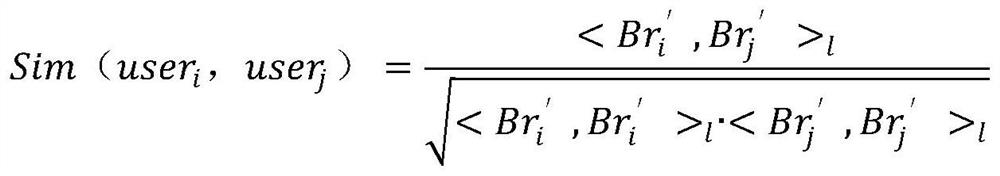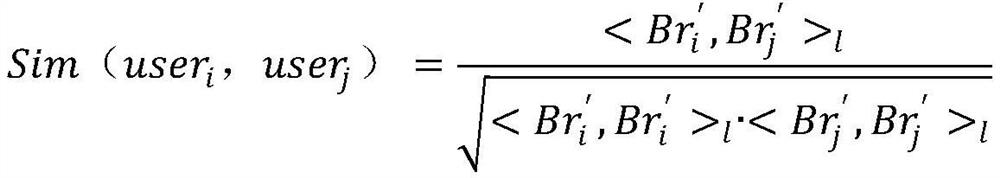Patents
Literature
141results about How to "Guarantee privacy and security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
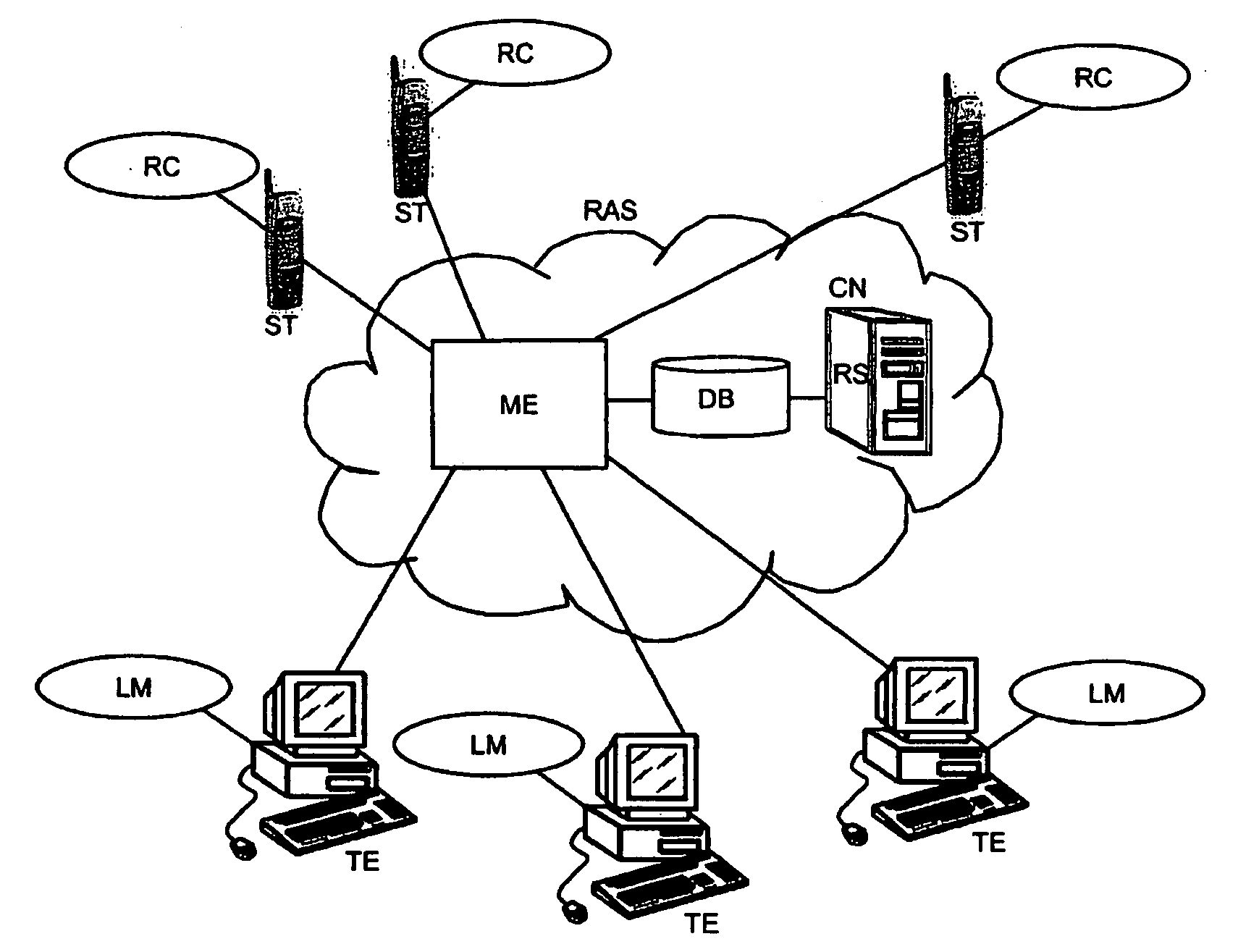
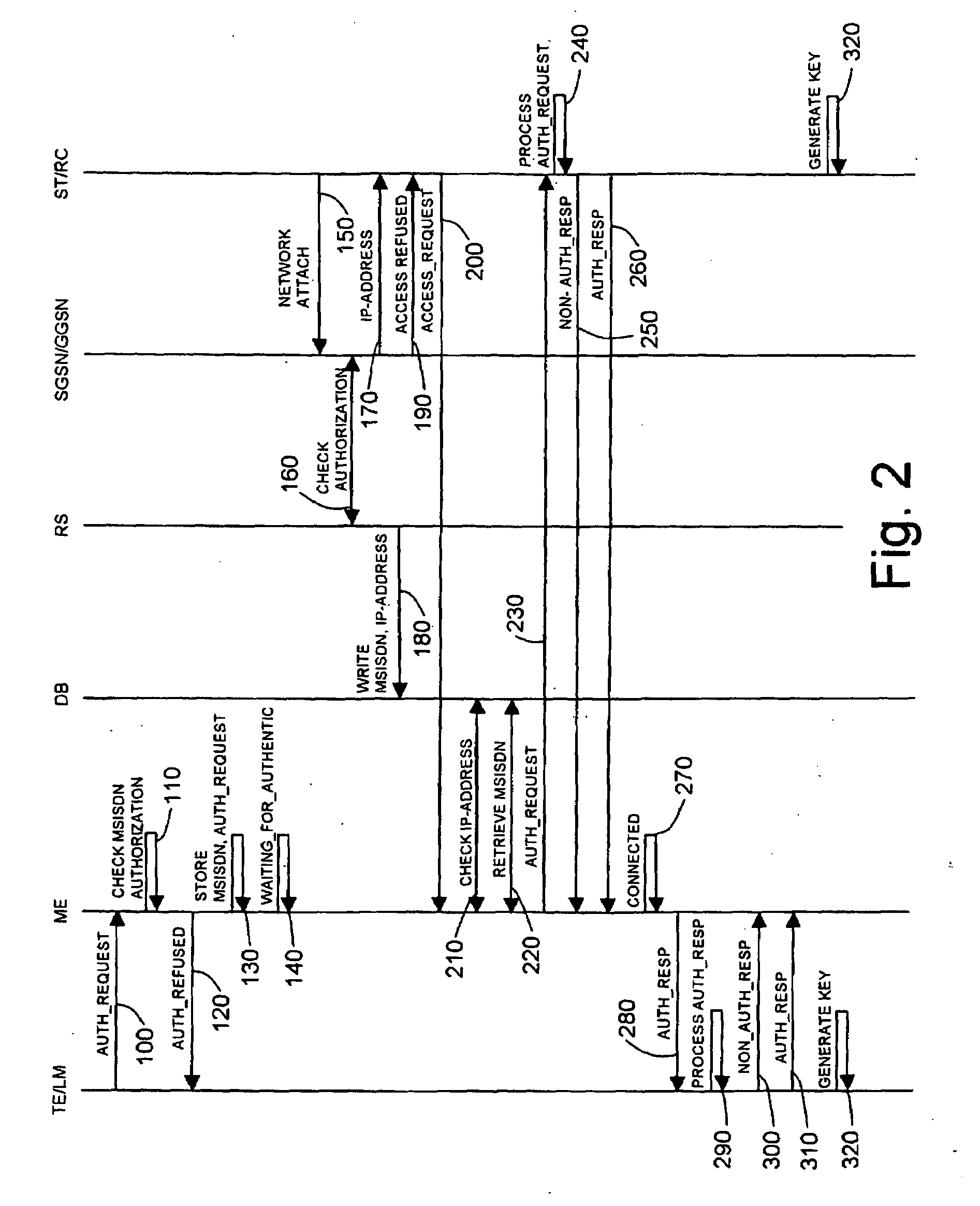
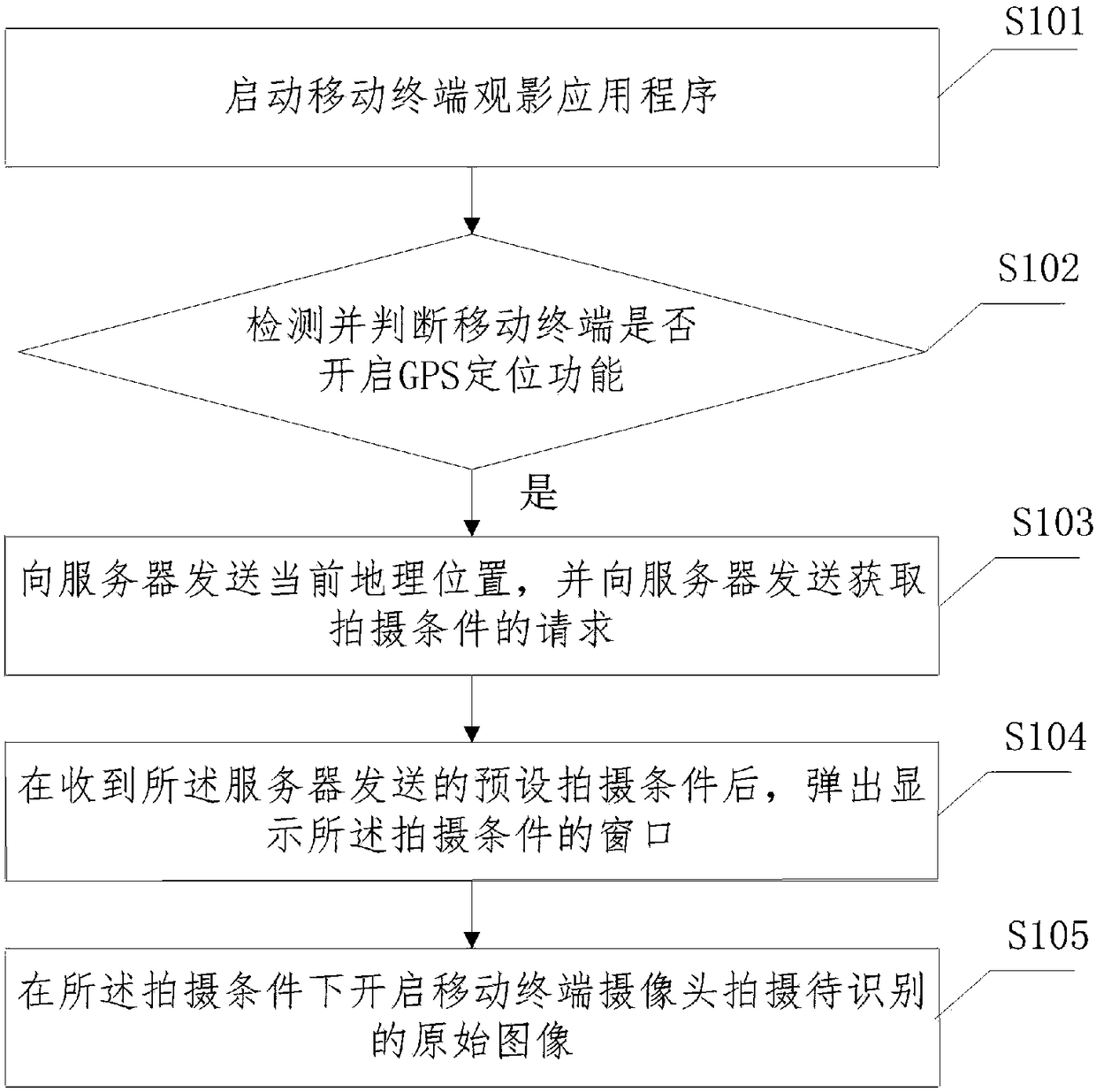
Remote Access System and Method for Enabling a User to Remotely Access Terminal Equipment from a Subscriber Terminal
ActiveUS20090019134A1Easy to implementEasy to installUser identity/authority verificationSubstation remote connection/disconnectionTerminal equipmentAuthentication
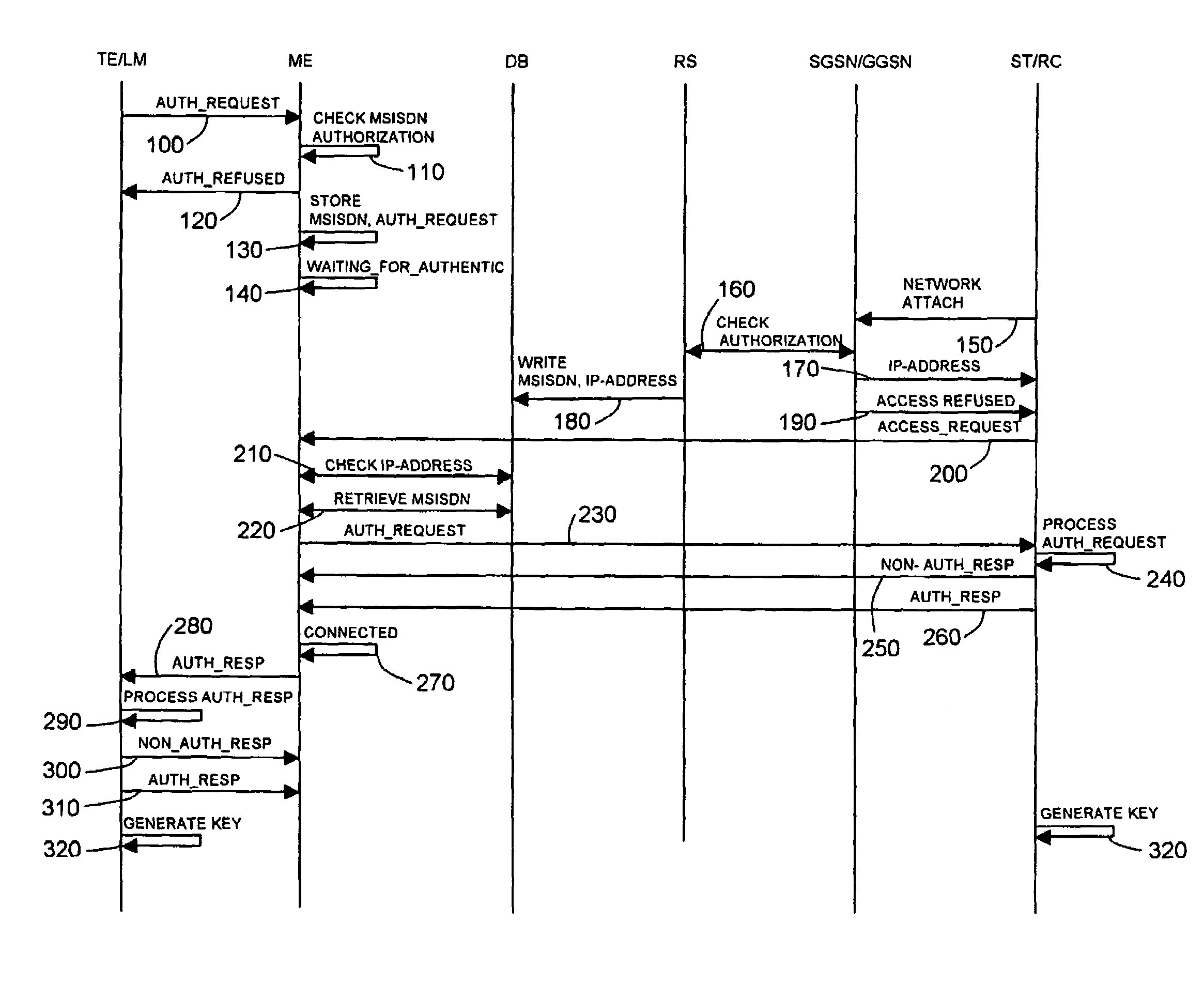
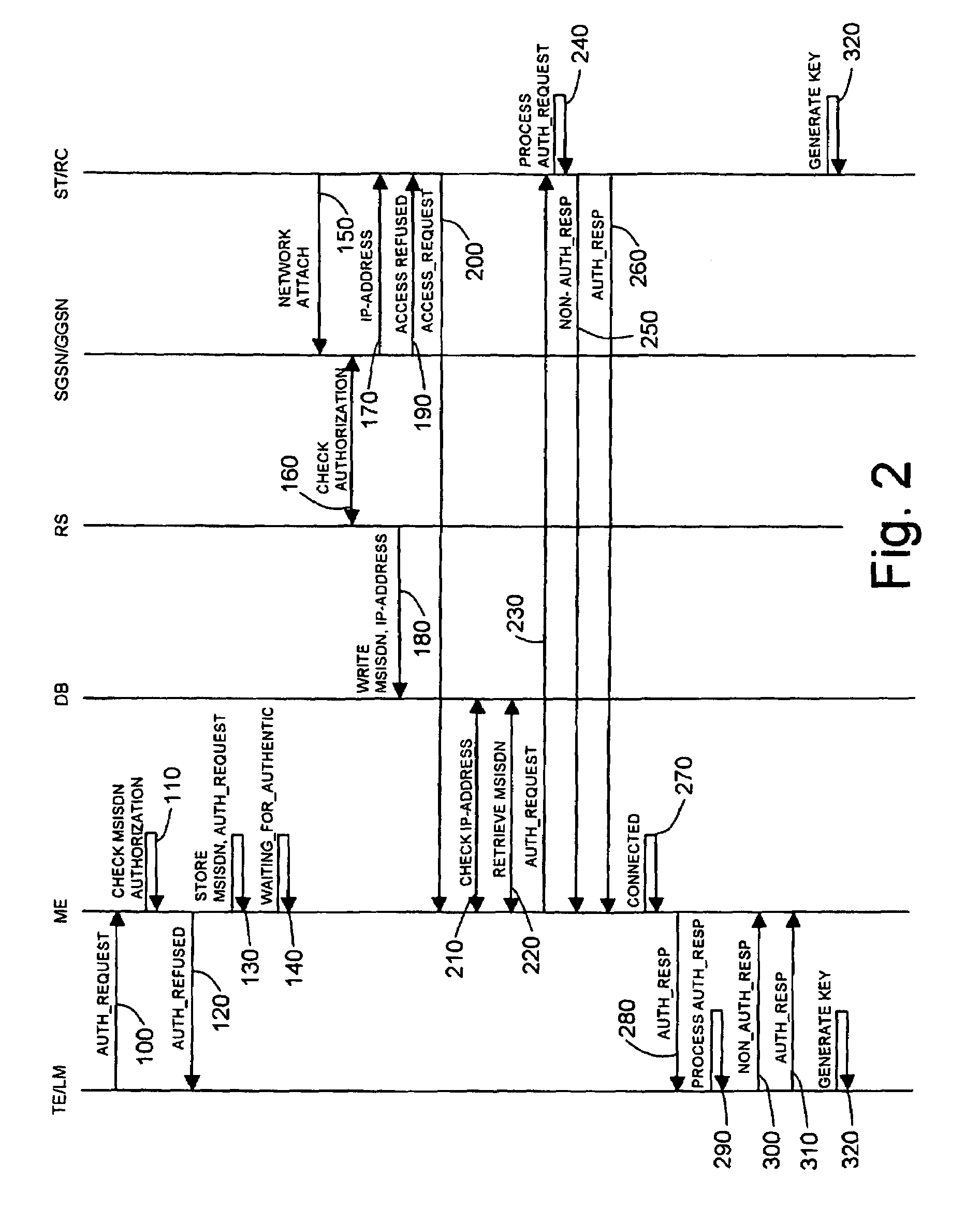
A method for enabling a subscriber terminal to remotely access terminal equipment, the terminal equipment storing identification data of the subscriber terminal, and the subscriber terminal being subscribed to a communication network and to a remote access service, wherein the method includes: receiving a request for authentication from the terminal equipment, the request for authentication including identification data of the subscriber terminal; receiving a request for access to the terminal equipment from the subscriber terminal; authenticating the subscriber terminal based on information from the communications network; forwarding the request for authentication from the terminal equipment to the subscriber terminal upon authenticating the subscriber terminal, the subscriber terminal processing the request for authentication to authenticate the terminal equipment; receiving an authentication notification from the subscriber terminal; forwarding the authentication notification from the subscriber terminal to the terminal equipment, the terminal equipment processing the authentication notification to authenticate said subscriber terminal; receiving an authentication notification from the terminal equipment; and enabling the subscriber terminal to remotely access the terminal equipment upon receiving the authentication notification from the terminal equipment.
Owner:TELECOM ITALIA SPA
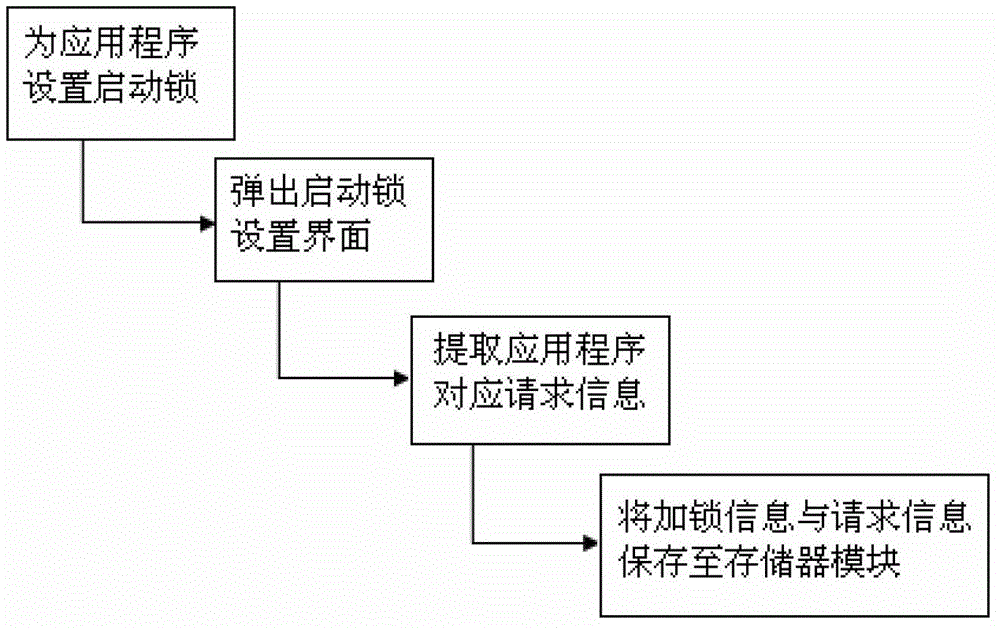
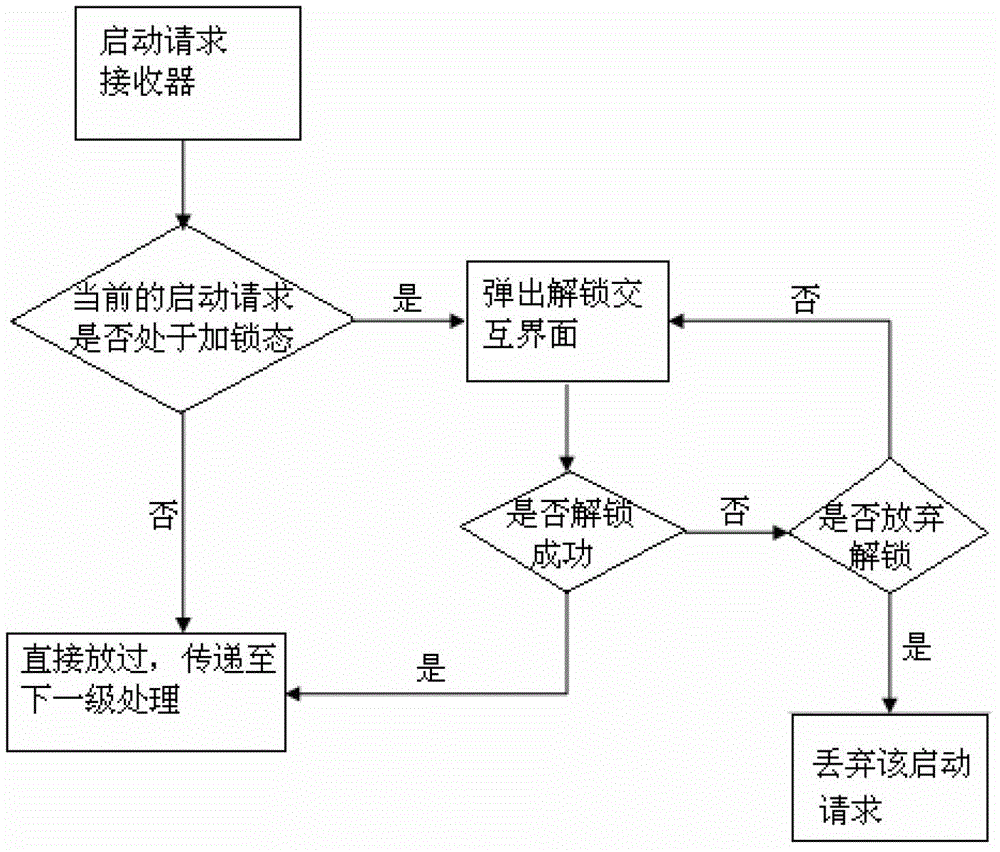
Starting lock for mobile terminal application program
ActiveCN103336924AFix security issuesGuarantee privacy and securityComputer security arrangementsOperational systemApplication software
The invention discloses a starting lock for a mobile terminal application program, and particularly relates to a starting lock of an application program. The starting lock for the mobile terminal application program comprises an operating system platform, the operating system platform is provided with an application program manager which manages at least one application program, and the application program manager comprises a locking module, a storage module and an unlocking module, wherein the storage module stores the locking information of the locking module and relevant starting request information. After the application program manager receives the starting request of an application program, the application program manager analyzes, identifies and judges the starting request, the unlocking module is started for the locked starting request, and the application program manager enables input unlocking information and locking information in the storage module to be matched and judged. According to the starting lock for the mobile terminal application program, the starting request information is extracted and stored during locking, the starting request information is detected, intercepted and captured in use, operation verification is conducted, and therefore individual privacy and information safety are further guaranteed in the using process of the application program.
Owner:宋易霄
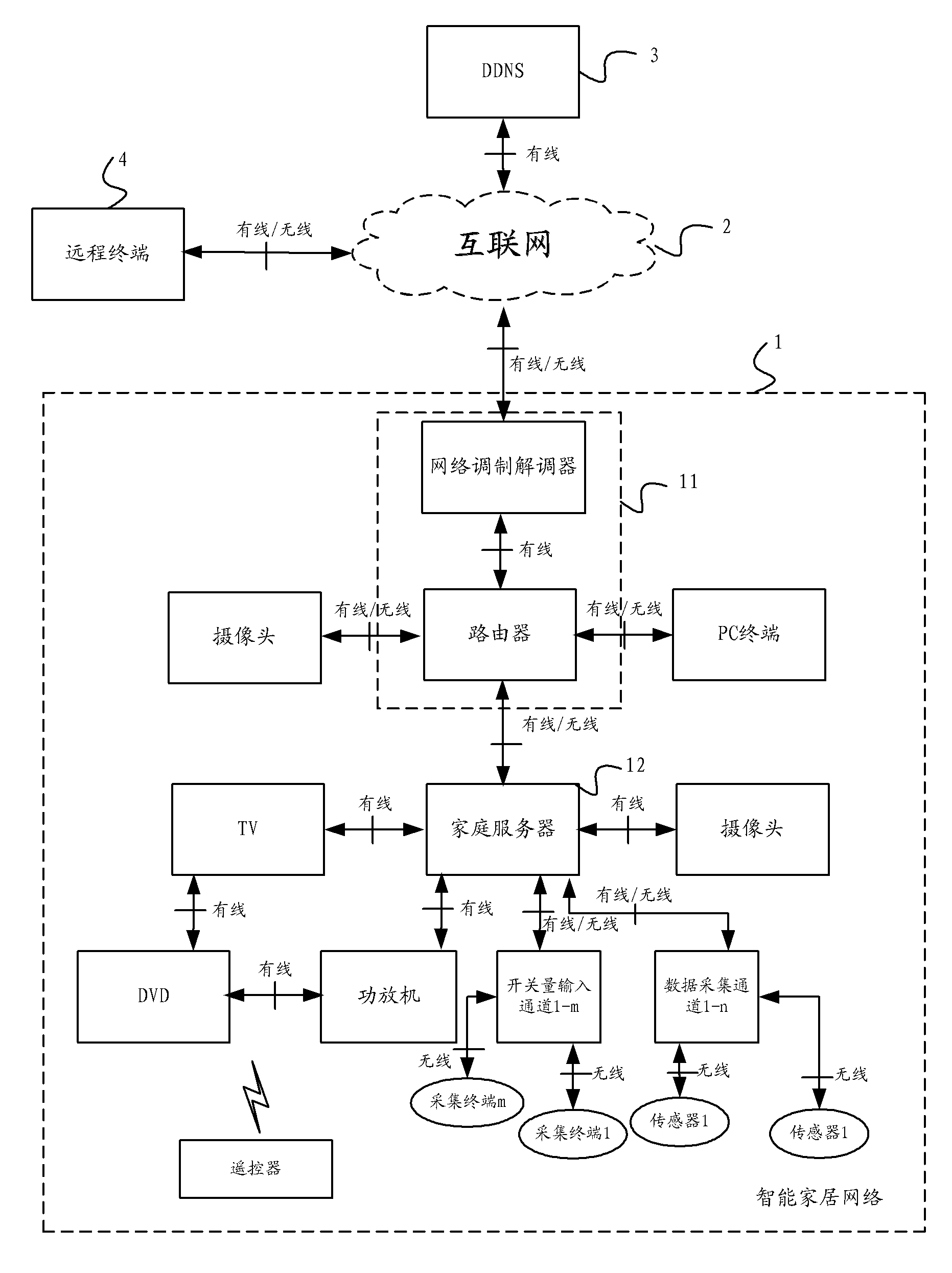
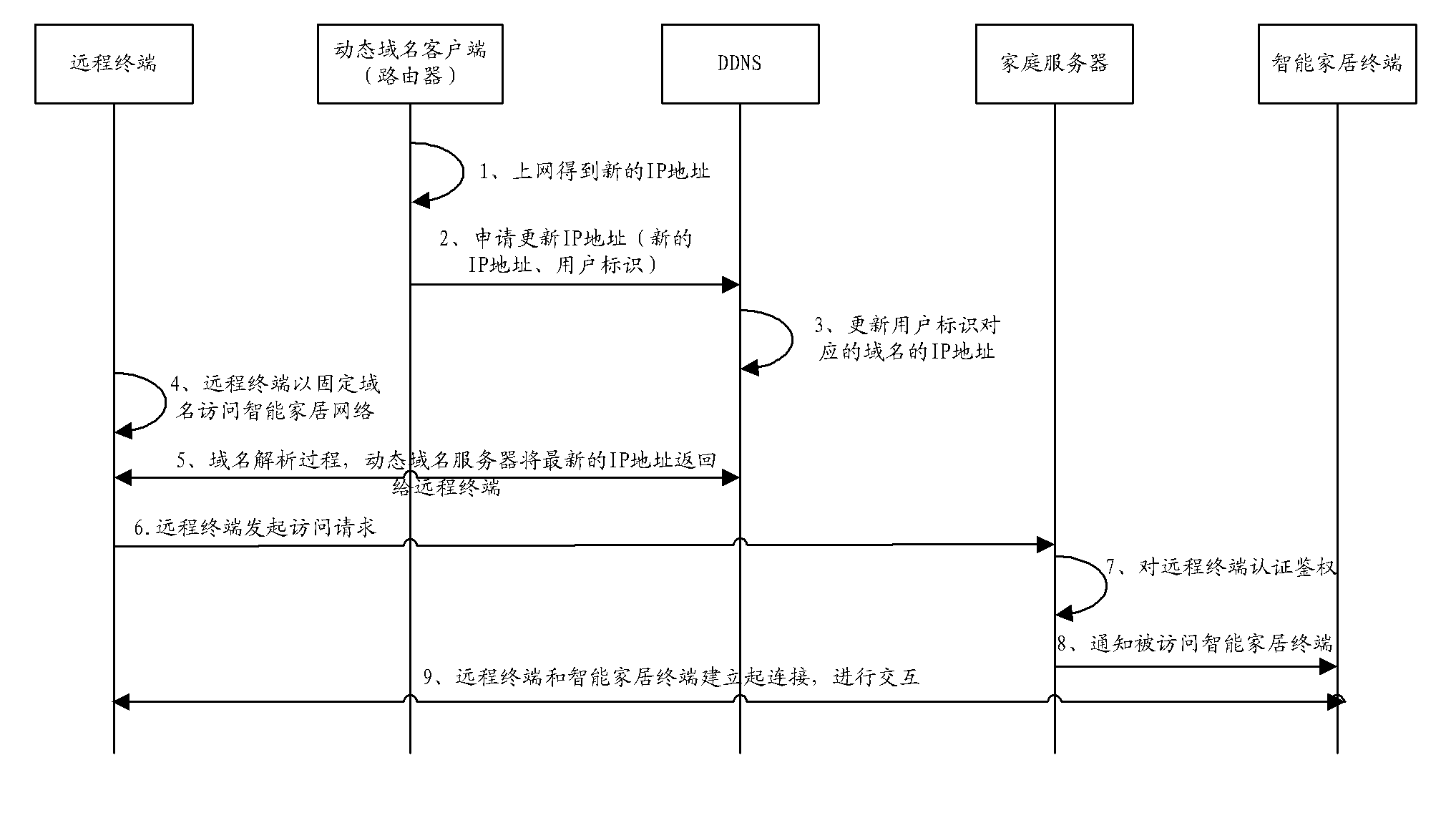
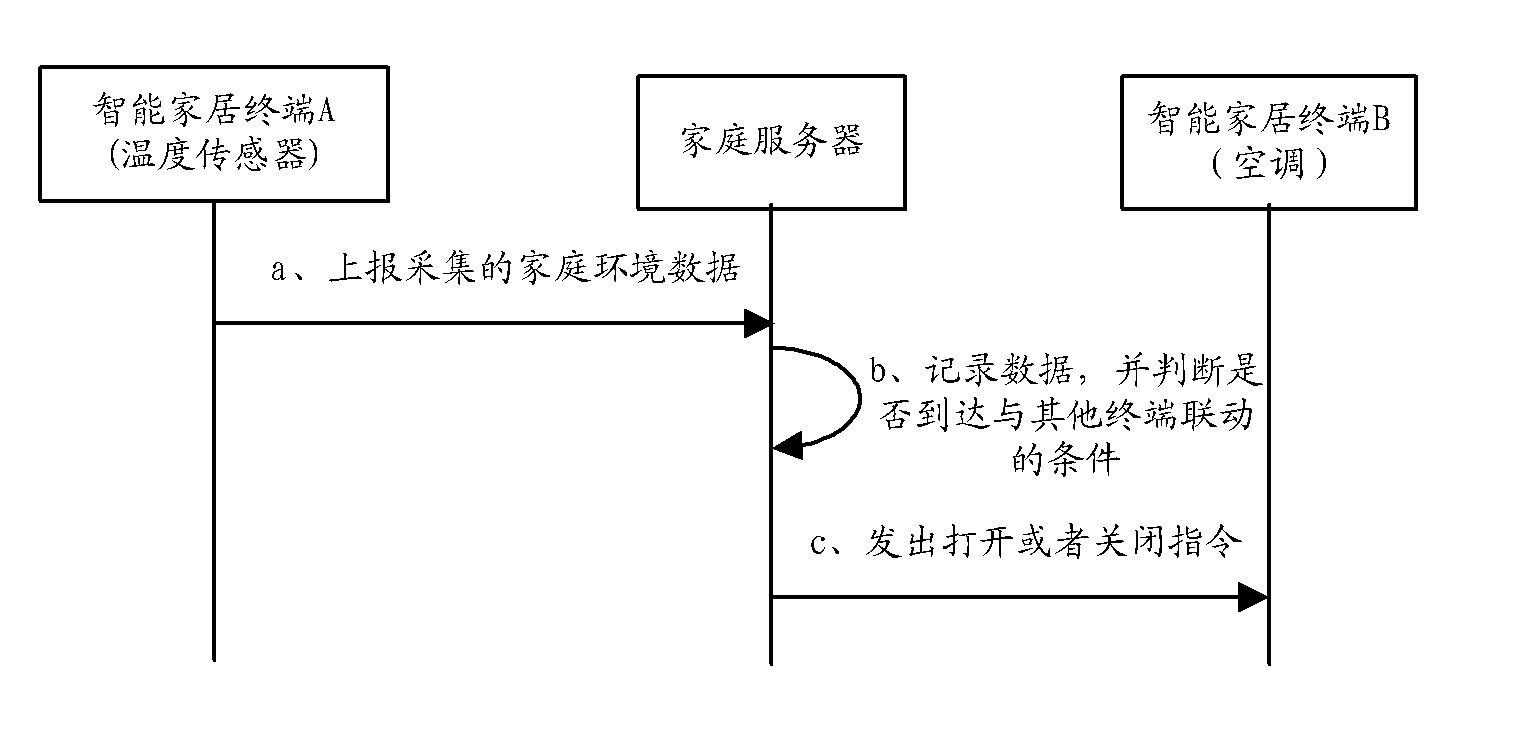
Intelligent home system
InactiveCN102546330AGuarantee privacy and securityGuarantee information securityData switching by path configurationDomain nameInternet communication
The invention provides an intelligent home system. The system comprises an intelligent home network, the Internet and a dynamic domain name server. The intelligent home network comprises network equipment, a home server and a plurality of intelligent home terminals, wherein the network equipment is in communication connection with the Internet, the home server is in communication connection with the network equipment and is used for information interaction with the network equipment, receiving information sent by the intelligent home terminals and sending control signals to the intelligent home terminals so as to control the work of the intelligent home terminals, and the intelligent home terminals are in communication connection with the home server. The dynamic domain name server is in communication connection with the Internet and is used for receiving a dynamic IP (Internet Protocol) address sent by the network equipment through the Internet, binding the dynamic IP address to the fixed domain name of the intelligent home network, and carrying out domain name resolution. With the adoption of the intelligent home system provided by the invention, the functions, such as video surveillance, leisure and entertainment, intelligent control of household appliances and home environment monitoring, can be achieved, and the customized customization, assembly and association can be achieved; and the information security can be guaranteed because no external operation service platform exists.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
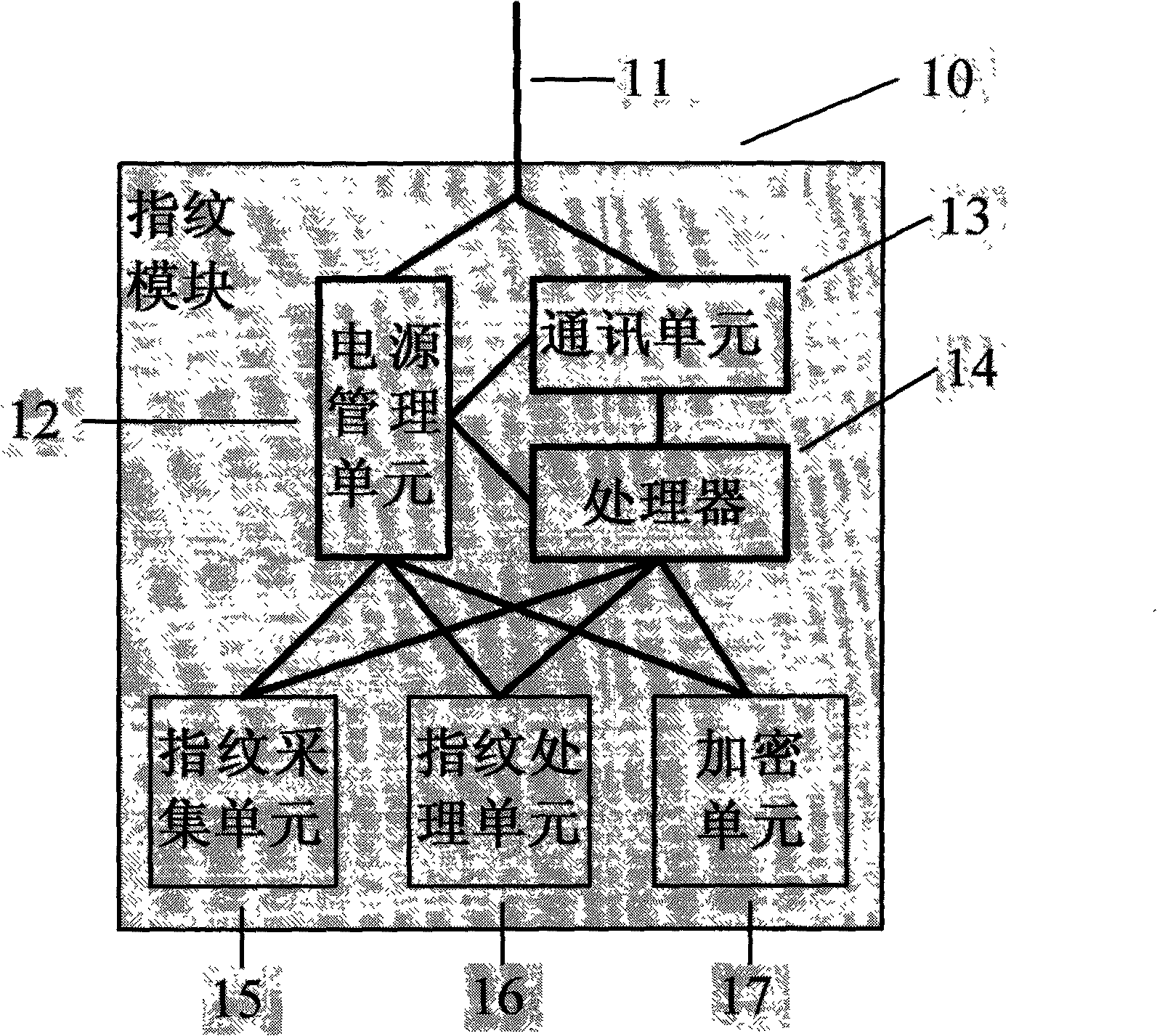
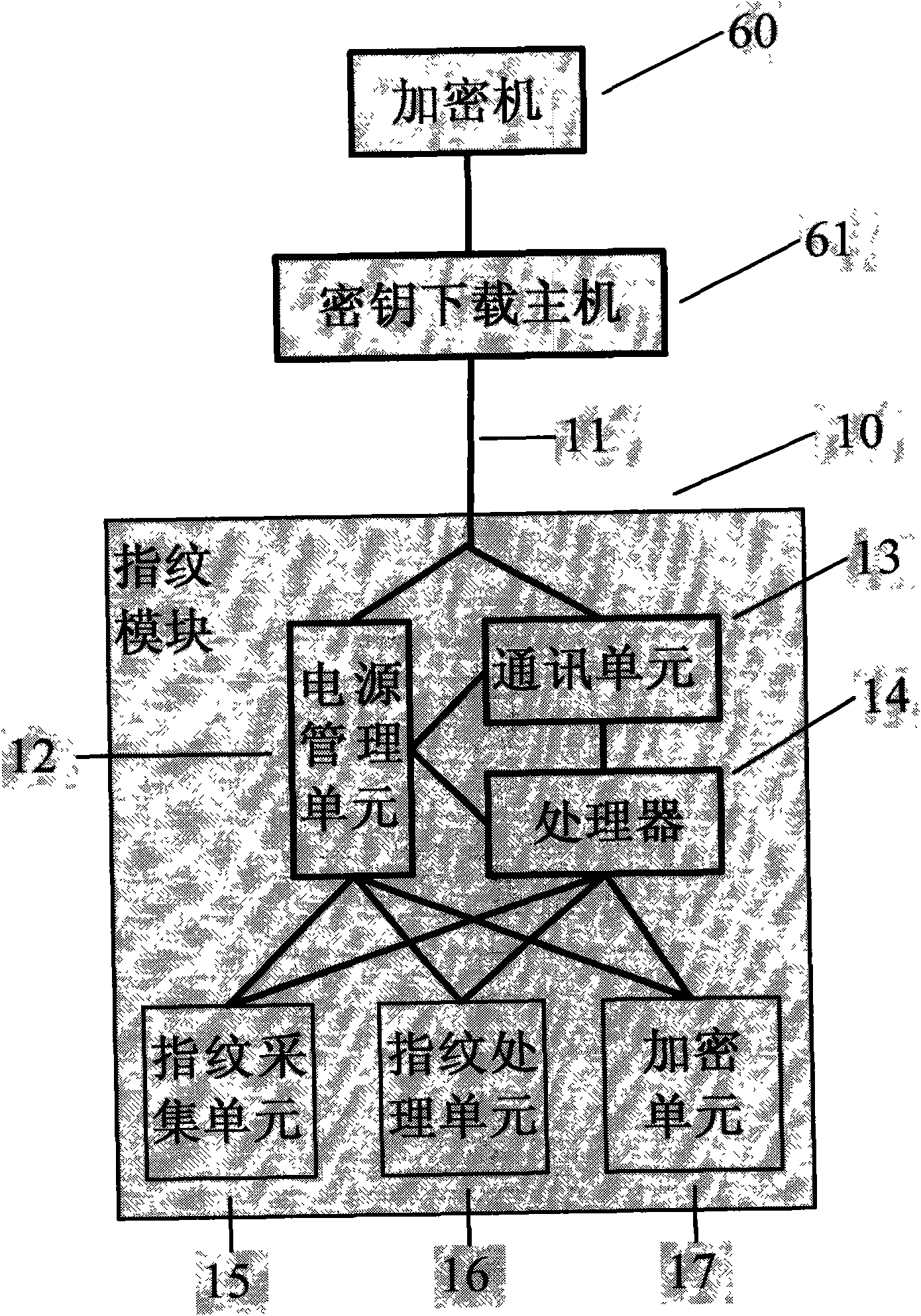
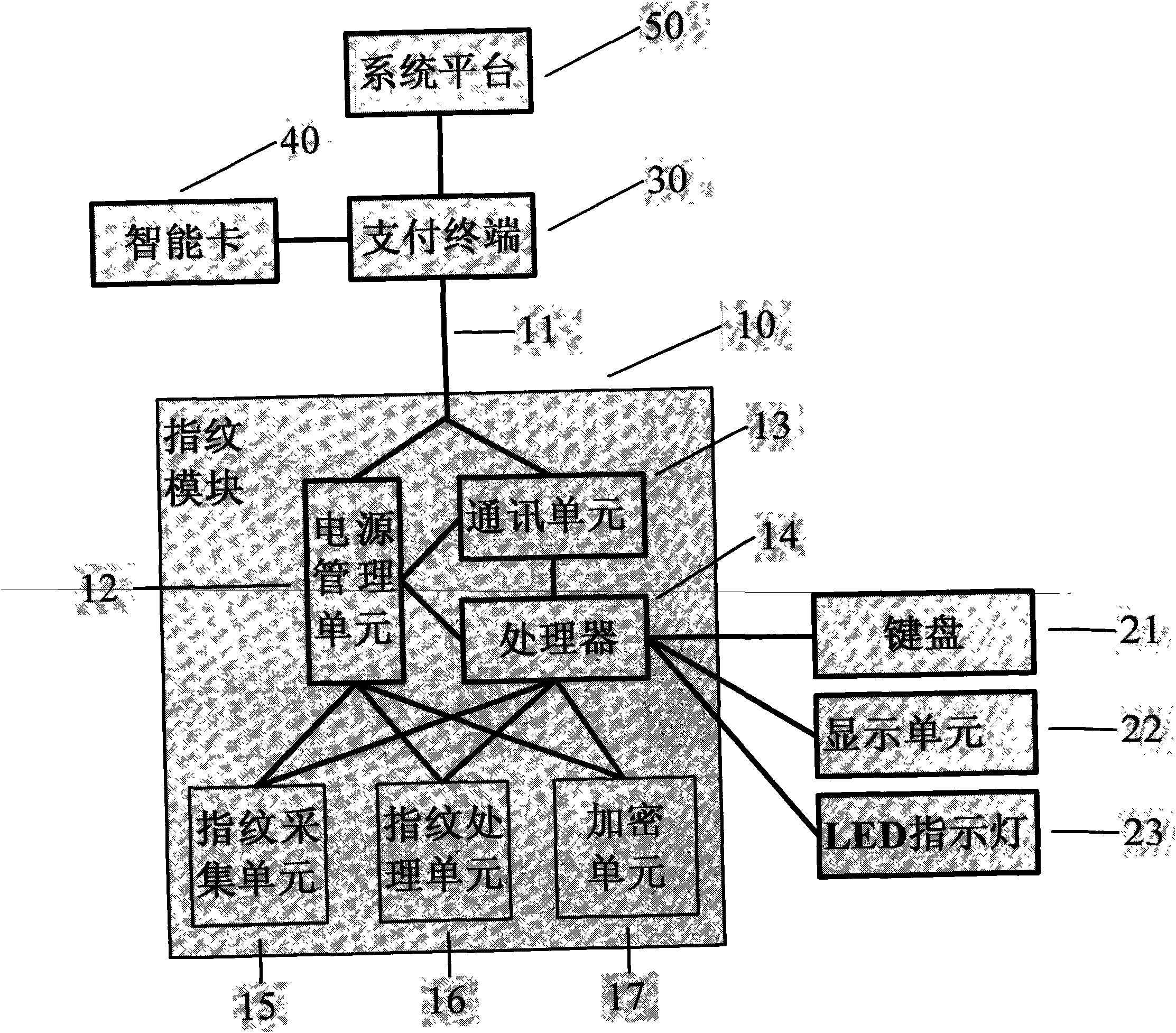
Fingerprint module with encryption unit
InactiveCN102176694AAvoid Forged Transaction RequestsGuarantee privacy and securityUser identity/authority verificationCharacter and pattern recognitionData validationComputer terminal
The invention provides a fingerprint module with an encryption unit, which is characterized in that the fingerprint module is connected with a payment terminal or arranged on the payment terminal by a communication line; the fingerprint module is provided with a fingerprint acquisition unit which is at least used for acquiring fingerprint image data of a user; the fingerprint module is provided with a fingerprint processing unit which is at least used for extracting fingerprint characteristic data from the fingerprint image data of the user; and the fingerprint module is provided with the encryption unit which is at least used for encrypting the fingerprint characteristic data of the user and / or adding an MAC (message authentication code) to the fingerprint characteristic data. The fingerprint characteristic data of the user are sent out after secret keys and dynamic random numbers are used to encrypt the fingerprint characteristic data of the user and / or add the MAC to the fingerprint characteristic data of the user in the fingerprint module; and a fingerprint data validation party validates the validity of the MAC firstly and / or carries out fingerprint matching on the decrypted MAC, thus avoiding the possibility that a lawbreaker counterfeits a transaction request after recording fingerprint data of the user, improving the system safety, ensuring the privacy of the fingerprint data of the user and the capital safety, and being beneficial to promoting applications of a fingerprint identification technology in the payment field.
Owner:张龙其
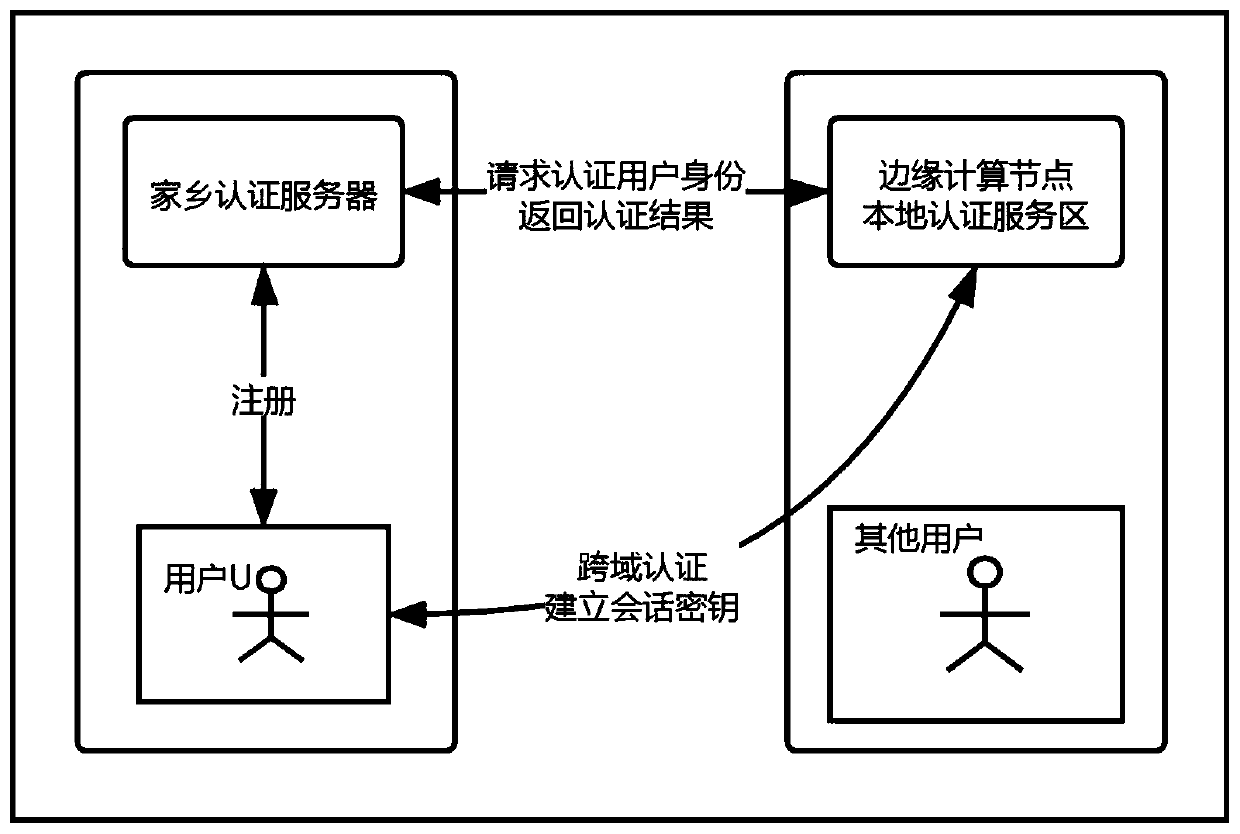
Cross-domain identity authentication method based on edge computing network architecture
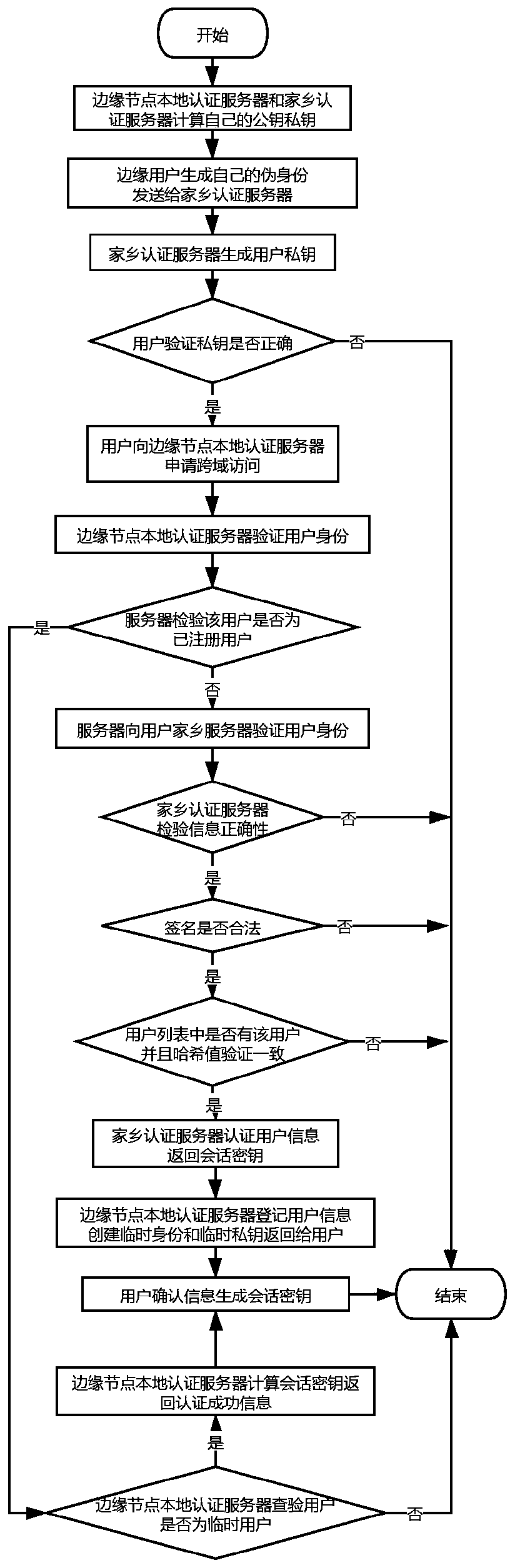
ActiveCN111355745AReduce computational overheadLow costKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEdge nodeNetwork architecture
The invention discloses a cross-domain identity authentication method based on an edge computing network architecture, and mainly solves the technical problems that in the prior art, key management and distribution are difficult, and user privacy is difficult to protect. The method comprises the following steps: 1) an edge node local authentication server and a home authentication server calculaterespective public and private keys; 2) the home authentication server generates a private key constructed by the user by using the pseudo identity; 3) the user applies for cross-domain access to theedge node local authentication server; 4) the edge node local authentication server sends information to a home authentication server of the user to verify the identity of the user; 5) the home authentication server authenticates the user information and returns a session key; 6) the local authentication server of the edge node calculates the session key and returns the authentication information;7) the user confirms the information to generate the session key. According to the method, the bidirectional verification security of the edge node equipment and the user can be effectively improved,the problems that the identity privacy of the user is exposed and the session is tracked are solved, and the method can be used for modern Internet of Things equipment.
Owner:XIDIAN UNIV
Screen unlocking method and device
InactiveCN104166518AEasy to rememberImprove securityInput/output processes for data processingUser inputEmbedded system
Owner:北京数字天域科技有限责任公司
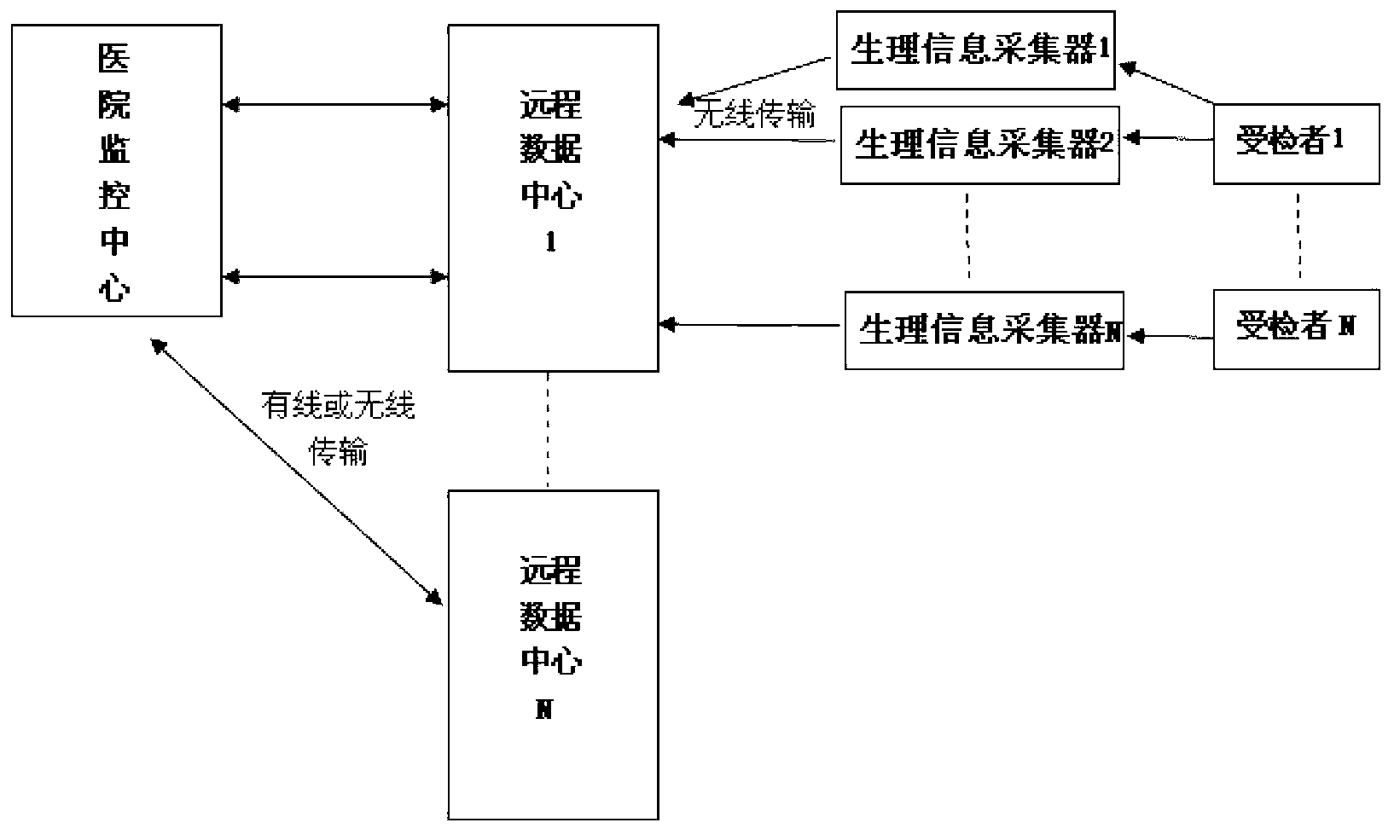
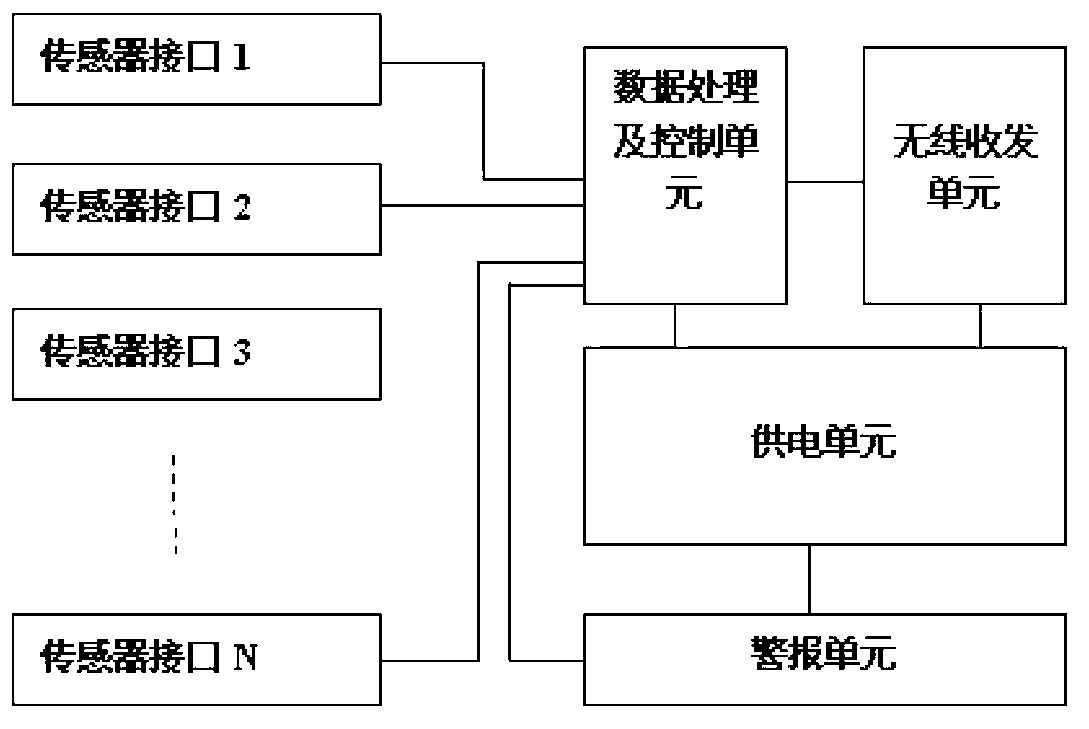
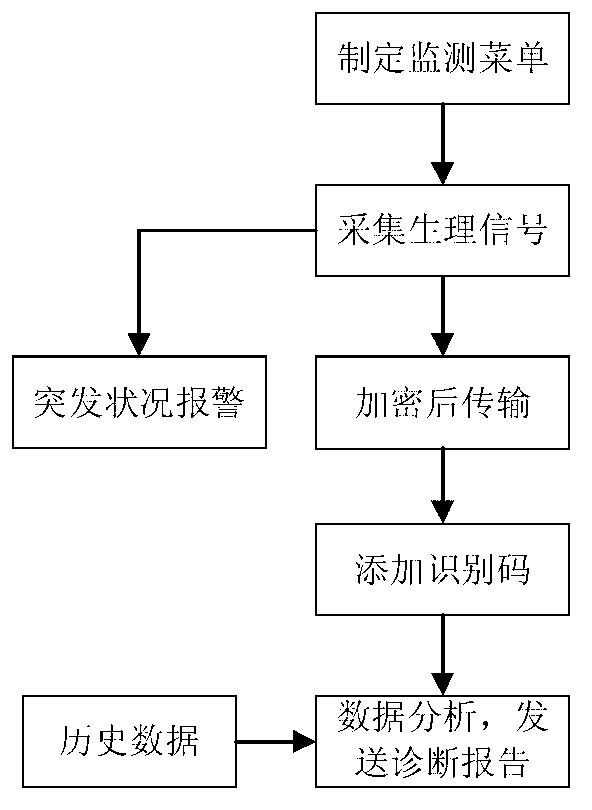
Physiological information monitoring system and monitoring method
ActiveCN103230261AGuarantee privacy and securitySimple structureElectric signal transmission systemsDiagnostic recording/measuringMedical emergencyInformation monitoring
The invention discloses a physiological information monitoring system comprising a physiological information collector, a remote data terminal and a hospital monitoring center, wherein the physiological information collector is used for collecting a physiological signal, encrypting the collected physiological signal data and transmitting the physiological signal data to the remote data terminal, the remote data terminal is used for adding an identification code on the received physiological signal data and transmitting the physiological signal data to the hospital monitoring center, and the hospital monitoring center is used for decrypting, storing and analyzing the physiological signal data and sending a diagnostic report to the remote data terminal. The invention further provides a monitoring method. The physiological information monitoring system and the physiological information monitoring method disclosed by the invention are used for solving the problem of low privacy safety of subjects and low utilization rate of monitoring information, the collected physiological signal data are transmitted after being encrypted, thereby preventing the physiological information of the subjects from being leaked by illegal monitoring in the transmission process; and the hospital monitoring center analyzes the received data and provides the diagnostic report to provide illness condition caution to the subjects in time.
Owner:MIANYANG DEHUI AUTOMATION TECH CO LTD
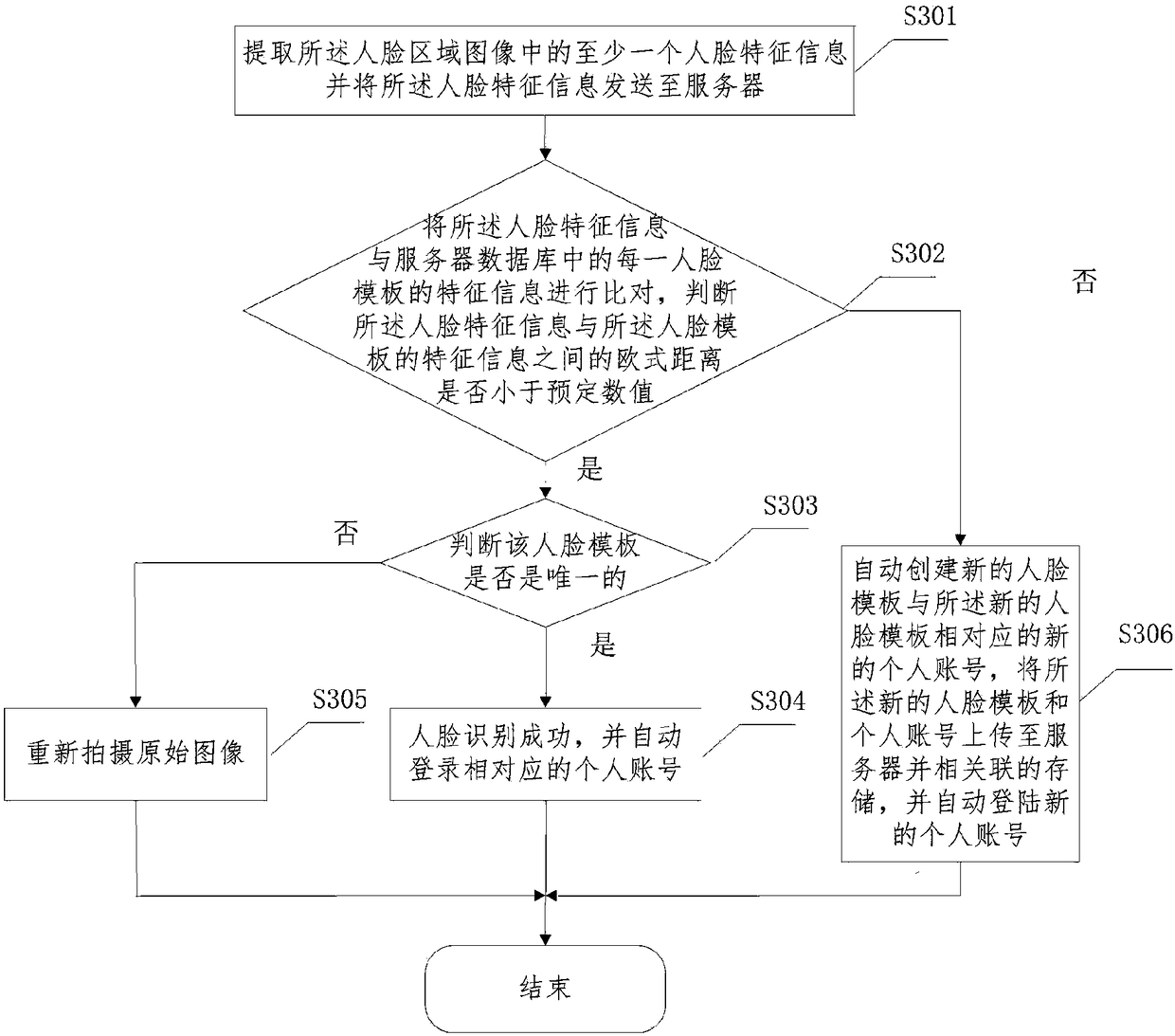
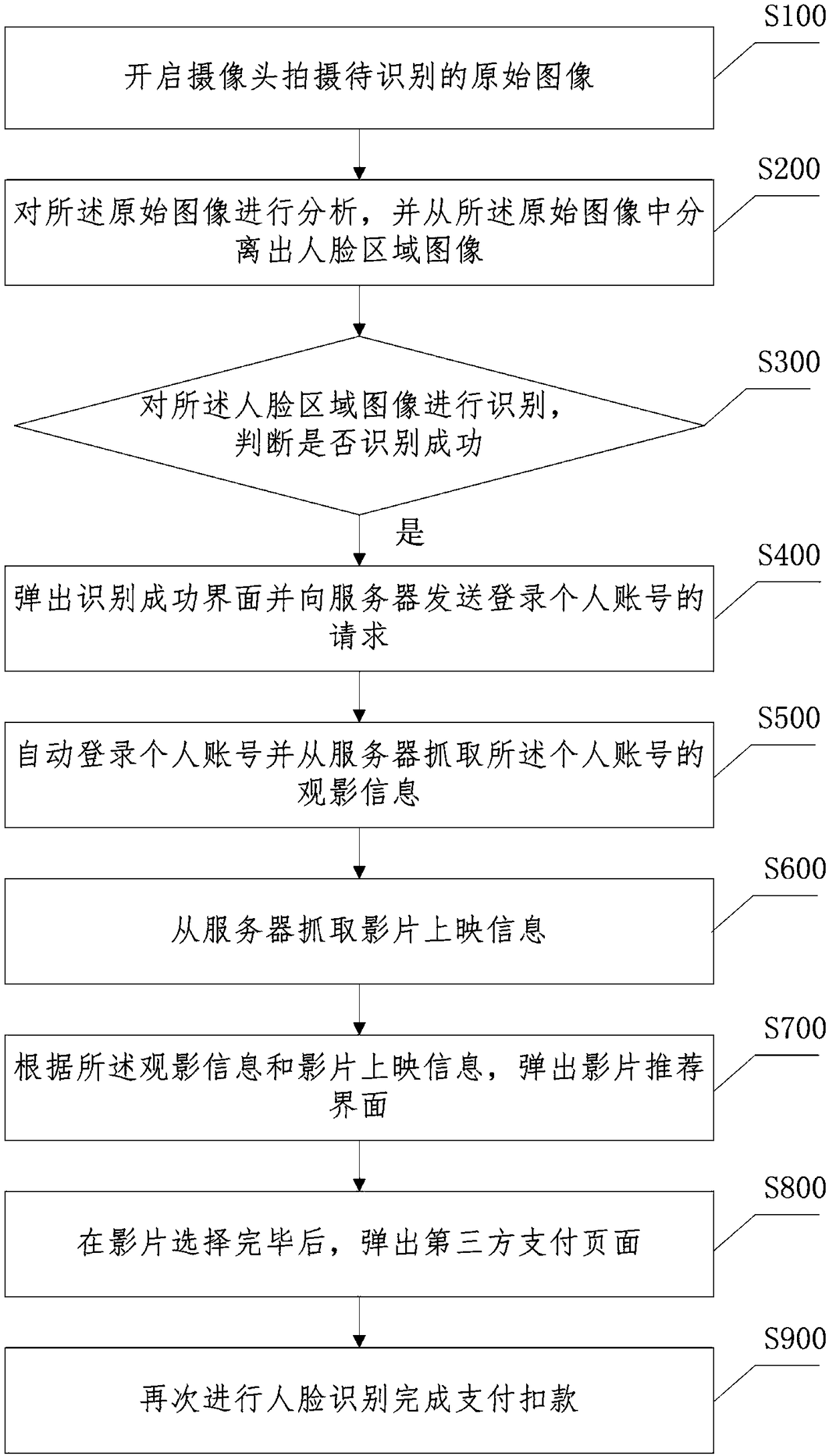
Quick face recognition method
InactiveCN108491806ASave yourself the hassle of buying tickets manuallyGuarantee privacy and securityBuying/selling/leasing transactionsSpoof detectionPattern recognitionThird-Party Payments
The invention provides a quick face recognition method. The method comprises the steps that a camera is started to shoot a to-be-recognized original image; the original image is analyzed, and a face region image is separated from the original image; the face region image is recognized, and whether recognition succeeds is judged; if recognition succeeds, a personal account is automatically logged in, and film watching information of the personal account is captured from a server; film release information is captured from the server; according to the film watching information and the film release information, a film recommendation interface is popped up; after a file is selected, a third-party payment page is popped up; and face recognition is performed again to complete payment deduction. According to the method, the camera is started to shoot the to-be-recognized face image, the face image is analyzed and recognized, the personal account is automatically logged in for ticket purchase after recognition succeeds, face recognition is performed again during payment, therefore, cinema ticket purchase operation is completed quickly and conveniently, and the trouble of manual ticket selling and management is omitted.
Owner:成都信达智胜科技有限公司
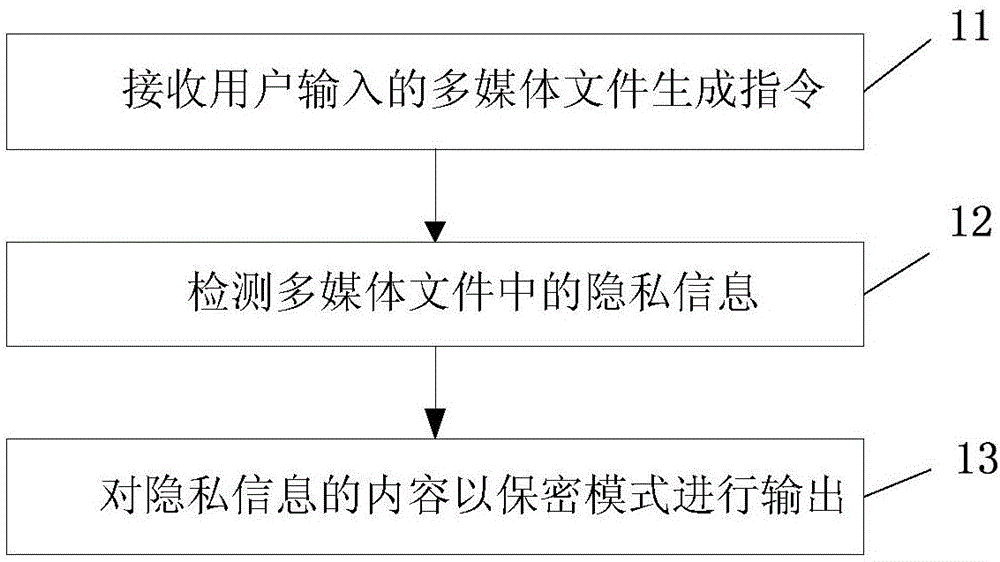
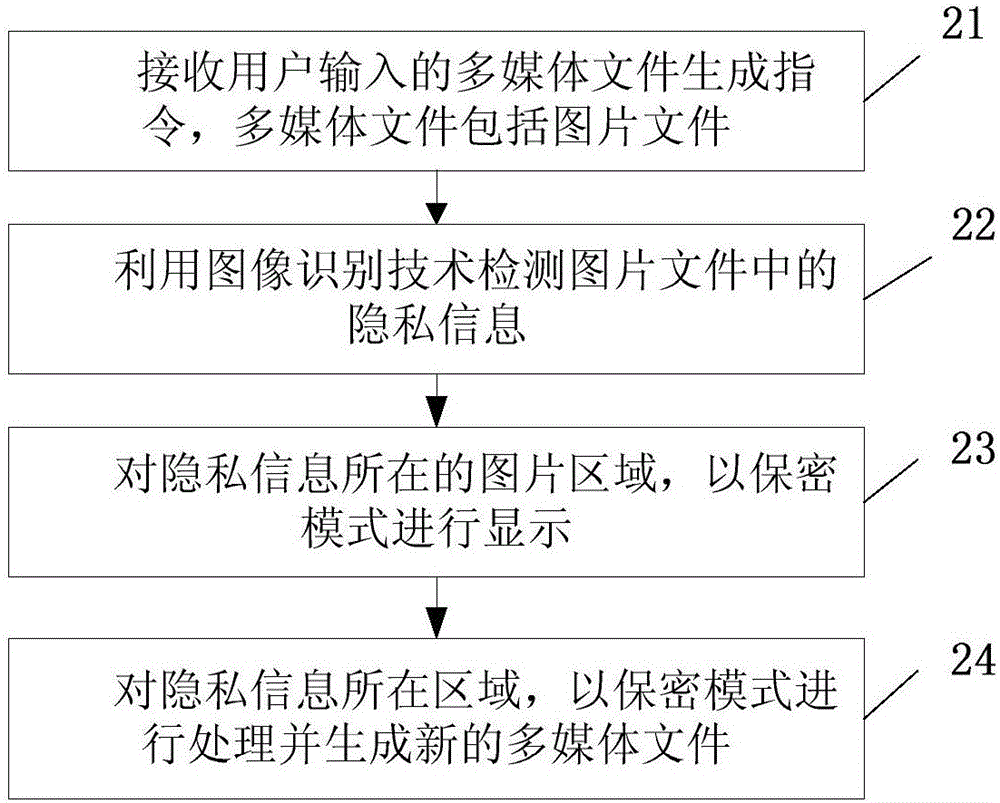
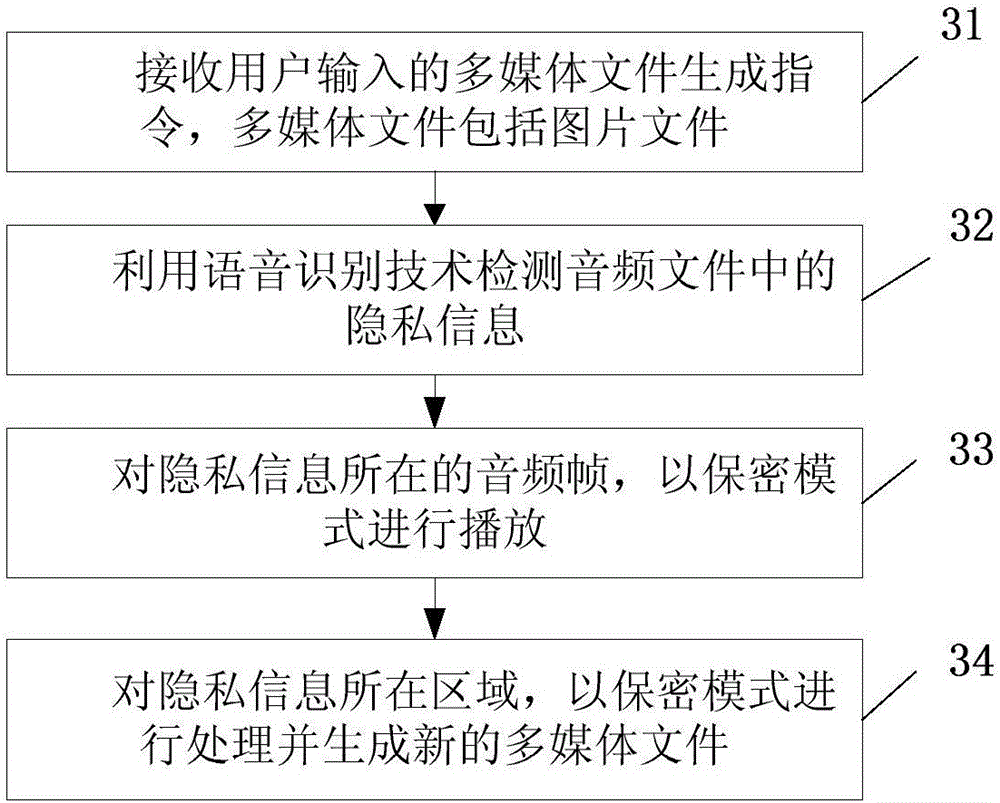
Protecting method for privacy information and mobile terminal of protecting method
InactiveCN106295398AGuarantee privacy and securityGuarantee property securityDigital data protectionUser inputInternet privacy
The invention relates to the field of mobile communication and provides a protecting method for privacy information and a mobile terminal of the protecting method. According to the protecting method, privacy information detection is carried out on a multimedia file input to the mobile terminal by a user, the privacy information is output in a secret mode, personal privacy in the multimedia file can be effectively prevented from being leaked, the privacy safety and property safety of the user are guaranteed, the material loss or the mind loss is avoided, and the user can use the mobile terminal more safely and relaxedly.
Owner:VIVO MOBILE COMM CO LTD
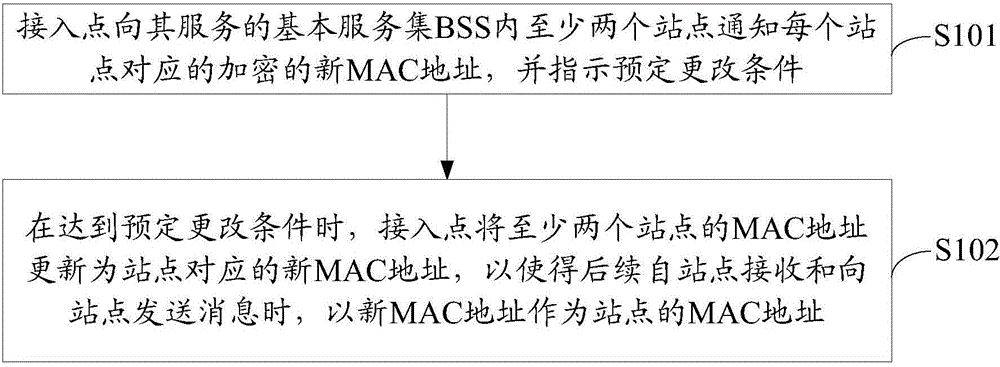
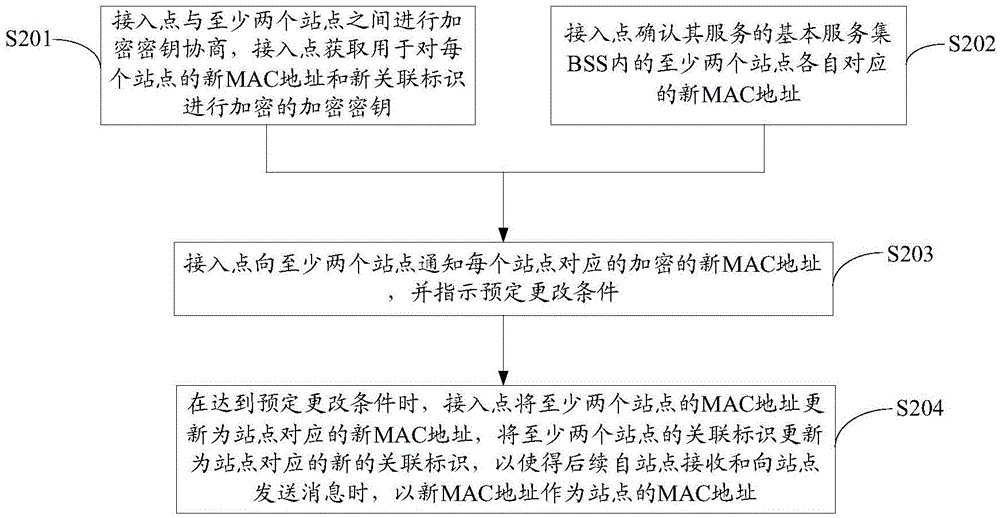
Method for distributing addressing identification, and access point, site and communication system
ActiveCN104955038AGuarantee privacy and securityNetwork topologiesSecurity arrangementCommunications systemComputer terminal
Disclosed are a method for allocating an addressing identifier, an access point, a station and a communication system. The method for allocating an addressing identifier comprises: notifying, by an access point, at least two stations of encrypted new MAC addresses corresponding to each station, and instructing a pre-determined change condition, so that the at least two stations respectively change respective MAC addresses into respective new MAC addresses when reaching the pre-determined change condition; and when the pre-determined change condition is reached, updating, by the access point, the MAC addresses of the at least two stations into new MAC addresses corresponding to the stations, so that the new MAC addresses are used as the MAC addresses of the stations when messages are received from the stations or sent to the stations subsequently. By means of the method above, the present invention prevents an eavesdropper tracking a terminal through the MAC addresses so as to acquire the privacy of a user, thereby guaranteeing the privacy security of the user.
Owner:HUAWEI DEVICE CO LTD
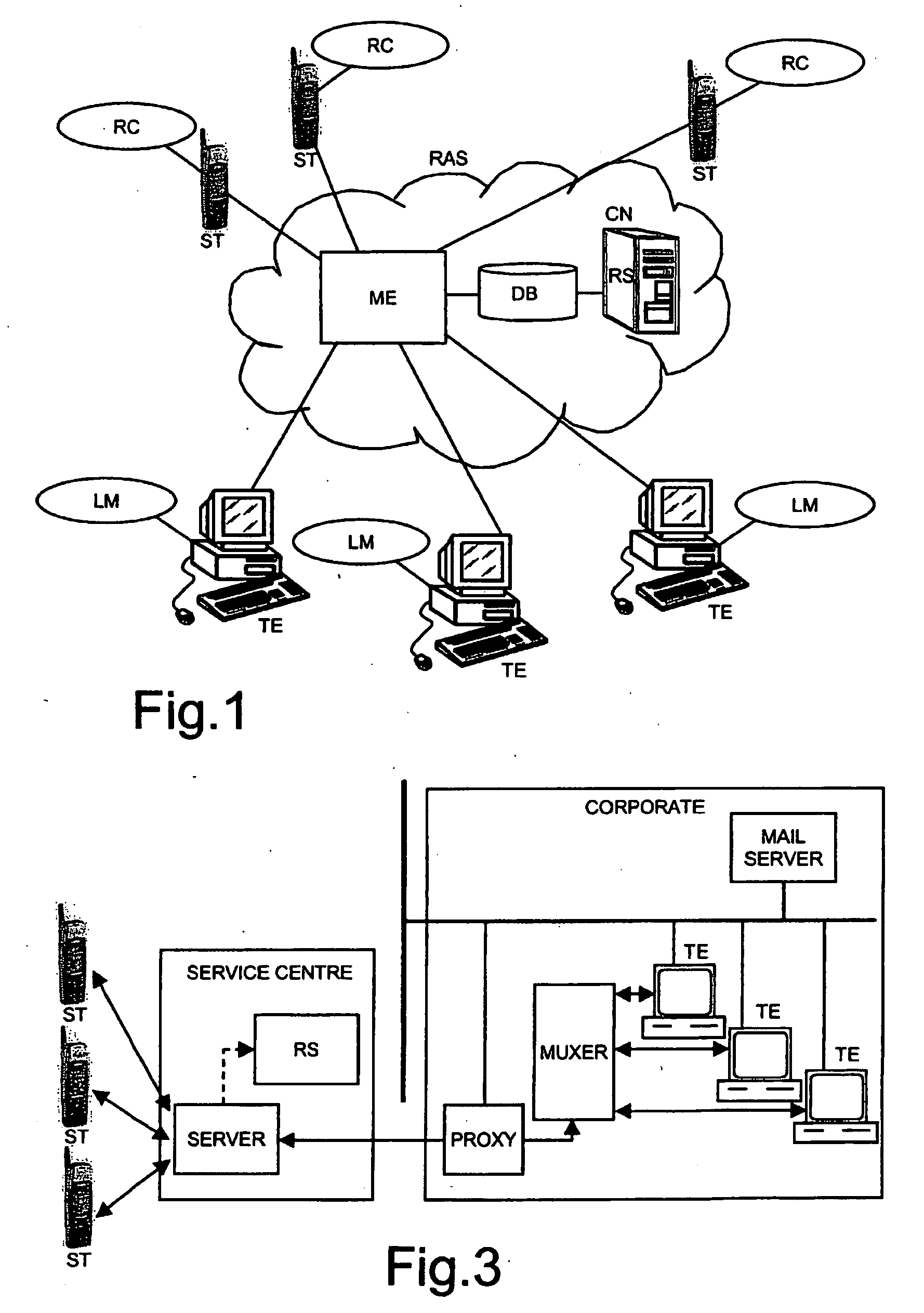
Remote access system and method for enabling a user to remotely access terminal equipment from a subscriber terminal
ActiveUS8156231B2Easy to implementEasy to installUser identity/authority verificationSubstation remote connection/disconnectionTerminal equipmentAuthentication
A method for enabling a subscriber terminal to remotely access terminal equipment, the terminal equipment storing identification data of the subscriber terminal, and the subscriber terminal being subscribed to a communication network and to a remote access service, wherein the method includes: receiving a request for authentication from the terminal equipment, the request for authentication including identification data of the subscriber terminal; receiving a request for access to the terminal equipment from the subscriber terminal; authenticating the subscriber terminal based on information from the communications network; forwarding the request for authentication from the terminal equipment to the subscriber terminal upon authenticating the subscriber terminal, the subscriber terminal processing the request for authentication to authenticate the terminal equipment; receiving an authentication notification from the subscriber terminal; forwarding the authentication notification from the subscriber terminal to the terminal equipment, the terminal equipment processing the authentication notification to authenticate said subscriber terminal; receiving an authentication notification from the terminal equipment; and enabling the subscriber terminal to remotely access the terminal equipment upon receiving the authentication notification from the terminal equipment.
Owner:TELECOM ITALIA SPA
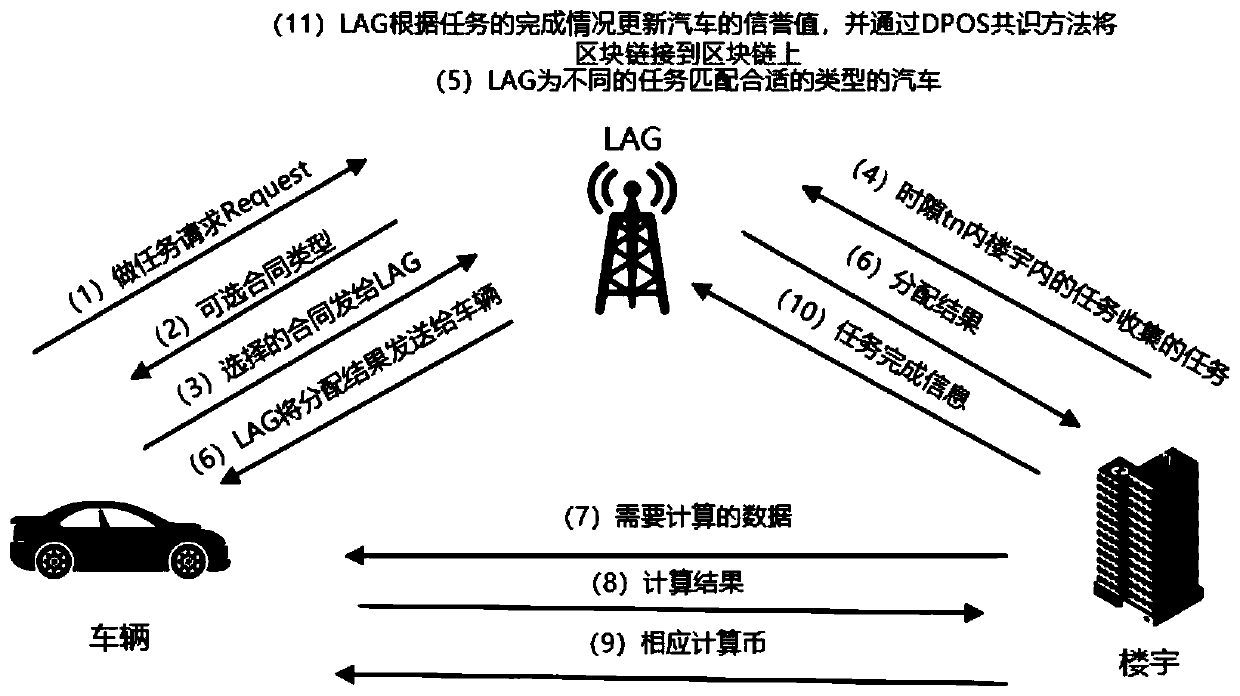
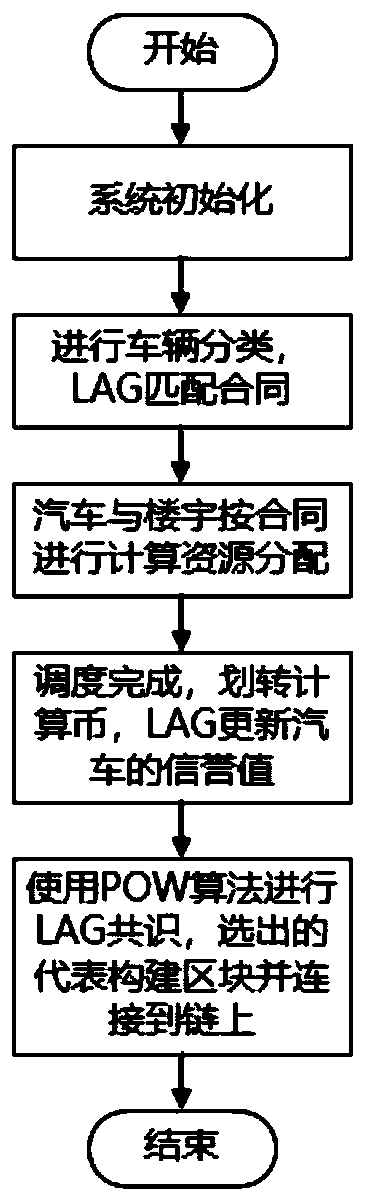
Vehicle computing resource allocation method in urban computing environment
ActiveCN110348670AImprove distribution efficiencyAchieve traceabilityResourcesThird partyUser privacy
The invention discloses a vehicle computing resource allocation method in an urban computing environment, and relates to related technologies such as a block chain, a contract theory and a reputationmechanism. Firstly, a framework of an alliance block chain is introduced, decentralization of the system is achieved, and traceability and non-modifiability of distributed records are also achieved; meanwhile, the contract theory is applied to the system, so that the problem of information asymmetry between entities in the resource allocation process is solved; the two measures ensure the privacysecurity of the user to a great extent, the willingness of the user to participate in computing resource allocation is improved, and the system is automatically executed through a corresponding algorithm, so that tedious procedures in a third-party mechanism are omitted, and the resource allocation efficiency is greatly improved; besides, in the process of selecting the corresponding task unloading vehicle for the building calculation task, the high-reputation vehicle is screened out through a reputation mechanism, and it is guaranteed that high-quality service is provided for the building.
Owner:GUANGDONG UNIV OF TECH
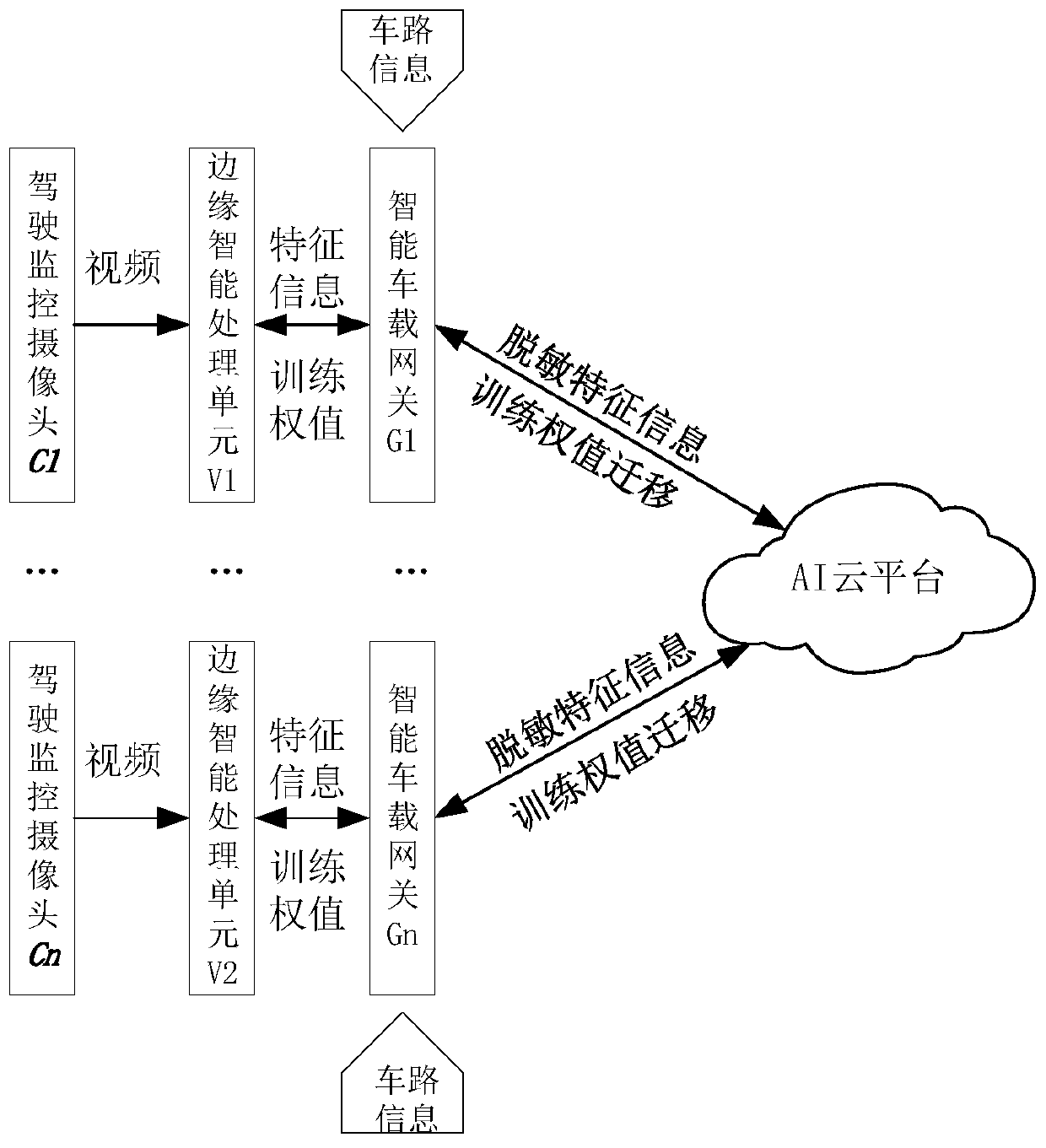
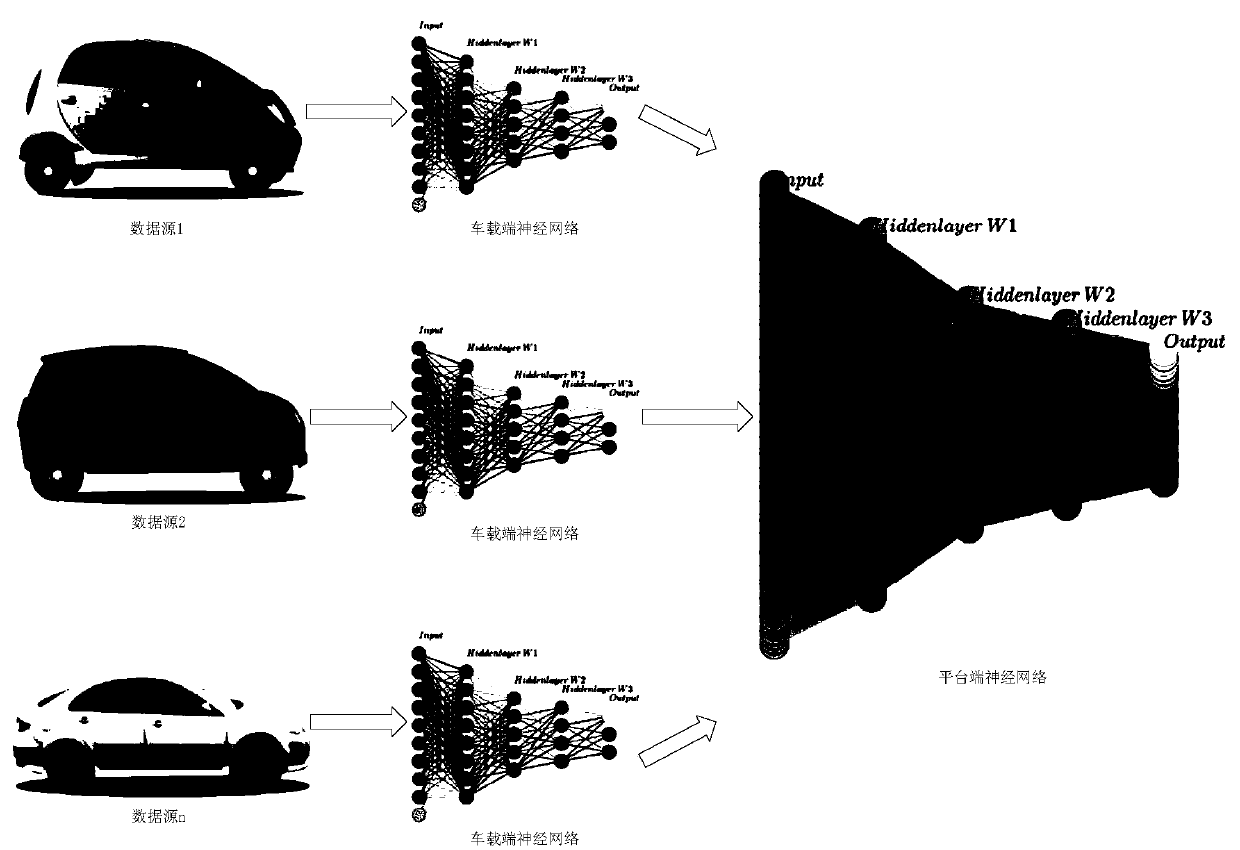
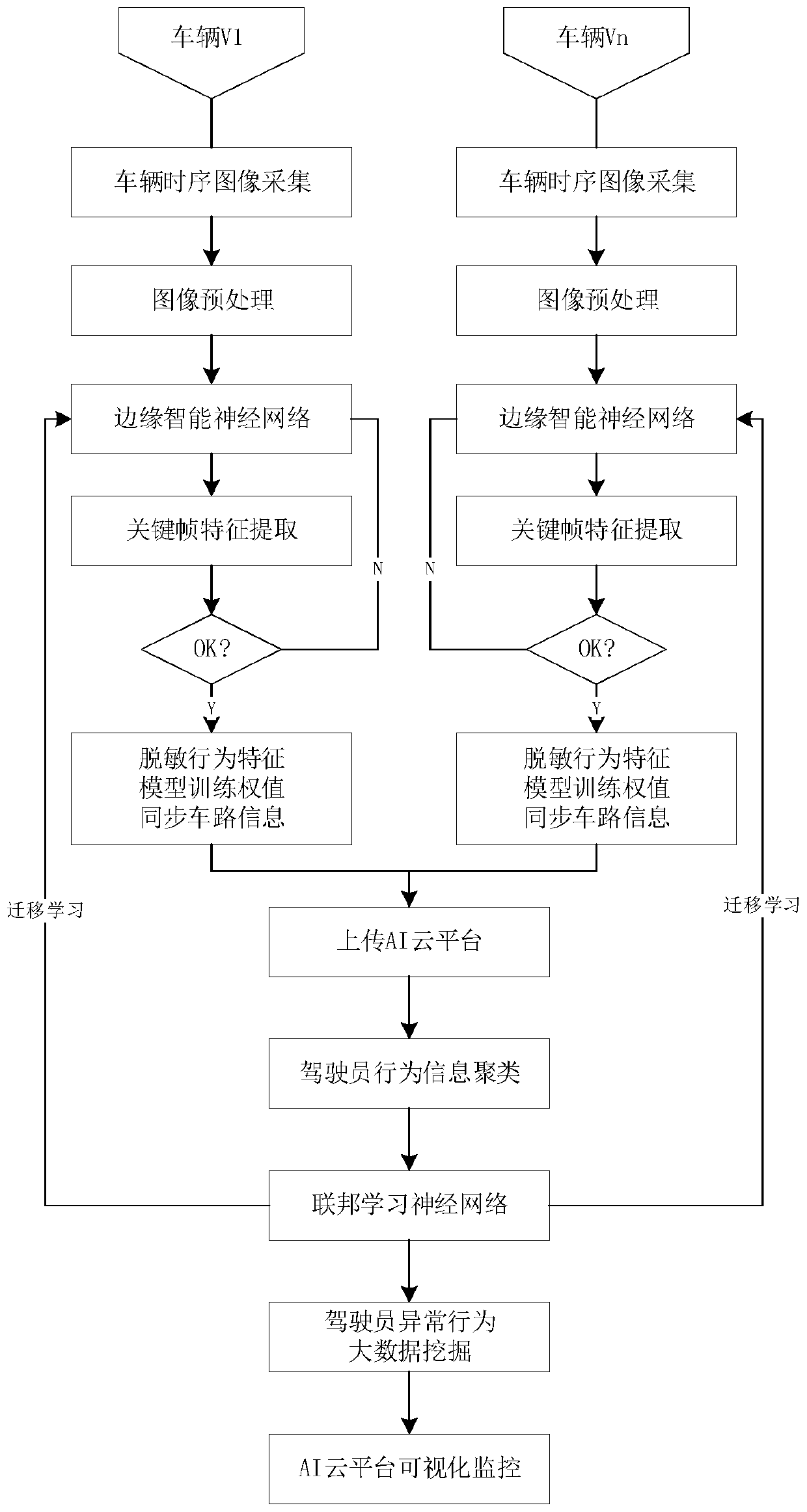
Driver behavior cloud-side collaborative learning system based on federated transfer learning
ActiveCN111476139AGuarantee privacy and securityRealize intelligent interconnectionInternal combustion piston enginesCharacter and pattern recognitionNeural network systemDriver/operator
The invention relates to a driver behavior cloud-side collaborative learning system based on federated transfer learning. The system comprises an AI cloud platform, an intelligent vehicle-mounted terminal, a deep neural network system for federated transfer learning and the like. The deep neural network system comprises a vehicle-mounted end neural network and a platform end neural network, and can realize federated model training and learning migration of non-original data transmission between the vehicle-mounted end neural network and the platform end neural network based on an AI cloud platform and intelligent vehicle-mounted terminals of a plurality of vehicles connected with the AI cloud platform. The method is used for intelligent automobile driver behavior perception and intention understanding, and compared with the prior art, the driver collaborative perception machine learning problem of a large-scale vehicle cluster is solved, and meanwhile driver privacy is protected.
Owner:TONGJI UNIV
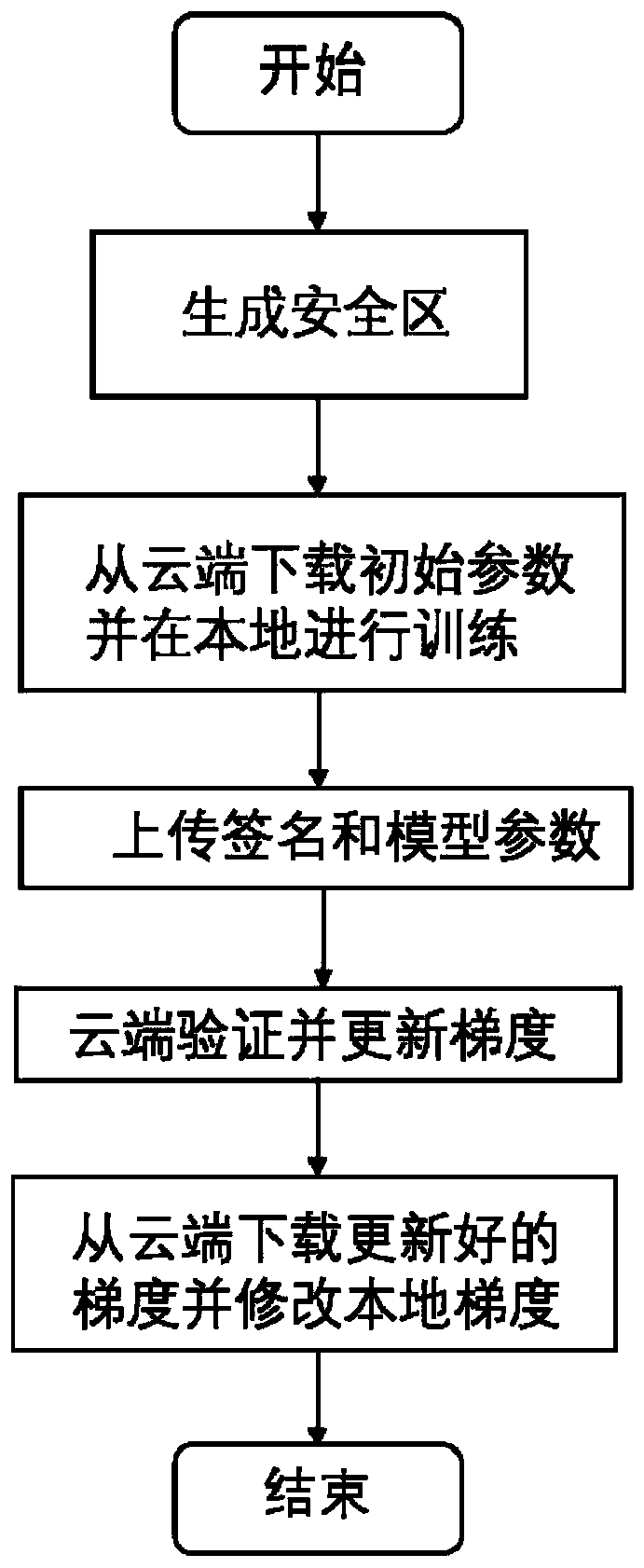
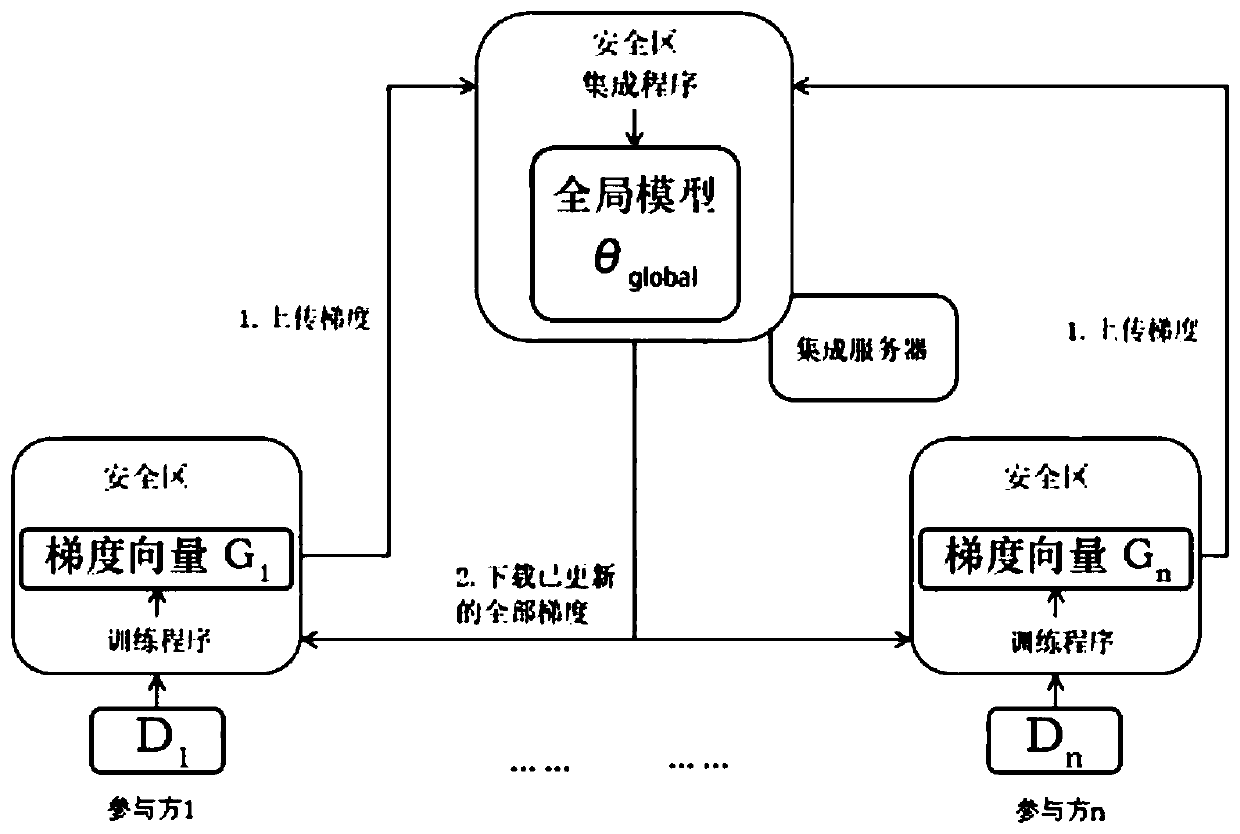
Federated learning method based on trusted execution environment
ActiveCN111241580AEnsure correct execution of the training algorithmGuarantee privacy and securityUser identity/authority verificationDigital data protectionData setDigital signature
The invention belongs to the field of data security, and discloses a federated learning method based on a trusted execution environment, which comprises the following steps: generating a security areabased on the trusted execution environment; downloading the initialized model parameters from the cloud by a local user; loading the training algorithm, the training data set, the training data example number and the initialized model parameters returned by the cloud into a security area; obtaining a trained model parameter gradient and generating a digital signature, performing local user identity authentication through a group signature algorithm, and uploading the trained model parameter gradient, a model integration algorithm and the local user identity authentication to a cloud; and enabling the cloud to verify the local user identity authentication, obtain the uploaded model parameter gradient and model integration algorithm after successful verification, placing the model parametergradient and model integration algorithm in a cloud security area, integrating the model, and updating the model parameter gradient. According to the invention, the trusted execution environment is used to generate the security area, the user cannot bypass the training process to directly give the training result, and the training integrity and the user privacy protection are realized.
Owner:GUANGZHOU UNIVERSITY
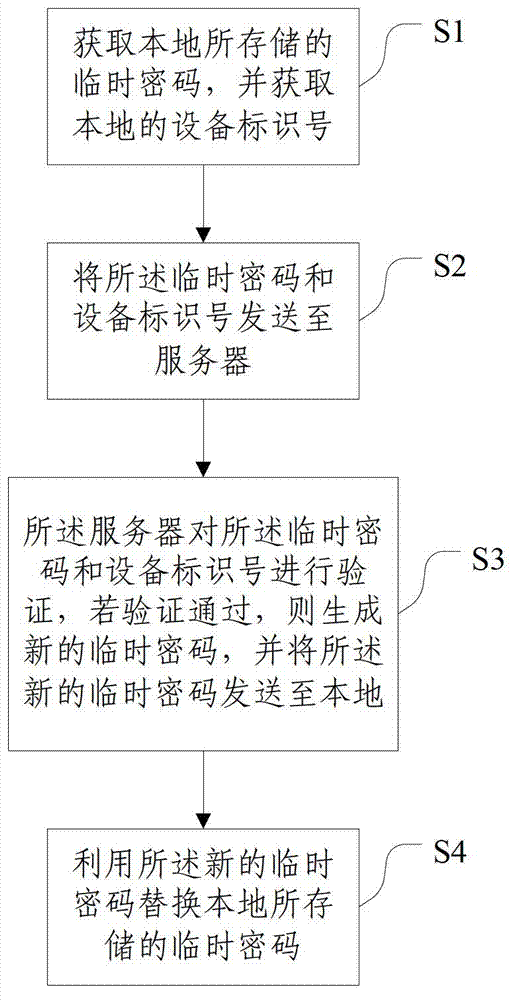
Client-side password storage method and service system
InactiveCN102769629AImprove securityGuarantee privacy and securityUser identity/authority verificationPasswordNetwork communication
The invention discloses a client-side password storage method and a service system, relating to the technical field of network communication. The method comprises S1: obtaining a temporary password stored in a local area and a local device identification number; S2: transmitting the temporary password and the device identification number to a server; S3: verifying the temporary password and the device identification number by the server, and if the confirmation is successful, generating a new temporary password and transmitting the new temporary password to the local area; and S4: replacing the temporary password stored in local area with the new temporary password. By storing the temporary password, a hacker is unlikely to obtain an original password of a user by attacking the password stored in the client side, therefore the storage safety of the password is increased, and the purposes of protecting privacy and property safety of the user are achieved.
Owner:OPZOON TECH
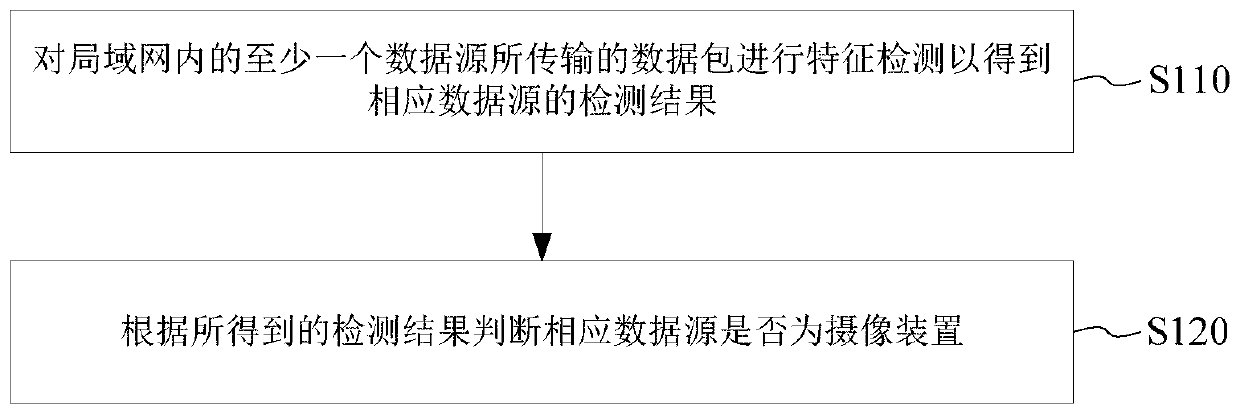
Method for identifying camera device in local area network, data exchange equipment and system
InactiveCN111541892AGuarantee privacy and securityImprove detection efficiencyTelevision systemsData packAnalysis data
The invention discloses a method for identifying a camera device in a local area network, a software system and data exchange equipment. The method comprises the steps of carrying out the feature detection of a data package transmitted by at least one data source in the local area network, so as to obtain a detection result of the corresponding data source, judging whether the corresponding data source is a camera device or not according to the obtained detection result, or sending the to-be-detected information containing the detection result to an analysis system, so that the analysis systemjudges whether a corresponding data source in the local area network is a camera device or not according to the obtained detection information. According to the method, the data packet transmitted bythe data exchange equipment in the local area network of the hotel is monitored, and the video data characteristics in the data packet are analyzed to determine the legality of the corresponding camera device, so that the leakage of the video data shot by the illegal camera device is avoided, and the privacy security of check-in users of the hotel is guaranteed.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
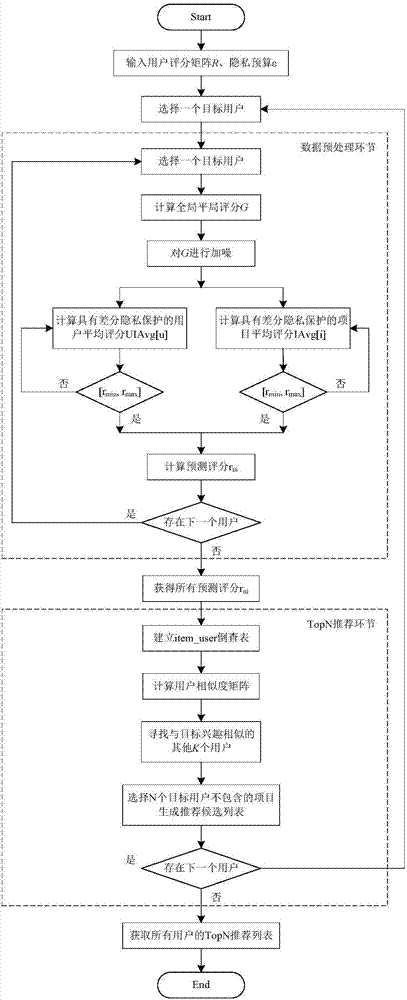
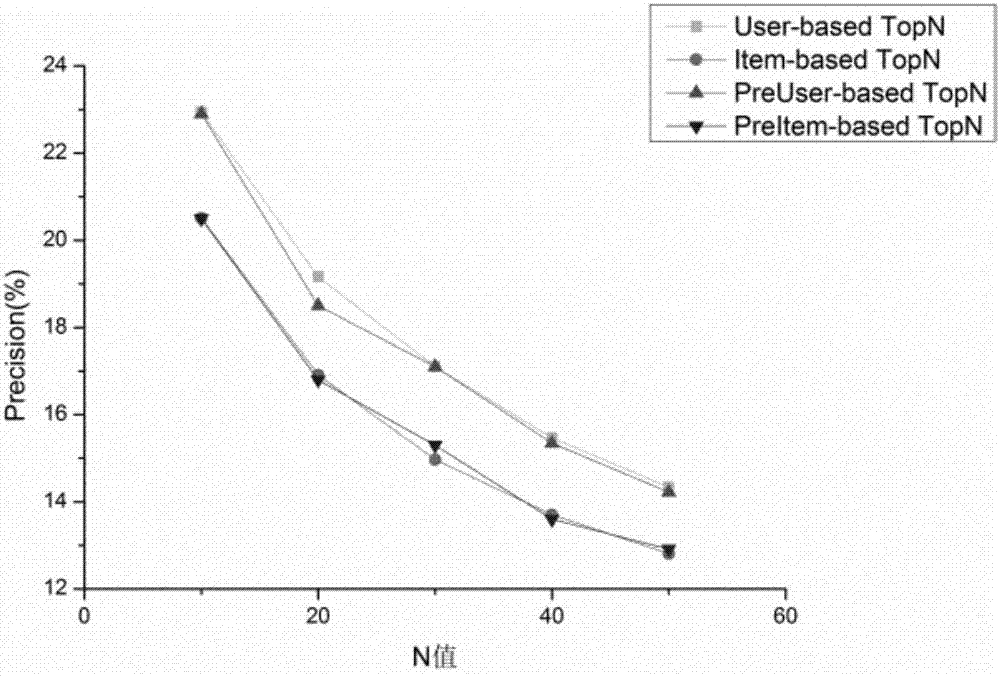
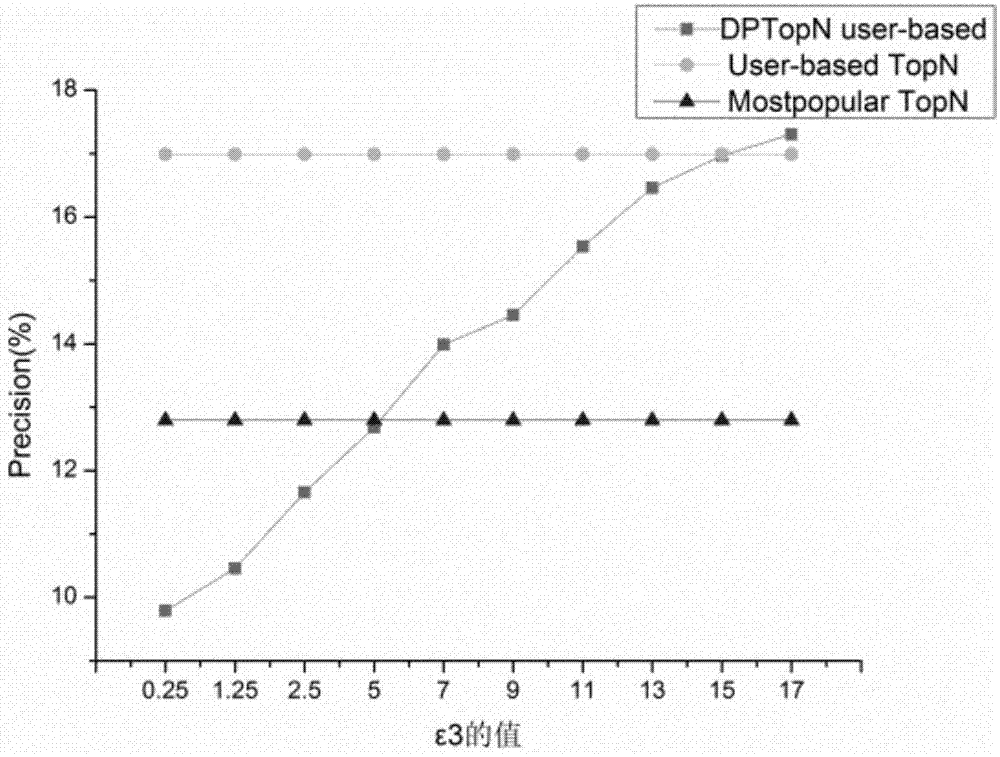
TopN collaborative filtering recommendation method based on differential privacy
InactiveCN107491557APrivacy protectionProtect raw scoring dataData processing applicationsSpecial data processing applicationsCosine similarityData set
The invention discloses a TopN collaborative filtering recommendation method based on differential privacy and relates to the technical fields of differential privacy technologies and collaborative recommendation. According to the method, Laplace noise is reasonably added to original input data Rm*n firstly to obtain user grading records (shown in the description) after disturbance, and then cosine similarity is utilized to calculate the similarity between a target user and other users. On one hand, the records meet an epsilon-differential privacy protection model by adding the Laplace noise to original user grading records, it is ensured that the records have higher availability while the privacy security of issued data sets is guaranteed, and original grading data of users is effectively protected; on the other hand, improvement starts from a recommendation algorithm itself, the problem that an existing TopN recommendation model leaks the privacy of the users is solved, attackers are prevented from speculating their browsing histories according to a recommendation list of the target user so as to obtain personal preferences of the users, and accurate recommendation can be provided for the users while the privacy of the users is protected.
Owner:XUZHOU MEDICAL UNIV
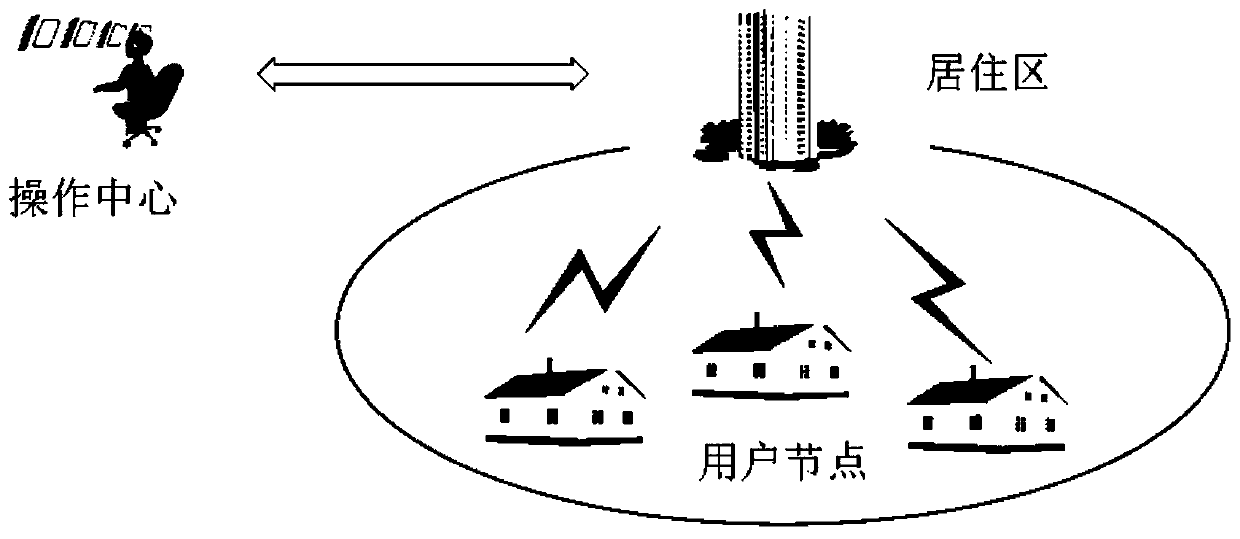
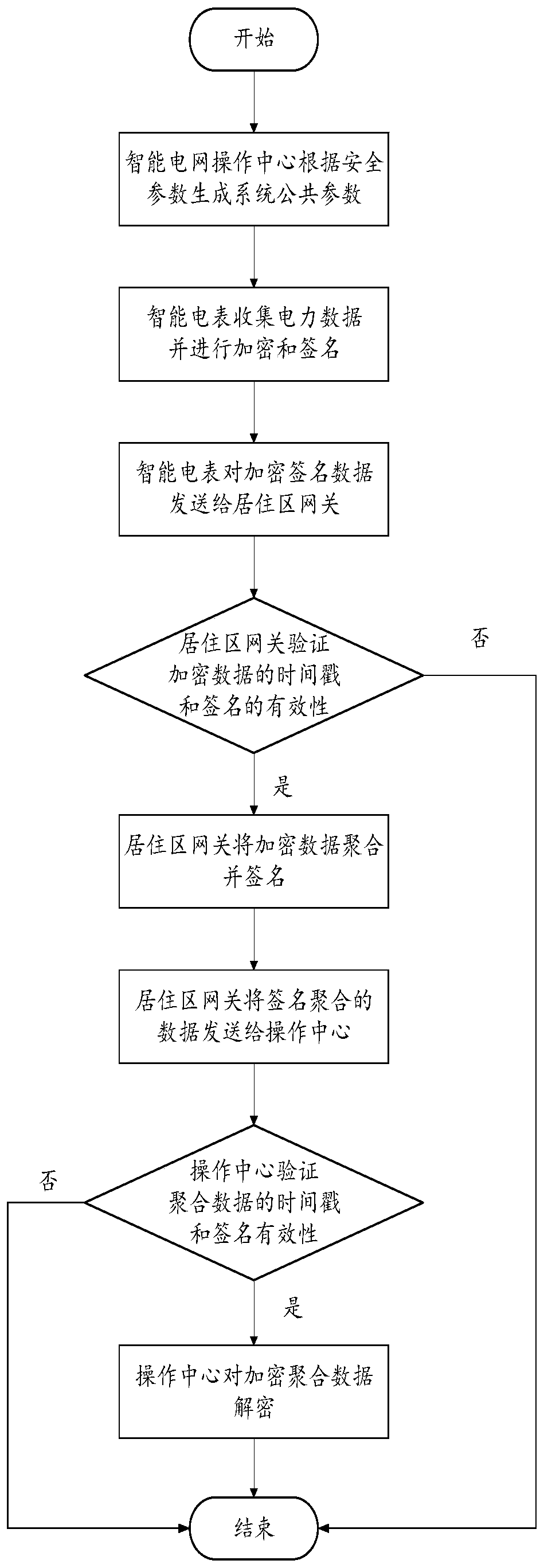
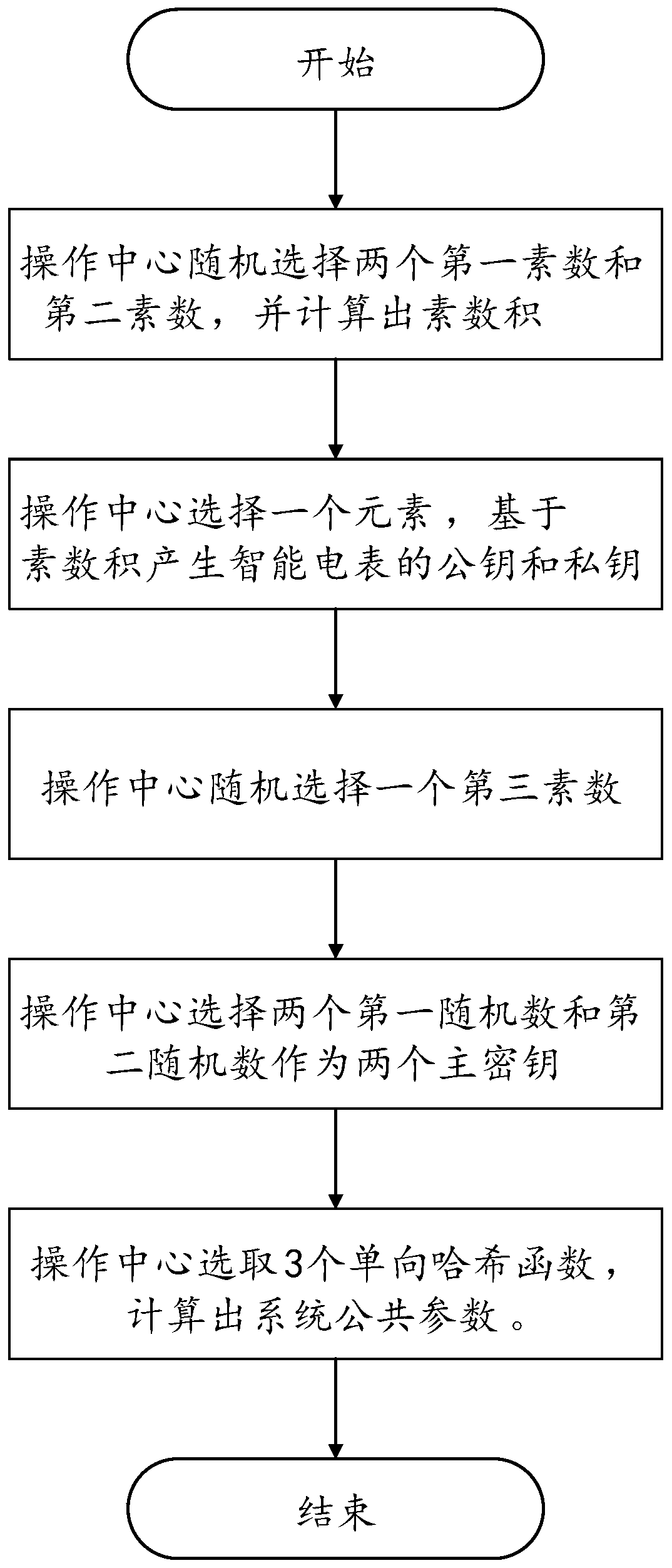
Anonymous authentication method and system based on tamper-proof equipment in intelligent power grid
ActiveCN111385306AGuarantee privacy and securityImprove securityUser identity/authority verificationCommunication with homomorphic encryptionTimestampCiphertext
The invention belongs to the field of power data security transmission in an intelligent power grid environment, and particularly relates to an anonymous authentication method and an anonymous authentication system based on tamper-proof equipment in a intelligent power grid. The anonymous authentication method comprises the steps that: an operation center of the intelligent power grid generates system public parameters according to safety parameters and distributes the system public parameters to intelligent electric meters and residential district gateways; the intelligent electric meter collects real-time electric power data, encrypts the electric power data by adopting an addition homomorphic encryption algorithm, signs the electric power data by using a private key of the intelligent electric meter, and sends a signed electric power data ciphertext to the residential district gateway; the residential district gateway authenticates the ciphertext after receiving the ciphertext, performs privacy protection aggregation on the ciphertext if the authentication succeeds, and sends an aggregated ciphertext signature to the operation center; and the operation center verifies the validity of a timestamp and a signature of the operation center, if the verification is valid, the aggregated ciphertext is decrypted by adopting the private key, and a plaintext message of the power data is obtained. According to the anonymous authentication method and the anonymous authentication system, the safety of the intelligent power grid system is greatly improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
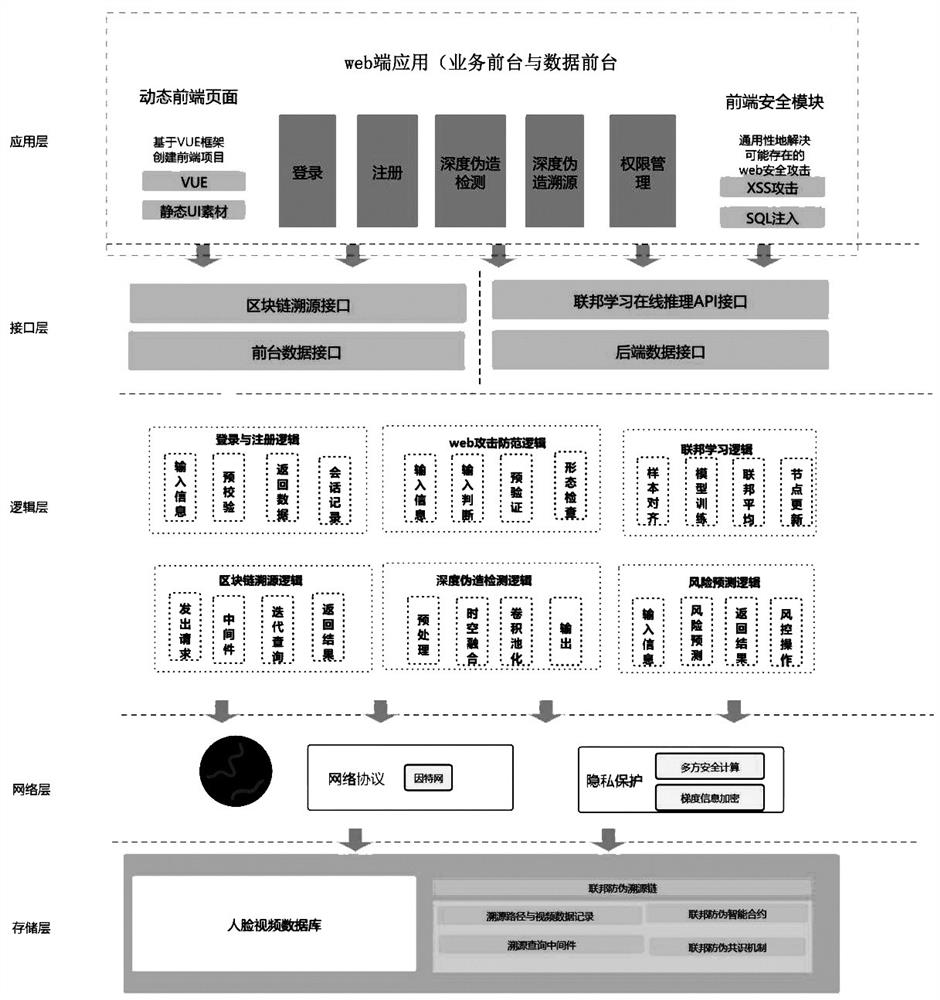
Deepfake traceability system based on big data federated learning architecture
ActiveCN113723220AImprove detection accuracyMaintain progressive relationshipCharacter and pattern recognitionNeural architecturesEngineeringLearning architecture
The invention discloses a deepfake traceability system based on a big data federated learning architecture. The system comprises: an application layer, an interface layer, a logic layer, a network layer, and a storage layer which are connected in sequence; the application layer is used for providing a deepfake traceability service for a user and obtaining user login and uploading data; the interface layer is used for providing interface service and realizing communication between a server side and a web side; the logic layer is used for dividing system functions and designing an algorithm to construct a model to realize system function logics; the network layer is used for carrying out parameter exchange and encrypting gradient information in a modeling process; the storage layer is used for receiving transmitted parameter information and encrypted information and storing the parameter information and the encrypted information in a local database and a blockchain network. According to the system, an overall architecture of federated anti-counterfeiting traceability chains is provided, a federated anti-counterfeiting mechanism, an abnormal traceability mechanism and a risk prediction mechanism are established, Web security threats can be prevented, and the problems of data poisoning and single-point failure for federated learning can be effectively solved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Identity authentication method and device
PendingCN111199032AAvoid distractionsImprove accuracy and robustnessDigital data authenticationMulti modalityEngineering
The invention provides an identity authentication method and device applied to the field of artificial intelligence AI. The invention can be specifically applied to intelligent terminal equipment suchas an intelligent robot for user identity authentication, and comprises the steps of acquiring information of multi-modal biological characteristics of a to-be-recognized user wherein the multi-modalbiological characteristics comprise at least two biological characteristics of the to-be-recognized user; performing identity authentication on the to-be-identified user in parallel according to at least two biological characteristics; and determining an identity authentication result of the to-be-identified user according to an identification result obtained by performing identity authenticationon the to-be-identified user in parallel, with the identity authentication result being obtained based on a confidence coefficient of matching of the multi-modal biological feature and a preset biological feature. According to the technical scheme, interference factors existing in identity authentication through a single biological feature can be effectively avoided, and therefore the robustnessand accuracy of the identity authentication method are improved.
Owner:HUAWEI TECH CO LTD
Multi-energy multilateral distributed transaction method based on blockchain technology
ActiveCN111178632AFair and just transactionEfficient transactionMarket predictionsFinanceConfidentialityTransaction data
The invention discloses a multi-energy multilateral distributed transaction method based on a blockchain technology. The method comprises the following steps: price information is initialized; all market main bodies participating in the transaction determine respective transaction strategies according to the known information, and publish the information to the energy block chain network; each benefit subject games contract price and contract energy; nash equilibrium of the game is achieved through a distributed algorithm, and under the condition of equilibrium price and demand, benefits of all benefit subjects are maximized; the supplier and the demander reach a consensus, sign an intelligent contract, record transaction information in the blockchain and publish the transaction information in the network; the transaction is executed; and value transfer and ending the transaction are completed. According to the method, multilateral transaction and energy transmission between a plurality of comprehensive energy service providers and a plurality of load aggregators in a region are realized, the problem of coordination and complementation of multiple energies is solved, fair, efficient, flexible and safe energy transaction of multi-party subjects is satisfied, and the confidentiality and reliability of transaction data are ensured.
Owner:SOUTHEAST UNIV
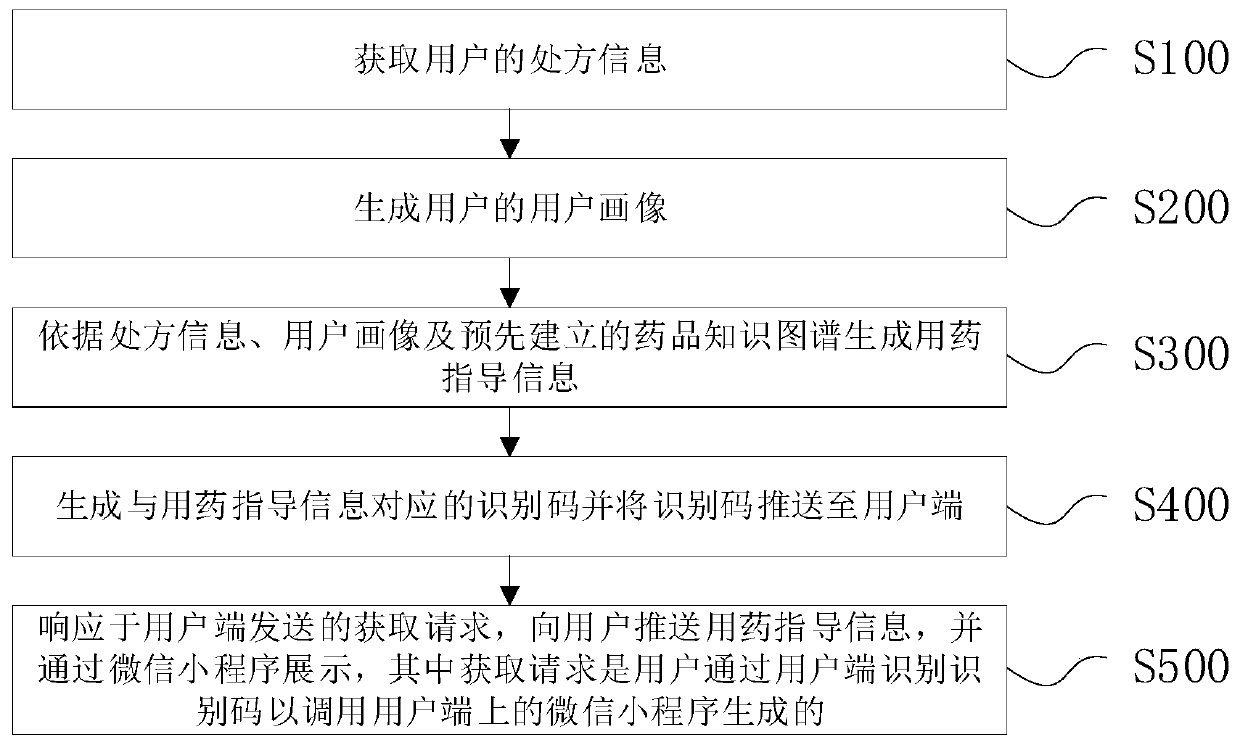
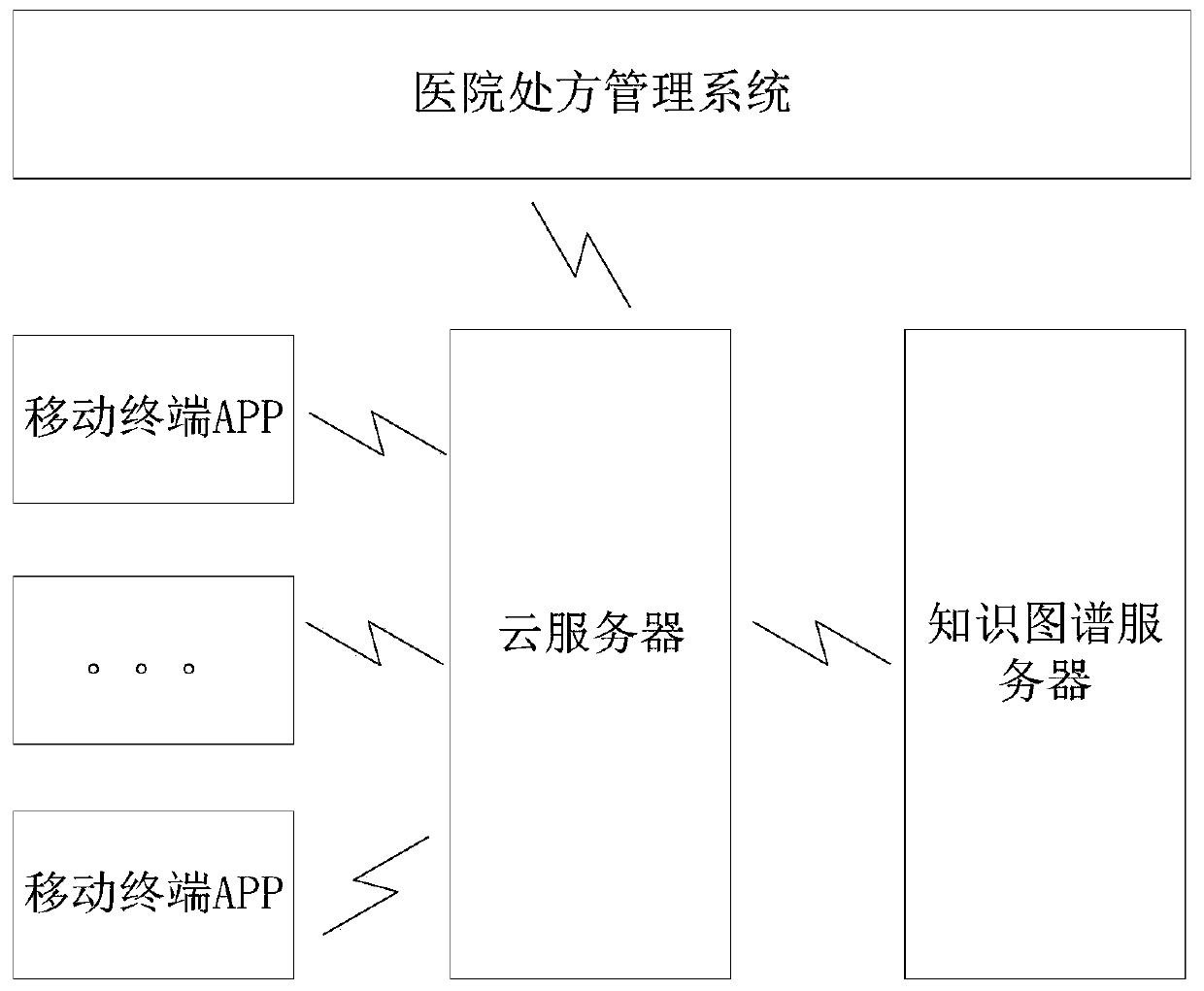
WeChat-applet-based medication guidance pushing method, device and equipment
InactiveCN111199784AGuarantee privacy and securityPrevent grabbingDrug and medicationsDigital data protectionDrug utilisationEngineering
The embodiment of the invention provides a WeChat-applet-based medication guidance pushing method, device and equipment and belongs to the technical field of medical artificial intelligence. The method comprises the steps: obtaining prescription information of a user; generating a user portrait of the user; generating medication guidance information according to the prescription information, a user portrait and a pre-established medicine knowledge graph; generating an identification code corresponding to the medication guidance information and pushing the identification code to a user side; and in response to an acquisition request sent by the user side, pushing medication guidance information to the user, and displaying the medication guidance information through a WeChat applet. The medication guidance information is generated for the user based on the user prescription information, the user portrait and the drug knowledge graph and pushed to the user in a WeChat applet mode, so thatthe problems that the existing user cannot accurately obtain the medication guidance, the network search recommendation range is too large, and the accuracy is low are effectively solved.
Owner:北京左医健康技术有限公司
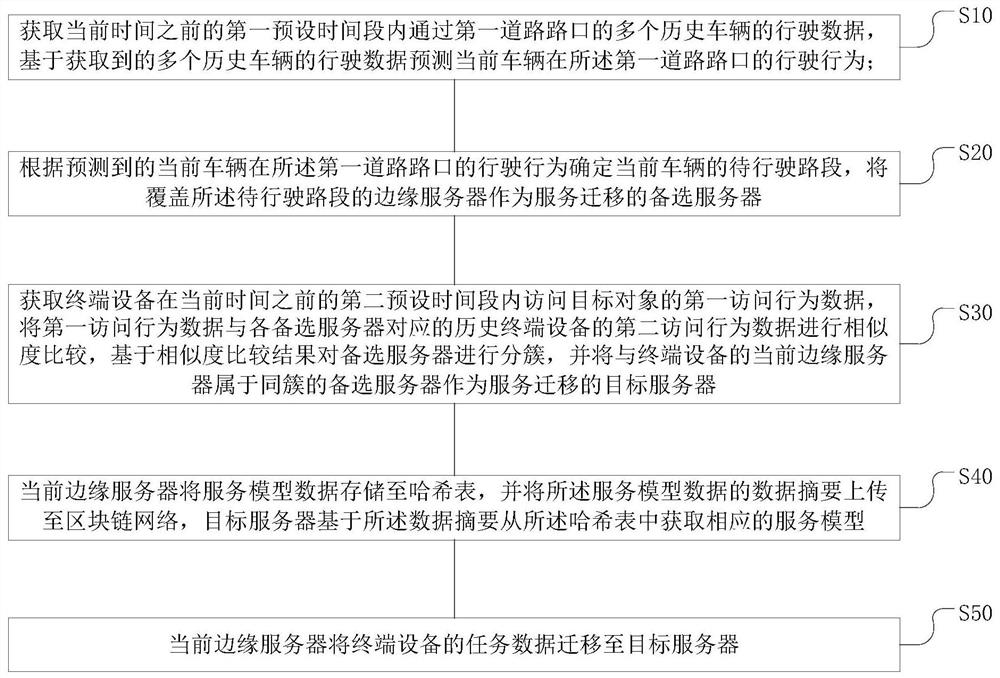
Vehicle terminal service migration method and system
ActiveCN113377743AImprove service experienceGuarantee privacy and securityDatabase distribution/replicationSpecial data processing applicationsEdge serverSimulation
The invention provides a vehicle terminal service migration method and system, and the method comprises the steps of obtaining the driving data of a plurality of historical vehicles passing through a first road intersection in a first preset time period, and predicting the driving behavior of a current vehicle at the first road intersection based on the obtained driving data; determining a to-be-driven road section of the current vehicle according to the predicted driving behavior, and taking an edge server covering the to-be-driven road section as an alternative server for service migration; obtaining first access behavior data of the terminal equipment, performing similarity comparison on the first access behavior data and second access behavior data of historical terminal equipment corresponding to each alternative server, clustering the alternative servers based on a comparison result, and taking the alternative server belonging to the same cluster as the current edge server as a target server; enabling the current edge server to store the service model data to a hash table, and enabling the target server to obtain a corresponding service model from the hash table; and enabling the current edge server to migrate the task data to the target server.
Owner:BEIJING UNIV OF POSTS & TELECOMM
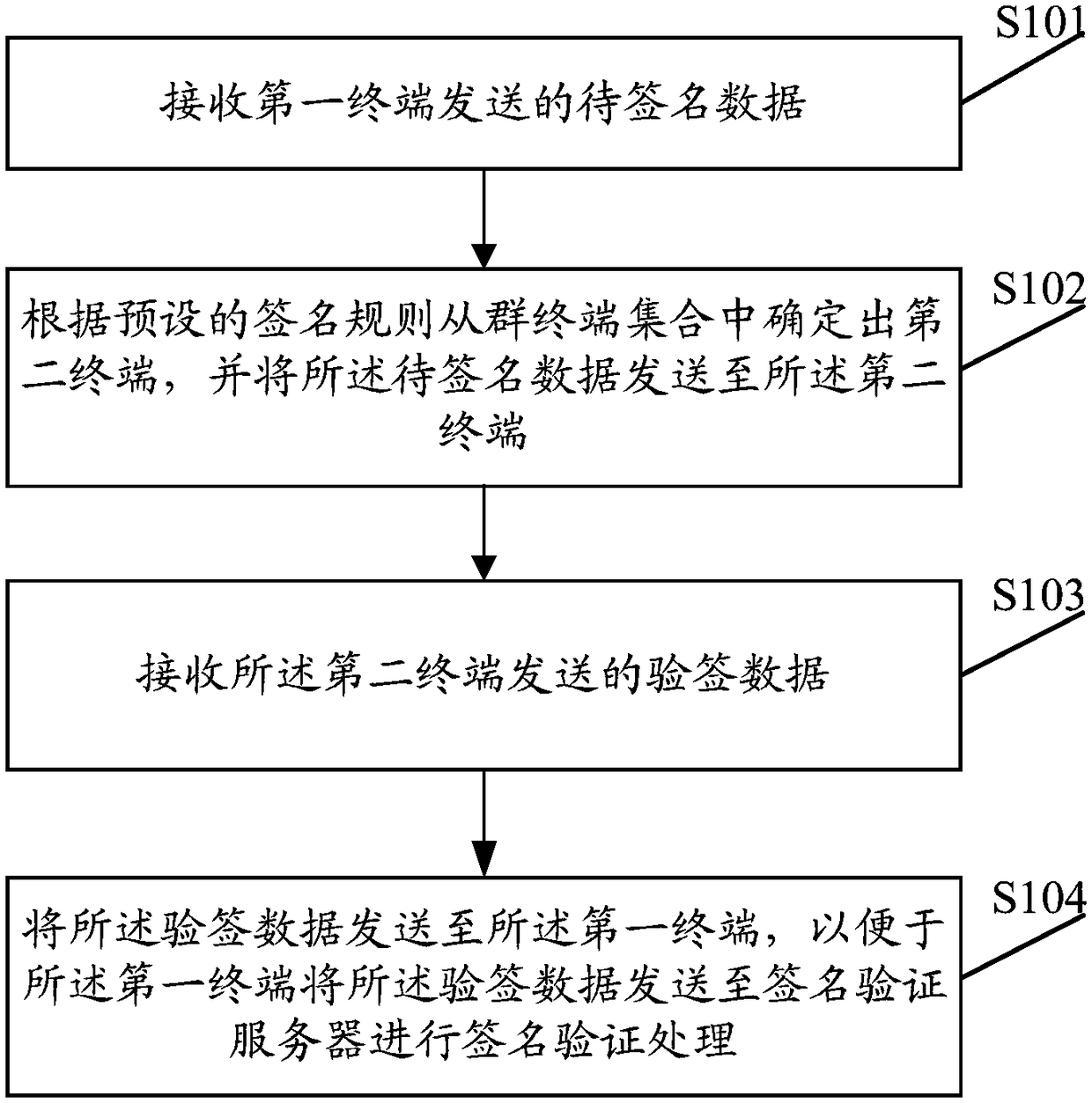
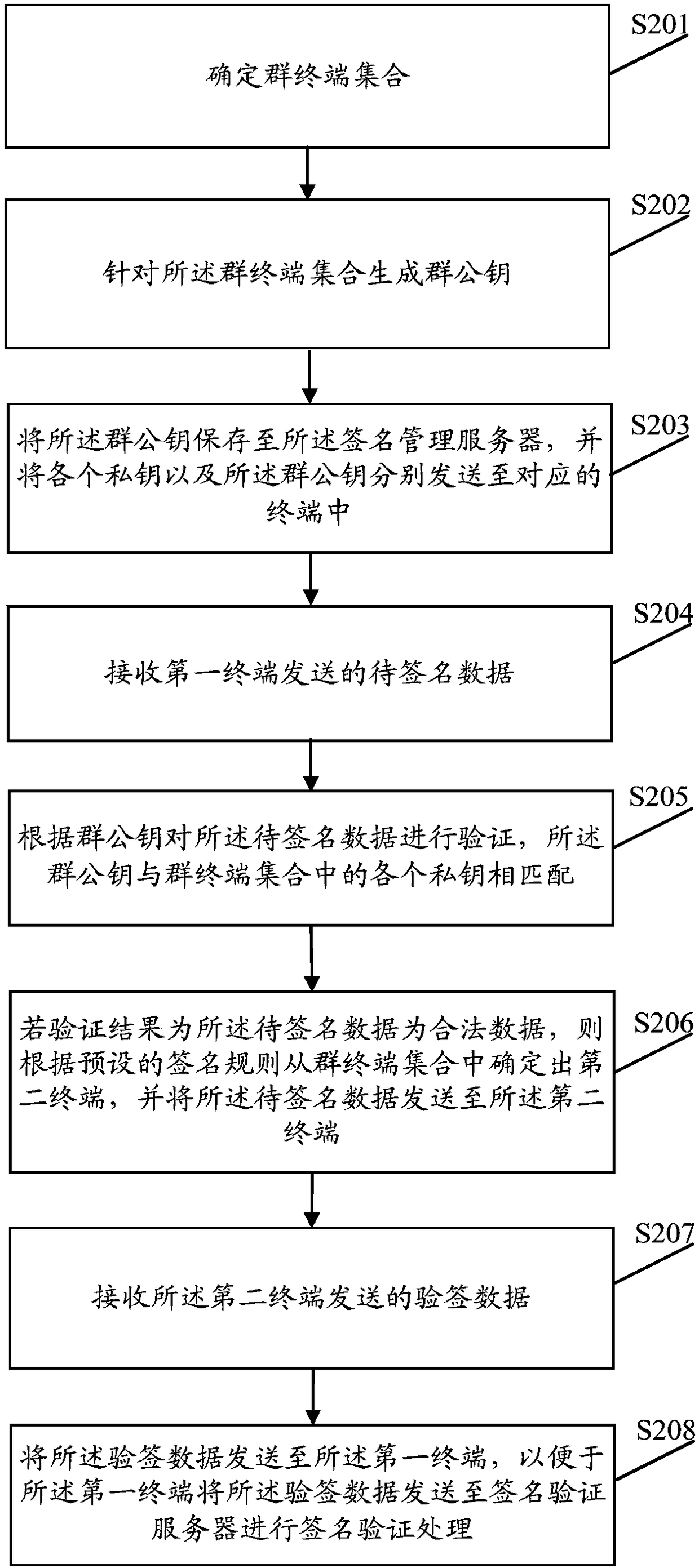
Signature authentication method, related device, and computer-readable storage medium
InactiveCN108289028AGuarantee privacy and securityUser identity/authority verificationAuthenticationComputer terminal
The embodiment of the invention discloses a signature authentication method, a related device, and a computer-readable storage medium, wherein the method includes: receiving to-be-signed data sent bya first terminal, wherein the first terminal is a terminal that initiates a signature verification behavior; determining a second terminal from a group terminal set according to a preset signature rule, and sending the to-be-signed data to the second terminal; receiving the signature verification data sent by the second terminal, wherein the signature verification data is the to-be-signed data signed by second terminal according to the private key of the second terminal; sending the signature verification data to the first terminal so that the first terminal sends the signature verification data to a signature verification server for signature verification. The signature authentication method can effectively protect the privacy of the terminal.
Owner:SHENZHEN GIONEE COMM EQUIP
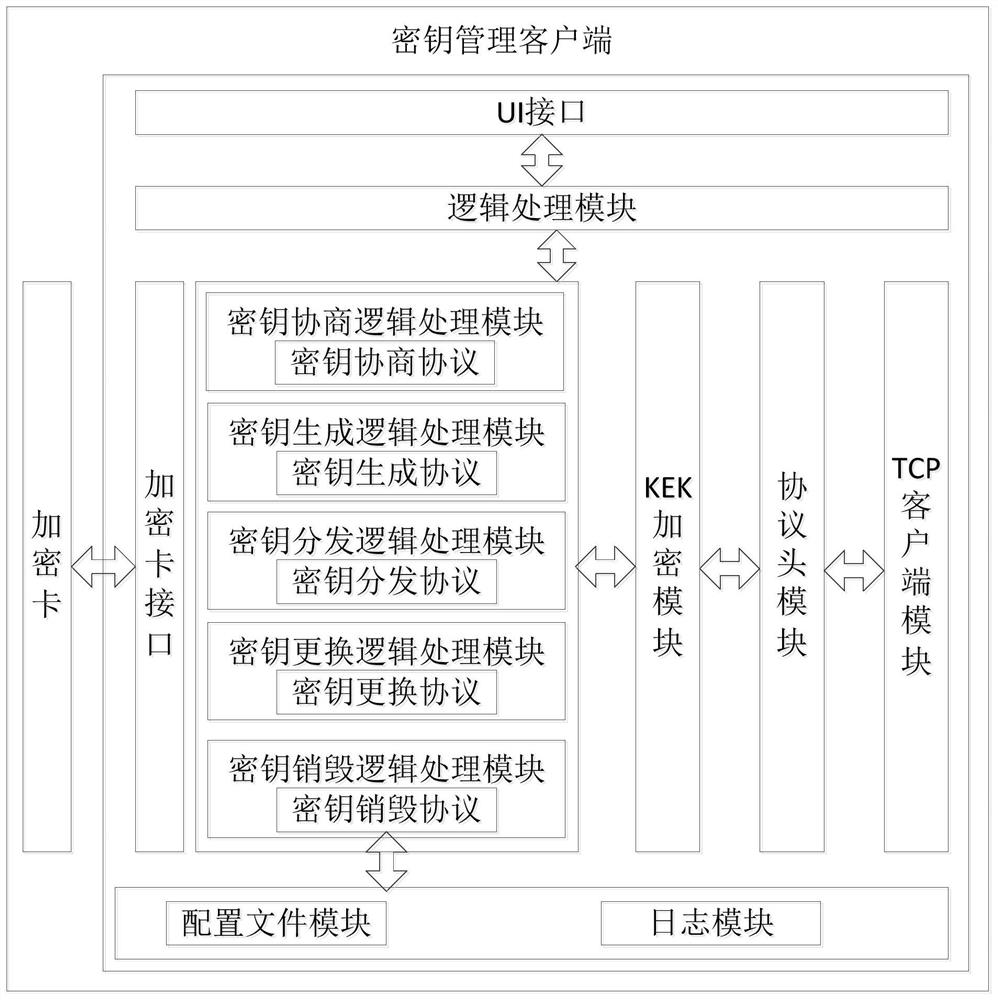
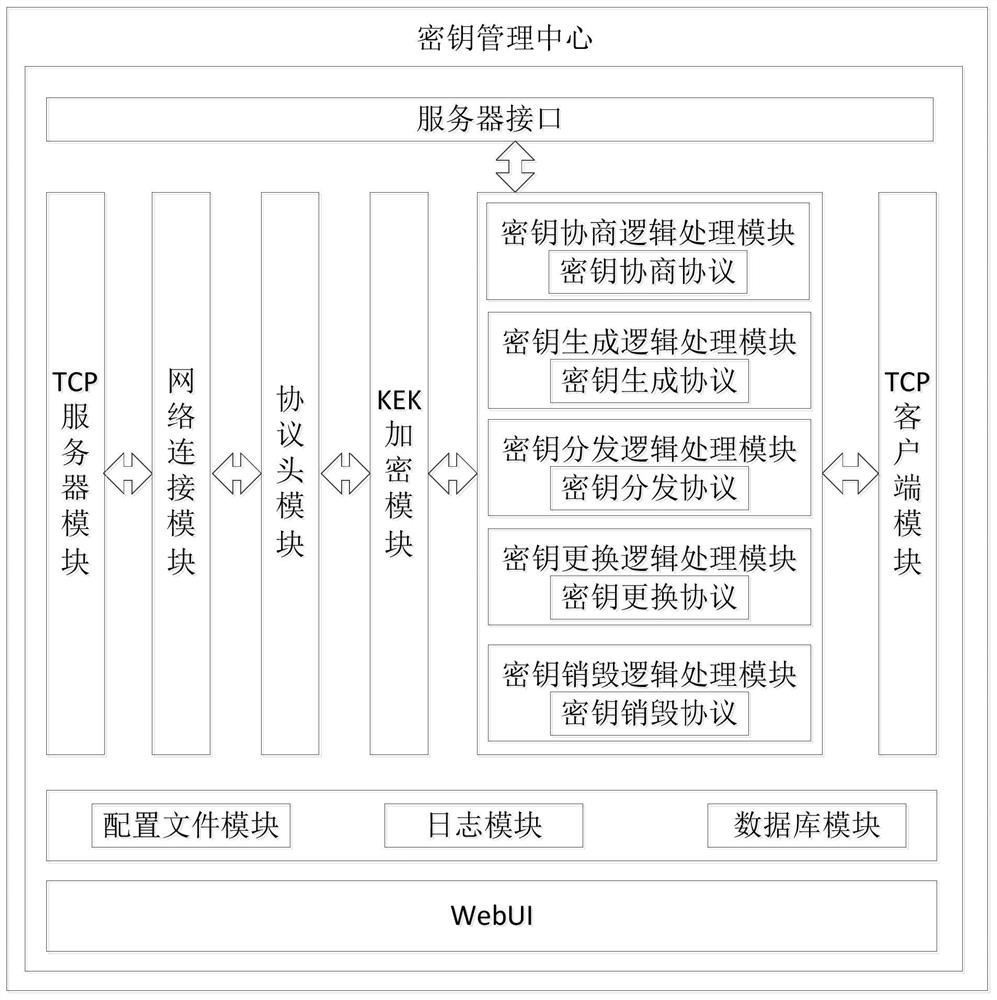
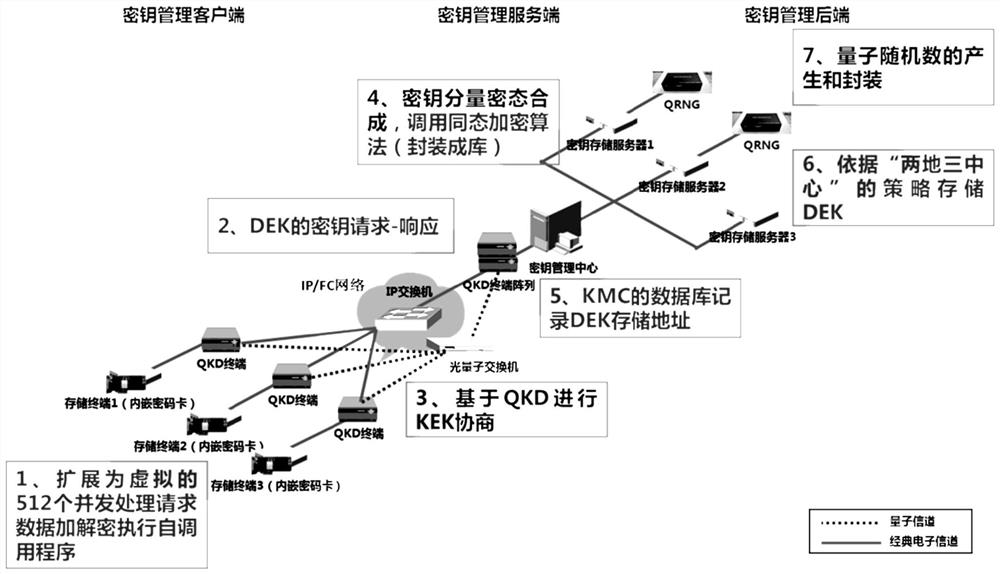
Secure storage-oriented key management protocol design method and system
ActiveCN112800439AGuarantee privacy and securityImprove production efficiencyDigital data protectionDigital data authenticationResource poolProtocol design
The invention discloses a secret key management protocol design method and system oriented to secure storage. The method comprises the steps: constructing a secret key request message through a secret key management client, transmitting the secret key request message to a secret key management center, receiving and analyzing a response message of the secret key management center, and providing a processing result of the request message for an application program; when the key management client obtains the key, the key is loaded into the password card to realize password operation; centralized password management is provided through a key management center, services which comprises key registration, query and revocation are provided, a key resource pool is partitioned, configured and managed, and administrator access, log recording and audit tracking are provided; secret keys are respectively generated and stored through a secret key generator and a secret key storage center in the secret key resource pool. According to the invention, the safety of the whole life cycle of key generation, distribution, storage, updating and destruction in the storage environment can be ensured.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
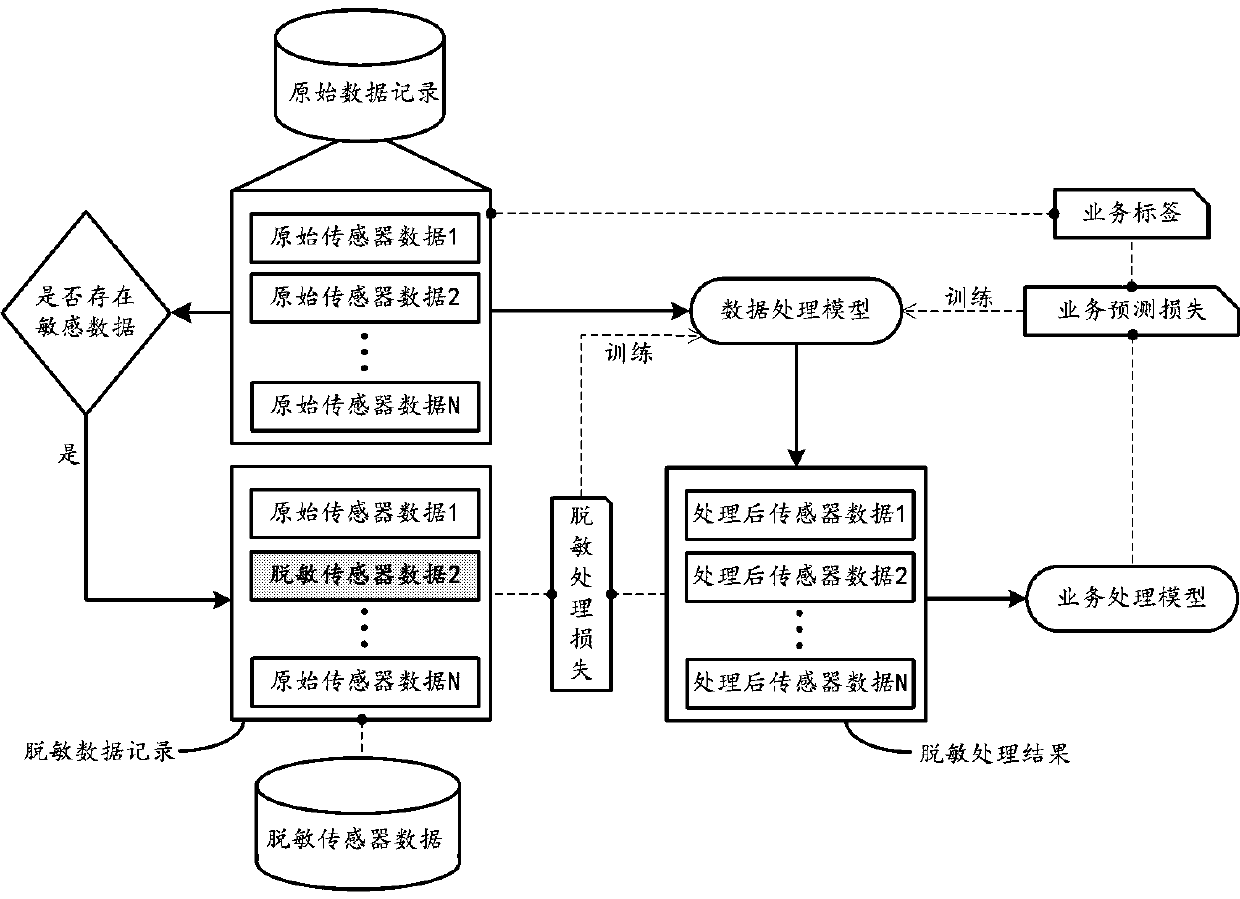
Data processing method and device for realizing privacy protection
ActiveCN111475855APrevent leakageGuarantee privacy and securityDigital data protectionPrivacy protectionEngineering
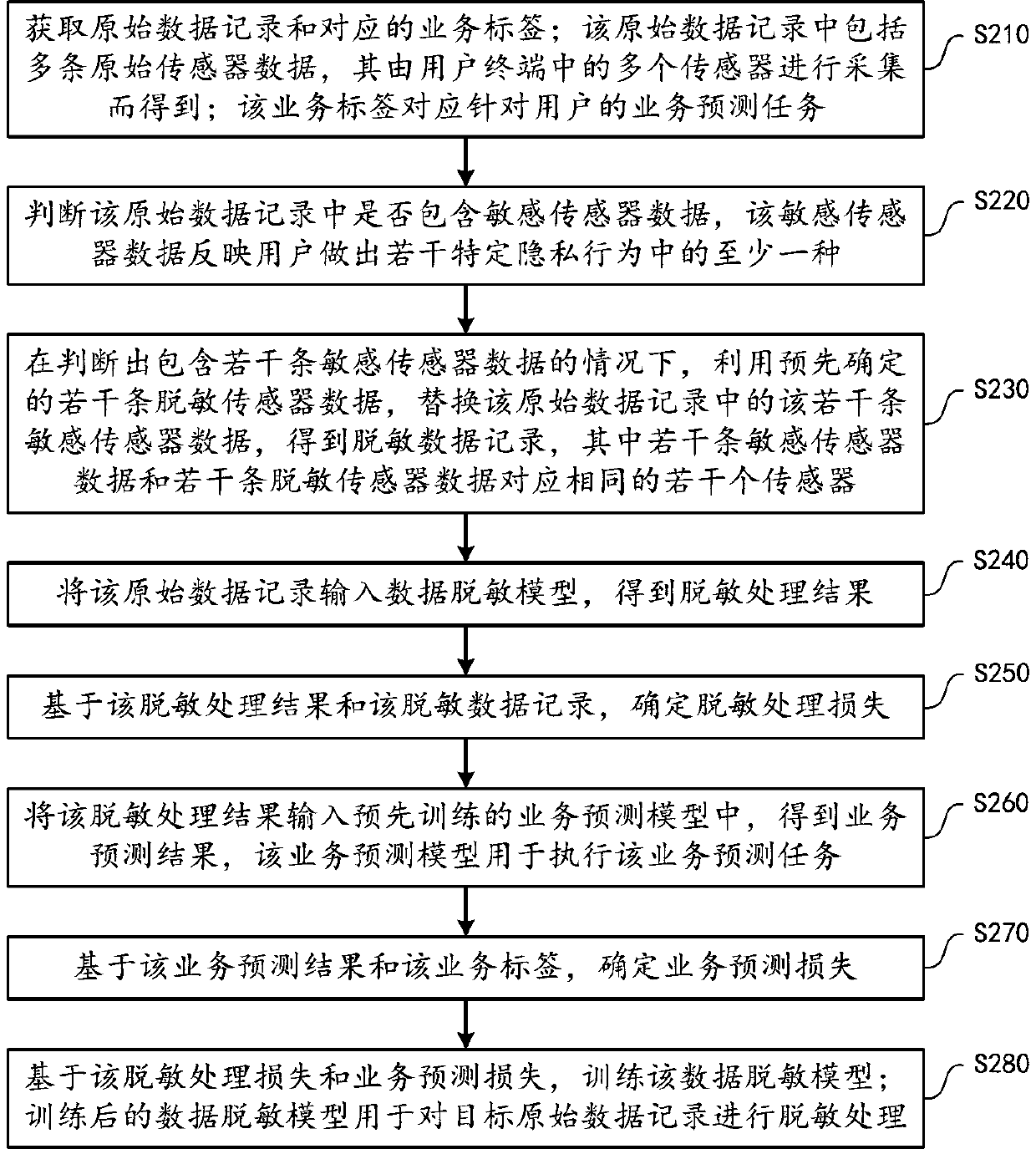
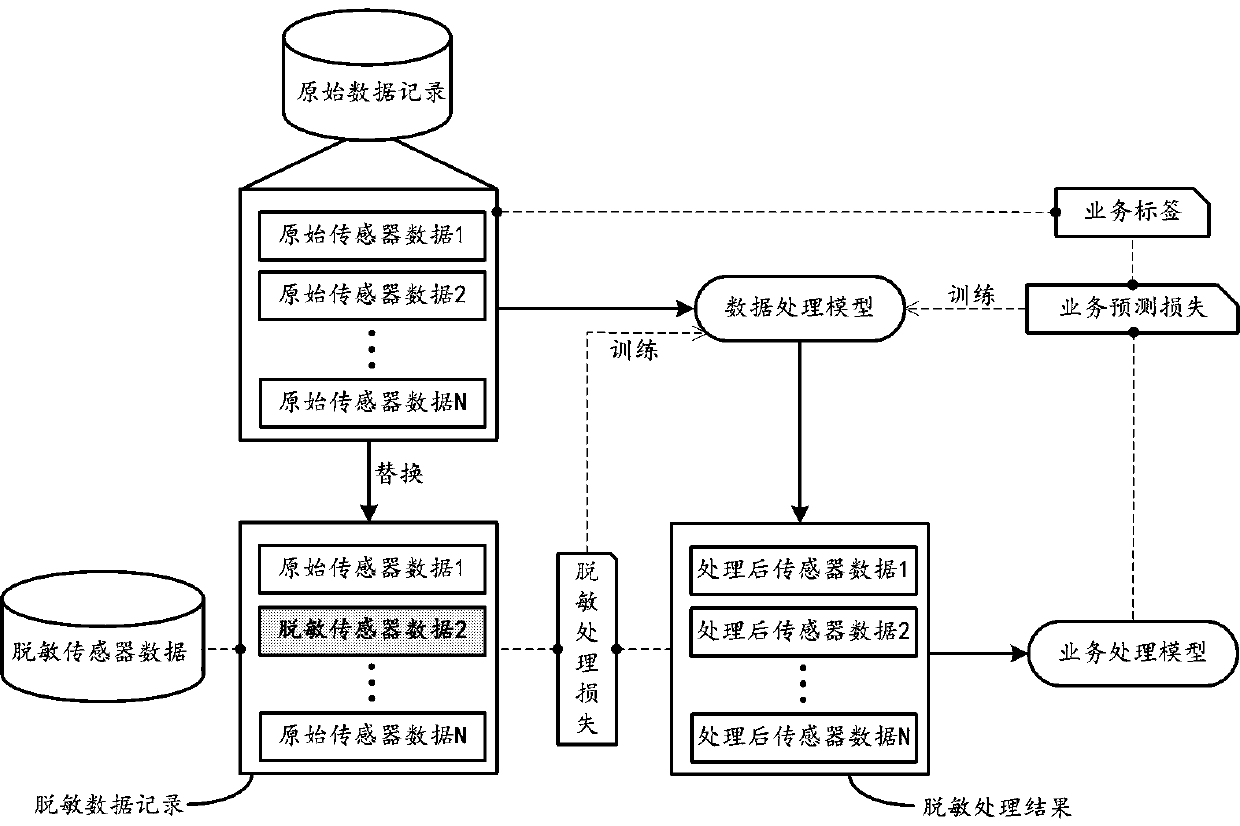
The embodiment of the invention provides a data processing method for realizing privacy protection, which comprises the following steps of: firstly obtaining a plurality of pieces of original sensor data collected by a plurality of terminal sensors to form an original data record, and obtaining a corresponding service label for a user; then, judging whether the original data record contains sensitive sensor data for reflecting a specific privacy behavior of the user or not; if yes, performing corresponding local replacement by utilizing neutral data to obtain a desensitized data record, and inputting the original data record into a data desensitization model to obtain a desensitization processing result; further, on one hand, based on the desensitization processing result and the desensitized data record, determining desensitization processing loss, and on the other hand, inputting the desensitization processing result into a pre-trained service prediction model to obtain a service prediction result, and determining service prediction loss according to the service prediction result and the service label; and training the data desensitization model based on the desensitization processing loss and the service prediction loss.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Graph data publishing privacy protection cluster anonymity method and system
InactiveCN109002468AGuarantee privacy and securityProtection attribute informationData switching networksSpecial data processing applicationsSocial graphPrivacy protection
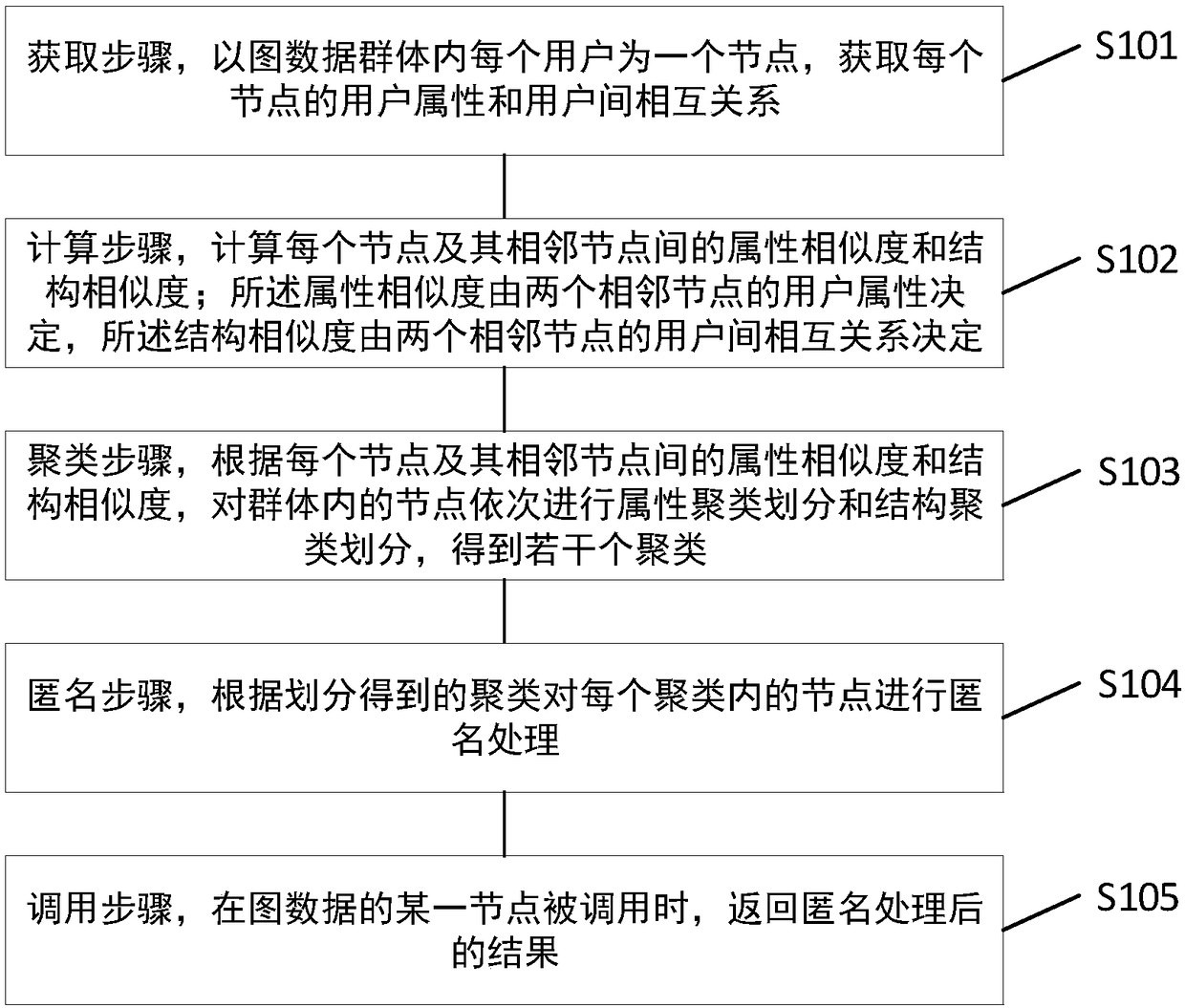
The invention discloses a graph data publishing privacy protection cluster anonymity method and system. With each user in a graph data group as one node, the user attributes and user-to-user relationships for each node are obtained; based on the same, the attribute similarity and structure similarity between each node and its neighboring nodes are calculated, and then the nodes in the group are subjected to attribute cluster division and structure cluster division in turn according to the calculation results to obtain multiple clusters; and the nodes in each cluster are treated anonymously according to the clusters obtained from the division. The invention applies cluster analysis technology to privacy protection of graph data release; firstly, the structure similarity and attribute similarity between nodes are calculated, graph attribute cluster division and graph structure cluster division performed in turn, and finally each cluster is processed anonymously, which can protect the attribute information and structure information of users at the same time and prevent all attacks with connecting edges and attribute values as background knowledge, so as to protect the privacy and security of social network graph data publishing.
Owner:ZHEJIANG JIESHANG ARTIFICIAL INTELLIGENCE RES & DEV CO LTD
Network security detection system
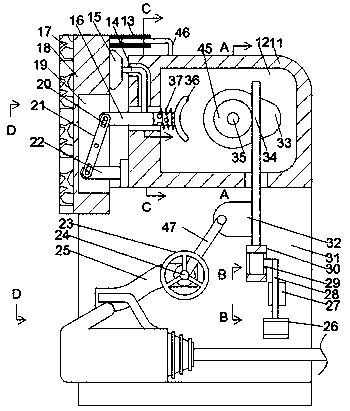
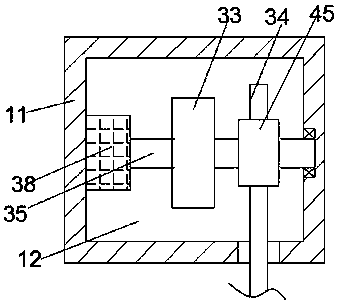
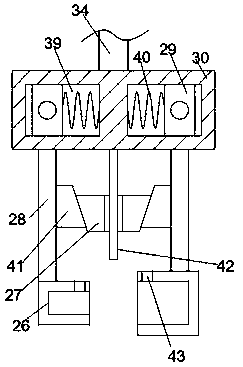
InactiveCN110110558AGuarantee privacy and securitySimple structureInternal/peripheral component protectionButt jointEngineering
The invention discloses a network security detection system. The network security detection system comprises a separating box, a track frame is fixedly connected to the end face of the lower side of the separating box, a butt joint groove which is through left and right is formed in the track frame, an unbuckling device capable of pressing a crystal head of a network cable is arranged in the buttjoint groove, a transmission cavity is formed in the separating box, and a lifting rod is slidably connected to the inner wall of the bottom end of the transmission cavity. According to the network security detection system, the buckling part of the crystal head can be removed, the network cable can be clamped, and the capacity of strongly limiting the displacement of the network cable is lost through the compensation of the air pressure difference value in the adsorption structure. The system is pushed to move towards the side far away from the case, and the network cable plug is horizontallypulled out, so that a computer is directly disconnected from the network.
Owner:嘉兴怀莲电子科技有限公司
An Internet of Things communication flow analysis method based on Android VPNService
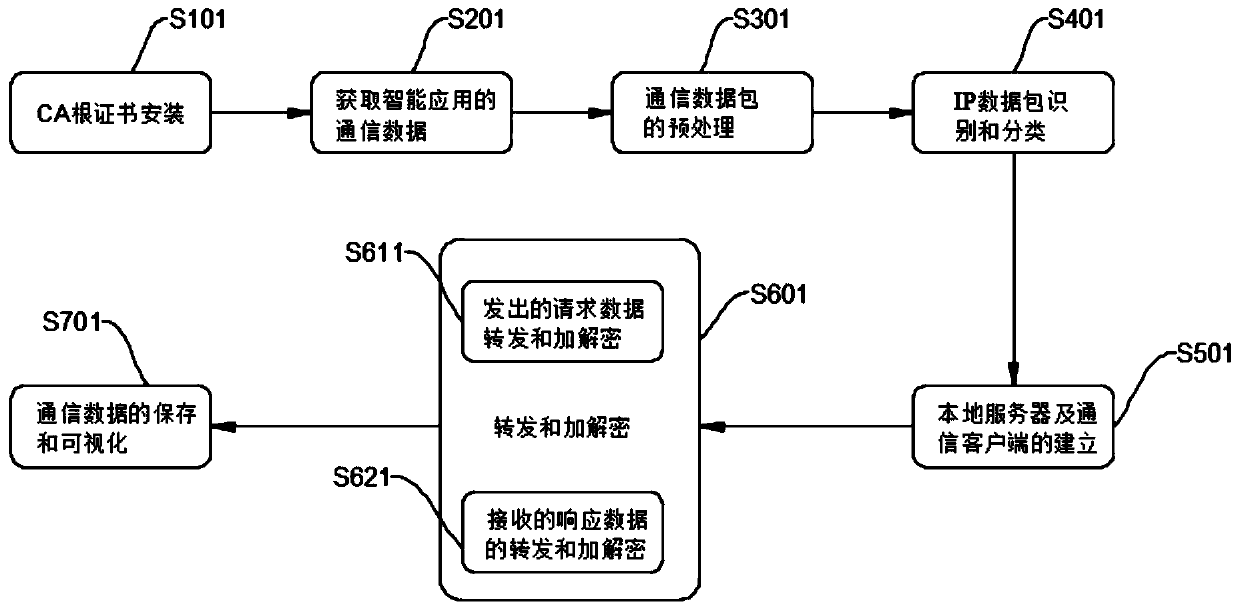
InactiveCN109729099AAvoid decryptionFacilitate analytical certificationNetworks interconnectionTraffic capacityRoot certificate
The invention discloses an Internet of Things communication traffic analysis method based on Android VPNService, relates to the technical field of Internet of Things security, and mainly aims to solvethe problem that security vulnerabilities of specific implementation of communication protocols cannot be analyzed. The analysis method comprises the following steps: CA root certificate installation: installing and creating a CA root certificate on an Android mobile phone end; Acquiring communication data of the intelligent application; Preprocessing the communication data packet; Establishing alocal server and a communication client; Forwarding, encryption and decryption: forwarding, encrypting and decrypting the data traffic of the unique session process of the intelligent application byusing the local server and the client; And storing and visualizing the communication data. The method is deployed at an Android mobile phone end, no root or other hardware support is needed, the operation is convenient, and the efficiency is high.
Owner:XIDIAN UNIV
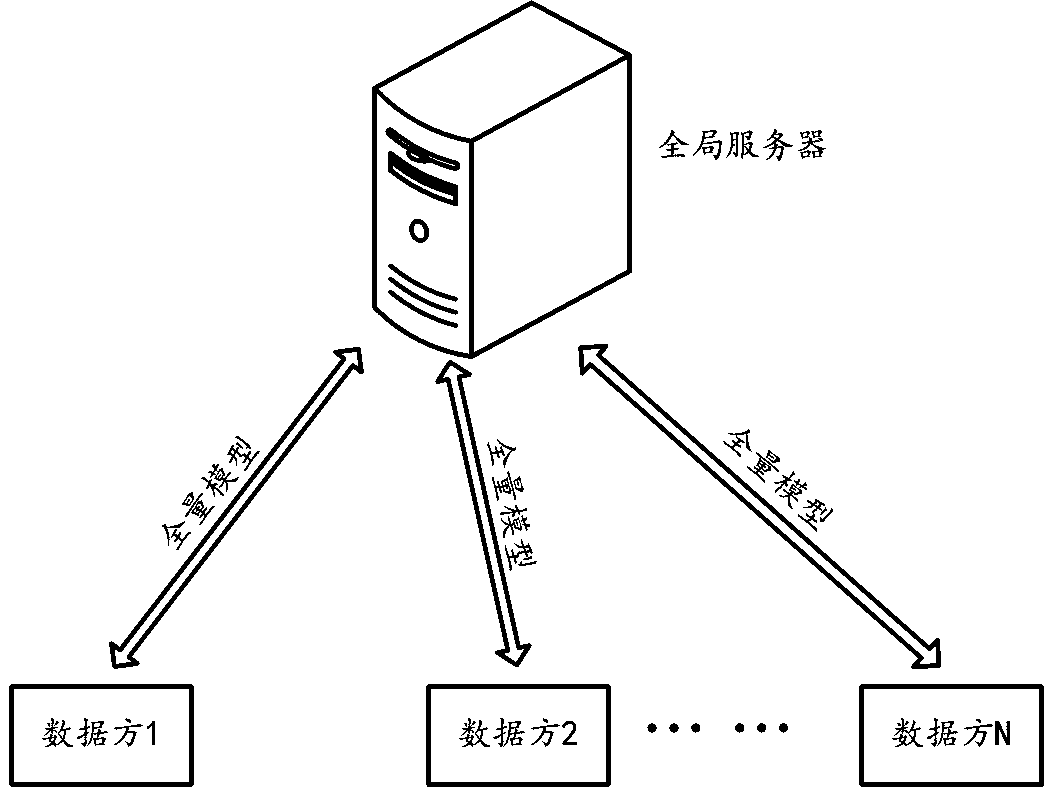
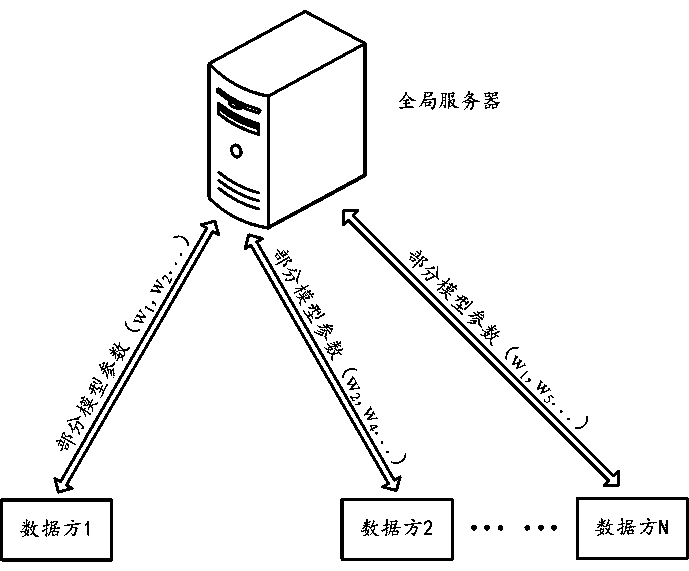
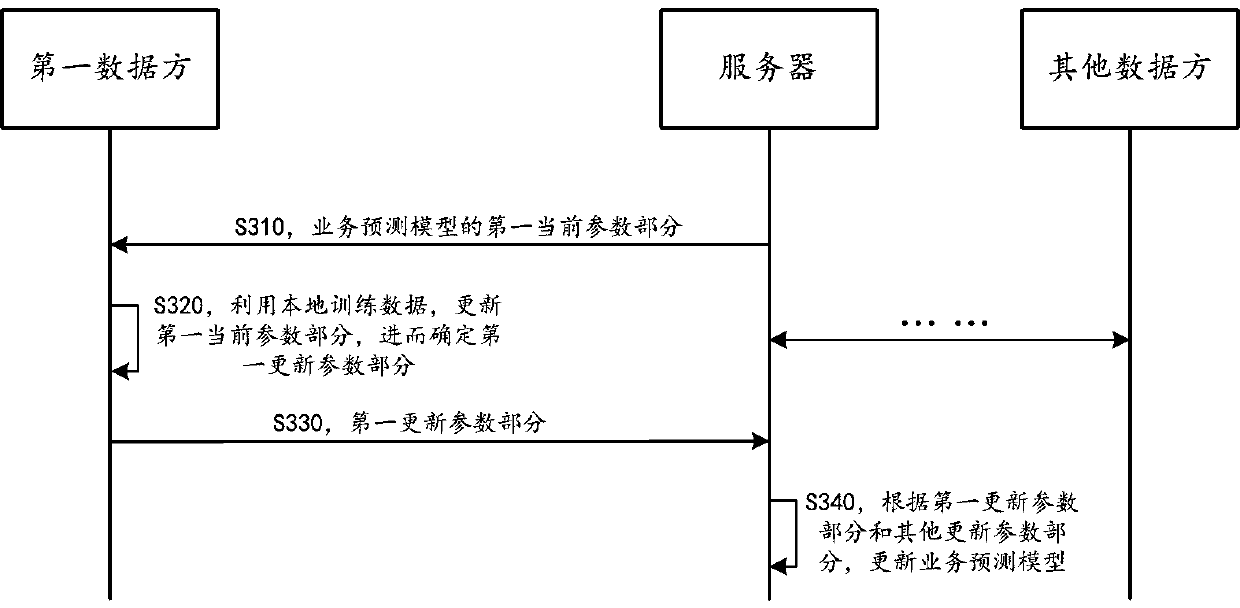
Multi-party collaborative business prediction model updating method for realizing privacy protection
ActiveCN111325417AGuarantee privacy and securityPrevent overfittingForecastingResourcesPrivacy protectionModel parameters
The embodiment of the invention provides a multi-party collaborative business prediction model updating method for realizing privacy protection. The multiple parties comprise a server and a pluralityof data parties; the server deploys a service prediction model for a service object. The method comprises the steps that any round of iterative updating is conducted on a service prediction model, andspecifically comprises the steps that a first data party participating in the round of iterative updating obtains a first current parameter part from a server, and the first current parameter part isobtained by conducting random selection based on current model parameters of the service prediction model; the first data party updates the first current parameter part by using local training data,and obtains a first updated parameter part based on at least one part of the updated parameter; the first data party partially uploads the first updating parameter to a server; and the server updatesthe service prediction model according to the first updating parameter part and other updating parameter parts received from other data parties participating in the current round of iterative updating.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com