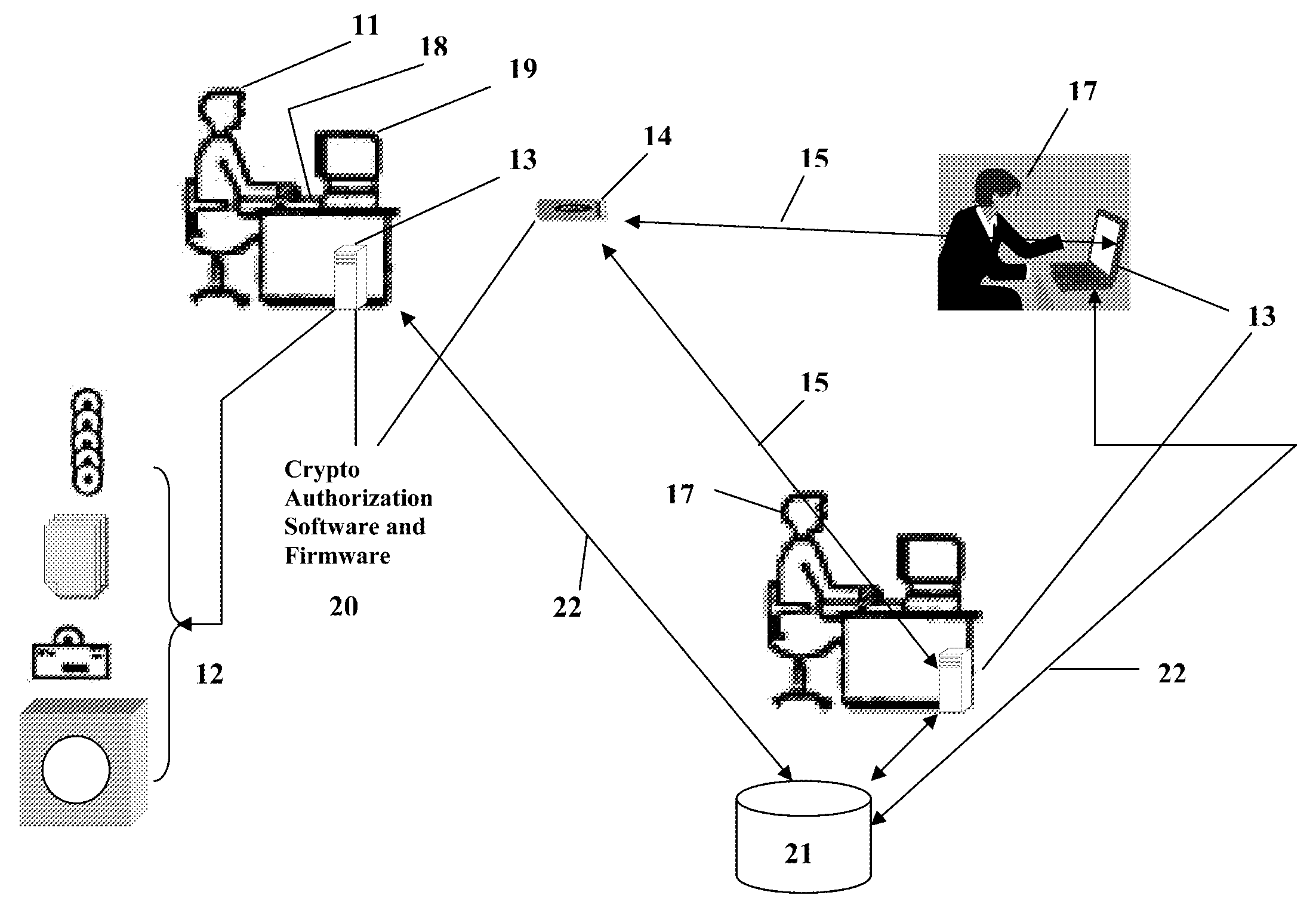
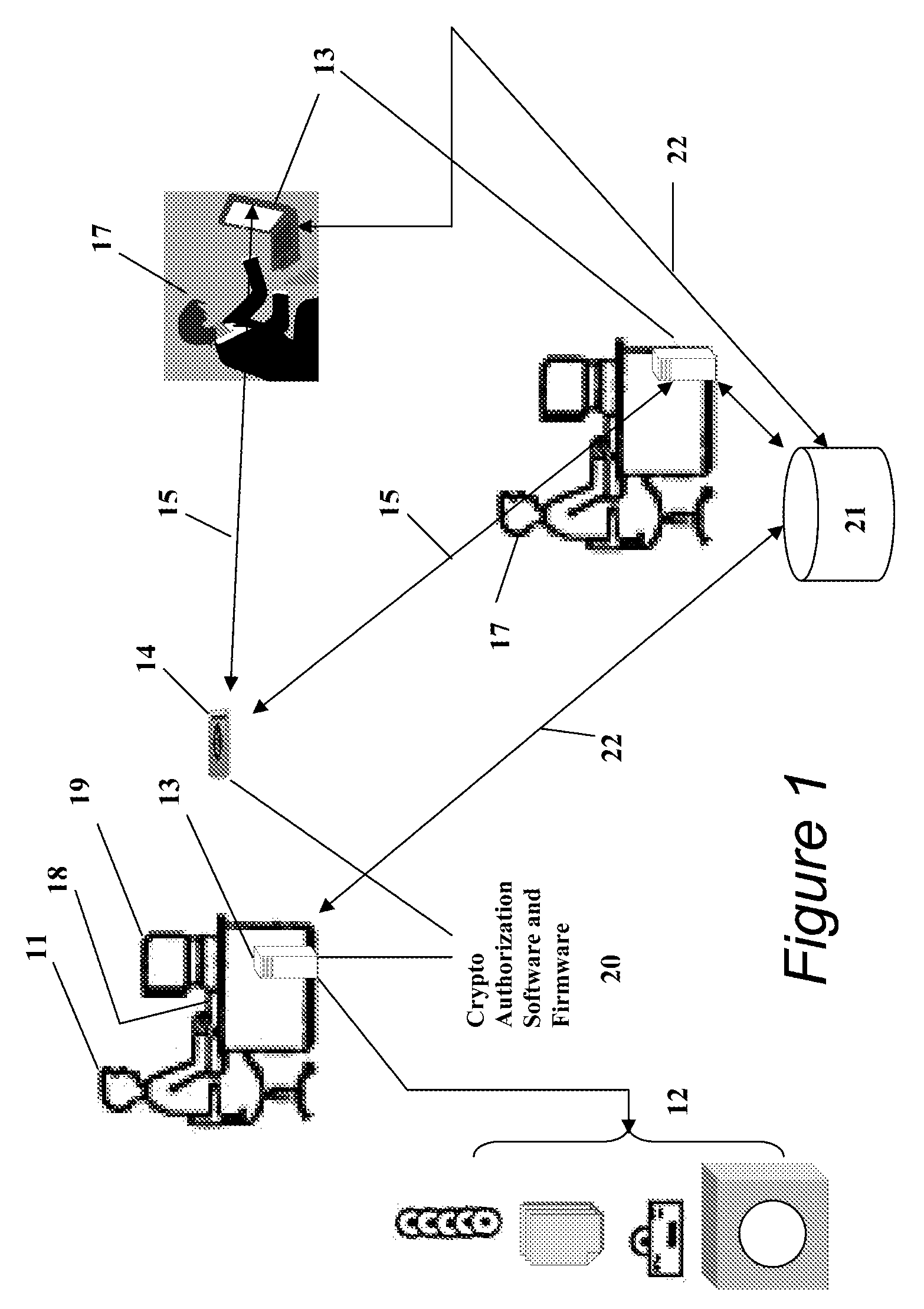
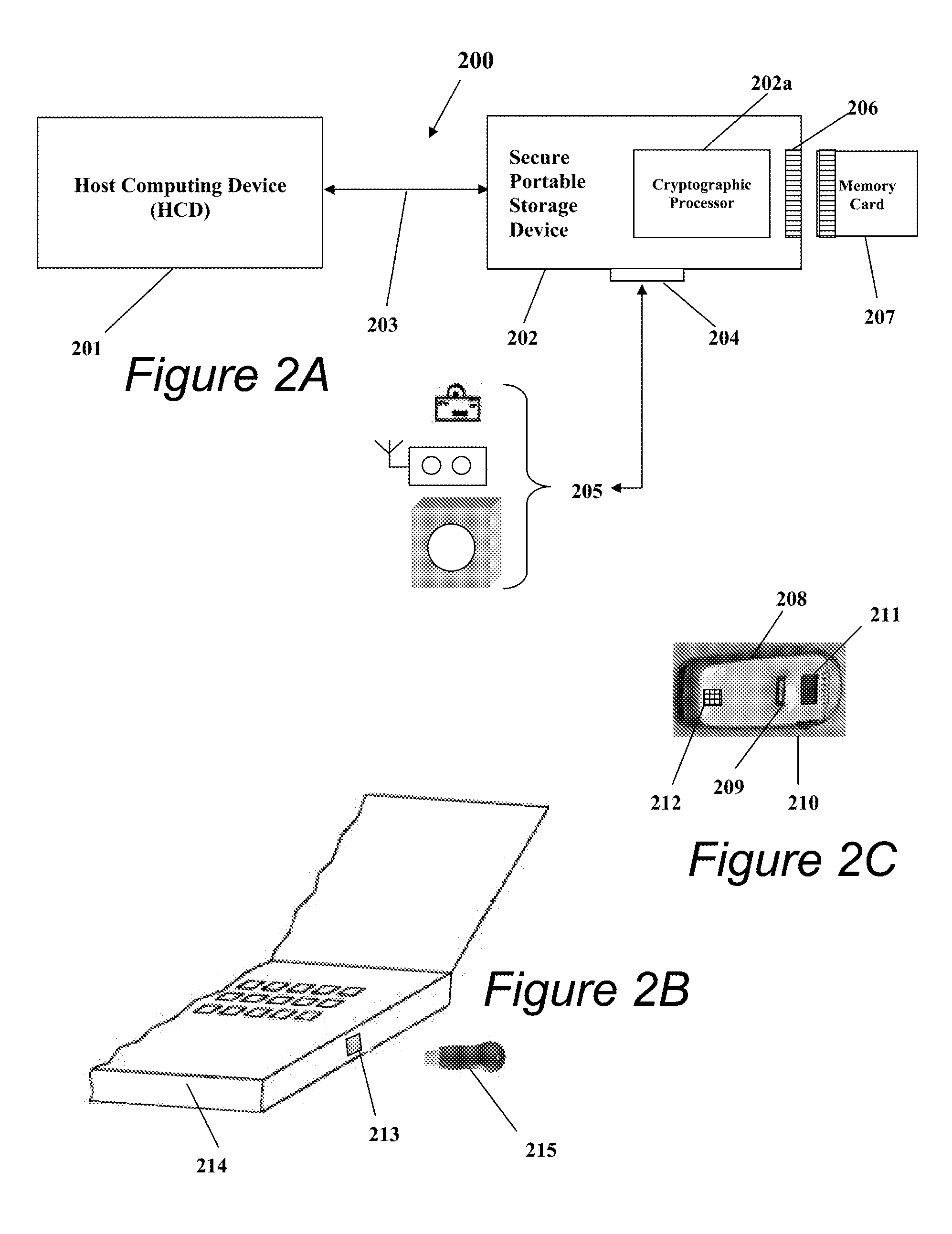
The exposed storage and transport of this proprietary information, particularly for the purposes of sharing among separate
collaboration groups, has significantly increased the risk of interception and theft by criminal elements, competitors, amateur thieves, computer hackers, terrorists, or political or industrial spies.
The physical mobility of these storage devices makes them vulnerable to theft, capture, loss, and possible misuse.
However,
thin client software greatly increases the
vulnerability of such data to hackers who are able to penetrate the firewalls and other mechanisms, unless the data is encrypted on the storage medium in such a way that only authorized users could make sense of it, even if an unauthorized user were able to access the encrypted files.
The sophistication of literally millions of mathematicians, computer engineers and scientists, many of whom can be hostile to the protection of digital
intellectual property for economic, political, or frivolous purposes, represents a great
threat to the
efficacy of simple implementations of
password security and
software encryption systems currently implemented on such portable encryption devices.
Furthermore, the difficulty and, in some cases, the inability to change security policies for access to such data forms yet another barrier to the commercial and institutional interests of the owners of the
intellectual property in controlled and directed sharing of such information, and of the user's ability to retrieve, search, and store such data in their daily activities.
In contrast, some users have adopted the use of hardware-based encryption solutions in order to prevent these problems, only to discover a few years later that their data was irretrievable because their cryptographic token was lost, stolen, or malfunctioned and they had no
backup or
recovery agent capability, or that interesting or even vital historical records could not be read because no information exists as to what keys were used to encrypt the documents, or what tokens or PINs were used.
It is easy to imagine that if these issues are a significant problem today, then the problem of encrypting data for personal privacy for 40 or 50 years, or even the life of the individual, will become overwhelming.
Because the secure portable encryption device may be used in a high
threat and high-risk environment, there is the possibility that the device could be lost, stolen, or captured by competitive or criminal forces, and later disassembled and even reverse engineered by a sophisticated and capable
adversary.
In many environments, it is not sufficient merely to
restrict the
physical access and ability to log on to the device to certain host computers within a given enclave.
Finally, it must be recognized that the long-term storage of encrypted data presents some very difficult problems in sorting, searching, or even finding any data that is relevant to a particular subject, without being forced to decrypt the entire archive in order to find something.
This process is difficult enough if the document is a
text document that can be searched relatively easily, but if the information that is sought is a photograph, drawing, sound recording, musical
score,
computer program, or other more abstract
data type, then the search process can be very difficult indeed.
In addition to the search difficulty, there is a cost associated with the long-term storage of any kind of data, encrypted or not, and it is often necessary to make an
intelligent decision as to what to save and what to discard.
But if the information is encrypted, making that decision effectively requires that the information be decrypted in order to examine it, and that may not be practical if terabytes, exabytes, or even petabytes of data are involved.
Even if the error is later detected, it may not be possible to correct it if the original source is no longer available.
In particular, depending on the Mode of Operation of the cryptographic
system, an uncorrected error may cause error propagation throughout the remainder of the decrypted file or message after the point of the error, rendering the data completely unintelligible.
This is a particular problem in the case of one-way transmissions, e.g., when the recipient is operating under “EMCON” (emissions control) or radio
silence conditions, as well as for one-way storage or archive operations.
However, the looming
threat on the
horizon is the possibility of highly parallel computations made possible by a form of computation called “
quantum computing.” At present, many of the cryptographic protocols, including RSA and ECC are believed to be secure, in that the effort which would be required to break them is considered computationally infeasible.
If realized, the difficulty of most of these problems would drop from exponential complexity to merely polynomial complexity, rendering currently deployed cryptographic systems and key lengths useless.
As of December 2006, as quoted in the New York Times, “Despite an almost four-and-half-year campaign on the part of the company (Microsoft), and the best interests of the computer industry, the threat from harmful
computer software continues to grow.
Attacks on personal computers and commercial, government and military data are now commonplace; indeed,
identity theft of passwords is the largest white-collar crime in the United States.
Yet passwords and PINs (Personal Identification Numbers), in most cases generated by human beings who are tempted to use native-language words, Social Security Numbers, telephone numbers, etc., are still the most used access security methods for protecting portable encryption devices, and among the most vulnerable to both
brute force dictionary attacks as well as sophisticated logic tracing.
One of the key deficiencies of prior art, therefore, is the widespread reliance on a stored PIN or
password that is used for comparison purpose, for
access control, or used for
password-based encryption to protect other cryptographic variables.
Such systems are optimized for protecting access to centralized sensitive data but are not adaptable to secure the user
authorization and access and decryption rights to data which is transportable via portable storage media.
Since the table data is external to the secured media on which the data is stored, the processes to authenticate the user and authorize decryption of the data are generally not cryptographically secure nor are they adaptable to be implemented by the portable storage device itself, even with the presence of
processing capability on the device.
In these cases, however, the individual secret shares themselves are maintained statically in multiple storage devices, generally on-line, where they are susceptible to attackers, particularly from within the institution, who can target the secret shares and recombine then to form the decryption key.
Such solutions are implemented for relatively static configurations of computing and storage devices and related communities of interest or tiers of users, and have not addressed the ability to so protect key encrypting keys when the data itself, and the means to encrypt and decrypt the data and to generate and recombine the shared secrets, are on a portable device.
 Login to View More
Login to View More  Login to View More
Login to View More