Method for authenticating point of sail (POS) file and method for maintaining authentication certificate
A certificate and document technology, applied in the field of POS application software certification, can solve the problems that are not conducive to certificate renewal and maintenance, and cannot better ensure the authenticity of application software, and achieve the effect of ensuring authenticity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
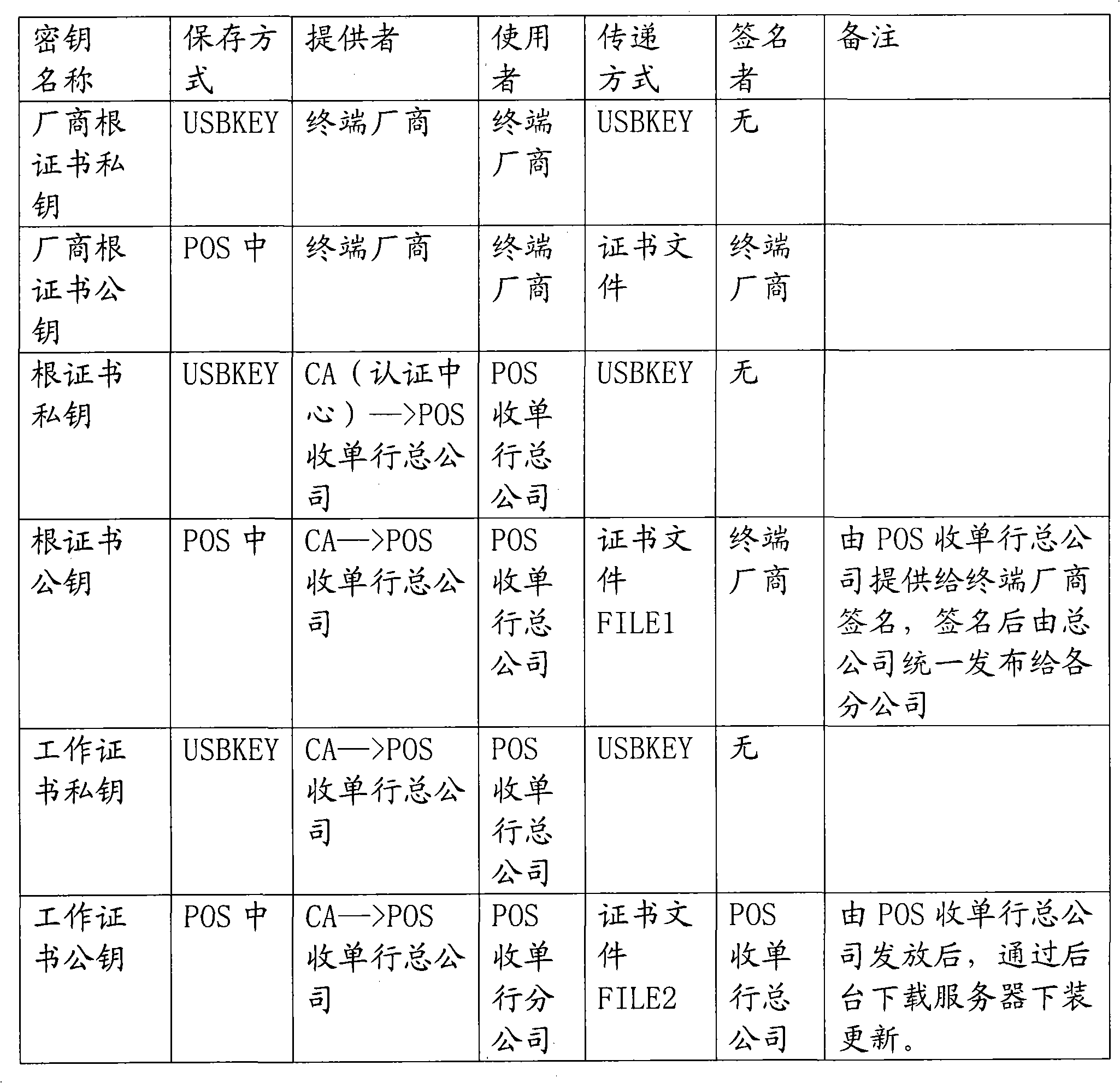
[0043] The invention proposes a set of POS digital signature scheme and management process based on secondary certificate management.
[0044] 1. POS secondary certificate management mechanism
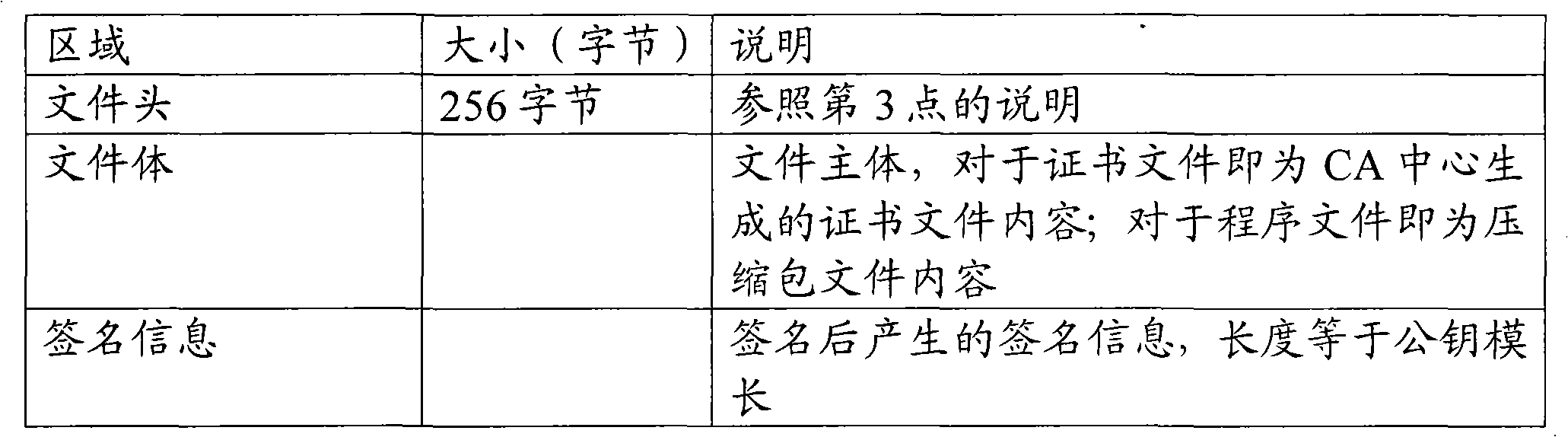
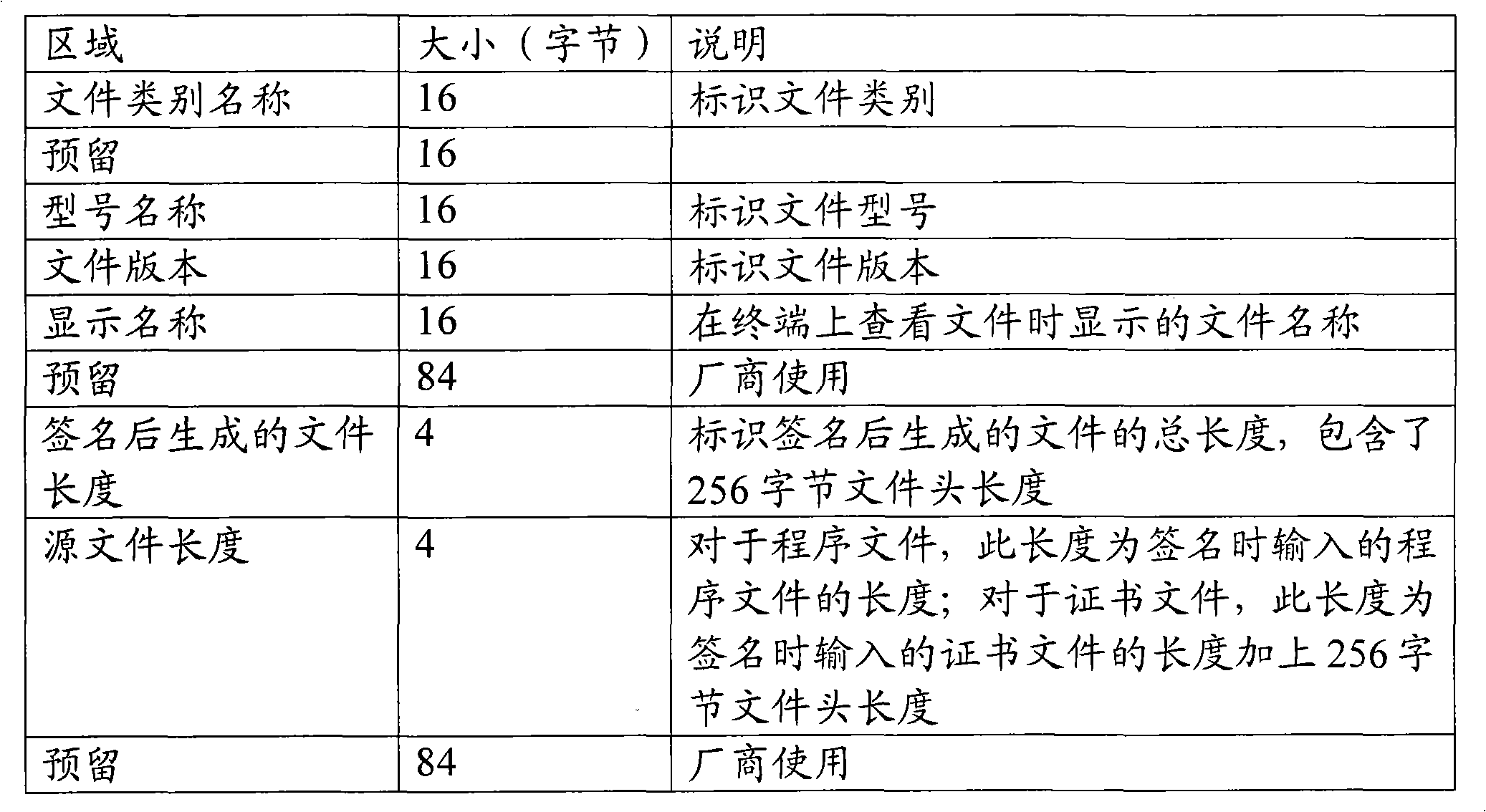
[0045]Use two-level certificate management, the first level is the root certificate, and the second level is the work certificate. The root certificate is used to verify the legitimacy of the work certificate, but cannot be used to verify the legitimacy of the application. The work certificate is used to verify the legitimacy of the downloaded software. Each certificate consists of a public key and a private key.
[0046] 1. As long as there are two certificates managed by the POS acquirer:
[0047] (1) root certificate (public, private key);
[0048] (2) Work certificate (public, private key).
[0049] Note: The private key used to sign the terminal application is parsed from the private key file. There are currently two ways to protect the private key, one is to encrypt and sav...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com