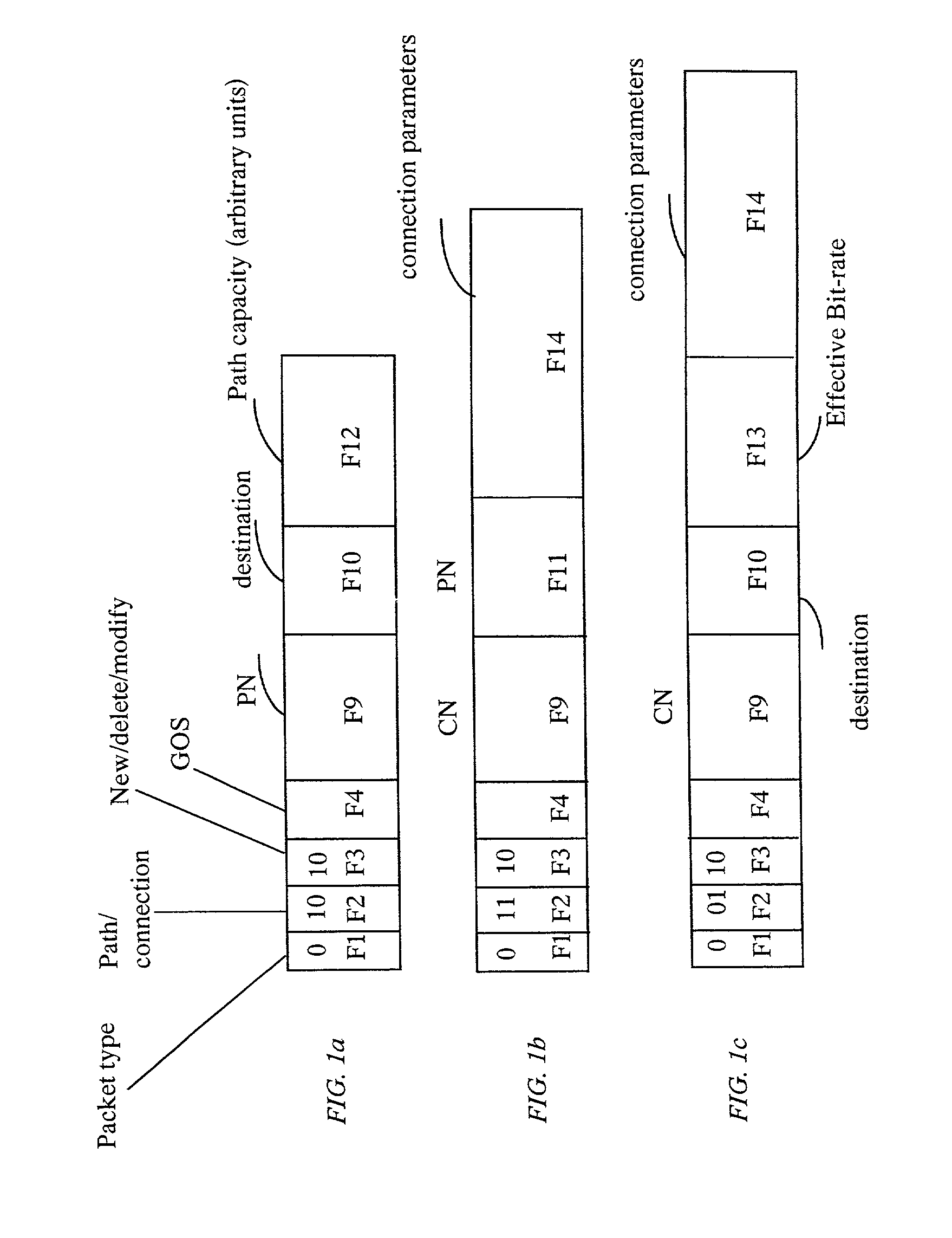
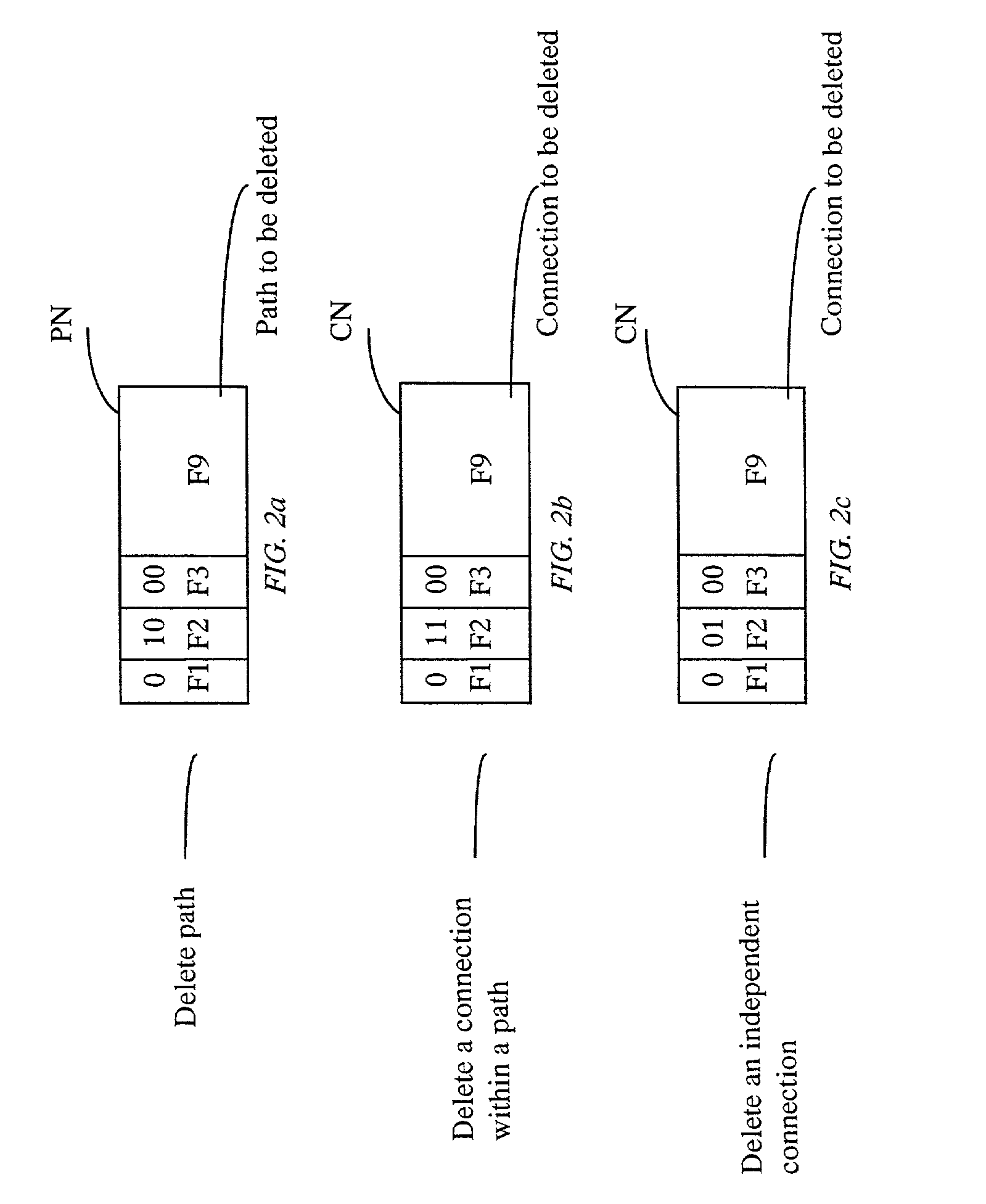
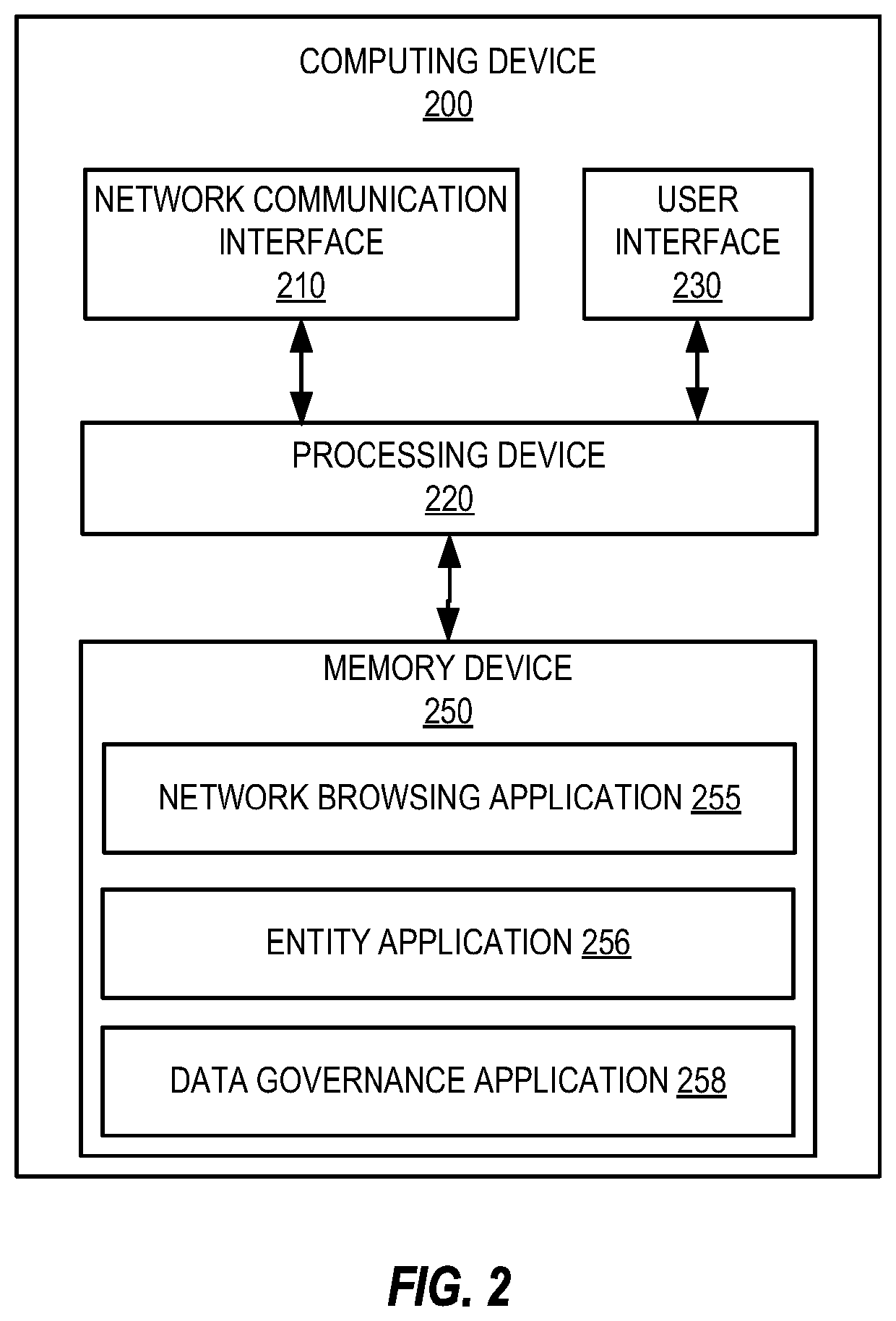
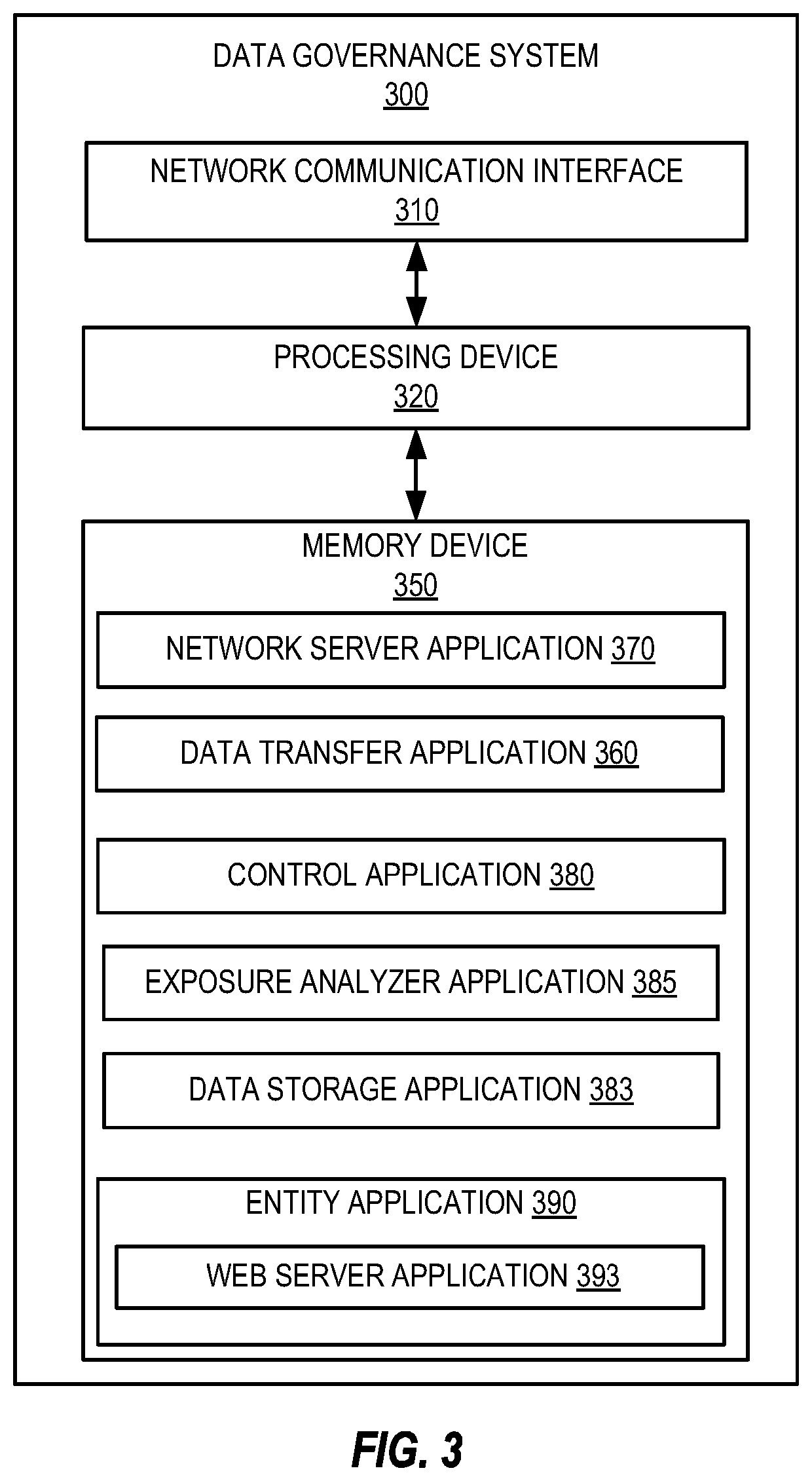
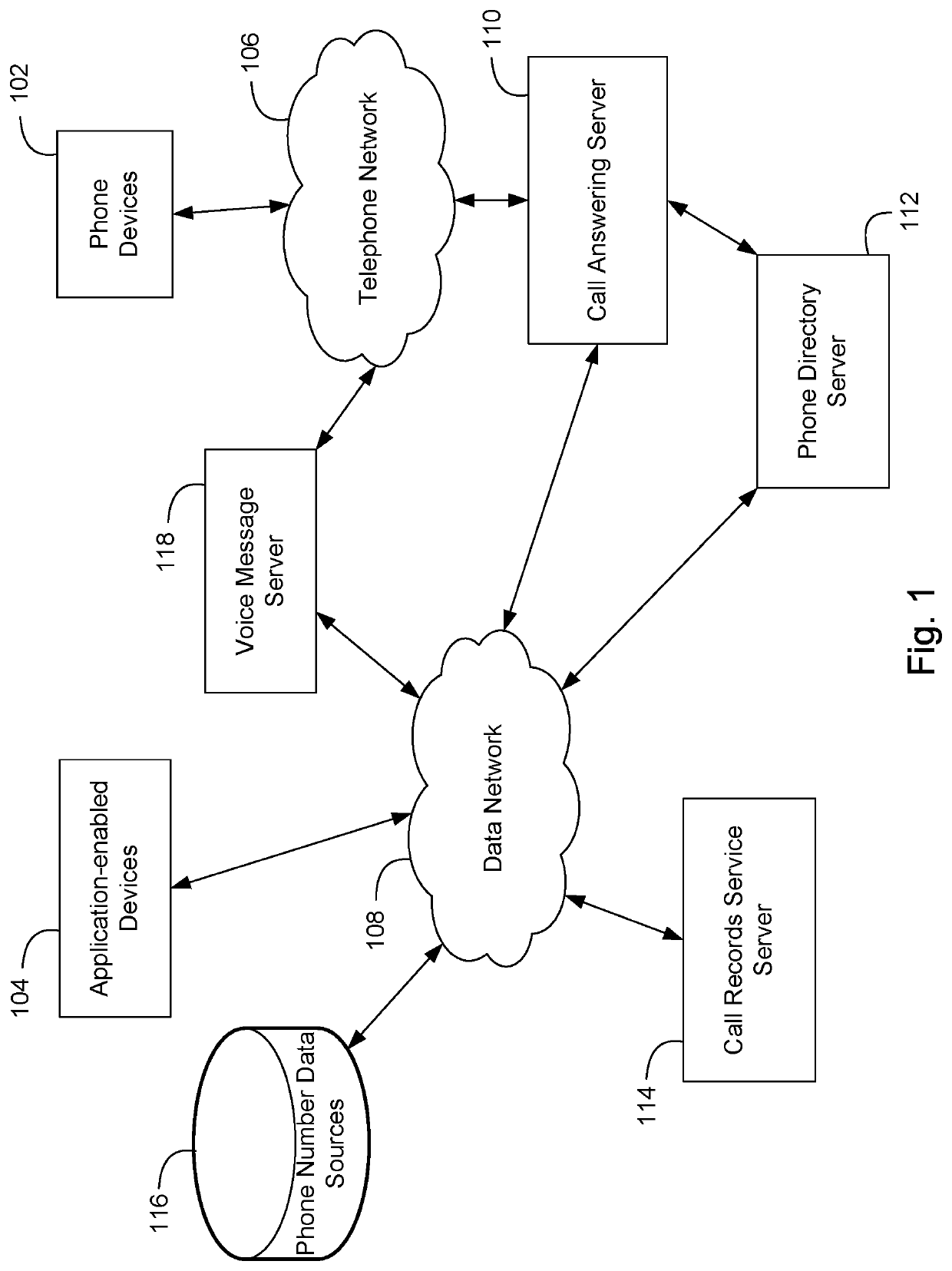
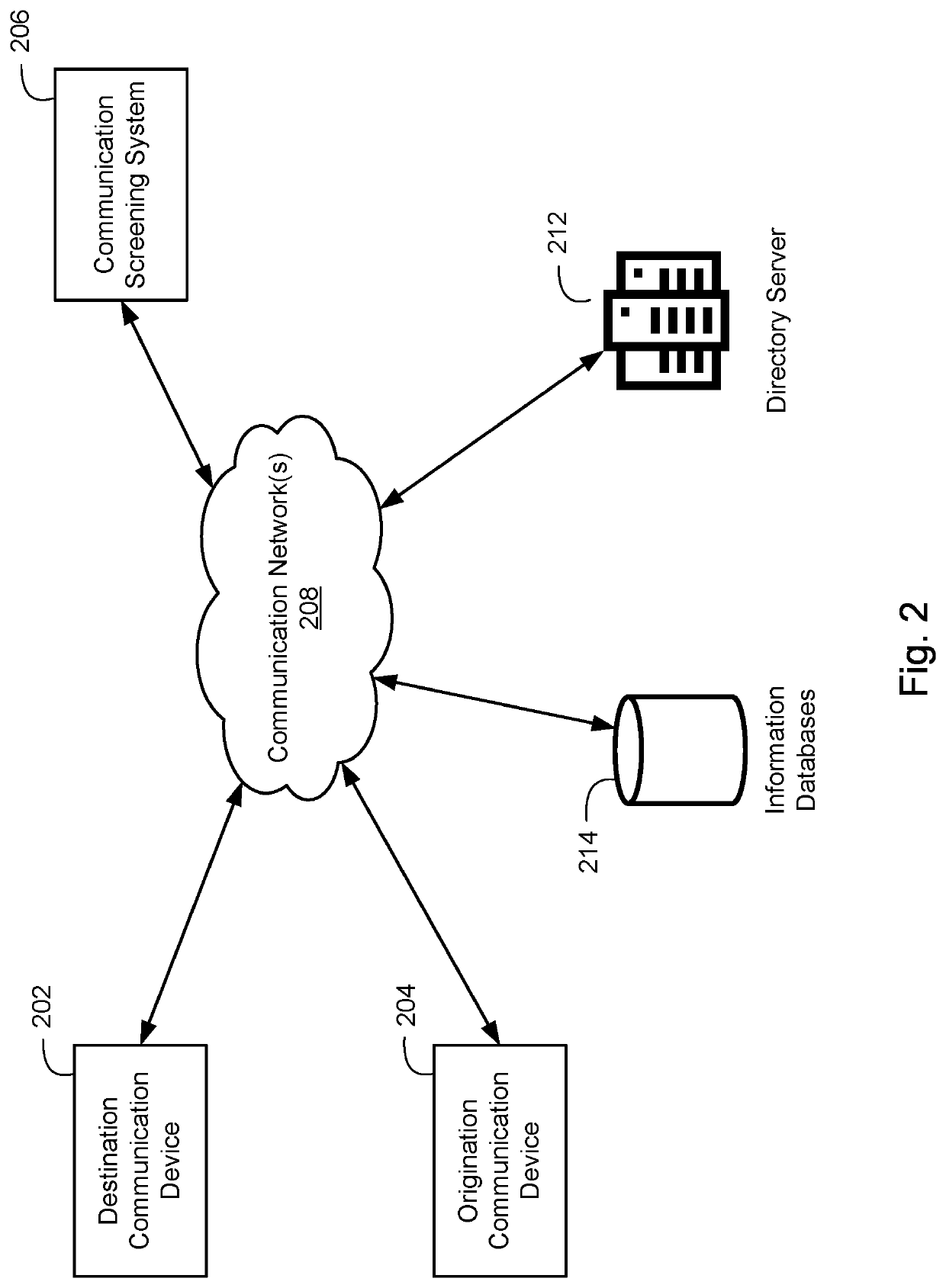
Patents
Literature
71 results about "Origination" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Origination in VOIP telephony refers to calls that originate in the PSTN public switched telephone network and are carried to their destination over the Internet. A VoIP call is initiated between two points, the initiation point is known as originator and the destination point is known as terminator.
Method and apparatus for optimization of wireless multipoint electromagnetic communication networks
InactiveUS20040095907A1Improve signal qualityReduce interference energyPower managementSpatial transmit diversityGlobal optimizationDiversity scheme
Exploiting the substantive reciprocity of internode channel responses through dynamic, adaptive modification of receive and transmit weights, enables locally enabled global optimization of a multipoint, wireless electromagnetic communications network of communication nodes. Each diversity-channel-capable node uses computationally efficient exploitation of pilot tone data and diversity-adaptive signal processing of the weightings and the signal to further convey optimization and channel information which promote local and thereby network-global efficiency. The preferred embodiment performs complex digital signal manipulation that includes a linear combining and linear distribution of the transmit and receive weights, the generation of piloting signals containing origination and destination node information, as well as interference-avoiding pseudorandom delay timing, and both symbol and multitione encoding, to gain the benefit of substantive orthogonality at the physical level without requiring actual substantive orthogonality at the physical level.
Owner:COMCAST CABLE COMM LLC
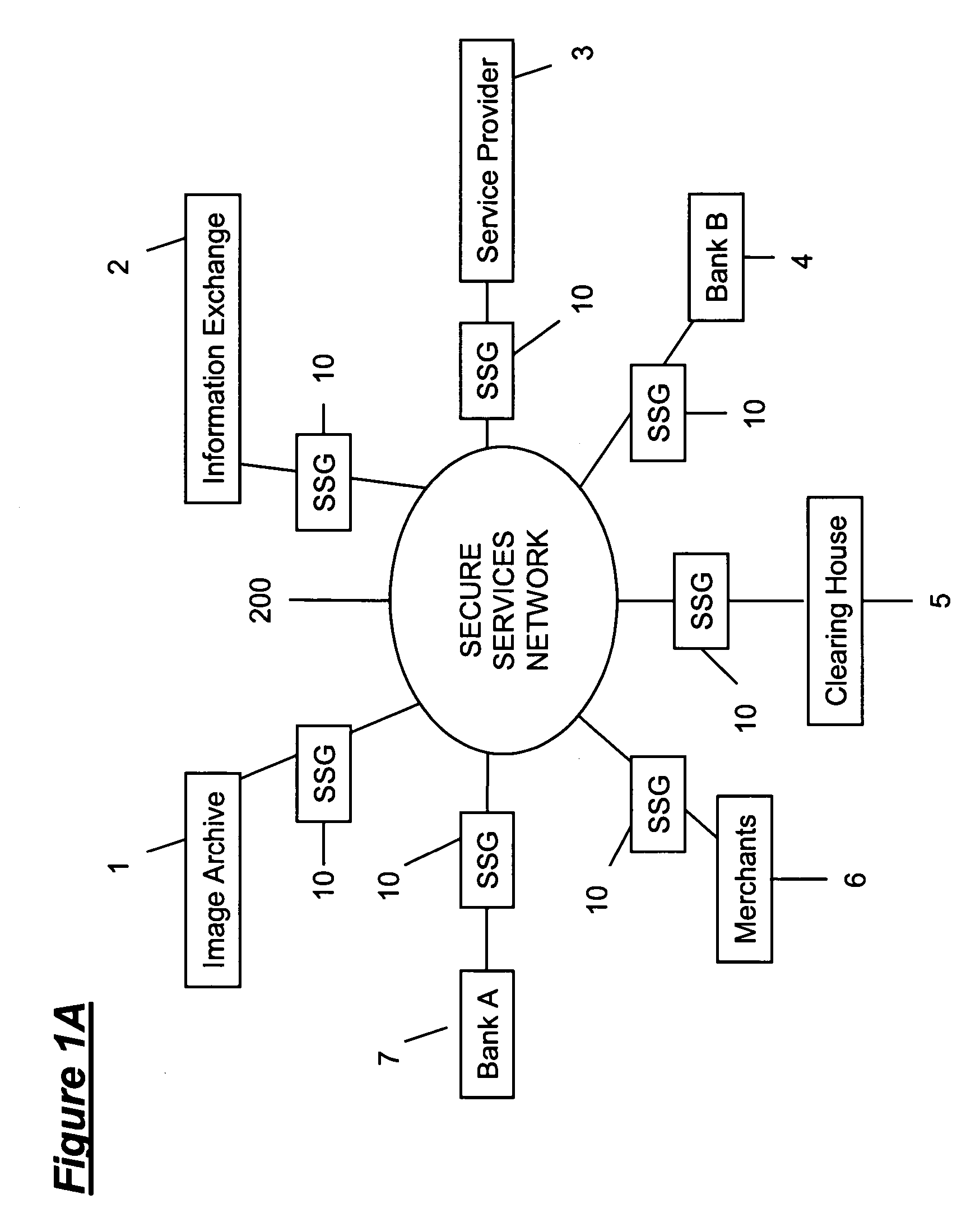
Secure service network and user gateway
ActiveUS20060107036A1Limited in functionally and participant reach and flexibilityLow costFinanceBilling/invoicingEngineeringPeer-to-peer
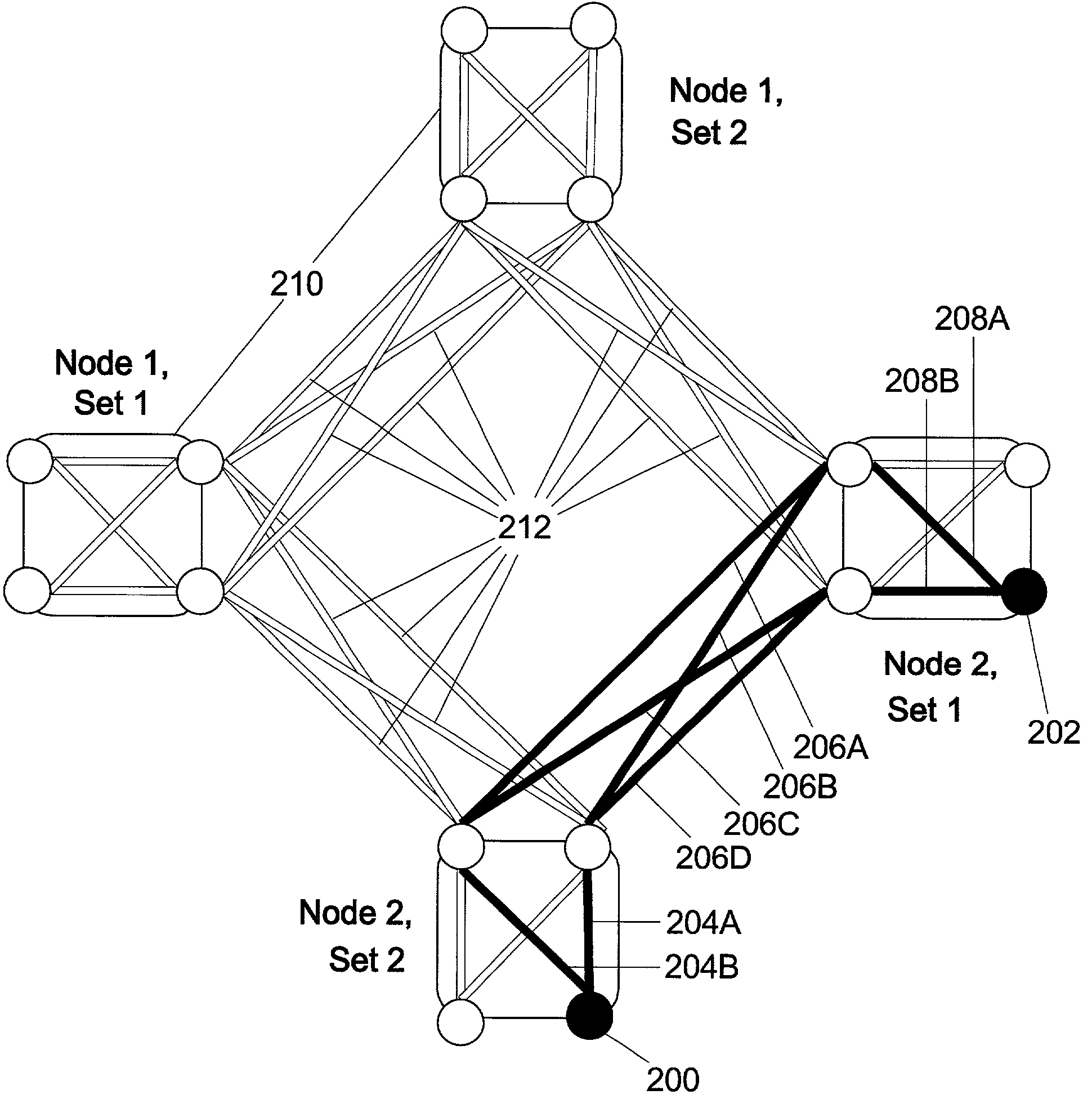
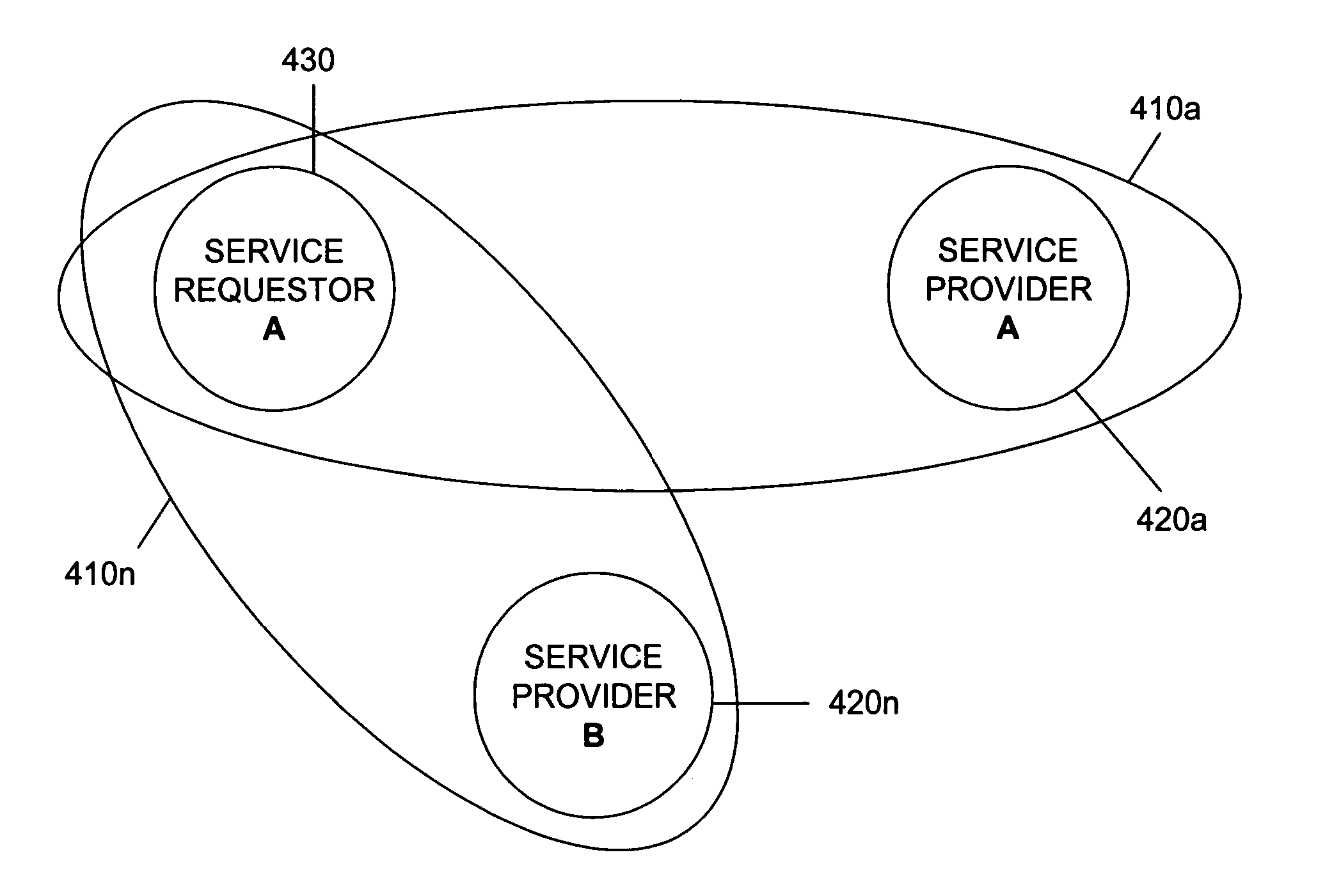
A secure service network (SSN) comprising an IP network infrastructure wherein the access of one participant to another participant in the network is controlled by a secure service gateway (SSG) in which a point of origination universal identifier (PoUID) represents a unique identifier for the participant within a participant's internal network domain and the interconnection of the SSGs within the SSN as a precondition of access creates a bilaterally secure peer to peer service connection. Participants in the network are service providers, service requesters, or both. A global secure service gateway (GSSG) may be interconnected in the SSN to provide a central access authority and management services.
Owner:WMR E PIN
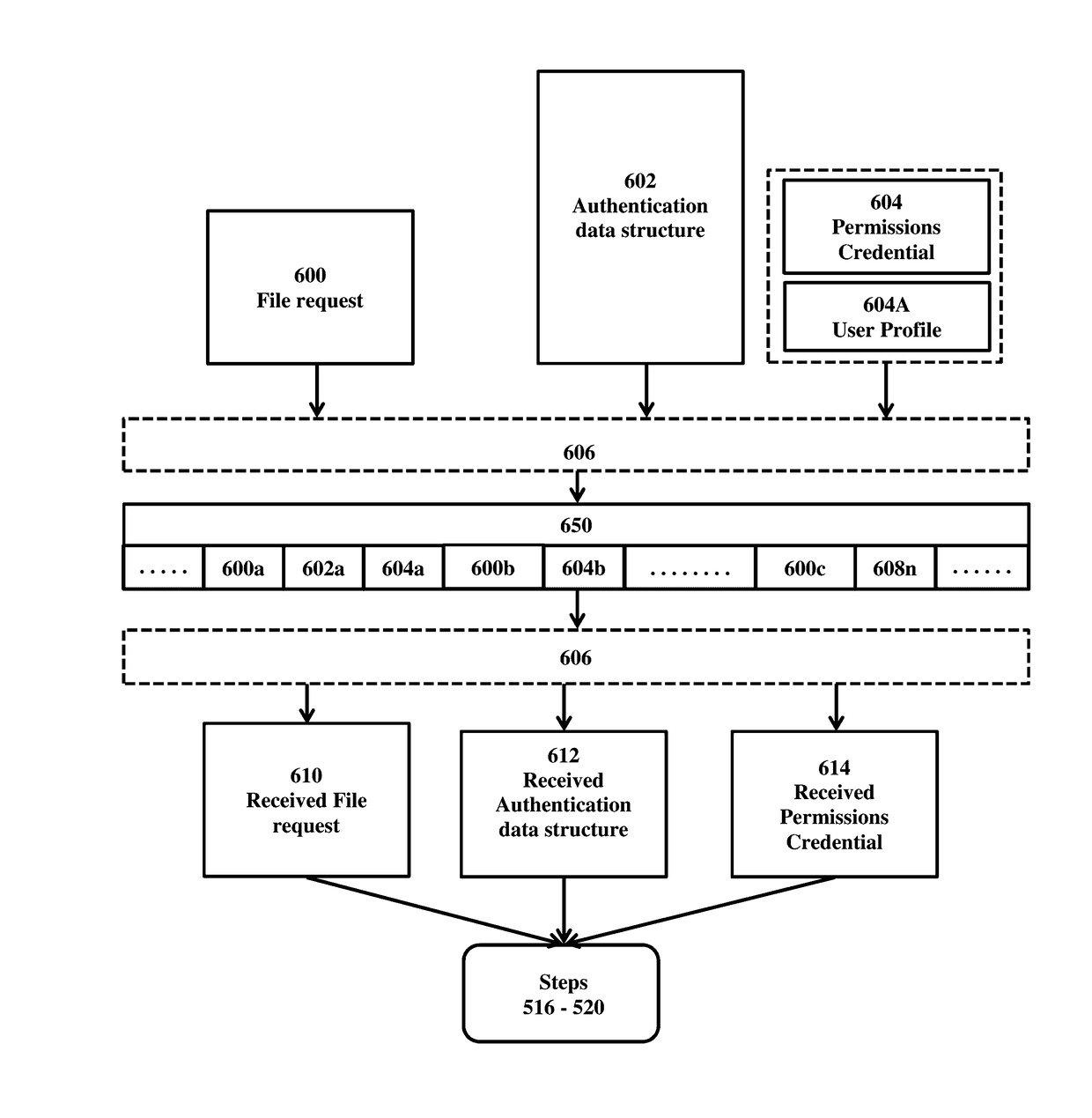
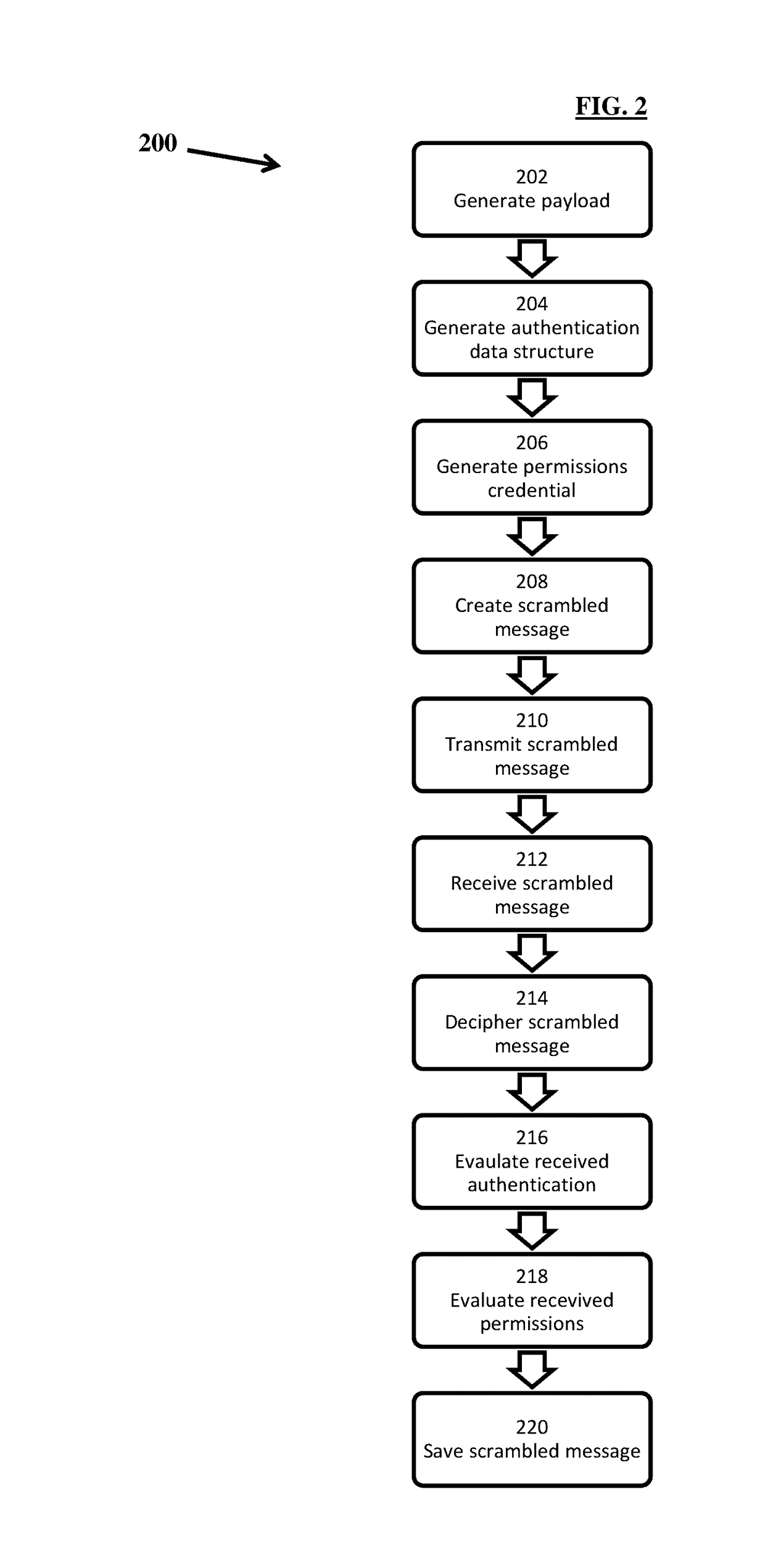
Method to secure file origination, access and updates
InactiveUS20170070495A1Digital data protectionTransmissionCommunications receiverAuthenticated data structures
A method to secure file origination, access and updates between a sender and a receiver is provided. The method includes generating a transmit payload to transmit to the receiver, generating an authentication data structure to transmit to the receiver, generating a permissions credential to transmit to the receiver, creating a scrambled message by combining and transforming the transmit payload, the authentication data structure, and the permissions credential, using a pre-determined scheme, transmitting the scrambled message to the receiver, receiving the scrambled message, applying the pre-determined scheme to recover a received payload, a received authentication data structure, and a received permissions credential, from the scrambled message, evaluating the received authentication data structure, and if authentication fails, ignoring the received payload, evaluating the received permissions credential, and if the received permissions credentials are insufficient, ignoring the received payload, and performing steps (a.)-(k.) for subsequent communications between the sender and the receiver.
Owner:CHERRY MICHAEL A +2
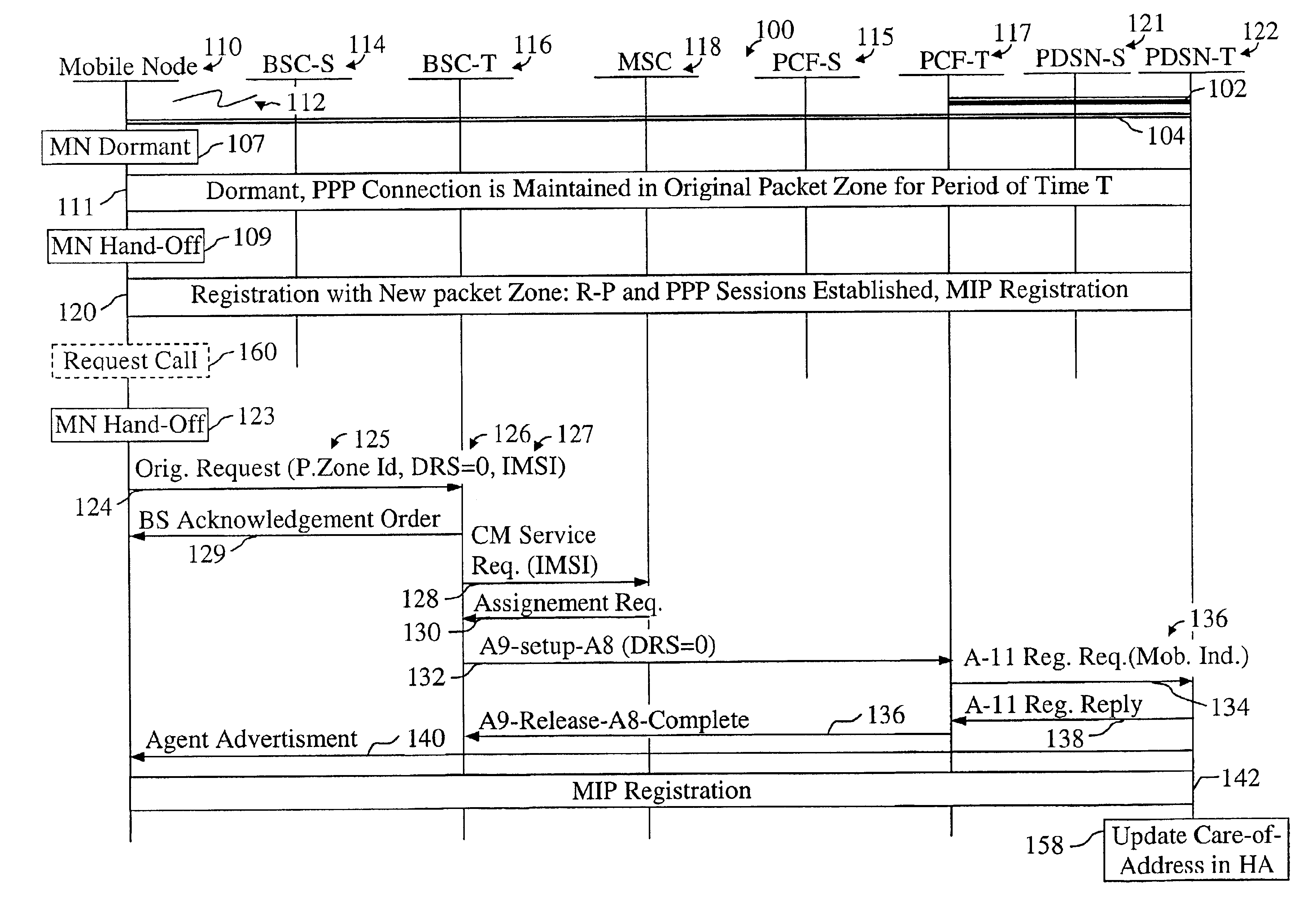
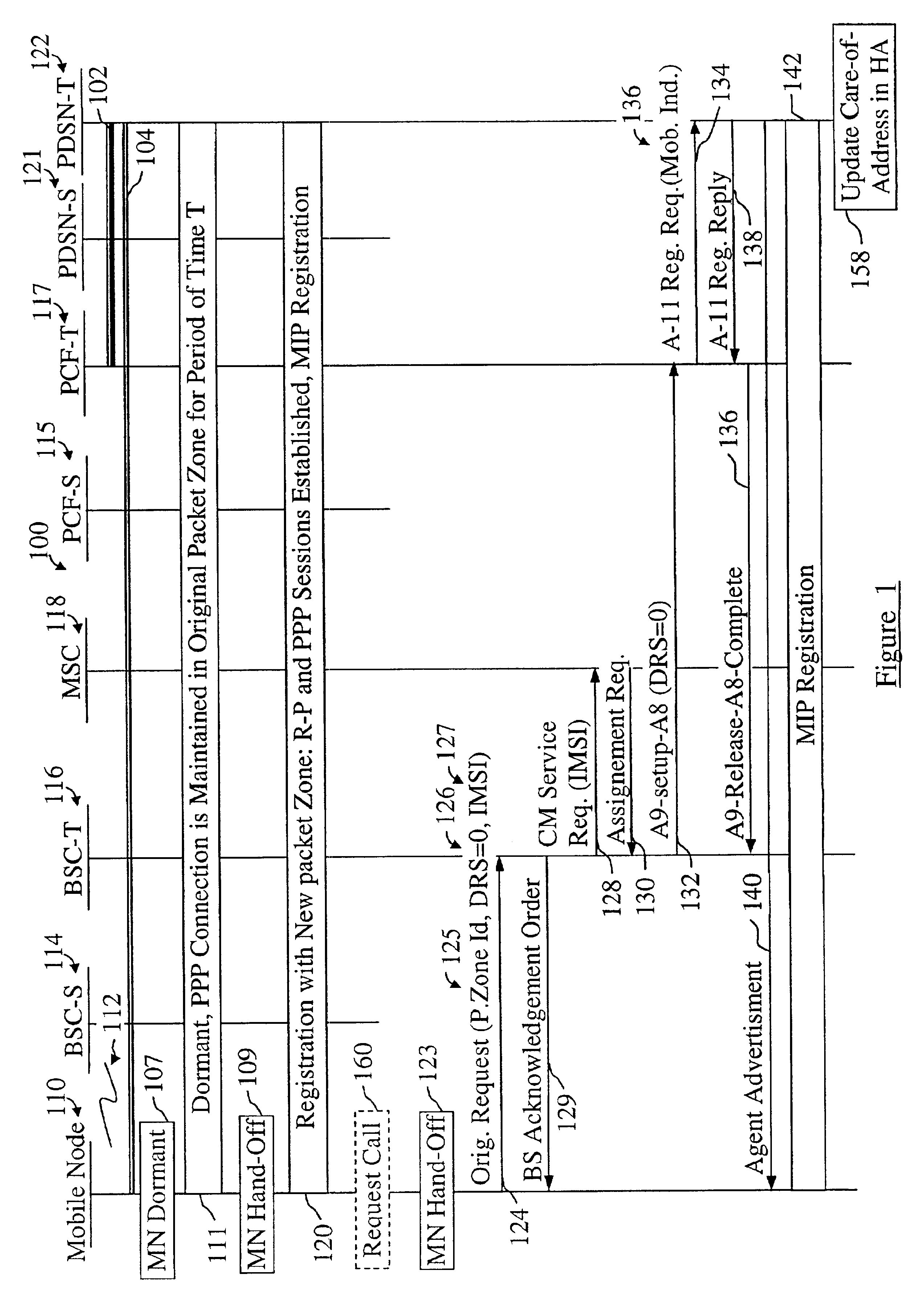
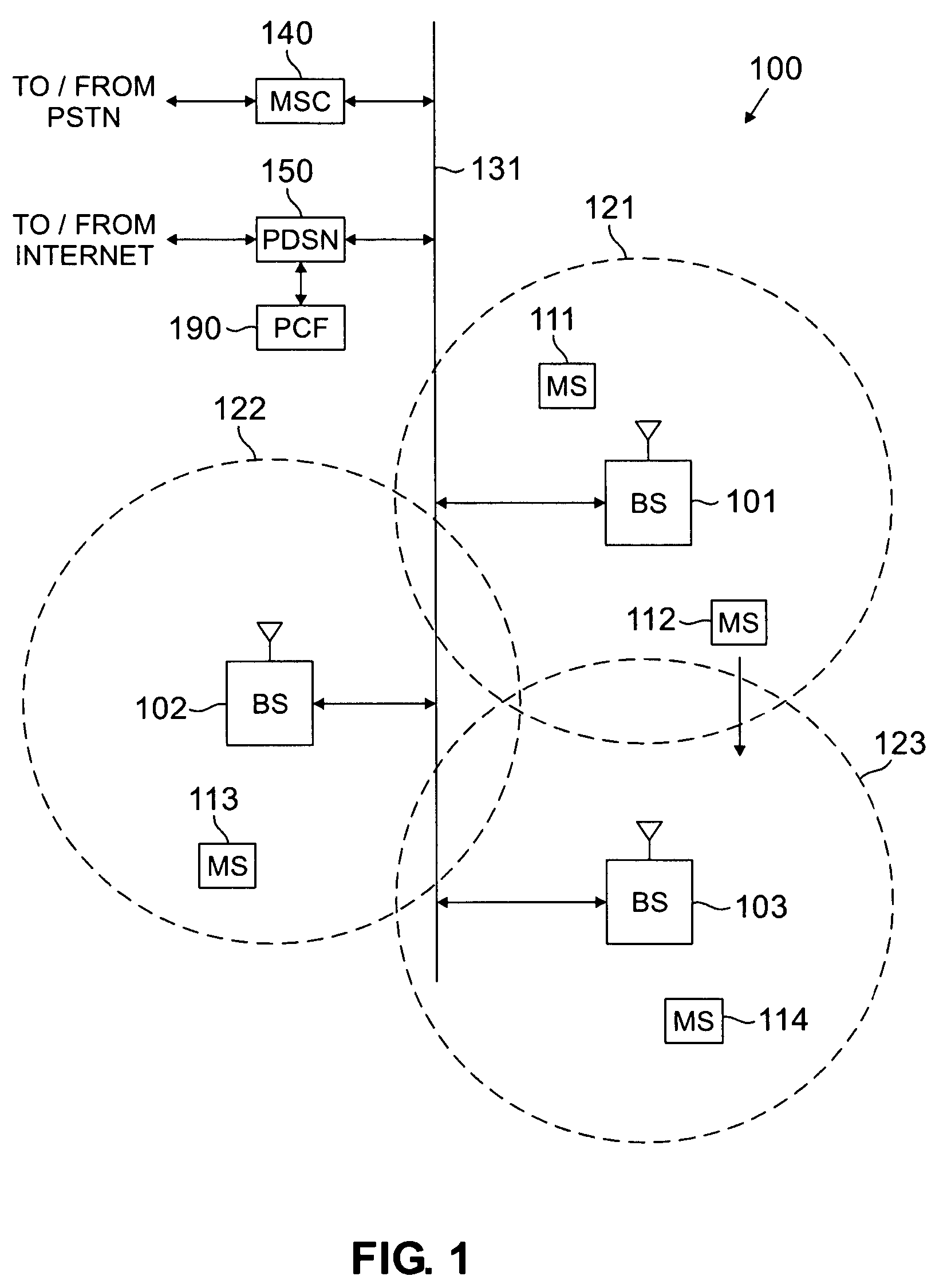
Mobile IP registration in selected inter-PDSN dormant hand-off cases in a CDMA2000-based cellular telecommunications network
InactiveUS6907016B2Time-division multiplexRadio/inductive link selection arrangementsPacket data serving nodeTelecommunications network
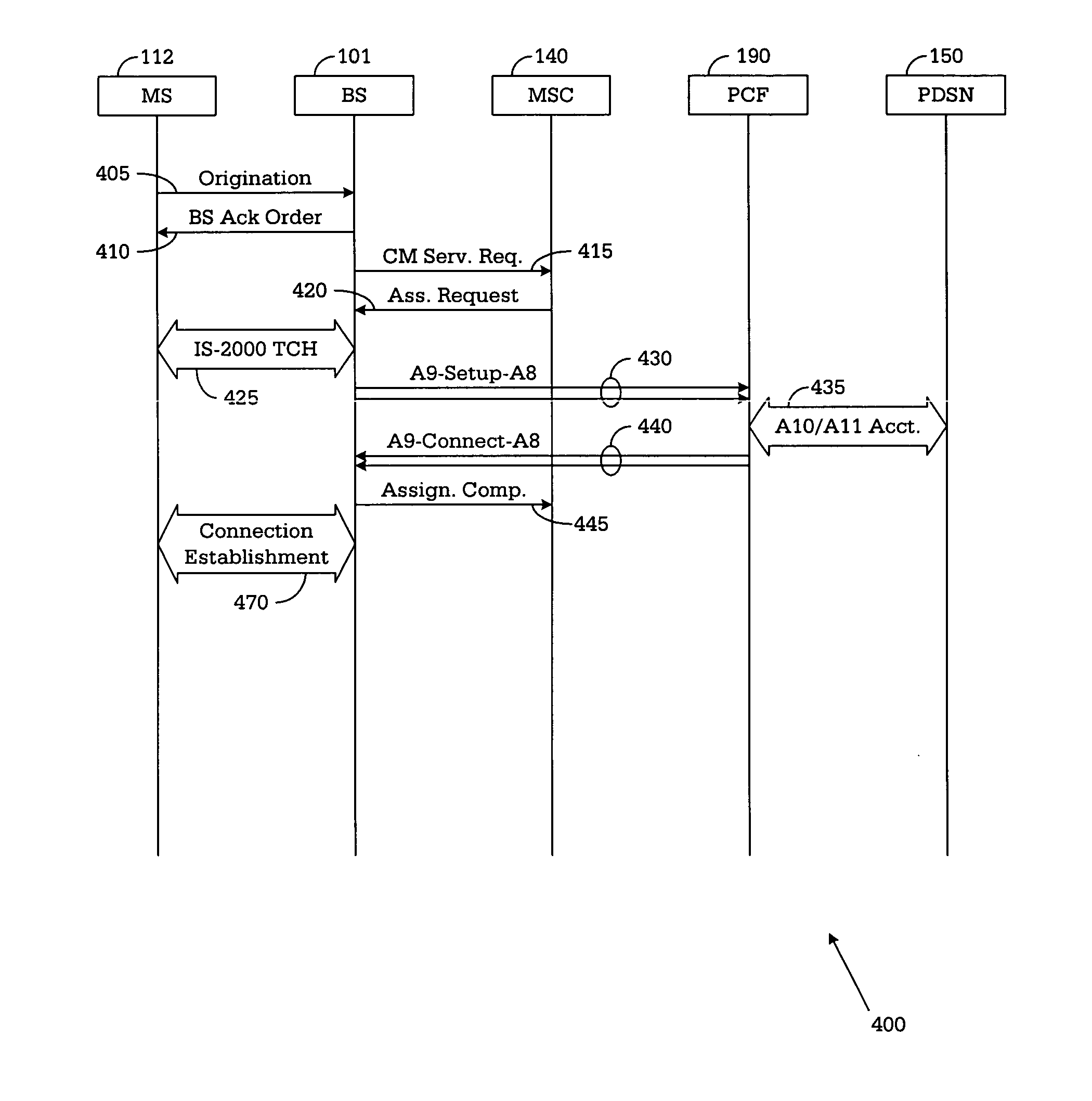
In a cellular telecommunications network, a method and system for performing dormant hand-off for a dormant Mobile Node (MN) between a source packet zone an a target packet zone, when the MN still has an active A10 and Point-to Point Protocol (PPP) connection in the target packet zone. According to the method, when handed-off, the MN issues an origination request with a Data Ready to Sent (DRS) parameter set to zero for the target Base Station Controller (BSC-T) which responsive to the request further sends an A9-setup-A8 registration request to a target Packet Control Function (PCF-T). The PCF-T then sends an A-11 Registration Request message to a Packet Data Service Node (PDSN-T) of the target packet zone. Responsive to the receipt of the Registration request, the PDSN-T sends an agent advertisement message to the MN and initiates the Mobile IP (MIP) registration procedure, and the MN can register the care-of-address information relating to the new serving PDSN, the PDSN-T, with its Home Agent (HA). According to another embodiment, the same method is to be used for performing a hand-off of the dormant MN to the target packet zone, when the MN, before issuing the origination request, demands the activation of a packet data session.
Owner:TELEFON AB LM ERICSSON (PUBL)
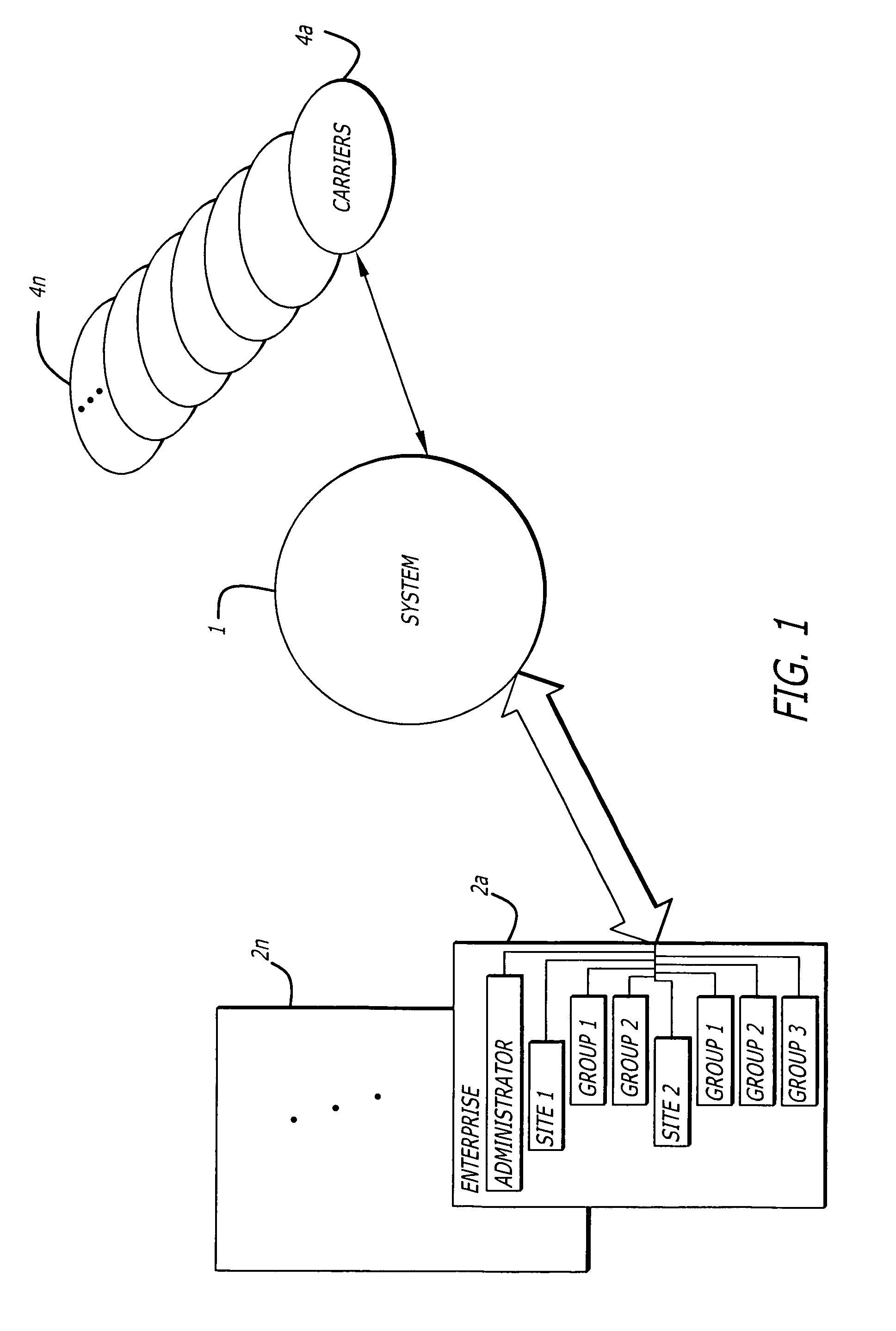
Apparatus, systems and methods for online, multi-parcel, multi-carrier, multi-service enterprise parcel shipping management
ActiveUS7774284B2Increase user productivityEasy to understandOffice automationBuying/selling/leasing transactionsBusiness enterpriseEngineering
The present invention provides a plurality of Enterprises with a single online user interface with which the Enterprise can provide Enterprise Shippers, shipping origination users and shipping intermediary users with an automated parcel management system for a plurality of supported Carriers for a plurality of services. The present invention provides for the hierarchical definition of users, including the establishment of at least one user for each Enterprise as a Super-Administrator with the highest level of privileges and authority for the Enterprise, and the identification of other users as Sub-Administrators, Desktop Users and Shipping Station Users. The present invention also provides for the hierarchical definition of organizational units within each Enterprise, including the definition of sites, groups within a site, and users within a group. The present invention further provides for a distinct definition of policies, privileges, and other types of specifications for each user level, each user, and each organizational unit. The present invention applies the user and organizational policies, privileges and other specifications as they apply to each particular user to drive the interactive interface with each particular user and to provide among other things, shipping options, shipping services, shipping rates, traveler and / or shipping label preparation, and shipment tracking.
Owner:AUCTANE INC +1
Systems and methods for handling voluminous calls to cell phones using transfer agent process
A computerized system for calling a plurality of cell phones in compliance with the TCPA, comprises a call center database; call center workstations operated by transfer agents; client workstations operated by client associates; and a computer processor that retrieves a cell phone number of a consumer to call, in response to an initiate call instruction from a respective transfer agent, dials the cell phone number, connects the call to the respective transfer agent if a live voice is detected; receives a transfer call request from the respective transfer agent, transfers the call with the one consumer to a client associate, using the cell number as the origination number of the call to identify the one consumer to the client associate, disconnects the connection between the one consumer and the respective transfer agent, and identifies a next consumer to call upon request by the transfer agent.
Owner:RADIUS SOLUTIONS
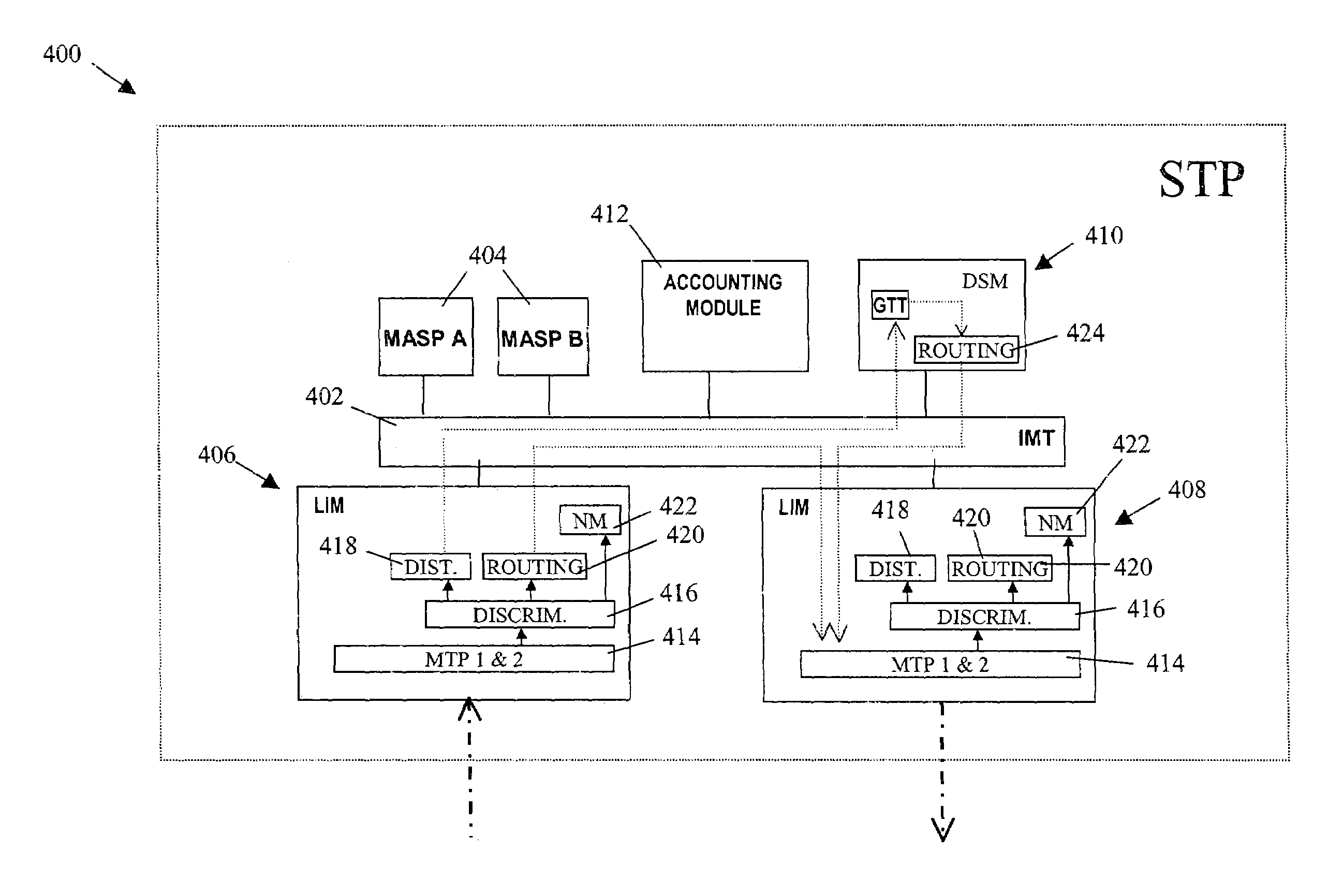
Methods and systems for routing signaling messages to the same destination over different routes using message origination information associated with non-adjacent signaling nodes
InactiveUS7088728B2Eliminate requirementsInterconnection arrangementsData switching by path configurationQuality of serviceNetwork addressing
Methods and systems for associating a plurality of different routes with the same destination and for routing signaling messages to the destination based on originating information associated with non-adjacent signaling nodes are disclosed. A routing database in a signal transfer point includes multiple routes to the same destination. The routes are distinguishable from each other in the routing database using message origination information associated with signaling nodes that are not adjacent to the signal transfer point. When a signaling message is received, origination and destination information in the signaling message are used in combination to select among multiple routes to a destination having a network address corresponding to the destination information in the signaling message. The signaling message is then routed over the route selected using the originating information. The selected route may be a high-speed route used to provide a particular quality of service.
Owner:TEKELEC GLOBAL INC
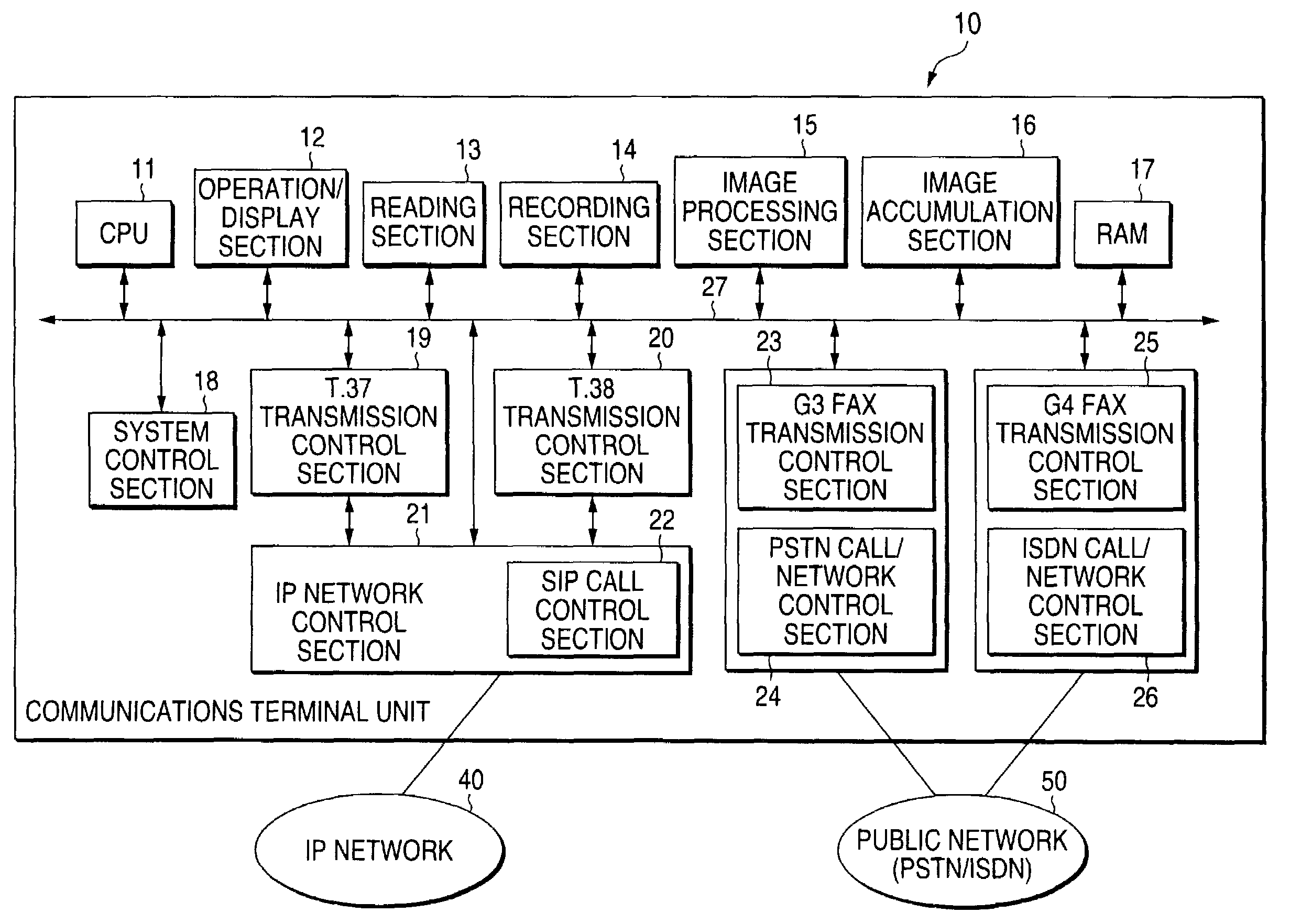
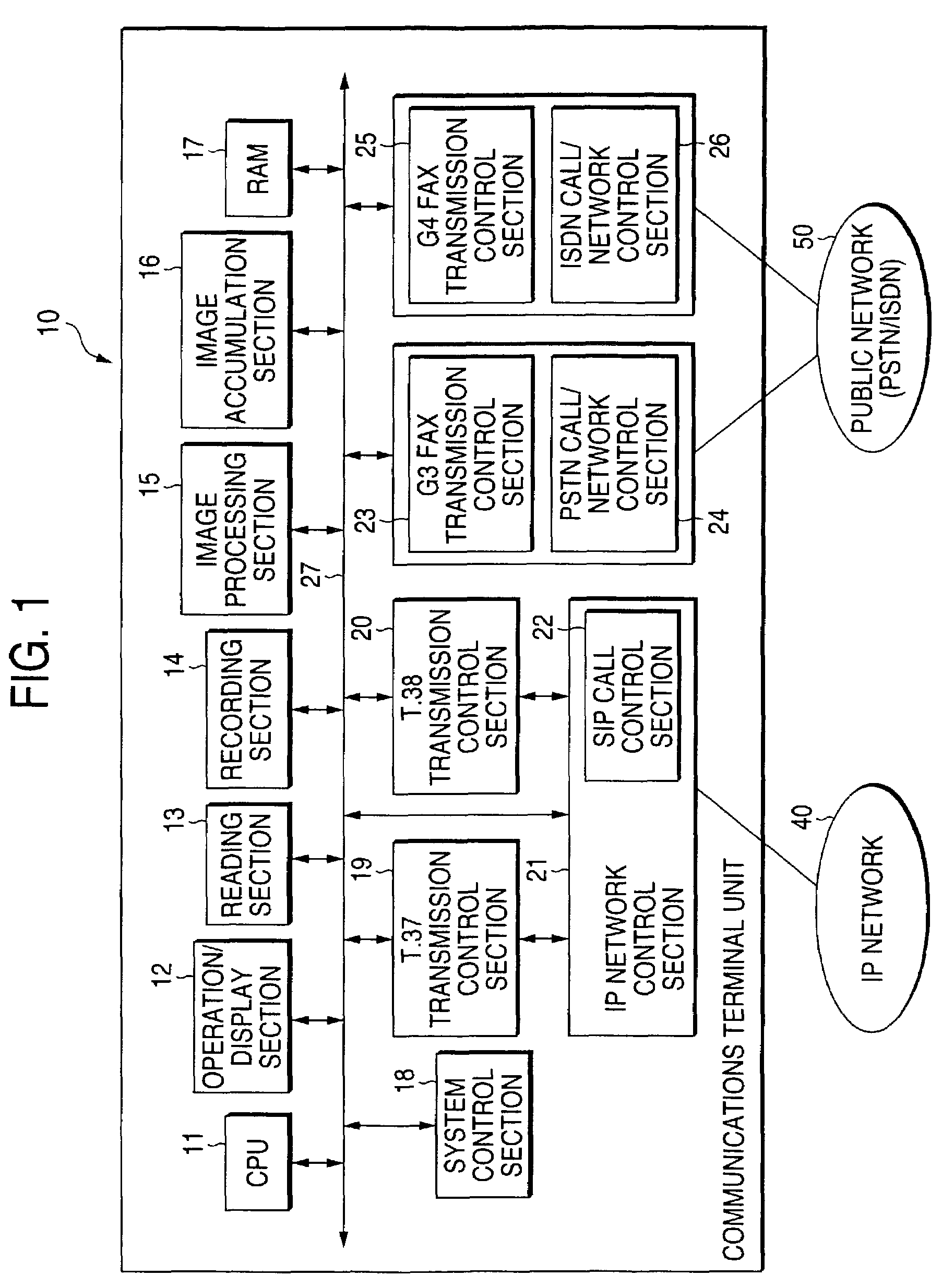
Communications terminal unit and method for controlling the same
InactiveUS7627097B2Communication cost increaseIncrease the number ofInterconnection arrangementsHybrid switching systemsTelecommunicationsInformation analysis
A communication terminal unit has a system control section including a call destination specification information analysis section that analyzes a destination number which is assigned to a communications terminal unit at the other end and input at the time of origination of a call. On the basis of a result of analysis of the destination number performed by the call destination specification information analysis section, a call origination network determination section automatically determines to originate a call over an IP network or over a public network through use of the destination information that has been subjected to analysis and through use of selected network setting information stored in a selected network setting storage section. Selected network setting information required to automatically determine to originate a call over the IP network or over the public network is stored in the call origination network determination section.
Owner:FUJIFILM BUSINESS INNOVATION CORP
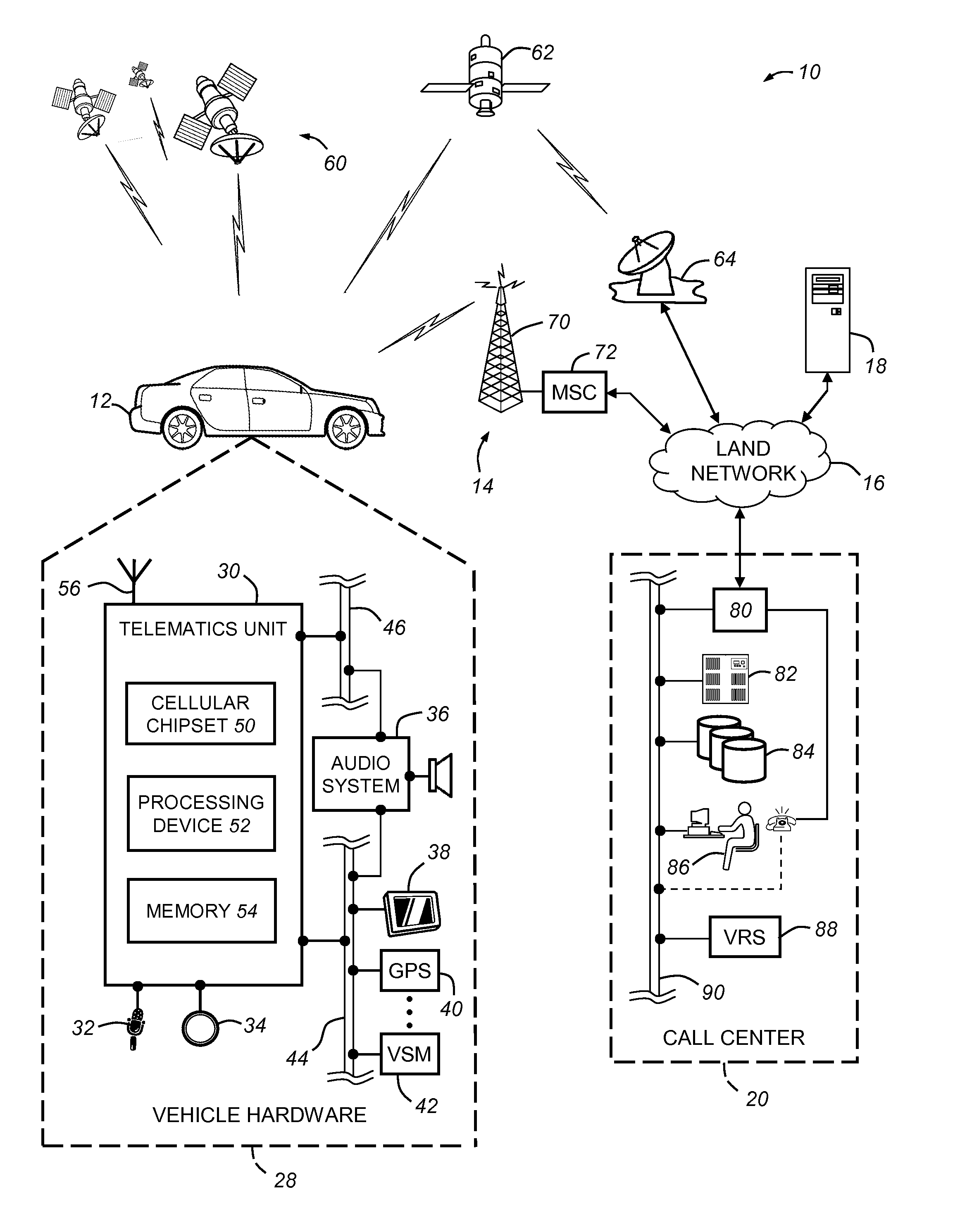
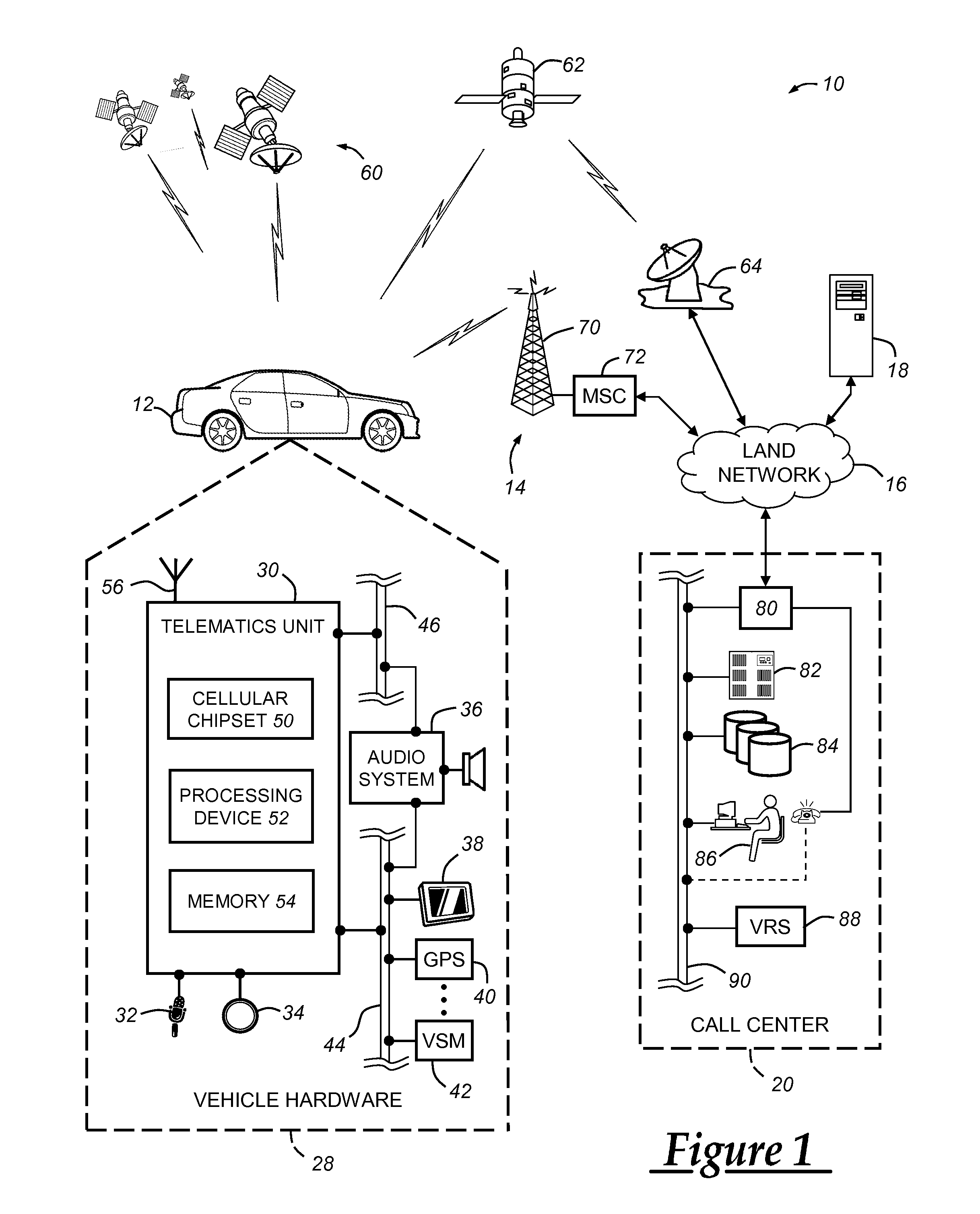
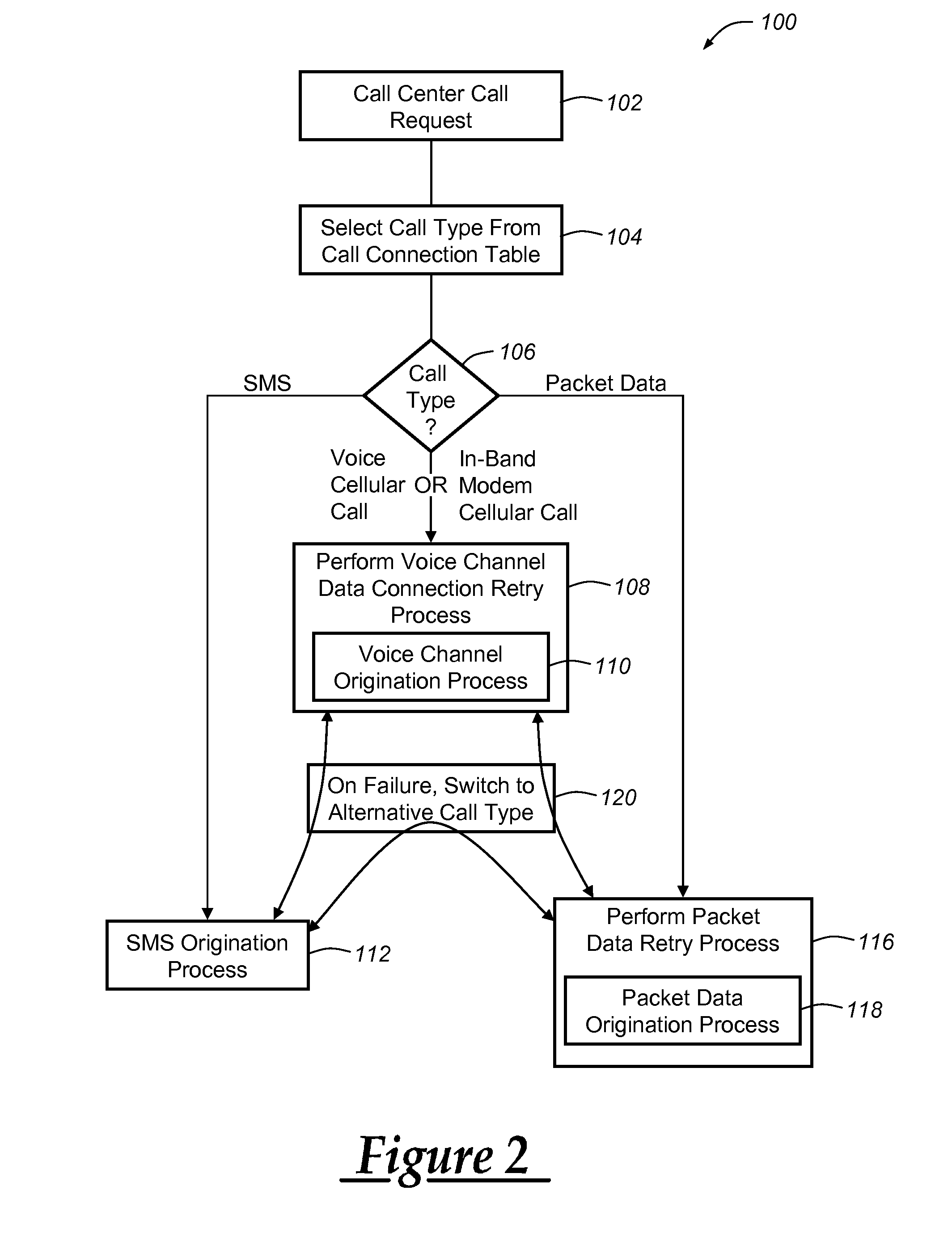
Voice fallback origination for vehicle cellular communication with a call center
InactiveUS20110039538A1Connection managementWireless commuication servicesModem deviceCellular communication
A system and method for making vehicle originated calls to a telematics service provider or other call center. The method includes identifying a call type associated with a desired wireless communication of speech or data to the call center, and then carrying out one of a number of different call connection processes depending on the call type. For voice channel cellular connections, an in-band modem cellular connection is preferably established in most instances using a connection retry strategy that includes primary, secondary, and possibly tertiary connection attempts each of which utilize at least one of a number of different voice and data call origination processes. The system and method can be carried out in connection with various cellular system technologies, but is especially suited for use with GSM systems.
Owner:GENERA MOTORS LLC
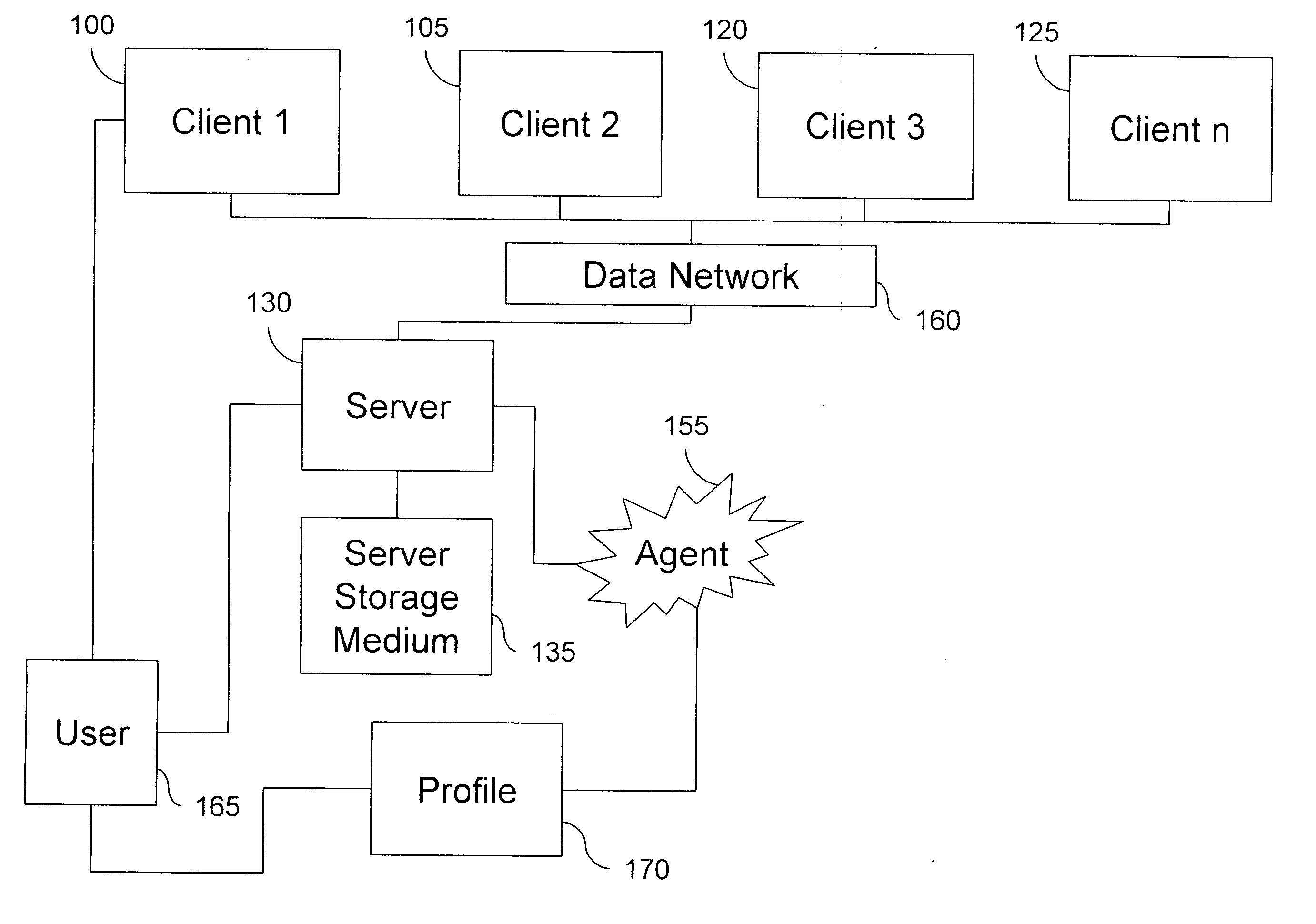
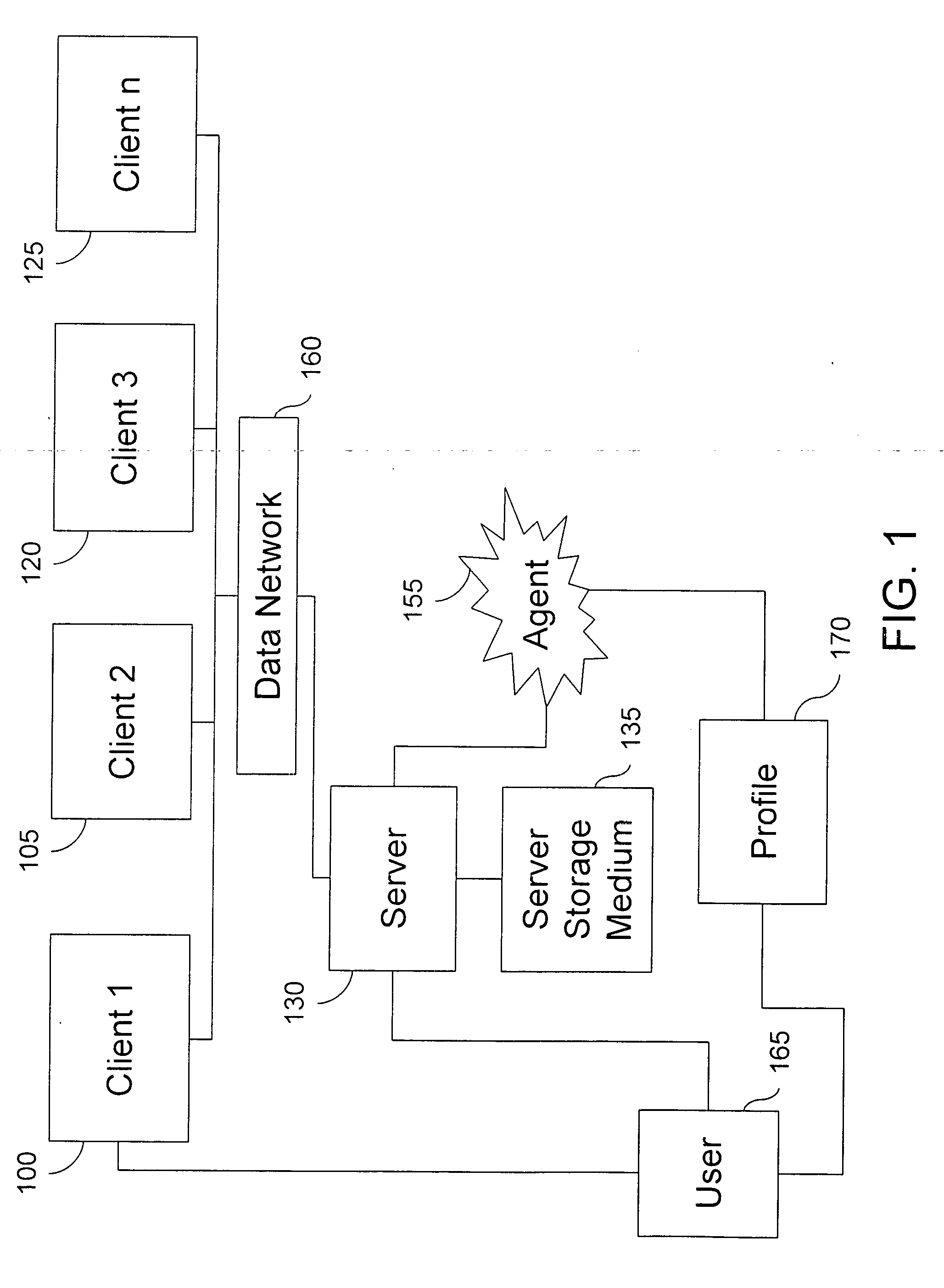
Method and system for an electronic agent traveling based on a profile
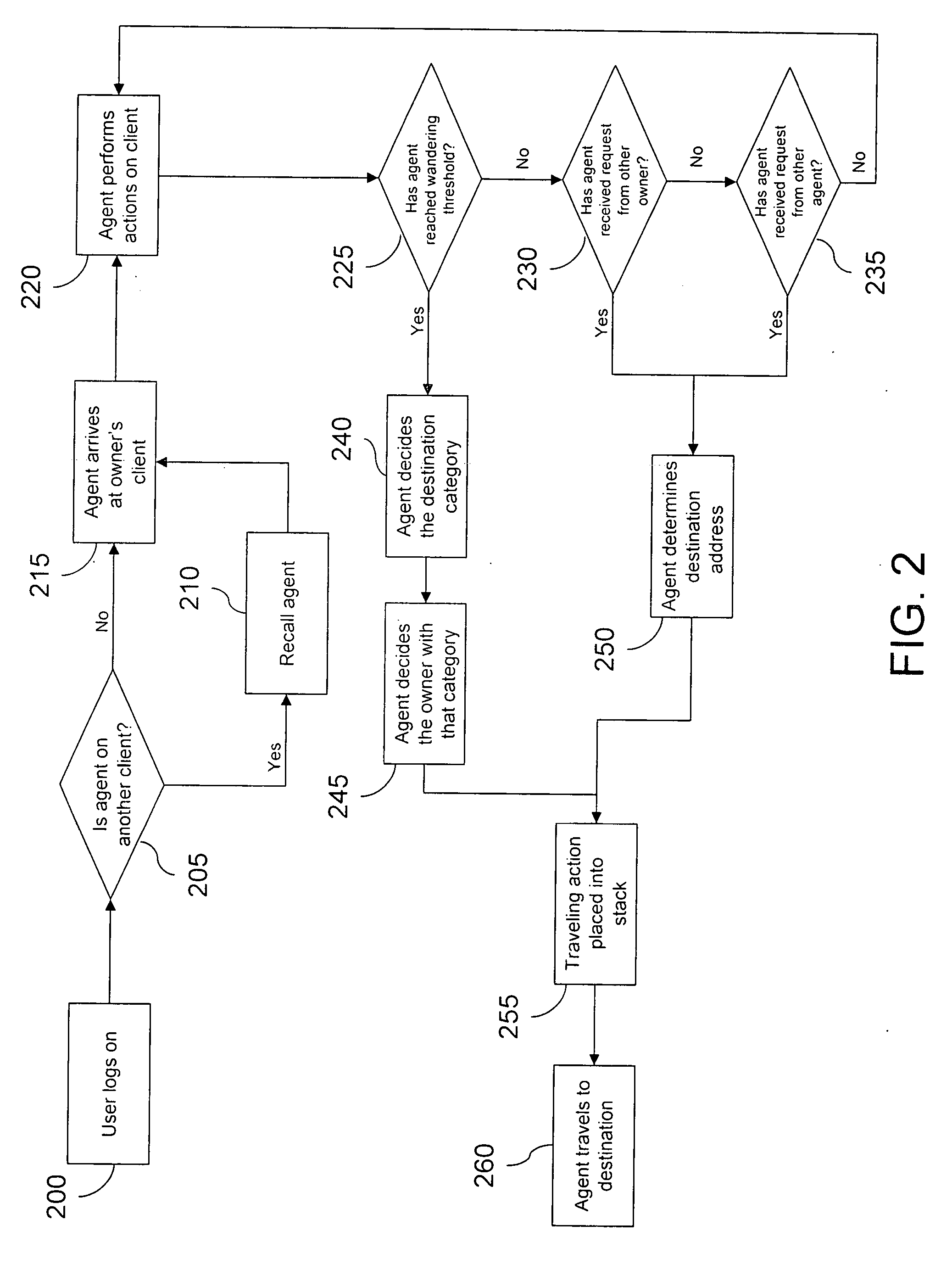
InactiveUS20060190524A1Easy to findEfficient methodMultiple digital computer combinationsTransmissionComputer scienceOrigination
A method and system is described for an electronic agent to automatically travel from an origination computer to a destination computer. The method comprises the monitoring of requests for travel, generating a list of possible destinations, determining the final destination, prioritizing the importance of the travel, and then finally inserting that traveling action into the stack. A system is further disclosed and claimed for enabling the above methodology over a data network.
Owner:BETHKE ERIK +2
Method fro dynamic load balance in distributed system based on session origination protocol
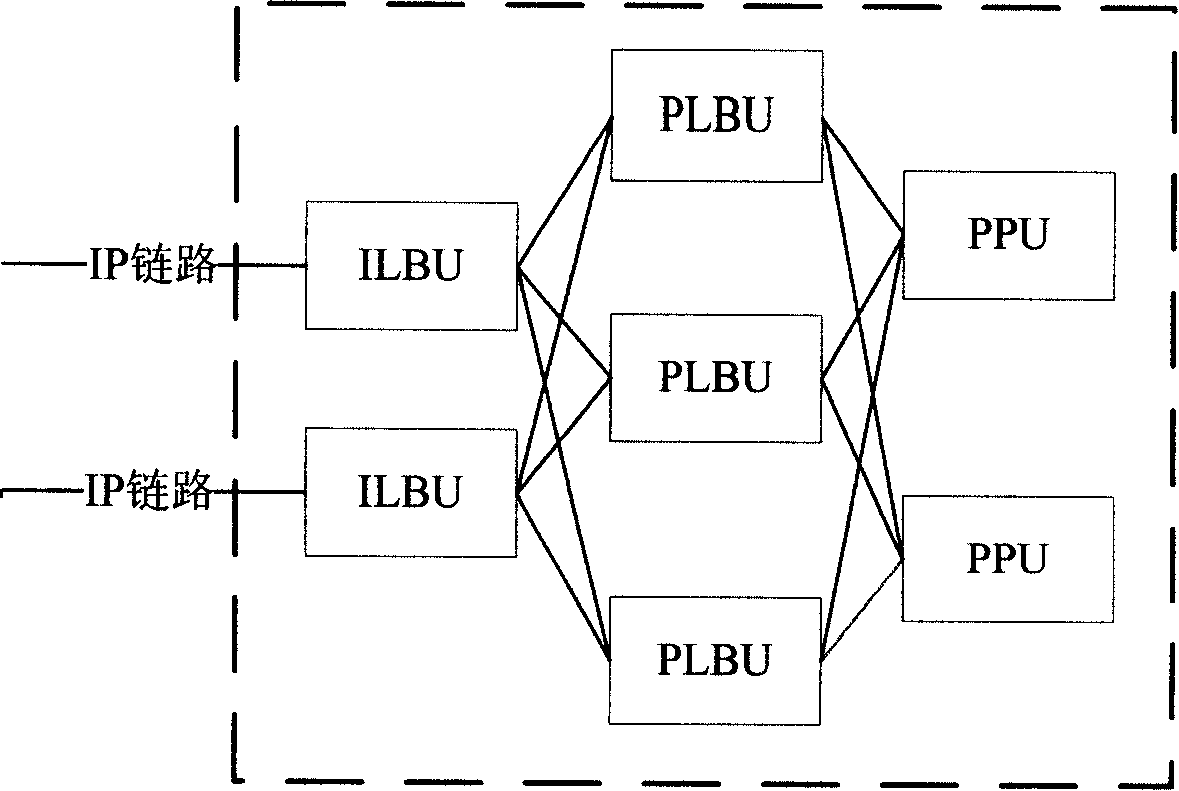
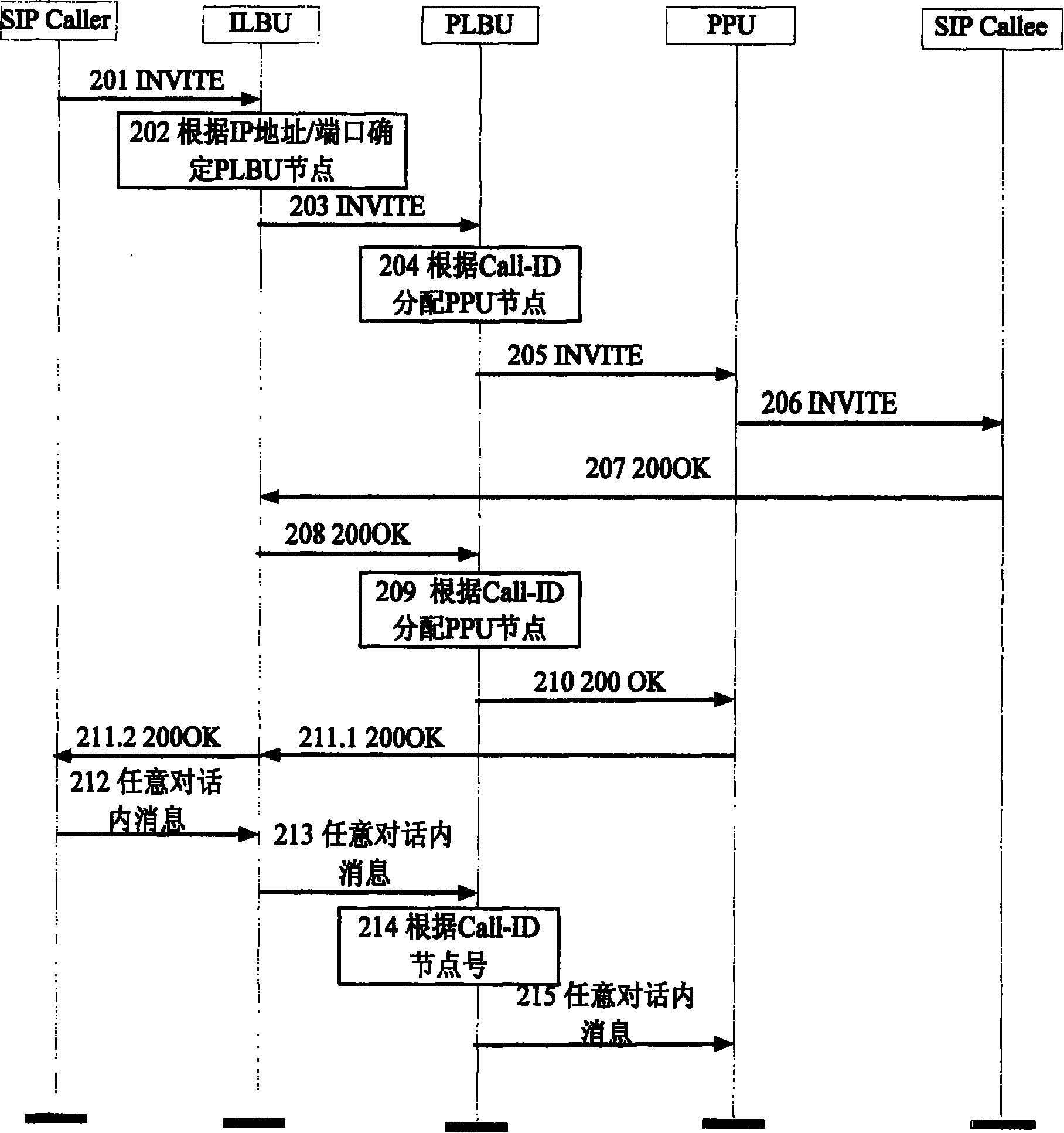
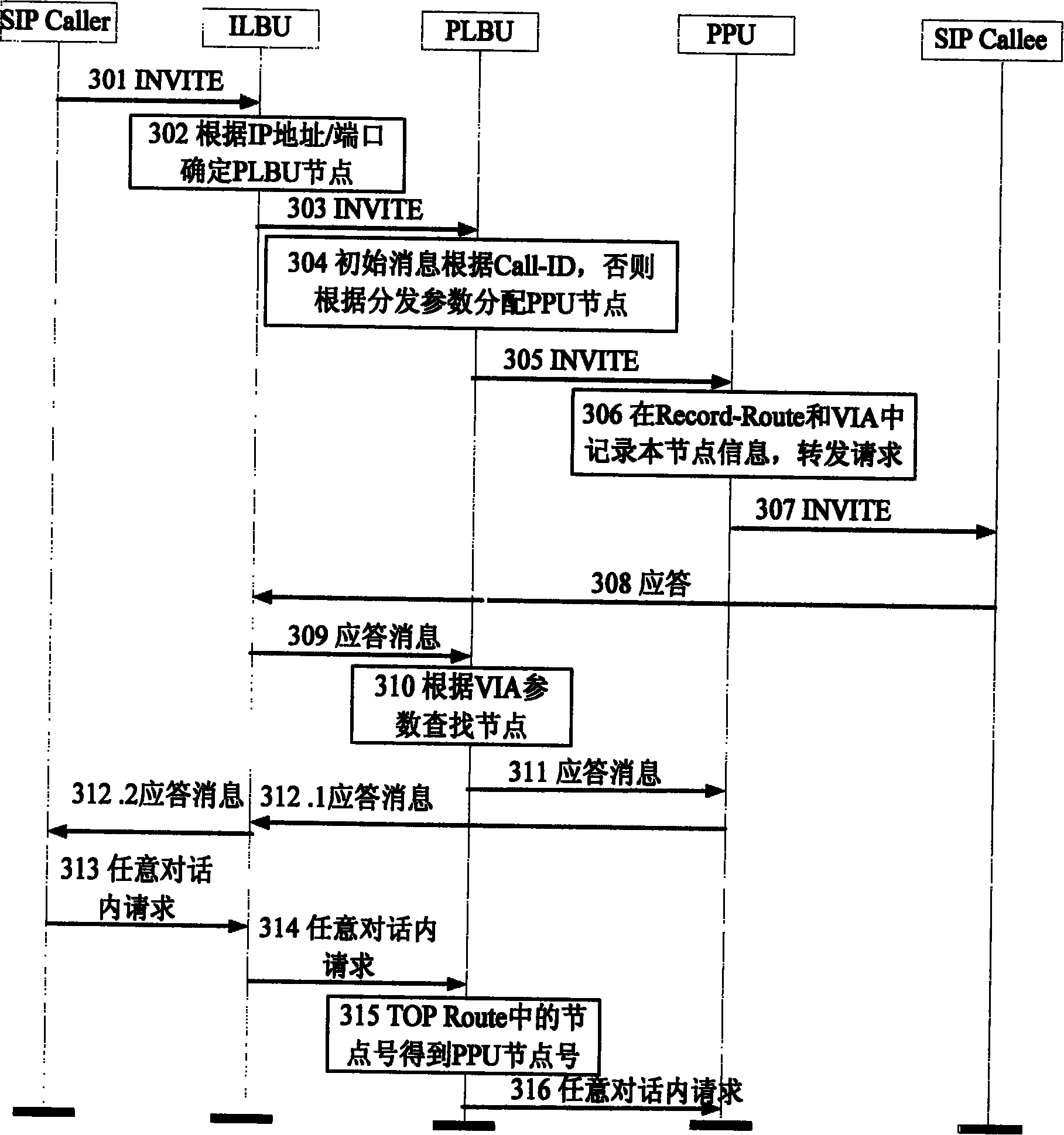
ActiveCN101166176AProcessing does not affectKeep statelessTransmissionSession Initiation ProtocolDistributed computing
SIP entity initiates message of SIP request. Receiving SIP message, ILBU sends the message to a PLBU process node based on address or port number of message. Decoding the SIP message, PLBU determines whether the message is a request on inside or outside conversation, or a response in order to carry out different processes. The method improves shortcoming of current fixed type HASH algorithm, and meanwhile keeps characteristic of no state of distributing procedure self. In the invention, no meter increasing or decreasing nodes in the system or adjusting distributing strategy of system will not influence on processing message of conversation so as to raise reliability and scalability of system greatly.
Owner:ZTE CORP
Apparatus and method for reactivating multiple packet data sessions in a wireless network
A mobile station capable of reactivating at least a dormant first data session and a dormant second data session associated with a first base station of a wireless network. The mobile station transmits to the first base station an Origination message comprising: i) a first Data Ready to Send (DRS) field indicating to the first base station that the dormant first data session is being reactivated; and ii) a second Data Ready to Send (DRS) field indicating that the dormant second data session is being reactivated.
Owner:SAMSUNG ELECTRONICS CO LTD
Universal transfer method and network with distributed switch
InactiveUS7061910B2Simple algorithmImproves connection setup rateMultiplex system selection arrangementsBroadcast transmission systemsFrame RelayTransfer mode
A method and a network for a universal transfer mode (UTM) of transferring data packets at a regulated rate are disclosed. The method defines a protocol that uses an adaptive packet header simplify packet routing and increase transfer speed. The protocol supports a plurality of data formats, such as PCM voice data, IP packets, ATM cells, frame relay and the like. The network preferably includes plurality of modules that provide interfaces to various data sources. The modules are interconnected by an optic core with adequate inter-module links with preferably no more than two hops being required between any origination / destination pair of modules. The adaptive packet header is used for both signaling and payload transfer.
Owner:CIENA
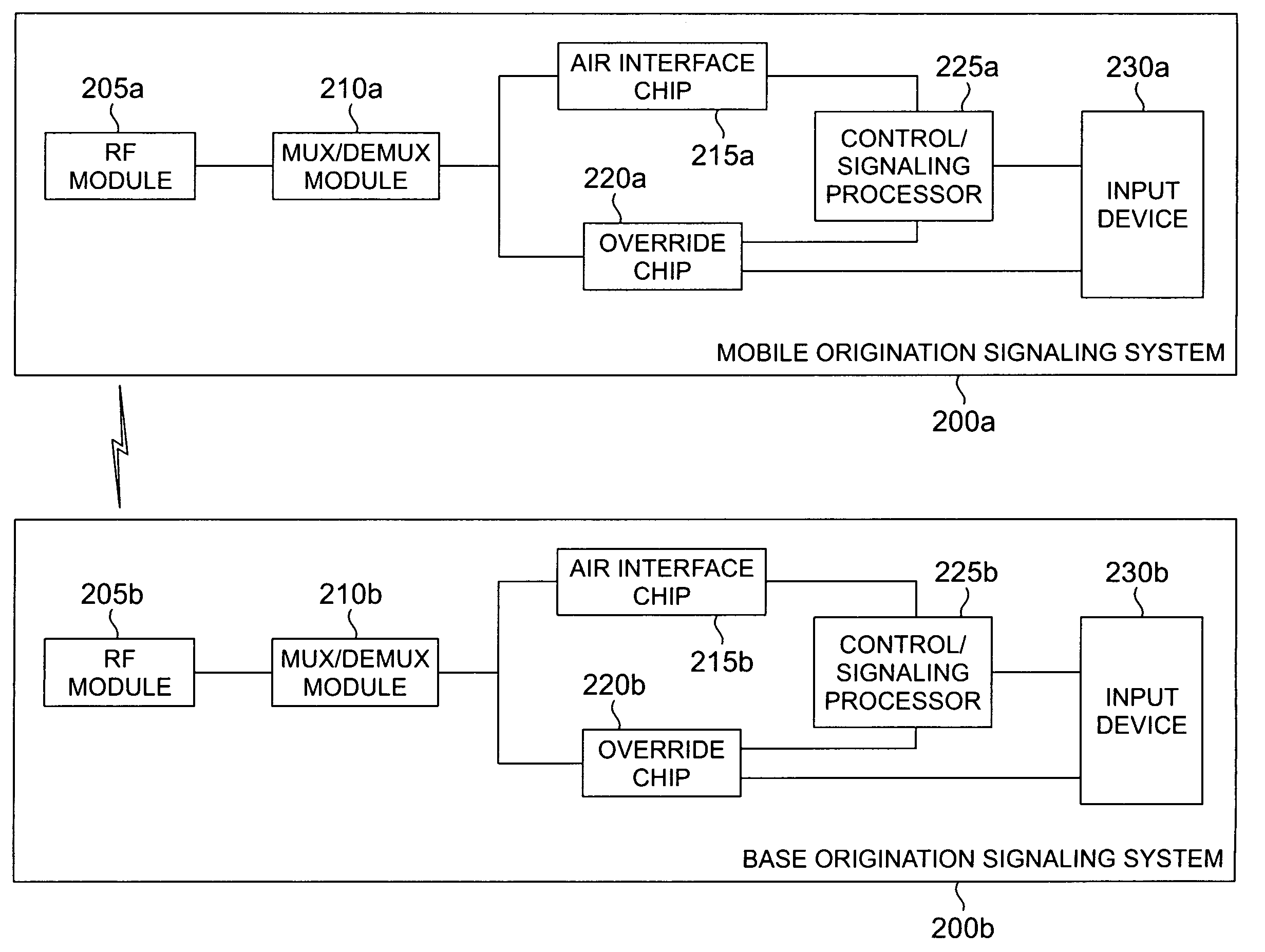
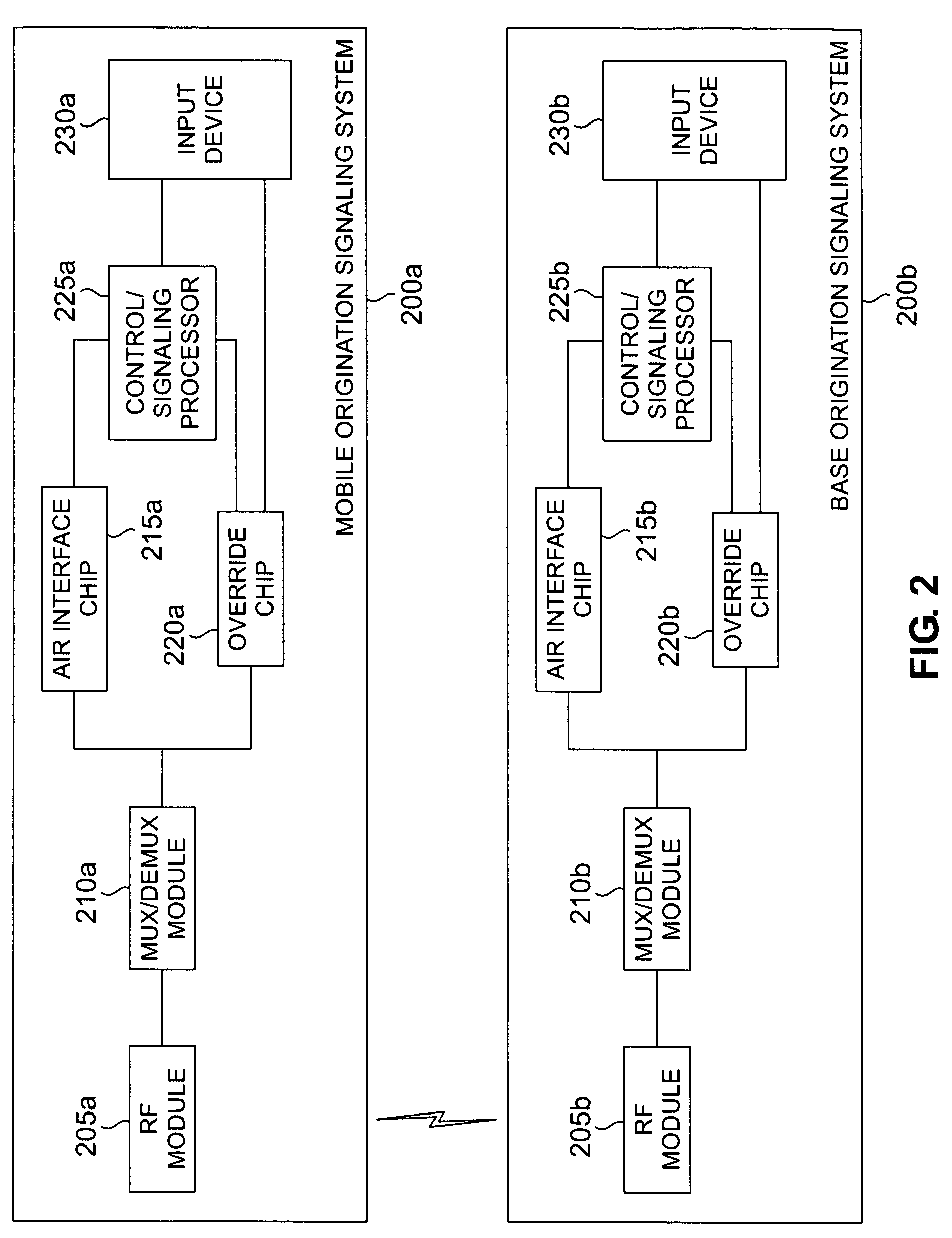
Method and system for origination signaling in a wireless network
ActiveUS7561896B2Eliminate and reduce disadvantageEliminate and reduce and problemBroadcast transmission systemsTime-division multiplexWireless networkReal-time computing
A method for origination signaling in a wireless network is provided. The method includes receiving a delayed feature request at an input device. The delayed feature request is directly provided from the input device to an override chip. An invitation message that is operable to request establishment of a delayed feature session is generated in the override chip based on the delayed feature request. The invitation message is sent to a base station.
Owner:SAMSUNG ELECTRONICS CO LTD
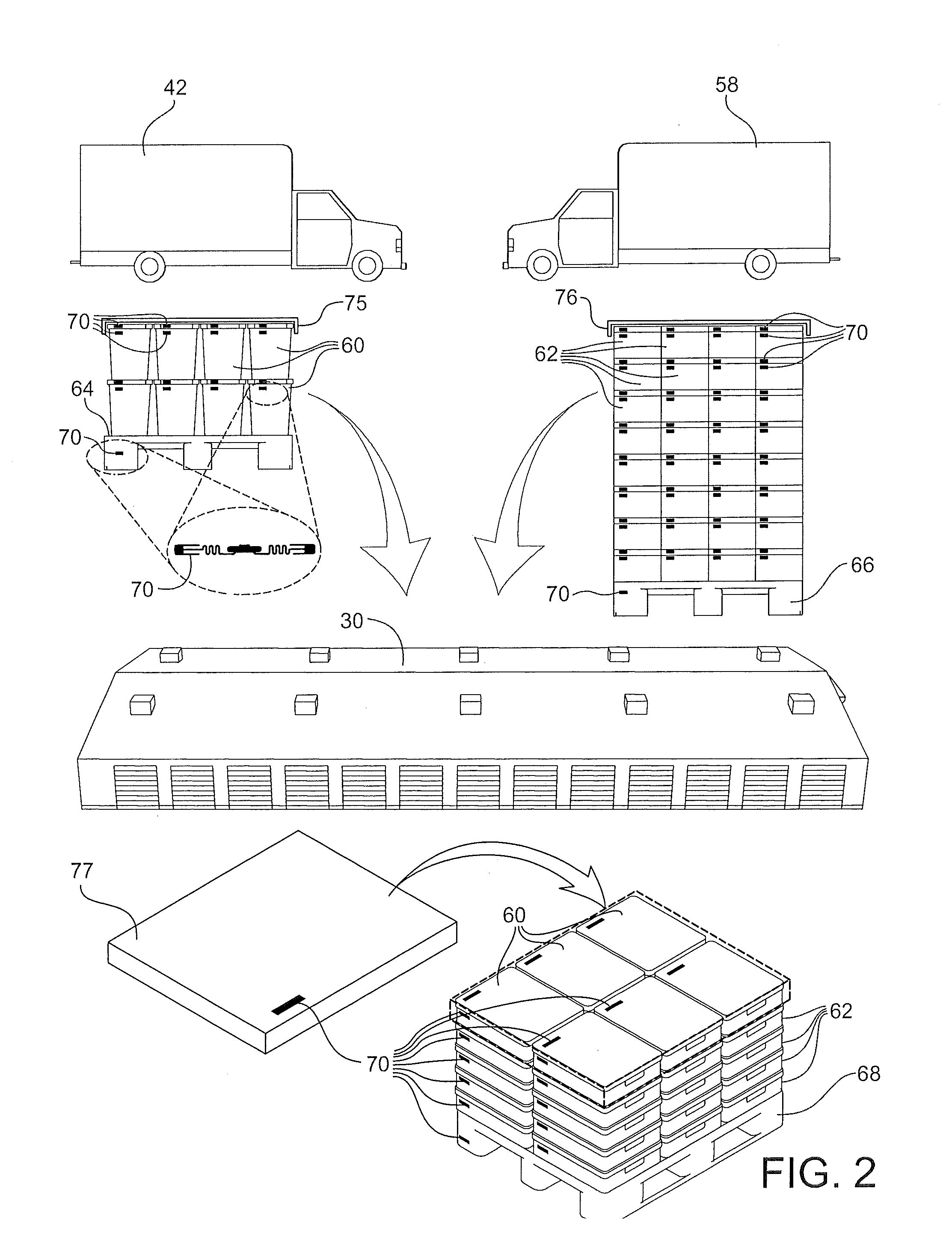
Closed-loop container indentification and tracking method and apparatus
A closed-loop box identification and tracking system that includes a plurality of boxes for being moved by at least one box transport apparatus between an origination point and a destination point, each box containing an RFID tag. At least one RFID reader / transmitter is provided to interact with the at least one box transport apparatus, and is adapted to read the RFID tags when in proximity to the RFID reader / transmitter and transmit the identification of the RFID tag. An RFID receiver and associated digital computer is provided for receiving, storing and processing the transmitted RFID identification for determining the location of the boxes from the processed RFID identification.
Owner:SCHAEFER SYST INT INC
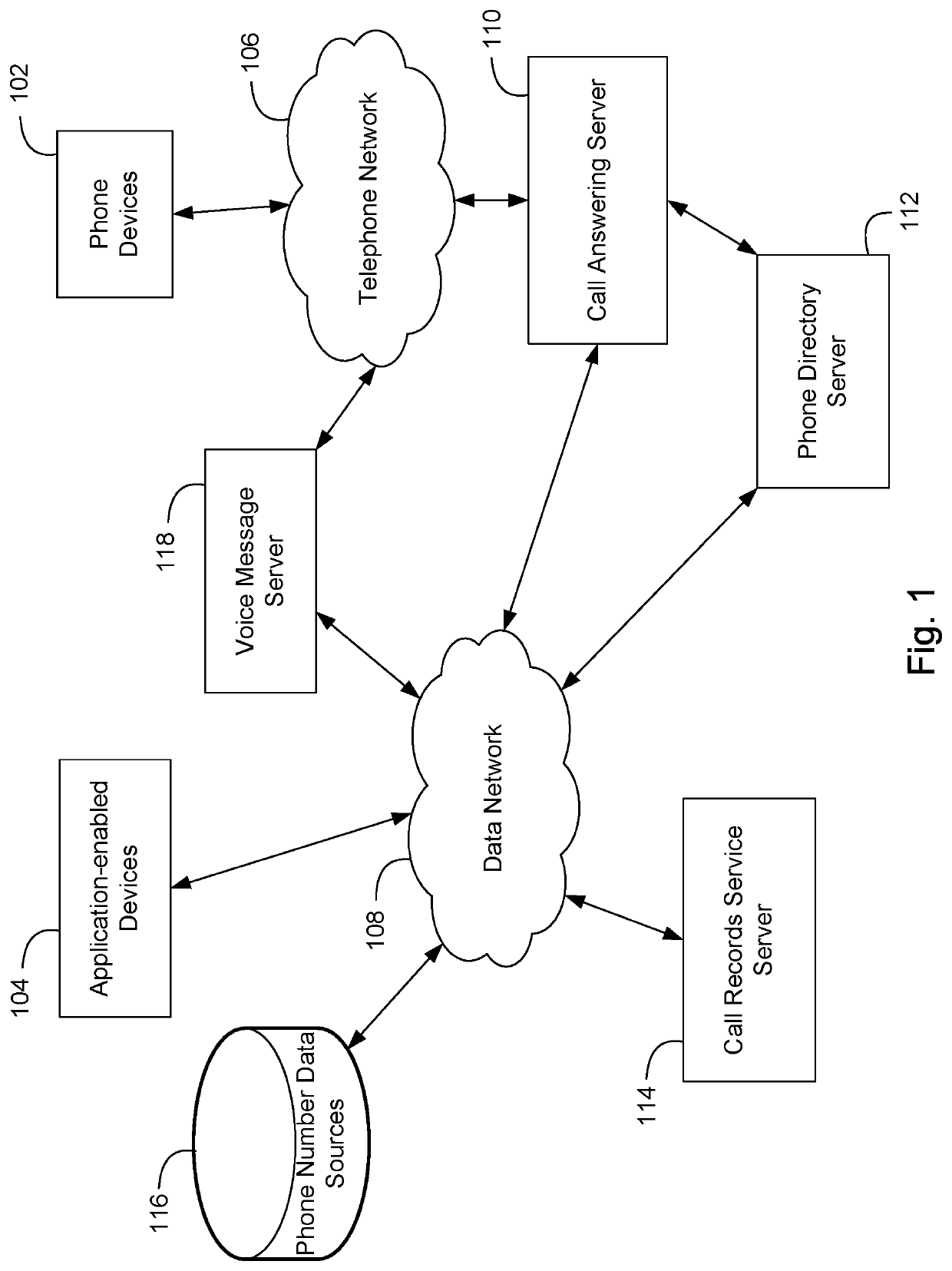
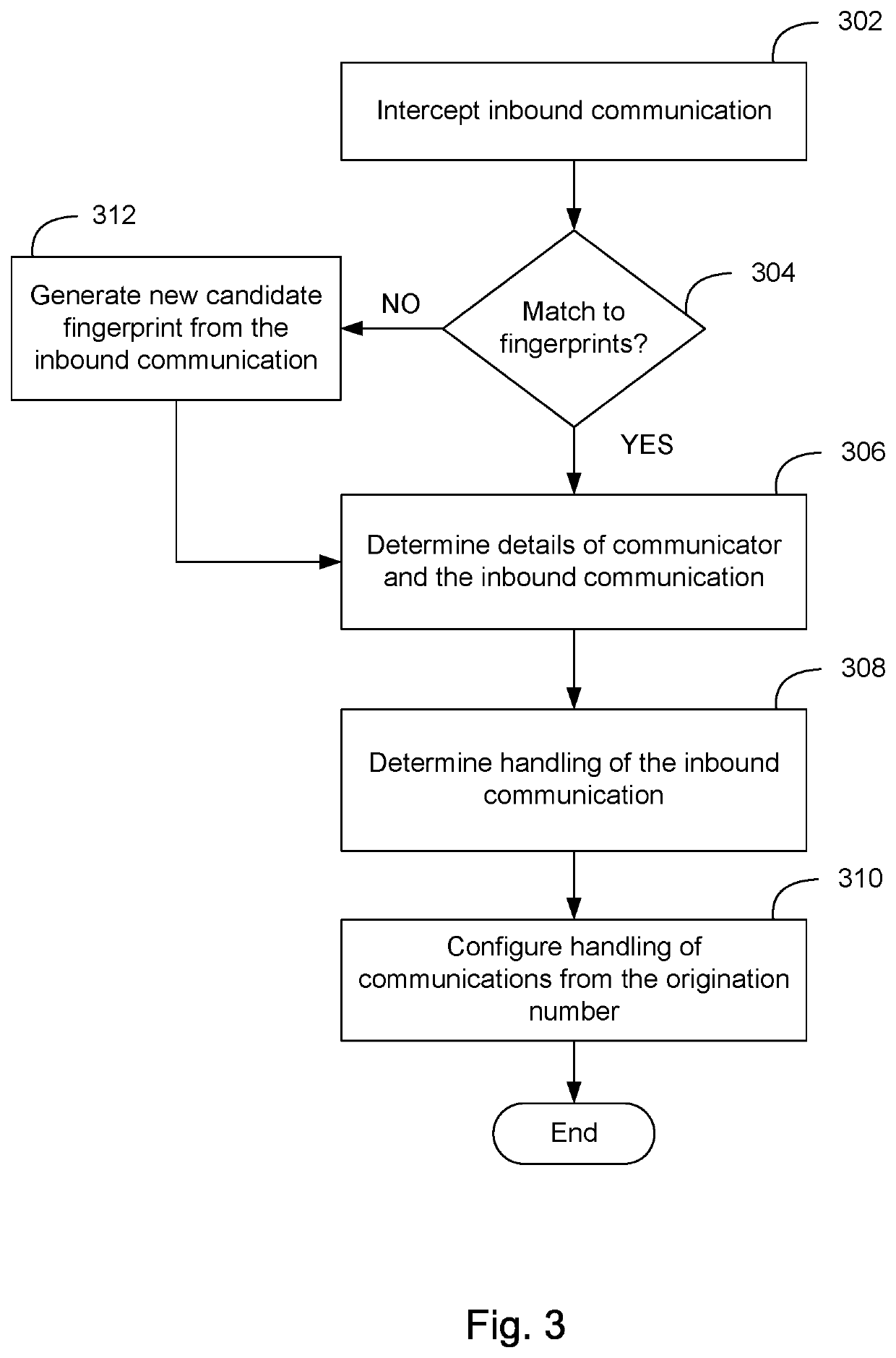
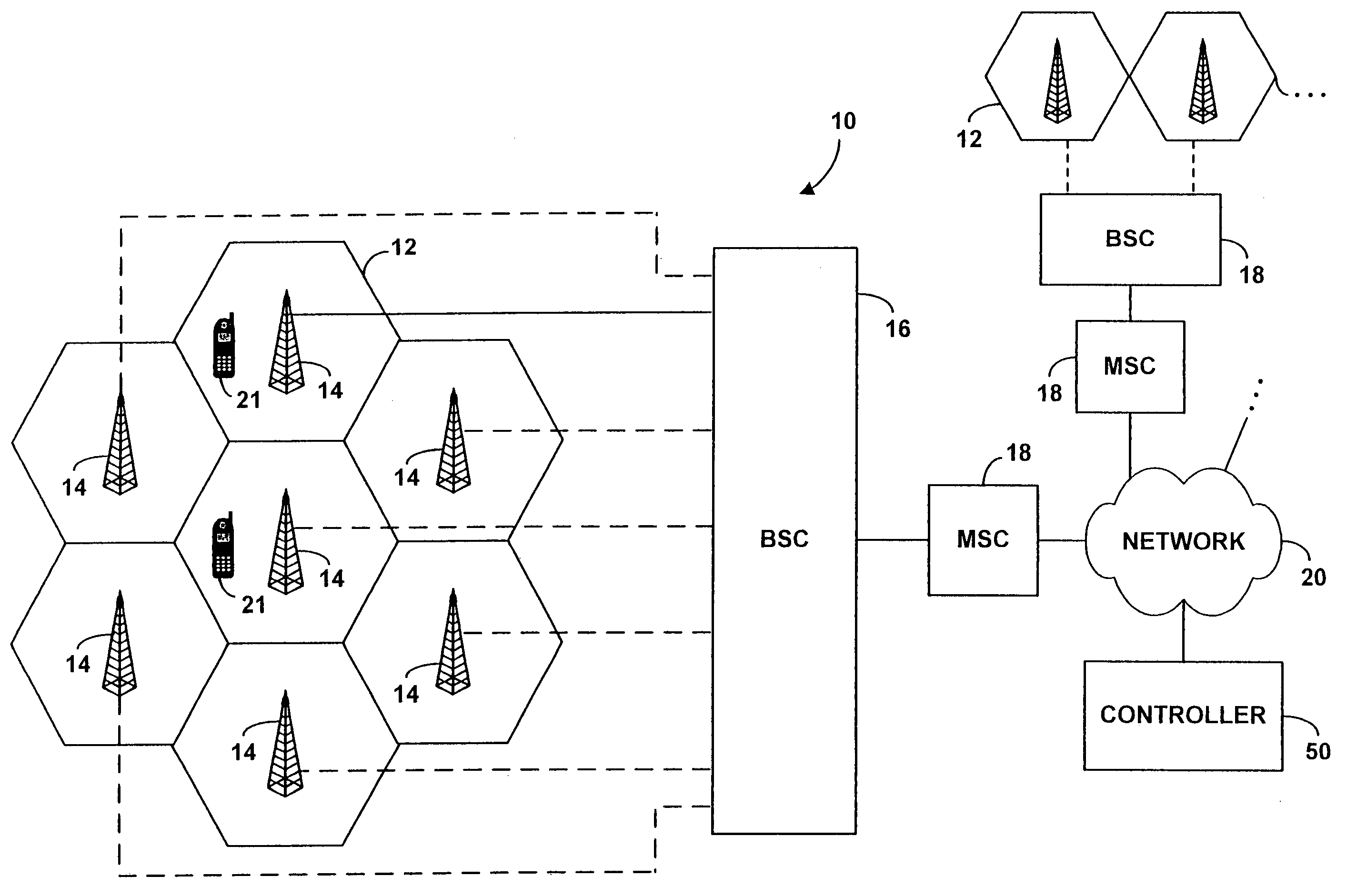
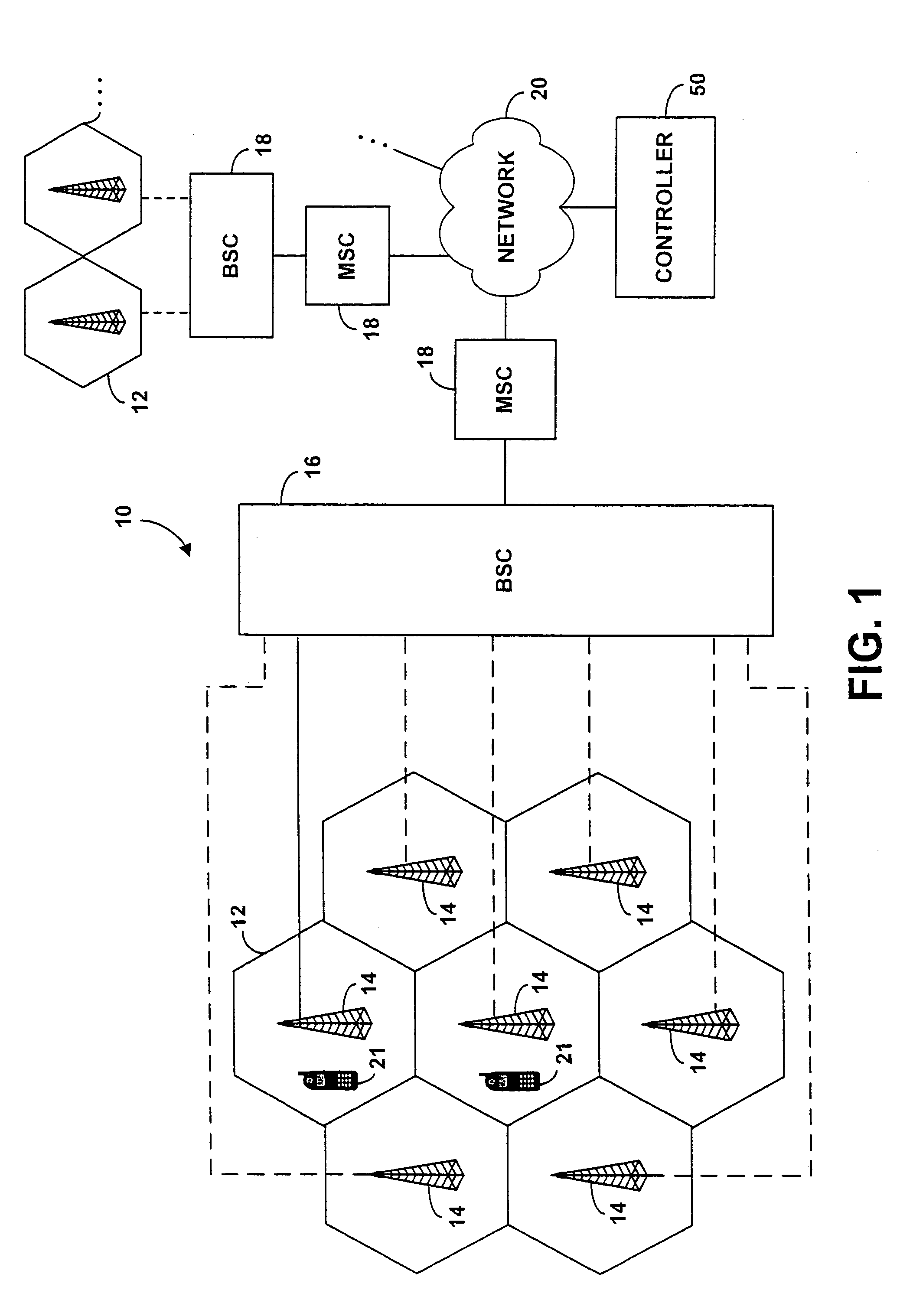
System and method for determining unwanted call origination in communications networks
ActiveUS10798241B1Easy to understandSpecial service for subscribersCalling susbscriber number recording/indicationCall originationVideo sequence
A method and system for discovering and locating the source of unwanted communication origination in a communications network, the method comprising compiling a communication campaign database storing data of one or more communication campaigns along with automatically identified instances of those campaigns, and simultaneously or sequentially matching those instances against known communication traffic of a set of cooperating telecommunication carriers. The one or more communications campaigns include a grouping of related fingerprints and patterns that identify a sequence of characters, audio or video associated with instances of a same likely campaigns, either legitimate or illegitimate / fraudulent.
Owner:YOUMAIL
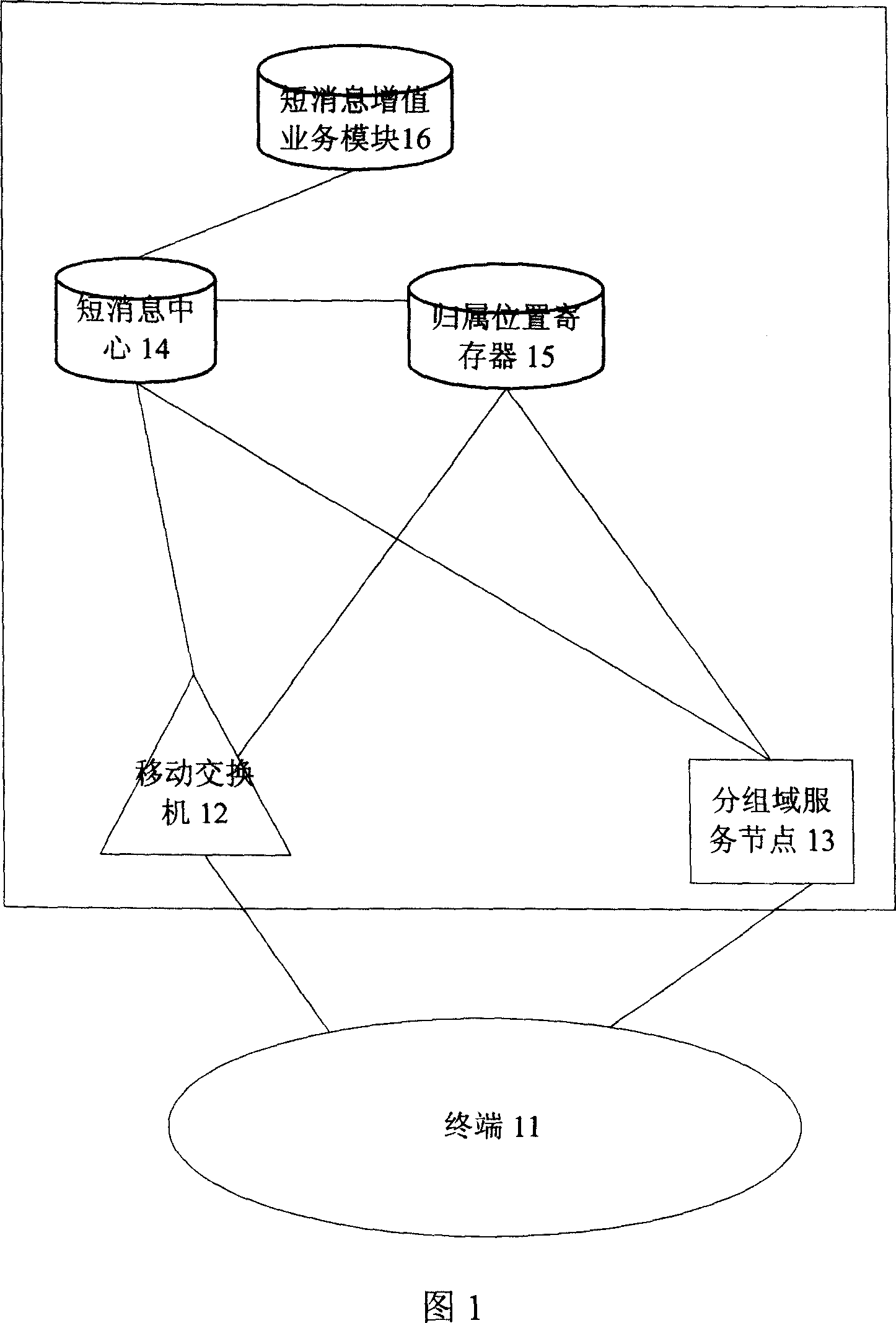
A device and method for realizing automatic SMS forward
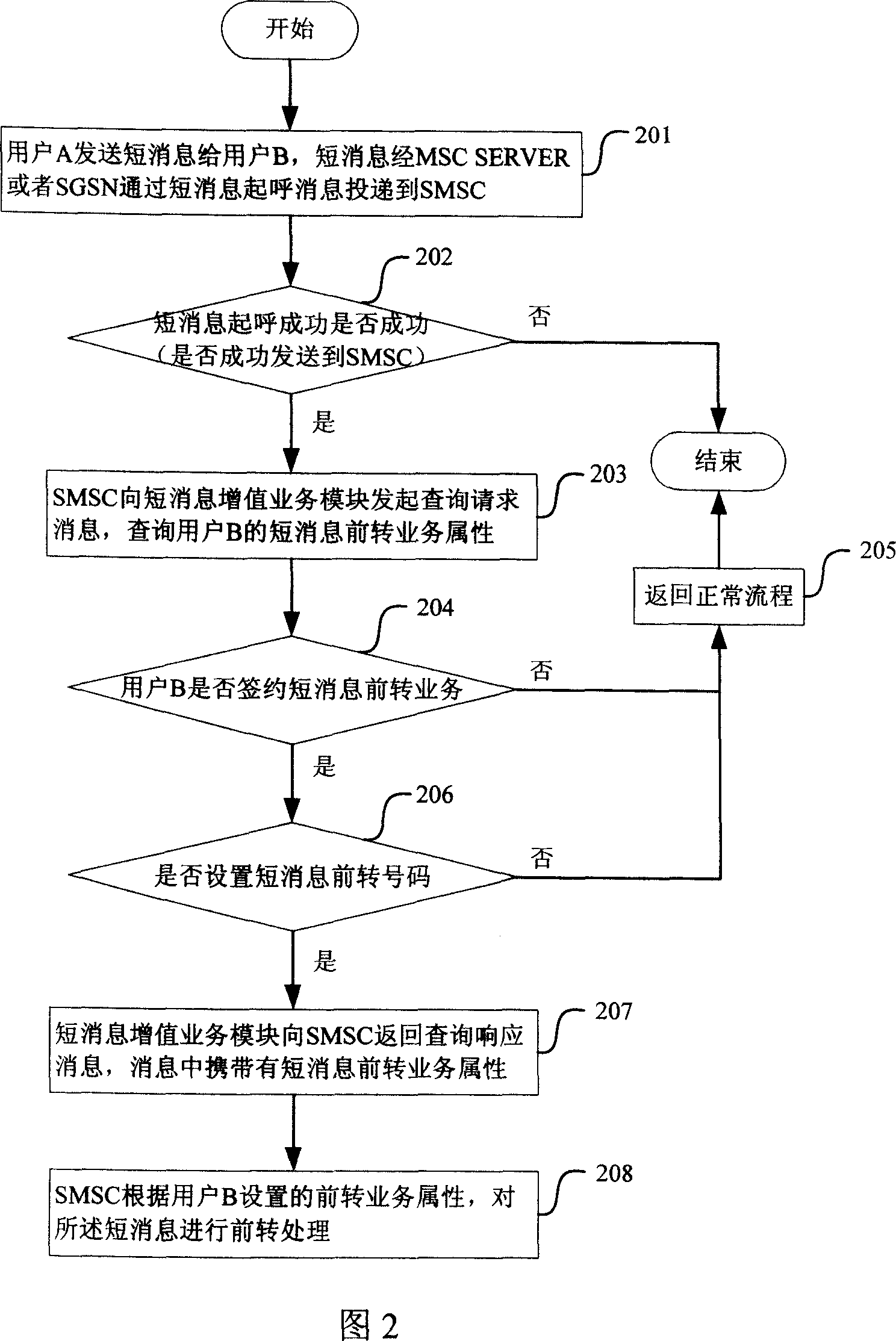
InactiveCN101146244AEnrich business experienceRead in timeSpecial service for subscribersCommmunication supplementary servicesComputer hardwareService experience
The invention discloses a device and a method for automatic short message forwarding. The device comprises a short message value-added service module for setting and saving the property of a short message forwarding service signed by a user. The method comprises: (a) a user A sends a short message to a user B, and a short message center, after completing the short message origination, sends a query request message to the short message value-added service module to inquire the property of the short message forwarding service of the user B; (b) the short message value-added service module receives the query request message, and then judges whether the user B signed the short message forwarding service and simultaneously sets a short message forwarding code C and feedbacks a query response message to the short message center, wherein the message carries the property of the short message forwarding service; (c) the short message center extracts the property of the short message forwarding service from the received query response message and performs the forwarding treatment of the short message according to the property of the forwarding service signed by the user B. The invention provides the user with rich service experiences.
Owner:ZTE CORP
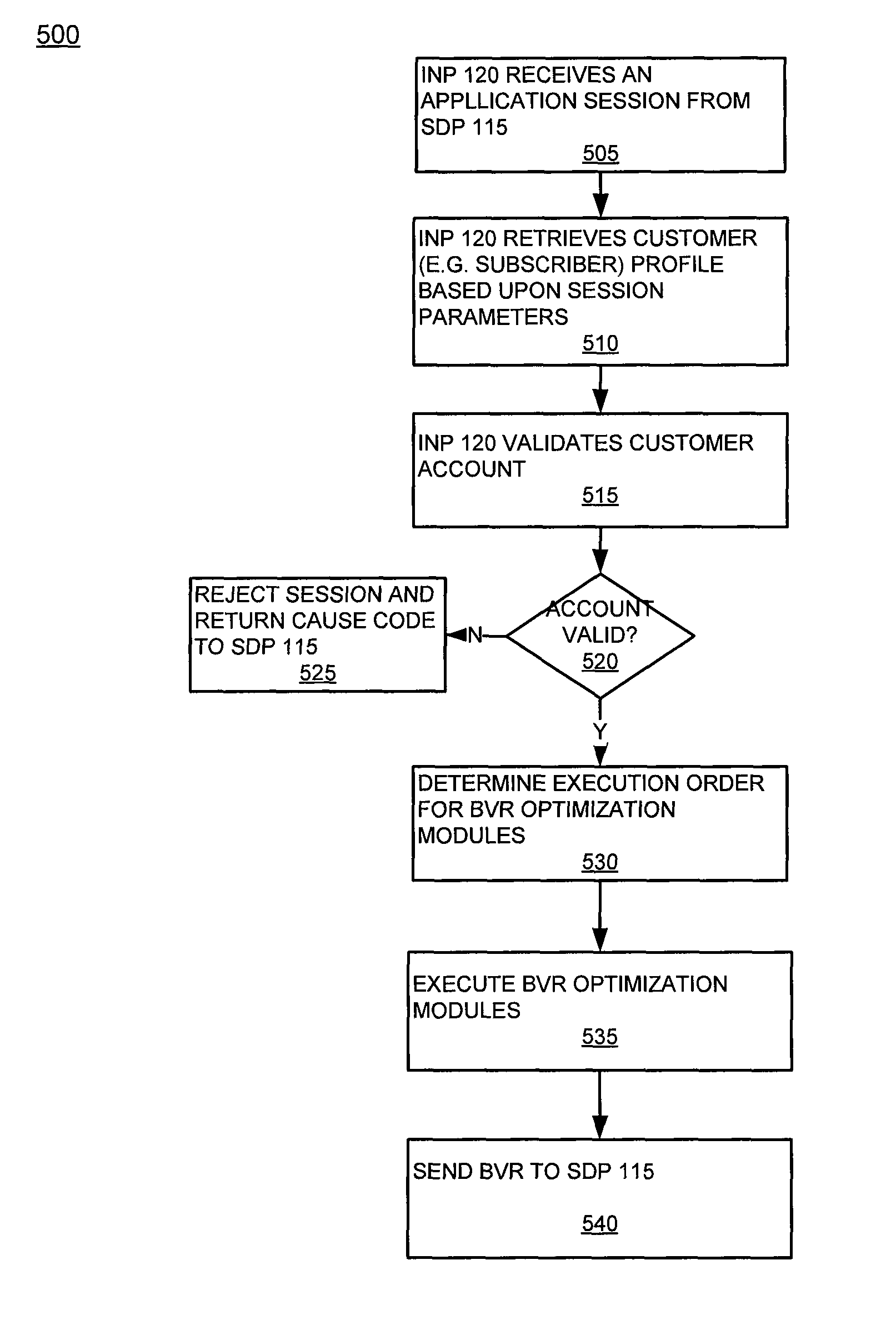
System and method for best value routing
A system determines, in real-time, the routing of communication services from origination to destination based on a number of selected criteria used to determine an optimal path. Best value routing enables carriers and service providers to route a session / call by using an advanced intelligent network solution to generate optimal routes / service providers for servicing a request.
Owner:PULSE NETWORKS +1
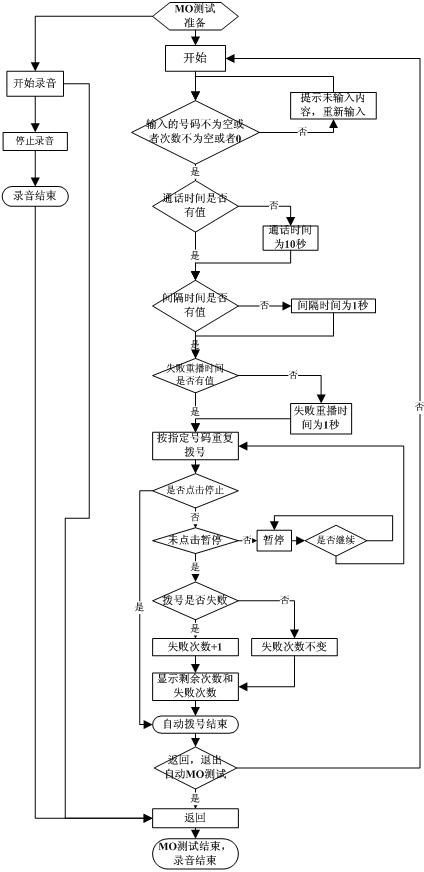
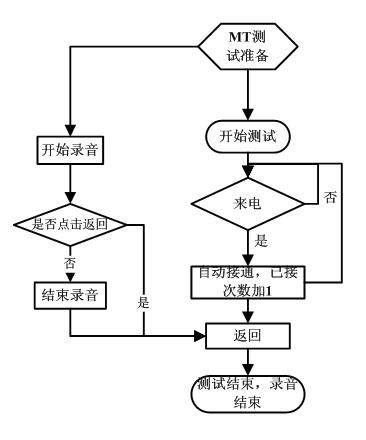
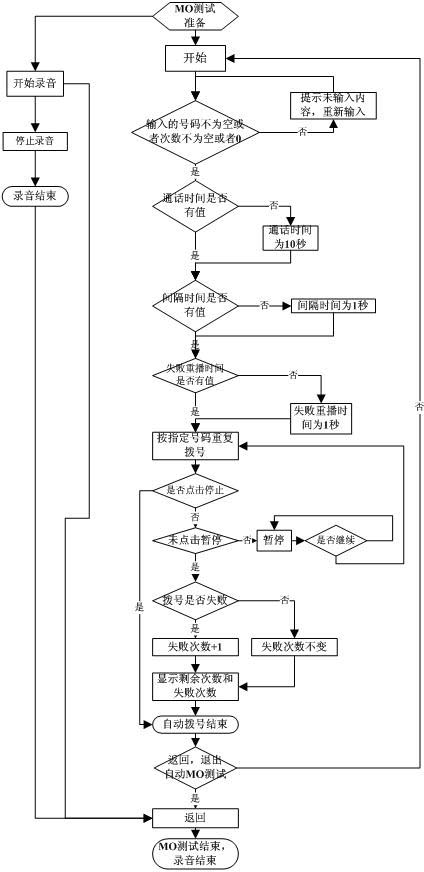
Method for realizing automatic mobile origination call (MO) and mobile termination call (MT) tests
ActiveCN102307254AReal-time transmissionImprove general performanceSubstation equipmentApplication programming interfaceRepeat testing
The invention discloses methods for realizing automatic mobile origination call (MO) and mobile termination call (MT) tests. An MO test is used for testing whether a mobile origination call function is normal or not, namely testing whether a calling communication function is normal or not when a mobile phone calls another mobile phone. An MT test is used for testing a mobile termination call function is normal or not, namely testing whether a receiving communication function is normal or not when the mobile phone is called by another mobile phone. In the MO test, a bottom-layer calling application programming interface (API) and own counter are called, and parameters such as call numbers, the number of calls, call time and the like in the test are recorded; and a media recorder interface records the sound information of receiver and a microphone, and stores the recorded sound information into a memory card. In the MT test, a message receiver monitors incoming calls, automatically answers the incoming calls under the condition of enabling automatic answering if the mobile phone is called, and records sounds, successful answering times and unsuccessful answering times. The method ishighly universal, and repeated development can be avoided; the method is implemented in automated scripts by practice; and automatic dialing and answering is realized, test records are recorded, the sounds recorded in the calls are stored, and repeated tests in data services are performed.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
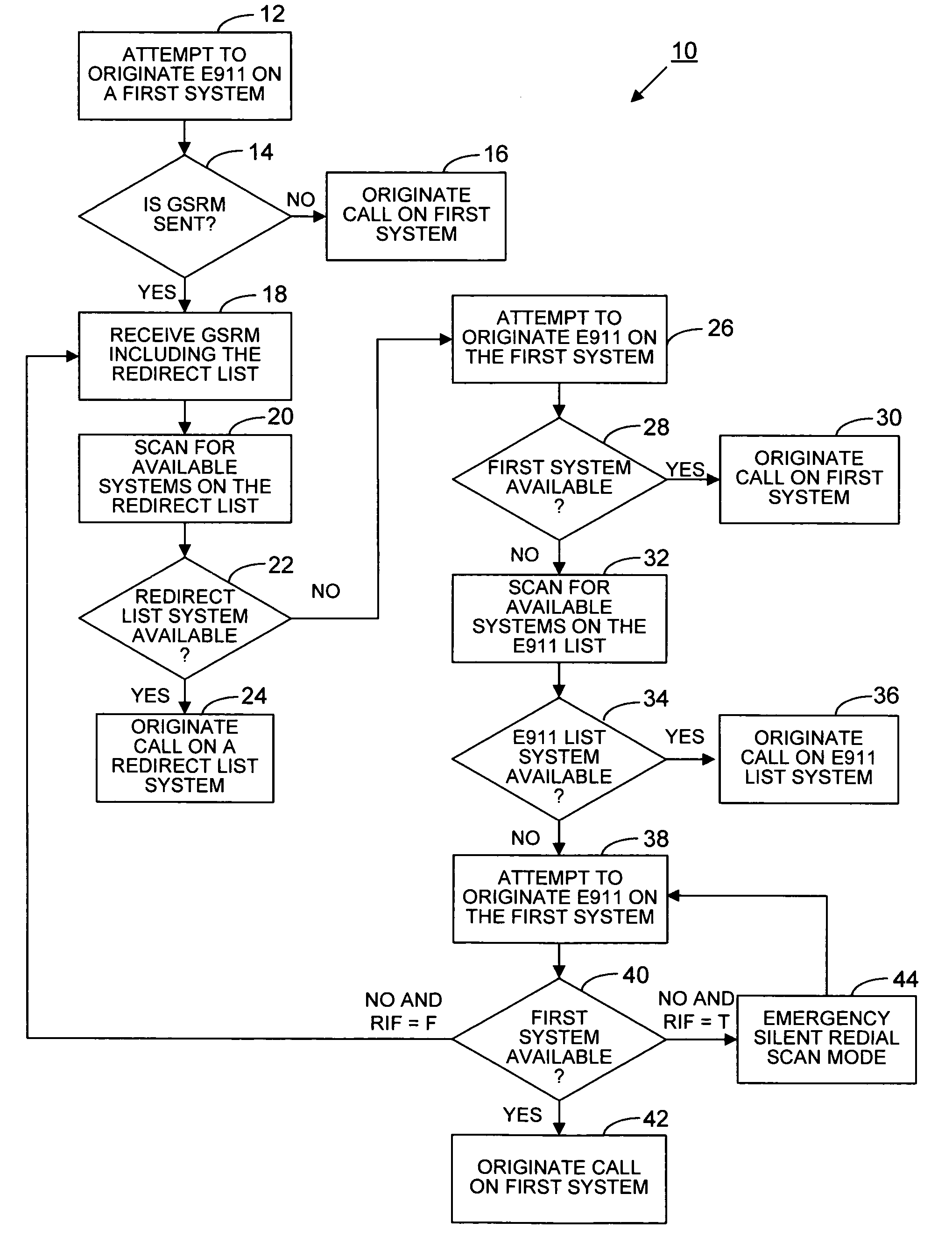
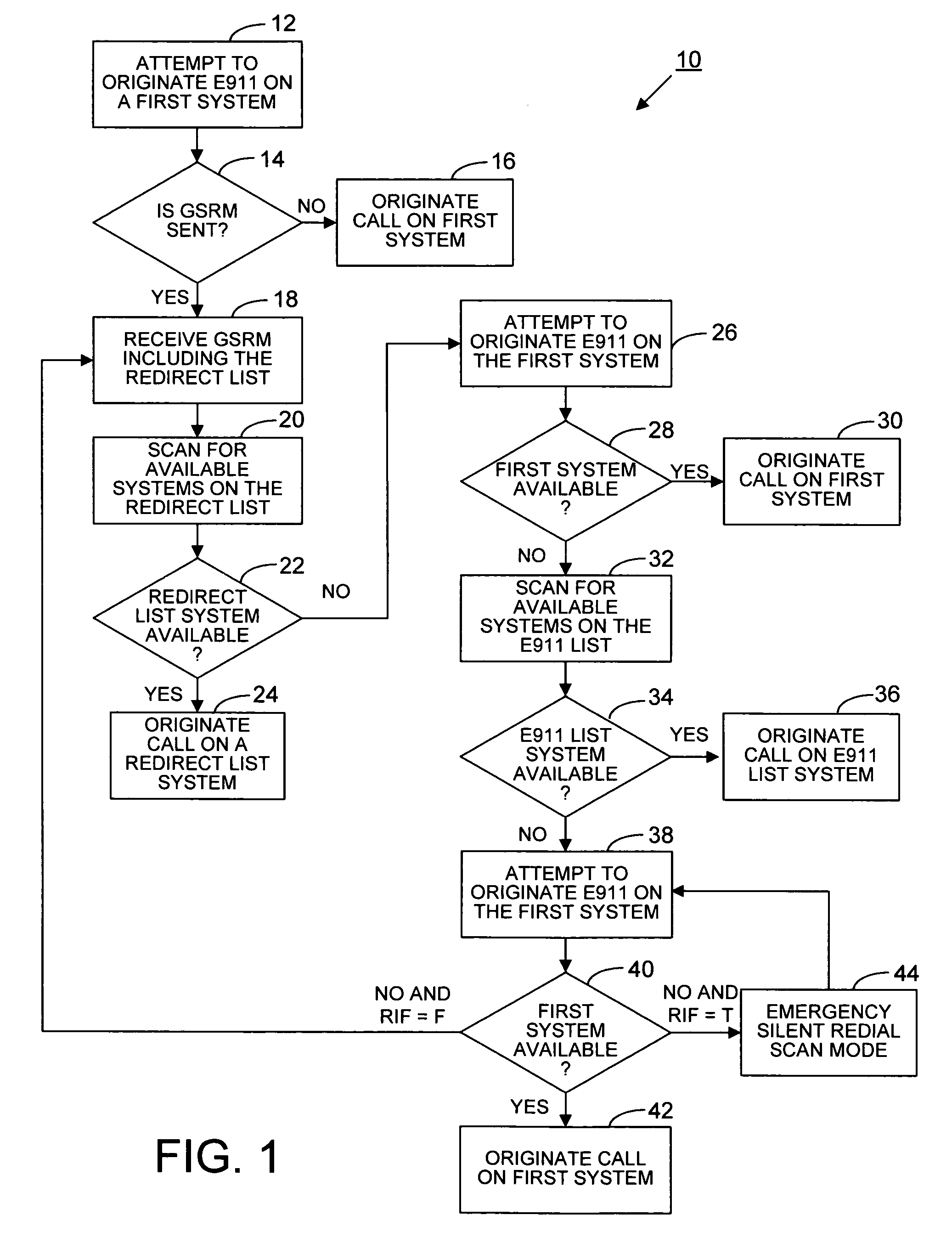
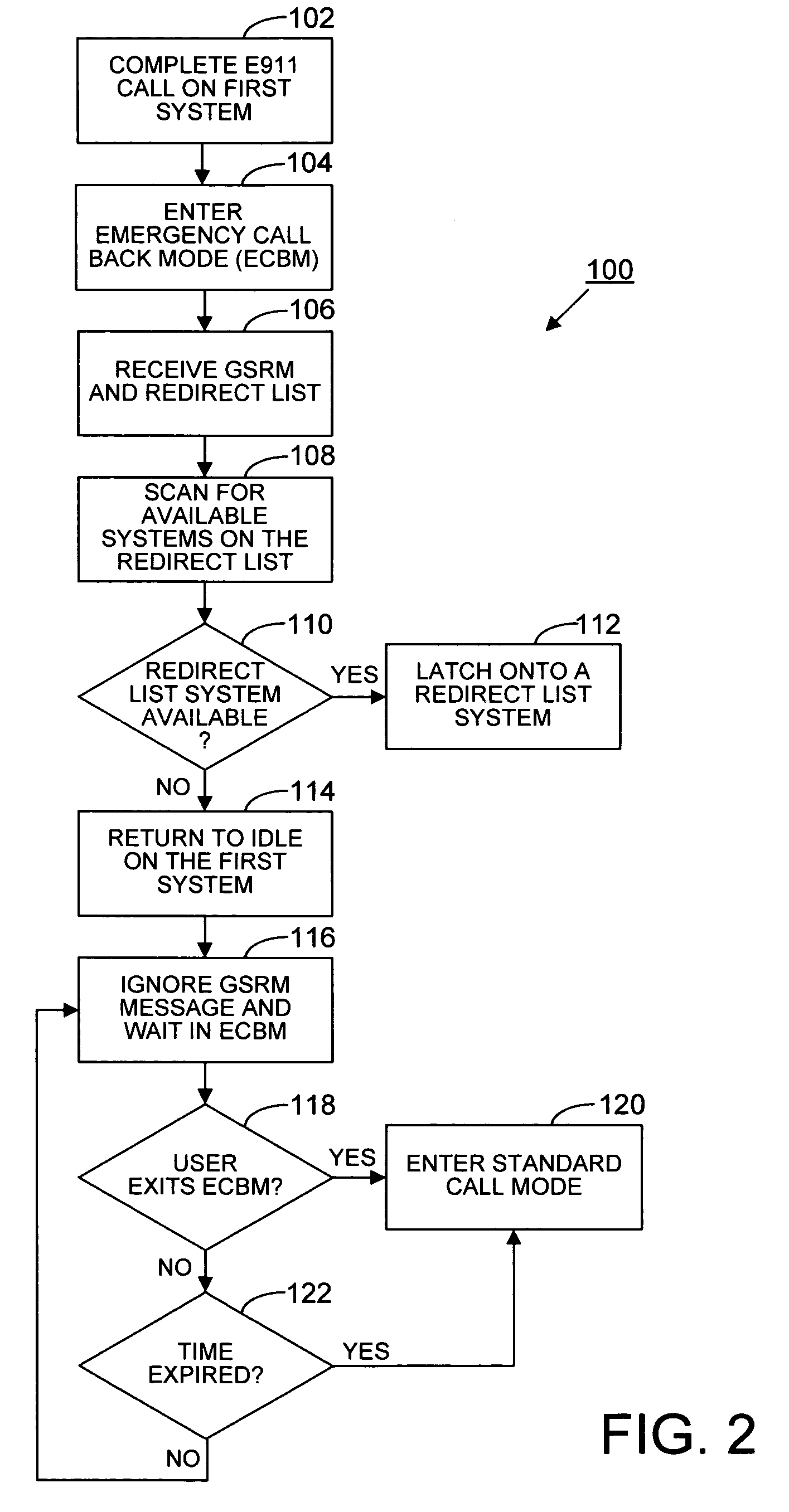
E911 behavior with GSRM in a wireless communication device
InactiveUS7463880B2Multiplex system selection arrangementsSpecial service for subscribersTelecommunicationsStandby system
A wireless communications device attempts to originate an emergency E911 call on a first system. If the system sends a global service redirection message (GSRM), including a redirect list, then the device scans alternate systems from the redirect list. if the redirect systems are not available, the device and again attempts to originate the E911 call on the first system. If the origination is not accepted on the first system, then the device scans an E911 list. If the device fails to acquire a system on the E911 list, the device returns to the first system to reattempt origination if the first system has directed the device to “return if failure”. If origination is not honored on the first system, the device enters an emergency silent redial scan mode and continues attempts at origination until accepted by the first system. After the wireless communication device has completed an E911 call to a Public Safety Answering Point (PSAP), it enters an emergency call back mode and idles on the system network so that it can receive emergency call backs from the PSAP. If the system sends a GSRM message, the device will scan the redirect list sent to the device in the GSRM message. However, if the systems of the redirect list are not available, the device will not scan an E911 list. Instead, the device will return to the redirecting system and ignore the GSRM messages and wait in the emergency call back mode.
Owner:KYOCERA CORP
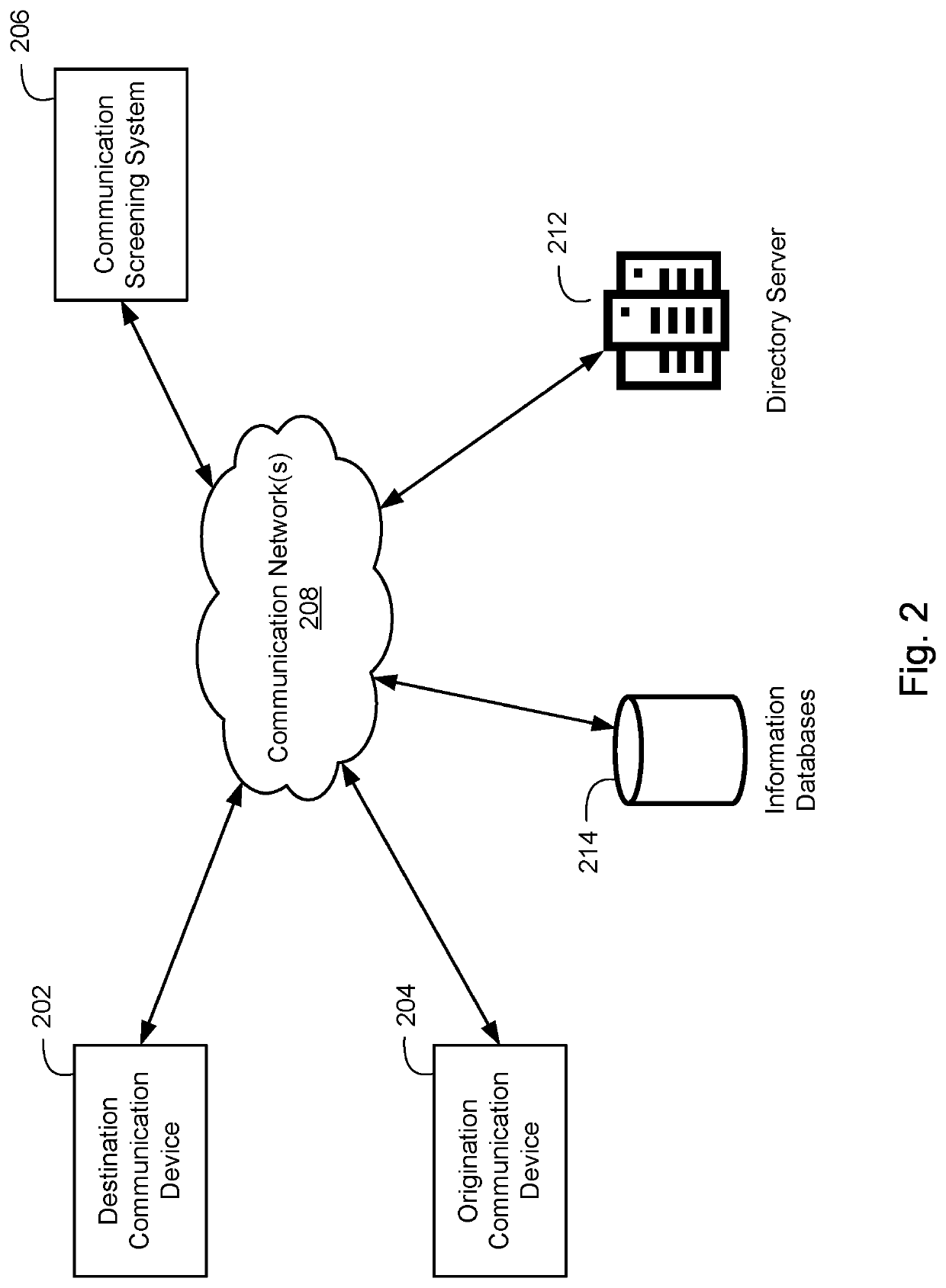
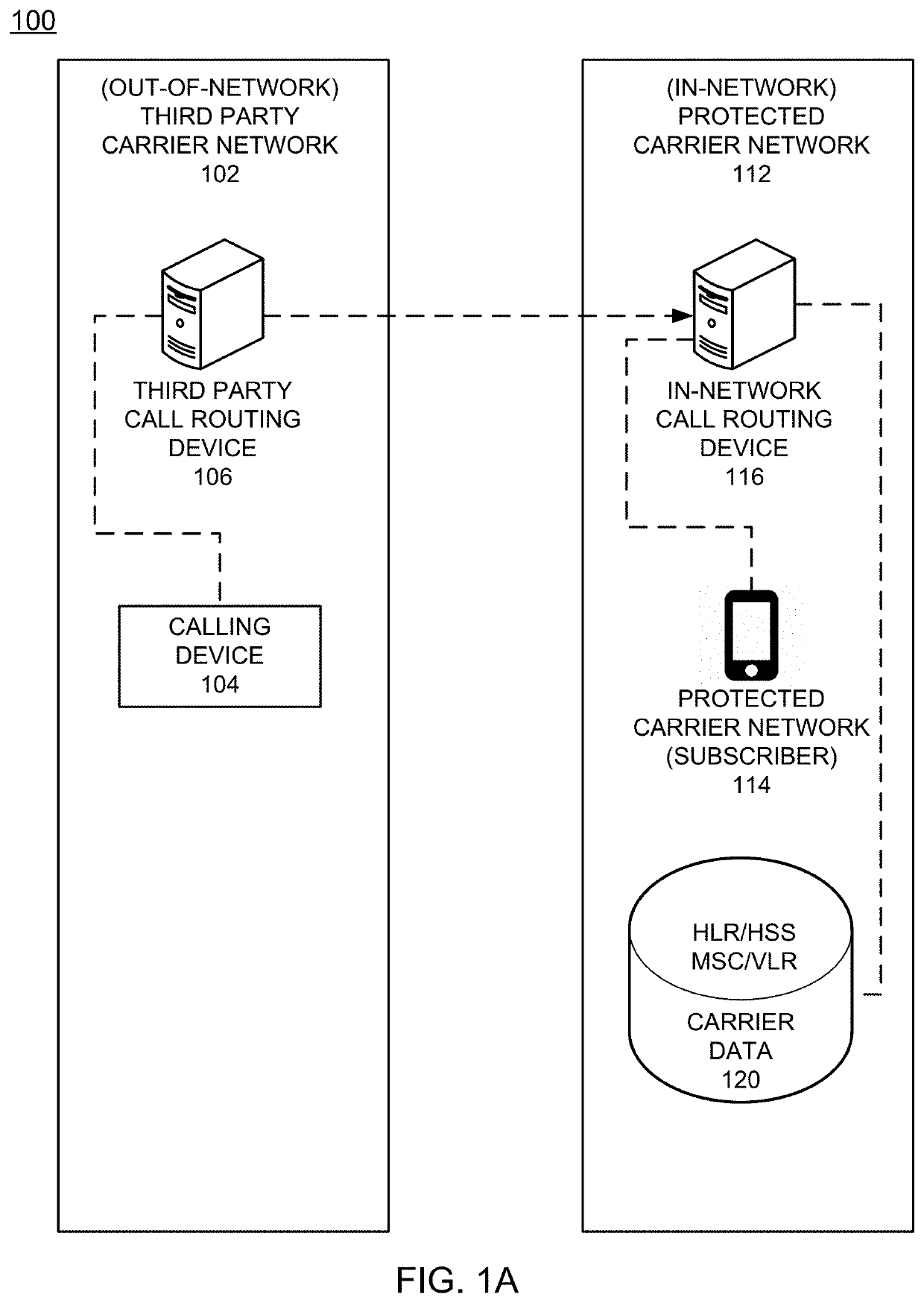
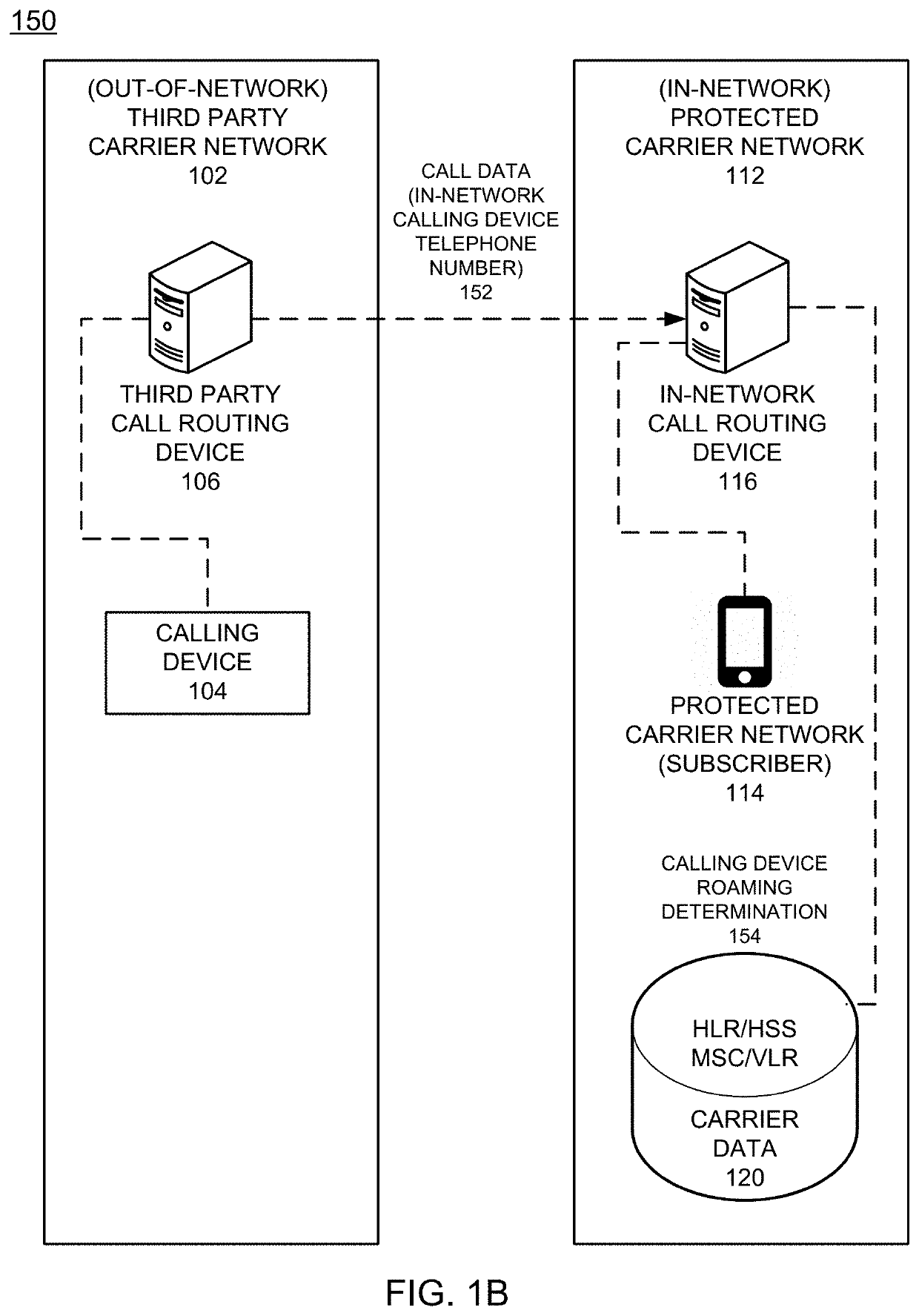
Call screening service for detecting fraudulent inbound/outbound communications with subscriber devices
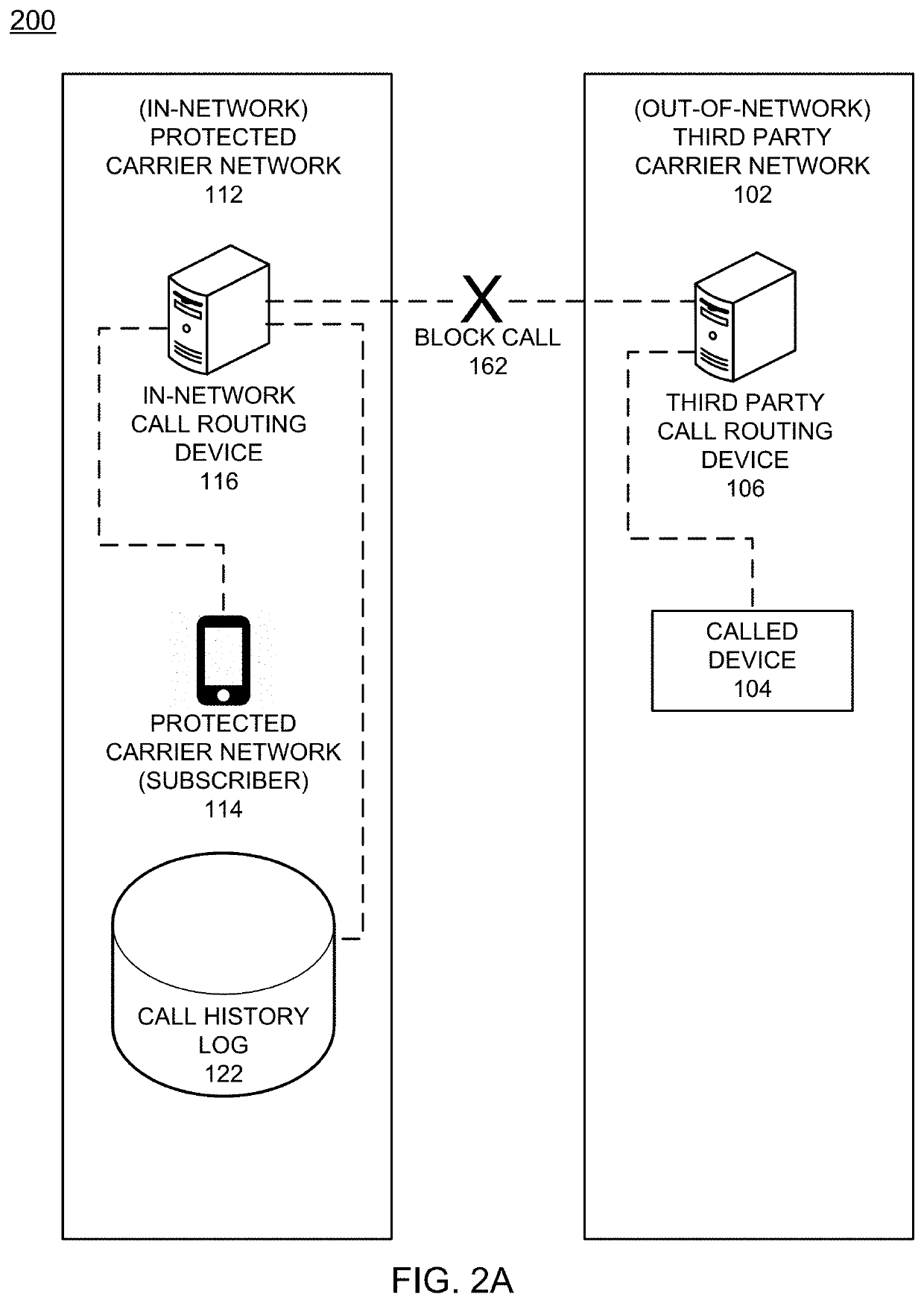
ActiveUS20210203779A1Raise the possibilitySpecial service for subscribersSupervisory/monitoring/testing arrangementsOutbound communicationScreening call
An example method of operation may include one or more of identifying an inbound call intended for a mobile device subscribed to a protected carrier network, determining the inbound call is assigned an origination telephone number that is subscribed to the protected carrier network, determining whether an inbound call origination source location indicates the protected carrier network or an out-of-network carrier network based on one or more call parameters received with the inbound call, and determining whether to transmit an indication to the mobile device that the inbound call has an elevated likelihood of being a scam call based on the inbound call origination source location.
Owner:FIRST ORION CORP
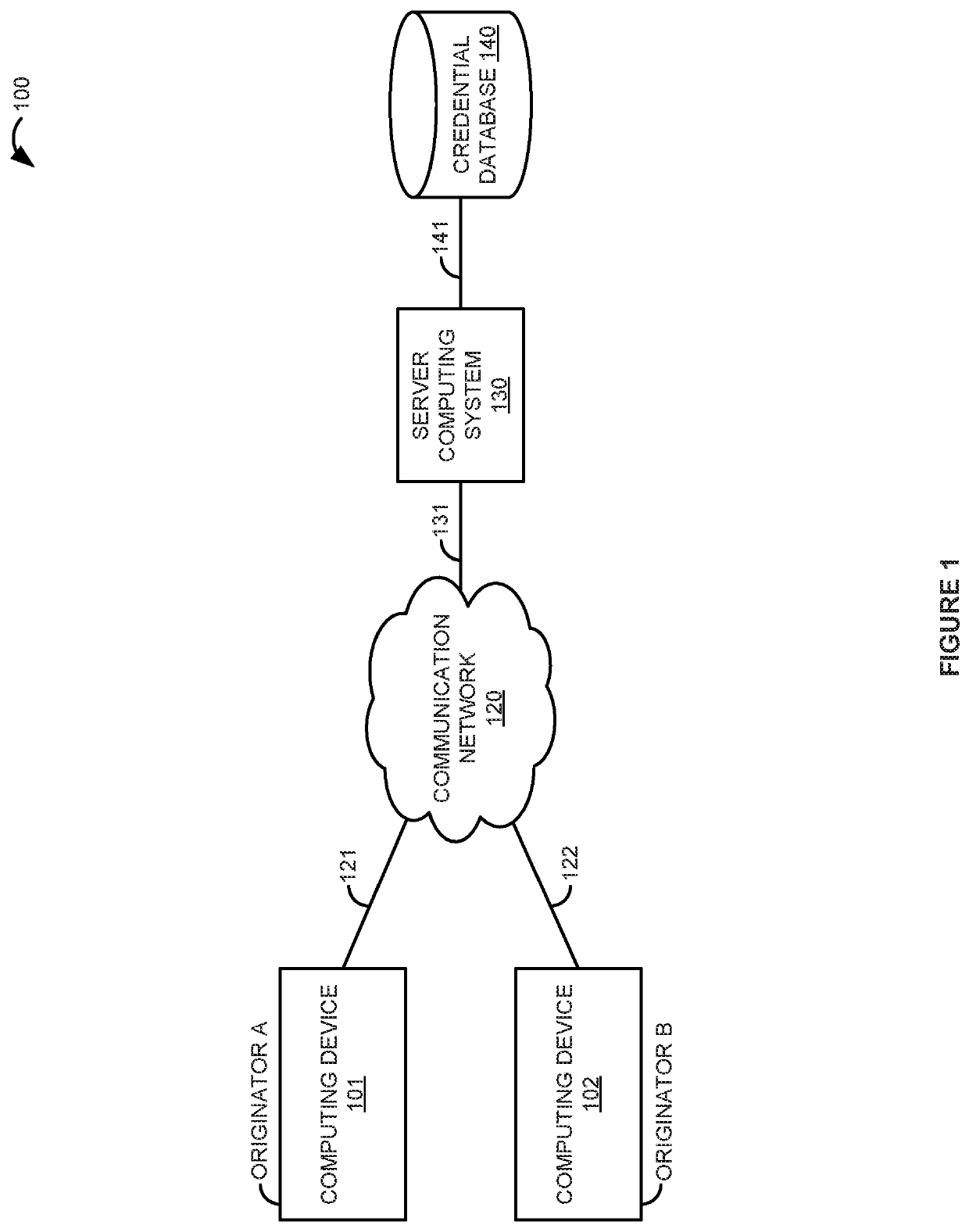
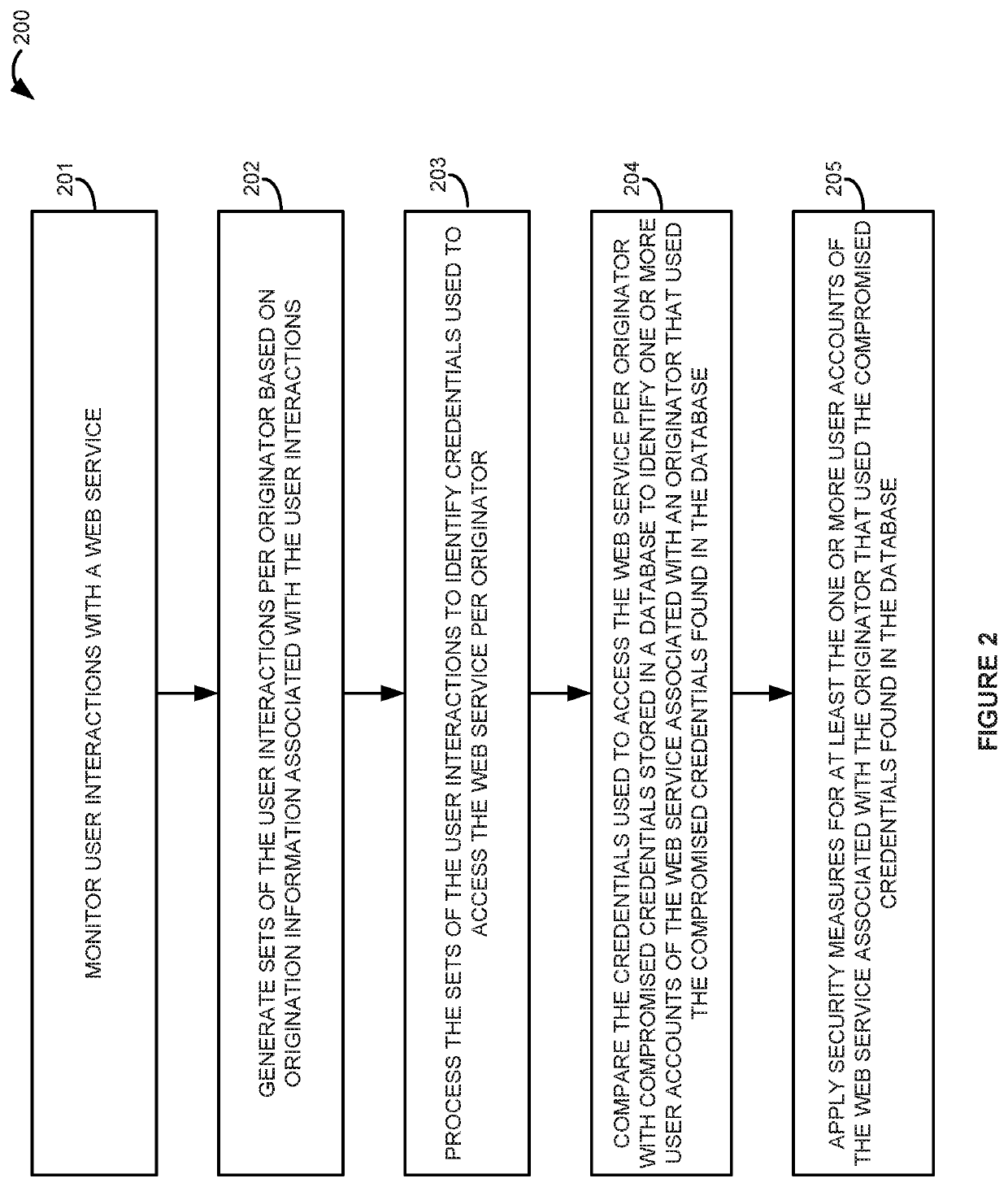
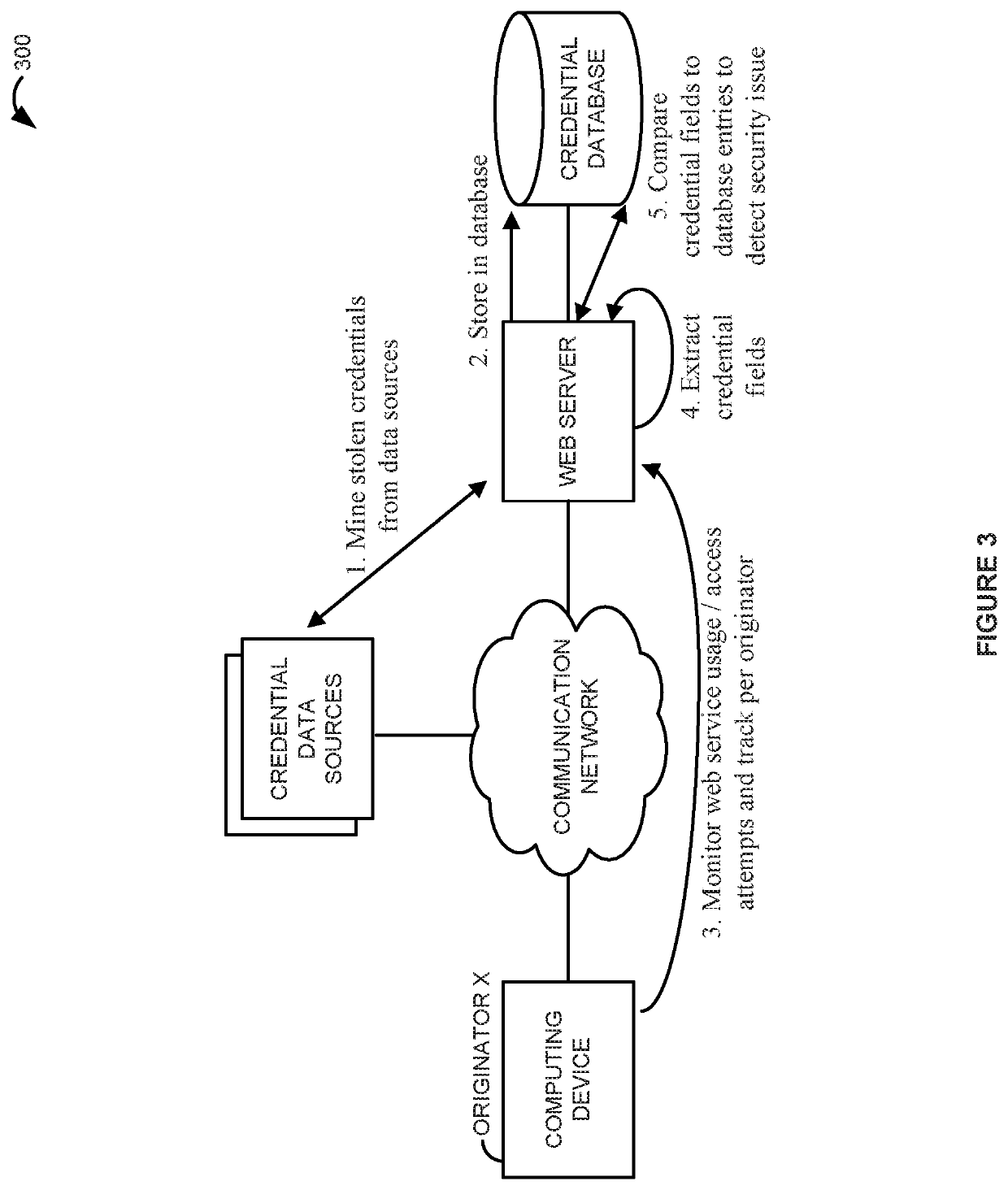
Stolen credential use prevention on a web service
Owner:STEALTH SECURITY INC
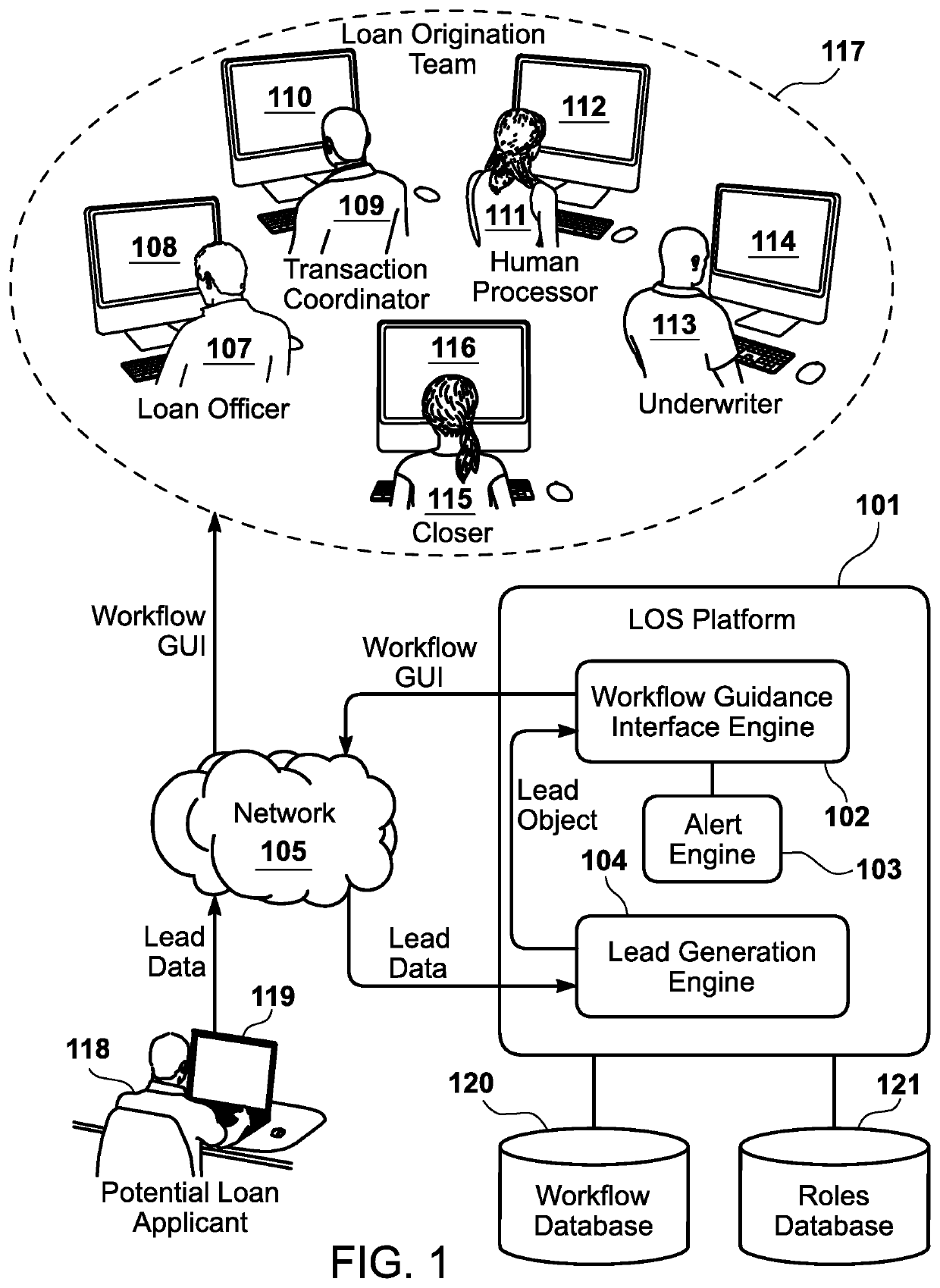
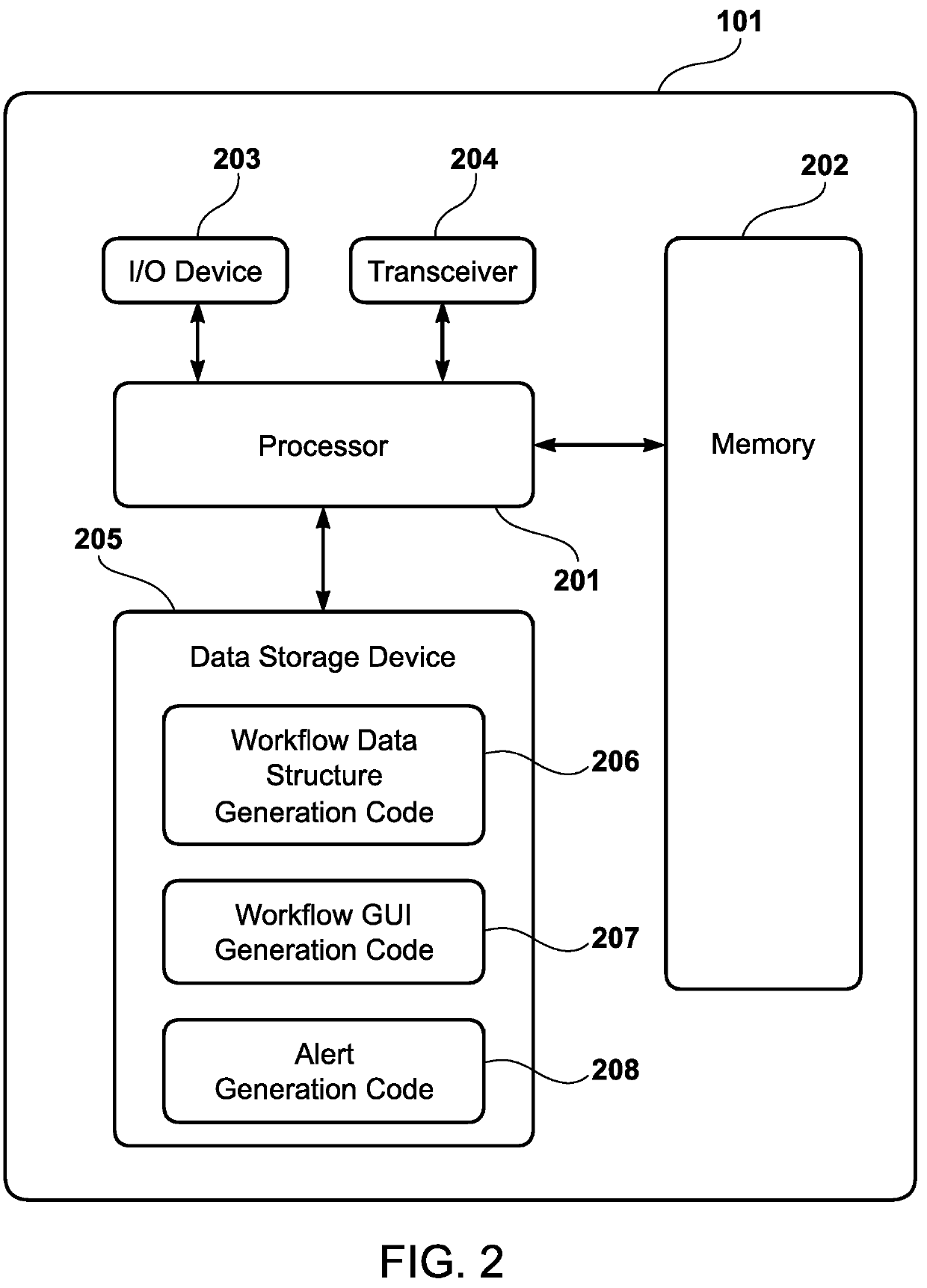
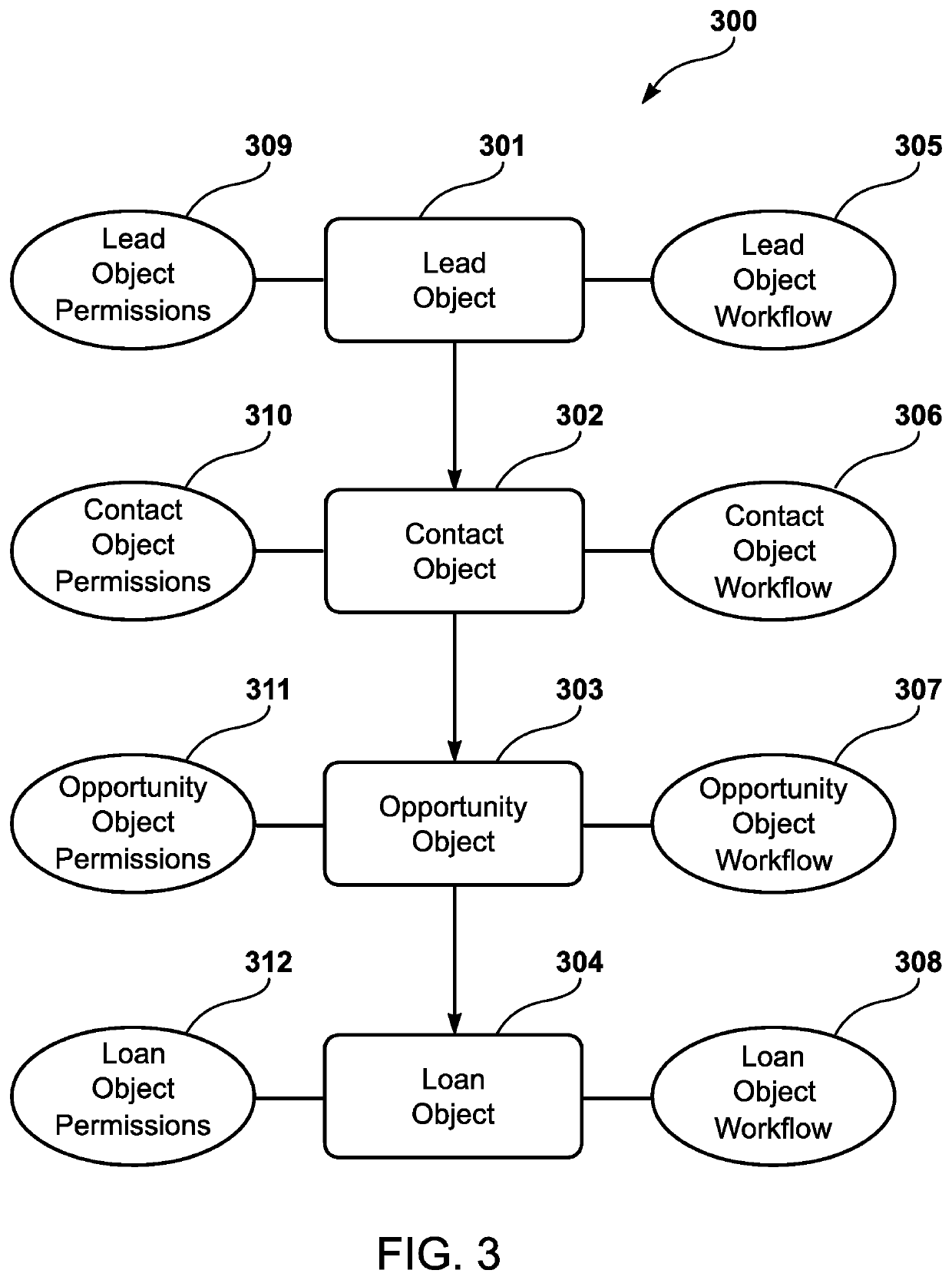
Workflow guidance interface for loan origination system
A computer-implemented loan origination system has a memory device that stores an object specific workflow data structure corresponding to each of a plurality of object-specific workflows. The object specific workflow data structure has a plurality of workflow rules corresponding to advancement through each of the plurality of object-specific workflows in a workflow guidance interface that provides a graphical representation of a loan origination workflow. The computer-implemented loan origination system has a processor that generates the workflow guidance interface, which simultaneously operates in conjunction with the computer-implemented loan origination system. The processor also generates a plurality of data objects, which include a lead object, a contact object, an opportunity object, and a loan object. The processor generates the plurality of object-specific workflows corresponding to each of the plurality of data objects.
Owner:PATCH LENDING LLC
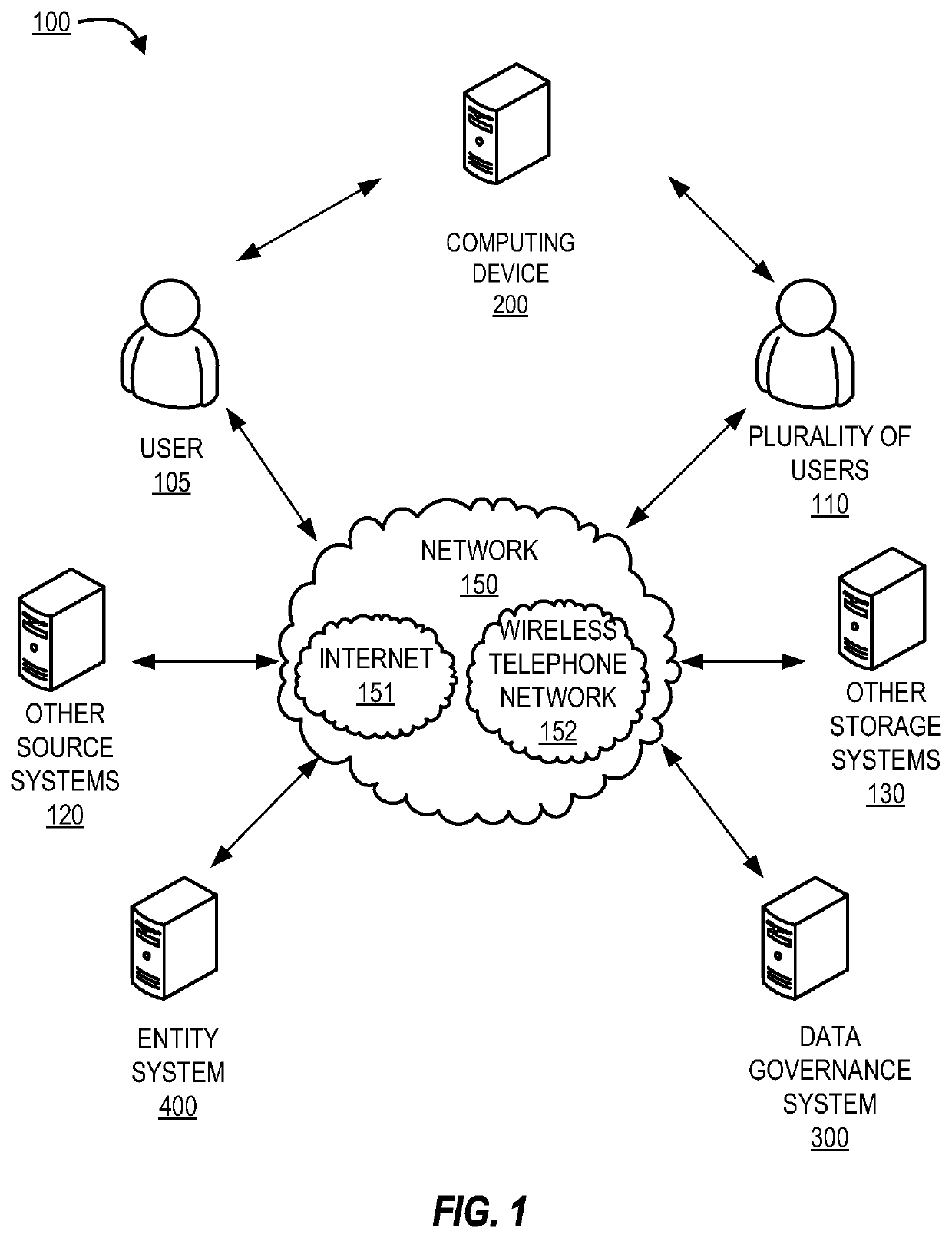
System for electronic data verification, storage, and transfer
Embodiments of the invention are directed to systems, methods, and computer program products for verifying, storing, and transferring data within an entity. The system is configured for receiving data from one or more source systems, generating a metadata, exposure, and control statement for the data, transferring the data and the metadata, exposure, and control statement to a system of origination, logically classifying the data in the system of record into one or more domains, transferring the data into one or more authorized data sources associated with the one or more domains, receiving a request from a user associated with a target system to retrieve a set of data from the one or more authorized data sources, and transferring the set of data from the one or more authorized data sources to the target system.
Owner:BANK OF AMERICA CORP
System and method for determining unwanted call origination in communications networks
ActiveUS20210014355A1Easy to understandSpecial service for subscribersSupervisory/monitoring/testing arrangementsCall originationEngineering
A method and system for discovering and locating the source of unwanted communication origination in a communications network, the method comprising compiling a communication campaign database storing data of one or more communication campaigns along with automatically identified instances of those campaigns, and simultaneously or sequentially matching those instances against known communication traffic of a set of cooperating telecommunication carriers. The one or more communications campaigns include a grouping of related fingerprints and patterns that identify a sequence of characters, audio or video associated with instances of a same likely campaigns, either legitimate or illegitimate / fraudulent.
Owner:YOUMAIL
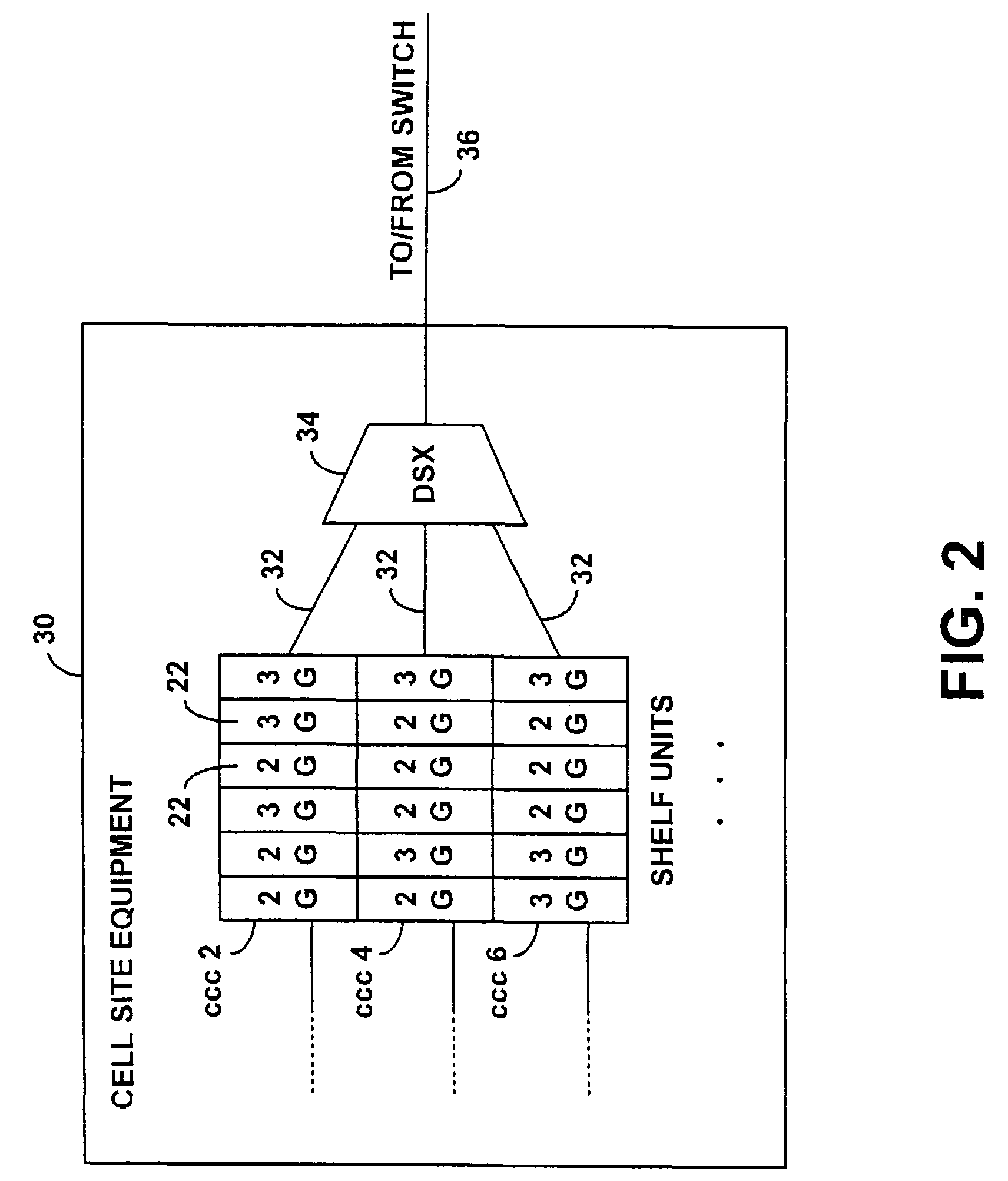
Reserving channel elements to maximize utilization of resources and prevent blocking of calls
InactiveUS7107037B1Interconnection arrangementsRadio/inductive link selection arrangementsGeneral purposeQuality of service
Channel elements at a cell site in wireless network are managed by reserving a portion of the channel elements for handling certain types of calls for which the reserved channel elements are capable of handling. At least some of the non-reserved channel elements will typically lack the capabilities of the reserved channel elements, due to there being previous generation or older technology. For example, in a cell cite having both 3G and 2G channel elements, a percentage of the 3G channel elements, such as 15 percent, are reserved for certain types of calls, such as 3G data call origination and 3G voice hand-ins. These are types of calls that the 2G channel elements do not support. The remaining 3G channel elements are not reserved. If the non-reserved channel elements are fully utilized, the reserved channel elements may, or may not, be released for general usage so as to prevent a blocking of calls, depending on quality of service considerations for the site. The reservation of channel elements can be via a configuration parameter issued from a central management entity to base station controllers, on either a system-wide basis, or on a targeted basis to particular base station controllers.
Owner:SPRING SPECTRUM LP
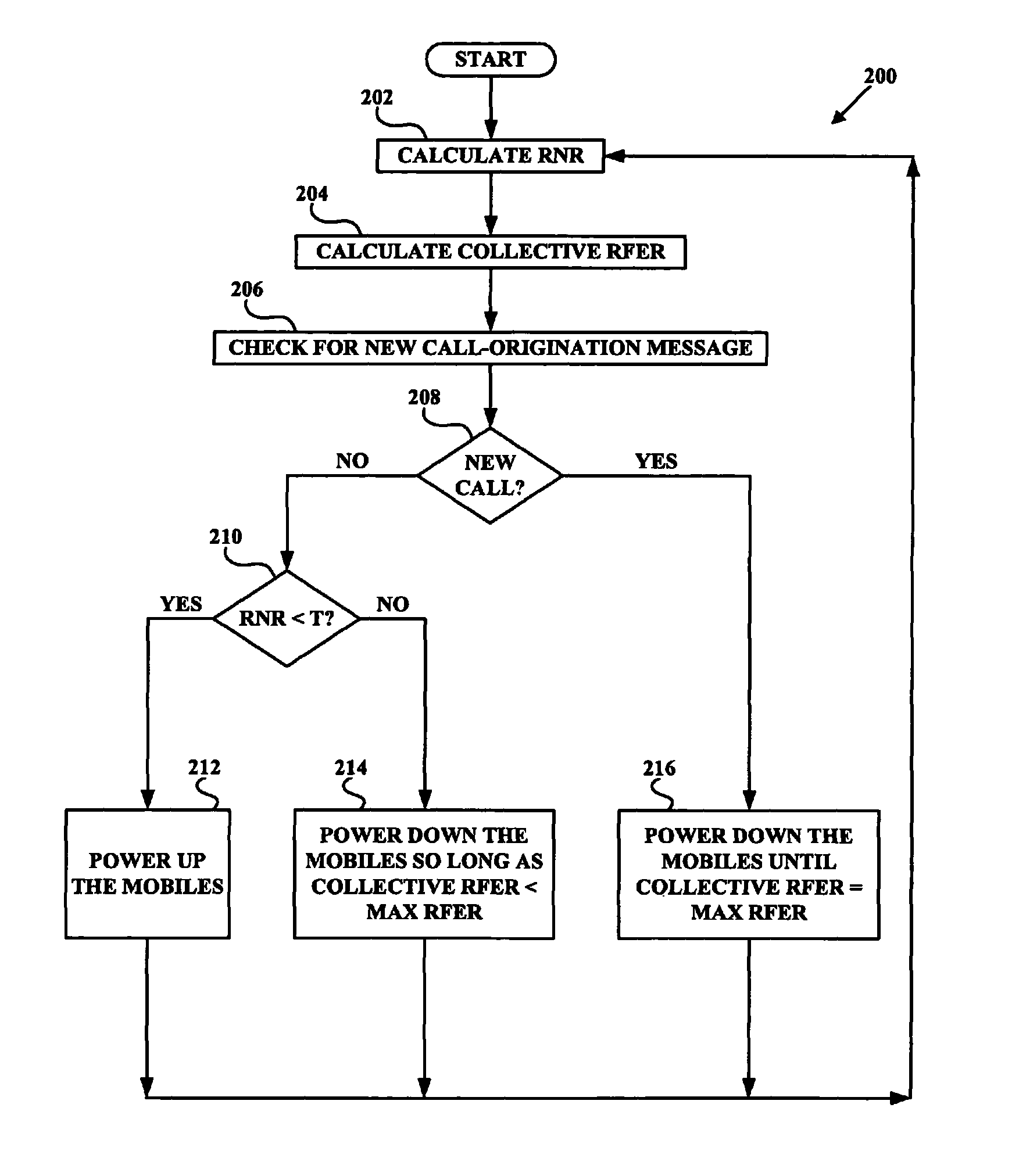
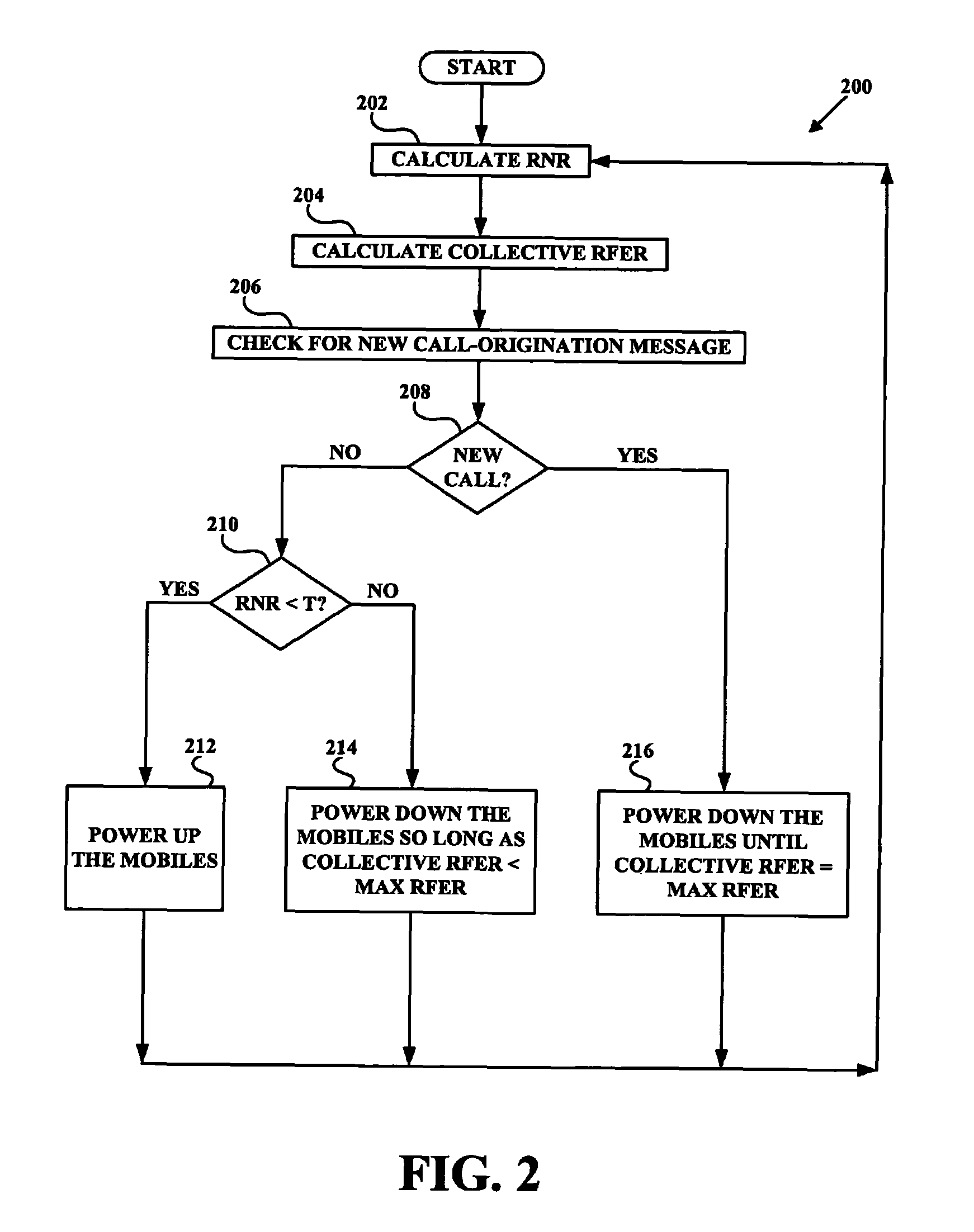
Conducting power control based on reverse-link RF conditions
Methods and systems are provided for conducting power control based on reverse-link RF conditions. In an embodiment, a base station periodically calculates a reverse noise rise (RNR), periodically calculates a collective reverse-link frame error rate (RFER), and periodically checks whether a new call-origination message has been received. If a call origination has not been received, the base station checks whether the RNR is less than a threshold. If the RNR is less than the threshold, the base station sends power-up commands to each of mobile stations. If the RNR is not less than the threshold, the base station sends power-down commands to each of the mobile stations so long as the collective RFER is less than a maximum RFER. If a call origination has been received, the base station sends power-down commands to each of the mobile stations until the collective RFER reaches the maximum RFER.
Owner:SPRINT SPECTRUM LLC
Attested end-to-end encryption for transporting sensitive data
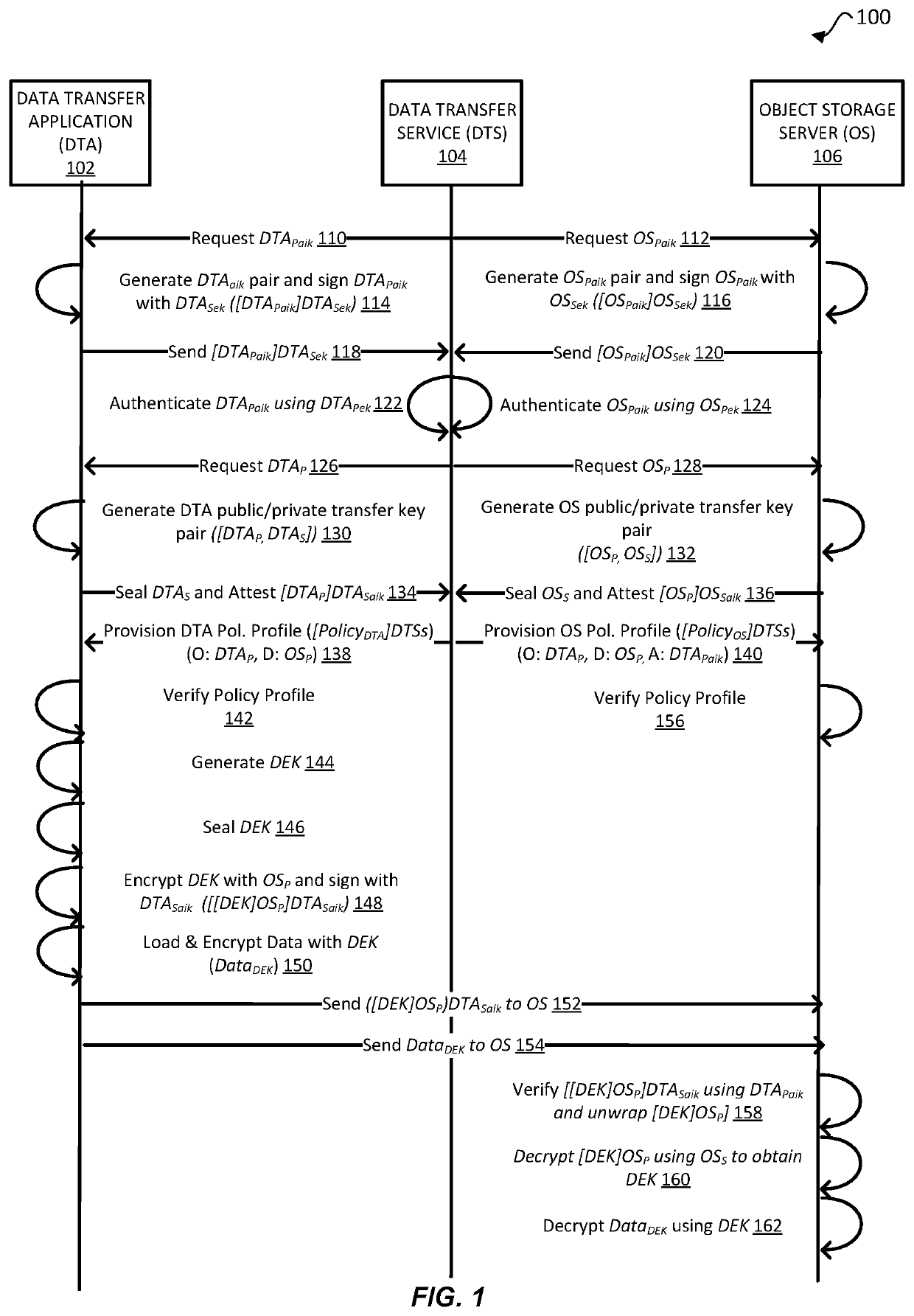
ActiveUS20220060323A1Key distribution for secure communicationBootstrappingEnd-to-end encryptionInternet privacy
Techniques are disclosed for enabling attested end-to-end encryption for transporting sensitive data between devices. In one example, an origination device receives and verifies, in a secure environment, a policy profile that includes an origination key of the origination device and a destination key of a destination device. The origination device generates and seals a data encryption key based on a characteristic of the secure environment. The origination device then encrypts the data encryption key with a public key of the destination device to form an encrypted data encryption key. The origination device then signs the encrypted data encryption key with a private attestation identity key of the origination device. The origination device encrypts the sensitive data with the sealed data encryption key to form encrypted data, and then transmits the signed encrypted data encryption key and the encrypted data to the destination device for subsequent decryption of the encrypted data.
Owner:ORACLE INT CORP
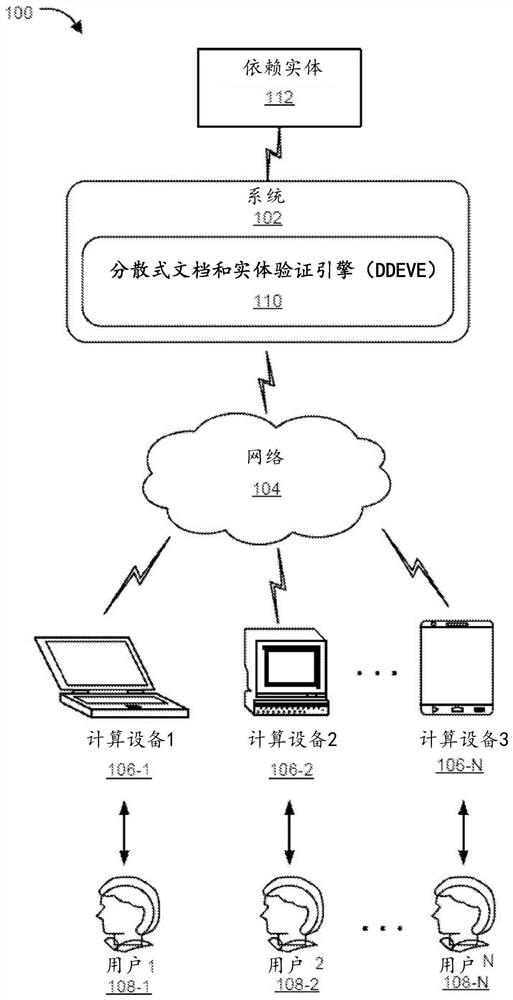
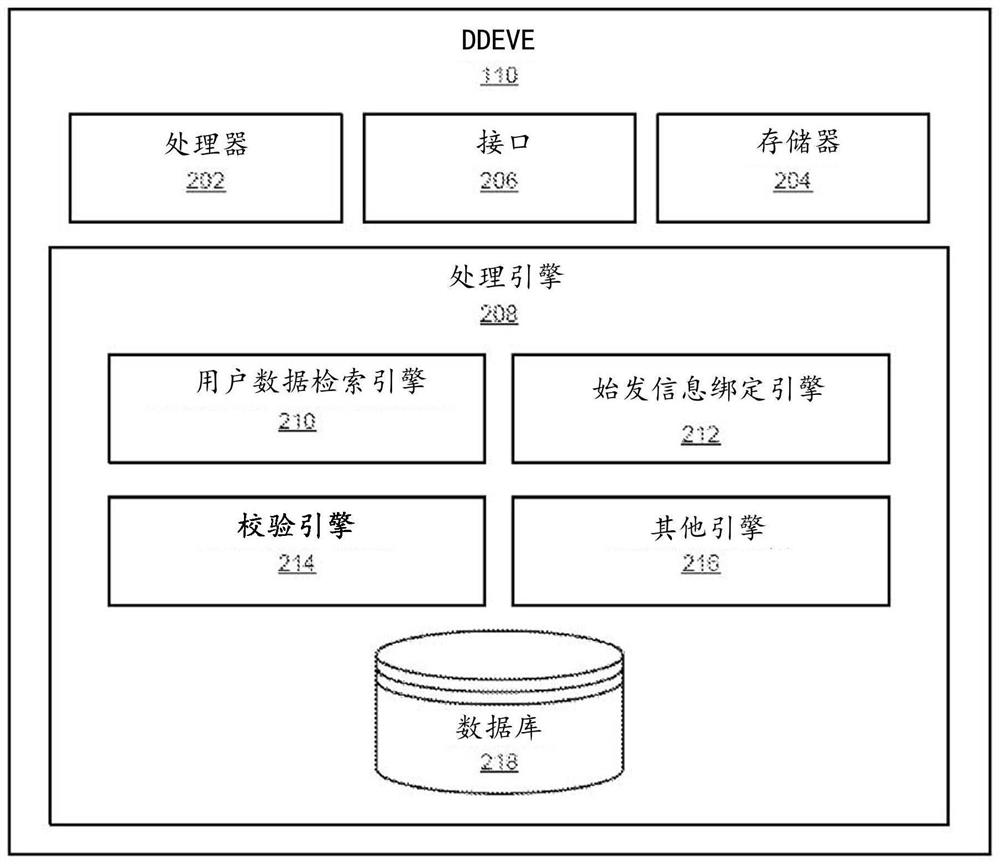
Decentralized document and entity verification engine
PendingCN112292682AUser identity/authority verificationDigital data protectionEngineeringDocumentation
A system and method enabling an entity to prove its identity and provide authentic documents / data / information therein at any time required based upon data retrieved froman independent cryptographically verifiable source (ICVS) through a secured channel is disclosed. The system enables a virtual and secure browser on a user computing device allowing a user to login and retrieve authentic information pertaining to the user from the ICVS in a verifiable and untamperable manner. The retrieved information is bounded with origination information of the ICVS and the bounded information is provided torelying entities as authentic information for verification. Also, cryptographic value of the authentic information can be stored in an immutable storage such as blockchain, so that the cryptographicvalue is used by the relying-party to validate integrity of the authentic information.
Owner:维沙尔古普塔
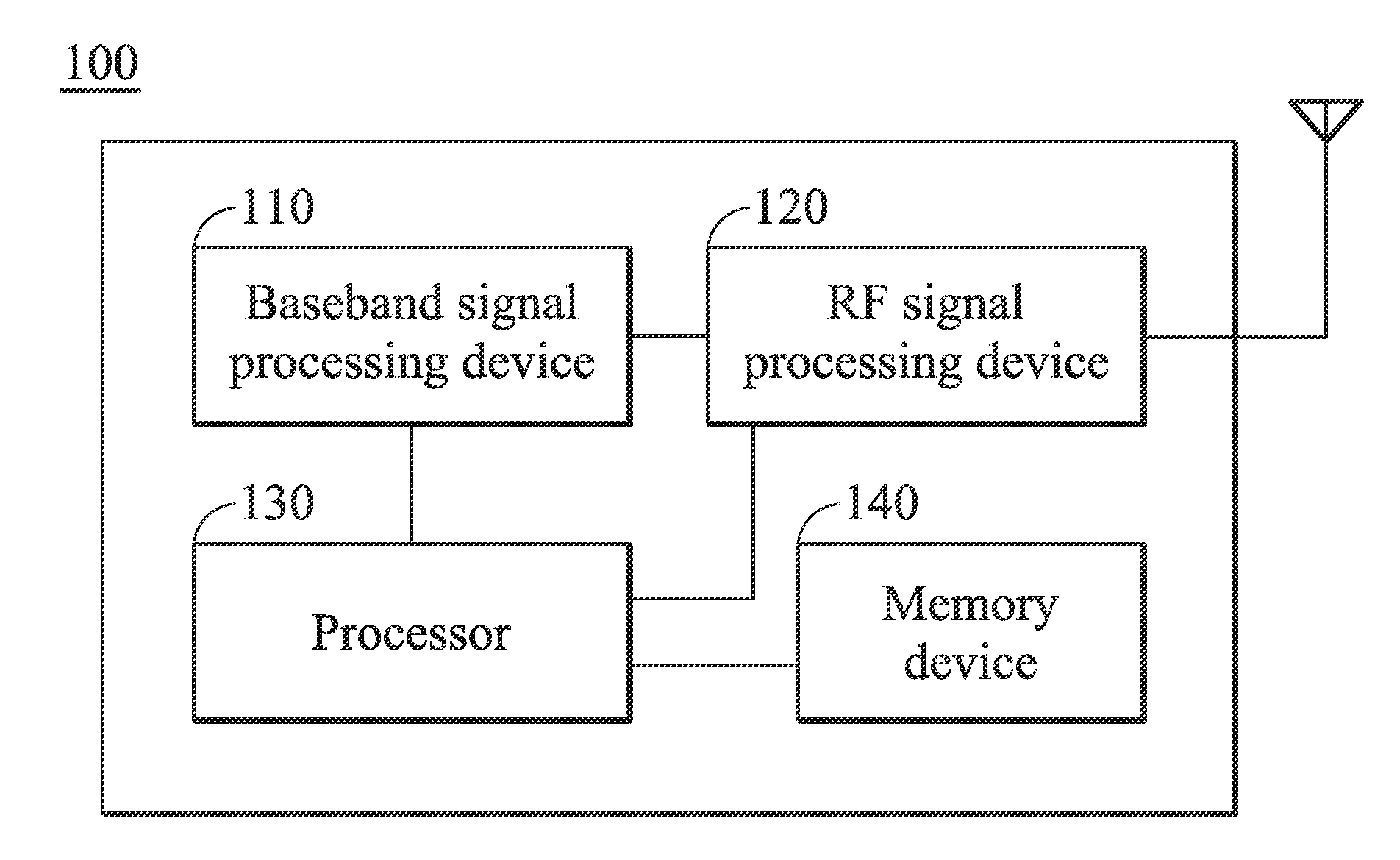
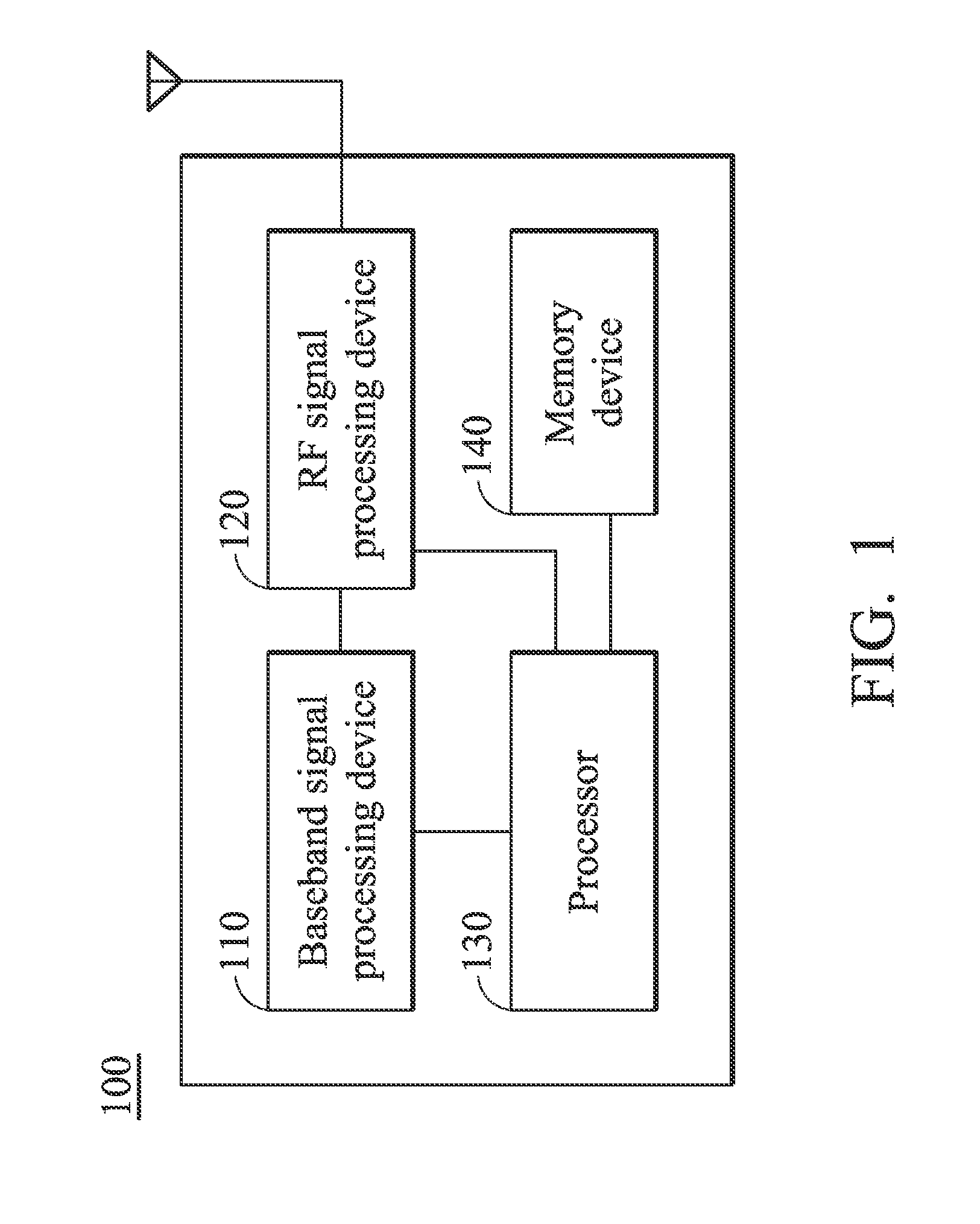
Methods for processing emergency call and communications apparatuses utilizing the same
A communications apparatus includes a baseband signal processing device, an RF signal processing device, a memory device, and a processor. The processor transmits a normal call-establishment signal with a remote identifier to a network to originate a normal call in response to a first call-origination request with the remote identifier, receives an indication message indicating that the normal call is routed as an emergency call from the network, records the remote identifier in the memory device, and when receiving a second call-origination request with the remote identifier, transmits an emergency call-establishment signal with the remote identifier to the network to originate an emergency call in response to the second call-origination request.
Owner:MEDIATEK INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com