Patents
Literature
406 results about "Root certificate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
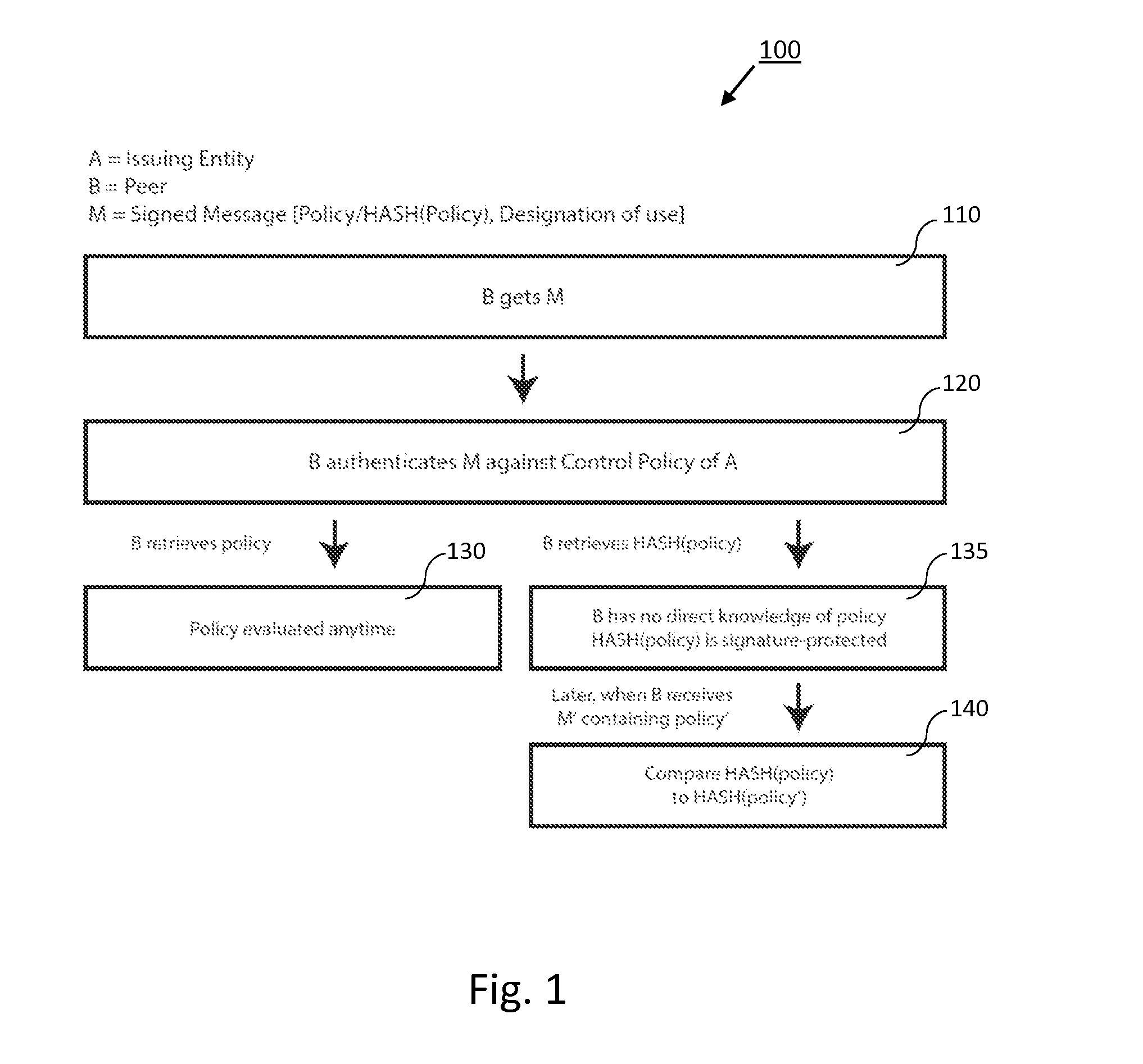
In cryptography and computer security, a root certificate is a public key certificate that identifies a root certificate authority (CA). Root certificates are self-signed and form the basis of an X.509-based public key infrastructure (PKI). Either it has matched Authority Key Identifier with Subject Key Identifier, in some cases there is no Authority Key identifier, then Issuer string should match with Subject string (RFC5280). For instance, the PKIs supporting HTTPS for secure web browsing and electronic signature schemes depend on a set of root certificates.
Generalized entity network translation (GENT)
ActiveUS20150244690A1Many choicesGood conditionUser identity/authority verificationPublic key infrastructure trust modelsSystem integrationRoot certificate
Generalized Entity Network Translation provides new state of the art methodology for extending RKI techniques into a truly generalized framework capable of operating at exceptional levels of authenticity without the need for roots, certificate authorities, or other static points in an infrastructure. More astounding is its ability to create trusted authentic entity relationships that require no externally stored state outside of the shared context between discrete peers. The present invention provides, among other things, novel improvements to blockchain-derived systems and provides strong proof of ownership, renewal, roll-backs, and localized state and many blockchain systems more palatable choices for system integration.
Owner:ENT TECH
Authorization infrastructure based on public key cryptography
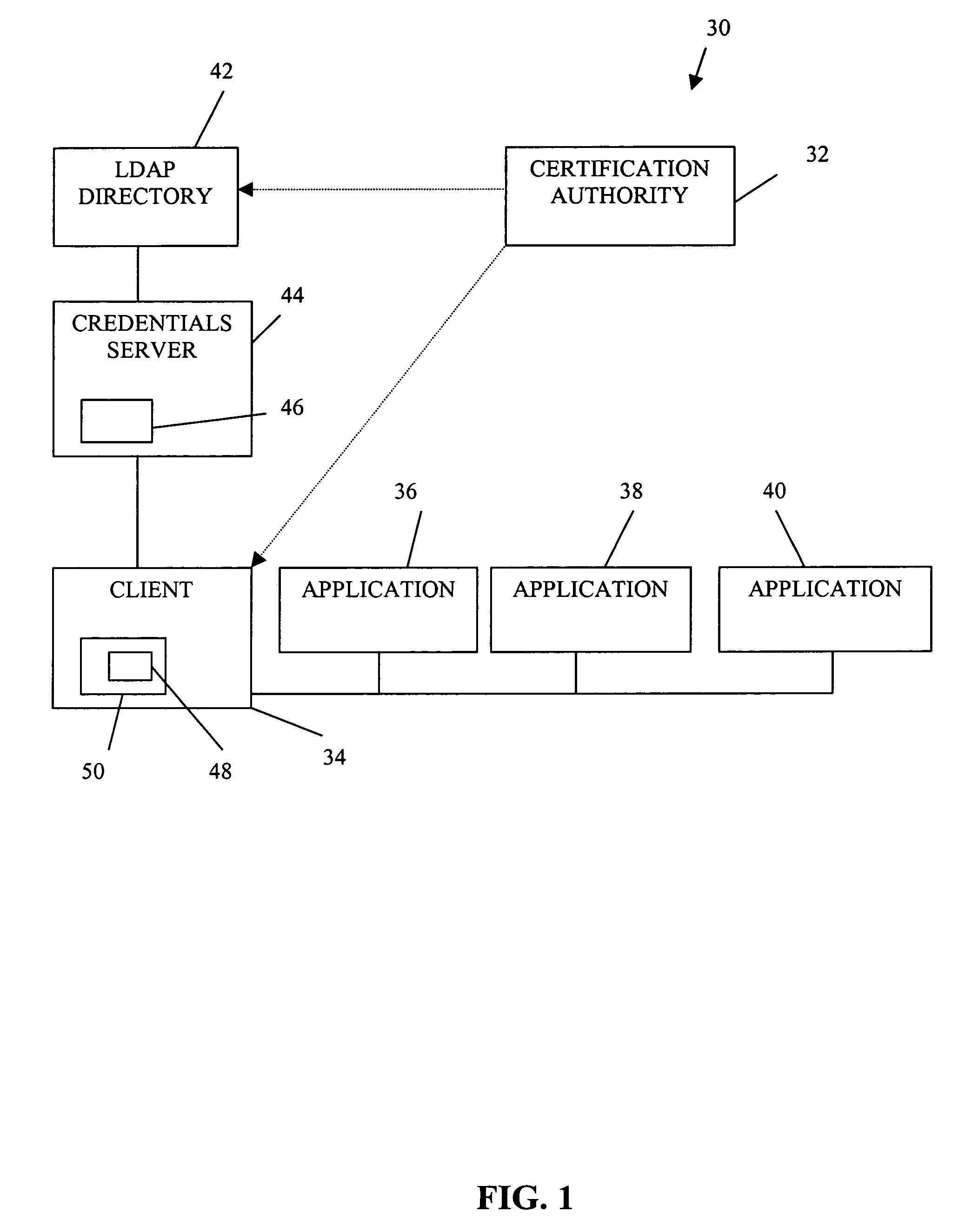
InactiveUS7340600B1Random number generatorsUser identity/authority verificationRoot certificateClient-side
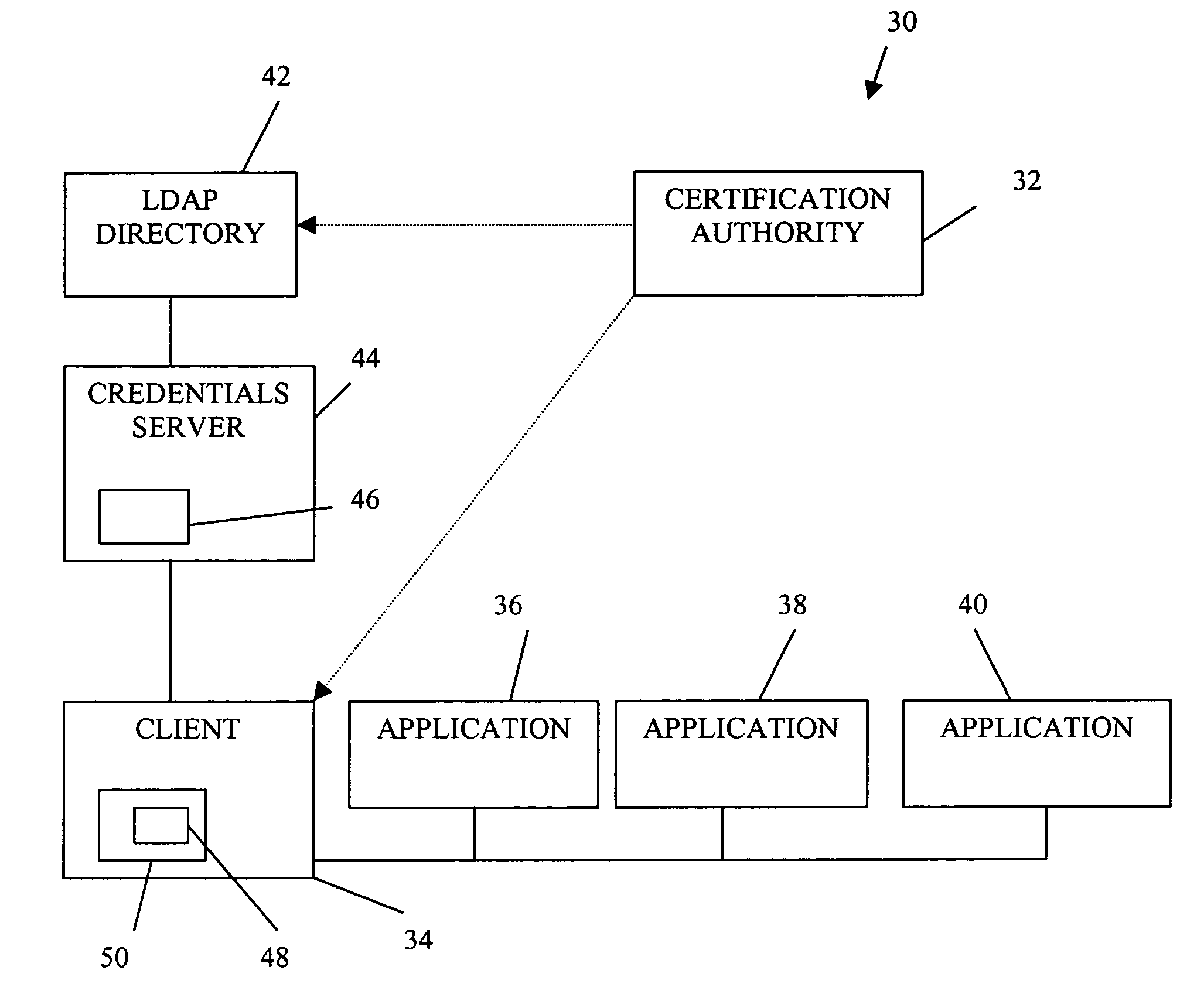
A public key authorization infrastructure includes a client program accessible by a user and an application program. A certificate authority issues a long-term certificate that binds a public key of the user to long-term identification information related to the user. A directory stores the issued long-term certificate and short-term authorization information related to the user. A credentials server issues a short-term certificate to the client. The short-term certificate binds the public key to the long-term identification information and to the short-term authorization information. The client presents the short-term certificate to the application program for authorization and demonstrates that the user has knowledge of a private key corresponding to the public key in the short-term certificate. The short-term certificate includes an expiration date, and is not subject to revocation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
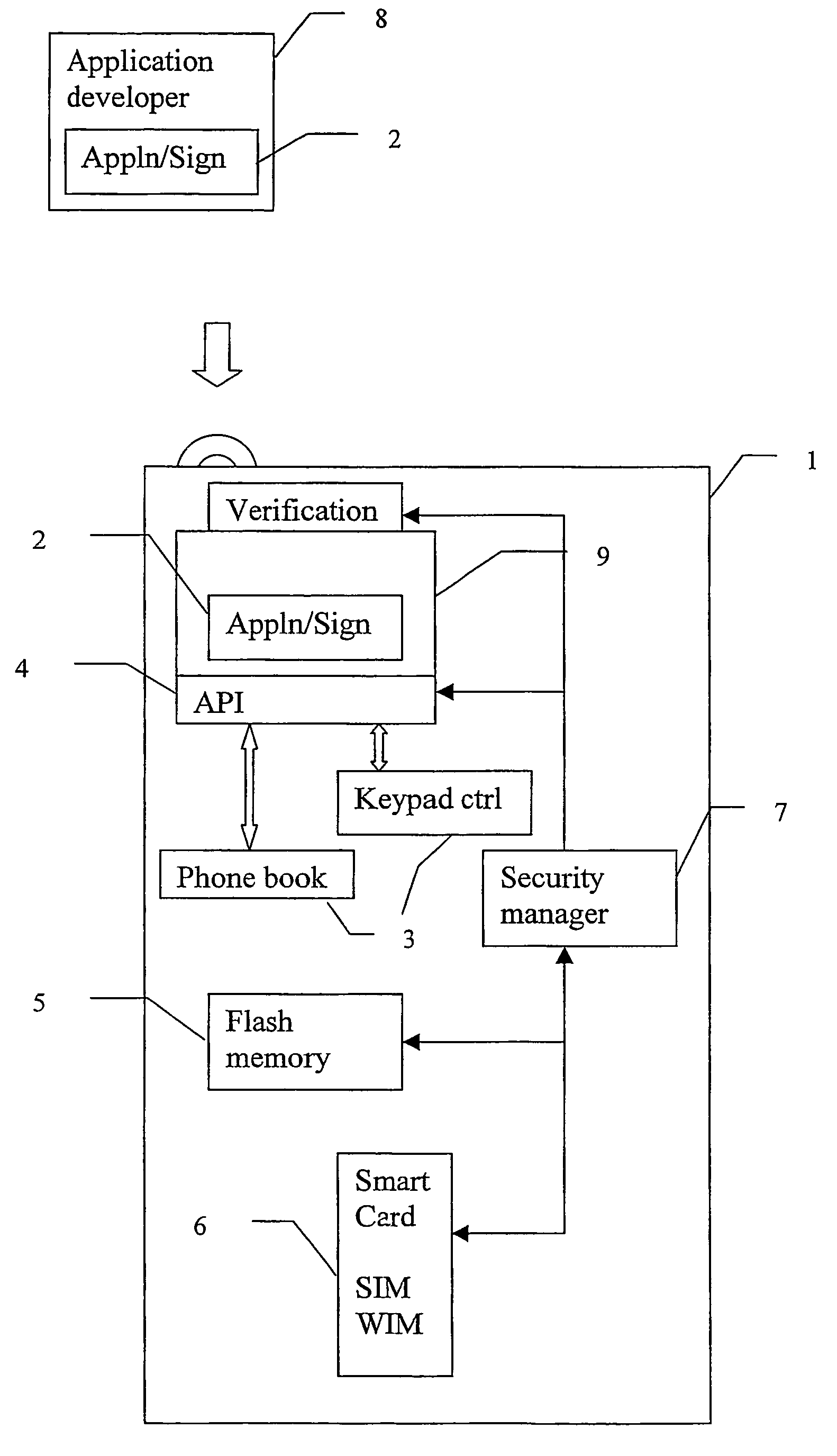
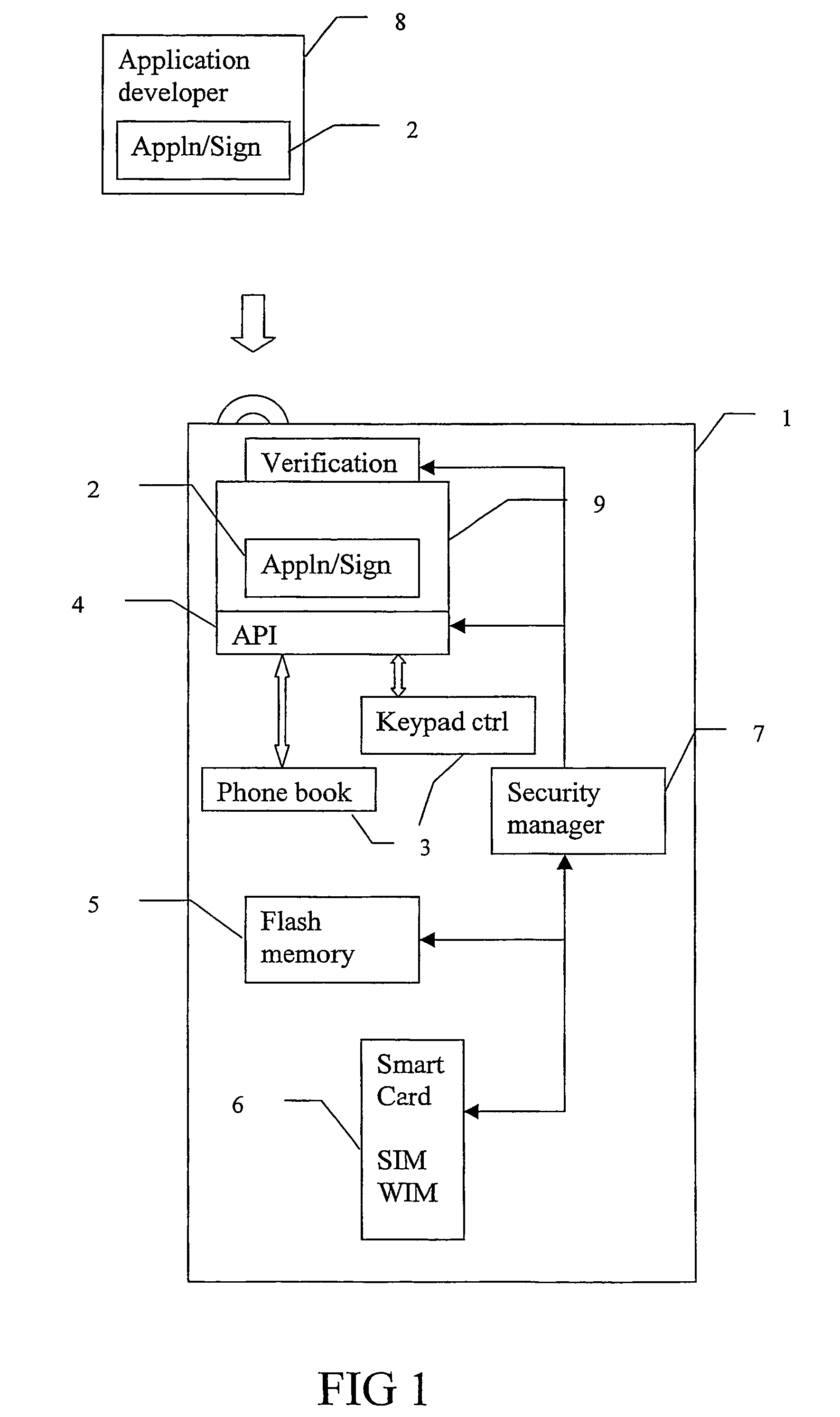
Method for loading an application in a device, device and smart card therefor
ActiveUS7900048B2Digital data processing detailsUser identity/authority verificationRoot certificateApplication procedure
An application is loaded into a device, such as downloading an application into a portable device, such as a mobile telephone, by downloading the application with a signature to the device. The signature of the application is coupled to a predefined attribute certificate stored in the device. The application and said attribute certificate are then installed together. The signature of the application may be coupled to a root certificate that in turn links the application to a predefined attribute certificate.
Owner:SONY CORP
Communication system and method in public key infrastructure
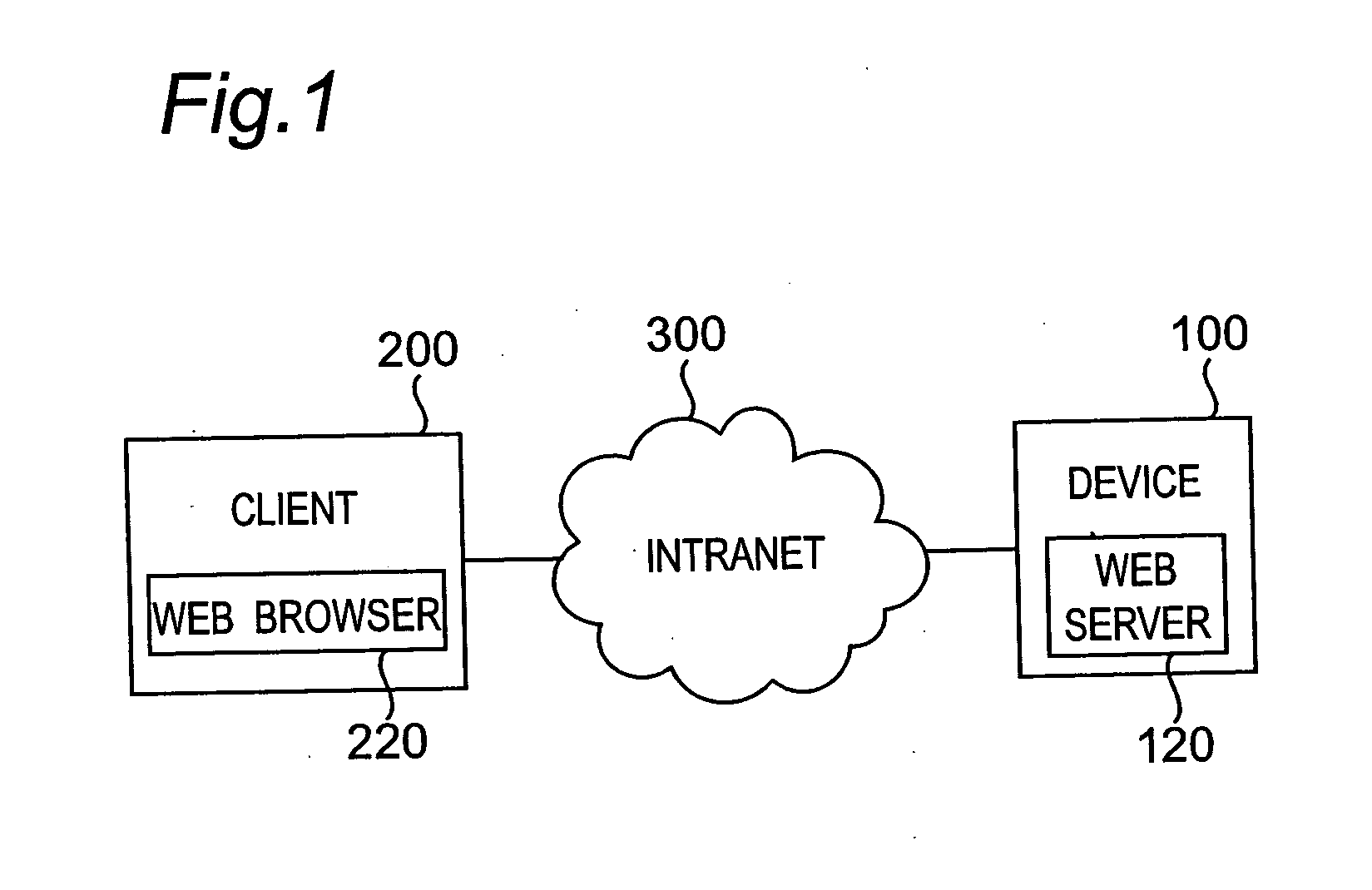
InactiveUS20050005097A1User identity/authority verificationCoding/ciphering apparatusRoot certificateCommunications system
In a communication system wherein a device and a client communicate data with each other through a network, the device holds a root certificate including a public key in a pair of the public key and a private key and signed with the public key. When data is sent, a certificate creator creates a second certificate including the root certificate designated as a certificate authority at a higher level and signed with the root certificate, and the second certificate is sent to the client. In the client, the root certificate has been stored beforehand, and a verifier verifies the signature of the second certificate with the root certificate.
Owner:MINOLTA CO LTD
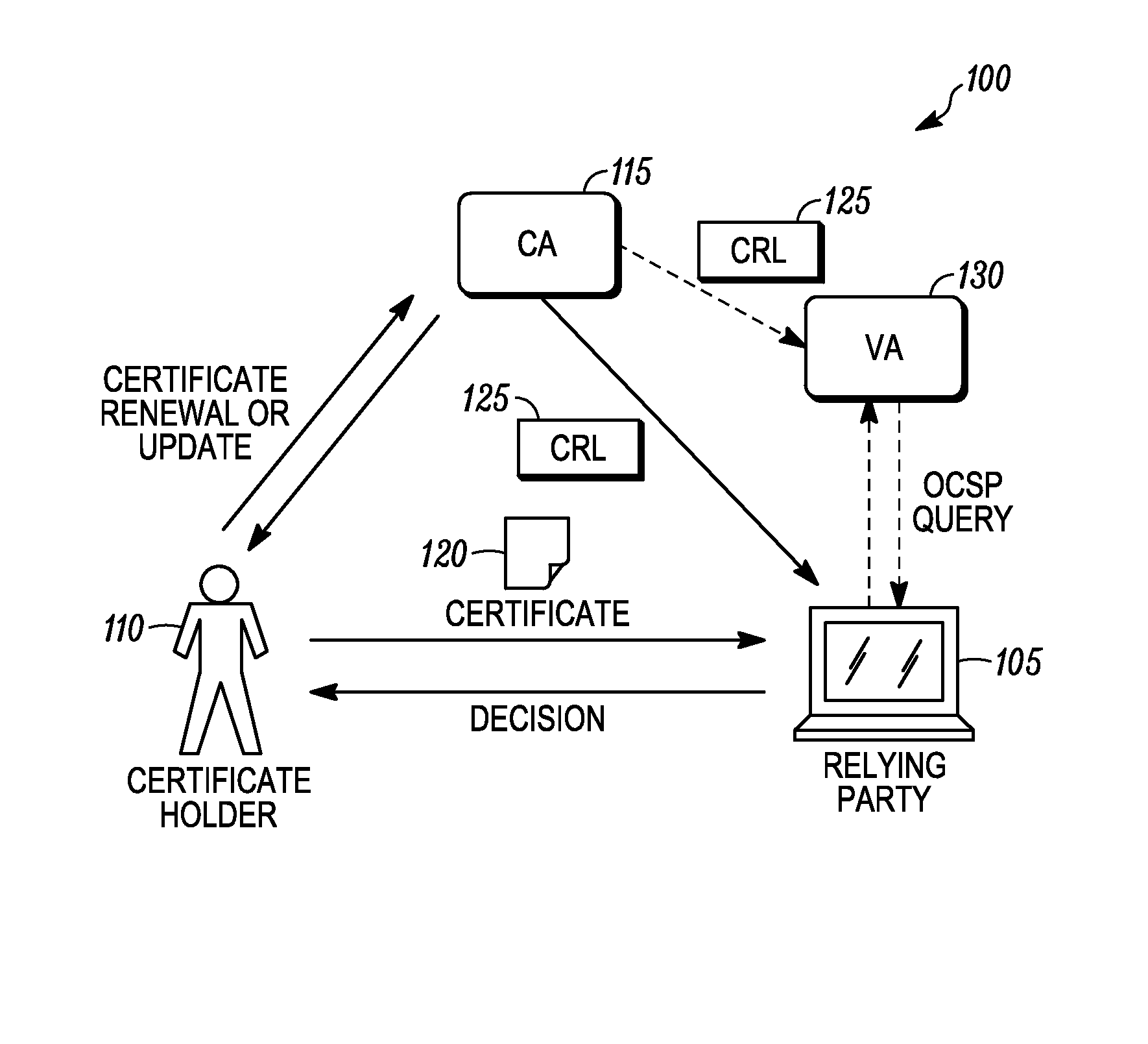
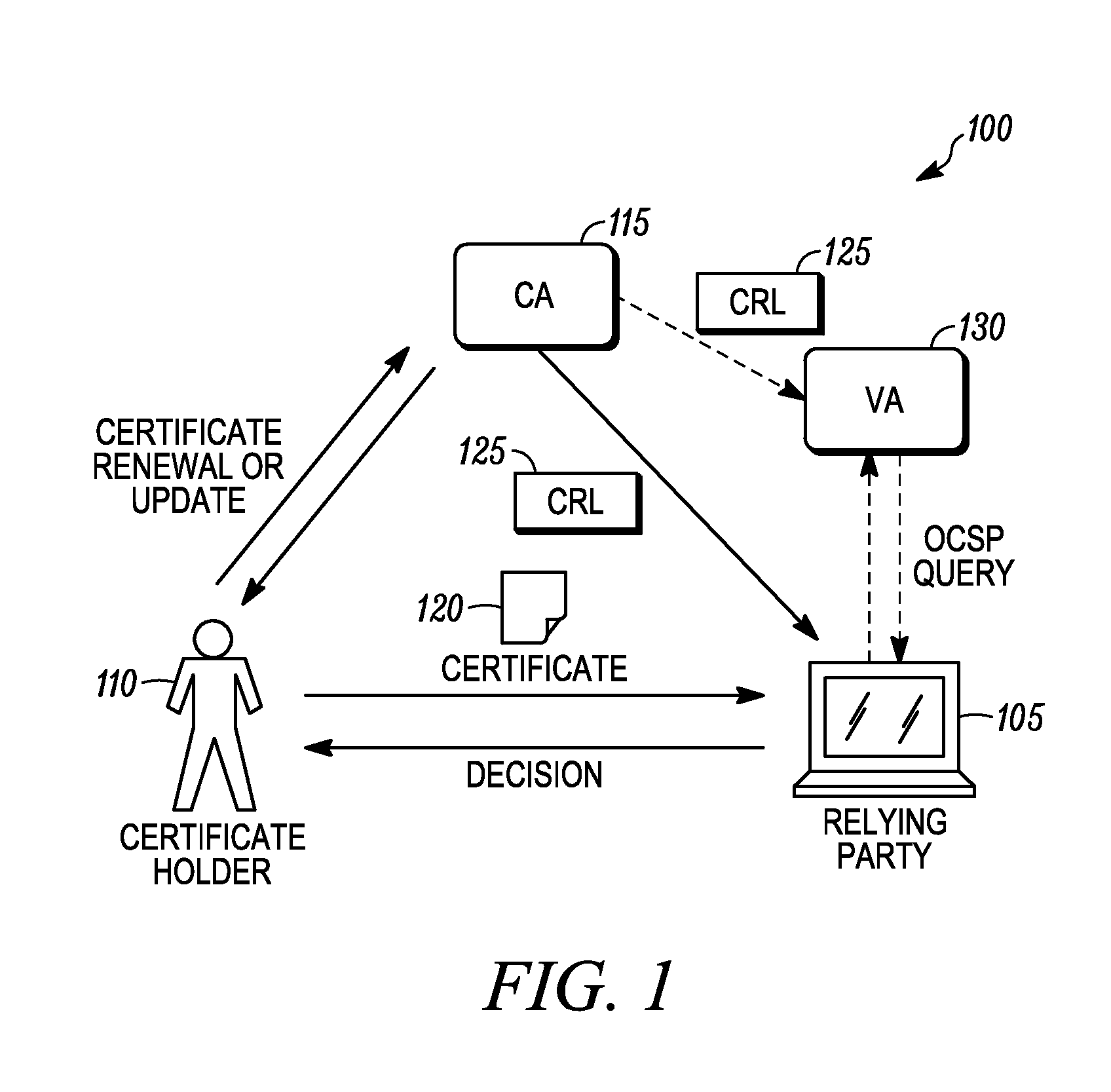
Certificate reissuance for checking the status of a certificate in financial transactions
InactiveUS6842863B1Easy to liftDigital data processing detailsUser identity/authority verificationRoot certificateFinancial transaction
A system for using a certificate authority to first provide a customer with a digital certificate, and then having a relying party that receives that digital certificate access a status authority (the certificate authority or its designated agent) to receive a reissued certificate on that certificate. The reissued certificate has a much shorter validity period, which ensures that the information is timely. Moreover, the certificate may serve as a receipt, including an accumulated record of the signatures (digital certificates) and policy applied throughout the financial transaction. As a result, each transfer of the transaction forms a digitally-signed chain of evidence recording each step of the transaction and policy applied thereto, whereby risk may be assumed and charged for appropriately and in accordance with the risk purchaser's policy.
Owner:MICROSOFT TECH LICENSING LLC
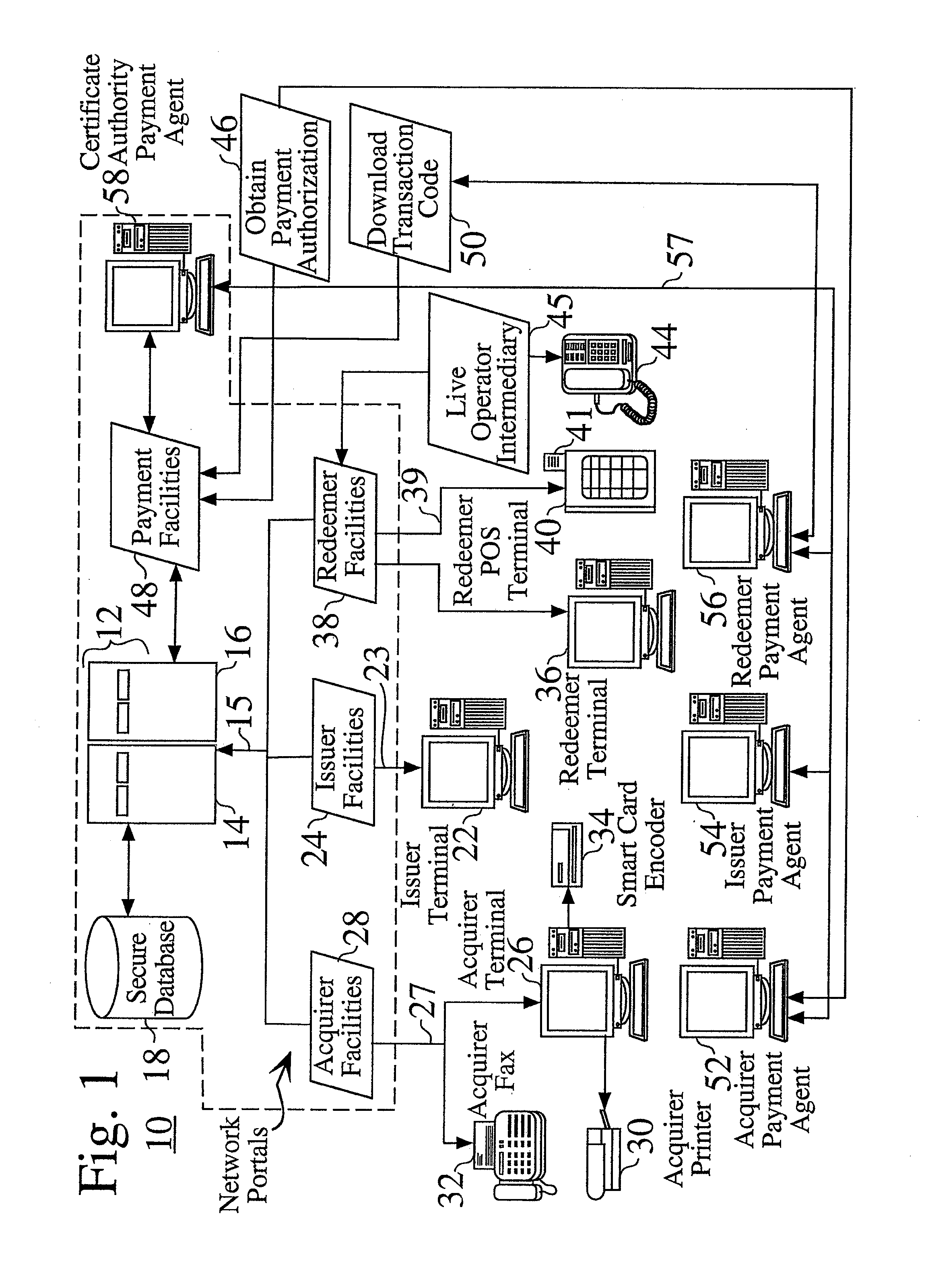
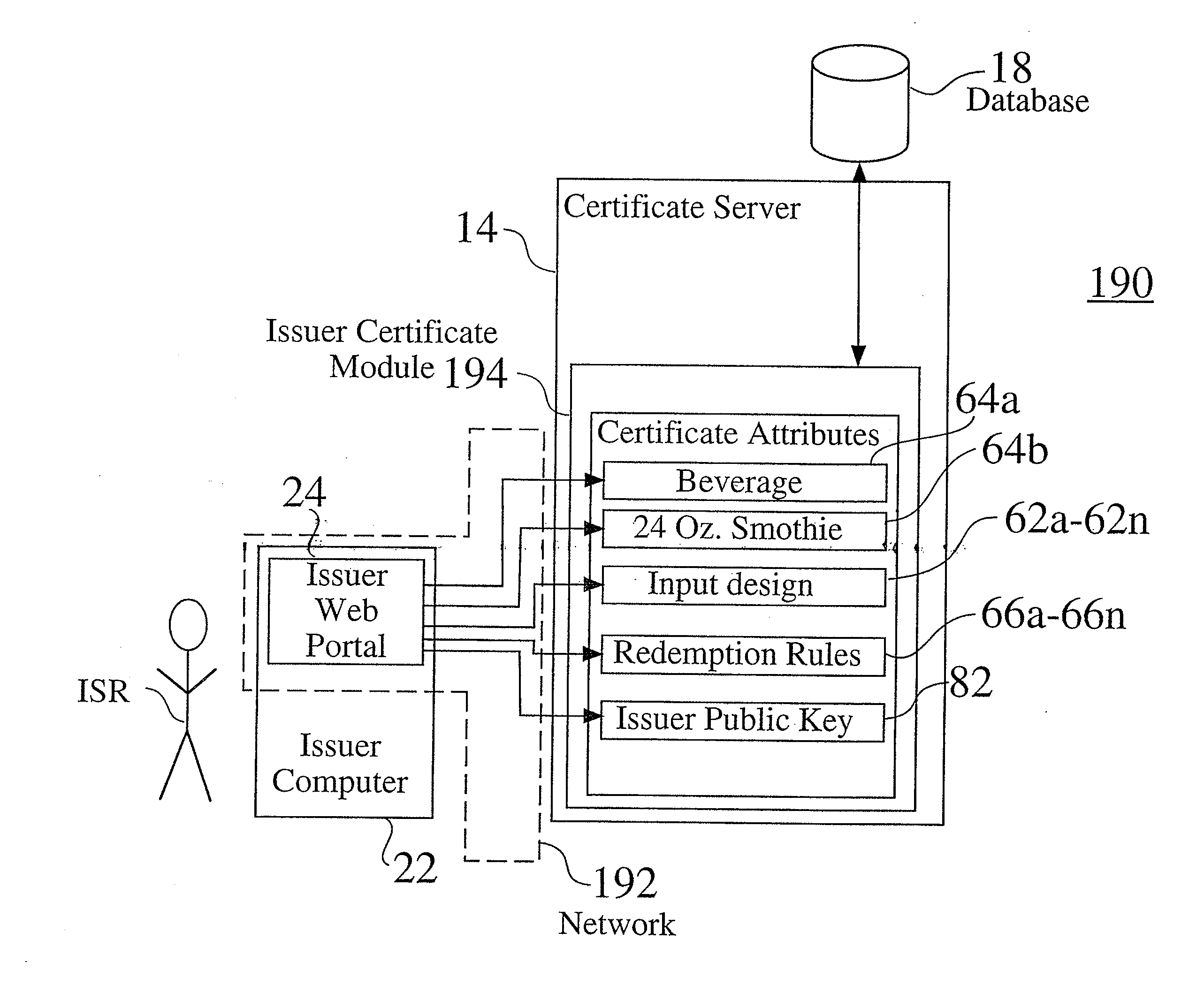
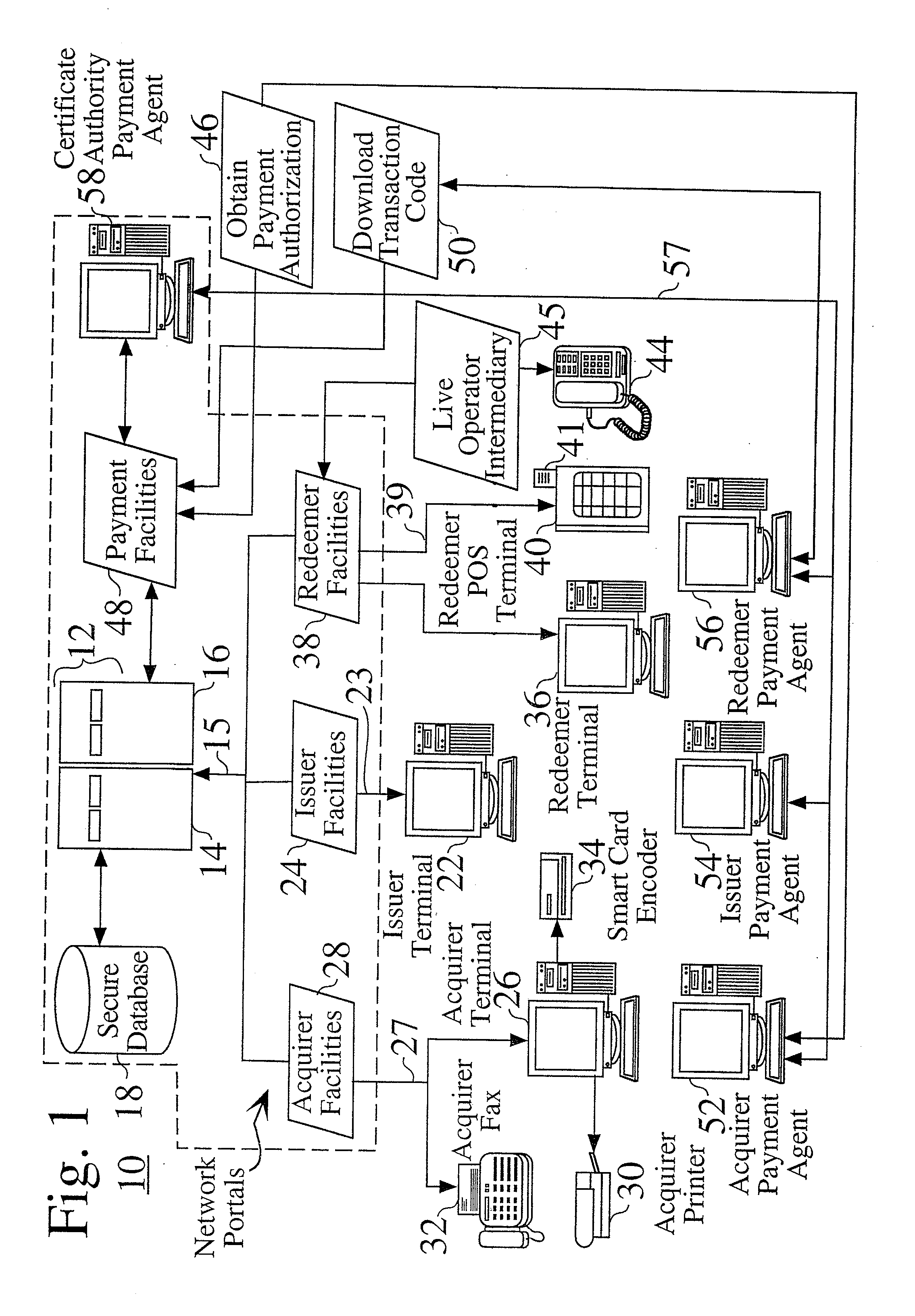
Secure system for the issuance, acquisition, and redemption of certificates in a transaction network
InactiveUS7209889B1User identity/authority verificationSecret communicationRoot certificateComputer security
A transaction network contains a networked certificate authority, by which one or more virtual certificates may be remotely defined and stored, such as by an issuer user through a issuer web portal interface. An acquirer user, through an acquirer web portal interface, may acquire one or more virtual certificates, which contain a public key portion, as well as a corresponding private key, which is established at the time of acquisition, and is stored at the certificate authority. At a redemption location associated with an acquired certificate, the acquirer (or an alternate recipient of an acquired certificate to whom the acquirer has communicated the established private key), submits the certificate information, along with the established private key, to redeem the certificate.
Owner:RATEZE REMOTE MGMT LLC +1
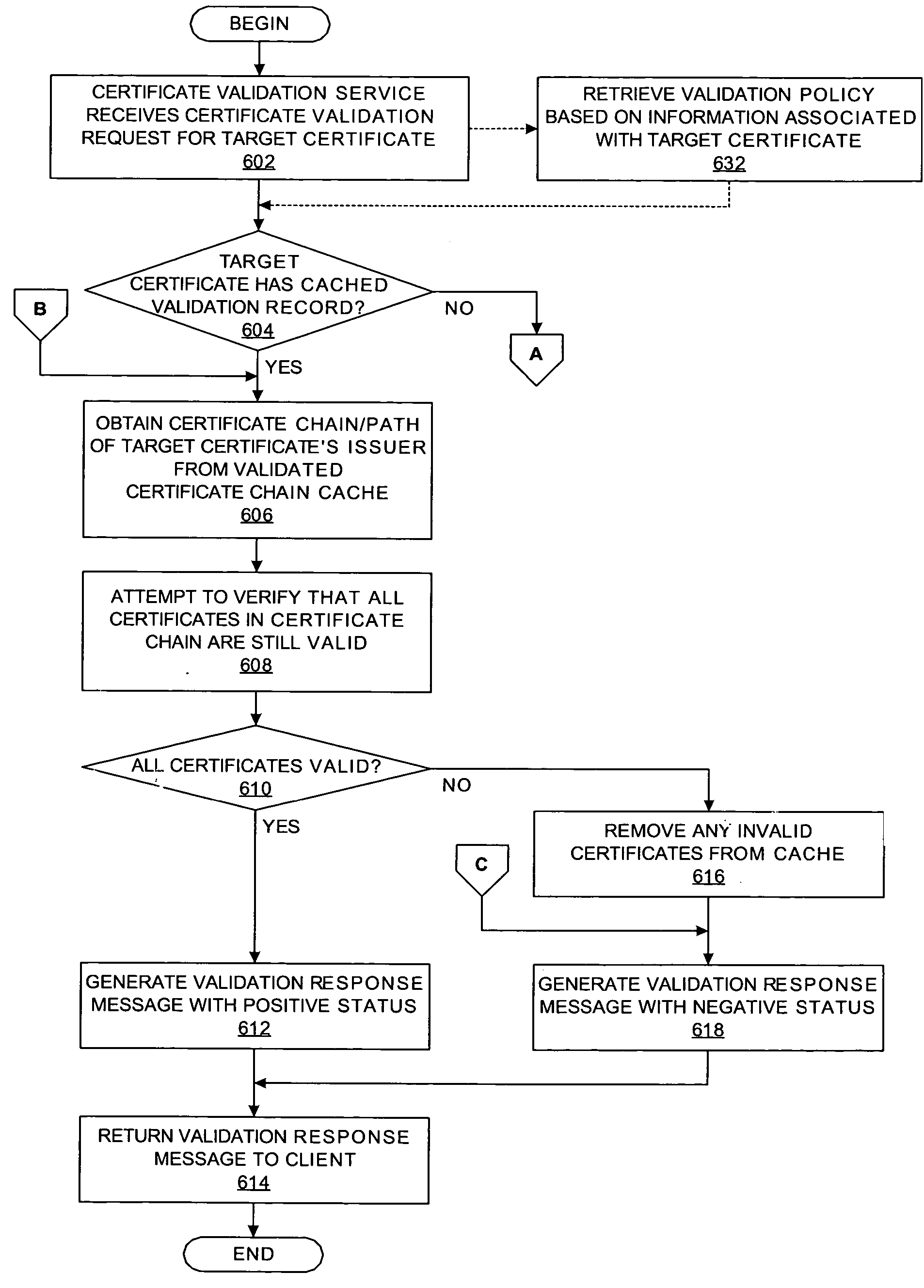
Method and system for certification path processing
InactiveUS20050278534A1Improve service efficiencyUser identity/authority verificationData processing systemRoot certificate
A method, an apparatus, a system, and a computer program product are presented for validating certificates. A certificate validation service receives a certificate validation request for a target certificate from a client, thereby allowing the client to offload certificate validation tasks into an online certificate validation service that is accessible and sharable by multiple components within a data processing system. In response to a determination that the target certificate is valid or invalid, the certificate validation service sends a certificate validation response with an indicating status value that the target certificate is valid or invalid. The certificate validation service is able to cache information about previously validated certificates and the associated certificate chains, thereby enhancing the efficiency of the service. Different certificate validation policies may be applied against target certificates based upon information associated with the target certificates.
Owner:IBM CORP
Method and system for managing identities in a peer-to-peer networking environment
InactiveUS20050177715A1Efficiently create modify deleteEfficiently list and manipulateUser identity/authority verificationRoot certificateDistributed computing
Disclosed is a system for organizing and storing information about multiple peer identities. New certificates are introduced that enable a user to efficiently create, modify, and delete identities and groups. New storage structures enable the user to list and search through existing identities, groups, and their related certificates. An identity certificate contains information about a peer identity. A group root certificate is created by a user when he decides to create a new group. When the group creator user wishes to invite another entity to join the group, it creates another type of certificate called a group membership certificate. The group membership certificate is logically “chained” to the group root certificate. The invitee checks the validity of these certificates by checking that the chaining has been properly done. The invitee may then be allowed to invite other entities to join the group by sending out its own group membership certificates.
Owner:MICROSOFT TECH LICENSING LLC
Security for device management and firmware updates in an operator network
InactiveUS20060039564A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsRoot certificateSmart card
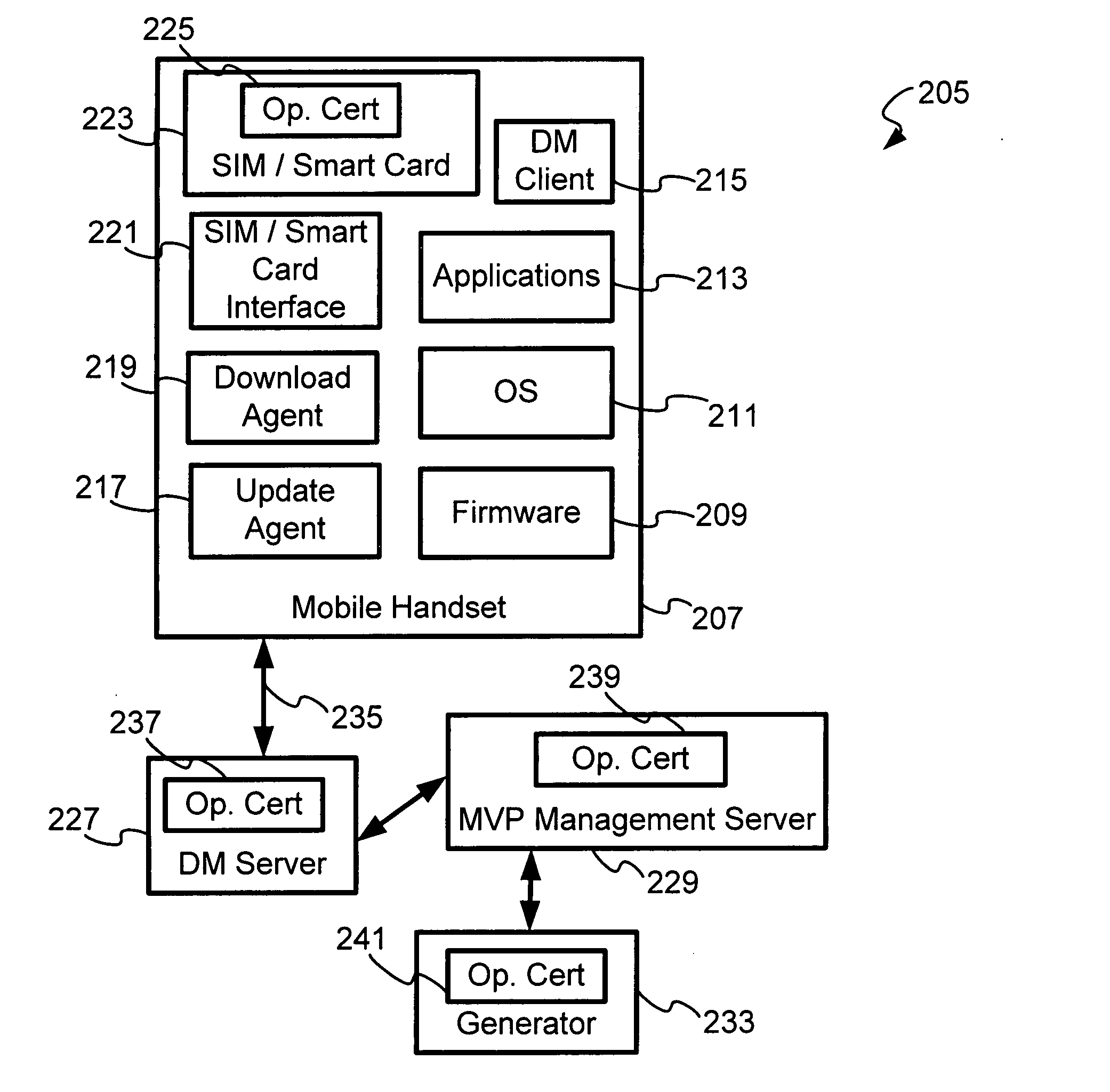
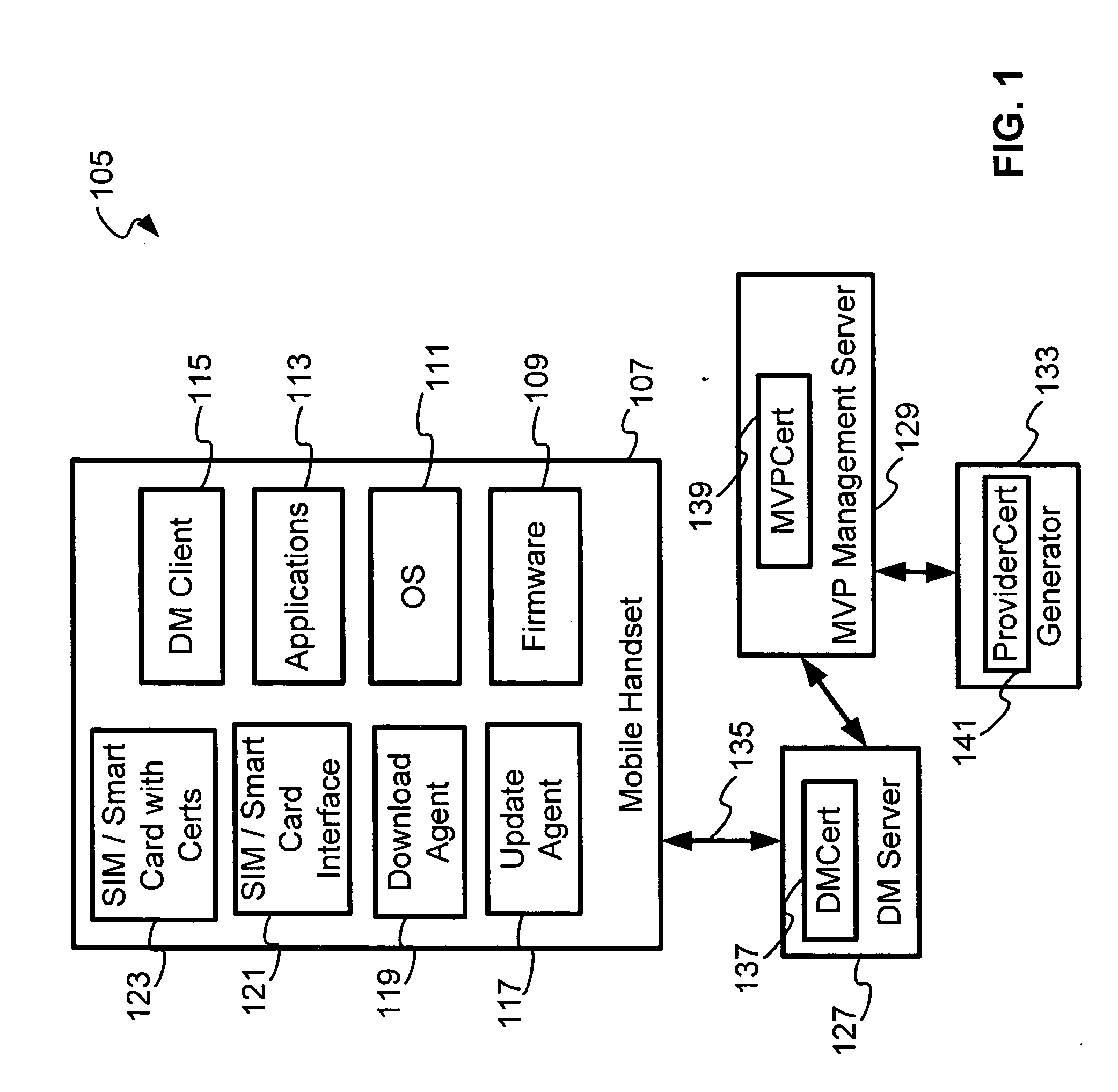
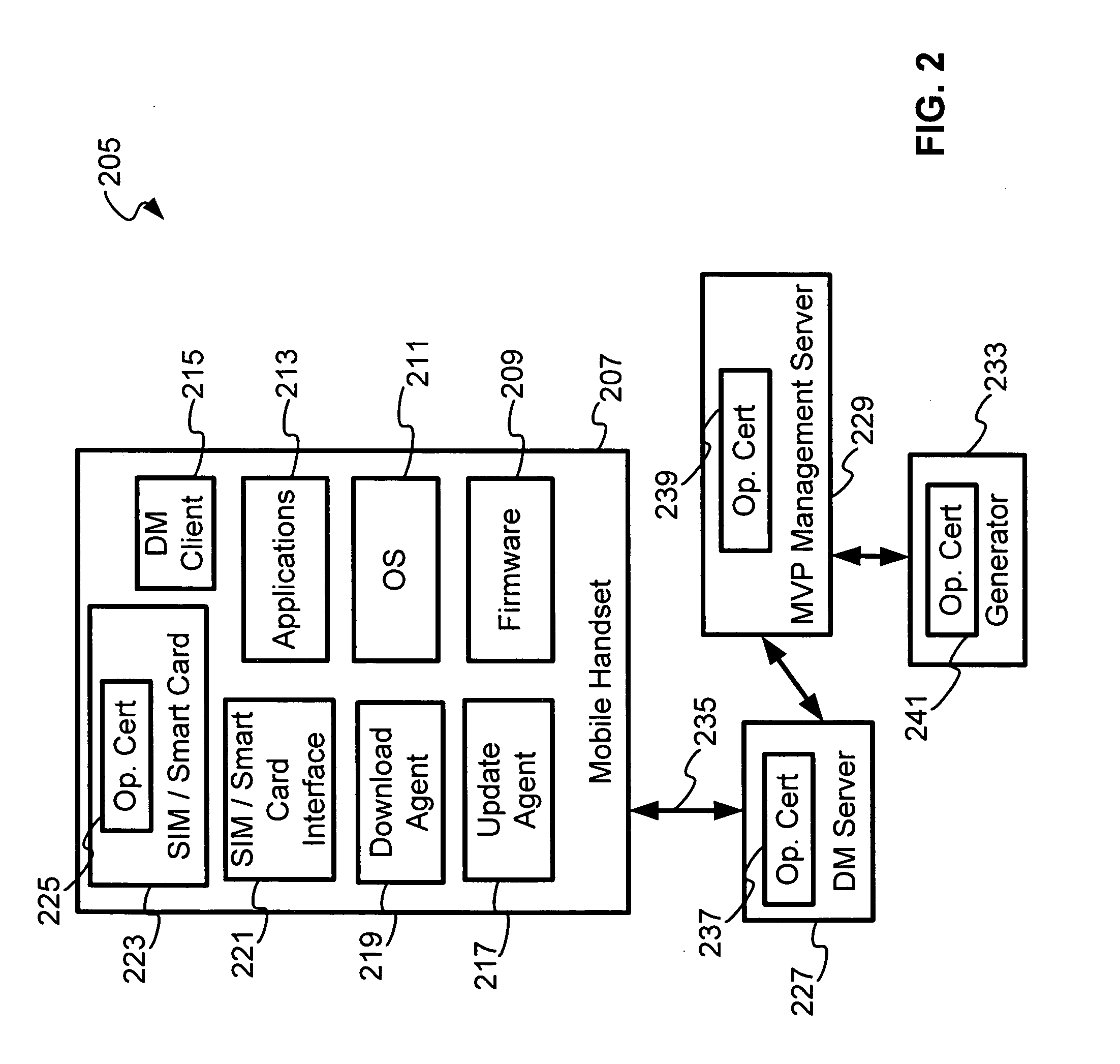
A SIM / Smartcards based approach to security within an operator's network (OMA device management system), by providing certificates to mobile devices as a way of authenticating the servers. A root certificate is stored in the SIM / Smartcard of each mobile device and accessed by the electronic device when the SIM / Smartcard is inserted into programmed card reader. Typically, in a OMA device management system, there are device management (DM) servers, mobile variance platform (MVP) server and generator; each are provisioned with a unique certificate that refers to a root certificate issued or associated with the operator, device management certificate (DMCert), mobile variance platform certificate (MVPCert) and provider certificate (ProviderCert), respectively. The mobile device authenticates each server session for Bootstrap provisioning and update package sessions originated by the servers, by verifying the root certificate with the certificates of the servers that accompany Bootstrap provisioning and update package messages.
Owner:HEWLETT PACKARD DEV CO LP
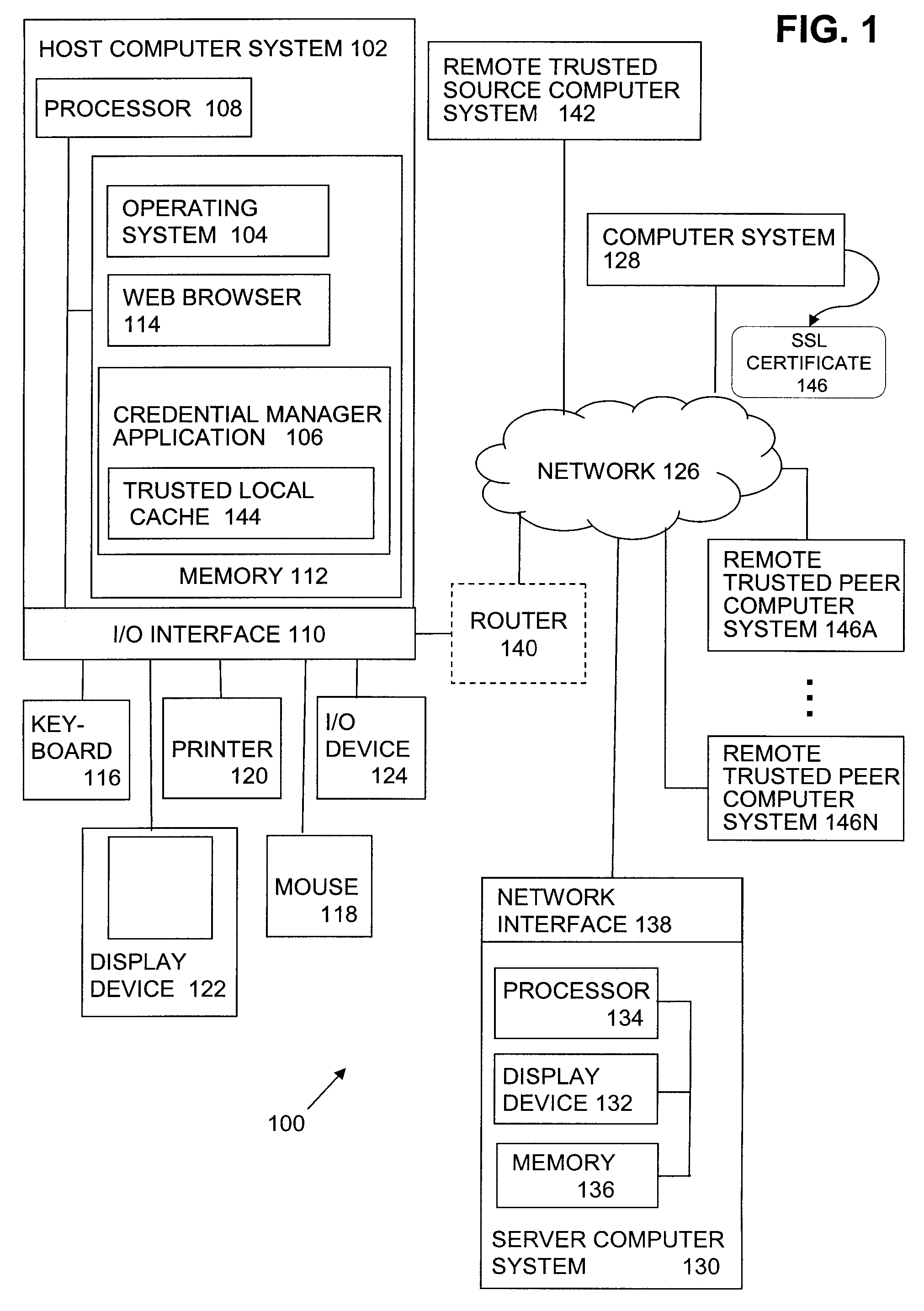
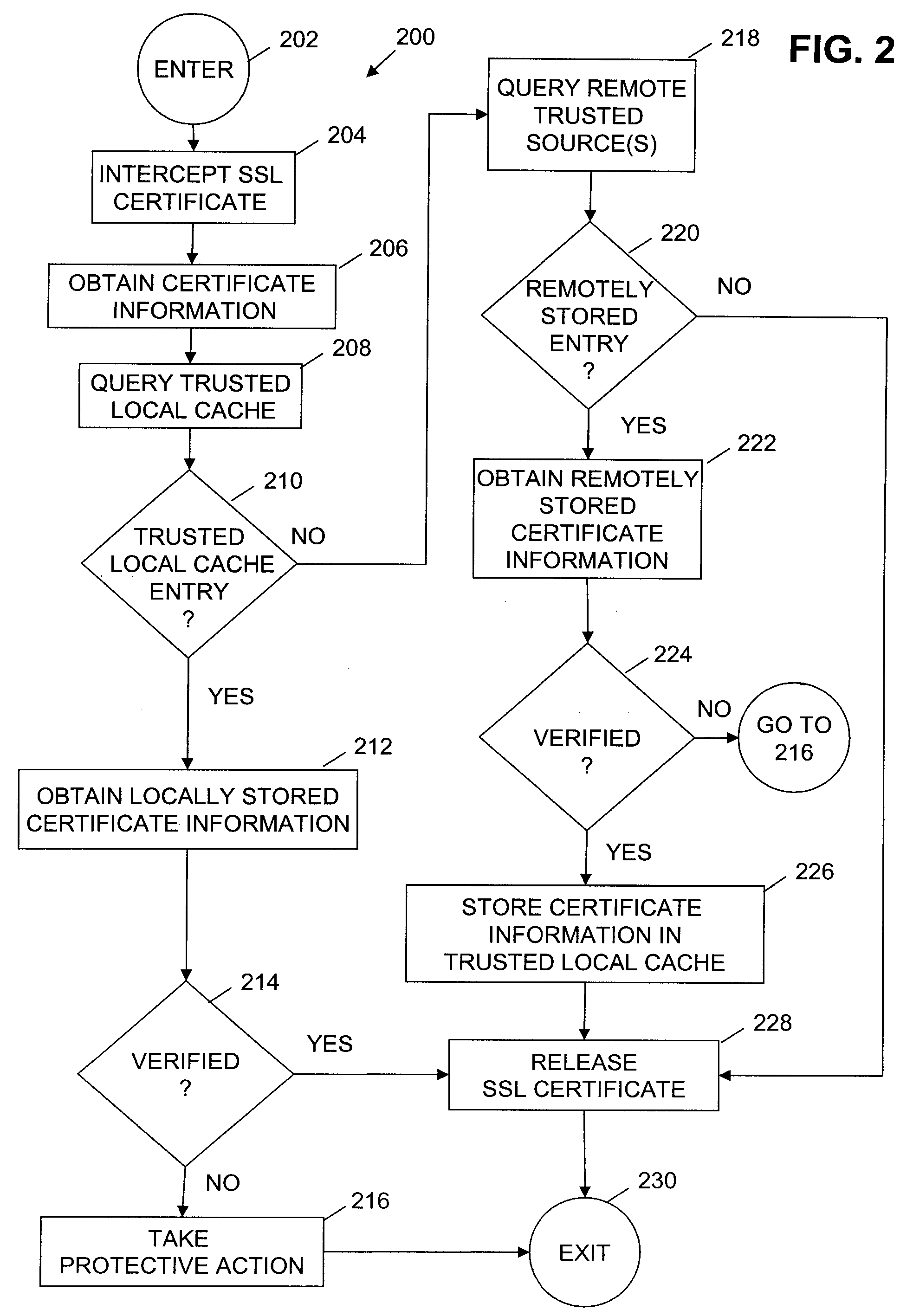
Method for detecting DNS redirects or fraudulent local certificates for ssl sites in pharming/phishing schemes by remote validation and using a credential manager and recorded certificate attributes
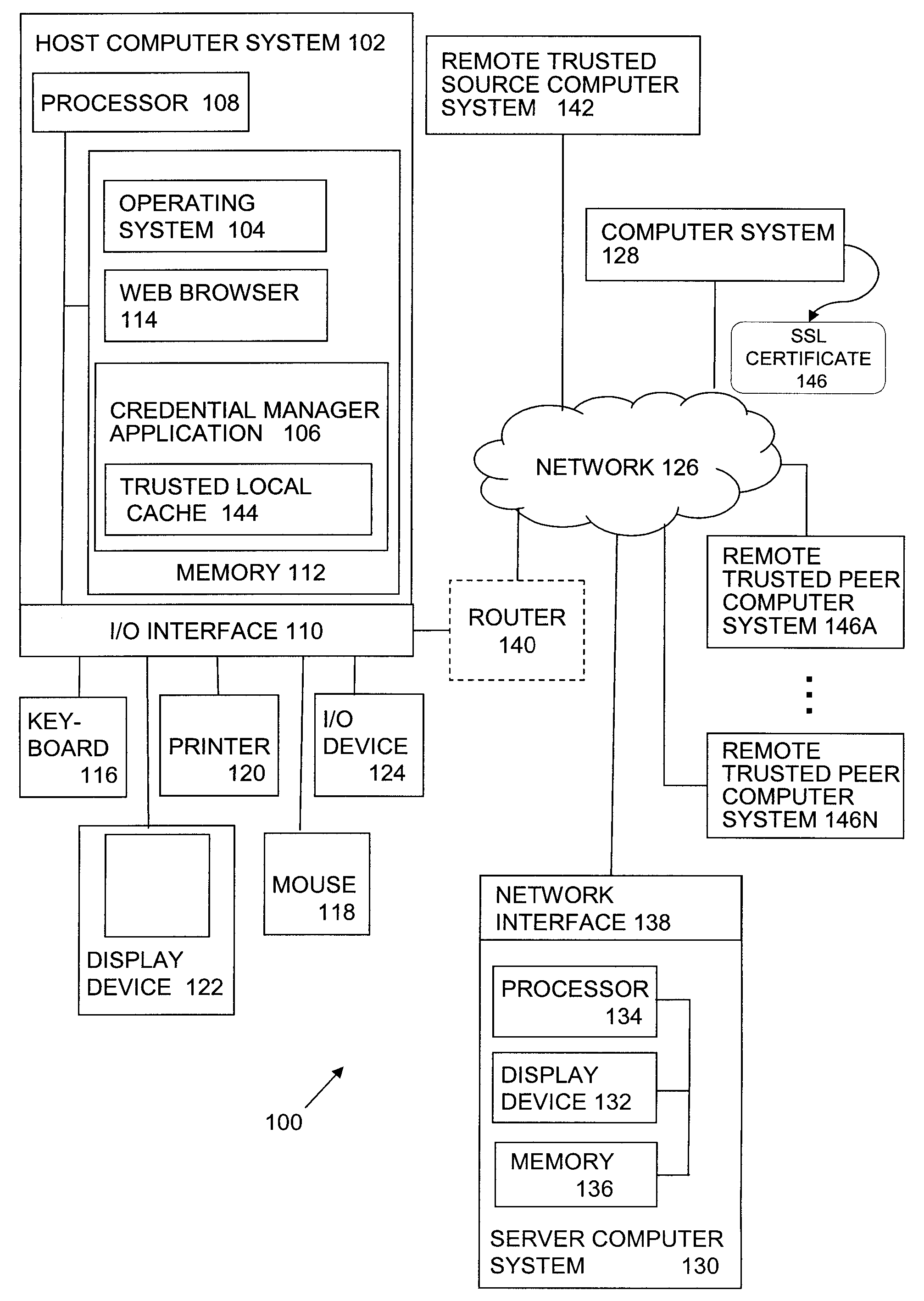
ActiveUS20090037997A1Digital data processing detailsUser identity/authority verificationDomain nameRoot certificate
Certificate information associated with a received certificate, such as a Secure Sockets Layer (SSL) certificate is stored in a trusted local cache and / or in one or more remote trusted sources, such as a single remote trusted source and / or a trusted peer network. When a site certificate is received on a host computer system, certificate information associated with the received site certificate is obtained and compared with the stored certificate information to determine whether or not the site certificate indicates malicious activity, such as a malicious DNS redirection or a fraudulent local certificate. When a site certificate is not found indicative of malicious activity, the site certificate is released. Alternatively, when a site certificates is found indicative of malicious activity protective action is taken. In some embodiments, a user's log-in credentials are automatically obtained from a trusted local cache and automatically submitted to a web site.
Owner:SYMANTEC CORP
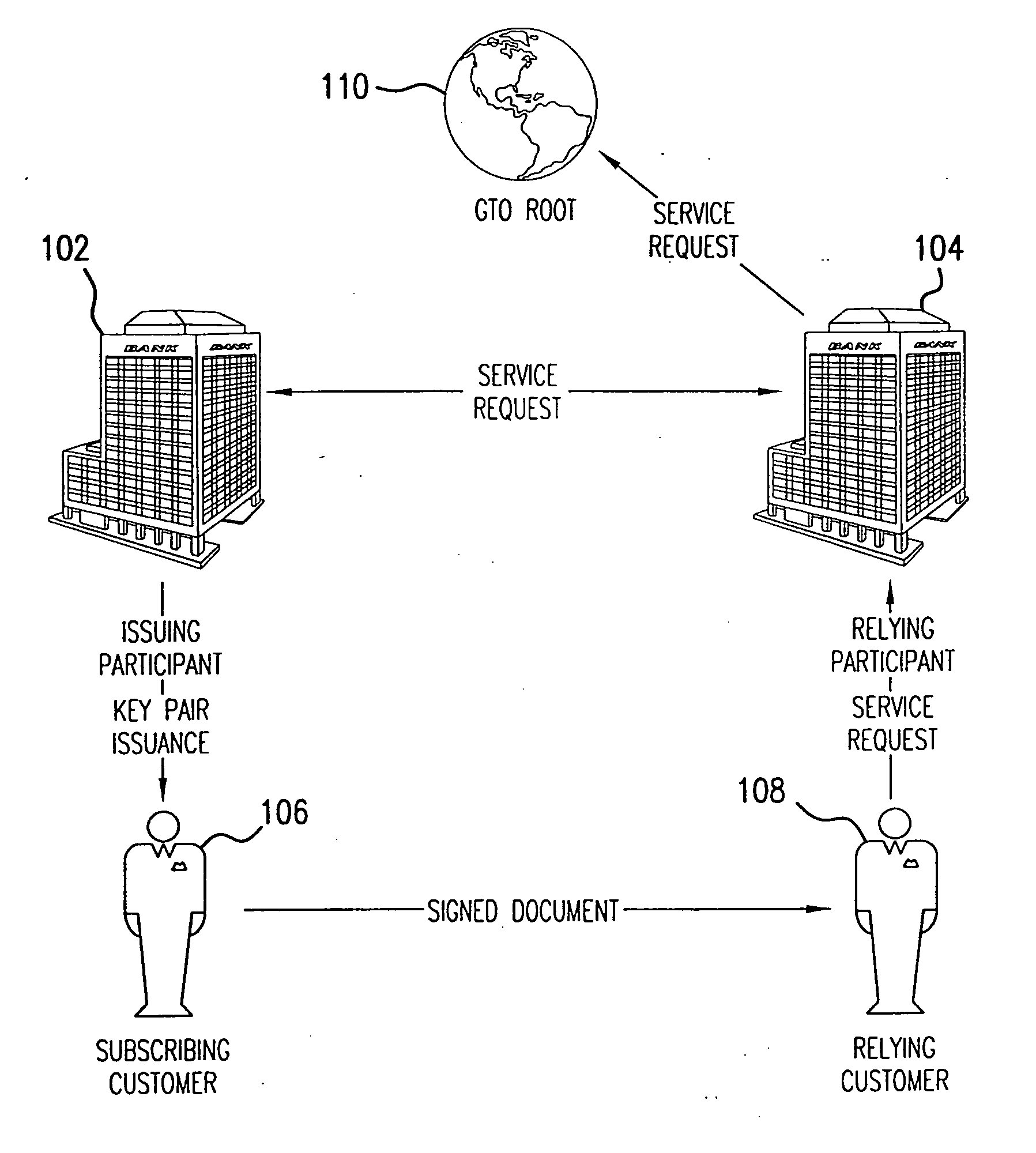
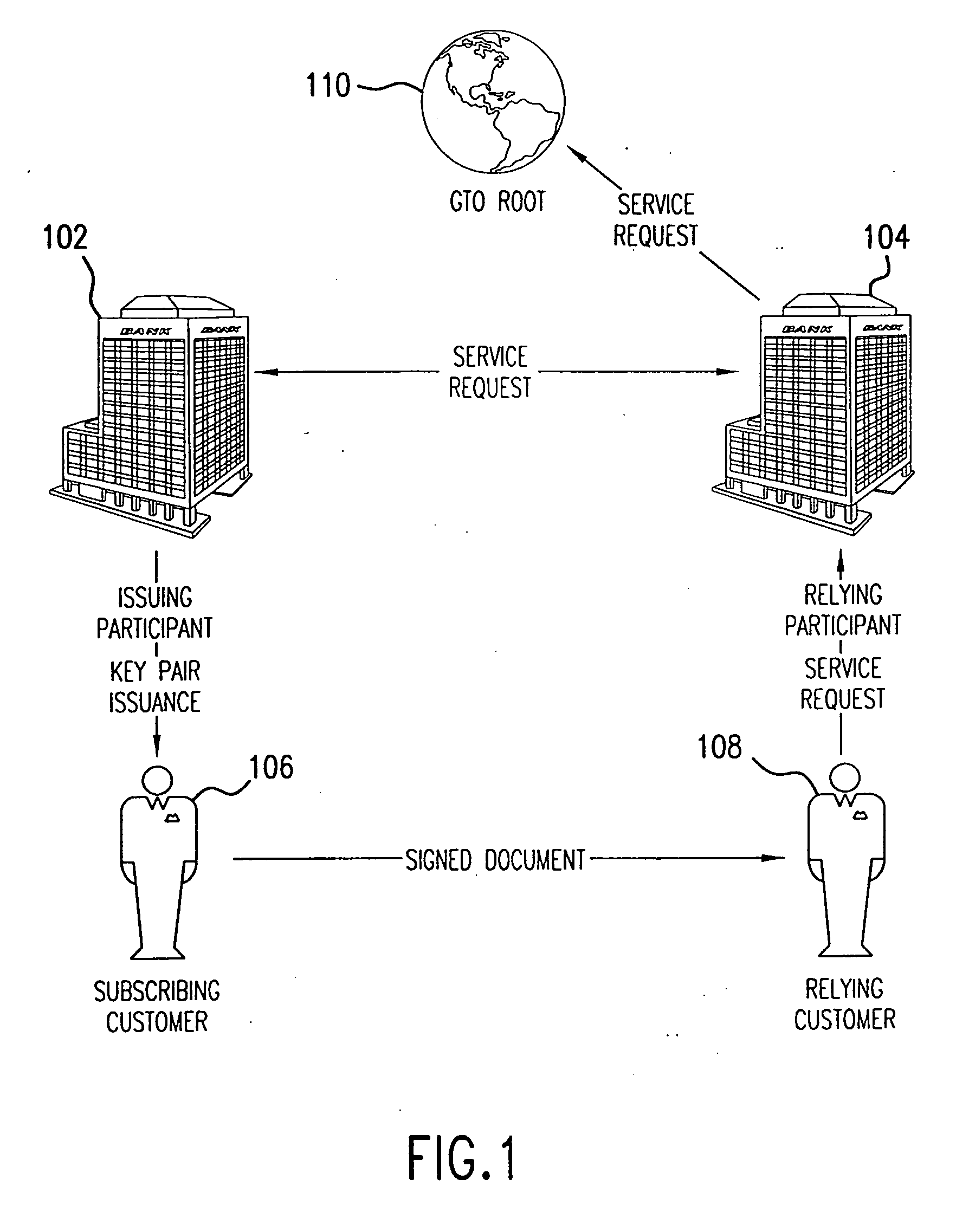
Transaction coordinator for digital certificate validation and other services
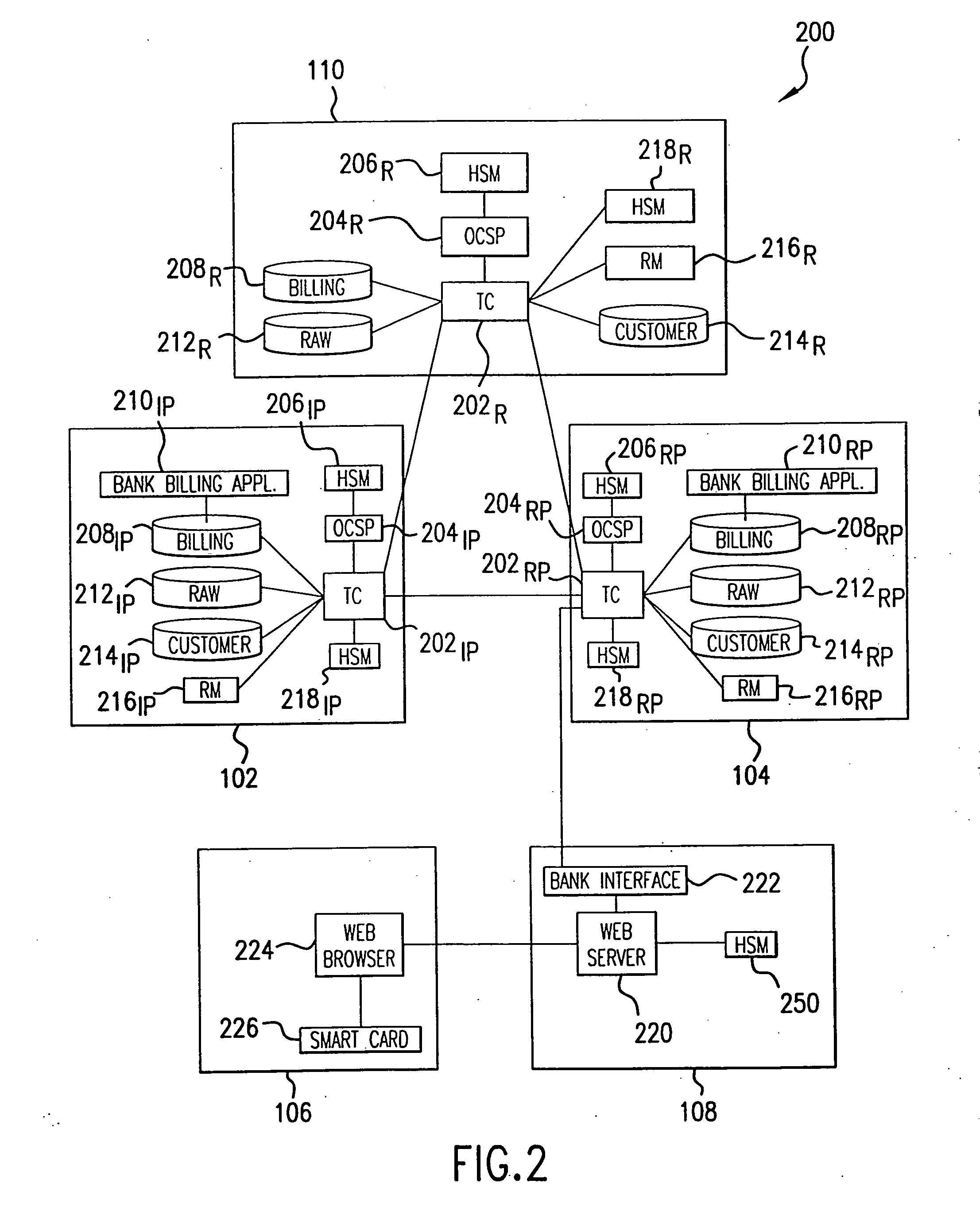
InactiveUS20070073621A1Easy to reuseEasy maintenanceCryptography processingPayment protocolsRoot certificateTransaction data
Systems and methods for facilitating electronic commerce by securely providing certificate-related and other services including certificate validation and warranty. In a preferred embodiment, these services are provided within the context of a four-corner trust model. The four-corner model comprises a buyer, or subscribing customer, and a seller, or relying customer, who engage in an on-line transaction. The buyer is a customer of a first financial institution, or issuing participant. The issuing participant operates a certificate authority and issues the buyer a hardware token including a private key and a digital certificate signed by the issuing participant. The seller is a customer of a second financial institution, or relying participant. The relying participant operates a certificate authority and issues the seller a hardware token including a private key and a digital certificate signed by the relying participant. The system also includes a root certificate authority that operates a certificate authority that issues digital certificates to the issuing and relying participants. At the time of a transaction, the buyer creates a hash of the transaction data, signs the hash, and transmits the transaction data, the signature, and its digital certificate to the seller. The seller may then request system services via a connection with its financial institution, the relying participant. The system services may include a certificate status check service and a warranty service. The certificate status check service allows the relying customer to validate the subscribing customer's certificate. The warranty service allows the relying customer to receive a collateral-backed warranty that the subscribing customer's certificate is valid. Each participant and the root entity is provided with a transaction coordinator for combining services and operations into a single transaction having the qualities of atomicity, consistency, isolation, and durability. The transaction coordinator provides a single consistent interface for certificate-status messages and requests, as well as messages and requests relating to other services.
Owner:DULIN CHARLES +4
Multiple cryptographic key security device
InactiveUS20060174125A1User identity/authority verificationPublic key infrastructure trust modelsRoot certificateDigital signature
A security domain for controlling PKI keys includes a root certificate authority, and one or more regional certificate authorities, each having a remote control and a postal security device. Different PKI keys are utilized to sign and to validate the authenticity of a digital signature for each certificate authority.
Owner:NEOPOST TECH SA
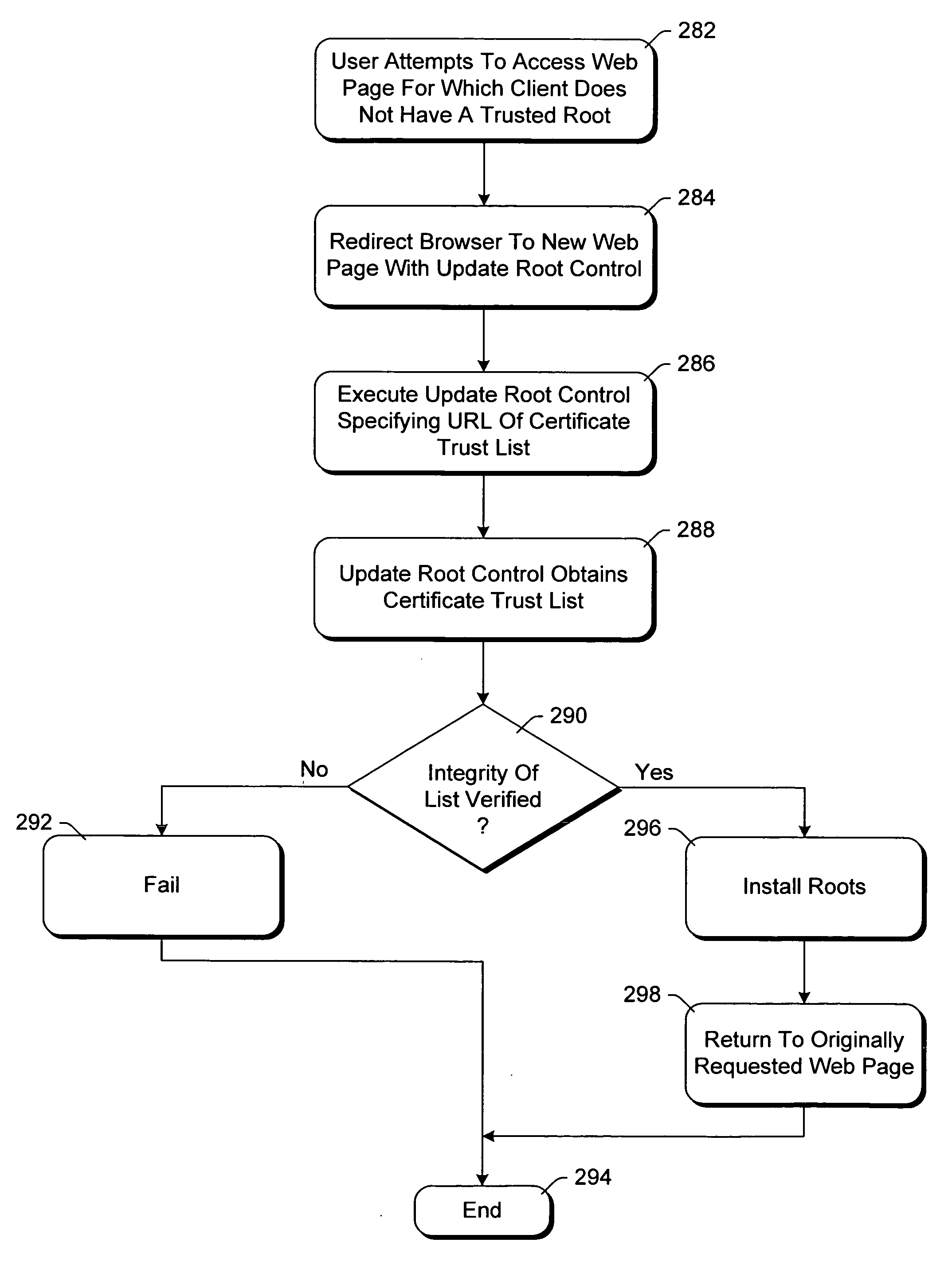
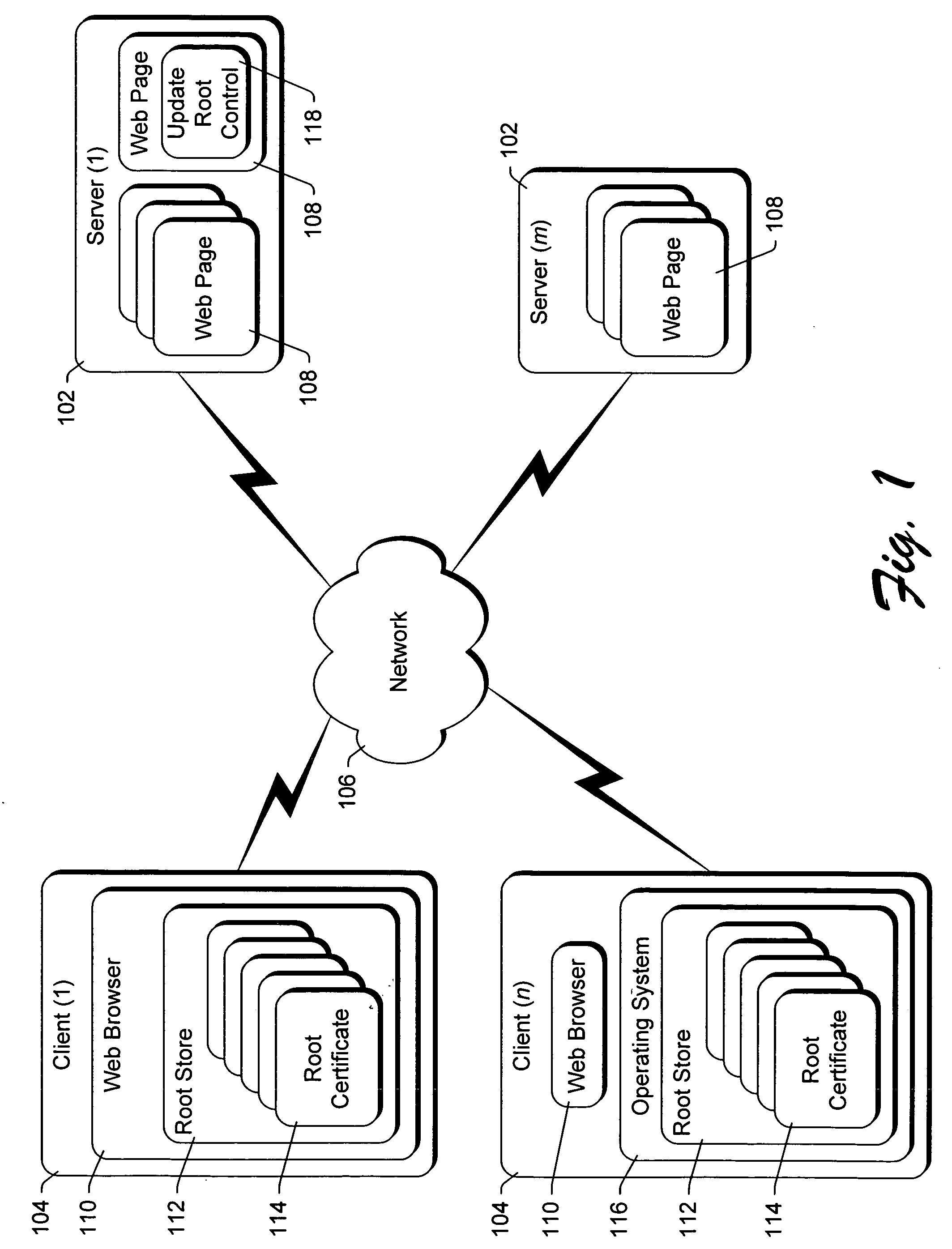
Updating trusted root certificates on a client computer
InactiveUS20050080899A1User identity/authority verificationMultiple digital computer combinationsRoot certificateClient-side
An update process is used to update root certificates in a root certificate store of a client computer, maintaining the integrity of the existing root certificates as well as any new root certificates. In accordance with certain aspects, the integrity of a certificate trust list identifying one or more root certificates is verified. The root certificate store of the client computer is modified in accordance with the certificate trust list if the integrity of the certificate trust list is verified.
Owner:MICROSOFT TECH LICENSING LLC
Method and device for enabling a trust relationship using an expired public key infrastructure (PKI) certificate
ActiveUS20100115267A1Digital data processing detailsAnalogue secracy/subscription systemsRoot certificateTrust relationship
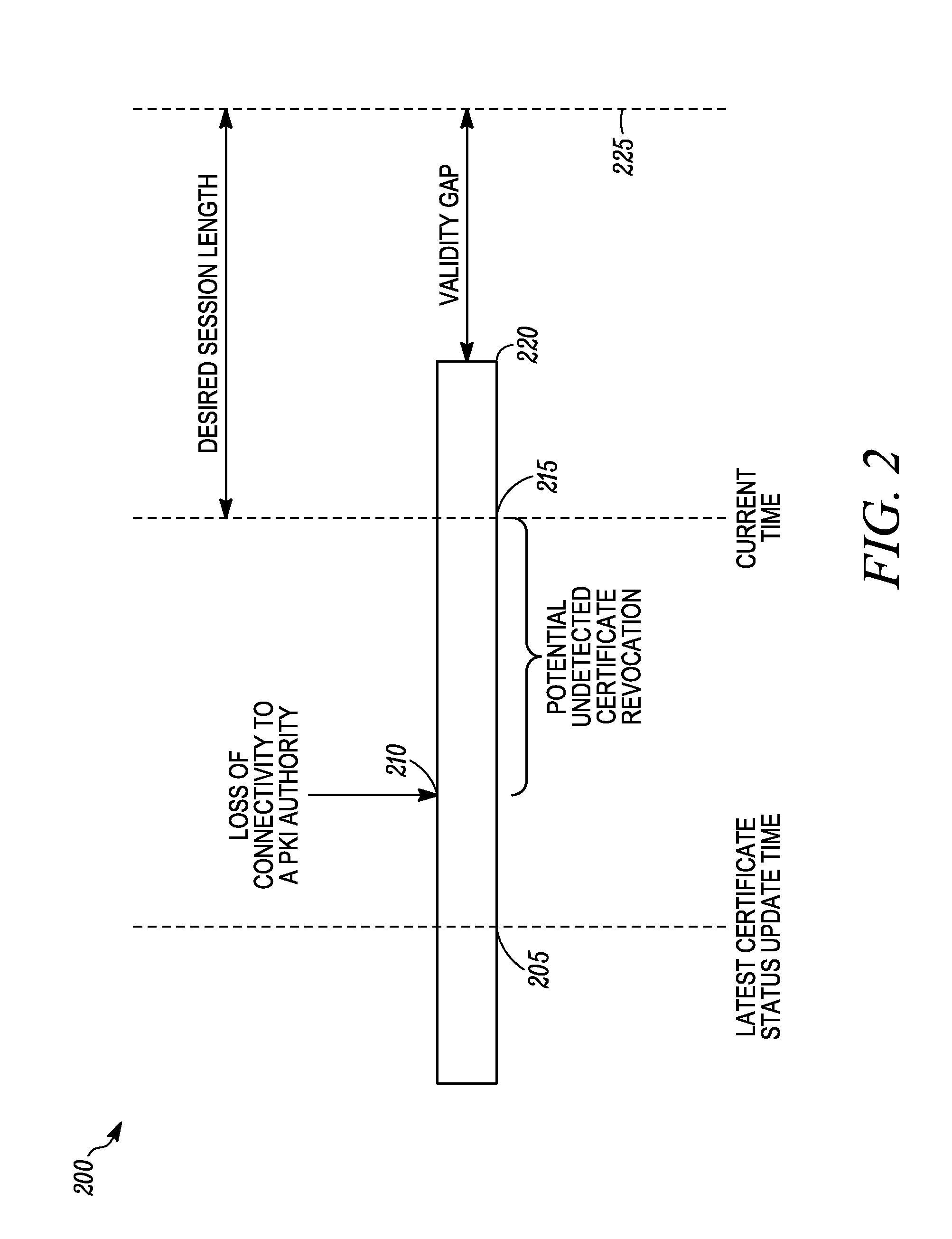
A method and device are useful for enabling a trust relationship using an expired public key infrastructure (PKI) certificate. The method includes determining at a relying party a maximum permissible grace period during which the PKI certificate can be conditionally granted a valid status (step 905). Next, at the relying party an uncertainty interval is determined, during which the relying party is unable to detect a revocation of the PKI certificate (step 910). A certificate grace period is then determined at the relying party from a function of the maximum permissible grace period, the uncertainty interval and at least one attribute defined in the PKI certificate (step 915). Using the PKI certificate, a trust relationship is then enabled between the relying party and a certificate holder of the PKI certificate, after determining the grace period and before an expiration of the grace period (step 920).
Owner:ARRIS ENTERPRISES LLC
Tandem encryption connections to provide network traffic security method and apparatus
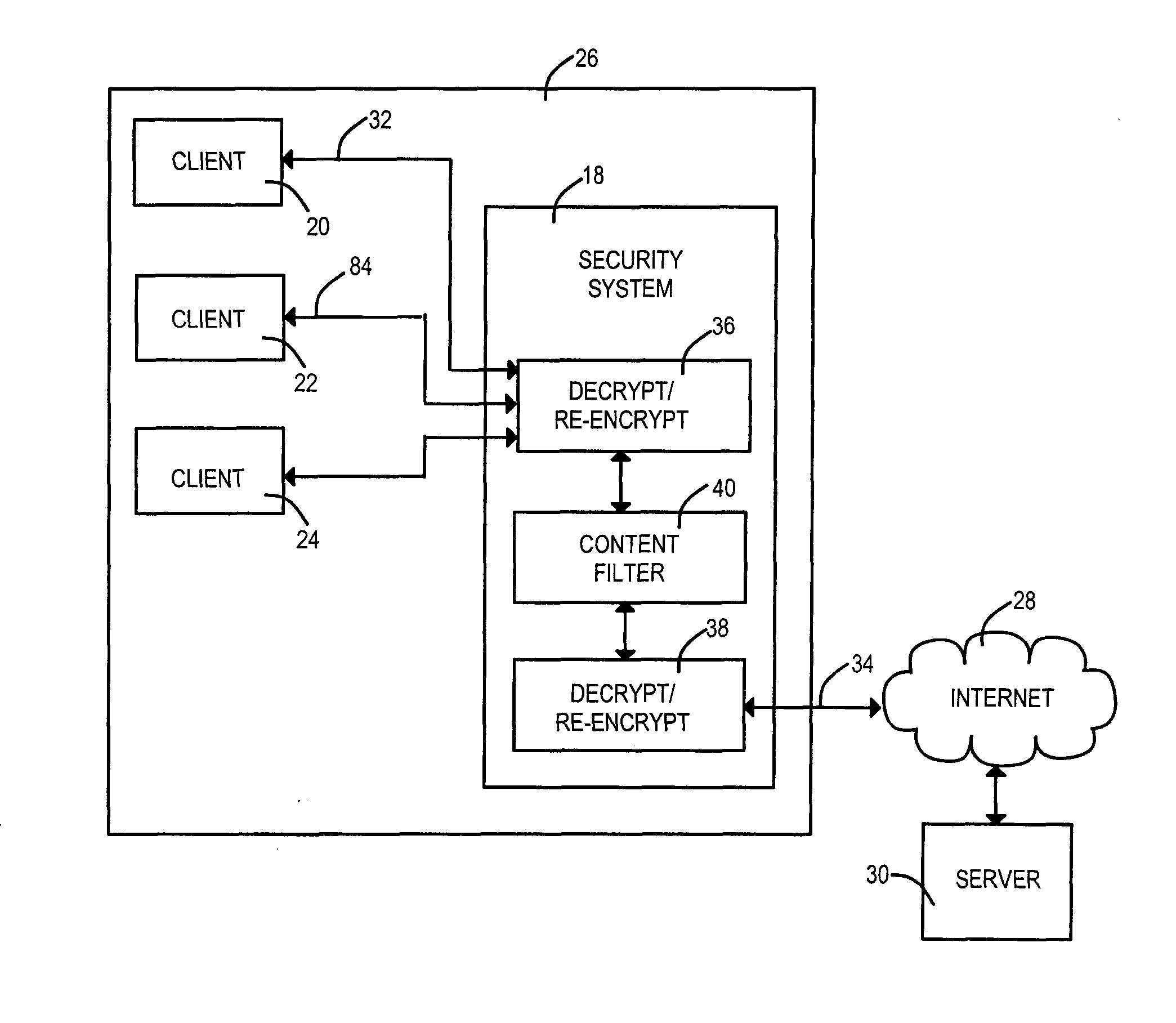
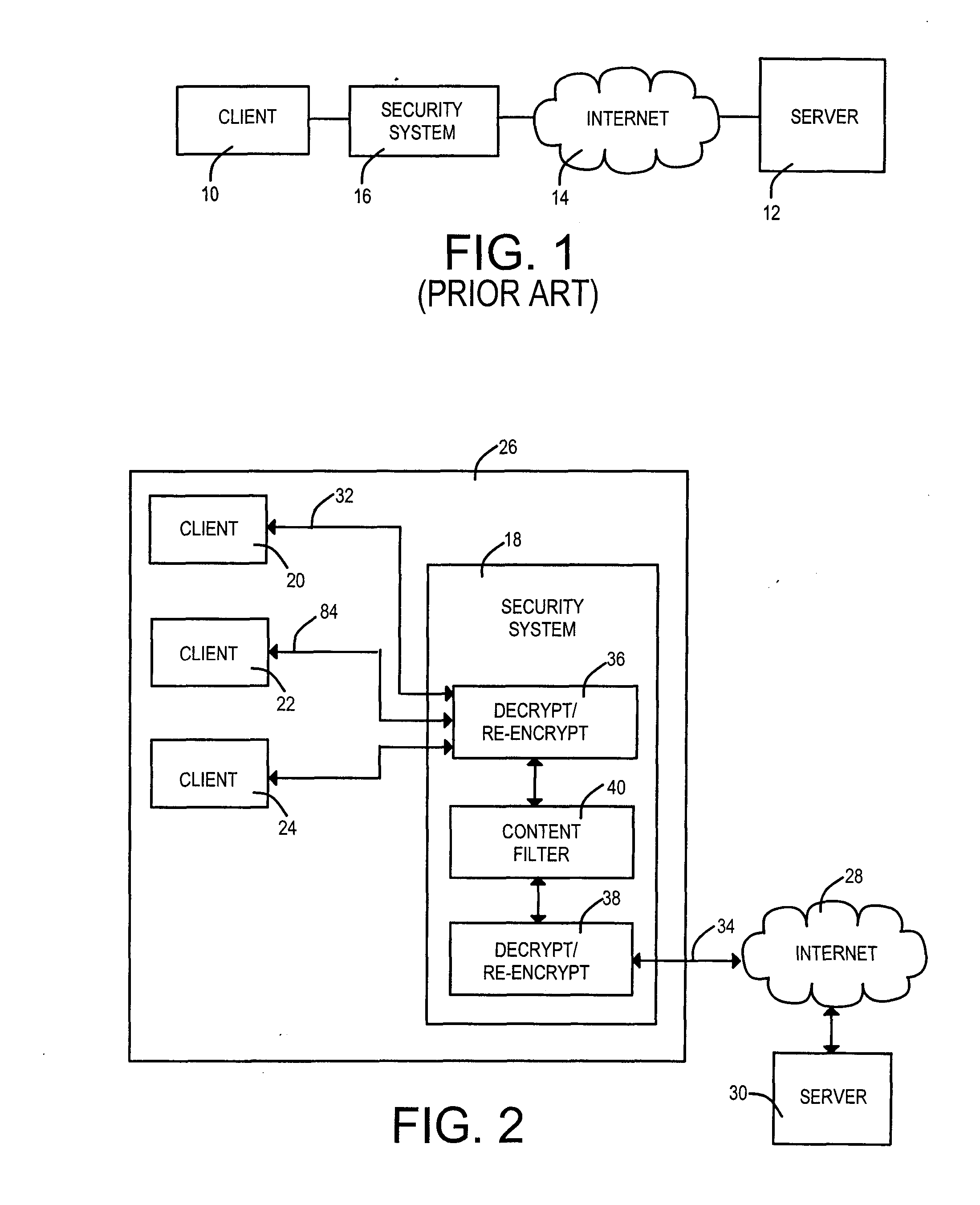
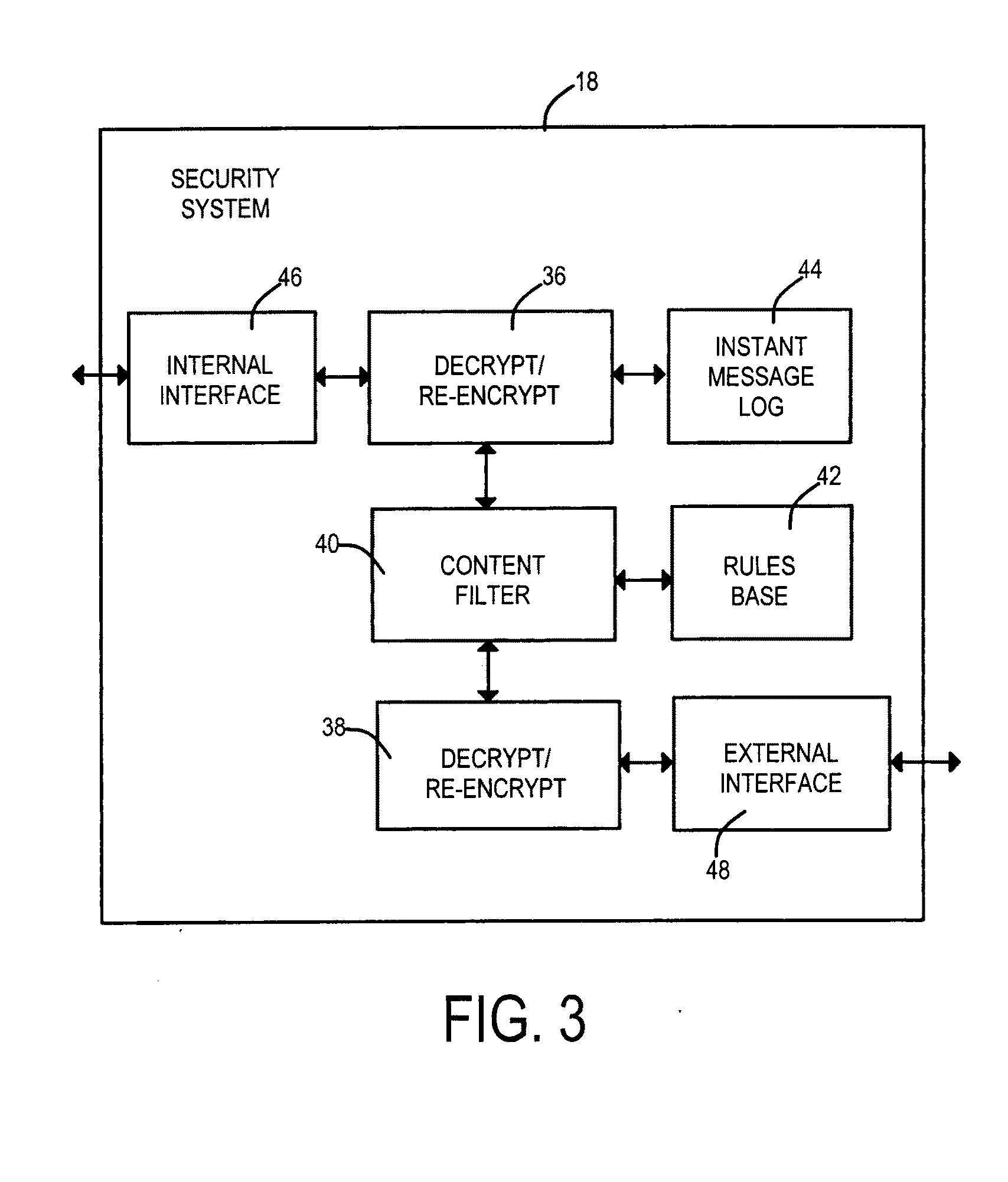
Security measures are applied to encrypted data exchanges by enabling content decryption, rule application, and content re-encryption at a network location. A certificate, self-signed or authenticated by an official Certificate Authority is obtained for and installed within the secure proxy apparatus. A link to a secure page is replaced with a link to a page having a fully qualified domain name of the proxy apparatus as the suffix. An encrypted session between the client is established between the client and the proxy apparatus without deceit in the later case. A first encryption-enabled connection is established from the first node to a content filter, while a second encryption-enabled connection is established from the content filter to the second node. Following decryption, a determination is made as to whether the content includes Undesired Data. Restricted material is blocked, while unrestricted material is re-encrypted and delivered to the destination node. For a self-signed certificate, the destination node comprises a private security system-signed root certificate installed in the destination node's Trusted Root Certification Authorities certificate store. In another aspect of the invention, at least one of encrypted Instant Messages, e-mail messages and web pages are decrypted and recorded at a location between sources and destinations of the transmissions. The look and feel is maintained of a single encrypted link between the requestor and the external source by the inventive use of a wildcard certificate within the network local to the requestor.
Owner:BARRACUDA NETWORKS
Certification apparatus and method
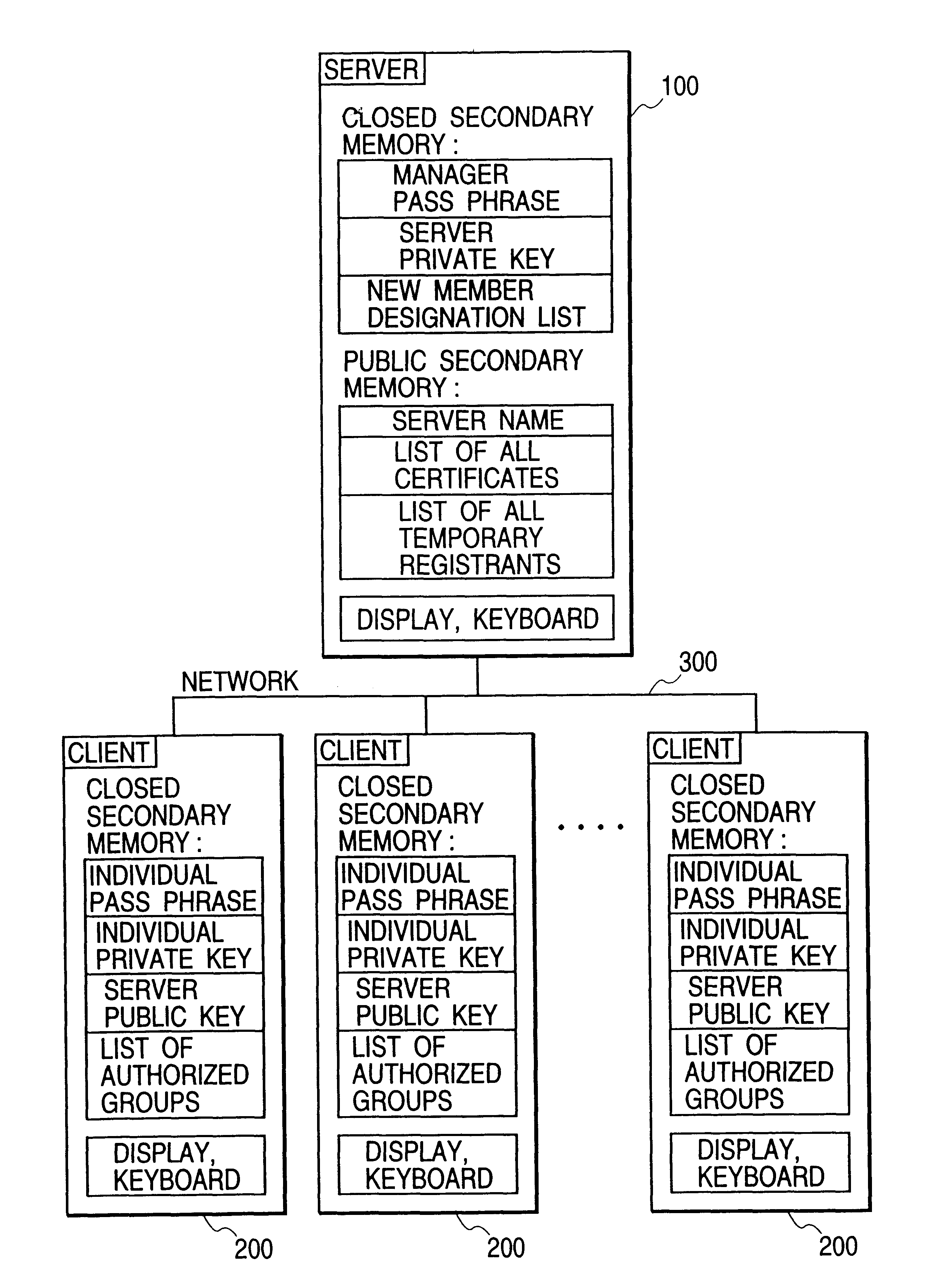
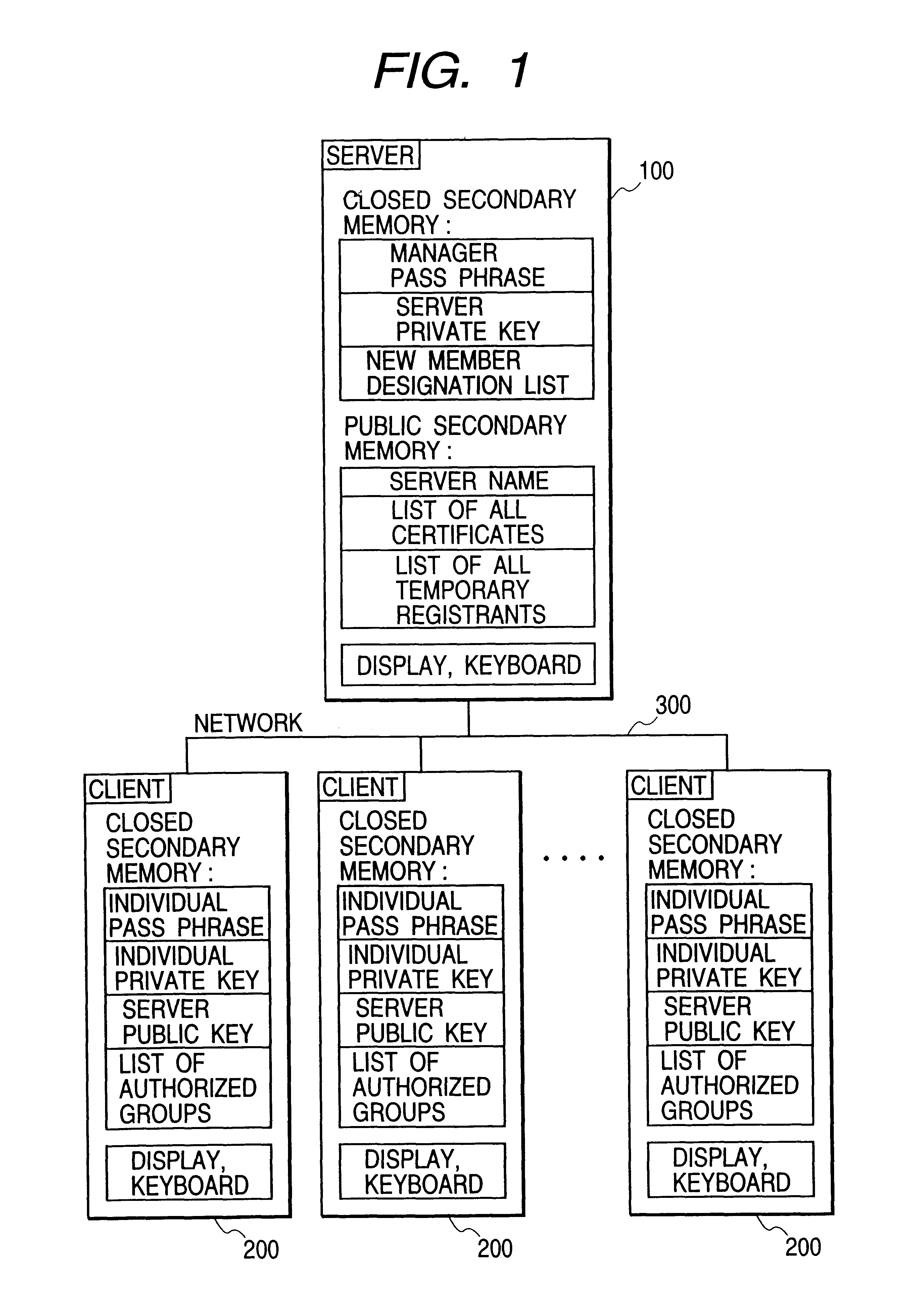
InactiveUS6748530B1Easy to handleKey distribution for secure communicationUser identity/authority verificationRoot certificateNetwork connection
Certification will be performed without the use of any external certification organizations in an organization such as an enterprise. A server and a plurality of clients are connected via a network to thereby constitute a certification system for the entire enterprise. A public secondary memory in the server holds a server name, a certificate list, a temporary registrant list and the like. The certificate list includes individual and group certificates, and the certificate includes specifying information on a certification target, a public key and signature by an responsible person of a group, to which the certification target belongs. The group responsible person signs the public key of the group member and specifying information by using the information on a registrant list to generate a certificate.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Method for authenticating point of sail (POS) file and method for maintaining authentication certificate
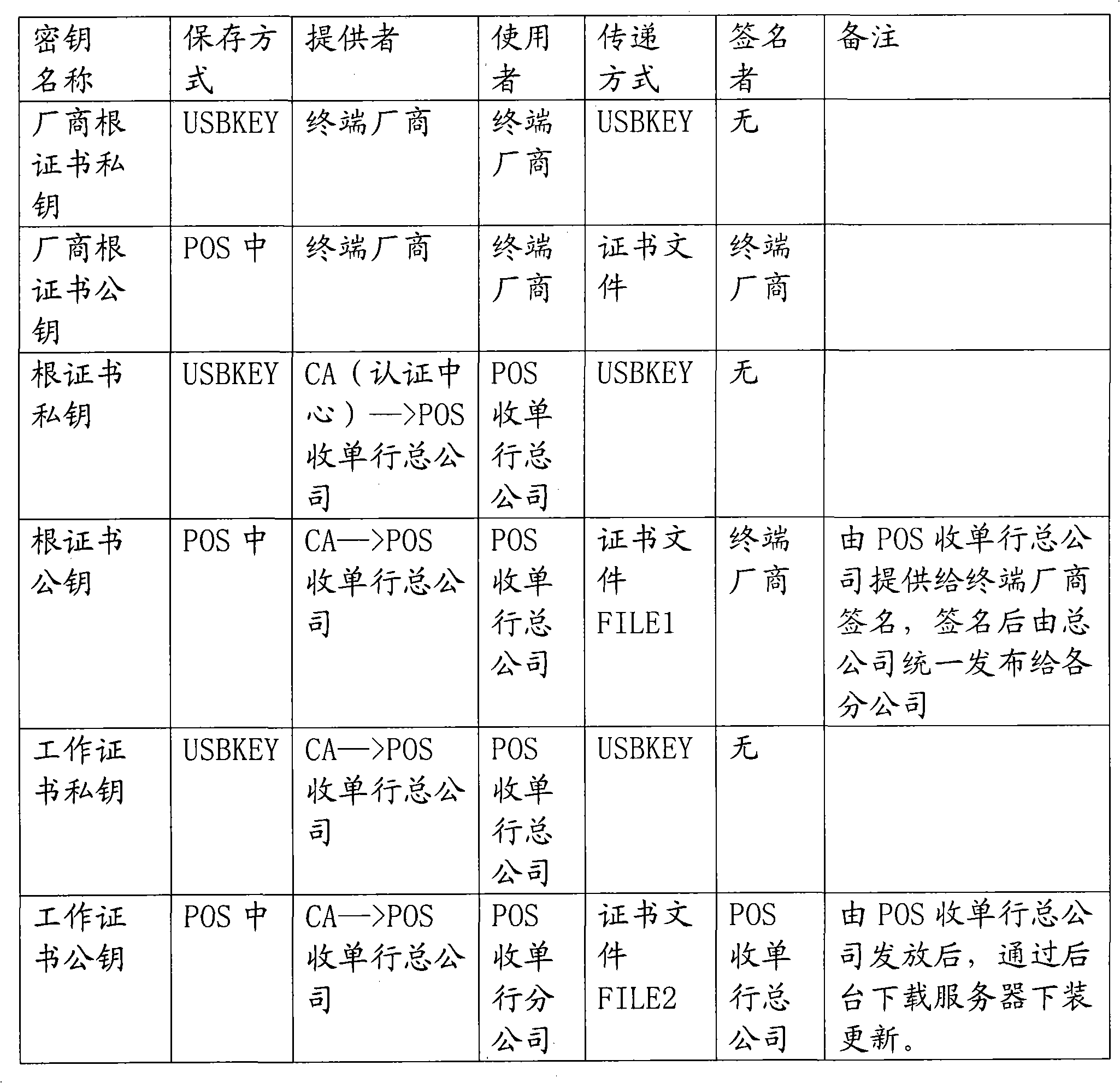
ActiveCN102064939AGuarantee authenticityMeet safety requirementsUser identity/authority verificationRoot certificateDigital signature
The invention provides a method for authenticating a point of sail (POS) file and a method for maintaining an authentication certificate. During the POS file authentication, a two-level certificate management-based POS digital signature scheme is adopted, wherein the first-level certificate is a root certificate and the second-level certificate is a working certificate; the root certificate can authenticate the legality of the working certificate, but cannot authenticate the legality of an application program; and the working certificate can authenticate the legality of downloaded POS software. A POS acquirer head office applies the root certificate and the working certificate from certificate authority (CA), provides a POS acquirer root certificate public key to a terminal manufacturer, performs digital signature to generate a root certificate public key file, returns the root certificate public key file to the head office and then issues the root certificate public key file to each branch office; each POS acquirer branch office receives the root certificate public key file transmitted by the head office; and the POS acquirer head office performs digital signature on a working certificate public key by a root certificate private key to generate a working certificate public key file and issue the working certificate public key file to each branch office. The method for authenticating the POS file and the method for maintaining the authentication certificate have the advantages of contributing to the update and the maintenance of the certificate per se and guaranteeing the authenticity of application software.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
Systems And Methods For Root Certificate Update
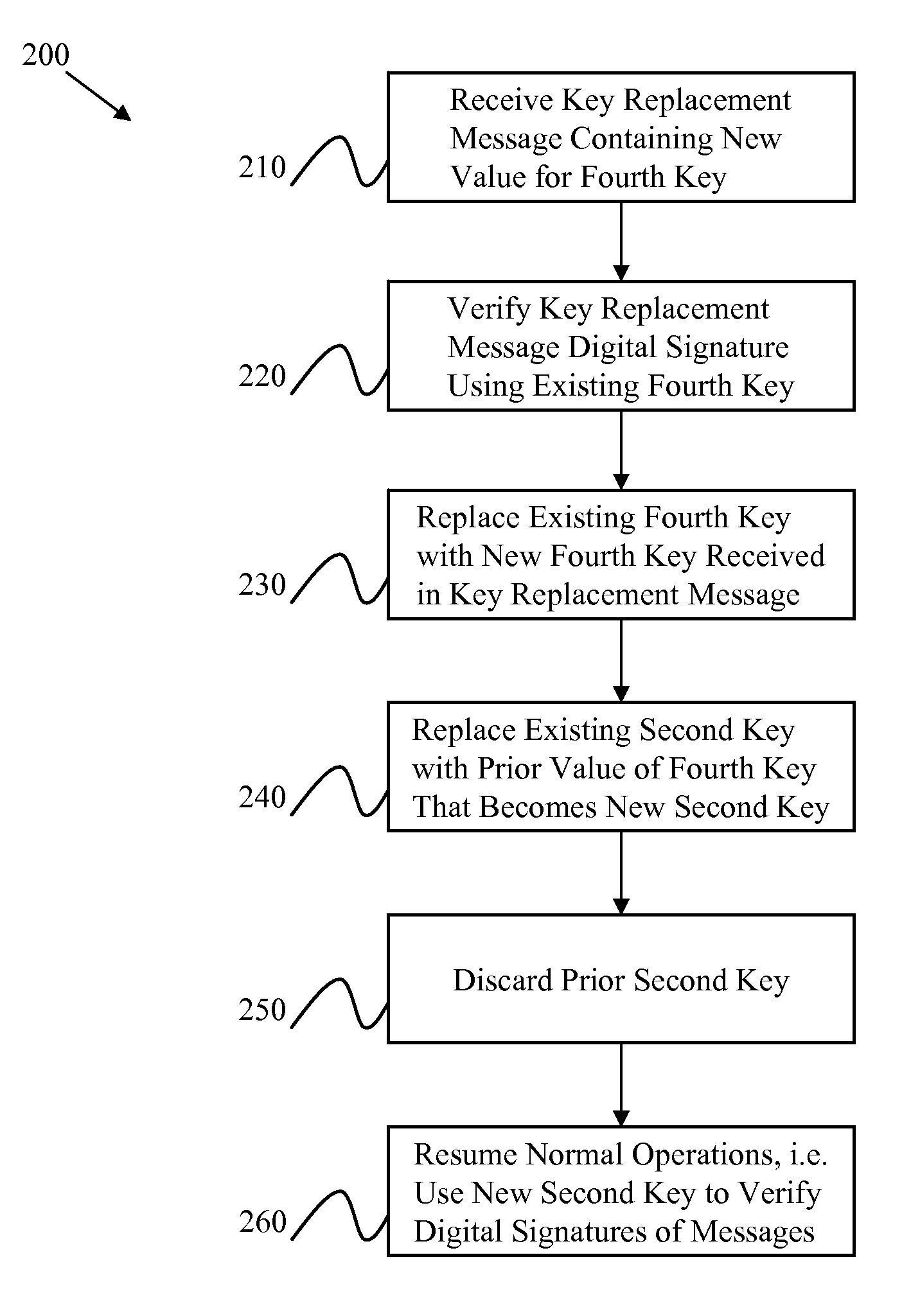
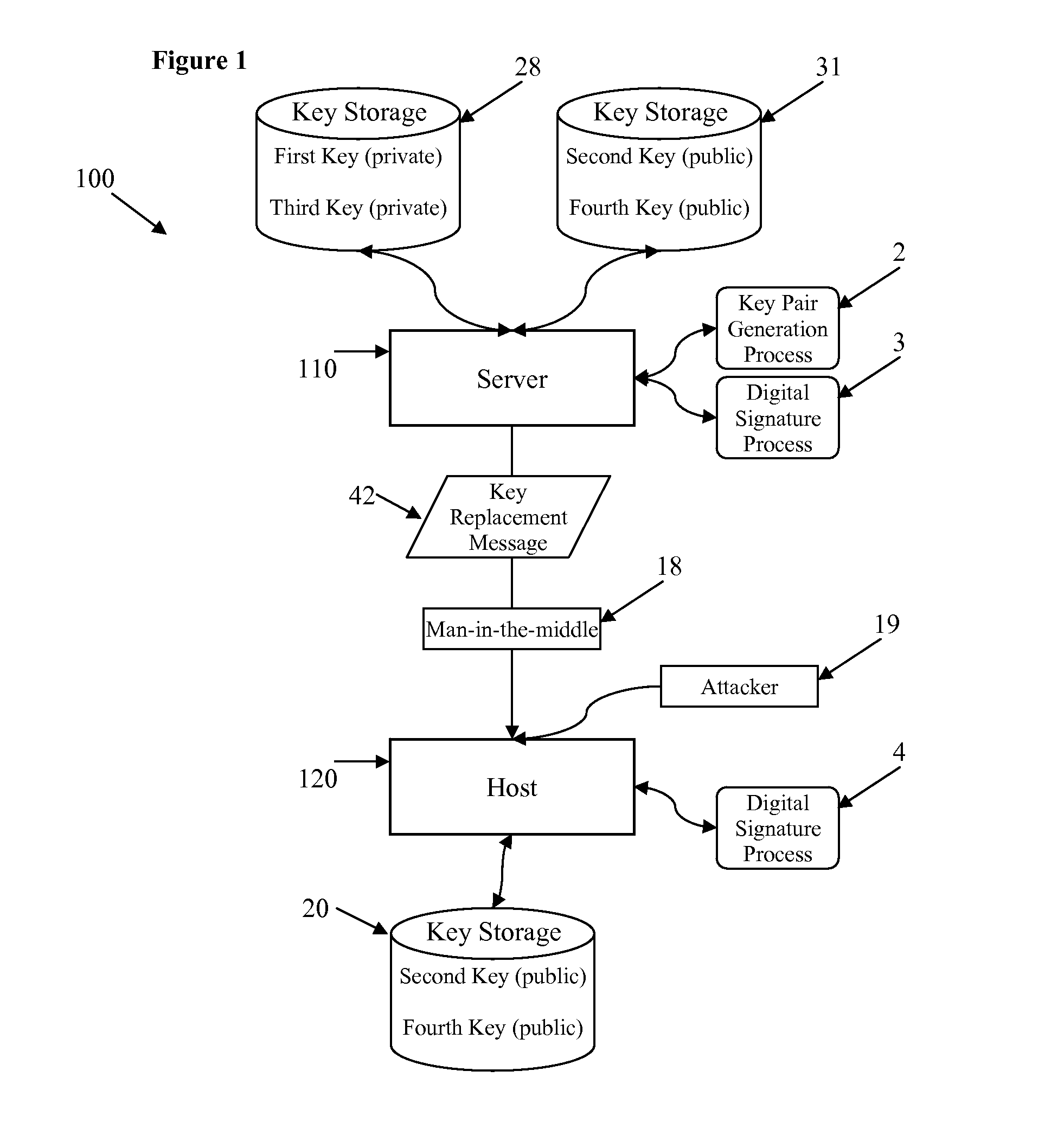
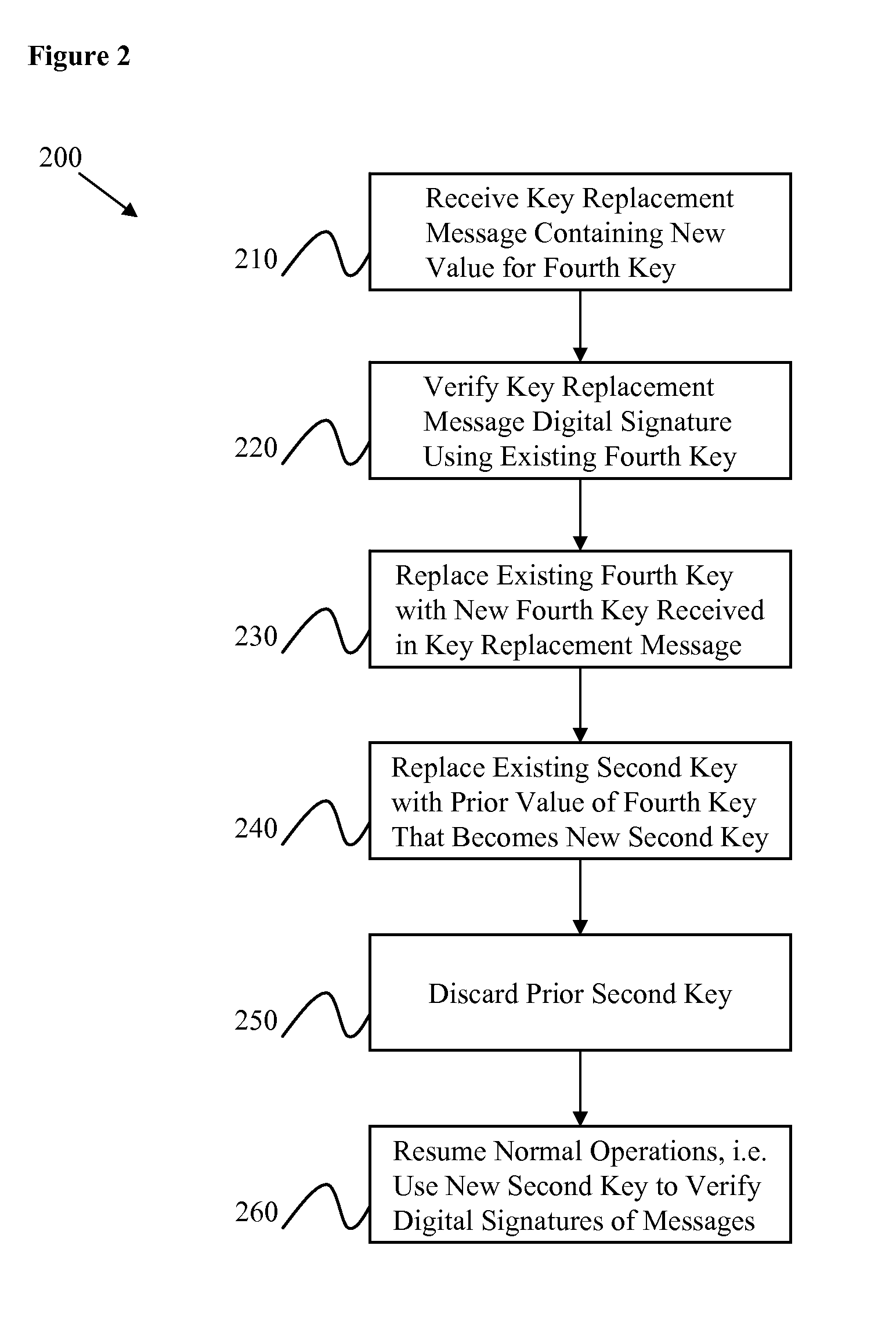
InactiveUS20080025514A1Multiple keys/algorithms usagePublic key for secure communicationComputer hardwareRoot certificate
Certain embodiments of the present invention provide a method for replacing a cryptographic key including receiving a key replacement message for replacing the cryptographic key, decrypting at least part of the key replacement message using at least part of the cryptographic key, reading from the key replacement message at least part of at least a first replacement cryptographic key or at least a first replacement cryptographic key precursor value that is used to derive a first replacement cryptographic key, and replacing the cryptographic key with at least part of the first replacement cryptographic key. The key replacement message includes encrypted data. The encrypted data having been encrypted using at least part of at least a third cryptographic key. Decrypting the encrypted data using at least part of the cryptographic key. The decrypting being associated with verifying a digital signature.
Owner:COOMBS JASON SCOTT
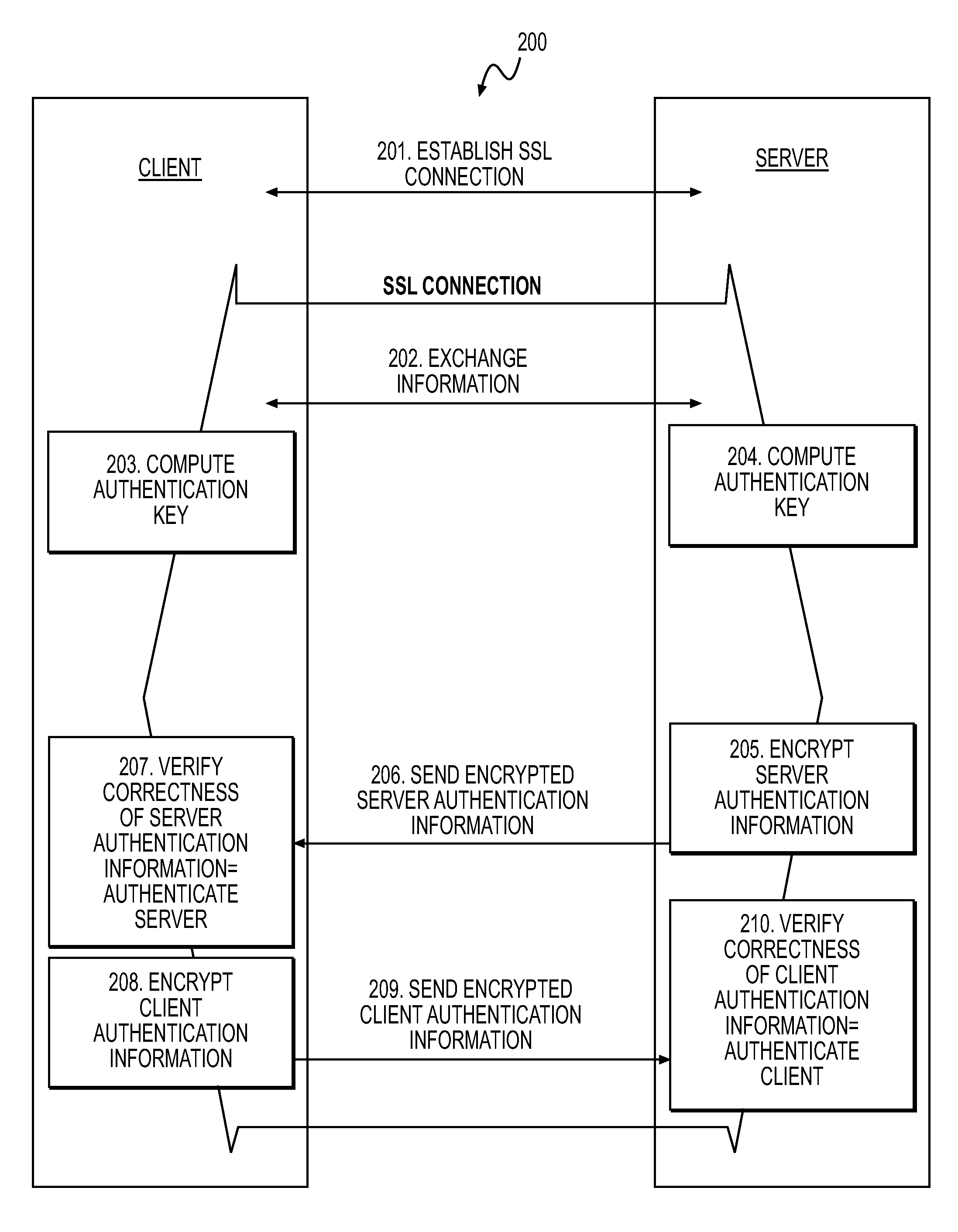
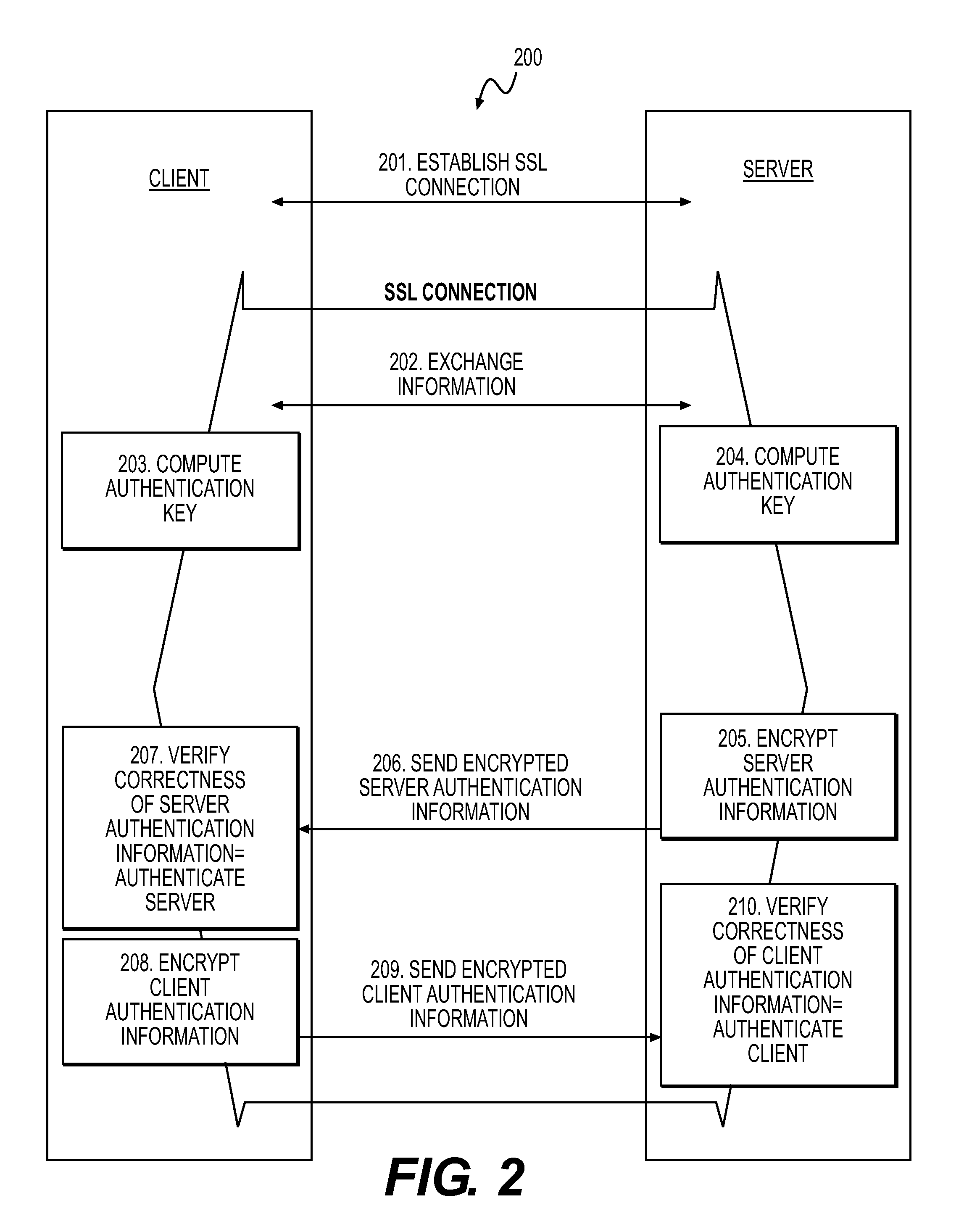
Use and generation of a session key in a secure socket layer connection
InactiveUS7975139B2Digital data processing detailsUser identity/authority verificationRoot certificateClient-side
The invention describes a method and system for verifying the link between a public key and a server's identity as claimed in the server's certificate without relying on the trustworthiness of the root certificate of the server's certificate chain. The system establishes a secure socket layer type connection between a client and a server, wherein the server transmits information including the server's public key to the client while establishing the connection. Next, a first information is sent from the client to the server. The client and the server create an identical authentication key using a shared secret known to the server and the client. Next, the server transmits a first encrypted message to the client, wherein the first encrypted message includes the server's public key encrypted with the authentication key. Then, the client decrypts the first encrypted message and verifies the correctness of that message including comparing the public key included in the decrypted first encrypted message to the public key transmitted during the set-up of the secure socket layer type connection to authenticate the client and to establish the trustworthiness of the server's public key and thereby the entire SSL connection. The client then transmits a second encrypted message to the server, wherein the second encrypted message is the first information encrypted with the authentication key. Finally, the server then decrypts the second encrypted message and verifies the correctness of the decrypted second encrypted message to authenticate the client.
Owner:ONESPAN NORTH AMERICA INC
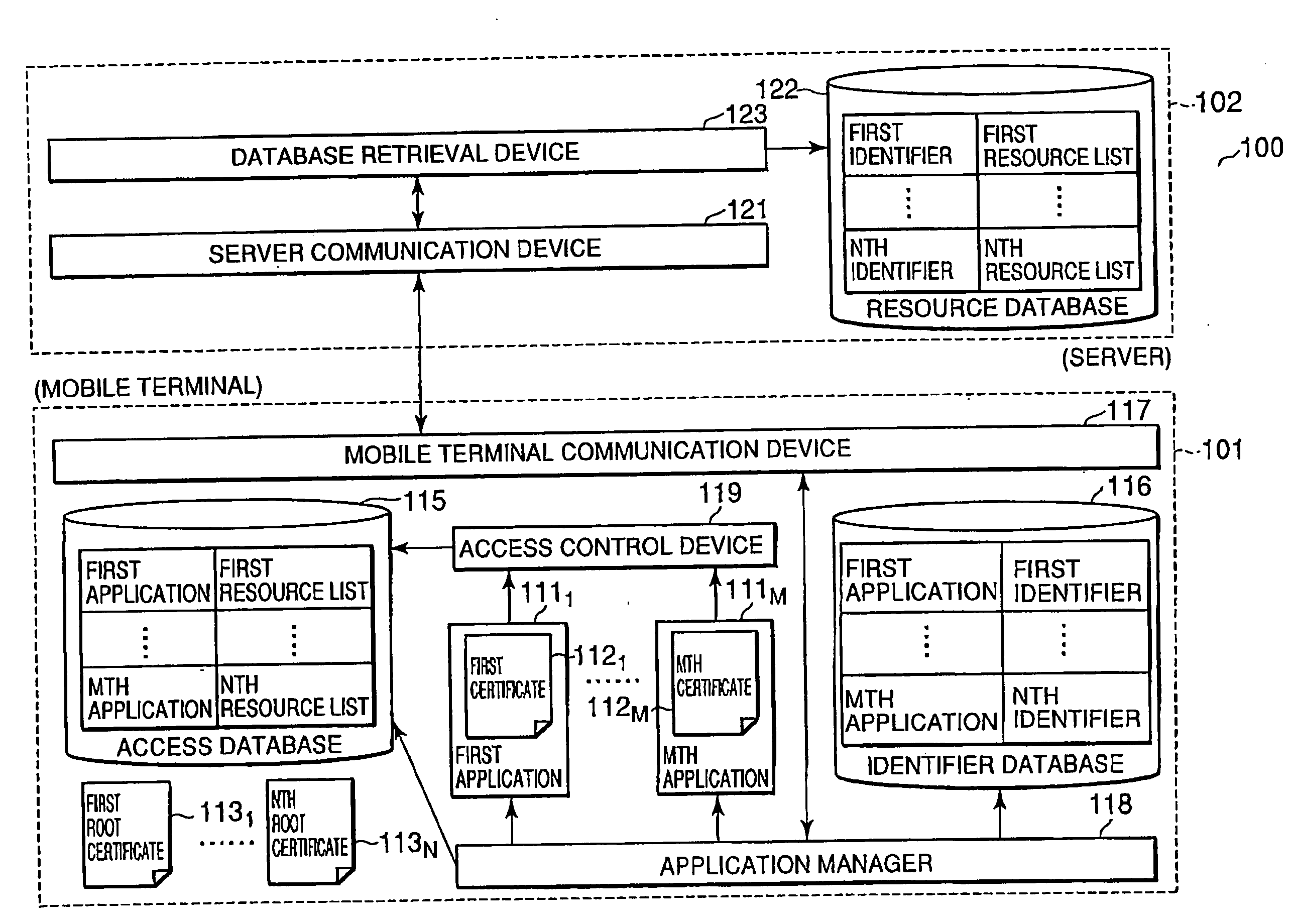
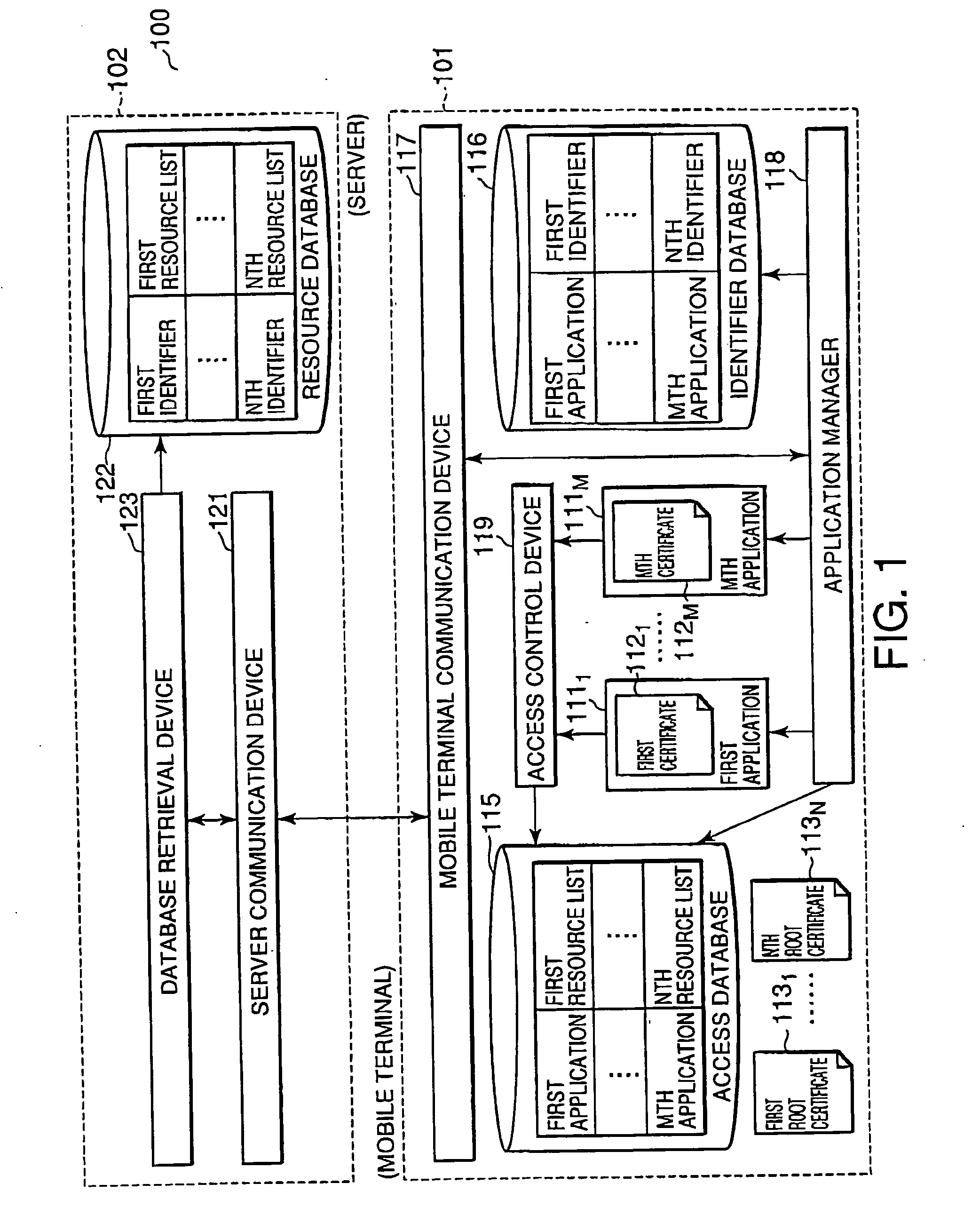
Mobile terminal, resource access control system for mobile terminal, and resource access control method in mobile terminal
InactiveUS20090205037A1Limited accessReduce necessitySpecific access rightsDigital data processing detailsRoot certificateComputer terminal
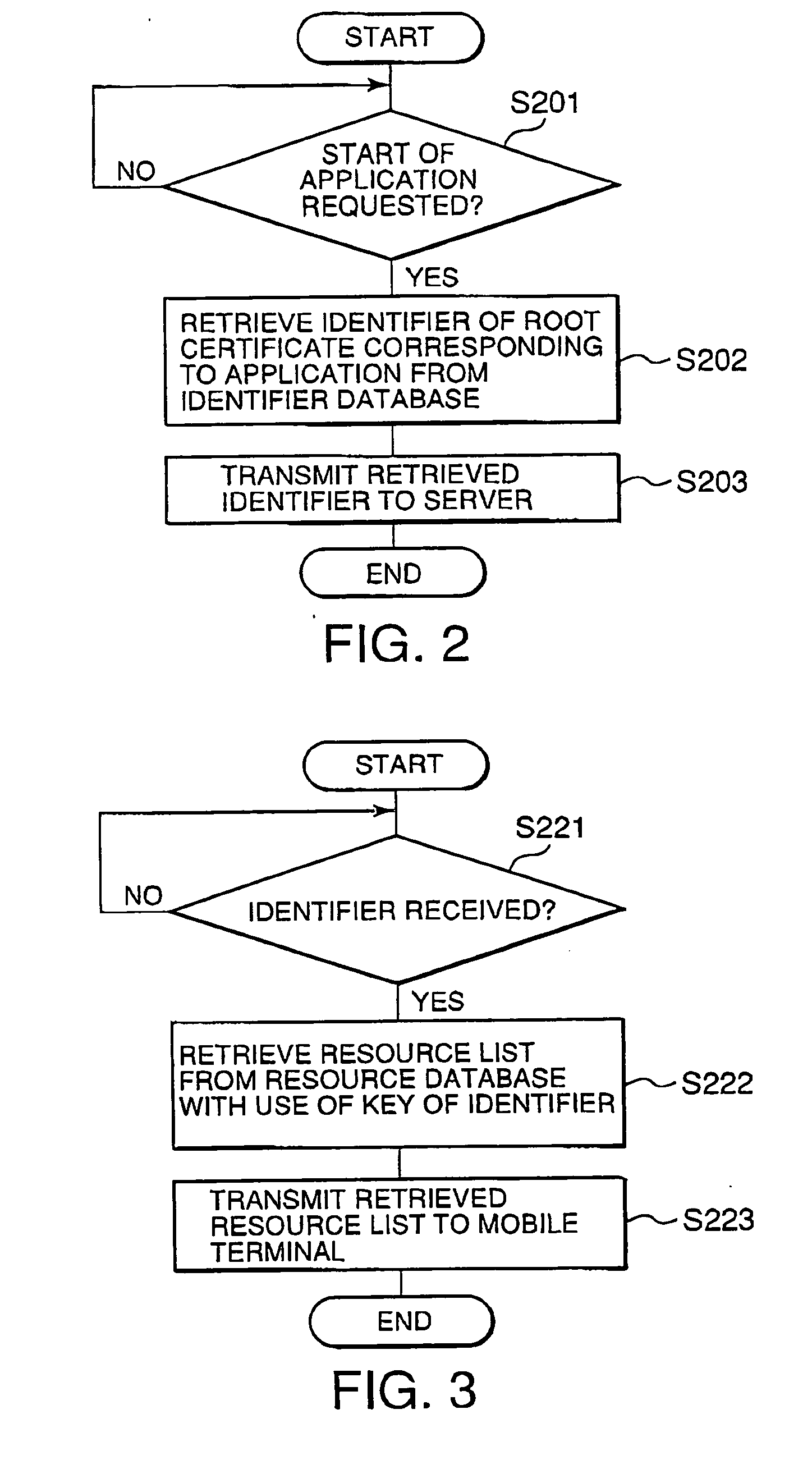
The present invention provides a mobile terminal, a resource access control system for a mobile terminal, and a resource access control method in a mobile terminal which can flexibly change resources that can be accessed by an application. An application manager 118 of a mobile terminal 101 transmits an identifier of a root certificate of an application to a server 102 at predetermined timing, e.g., when the application is started, to thereby retrieve a corresponding resource list from a resource database 122. The corresponding resource list is added to an access database 115, or the contents of the access database 115 are updated with the corresponding resource list. Access to resources specified by the resource list is permitted. When the resource list is changed, the contents of the resource list may be transmitted from the server 102 to the mobile terminal 101 by a push type notification.
Owner:NEC CORP
User authentication system
ActiveUS20110246764A1Public key for secure communicationDigital data processing detailsThird partyRoot certificate
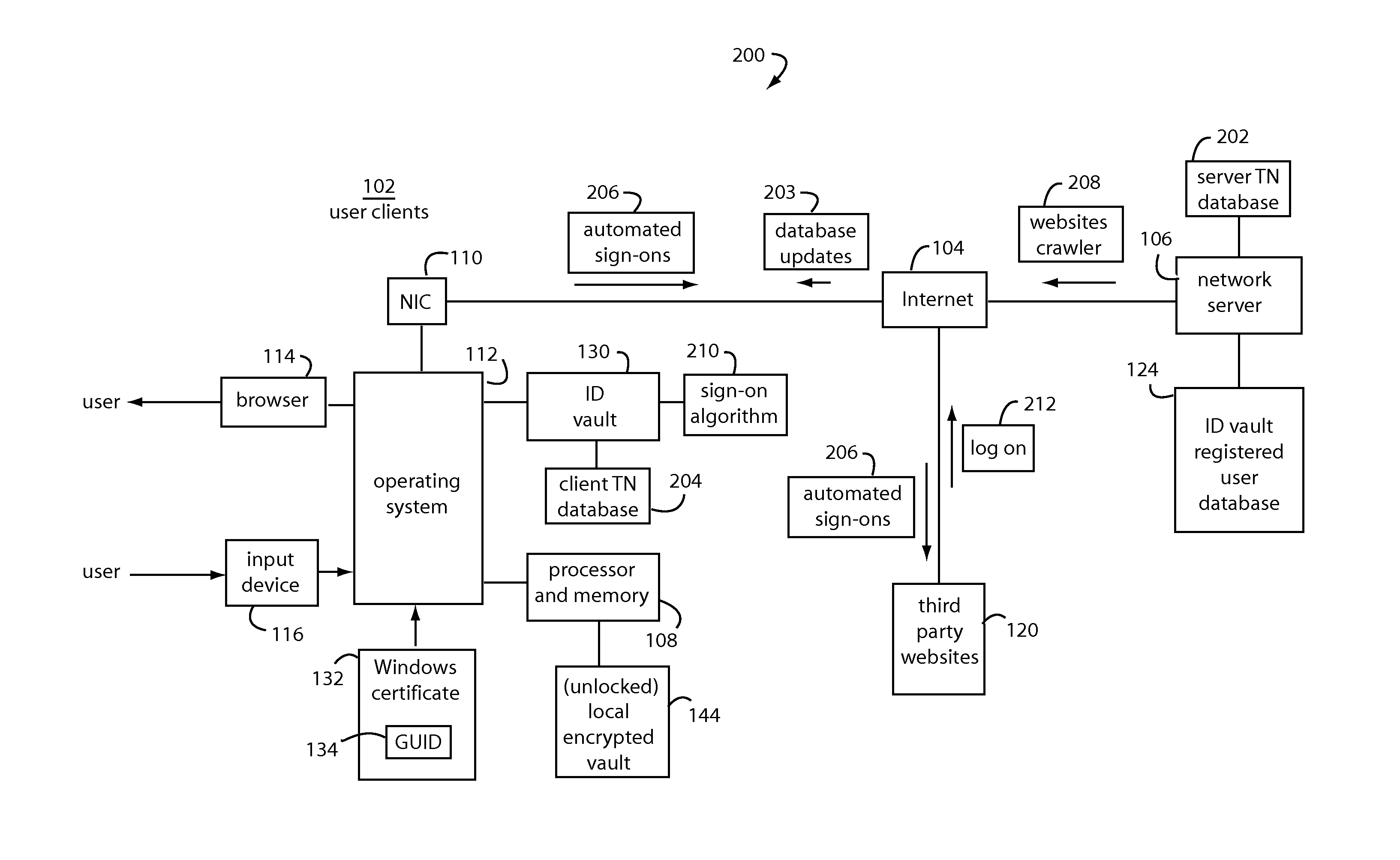
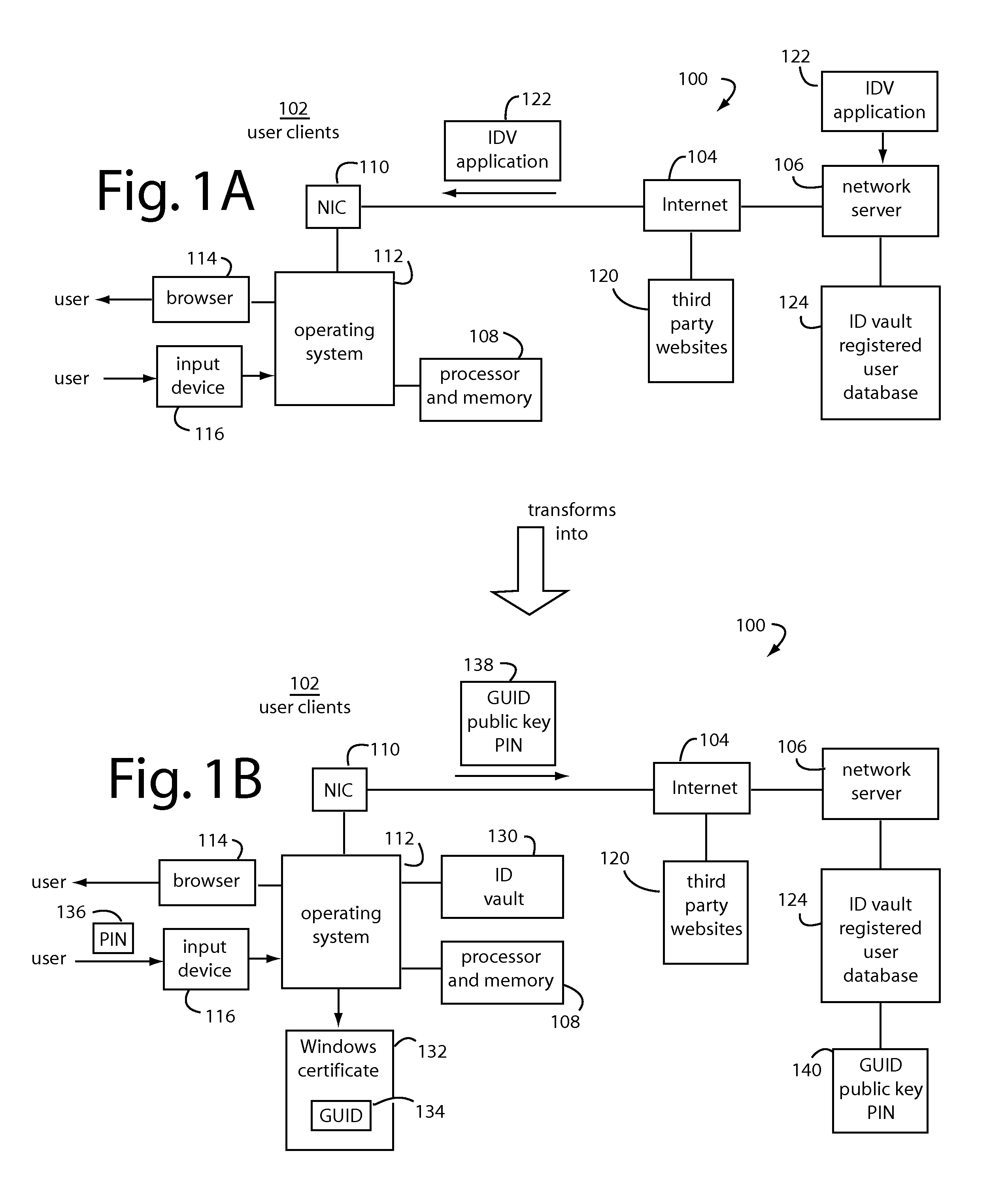
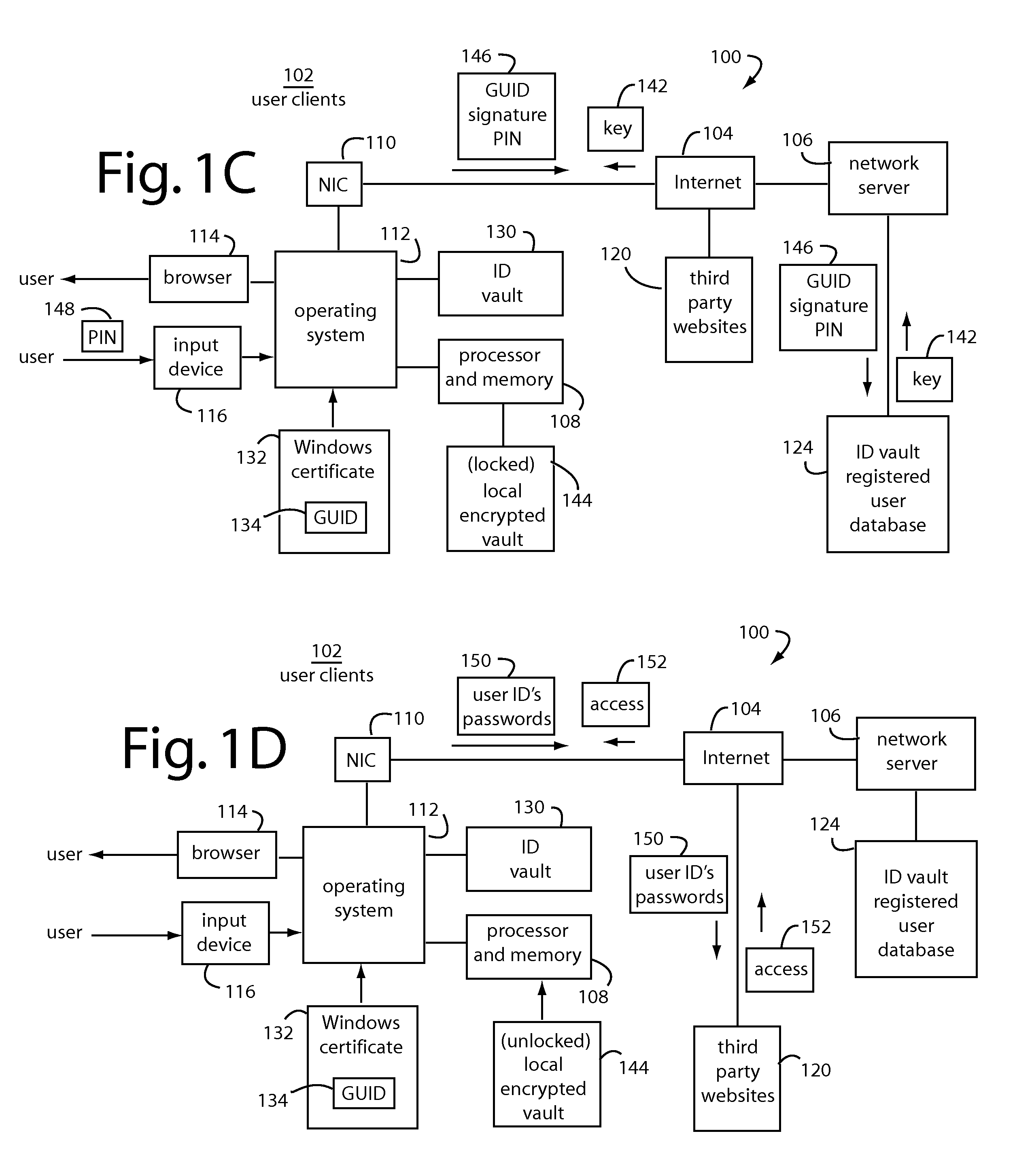
An ID vault computer control program detects when a user's browser navigates to a third-party website that requires a user ID and password. If it hasn't done so already, it automatically requests a decryption key for a local encrypted vault file from a network server by supplying a personal identification number (PIN) from the user through the input device, a copy of the GUID, and a signature of GUID using a private key for the root certificate. If a decryption key is returned from the network server, the local encrypted vault file is unlocked and automatically supplies a corresponding user ID and password to log-on to the third-party website without the user.
Owner:INTERSECTIONS LLC +1
Medical data platform based on block chain technology
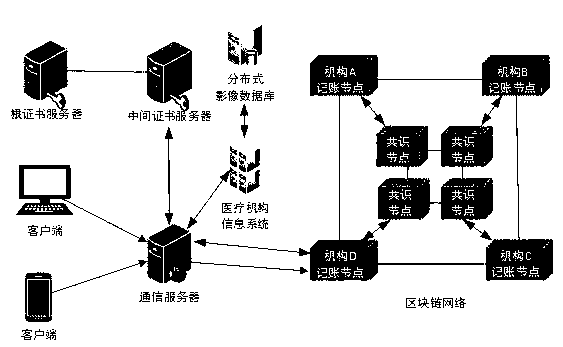
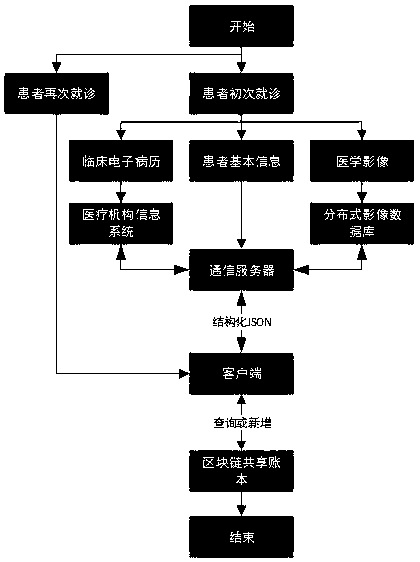
InactiveCN109243548AIsolation damageReduce risk of leakageDigital data information retrievalPublic key for secure communicationData synchronizationData platform
The invention discloses a medical data platform based on the block chain technology. The medical data platform comprises a terminal, a server module, a data storage module and a block chain network. The terminal exchanges data with the data storage module and the block chain network through the server module. The server module comprises a communication server, an intermediate certificate server and a root certificate server and is used for processing data interaction between the modules and allocating certificates to the block chain network nodes. The data storage module comprises a medical information system and a distributed image database and is used for data storage. The block chain network comprises multiple institutional accounting nodes and multiple consensus nodes. The accounting nodes perform mutual data synchronization. The medical data platform based on the block chain technology has the advantages that the existing medical information is stored in the block chain shared account book so that all the medical institutions can share the medical information related to the patients, and the privacy protection function of the medical data can be realized by using the encryption algorithm and thus sharing of the medical data can be facilitated and the security of the sensitive information can also be protected.
Owner:GUANGDONG UNIV OF TECH
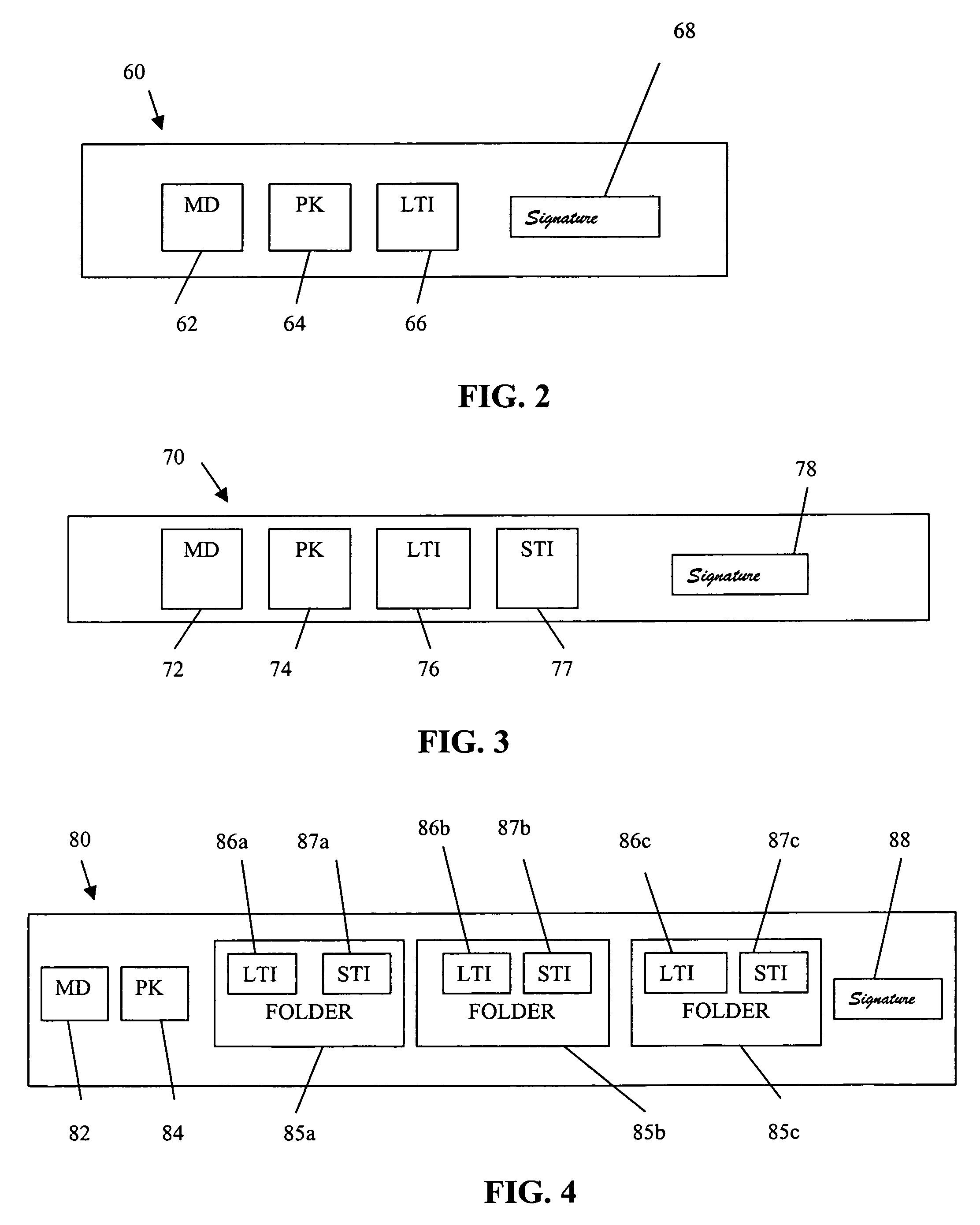
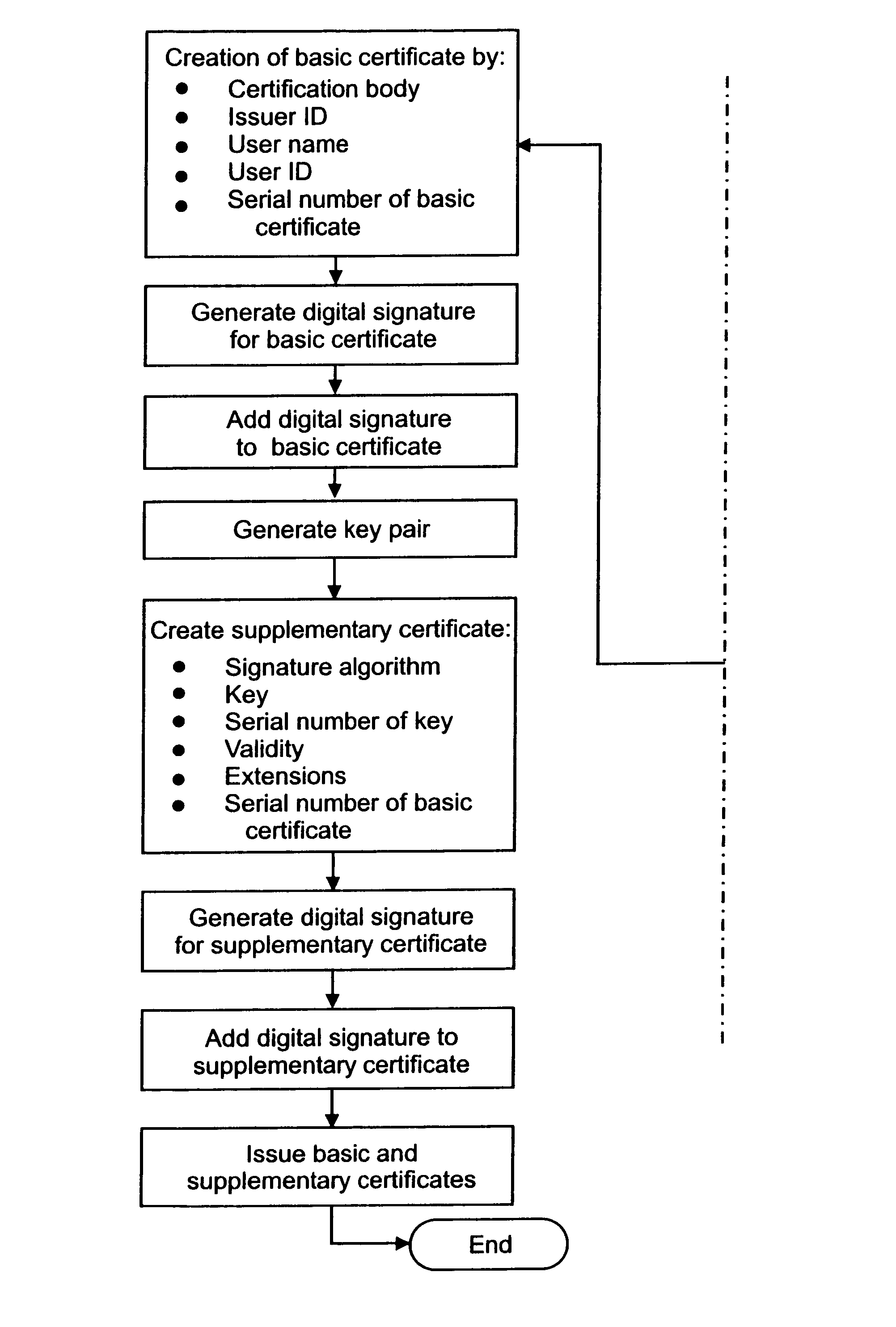
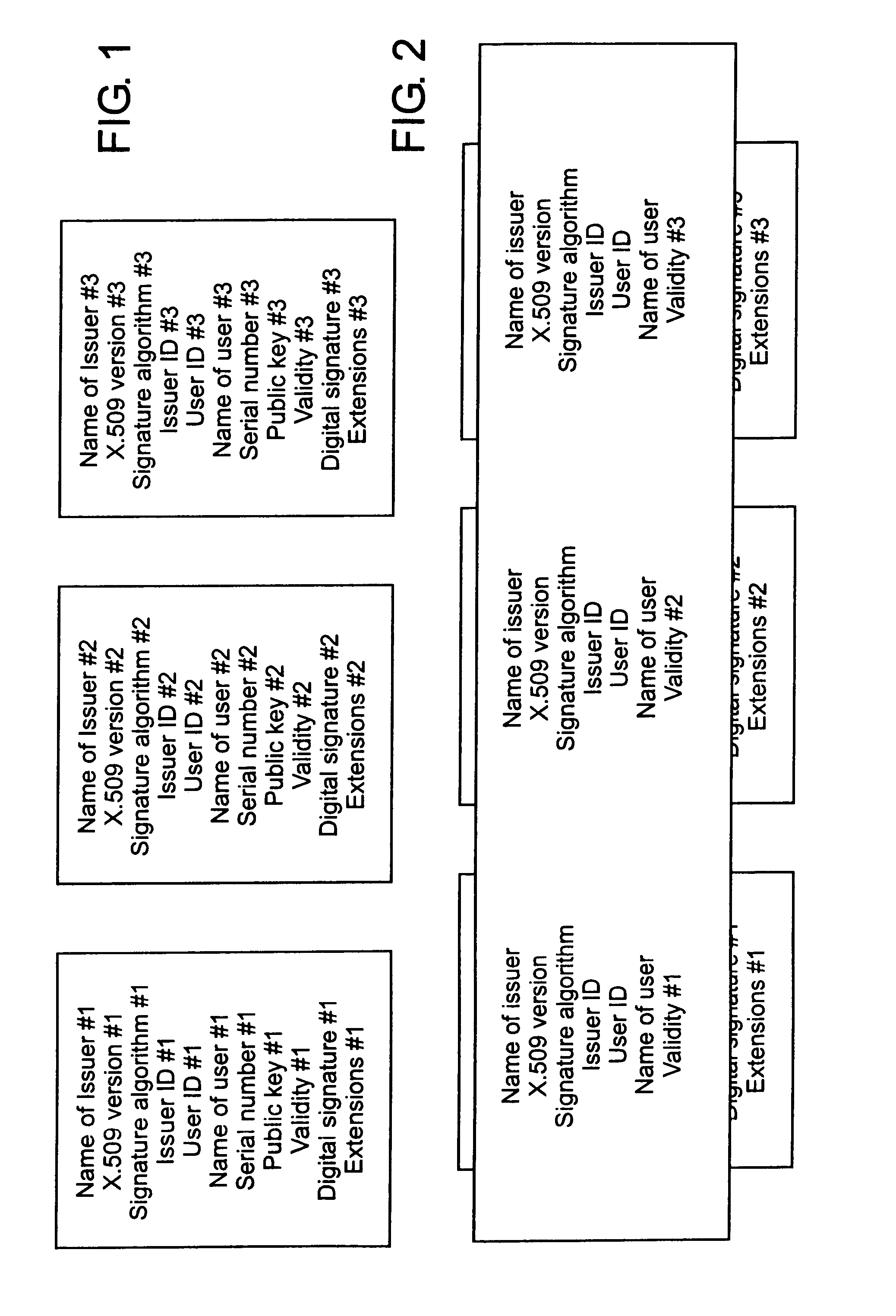
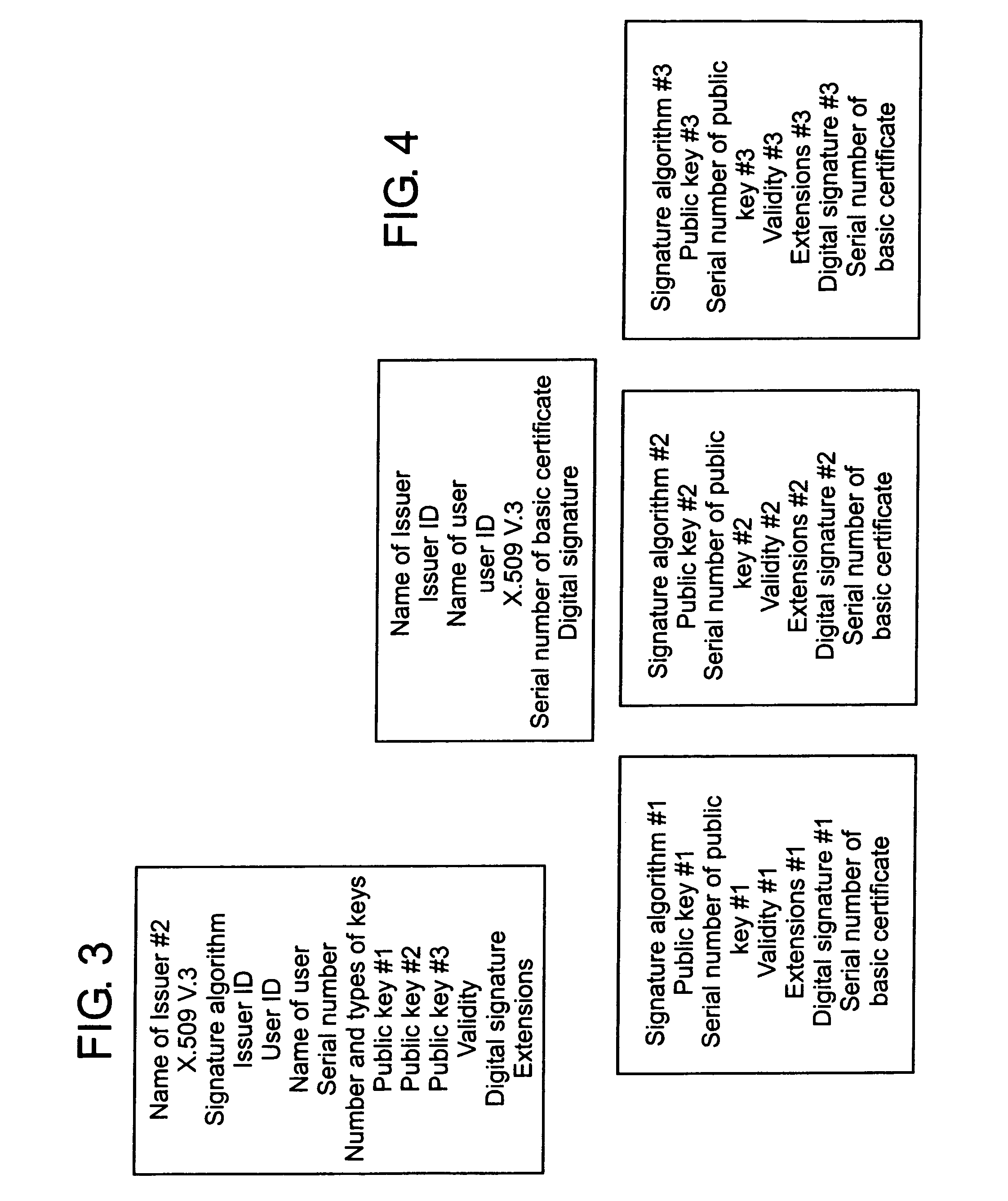
Certification of multiple keys with new base and supplementary certificate types
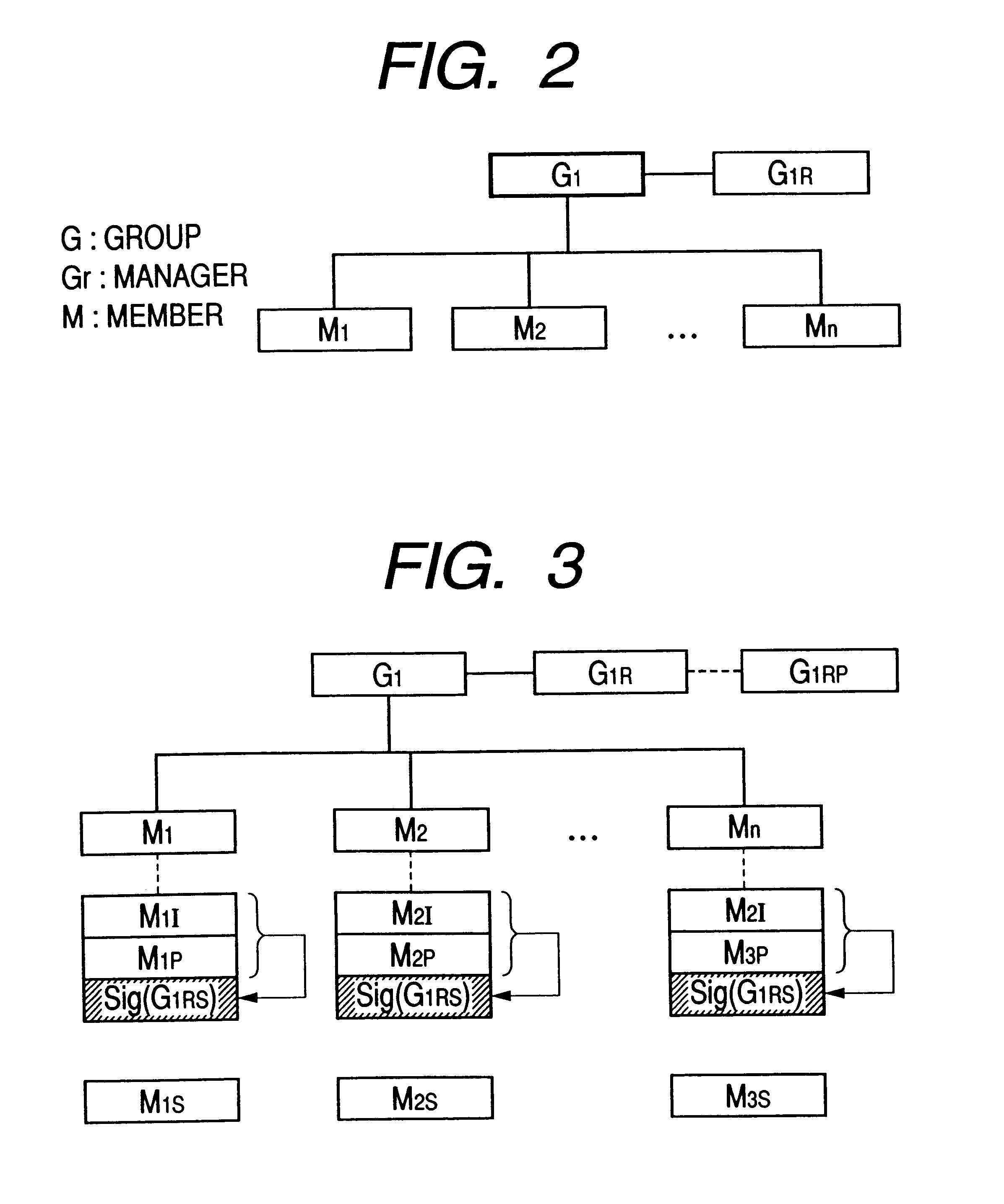
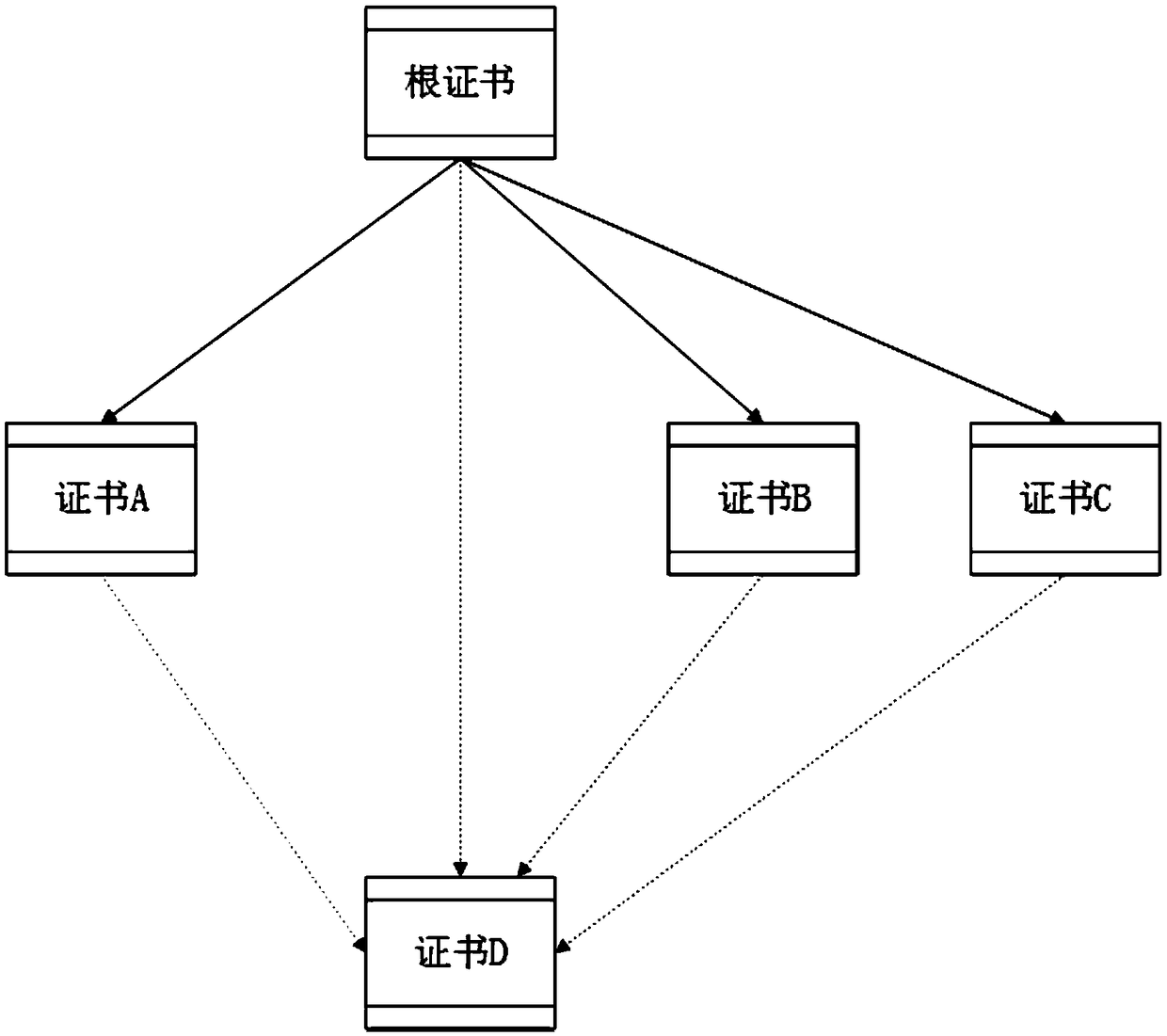
InactiveUS6981147B1Good flexibilityReduce memory requirementsUser identity/authority verificationDigital data authenticationRoot certificateKey authentication
A method for creating, storing and reading a new certificate type for certification of keys is provided. In the new certificate type, several certificates, containing a minimum quantity of redundant data fields, are collated to form one certificate and all redundant information on the certificates is eliminated. An embodiment of the new certificate type is the group certificate. The group certificate is used where several keys are to be issued at the same time for the same user by the same certification instance. By means of the group certificate, all redundant data elements are eliminated and all data elements for a set of several keys subject to certification are grouped into one certificate. This substantially reduces the memory requirement, and handling of the certificates is simplified for the communication partners. A further embodiment of the new certificate type is the basic and supplementary certificate combination. This form of certification is used where certificates are issued at different times for the same user by the same certification body. The memory requirement is consequently somewhat more than for group certificates, but greater flexibility is gained in use of the keys.
Owner:IBM CORP
Secure system for the issuance, acquisition, and redemption of certificates in a transaction network
Owner:BUFFALO PATENTS LLC
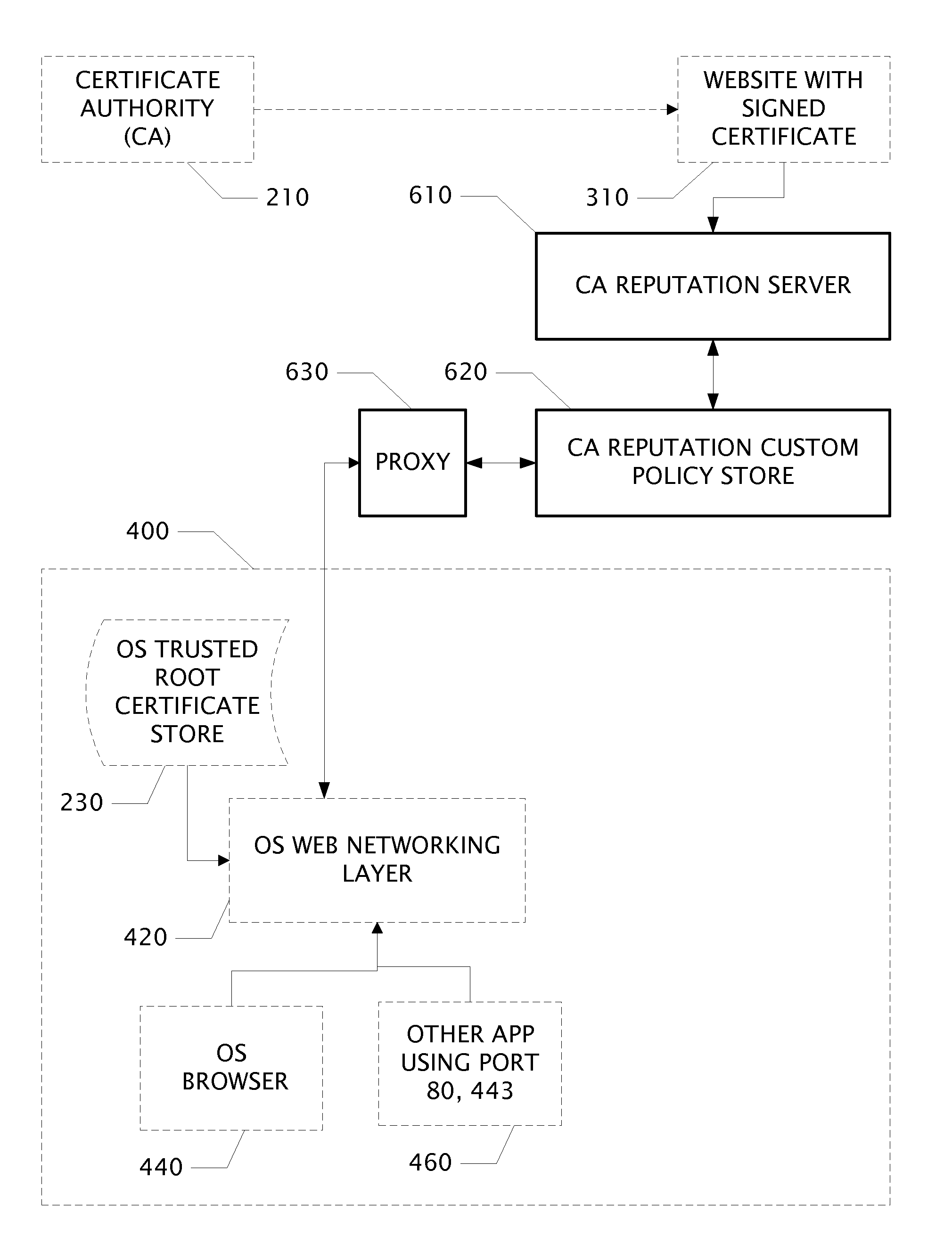
System and Web Security Agent Method for Certificate Authority Reputation Enforcement
InactiveUS20130061281A1Internal/peripheral component protectionDigital data authenticationThird partyRoot certificate
Owner:BARRACUDA NETWORKS
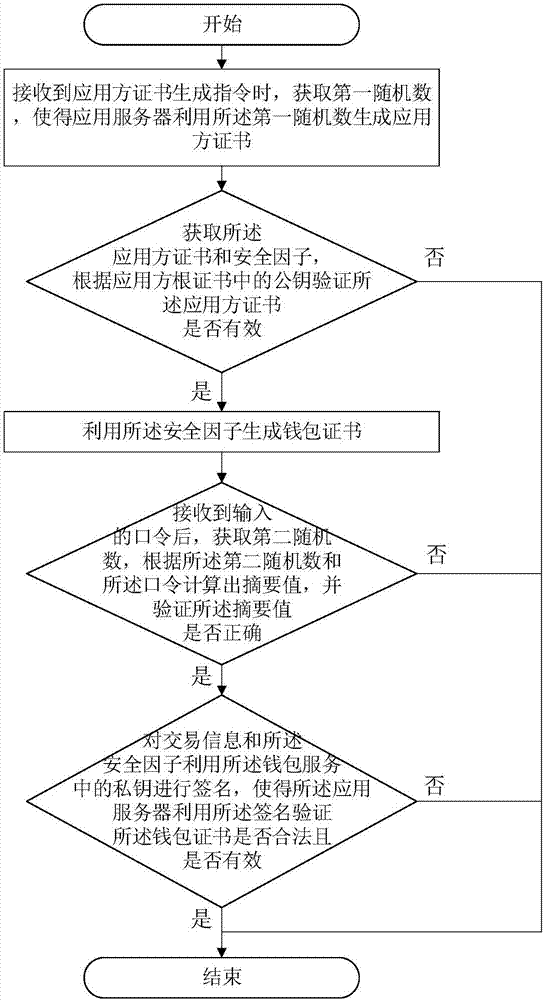
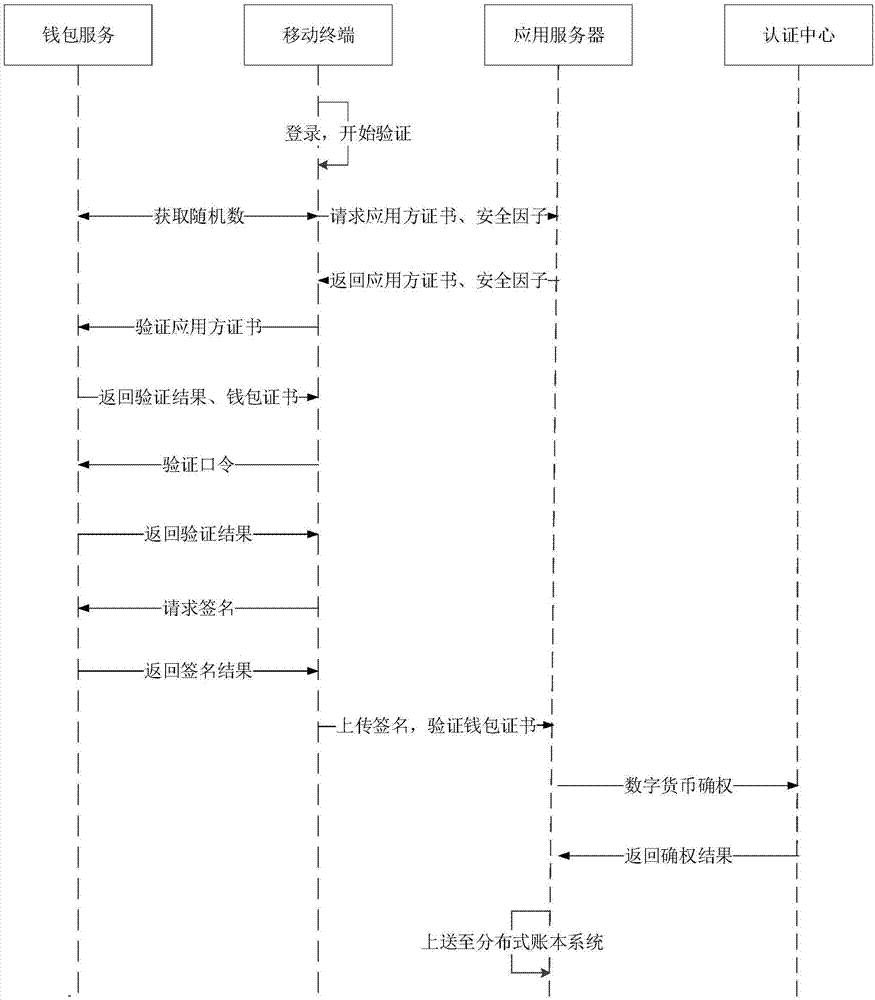
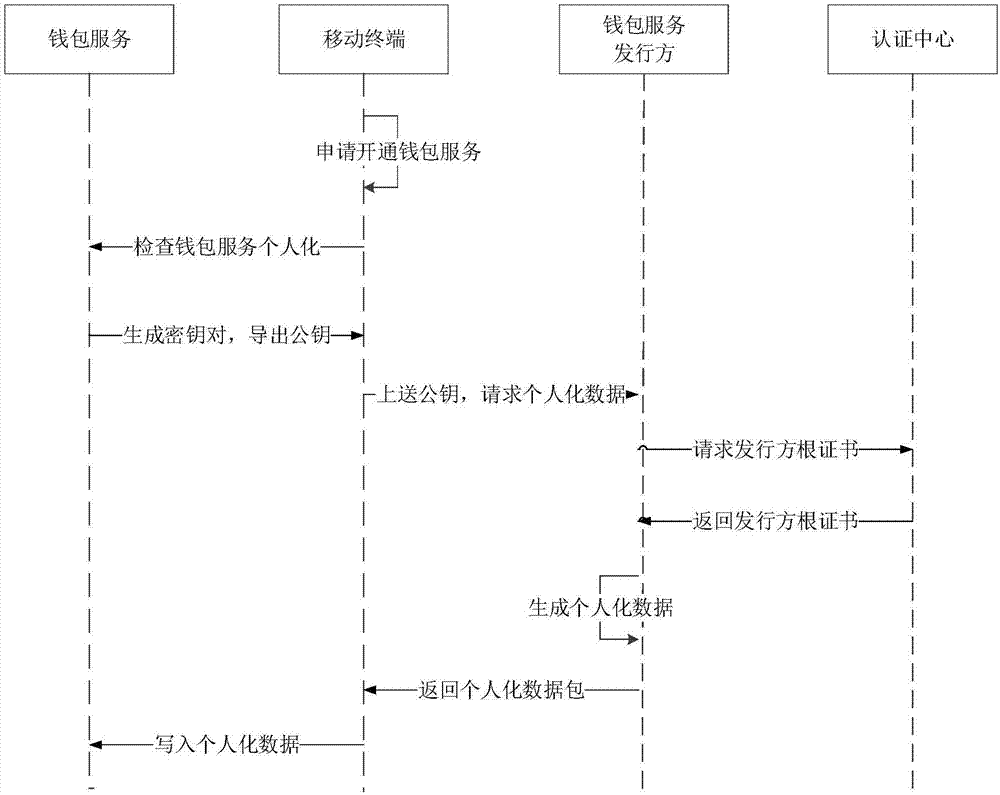
Digital identity verification method, apparatus and system based on block chains
The invention provides a digital identity verification method based on block chains. The method comprises the following steps: when an application party certificate generating instruction is received,obtaining a first random number, so that an application server generates an application party certificate by using the first random number; obtaining the application party certificate and a securityfactor, and verifying whether the application party certificate is effective according to a public key in an application party root certificate; if so, generating a wallet certificate by using the security factor; after an input password is received, obtaining a second random number, calculating a summary value according to the second random number and the password, and verifying whether the summary value is correct; and if so, singing transaction information and the security factor by using a private key in purse service, so that the application server verifies whether the wallet certificateis legal and effective by using the signature. By adoption of the random numbers, the signature and various certificates, high-security digital identity verification between block chains is achieved.The invention further provides a digital identity verification apparatus and system based on block chains, which have the above beneficial effects.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院
Method and device for deploying blockchain network and computer storage medium
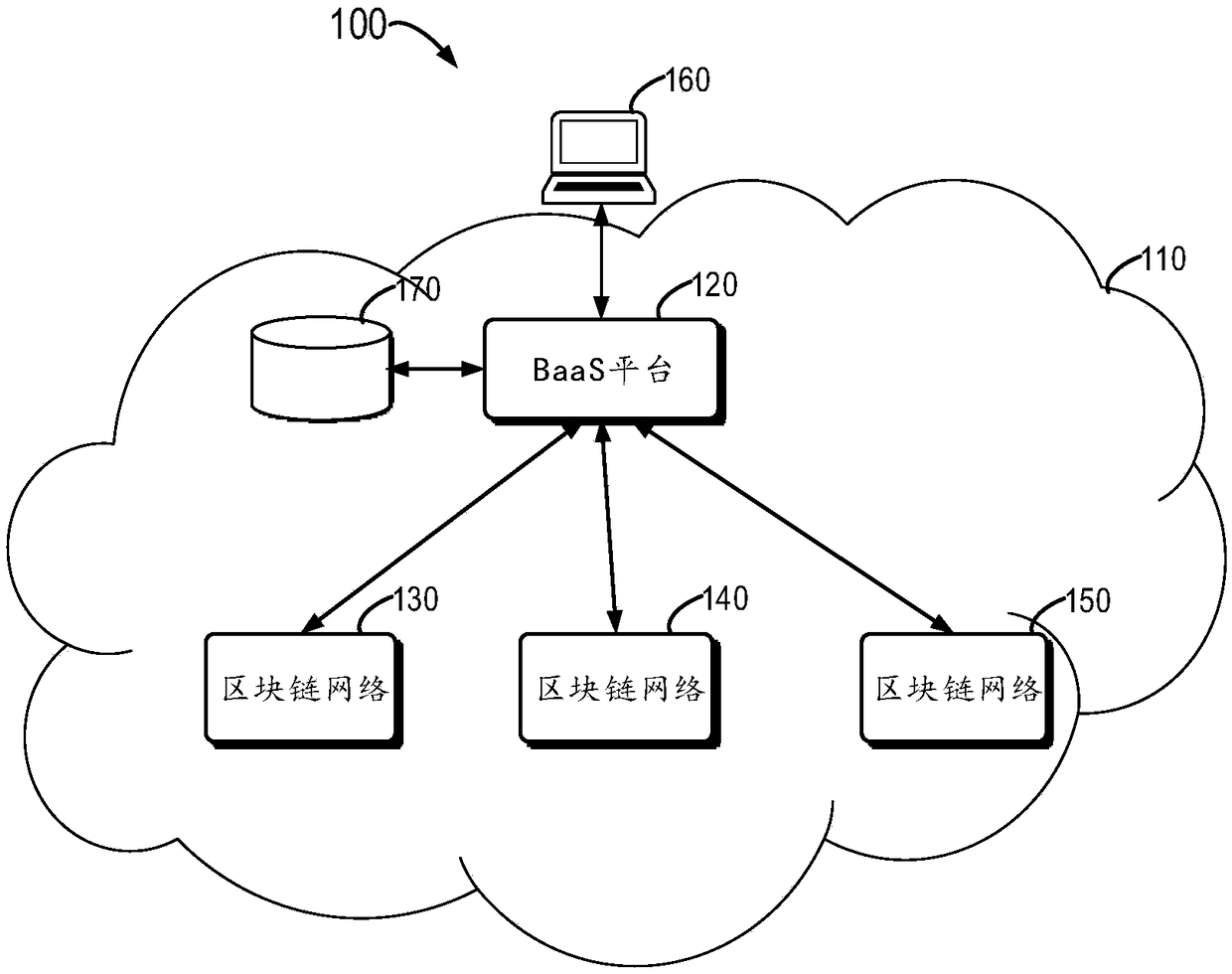
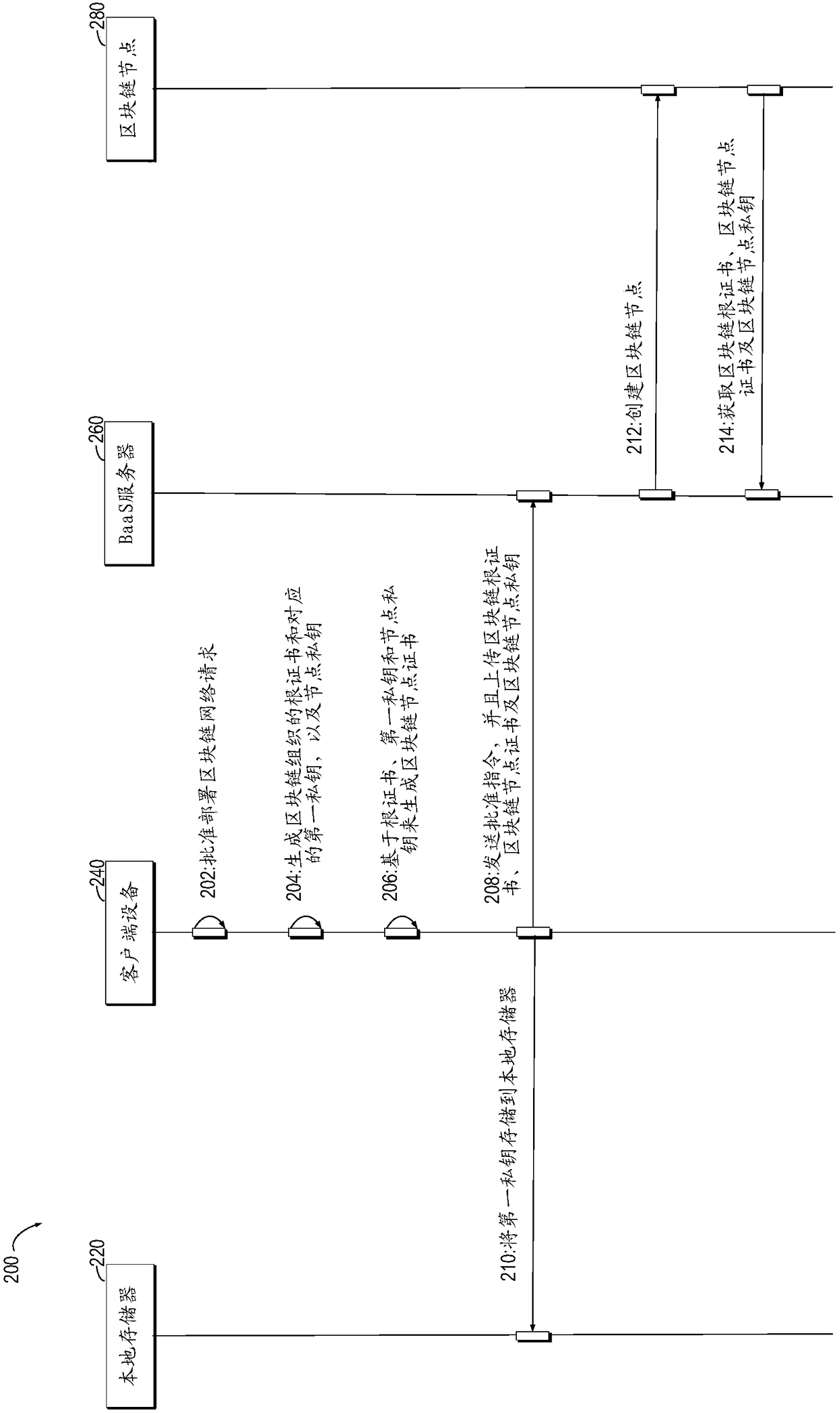
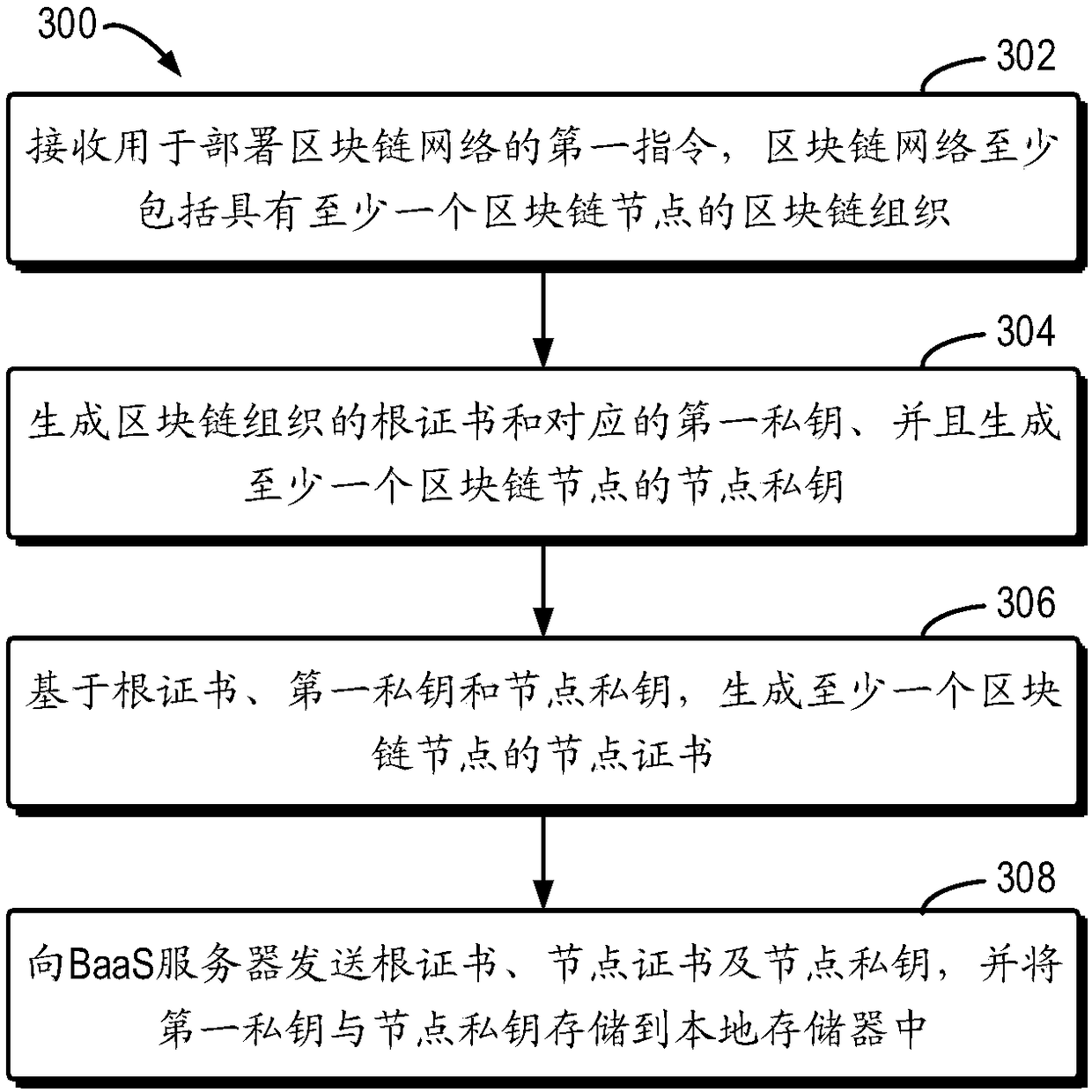
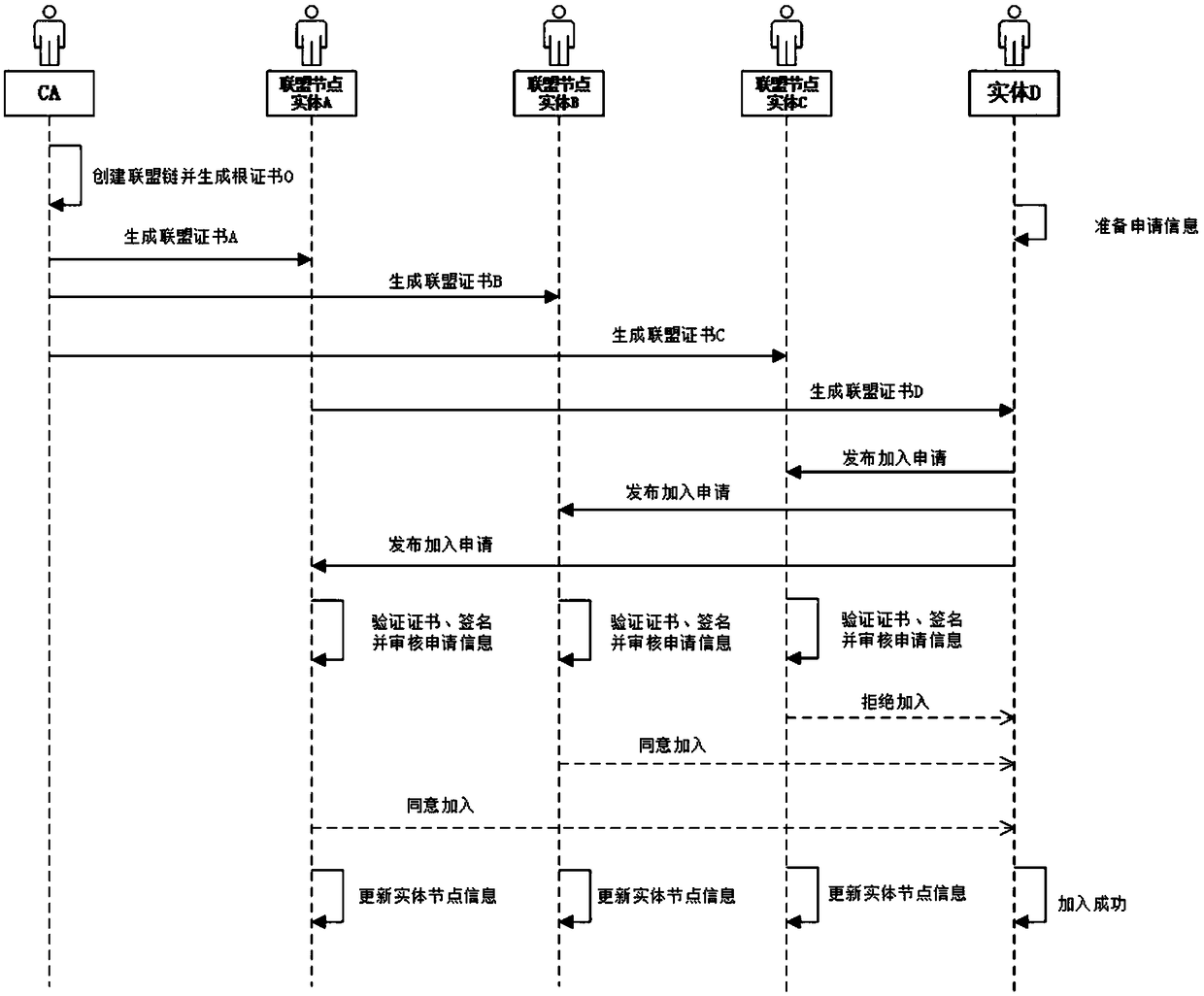
An embodiment of the present invention relates to a method for deploying a blockchain network, a client device and a BssA server. The method comprises a step of receiving a first instruction for deploying the blockchain network at the client device, wherein the blockchain network at least includes a blockchain organization with at least one blockchain node, and the client device is coupled to theBaaS server in a communicated mode, a step of responding to the first instruction, generating a root certificate of the blockchain organization and a corresponding first private key, and generating anode private key of the at least one blockchain node, a step of generating a root certificate of the at least one blockchain node based on the root certificate, the first private key and the node private key, and a step of sending the root certificate, the node certificate and the node private key to the BaaS server and storing the first private key and the node private key into a local memory coupled to the client device.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
Information processing apparatus, control method for the apparatus, and information processing system
InactiveUS20080120610A1Program loading/initiatingProgram/content distribution protectionRoot certificateSecure communication
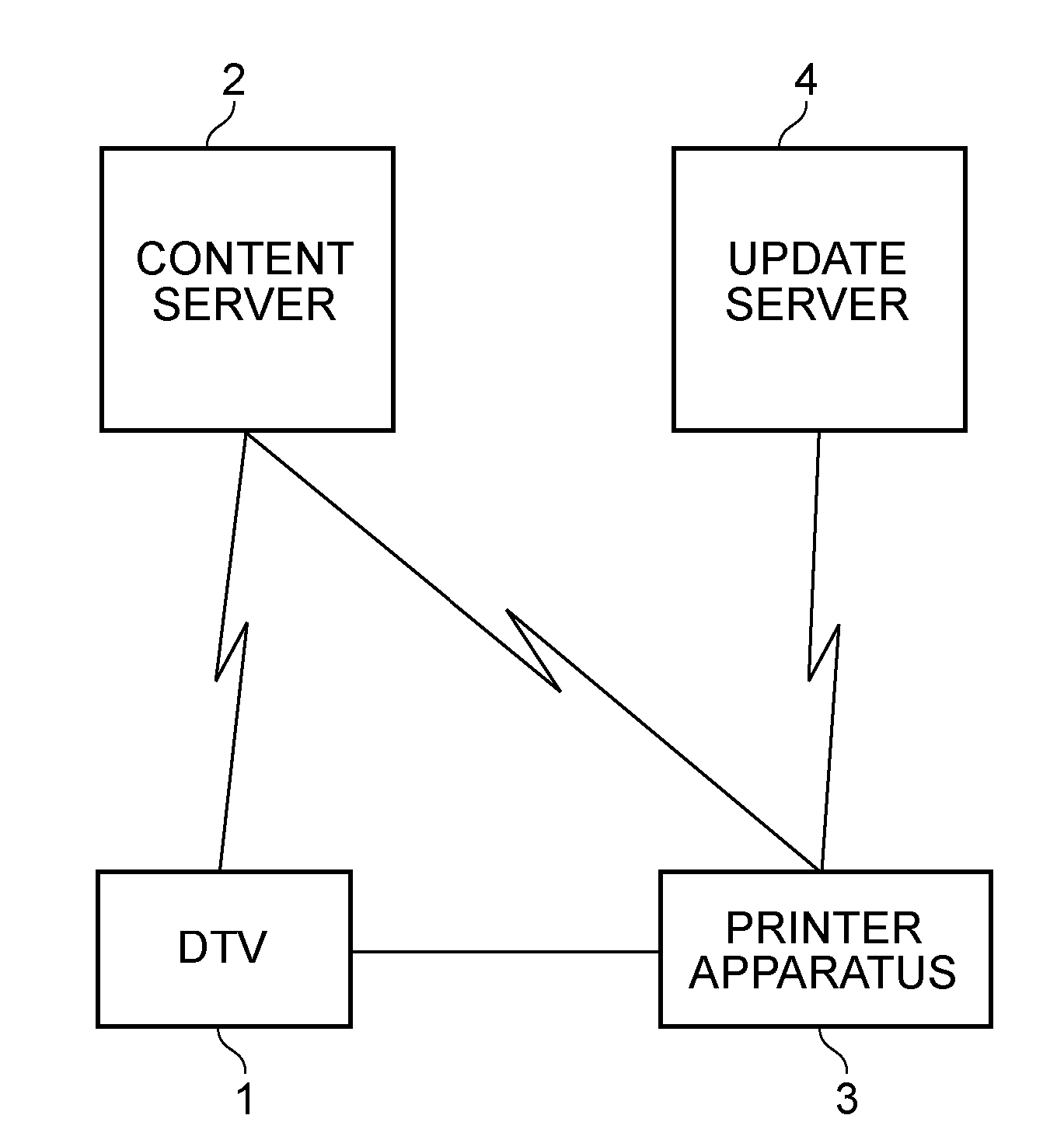
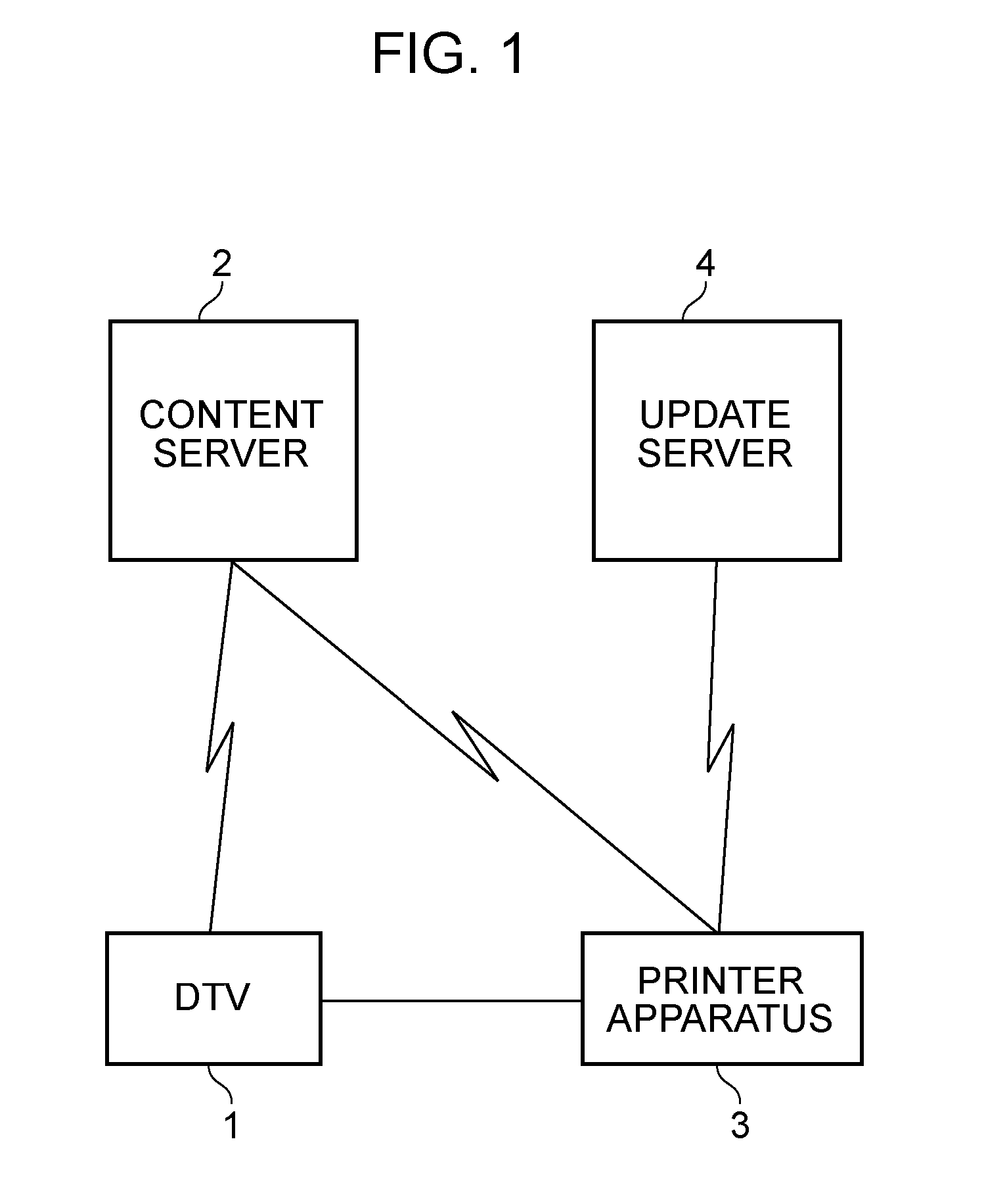
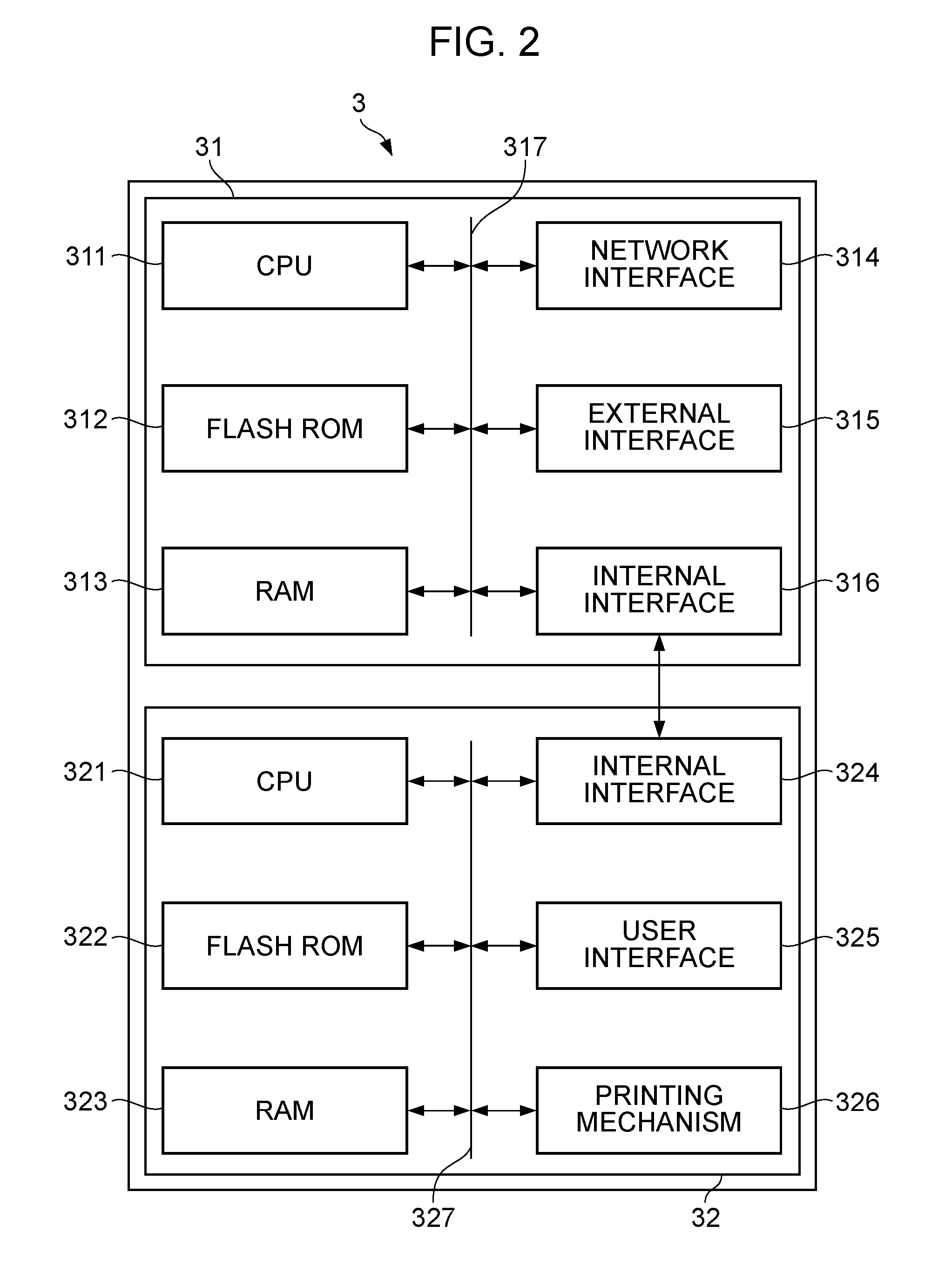
Update firmware is stored as one binary file. The binary file includes firmware data necessary for operating a controller unit and root certificate data necessary for a printer apparatus to establish secure communication with a content server. Specific information in the root certificate data is extracted from the update firmware, and the extracted specific information is used to update a management table of the root certificate provided in a RAM. With this configuration, it is possible for an information processing apparatus to reliably acquire and update the root certificate data without greatly changing the original functional configuration.
Owner:CANON KK
Manufacture link multi-entity security synergy method based on blockchain
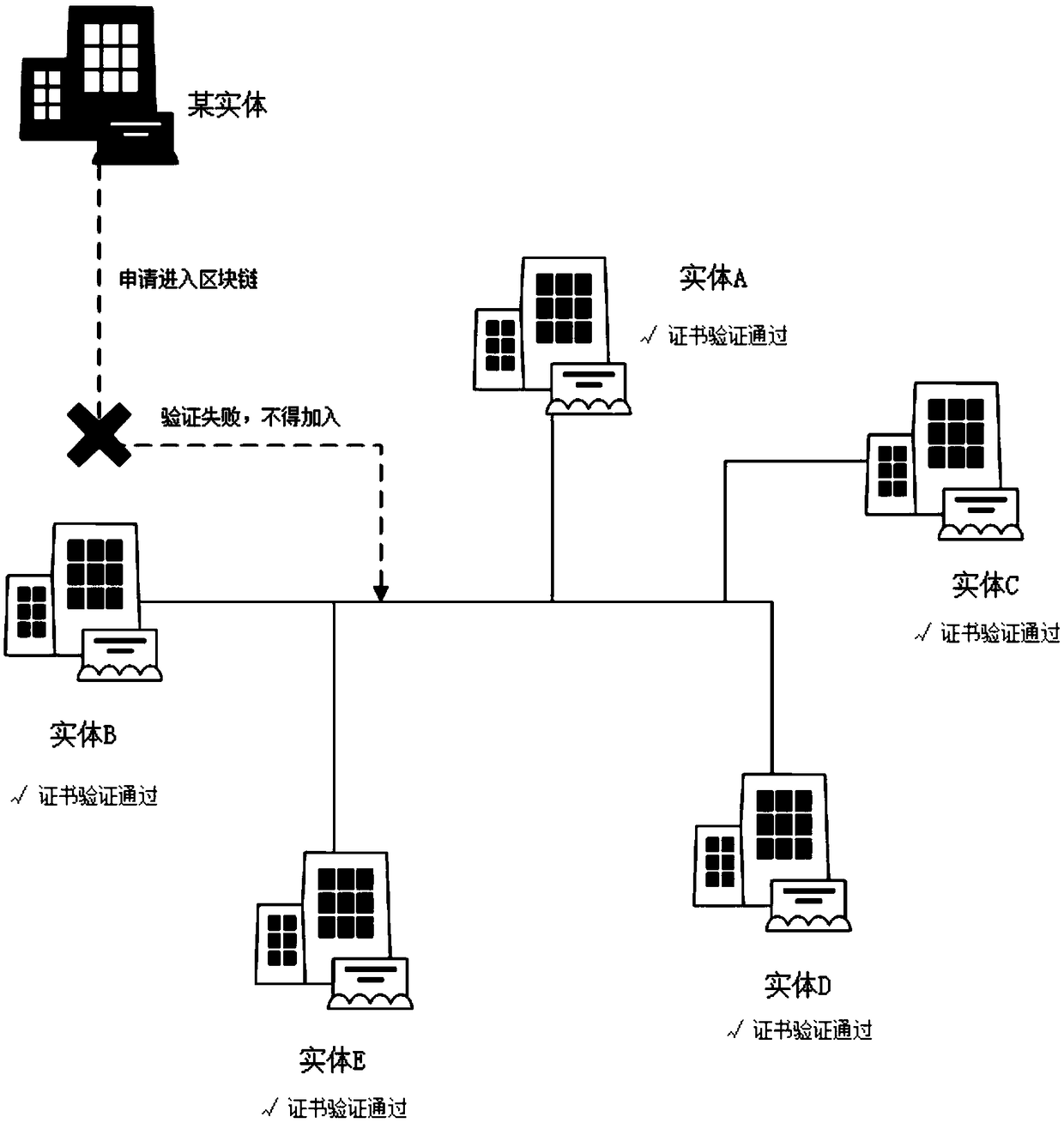
InactiveCN108765058AAchieve protectionSolve the problem of high physical production costsKey distribution for secure communicationUser identity/authority verificationRoot certificateSmart contract
The invention provides a manufacture link multi-entity security synergy method based on a blockchain. The method comprises the following steps that: firstly, creating a root certificate by the CA (Certificate Authority), and verifying a new certificate which applies to be added into an entity; then, when a bid inviting entity in a trusted network initiates a synergy requirement, releasing requirement information and the signature of the requirement information to the trusted network through ''a smart contract for bid inviting releasing''; when a bidding entity receives the synergy requirement,through negotiation between a ''smart contract for communication key negotiation'' and the bid inviting entity, forming a shared secret key for decrypting the bidding information of the correspondingentity, and releasing encrypted bidding information and singed bidding information into the trusted network; after the bid inviting entity receives the bidding information, checking the credit information of the bidding entity, combining with the credit of the bidding entity to comprehensively evaluate all bidding information, and preferentially selecting one bidding entity as a bid winning entity to carry out synergy product production with the bid inviting entity; and finally, checking and accepting a product delivered by the bid winning entity by the bid inviting entity, and after the product is qualified, carrying out credit evaluation on the bid winning entity.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
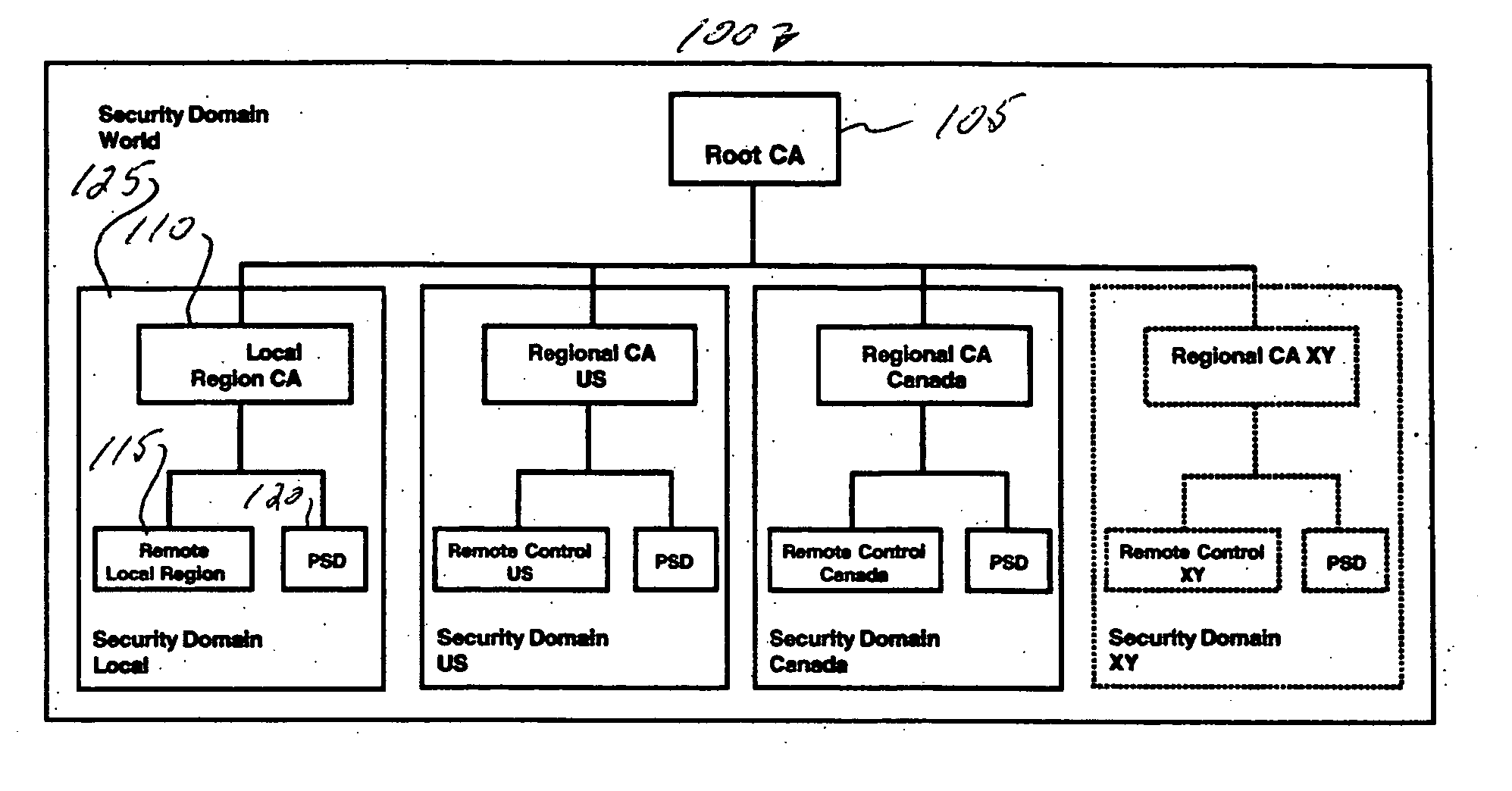
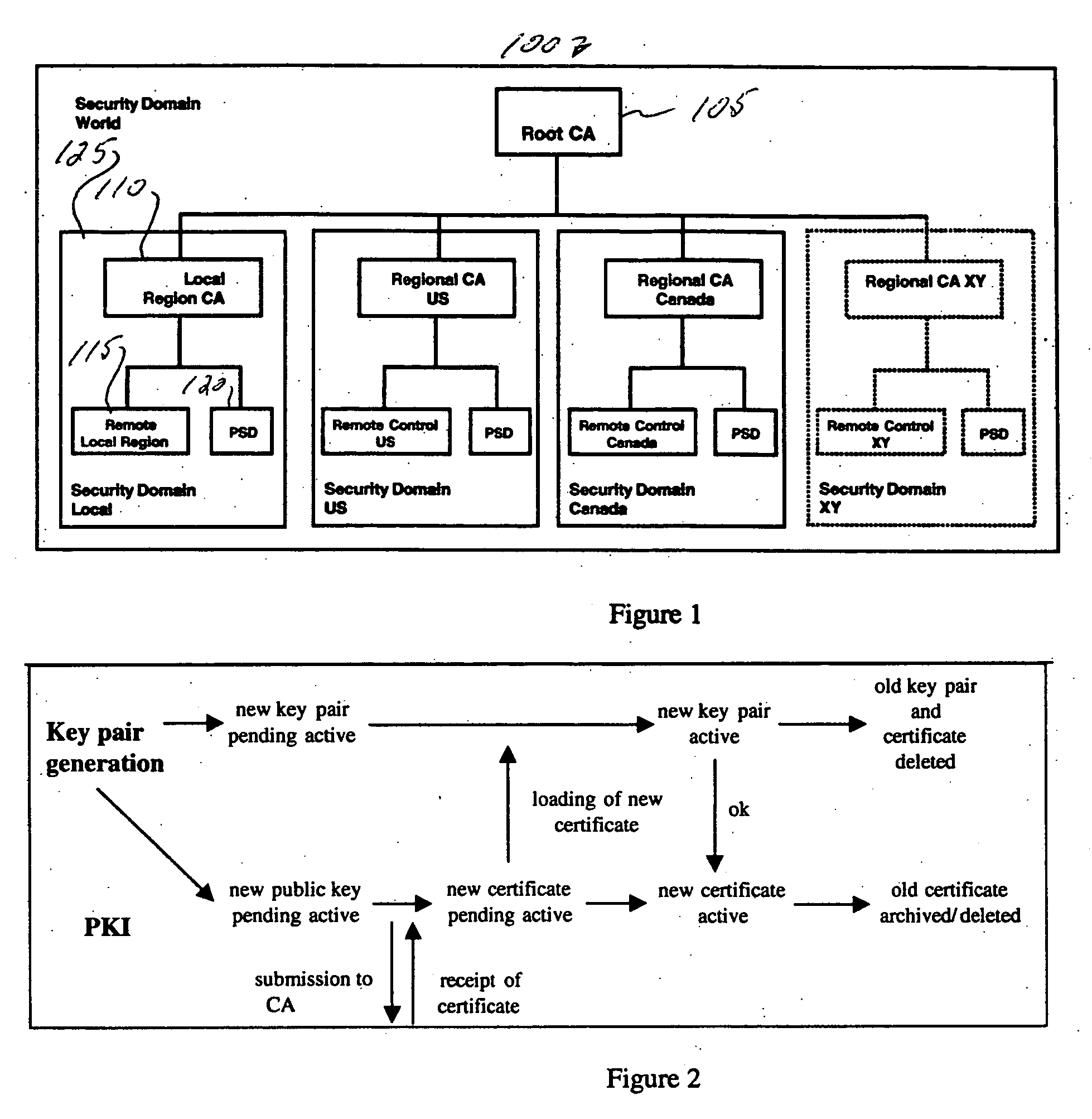
Flexible System And Method To Manage Digital Certificates In A Wireless Network
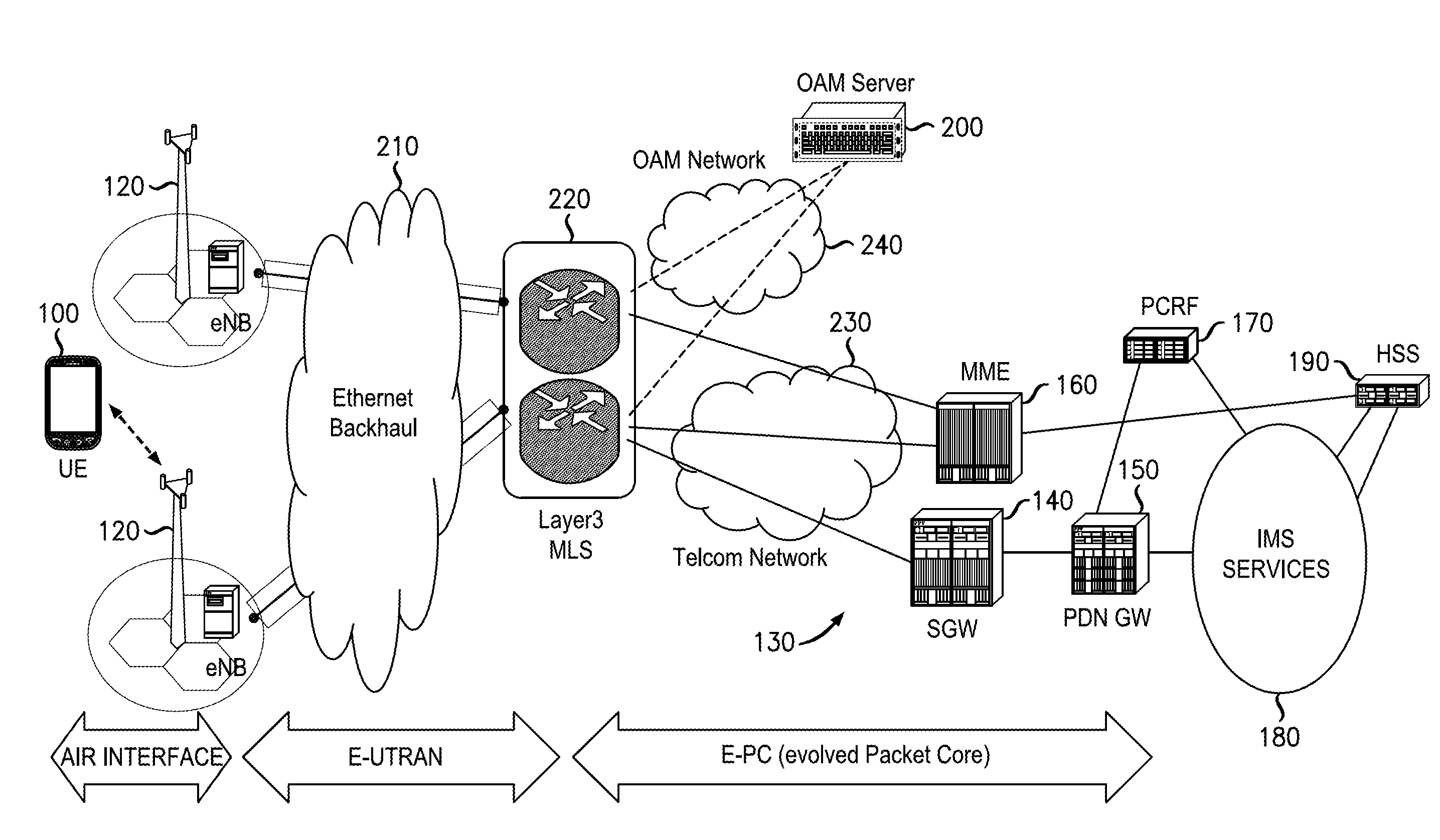
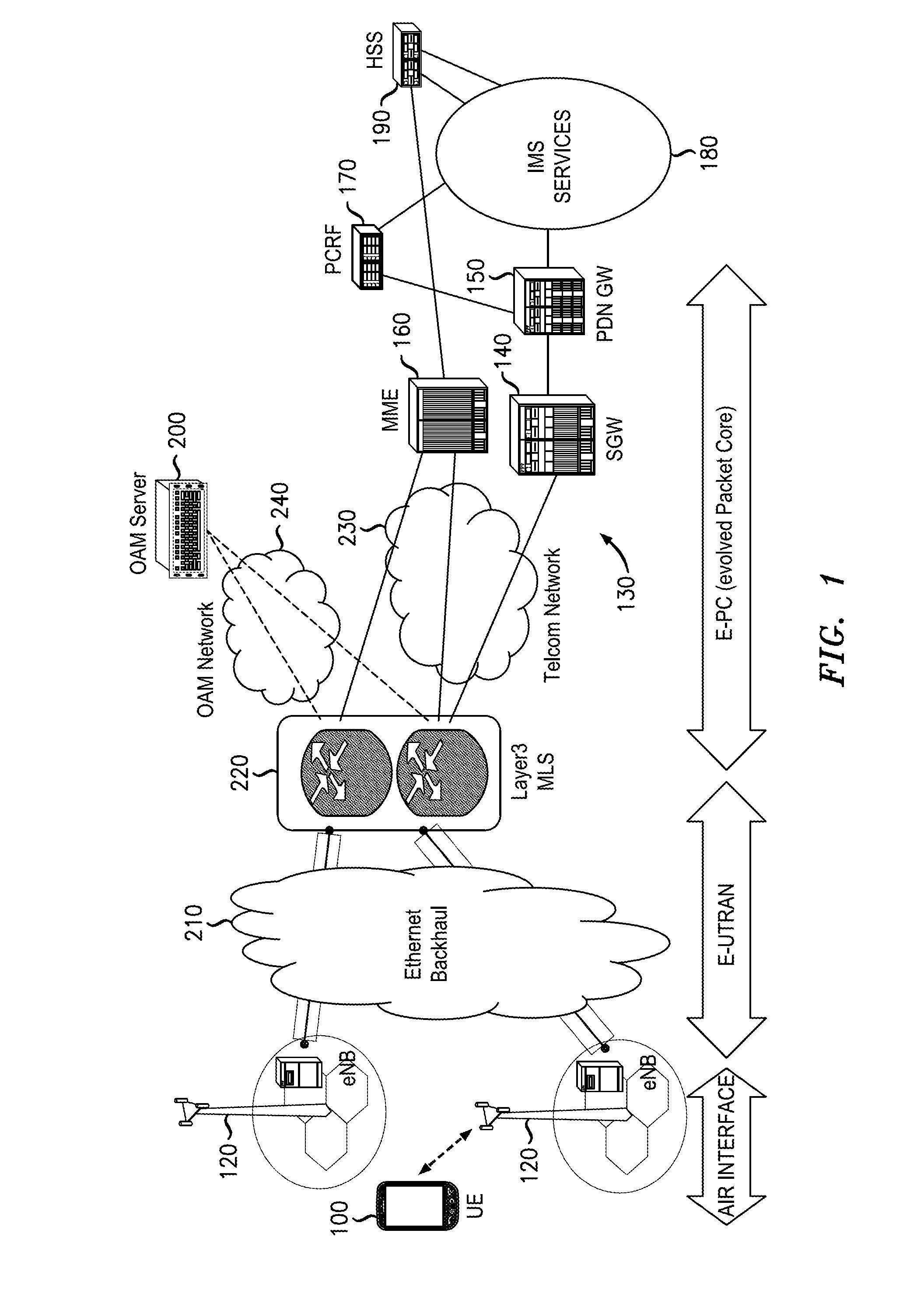
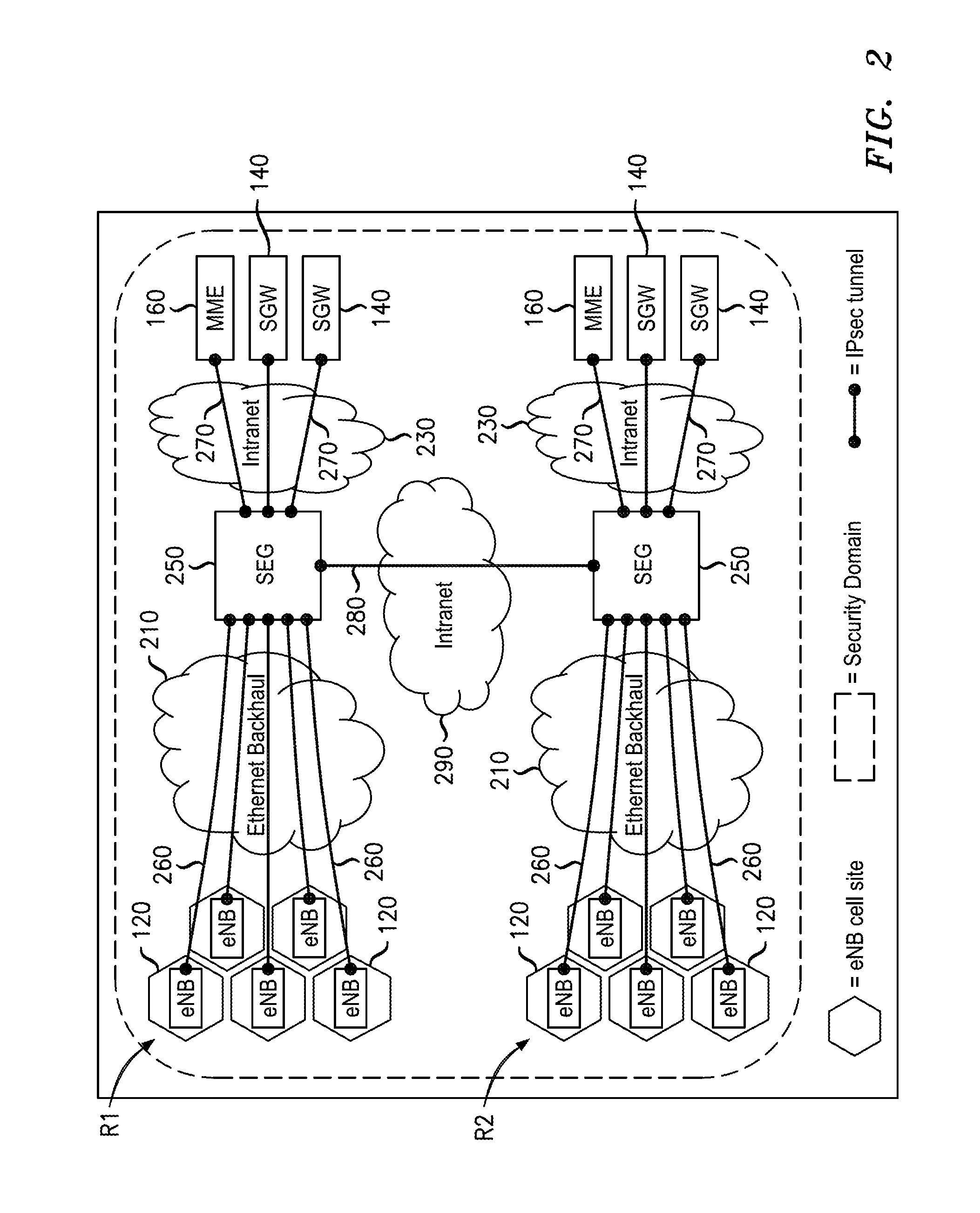
InactiveUS20120246466A1User identity/authority verificationPublic key infrastructure trust modelsRoot certificateWireless mesh network
An infrastructure is provided for managing the distribution of digital certificates for network security in wireless backhaul networks. In embodiments, a root certificate management system (root CMS) processes requests for digital certificates, issues root certificates, automatically authenticates surrogate certificate management systems (sur-CMSs), and automatically processes certificate requests and issues certificate bundles to sur-CMSs that are successfully authenticated. The infrastructure includes sur-CMSs to which are assigned base stations within respective regions. Each sur-CMS automatically authenticates its own base stations and automatically processes certificate requests and issues certificate bundles to base stations that are successfully authenticated. A certificate bundle issued to a base station includes a digital certificate, signed by the issuing sur-CMS, of a public key of such base station, and at least one further digital certificate, including a self-signed certificate of the root CMS.
Owner:ALCATEL LUCENT SAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com