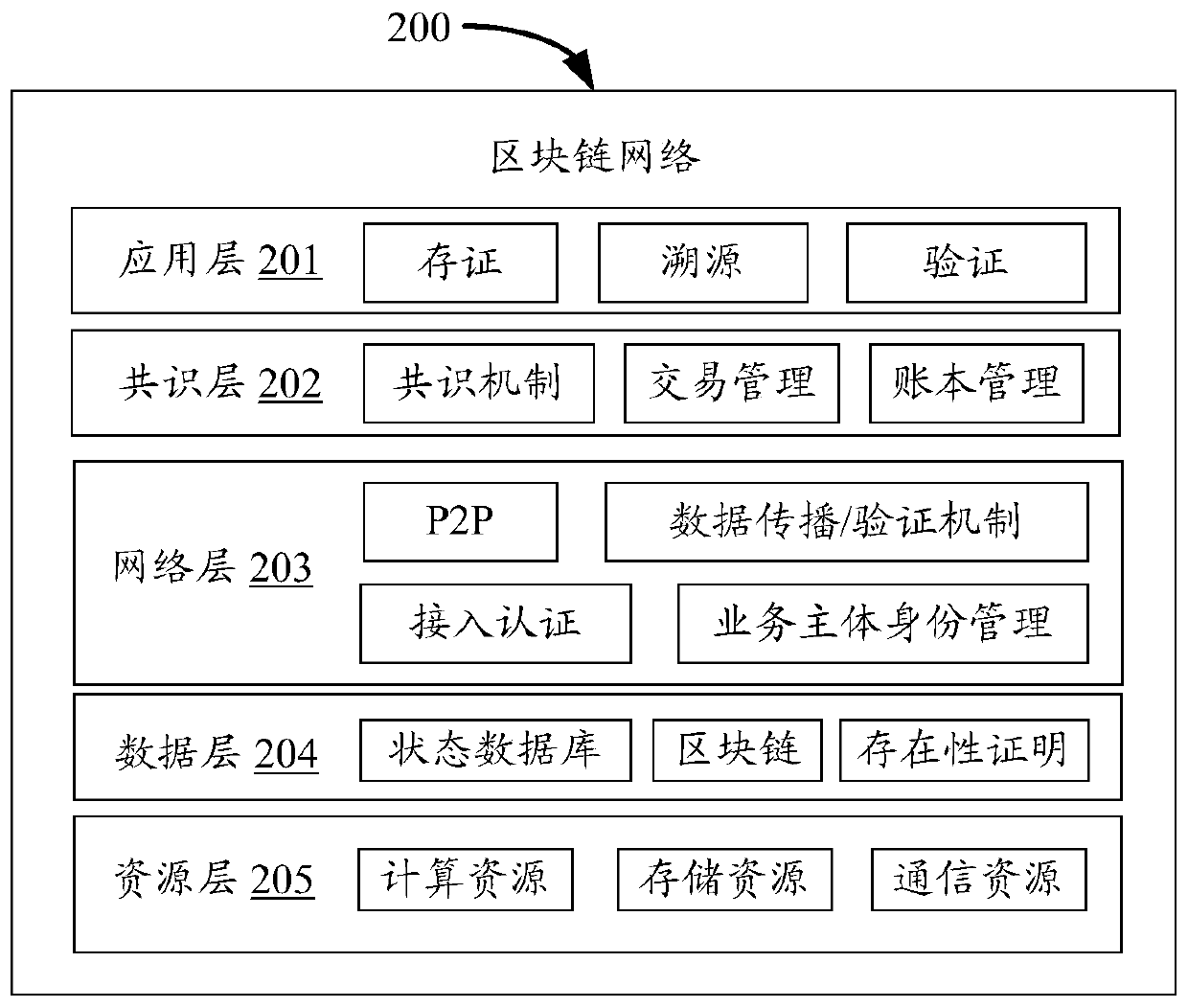
Patents
Literature
268 results about "Data authenticity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data authenticity also means that a digital object is indeed what it claims to be or what it is claimed to be. Find more terms and definitions using our Dictionary Search.
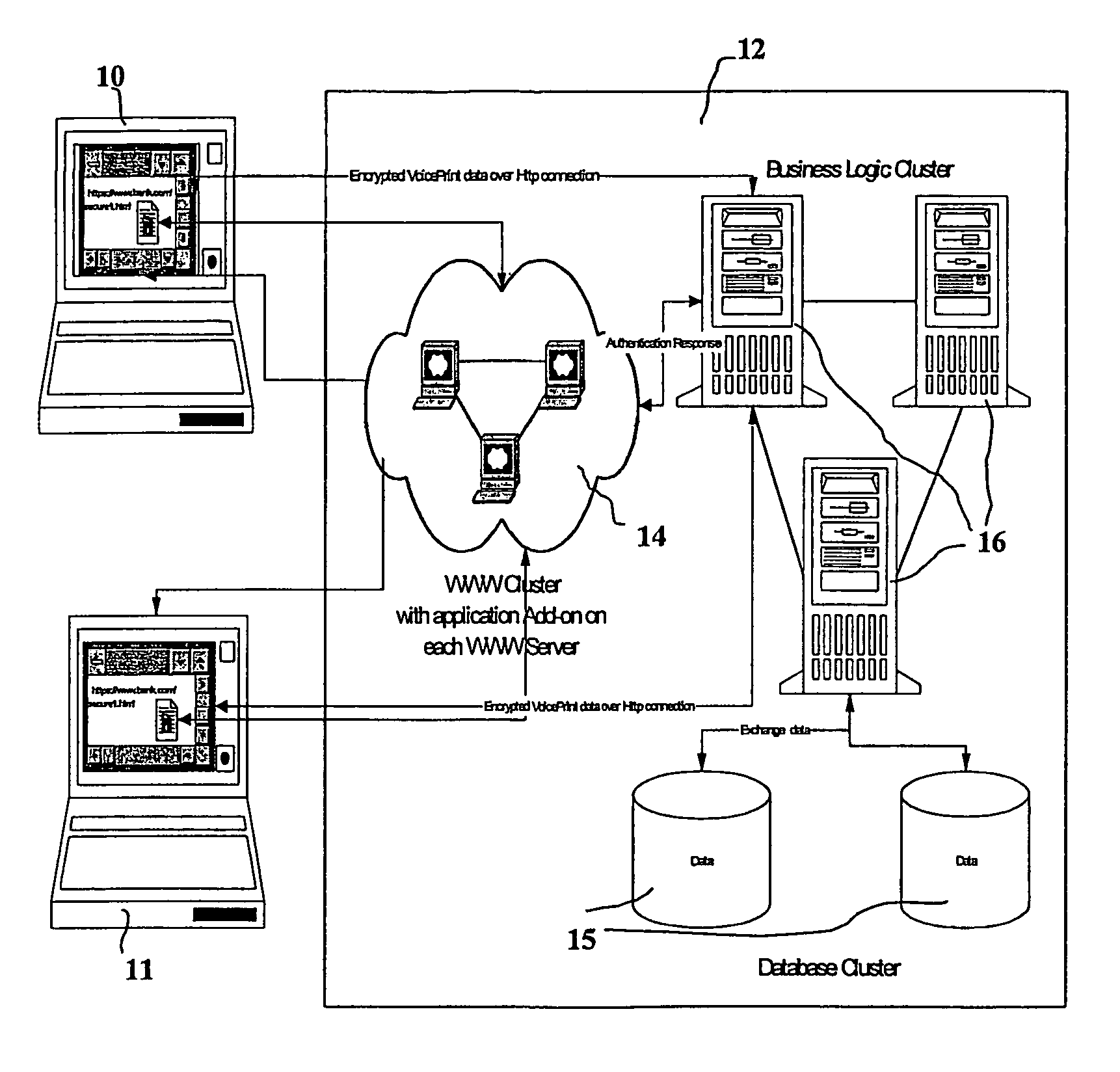
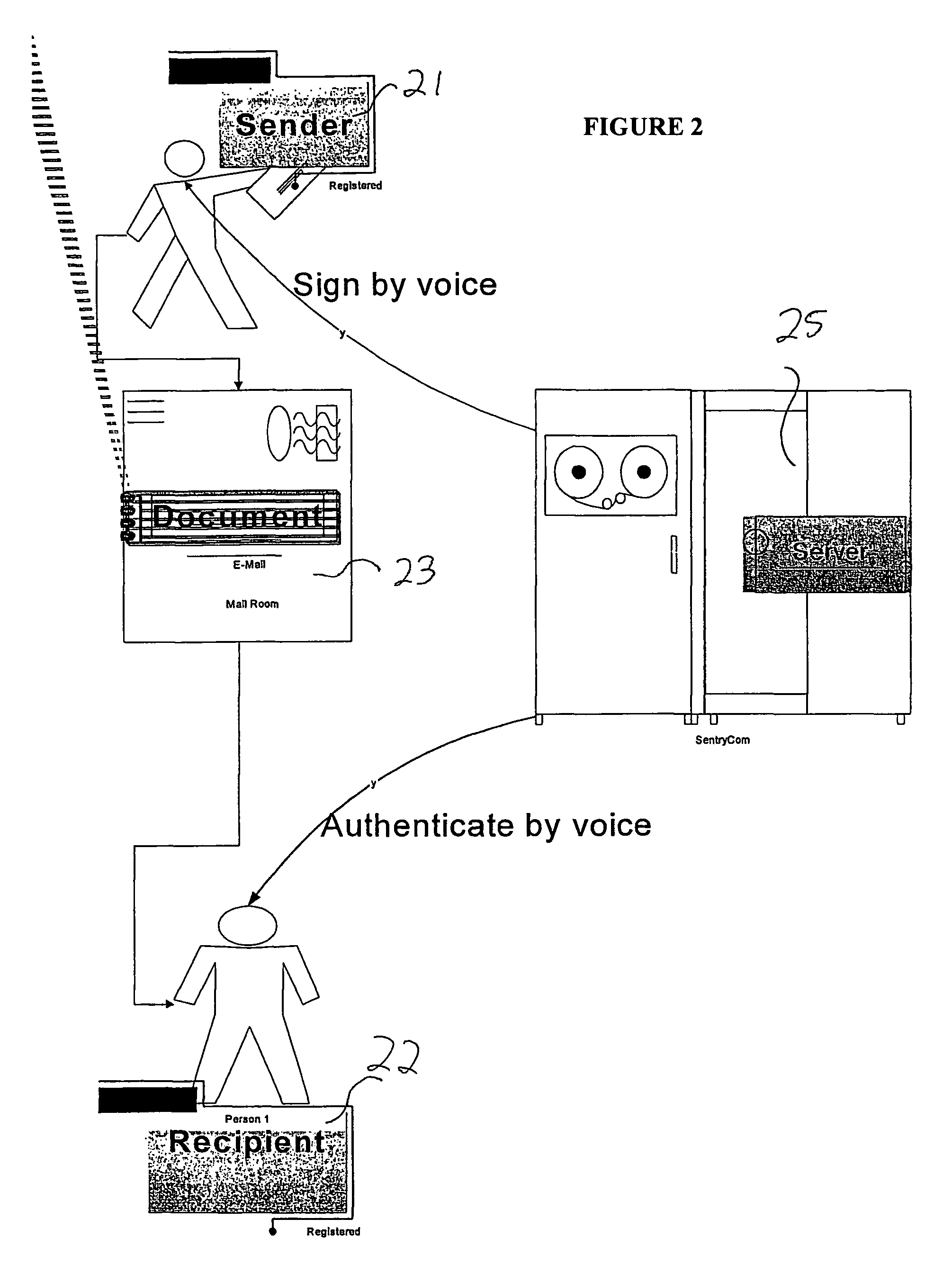
Biometric-based system and method for enabling authentication of electronic messages sent over a network
InactiveUS7689832B2Digital data processing detailsUser identity/authority verificationReal time validationData authenticity
A network based mechanism for real time verification and authentication of data and user identities. The present invention enables a method whereby biometric elements, such as voice prints, are utilized to enhance the Public Key Infrastructure as a means to decrypt data and verify data authenticity, such that the user's private key is authenticated remotely on a one-time basis. The present invention comprises an authentication server (25) with various software modules that enable authentication of user identity, secure user access to data, digital signatures, secure messaging and secure online transactions.
Owner:SENTRYCOM
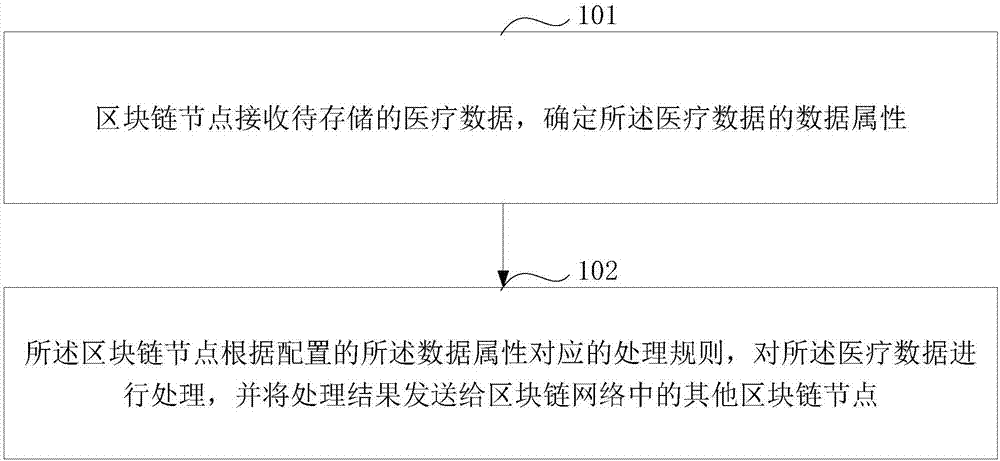
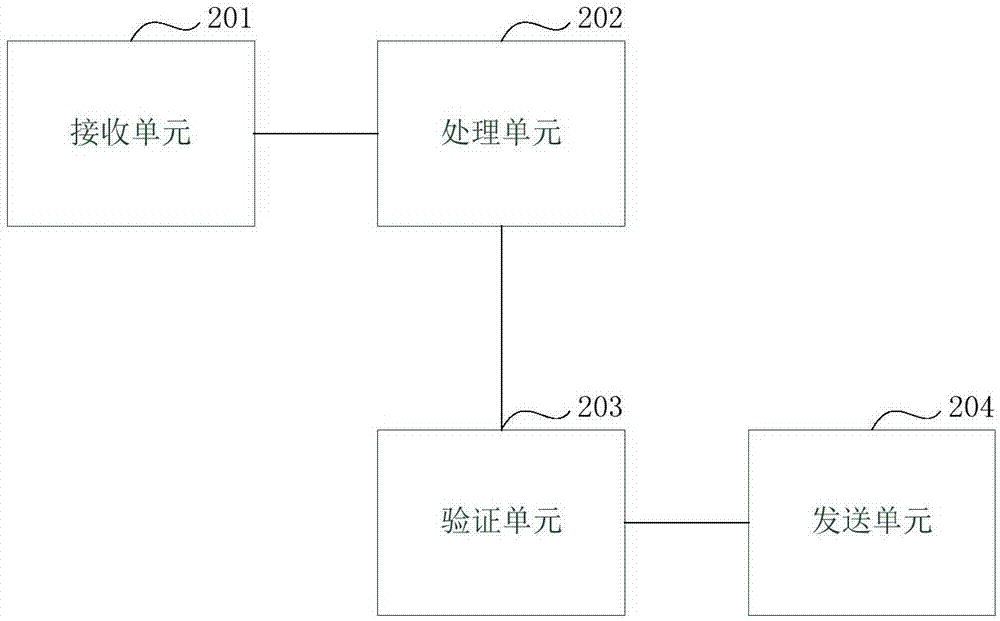
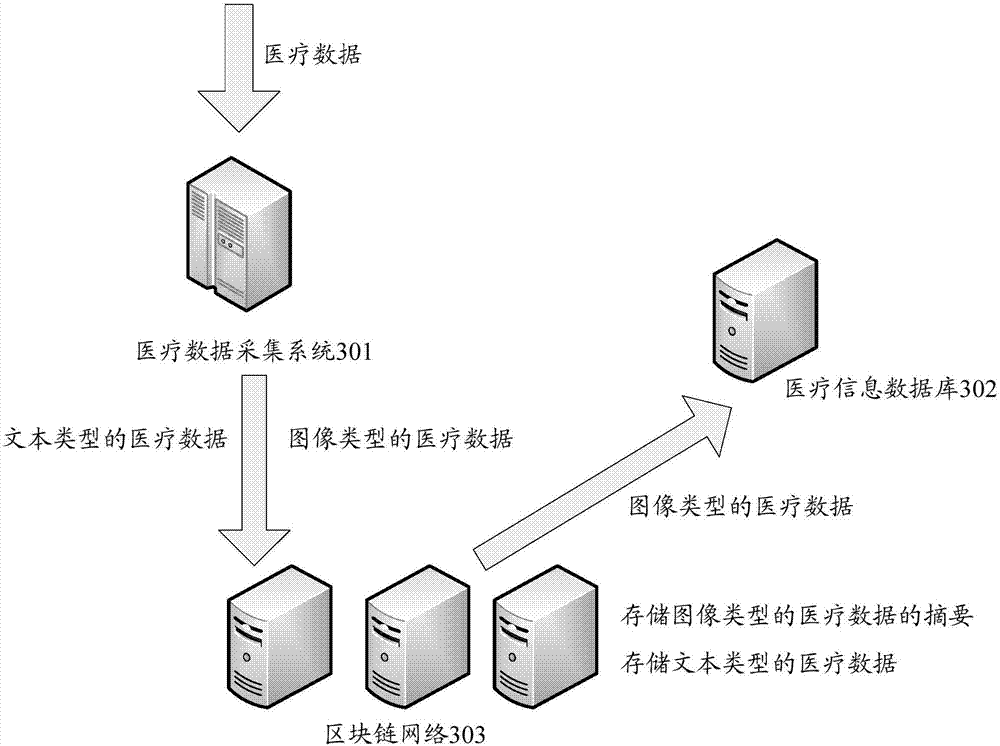
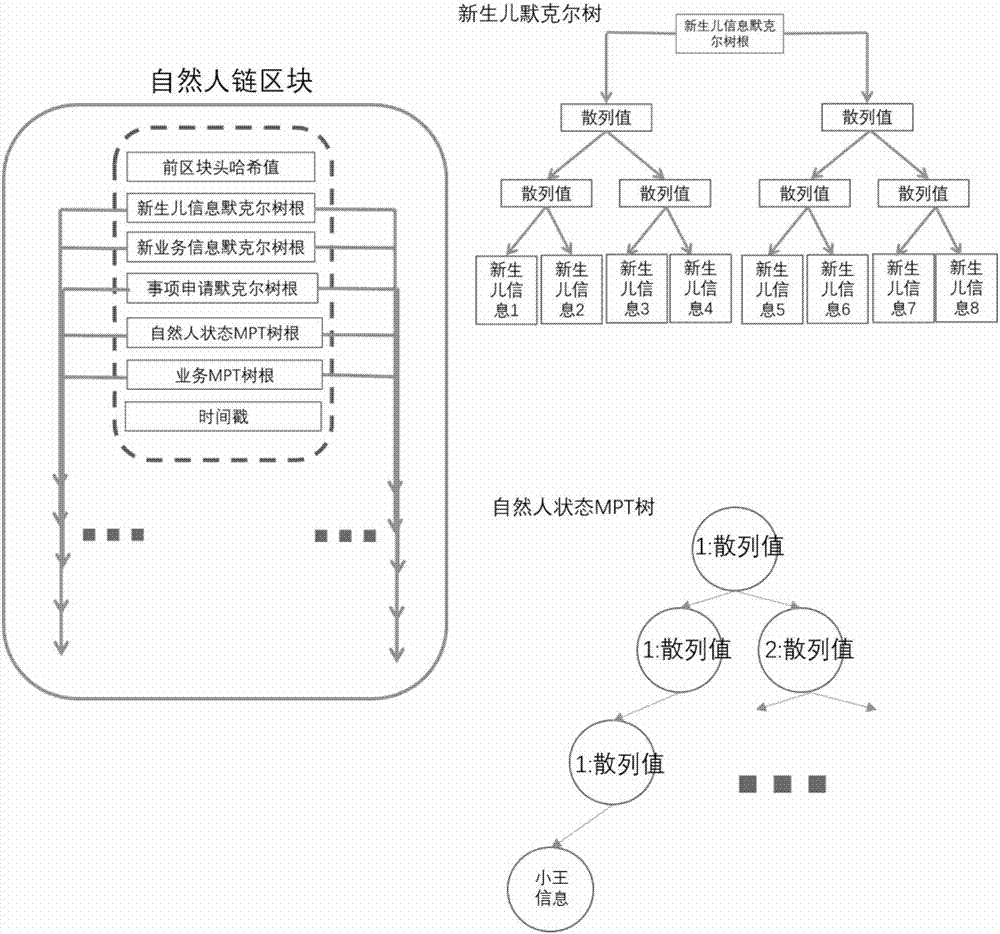
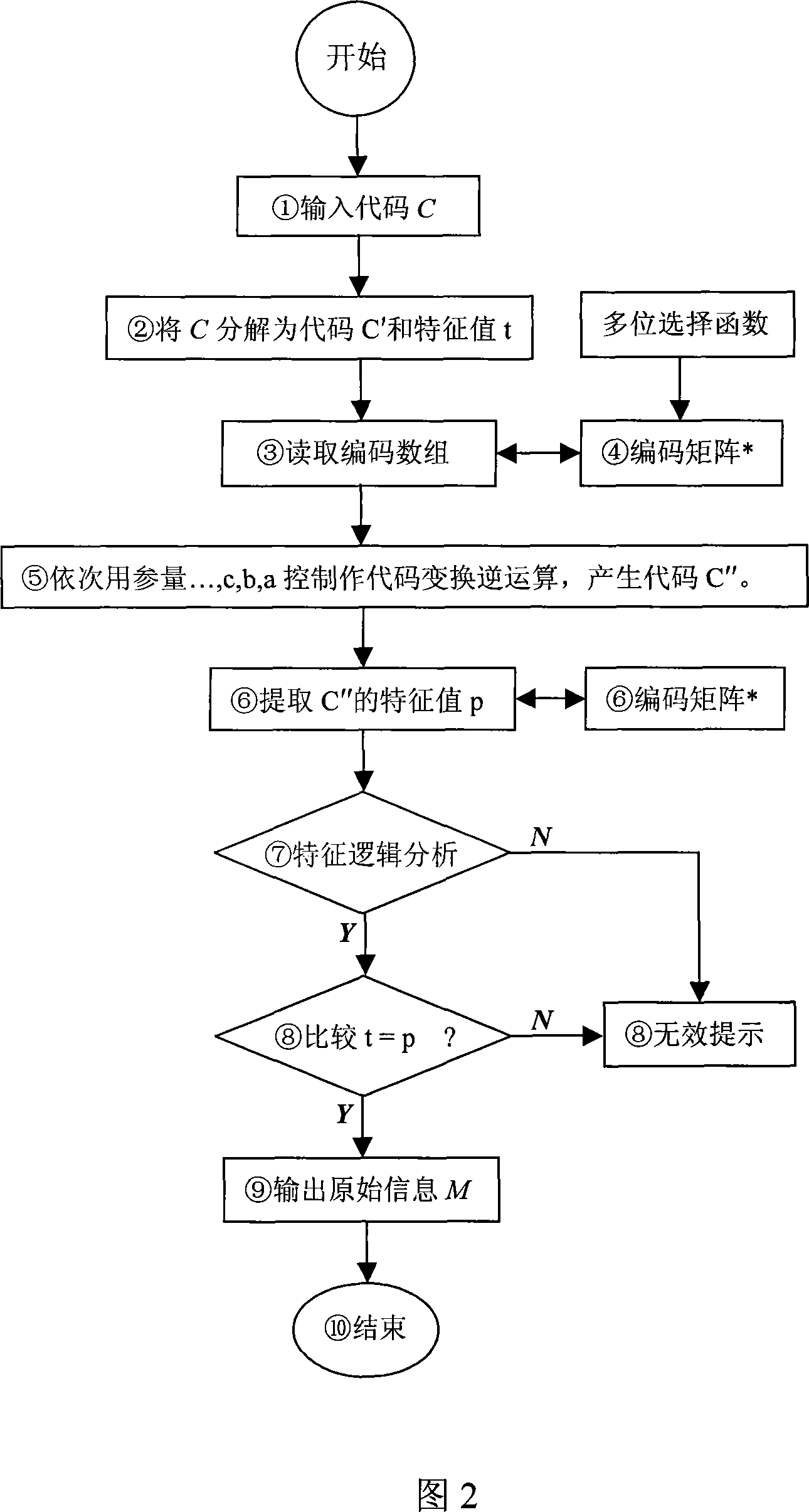
Method and device for data processing based on block chain
ActiveCN107426170AGuarantee authenticityNot tampered withComputer security arrangementsSpecial data processing applicationsTamper resistanceData authenticity
The present invention discloses a method and device for data processing based on a block chain. The method comprises: when a block chain node receives business data to be stored, determining the data attributes of the business data; if the data attributes of the business data is a text type, employing a preset private key in a public and private key pair corresponding to the user identification included in the business data to perform encryption processing of the business data; and if the data attributes of the business data is an image type, determining the abstract of the business data, and employing preset private key in a public and private key pair corresponding to the user identification included in the business data to perform encryption processing of the abstract. The features of decentration, openness and transparency, tamper resistance and dependability of the block chain technology are employed to employ different processing modes according to the data attributes of the business data to store the business data into the block chain network so as to ensure the business data authenticity and ensure that the business data is not tampered.
Owner:ADVANCED NEW TECH CO LTD
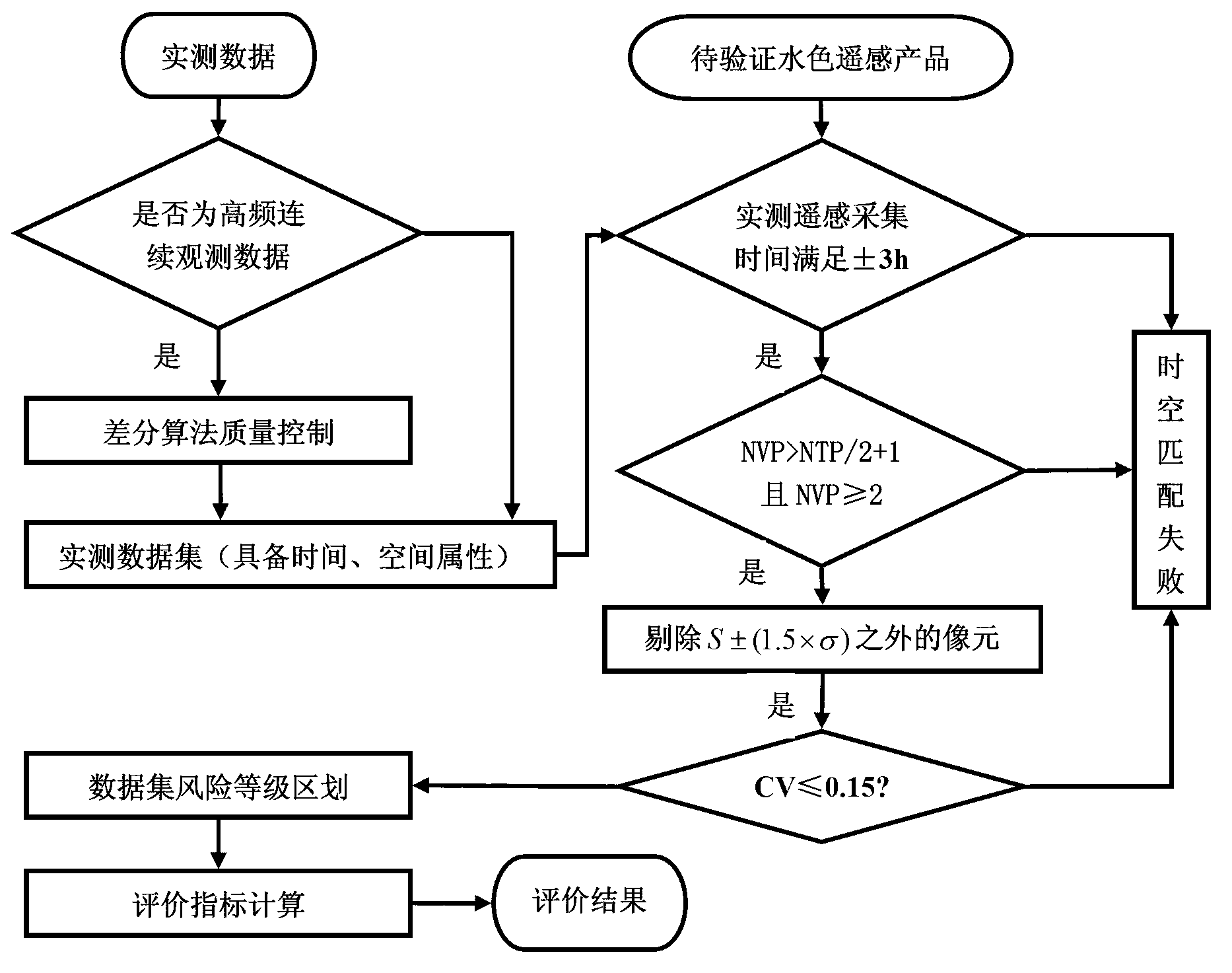
Method for checking reality of ocean color remote sensing product
InactiveCN103020478AHave diversityReasonableSpecial data processing applicationsData setData authenticity
The invention discloses a method for checking the reality of an ocean color remote sensing product. The method comprises the following steps: (1) reconstructing a long time sequence remote sensing data set; (2) computing and integrating based on the time-space variation characteristics of the remote sensing data set; (3) carrying out quality control and screening on a practical measurement data set for checking the remote sensing product; (4) checking generation of data sets by practical measurement-remote sensing data based on a time-space matching rule; (5) carrying out risk level division on the eligible matched data sets; and (6) computing indexes for checking the data reality of the remote sensing product. According to the method, the representativeness and the reasonability between the remote sensing product data and the checking practical measurement data can be checked, the matched data sets are screened and generated, and an evaluation method for different risk levels is obtained, so that the evaluation results are diversified and reasonable, the uncertain risk in the checking process is lowered, and the checking credibility is improved.
Owner:HANGZHOU NORMAL UNIVERSITY
Method and system based on USBKey online banking trade information authentication
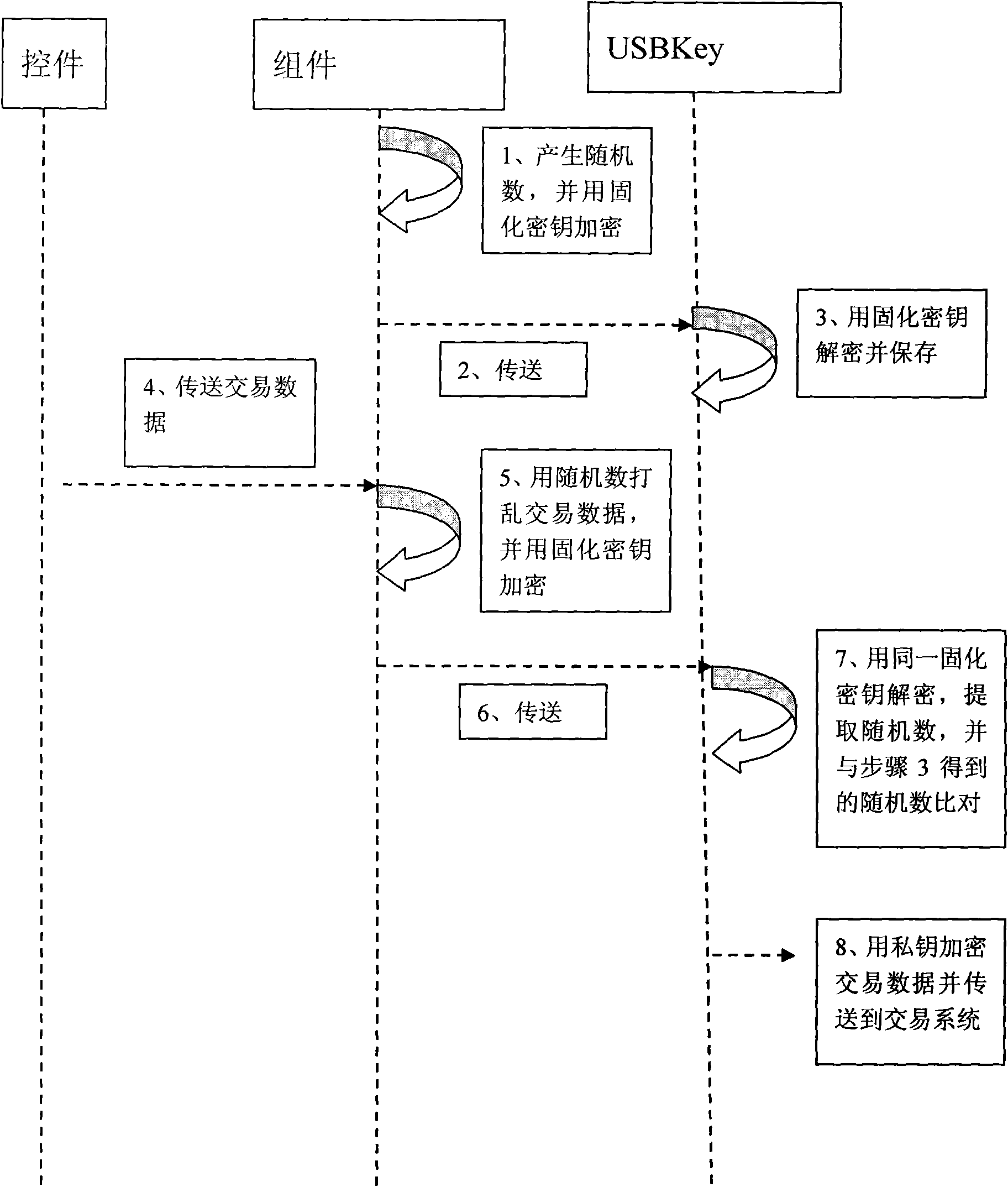
The invention discloses a method based on USBKey online banking trade information authentication; when being used for the first time, system software is automatically mounted into an operating systemand a solidifying key is mounted simultaneously; when a user finishes pressing a trade fingerprint to confirm the trade, application software generates a random number and uses the solidifying key toencrypt and transmit to a USBKey; meanwhile, the application software uses the random number to implement inserting and upsetting on the received trade data and uses the solidifying key to encrypt andtransmit to the USBKey; the USBKey uses the shared solidifying key to decrypt to obtain one random number and a string of trade data upset by the random number, uses the shared key to take out the random number inserted into the trade data and compares the random number with the random number obtained by directly deciphering, and the random number is confirmed to be true and valid if the resultsare the same. The invention can guarantee the trade information to be safely transferred in the network links by establishing a data truth authentication system, stop the trade information from beingmaliciously altered and protect the user trade to be safely and validly executed.
Owner:ZHEJIANG WELLCOM TECH
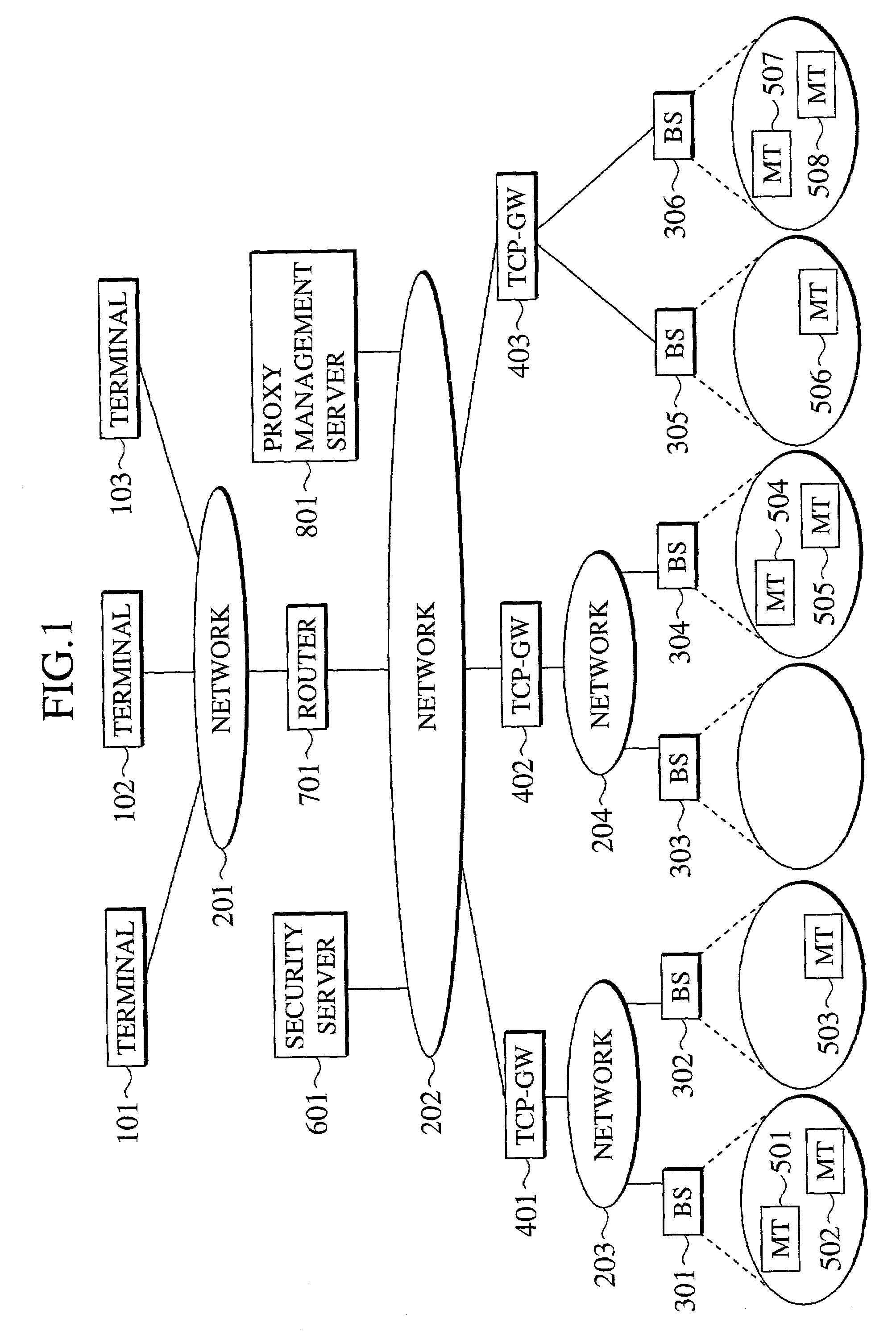
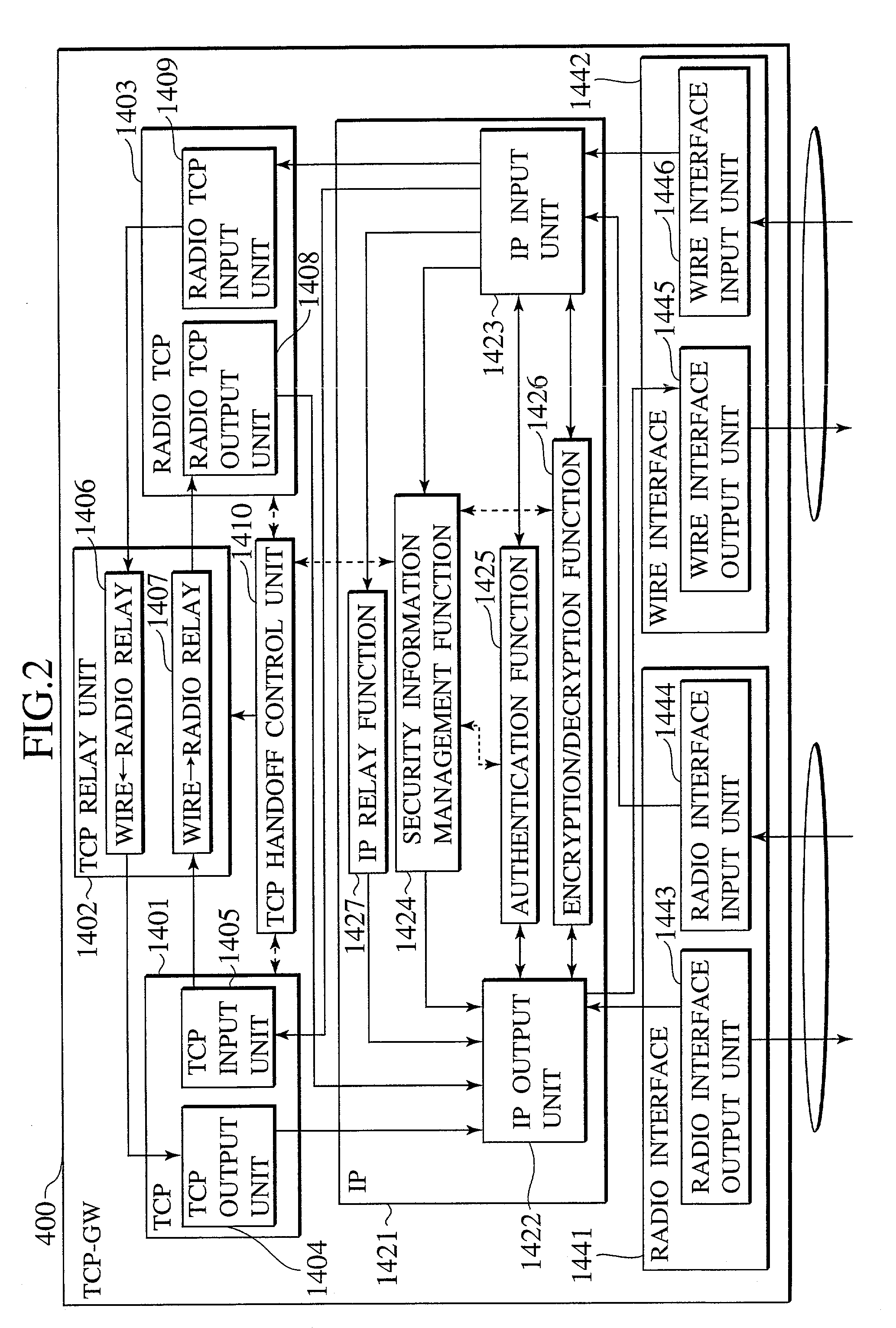
Communication control scheme using proxy device and security protocol in combination
InactiveUS7143282B2Efficient data communicationEfficient workTime-division multiplexData switching by path configurationSecurity associationData authenticity
In a gateway device for carrying out a data relaying at a transport or upper layer between a first terminal device and a second terminal device which are capable of carrying out communications through networks, information regarding a security association set up between the first terminal device and the second terminal device in order to carry out communications with guaranteed data secrecy or in order to carry out communications with guaranteed data authenticity managed, and the decryption / encryption processing or the authentication processing is carried out according to the managed information regarding the security association along with the data relaying at the transport or upper layer.
Owner:KK TOSHIBA
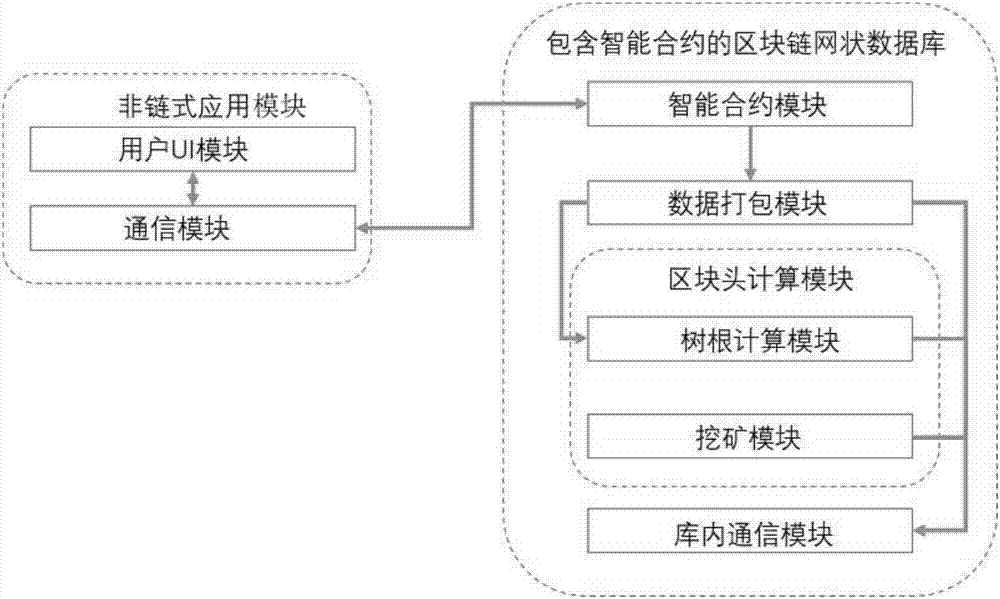
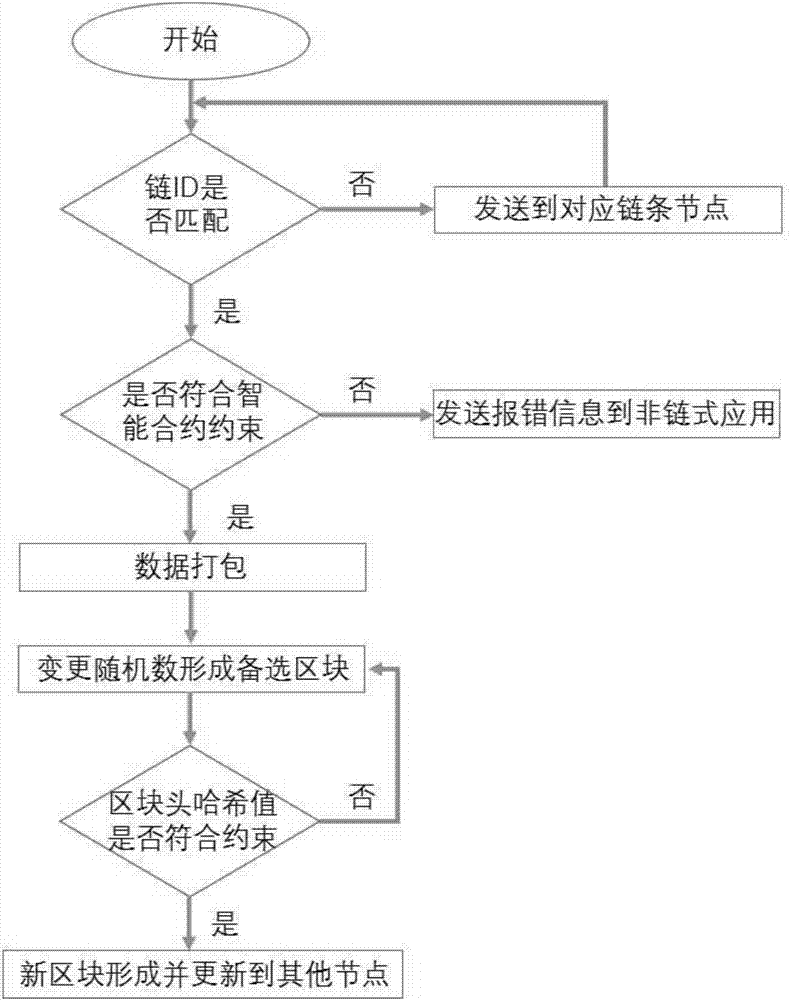
Blockchain net type database comprising smart contract and work method
InactiveCN107103098AGuarantee authenticitySpeed up developmentSpecial data processing applicationsData authenticitySmart contract
The invention provides a blockchain net type database comprising a smart contract. The blockchain net type database comprises a smart contract module, a data packaging module, a block head calculating module and an in-database executing module, wherein the smart contract module is connected with the data packaging module, and the data packaging module is connected with the block head calculating module and the in-database executing module; the smart contract module is a user-defined mode and used for verifying and processing data according to user-defined constraint; the data package module organizes data in a tree chain mode; the in-database executing module adopts a PBFT algorithm to ensure consistency between a main node and backup modes. The invention further provides a working method of the blockchain net type database comprising the smart contract. The general core library of the blockchain system is provided, and the development speed of blockchain application can be accelerated; multi-chain interaction can be achieved, the condition that part of nodes cannot take part in a network as a single chain mode account book is too large can be avoided, and data authenticity can be ensured through service logic dependent relation between chains.
Owner:曾建伟
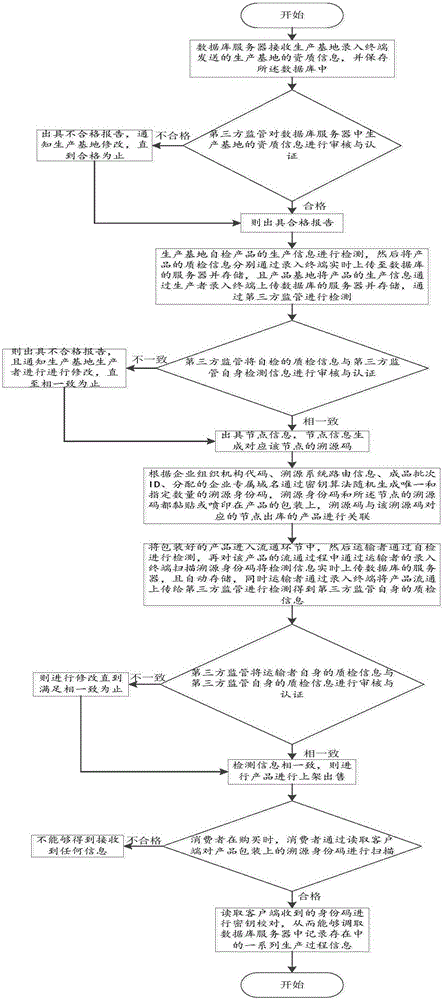
Product quality control traceability method
The invention provides a product quality control traceability method which is applied to a product traceability system. The product traceability system comprises input terminals and a server which is provided with a database which stores product information. The product information comprises the node information of a number of nodes in the whole product chain from raw materials to finished products. A number of input terminals are comprised. A number of steps are comprised, and audit and certification are carried out from production to circulation through third-party supervision. The data authenticity in product production and circulation is improved. The whole production process is effectively supervised. Unqualified agricultural products into the market are greatly reduced. The phenomenon of production chain reputation fall is avoided.
Owner:杭州维甄科技有限公司
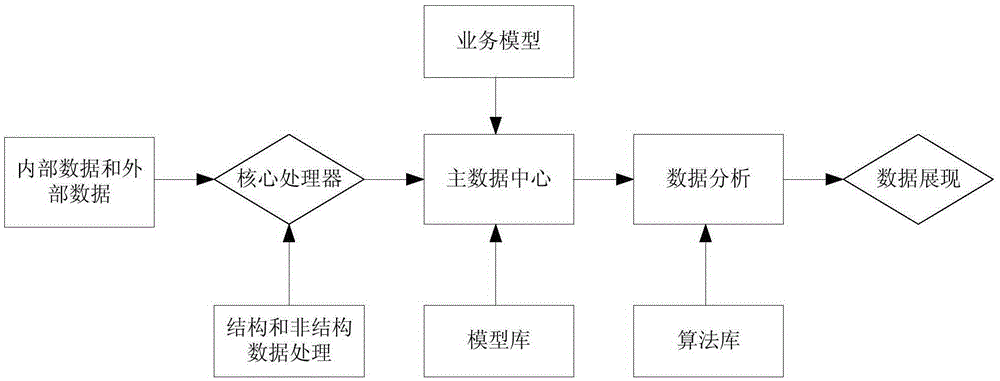
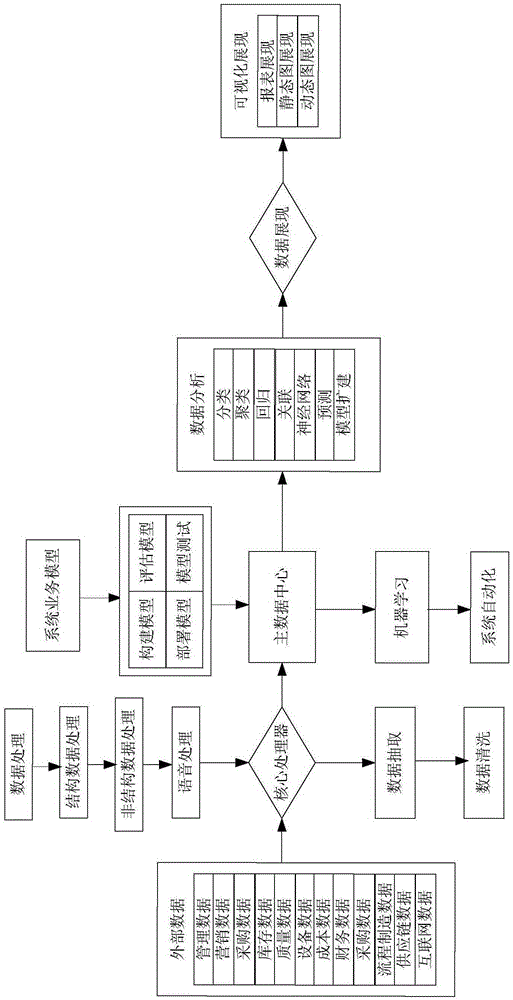
Method for modeling, analyzing, and self-optimizing multi-source business big data
InactiveCN105260835AImprove collection effectGuarantee authenticityResourcesSpecial data processing applicationsPersonalizationData authenticity
The invention provides a method for modeling, analyzing, and self-optimizing multi-source business big data. The method comprises steps of: receiving internal data from an enterprise system and external data from the Internet; analyzing the internal data and the external data in order to classify the internal data and the external data into structured data and unstructured data; converting the unstructured data into corresponding text content and extracting and cleaning the converted unstructured data and the structured data; establishing multiple business models according an internal demand of an enterprise, and enabling the business models to perform self-learning and self-optimization according to data input in order to automatically generate a master data center; processing and analyzing data in the master data center in order to obtain a business analysis result; and displaying the business analysis result by using a digital and graphical interface. The method accurately analyzes business data on the premise of data authenticity in order that the business data models are automatically established, optimized and expanded and correlation analysis and display for individualized demands are solved.
Owner:BEIJING ALAZIN TECH CO LTD
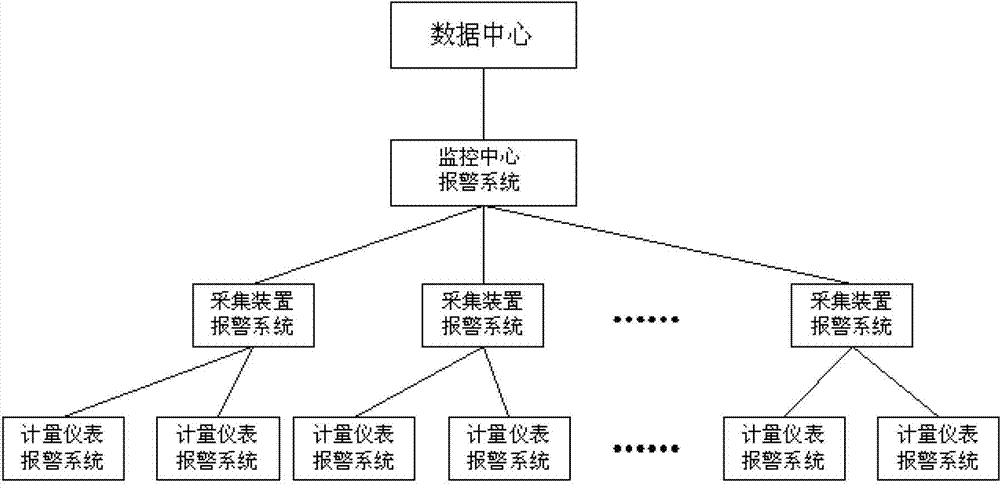
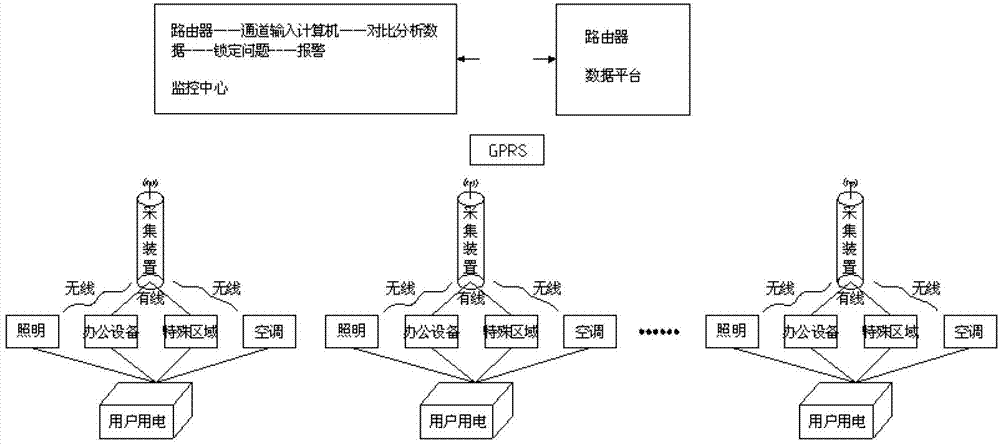
Energy consumption acquiring, monitoring, analyzing and alarming system for independent rooms in office building
ActiveCN102929232AMonitor energy consumptionEasy to operateProgramme total factory controlElectricityReal-time data
The invention relates to an energy consumption monitoring system for a building. The system attracts the attention of people by an alarm mode, and adjustment or system upgrading is performed. Data required by field research is provided conveniently and quickly, time and labor are saved for national research, and the data authenticity and timeliness are optimized. According to the technical scheme, the energy acquiring, monitoring, analyzing and alarming system for independent rooms in an office building comprises metering devices, acquisition devices, a monitoring center and alarming devices; the metering devices are used for metering power consumption real-time data of all users; the acquisition devices are connected with the metering devices at all tail ends through a network, and transmit the obtained real-time data to the monitoring center through a wireless network; the monitoring center is used for storing and analyzing real-time data; and according to the alarm devices, three stages of alarming systems are used for alarming, a first-stage alarming system is connected with the metering devices, a second-stage alarming system is connected with the acquisition devices; and a third-stage alarming system is connected with the monitoring system. The energy acquiring, monitoring, analyzing and alarming system for the independent rooms in the office building is mainly applied to monitoring of the energy consumption of buildings.
Owner:TIANJIN UNIV
Digital antenna test system and method
PendingCN106970271AIncrease authenticityFast testAntenna radiation diagramsHigh level techniquesData authenticityBus
The invention discloses a digital antenna test system and method. The system comprises a digital antenna probe array, digital test equipment, a data bus and a center industrial control computer, wherein the digital test equipment is connected with a to-be-tested antenna structure, the digital antenna probe array is connected with the to-be-tested antenna structure through a space wireless channel, the to-be-tested antenna structure, the digital antenna probe array, the digital test equipment and the center industrial control computer are connected with the data bus, the digital antenna probe array comprises N digital antenna probes, and the N is a natural number not smaller than 2. As all the spatial domain radiation signals can be simultaneously acquired one time, a test speed is improved by N times; as the radiation signals in all directions are simultaneously acquired in real time, antenna test data including directional diagrams and polarized characteristics has higher authenticity.
Owner:旷良彬
Data change recovery algorithm capable of restoring data authenticity in cloud storage
ActiveCN106612172AGuaranteed confidentialityEfficient use ofEncryption apparatus with shift registers/memoriesComputer hardwareConfidentiality
Provided is a data change recovery algorithm capable of restoring data authenticity in cloud storage. A Hash value of a file serves as a root key of an encryption system, a file block is encrypted, a verification label of the file block is stored, a data block of F is converted into a matrix, an integrity indication code generation function is designed to implement calculation on the matrix, an obtained value is coded, a final integrity indication code is generated, the final integrated indication code is stored in a cloud space together with ciphertext data and ciphertext Hash data, when data is damaged, content of the original data block can be recovered according to order of the integrity indication code, and due to that the root key of encryption equals the Hash value of the file content, the two Hash values can be compared to obtained the authenticity of a restored file. Under the condition that the data is recovered to the largest degree, the data confidentiality is ensured; a storage space is utilized effectively; and the system cost is reduced.
Owner:中智贵阳人力资本科技有限公司
Enterprise risk assessment method based on various kinds of operation data
InactiveCN104992234AHigh precisionOvercome the risk of assessment errorFinanceForecastingData ingestionData authenticity
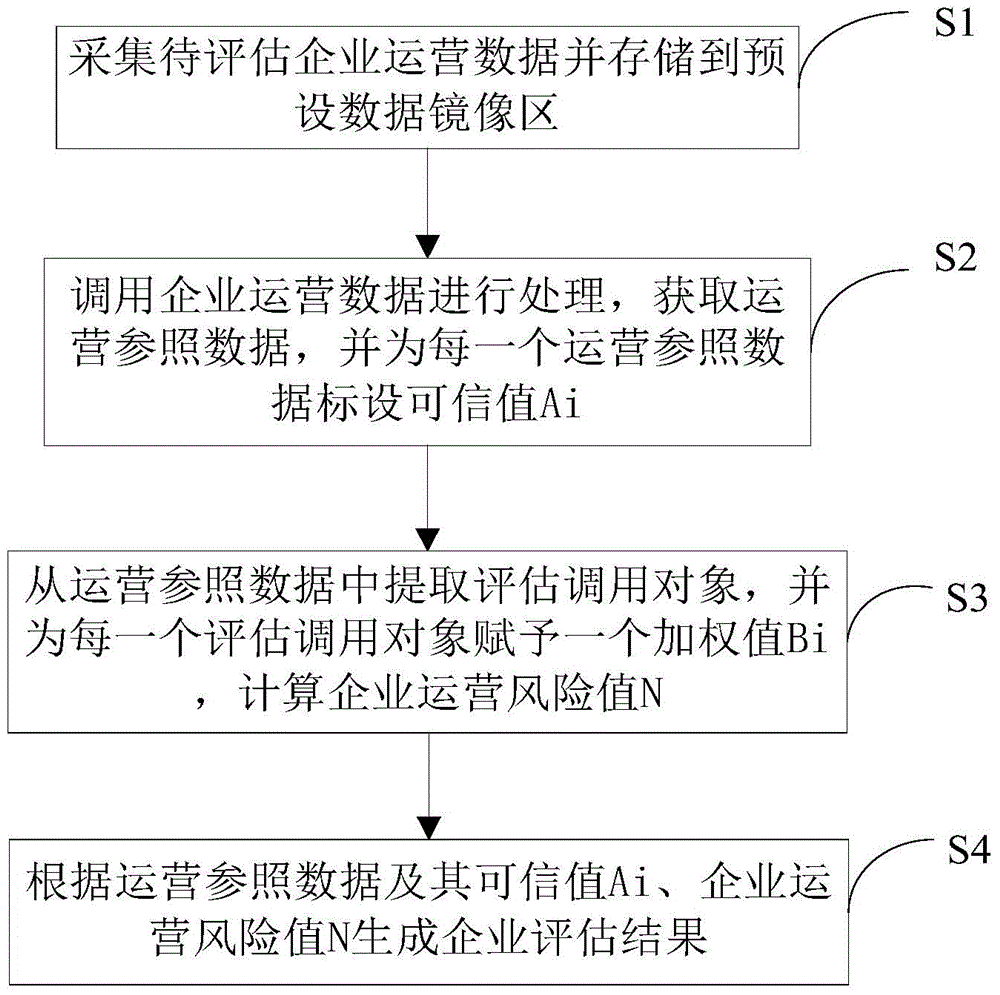
The invention discloses an enterprise risk assessment method based on various kinds of operation data. The method comprises the following steps of S1, collecting operation data of an enterprise to be assessed and storing the data to a preset data mirror image area, wherein the enterprise operation data comprises ERP data, HR data and financial data; S2, according to a preset data extraction model, calling the enterprise operation data and processing, acquiring operation reference data and marking a trusted value Ai for each operation reference data; S3, according to a preset risk calculating model, extracting assessment calling objects from the operation reference data, giving one weighted value Bi for each assessment calling object, and calculating an enterprise operation risk value N according to the trusted value Ai and the weighted value Bi of each assessment calling object; S4, according to the operation reference data, the trusted value Ai and the enterprise operation risk value N, generating an enterprise assessment result. Financial data authenticity of the enterprise and especially middle and small-sized enterprises is low so that an assessment error risk is generated. By using the method of the invention, the above problem is overcome so that accuracy of enterprise risk assessment is increased.
Owner:合肥智权信息科技有限公司
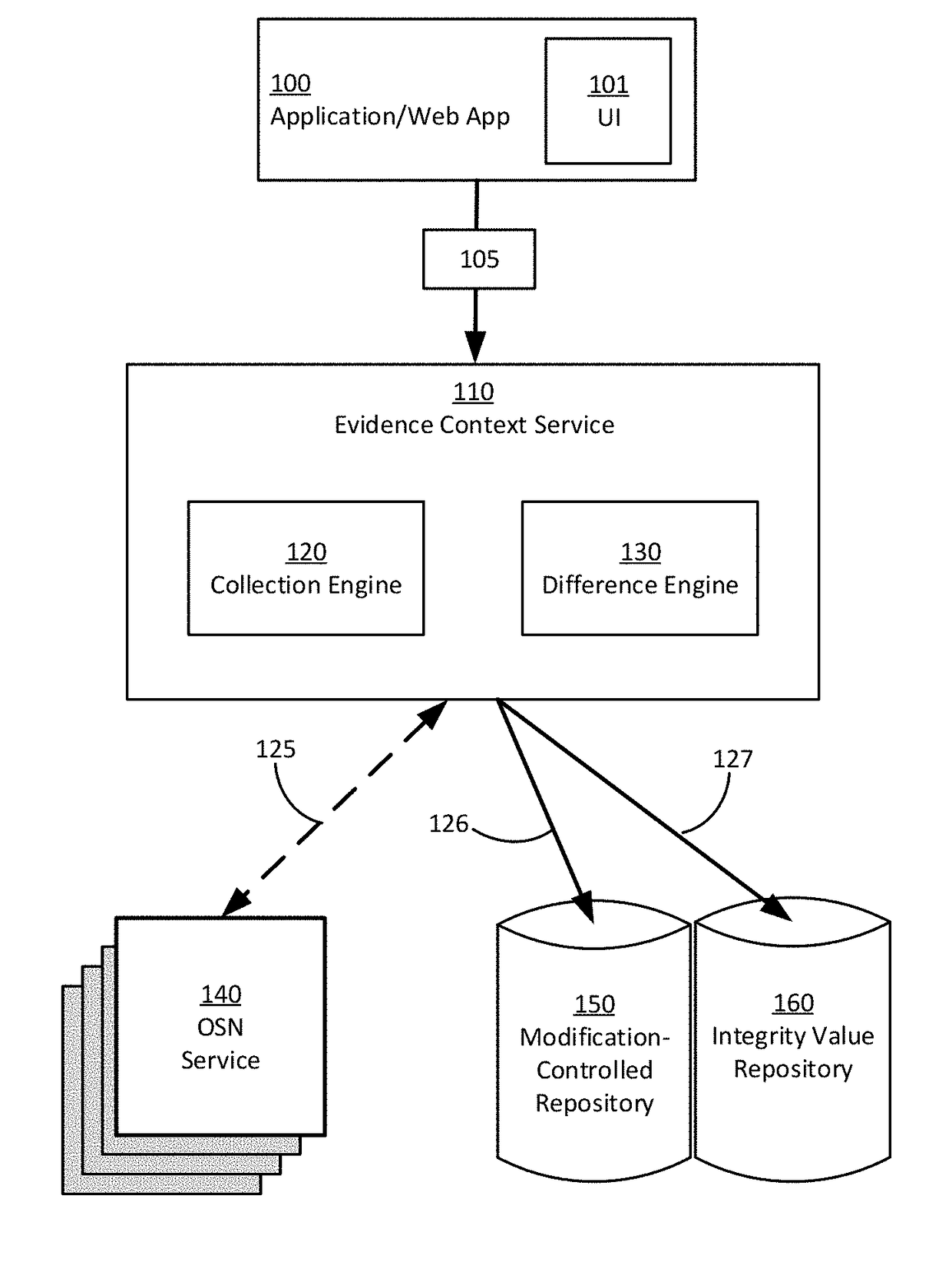
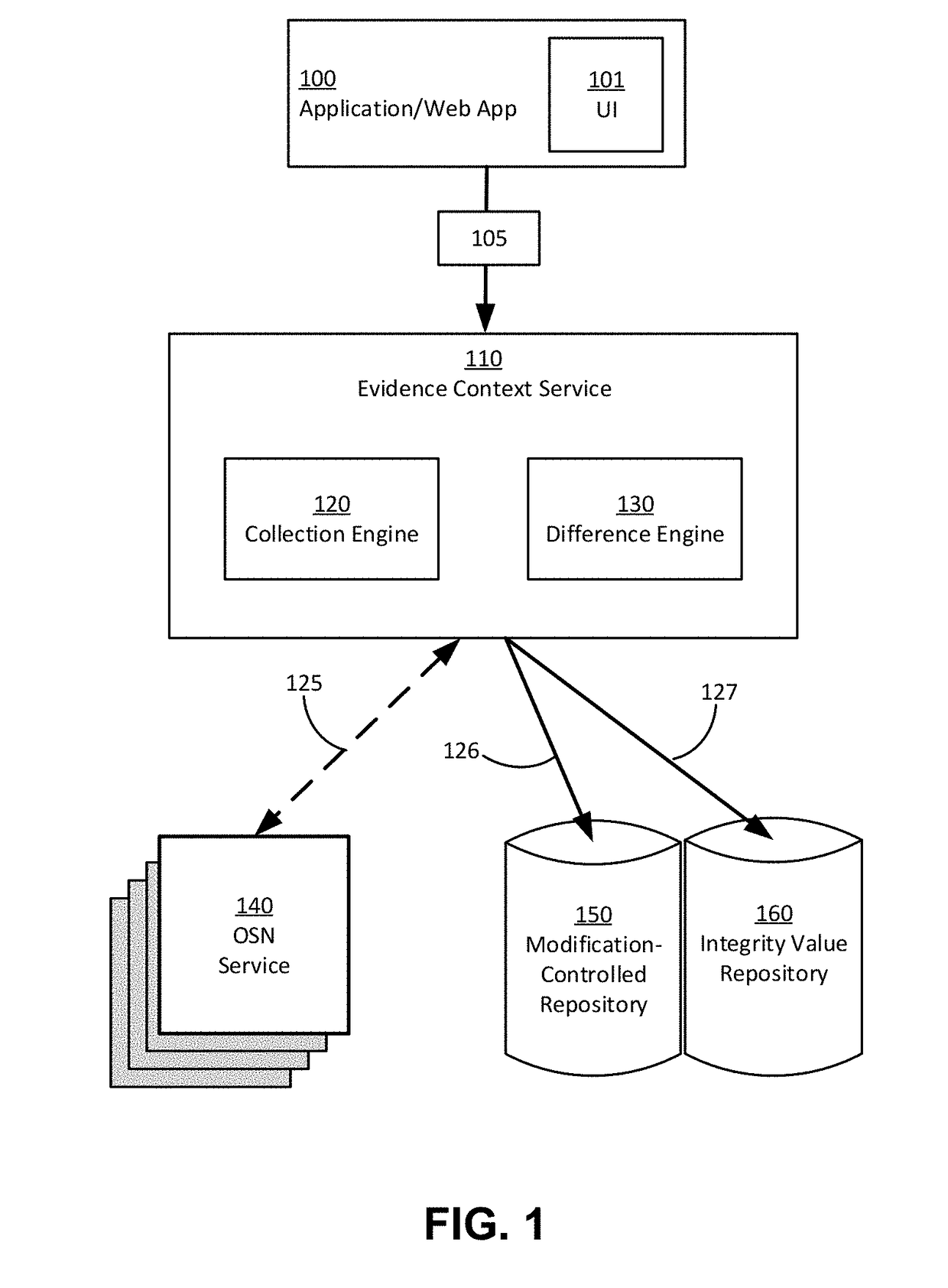
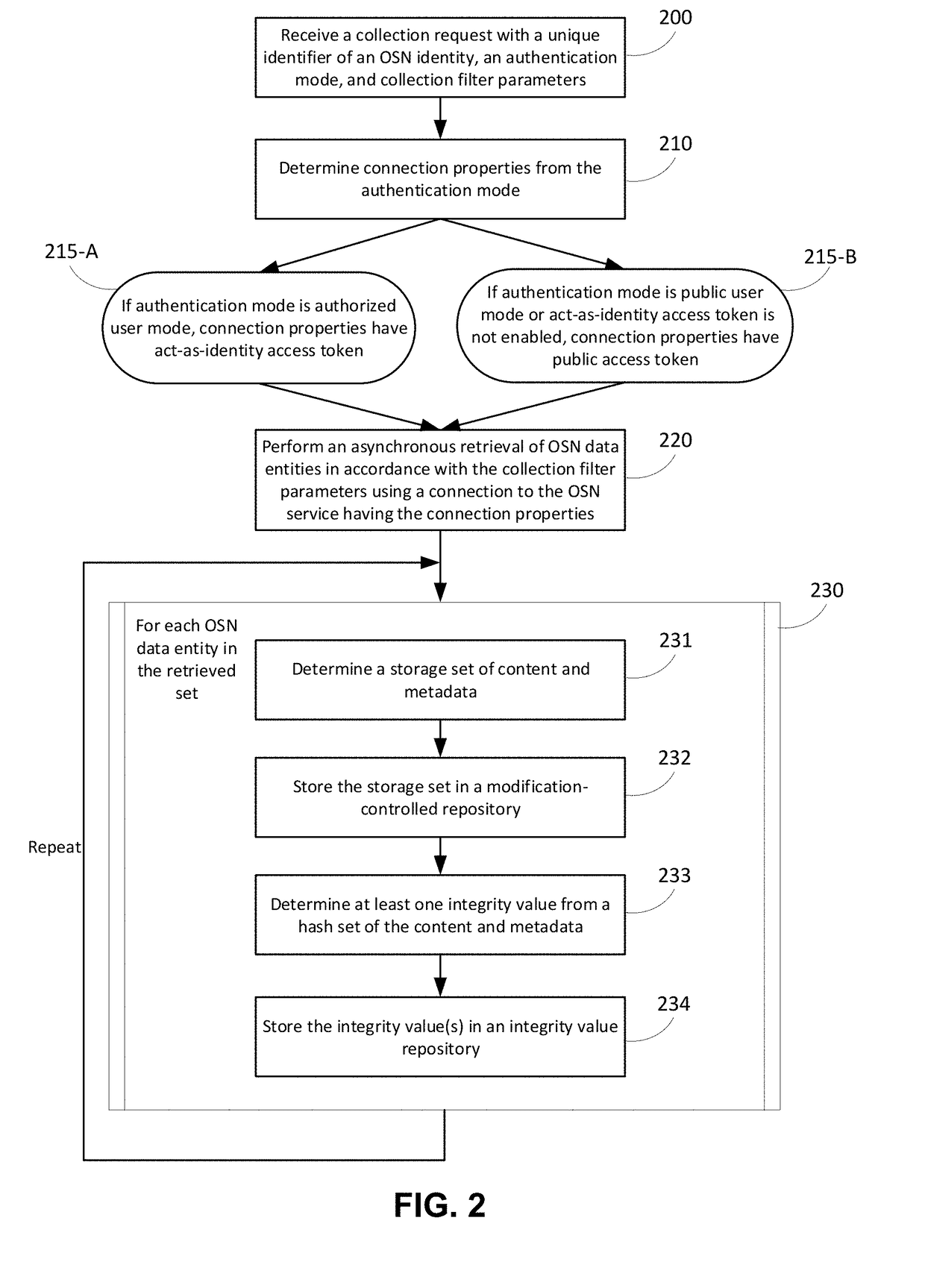
Targeted collection and storage of online social network data in evidence domains
InactiveUS20180137199A1Enhanced informationImprove targetingData processing applicationsWeb data indexingData entitySocial web
Techniques and systems are provided for selecting, collecting, and storing online social network (OSN) data pertinent to an evidence context. A collection request with content filter parameters, an authentication mode, and a targeted OSN identity is received. A unique content and user perspective is determined to build an OSN connection that is used to asynchronously retrieve targeted OSN data entities in accordance with the content filter parameters. Filtered OSN data is assembled and stored in a modification-controlled repository. An integrity value for certifying the authenticity of stored OSN data is stored in an integrity value repository. Some implementations include methods for targeting information of evidentiary value by repeating a collection request at a timed interval and determining the existence of added, modified, or deleted OSN data from prior retrieval instances.
Owner:SOCIAL EVIDENCE LLC
Measurement authentication method based on digital signature
InactiveCN101123502ASolving difficult-to-verifiable problemsReduce difficultyTariff metering apparatusUser identity/authority verificationData authenticityDigital signature
The present invention relates to a measuring value authentication method based on digital signatures, which utilizes a password algorithm with identification ability to digitally sign the measuring value of a measuring meter, such as an electricity meter, a water meter, a gas meter, a heat energy meter, etc., and a measuring value electronic authentication system consists of a coder and a decoder that are based on the password algorithm. The coder connected with the measuring meter reads a measuring value and then utilizes an encryption algorithm to realtimely convert the measuring value and the user identity information into a code, that is, a digital signature; whereas the decoder utilizes a decryption algorithm to revert the code back to the corresponding measuring value and the user identity information, that is, a verification digital signature. The basic operation of the measuring value electronic authentication is divided into two steps, the authentication registration and the authentication, wherein the authentication registration is a process in which a service provider registers the code generated by the coder, and the authentication is a process in which the service provider utilizes the decoder to revert the code obtained by the authentication registration back to the corresponding measuring value and the user identity information. Characterized in strong conditionality and simple operation, the present invention eliminates the defect that the authenticity of data is hard to be verified in manual metering.
Owner:ZHEJIANG UNIV
Data safety audit method based on identification
The invention provides a data safety audit method based on identification. The data safety audit method based on the identification can guarantee data authenticity and integrity of an audited server through small calculated amount and communication amount. In the step of data block signing, a data block serial number and data block data together generate flag value, in an audit step of challenging of response value, the data block serial number is participated into the audit process of the data block, therefore, the audited server can be prevented from using unchallenged legal data to replace the challenged data, and safety and effectiveness of data audit are guaranteed.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
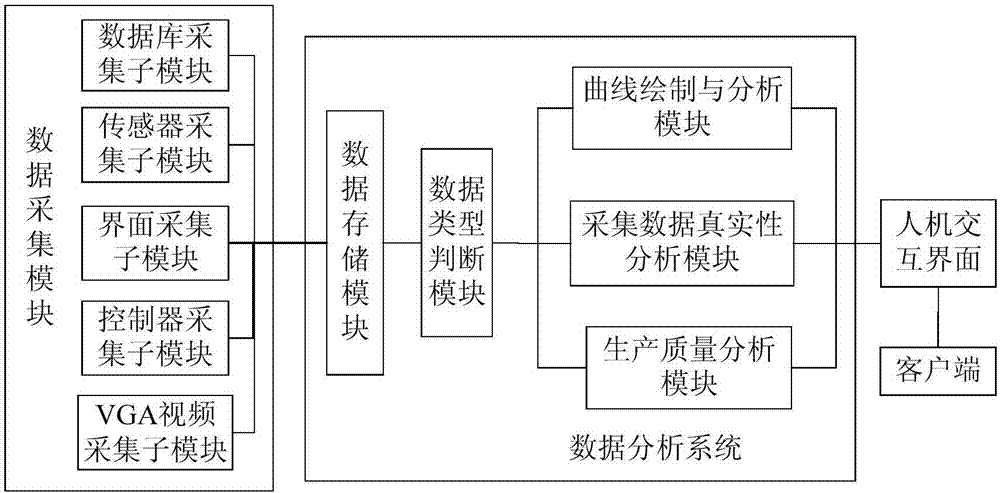
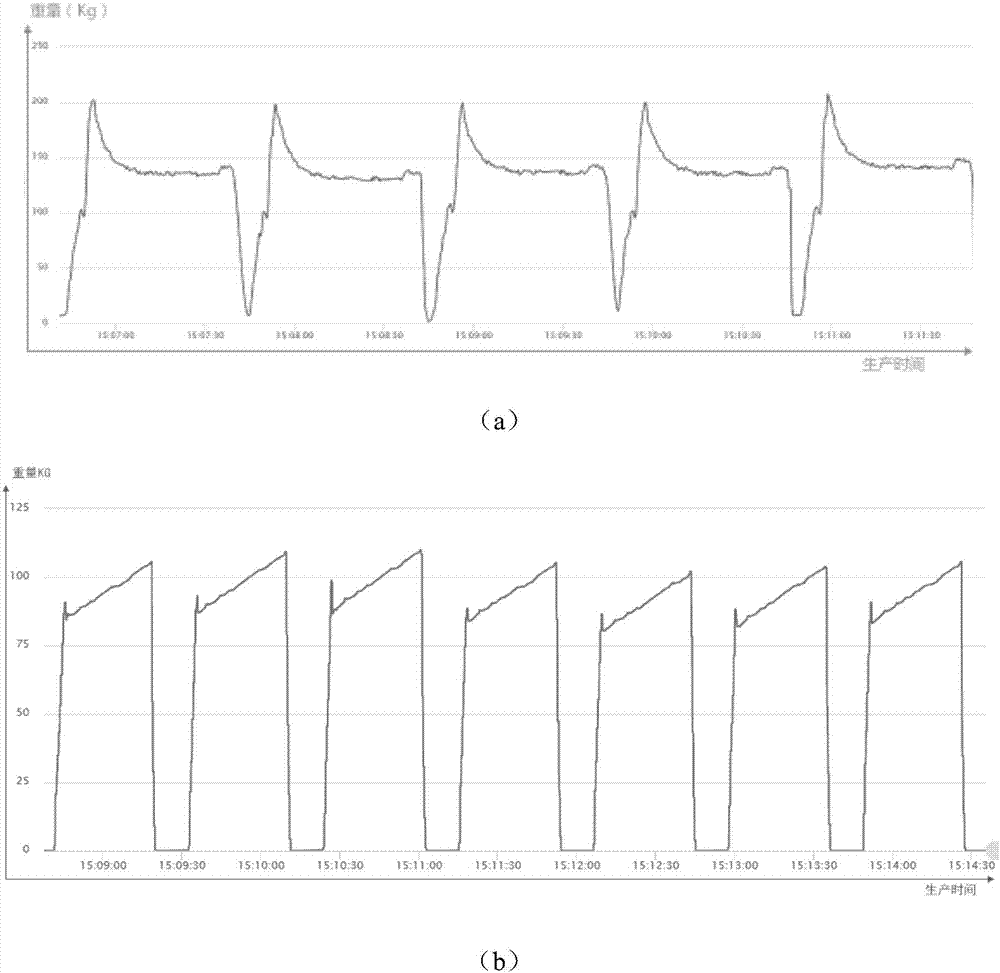
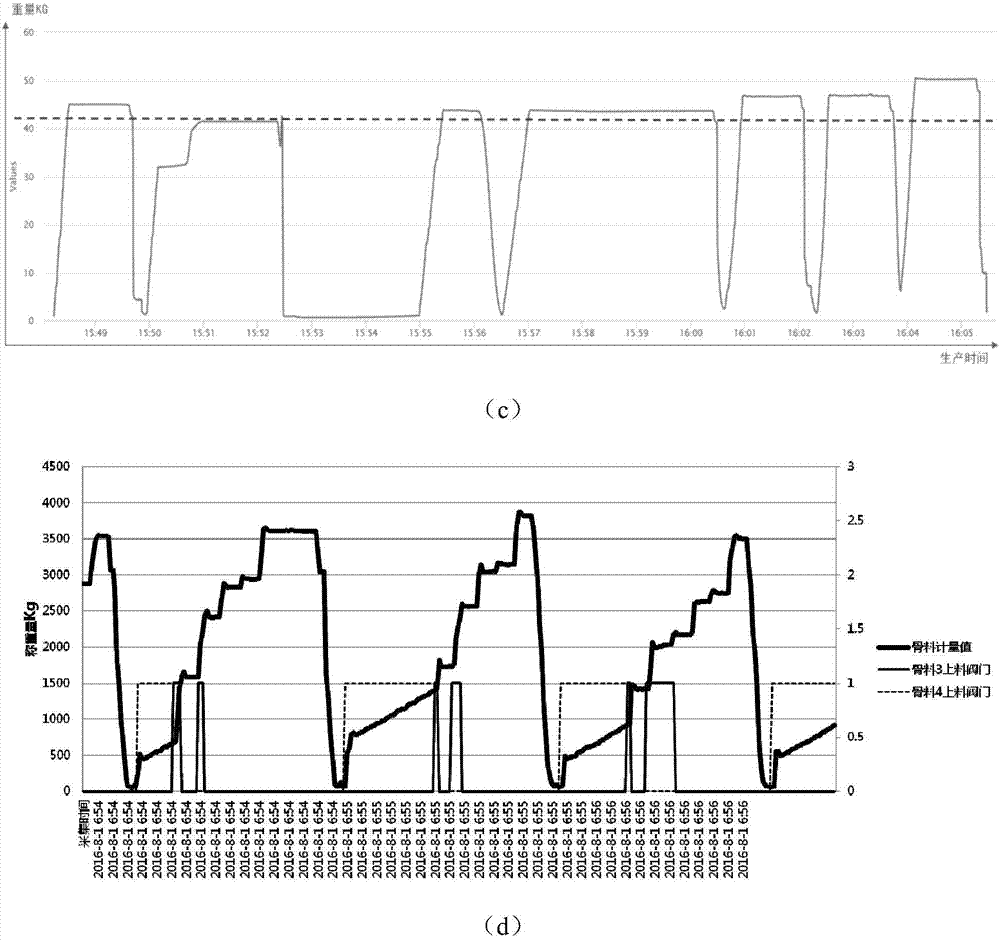
Stirring device production quality monitoring system based on multiple data sources and method
InactiveCN106952033AMonitor Dynamic Weighing AccuracyRealize intelligent early warningResourcesManufacturing computing systemsData authenticityData acquisition
The invention provides a stirring device production quality monitoring system based on multiple data sources and a method, and relates to the technical field of stirring device production quality monitoring. A data acquisition module is used for acquiring production data; a data storage module, a data type judgment module, a curve drawing and analysis module, an acquired data authenticity analysis module and a production quality analysis module in a data analysis system are used for carrying out deep analysis on the production data and monitoring operation states of stirring devices, authenticity of the acquired data and whether the production quality meets a regulated requirement. A human-machine interaction interface displays monitoring results. According to the invention, dynamic weighing accuracy of stirring devices in a blending process can be effectively monitored; it is achieved that an intelligent early warning is given out for fault stirring devices, and the operation states of the stirring devices, whether the acquired data is true and accurate and whether the production quality meets a regulated requirement are monitored, so quality risks are effectively eliminated, and powerful technical support is provided for stabilized soil / concrete / mixture quality monitoring of a construction project.
Owner:沈阳新一代信息技术有限公司
Multi-source-data-based automatic modeling method and system of three-dimension model of geological structural surface
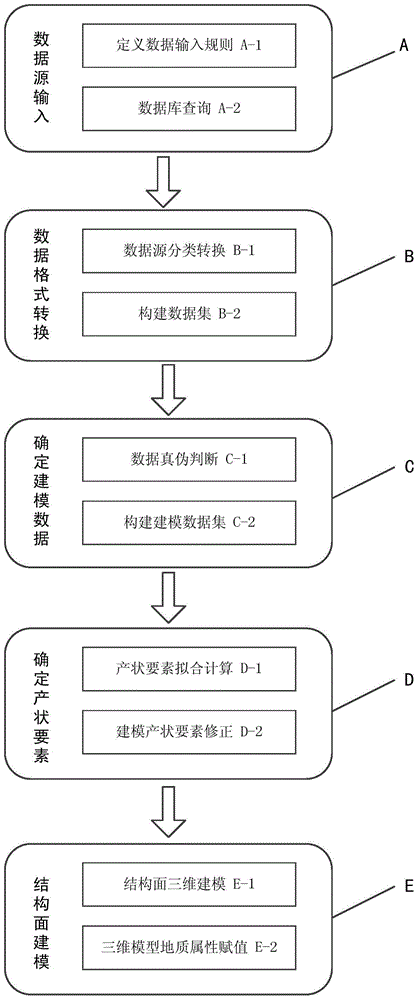
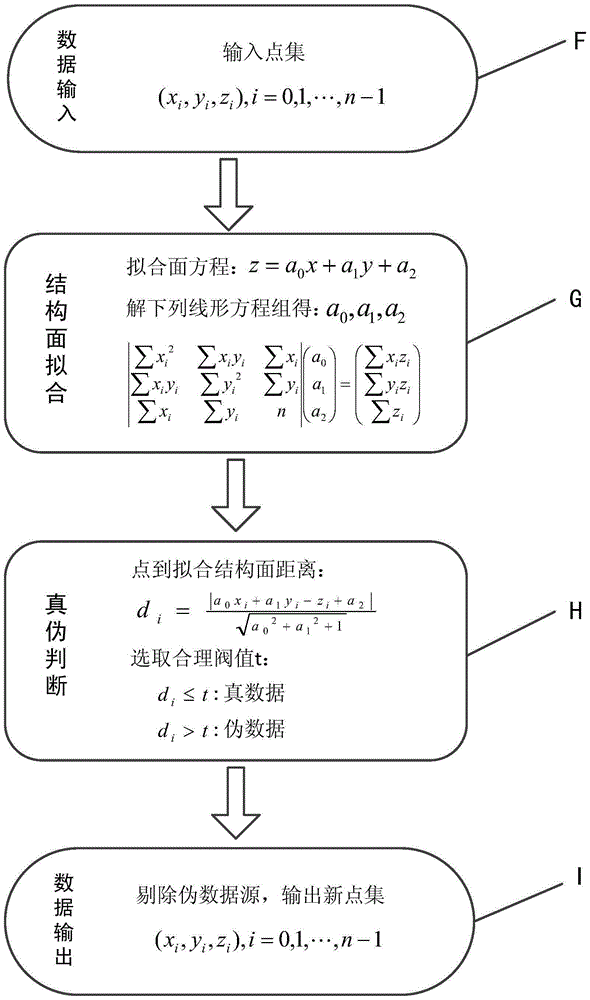
ActiveCN105205864ASolve data authenticity judgmentSolve the automated modeling process3D modellingData setData authenticity
The invention discloses a multi-source-data-based automatic modeling method and system of a three-dimension model of a geological structural surface. The method comprises: S1, carrying out data source inputting; to be specific, defining a data input rule and searching data meeting the rule from an engineering geological database; S2, carrying out data format conversion; to be specific, converting various inputted data sources into ones in a uniform format and constructing a basic data set; S3, determining modeling data; to be specific, determining data authenticity of the data sources, extracting data meeting the requirement, and constructing a modeling data set; S4, determining elements of attitude; to be specific, fitting and correcting structural surface modeling elements of attitude based on the modeling data set; and S5, carrying out structural surface modeling; to be specific, establishing a structural surface three-dimension model according to the modeling data set and the elements of attitude of the structural surface and adding a corresponding geological attribute to the three-dimension model. With the method and system, the data authenticity determination of the data sources of the geologic structural surface and the automatic modeling process of the three-dimension model of the three-dimension model of the geologic structural surface are realized; and the accuracy and efficiency of the three-dimension modeling of the geologic structural surface are improved.
Owner:POWERCHINA BEIJING ENG
Sales management system for network
InactiveCN108564273AIncrease authenticityNo redundant functionsCustomer relationshipResourcesTablet computerThird party
The invention belongs to the technical field of networks and discloses a sales management system for a network. Nine modules of home page, task calendar, sales system, personal customer, customer service system, financial system, common tools, system management and recycling station are set. Customer data has wide sources and high authenticity. System data mainly comes from a recruitment website,a user can register for the recruitment website by himself or herself through a mobile phone, a tablet computer, a PC and the like to be a system customer and also can become the system customer through the participation in a job fair, the manual entry by a salesperson and the like. The data obtained by the recruitment website and the job fair is more authentic. The system can view the informationof an enterprise customer from a third party through an interface, and the authenticity of the data is improved. The system has no redundant function and is seamlessly connected to the recruitment website. The system is specially developed for the recruitment website and has no other redundant function, and at the same time, the functions of consultant management, job management and the like which do not exist in a similar system are added.
Owner:江苏艾克斯信息科技有限公司
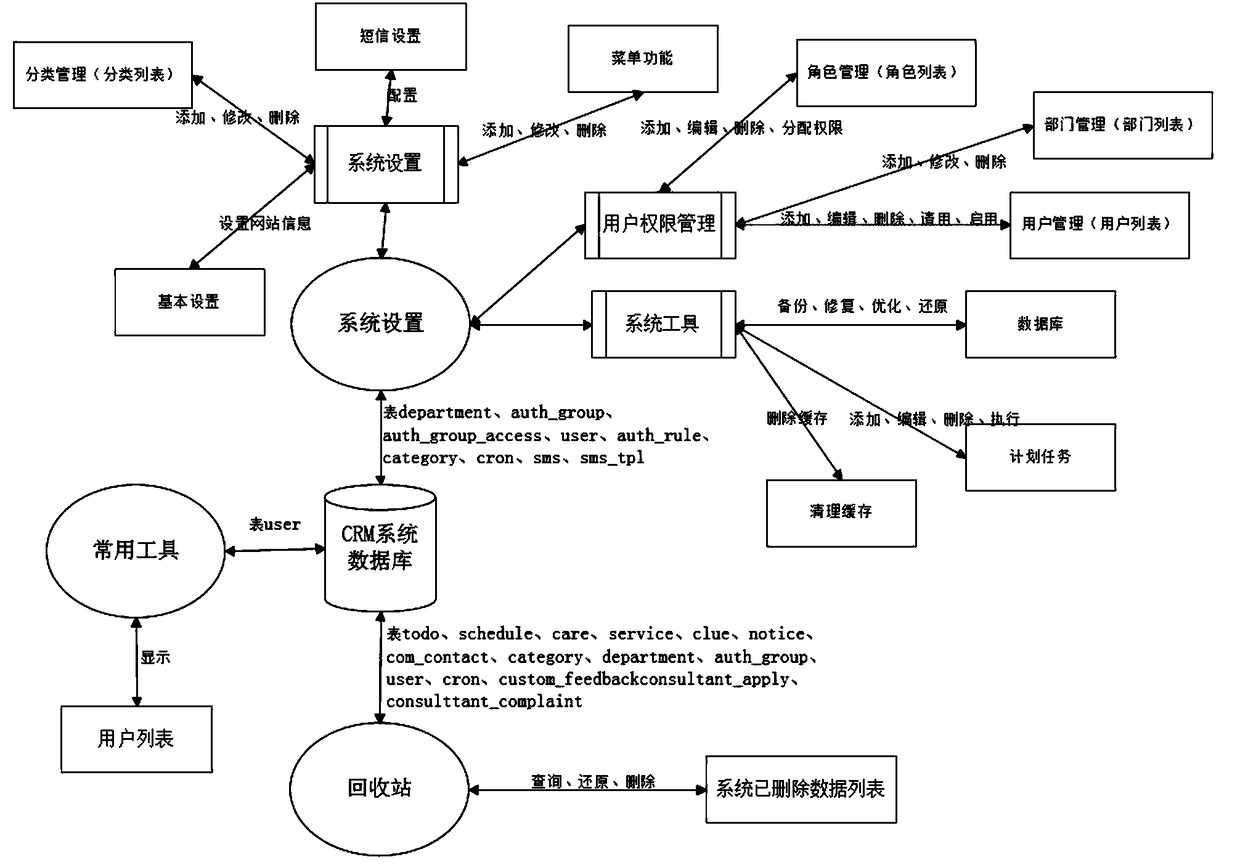
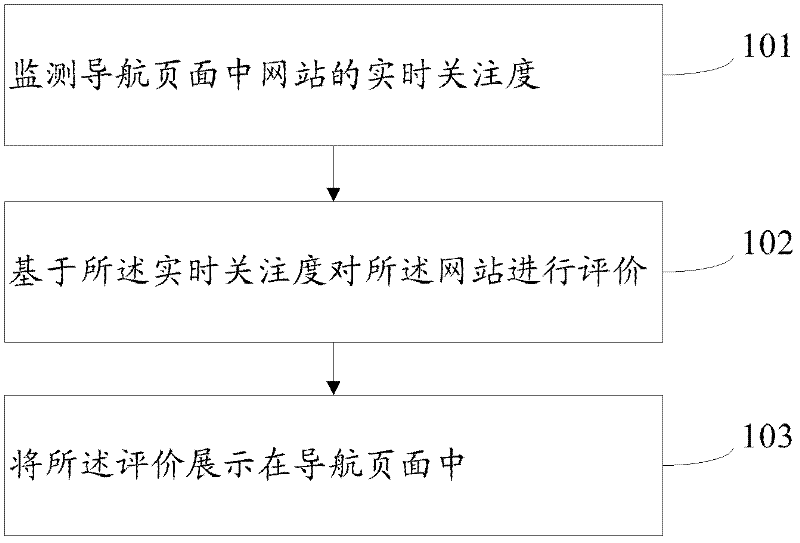
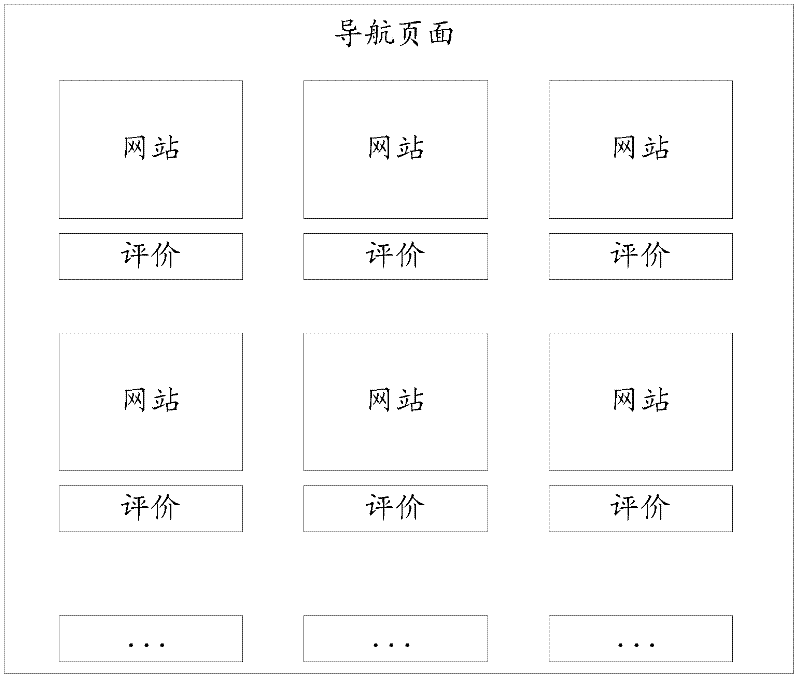
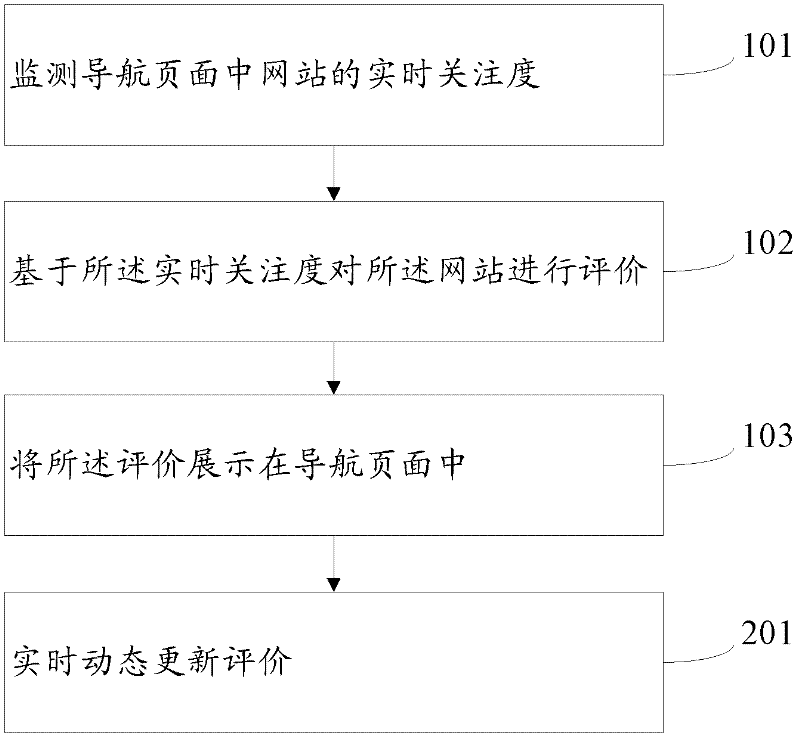
Navigation page data processing method and navigation page data processing device
InactiveCN102609511AAvoid mindless clicksThe test result is accurateSpecial data processing applicationsData displayData authenticity
The invention provides a navigation page data processing method, which includes steps: monitoring real-time attention of websites in a navigation page; evaluating the websites based on the real-time attention; and displaying the evaluation in the navigation page. The invention further provides a navigation page data processing device for implementation of the method. Using the navigation page data processing method and the navigation page data processing method device can enrich display information of the navigation page and detect authenticity of data displayed by the websites in the navigation page.
Owner:BEIJING QIHOO TECH CO LTD +1
Information collection system and method for machine manufacturing workshop in production process based on machine vision
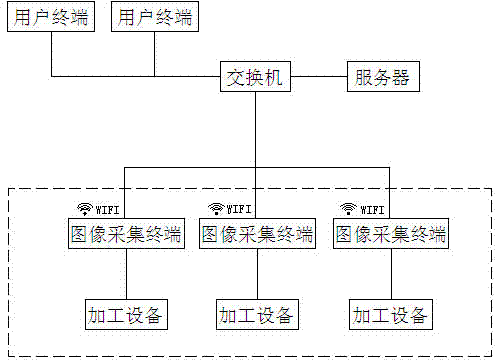
InactiveCN104281132AGuarantee authenticityLow costTotal factory controlProgramme total factory controlData informationCollection system
The invention discloses an information collection system and method for a machine manufacturing workshop in the production process based on machine vision, and belongs to the technical field of automation control and production and management modernization in the manufacturing industry. The system comprises a plurality of processing devices, each processing device is provided with an image collection terminal capable of collecting image data, the image collection terminals are connected with a network switch through Ethernet cables, and the network switch is connected with a data server through an Ethernet cable. The network switch is further connected with user terminals capable of calling data information in the data server through Ethernet cables. The information collection system and method for the machine manufacturing workshop in the production process based on machine vision have the advantages that collected image information is processed and converted into workpiece state information through the method that actual data are matched with server data instead of conducting simple size and color judgment according to the image information, manual counting and form filling are of no need, data authenticity can be guaranteed, the cost is greatly lowered, and the production management efficiency is improved.
Owner:ZHENJIANG COLLEGE
Car performance detecting method and car comprehensive performance evaluating method
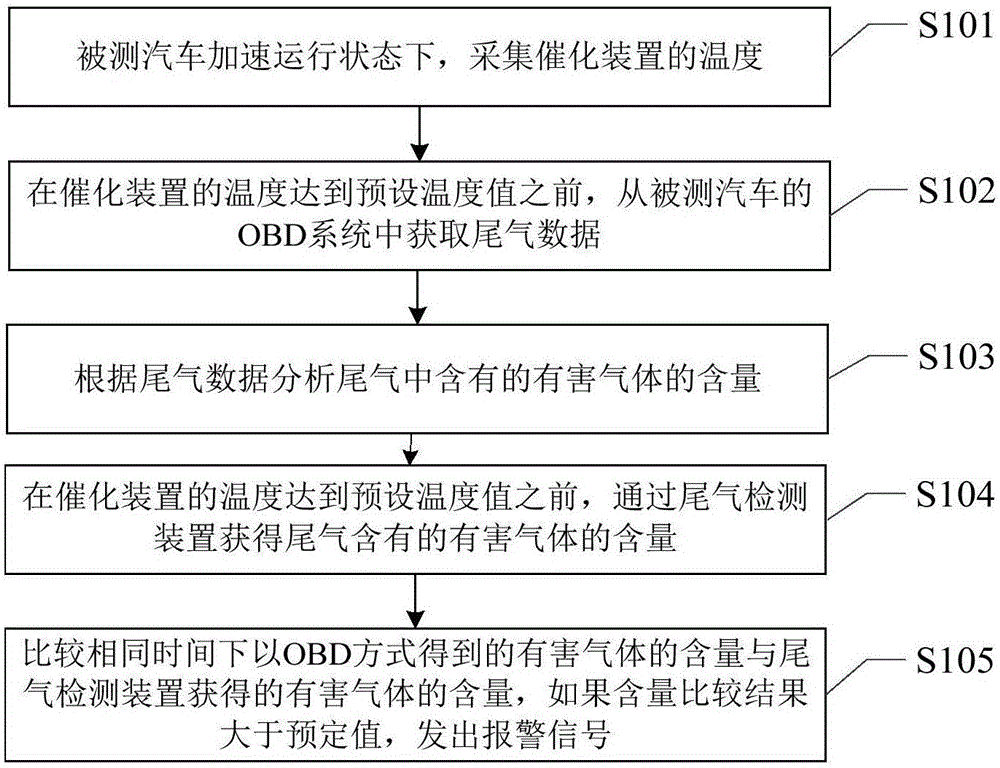
The invention relates to a car performance detecting method and a car comprehensive performance evaluating method. The car performance detecting method includes: collecting the temperature of the catalyzing device of a to-be-detected car when the to-be-detected car is in an operating state; acquiring tail gas data from the OBD system of the to-be-detected car before the temperature of the catalyzing device reaches preset temperature; analyzing the harmful gas content in tail gas according to the tail gas data. The car performance detecting method has the advantages that the tail gas data of the to-be-detected car is obtained through detecting before the temperature of the catalyzing device of the to-be-detected car reaches the preset temperature, the problem that gas such as CO in the tail gas is decomposed at high temperature after the catalyzing device treatment in an existing detecting method and the authenticity of the detecting data is affected can be avoided, and the detected tail gas data is accurate and real. The car comprehensive performance evaluating method has the advantages that the method uses American lemon law as reference, a mathematical model is used to comprehensively consider aspects such as environment protection performance, safety performance, economy and power performance, and the evaluation is objective and real.
Owner:汪林
Deposit method and system based on 5G architecture and block chain
ActiveCN109361688ASolve the problem of authenticityResolve trust issuesTransmissionComplete dataData authenticity
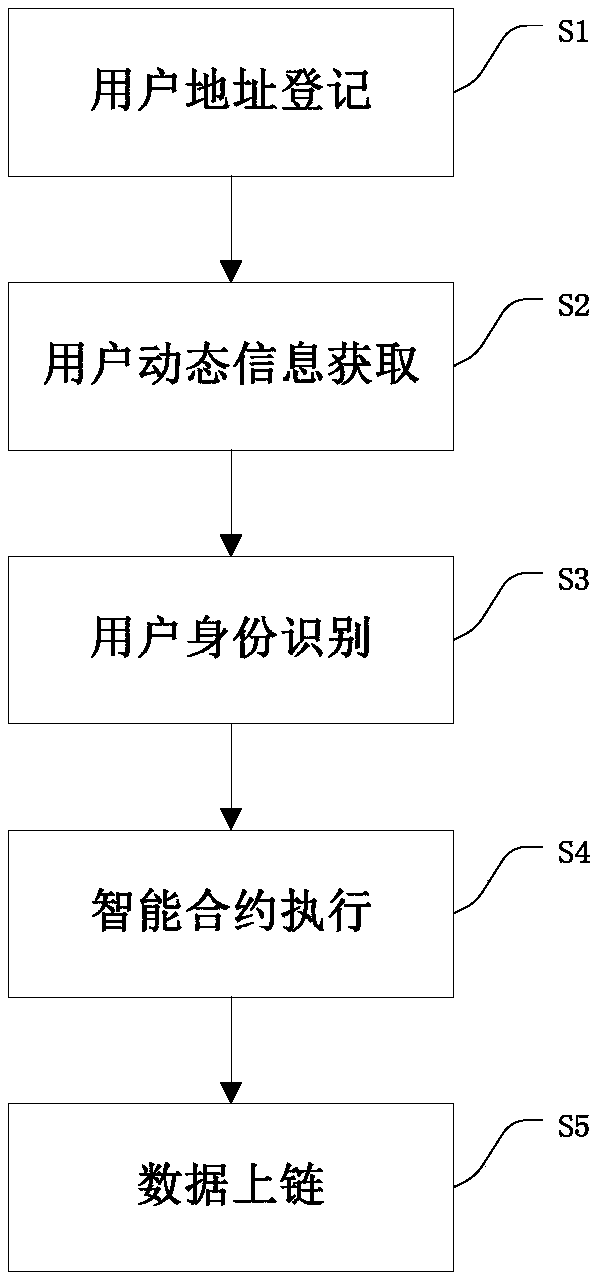
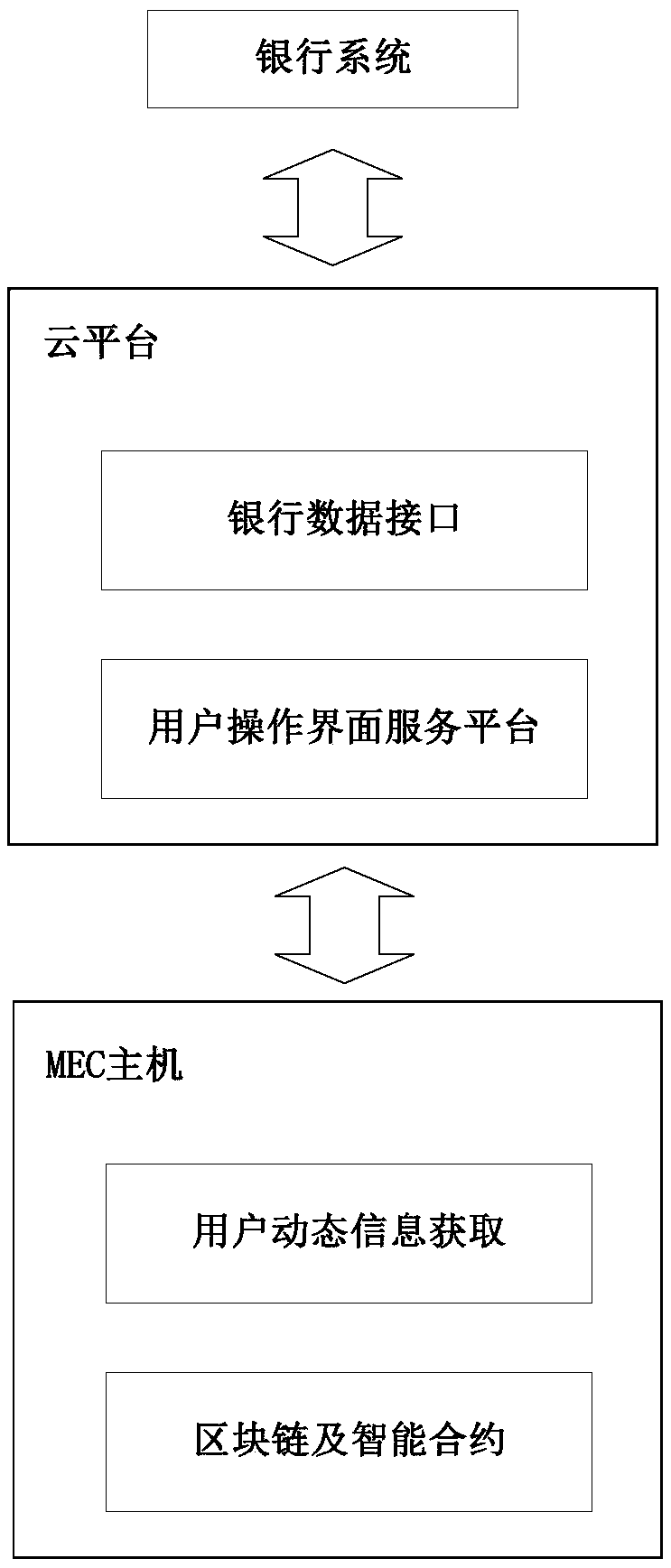
A deposit method and system based on a 5G architecture and a block chain are provided. The deposit method comprises: communication address registration, for communication and / or identification on operator's identity; user's dynamic information acquisition, where a user accesses a 5G platform through a communication address thereof and sends request information, and the 5G platform acquires the request information through a corresponding routing interface, and obtains a communication address of the user by mobile edge computing; user identification, where the 5G platform sends the communicationaddress to a cloud platform, to verify the identity of the user; smart contract execution, where after the identification succeeds, a corresponding smart contract is executed according to the requestinformation; and data upload, where the process of user address registration, user's dynamic information acquisition and smart contract execution is uploaded to the block chain to complete data recording. The method and the system can realize automatic processing of the deposit process, and solve the problems of data authenticity, authenticity of the user identity and trust between users.
Owner:大唐高鸿信息通信(义乌)有限公司
Enterprise risk assessment system based on a plurality of operating data
InactiveCN104966227AHigh precisionOvercoming the problem of low authenticityFinanceData ingestionData authenticity
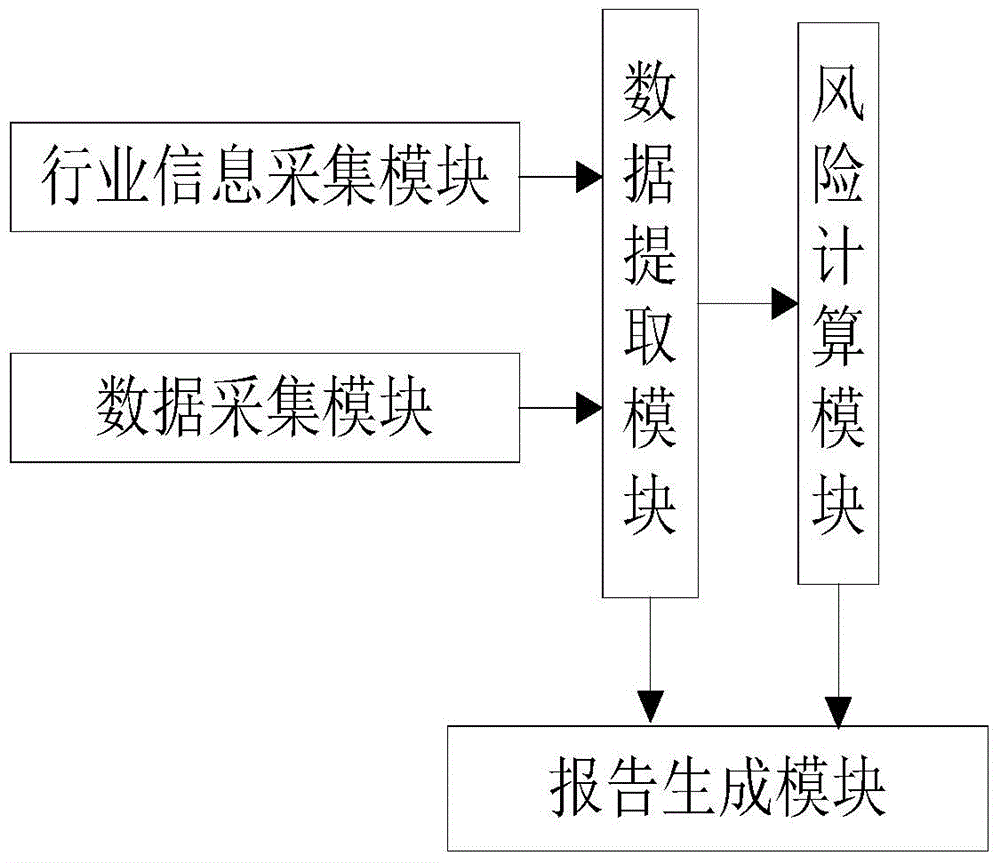
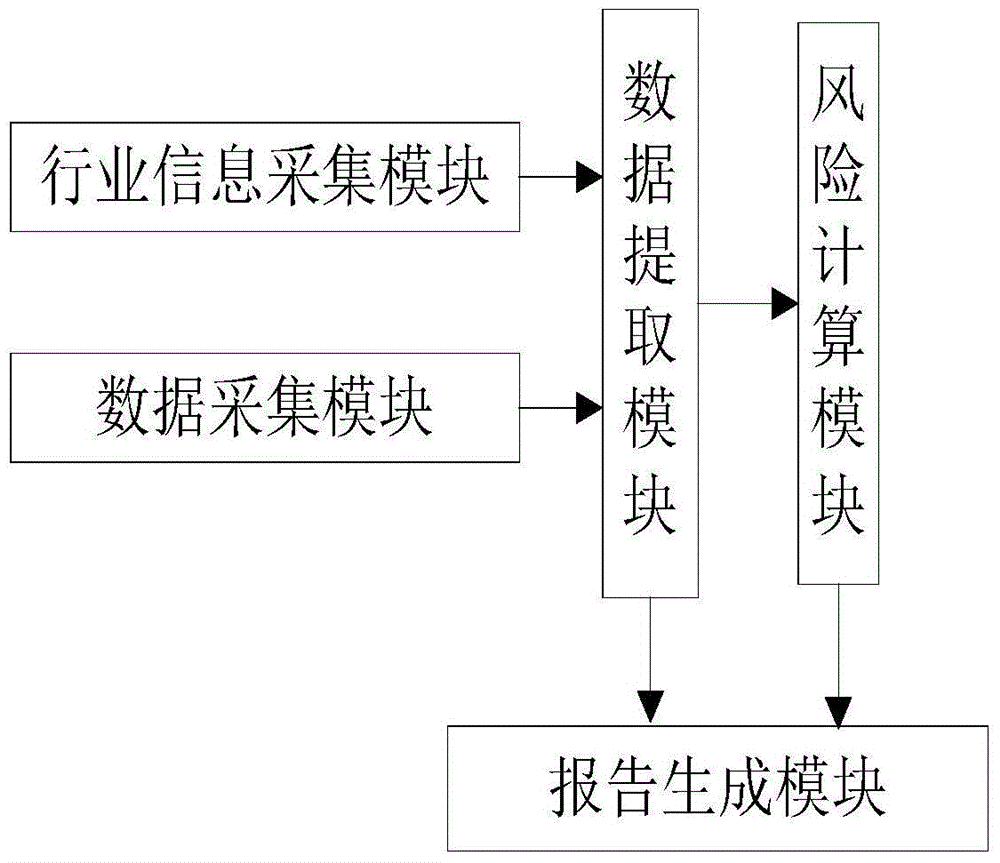
The present invention discloses an enterprise risk assessment system based on a plurality of operating data, comprising a data acquisition module, a data extraction module, a risk calculating module and a report generation module; wherein the data acquisition module is used for acquiring enterprise operating data to be assessed and storing the enterprise operating data to a preset data mirroring area, wherein the enterprise operating data comprises EPR data, HR data and financial data; the data extraction module is connected with the data acquisition module and is used for calling the enterprise operating data from the data mirroring area according to a preset data extraction model to perform processing, obtaining operation reference data, and marking each operation reference data with a trusted value Ai. According to the enterprise risk assessment system of the present invention, more comprehensive data such as the ERP data, the HR data and the financial data are combined to serve as the basis of enterprise risk assessment, thus the problem that enterprises, especially middle and small-sized enterprises, have low authenticity in financial data can be overcome, thereby improving accuracy of the enterprise risk assessment.
Owner:合肥智权信息科技有限公司
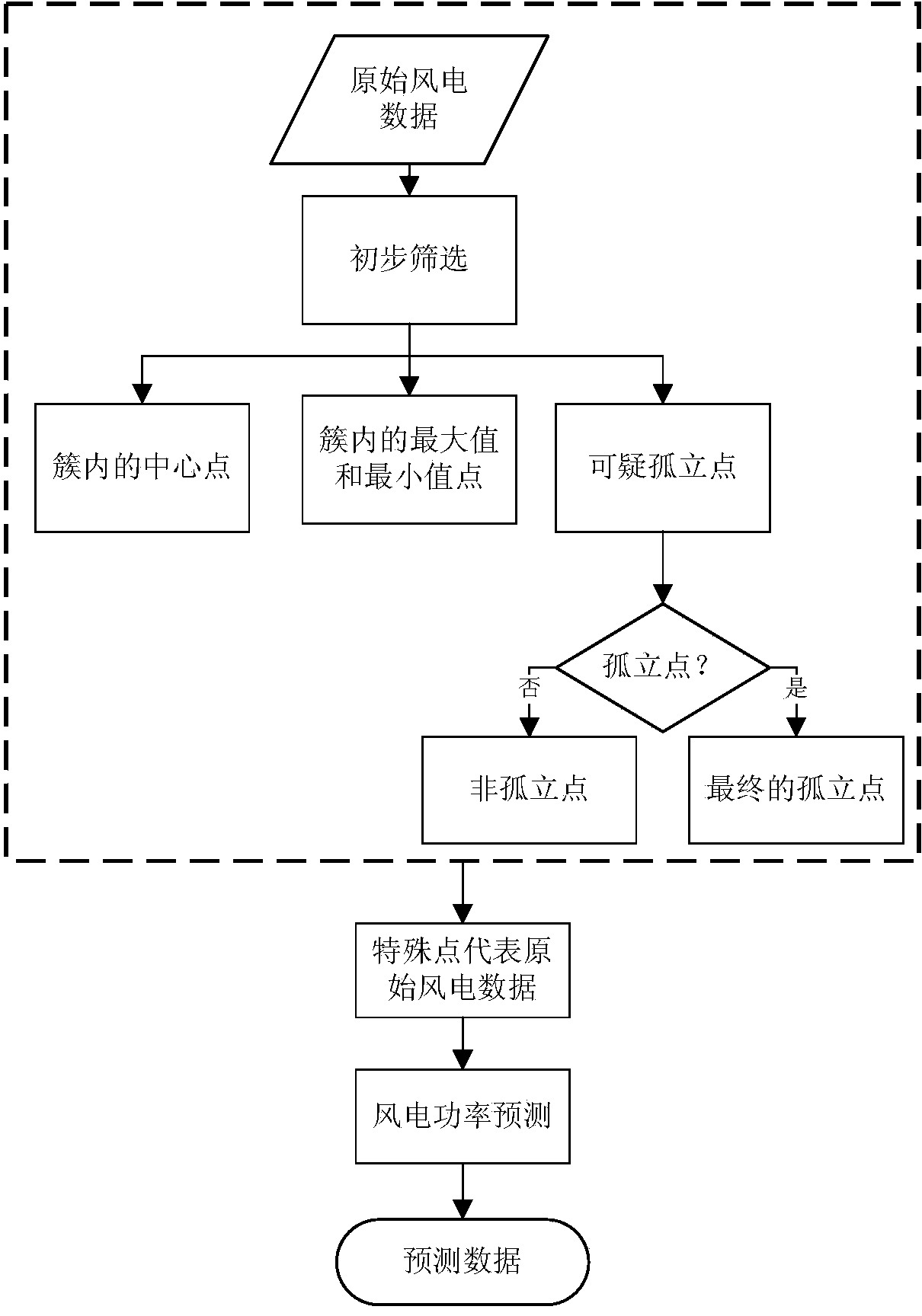
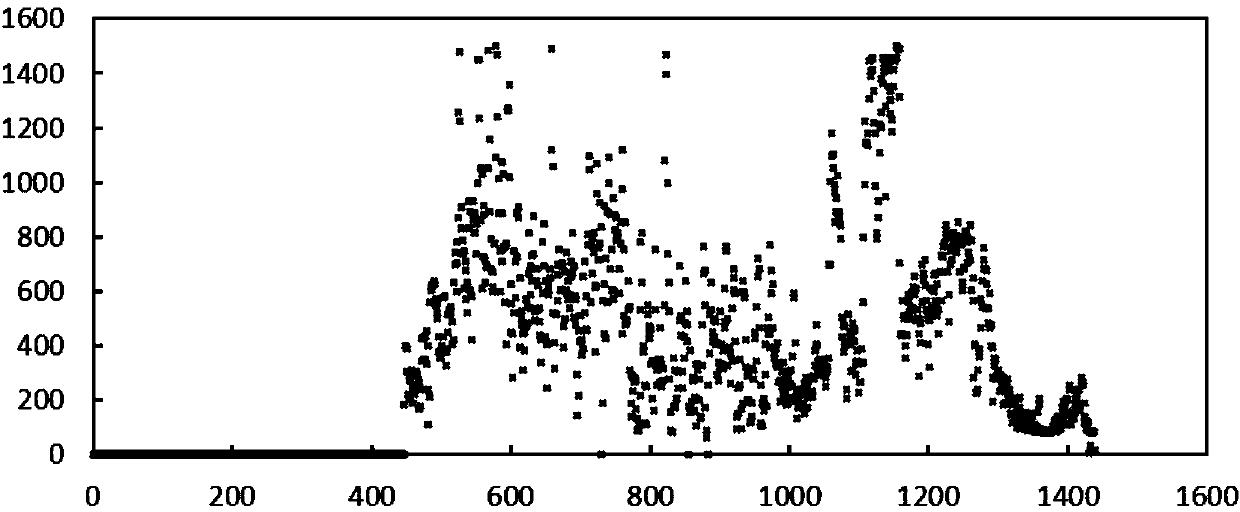
Wind power data preprocessing method, wind power forecast method and system
InactiveCN104182803AImprove forecasting efficiencyReduce data volumeForecastingElectricityPretreatment method
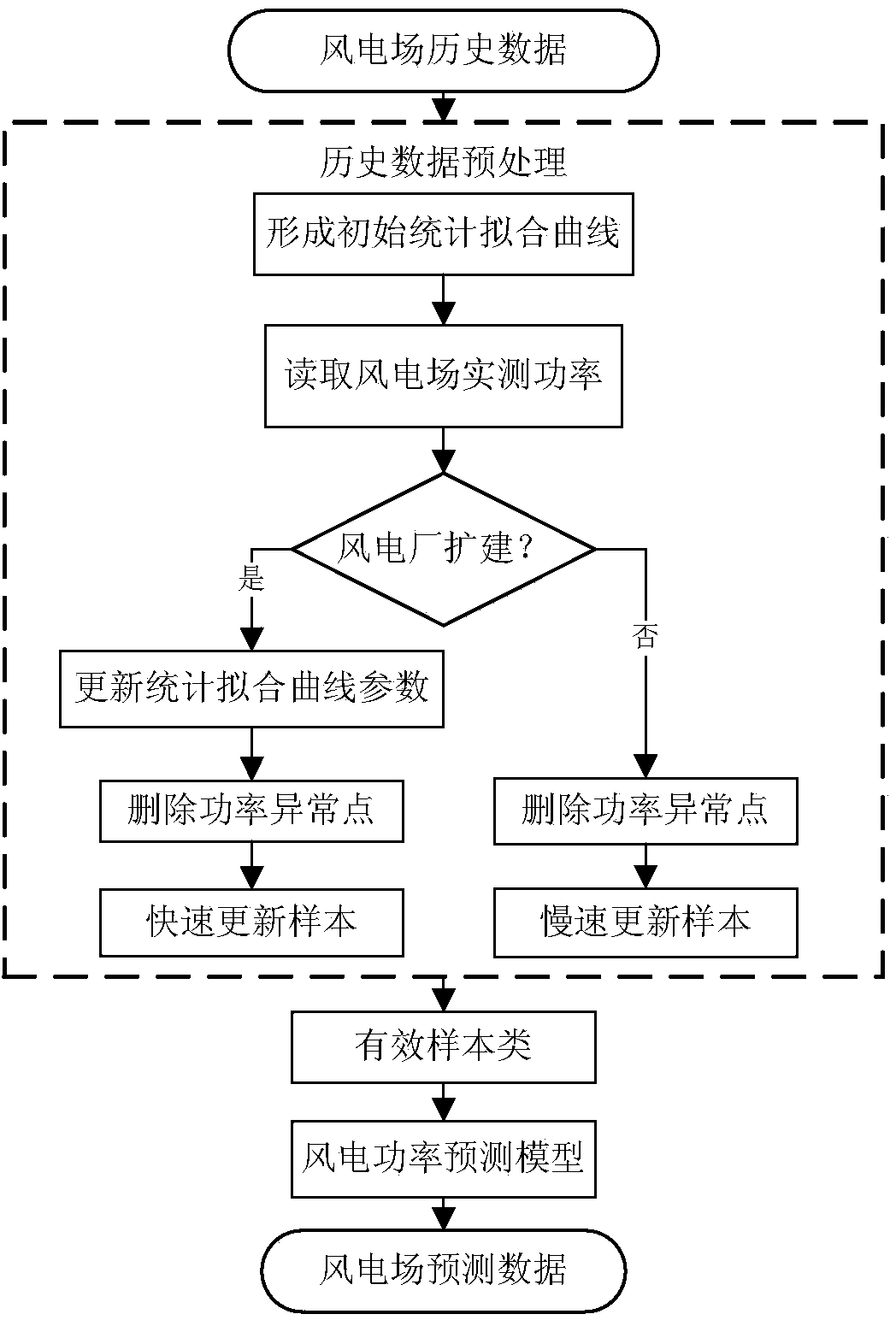
The invention provides a wind power data preprocessing method used for wind power forecast, a wind power forecast method and a system. The wind power data preprocessing method comprises the steps of clustering wind power data so as to form clusters and obtain isolated points outside the clusters, and extracting a center point from each cluster; and based on the difference between the power value of the isolated points outside the clusters and the power value of the points in the clusters, screening out one isolated point or more isolated points from the isolated points outside the clusters. The wind power forecast method comprises the steps of selecting partial data from collected wind power data by the wind power data preprocessing method; and forecasting wind power information according to the selected data. According to the method, the forecast efficiency of the wind power is improved due to extraction of special points from original wind power data; and data authenticity is guaranteed in extraction of the special points, so that the forecast precision of the wind power is improved.
Owner:NORTHEAST DIANLI UNIVERSITY
Archive management method and device based on block chain and storage medium
PendingCN110543545AQuick checkAccurate verificationDigital data protectionText database indexingData authenticityChain network
The invention provides an archive management method and device based on a block chain and a storage medium. The method comprises the following steps: in response to a storage request for a target file, storing first file information corresponding to the target file to a block chain network; receiving a first verification request for first archive data of the target archive, wherein the first verification request is used for requesting to verify the authenticity of the first archive data; determining second file information of the target file based on the first verification request; sending a second verification request carrying the second archive information to the block chain network, so that the block chain network determines and returns a verification result representing the authenticity of the first archive data based on the first archive information and the second archive information; and sending the verification result returned by the block chain network. According to the invention, the authenticity of the archive data can be quickly and accurately verified.
Owner:TENCENT TECH (SHENZHEN) CO LTD
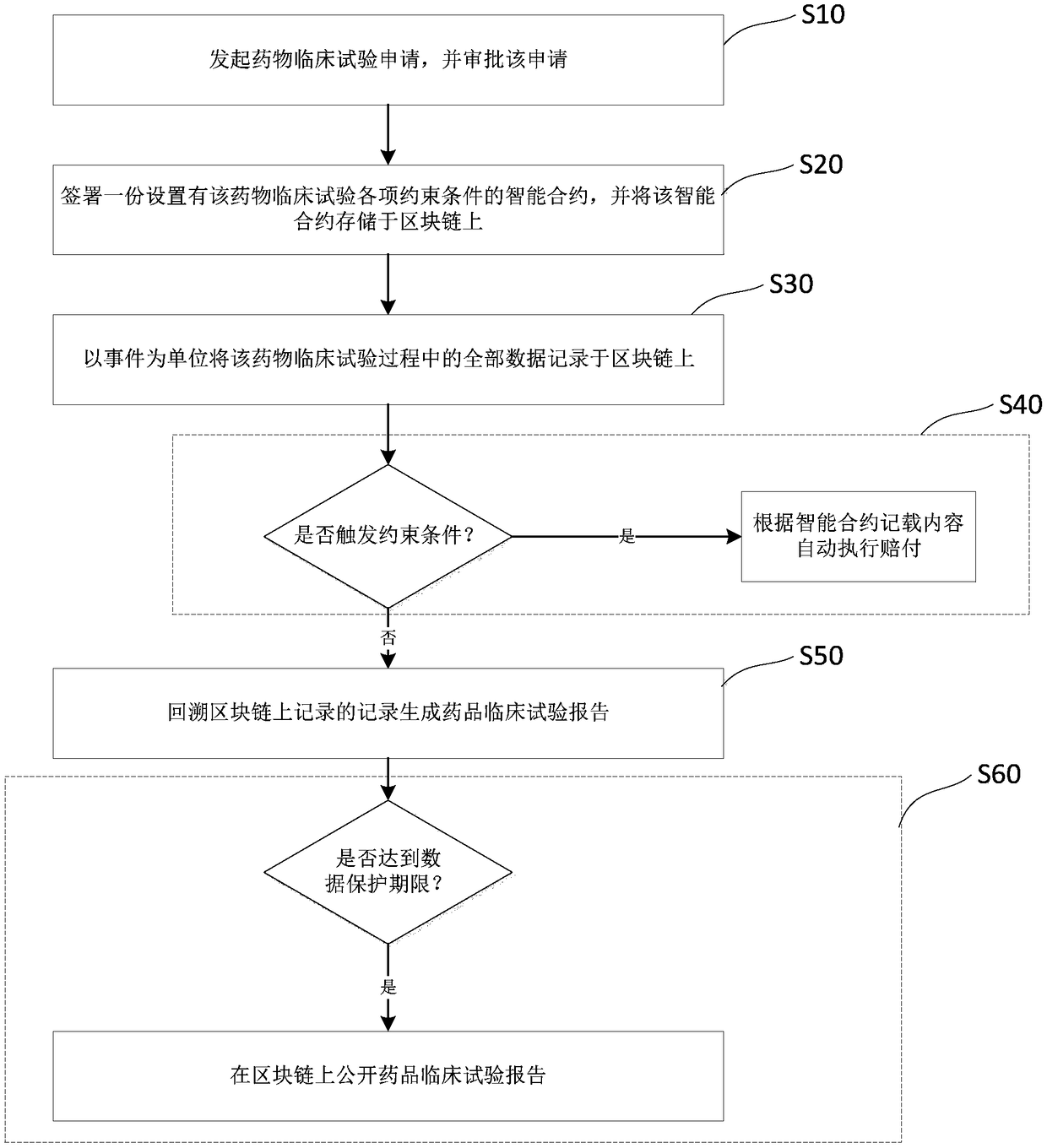
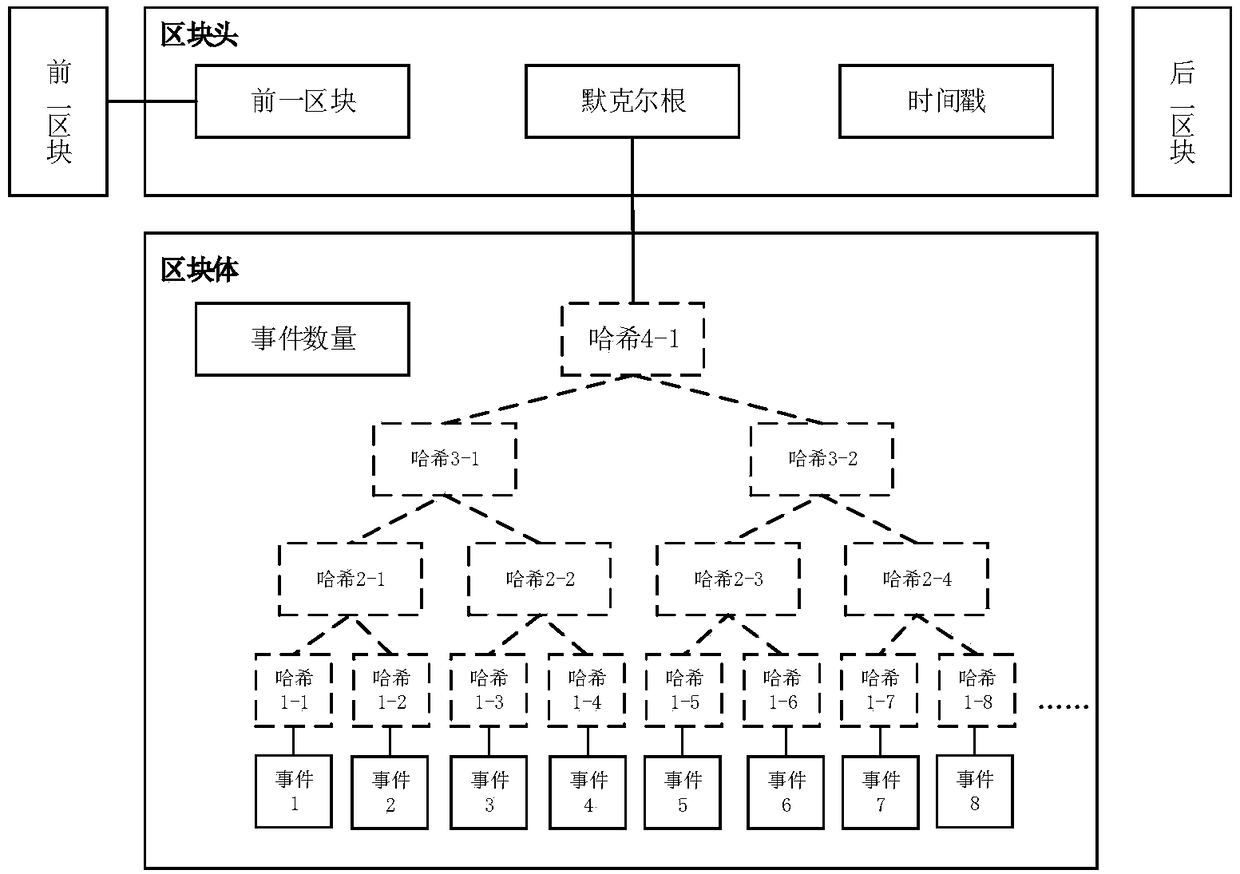
Drug clinical trial monitoring method and system based on block chain, device and medium
InactiveCN109065101AGuaranteed to be true and reliableProtection of rights and interestsDrug referencesSpecial data processing applicationsData authenticityEvent trigger
The invention discloses a drug clinical trial monitoring method and system based on the block chain, a device and a medium and relates to the technical field of the drug clinical trial. The block chain technology is introduced, test records are maintained jointly by participants in the drug trial and stored in a block chain in a chronological order through the chain structure, through use of the block chain, characteristics can be only added and are non-tamperable and deleteable, and data authenticity and validity are guaranteed; rights of subjects are better protected through the intelligentcontract technology, an informed consent is stored in the block chain in the form of an intelligent contract, during the test, the physiological data of the subjects are obtained in real time throughdocking with the medical device, once the event triggering a contract suspension clause is monitored, payment is automatically executed according to the contract terms; through the decentralized storage idea, defects including large cost of data storage space, incomplete privacy protection and weak anti-attack ability existing in a centralized drug test management system in the prior art are solved.
Owner:INST OF SOFTWARE APPL TECH GUANGZHOU & CHINESE ACAD OF SCI
Full-automatic COD analysis meter
InactiveCN106290353AGuarantee authenticityReduce manual operationsChemical analysis using titrationMaterial analysis by observing effect on chemical indicatorData authenticityBiochemical engineering
The invention relates to a full-automatic COD analysis meter. The full-automatic COD analysis meter comprises a heating unit, a condensation unit, a clamping unit and a titration unit which are arranged in sequence. A liquid adding unit is arranged beside the heating unit and the condensation unit. An automatic equipment testing unit is arranged beside the condensation unit. The full-automatic COD analysis meter has the advantages that due to the arrangement of the heating unit, the condensation unit, the clamping unit, the titration unit and the liquid adding unit, manual operations are reduced, and the automatic degree is high; in addition, due to the arrangement of the automatic equipment detection unit, automatic detection can be performed, and experiment data authenticity is ensured.
Owner:海安华达石油仪器有限公司
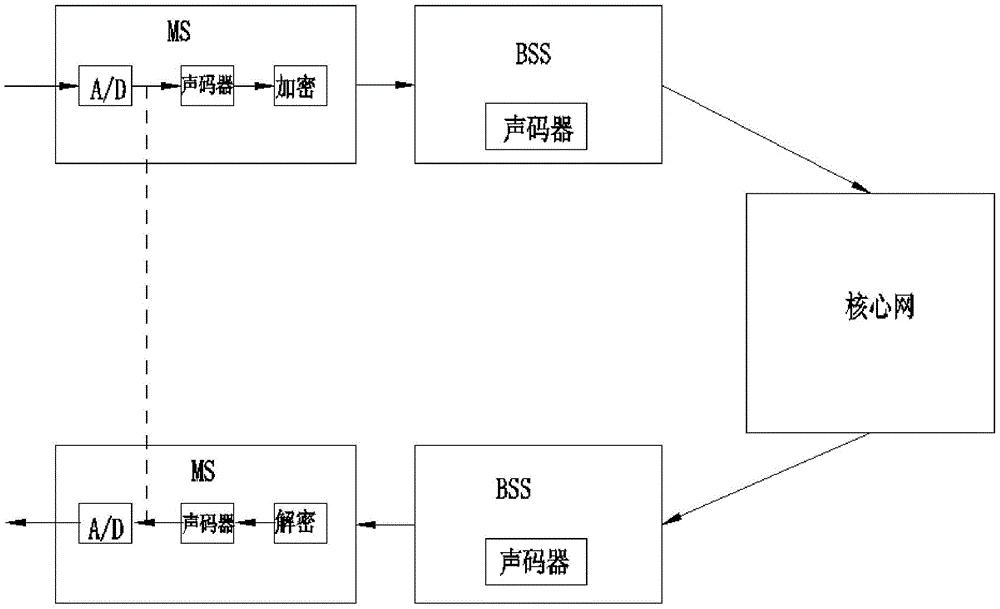
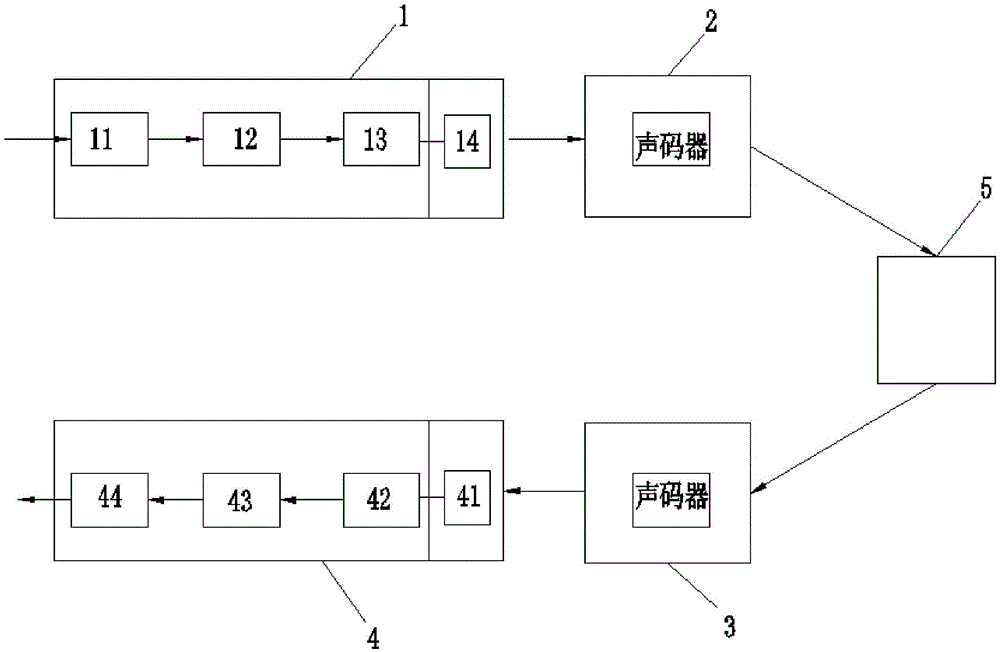
End-to-end voice encryption communication method and device for mobile terminals
InactiveCN105471899AImprove privacyIncrease anti-eavesdroppingTransmissionData authenticityVoice communication
The invention provides an end-to-end voice encryption communication method and an end-to-end voice encryption communication device for mobile terminals. The method comprises the following steps of A / D data collection, specifically including dividing input voice communication signals into voice frames with fixed length by A / D conversion; encryption, specifically including dynamically obtaining a key through operation of an access point, and then encrypting the voice frames; modulation, specifically including synthesizing encrypted data into voice signals by a modulator; vocoder processing and base station transmission, specifically including performing coding, encryption and other treatments on the synthesized voice signals by a mobile communication vocoder, after coding, sending to a base station by a terminal through a cell channel, and then transmitting to a receiving terminal by the base station; demodulation, specifically including demodulating the voice signals into encrypted voice frames by a demodulator; and decryption, specifically including decrypting the encrypted voice frames according to the algorithm and key appointed by two parties in an end-to-end manner. The end-to-end voice encryption communication method and device for mobile terminals is simple in structure, reasonable in design, capable of implementing based on the inherent coding / decoding and encryption algorithm of the mobile communication protocol, and low in distortion rate, and can pass through the voice data authenticity detection of the base station.
Owner:ZHEJIANG TECHAIN ELECTRONICS TECH CO LTD
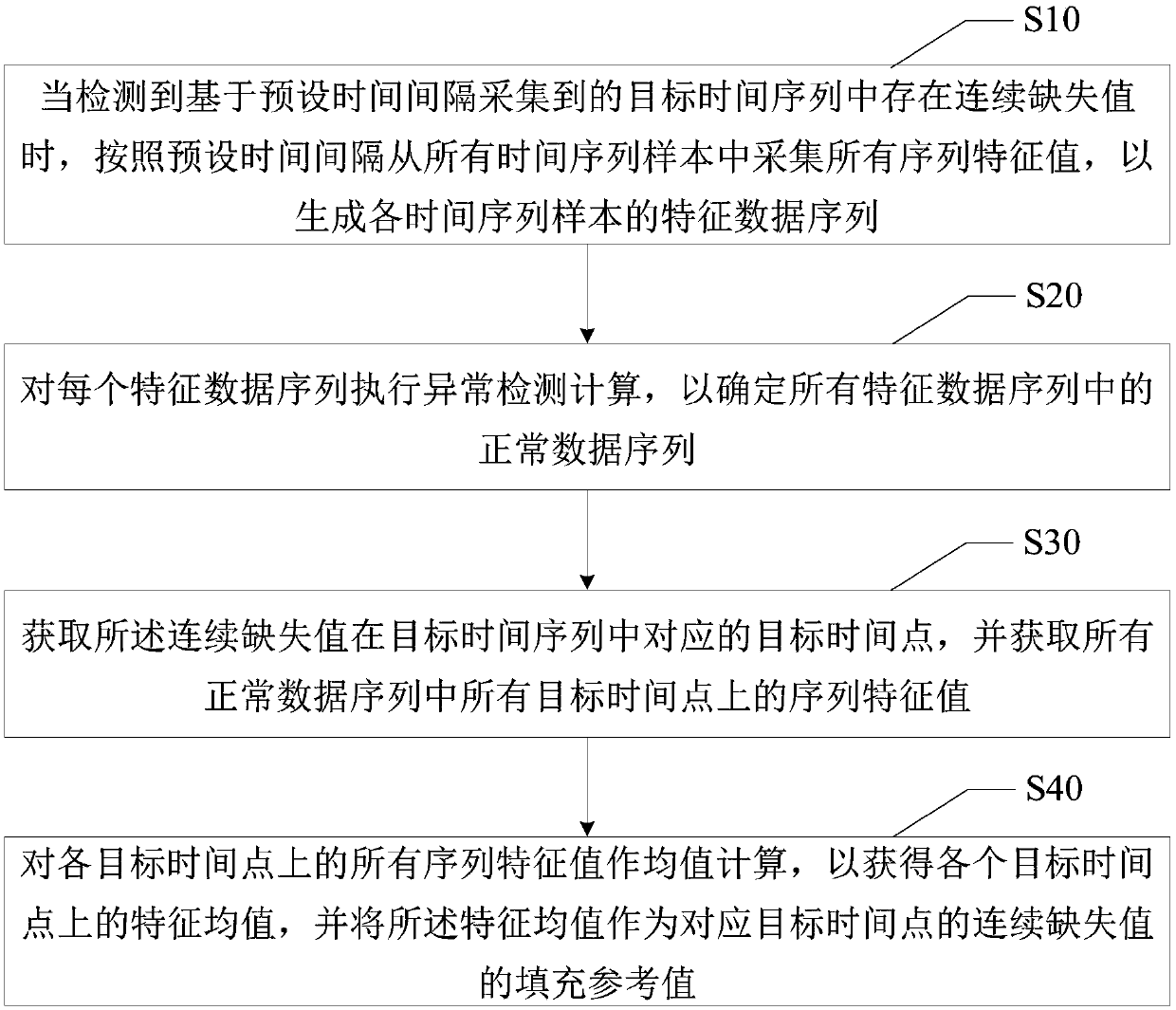
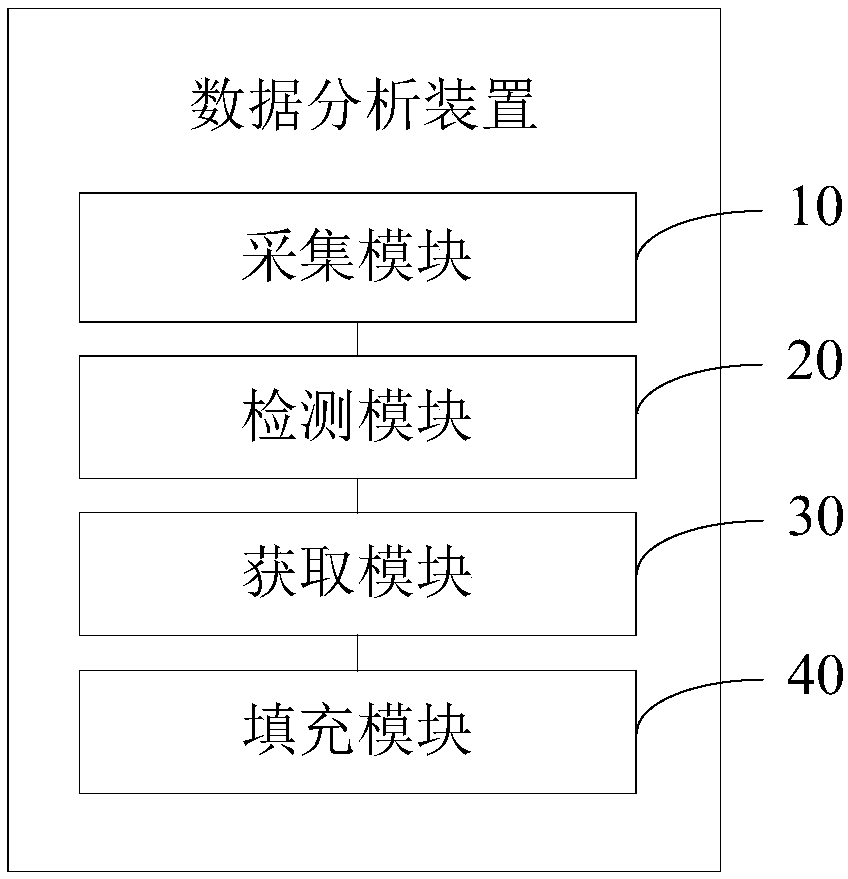
Continuous missing value filling method, data analysis device, terminal and storage medium
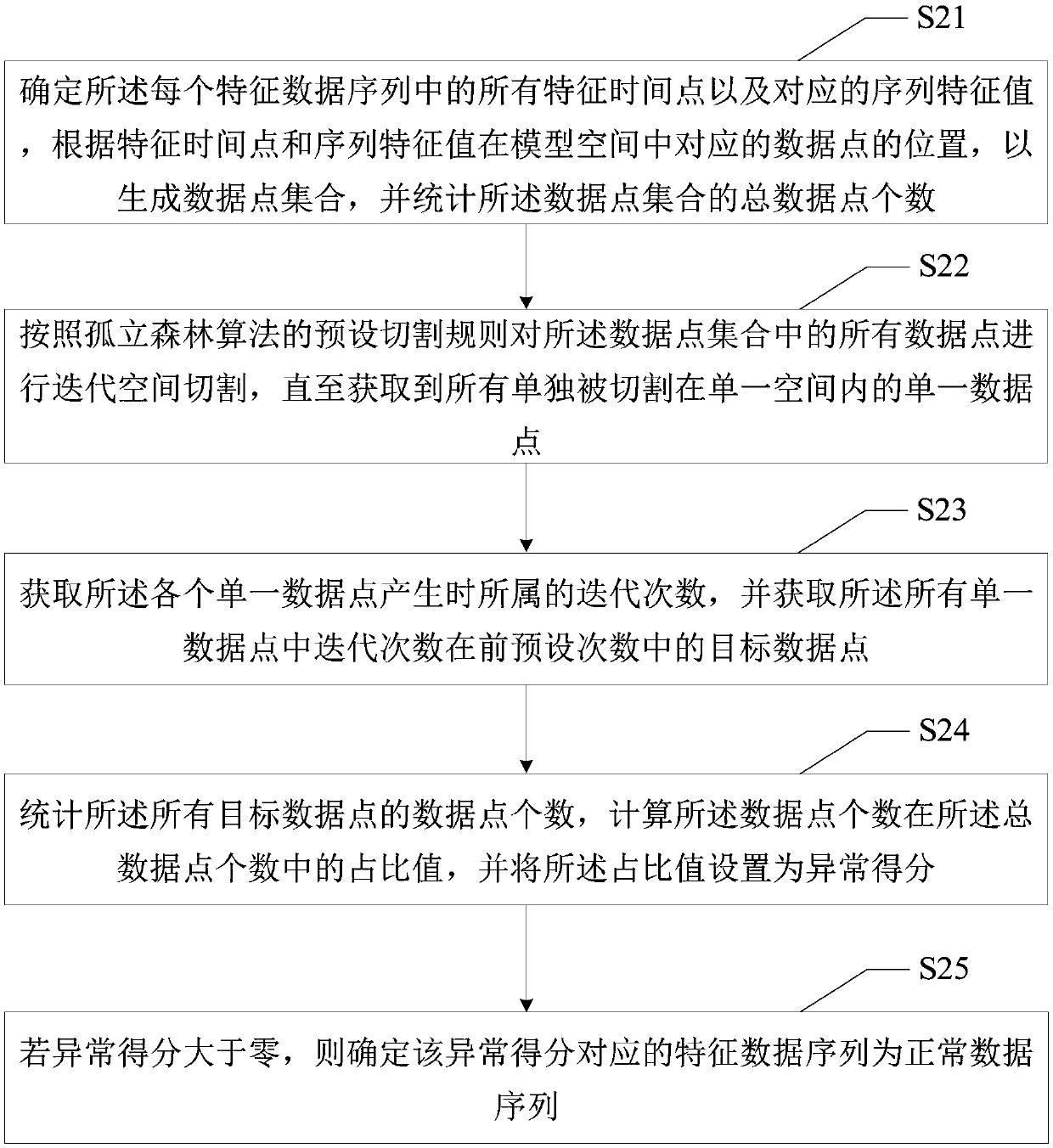
PendingCN109947812APreserve distribution propertiesEnsure data reliabilityDigital data information retrievalComplex mathematical operationsAlgorithmAnomaly detection
The invention discloses a continuous missing value filling method, a data analysis device, a data analysis terminal and a computer readable storage medium. The continuous missing value filling methodcomprises the steps that if it is detected that continuous missing values exist in a target time sequence collected on the basis of a preset time interval, collecting all sequence characteristic values from all time sequence samples according to the preset time interval, so that a characteristic data sequence of all the time sequence samples is generated; Performing anomaly detection calculation on each feature data sequence to determine normal data sequences in all the feature data sequences; Obtaining corresponding target time points of the continuous missing value in a target time sequence,and obtaining sequence characteristic values on all the target time points in all the normal data sequences; And carrying out mean value calculation on all sequence characteristic values on each target time point, and taking the characteristic mean value as a filling reference value of the continuous missing value of the corresponding target time point. The data authenticity of the time sequenceis improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Data processing method and device
ActiveCN107748752AEnsure consistencyGuarantee authenticitySpecial data processing applicationsData setData authenticity
The invention relates to the technical field of big data, in particular relates to a data processing method and device, and the problem that data authenticity cannot be guaranteed during data processing by a big data platform in the prior art is solved. The data processing method is that an initial data set is extracted from a designated source system by a designated tool and loaded, and then theloaded initial data set is divided into a plurality of initial data subsets; whether initial data bars are required for modification is determined for the current initial data subsets by batches; increment combination operation is executed to to-be-modified initial data subsets, so a corresponding target data subset is acquired; an incidence relation is built for a plurality of target data bars contained in each acquired target data subset according to a preset business logic rule; therefore, a designated big data platform can be linked with the designated source system via the designated tool; besides, even the data are loaded to the designated big data platform and then modified, data consistency can still be guaranteed via the increment combination operation; therefore, data authenticity can be guaranteed and user experience can be improved.
Owner:新智云数据服务有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com