Patents
Literature
843 results about "Secret sharing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
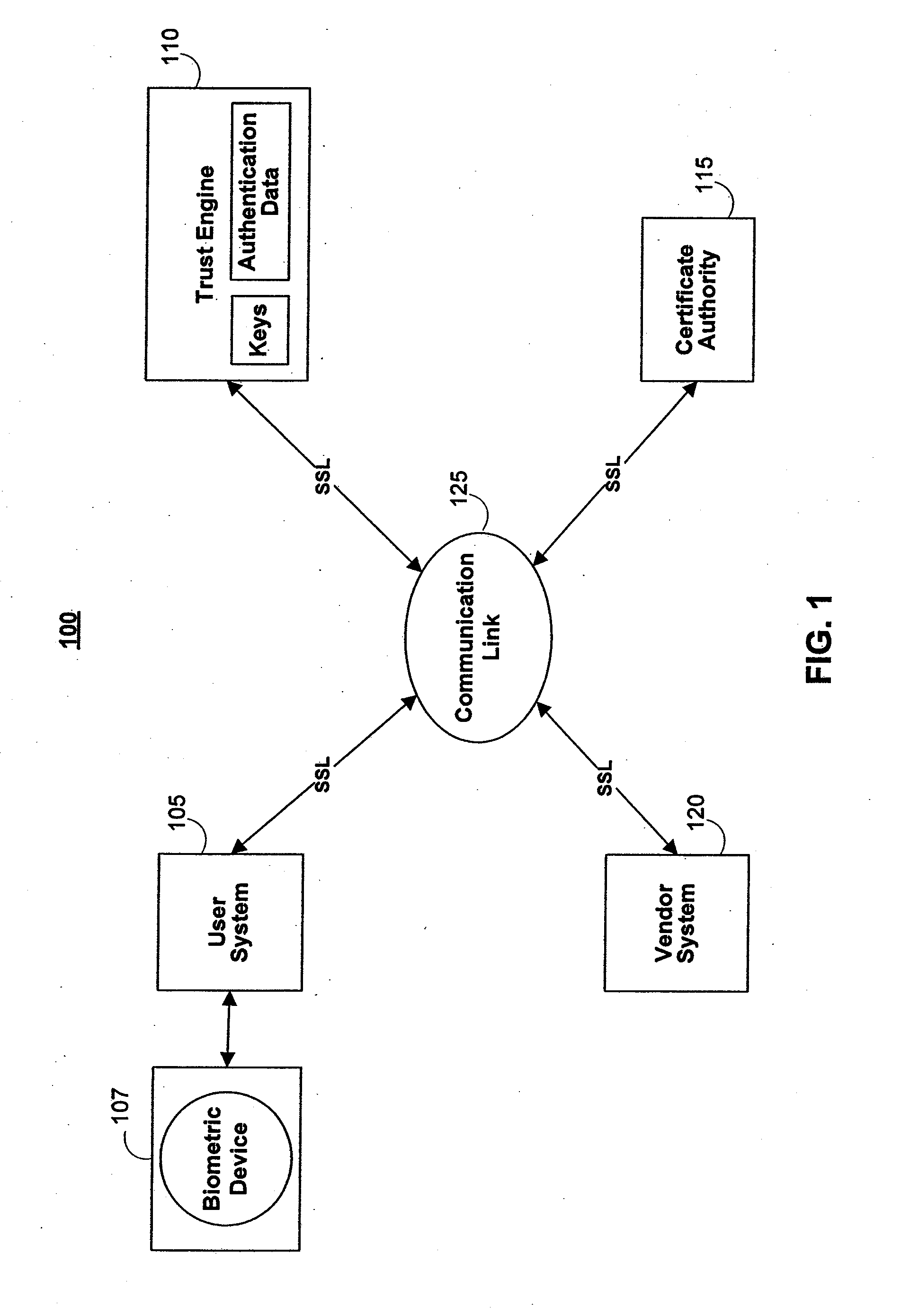
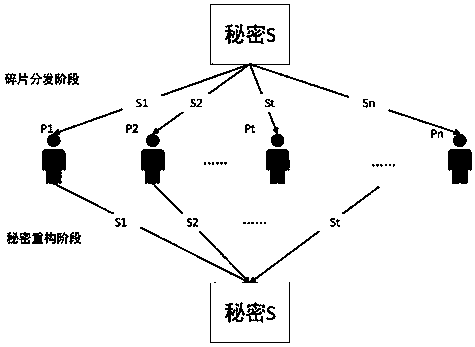
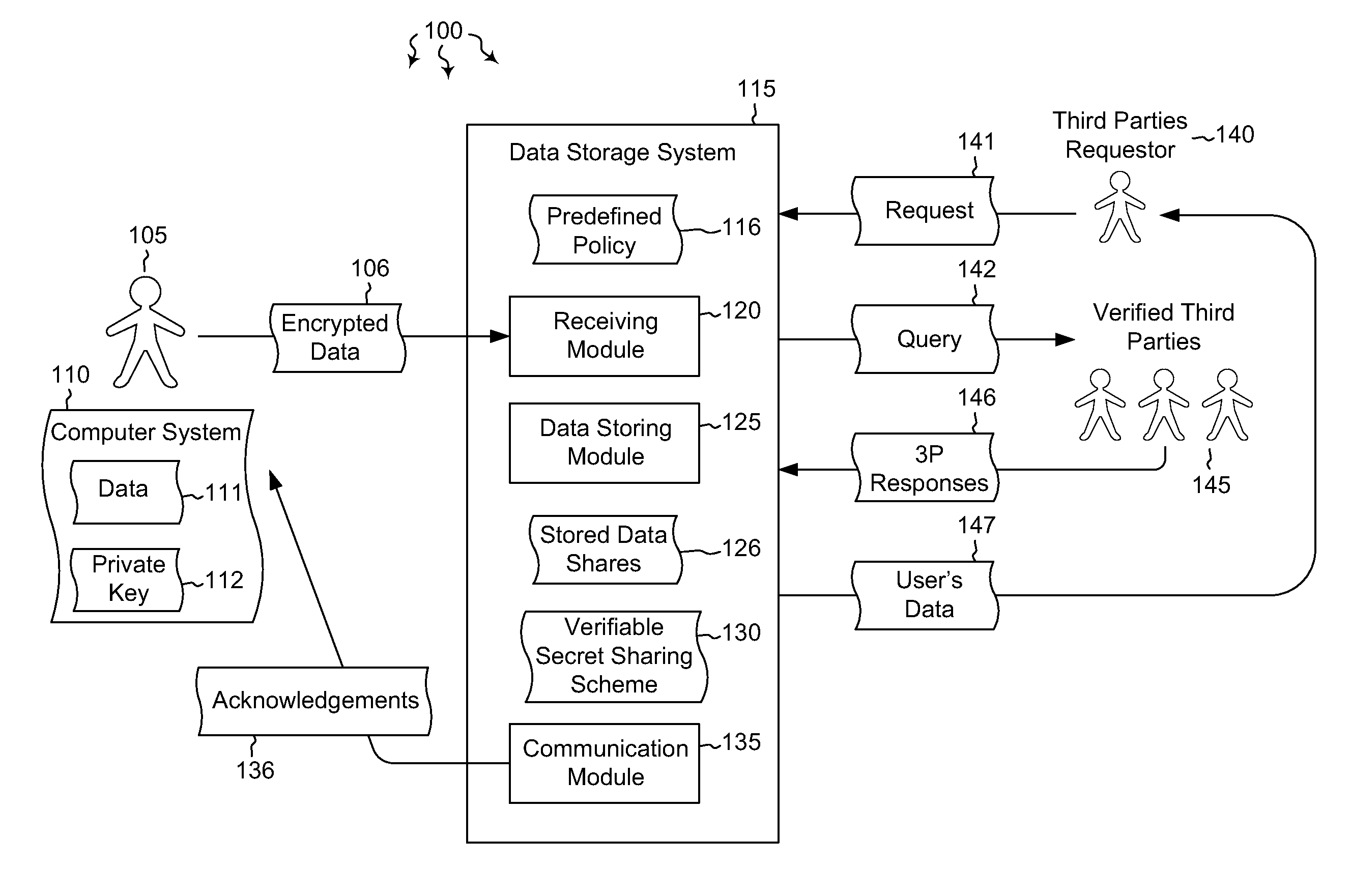
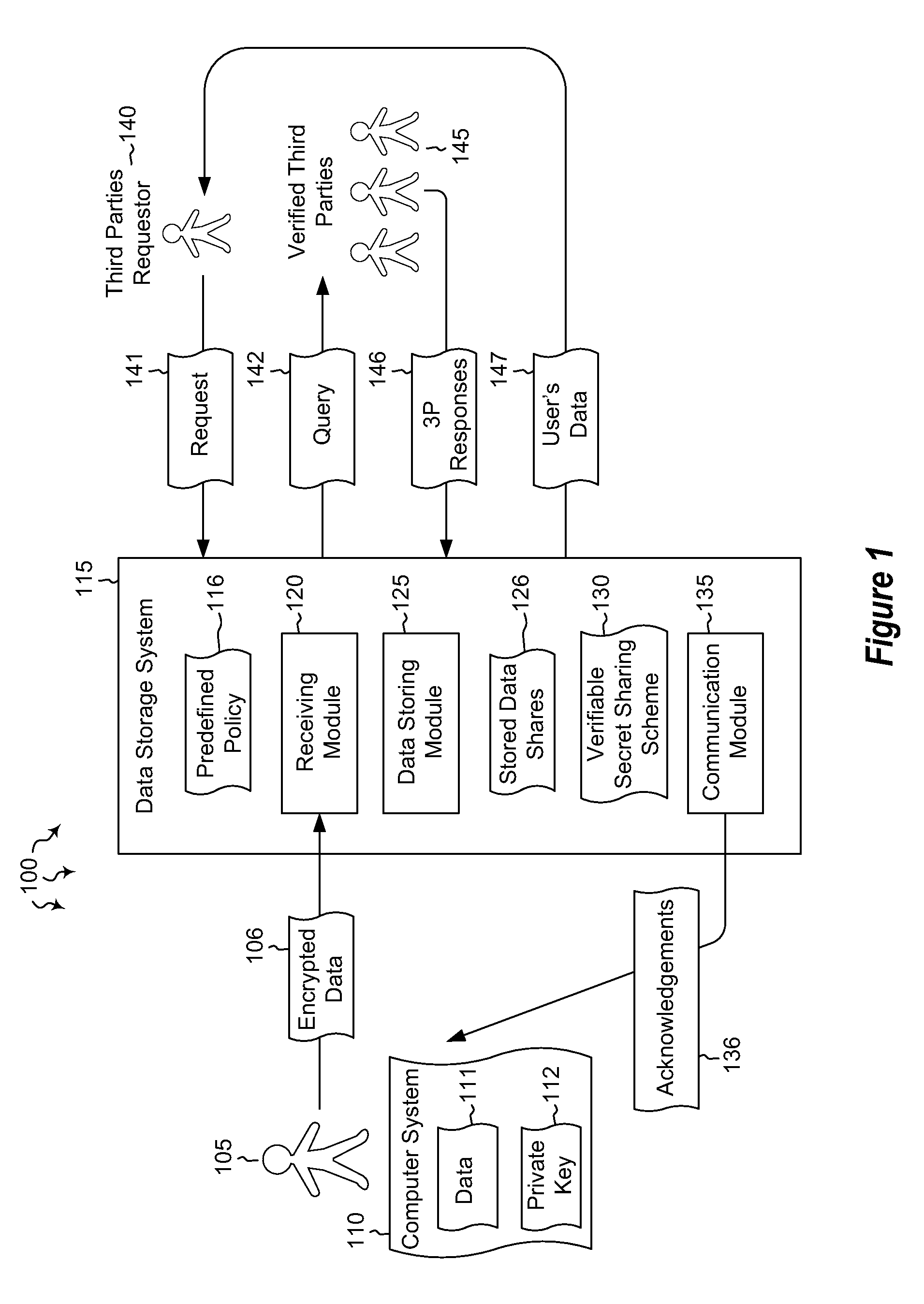
Secret sharing (also called secret splitting) refers to methods for distributing a secret amongst a group of participants, each of whom is allocated a share of the secret. The secret can be reconstructed only when a sufficient number, of possibly different types, of shares are combined together; individual shares are of no use on their own.
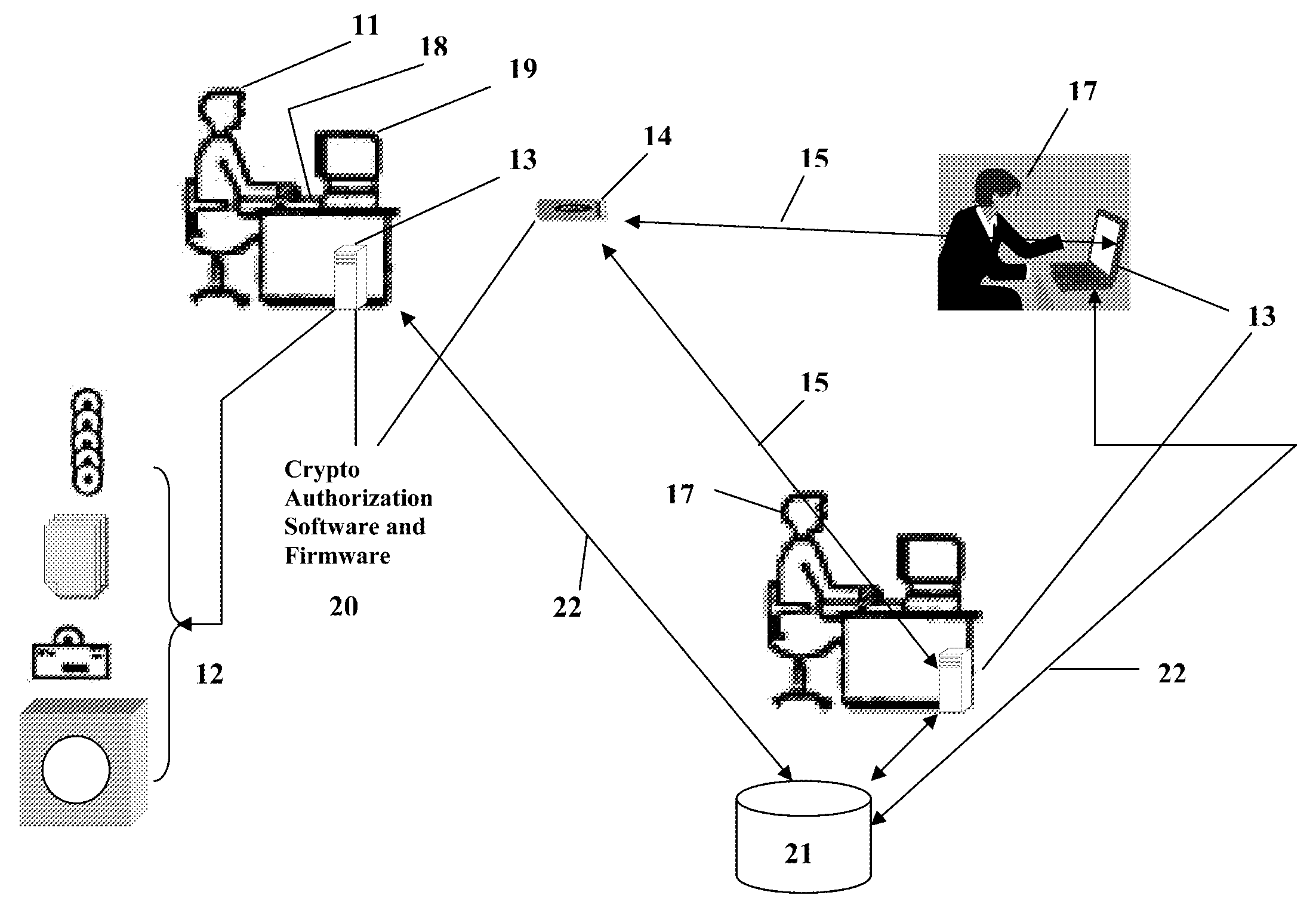
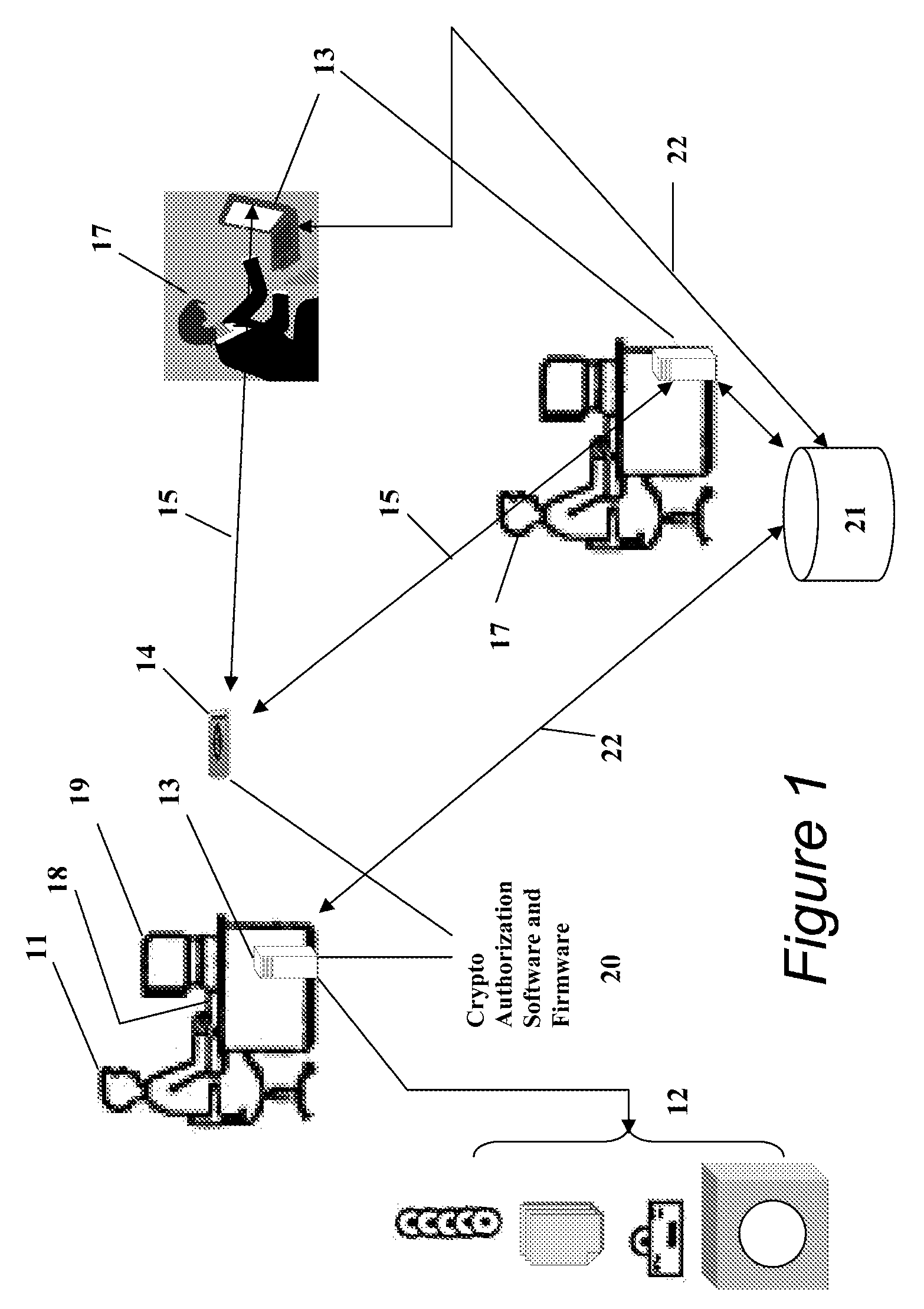
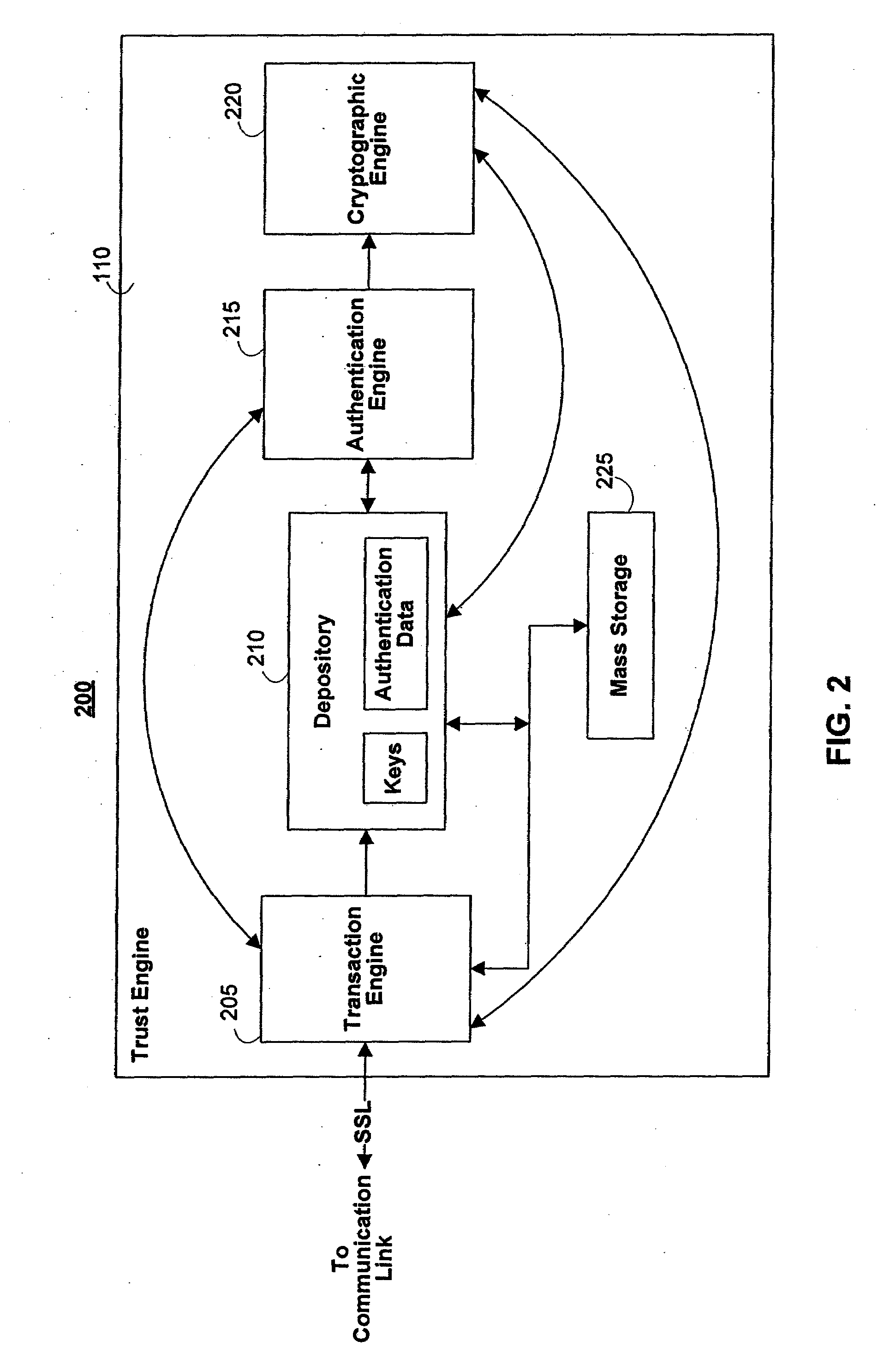
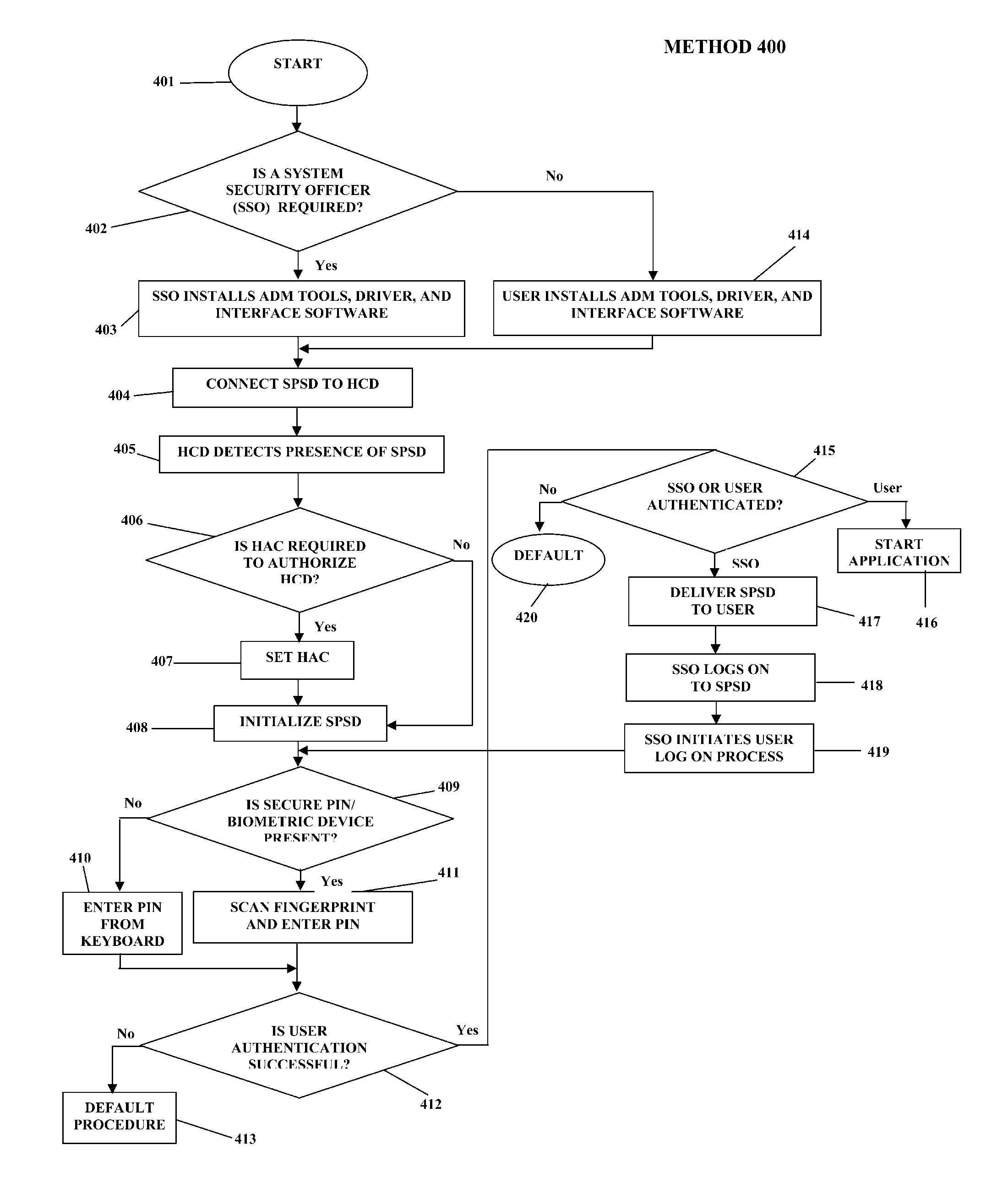
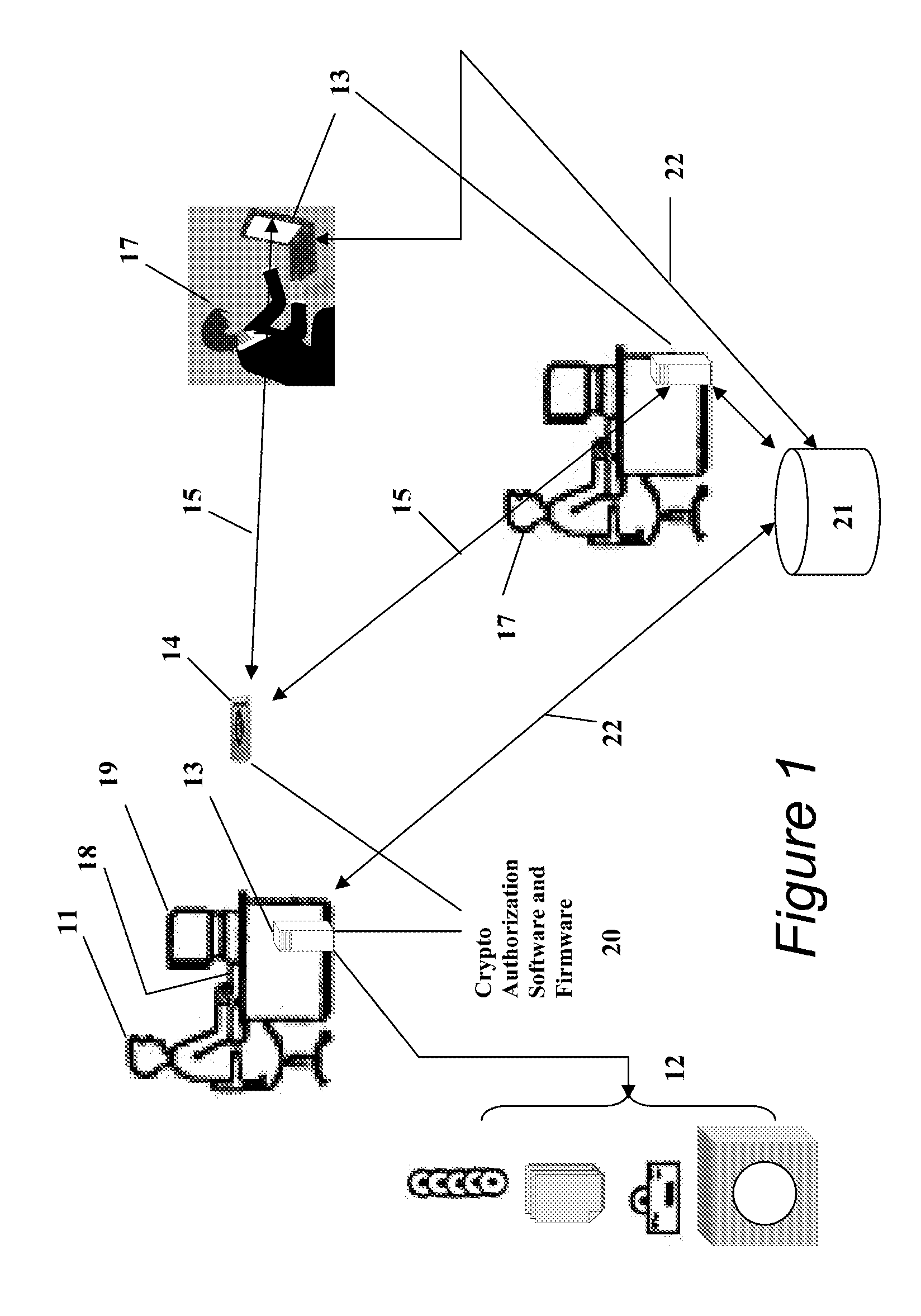
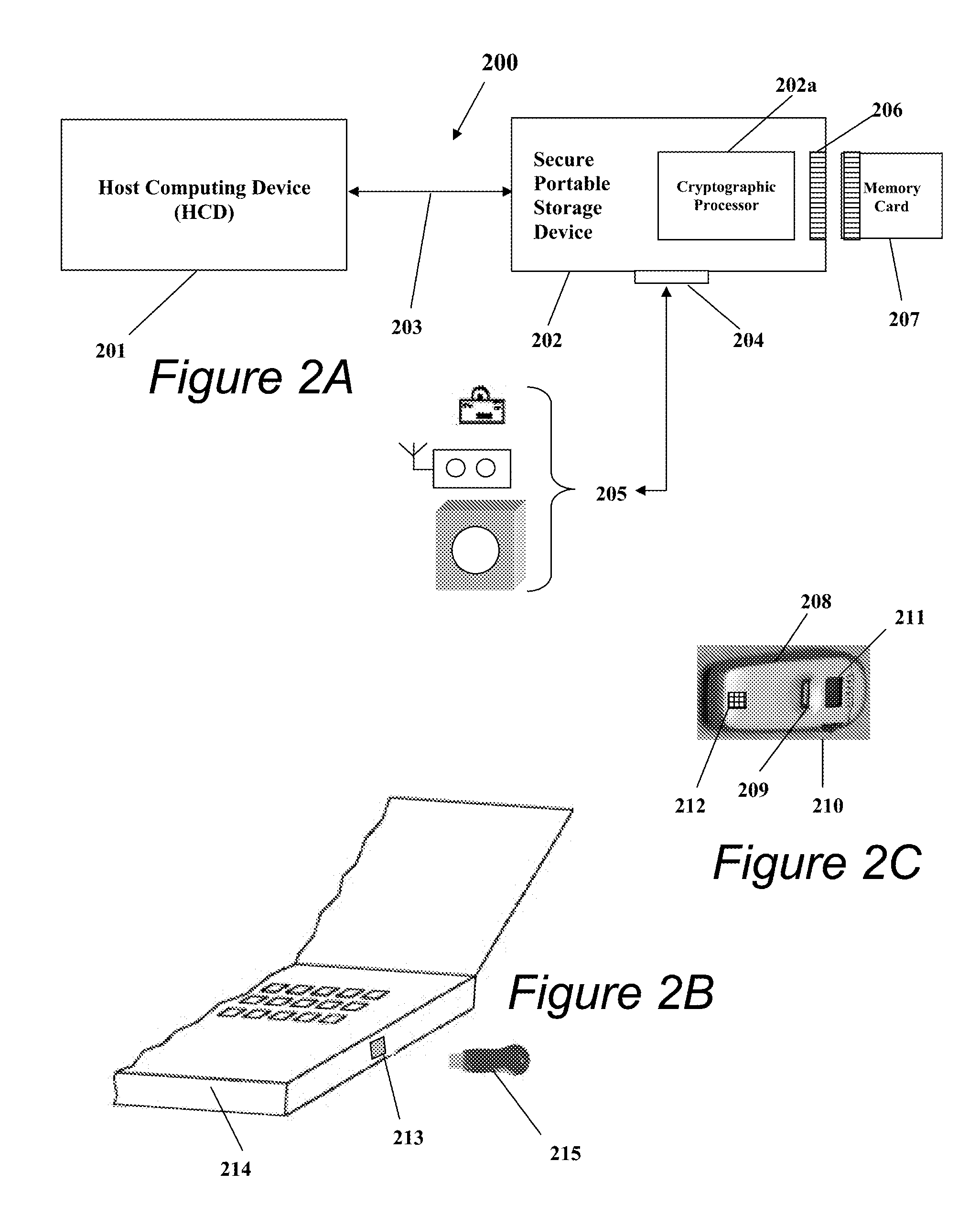
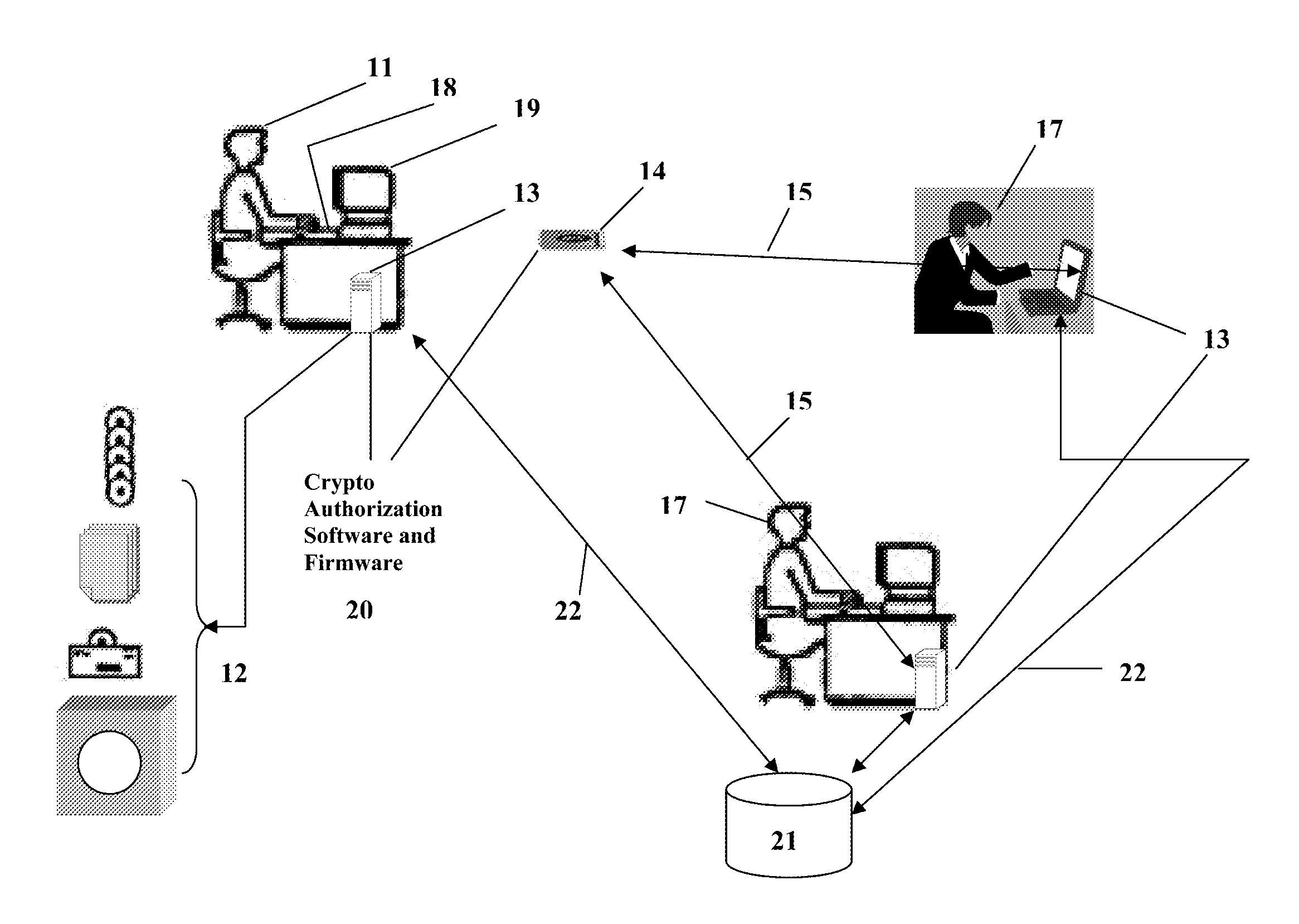
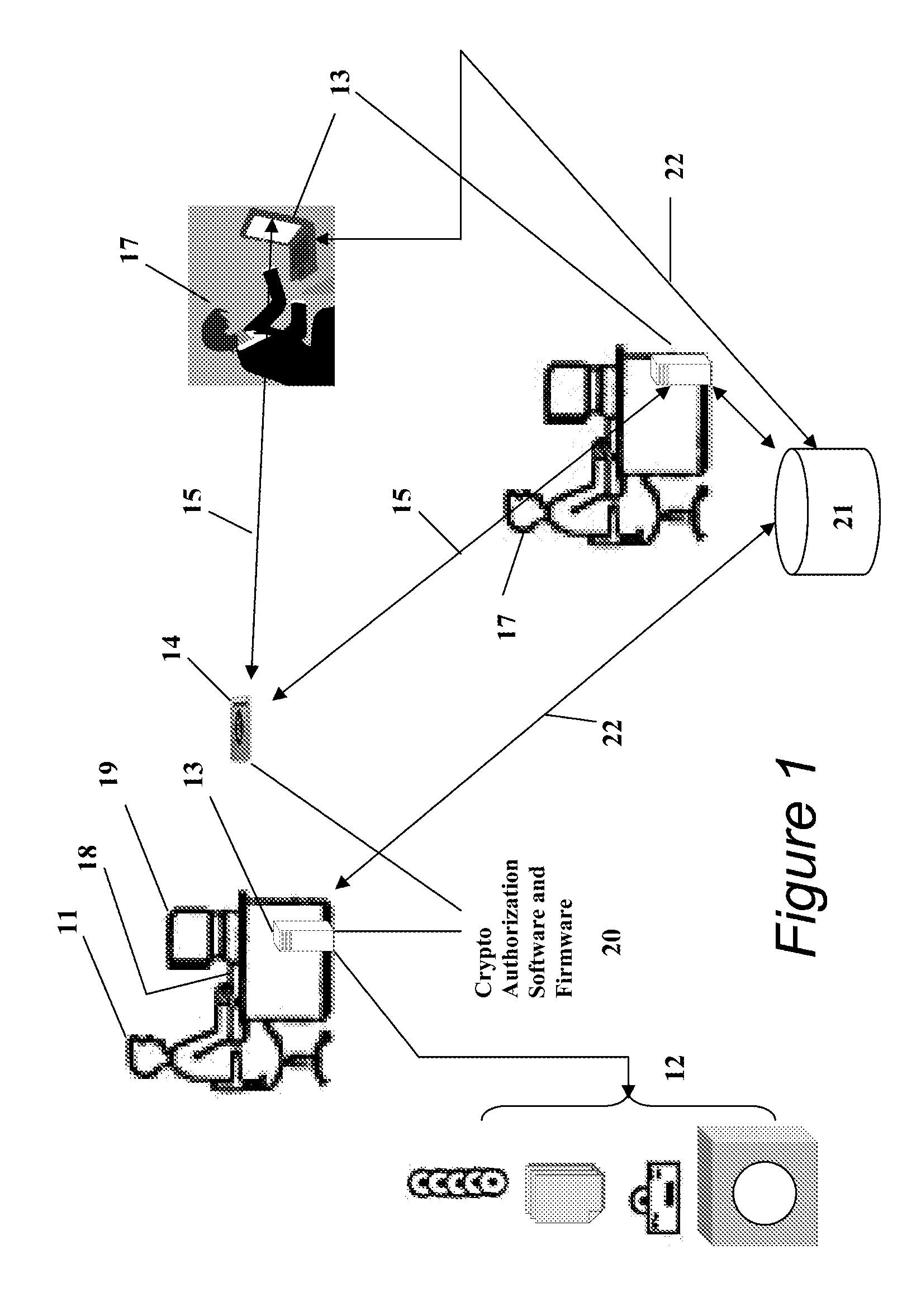
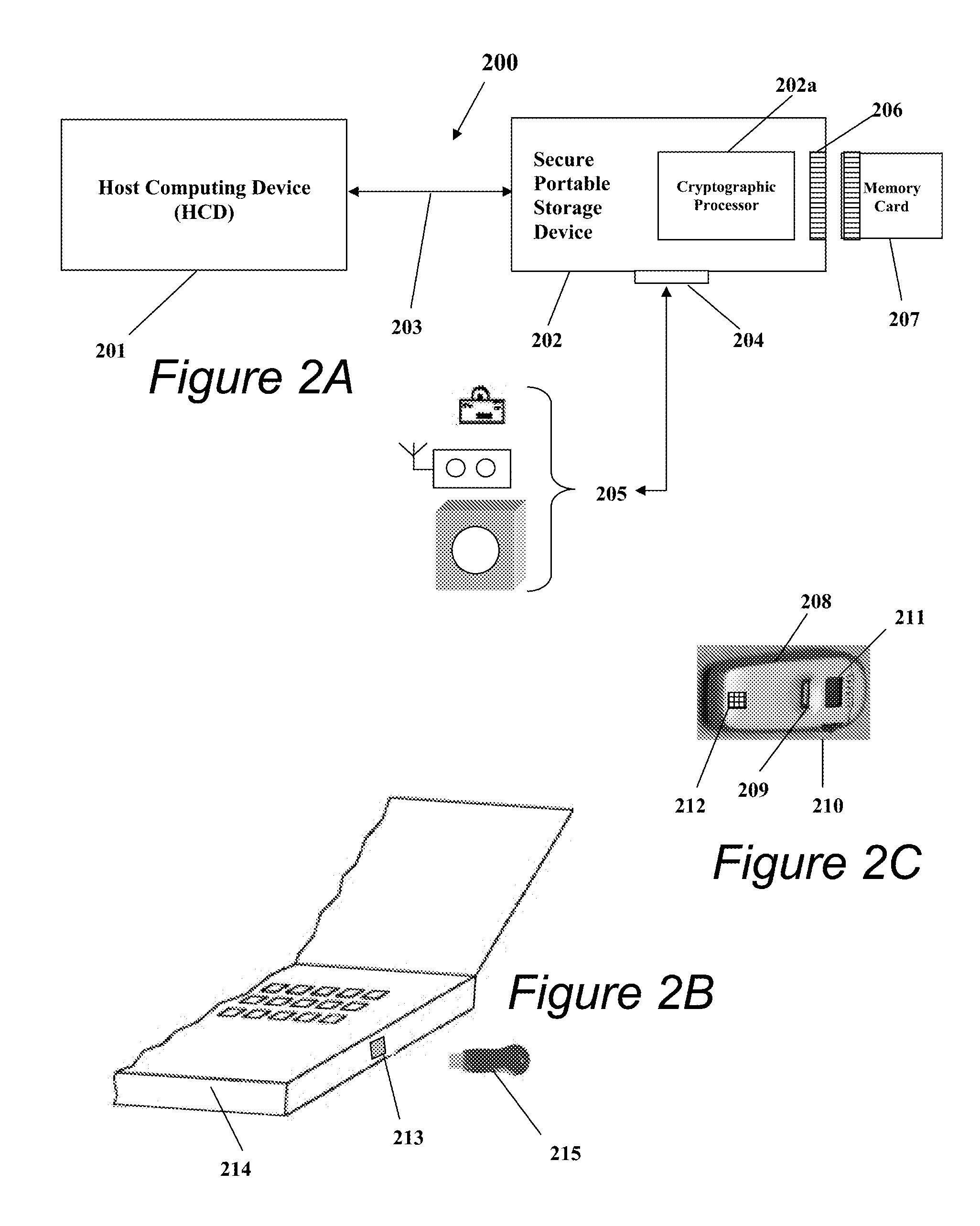
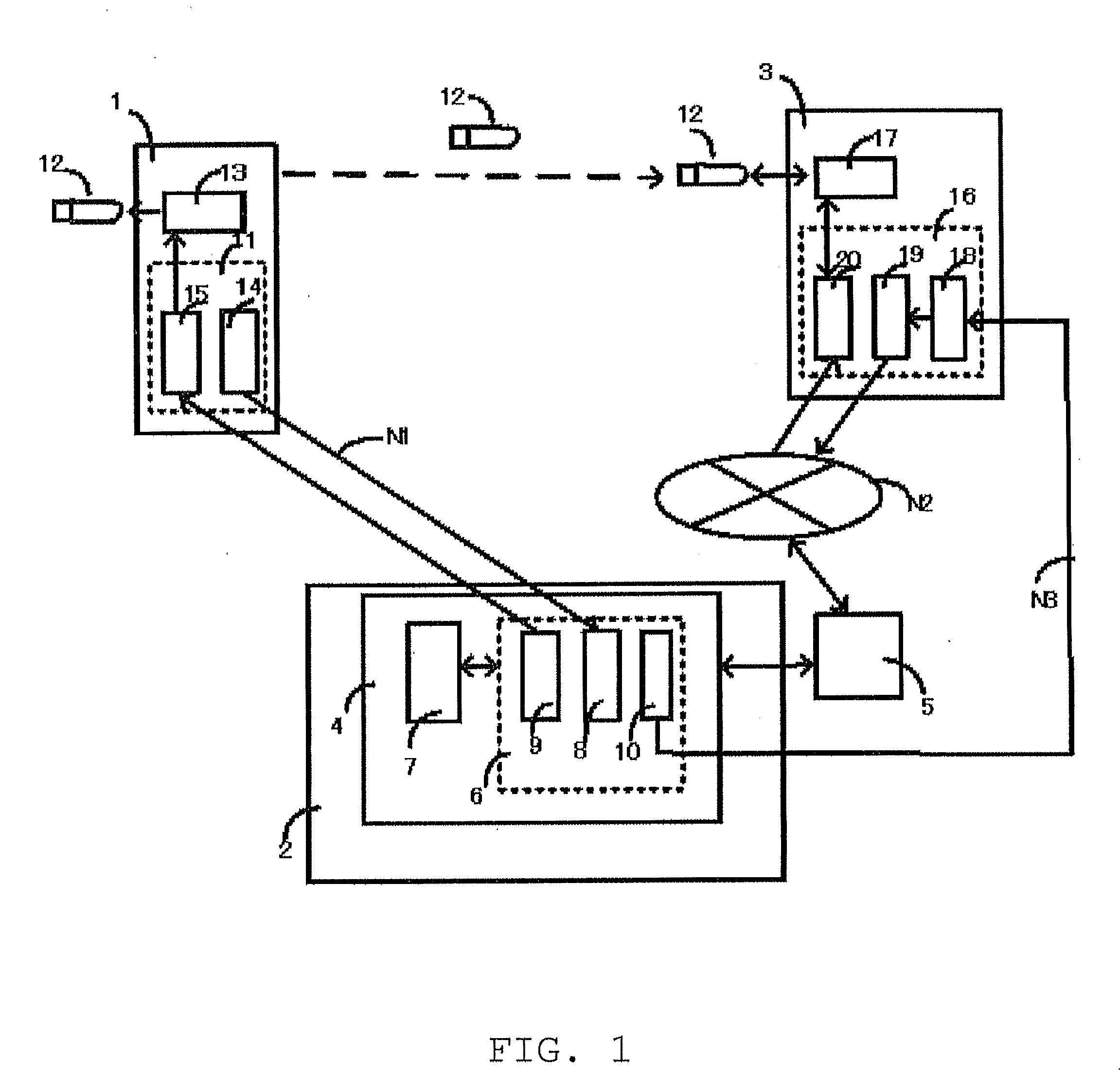
Portable Data Encryption Device with Configurable Security Functionality and Method for File Encryption
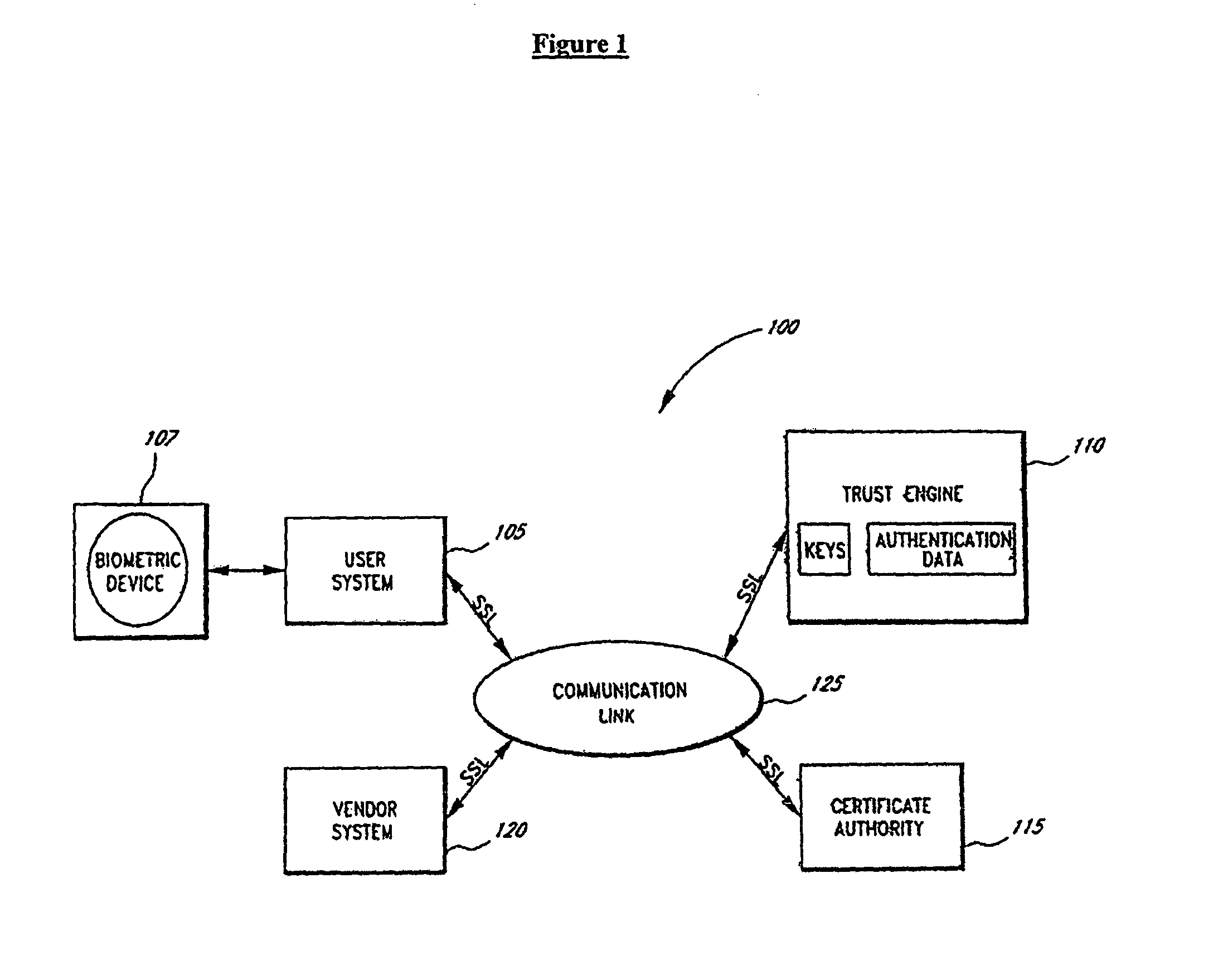
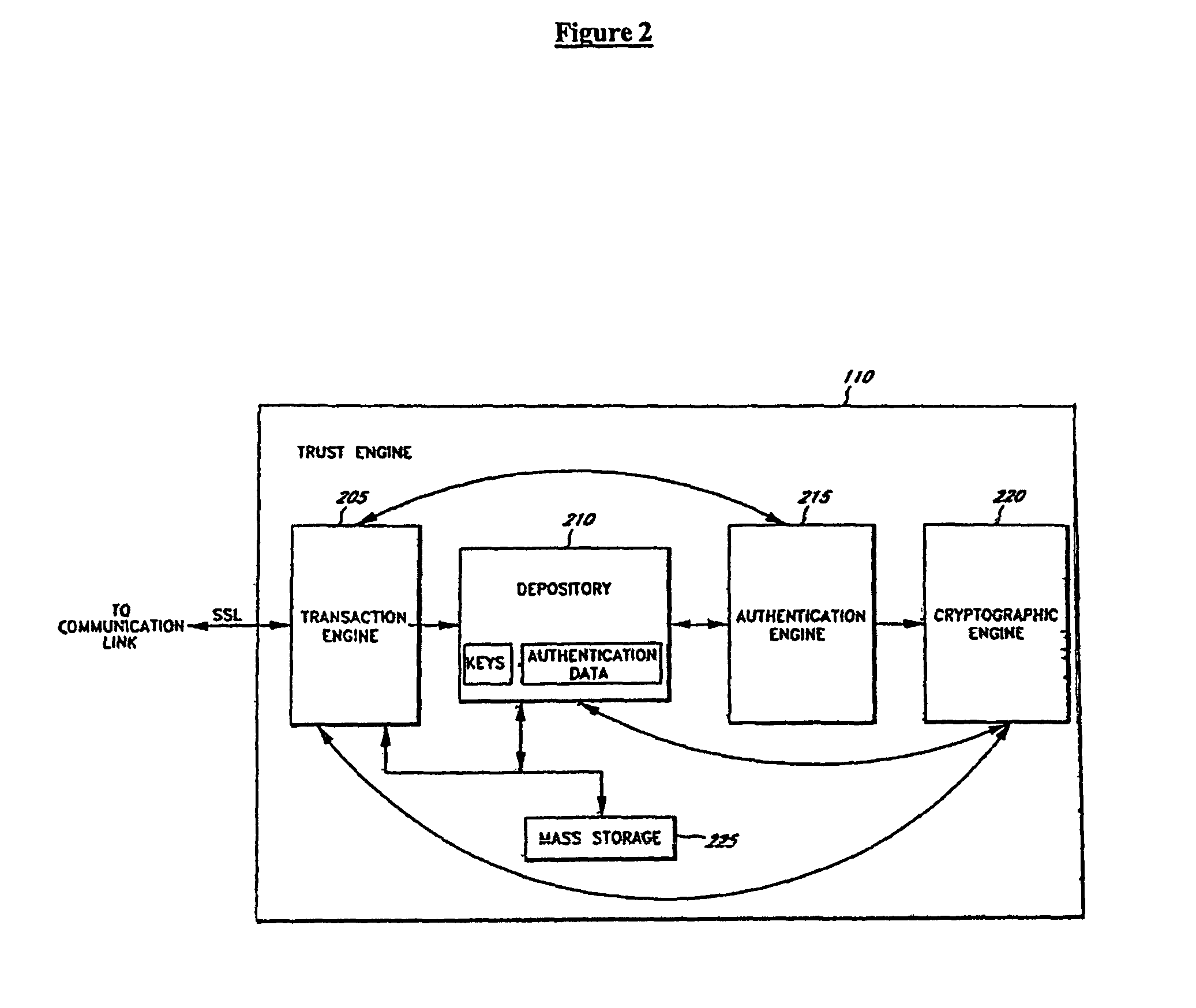
InactiveUS20080263363A1Mitigates and eliminates vulnerabilityUser identity/authority verificationInternal/peripheral component protectionComputer hardwarePlaintext
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
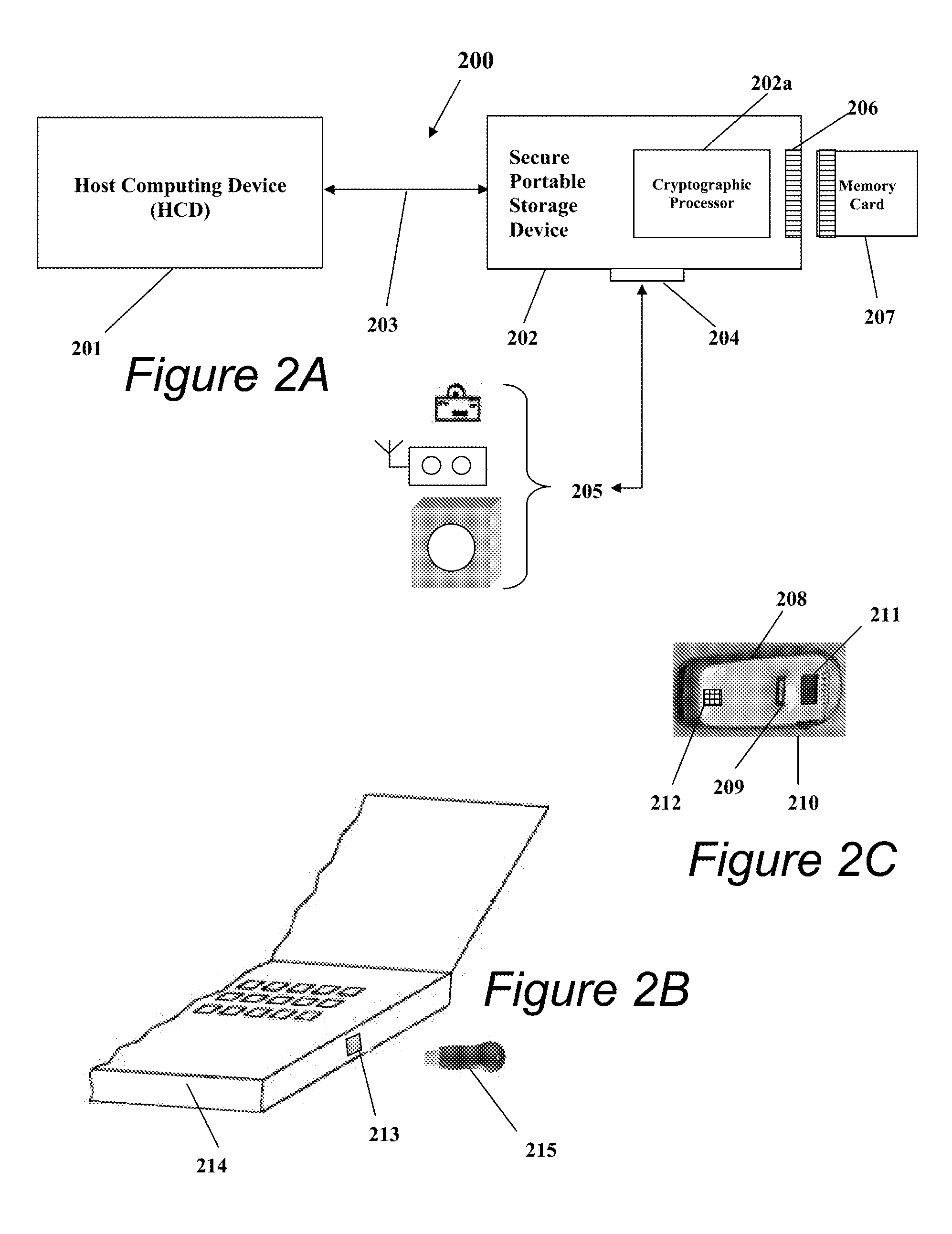
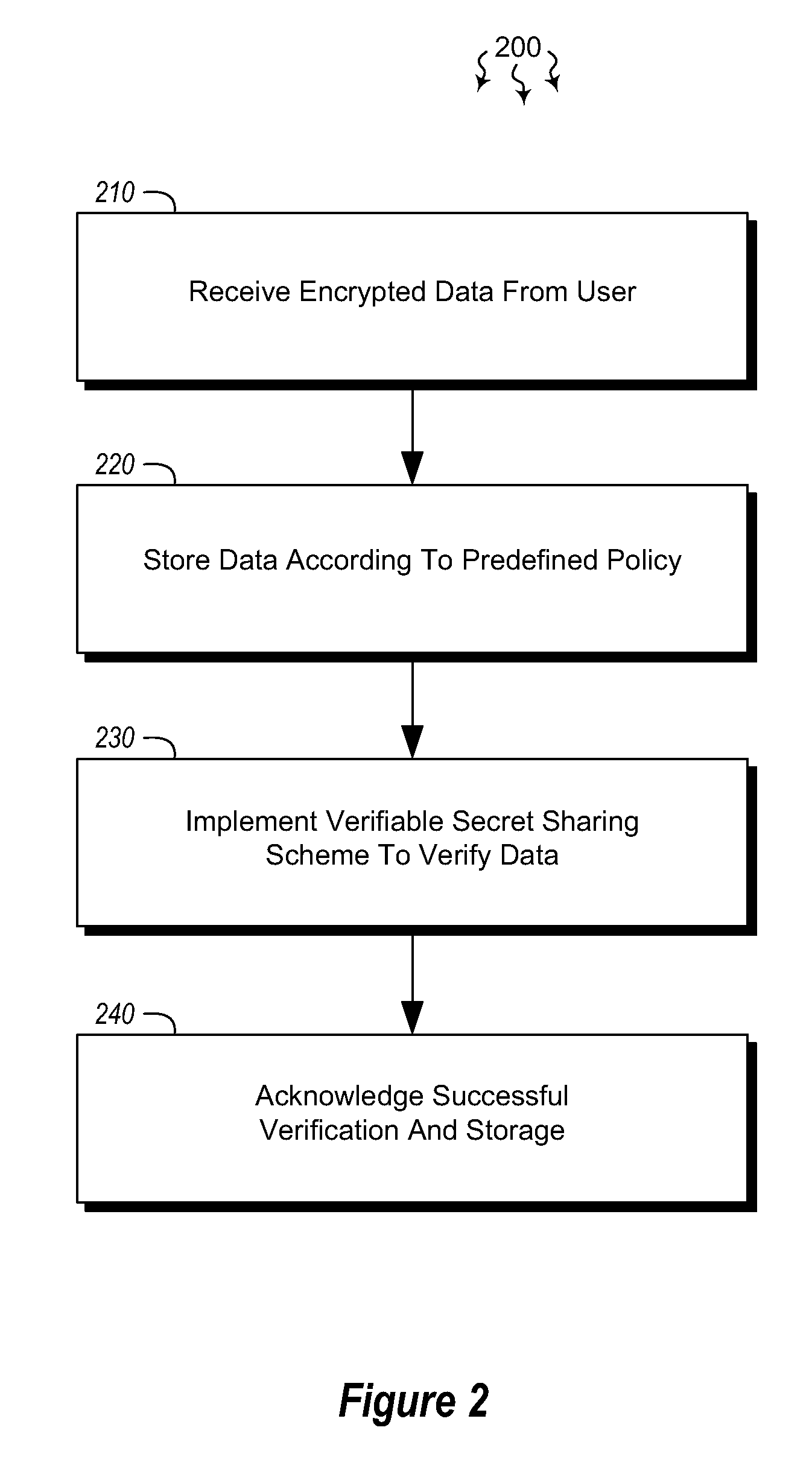
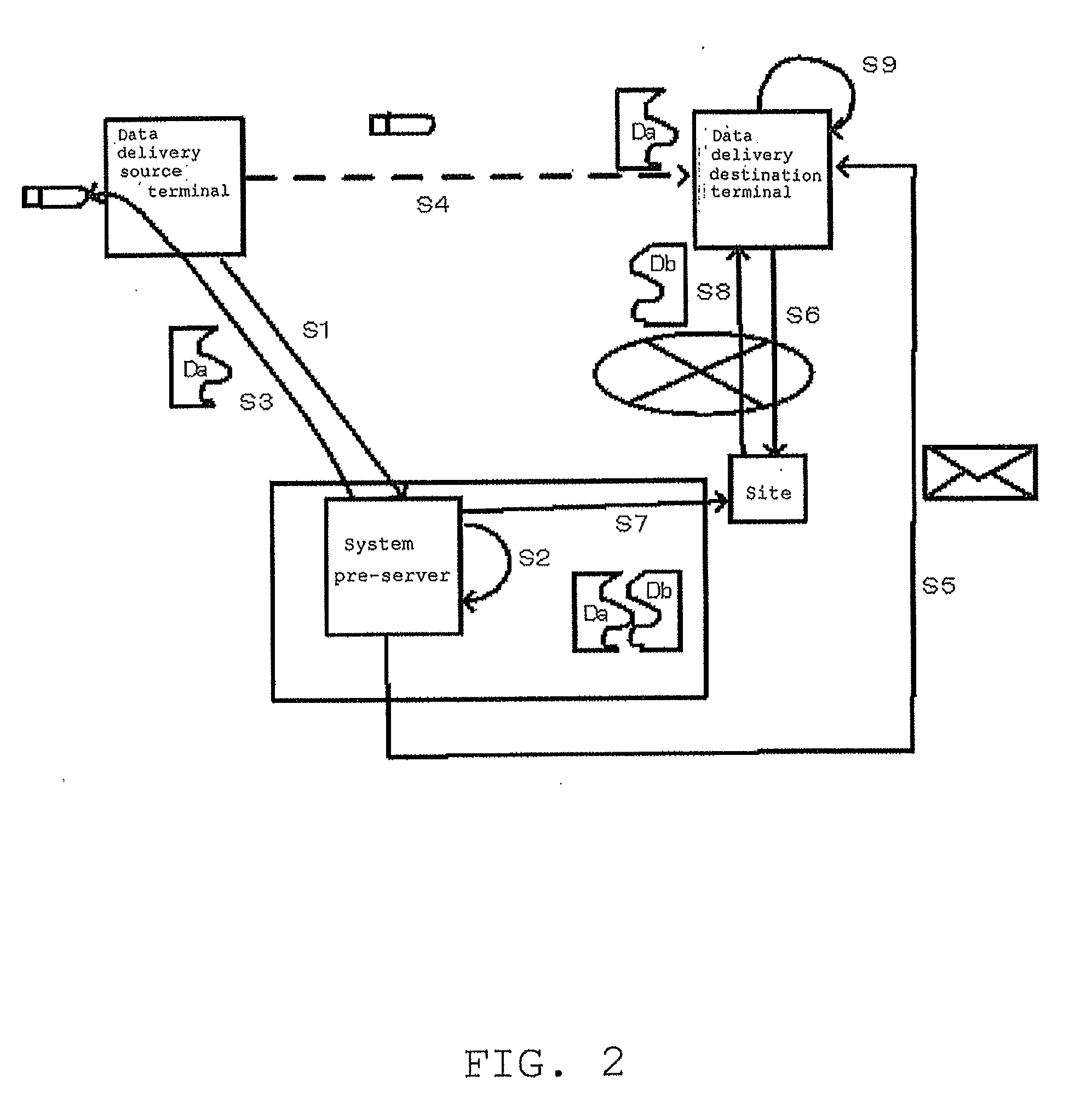
Systems and methods for securing data using multi-factor or keyed dispersal
ActiveUS20090177894A1Minimal compute resourceAvoid the needUnauthorized memory use protectionHardware monitoringInformation dispersalOriginal data
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths. A keyed information dispersal algorithm (keyed IDA) may also be used. The key for the keyed IDA may additionally be protected by an external workgroup key, resulting in a multi-factor secret sharing scheme.
Owner:SECURITY FIRST INNOVATIONS LLC
Portable data encryption device with configurable security functionality and method for file encryption
ActiveUS9049010B2Mitigates and eliminates vulnerabilityKey distribution for secure communicationUser identity/authority verificationPlaintextComputer hardware
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
Systems and methods for distributing and securing data
ActiveUS20080137857A1Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
Block chain key trusteeship and recovery method and device based on secrecy sharing technology
InactiveCN107623569ASafekeepingSafe recoveryKey distribution for secure communicationRecovery methodRestoration method
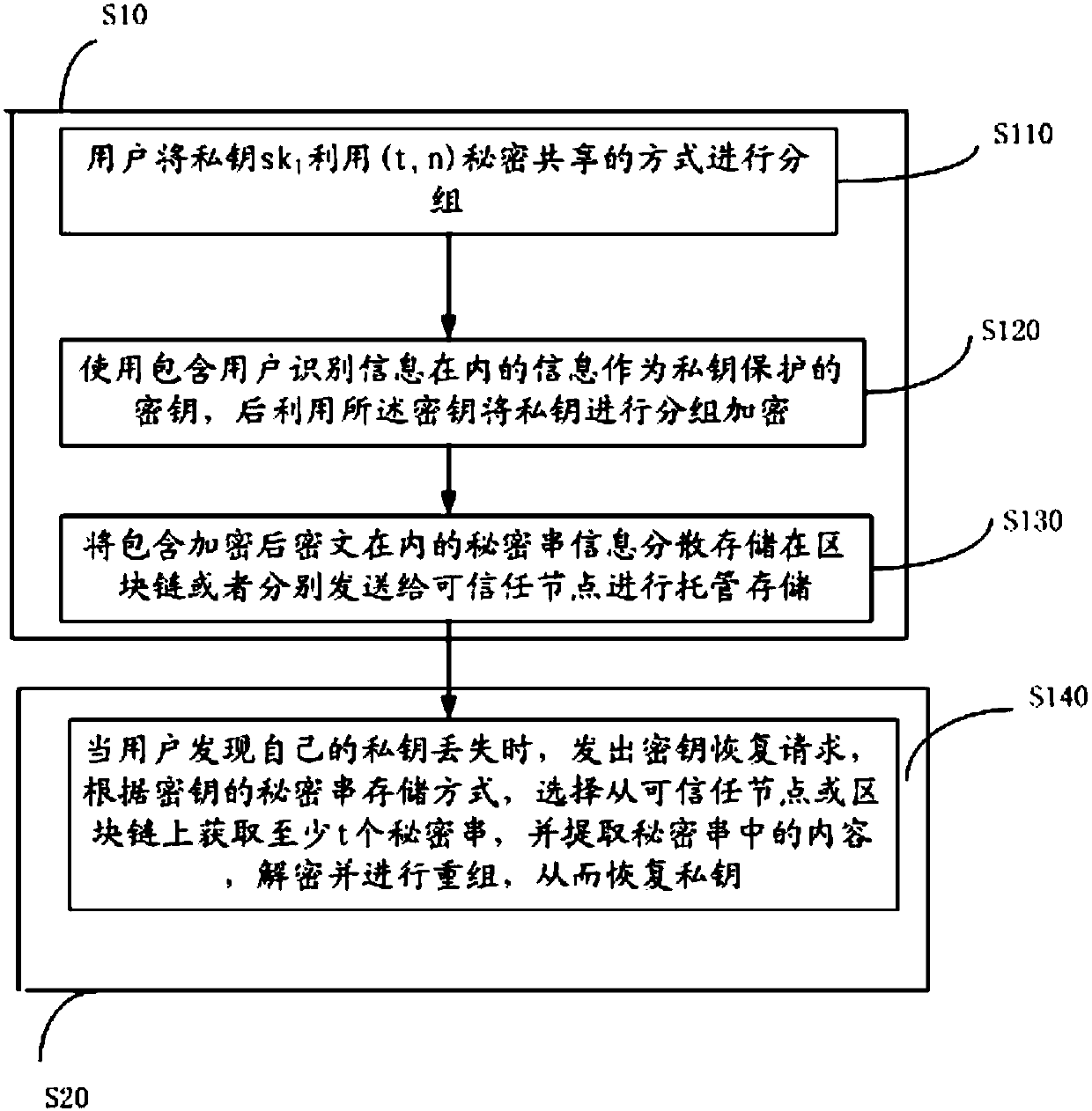
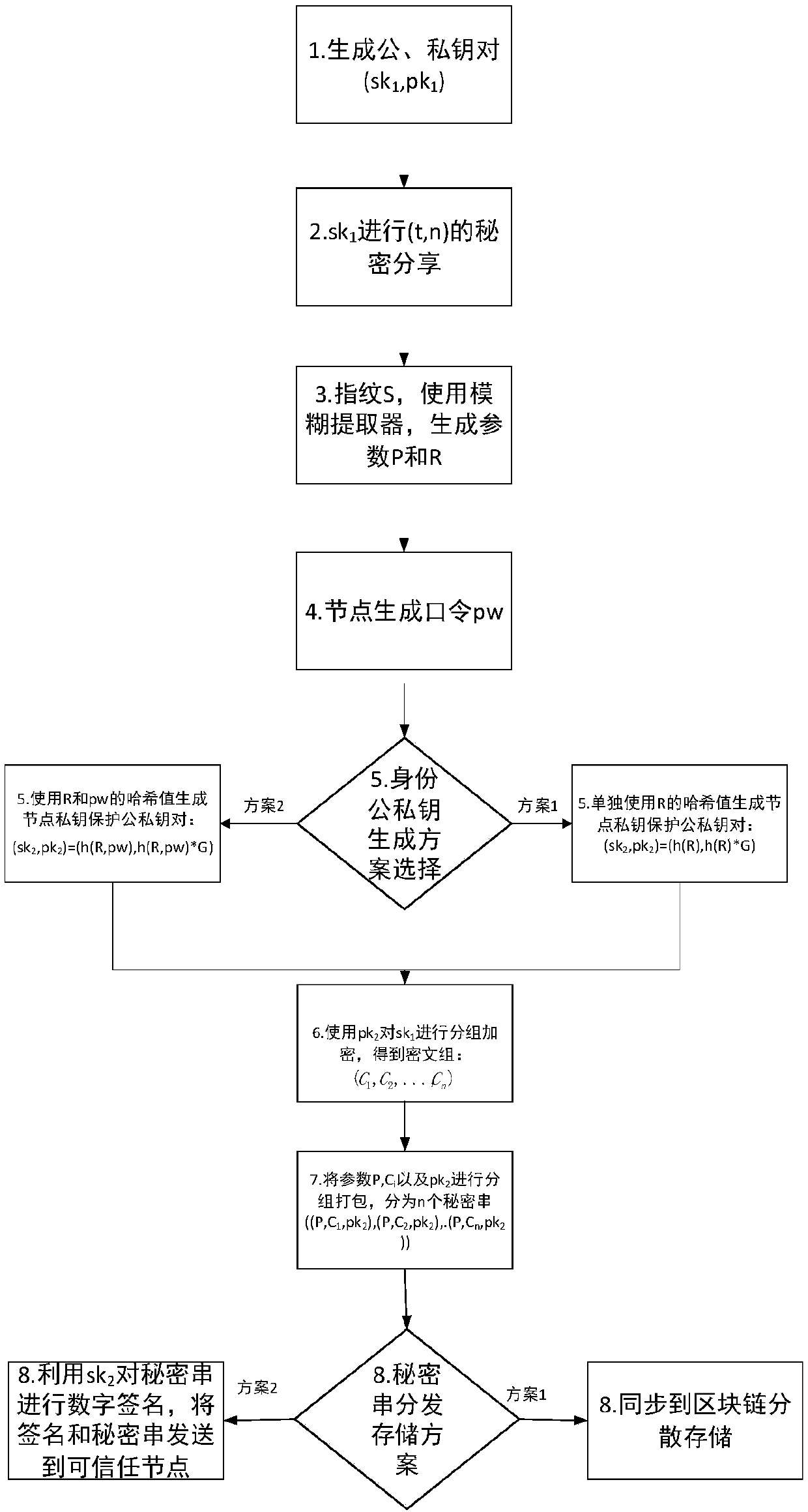
The invention discloses a block chain key trusteeship and recovery method and device based on a secrecy sharing technology. The method comprises the steps that A1, a user groups a private key sk1 in a(t, n) secrecy sharing mode, wherein the n is the number of fragments of shared secrecies obtained by splitting the private key, the t is the minimum number of the fragments for recovery of the private key, and the t is greater than or equal to 2 and is smaller than or equal to the n; A2, information containing user identification information is taken as a private key protection key, and then grouping encryption is carried out on the private key through utilization of the key; and A3, secrecy string information containing encrypted ciphertexts is dispersely stored to a block chain or is sentto trusted nodes for trusteeship and storage, when the user discovers that own private key is lost, a key recovery request is generated, at least t secrecy strings are obtained from the trusted nodesor the block chain in a secrecy string storage mode of the key, and the content in the secrecy strings is extracted, decrypted and recombined, so the private key is recovered. According to the methodand the device, the secrecy sharing technology is applied to a block chain scene for the first time, thereby solving the private key trusteeship and recovery security problem.
Owner:JUZIX TECH SHENZHEN CO LTD
Threshold and identity-based key management and authentication for wireless ad hoc networks
InactiveUS20060023887A1Reduce usageReduce resource requirementsKey distribution for secure communicationPublic key for secure communicationConfidentialityWireless ad hoc network
As various applications of wireless ad hoc network have been proposed, security has become one of the big research challenges and is receiving increasing attention. The present invention provides for a distributed key management and authentication approach by deploying the recently developed concepts of identity-based cryptography and threshold secret sharing. Without any assumption of pre-fixed trust relationship between nodes, the ad hoc network works in a self-organizing way to provide the key generation and key management service, which effectively solves the problem of single point of failure in the traditional public key infrastructure (PKI)-supported system. The identity-based cryptography mechanism provided not only to provide end-to-end authenticity and confidentiality, but also saves network bandwidth and computational power of wireless nodes.
Owner:UNIVERSITY OF CINCINNATI
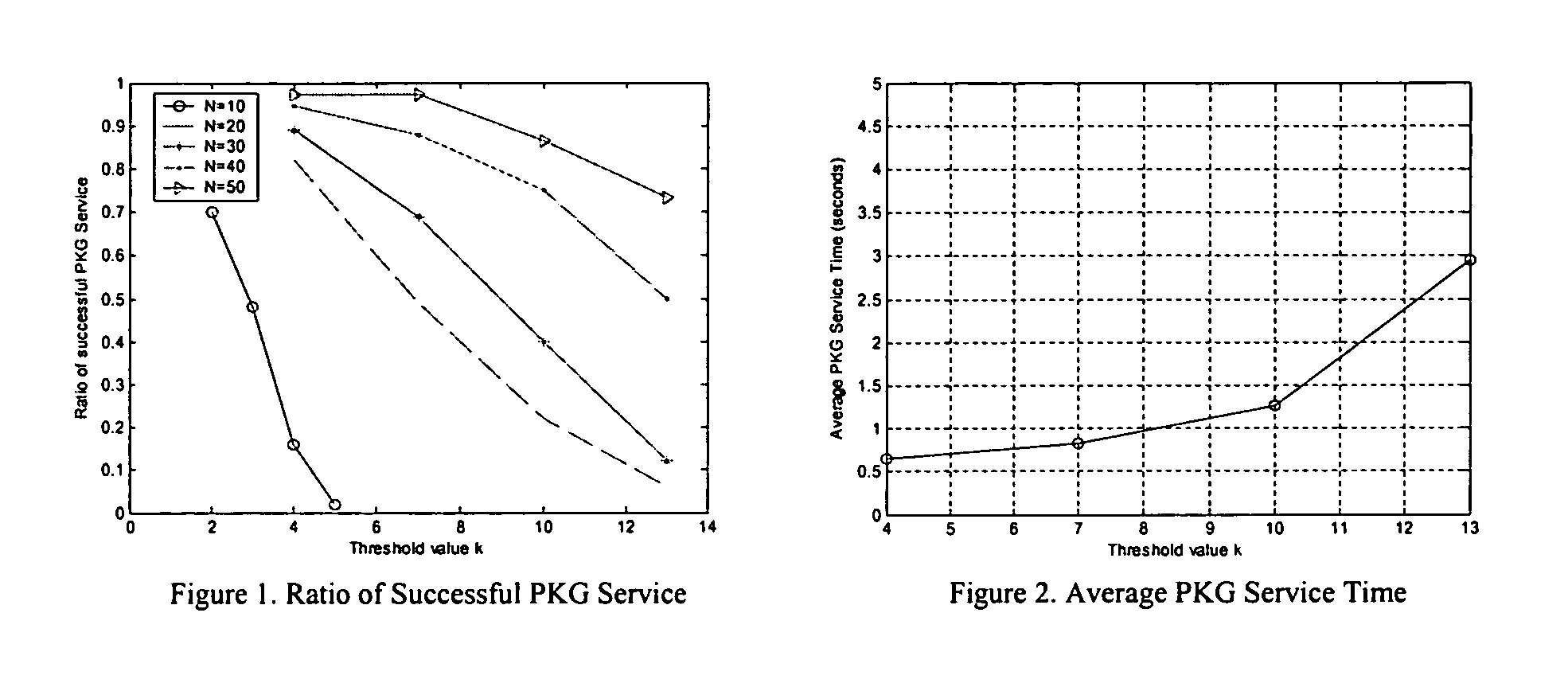
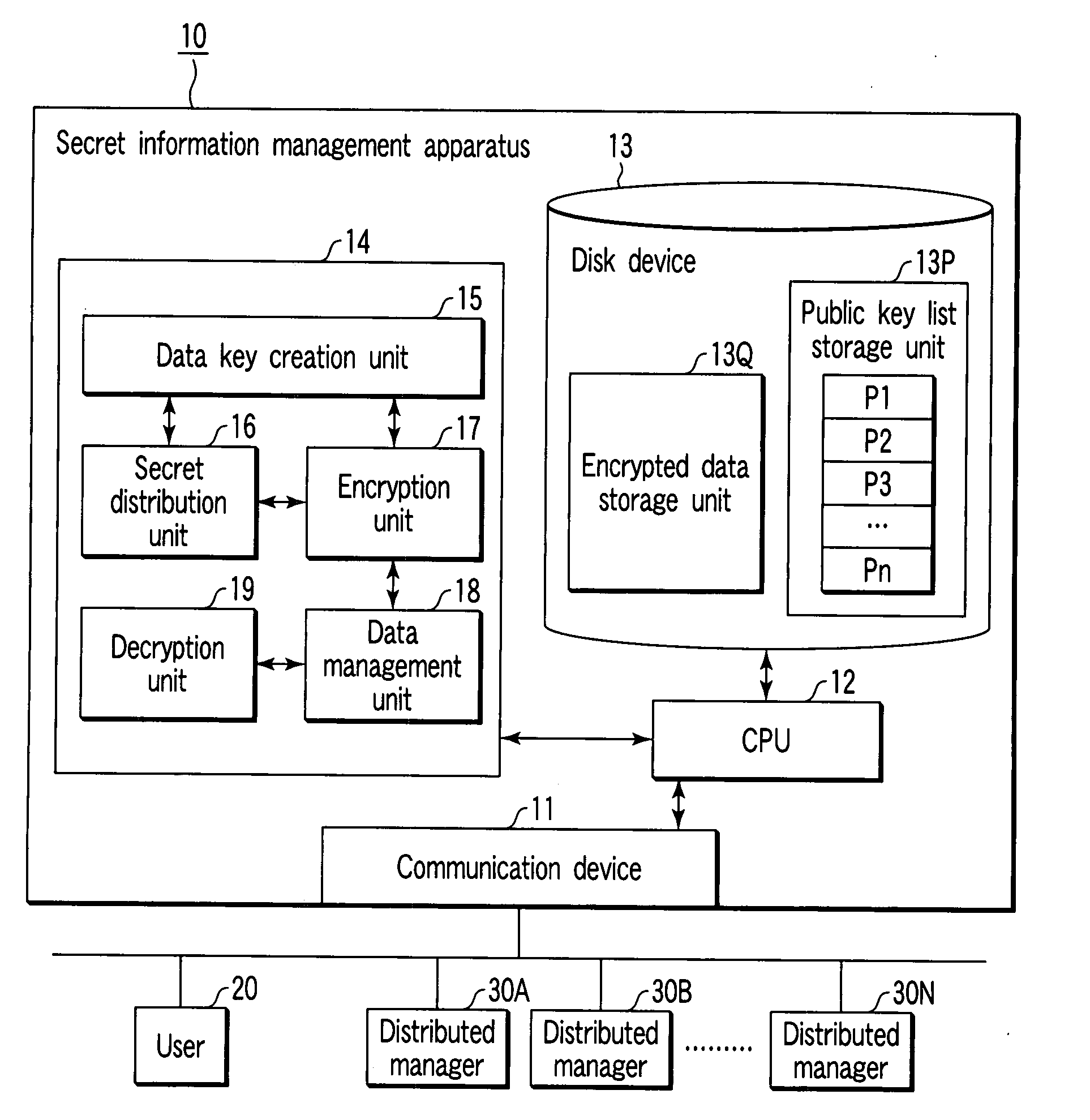
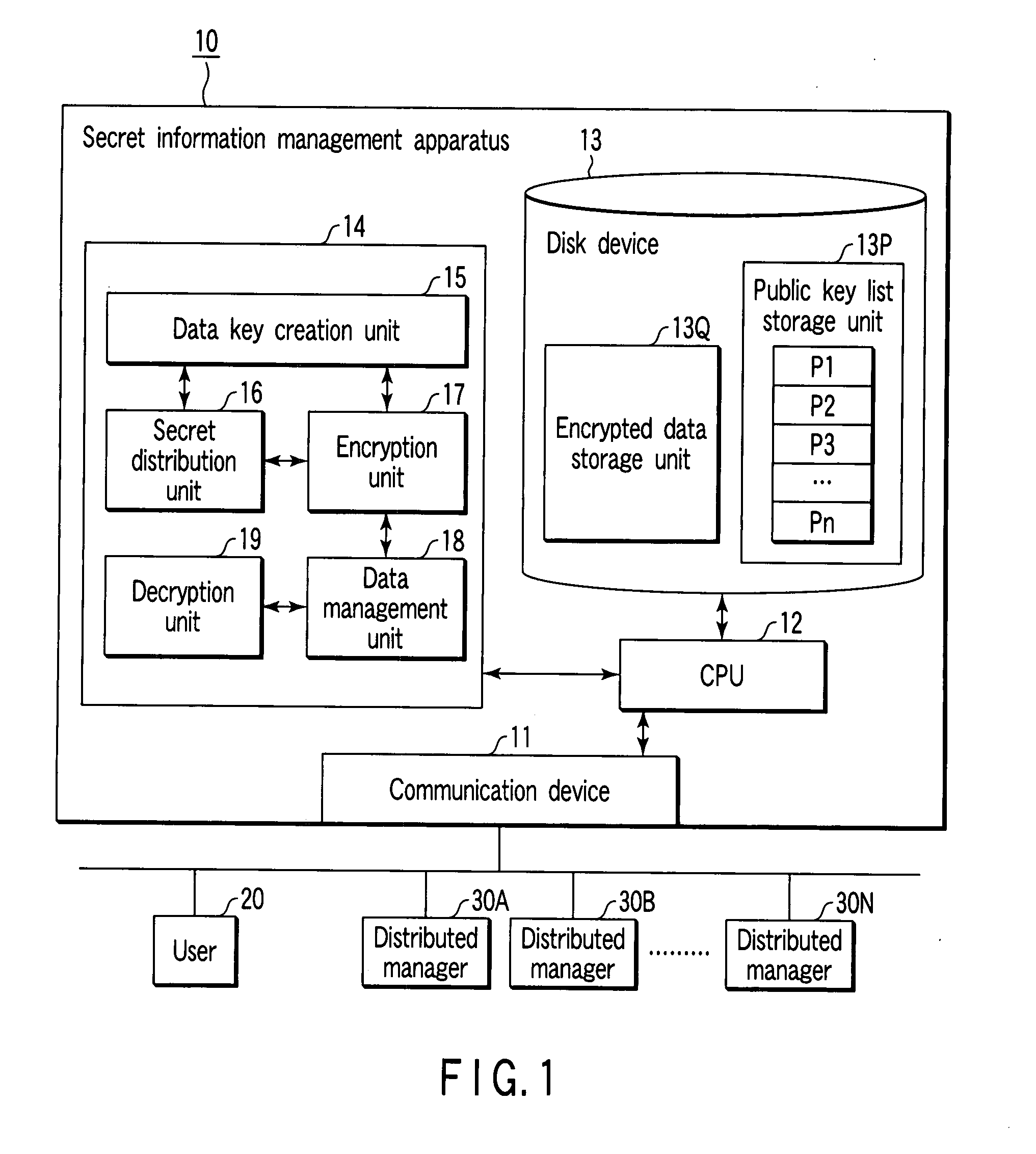
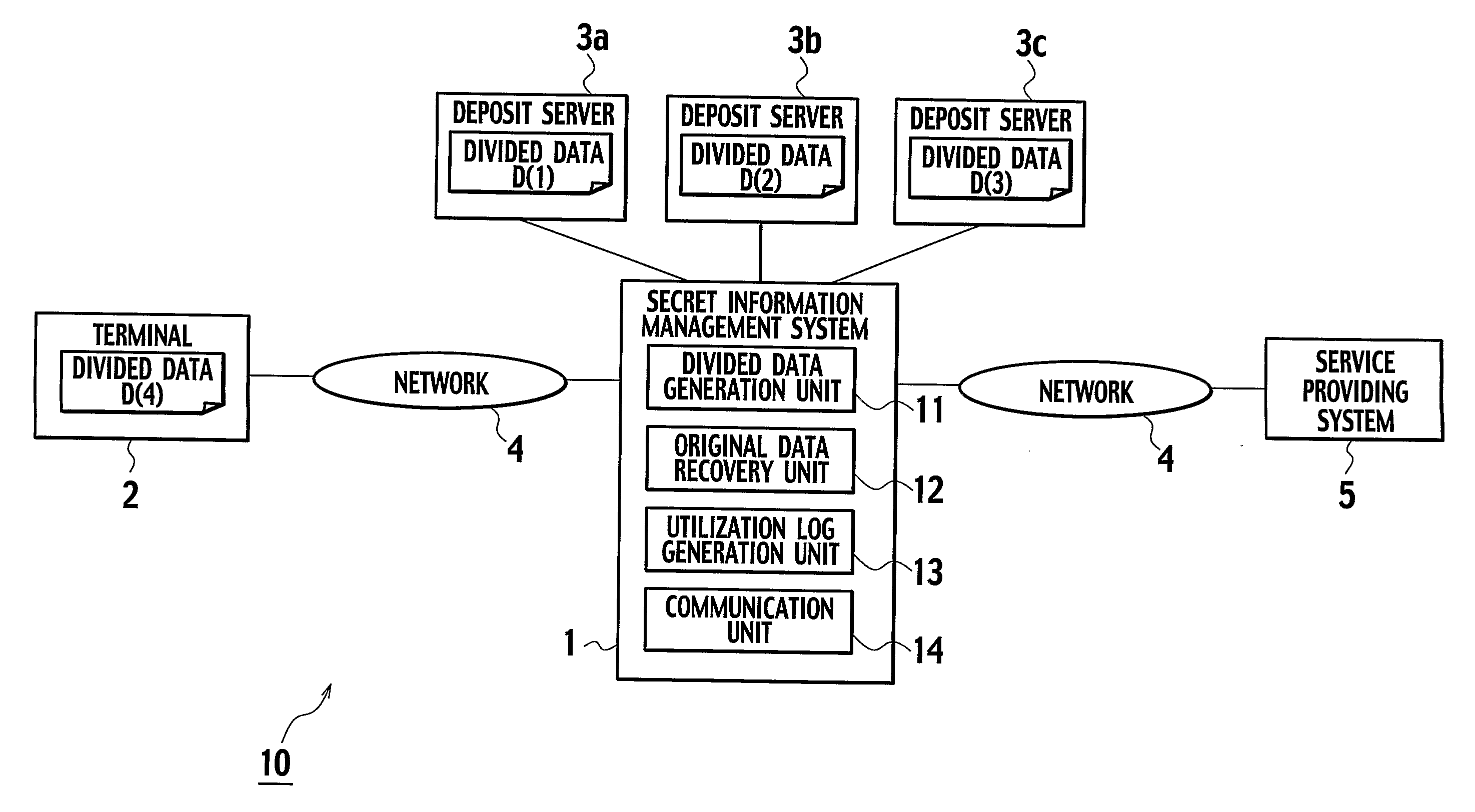
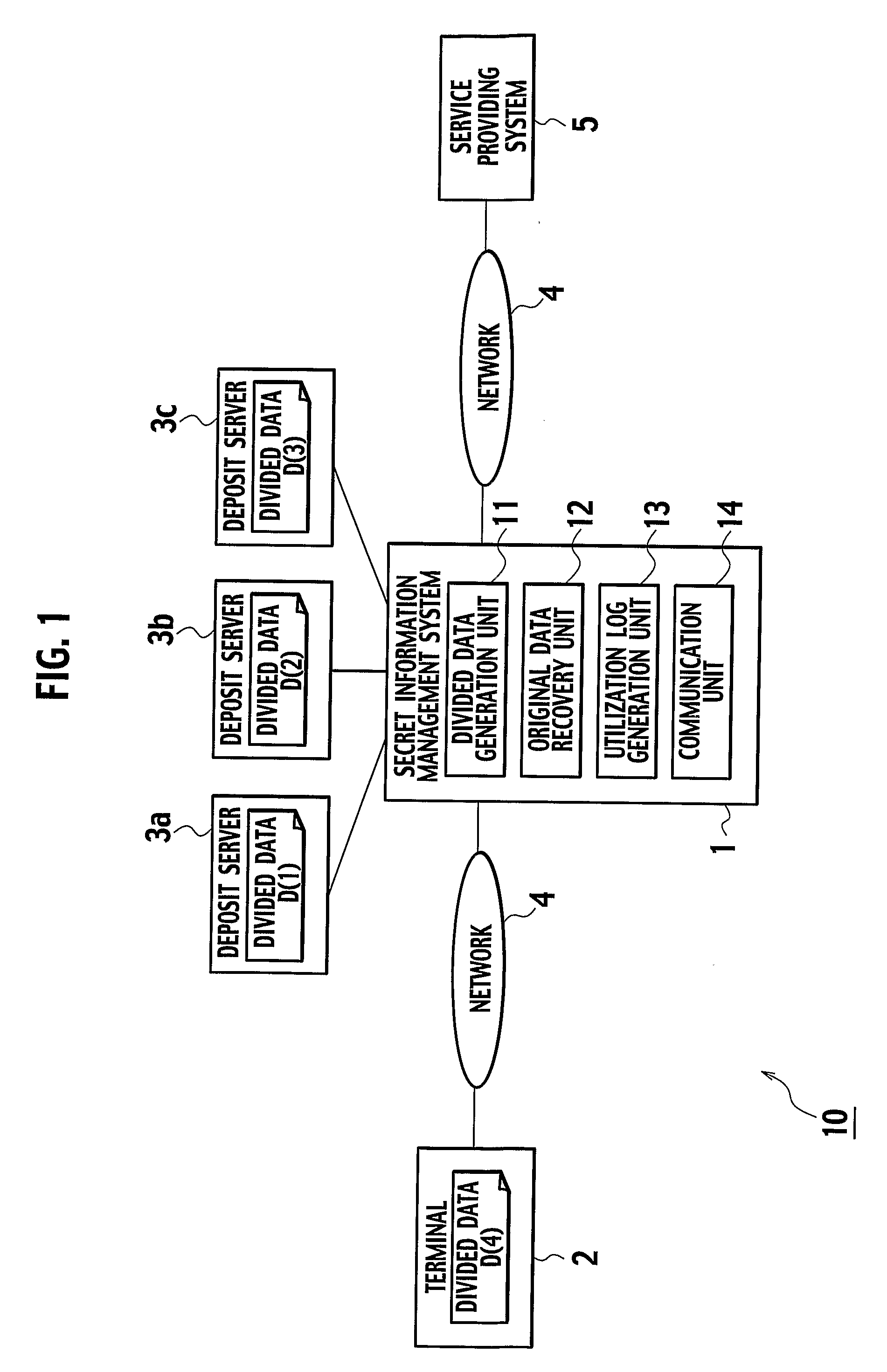
Secret information management apparatus and secret information management system
InactiveUS20080095375A1Key distribution for secure communicationPublic key for secure communicationManagement systemEncryption
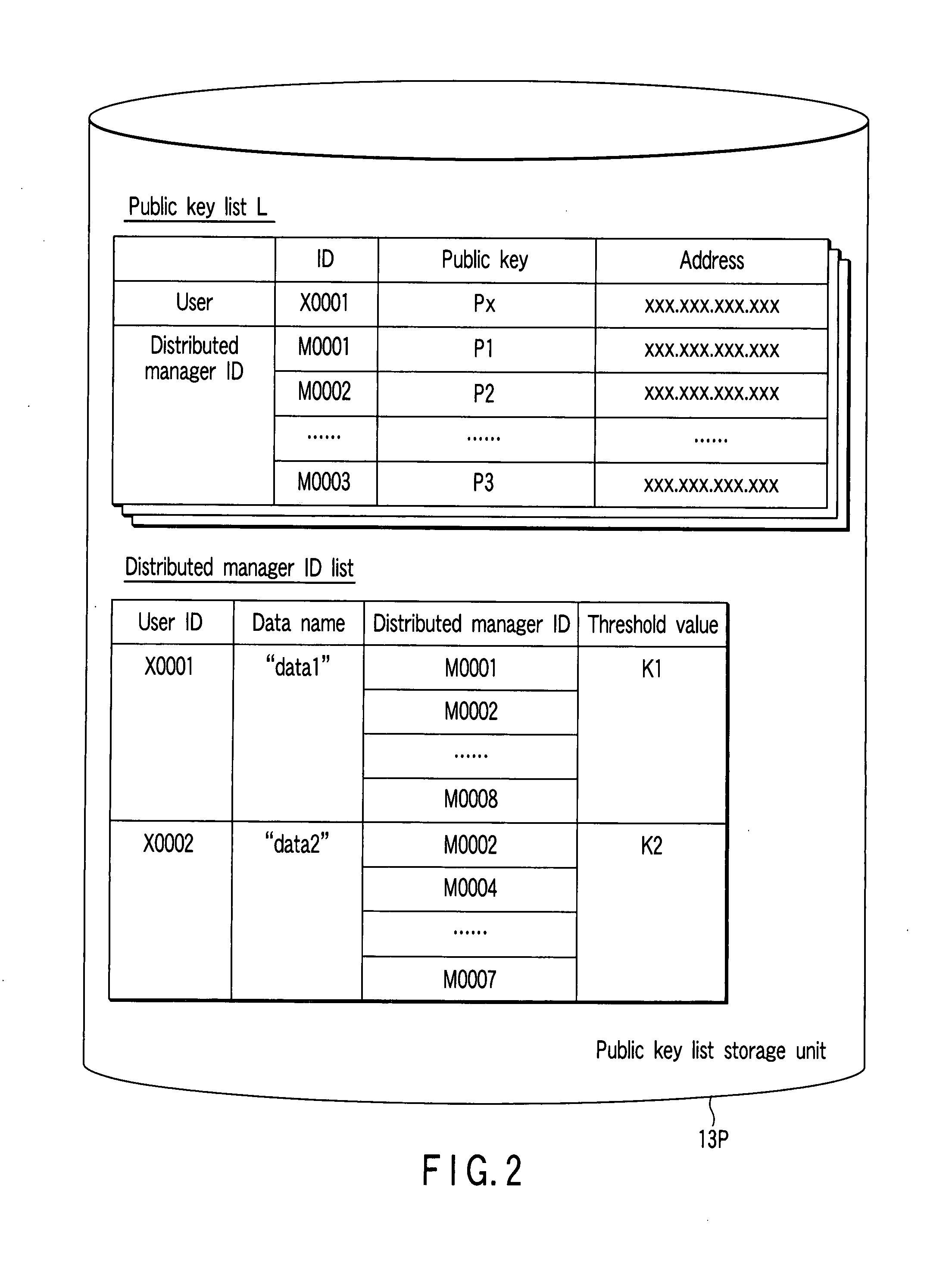
In a secret information management system, a secret information management apparatus comprises a secret distribution unit which secretly distributes a data key k using a (k, n) threshold secret sharing scheme and creates n distributed keys B1, B2, . . . , Bn in the decryption of data D input from a user terminal, an encryption unit which creates n encrypted distributed keys EP1(B1), EP2(B2) . . . , EPn(Bn) using n distributed manager public keys P1, P2, . . . Pn, and an encrypted data storage unit which stores encrypted data EK(D), an encrypted data key EPx(K) and the n encrypted distributed keys in association with each other.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP +1
Network Security System
InactiveUS20090077379A1Limited accessSynchronising transmission/receiving encryption devicesUser identity/authority verificationComputer hardwareSecret share
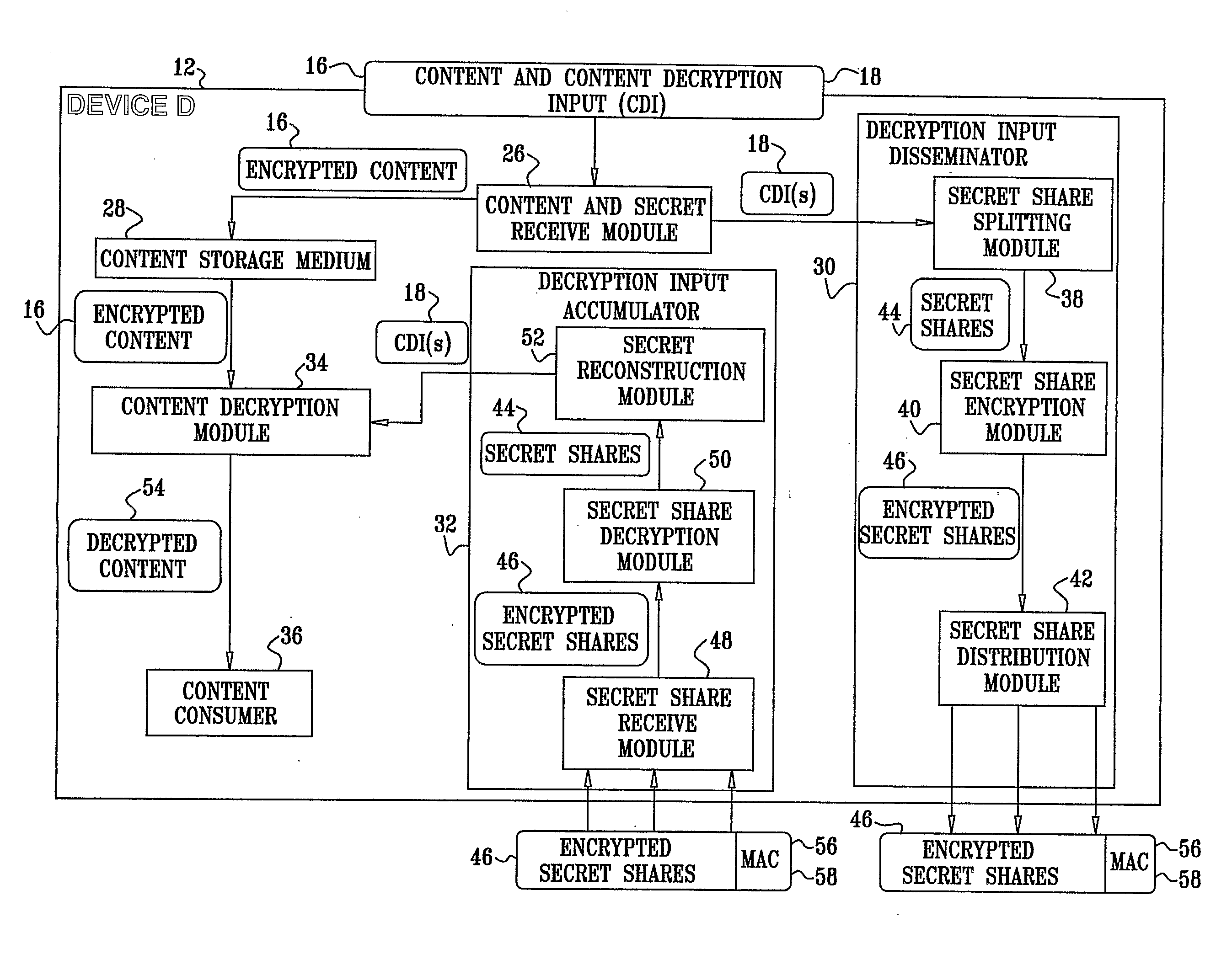
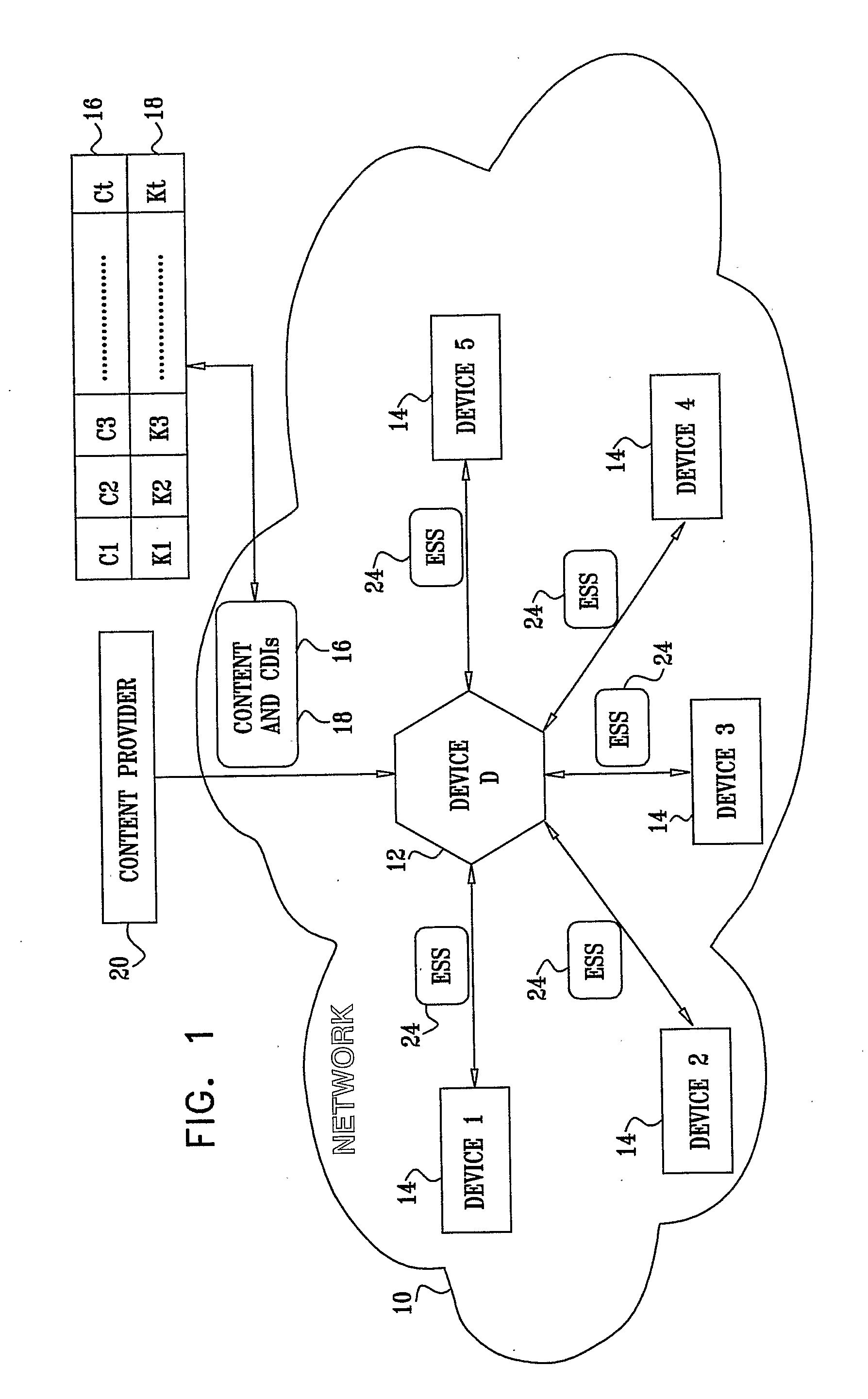
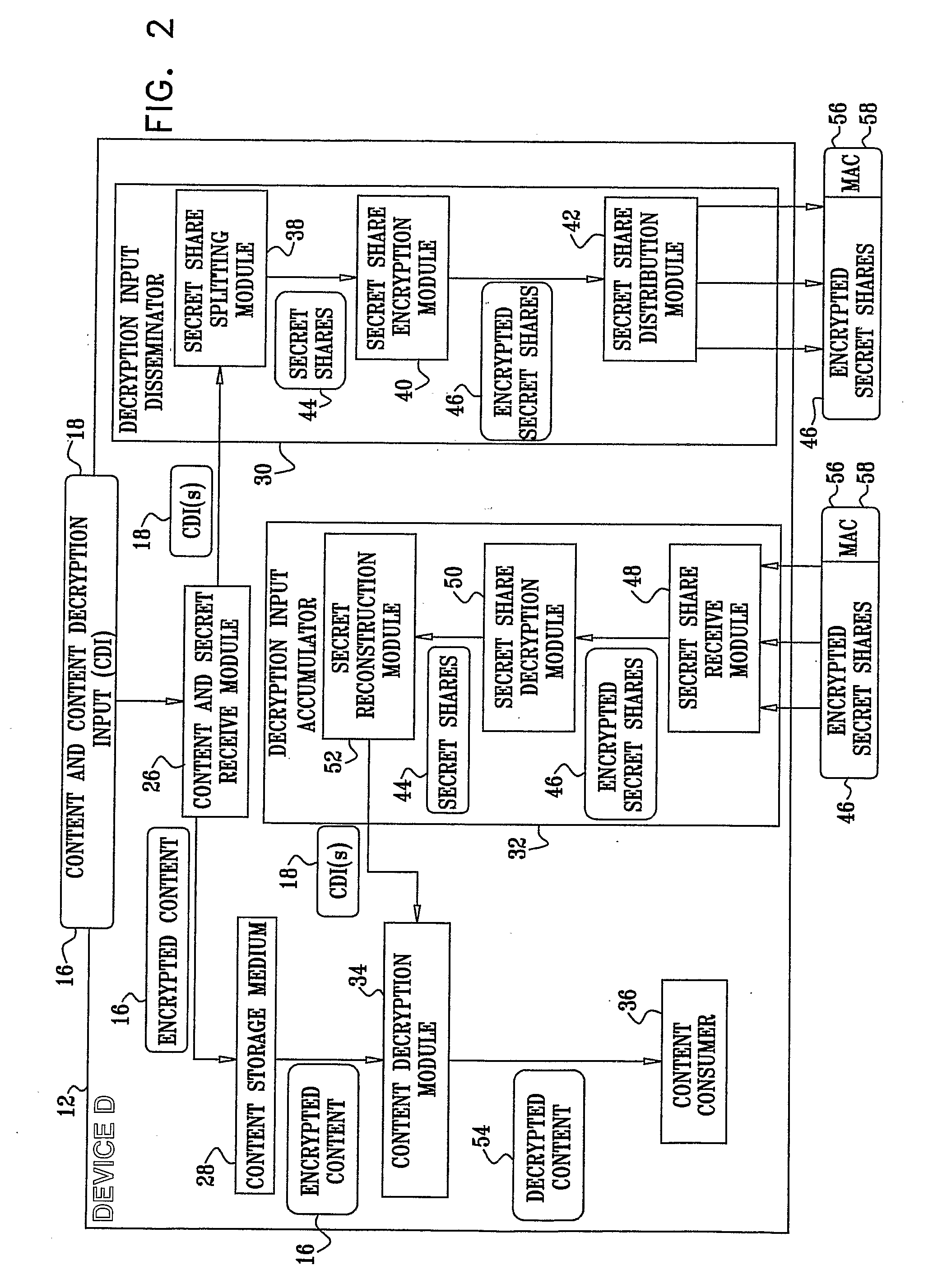
A system for restricting access to encrypted content stored in a consuming device (12) which is part of a network (10) including other devices (14), the system including a content storage medium to store the encrypted content, a secret-share distribution module to distribute secret-shares to the other devices (14), a secret-share receive module to receive the secret-shares from the other devices (14), a secret reconstruction module to form a content decryption input from the secret-shares received by the secret-share receive module, a content decryption module to receive the encrypted content from the content storage medium and the content decryption input from the secret reconstruction module and decrypt the encrypted content using the content decryption input thereby rendering decrypted content, and a content consumer to use the decrypted content, wherein the secret shares distributed to the other devices (14) are in an encrypted format for decryption by the consuming device (12) or the other devices (14).
Owner:CISCO TECH INC +1
Cloud key escrow system
ActiveUS20120321086A1Data augmentationKey distribution for secure communicationDigital data processing detailsThird partyData access
Owner:MICROSOFT TECH LICENSING LLC
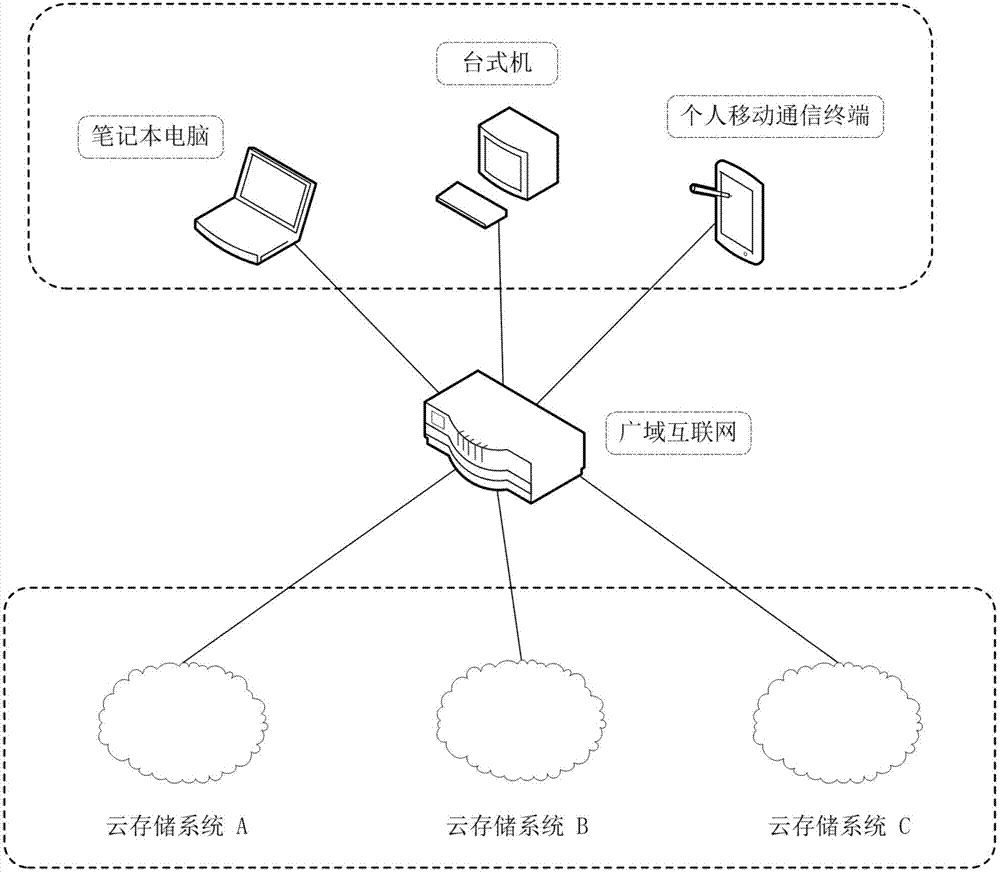
Safe storage method based on a plurality of cloud storage systems and system thereof
InactiveCN103118089AImprove fault toleranceAvoid inaccessibilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCode moduleCiphertext
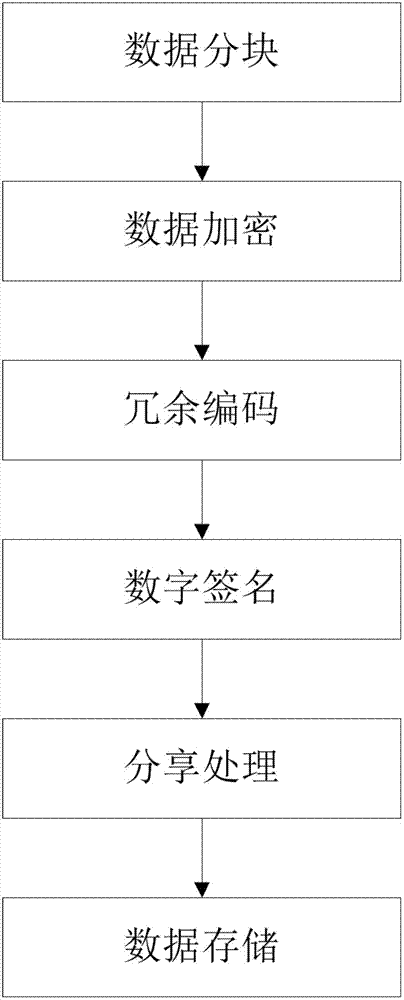
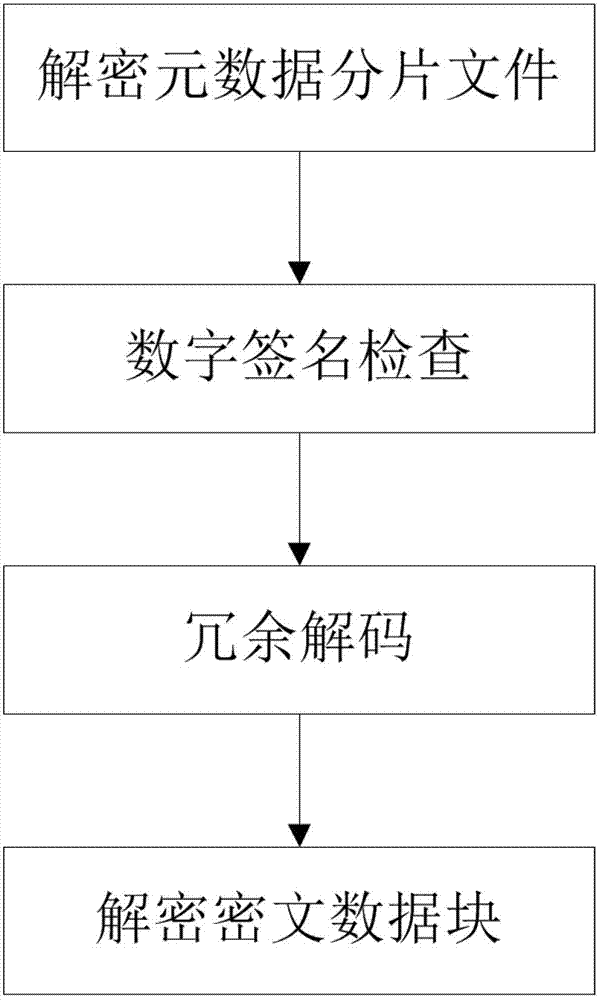
The invention belongs to the technical field of computer storage, and provides a safe storage method based on a plurality of cloud storage systems and a system thereof. The method and the system can achieve the purpose that in the plurality of existing cloud storage systems, safety of data and metadata can be guaranteed at the same time. The safe storage method comprises a step of data writing operation and a step of data reading operation, wherein the step of data writing operation comprises the sub-steps of data partitioning, data encryption, redundancy encoding, digital signature, sharing processing, and data storage. The step of data reading operation comprises the sub-steps of metadata partition file decryption, digital signature inspection, redundancy decoding and cipher text data block decryption. The safe storage system comprises an encryption and decryption coding module, a redundancy encoding module, a secret sharing module and a digital signature module. By means of the method and the system, metadata privacy and high availability can be guaranteed, and meanwhile, a user does not need to store any metadata information for indexing and data query.
Owner:HUAZHONG UNIV OF SCI & TECH
Method for Voting with Secret Shares in a Distributed System
ActiveUS20110022883A1Eliminate pointLess reliableKey distribution for secure communicationDigital data processing detailsFailoverSecret share
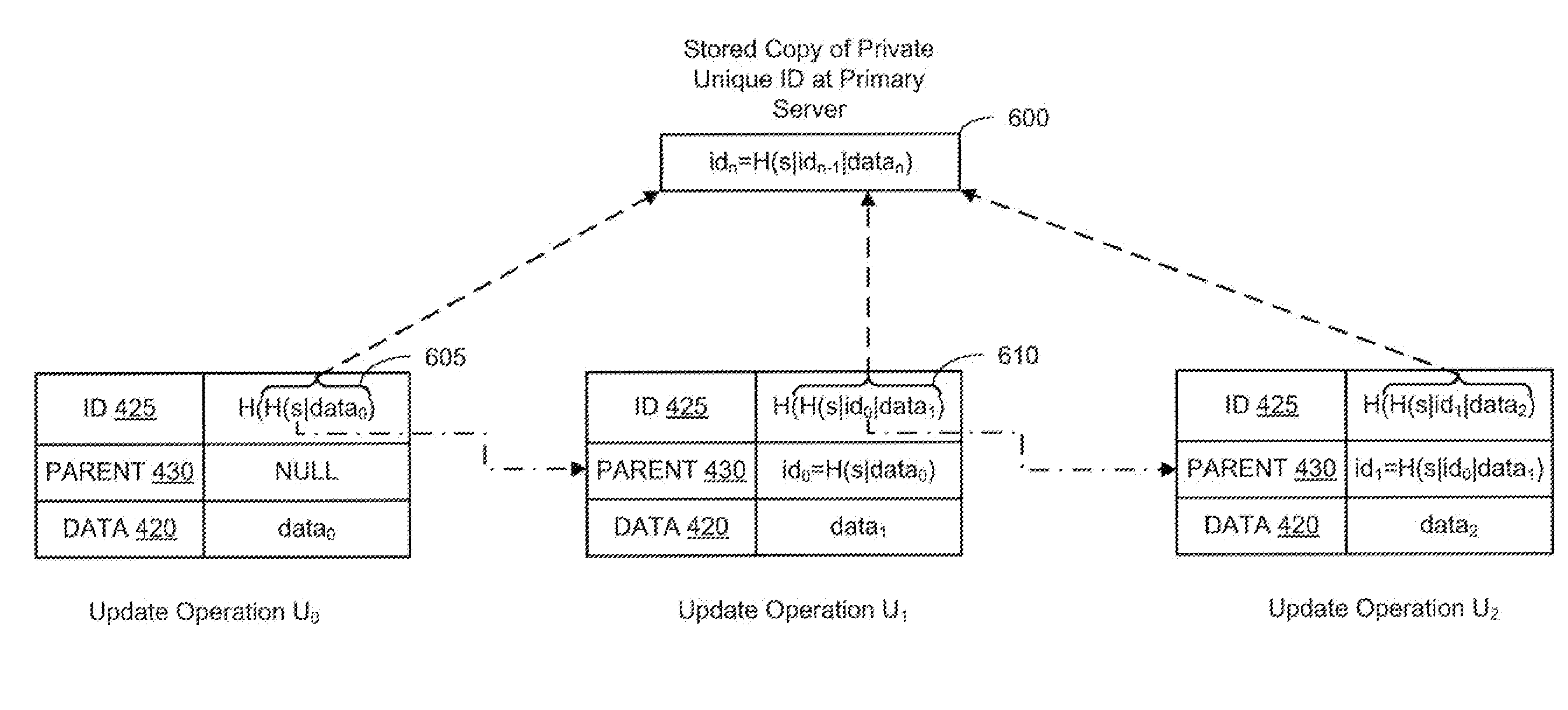
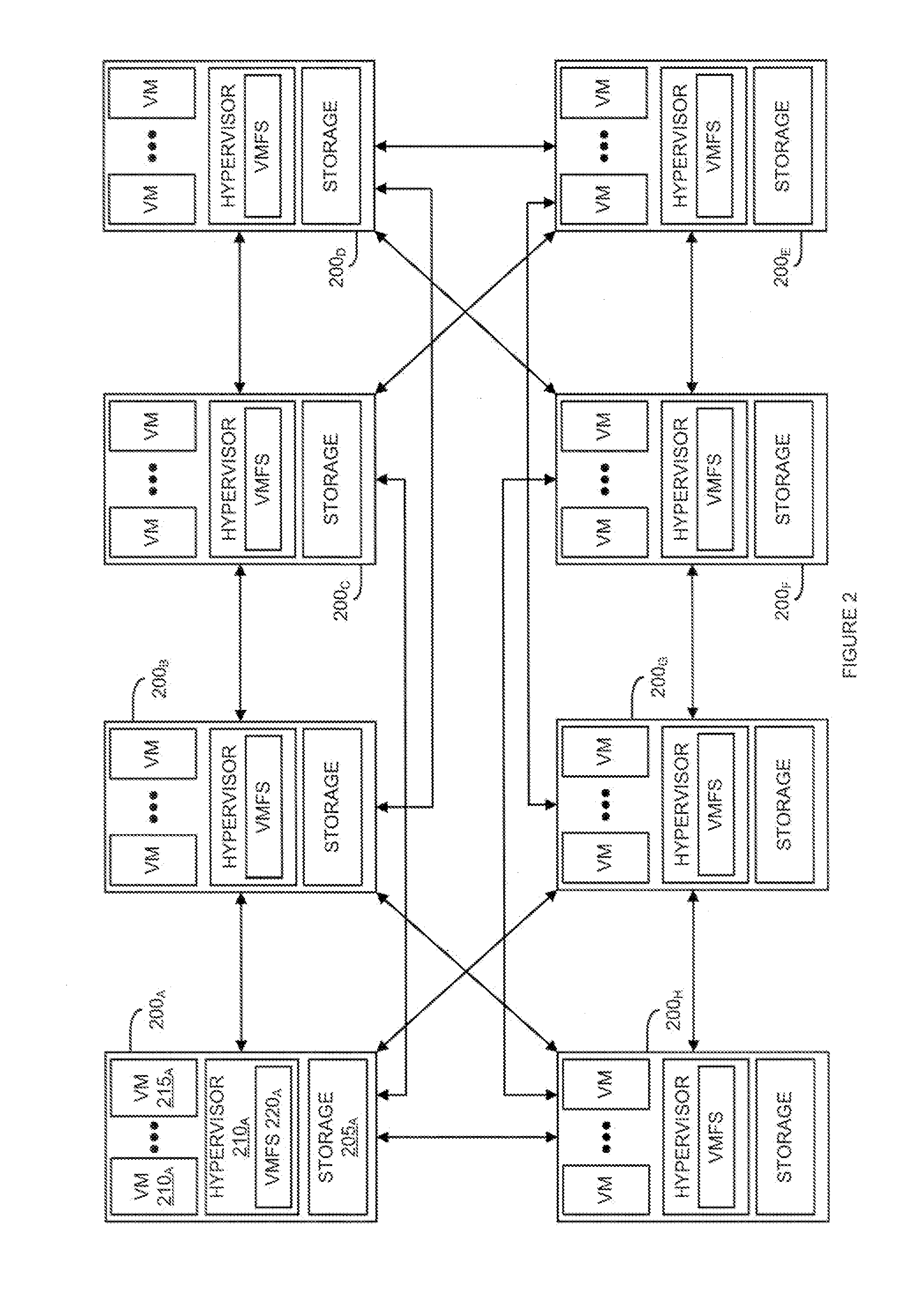
A replicated decentralized storage system comprises a plurality of servers that locally store disk images for locally running virtual machines as well as disk images, for failover purposes, for remotely running virtual machines. To ensure that disk images stored for failover purposes are properly replicated upon an update of the disk image on the server running the virtual machine, a hash of a unique value known only to the server running the virtual machine is used to verify the origin of update operations that have been transmitted by the server to the other servers storing replications of the disk image for failover purposes. If verified, the update operations are added to such failover disk images. To enable the replicated decentralized system to recover from a failure of the primary server, the master secret is subdivided into parts and distributed to other servers in the cluster. Upon a failure of the primary server, a secondary server receives a threshold number of the parts and is able to recreate the master secret and failover virtual machines that were running in the failed primary server.
Owner:VMWARE INC
Data file security privacy storage and sharing method based on a block chain
ActiveCN109768987AImplement security managementRealize ciphertext sharingUser identity/authority verificationCiphertextData file
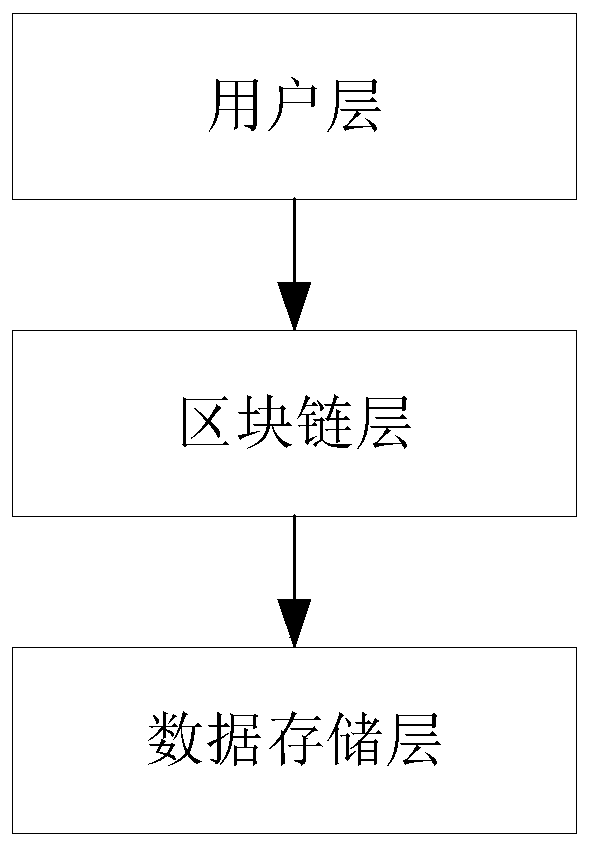
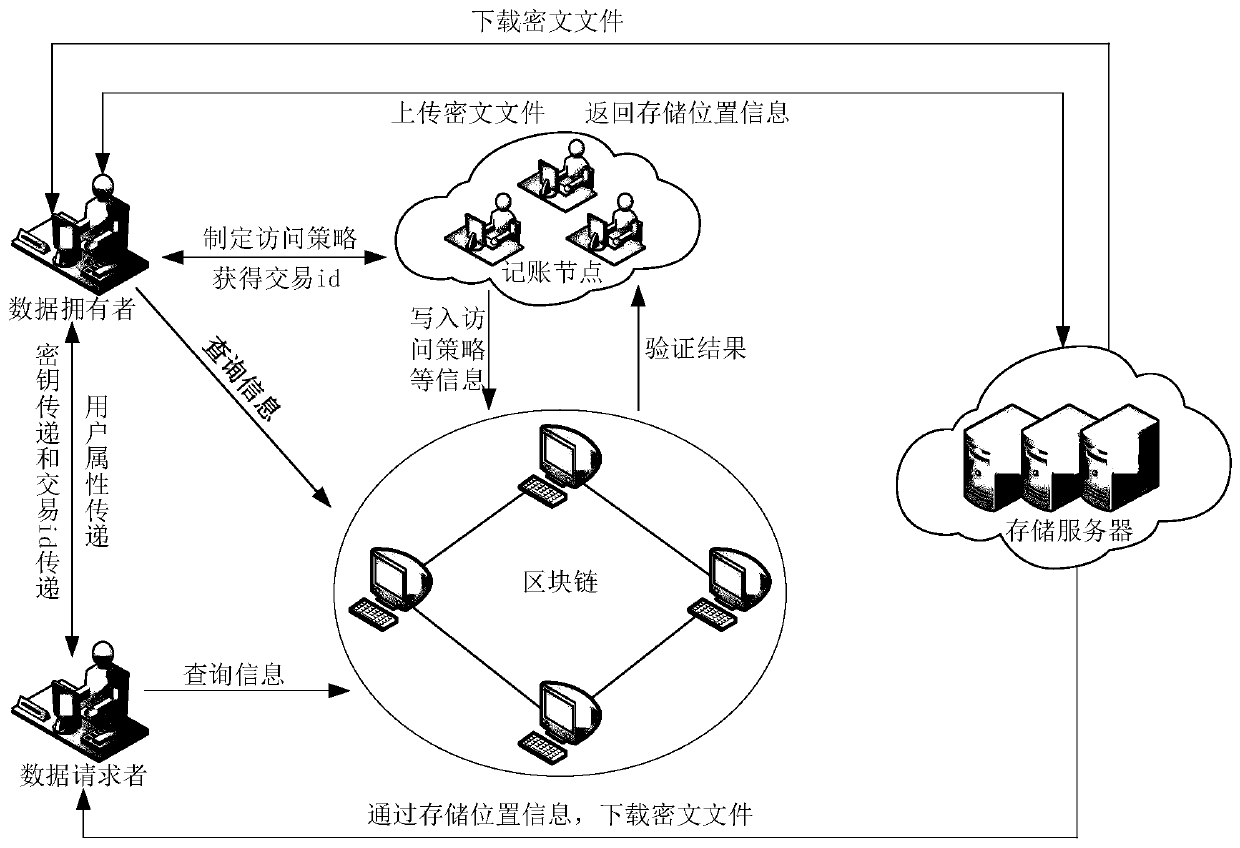
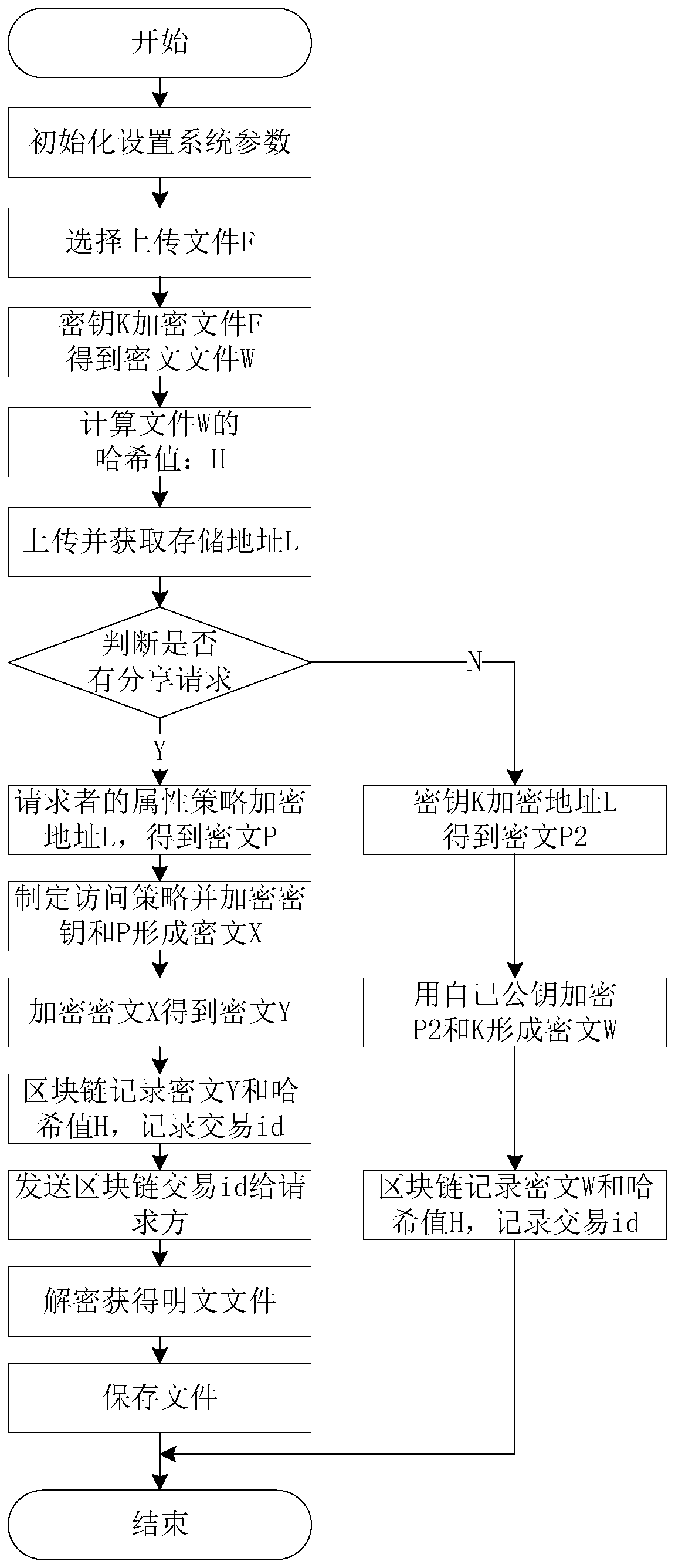
The invention relates to the field of computers and data storage, in particular to a data file security privacy storage and sharing method based on a block chain, which comprises a user layer, a blockchain layer and a data storage layer, and is characterized in that the user layer is used by a user to encrypt and upload data, encrypt and share data and receive data shared by other users; the blockchain layer is used for public storage of hash check codes of double encrypted ciphertext data and cloud storage data, and files are shared among users through transaction id; the data storage layeris used for storing and downloading ciphertext data; according to the invention, the availability and integrity of cloud storage data are effectively ensured; the user can conveniently verify the access permission, multi-user sharing of the data is achieved, the storage overhead and management overhead of the user on the secret key are reduced, the control force of the data owner on the data is improved, ciphertext sharing of the data is achieved, and the safety and privacy of the storage system are improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Dispersed storage network data slice integrity verification
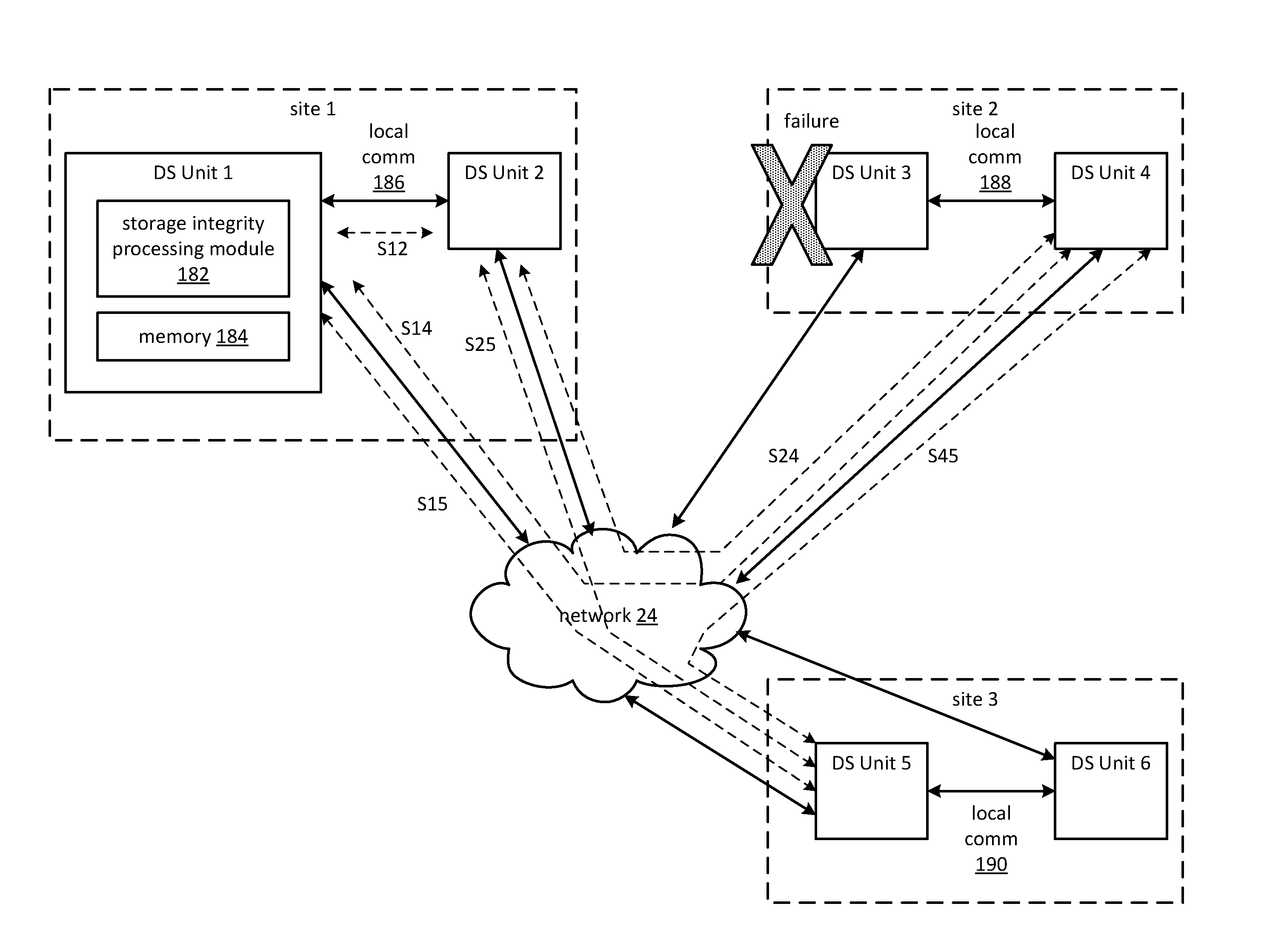
InactiveUS20110126295A1Digital data information retrievalError detection/correctionData segmentSecret share
A method begins with a processing module issuing a retrieval request, receiving secret shares of a set of secret shares to produce received secret shares, and receiving encoded data slices of a set of encoded data slices. The method continues with the processing module decoding the received secret shares to recapture a message authentication key when a threshold number of the secret shares is received. The method continues with the processing module identifying a received encoded data slice of the received encoded data slices having an authentication code associated therewith when a threshold number of the encoded data slices is received. The method continues with the processing module verifying the authentication code based on the message authentication key and the received encoded data slice. The method continues with the processing module decoding the received encoded data slices to recapture a data segment when the authentication code is verified.
Owner:PURE STORAGE
Efficient techniques for sharing a secret
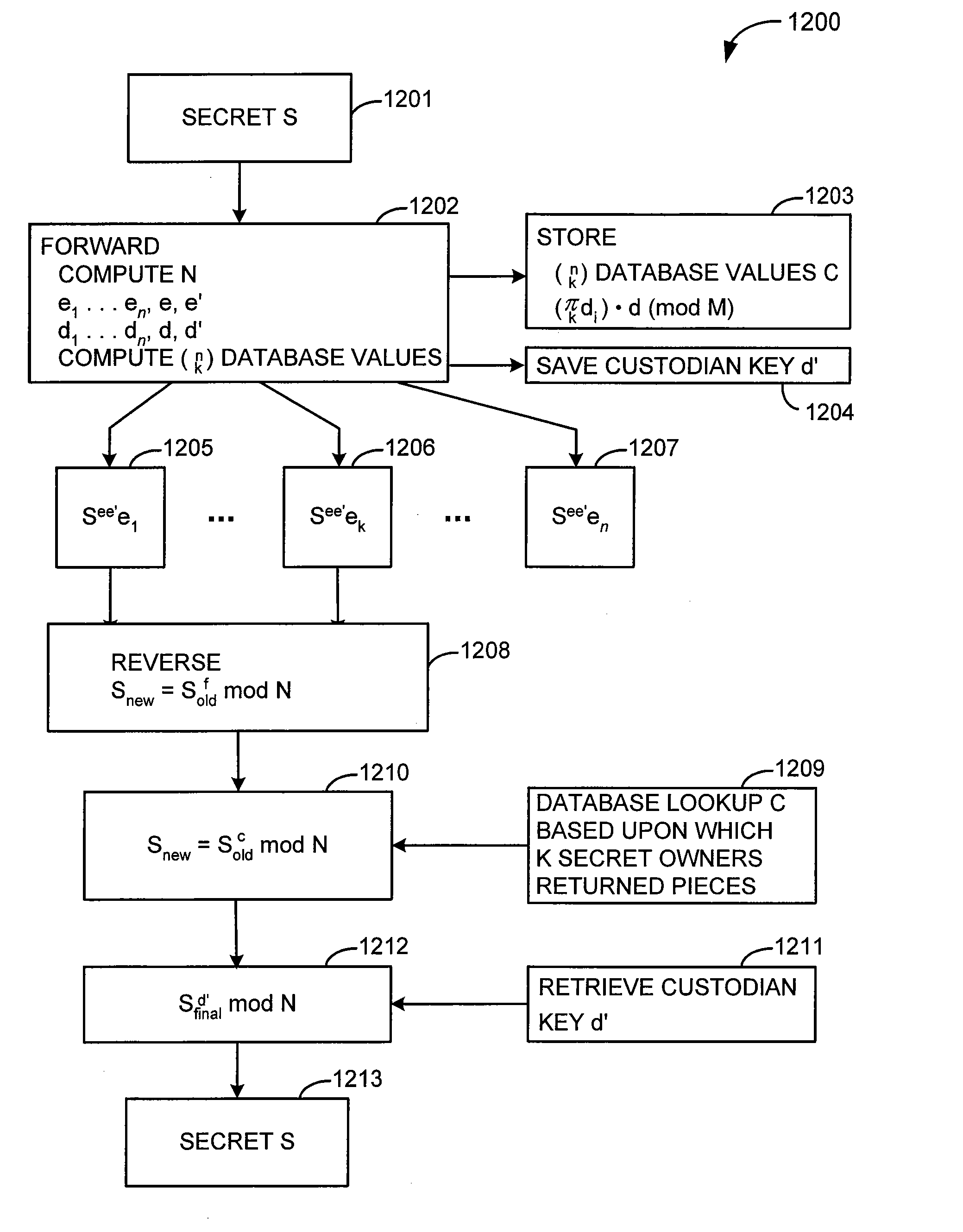
InactiveUS7167565B2Adequate protection against disk attackComputationally efficientKey distribution for secure communicationMultiple keys/algorithms usageKey distributionModulo operation
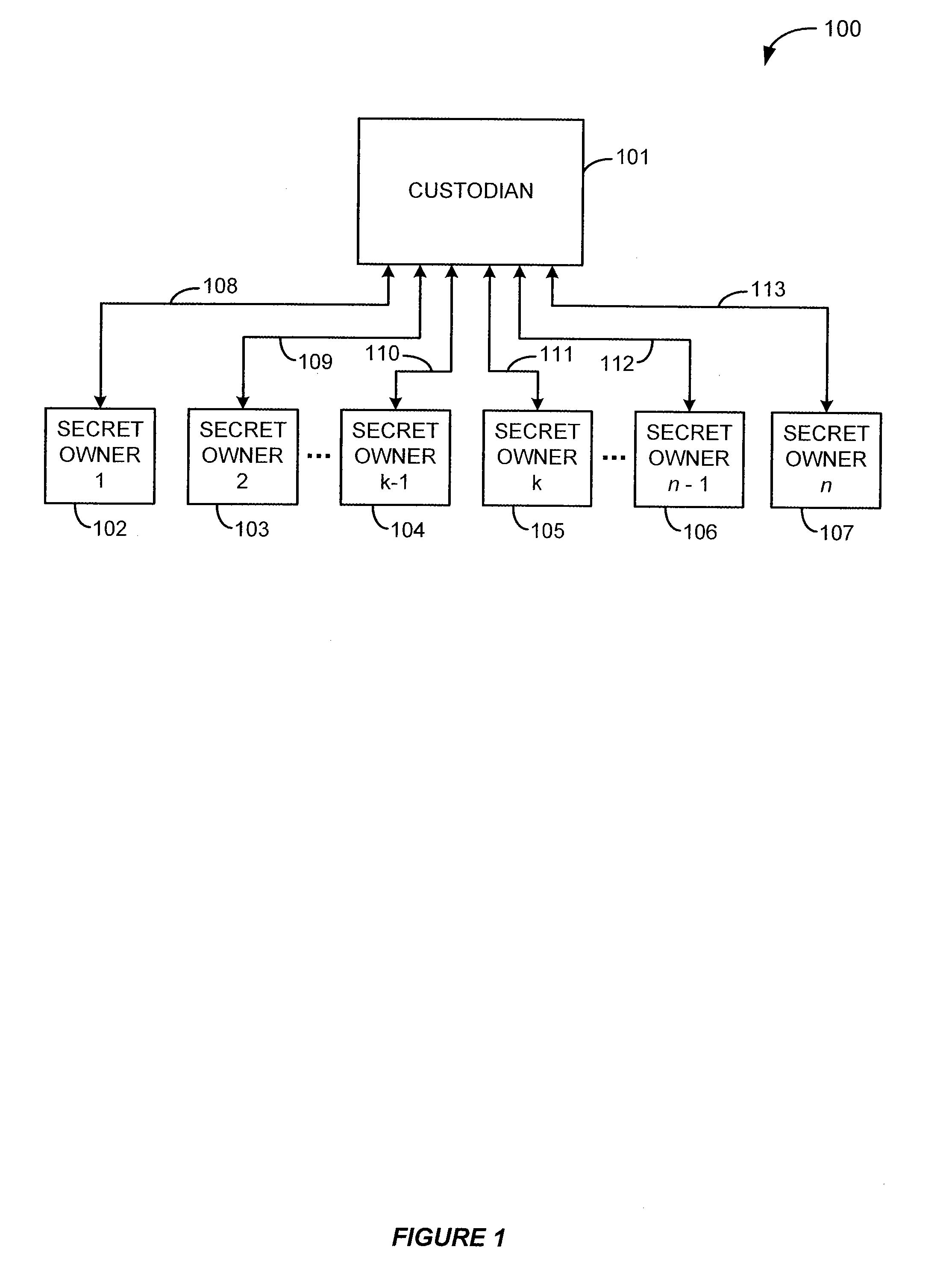
An n person secret sharing solution computes n unique keys to be distributed to the secret owners along with an exponentiated version of the secret. The custodian performs an exponent / modulo operation each time one of the keys is received from one of the secret owners. Alternatively, n+1 keys are created by the custodian, and the custodian retains one key after distributing the remaining n keys to the secret owners. After the custodian has received and processed the n keys from the secret owners, he performs an exponent / modulo operation using his own retained key. According to another aspect, a k out of n secret sharing solution involves computing and storing a database having an entry for each unique combination of k keys that could be returned from among the n keys. After k keys have been received, the custodian looks up in the database the entry corresponding to the particular unique combination of secret owners who returned keys. The custodian performs another exponent / modulo operation using the entry retrieved from the database in order to reconstruct the original secret. According to an embodiment, the custodian computes n+1 keys, distributes n of the keys to the secret owners, and keeps one of the keys for himself. The custodian retrieves his own key and performs a final exponent / modulo operation in order to reconstruct the original secret. According to another aspect, a k out of n secret sharing solution involves encrypting the original secret before applying any conventional k out of n secret sharing solution.
Owner:CA TECH INC
Security data item level database encryption system
ActiveCN102236766ADigital data protectionSpecial data processing applicationsHash functionCiphertext
The invention relates to a security data item level database encryption method. Confidential data is encrypted by a data item level particle size; a hash function is used for deriving an encryption key of each data item according to a derived key and unique positioning information of the data item, even the data item encryption keys for encryption of all integral databases can be derived by using one key to reduce the using amount of the keys and facilitate key management; and a stream cipher algorithm is used for encrypting the data items to avoid filling. A ciphertext index is also encrypted by the stream cipher algorithm; each field (column) is encrypted by using the same key; therefore, searching keywords can be encrypted and then ciphertexts of corresponding fields are matched in spite of precise complete or incomplete searching. The method also has complete security functions of key management, secret sharing, security backup, mandatory access control, security connection and the like.
Owner:WANBANG CHARGING EQUIP CO LTD +1
Privacy protection method in face authentication system based on edge calculation
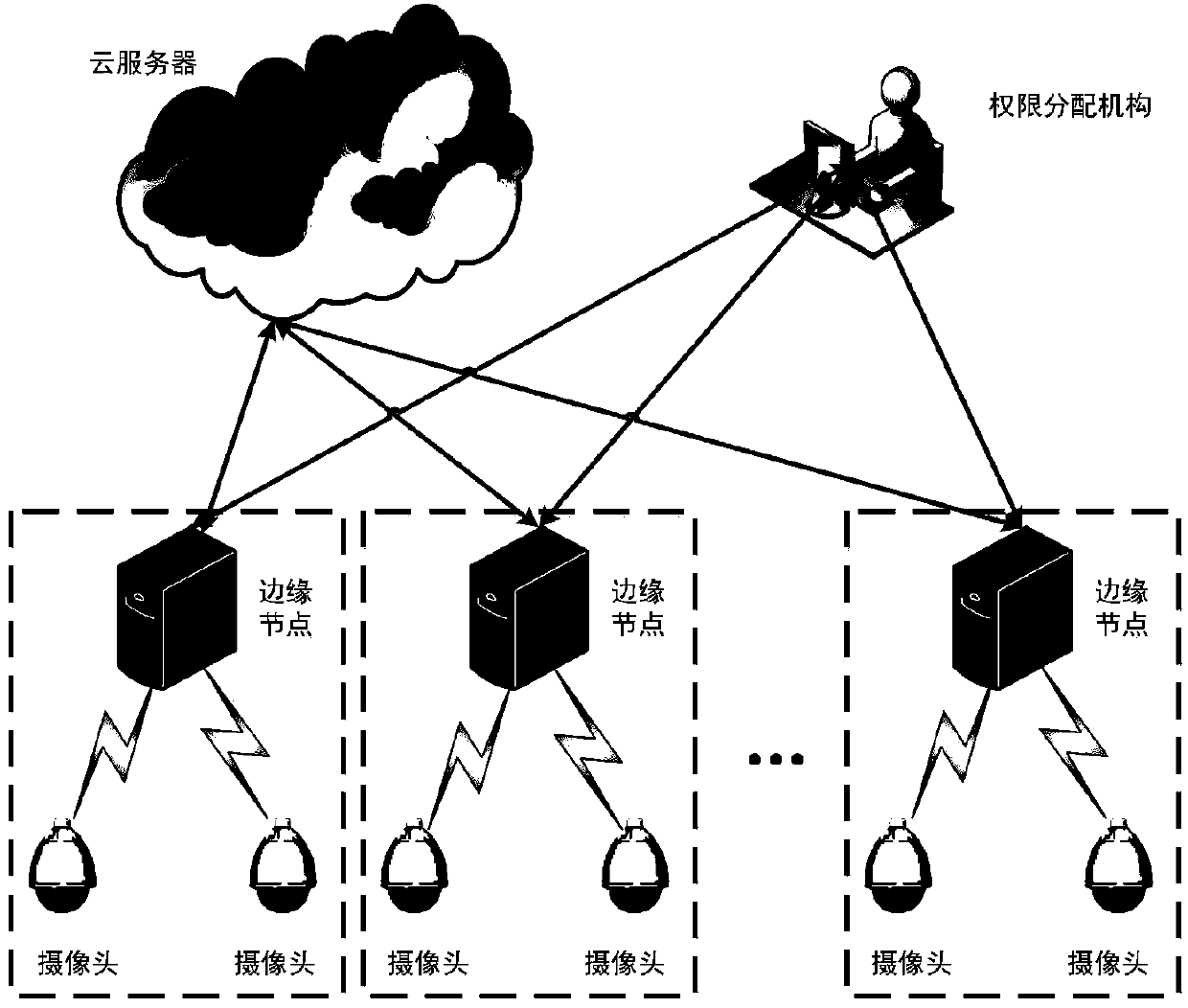
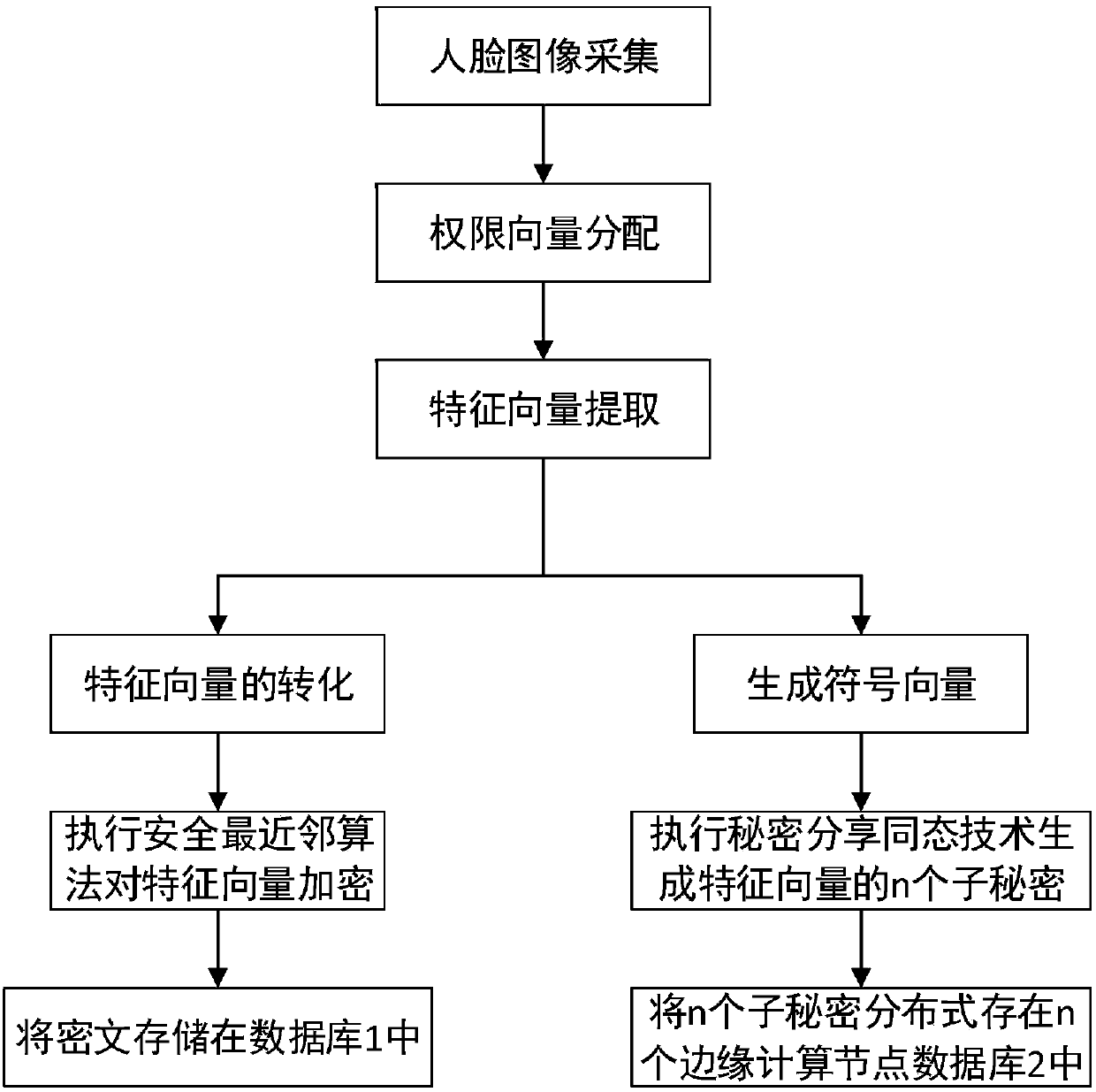
ActiveCN108446680APrivacy protectionProtect face recognition functionCharacter and pattern recognitionTransmissionPlaintextFault tolerance
The invention belongs to the technical field of privacy protection in cloud computing and discloses a privacy protection method in face authentication system based on edge calculation. The method comprises the steps that: a camera collects a face image and uploads the face image to a connected edge computing node, an authority assigning mechanism sends a permission vector Li of a user to the edgecomputing node after collecting user face information, an edge computing device carries out feature extraction on a face image of a user requesting registration to obtain a feature vector by using a method based on a deep convolutional neural network, a safe nearest neighbor algorithm is performed to encrypt the feature vector of a registered user, and a secret sharing homomorphic algorithm is performed and n sub-secrets are generated according to the feature vector and are distributively stored in n edge computing devices. The direct upload of sensitive data to a cloud server is avoided, theprivacy of the face data is protected, and the fault tolerance of a system is improved. Results prove that the accuracy of face recognition under a ciphertext of the present invention is completely equal to the accuracy of face recognition under a plaintext.
Owner:XIDIAN UNIV
Resilient secret sharing cloud based architecture for data vault
InactiveUS20170005797A1Increase choiceKey distribution for secure communicationMultiple keys/algorithms usageSecret shareComputer network
A method of securely storing data including: providing, within a secure data storage system, a plurality of secret sharing methods for selection and identifying a striping policy for storage of the data, in accordance with input preferences. The data can be split into N secret shares according to a secret sharing method, the selection being determined by the striping policy, wherein a threshold number, T, of such shares is sufficient to recover the data, where T is less than N, generating metadata associated with the data, the metadata identifying the selected secret sharing method and storing the metadata within the secure data storage system and writing the secret shares to storage that includes storage outside the secure data storage system, such that, when at least T shares are retrieved, the metadata can be recalled to identify the selected secret sharing method for recovery of the data.
Owner:LEADING SOFTWARE LTD
Crytographic communication apparatus
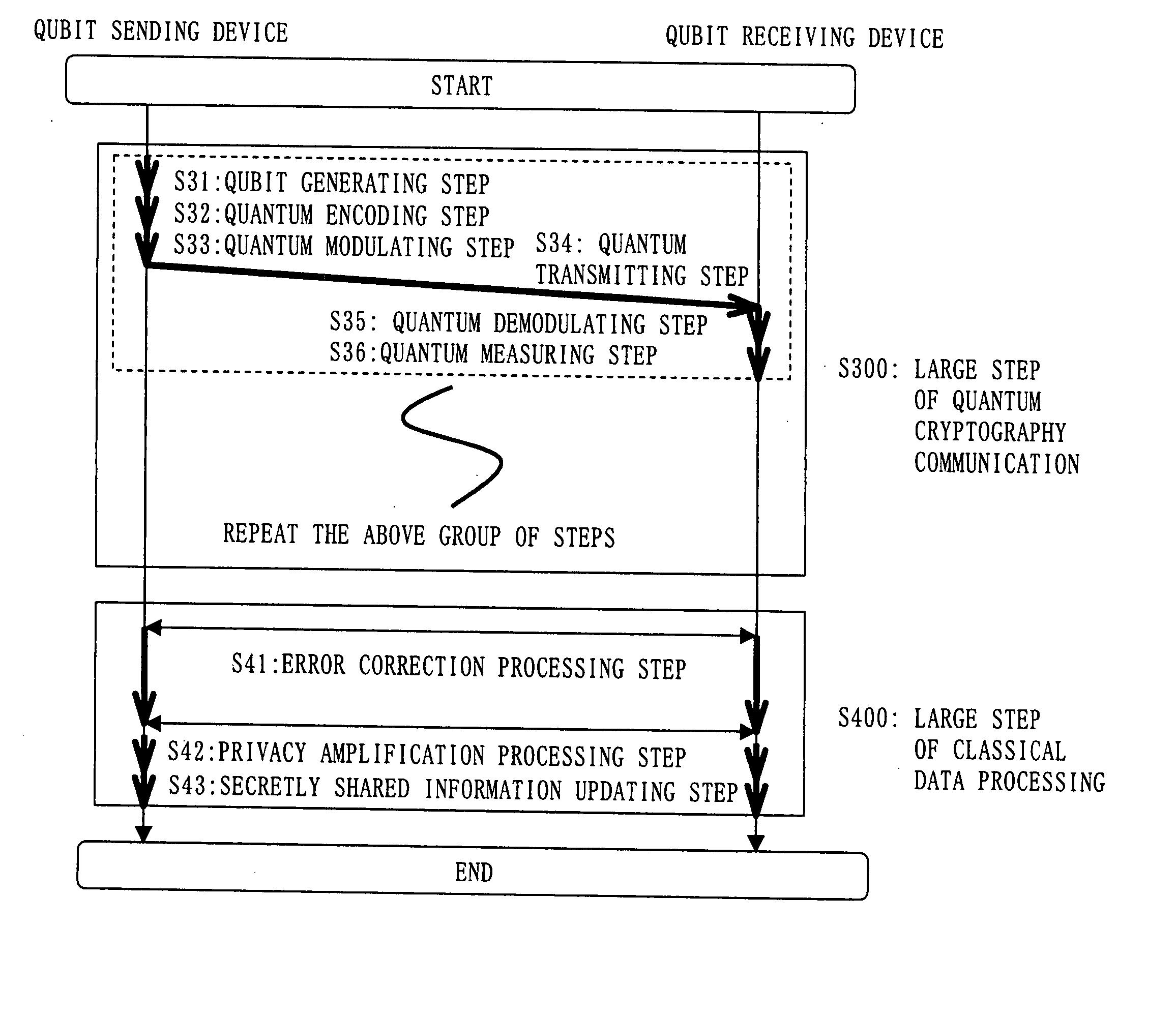
InactiveUS20050157875A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesPseudo random number generationQuantum electrodynamics
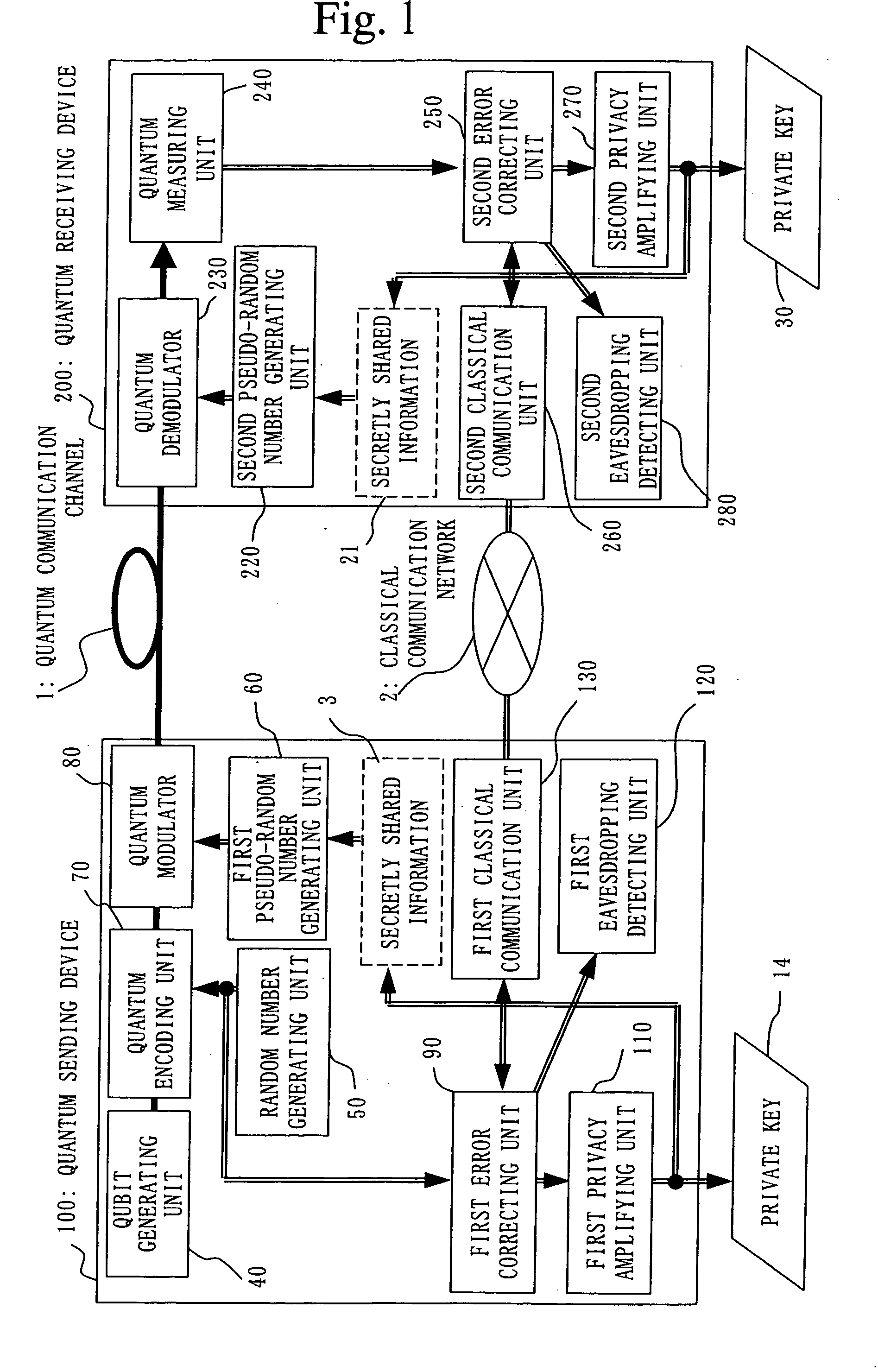
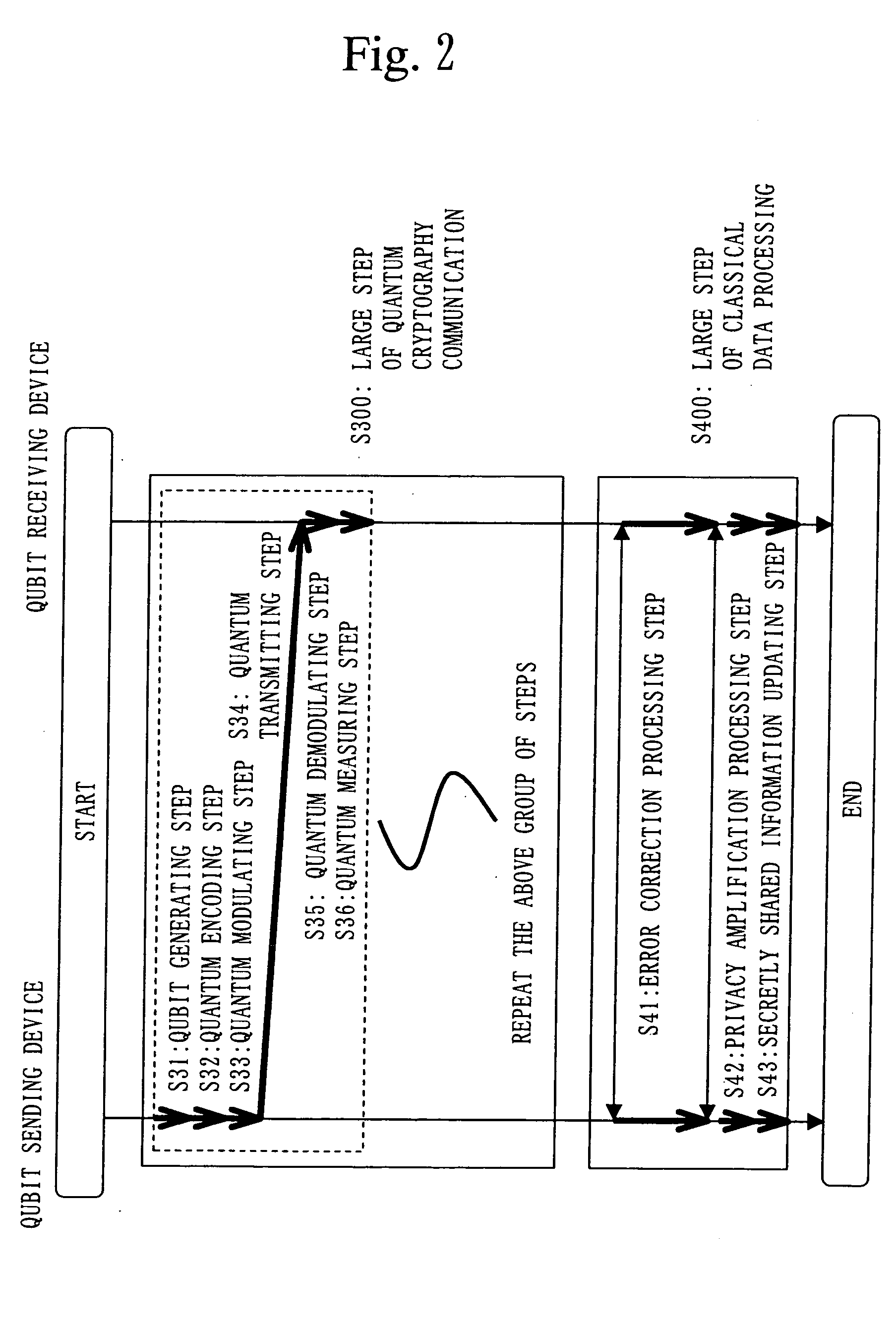
A qubit generating unit 40 generates a qubit having a predetermined quantum state. A qubit encoding unit 70 performs quantum encoding of the generated qubit. A first pseudo-random number generating unit 60 generates a first pseudo-random number from secretly shared information 3 which has been secretly shared with the quantum receiving device 200 in advance. A quantum modulator 80 performs quantum modulation of the qubit on which quantum encoding has been performed based on the first pseudo-random number and sends the modulated qubit to the quantum receiving device 200. A second pseudo-random number generating unit 220 generates a second pseudo-random number from secretly shared information 21 which has been secretly shared with the above quantum sending device 100 in advance synchronously with generation of the above first pseudo-random number. A qubit demodulator 230 performs quantum demodulation of the qubit which has been received from the quantum demodulator 80 based on the second pseudo-random number.
Owner:MITSUBISHI ELECTRIC CORP
Secure outsourced computation
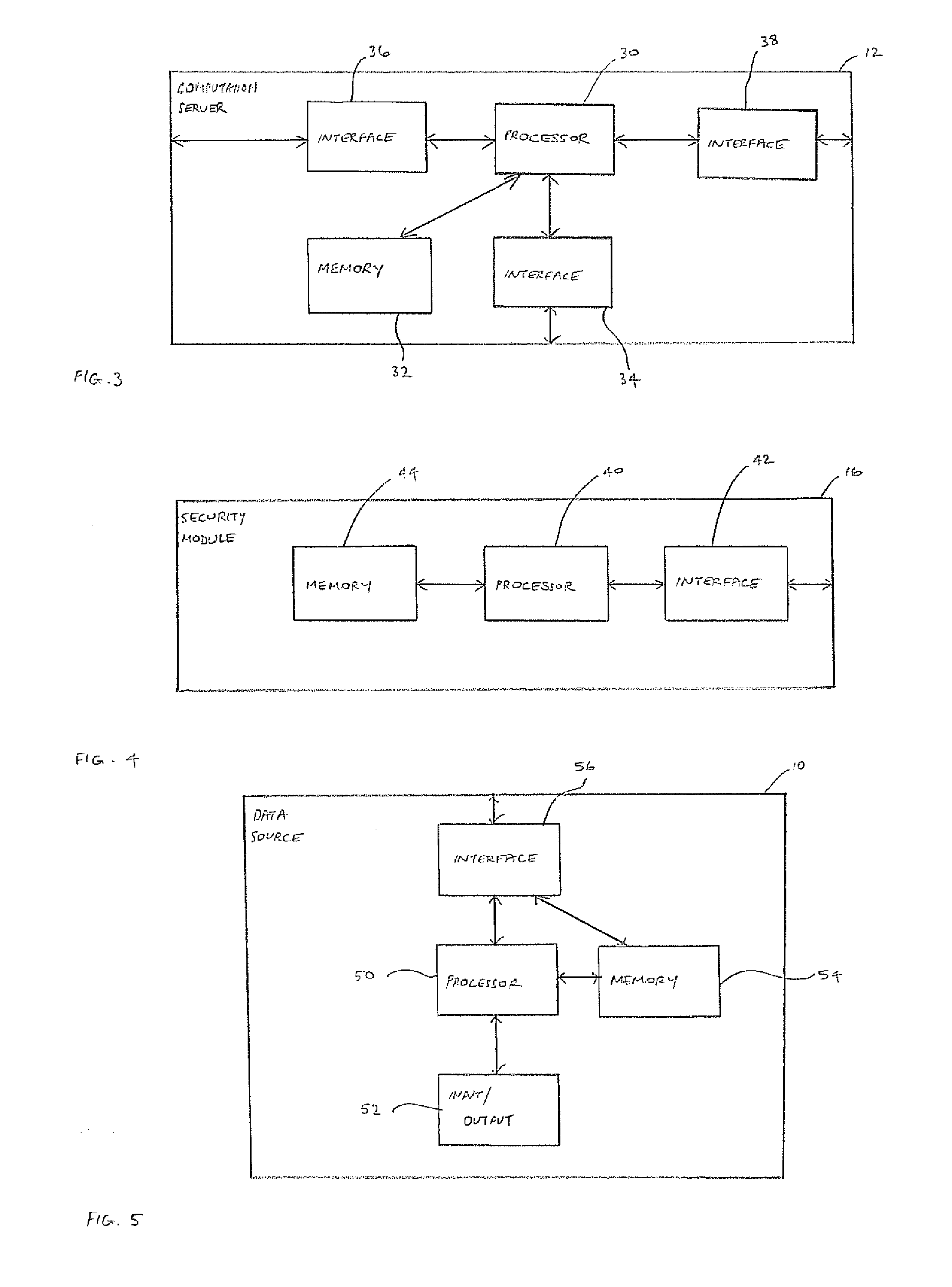
PendingUS20120002811A1Few constraintsSecret communicationSecuring communicationComputer securitySecret sharing
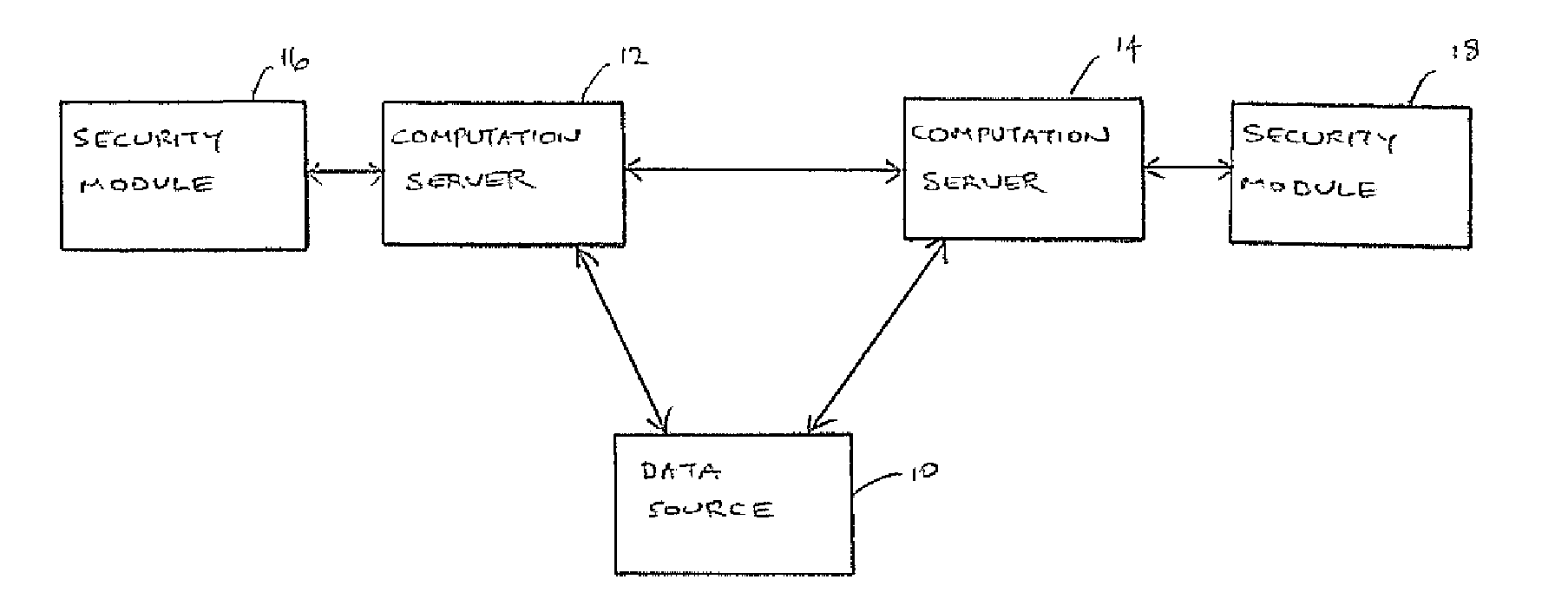
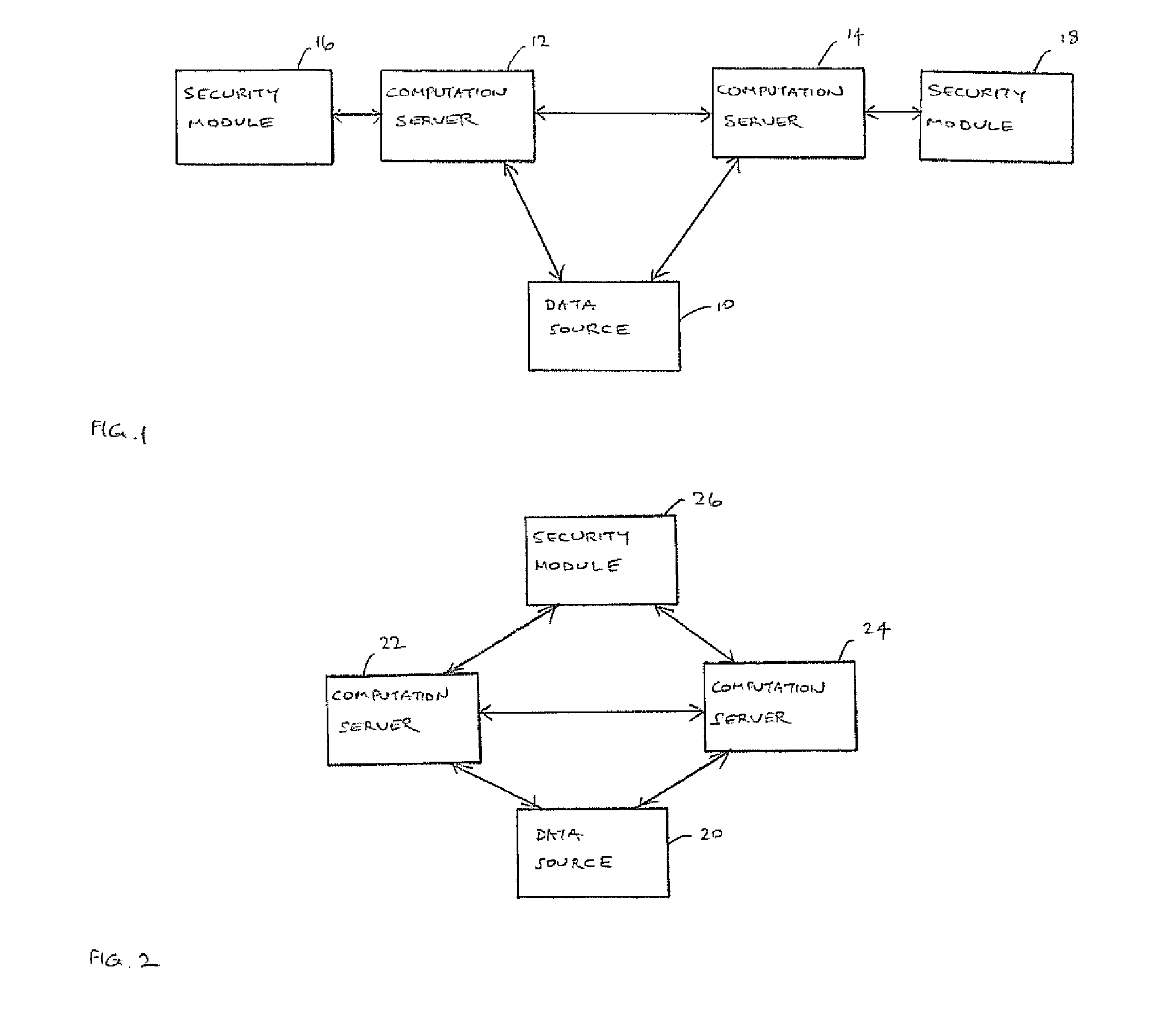
Secure outsourced computation on data can be achieved by transmitting shares of the data to respective computation servers; establishing respective connections between each of the computation servers and respective security modules, wherein each security module contains respective security data, the security data on the security modules being related by means of a Linear Secret Sharing Scheme; computing respective shares of a computation result in the computation servers, using the respective shares of the data and the respective security data; returning the shares of the computation result to a data owner; and obtaining the computation result from the respective shares of the computation result.
Owner:UNIV OF BRISTOL
Multi-drive cooperation to generate an encryption key
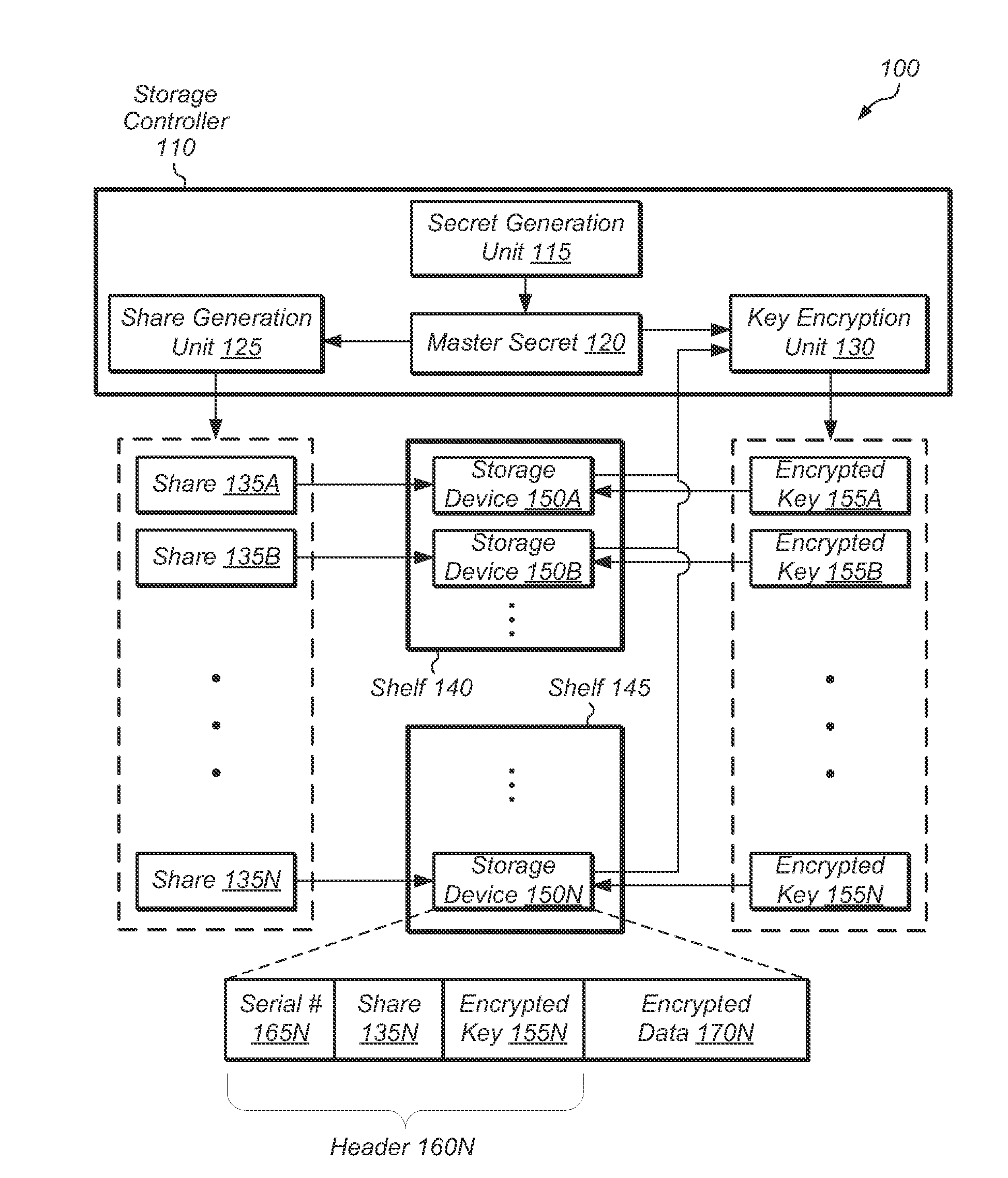
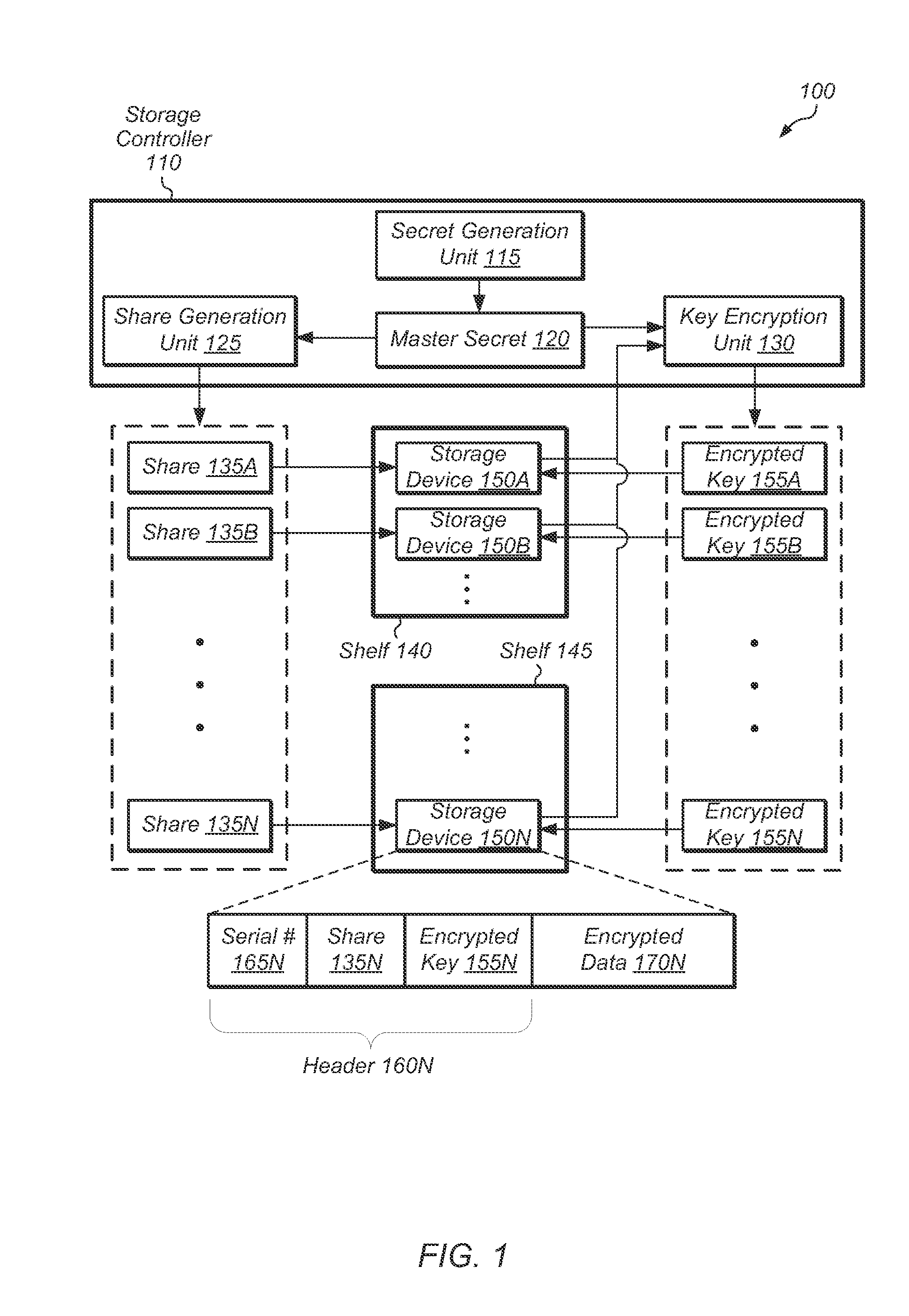
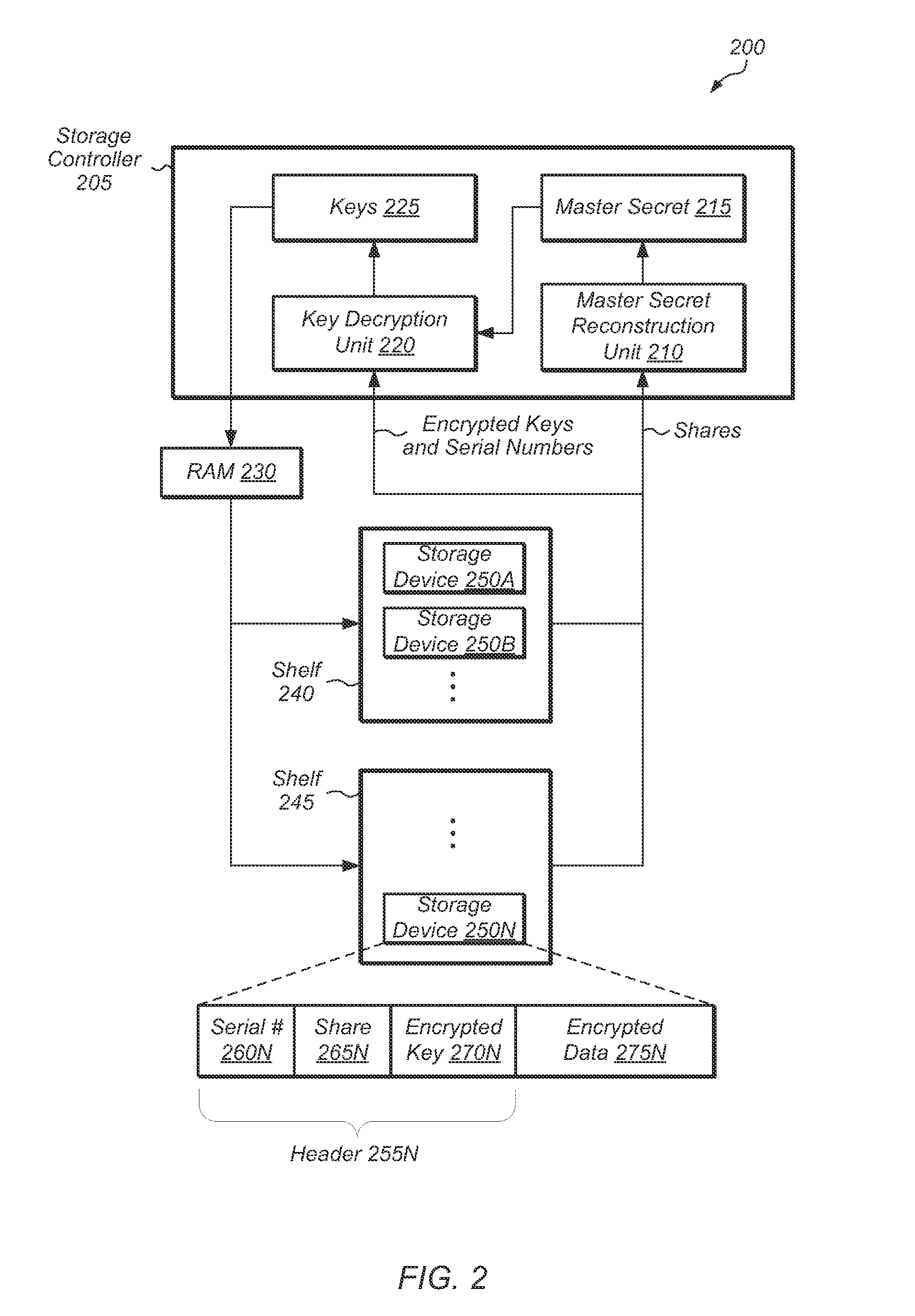
ActiveUS20140089683A1Prevent unauthorized accessUnauthorized memory use protectionHardware monitoringThreshold numberShared secret
A system, method, and computer-readable storage medium for protecting a set of storage devices using a secret sharing scheme. The data of each storage device is encrypted with a key, and the key is encrypted based on a shared secret and a device-specific value. Each storage device stores a share and its encrypted key, and if a number of storage devices above a threshold are available, then the shared secret can be reconstructed from the shares and used to decrypt the encrypted keys. Otherwise, the secret cannot be reconstructed if less than the threshold number of storage devices are accessible, and then data on the storage devices will be unreadable.
Owner:PURE STORAGE
Secret information management scheme based on secret sharing scheme
ActiveUS20070160197A1Without any changeKey distribution for secure communicationDigital data processing detailsData storingData store
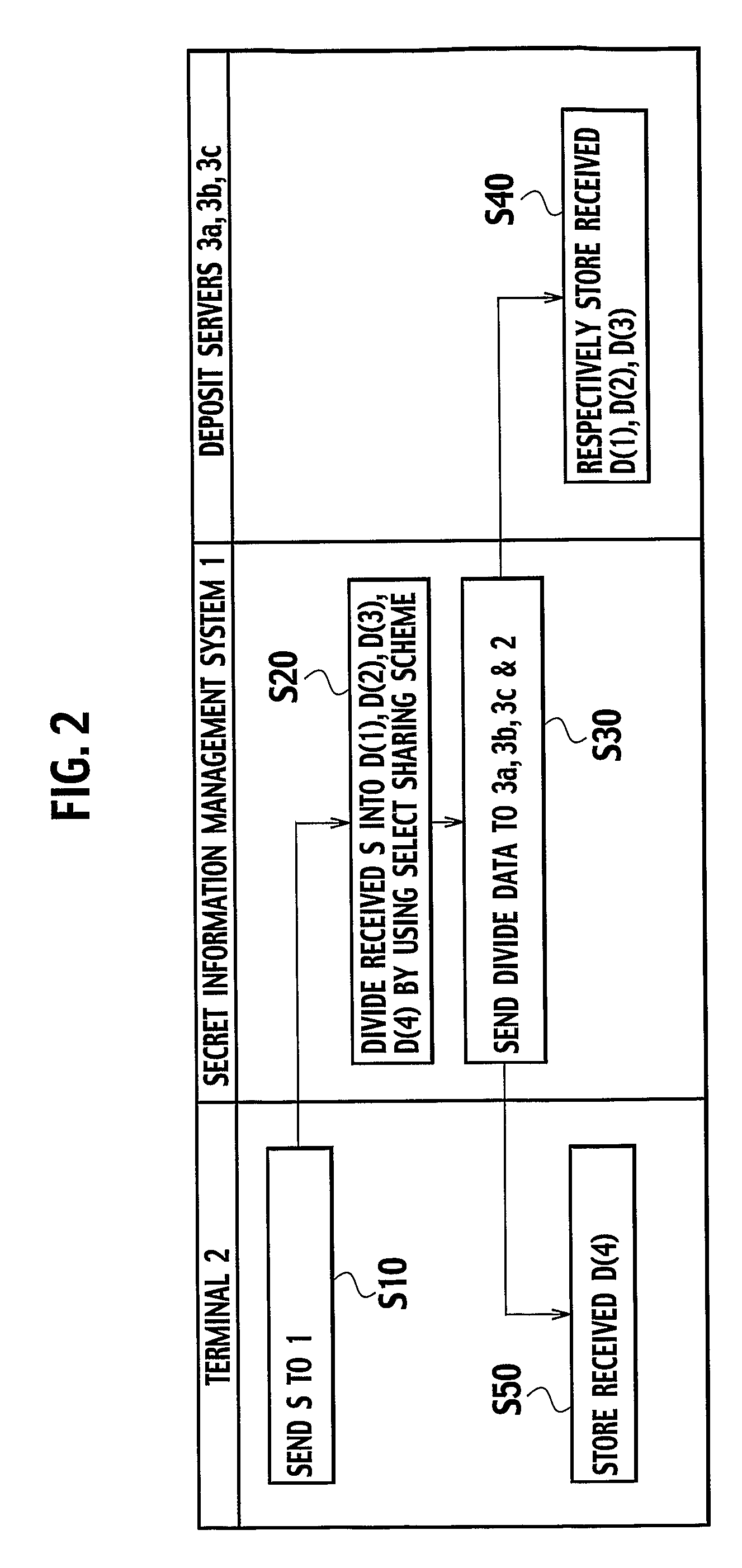
In a secret information management system for managing a secret information of a user, the secret information is divided into a plurality of divided data by using a secret sharing scheme, such that the secret information can be recovered from a prescribed number of the divided data, and a part of the plurality of divided data is stored into a terminal of the user as user's divided data while a rest of the plurality of divided data are stored into one or more of deposit servers. Then, a plurality of re-divided data different from the plurality of divided data are generated, from a combination of the prescribed number of the divided data among the divided data stored in the deposit servers by using the secret sharing scheme, and a part of the plurality of re-divided data is stored into the terminal as newly generated user's divided data while a rest of the plurality of re-divided data are stored into the deposit servers as newly generated divided data.
Owner:NTT COMM CORP
Image hiding and authentication method based on secret sharing
ActiveCN103761702AImprove securityDifferences in Statistical PropertiesImage data processing detailsPattern recognitionHash function
The invention discloses an image hiding and authentication method based on secret sharing, and belongs to the technical field of secret image sharing. The image hiding and authentication method is characterized by comprising the steps that firstly, difference Huffman encoding is conducted on a secret image, every three generated bit sequences are set to be one group to be converted into decimal numbers which are used as coefficients of a sharing polynomial in the Shamir (k, n) threshold scheme, the k and the n are positive integers, the k is smaller than or equal to the n, and n shadow images are generated; secondly, n significant carrier images are selected, the generated shadow images are embedded into the carrier images in a matrix encoding mode, authentication bits generated by the hash function are also embedded into the carrier images, and n disguise images are formed and are in the charge of n different participants respectively. The disguise images generated through the image hiding and authentication method has higher visual quality, existence of secret information cannot be perceived by attackers easily, and the safety of the secret information is ensured. Meanwhile, before the secret information is recovered, the disguise images provided by each participant need to be authenticated, only the disguise images passing through authentication can participate in recovery of the secret information, and the safety of the secret information is further strengthened.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
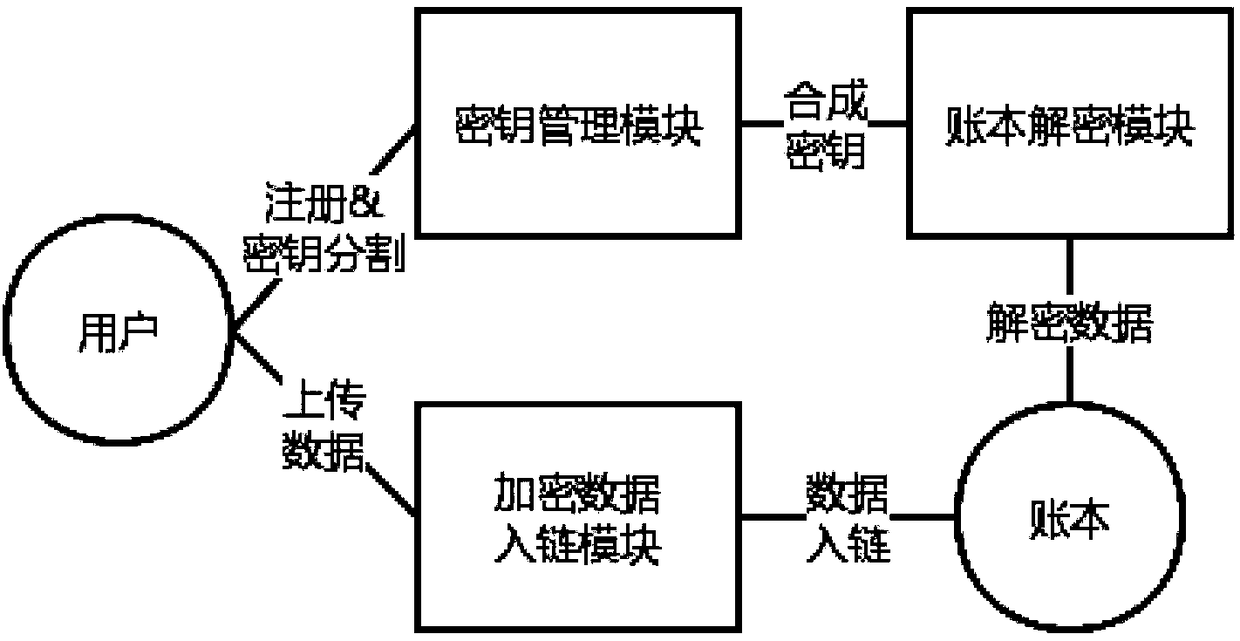
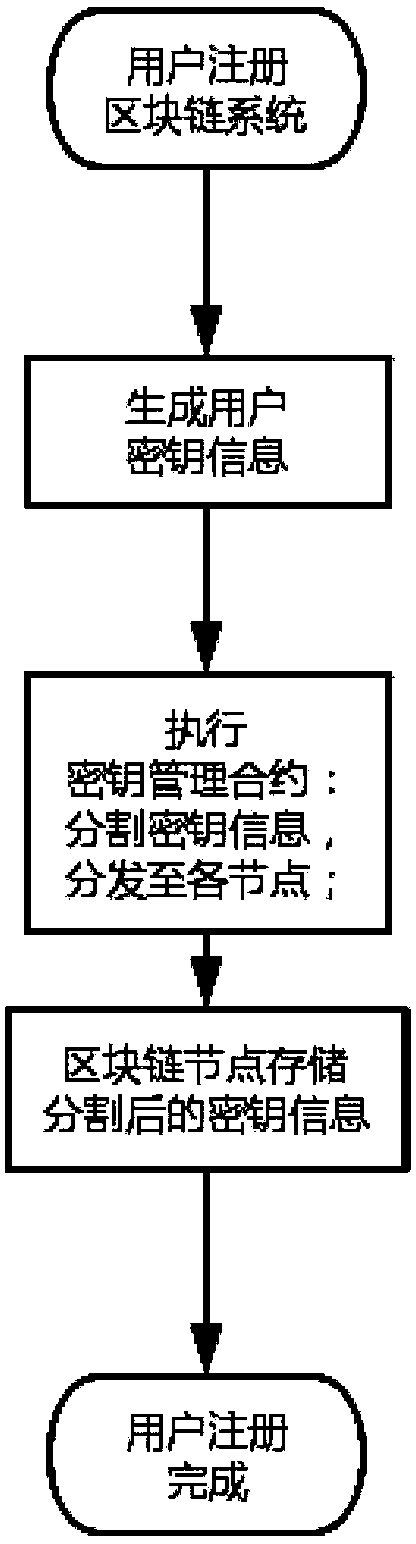
Blockchain encryption ledger based on secret sharing
ActiveCN108809652AGuaranteed privacyImprove usabilityKey distribution for secure communicationUser identity/authority verificationKey storageKey generation
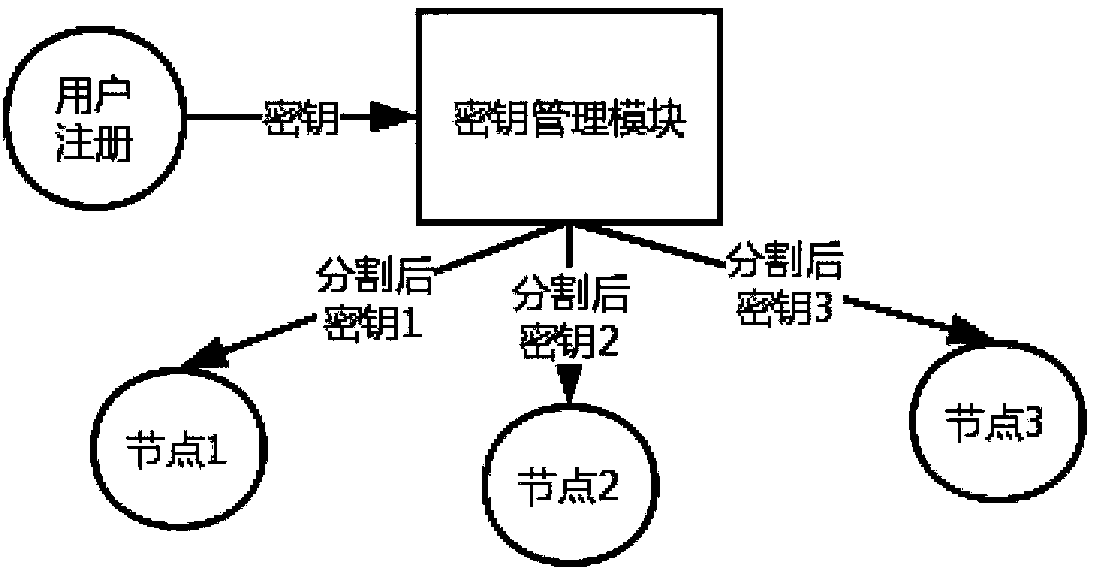
The invention discloses a blockchain encryption ledger based on secret sharing. The blockchain encryption ledger based on secret sharing comprises a key management module, an encryption data in-chainmodule and a ledger decryption module; the key management module is responsible for registration and key generation of a user; key segmentation is realized by utilization of a secret sharing technology; each node of the blockchain is responsible for cooperatively storing segmented key information; each node only can grasp incomplete key information; the encryption data in-chain module is responsible for processing the data uploading request of the user, and storing user encryption data passing signature verification in the blockchain ledger; the ledger decryption module is responsible for processing a ledger decryption request; only after the blockchain nodes reach a decryption consensus, a decryption key can be synthesized; and then, decryption of the encryption ledger is completed. According to the blockchain encryption ledger based on secret sharing disclosed by the invention, the user key security storage problem can be solved by utilization of the secret sharing technology; furthermore, the accidental leakage behaviours of a part of blockchain nodes on the privacy data of the ledger can be effectively avoided; the user key storage security is ensured; and furthermore, the credibility of the blockchain system is improved.
Owner:安徽航天信息有限公司
Model parameter training method and device based on federal learning
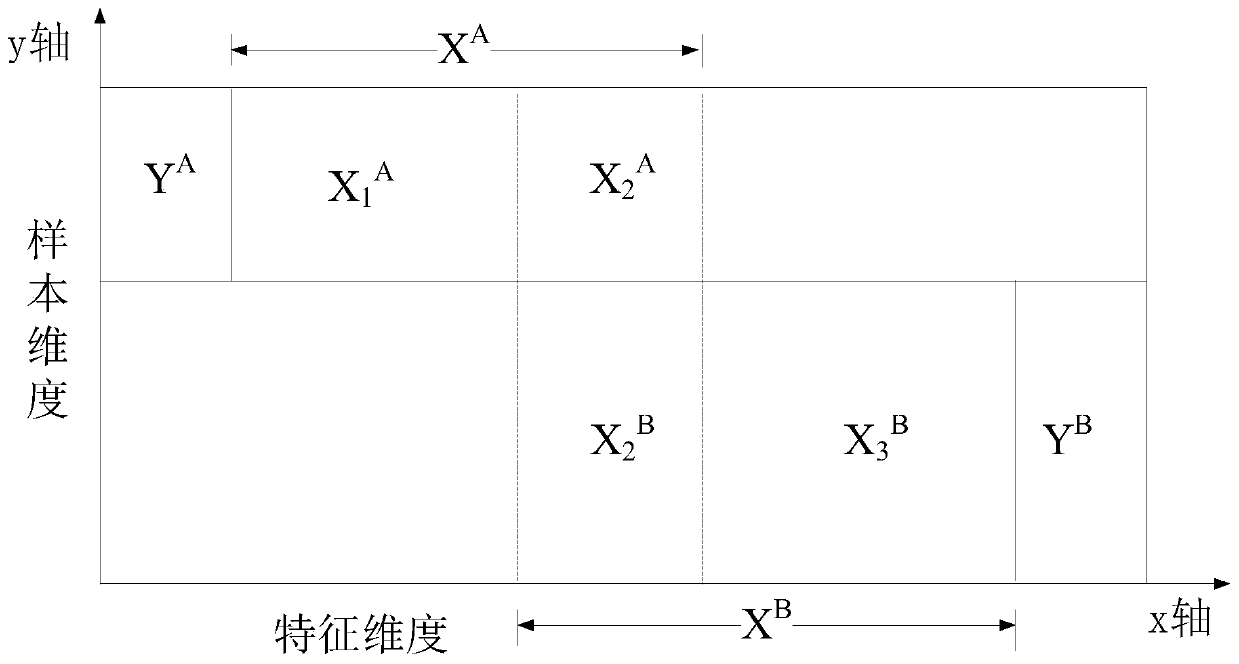
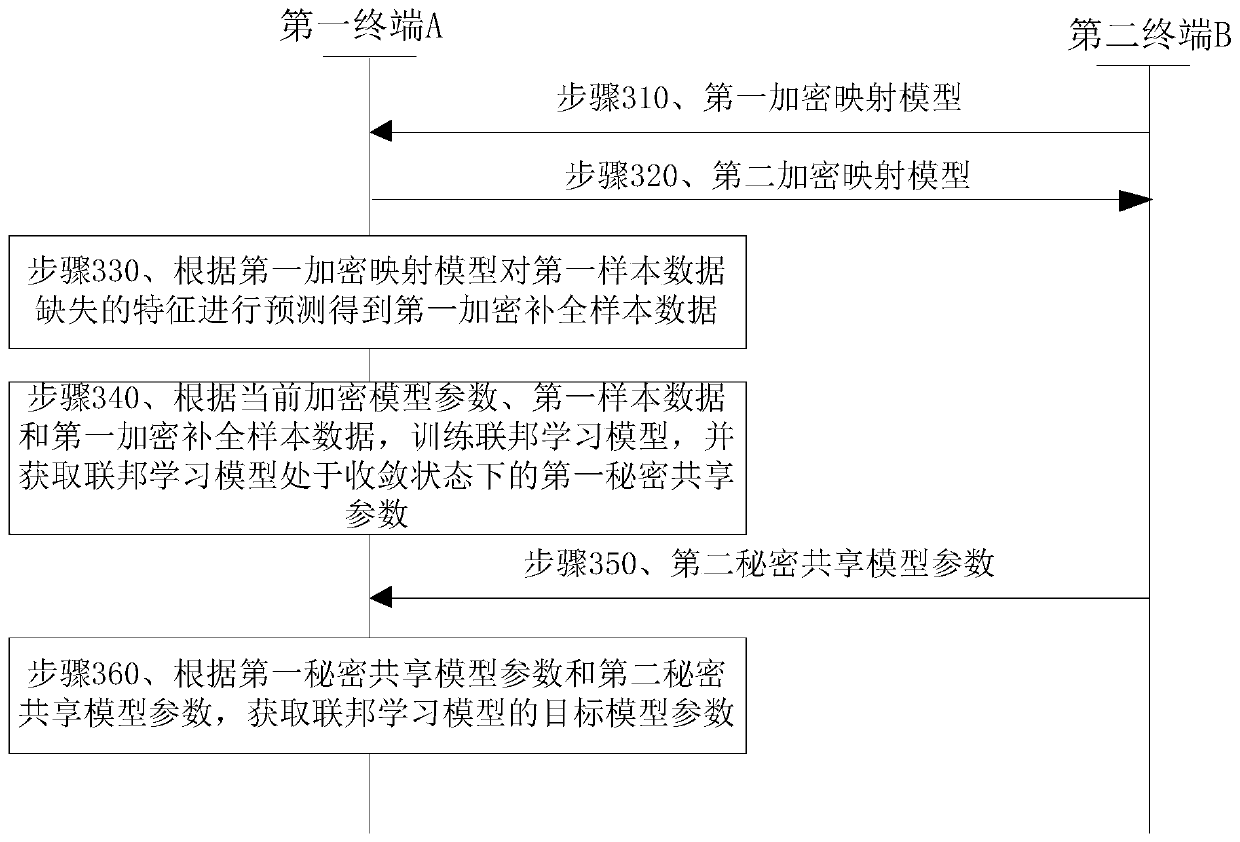
ActiveCN110288094AImprove experienceProtect private dataMachine learningPattern recognitionModel parameters
The invention discloses a model parameter training method and device based on federal learning. The method comprises the steps of using a first terminal to receive a first encryption mapping model sent by a second terminal; predicting the missing feature of the first sample data according to the first encryption mapping model to obtain the first encryption complement sample data; training a federal learning model according to the current encryption model parameters, the first sample data and the first encryption completion sample data, and obtaining a first secret sharing loss value and a first secret sharing gradient value; and if it is detected that the federal learning model is in a convergence state, obtaining a target model parameter according to the updated first secret sharing model parameter corresponding to the first secret sharing gradient value and a second secret sharing model parameter sent by the second terminal. According to the method, by adopting a secret sharing mode, the training process of the federated learning model does not need the assistance of a second collaborator, and the user experience is improved.
Owner:WEBANK (CHINA)
Shared information distributing device, holding device, certificate authority device, and system
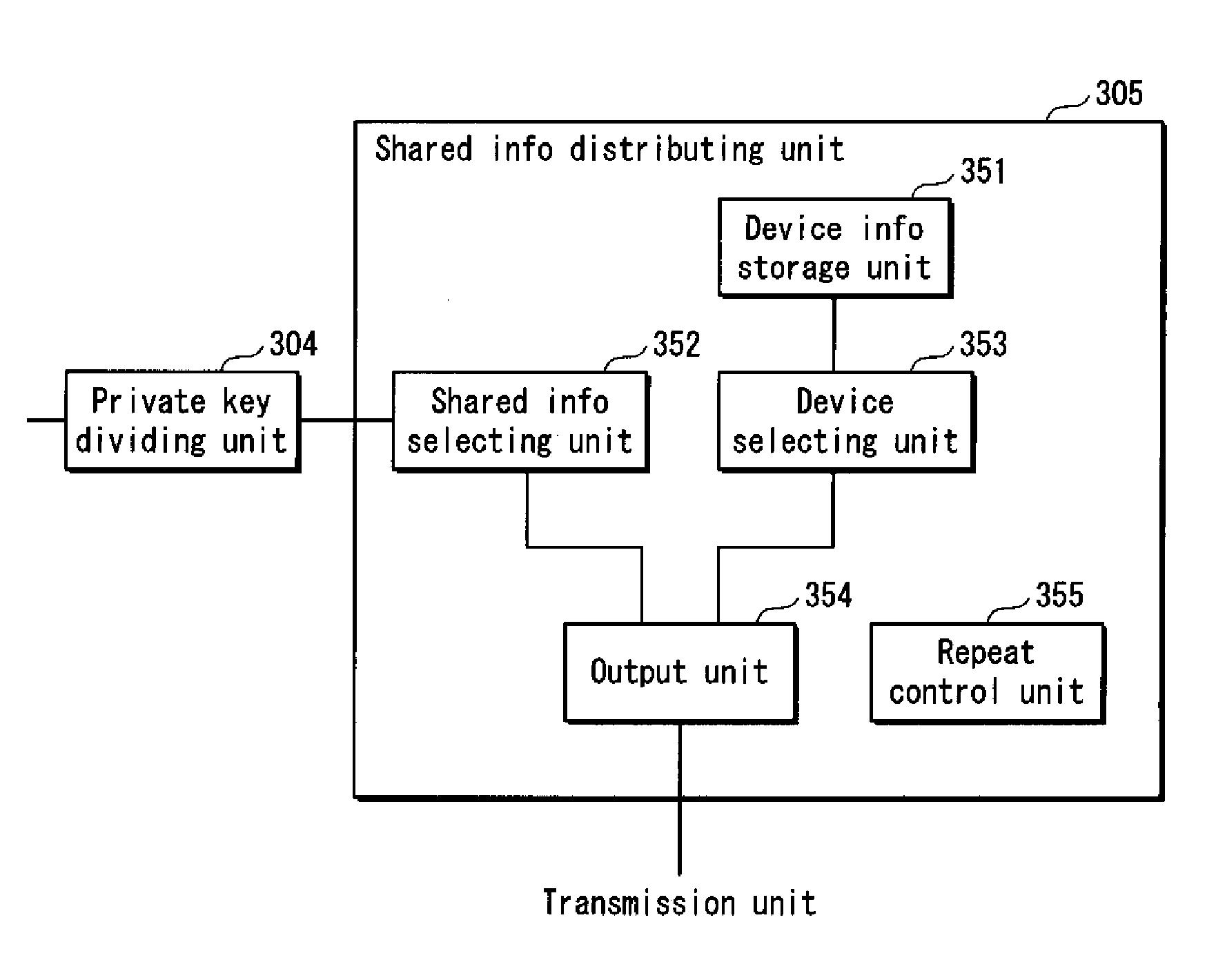
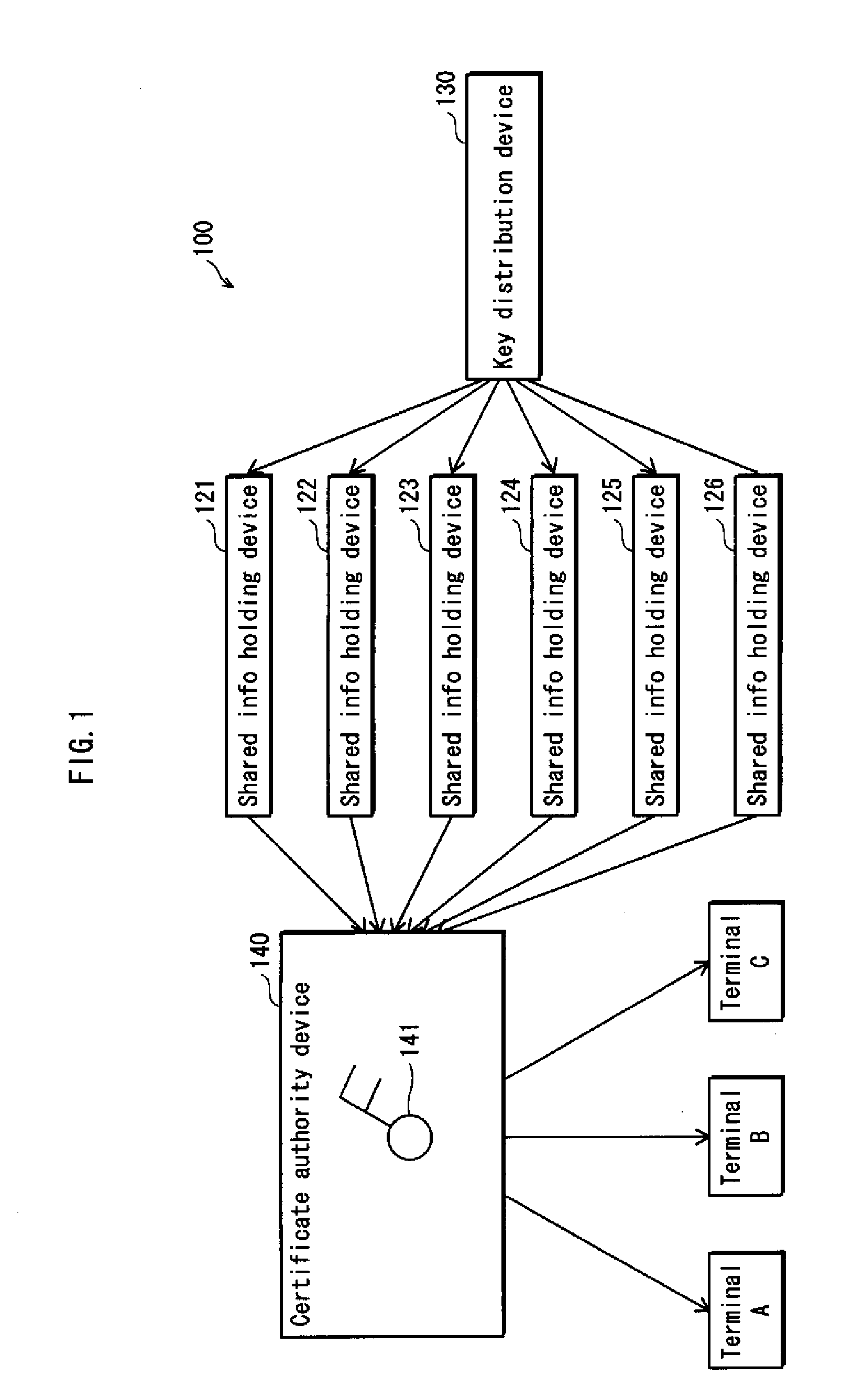
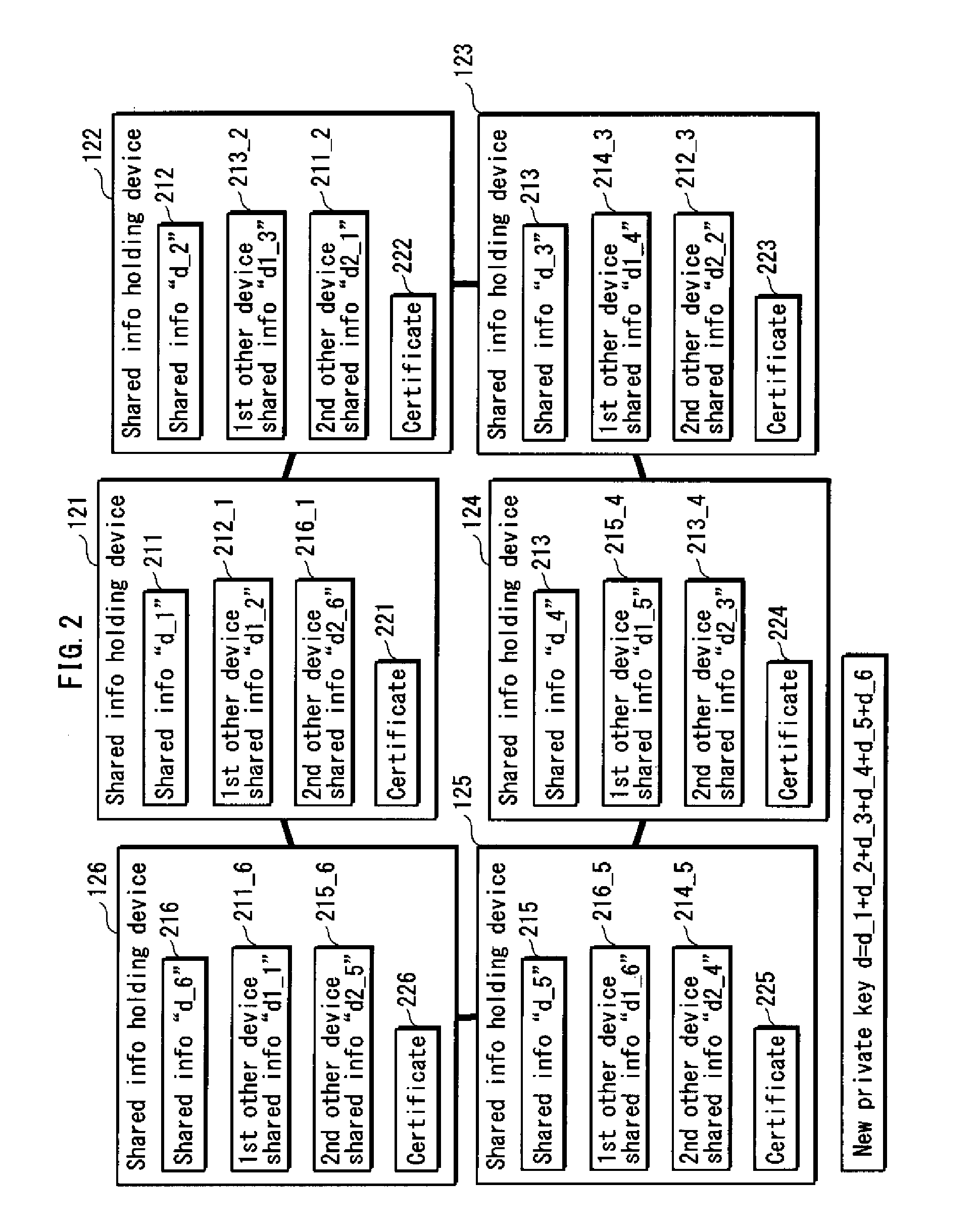
ActiveUS20100235588A1Increase redundancySure easyMemory adressing/allocation/relocationSecuring communicationCertificate authorityComputer security
A distributing device for generating private information correctly even if shared information is destroyed or tampered with. A shared information distributing device for use in a system for managing private information by a secret sharing method, including: segmenting unit that segments private information into a first through an nth pieces of shared information; first distribution unit that distributes the n pieces of shared information to n holding devices on a one-to-one basis; and second distribution unit that distributes the n pieces of shared information to the n holding devices so that each holding device holds an ith piece of shared information distributed by the first distribution unit, as well as a pieces of shared information being different from the ith piece of shared information in ordinal position among n pieces of shared information, “i” being an integer in a range from 1 to n.
Owner:PANASONIC CORP
Systems and methods for distributing and securing data
ActiveUS8155322B2Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
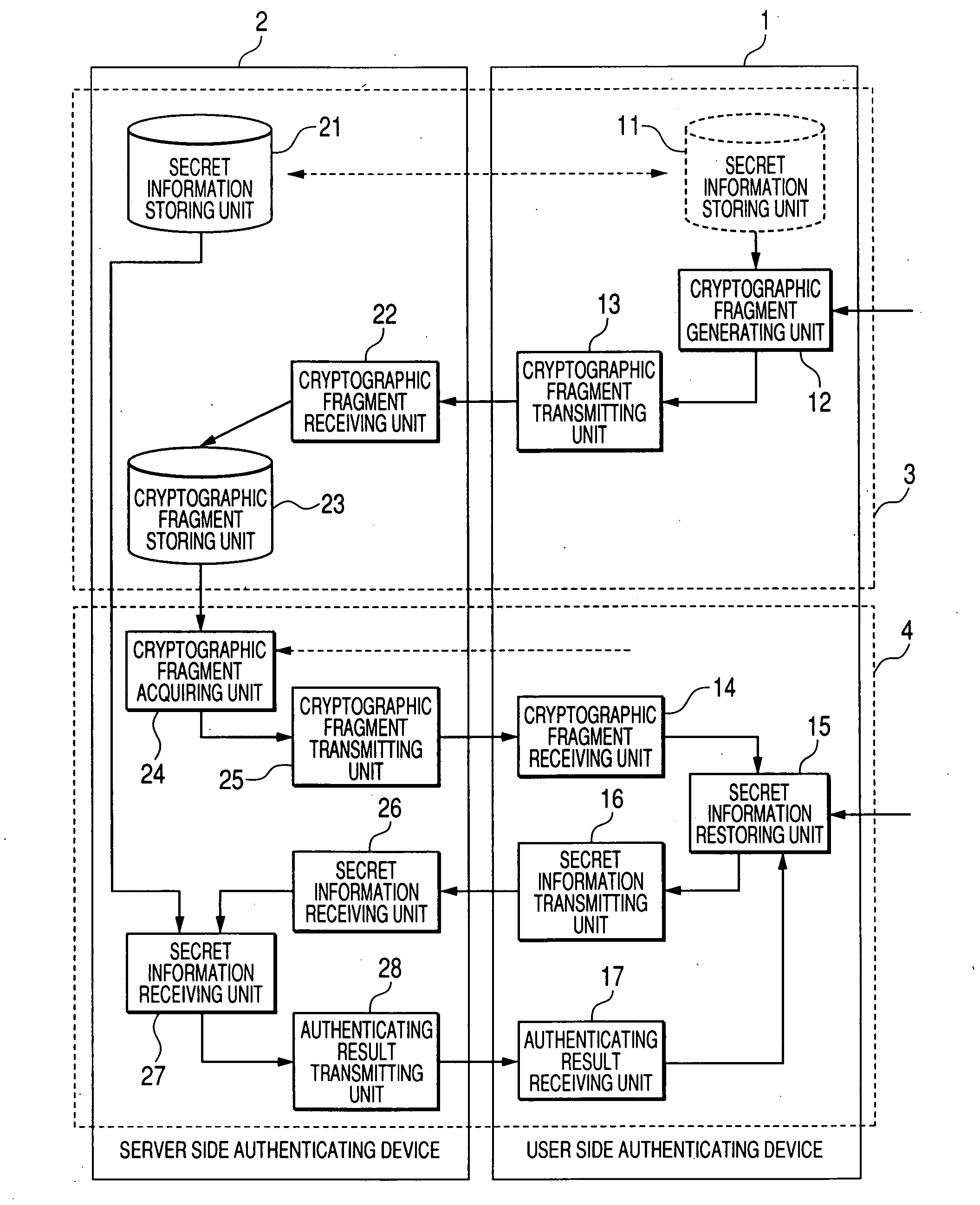
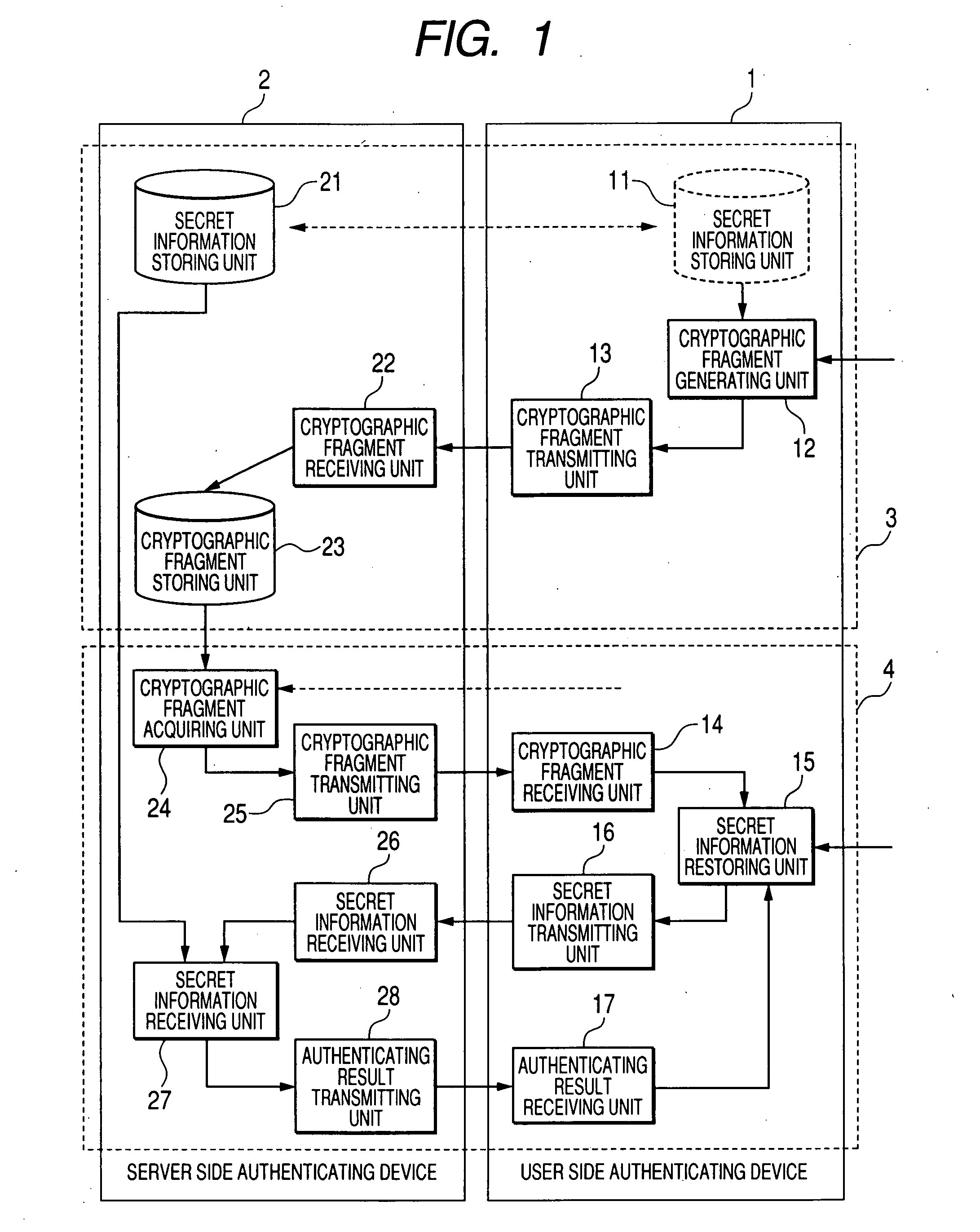
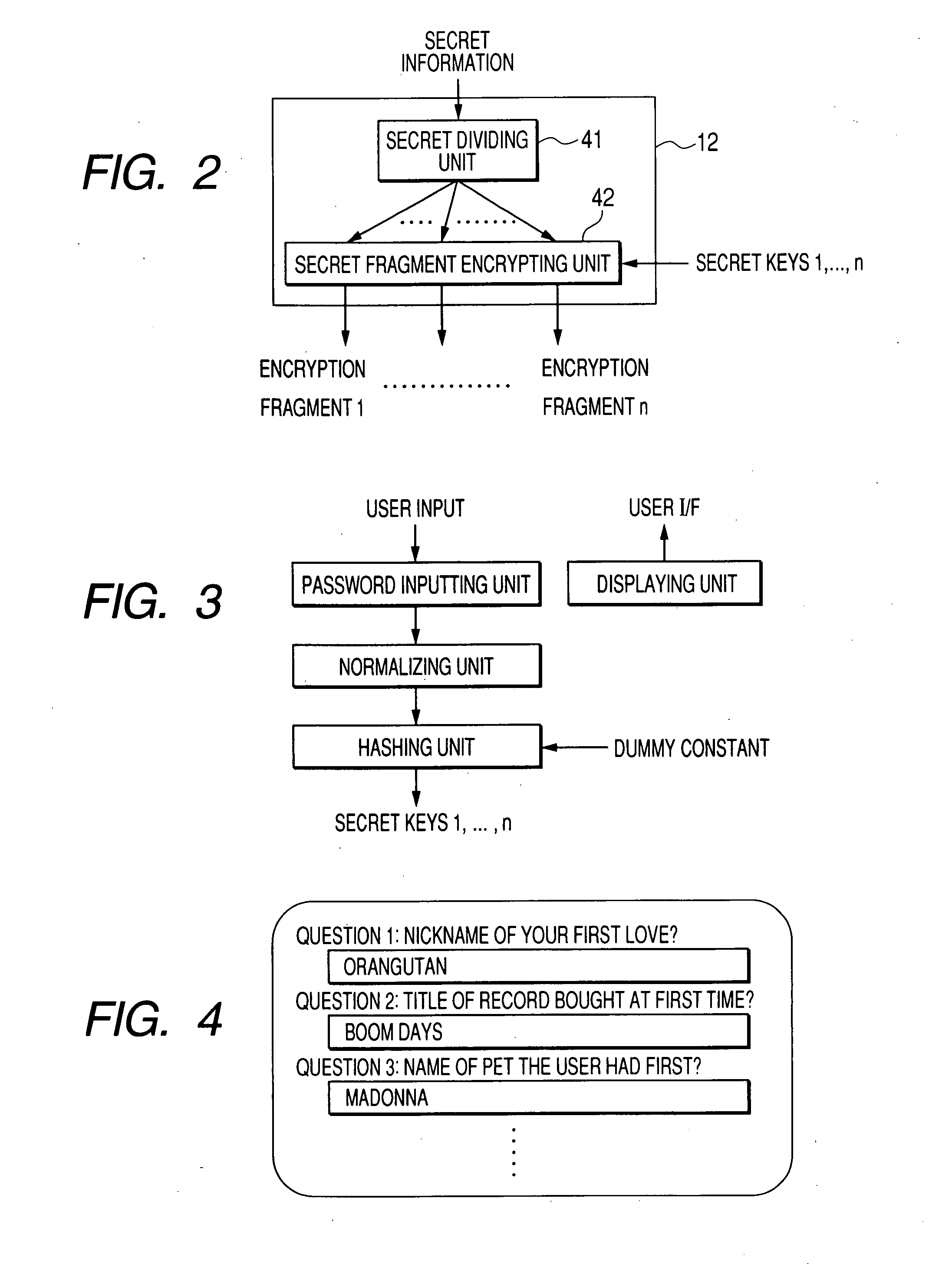
User authentication method, user authenticating device and program product
An authenticating device communicating with a server device includes: a dividing unit that divides secret information into plural secret fragments by a threshold secret sharing scheme; a first generating unit that generates plural cryptographic fragments by encrypting the secret fragments using first plural passwords; a first transmitting unit that transmits the cryptographic fragments to the server device; a first receiving unit that receives the cryptographic fragments from the server device, a second generating unit that generates plural secret fragment candidates by decrypting the cryptographic fragments using second plural passwords; a third generating unit that obtains a verifying information candidate by the threshold secret sharing scheme using a group of the secret fragment candidates; a second transmitting unit that transmits the verifying information candidate to the server device; and a second receiving unit that receives result information of comparing the verifying information candidate with verifying information in the server device.
Owner:KK TOSHIBA
Portable Data Encryption Device with Configurable Security Functionality and Method for File Encryption
ActiveUS20130046993A1Mitigates and eliminates vulnerabilityUser identity/authority verificationUnauthorized memory use protectionComputer hardwarePlaintext
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
Encryption method, encryptor, and encryption system for encrypting electronic data by splitting electronic data
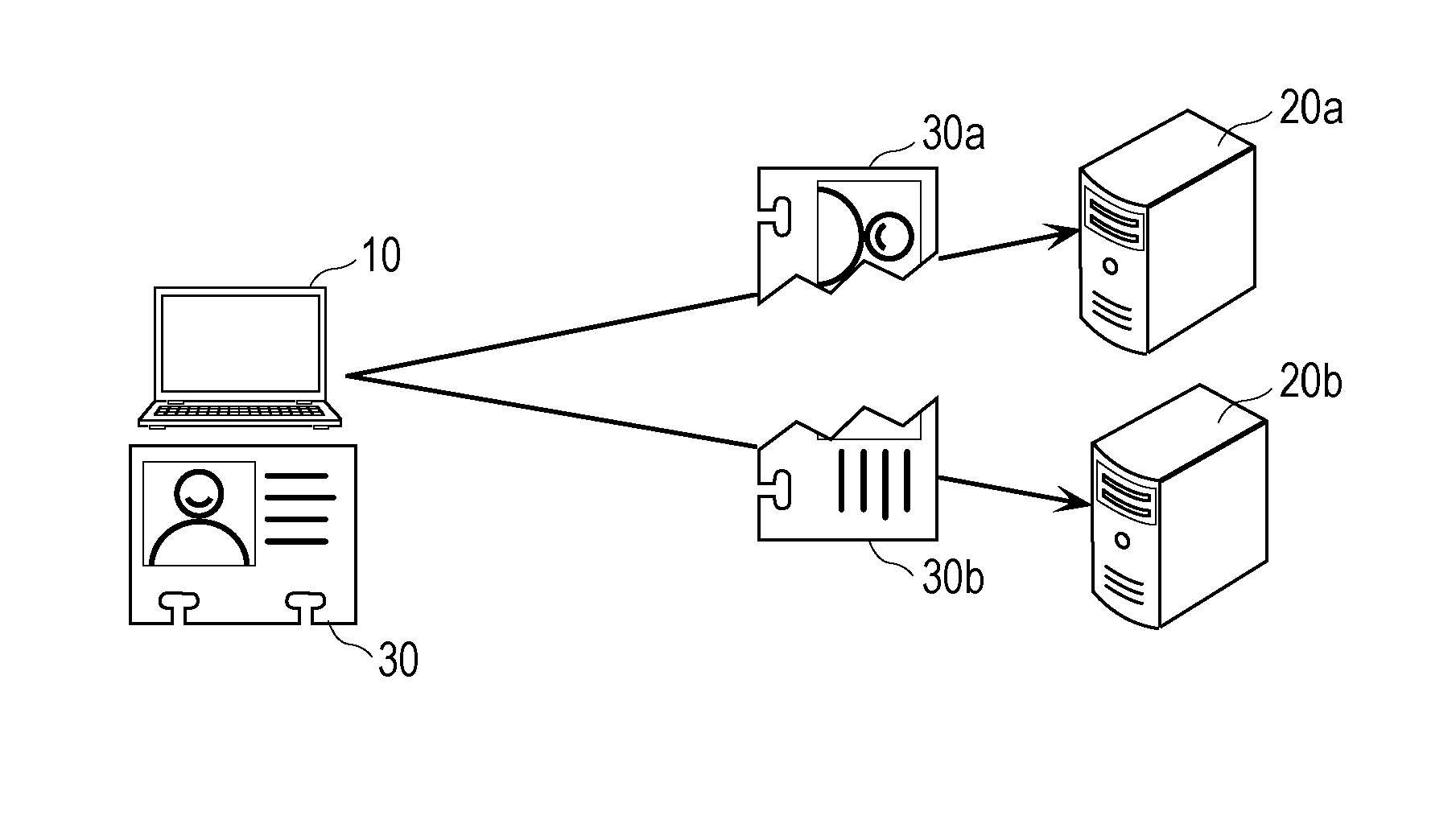
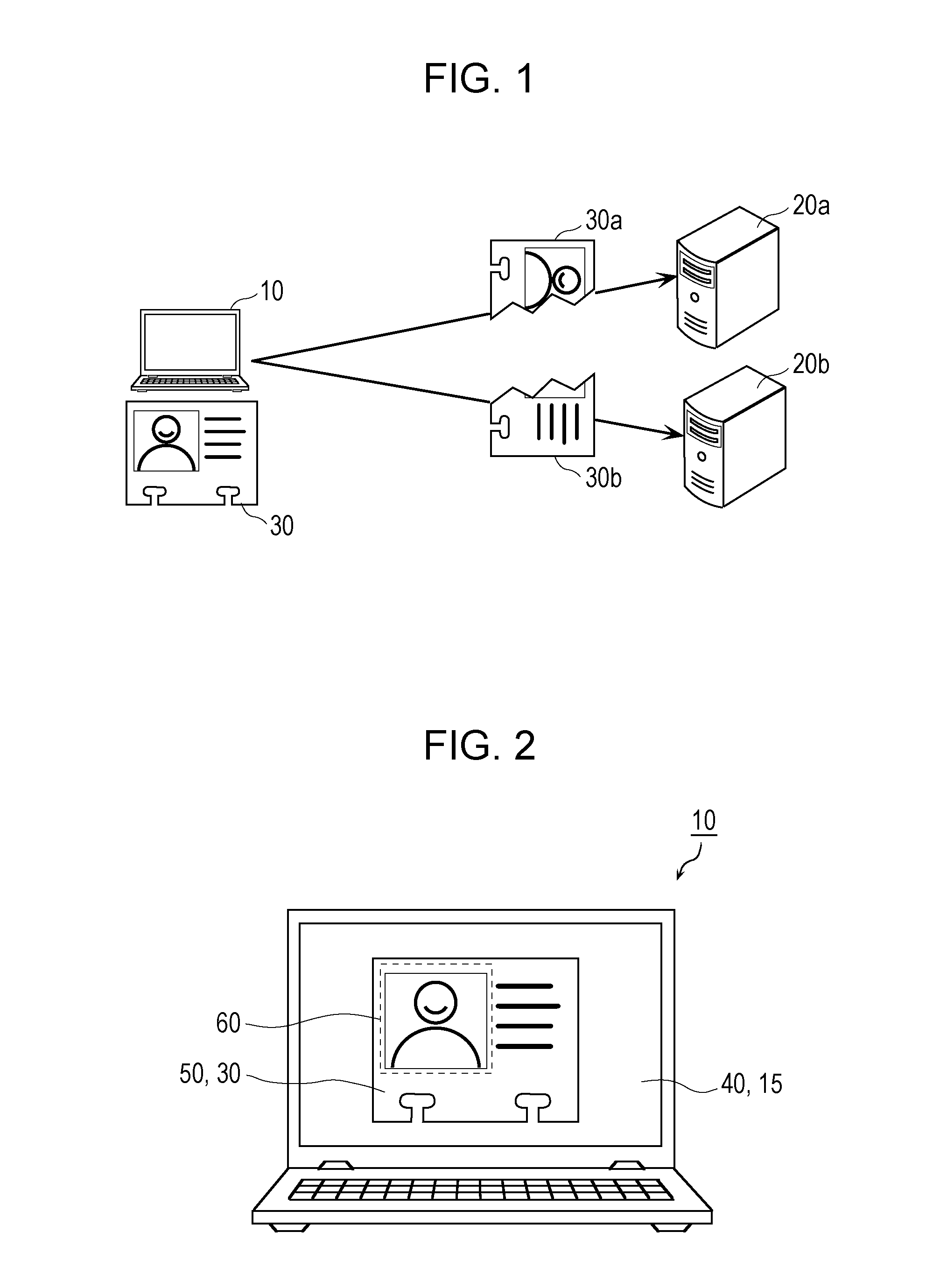
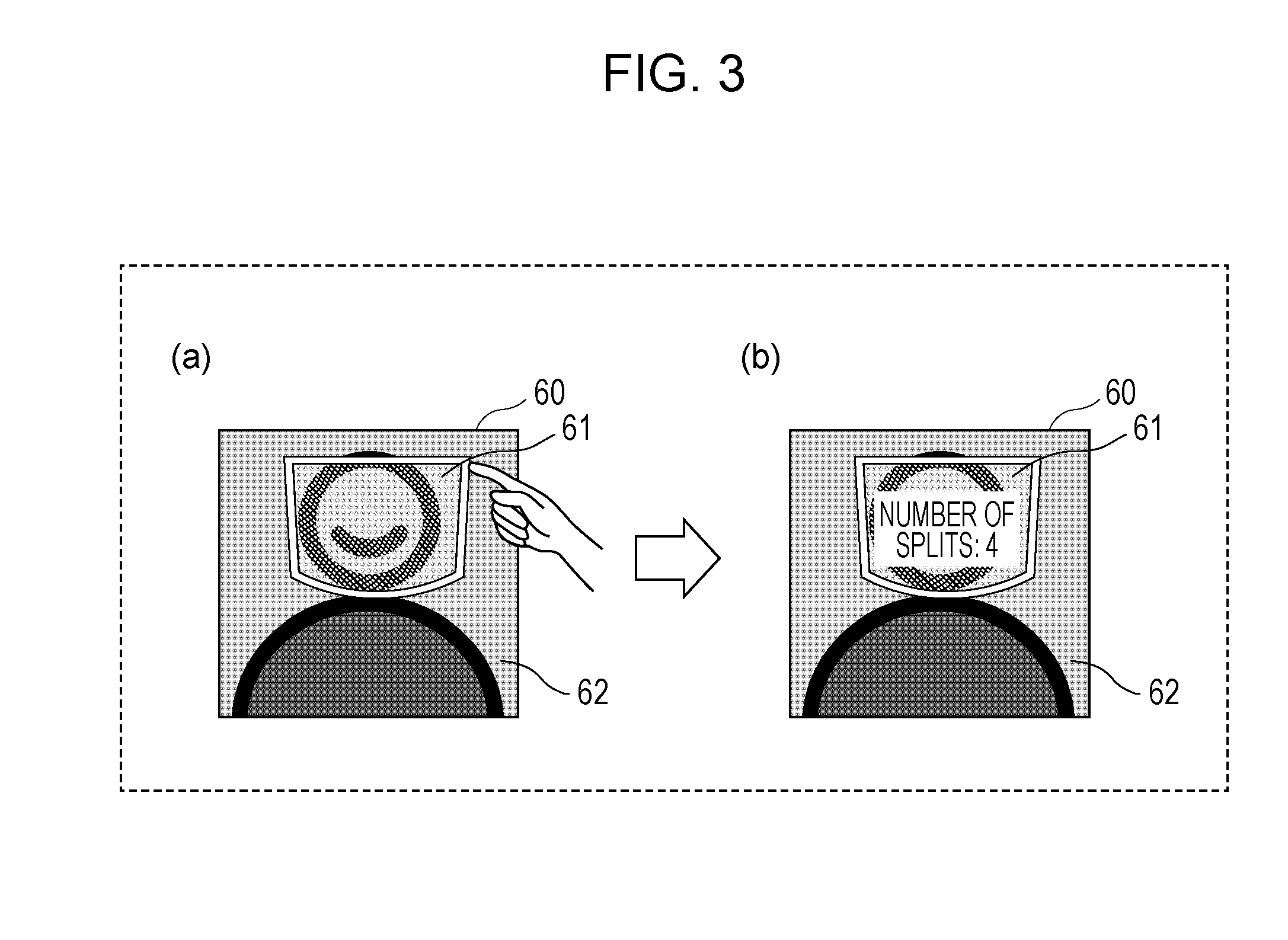
ActiveUS20160119134A1Improve confidentialityEasy to implementKey distribution for secure communicationUser identity/authority verificationXML EncryptionElectronic data
An encryption method includes displaying encryption target data on a display screen as an image, performing first acceptance in which designation of an at least partial region of the displayed image is accepted, performing second acceptance in which designation regarding splitting of the designated at least partial region is accepted, and splitting data that is included in the encryption target data and corresponds to the designated at least partial region in accordance with the designation regarding the splitting under a secret sharing scheme.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com