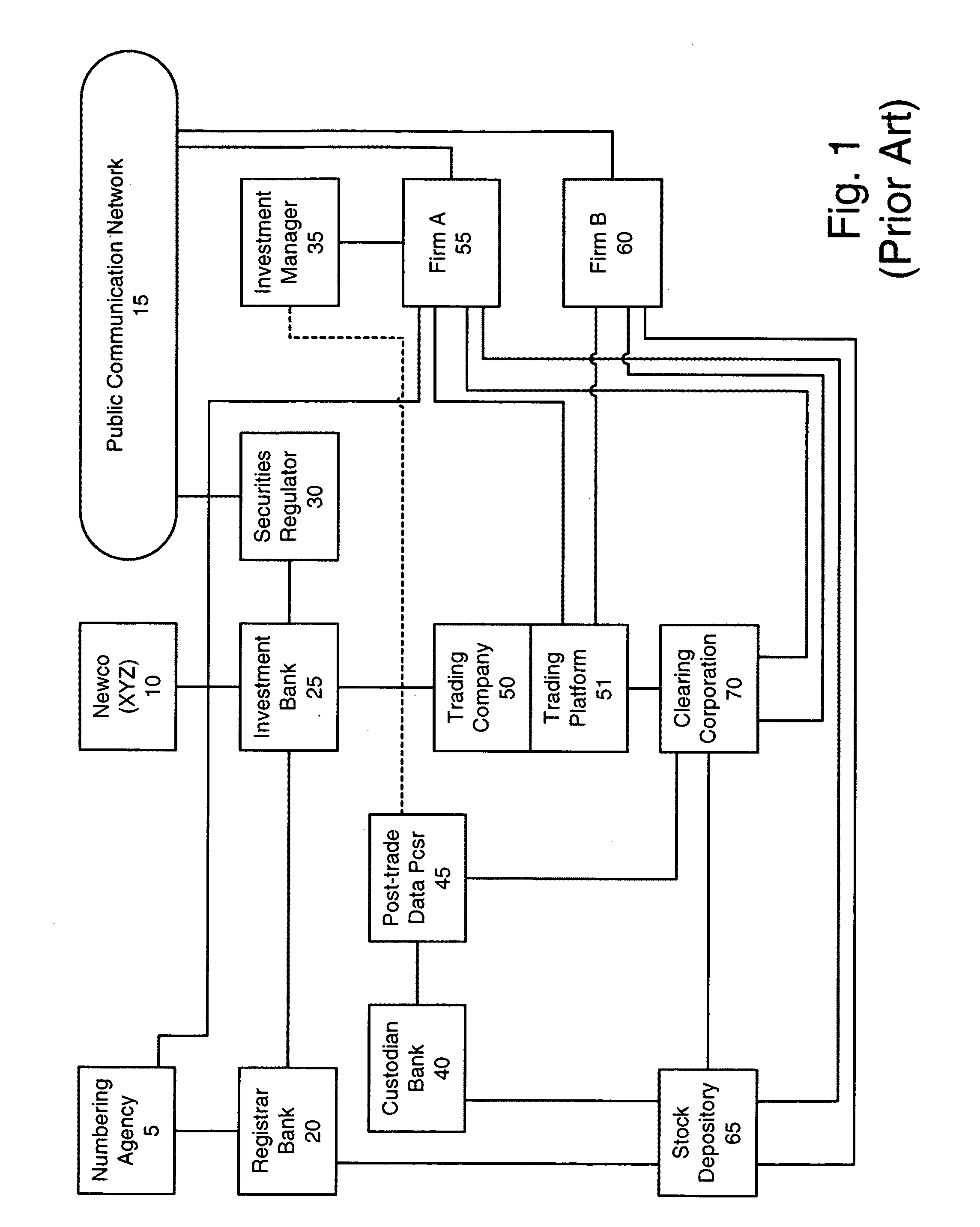
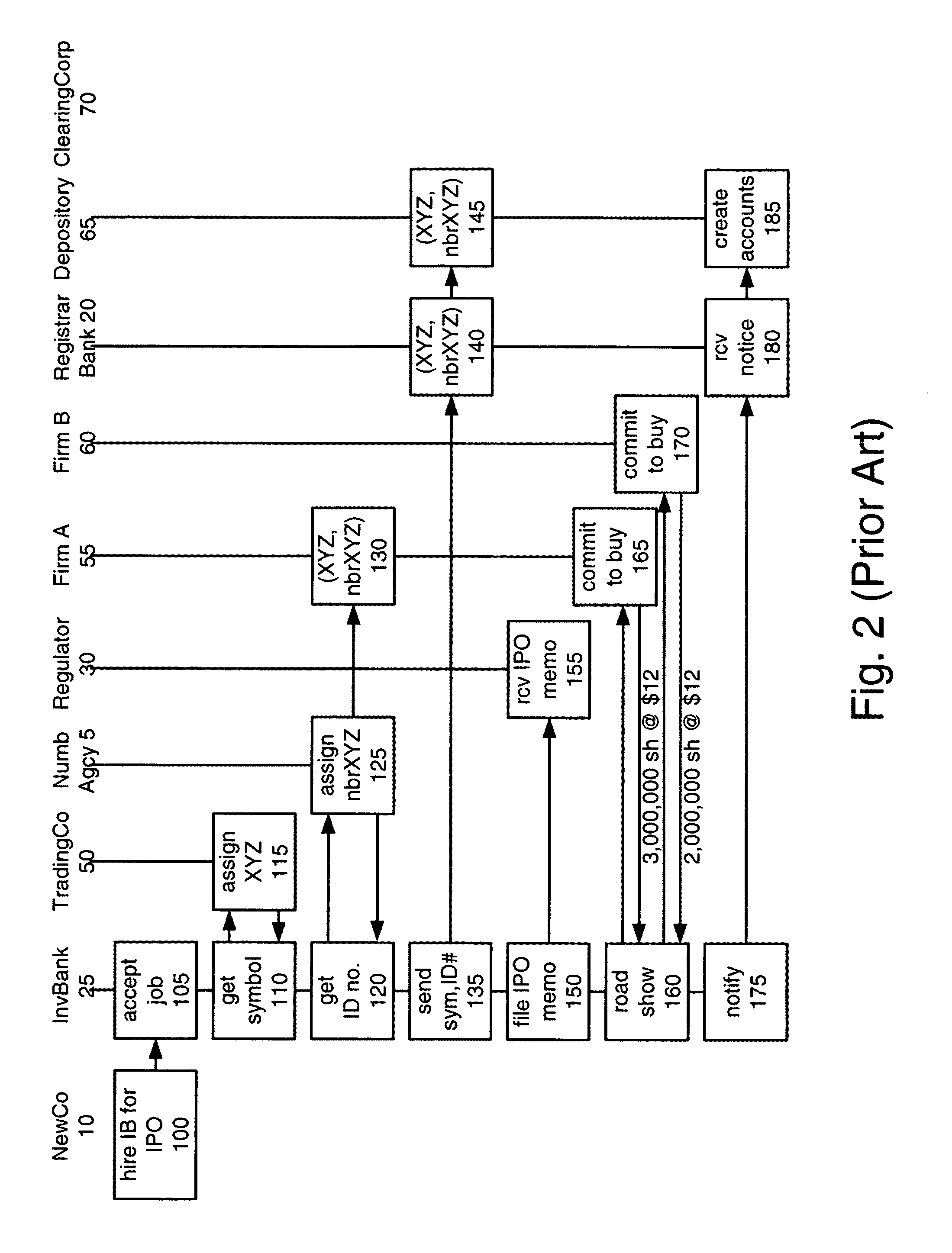
Patents
Literature
61 results about "Universal Identifier" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
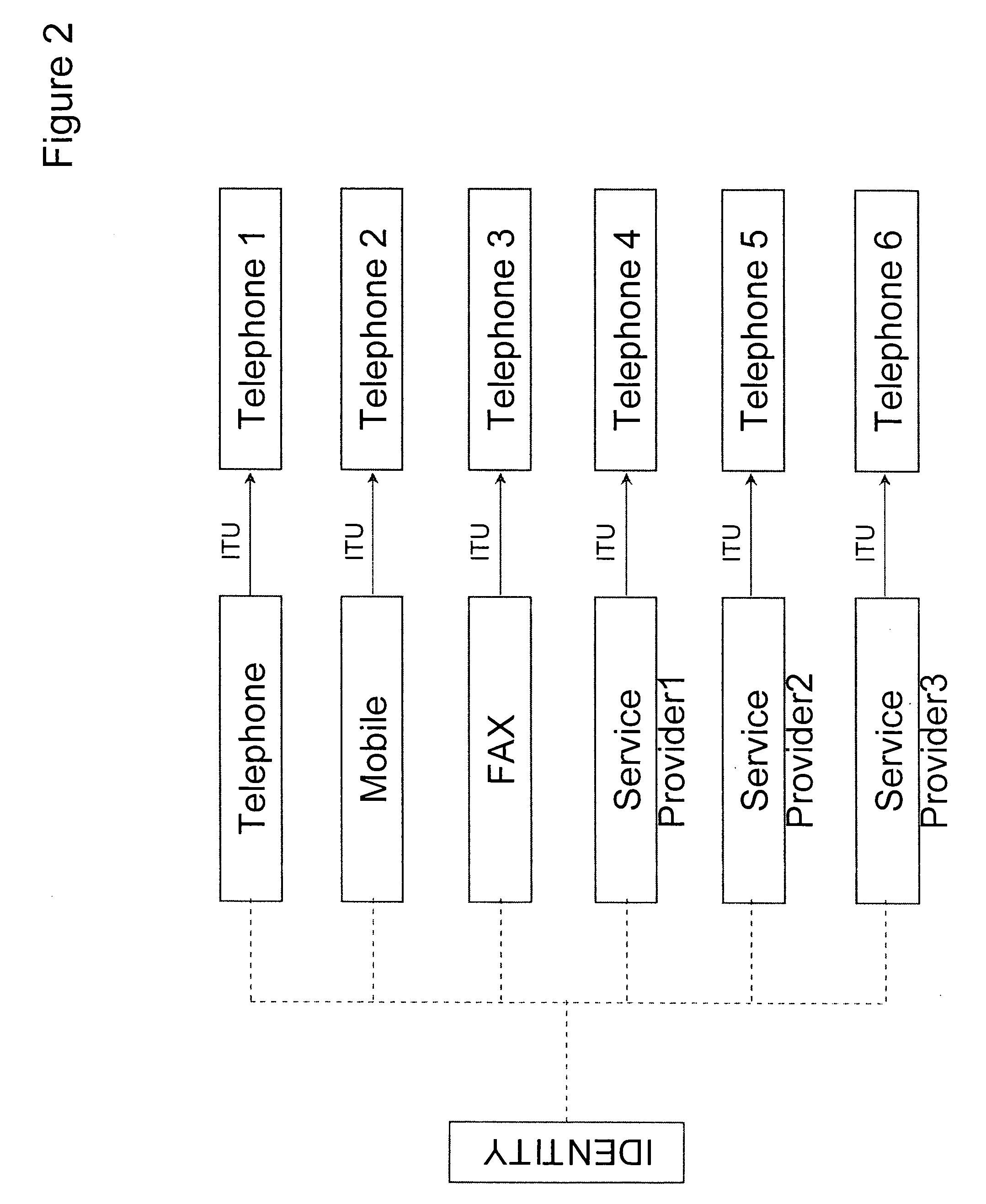
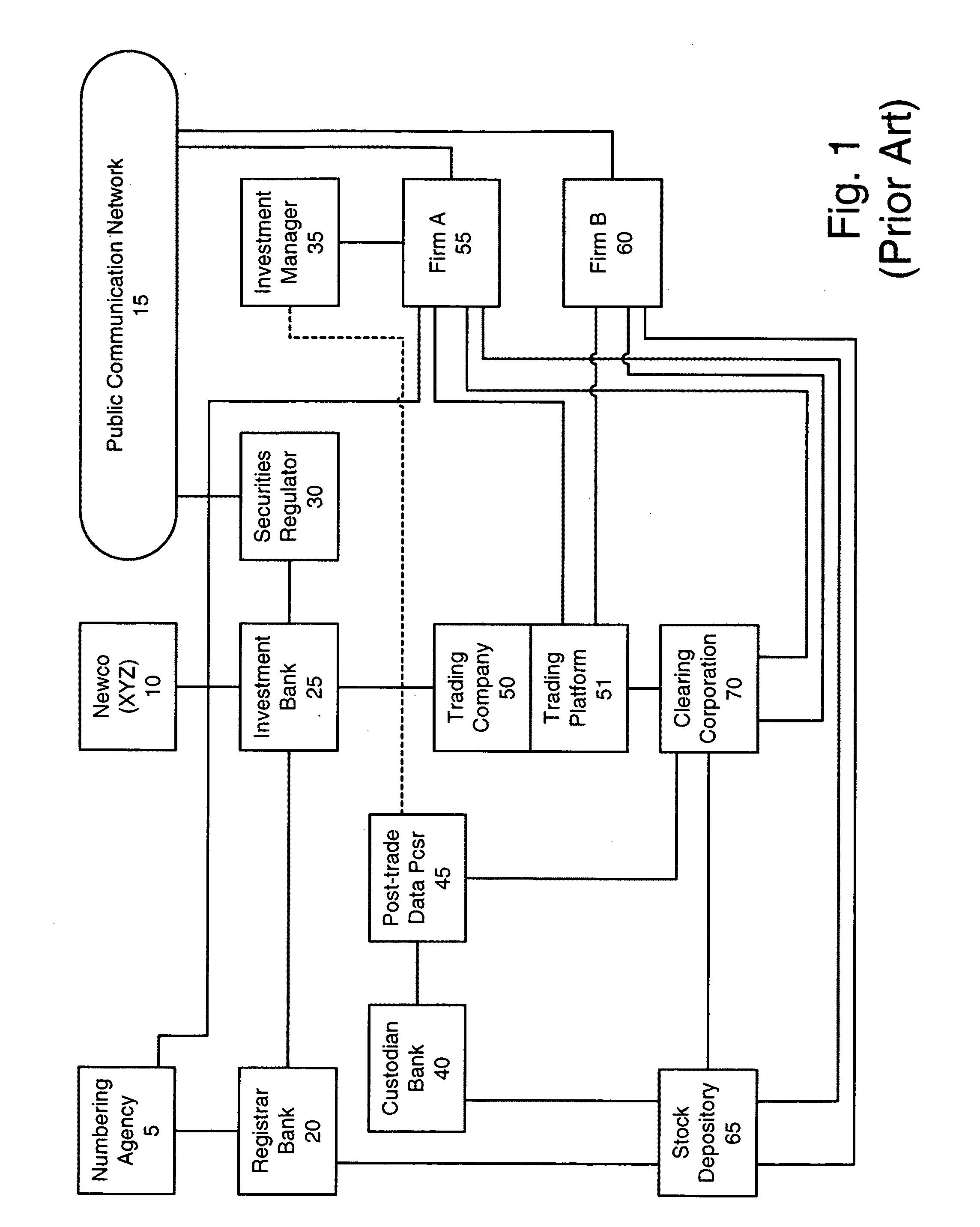
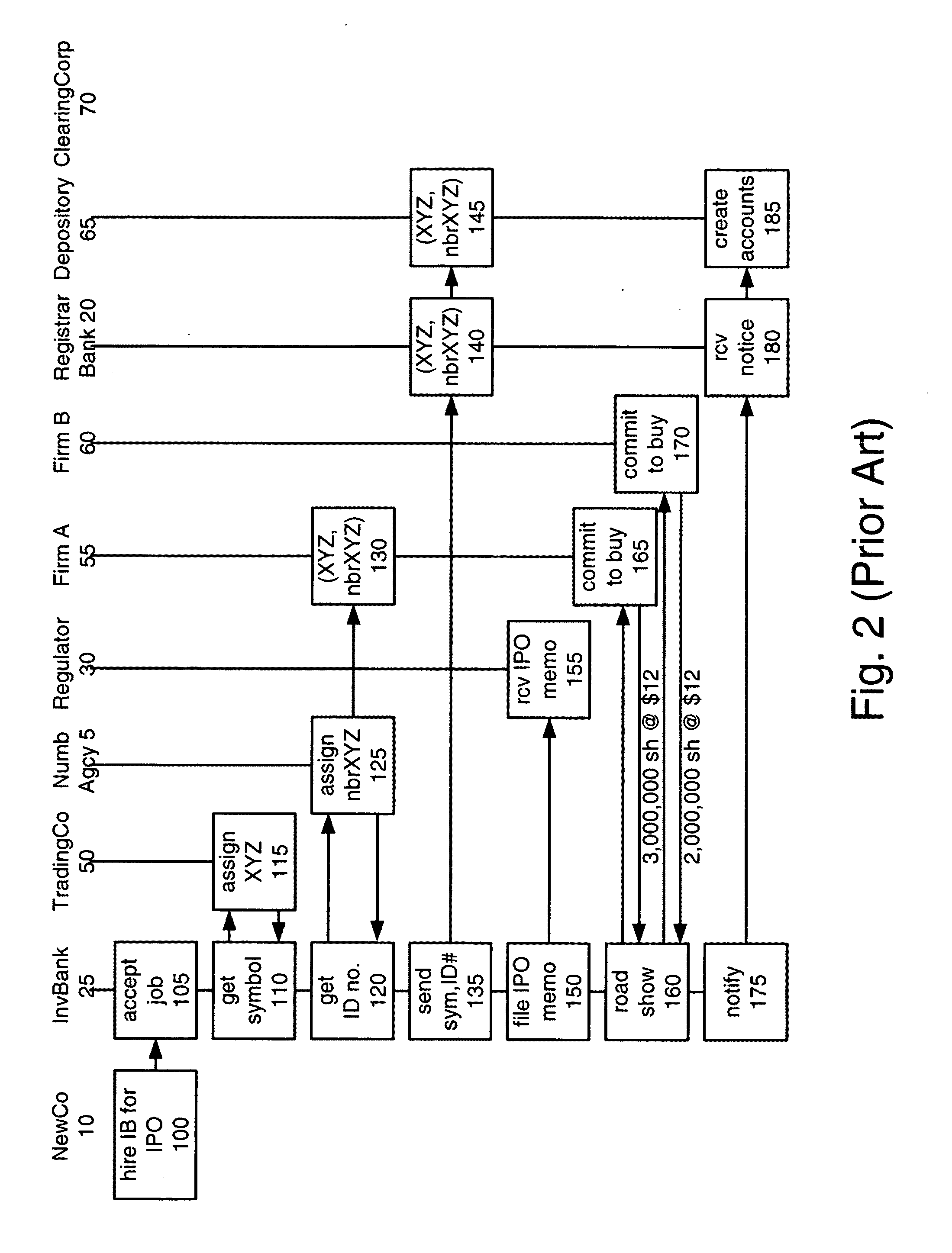
A UUID (Universal Unique Identifier) is a 128-bit number used to uniquely identify some object or entity on the Internet.
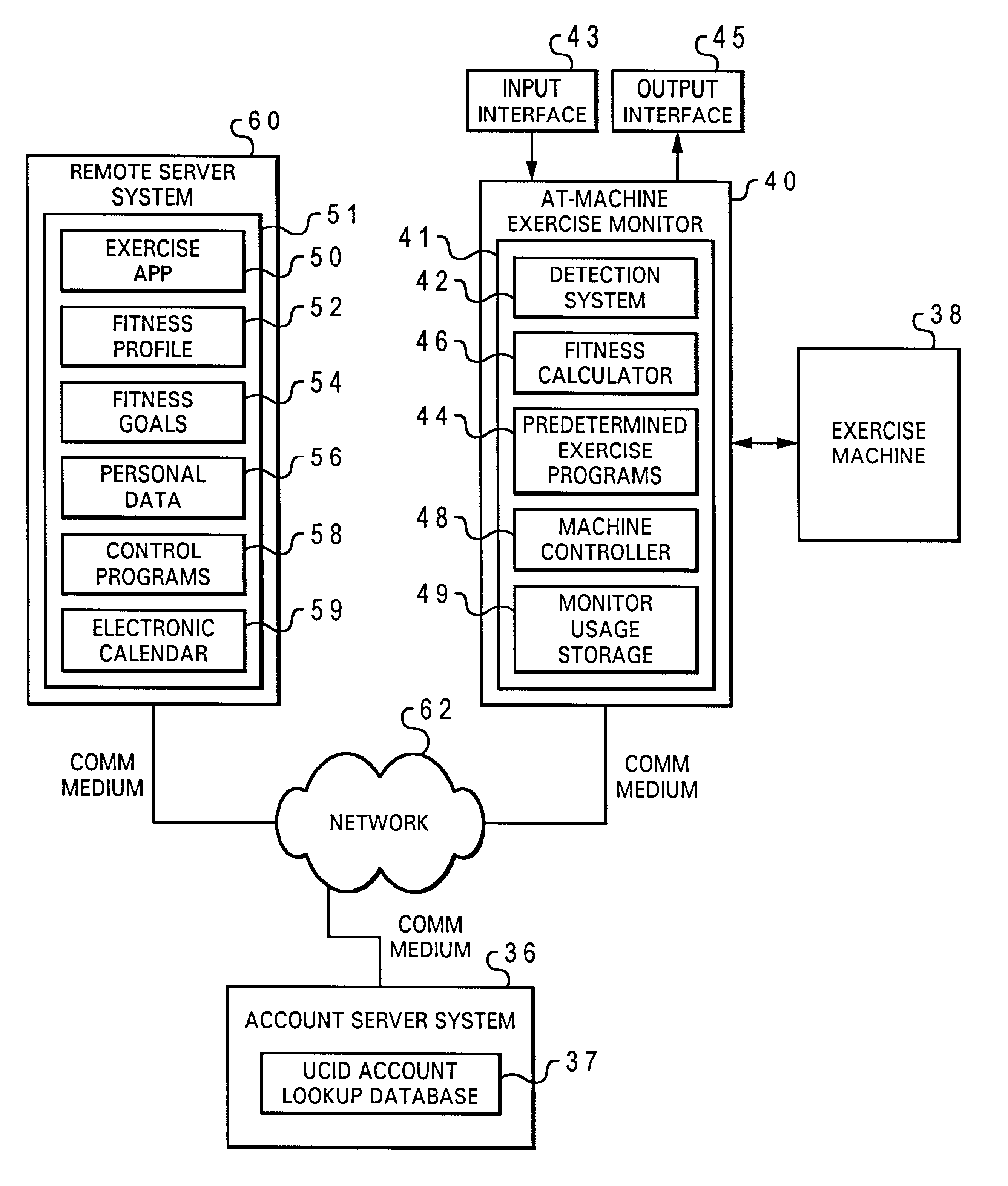
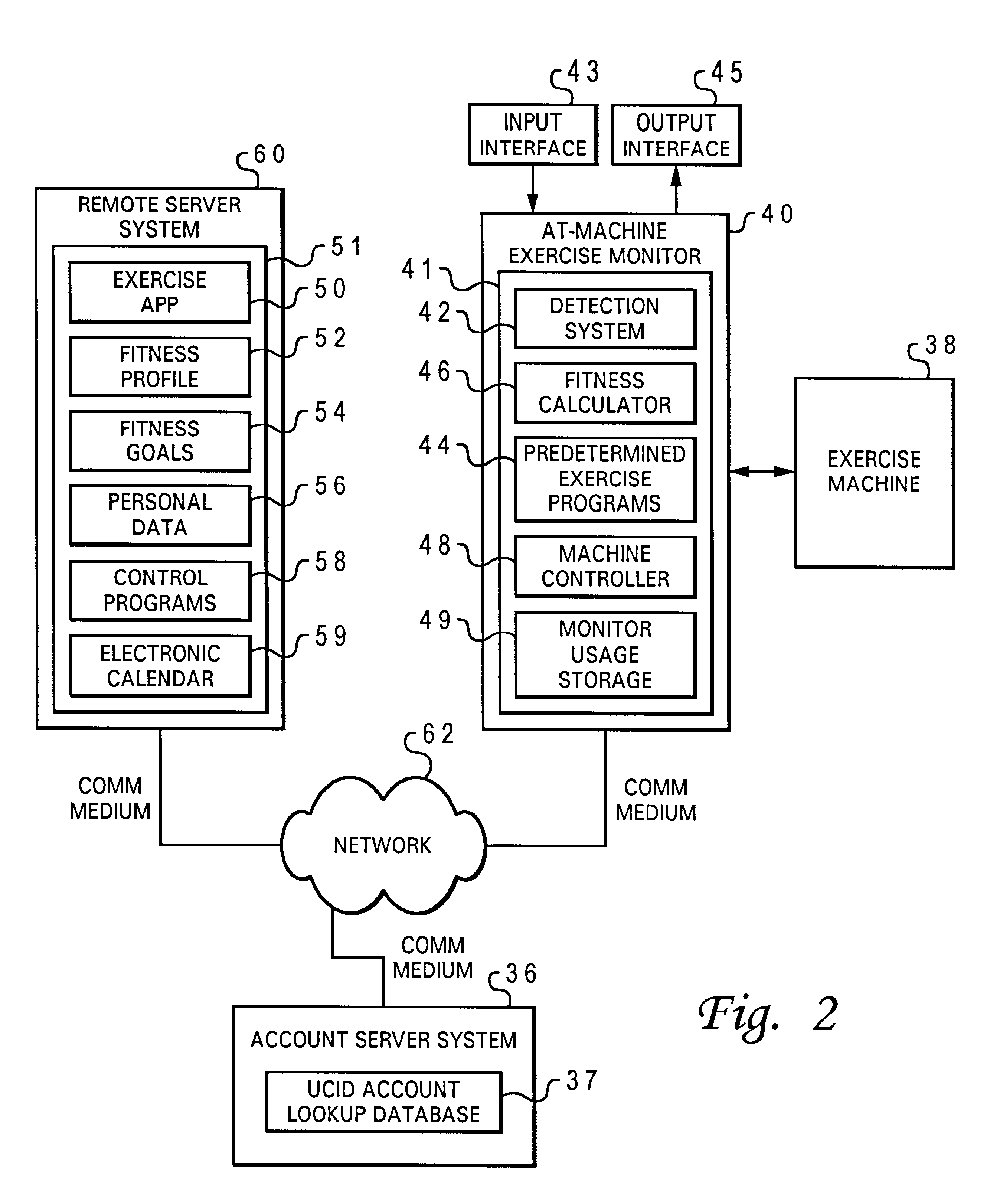
Monitoring fitness activity across diverse exercise machines utilizing a universally accessible server system
InactiveUS6601016B1Physical therapies and activitiesGymnastic exercisingUser identifierExercise machine
According to the present invention, current fitness indicators for a particular user are detected by a particular exercise machine monitoring device that monitors exercise performed by the particular user on a particular exercise machine. The current fitness indicators are transmitted in a particular transmittable data format to a universally accessible server system in accordance with a universal identifier associated with the particular user and stored at said universally accessible server system in accordance with the universal identifier as current fitness activity, such that real-time fitness activity for a user computed from fitness activity received from any of multiple diverse exercise machines over a period of time is monitored by a universally accessible server system according to a universal identifier for a particular user.
Owner:ICON HEALTH & FITNESS INC
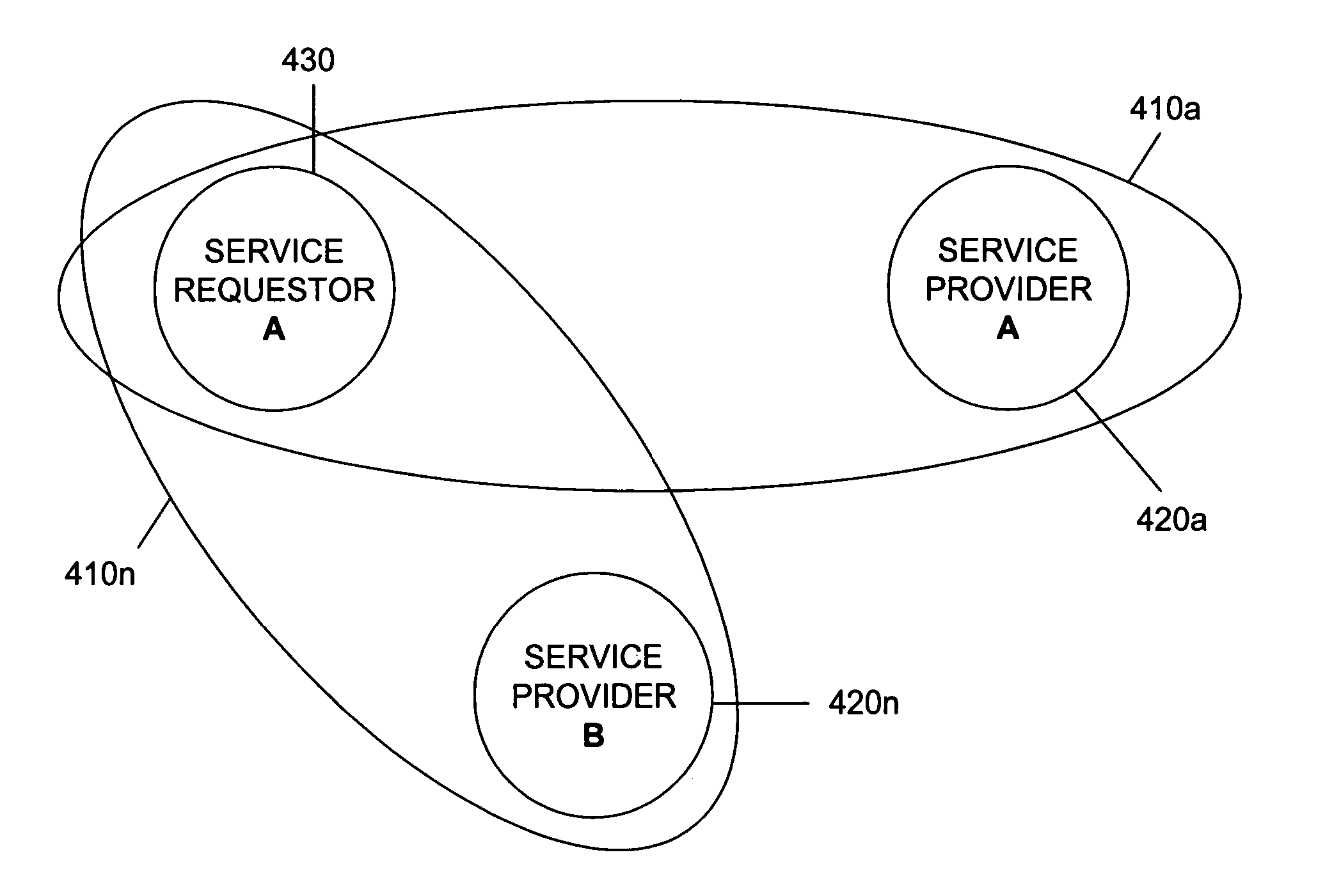
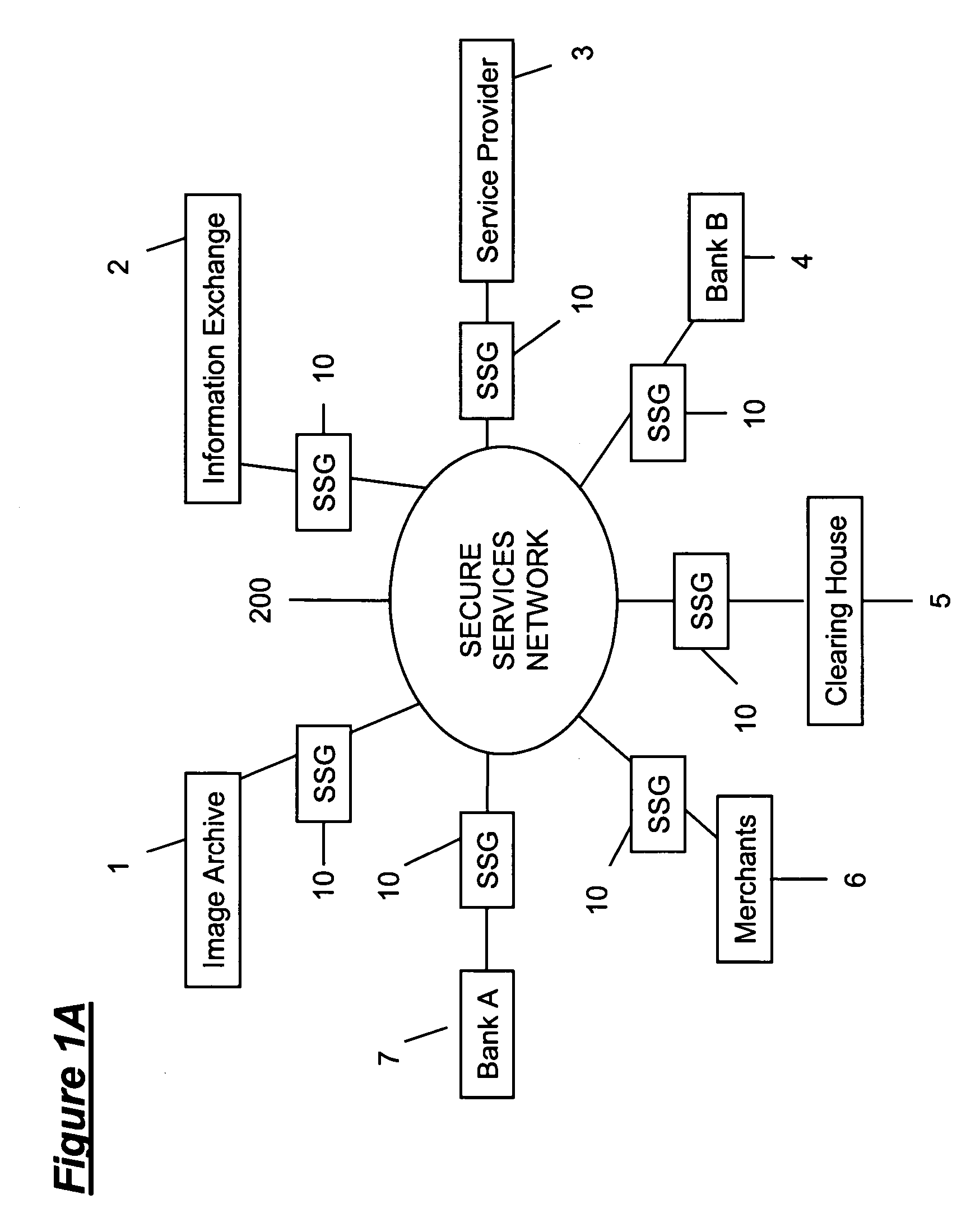
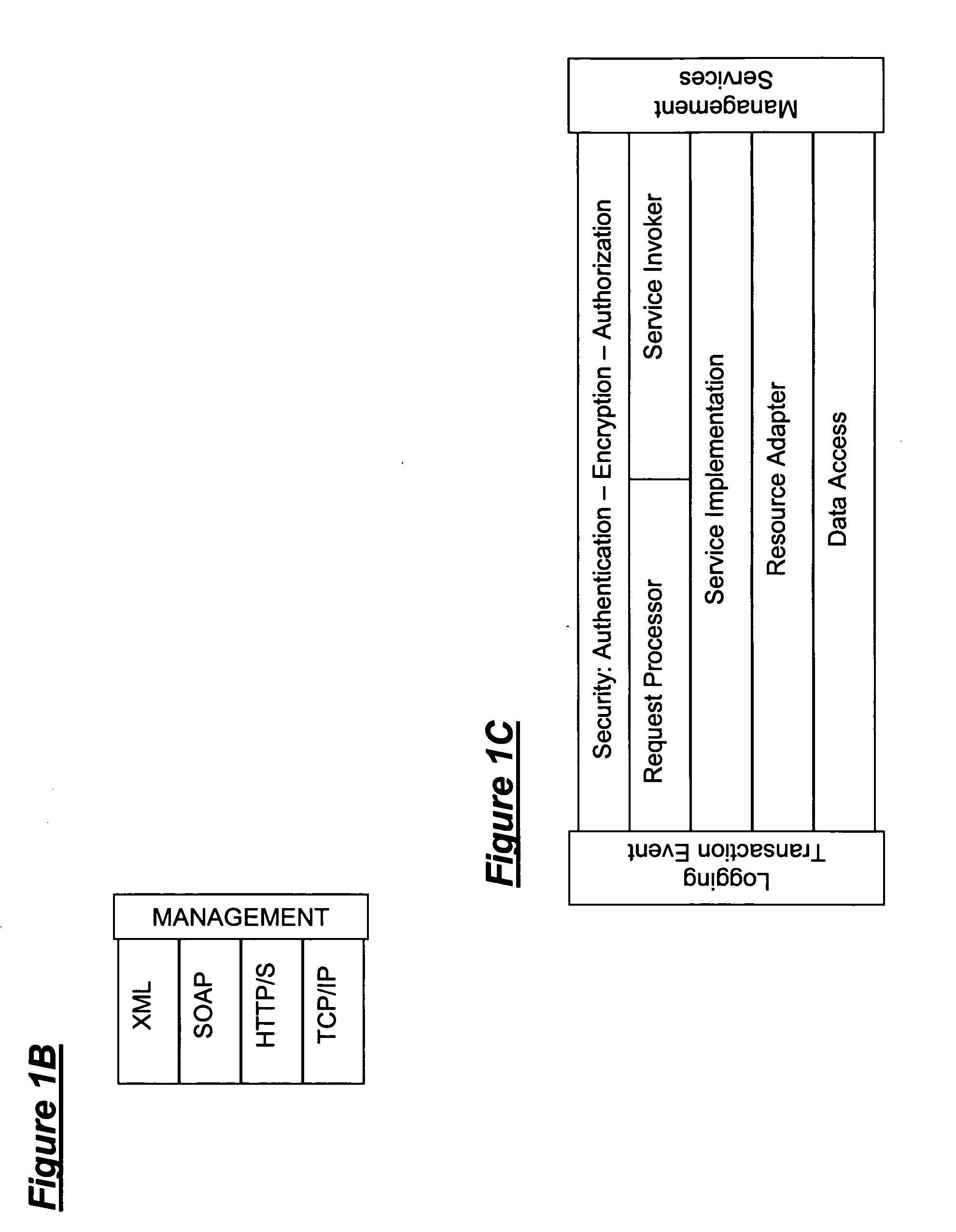
Secure service network and user gateway
ActiveUS20060107036A1Limited in functionally and participant reach and flexibilityLow costFinanceBilling/invoicingEngineeringPeer-to-peer
A secure service network (SSN) comprising an IP network infrastructure wherein the access of one participant to another participant in the network is controlled by a secure service gateway (SSG) in which a point of origination universal identifier (PoUID) represents a unique identifier for the participant within a participant's internal network domain and the interconnection of the SSGs within the SSN as a precondition of access creates a bilaterally secure peer to peer service connection. Participants in the network are service providers, service requesters, or both. A global secure service gateway (GSSG) may be interconnected in the SSN to provide a central access authority and management services.
Owner:WMR E PIN
System and method to control transactions on communication channels based on universal identifiers
InactiveUS20070073888A1Minimizing effect of changeMultiple digital computer combinationsTransmissionOutbound communicationAutomatic routing
The present invention is a method to control communication channels using universal and persistent identifiers in circuit / packet switched or converged networks. The method involves linking domain specific addresses or concrete identifiers of communication end points within or across channels, domains and networks with an abstract, persistent and universal identifier that represents the single point of contact or principal identity of the user. The principal identity can specify parameters of inbound / outbound communication relationships with other specified / unspecified users / entities inter-alia through default / specific levels of control in communication relationships on / across / through normal or alternate channels, domains, applications, networks, etc., based on universal / persistent identifiers such as XRI. All transactions originating from, or terminating on, the principal identity are authenticated, asserted securely and routed automatically to an appropriate channel based on the principal identity's current context (state, location, presence, etc.) and privileges (or contracts) defined in rules created by the principal identity for access, usage, privacy, synchronization, compliance, expiry, etc. The principal identity is also empowered with multi-level control over attributes and metadata including rules for what data to expose / share and what data to eclipse / hide for which user. Control / user data, or traffic, and program / client / sequence logic, may be resident / executed / exchanged / carried on, or across, diverse networks / channels / media / devices / domains etc.
Owner:AMSOFT SYST PTE LTD
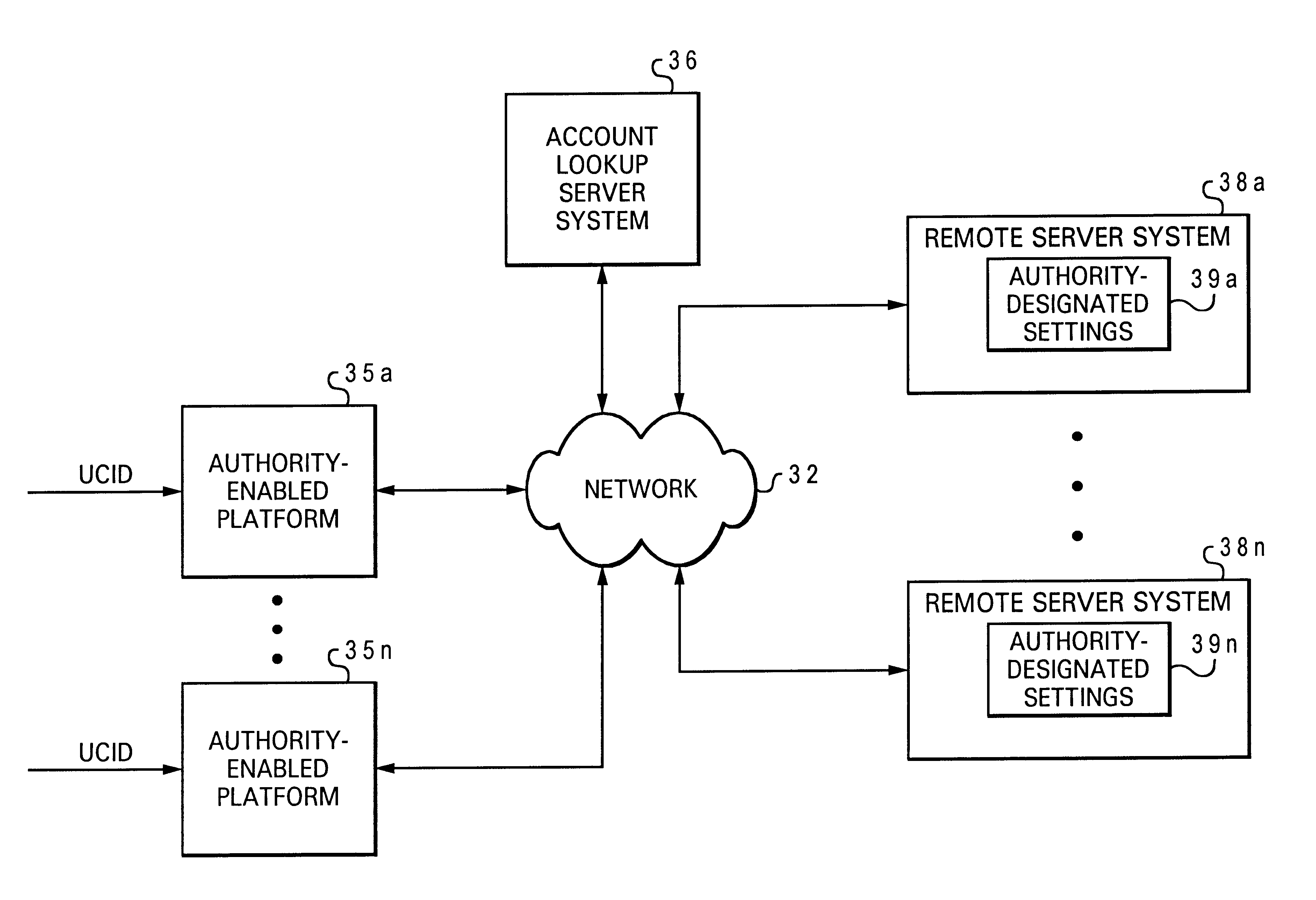
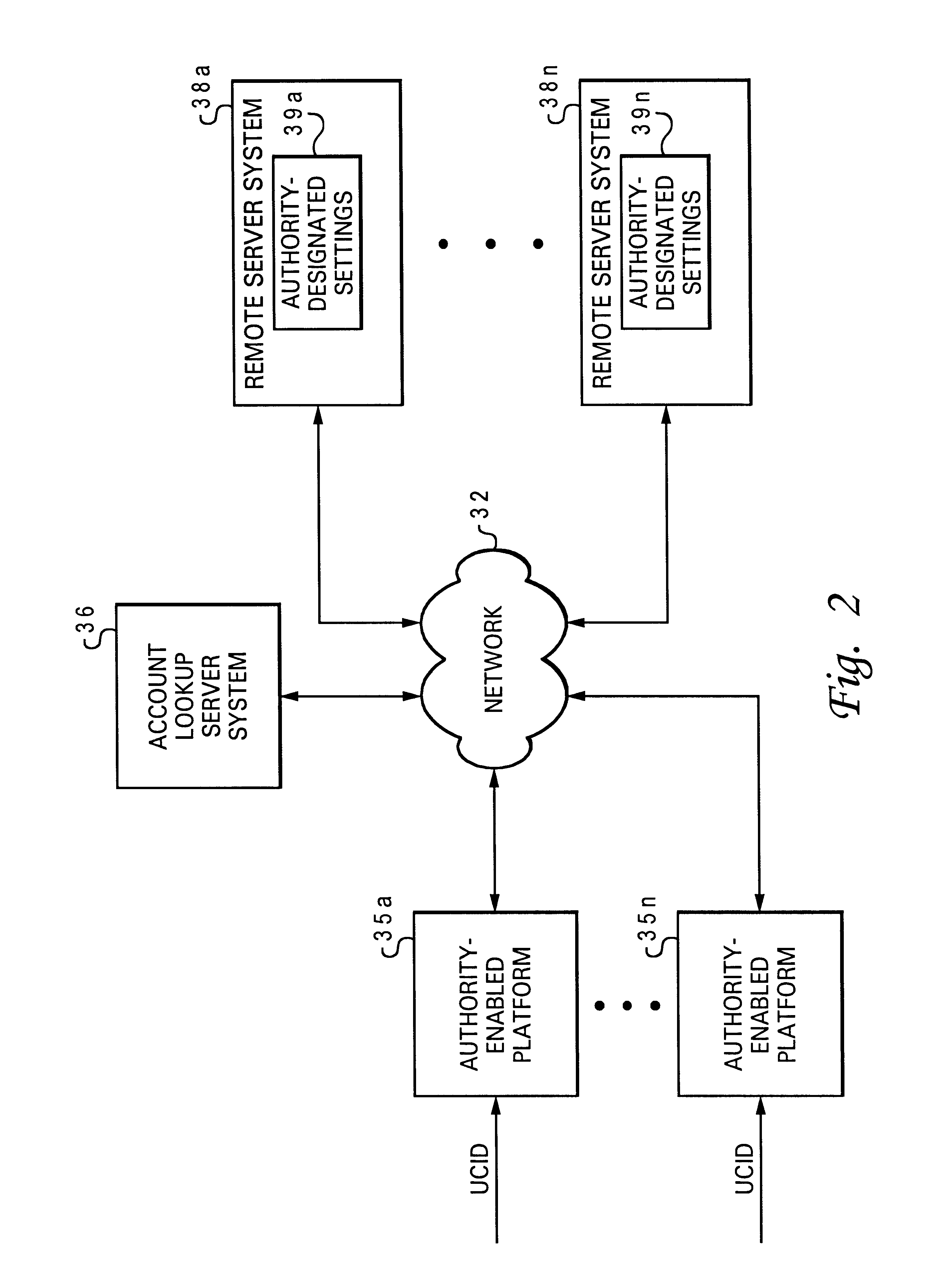
Monitoring and managing user access to content via a universally accessible database
InactiveUS6658415B1Data processing applicationsComputer security arrangementsUniversal IdentifierDatabase
In accordance with the present invention, multiple authority-designated settings are accessed at an authority-enabled system via a network from a universally accessible database according to a particular universal identifier associated with a particular user. The particular user is only allowed access to a selection of multiple of types of content from the authority-enabled system that are enabled according to the authority-designated settings received at the authority-enabled system, such that an authority-enabled system enforces an authority-designated access policy for a particular user received via a universally accessible database.
Owner:IBM CORP
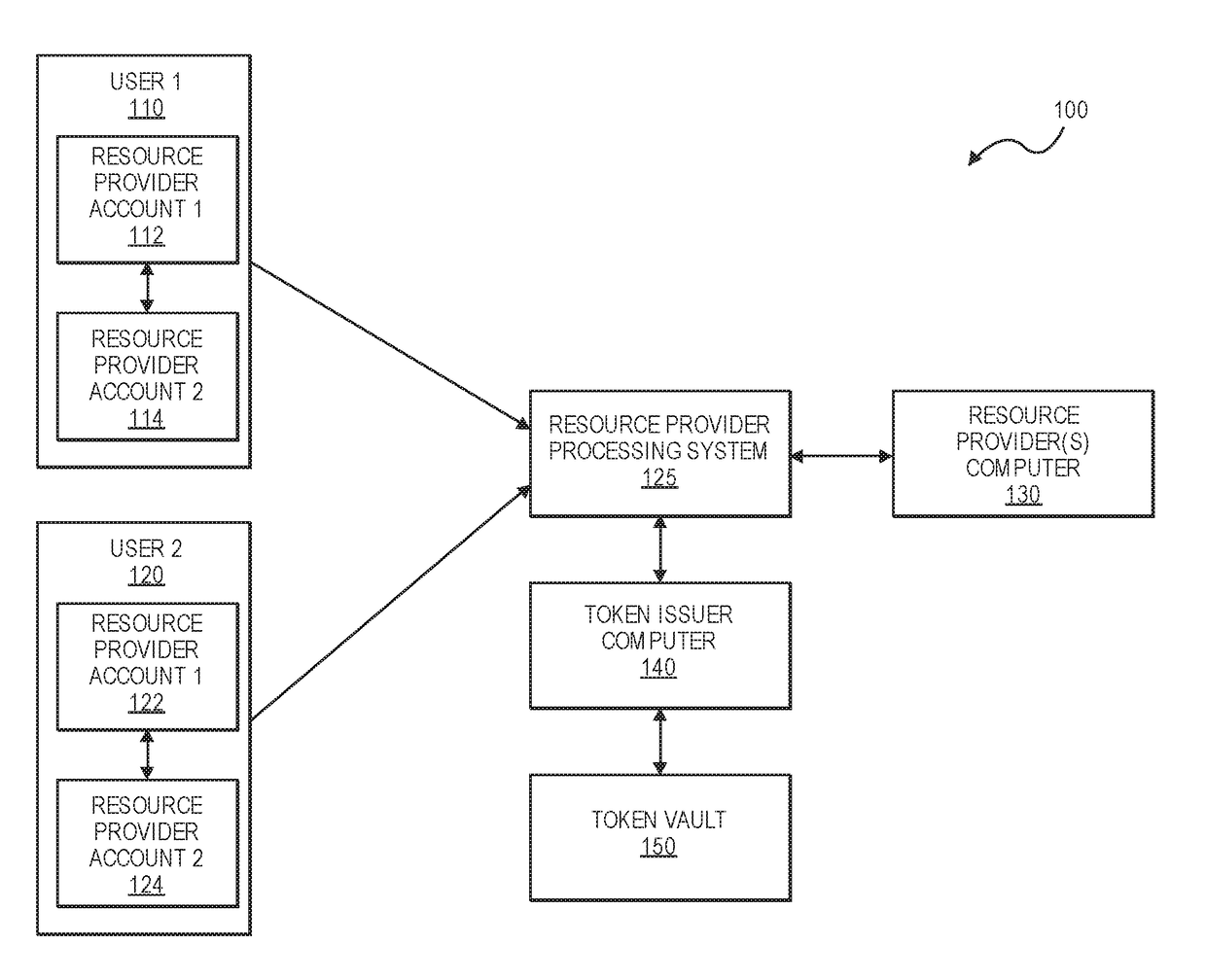
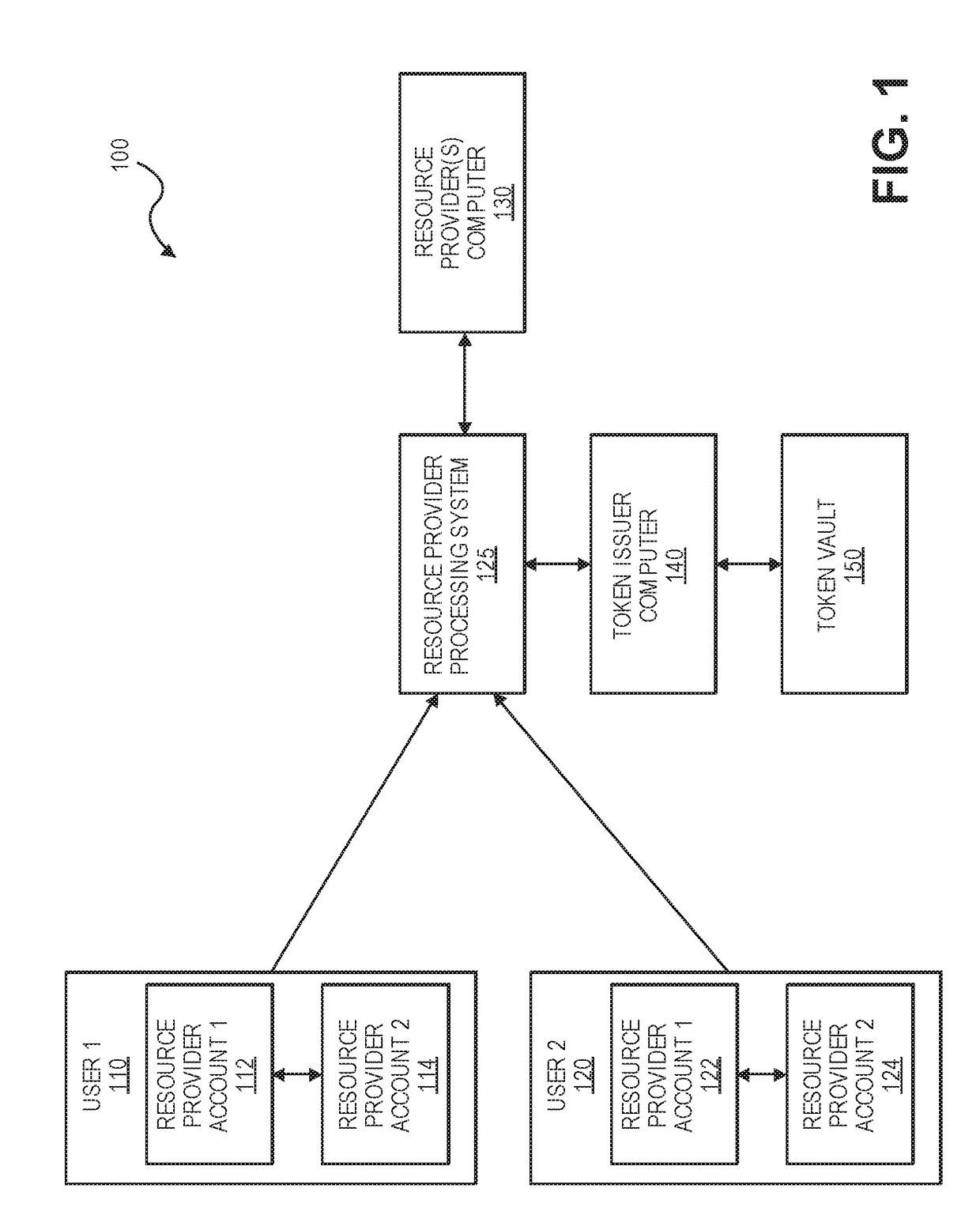
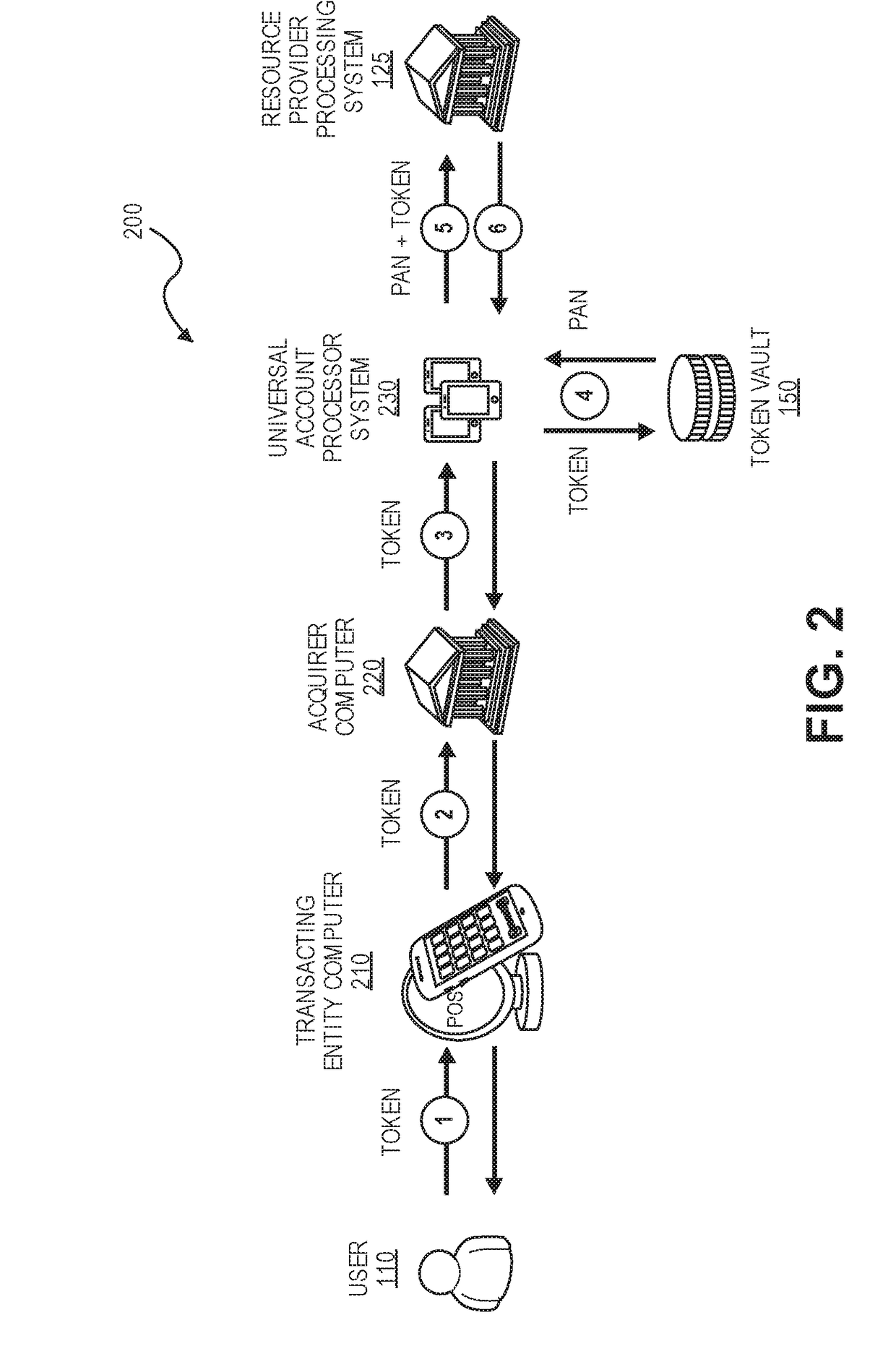
Resource provider account token provisioning and processing
Embodiments are directed to issuing tokens for identifiers associated with a resource provider account specific to the resource provider issuing the account. A resource provider processor system interfaces with a resource provider computer to validate account eligibility upon receiving a token request message. If the account is eligible for token generation, the resource provider processor system generates a universal identifier corresponding to the identifier associated with the resource provider account and returns the universal identifier to the token requestor. The token requestor may send a token request message to a token issuer for obtaining a token using the universal identifier. Accordingly, the universal account identifier can be used to provision a token into a digital wallet. Transactions using the token may be processed with the resource provider processor system acting as an account issuer.
Owner:VISA INT SERVICE ASSOC
Local area network with one or more virtual groups of core equipments appropriate for layer 2 switching
ActiveUS20060018302A1Multiplex system selection arrangementsDigital computer detailsUniversal IdentifierEngineering
A local area network comprises a peripheral equipment effecting layer 2 switching and including physical link aggregation means, and first and second core equipments effecting layer 2 switching and including physical link aggregation means. The peripheral equipment is connected to the first and second core equipments by first and second physical links, and the first and second core equipments are connected to each other by a third physical link. The first and second core equipments also respectively comprise first and second management means each adapted to detect the presence of the core equipment in which they are not installed via the third physical link coupling them and in the event of mutual detection to instruct the transmission of a common identifier to the peripheral equipment so that it considers the first and second core equipments as a single layer 2 switch and its aggregation means aggregate the first and second physical links with the aggregation means of the first and second core equipments.
Owner:RPX CORP
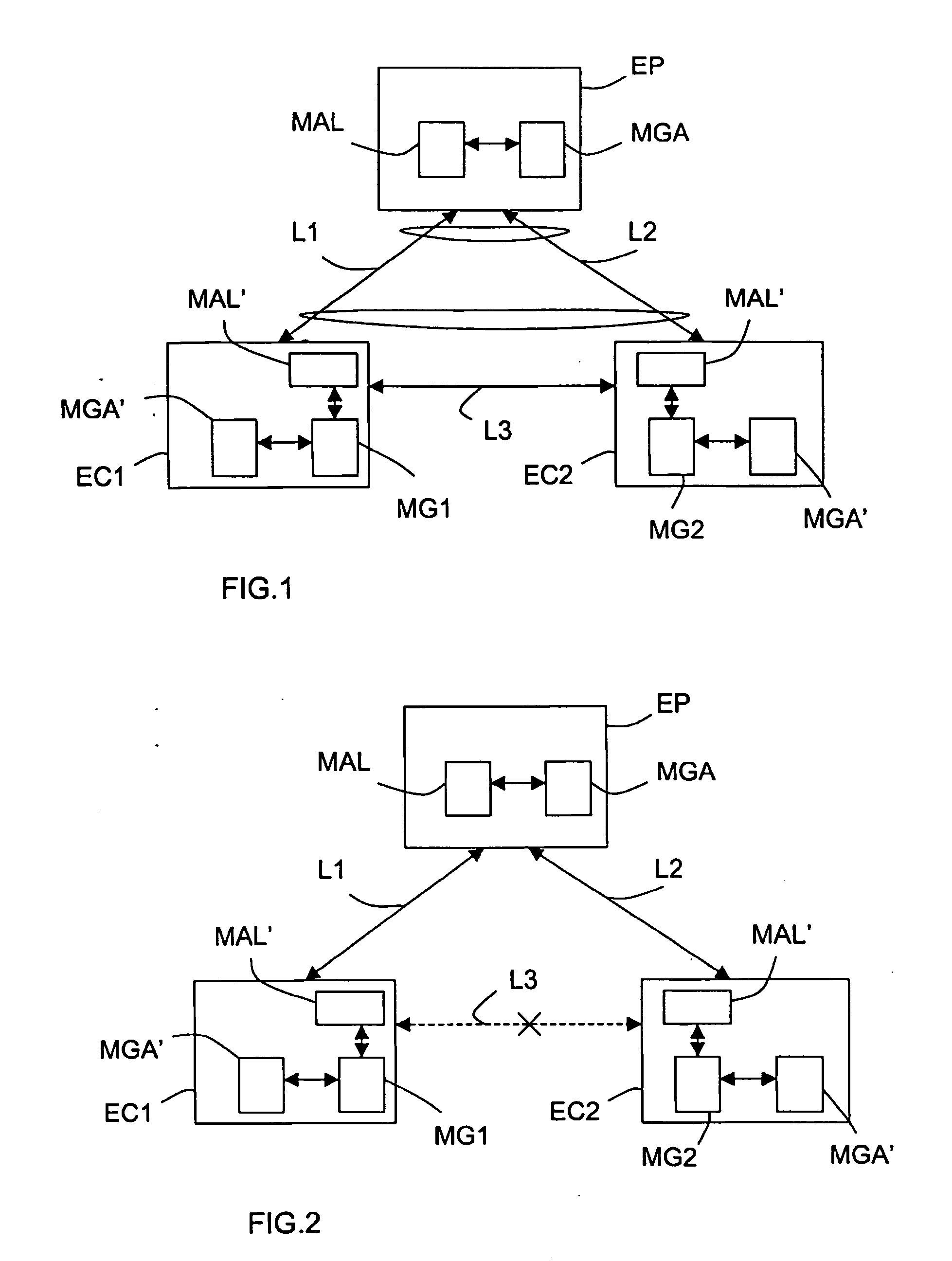
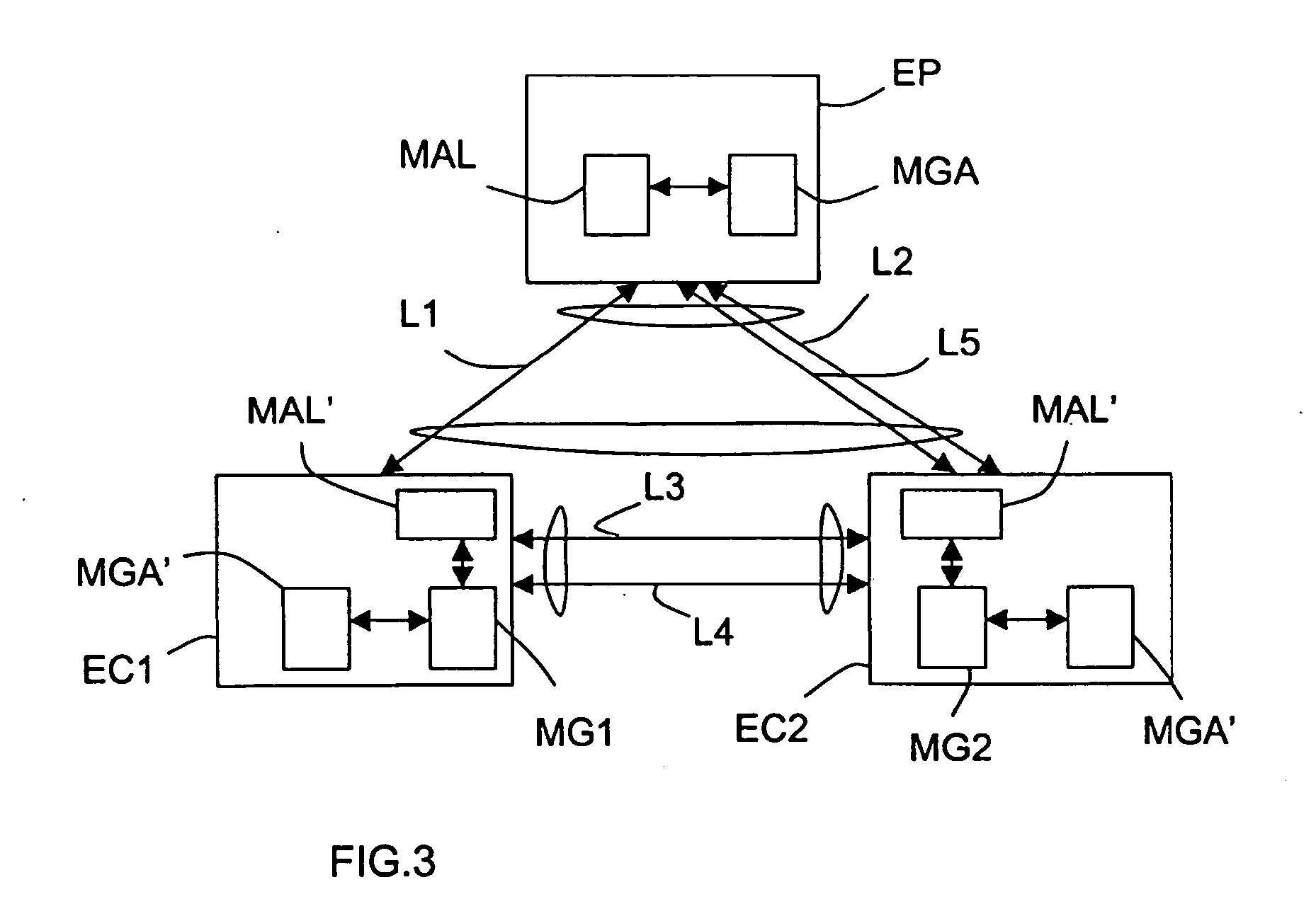
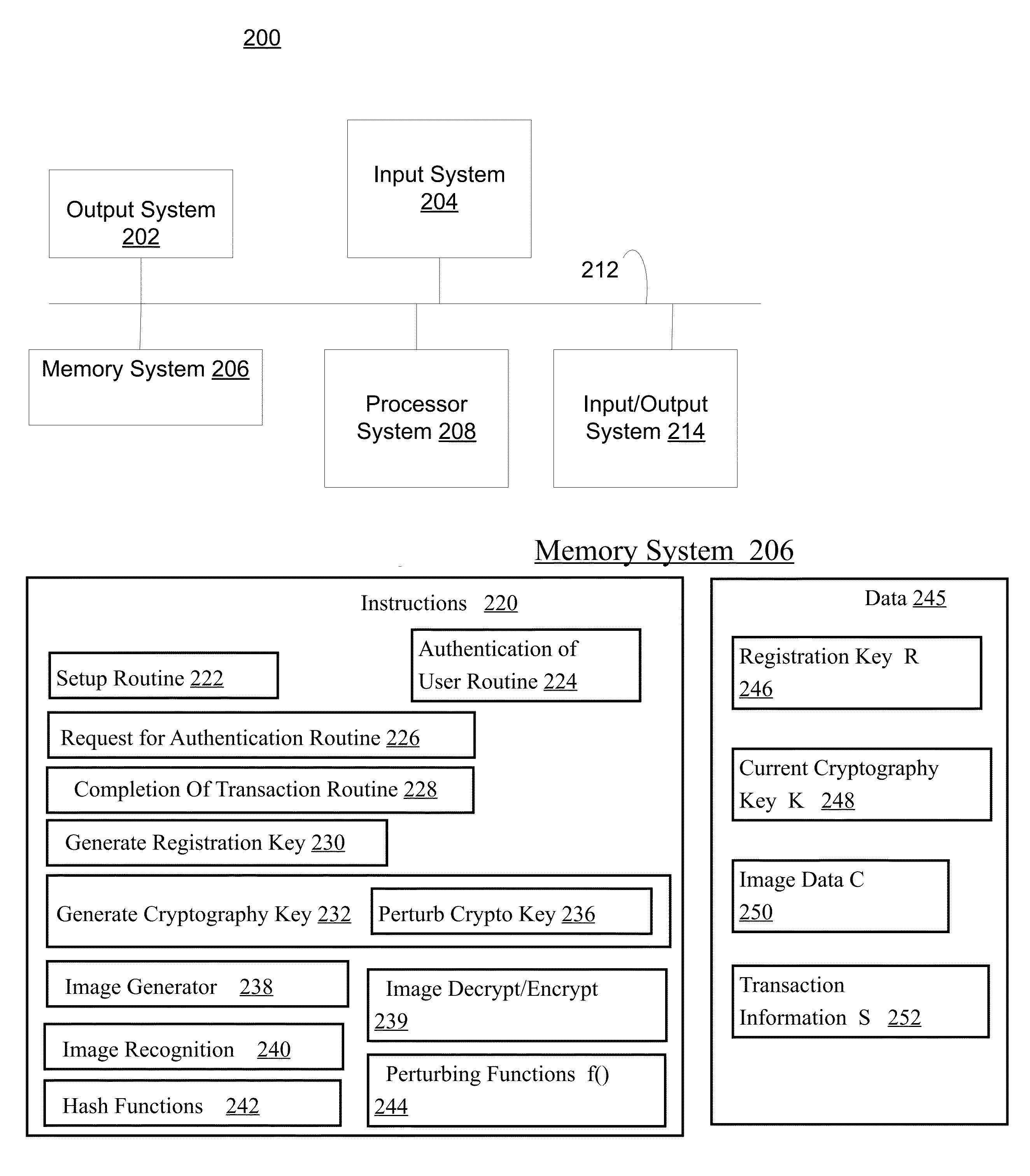
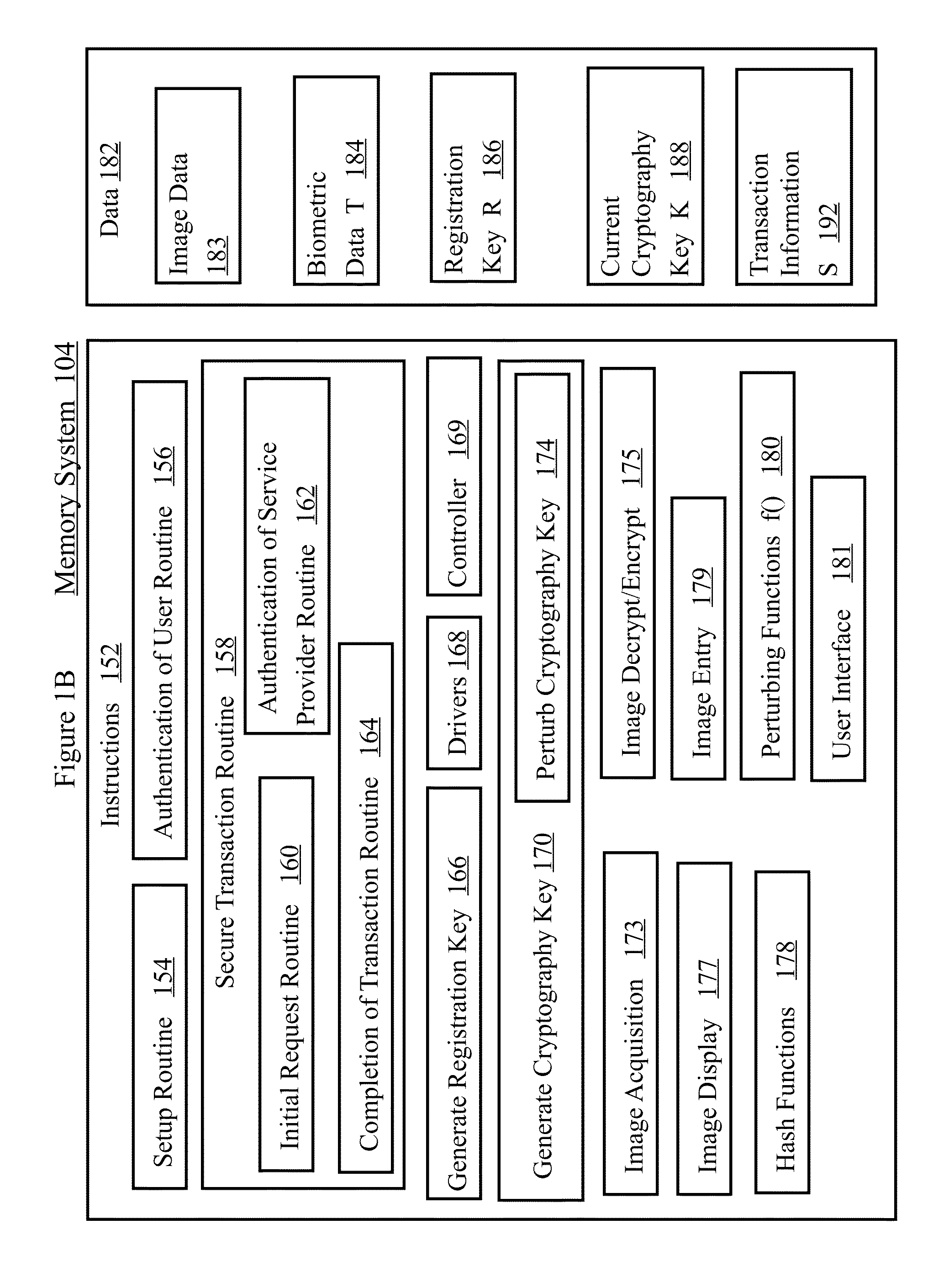
Visual image authentication and transaction authorization using non-determinism
InactiveUS20150067786A1Multiple keys/algorithms usageDigital data processing detailsPattern recognitionService provision
Methods and systems described herein perform a secure transaction. A display presents images that are difficult for malware to recognize but a person can recognize. In at least one embodiment, a person communicates transaction information using visual images received from the service provider system. In at least one embodiment, a universal identifier is represented by images recognizable by a person, but difficult for malware to recognize.In some embodiments, methods and systems are provided for determining whether to grant access, by generating and displaying visual images on a screen that the user can recognize. In an embodiment, a person presses one's finger(s) on the screen to select images as a method for authenticating and protecting communication from malware.In at least one embodiment, quantum randomness helps unpredictably vary the image location, generate noise in the image, or change the shape or texture of the image.
Owner:FISKE MICHAEL STEPHEN
Identity and preference management via universal identifier
InactiveUS20080104199A1Multiple digital computer combinationsMarketingUser identifierUniversal Identifier
A system is disclosed for utilizing a universal identifier (“ID”) that allows for access to information associated with the ID. The ID may be a substitute for a variety of information, such as contact information. When a user requests information for a given ID, an ID server may provide that information.
Owner:OATH INC
Exchanging a contact profile between client devices during a communication session
ActiveUS20140254434A1Special service provision for substationMultiplex system selection arrangementsClient-sideUniversal Identifier
In an embodiment, a client device (CD) maintains a contact profile for a user of the CD, the contact profile including a universal identifier (UID) for the user and a list of devices and addresses at which the user of the CD can be contacted. The CD establishes a communication session with a remote CD (RCD) via a given contact address from the set of contact addresses for the RCD. The CD shares, in response to the communication session establishment, at least a portion of the contact profile to the RCD. The RCD generates and / or updates a given contact profile for the user of the CD that is maintained on the RCD based on the shared contact profile. The RCD can also share its profile with the CD in response to the communication session establishment, causing the CD to generate and / or update a contact profile for the RCD.
Owner:QUALCOMM INC
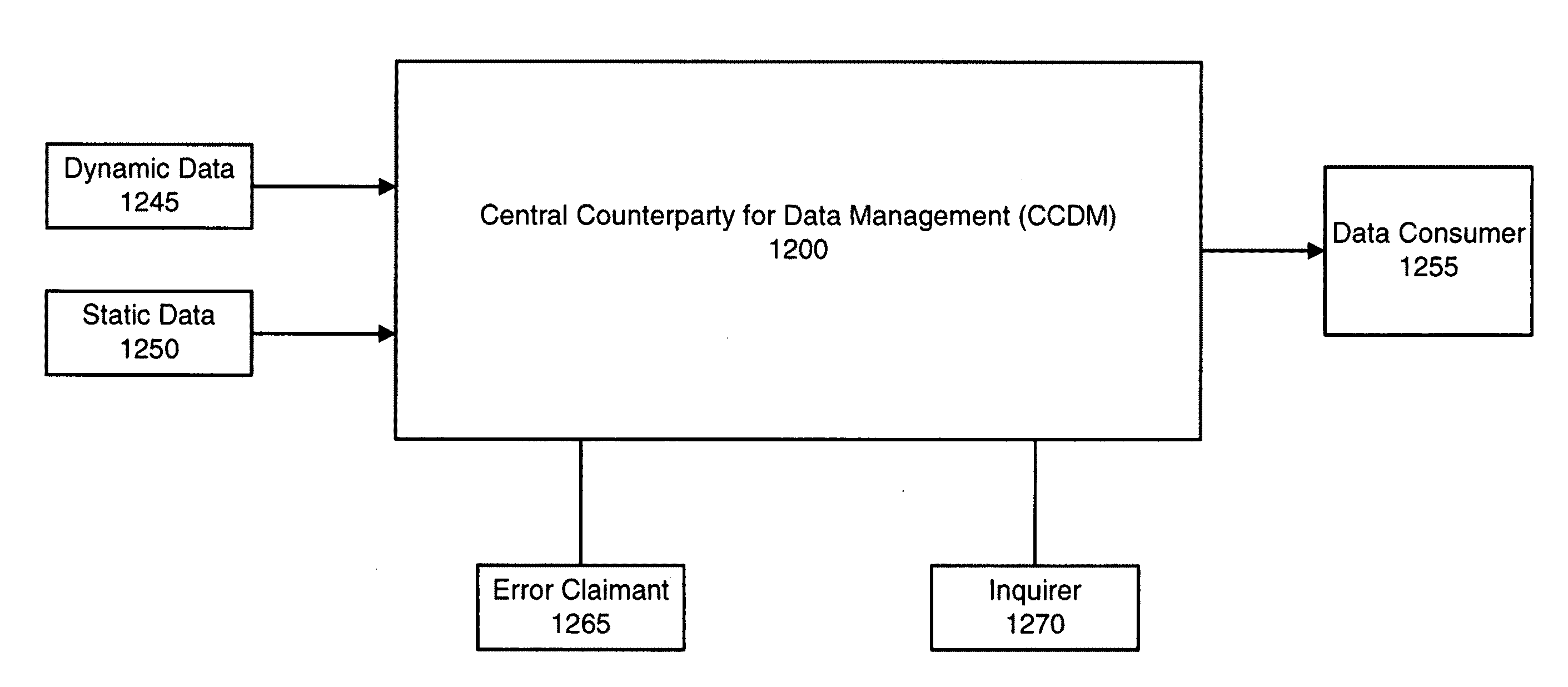
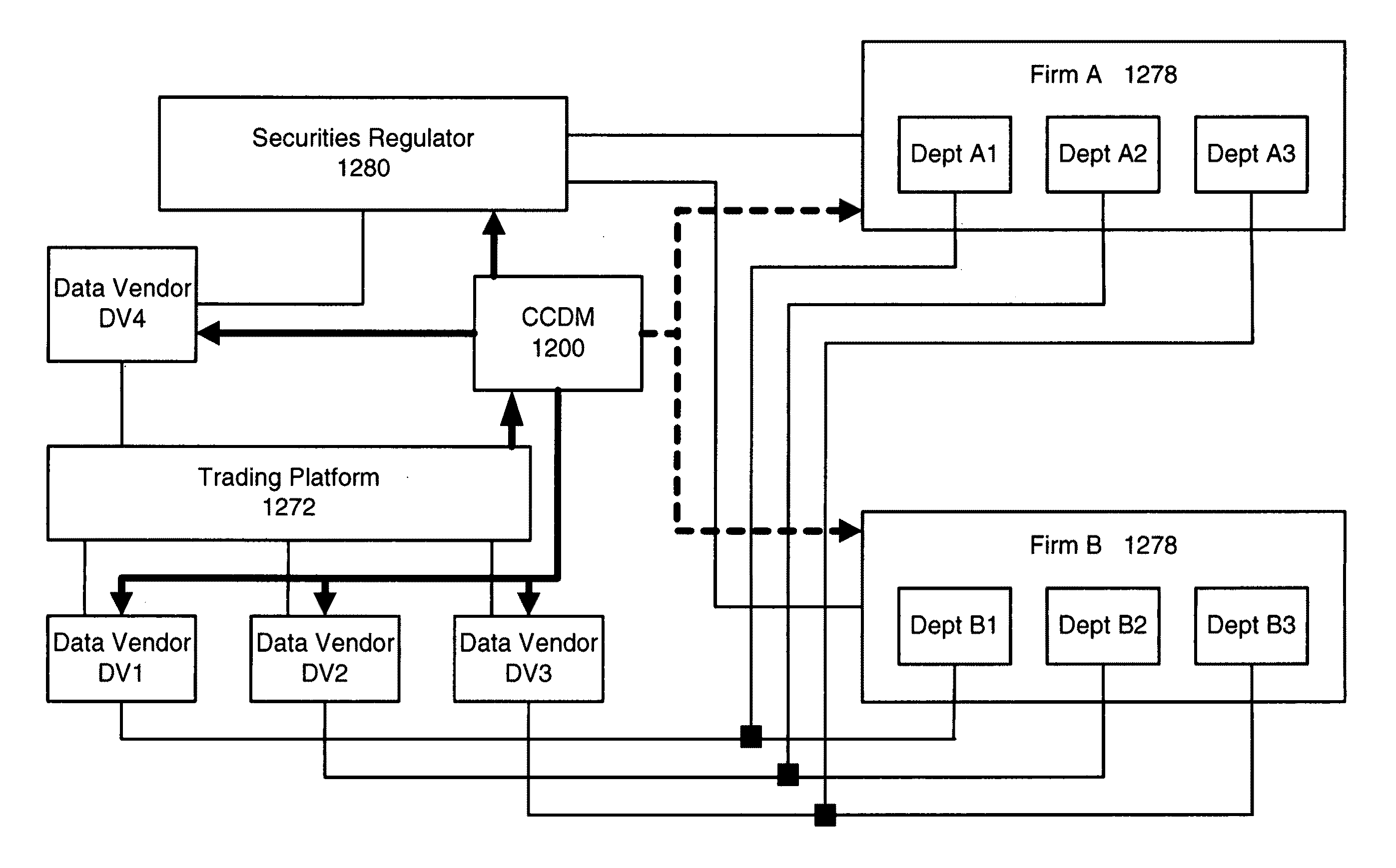
Central counterparty for data management
A central counterparty for data management (CCDM) receives data relating to financial transactions, associates the data with metadata to create reference data, stores the reference data and provides the reference data in “push” and “pull” ways. The “push” techniques for providing the data include distributing on a data feed, sending the data to parties known to be relevant to the transaction, and sending the data to parties who have a standing query that is satisfied by the data. The “pull” techniques for providing the data include responding to queries received from a variety of parties. The CCDM generates and distributes unique, unambiguous and universal identifiers (U3id's) and associates the U3id identifiers with the reference data.
Owner:FINANCIAL INTERGROUP HLDG
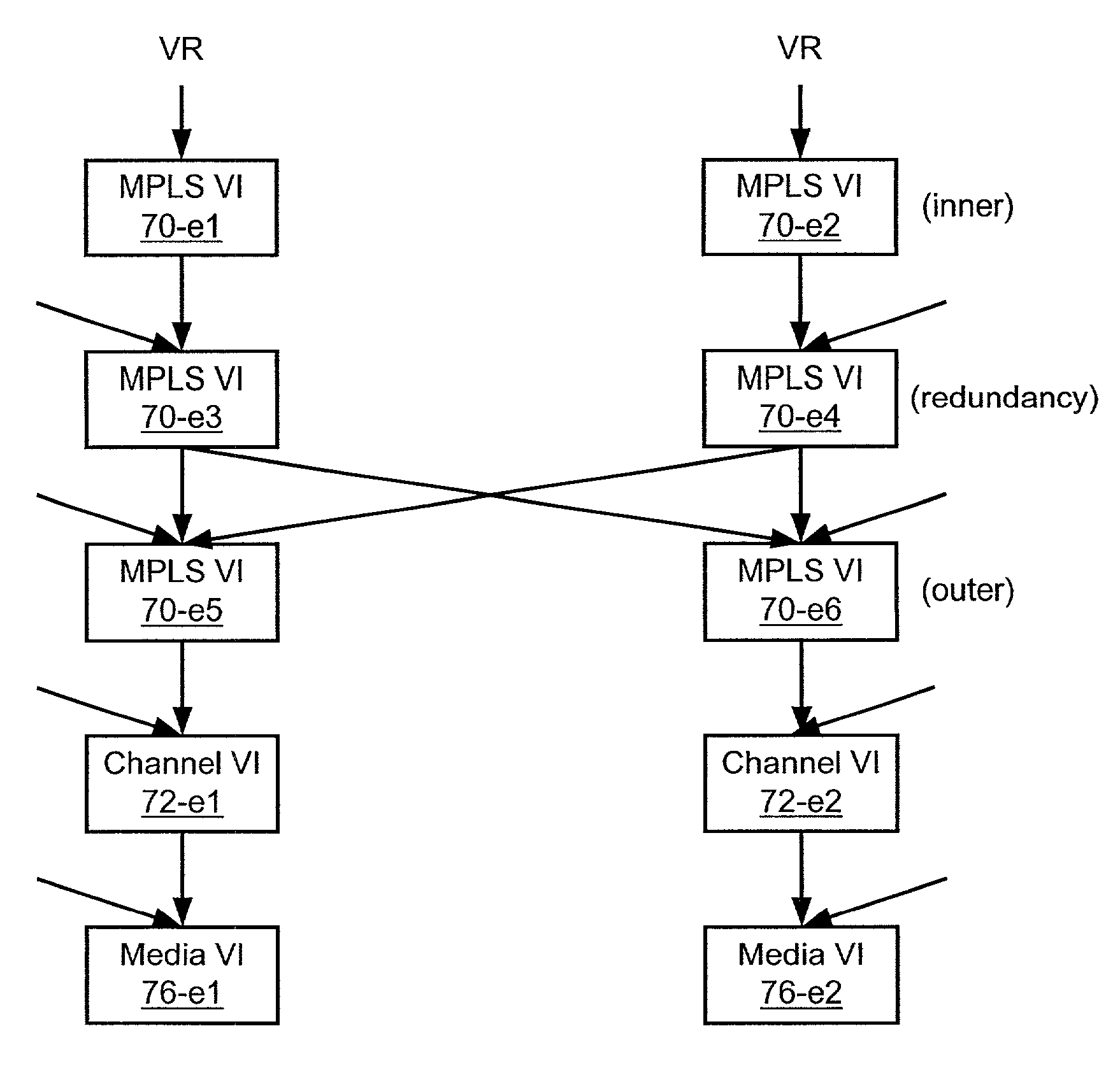
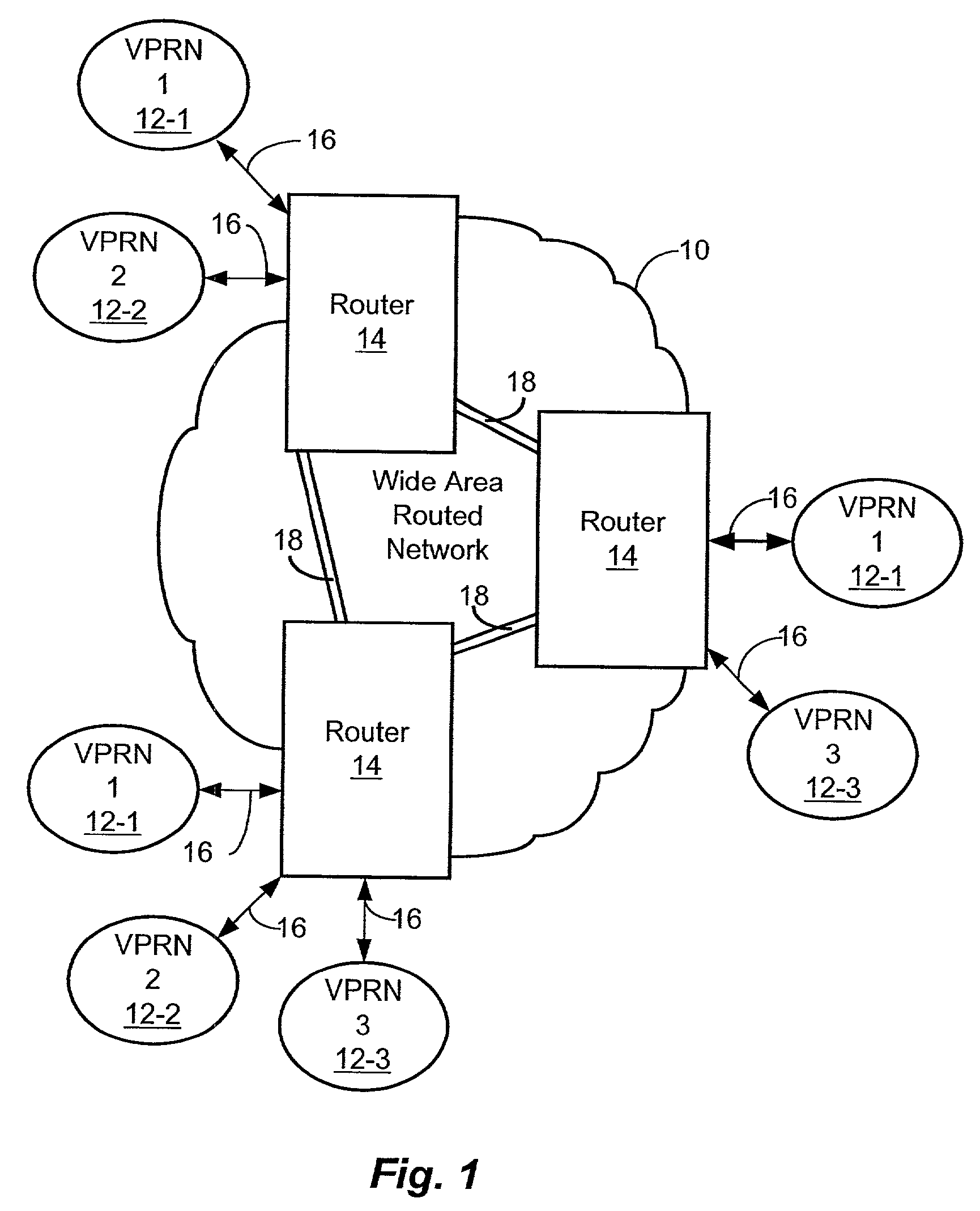
Network device virtual interface
InactiveUS7242665B2Easy to changeHighly configurableError preventionTransmission systemsLabel switchingHuman–computer interaction
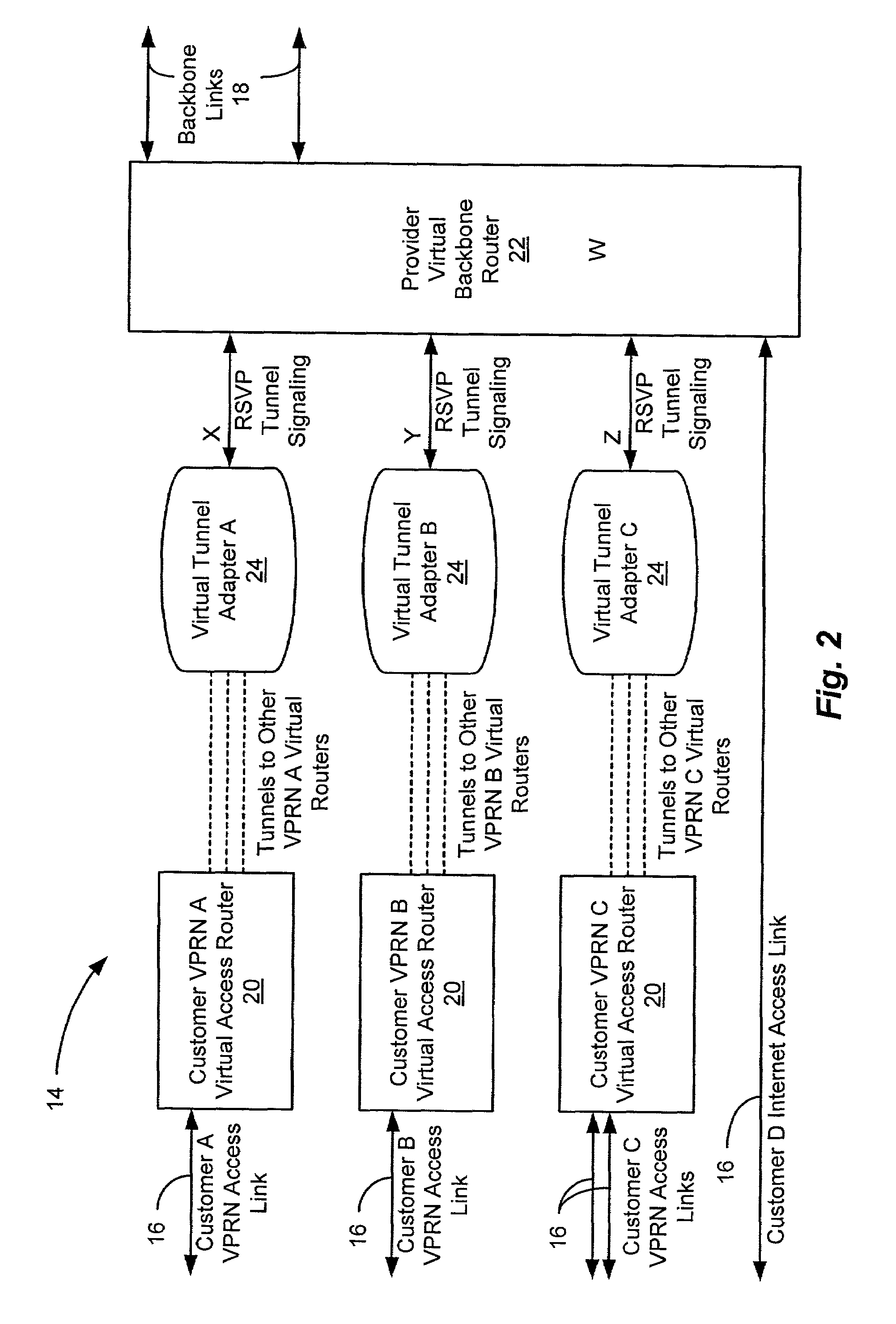
A network device includes a virtual router subsystem having potentially numerous virtual routers associated with corresponding different virtual private routed networks (VPRN) and employing generic interface identifiers to identify interfaces at which VPRN traffic is received or transmitted. A virtual interface subsystem couples the virtual router subsystem to physical interfaces of the device. The virtual interface subsystem includes virtual interfaces organized into linked sets, and each set associates a generic identifier of a virtual router with a physical interface to another network device serving the same VPRN. A basic type of set includes two VIs for interfacing a virtual router to a customer access link, and a more complicated set includes multiple pairs of several types of VIs to interface a virtual router to redundant label-switched paths on a channel-oriented backbone link such as an ATM link.
Owner:TELEFON AB LM ERICSSON (PUBL)
Managing an environment via a universally accessible server system
InactiveUS6636808B1Temperature control without auxillary powerAir-treating devicesMeasurement deviceControl system
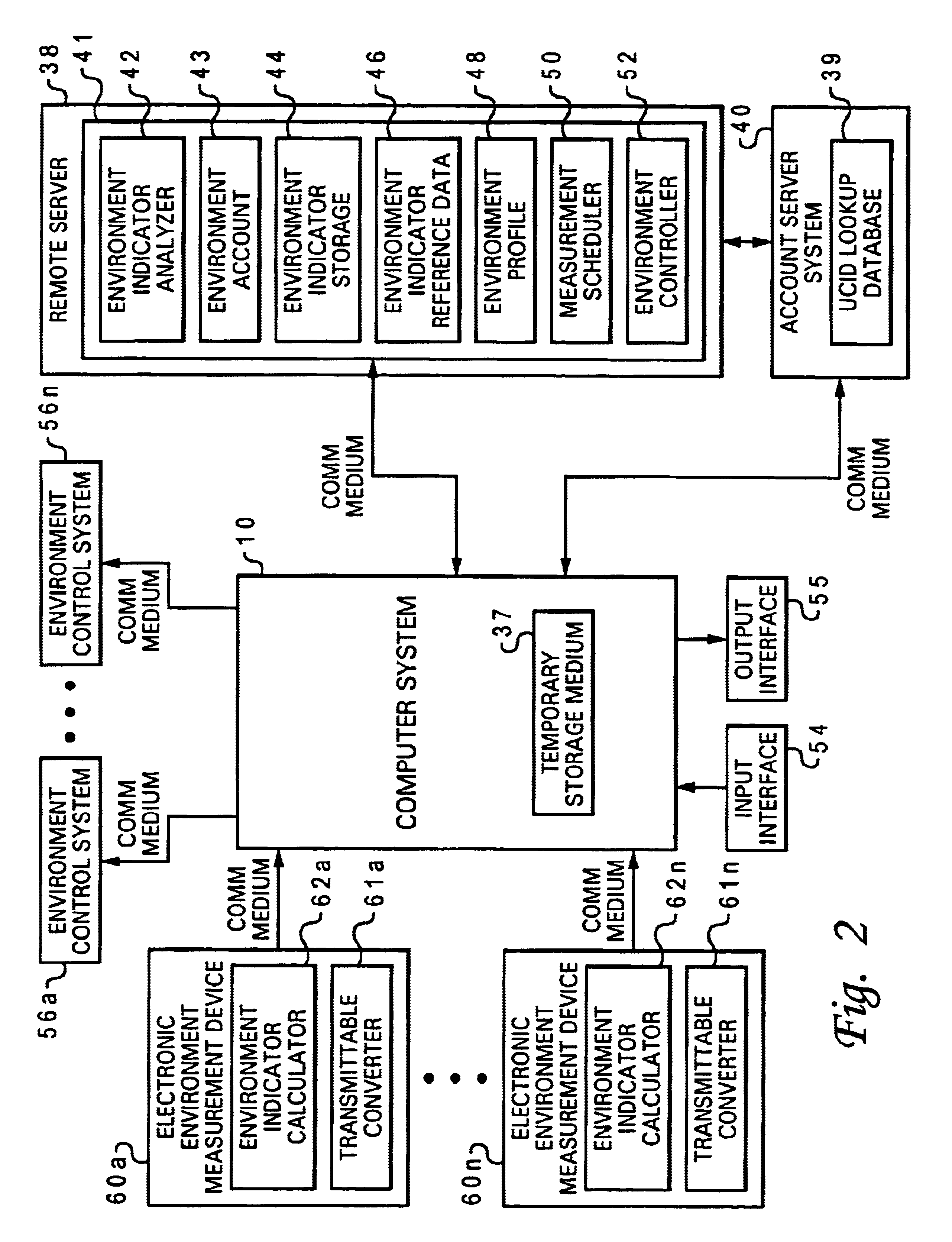
According to the present invention, environment indicators computed for a particular environment are converted into a common transmittable data format, wherein each of the environment indicators is computed by an electronic environment measurement device from among multiple diverse electronic environment measurement devices. The environment indicators are transmitted in the transmittable data format to a universally accessible server system in association with a particular universal identifier for a particular user. The universally accessible server system analyzes each of the environment indicators according to an environment sensitivity profile stored within the universally accessible server system in association with the universal identifier. Control signals are determined at the universally accessible server system for adjusting multiple environment control systems that control the particular environment in response to the analysis. The particular environment is adjusted as controlled by the environment control systems according to the control signals, such that a particular environment is temporarily managed via a universally accessible server system according to an environment sensitivity profile associated with a particular user.
Owner:IBM CORP
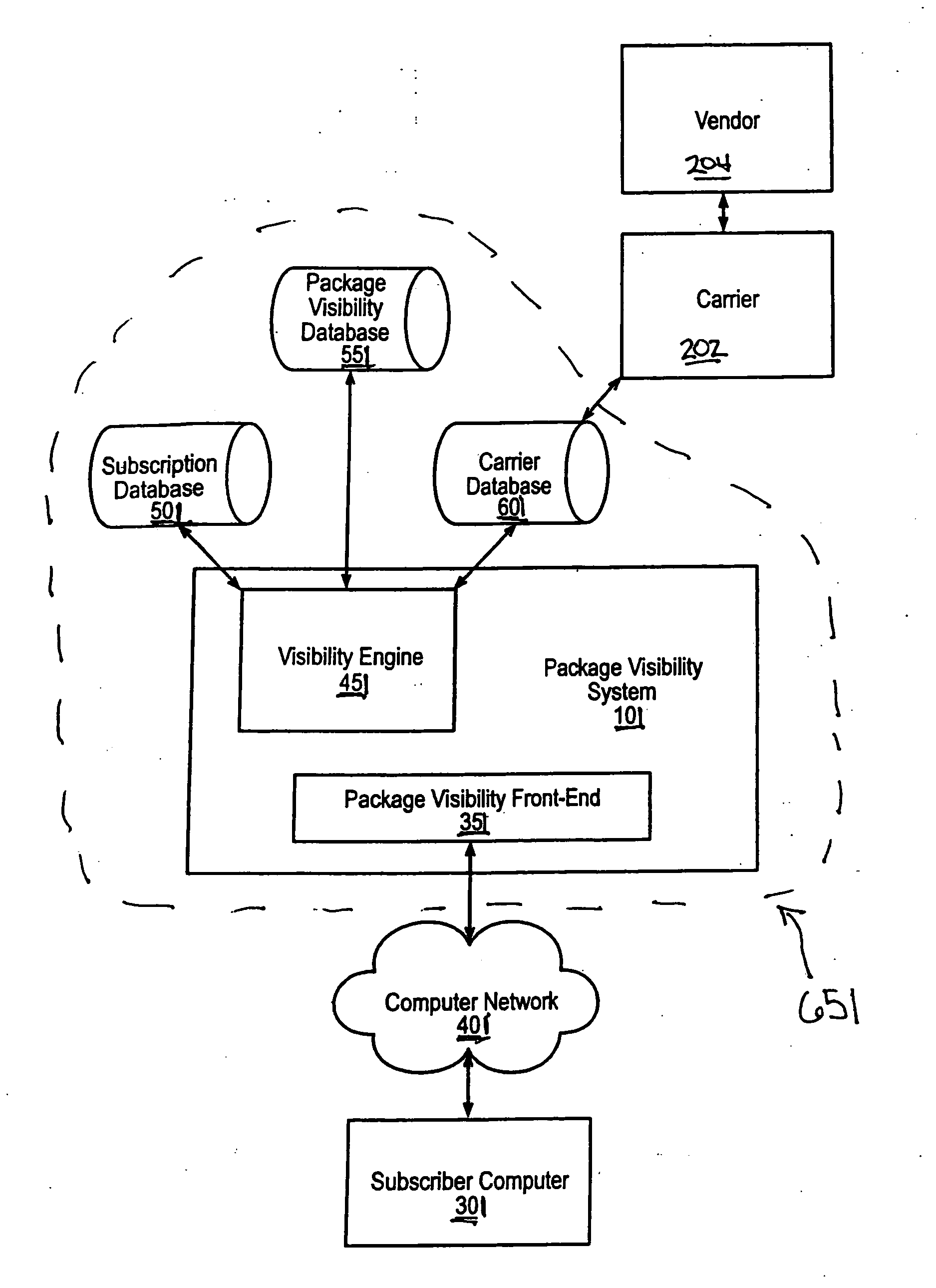
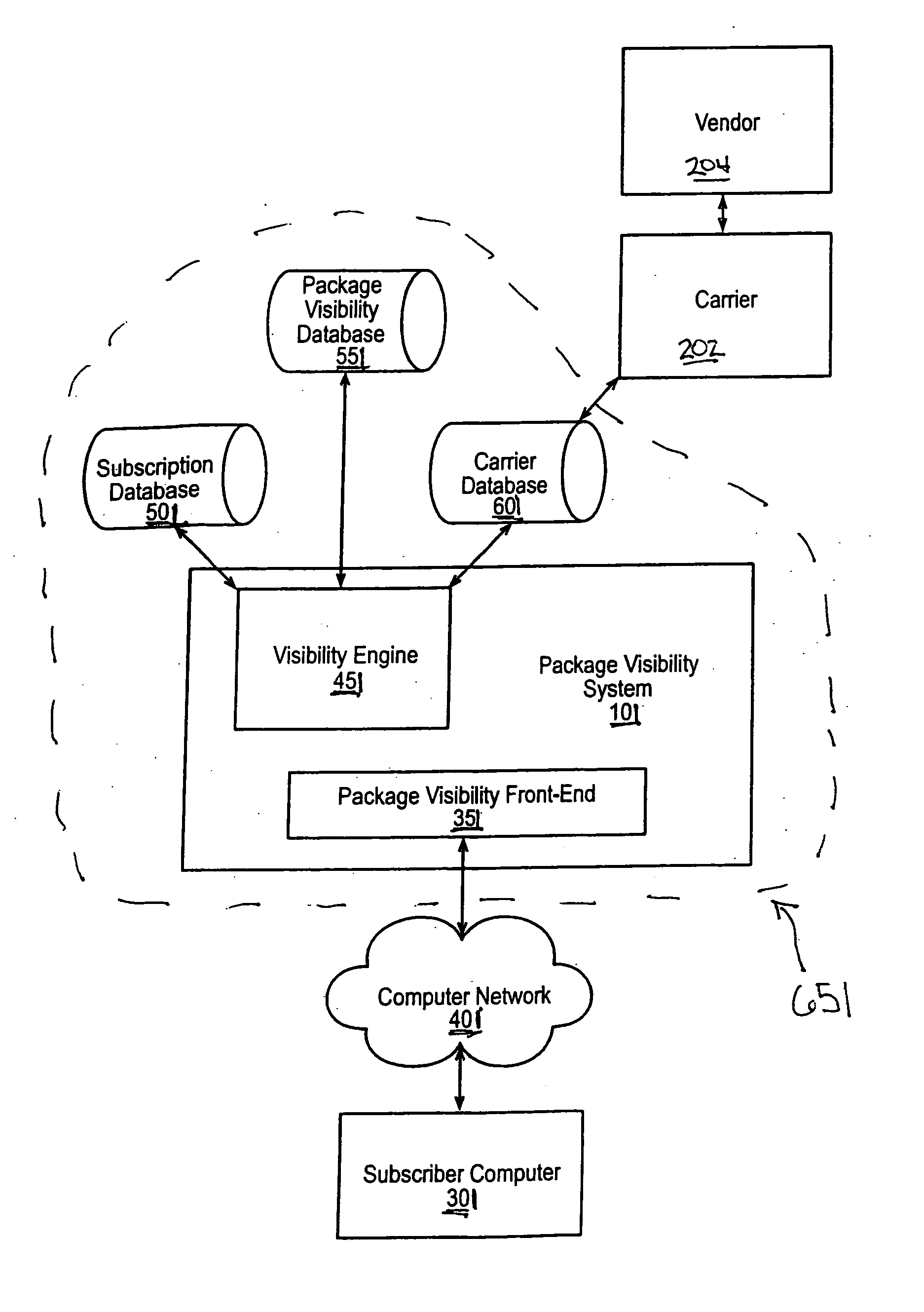
Universal identifier systems in supply chain logistics
The present invention is generally directed to systems and methods to provide a user with visibility to certain packages that are transported by one or more carriers and that have a universal identifier included in each package's package level detail information. The universal identifier may be used to access the package level detail information in each package by the parties to a shipping transaction and by third-parties that are not the shipper, recipient or intended recipient of the packages.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
Central counterparty for data management
A central counterparty for data management (CCDM) receives data relating to financial transactions, associates the data with metadata to create reference data, stores the reference data and provides the reference data in “push” and “pull” ways. The “push” techniques for providing the data include distributing on a data feed, sending the data to parties known to be relevant to the transaction, and sending the data to parties who have a standing query that is satisfied by the data. The “pull” techniques for providing the data include responding to queries received from a variety of parties. The CCDM generates and distributes unique, unambiguous and universal identifiers (U3id's) and associates the U3id identifiers with the reference data.
Owner:FINANCIAL INTERGROUP HLDG
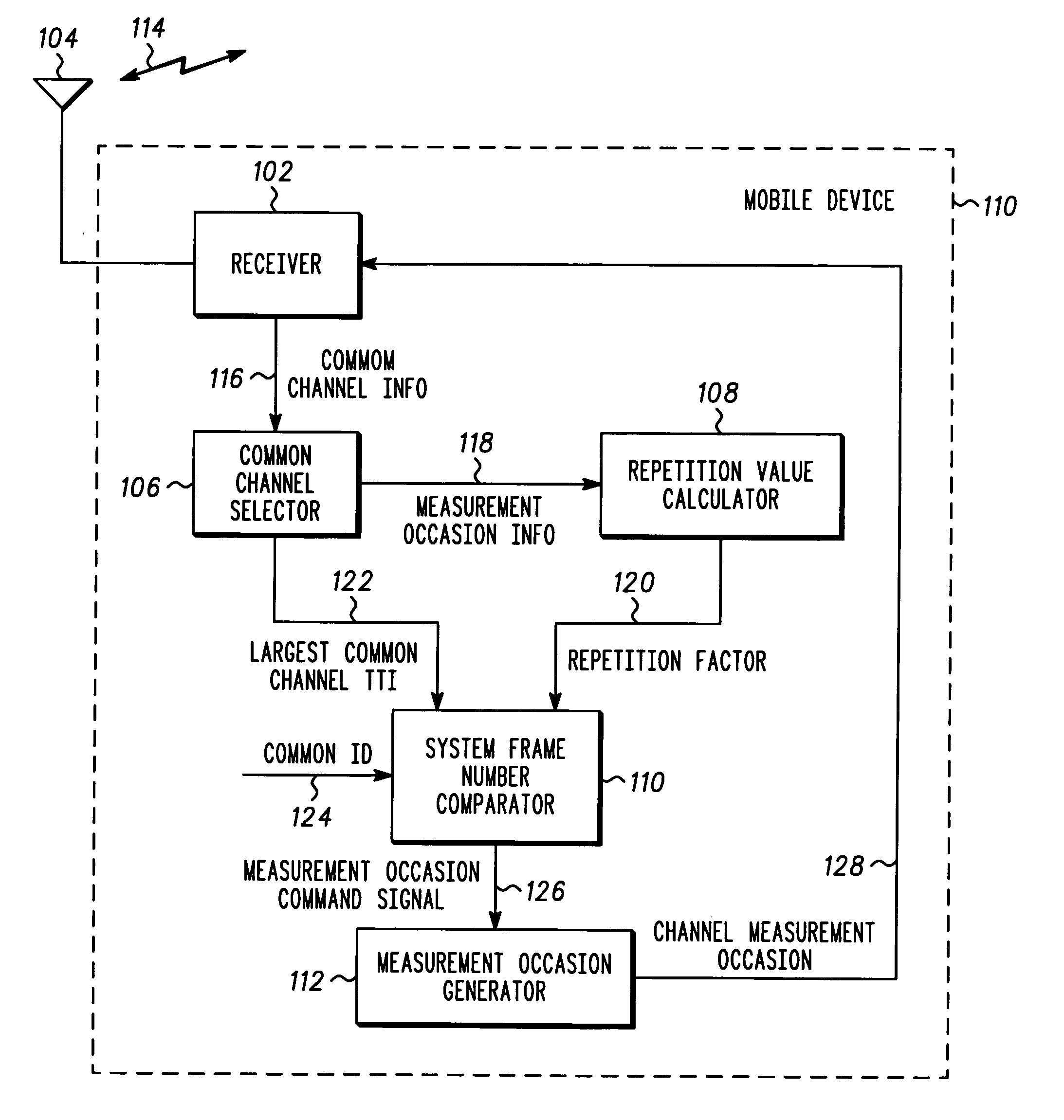
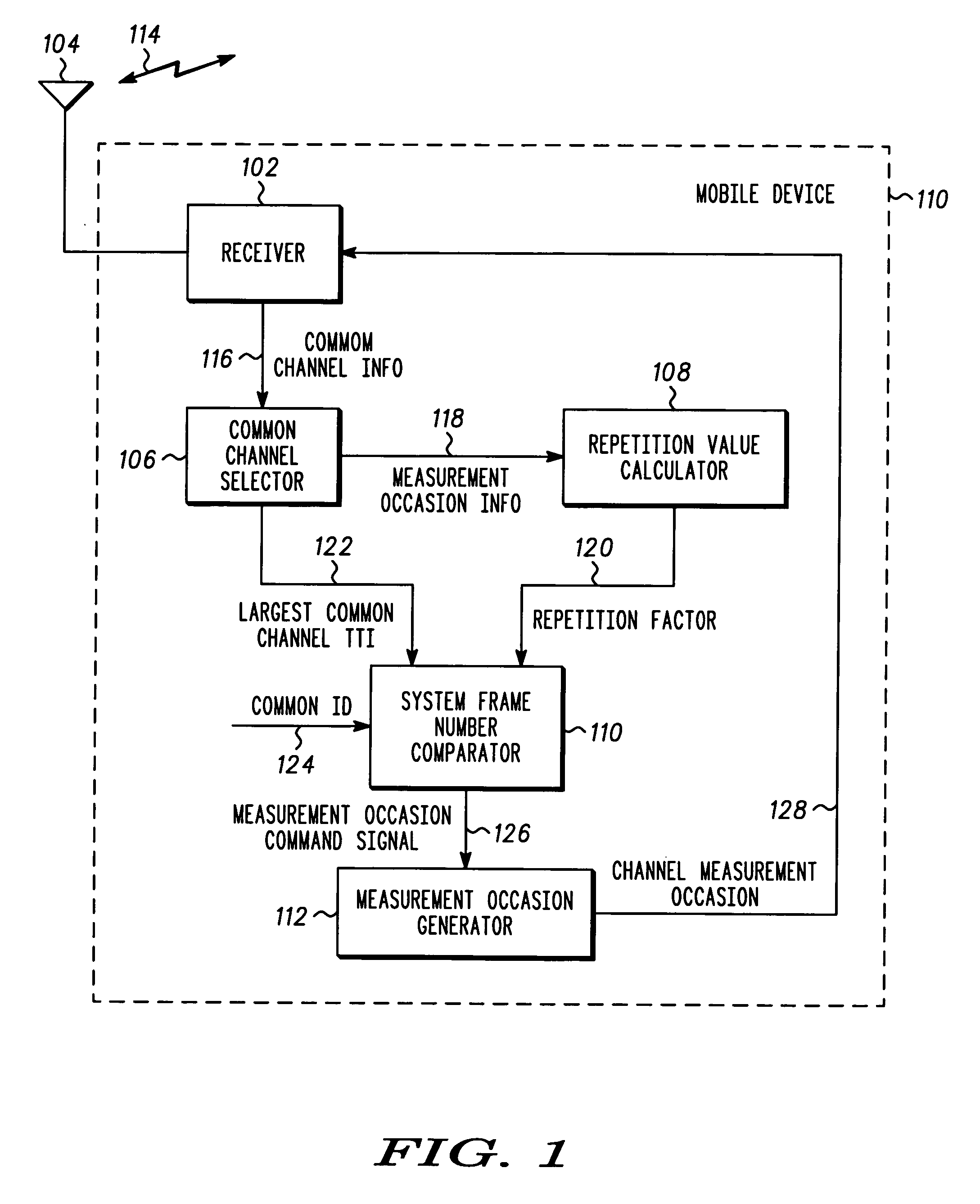
Method and apparatus for interrupting a transmission of a multicast signal
InactiveUS20050100037A1Time-division multiplexBroadcast service distributionUniversal IdentifierComparator
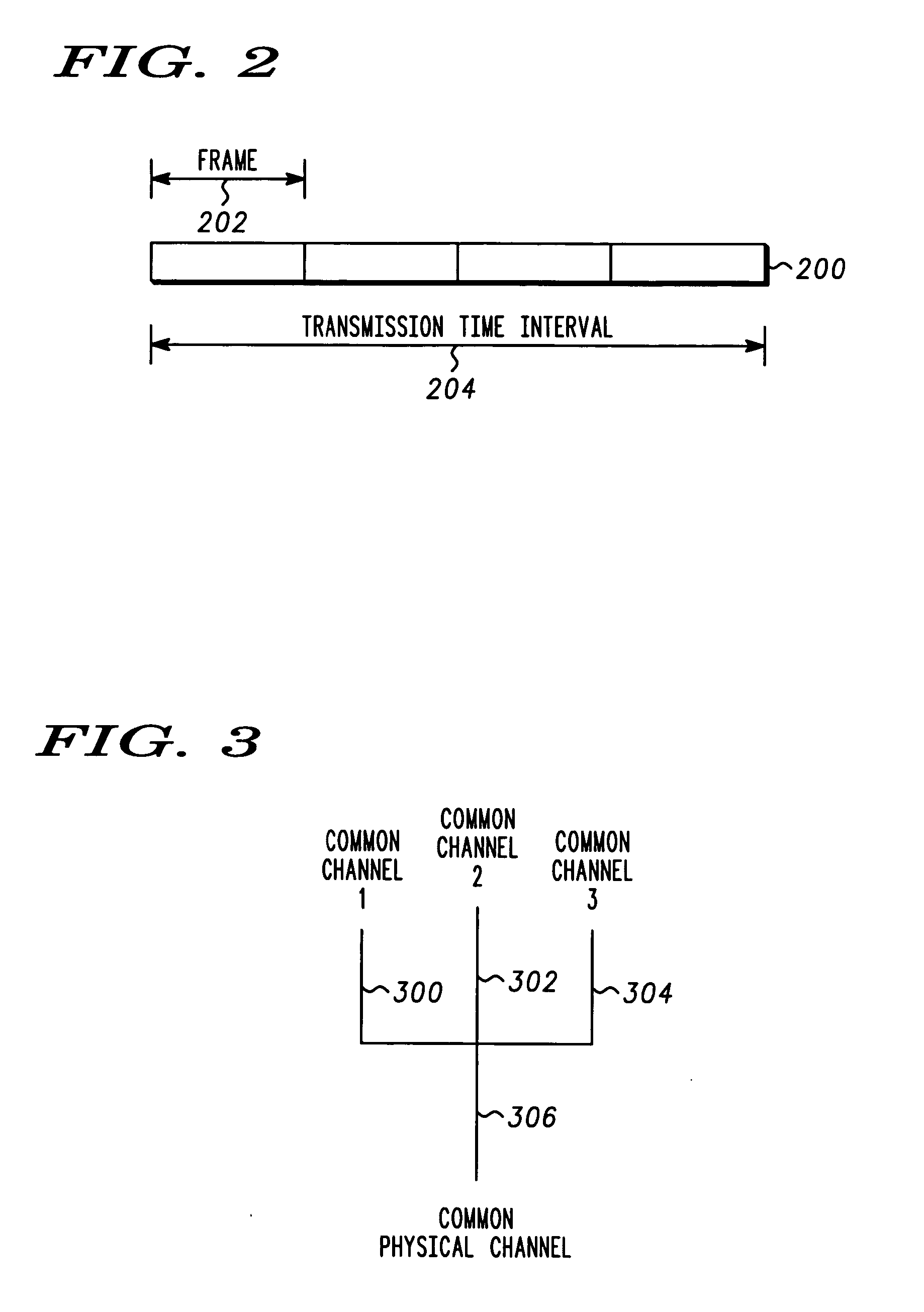
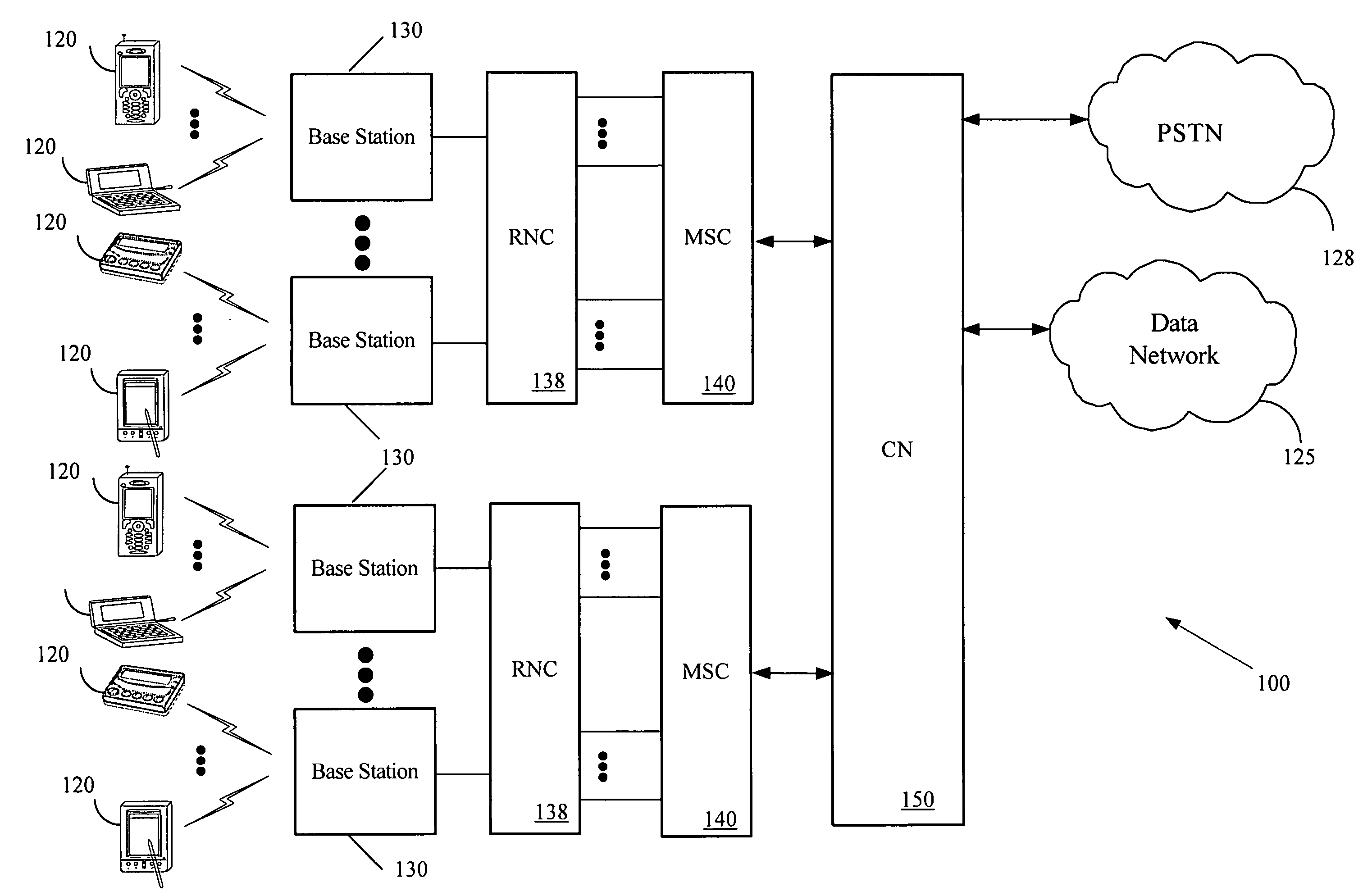
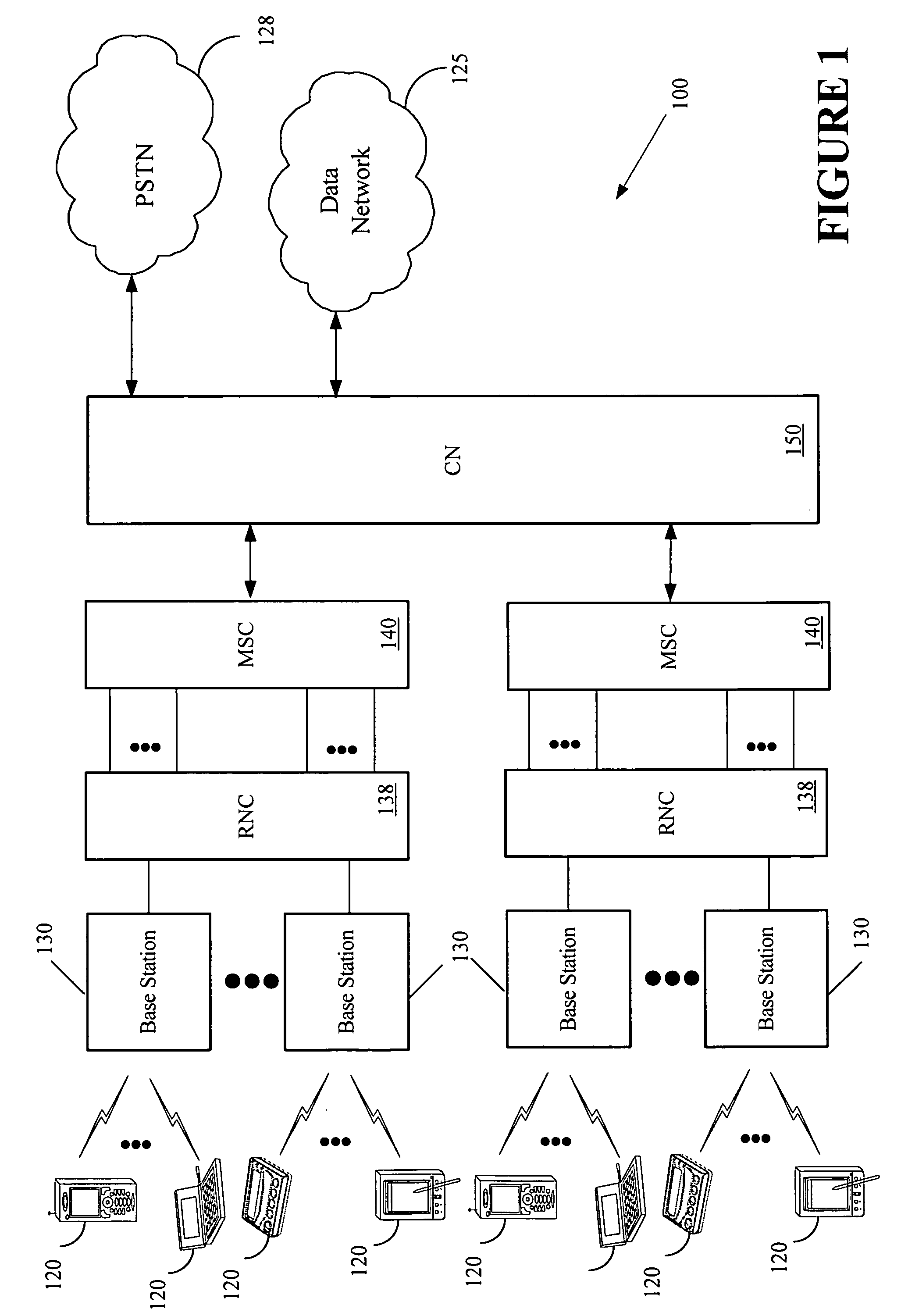
A method and apparatus for interrupting a transmission of a multicast signal includes a common channel selector (106) coupled to a receiver (102) to receive common channel information (116) therefrom. A repetition value calculator (108) receives measurement occasion information (118) from the common channel selector (106) to calculate a repetition factor (120). A system frame number comparator (110) determines if a channel measurement occasion (128) should be performed based on the repetition factor (120), a common identifier (124) and a largest common channel transmission time interval (122). The method and apparatus further includes a measurement occasion generator (112) coupled to the system frame number comparator (110), wherein if a measurement occasion is to be performed, a measurement occasion command signal (126) is provided to the measurement occasion generator (112) and the measurement occasion generator generates the channel measurement occasion (128).
Owner:GOOGLE TECH HLDG LLC
Method for transition from traditional internet to universal identifier network
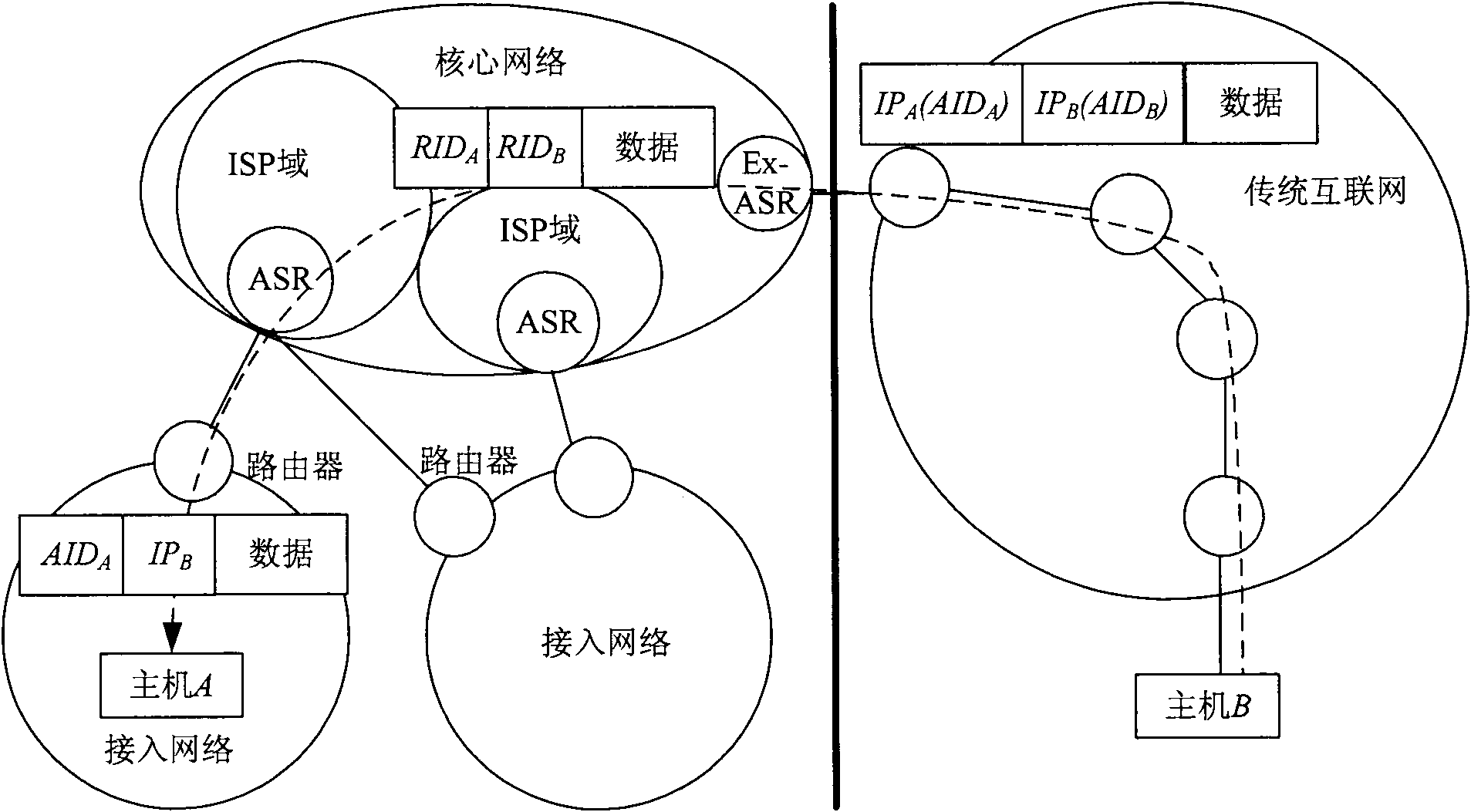
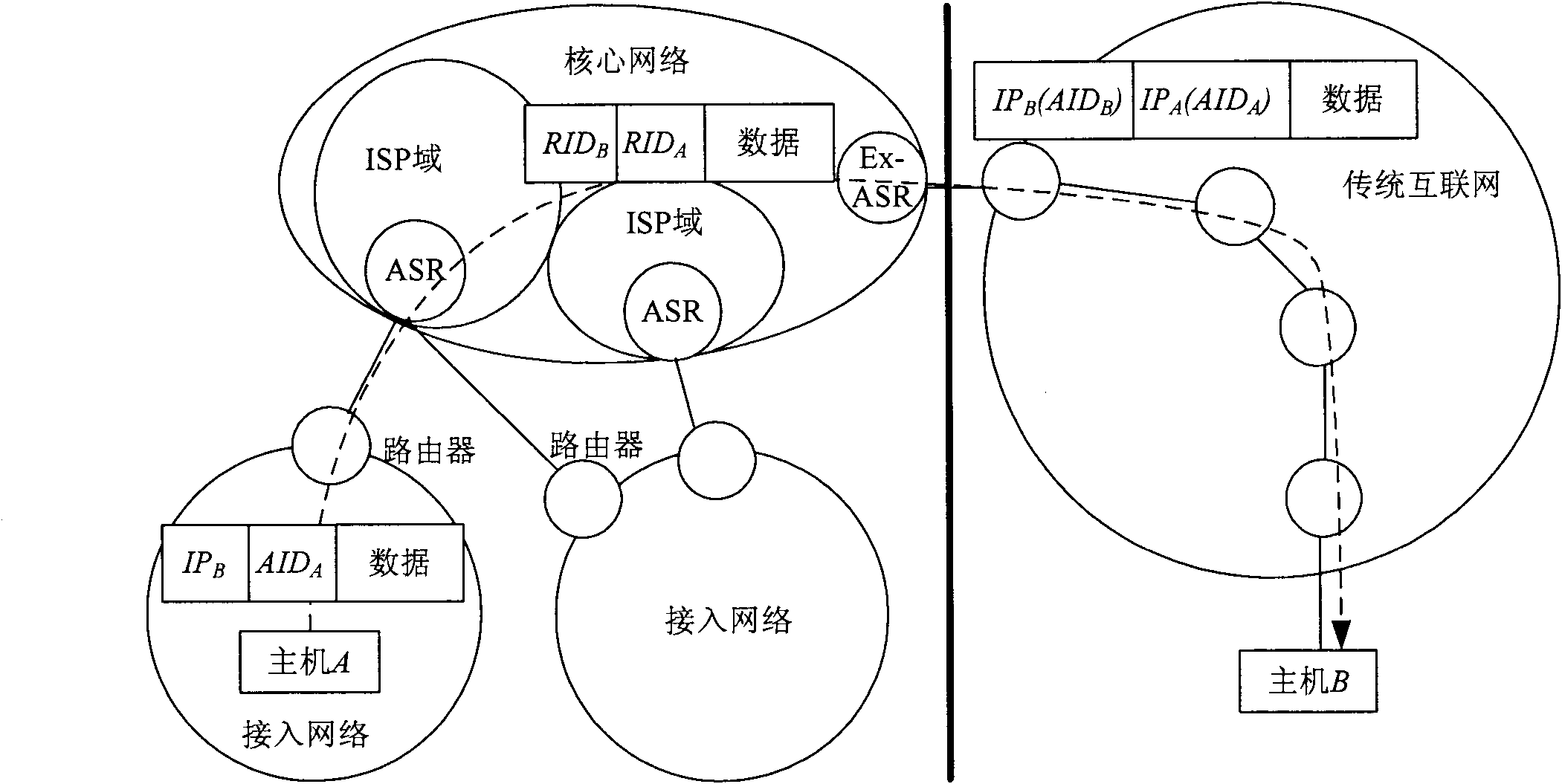
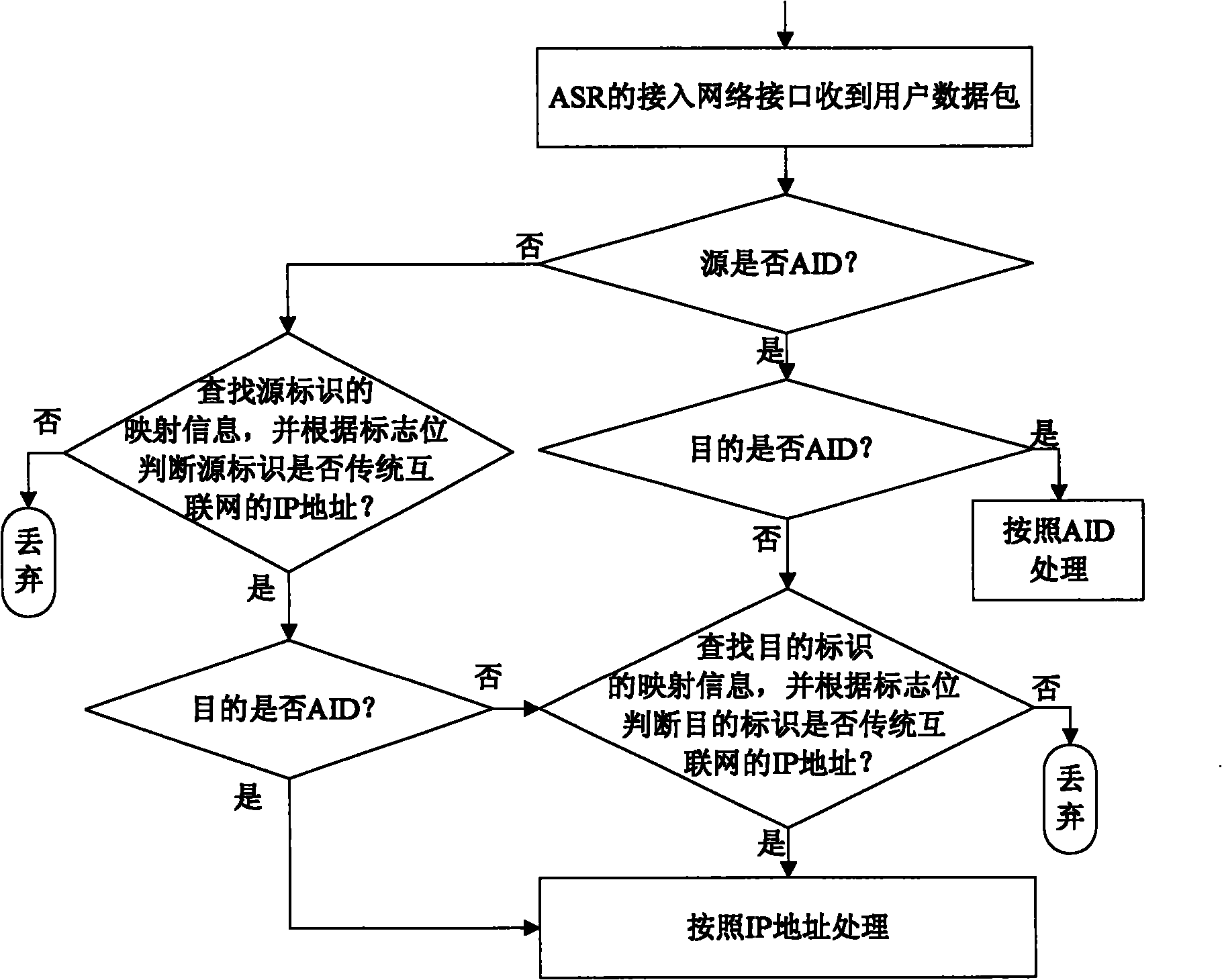
InactiveCN101938413ARouting scalability problem solvedLocation Privacy ProtectionNetworks interconnectionIp addressNetwork packet
The invention discloses a method for transition from the traditional internet to a universal identifier network, which allows users of the traditional internet to communicate with users of a universal identifier network without upgrading by introducing an expansion access switched router Ex-ASR. When the users of the traditional network communicate with those of the universal identifier network, a data packet is sent to an expansion access switched router, and an access identifier and an IP address in the data packet are replaced by a switched routing identifier to be transmitted in a core network of the universal identifier network; and for the access switched router of an opposite terminal, the switched routing identifier is replaced by the access identifier and the IP address to send a message to a target node. The invention provides a method to solve the problem of intercommunication between the traditional internet and the universal identifier network, so that the users of the traditional internet can operate normally and independently without suffering from any influence of the universal network; and the method is favorable for the further development of the universal identifier network.
Owner:BEIJING JIAOTONG UNIV
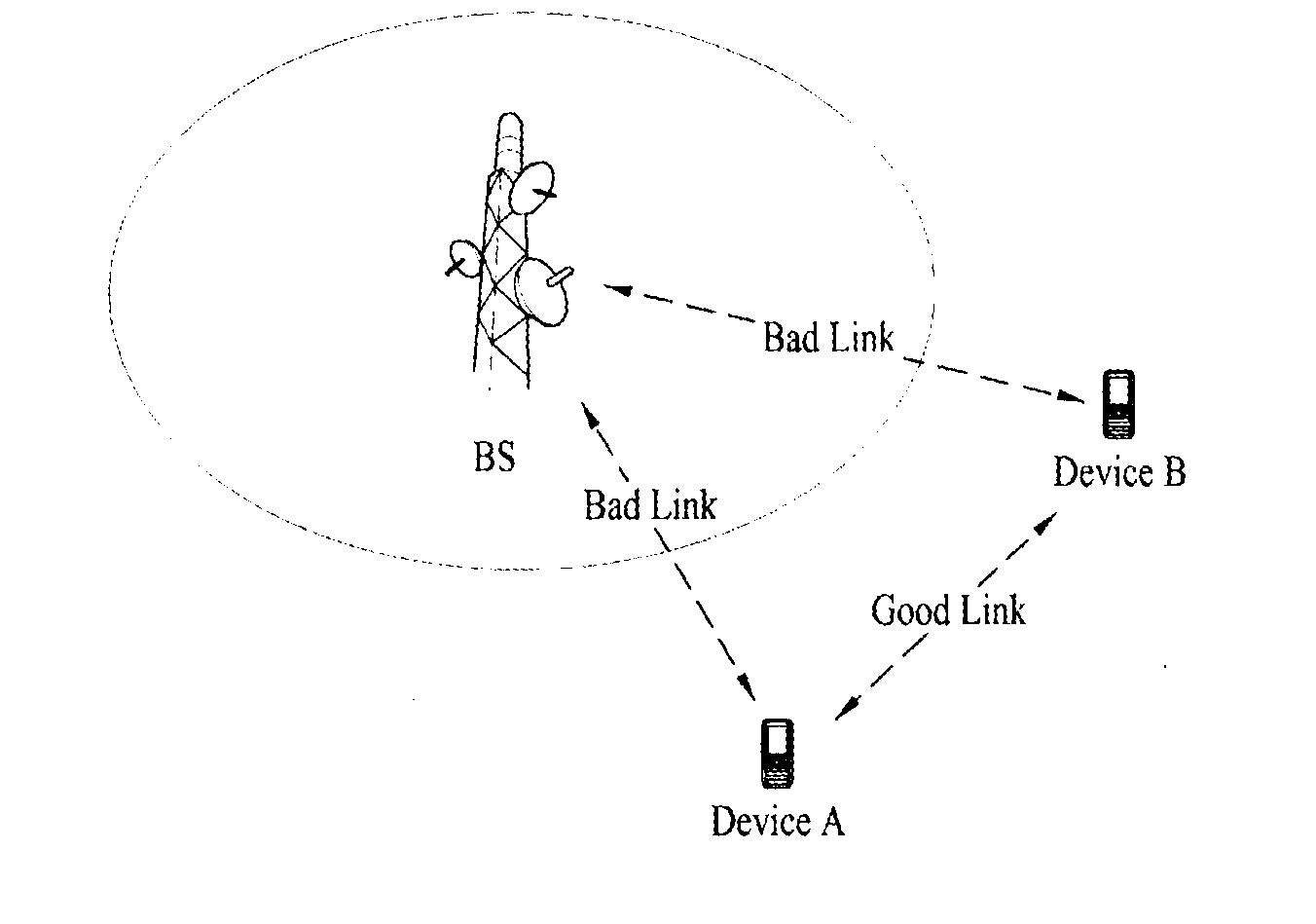
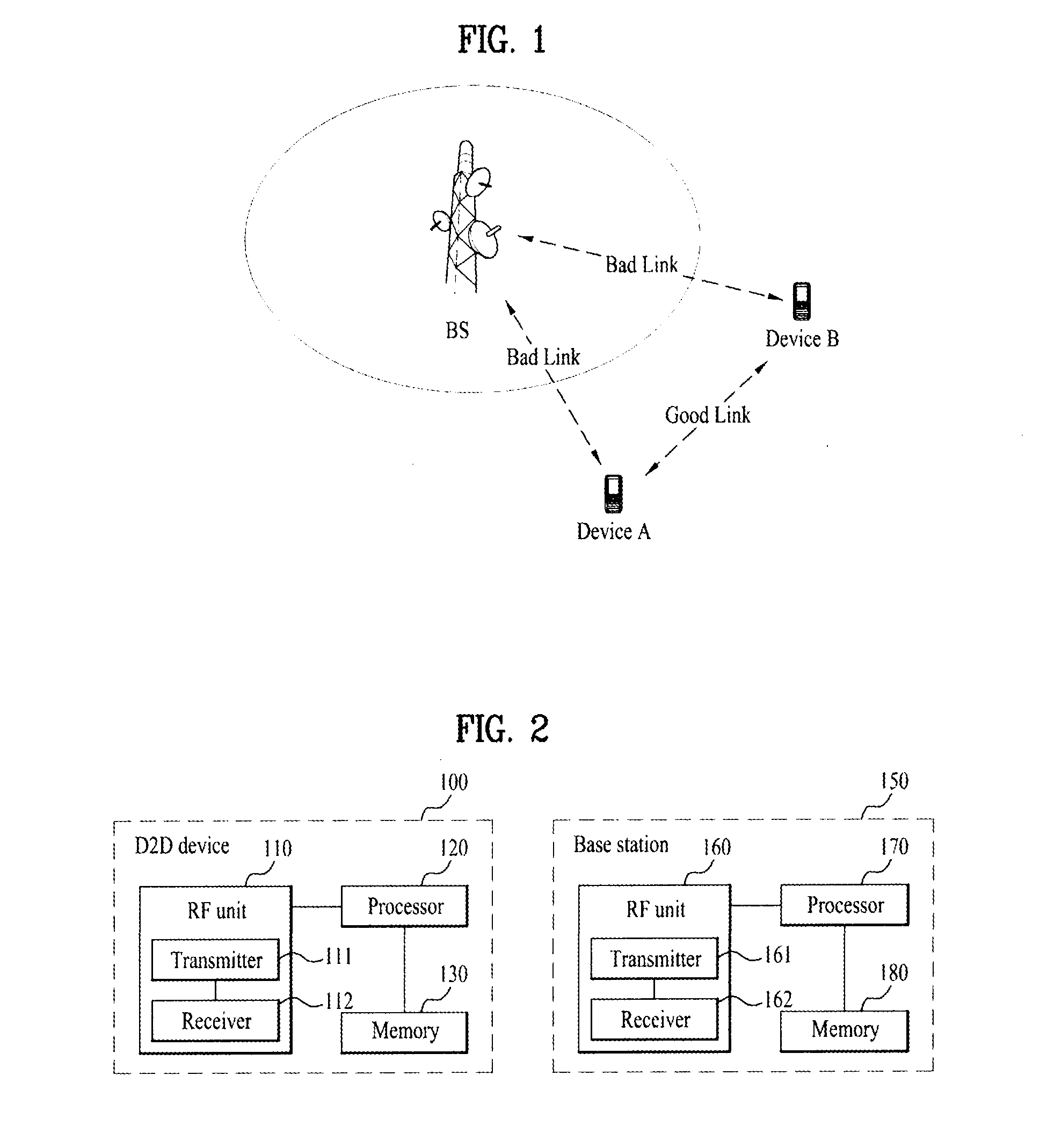
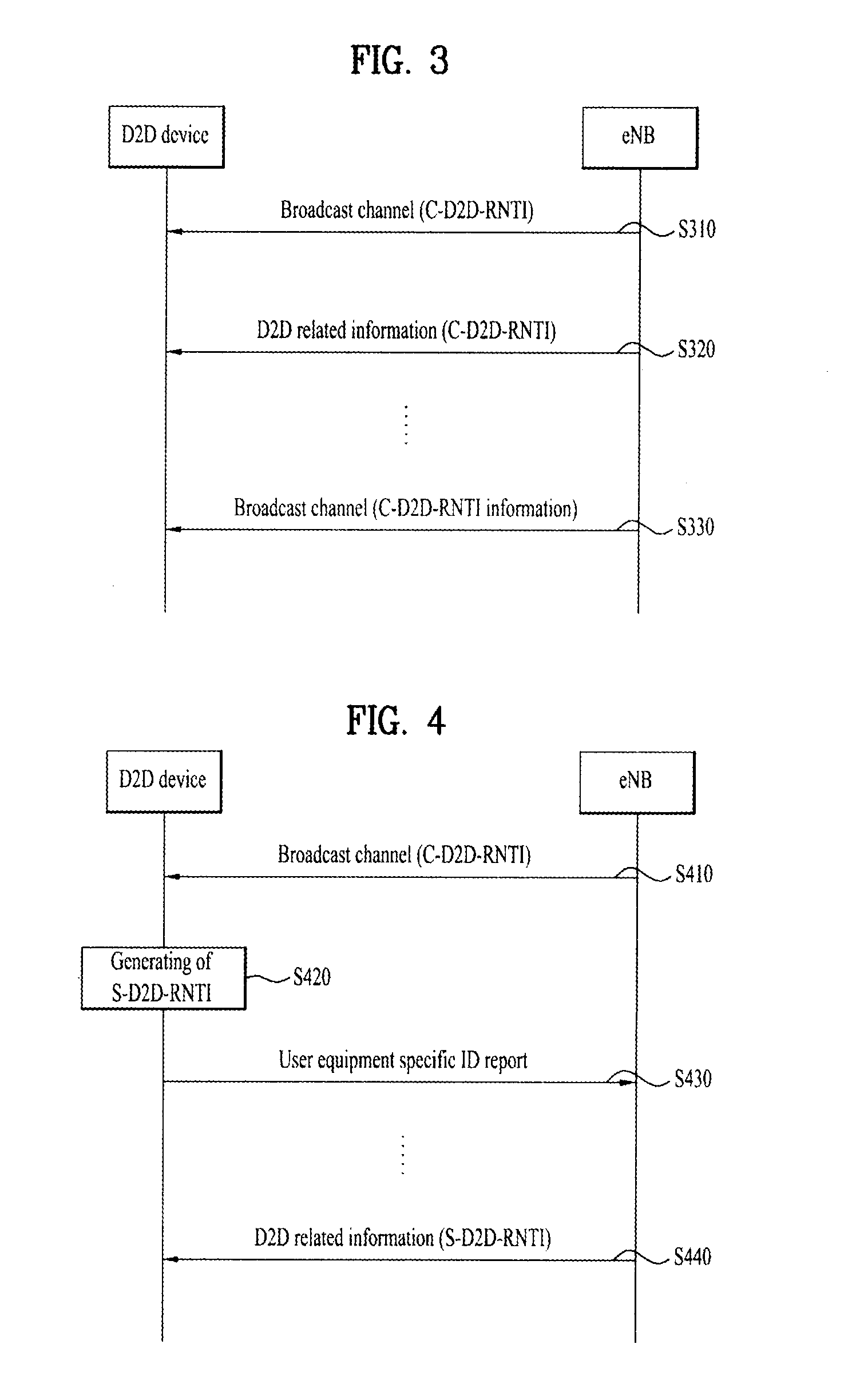
Definition of new identifier in wireless access system that supports device to device communication, and transmission method and device using same
ActiveUS20140355483A1Efficient communicationAvoid misunderstandingAssess restrictionConnection managementUniversal IdentifierDevice to device
The present invention provides definition of an identifier which is required for recognizing information essential for device to device communication, a transmission method thereof, and devices that support the same. The method for supporting device to device (D2D) communication in a wireless access system that supports D2D communication as one embodiment of the present invention comprises the steps of allowing a first D2D device to receive, from a base station, a broadcast message which contains a common D2D identifier (C-D2D-RNTI) for all D2D devices that perform D2D communication; and allowing the first D2D device to receive the transmitted D2D-related information by using the C-D2D-RNTI. In this situation, the wireless access system can support both D2D communication and cellular communication for a normal terminal instead of the D2D device.
Owner:LG ELECTRONICS INC
System and method for modifying a host user interface
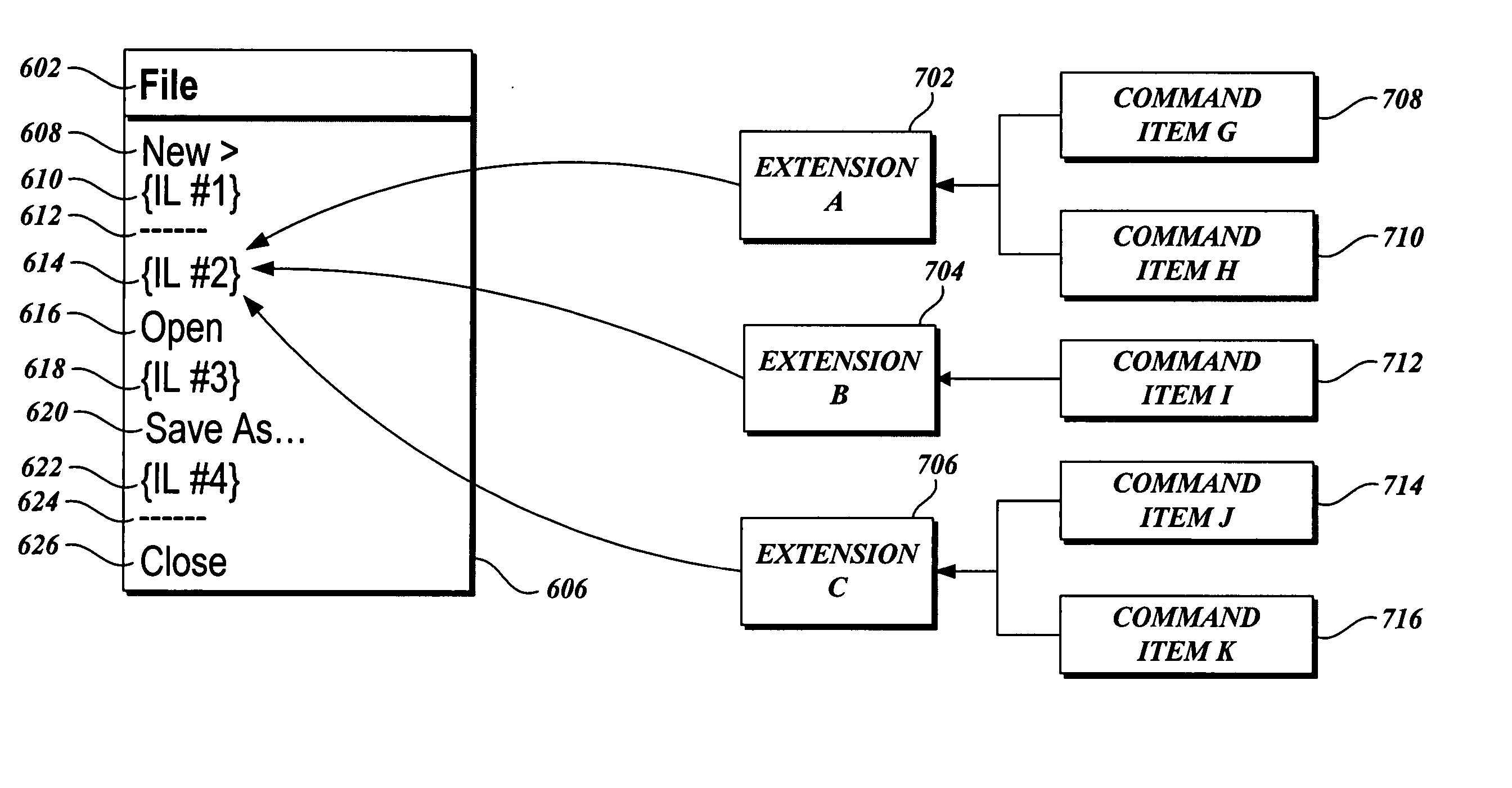
InactiveUS20050091641A1Safely modifySimple interfaceExecution for user interfacesSpecial data processing applicationsComputer scienceUniversal Identifier
A method, system, and computer-accessible medium are provided for safely modifying a host user interface with one or more extension user interfaces. The system comprises command item and insert location data structures, and host and extension programming interfaces. The programming interfaces facilitate negotiating modifications to a host user interface (UI) with extension commands specified by the extension in the command item data structure at locations specified by the host in the insert location data structure. The command item and insert locations are uniquely identified with unique universal identifiers (UUID) that enable the host to control the modification of the host UI by multiple extensions. The command item data structure contains the command's UI. The host modifies the host UI to insert the extension's commands in accordance with the command's UI.
Owner:MICROSOFT TECH LICENSING LLC
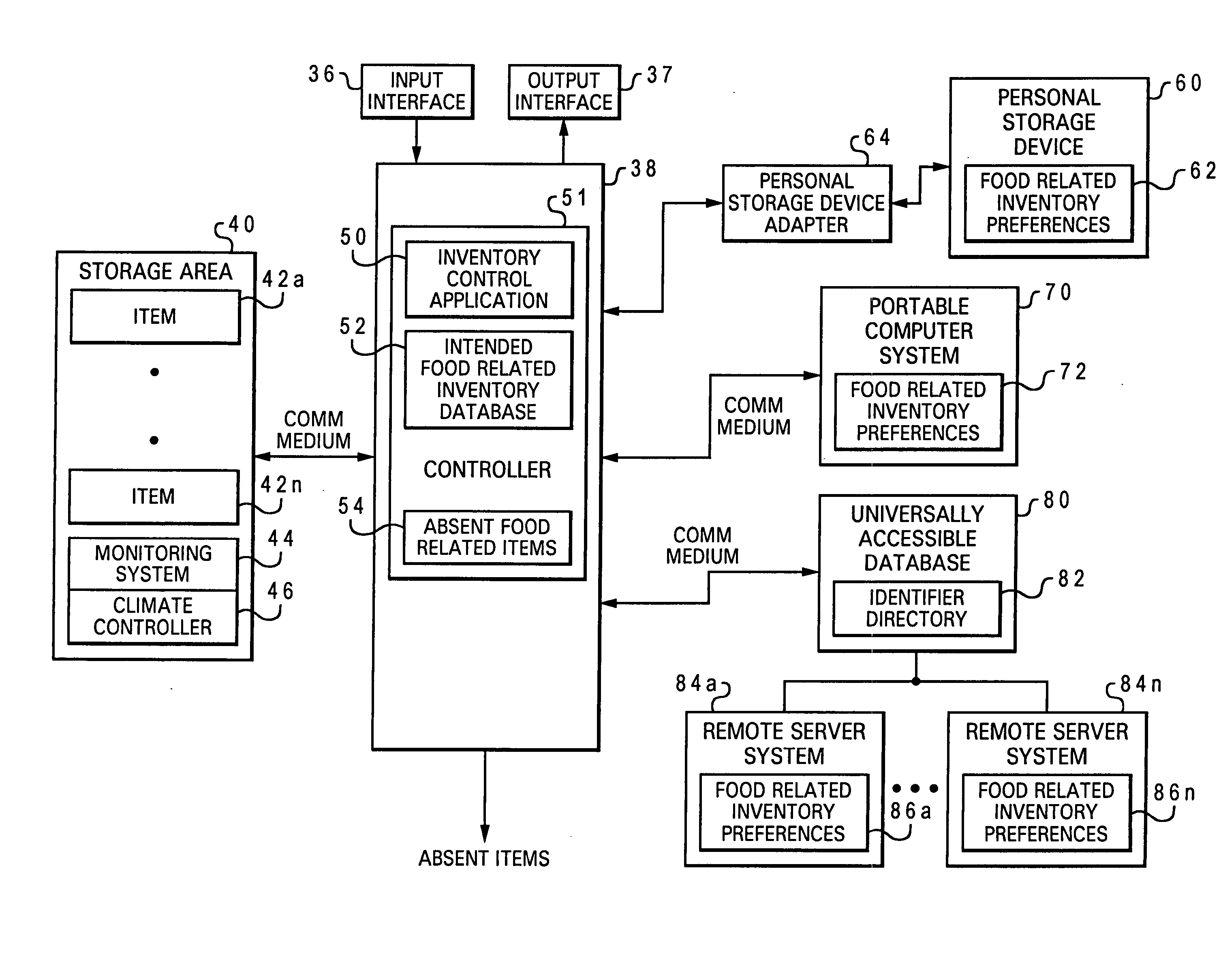
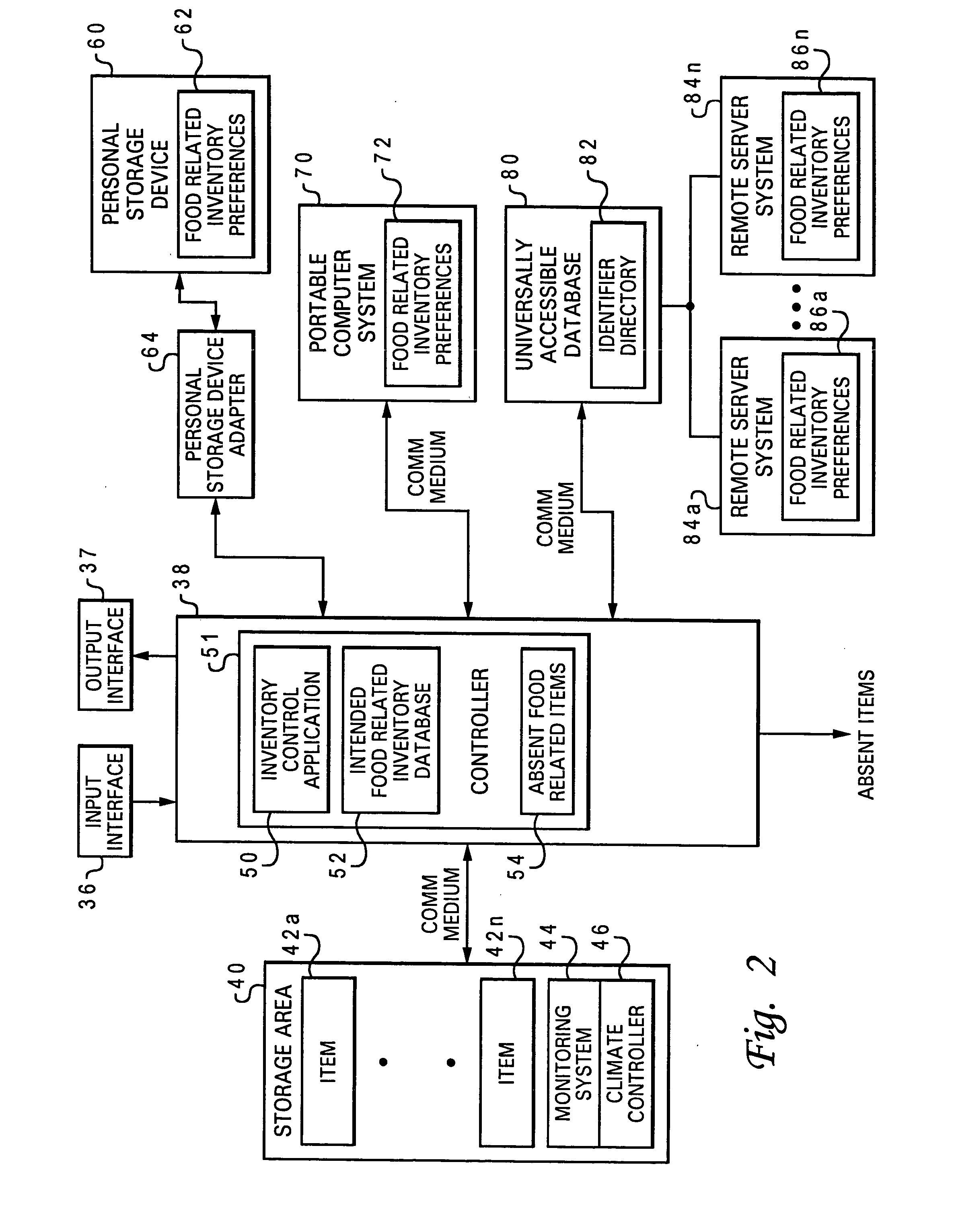
Managing store inventory
InactiveUS20040078272A1Hand manipulated computer devicesLogisticsComputerized systemUniversal Identifier
In accordance with the present invention, multiple selections of food-related items that are absent from multiple homes are accessed at a computer system associated with a store via a universally accessible database according to multiple universal identifiers that are each respectively associated with one of the homes. The selections of food-related items that are absent from multiple homes are compared with a database of current food-related inventory for the store. Future food-related orders for the store are adjusted according the multiple selections of food-related items, such that inventory for said particular store is managed in response to accessing inventory requirements for multiple homes.
Owner:BROWN MICHAEL WAYNE +2
Visual image authentication
ActiveUS20160034682A1Multiple keys/algorithms usageDigital data processing detailsAlice and BobKey exchange
Methods and systems described herein perform a secure transaction. A display presents images that are difficult for malware to recognize but a person can recognize. In at least one embodiment, a person communicates transaction information using visual images received from the service provider system. In at least one embodiment, a universal identifier is represented by images recognizable by a person, but difficult for malware to recognize.In some embodiments, methods and systems are provided for determining whether to grant access, by generating and displaying visual images on a screen that the user can recognize. In an embodiment, a person presses ones finger(s) on the screen to select images as a method for authenticating and protecting communication from malware.In at least one embodiment, quantum randomness helps unpredictably vary the image location, generate noise in the image, or change the shape or texture of the image.In some embodiments, visual image authentication helps Alice and Bob detect if Eve has launched a man-in-the-middle attack on their key exchange.
Owner:FISKE SOFTWARE
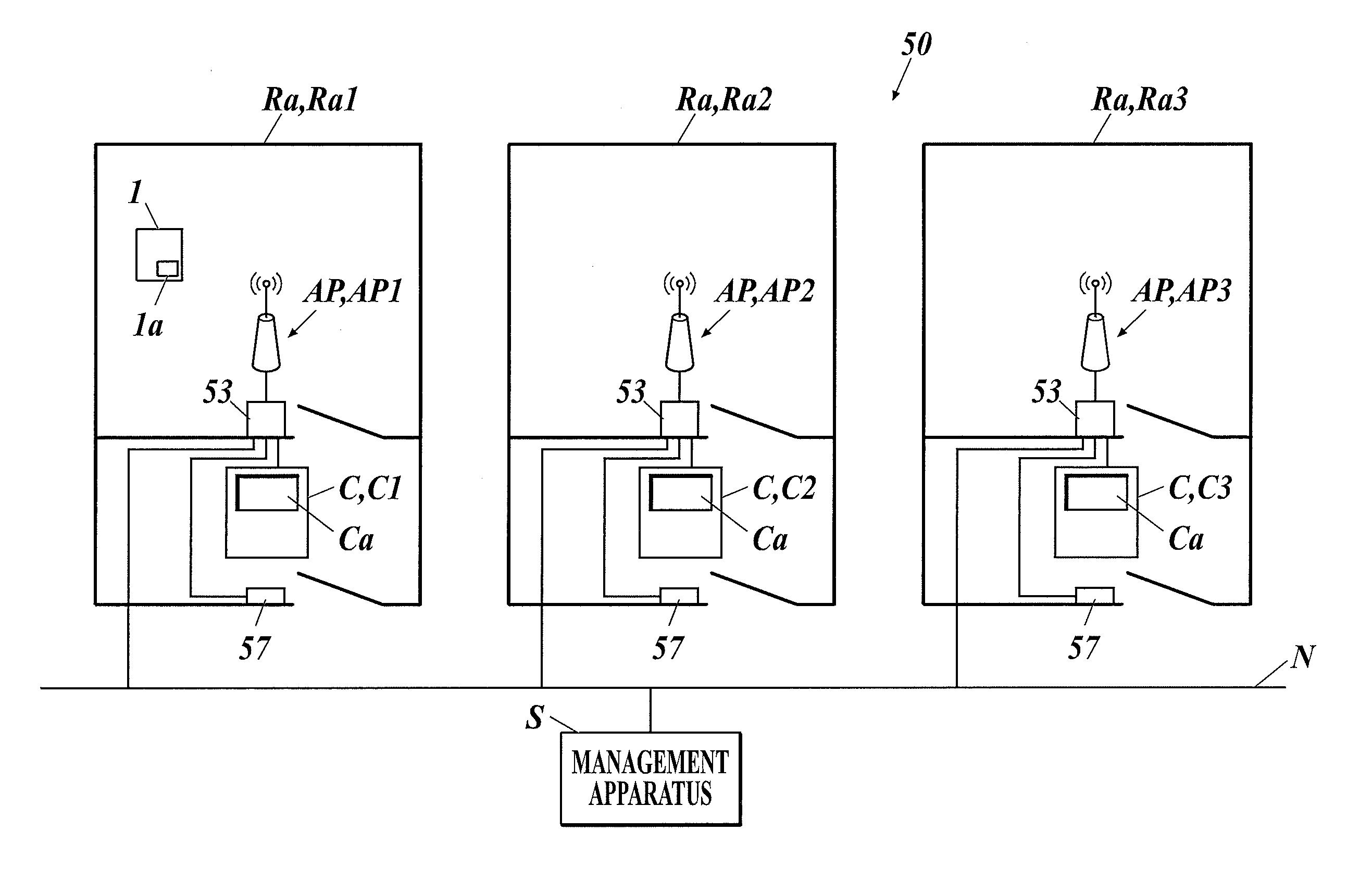
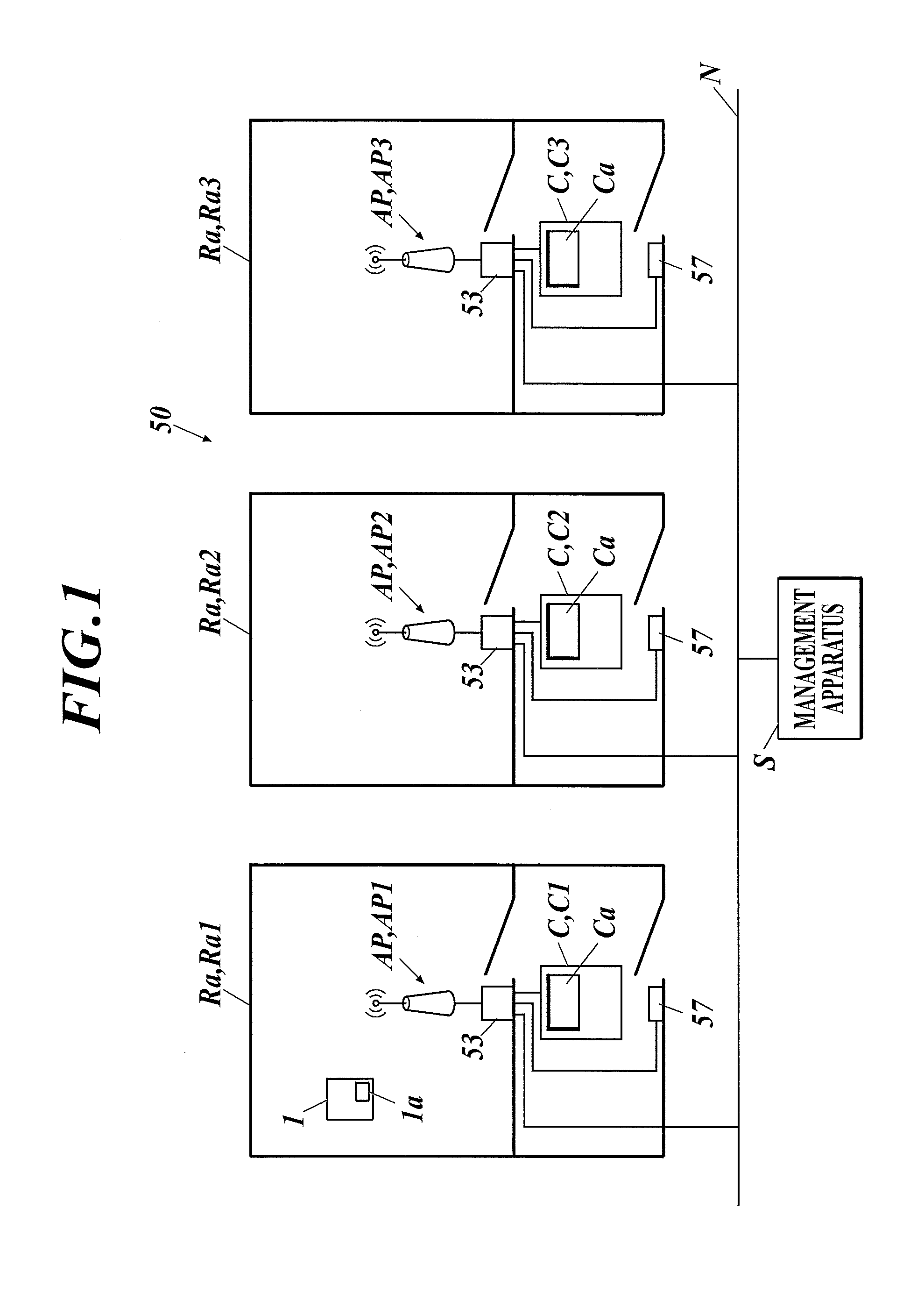
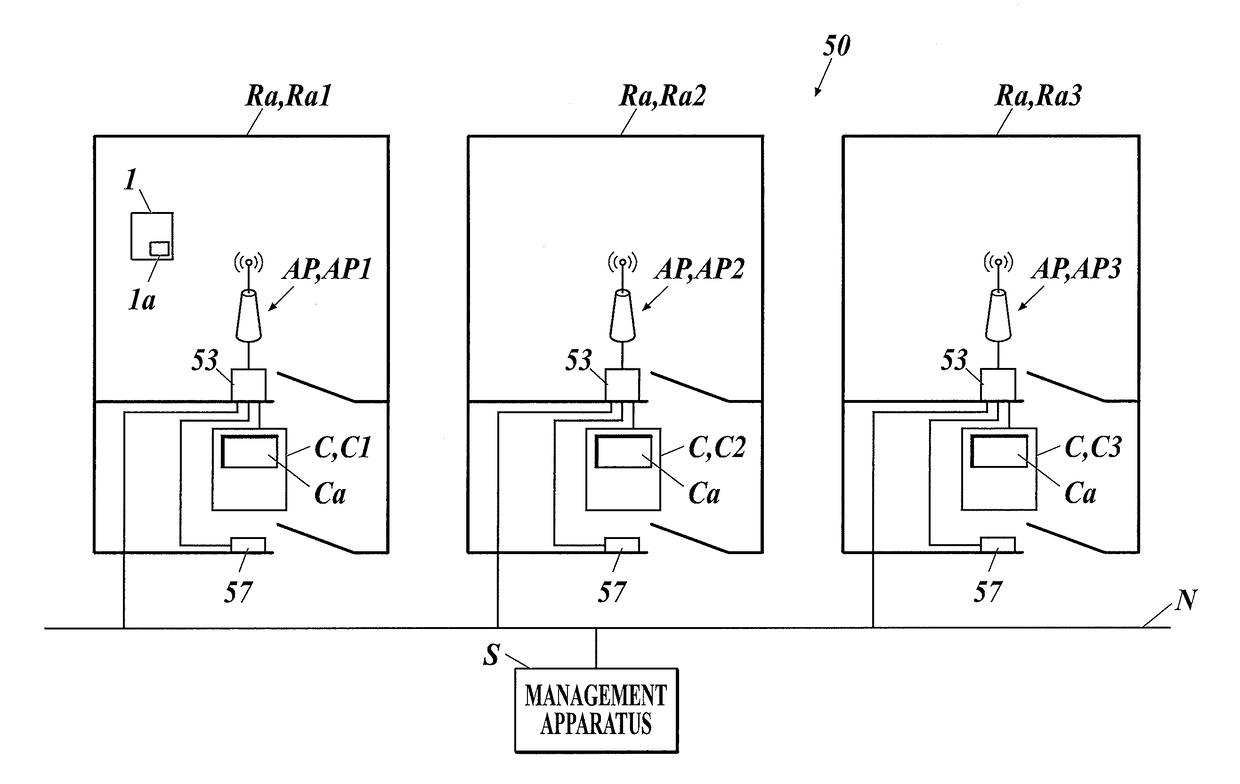
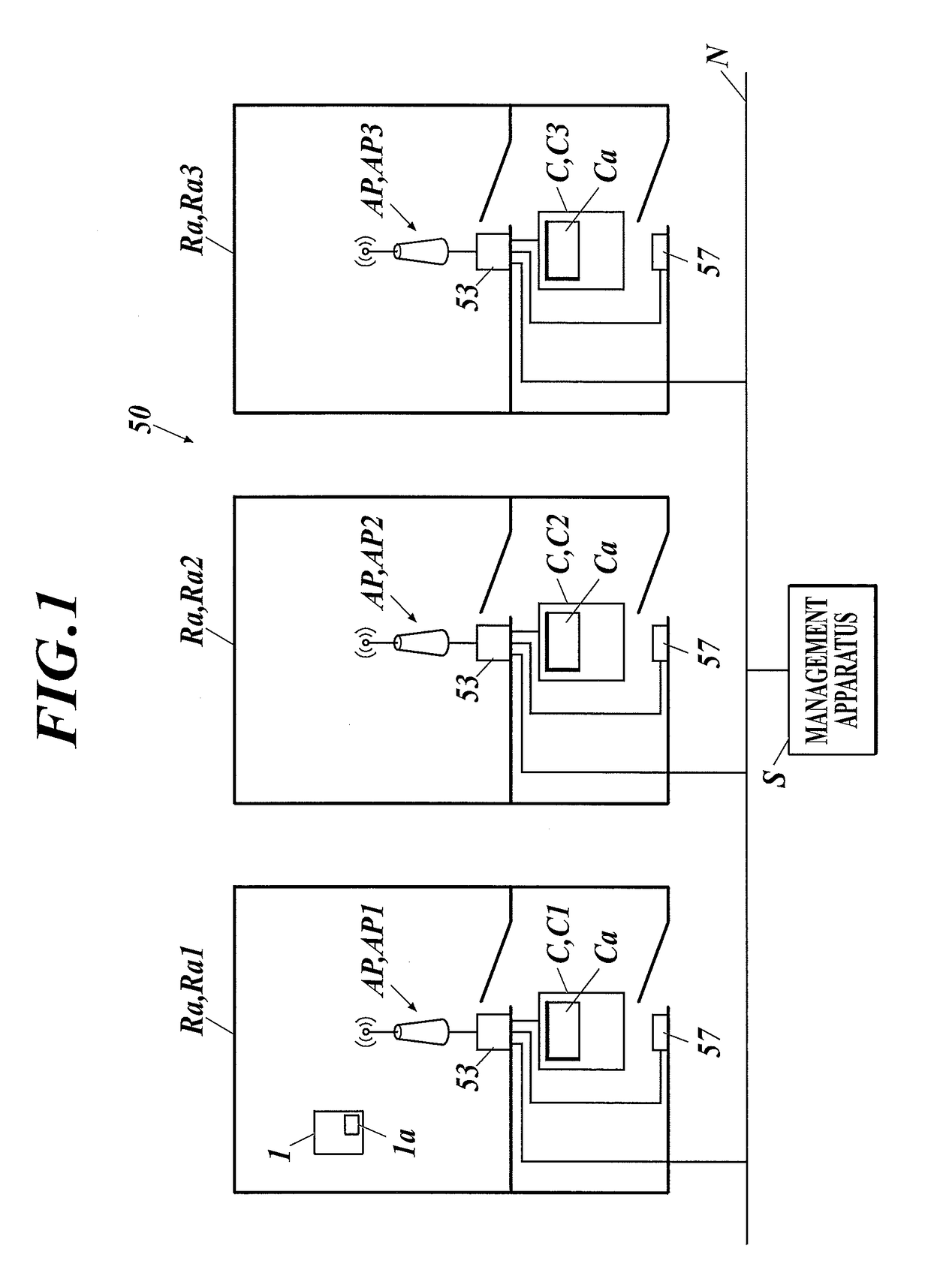
Radiographic image photographing system
The radiographic image photographing system includes an information acquisition member which acquires information on the radiographic image photographing device from an information presentation member of the radiographic image photographing device in a non-contact manner. When the information acquisition member makes the notification of the acquired information on the radiographic image photographing device, the management apparatus notifies the wireless communication member of the radiographic image photographing device of an identifier dedicated to an access point correlated with the information acquisition member. The wireless communication member of the radiographic image photographing device conducts wireless communication with the access point using a general-purpose identifier in a default state, and using the identifier dedicated to the access point after receiving the notification of the identifier dedicated to the access point from the management apparatus.
Owner:KONICA MINOLTA INC
Method to provide authentication using a universal identifier
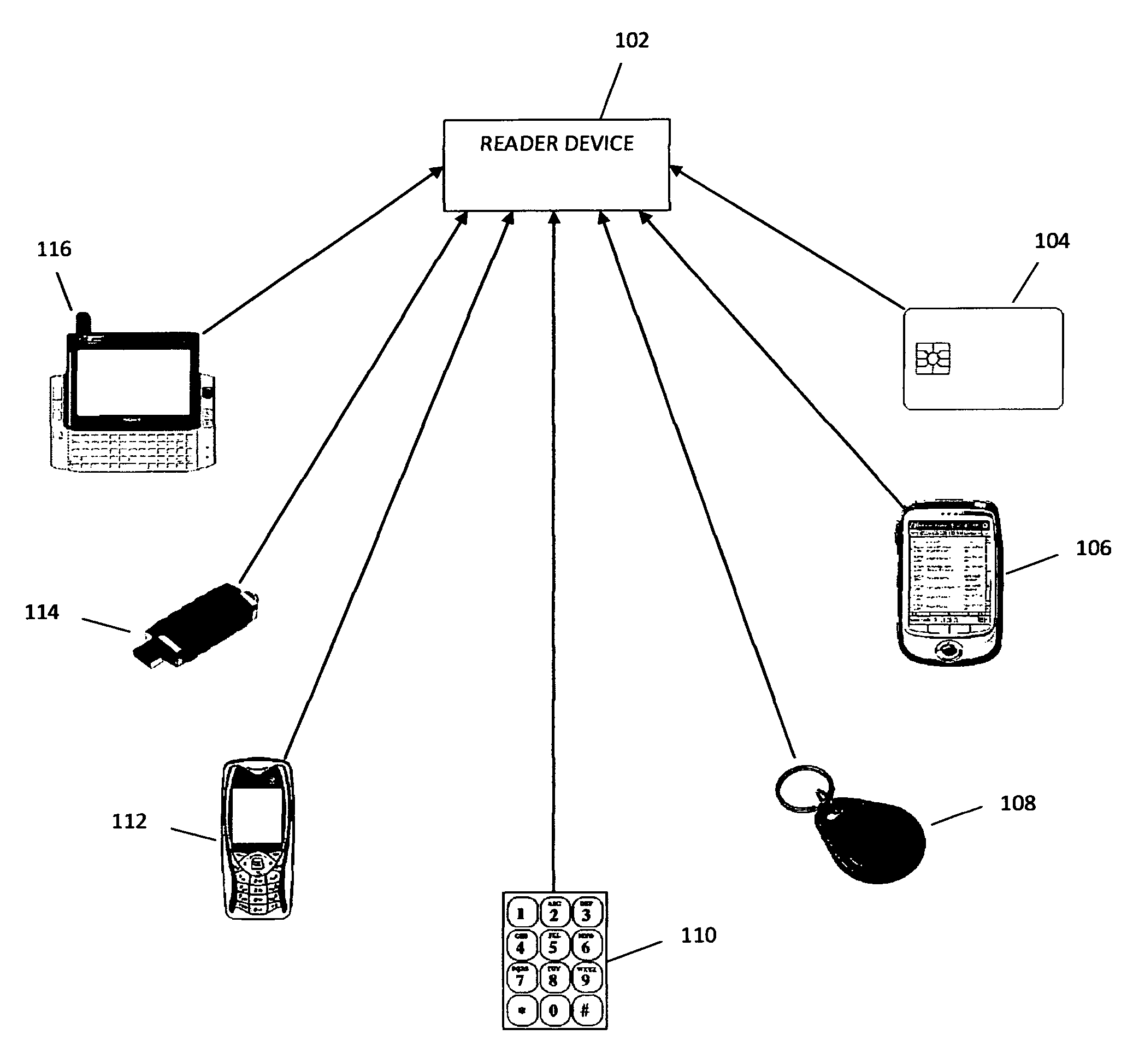
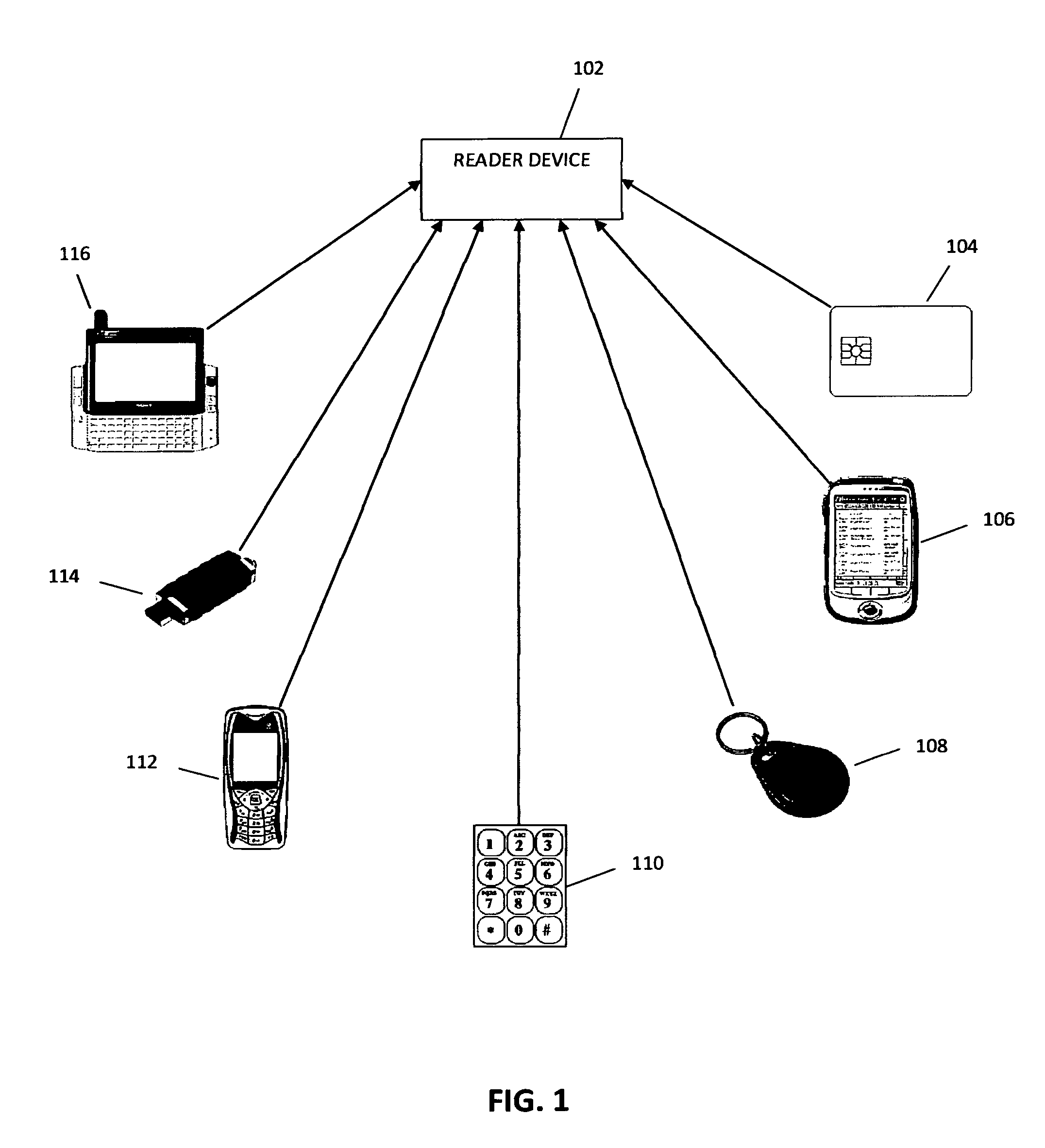
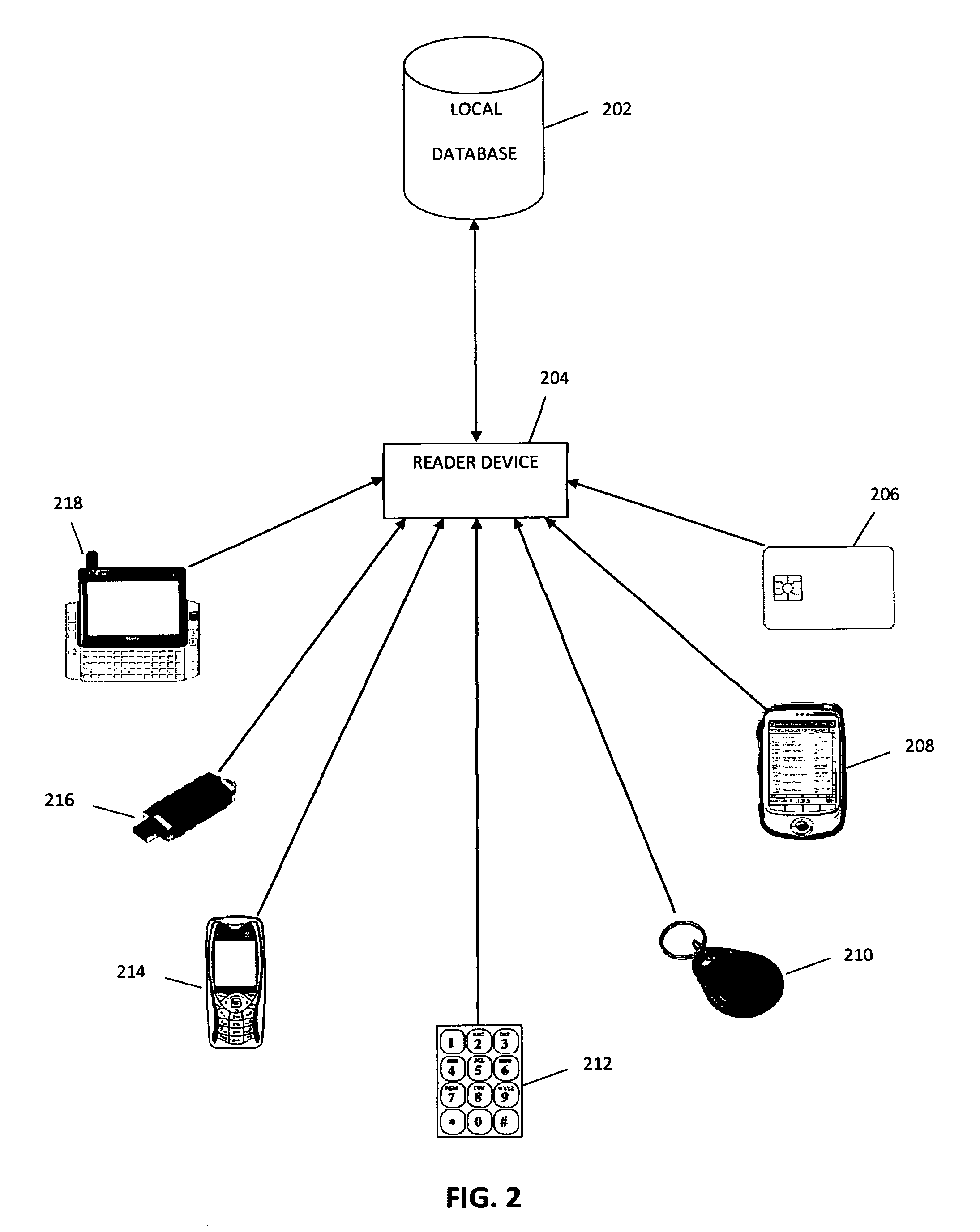
ActiveUS8677139B1Digital data processing detailsUser identity/authority verificationBiometric dataUser identifier
Once an individual is issued a Universal Identifier (UID) it uniquely identifies that person anywhere in the world. The UID could be embedded in any type of device, token or apparatus that is capable of transmitting it (only several bytes of data) to a reader device. Alternatively, for the purposes of authentication the UID could also be entered via a keypad or via any other means. The code scheme for a UID could be any type of symbol sequence that is capable of providing enough combination to cover the entire expected human population. Although it can also be used without biometric data the intended use of the UID is in conjunction with biometric authentication. The Universal Identifier is universal from two aspects: first it is a global or worldwide identifier for people around the world; second it is to be used most generally in any type of transactions, processes or scenarios where authentication is needed. UIDs are issued by an Identity Clearinghouse (IC) or Universal Authentication Authority (UAA) or a Centralized Identity Management Service (CIMS) after verifying the uniqueness of submitted biometric and personal data.
Owner:KALOCSAI PETER
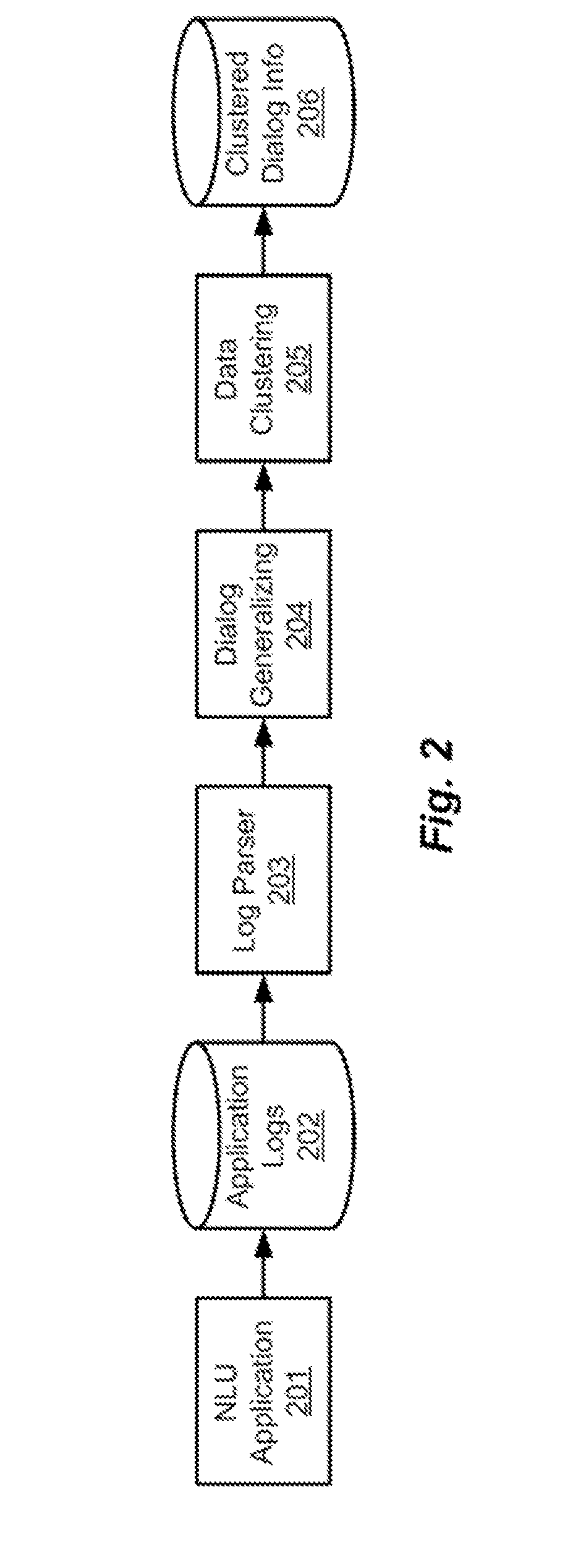
Unsupervised Clustering of Dialogs Extracted from Released Application Logs
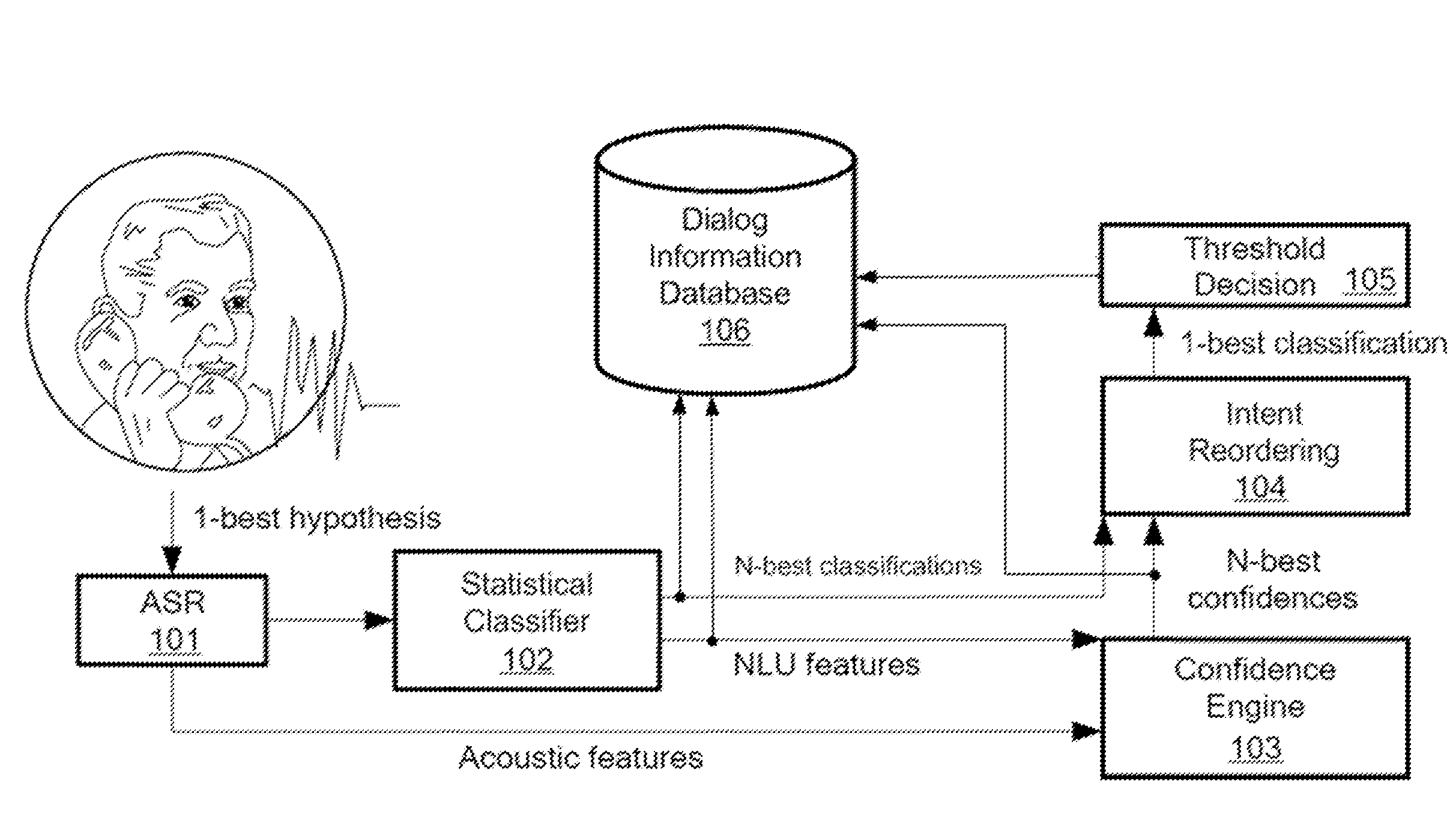
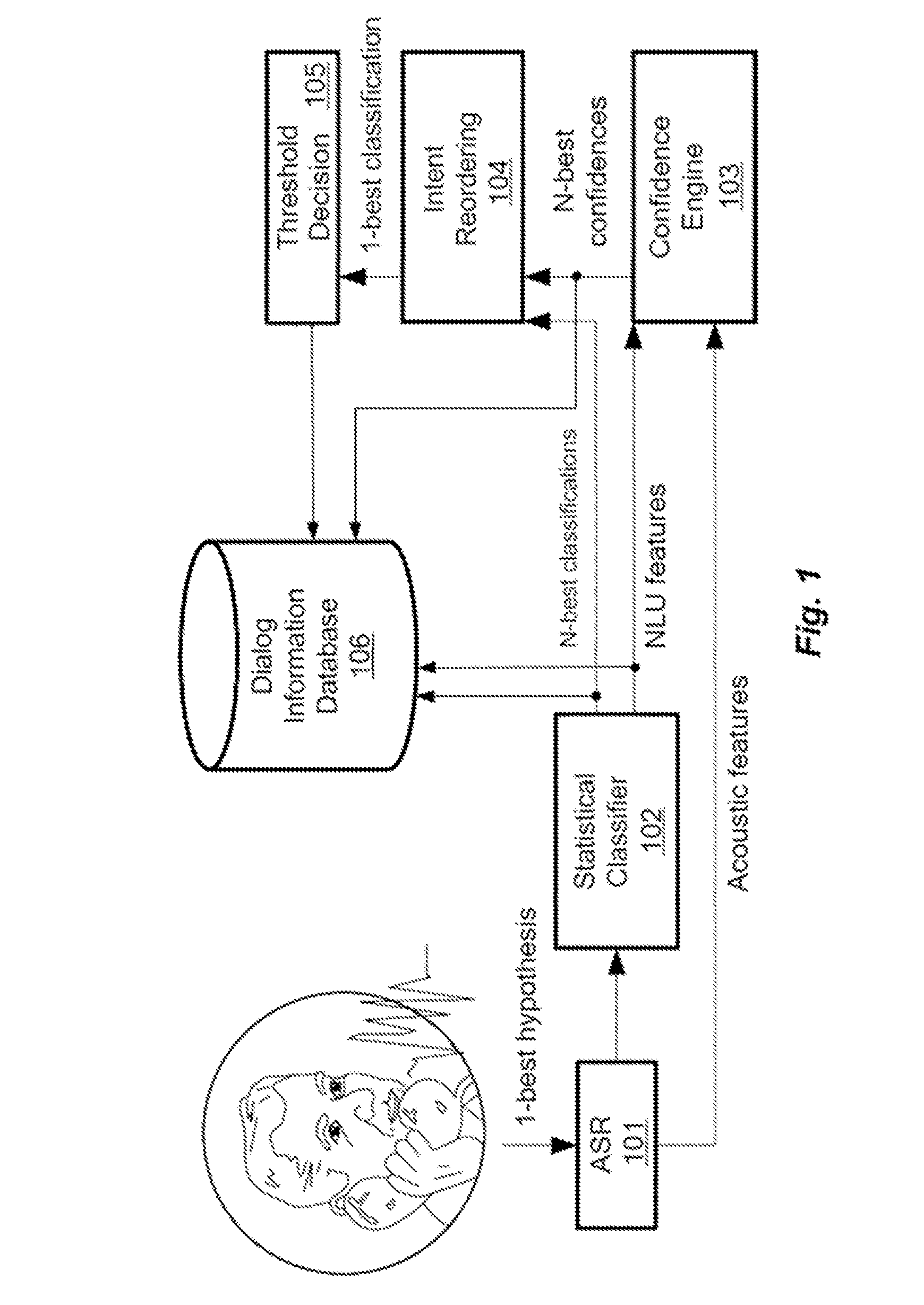
ActiveUS20150051910A1Natural language data processingSpeech recognitionNatural language understandingUnsupervised clustering
A natural language understanding system performs automatic unsupervised clustering of dialog data from a natural language dialog application. A log parser automatically extracts structured dialog data from application logs. A dialog generalizing module generalizes the extracted dialog data to generalization identifier vectors. A data clustering module automatically clusters the dialog data based on the generalization identifier vectors using an unsupervised density-based clustering algorithm without a predefined number of clusters and without a predefined distance threshold in an iterative approach based on a hierarchical ordering of the generalization.
Owner:NUANCE COMM INC
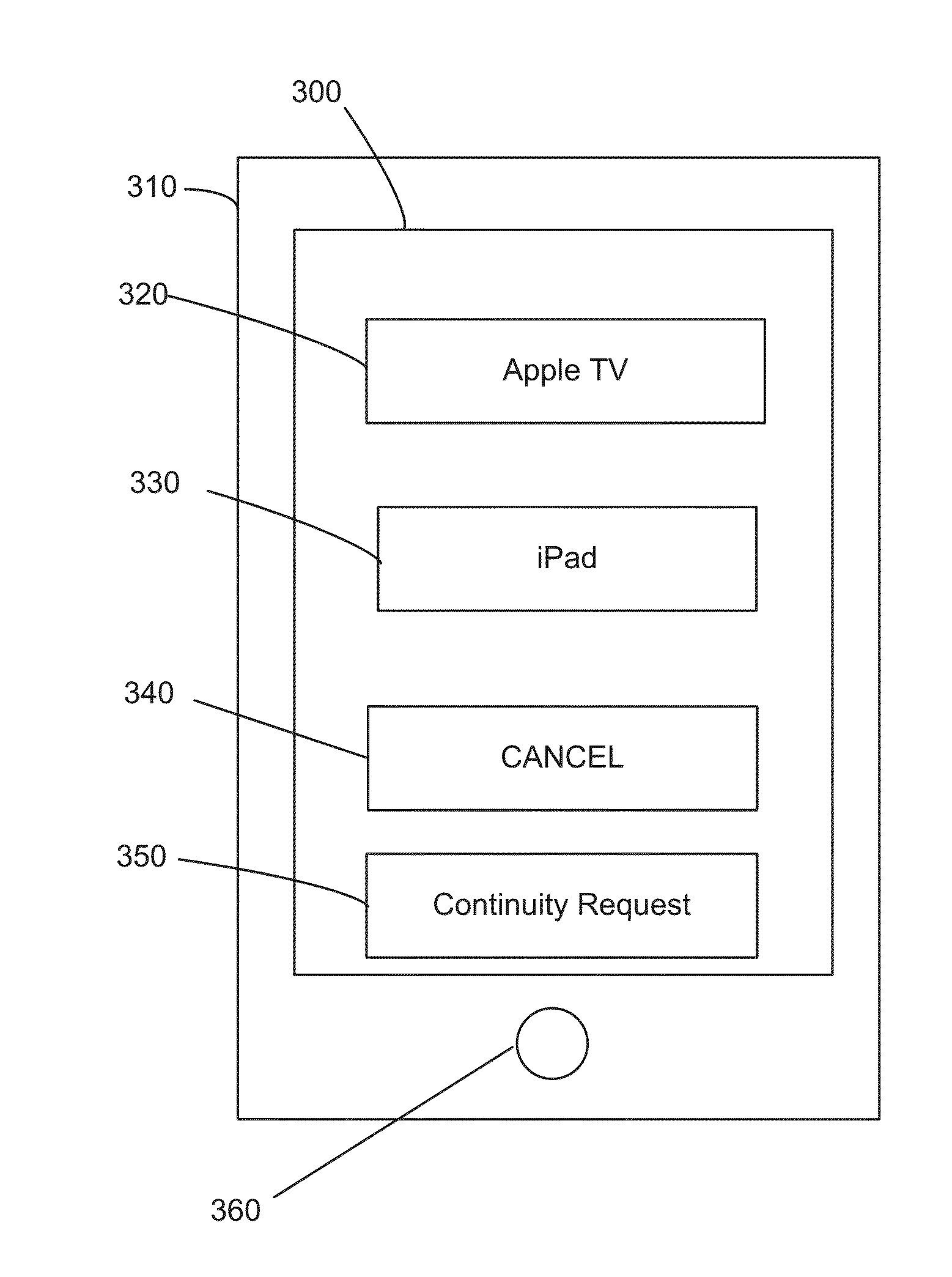
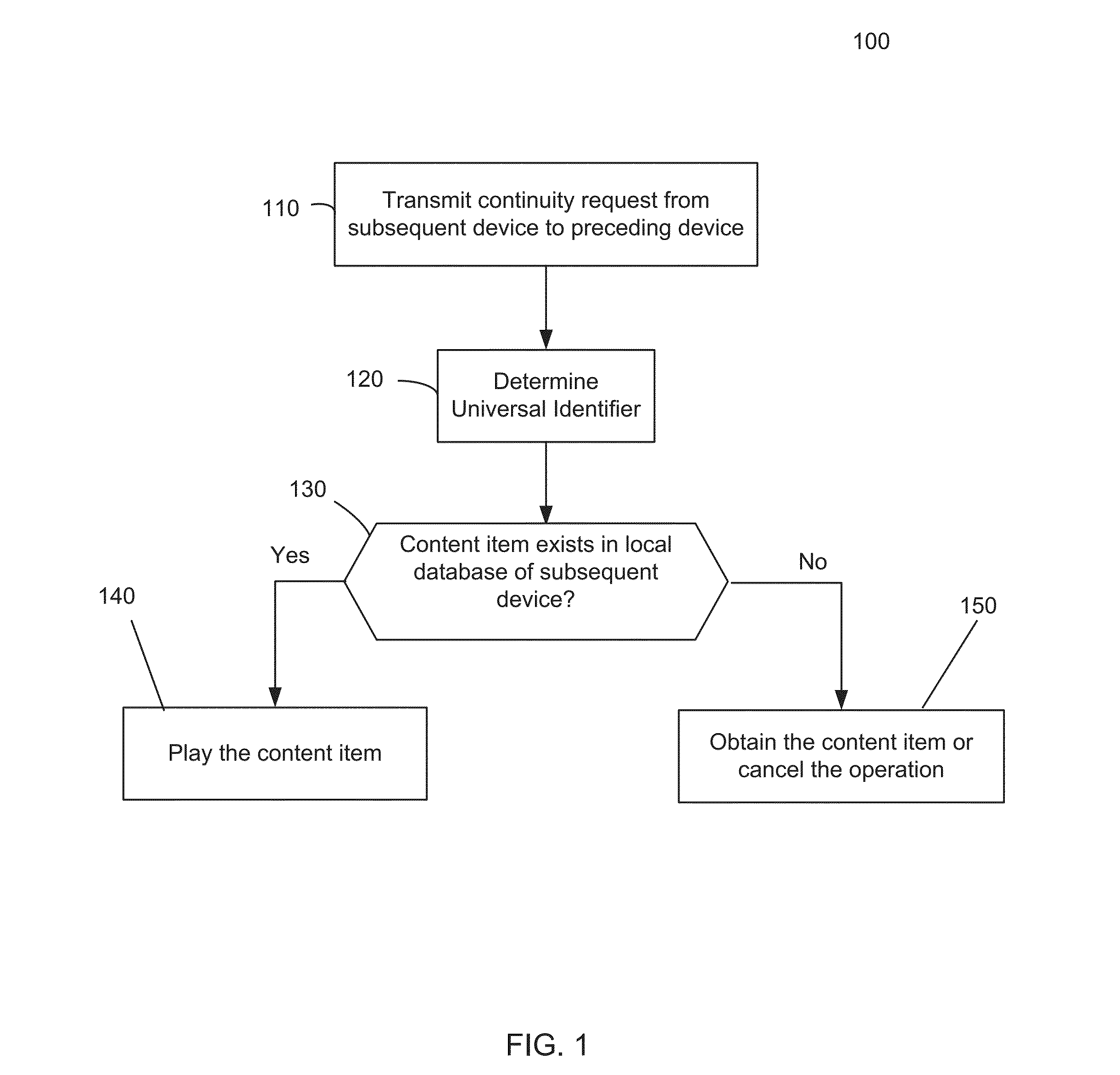
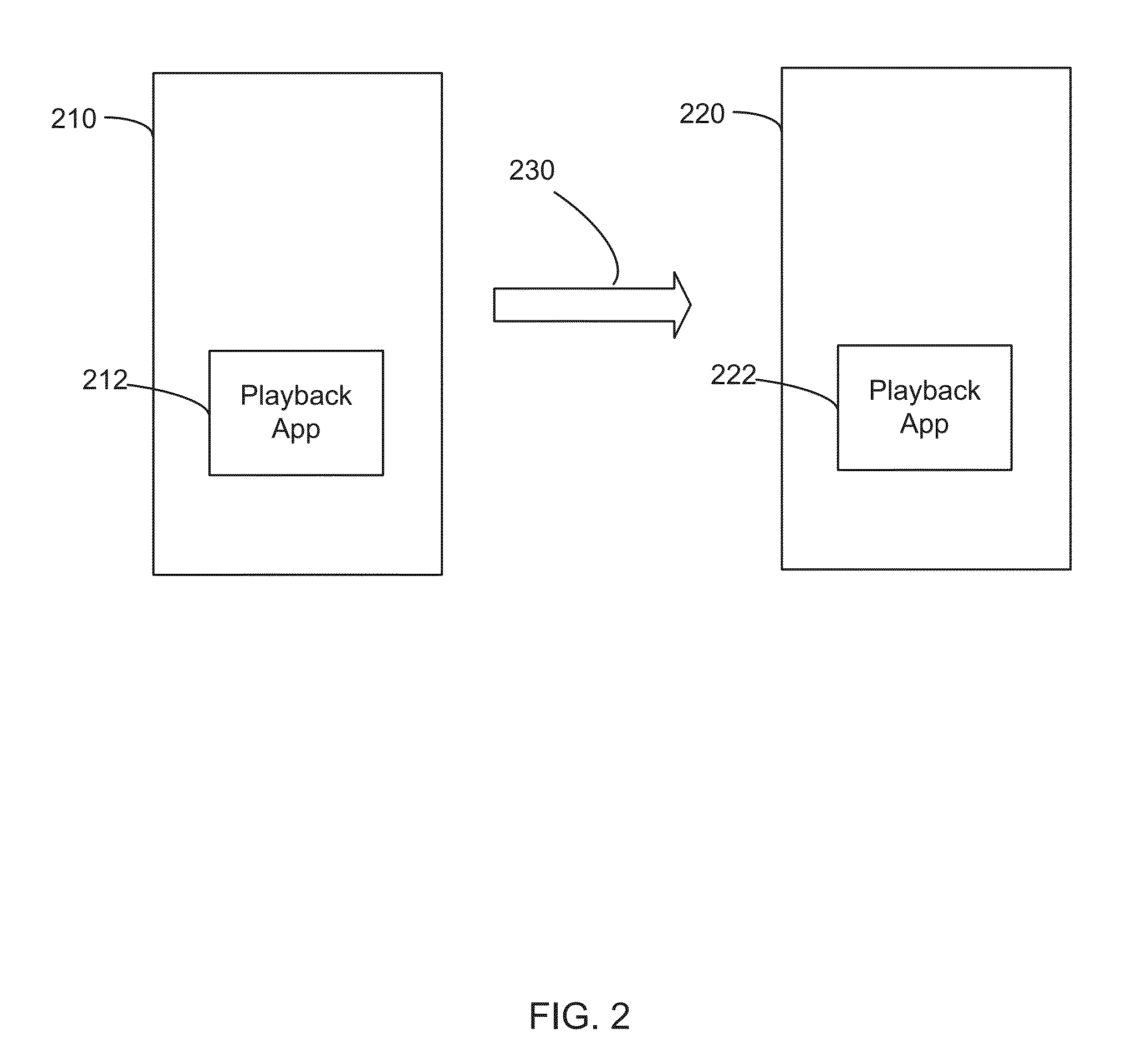
Universal identifier
ActiveUS20150347511A1Multimedia data queryingDigital data processing detailsUniversal IdentifierComputer science
A user listening to a content item on a preceding device and wishes to continue with the listening experience on a subsequent device initiates a continuity request from the subsequent device to the preceding device. The preceding device responds to the received continuity request by determining a multiverse identification that is contained in the continuity request, such that the multiverse identification uniquely identifies the content item that is currently playing on the preceding device over all known playback devices with which it has communicated. The subsequent device determines if the content item exists in a local database of the subsequent device and, if it exists, the subsequent device plays the content item from the local database of the subsequent device, and otherwise obtains the content item.
Owner:APPLE INC
Universal identifier methods in supply chain logistics
The present invention is generally directed to methods to provide a user with visibility to certain packages that are transported by one or more carriers and that have a universal identifier included in each package's package level detail information. The universal identifier may be used to access the package level detail information in each package by the parties to a shipping transaction and by third-parties that are not the shipper, recipient or intended recipient of the packages.
Owner:UNITED PARCEL SERVICE OF AMERICAN INC
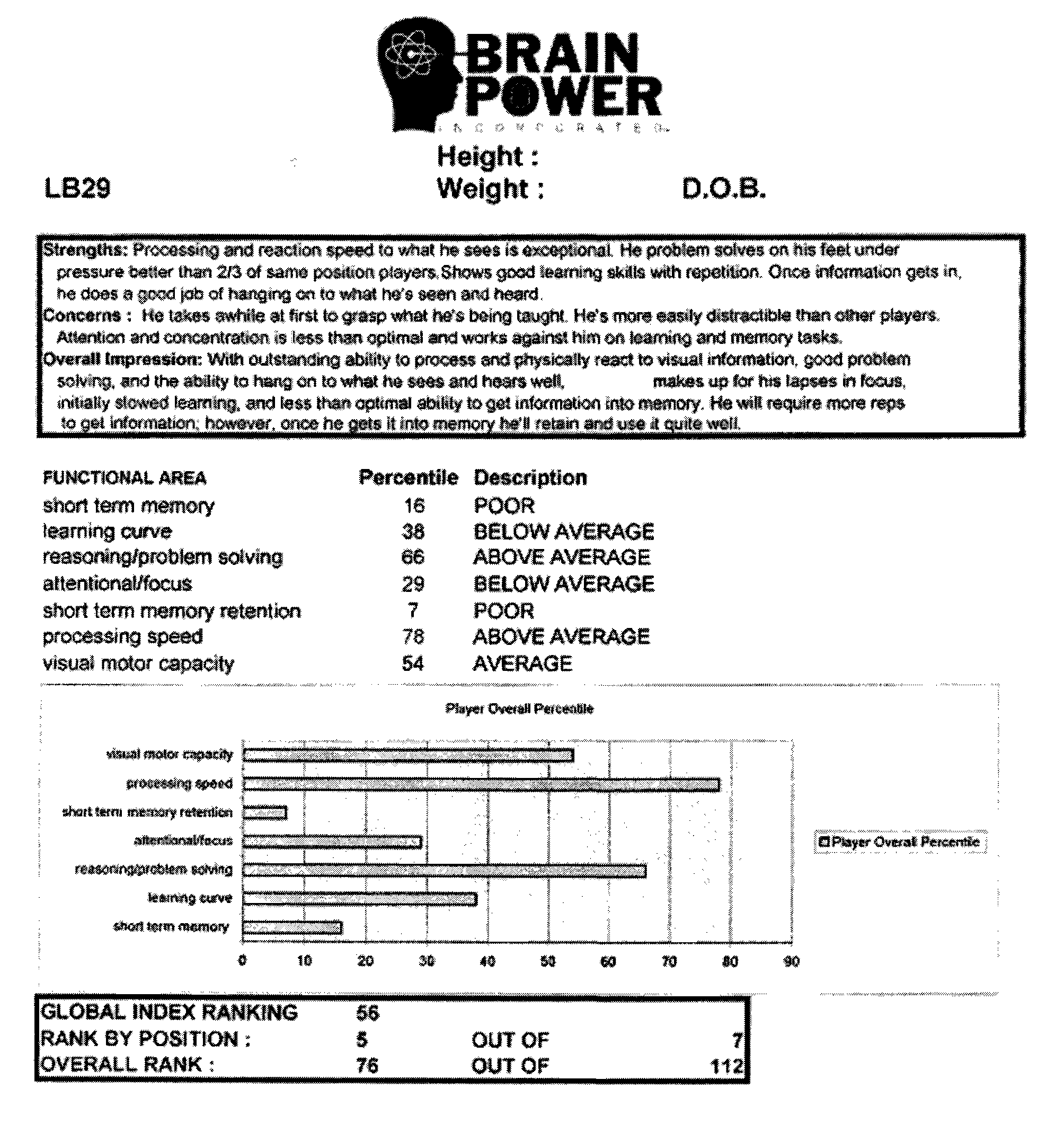
Method and System for Evaluating Athletes
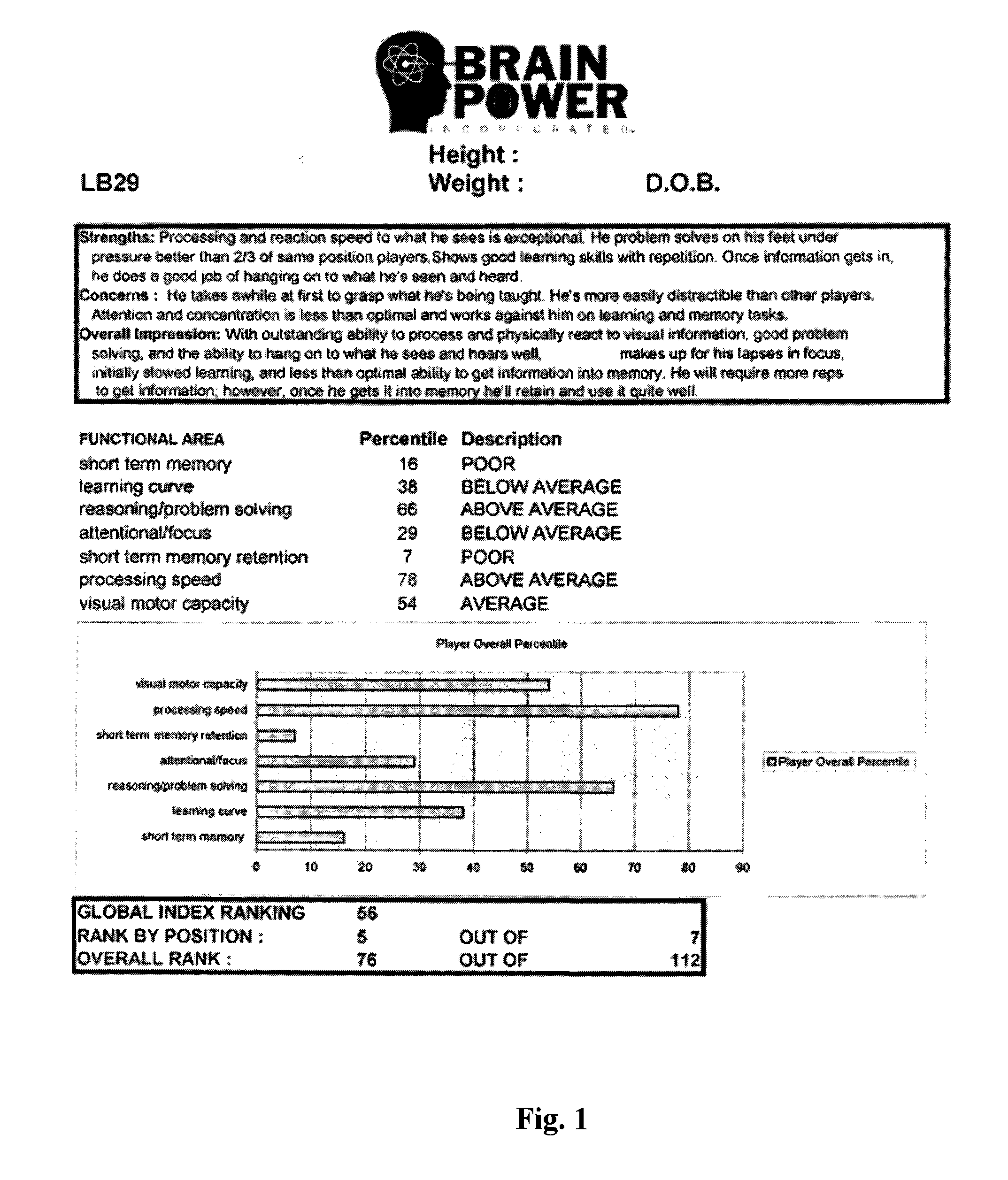
A method and system of evaluating athletes includes the steps of subjecting an athlete to a first battery of objective tests directed to the athlete's functioning brain capacity; determining a set of test scores for the athlete; providing a data base comprising of competitive test scores from another athlete sharing at least one common identifier with the athlete being evaluated; comparing the test scores of both athletes; and ranking the test scores the athlete being evaluated relative to the competitive test scores of the other athlete. In one embodiment, the objective tests are directed to measuring the athlete's short term memory, learning, reasoning / problem solving, attentional focus, short term memory retention, processing speed, and visual motor capacity.
Owner:JOHNSON DANIEL A
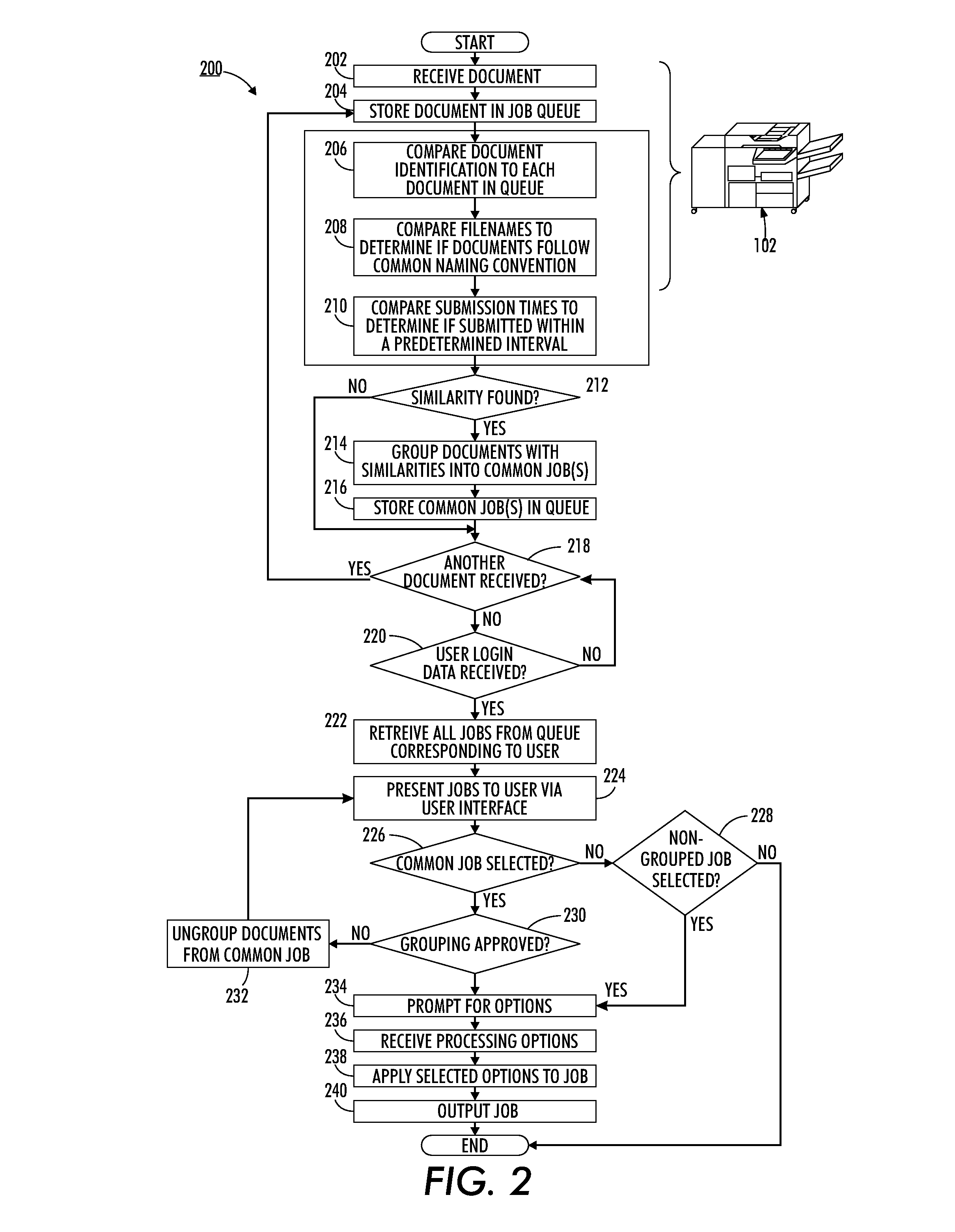
Automatic aggregation of multiple documents into a common processing job
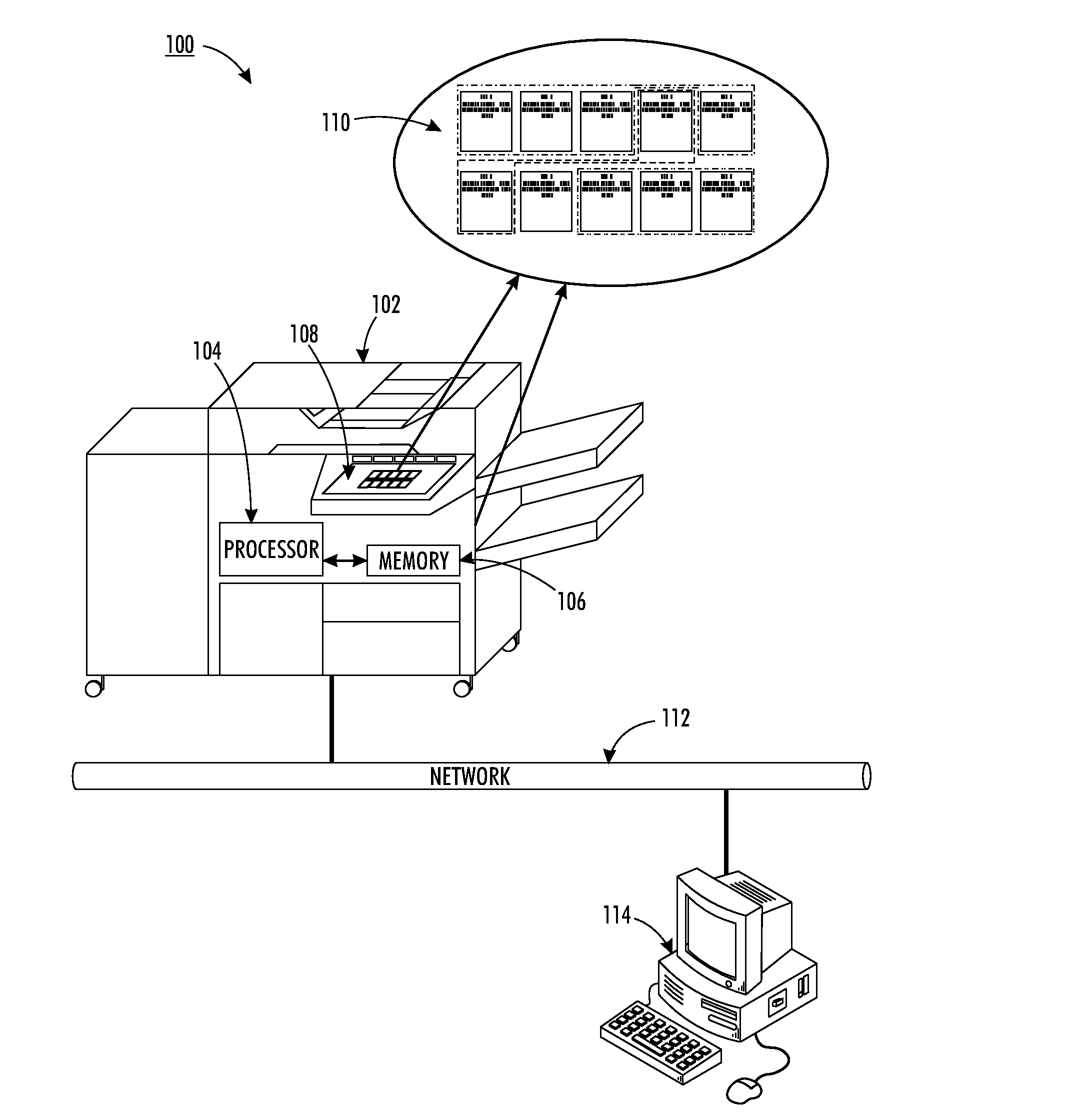
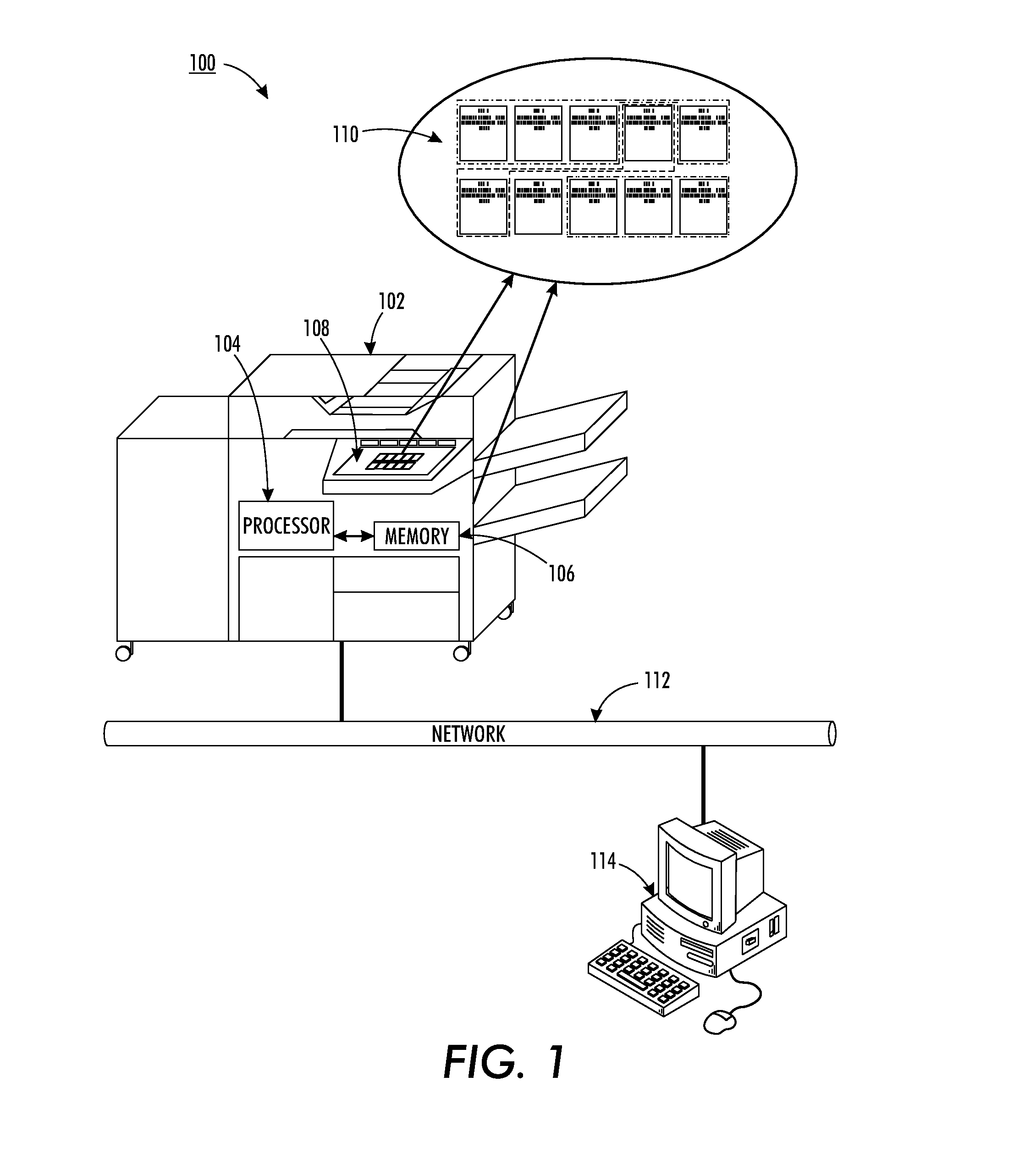
InactiveUS20130077112A1Visual presentation using printersDigital output to print unitsDocumentation procedureDocument preparation
As set forth herein, methods and systems for automatic grouping of individual print jobs into a common job at a multifunction device. Received jobs stored in a job processing queue are analyzed to determine the filenames, submission times, and other related identification data. Those jobs sharing a common naming convention, submission time interval, or other common identifiers, are automatically grouped into a single, common job. Upon login, the user is able to approve or disapprove the grouping. For an approved grouping, the user is able to select finishing options via the user interface of the multifunction device to be applied to the common job. The common job, in which the finishing options have been propagated through each formerly individual job, is then output as if it were a single job by the multifunction device.
Owner:XEROX CORP
Radiographic image photographing system
The radiographic image photographing system includes an information acquisition member which acquires information on the radiographic image photographing device from an information presentation member of the radiographic image photographing device in a non-contact manner. When the information acquisition member makes the notification of the acquired information on the radiographic image photographing device, the management apparatus notifies the wireless communication member of the radiographic image photographing device of an identifier dedicated to an access point correlated with the information acquisition member. The wireless communication member of the radiographic image photographing device conducts wireless communication with the access point using a general-purpose identifier in a default state, and using the identifier dedicated to the access point after receiving the notification of the identifier dedicated to the access point from the management apparatus.
Owner:KONICA MINOLTA INC
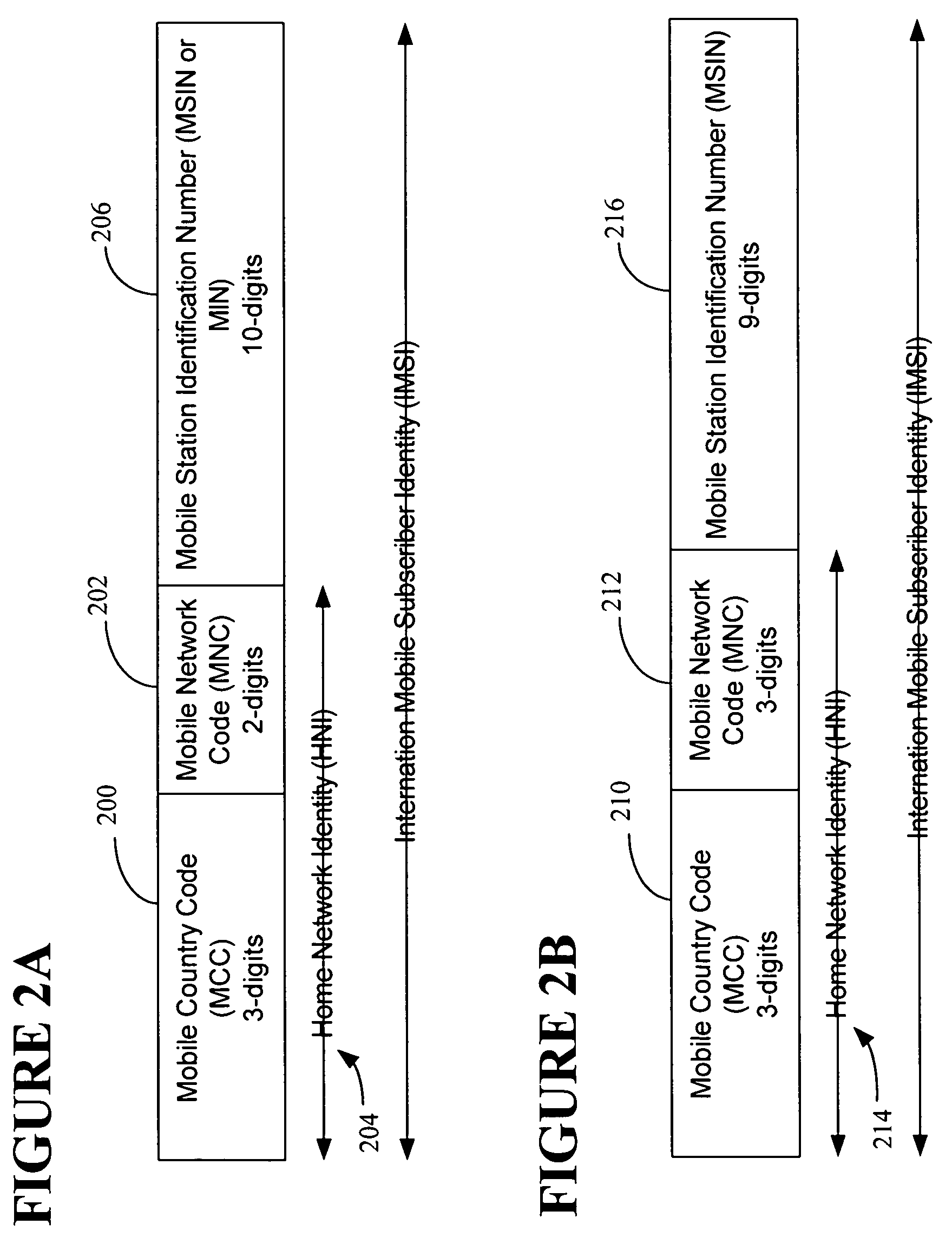
Method for migrating a mobile station identity from a mobile identification number to an international mobile station identity
InactiveUS20070082670A1Radio/inductive link selection arrangementsWireless commuication servicesMobile identification numberMobile network code
In one aspect of the instant invention, a method is provided for controlling international roaming in a communications system. The method comprises storing a 15-digit universal identifier in a mobile device in two locations ordinarily used to store a 15-digit MIN-based-IMSI and a 15-digit true IMSI. The universal identifier is comprised of a 10-digit Mobile Identification Number (MIN) and a 5-digit Home Network Identifier (HNI), which is comprised of a 3-digit Mobile Country Code (MCC) and a 2-digit Mobile Network Code (MNC). Generally, the communications system uses the universal identifier to control international roaming. However, the mobile device transmits only the 10-digit MIN in response to the mobile device being within a home network. To form the 15-digit universal identifier, the home network appends its HNI to the received MIN. When the mobile device is outside of its home network, the mobile device transmits the entire 15-digit universal identifier.
Owner:LUCENT TECH INC
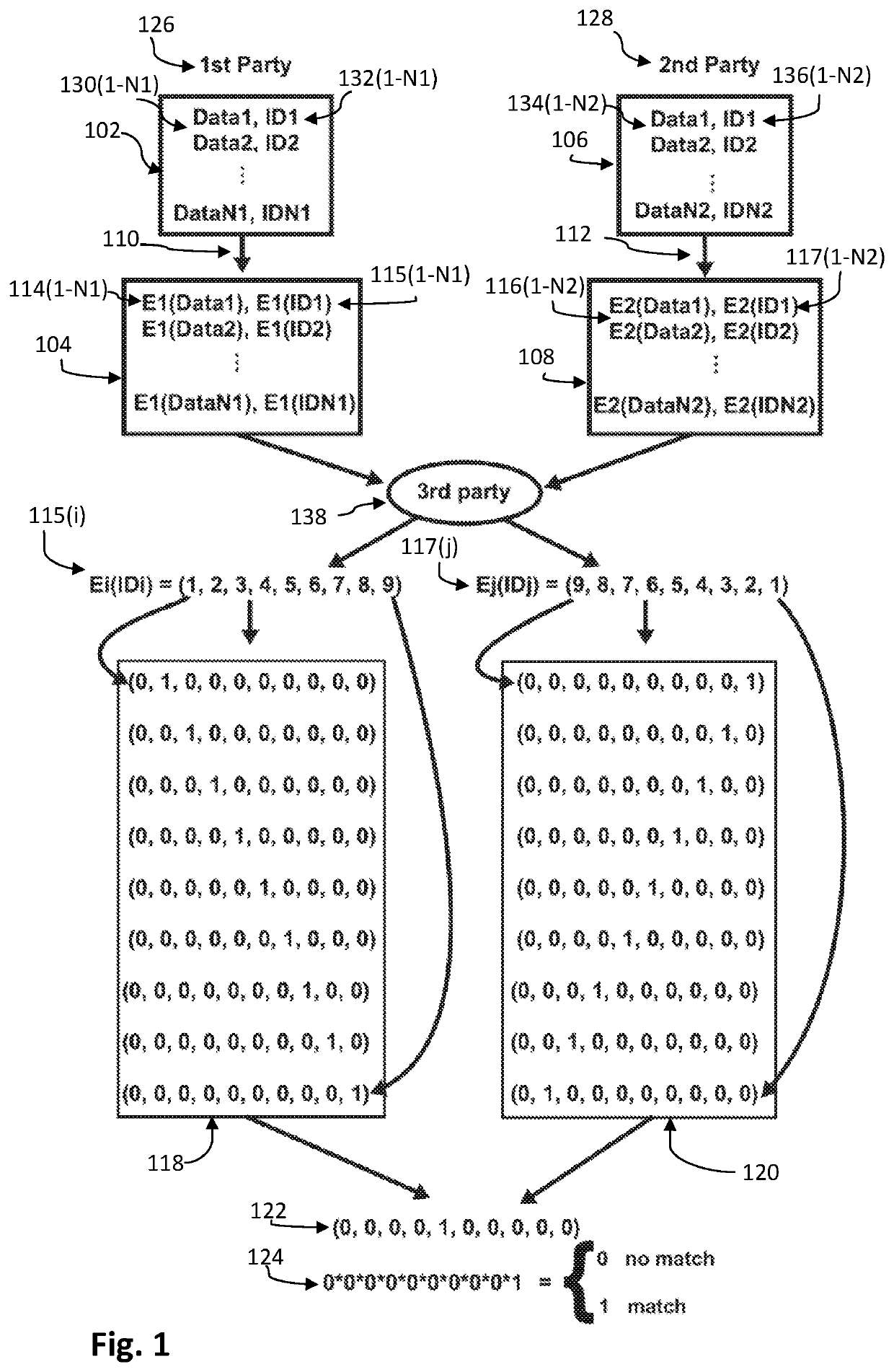
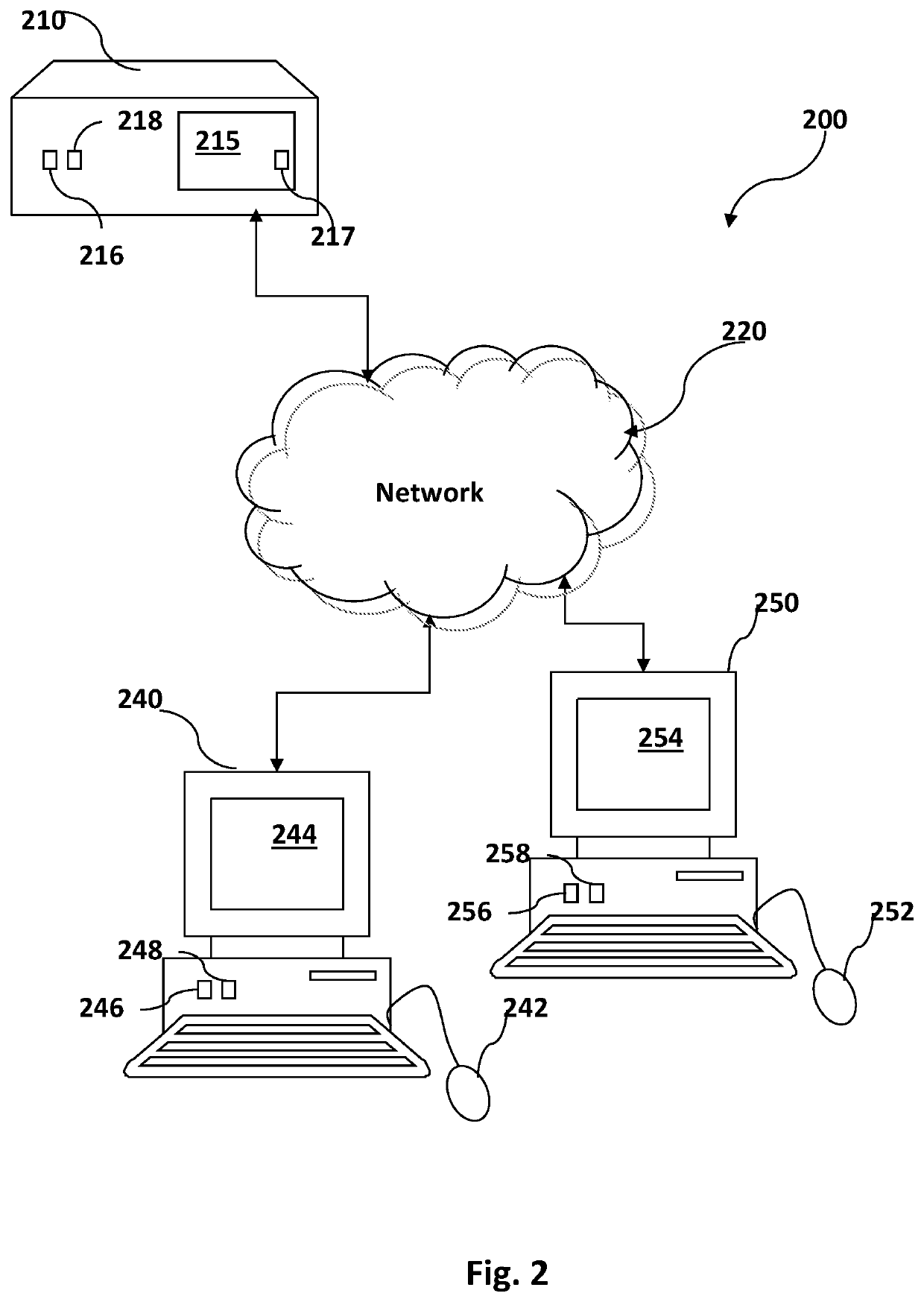
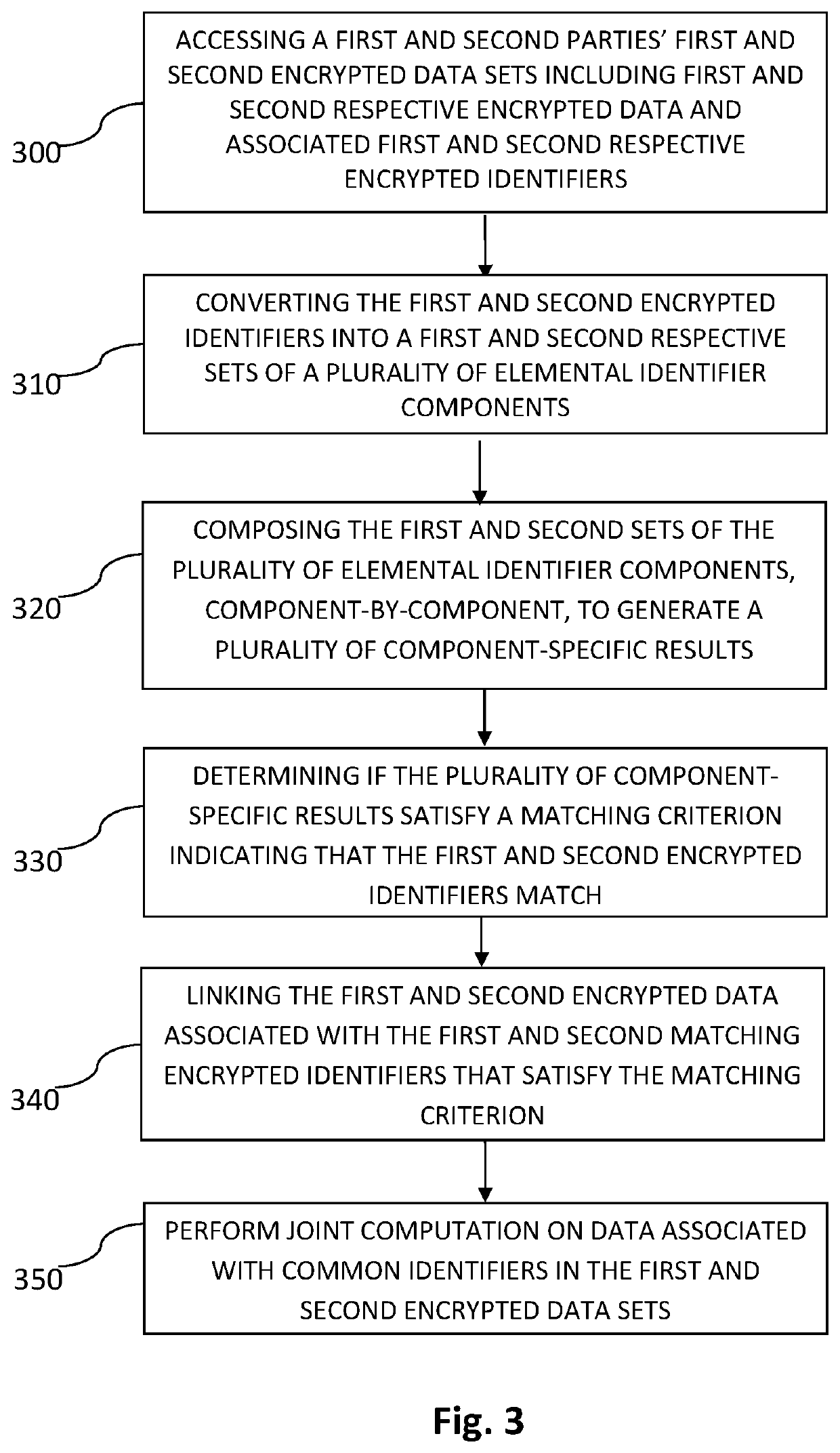
Linking encrypted datasets using common identifiers
ActiveUS20210157932A1Key distribution for secure communicationDigital data protectionData setIdenticon
A device, system and method for linking encrypted data sets using common encrypted identifiers in encrypted space. A first and second parties' encrypted data sets may include first and second respective encrypted data and associated first and second respective encrypted identifiers. The first and second encrypted identifiers may be converted into a first and second respective sets of a plurality of elemental identifier components. Each of the plurality of elemental identifier components in each component set characterizes a distinct numeric property of the corresponding converted encrypted identifier. The first and second sets of the plurality of elemental identifier components may be composed, component-by-component, to generate a plurality of component-specific results. If the plurality of component-specific results are determined to satisfy a matching criterion indicating that the first and second encrypted identifiers match, the first and second encrypted data associated with the first and second matching encrypted identifiers may be linked.
Owner:DUALITY TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com