile routers to a clusterhead in a tree-based ad hoc mobile network
ActiveUS20050265259A1Minimal overheadFast convergenceAssess restrictionNetwork topologiesMobile WebNetwork topology
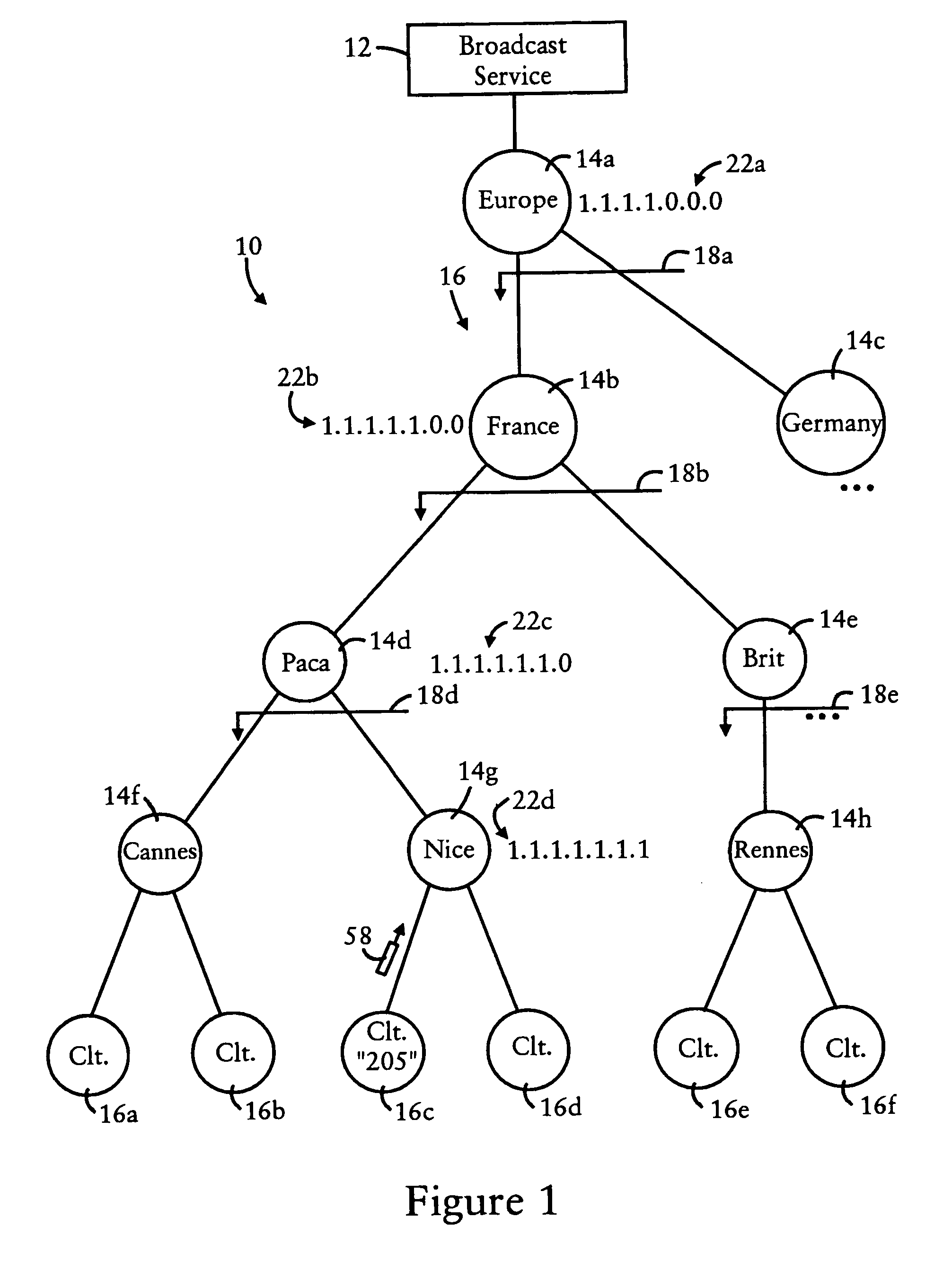
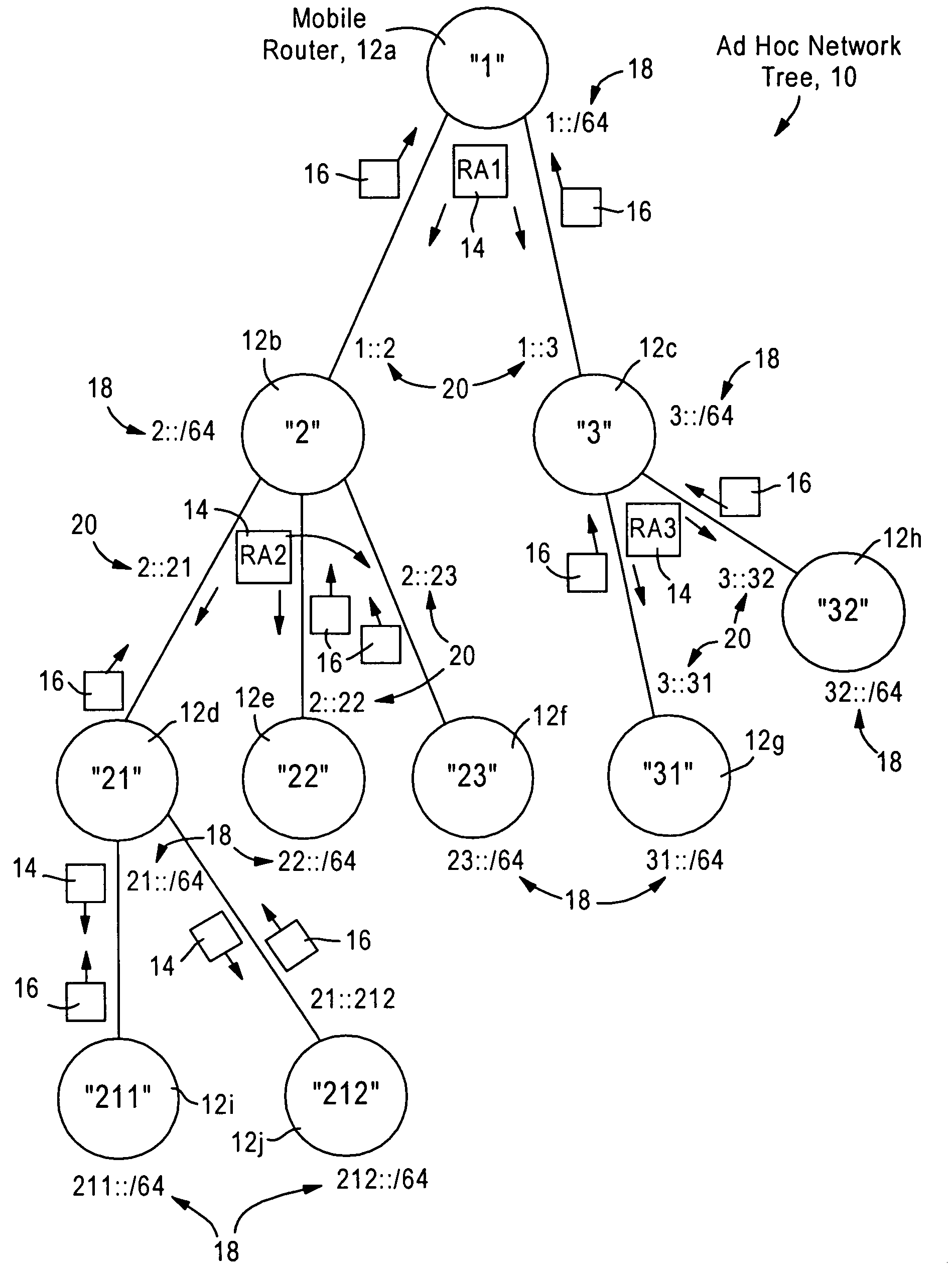
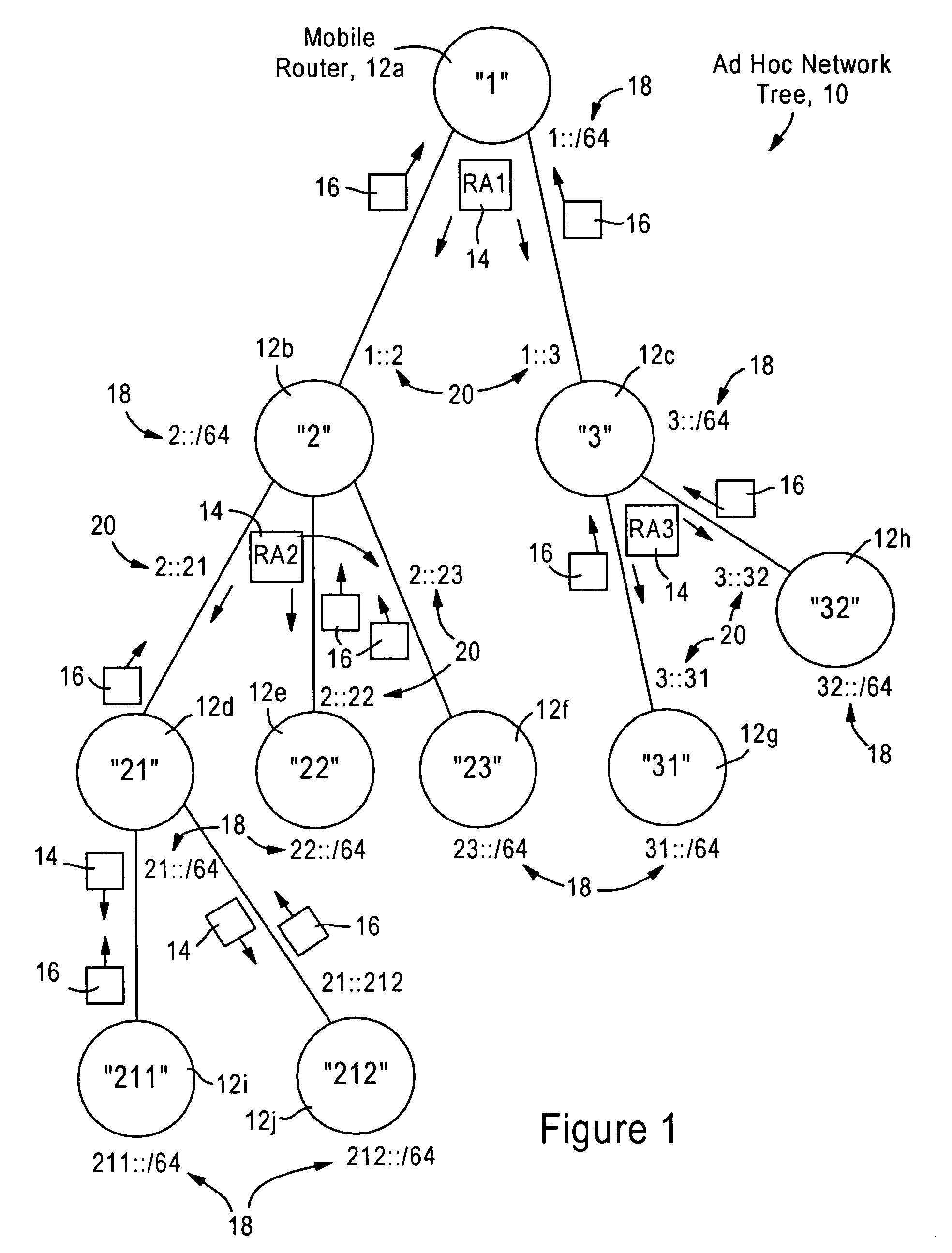
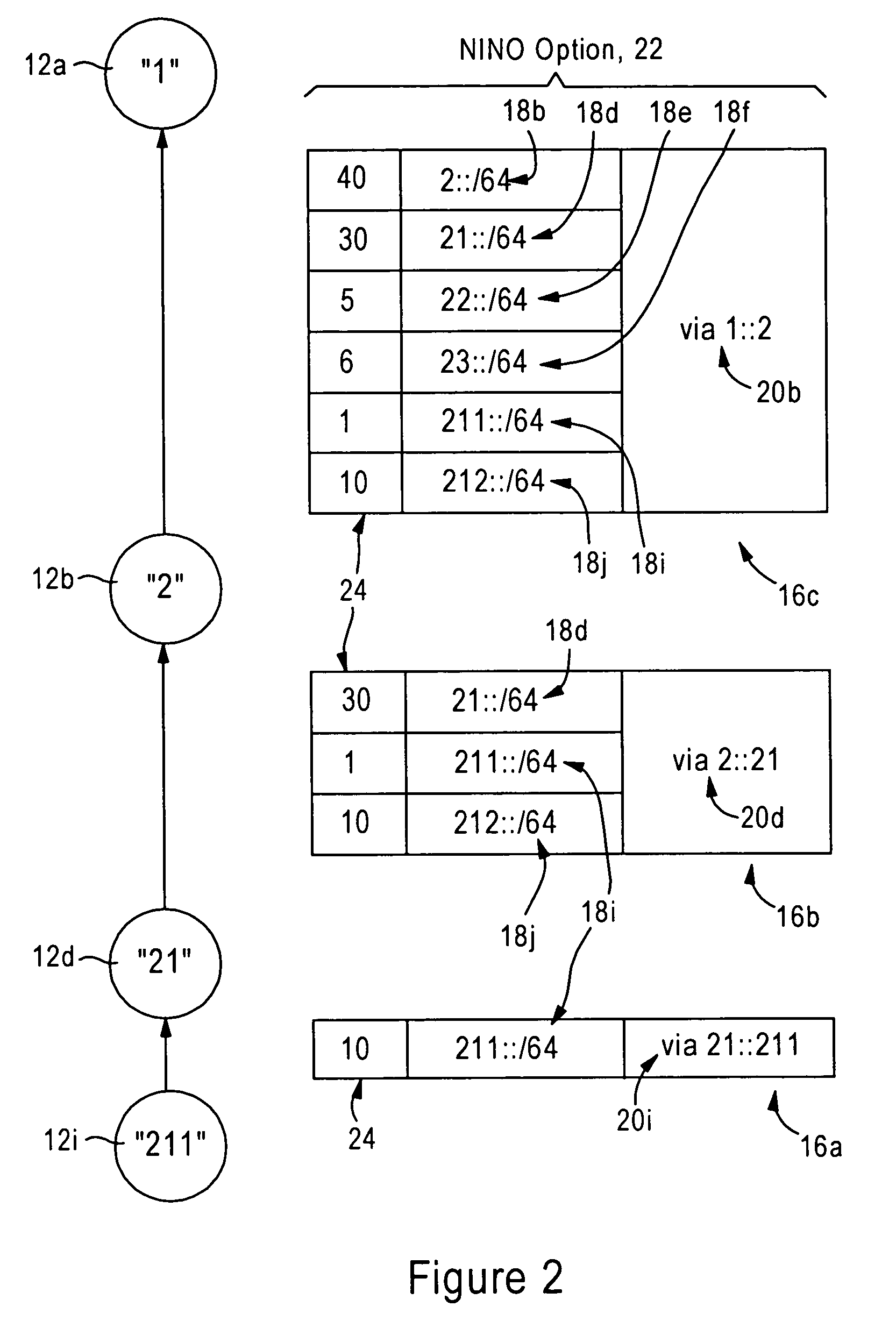
Mobile routers establish a tree-based network topology in an ad hoc mobile network, the tree-based network topology having a single clusterhead and attached mobile routers. Each attached mobile router has a default egress interface configured for sending messages toward the clusterhead, and ingress interfaces configured for receiving messages from attached network nodes that are away from the clusterhead. A neighbor advertisement message received from an ingress interface away from a clusterhead is used by the attached mobile router to identify specified network prefixes that are reachable via the source of the neighbor advertisement message. The attached mobile router outputs on its default upstream interface a second neighbor advertisement message that specifies the network prefix used by the attached mobile router, and the specified network prefixes from the neighbor advertisement message received on the ingress interface. Hence, connectivity is established with minimal routing overhead.
Owner:CISCO TECH INC
Arrangement for providing optimized connections between peer routers in a tree-based ad hoc mobile network
InactiveUS20060227724A1Reduce necessityAvoid congestionError preventionFrequency-division multiplex detailsEngineeringSelf-organizing network
Mobile routers in a tree-based network topology with a single clusterhead in an ad hoc network establish connectivity based on each attached mobile router sending a neighbor advertisement message to an attachment mobile router via a corresponding egress interface. Any neighbor advertisement message received by a mobile router is used to identify specified network prefixes that are reachable via the source of the neighbor advertisement message. Each attached mobile router outputs to its attachment router another neighbor advertisement message that specifies the network prefix used by the mobile router, and the specified network prefixes from its attached mobile routers. The mobile router also identifies peer mobile routers having the same depth, and selectively shares limited routing information with the peer routers, enabling the mobile router to bypass the clusterhead and reach remote prefixes via the peer routers without burdening the tree.
Owner:CISCO TECH INC
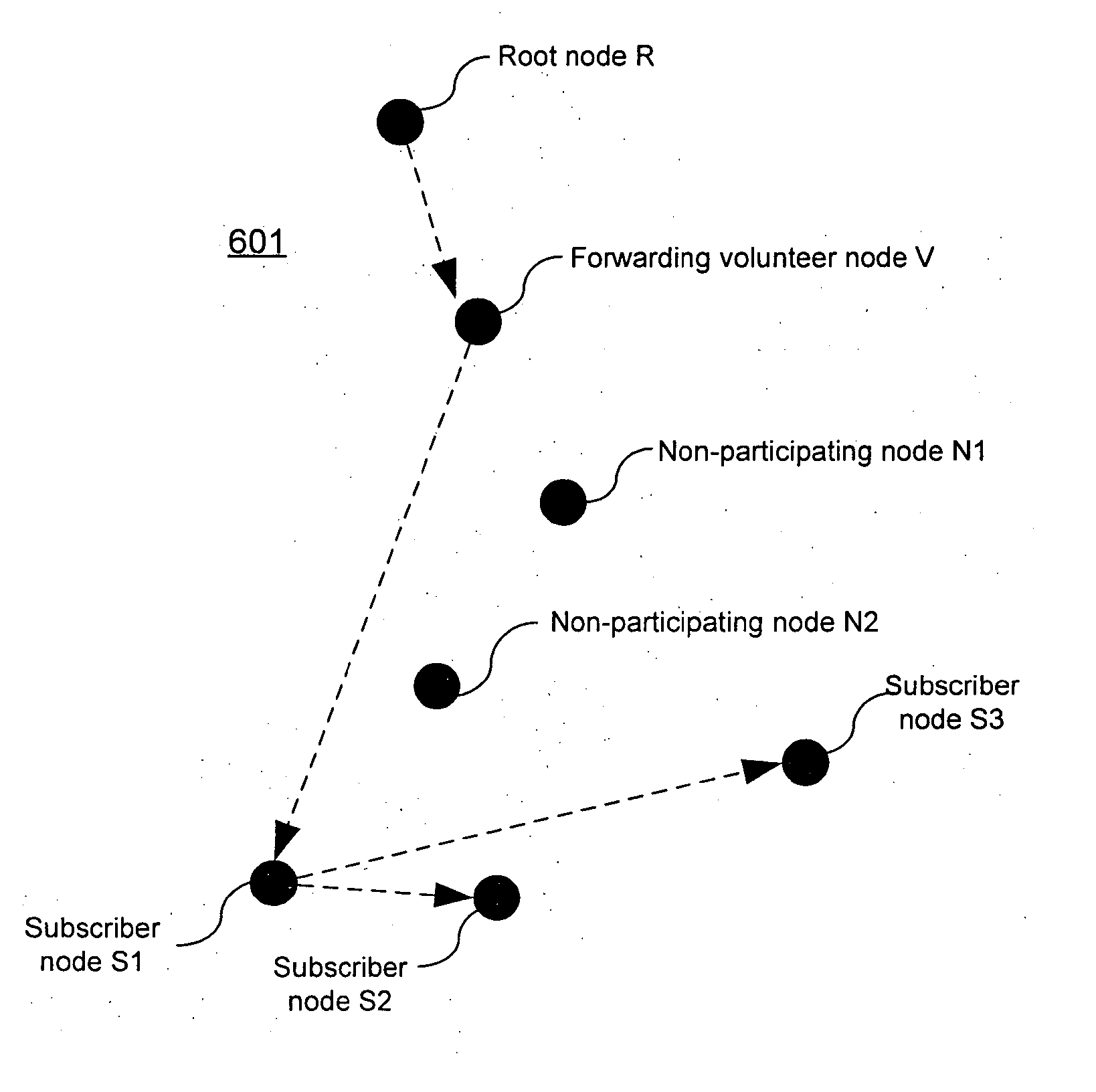
Scalable, fault tolerant notification method
InactiveUS20050086469A1Reliable deliveryPrevent malicious and faulty nodesSpecial service provision for substationSecuring communicationClient-sideTree based
A scalable, fault-tolerant, federated event notification method is described, wherein clients express interest in a topic by subscribing, and published event notifications are delivered to all current topic-subscribers. Event notifications are disseminated by a multicast tree that does not require participation by unwilling nodes. The multicast tree is constructed so that nodes belonging to the organization owning the tree do not rely on nodes outside the organization to forward message traffic. Event notifications are delivered using redundant tree-based application-level multicast to ensure reliable delivery.
Owner:MICROSOFT TECH LICENSING LLC
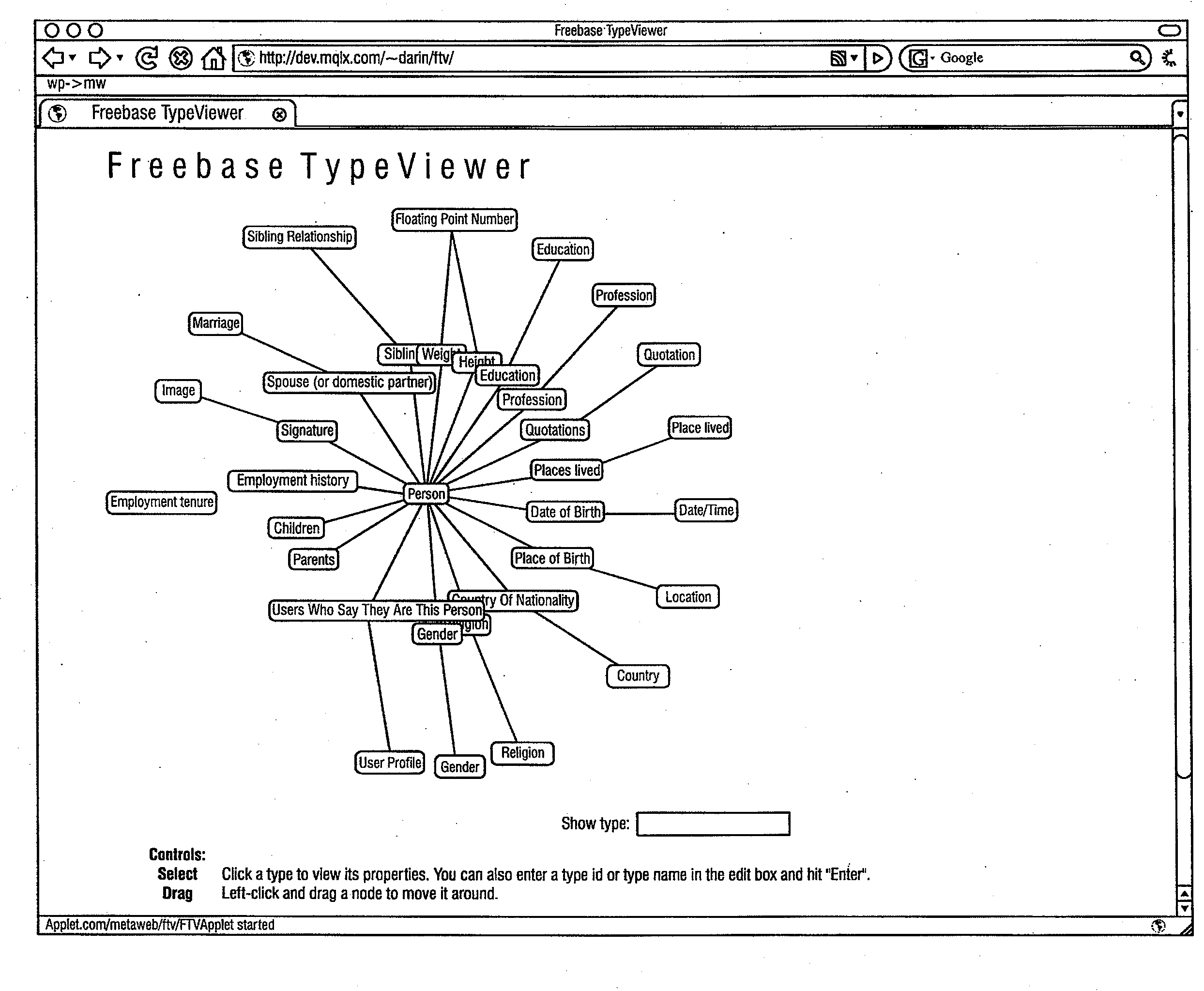
User contributed knowledge database
InactiveUS20090024590A1Emphasizes scalability and performance and correctnessSimple powerDigital data processing detailsWebsite content managementGraphicsWeb site
A large open database of information has entries for commonly understood data, such as people, places and objects, which are referred to as topics. The database has a type system and contains attributes and relationships between topics. The invention also comprises a powerful query language and an open API to access the data and a website where contributors can update the data or add new topics and relationships. The elements of the invention comprise a scalable graph database, a dynamic user contributed schema representation, a tree-based object / property query language, a series of new Web service APIs, and set of AJAX dynamic HTML technologies.
Owner:GOOGLE LLC
System and method for recognizing faults in machines
InactiveUS6907545B2Overcome deficienciesDetecting faulty hardware by remote testElectric testing/monitoringComputer scienceFault recognition
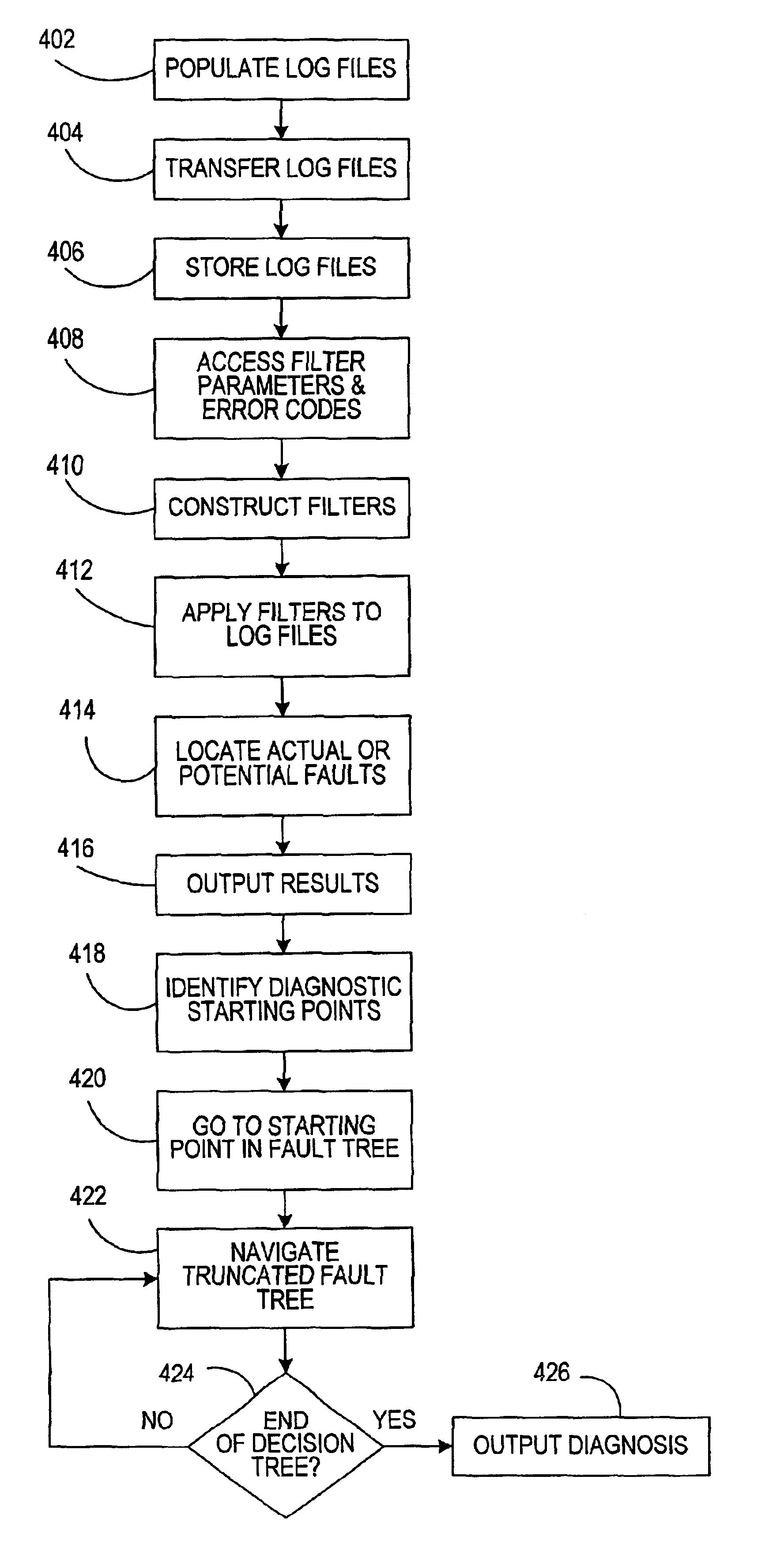
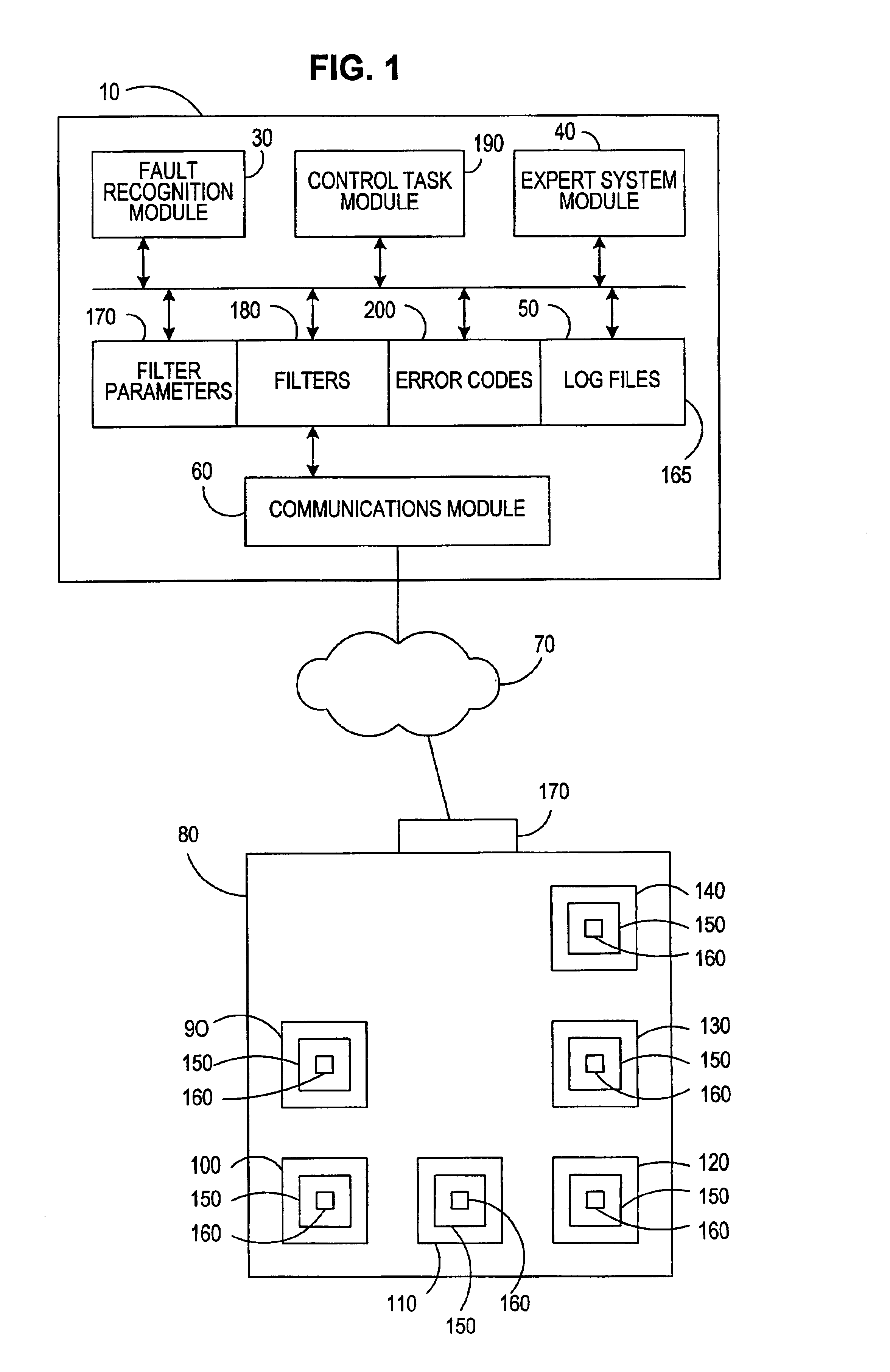
A system and method for diagnosing one or more faults or one or more potential faults in a machine. The system and method has a communications module for communicating machine data between the machine and the system. It also has a fault recognition module for analyzing the machine data, which can determine one or more faults or potential faults in the machine. An expert system module having a fault tree is guided through only a truncated portion of the fault tree based upon output from the fault recognition module.
Owner:PITNEY BOWES INC
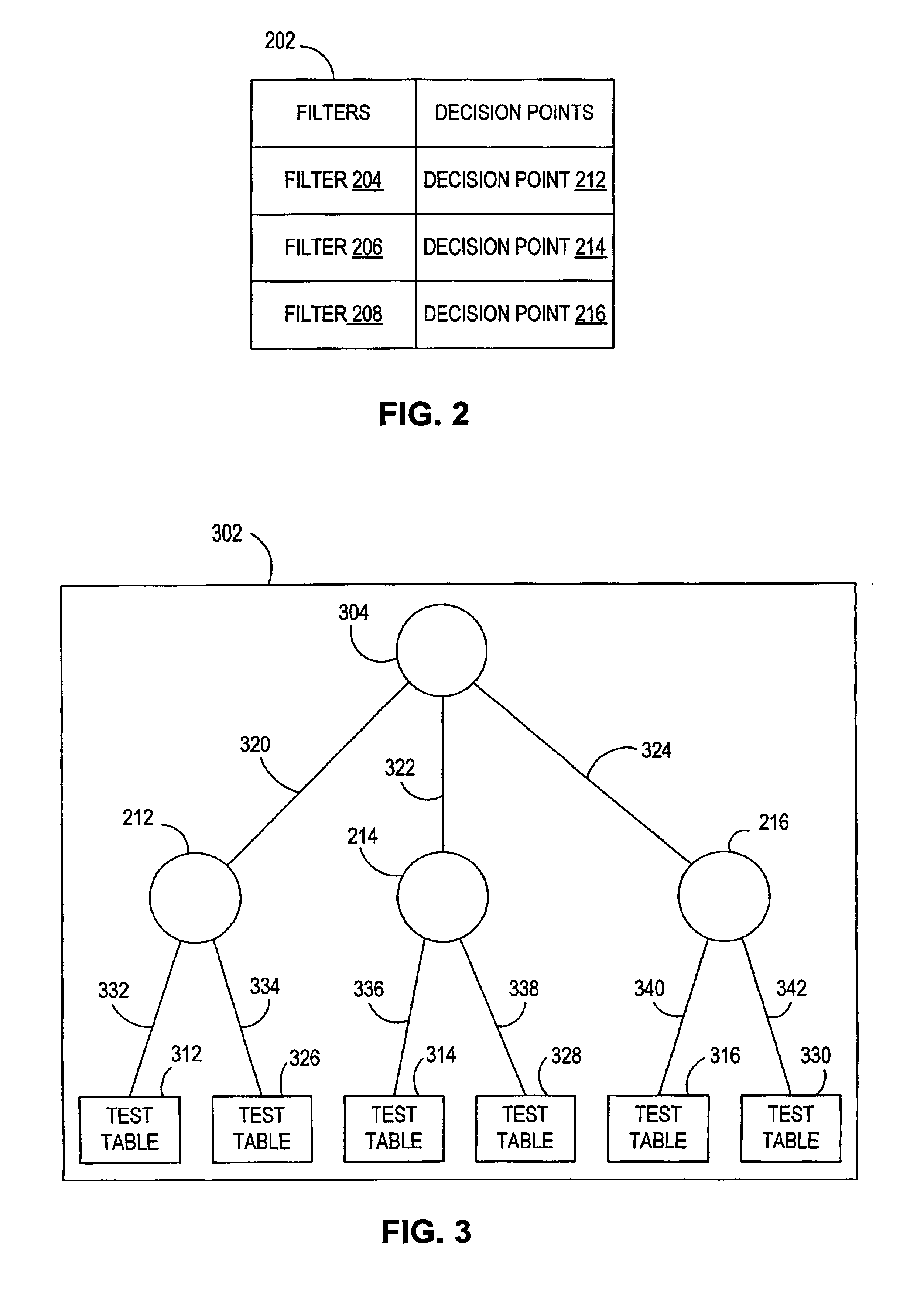
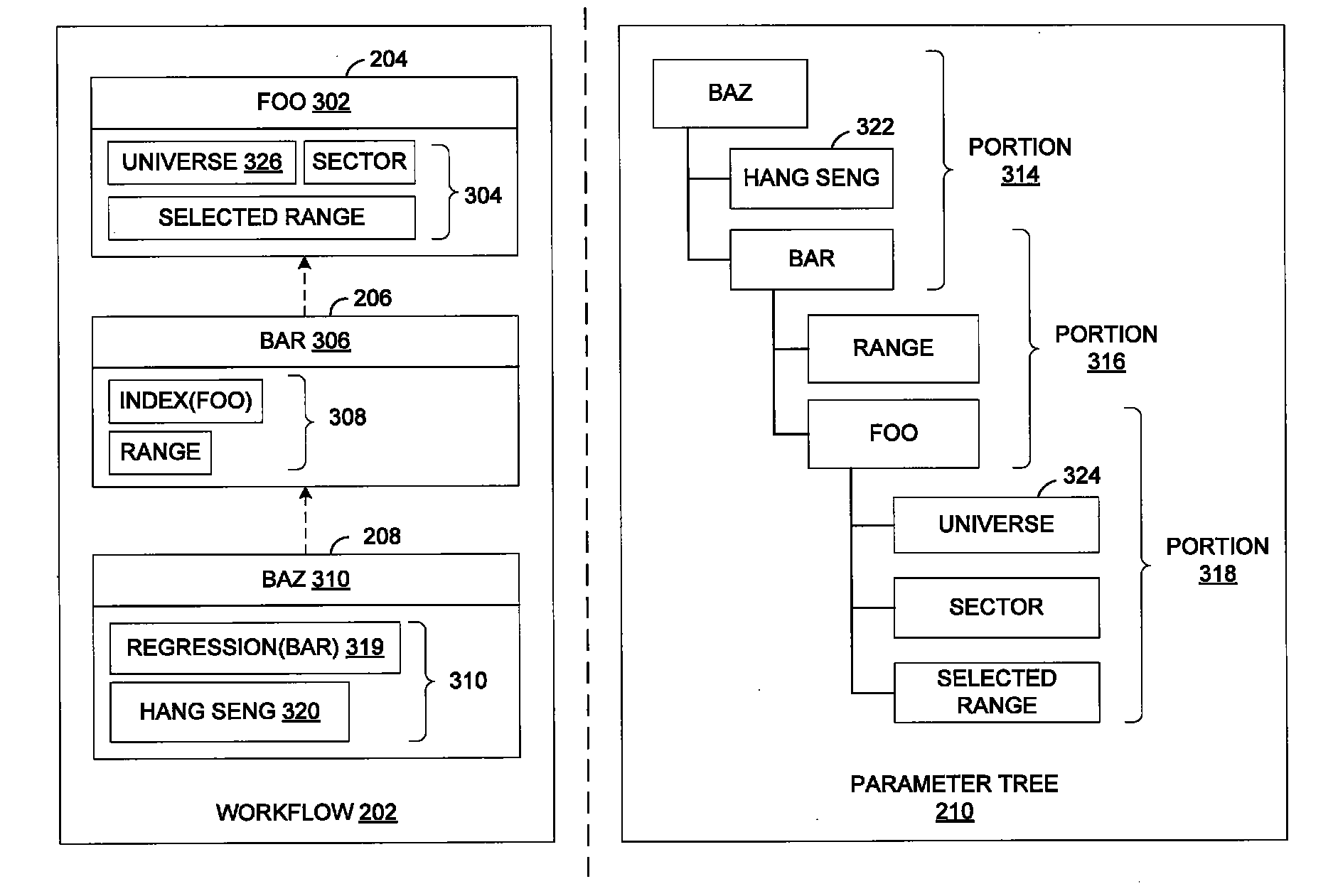
System and method for parameterizing documents for automatic workflow generation
ActiveUS8732574B2Redoes any synchronization neededQuick buildFinanceMultiprogramming arrangementsData miningDocumentation
One embodiment of the present invention sets forth a method for generating a new workflow for an application. The method includes generating a parameter tree related to a current workflow, wherein the parameter tree includes a different node corresponding to each parameter included in one or more documents associated with the current workflow, modifying a value associated with a first node included in the parameter tree based on an input, wherein the first node corresponds to a first parameter included in a first document associated with the current workflow, evaluating a second document associated with the current workflow based on the modified value associated with the first node, and generating the new workflow based on the evaluated second document.
Owner:PALANTIR TECHNOLOGIES
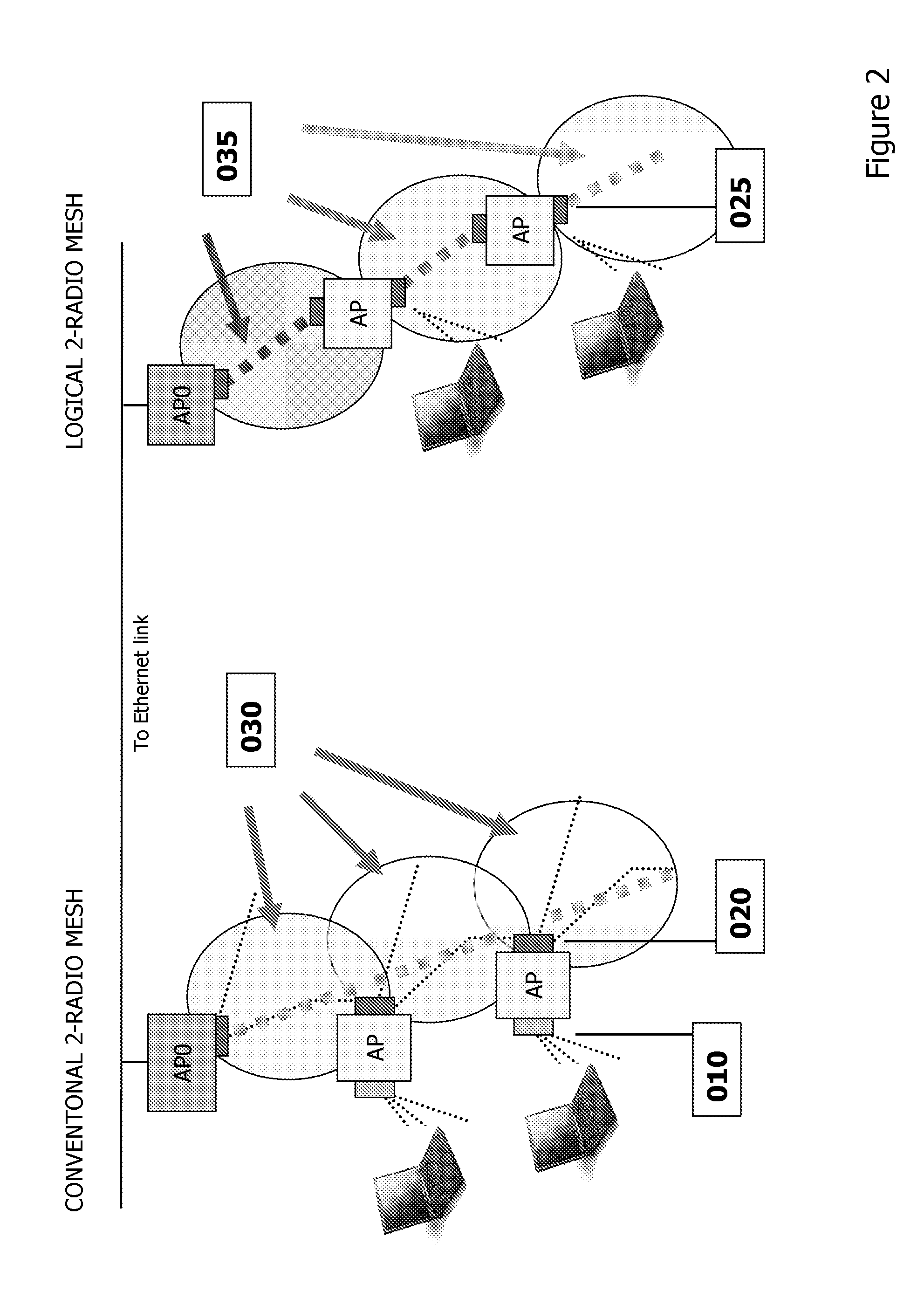
Chirp networks
ActiveUS20150304879A1Low costEfficient transportError preventionTransmission systemsPacket lossRouting table
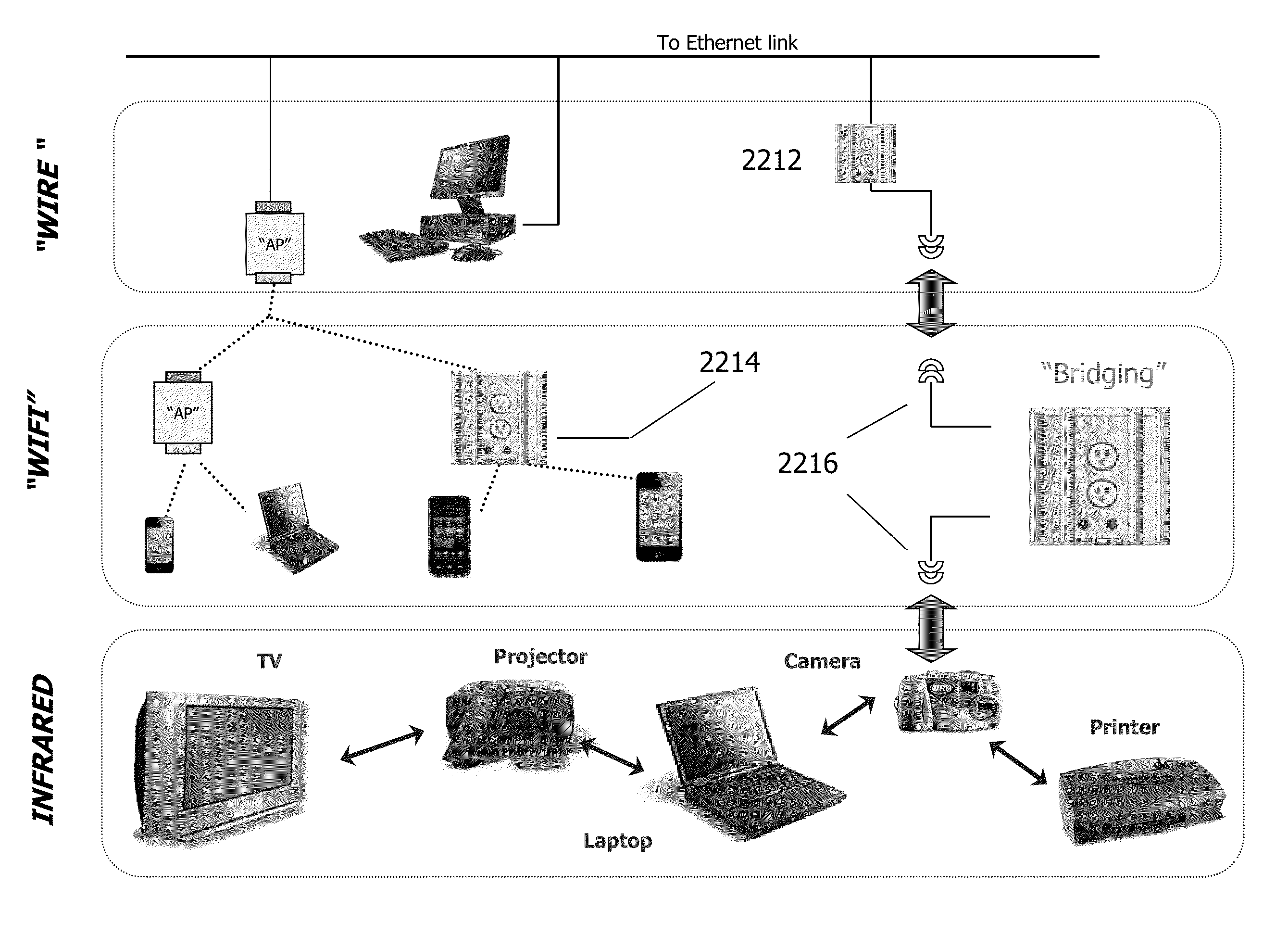
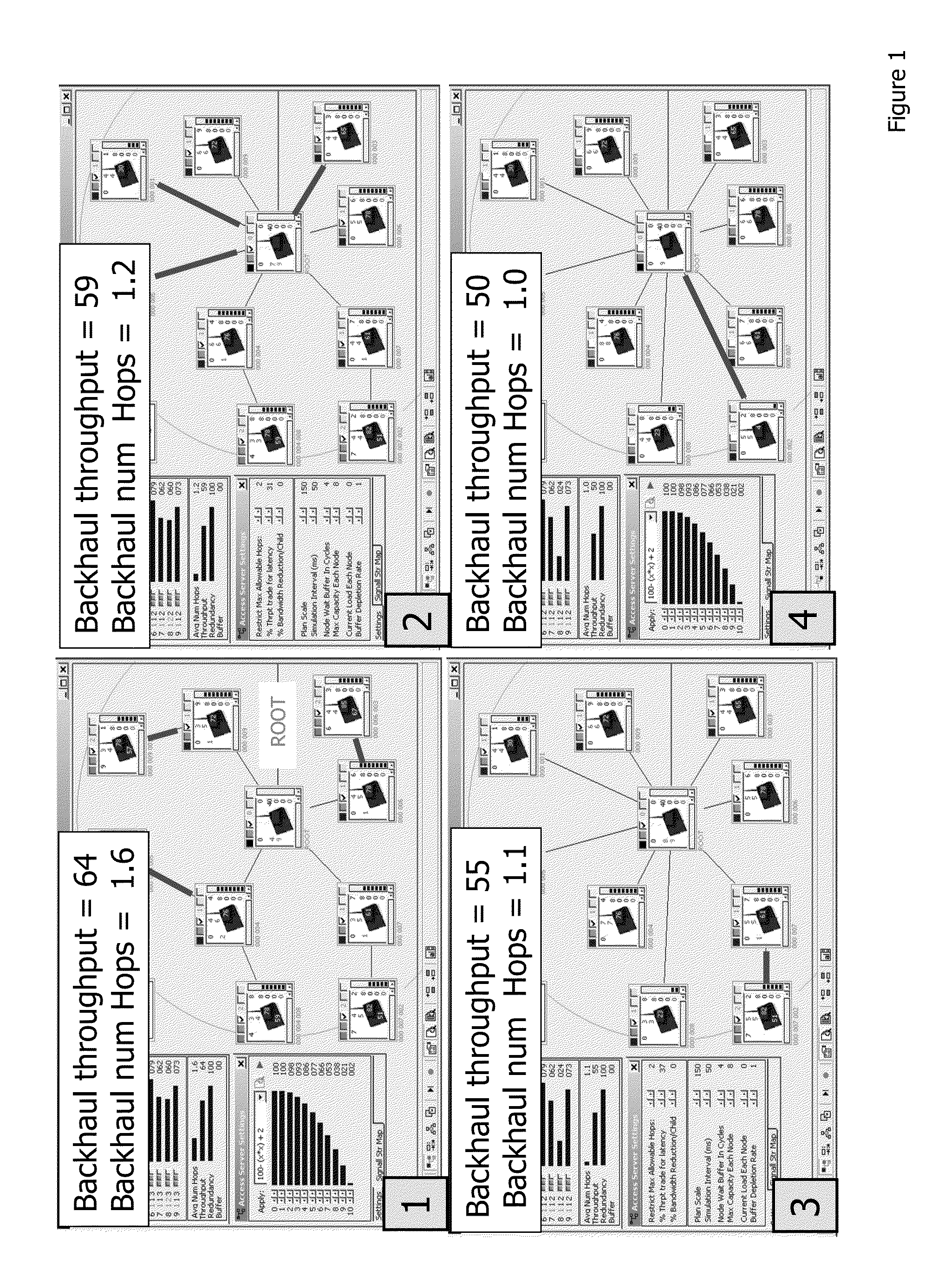
A network combining wireless and wired elements is described, using a multi-slot modular mesh node to house diverse transceiver elements (e.g. IR, Wi-Fi, Powerline). A radio agnostic tree based mesh network is formed, based on what type of wireless links are formed on the uplink and downlink of the backhaul and what type of radios are used for the Access Points AP. In addition to servicing IP based clients (e.g. Wi-Fi, WiMax, Bluetooth), the modular mesh nodes APs may also serve as receivers / collectors for low cost chirp devices. The method of transport is standard IP based packets yet security is inherent in this chirp-based implementation: only mesh nodes are privy to the routing tables that indicate that packet addresses are not IP. Multiple methods to obfuscate packet flow are presented. An organic approach to providing category / class based form of data type identification is proposed, to support a (dynamic) M2M Social Network Applications in-device discovery, registration and control are presented.
Owner:MESHDYNAMICS
Backup operations in a tree-based distributed file system
ActiveUS20160034356A1Digital data information retrievalDigital data processing detailsDistributed File SystemFile system
Techniques for cloning, writing to, and reading from file system metadata. Cloning involves identifying a first set of pointers included in a first root node in a file system metadata tree structure that stores file system metadata in leaf nodes of the tree structure, creating a first copy of the first root node that includes the first set of pointers, creating a second copy of the first root node that includes the first set of pointers, associating the first copy with a first view, and associating the second copy with a second view. Reading generally involves traversing the tree structure towards a target leaf node that contains data to be read. Writing generally involves traversing the tree structure in the same manner, but also creating copies of any nodes to be modified if those nodes are deemed to have a different treelD than a particular root node.
Owner:COHESITY
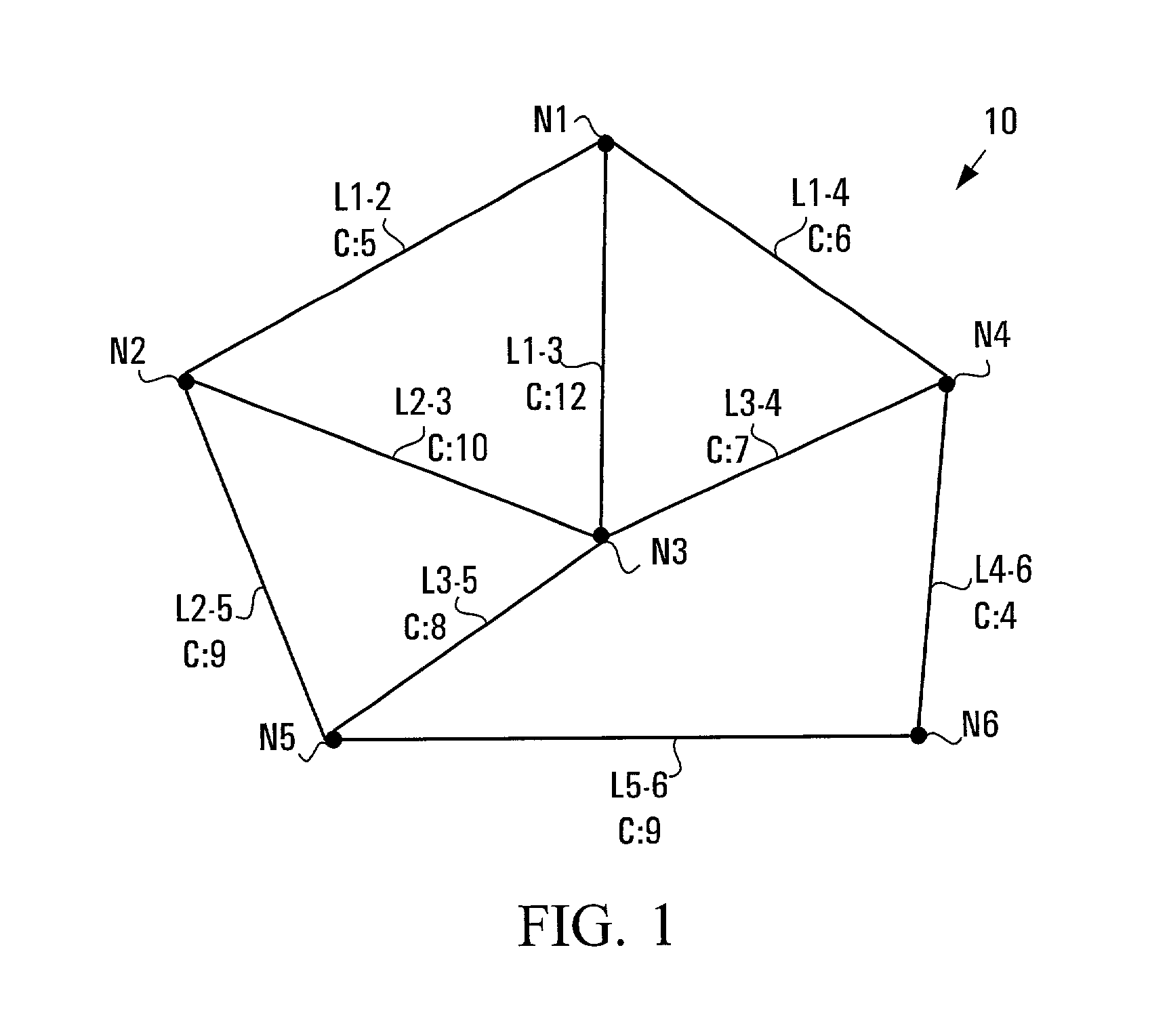
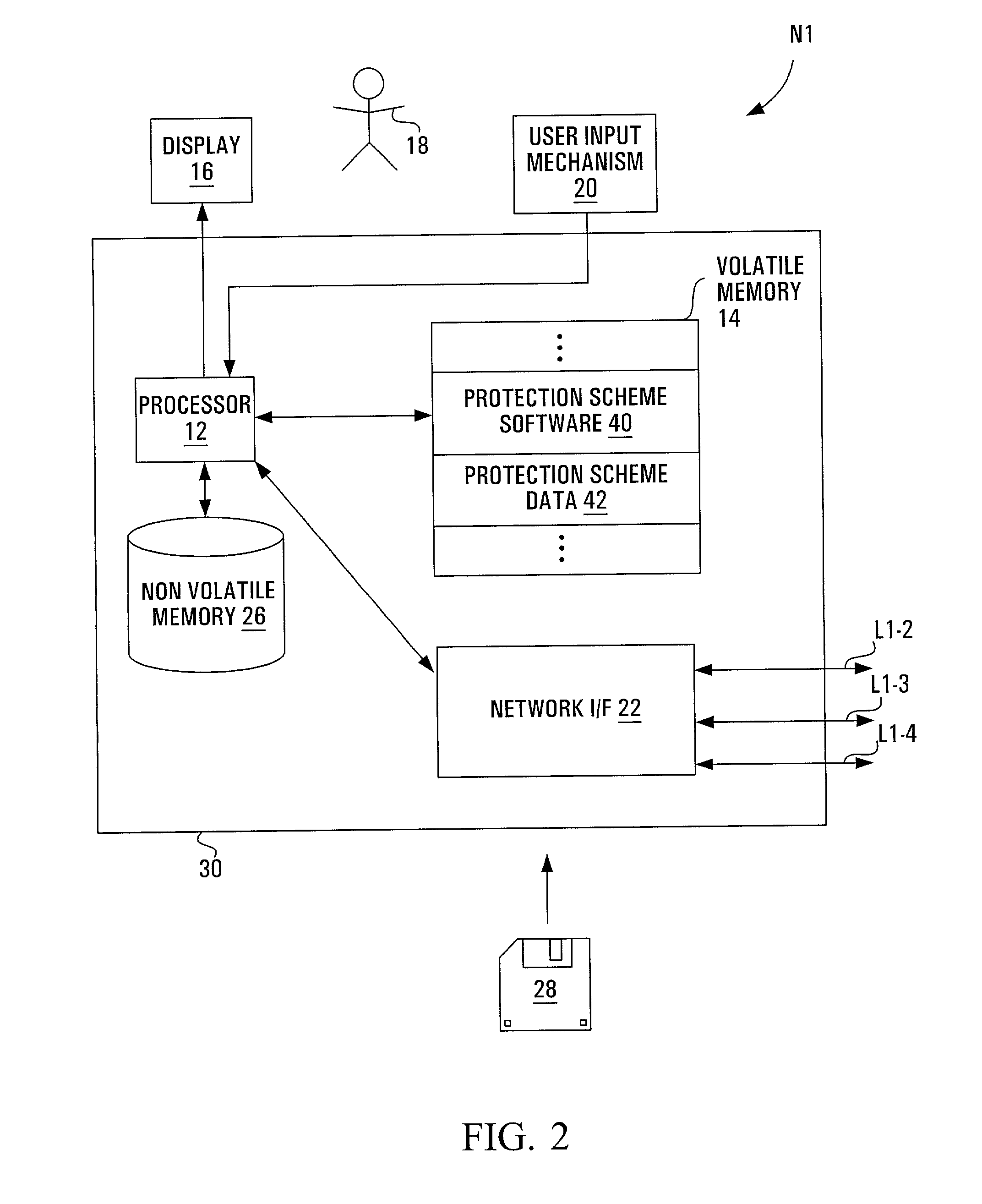
Hierarchical tree-based protection scheme for mesh networks
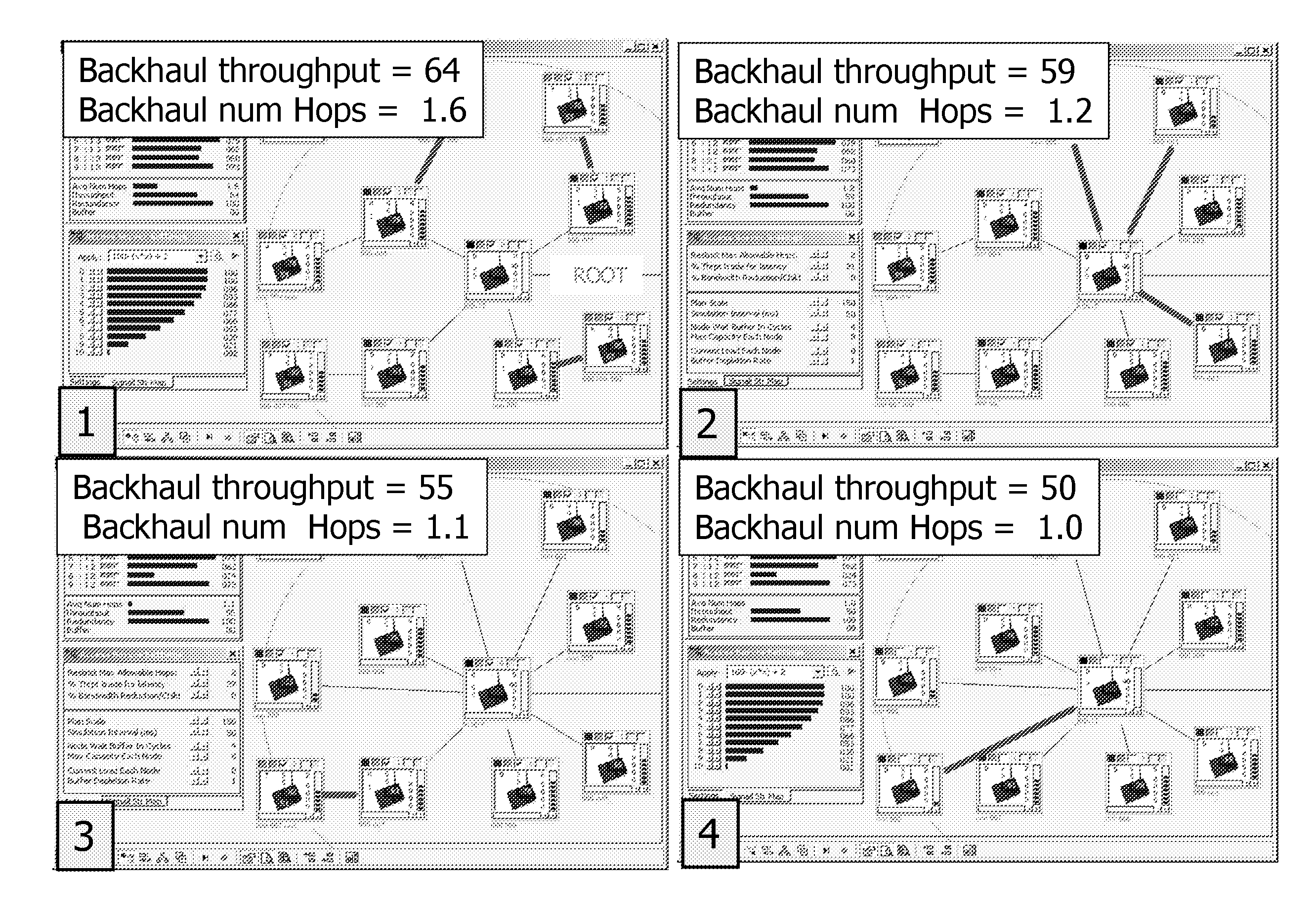
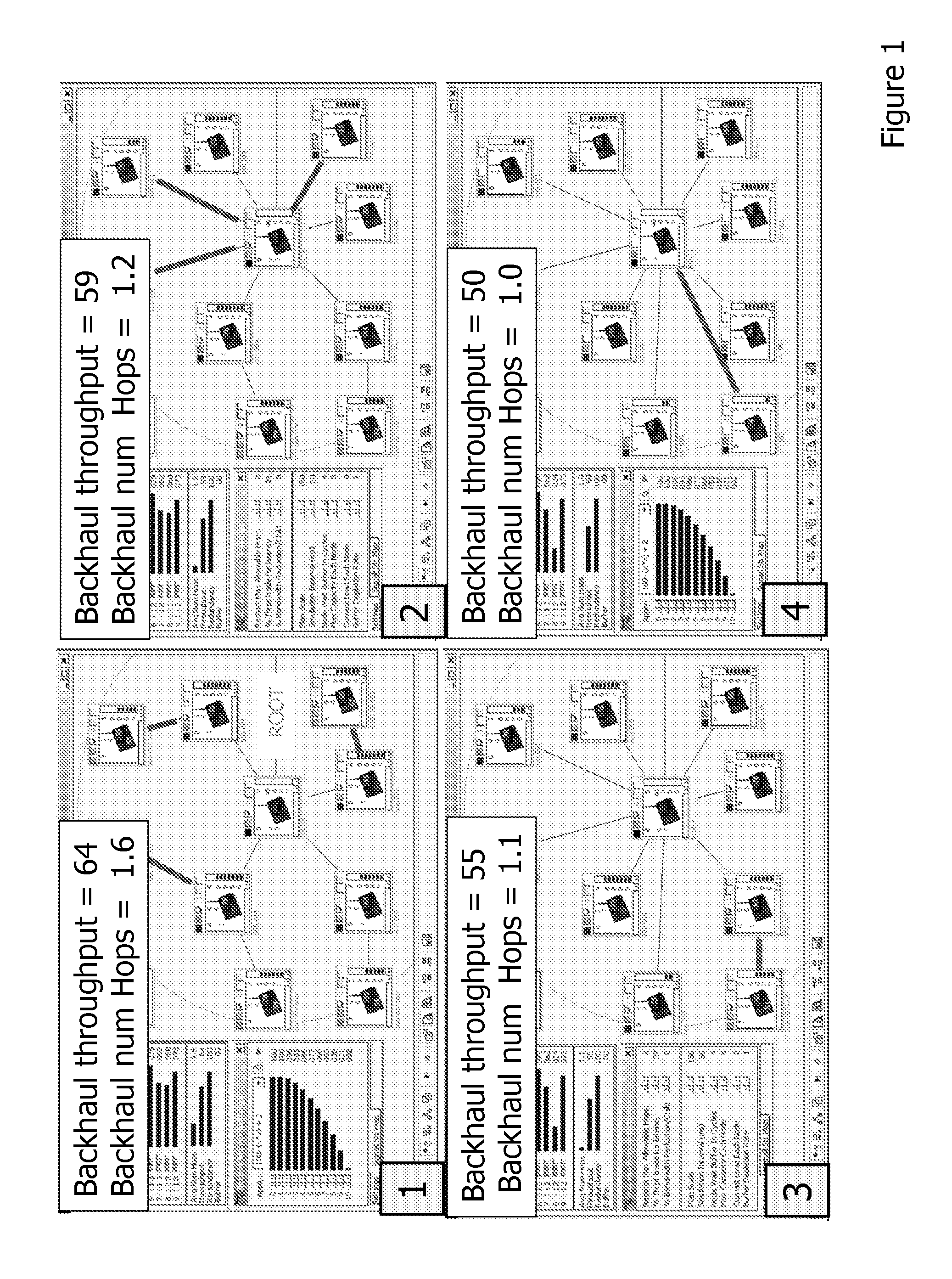
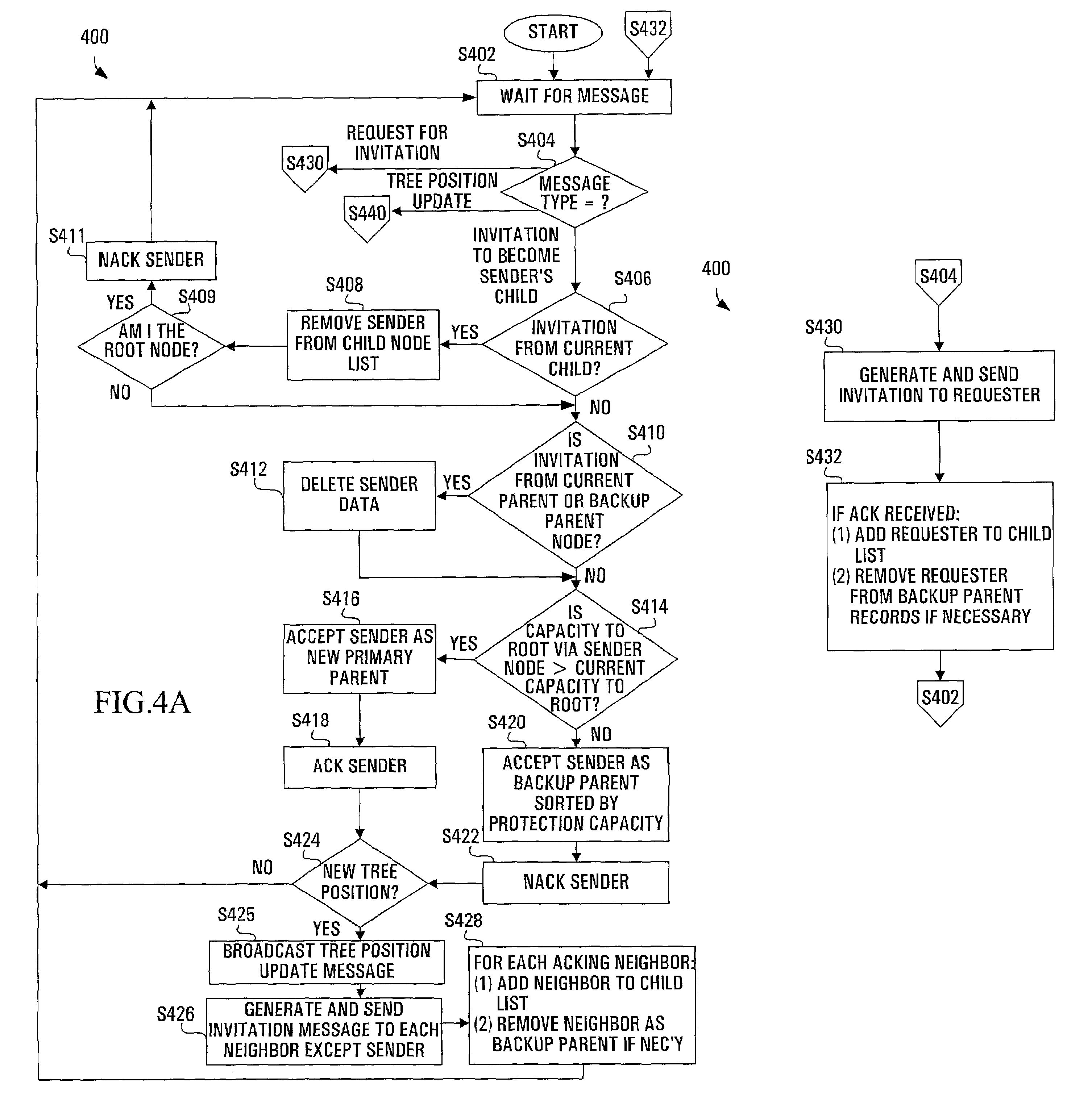
ActiveUS7203743B2More capacityFast protection switchingMultiple digital computer combinationsTransmissionNetwork topologyDistributed computing
In a hierarchical tree-based protection scheme, a node in a mesh network is designated as a root node of a spanning hierarchical protection tree and subsequently invites each adjacent node to become its child within the tree. If the inviting node provides a more capacious protection path to the root node than is currently enjoyed by the invitee, the invitee designates the inviting node as its primary parent and assumes a new tree position. Otherwise, the invitee designates the inviting node as a backup parent. A node assuming a new tree position invites all adjacent nodes except its parent to become its child. The invitations propagate throughout the network until a spanning hierarchical protection tree is formed. Upon a subsequent failure of a straddling link, the tree may be used to re-route data. Further, given a tree link failure, protection switching is quickly achieved at a disconnected node through use of a backup parent as the new primary parent. Dynamic tree reconfiguration in the event of network topology changes may be limited to the network area surrounding the change.
Owner:CIENA
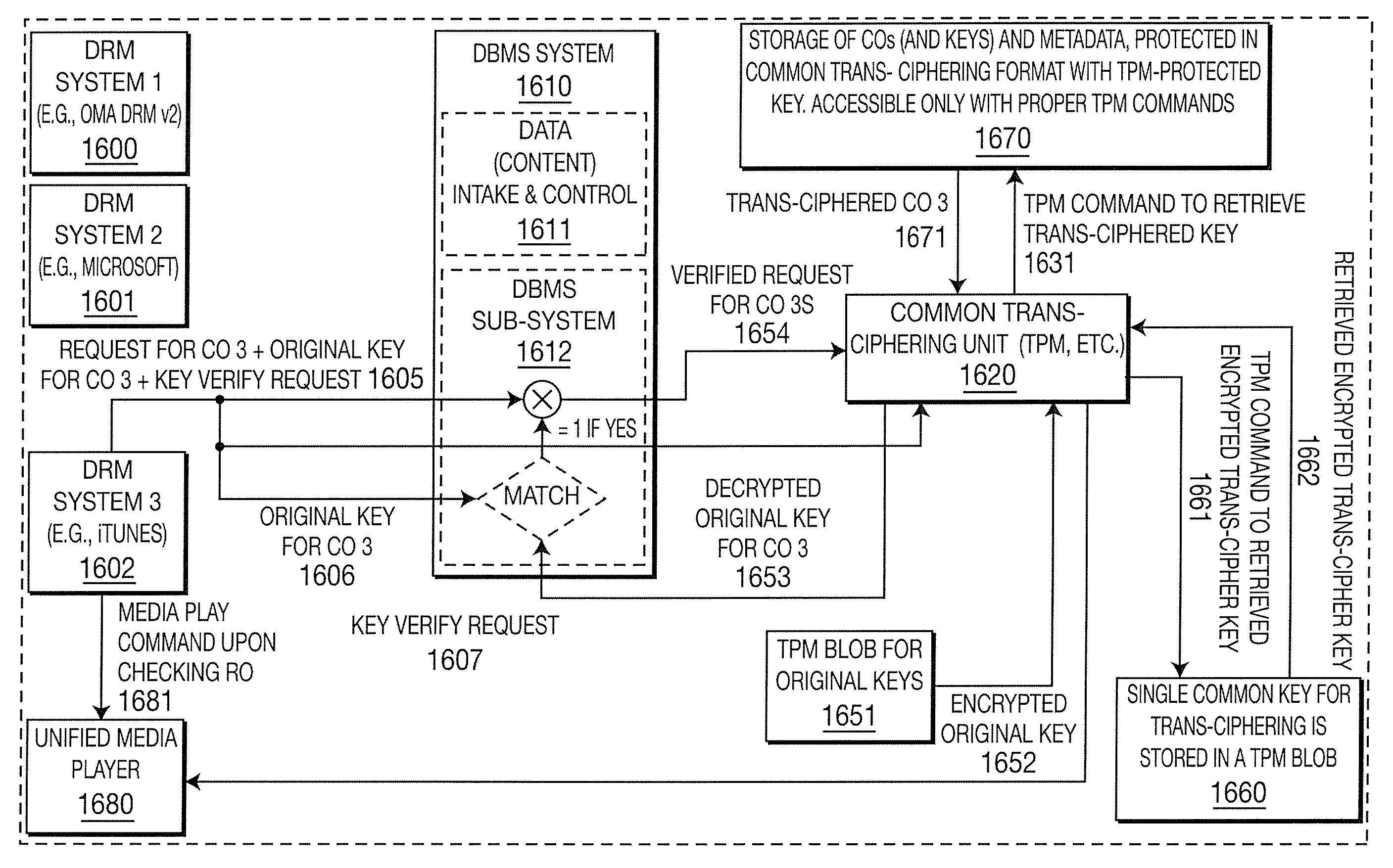
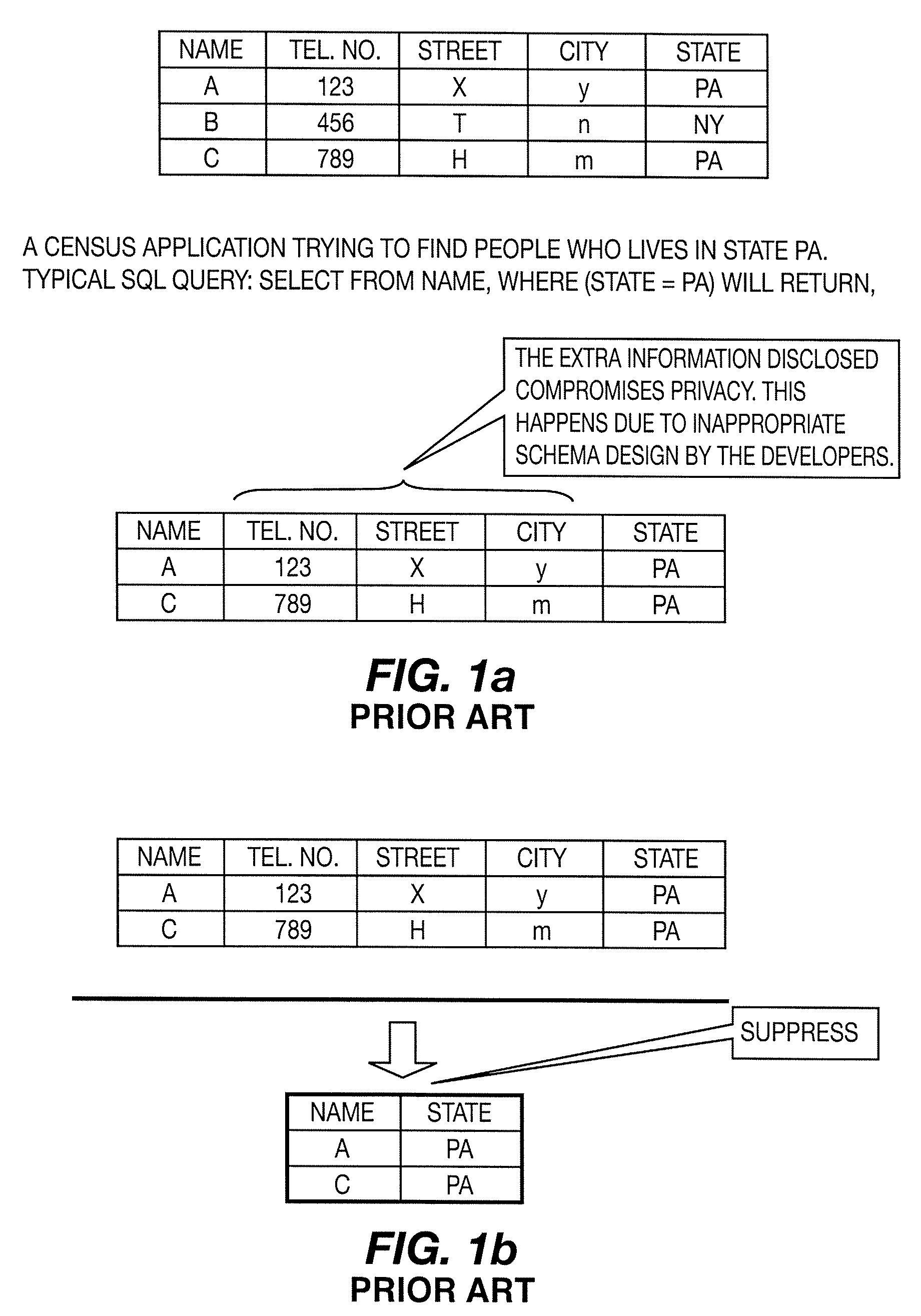
Techniques for database structure and management
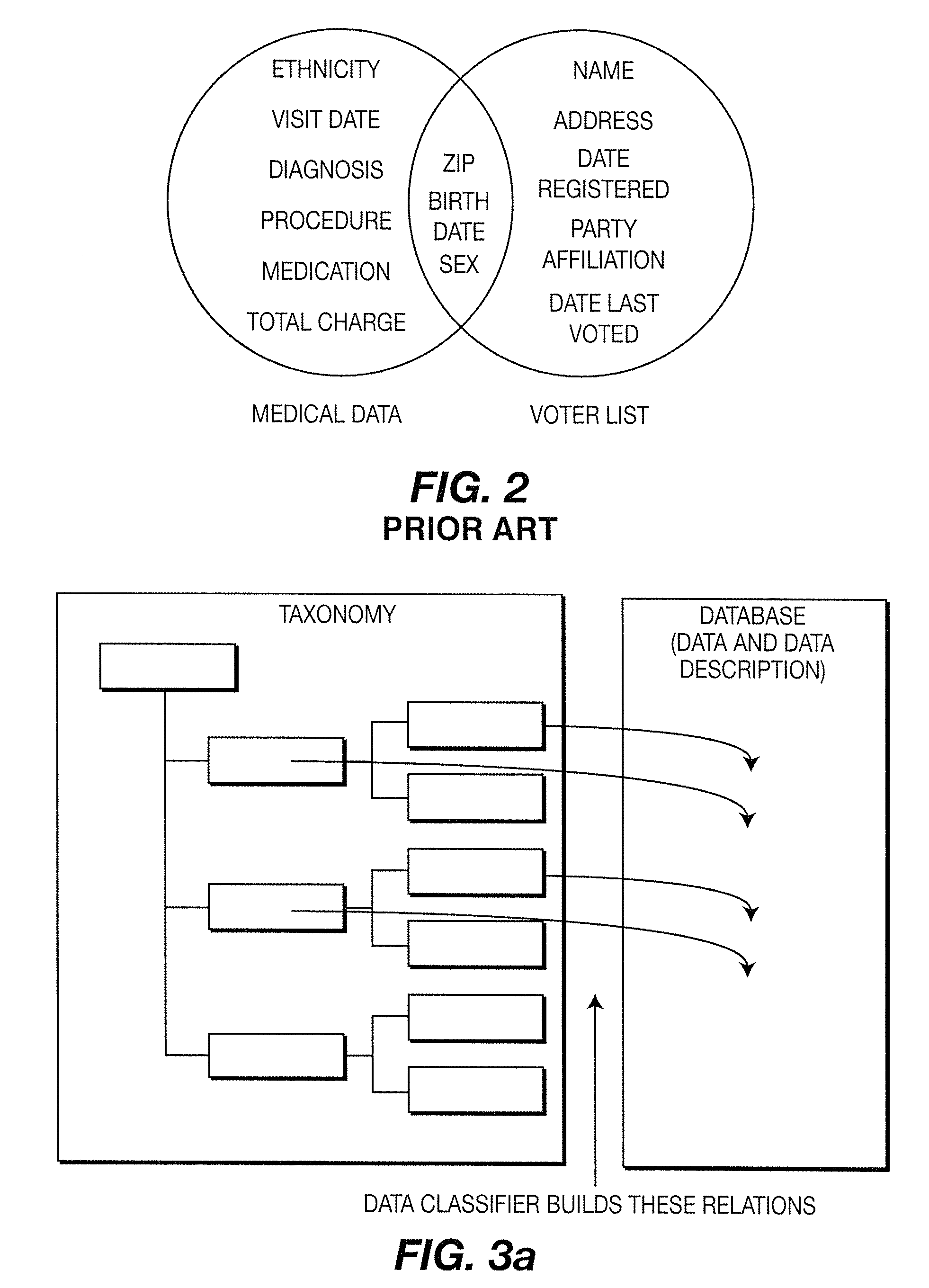
InactiveUS20080189250A1Efficient processingFacilitates seamless and organic handover of service and network accessDigital data processing detailsAnalogue secracy/subscription systemsDatabase structureUser agent
An embodiment is related to a database system for protecting data privacy and efficient organization of data. An enhanced database system comprises a DBMS, a data classifier, a database of applications and a rules and policy unit. The DBMS includes a query processor for processing a query from a user. The rules and policy unit outputs a pointer to a node within the data classification tree based on several criteria. In accordance with another embodiment, a DBMS residing within a communication network organizes data related to the ID of mobile users. In accordance with another embodiment, an enhanced database system comprises a DRM user agent and a DBMS. The DRM user agent receives a CO protected by DRM. The DBMS stores the CO and controls access to the CO based on restrictions specified in an RO associated with the CO.
Owner:INTERDIGITAL TECH CORP
Methods and systems for modeling using classification and regression trees
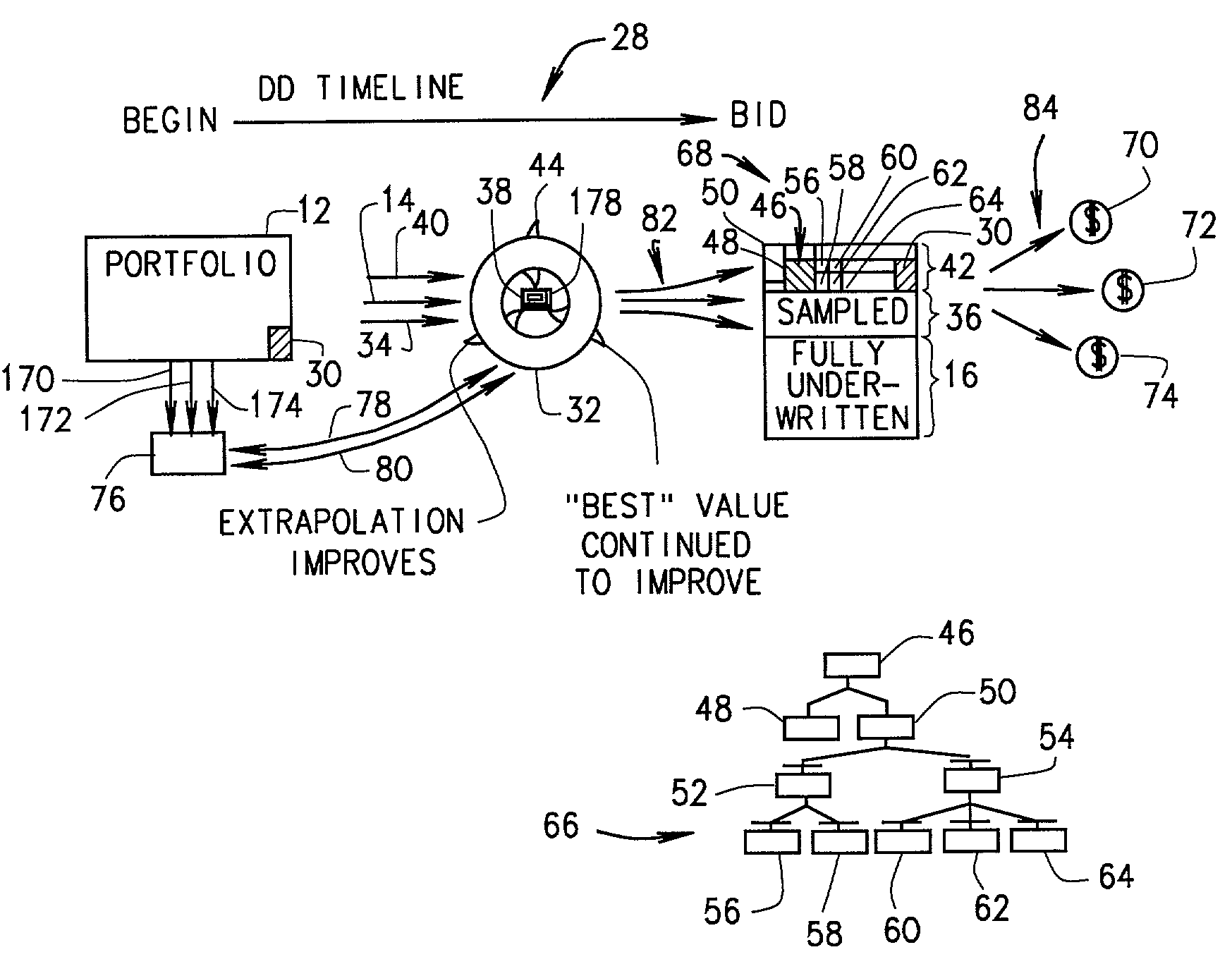
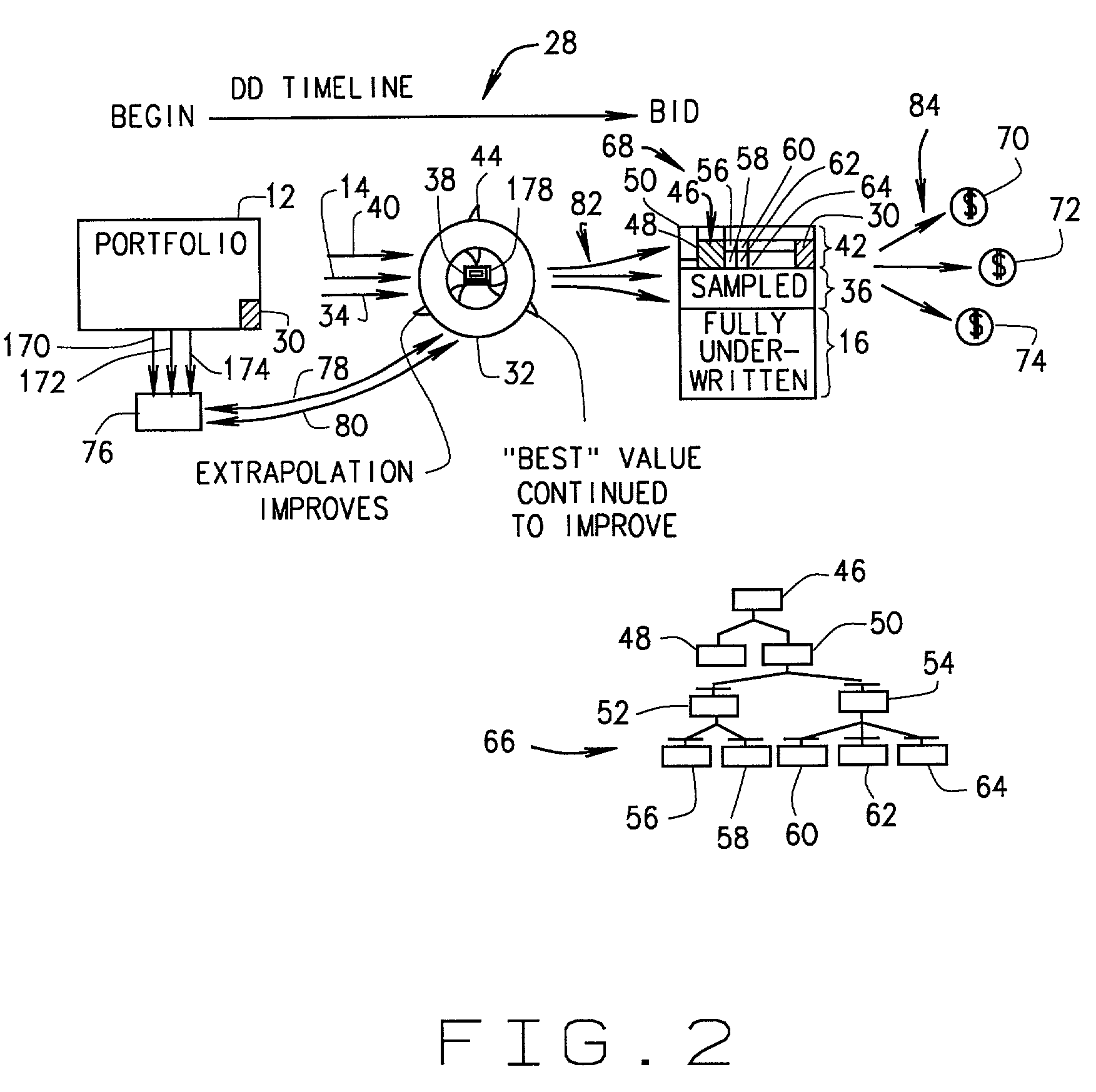
A method of valuation of large groups of assets using classification and regression trees is described. The method includes defining relevant portfolio segmentations, assessing performance of the classification and regression tree based model against a simple model and ranking all portfolio segments based upon performance of the models. Iterative and adaptive statistical evaluation of all assets and statistical inferences are used to generate the segmentations. The assets are collected into a database, grouped by credit variable, subdivided by ratings as to those variables and then rated individually. The assets are then regrouped and a collective valuation is established by cumulating individual valuations.
Owner:GENERAL ELECTRIC CO
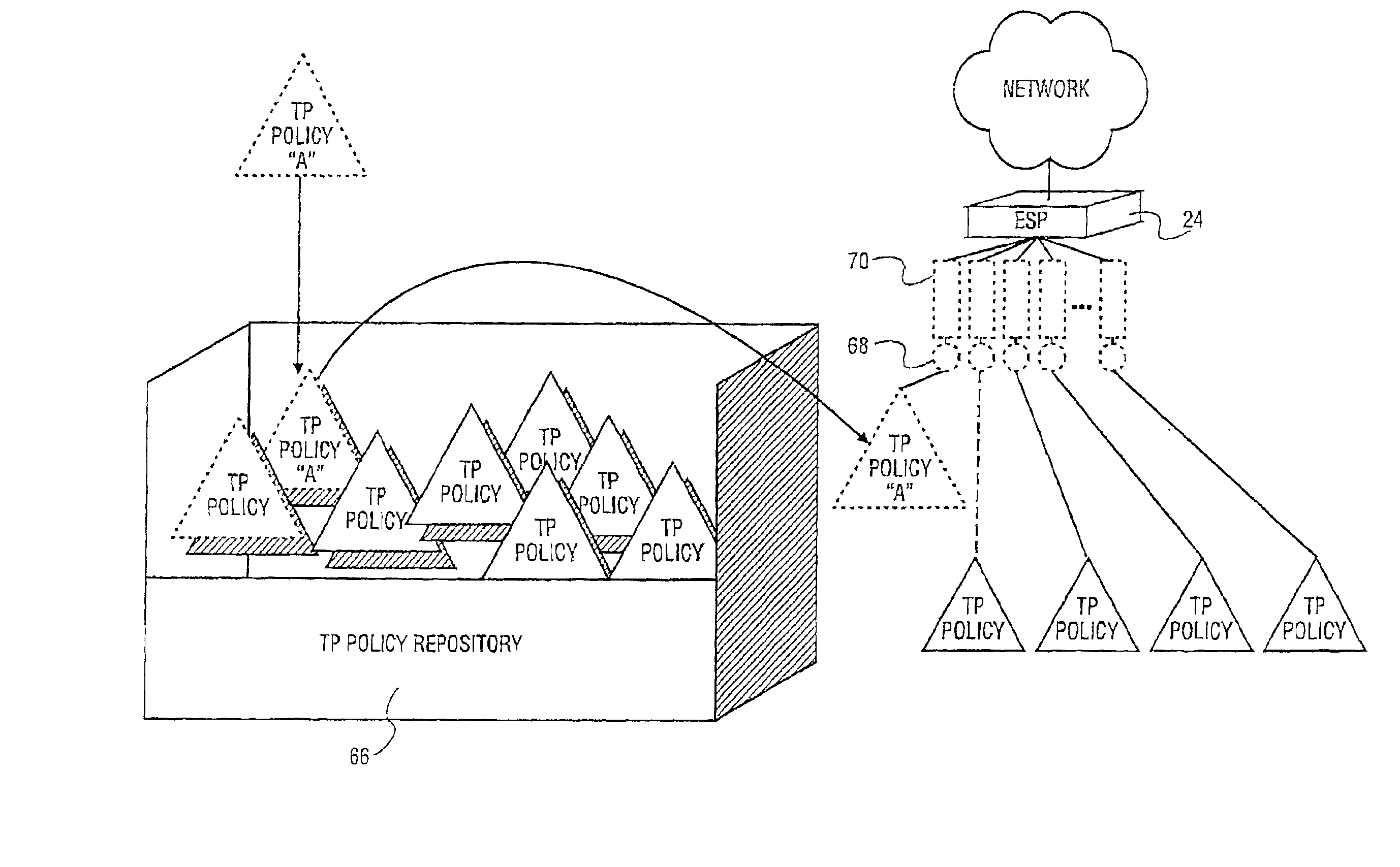
Policy change characterization method and apparatus
ActiveUS6980555B2Data switching by path configurationMultiple digital computer combinationsQuality of serviceTree based
A method and apparatus is described for receiving a new policy tree at a network element in a network. The network element stores a current policy tree of classes for quality of service of packets being processed by the network element. Classes of the current policy tree are compared with the classes of the new policy tree. Classes of the current policy tree are selectively deleted and classes of the new policy tree are selectively added to the current policy tree based on the comparison of the classes.
Owner:TELEFON AB LM ERICSSON (PUBL)
Arrangement in a router for establishing multicast group hierarchy and coalescence
InactiveUS7519733B1Special service provision for substationMultiple digital computer combinationsBroadcast packetClient-side
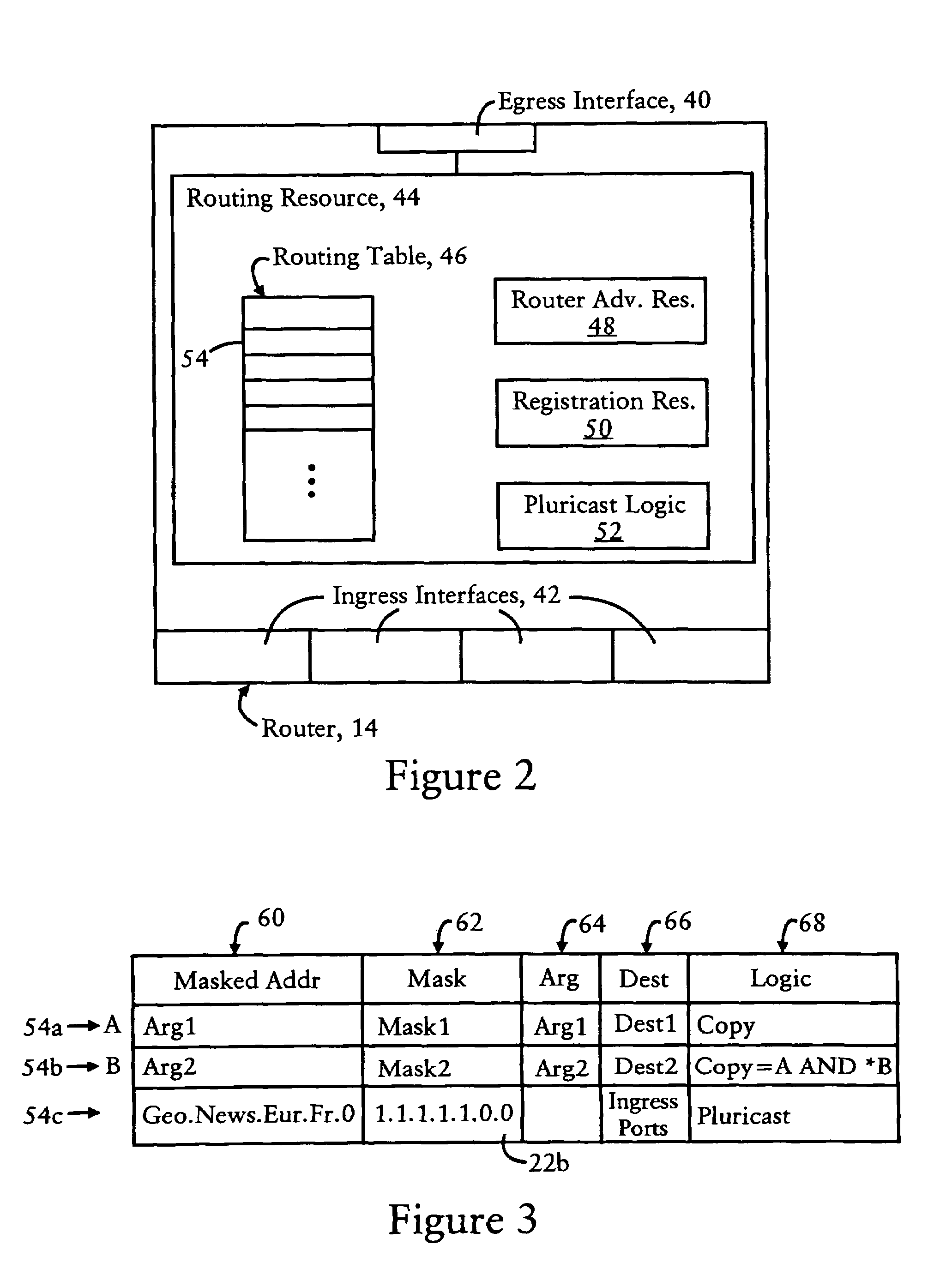
Routers of a content network include routing entries that specify aggregation levels, enabling the routers to establish a tree-based topology within an aggregation realm for distribution of broadcast packets. Each router is configured to have a prescribed aggregation level within the aggregation realm, and identify a network-directed broadcast packet based on detecting a prescribed pluricast code at a corresponding prescribed prefix location relative to the prescribed aggregation level. Each router also is configured for storing a registration request within its routing entries, and propagating the registration request to other routers within the aggregation realm. Each registration request includes a bit mask according to one of the prescribed aggregation levels. Hence, client-based registration requests can be propagated throughout the aggregation realm for rules-based coalescence of subscriber groups throughout the aggregation realm.
Owner:CISCO TECH INC
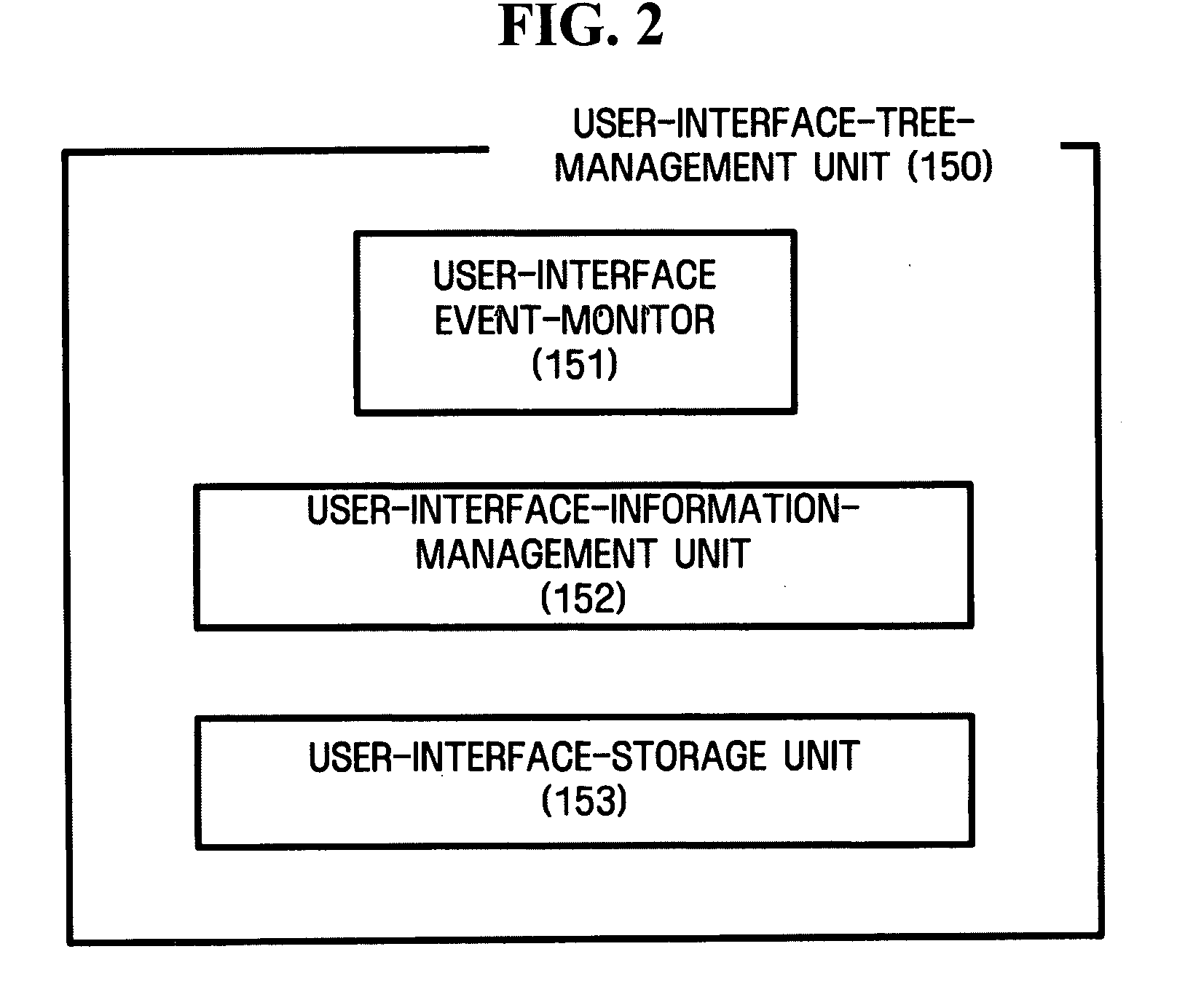
Apparatus and method for setting user interface according to user preference
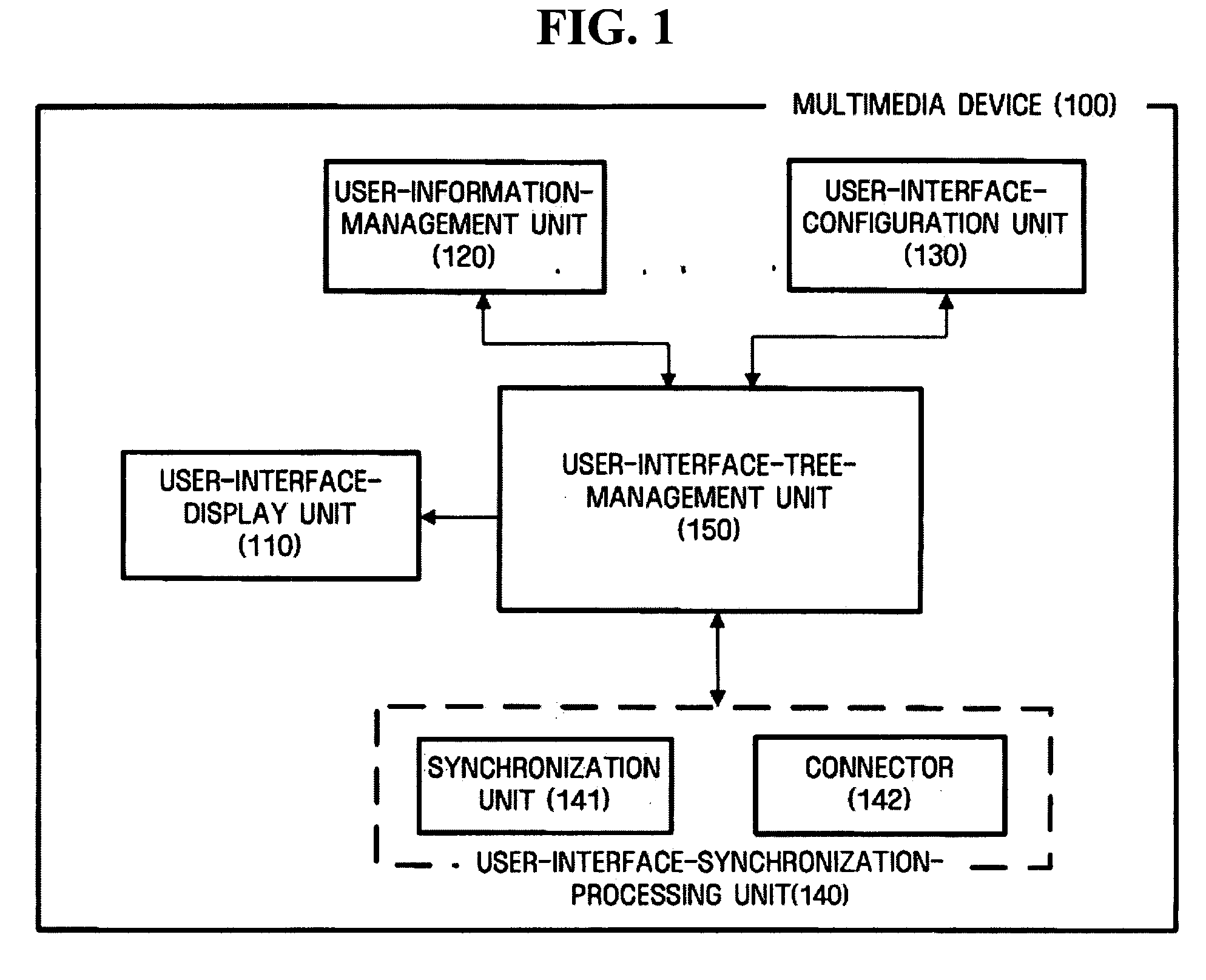
Provided are an apparatus and method for setting a user interface according to user preferences, more particularly, an apparatus and method for setting the user interface according to the user preferences, in which the user interface can be set up by reflecting the user preferences, and the set user interface is synchronized in order to be used in other devices. The apparatus includes a user-interface-configuration unit that is notified of an update and rearrangement of a predetermined user interface element by a user, a user-information-management unit that manages security information of the user that reconfigures the user interface element, and a user-interface-tree-management unit that reconfigures a predetermined user-interface tree based on the reconfigured user-interface element.
Owner:SAMSUNG ELECTRONICS CO LTD
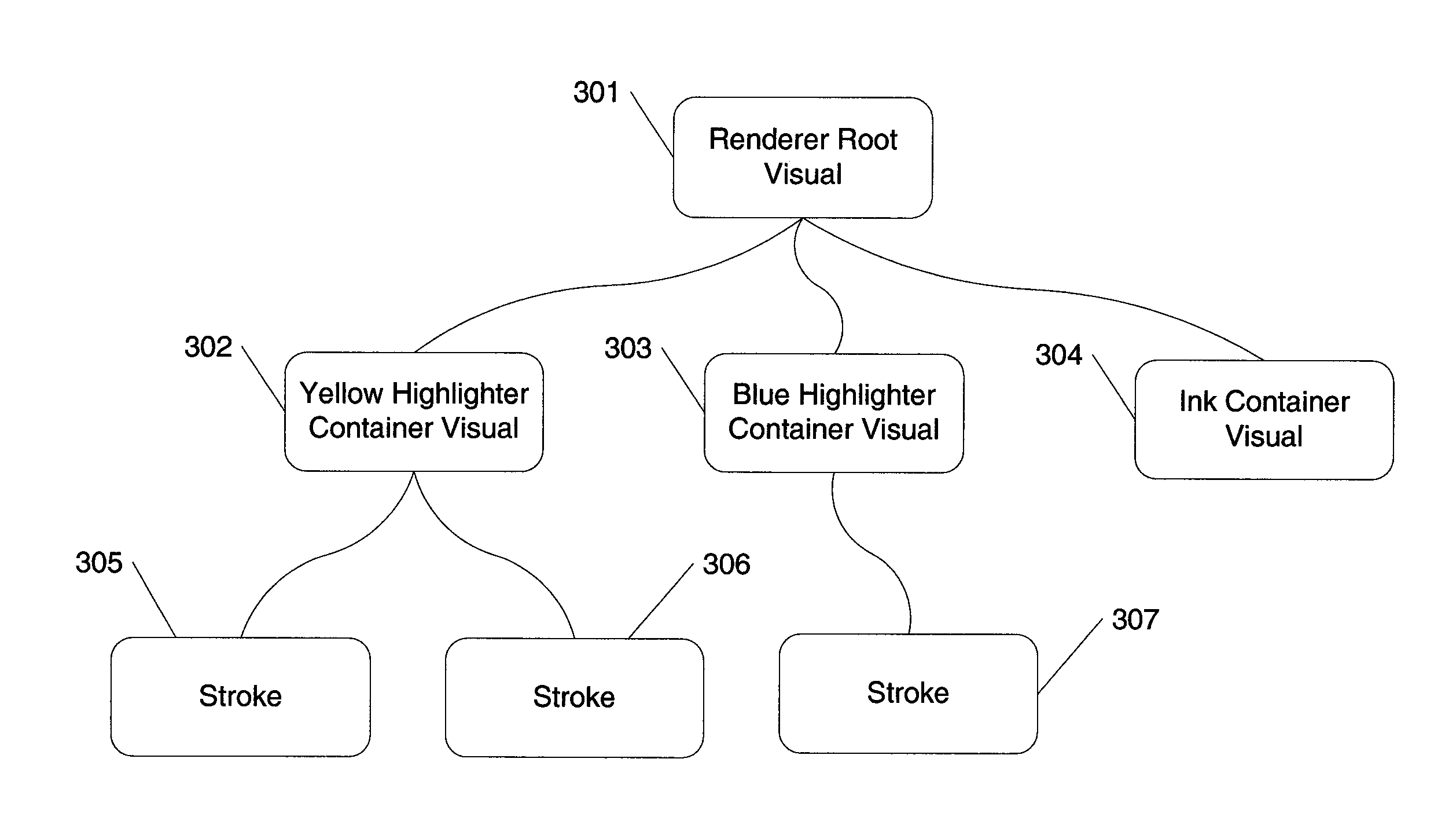
Programmatical Access to Handwritten Electronic Ink in a Tree-Based Rendering Environment
InactiveUS20060274057A1Easy to controlImprove experienceCathode-ray tube indicatorsInput/output processes for data processingComputer graphics (images)Collection Object
A system and method for performing ink related operations in a tree-based presentation system is described. Ink-related programmatical interfaces may relate to interactions with a stroke object, a stroke collection object, and ink input elements.
Owner:MICROSOFT TECH LICENSING LLC
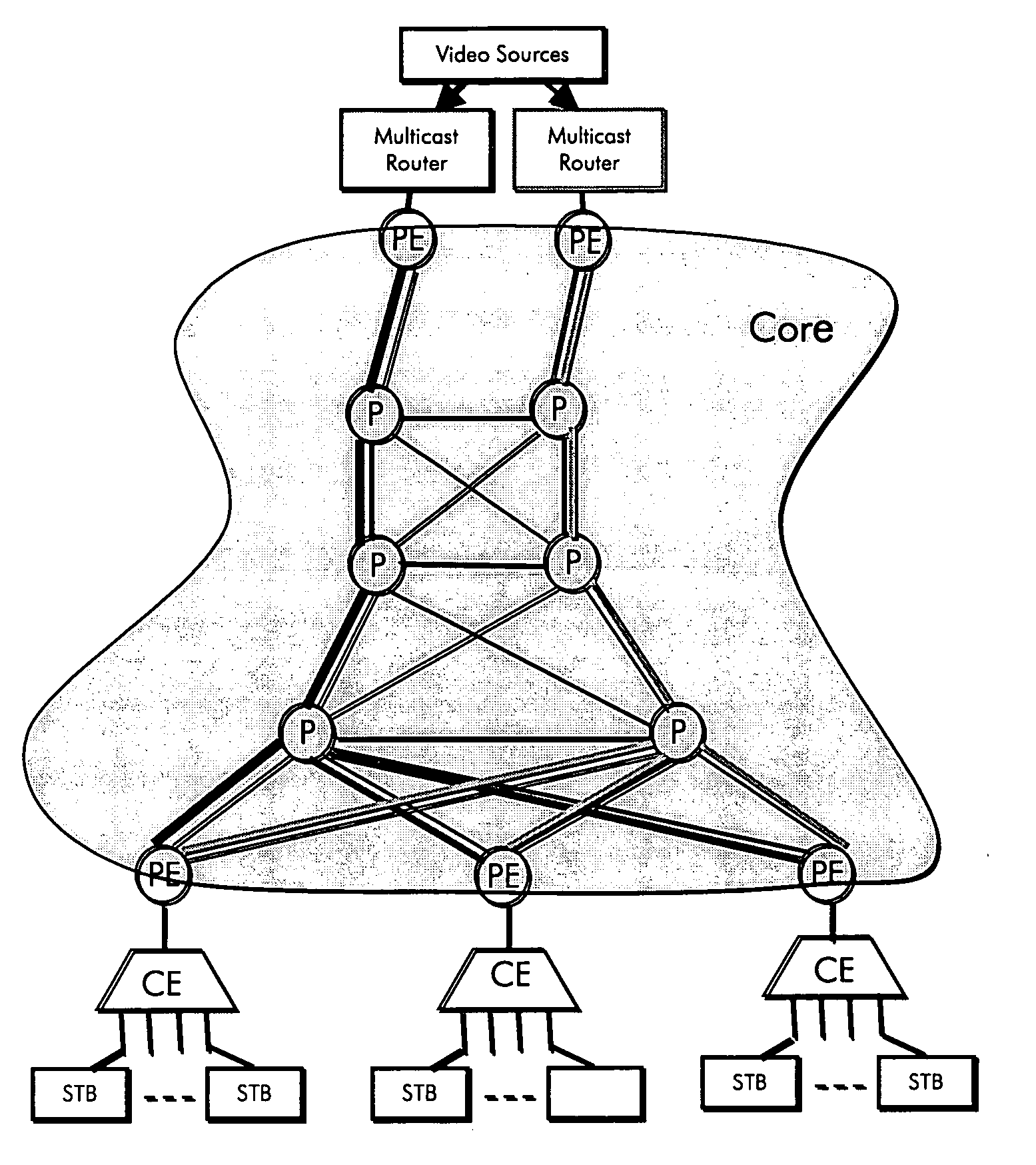
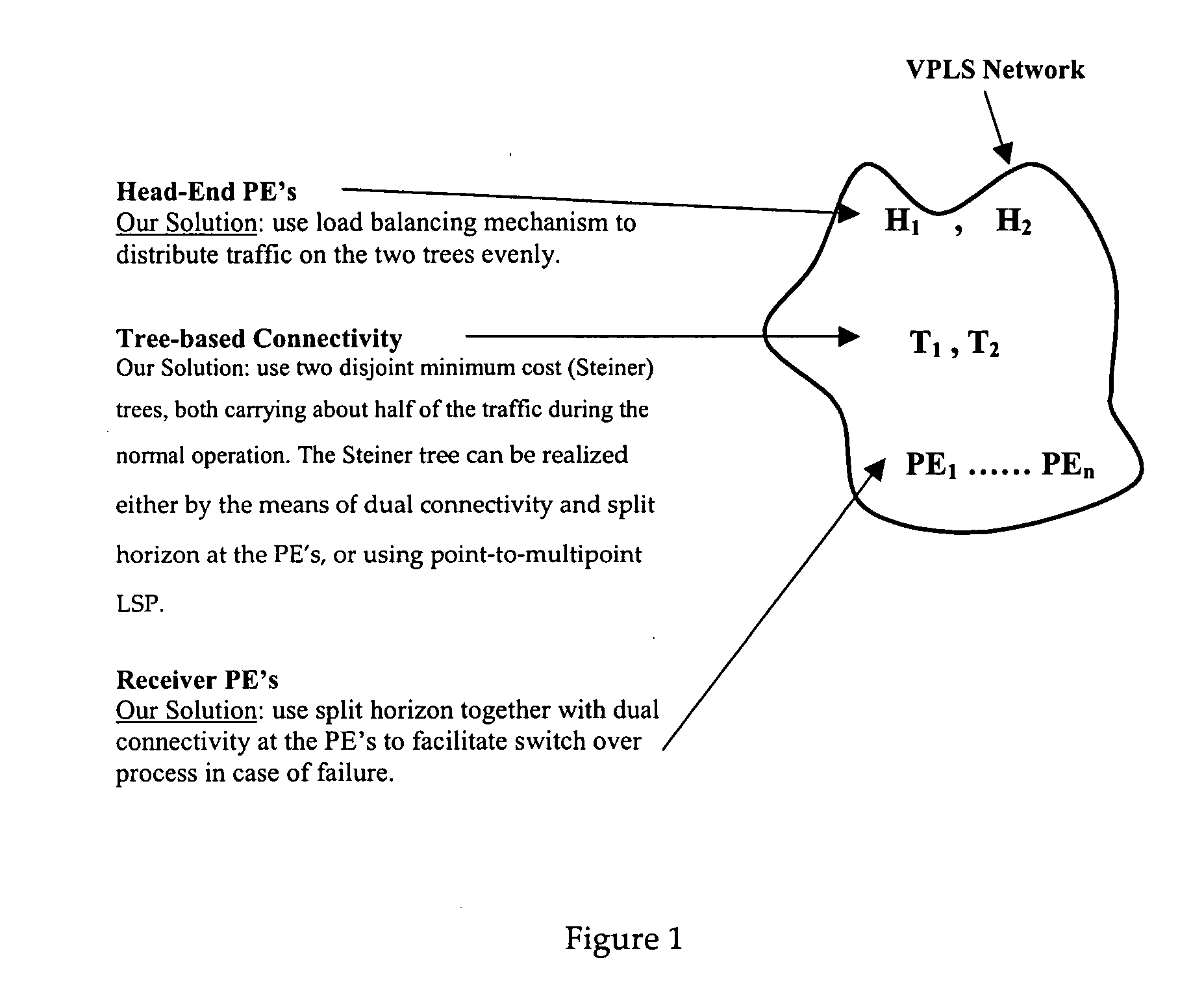
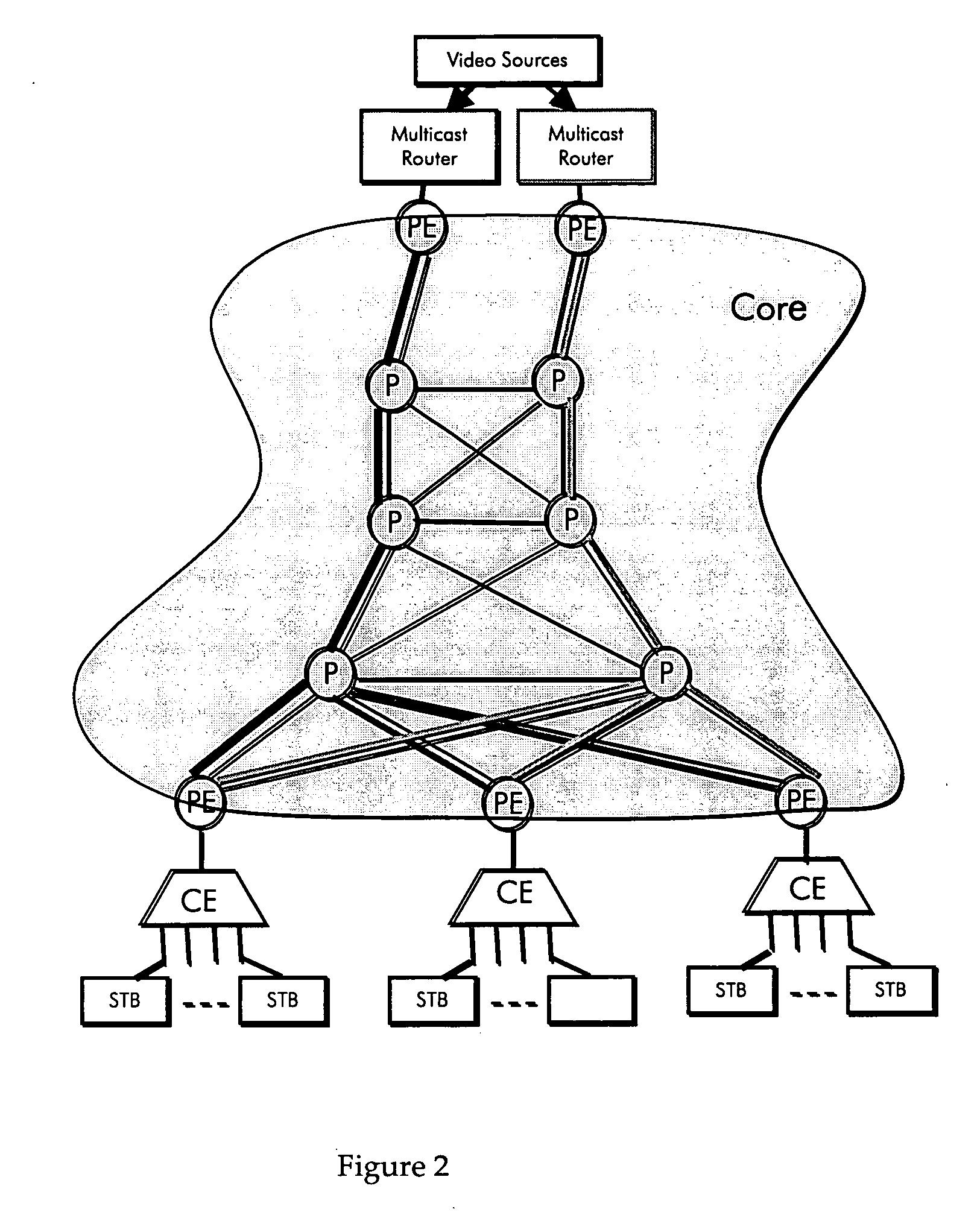
Resiliency in minimum cost tree-based VPLS architecture
InactiveUS20070047556A1Easy to convertEfficient and easy to distributeSpecial service provision for substationTime-division multiplexHorizonNetwork management
A system for providing resilient multimedia broadcasting services over a VPLS network is described. A network Management System (NMS) calculates disjoint minimum cost trees using the Steiner algorithm executed with extra steps to result in the disjoint trees. Destination PE routers in the VPLS network are connected to the disjoint trees so that they can be serviced by either tree in the case of a fault. Each of the disjoint trees is provisioned with enough bandwidth to carry all of the services provided by the VPLS network. Under normal operation, however, the services are distributed evenly over the trees. In the event of a fault, the services on the faulty tree are switched to the other tree using split horizon bridging. Each Steiner tree can also be realized using poin-to-multipoint LSPs which is fully protected by a precomputed point-to-mulltipoint LSP.
Owner:WSOU INVESTMENTS LLC
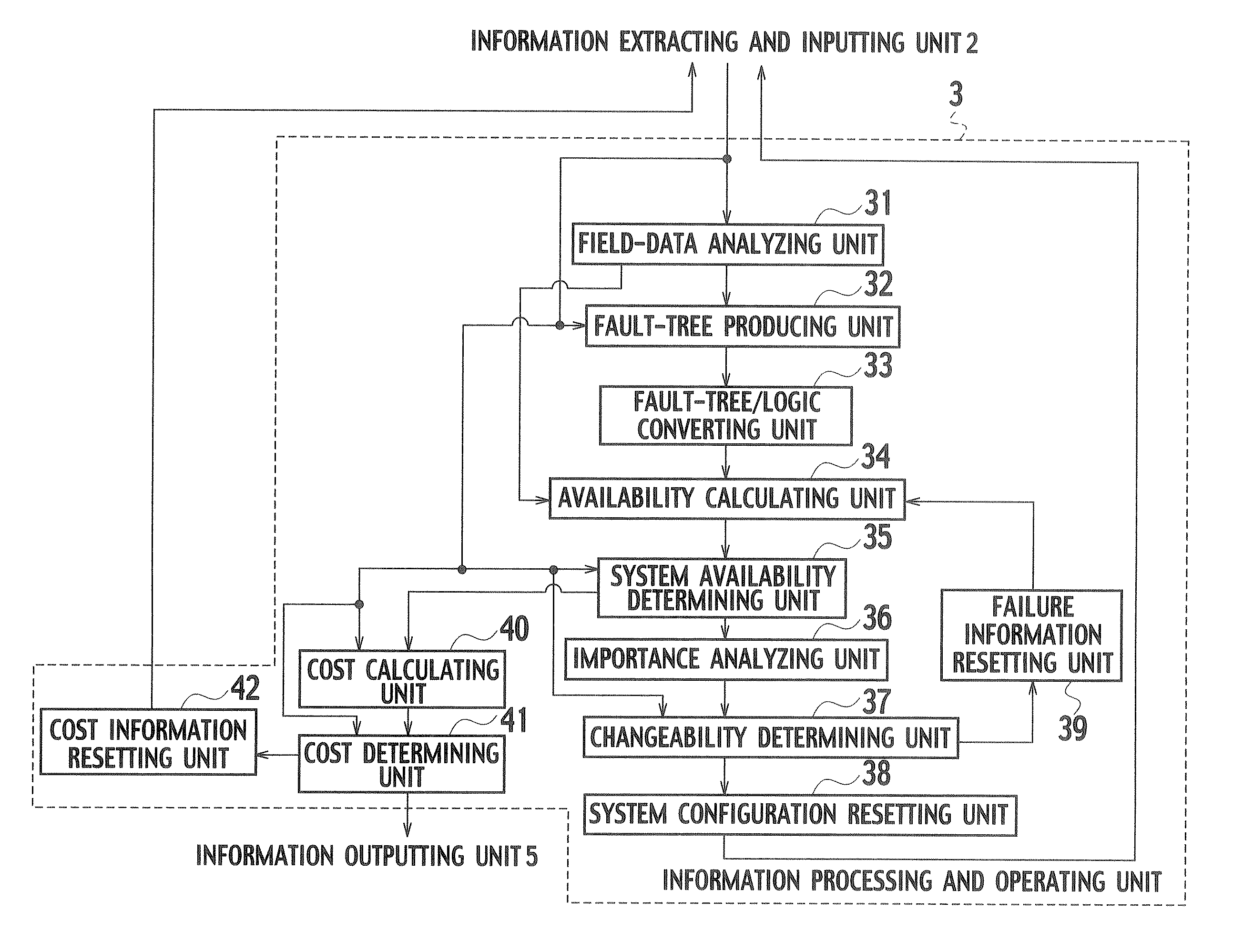
Reliability evaluation system, reliability evaluating method, and reliability evaluation program for information system
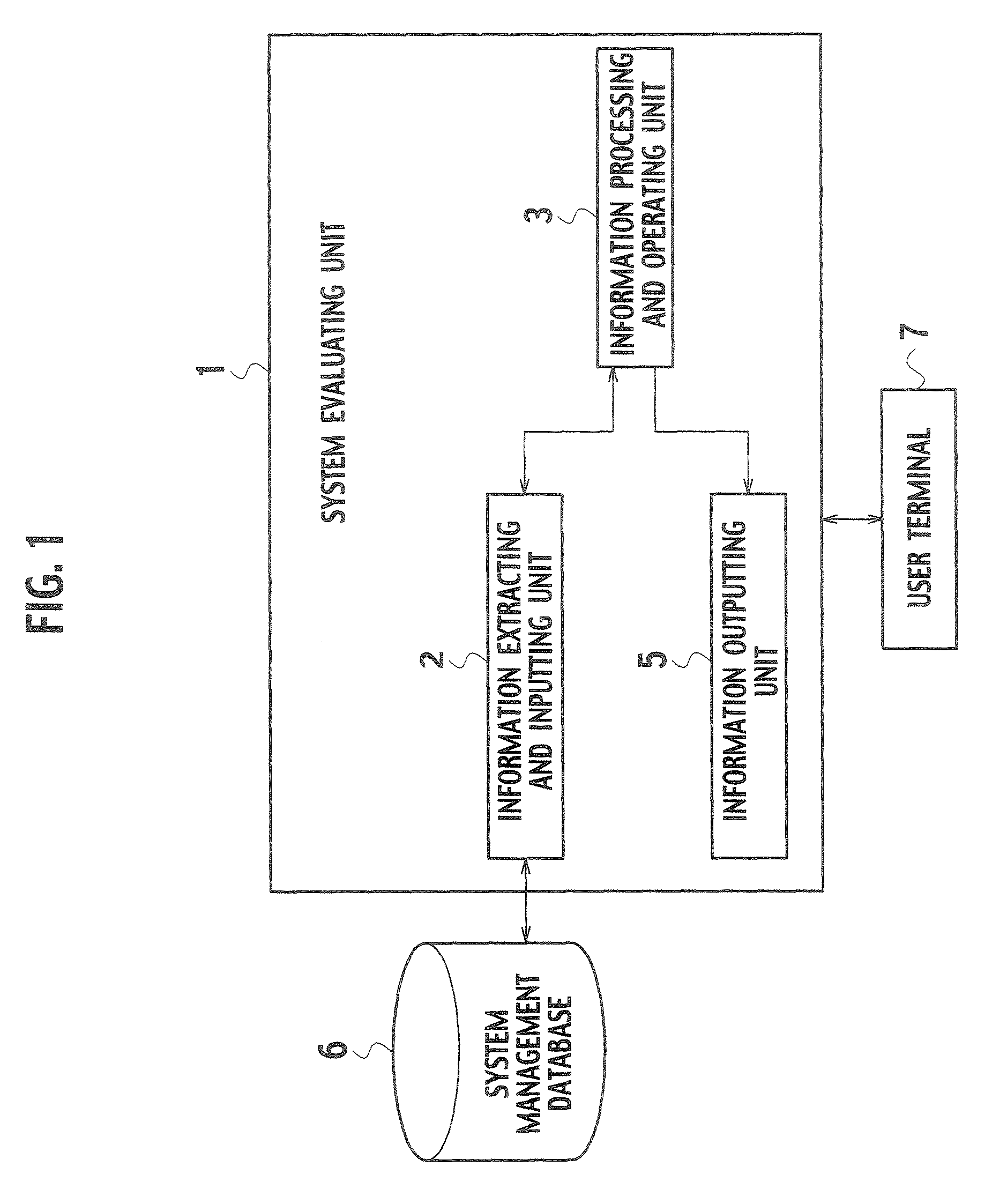
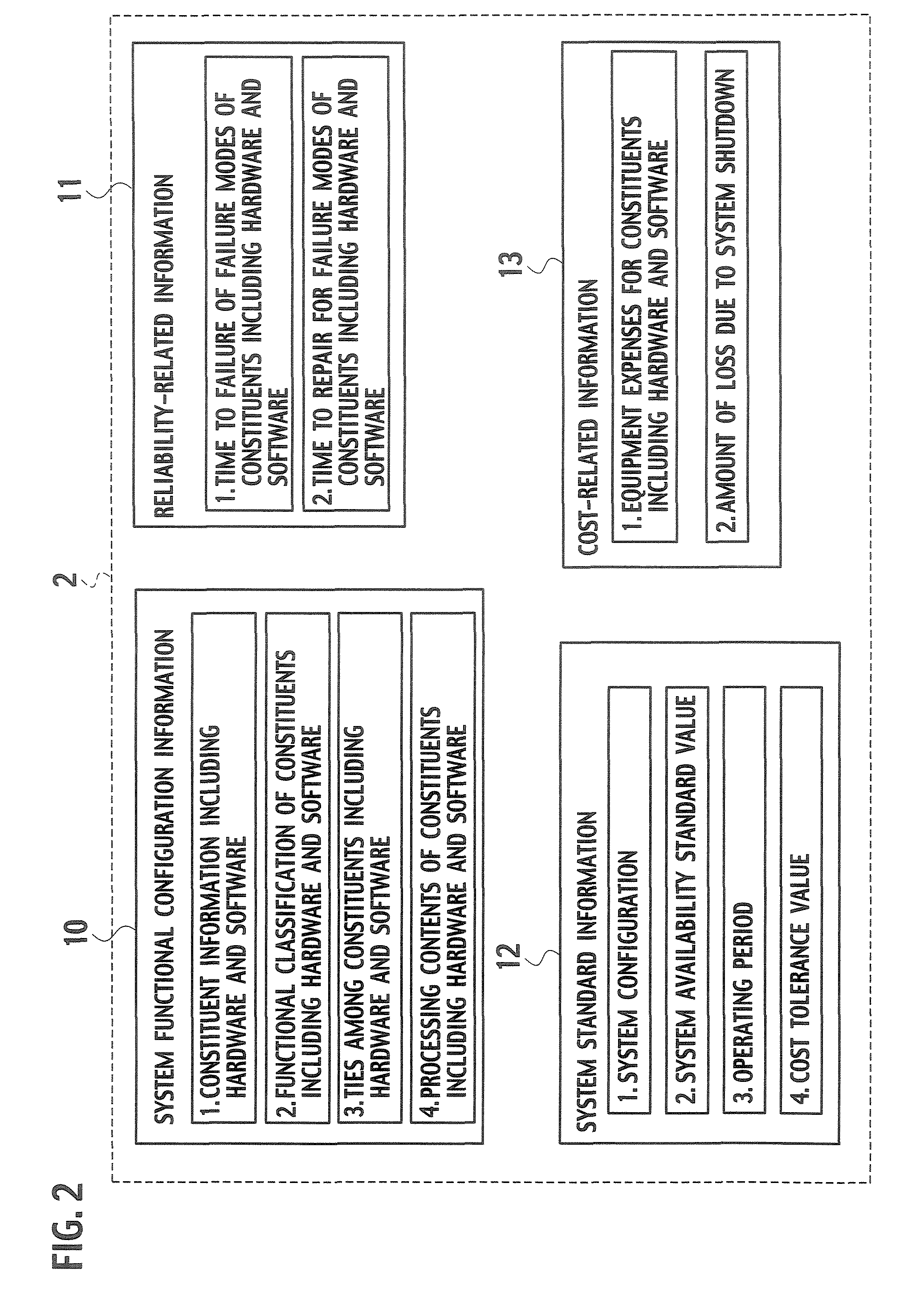
InactiveUS7730363B2Reduce the burden onImprove usabilityTesting/monitoring control systemsReliability/availability analysisEvaluation systemComputer science
A system includes an input unit (2) to which failure information corresponding to failure modes of constituents indicating software and hardware, a system configuration information and a standard value of system availability are inputted, a producing unit (32) producing a fault tree based on the system configuration information, a calculating unit (34) calculating unavailability corresponding to the failure modes based on a result of analyzing the failure information, and calculating system availability based on the calculated unavailability and the fault tree, a determining unit (35) determining whether the system availability meets the standard value, an extracting unit (36) extracting a basic event related to an increase in the system availability when the system availability is determined to be below the standard value, and resetting units (38, 39) resetting new unavailability and the like based on whether it is possible to reduce the unavailability of the extracted basic event.
Owner:TOSHIBA SOLUTIONS
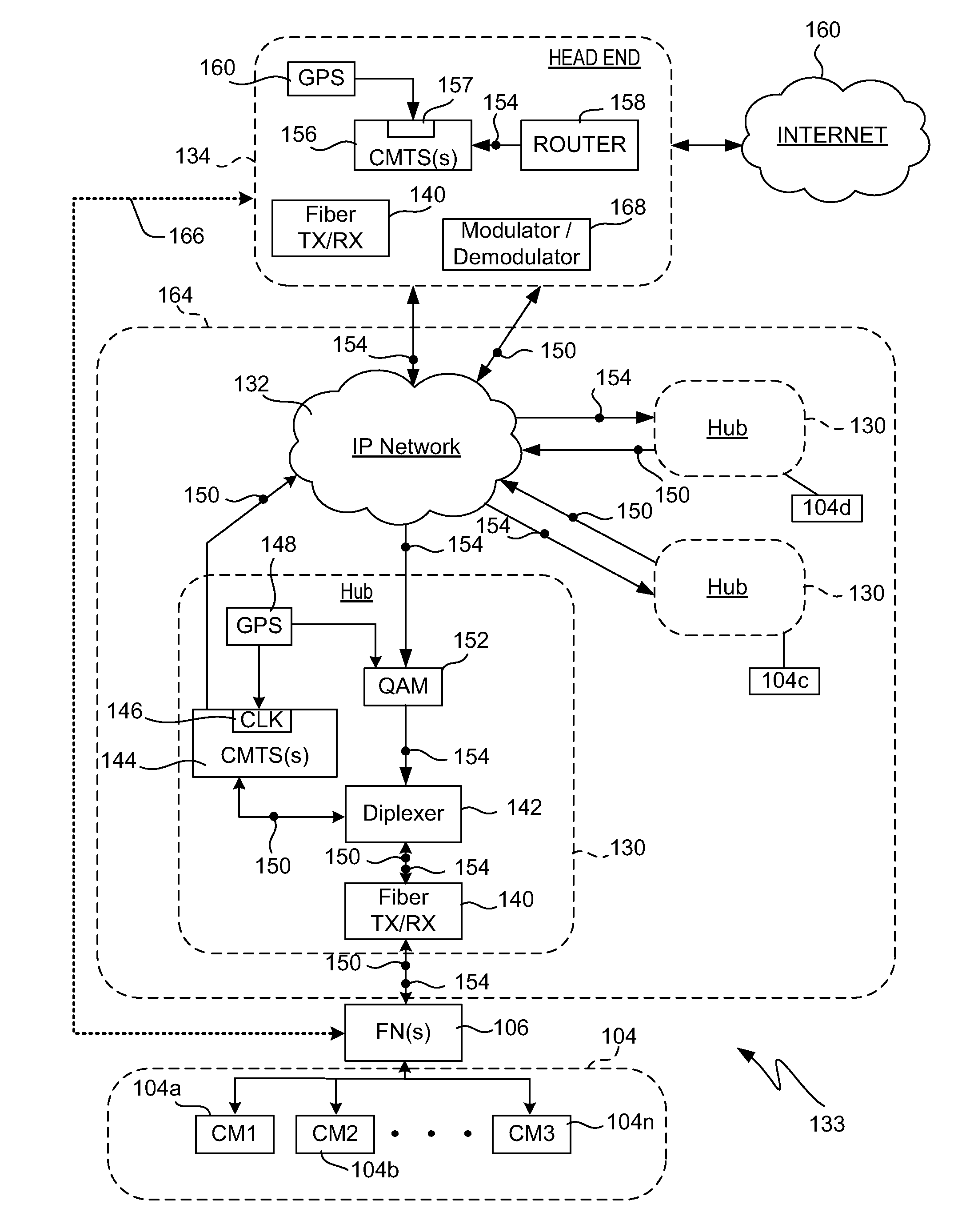
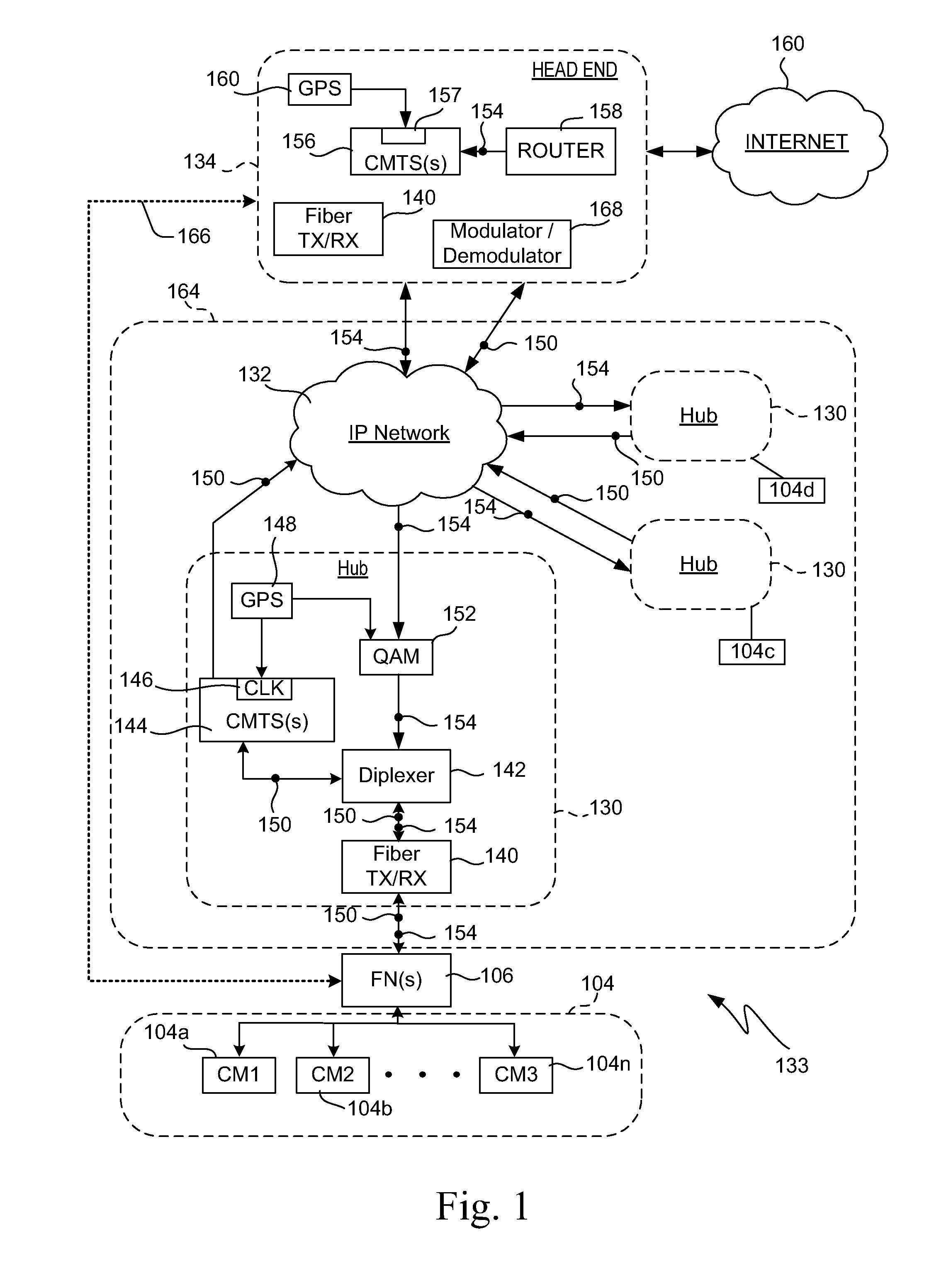
Traffic Flow Scheduling Techniques Implemented on Bonded Channels of a Shared Access Cable Network
Owner:CISCO TECH INC
Method and System for Machine Learning Based Classification of Vascular Branches
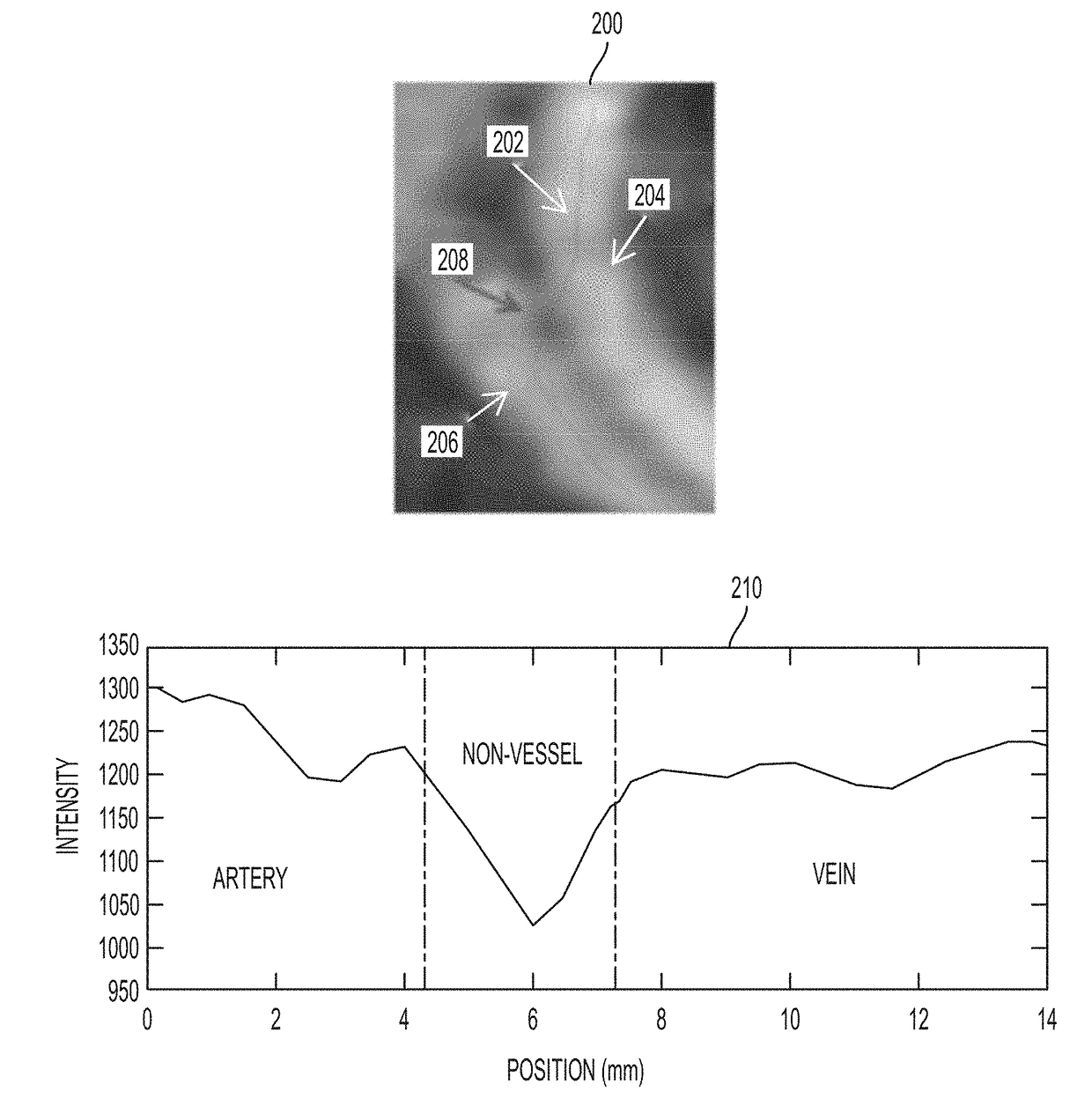
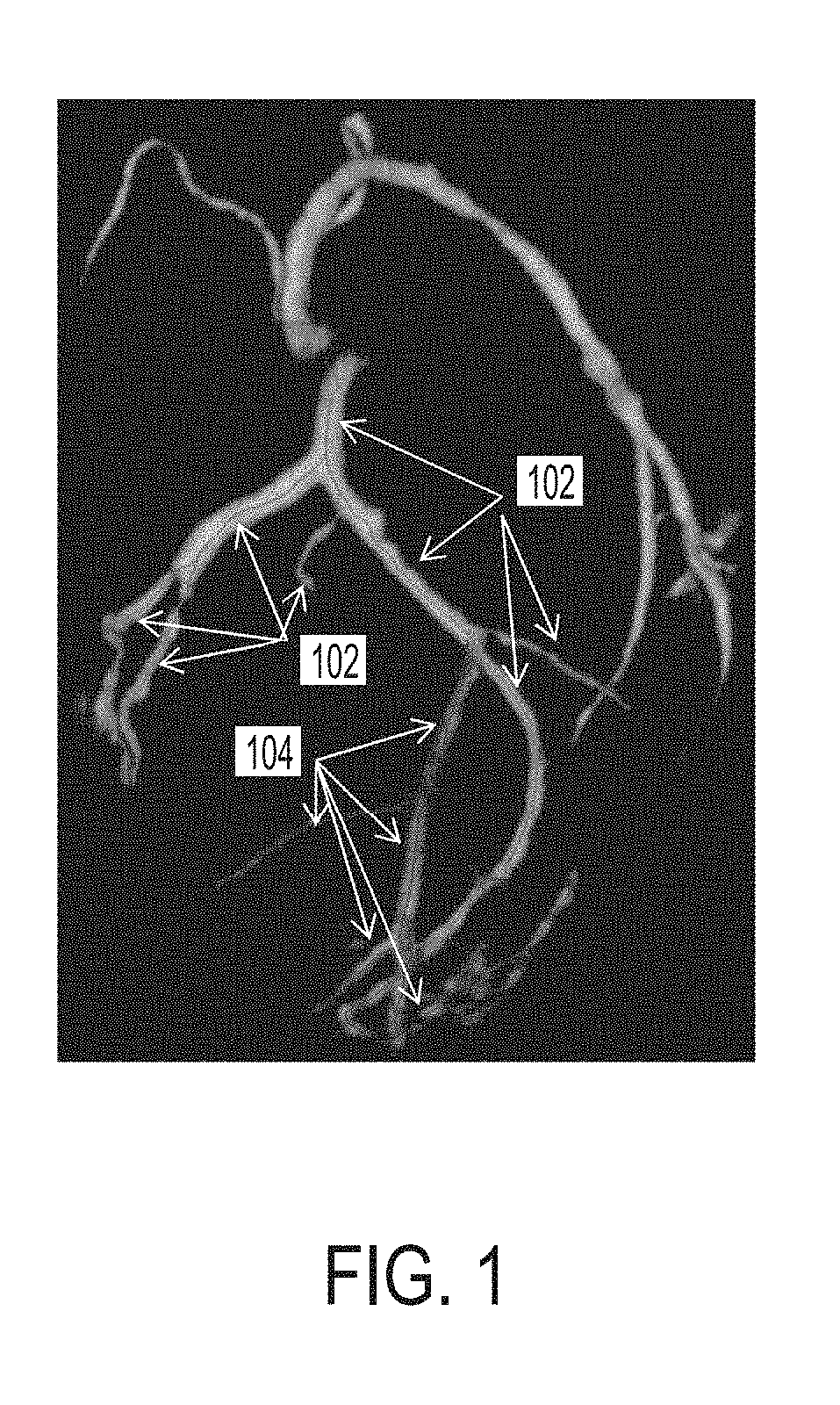
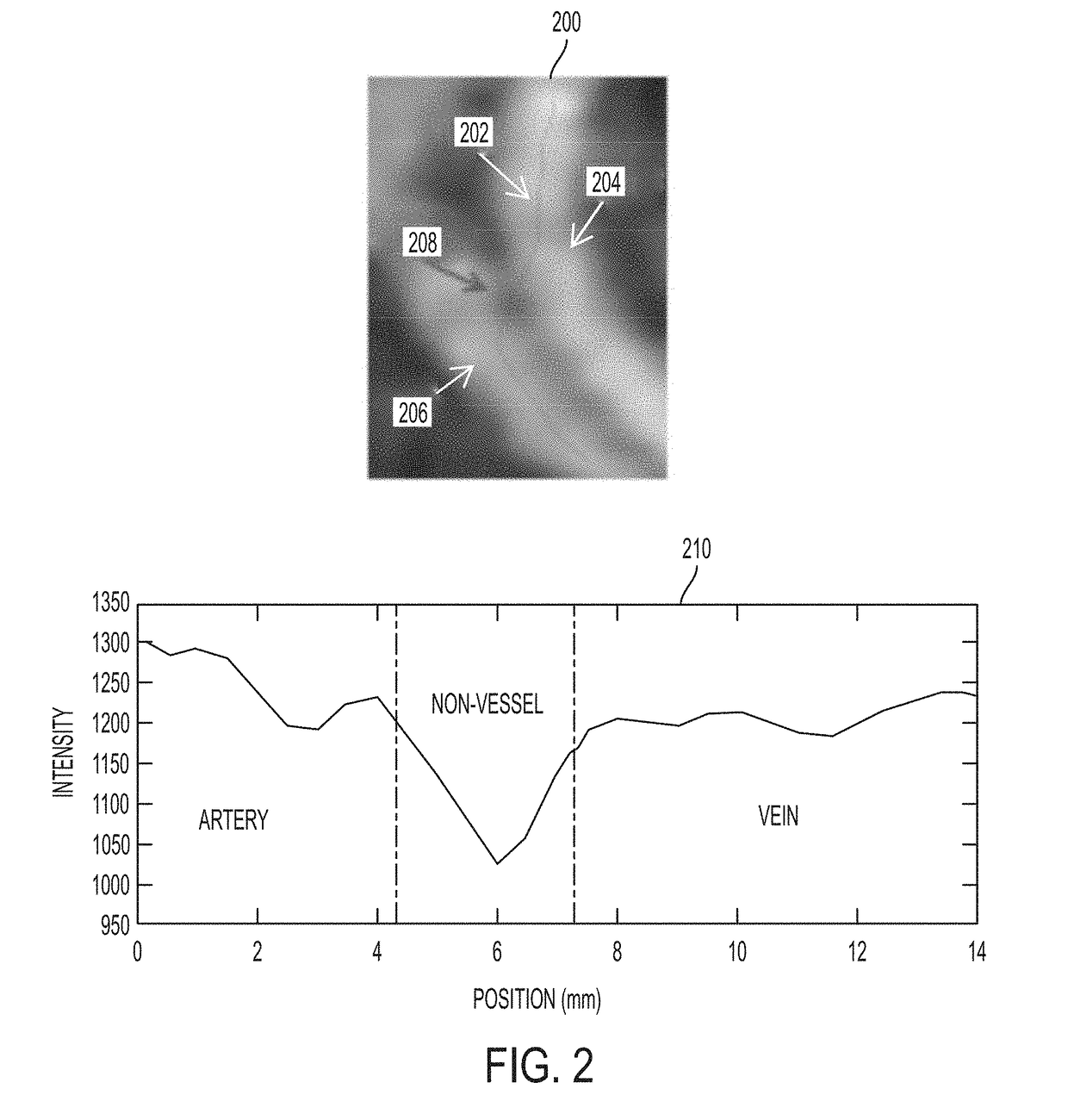
A method and apparatus for learning based classification of vascular branches to distinguish falsely detected branches from true branches is disclosed. A plurality of overlapping fixed size branch segments are sampled from branches of a detected centerline tree of a target vessel extracted from a medical image of a patient. A plurality of 1D profiles are extracted along each of the overlapping fixed size branch segments. A probability score for each of the overlapping fixed size branch segments is calculated based on the plurality of 1D profiles extracted for each branch segment using a trained deep neural network classifier. The trained deep neural network classifier may be a convolutional neural network (CNN) trained to predict a probability of a branch segment being fully part of a target vessel based on multi-channel 1D input. A final probability score is assigned to each centerline point in the branches of the detected centerline tree based on the probability scores of the overlapping branch segments containing that centerline point. The branches of the detected centerline tree of the target vessel are pruned based on the final probability scores of the centerline points.
Owner:SIEMENS HEALTHCARE GMBH
International information search and delivery system providing search results personalized to a particular natural language
Documents containing information about product offerings in various natural languages are passed through transitional translation layers which convert the data to a single computer language using a universal character set encompassing the character sets used in all supported natural languages. The documents are stored in their original natural languages and in English with documents segmented into components which components are identified by search terms arranged in a taxonomy tree based on product types. The names of the products in the national languages are added to the English language documents enabling quick keyword searches when the product name or number is known. A bi-directional inverted index is provided for access by the keyword search terms so that keywords with the same meaning in different languages are accessible together when the keyword in one of the languages is queried.
Owner:IBM CORP
Trustworthy structural synthesis and expert knowledge extraction with application to analog circuit design
ActiveUS20090307638A1Detecting faulty computer hardwareCAD circuit designAnalog circuit designAnalytic model
A system and method that does trustworthy multi-objective structural synthesis of analog circuits, and extracts expert analog circuit knowledge from the resulting tradeoffs. The system defines a space of thousands of possible topologies via a hierarchically organized combination of designer-trusted analog building blocks, the resulting topologies are guaranteed trustworthy. The system can perform a search based on a multi-objective evolutionary algorithm that uses an age-layered population structure to balance exploration vs. exploitation, with operators that make the search space a hybrid between vector-based and tree-based representations. A scheme employing average ranking on Pareto fronts is used to handle a high number of objectives. Good initial topology sizings are quickly generated via multi-gate constraint satisfaction. To explicitly capture expert analog design knowledge, data mining is employed on the sized circuits to: automatically generate a decision tree for navigating from performance specifications to topology choice, to do global nonlinear sensitivity analysis, and to generate analytical models of performance tradeoffs.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
Tree-based thread management
ActiveUS20150205607A1Increase speedAvoid bad consequencesDigital computer detailsSpecific program execution arrangementsMulti processorParallel computing
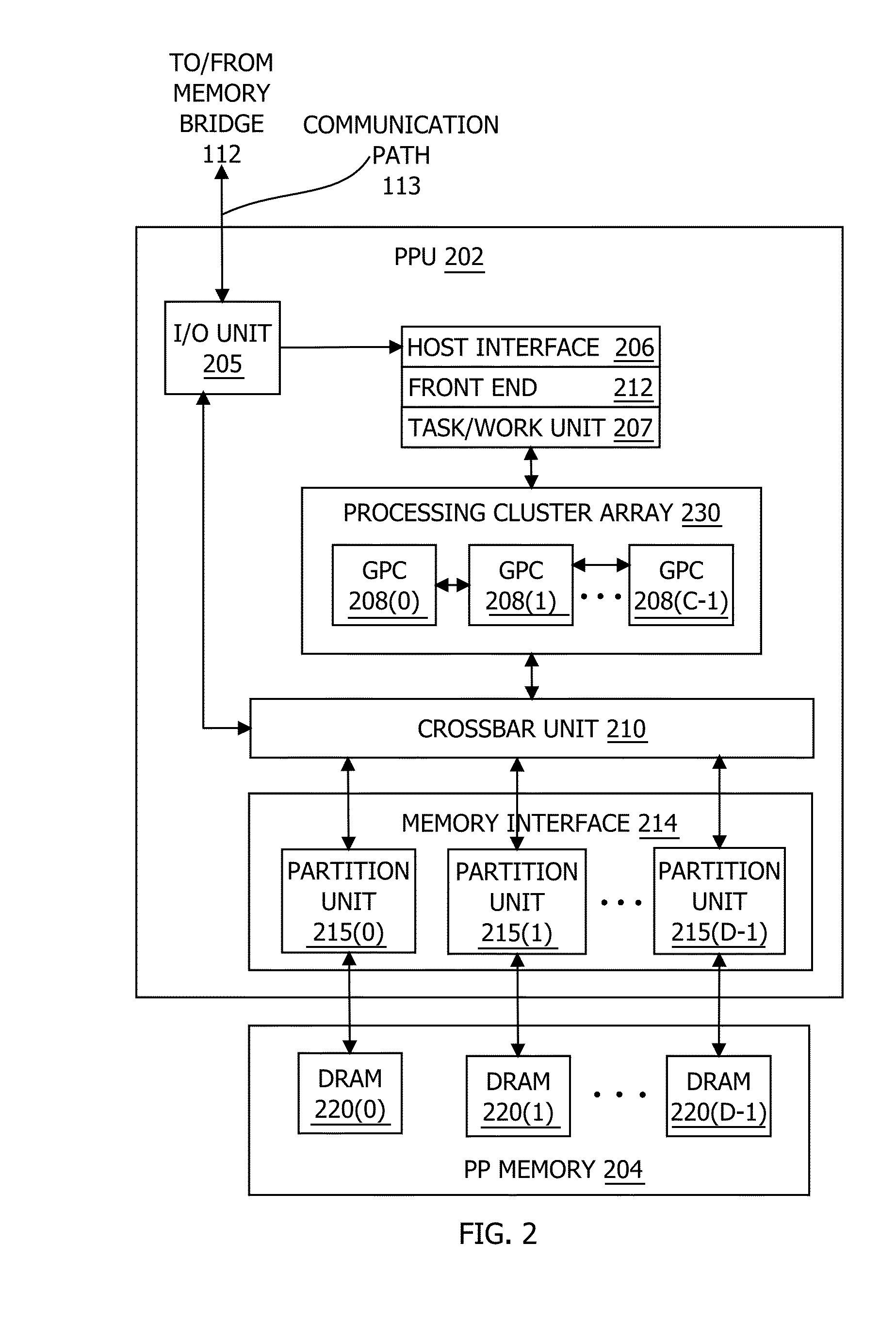
In one embodiment of the present invention, a streaming multiprocessor (SM) uses a tree of nodes to manage threads. Each node specifies a set of active threads and a program counter. Upon encountering a conditional instruction that causes an execution path to diverge, the SM creates child nodes corresponding to each of the divergent execution paths. Based on the conditional instruction, the SM assigns each active thread included in the parent node to at most one child node, and the SM temporarily discontinues executing instructions specified by the parent node. Instead, the SM concurrently executes instructions specified by the child nodes. After all the divergent paths reconverge to the parent path, the SM resumes executing instructions specified by the parent node. Advantageously, the disclosed techniques enable the SM to execute divergent paths in parallel, thereby reducing undesirable program behavior associated with conventional techniques that serialize divergent paths across thread groups.
Owner:NVIDIA CORP
Arrangement for providing network prefix information from attached mobile routers to a clusterhead in a tree-based ad hoc mobile network
ActiveUS7428221B2Minimal overheadFast convergenceError preventionFrequency-division multiplex detailsMobile WebNetwork topology
Mobile routers establish a tree-based network topology in an ad hoc mobile network, the tree-based network topology having a single clusterhead and attached mobile routers. Each attached mobile router has a default egress interface configured for sending messages toward the clusterhead, and ingress interfaces configured for receiving messages from attached network nodes that are away from the clusterhead. A neighbor advertisement message received from an ingress interface away from a clusterhead is used by the attached mobile router to identify specified network prefixes that are reachable via the source of the neighbor advertisement message. The attached mobile router outputs on its default upstream interface a second neighbor advertisement message that specifies the network prefix used by the attached mobile router, and the specified network prefixes from the neighbor advertisement message received on the ingress interface. Hence, connectivity is established with minimal routing overhead.
Owner:CISCO TECH INC
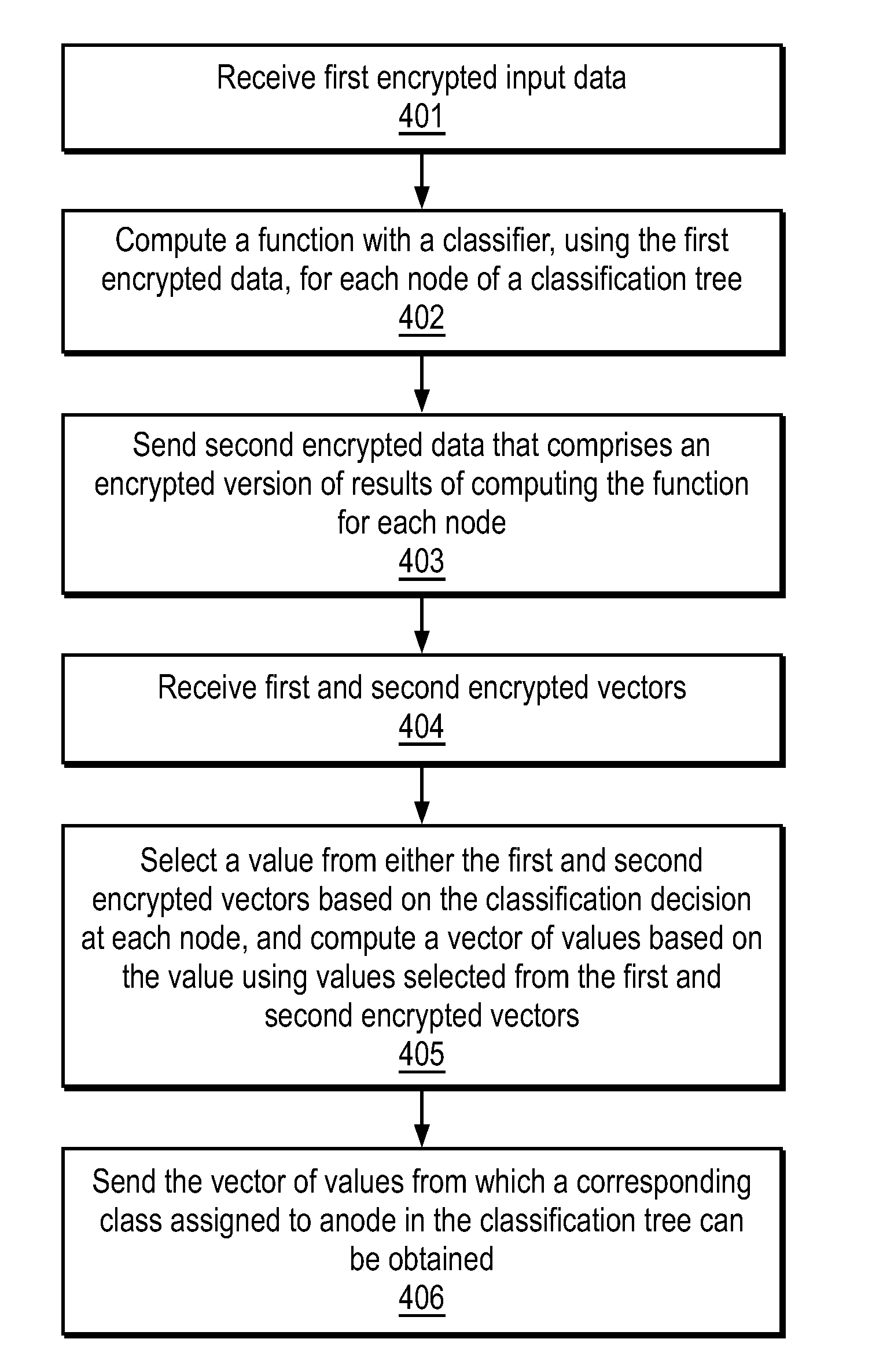
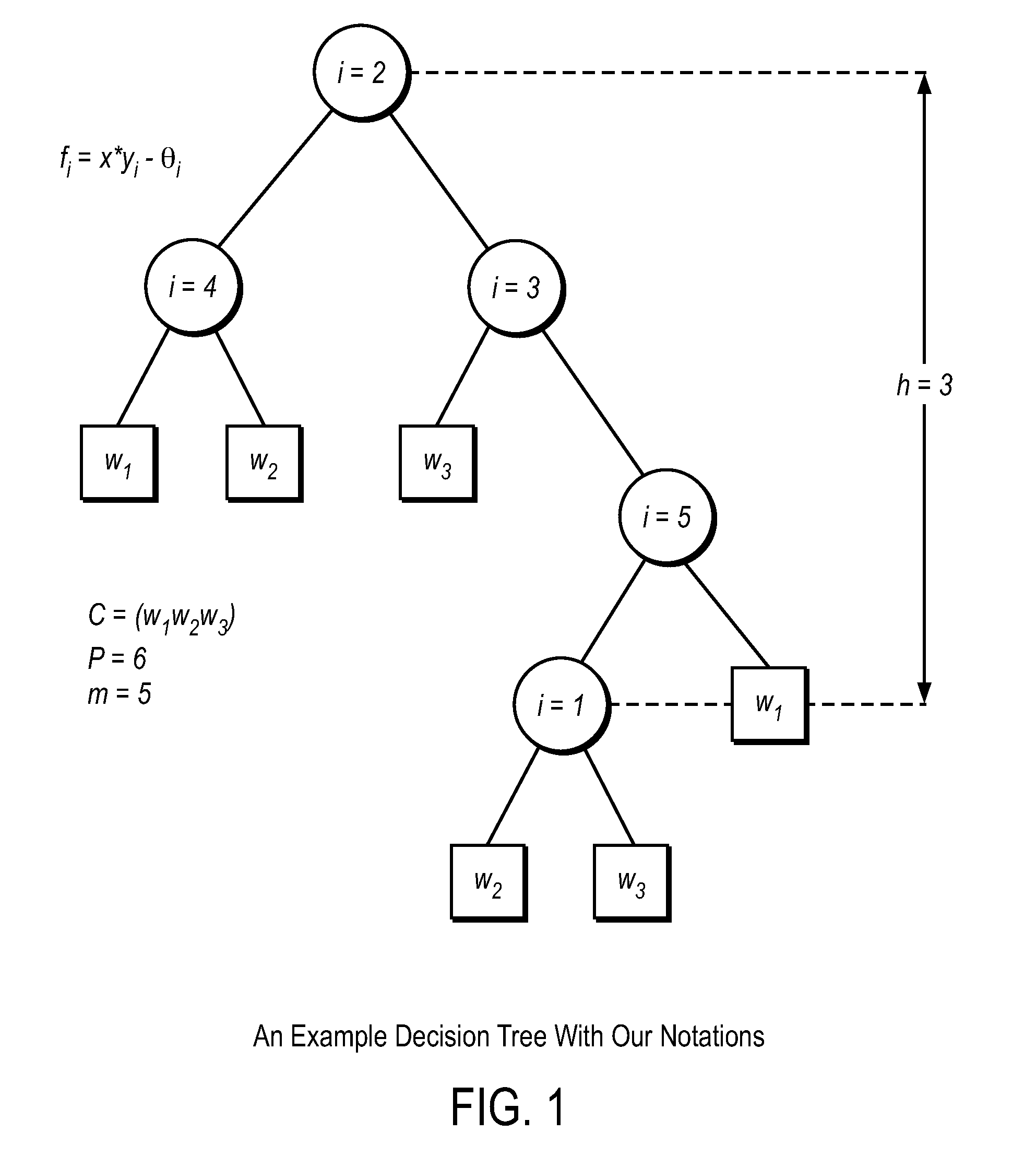
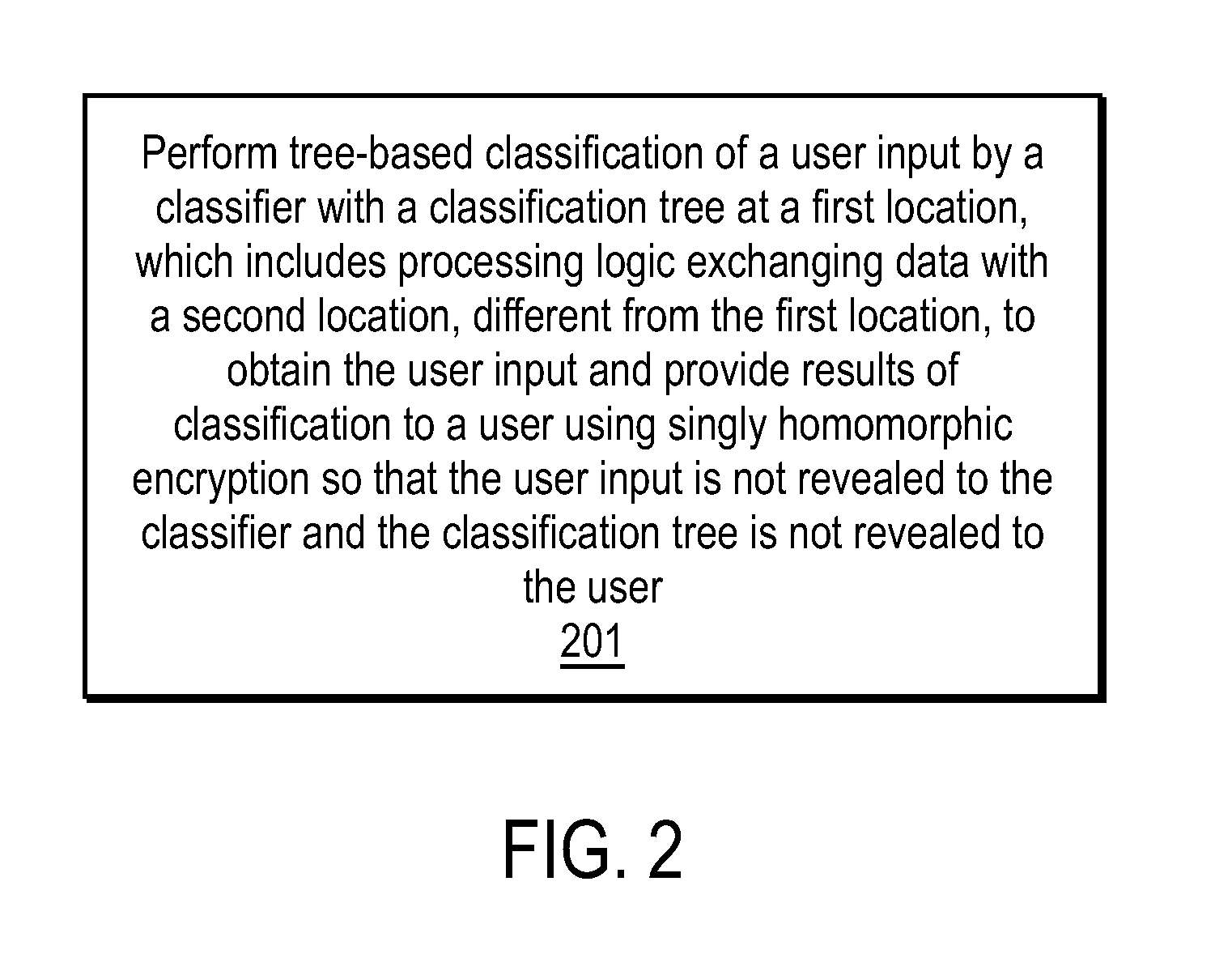
Efficient, remote, private tree-based classification using cryptographic techniques
InactiveUS20120201378A1Digital data protectionInternal/peripheral component protectionUser inputData mining
A method and apparatus are disclosed herein for classification. In one embodiment, the method comprises performing tree-based classification of a user input by a classifier with a classification tree at a first location, including exchanging data with a second location, different from the first location, to obtain the user input and provide results of classification to a user using singly homomorphic encryption so that the user input is not revealed to the classifier, the classification tree is not revealed to the user and the classifier's output is not revealed to the classifier.
Owner:RICOH KK
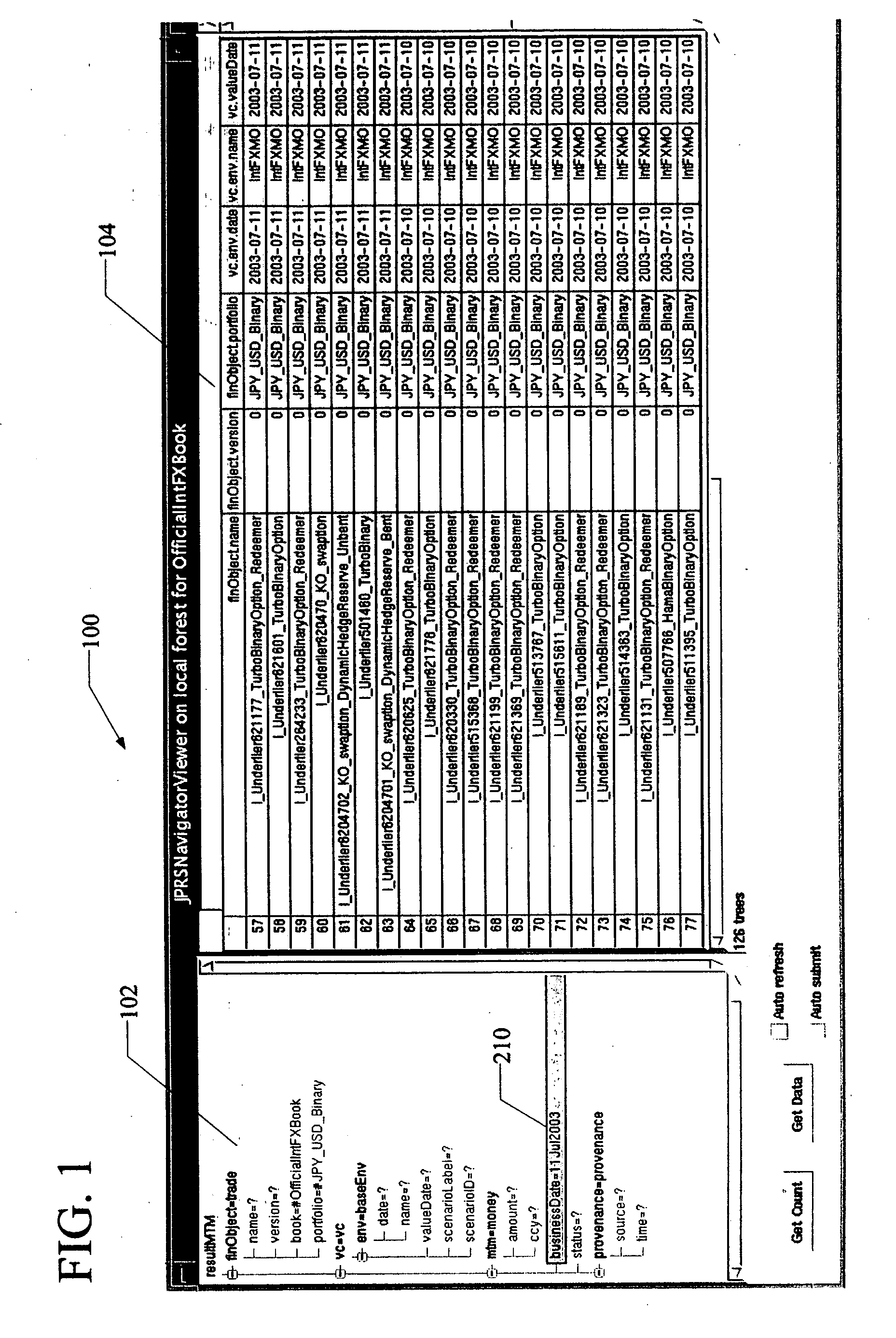
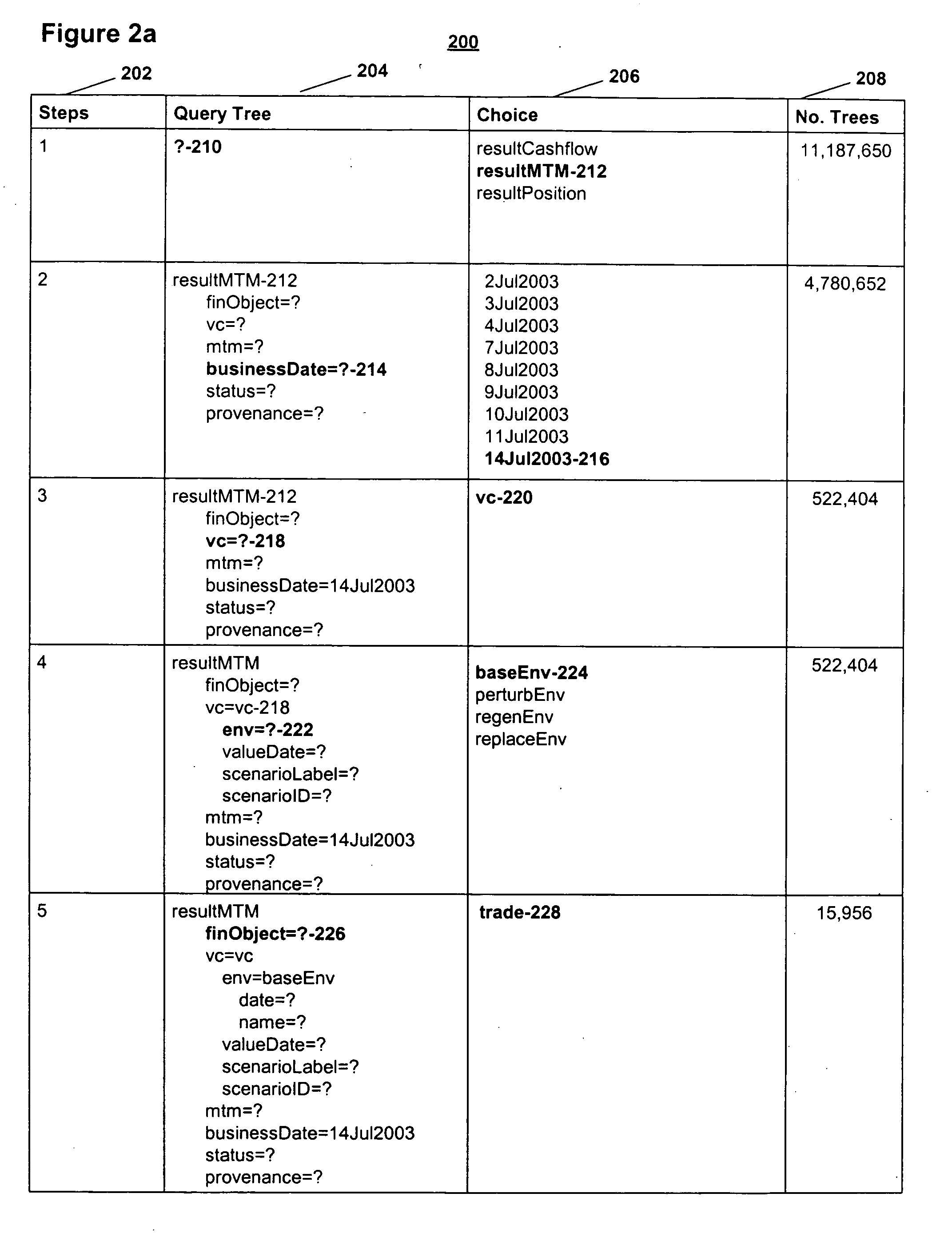
Update of a tree-based database
InactiveUS20050065964A1Easy accessSimple processDigital data information retrievalSpecial data processing applicationsGraphicsGraphical user interface
Data items are represented by trees and stored in a database, the collection of data items defining a forest. Queries and masks are also represented by trees. A method for navigating the forest of data items is disclosed in the context of a graphical user interface. A set of operations on trees are defined such that the data items can be queried on the basis of structure as well as node values. That is, the query can include a specification of the relationship between nodes in a tree, as well as the data in the nodes themselves. Exemplary implementations of such operations are disclosed in the context of a database update procedure. Additionally disclosed are methods for efficiently storing and processing the forest of data items.
Owner:JPMORGAN CHASE BANK NA
Chirp networks
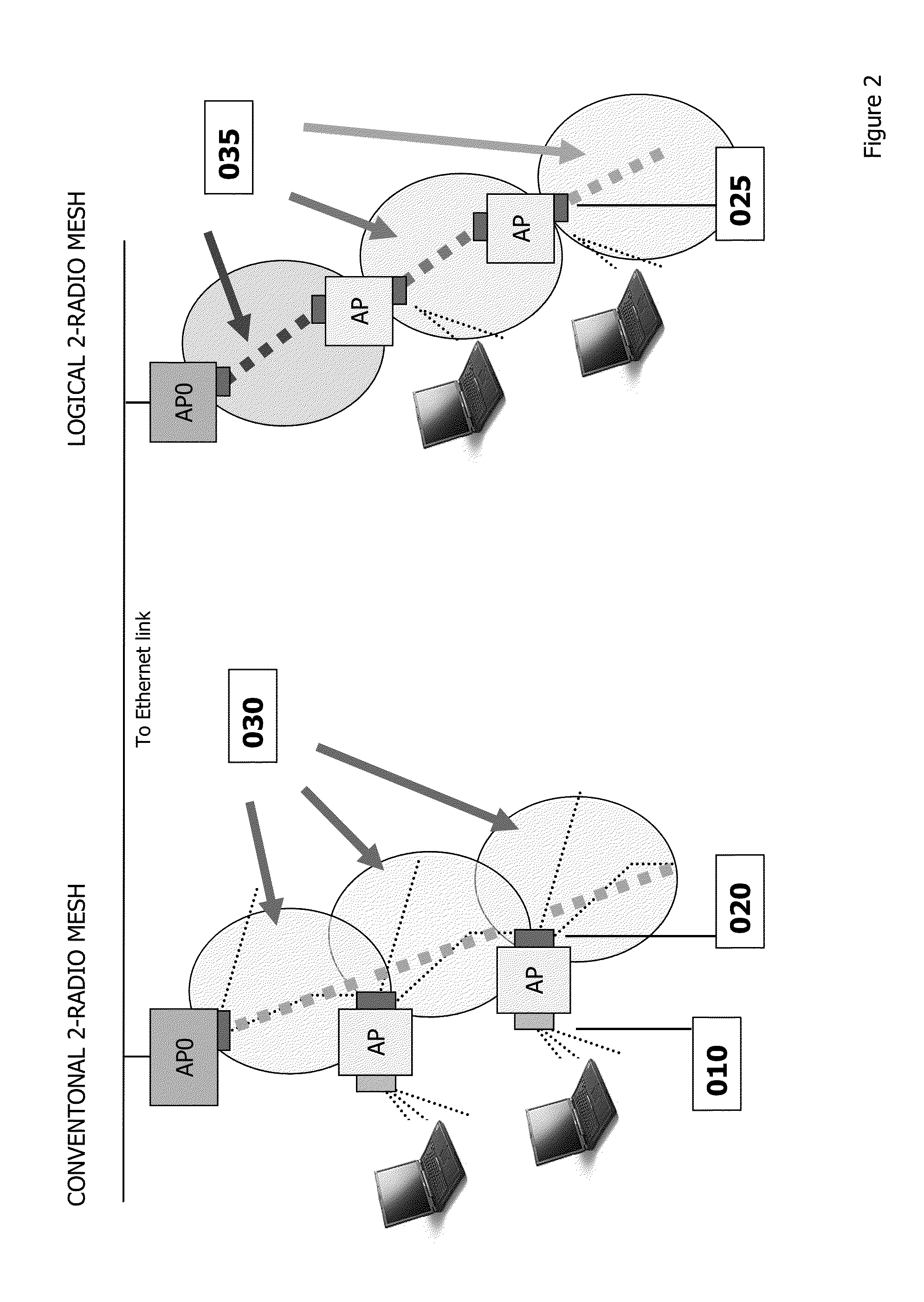
A wire-less / Wired mesh network is described, using a multi-slot modular mesh node to house diverse transceiver elements (e.g. IR, Wi-Fi, Powerline). A radio agnostic tree based mesh network is formed, based on what type of wire-less links are formed on the uplink and downlink of the backhaul and what type of radios etc are used for the Access Points AP, see FIG. 17,23.In addition to servicing IP based clients (e.g. Wi-Fi, WiMax, Bluetooth), the modular mesh nodes APs may also serve as receivers / collectors for low cost chirp devices. These devices are not “agile” and therefore contentious. APs, servicing these devices, alleviate potential contention by multiple means including: sending out a “incoming” CTS, efficient delivery through container based schedulable bus deliveries, and its reverse (moving chirp transmission times to be sequential).Multiple approaches for “pollen” to reach the intended “flower” in a timely manner are described. The method of transport is standard IP based packets yet security is inherent in this pollen-flower based system: only mesh nodes are privy to the routing tables that indicate that packet addresses are not IP. Multiple options to further obfuscate packet flow are presented.A multi-agent based approach driving business process flow is described. Such agents can also provide specialized mesh network routing e.g. navigation agents for chirp devices.Tree based routing and logical radio abstractions are revisited.An organic approach to providing category / class based form of data type identification is proposed, to efficiently match publishers and subscribers, based on the type of data being sought. A private, secure and natively Publish / Subscribe M2M community is engendered at the edge. It has loosely, dynamic and ad hoc couplings to big data servers, also operating on their own private exchange / market place, using a real time publish / subscribe infrastructure with content categories used as part of pollen identification.
Owner:DYNAMIC MESH NETWORKS
Method and apparatus for reduced resolution partitioning
ActiveUS8363936B2Character and pattern recognitionDigital video signal modificationImage resolutionAlgorithm
There are provided methods and apparatus for reduced resolution partitioning. An apparatus includes an encoder for encoding video data using adaptive tree-based frame partitioning, wherein partitions are obtained from a combination of top-down tree partitioning and bottom-up tree joining.
Owner:INTERDIGITAL VC HLDG INC
Arrangement for providing optimized connections between peer routers in a tree-based ad hoc mobile network
InactiveUS7366111B2Reduce necessityAvoid congestionError preventionFrequency-division multiplex detailsEngineeringSelf-organizing network
Mobile routers in a tree-based network topology with a single clusterhead in an ad hoc network establish connectivity based on each attached mobile router sending a neighbor advertisement message to an attachment mobile router via a corresponding egress interface. Any neighbor advertisement message received by a mobile router is used to identify specified network prefixes that are reachable via the source of the neighbor advertisement message. Each attached mobile router outputs to its attachment router another neighbor advertisement message that specifies the network prefix used by the mobile router, and the specified network prefixes from its attached mobile routers. The mobile router also identifies peer mobile routers having the same depth, and selectively shares limited routing information with the peer routers, enabling the mobile router to bypass the clusterhead and reach remote prefixes via the peer routers without burdening the tree.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com