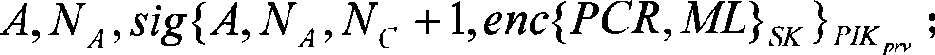Patents
Literature
4121results about How to "Guarantee authenticity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
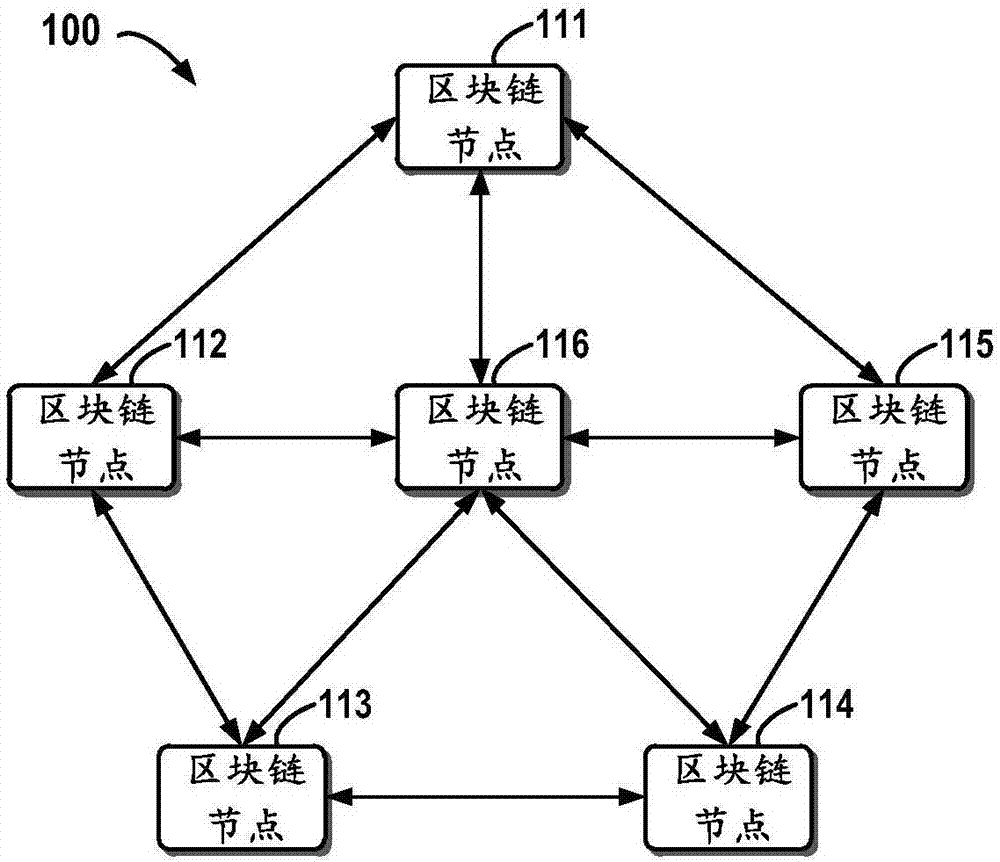
Block chain-based distributed storage
InactiveCN107273410ASolve the problem of limited node capacityAchieve tamper resistanceFile access structuresSpecial data processing applicationsTamper resistanceDistributed File System
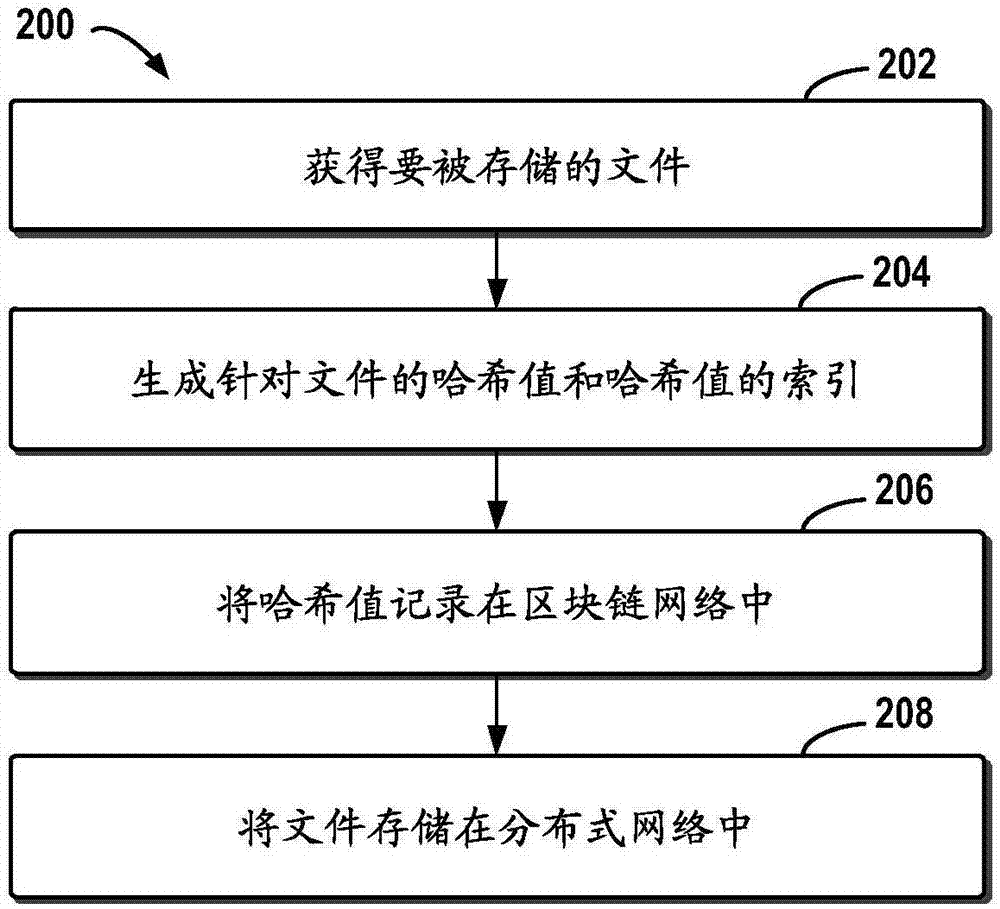
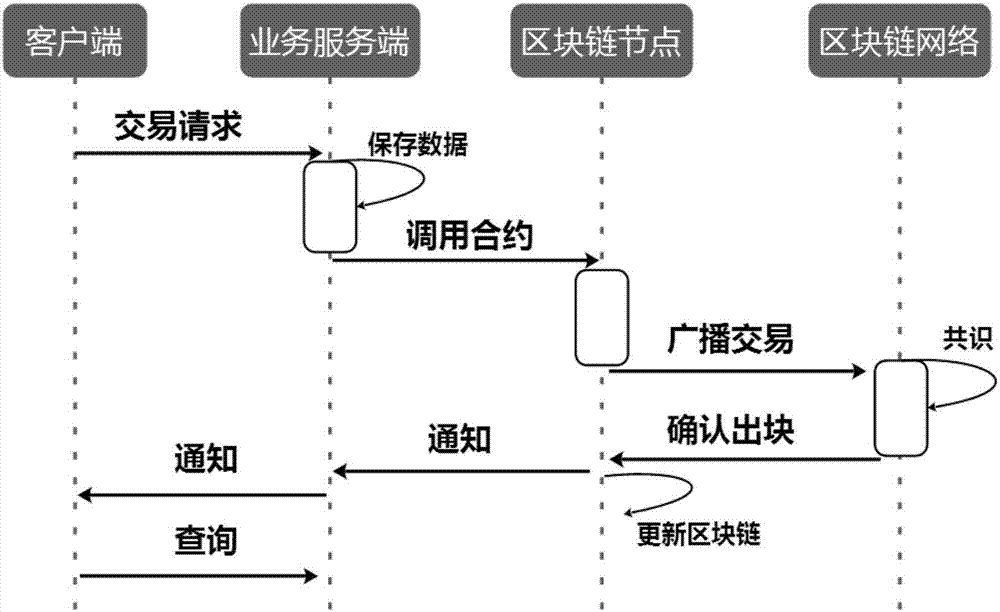
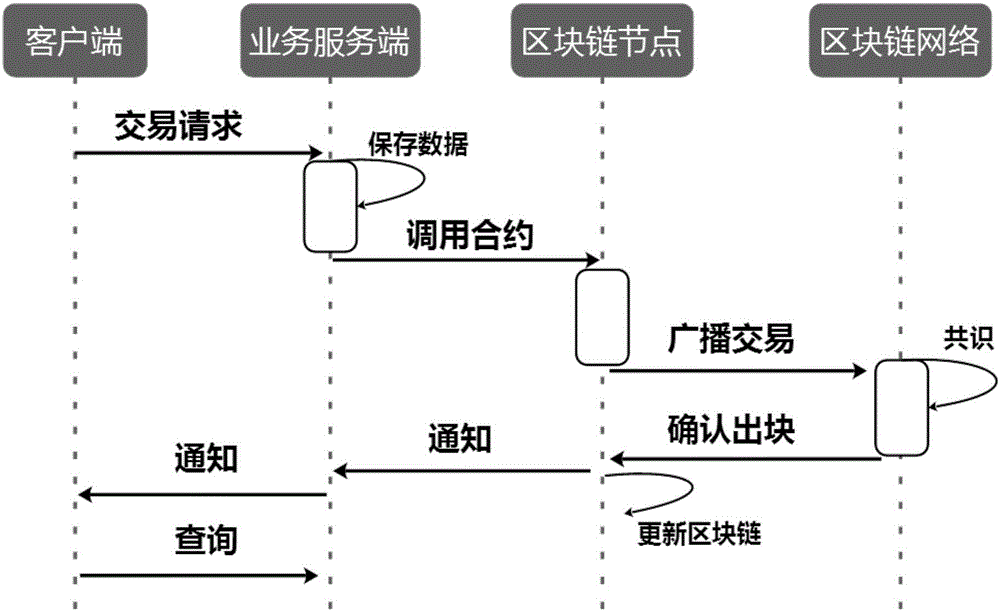
The embodiment of the disclosure relates to block chain-based distributed storage, and discloses a block chain-based distributed storage method. The method includes: obtaining a file which needs to be stored, and generating a hash value and an index of the hash value for the file. The method also includes: recording the hash value in a block chain network, and storing the file in a distributed network, wherein the file is located on the basis of the hash value in the distributed network. Therefore, according to the embodiment of the disclosure, tampering proofing and the distributed storage of the file can be realized through combining a block chain and a distributed file system, thus the problem of the limited capacity of block chain nodes is solved, and the authenticity and the availability of the stored file are effectively guaranteed.
Owner:SHANGHAI DIANRONG INFORMATION TECH CO LTD
Method for constructing financial asset trading system based on alliance chain
InactiveCN107025602AProtect interestsReduce credit riskFinanceElectronic credentialsData miningComputer science
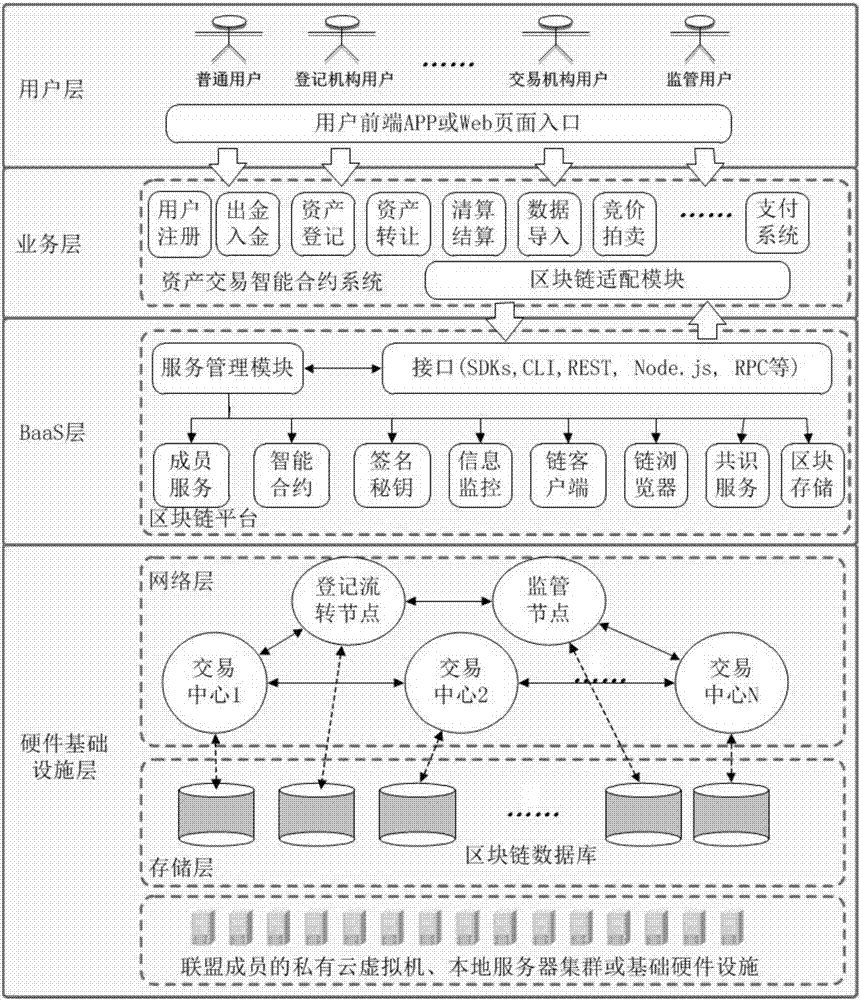
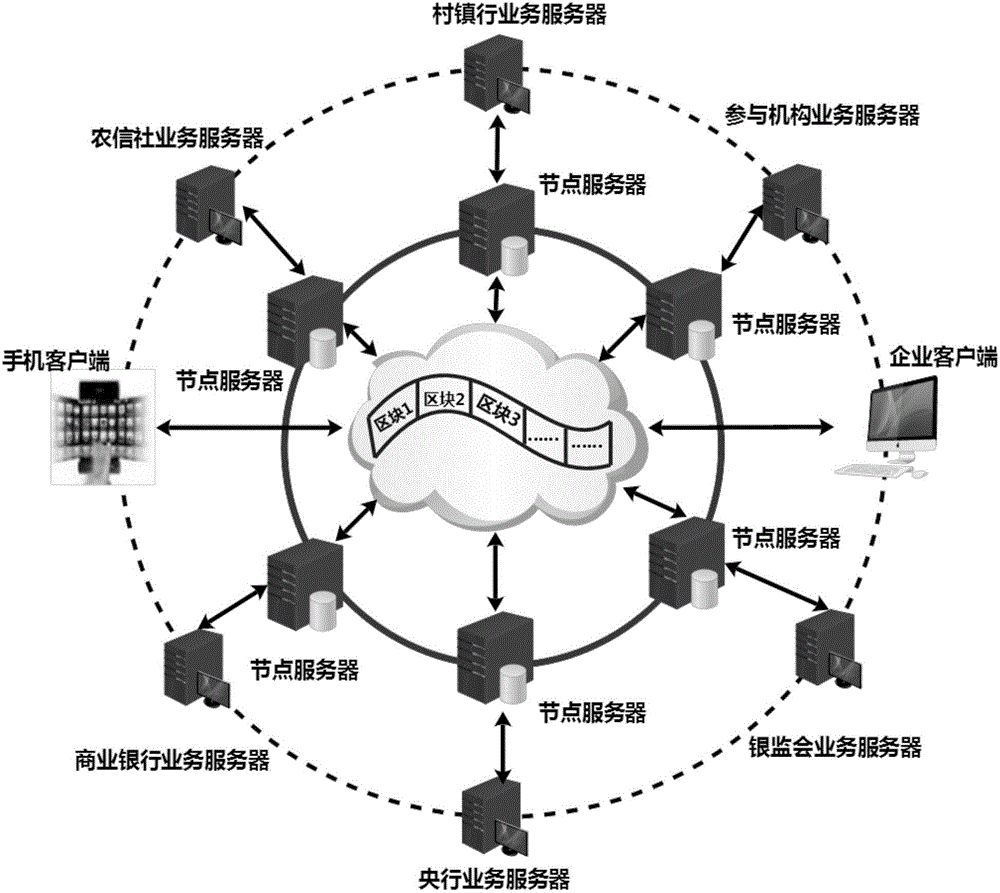
The invention discloses a method for constructing a financial asset trading system based on an alliance chain. With an alliance chain as a technical support, a novel financial asset digital unique certificate is provided based on the existing laws and regulations. The system uses a distributed technology architecture. All participants jointly maintain the ledger of financial asset trading. It is ensured that the trading of financial assets is open, transparent, real and credible. The credit risk of trading is reduced. The cross-platform and cross-region flow of financial assets is promoted. Tedious manual account checking work between platforms is omitted. In addition, the block chain technology is applied to the field of financial asset trading for the first time. A unified and standardized financial asset trading platform is established. Digital management of financial assets is realized. The credit risk of trading can be prevented effectively. The efficiency of trading and supervising is improved. The trading cost is reduced.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Identity authentication method, identity authentication server and identity authentication device
ActiveCN102916968AImprove securityEnsure safetyKey distribution for secure communicationUser identity/authority verificationPasswordAuthentication server
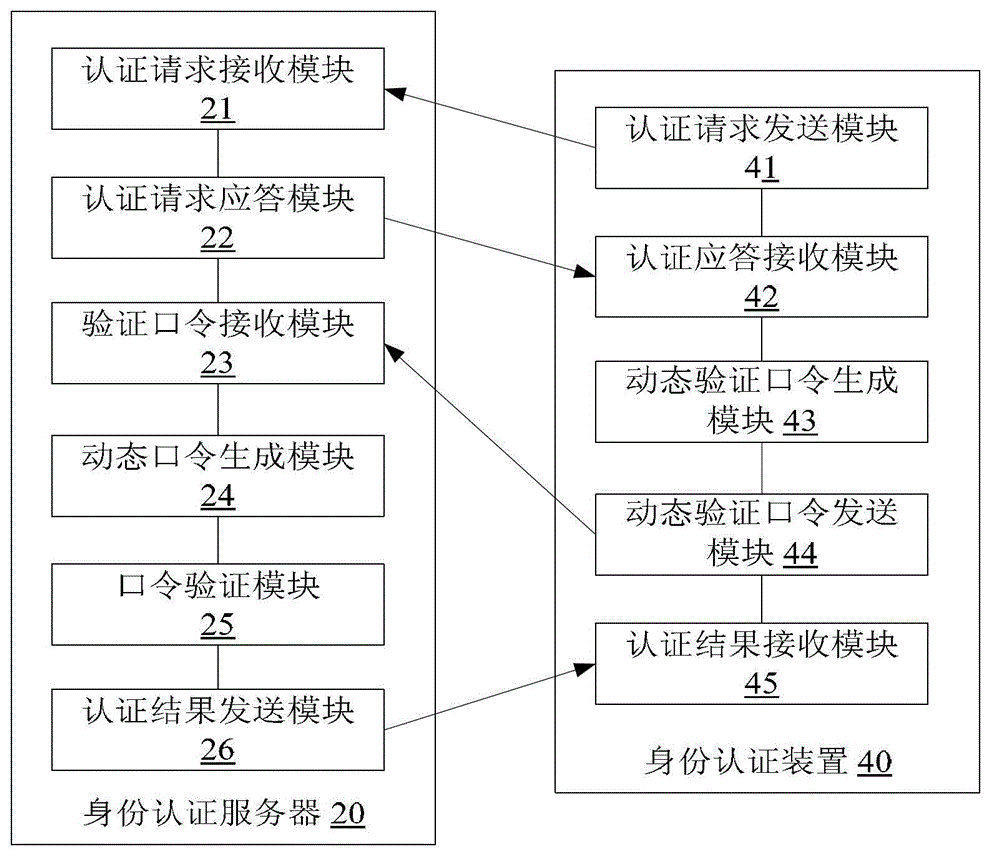
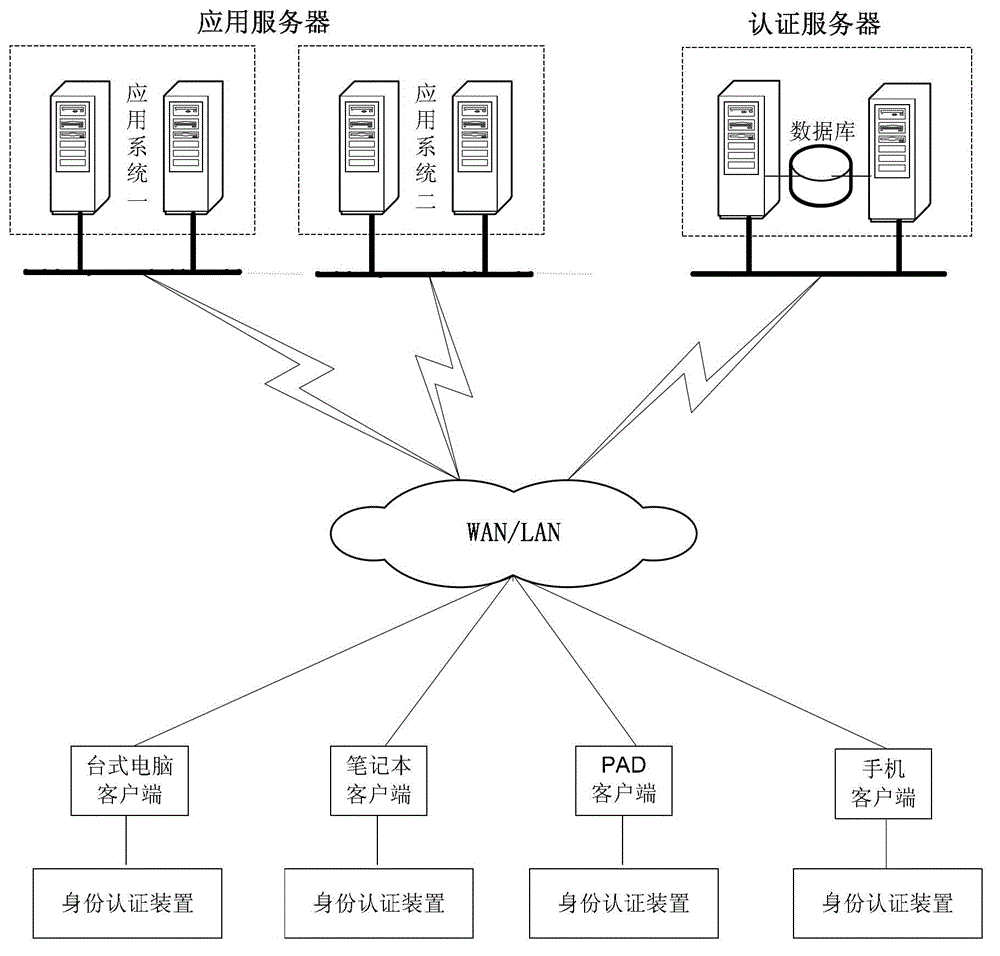
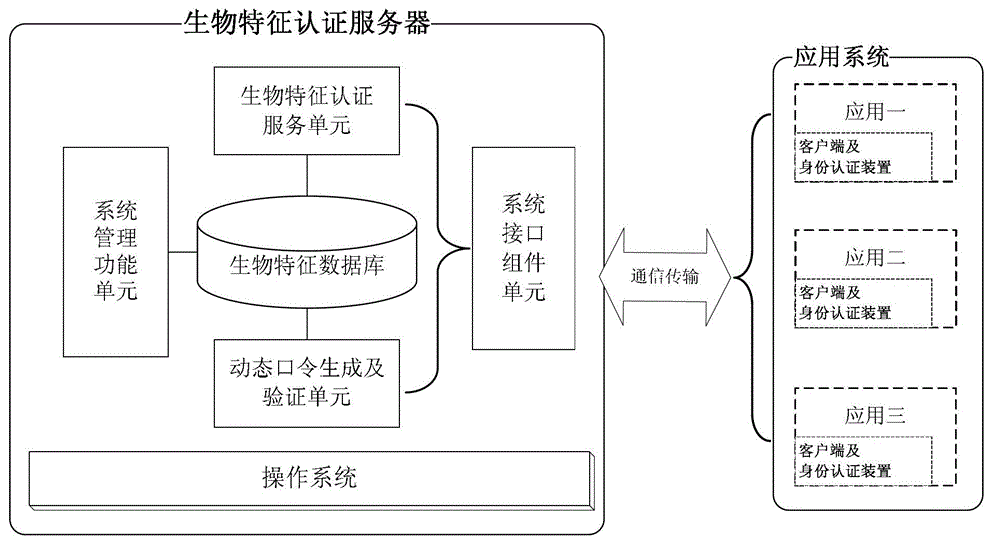
The invention discloses an identity authentication method, an identity authentication server and an identity authentication device. The method comprises the steps that the authentication server receives a biological characteristic authentication request sent by a client, returns challenges generated randomly to the client and receives a dynamic verification password sent by the client, wherein the dynamic verification password is generated by the client time when the challenges are received, the challenges, a biological characteristic of a user and a first seed key prestored in the client; the authentication server generates a dynamic password according to the time of the authentication server when the dynamic verification password is received, the challenges, the biological characteristic of the user and a second seed key; and the authentication server verifies whether the dynamic password is consistent with the dynamic verification password and returns an identity authentication result to the client according to a verification result. With the adoption of the identity authentication method, the identity authentication server and the identity authentication device, the safety of the dynamic password is ensured through the biological characteristic, and the authenticity and reliability of the identity authentication of the user are guaranteed.
Owner:BEIJING EYECOOL TECH CO LTD +1
Logistics tracking method based on block chain
InactiveCN106022681ASolve the problem of real name systemGuarantee authenticityLogisticsPhysical spaceDigital fingerprint
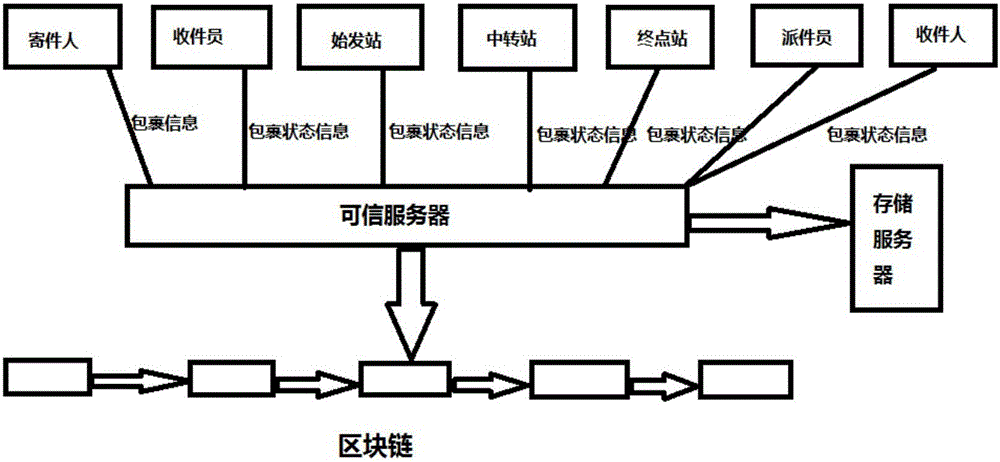
The invention discloses a logistics tracking method based on a block chain. The method comprises steps that a user sending node uploads parcel information to a main node; the main node generates a digital fingerprint for the parcel information uploaded by the user sending node, writes the digital fingerprint and a corresponding time stamp into a block chain, broadcasts the block chain in all nodes; each logistics node generates parcel state information successively according to the digital fingerprint, the node information of the logistics node and the node information of a next logistics node in accordance with a parcel physical space transfer path; a corresponding user receiving node signs for the parcel, generates parcel receiving information and uploads the parcel receiving information to the main node in order for the main node to write the parcel receiving information into the block chain. The logistics tracking method applies the block chain technology to the logistics field, guarantees the traceability of the authenticity and the state of logistics information by using the unchangeable characteristic of the block chain, saves the logistics information and update state information fast and efficiently according to the characteristic of a private chain in order to satisfy a requirement for logistics instantaneity.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Consortium chain-based digital bill trading system construction method
InactiveCN106780033AImprove safety and reliabilityAvoid reconciliation workFinanceTechnical supportBlockchain
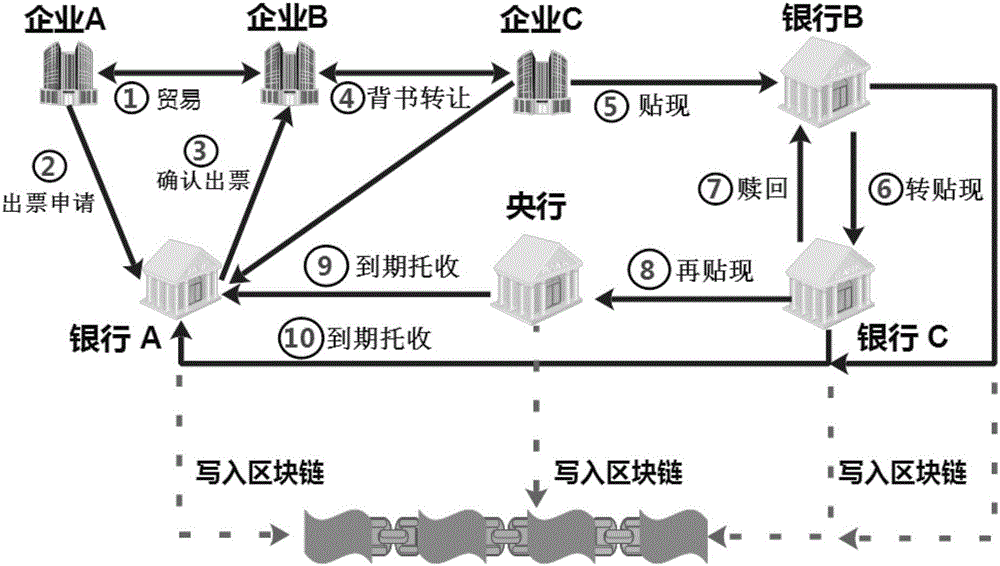
The invention discloses a consortium chain-based digital bill trading system construction method, which develops a brand-new bill display form, namely, a digital bill in combination with existing bill attributes, laws and regulations and market by taking a consortium chain as technical support. Compared with an existing electronic bill, the digital bill is totally different from the electronic bill in technical framework, not only has all functions and advantages of the electronic bill but also fuses the advantages of a block chain technology, and is a securer, more intelligent, more convenient and more promising bill form. In addition, the block chain technology is applied to the field of bill businesses for the first time; a unified standard bill trading platform is established; the problems of trade background forgery, bill authenticity authentication failure, paper bill multi-time selling, non-synchronous electronic bill discounting and bill endorsing, and the like are solved; and various risks are effectively managed, controlled and prevented.
Owner:HANGZHOU YUNXIANG NETWORK TECH
Electronic document safe sharing system and method thereof
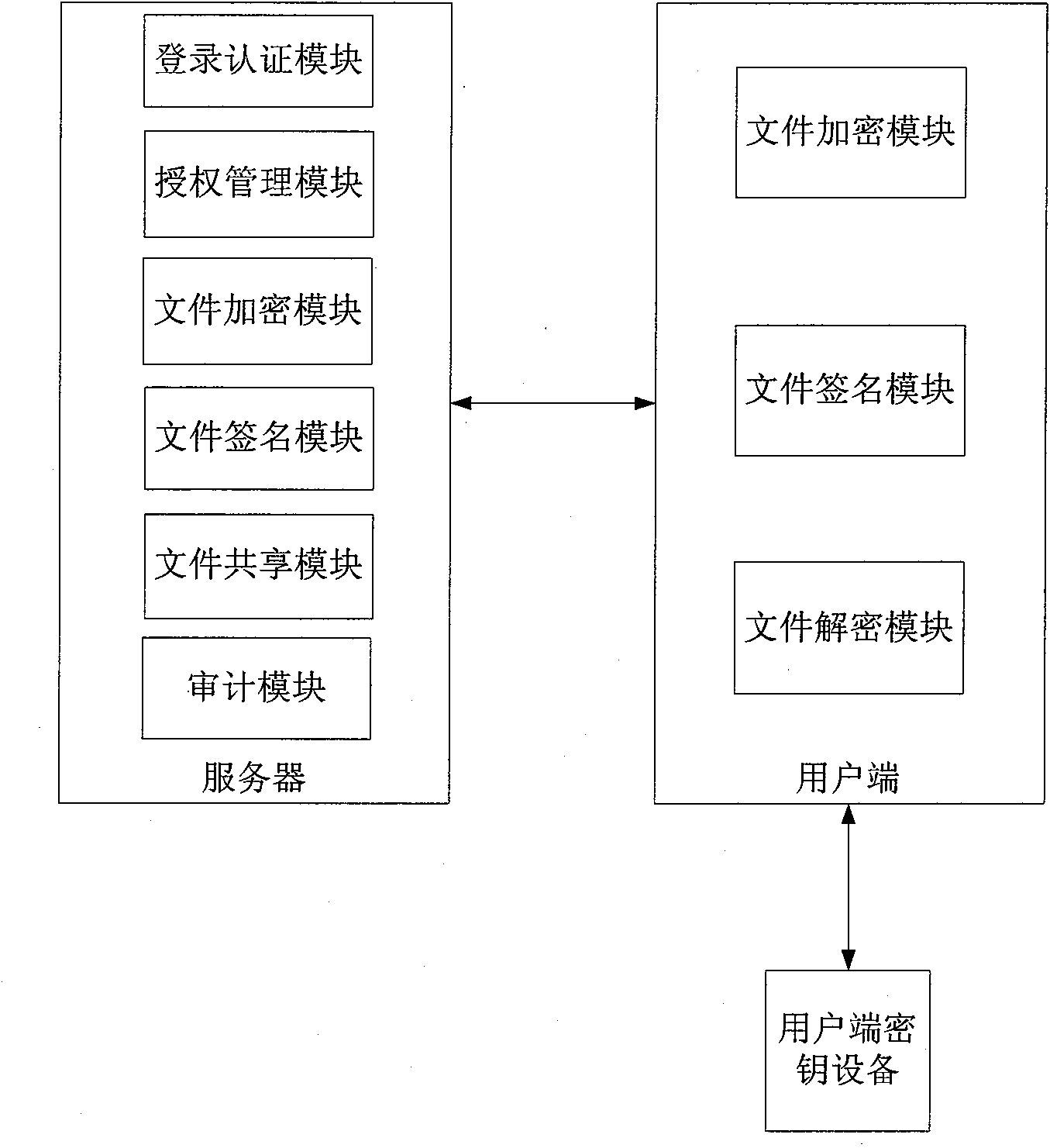
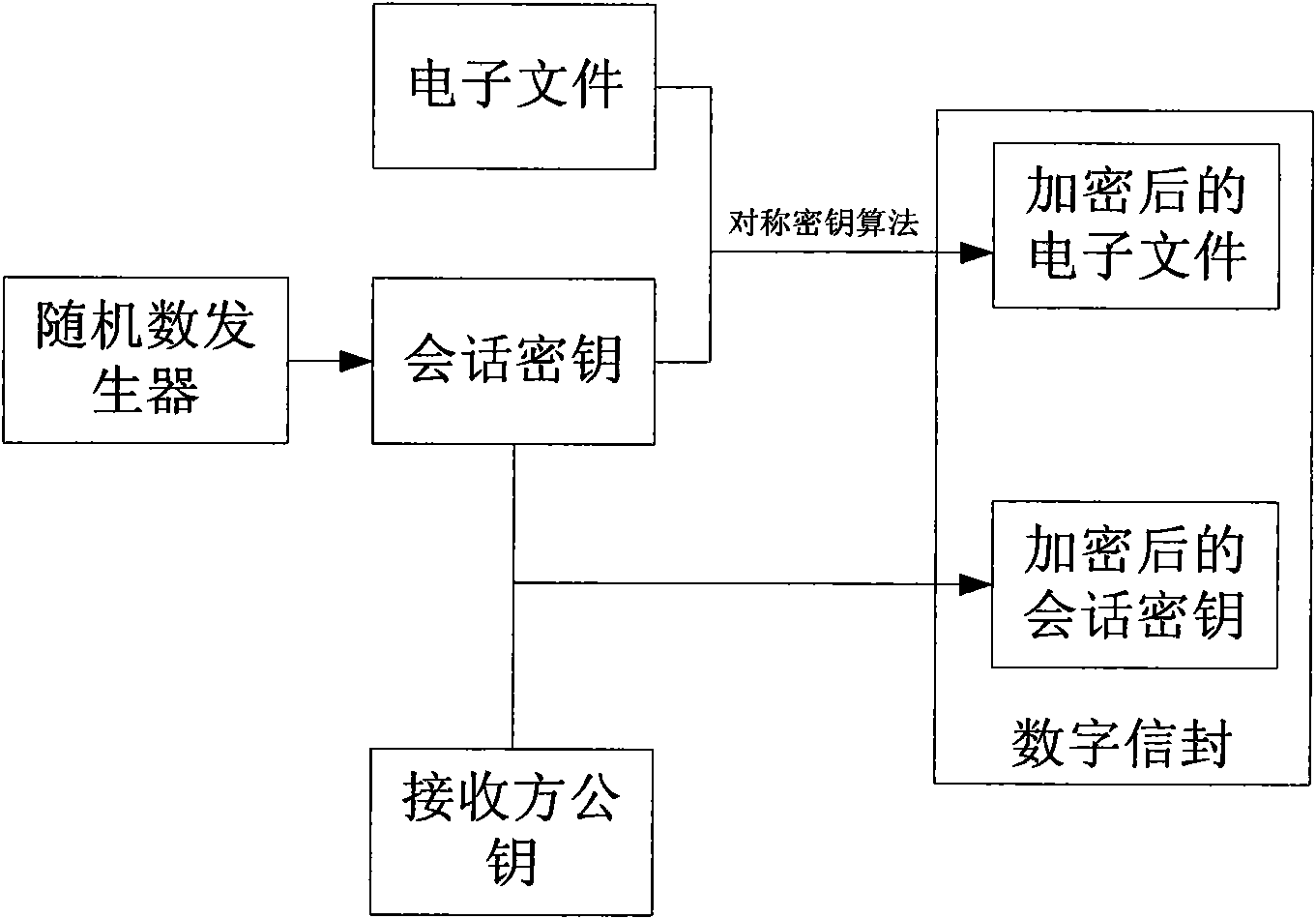
InactiveCN101989984AGuarantee authenticitySafe storagePublic key for secure communicationUser identity/authority verificationClient-sideSafe storage
The invention discloses an electronic document safe sharing system which can realize safe storage and fully sharing of secret document. The electronic document safe sharing system comprises a document encrypting module and a document decrypting module; wherein the document encrypting module utilizes a session key to symmetrically encrypt electronic document data, receiver identification (public key) is utilized to asymmetrically encrypt the session key, and finally the encrypted symmetric key and encrypted electronic document data are packed into a digital envelop; and the document decrypting module utilizes an own private key to decrypt the digital envelop. The electronic document safe sharing method of the invention takes CPK combined public key or CPK compound public key technology as the basis, flexible digital signature and secret key exchange capacity thereof are utilized, and a confidential document management system which is from a server to a client, contains information storage and transmission to each use link and is integrated with document data encryption, access control, authorization management, dynamic key exchange and process audit trail into a whole is constructed.
Owner:BEIJING E HENXEN AUTHENTICATION TECH +1
Authentication system based on address, device thereof, and program
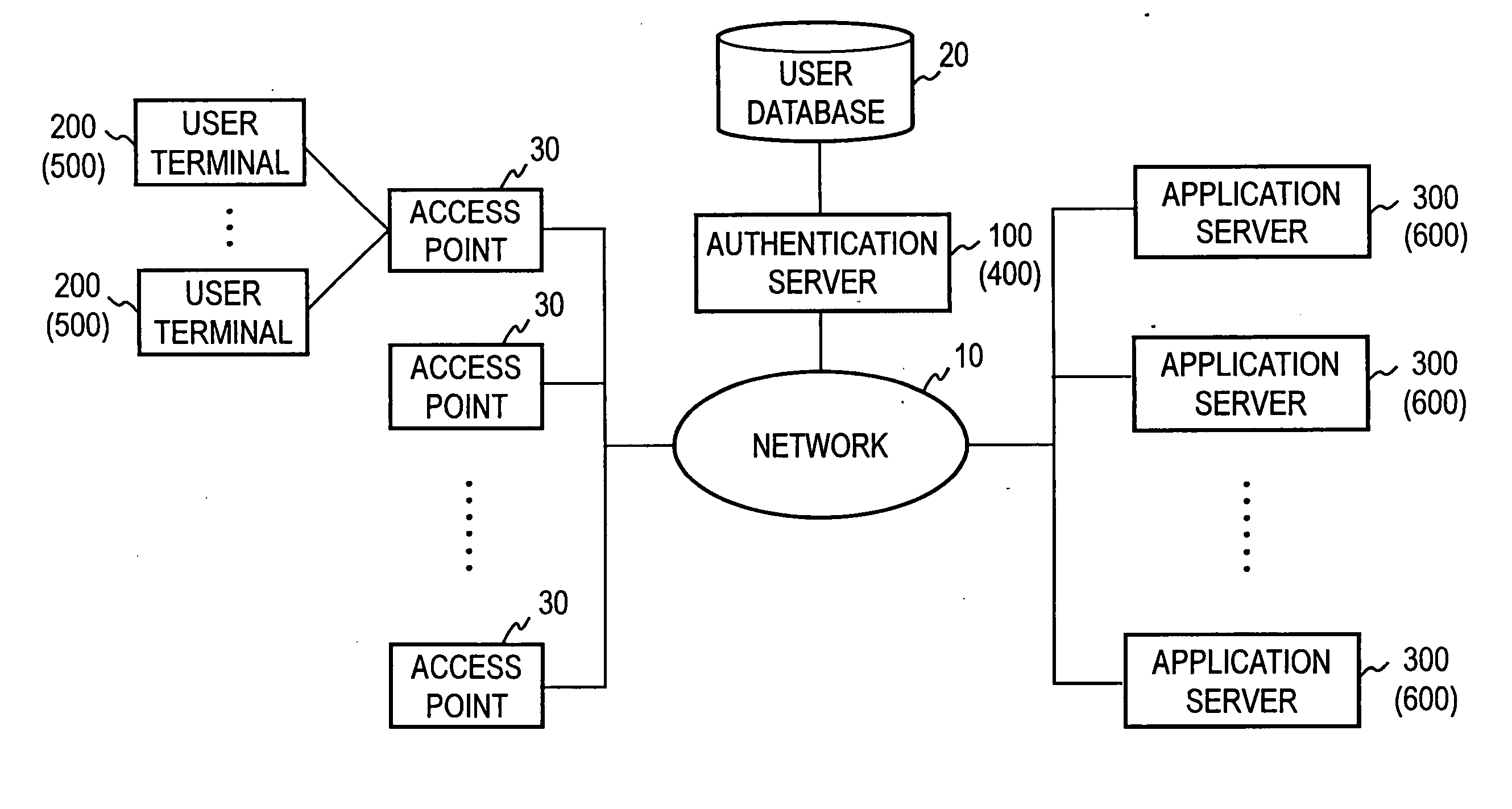
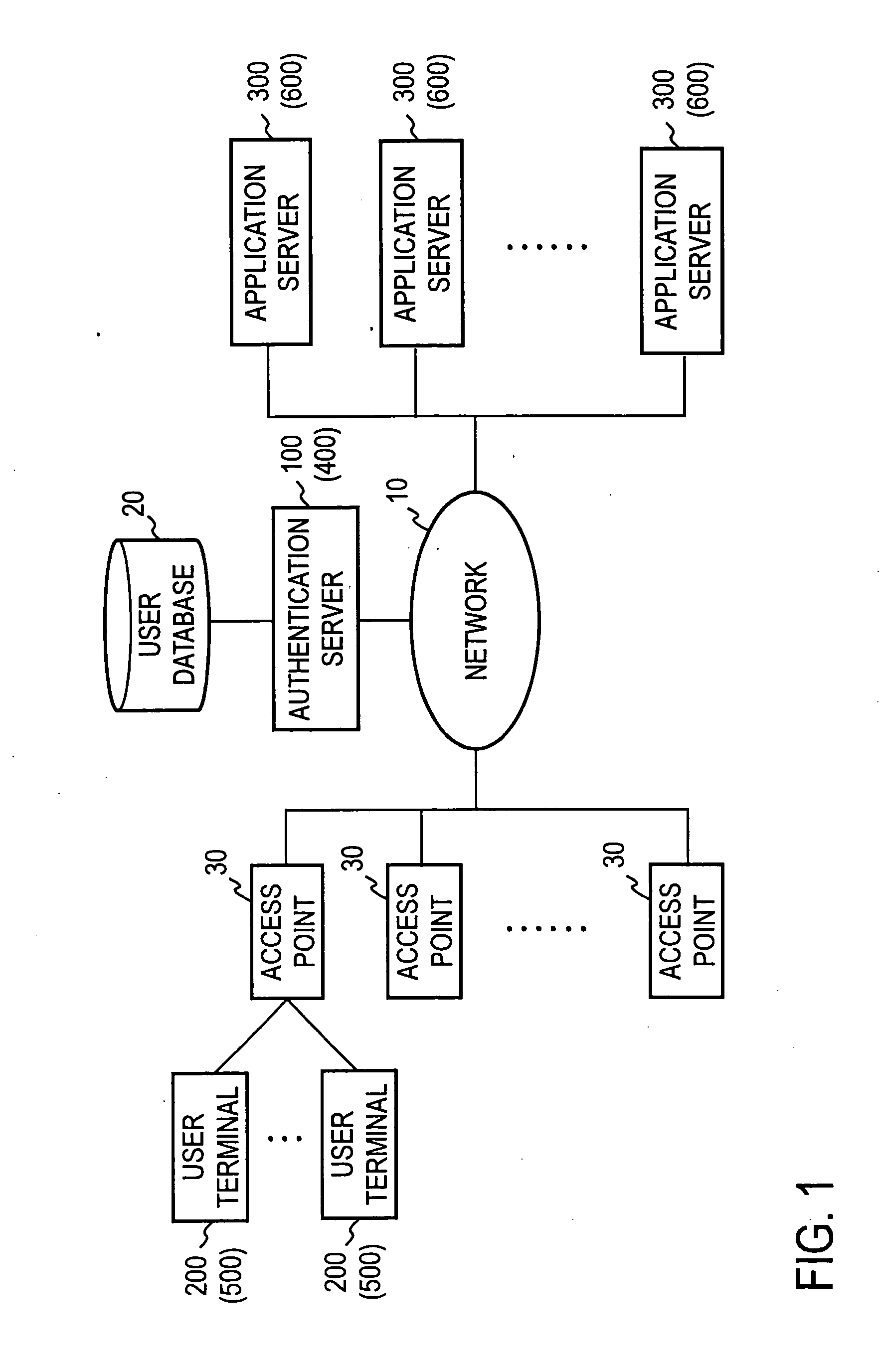
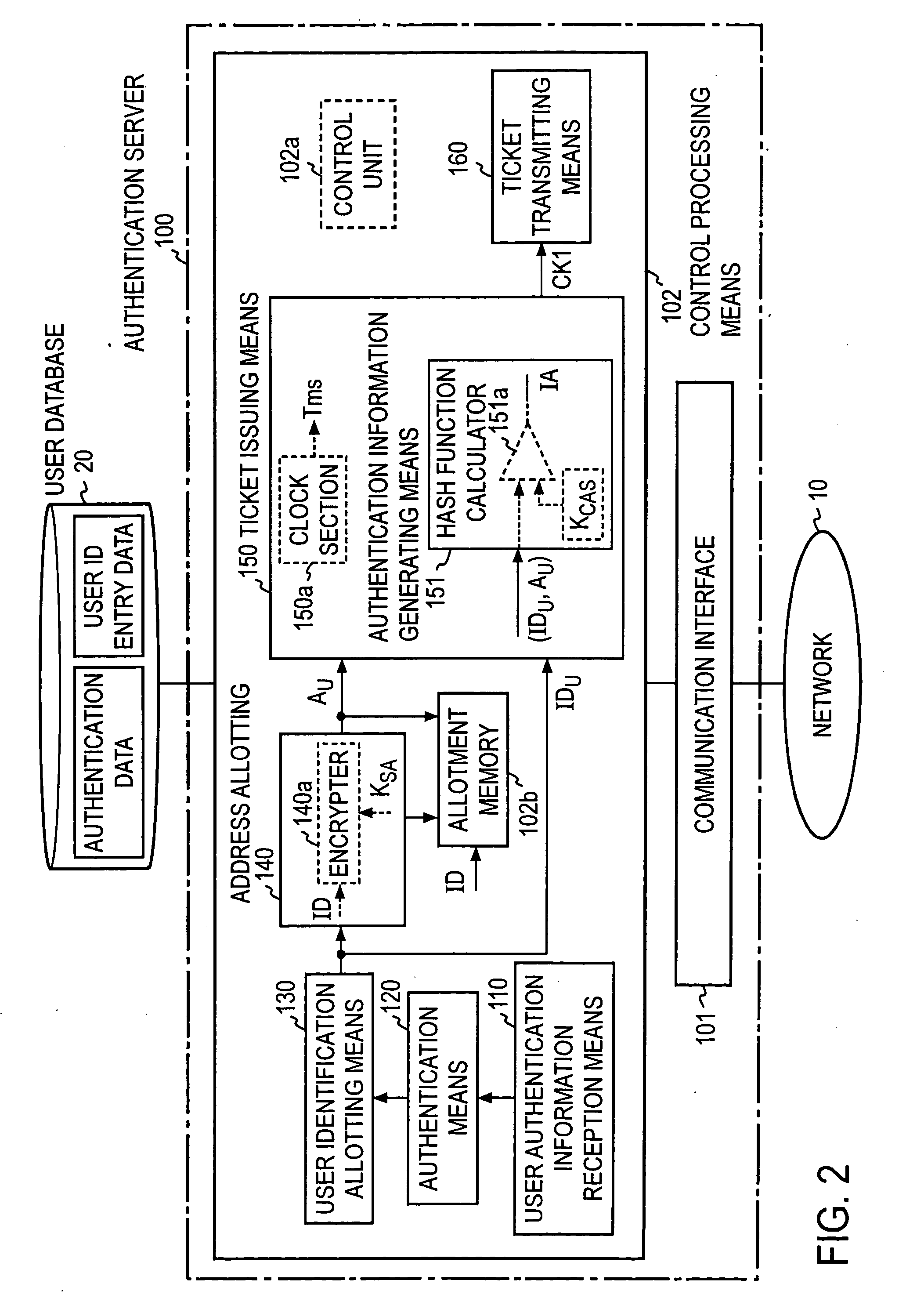
ActiveUS20060048212A1Guarantee authenticityDigital data processing detailsUser identity/authority verificationApplication serverIp address
An address allocated to a user by an authentication server is used as an IP address of a packet which is transmitted from a user terminal, preventing an illicit use if the IP address were eavesdropped. An authentication server 100 performs an authentication of a user based on a user authentication information which is transmitted from the user terminal, and upon a successful authentication, allocates an address to the user terminal, and issues a ticket containing the address to be returned to the user terminal. The user terminal sets up the address contained in the ticket as a source address, and transmits the ticket to the application server 300, requesting a session to be established. After verifying that the ticket is authentic, the server 300 stores the ticket and establishes a session with the user terminal. The user terminal transmits a service request packet containing the source address to the server 300 utilizing the session. If the source address coincides with the address contained in the stored ticket, the server 300 provides a service to the user.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Method and device for data processing based on block chain
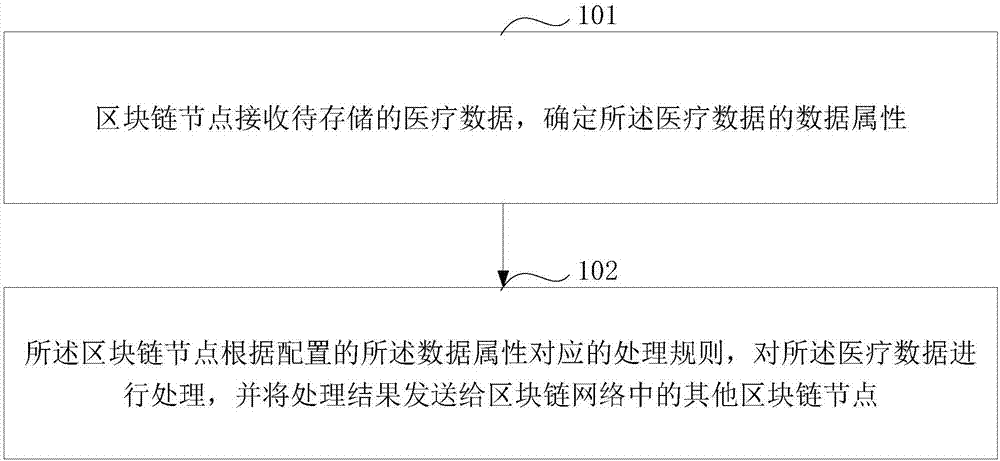
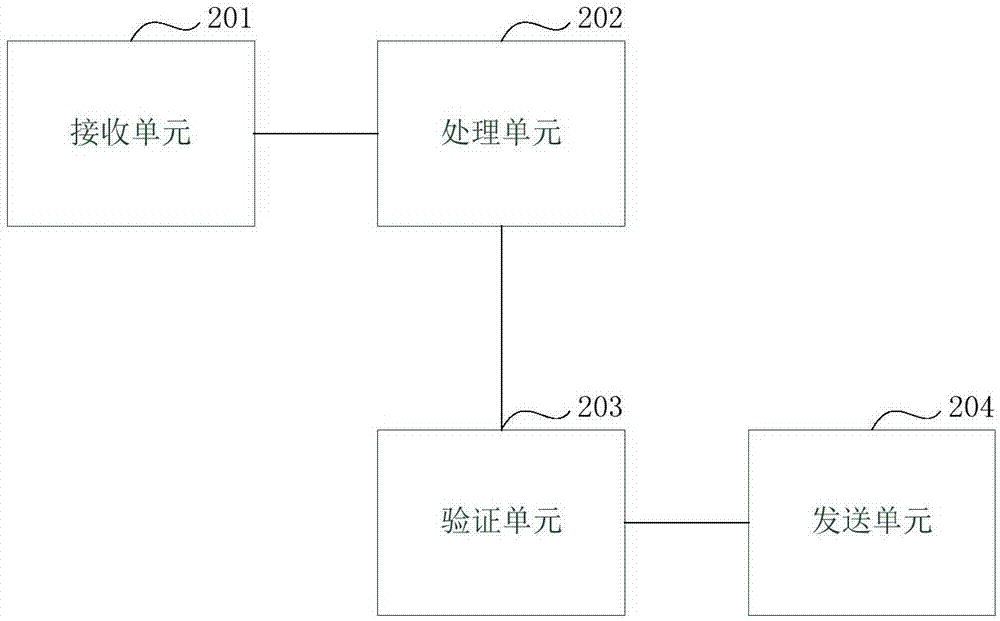
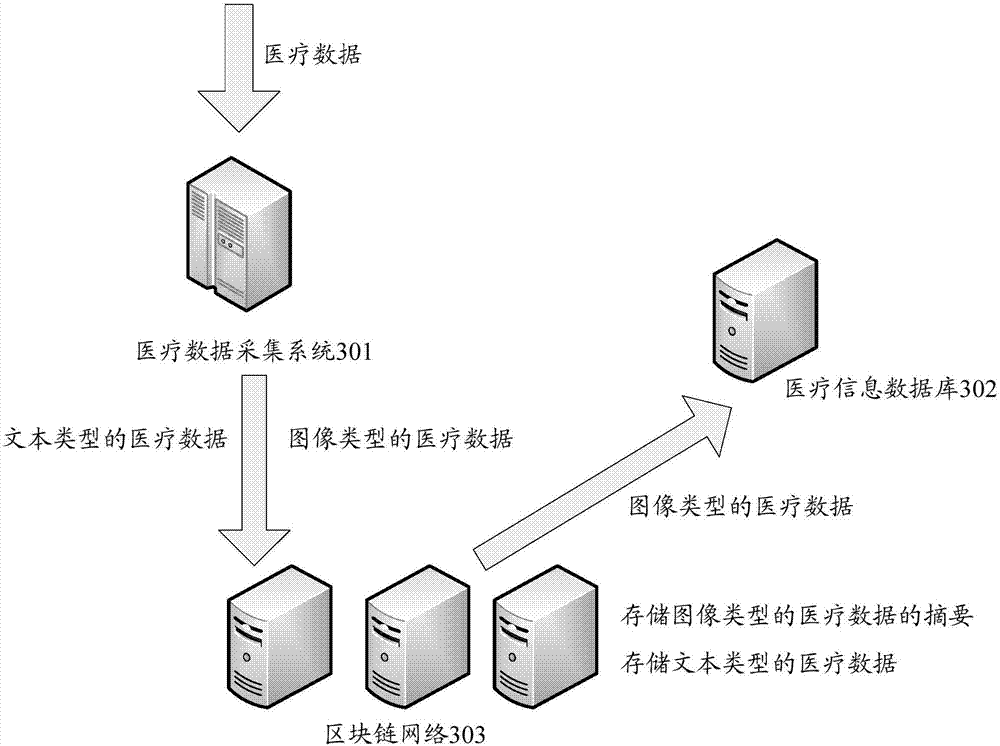
ActiveCN107426170AGuarantee authenticityNot tampered withComputer security arrangementsSpecial data processing applicationsTamper resistanceData authenticity
The present invention discloses a method and device for data processing based on a block chain. The method comprises: when a block chain node receives business data to be stored, determining the data attributes of the business data; if the data attributes of the business data is a text type, employing a preset private key in a public and private key pair corresponding to the user identification included in the business data to perform encryption processing of the business data; and if the data attributes of the business data is an image type, determining the abstract of the business data, and employing preset private key in a public and private key pair corresponding to the user identification included in the business data to perform encryption processing of the abstract. The features of decentration, openness and transparency, tamper resistance and dependability of the block chain technology are employed to employ different processing modes according to the data attributes of the business data to store the business data into the block chain network so as to ensure the business data authenticity and ensure that the business data is not tampered.
Owner:ADVANCED NEW TECH CO LTD
Safety communication secret key negotiation interaction scheme
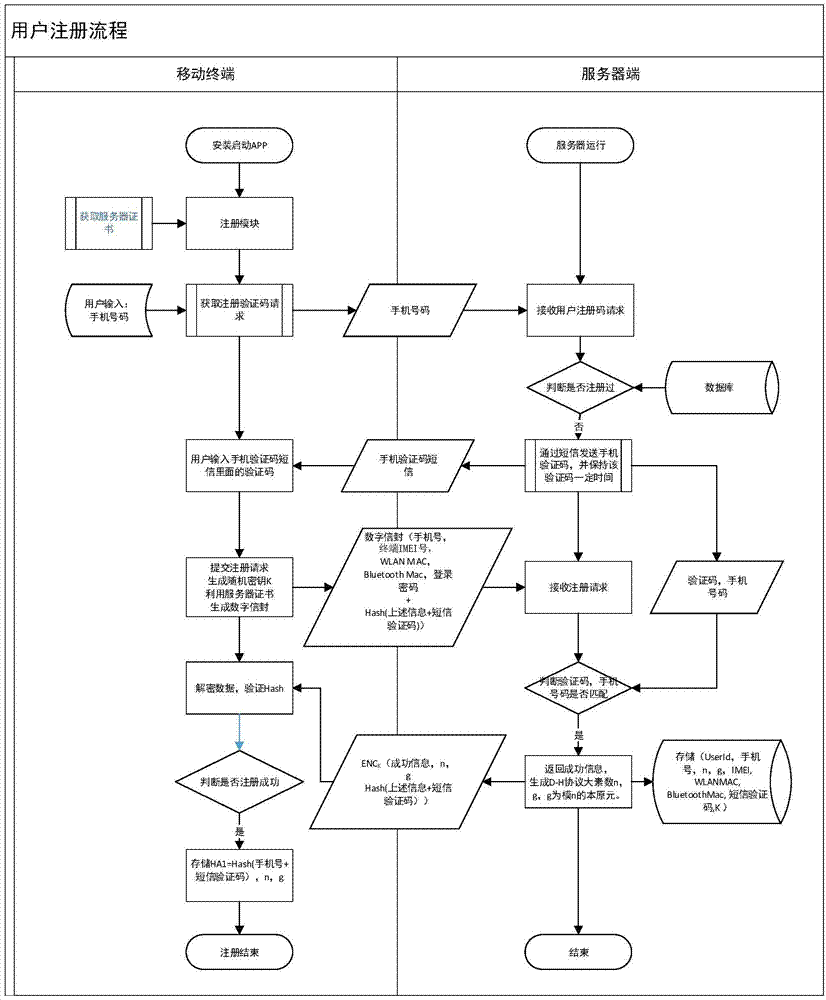
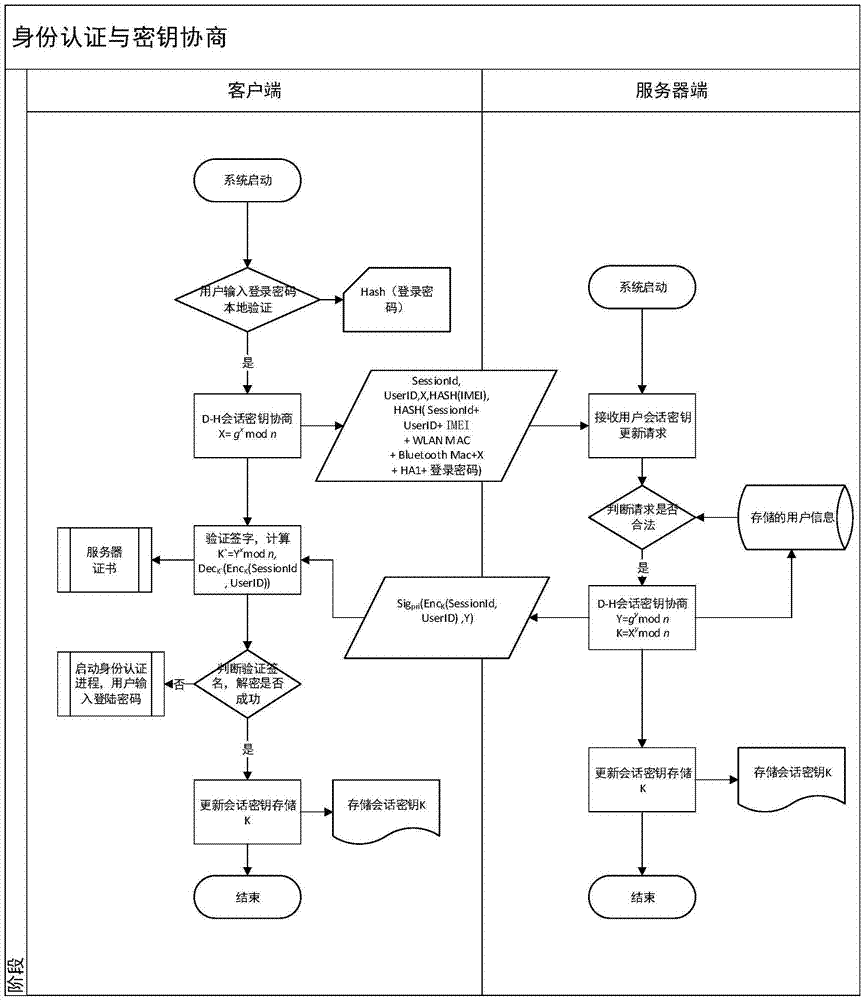
ActiveCN104506534AGuarantee authenticityEnsure communication securityKey distribution for secure communicationUser identity/authority verificationThe InternetNetwork service
The invention provides a method for safety communication between an application on a mobile terminal and a network server. Shared secrets of a user and a server are overlapped and bound with an identification code of mobile intelligent terminal equipment and a mobile phone number of the user by utilizing a cryptology; then the obtained product is applied to an identity authentication system to implement authentication on a client side; a digital certificate and a digital signature mechanism are utilized to implement authentication on the server; a session key is established with a network server by utilizing a Differ-Hellman secret key negotiation protocol so as to carry out safety data communication. The method is characterized in that the shared secrets are overlapped and bound with identification code of the machine and the mobile phone number of the user and the shared secrets are updated regularly; even though information is stolen by an attacker, a system still cannot be influenced. The user not only needs to provide a login password, but also needs to use the system on designated equipment. The method can ensure that the user carries out safety communication with the server on internet by the mobile equipment.
Owner:QINGDAO WEIZHIHUI INFORMATION
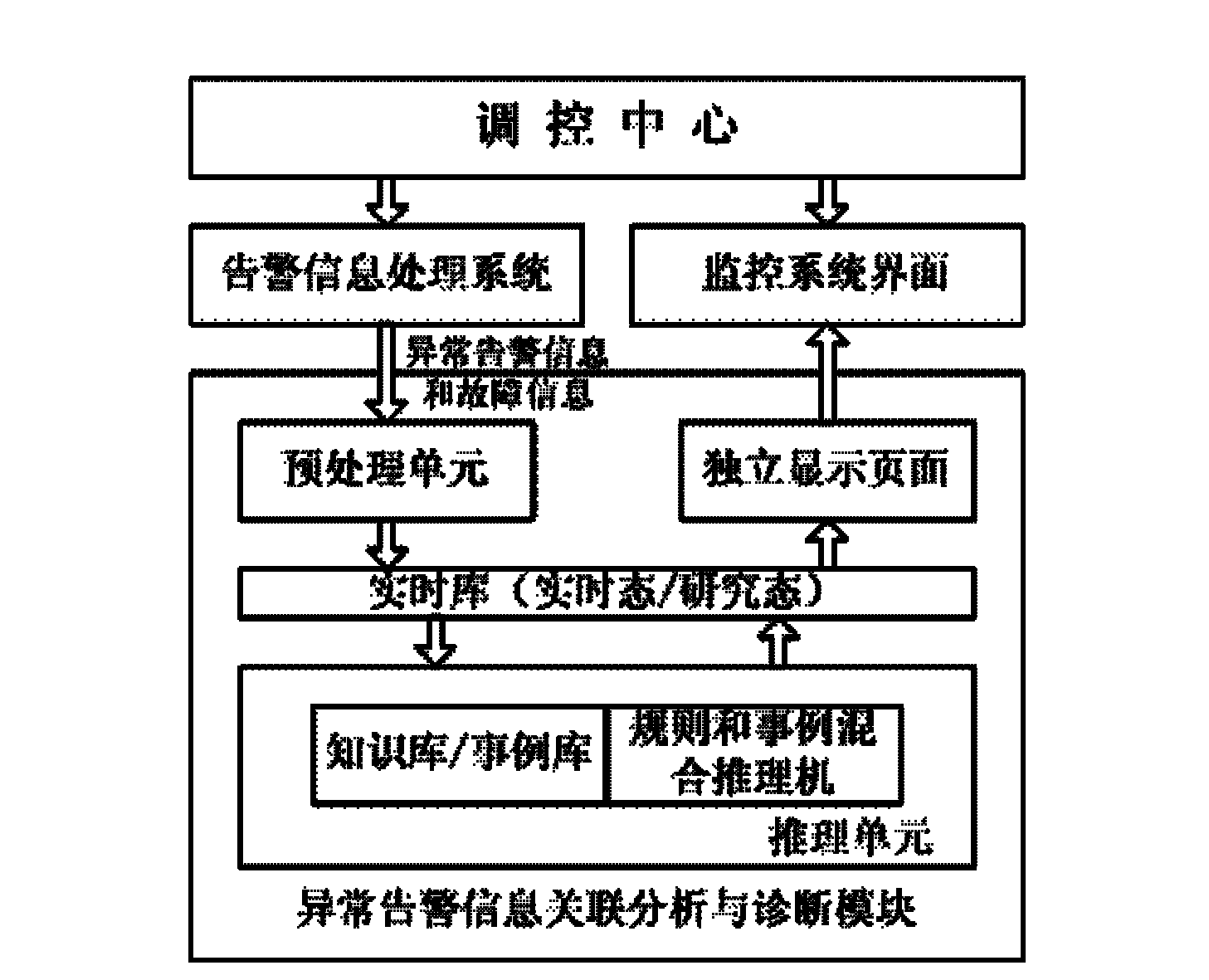
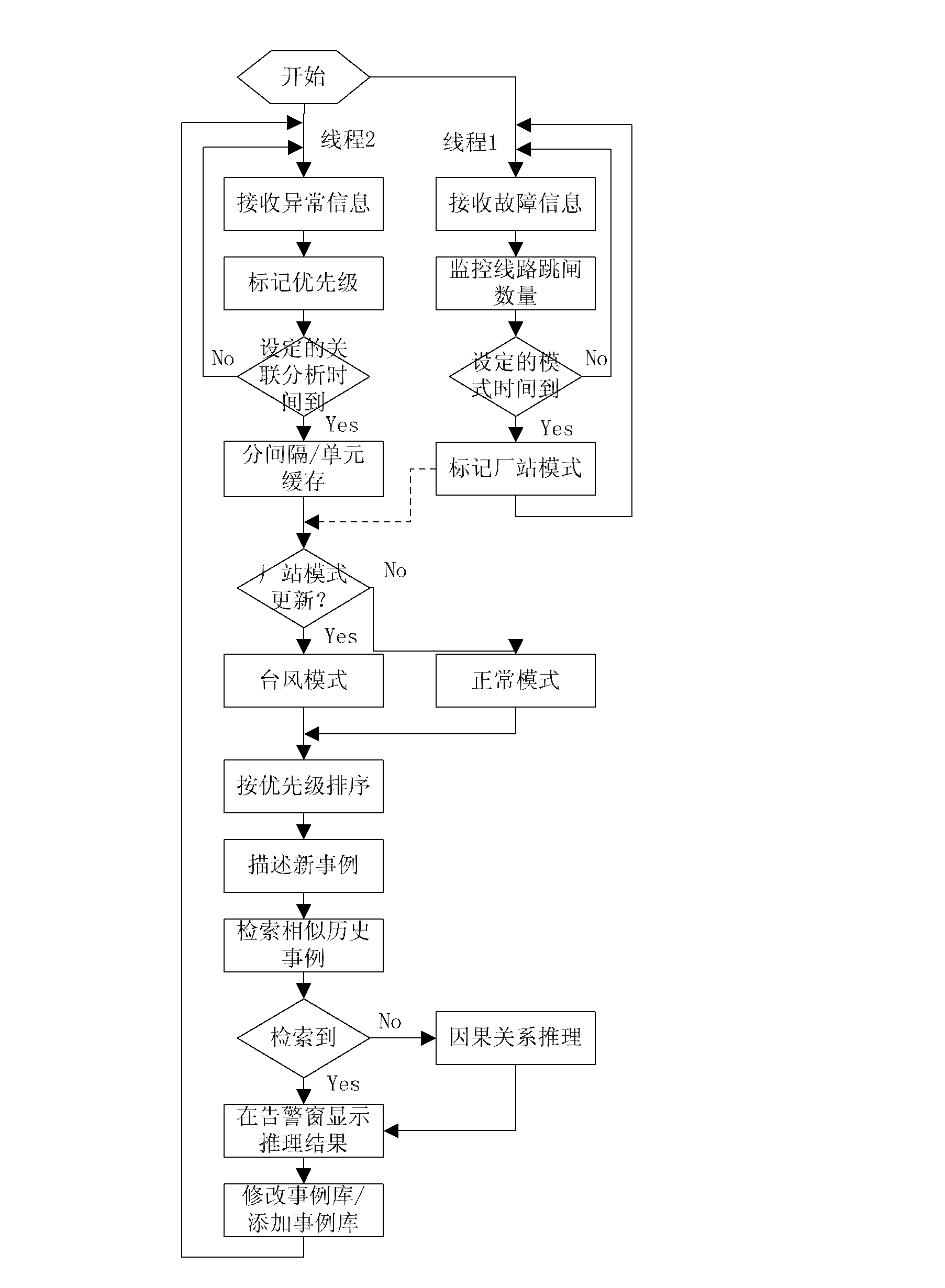
District power network equipment abnormal alarm signal association analysis and diagnosis method
InactiveCN102638100AIntegrity guaranteedGuarantee authenticityCircuit arrangementsInformation processingPower system scheduling
The invention discloses a district power network equipment abnormal alarm signal association analysis and diagnosis method in the field of automation of scheduling of electric power systems. According to the method disclosed by the invention, the weather situation of a plant station region at which abnormal alarm information is located can be automatically identified so as to determine the information processing mode. The method disclosed by the invention has the beneficial effects that by realizing intelligent association analysis and auxiliary decision making of the equipment abnormal alarm information under the real-time state, and performing playback on historical alarm information and performing real-time treatment on manual set information under the research state, the abnormal treatment time is greatly reduced, the incidence of accidents is reduced, a real-time, rich and intelligent auxiliary decision-making support is provided for regulation and control staff, and the safe, high-quality, economical and stable operation of an electric fence is further ensured.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Credit recording system and method based on block chain
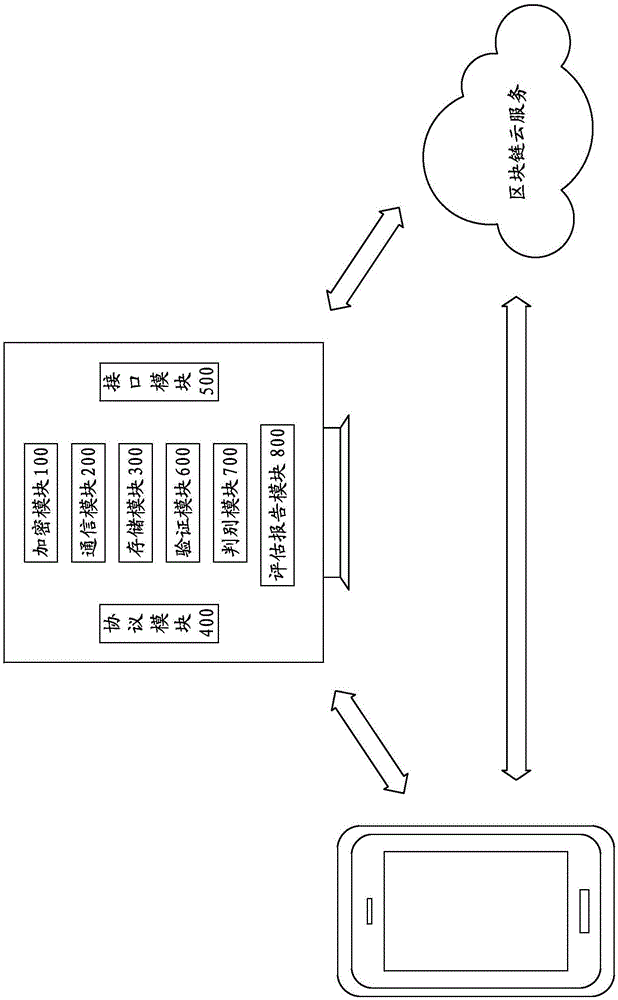
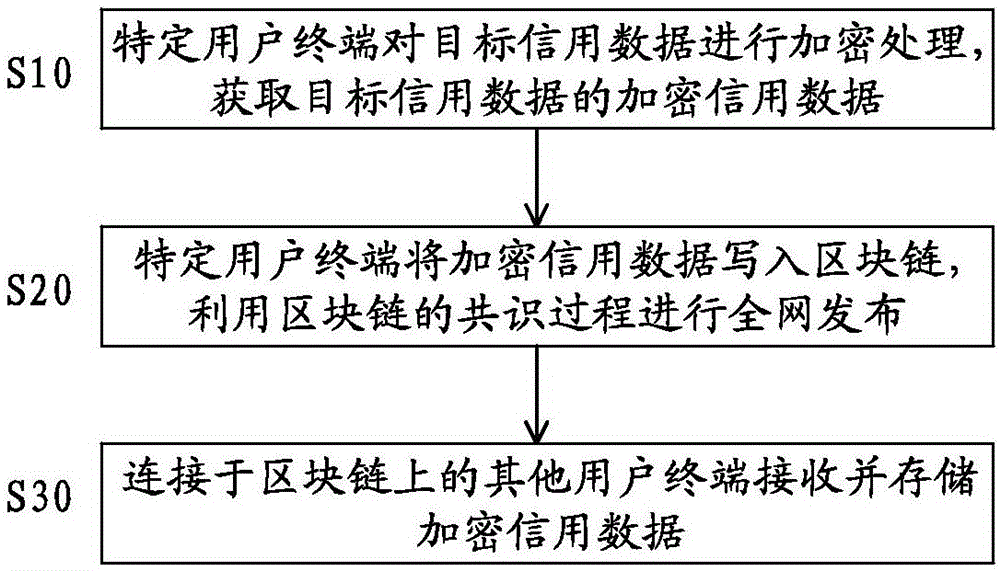
ActiveCN106485167AWide variety of sourcesReduce complexityDigital data protectionExtensibilityComputer terminal
The invention discloses a credit recording system and method based on a block chain. The credit recording system comprises a plurality of user terminals which are connected to the block chain and used for acquiring and verifying credit data, wherein each user terminal is installed with an encryption module for encrypting target credit data to be transmitted to form encrypted credit data, a communication module for transmitting the encrypted credit data together with the block chain, and a storage module for storing the target credit data of the user terminal and other encrypted credit data transmitted by the block chain. The credit data are wide in sources, independent, reliable and real; the cleaning and sieving complexity of the credit data are lowered greatly; and the credit recording system and method have flexible and diverse application scenes and high extensibility.
Owner:CENTRIN DATA SYST
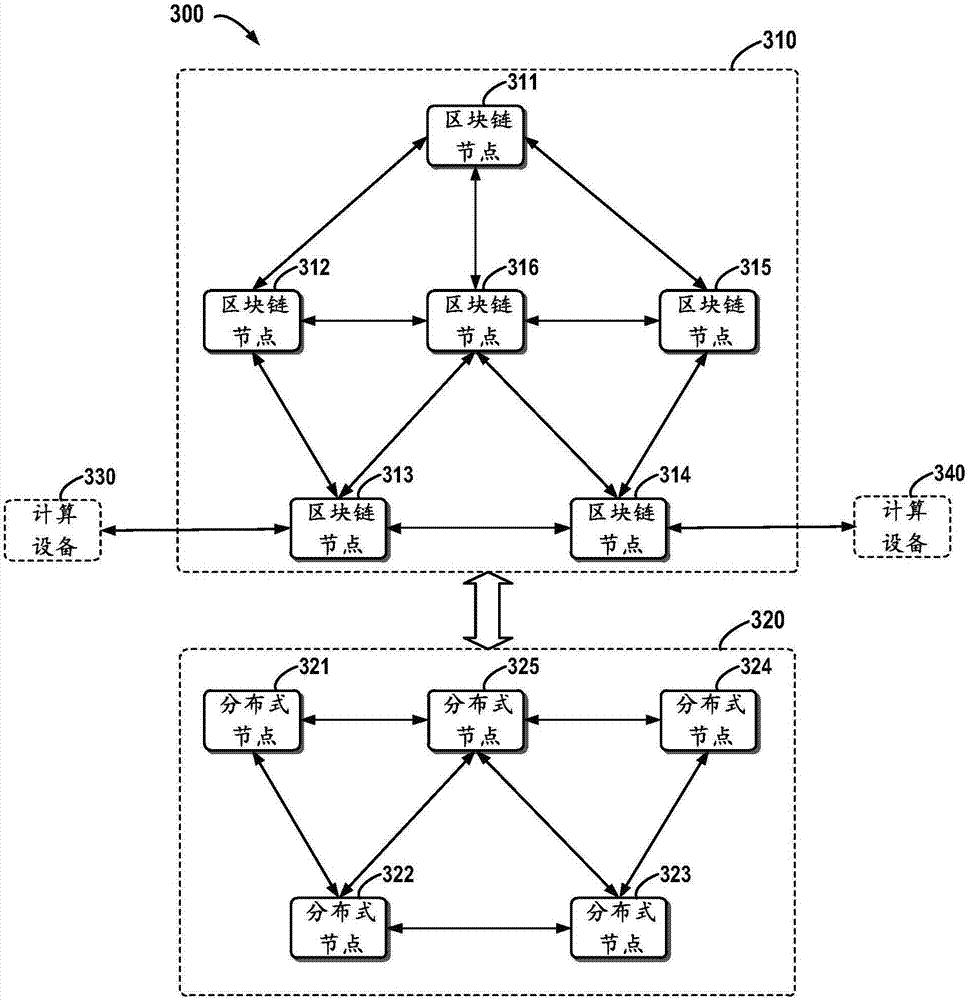
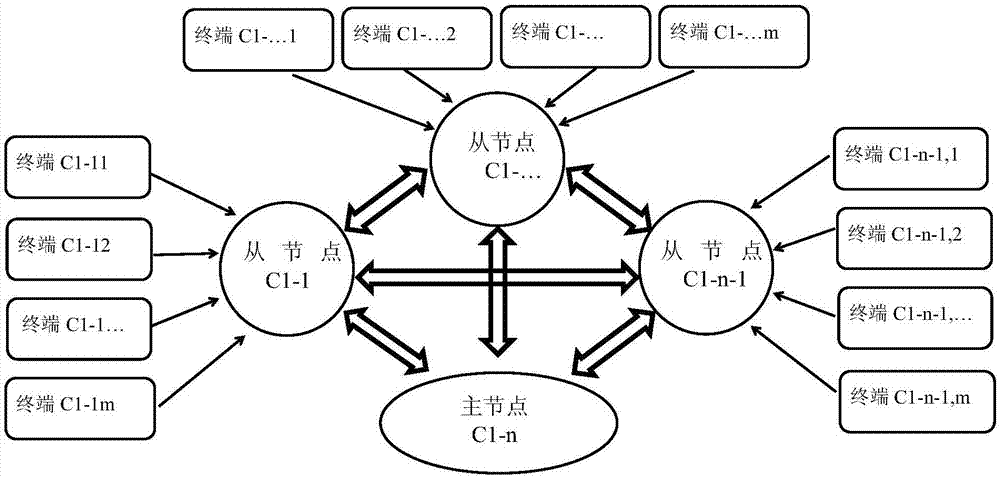
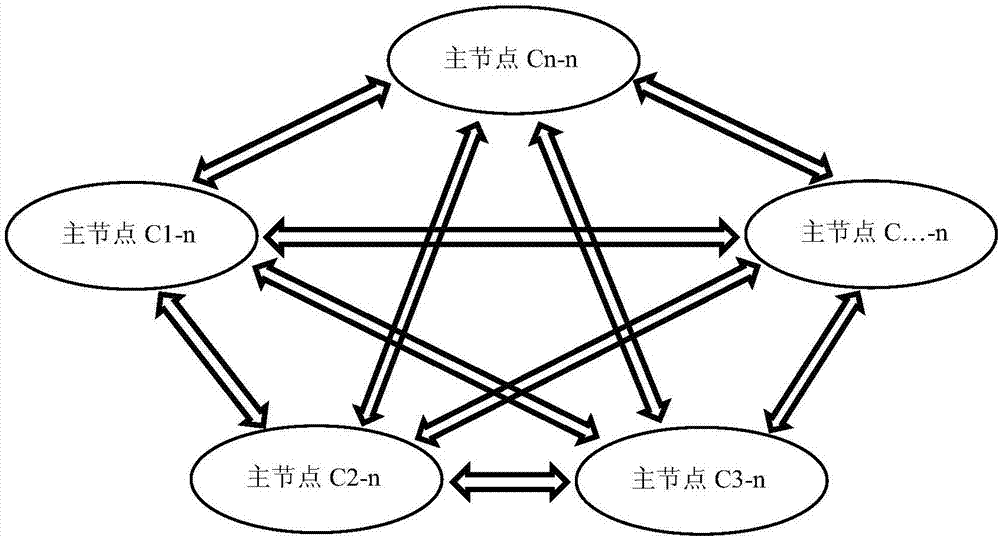
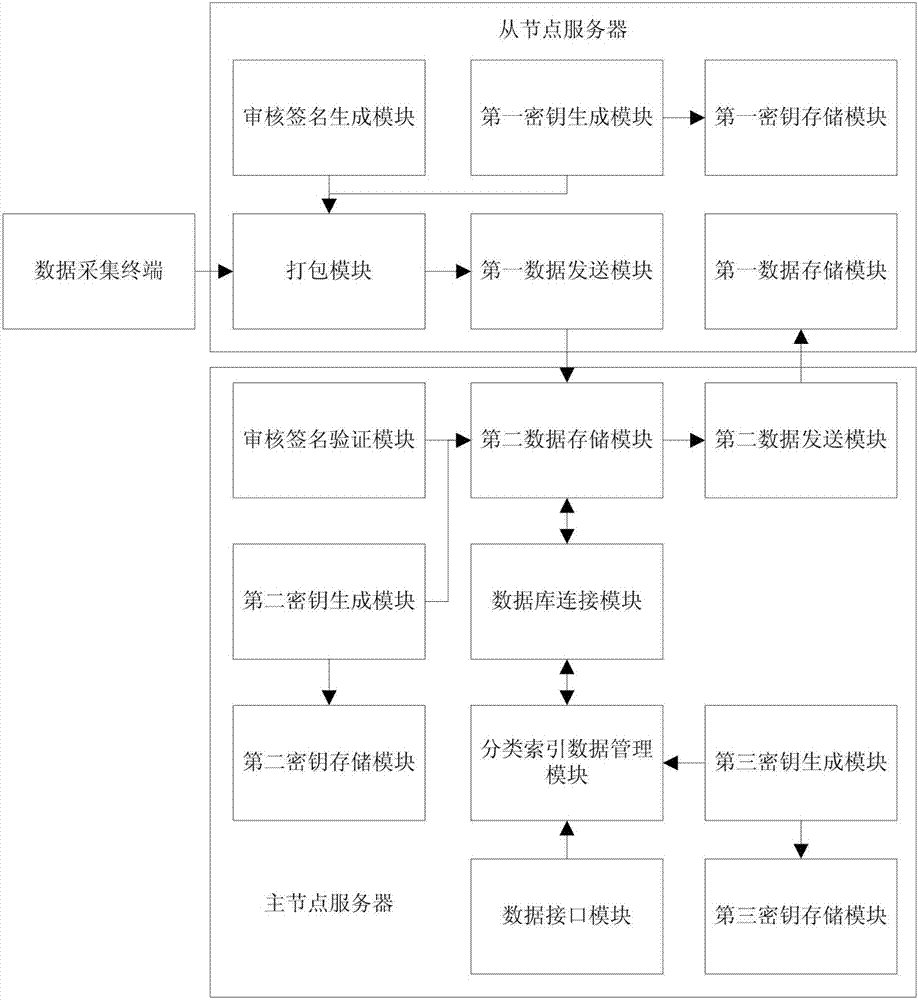
Data management system and method based on composite blockchain network
InactiveCN107222482AIntegrity guaranteedGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationAuthorization ModeStructure of Management Information
The invention relates to a data management system and method based on a composite blockchain network, wherein the system comprises a first-level blockchain network and at least one second-level blockchain network; the second-level blockchain network comprises multiple mutually connected slave node servers; the second-level blockchain network sets a master node server in all the slave node servers; and the master node servers in all the second-level blockchain networks are mutually connected, so that the first-level blockchain network is formed. By means of the data management system and method disclosed by the invention, the integrity, the authenticity and the standardization of data can be ensured through audit signature verification of the composite multi-level blockchain network; the security of the data is ensured in a hierarchical encryption and multiple authorization mode; structural design of hierarchical storage of detailed data and classified index data is carried out through a blockchain technology and the composite multi-level network; therefore, the data is relatively smooth to interconnect, intercommunicate and exchange; furthermore, audit tracing can be realized; and the data retrieving, applying and sharing efficiency can be increased.
Owner:黑龙江卓亚科技有限公司
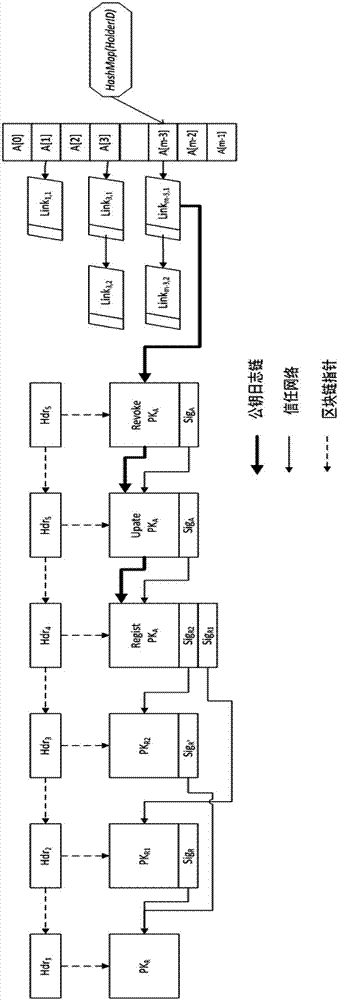
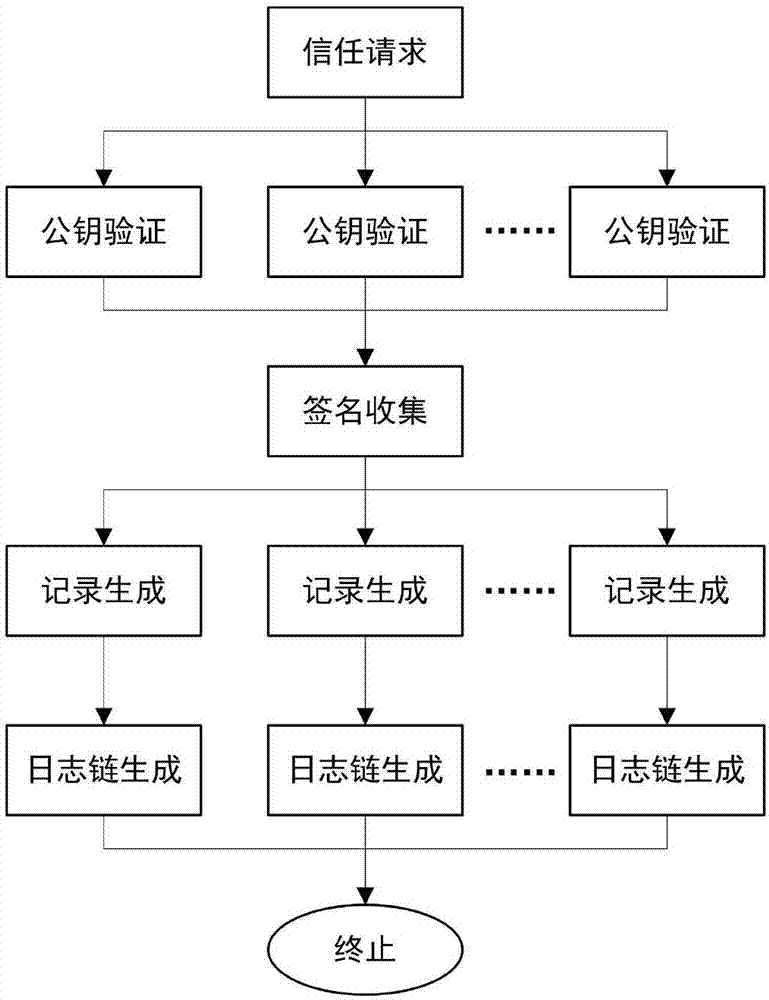
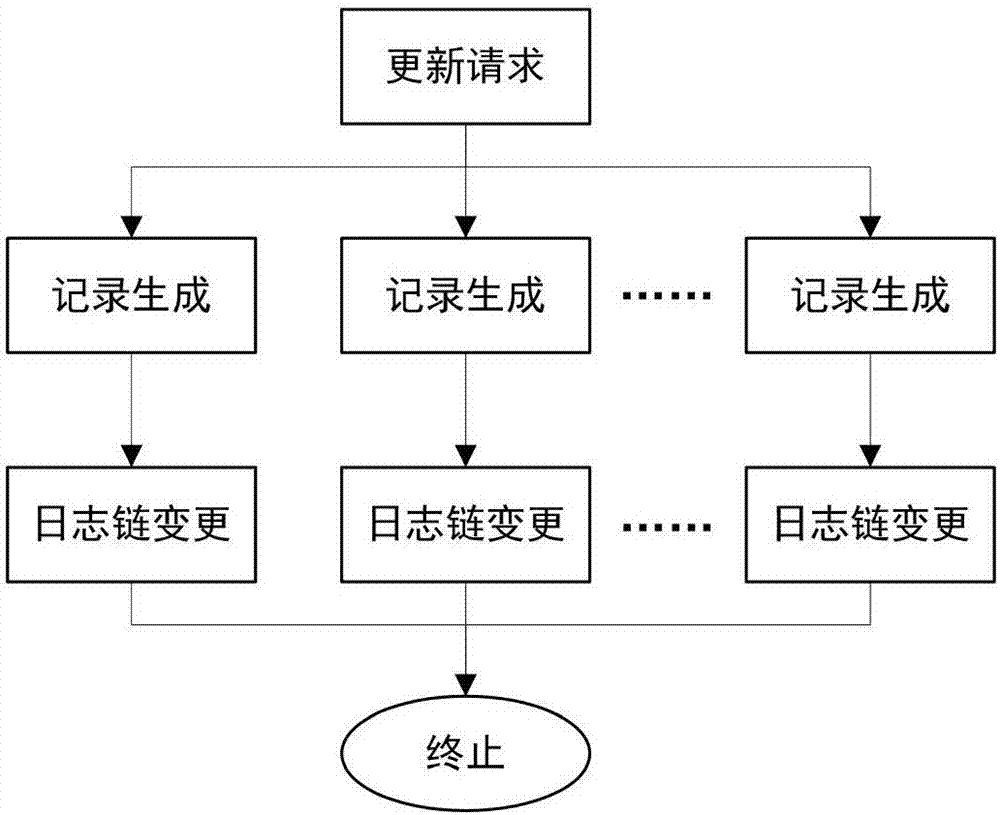
Decentralized public key management method and system based on trusted network
ActiveCN107070644AEfficient verificationEfficient queryKey distribution for secure communicationStructure of Management InformationUser identifier
The invention mainly belongs to the technical field of information security, and specifically relates to a novel decentralized public key management method and a trusted model. The method is constructed on distributed data network platforms such as a block chain and P2P (Peer to Peer) in order to ensure that all nodes in the platforms can participate in maintenance of whole-life-cycle management of public keys of users, and the changes of the public keys of the users in various states in a life cycle are recorded in a bill form. Through the method, public keys passing verification can be recorded and added into a consistent public key storage structure of a platform to be saved; a public key log chain is generated for all public key records of the same user according to a time sequence, and an authentication chain and a trusted network are formed on the basis of a referrer signature; and efficient search of the public keys can be realized on the basis of user identifiers. Through adoption of the method, the public keys of the users can be issued and acquired conveniently and accurately, and the effectiveness, correctness, consistency and non-fraudulence of acquired public keys are ensured. The method can be taken as an infrastructure supporting authentication, encryption, integrity and accountability services.
Owner:UNIV OF SCI & TECH BEIJING
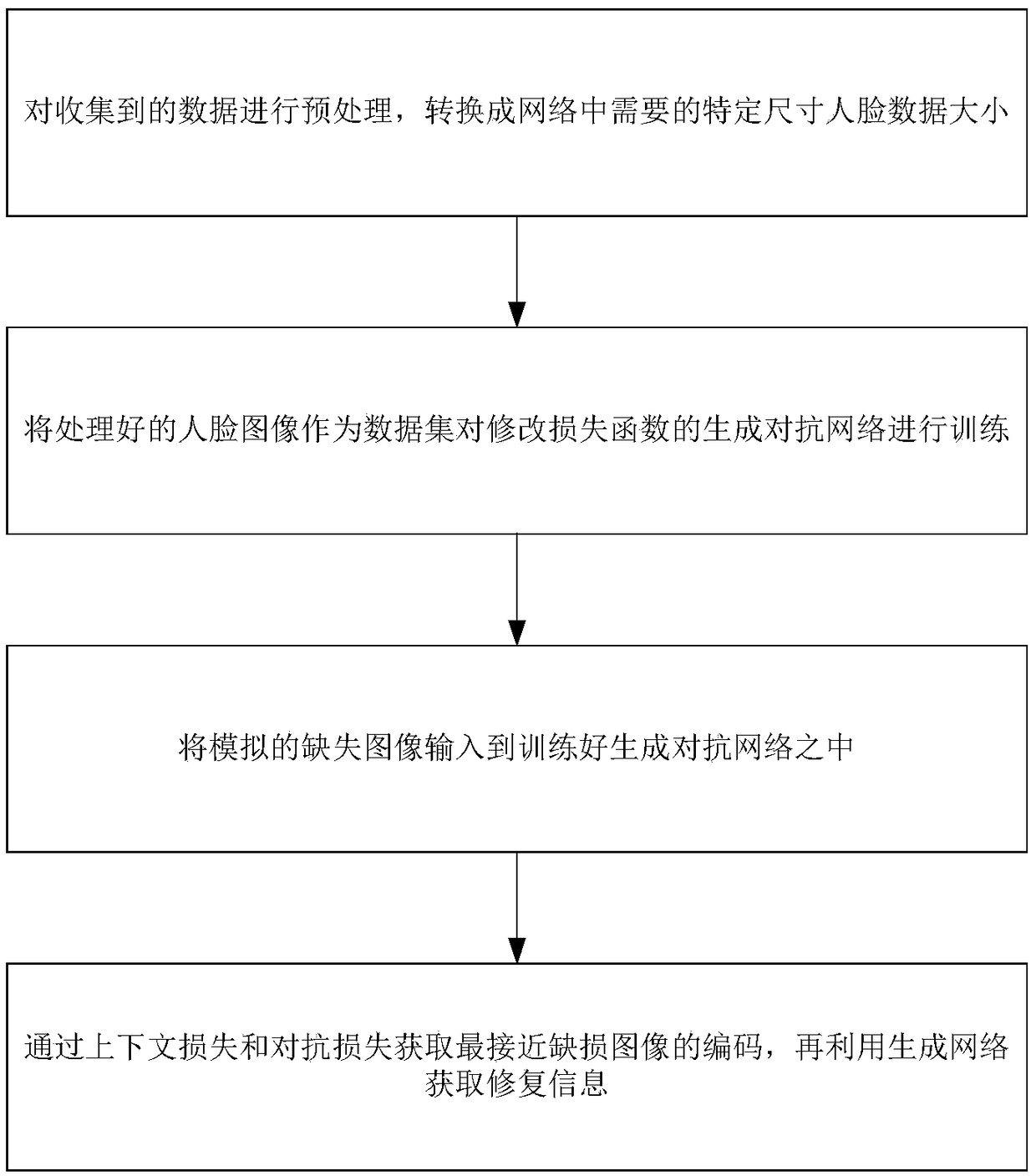
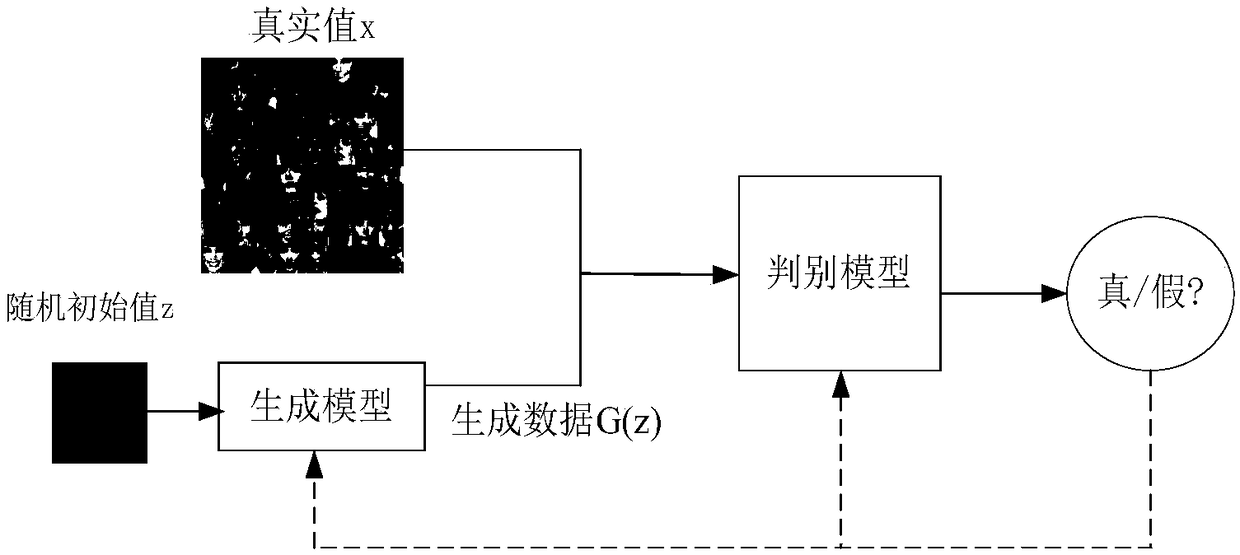
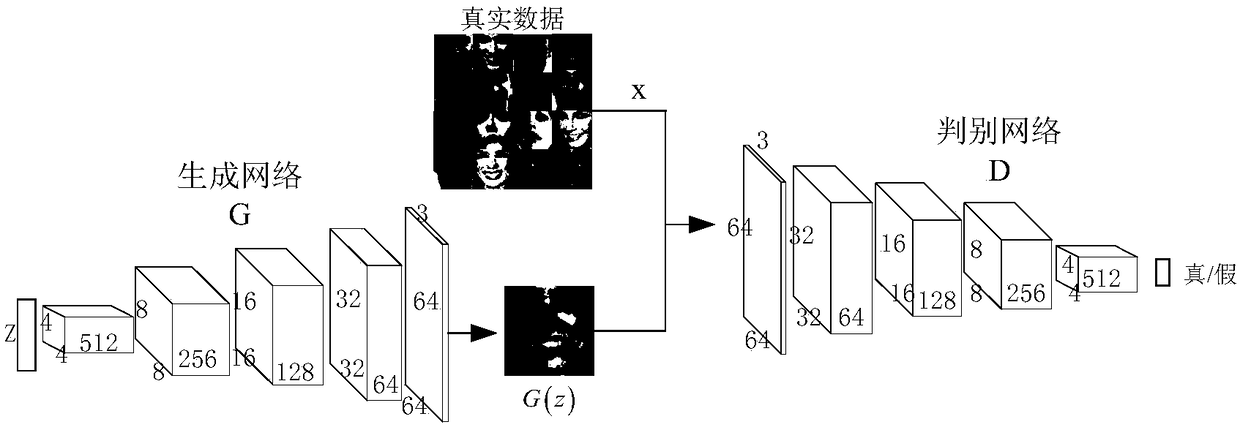
A face image restoration method based on a generation antagonism network
ActiveCN109377448AImprove stabilityGuarantee authenticityImage enhancementImage analysisData setTraining phase
The invention discloses a face image restoration method based on a generation antagonism network. The method comprises the following steps: a face data set is preprocessed, and a face image with a specific size is obtained by face recognition of the collected image; In the training phase, the collected face images are used as dataset to train the generating network and discriminant network, aimingat obtaining more realistic images through the generating network. In order to solve the problems of instability of training and mode collapse in the network, the least square loss is used as the loss function of discriminant network. In the repairing phase, a special mask is automatically added to the original image to simulate the real missing area, and the masked face image is input into the optimized depth convolution to generate an antagonistic network. The relevant random parameters are obtained through context loss and two antagonistic losses, and the repairing information is obtainedthrough the generated network. The invention can not only solve the face image repairing with serious defective information, but also generate a face repairing image which is more consistent with visual cognition.
Owner:BEIJING UNIV OF TECH
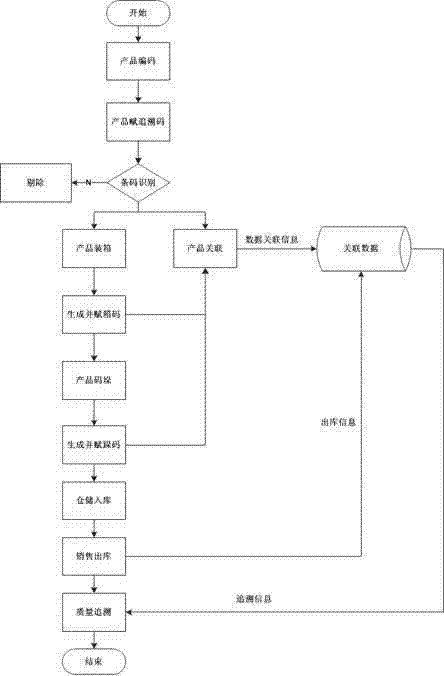
Quality safety tracing method for food processing enterprises
InactiveCN103761546ANo repeated codes appearMeet randomnessCo-operative working arrangementsDebit schemesProduction lineRelational database
The invention discloses a quality safety tracing method for food processing enterprises. The quality safety tracing method includes the steps that a laser coder generates random tracing codes according to a coding rule when a laser marking machine in a production line device is dynamically read in an on-line tagging mode; the laser marking machine carries out tracing mode marking on products on a production line, and two-dimension codes and plain codes are all marked on packages; a fixed reader is used for scanning and reading designated tagged code portions of the products; the two-dimension codes are successfully scanned and read, the tracing codes are recorded, and relevance between the tracing codes and commodity attribute information is completed; if the two-dimension codes fail to be scanned, the two-dimension codes will be removed through a removing device; the commodity tracing code information and the commodity attribute information are recorded into a relational database; after the products are packaged, package code data and product tracing code data are related; the products are stacked, stacking codes and tagged stacking codes are generated, and the stacking codes and the product package code data are related; the stacking codes are scanned, storage of the products is completed, delivery orders and the stacking codes are scanned to complete delivery, and the database records delivery information.
Owner:武汉华工赛百数据系统有限公司
Multifunctional remote medical care system based on multi-network fusion
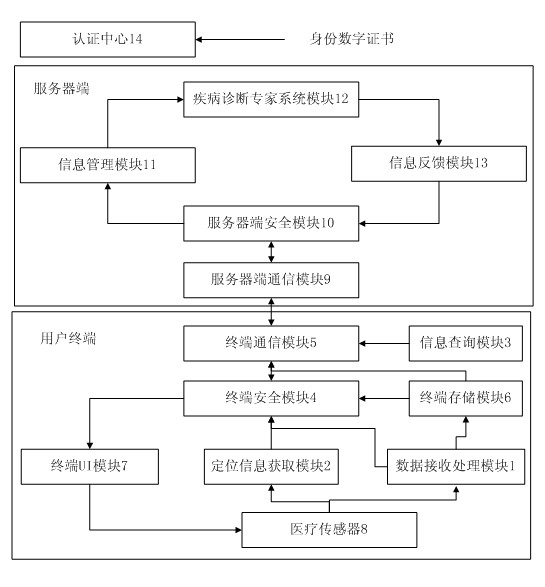
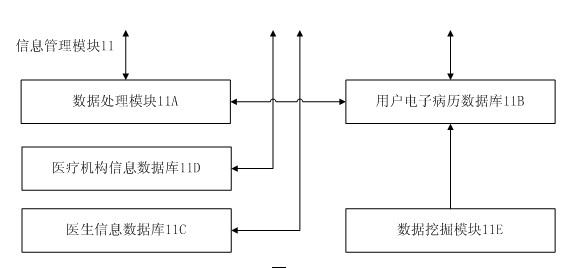
InactiveCN102085116AConvenient treatmentTimely treatmentSurgeryDiagnostic recording/measuringMedical recordFunctional expansion
The invention discloses a multifunctional remote medical care system based on multi-network fusion. The system involves the processes of registration from an entity to an authentication center, establishment of electronic medical record, data acquisition, remote diagnosis and information feedback; and a user terminal comprises a smart phone and a medical sensor. The smart phone comprises a data receiving processing module, a location-information acquisition module, an information querying processing module, a terminal safety module, a terminal communication module, a terminal storage module and a terminal UI (User Interface) module, wherein the medical sensor is provided with a wireless network interface and can be placed on a third medical sensor placed on the body of a user, a system server side comprises a server communication module, an information management module, a server-side safety module, a disease diagnostician system module, an information feedback module and an authentication center. The multifunctional remote medical care system based on multi-network fusion has the characteristics of rapid response, capability of detecting pathological changes in time, convenience and rapidness and the like, is easy for functional expansion, and has a greater upgrading function.
Owner:HUAZHONG UNIV OF SCI & TECH
Multi-sensing-data space-time synchronization method and road multi-sensing-data vehicle-mounted acquisition system
ActiveCN104112363AResolution timeSolving Consistency IssuesDetection of traffic movementSensing dataCognition
The invention provides a multi-sensing-data space-time synchronization method and a road multi-sensing-data vehicle-mounted acquisition system. The invention proposes the multi-sensing-data space-time synchronization realization method, and the multi-sensing-data space-time synchronization refers to one-to-one alignment of a plurality of paths of video data and GPS position data of a driving vehicle in a time dimension of a single frame of data and a space dimension of different acquisition devices. At the same time, the invention also discloses the vehicle-mounted system of road traffic environment multiple sensing data. The system is capable of real-time recording of multiple sensing data of a road traffic environment of the driving vehicle, such as the plurality of paths of video data and the GPS position data of the driving vehicle. The disorderly multiple sensing data acquired by the acquisition system can only be used alone because incapable of interaction with different kinds of data. However, the multiple sensing data which undergo the space-time synchronization is capable of reproducing driving scenes in a seamless transition manner so that the system is capable of providing comprehensive and objective real data and offline simulation verification data for hot researching problems such as visual scene understanding and environment cognition of unmanned vehicles and the like.
Owner:XI AN JIAOTONG UNIV
Remote proving method in trusted computation environment
InactiveCN101477602AGuarantee authenticityGuaranteed privacyInternal/peripheral component protectionTransmissionMan-in-the-middle attackDigital signature
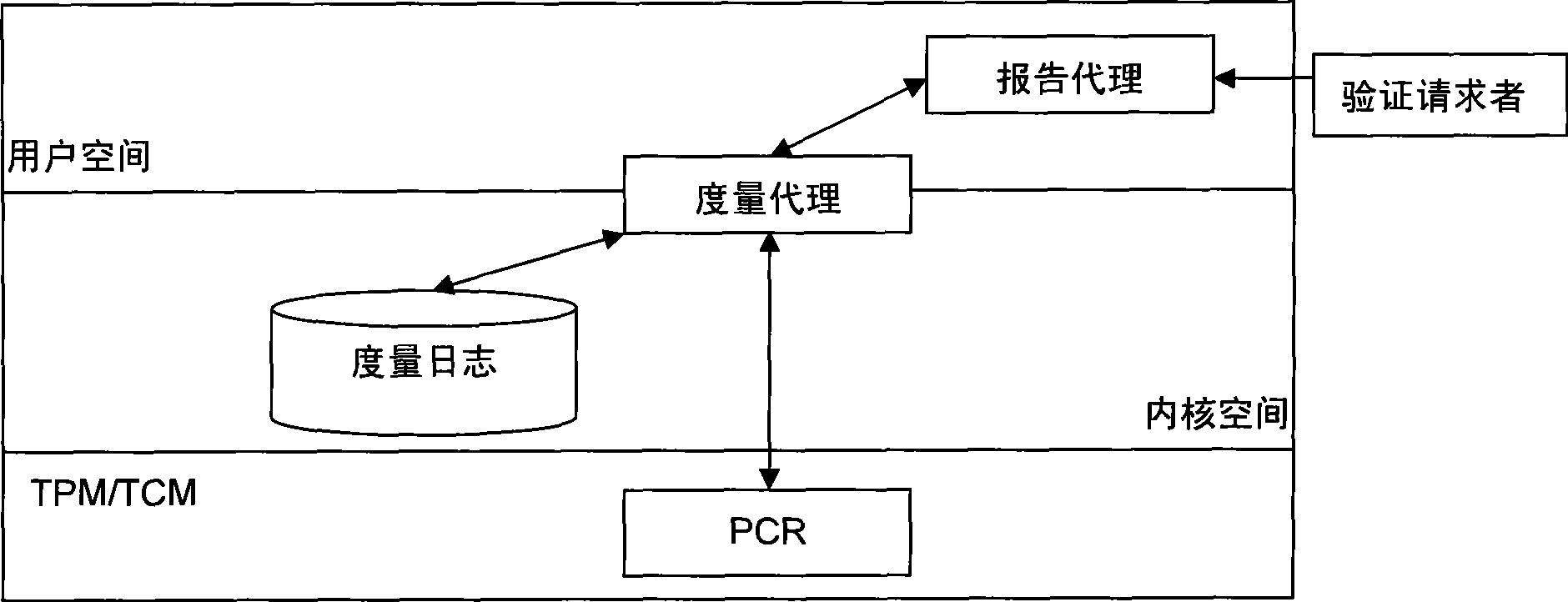
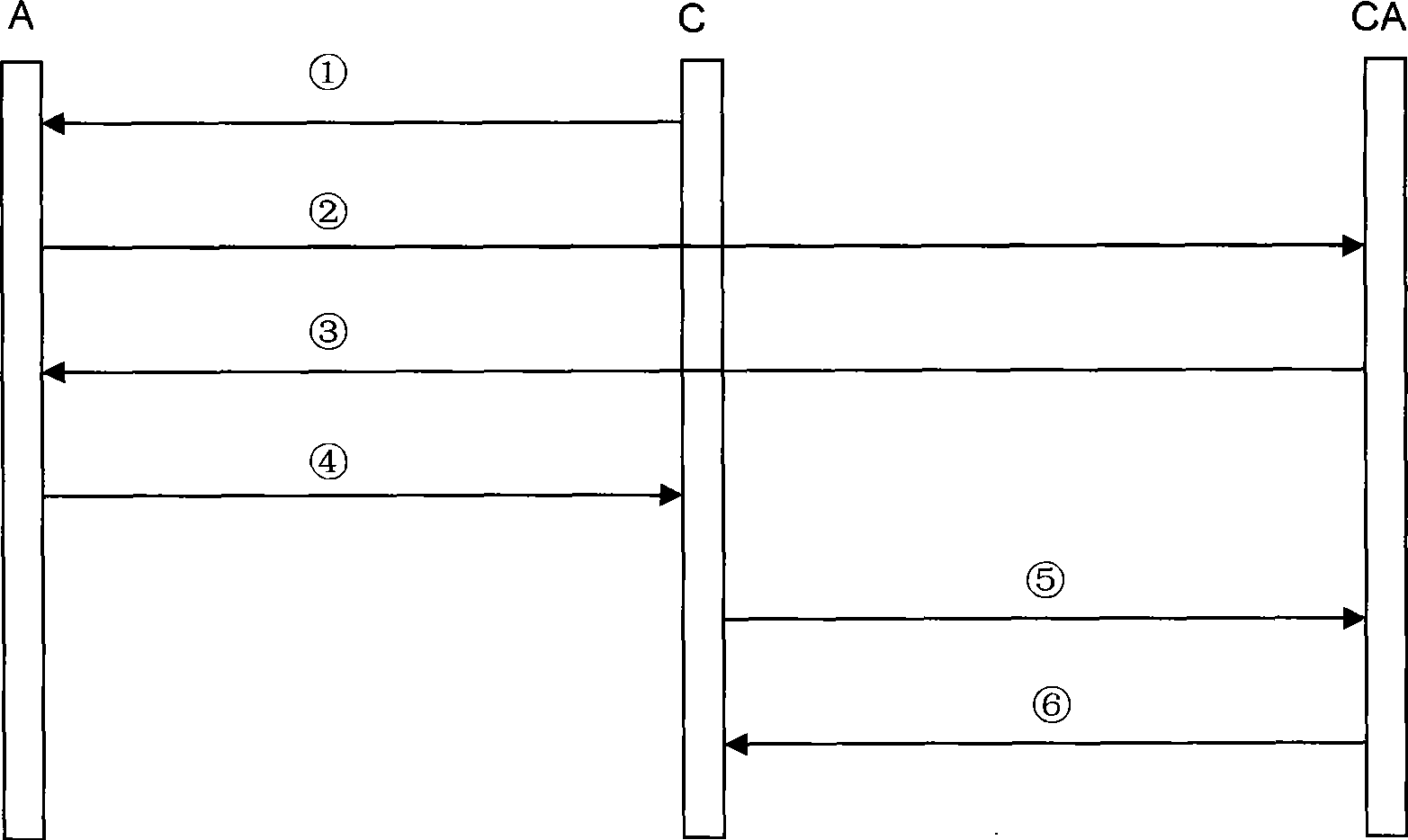
The invention provides a method for remote attestation in a trusted computing environment. The method is characterized in that secure session key is adopted for encrypting the metric value and the metric log of trusted platform to be verified, and signs for encryption result data. The method is based on a security chip TPM / TCM; the adopted remote attestation framework comprises three parts: an integrity measuring mechanism, a reporting mechanism and a validation mechanism, which are achieved by an integrity measuring agency, a report agency and a verification requestor, wherein, the measuring agency, the report agency and the verification requestor are installed in the trusted platform to be verified. The method ensures that the authenticity of the integrity measuring value and the measuring log and the privacy of the platform are kept; the replay attack, impersonation attack and man-in-the-middle attack are effectively prevented; the method is used for proving to the verification requestor that the running environment of the platform is credible, or used for self-test of the platform running environment; the method can be used for not only proving to the requestor that the platform running environment is credible, but also the self-test of the platform running environment; and the method is more suitable for a fair and open network environment.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
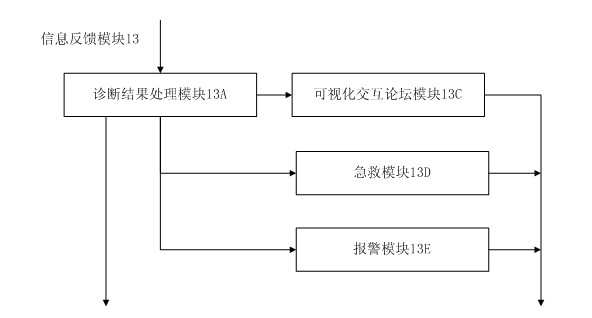
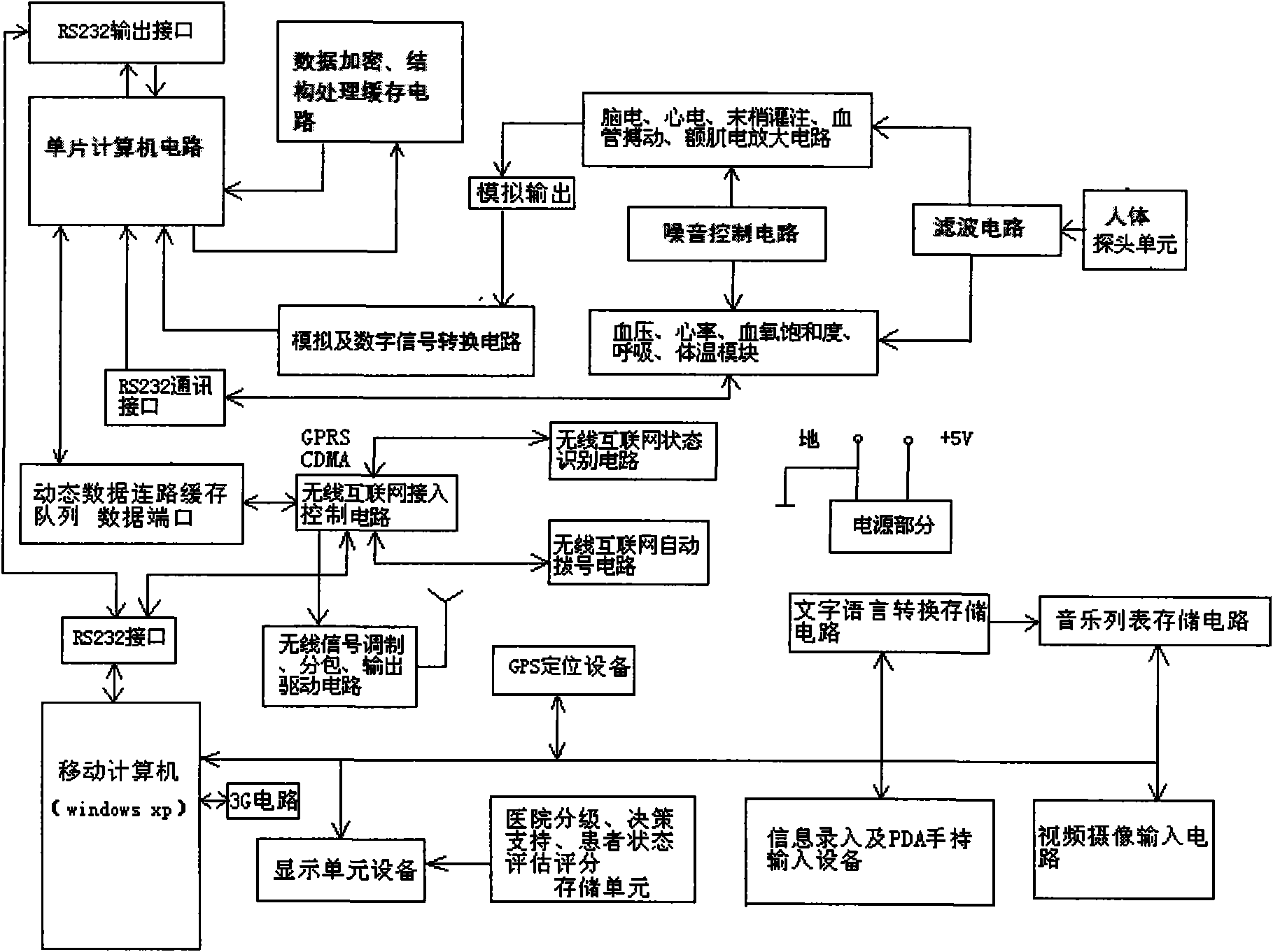
Emergency medical rescue wireless mobile information management method and platform
InactiveCN101599110ARealize acquisitionElimination distanceTransmissionSpecial data processing applicationsEmergency rescueHand held devices
The invention discloses an emergency medical rescue wireless mobile information management method and a platform, and the central content of the method is built on the basis of a regional monitoring information wireless network management system in a wide area. The invention comprises a handheld PDA device, a mobile monitoring information management system and an emergency rescue dispatching information management system, wherein, the handheld PDA device is used for rapidly inputting and transmitting the basic conditions and illness information of patients on the incidence scene; the mobile monitoring information management system belonging to the mobile ambulance onboard part is in charge of the acquisition and transmission of the monitoring information, the basic information of patients and treatment and rescue information, voice and video instant messaging, GPS location and real-time traffic enquiries; and the emergency rescue dispatching information management system arranged in the emergency rescue dispatching management center in fixed places is in charge of dispatching management and real-time monitoring of the comprehensive information. In the invention, the information of the emergency rescue process is digitalized; the rescue medical information of patients from different regions such as the incidence site, transport process, reception hospital, rescue in hospital, dispatch and control and the like can be shared in real time and synchronously, thus building a new rescue mode in which the information runs first with the non-arrival of patients.
Owner:PEOPLES HOSPITAL PEKING UNIV +1
Shared vehicle management method, server, system and computer readable storage medium
ActiveCN107563846AImprove transaction efficiencyGuarantee authenticityUser identity/authority verificationBuying/selling/leasing transactionsService selectionManagement system
The invention discloses a shared vehicle management method comprising the following steps: obtaining vehicle information posted on a block chain by vehicle ends and intelligent contracts formed by thevehicle information, and sending the vehicle information and the intelligent contracts to a user terminal; receiving a vehicle sharing request sent by the user terminal according to the vehicle information and the intelligent contracts, obtaining a target vehicle and an intelligent contract corresponding to the vehicle sharing request, and sending the corresponding target vehicle and the intelligent contract to the user terminal; receiving service selection information sent by the user terminal according to the target vehicle and the corresponding intelligent contract, and determining whetherthe user terminal satisfies with the vehicle usage conditions or not; if yes, associating the vehicle end with the user terminal. The invention also discloses a server, a shared vehicle management system and a computer readable storage medium. The method and system can improve the trading efficiency, and can ensure the information authenticity and security.
Owner:SHENZHEN ECHIEV AUTONOMOUS DRIVING TECH CO LTD
Driving behavior assessment and vehicle driving state monitoring early warning system and method
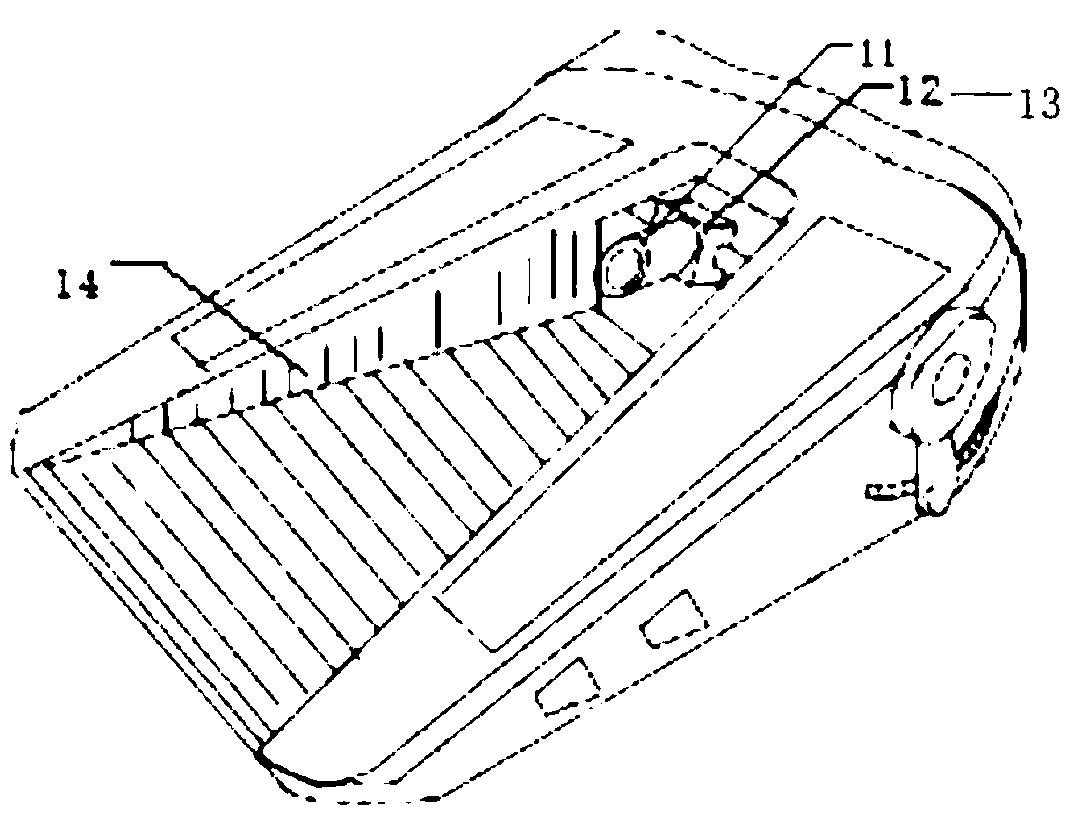
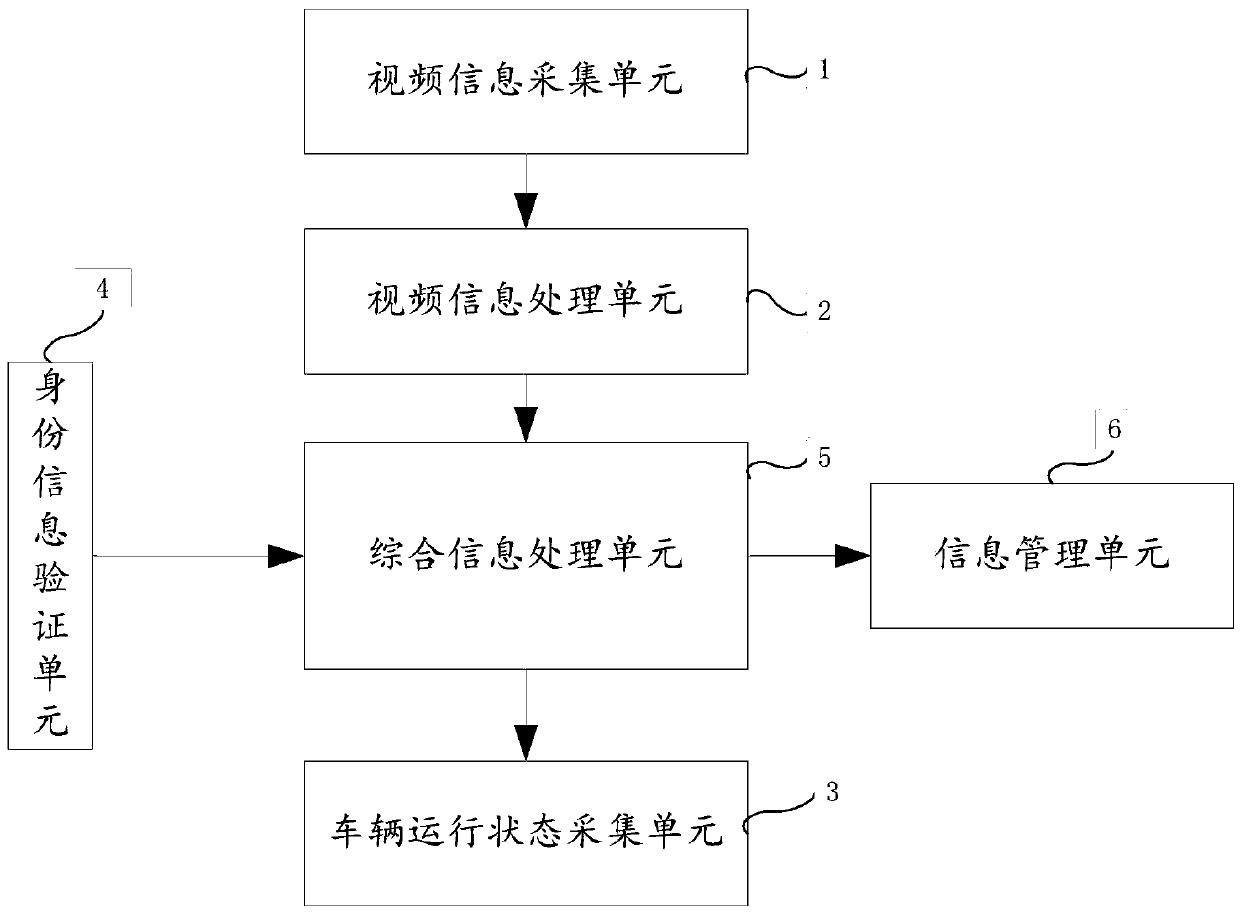
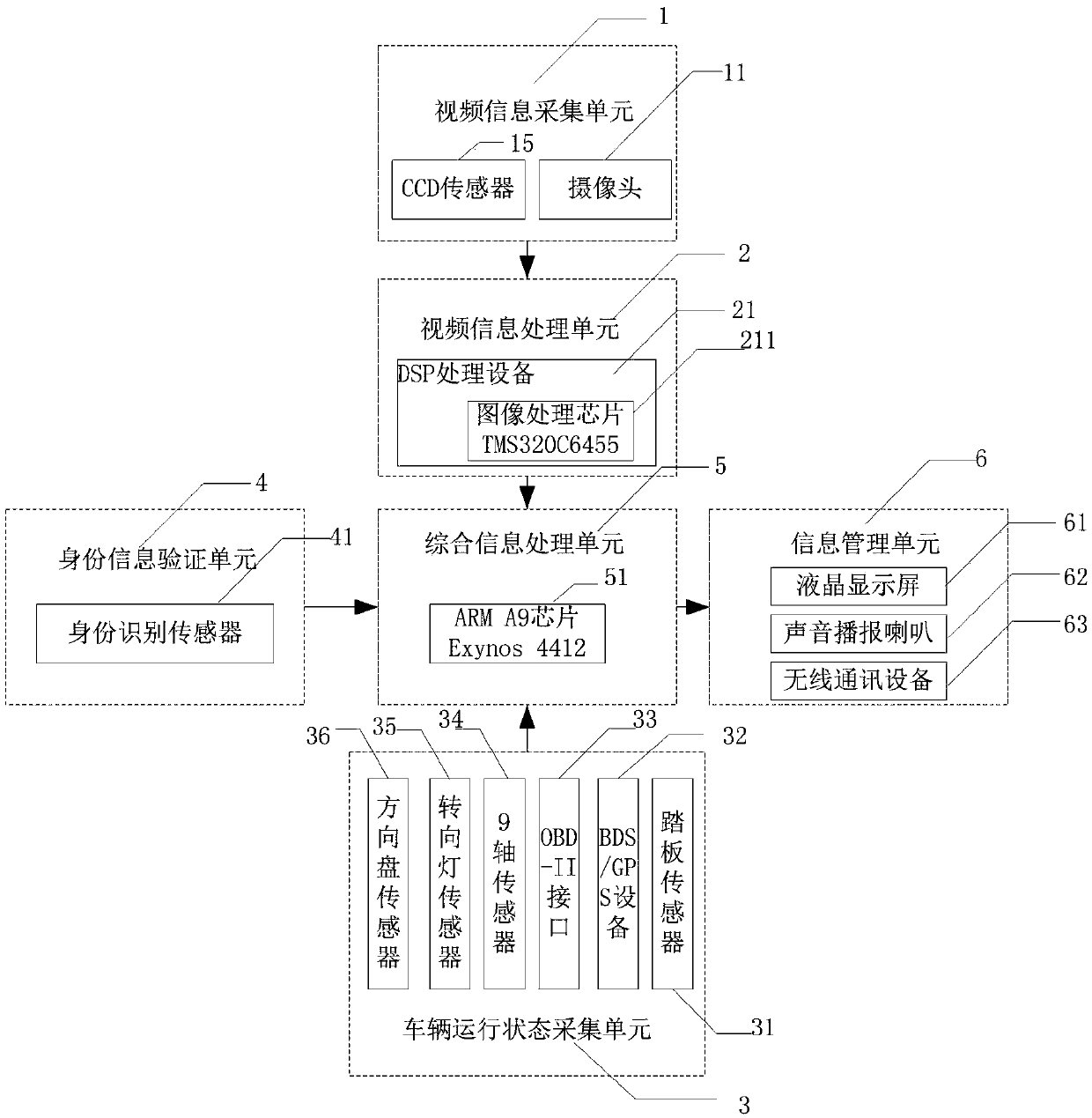
ActiveCN105513358AEasy to driveGuaranteed stabilityDetection of traffic movementClosed circuit television systemsWeight distributionCondition monitoring
The invention relates to a driving behavior assessment and vehicle driving state monitoring early warning system and method. The method comprises a video information collection unit, a video information processing unit, an identity information verification unit, a vehicle running state collection unit, an integrated information processing unit and an information management unit. The system constructs an assessment mechanism specific to driving behaviors, collects road condition video information, vehicle driving state information and driver vehicle operation process data information, excavates data characteristics, and performs weight distribution, information fusion and comprehensive determination, thereby realizing real time assessment of driving behaviors, and providing early warning specific to possible dangers.
Owner:烟台中正新技术有限公司
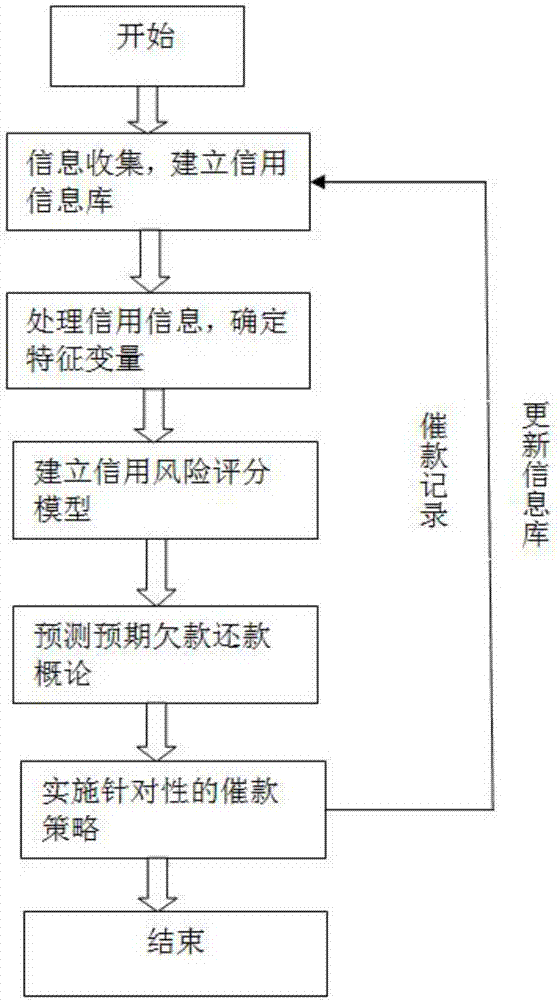
Urgent collection method based on credit score and urgent collection device thereof
InactiveCN106952155ABeneficial technical effectImprove the effect of collectionFinanceRisk levelData dredging
The invention discloses an urgent collection method based on the credit score and an urgent collection device thereof. The urgent collection method comprises the steps of collecting urgent collection object credit information, processing the collected credit information, establishing a credit risk scoring model, predicting the overdue debt collection probability and performing the targeted urgent collection strategy. The risk level can be automatically judged according to the urgent collection score result so that the urgent collection strategy of the client can be reasonably determined, the urgent collection effect can be enhanced and the bad debt loss can be reduced. Data mining acts as the analysis technology so that the modeling time can be saved and the data support can be provided for the urgent collection industry. Besides, user information can also be updated in real time, the urgent collection risk score can be more accurately predicted, the most appropriate urgent collection strategy can be performed and the urgent collection task efficiency can be enhanced.
Owner:深圳前海纵腾金融科技服务有限公司
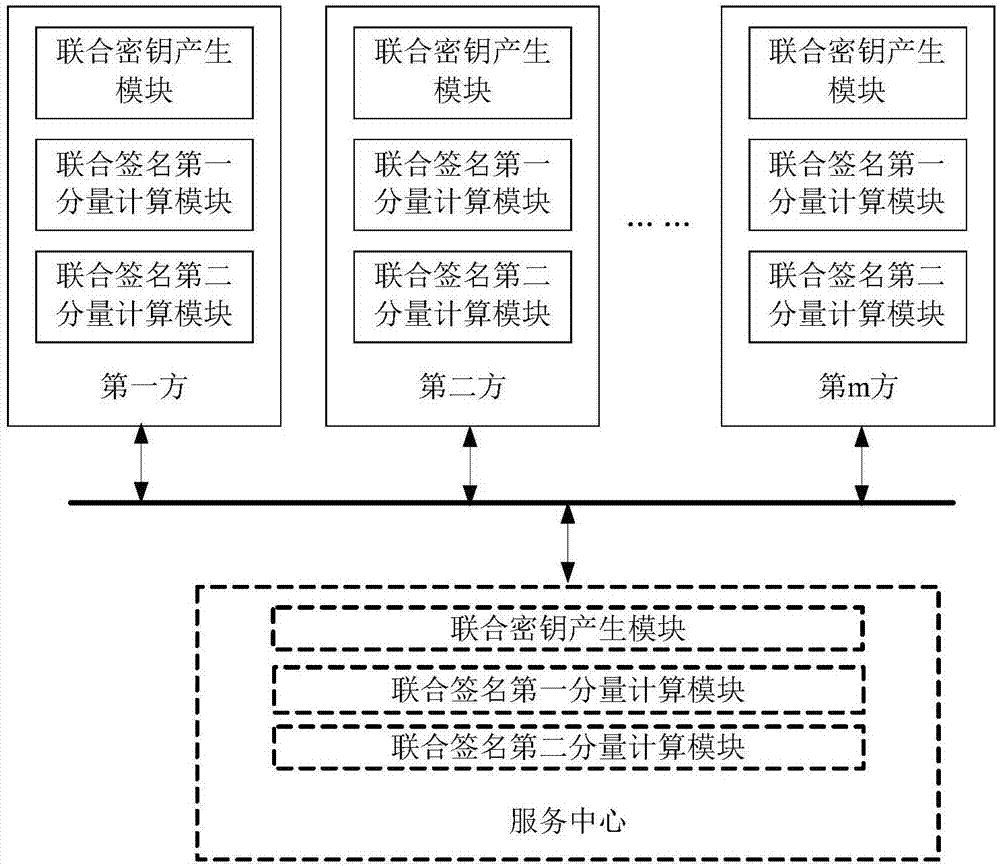
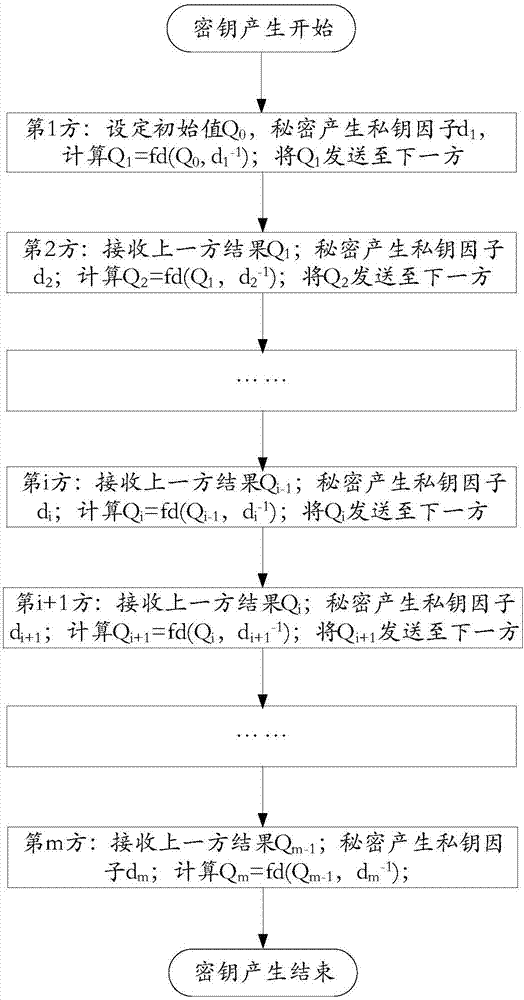
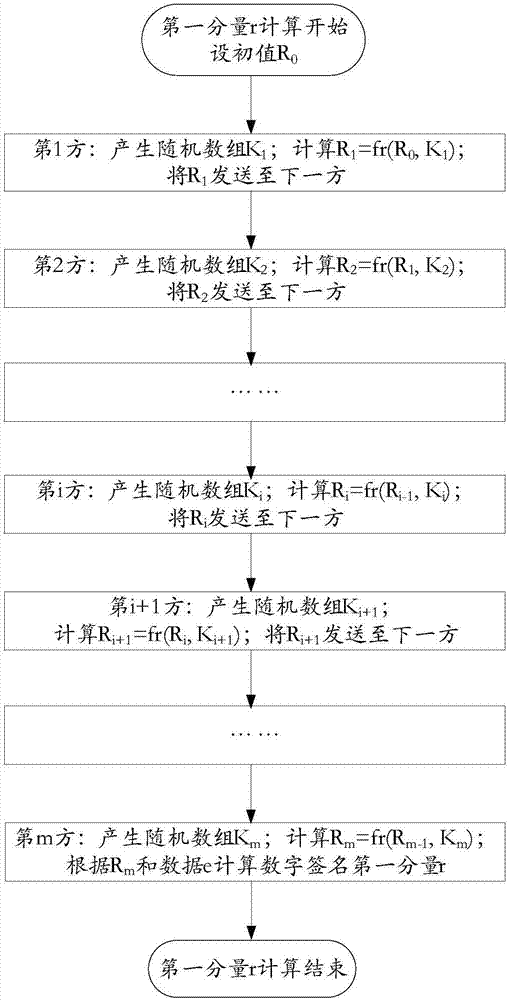
Multiparty joint key production and digital sign method and system
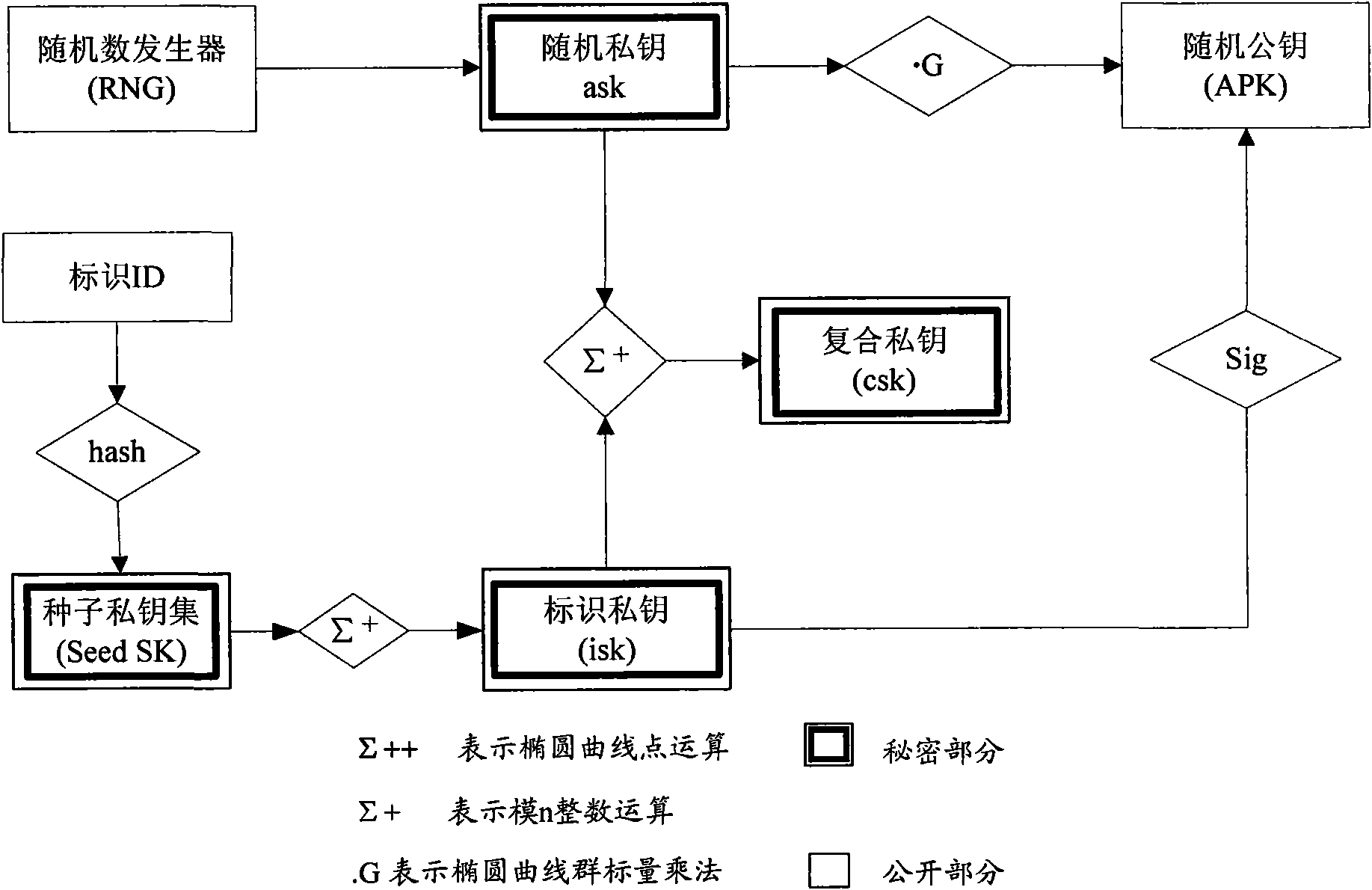
ActiveCN107017993AImprove protectionPrevention and control measures are effectiveKey distribution for secure communicationPublic key for secure communicationDigital signatureEngineering
The invention provides a multiparty joint key production and digital sign method and system. A joint sign private key d is composed of m private key factors di. The i is equal to [1, m]. The m is greater than or equal to 3. The m private key factors di are produced by the joint parties independently and secretly when the private key is produced and are stored in own devices secretly. The joint digital sign is finished by the parties according to a certain sequence and is finished jointly through utilization of the secretly stored key factors di based on calculation. The system comprises m joint parties. Each joint party has an independent subsystem. Each subsystem is composed of three parts: a joint key production module, a joint sign first component calculation module and a joint sign second component calculation module. According to the method and the system, the multiparty joint key production and digital sign method of an SM2 cryptographic algorithm and various formed systems: acentric and centered systems are realized. The digital sign is no longer finished by a single individual and is finished by multiple parities jointly.
Owner:BEIJING JN TASS TECH
Multi-disease chronic disease information management system
InactiveCN104834989ARealize unified managementGuarantee authenticityResourcesSystems managementDisease cause
The present invention provides a multi-disease chronic disease information management system relating to the computer field and used for solving the problem that the conventional chronic disease management system can not realize the multi-department multi-disease same system management. The system provided by the present invention comprises a database, an application server, a plurality of hospital clients and a plurality of patient clients. The database stores the health examination data of patients, the doctor suggestion, the health data reference ranges of the examination items and the health state assessment indexes of various chronic diseases, and the application server obtains the health examination data of the appointed patient, the corresponding health data reference ranges, the health state assessment indexes of various chronic diseases and the doctor suggestion from the database according to a first query instruction sent by the hospital / patient client to obtain a chronic disease assessment result and return the chronic disease assessment result of the current appointed patient and the data to the hospital / patient client. By the above scheme, the communication interaction of the multiple medical departments and the patients about the multi-disease chronic disease is realized.
Owner:BEIJING SHIJITAN HOSPITAL CAPITAL MEDICAL UNIVERSTY
Design and implementation of multi-person indoor environment state monitoring system based on WiFi channel state information
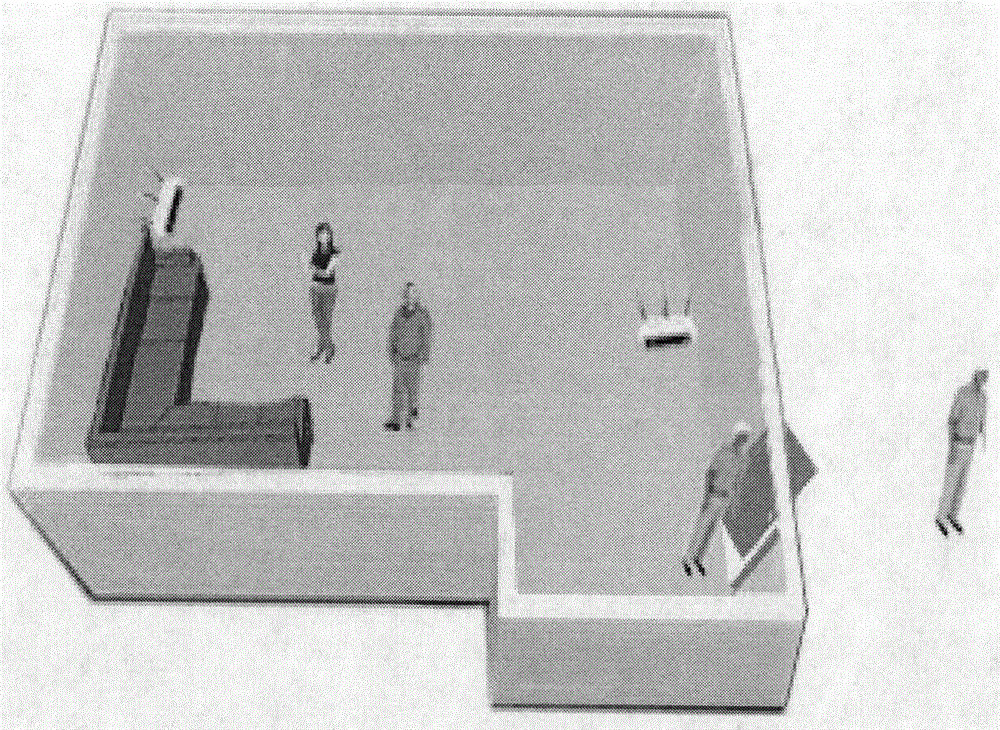
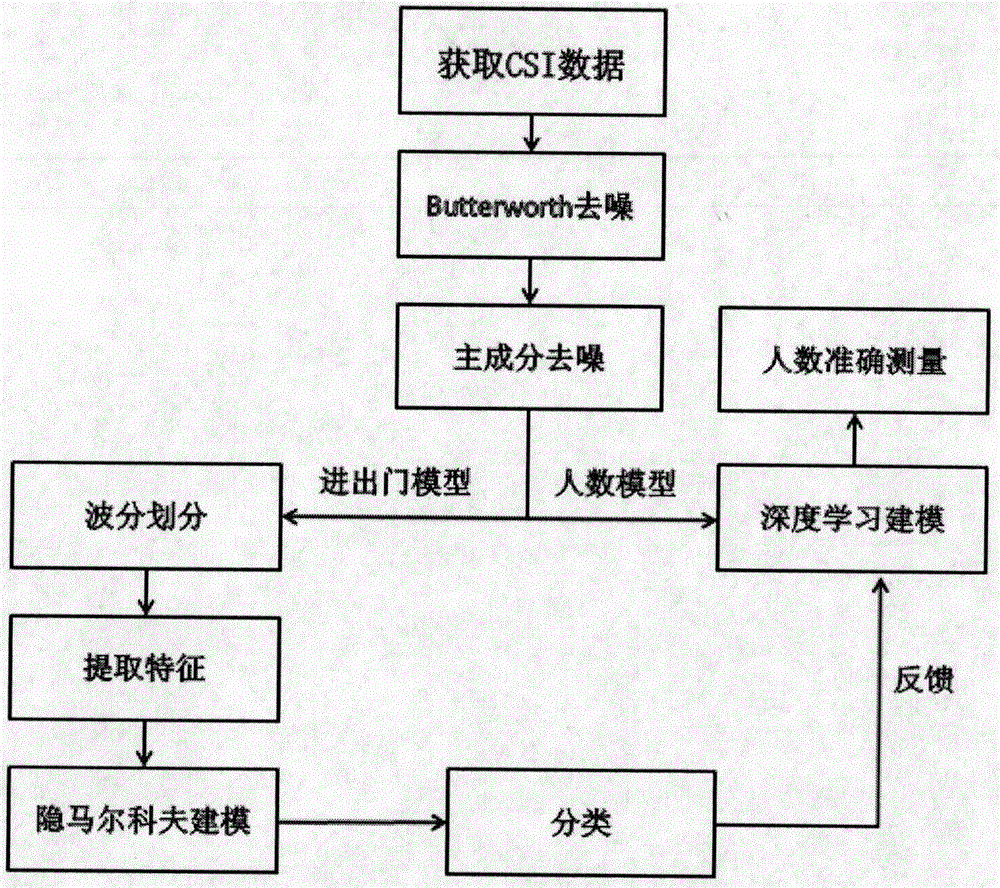
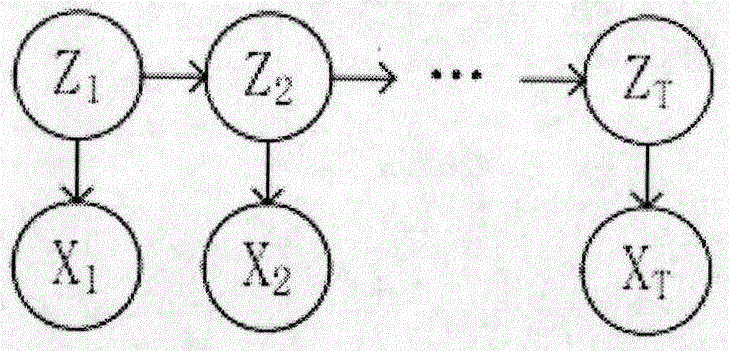
ActiveCN106658590AGuarantee authenticityNetwork topologiesCharacter and pattern recognitionChannel state informationEnvironmental noise
The invention discloses design and implementation of a multi-person indoor environment state monitoring system based on WiFi channel state information. According to the design and implementation provided by the invention, whether people come in and go out from a room is mainly monitored, and the number of people in the room is determined. According to the design and implementation provided by the invention, WiFi signals are applied to multi-person environmental perception for the first time, CSI (Channel State Information, channel state information) is obtained by use of the widely used WiFi signals, the CSI data are analyzed and processed, an effective denoising method is adopted to remove the environmental noise and extract the waveform, an indoor access monitoring model is established by using a hidden Markov method, a people number recognition model is established by using a neural network, and the people number recognition model is corrected by the access monitoring model, thereby further improving the people number recognition accuracy and effectively monitoring the indoor environmental state.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Metadata based rapid statistic form generation method and system
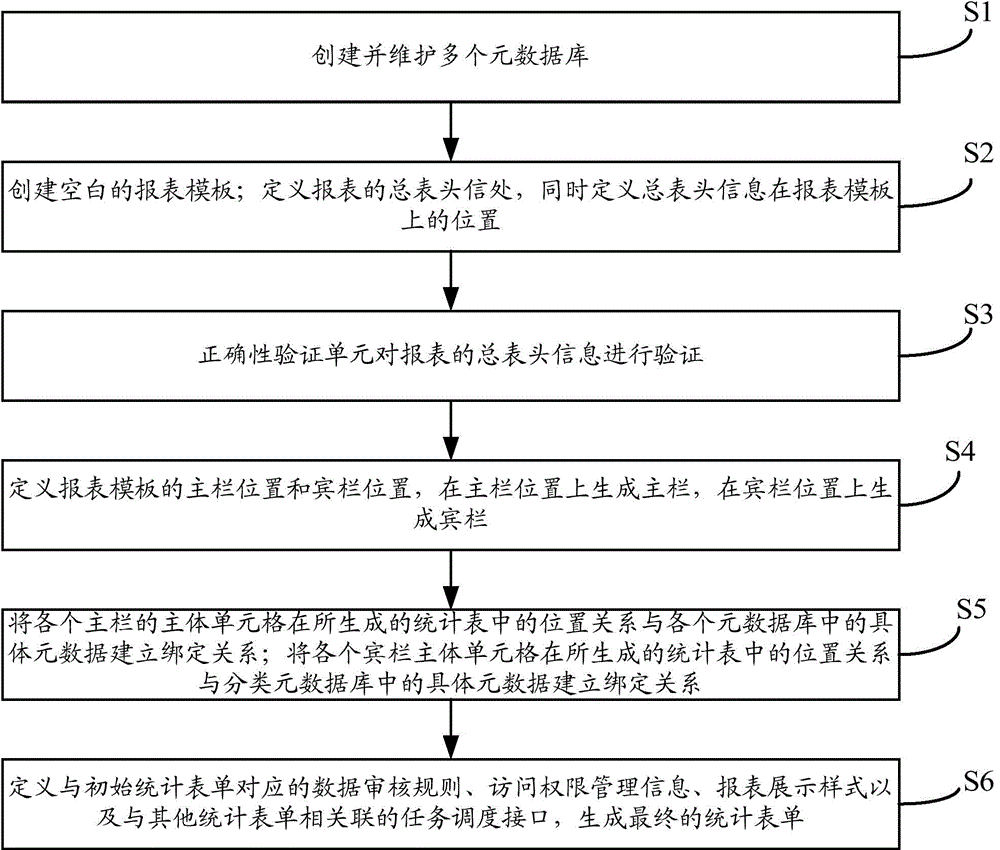
ActiveCN105320690ASimplify how survey indicators are customizedConvenient management of indicator library informationSpecial data processing applicationsMetadata managementForm generation
The invention provides a metadata based rapid statistic form generation method and system. The system comprises a metadata base management module and a report customization module, wherein the metadata base management module comprises an attribute metadata base definition unit, a measurement unit metadata base definition unit, a classified metadata base definition unit and a shared index metadata base definition unit; the report customization module comprises a report attribute definition unit, a template definition unit, an index definition unit, a report style definition unit, a management authority definition unit, an access definition unit and a preview definition unit. Through configuration of report structure rules, when a report structure changes, a report engine adjusts a report structure automatically according to changes, a new report is generated, and the flexibility of report customization is improved; a metadata management mode is adopted for managing index names and index attributes; when index names and index attributes change, all that is required is to modify metadata in the metadata base, and the surveying index customization mode is simplified.
Owner:BEIJING ZHONGHAIJIYUAN DIGITAL TECH DEV CO LTD
Method and system for identity verification of digital certificate based on TEE (Trusted Execution Environment)
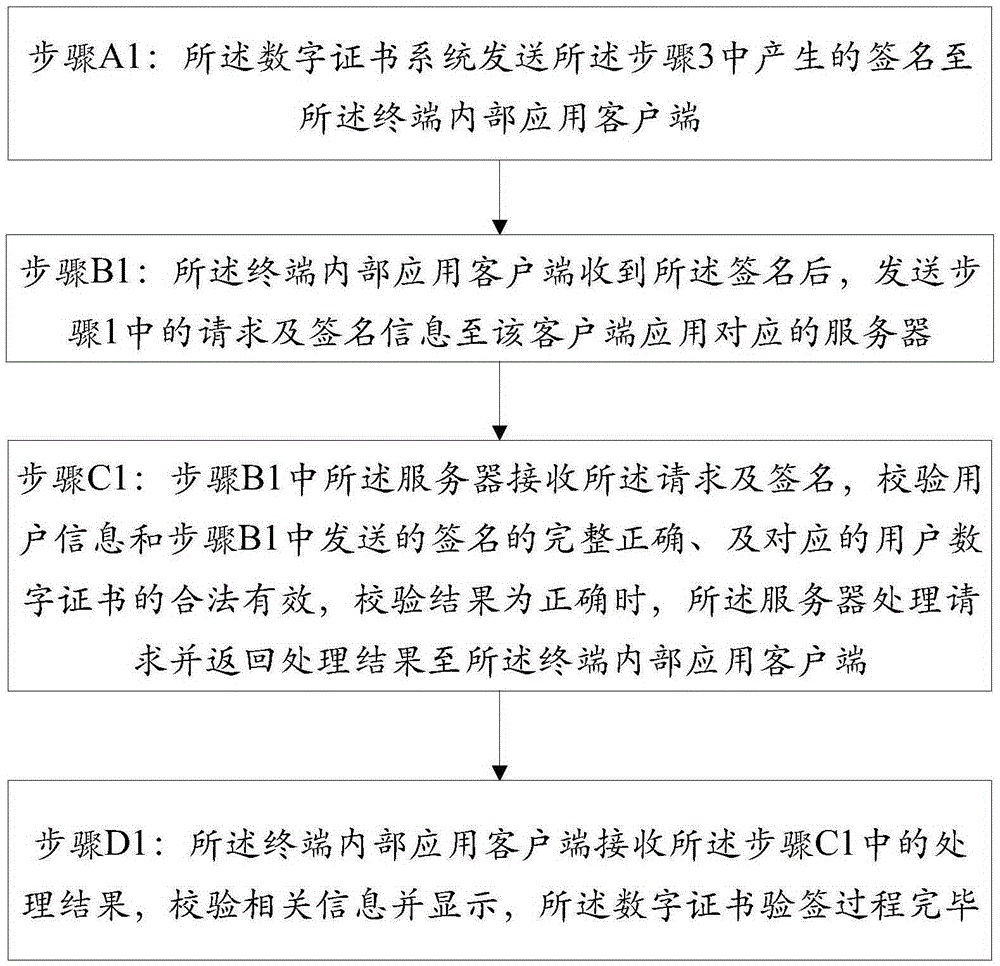
ActiveCN105429760AEnsure true willEnsure that the identity verification process can reflect the true willUser identity/authority verificationPasswordPersonal identity verification
The invention discloses a method for identity verification of a digital certificate based on a TEE (Trusted Execution Environment). The method comprises pre-configuration of a digital certificate system through a terminal, a digital certificate signature process and a digital certificate signature verification process. The method is characterized in that the terminal is provided with the TEE; the digital certificate signature process is carried out on the terminal and is used for utilizing a private key of the digital certificate to sign for a user request; the digital certificate signature verification process is used for authenticating identity of a requested user, and the authentication method comprises verification of validity and effectiveness of the digital certificate and integrity and correctness of the signature, wherein the digital certificate signature process is carried out under the TEE; the sensitive information, such as a user key, identity information, biological characteristic information and password information, is stored through a secure storage module, so that the problems that the signature process is carried out in REE and the sensitive information of the user is stored under the REE environment to cause privacy disclosure and stolen hidden danger of property in the prior art are avoided.
Owner:神州融安数字科技(北京)有限公司
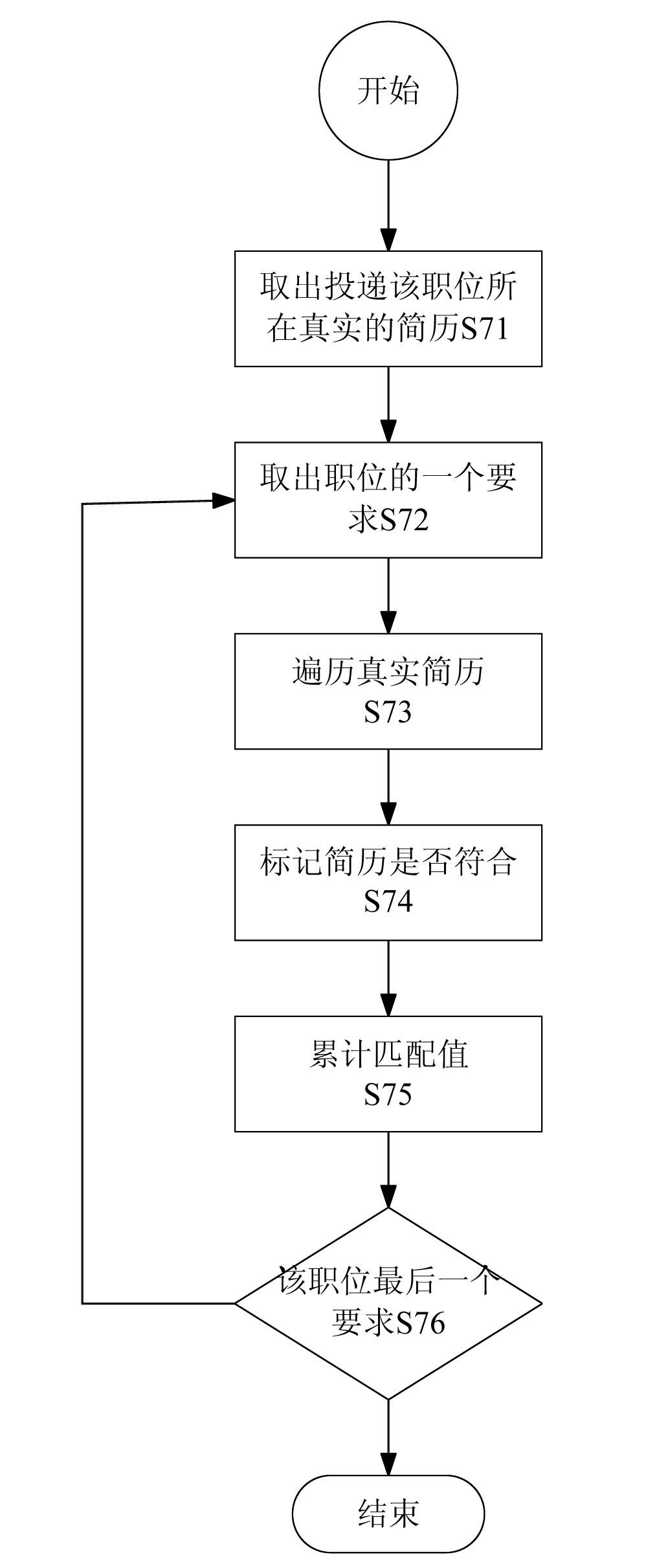
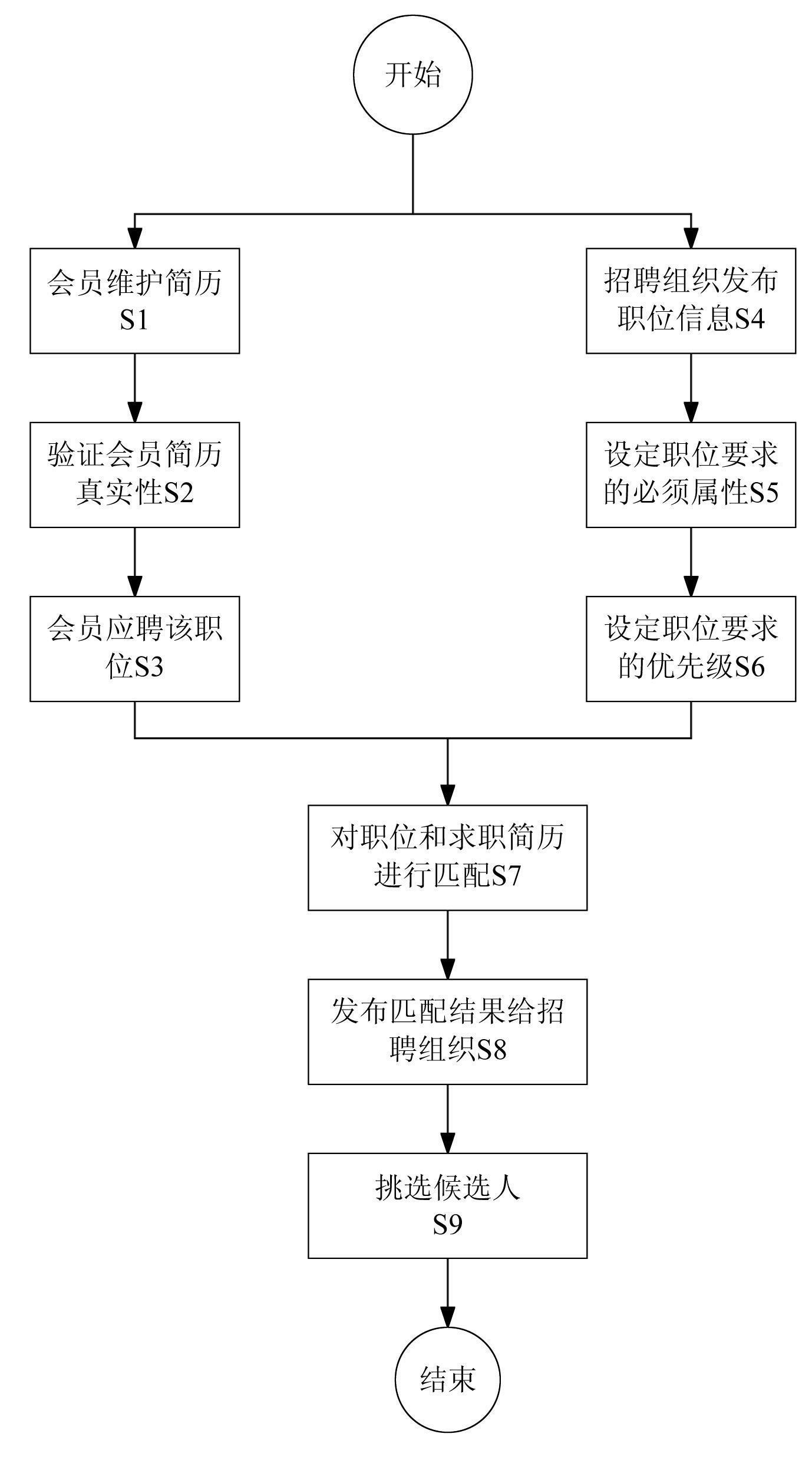
Job seeker resume recommendation processing method and system
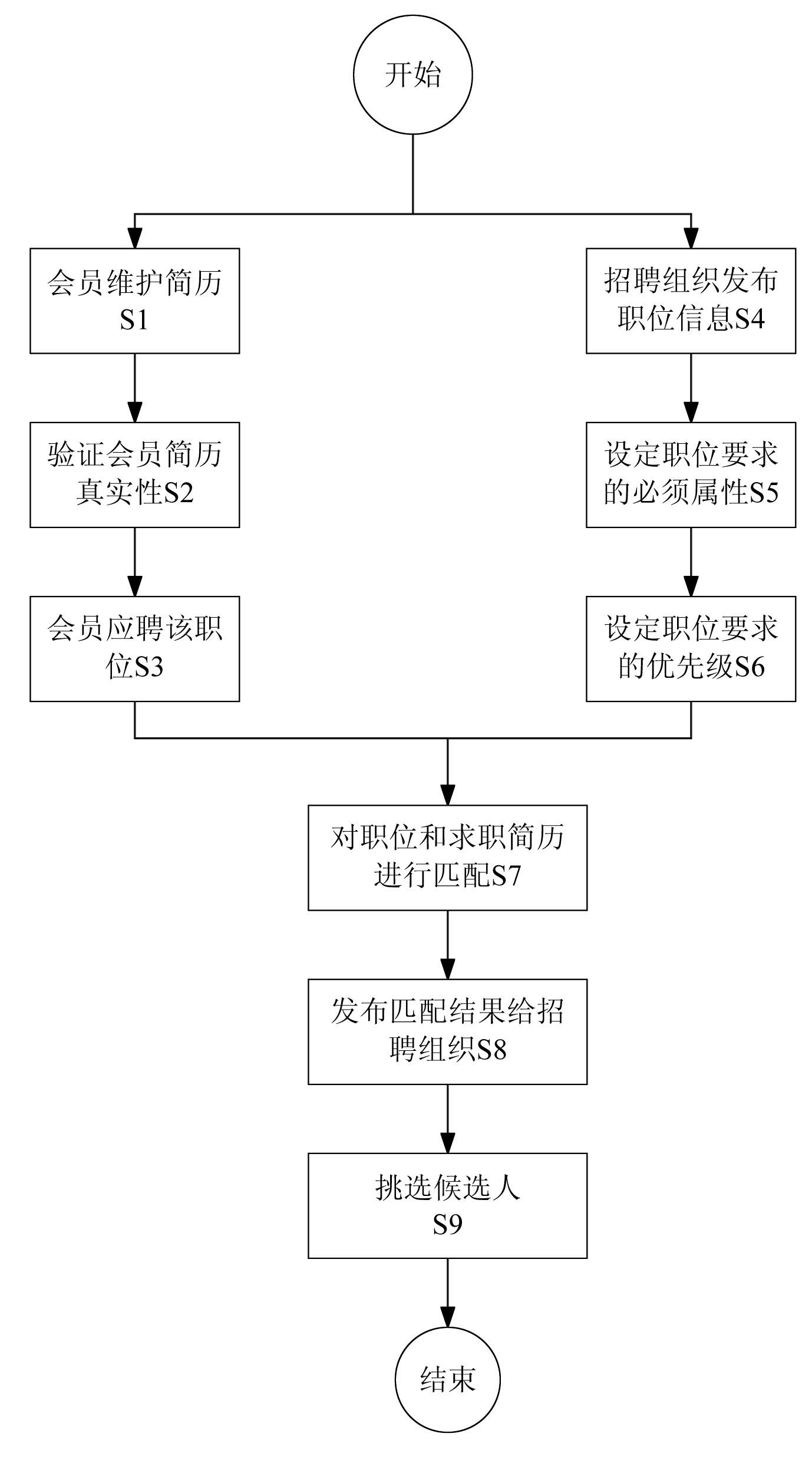
InactiveCN102117323AGuarantee authenticityResolution timeResourcesSpecial data processing applicationsExact matchRecruitment methods
The invention discloses a processing method and a processing system for accurately recommending resumes. The method comprises the following steps of: establishing a member resume database and the recruitment information of an enterprise, setting whether vacant position requirements are necessarily met or not, and setting priorities; and sequentially performing accurate matching with key attributes of the job seeker resumes in combination with rules of matching the position requirements with the resumes according to whether the vacant position requirements are necessarily met or not and the priorities, and accurately pushing the job seeker resumes meeting the requirements to a recruitment group according to a matching degree sequence. By the method and the system, the recruitment group can accurately screen corresponding candidates, the recruitment efficiency can be improved, the recruitment cost can be reduced, and simultaneously, the job seeker resumes meeting the requirements may not be omitted.
Owner:SHENZHEN AISI OUNA INFORMATION CONSULTING
Method for monitoring and measuring full section of tunnel through three-dimensional laser
InactiveCN102564393AGuarantee authenticityAvoid human influenceProfile tracingPoint cloudMaterial resources
The invention relates to a method for monitoring and measuring a full section of a tunnel through three-dimensional laser, and belongs to the field of tunnel engineering construction monitoring. The method comprises the following steps of: arranging target points in a tunnel to be measured according to a requirement; determining whether to adopt one-station scan or multi-station scan according to the monitoring length of the tunnel; erecting an instrument at a proper position and scanning the full section of the tunnel; after the scan is finished, importing data into a computer; registering point cloud data acquired through the scan to generate a three-dimensional model by applying three-dimensional data processing software; and generating a comparison model by combining a previous three-dimensional model for the same tunnel at different time, and selecting a specific section and characteristic points to generate a variation analysis chart and a variation analysis sheet for a corresponding position. By the method, the full section of the tunnel is monitored in real time, the speed and accuracy of monitoring and measuring work are improved, manpower and material resources are saved, the speed and quality for monitoring and measuring the tunnel are improved, and reliable guarantee is provided for tunnel engineering construction.
Owner:BEIJING UNIV OF TECH +1
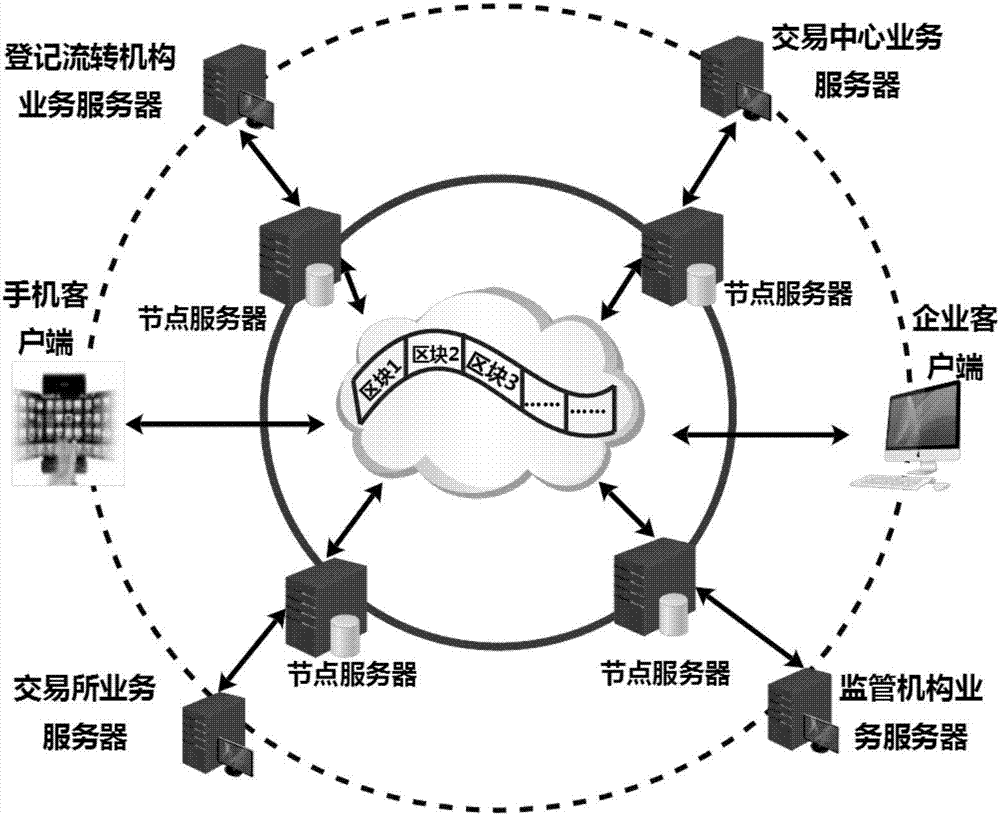
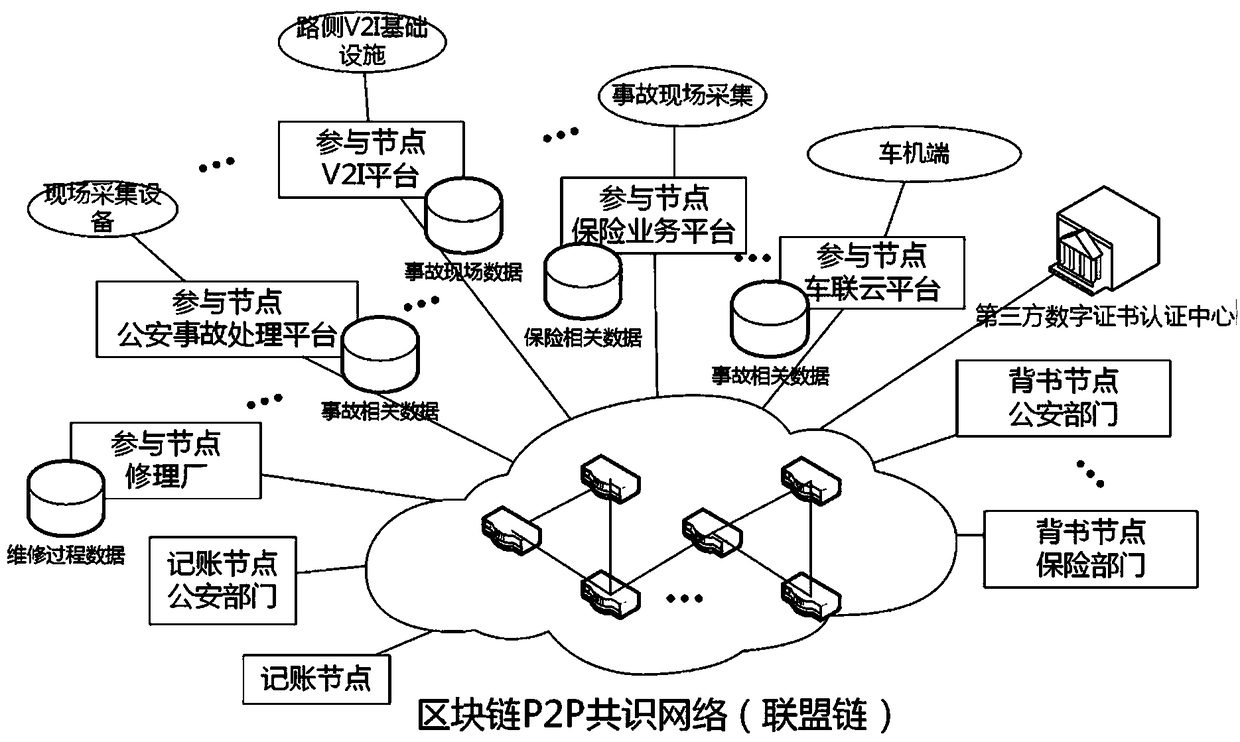
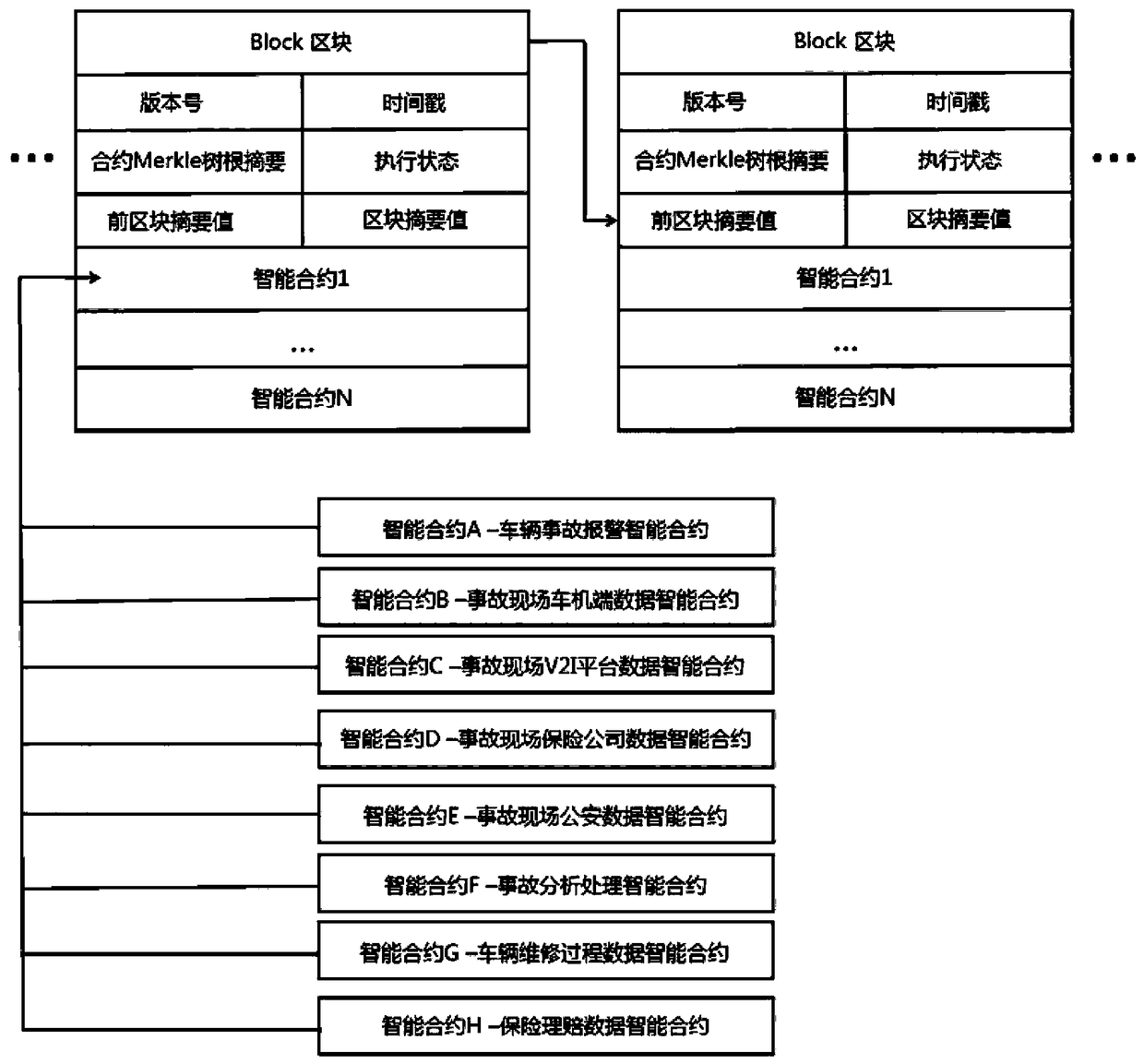
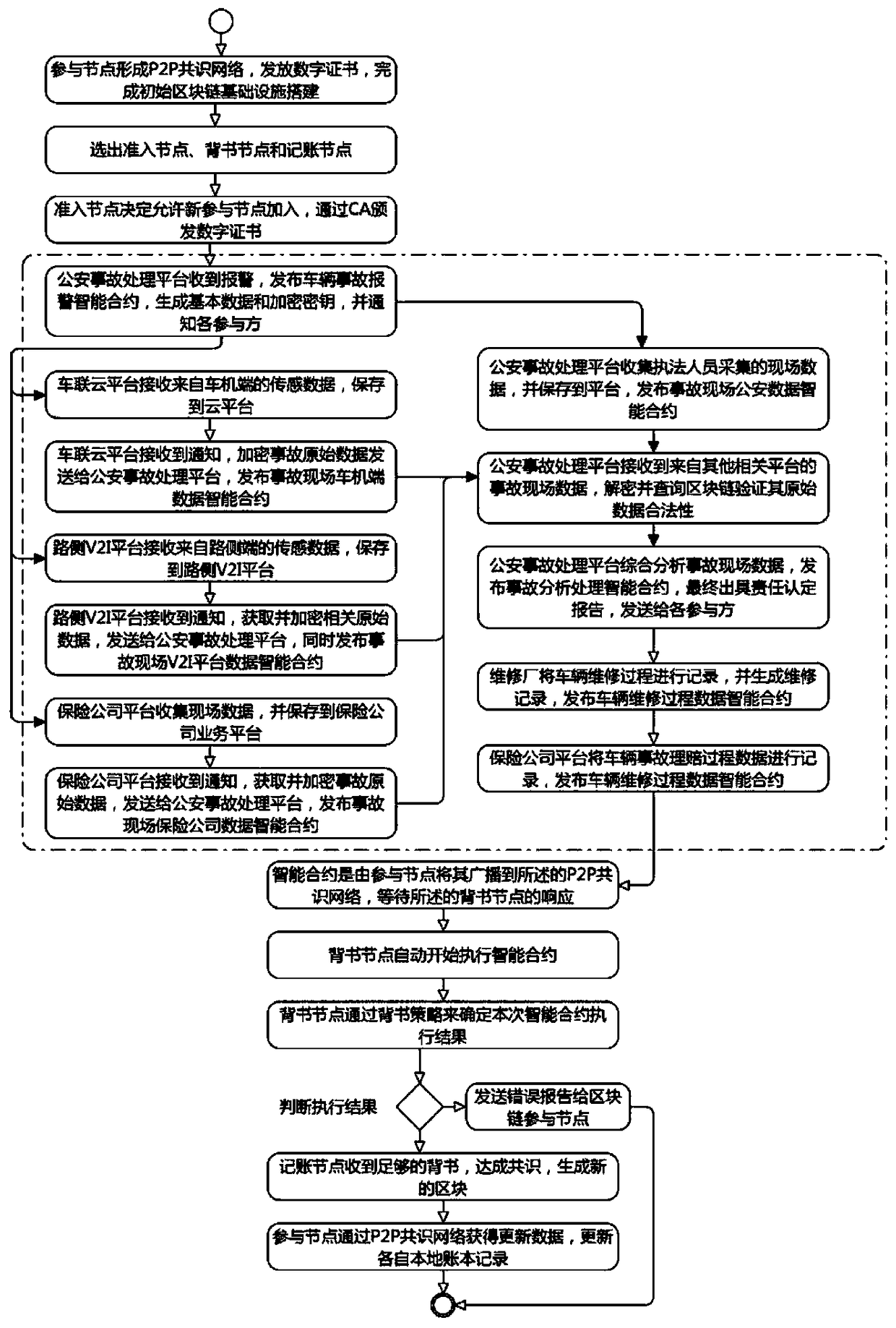
Network connected vehicle accurate accident handling method based on block chain
InactiveCN108446992AImprove accuracyImprove processing speedFinanceUser identity/authority verificationReal-time computingBlockchain
The invention discloses a network connected vehicle accurate accident handling method based on block chain. The implementation process of the method comprises: 1, firstly, through a block chain technology, connecting all participated joints which are associated with accident handling, based on a P2P consensus network, establishing an alliance chain, putting life cycle of accident handling in the block chain to record; through an intelligent terminal on a vehicle accident site, acquiring on-site data and uploading, the participated joints which are associated with accident handling completing accident handling. Compared with the prior art, the network connected vehicle accurate accident handling method based on block chain effectively solves a mutual trust problem of involve parties throughan unified and decentralized method, improves accident responsibility confirmation accuracy rate and handling speed, and provides an accident retroactive function, improves transparency of accident handling process, shortens accident handling time, and saves vehicle accident handling cost.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com