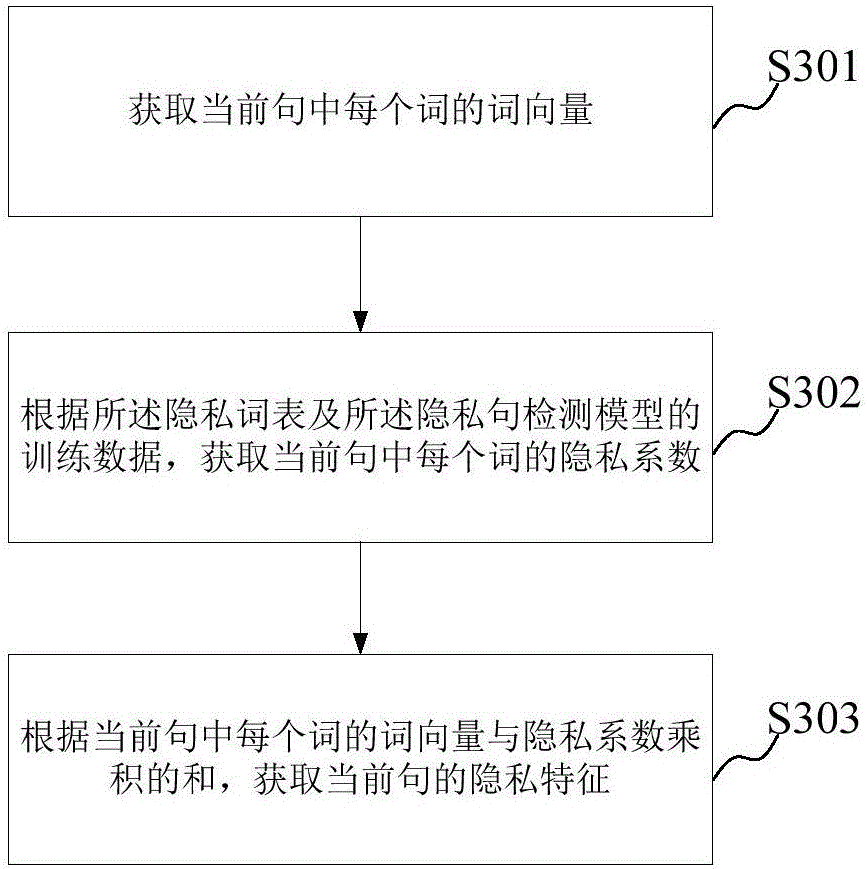
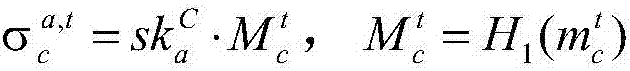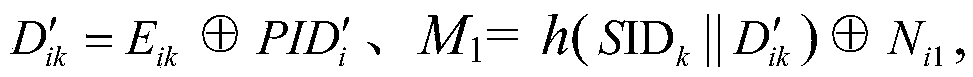Patents
Literature
1072results about How to "Protection of rights and interests" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
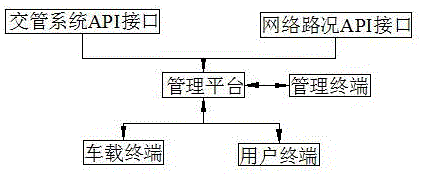
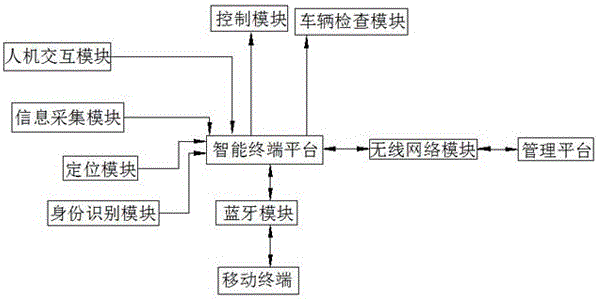
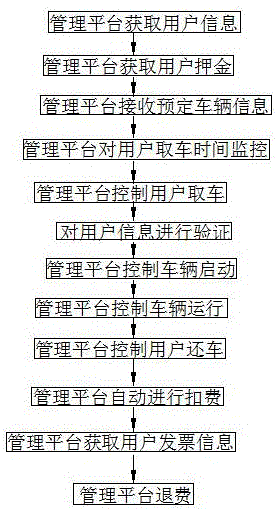
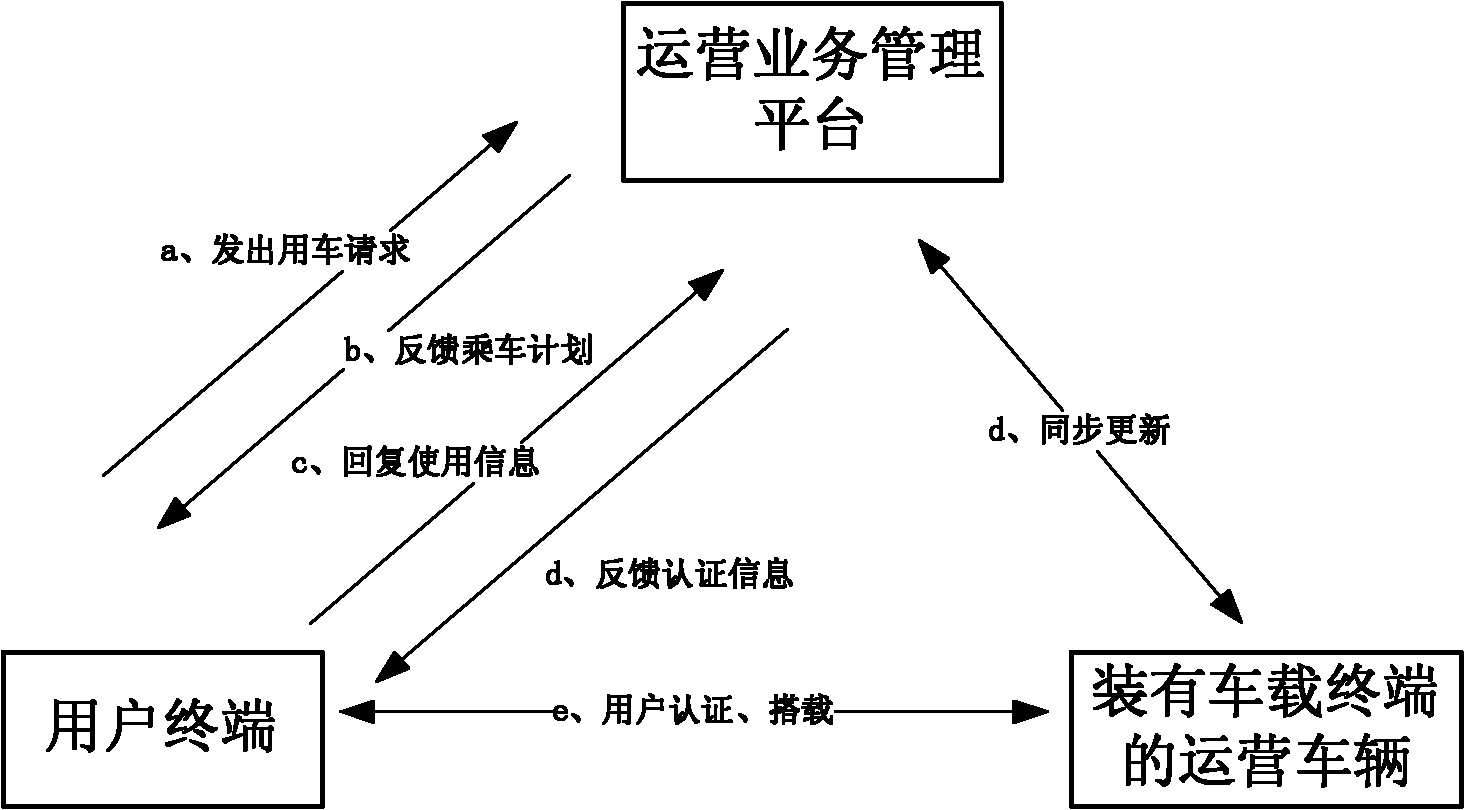
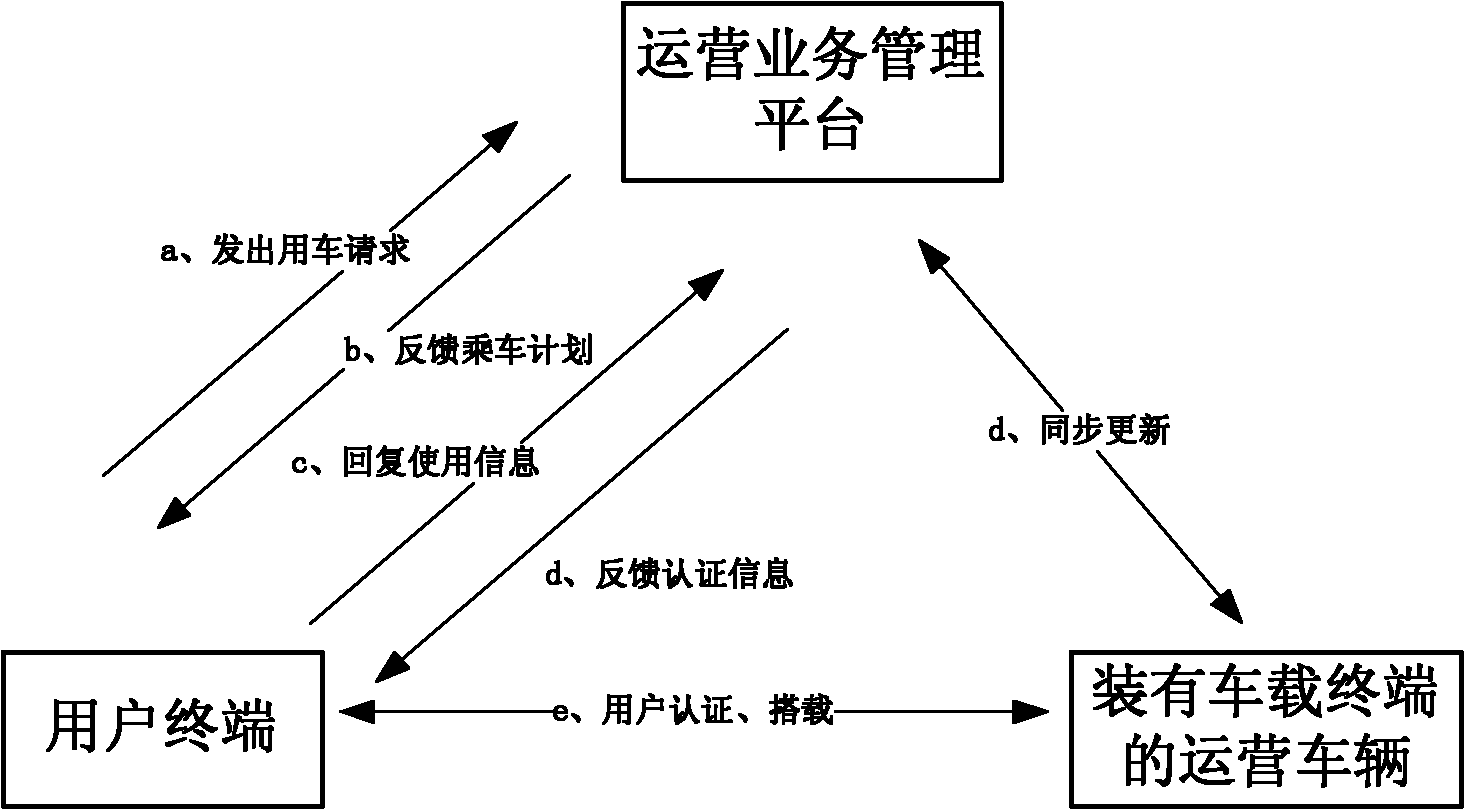
Unattended electric car rental system and rental method
ActiveCN104992364AEasy to useProtect the rights and interests of usersBuying/selling/leasing transactionsData transmissionAutomatic deduction
Provided are an unattended electric car rental system and a rental method. The system comprises a vehicle-mounted terminal, a user terminal and a management platform; and the vehicle-mounted terminal and the user terminal both perform data transmission with the management platform, and a wireless connection is formed between the vehicle-mounted terminal and the user terminal. The method comprises steps of: the management platform obtaining user information, obtaining user deposit, receiving information of a reserved vehicle, monitoring a time when a user picks up the vehicle, controlling the user to pick up the vehicle, verifying the user information, controlling starting up and running of the vehicle, controlling the user to return the vehicle, the management platform performing automatic deductions, and introducing a whole process of implementation of vehicle renting. The system provided by the invention is novel in design, and is convenient for the user to use; a rental process does not need the participation of staff members, thereby implementing unmanned renting. The method provided by the invention provides more convenience for the user in a renting process, and real-time feedback of information enables the user to timely obtain related information, thereby ensuring rights and interests of rental enterprises and users.
Owner:联世海富威海智慧科技有限公司
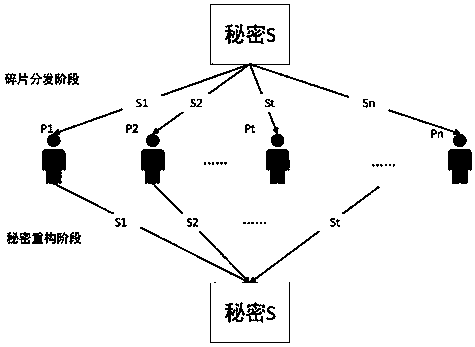
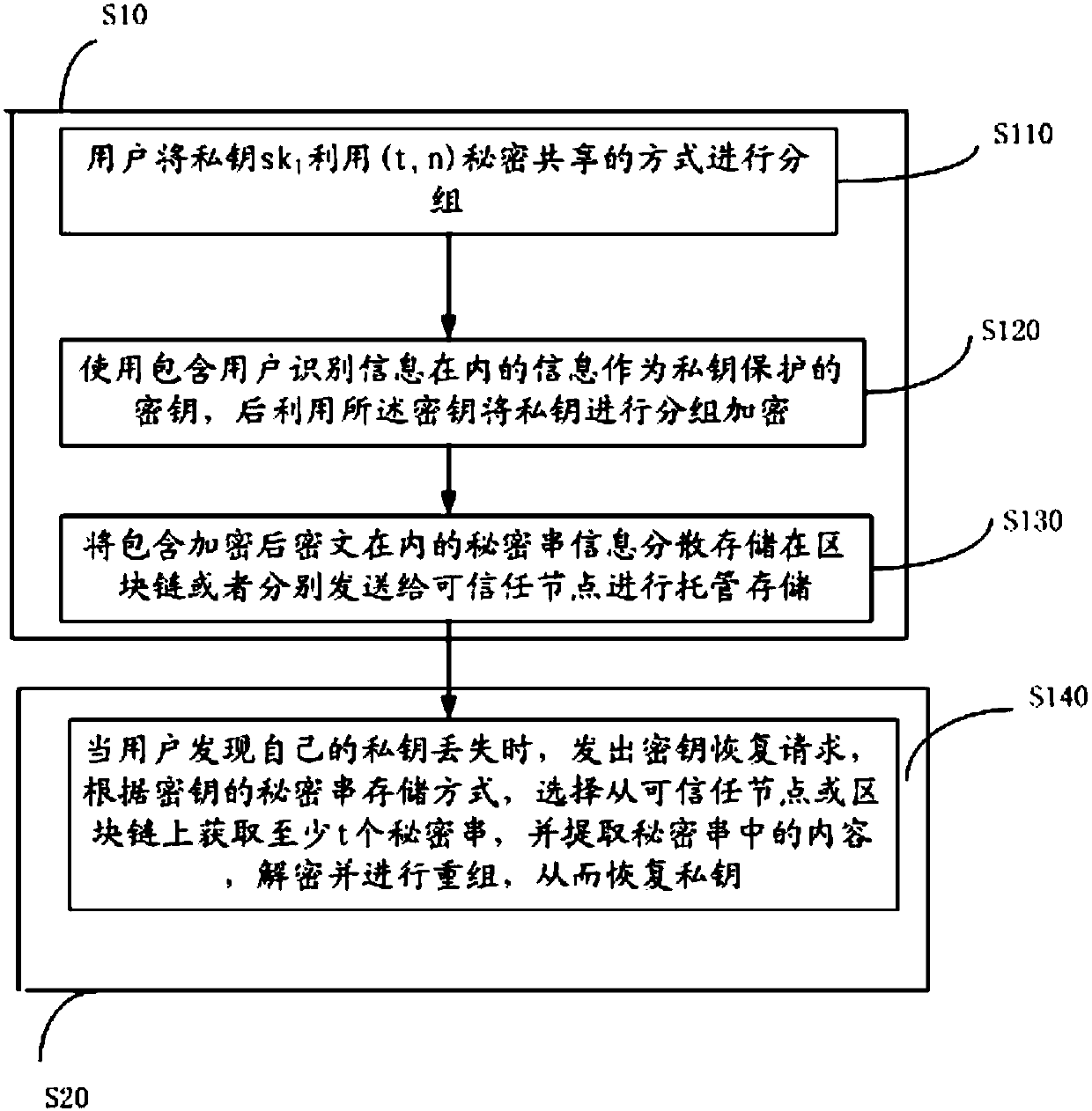
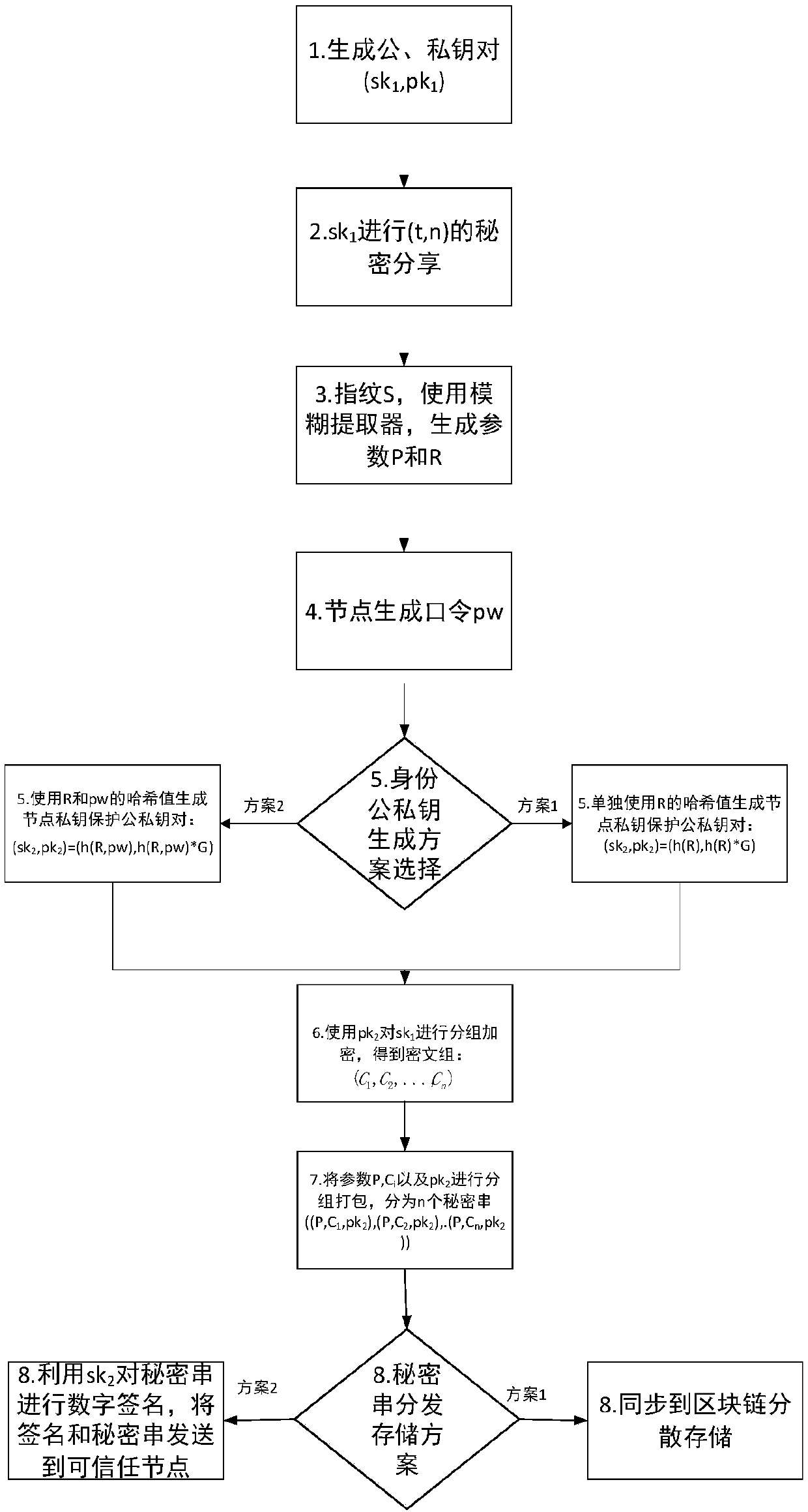
Block chain key trusteeship and recovery method and device based on secrecy sharing technology
InactiveCN107623569ASafekeepingSafe recoveryKey distribution for secure communicationRecovery methodRestoration method
The invention discloses a block chain key trusteeship and recovery method and device based on a secrecy sharing technology. The method comprises the steps that A1, a user groups a private key sk1 in a(t, n) secrecy sharing mode, wherein the n is the number of fragments of shared secrecies obtained by splitting the private key, the t is the minimum number of the fragments for recovery of the private key, and the t is greater than or equal to 2 and is smaller than or equal to the n; A2, information containing user identification information is taken as a private key protection key, and then grouping encryption is carried out on the private key through utilization of the key; and A3, secrecy string information containing encrypted ciphertexts is dispersely stored to a block chain or is sentto trusted nodes for trusteeship and storage, when the user discovers that own private key is lost, a key recovery request is generated, at least t secrecy strings are obtained from the trusted nodesor the block chain in a secrecy string storage mode of the key, and the content in the secrecy strings is extracted, decrypted and recombined, so the private key is recovered. According to the methodand the device, the secrecy sharing technology is applied to a block chain scene for the first time, thereby solving the private key trusteeship and recovery security problem.
Owner:JUZIX TECH SHENZHEN CO LTD
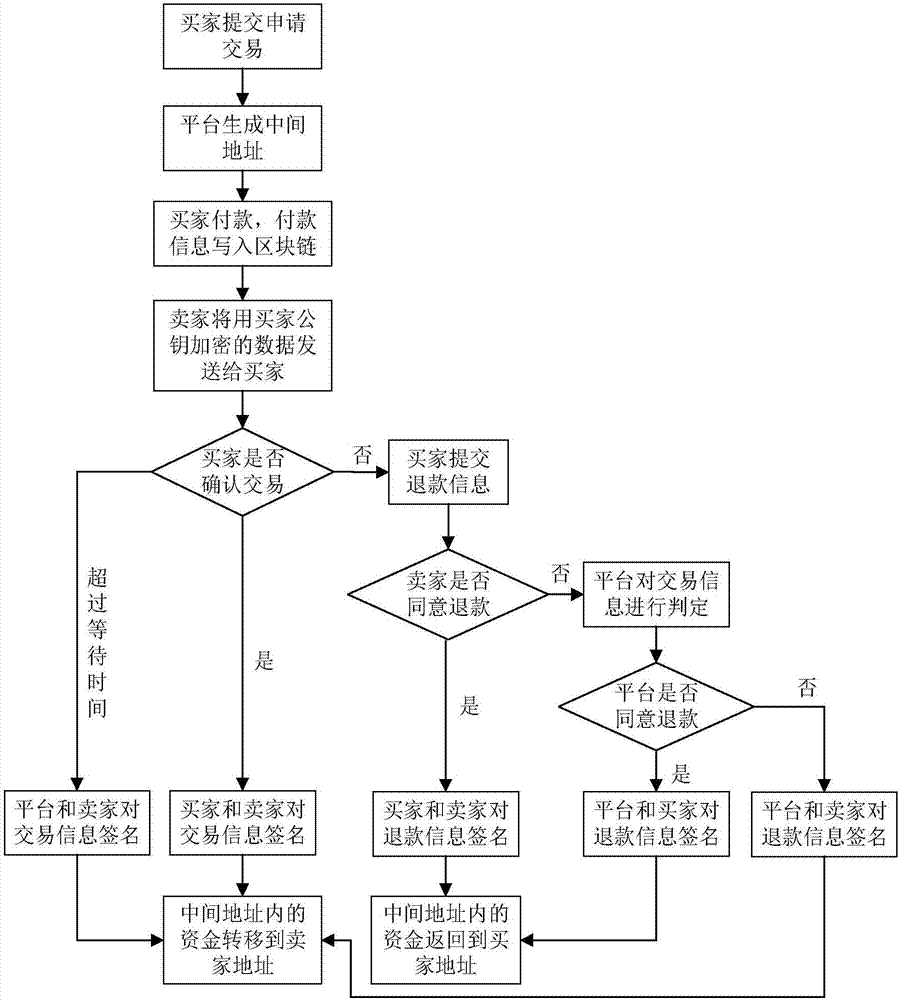
Multi-signature transaction information processing method for data transaction platform based on block chain
ActiveCN107038578AEnsure information securityEnsure safetyPayment protocolsInformation processingPayment
The invention discloses a multi-signature transaction information processing method for a data transaction platform based on a block chain. Each of a buyer and a seller generates a transaction key pair at self client, and the data transaction platform generates and distributes a single transaction key pair for each transaction process; the seller releases data to be transacted on the block chain via the data transaction platform; after the buyer submits a transaction application, an intermediate address is generated according to a three-party public key, money is transferred to the intermediate address after payment, and the seller receives the money, writes the money into the block chain, then encrypts data and sends the encrypted data to the buyer; after the buyer receives the data, if transaction is acknowledged, the double parties sign, and the money is transferred to the address of the seller; and if objection exists, the data transaction platform makes a judgment, and determines to transfer the money to the buyer or the seller according to the judgment result. Data and transaction information during transaction of the double parties are processed in a special regional chain manner, and meanwhile, the data transaction platform cannot embezzle the transaction money, so that the security of digital assets during transaction is further guaranteed.
Owner:浙江数秦科技有限公司
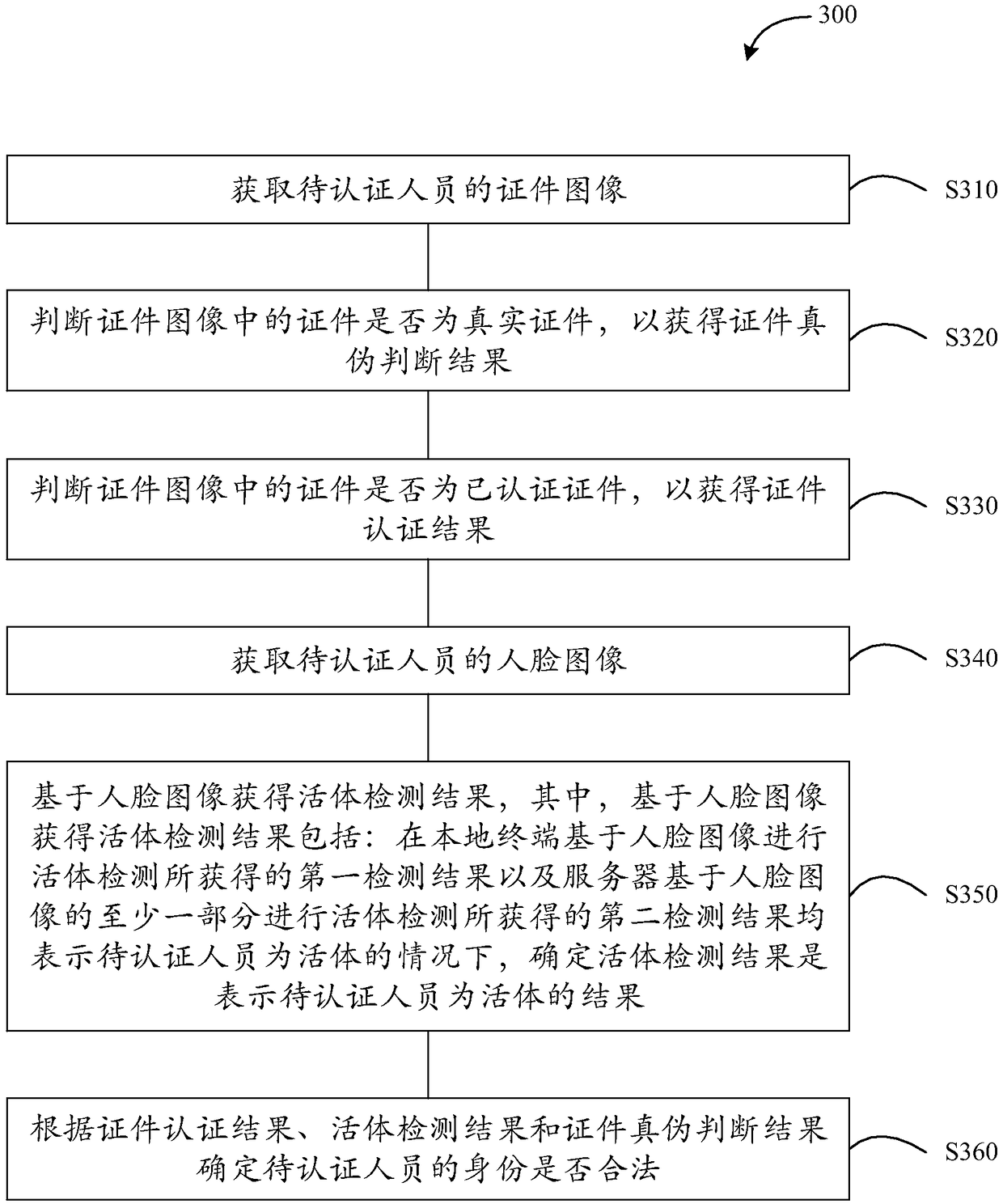
Identity authentication method and apparatus
ActiveCN106778525AImprove securityProtection of rights and interestsNeural architecturesSpoof detectionPasswordUser authentication
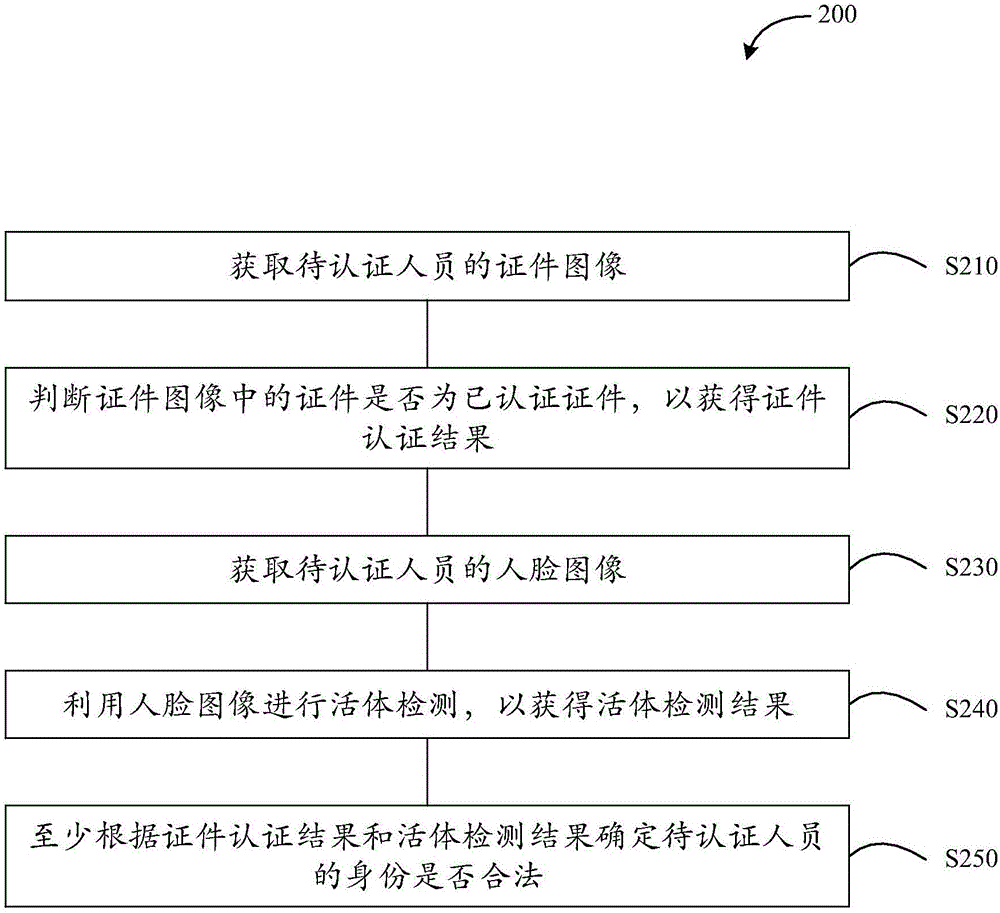
Embodiments of the invention provide an identity authentication method and apparatus. The method comprises the steps of obtaining a certificate image of to-be-authenticated personnel; judging whether a certificate in the certificate image is an authenticated certificate or not, thereby obtaining a certificate authentication result; obtaining a human face image of the to-be-authenticated personnel; performing living body detection by utilizing the human face image, thereby obtaining a living body detection result; and determining whether an identity of the to-be-authenticated personnel is legal or not at least according to the certificate authentication result and the living body detection result. According to the method and the apparatus, whether the identity of the to-be-authenticated personnel is legal or not is determined in combination with the authenticated certificate judgment and the living body detection, so that compared with a conventional mode of performing identity authentication based on a password or the certificate only, the identity authentication method and apparatus has the advantages that the authentication result is more accurate, and the security of user authentication can be improved, so that user rights and interests can be effectively ensured.
Owner:BEIJING KUANGSHI TECH +1
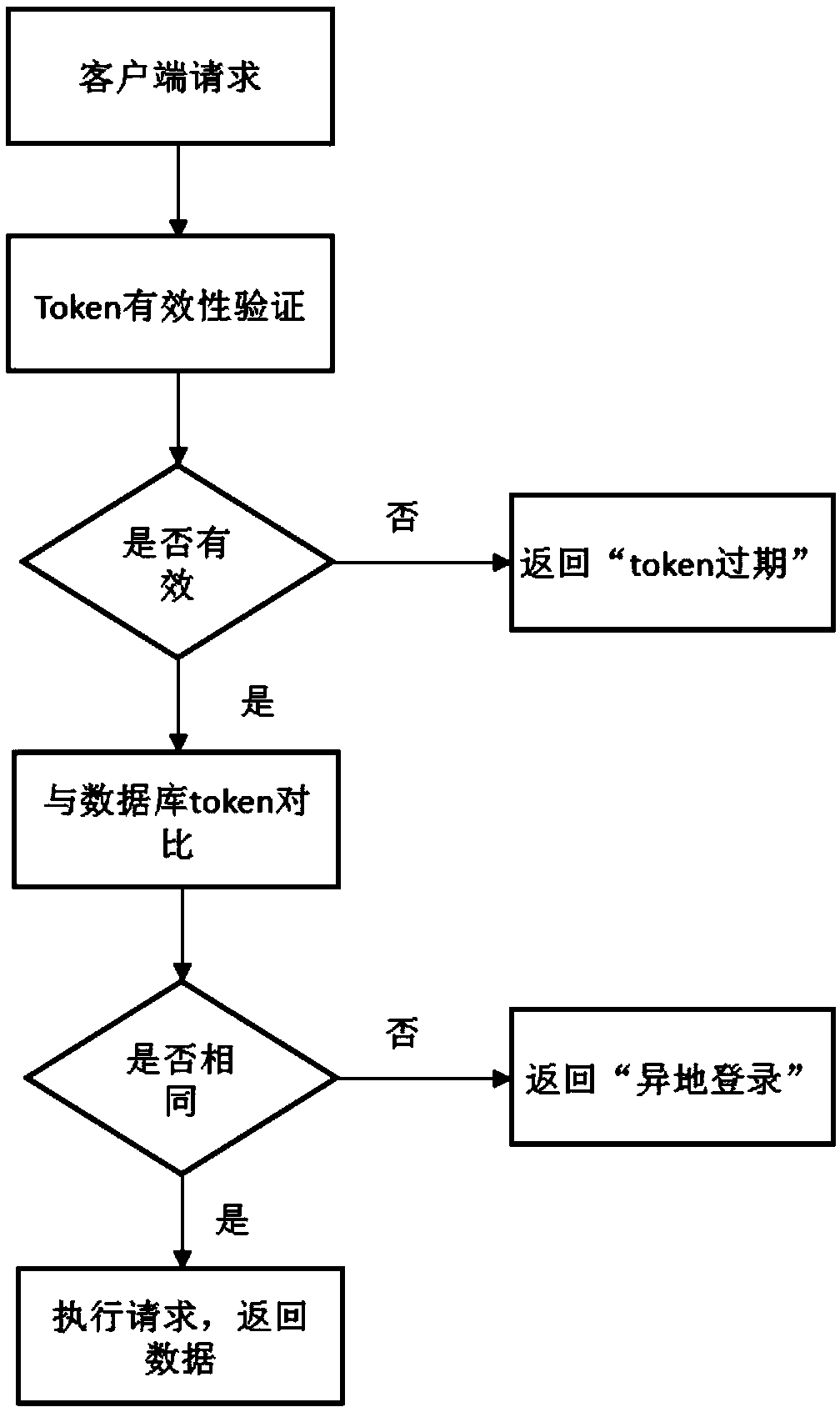
Token-based client identity verification method and system
ActiveCN109309683AProtection of rights and interestsAvoid Simultaneous LoginsTransmissionPasswordUser identifier
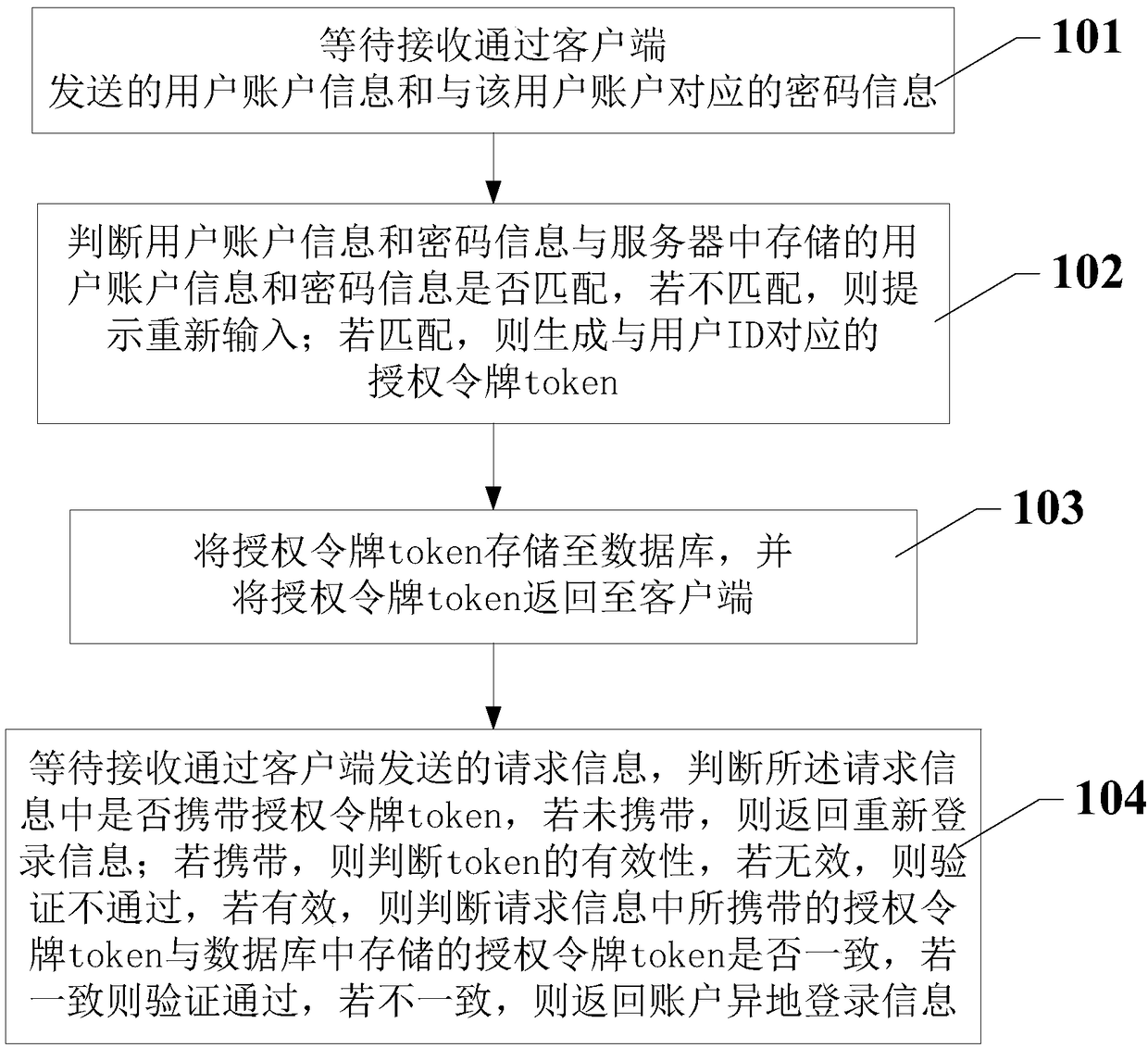
The invention discloses a token-based client identity verification method and system, and relates to the field of information technology. The method comprises the following steps: waiting for to receive a user name and password information sent by a client; judging whether the user name and the password information match with the user name and the password information stored in a server, and if not, prompting re-input; if so, generating an authorization token corresponding to a user ID; storing the authorization token in a database and returning the authorization token to the client; waiting for to receive request information sent by the client, and judging whether the request information carries the authorization token: if the request information carries the authorization token, judging whether the authorization token is valid, and if the authorization token invalid, returning re-login information; if the authorization token is valid, judging whether the authorization token stored inthe database is consistent with the authorization token carried in the request information, and if so, indicating that the verification is passed; if not, indicating that the verification fails, and returning account remote login information; and if the request information does not carry the authorization token, returning the re-login information.
Owner:TAIHUA WISDOM IND GRP CO LTD
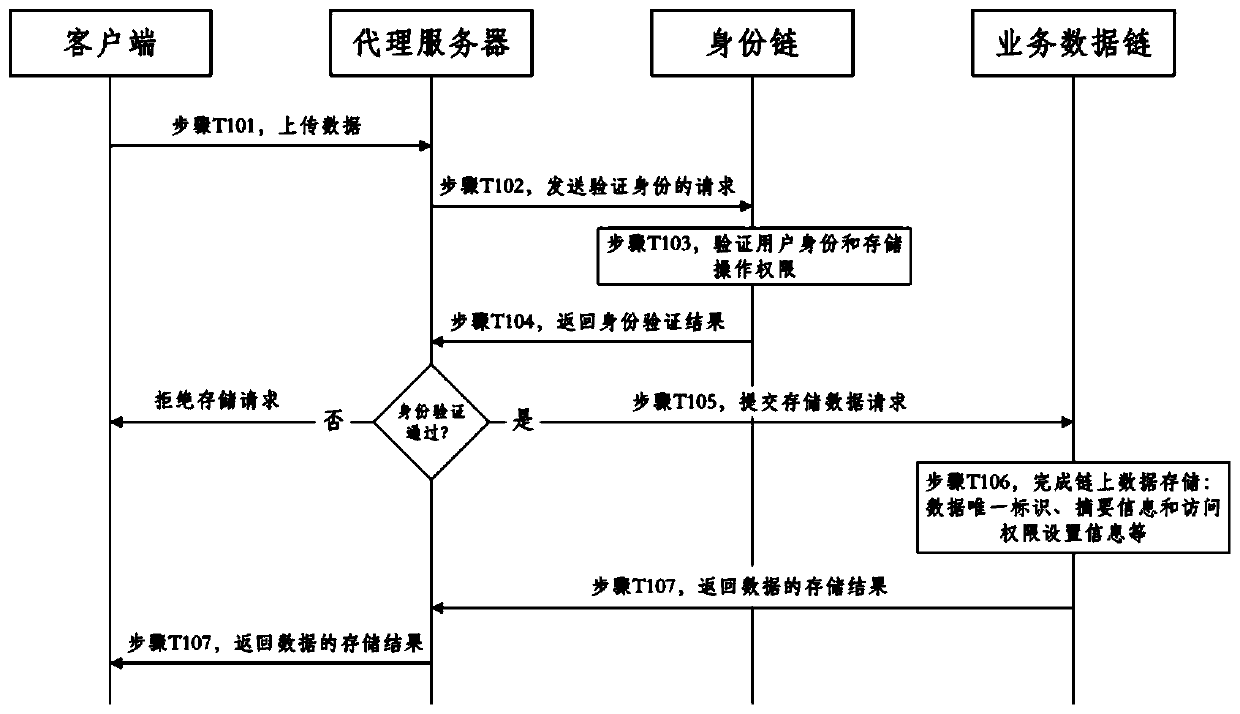
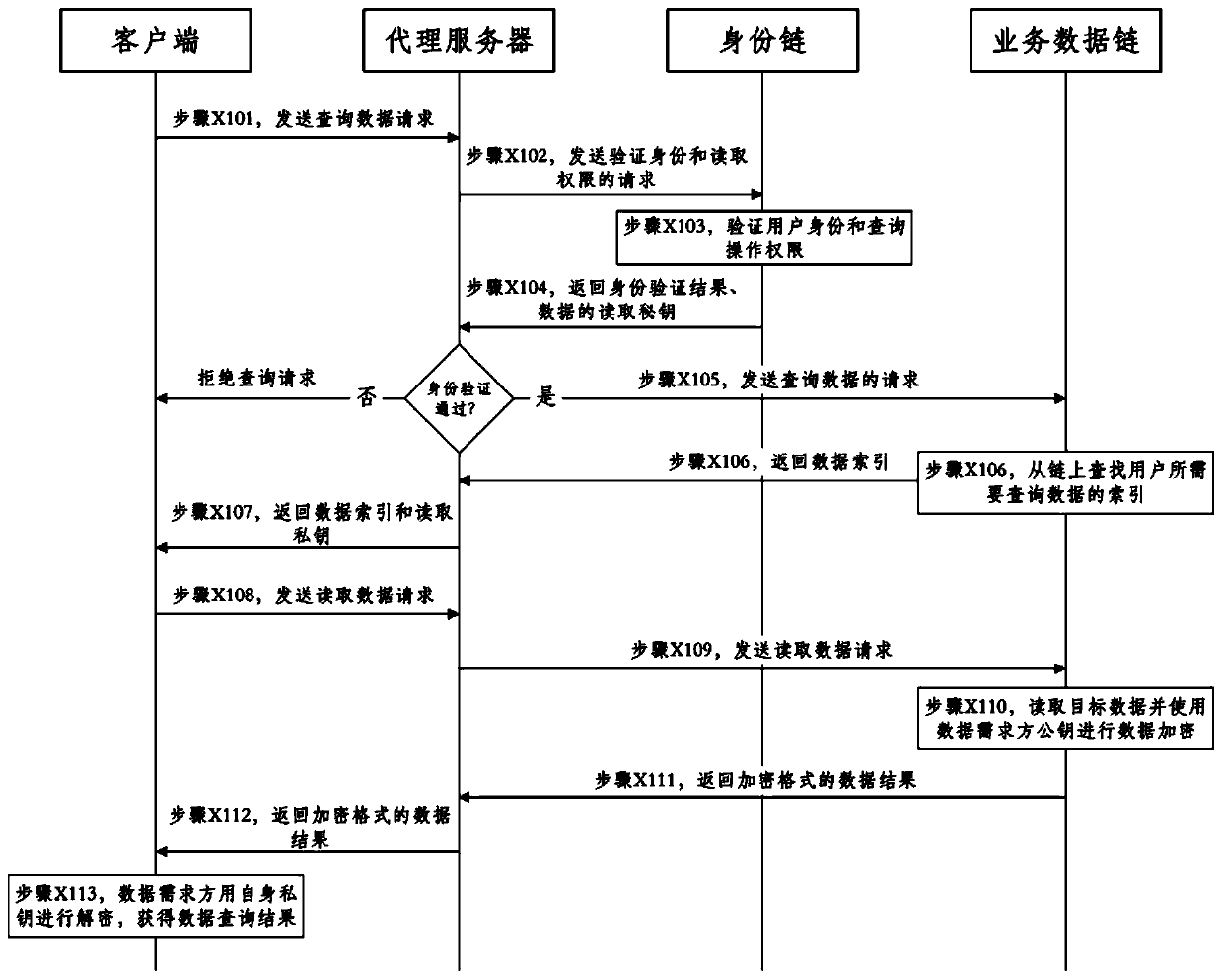
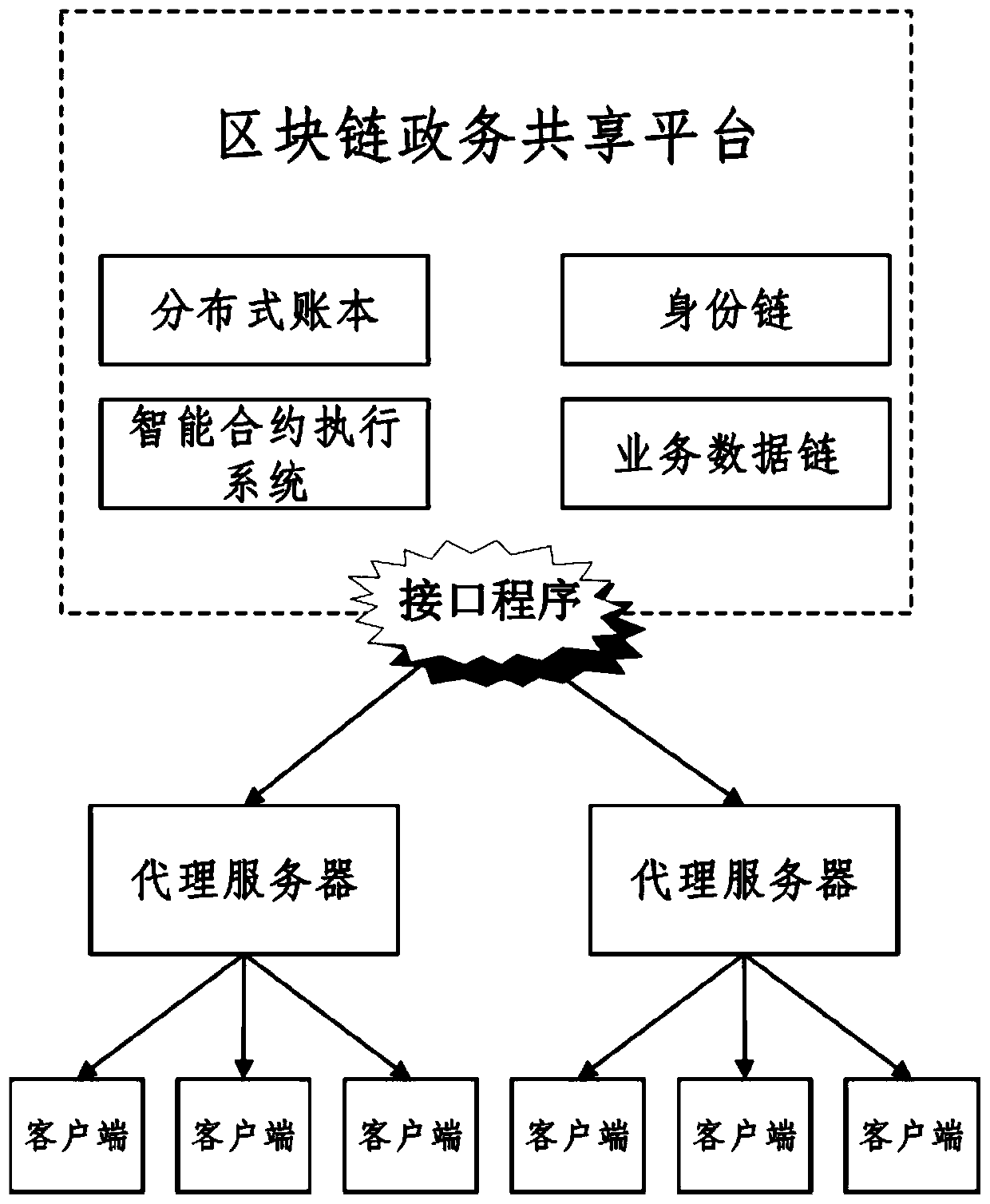
Government affair data storage and query method and system based on block chain double-chain structure
ActiveCN110109930AEnsure safetyGuaranteed controllableData processing applicationsDigital data protectionStructure of Management InformationClient-side
The invention provides a government affair data storage and query method and system based on a block chain double-chain structure. The government affair data storage method based on the block chain double-chain structure comprises the steps that a client uploads the data to a proxy server; the proxy server sends a data storage request to the identity chain and verifies the user identity and the data storage request; the identity chain verifies the identity of the user who makes the request and the storage operation authority, and returns a verification result to the proxy server; if the verification does not pass, the proxy server sends a data storage rejection request to the client; if the verification passes, the proxy server submits a data storage request to a service data chain, and the service data chain completes a consensus process according to the data storage request of the client and stores the data related information in a block chain system state database; and the service data chain feeds back a storage result to the client through the proxy server.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
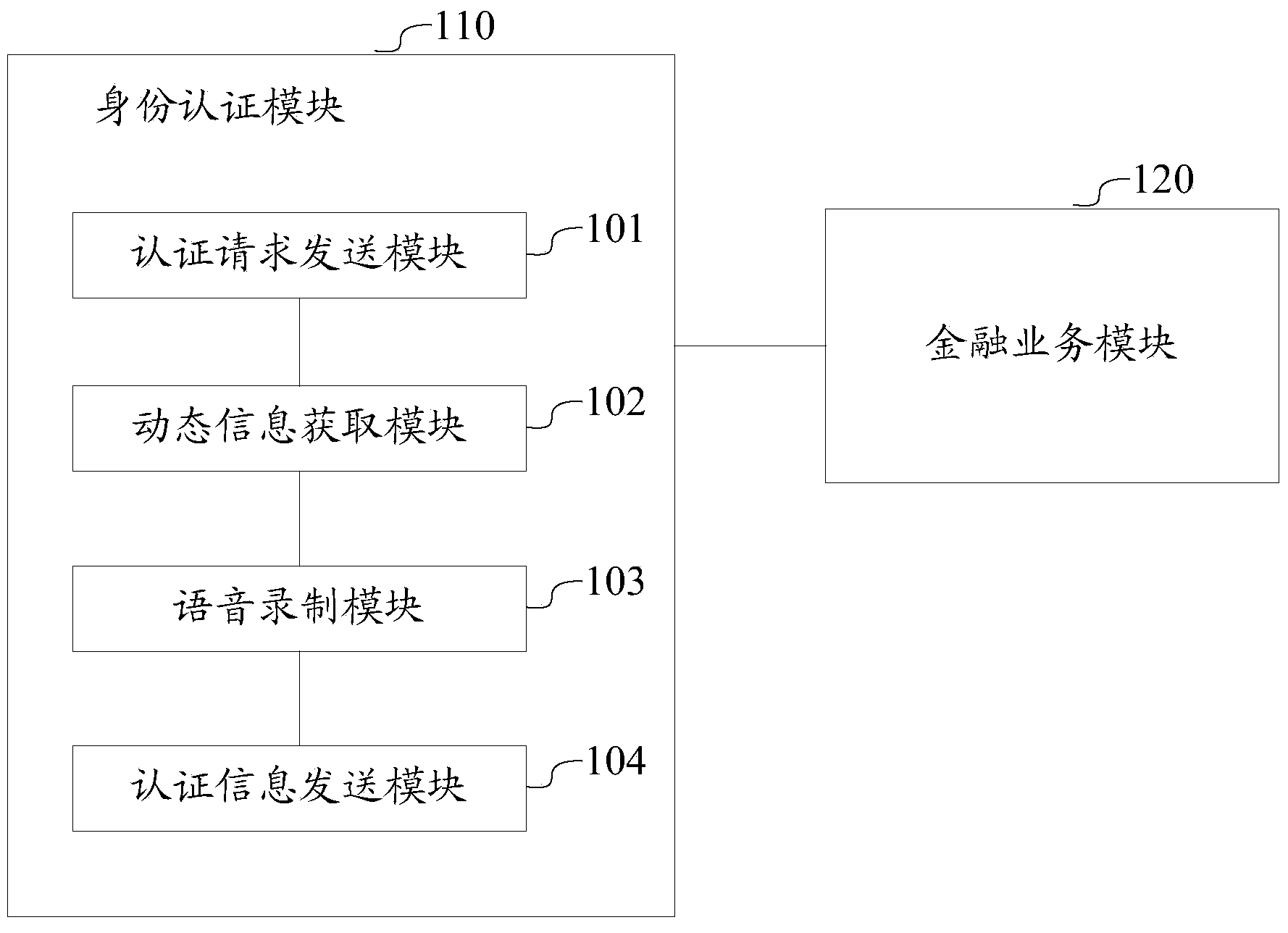
Client side, server side and identity authentication system and method
InactiveCN103986725AEasy accessProtection of rights and interestsSpeech analysisTransmissionClient-sideAuthentication system
The invention discloses a client side, a server side and an identity authentication system and method. The method includes the steps that vocal print characteristics of a user are reserved and used as the vocal print recognition reference characteristics in the user identity authentication process; in the following process, when an authentication request of the client side user is received and identity authentication is conducted; dynamic verification codes generated at random are sent to the client side user, the user is made to read the dynamic verification codes in a voice mode to generate voice information, correctness of voice information of the user is verified based on the dynamic verification codes and reserved reference characteristics, when the vocal print characteristics included in the voice information are the same as the reference characteristics and semantic content included in the voice information is the same as the semantic content of the dynamic verification codes, the user can pass identity authentication. It can be shown that on the basis of biological characteristics (vocal print) and by the combination of the dynamic information verification principle, user identity authentication is achieved, and compared with an existing authentication mode based on physical equipment, the identity authentication method is higher in safety and can guarantee user benefits to the higher degree.
Owner:AGRICULTURAL BANK OF CHINA
Intelligent investment product collocation method based on block chain intelligent contract technology
InactiveCN107578337AGuarantee authenticityProtection of rights and interestsFinanceRisk ControlTimestamp
The invention discloses an intelligent investment product collocation method based on the block chain intelligent contract technology. According to the method, the authenticity and non tamperability of the data on the chain are guaranteed by block chain consensus, authentication, timestamp and other technical means, and the participants on the chain can see the same and real information; the intelligent contract is automatically executed without artificial interference and supervision in the process of work can be performed to ensure the interests of customers. Being different from the centralized central registration and settlement mechanism, the system of the invention adopts the distributed technical architecture, the participants jointly maintain the product life cycle, thereby ensuring that the products are open and transparent and credible, effectively reducing the credit risk and avoiding the lack of supervision and risk control, resulting from that the product contents and operation means are opaque, and thus the customer rights and interests are not guaranteed.
Owner:HANGZHOU YUNXIANG NETWORK TECH
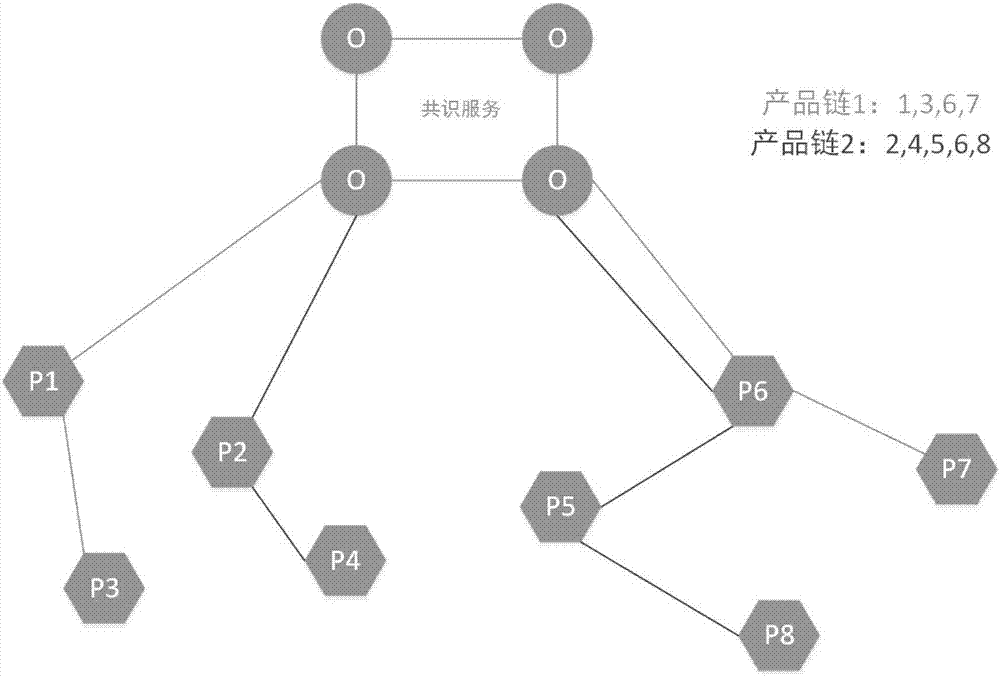
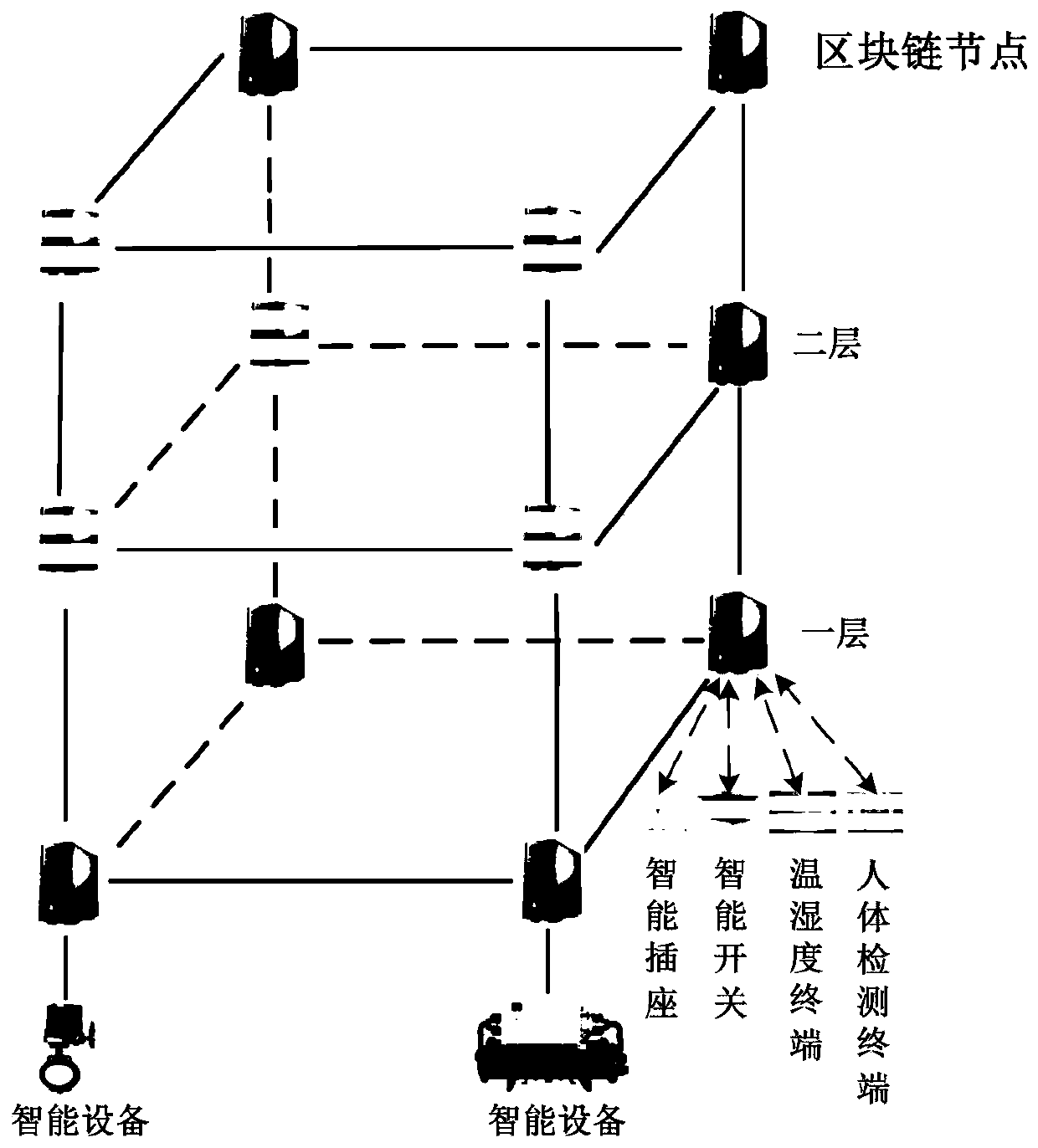
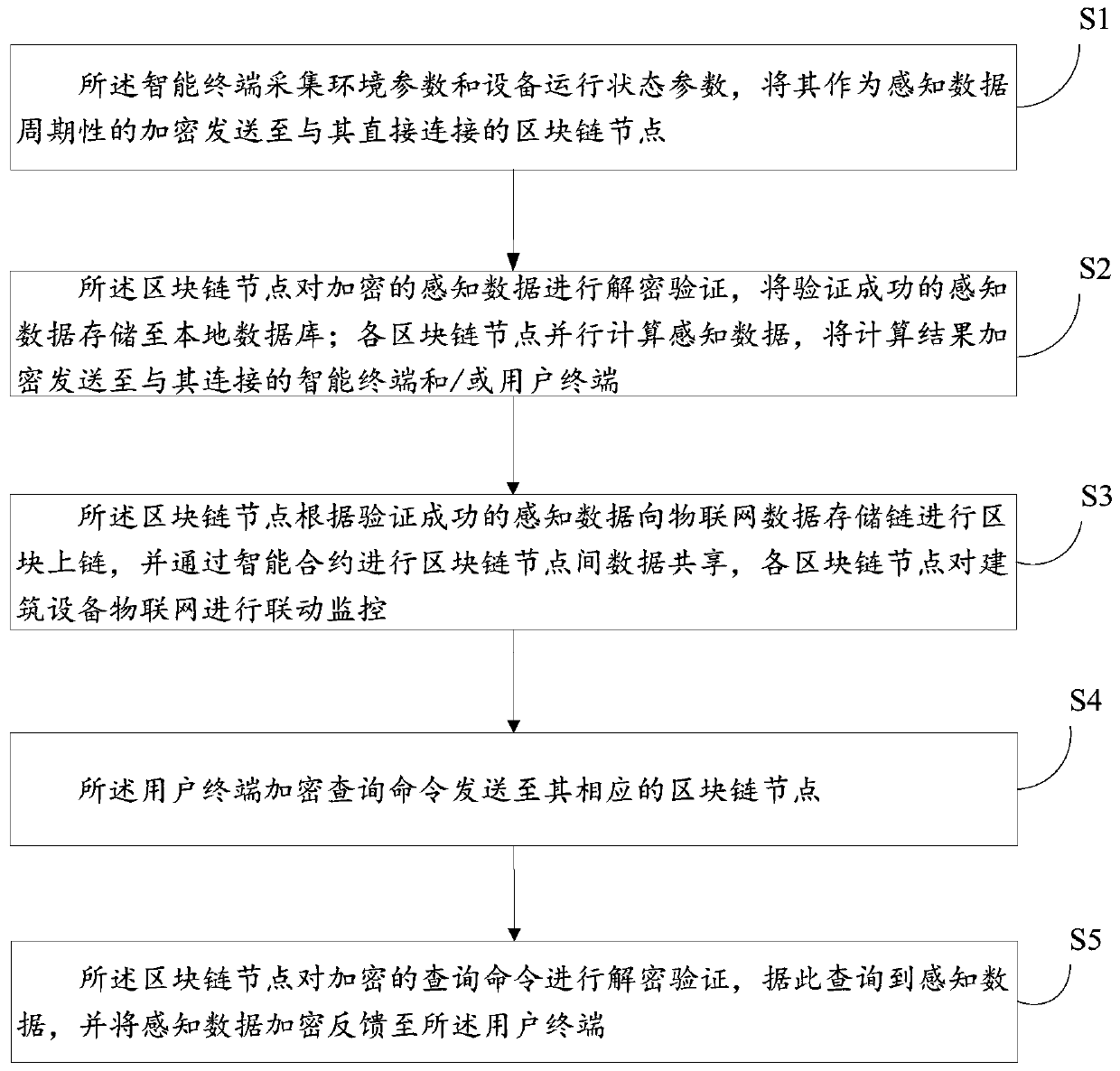
A flattened building equipment Internet of Things monitoring system and method based on a block chain
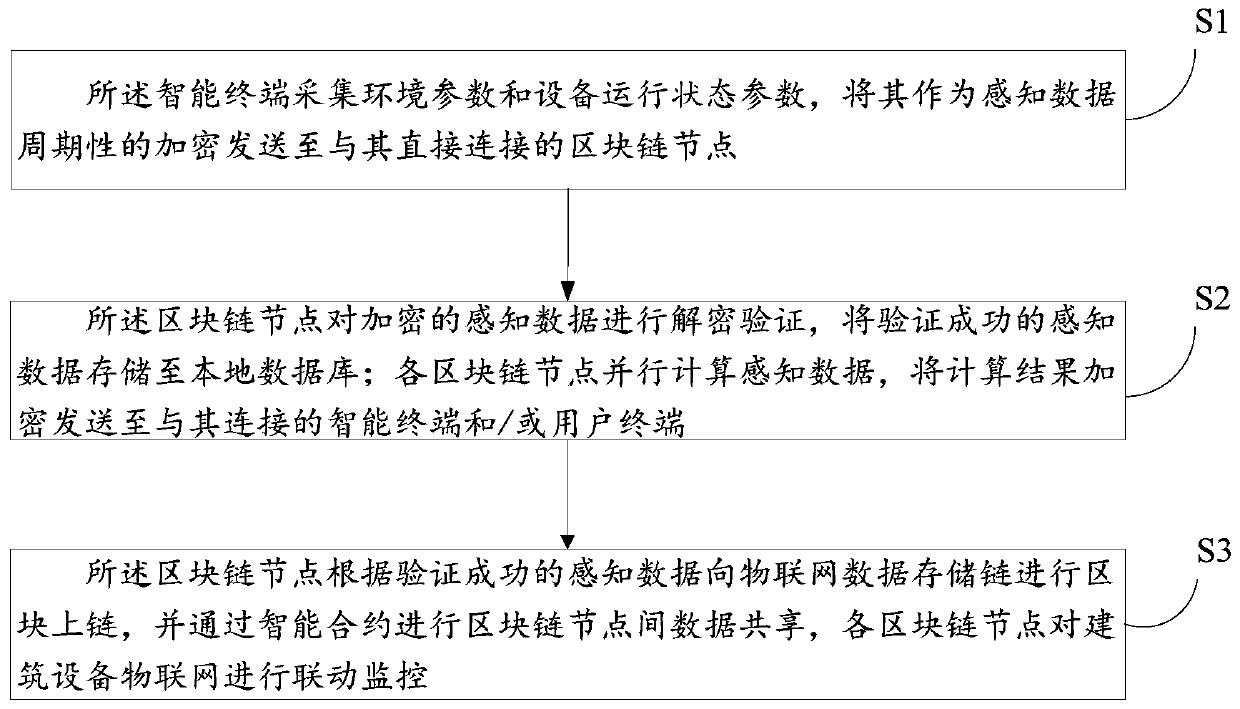
The invention discloses a flat building equipment Internet of Things monitoring system and method based on a block chain. The system comprises a plurality of block chain nodes, a plurality of intelligent terminals and a plurality of user terminals, the block chain nodes are deployed in a building subspace. wherein the blockchain nodes are respectively connected with a user terminal and intelligentterminals arranged in the building subspace, are in one-to-one correspondence with the building subspaces, and are configured to authenticate the intelligent terminals, decrypt the received intelligent terminal data, store and carry out parallel computing, and carry out data sharing among the blockchain nodes through an intelligent contract; the intelligent terminal is configured to collect environment parameters and equipment operation state parameters, and periodically encrypt and send the environment parameters and the equipment operation state parameters as sensing data to the blockchainnode directly connected with the intelligent terminal; and the user terminal is configured to perform data interaction with the block chain node.
Owner:SHANDONG JIANZHU UNIV
Taxi guiding and dispatching system
ActiveCN105006145AImprove operational efficiencyAvoid grabbing ordersRoad vehicles traffic controlComputer terminalPredictability
The invention provides a taxi guiding and dispatching system, which belongs to the field of taxi dispatching system. The taxi guiding and dispatching system provided by the invention comprises a vehicle-mounted terminal, a passenger terminal and a server, and is characterized in that: the vehicle-mounted terminal, the passenger terminal and the server communicate with one another through a network; and the server collects online information of the passenger terminal and the vehicle-mounted terminal, establishes and maintains a supply-demand link relation between taxis and passengers through an intelligent dispatching mechanism, sends travel information of a dispatched taxi to the passenger terminal according to the supply-demand link relation, and sends passenger requirement information dispatched to the vehicle-mounted terminal and an optimal driving route planned for the same to the vehicle-mounted terminal. The taxi guiding and dispatching system can recommend the optimal driving route, improves operating efficiency, reduces operating cost, protects the environment, minimizes the participation of the driver in the whole link so that the driver can concentrate on driving, ensures the safe driving of the driver, reports passenger travel information in real time, and has a certain predictability in passenger riding arrangement.
Owner:山东睿达电子科技有限责任公司
Ownership based digital copyright work protection-transaction-issuing method and system
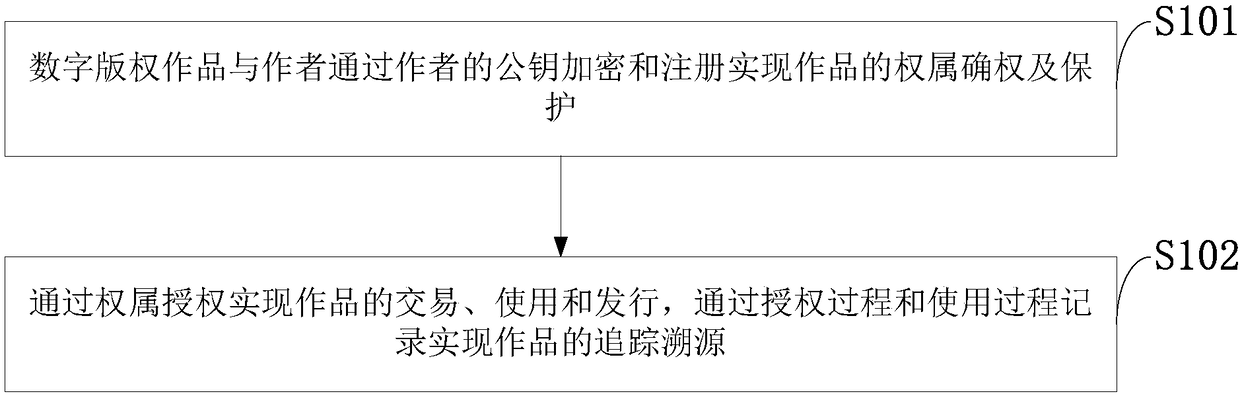
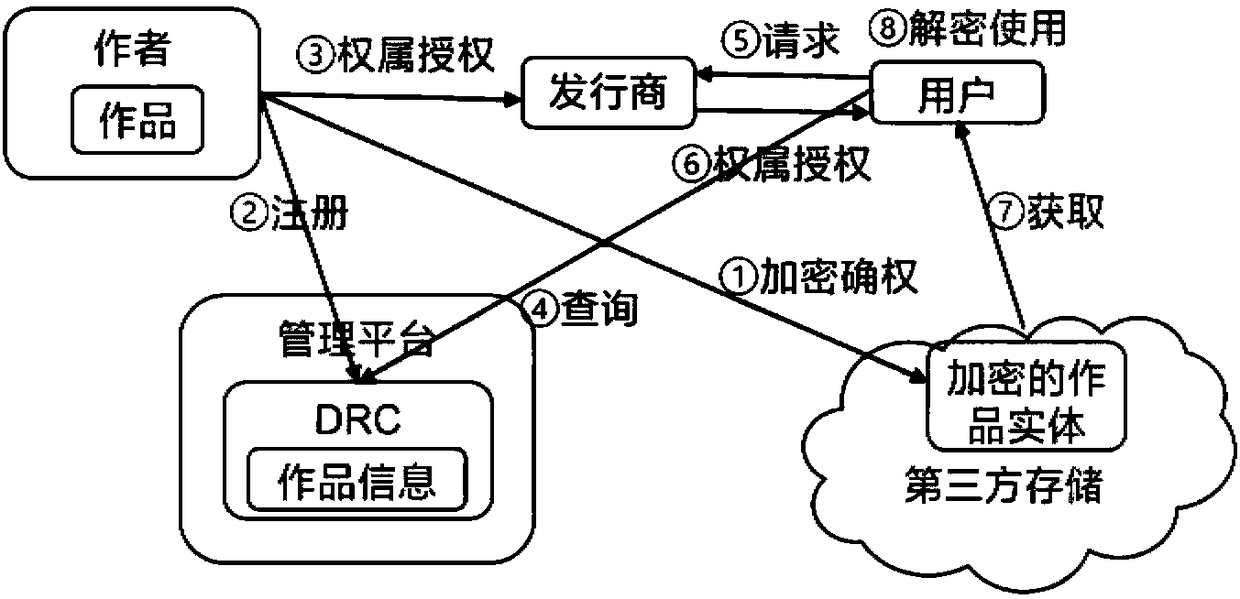
InactiveCN108389059AProtect interestsProtection of rights and interestsTransmissionCommerceAuthorizationEncryption
The invention discloses an ownership based digital copyright work protection-transaction-issuing method and system, and belongs to the technical field of direction data protection. According to the method, an author declares and protects the ownership of a digital copyright work by public key encryption and registration; and the work is transacted, used and issued by authorization, and the work istracked and traced via recording in authorization and using processes. Via the encrypted ownership declaration and authorization methods, the problem that a traditional digital copyright protection method has deficiency in the aspects of preventing non-authorized use and pirates, help is provided for protection and shared use of the digital copyright work, and benefit and rights of the author canbe protected.
Owner:CHENGDU UNIV
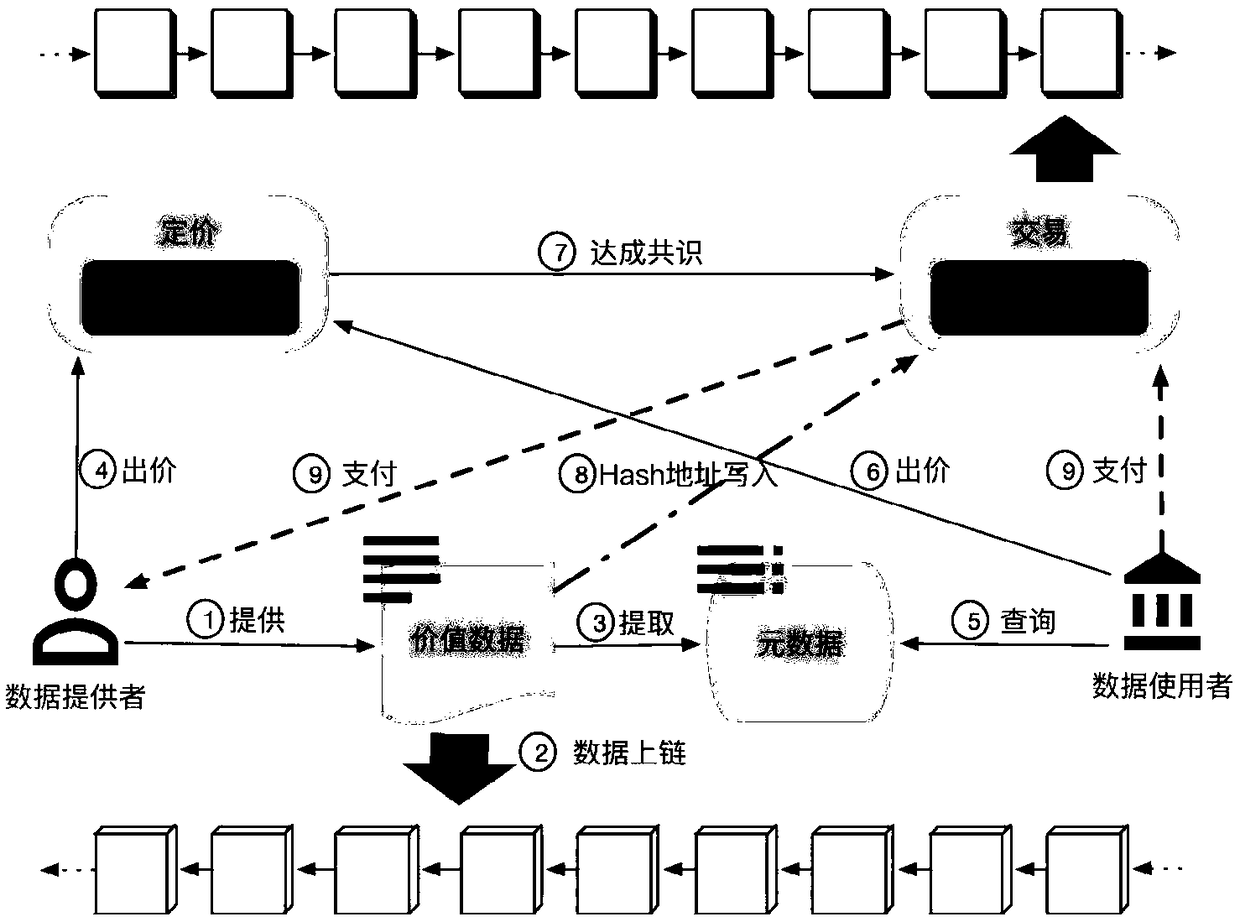
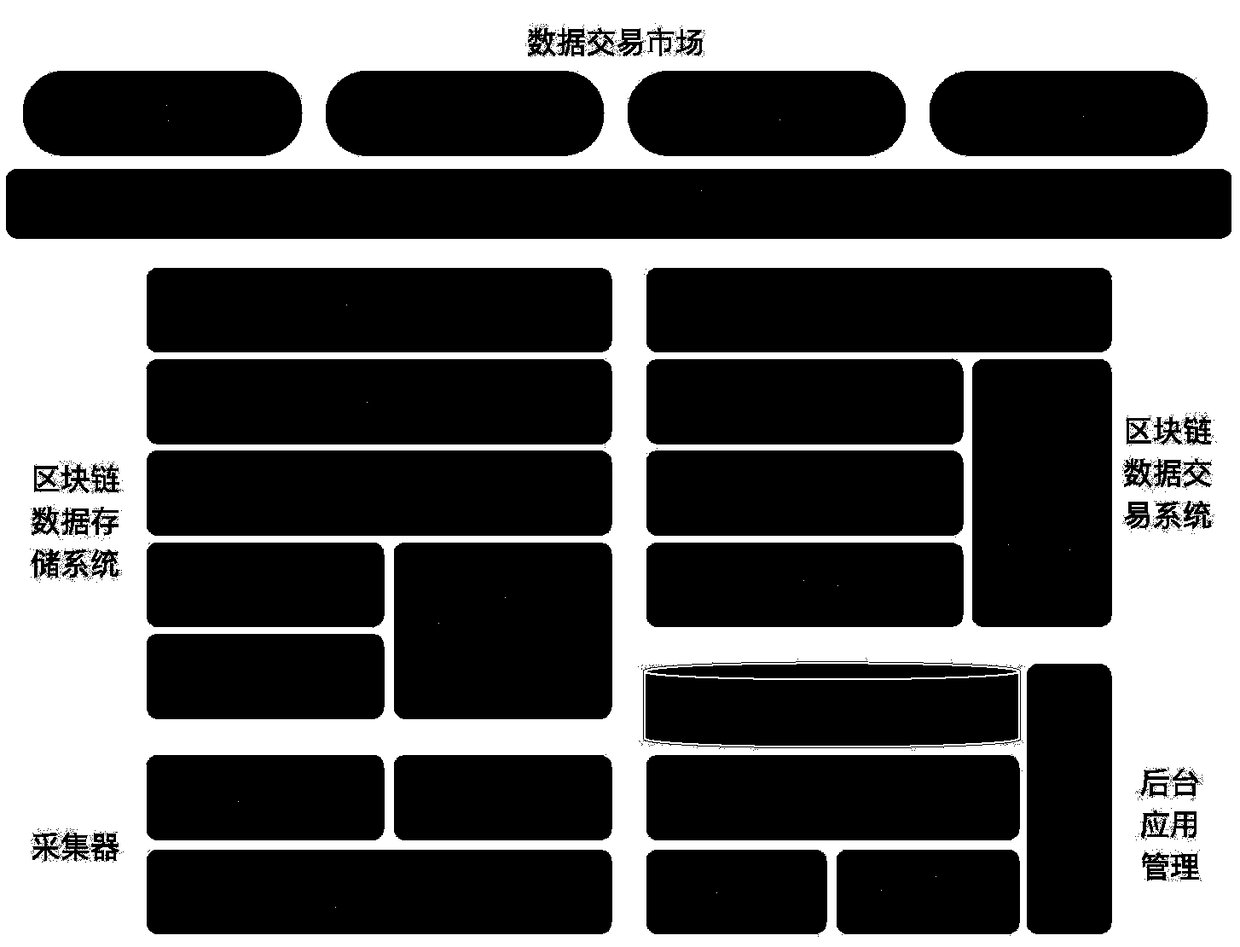
A data trading system based on a block chain and an implementation method thereof
InactiveCN109242636AData acquisition barriers are highLower barriers to accessFinanceDigital data protectionData providerData acquisition
The invention discloses a data trading system based on a block chain and an implementation method thereof. The invention comprises a data collector, a background application management module, a blockchain data storage module based on a federation chain, a block chain data transaction module based on a public chain, and a user display terminal. The data collector interacts with the background application management system, The block chain storage module stores the data obtained by the collector in a distributed manner, and the block chain data transaction module stores the information and transaction information exchanged between the data collector and the background application management system in a decentralized manner and controls the transaction flow, and the user operates the user display terminal. The invention can encourage data providers to participate in data flow and reduce data acquisition barriers, protect the rights and interests of data providers and make full use of data value. It solves the contradiction between the high efficiency of data transaction and the high cost of current block chain. Data pricing strategies are implemented in a more concise, efficient, and executable manner.
Owner:盈盈(杭州)网络技术有限公司
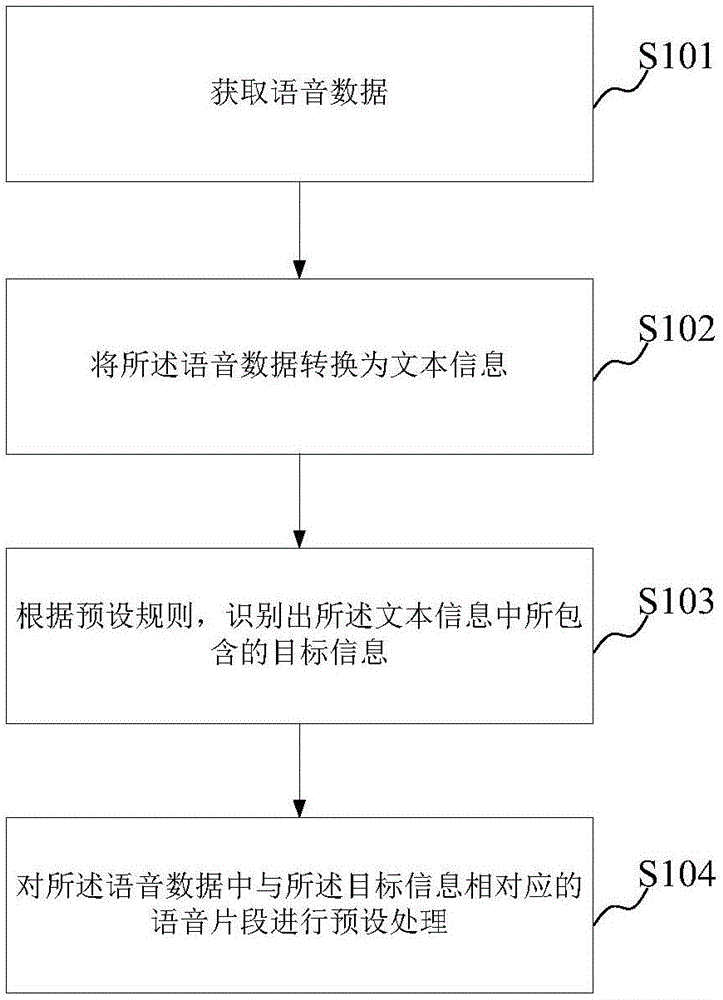
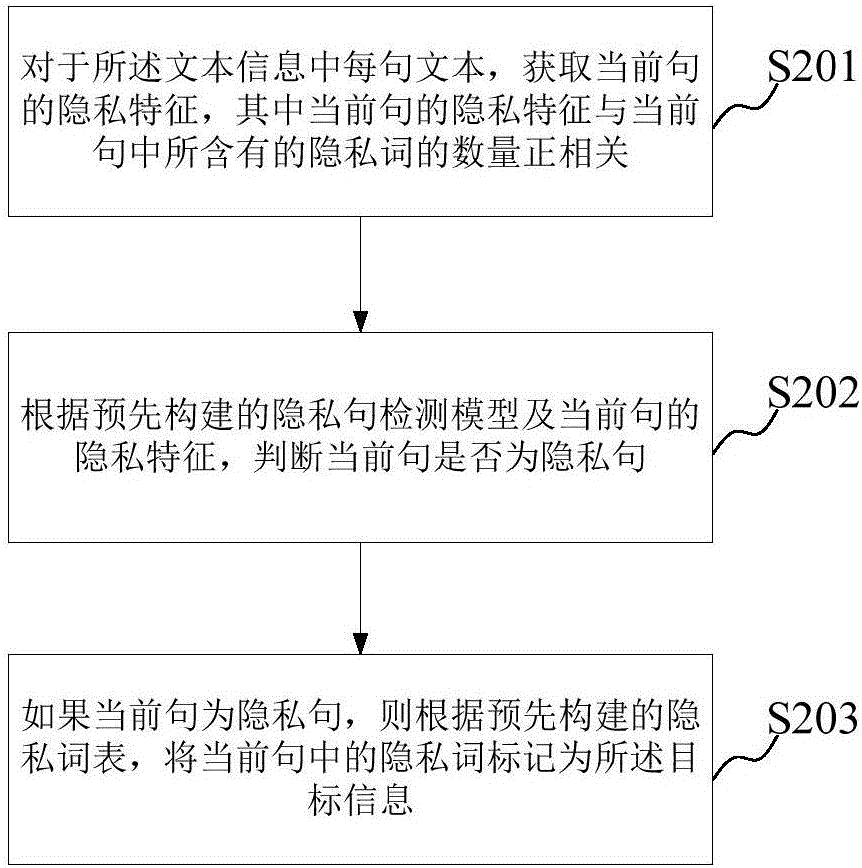
Voice processing method and device
ActiveCN106504744AEliminate concernsRemove obstaclesSpeech recognitionSpeech synthesisPrivacy protectionSpeech sound
The embodiment of the invention provides a voice processing method and device. The method comprises: obtaining voice data, converting the voice data into text information; according to a preset rule, identifying target information included by the text information; and carrying out pretreatment on a voice segment corresponding to the target information in the voice data. According to the embodiment of the invention, after conversion from the voice data into the text information, the target information including privacy of a speaker in the text information is identified based on the preset rule; and then the pretreatment is carried out on the voice segment corresponding to the target information in the voice data, wherein the pretreatment includes deleting the voice segment. Therefore, the content of the target information like privacy of the speaker can not be obtained by others and thus the rights of the speaker are protected, thereby eliminating the consideration and obstacle of the voice data during the transmission process and realizing privacy protection and voice transmission simultaneously.
Owner:IFLYTEK CO LTD
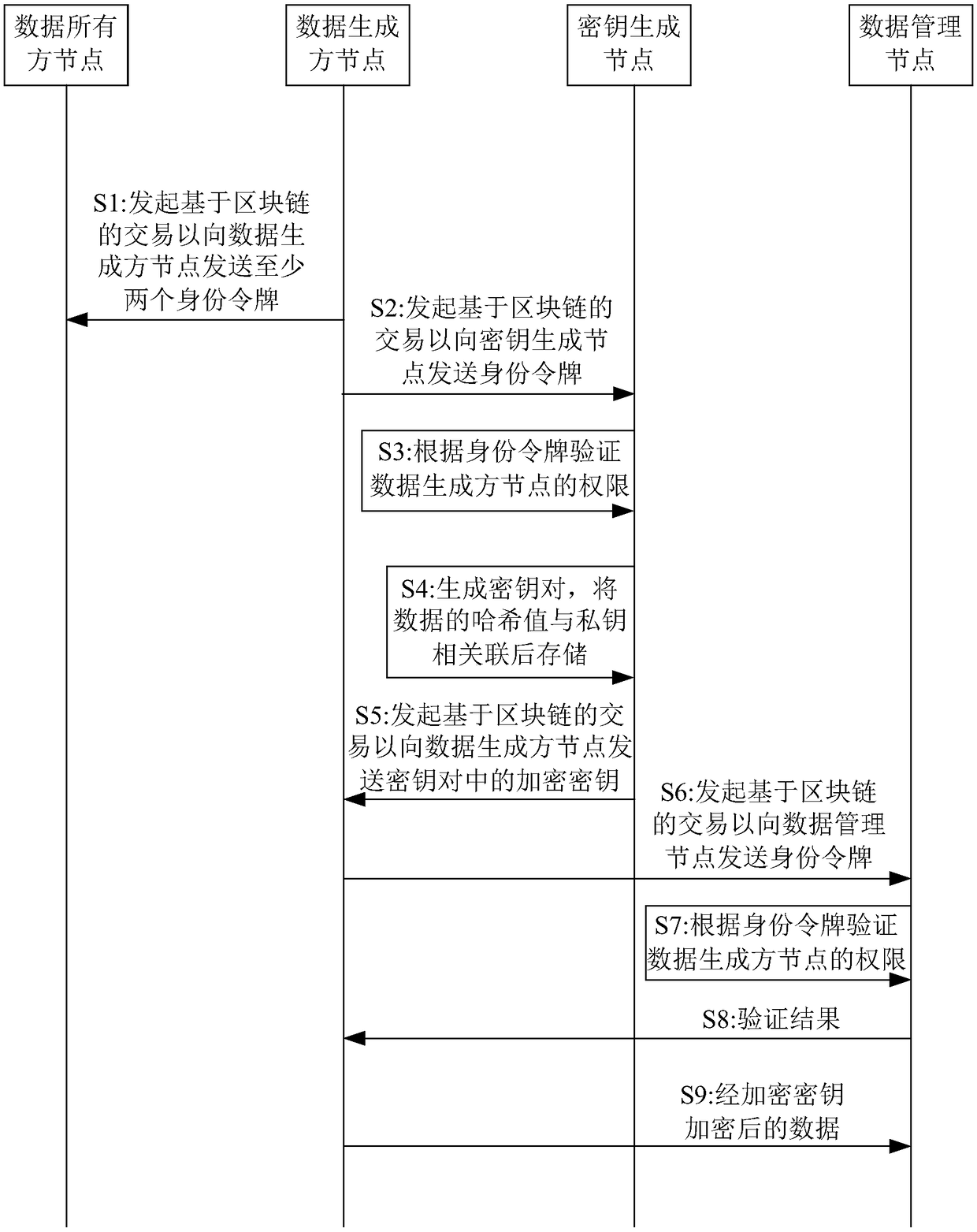
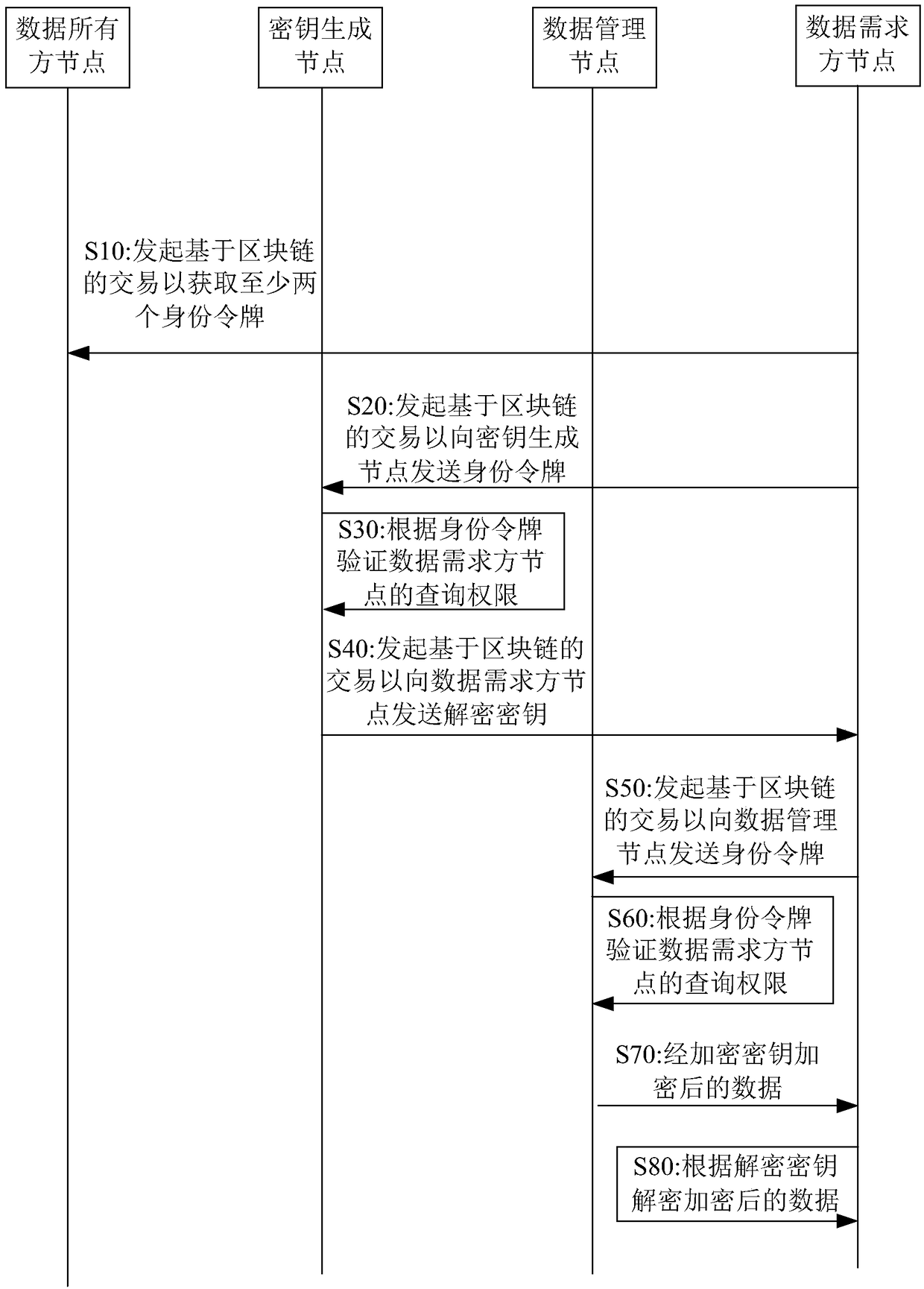
Blockchain-based data processing method, blockchain-based data processing system and computer-readable storage medium
ActiveCN108848063AImprove securityImprove confidentialityKey distribution for secure communicationUser identity/authority verificationData processing systemConfidentiality
The invention discloses a blockchain-based data processing method, a blockchain-based data processing system and a computer-readable storage medium, wherein a data owner node respectively grants the permission of uploading and querying data to a data generator node and a data demander node through identity tokens; the data generator node obtains an encryption key used for encrypting the data through the identity token so as to upload the data to a data management node after encrypting the data; and the data demander node obtains a corresponding decryption key and the encrypted data through theidentity token so as to obtain the data. Thereby, the security and the confidentiality of the data are improved; furthermore, the data owner node participates management of the data itself; therefore, the right of the data owner can be ensured; and the data processing efficiency can be increased.
Owner:苏州朗润创新知识产权运营有限公司
Self-service car returning method in car sharing process and car sharing method based on self-service car returning
InactiveCN105913308AEfficient sharingProtection of rights and interestsBuying/selling/leasing transactionsUser needsTimestamp
A self-service car returning method in the car sharing process and a car sharing method based on self-service car returning belong to the field of car sharing. The methods are disclosed in order to solve the problem that the procedure of car returning is complicated for car sharing as a car user needs to return a car to a car owner and the car owner needs to check the car face to face. The self-service car returning method is characterized by comprising the following steps: S1, a car user parks a car at an agreed location at the end of car sharing; the car user submits a car returning application through the APP client thereof, and takes an image of the car using an APP and uploads the image to a cloud platform server as the car checking basis for car returning, and the cloud platform server automatically adds a timestamp when the APP client of the car user uploads the image, carries out backup and image processing and comparing, makes out new damaged points generated after the car user picks up the car, and pushes the new damaged points to the APP client of a car sharer; and S3, the car sharer receives the car returning application, checks the car based on the image pushed by the APP client of the car user, and / or checks the car at the car location, and / or does not check the car.
Owner:DALIAN ROILAND SCI & TECH CO LTD
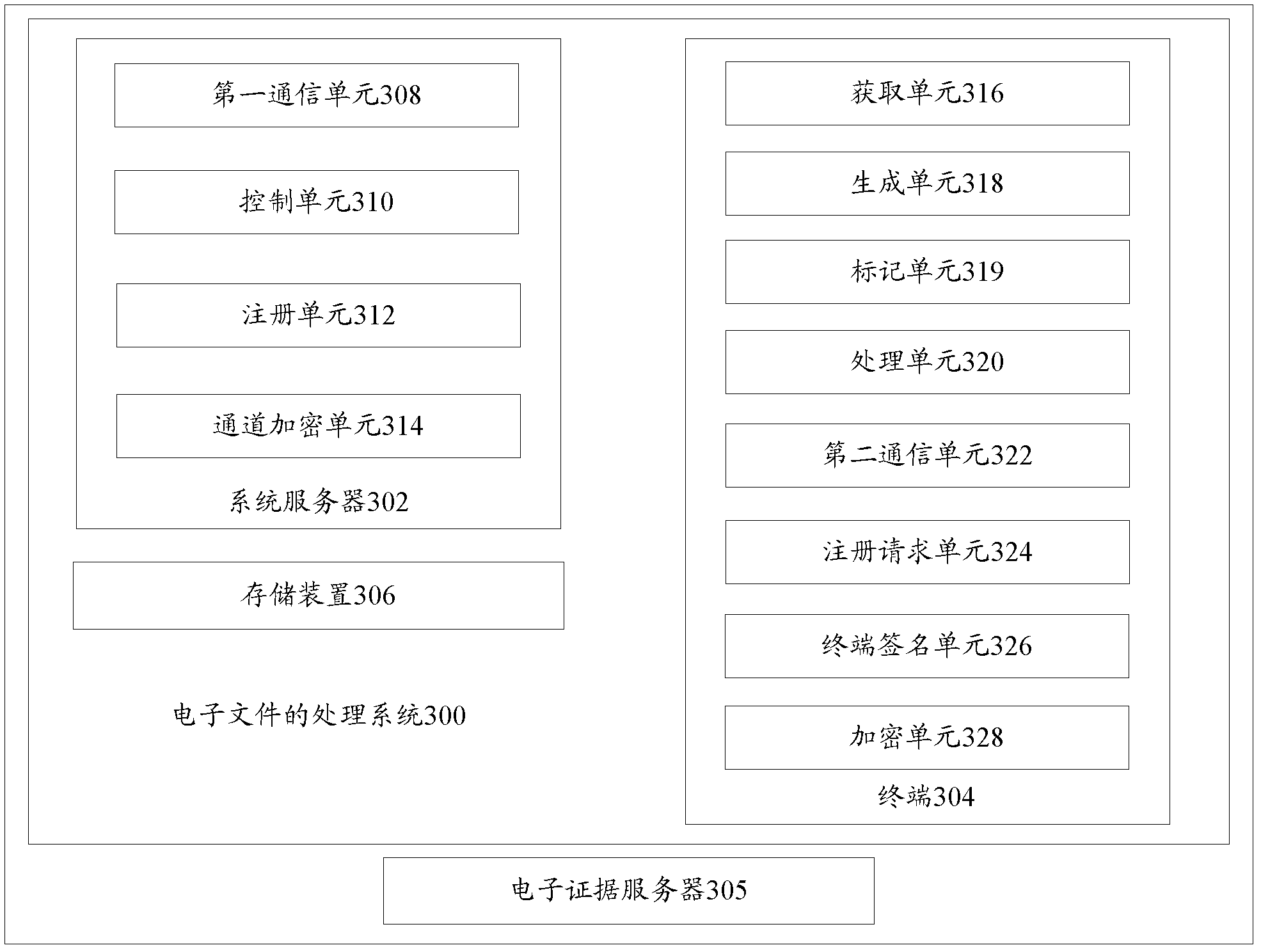
Electronic document processing method, processing system and verification system
ActiveCN102325139AProtection of rights and interestsUser identity/authority verificationElectronic documentTimestamp
The invention provides an electronic document processing method. The method comprises the following steps of: step 102, acquiring an electronic document, generating an electronic evidence package for the electronic document, and storing the electronic evidence package after marking a timestamp on the electronic evidence package, wherein the electronic evidence package comprises the electronic document; and step 104, generating evidence-obtaining information by using the electronic document and the electronic evidence package, and transmitting and storing the evidence-obtaining information to an electronic evidence server through a transmission channel. Correspondingly, the invention also provides an electronic document processing system and an electronic document verification system. Through the technical scheme of the invention, an operation process in a computer and a network interaction process can be cured and preserved so that non-repudiation evidences are generated; and rights and interests of a user are protected through verifying relevant evidences.
Owner:上海榕安科技有限公司
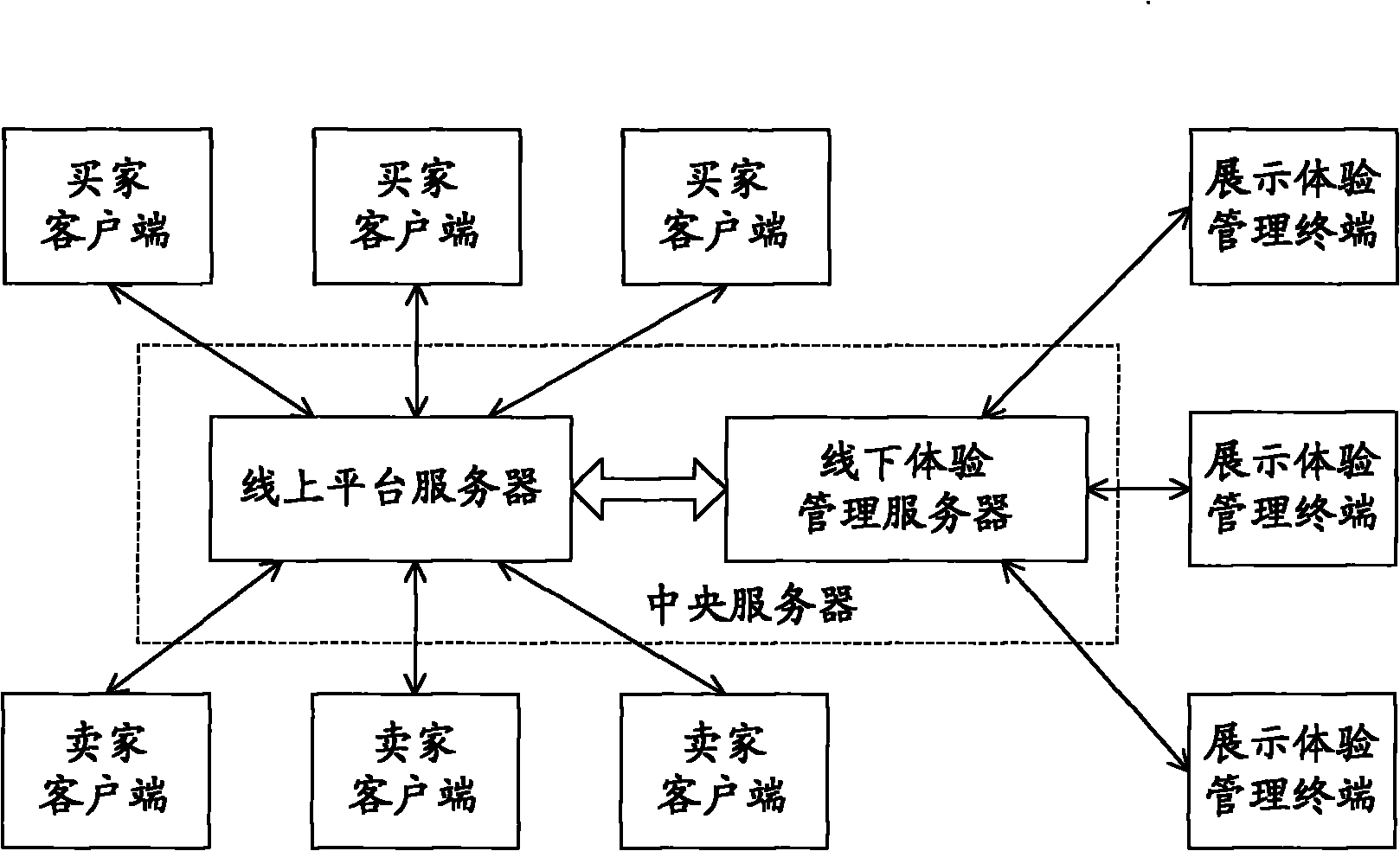
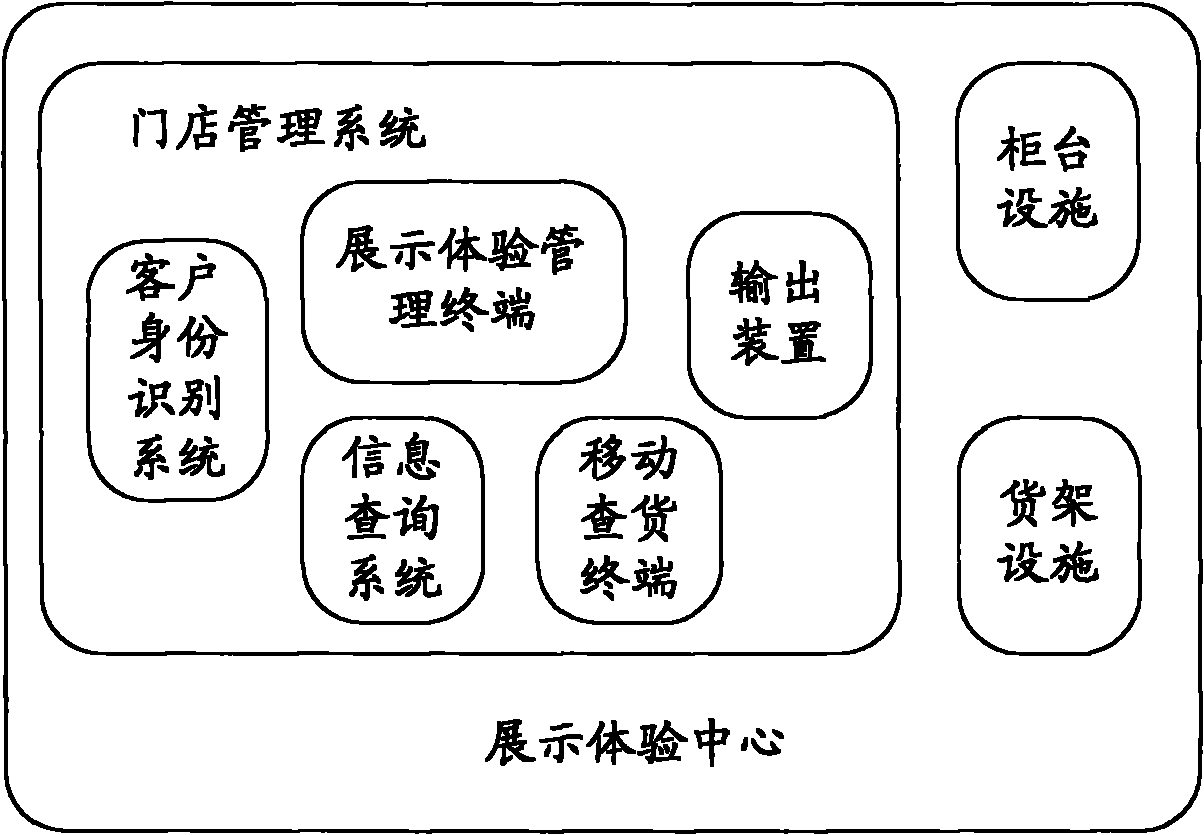
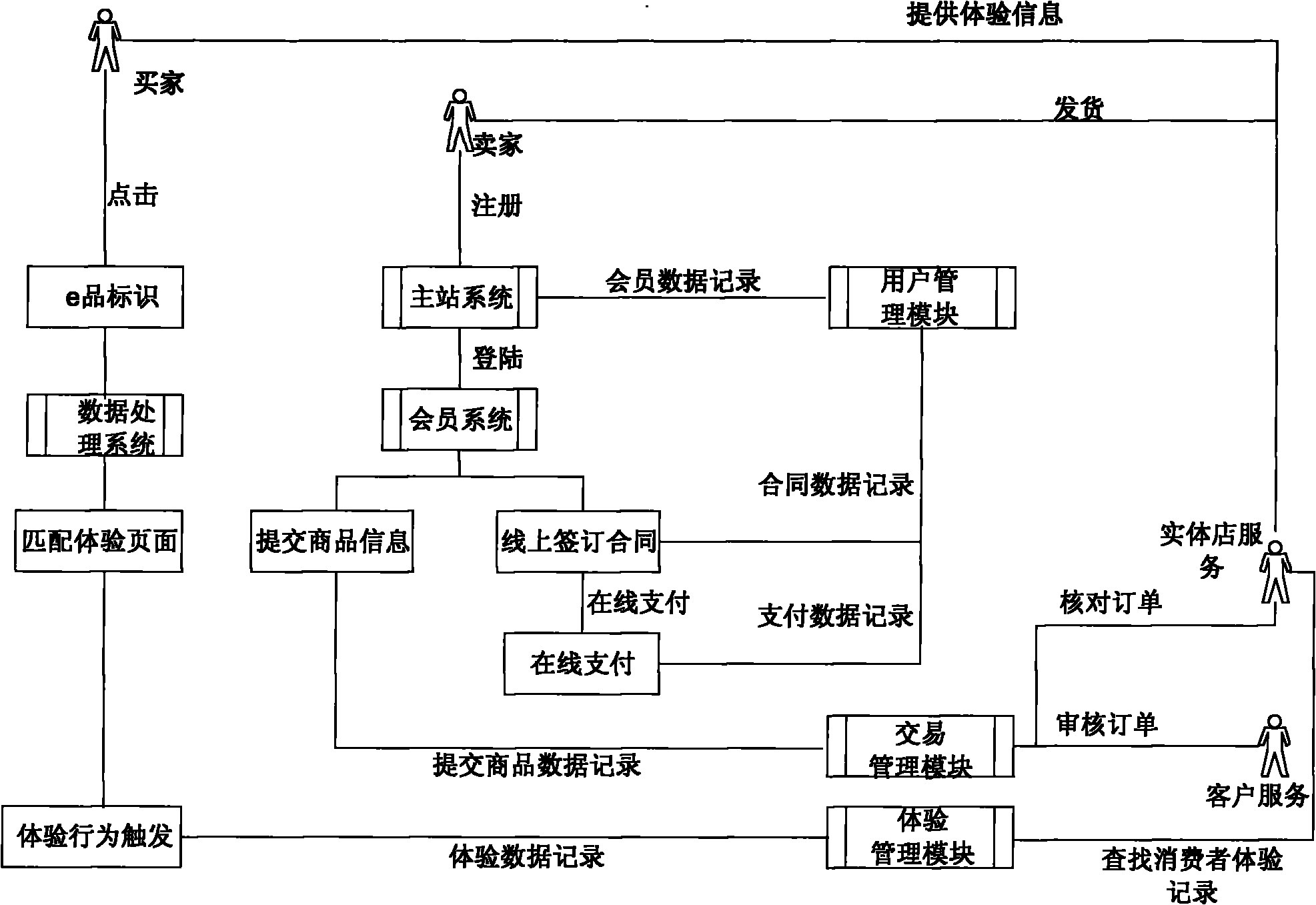
Off-line experience store management system and method
The invention relates to an off-line experience store management system. The system comprises an experience management system terminal and a client identification system, an information query system, a mobile query terminal and an output device which are connected with the experience management system terminal in a communication way, wherein the experience management system terminal is connected with a remote central server in a communication way and performs data interaction and the synchronization of an experience goods database; the client identification system is used for identifying experience sheet numbers of clients coming into a store, transmits the experience sheet numbers to the experience management system terminal and generates experience serial numbers of the clients; the output device is used for displaying information to users in the store according to instructions of the experience management system terminal; the information query system is communicated with the experience management system terminal and is used for providing real-time query of store inventories and experience information for the clients or salesclerks; and the mobile query terminal is used for reading all the goods information of the store and uploading the goods information to the experience management system terminal. Therefore, the system can realize mutual combination of an on-line system and an off-line system and provides an integrated shopping platform.
Owner:BEIJING HUSNG CHUANGZHAN TECH
Limiting stop-free and fixed line-free public transportation operating system and method
InactiveCN102147970AOptimizing the travel plan of a single operating vehicleEasy to controlArrangements for variable traffic instructionsPersonalizationPublic transport service
The invention relates to a limiting stop-free and fixed line-free public transportation operating system and method. By using the invention, a driving plan of at least one public transportation operating vehicle can be made or modified according to an individual traffic service request of a user, wherein the driving plan comprises information such as a driving route. stops and the like, so that the driving plan of the vehicle and the departure point and / or destination point of the user can be matched in the appointed time period, thereby forming a public transportation service unit which can meet the public individual transportation requirement. By combining and optimizing all the public transportation service units, the public transportation system can provide an economic, efficient and individual transportation service for the public. The invention fuses the expressage vehicle management concept, the vehicle sharing idea and the bus operation, enhances the ability of the common people to control public transportation vehicles, and alleviates various social and environmental problems caused by the public transportation vehicles.
Owner:顾泰来
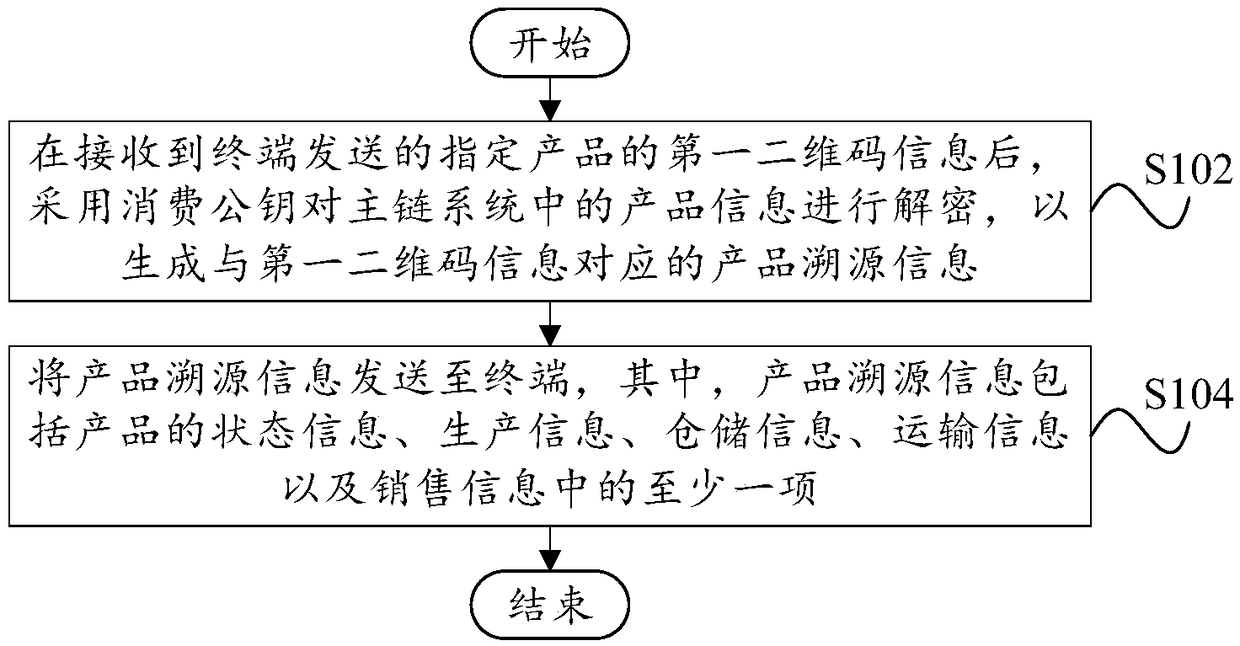
A liquor traceability system based on block chain
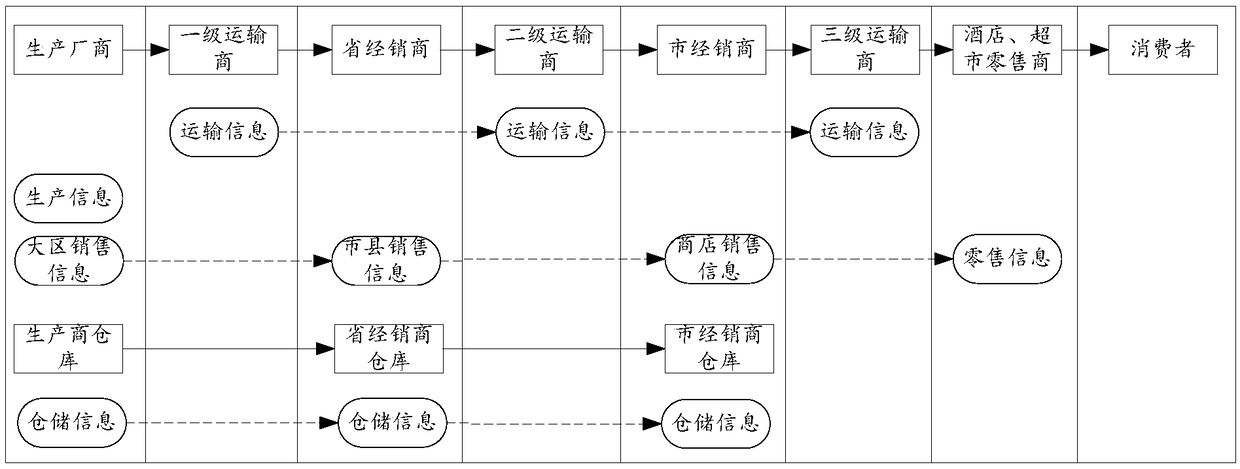
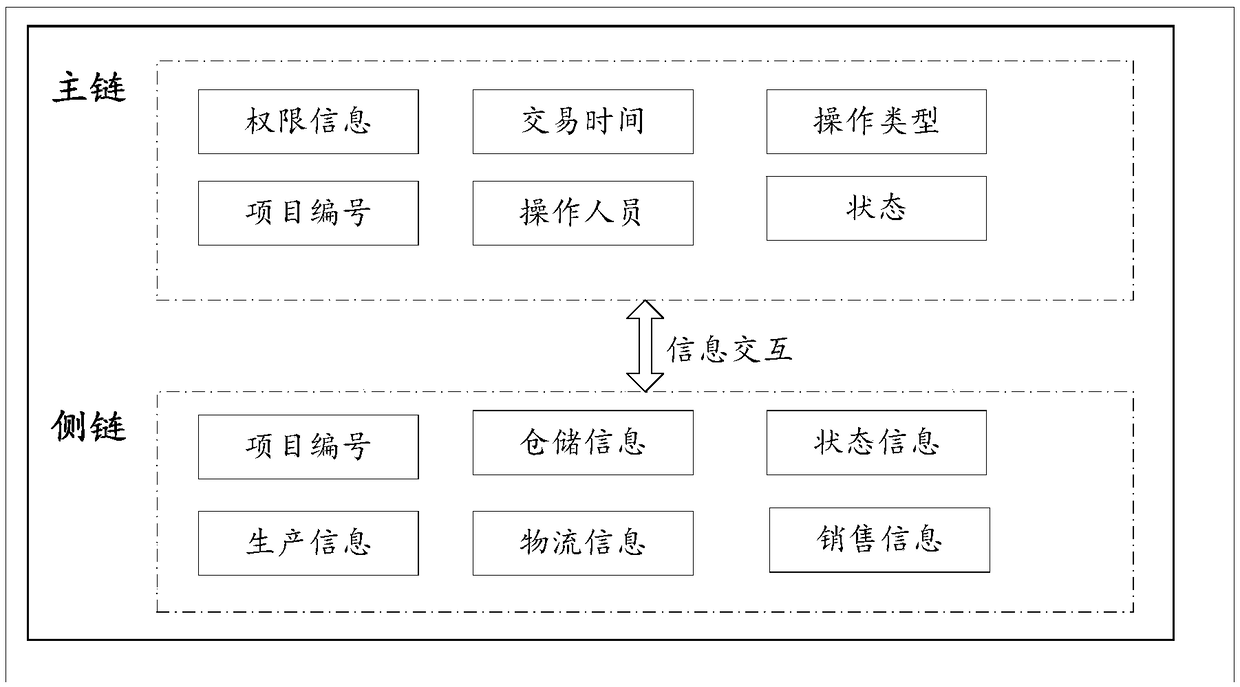
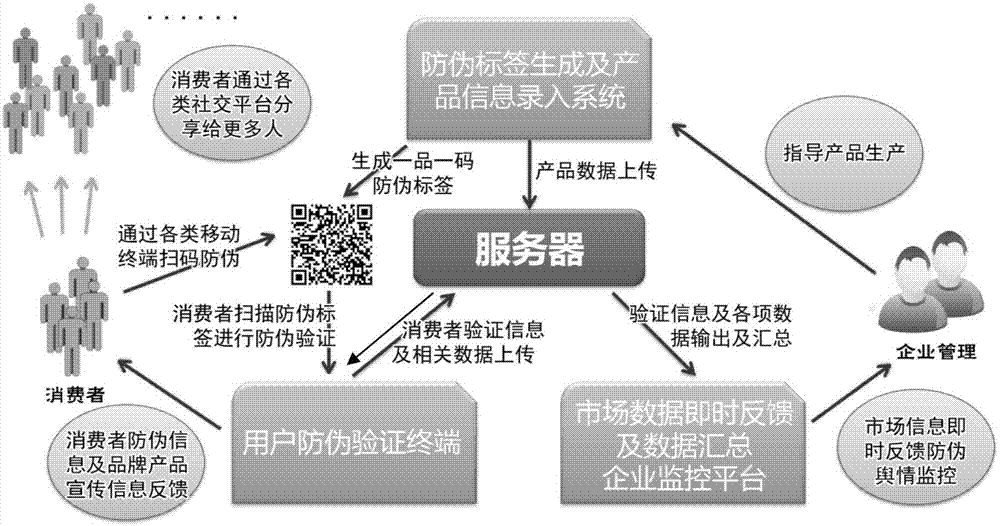
InactiveCN109146516AIncrease profitGuaranteed real-timeParticular environment based servicesUser identity/authority verificationProduct traceabilityComputer terminal
The invention provides a liquor traceability system based on a block chain, comprises a traceability method, a traceability device, a server and a storage medium, wherein, the traceability method based on a block chain comprises the following steps: after receiving the first two-dimensional code information of a designated product sent by a terminal, decrypting the product information in a main chain system by using a consumption public key to generate product traceability information corresponding to the first two-dimensional code information; the product traceability information being transmitted to the terminal, wherein the product traceability information includes at least one of status information, production information, warehousing information, transportation information and sales information of the product. The technical proposal of the invention can effectively supervise each link of product production and sales, can reliably trace the source of product sales process, is conducive to cracking down on fake and inferior products, and protects the rights and interests of consumers and manufacturers.
Owner:佛山鑫达智汇科技有限公司
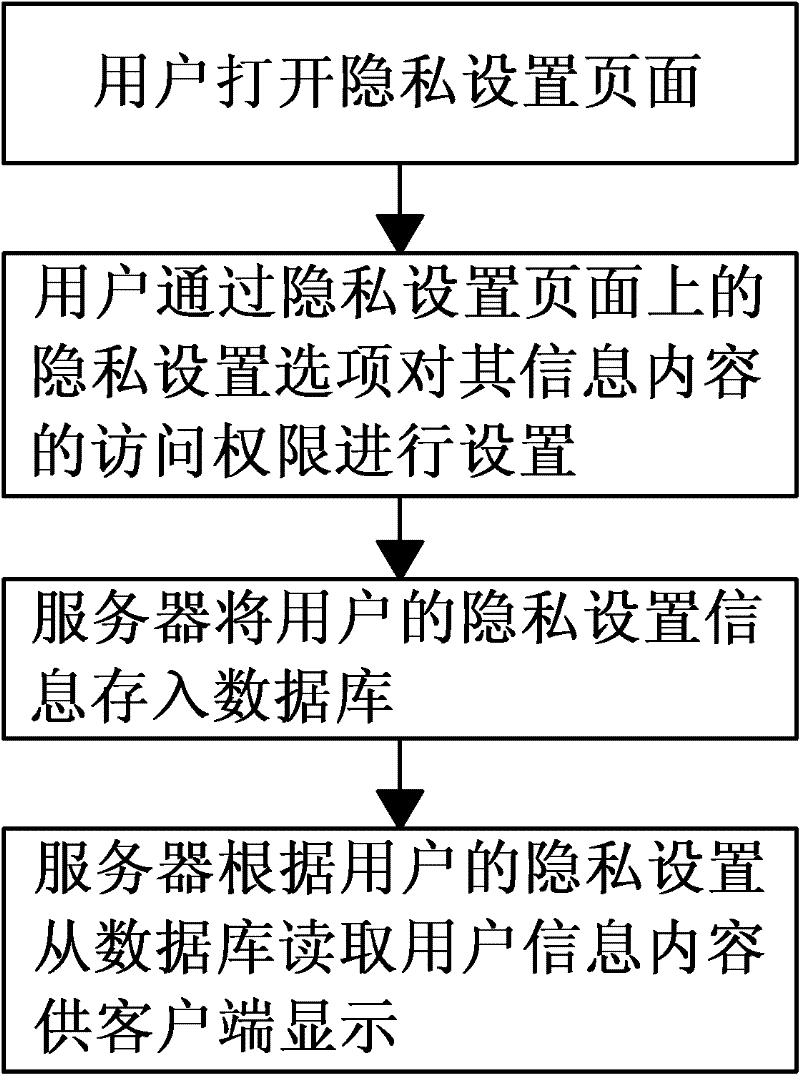
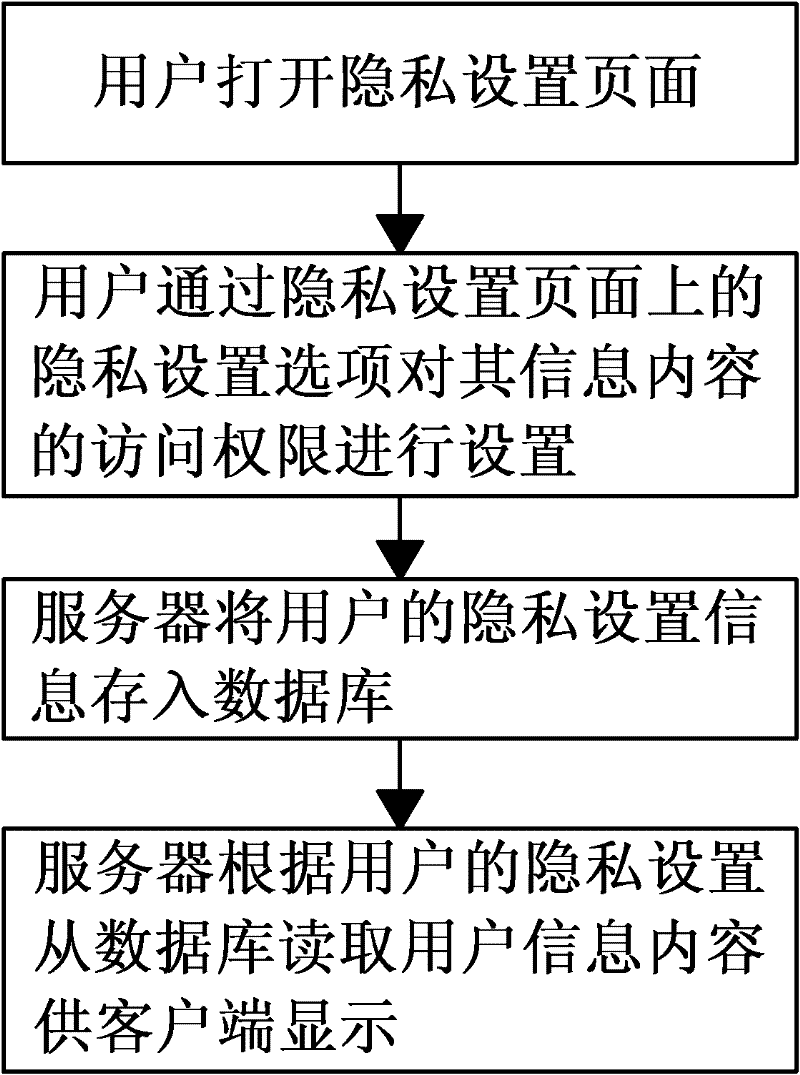
Method and system for protecting user privacy
InactiveCN102185826APrevent leakageProtection of rights and interestsTransmissionClient-sideUser privacy
The invention discloses a method and a system for protecting user privacy. The method includes the following steps of: S1, a user opens a privacy setting page; S2, the user sets the access right of the information content through the privacy setting options on the privacy setting page; S3, a server stores the privacy setting information in a database; S4, the server reads the user information content from the database for user-side display based on the user privacy setting. The method and the system for protecting the user privacy can control the flow direction of the user private information, thus avoiding the disclosure of the user private information, effectively guaranteeing the user rights, and reducing the disputes between the user and a social website.
Owner:BEIJING PEOPLE HAPPY INFORMATION TECH
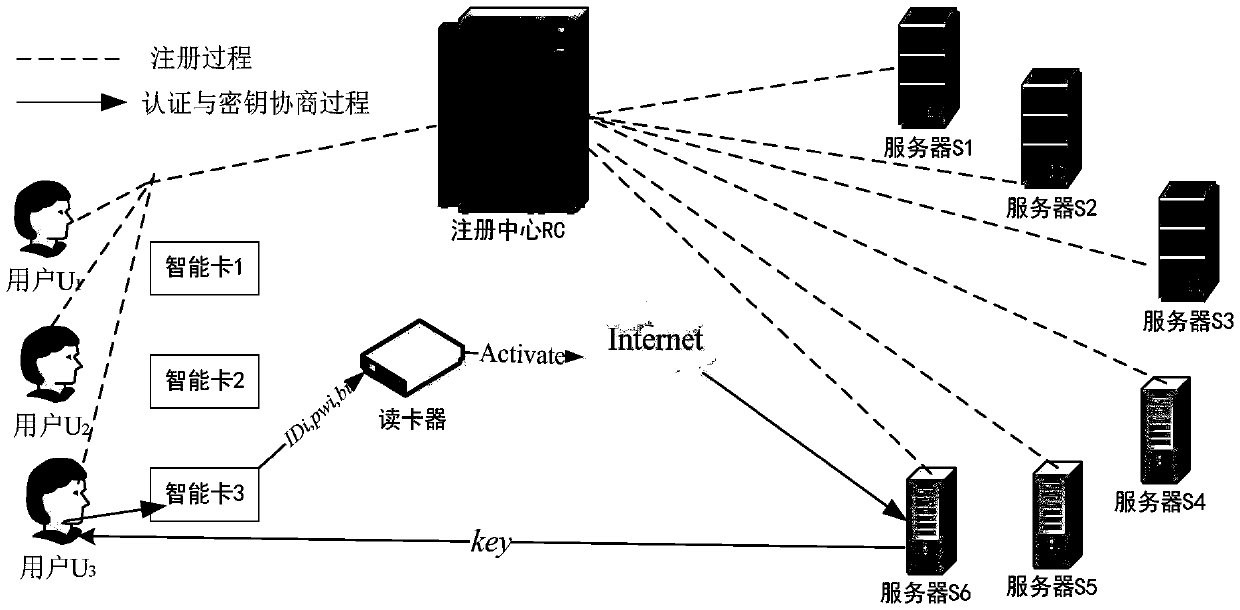
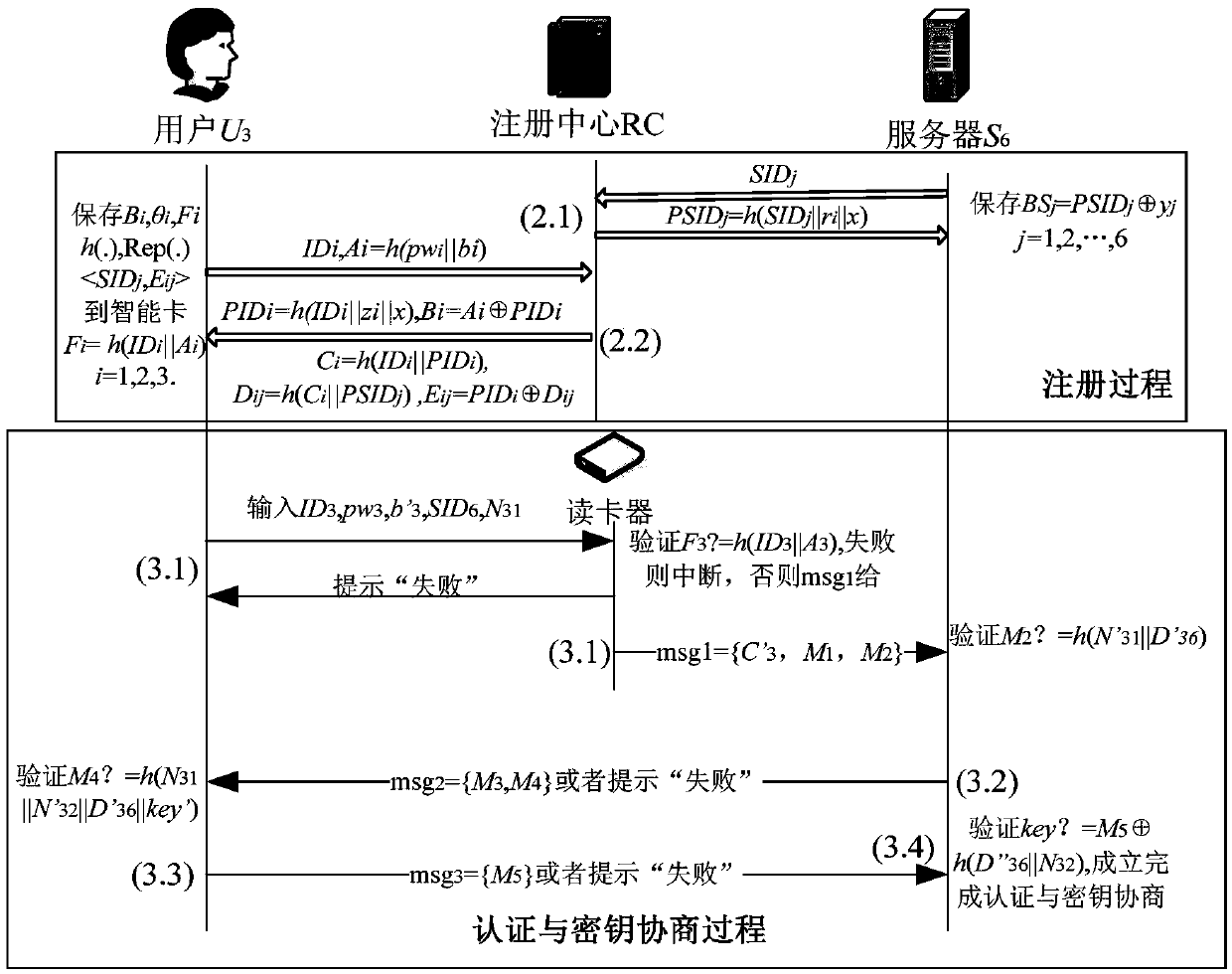
Lightweight anonymous authentication and key negotiation method in multi-server environment
The invention relates to a lightweight anonymous authentication and key negotiation method in a multi-server environment and belongs to the technical field of information safety. The method is characterized by achieving the anonymous authentication and key negotiation in the multi-server environment by means of the following three steps: (1) building a system and selecting system parameters; (2) registering in a registering center RC by a server and a user; (3) carrying out authentication and key negotiation by the user and a remote server so as to provide subsequent communication session keys. The lightweight anonymous authentication and key negotiation method is applicable to remote authentication of a mobile terminal and servers with low calculation capability, memory space and communication capability; the mobile terminal can log in any server registered by RC through a user name and a password; the server only can authenticate that the user is a valid user and cannot know the specific identity of the user, so that the privacy of the user is protected; the lightweight anonymous authentication and key negotiation method is excellent in expansibility; the two-party negotiation session keys are determined by random numbers Ni1 and Ni2 selected by authenticating for each time by two parties; the independence and the forward and backward security of the session keys are ensured.
Owner:深圳市迅威恒达信息技术有限公司
Anti-stealing link method of internet content delivery network
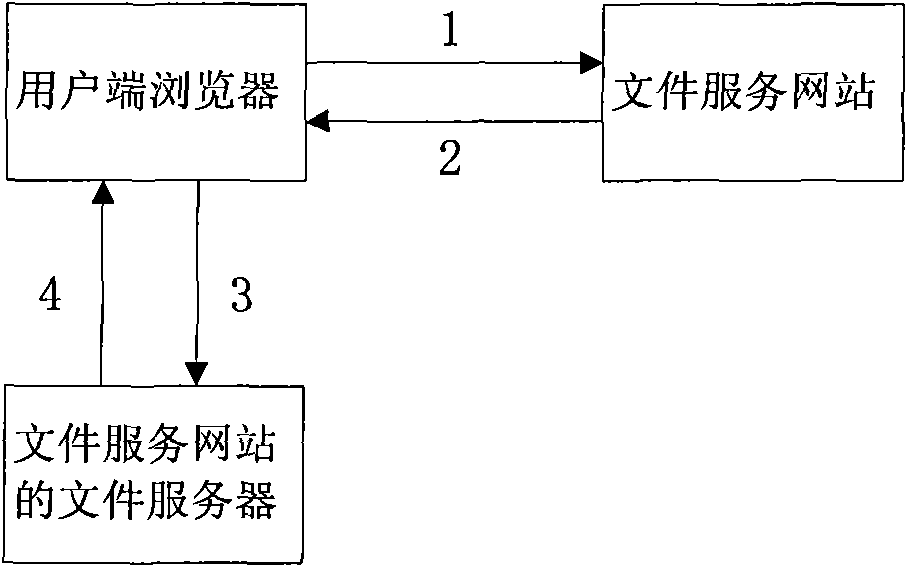
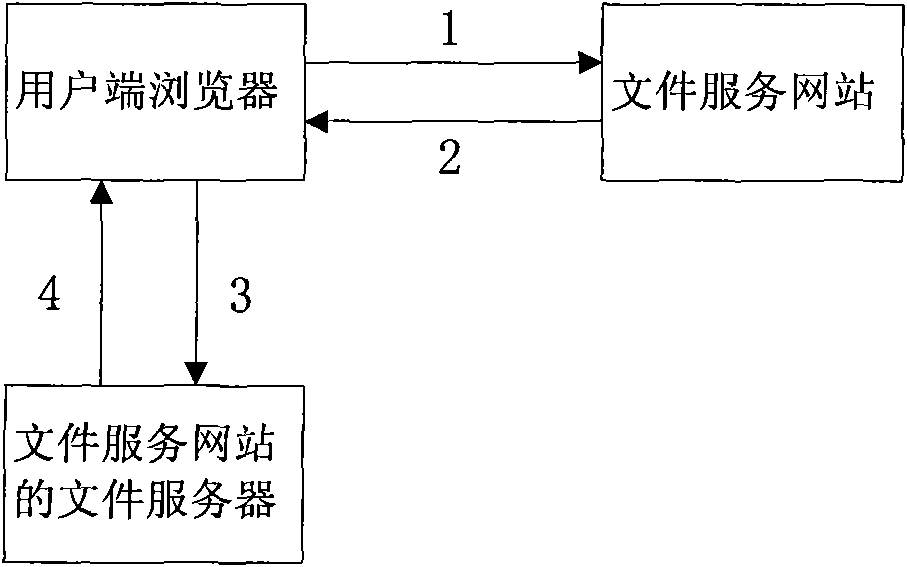
ActiveCN101815060AProtection of rights and interestsRaise the bar for hotlinkingTransmissionSpecial data processing applicationsInternet contentHyper text transport protocol
The invention relates to an anti-stealing link method of an internet content delivery network, comprising the following steps: (1) a user side requests a file server website to provide a file download link through a browser; (2) the file server website returns the file download link in which HTTP (Hyper Text Transport Protocol) User-Agent information of the browser at the user side is introduced; (3) the browser at the user side initiates a file download request to a file server of the file server website through the file download link; (4) after receiving the file download request, the file server of the file server website checks the HTTP User-Agent information in the file download link and User-Agent information in the file download request, if the HTTP User-Agent information in the file download link and the User-Agent information in the file download request are consistent, then the request is judged to be a legal request, and file download service is provided for the request; otherwise, the request is judged to be a stealing link, and the file download service is refused to be provided for the request. The invention improves the threshold of the stealing link and effectively protects the right and the interest of the file server website.
Owner:阿里巴巴(中国)网络技术有限公司
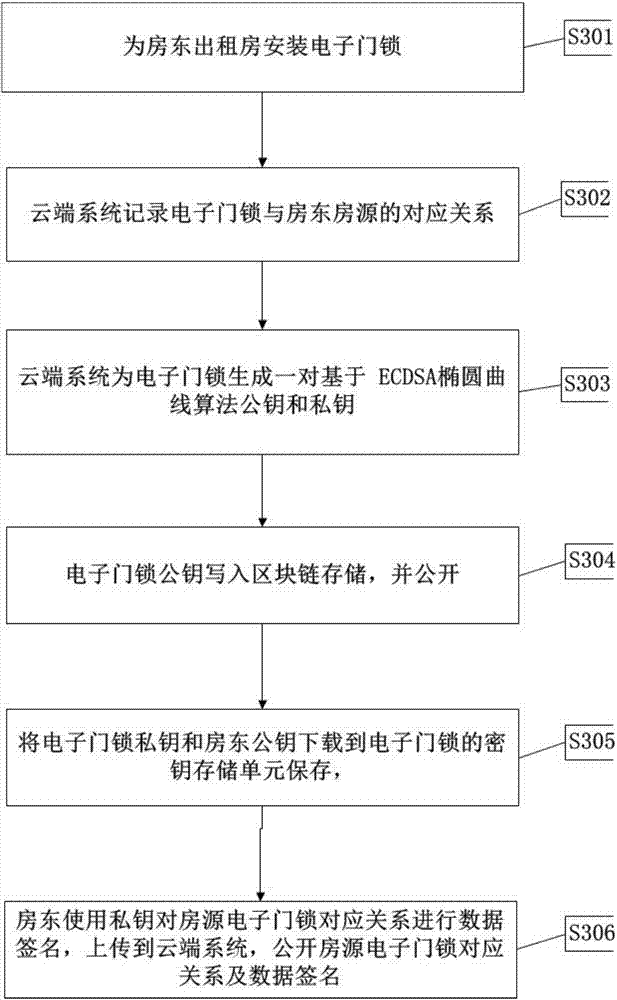
House renting platform and network fingerprint electronic door lock system
InactiveCN107958412AJudging the authenticity and validityGuaranteed to be true and effectiveUser identity/authority verificationIndividual entry/exit registersEnd systemEngineering
The invention discloses a house renting platform and network fingerprint electronic door lock system comprising a cloud end system, a data storage system, a block chain storage system, a tenant clientend, a landlord client end, and an electronic lock; the house renting platform and network fingerprint electronic door lock system can effectively check the landlord and tenant ID information, and uses the tenant fingerprint as the key; the system is easy to use, can record the tenant renting process, and can form a tenant credit file.
Owner:云南飞网科技有限公司
Product personalized customization display system achieved through Internet and two-dimensional codes
InactiveCN104463660AClear and complete purpose of gift givingAvoid reuseBuying/selling/leasing transactionsPersonalizationGift giving
The invention provides a product personalized customization display system achieved through the Internet and two-dimensional codes and belongs to the field of two-dimensional code customization platforms. The product personalized customization display system achieved through the Internet and the two-dimensional codes comprises two-dimensional code labels and an information platform, and a gift recipient can know information wanted to be expressed and completely understand the gift giving intention through the information platform by using a terminal device capable of scanning the two-dimensional codes and a server carrying the information platform.
Owner:SHANDONG TAIBAO PREVENTING COUNTERFEIT
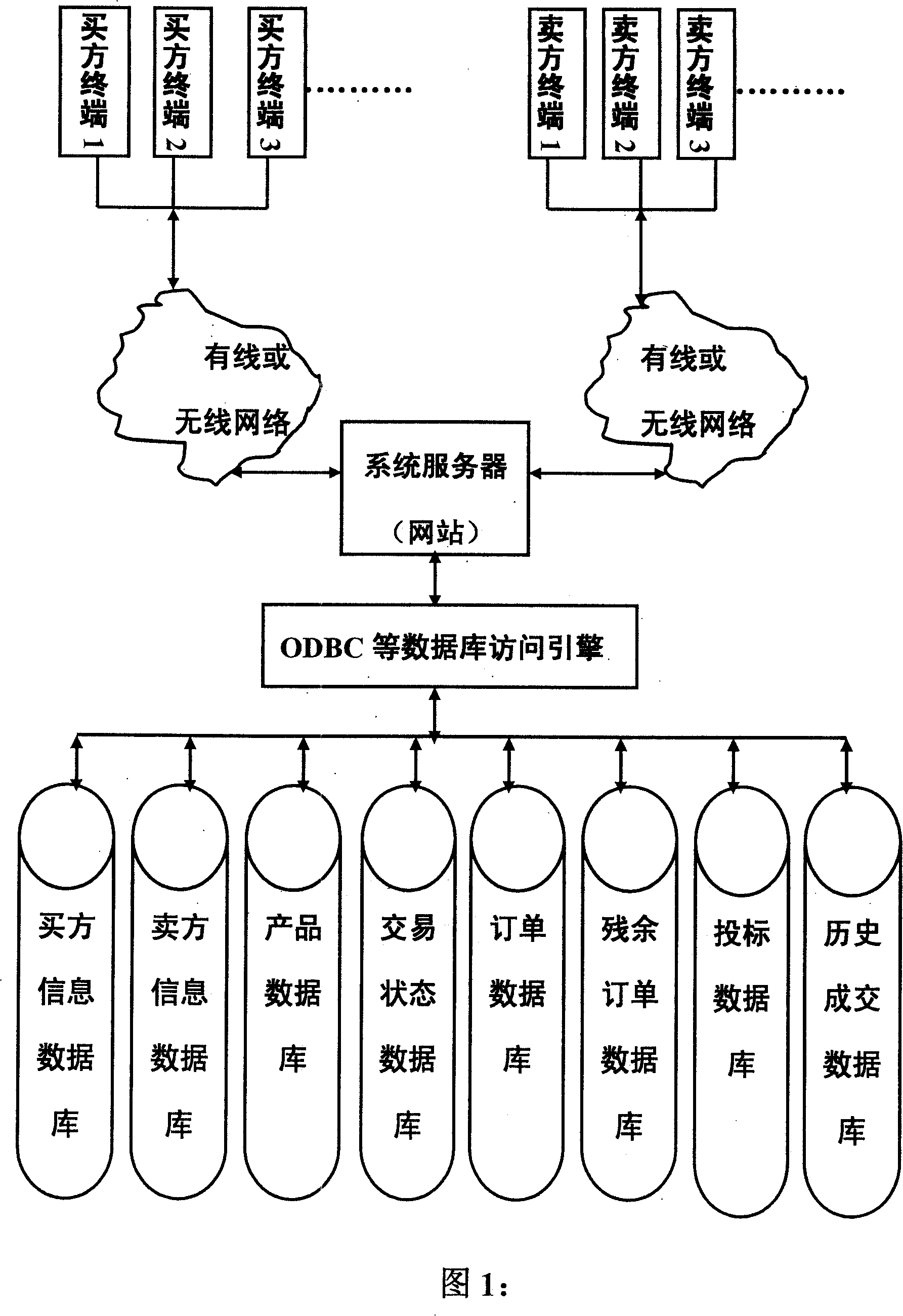
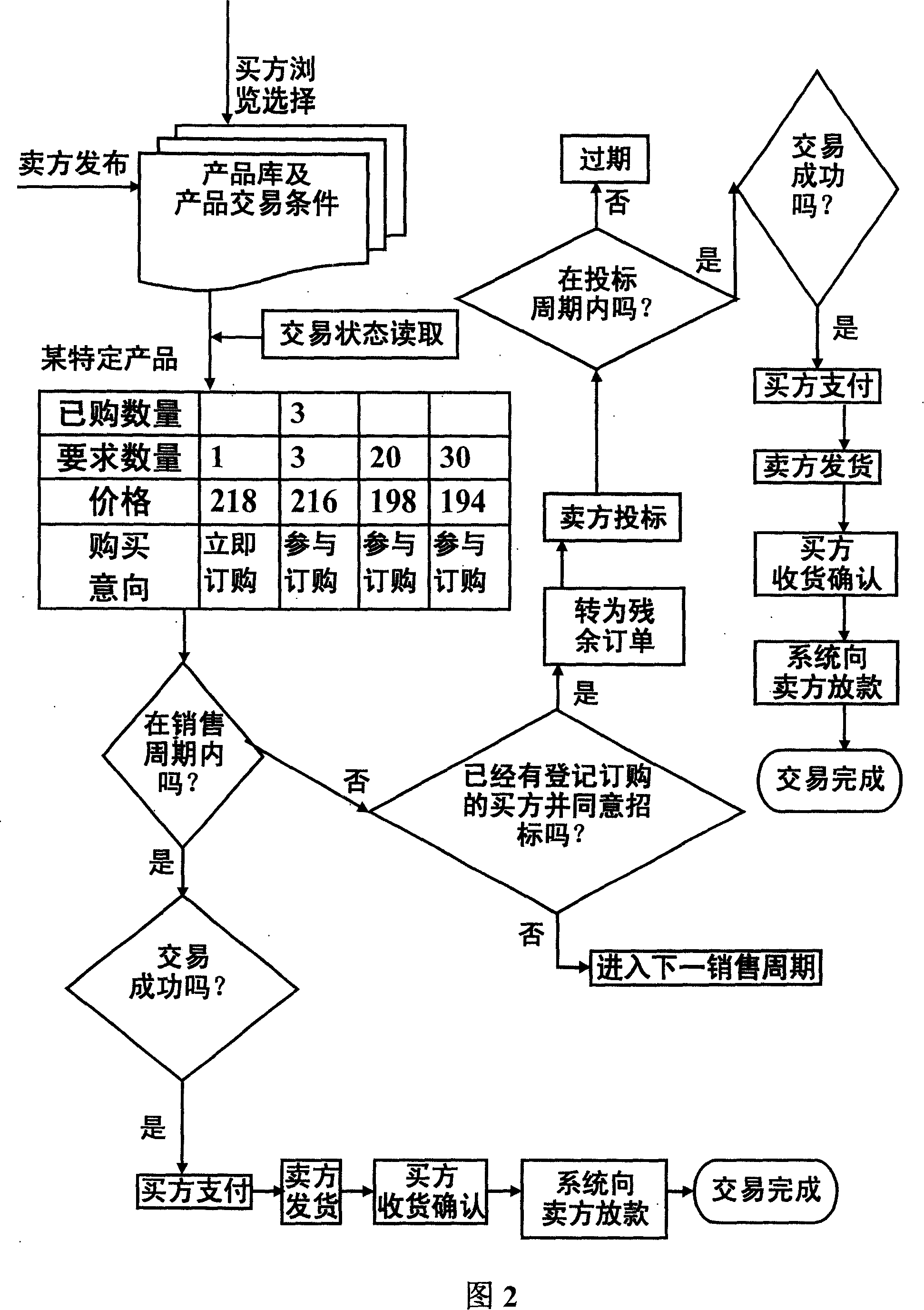
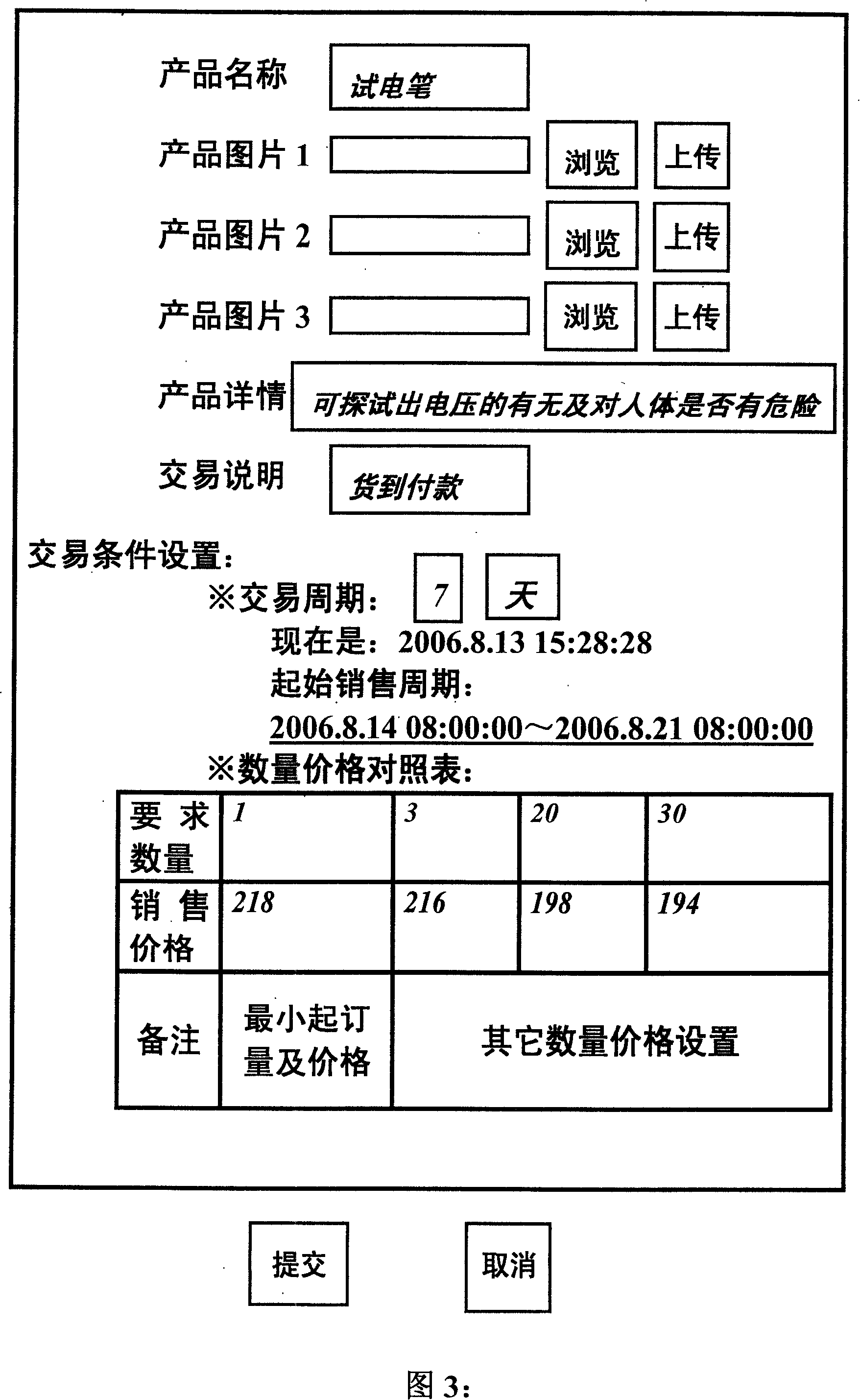
Commodity transaction mode under information network surroundings
InactiveCN101140650AReduce logistics costsReduce intermediate linksBuying/selling/leasing transactionsSystem structureData mining
A commodity exchange mode in an information network environment: The invention relates to a commodity exchange mechanism of group bargaining in the information network environment, as well as a relevant implementation method and a system structure. The invention aims at the following problems that are universally utilized in prior electronic commerce (in particular in B2C, B2B and C2C modes): Buyers are in weaker situations in market in commodity exchange mechanism and relevant implementation method, and market efficiency is rather low and etc. The invention submits a commodity exchange mode with rather high efficiency in the information network environments. Divide the commodity exchange process into the following two stages: Group bargaining stage and remaining order bidding stage. In the group bargaining stage, the conclusion policies include demands polymerization and graded bargaining conclusion. The invention provides the commodity exchange mechanism to enlarge sales opportunity of commodity and products (services) and increase sales speed, considerably increase buyers' negotiation situation levels, increase consumers' effects, and further increase exchange success rate, lower exchange cost and improve market efficiency.
Owner:高思兵
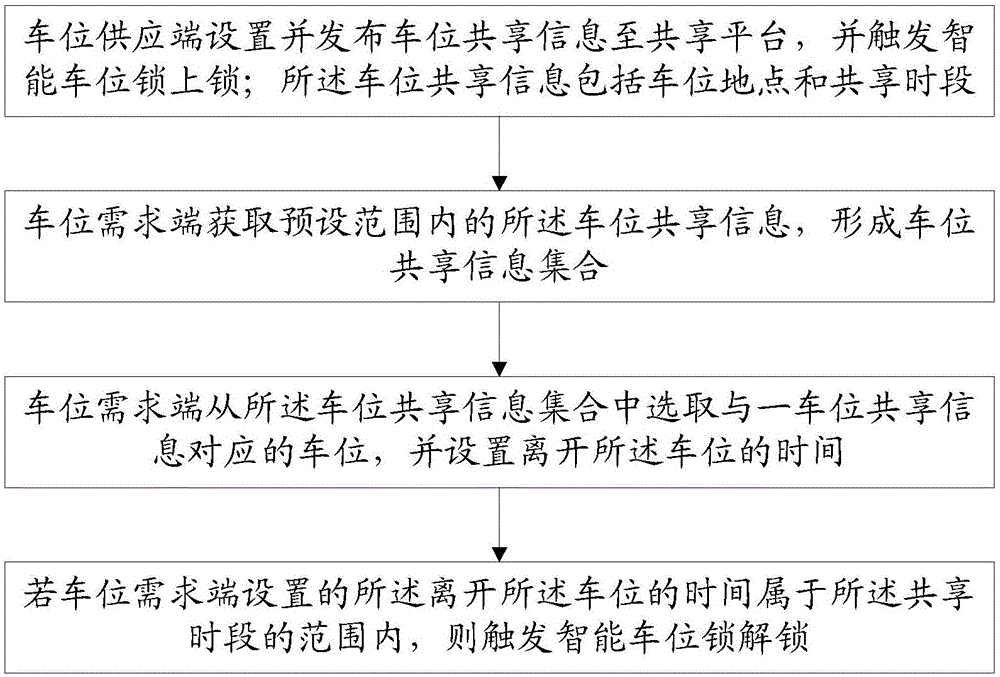
City private parking position sharing exchange service method and system
ActiveCN106504576AIncrease usageFree from abuseTransportation facility accessParticular environment based servicesInformation sharingParking space
The invention relates to the field of information sharing, and especially relates to a city private parking position sharing exchange service method and system. The method comprises the following steps: a parking position supply chain setting and issuing parking position sharing information to a sharing platform, and triggering an intelligent parking position lock to be locked, wherein the parking position information comprises parking position places and sharing periods; a parking position demand end obtaining the parking position sharing information in a preset scope to form a parking position sharing information set; the parking position demand end selecting a parking position corresponding to one piece of the parking position sharing information from the parking position sharing information set and setting time of departure from the parking position; and if the time of departure from the parking position, set by the parking position demand end belongs to the scope of the sharing periods, triggering the intelligent parking position lock to be unlocked. According to the invention, city private parking position information can be shared, and the utilization rate of parking positions is improved.
Owner:FUJIAN UNIV OF TECH
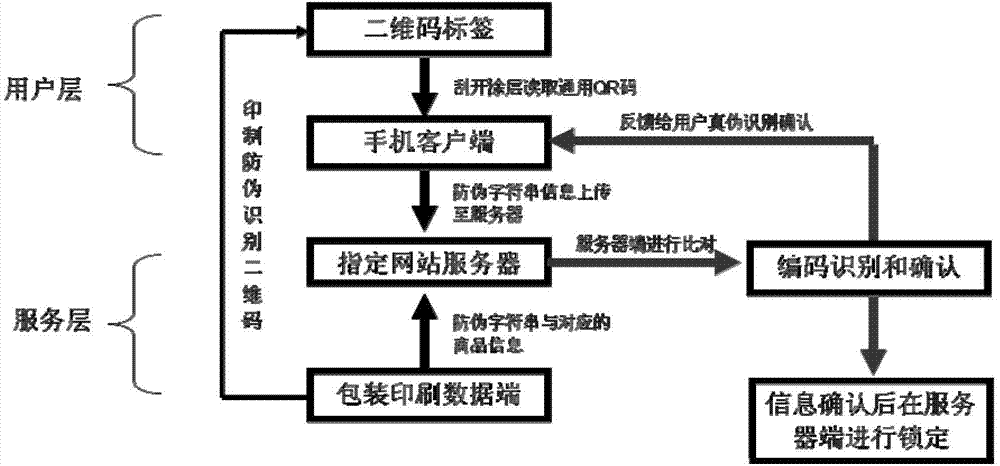
Tracing anti-fake market interaction integration system and method
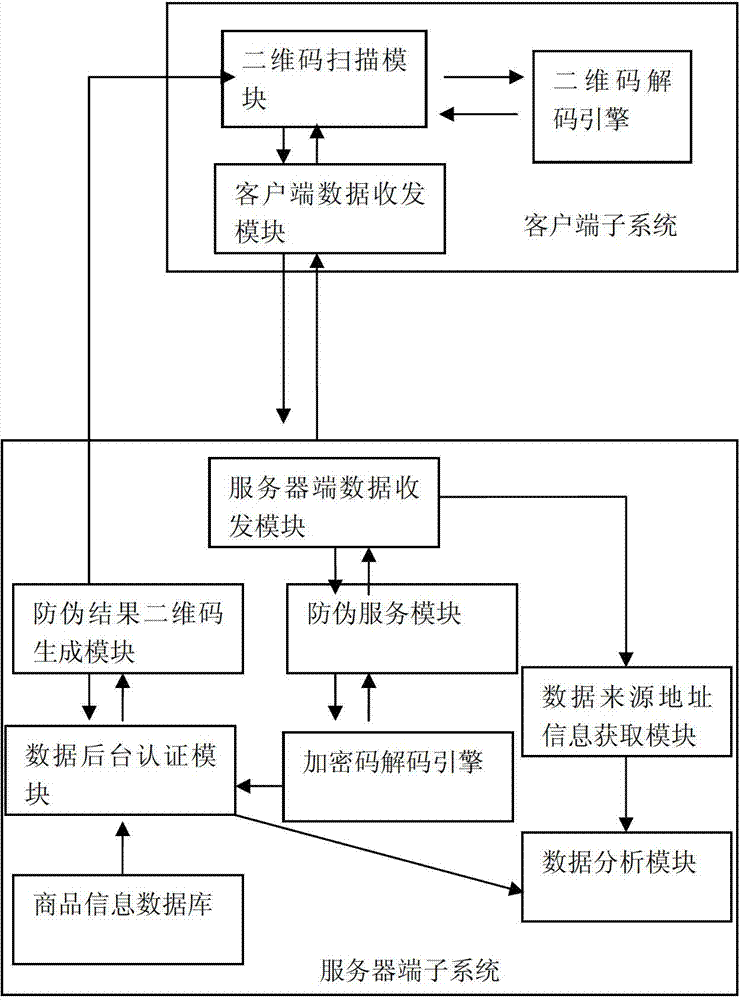
ActiveCN103325042AAnti-counterfeiting is the most detailedGuarantee the strength of anti-counterfeiting certificationCommerceSoftware engineeringAuthentication
The invention discloses a tracing anti-fake market interaction integration system and method. The tracing anti-fake market interaction integration system and the tracing anti-fake market interaction integration method break through limitation on the cover degree of an existing tracing anti-fake system, achieve the purpose that one product is provided with one code, and put anti-fake into practice for every consumer. The anti-fake method that one product is provided with one code is adopted in the whole process of product delivery and sale. The method includes the steps of correspondence of identification codes to goods and correspondence of the identification codes to spraying in the process of anti-fake code generation and subsystem generation, then based on identification code scanning and network transmission, the most detailed anti-fake is achieved under the condition of little expenditure, and anti-fake and authentication effort for each product is guaranteed.
Owner:黄梅
A distributed parking sharing system based on a block chain and an implementation method
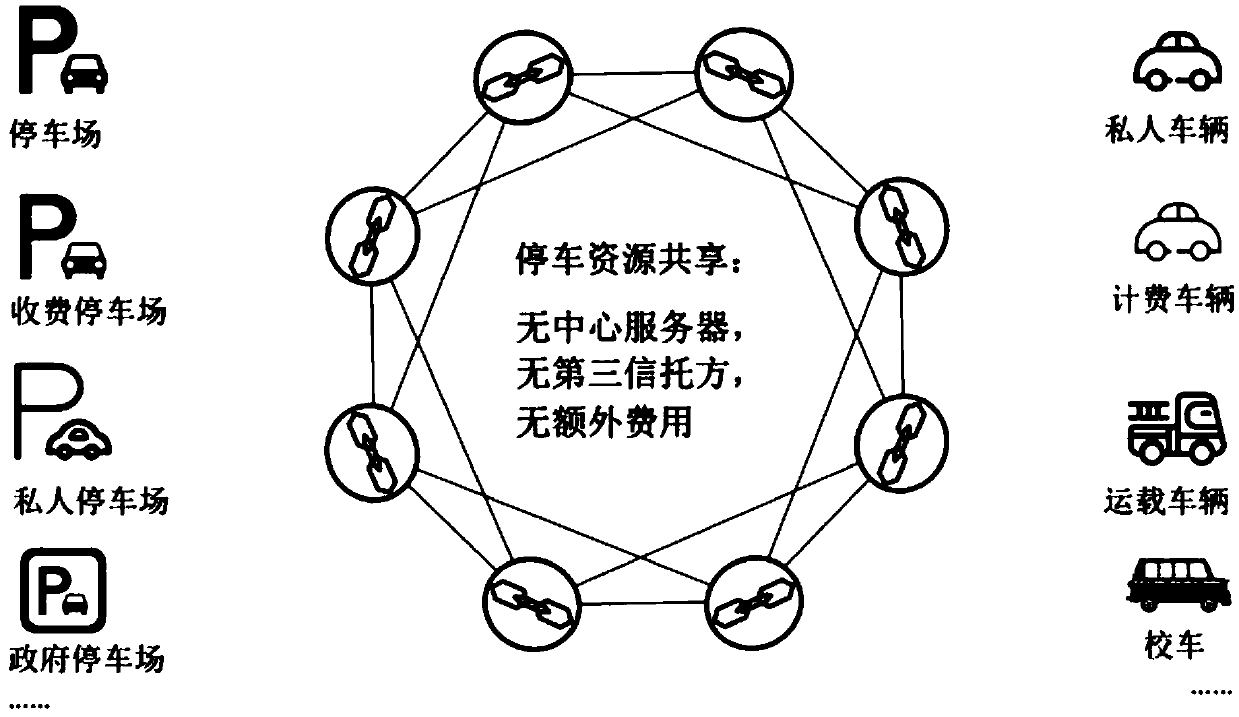
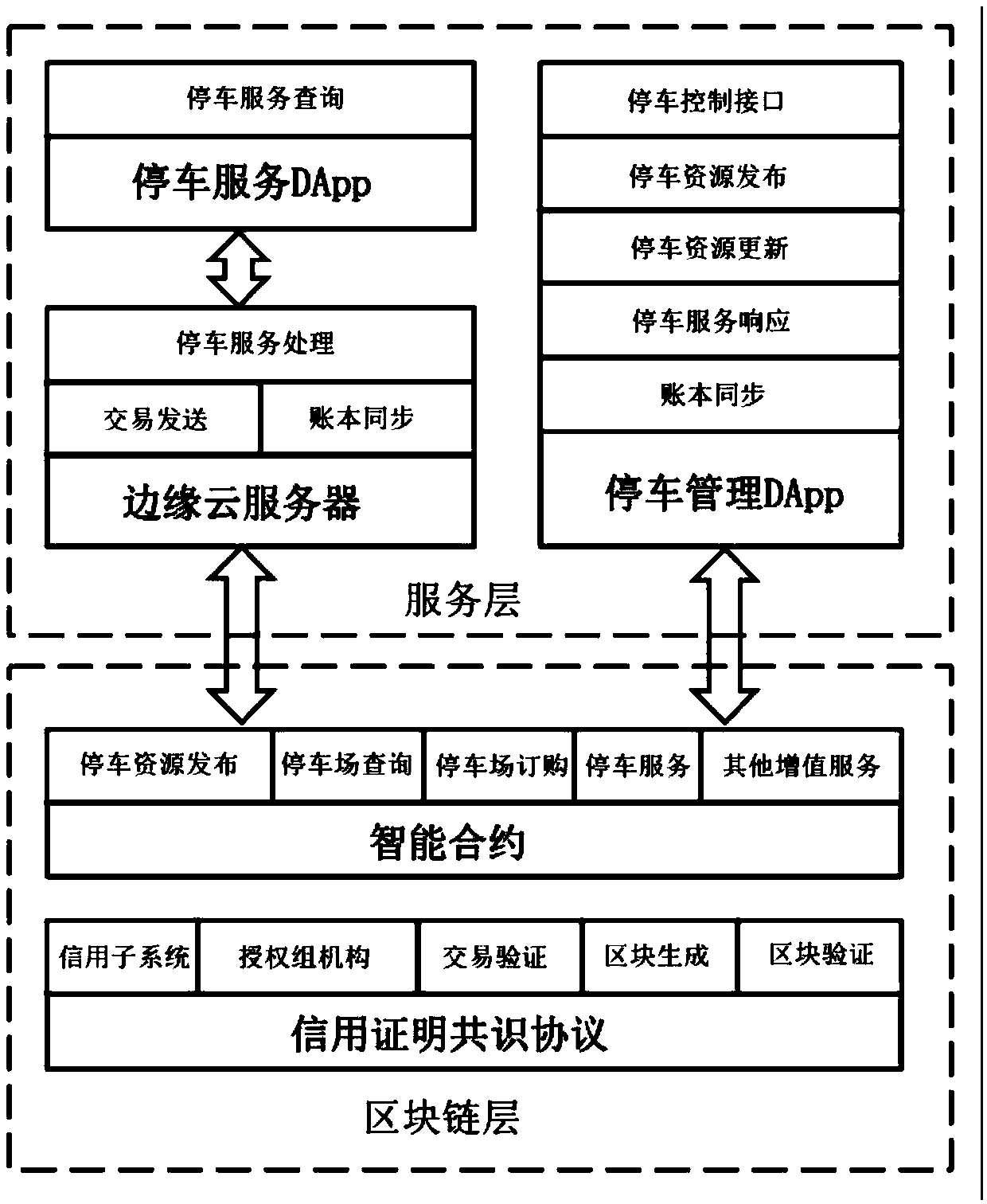
InactiveCN109636547AReduce construction costsReach the consensus of the whole networkFinanceBuying/selling/leasing transactionsChain networkSmart contract
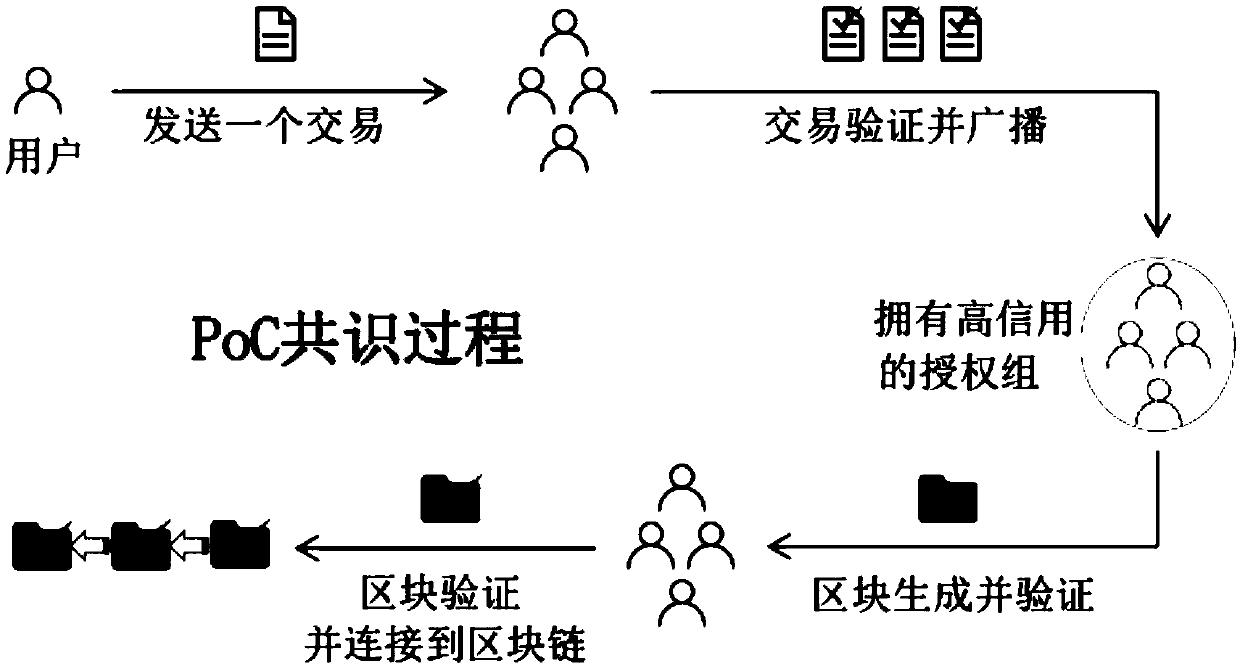
The invention belongs to the technical field of block chains, and discloses a distributed parking sharing system based on a block chain and an implementation method. the distributed parking sharing system based on the block chain comprises a block chain layer and a service layer; The block chain layer is used for defining business models of various parking related services by using an intelligentcontract and Operating in a transparent and trusted manner through the smart contract; Parking lot reservation and parking service transaction records of the smart contract are collected and packagedinto a data block in a block chain network; a data block is generated and a block chain account book is managed through a PoC (Point of Credit) based consensus protocol; And the service layer is usedfor providing a service interface through a distributed application program (DApps). The problem that urban parking is difficult is solved; A prototype system is established to verify the system, anda result shows that the new scheme provided by the invention can effectively realize parking resource sharing and service.
Owner:ZHEJIANG NORMAL UNIVERSITY
Identity authentication method and device and computer storage medium
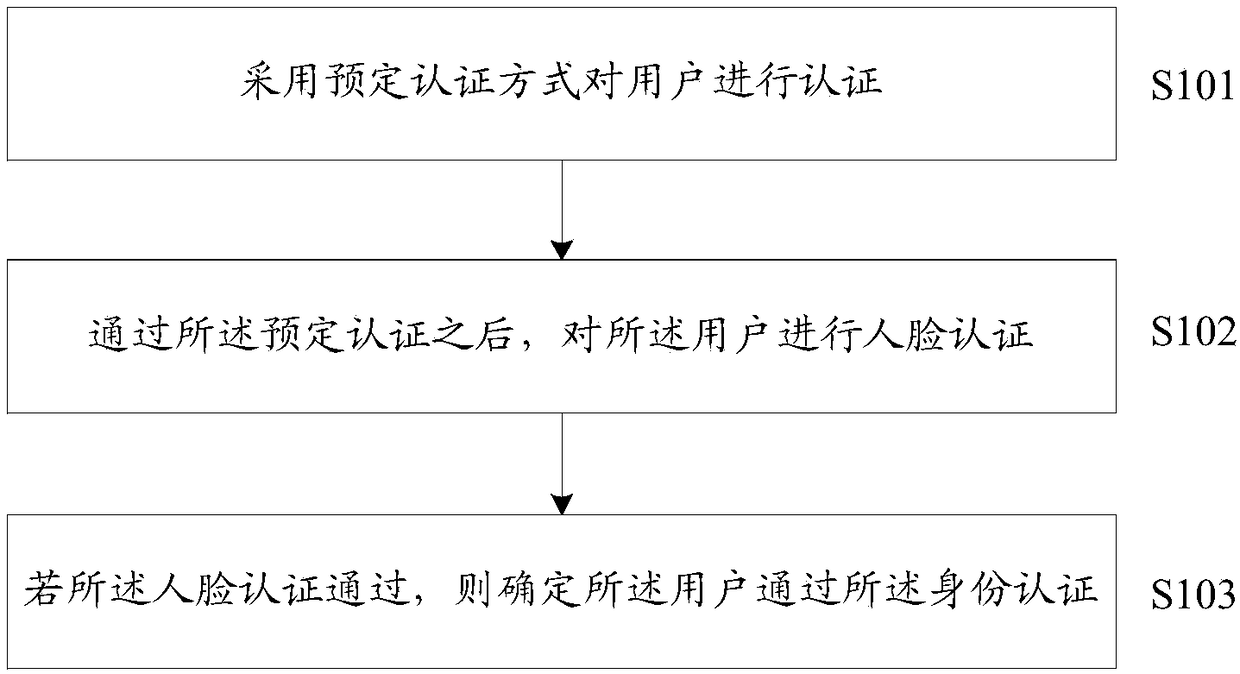
ActiveCN108804884AProtection of rights and interestsEnsure safetyDigital data authenticationSpoof detectionAuthentication
The embodiment of the invention provides an identity authentication method and device and a computer storage medium. The method comprises the steps that a predetermined authentication mode is adoptedto perform authentication on a user; after the user passes the predetermined authentication, facial authentication is performed on the user; and if the user passes the facial authentication, it is determined that the user passes identity authentication. It is thus obvious that through the embodiment, in the identity authentication process, security can be guaranteed through the dual authenticationmodes of predetermined authentication and facial authentication, and therefore the rights and interests of the user are safeguarded.
Owner:BEIJING KUANGSHI TECH +1
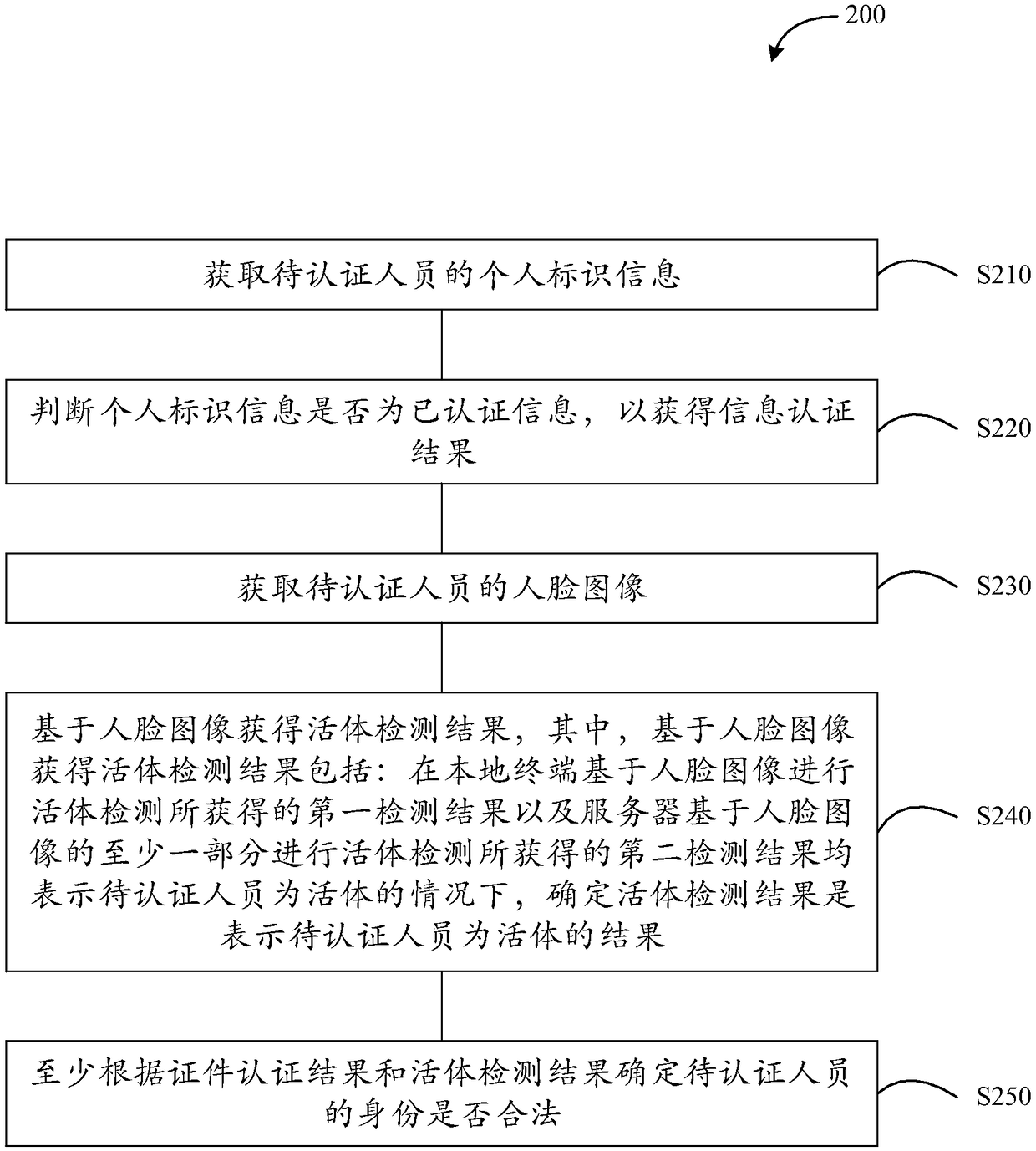
Identity authentication method, device and system, terminal, server and storage medium
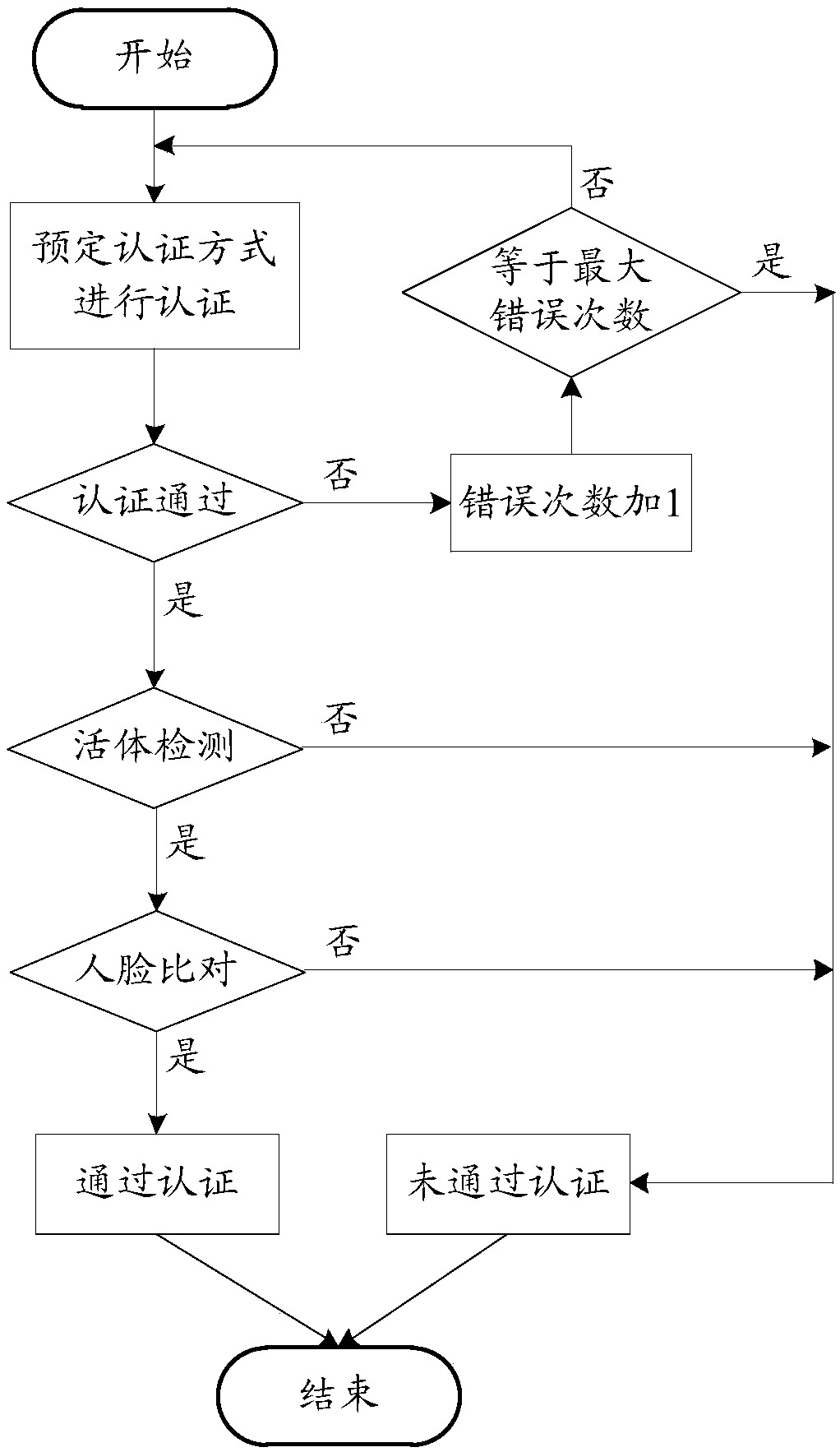
InactiveCN108573202AProtection of rights and interestsImprove securitySpoof detectionInternet privacyLiving body
The embodiment of the invention provides an identity authentication method, device and system, a terminal, a server and a storage medium. The method comprises steps of acquiring personal identifier information of a to-be-authenticated person; judging whether the personal identifier information is the authenticated information so as to acquire an information authentication result; acquiring a faceimage of the to-be-authenticated person; based on a face image, acquiring a living body detection result, wherein under the condition that a first detection result acquired in living body detection carried out by a local terminal based on a face image and a second detection result acquired in living body detection carried out by a server based on at least one part of the face image represent thatan authentication worker is a living body, the living body detection result is determined to be the result for representing the to-be-authenticated worker is a living body; and at least according to the information authentication result and the living body detection result, whether the identity of the to-be-authenticated worker is legal. According to the invention, by combining the authenticated information judgment and double living body detections, whether the identity of the to-be-authenticated worker is legal is determined.
Owner:BEIJING KUANGSHI TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com