Linking encrypted datasets using common identifiers
a common identifier and encryption technology, applied in the field of data encryption, decryption and security, can solve the problems of prohibitively slow, security risks, and difficult correlating encrypted identifiers in encrypted space using current methods, and achieve the effect of reducing the number of identifiers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
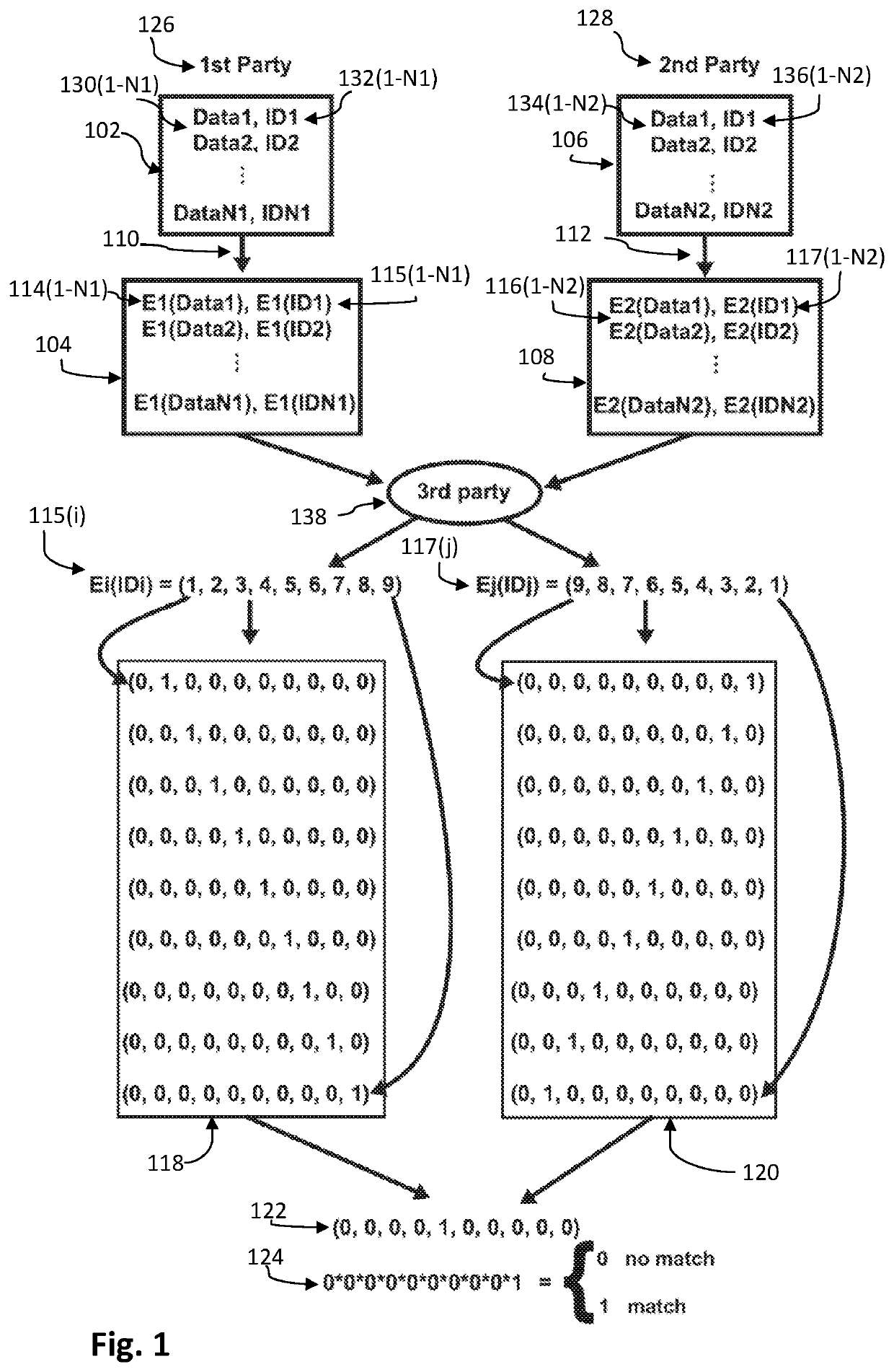
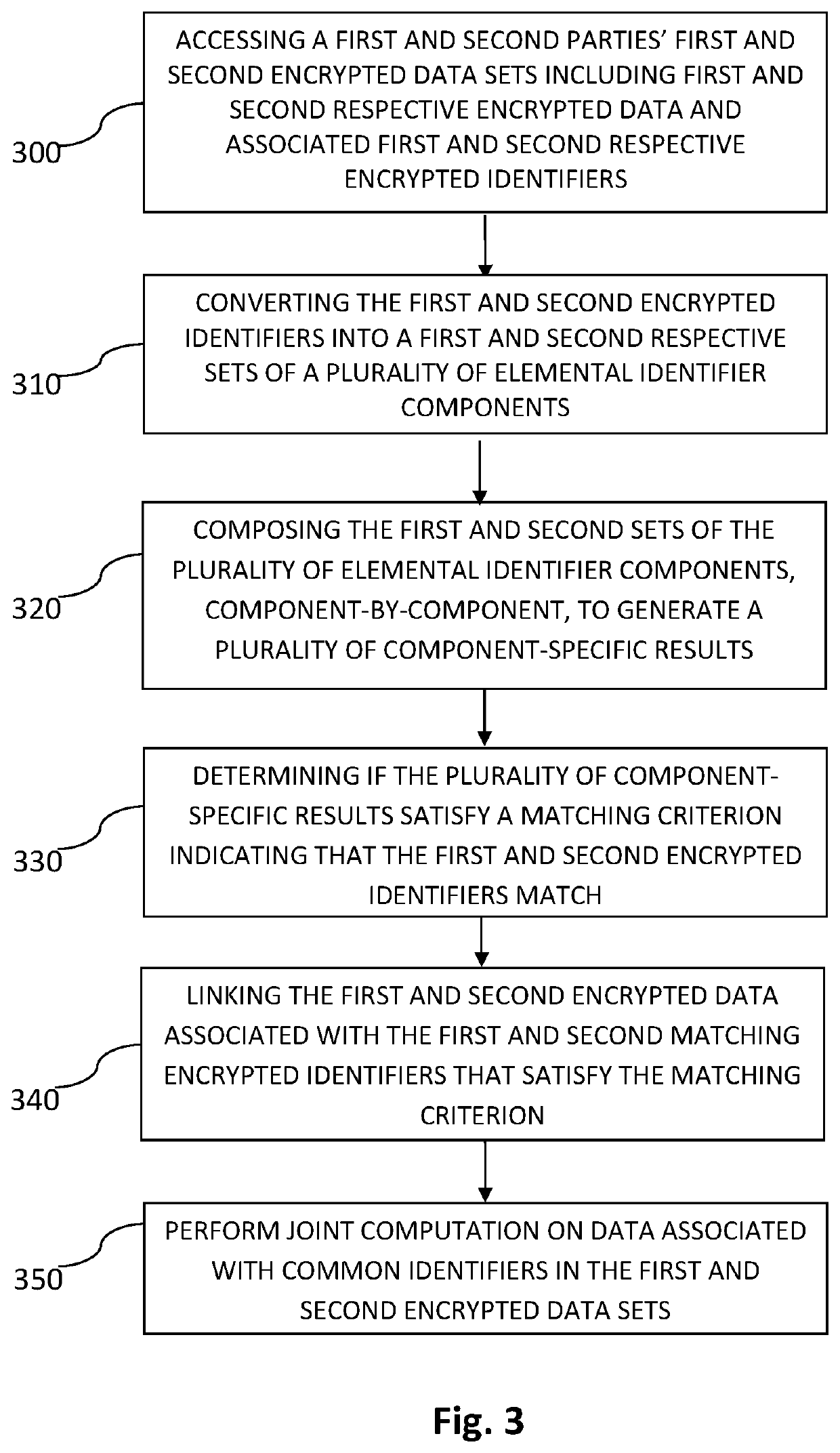
[0007]Embodiments of the invention solve this long felt need in the art by providing a device, system, and method for linking two or more encrypted datasets based on common identifiers (IDs) (or their hashes or derivative thereof). The IDs (or their hashes or derivatives) may also be encrypted.
[0008]In an embodiment of the invention, a device, system and method is provided for linking encrypted data sets using common encrypted identifiers in an encrypted space. A first and second parties' respective encrypted data sets may include first and second respective encrypted data and associated first and second respective encrypted identifiers. The data and identifiers typically cannot be unencrypted without one or more secret decryption keys. The first and second encrypted identifiers may be converted into a first and second respective sets of a plurality of elemental identifier components. Each of the plurality of elemental identifier components in each component set characterizes a dist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com