Patents
Literature
133results about How to "Minimal overhead" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Medium access control (MAC) protocol for wireless ATM
InactiveUS6198728B1Structure is limitedMinimize timePower managementNetwork traffic/resource managementNetwork communicationMedia access control
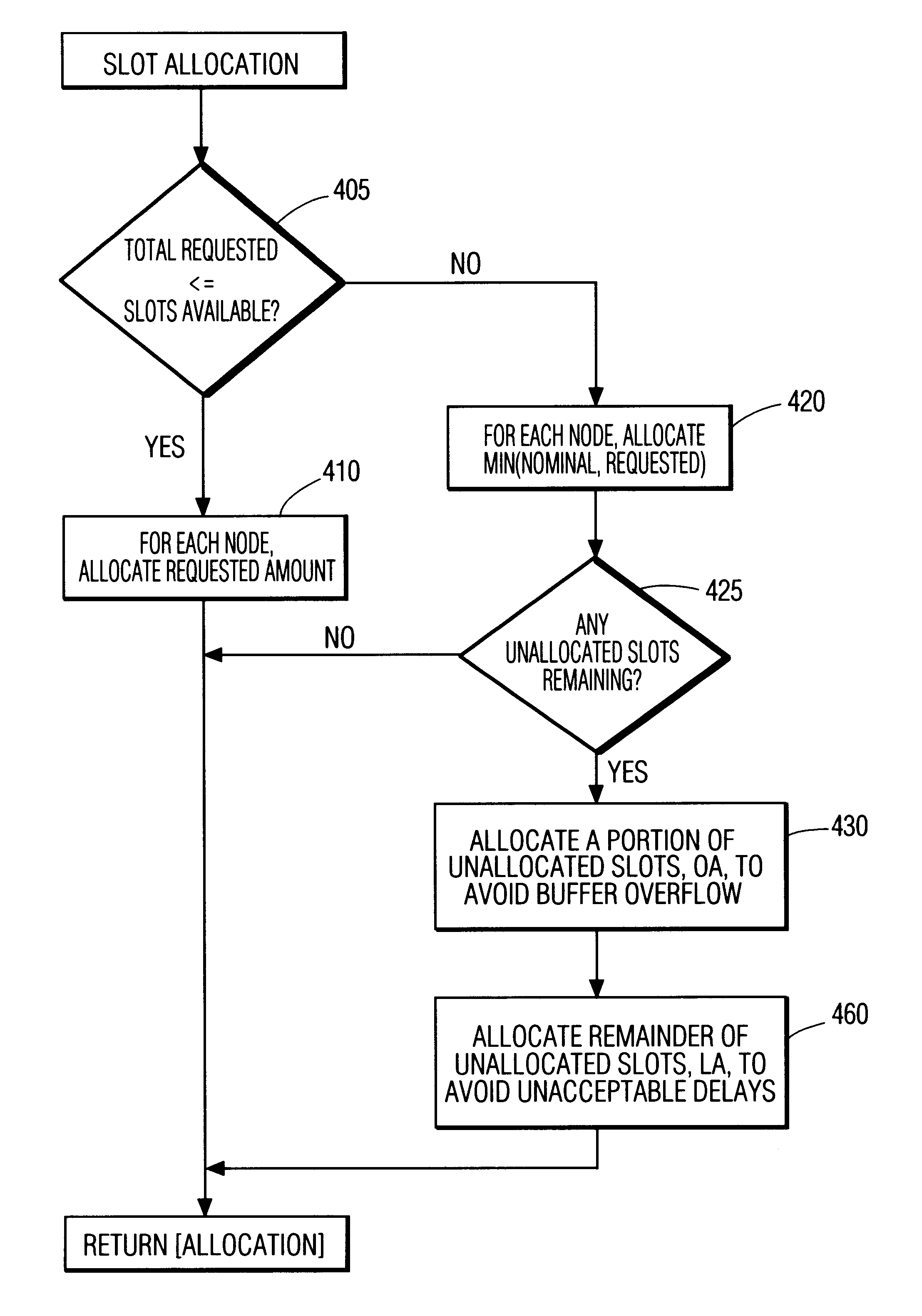
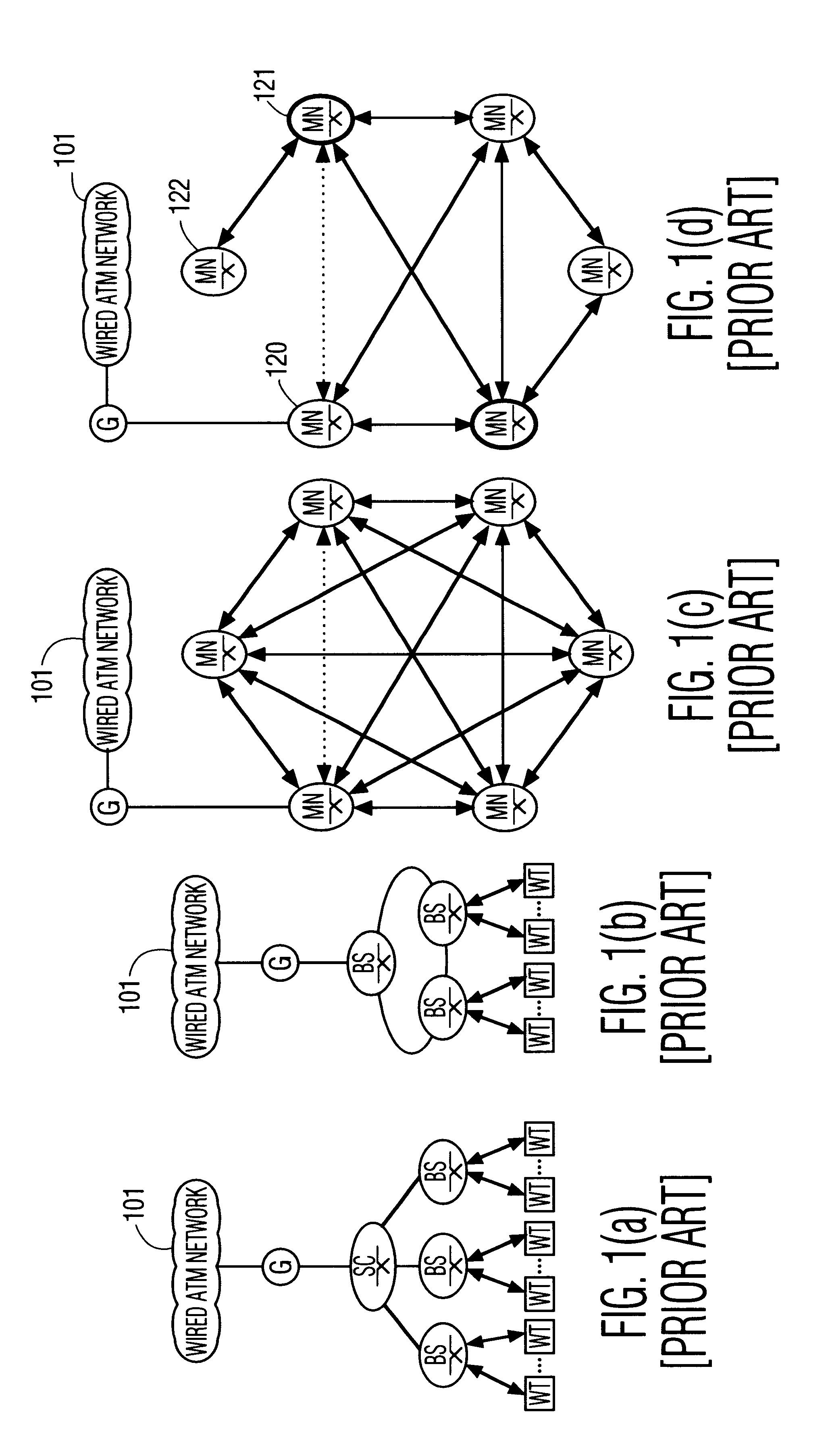
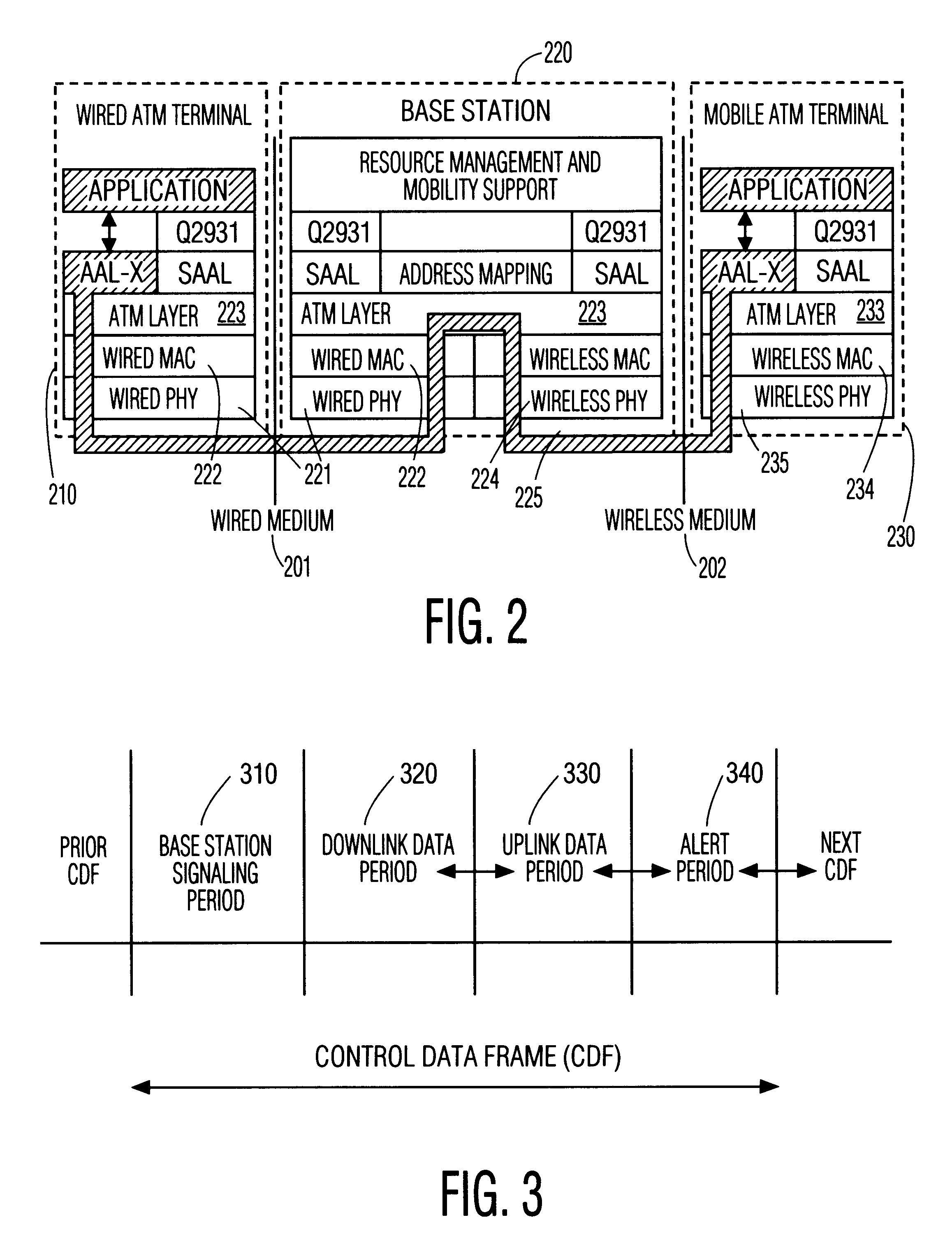
A protocol, method, and apparatus for managing network communications which are particularly well suited for ATM communications across a wireless medium. Contiguous time slots within a frame are allocated to each node having traffic to send. Each node is assured a nominal bandwidth, and excess bandwidth is distributed by demand. The allocation of excess bandwidth can be dependent upon the size of the buffer at each node, as well as the time-criticality of each message. Nodes communicate their requests for allocation by appending such control information to the first of their transmitted packets. The allocation, of each node's transmit and receive time slots, is transmitted to all the nodes at the beginning of each frame. Thereafter, each node need not participate on the network until their allocated time periods, thereby allowing portable devices to enter inactive states to conserve power. The network is operated in a connection mode; connections are established in a relatively non-interfering manner by the use of periodically occurring beacons. Inactive, unconnected, nodes need only monitor the network during these beacon periods, further allowing for power conservation.
Owner:UNILOC 2017 LLC
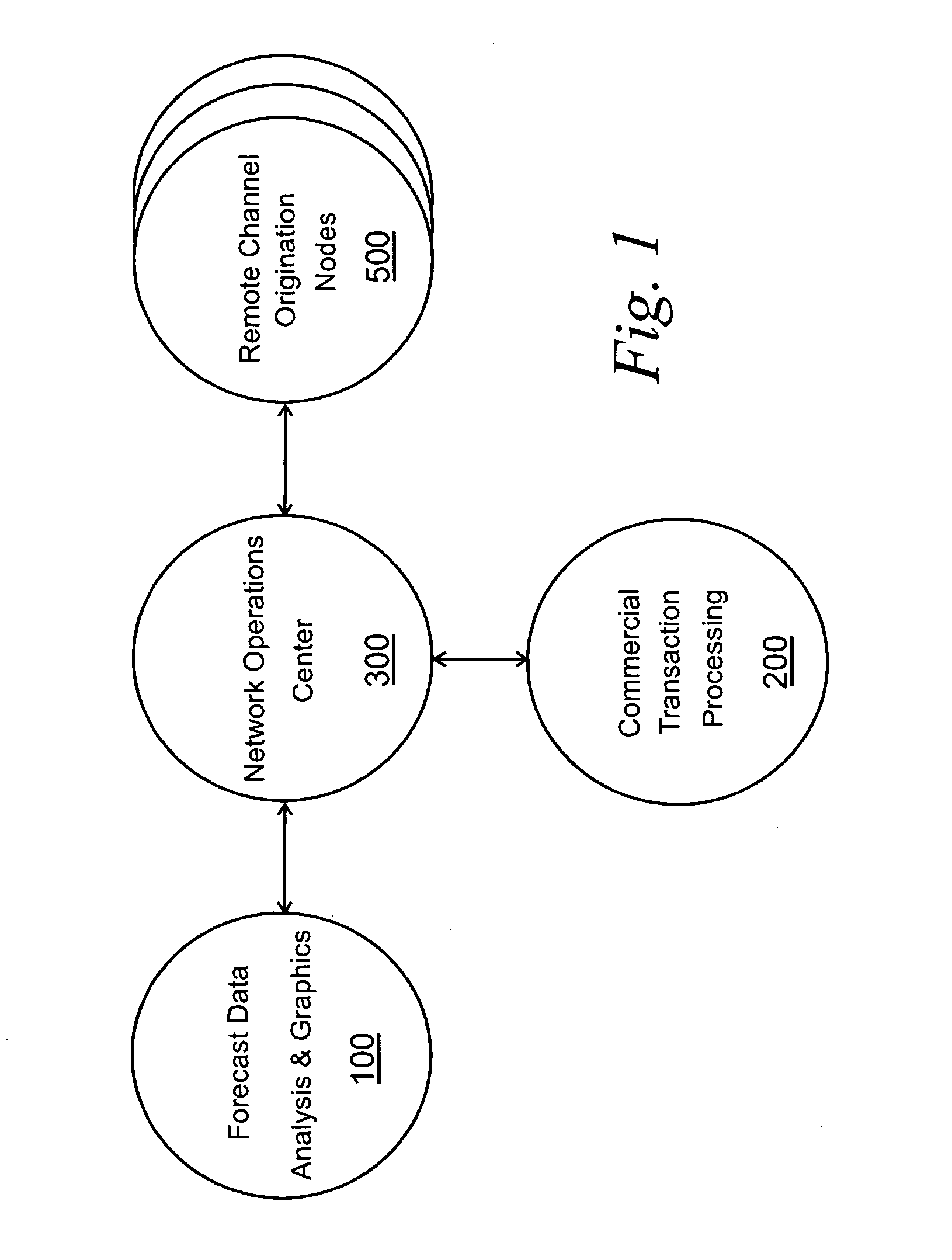
Encapsulated, streaming media automation and distribution system
ActiveUS20050060759A1Low costReduce operating costsTelevision system detailsGHz frequency transmissionDisplay deviceApplication software
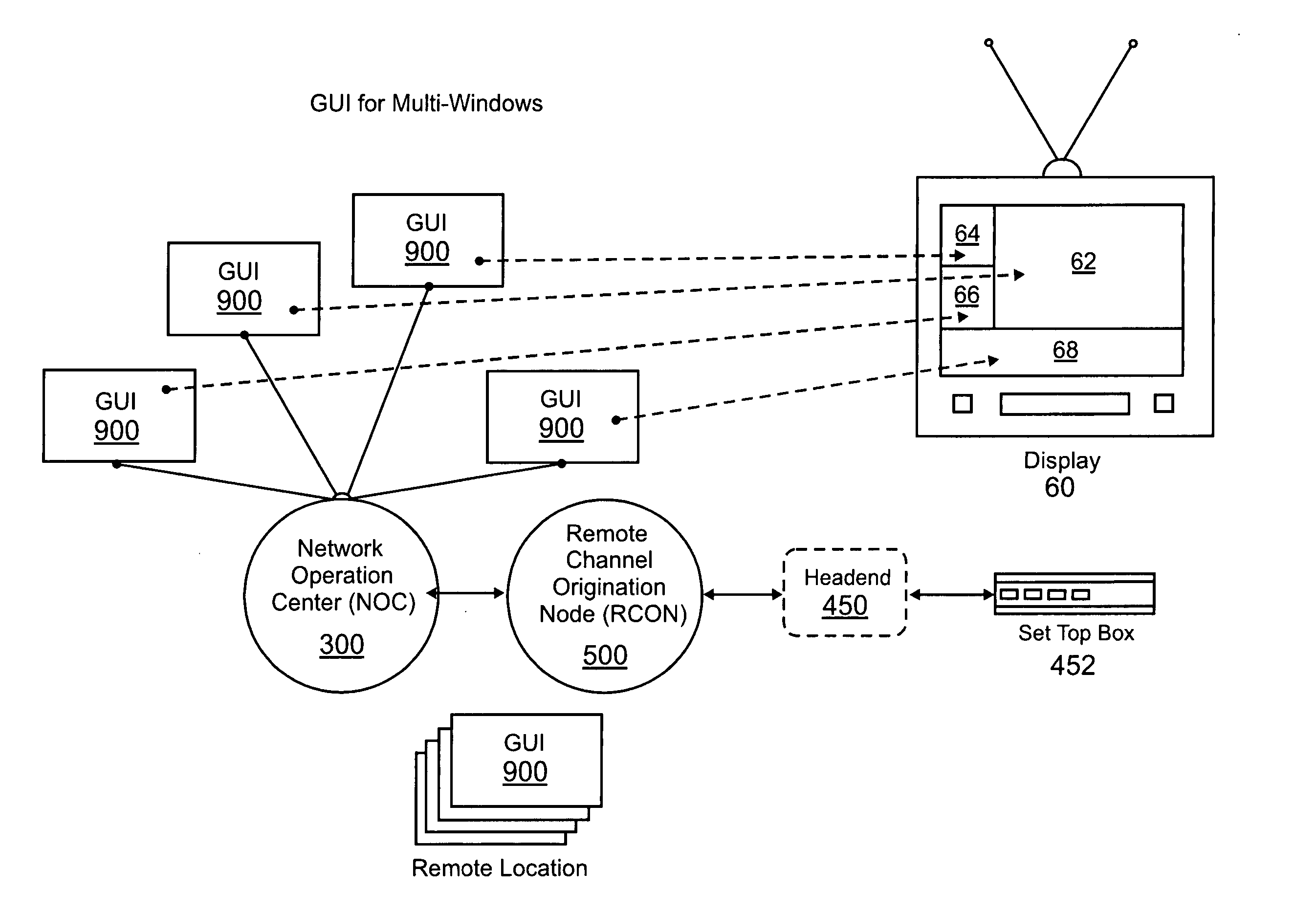
Disclosed are systems and methods for creating and distributing programming content carried by a digital streaming media to be a plurality of remote nodes located over a large geographic area to create customized broadcast quality programming at the remote nodes. At the remote nodes, a multi-window screen display simultaneously shows different programming including national programming and local programming content. The remote nodes utilize a remote channel origination device to assemble the customized programming at the remote location that can be controlled from a central location. An encapsulated IP and IP encryption system is used to transport the digital streaming media to the appropriate remote nodes. Also disclosed is a graphical user interface (“GUI”) providing a software control interface for creating and editing shows or programs that can be aired or played on a remote display device having a multi-window display. The intuitive GUI Software provides the user the ability to easily manage and assemble a series of images, animations and transitions as a single broadcast quality program to be displayed on a remote display device. Another application software system is capable of automating the production of audio narration reports. The disclosed audio concatenation engine automates the creation of audio narration using prerecorded audio segments to minimize the requirement for live, on-air personnel to record audio narration segments.
Owner:CALLAHAN CELLULAR L L C
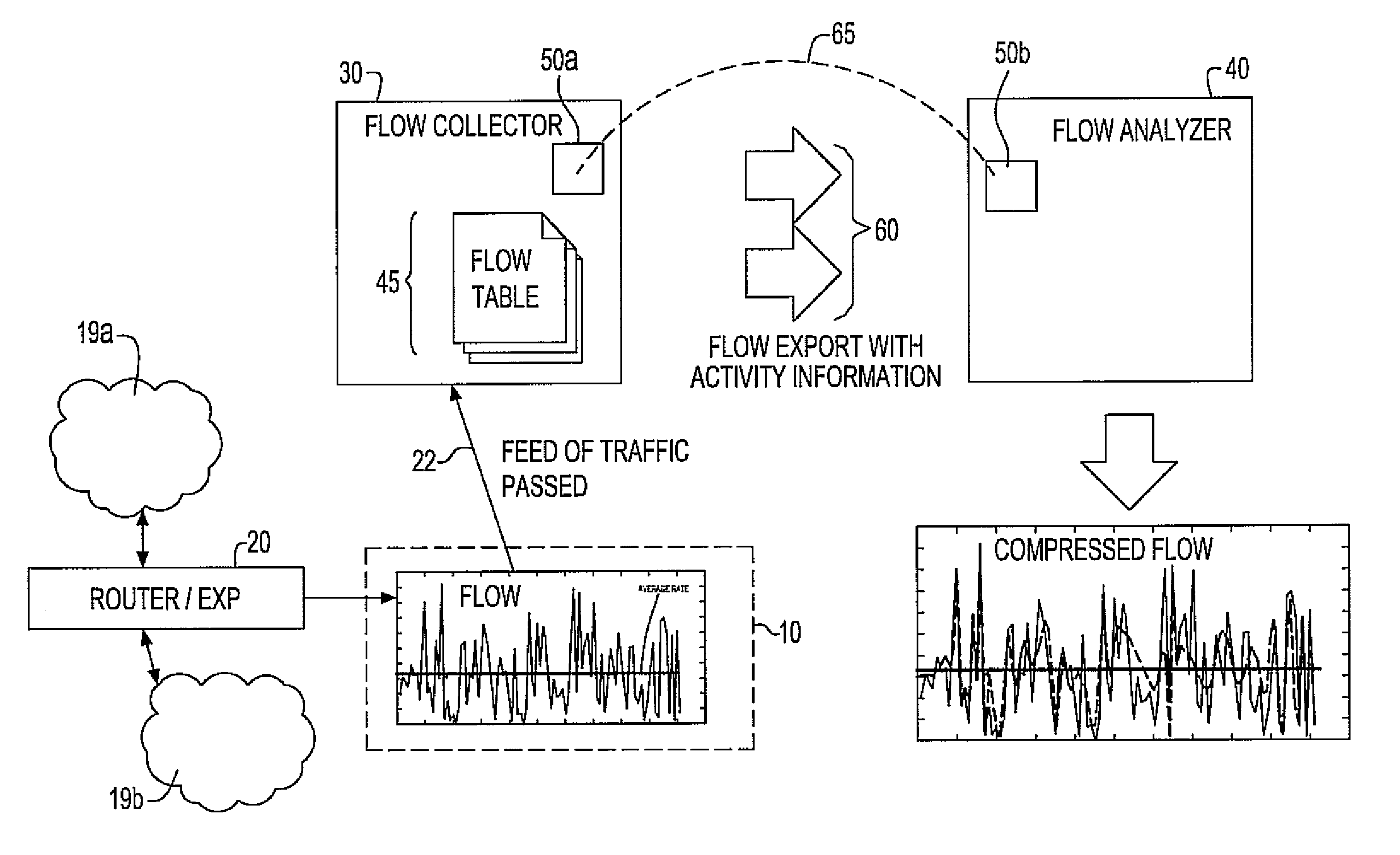
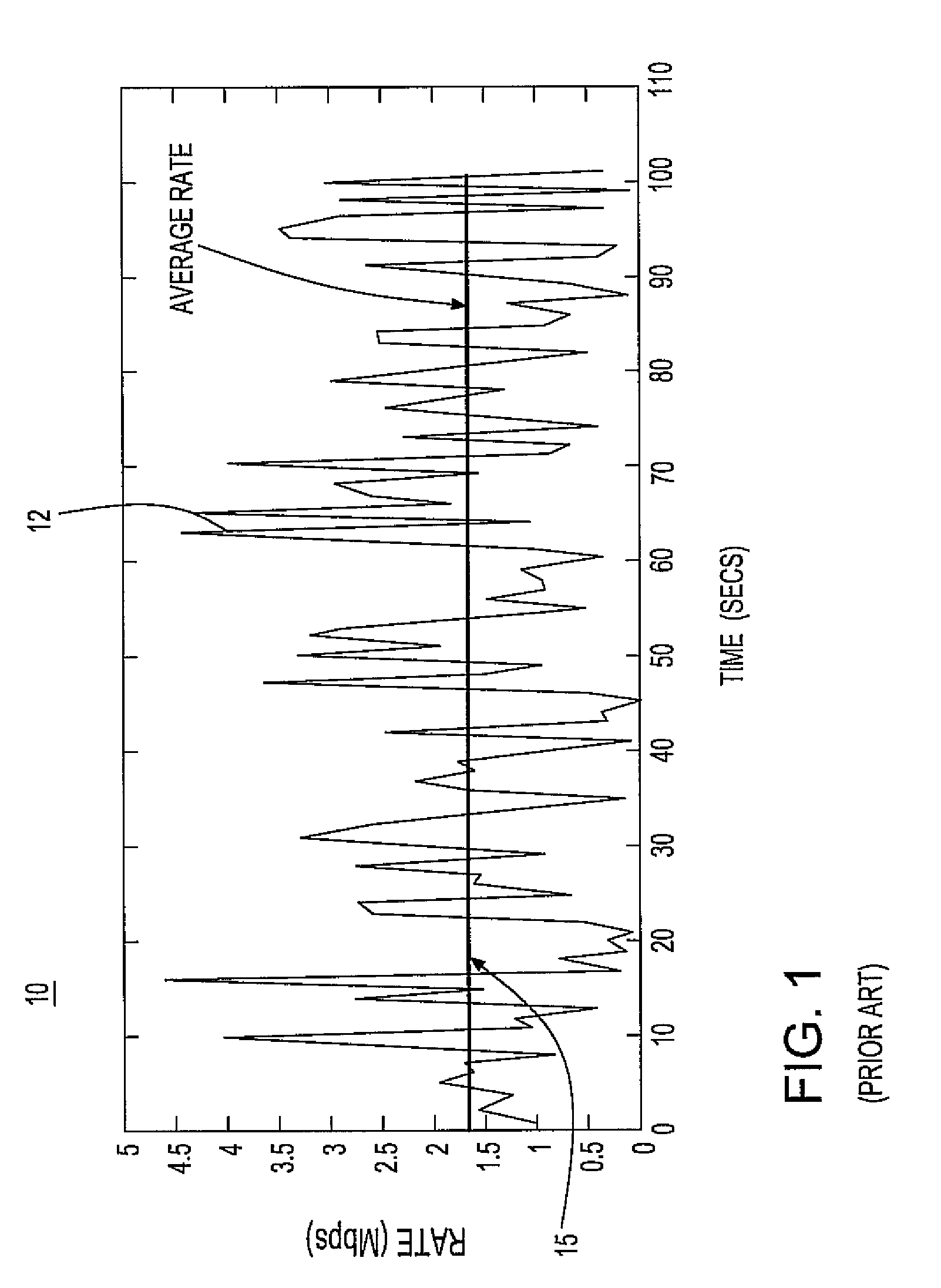
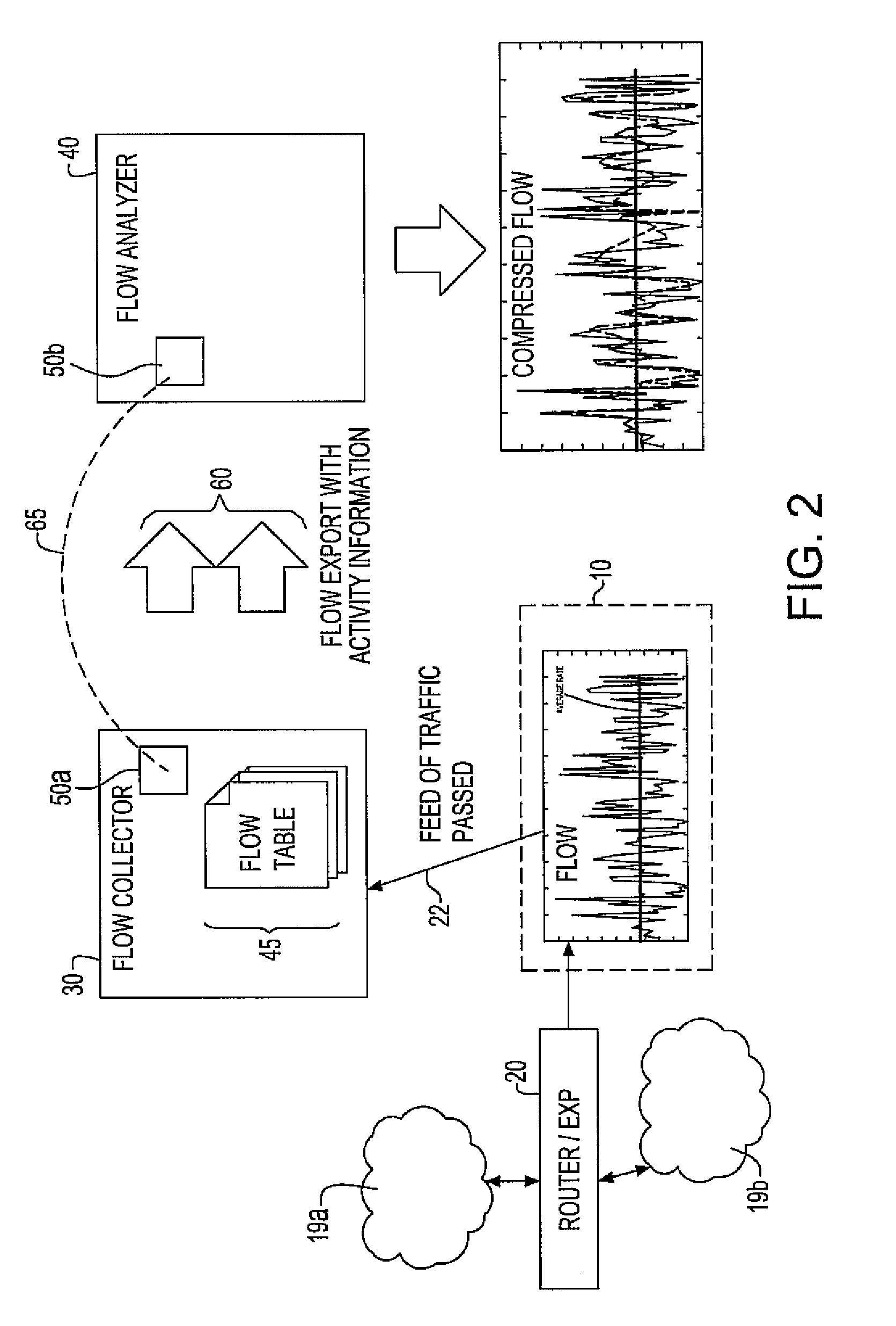
System and method for network flow traffic rate encoding
InactiveUS7911975B2Improve reporting activityRegulation stabilityError preventionTransmission systemsTraffic capacityNetwork packet
A system and method for monitoring packetized traffic flow in a network and enabling approximation of the rate information of a network flow. The method for monitoring network traffic flow includes receiving, at a network packet flow collector device, packetized traffic flow signals to be monitored; sampling said received packetized traffic flow signals in time to form an approximation of the packet flow rate in time; generating packet flow activity data comprising data representing the sampled traffic flow signals sampled in time; communicating the packet flow activity data to a network packet flow analyzer device and processing the flow activity data to form signals representing an approximate version of the network traffic flow in the network, the analyzer processing the traffic flow signals for reconstructing the rate of the netflow as a function of time. The flow analyzer then generates a compressed version of the network traffic flow signals in the network, the compressed network traffic flow signals comprising relevant approximation of the packet flow rate in time.
Owner:INT BUSINESS MASCH CORP
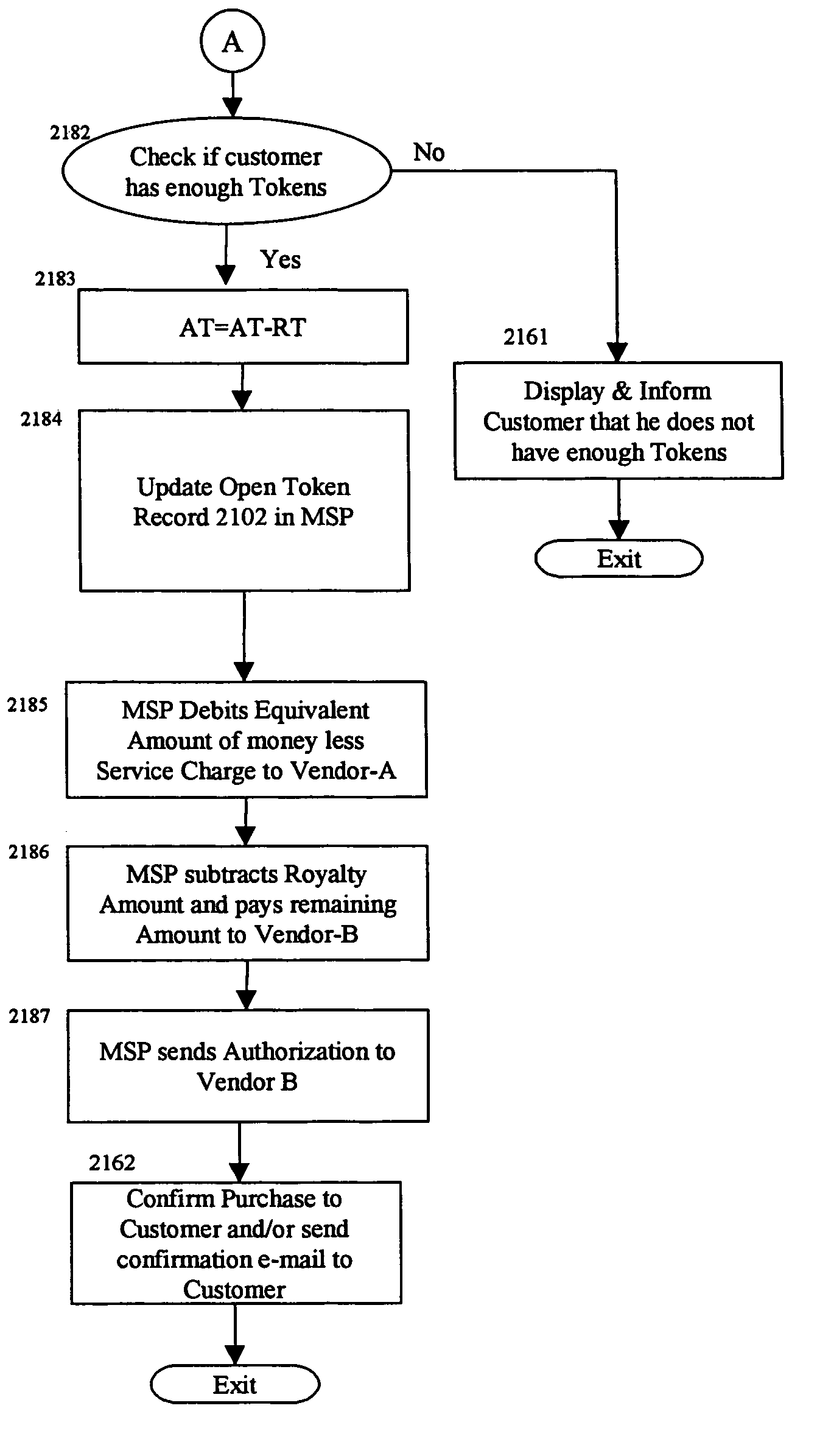
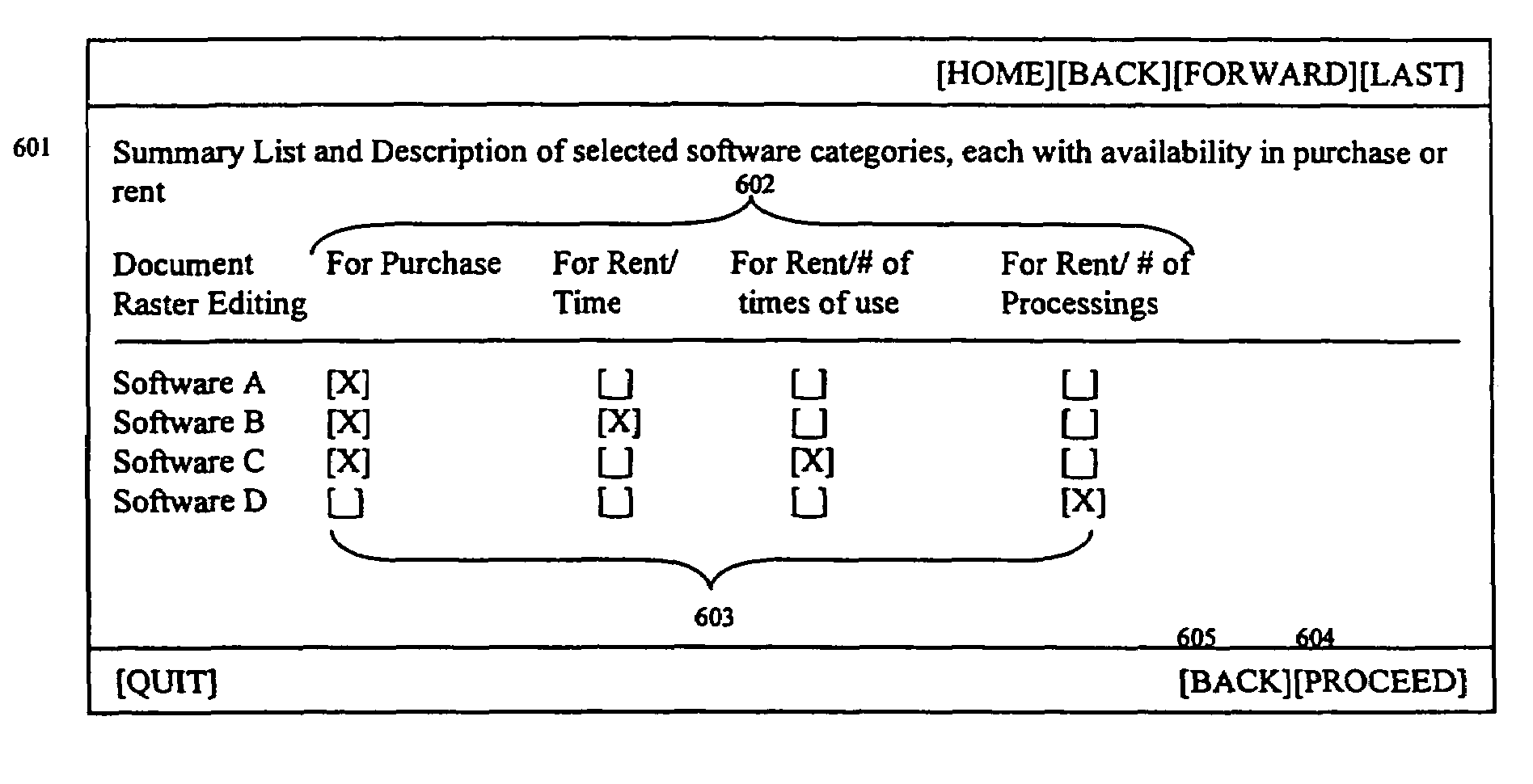
Method and apparatus for conducting electronic commerce transactions using electronic tokens
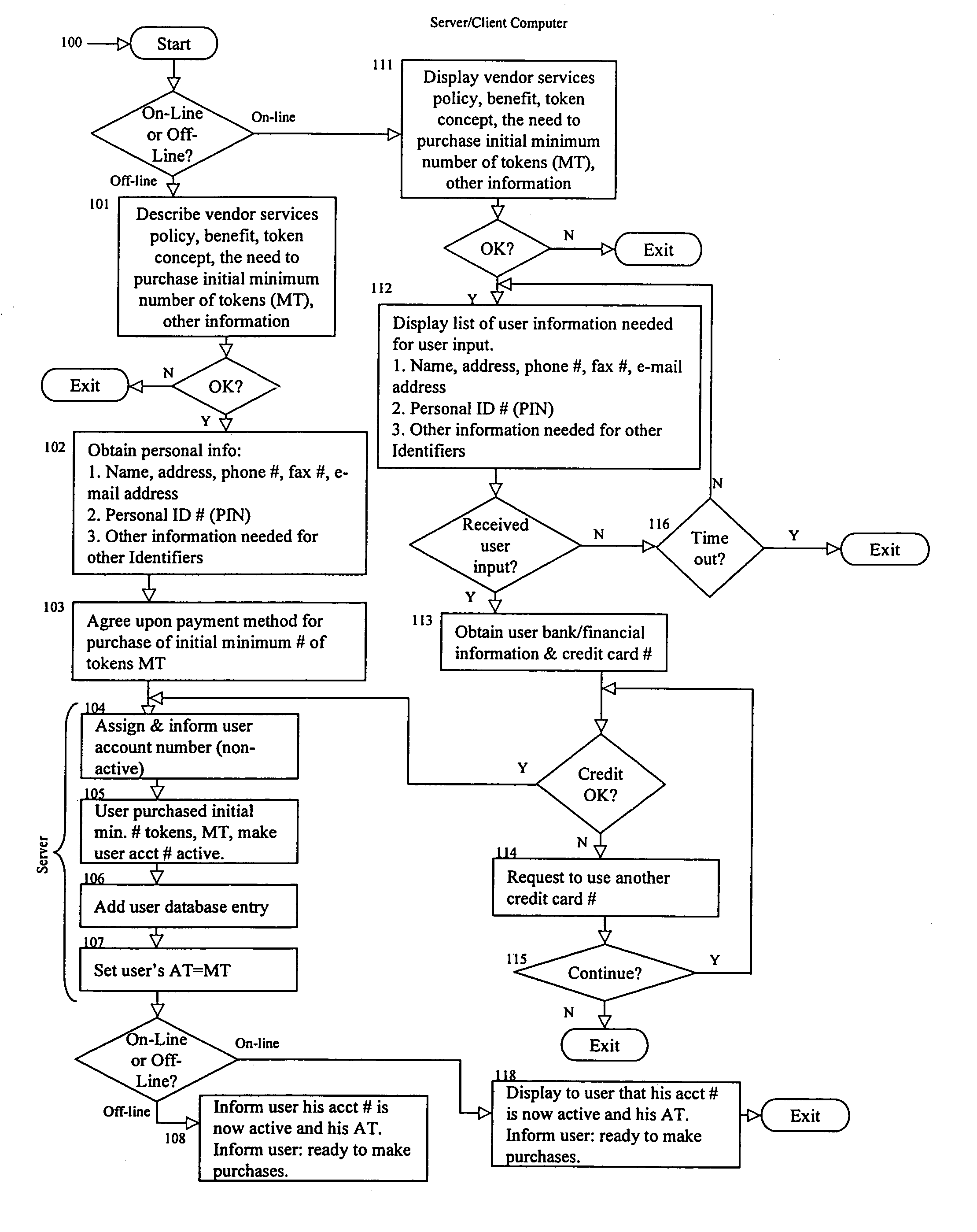
Methods and apparatus for conducting electronic commerce using electronic tokens are described. The electronic tokens are issued and maintained by a vendor, who also provides products and services that can be purchased or rented using the electronic tokens. The electronic tokens may be purchased from the vendor either on-line, using a credit card, or off-line, using a check, money order, purchase order, or other payment means. Because the vendor is the issuer of the electronic tokens, there is no need for transactions to be handled by a third party, such as a bank or other organization. This reduces the overhead involved in conducting electronic commerce, and provides the vendor with a greater amount of control. Additionally, the vendor maintains total control over the price of the electronic tokens at any time. For vendors who offer software products for sale or rental, use of electronic tokens makes a variety of rental arrangements practical. Additionally, a user registers and purchases electronic tokens at the vendor. The user may purchase products at any other vendors who conduct electronic commerce using electronic tokens.
Owner:AML IP LLC
Method and apparatus for conducting electronic commerce transactions using electronic tokens
InactiveUS7177838B1Minimal overheadFinanceApparatus for meter-controlled dispensingThird partyCredit card
Methods and apparatus for conducting electronic commerce using electronic tokens are described. The electronic tokens are issued and maintained by a vendor, who also provides products and services that can be purchased or rented using the electronic tokens. The electronic tokens may be purchased from the vendor either on-line, using a credit card, or off-line, using a check, money order, purchase order. Because the vendor is the issuer of the electronic tokens, there is no need for transactions to be handled by a third party, such as a bank or other organization. This reduces the overhead involved in conducting electronic commerce, and provides the vendor with a greater amount of control. Additionally, the vendor maintains total control over the price of the electronic tokens at any time. For vendors who offer software products for sale or rental, use of electronic tokens makes a variety of rental arrangements practical, including rental for short periods of time, for a specific number of uses, or for a specific number of processings.
Owner:AML IP LLC
System and method for creating and managing virtual services
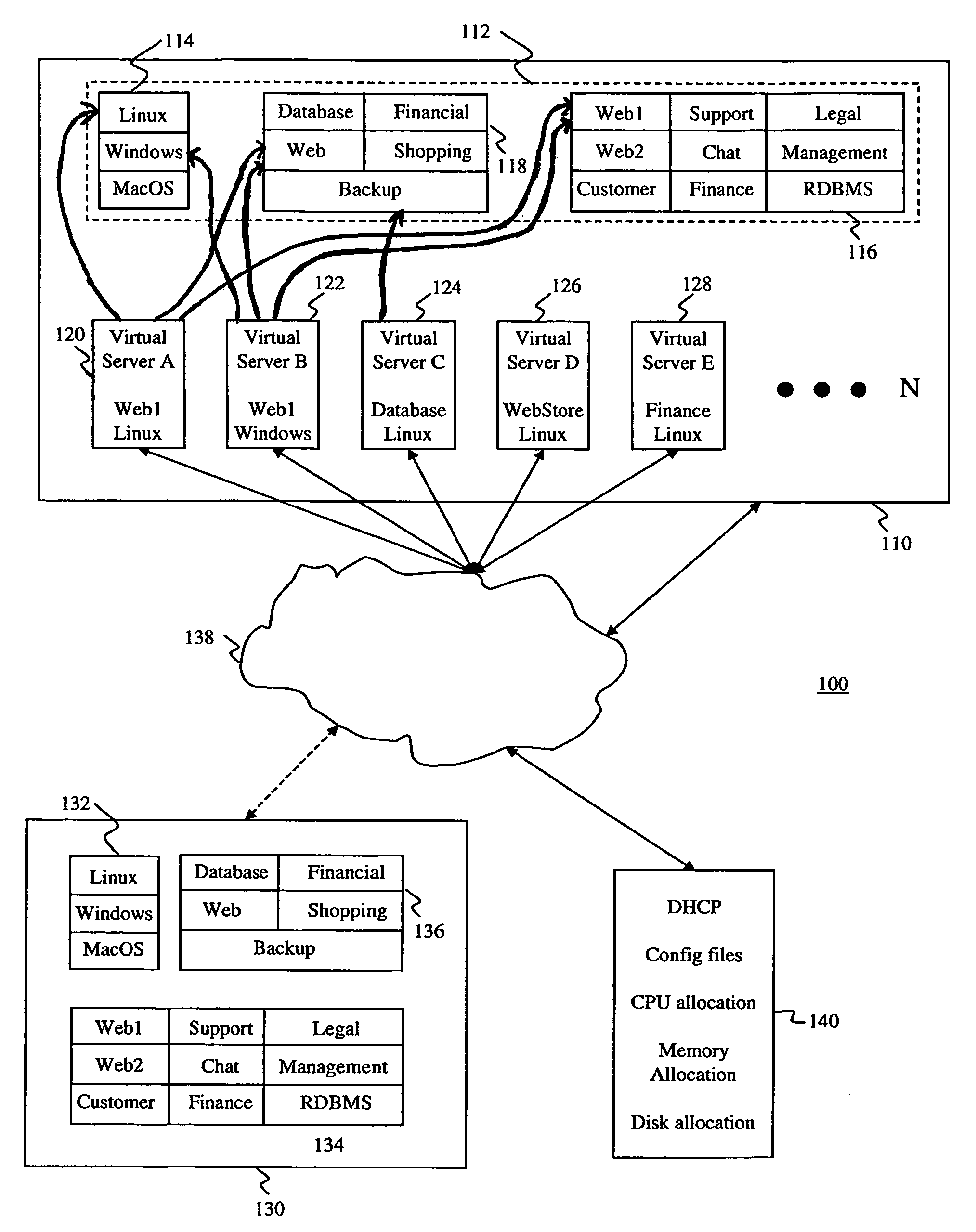
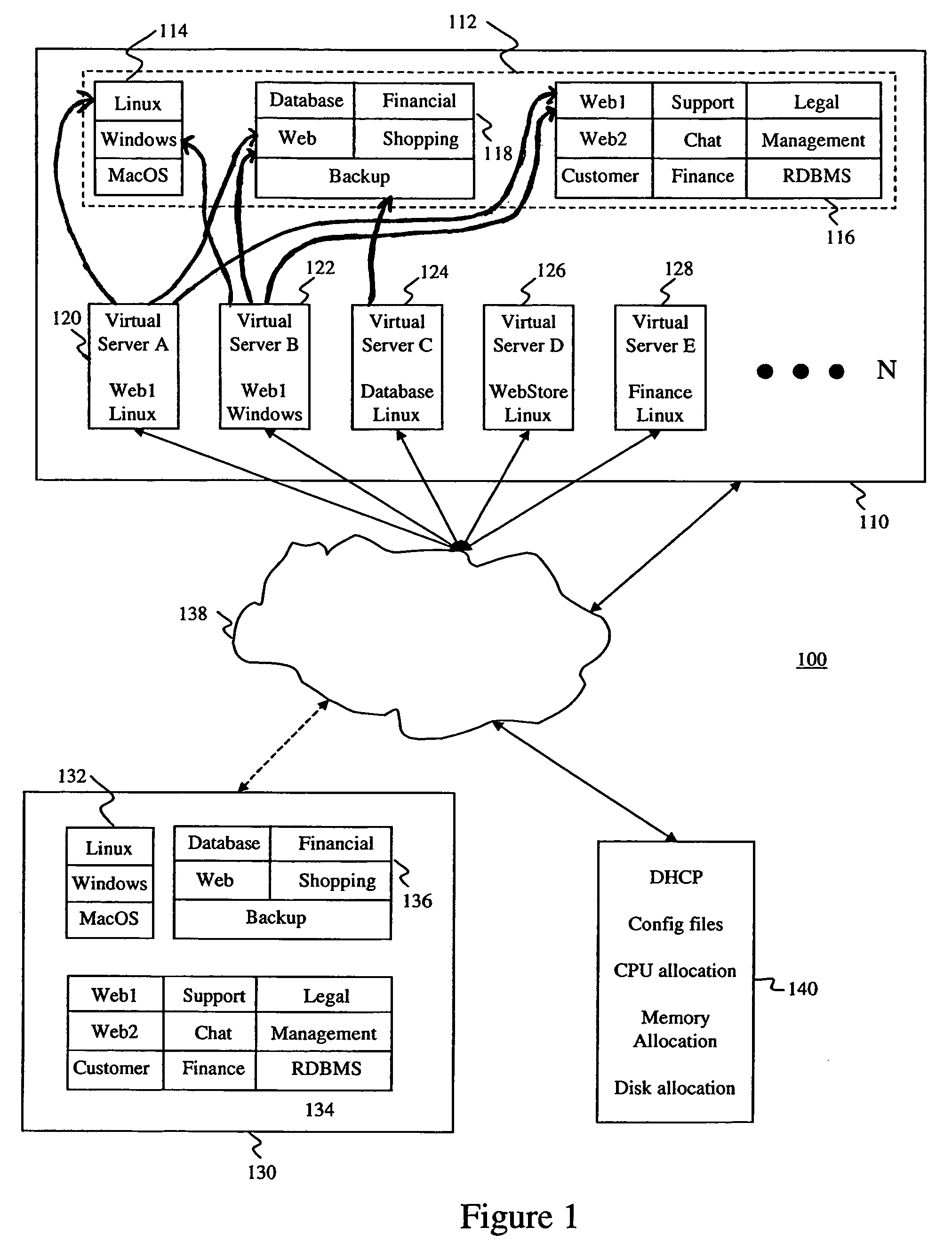
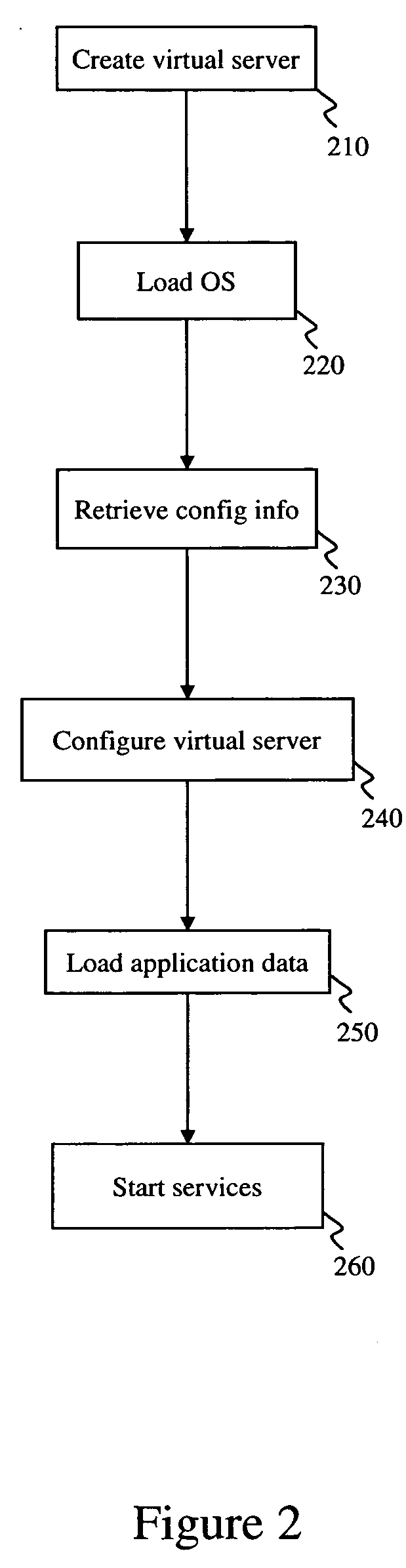
InactiveUS20060184653A1Lower Level RequirementsMinimal overheadMultiple digital computer combinationsProgram controlOperational systemApplication software
A method of creating and managing virtual servers utilizes separate master copies of information such as operating systems, configuration files, and application programs. When a virtual server is created, it loads an appropriate operating system and configuration information. During the boot process, the virtual server is configured to provide a predetermined service. Appropriate application programs are subsequently loaded to support the service configuration. Multiple virtual servers can be created and configured using the master copies of information, thus reducing the amount of customization required by each virtual server. Virtual servers can be easily restarted from failures with minimal loss of data.
Owner:RED HAT
Integrated mechanism for suspension and deallocation of computational threads of execution in a processor
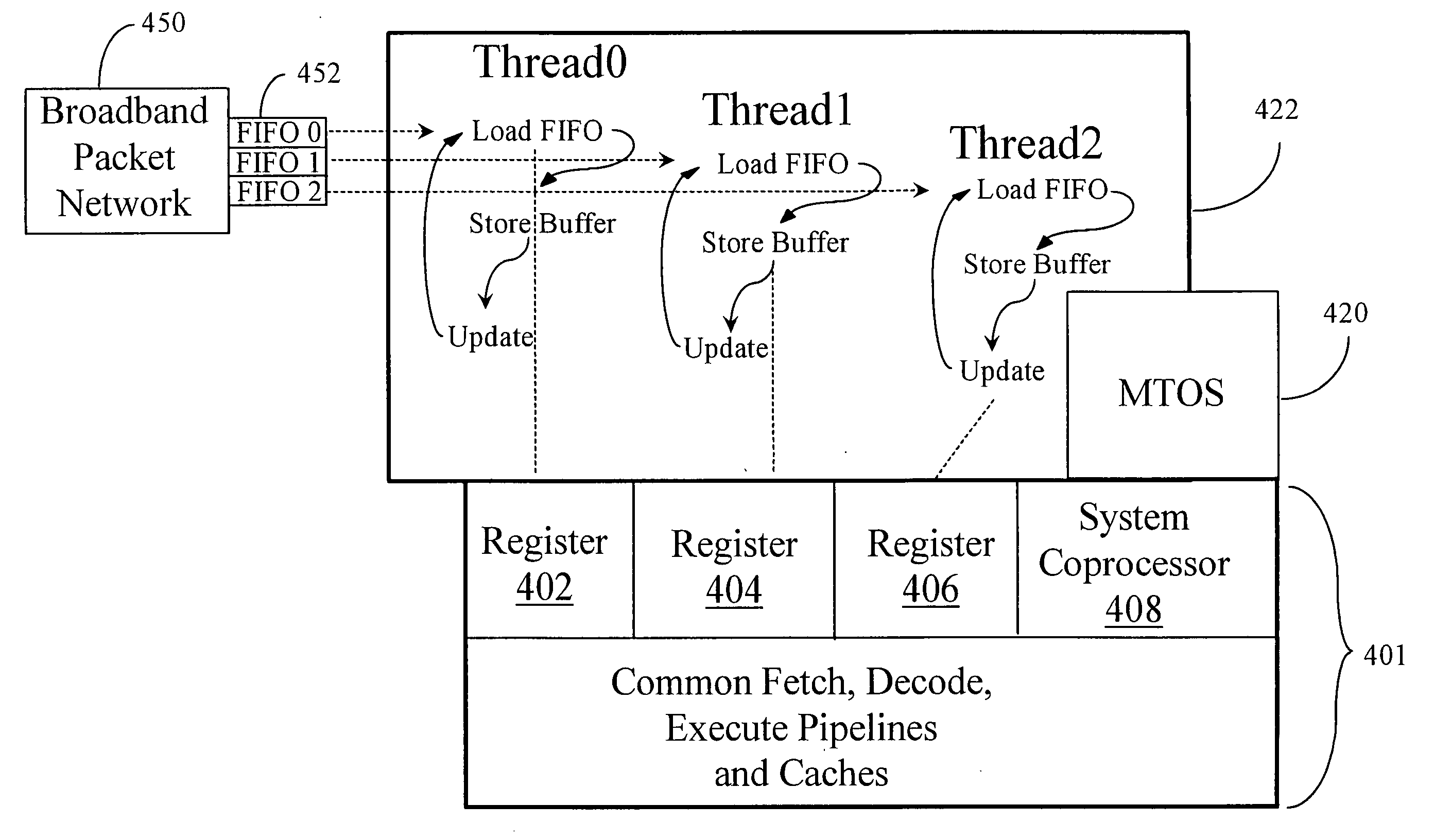
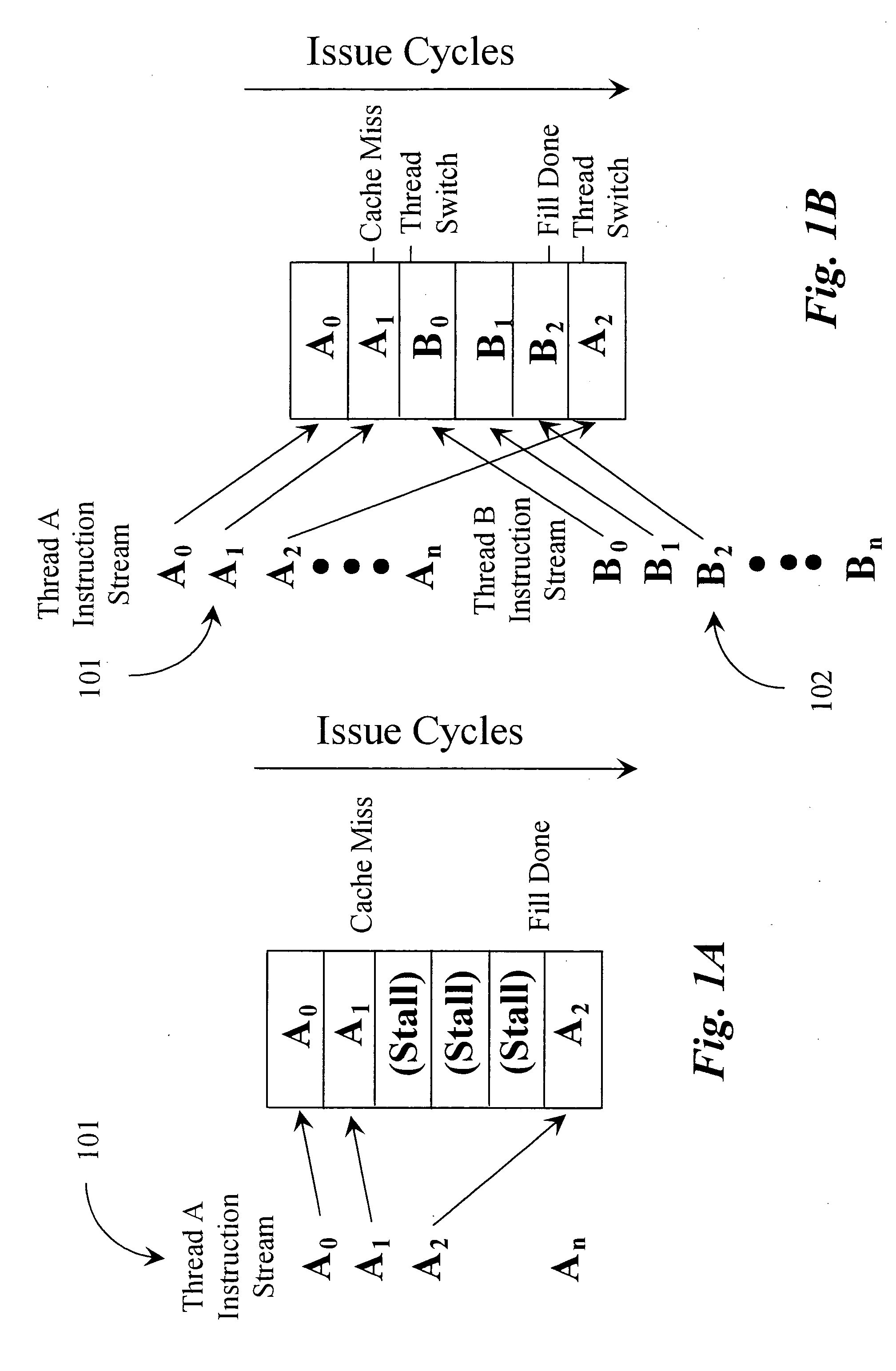
InactiveUS20050050305A1Minimize overheadMinimal overheadProgram initiation/switchingSoftware engineeringProgram ThreadComputer science
A mechanism for processing in a processor enabled to support and execute multiple program threads includes a parameter for scheduling a program thread and an instruction disposed within the program thread and enabled to access the parameter. When the parameter equals a first value the instruction, when issued by a program thread, reschedules the program thread in accordance with one or more conditions encoded within the parameter.
Owner:MIPS TECH INC
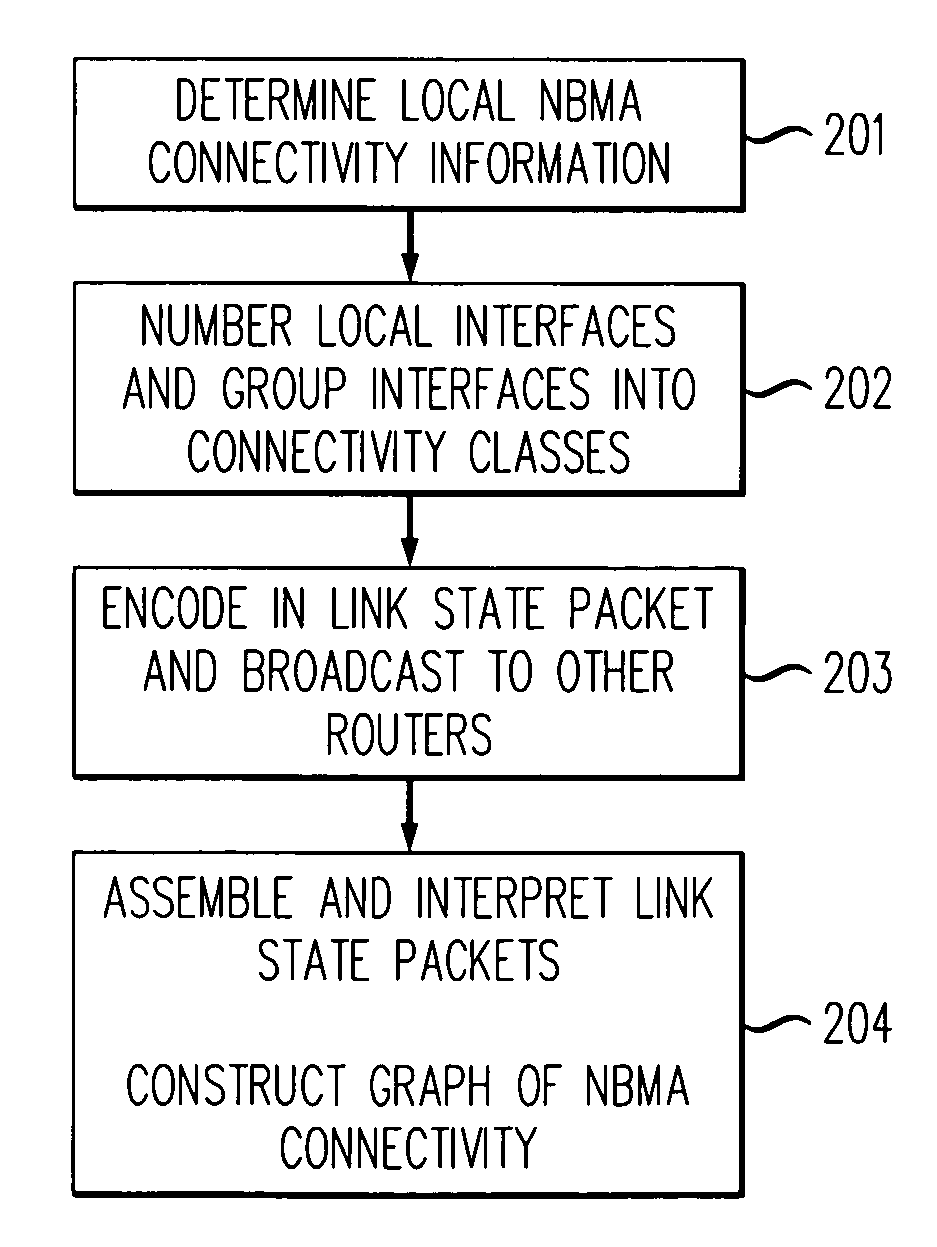
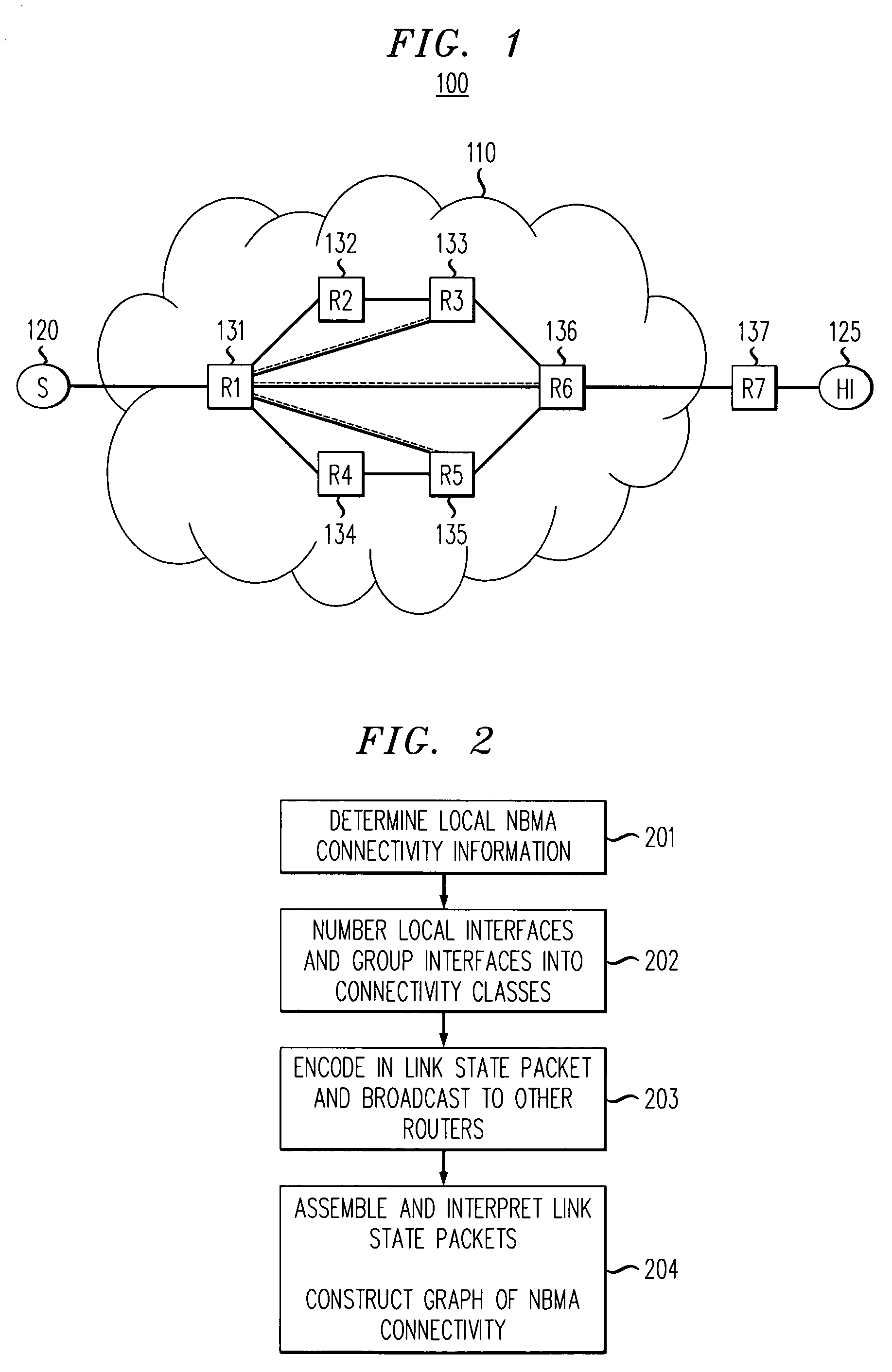
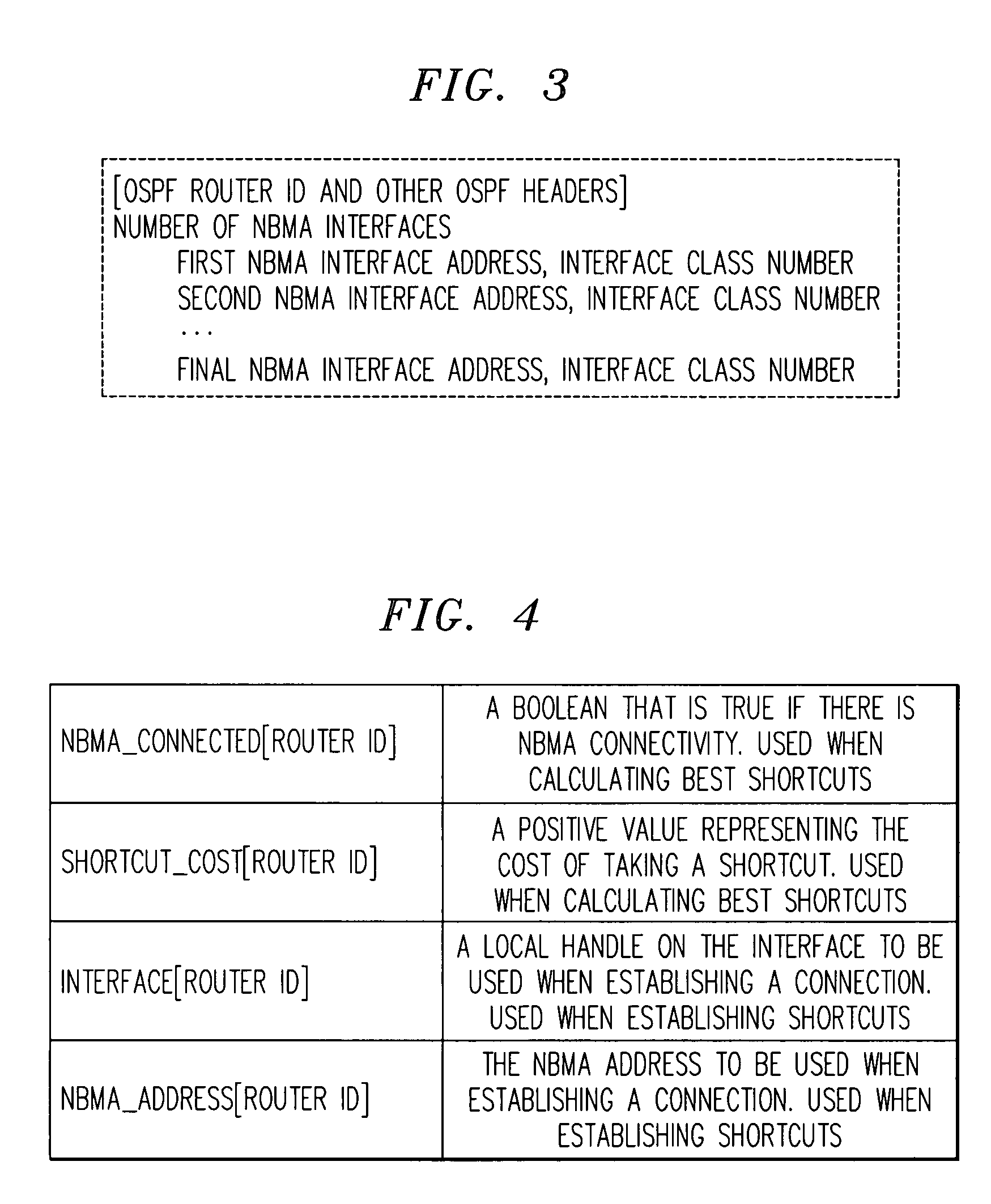
Method for determining non-broadcast multiple access (NBMA) connectivity for routers having multiple local NBMA interfaces
InactiveUS7808968B1Avoid overheadIntroduce latencyData switching by path configurationTier 2 networkLink state packet
The present invention discloses an efficient architecture for routing in a very large autonomous system where many of the layer 3 routers are attached to a common connection-oriented layer 2 subnetwork, such as an ATM network. In a preferred embodiment of the invention, a permanent topology of routers coupled to the subnetwork is connected by permanent virtual circuits. The routers can further take advantage of both intra-area and inter-area shortcuts through the layer 2 network to improve network performance. The routers pre-calculate shortcuts using information from link state packets broadcast by other routers and store the shortcuts to a given destination in a forwarding table, along with corresponding entries for a next hop along the permanent topology. The present invention allows the network to continue to operate correctly if layer 2 resource limitations preclude the setup of additional shortcuts.
Owner:AT&T INTPROP I L P
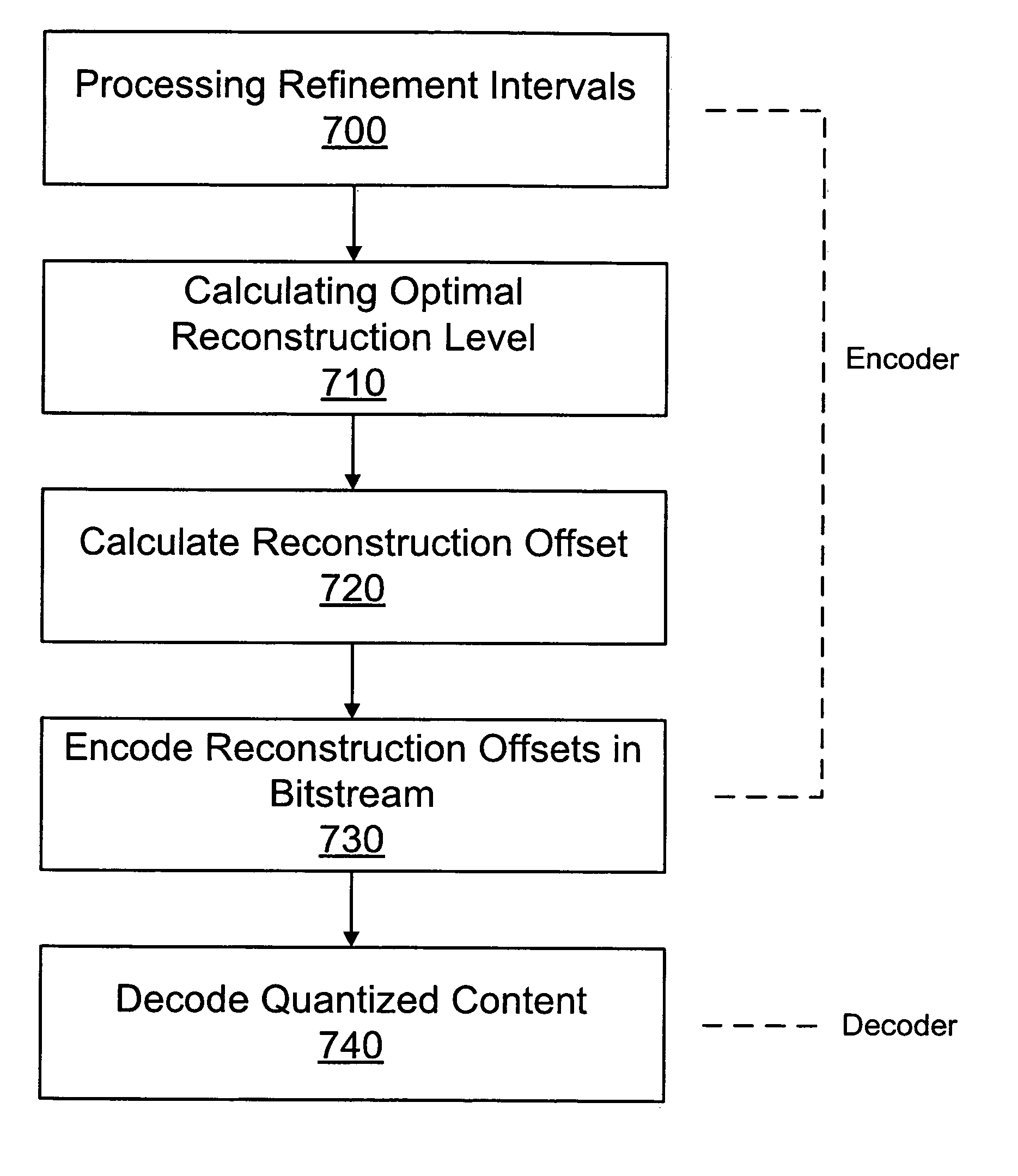
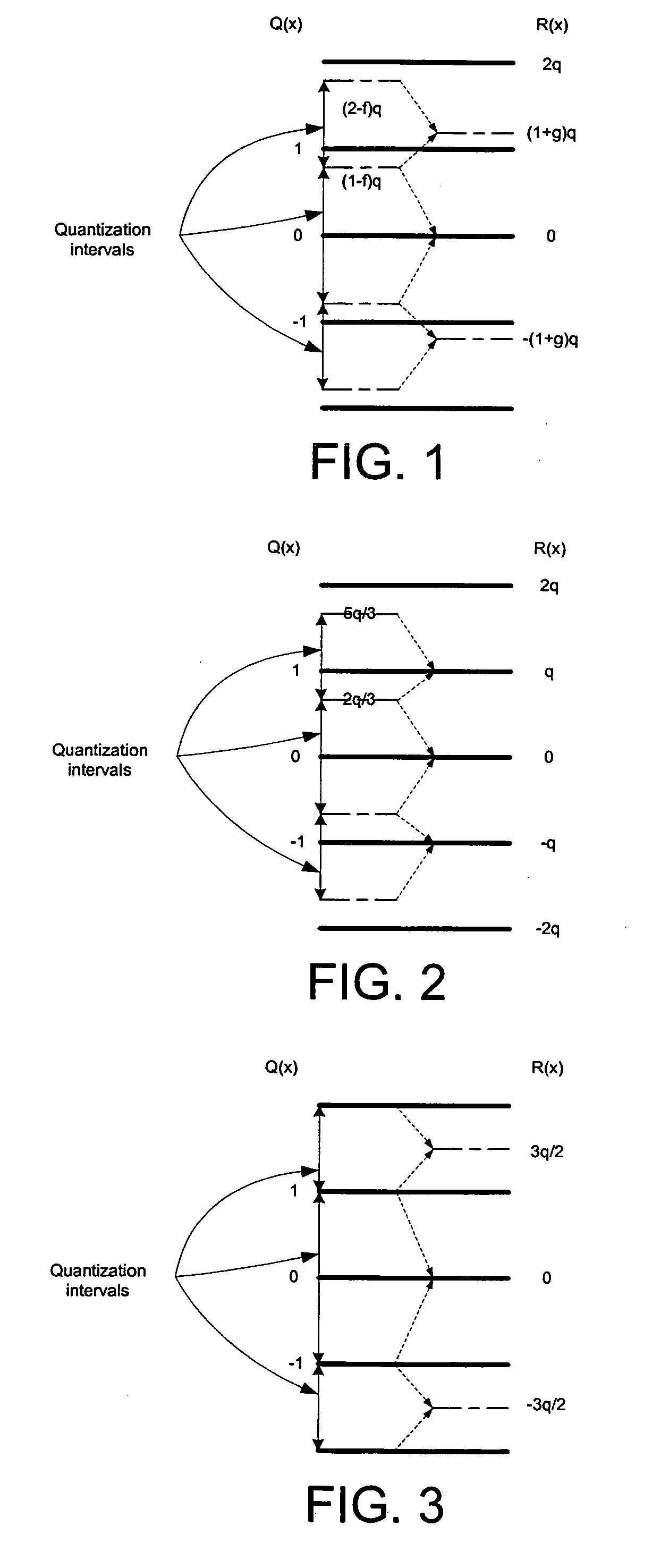
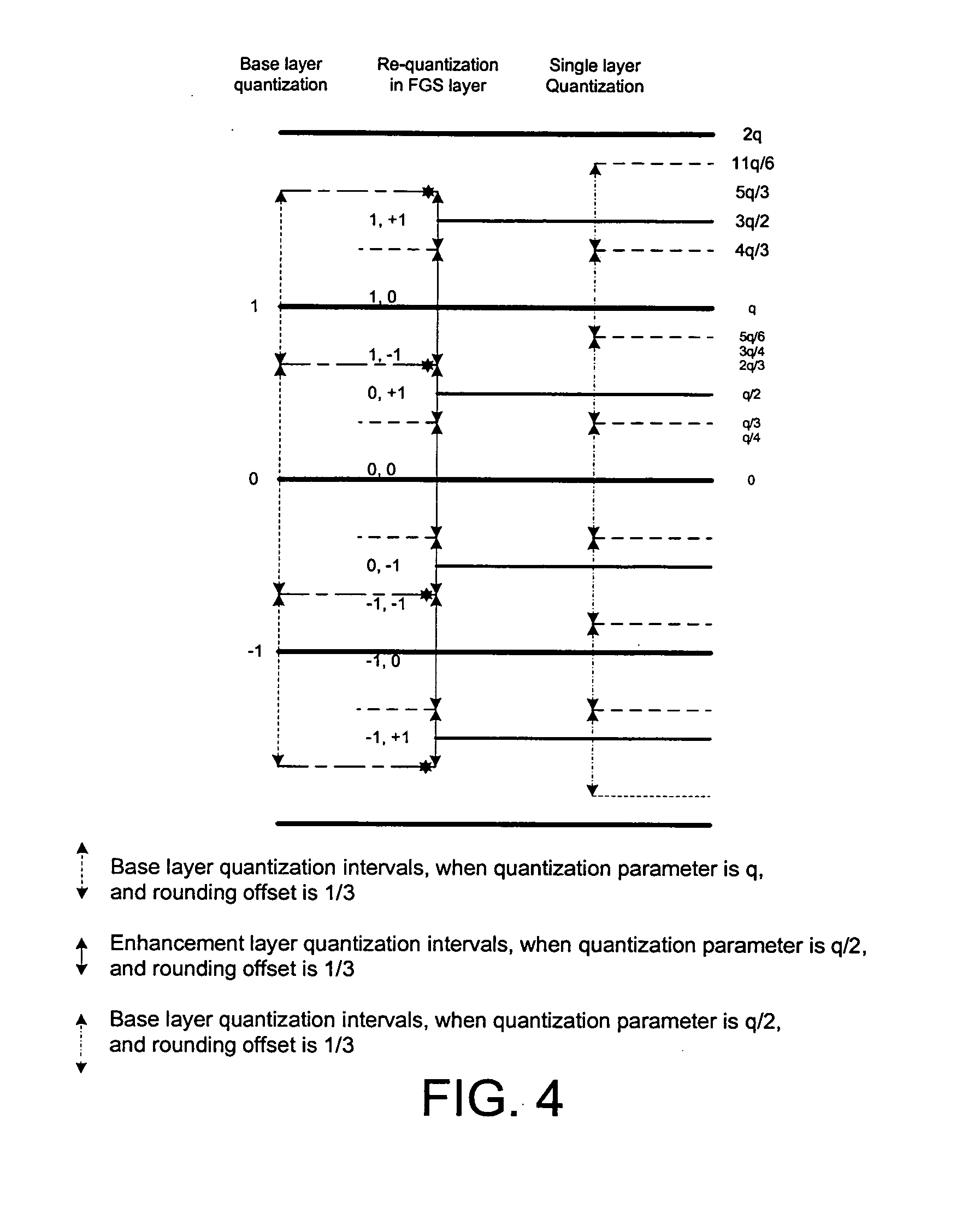
System and method for progressive quantization for scalable image and video coding
InactiveUS20070147497A1Enhance layeringMinimal numberColor television with pulse code modulationColor television with bandwidth reductionPattern recognitionVideo encoding
An improved system and method for dequantizing progressively quantized signals in scalable image and video coding. A decoder performs simple dequantization, such as normal uniform dequantization, on coded content using a quantization index and a nominal quantization step size to obtain a nominal reconstruction level. The result is then adjusted by adding the reconstruction offset to obtain the final reconstruction value.
Owner:NOKIA CORP
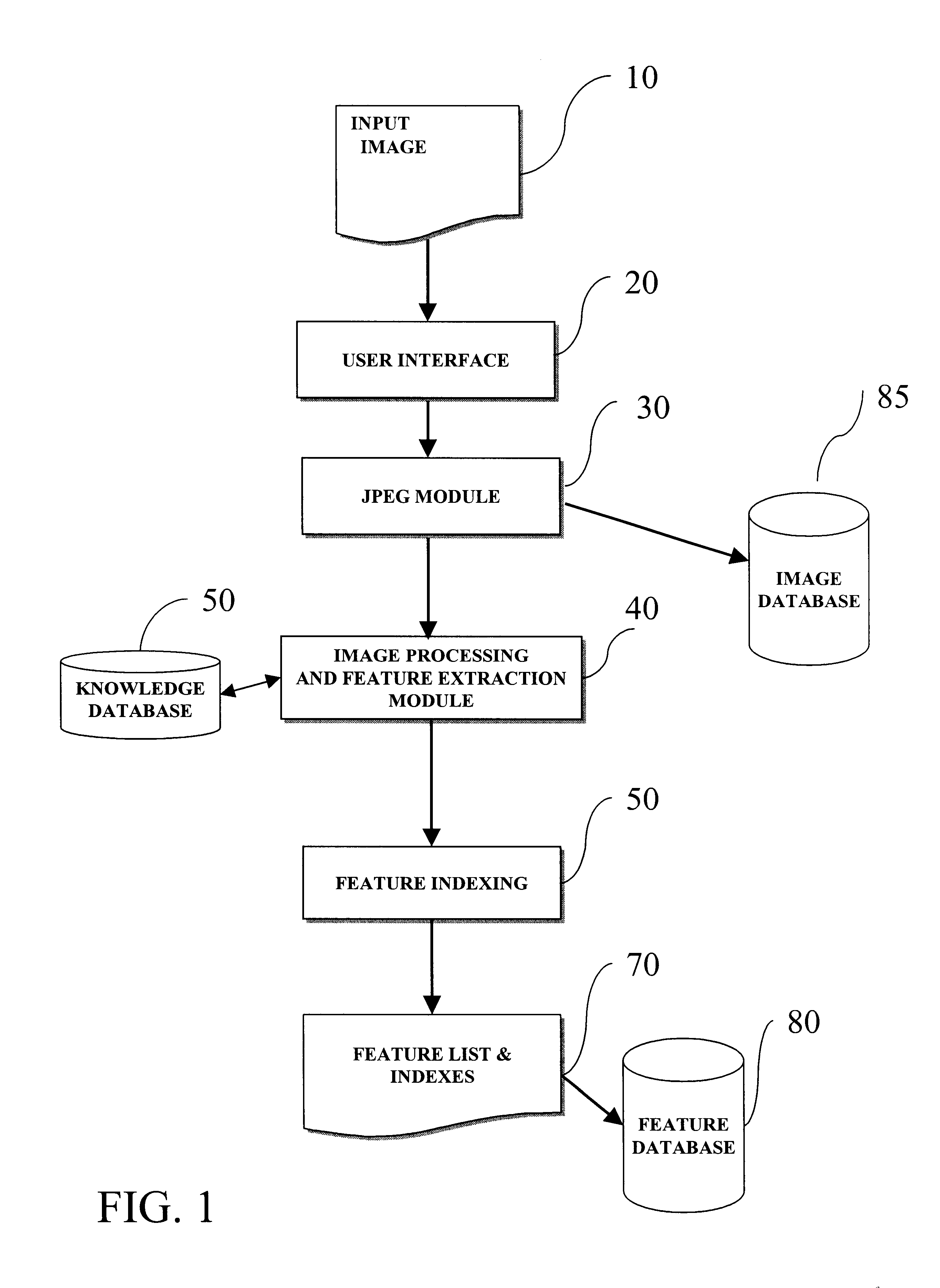
Method for computerized indexing and retrieval of digital images based on spatial color distribution
InactiveUS6594386B1Improve performanceMinimal overheadDigital data information retrievalDigital data processing detailsPersonal computerImage compression
In the context of image database systems, a method for indexing and retrieval of images by their color content and the spatial distribution of color is disclosed. The method is implemented as a software tool that runs on a personal computer and enables the computer to find a desired image from an image database. The user interface allows the user to describe the desired image, and the tool searches the repository for any images that satisfy the description. The description of the composite image may include information on shapes, texture, presence or absence of objects, and color. The process of search and retrieval of images makes use of a method that determines whether a specific color, or a combination of colors, is present in an image. Further, the method determines the location where the specific color or color combination can be found. By analyzing the results of comparisons between the features found in the composite image and in the stored images, the tool retrieves those images that satisfy the description of the query, image. Calculation of color-related features makes significant use of the calculations that are made in the process of image compression which is an essential step prior to image storage. The process of search and retrieval on the basis of features relating to color are provided via a library of routines that perform the necessary tasks.
Owner:GOLSHANI FOROUZAN +1
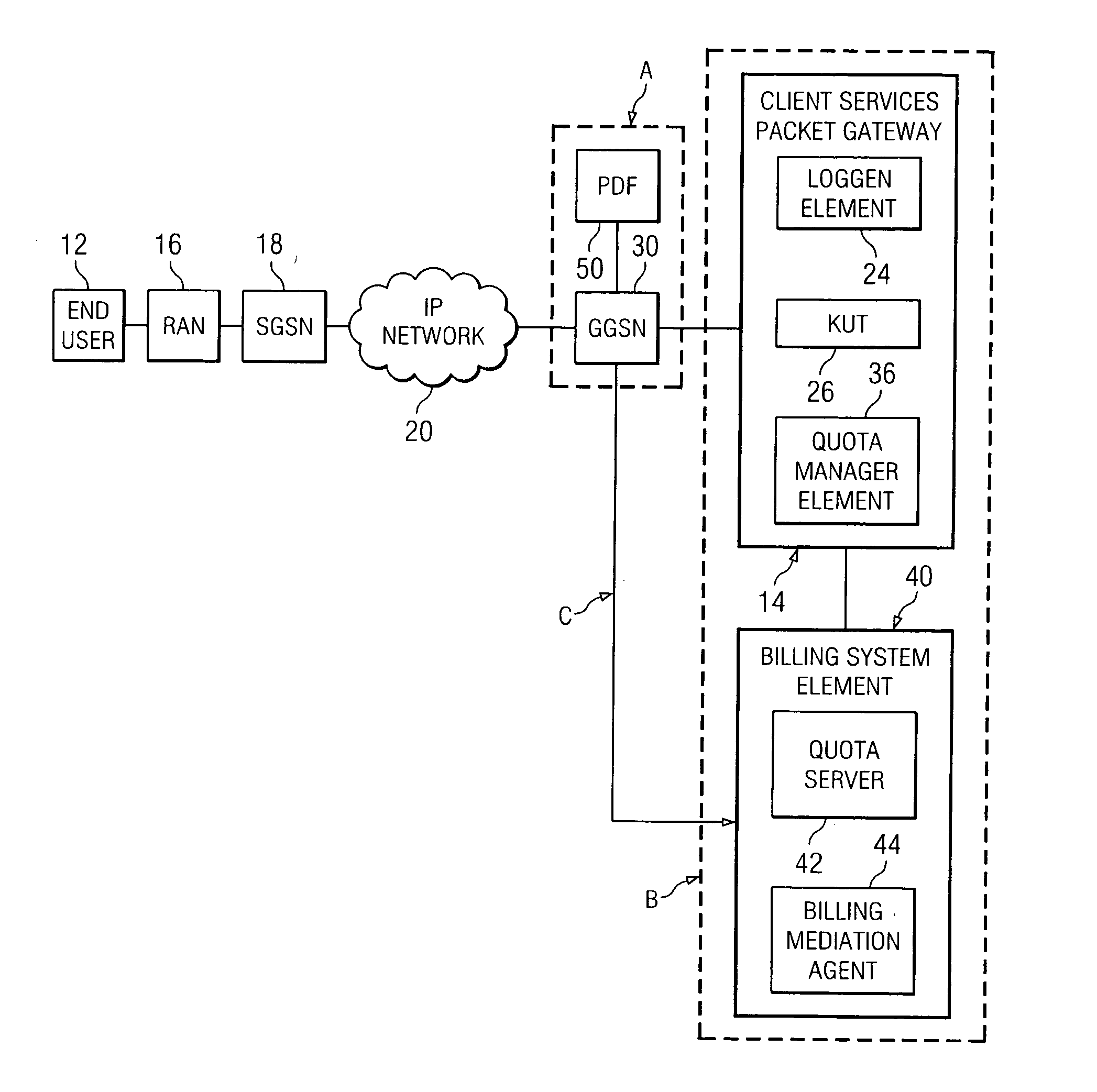
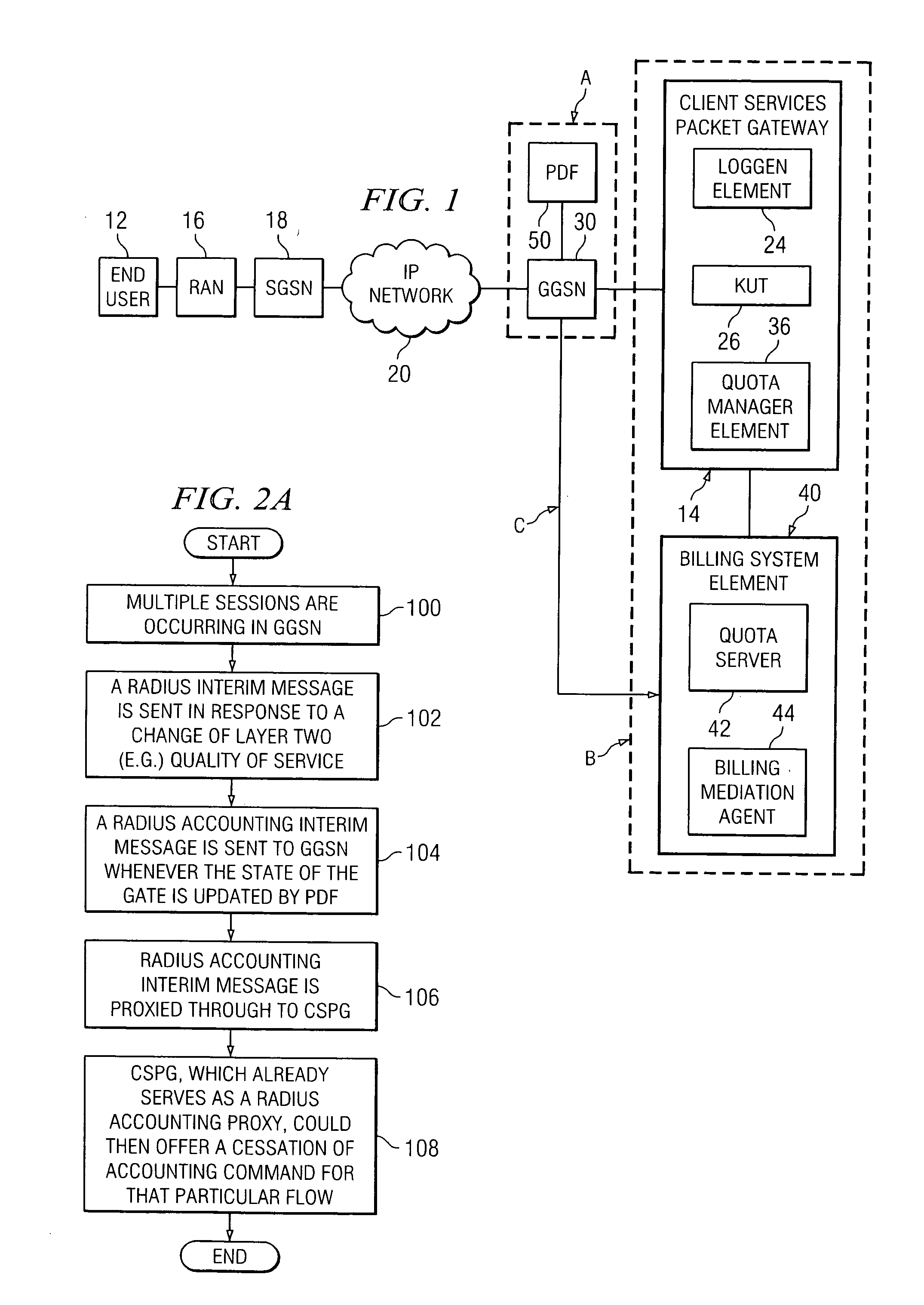
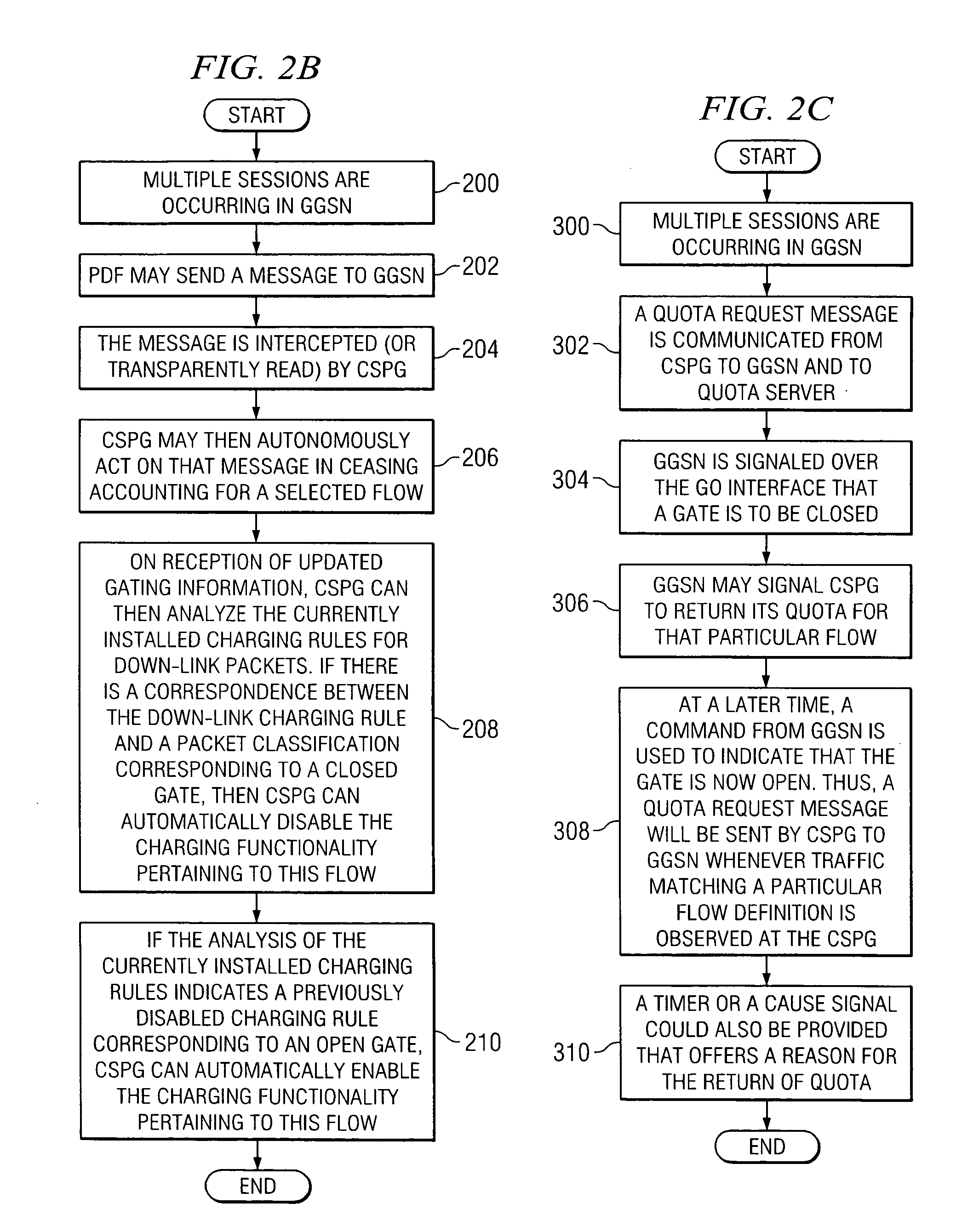
System and method for signaling information in order to enable and disable distributed billing in a network environment
ActiveUS20060029084A1Reduce disadvantagesReduce problemsMetering/charging/biilling arrangementsError preventionQuality of serviceClient-side
An apparatus for signaling information in a network environment is provided that includes an access gateway operable to establish one or more packet data protocol (PDP) links on behalf of an end user. The access gateway is operable to communicate a message associated with a change in quality of service, locale, or policy enforcement relating to a selected one of the PDP links to a client services packet gateway (CSPG). The CSPG responds to the message by providing an accounting command for the selected PDP link such that synchronization is achieved between accounting information and a state associated with the selected PDP link.
Owner:CISCO TECH INC
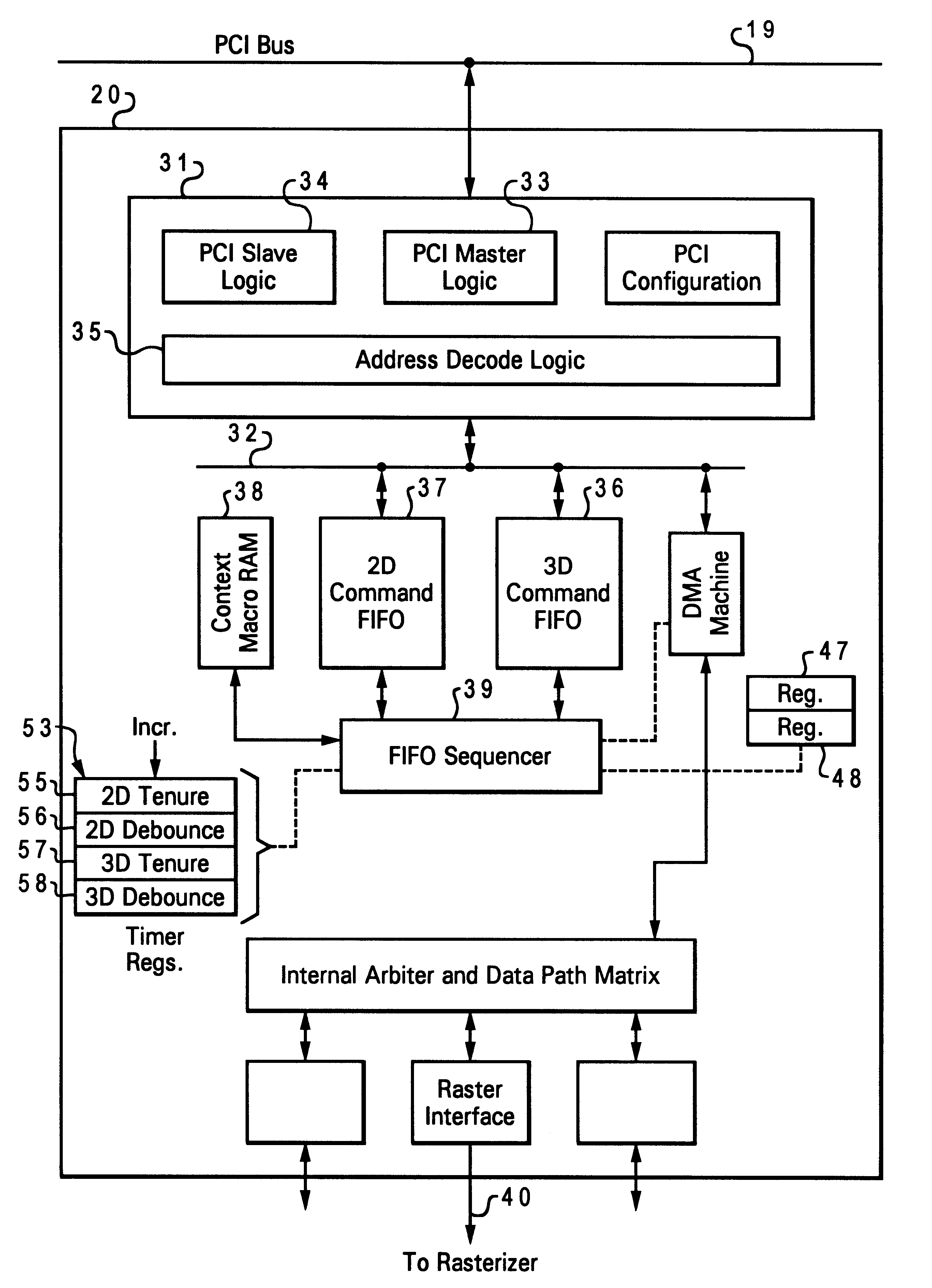
Computer graphics system with dual FIFO interface
InactiveUS6252600B1Minimum delayEasy to useImage memory managementCathode-ray tube indicatorsGraphic systemComputerized system
A computer system has a graphics subsystem employing a rasterizer and a frame buffer, with a digital-to-analog converter for producing drive signals to a video display. A bus interface acts as a gateway between a PCI bus and the graphics subsystem; this interface manages commands and DMAs passing between the host processor and various parts of the graphics subsystem. Within the interface, two command FIFOs are employed, one for storing commands / data sent from the host for 2D display (window management) and another for 3D applications. Using two command FIFOs eliminates the need for host semaphore, FIFO draining, and the latency associated with these operations. Timers are provided in the interface, associated with the two command FIFOs, to manage and regulate the frequency with which the system automatically switches between 2D and 3D FIFO processing. Host intervention is minimized by use of a context macro store for holding locally the sequences for context save and context restore which are used repeatedly.
Owner:IBM CORP
Device and method for transmitting reference signal in multi-antenna system
ActiveUS20150288497A1Minimal overheadReduce transmission overheadSpatial transmit diversityPilot signal allocationChannel state informationRSS
The present invention relates to a device and a method for transmitting a reference signal in a multi-antenna system. The present specification discloses a method for receiving a reference signal, the method comprising the steps of: receiving, from a base station, first channel state information (CSI) reference signal (CSI-RS) configuration information including individual parameters necessary when a terminal receives a first CSI-RS from a horizontally adjacent horizontal representative antenna among the all of the transmission antennas of the base station and second CSI-RS configuration information including individual parameters necessary when the terminal receives a second CSI-RS from a vertically adjacent vertical representative antenna; and receiving the respective first and second CSI-RSs from the base station on the basis of the first CSI-RS configuration information and the second CSI-RS configuration information.
Owner:PANTECH CORP
Method and apparatus for conducting electronic commerce transactions using electronic tokens
InactiveUS7376621B1Accurate recordInhibit transferComplete banking machinesFinanceThird partyCredit card
Methods and apparatus for conducting electronic commerce using electronic tokens are described. The electronic tokens are issued and maintained by a vendor, who also provides products and services that can be purchased or rented using the electronic tokens. The electronic tokens may be purchased from the vendor either on-line, using a credit card, or off-line, using a check, money order, purchase order, or other payment means. Because the vendor is the issuer of the electronic tokens, there is no need for transactions to be handled by a third party, such as a bank or other organization. This reduces the overhead involved in conducting electronic commerce, and provides the vendor with a greater amount of control. Additionally, the vendor maintains total control over the price of the electronic tokens at any time. For vendors who offer software products for sale or rental, use of electronic tokens makes a variety of rental arrangements practical including rental for short periods of time, for a specific number of uses, or for a specific number of processing.
Owner:AML IP LLC
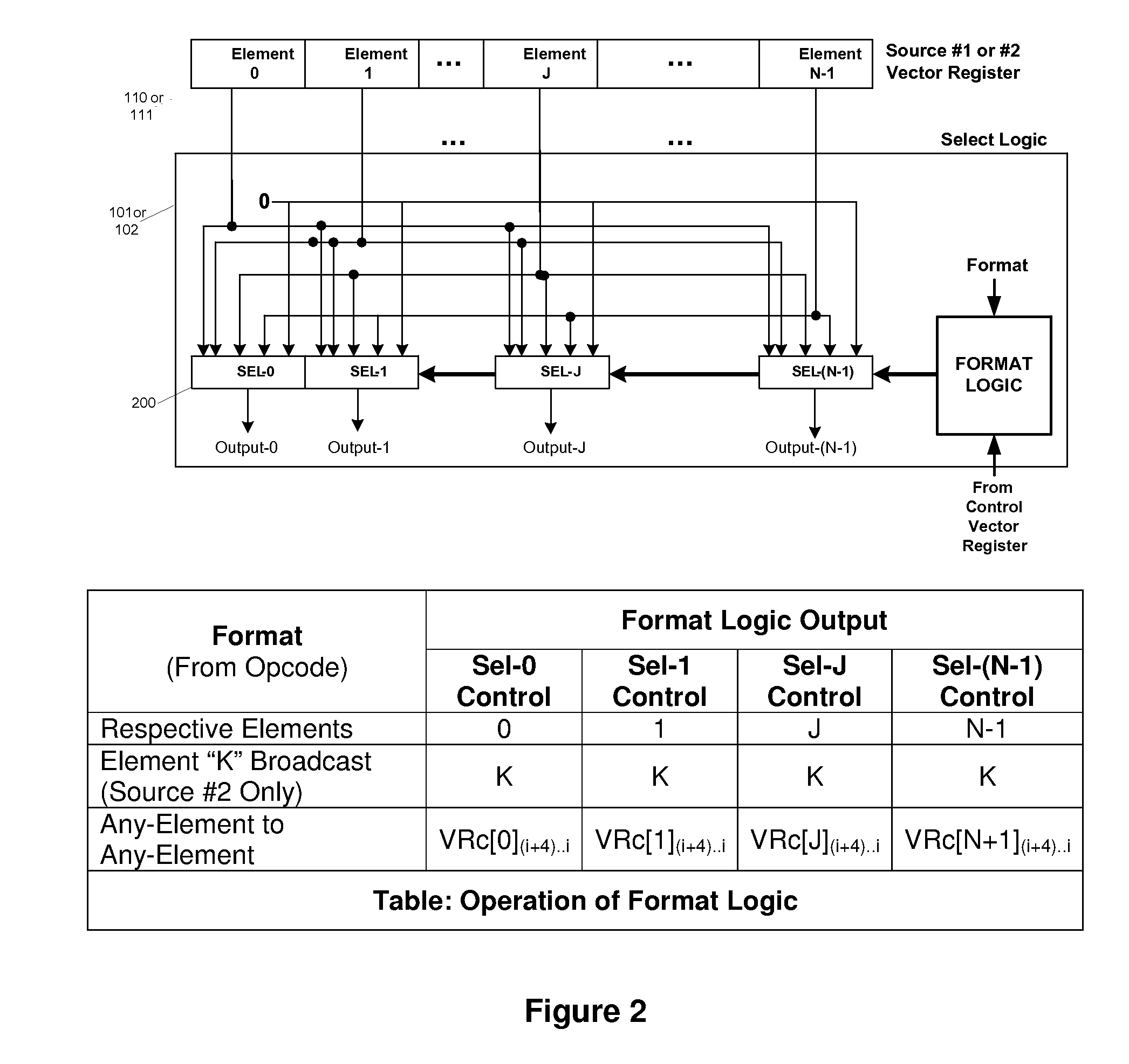
Efficient handling of vector high-level language conditional constructs in a SIMD processor
InactiveUS7793084B1Minimize the numberLow costConditional code generationDigital computer detailsVector elementSimd processing
The present invention provides an efficient method to implement nested if-then-else conditional statements in a SIMD processor, which requires only one vector compare instruction for both if and else parts of the conditional construct. No stack and stack-handling instructions are needed for vector condition codes. Two condition code flag bits representing if and else parts of testing per element provide for nesting of multiple if-then-else. All SIMD instructions are conditional including the vector compare instruction, and this provides a method for aggregating multiple conditions in nested if-then-else statements. M full levels of if-then-else nesting requires (2M−1) nodes or vector test instructions and 2M+1 condition code flags per vector element. Also, capability to compare any element of first source vector register with any element of second source vector is provided.
Owner:CUE BIOTECH
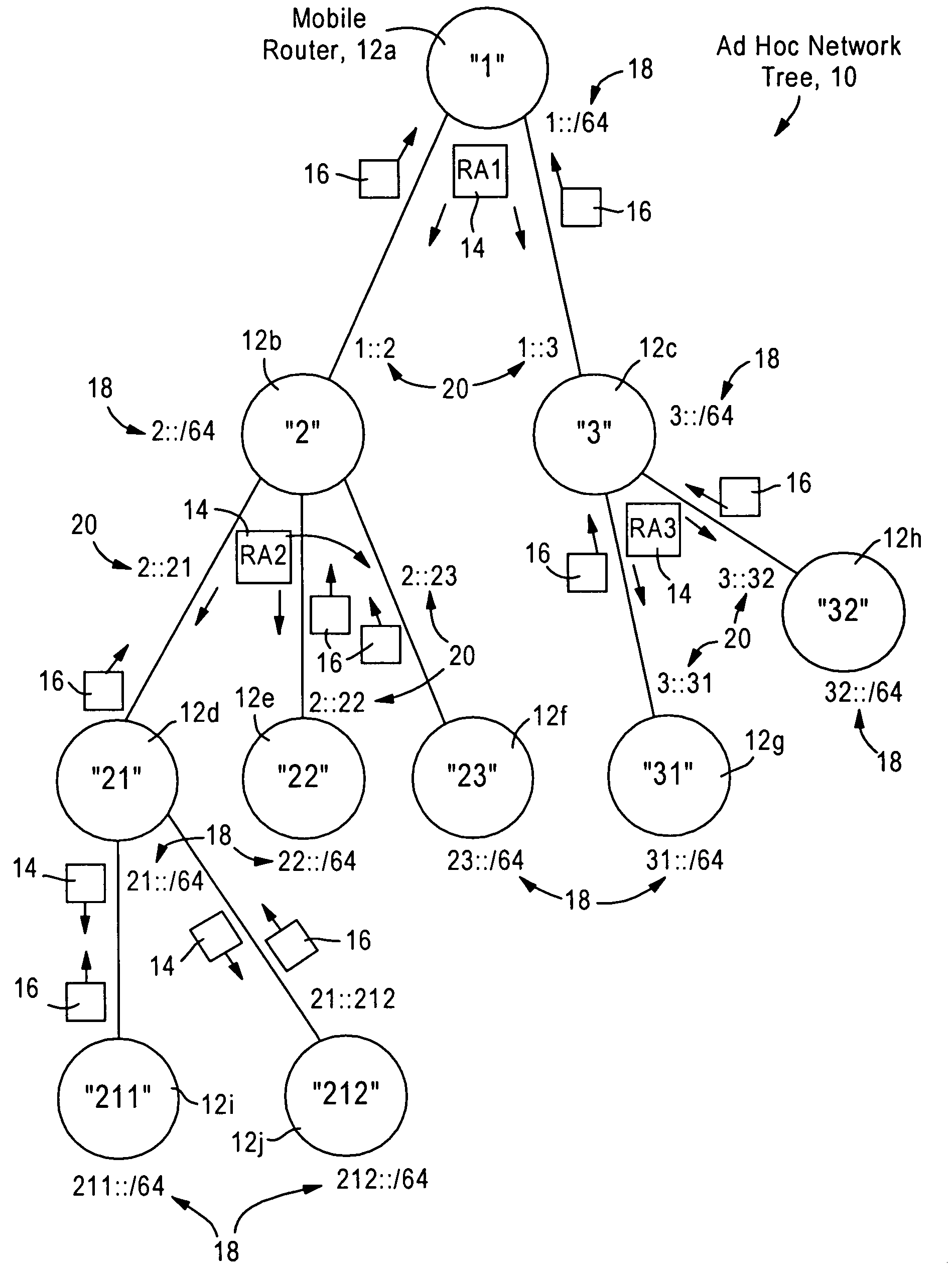
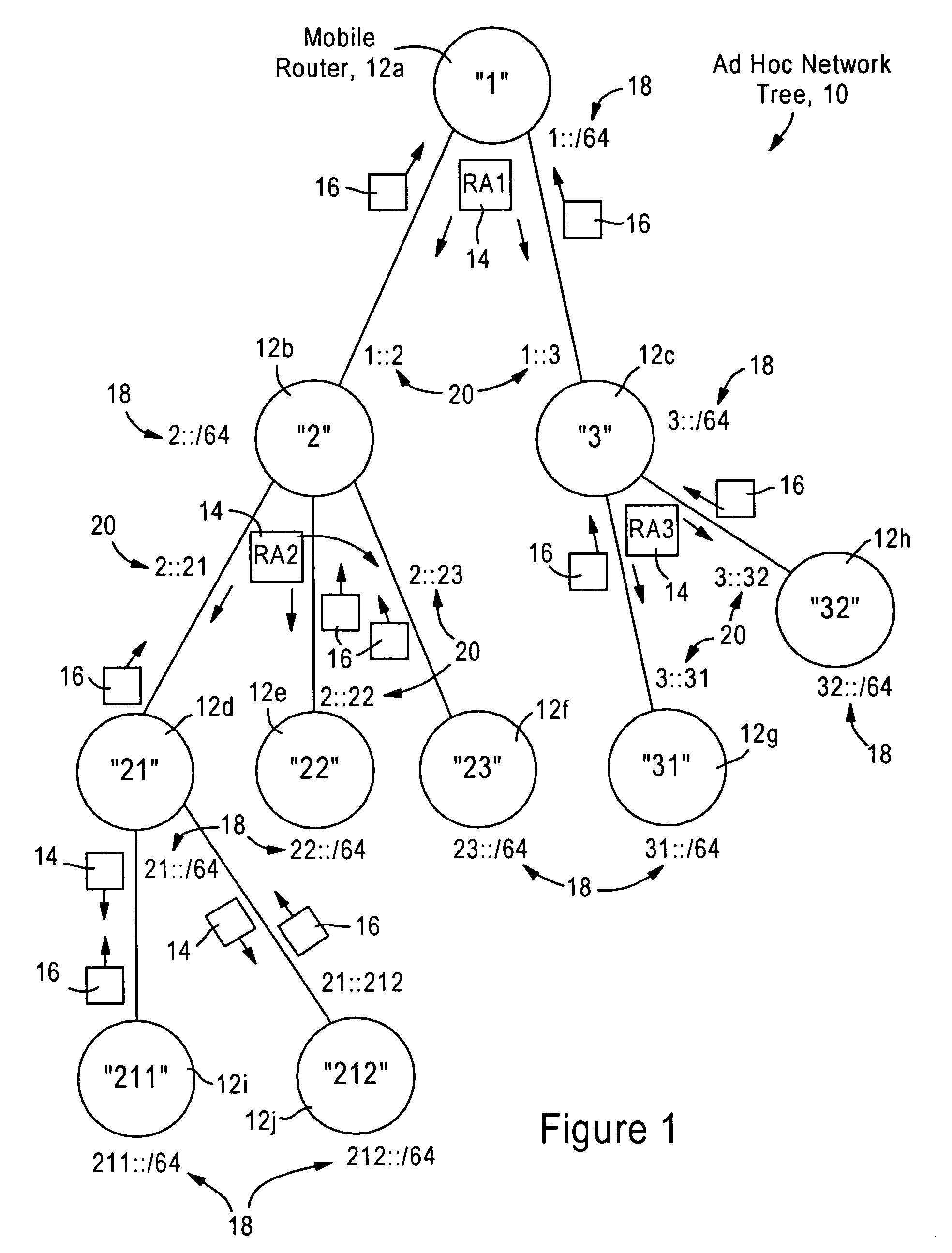
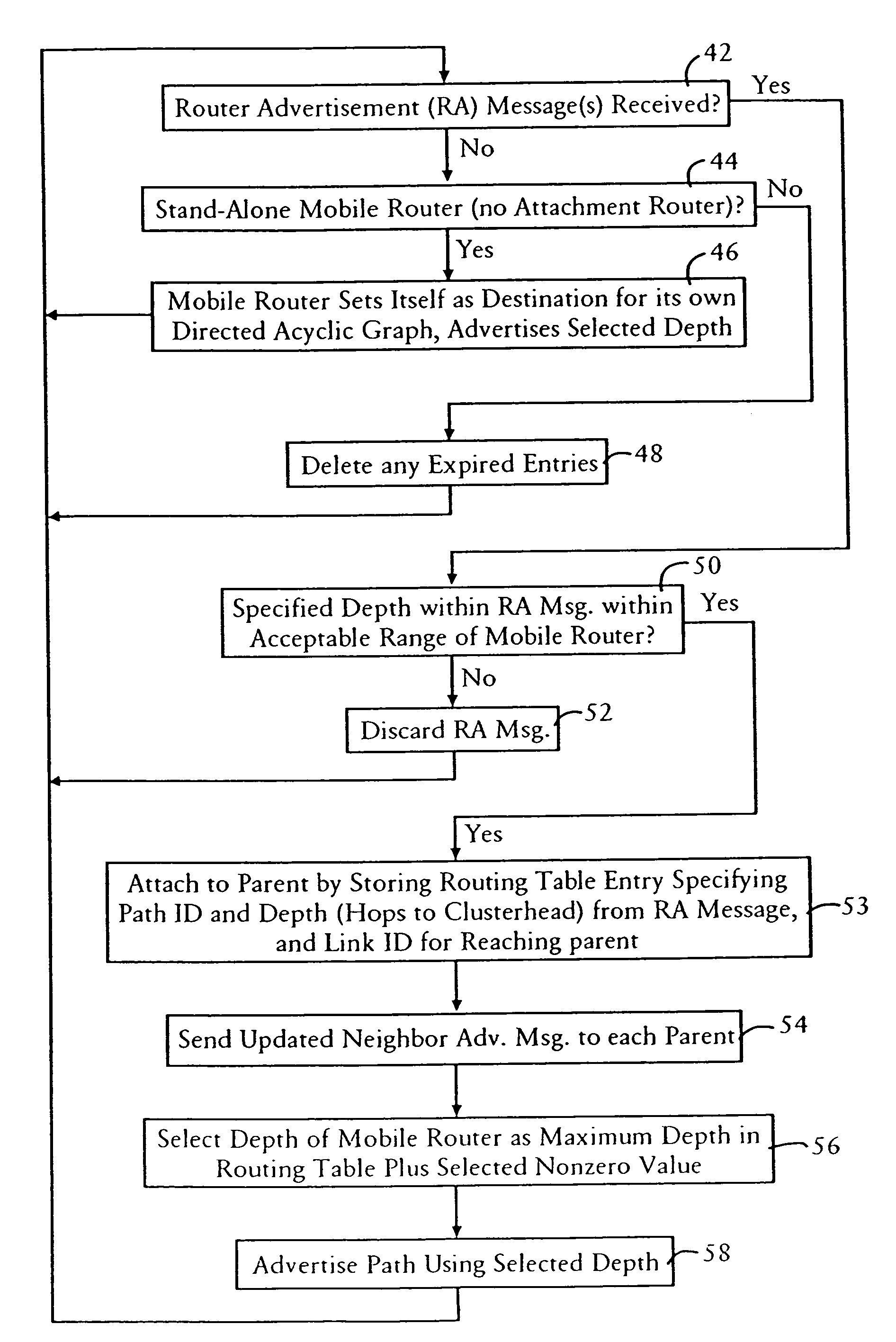
Arrangement for providing network prefix information from attached mobile routers to a clusterhead in a tree-based ad hoc mobile network
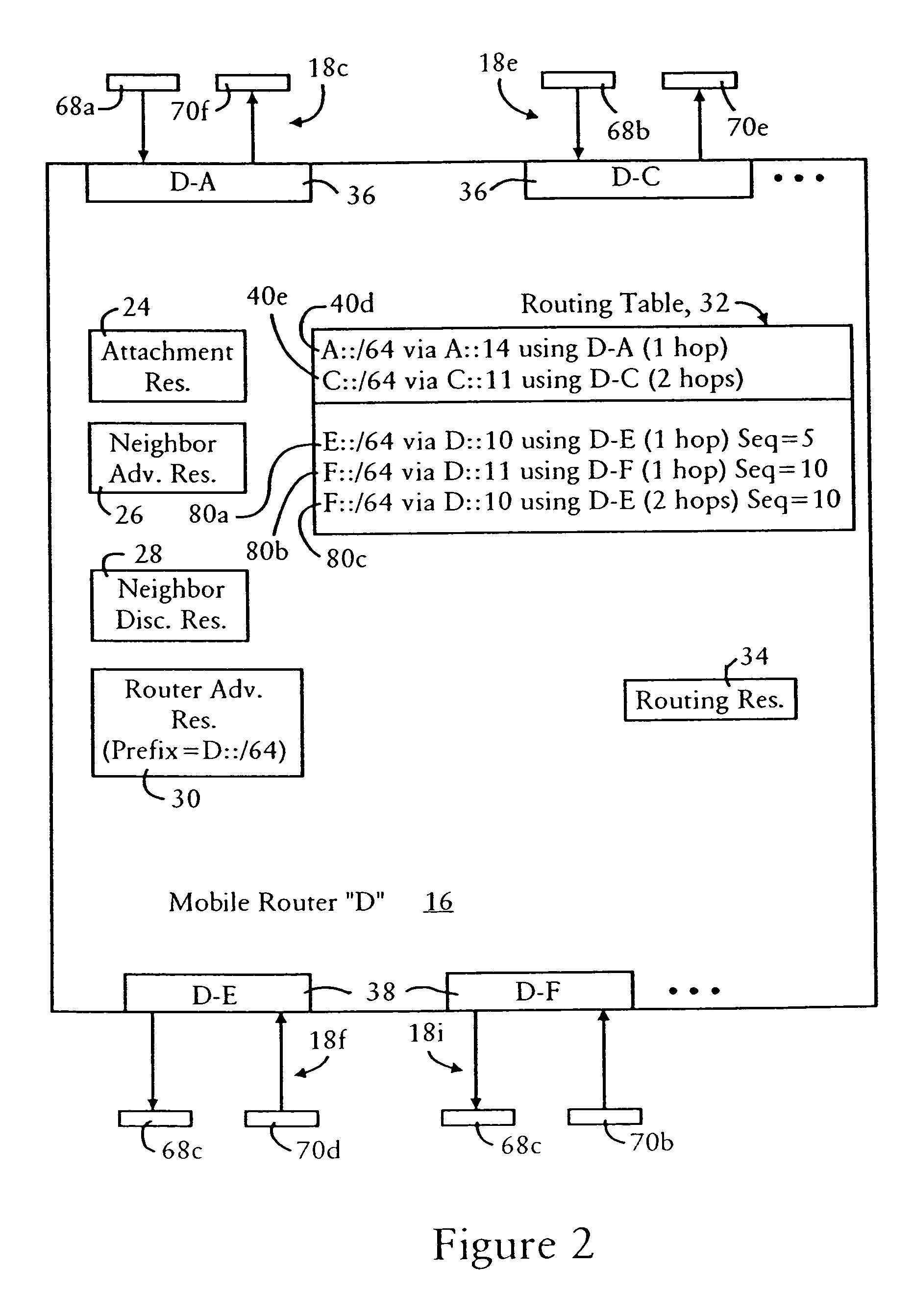
ActiveUS7428221B2Minimal overheadFast convergenceError preventionFrequency-division multiplex detailsMobile WebNetwork topology
Mobile routers establish a tree-based network topology in an ad hoc mobile network, the tree-based network topology having a single clusterhead and attached mobile routers. Each attached mobile router has a default egress interface configured for sending messages toward the clusterhead, and ingress interfaces configured for receiving messages from attached network nodes that are away from the clusterhead. A neighbor advertisement message received from an ingress interface away from a clusterhead is used by the attached mobile router to identify specified network prefixes that are reachable via the source of the neighbor advertisement message. The attached mobile router outputs on its default upstream interface a second neighbor advertisement message that specifies the network prefix used by the attached mobile router, and the specified network prefixes from the neighbor advertisement message received on the ingress interface. Hence, connectivity is established with minimal routing overhead.
Owner:CISCO TECH INC
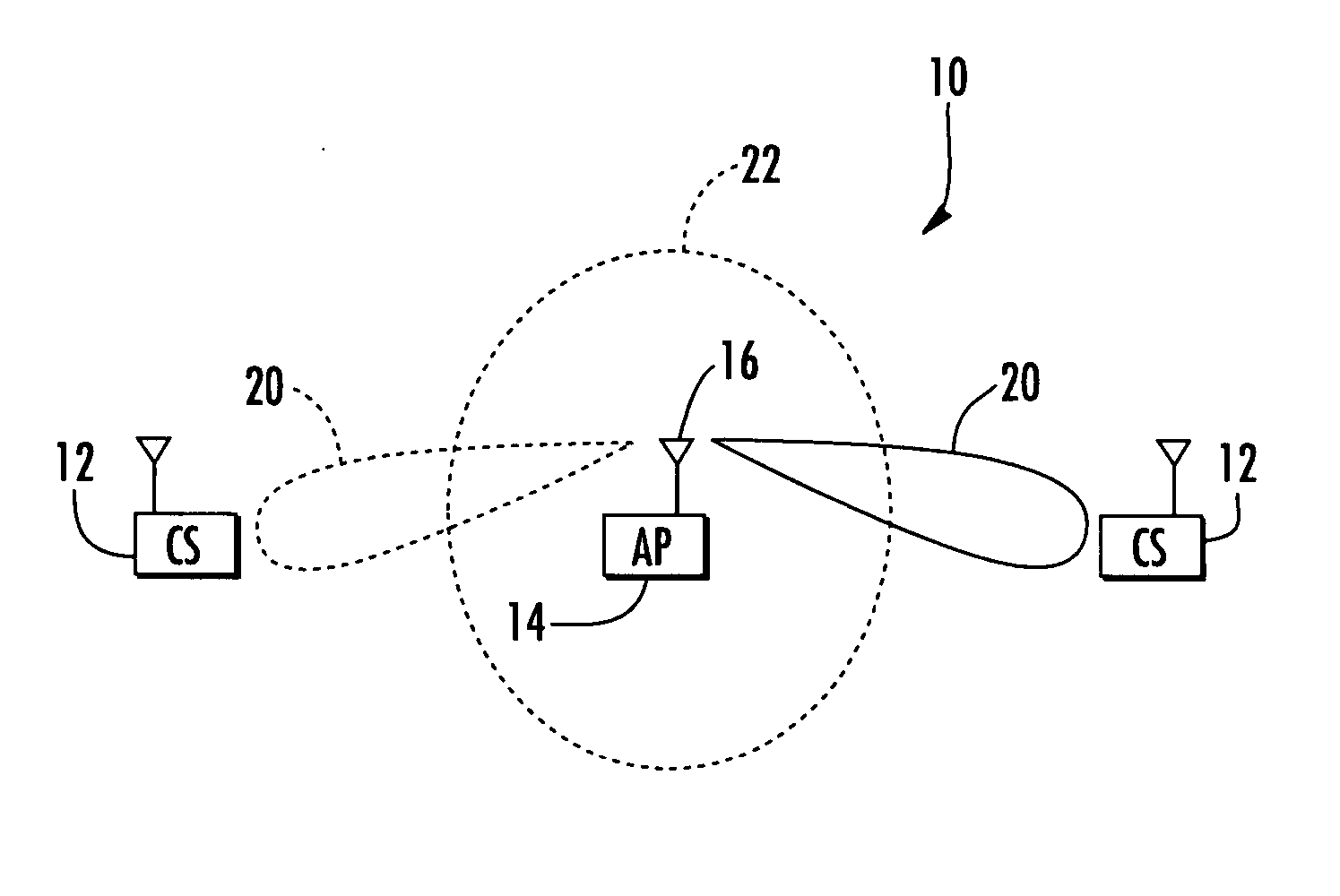
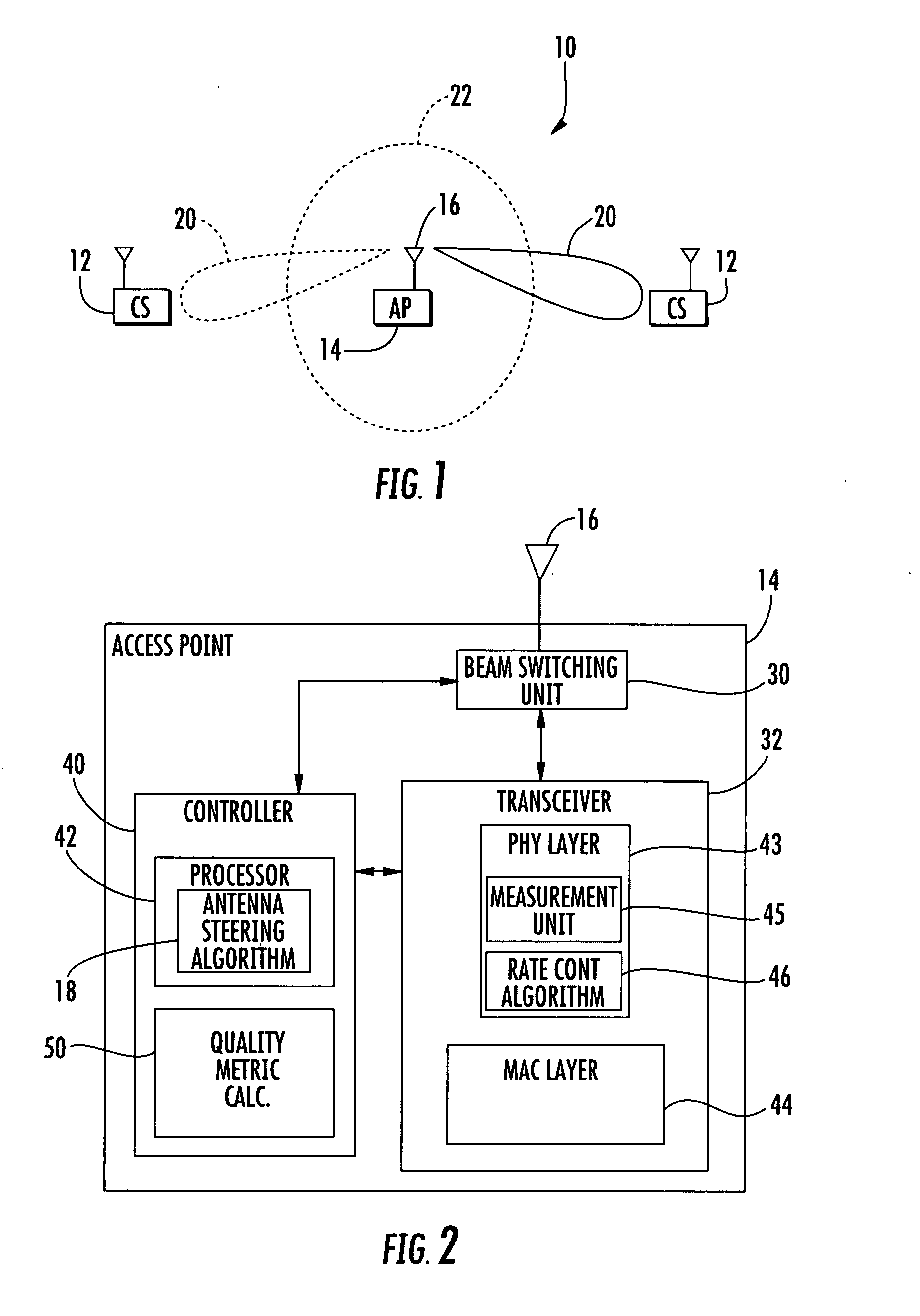
Deviation based antenna control algorithm for an access point
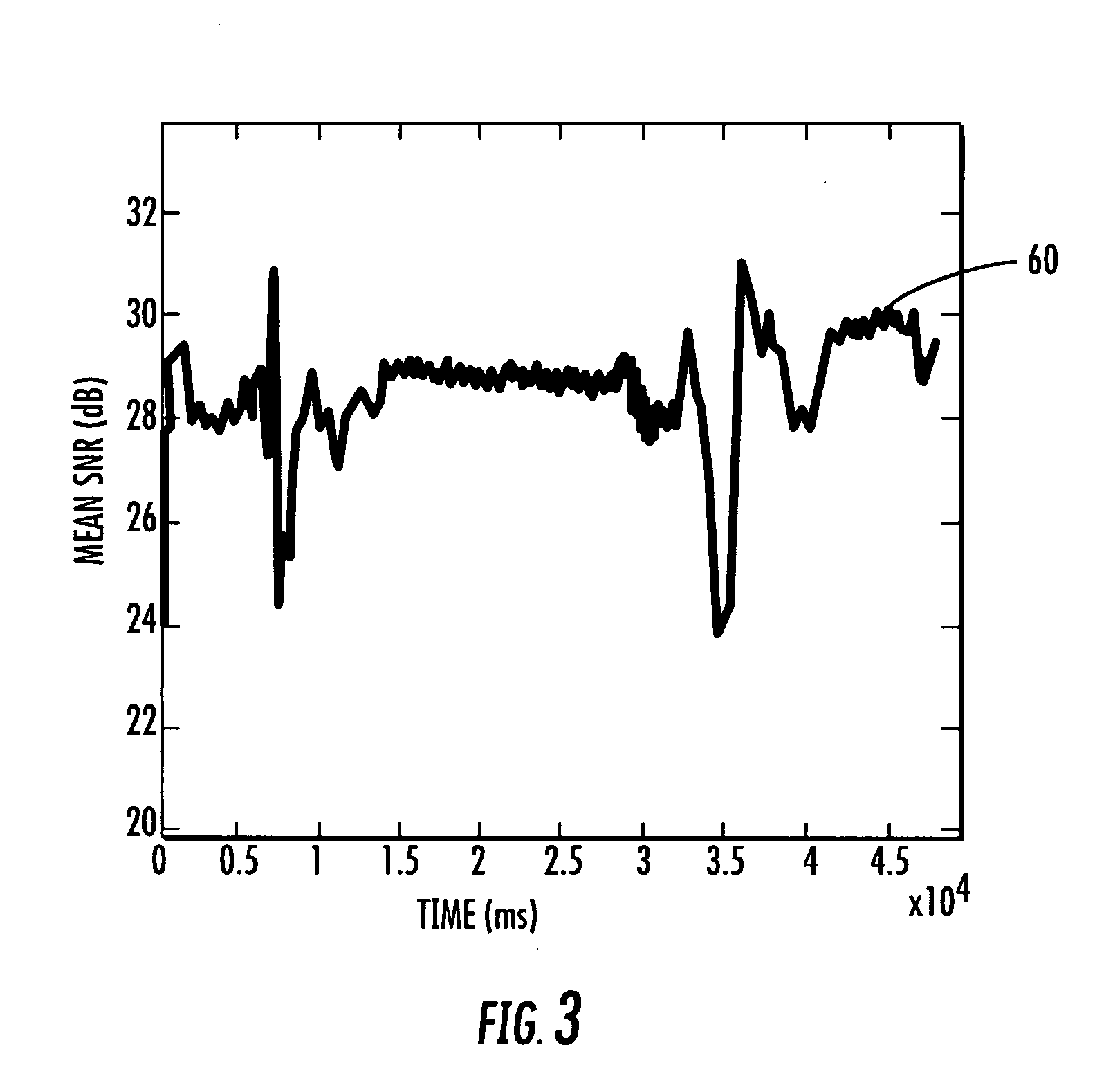
InactiveUS20070232359A1Minimal overheadQuickly to environmental changeSpecial service provision for substationMultiplex system selection arrangementsSignal-to-noise ratio (imaging)Directional antenna
An access point operating in a wireless communication network includes a smart antenna for generating directional antenna beams. A method for operating the access point includes communicating with a client station using a selected directional antenna beam, with the client station initially being in a stationary position. Signal to noise ratios of signals received from the client station within a time interval are measured. At least one variation metric of a mean of the measured signal to noise ratios within the time interval is determined. This at least one determined variation metric is compared to a threshold for determining if the client station is moving.
Owner:INTERDIGITAL TECH CORP
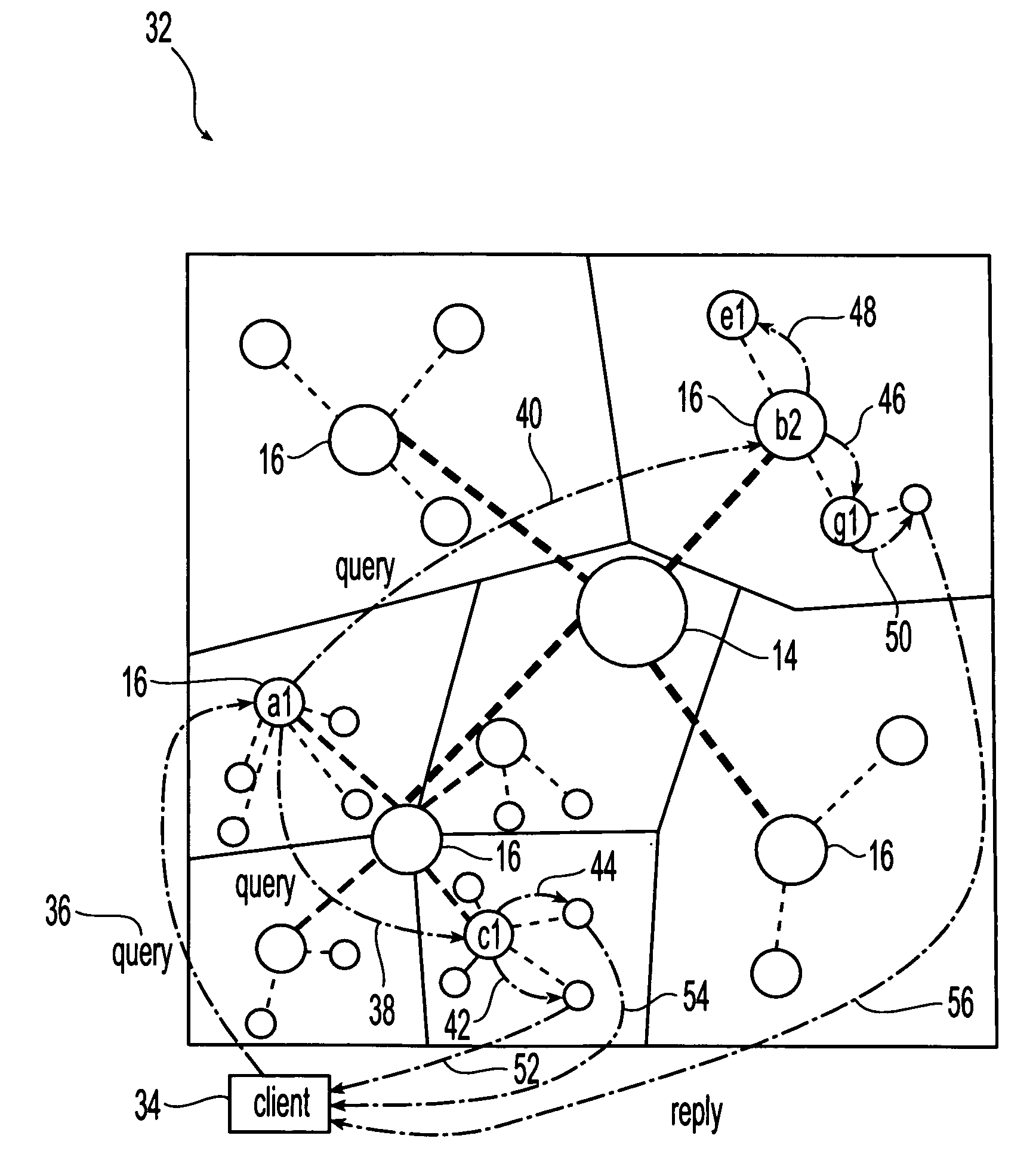
Method and system for federated resource discovery service in distributed systems
InactiveUS20070299804A1Fine granularityMinimal overheadDigital data information retrievalDigital data processing detailsComputing systemsData shipping
Methods and systems are provided for identifying and allocating resources disposed within a plurality of distributed and autonomous computing systems, each of which may have its own legacy resource discovery service. Resource identification servers disposed within each one of the distributed computing systems communicate resource attribute data to a tree hierarchy of dedicated servers. The resource attribute data are maintained in native formats within the distributed computing systems and are mapped to a common format provided by the dedicated servers. The resource attribute data are aggregated at each node within the tree hierarchy, communicated up through the tree hierarchy to one or more root nodes and replicated down through all of the nodes. Additional system robustness is provided through period resource checks and resource attribute data updates. Resource allocation queries are submitted to any level node within the hierarchy and forwarded to the proper computing system for processing.
Owner:IBM CORP
System And Method Of Memory Access Of Multi-Dimensional Data
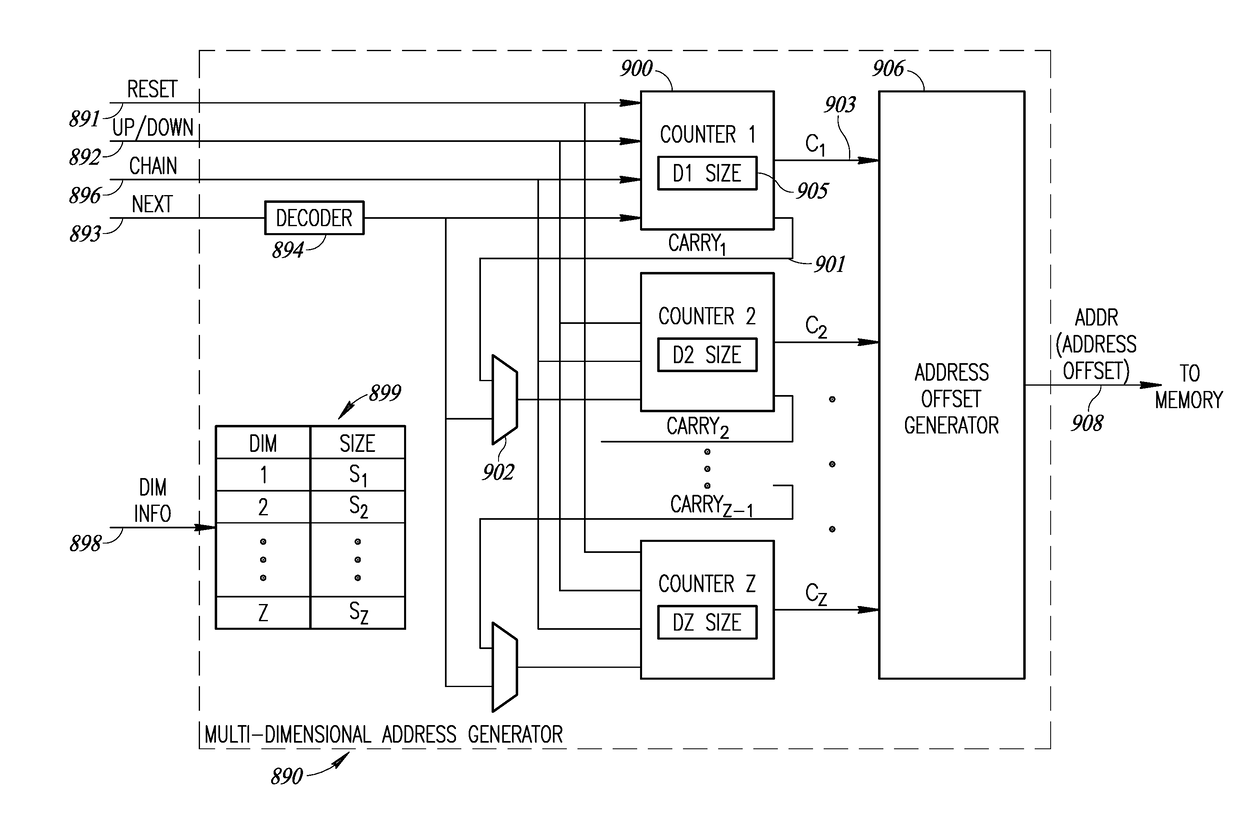
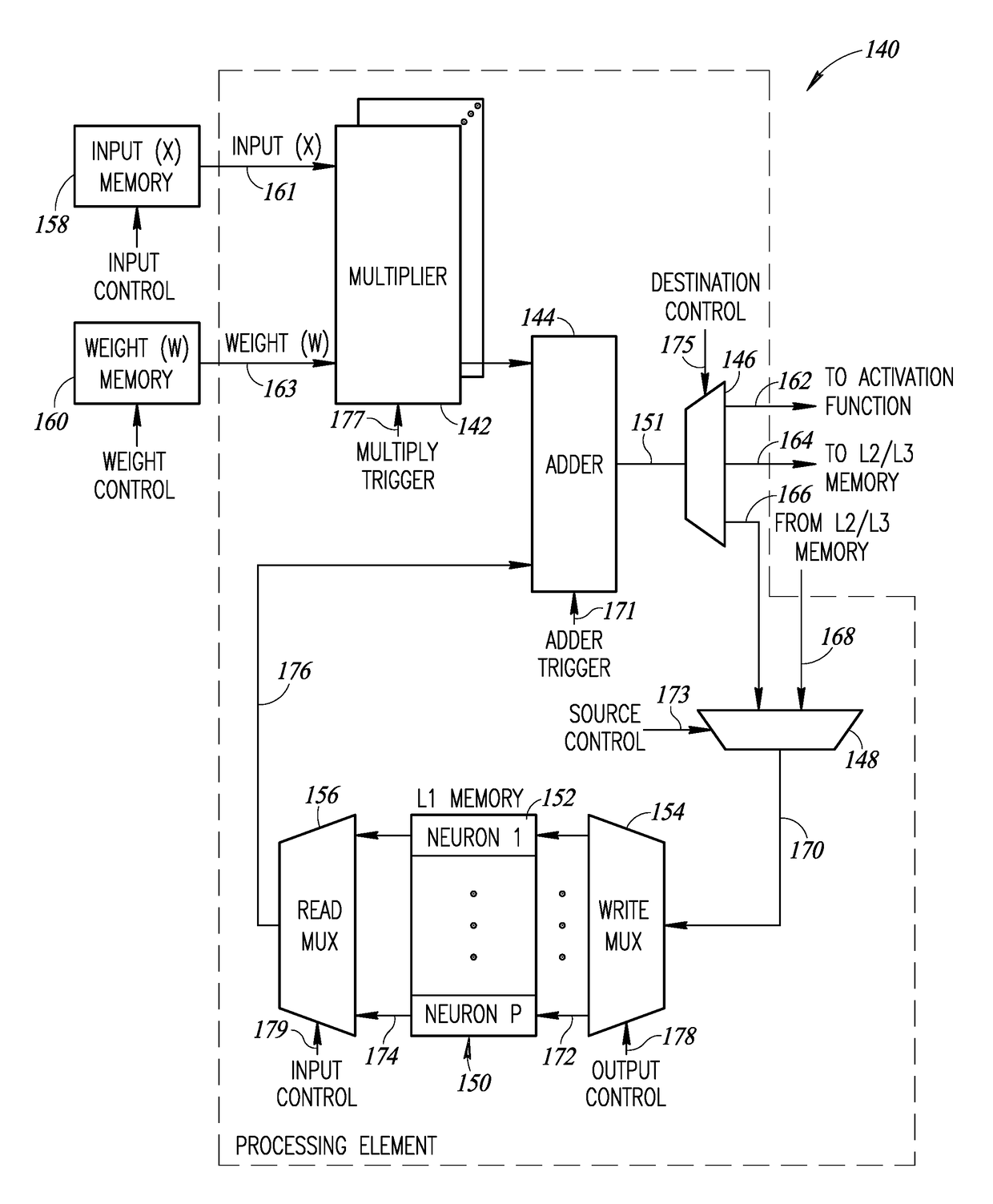
ActiveUS20180285254A1More efficientIncrease unit densityDigital data processing detailsMemory adressing/allocation/relocationLean controlNerve network
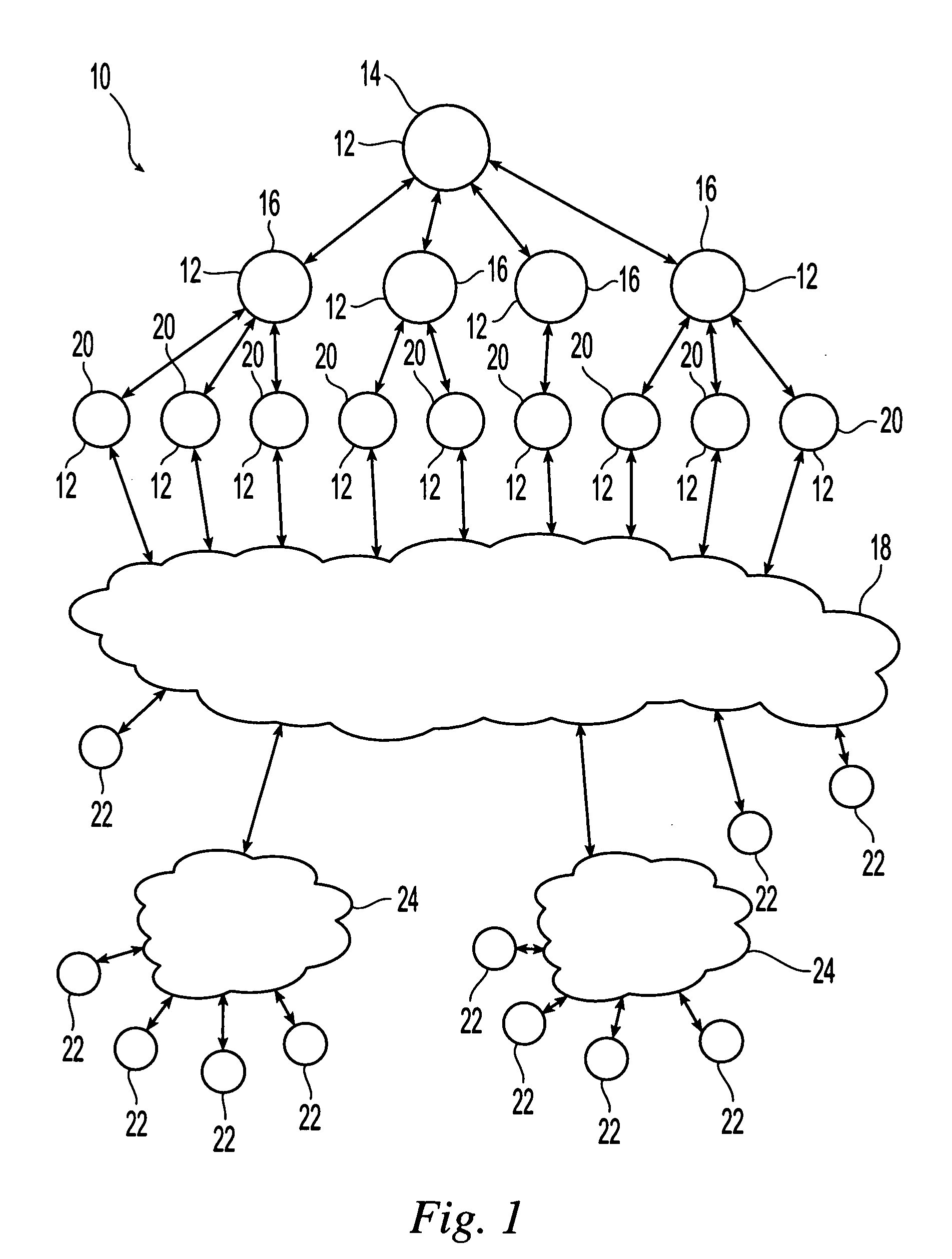
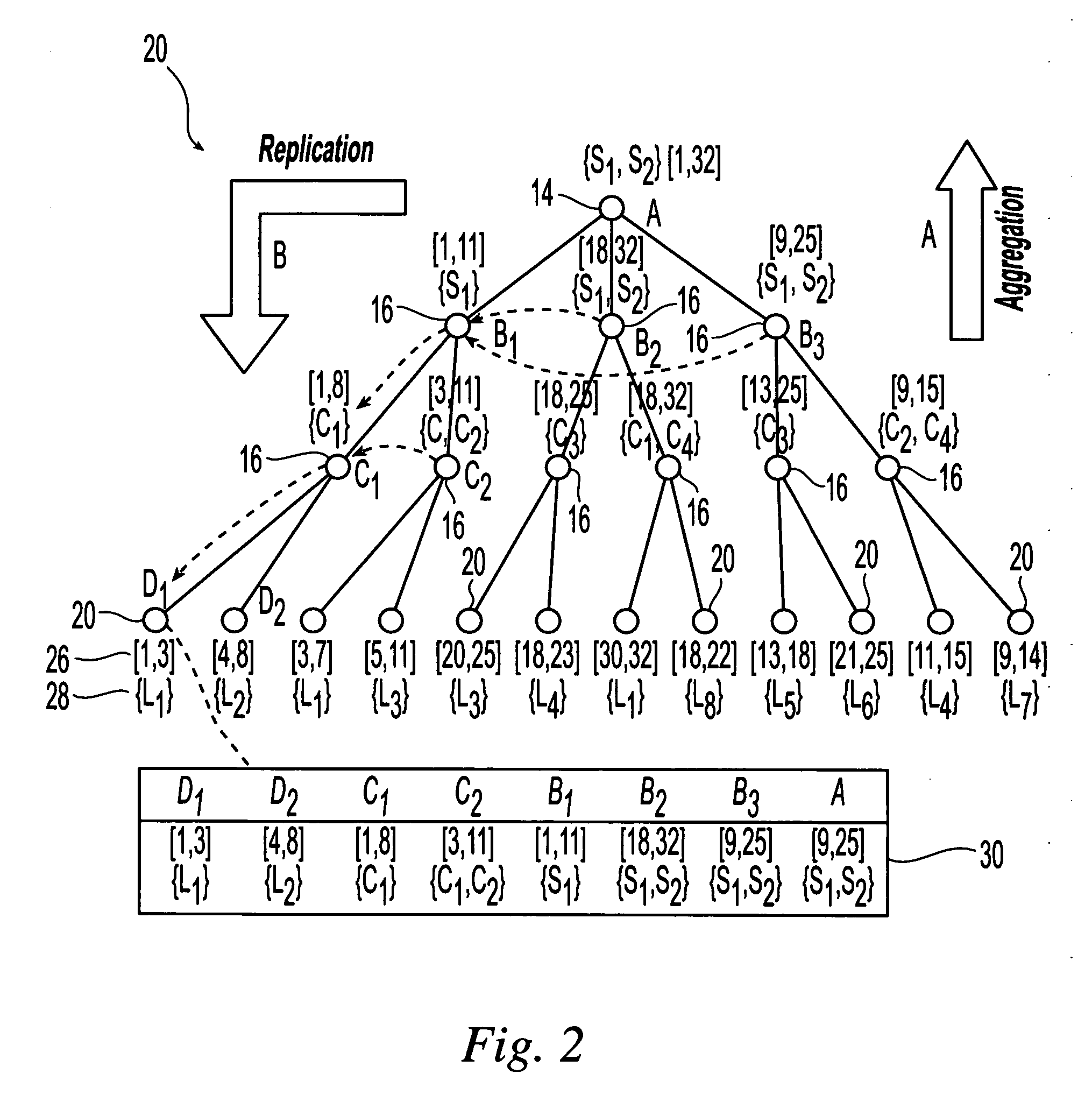
A novel and useful system and method of accessing multi-dimensional data in memory. The invention is applicable to neural network (NN) processing engines adapted to implement artificial neural networks (ANNs). The NN processor is constructed from self-contained computational units organized in a hierarchical architecture. The homogeneity enables simpler management and control of similar computational units, aggregated in multiple levels of hierarchy. Computational units are designed with minimal overhead as possible, where additional features and capabilities are aggregated at higher levels in the hierarchy. On-chip memory provides storage for content inherently required for basic operation at a particular hierarchy and is coupled with the computational resources in an optimal ratio. Lean control provides just enough signaling to manage only the operations required at a particular hierarchical level. Dynamic resource assignment agility is provided which can be adjusted as required depending on resource availability and capacity of the device.
Owner:HAILO TECH LTD
Fluidically isolated pumping and metered fluid delivery system and methods
InactiveUS20030143754A1Avoid damageMinimize electric power consumptionBioreactor/fermenter combinationsFunctional valve typesBall bearingBiological fluids
An apparatus and method for pumping and optionally mixing of small quantities of biological fluid wherein the pumping mechanism is segregated from the biological fluid being pumped. The micro-pump pushes the biological fluid by compressing a cartridge housing the blood and reagents with collapsible walls with a roller or ball bearing, synchronized perpendicular plungers, or an acutely-angled member to push the biological fluid by collapsing the walls of the cartridge in the direction of flow.
Owner:AGILENT TECH INC
Fluidically isolated pumping and metered fluid delivery system and methods
InactiveUS7056475B2Minimize electric power consumptionMinimal overheadBioreactor/fermenter combinationsBiological substance pretreatmentsBall bearingEngineering
Owner:AGILENT TECH INC
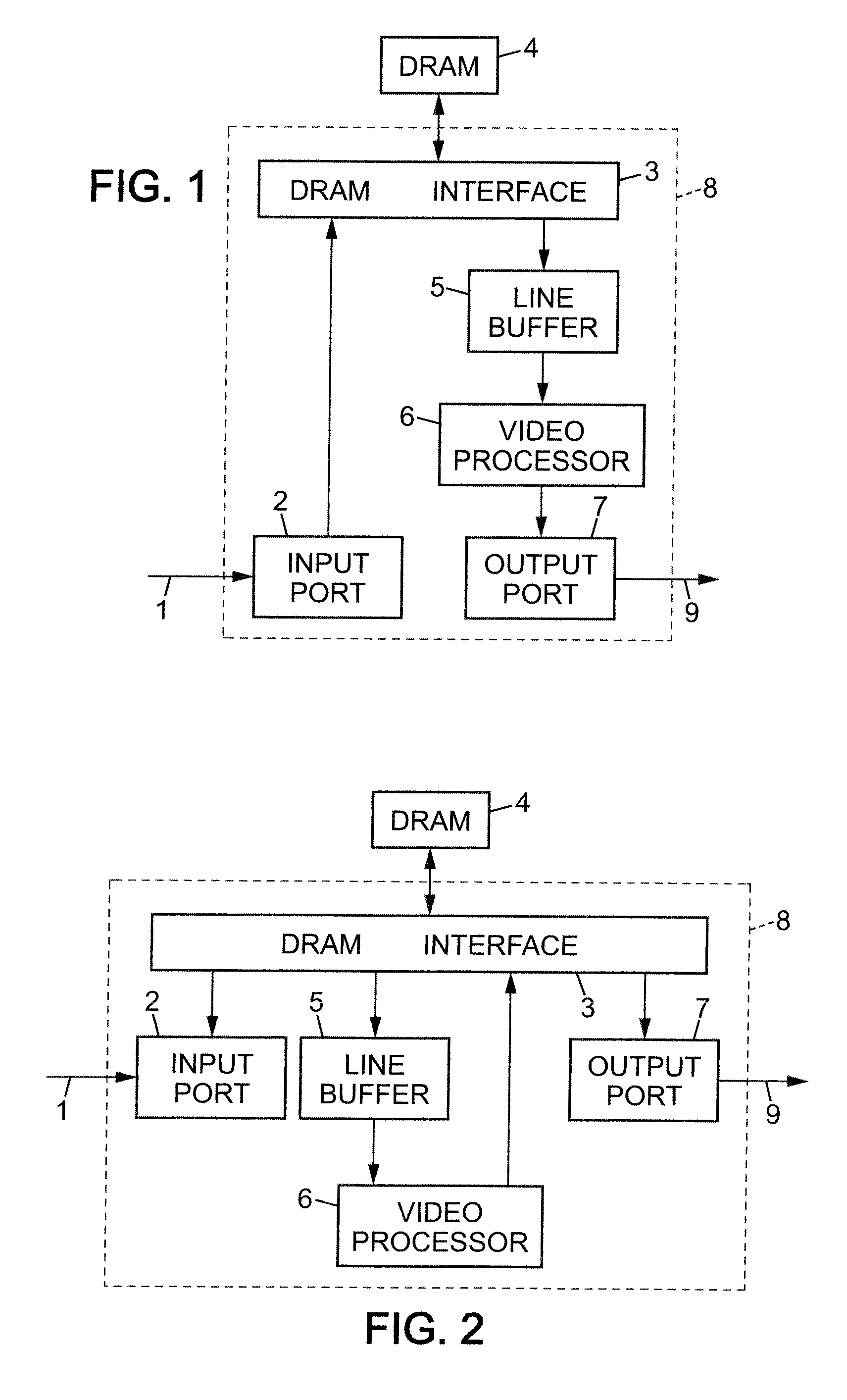
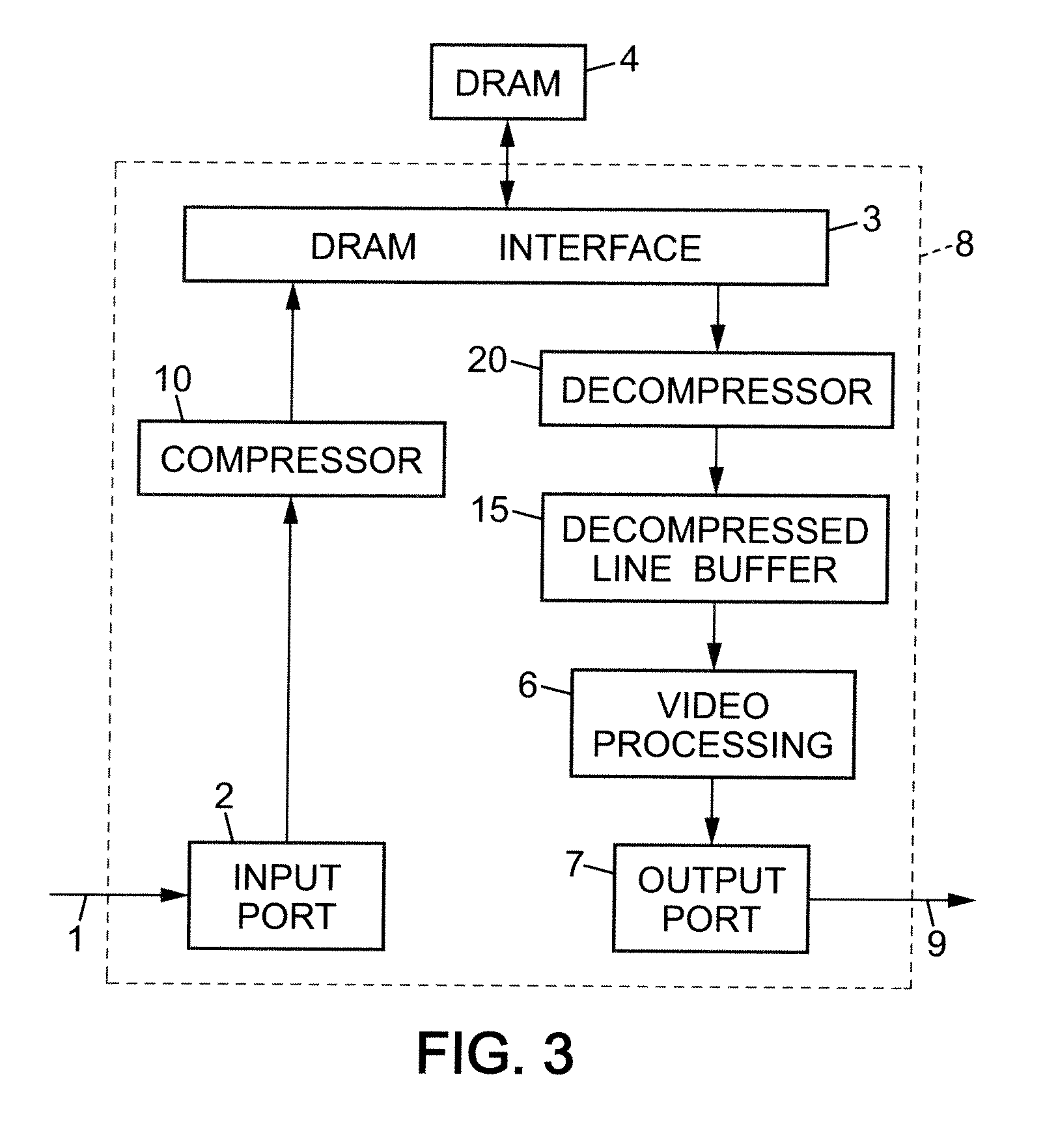
Frame buffer compression for video processing devices
ActiveUS20100220783A1Increase the compression ratioQuality improvementColor television with pulse code modulationColor television with bandwidth reductionVideo processingComputer science
For compressing a video signal, a local multiscale transform is applied to a frame of the video signal to obtain coefficient blocks. The coefficients of each block are distributed into a plurality of coefficient groups, and for at least one of the groups, a common exponent is determined for encoding the coefficients of the group, and respective mantissas are determined for quantizing the coefficients of the group in combination with the common exponent. Coding data including each exponent determined for a coefficient group and the mantissas quantizing the coefficients of the group in combination with this exponent are stored in an external frame buffer.
Owner:ZORAN CORPORATION
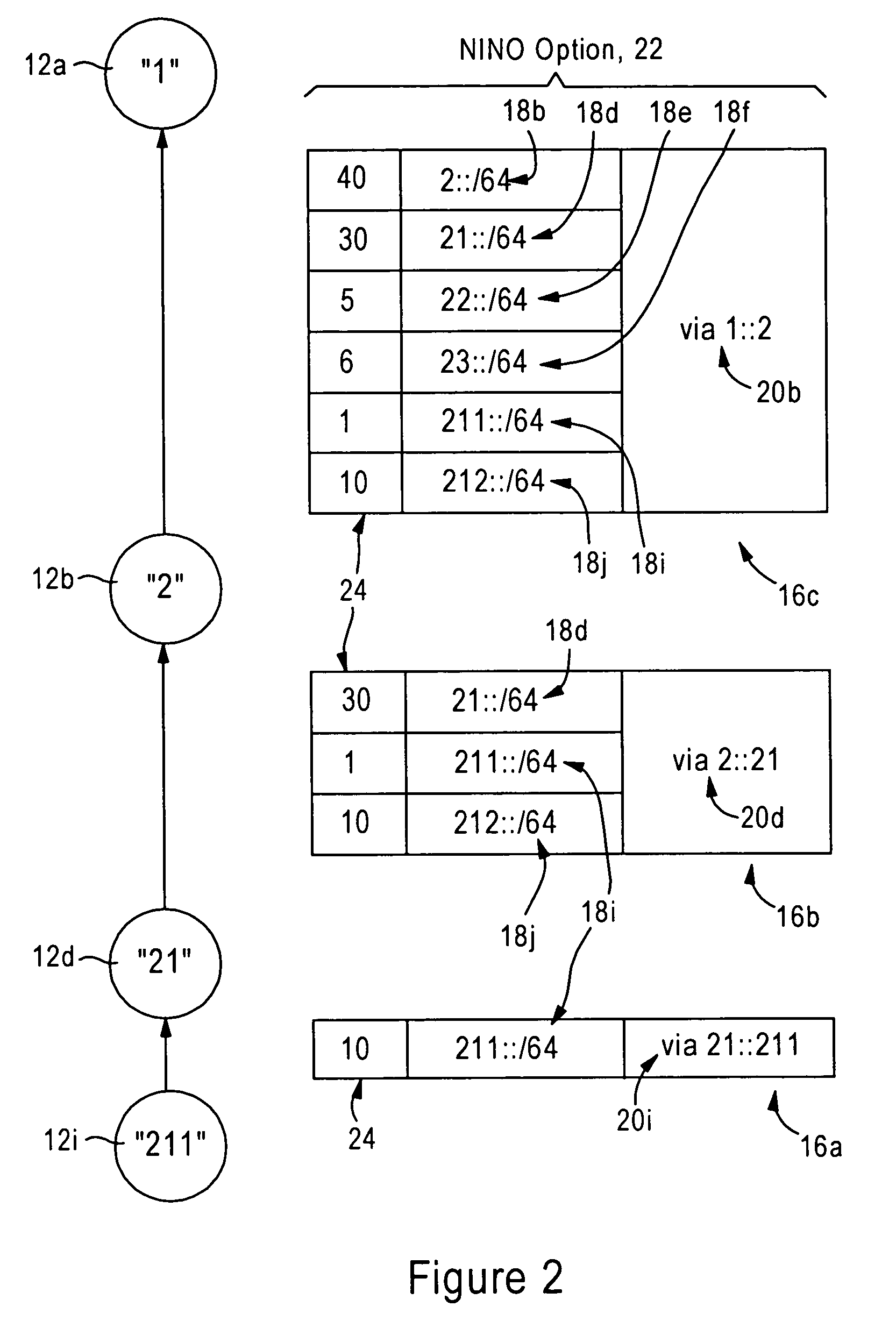
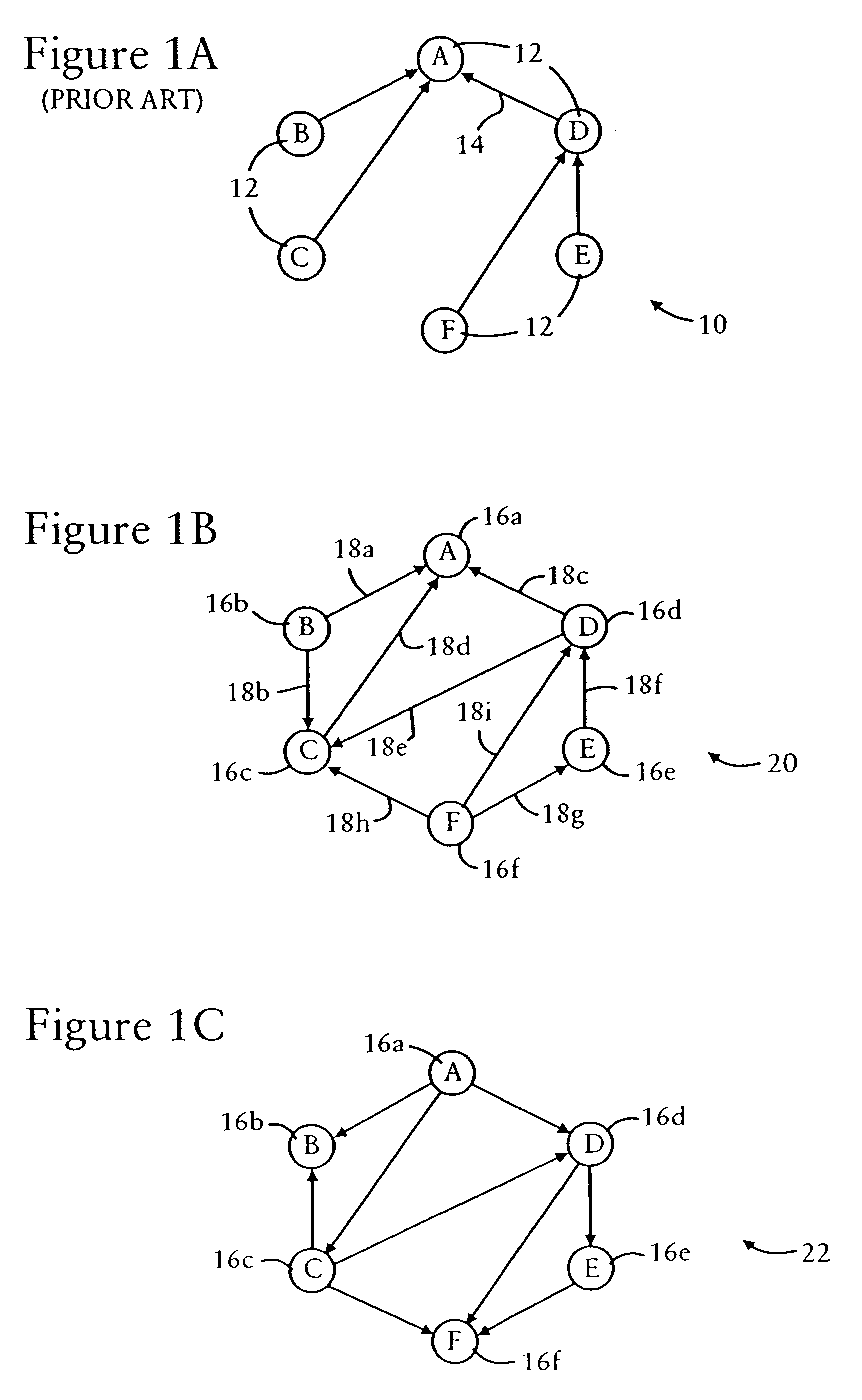
Directed acyclic graph discovery and network prefix information distribution relative to a clusterhead in an ad hoc mobile network
ActiveUS7860025B2Processing requirement is minimalReliable transmissionDigital computer detailsTime-division multiplexMobile WebDirected acyclic graph
Each mobile router in an ad hoc mobile network is configured for concurrently attaching to multiple parents advertising respective parent depths relative to a clusterhead of the ad hoc mobile network. The mobile router selects an advertised depth relative to the clusterhead based on adding a prescribed increment to a maximum one of the parent depths, enabling the mobile routers to form a directed acyclic graph relative to the clusterhead. Each mobile router sends to each of its parents a neighbor advertisement message specifying at least one reachable prefix, a corresponding cost for reaching the reachable prefix, and a corresponding sequence identifier that enables the parents to validate the neighbor advertisement message relative to stored router entries. Hence, mobile routers automatically can form a directed acylic graph relative to the clusterhead, and can distribute routing information with minimal overhead.
Owner:CISCO TECH INC
Memory and processor efficient network communications protocol
InactiveUS20060098662A1Minimal overheadData switching by path configurationForward error control useTelecommunicationsNetwork Communication Protocols
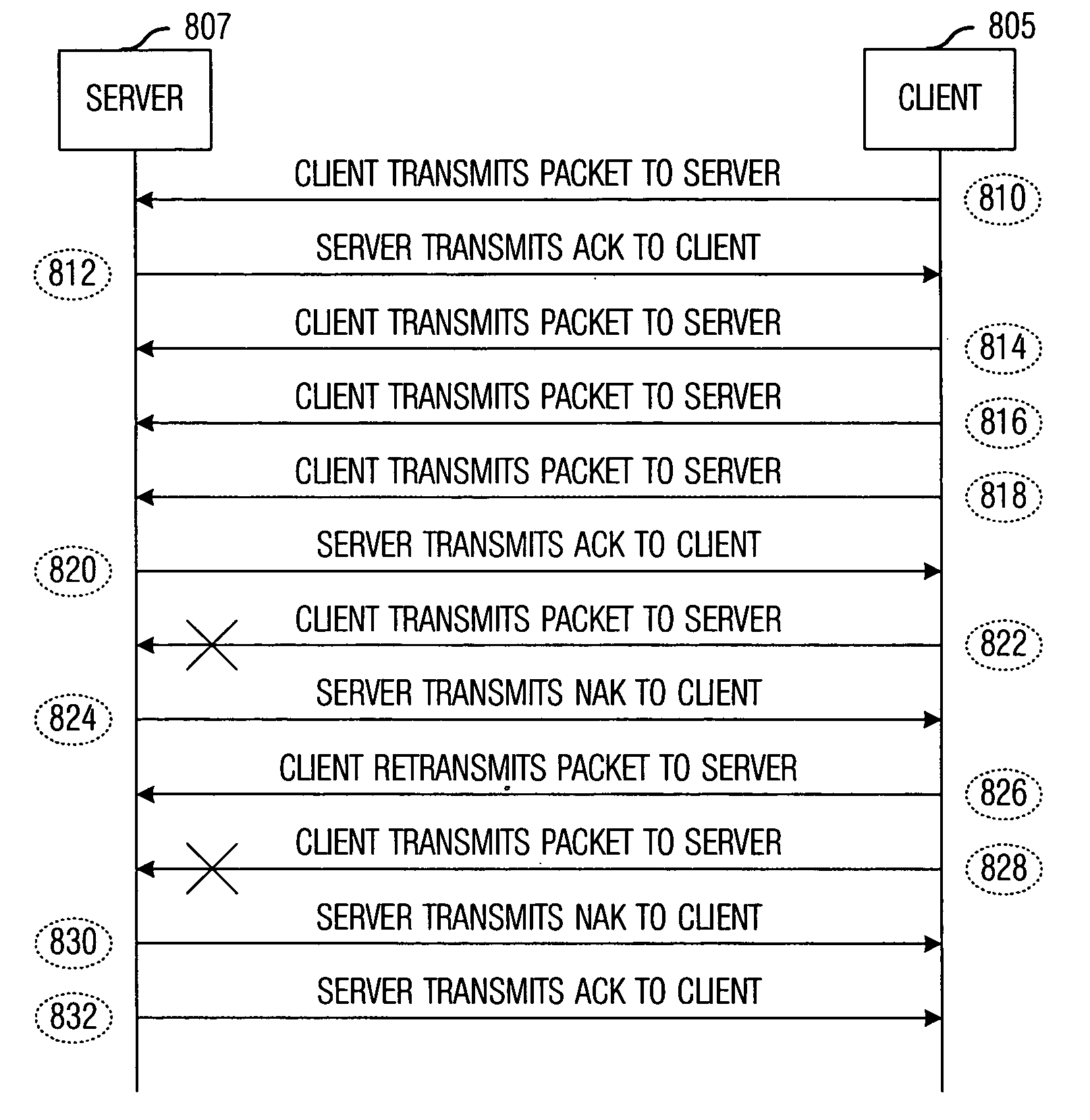
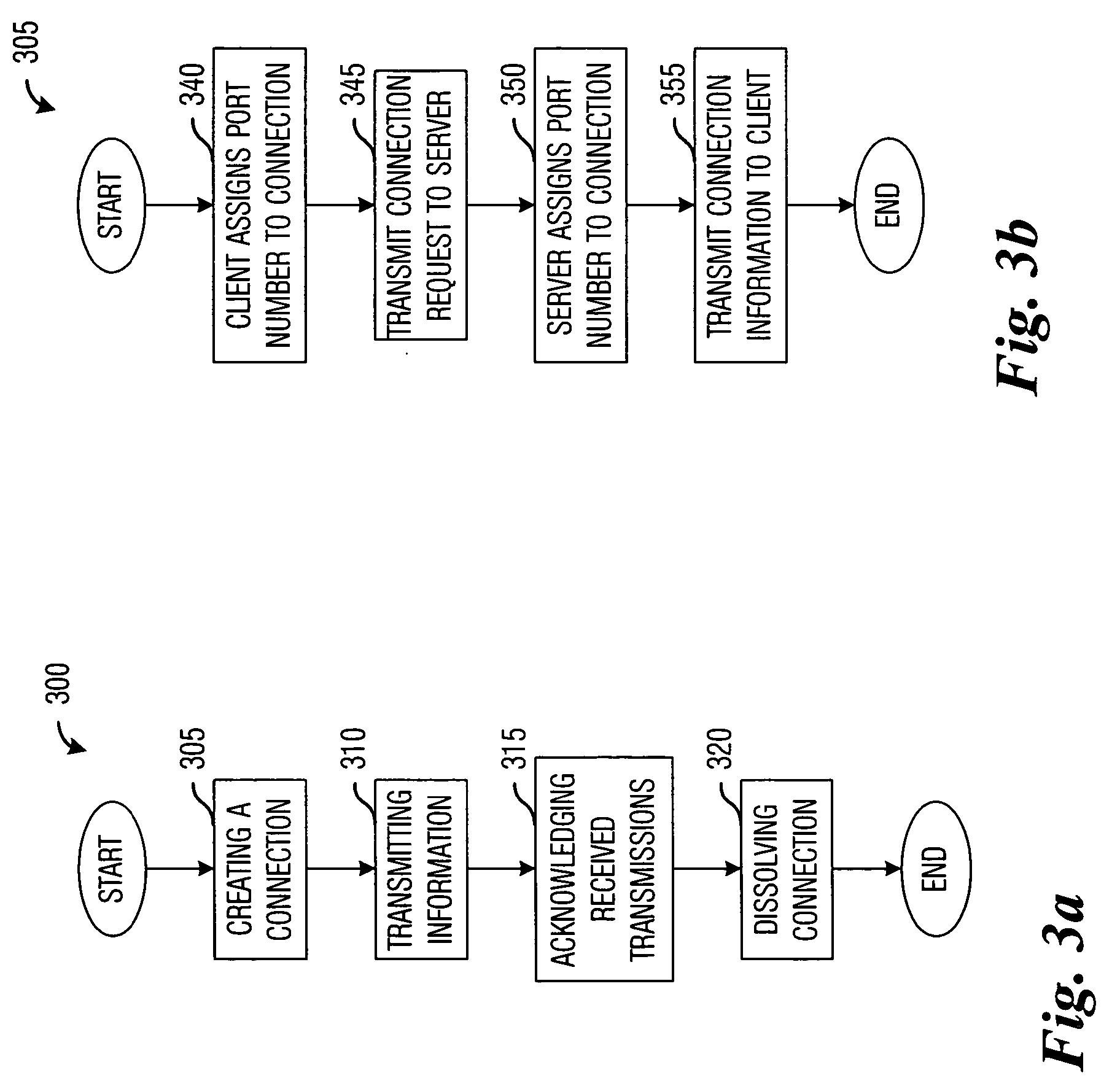
System and method for a full featured network communications protocol that is both memory and processor efficient. A preferred embodiment comprises a method for transmitting information between electronic devices, the method comprising creating a connection between a pair of electronic devices, sending a packet between the pair, acknowledging a receipt of the packet by a receiver of the packet, and dissolving the connection when it is no longer needed. The creating of the connection comprises assigning a port number to the connection at an initiating electronic device and then transmitting a connection request containing the port number to a servicing electronic device. After the transmitting, the creating further comprises receiving a second port number to the connection from the servicing electronic device.
Owner:TEXAS INSTR INC
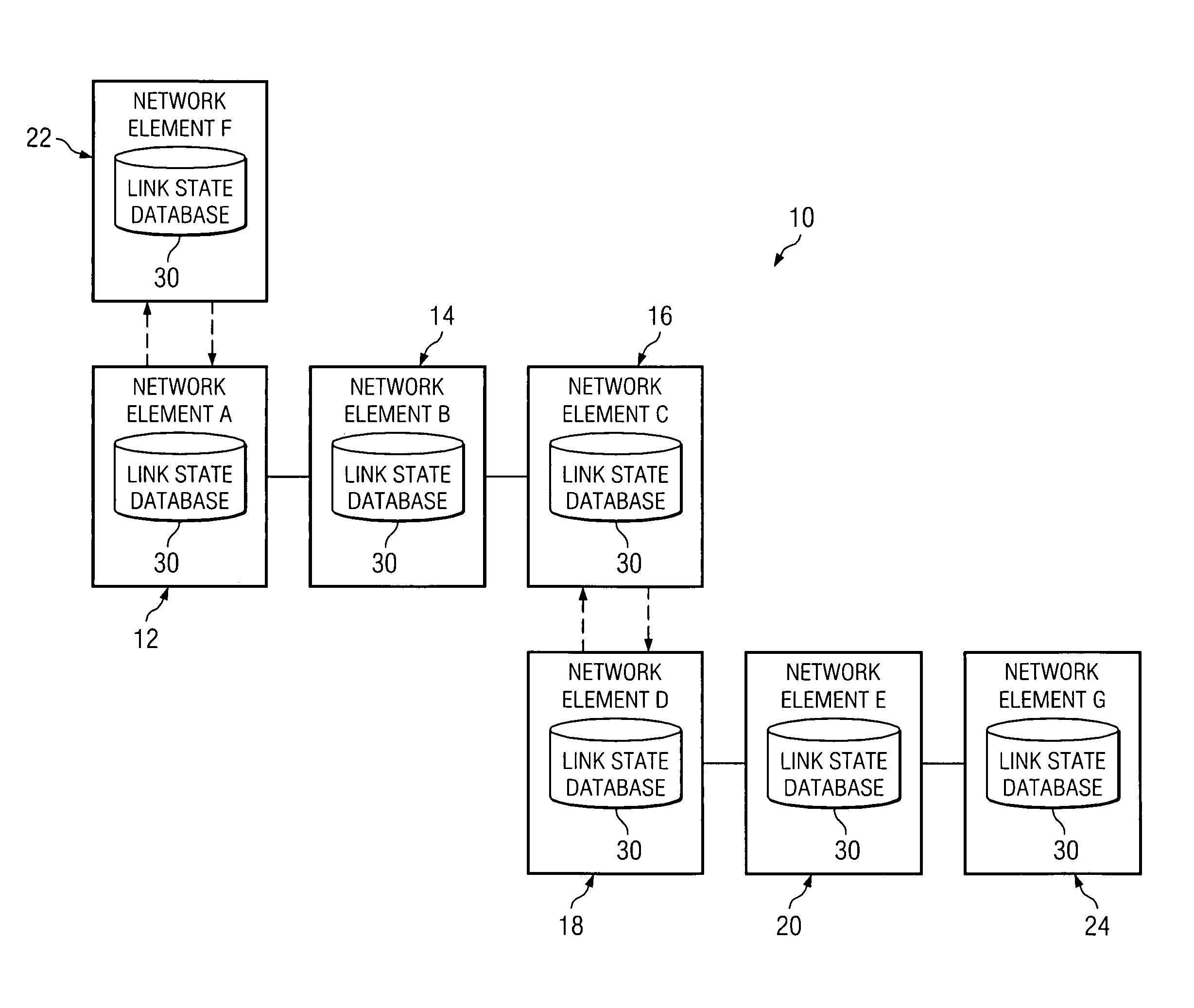
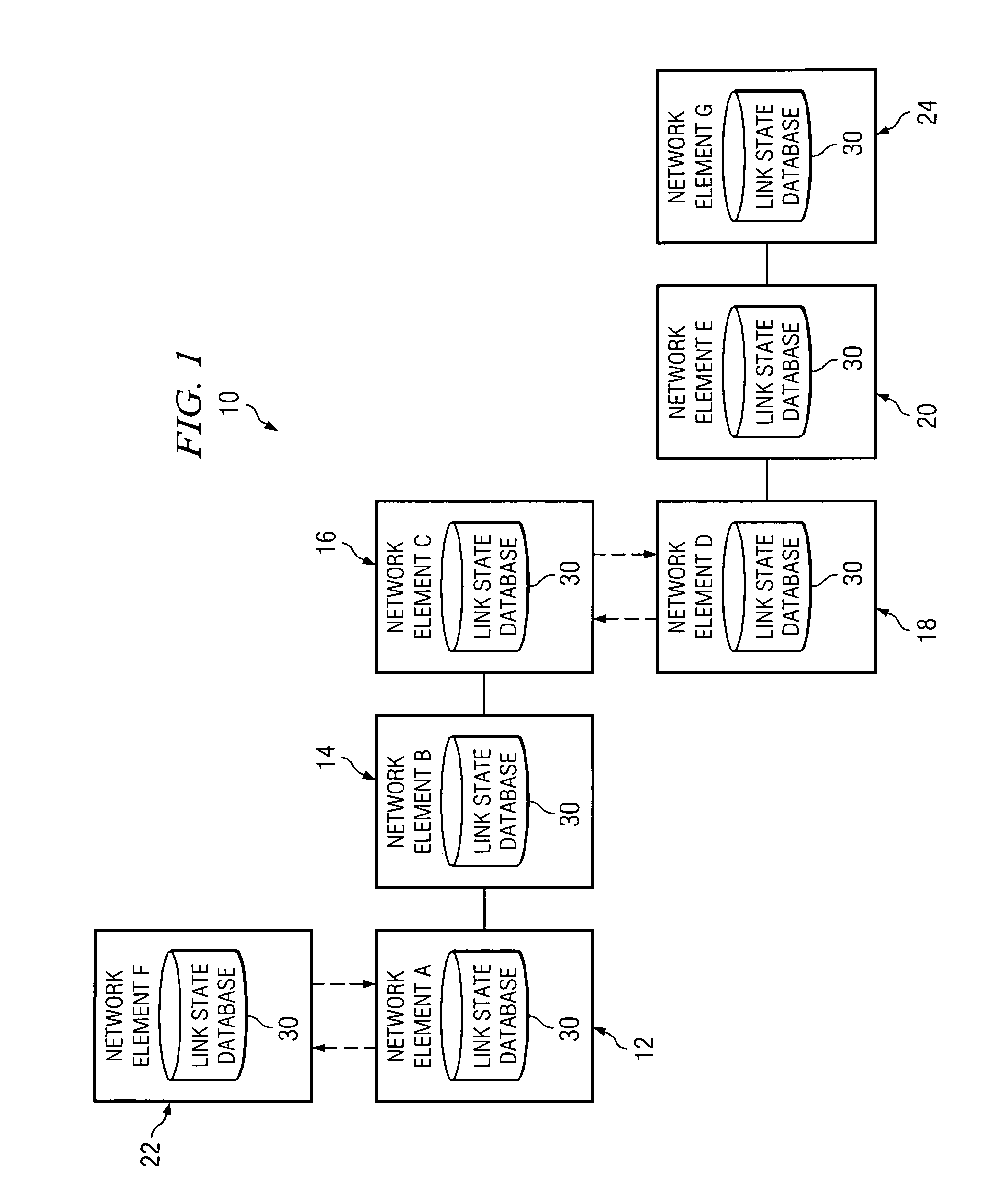
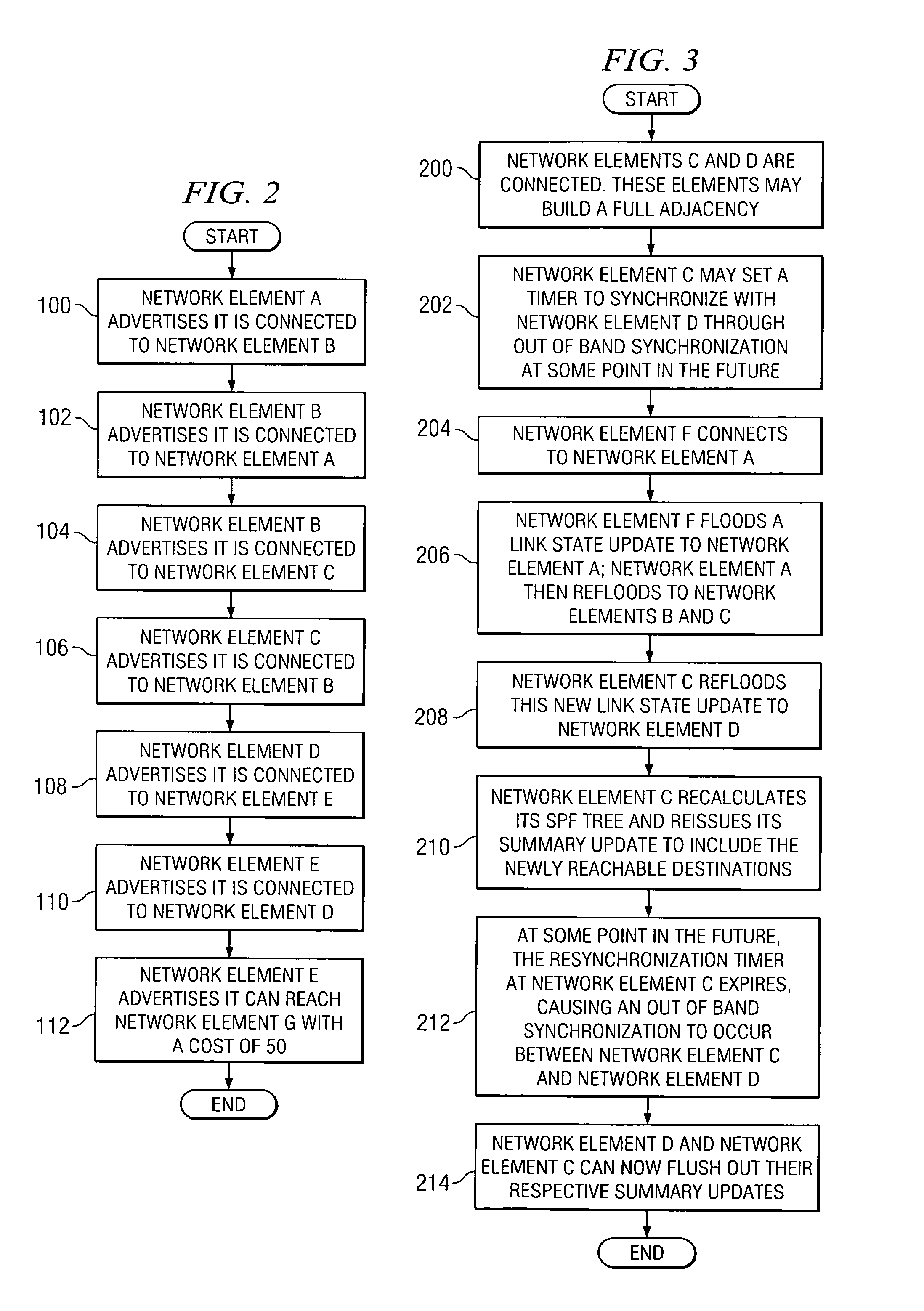
System and method for synchronizing link state databases in a network environment
ActiveUS7391730B1Avoid modificationRealize the operationError preventionTransmission systemsDistributed computingWeb environment
A method for communicating packets in a network environment is provided that includes communicating, by a first network element, a first summary update to a second network element. The method further includes receiving a second summary update from the second network element. The exchange of the first and second summary updates achieves adjacency between the first and second network elements. The first and second summary updates include, at least, locally generated state information and a single link state.
Owner:CISCO TECH INC
Neural Network Processing Element Incorporating Compute And Local Memory Elements
ActiveUS20180285727A1High computational unit densityReduce power consumptionResource allocationDigital data processing detailsLean controlNerve network
A novel and useful neural network (NN) processing core adapted to implement artificial neural networks (ANNs) and incorporating processing circuits having compute and local memory elements. The NN processor is constructed from self-contained computational units organized in a hierarchical architecture. The homogeneity enables simpler management and control of similar computational units, aggregated in multiple levels of hierarchy. Computational units are designed with minimal overhead as possible, where additional features and capabilities are aggregated at higher levels in the hierarchy. On-chip memory provides storage for content inherently required for basic operation at a particular hierarchy and is coupled with the computational resources in an optimal ratio. Lean control provides just enough signaling to manage only the operations required at a particular hierarchical level. Dynamic resource assignment agility is provided which can be adjusted as required depending on resource availability and capacity of the device.
Owner:HAILO TECH LTD
Method of generating and presenting kernel data
ActiveUS7099866B1Minimal slowdownMinimizes numberData processing applicationsDigital data processing detailsData sourceSemantics
IDDS is implemented as a kernel resident data source which provides per-system call audit records into user space in a timely manner. Each invocation of a system call is audited and a record of the activity is placed into a circular buffer in the kernel. A user-space process reads the data from the buffer via a device driver interface. A device driver provides a clean interface between the kernel and the IDS. The semantics of device drivers are familiar to most UNIX programmers, following the standard file-based open-read-write-close paradigm.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
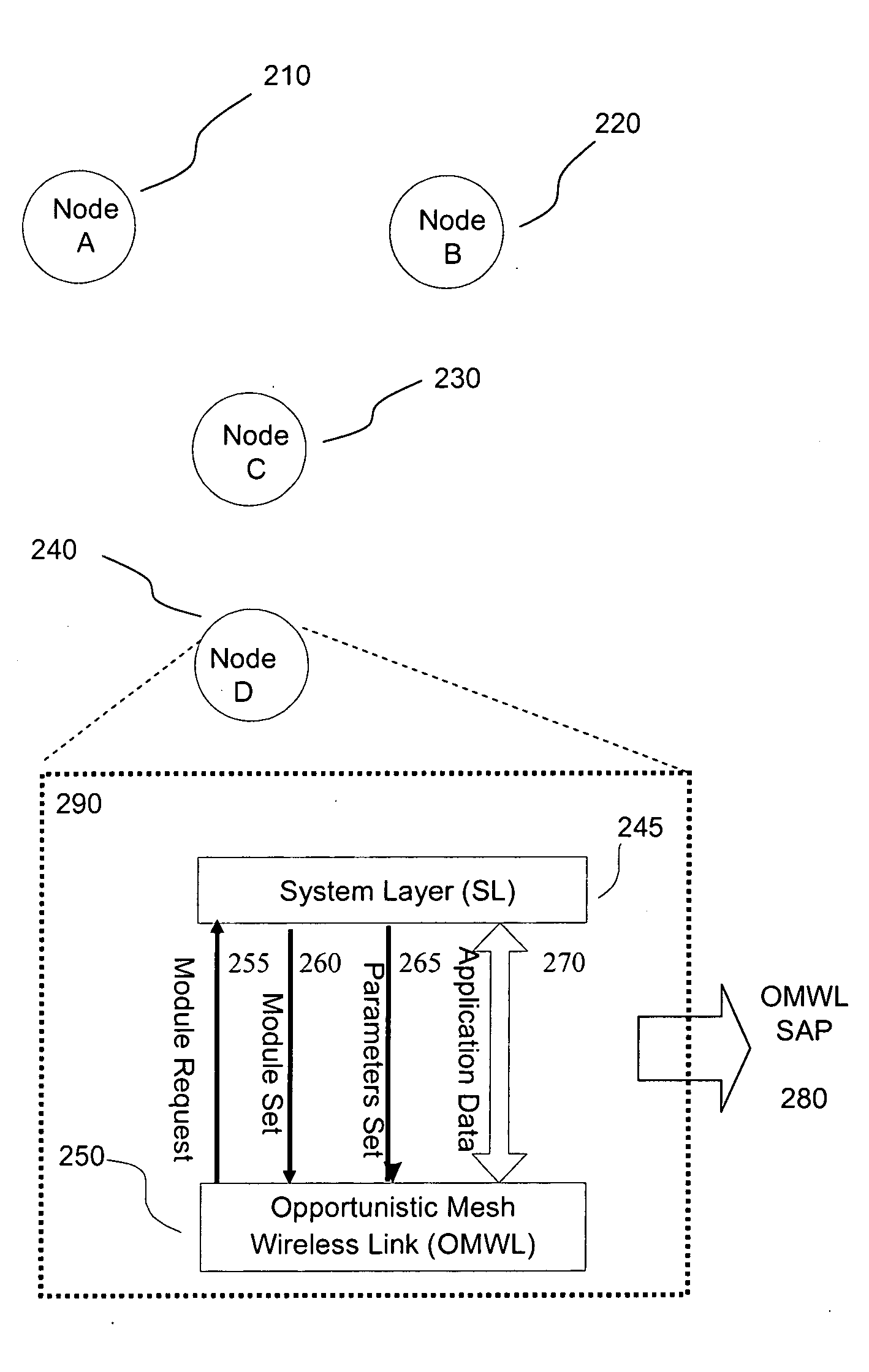
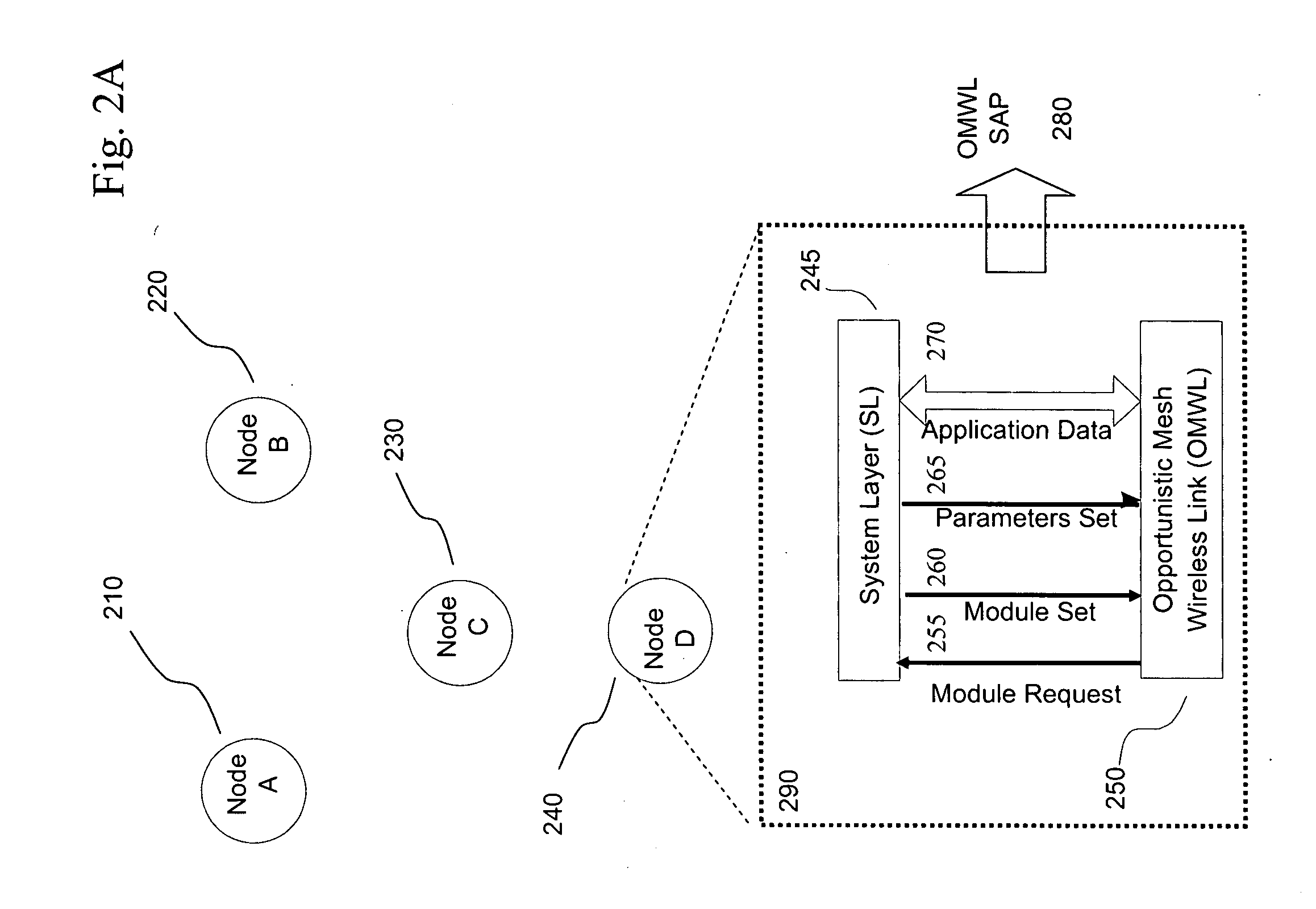
Opportunistic wireless mesh network methods
ActiveUS20080075010A1Improve performanceMinimal overheadBroadcast with distributionEnergy efficient ICTReference modelWireless mesh network
The invention relates to opportunistic wireless mesh networks which operate under random networking conditions. Such random network conditions typically limit the effectiveness of prior art wireless mesh networks, and more particularly to those supporting low power devices within the wireless network. Random network conditions include: random power supply, random node distribution, random node mobility, high mobility of nodes, random wireless link fluctuations, and random application traffic. The opportunistic wireless mesh network utilizes a two-layer architecture Embedded Wireless Interconnect (EWI) framework, which is adopted as the architecture reference model. A mesh network according to the invention supports opportunistically determining both mesh interconnections and network transmission routes by providing nodes with broadcast modules and unicast modules. The methods provide novel low power opportunistic wireless mesh networks that support interconnection with existing network infrastructures such as Open System Interconnect (OSI) based wired or wireless networks. Network embodiments provide protocol translation at network borders to allow micro- and macro-mobility management for wireless devices and their associated users. Additionally embodiments of the opportunistic wireless mesh networks address reduction in power consumption.
Owner:SENNET COMM
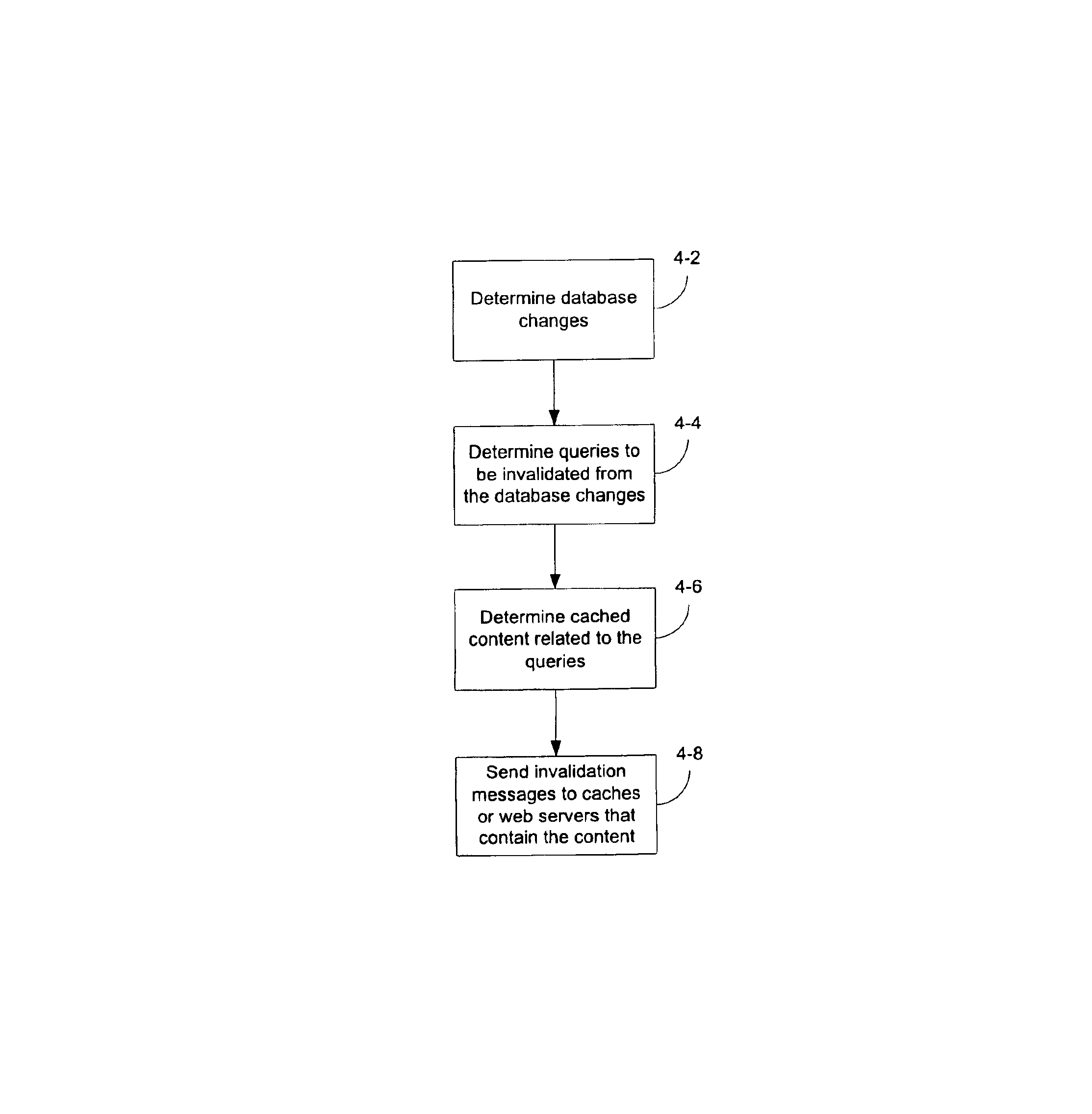
System and methods for invalidation to enable caching of dynamically generated content
InactiveUS6889234B1Minimal overheadTechnique is effectiveDatabase updatingData processing applicationsDatabase
Various systems and methods are describe for determining dynamically generated content to be invalidated as a result of changes to underlying data. In one method, invalidation processing is performed using a delayed version of the database that reflects the state of the database at the beginning of a preceding processing cycle, and an update log that reflects all updates since the beginning of the preceding processing cycle. In another method, invalidation processing is performed by locking a database which is locked during processing so as to reflect the state of the database at the beginning of processing, and an update log that reflects all updates to the database since the beginning of the preceding processing cycle. In another method, invalidation processing uses the database while it is freely updated during said processing, and the update log of the database.
Owner:NEC CORP
Probabilistic framework for the highly efficient correlation of call chains with hardware events
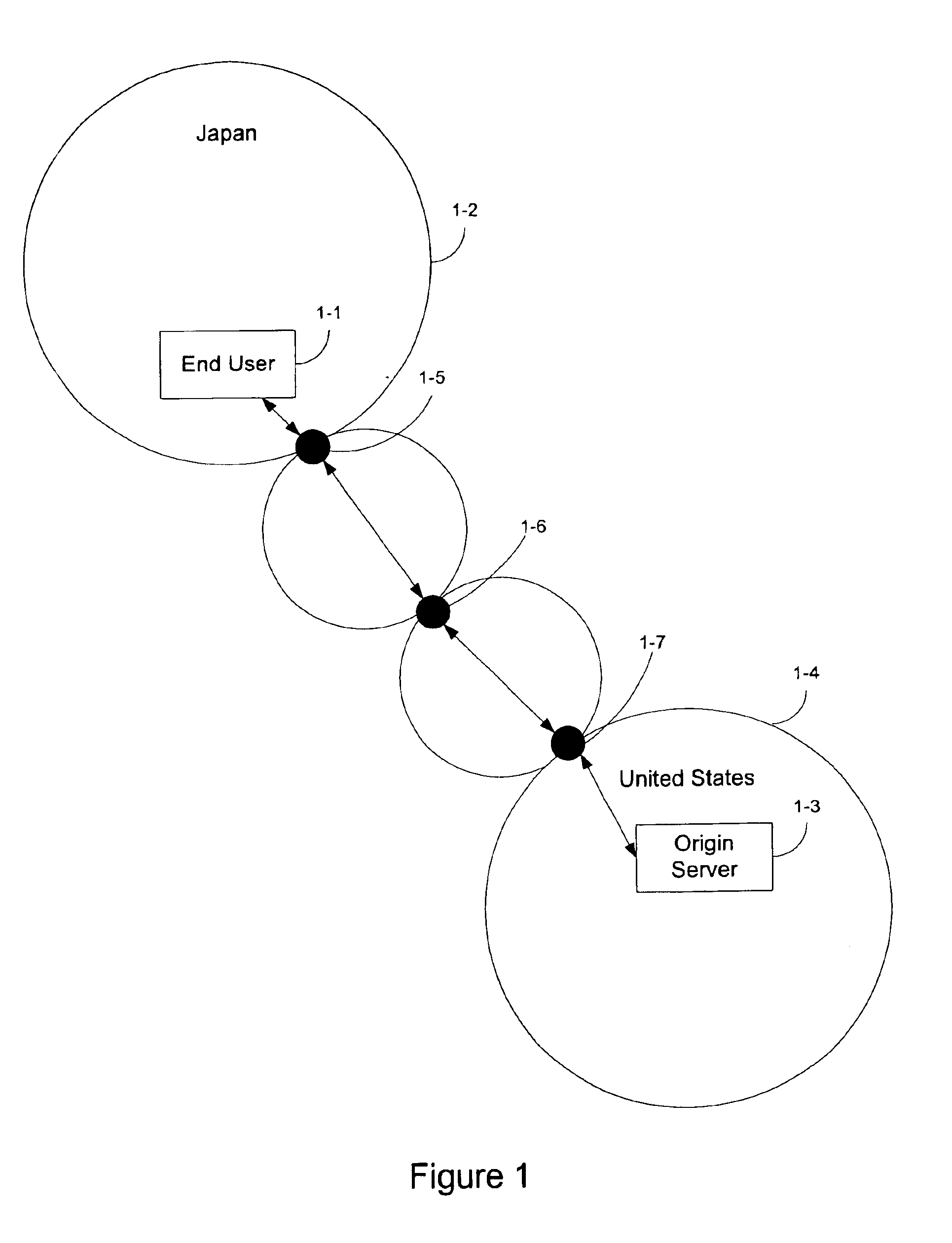
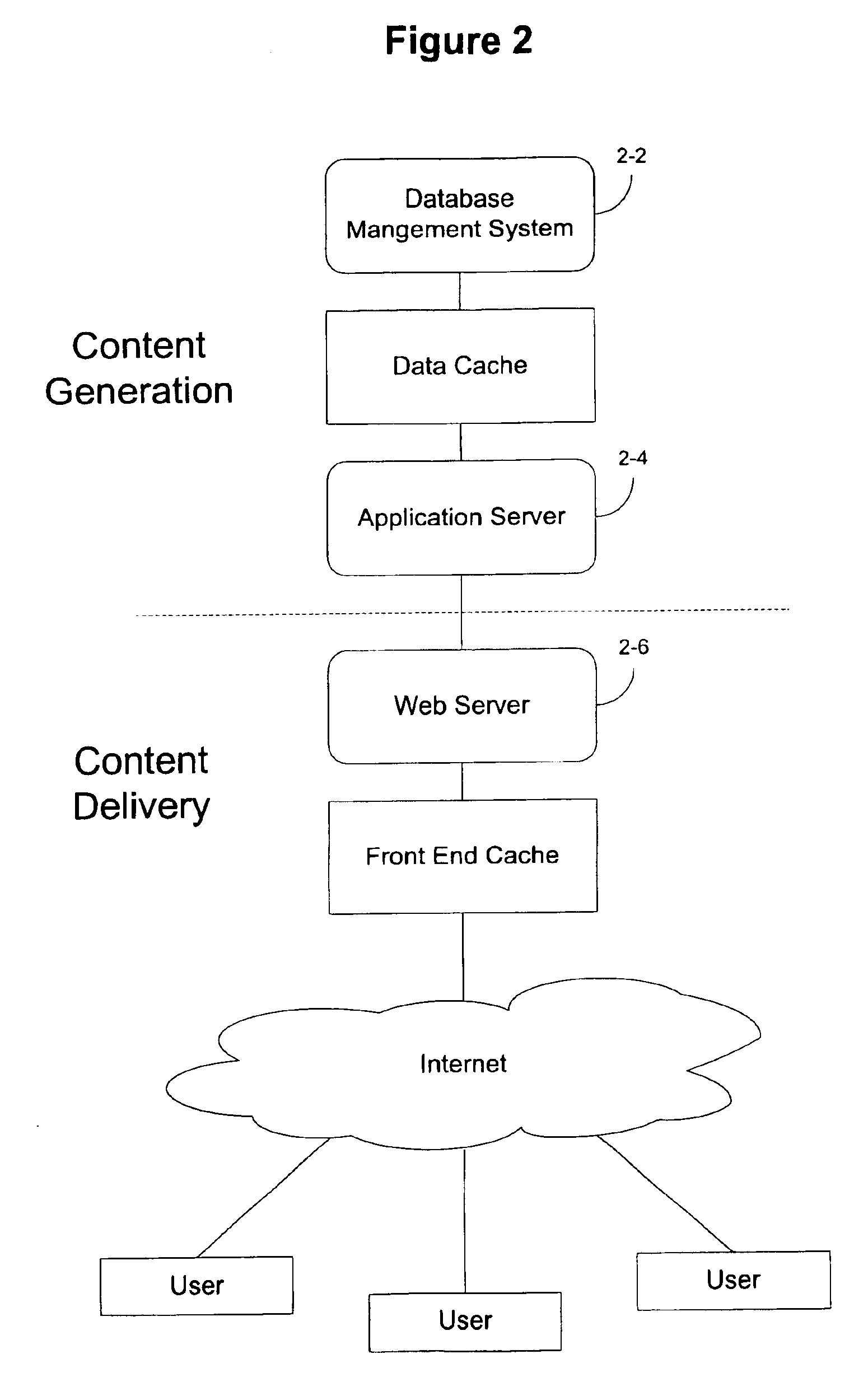
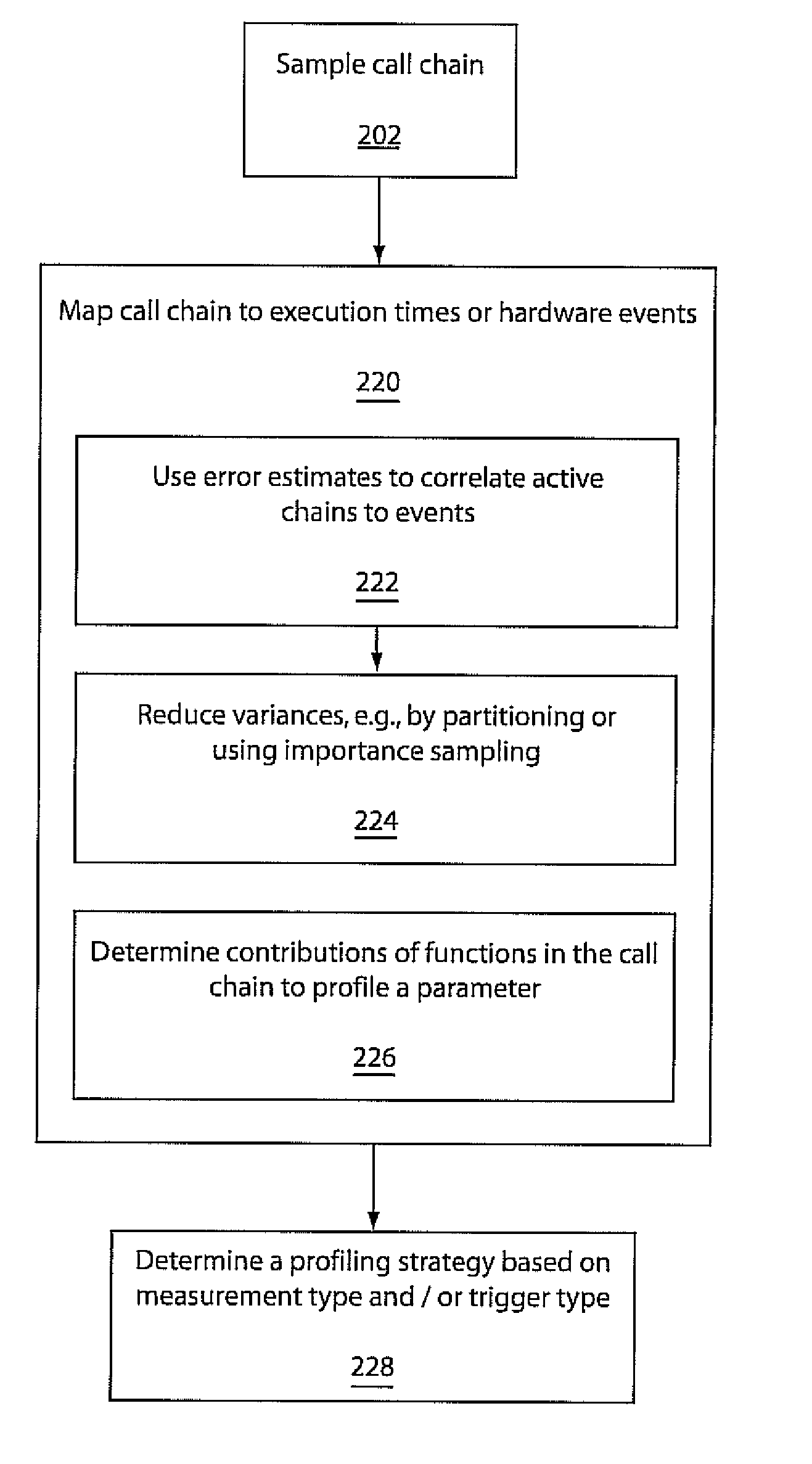
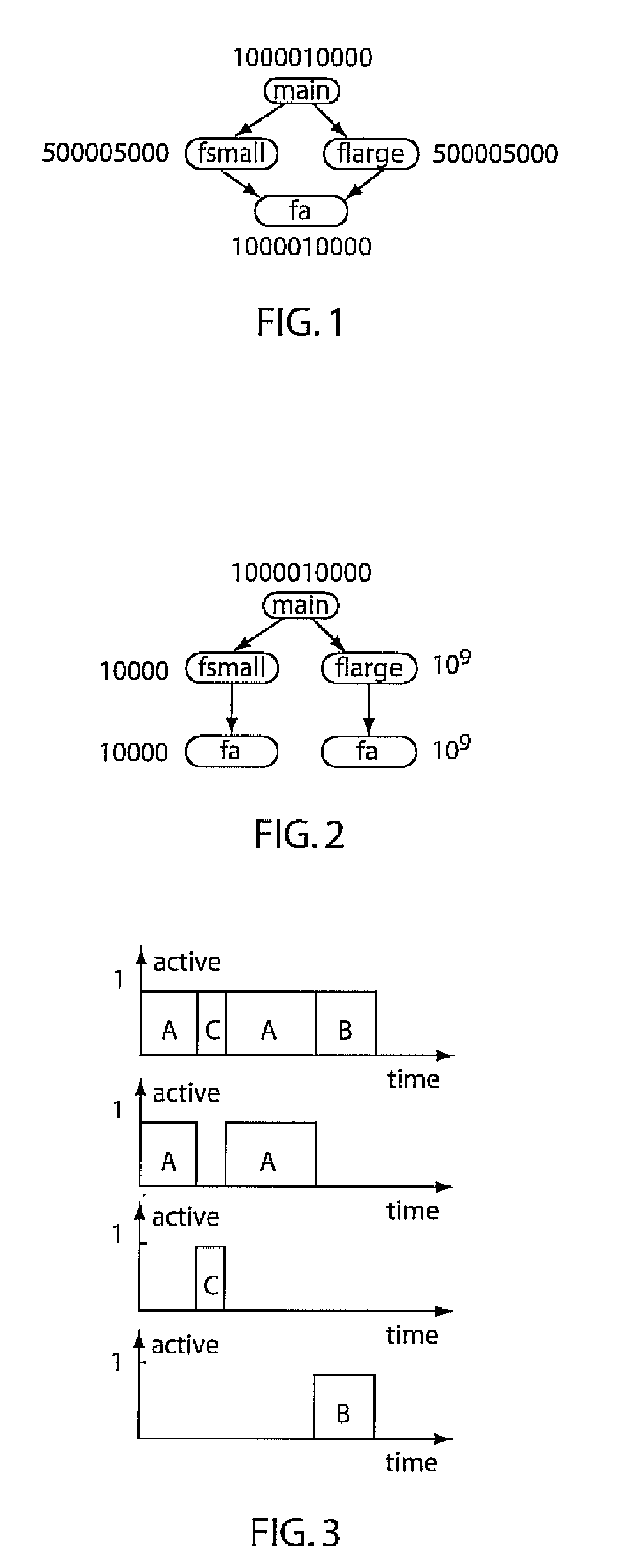
ActiveUS20100017791A1Minimal overheadSufficiently accurate insightError detection/correctionDigital computer detailsOperating systemProbabilistic framework
A system and method for correlation of resources with hardware events includes event driven sampling a call chain of functions at to determine when functions of the call chain are active. The call chain is mapped to execution times based upon a probabilistic integration of the functions such that when portions of the call chain are active, resources associated with call chain activity are correlated with hardware events.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com