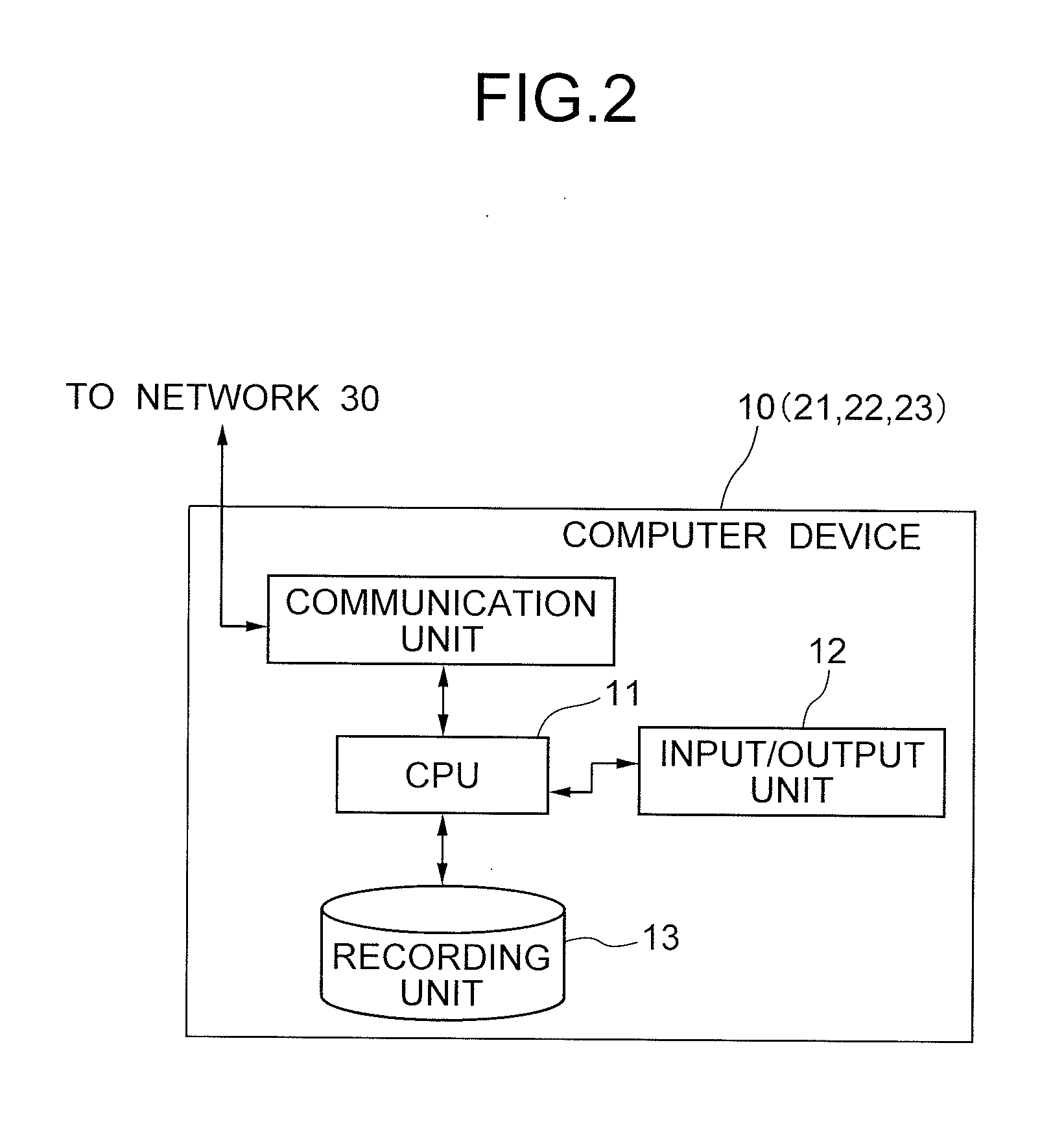
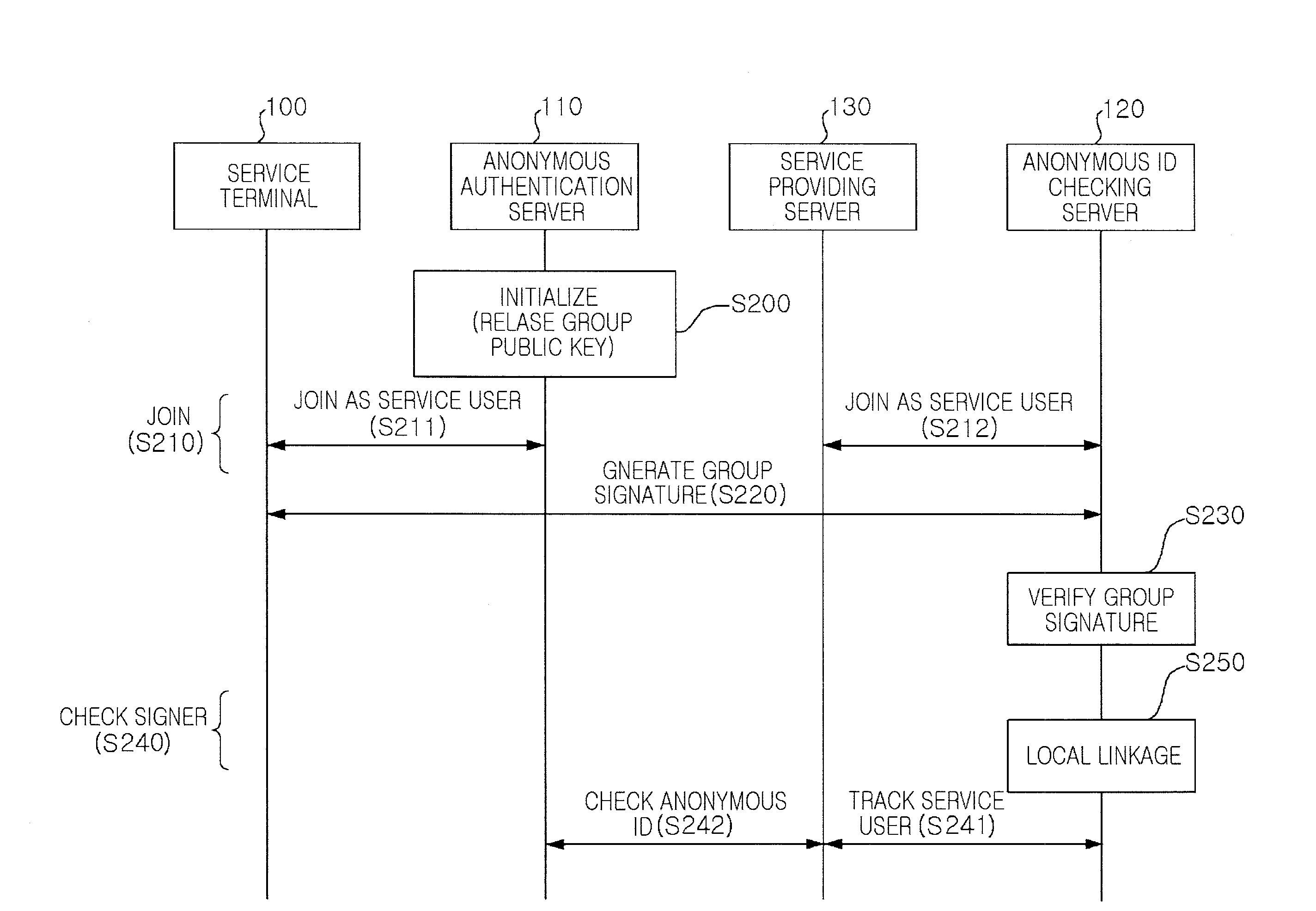
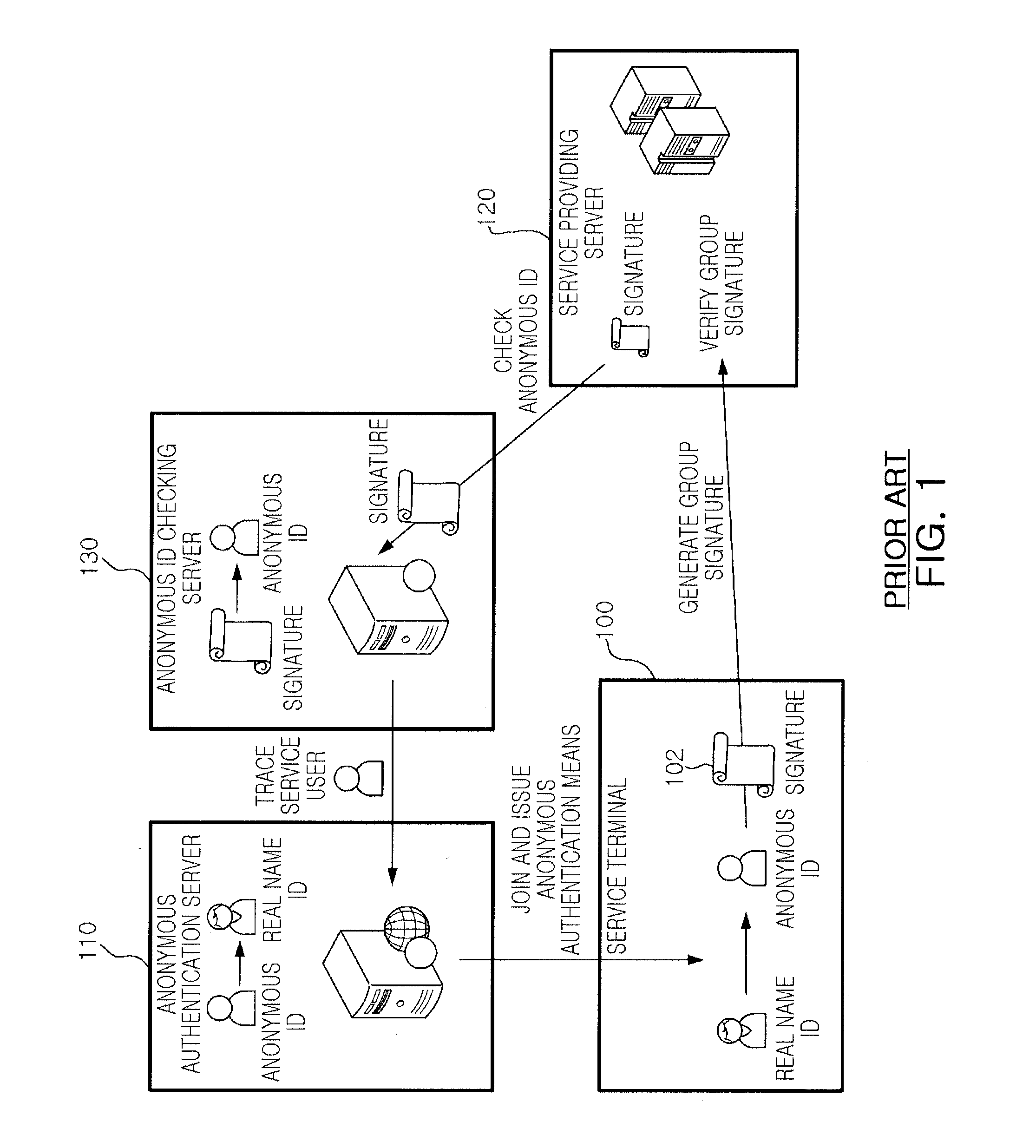
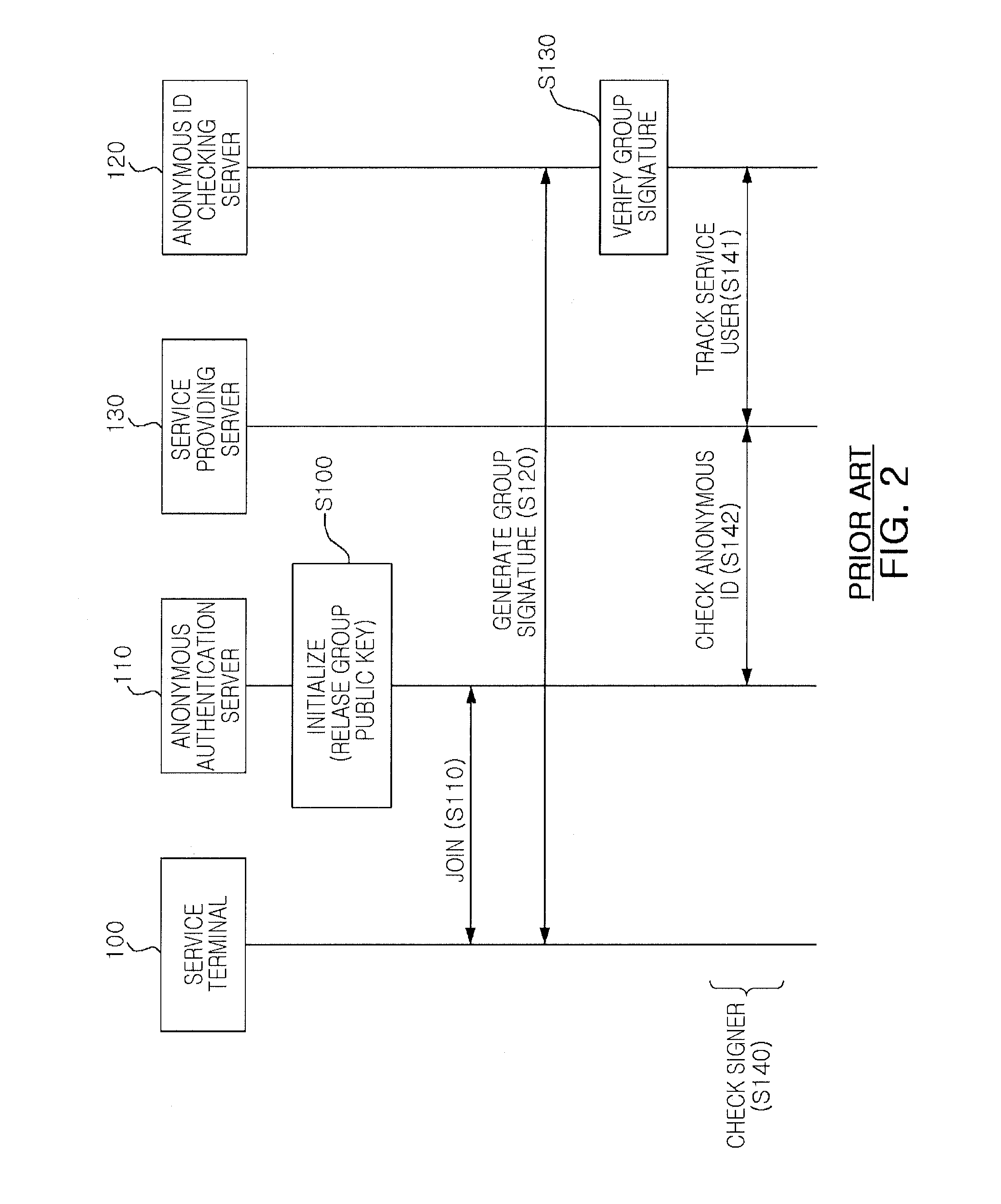
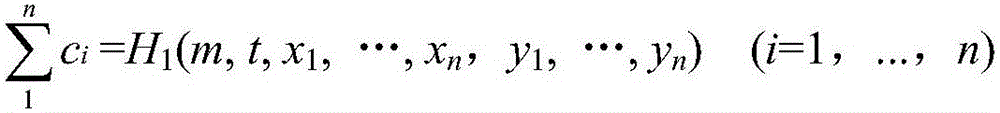Patents
Literature
211 results about "Anonymous authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Anonymous biometric authentication
InactiveUS20020112177A1Digital data processing detailsUser identity/authority verificationInternet privacyAnonymous authentication
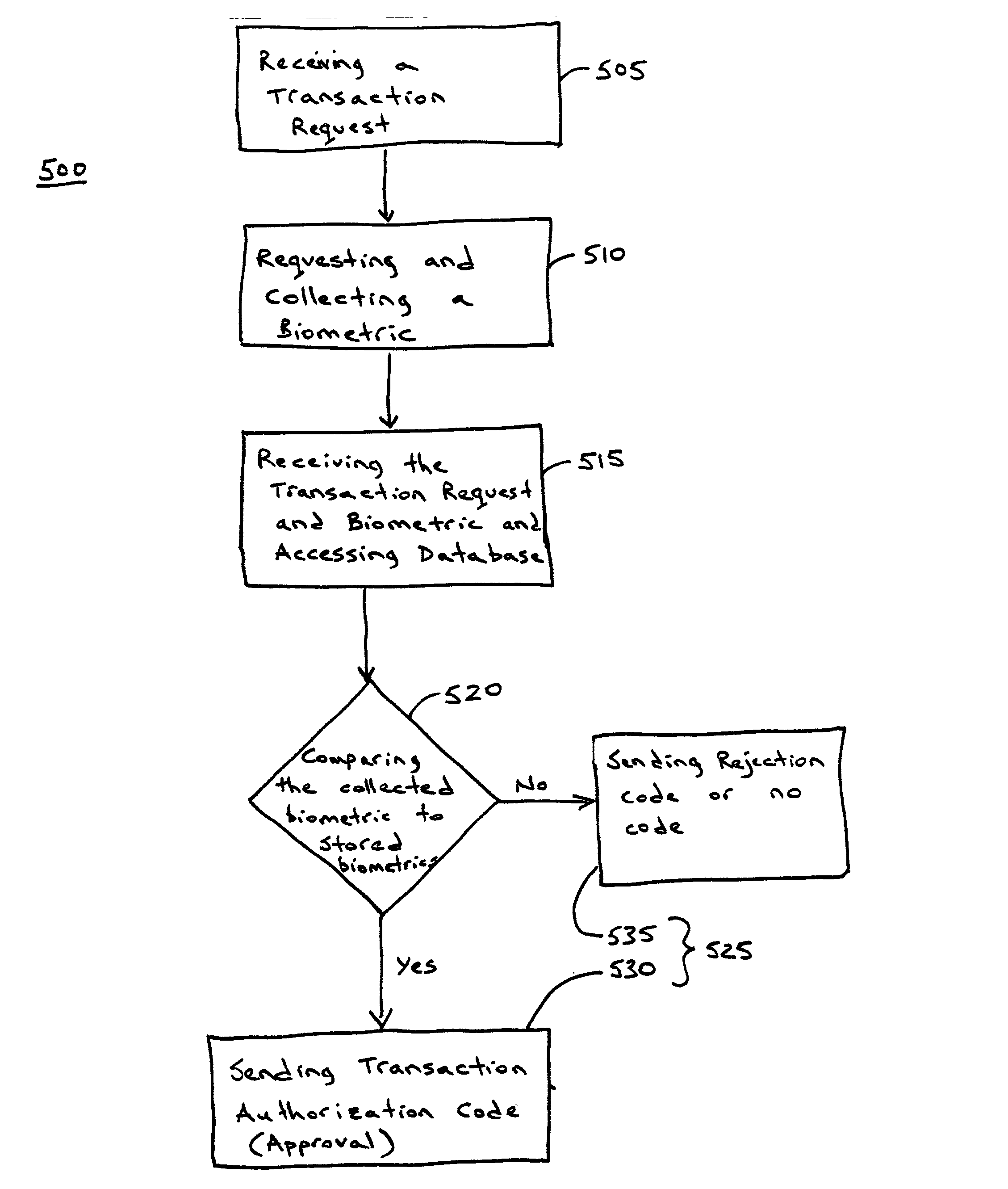
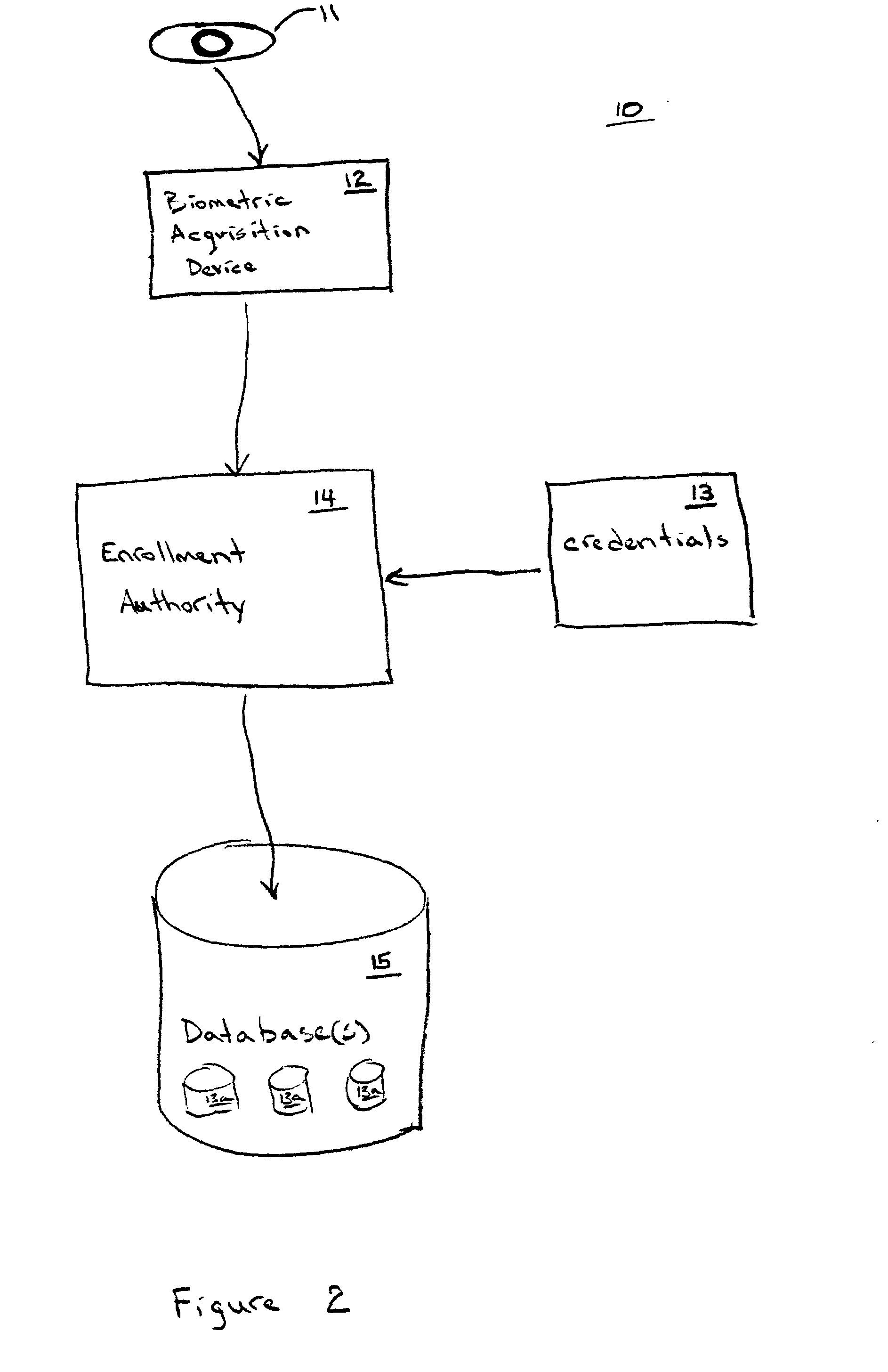
The use of an anonymous biometric authentication system and method that use biometrics to anonymously authenticate an individual and grant certain privileges based on the anonymous authentication is provided. The system and method permit enrollment of an individual by submission of a first biometric and associated identity documents or credentials to an enrollment authority. The enrollment authority verifies the identity of the identity of the individual submitting the biometric using the credentials which are then returned to the individual or discarded. The first biometric is stored in a database for later retrieval in anonymously authenticating an individual seeking to exercise certain privileges. No other personal identity information is stored along with the biometric during the enrollment process. When an individual later seeks to exercise certain privileges, they must submit a second biometric that is compared to the stored biometrics in the database in order to anonymously authenticate the identity of the individual as having access to such privileges. No other personal information is captured, collected, or solicited during the authentication process. Privileges are granted to an individual based on the comparison of the later captured biometric to the stored biometrics in the database. Alternatively, the anonymous biometric authentication system can be designed to avoid repeat offenders by capturing a biometric of an individual seeking to exercise a privilege and denying the privilege if the captured biometric is matched to a biometric stored in a database containing the biometrics of previous offenders. Preferably, the system and method include capture and storage of a powerful biometric identifier based on the iris of the eye which uniquely identifies the individual that has submitted the biometric. Anonymous biometric authentication allows verification of the identity of an individual seeking certain privileges while at the same time protecting the privacy of personal information about the individual.
Owner:IRIDIAN TECH
Anonymous authenticated communications
InactiveUS7234059B1Maintaining anonymityKey distribution for secure communicationPublic key for secure communicationComputer networkElectronic communication
Owner:SANDIA NAT LAB
Method and system with authentication, revocable anonymity and non-repudiation
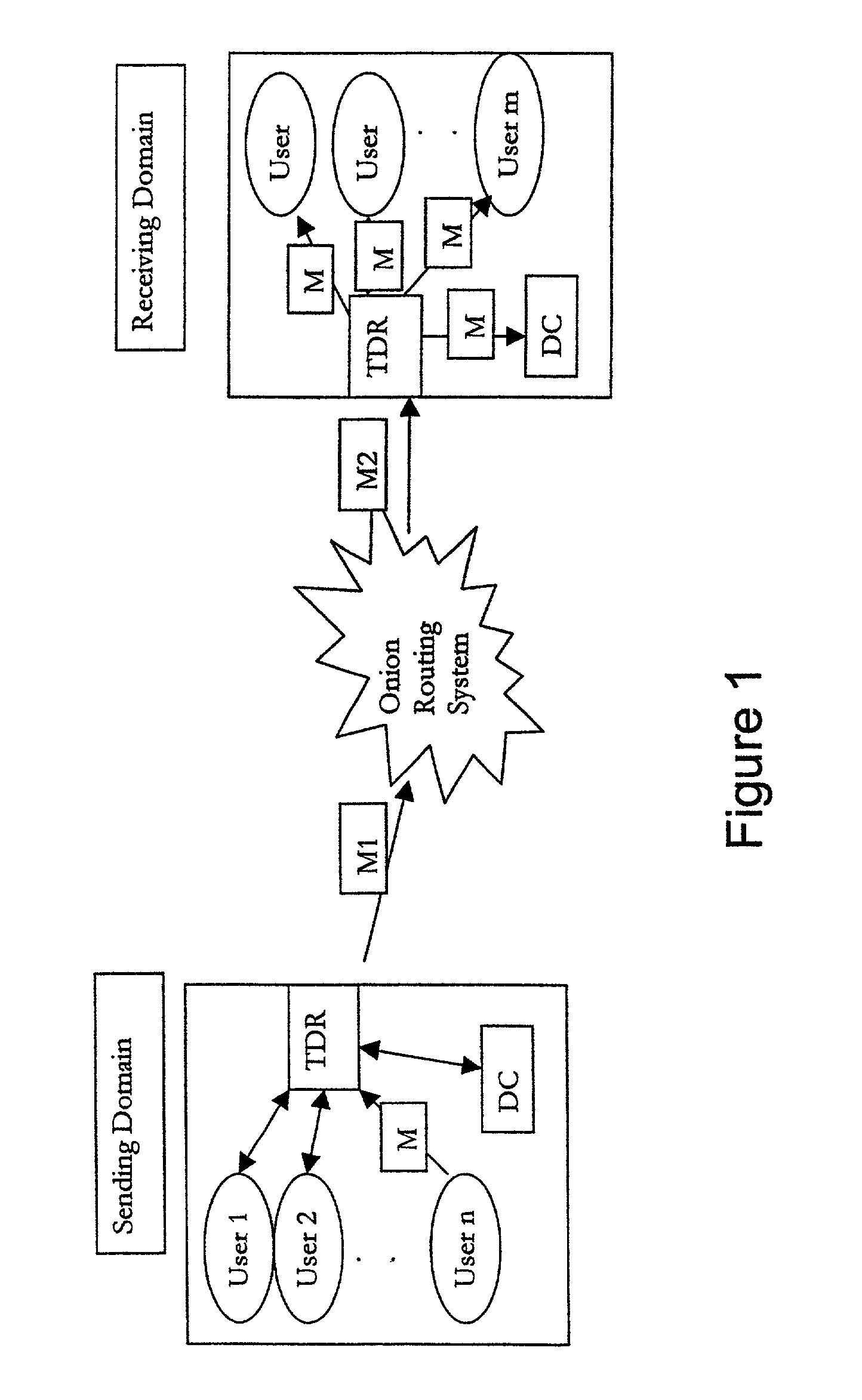
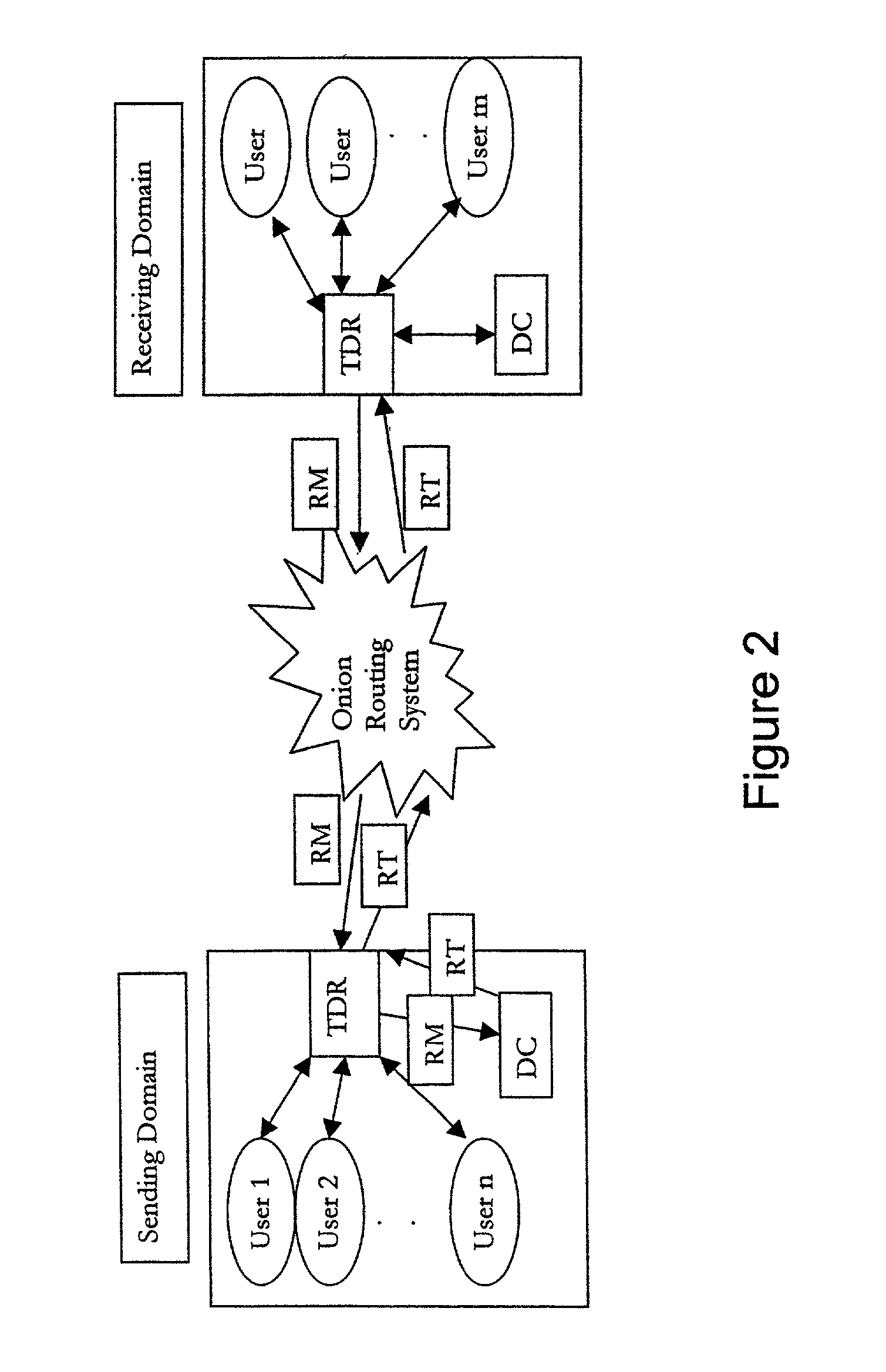
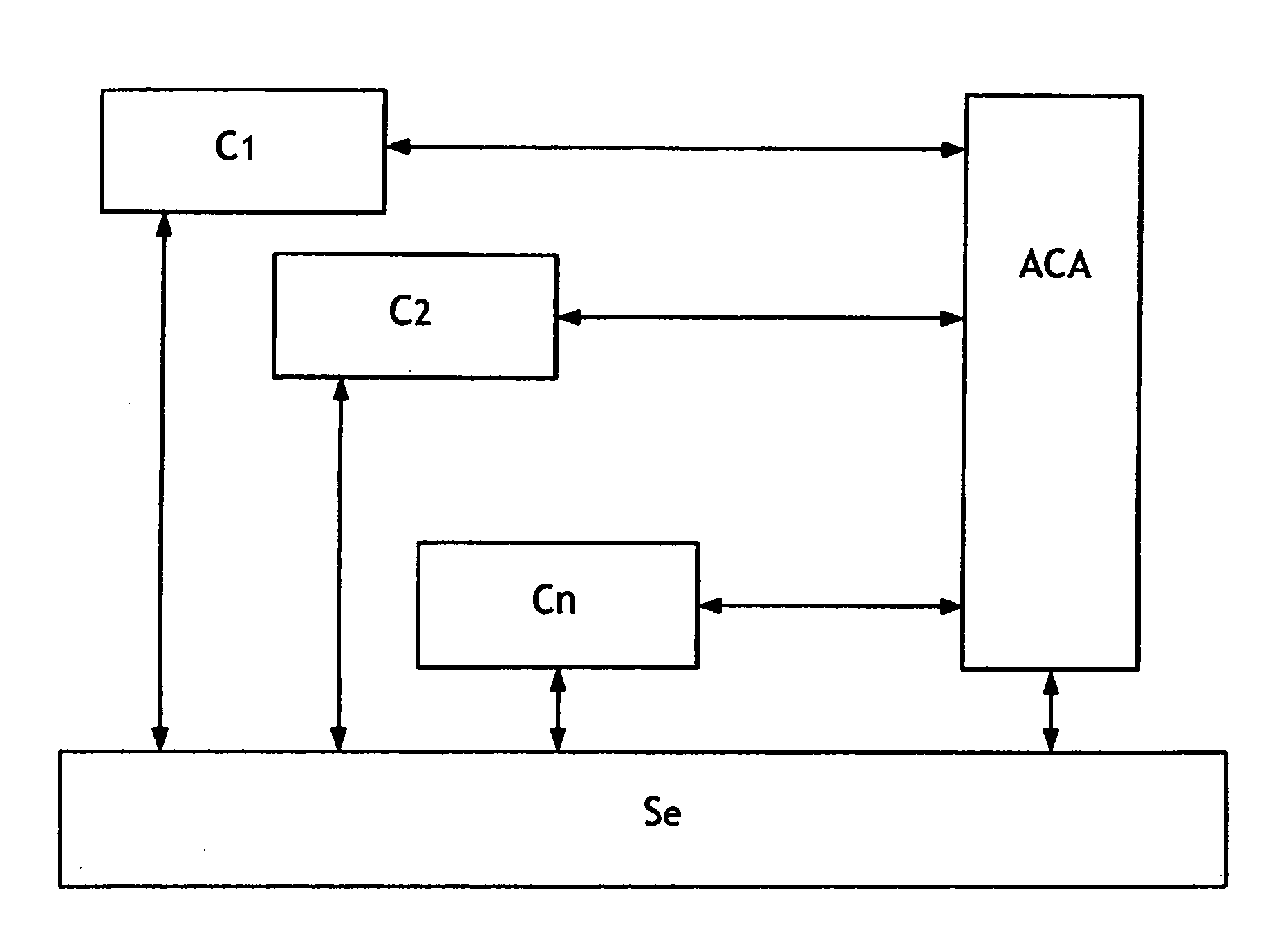
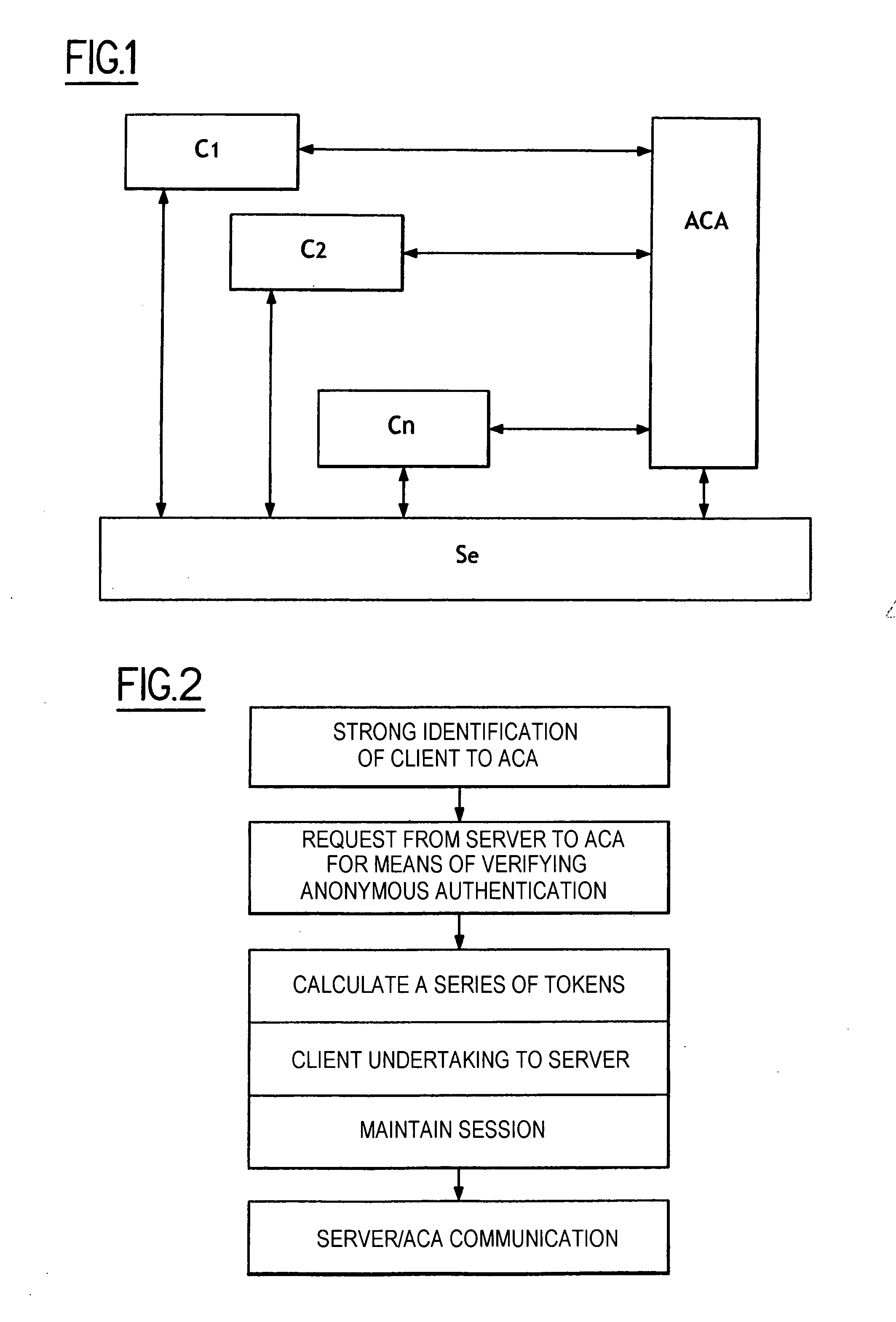
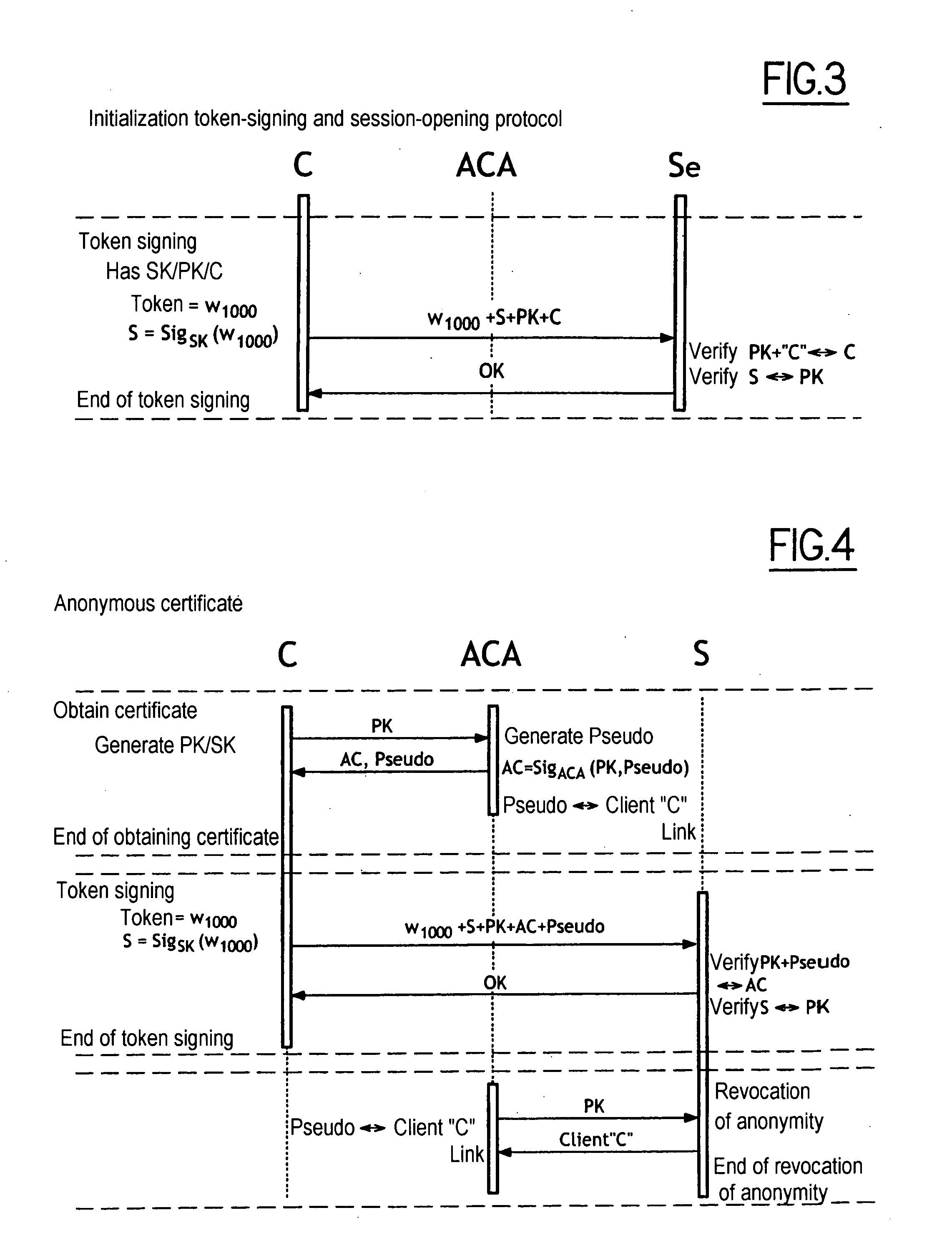
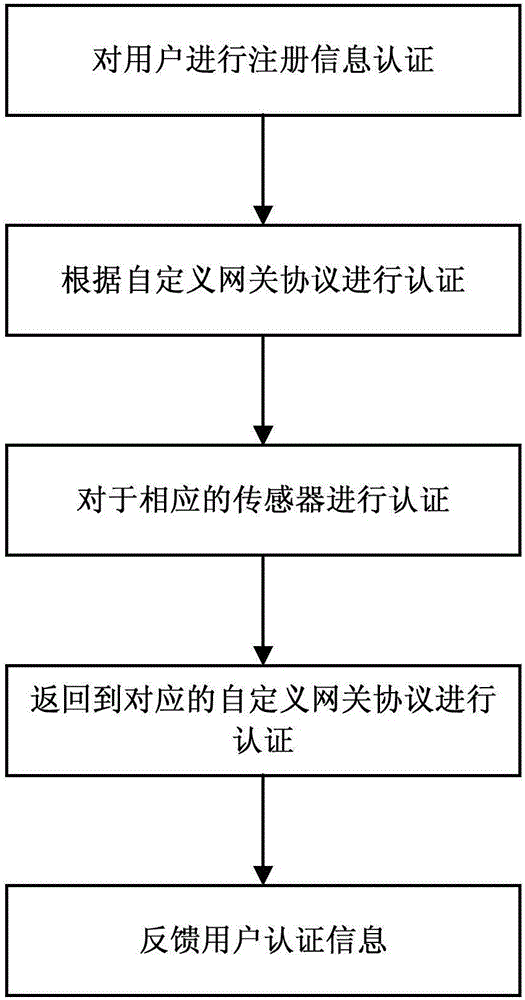
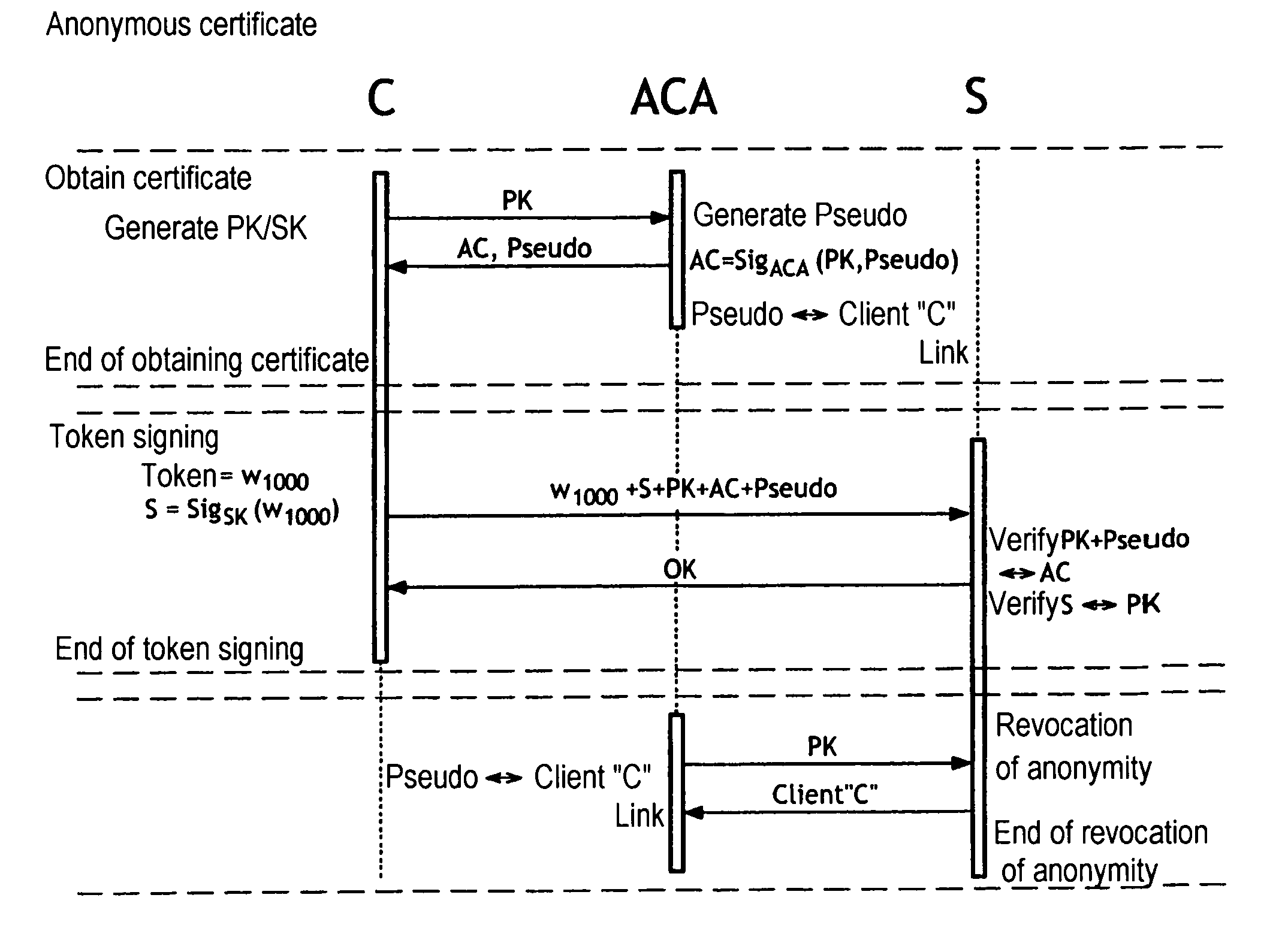
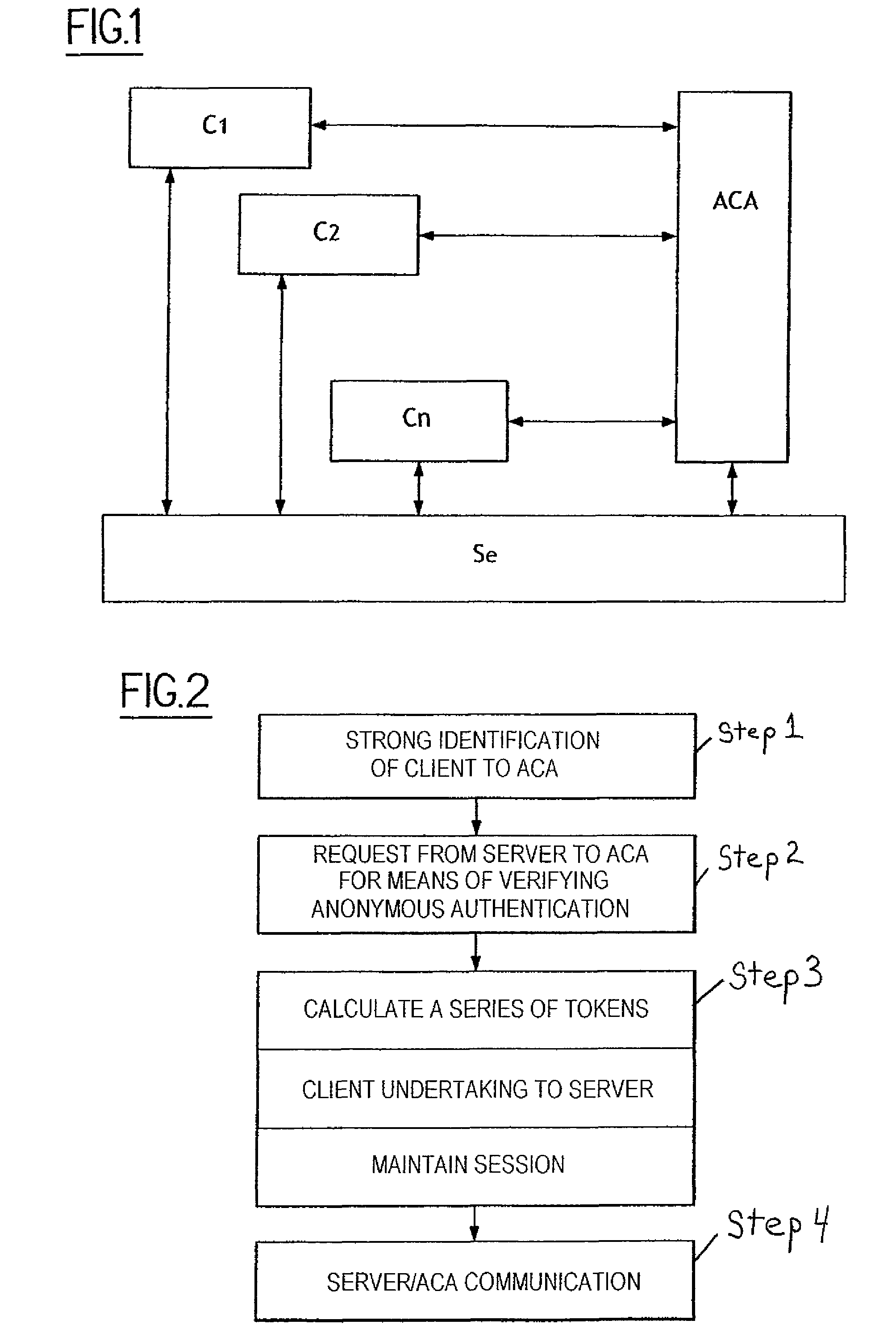
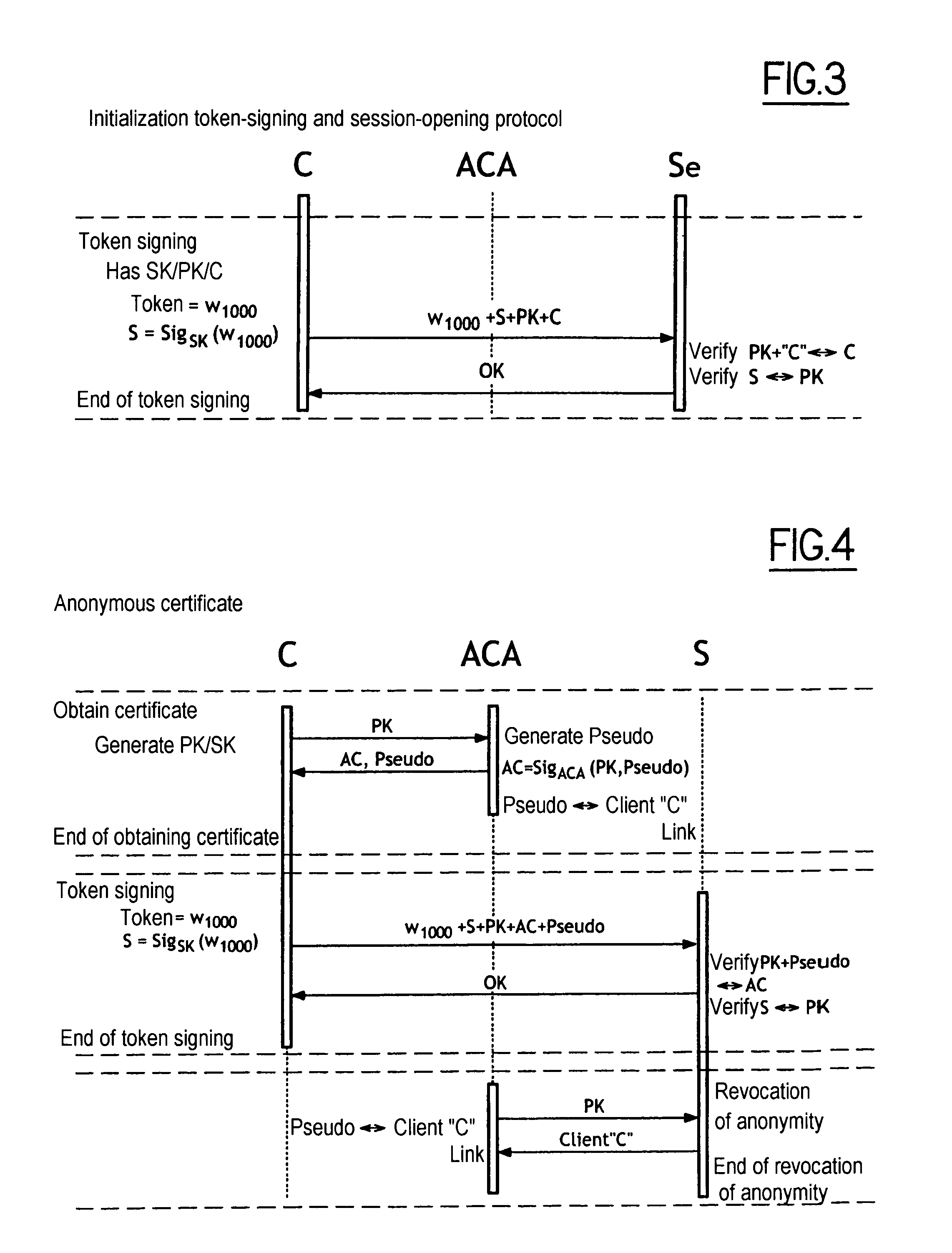
The present invention relates to a method of access to a service consisting in i) identifying and registering a client (C), ii) authenticating the client to an anonymous certification authority, iii) authenticating the client by producing an anonymous signature and opening and maintaining an anonymous authentication session with a server (Se), and iv) selectively allowing contact between the server (Se) and the anonymous certification authority (ACA) to revoke the anonymity of the client (C) using the signature provided in step iii). The invention also relates to a system for opening and maintaining an authentication session guaranteeing non-repudiation.
Owner:FRANCE TELECOM SA
Anonymous authentication system and anonymous authentication method
InactiveUS20100174911A1Privacy protectionPrevented excessively chargingDigital data processing detailsUser identity/authority verificationData validationUser device
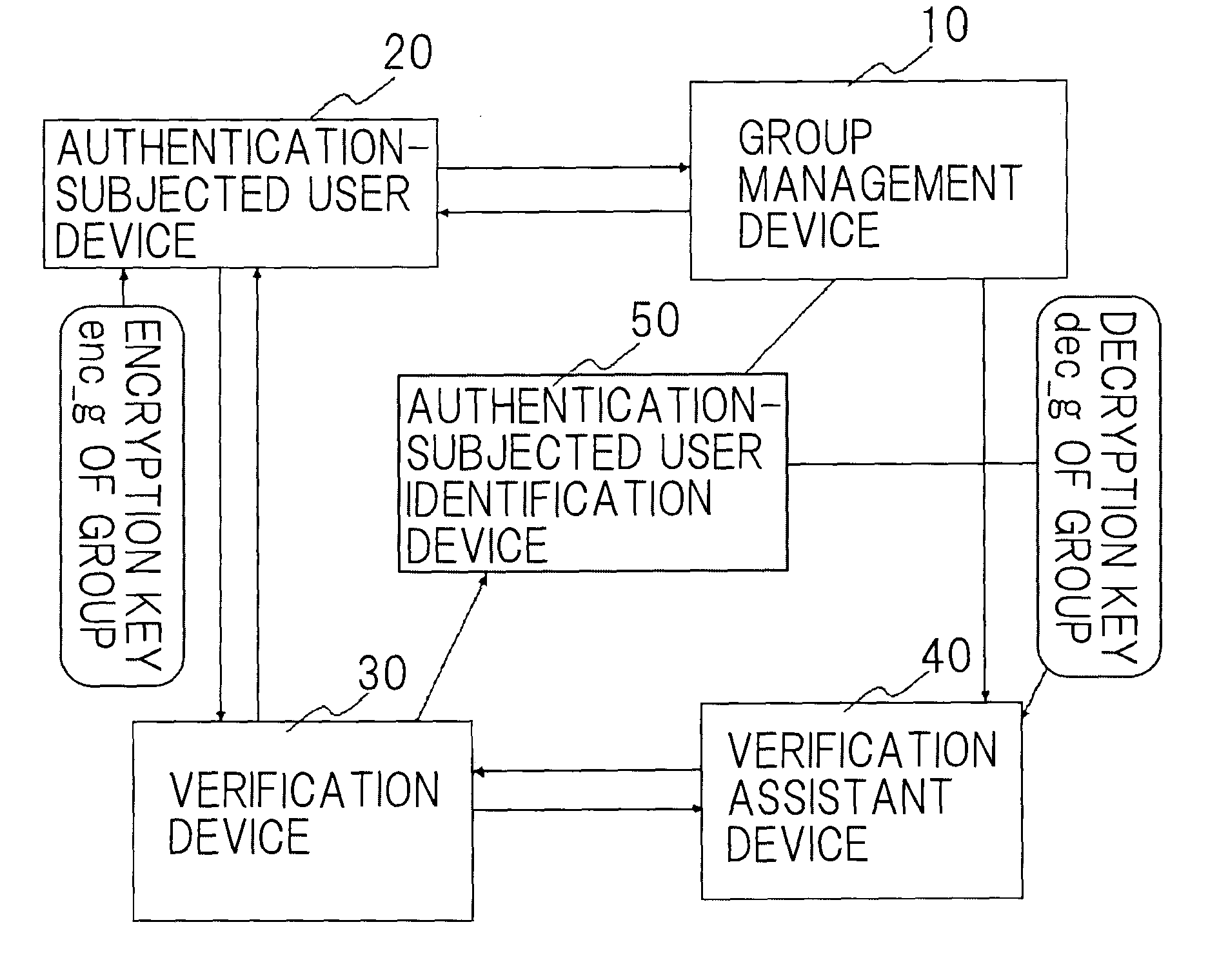
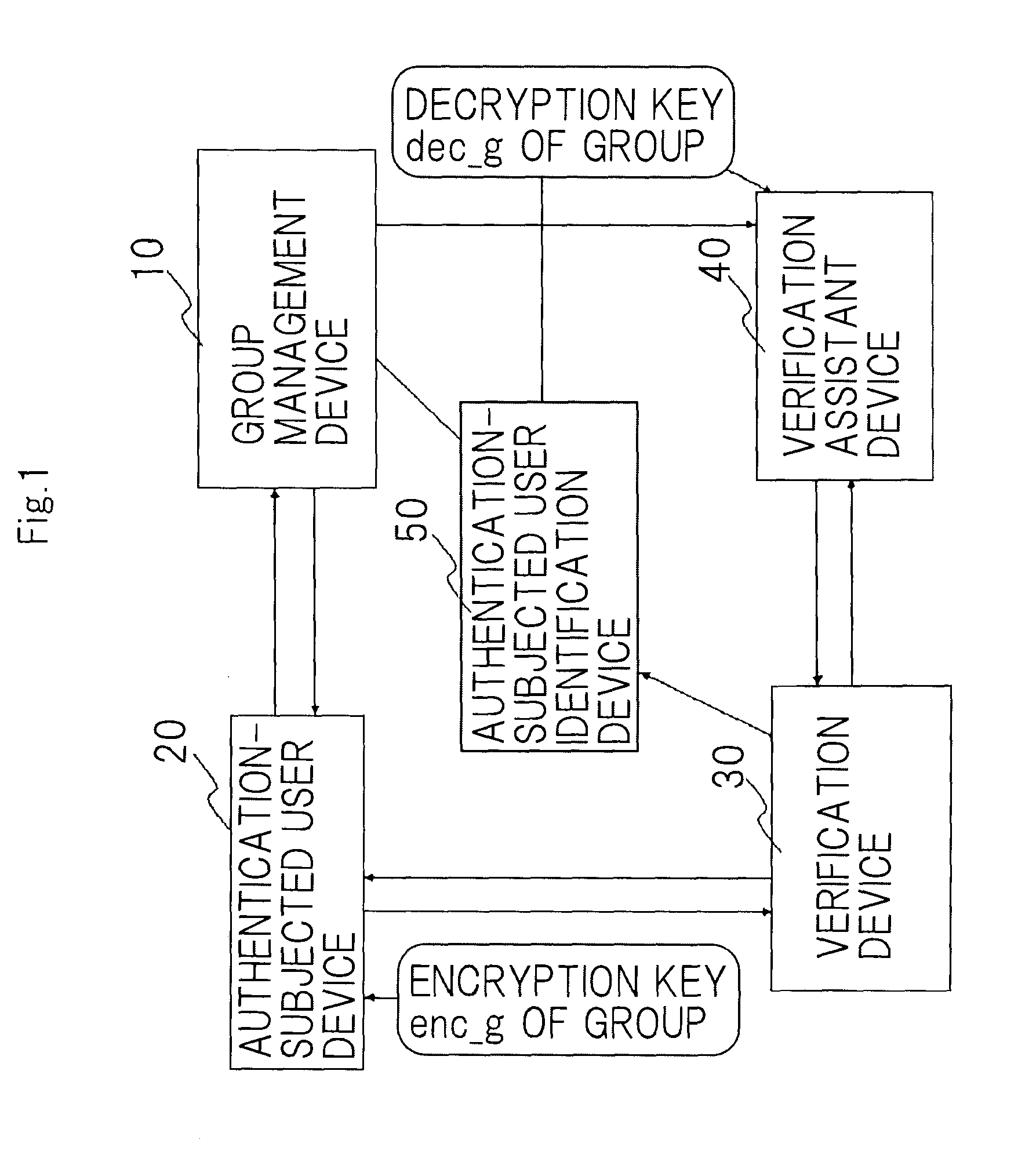
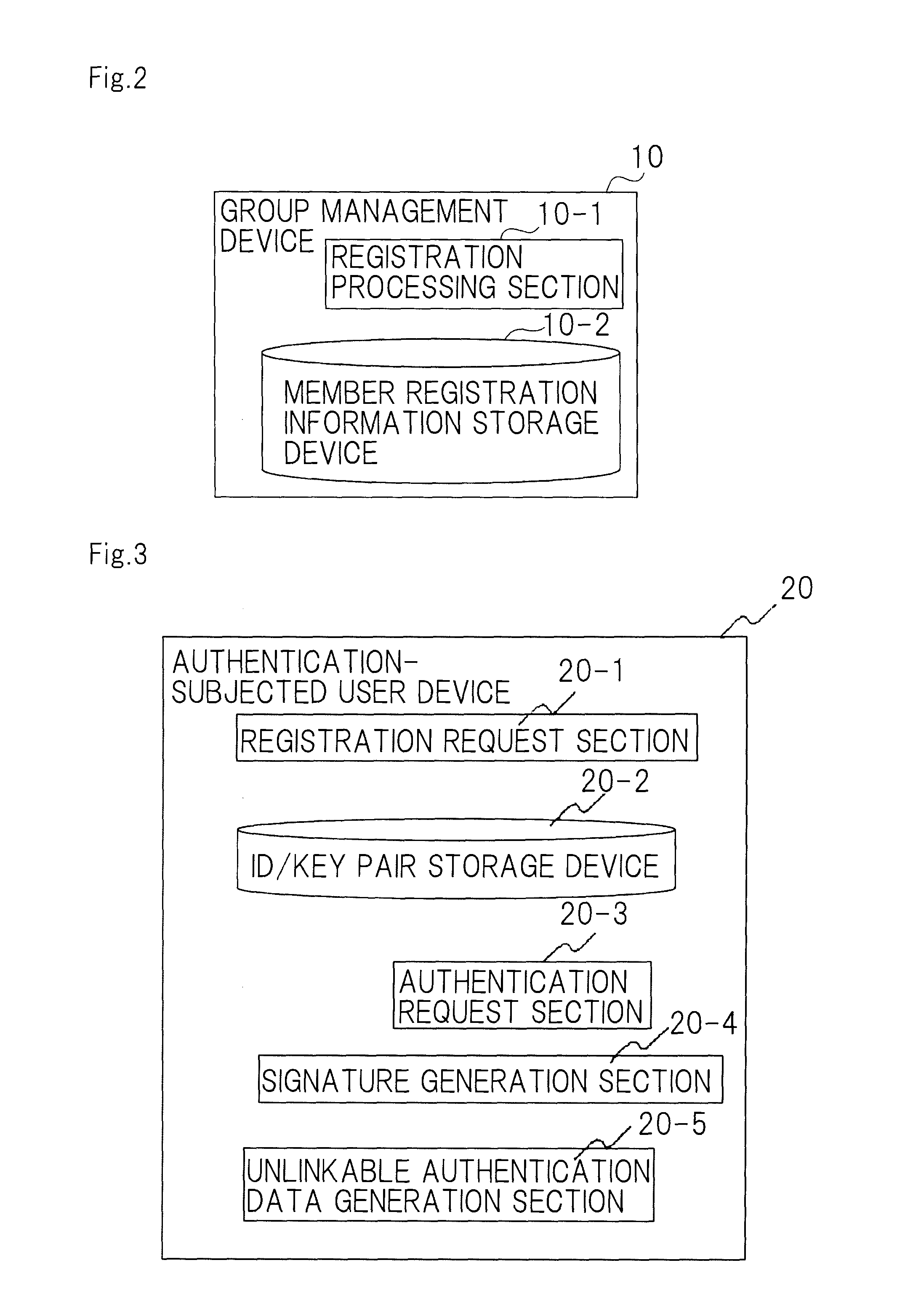
A disclosed anonymous authentication system comprises a group management device, an authentication-subjected user device, a verification device and an authentication-subjected user identification device. A user previously registers a verification key in the group management device such that his signature can be verified. For authentication, the user generates his or her own signature using the authentication-subjected user device, and encrypts the signature using an encryption key of the group to generate authentication data. The verification device authenticates the signature in collaboration with a verification assistant who has a decryption key of the group. The authentication-subjected user identification device that has the decryption key of the group decrypts the authentication data as required to identify a user who is to be authenticated.
Owner:NEC CORP
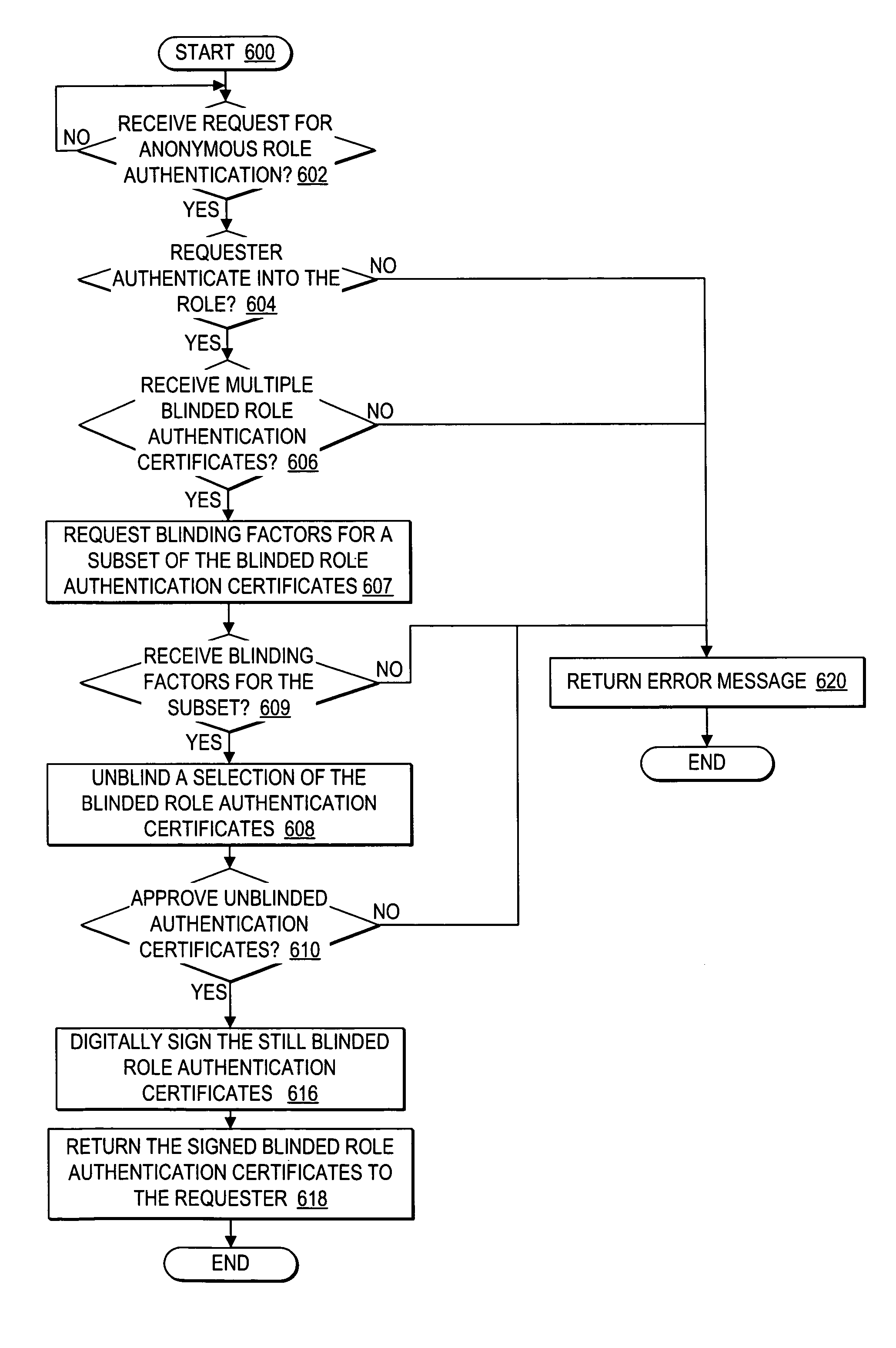
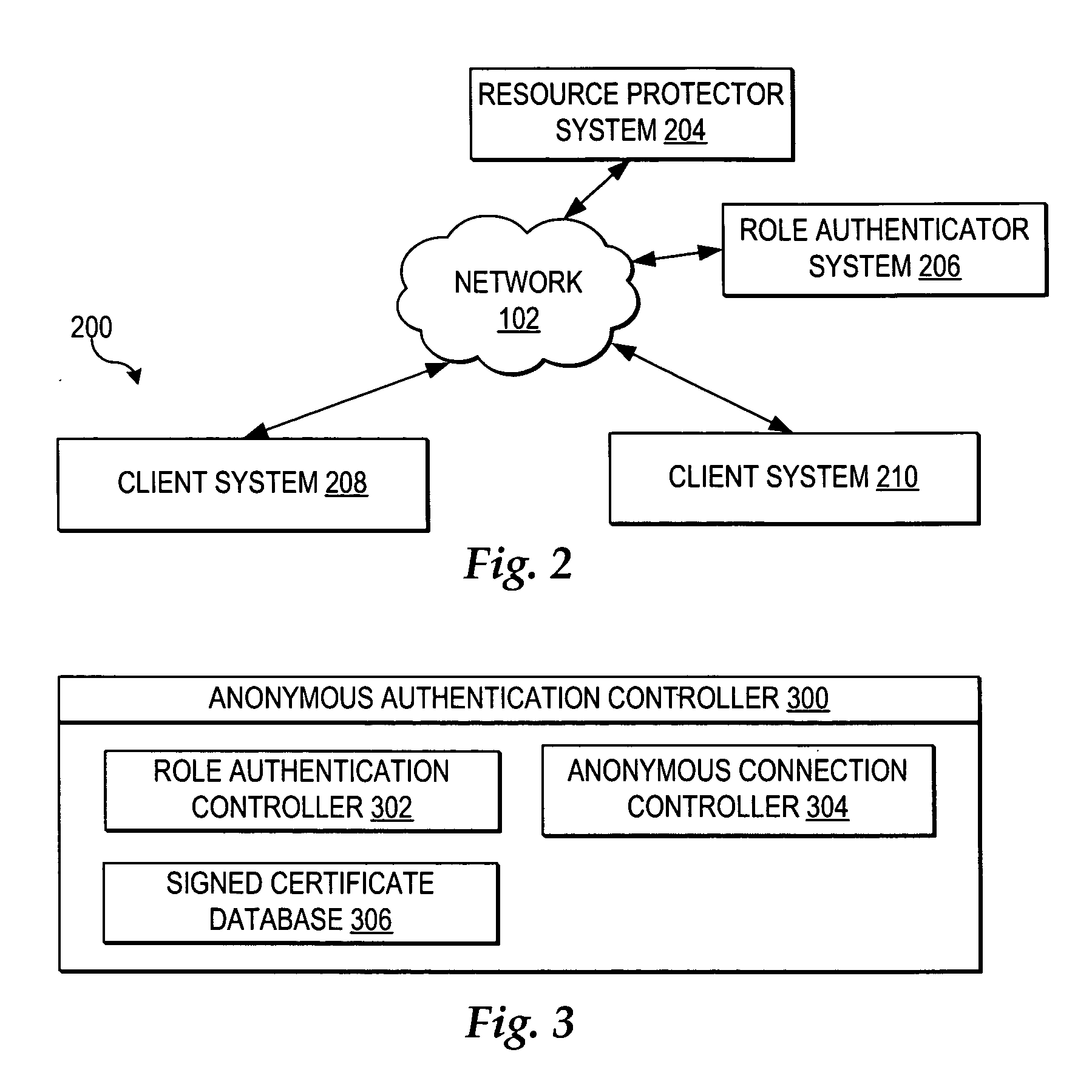
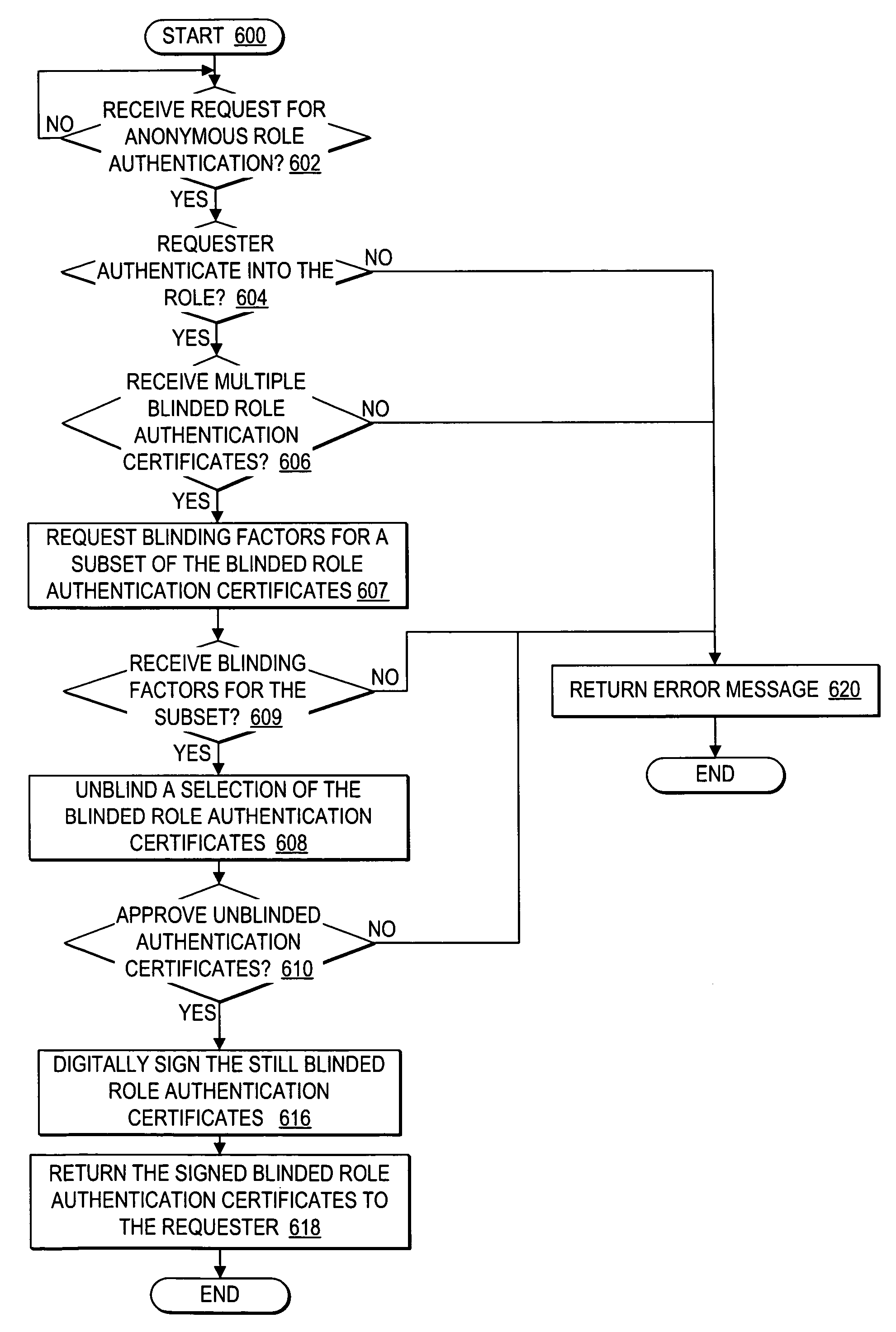
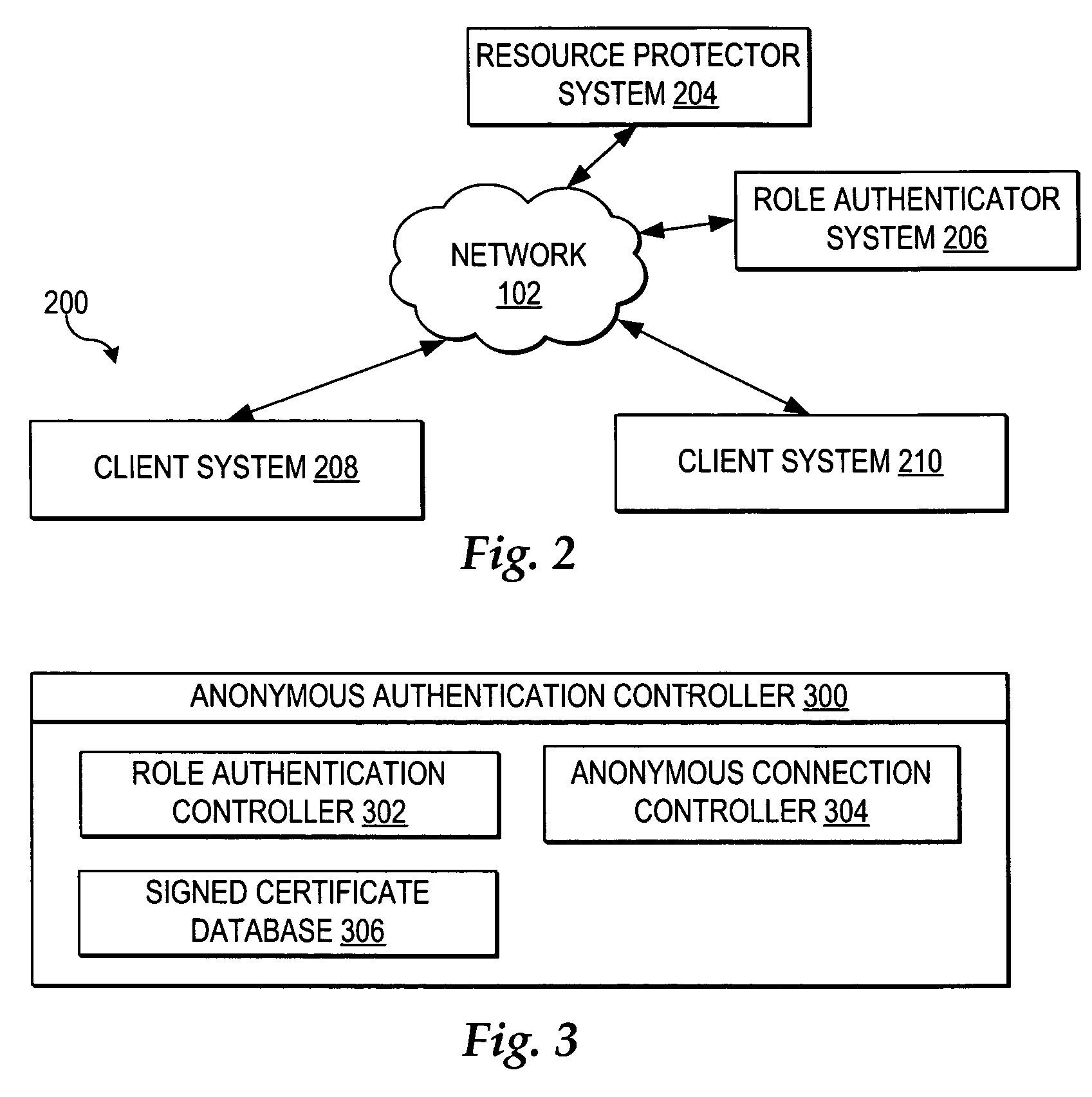
User controlled anonymity when evaluating into a role
InactiveUS20050283608A1Enhanced authenticationImprove identityDigital data processing detailsUser identity/authority verificationThird partyResource protection
A method, system, and program for user controlled anonymity when evaluating into a role are provided. An anonymous authentication controller enables a user to control anonymity of the user's identity for role based network accesses to resources, without requiring reliance on any single third party to maintain user anonymity. First, a role authentication certificate is received from a role authenticator, wherein the role authentication certificate certifies that the holder of the role authentication certificate is a member of a particular role without allowing the role authenticator issuing the role authentication certificate the ability to track an identity of a user holding the role authentication certificate. Next, an anonymous channel is established for anonymously presenting the role authentication certificate to a resource protector, wherein the resource protector requires the user to authenticate into the particular role to access a resource, wherein the role authentication certificate authenticates the user into the particular role without enabling the resource protector to ascertain the identity of the user, such that the user is in control of maintaining user anonymity for authenticated role-based accesses.
Owner:IBM CORP
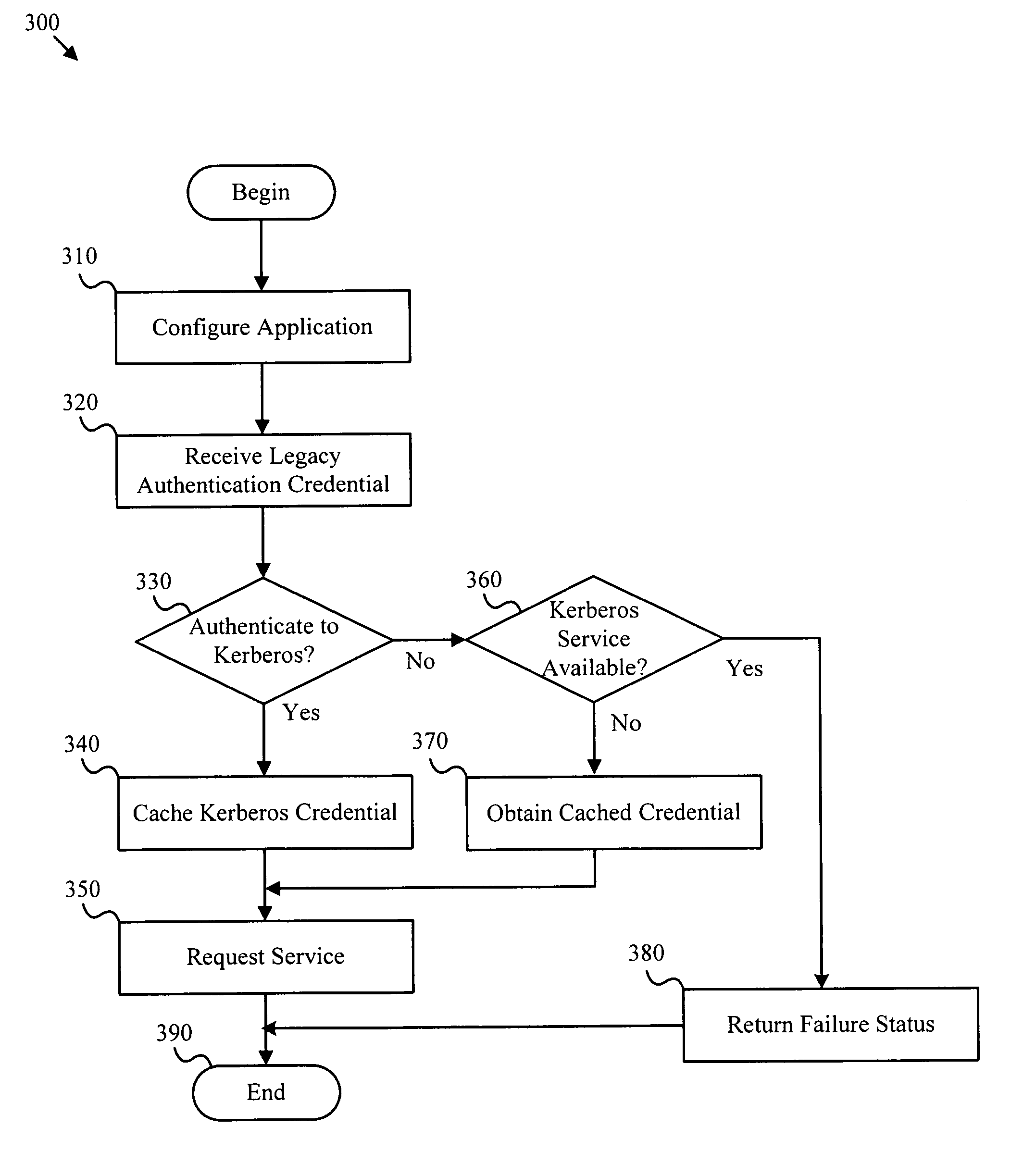
Apparatus, systems and methods to provide authentication services to a legacy application
ActiveUS7904949B2Digital data processing detailsUser identity/authority verificationInternet Authentication ServicePassword
Owner:QUEST SOFTWARE INC
Authorized anonymous authentication
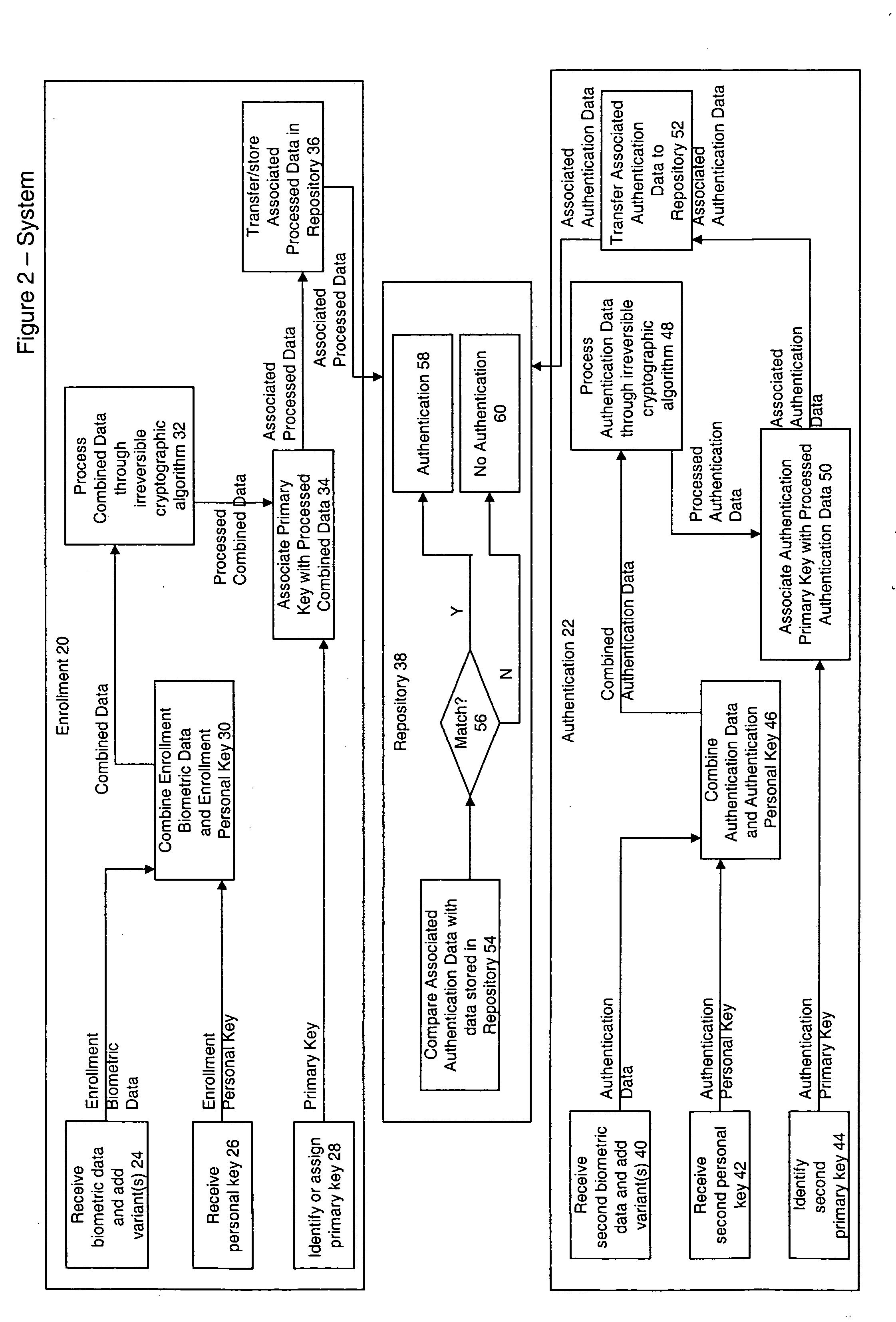
ActiveUS20050060556A1Public key for secure communicationDigital data processing detailsComputer hardwareBiometric data
A method, program and system for processing data is disclosed. The method, program and system comprising the steps of: (a) receiving (e.g., during an enrollment process) a first biometric data and a first personal key, (b) processing the first biometric data and the first personal key through an irreversible cryptographic algorithm, sometimes after: (i) generating one or more variants from the first biometric data, (ii) processing the first personal key through a reversible cryptographic algorithm, and (iii) adding salt to the first biometric data or first personal key, (c) receiving (e.g., during an authentication process) a second biometric data and a second personal key, (d) processing the second biometric data and the second personal key through the irreversible cryptographic algorithm, (e) comparing the second processed data to the first processed data, and (f) generating a signal pertaining to the comparison of the second processed data to the first processed data, such as: (i) a confirmation reflecting authentication when the second processed data matches the first processed data (sometimes allowing access to a facility or system) or (ii) a denial reflecting no confirmation when the second processed data does not match the first processed data.
Owner:IBM CORP
Apparatus system and method to provide authentication services to legacy applications
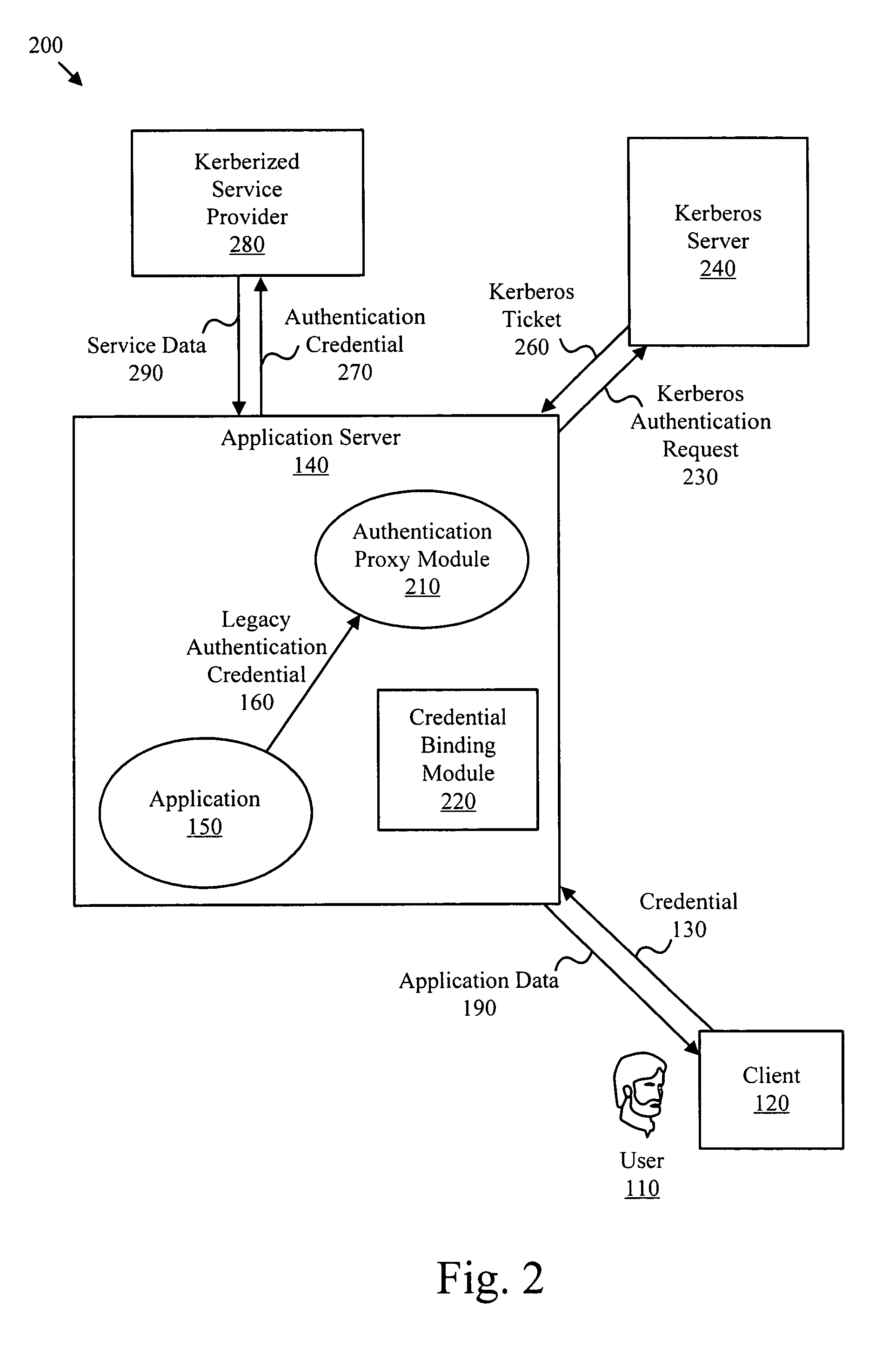
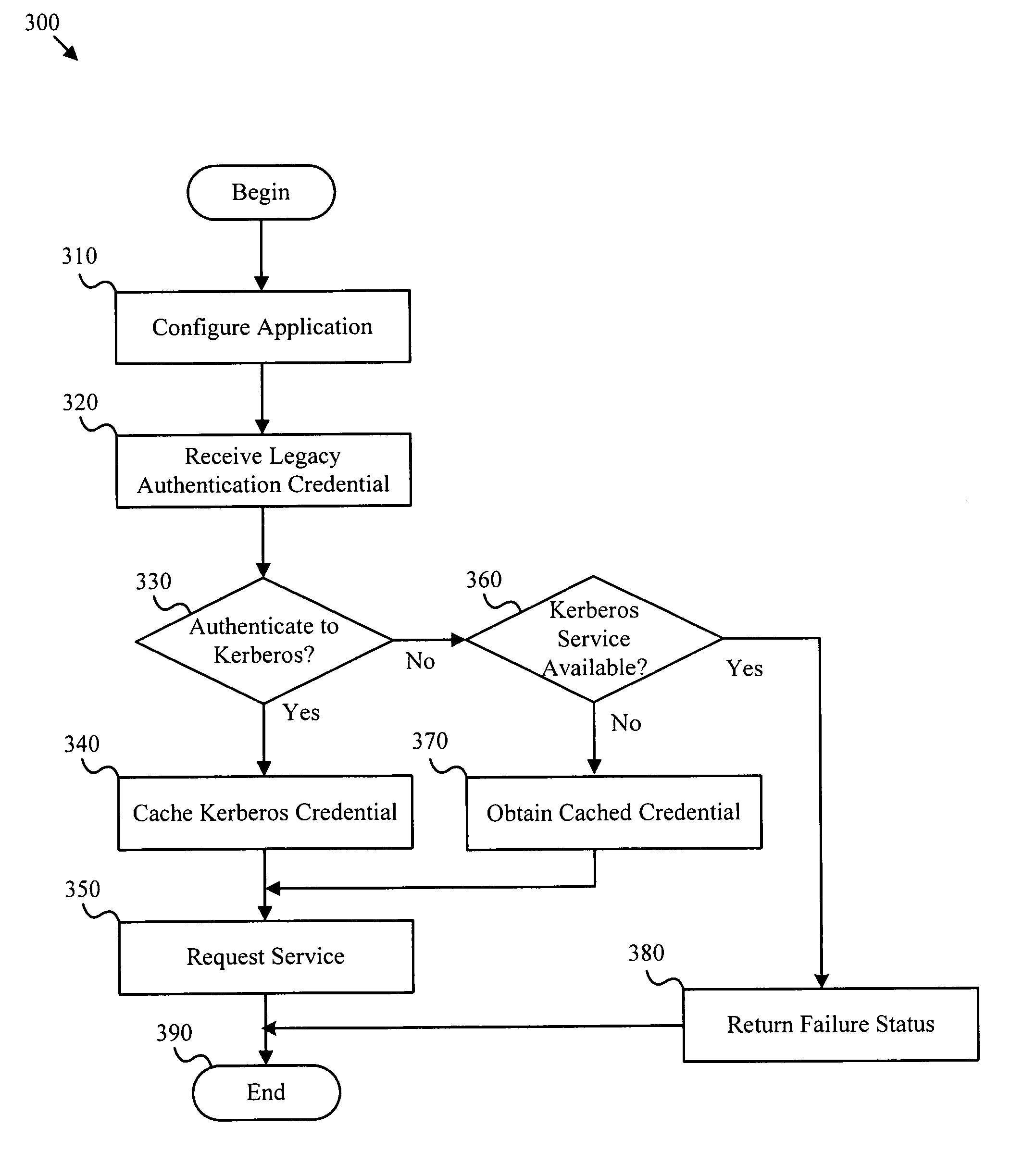
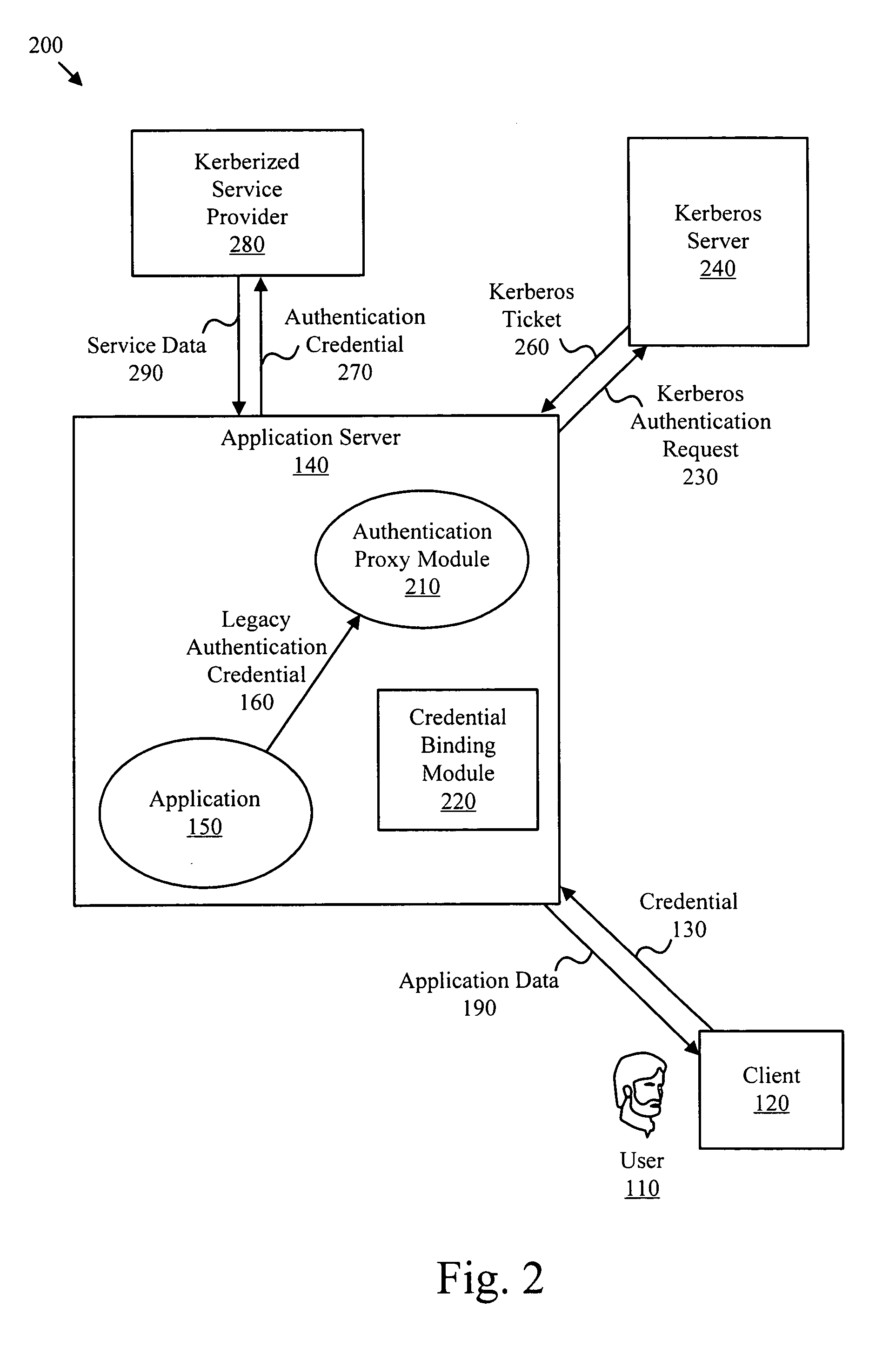
ActiveUS20070143836A1Improve safety benefitsDigital data processing detailsUser identity/authority verificationPasswordAnonymous authentication
Authentication credentials from legacy applications are translated to Kerberos authentication requests. Authentication credentials from the legacy application are directed to an authentication proxy module. The authentication proxy module acts as a credential translator for the application by receiving a set of credentials such as a user name and password, then managing the process of authenticating to a Kerberos server and obtaining services from one or more Kerberized applications, including Kerberos session encryption. A credential binding module associates a user corresponding to authentication credentials from a legacy authentication protocol with one or more Kerberos credentials. Anonymous authentication credentials may be translated to authentication requests for a network directory services object, such as a computer object or service object.
Owner:QUEST SOFTWARE INC
Pseudonym-based anonymous authentication and key negotiation optimization method and optimized authentication analysis method for Internet of Things
ActiveCN106657124AAchieve non-traceabilityAvoid attackTransmissionKey-agreement protocolThe Internet
The invention provides a pseudonym-based anonymous authentication and key negotiation optimization method and optimized authentication analysis method for the Internet of Things. The method comprises the following steps: S1, a user and a sensor node separately register a gateway node, and for the difference of the user and the sensor node, a user registration protocol and a sensor node registration protocol different from each other are adopted; and S2, after the registration, the user logs in the system through a user login protocol and an authentication and key negotiation protocol, and under the assistance of the gateway node, the sensor node requiring access realizes mutual authentication and a negotiation shared session key. By adoption of the method provided by the invention, better anonymity, non-traceability and security are realized.
Owner:YICHUN UNIVERSITY
Method and system with authentication, revocable anonymity and non-repudiation
The present invention relates to a method of access to a service consisting in i) identifying and registering a client (C), ii) authenticating the client to an anonymous certification authority, iii) authenticating the client by producing an anonymous signature and opening and maintaining an anonymous authentication session with a server (Se), and iv) selectively allowing contact between the server (Se) and the anonymous certification authority (ACA) to revoke the anonymity of the client (C) using the signature provided in step iii). The invention also relates to a system for opening and maintaining an authentication session guaranteeing non-repudiation.
Owner:FRANCE TELECOM SA
Cross-domain anonymous authentication method and system based on block chain
ActiveCN112039872ANo additional overheadNo secondary registration requiredKey distribution for secure communicationUser identity/authority verificationPrivacy protectionEngineering
The invention provides a cross-domain anonymous authentication method and system based on a blockchain. A trusted key generation center is set to issue a public and private key pair to a registrationcenter, and deploy key information of a blockchain smart contract management communication party; the registration center provides registration service for a common user, generates a signature to realize certificate authentication service, and stores communication party identification information and public key information related to a service system into the blockchain intelligent contract in a privacy protection mode; when two communication parties carry out mutual authentication, authentication information is sent in an anonymous mode, a blockchain intelligent contract query interface is called to check identification information of a user, and whether a public key of the user is registered or not is checked and authenticated; the smart contract manages the identification information and the key information, provides real-time update of the user identification information and the key information, so that the method avoids the problems of introduction of single-point fault attacks, asynchronous update, high communication overhead and the like, and supports user cross-domain authentication service. The anonymous authentication technical scheme has good security, stability and reliability.
Owner:武汉见邦融智科技有限公司 +1
Traceable anonymous authentication method based on elliptic curve
InactiveCN105812369AImprove securityPublic key for secure communicationUser identity/authority verificationRing signatureDigital Signature Algorithm
The invention discloses a traceable anonymous authentication method based on an elliptic curve. The method comprises following stages of initializing a system and generating a secrete key, generating anonymous signatures, authenticating the signatures, linking and tracing nodes. According to the method, a ring signature algorithm in a data signing process is improved; the ring signatures and the elliptic curve are combined; the linkage performance is increased; moreover, traceability to malicious nodes is provided, thus finding out the malicious nodes efficiently and accurately; the network security is improved; a critical value is unnecessary; an efficient hop-by-hop message authentication mechanism is provided; the privacy leakage problem of sending nodes in a wireless sensor network can be solved; moreover, the reality and integrity of the sent messages are ensured; and the malicious nodes can be traced if necessary.
Owner:GUANGDONG UNIV OF PETROCHEMICAL TECH
User controlled anonymity when evaluating into a role
InactiveUS7472277B2Enhanced authenticationImprove identityDigital data processing detailsUser identity/authority verificationThird partyResource protection
A method, system, and program for user controlled anonymity when evaluating into a role are provided. An anonymous authentication controller enables a user to control anonymity of the user's identity for role based network accesses to resources, without requiring reliance on any single third party to maintain user anonymity. First, a role authentication certificate is received from a role authenticator, wherein the role authentication certificate certifies that the holder of the role authentication certificate is a member of a particular role without allowing the role authenticator issuing the role authentication certificate the ability to track an identity of a user holding the role authentication certificate. Next, an anonymous channel is established for anonymously presenting the role authentication certificate to a resource protector, wherein the resource protector requires the user to authenticate into the particular role to access a resource, wherein the role authentication certificate authenticates the user into the particular role without enabling the resource protector to ascertain the identity of the user, such that the user is in control of maintaining user anonymity for authenticated role-based accesses.
Owner:INT BUSINESS MASCH CORP
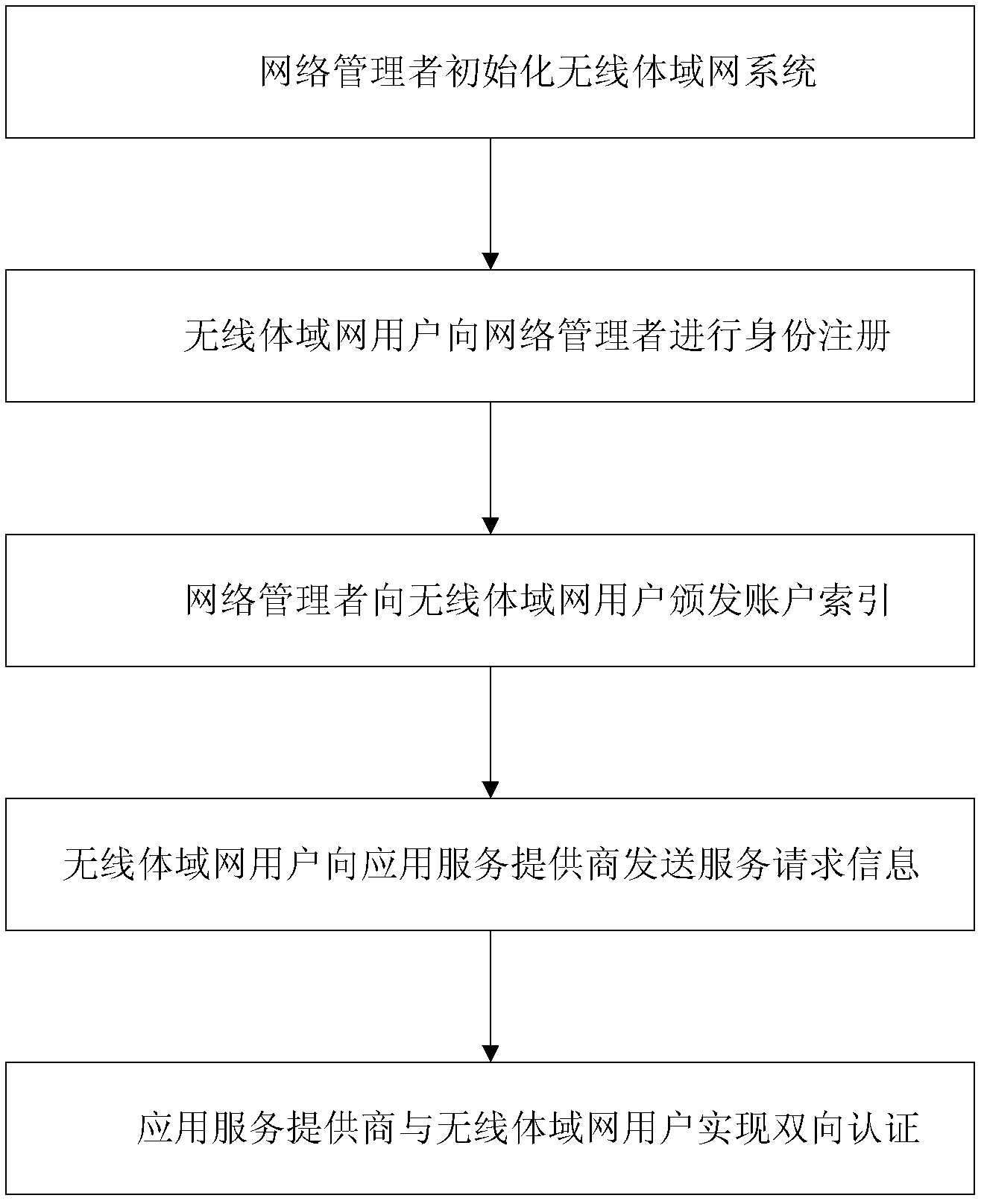
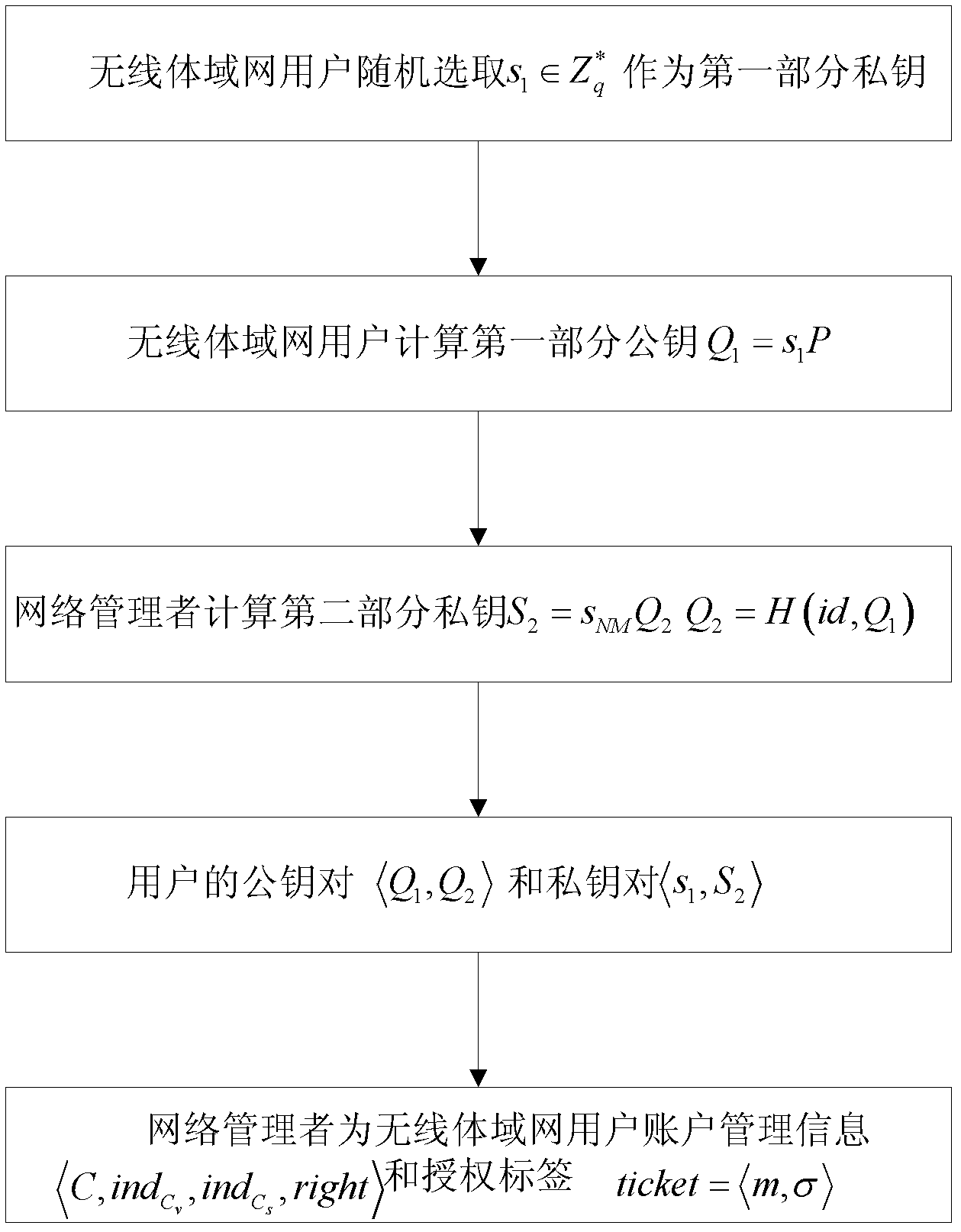
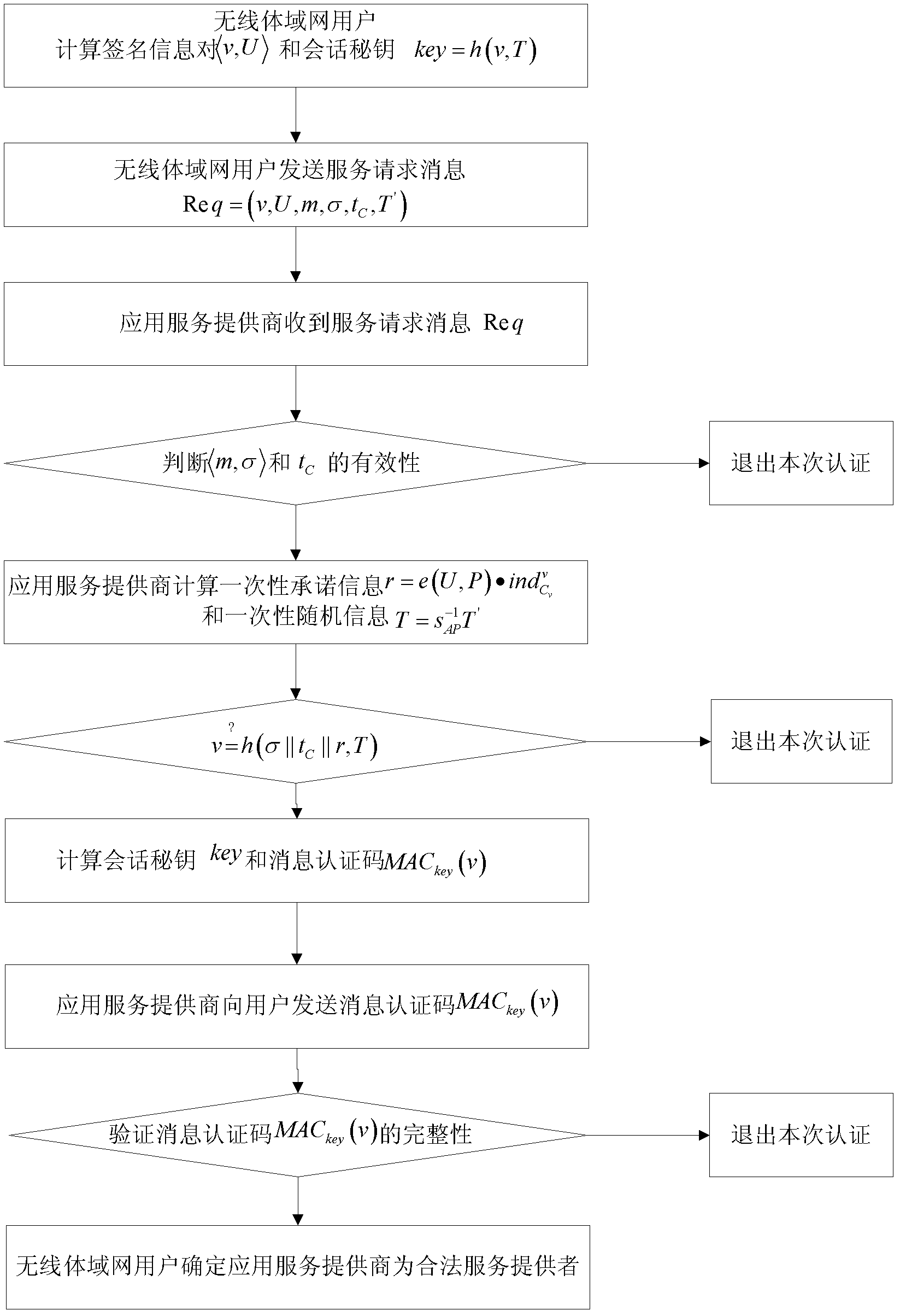
Certificate-free remote anonymous authentication method for wireless body area network
InactiveCN102624530AGood anonymityImprove securityPublic key for secure communicationUser identity/authority verificationComputation complexityBody area network
The invention discloses a certificate-free anonymous authentication method for a wireless body area network, which mainly solves the anonymity problem of wireless body area network remote authentication, and mainly comprises the steps as follows: 1) a network manager initializes a whole wireless body area network system; 2) a wireless body area network user carries out identity register from the network manager; 3) the network manager issues an account index to the wireless body area network user; 4) the wireless body area network user uses the account index to disguisedly send a service request to the network manager; and 5) bidirectional authentication between an application service provider and the wireless body area network user is achieved. According to the invention, a certificate is not required, the defect of no key escrow is avoided, the security performance is high, the degree of complexity of calculation is low, and the method can be used for remote medical treatment monitoring and on other application occasions.
Owner:XIDIAN UNIV
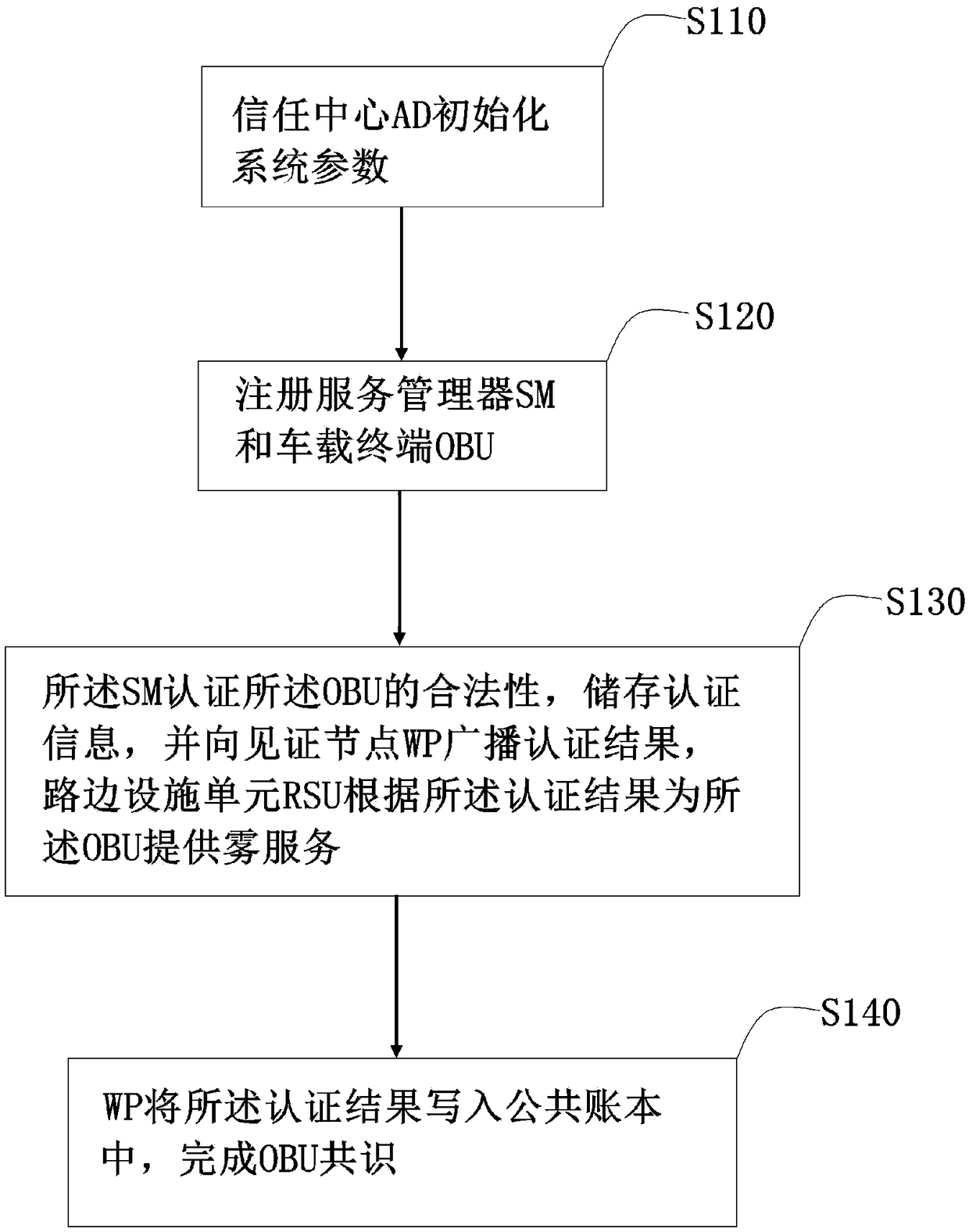
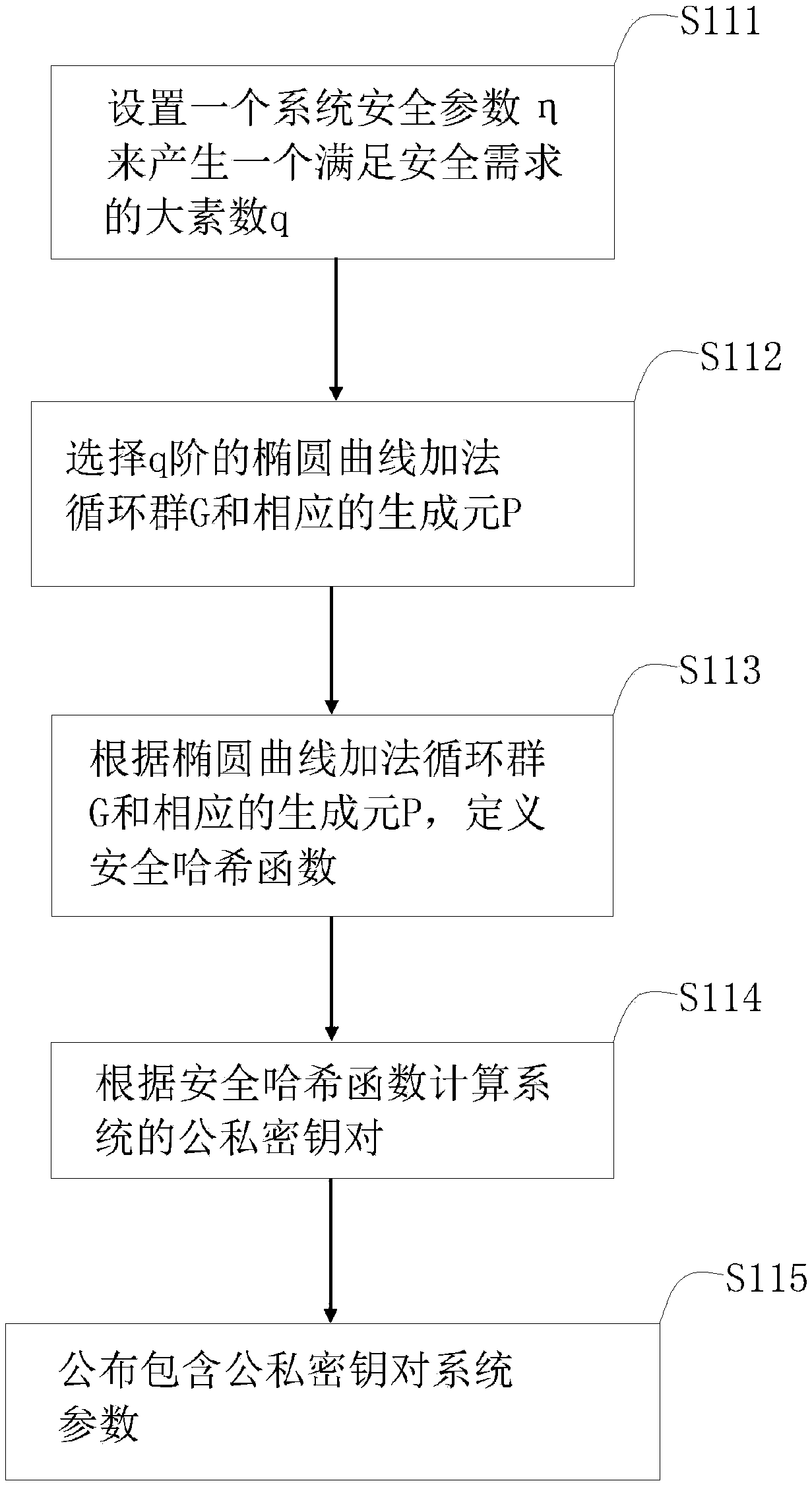
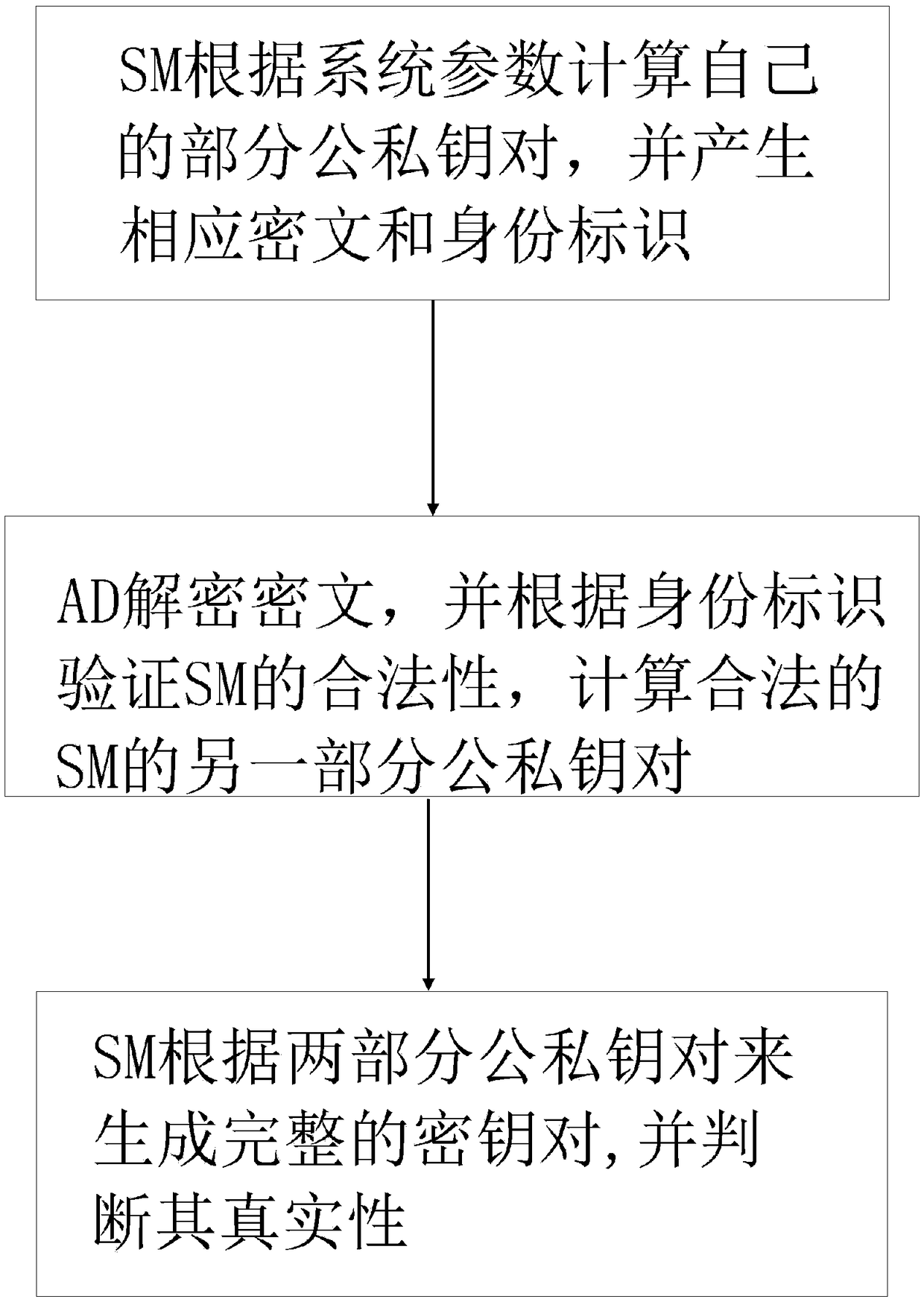
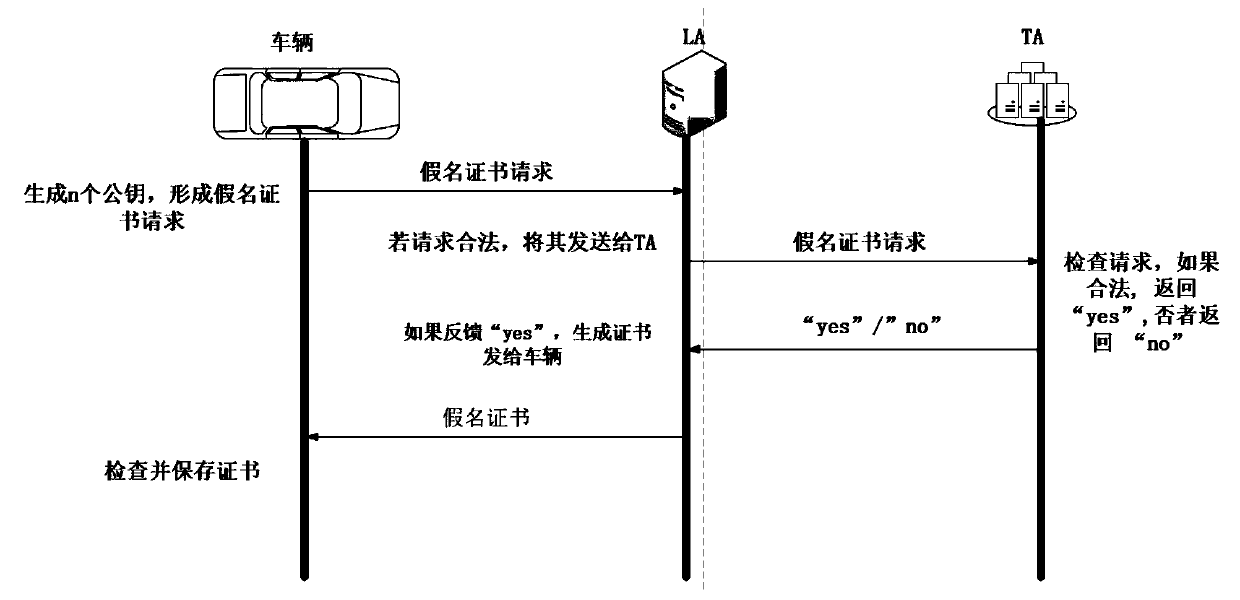
Vehicle fog data light-weight anonymous access authentication method based on blockchain assistance
InactiveCN109194610AProtect private informationEnhanced anonymityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPublic accountOn board
The present invention provides a vehicle fog data light-weight anonymous access authentication method based on blockchain assistance, and relates to the technical field of network communication safetyof urban traffic operation management. The method comprises the steps of: arranging one witness node (WP) in a management range of each service manager (SM), initializing system parameters through antrusted center AD, and registering the SM and a OBU (On Board Unit); allowing the SM to authenticate the validity of the OBU, storing the authentication information, broadcasting an authentication result to the WP, and providing fog service to the OBU according to the authentication result by a roadside facility unit RSU; and writing the authentication result into a public account by the WP to complete OBU consensus. The vehicle fog data light-weight anonymous access authentication method based on blockchain assistance can protect the user privacy information while ensuring the identity authenticity of a vehicle user accessing the fog service so as to achieve the vehicle anonymous authentication and allow users to select the time and the frequency of replacement of the pseudonym by themselves; the non-interactive autonomous cross-domain authentication is achieved, and the communication delay is effectively reduced; and moreover, the authentication information management is simplified,and the risk that a single database is tampered is effectively avoided.
Owner:BEIJING JIAOTONG UNIV
Anonymous authentication scheme under vehicular ad hoc network based on biometric encryption technology
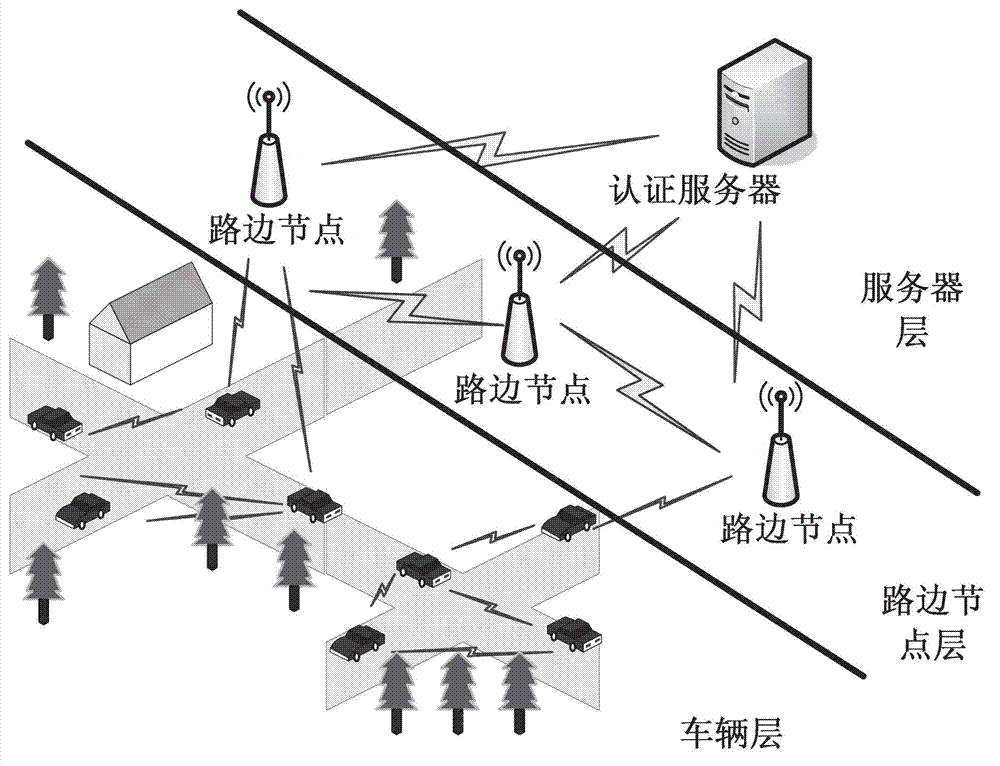
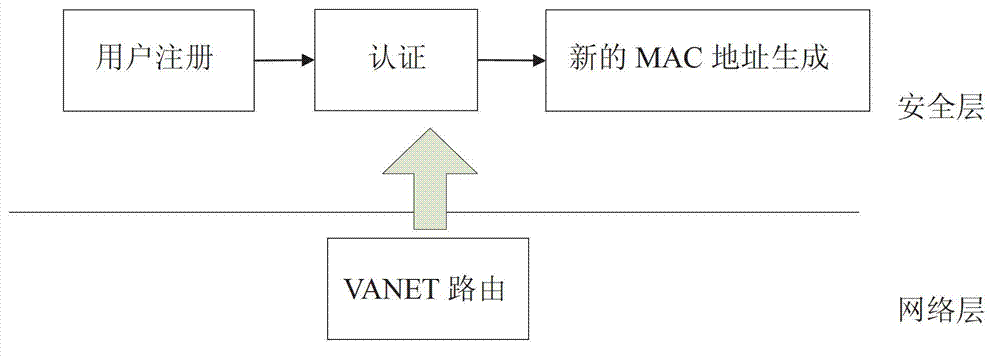
InactiveCN102904896AProtect biological privacyProtect real identityParticular environment based servicesUser identity/authority verificationCiphertextAnonymous authentication
The invention discloses an anonymous authentication scheme under a vehicular ad hoc network based on a biometric encryption technology, belonging to the technical field of information security, and particularly relating to a biometric encryption algorithm and an MAC (Media Access Control) address hiding technology. The anonymous authentication scheme is characterized in that the biometric encryption technology is used for organically combining a biological template of a user with a secret key to generate a biological ciphertext; the biological ciphertext hides biological characteristics and information of the secret key, and is used for representing a unique identity of one user; the generation of the biological ciphertext is unidirectional, and the biological information and the encrypted secret key are mutually independent; and a new MAC address is generated while the users negotiate a session key, thus the subsequent anonymous communication is realized. The anonymous authentication scheme has the advantages and the beneficial effects that the biometric encryption technology solves the problem of leakage of the biological template, the unidirectional generation of the ciphertext ensures that an attacker can not crack the biological information through the secret key; and the MAC address hiding technology can protect the real identifies of the users, thus the anonymous communication is realized, and the higher service quality is ensured by easily updated characteristics.
Owner:DALIAN UNIV OF TECH
A coalition taxi-hailing method and system for privacy protection
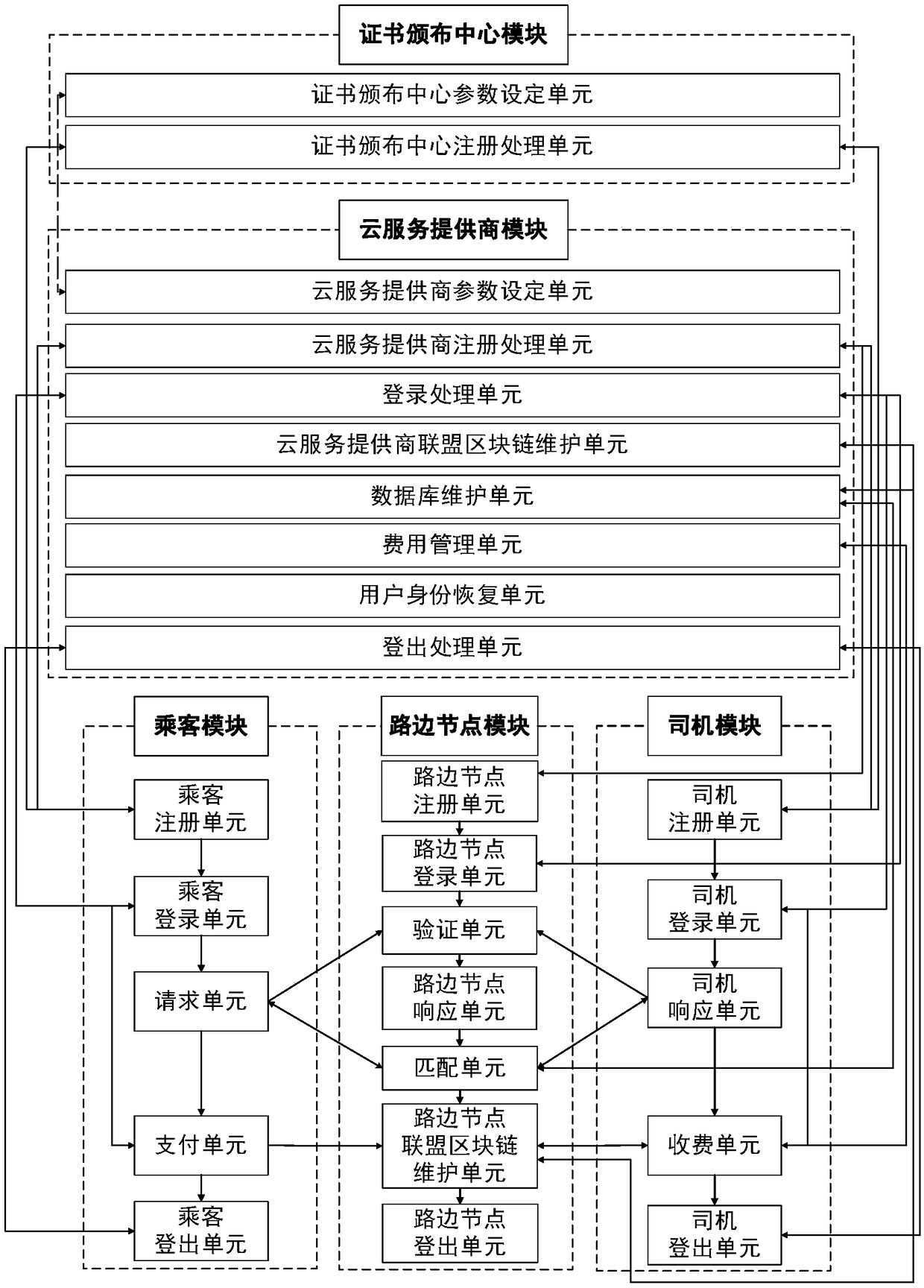
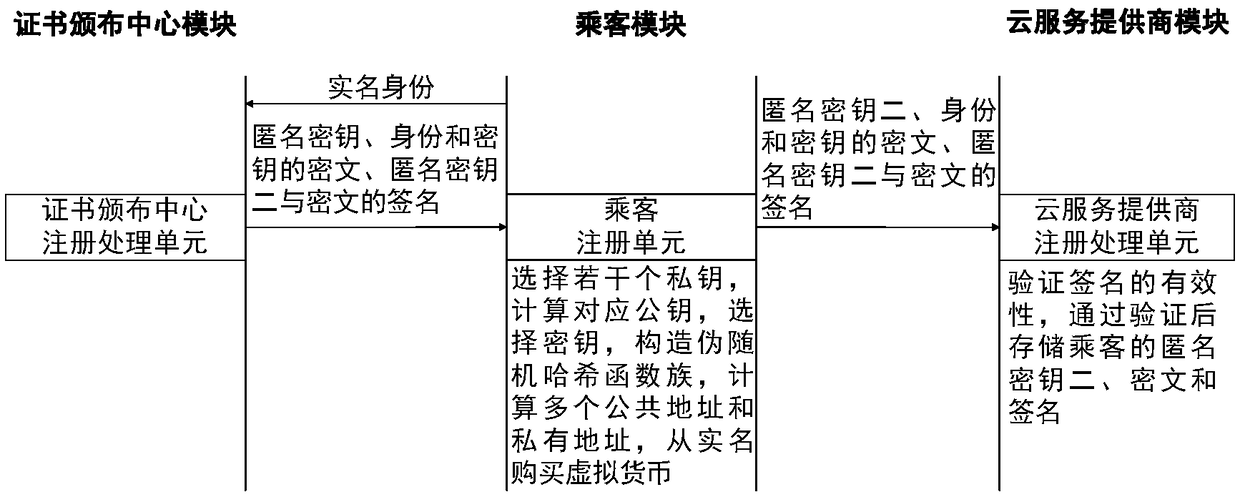
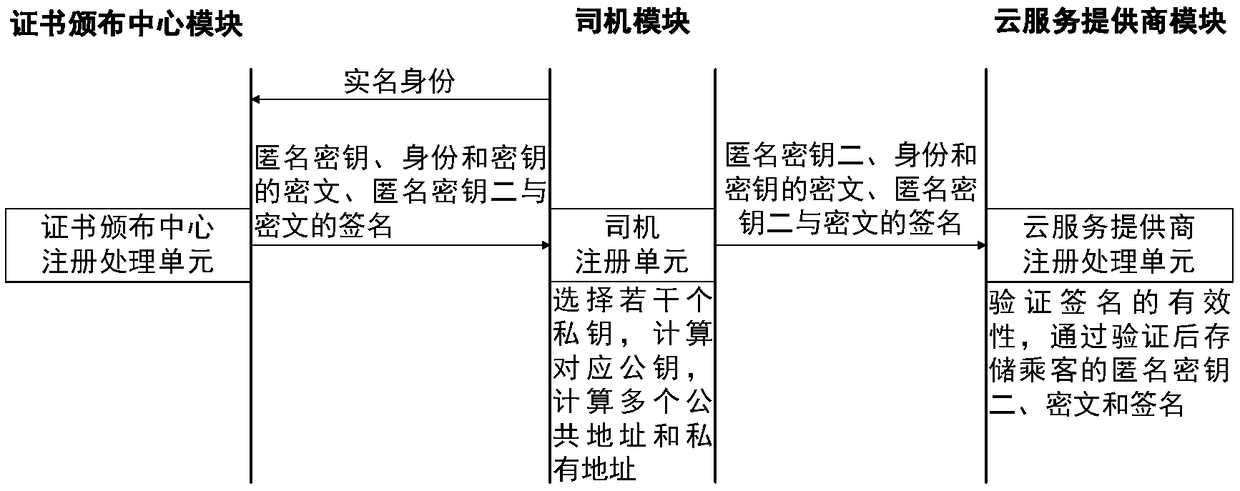
ActiveCN109345438AProtection securityGuarantee authenticityAnonymous user systemsUser privacyPrivacy protection
The invention relates to a coalition taxi-hailing method and system for privacy protection, belonging to the technical fields of anonymous authentication, privacy protection and block chain. Comprisesa plurality of taxi-hailing cloud service providers sharing a data component of a user, a coalition taxi-hailing platform, a passenger sending a coalition taxi-hailing request to a roadside node, a roadside node verifying the identity and data of the passenger, broadcasting the request in its coverage area, and a driver receiving the broadcasting sending a coalition taxi-hailing response to the roadside node; The roadside node verifies the identity and data of the driver, and sends the matched driver information to the corresponding passenger. The passenger sends confirmation message to the roadside node after contacting the driver, starts the alliance to take a taxi, and the passenger pays the fare anonymously to the driver; Roadside nodes maintain federated block chains. The taxi-hailing method and system provide timely taxi-hailing service for passengers, provide commercial benefits for cloud service providers, protect user privacy and cloud service providers' commercial secrets, and reduce computational and communication overhead on the basis of existing protocols.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
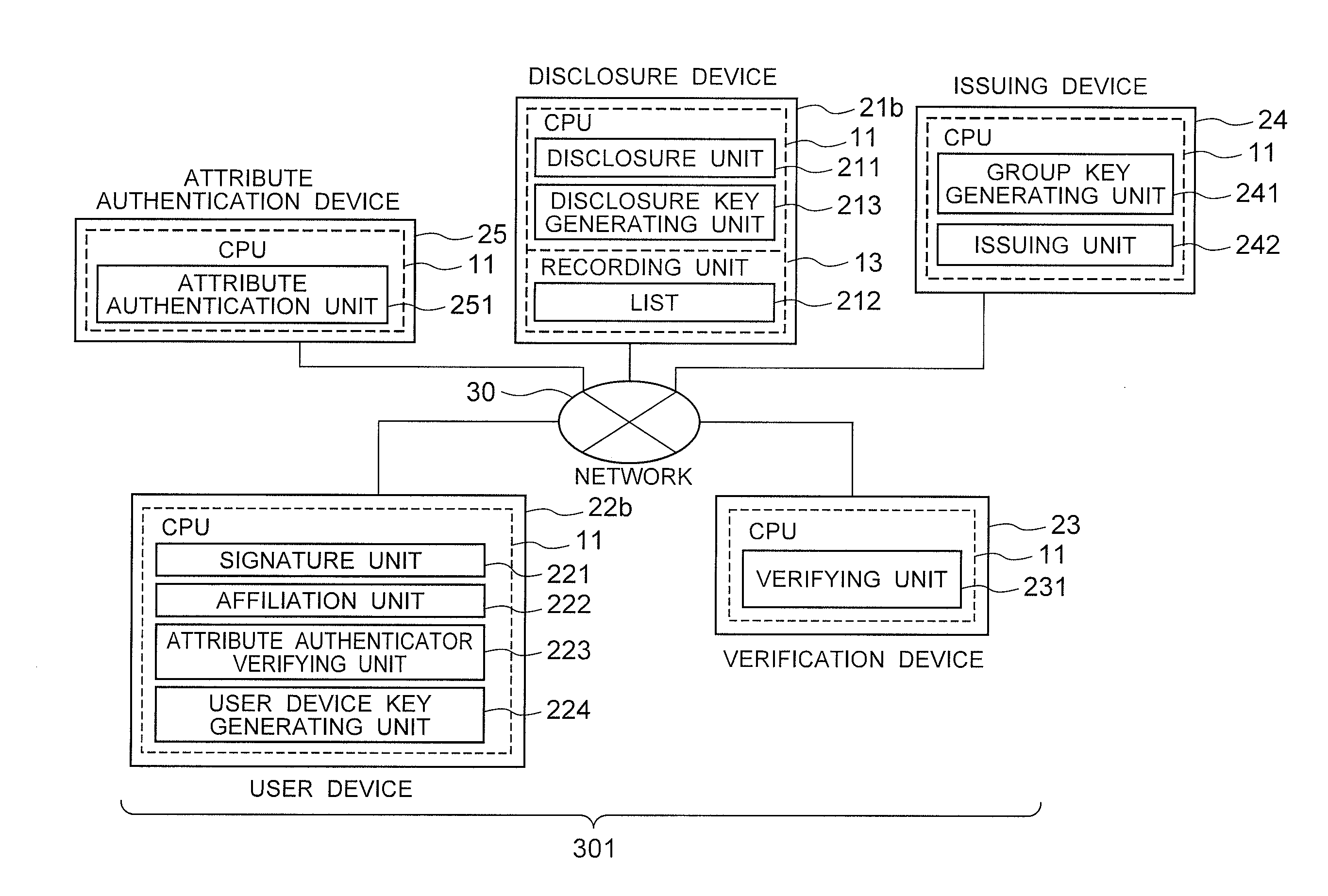
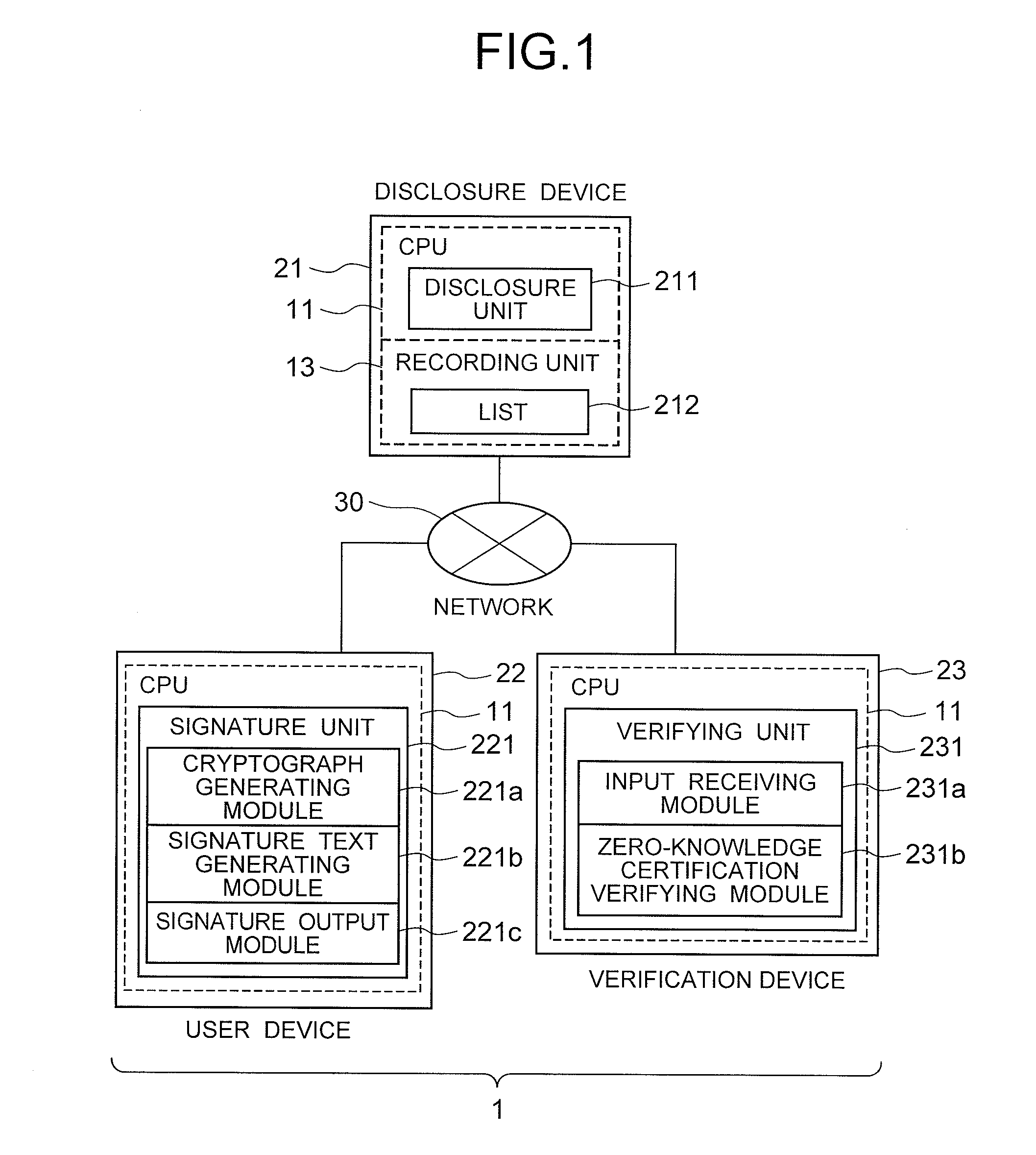
Anonymous authentication signature system, user device, verification device, signature method, verification method, and program therefor
InactiveUS20120124379A1Reduce in quantityReduce the number of timesPublic key for secure communicationUser identity/authority verificationUser deviceValidation methods
The user device includes: a recording unit which stores system parameters as respective parameters given in advance, a disclosure public key, a user public key, a user private key, a member certificate, and an attribute certificate; an input / output unit which receives input of the document from the user and an attribute the user intends to disclose; a cryptograph generating module which generates a cryptograph based on the inputted document, the attribute to be disclosed, and each of the parameters; a signature text generating module which generates a zero-knowledge signature text from the generated cryptograph; and a signature output module which outputs the cryptograph and the zero-knowledge signature text as the signature data. The user public key and the attribute certificate are generated by using a same power.
Owner:NEC CORP
Anonymous authentication service method for providing local linkability
There is provided an anonymous service method of providing local linkability. The anonymous service method providing local linkability according to exemplary embodiments of the invention, an anonymous authentication operation based on a short group signature is performed, for which the concept of a local linkability is introduced to secure linkability within the same service domain. Namely, in the interior of a service provider, a virtual index having a fixed value is calculated for each service user, and in this case, although a plurality of service providers collude with each other, they cannot calculate a virtual index having the same value, whereby the linkability can be secured within the same service domain but not within the interiors of different service domains.
Owner:ELECTRONICS & TELECOMM RES INST
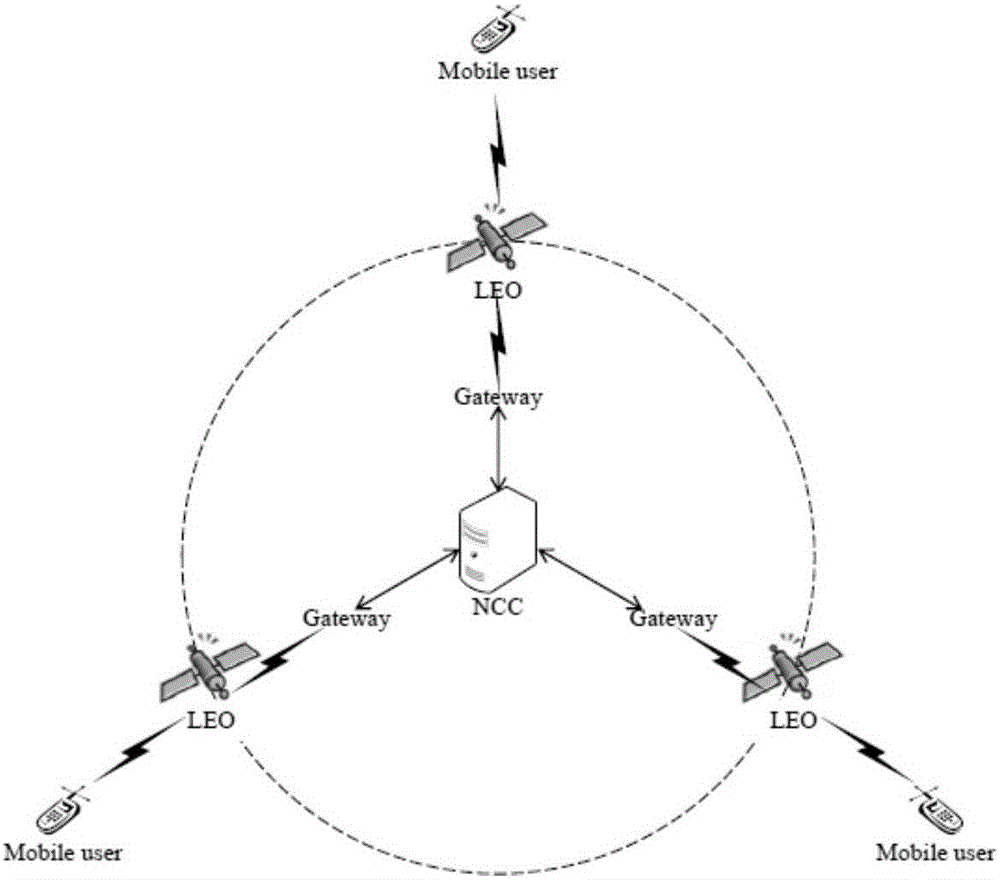
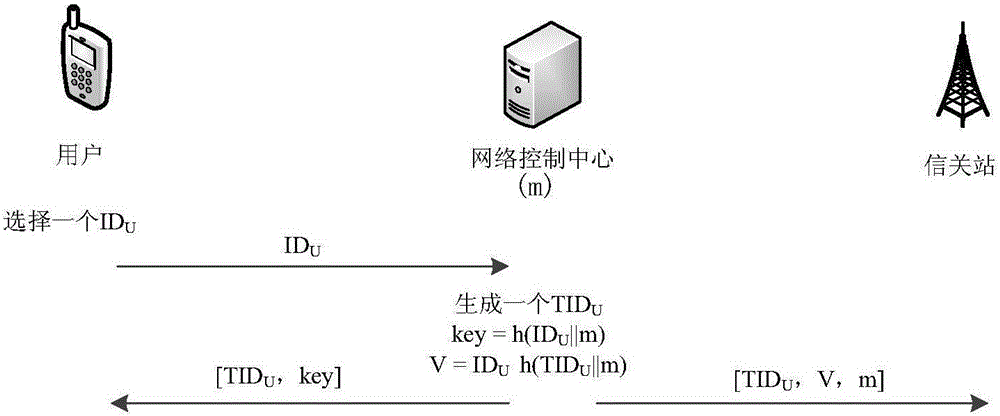
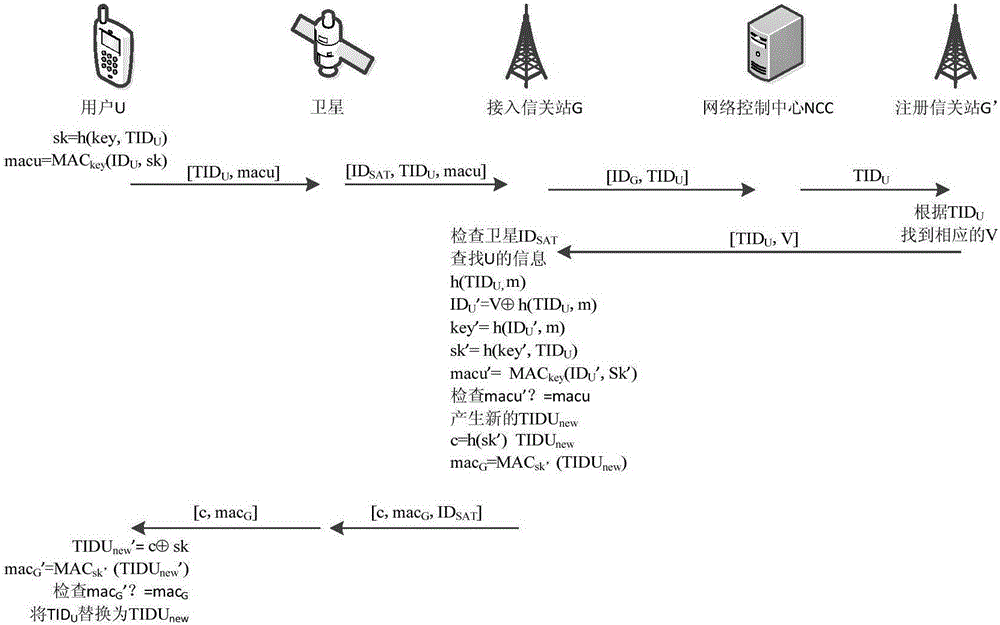
Gateway station-based satellite network anonymous authentication method
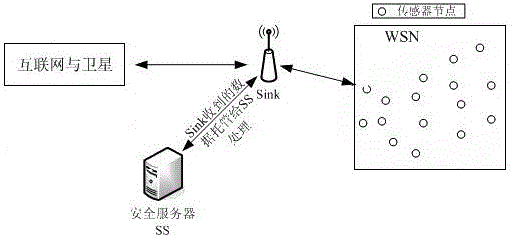
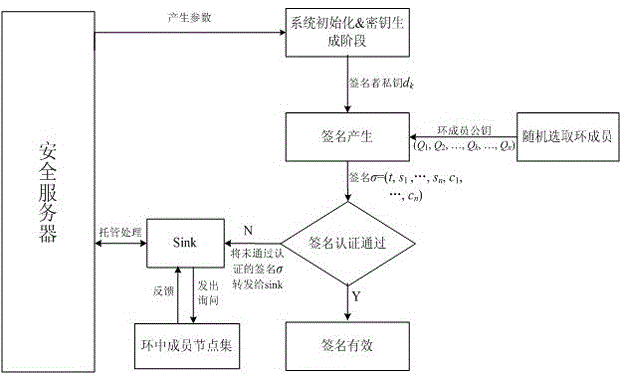
ActiveCN105827304AImprove securityImplement anonymous authenticationRadio transmissionSecurity arrangementNetwork controlAnonymous authentication
The present invention provides a gateway station-based satellite network anonymous authentication method. The conventional satellite network authentication methods all adopt a network control center (NCC) to authenticate users, and in order to reduce the authentication calculation amount of the NCC, the gateway station-based satellite network anonymous authentication method of the present invention enables an authentication function to transfer to a gateway station G, thereby relieving the burdens of the NCC. The gateway station-based satellite network anonymous authentication method of the present invention adopts a message authentication code (MAC) during an authentication process, thereby realizing the anonymous authentication of the users, and protecting the privacy of the users. According to the present invention, after the security authentication of a satellite network to the users is realized, the security authentication of the users to the satellite network is finished, thereby achieving a bidirectional authentication purpose, and further improving the network security. The authentication method of the present invention mainly comprises two stages, namely a registration stage and an authentication stage.
Owner:NANJING UNIV OF POSTS & TELECOMM
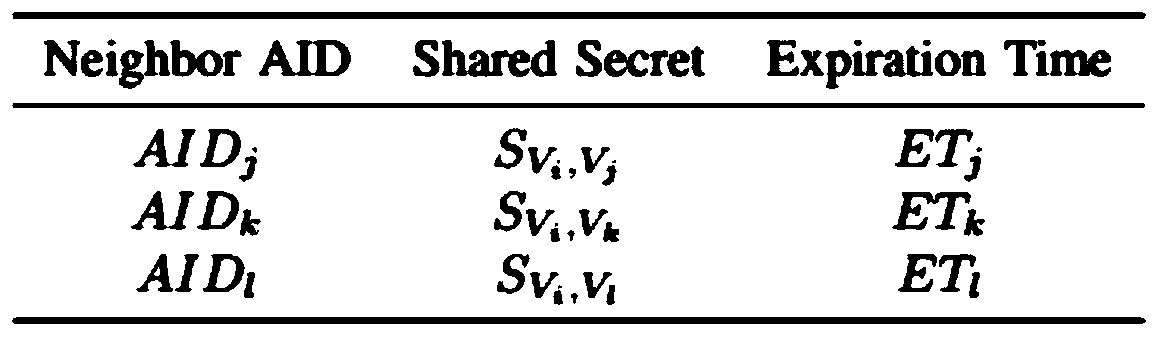
An inter-vehicle message anonymous authentication method and system in an Internet of Vehicles environment
ActiveCN109788482AShort timeMeet privacy requirementsKey distribution for secure communicationUser identity/authority verificationHash-based message authentication codeThe Internet
The invention relates to an inter-vehicle message anonymous authentication method and system in an Internet of Vehicles environment, in the method, each vehicle has a unique identity, and in communication, a short-term pseudonymous certificate needs to be obtained through TA authentication in advance and is used for proving the legal identity of the vehicle. The vehicle negotiates with each neighbor vehicle a communication authentication secret key through the pseudonym certificate, and then based on the communication secret key, signature and signature verification can be realized through simple and rapid HMAC. Compared with a previous message authentication mode, the method has the advantages that the time required for message authentication each time is shortened on the whole, and the environment of vehicle information communication is improved.
Owner:WUHAN UNIV
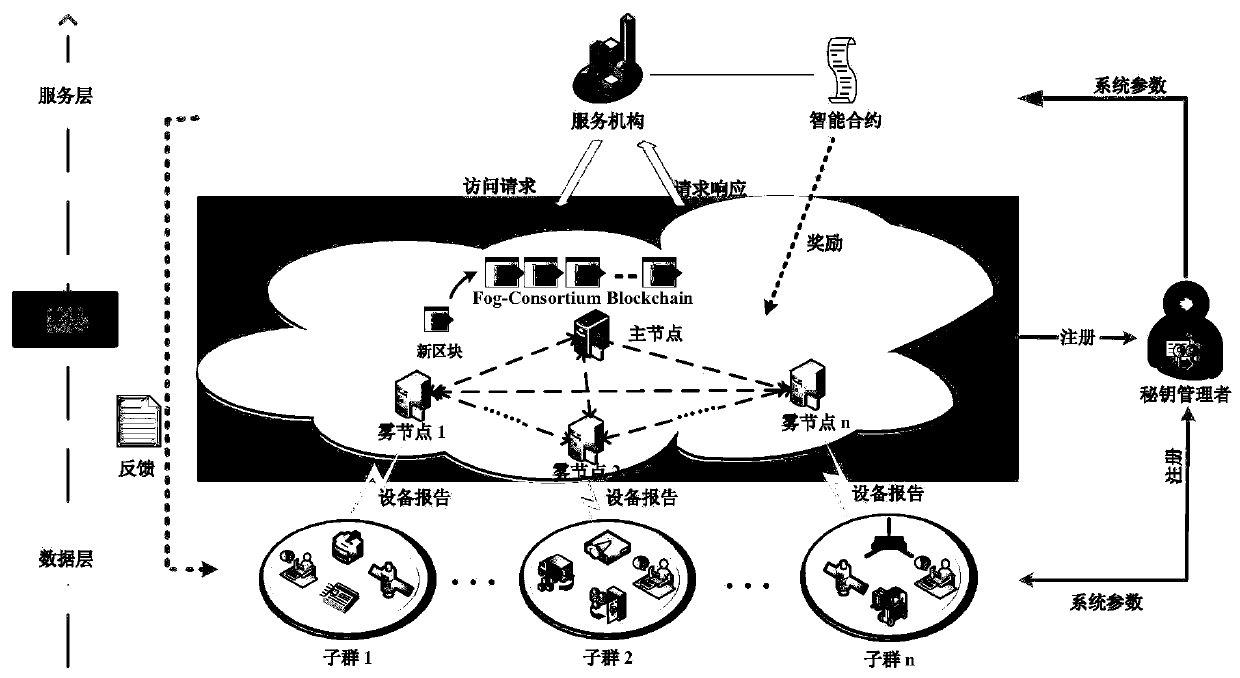
Security distributed aggregation and access system and method based on fog alliance chain
ActiveCN111372243AReduce transmission overheadResist curiosityPublic key for secure communicationSecurity arrangementData integrityConfidentiality
The invention discloses a security distributed aggregation and access system and method based on a fog alliance chain, and aims to solve the problem that most of current data aggregation schemes are designed based on a centralized mode, face single-point faults and tampering threats, and have security and performance improvement space. In order to solve the challenge, a distributed aggregation framework is designed in combination with fog computing and an alliance chain, single-point faults and tampering crisis are solved, and powerful support is provided for safe collection, communication andstorage of data. Meanwhile, a Paillier homomorphic algorithm of a threshold version is fused, a safe access control mechanism with a fault-tolerant function is designed, and confidentiality and privacy of data on a chain are guaranteed. Meanwhile, an efficient anonymous authentication method is provided, and identity privacy and data integrity can be guaranteed. Finally, the comparative analysisresult of the method and the existing method shows that the method can resist malicious attacks and ensure the system security, and compared with other existing methods, the method has lower calculation and communication costs.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and system for sharing anonymous resource
InactiveCN101834853AProtect personal privacyProtection of personal informationTransmissionResource managementResource Provider
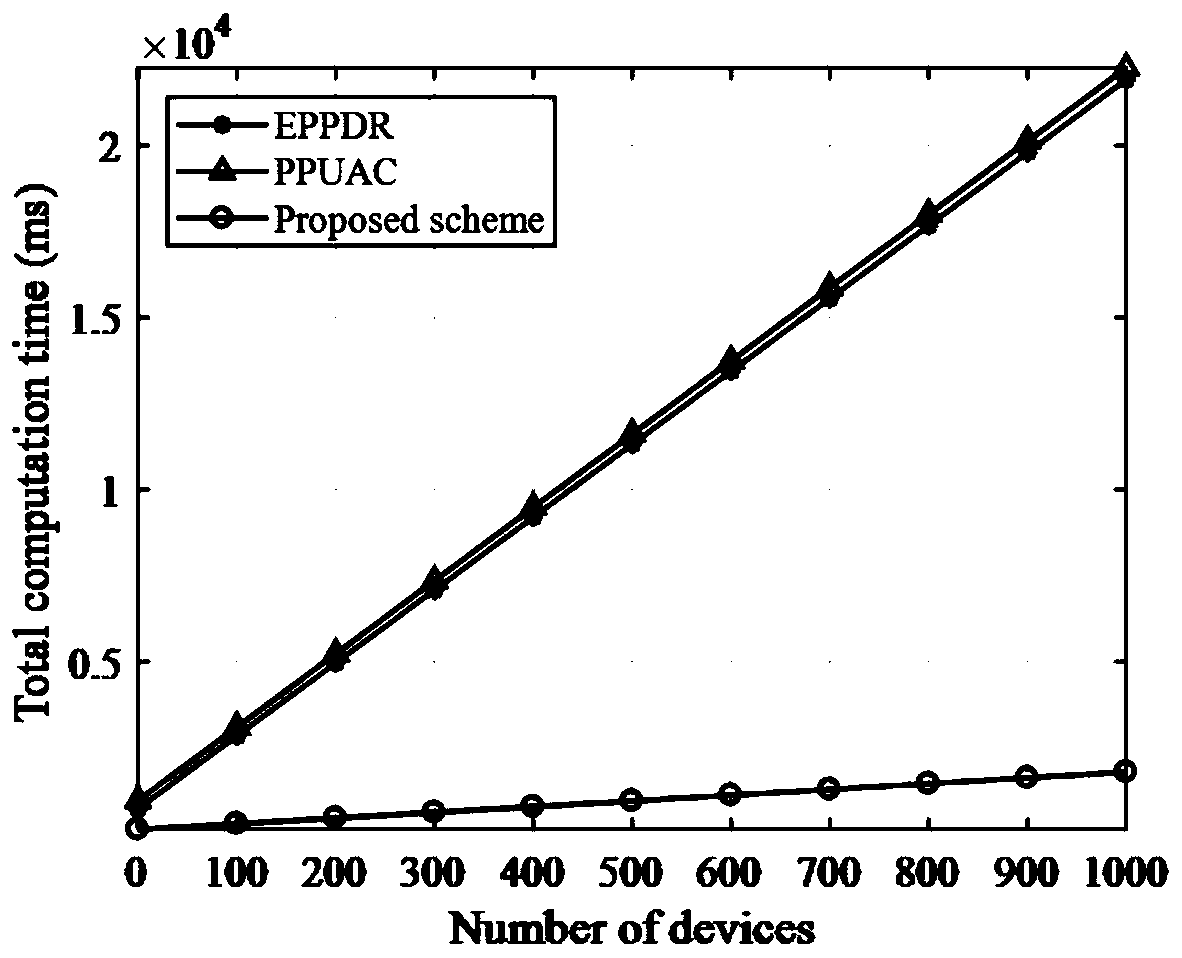
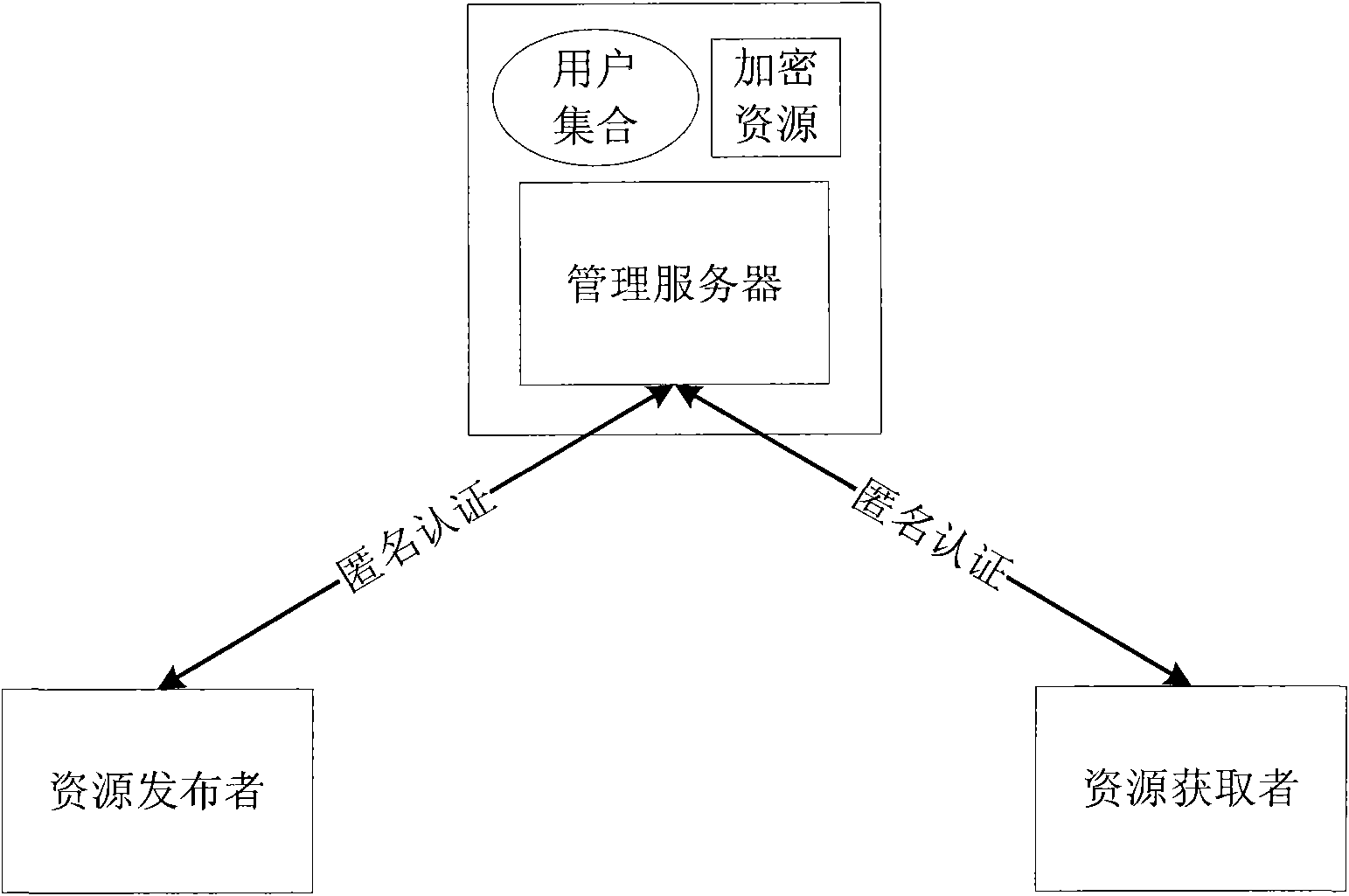
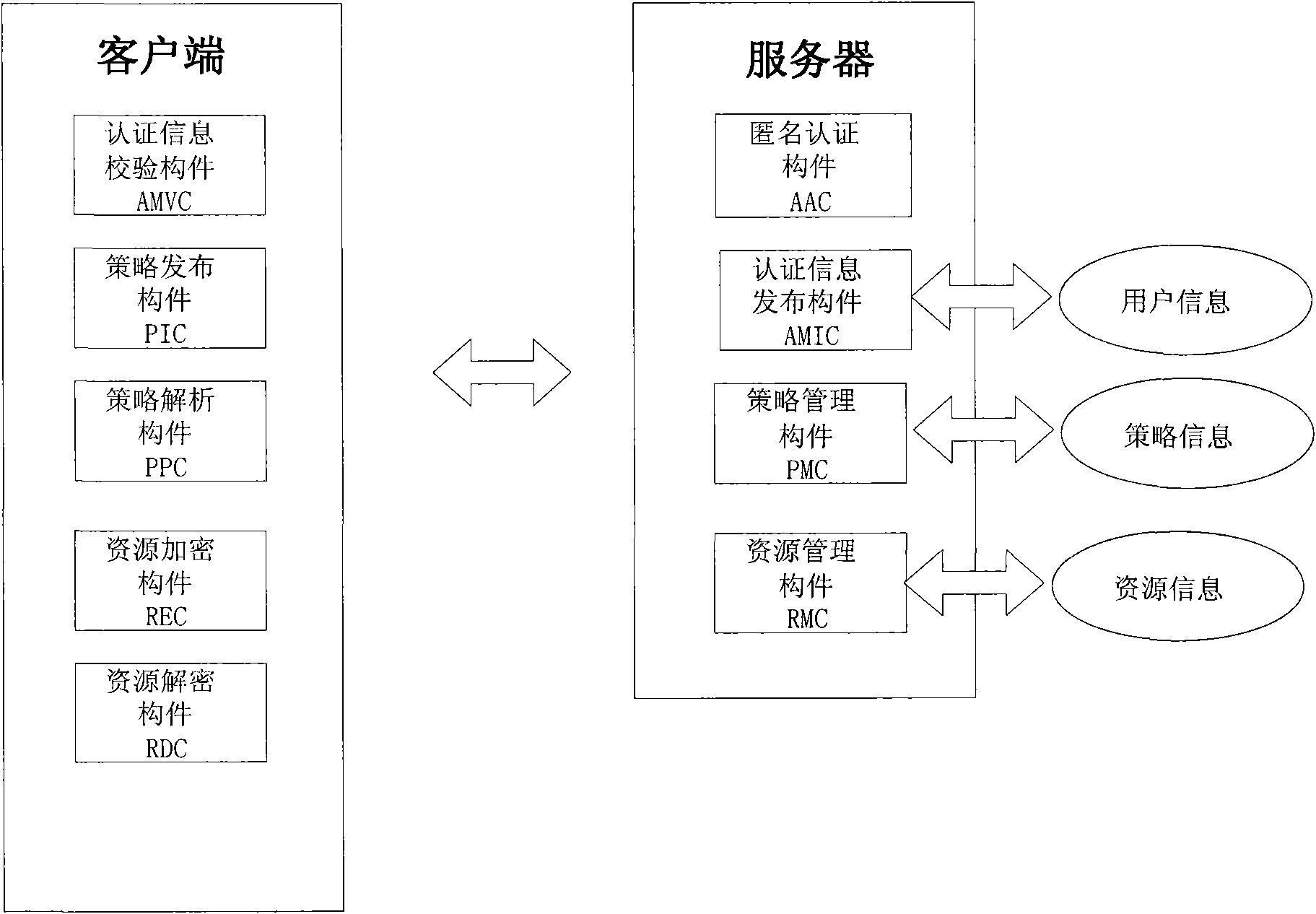
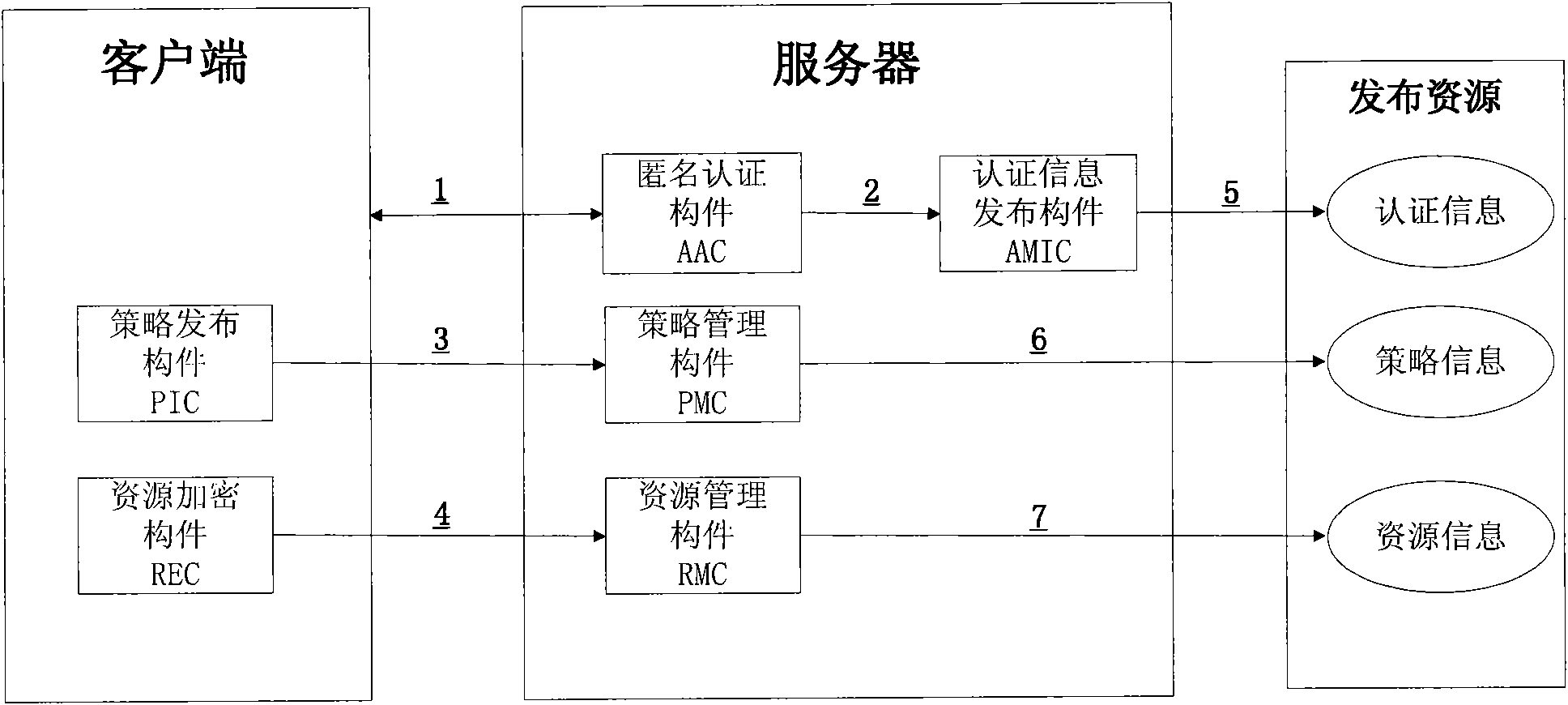
The invention discloses a method and a system for sharing an anonymous resource, which belong to the technical field of computer information. The method for sharing the resource comprises the following steps that: a resource provider initiates a resource publishing request to a resource management server; the resource management server performs an anonymous authentication on the request; the resource provider generates a resource acquisition strategy, uses the resource acquisition strategy as a cipher key to encrypt the resource, and sends the acquisition strategy and the encrypted resource to the resource management server; the resource management server stores a binary group and releases resource description information; a resource acquirer retrieves the resource description information and initiates a resource acquisition request; the resource management server performs the anonymous authentication on the resource acquirer; and the resource acquirer acquires and decrypts the resource after acquiring a strategy verification. The invention also discloses a system sharing the resource, which corresponds to the method. The method and the system can be used for computer information technical application such as network resource sharing and the like.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
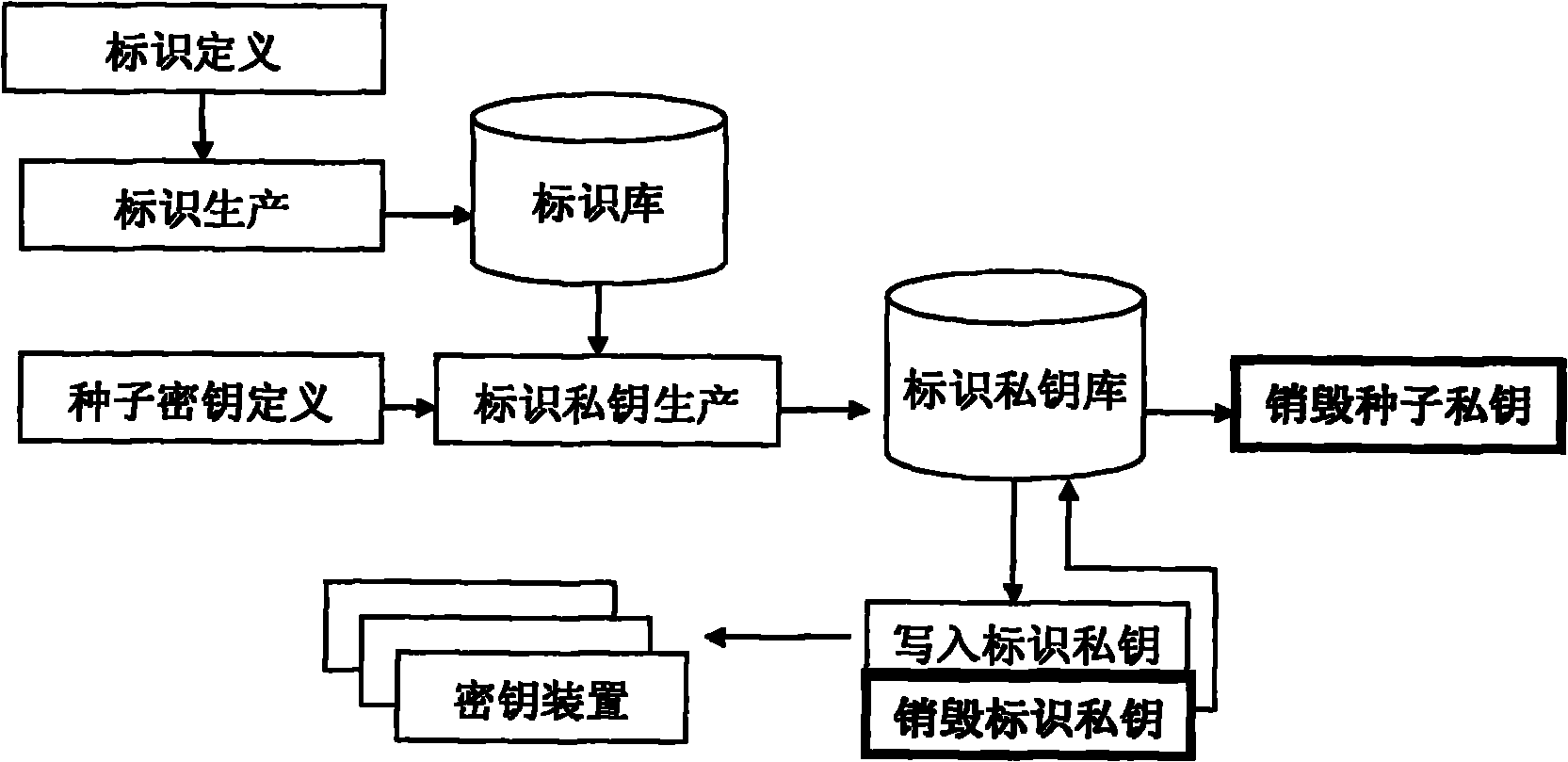
Secret key devices for supporting anonymous authentication, generation method and unlocking method thereof
ActiveCN101958796ABreak through application bottlenecksEnable secure interactionsKey distribution for secure communicationUser identity/authority verificationAnonymous authenticationAnonymous identifier
The invention provides identification authentication-based technology, and relates to secret key devices for supporting anonymous authentication. Identification secret keys generated by anonymous identifiers are stored in the secret key devices. The generation method of the secret key devices for supporting the anonymous authentication comprises the following steps of: defining and generating at least one anonymous identifier; defining a seed secret key pair, wherein the seed secret key pair consists of a seed public key and a seed private key; allowing the anonymous identifiers to generate identification private keys corresponding to the anonymous identifiers respectively through the seed private key; and writing the generated identification private keys into each secret key device. The invention also provides a back-up unlocking method of the dual secret key devices. The devices and the method can support requirements of social and publics on anonymous safety service, and reduce theapplication threshold of the authentication technology greatly.
Owner:北京联合智华微电子科技有限公司
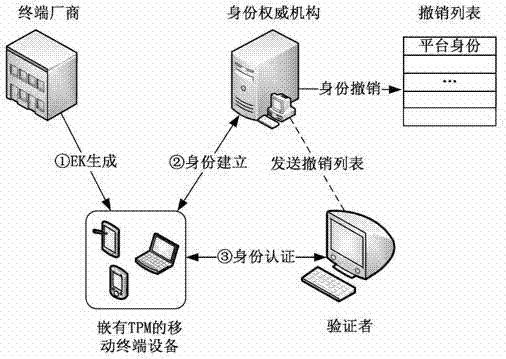
Direct anonymous attestation method applied to credible mobile terminal platform
ActiveCN102970682AReduce computational overheadImprove safety and reliabilitySecurity arrangementThree stageTrusted Platform Module
The invention provides a direct anonymous attestation method applied to a credible mobile terminal platform, which can realize the generation of a platform endorsement key (EK) pair, the establishment and revocation of a platform identity and the authentication of a mobile terminal identity by adopting a method based on identity signature and zero-knowledge proof signature. The method is divided into three stages, namely a system initialization stage, an identity establishment stage and an identity verification stage and comprises 9 steps in total, and the method is specifically as follows: stage 1: system initialization: step 1: performing the system initialization on a manufacturer; step 2: performing the system initialization on an identity authoritative institution; step 3: initializing an equipment EK pair; stage 2: identity establishment: step 4: sending a challenge number; step 5: making a response by terminal equipment; step 6: verifying and issuing an identity certificate; and the stage 3: identity verification: step 7: sending a challenge number; step 8: responding by the terminal equipment; and step 9: verifying the legitimacy of the identity certificate. The method provided by the invention meets the requirements of anonymous authentication for correctness, unforgeability and untraceability, and is suitable for a mobile terminal platform which has limited computational resources and is embedded with a TPM (trusted platform module).
Owner:BEIHANG UNIV
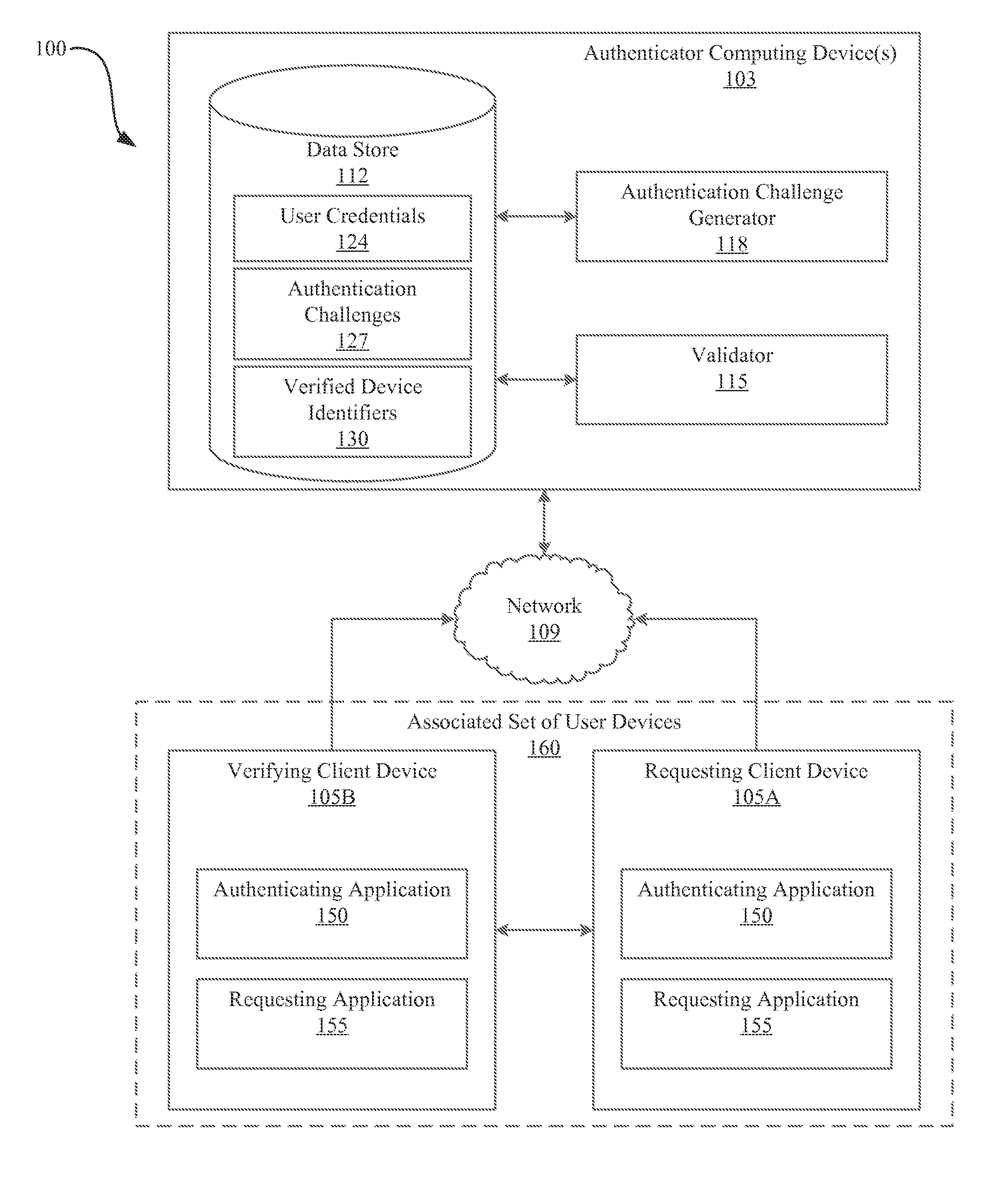
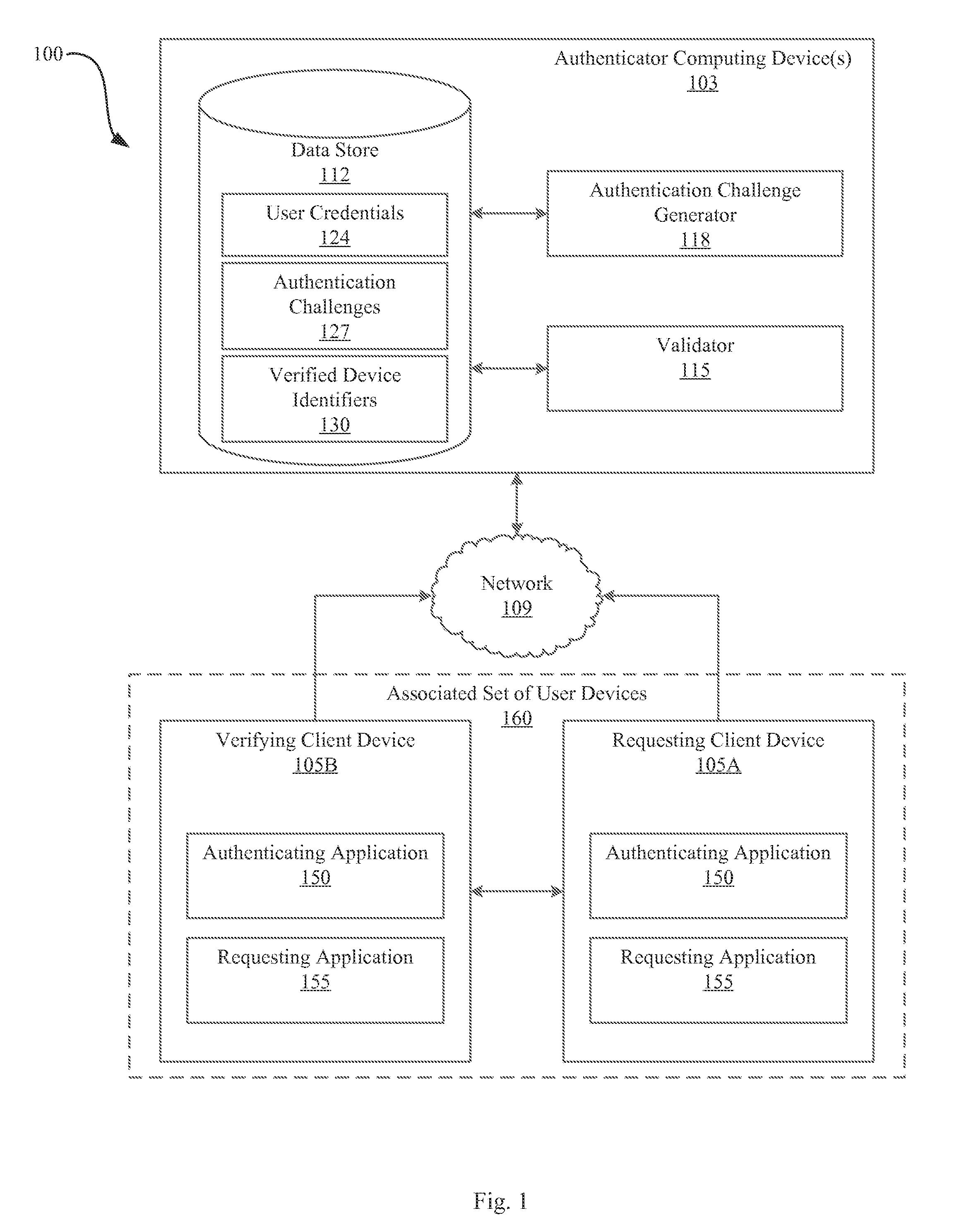
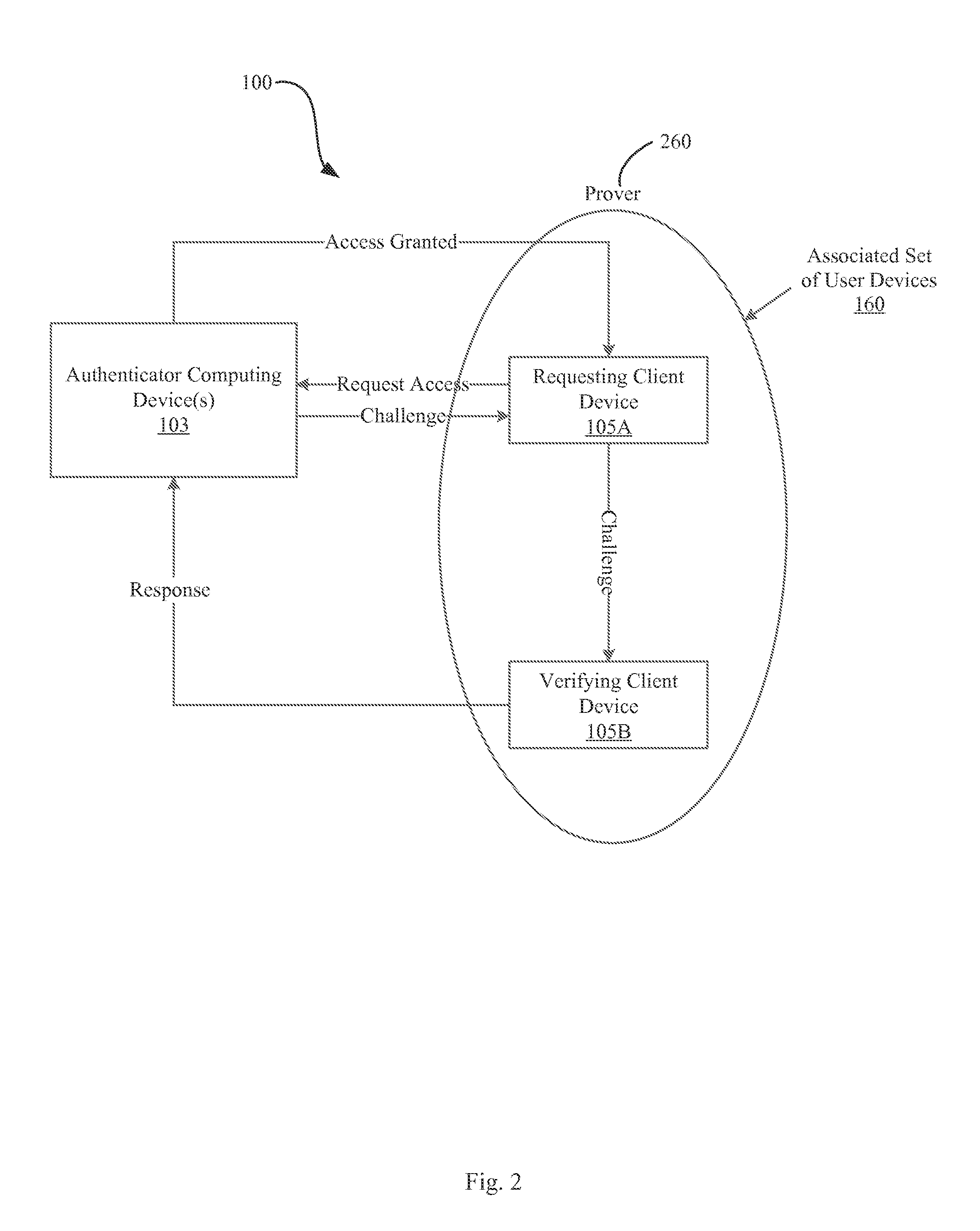
Systems and methods for anonymous authentication using multiple devices
ActiveUS20160182500A1Improve securityEnhanced anonymityUser identity/authority verificationUser deviceInternet privacy
A system and method of anonymous authentication is described. In operation, the authenticator receives a request to access a resource from one of the user devices of an associated set of user devices, wherein each of the user devices is registered to at least one user requesting access to the resource registered to at least two users. The authenticator generates and transmits an authentication challenge in response to the request to a subset of the user devices. A user device subsequently generates and transmits a response to the authentication challenge to the authenticator. The authenticator determines whether the responses received from the one or more user devices constitutes a valid response and grants any one or more of the user devices of the associated set of user devices access to the resource if the responses received from the user devices constitutes a valid response to the authentication challenge.
Owner:UNIV OF SOUTH FLORIDA
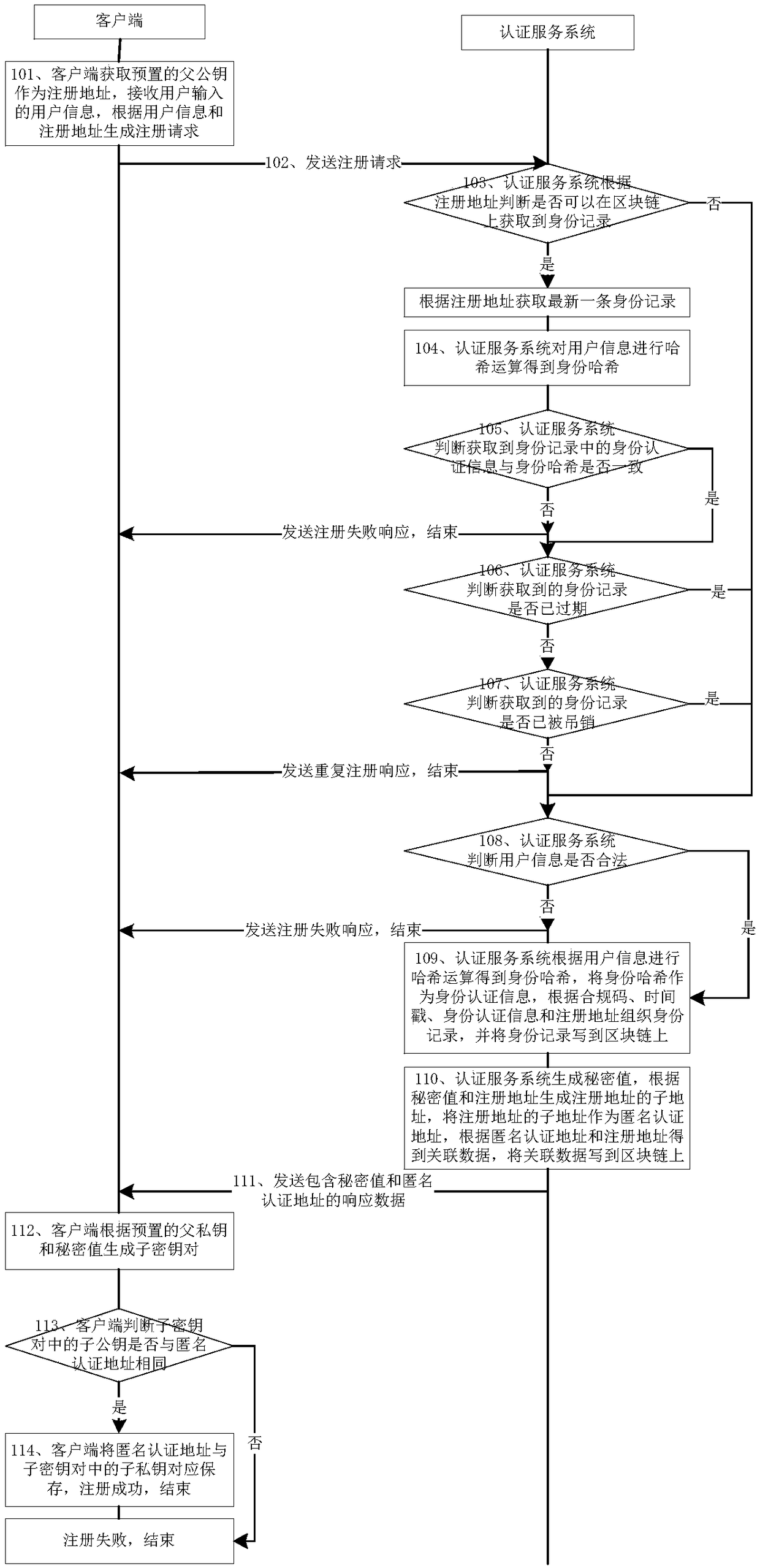
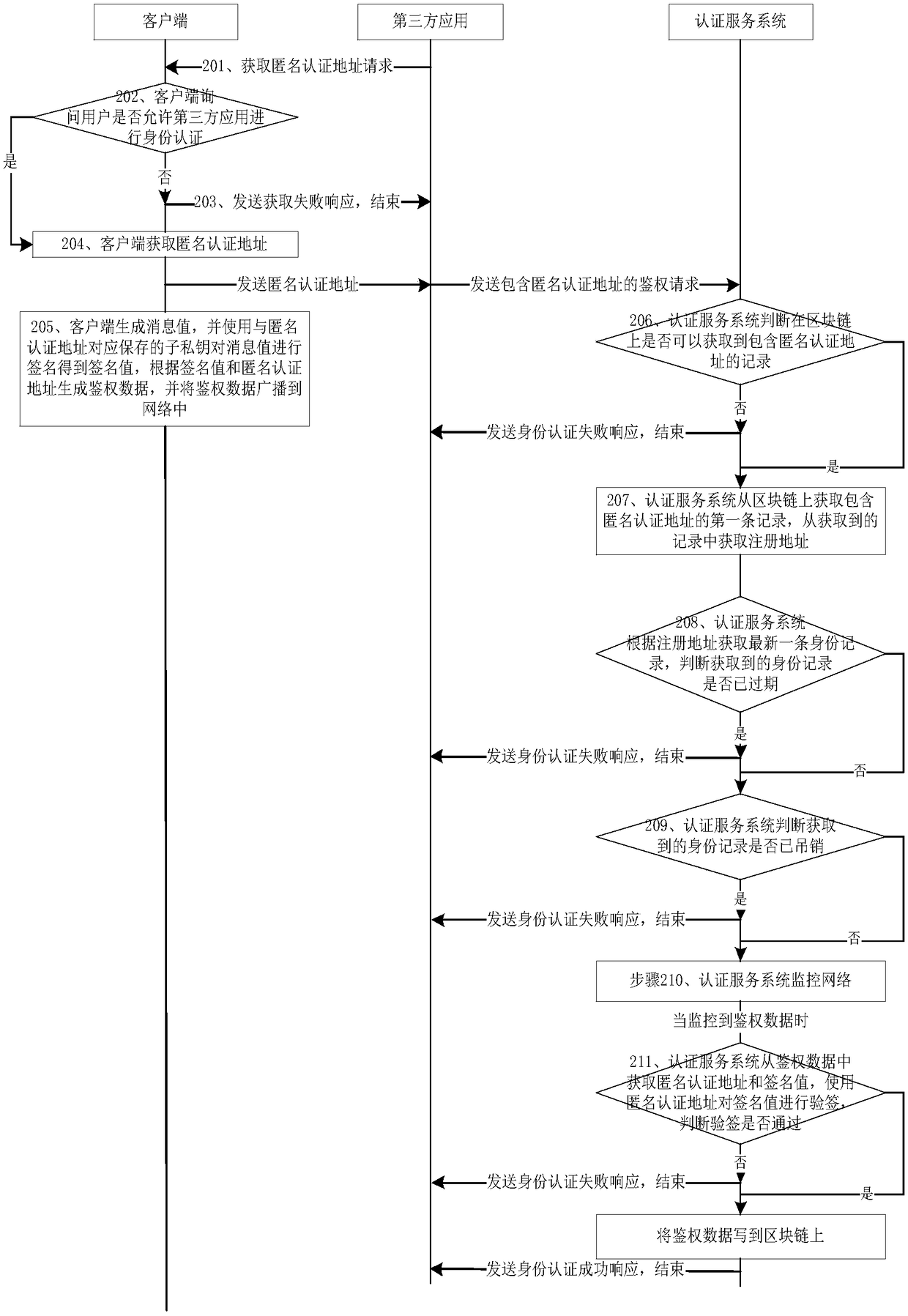
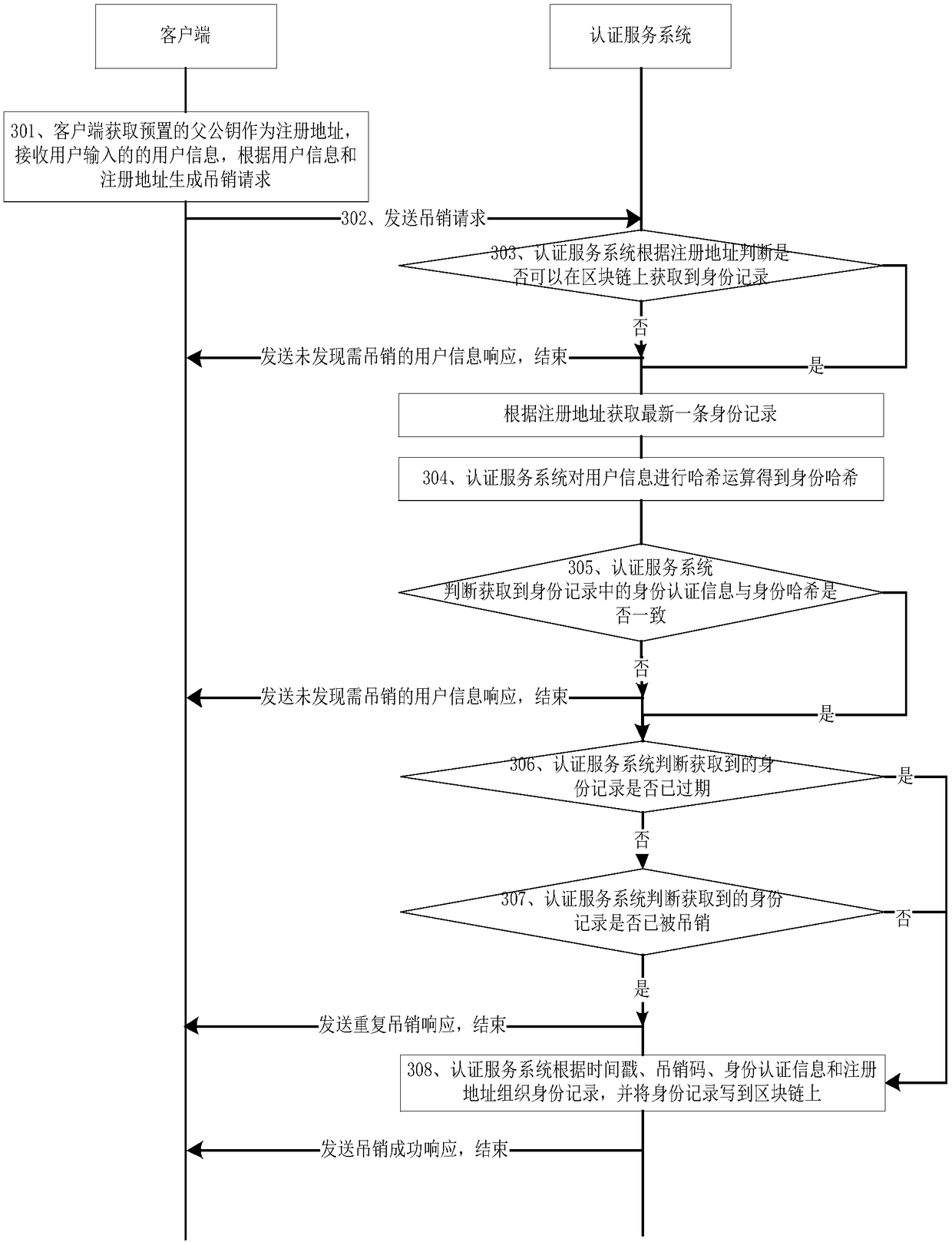
Blockchain-based anonymous identity authentication method and device
ActiveCN108809953AImplement anonymous authenticationPrevent leakageTransmissionThird partyThe Internet
The invention relates to the technical field of Internet, and particularly relates to a blockchain-based anonymous identity authentication method and device. The method includes the following steps: when a third-party application receives a login request initiated by a user through a client, acquiring an anonymous authentication address from the client; enabling the third-party application to sendan authentication request including the anonymous authentication address to an authentication service system, and simultaneously enabling the client to generate a message value, signing the message value by using a sub-private key saved corresponding to the anonymous authentication address to obtain a signature value, generating authentication data according to the signature value and the anonymous authentication address, and broadcasting the authentication data to networks; and when an authentication server monitors the authentication data including the anonymous authentication address, performing signature verification on the signature value by using the anonymous authentication address; and when the signature verification is successful, writing the authentication data to a blockchain,sending an identity authentication success response to the third-party application, and ending the process. By adopting the technical scheme provided by the invention, the anonymous verification of user information performed by a verifier can be achieved.
Owner:FEITIAN TECHNOLOGIES
Method and Device for Information System Access Authentication
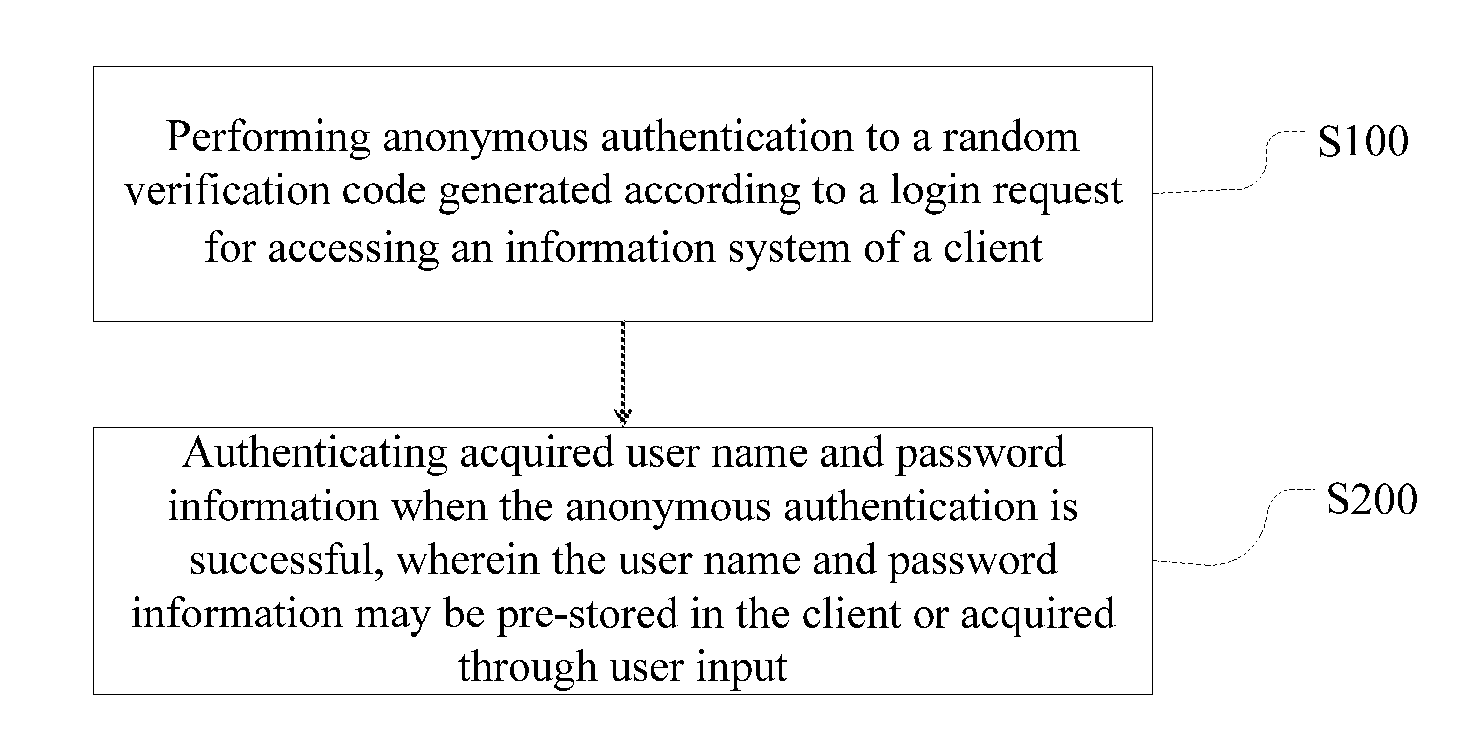
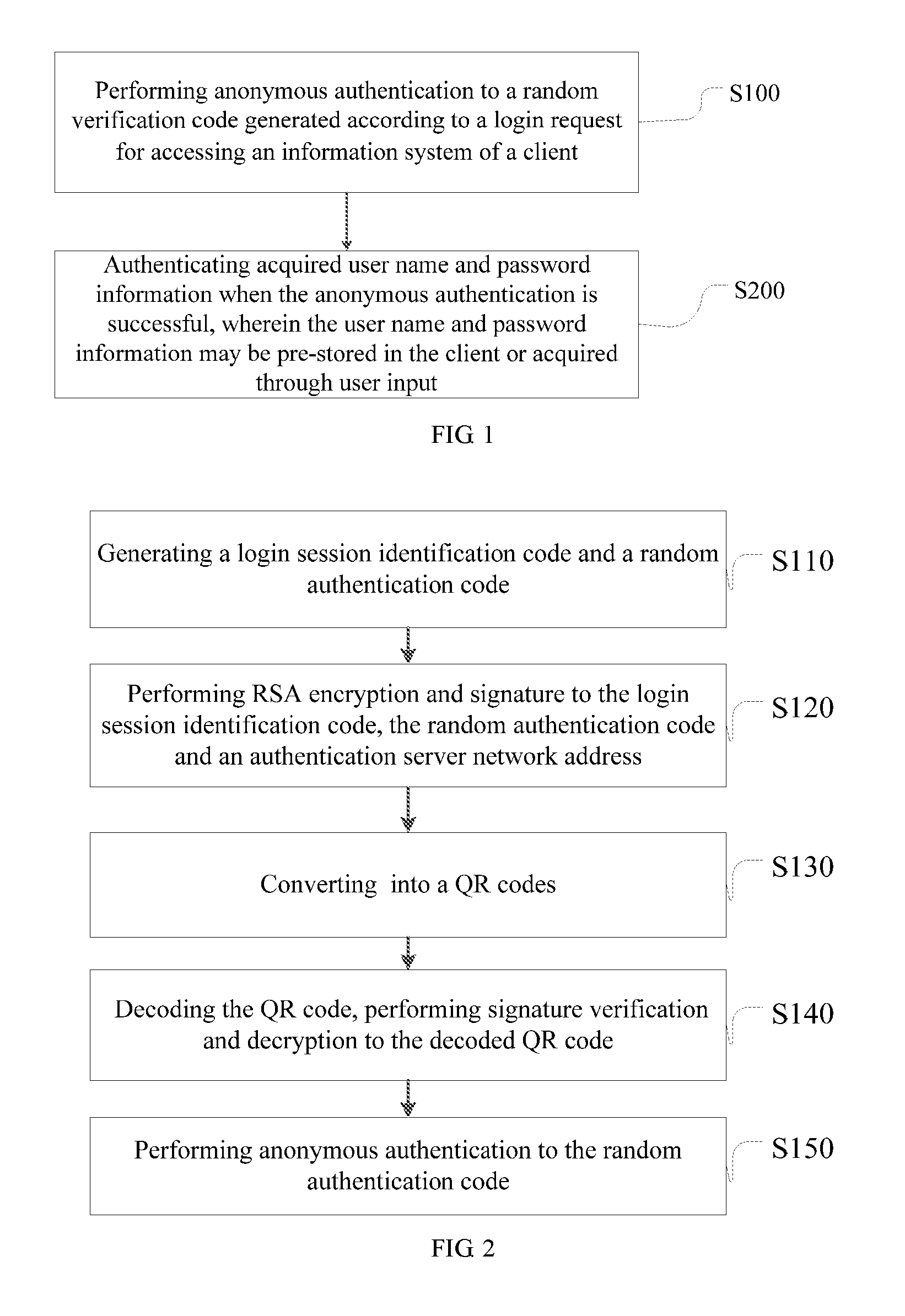
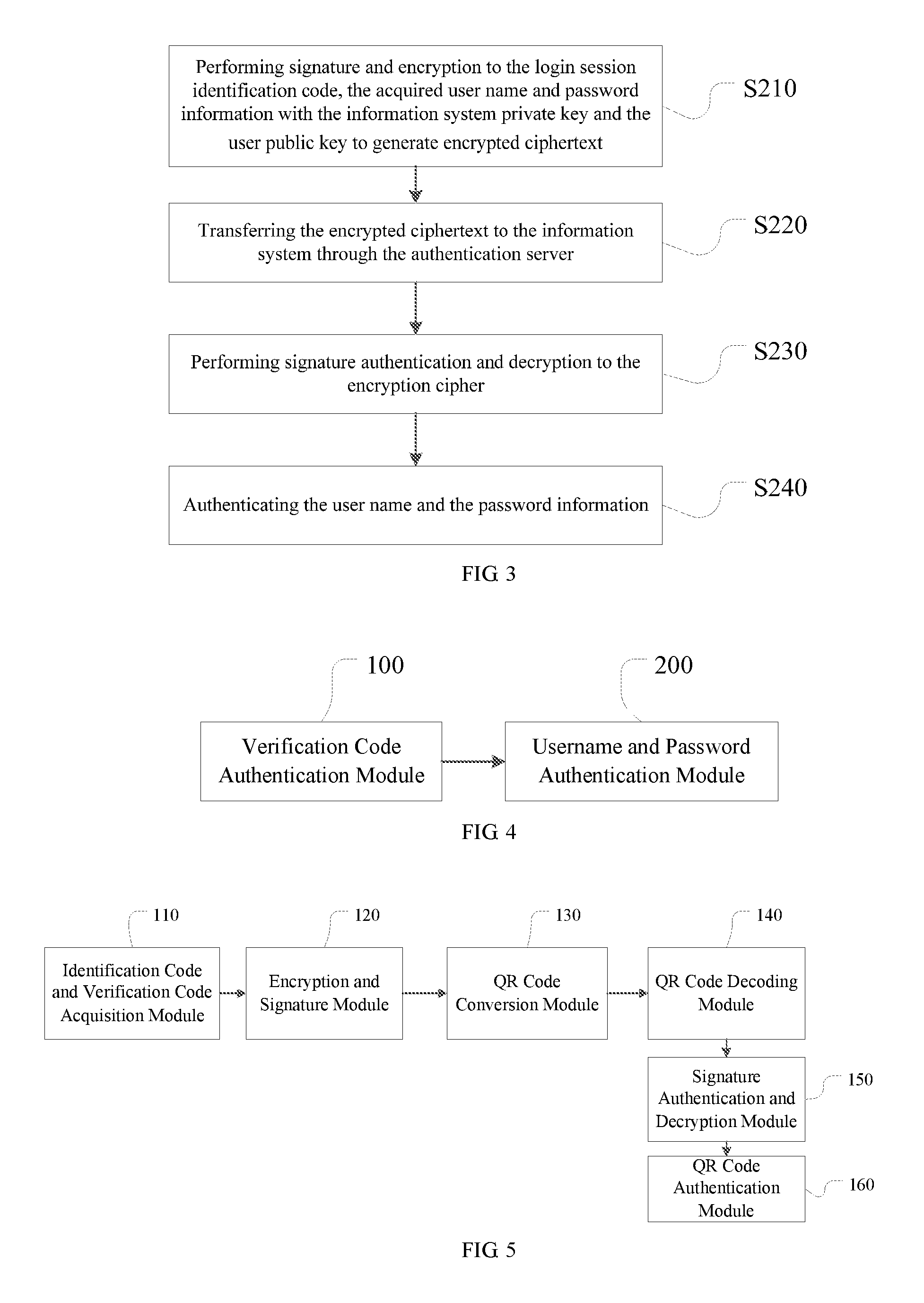
ActiveUS20160269181A1Reduce riskImprove securityUser identity/authority verificationSecurity arrangementPasswordAnonymous authentication
A method and a device for information system access authentication are disclosed. The method includes: performing anonymous authentication to a random verification code generated according to a login request for accessing an information system of a client, and authenticating acquired user name and password information when the anonymous authentication is successful. The device includes an verification code authentication module and a user name and password authentication module connected to the verification code authentication module, wherein the verification code authentication module is configured to perform anonymous authentication to a random verification code generated according to a login request for accessing an information system of client; and the user name and password authentication module is configured to authenticate acquired user name and password information when the anonymous authentication is successful. The present disclosure uses a two-stage and two-factor authentication method such that the security of the login information is improved without increasing the complexity of the user's login.
Owner:MACAU UNIV OF SCI & TECH +1
Vehicle-mounted network anonymous authentication system and method based on ring signature and vehicle communication platform
ActiveCN109802956ARealize communicationAuthentication securityUser identity/authority verificationCommunications securityRelevant information
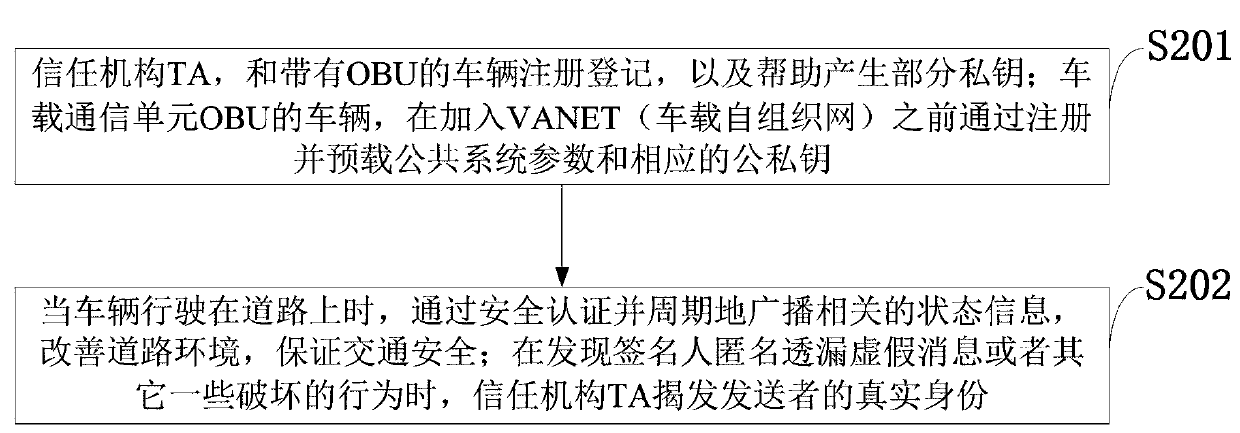
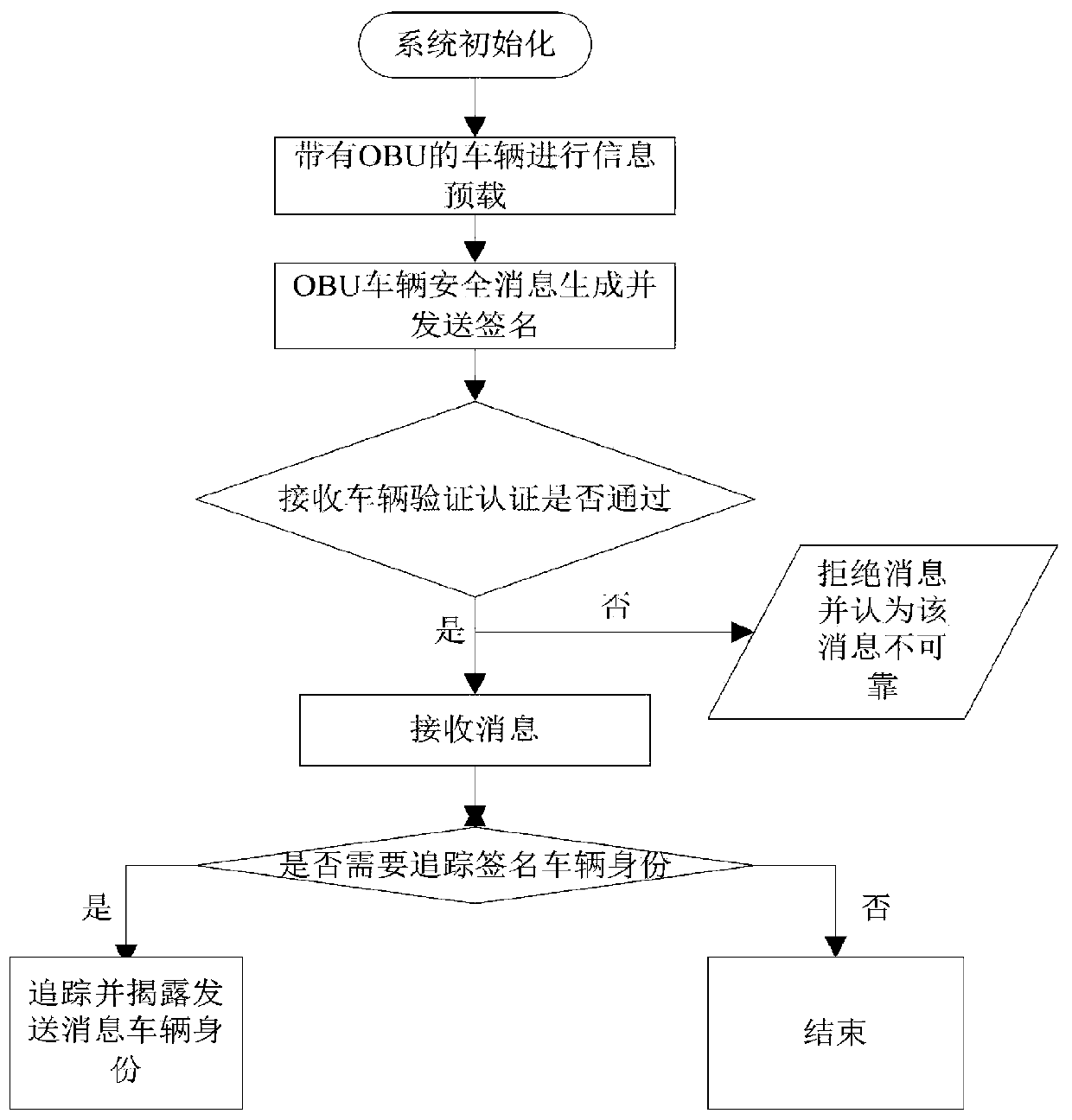
The invention belongs to the technical field of vehicle communication security, and discloses a vehicle-mounted network anonymous authentication system and method based on a ring signature, and a vehicle communication platform. The trust mechanism and the vehicle with the OBU are registered to generate a part of private keys; A vehicle of the OBU is registered and preloaded with public system parameters and corresponding public and private keys before being added into the vehicle-mounted ad hoc network. When the vehicle runs on a road, related state information is periodically broadcasted after safety certification; And when the signer finds that the signer anonymously leaks the false message or the behavior that the signer is damaged, the trust mechanism uncovers the real identity of thesender. According to the invention, the certificateless public key cryptosystem and the ring signature are combined to form the certificateless ring signature, so that anonymity and unforgeability aremet, and meanwhile, security authentication is met; A traceable algorithm is formed by adding related information to effectively solve the problem that when a signer anonymity leaks false messages orother destructive behaviors, identity tracking and revocation are carried out according to the received messages.
Owner:XIAN UNIV OF POSTS & TELECOMM
User anonymous identity authentication protocol based on k-pseudonym set in wireless network
ActiveCN104283899AReduce resource consumptionTransmissionSecurity arrangementWireless mesh networkUser authentication
The invention discloses a user anonymous identity authentication protocol based on a k-pseudonym set in a wireless network. In the protocol, a user sends the information includes the k-pseudonym set of the true identity label of the user and the information encrypted through the true user shared key to an authentication server, the authentication server completes user authentication within the range of the traversal and the calculation of k pieces of user information; the average number of users needing traversal is half the sum of k and 1, and two types of methods for constructing the k-pseudonym set are provided at the same time. According to the protocol, anonymous authentication is achieved on the basis of a shared key by introducing the k-pseudonym set, and the resource loss, generated during anonymous authentication, of the user and the authentication server is lowered.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com