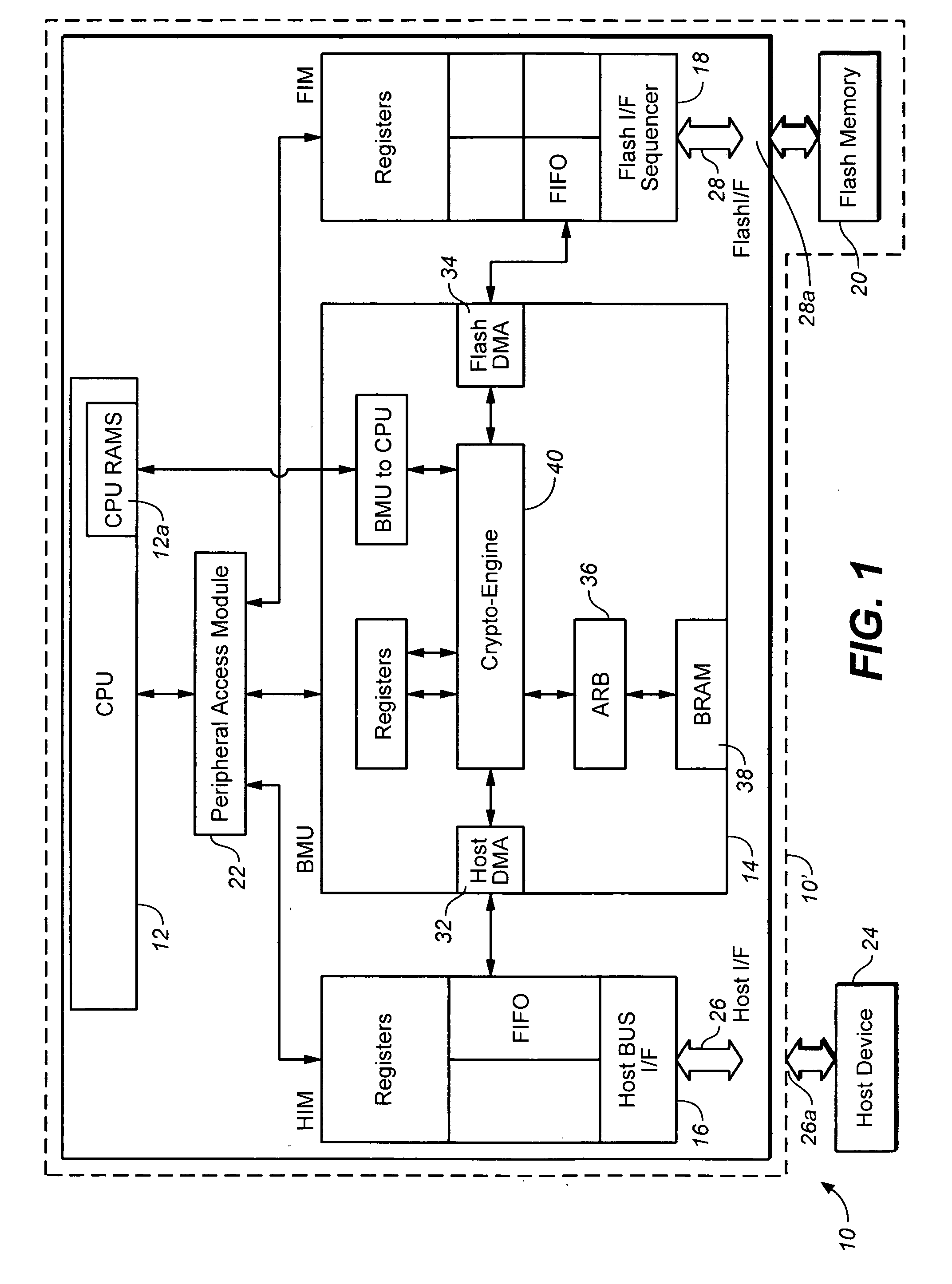
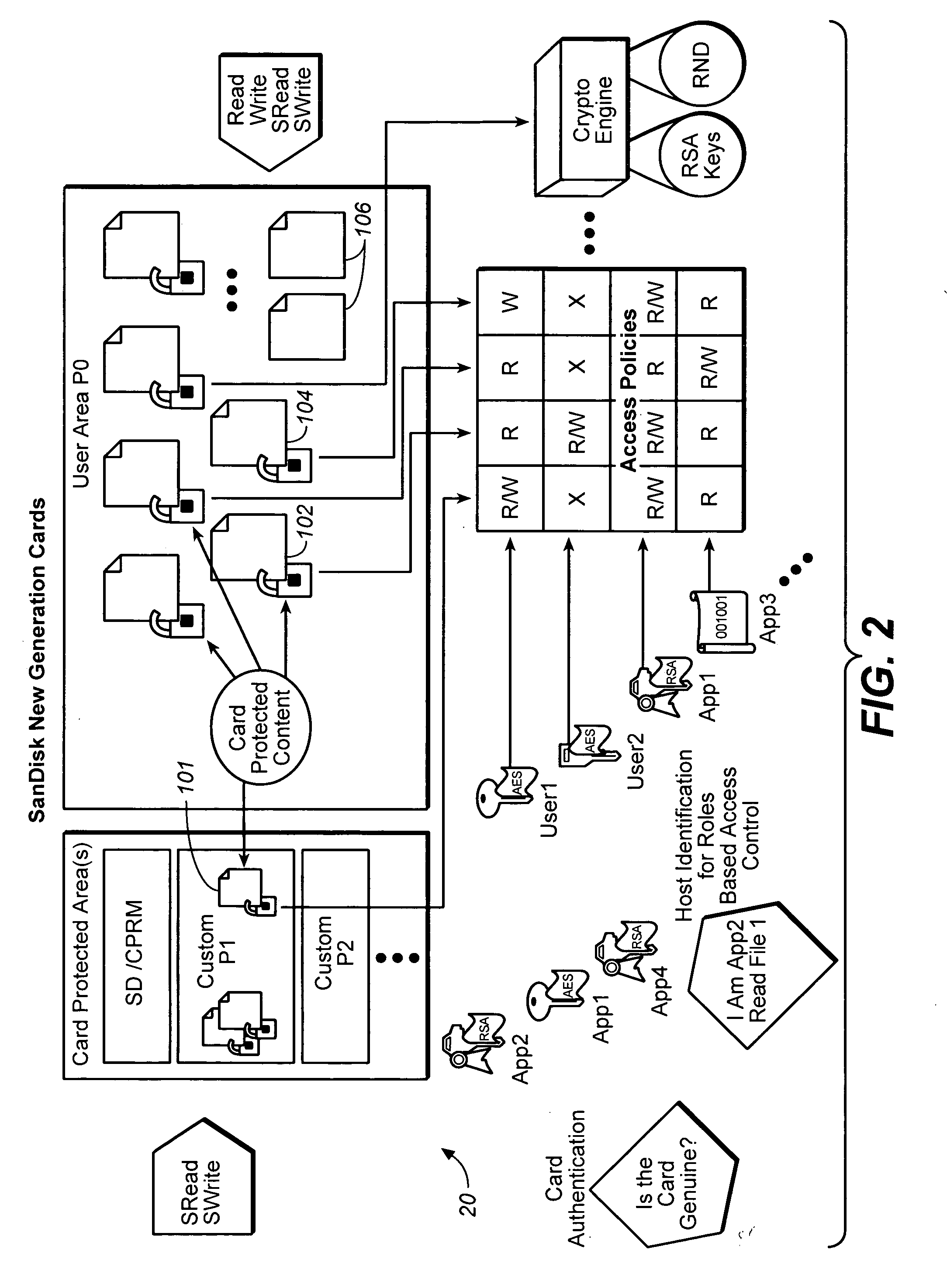
Patents
Literature
23697results about "Internal/peripheral component protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
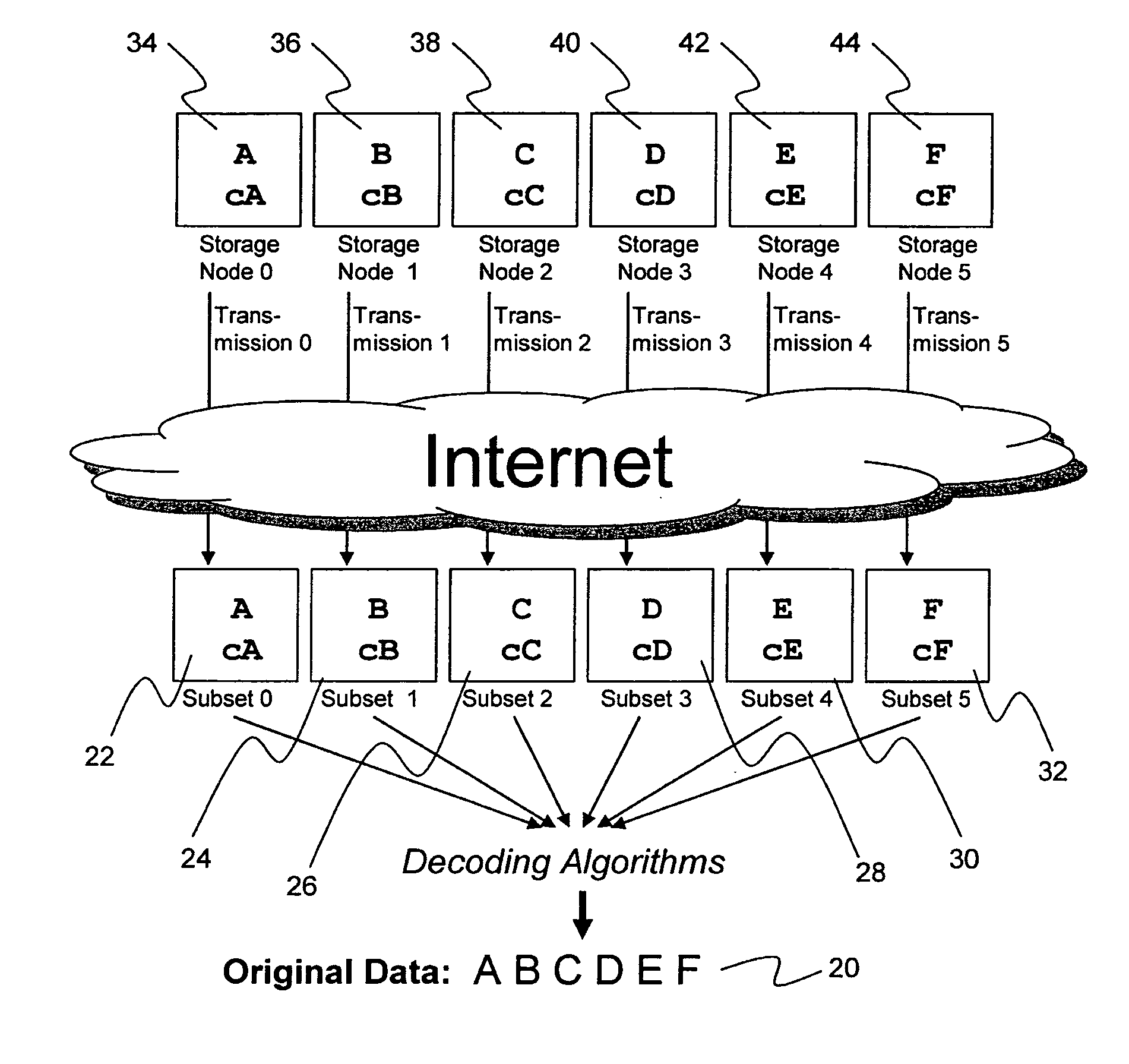
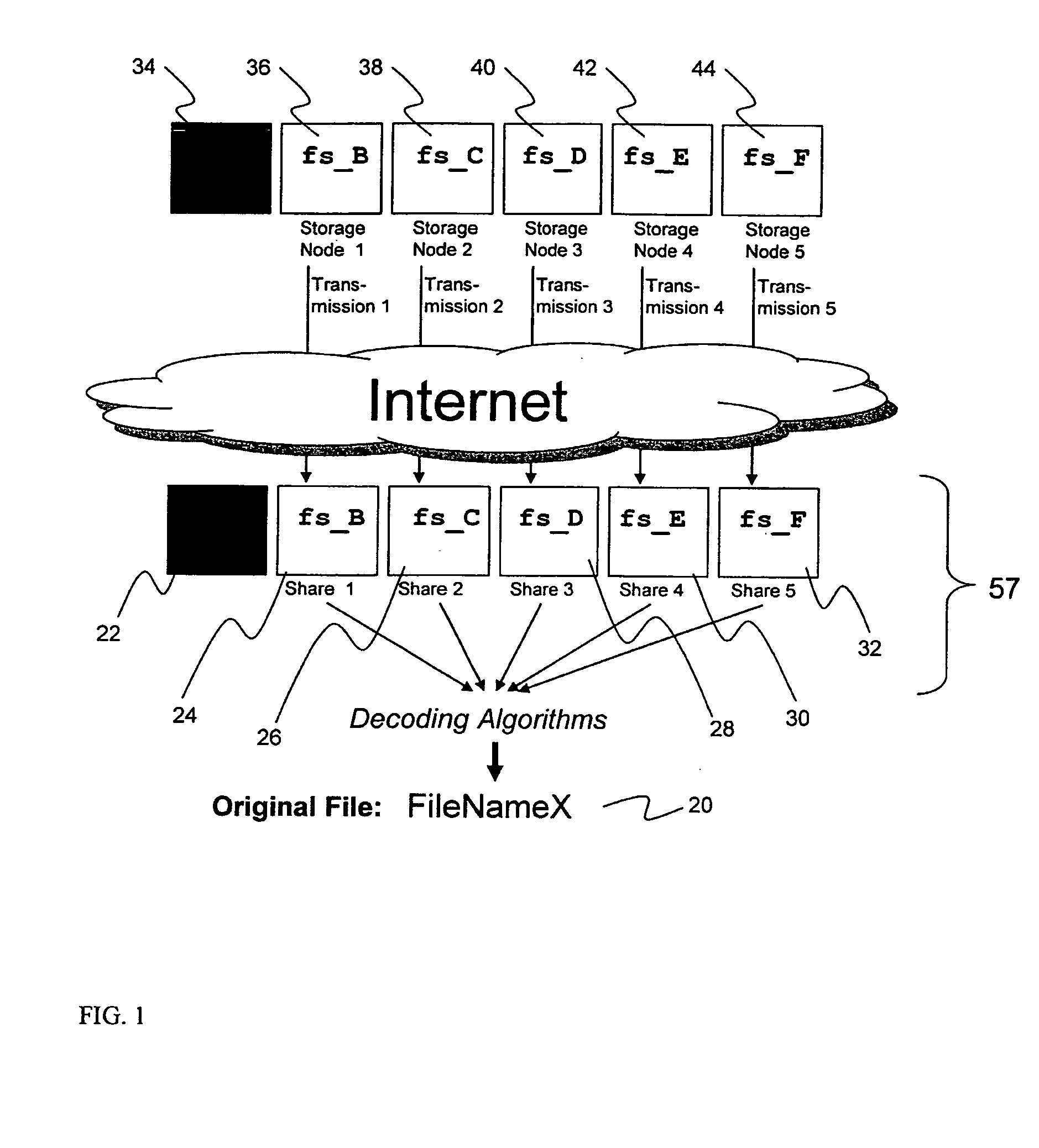
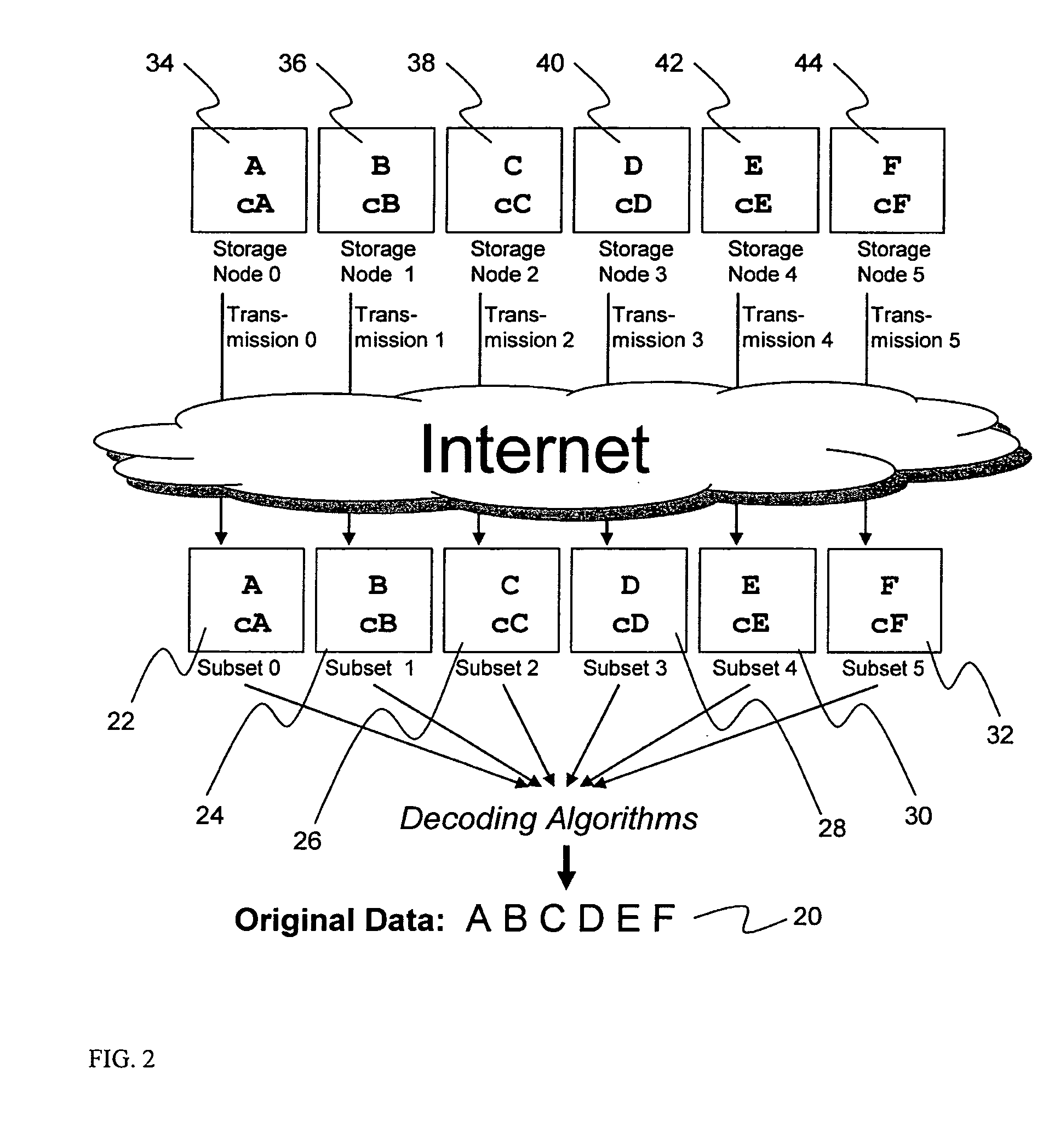
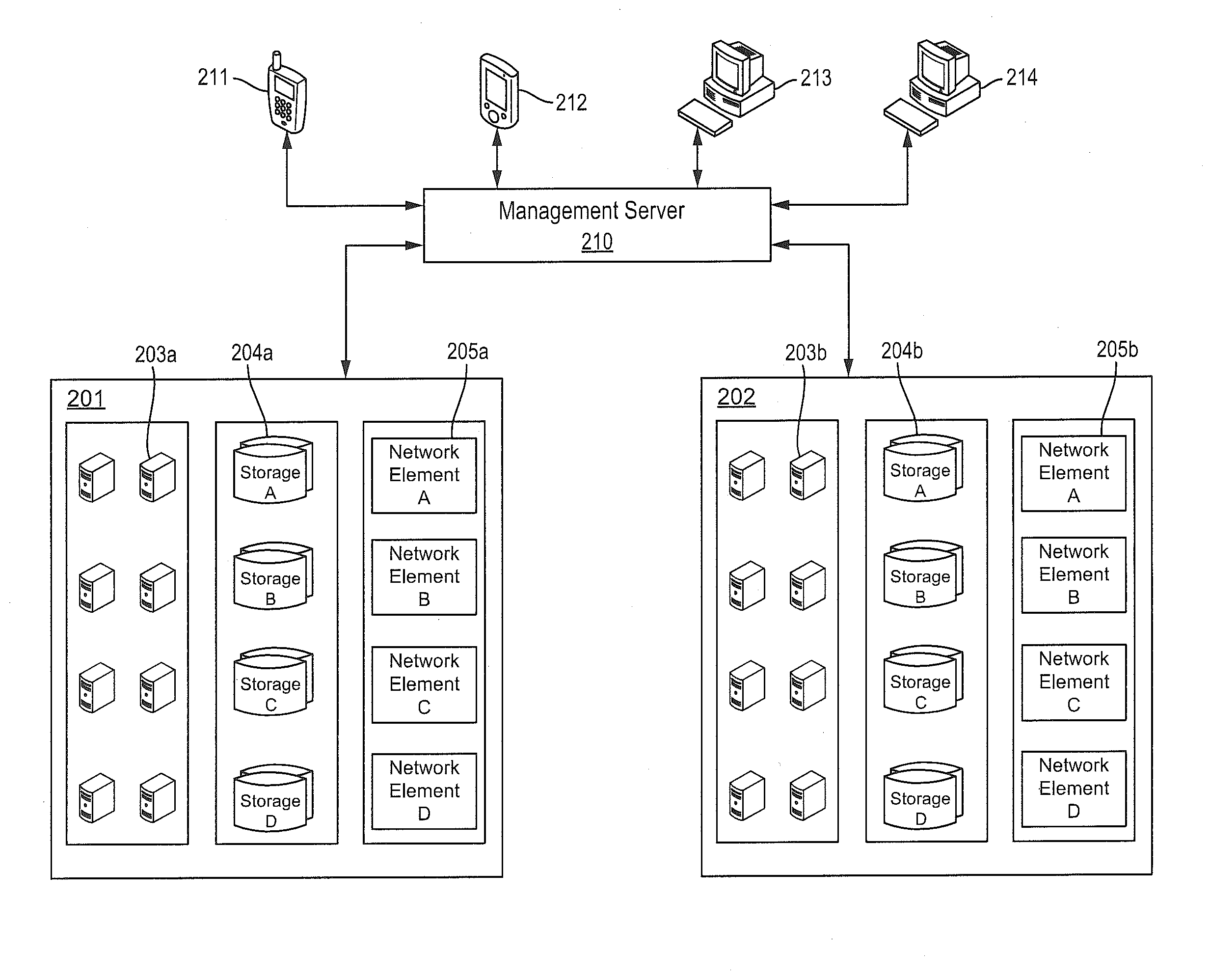
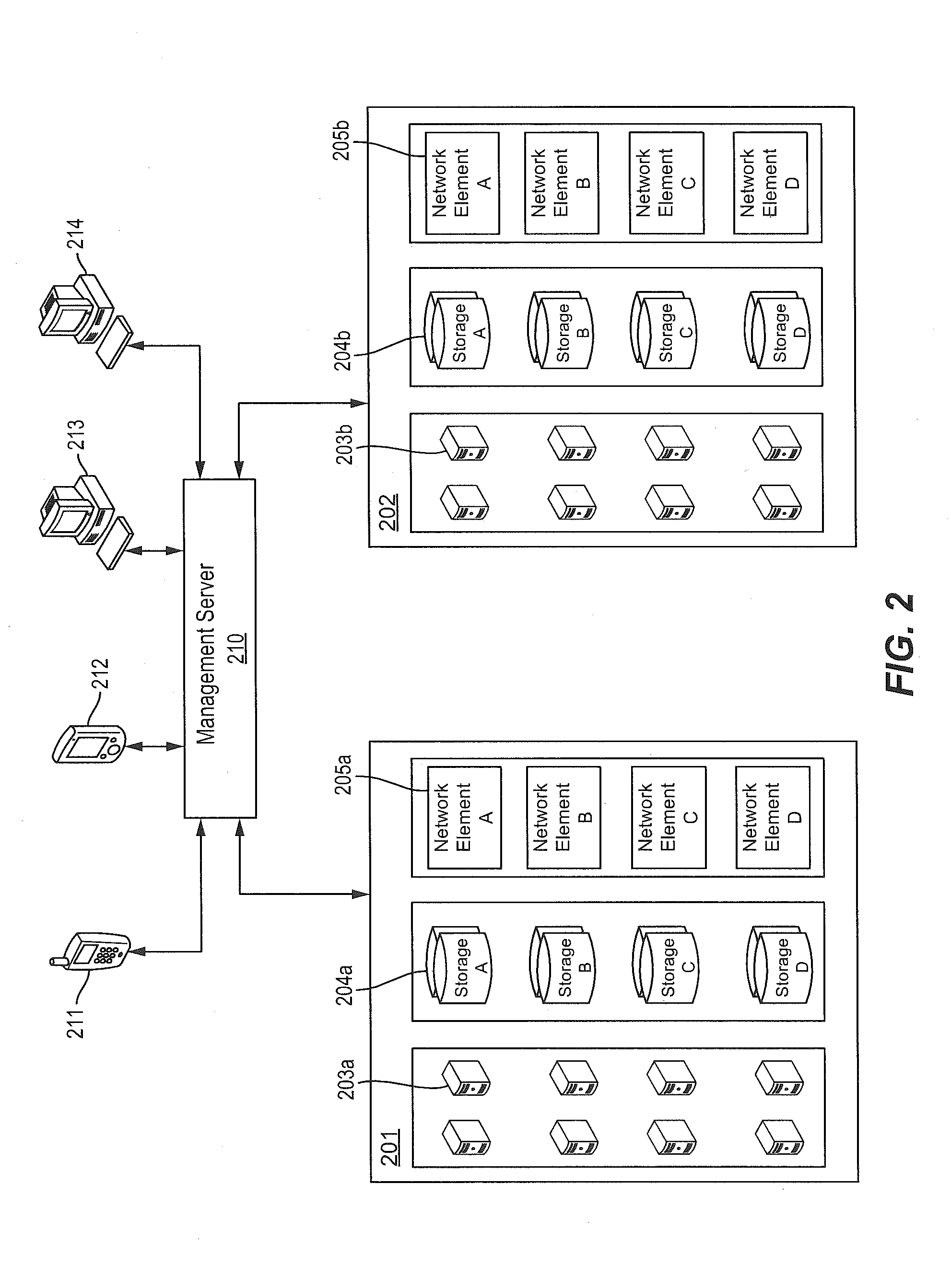
System for rebuilding dispersed data
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
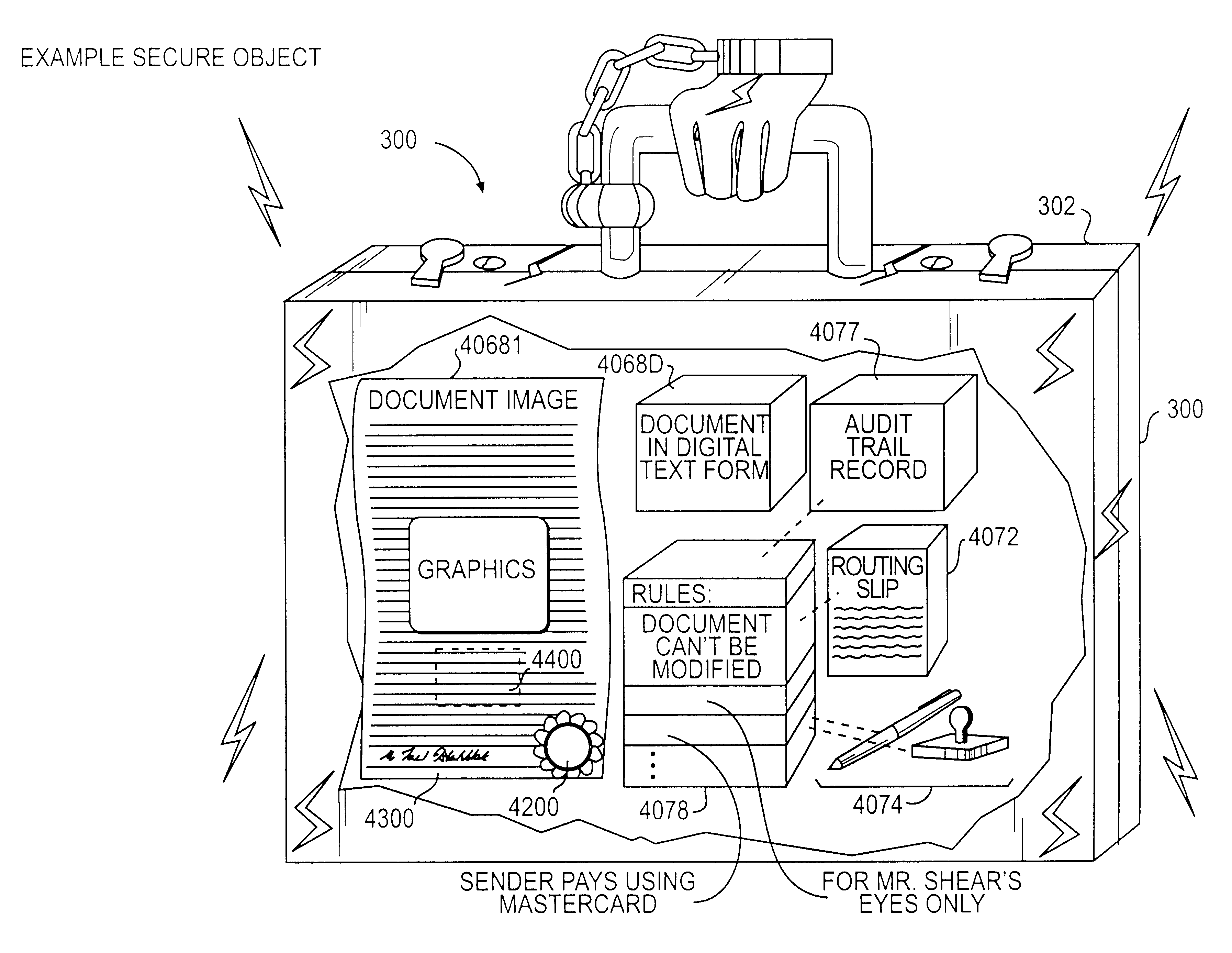
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
Software-based method for gaining privacy by affecting the screen of a computing device
InactiveUS7779475B2Improve privacyMinimal impactDigital data processing detailsUnauthorized memory use protectionGraphicsInternet privacy
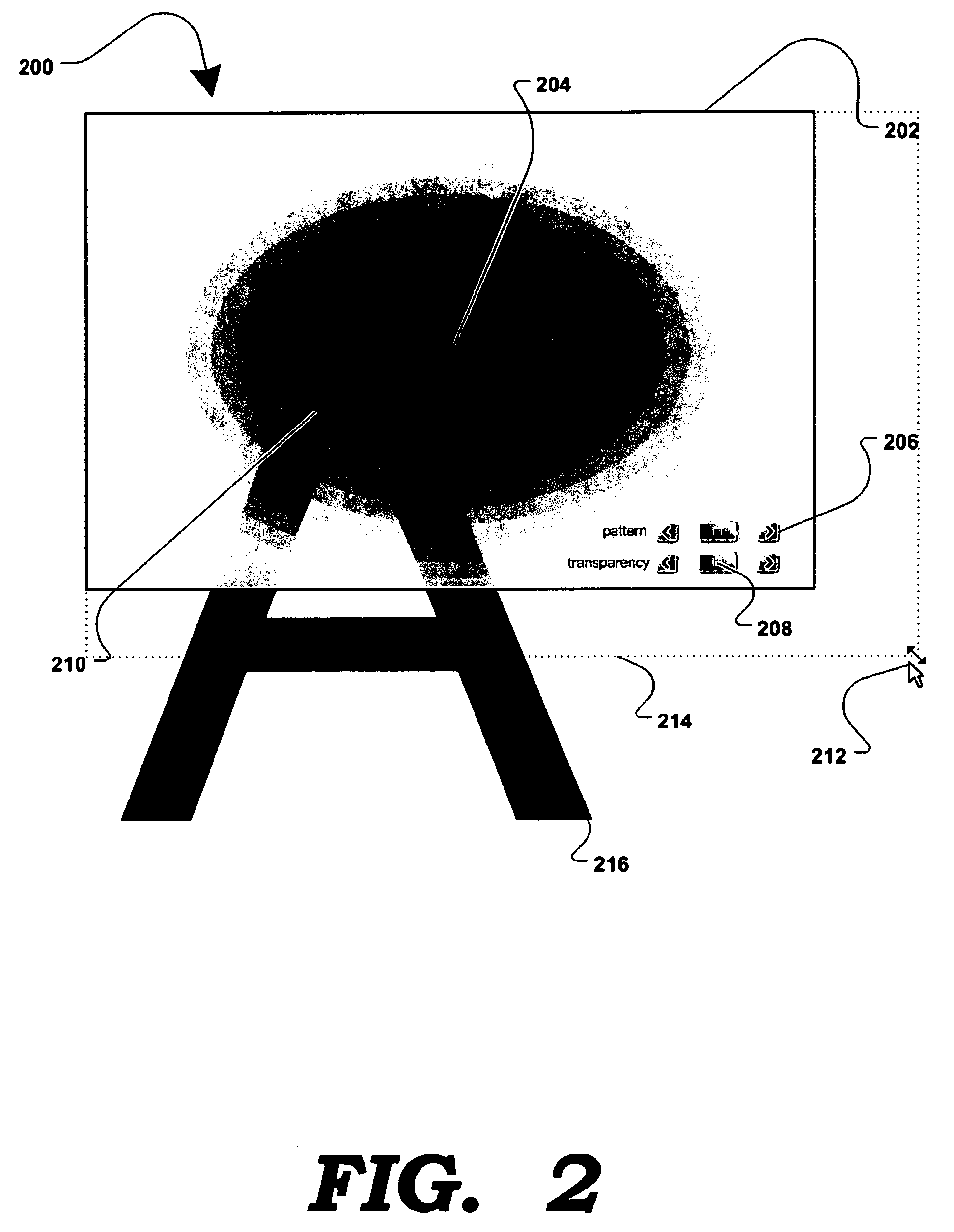
A method and apparatus for allowing the user of an electronic device to enhance privacy over a display with the use of software, are disclosed. A security window including a translucent graphical effects region may be displayed on the electronic device such that it overlays content the user may choose to protect. The security window allows the protected content to remain discernable for the user of the device yet substantially indiscernible to a person at a further distance and / or greater viewing angle from the screen of the device. One or more security windows, each of which may be of any size, shape, texture, translucency level and any other graphical or behavioral properties may be displayed on the display associated with the electronic device. The user may control the size, shape, texture, translucency level and any other graphical or behavioral properties of the security window and graphical effects region. The user may invoke or terminate a security window with the single click of a button. Security windows may automatically attach to applications in focus, or be attached in response to a user command, and allow uninterrupted usability of those applications.
Owner:PETNOTE
Conductive tamper switch for security devices
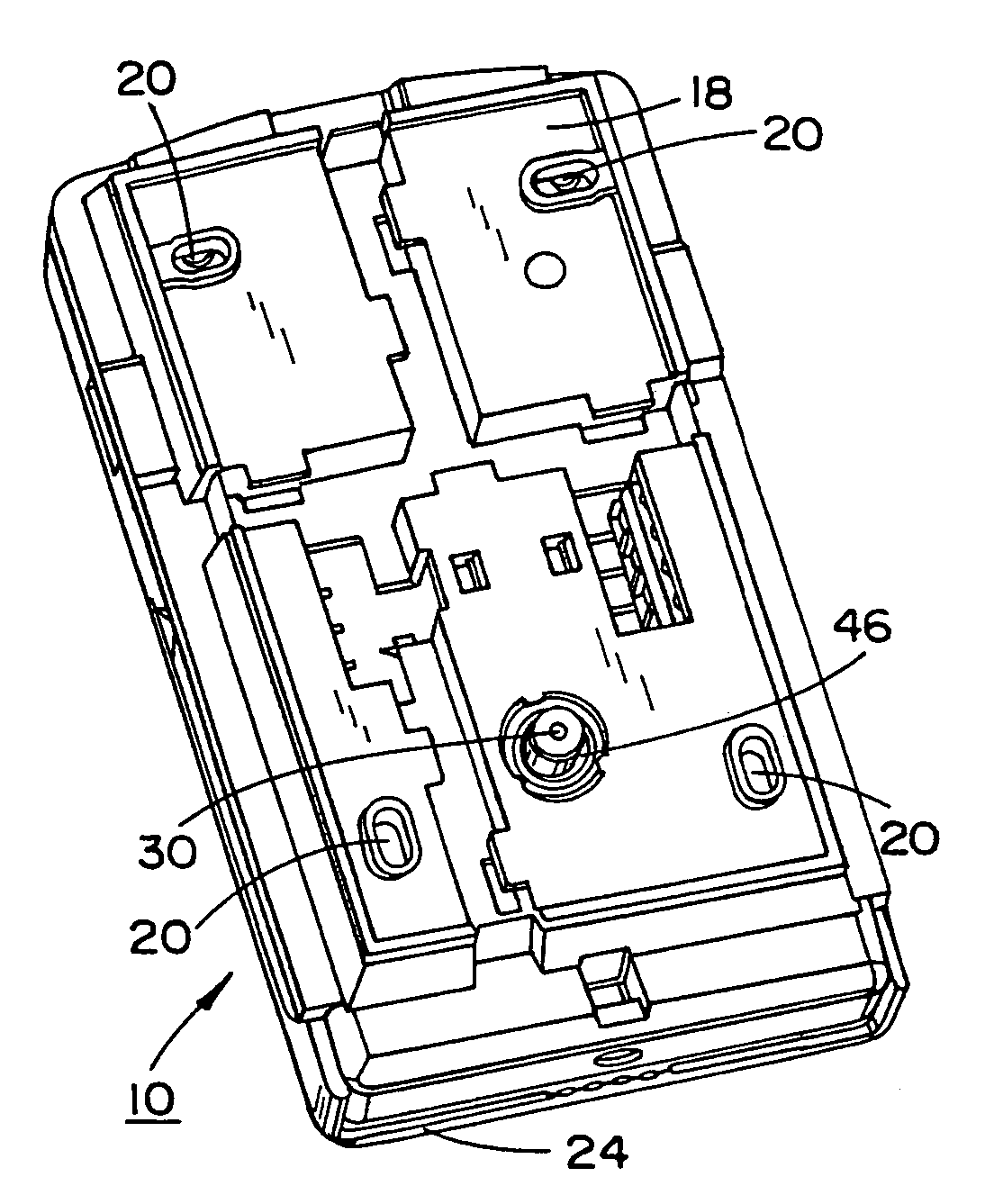
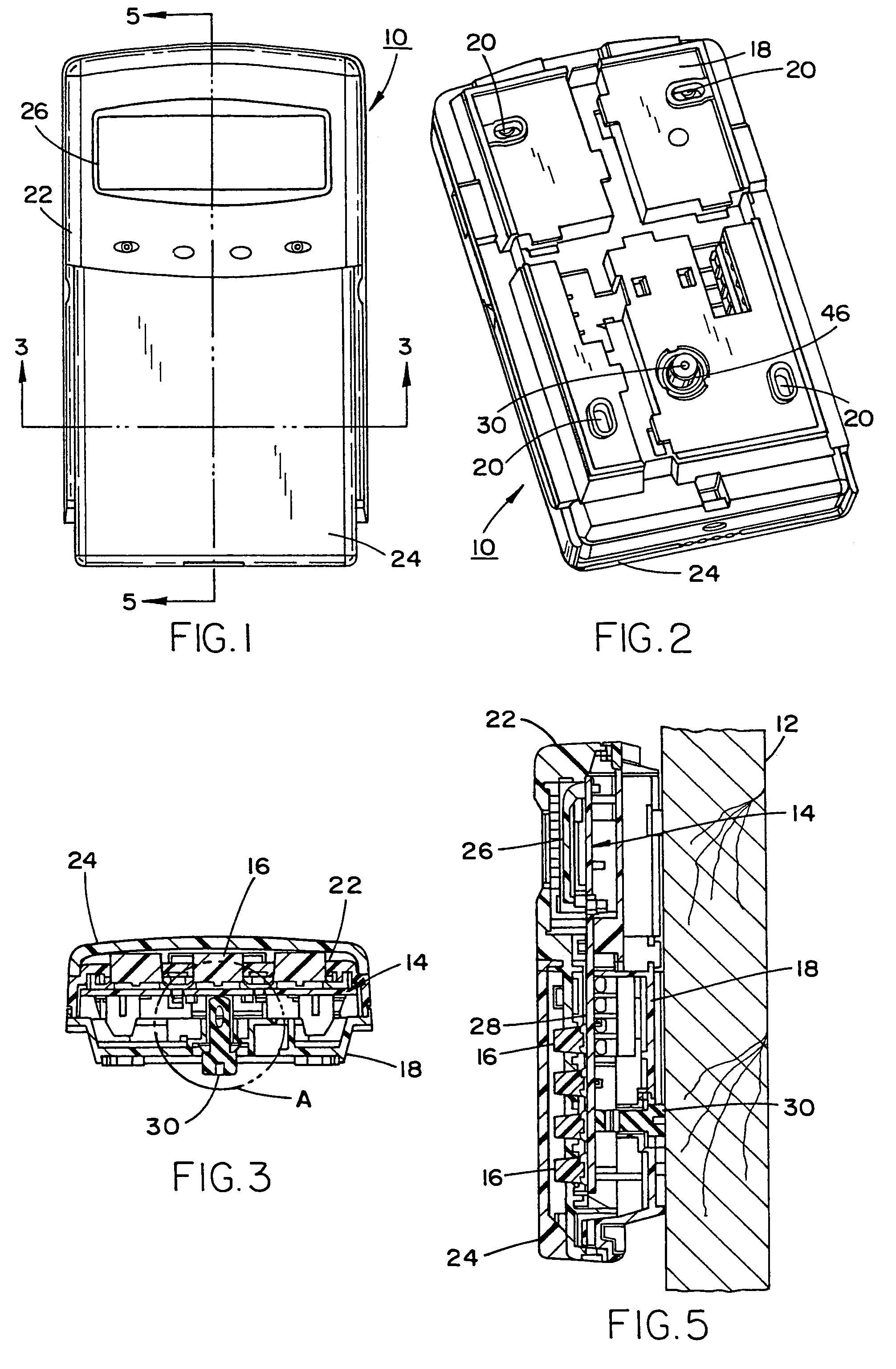
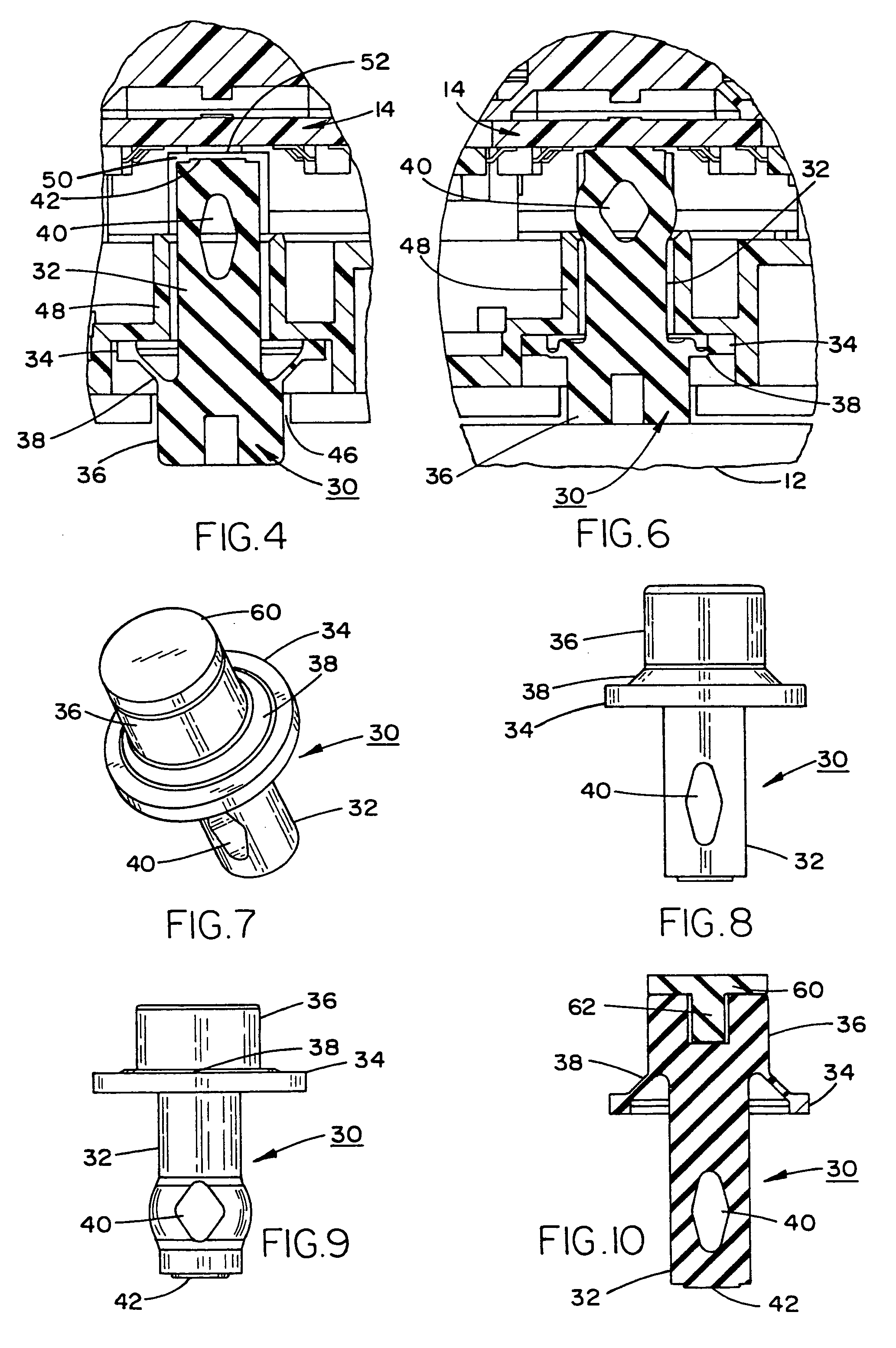
InactiveUS7388484B2Highly efficient and reliable in operationCost-effectively mountedInternal/peripheral component protectionRadio/inductive link selection arrangementsMonitoring siteFire alarm system
A tamper switch mechanism utilized in security interface devices such as keypad installations to render them tamper-resistant, wherein the devices are generally connected to burglar alarm and fire alarm systems. More particularly, provided is a conductive tamper switch which is installed in a security interface device, such as a keypad, which upon an unauthorized attempt to dislodge the device or keypad from a wall or surface on which it is mounted, will trigger an alarm or generate a warning signal at a monitoring site indicative that an effort at tampering with the device has been effected. Also disclosed is a method of providing the tamper switch mechanism in a security interface device, such as a keypad installation.
Owner:HONEYWELL INT INC
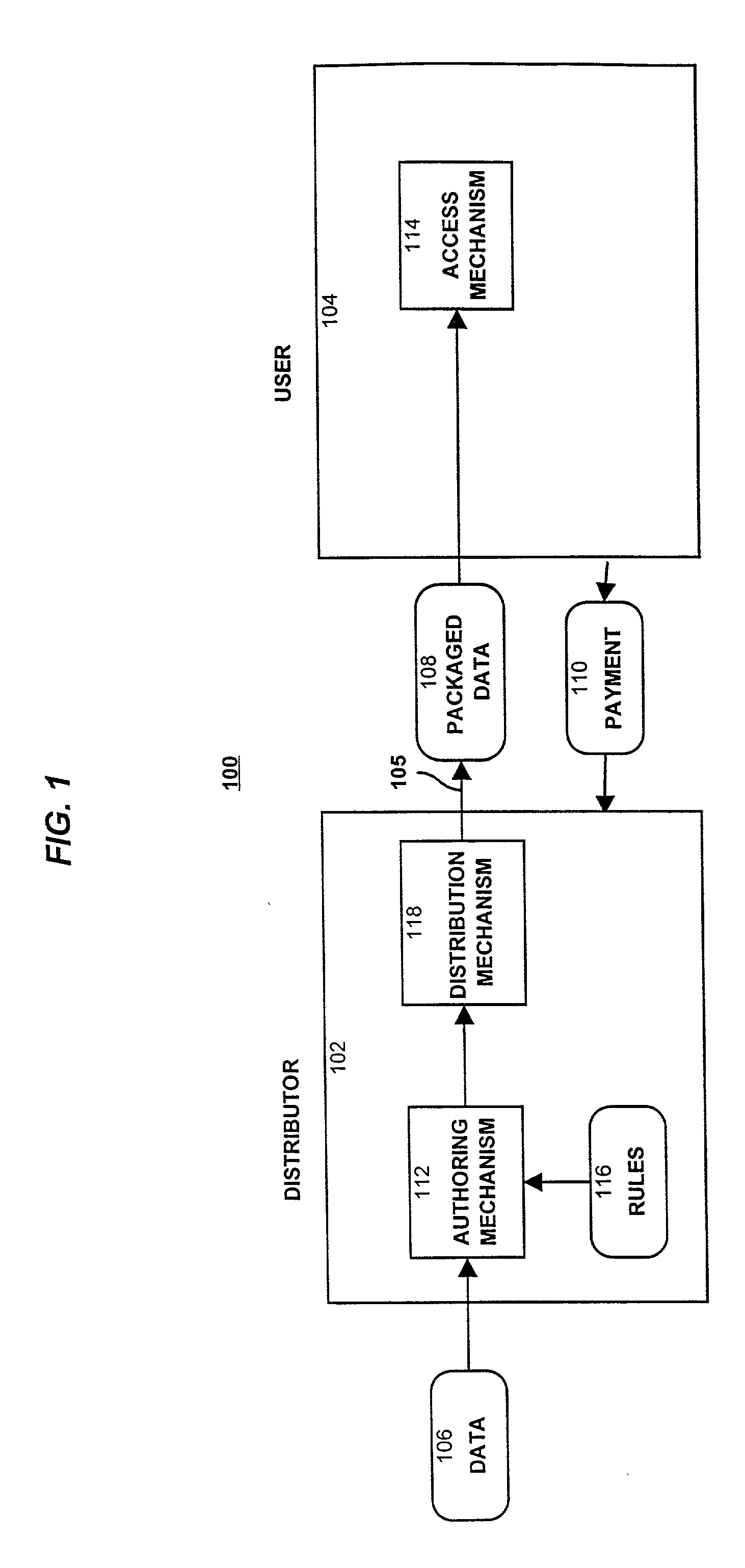
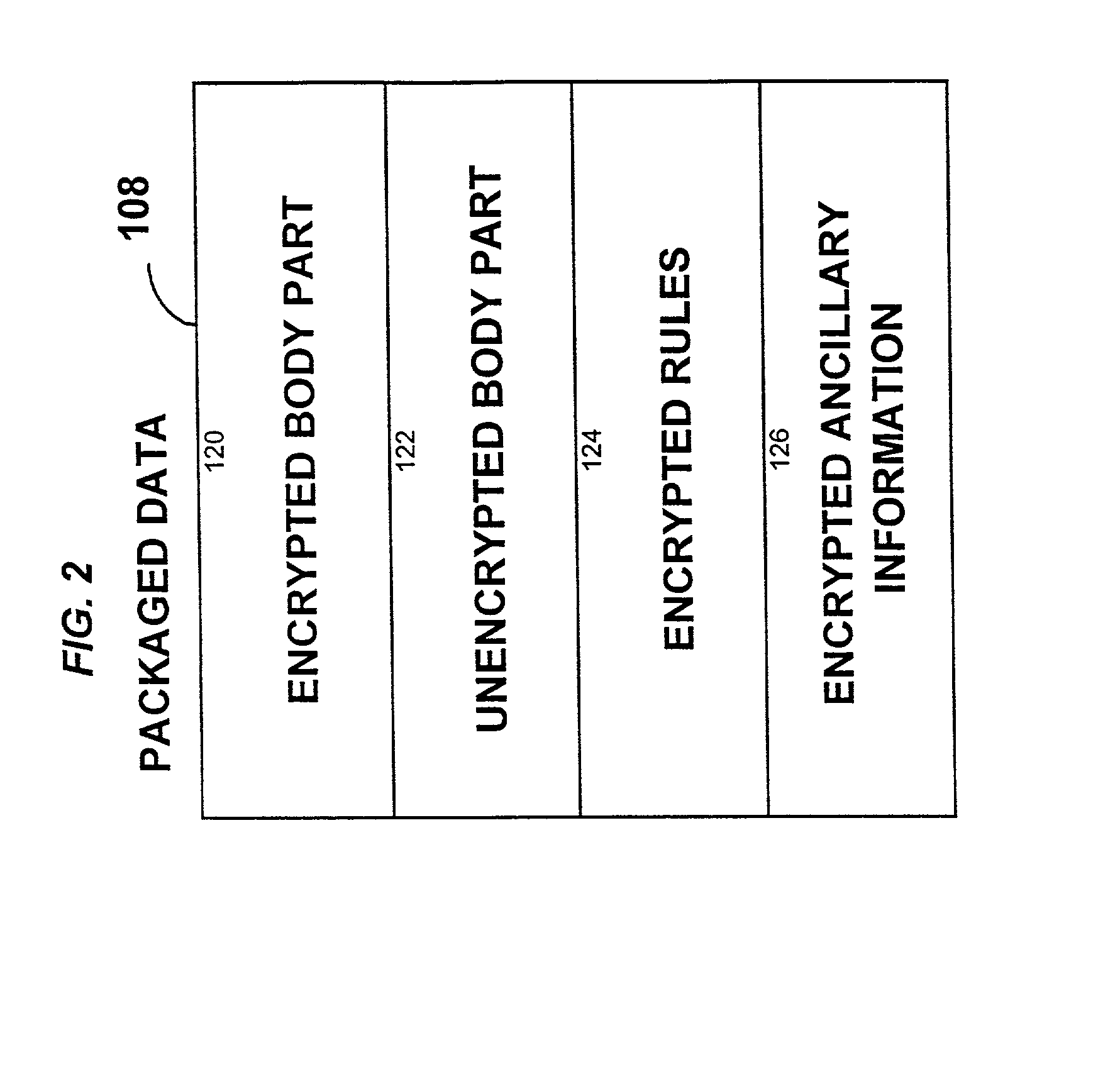
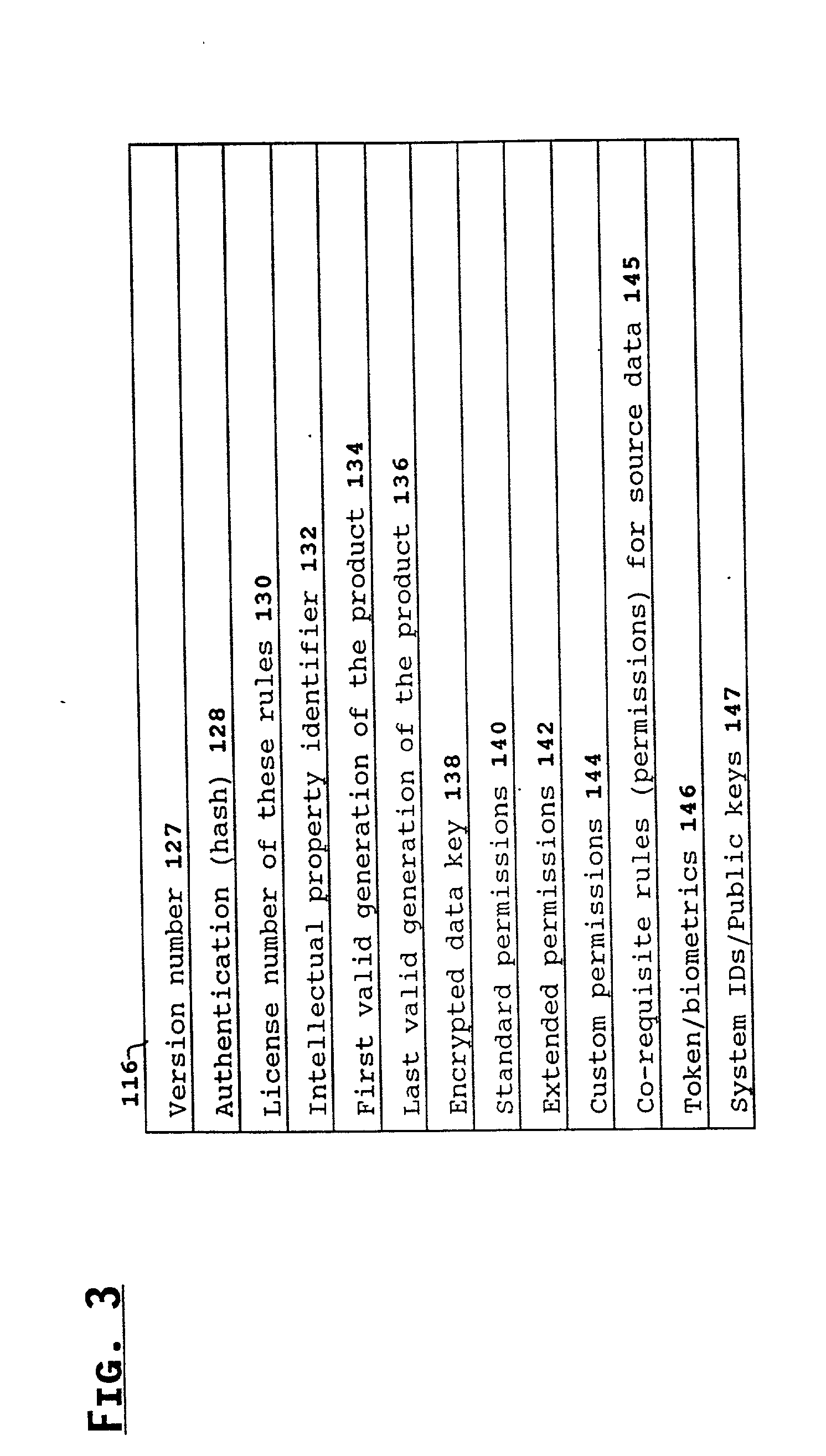
System for controlling access and distribution of digital property
InactiveUS6314409B2Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
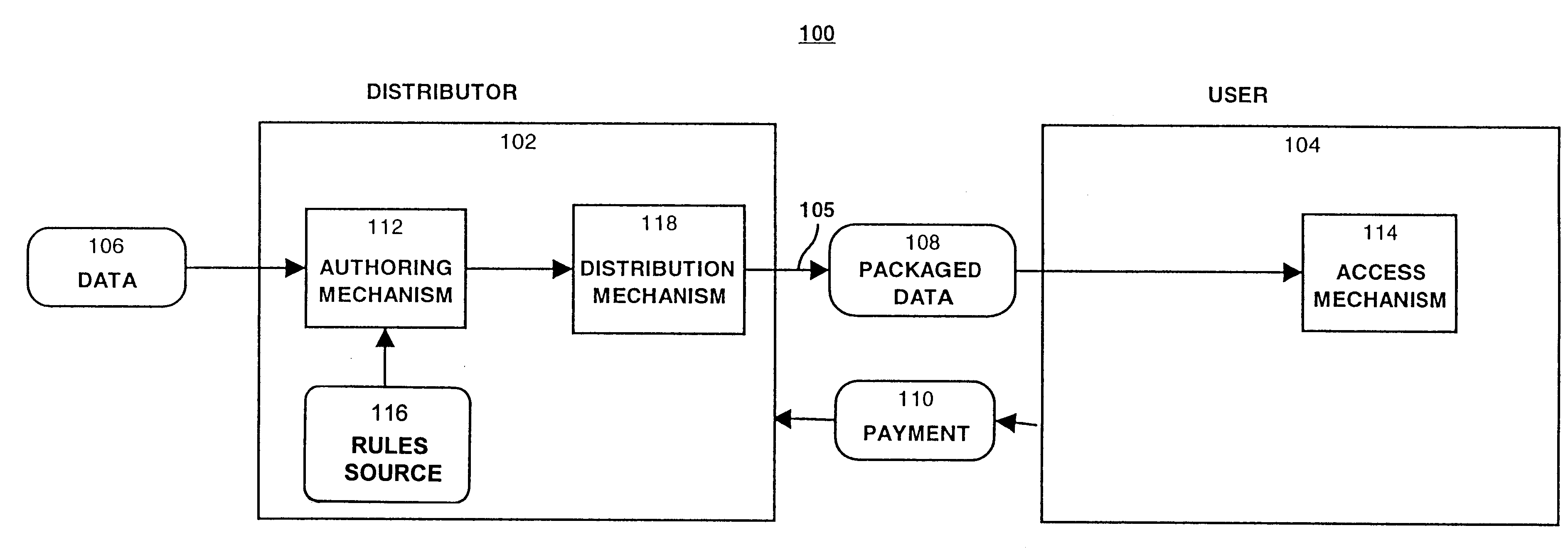
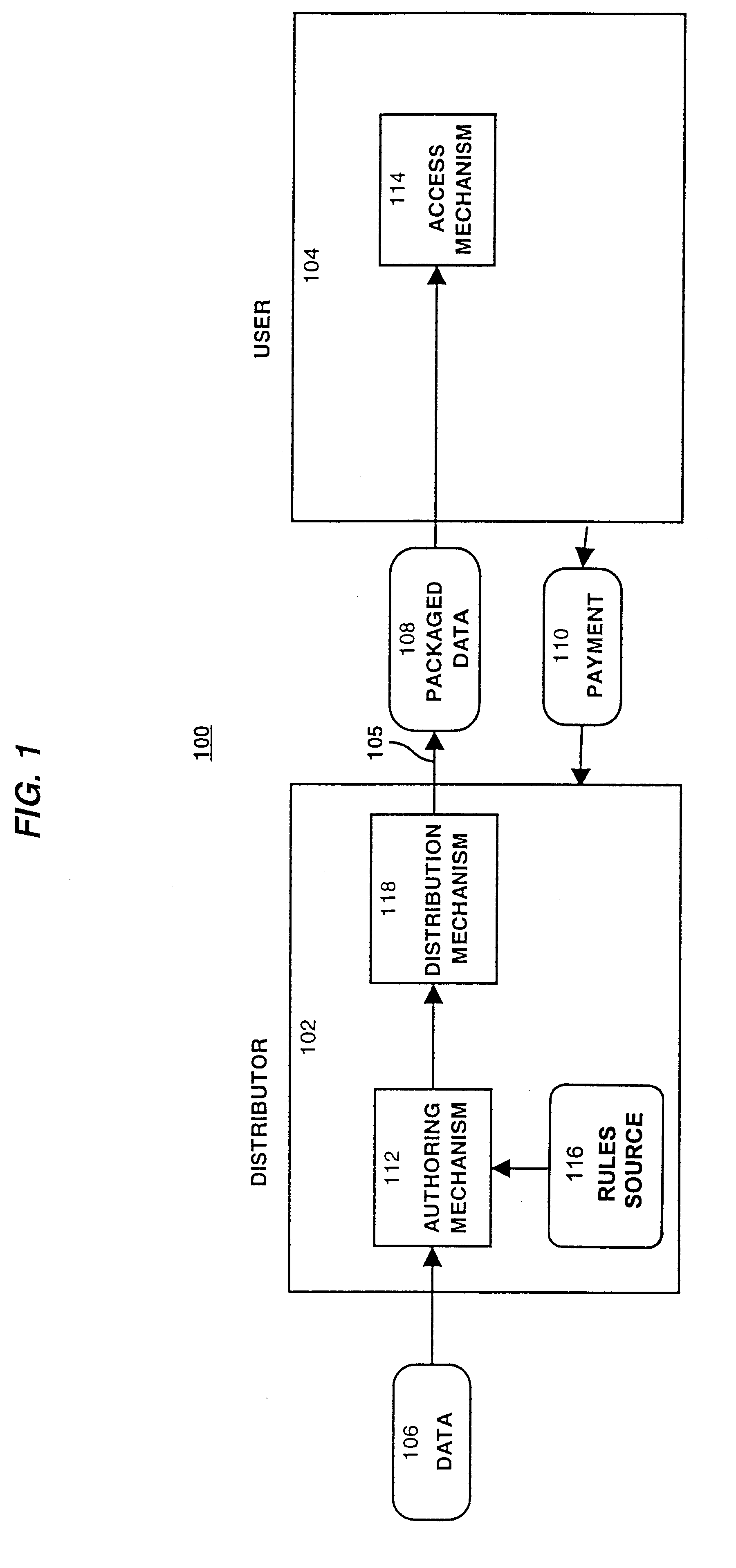
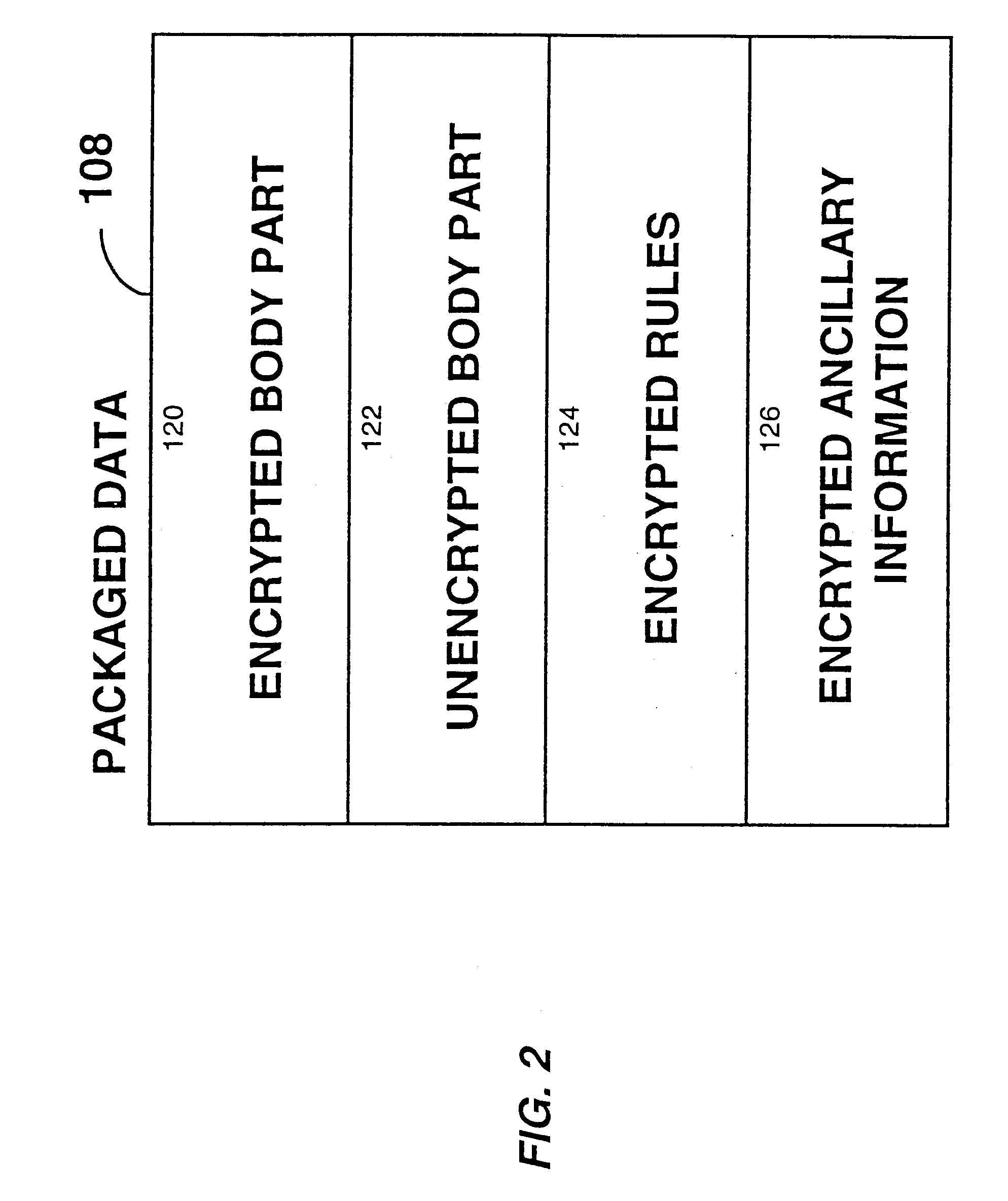
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
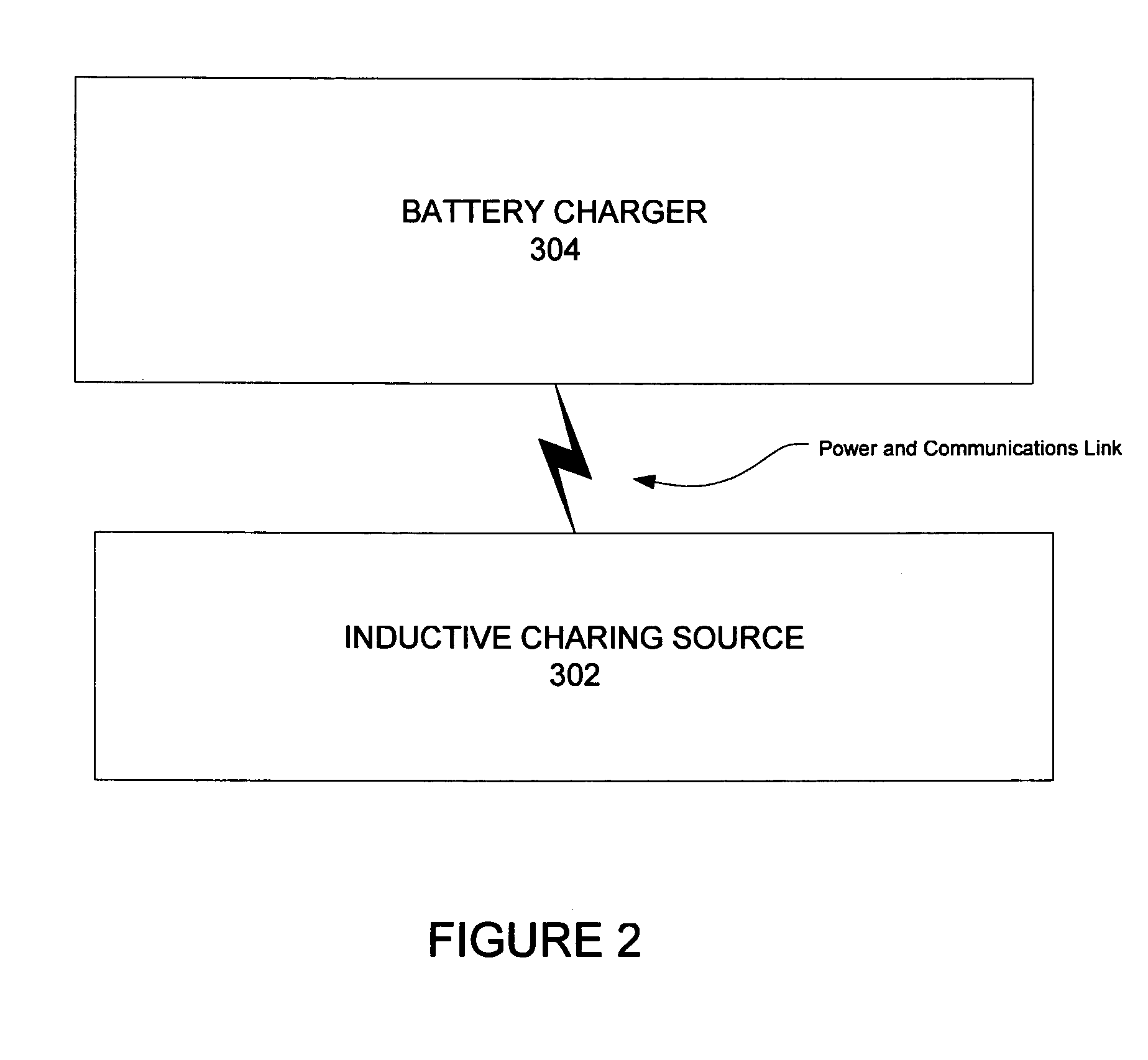
Inductive battery charger
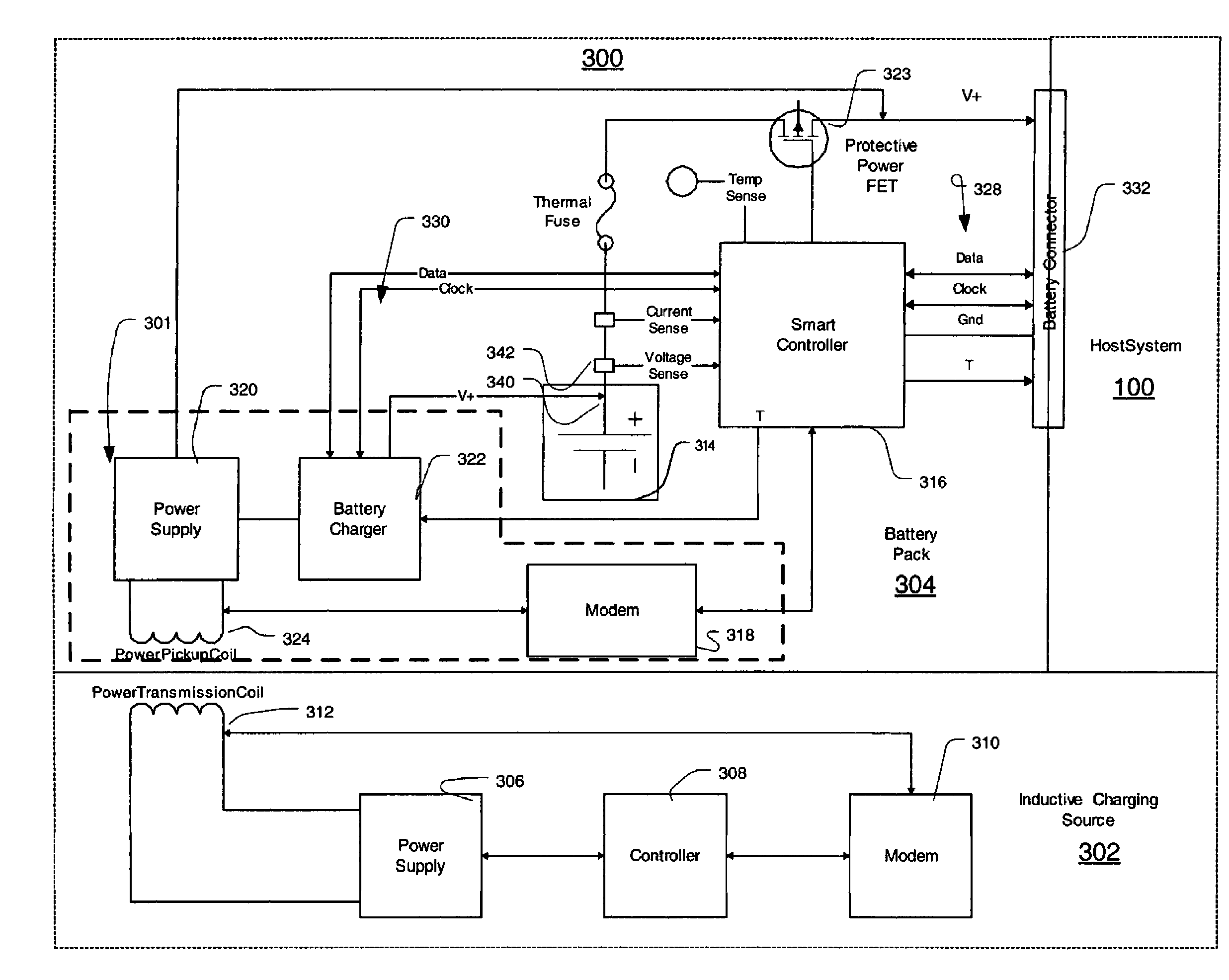
InactiveUS7375493B2Circuit authenticationVolume/mass flow measurementElectrical batteryReceiver coil
An inductive charging system transfers energy by inductively coupling a source coil on a power source to a receiver coil for a battery charger. Source current may be received in the battery charger and converted for charging a battery pack. A wireless communication arrangement may also provide for authentication of devices that are allowed by the source to be powered or otherwise charged.
Owner:MICROSOFT TECH LICENSING LLC
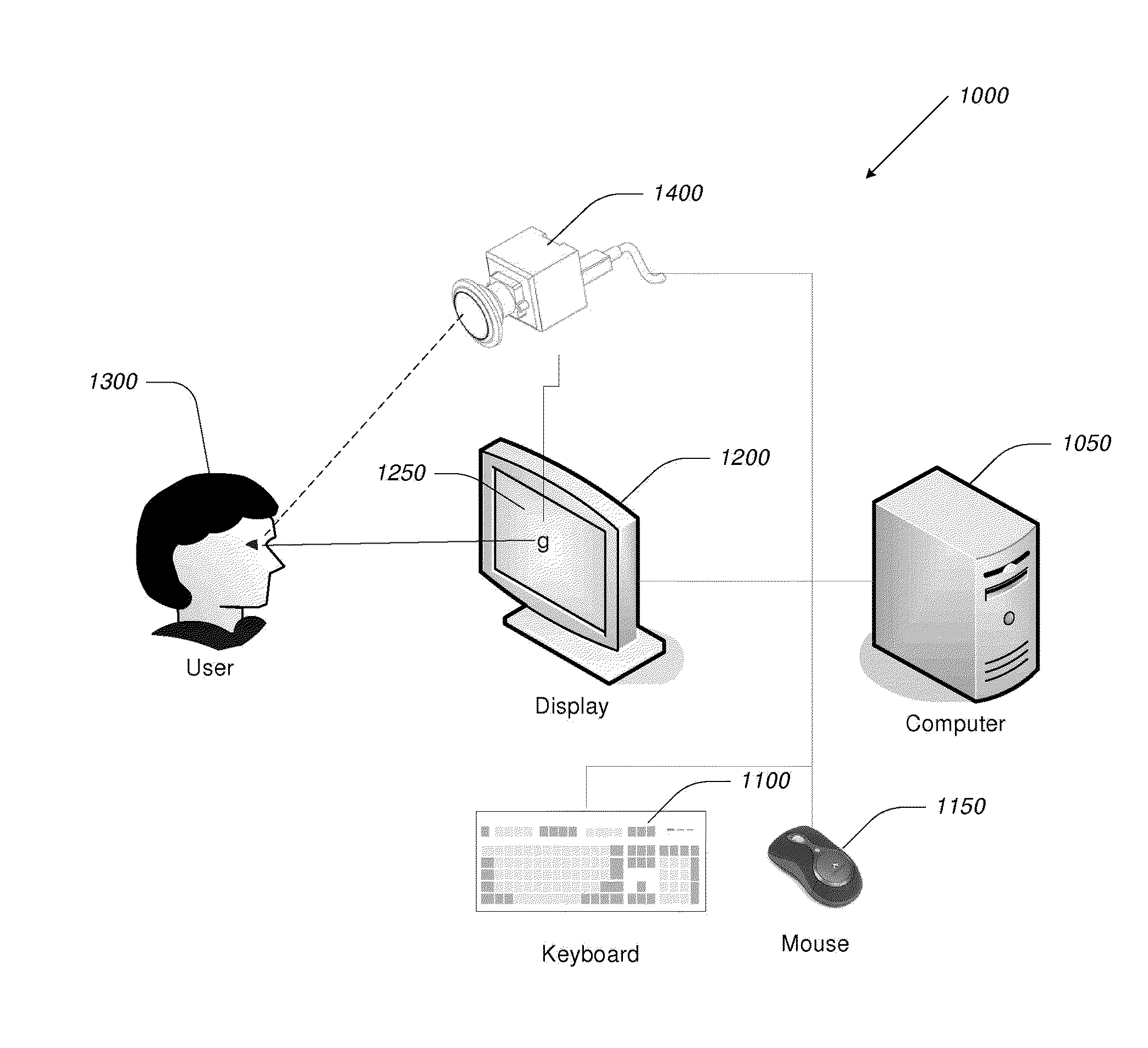
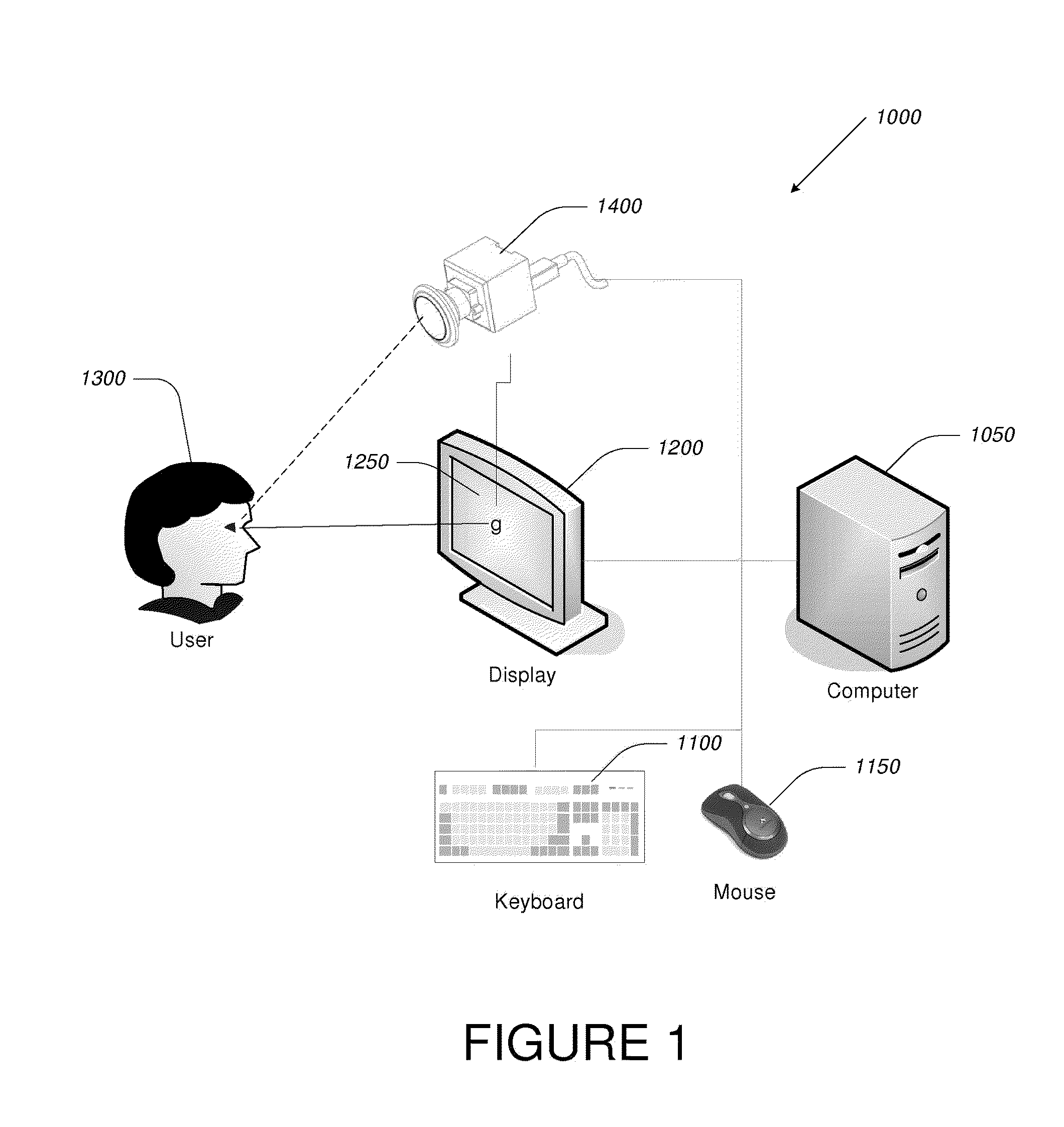
Video-Based Privacy Supporting System
ActiveUS20100205667A1Improve securityPrivacy protectionDigital data processing detailsUnauthorized memory use protectionDisplay deviceOutput device
Computer display privacy and security for computer systems. In one aspect, the invention provides a computer-controlled system for regulating the interaction between a computer and a user of the computer based on the environment of the computer and the user. For example, the computer-controlled system provided by the invention comprises an input-output device including an image sensor configured to collect facial recognition data proximate to the computer. The system also includes a user security parameter database encoding security parameters associated with the user; the database is also configured to communicate with the security processor. The security processor is configured to receive the facial recognition data and the security parameters associated with the user, and is further configured to at least partially control the operation of the data input device and the data output device in response to the facial recognition data and the security parameters associated with the user.
Owner:TOBII TECH AB
Authentication and authorization methods for cloud computing security
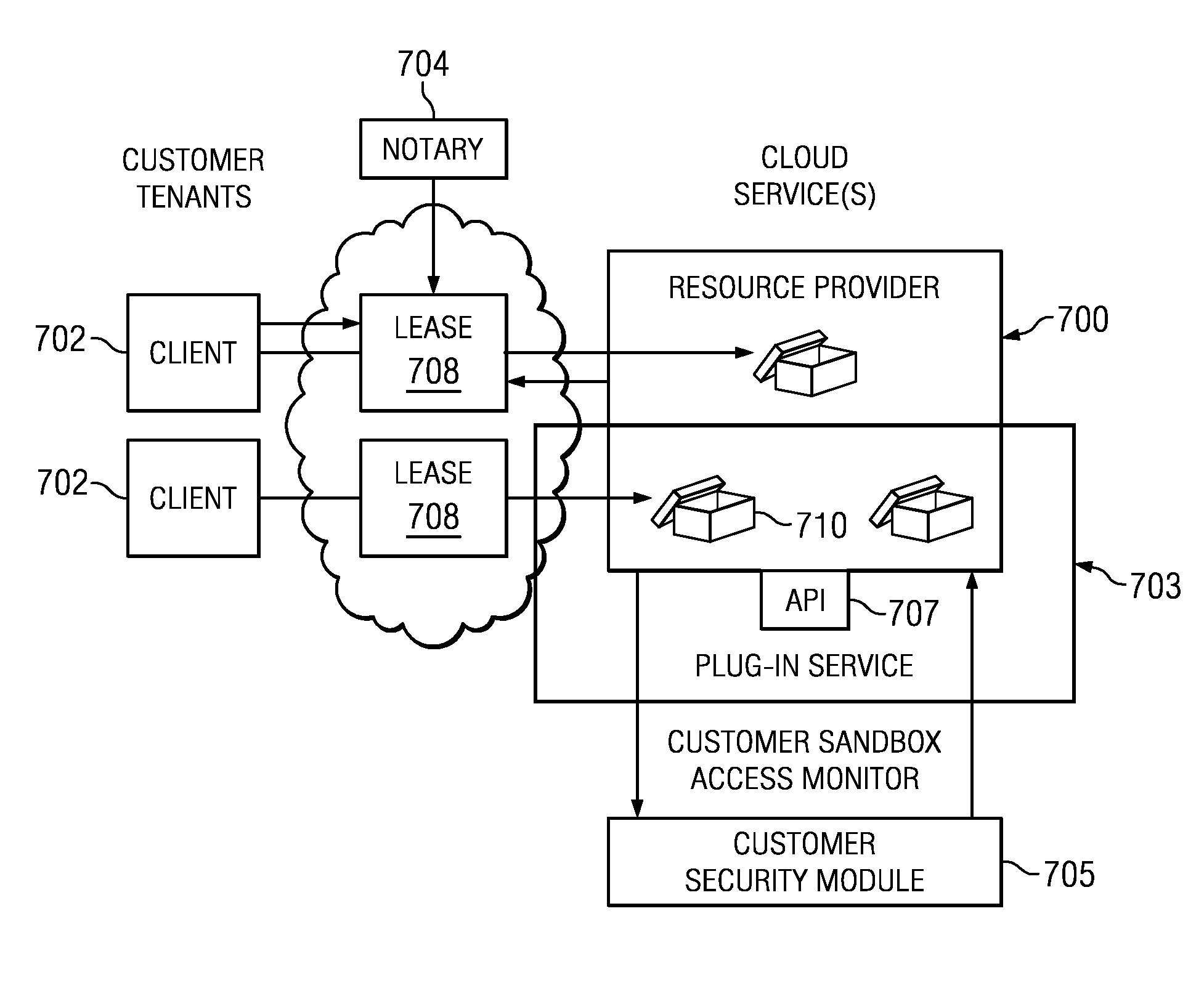
ActiveUS8769622B2Retain controlKey distribution for secure communicationDigital data processing detailsResource poolThird party
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
Storage mapping and partitioning among multiple host processors in the presence of login state changes and host controller replacement
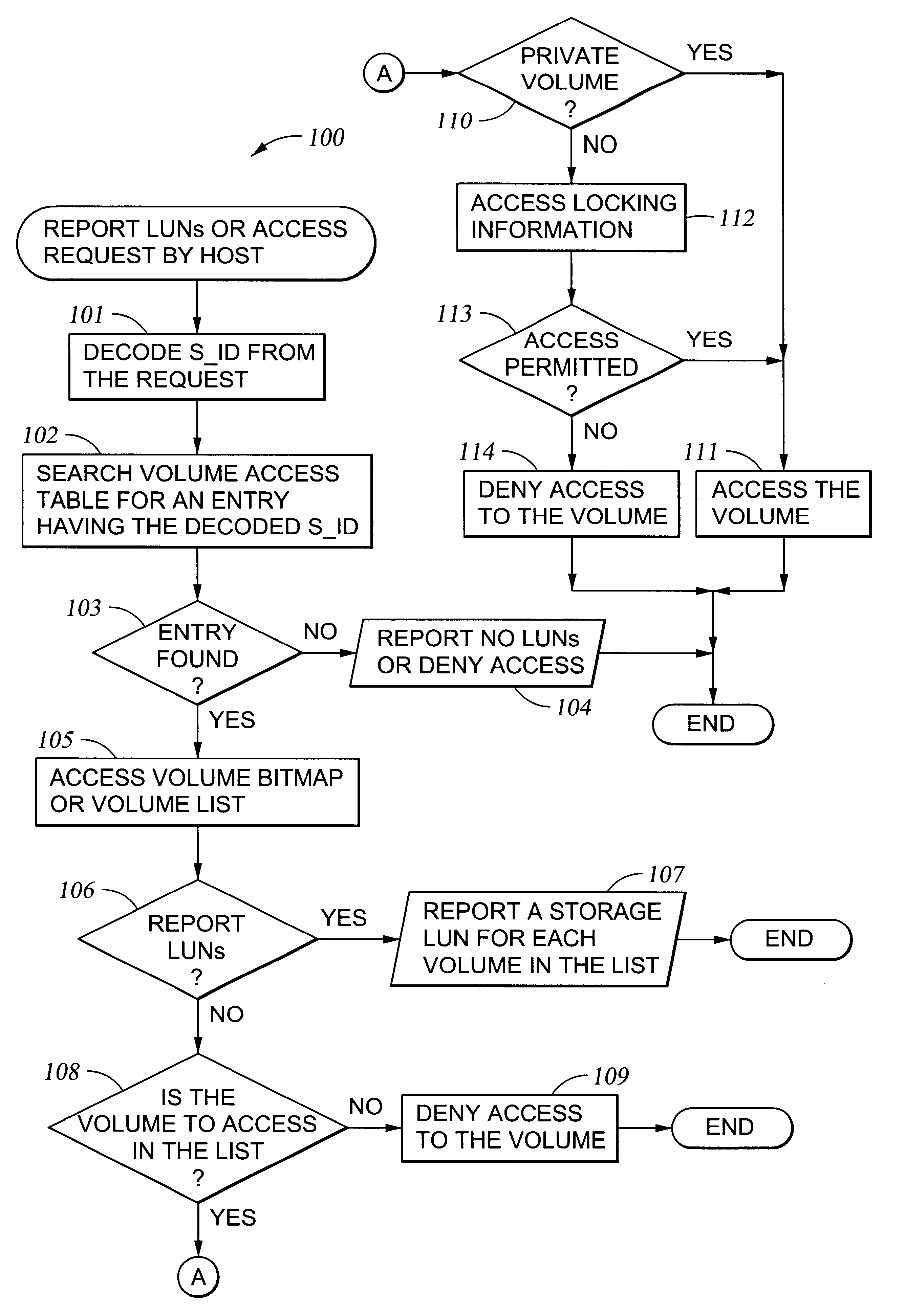
InactiveUS6260120B1Input/output to record carriersData processing applicationsData portControl store
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
Authentication and authorization methods for cloud computing security platform
ActiveUS20130007845A1Retain controlDigital data processing detailsUser identity/authority verificationThird partyResource pool
An authentication and authorization plug-in model for a cloud computing environment enables cloud customers to retain control over their enterprise information when their applications are deployed in the cloud. The cloud service provider provides a pluggable interface for customer security modules. When a customer deploys an application, the cloud environment administrator allocates a resource group (e.g., processors, storage, and memory) for the customer's application and data. The customer registers its own authentication and authorization security module with the cloud security service, and that security module is then used to control what persons or entities can access information associated with the deployed application. The cloud environment administrator, however, typically is not registered (as a permitted user) within the customer's security module; thus, the cloud environment administrator is not able to access (or release to others, or to the cloud's general resource pool) the resources assigned to the cloud customer (even though the administrator itself assigned those resources) or the associated business information. To further balance the rights of the various parties, a third party notary service protects the privacy and the access right of the customer when its application and information are deployed in the cloud.
Owner:IBM CORP
Secure network switching infrastructure
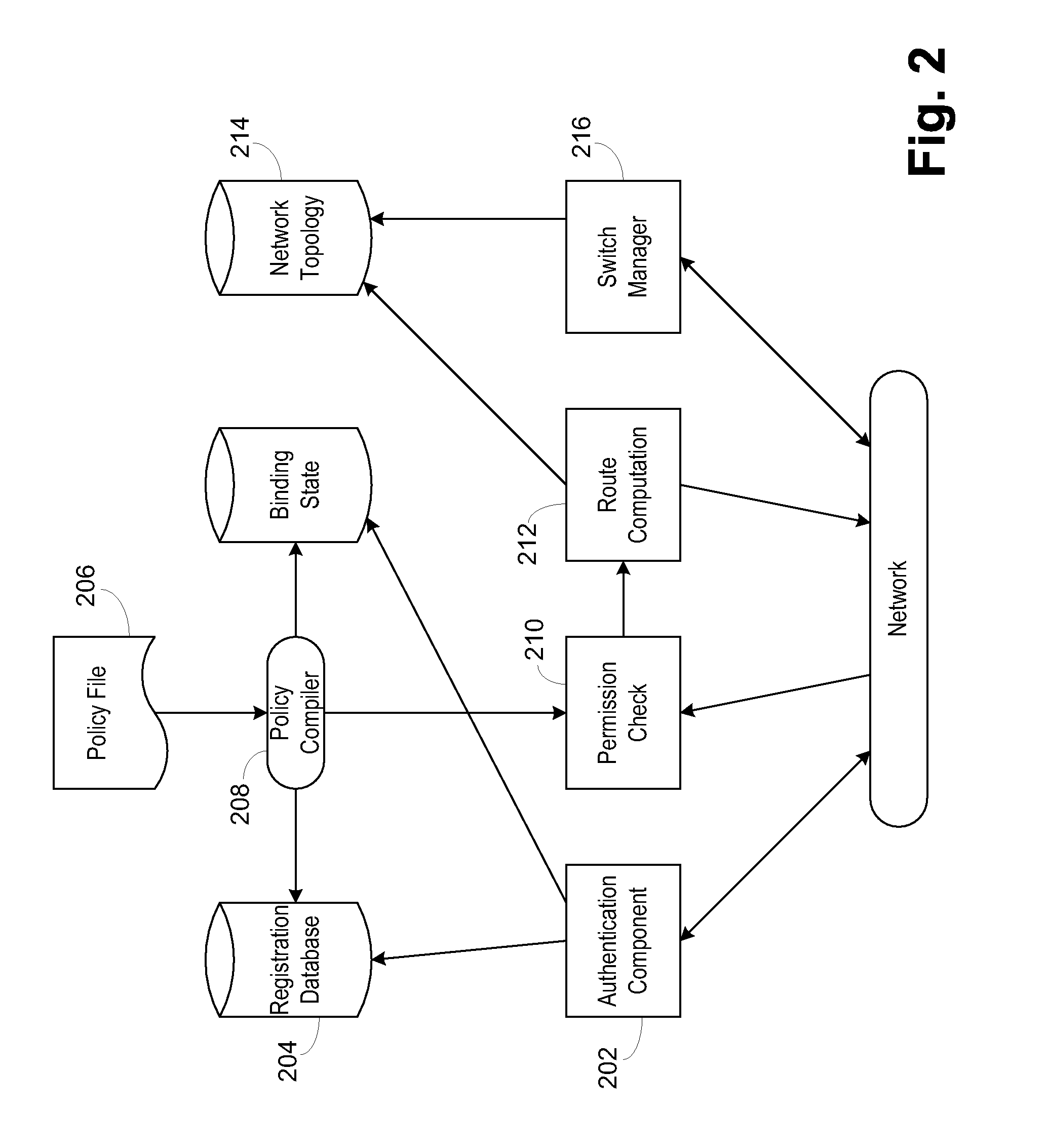
InactiveUS20080189769A1Reduces the trusted computing baseReduce overheadDigital data processing detailsUser identity/authority verificationNetwork packetNetwork control
Use of a centralized control architecture in a network. Policy declaration, routing computation, and permission checks are managed by a logically centralized controller. By default, hosts on the network can only route to the network controller. Hosts and users must first authenticate themselves with the controller before they can request access to the network resources. The controller uses the first packet of each flow for connection setup. When a packet arrives at the controller, the controller decides whether the flow represented by that packet should be allowed. The switches use a simple flow table to forward packets under the direction of the controller. When a packet arrives that is not in the flow table, it is forwarded to the controller, along with information about which port the packet arrived on. When a packet arrives that is in the flow table, it is forwarded according to the controller's directive.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Inductively charged battery pack
ActiveUS7375492B2Enabling user convenienceMaximizes flexibility and efficiency and safetyCircuit authenticationVolume/mass flow measurementElectrical batteryEngineering
An inductive charging systems transfers energy by inductively coupling a source coil on a charging source to a receiver coil on a charging portion of a battery pack. The source current is received in the battery pack and converted to direct current for storage in the battery pack cells. Communication between a charging source and the charging portion is provided. A wireless communication arrangement provides for authentication of devices that are allowed by a source to be charged.
Owner:MICROSOFT TECH LICENSING LLC
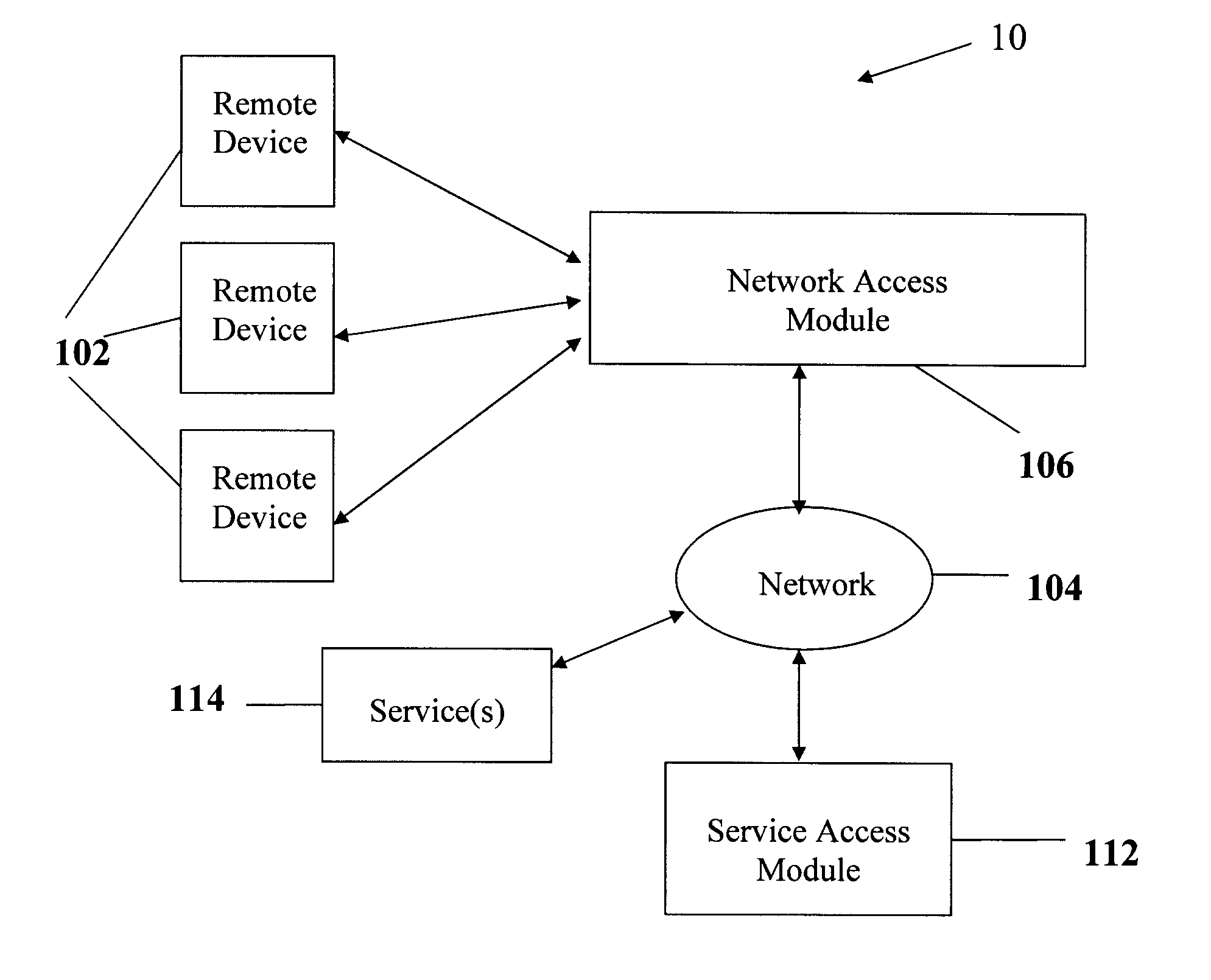
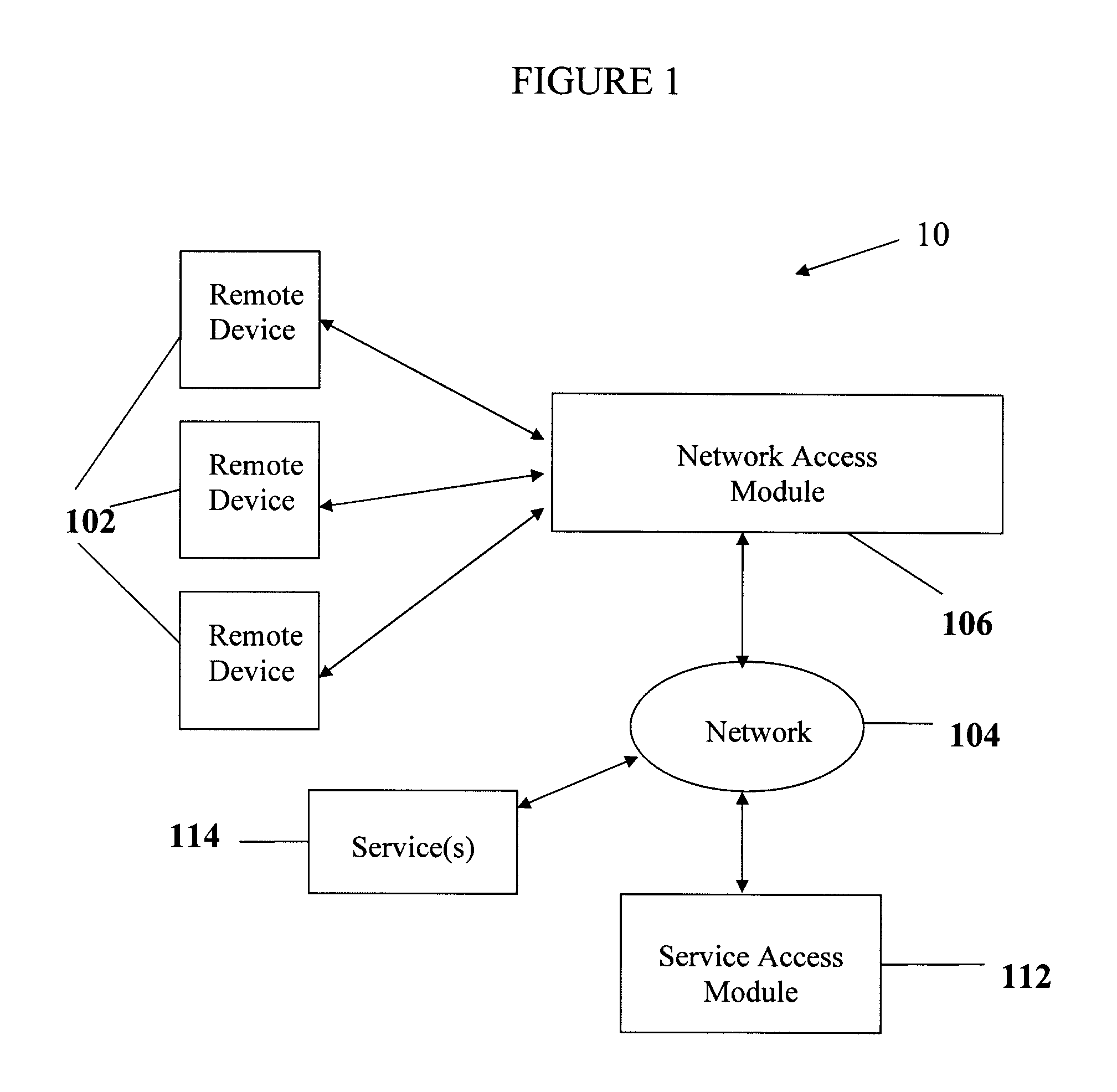
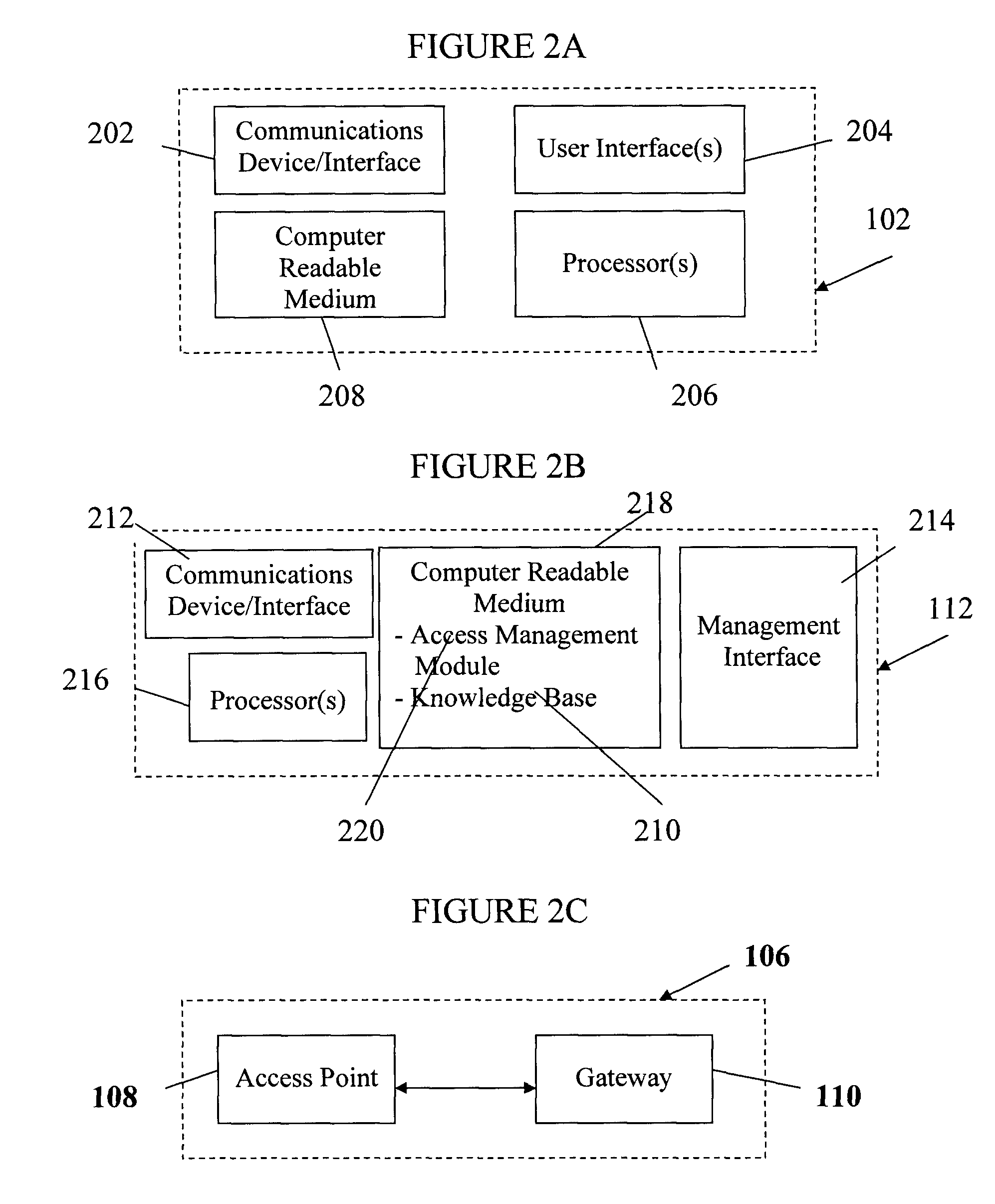
Remote service access system and method
InactiveUS20100107225A1Limited accessDigital data processing detailsMultiple digital computer combinationsData validationComputer network
A wireless service access system and method are disclosed. One aspect of the disclosed system provides a remote device wireless access to one or more services over a communication network, the system comprising a network access module adapted for communicating wirelessly with the remote device and for receiving therefrom identifying data; and a service access module, communicatively linked to the network access module, for authenticating the remote device based on the identifying data and authorizing access to the one or more services thereto via the network access module.
Owner:DATAVALET TECH
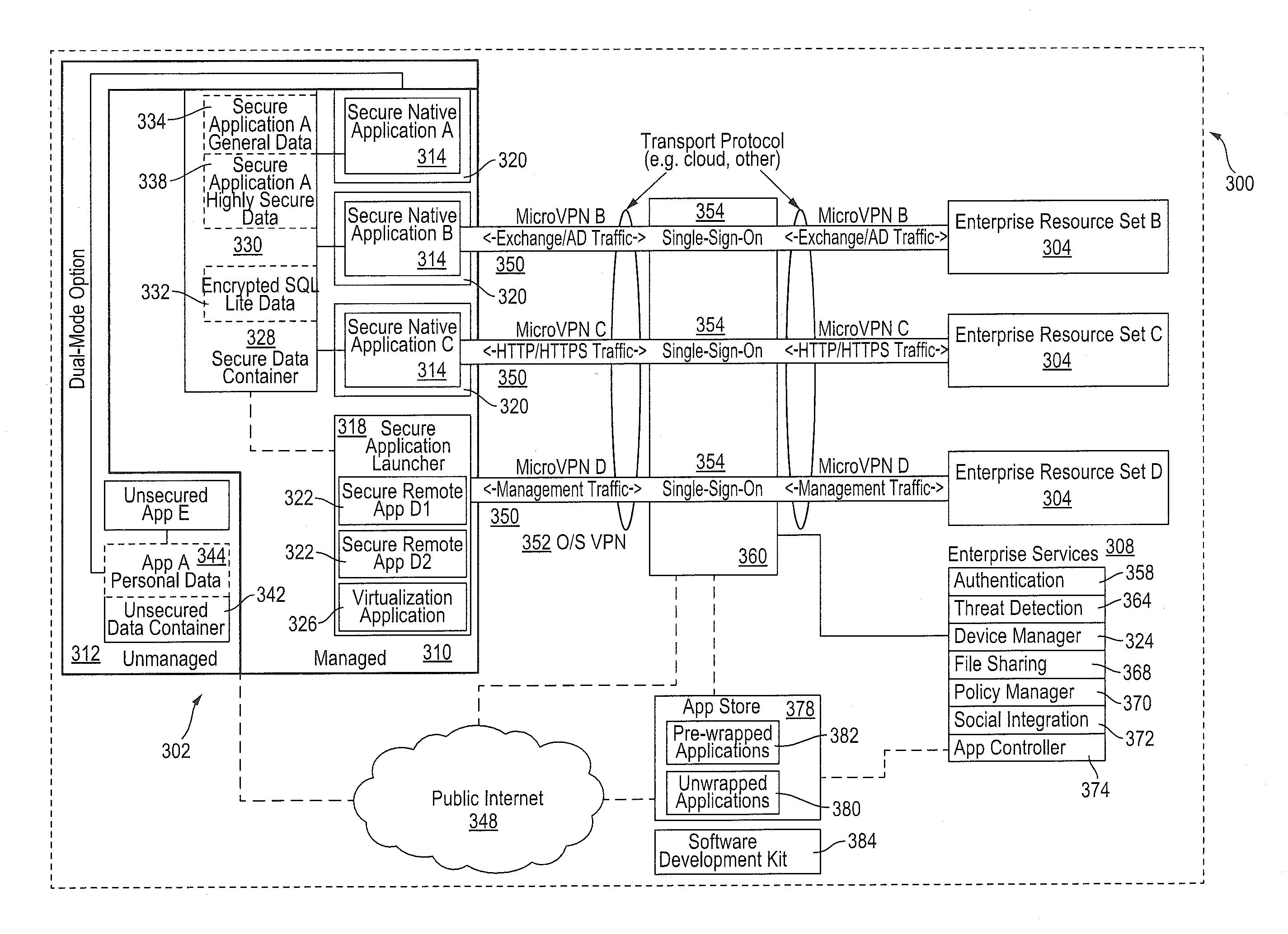
Policy-Based Application Management
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
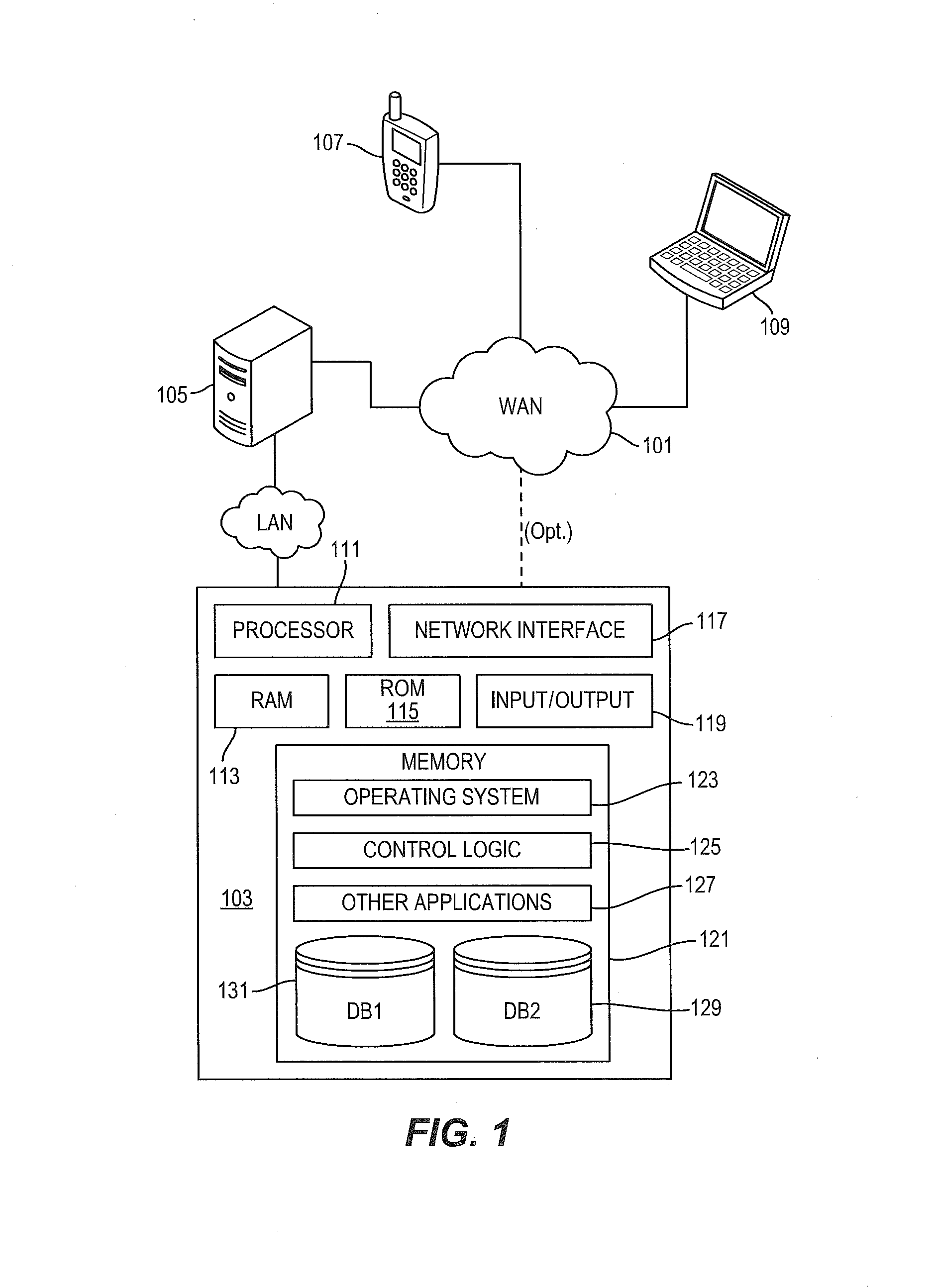
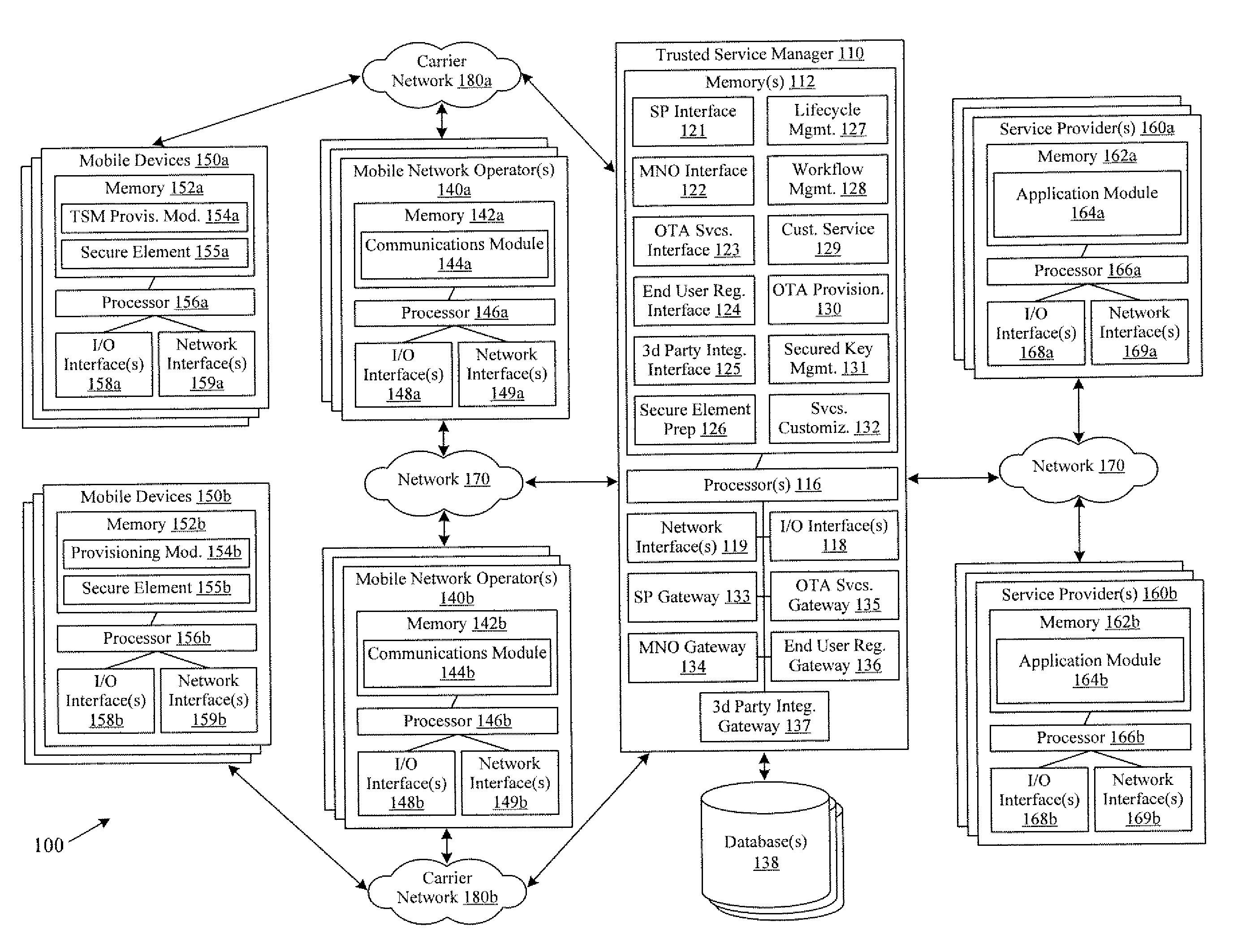
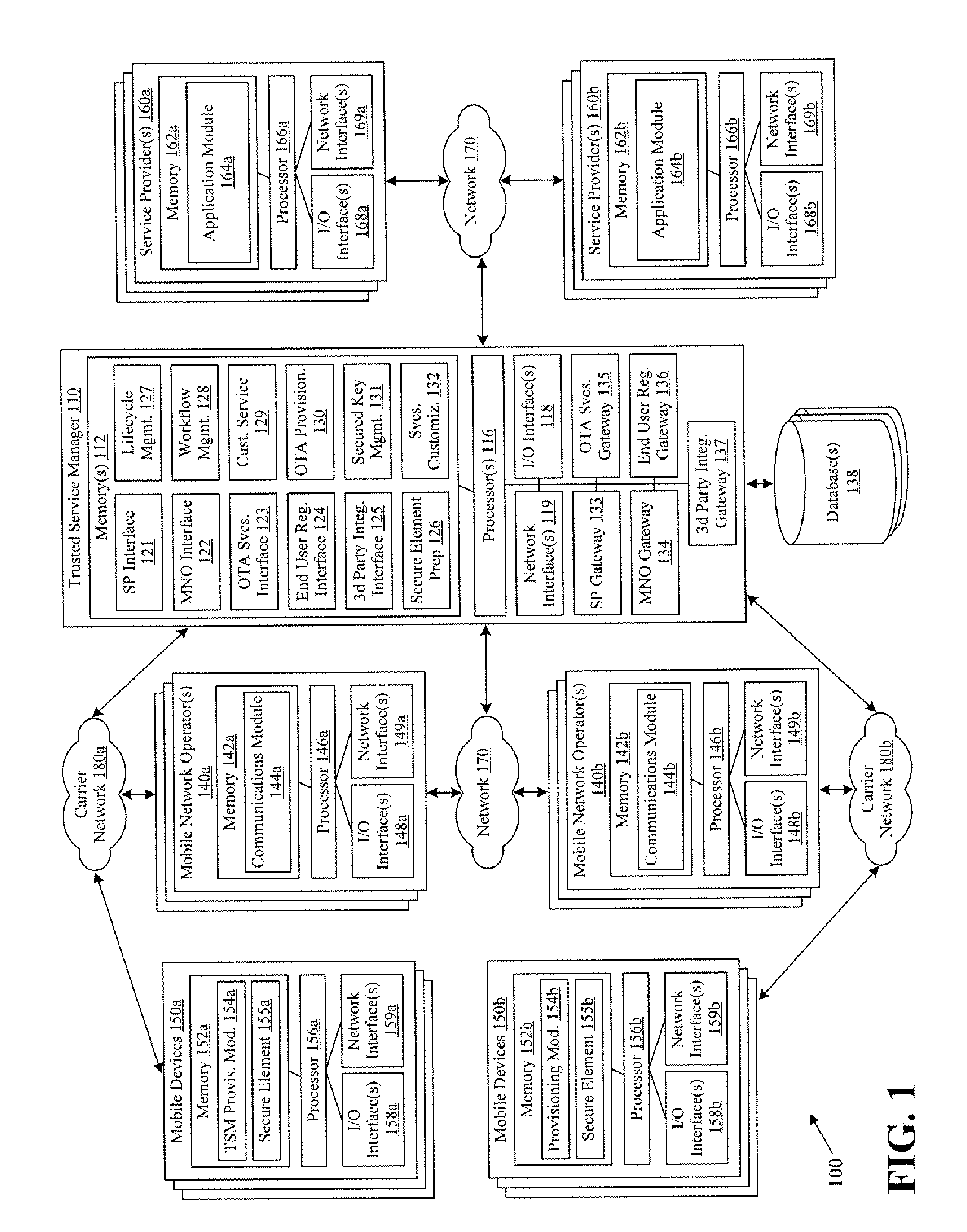
Systems and methods for providing trusted service management services
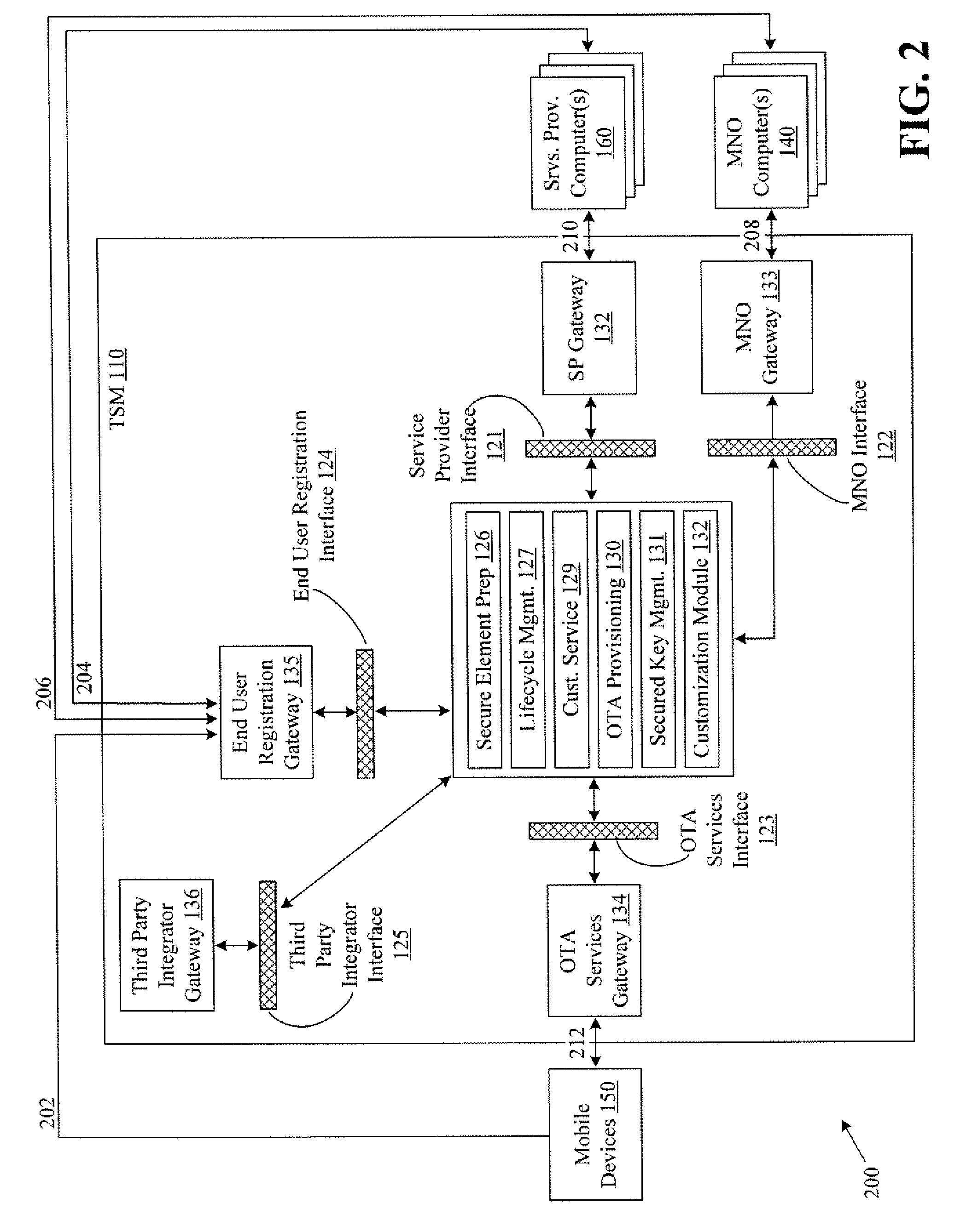
InactiveUS20100291904A1Easy maintenanceOptimize networkService provisioningSpecial service for subscribersService provisionMobile device
Embodiments of the invention provide systems and methods for providing trusted service management services. According to one embodiment, a system can include at least one service provider gateway operable to receive and transmit messages with multiple service providers; at least one mobile network operator gateway operable to receive and transmit messages with multiple mobile network operators; at least one provisioning gateway operable to transmit mobile device application data with multiple mobile devices and to receive messages from the plurality of mobile devices. The system can further include a processor operable to execute computer-executable instructions to: facilitate service provider communications by providing a common service provider interface for the service providers; facilitate mobile network operator communications by providing a common mobile network operator interface for the mobile network operators; facilitate provisioning multiple mobile device applications with the mobile devices; and facilitate communications with the mobile devices.
Owner:FIRST DATA
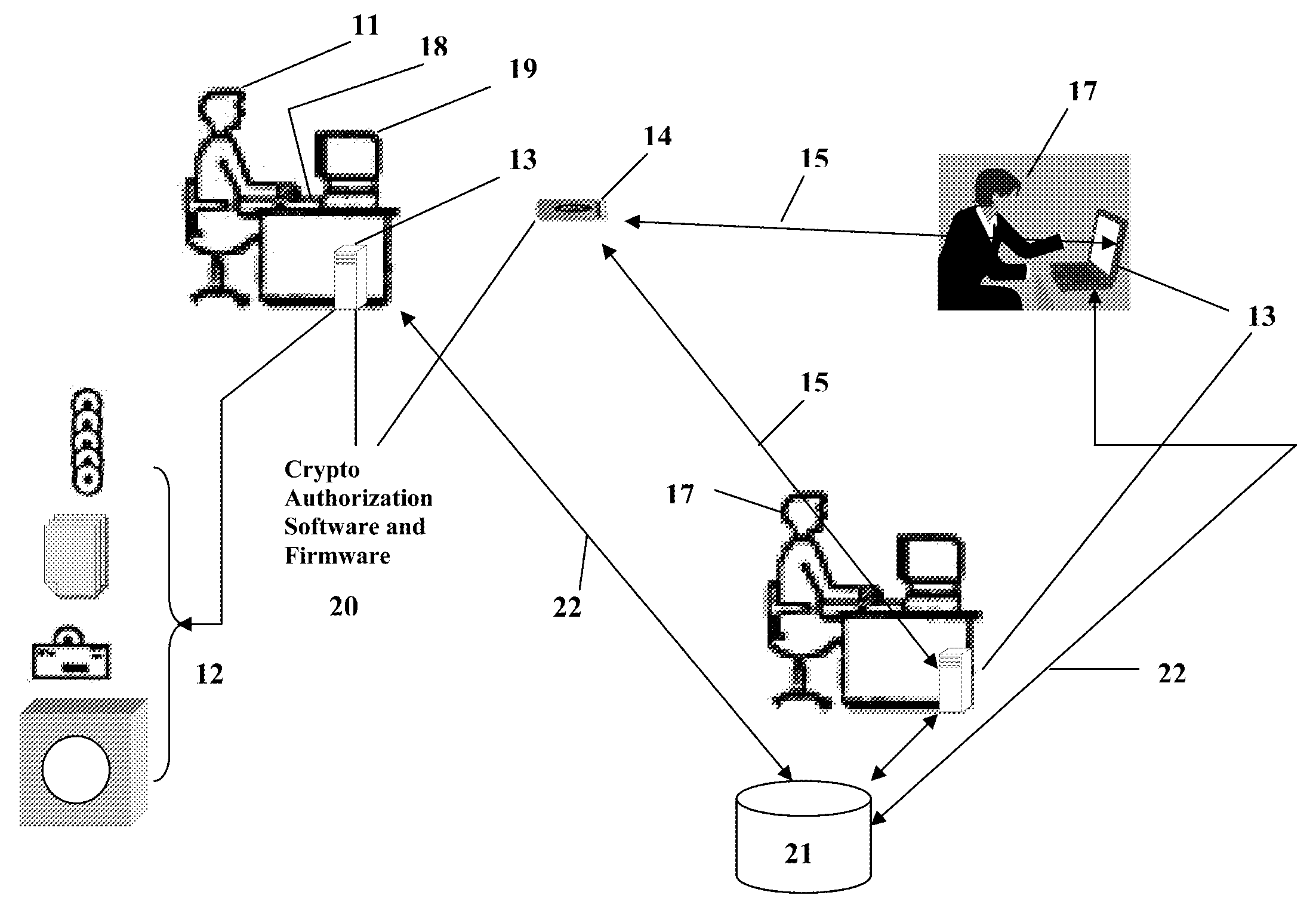
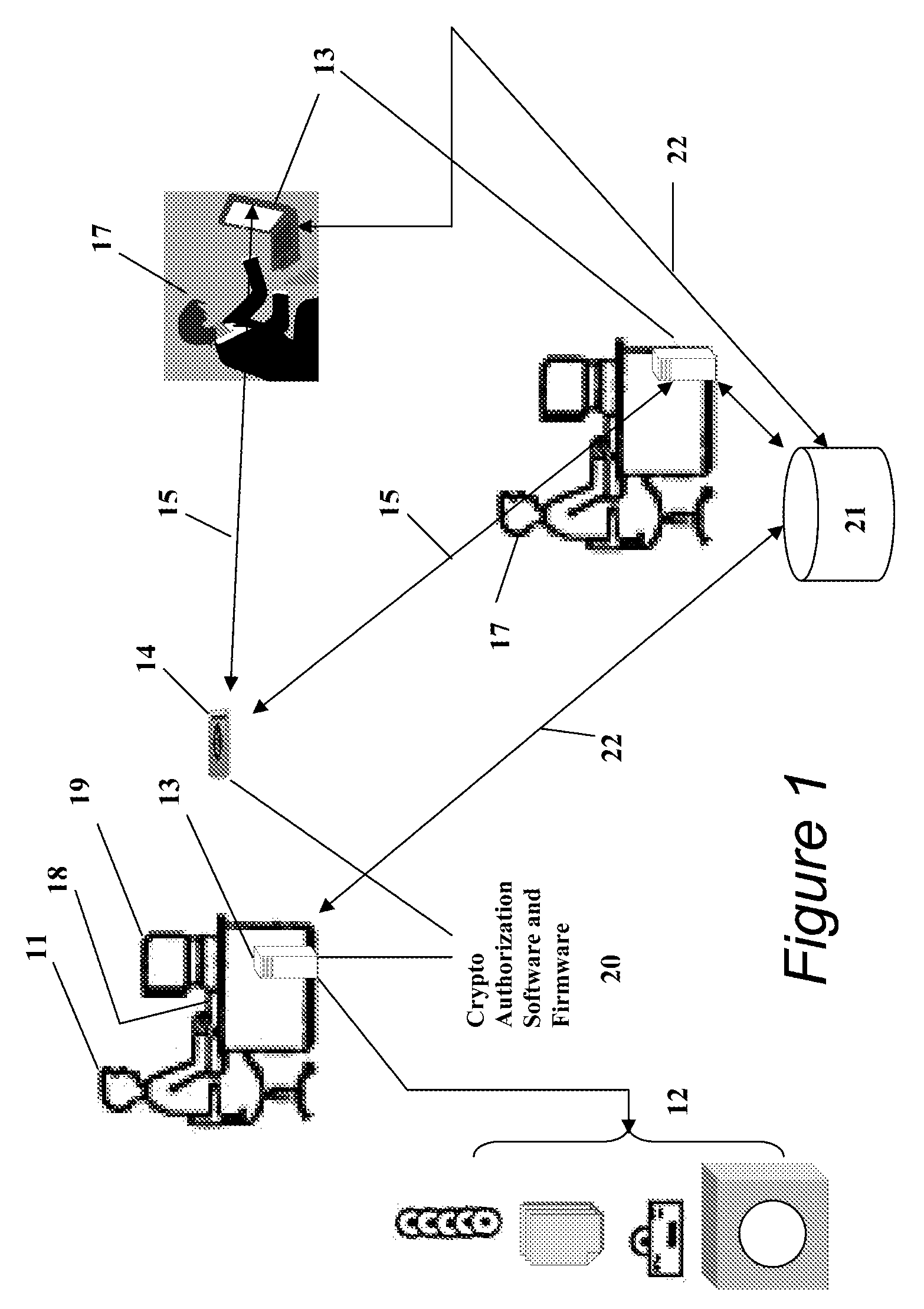
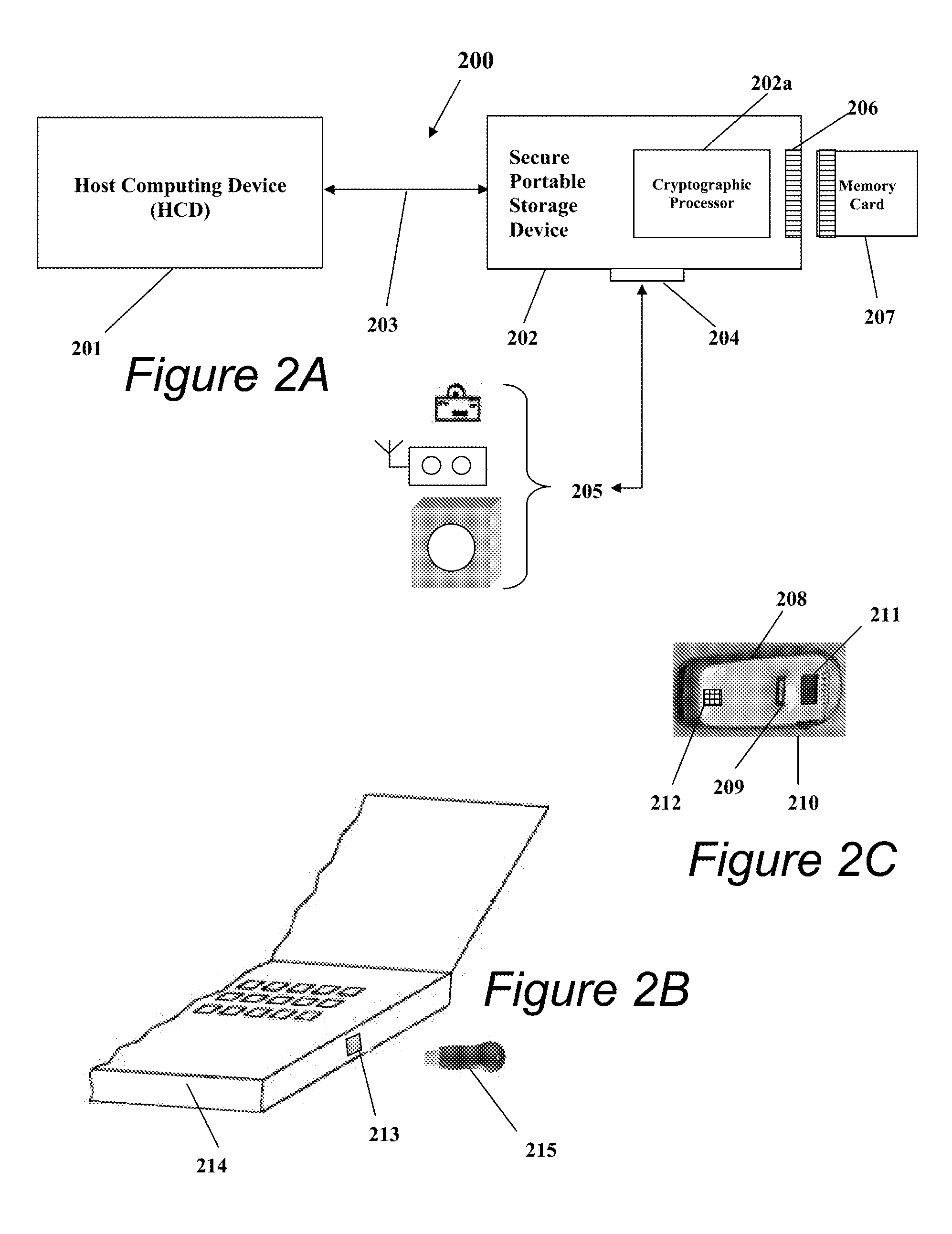
Portable Data Encryption Device with Configurable Security Functionality and Method for File Encryption
InactiveUS20080263363A1Mitigates and eliminates vulnerabilityUser identity/authority verificationInternal/peripheral component protectionComputer hardwarePlaintext
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
Policy-Based Application Management
ActiveUS20140032691A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
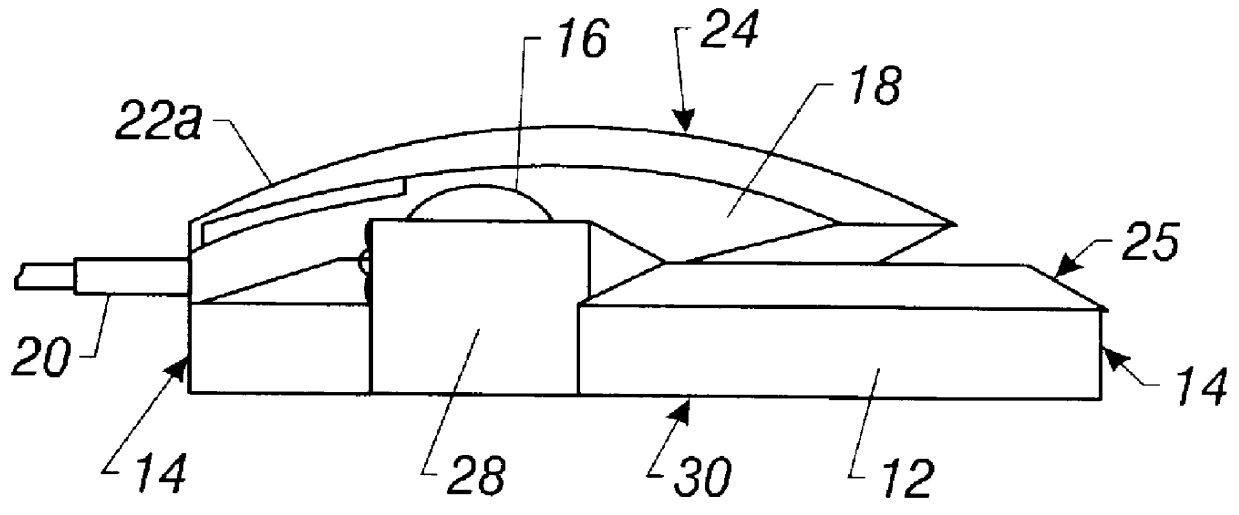
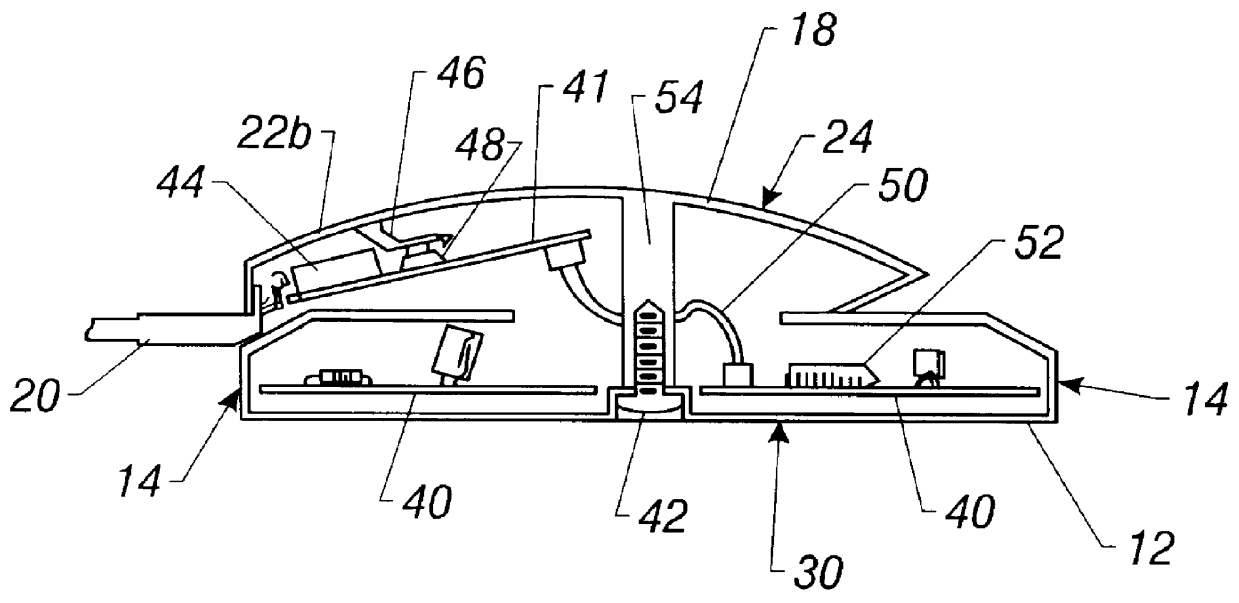
Pointing device with biometric sensor
InactiveUS6148094ACathode-ray tube indicatorsInternal/peripheral component protectionComputerized systemPointing device
A pointing device incorporates a biometric sensor at a location such that when operating the pointing device in a normal manner, a user's hand rests naturally in a position to place a finger of the user's hand in proximity to and readable by the biometric sensor. In one embodiment, a computer trackball pointing device includes a fingerprint sensor which is equally well suitable for use by either a right-handed or a left-handed user. Along with positional information from a position sensor and user selection information from at least one user-depressable button, the pointing device also conveys to an attached computer system information associated with the user's identity detected by the fingerprint sensor. Such a pointing device is well suited to both transparent verification as well as continuous verification, for if a user removes his or her hand from the natural position when using the device, the user's fingerprint will no longer be detectable by the fingerprint sensor, and the computer system to which the pointing device is attached can be alerted as to the need to re-authenticate any additional attempts at using the pointing device.
Owner:DALTON PATRICK ENTERPRISES
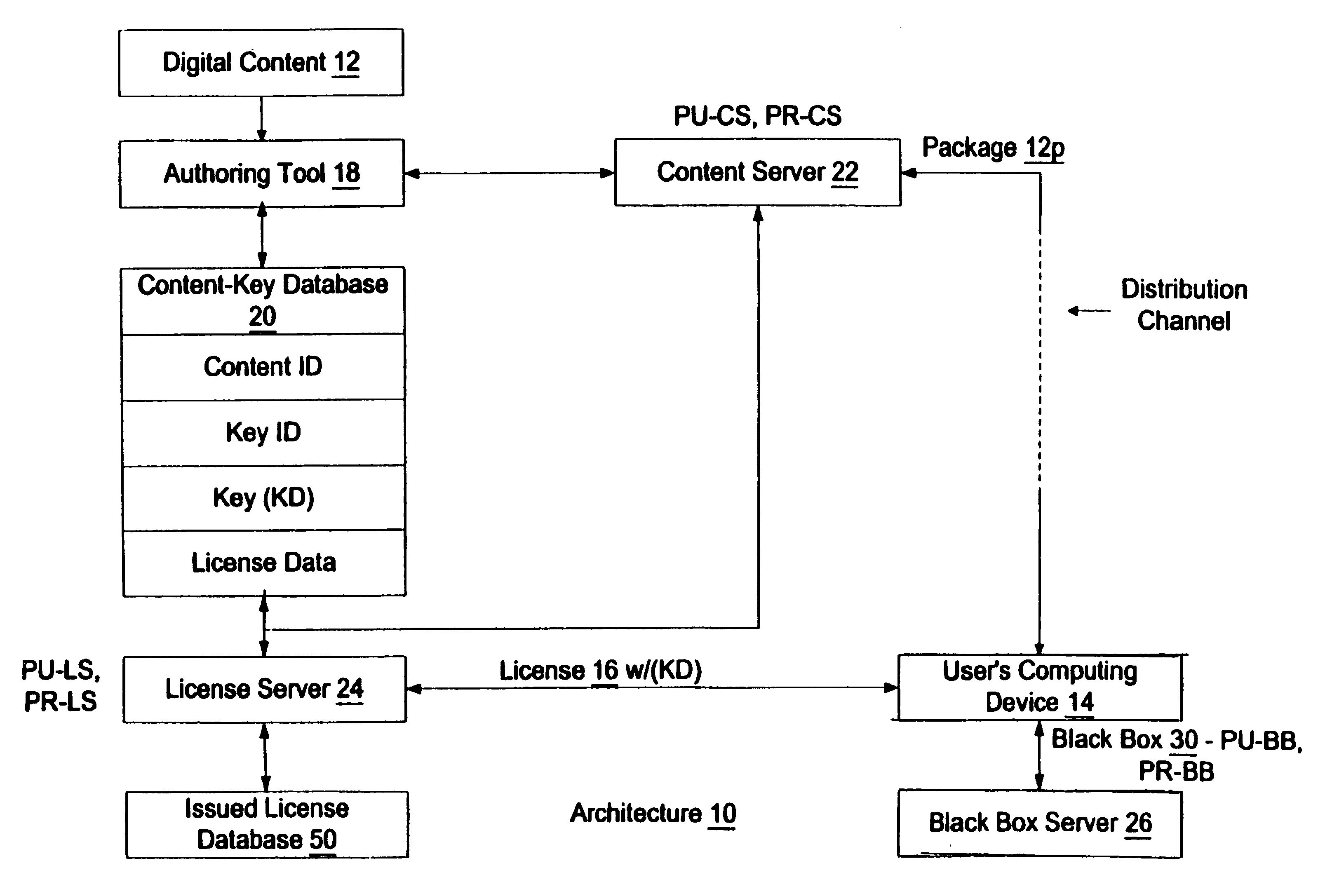
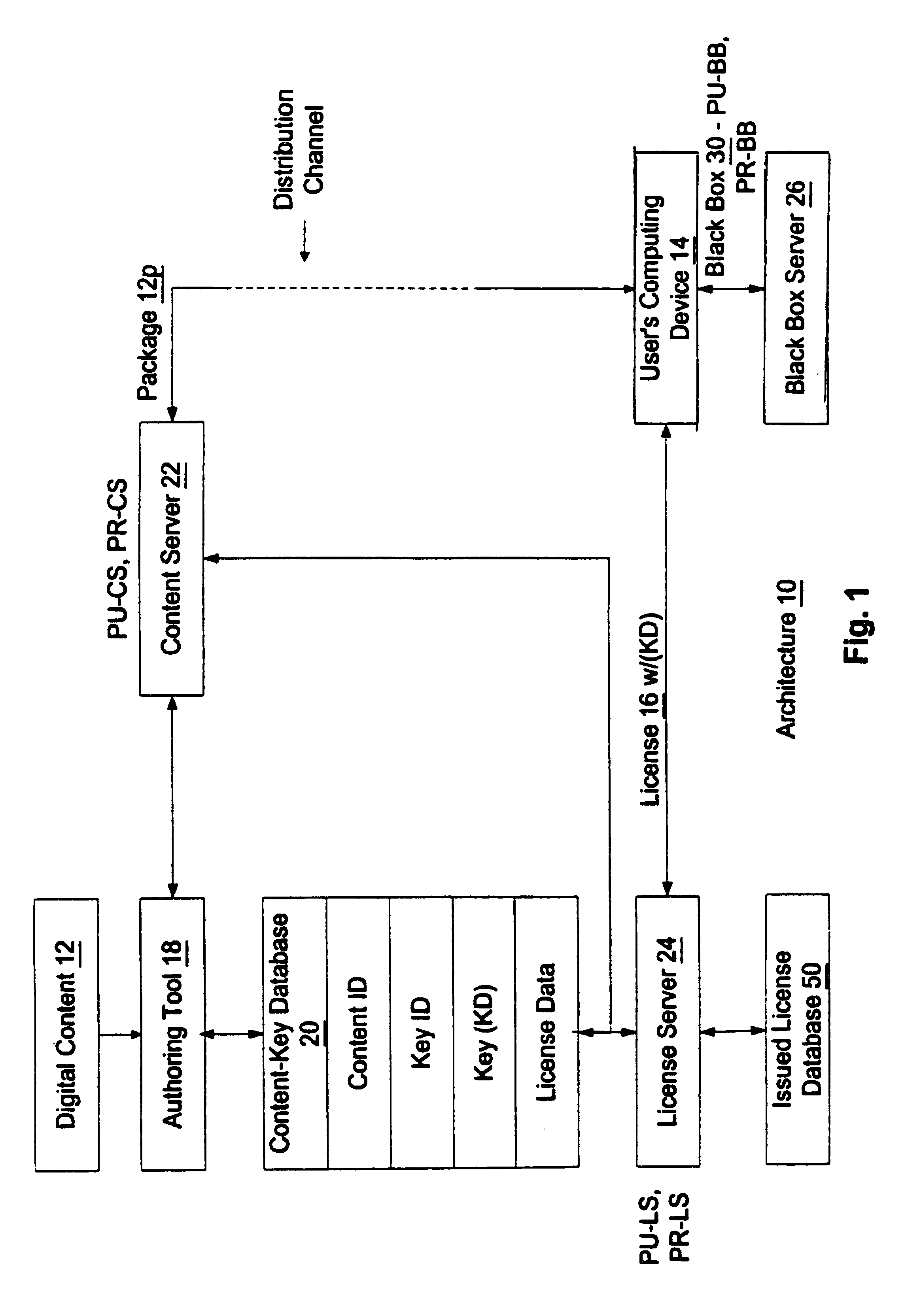
Enforcement architecture and method for digital rights management
InactiveUS7103574B1Satisfies needKey distribution for secure communicationDigital data processing detailsDigital contentNumber content
An enforcement architecture and method for implementing digital rights management are disclosed. Digital content is distributed from a content server to a computing device of a user and received, and an attempt is made to render the digital content by way of a rendering application. The rendering application invokes a Digital Rights Management (DRM) system, and such DRM system determines whether a right to render the digital content in the manner sought exists based on any digital license stored in the computing device and corresponding to the digital content. If the right does not exist, a digital license that provides such right and that corresponds to the digital content is requested from a license server, and the license server issues the digital license to the DRM system. The computing device receives the issued digital license and stores the received digital license thereon.
Owner:MICROSOFT TECH LICENSING LLC
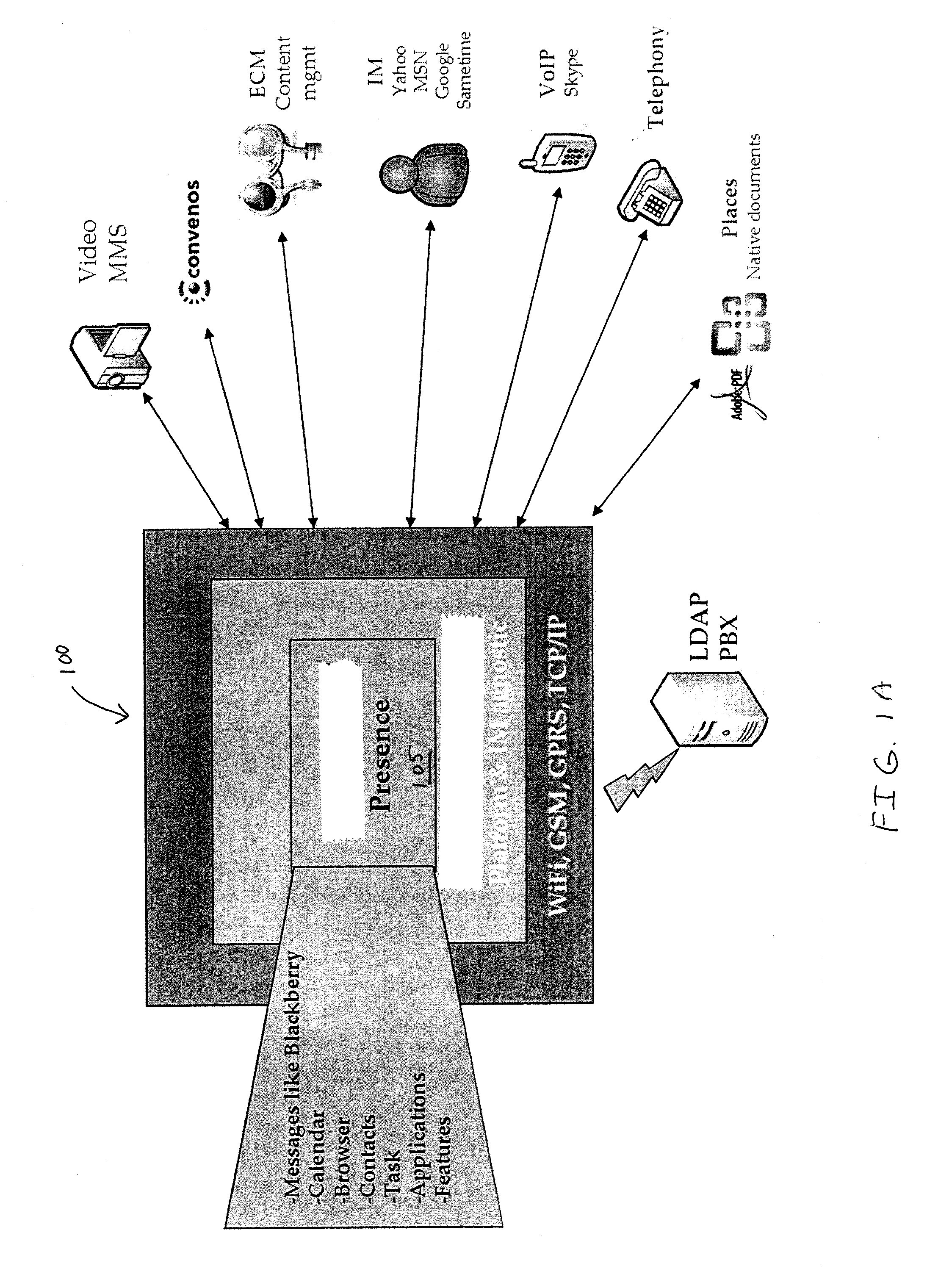
Apparatus, system, method, and computer program product for collaboration via one or more networks
InactiveUS20090019367A1Work well togetherFacilitate conferencing and collaborationDigital data protectionMultiple digital computer combinationsVirtual conferenceSpeech sound
A collaboration architecture supports virtual meetings, including web conferencing and collaboration. Presence information is aggregated from different types of communication services to provide a generic representation of presence. In one implementation, collaboration lifecycle management is provided to manage meetings over the lifecycle of a project. Audio options include voice over internet protocol (VoIP) and conventional PTSN phone networks, which are supported in one implementation by an audio conferencing server.
Owner:CONVENOUS
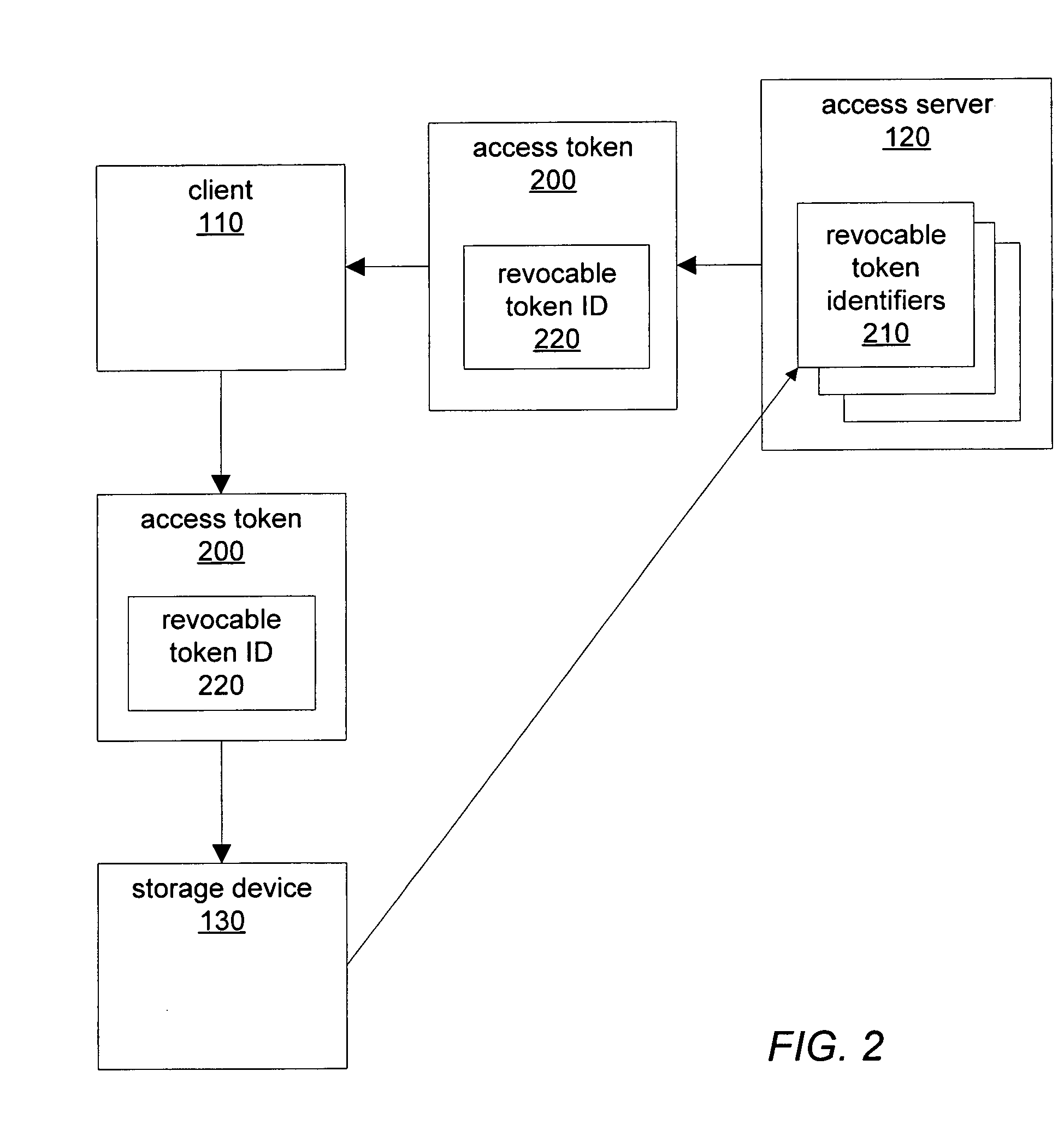
Secure storage access using third party capability tokens
ActiveUS8042163B1Digital data processing detailsMultiple digital computer combinationsThird partyClient-side
A method for revocable token identifiers may be employed in a shared storage environment. An access server may generate access tokens and include revocable token identifiers previously obtained from storage devices. When clients present access tokens to storage devices during storage requests, storage devices may check the validity of access tokens by verifying that the revocable token identifiers were previously issued to the access server. An access server may request that the storage device revoke revocable token identifiers. Storage devices may deny any future storage requests including revoked token identifiers. Additionally, an access token may include instructions specifying operations for a storage device to perform in conjunction with a storage request. A trusted server may issue grantor tokens granting permissions for access servers to use when issuing access tokens. An access server may then include such a grantor token in access tokens that it generates and issues to clients.
Owner:CA TECH INC
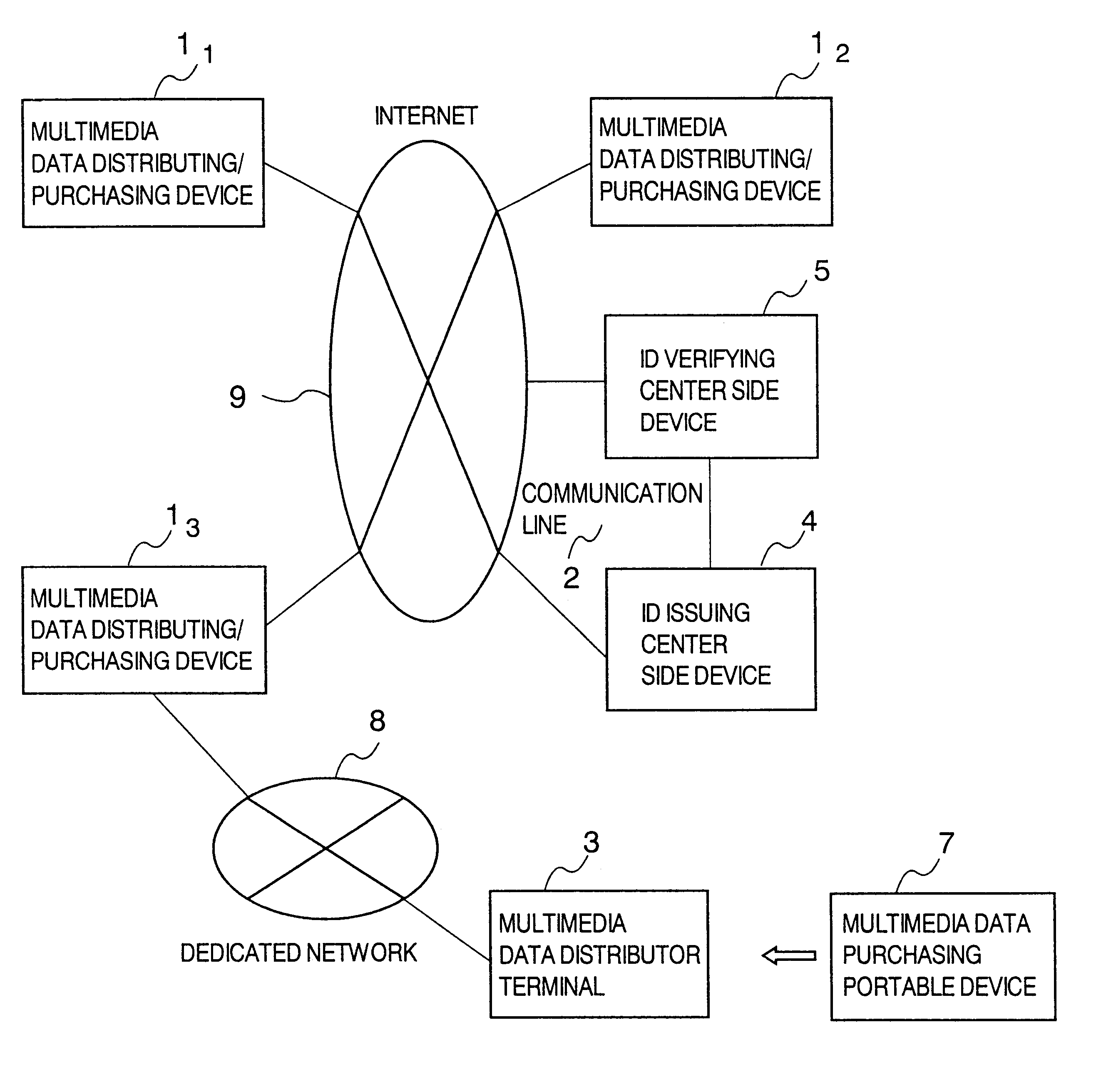
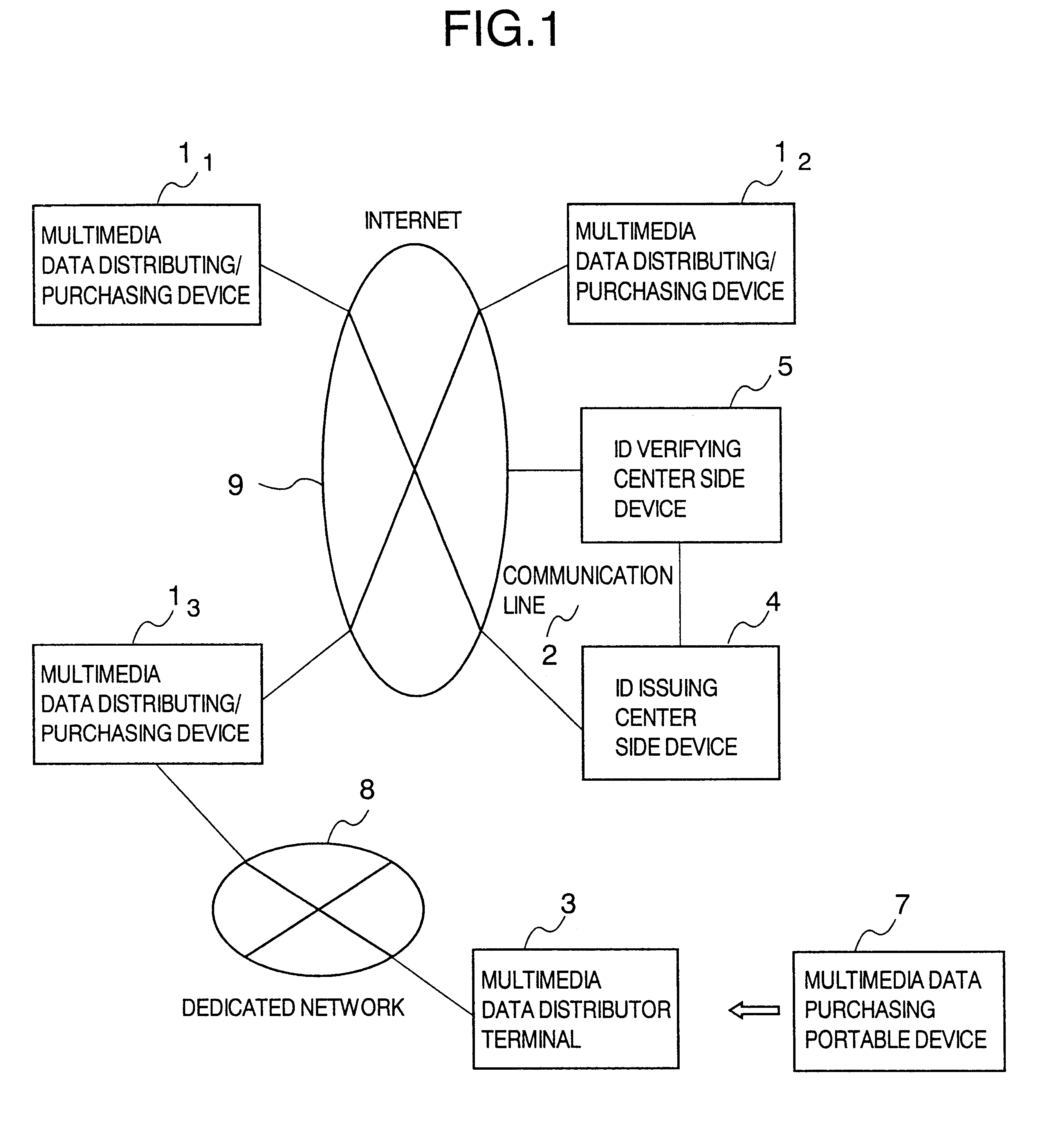
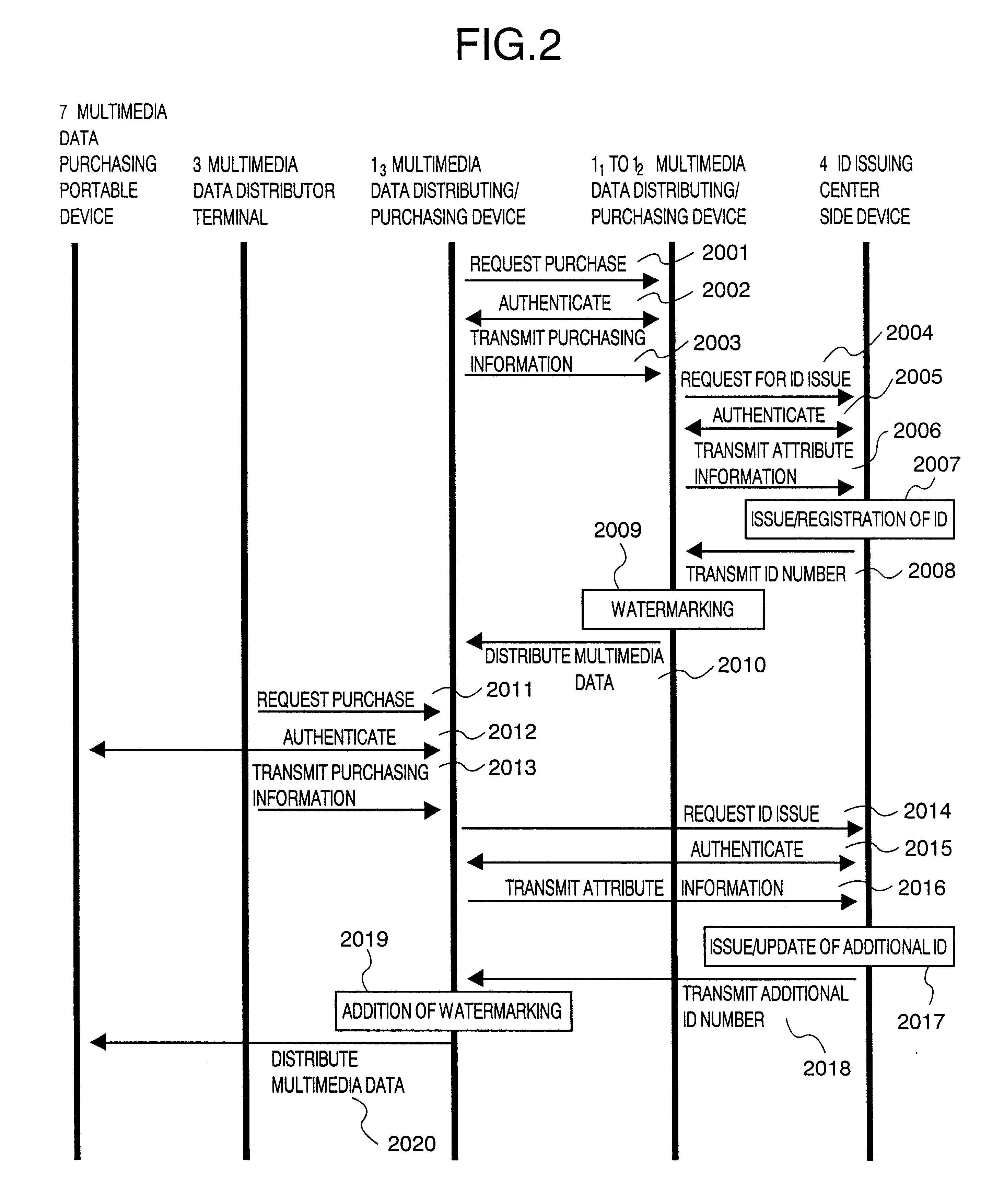
Method and system for distributing multimedia data with management information
InactiveUS6889211B1Data processing applicationsDigital data protectionInformation embeddingManagement information systems
A multimedia data distributing system comprising an ID issuing center side device and a multimedia data distributor side device for distributing multimedia data as electronic data to a purchaser of the multimedia data. The multimedia data distributor device includes: an attribute information transmitting unit that transmits attribute information of the electronic data indicating the multimedia data to be distributed, to the ID issuing center side device; a watermark information embedding unit that embeds information specifying the ID number transmitted from the ID issuing center side device in response to the attribute information transmitted to the attribute information transmitting unit, as an watermark information in the electronic data indicating the multimedia data to be distributed; and a distribution unit that distributes the electronic data indicating the multimedia data, in which the information specifying the ID number is embedded as the watermark information by the watermark information embedding unit, to the purchaser of the multimedia data. The ID issuing center side device includes: an ID number generating unit that generates a unique ID number and registering the generated ID number in a database in a manner to correspond to the attribute information transmitted by the distributor of the multimedia data; and an ID number transmitting unit that transmits the information specifying the generated ID number to the multimedia data distributor device.
Owner:HITACHI LTD
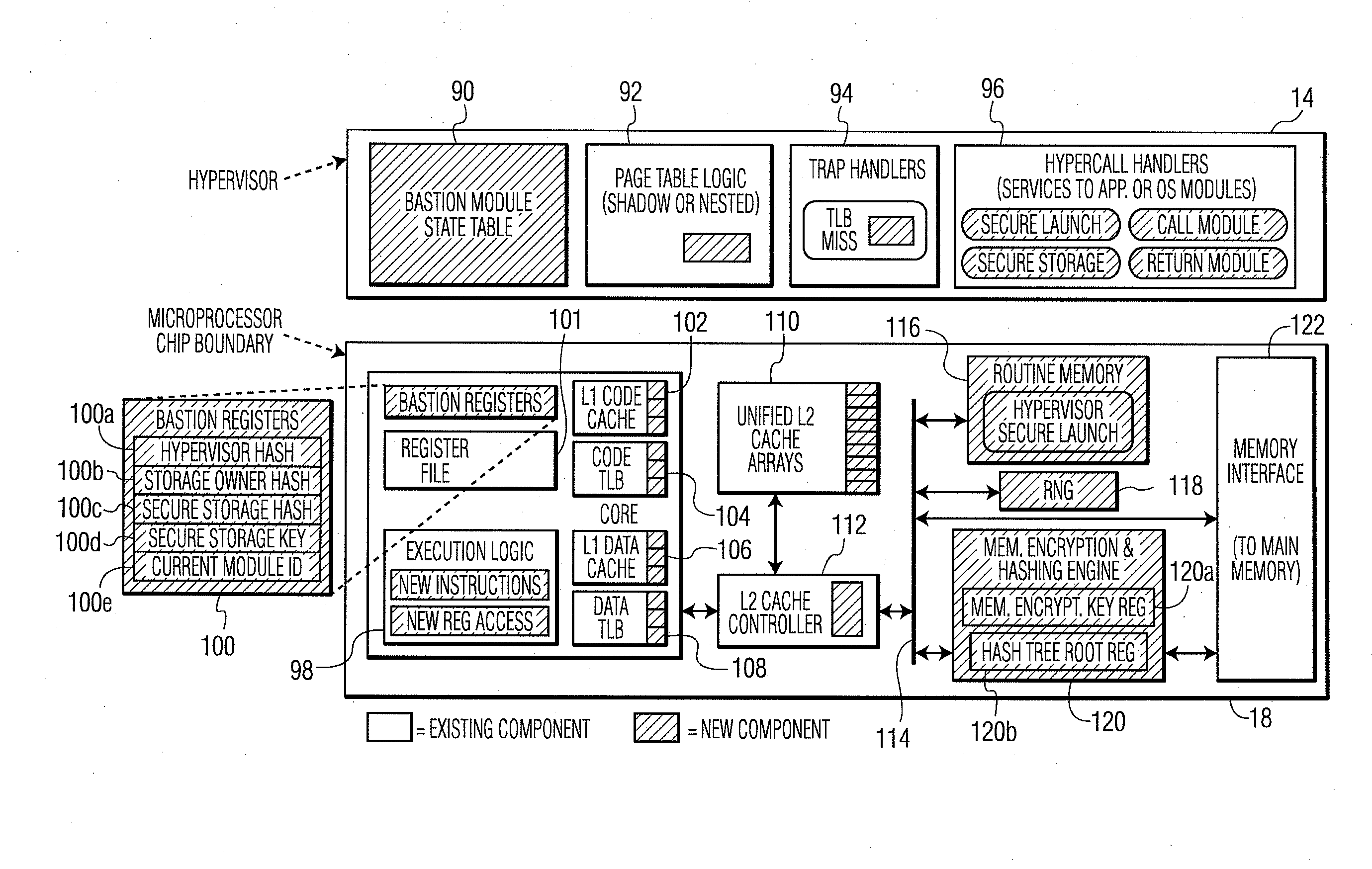
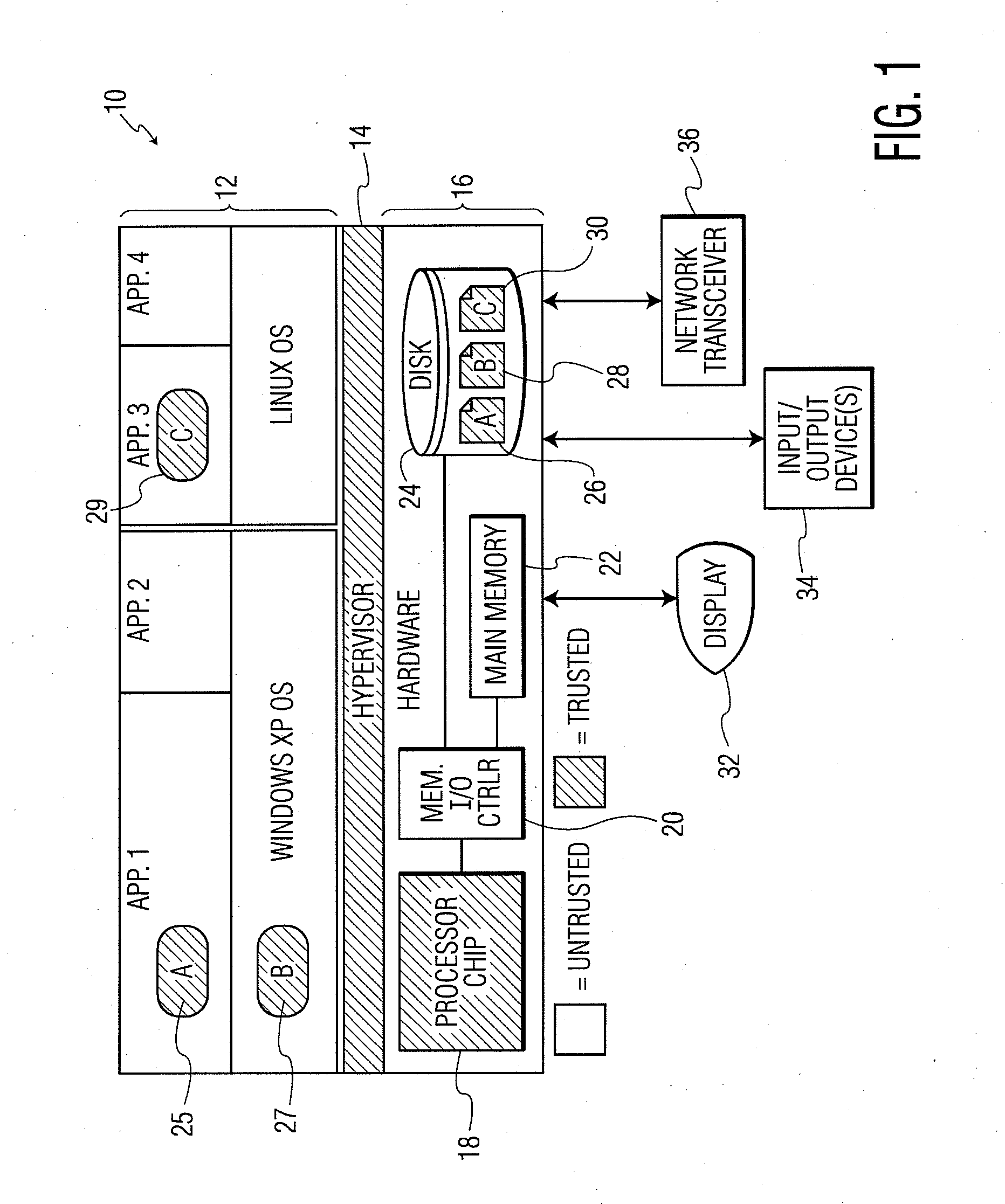
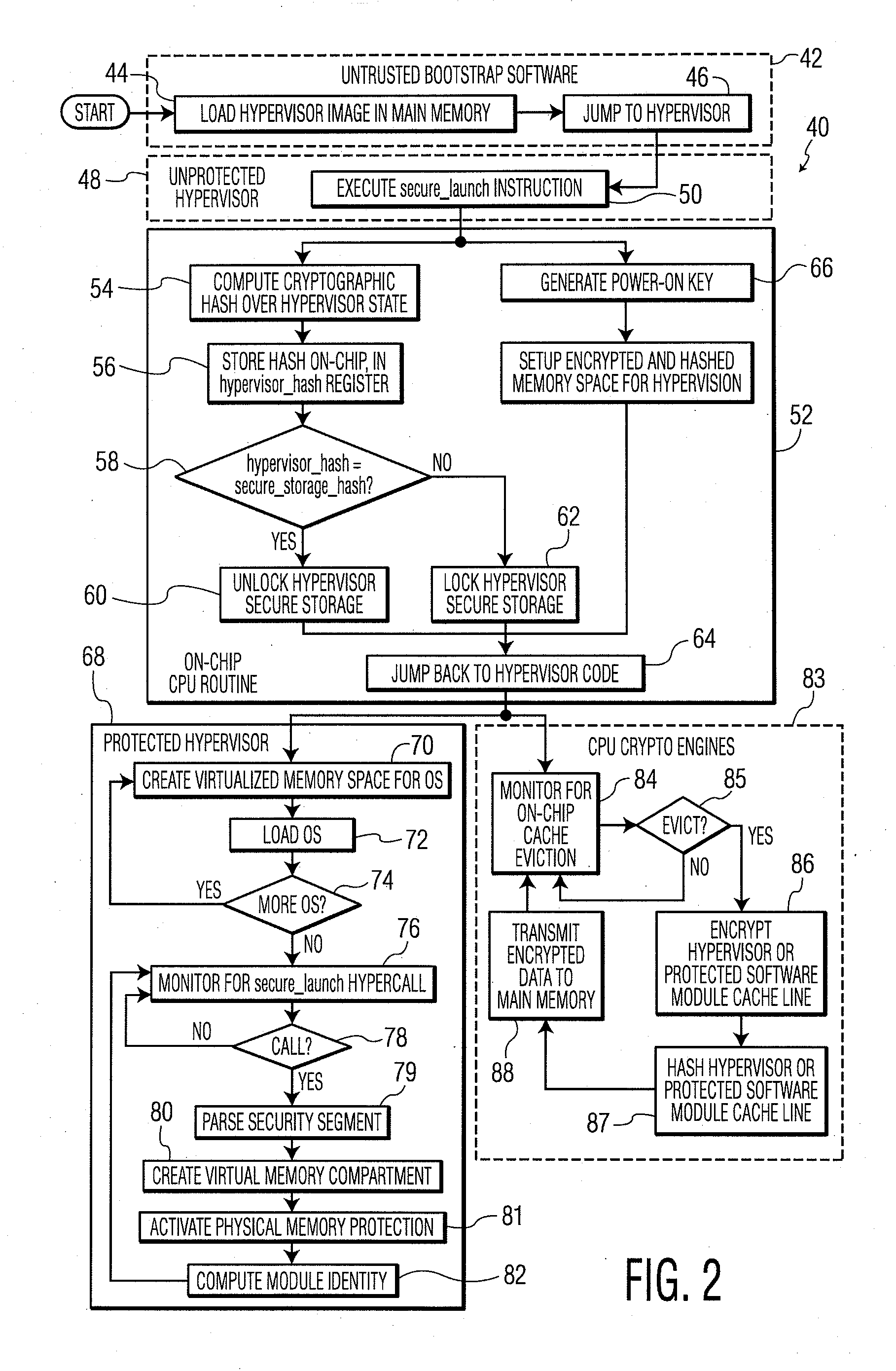
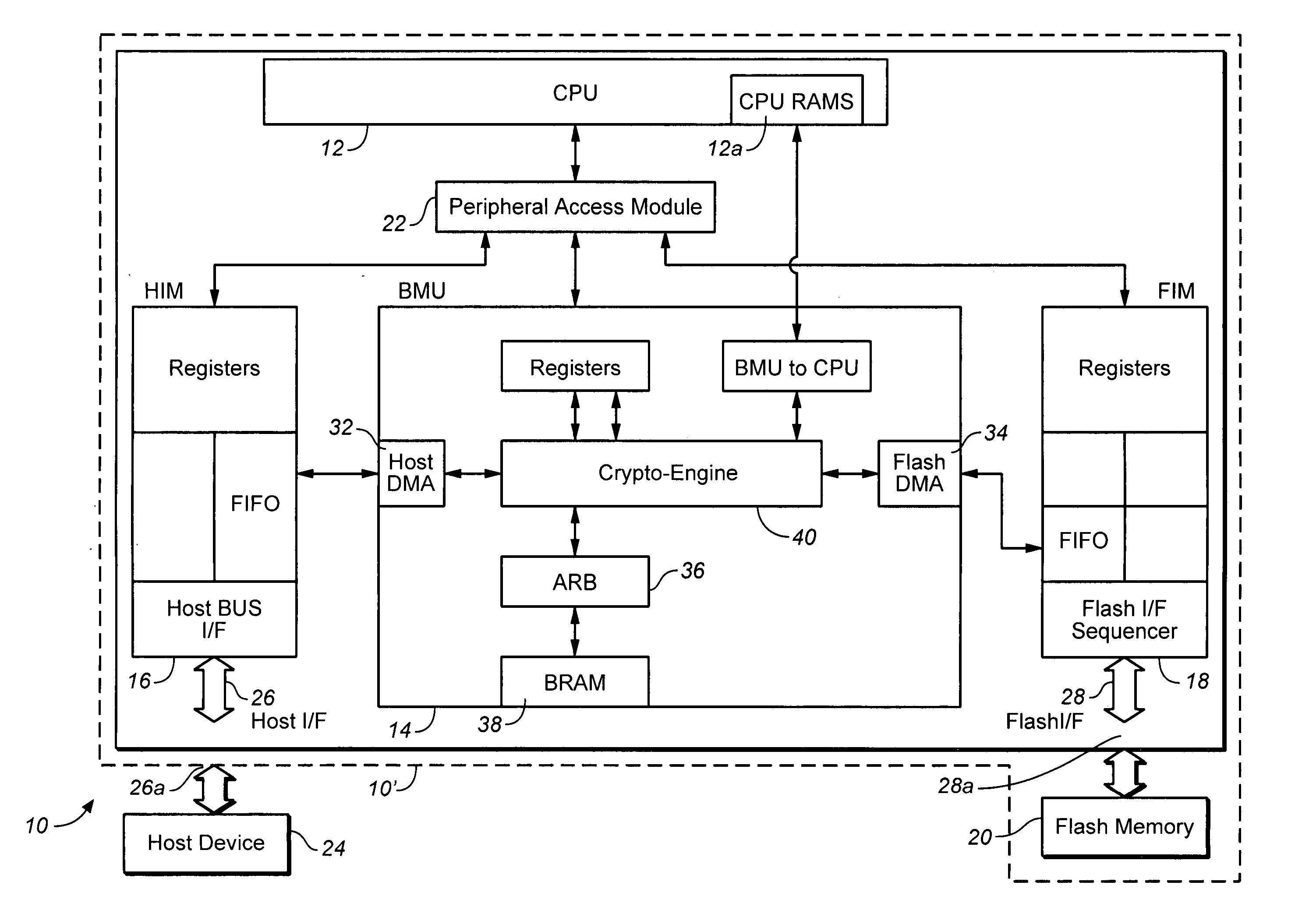
System and Method for Processor-Based Security
ActiveUS20100281273A1Avoid accessUnauthorized memory use protectionHardware monitoringExternal storageMemory interface
A system and method for processor-based security is provided, for on-chip security and trusted computing services for software applications. A processor is provided having a processor core, a cache memory, a plurality of registers for storing at least one hash value and at least one encryption key, a memory interface, and at least one on-chip instruction for creating a secure memory area in a memory external to the processor, and a hypervisor program executed by the processor. The hypervisor program instructs the processor to execute the at least one on-chip instruction to create a secure memory area for a software area for a software module, and the processor encrypts data written to, and decrypts data read from, the external memory using the at least one encryption key and the verifying data read from the external memory using the at least one hash value. Secure module interactions are provided, as well as the generation of a power-on key which can be used to protect memory in the event of a re-boot event. Lightweight, run-time attestation reports are generated which include selected information about software modules executed by the processors, for use in determining whether the processor is trusted to provide secure services.
Owner:CORESECURE TECH LLC
Virtual cores and hardware-supported hypervisor integrated circuits, systems, methods and processes of manufacture
InactiveUS20070226795A1Alteration can be preventedMemory loss protectionError detection/correctionNon real timeElectronic systems
An electronic system (1400) includes a processor (1422, 2610) having a pipeline, a bus (2655) coupled to the pipeline, a storage (1435, 1440, 2650) coupled to the bus (2655), the storage (1435, 2650) having a real time operating system (RTOS) and a real-time application, a non-real-time operating system (HLOS), a secure environment kernel (SE), and a software monitor (2310); and protective circuitry (2460) coupled to the processor and operable to establish a first signal (VP1_Active) and a second signal (NS) each having states and together having combinations of the states representing a first category (2430) for the real-time operating system and the real-time application, a second category (2420) for the non-real-time operating system, and a third category (2450) for the secure environment kernel.
Owner:TEXAS INSTR INC
Method and apparatus for content protection in a personal digital network environment
InactiveUS20050144468A1Easy to disassembleReliable lockingTelevision system detailsUser identity/authority verificationGraphicsVideo processing
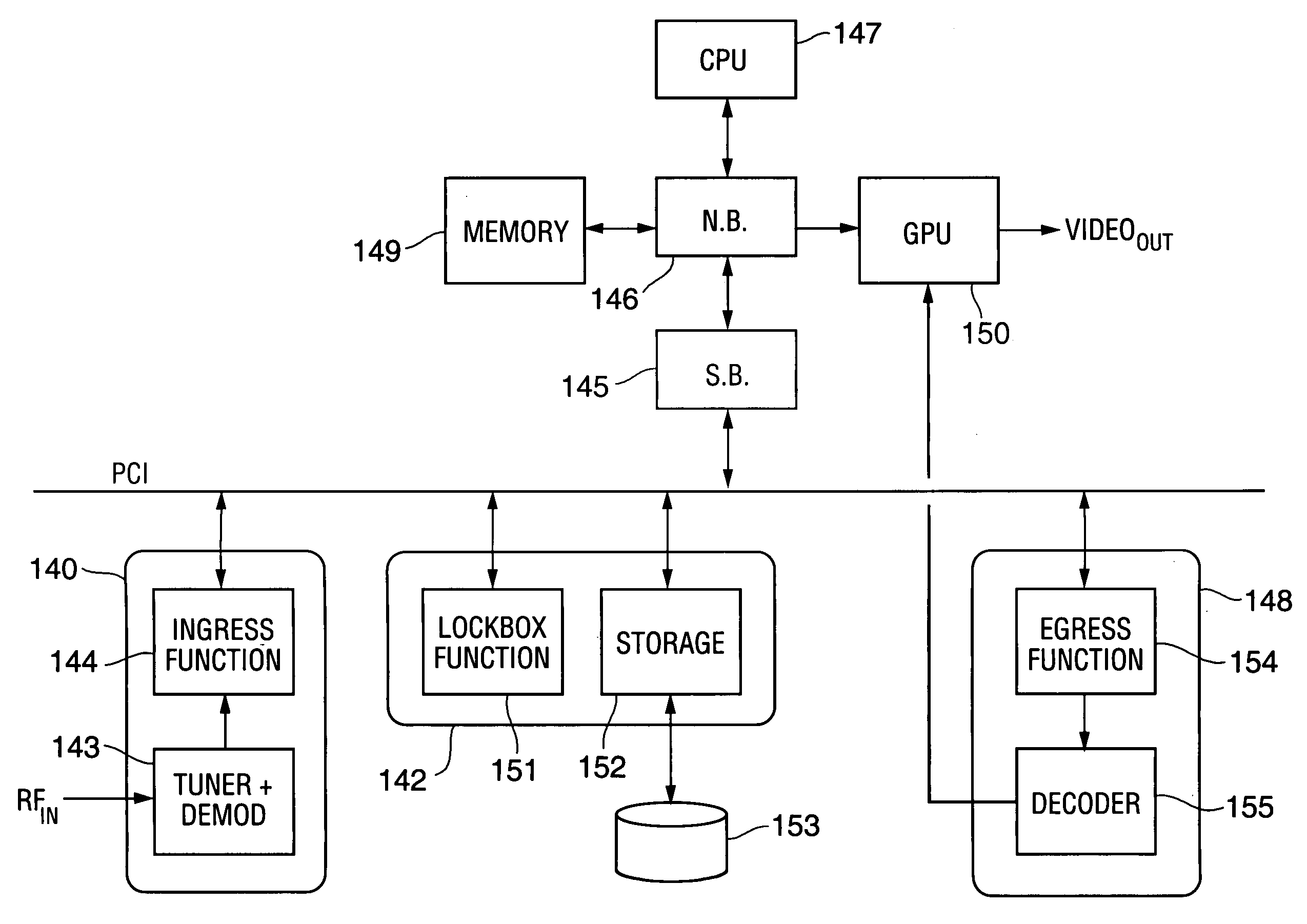
In some embodiments, the invention is a personal digital network (“PDN”) including hardware (sometimes referred to as Ingress circuitry) configured to transcrypt encrypted content that enters the PDN. Typically, the transcryption (decryption followed by re-encryption) is performed in hardware within the Ingress circuitry and the re-encryption occurs before the decrypted content is accessible by hardware or software external to the Ingress circuitry. Typically, transcrypted content that leaves the Ingress circuitry remains in re-encrypted form within the PDN whenever it is transferred between integrated circuits or is otherwise easily accessible by software, until it is decrypted within hardware (sometimes referred to as Egress circuitry) for display or playback or output from the PDN. Typically, the PDN is implemented so that no secret in Ingress or Egress circuitry (for use or transfer by the Ingress or Egress circuitry) is accessible in unencrypted form to software or firmware within the PDN or to any entity external to the PDN. Other aspects of the invention are methods for protecting content in a PDN (e.g., an open computing system) and devices (e.g., multimedia graphics cards, set top boxes, or video processors) for use in a PDN.
Owner:OPTIMUM CONTENT PROTECTION
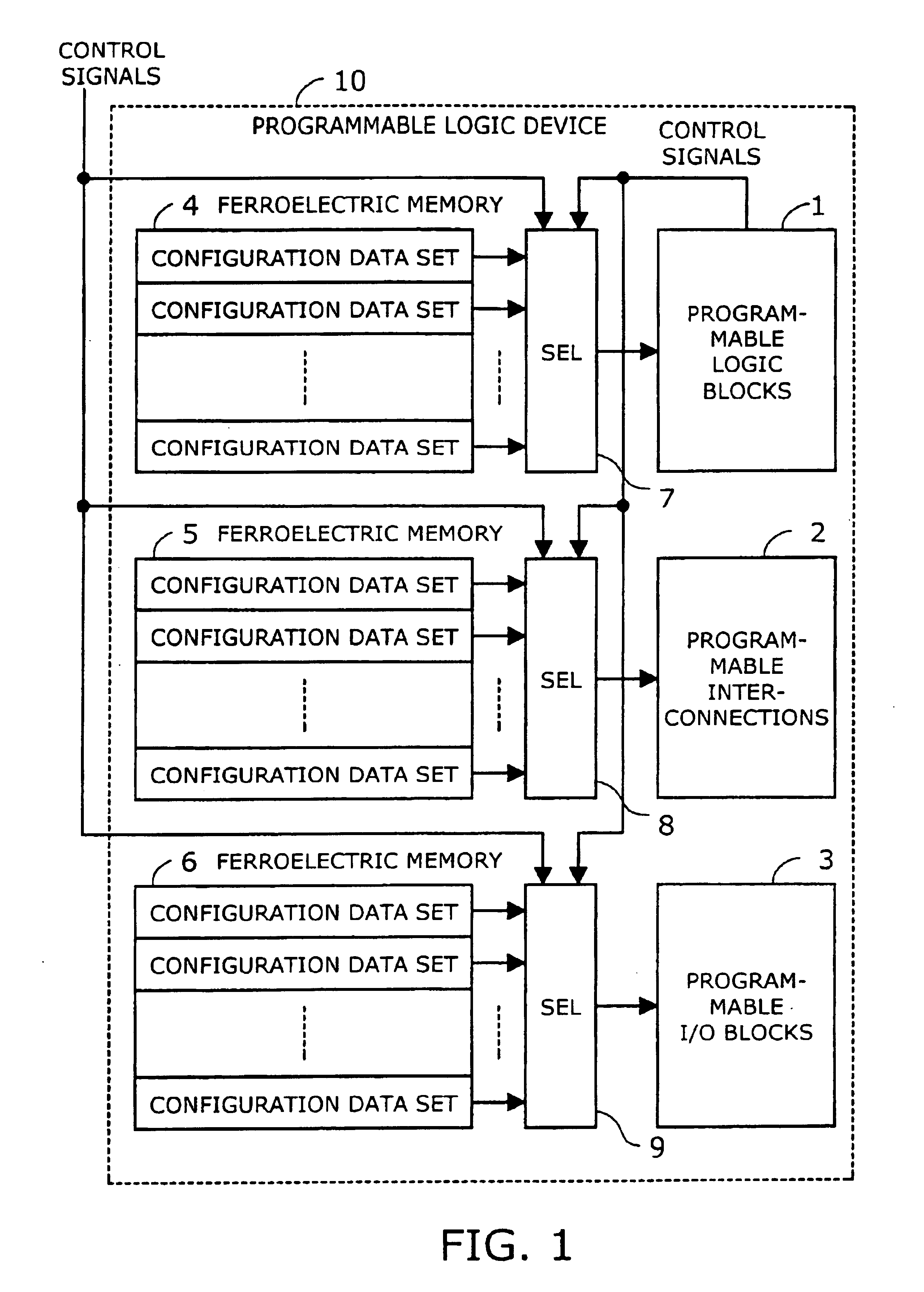
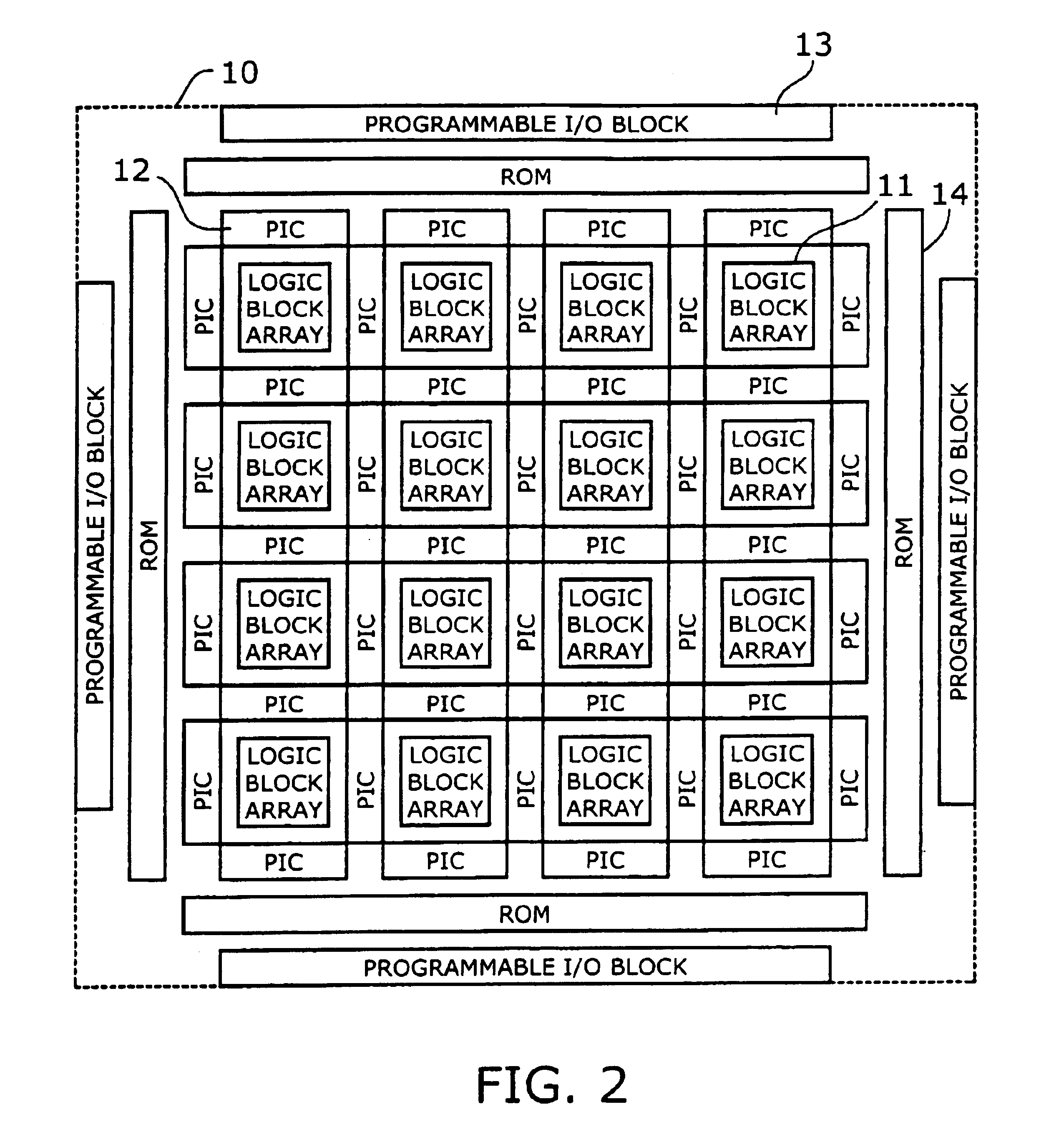
Programmable logic device with ferroelectric configuration memories
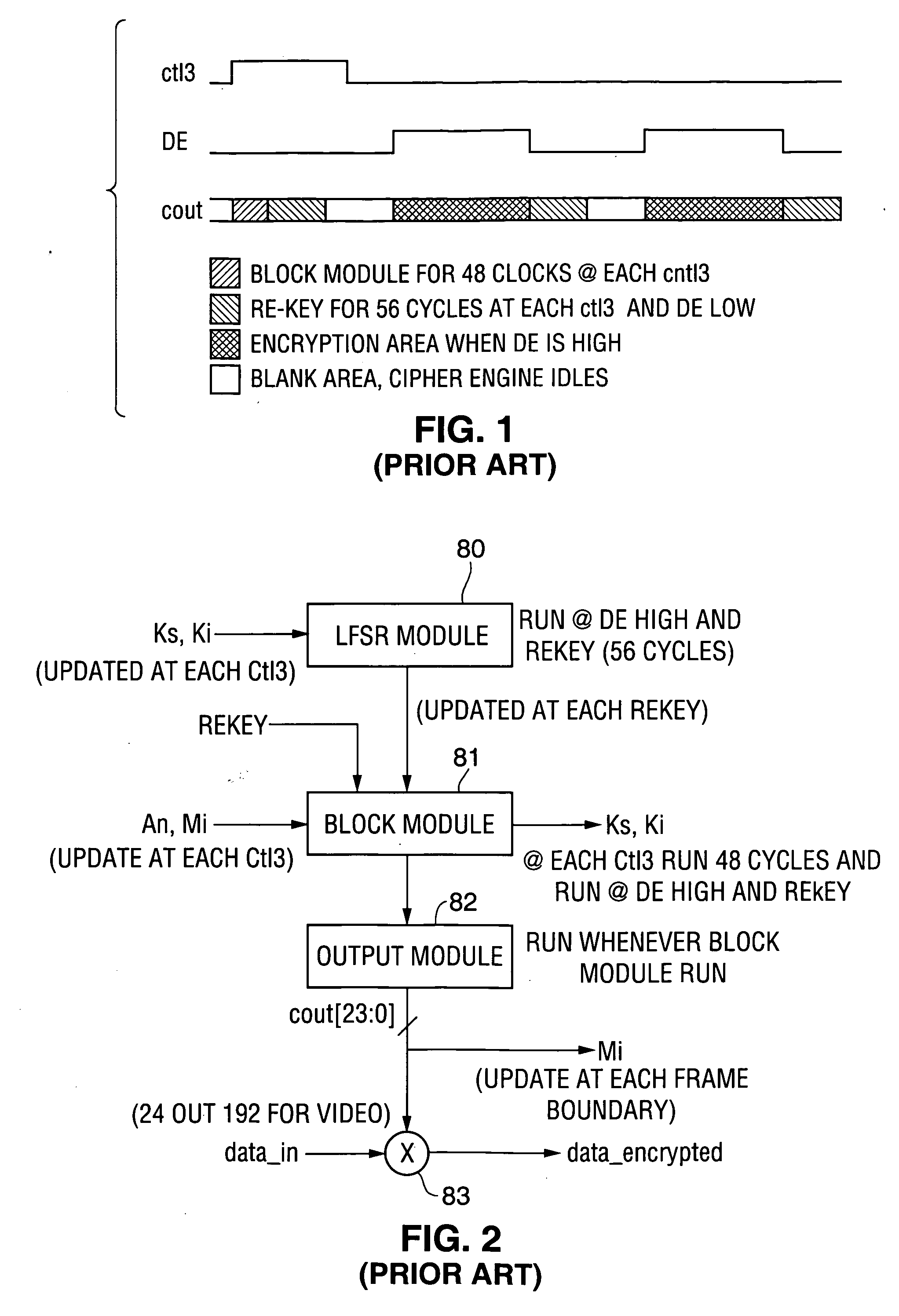
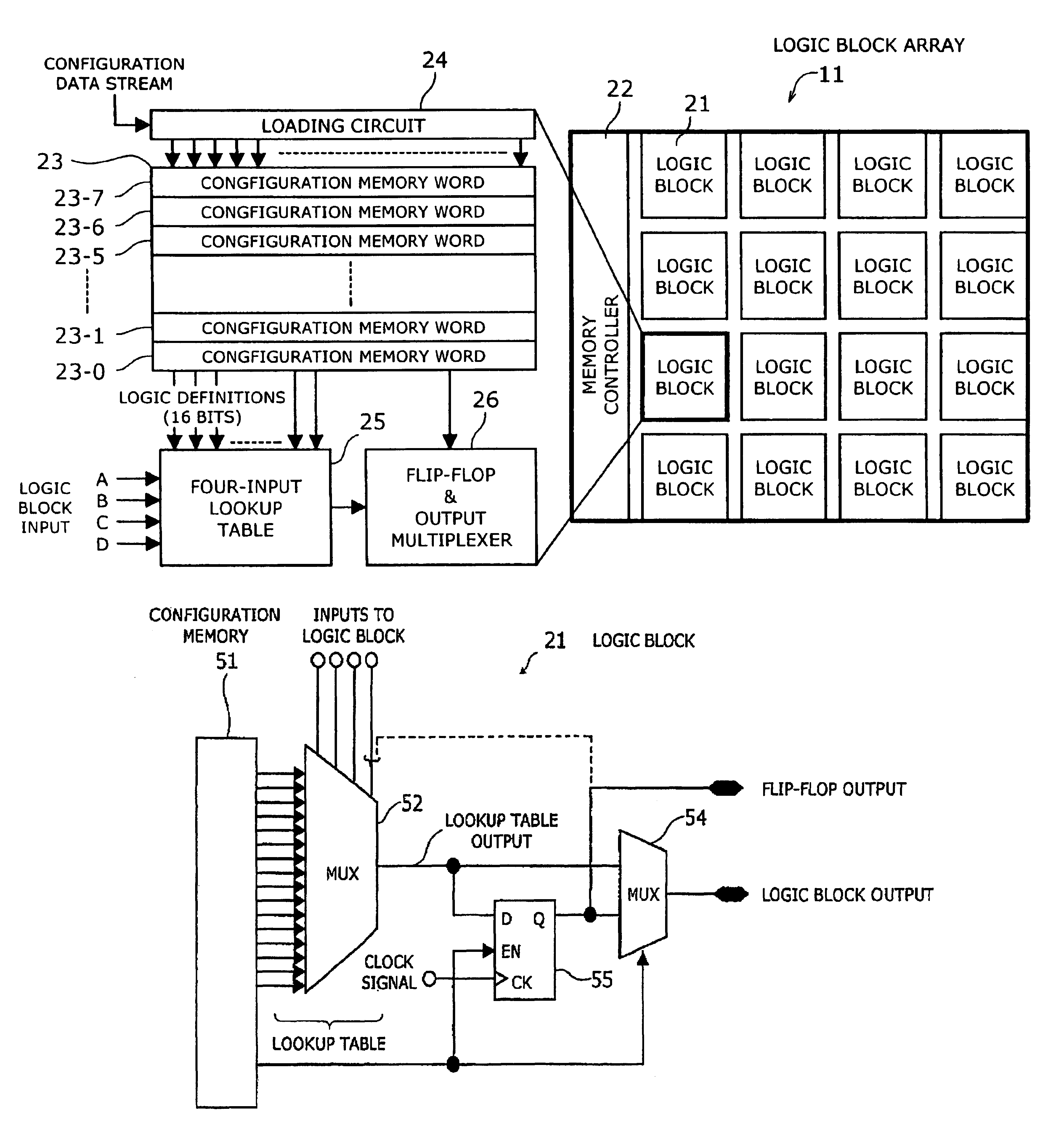
InactiveUS6924663B2Increase the effective amountEfficient architectureDigital storageInternal/peripheral component protectionElectricityData stream
A programmable logic device with ferroelectric configuration memories storing multiple configuration data sets. The device has programmable logic blocks, interconnections, and I / O blocks to provide desired logic functions. Those building blocks can be dynamically reconfigured by changing the selection of configuration data stored in the device's integral configuration memories. The configuration memories are divided into groups, so that they can be loaded concurrently with multiple configuration data streams. To protect the content of configuration memories from unauthorized access, the device employs an authentication mechanism that uses security IDs stored in the configuration memories. The device has a memory controller to provide an appropriate power supply sequence for ferroelectric memory cells to ensure the reliable data retention when the device is powered up or shut down.
Owner:FUJITSU SEMICON LTD
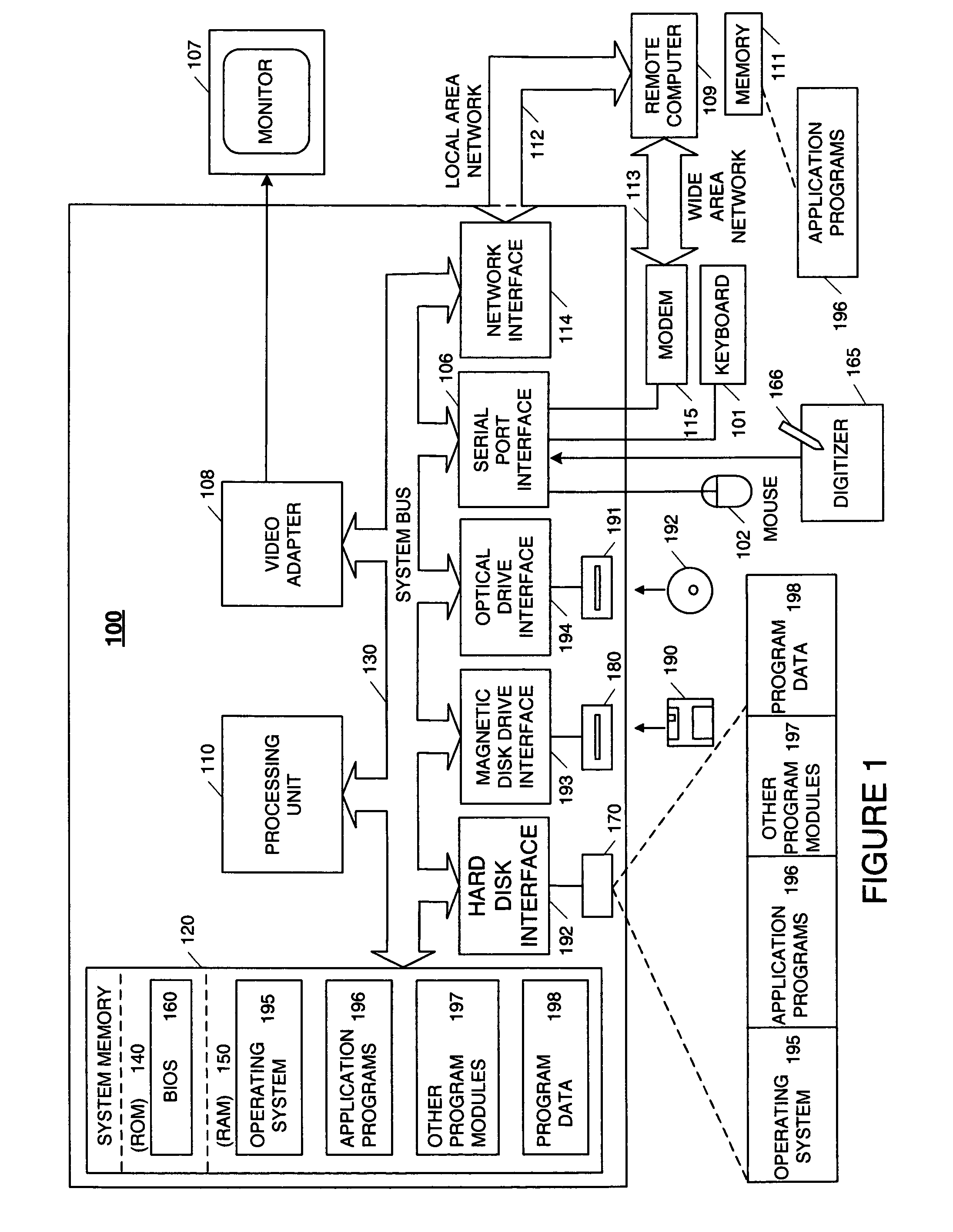
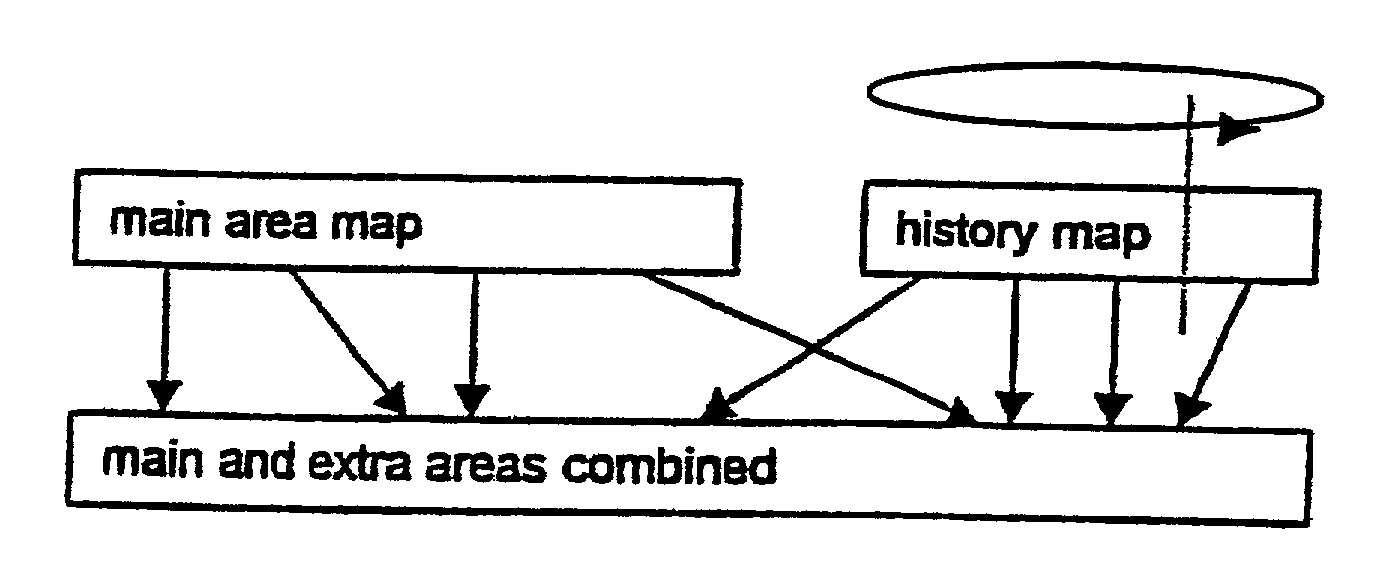
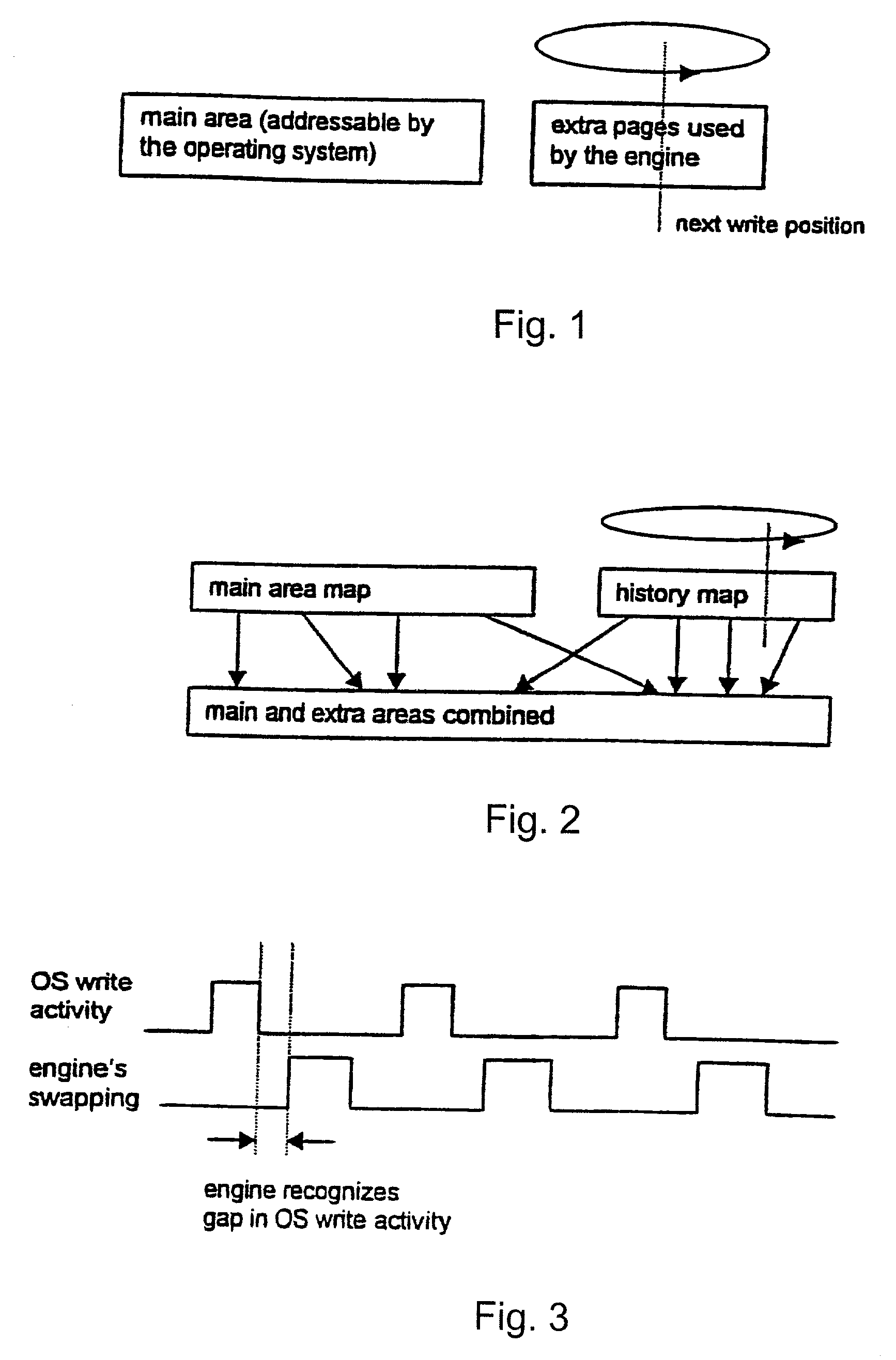
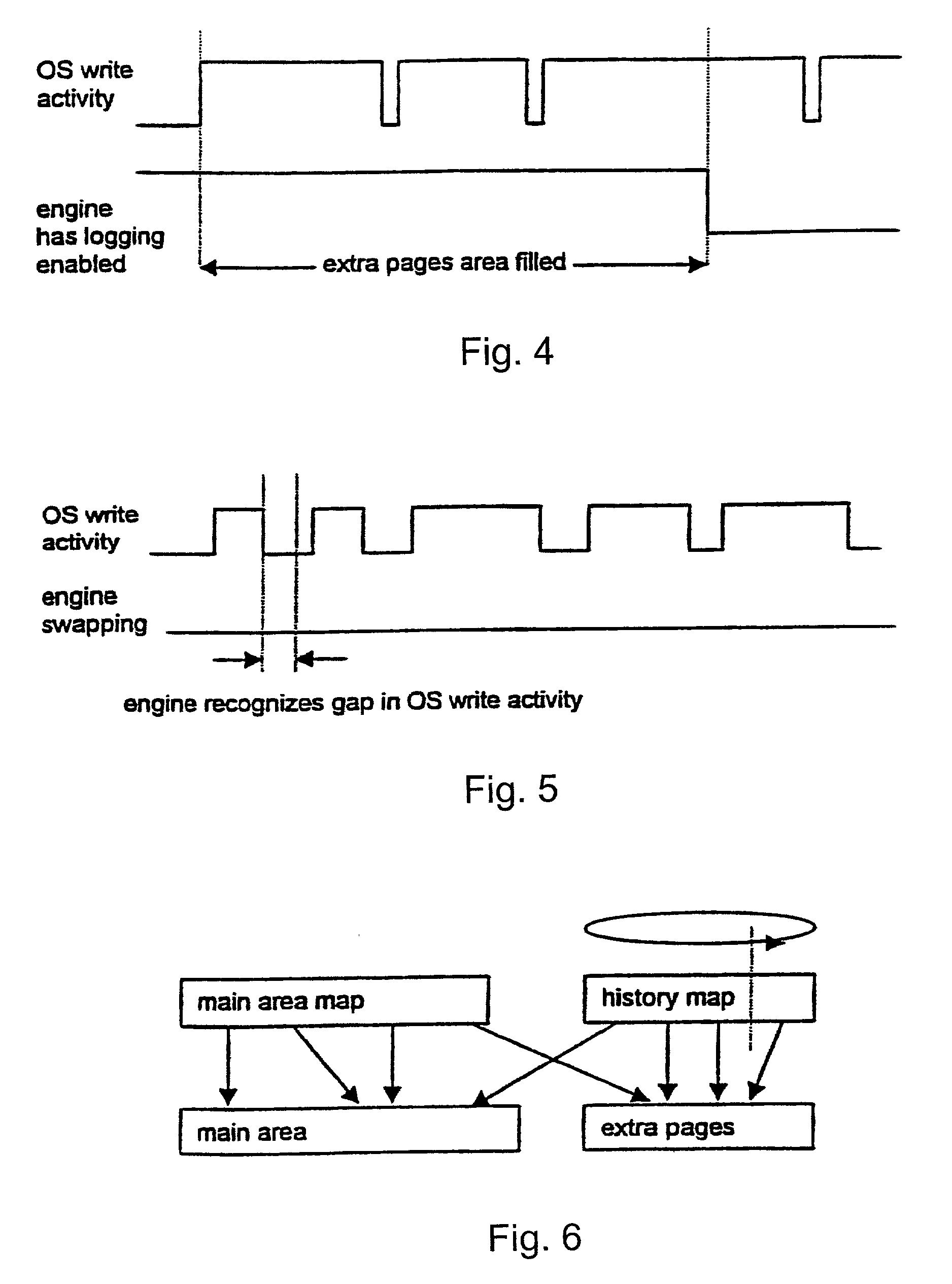
System and method for restoring a computer system after a failure
InactiveUS20020049883A1Memory adressing/allocation/relocationInternal/peripheral component protectionOperational systemOriginal data
A method and apparatus for reverting a disk drive to an earlier point in time is disclosed. Changes made to the drive are saved in a circular history buffer which includes the old data, the time it was replaced by new data, and the original location of the data. The circular history buffer may also be implemented by saving new data elements into new locations and leaving the old data elements in their original locations. References to the new data elements are mapped to the new location. The disk drive is reverted to an earlier point in time by replacing the new data elements with the original data elements retrieved from the history buffer, or in the case of the other embodiment, reads to the disk are mapped to the old data elements stilled stored in their original locations. The method and apparatus may be implemented as part of an operating system, or as a separate program, or in the controller for the disk drive. The method and apparatus are applicable to other forms of data storage as well. Also disclosed are method and apparatus for providing firewall protection to data in a data storage medium of a computer system.
Owner:NORTONLIFELOCK INC
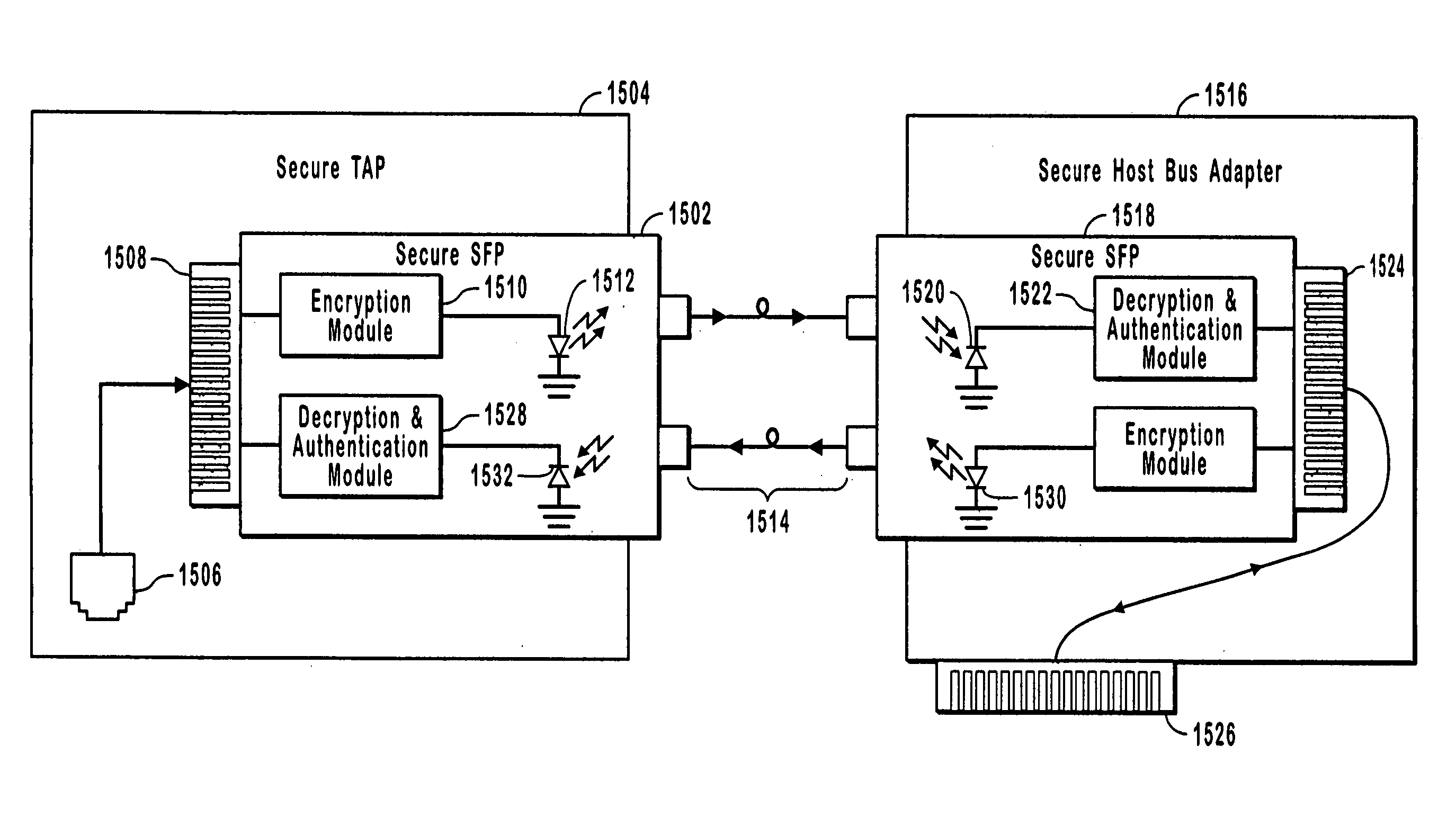
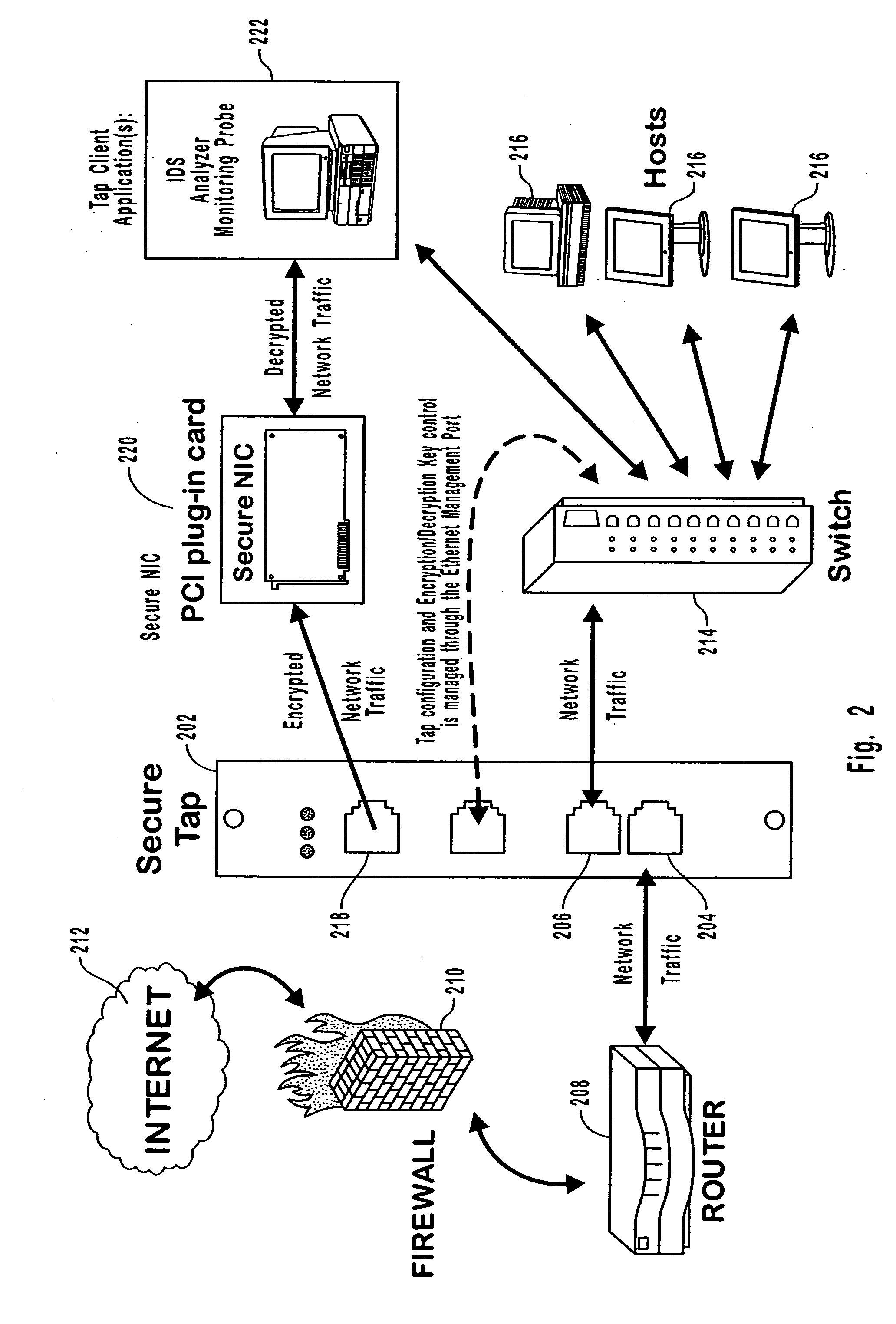
Secure network access devices with data encryption
InactiveUS20050114663A1Avoid readingUser identity/authority verificationInternal/peripheral component protectionUsage dataEncryption
Secure point to point network communications. Secure point to point network communications are accomplished by sending data across a secure link. Trusted partners at the link are matched to each other. To ensure that no un-trusted partners are on the link, authentication is performed. One of the points may be a secure tap. The secure tap authenticates a trusted partner by receiving a hardware embedded encryption key or value derived from the hardware embedded encryption key from the trusted partner. Data sent on the trusted link is encrypted to prevent interception of the data. The secure tap polices the link to ensure that no un-trusted partners are attached to the link and that the trusted partner is not removed from the link. If un-trusted partners are added to the link or trusted partners removed from the link, the secure tap ceases sending data.
Owner:FINISAR
System for controlling access and distribution of digital property
InactiveUS20010021926A1Key distribution for secure communicationMultiple keys/algorithms usageTamper resistanceData access
A method and device are provided for controlling access to data. Portions of the data are protected and rules concerning access rights to the data are determined. Access to the protected portions of the data is prevented, other than in a non-useable form; and users are provided access to the data only in accordance with the rules as enforced by a mechanism protected by tamper detection. A method is also provided for distributing data for subsequent controlled use of those data. The method includes protecting portions of the data; preventing access to the protected portions of the data other than in a non-useable form; determining rules concerning access rights to the data; protecting the rules; and providing a package including: the protected portions of the data and the protected rules. A user is provided controlled access to the distributed data only in accordance with the rules as enforced by a mechanism protected by tamper protection. A device is provided for controlling access to data having protected data portions and rules concerning access rights to the data. The device includes means for storing the rules; and means for accessing the protected data portions only in accordance with the rules, whereby user access to the protected data portions is permitted only if the rules indicate that the user is allowed to access the portions of the data.
Owner:HANGER SOLUTIONS LLC
Method for secure storage and delivery of media content
InactiveUS20070043667A1Easy accessSimple manufacturing processRecord information storageInternal/peripheral component protectionContent distributionService provision
The memory device contains control structures that allow media content to be stored securely and distributed in a manner envisioned by the content owner, or service providers involved in the distribution. A wide variety of different avenues become available for distributing media content using such memory devices, such as where the devices contain one or more of the following: abridged preview media content, encrypted unabridged media content, prepaid content, rights and / or rules governing access to such content. The memory device has a type of control structures that enable a service provider (who can also be the content owner) to create a secure environment for media content distribution where end users and terminals register with the service provider, and gain access to the content in a manner controlled by the service provider. The various components to be loaded (e.g. abridged preview media content, encrypted unabridged media content, prepaid content, rights and / or rules governing access to such content) may be generated and loaded in a secure and efficient manner.
Owner:SANDISK TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com