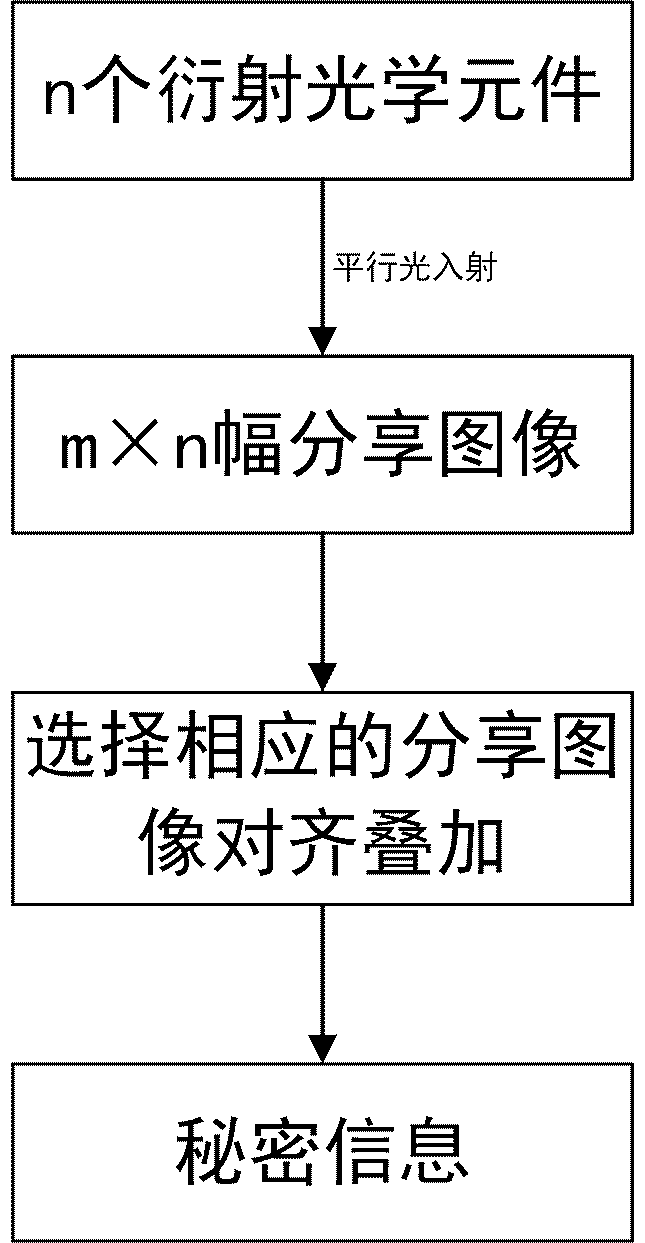
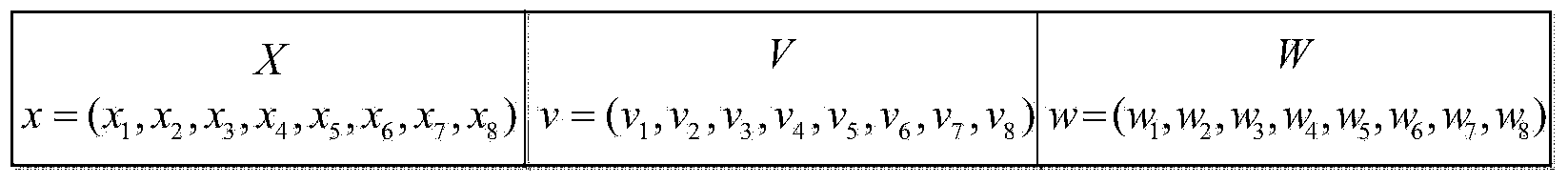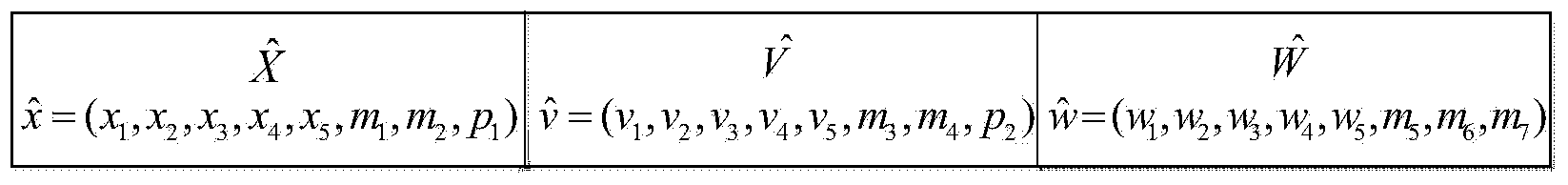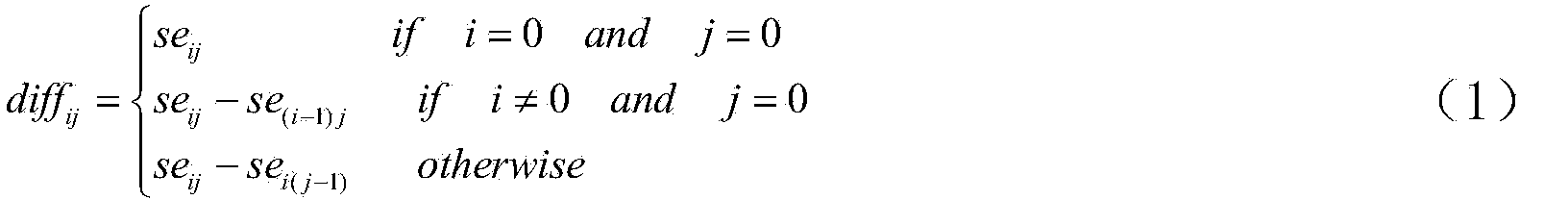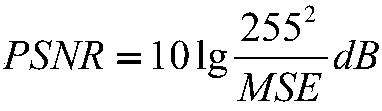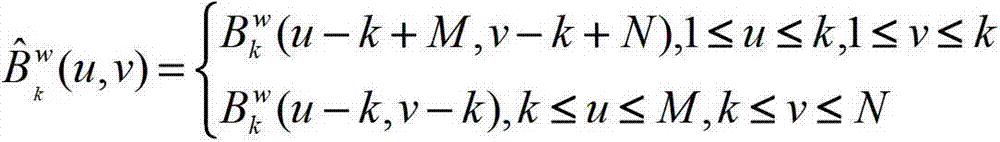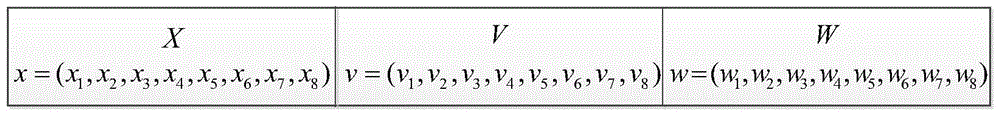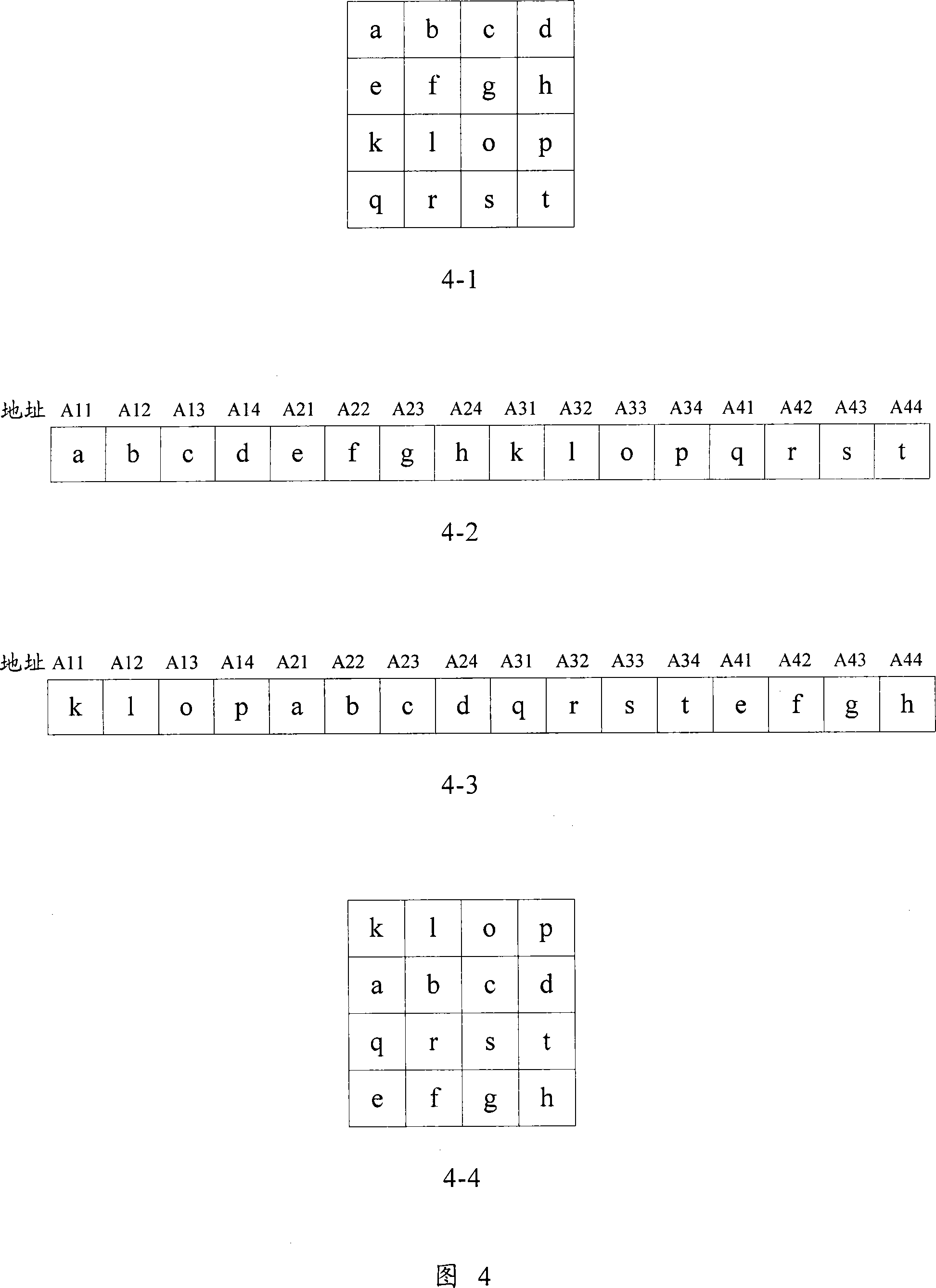Patents
Literature
76 results about "Image hiding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
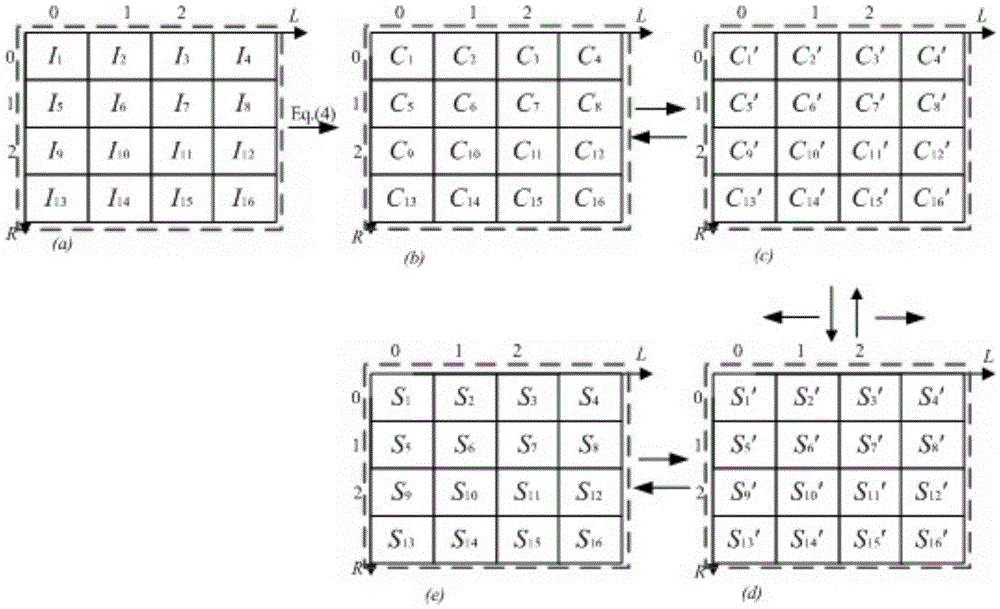
Image hiding and authentication method based on secret sharing
ActiveCN103761702AImprove securityDifferences in Statistical PropertiesImage data processing detailsPattern recognitionHash function
The invention discloses an image hiding and authentication method based on secret sharing, and belongs to the technical field of secret image sharing. The image hiding and authentication method is characterized by comprising the steps that firstly, difference Huffman encoding is conducted on a secret image, every three generated bit sequences are set to be one group to be converted into decimal numbers which are used as coefficients of a sharing polynomial in the Shamir (k, n) threshold scheme, the k and the n are positive integers, the k is smaller than or equal to the n, and n shadow images are generated; secondly, n significant carrier images are selected, the generated shadow images are embedded into the carrier images in a matrix encoding mode, authentication bits generated by the hash function are also embedded into the carrier images, and n disguise images are formed and are in the charge of n different participants respectively. The disguise images generated through the image hiding and authentication method has higher visual quality, existence of secret information cannot be perceived by attackers easily, and the safety of the secret information is ensured. Meanwhile, before the secret information is recovered, the disguise images provided by each participant need to be authenticated, only the disguise images passing through authentication can participate in recovery of the secret information, and the safety of the secret information is further strengthened.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
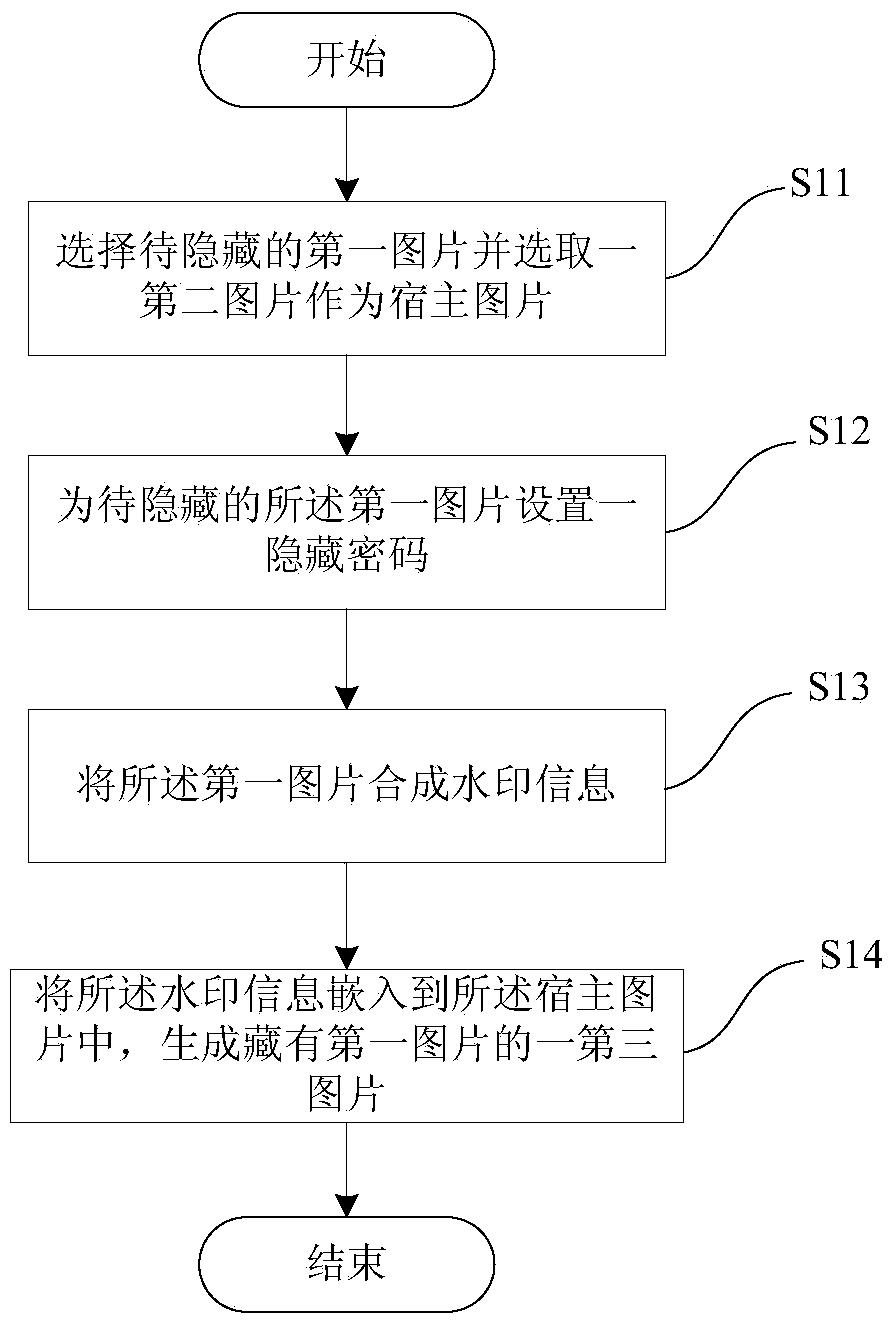
Picture hiding and acquiring method and intelligent terminal
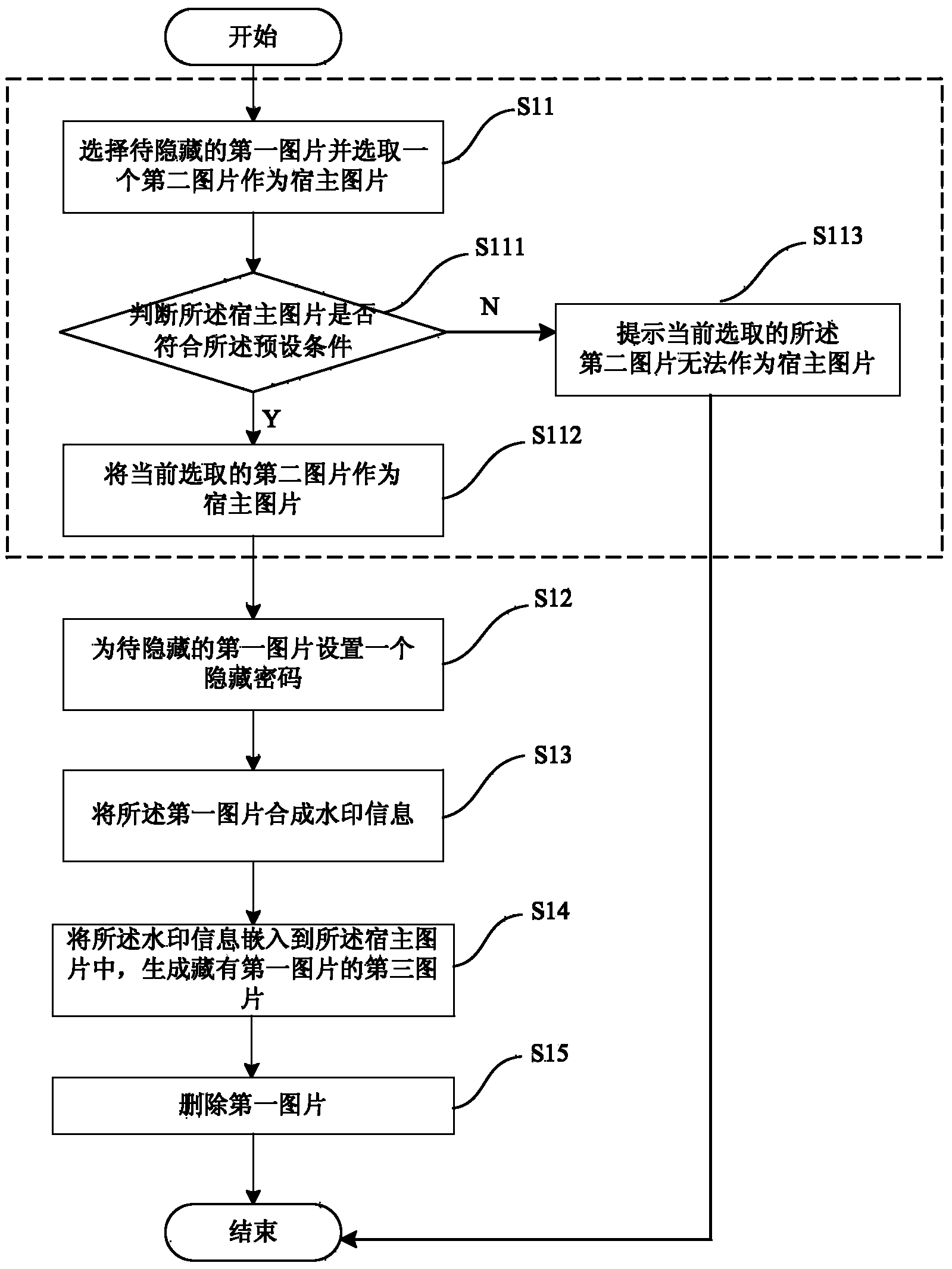
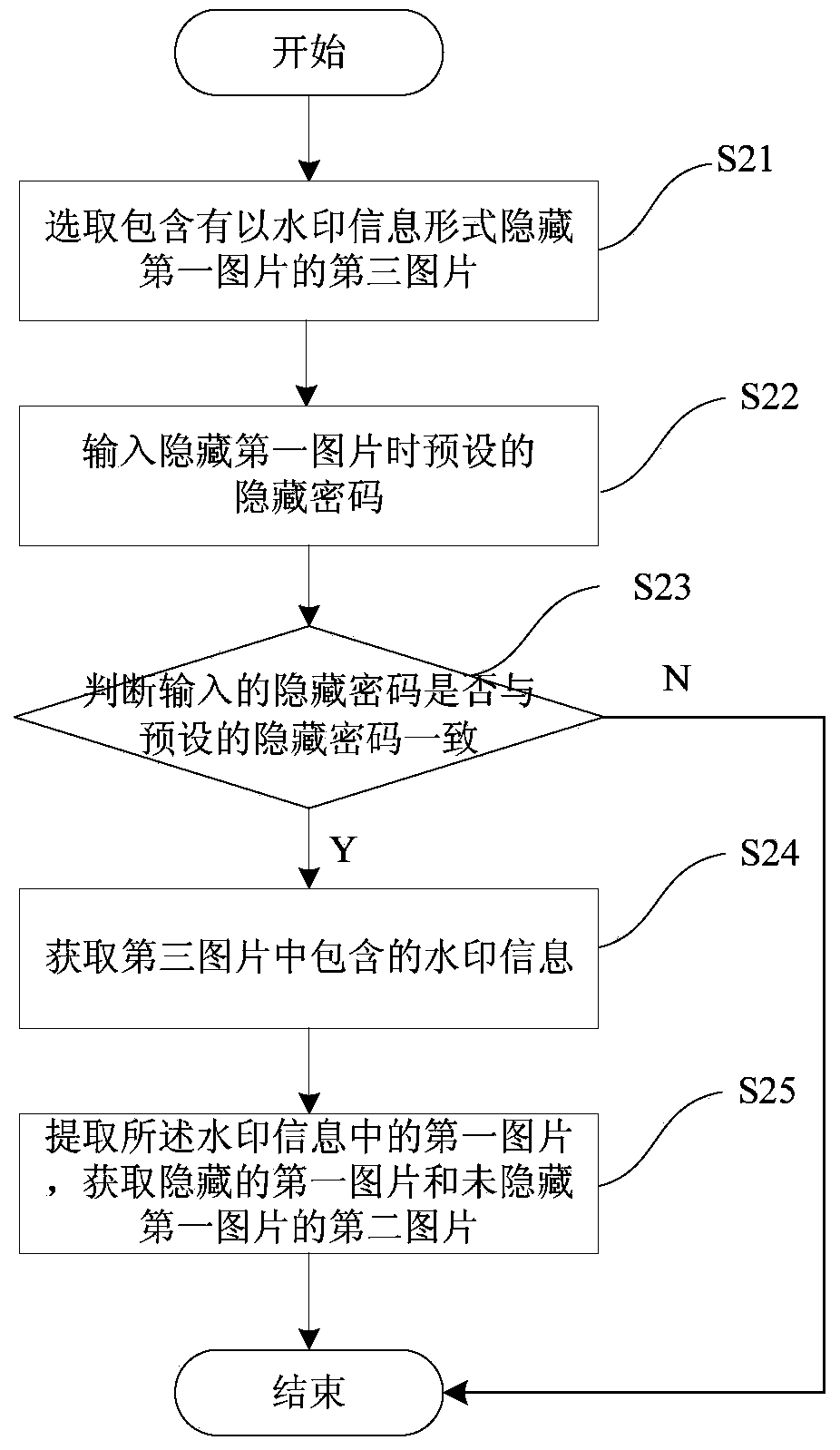
InactiveCN103824249ATo achieve the purpose of confidentialityData confidentialityImage data processing detailsConfidentialityPassword
The invention provides a picture hiding and acquiring method and an intelligent terminal. The method comprises the following steps: selecting a first picture to be hidden and selecting a second picture as a host picture; setting a hidden password for the first picture to be hidden; synthesizing the first picture into watermarking information; embedding the watermarking information into the host picture to generate a third picture with the first picture hidden. According to the picture hiding and acquiring method and the intelligent terminal, only other pictures are needed to be selected as the host picture, and the pictures are hidden in the host picture through an invisible watermarking technology, so as to reach the aim of keeping the picture confidentiality; otherwise, the hidden pictures can be extracted from the host picture and can be checked. Therefore, the privacy of users can be well protected, so that the data on mobile phones and other intelligent terminals is safe and private.
Owner:PHICOMM (SHANGHAI) CO LTD
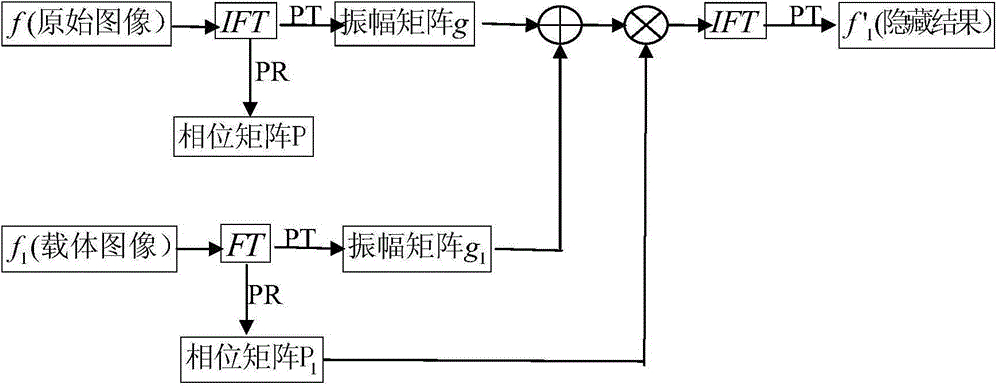
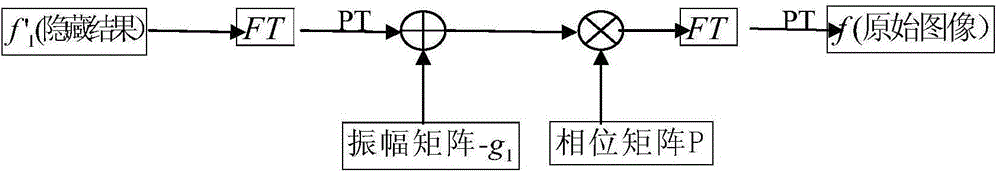
Phase-cut Fourier transform based image hiding method, image restoring method and image encrypted transmission method
InactiveCN104794675AImprove practicalityQuick hideImage data processing detailsImage hidingComputer vision
The invention discloses a phase-cut Fourier transform based image hiding method, an image restoring method and an image encrypted transmission method. The image hiding method includes: subjecting a to-be-hidden image f to Fourier inverse transform prior to extracting an amplitude matrix g(x, y) and a phase matrix P(x, y) of the image subjected to Fourier inverse transform, and subjecting a carrier image f1 to Fourier transform prior to extracting an amplitude matrix g1(u, v) and a phase matrix P1(u, v) of the image subjected to Fourier transform; enabling g'1 (u, v)=g1(u, v)+g(x, y), then multiplying the g'1 (u, v) by the P1(u, v), obtaining a hidden result after Fourier transform and extracting an amplitude matrix f'1(x, y) of the hidden result so as to obtain a final hidden result image. The image restoring method is implemented by taking the P(x, y) as a private decryption key and performing the image hiding method reversely. The phase-cut Fourier transform based image hiding method, the image restoring method and the image encrypted transmission method have the advantages that difference between the obtained hidden result and the carrier image is small, so that deception is achieved; original information can be restored completely, and the problems of image quality degradation and the like are avoided; calculated quantity is small, and high safety during encrypted transmission is achieved.
Owner:SOUTH CHINA NORMAL UNIVERSITY
Invisible code graphics, processing method thereof and anti-fake application
The invention discloses invisible code graphics, a processing method of the invisible code graphics and anti-fake application and belongs to the field of information processing. The processing method includes a processing method with the image hiding technology and the coding technology combined. Images are divided into two parts, two different screening manners are adopted for screening the two parts of the images respectively, amplitude-modulating screening is conducted on an information hiding part, frequency modulating screening is conducted on the other part of the images, and meanwhile coding information is recorded according to the sequence of exposing pixel points in a grid of an area needing information hiding so that the purpose of information hiding can be achieved. The hidden code graphics serves as anti-fake labels, after the labels are copied by a common copying machine, the images with amplitude-modulating dot screening can be well shown, however, the images with amplitude-modulating dot screening cannot be completely shown, and therefore the code graphics can be shown and initial fake prevention is achieved. Meanwhile, buried coded messages can be obtained through an image sensor, and therefore authenticity is identified after the coded messages are compared with content on certificates and securities.
Owner:广东绿之彩科技股份有限公司
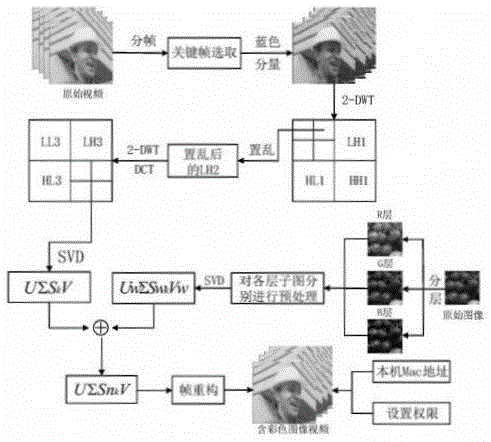
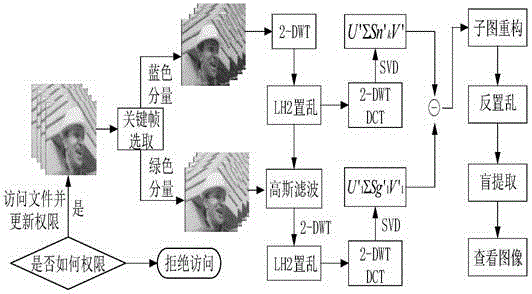
An image hiding method based on a video carrier and under an off-line controllable mechanism
ActiveCN105118018AAchieve effectivenessAchieve controllabilityImage data processing detailsProgram/content distribution protectionColor imageSingular value decomposition
The invention discloses an image hiding method based on a video carrier and under an off-line controllable mechanism. A key frame of a video is firstly subjected to 2-DWT transformation; then Arnold transformation is carried out on sub-bands; through characteristics of singular value decomposition and multi-resolution characteristics of wavelet transformation, images are embedded in sub-band singular values which have undergone scrambling; when the video is under different attacks, blind extraction of the image can be realized; and the blind extraction specifically comprises two steps which are color image confidential storage and color image extraction checking. As technology of embedding and extraction of the color image in the video and the technology of limited frequency checking and anti-copying in an image off-line condition, the method of the invention is the image confidential storage technology based on the video carrier and under the off-line controllable mechanism, and can solve problems of confidentiality and storage of confidential and private images, thereby reaching a purpose of protecting private and confidential information, and realizing validity and controllability access of the image in an extent of competence.
Owner:ANHUI UNIVERSITY
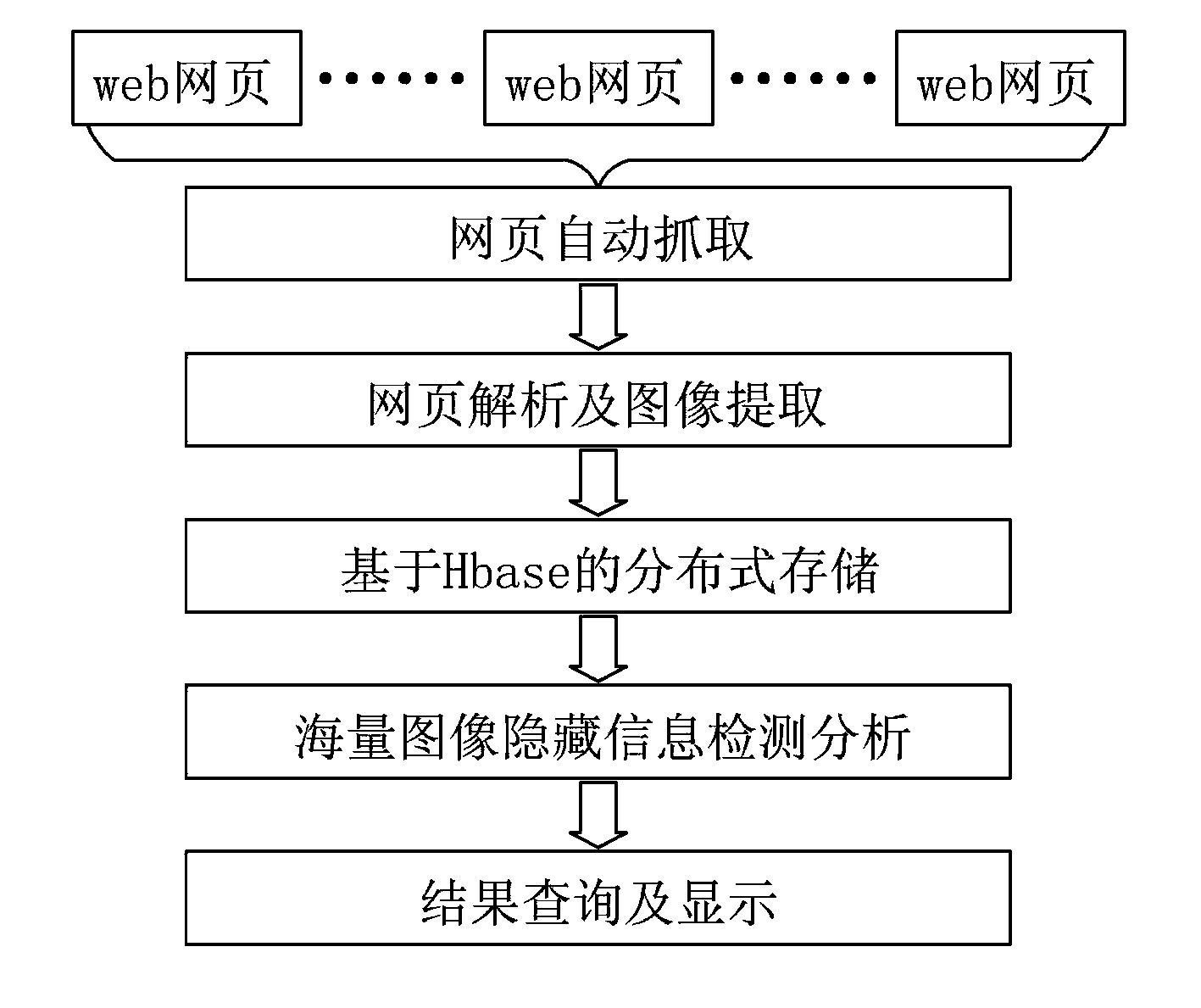
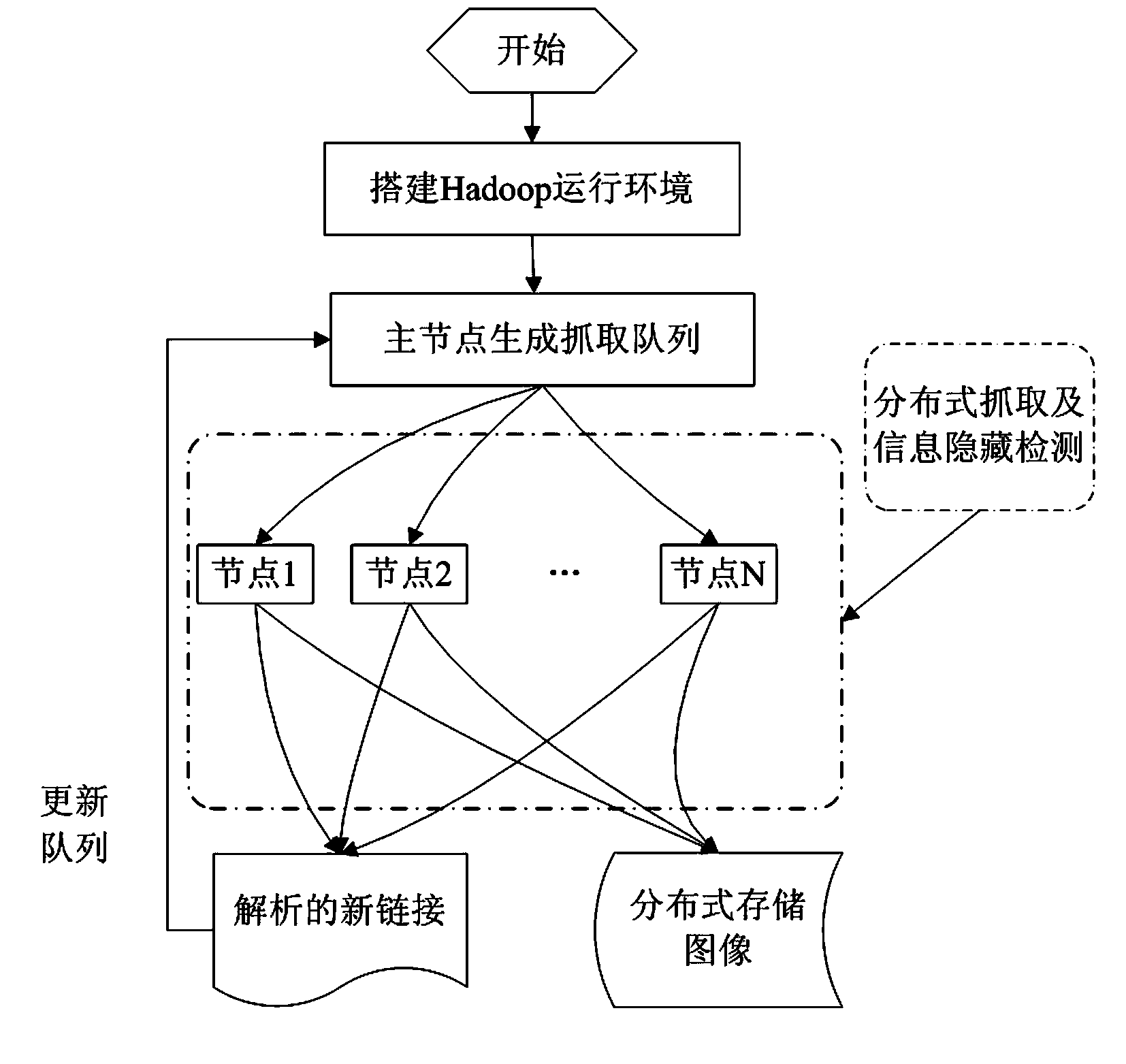
Distributed information hiding detection method facing mass web images
ActiveCN103455597AMaintain securityImprove good performanceSpecial data processing applicationsCovert communicationImage detection
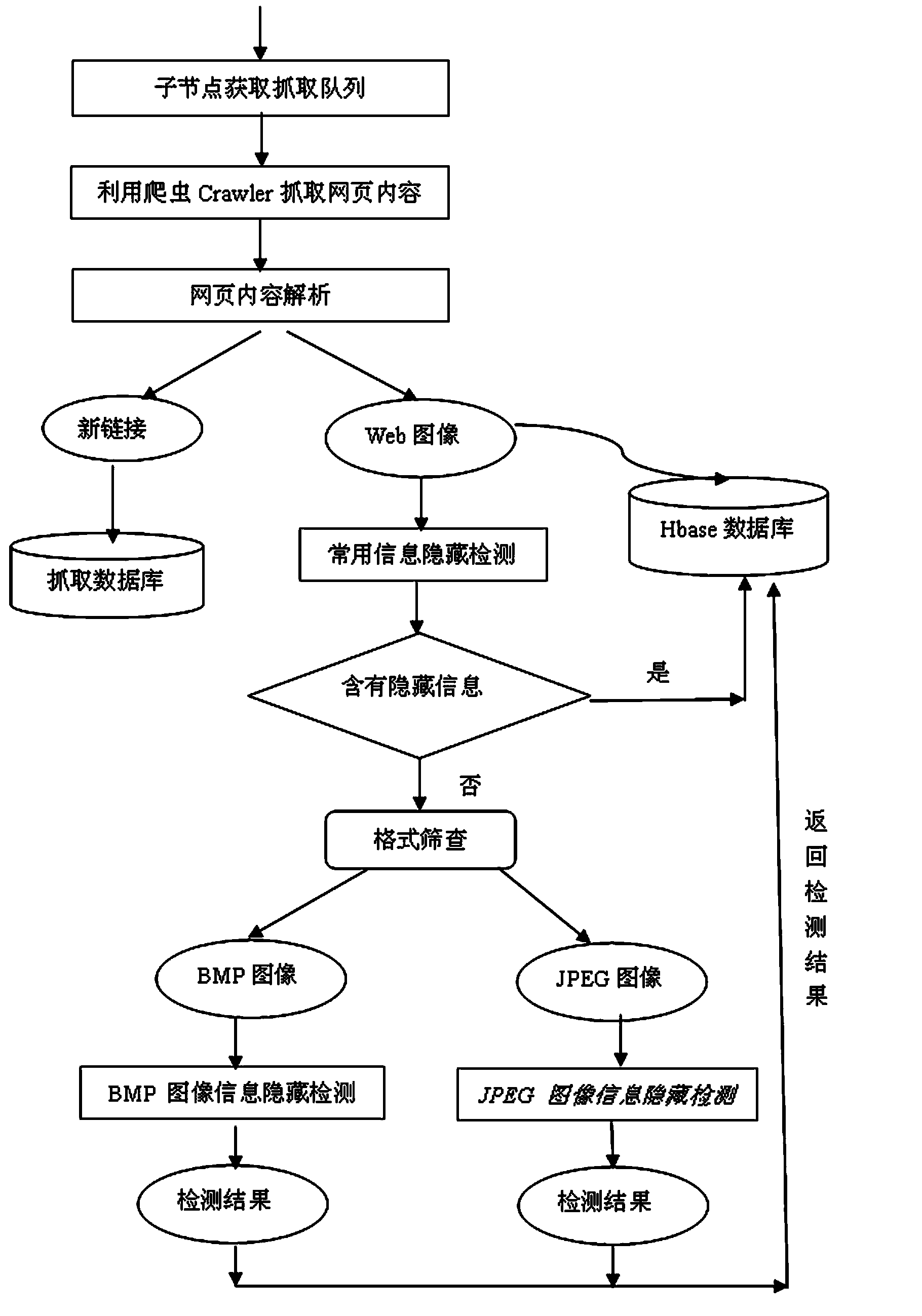
The invention relates to a distributed information hiding detection method facing mass web images, which comprises the following steps of: a, setting up a Hadoop operation environment on a cloud computing platform; b, generating a Nutch crawling queue; c, according to a MapReduce architecture of the Hadoop, carrying out distributed webpage crawling; d, analyzing a webpage and extracting images in the webpage; 3, storing the extracted web images by adopting Hbase; f, carrying out universal blind detection of the images; g, screening out images with a BMP (Bitmap) format and a JPEG (Joint Photographic Experts Group) format; h, detecting the images with the BMP format; and i, detecting the image with the JPEG format. The image hiding detection method disclosed by the invention adopts open source technologies such as Hadoop, Nutch and the like, is easy to design, develop and implement, has a good detection effect, is suitable for extraction of mass images and detection of hidden information in the current network environment and has important practical significance for finding out and tracking lawless people who utilize public channels to carry out covert communication and maintaining national information security.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
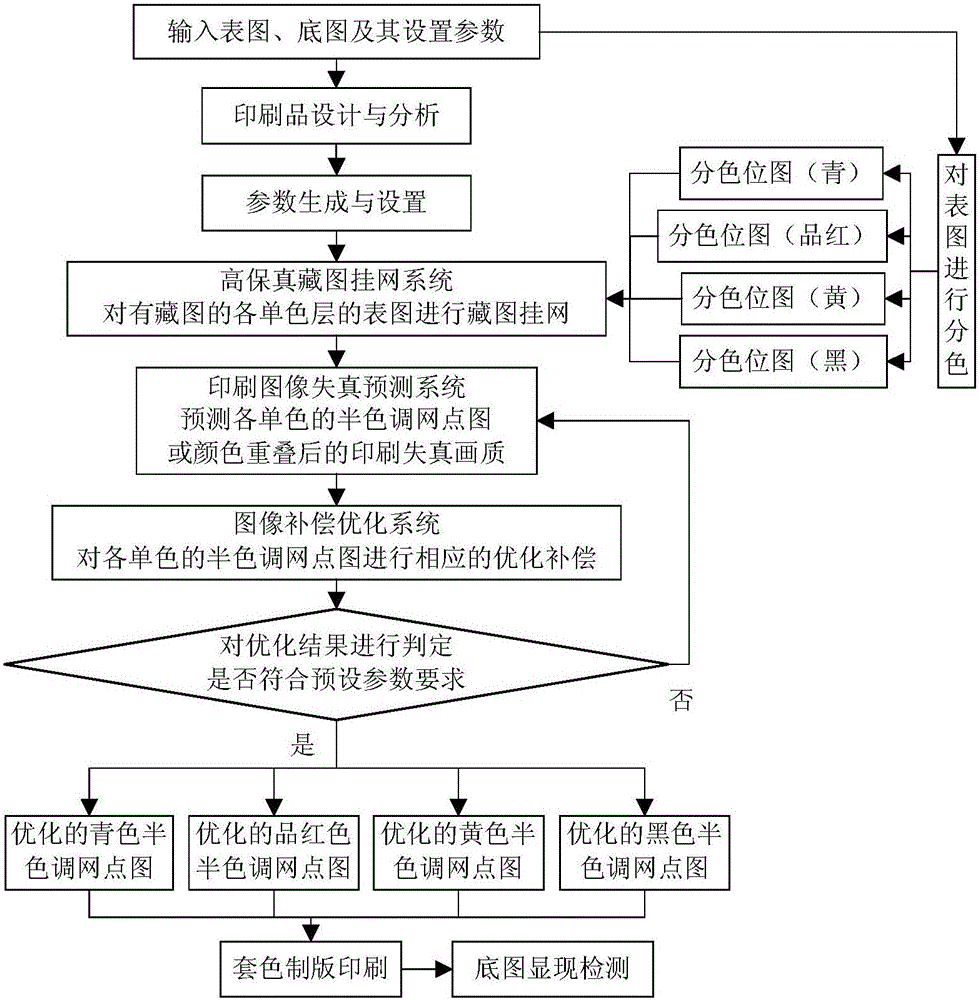
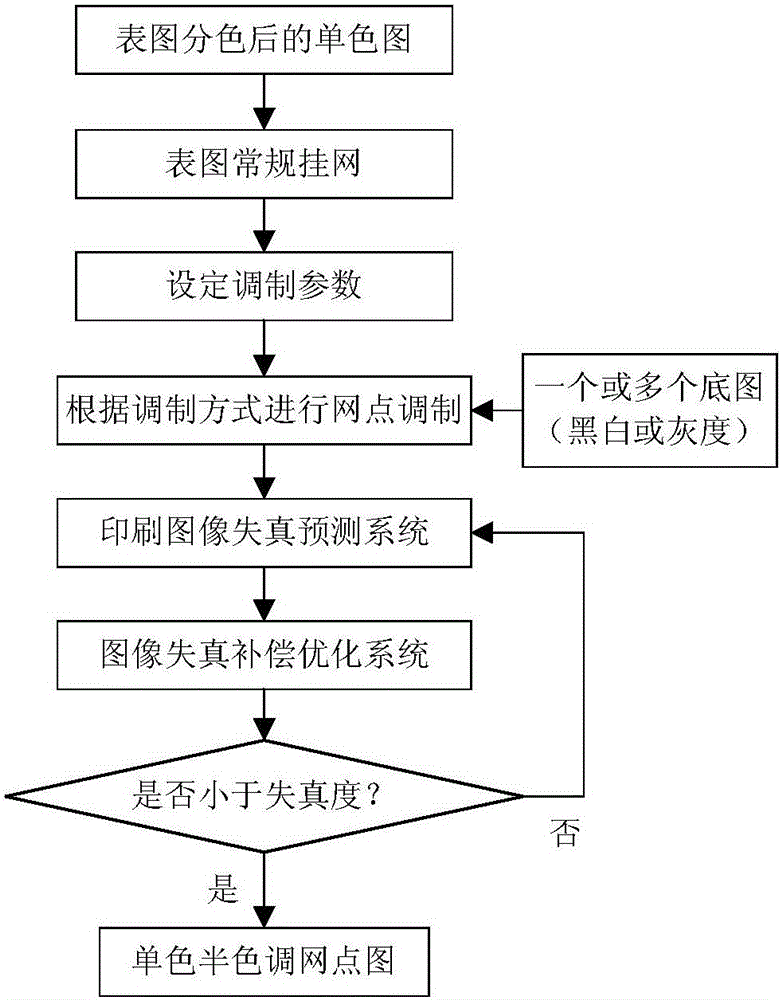
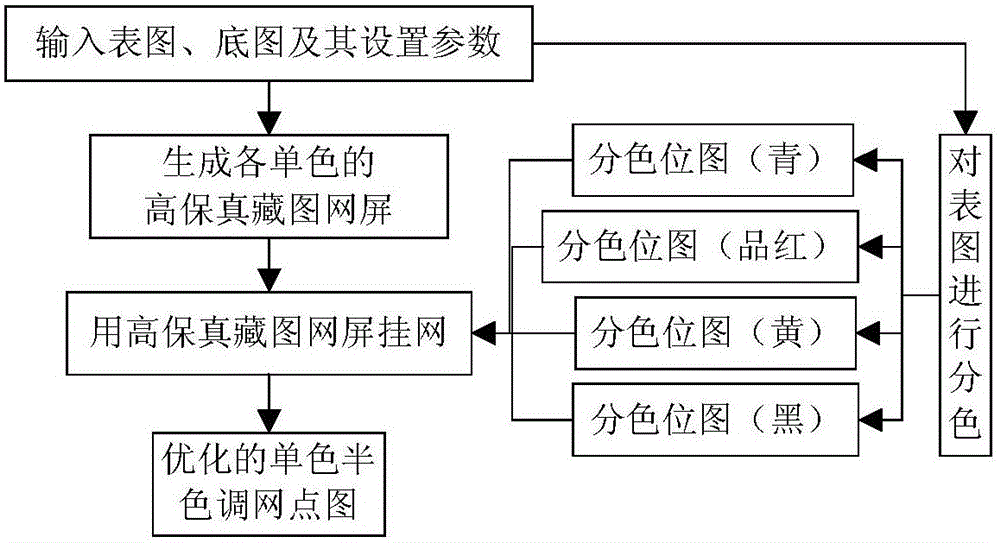
High-fidelity hidden image figure screen frequency determination method and system based on direct correction
ActiveCN106157336AQuality improvementExpand the scope of selectionImage enhancementImage analysisImage resolutionGray level
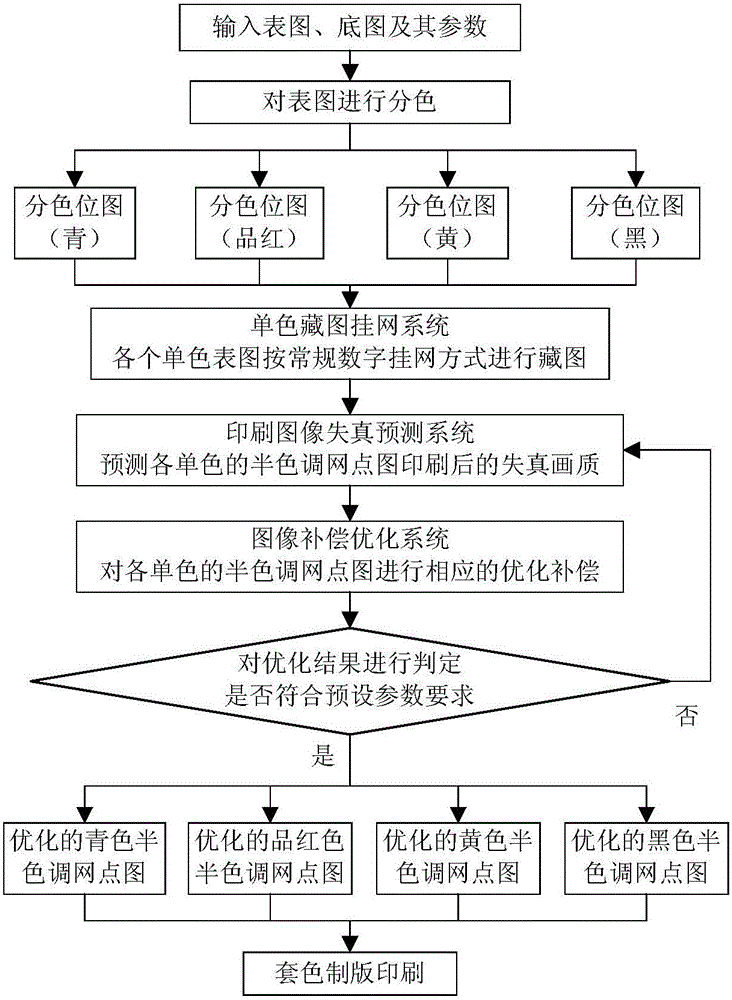
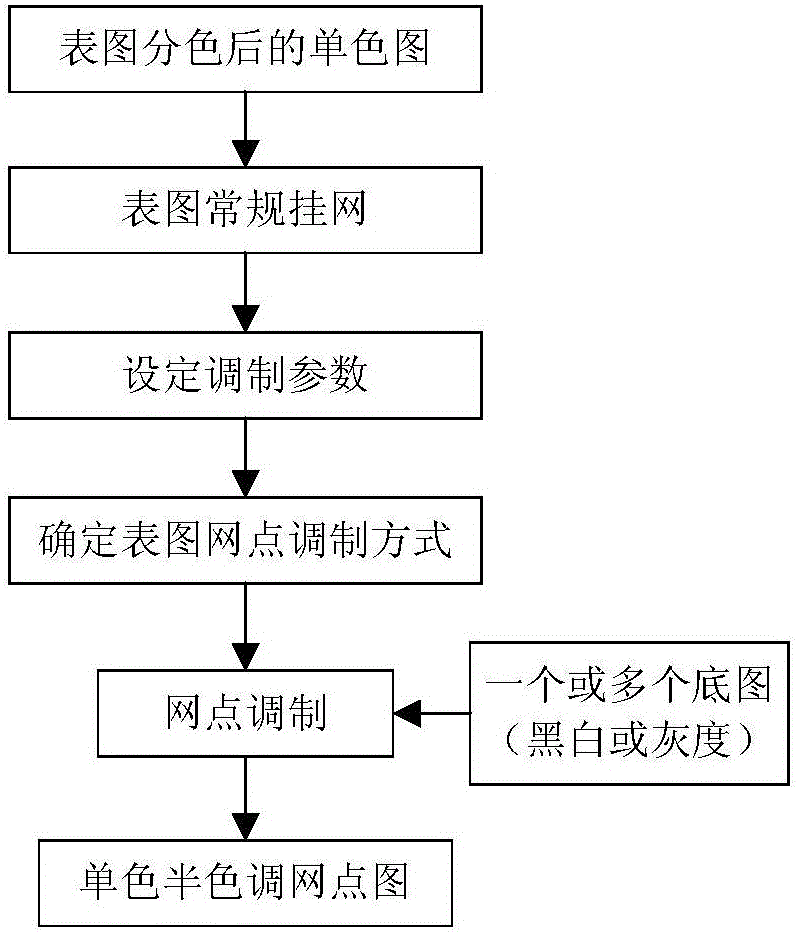
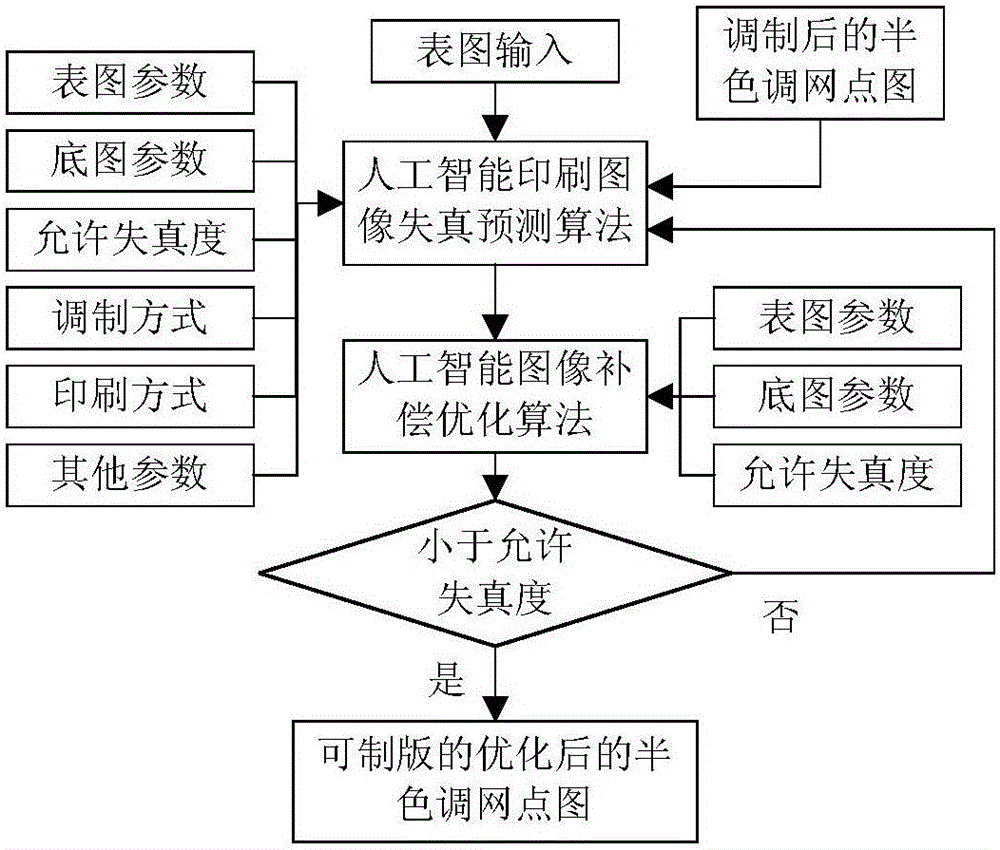
The invention provides a high-fidelity hidden image figure screen frequency determination method and system based on direct correction, and relates to the technical field of anti-counterfeiting printing. The method includes the steps that after a bottom image is hidden in a surface image at a conventional screen frequency, image defects caused in the image hiding and printing processes are quantitatively and accurately predicted through a printed image distortion prediction system, accurate alignment compensation is carried out through an image compensation optimization system, and a high-fidelity printed product including the bottom image is obtained. The system comprises a color separation module, a screen frequency determination module, a screen point modulation module, a printed image distortion prediction module, an image distortion compensation optimization module, an optimization result judgment module and a platemaking printing module. By means of the high-fidelity hidden image figure screen frequency determination method and system based on direct correction, the multilayer high-definition and multi-gray level bottom image is hidden under the condition that the high fidelity of the surface image is guaranteed, the quality of the surface image can be effectively improved, the selection range can be widened, the bottom image is large in modulation amplitude, good in visual effect and high in resolution ratio, and the high-fidelity hidden image figure screen frequency determination method and system based on direct correction are suitable for various screen point modulation modes and a combination thereof.
Owner:臧戈平
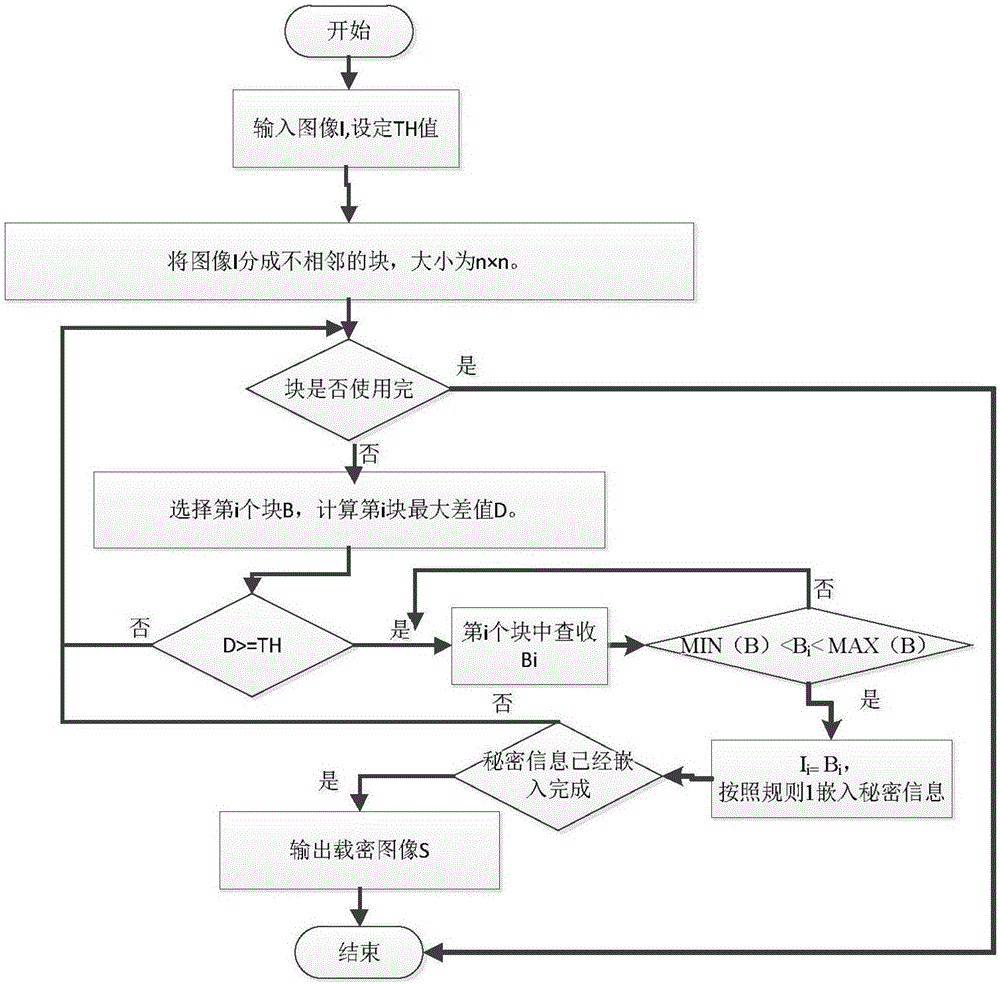
Reversible image hiding algorithm based on AMBTC algorithm
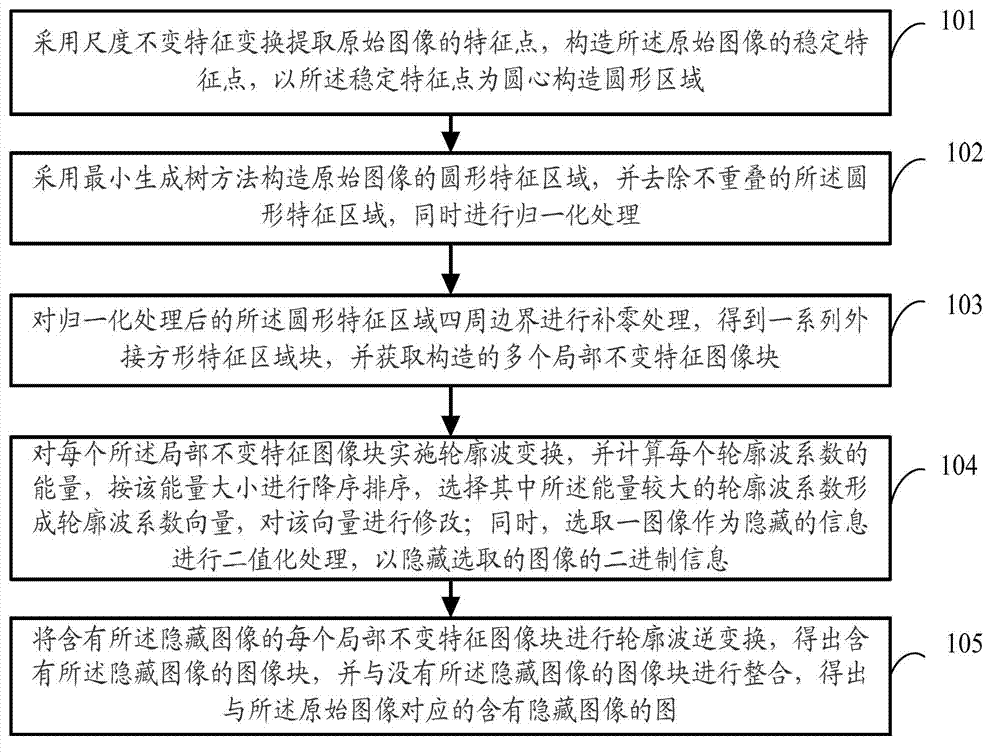
The invention discloses a reversible image hiding algorithm based on an AMBTC algorithm. The reversible image hiding algorithm comprises an RIHA algorithm. The RIHA algorithm comprises the following steps: (1), inputting a carrier image C; (2), entering the step (13) if all sub-blocks of the carrier image C are used, and otherwise, selecting a next k*k sub-block; (3), solving synthetic information Cv so as to obtain C'; (4-11), calculating W0,j and W1,j according to Pj of the jth sub-block; performing Cv embedding by selecting different steps according to values of W1,j and W0,j, entering the step 12 after all secrete information is embedded, and otherwise, entering the step 2; (12), reversely rotating in Ro*90 DEG, and outputting an image; and (13), ending. The RIHA algorithm provided by the invention has relatively high capacity and relatively low image distortion; the RIHA algorithm can avoid the effectiveness loss condition of the NRDH algorithm; the RIHA algorithm is more steady and reliable; and the output image quality is further improved.
Owner:XIHUA UNIV
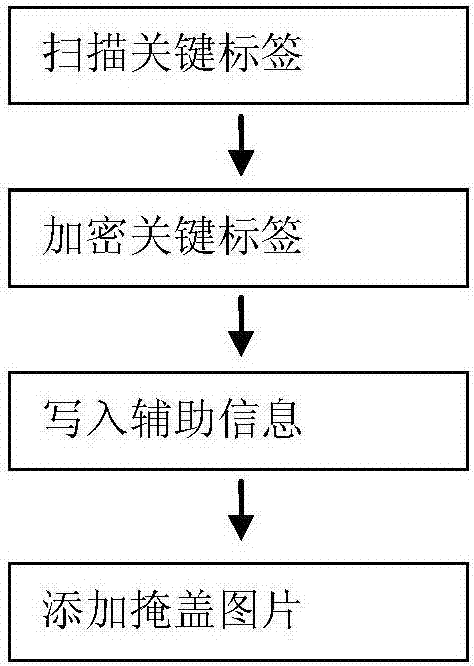
Picture hiding method for protecting personal privacy, restoration method and picture hiding system
ActiveCN107481181AEncryption avoidanceImprove processing efficiencyImage data processing detailsTransmissionPasswordRestoration method
A picture hiding method for protecting personal privacy comprises the steps of 1.1) determining a picture key tag parsing table; 1.2) scanning an original picture, and recording key tag storage bytes and corresponding positions to generate a list; 1.3) obtain a password character string according to an encrypted password or / and a randomly generated password, the password character string having a length the same as the number of key tags; 1.4) changing the key tag storage bytes in the list into password characters in the password character string; 1.5) sequentially taking out elements of the password character string and elements in the list to obtain a new string, and encrypting the new string to obtain an encrypted string; 1.6) writing in auxiliary information; and 1.17) after image start tag storage bytes covering up the picture is removed, splicing the remaining part to the tail part of arr_byte to complete the hiding of the original picture. Also provided are a picture restoration method for protecting personal privacy and a picture hiding system. According to the invention, the picture processing efficiency is high when massive pictures are processed.
Owner:ENJOYOR COMPANY LIMITED
Presswork expression enhancement method and system based on high-fidelity image-hiding
ActiveCN106204663AOptimized for clarityContrast OptimizationImage enhancementImage analysisImage hidingComputer vision
The invention provides a presswork expression enhancement method and system based on high-fidelity image-hiding, and relates to the technical field of presswork expression. The method comprises the following steps: determining a design parameter through the early design and before-printing analysis to the presswork, hiding multilayer high-definition base images associated with a surface image under a full-color high-quality surface image through the adoption of a high-fidelity image-hiding netting system; through the prediction and optimal compensation of the color overlapping, obtaining the presswork with high expression by a printing system, wherein each layer of clear base image can be gradually observed through the corresponding detection measurement. Through the adoption of the presswork expression enhancement method and system based on the high-fidelity image-hiding provided by the invention, the complete causal relationship between the surface image and the base image can be expressed, the expression of the presswork is effectively improved, and the selection range of each of the surface image and the base image is enlarged.
Owner:臧戈平
Anti-fake label and manufacture method thereof
InactiveCN101789202AStrong anti-counterfeiting functionNot easy to imitateStampsIdentification meansColor imageGrating
Owner:SICHUAN YIBIN WULIANGYE GROUP
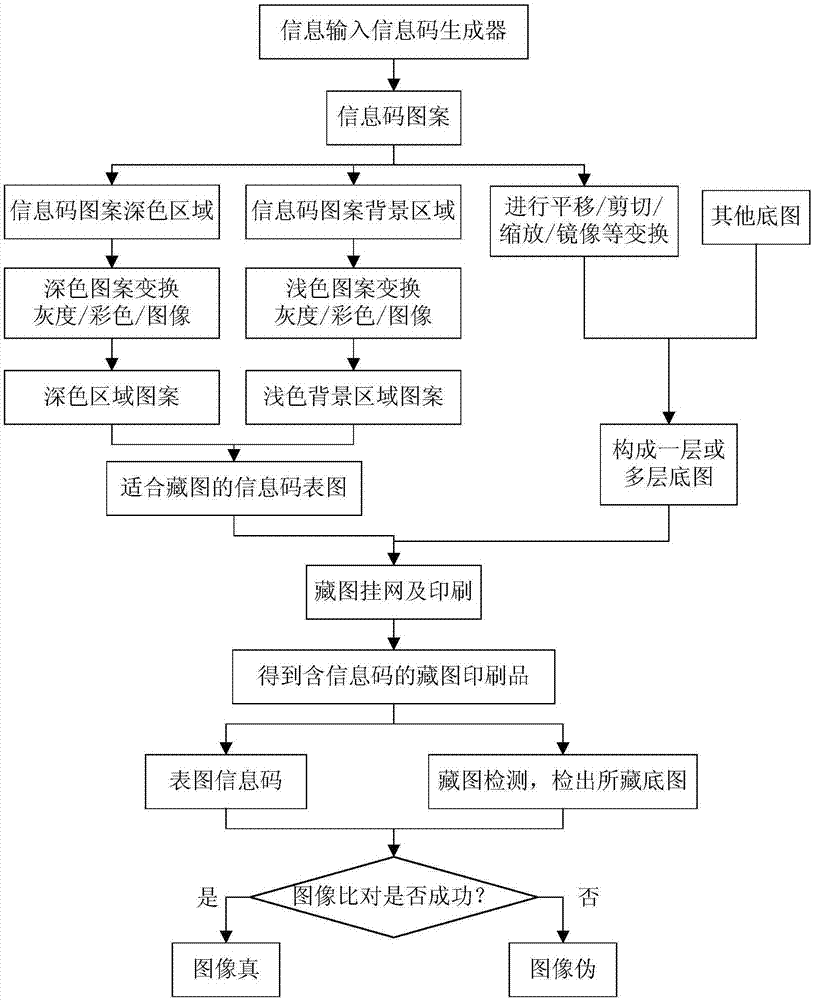
Anti-counterfeiting method for high-fidelity image hiding in information code area
ActiveCN107578079ADoes not affect normal readingDoes not affect detectabilityRecord carriers used with machinesImage hidingSystem optimization
The invention provides an anti-counterfeiting method for high-fidelity image hiding in an information code area, and relates to the technical field of anti-counterfeiting printing. The method comprises the steps that the local or whole information code area is adjusted as an image hiding area aiming at an surface image suitable for image hiding optimized by a specific printing system, so that theinformation code surface image containing the image hiding area is obtained; anti-counterfeiting image hiding screening and printing are conducted on a base image which needs to be hidden in the imagehiding area through the specific printing system; during color separation, screening and printing, at least one local or whole color separation is half-tone in the image hiding area. According to themethod, reading and detection of an information code through a code scanning machine or a mobile phone are not affected, and meanwhile, one or more base images can be hidden under the information code area; the information code of the surface image can be read by a conventional means, and the base images can be read and detected by an optical means or a scanning means or the mobile phone corresponding to image hiding, so that the purpose of counterfeiting resistance is achieved.
Owner:臧戈平
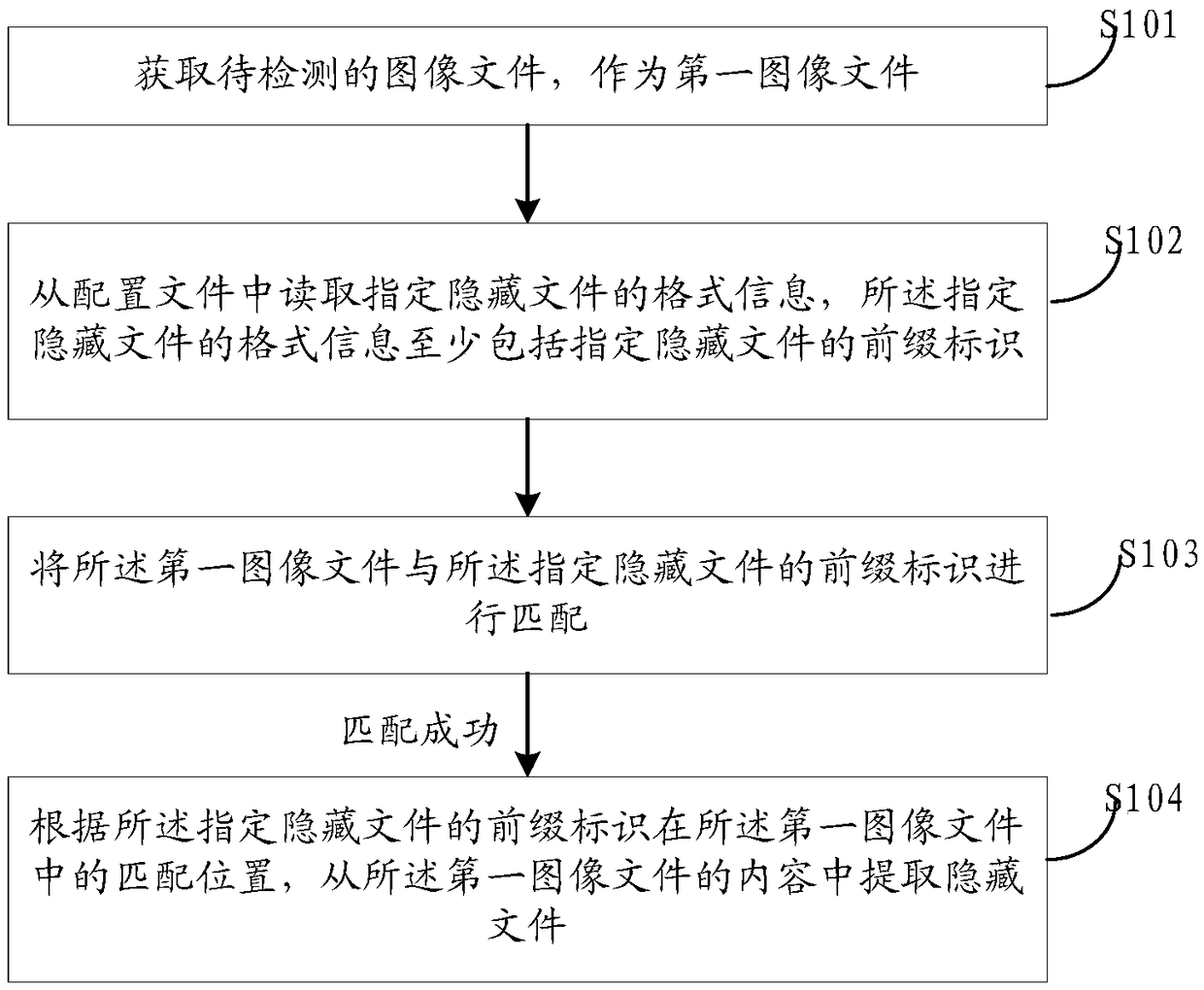
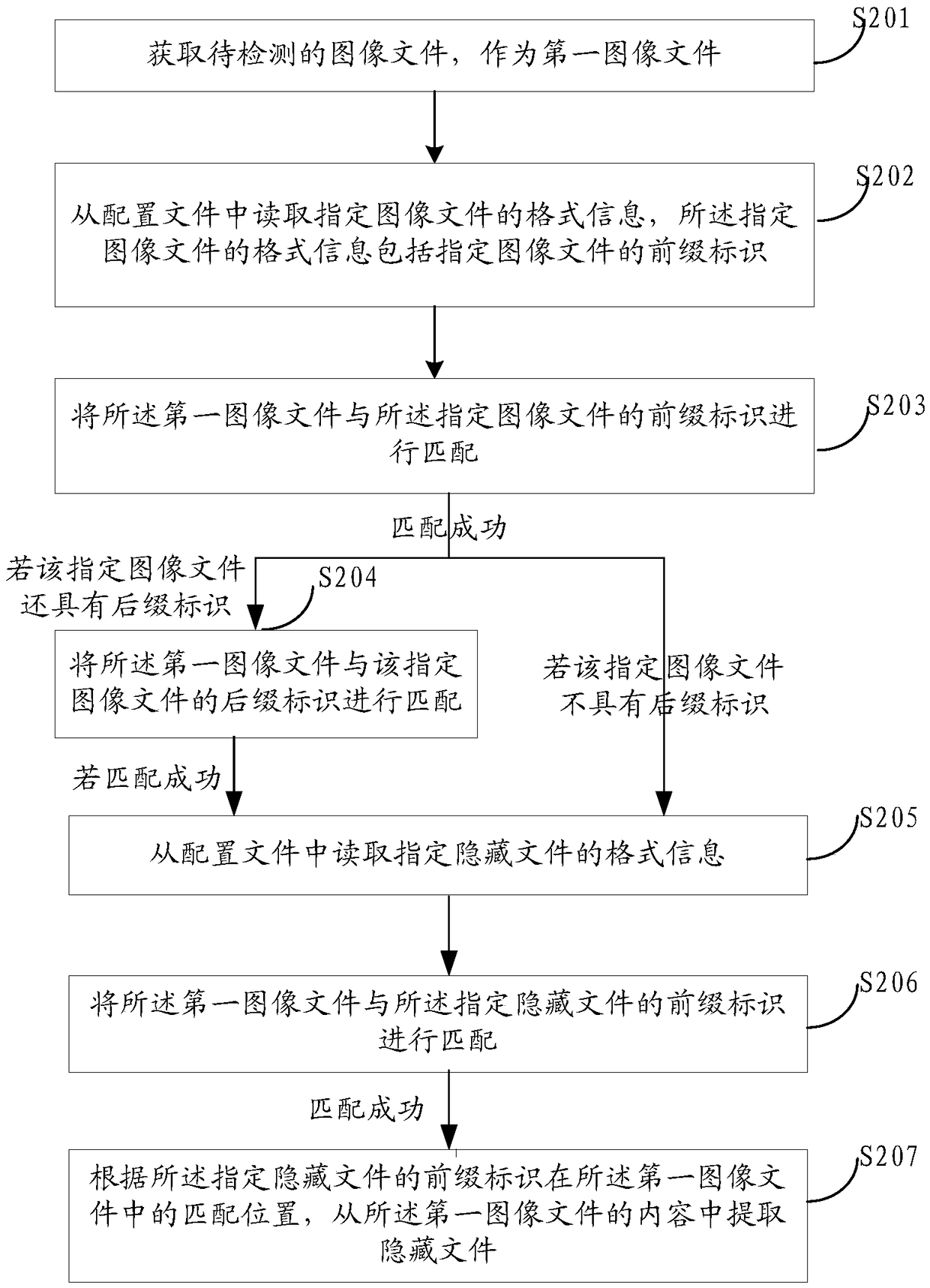
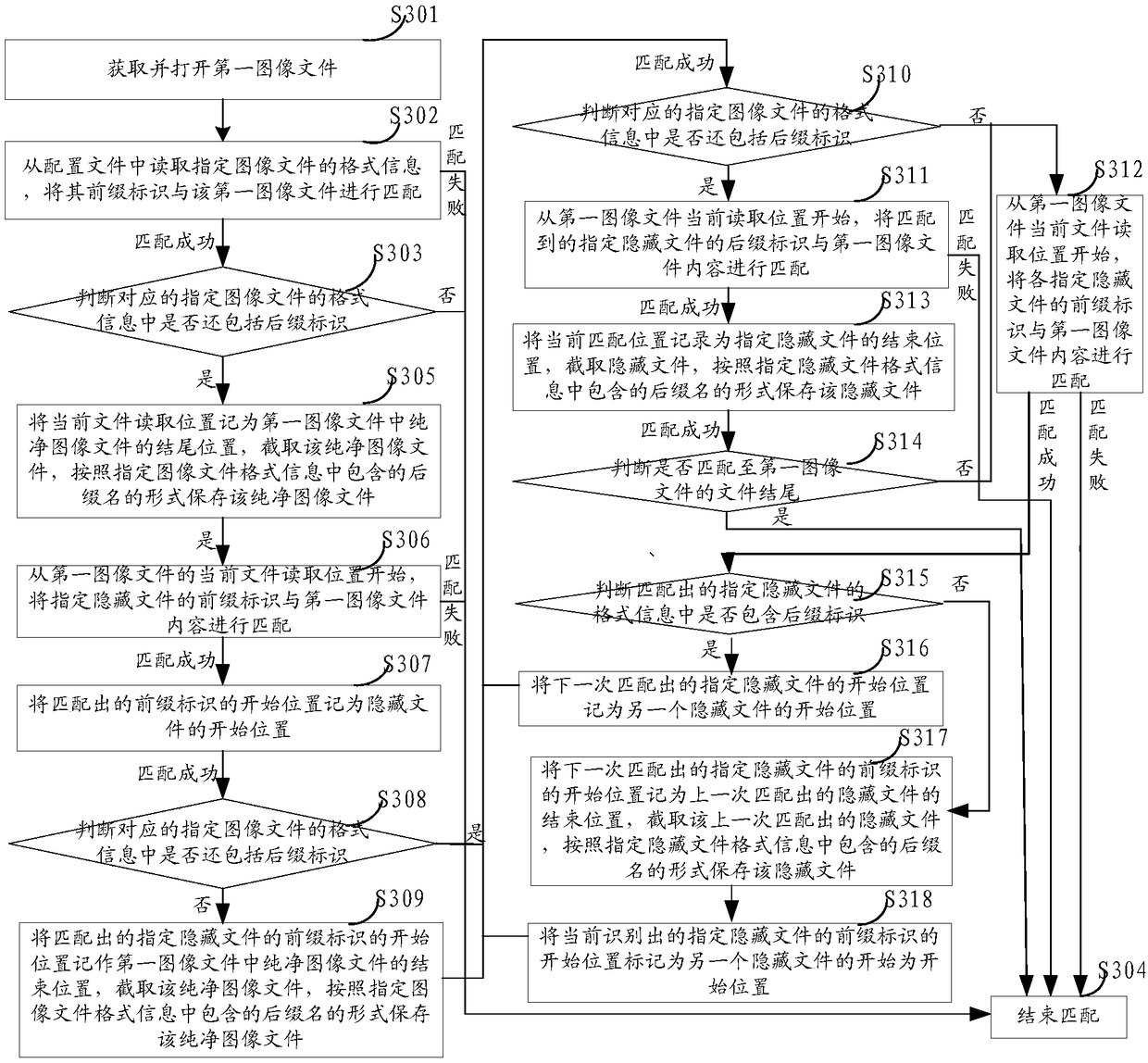
Method, device and apparatus for detecting image hiding information
ActiveCN109241780AImplement automatic detectionImprove detection efficiencyInternal/peripheral component protectionPlatform integrity maintainanceImage hidingComputer science
The invention provides a method for detecting image hiding information. The method comprises the following steps: acquiring an image file to be detected as a first image file; Reading format information of a specified hidden file from a configuration file, and matching the first image file with a prefix identification of the specified hidden file; If the matching is successful, extracting the hidden file from the contents of the first image file according to a matching position identified in the first image file by the prefix of the specified hidden file. Compared with the manual detection inthe prior art, the method can improve the detection precision and the detection efficiency, in addition, the method carries the format information of the specified hidden file required by the detection process with the configuration file, and in practical application, the configuration file can be updated in real time according to the actual detection requirements, and has high scalability. In addition, the present application also provides a corresponding device and apparatus.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Information hiding transmission method based on hybrid image processing
ActiveCN108521535ATo achieve the effect of safe transmissionControl hidden capacityPictoral communicationComputer hardwareImaging quality
The invention provides an information hiding transmission method based on hybrid image processing. An original image is pre-processed into an airspace-transform domain hybrid image; due to block optimization and hybrid processing, massive information hiding on optimized airspace data is directly carried out; therefore, the image hiding capacity and the hiding recovery image quality are improved; and the information hiding transmission method based on hybrid image processing has the characteristics of being high in performance, low in complexity and easy in software and hardware implementation,and has practical value in all kinds of image information hiding transmission systems.
Owner:XIAN INSTITUE OF SPACE RADIO TECH
Contourlet information hiding method based on images
ActiveCN103093464AGood visual imperceptibilitySuppression of Pseudo-Gibbs PhenomenonImage analysisImage hidingContourlet
The invention discloses a contourlet information hiding method based on images. The contourlet information hiding method is capable of resisting geometric attacking information such as image rotation, scale vibration, shearing, combination attack and warping, when only part images exist, the contourlet information hiding method can still ensure the specific hiding positions of information according to extracted or constructed characteristics so as to detect the hidden information in the images; the contourlet information hiding method can be applied to multi-media carrier copyright and other fields such as secret communication and electronic countermeasure; good visual imperceptibility of the information hiding method is achieved, tracks of information hiding can not be detected, and meanwhile balance of imperceptibility of information hiding and robustness is achieved; and a circular translation operation is adopted before contourlet transformation is conducted to partial invariant feature image blocks, and therefore the phenomenon of pseudo-Gibbs generated in the process of image hiding information can be restrained well.
Owner:SICHUAN JIUZHOU ELECTRIC GROUP
Picture hiding method and device
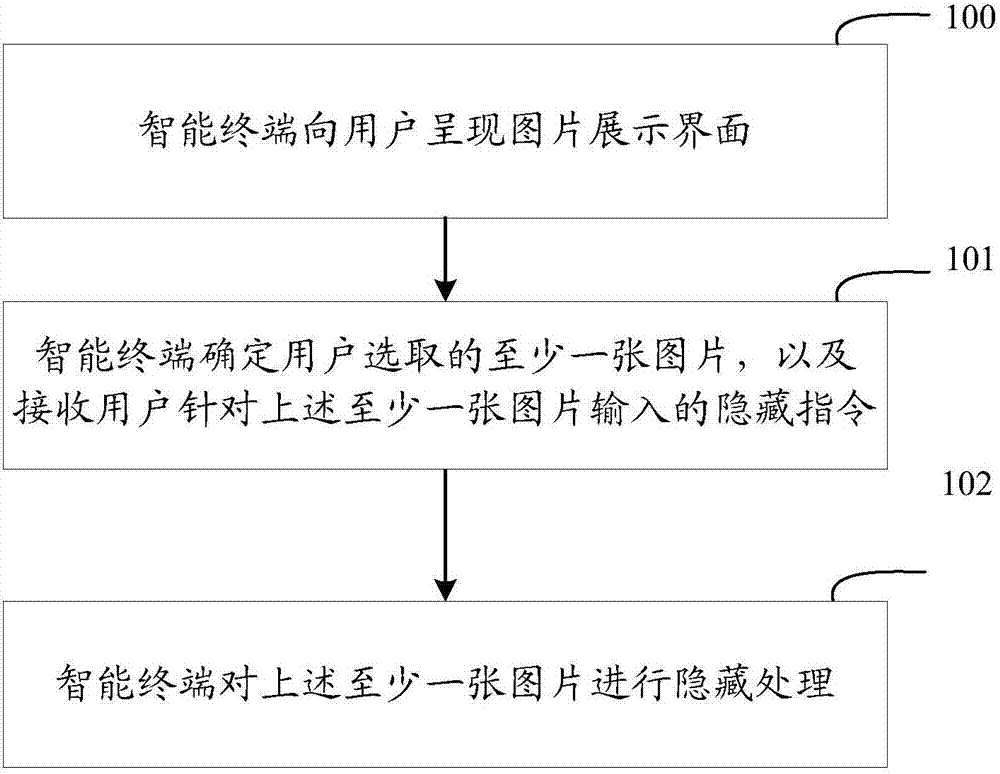
InactiveCN107992765AImprove performance qualityImprove service qualityDigital data protectionInput/output processes for data processingInternet privacyUser input
The invention relates to an intelligent terminal technology, in particular to a picture hiding method and device. The method and device are used for preventing user privacy disclosure. The method comprises the steps that after an intelligent terminal displays a picture presentation interface to a user, if it is determined that the user inputs a hiding instruction for at least one picture in the picture display interface, the pictures are hidden. In this way, pictures related to user privacy can be hidden in a targeted mode, user privacy disclosure is effectively prevented, the information security is protected, the service performance and service quality of the intelligent terminal are improved, and the user experience is effectively improved.
Owner:GREE ELECTRIC APPLIANCES INC
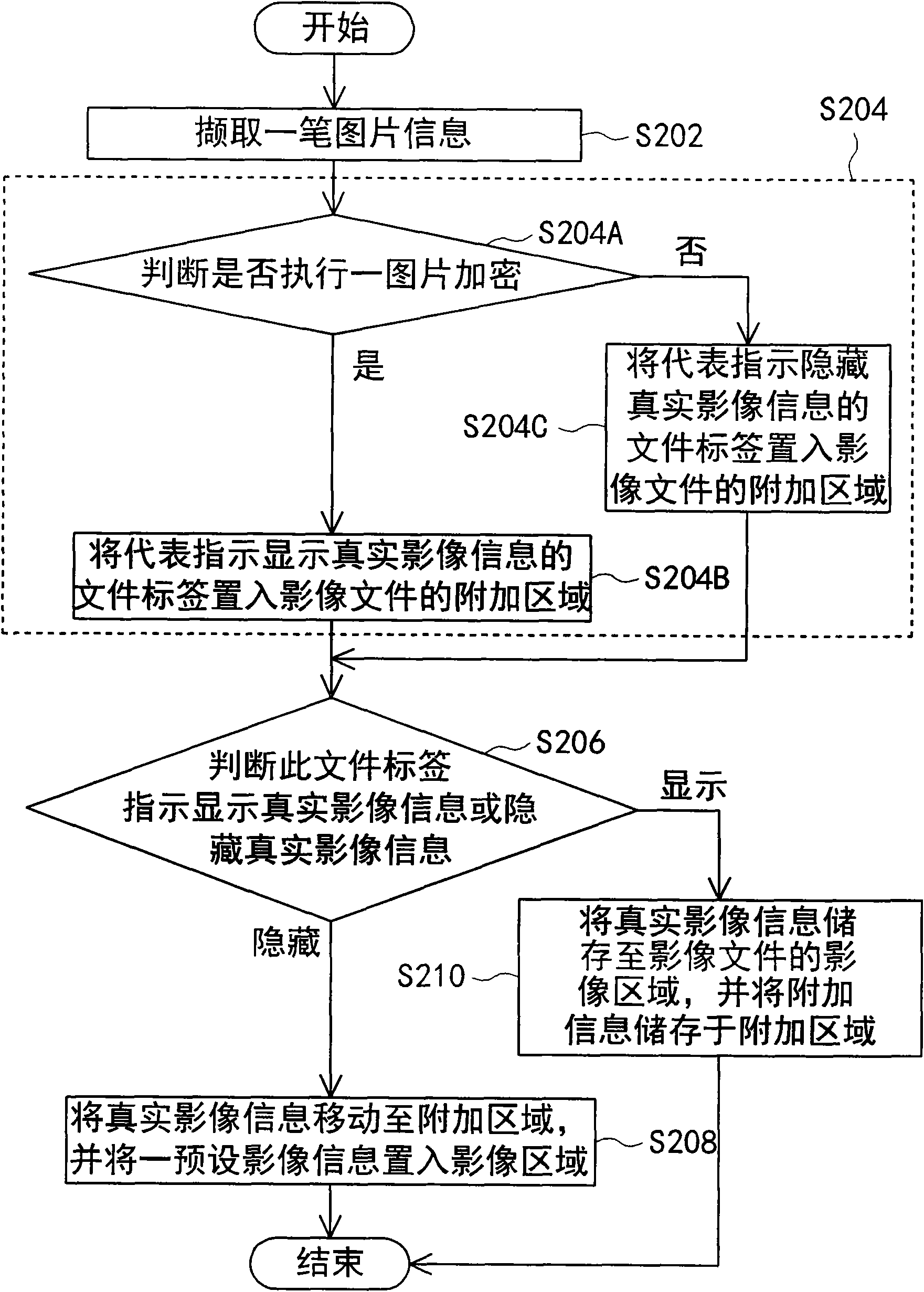
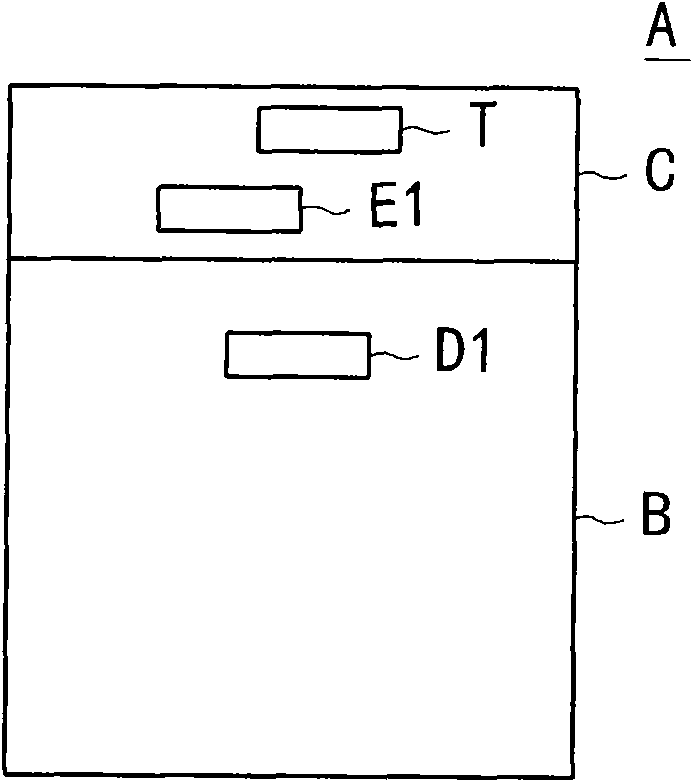
Image acquisition device and image hiding method thereof
InactiveCN102065201APrivacy protectionImprove data securityTelevision system detailsColor television detailsImage hidingComputer science
The invention discloses an image acquisition device and an image hiding method thereof. The image hiding method comprises the following steps of: firstly, acquiring picture information which comprises real image information and additional information; secondly, placing a file tag into an additional region of an image file; thirdly, if the file tag instructs displaying the real image information, storing the real image information in an image region of the image file and storing the additional information in the additional region of the image file; and lastly, if the file tag instructs hiding the real image information, moving the real image information to the additional region and placing preset image information into the image region.
Owner:INVENTEC CORP
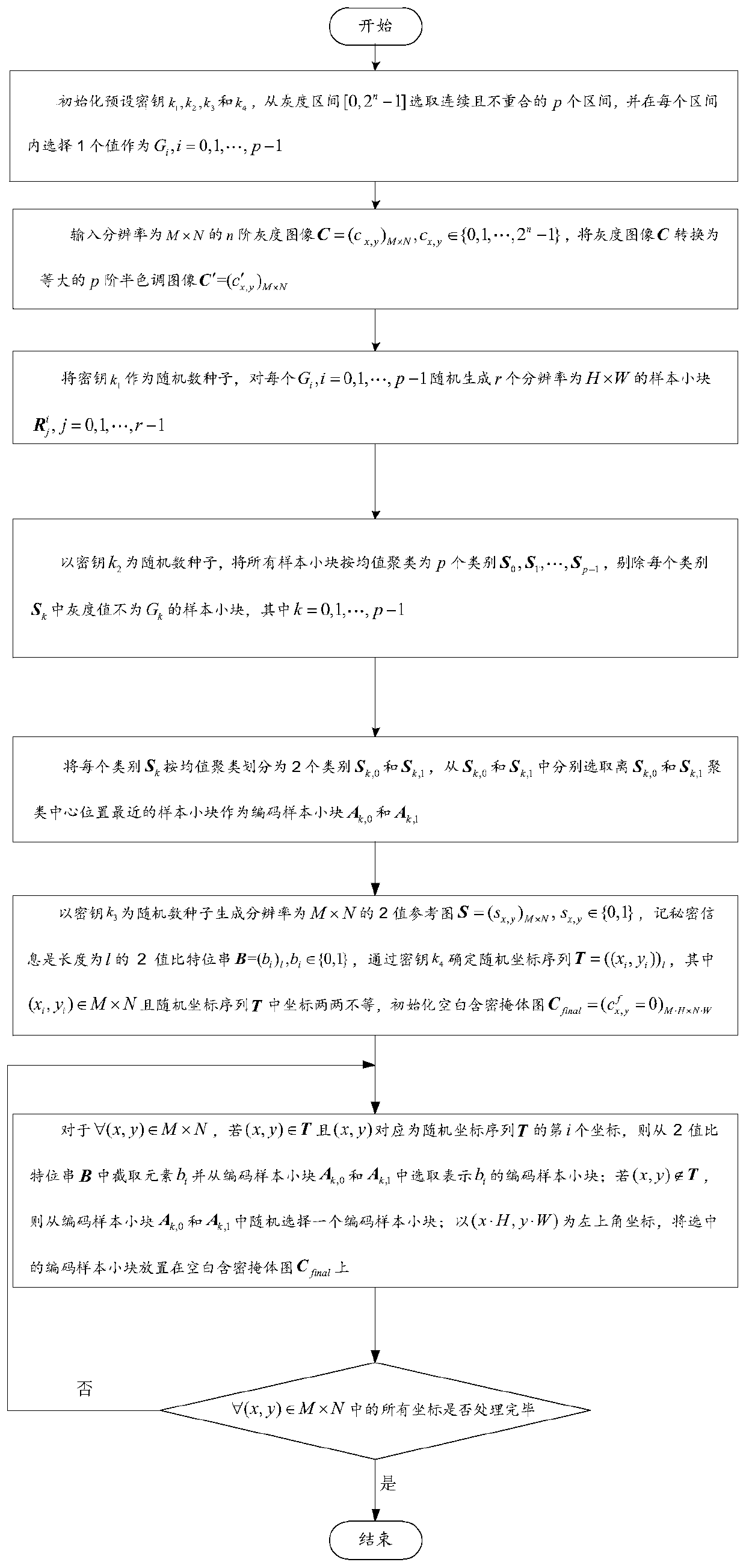
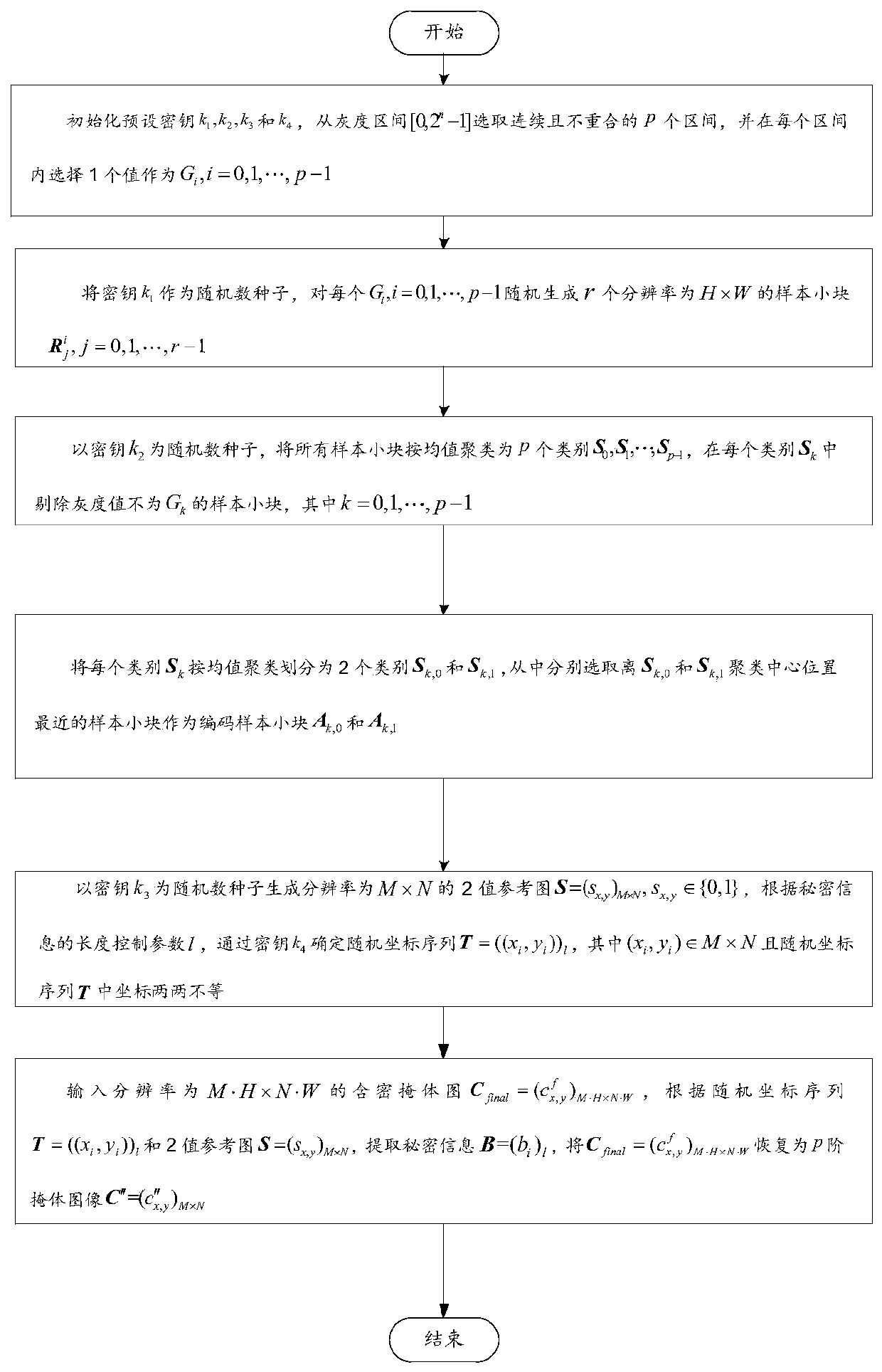
Image hiding and recovering method and device and storage medium
ActiveCN110430336ASolve hidden common problemsImprove visual qualityImage enhancementCharacter and pattern recognitionPattern recognitionReference image
The invention belongs to the crossing field of image information security and digital image signal processing and discloses an image hiding and recovering method and device and a storage medium, and the method comprises the steps: taking generated black and white noisy point small blocks with different gray scales as candidate sample small blocks, filtering similar sample small blocks with different gray scales through secondary clustering coding, and screening coding sample small blocks with the same gray scale for secret information coding representation; and finally, placing coded sample small blocks with different gray scales through a random binary reference image in combination with a random secret embedding position to generate a secret-containing shelter. During recovery, coded sample small blocks are generated by the secret key, and secret information is extracted by combining the binary reference image and the secret embedding position. Compared with the prior art, the invention has the advantages that the meaningful image with good visual quality can be generated, no splicing trace is generated, no modification embedding is involved, and the invention has good anti-attack capability; no matter how secret information is embedded, the secret-containing shelter can be recovered into a multi-order halftone shelter image in an equal-quality and lossless mode, the embedding and extracting process completely depends on a user secret key, and high safety is achieved.
Owner:SHAANXI NORMAL UNIV
Reversible data hiding method for high dynamic range image
ActiveCN104021518AIncrease hidden capacityImprove visual effectsImage data processing detailsPattern recognitionImaging quality
The invention discloses a reversible data hiding method for a high dynamic range image. The reversible data hiding method comprises a data embedding process and a data extracting process, wherein the data extracting process is inverse operation of the data embedding process, and the data embedding process comprises the following steps of converting a rgb image into an RGBE image, and dividing to-be-embedded data into three parts in sequence for embedding the three parts into rgb three channels corresponding to the RGBE image; dividing all pixels of a certain embedding channel of the rgb three channels into two types: S1 and S2, dividing the corresponding embedded data into two types corresponding to S1 and S2, wherein in an embedding process, one type of data is embedded to S1, and then the same process is repeated for embedding the other type of data to S2. The reversible data hiding method disclosed by the invention achieves a purpose of embedding more data by sacrificing least image quality. Compared with the existing reversible HDR (high dynamic range) image hiding algorithm, the hiding algorithm disclosed by the invention improves hiding capacity simultaneously when guaranteeing reversible hiding, and guarantees a better visual effect.
Owner:SHANDONG UNIV
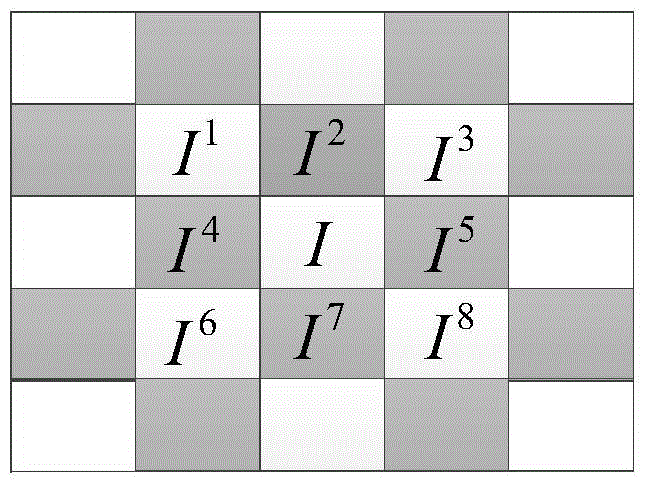
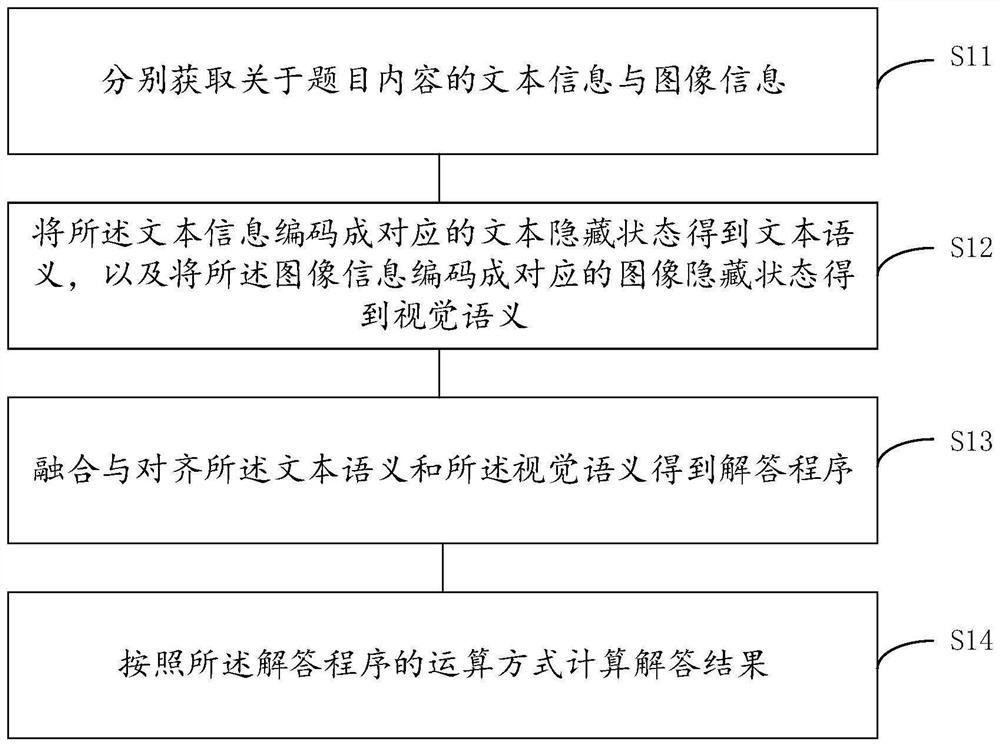
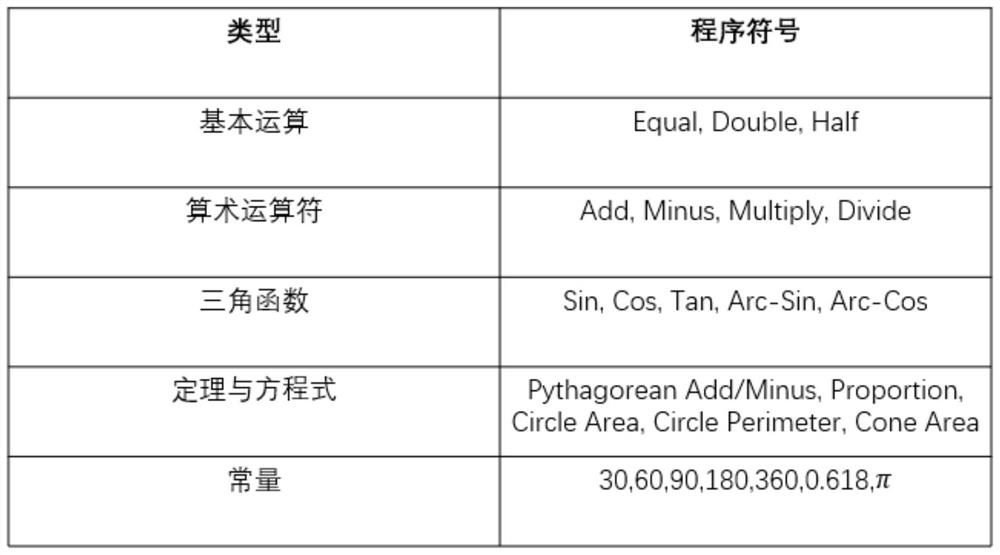
Geometric question answering method and model based on deep learning and multi-modal numerical reasoning
PendingCN113672716AImprove accuracyPracticalSemantic analysisNeural architecturesPattern recognitionBi modal
The invention discloses a deep learning and multi-modal numerical reasoning-based geometric question answering method and a text and image bimodal combined neural network model. The method comprises the following steps: respectively acquiring text information and image information about question contents; encoding the text information into a corresponding text hiding state to obtain text semantics, and encoding the image information into a corresponding image hiding state to obtain visual semantics; fusing and aligning the text semantics and the visual semantics to obtain an answering program; and calculating an answering result according to the operation mode of the answering program. According to the method, the answering accuracy can be increased, the processing efficiency can be improved, and the technology which has good accuracy and high practicability and can autonomously generate the code sequence of the answer through deep learning is achieved.
Owner:SUN YAT SEN UNIV SHENZHEN +1
A Method of Image Hiding and Authentication Based on Secret Sharing
ActiveCN103761702BImprove securityDifferences in Statistical PropertiesImage data processing detailsHash functionInformation recovery
The invention discloses an image hiding and authentication method based on secret sharing, and belongs to the technical field of secret image sharing. The image hiding and authentication method is characterized by comprising the steps that firstly, difference Huffman encoding is conducted on a secret image, every three generated bit sequences are set to be one group to be converted into decimal numbers which are used as coefficients of a sharing polynomial in the Shamir (k, n) threshold scheme, the k and the n are positive integers, the k is smaller than or equal to the n, and n shadow images are generated; secondly, n significant carrier images are selected, the generated shadow images are embedded into the carrier images in a matrix encoding mode, authentication bits generated by the hash function are also embedded into the carrier images, and n disguise images are formed and are in the charge of n different participants respectively. The disguise images generated through the image hiding and authentication method has higher visual quality, existence of secret information cannot be perceived by attackers easily, and the safety of the secret information is ensured. Meanwhile, before the secret information is recovered, the disguise images provided by each participant need to be authenticated, only the disguise images passing through authentication can participate in recovery of the secret information, and the safety of the secret information is further strengthened.
Owner:TAIYUAN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Image processing method and mobile terminal
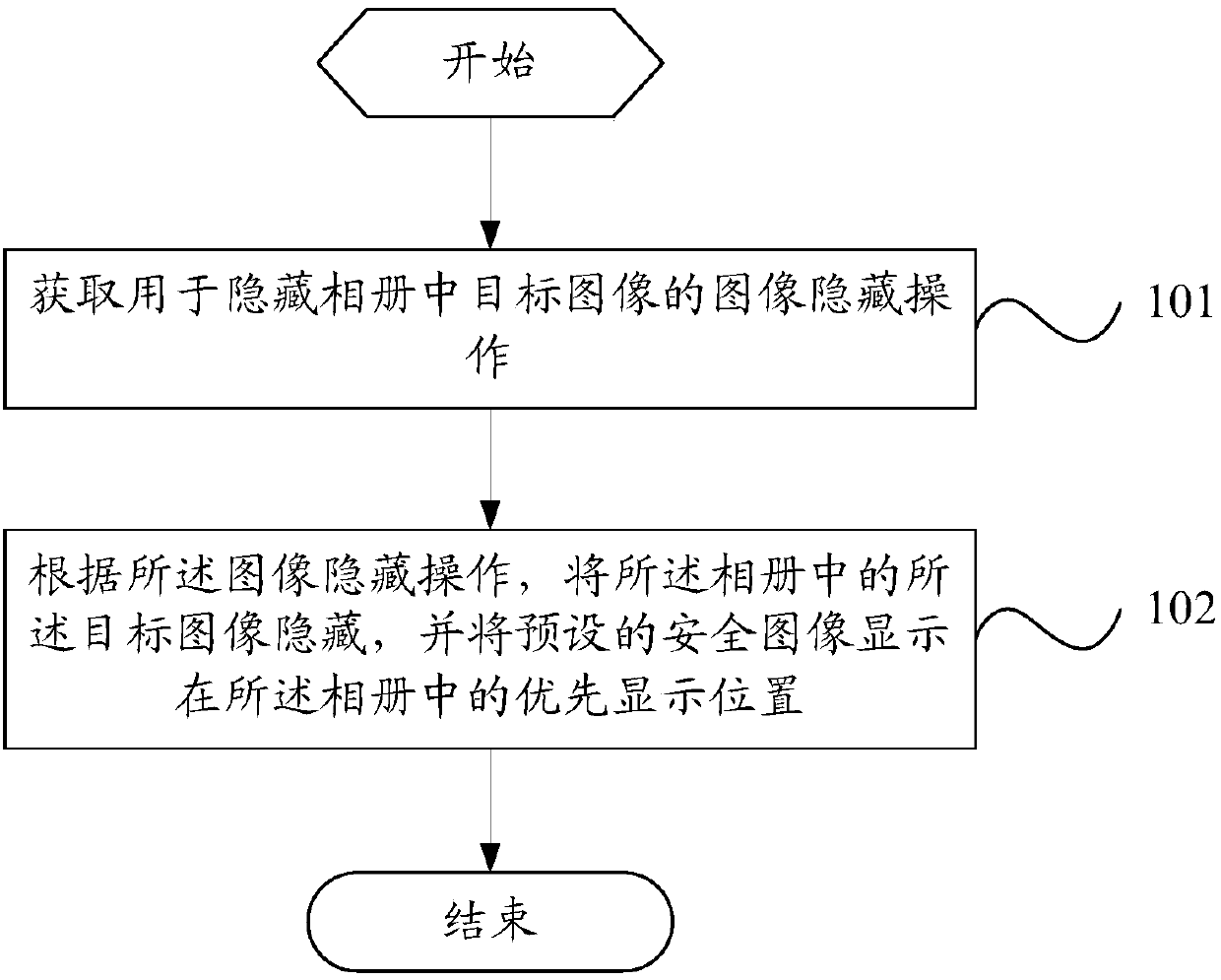
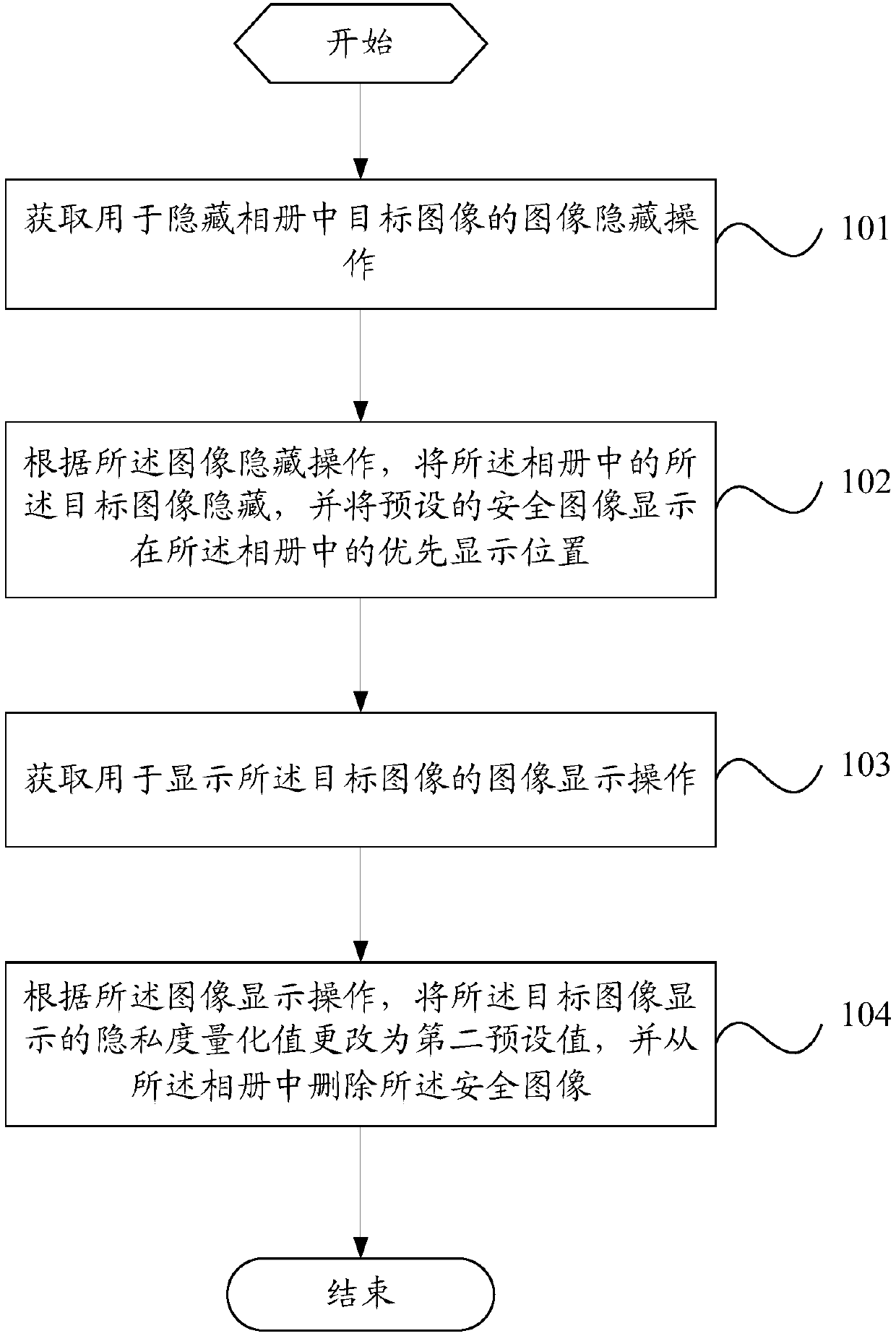
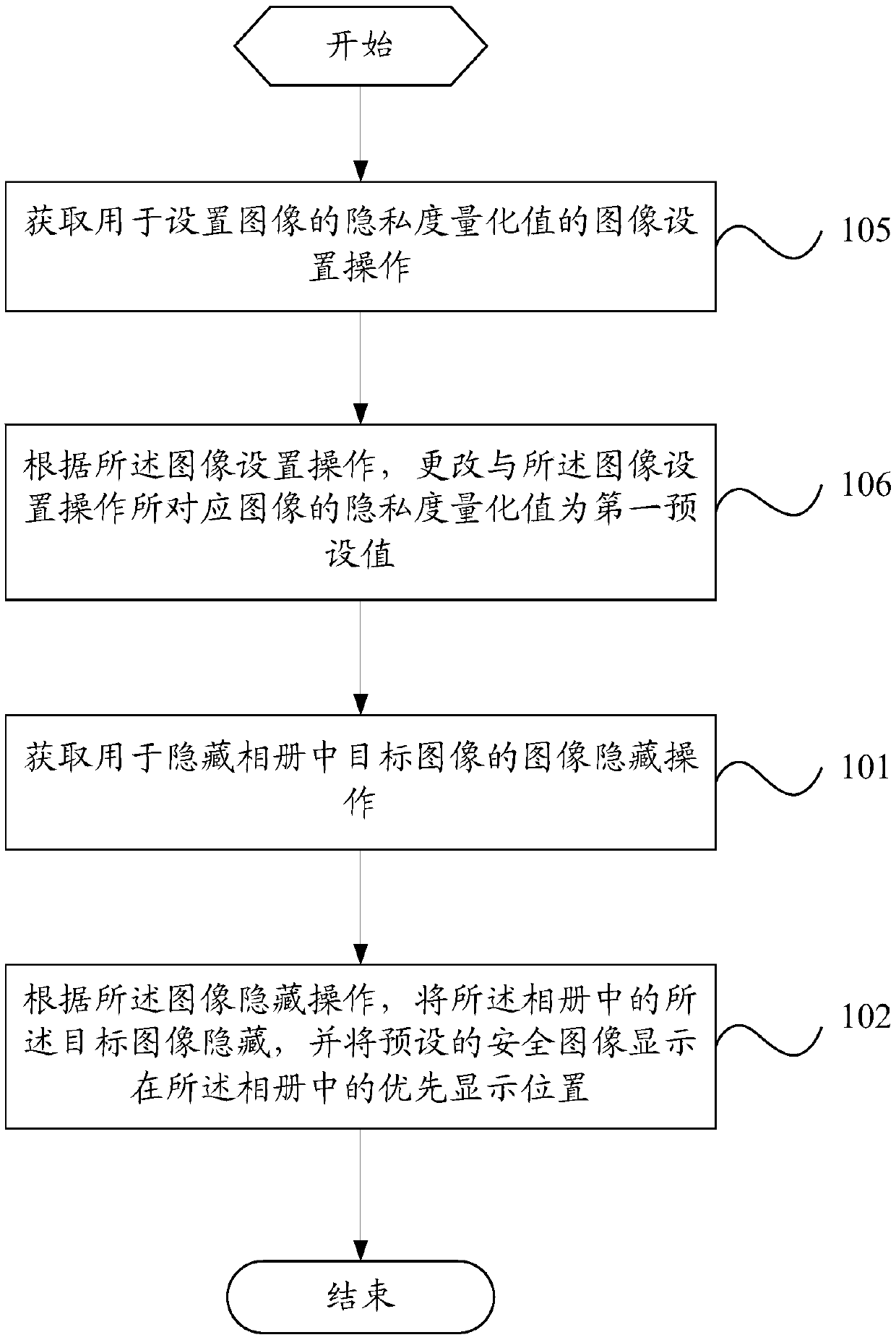
ActiveCN107911563AGuarantee privacy and securityHave hidden needsTelevision system detailsColor television detailsImaging processingPrivacy protection
The invention provides an image processing method and a mobile terminal, related to the technical field of communication. The image processing method comprises the following steps: obtaining an imagehiding operation used to hide a target image in an album; and hiding the target image in the album according to the image hiding operation, and displaying a preset secure image in the preferred display position in the album. The image processing method is used to solve the problem that the image encryption has a hidden security danger because the whole encryption of the image privacy protection inthe prior art makes other people know that the encrypted images exist in the mobile terminal.
Owner:VIVO MOBILE COMM CO LTD
Method and device for realizing image hiding
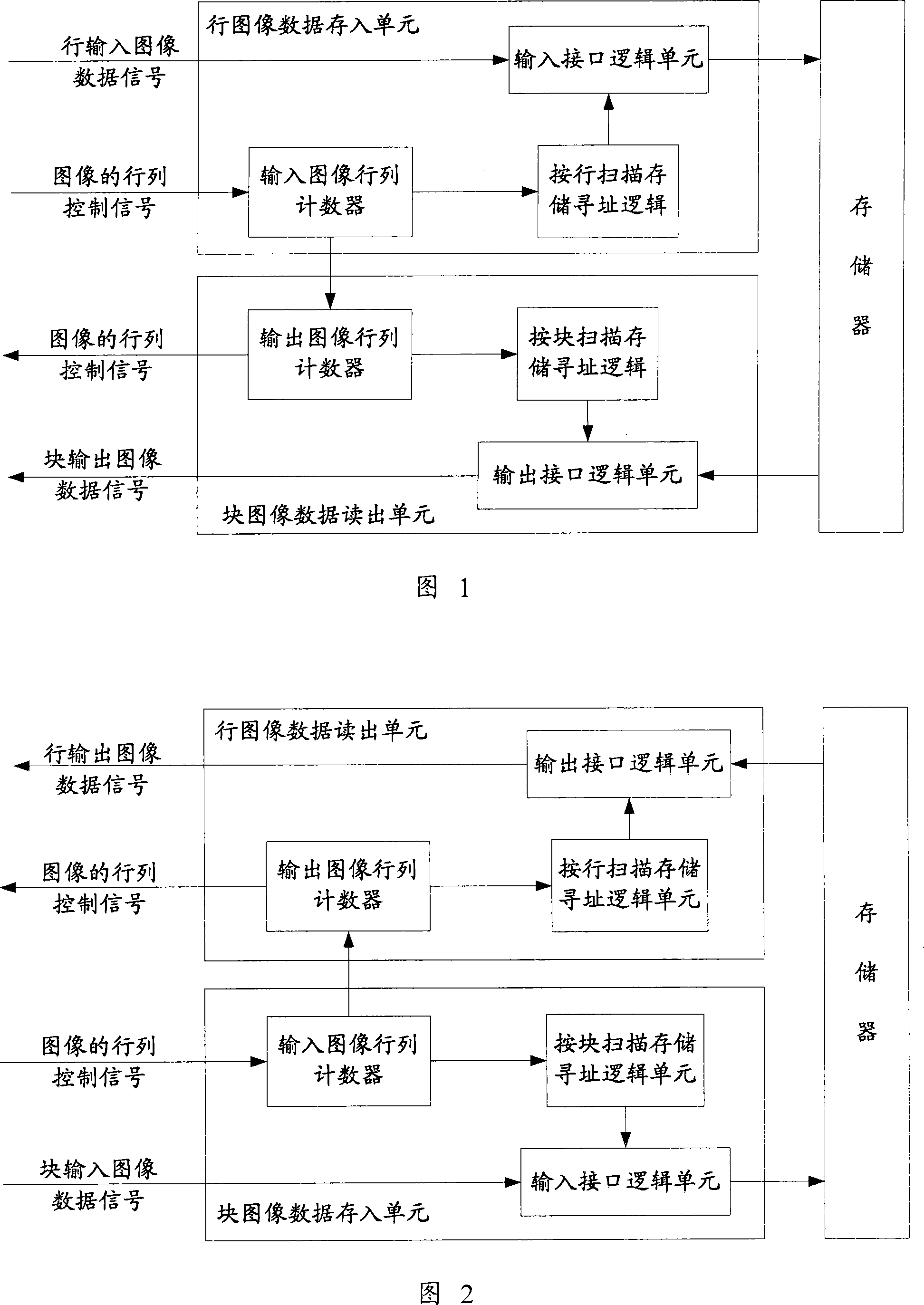
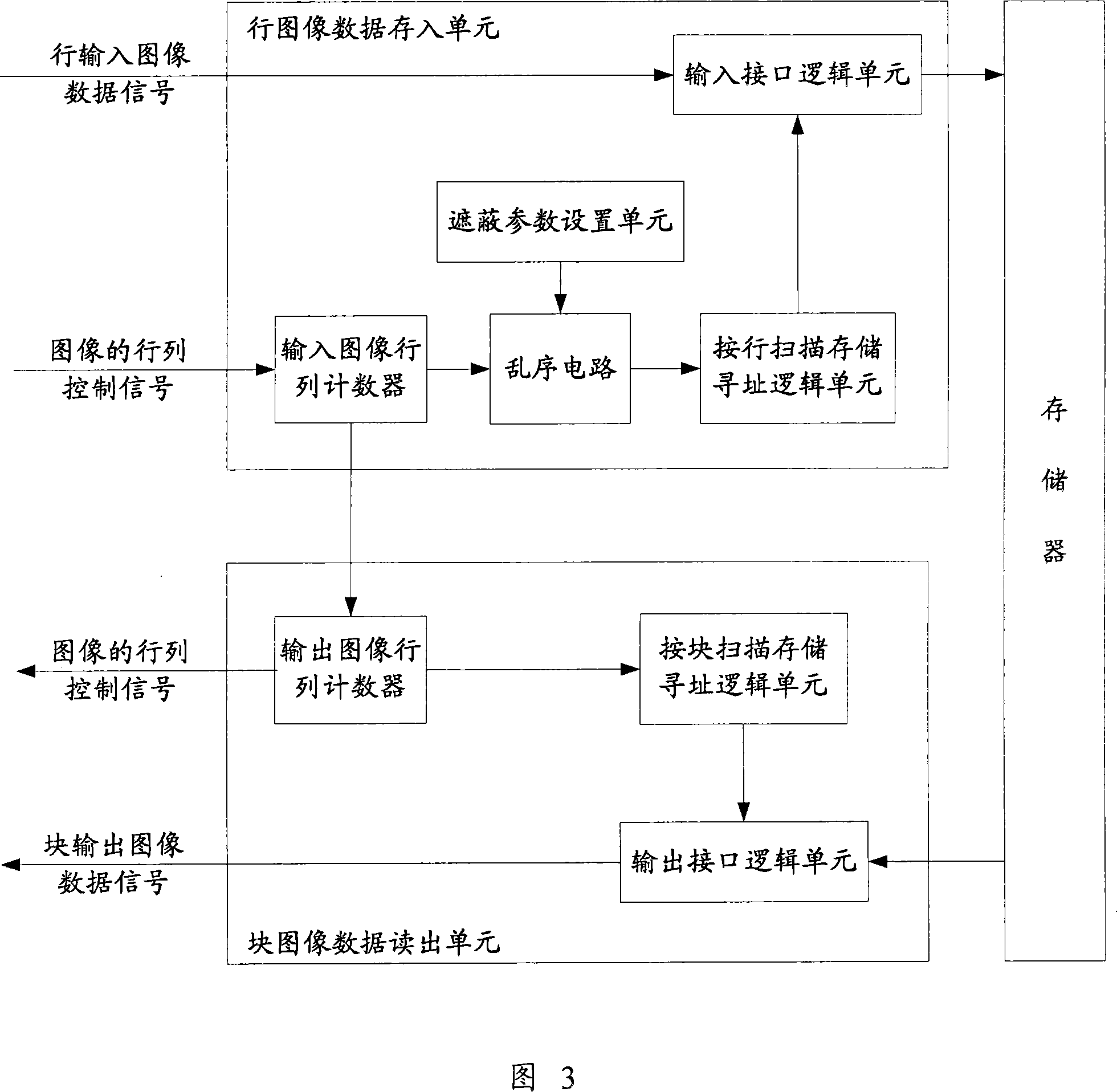
InactiveCN101022549AImplement image maskingImage masking is simplePulse modulation television signal transmissionDigital video signal modificationControl signalData signal
A method for covering image includes setting parameter of covering area, confirming image data of covering area to cover image data at covering area according to column / line control signal of image and set parameter of covering area in conversion process between line image data signal and block image data signal at image compression / decompression course. The device used for realizing said method is also disclosed.
Owner:VIMICRO CORP
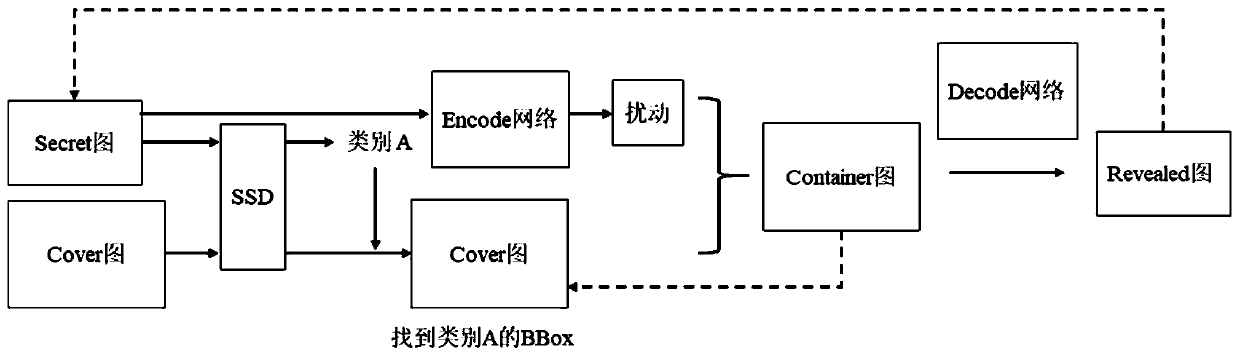
Depth adaptive image hiding method based on adversarial sample generation
ActiveCN110889797AQuantity excellentExcellent qualityImage data processing detailsNeural architecturesPattern recognitionCovering graph
The invention relates to a depth adaptive image hiding method based on adversarial sample generation, which comprises the following steps: firstly, designing an experimental sample, and determining asecret graph and a cover graph for receiving hidden information; secondly, establishing an SSD network selected by a local hidden patch, and finding out an area most suitable for hiding the secret graph in the cover graph; then, establishing an encode network, generating disturbance through the encode network by using an adversarial sample method for the secret graph, and directly adding the disturbance to a selected area of the cover graph to generate a container graph with hidden information; then, establishing a code network, and solving a real graph which is highly similar to the set graph; and finally, training and testing an encode network and a code network, and updating a coding network for each group of inputs to realize personalized hiding of each group of images. Through the above three main steps, the method can achieve the adaptive local hiding of the image while maintaining the good hiding and restoring effect of coding, improves the reconstruction quality of image hiding, and enlarges the actual application range of image hiding.
Owner:ZHEJIANG UNIV
Multi-backup image hiding and restoring method based on weight
The invention discloses a multi-backup image hiding and recovering method based on weight. The method is characterized by comprising the following steps that 1) image information is hidden, and 2) hidden images are restored, wherein in the first step that the image information is hidden, (1) the image information is hidden according to the multiple backup information, (2) the hidden number is determined according to the weight, and (3) hiding is carried out according to the weight. According to the method, high orders of the pixels of the hidden images restored through the method are more, andthe restored hidden images has a relatively high peak signal-to-noise ratio.
Owner:苏州京日科技有限公司
Adaptive image information hiding method based on critical value
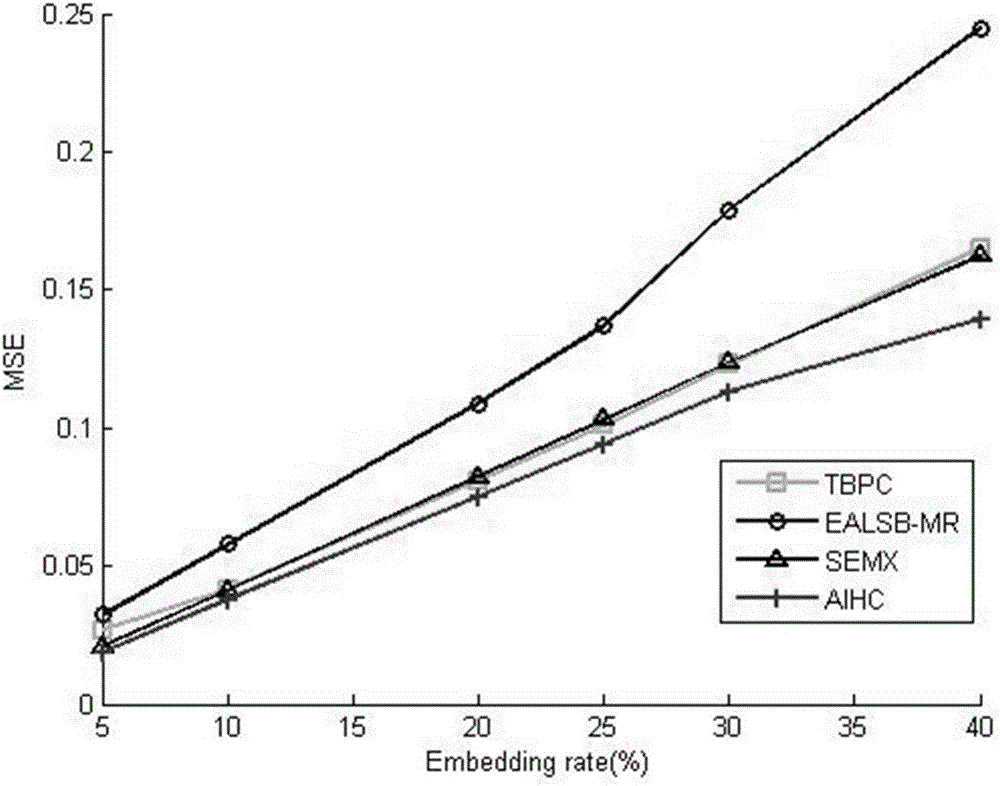
InactiveCN106530204AAvoid missingImprove securityImage data processing detailsAlgorithmImaging quality
The invention provides an adaptive image information hiding method based on a critical value. By combining a critical value of a subblock and an adaptive judgment critical block, an AIHC information hiding algorithm is provided. Through the AIHC algorithm, the capacity of image hiding is improved and through adaptively embedded secret information, safety is improved. The algorithm can be finished under the polynomial time complexity, thereby achieving simplicity. The secret information is extracted in the AIHC algorithm without additional information. Under the circumference that the image quality is kept, capacity is increased. The performance of the provided AIHC algorithm is better than that of other similar algorithms.
Owner:XIHUA UNIV
Multi-image optical hiding system based on visual password
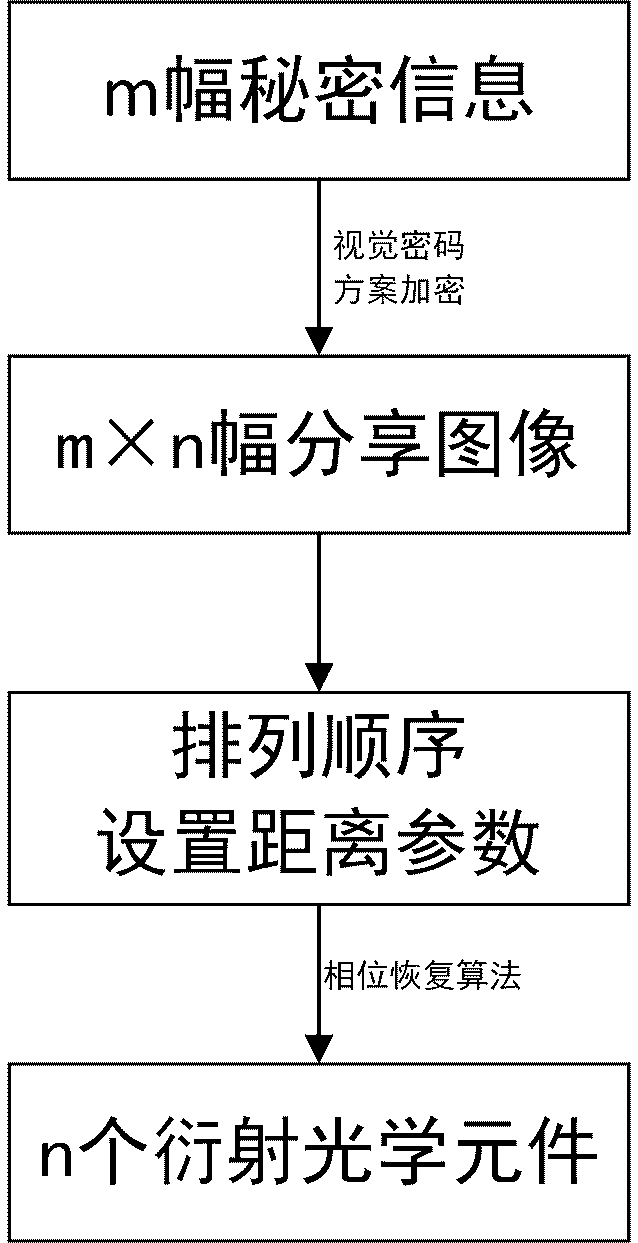
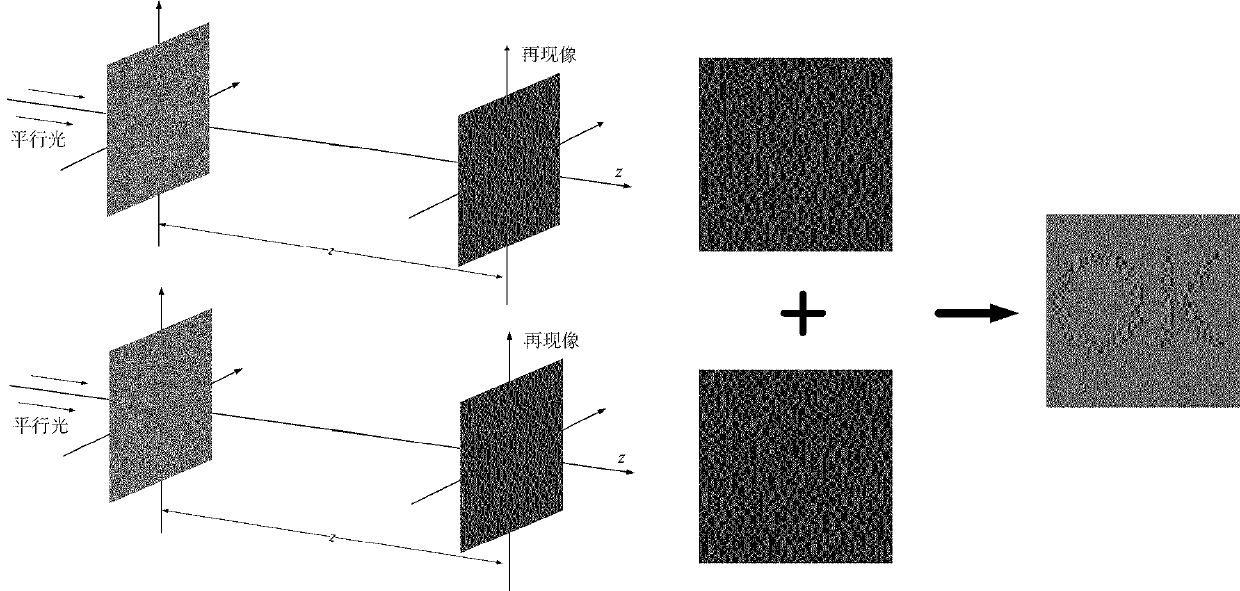
InactiveCN111385435ALarge information capacityImprove concealmentPictoral communicationMulti-imageImage hiding
The invention discloses a multi-image hiding system based on a visual password. The multi-image hiding system encrypts a plurality of images based on a visual password scheme to obtain a plurality ofshared images, thereafter, a diffractive optical element is designed by using a phase retrieval algorithm, so that after the obtained diffractive optical element is irradiated by laser, different shared images are reproduced at different positions in a rear space, the corresponding shared images are aligned and superposed, and secret information can be decrypted, therefore, the method belongs to non-coherent superposition, is simple and convenient to operate and can effectively suppress noise. According to the multi-image hiding system, the diffractive optical element is used for hiding the plurality of shared images obtained after encryption through adopting the visual password scheme, the controllability of the diffractive optical element on a three-dimensional light field is effectivelyutilized, and the hiding of a plurality of pieces of encrypted information is realized.
Owner:UNIVERSITY OF CHINESE ACADEMY OF SCIENCES
Novel image hiding method based on chaotic differential
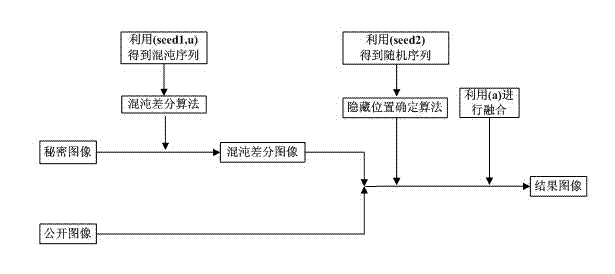
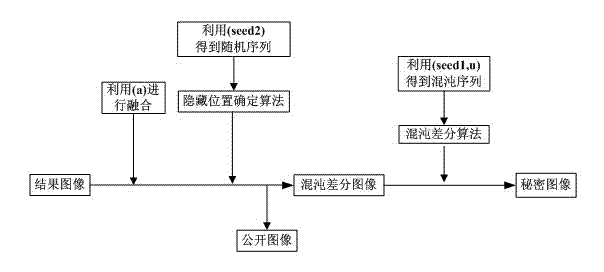
InactiveCN104504646AReduce distortionWide selection of sizesImage data processing detailsImage hidingComputer vision
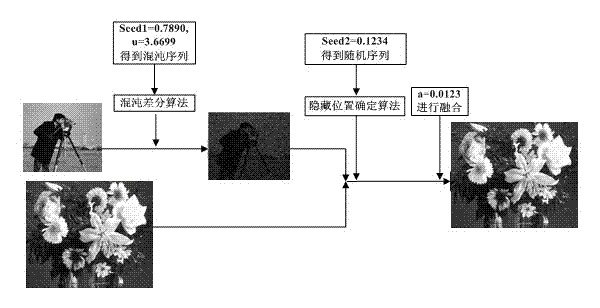
The invention discloses a novel image hiding method based on chaotic differential. The method mainly includes a hiding process of a transmitting end and a recovery process of a receiving end. At the transmitting end, firstly, a chaotic matrix with the size as same as that of a secret image is generated by the aid of secret keys seed1 and u, differential operation is performed for the chaotic matrix and the secret image to obtain a chaotic differential image, secondly, the position of each pixel in the secret image to be hidden in a public image is determined according to a random sequence obtained by a secret key seed2, and finally, the chaotic differential image is hidden in the public image through a common fusion technique. At the receiving end, the recovery process of the secret image is an inverse process of hiding the secret image at the transmitting end. The method is small in calculated amount and wider in applicable range, and is more reliable and uniform by the aid of chaotic encryption. The secret image before hiding is subjected to differential processing, the recovered secret image is lower in distortion, and the size of the public image does not need to be as same as that of the secret image.
Owner:CHONGQING COLLEGE OF ELECTRONICS ENG +1
Picture hiding method and device, picture restoring method and device, and terminal device
The invention is applicable to the technical field of information security, and provides a picture hiding method, a picture restoring method, a picture restoring device and a terminal device. The invention comprises the following steps: dividing pixel points of a read privacy picture into blocks with designated size; DCT blocks of a specified size; extracting a preset amount of data to be hidden from all blocks with designated size after DCT transformation to obtain data columns of all data to be hidden; calculating the size of the data column; calculating a hidden capacity of the read auxiliary picture according to a preset hidden policy; comparing the size of the data column with the hiding capacity of the auxiliary picture to determine whether the hiding capacity of the auxiliary picture meets the hiding requirement; if so, a bar code is generated according to the width and height of the auxiliary picture; replacing the data to be hidden in the data column with the pixel values of the same number in the auxiliary picture to obtain a first hidden picture; a bar code being superimposed on the first hidden picture to obtain a second hidden picture. The method can effectively realize picture hiding.
Owner:深圳市TCL高新技术开发有限公司
Multi-image hiding method based on secret sharing
The invention discloses a multi-image hiding method based on secret sharing, and belongs to the field of information security. The invention provides a multi-image hiding method based on secret sharing in order to protect the safety of hidden image content, improve the algorithm robustness and expand the hiding capacity. The method comprises the following steps of: firstly, partitioning k carrierimages, scrambling image blocks by using two-dimensional Zig transform, and respectively mapping the scrambled image blocks from a spatial domain to a discrete cosine transform (DCT) domain; secondly,embedding the hidden image bits into k carrier images by using an additive spread spectrum algorithm or a multiplicative spread spectrum algorithm; and finally, mapping the disguised DCT coefficientsback to a spatial domain, performing scrambling recovery on the image blocks by using two-dimensional zigzag inverse transformation, and splicing the image blocks according to an original sequence toobtain k disguised images. Experiments show that the algorithm is efficient, good in embedding effect, large in hiding capacity, high in robustness and high in safety.
Owner:CHINA UNIV OF MINING & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com