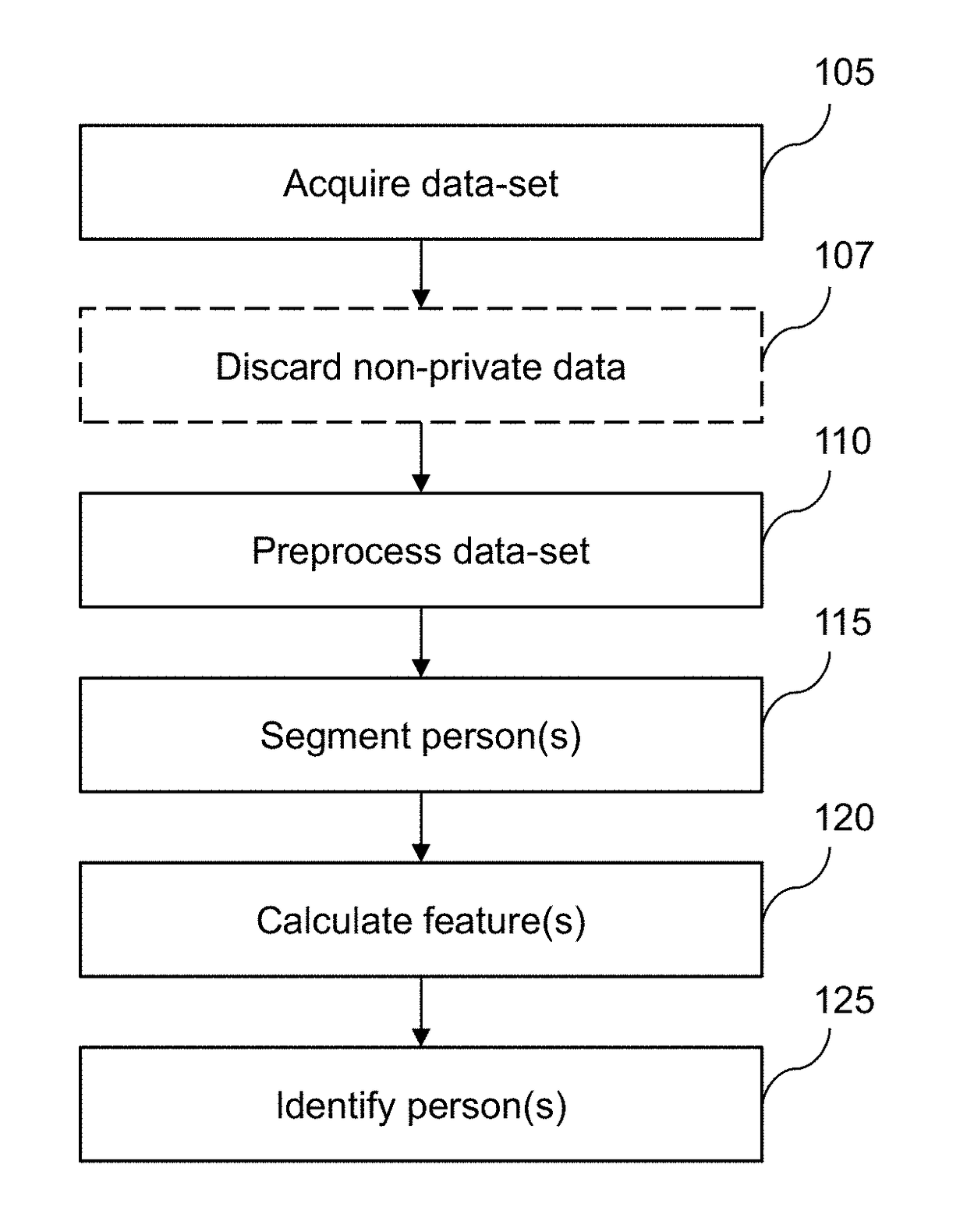
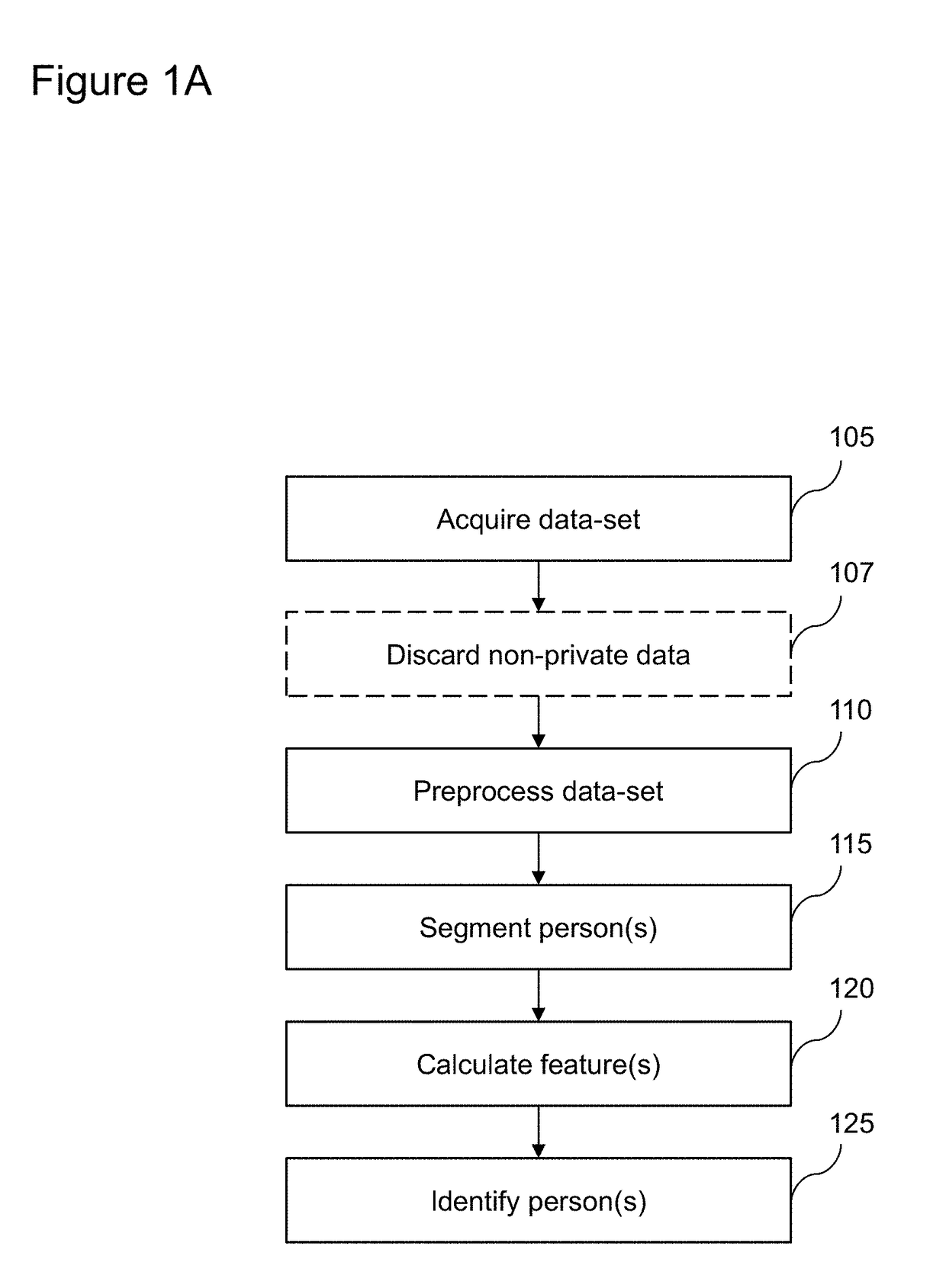
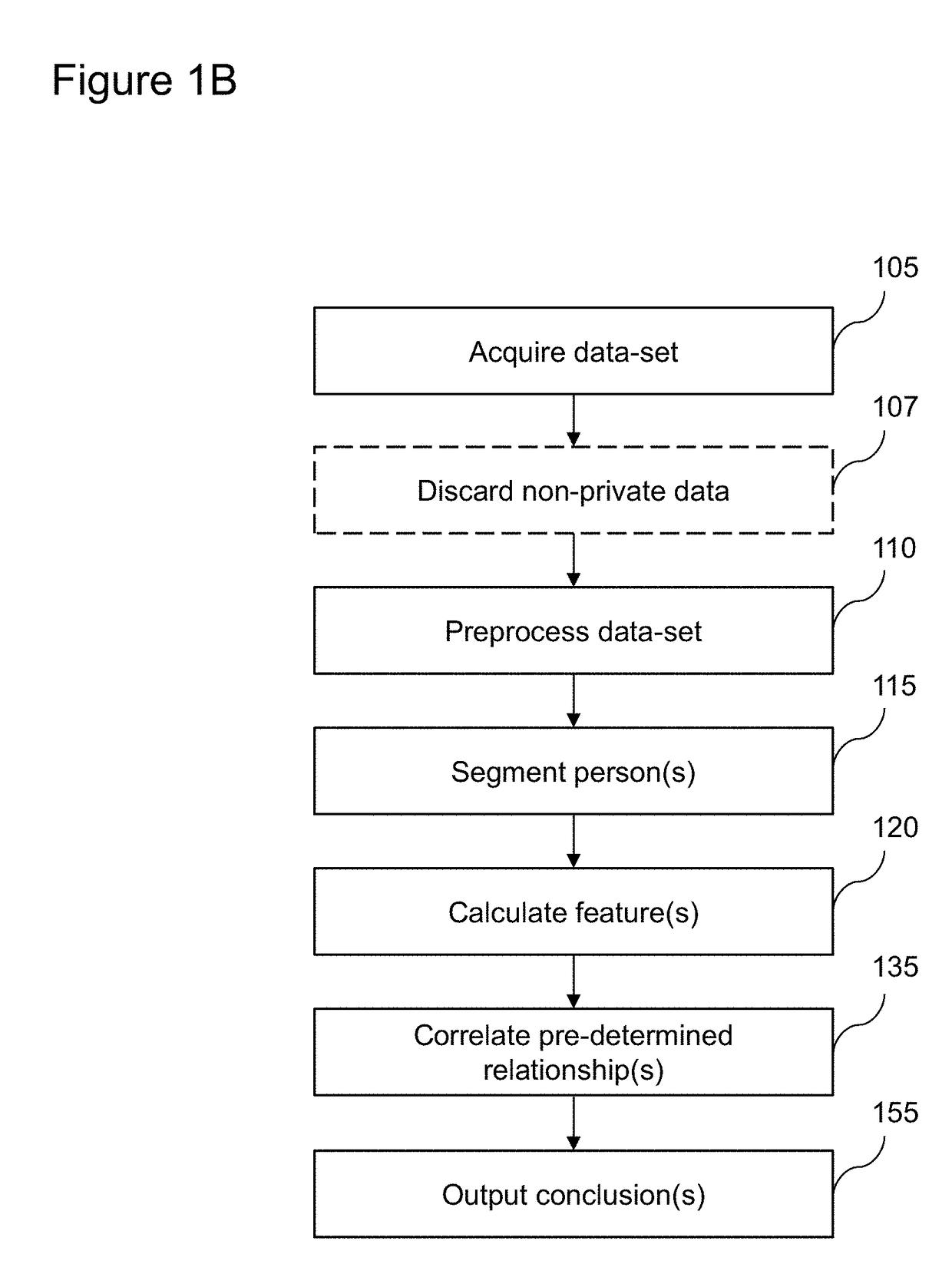
Patents
Literature
662results about How to "Protect personal privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
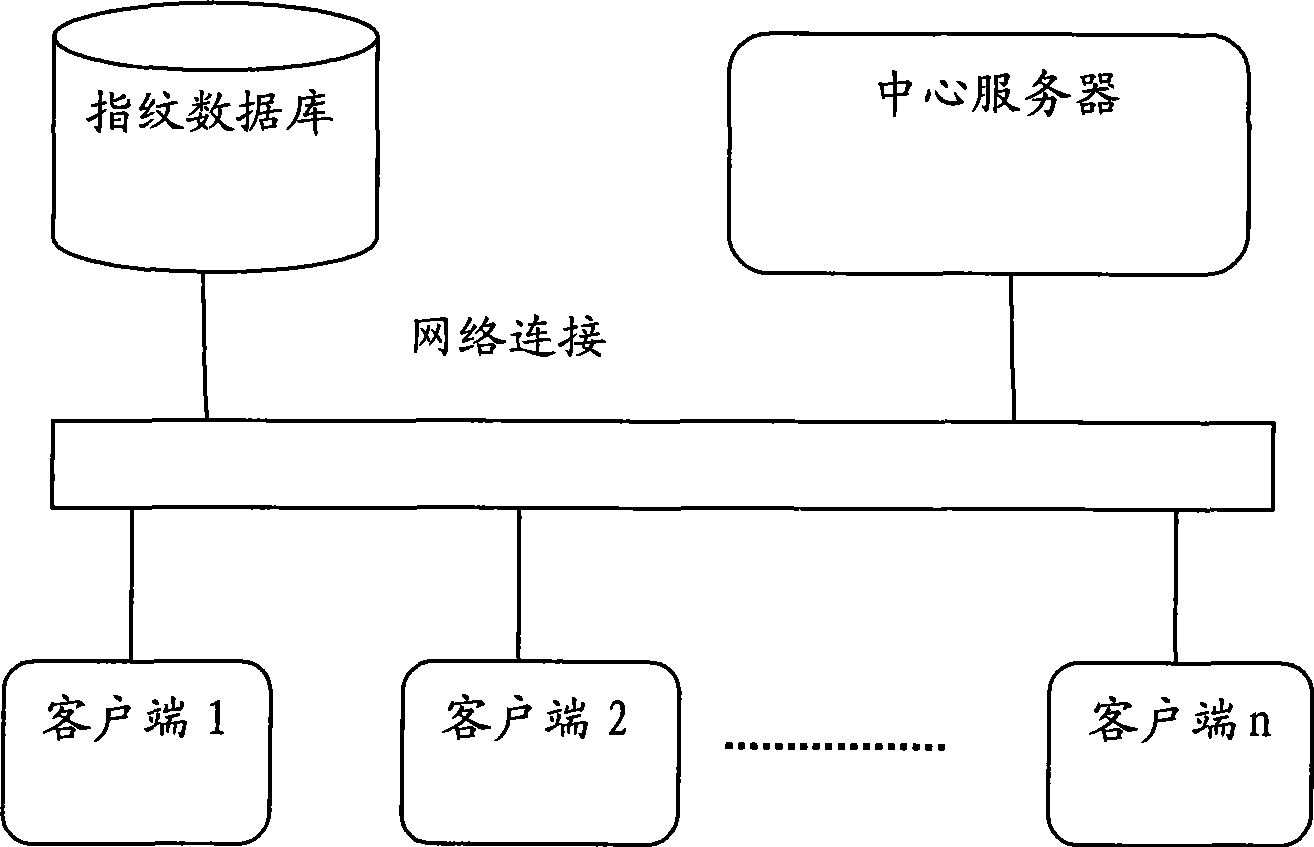
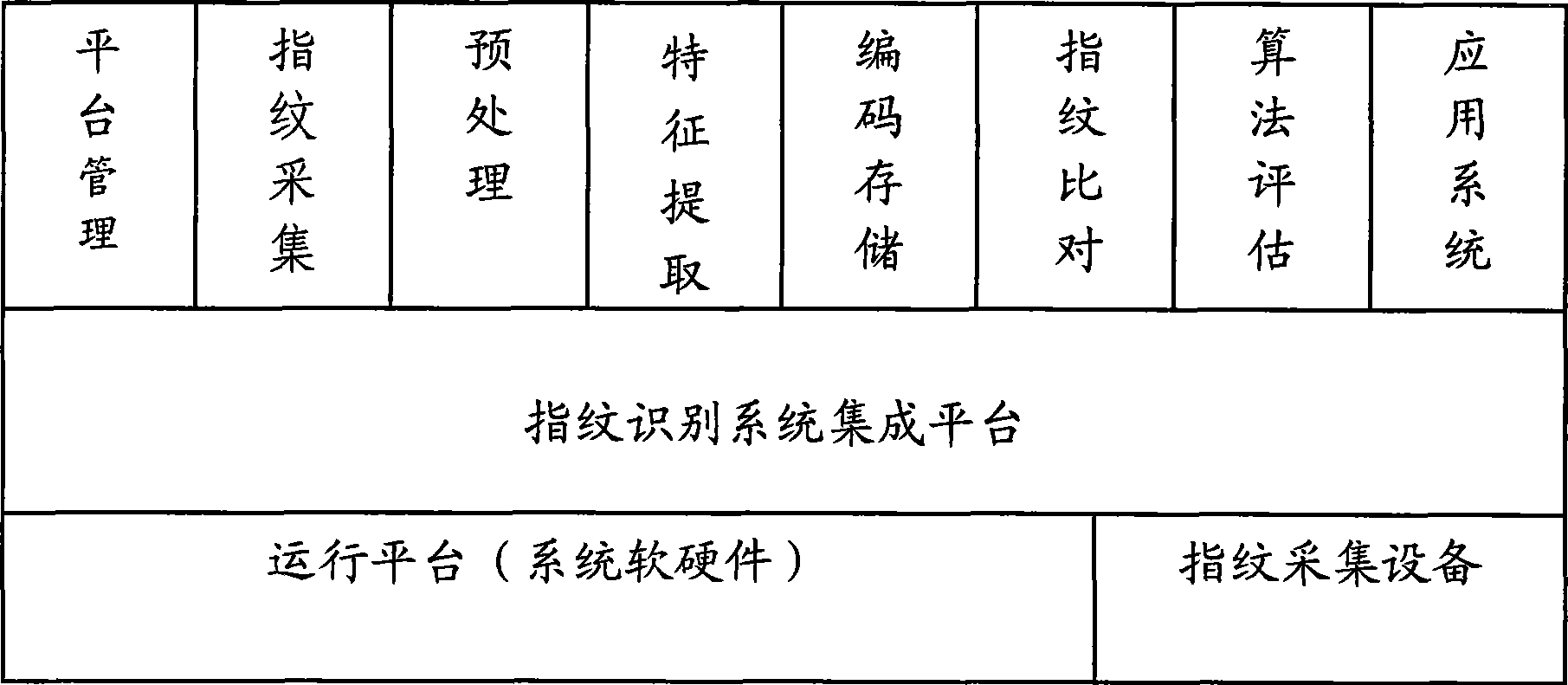
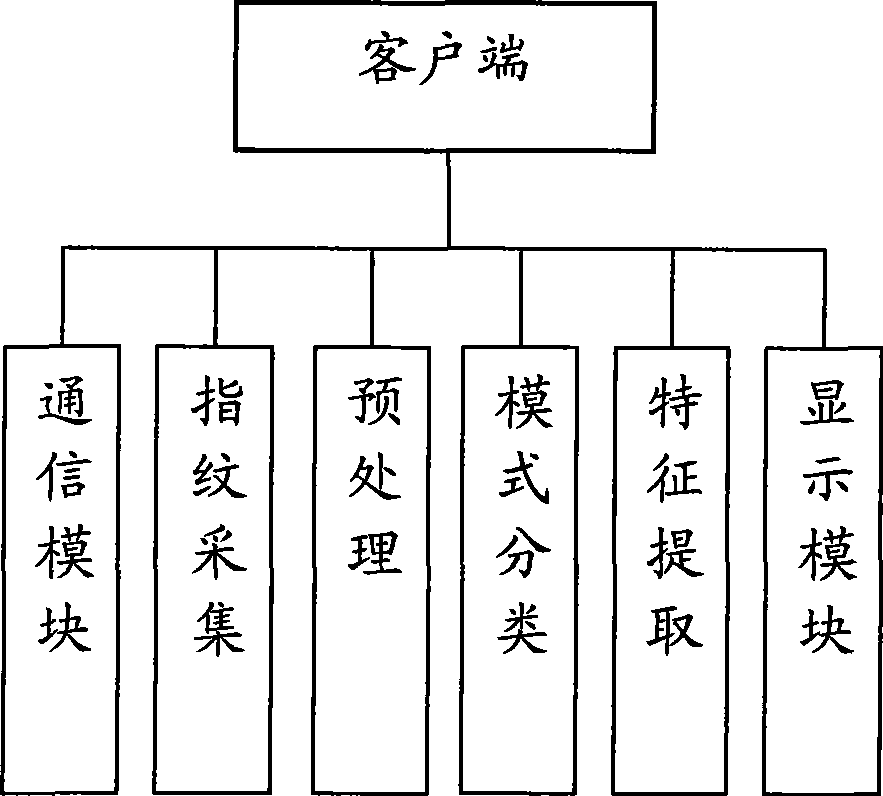
Fingerprint recognition system and control method
InactiveCN101414351AAvoid accessEasy constructionUser identity/authority verificationCharacter and pattern recognitionCapital investmentFingerprint database
The invention discloses a fingerprint identifying system which comprises three large parts of a fingerprint database, a central server and a client terminal; the fingerprint database is mainly used for memorizing the fingerprint characteristic information after digital coding; the central server is mainly responsible for validating the validity of the client terminal, receiving the fingerprint characteristic data, comparing the characteristics and returning the fingerprint identifying result; the client terminal is mainly responsible for collecting the fingerprint, extracting and uploading the fingerprint characteristic data. The system overcomes the defects of the prior art, can provide an online / offline fingerprint identifying system the basic algorithm library of which can be seamlessly expanded and the functions of which can be selected and matched. The fingerprint identifying system can lead a user to obtain the ID identification and authentication services with high quality under the situation of not needing a great amount of capital investment.
Owner:章毅 +2
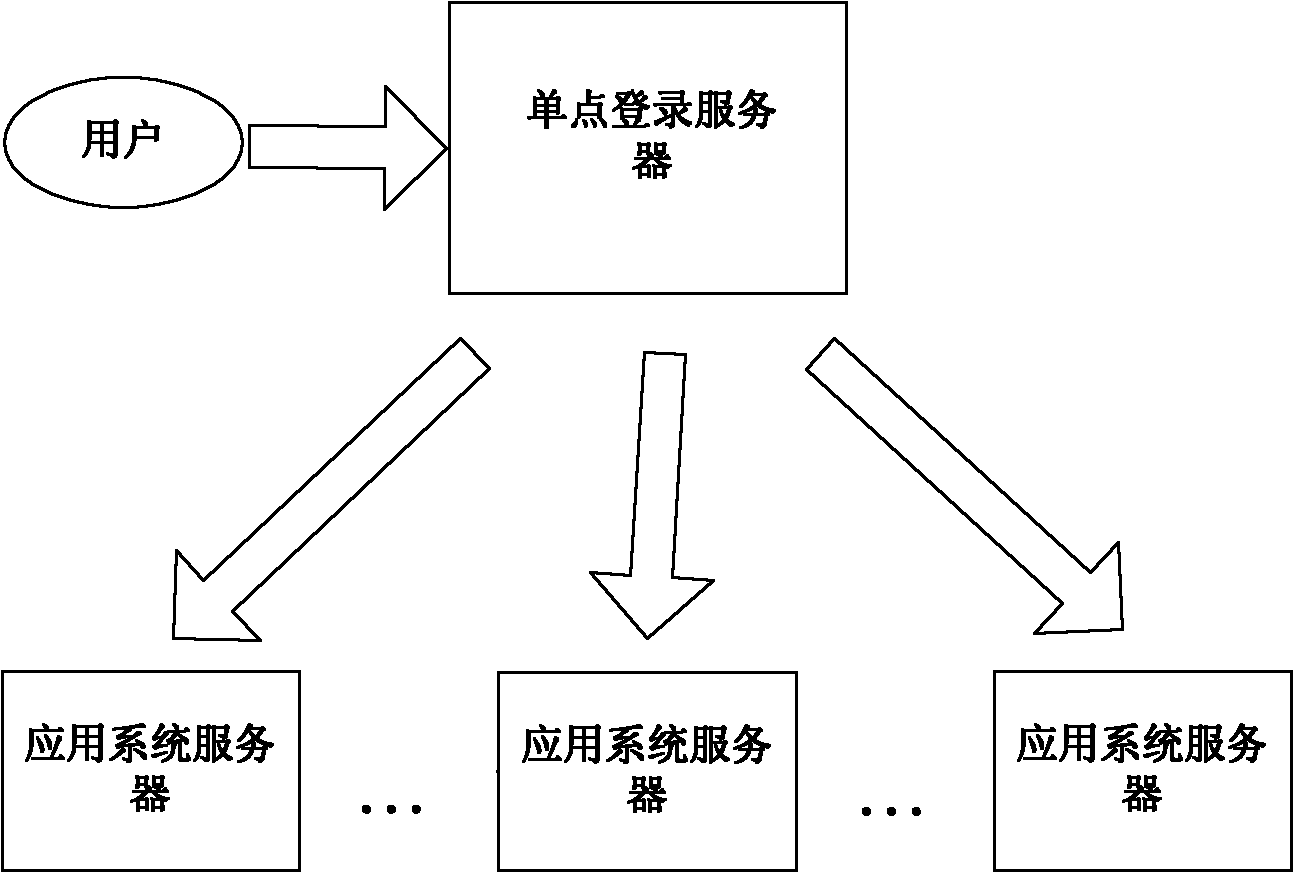
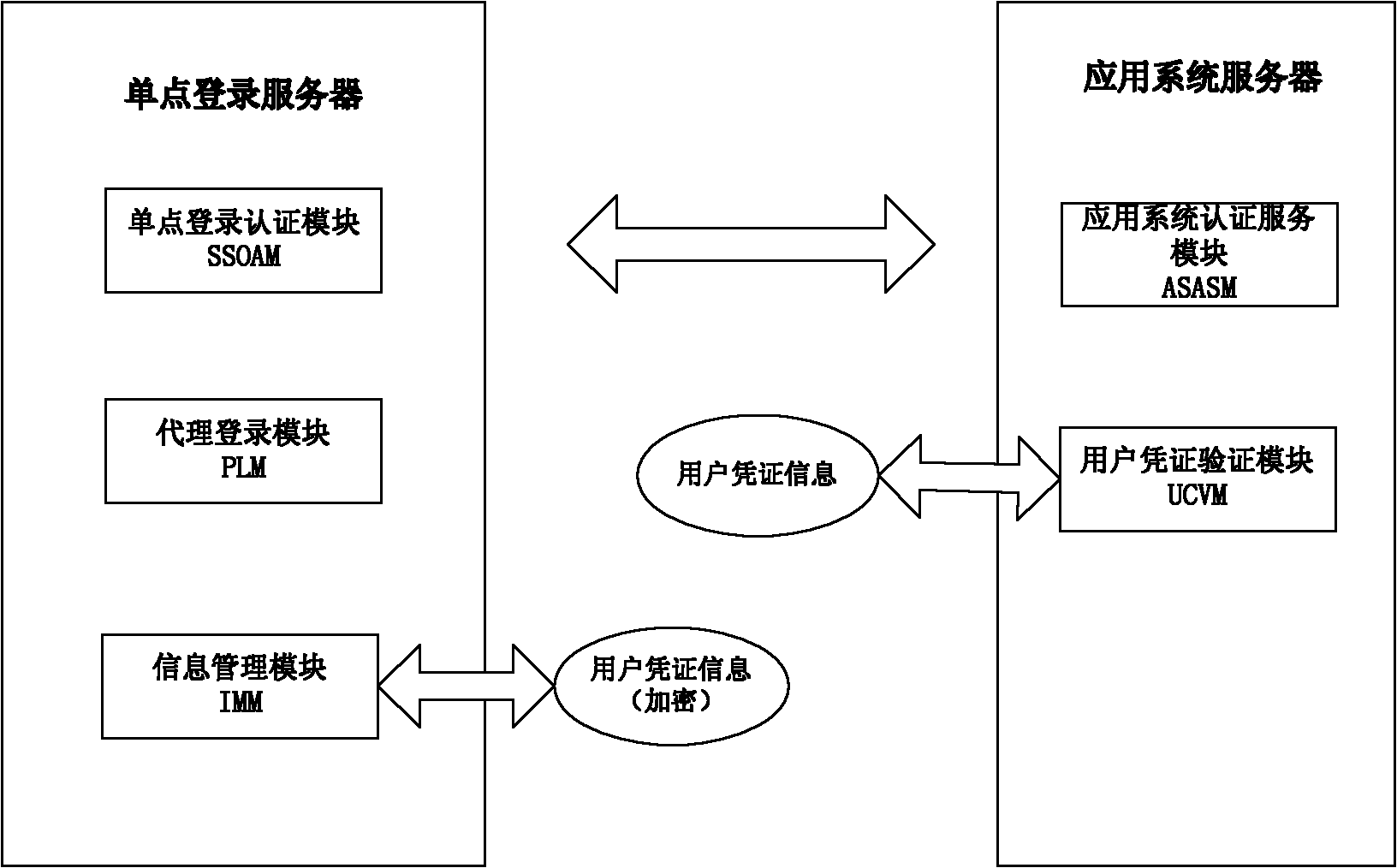
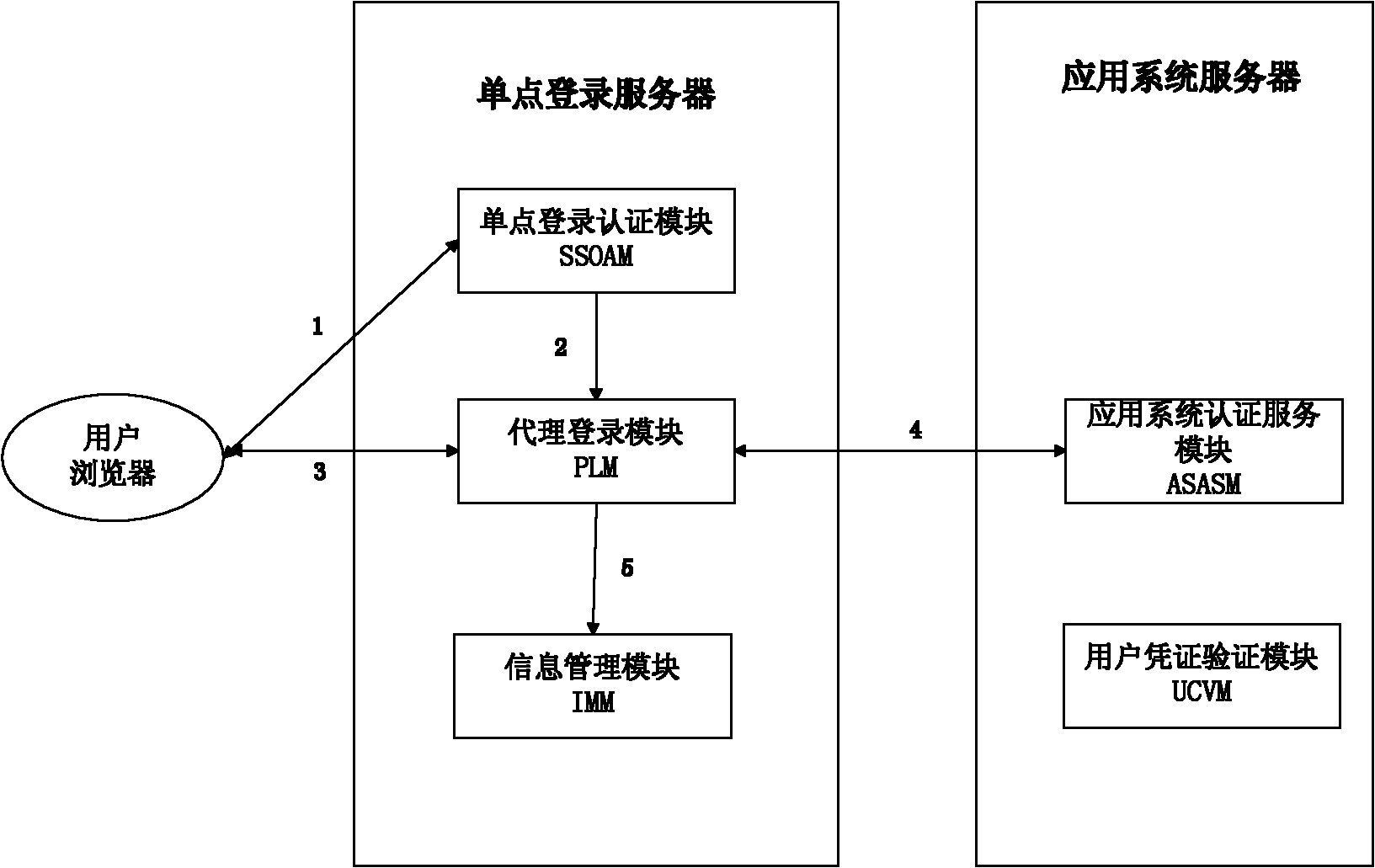
Agent-based single sign on (SSO) method and system
InactiveCN102111410AThe configuration cost is reasonableProtect personal privacyUser identity/authority verificationApplication serverCiphertext
The invention discloses an agent-based single sign on (SSO) method and system, belonging to the technical field of computer information. In the method, a user (U) registers and acquires a user certificate (C) in an application server (S); the U logs in an SSO server (L) and sends a certificate setting request; the L stores user identifications, application server identifications and ciphertext (C') in an associated manner; the U logs in the L and requests to access the S; the L is interacted with the S to acquire a token issued by the S and a signature (sig) of the S for the token; the L usesa self-private key to sign the token to acquire sig' and then searches the C' associated with the U identifications and the S identifications as well as sends the C', the token and the sig' to the U;the U uses a private key in the user C to decrypt c' so as to acquire C, and sends SSO server identifications, the C, the token and the sig' to the S; and the S verifies the token and the sig', if the token and the sig' pass the verification, the user C is continued to be verified; and if the user C passes the verification, the U is permitted to log in. The invention also discloses an SSO system corresponding to the SSO method.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
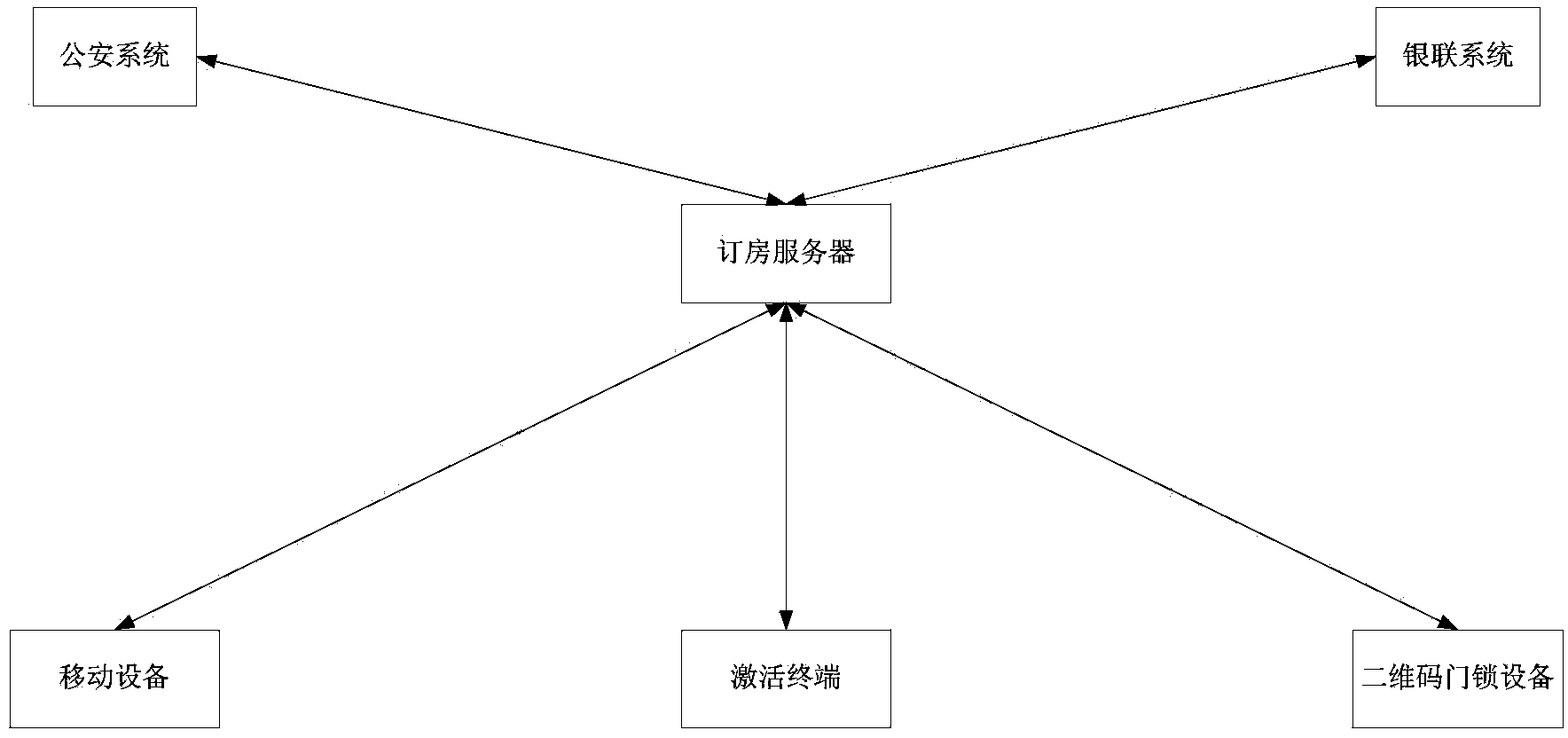
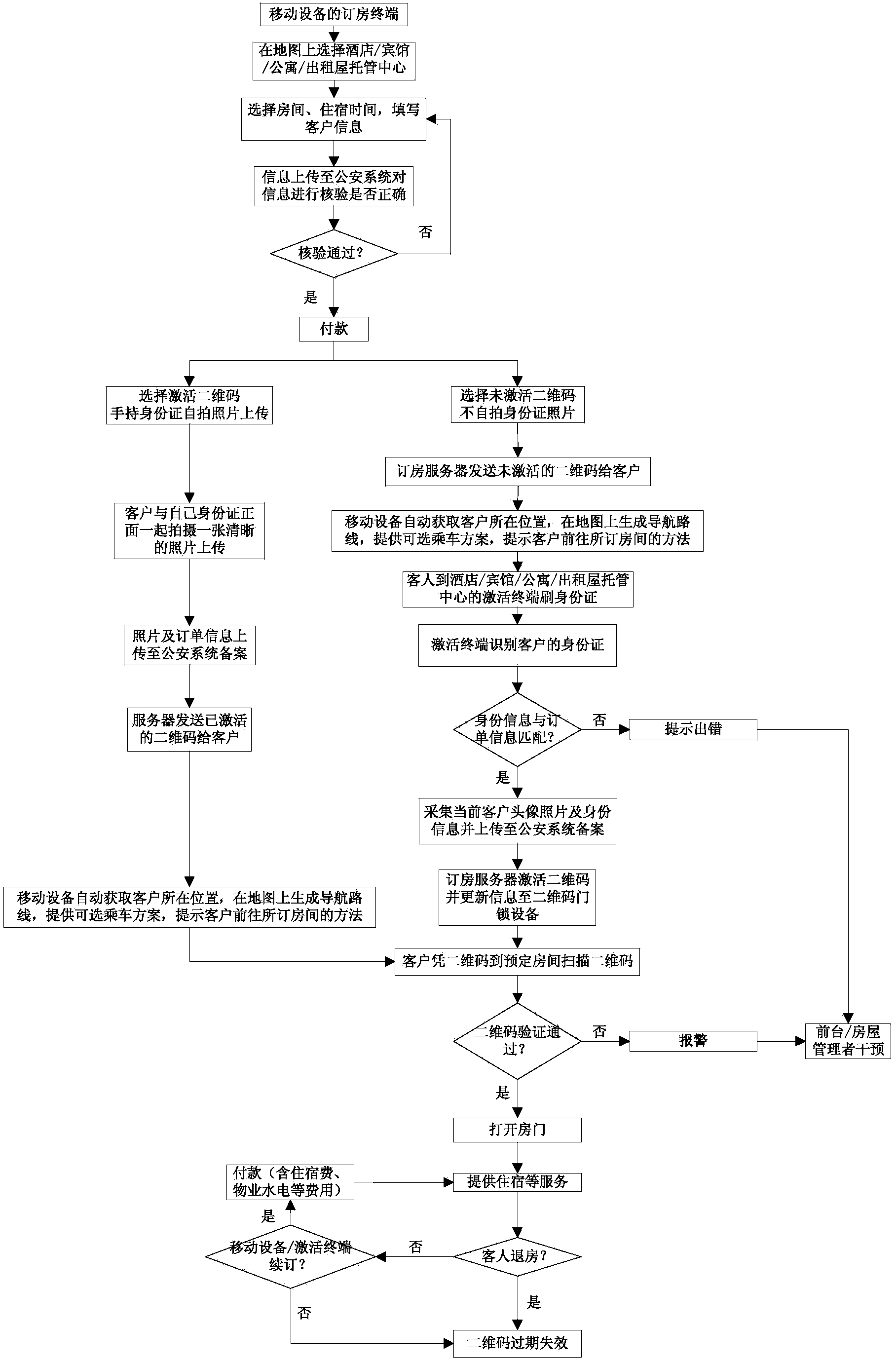
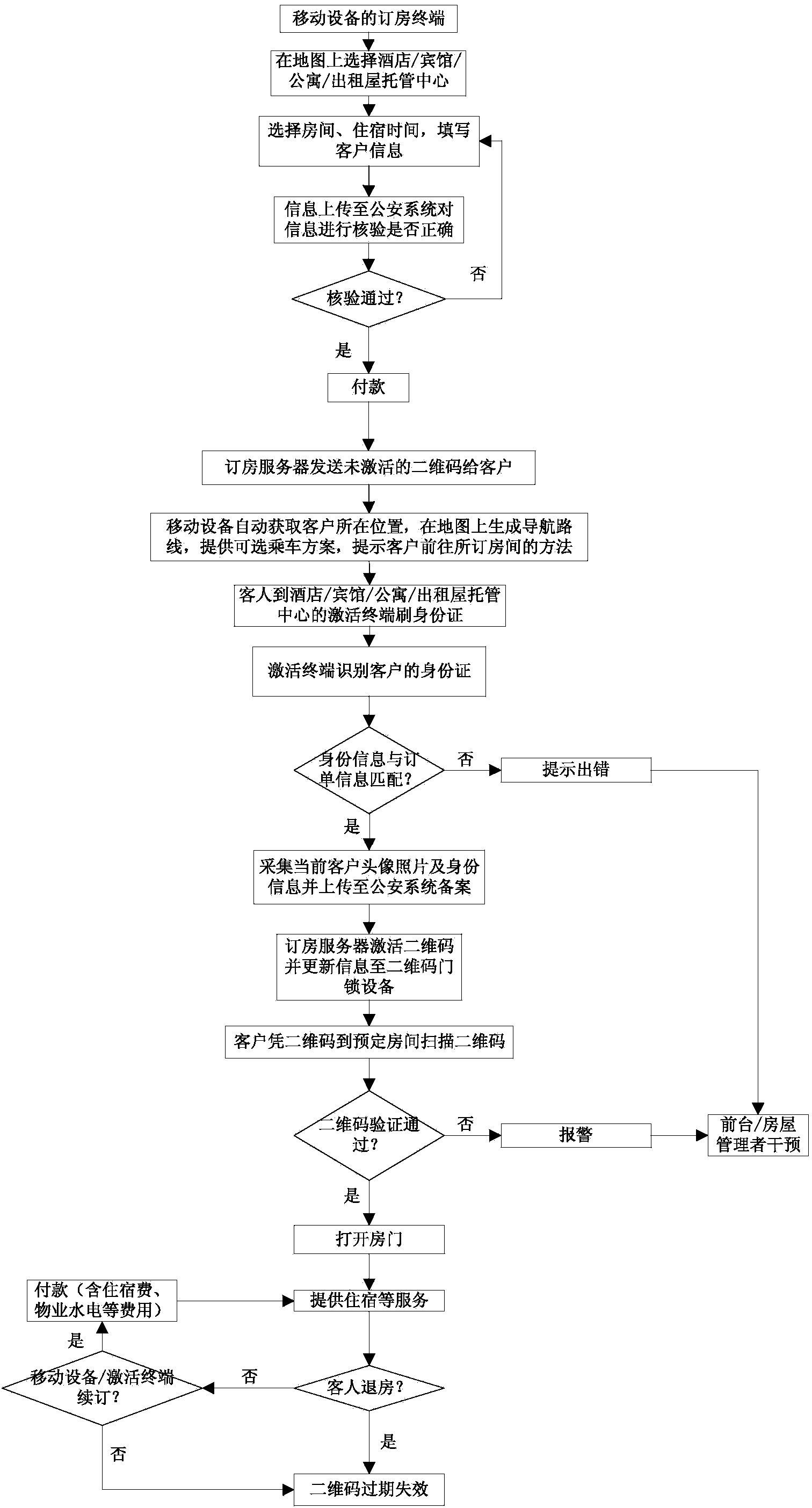
Self-service room reservation method and system based on mobile device
ActiveCN104182798AGood choiceProtect personal privacyReservationsPayment architectureApartmentSelf-service
The invention discloses a self-service room reservation method and system based on a mobile device. The method comprises the following steps that a room reservation terminal of the mobile device displays the positions of all hotels or guesthouses or apartments or rental house hosting centers having unoccupied rooms according to needs of a client in a map mode; after the client selects the needed hotel or the guesthouse or apartment or rental house hosting center on the map, selects a room and accommodation time and fills in client information, the room reservation terminal uploads the information to a room reservation server; the room reservation server extracts identity information and uploads the identity information to a public security system; the public security system verifies the identity information, judges whether the identity information is correct or not and feeds a verification result back to the room reservation server, and if the identity information is correct, the room reservation terminal reminds the client to carry out payment operation; if the identity information is incorrect, the client needs to submit the identity information again. According to the self-service room reservation method and system based on the mobile device, the client can reserve the room, rent the room and check in through self-service completely, reception services are avoided, the information is verified through the public security system, safety and high efficiency are achieved, and management is convenient.
Owner:广州商景网络科技有限公司
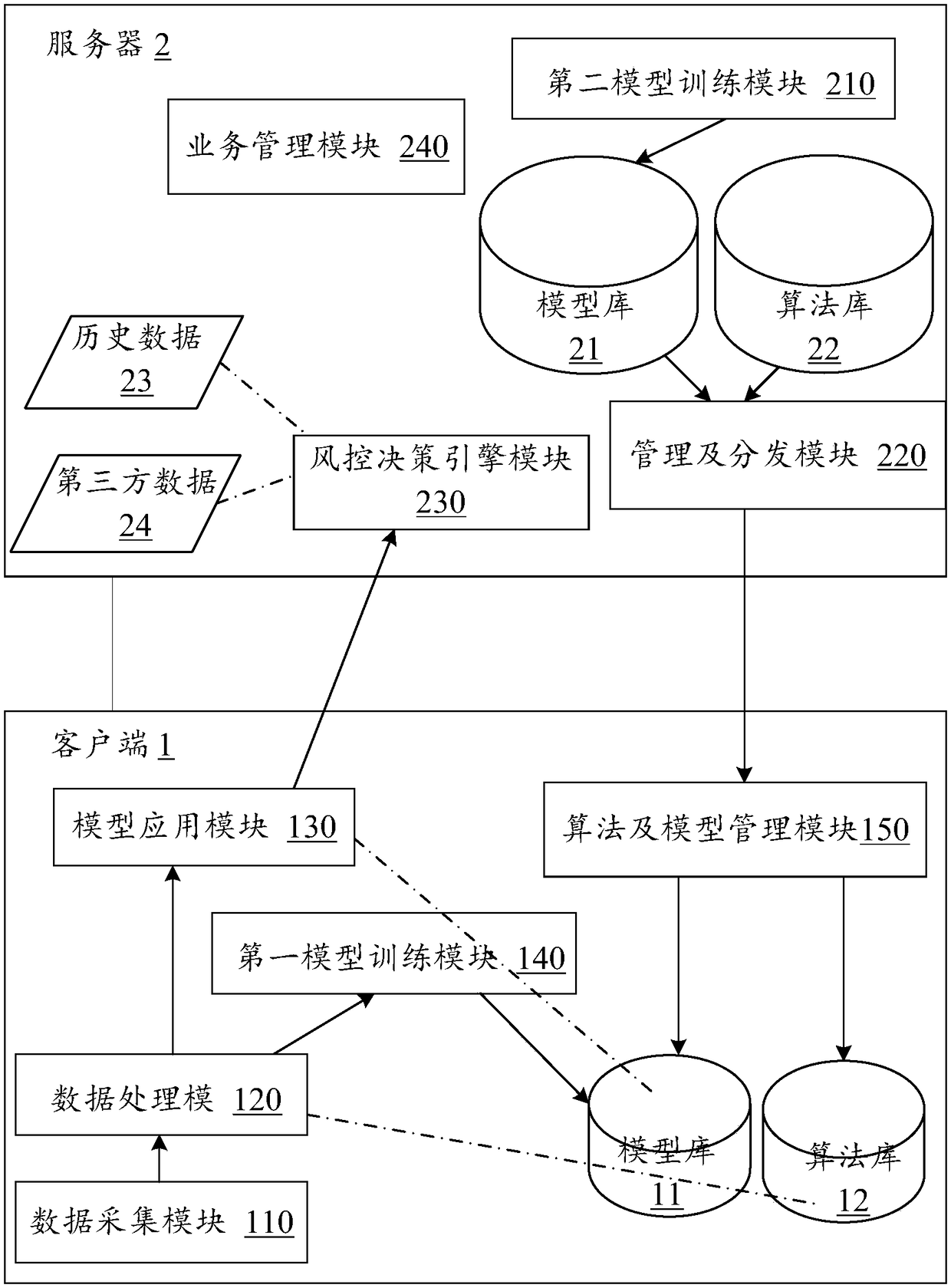
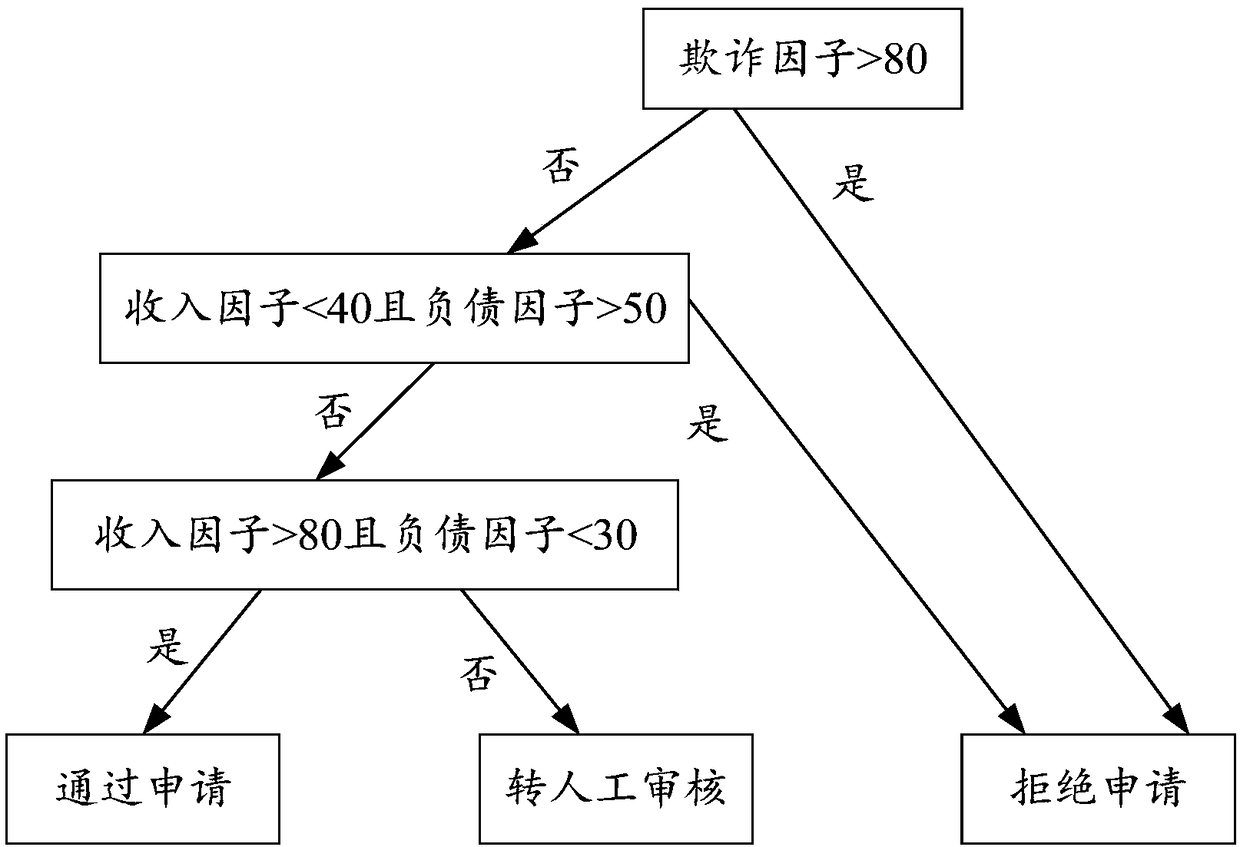
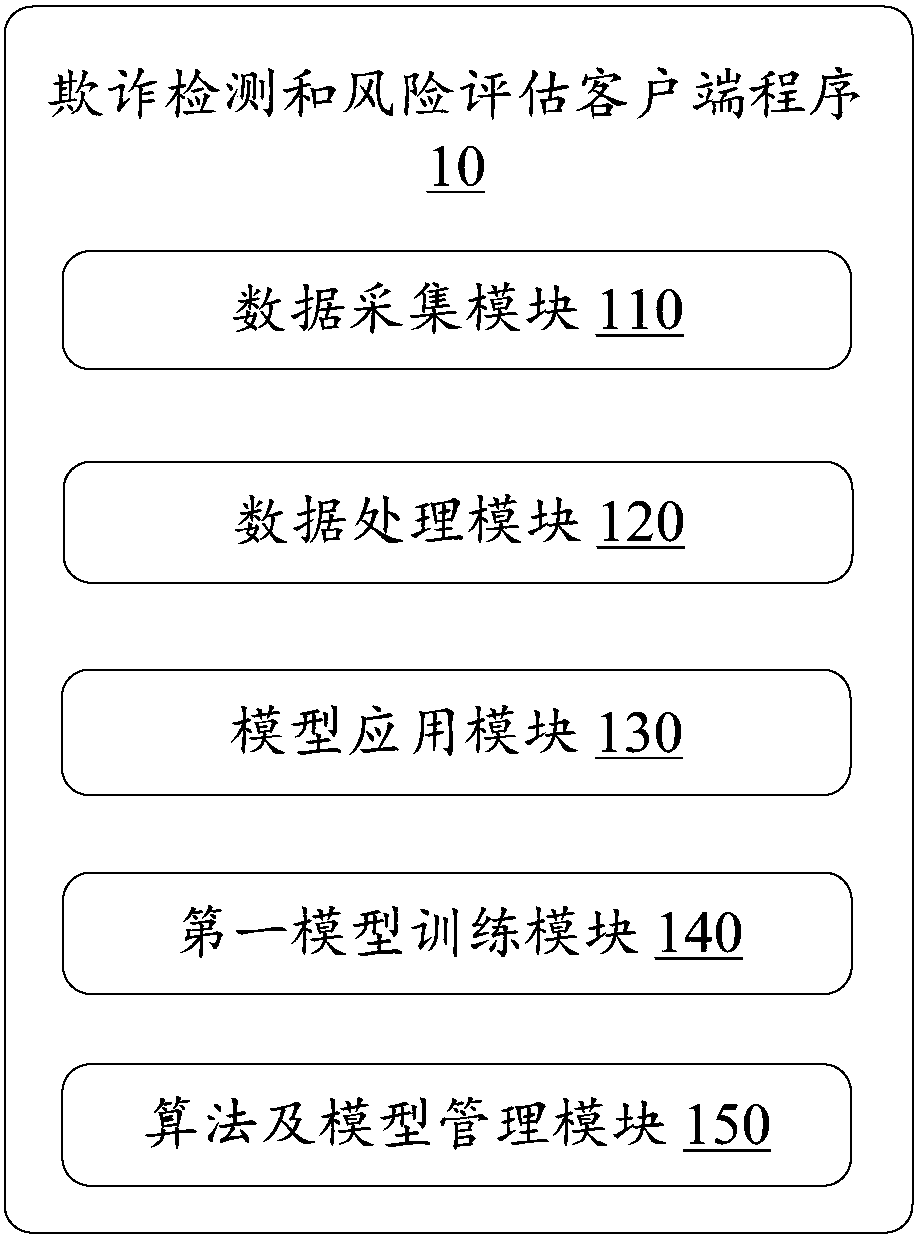
Fraud detecting and risk assessing method and system, equipment and storage medium
ActiveCN108596434AImprove experienceAlleviate the pressure of data transmissionEnsemble learningVersion controlRisk ControlData matching
The invention provides a fraud detecting and risk assessing method and system, equipment and a computer-readable storage medium. The method comprises the following steps of: collecting original data of a client user; extracting characteristic data from the original data by utilizing a data processing algorithm; inputting the characteristic data into a pre-trained machine learning model matched with the characteristic data, generating a model output result and uploading the model output result to a server; and outputting a fraud detecting and risk assessing result by utilizing a risk control decision engine and in combination with the model output result and historical data and third party data associated with the client user. By utilizing the method provided by the invention, the computingcapacity of client equipment can be fully utilized to reduce the computing pressure on the server; and a client does not need to upload the original data to the server, so that the data transmissionpressure between the client and the server and the risk of the leakage of privacy data and security information of the user can also be reduced.
Owner:WELAB INFORMATION TECH SHENZHEN LTD
Method and system for behavior detection
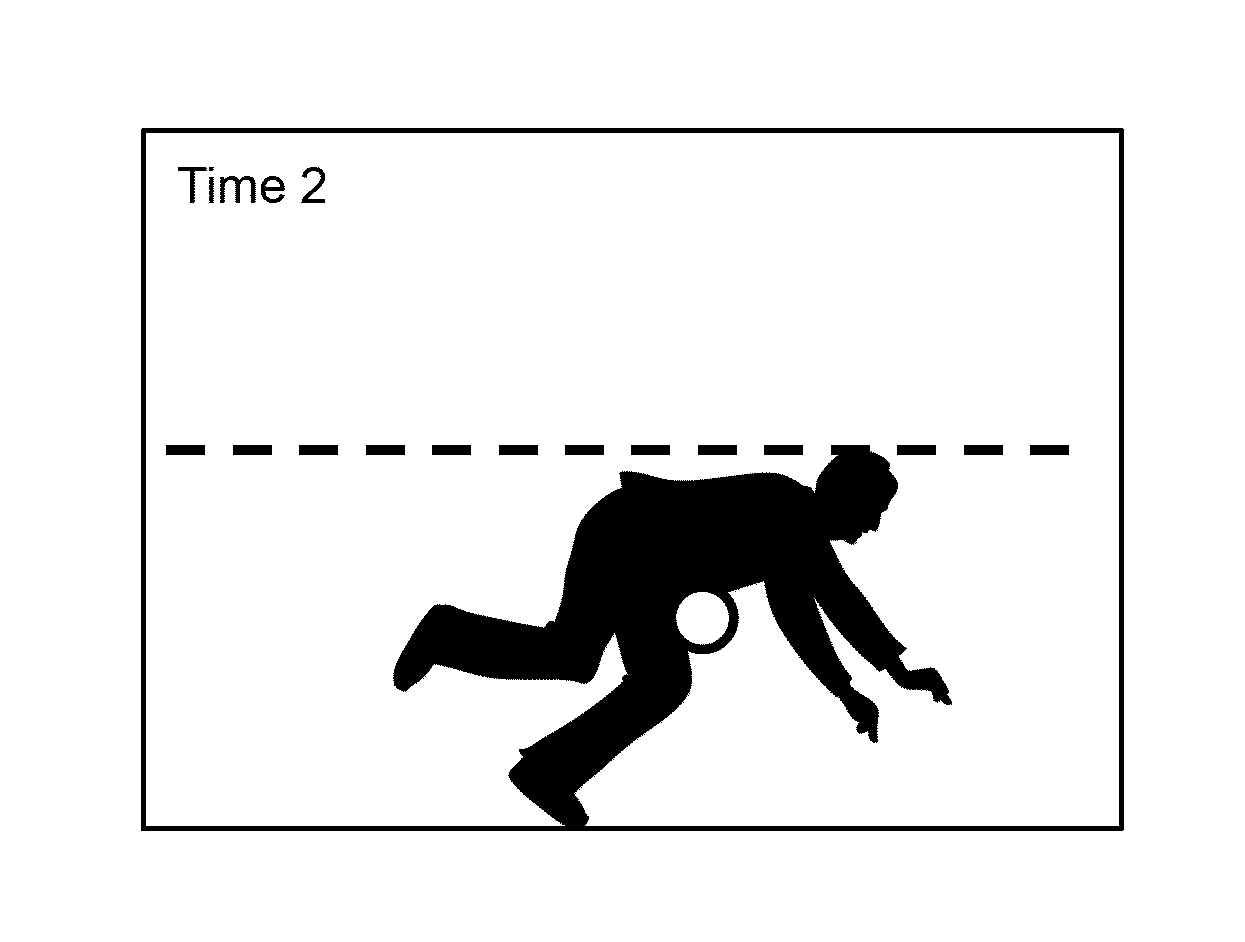
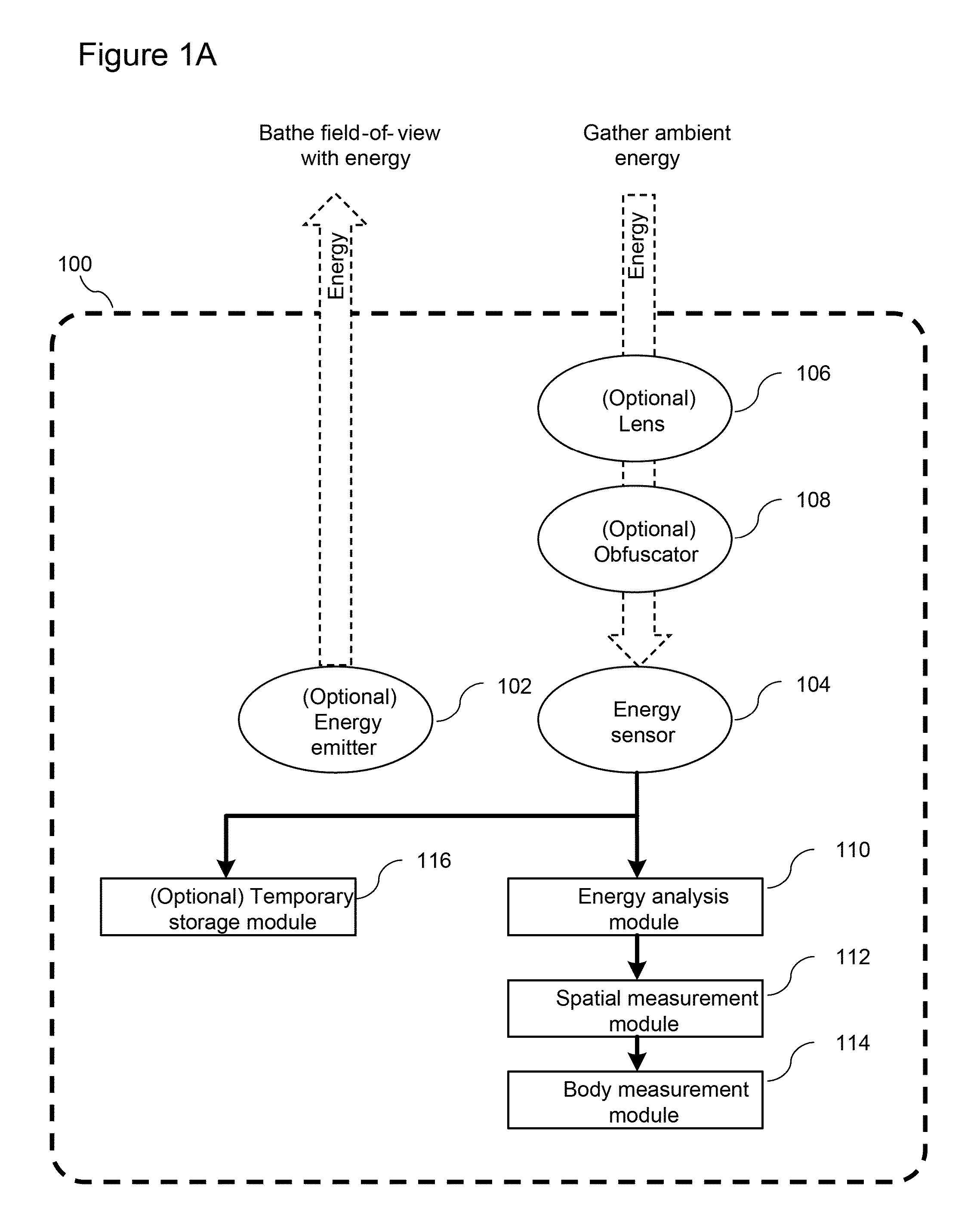
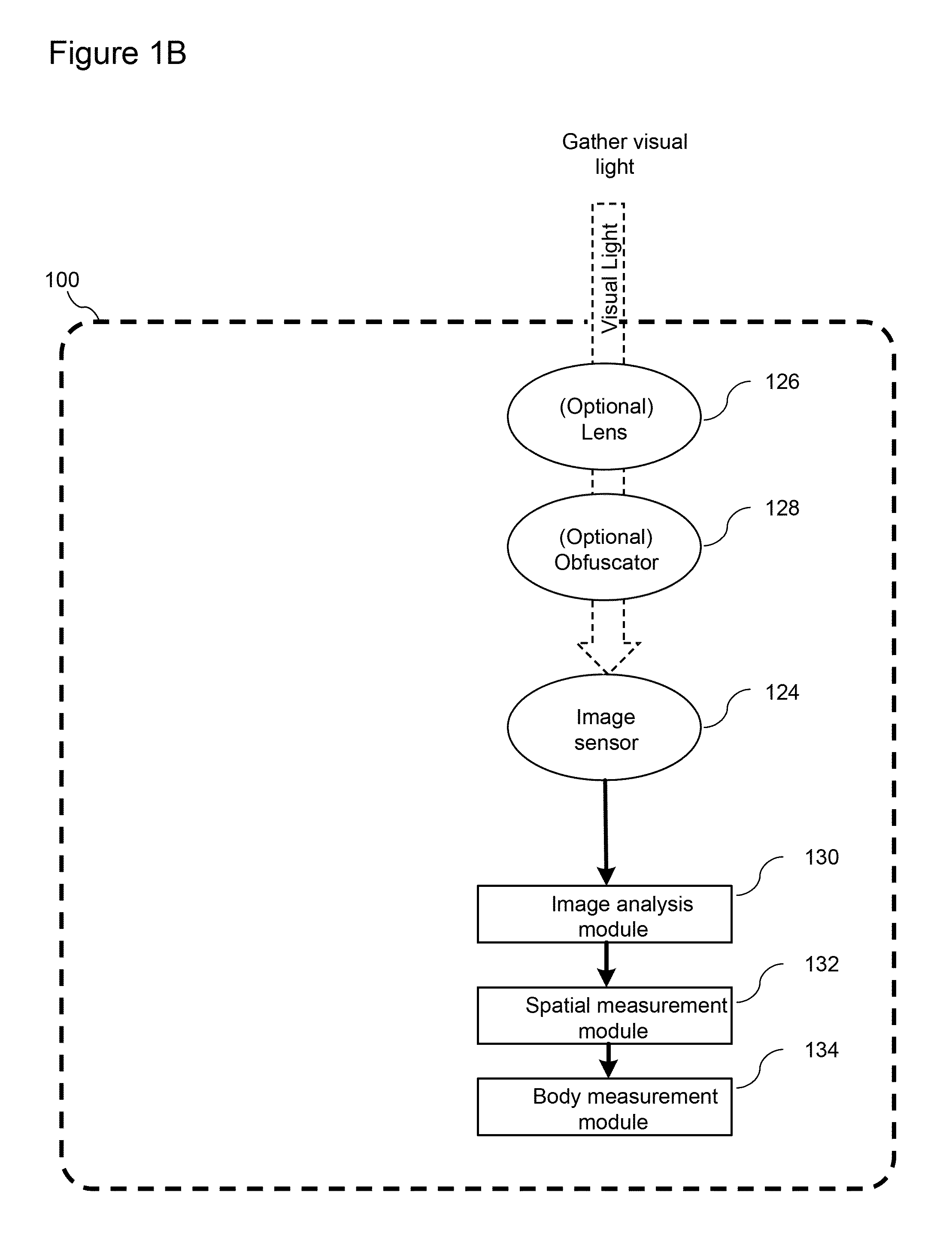
ActiveUS20150213702A1Prevent and cancel transmission of imageMinimize and prevent and transmission of imageImage enhancementImage analysisField of viewComputer science
Described herein are systems and methods for automatically detecting a behavior of a monitored individual, for example, that the individual has fallen. In certain embodiments, a system is presented that includes one energy sensor (e.g., a camera of a mobile electronic device) configured to capture reflected energy (e.g., light) within a field-of view; an optional lens to modify the distance or angular range of the field-of-view; and an optional image obfuscator to blur or distort the images received by the energy sensor, thereby preserving privacy. Techniques are described for determining spatial measurements and body measurements from the images and using these measurements to identify a behavior of the monitored individual, for example, a fall.
Owner:ATLAS5D
Anti-monitoring method and system for mobile terminal
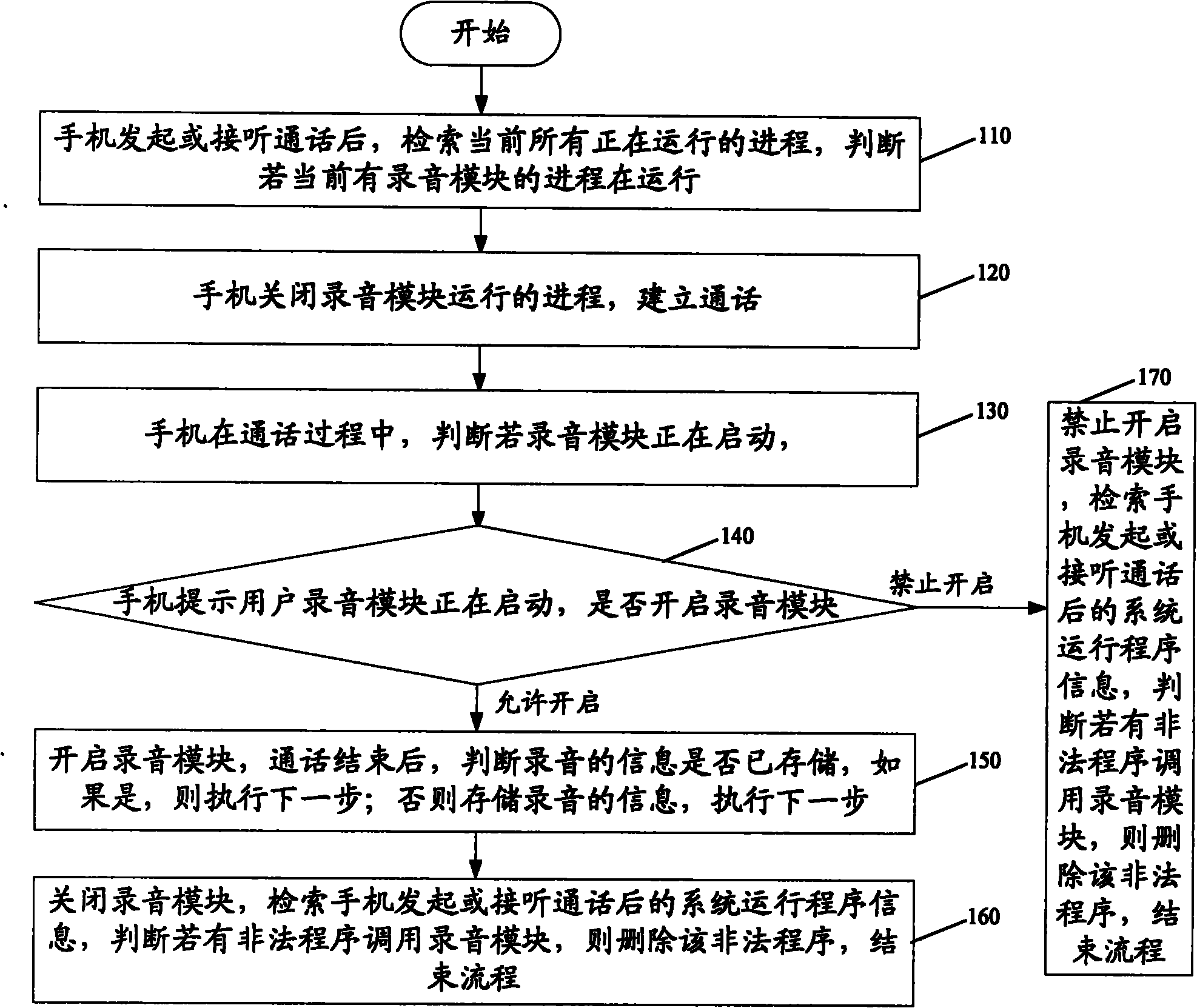
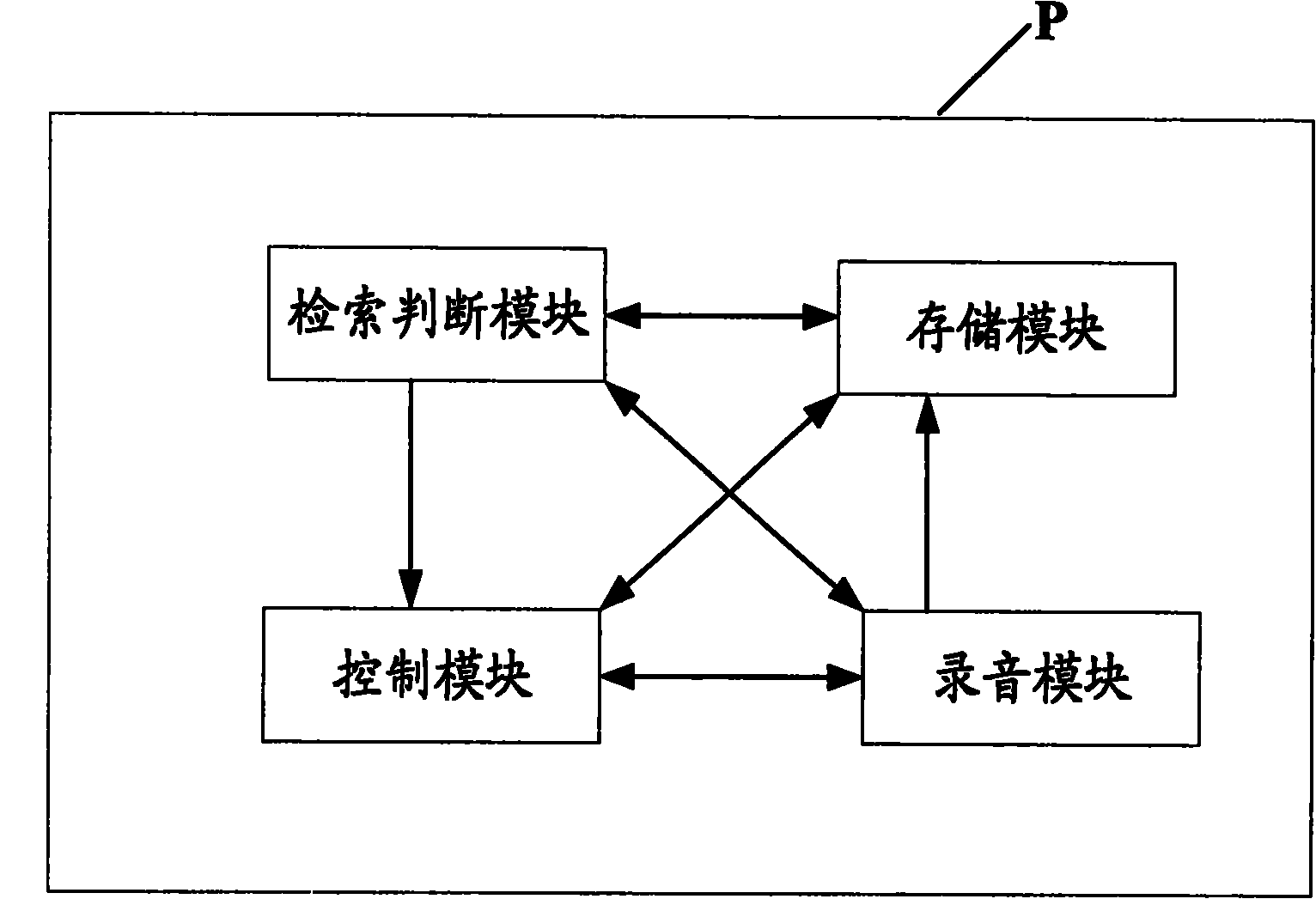
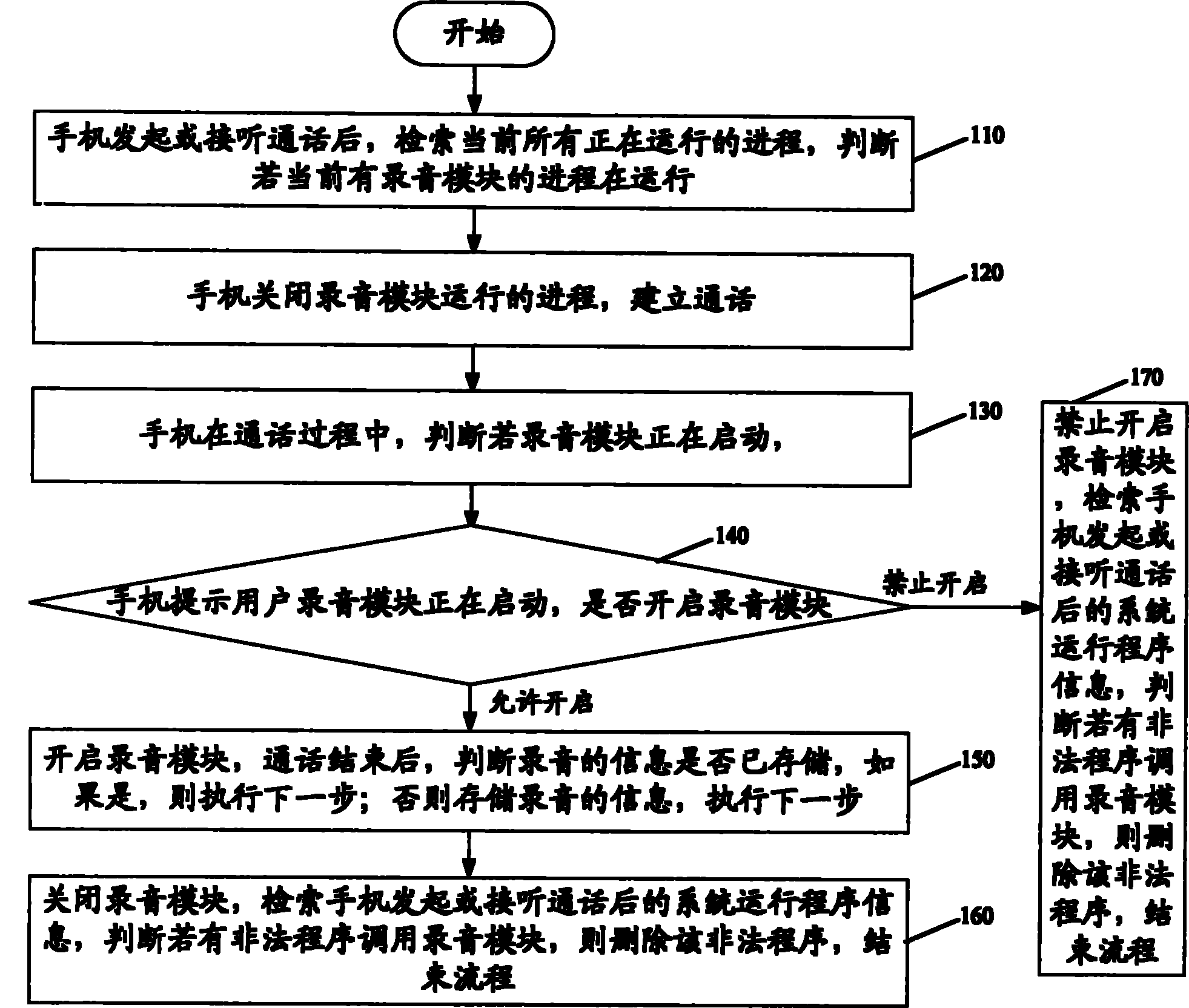
The invention provides an anti-monitoring method and system for a mobile terminal. The anti-monitoring method comprising the following steps: when the mobile terminal initiates or answers a call, indexing the process of an existing running program; and if judging that the process of a sound recording module runs currently, closing the process of the sound recoding module, and establishing conversation. The anti-monitoring method and system are used to ensure that conversation content of a user can not be recorded and spread illegally during the conversation, thus effectively protecting individual privacy and safety of the user, and improving degree of satisfaction of the user.
Owner:BEIJING QIHOO TECH CO LTD
Double screen notebook computer
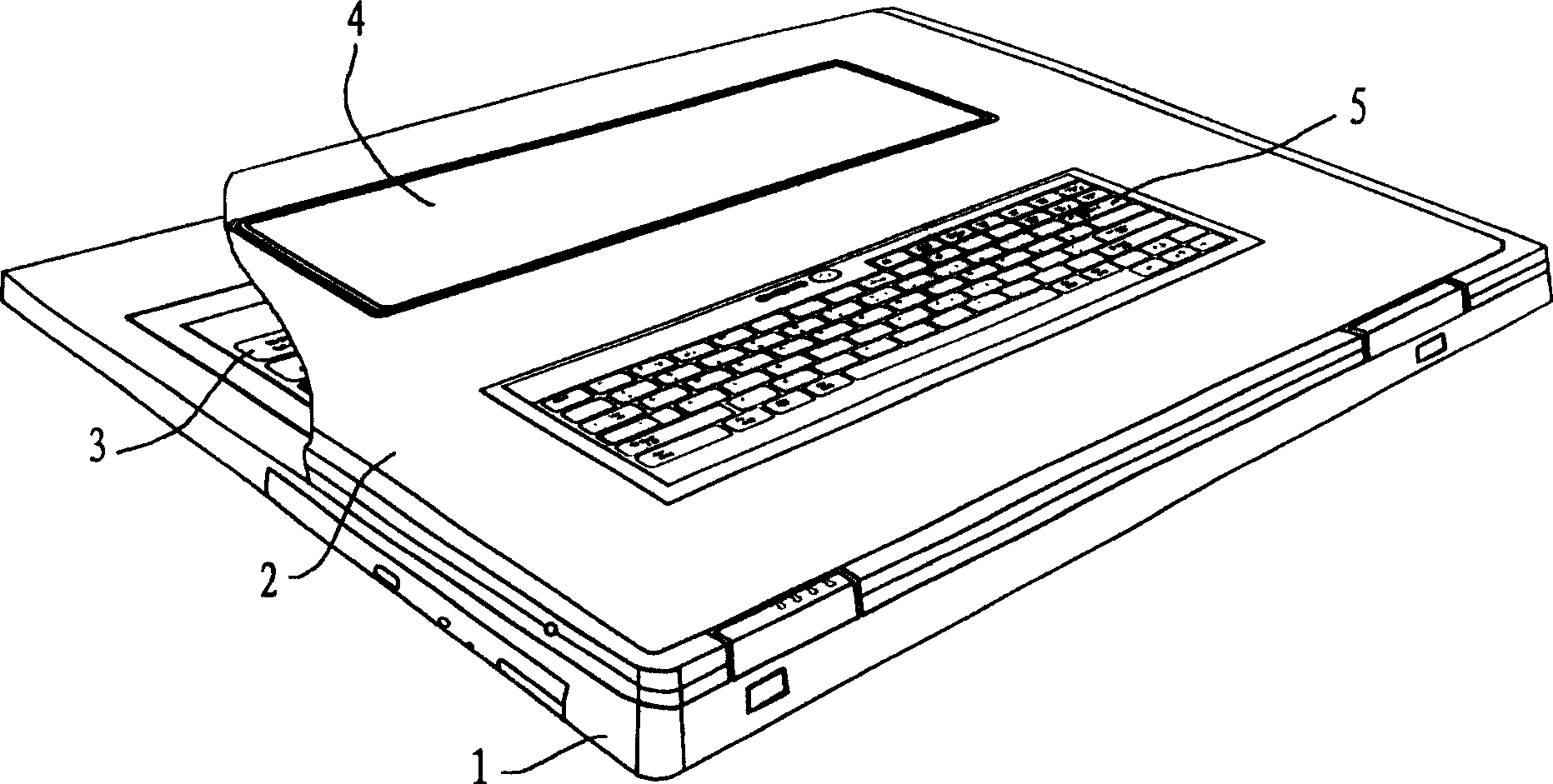
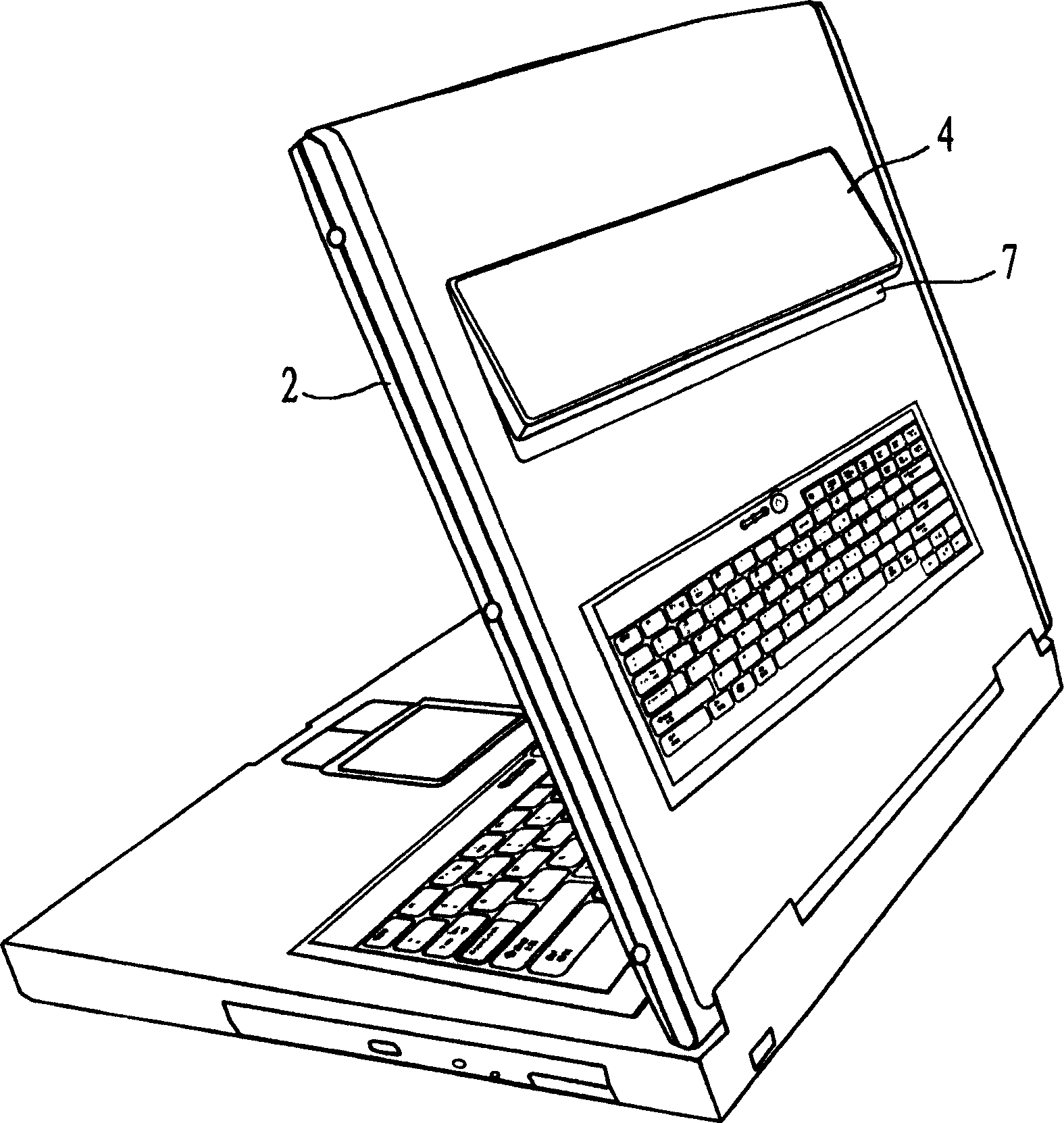
InactiveCN1690915ASave electricityProtect personal privacyDigital data processing detailsDisplay deviceComputer engineering
The invention discloses two-screen notebook computer, which comprises main machine with main keyboard and main display connected to main machine side; wherein, there is at least one assist display and corresponding assist keyboard set on back of main display, which solves the problem that existing notebook computer can be operated only one people, two persons can use one notebook synchronous to communicate on the main and assist displays face to face; and it can meet people to operate and use notebook on little space and on journey, also conserve energy.
Owner:秦建忠
Systems and methods to identify persons and/or identify and quantify pain, fatigue, mood, and intent with protection of privacy
ActiveUS20180039745A1Accurate identificationProtect personal privacyDisease diagnosisMedical imagesIdentity recognitionMood
The disclosed technology enables, among other things, the identification of persons and the characterization of mental perceptions (e.g., pain, fatigue, mood) and / or intent (e.g., to perform an action) for medical, safety, home care, and other purposes. Of significance are applications that require long-term patient monitoring, such as tracking disease progression (e.g., multiple sclerosis), or monitoring treatment or rehabilitation efficacy. Therefore, longitudinal data must be acquired over time for the person's identity and other characteristics (e.g., pain level, usage of a cane). However, conventional methods of person identification (e.g., photography) acquire unnecessary personal information, resulting in privacy concerns. The disclosed technology allows measurements to be performed while protecting privacy and functions with partial or incomplete measurements, making it robust to real-world (noisy, uncontrolled) settings, such as in a person's home (whether living alone or with others).
Owner:ATLAS5D
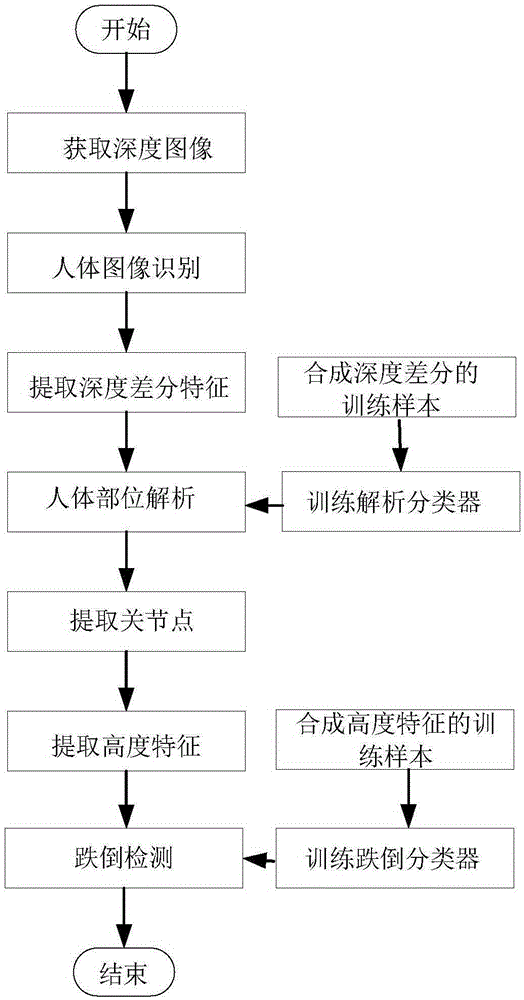
Fall-down behavior real-time detection method based on depth image
ActiveCN105279483AIllumination invariancePrivacy protectionCharacter and pattern recognitionFeature vectorNODAL
The invention discloses a fall-down behavior real-time detection method based on a depth image. The method comprises steps of depth image obtainment, human body image identification, depth difference feature extraction, human body part analysis, articulation point extraction, height feature extraction and fall-down behavior detection. Based on a depth image, a specific depth difference feature is selected on an identified human body image; a random forest classifier is used for analyzing human body parts; a human body is divided into a head part and a trunk part; articulation points are detected, and then a height feature vector is extracted; and a support vector machine classifier is used for detecting whether a detected object is in fall-down state. The invention provides the fall-down behavior detection method, improves the operation speed, and achieves timeliness of fall-down behavior detection. The depth image is utilized for fall-down behavior detection. On one hand, the method is free of influences of illumination and can be operated in an all-weather manner, and on the other hand, personal privacy can be protected compared with a colorful image. Only one depth sensor is required in terms of hardware support, and the advantage of low cost is achieved.
Owner:HUAZHONG UNIV OF SCI & TECH
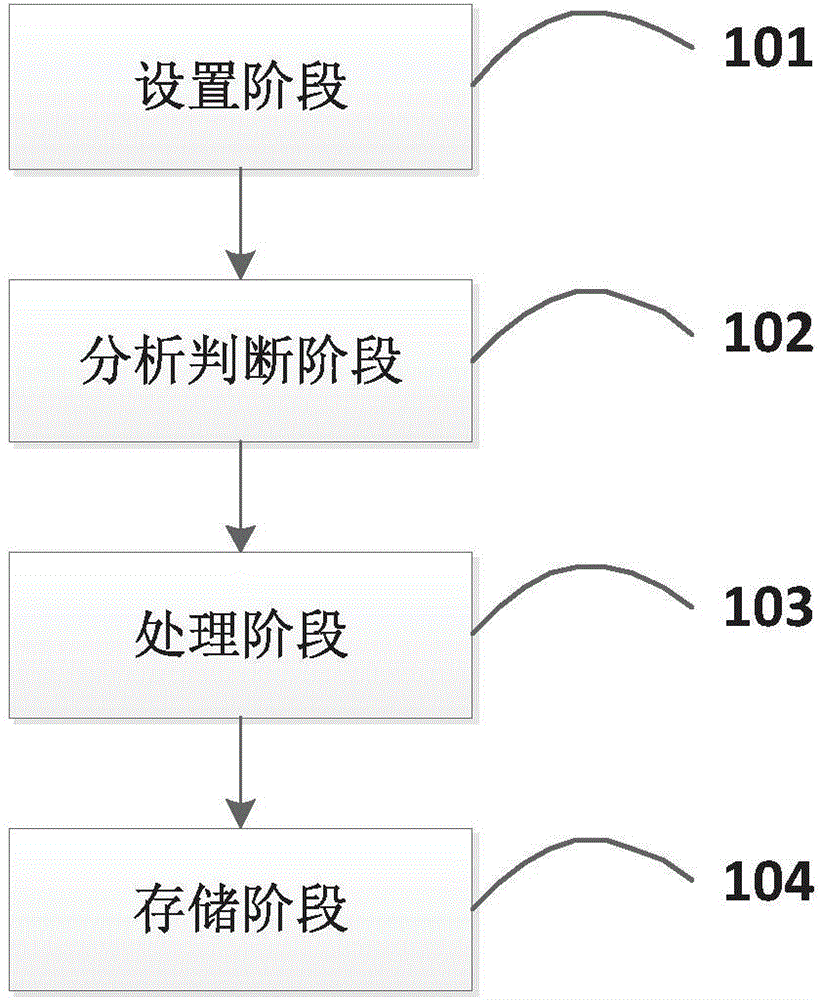
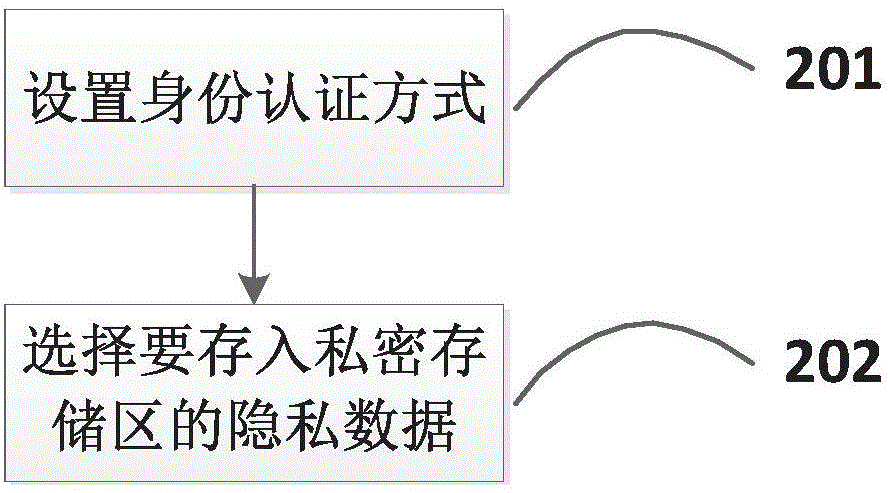
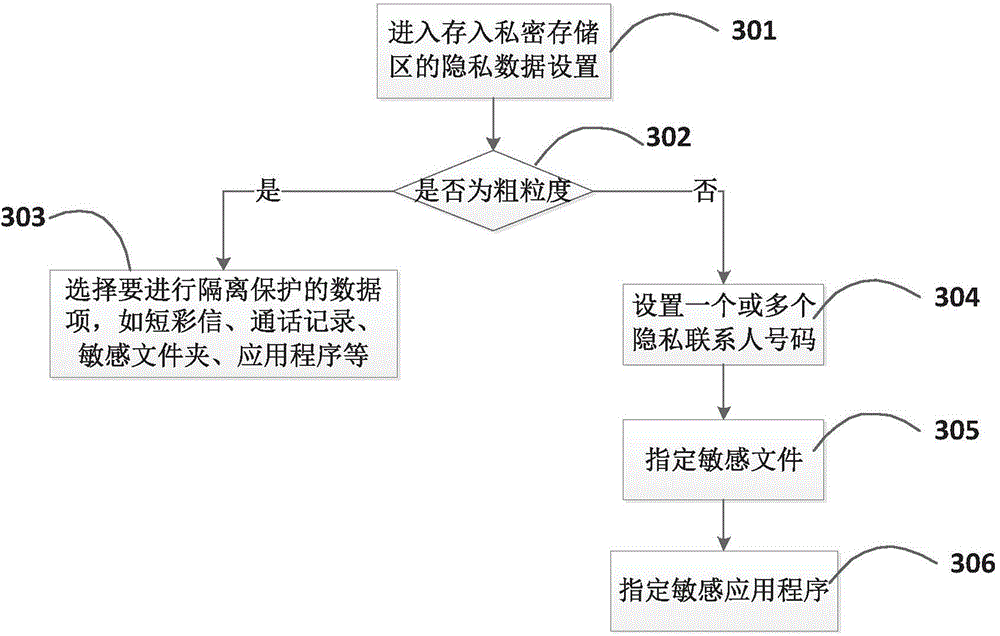
Isolation protection system and isolation protection method of private data in mobile phone
The invention provides an isolation protection system and an isolation protection method of private data in a mobile phone, which belongs to the field of mobile communication and information security. The system comprises a privacy storage area, an ordinary storage area, a setting module, an analysis judging module and a processing module, wherein the privacy storage area is used for storing the private data to be isolated and protected; data in the privacy storage area is stored in an encryption manner; the ordinary storage area is used for storing non-isolated protection data; the setting module is used for setting an identity authentication way and selecting private data needing to be stored into the privacy storage area; the analysis judging module is used for monitoring a system event in real time, when a data writing request is received, the analysis judging module judges whether the data writing request is the private data to be isolated and protected or not and transmits the judgment result to the processing module; when a private data access request is received, the identity authentication is carried out on a user according to the set identity authentication way; the processing module is used for encrypting the data when the judgment result of the analysis judging module is the data writing request and is the private data to be isolated and protected and transmitting a writing request to the storage module.
Owner:BEIJING UNIV OF POSTS & TELECOMM
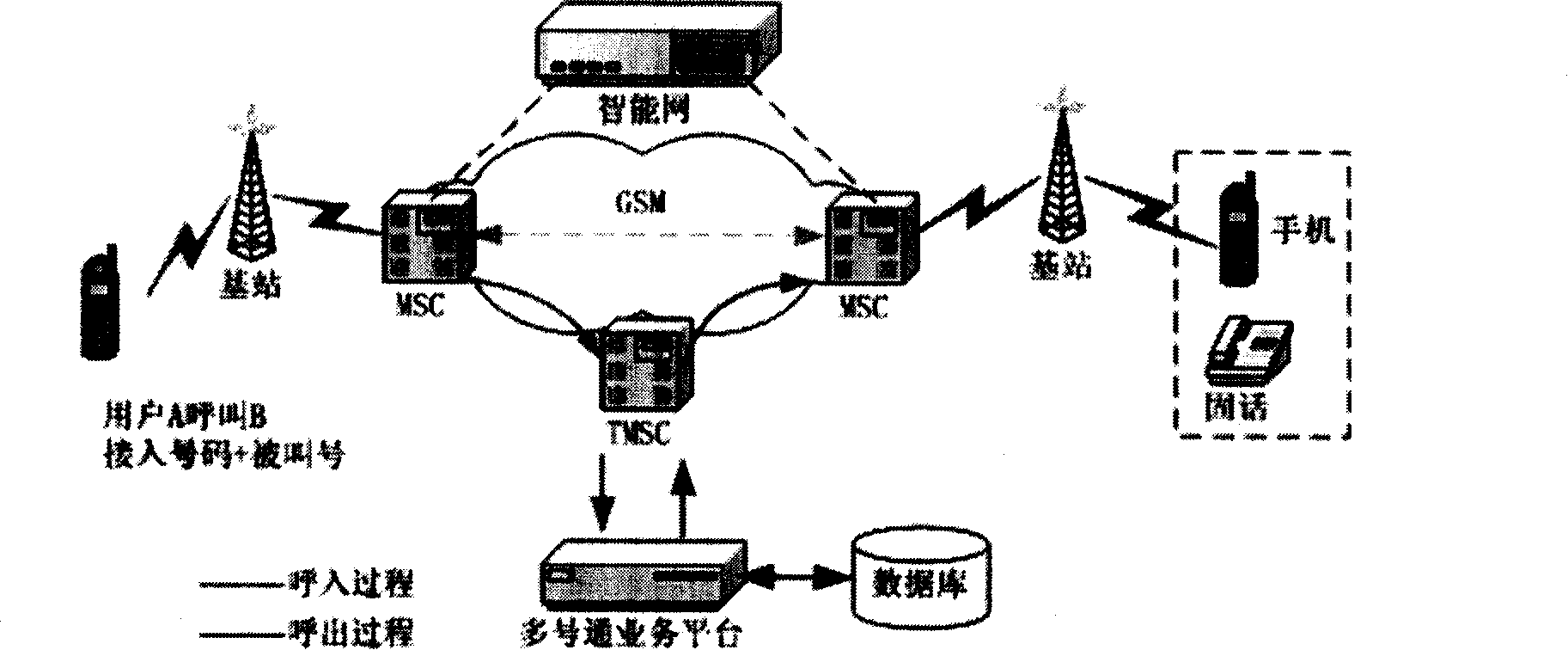
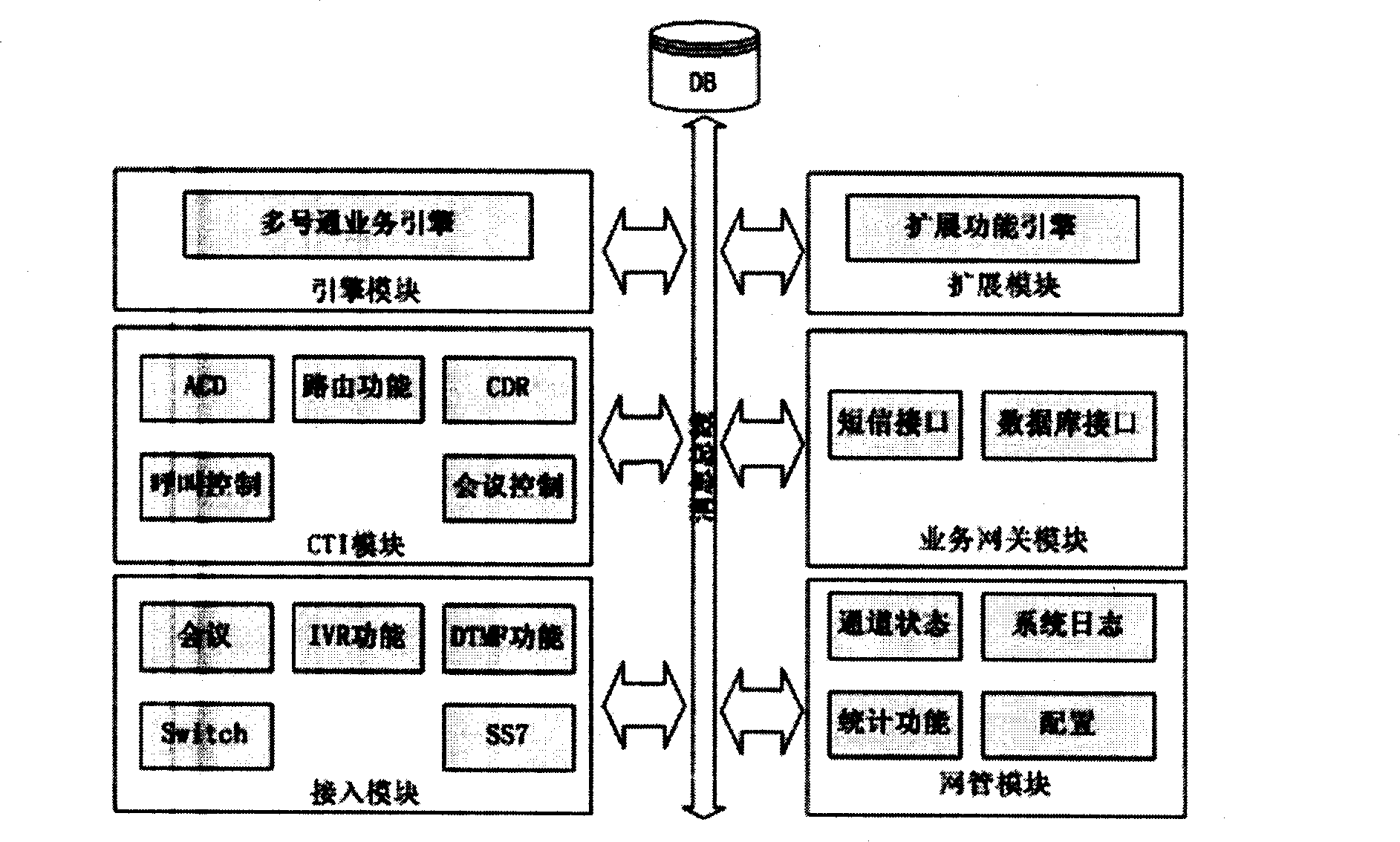
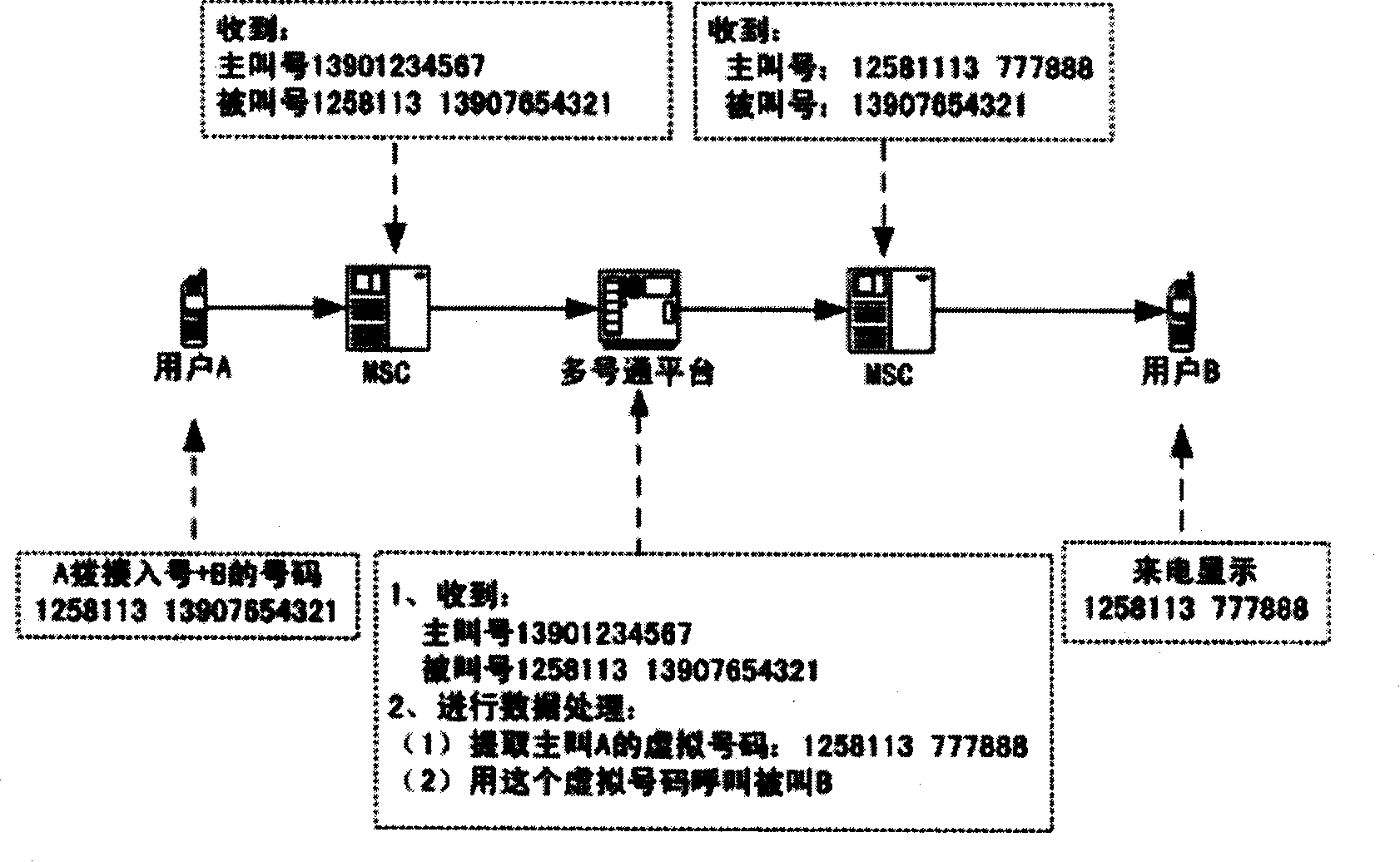
Mobile phone virtual number use method and device
InactiveCN101175236AImprove communication efficiencyExpand profit pointsRadio/inductive link selection arrangementsNetwork data managementBase stationMobile phone
The present invention relates to the use method of virtual mobile phone numbers and a device. The device includes a multi-number call platform, a database, mobile switching centers (MSC), tandem mobile switching centers (TMSC), base stations, mobile terminals and telephones. The multi-number call platform and the database are positioned at the lower layer, the mobile switching centers (MSC) and the tandem mobile switching centers (TMSC) are positioned at the second layer, and the base stations, the mobile terminals and the telephones are positioned at the third layer. The multi-number call platform receives a calling number and a called number, which are sent by a mobile switching center (MSC) and a tandem mobile switching center (TMSC) and then are converted into a virtual calling number; the mobile switching center (MSC) and the tandem mobile switching center (TMSC) first send the received calling and called numbers to the multi-number call platform and then receive the virtual number sent by the multi-number call platform, the received calling and called numbers are again sent to the mobile switching centers (MSC) and the tandem mobile switching centers (TMSC); the information emitted by the mobile terminals or the telephones is sent to the mobile switching center (MSC) via base stations; the multi-number call platform is provided with an independently installed multi-number call system module. The present invention can really realize the function of one mobile phone with multiple numbers.
Owner:CHINA MOBILE GRP FUJIAN CO LTD
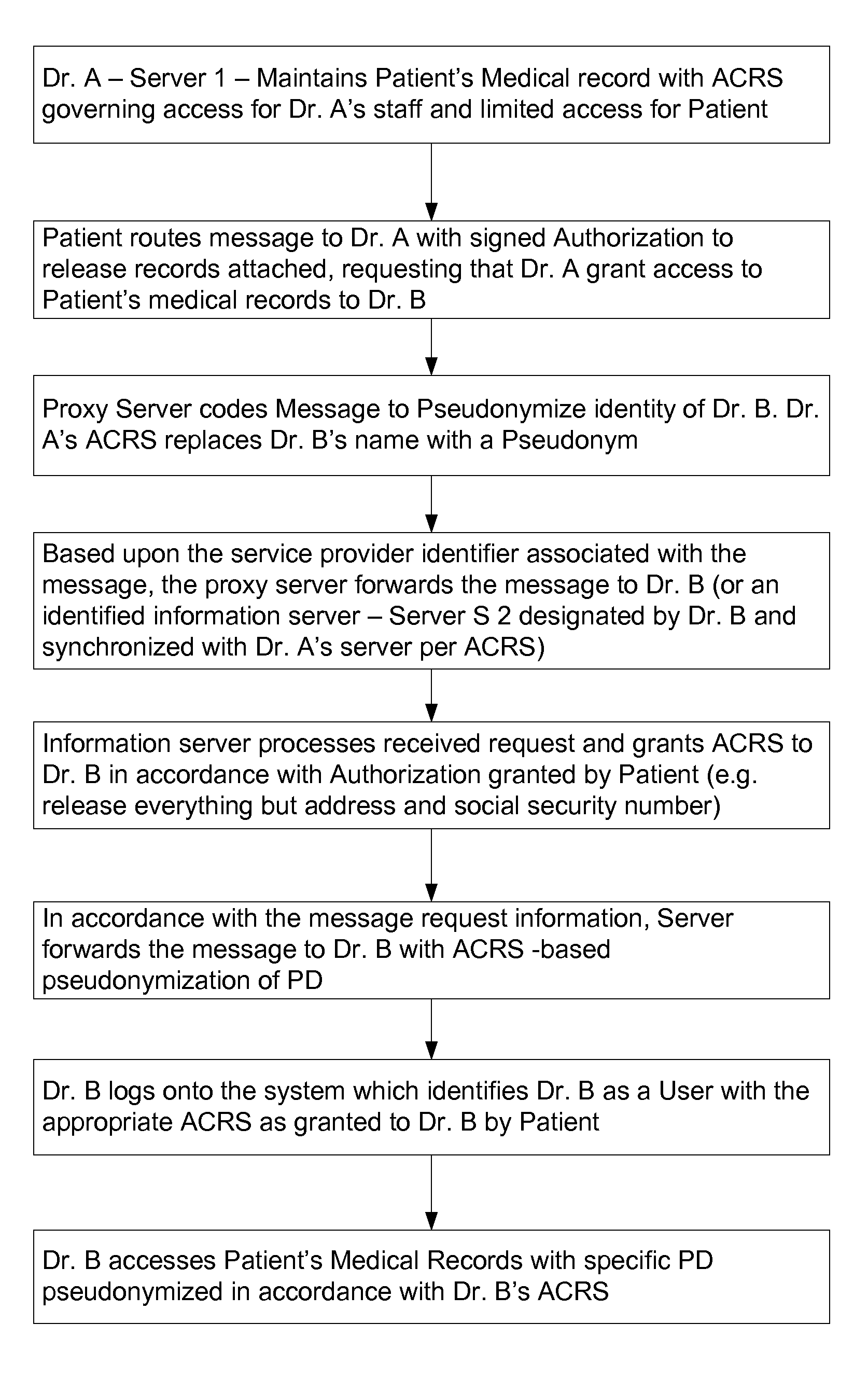
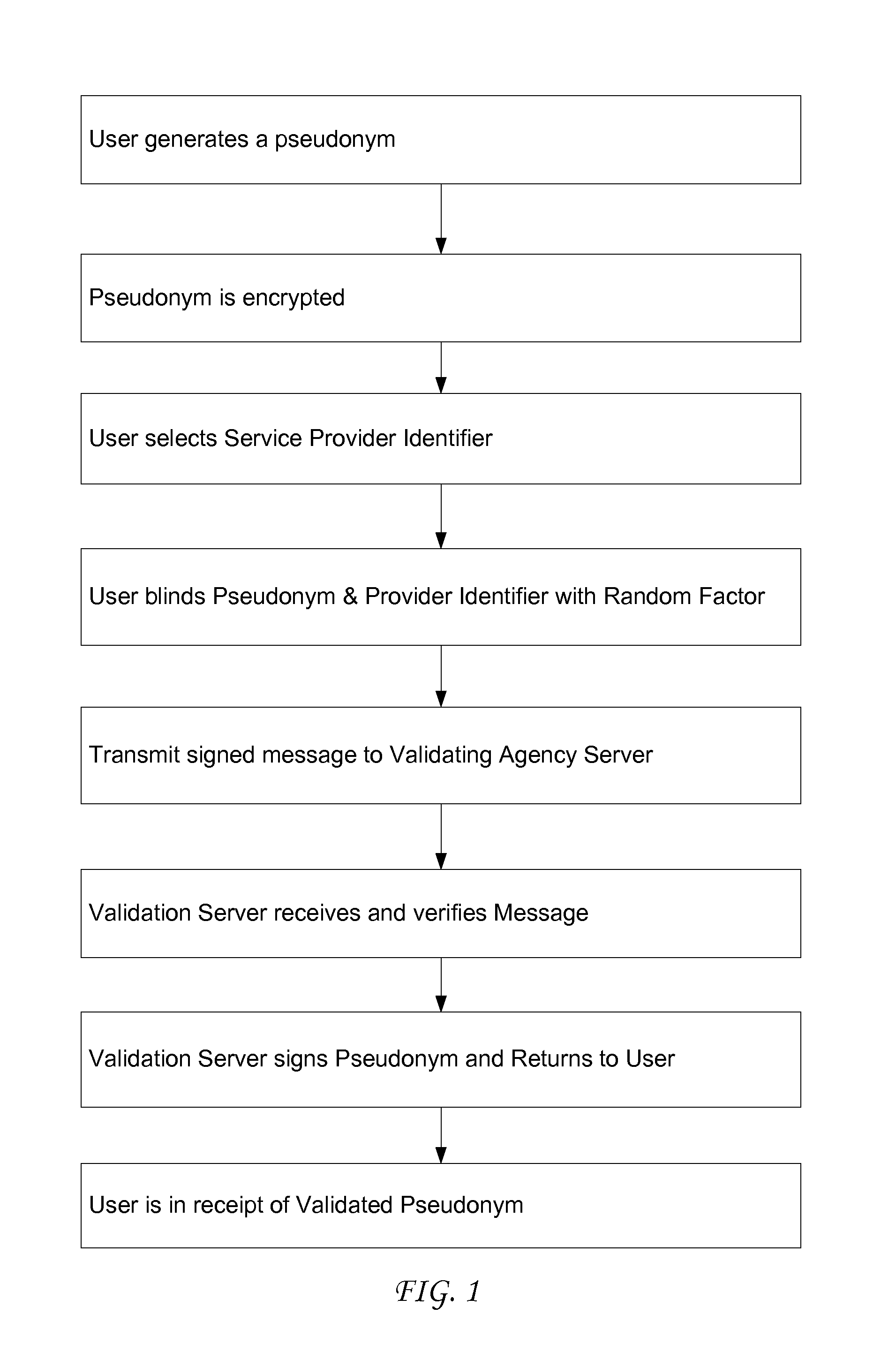
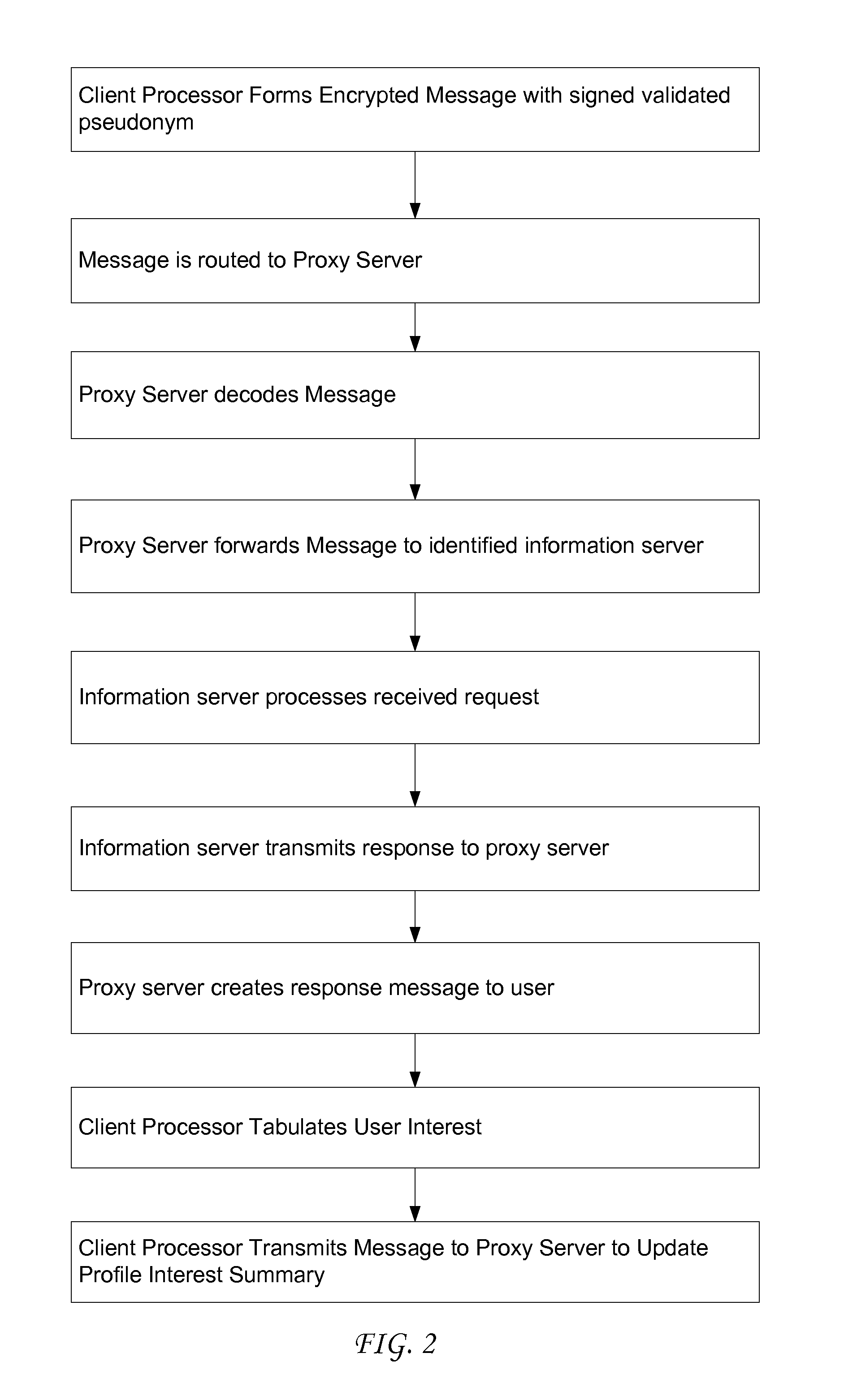
Use of proxy servers and pseudonymous transactions to maintain individual's privacy in the competitive business of maintaining personal history databases
InactiveUS7844717B2Protect data privacyPrivacy can be assuredComputer security arrangementsMultiple digital computer combinationsData accessProxy server
A system is provided that preserves data privacy for the Individual-I and Private Data Owner (PDO) while granting data access to the User-U and Accessor who need such data to perform their usual and customary business functions. The method and system completely control the User's access to the Private Data Owner's Private Data by replacing Identifying Information for the User-U, Individual-I, Accessor and PDO with pseudonyms. This assures the overall privacy of individuals, throughout the course of collecting, storing, accessing, analyzing and sharing detailed private records among different organizations engaged in providing and / or consuming services and / or products. Access Control Rule Sets (“ACRS”) consist of instructions which prescribe the terms and conditions for permitting Users to access the PDO's Pseudonymized and Actual Private data in accordance with the rules governing their authorization to access such data.
Owner:HERZ FREDERICK S M +2
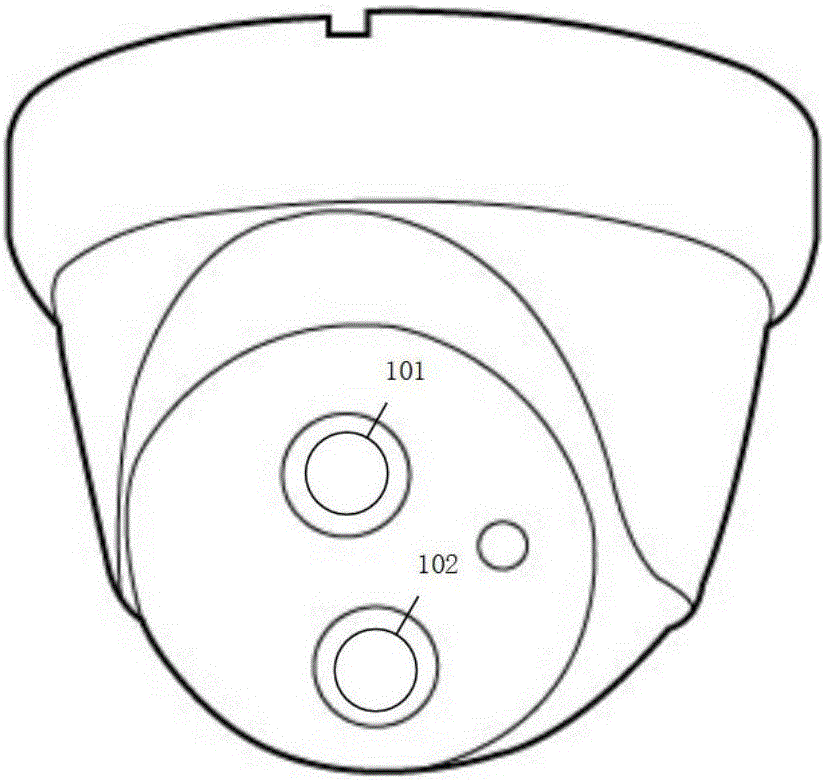
Smart home old age support video monitoring abnormal behavior system and method
ActiveCN106027978AAccurate identificationFully describeClosed circuit television systemsAcquiring/recognising facial featuresVideo monitoringMonitoring system
The invention discloses a smart home old age support video monitoring abnormal behavior system and method, and belongs to the technical field of mode identification and computer vision. The monitoring system provided by the invention comprises a double-lens monitoring camera, a video processing node and a communication center. According to the system, the indoor activity condition can be monitored in real time through the double-lens monitoring camera; an abnormal behavior is processed through the video processing node; whether there is an abnormal behavior activity or not is detected by taking face expressions as auxiliary identification; and abnormal behavior alarm information is sent to a user through the communication center. According to the system and the method, the body activity state can be monitored in real time, and alarm is generated when there is the abnormal condition. The system and the method have the advantages of wide application range, high security and stable and reliable identification.
Owner:NANJING UNIV OF TECH
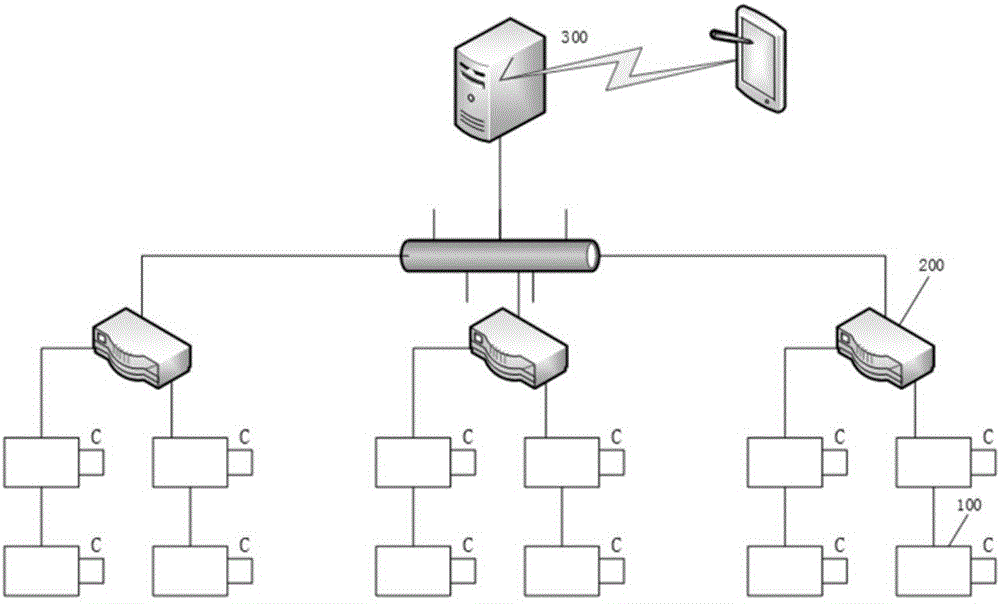
Security and protection service network based on Internet of Things
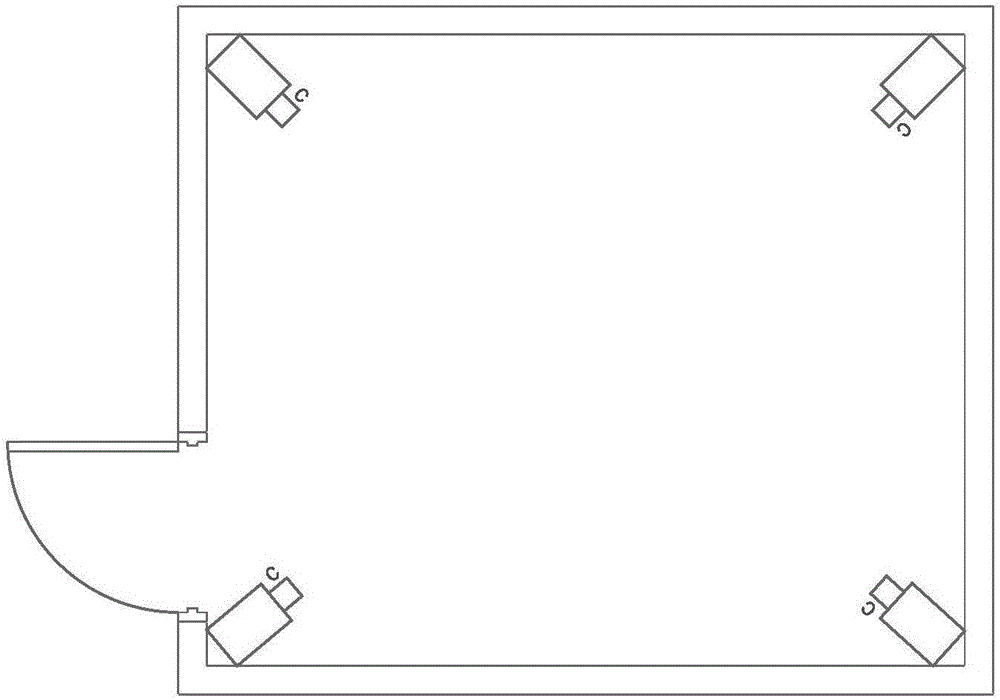
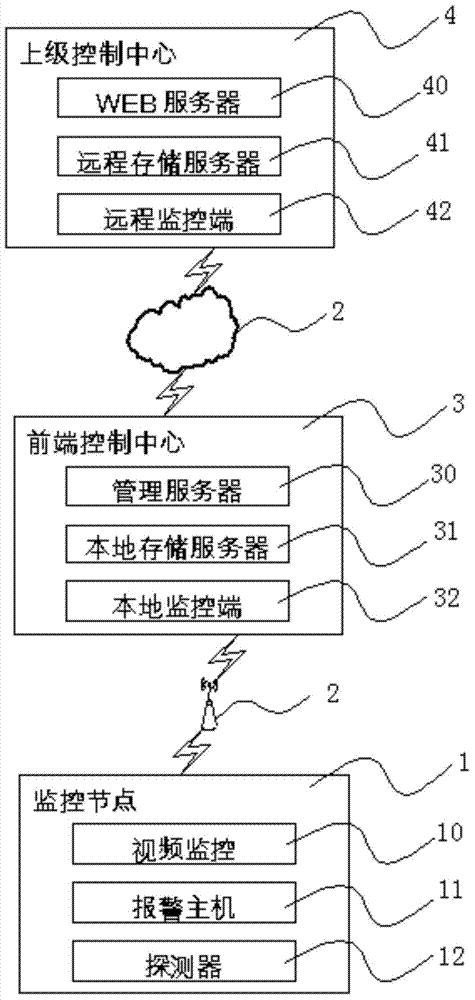
ActiveCN103578240AReduce false alarm rateImprove processing efficiencyClosed circuit television systemsAlarmsAlarm messageAutomatic steering
The invention discloses a security and protection service network based on the Internet of Things. The security and protection service network comprises a monitoring node, a front end control center and a superior control center. The monitoring node is composed a video monitor, an access controller, a perimeter alarm and a detector; the front end control center is composed of a management server, a local storage server and a local monitoring end; the superior control center is composed of a Web server, a remote storage server and a remote monitoring end. The security and protection service network can send a control instruction to a camera in the area where the security and protection service network is located according to various alarm messages detected by the detector and an alarm host, the camera receives the instruction and automatically turns towards an alarming situation to carry out snapshooting or video recording, and an alarm and audio and visual information are sent to a superior monitoring center or related organizations after the alarming situation is determined through synthetic judgment and analysis; besides, different motoring authorities can be given to different users; the security and protection service network further has the advantages of data security and extension flexibility.
Owner:WUXI KAIYI IOT TECH DEV
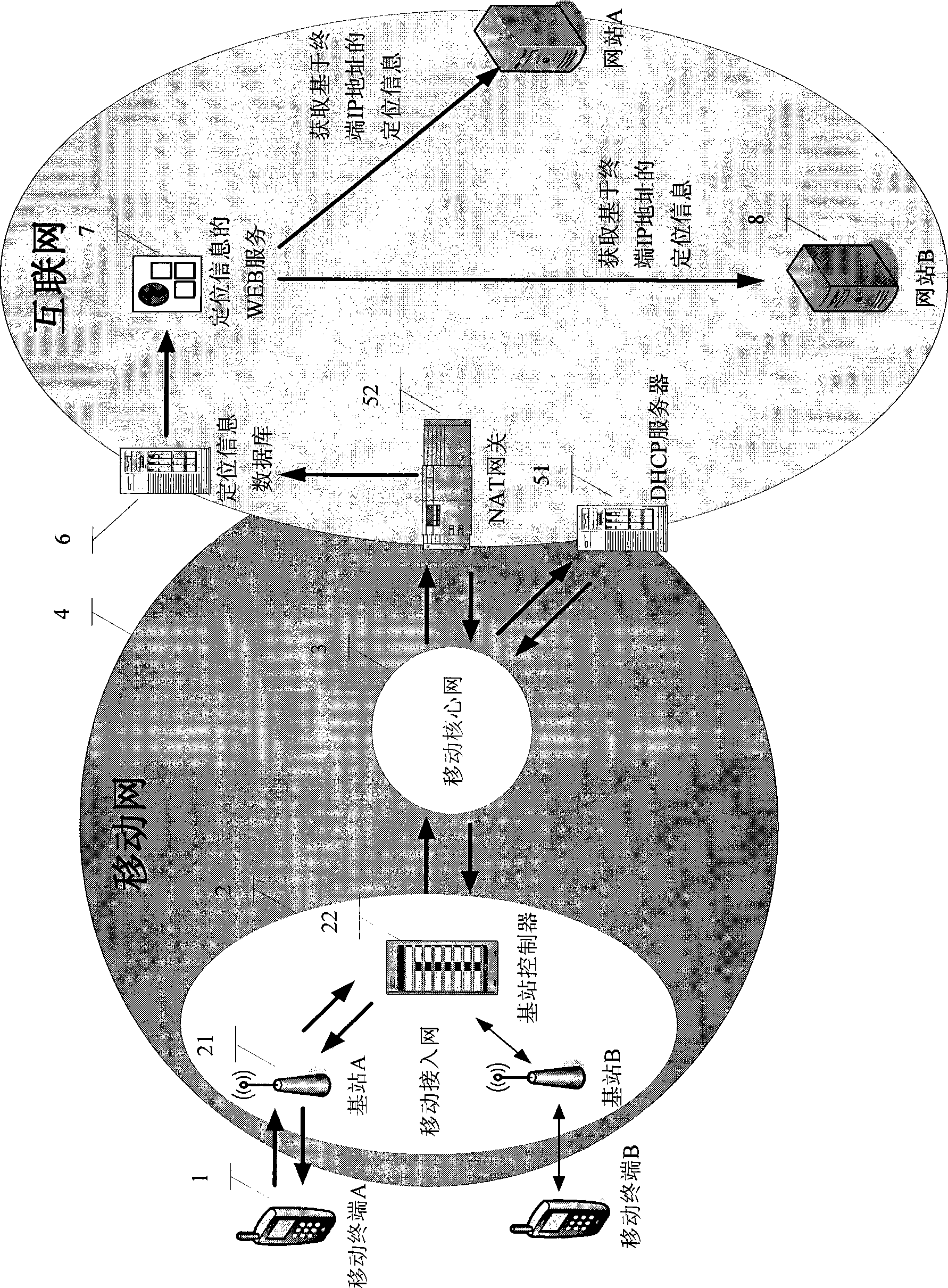
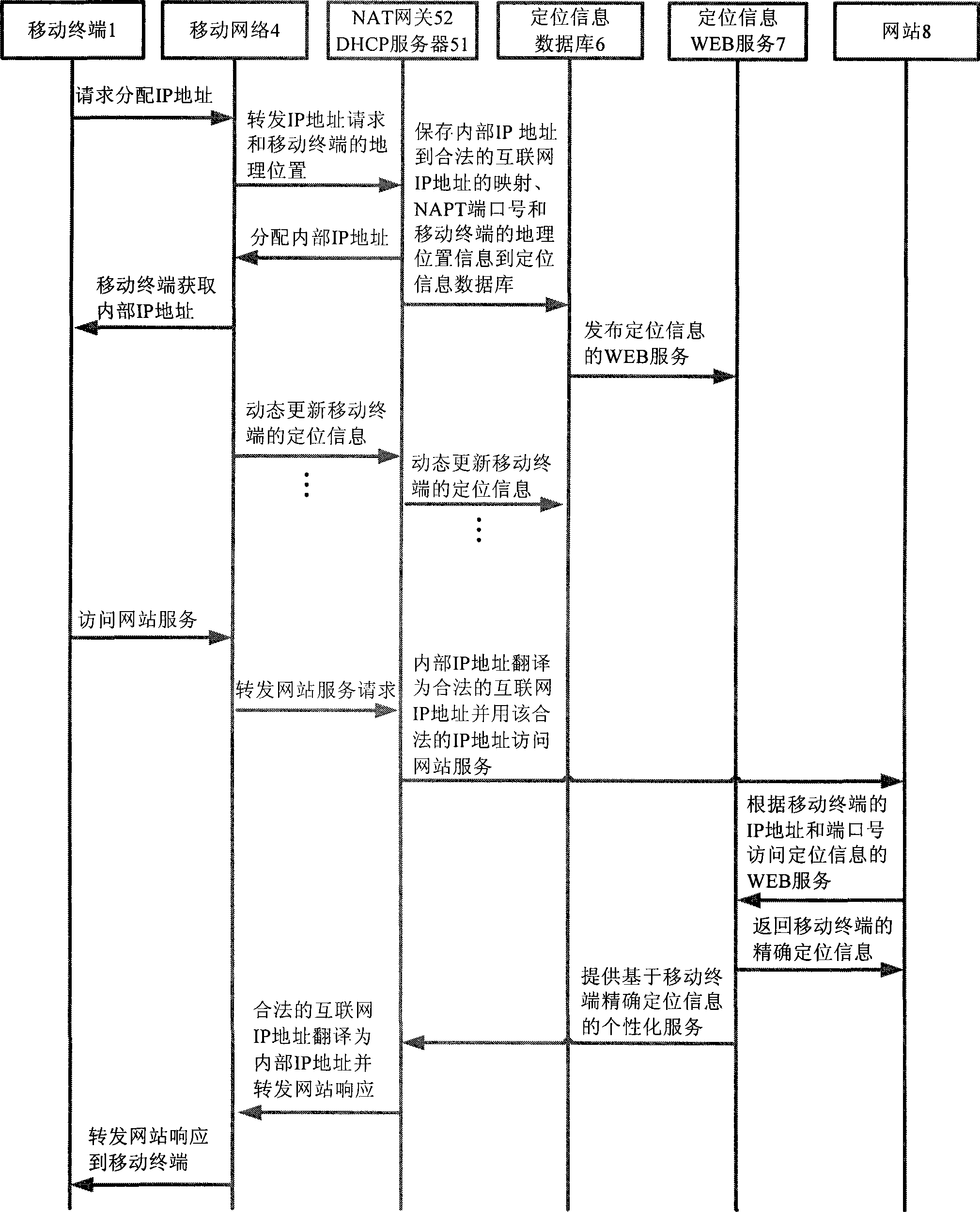
Method for obtaining computer accurate geological position information based on IP address information
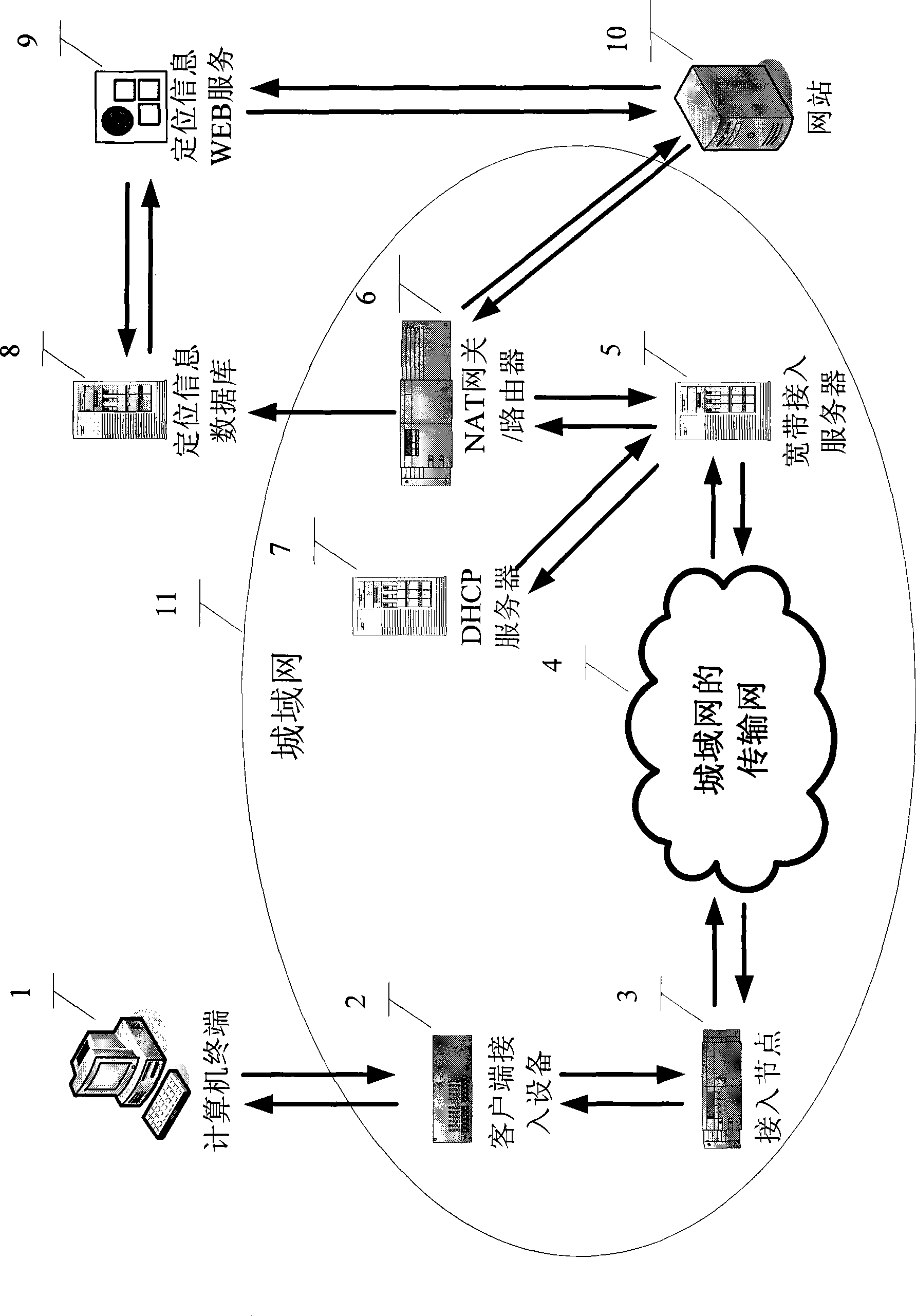
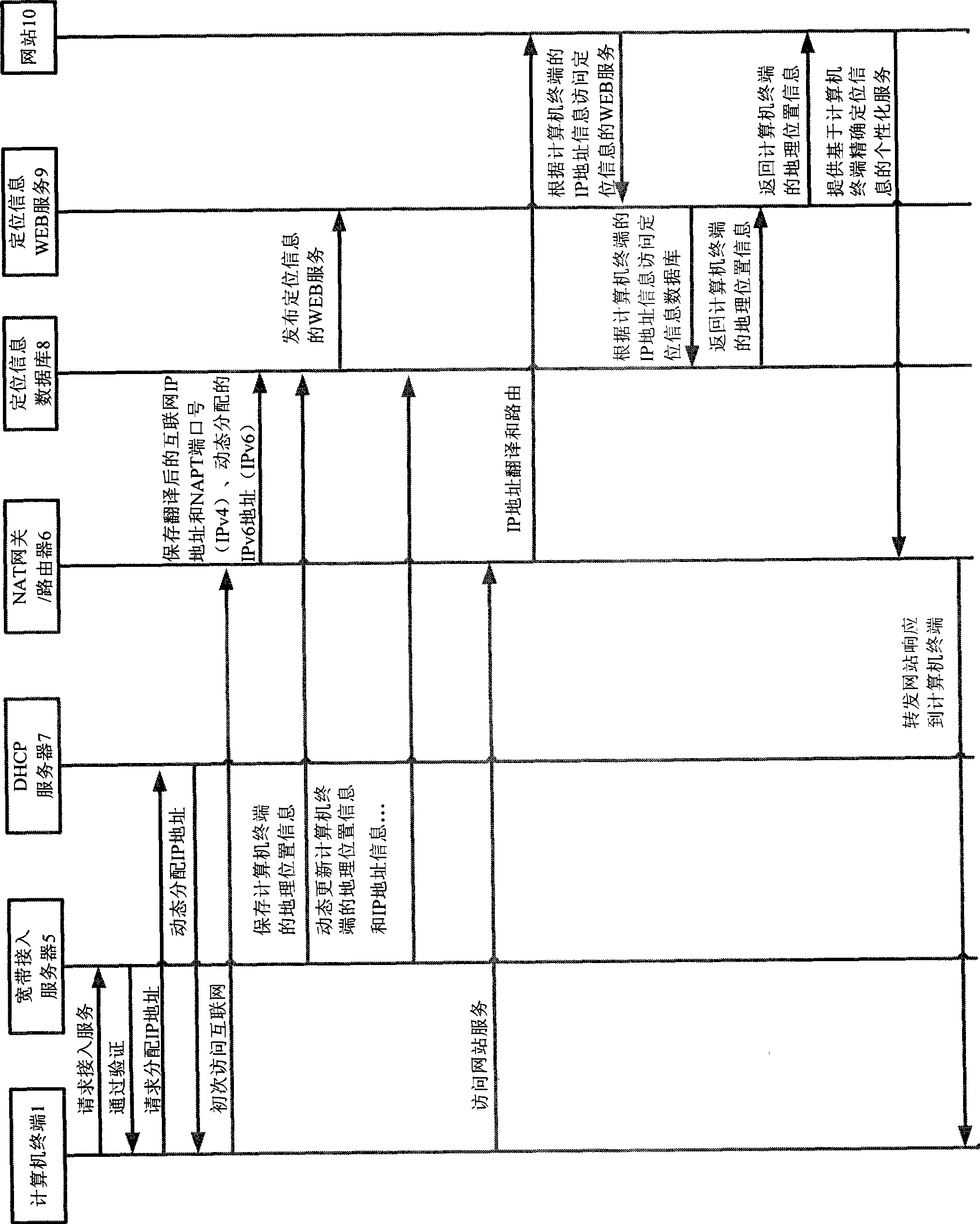
InactiveCN101383855AProtect personal privacyDoes not involve real informationData switching by path configurationIp addressPersonalization service
The invention relates to a method for obtaining an accurate geographical position based on IP address information. The invention has the key points that a computer terminal is preserved in a location information database by an IP address (IPv6) dynamically distributed by a DHCP server, an IP address and a port number (IPv4) translated by an NAT gateway / a router as well as the accurate geographical position information of the computer terminal obtained by that a wideband accesses a server, and is published to be location information WEB service supplied for website visiting; a website visits the location information WEB service according to the IP address information of the computer terminal which is interacted with the website to obtain the accurate location information of the computer terminal, thereby personalized service based on the accurate location information is provided for a computer user.
Owner:沈阳 +1
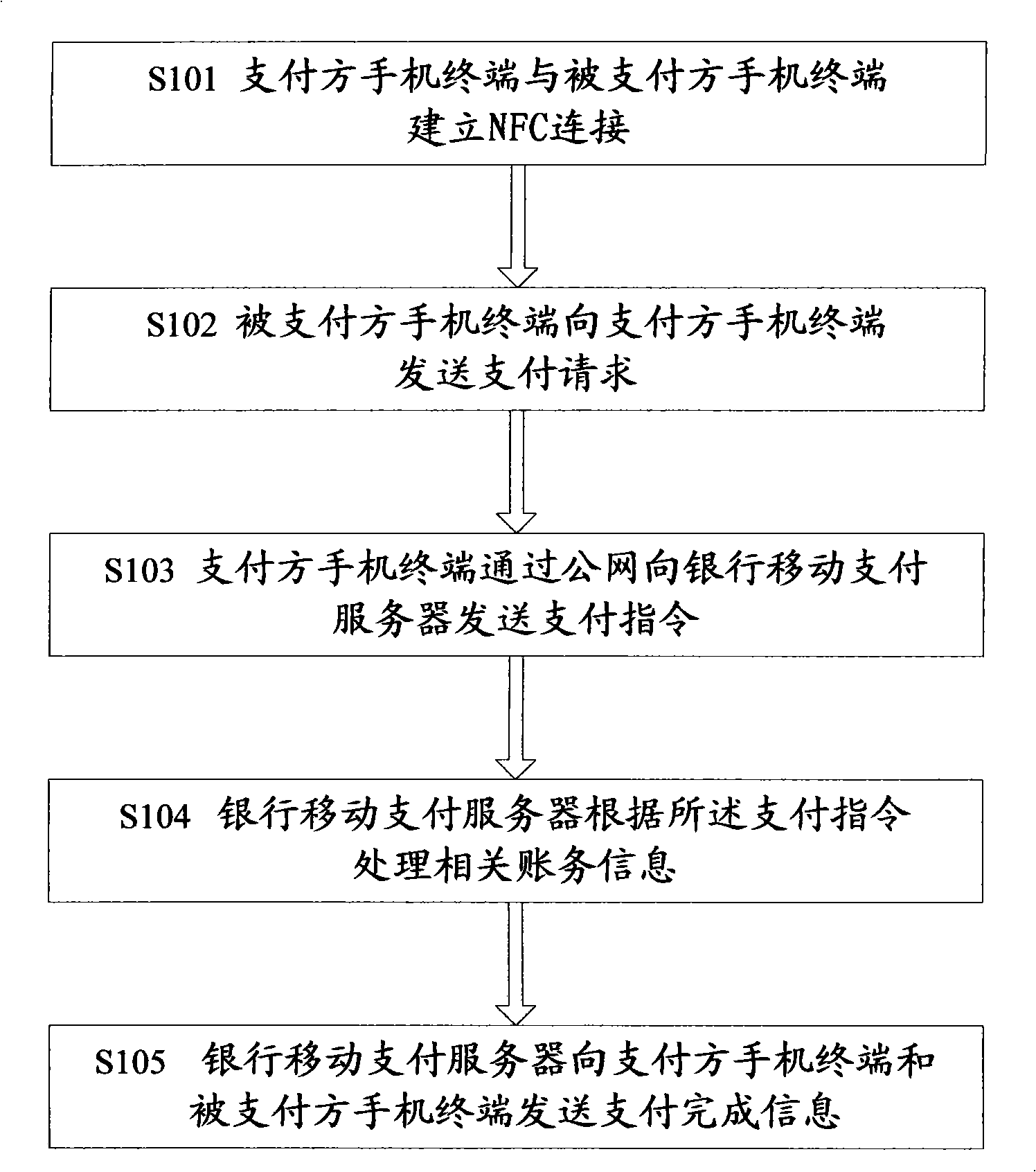
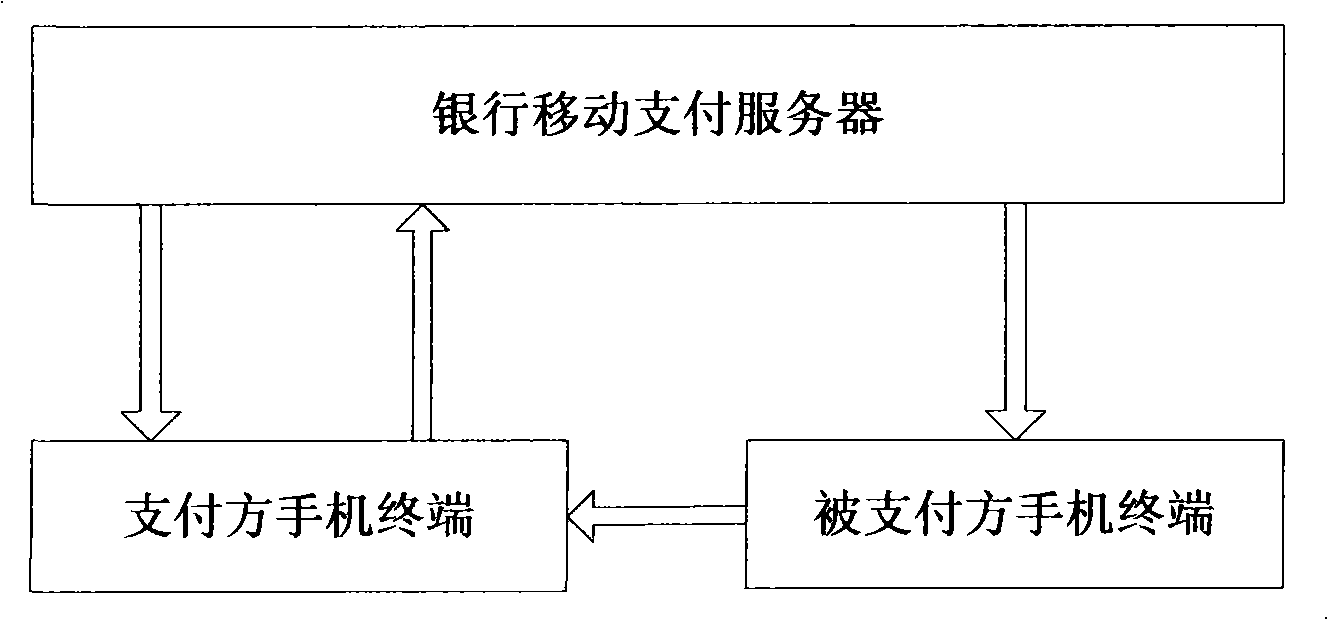
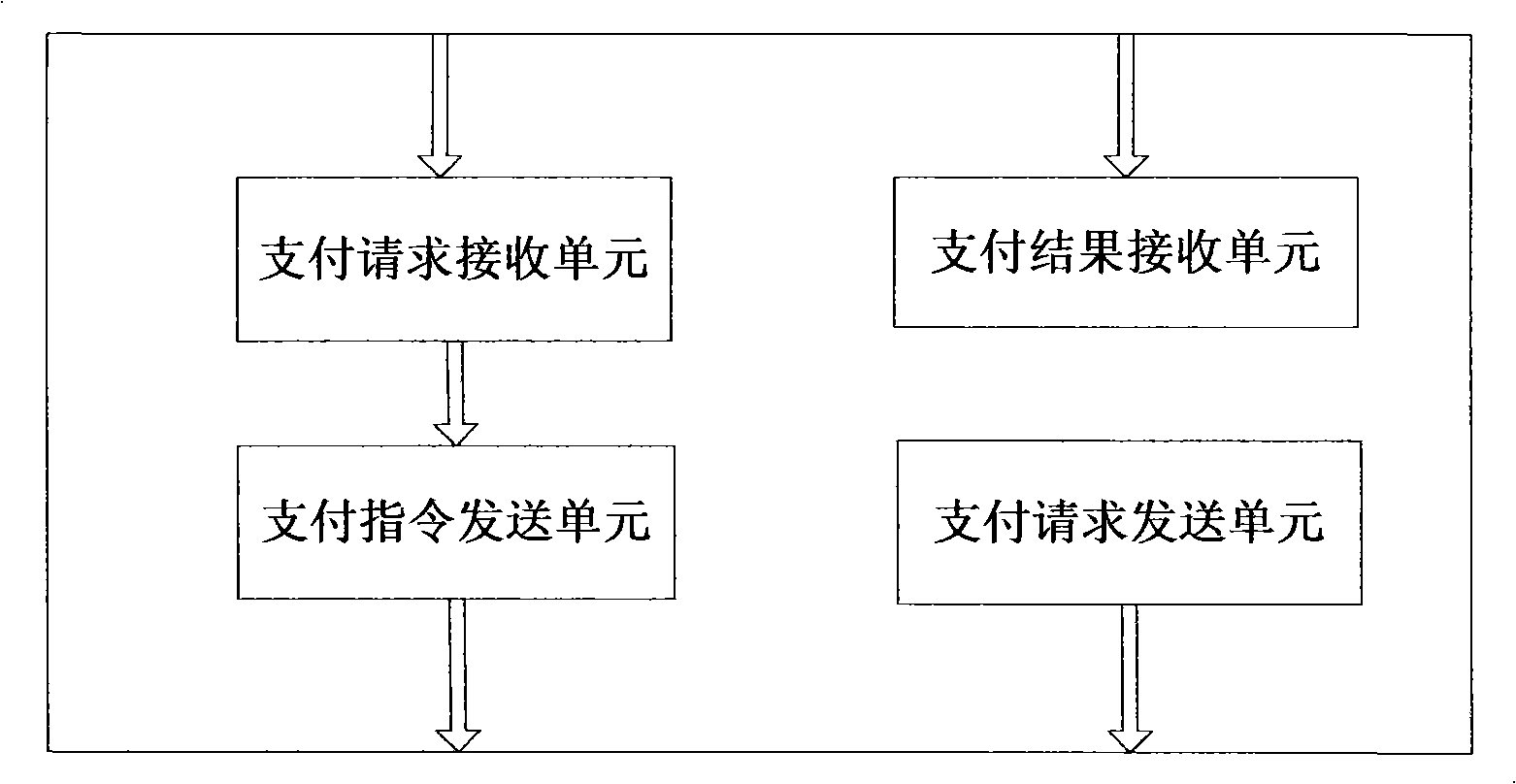
NFC mobile phones payment terminal, payment procedure and system
InactiveCN101290669AReduce riskTransmission data is accurate and reliablePayment architectureMobile paymentMobile phone
The invention discloses an NFC mobile phone payment terminal, a payment method and a system. The invention is designed to solve the problems that the prior mobile phone payment mode is troubled in operation and easy to go wrong; the system comprises a mobile phone terminal of a paying party, a mobile phone terminal of a paid party and a bank mobile payment server; the mobile phone terminal of the paid party is used for sending a payment request to the mobile phone terminal of the paying party by an NFC signal; and the mobile phone terminal of the paying party is used for receiving the payment request and sending a payment command to the bank mobile payment server according to the payment request; the bank mobile payment server receives the payment request, processes relevant financial information and sends an operation result to the mobile phone terminal of the paid party and the mobile phone terminal of the paying party. The NFC mobile phone payment terminal, the payment method and the system are suitable for consumption settlement between a consumer and a merchant and payment transfer among individuals.
Owner:BEIJING AIO TIME INFORMATION TECH
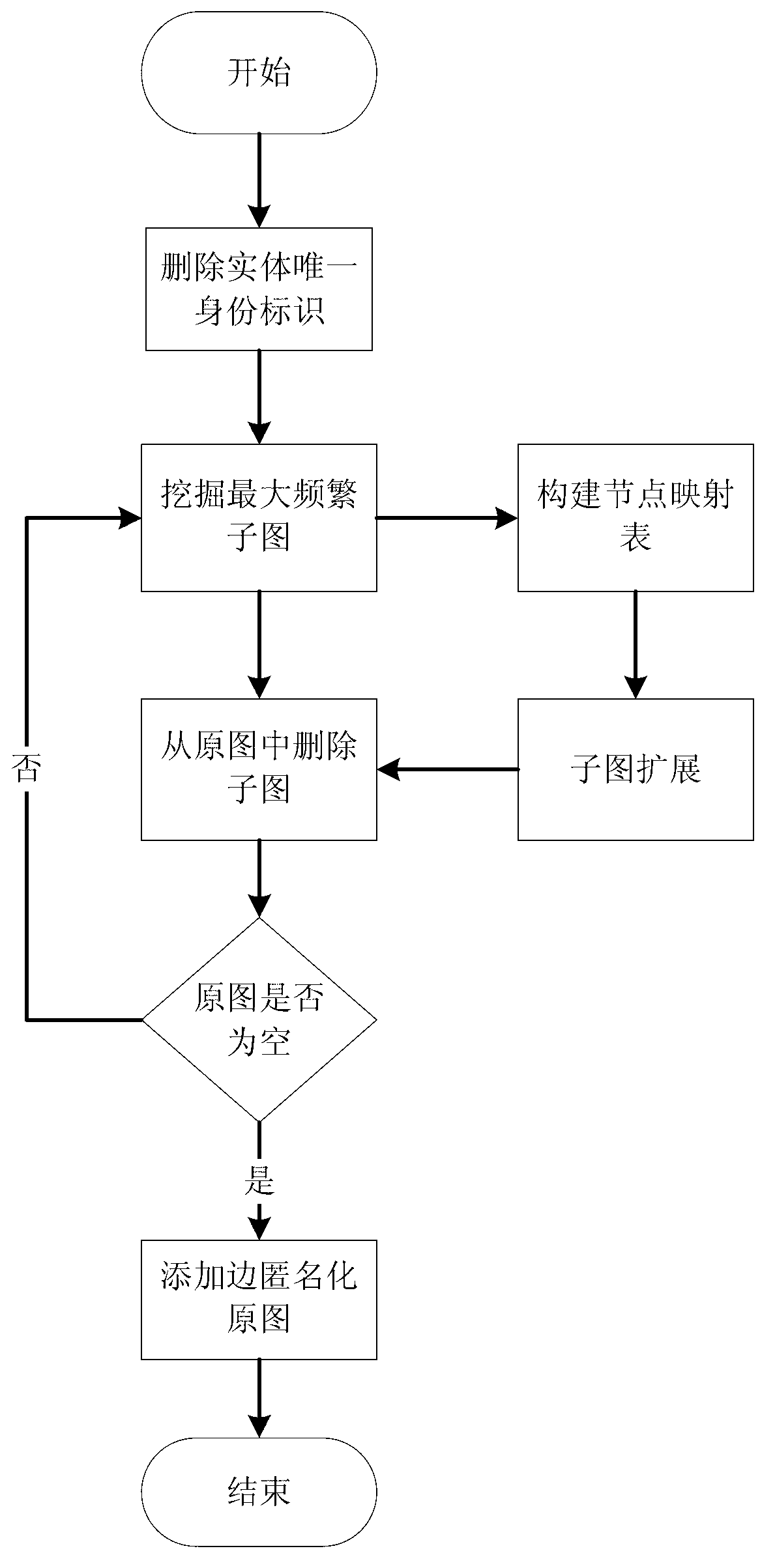
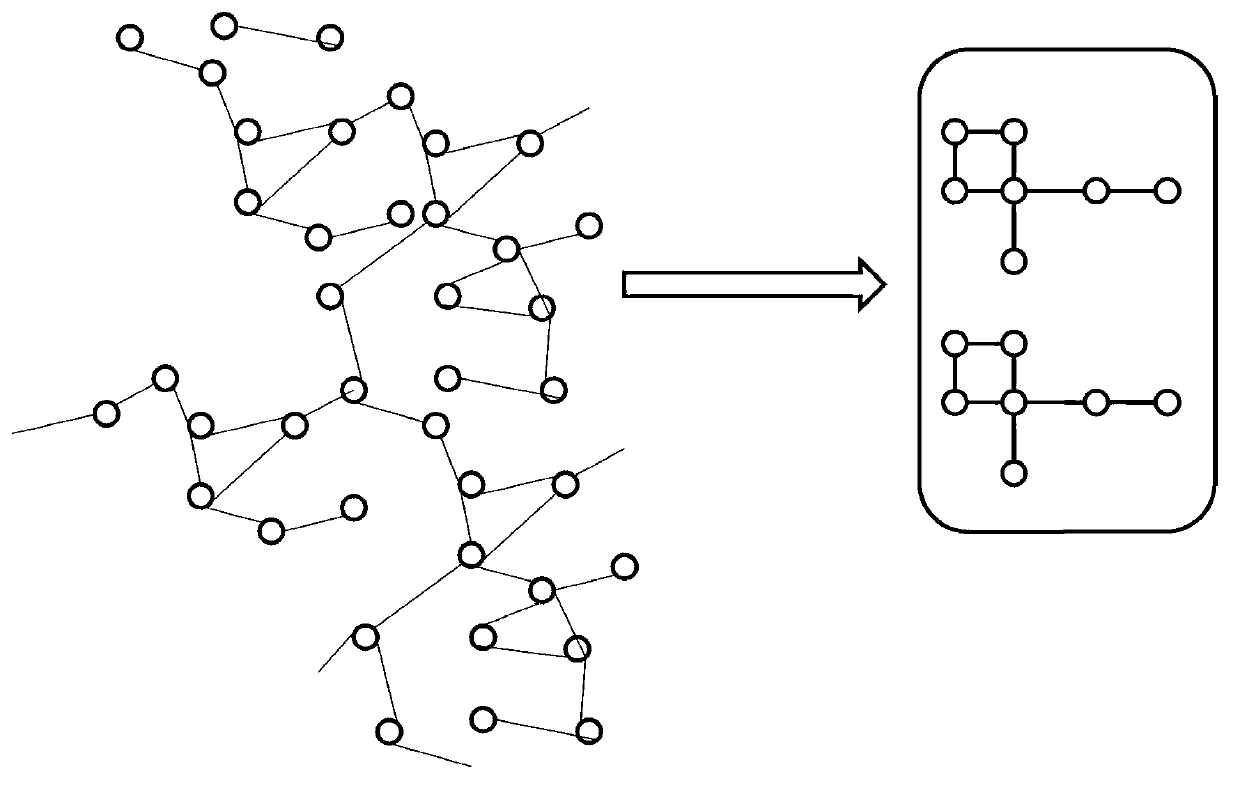
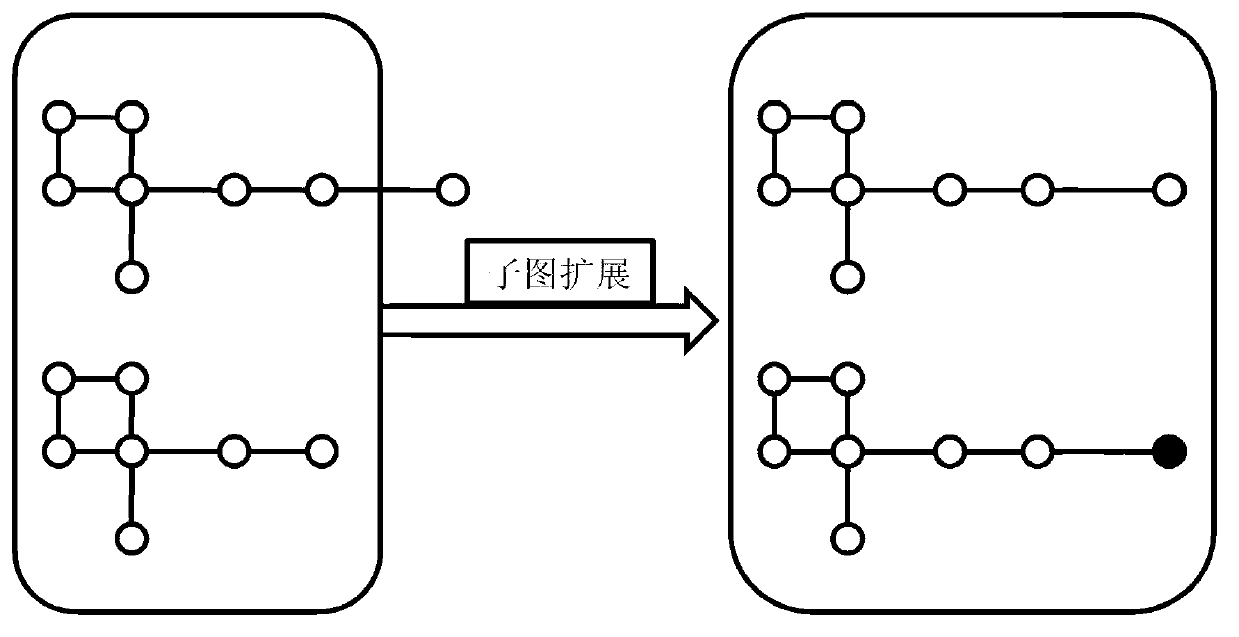
Privacy protecting method for social network based on undirected graph modification
ActiveCN103218397AAvoid repositioningProtect personal privacyDigital data protectionSpecial data processing applicationsNODALUndirected graph
The invention discloses a privacy protecting method for a social network based on undirected graph modification. The method comprises the following steps: (1) establishing an undirected graph of the social network; (2) digging the maximum frequent subgraph; (3) establishing a node mapping relation; (4) iteratively expanding the subgraph and improving the mapping table; and (6) forming an anonymity isomorphic graph by adding mapping lines and virtual nodes to the undirected graph. According to the method, the virtual nodes are added, so that each node has other nodes symmetrical thereto, so that re-positioning of user identity is avoided, and personal privacy safety of the user is effectively protected. In addition, the local structure of the social network is finely modified, social network graph data can be externally and safely issued, so that the method is suitable for researching characteristic analysis and statistics of the local structure of the social network, and promotes data digging technology in research and application in the field of social network.
Owner:ZHEJIANG UNIV
Method for obtaining terminal real time accurate geographic position based on the mobile terminal IP address
InactiveCN101374249AReal-time accurate geographic location informationGeographical information is accurateRadio/inductive link selection arrangementsNetwork connectionsMobile WebIp address
The invention relates to a method for acquiring real-time accurate geographical position of a mobile terminal based on the IP address of the mobile terminal. The method is characterized in that the IP address distributed by a DHCP server of the mobile terminal, the IP address translated by a NAT gateway and a port number of the mobile terminal, and the real-time accurate geographical position of the mobile terminal acquired by the mobile network are stored in a location information database and are released as WEB service of location information for website access; the website can access the WEB service of the location information according to the IP address information of the mobile terminal interacting with the website to acquire the real-time accurate location information of the mobile terminal, thereby providing personalized service for a mobile user based on the real-time accurate location information.
Owner:彭亮 +1
Information interaction control method and device
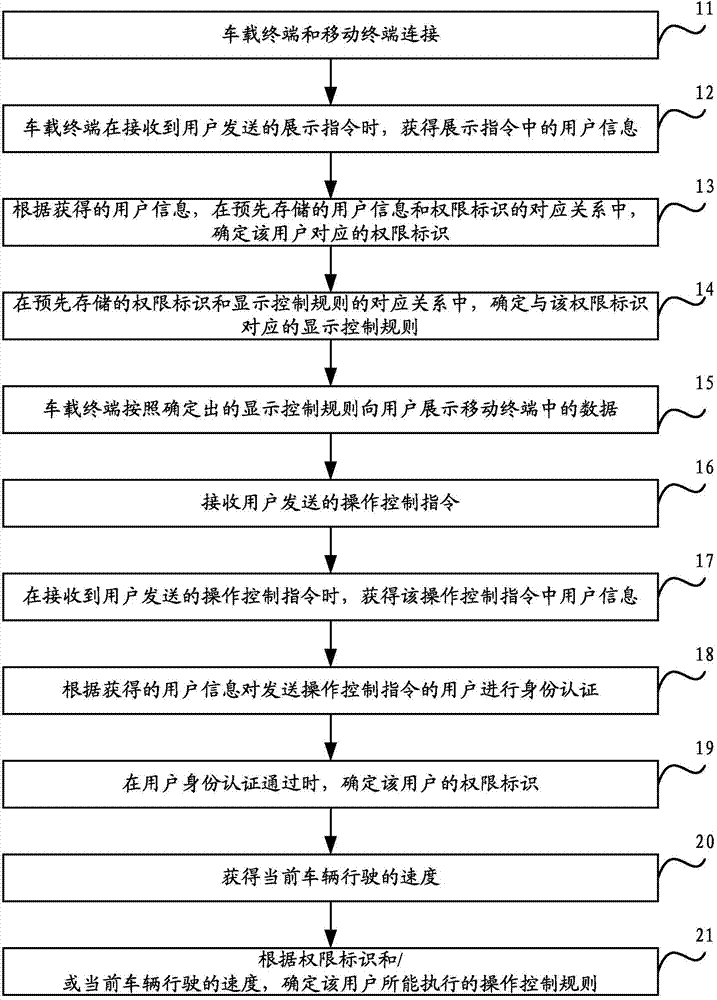
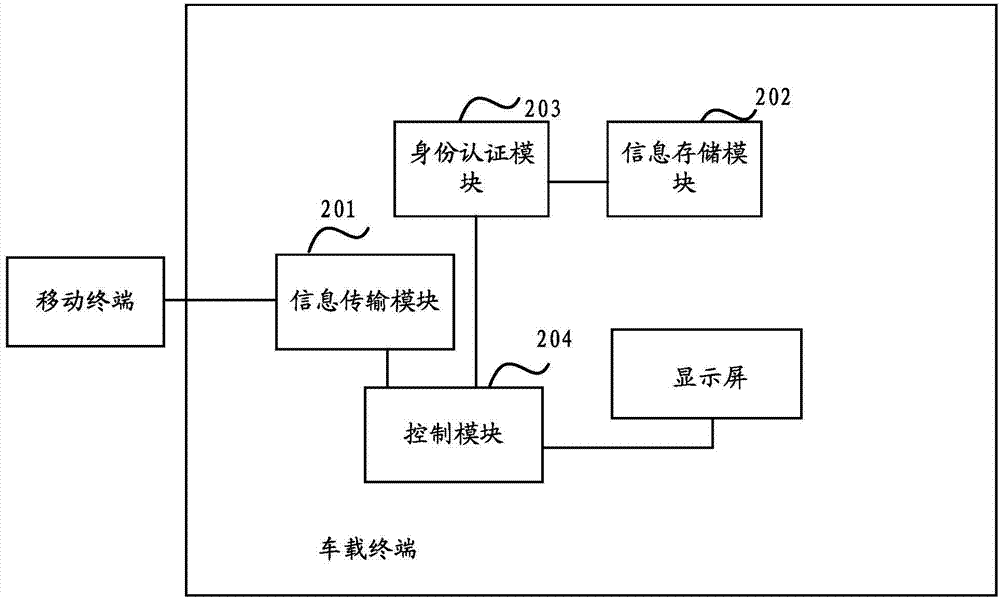
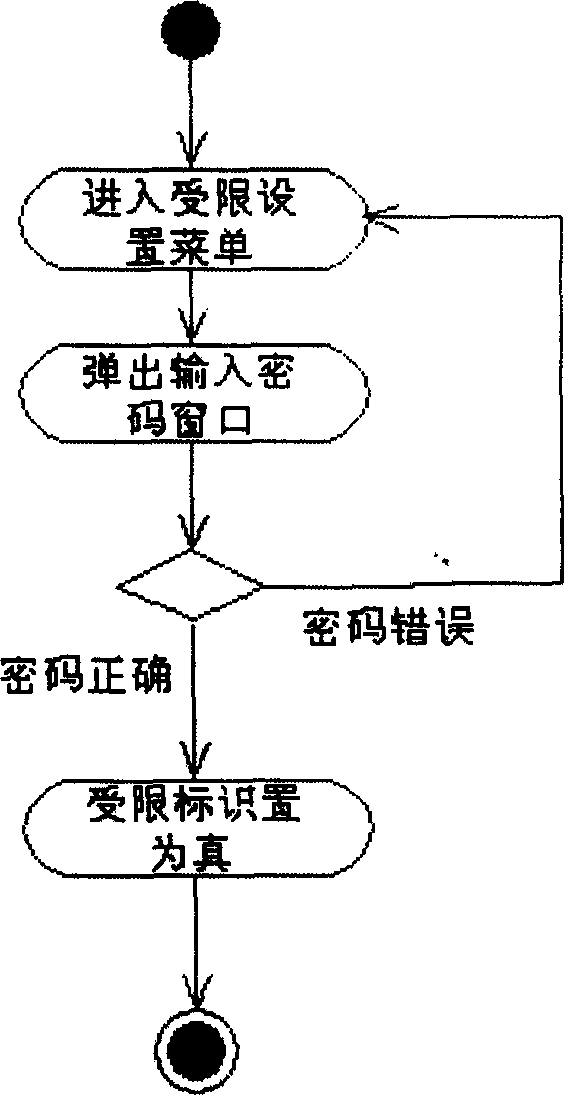
InactiveCN104751031AImprove securityProtect personal privacyDigital data authenticationEmbedded systemUser information
The invention discloses an information interaction control method and device and aims to, at the premise that information of a mobile terminal is shared at a vehicle-mounted terminal, protect individual private data and improve data storage safety. The information interaction control method includes connecting the vehicle-mounted terminal and the mobile terminal, and subjecting the vehicle-mounted terminal to acquiring user information contained in the display command as receiving a display command sent by the user; according to the user information, determining a limit identifier corresponding to the user from a pre-stored corresponding relation of the user information and the limit identifiers, to be specific, the limit identifiers present limits of the user to operate data in the mobile terminal; in a corresponding relation of the limit identifiers and display control rules, determining the display control rule corresponding to the limit identifier; subjecting the vehicle-mounted terminal to displaying the data in the mobile terminal to the user according to the display control rule.
Owner:CHINA MOBILE COMM GRP CO LTD
System and method for realizing smart card authentication based on voiceprint recognition
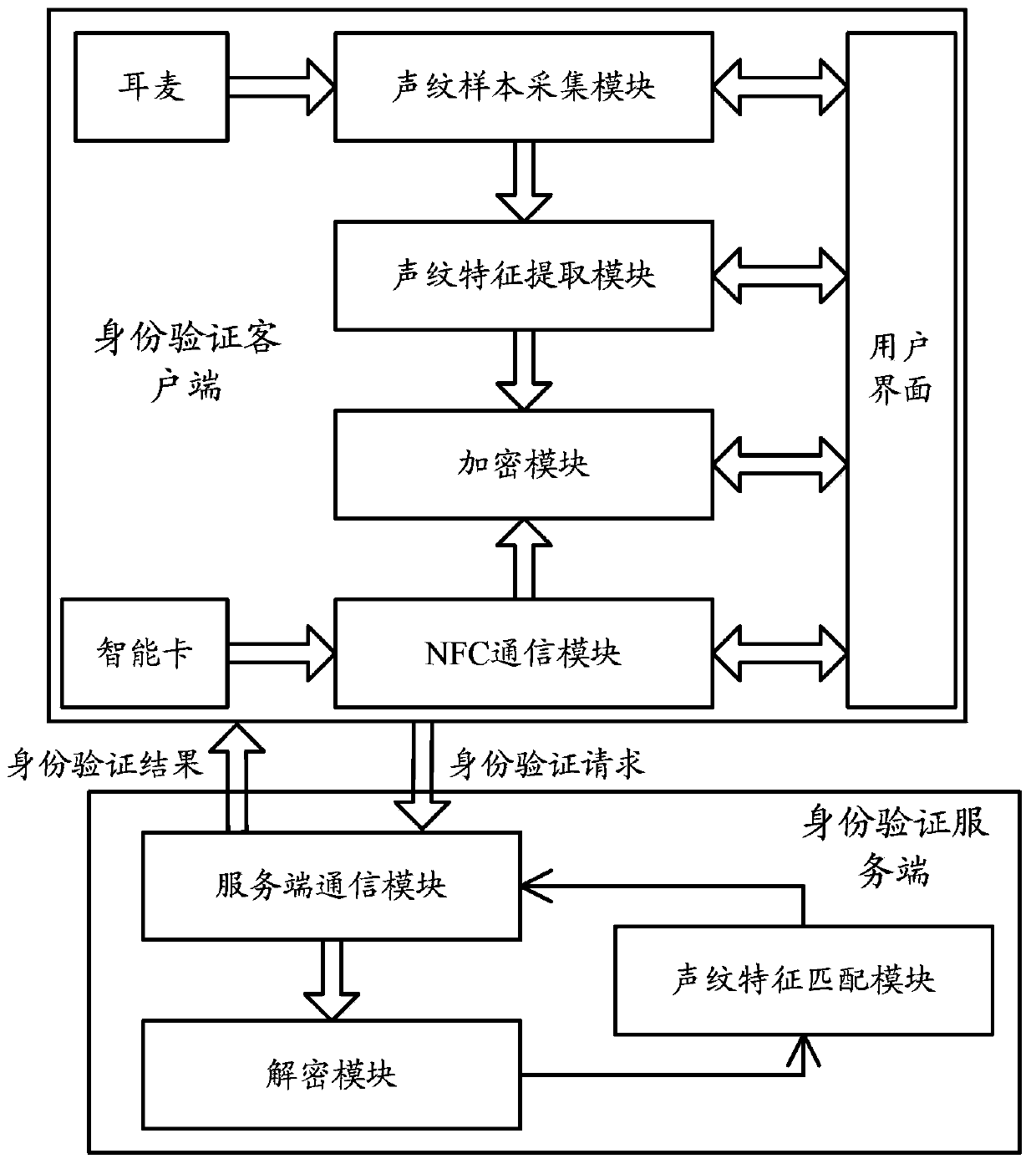
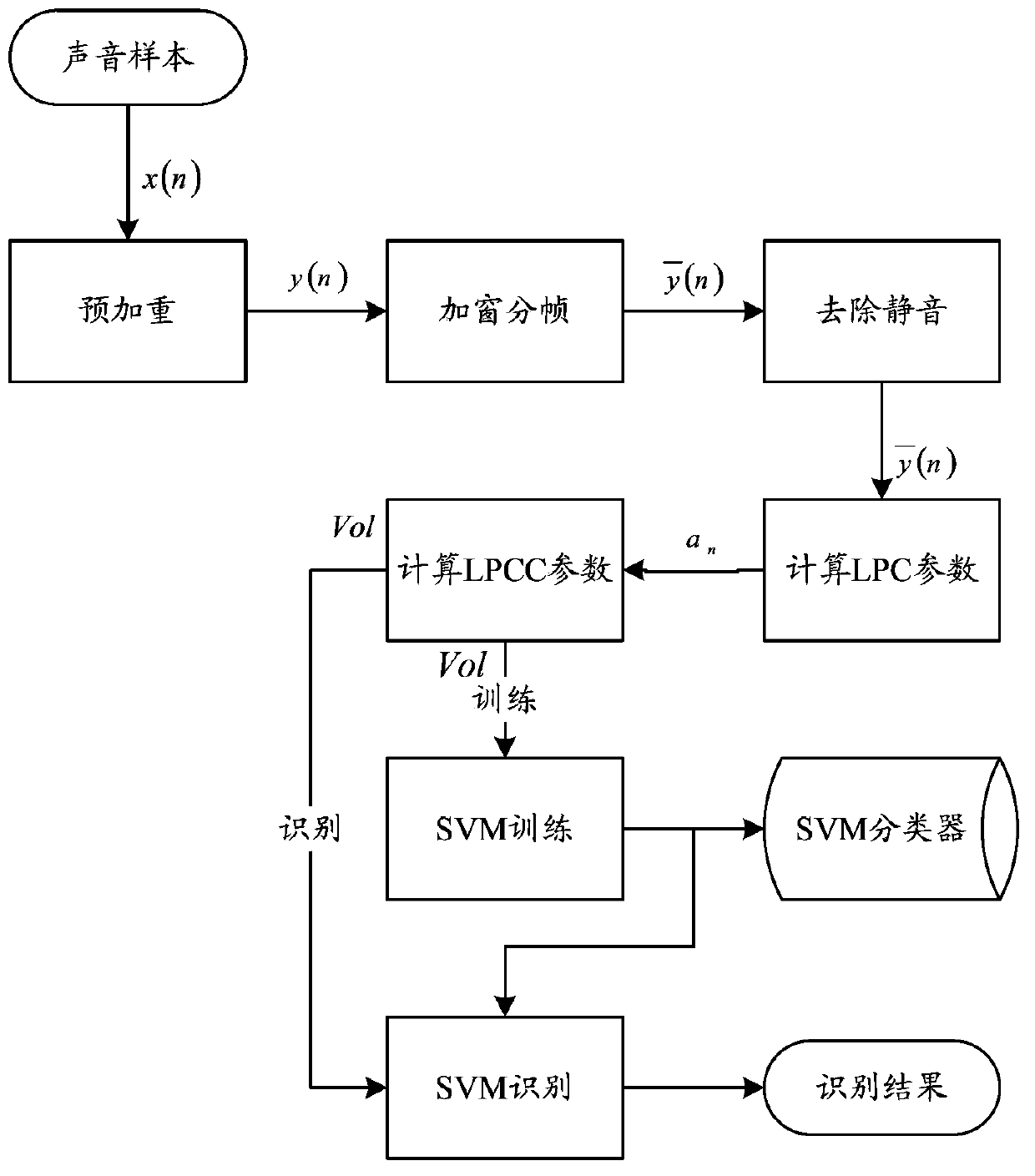
ActiveCN103391201AProtection securityGuaranteed to complete effectivelyUser identity/authority verificationSpeech analysisRead throughAuthentication server
The invention relates to a system for realizing smart card authentication based on voiceprint recognition. The system comprises an authentication client and an authentication server, wherein the authentication client comprises a voiceprint sample acquisition module, a voiceprint feature extraction module and an NFC (near field communication) module; the authentication server comprises a server communicating module and a voiceprint feature matching module; the server communicating module is used for receiving authentication request information sent by the authentication client and judging the validity of the authentication request and returning to an authentication result. The invention further relates to a method for realizing the smart card authentication based on the voiceprint recognition. With the adoption of the structure of the system and the method for realizing the smart card authentication based on the voiceprint recognition, related information on a smart card can be read through an NFC function, the irreplaceable, anti-theft and anti-lost characteristics of a voiceprint are used, the authentication can be guaranteed to be finished effectively, and a wider application range is provided.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Method, apparatus and electronic device for acquiring and feeding back user resources
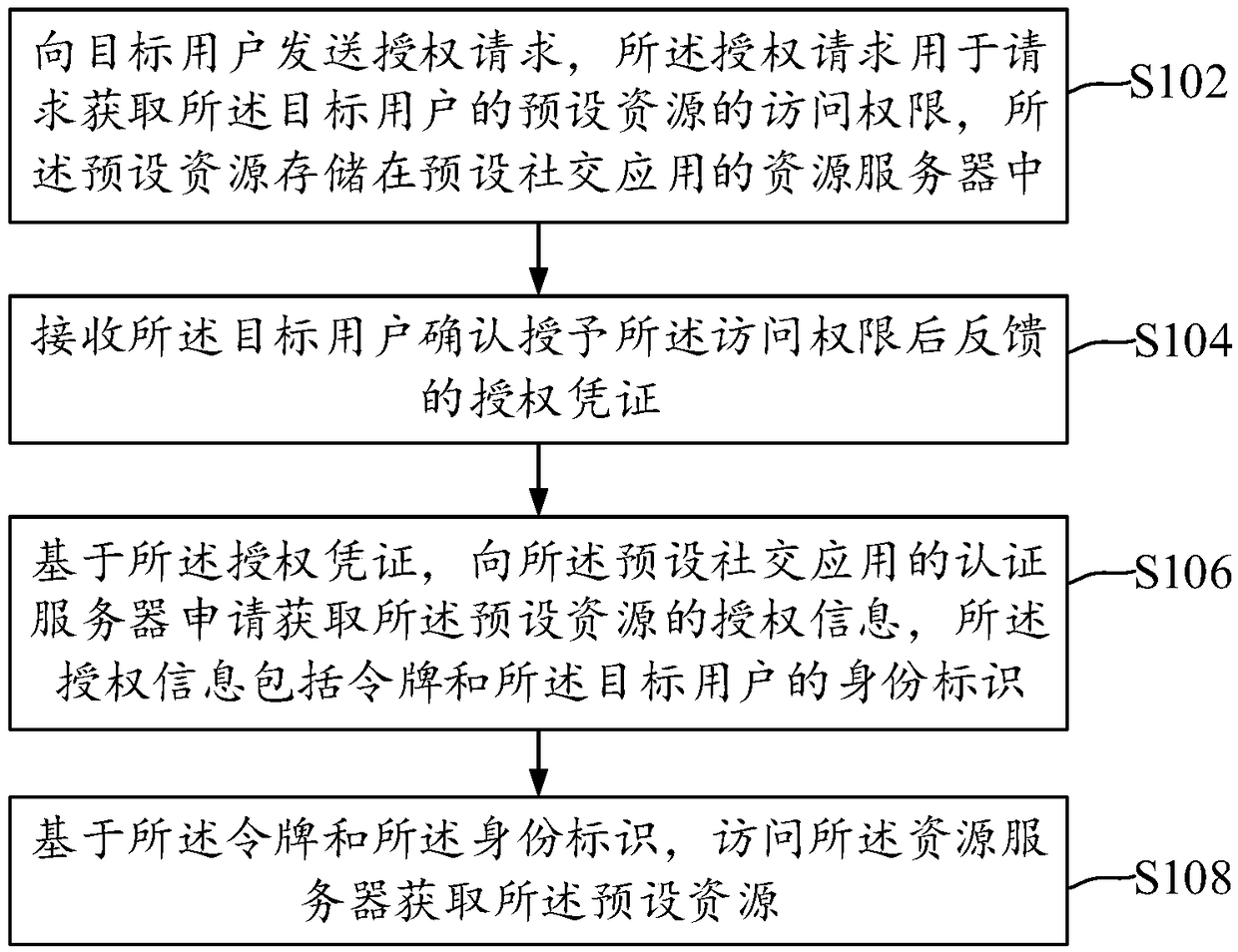
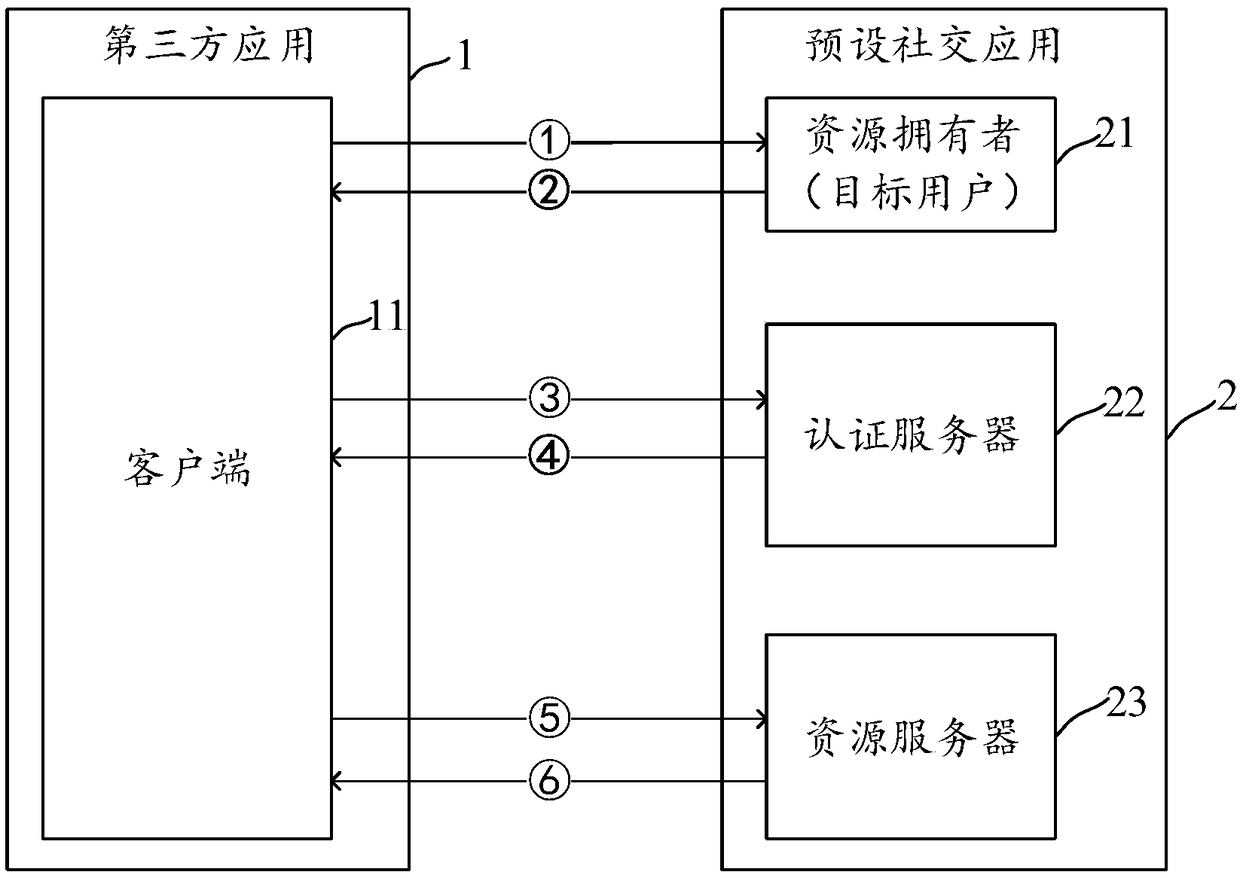
ActiveCN109033774AAvoid passing situationsProtect personal privacyDigital data authenticationAuthorization certificateResource based
The invention discloses a method, a device and an electronic device for obtaining and feeding back user resources. The method for obtaining user resources can send an authorization request for obtaining access rights of preset resources of the target user to a target user. The preset resources are stored in a resource server of a preset social application. Authorization credentials fed back by thetarget user are received after confirming the granting of the access right; it is applied for obtaining authorization information of the preset resources from an authentication server of the preset social application based on the authorization certificate, the authorization information comprises a token and an identity of the target user; the resource server is accessed to obtain the preset resource based on the token and the identity.
Owner:ADVANCED NEW TECH CO LTD
Method and device for creating business and deploying business
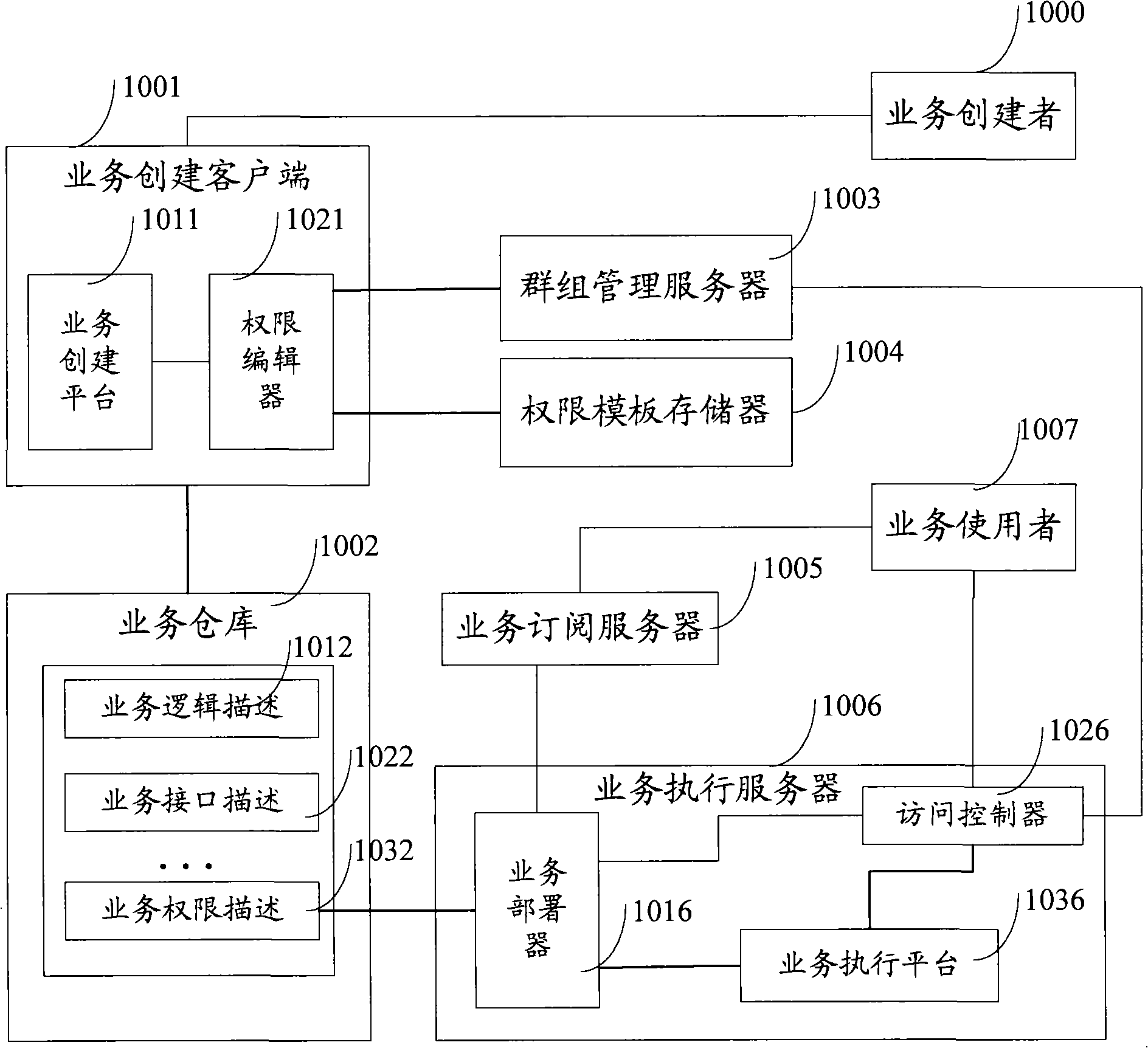
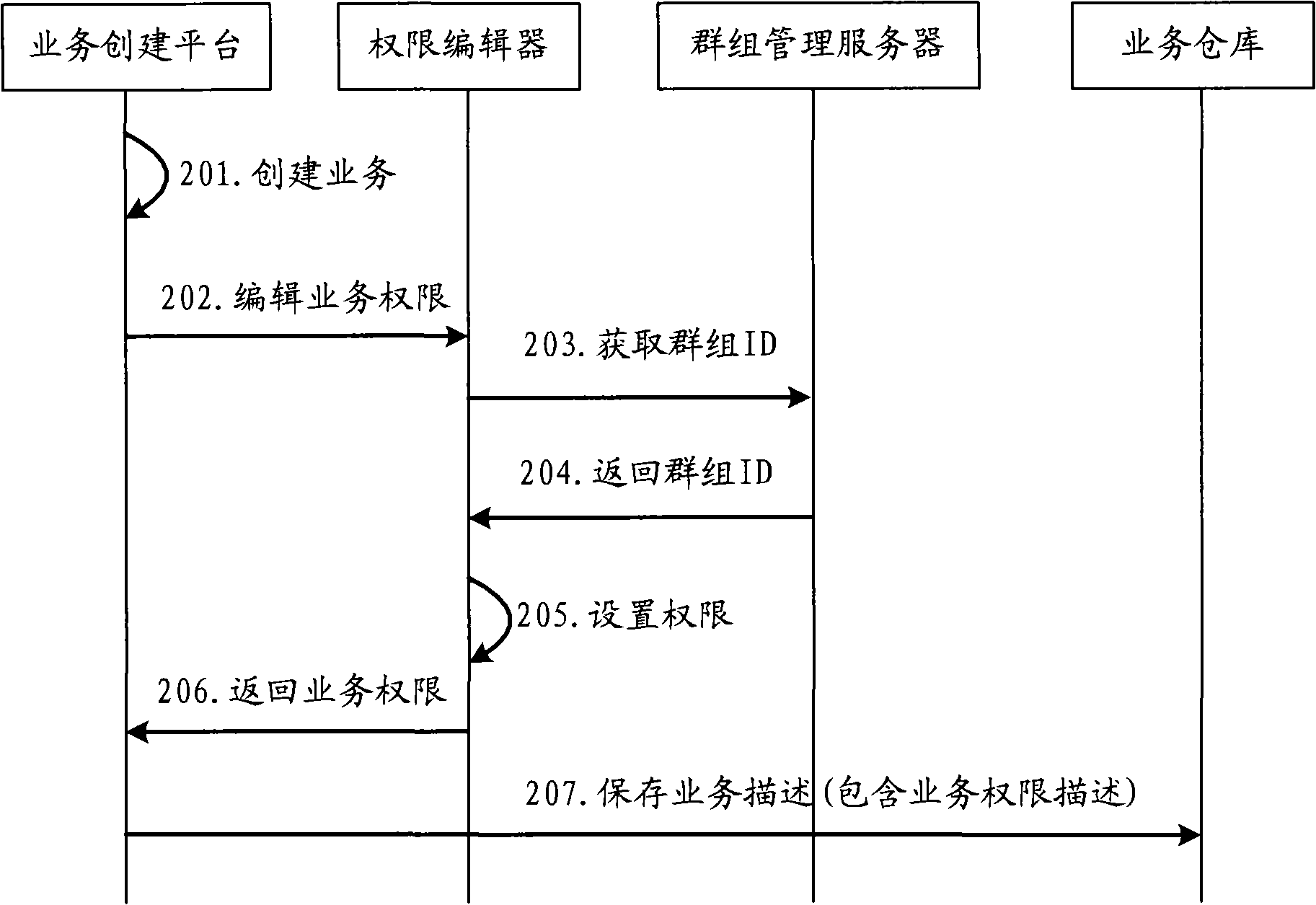
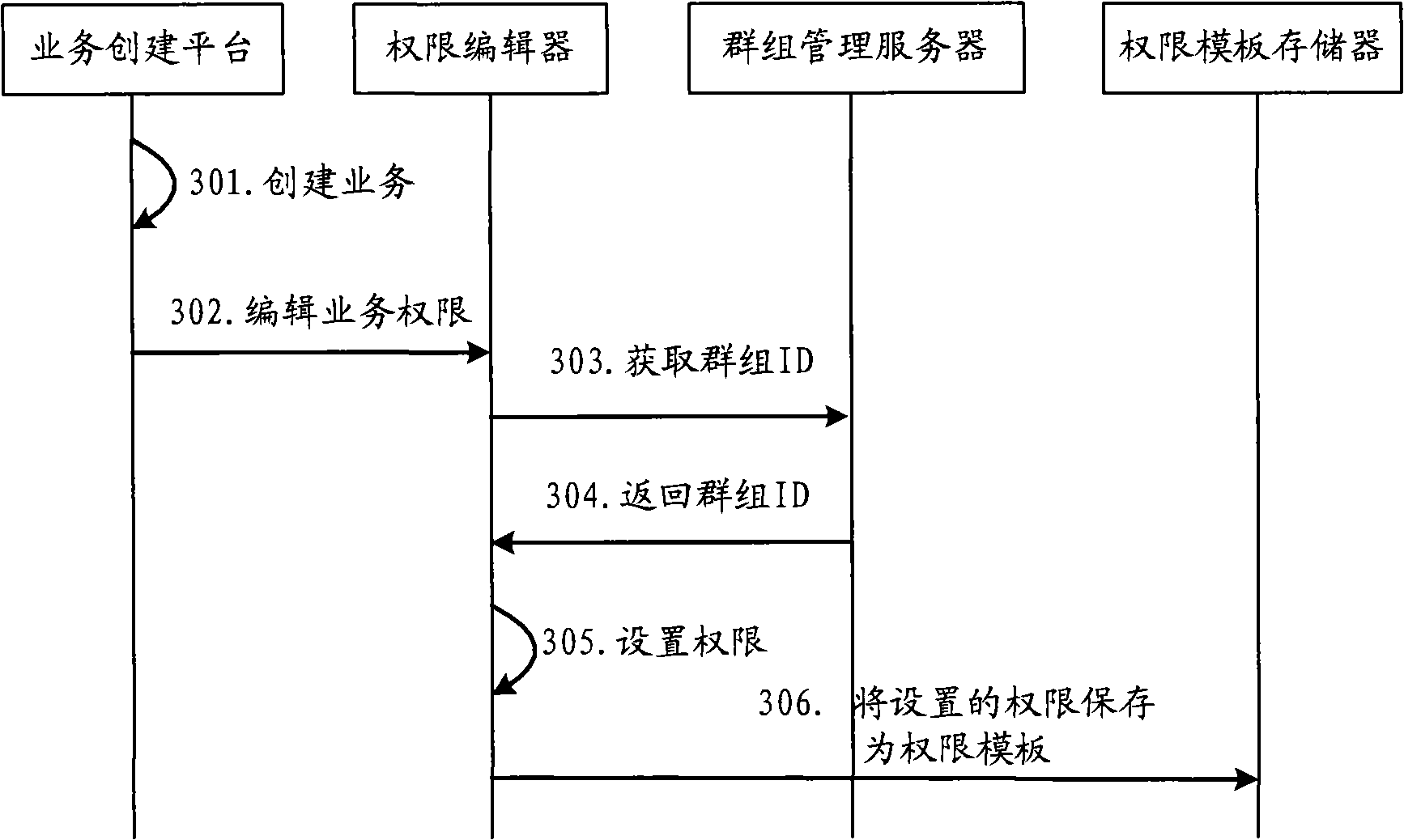
ActiveCN101321306AAdapt to many business typesAdapt to needsSpecial service for subscribersTransmissionBusiness classKnowledge management
Embodiment of the invention provides a method for establishing businesses, comprising: a right editor obtains group ID of the business establisher from a group management server to set business access right information for the group ID; the business access right information is regarded as a part of the business description files and saved therein. The invention further provides a method and device for disposing businesses, and a device for establishing businesses. The business establisher may actively preset a right for business access by using embodiment of the invention, adapting a new demand with numerous business types and numerous business users presently, so that the system manager may release from complicated and enormous business right set works to improve efficiency of business issuing operation.
Owner:HUAWEI TECH CO LTD
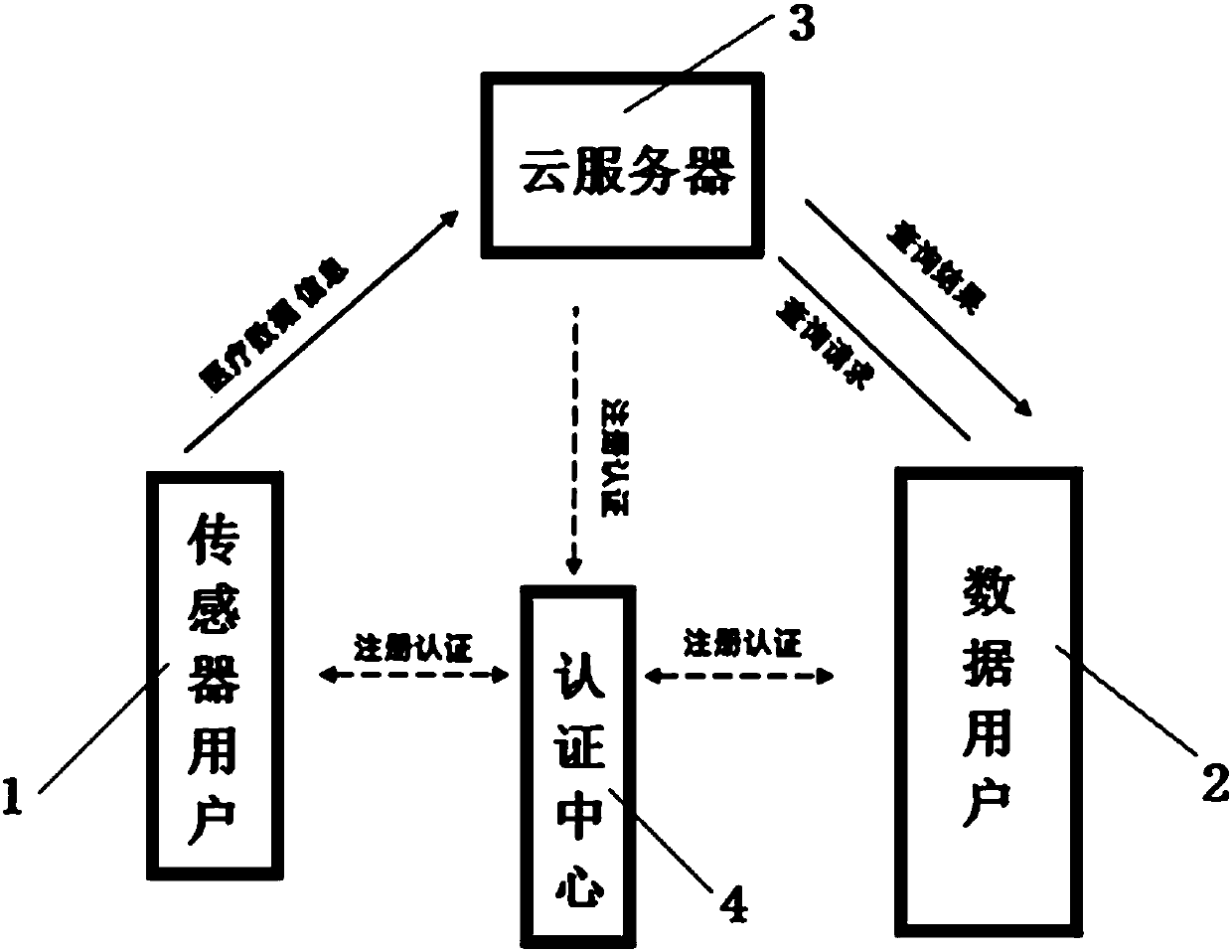
Cloud medical data monitoring system and monitoring method with efficient privacy protection function
ActiveCN106650205AProtect personal privacyEfficient queryTelemedicineSpecial data processing applicationsCiphertextData information
The invention discloses a cloud medical data monitoring system with an efficient privacy protection function, and a cloud medical data monitoring method with the efficient privacy protection function. The monitoring system comprises a sensor user used for providing medical data information, a data user used for querying the medical data information, a cloud server used for receiving a query request of the data user and sending the medical data information of the sensor user to the data user, and an authentication center used for performing registration authentication on the sensor user, the data user and the cloud server, wherein the sensor user encrypts the medical data information through encoding and uploads the encrypted medical data information to the cloud server; the cloud server directly performs query and vital sign situation analysis on a ciphertext without decrypting data; and the data user decrypts the ciphertext through a secret key and reads a query result. The monitoring method comprises five stages of system establishment, user registration, data acquisition, query request generation and query result returning. According to the system and the method, a ciphertext data query function is realized through encoding, and reliability and high efficiency are achieved.
Owner:XIDIAN UNIV
Monitoring front end and terminal, monitoring system as well as audio/video signal encryption and decryption methods
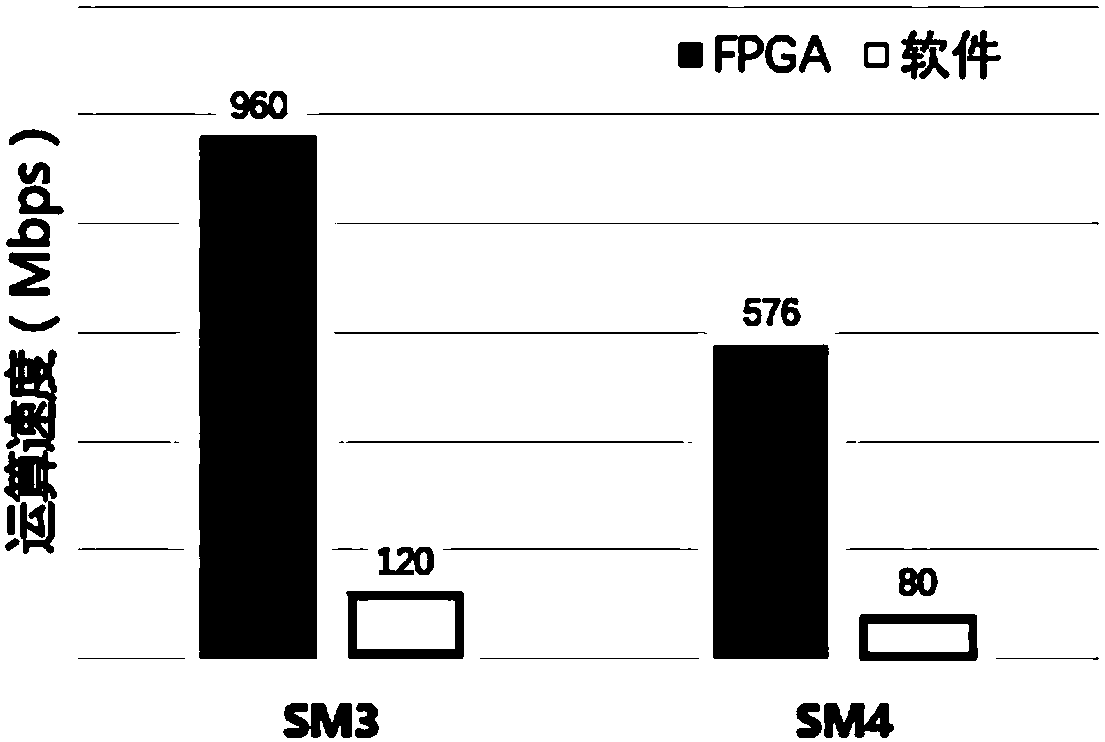
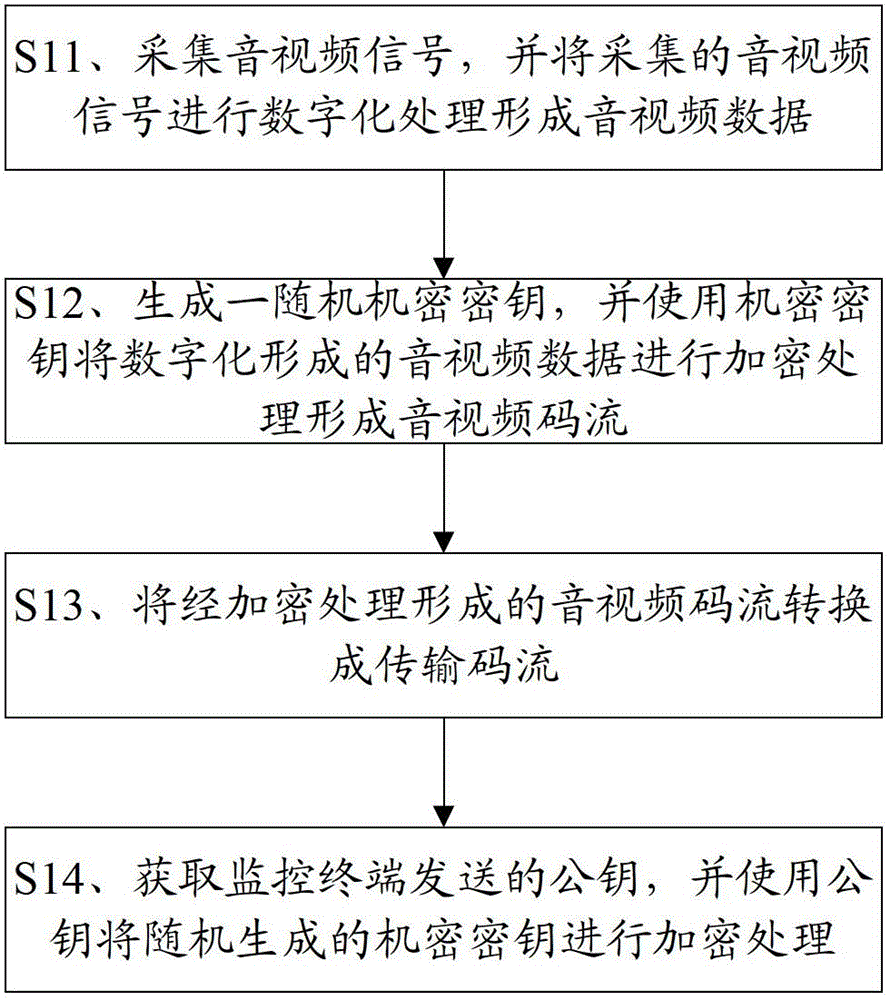
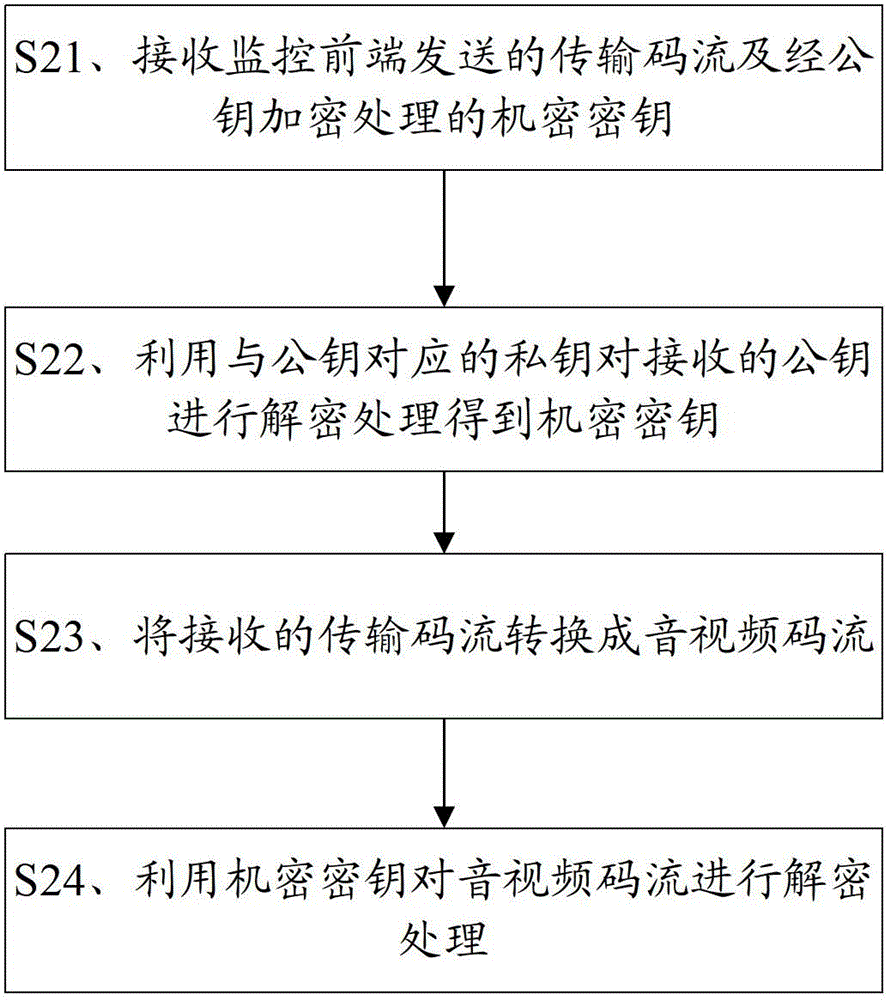
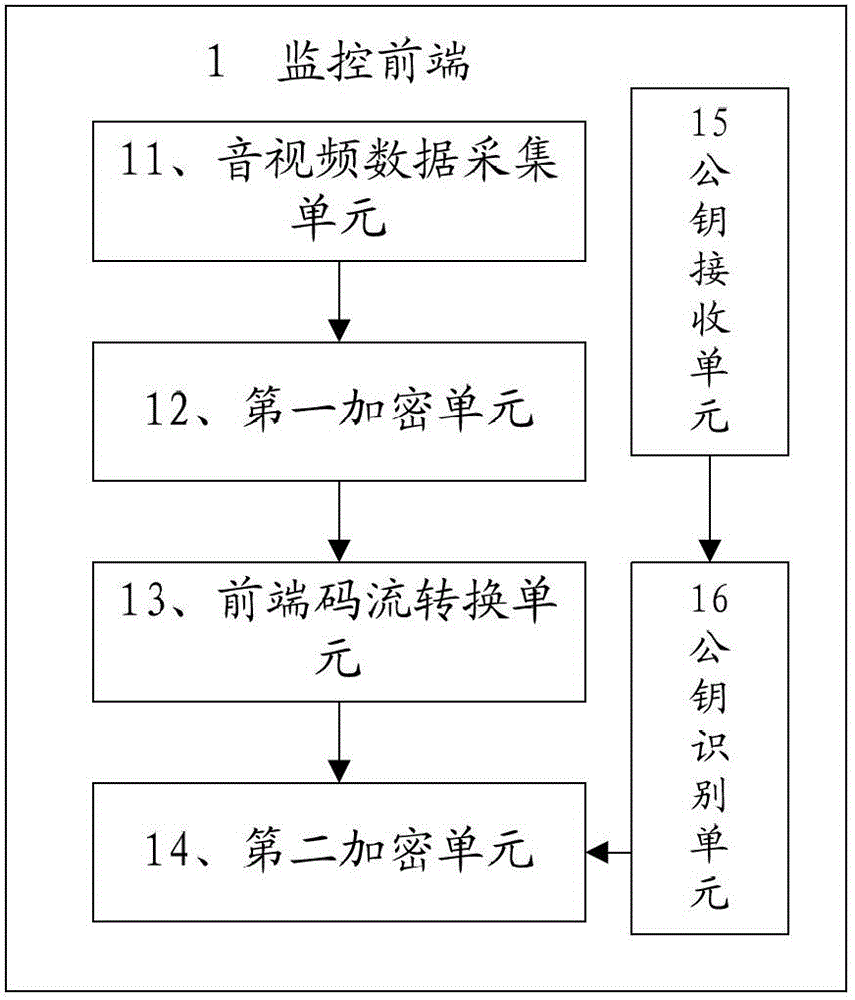
InactiveCN102724563AProtect personal privacyImproved personal privacyClosed circuit television systemsSelective content distributionMonitoring systemEncryption
The invention provides a monitoring front end and a terminal, a monitoring system as well as audio / video signal encryption and decryption methods. The audio / video signal encryption method comprises the following steps of: S11, collecting a video signal, and carrying out digital processing on the collected audio / video signal so as to form audio / video data; S12, generating a random private and confidential key, and utilizing the private and confidential key to carry out encryption treatment on the audio / video data formed by digitalization so as to form audio / video code stream; S13,converting the audio / video code current formed by the encryption treatment into transmission code current; and S14, obtaining a public key sent by a monitoring terminal, and utilizing the public key to carry out encryption treatment on the private and confidential key on the randomly generated private and confidential key. The audio / video signal encryption method provided by the invention can improve the safety feature of the whole monitoring system, and the privacy of users can obtain farthest protection.
Owner:SHENZHEN VIHI VISION TECH
Personal information protection method for handset
InactiveCN1477890AImprove protectionProtect personal privacyRadio/inductive link selection arrangementsSecurity arrangementElectricityComputer science
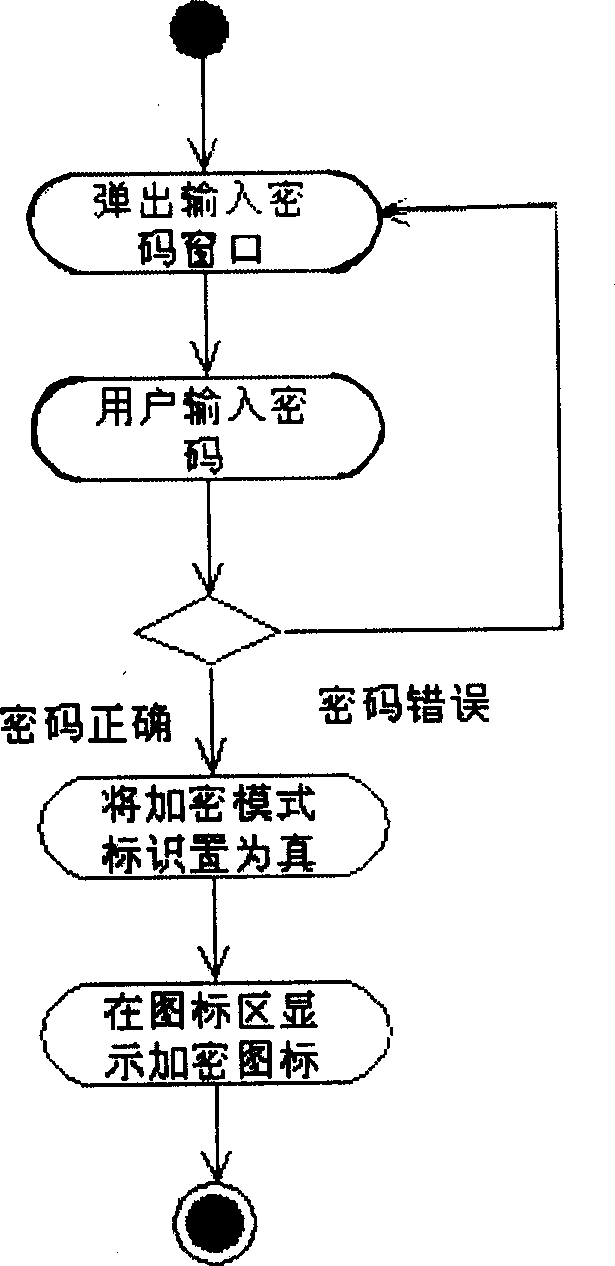
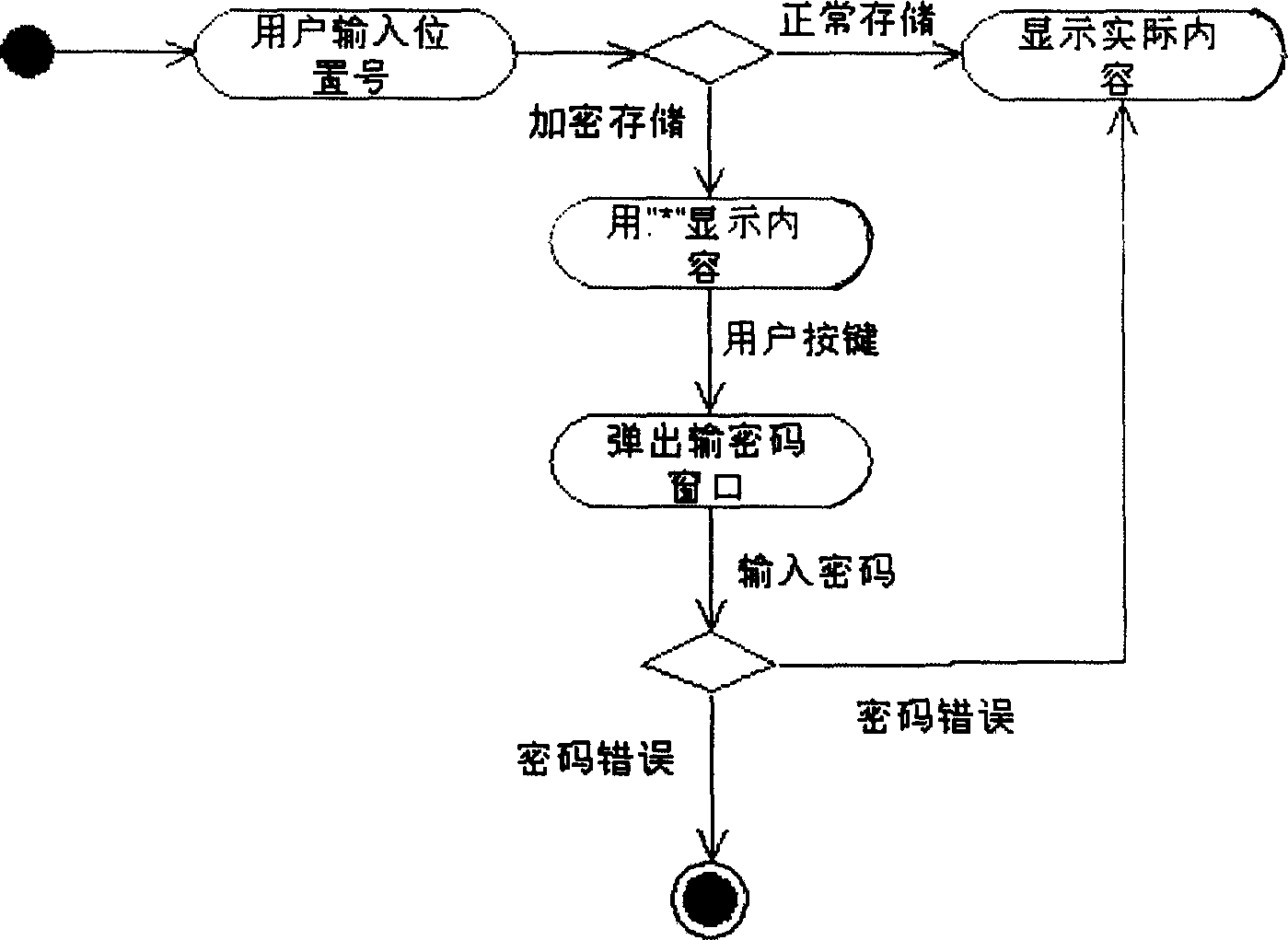
The present invention relates to a personal information protection method for hand set, belonging to the field of mobile communication technology. The method mainly includes the following steps: adopting encryption technique to produce enciphering mode and define hand set cipher code, adding submenu with enciphering mode on the management menu, setting commitment function and identification valuefor enciphering mode and adding restricted function for telephone dictionary, etc. The invention can be extensively in hand set and other mobile communication terminals.
Owner:HISENSE +1
Human body action function detection system, detection method and detector
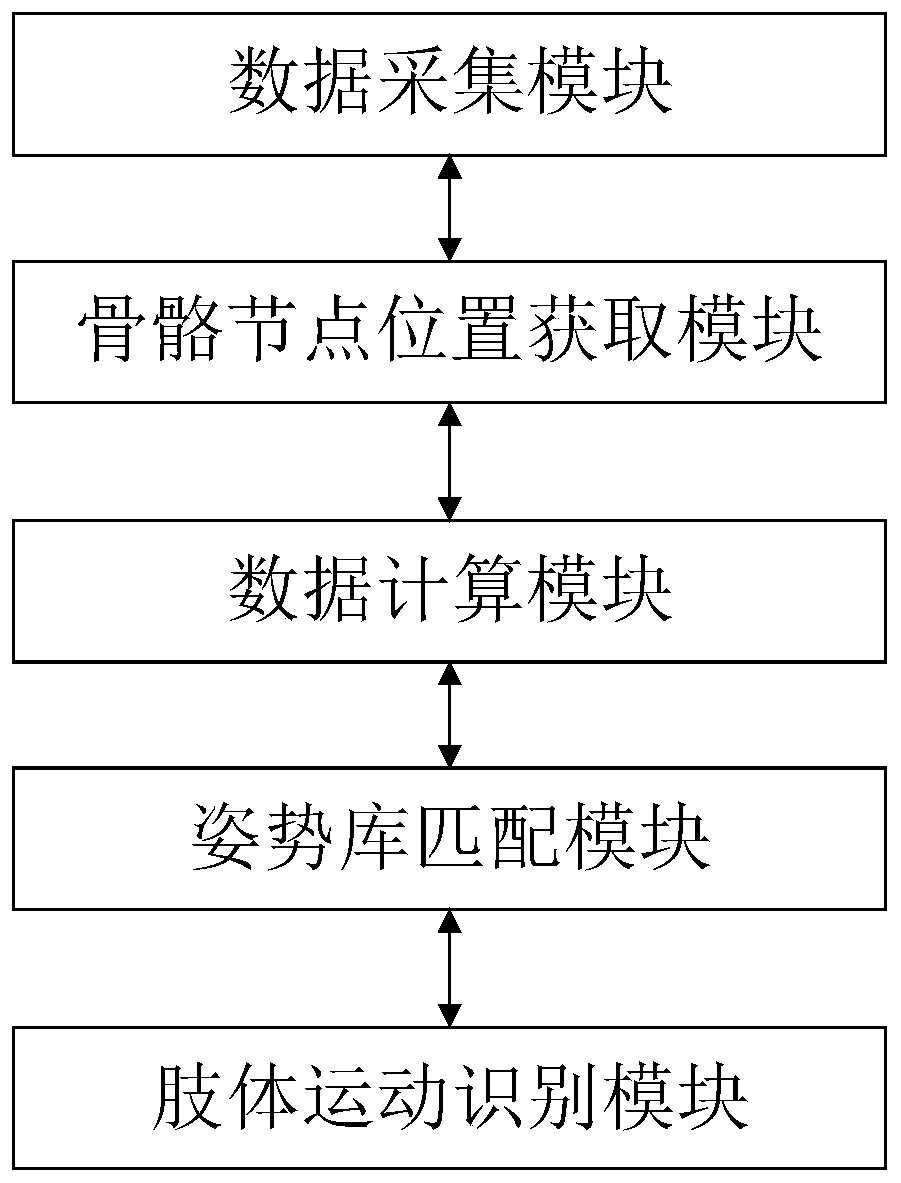
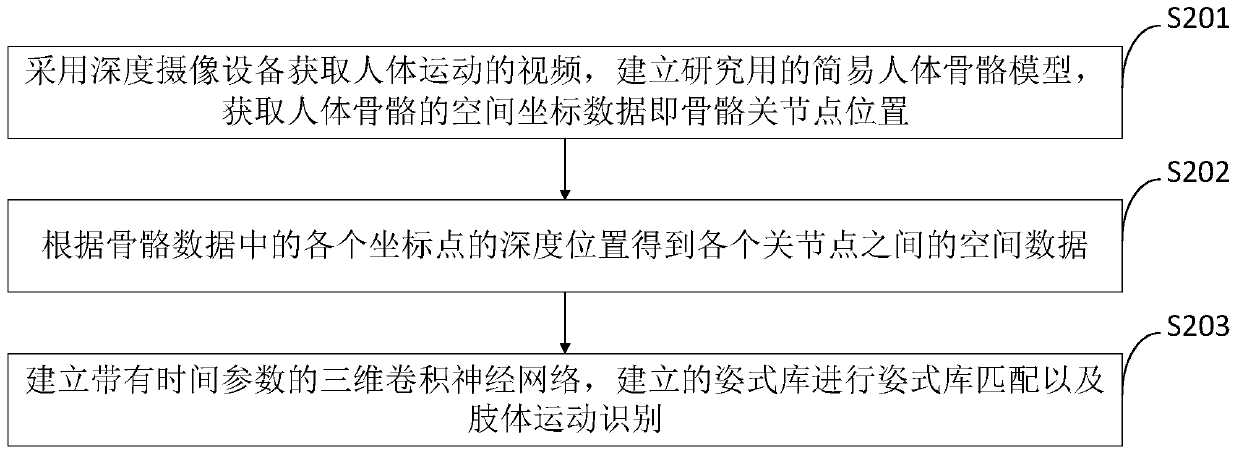
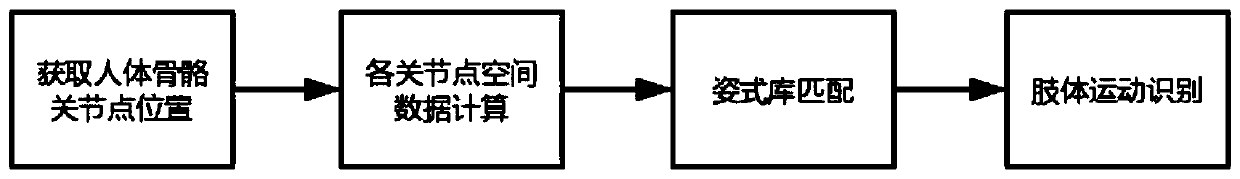
ActiveCN110969114AProtect personal privacyImprove accuracyImage enhancementImage analysisHuman bodyData acquisition
The invention belongs to the technical field of human body data identification, and discloses a human body action function detection system, a detection method and a detector. A data acquisition module adopts depth camera equipment to acquire a human body motion video; a skeleton node position acquisition module is used for establishing a simple human skeleton model for analysis and acquiring spatial coordinate data of human skeletons; a data calculation module is used for obtaining spatial data among the articulation points according to the depth positions of the coordinate points in the skeleton data; a posture library matching module is used for matching the spatial data with a posture library template obtained by performing machine learning on a large number of data samples; and a limbmovement recognition module is used for limb recognition. According to the invention, synchronous detection of motion data of multiple parts in functional action detection such as deep squatting by lifting hands, three-dimensional forward bending and lateral bending of a standing person is creatively realized, and quantification of functional action detection data is realized.
Owner:四川省骨科医院 +1
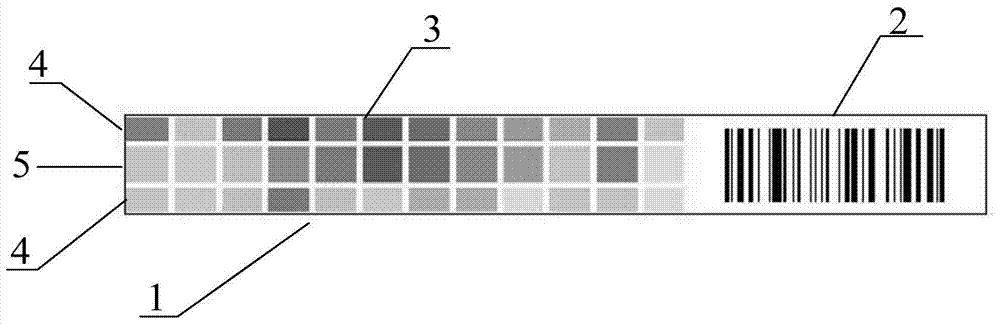
Novel test paper strip as well as preparation and application thereof
ActiveCN103926241AImprove accuracyMeet testing needsMaterial analysis by observing effect on chemical indicatorPulp and paper industryModel Number
The invention provides a novel test paper strip as well as preparation and application of the novel test paper strip. The preparation comprises the following steps: A, preparing a base plate with the corresponding size; B, coating the base plate with a test paper plate which is matched with the base plate and contains reaction chemicals; C, printing bar codes on the base plate, wherein information of the bar codes comprises the modes of the test paper strips, true and false information, and the cis-trans states of the strips; and judging the cis-trans states by scanning the bar codes by a phone App; D, coloring the base plate, wherein the colors are colors with the standard values; E, cutting the test paper plate along small square blocks coated with glue, wherein only the test paper plate is cut and the base plate is not cut; and rotating and blowing off the test paper plate which is not coated with the glue by wind; and F, cutting the base plate along lines among the bar codes so as to obtain the test paper strip. By adopting the scheme, the accuracy that an intelligent phone directly scan and read color data can be improved greatly, so that the practicability of phone applications can meet the detection requirements.
Owner:广东派特埃尔生物科技有限公司
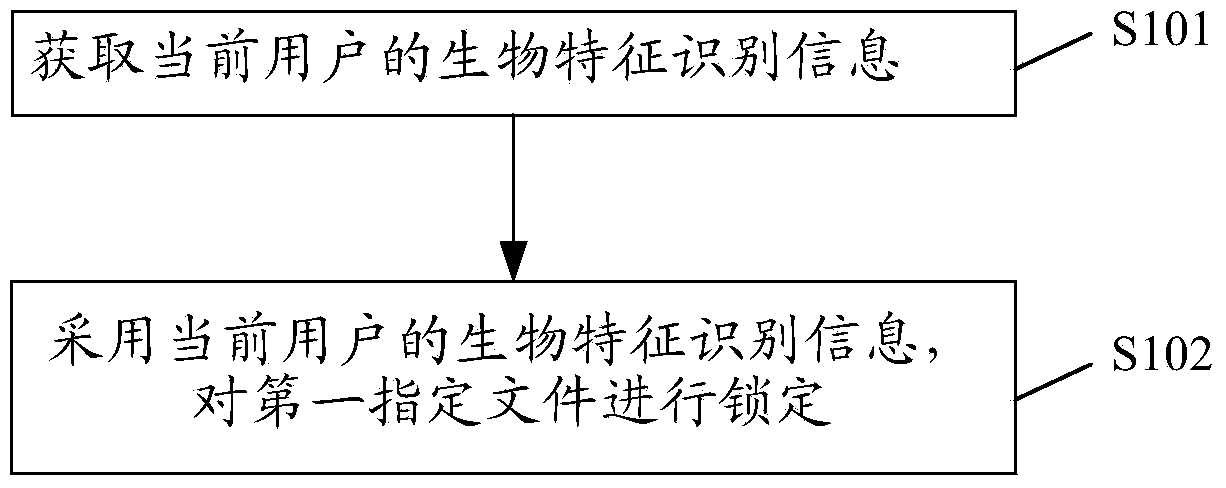
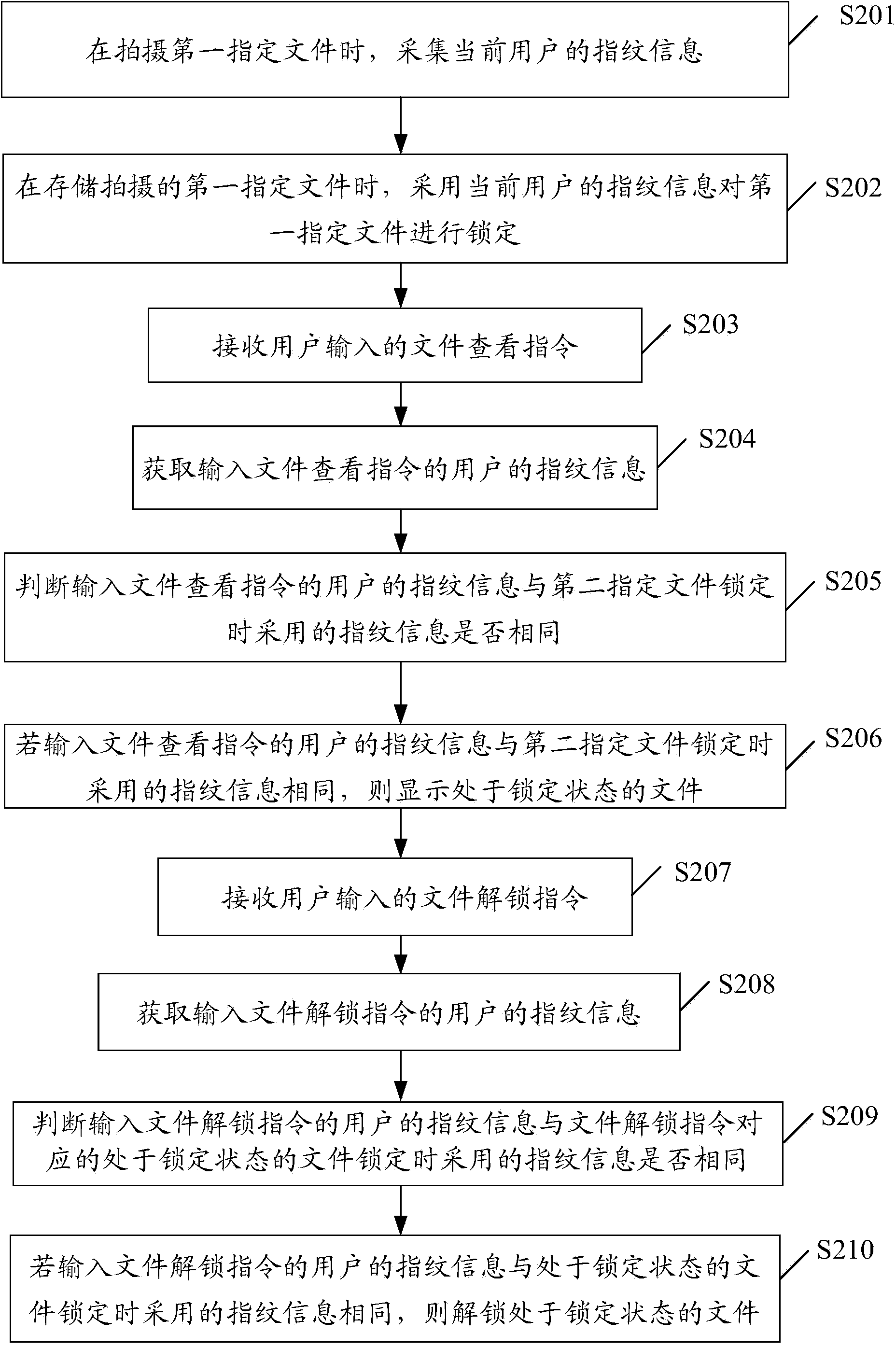
File locking method and device
InactiveCN104112091AProtect personal privacyImprove experienceDigital data authenticationSpeech recognitionFile lockingComputer science
The invention provides a file locking method and belongs to the technical field of electronic equipment. The file locking method comprises the steps of obtaining biological feature recognition information of a current user, wherein the biological feature recognition information comprises fingerprint information or voice print information or iris information or facial information; locking a first specified file according to the biological feature recognition information of the current user. Because the specified file is locked according to the biological feature recognition information, pictures or videos can be hidden, personal privacy of the current user is effectively protected, and user experience is enhanced. In addition, users can select files for locking according to needs, so that use is very flexible. The invention further provides a file locking device.
Owner:XIAOMI INC
Intelligent control system for nursing bed
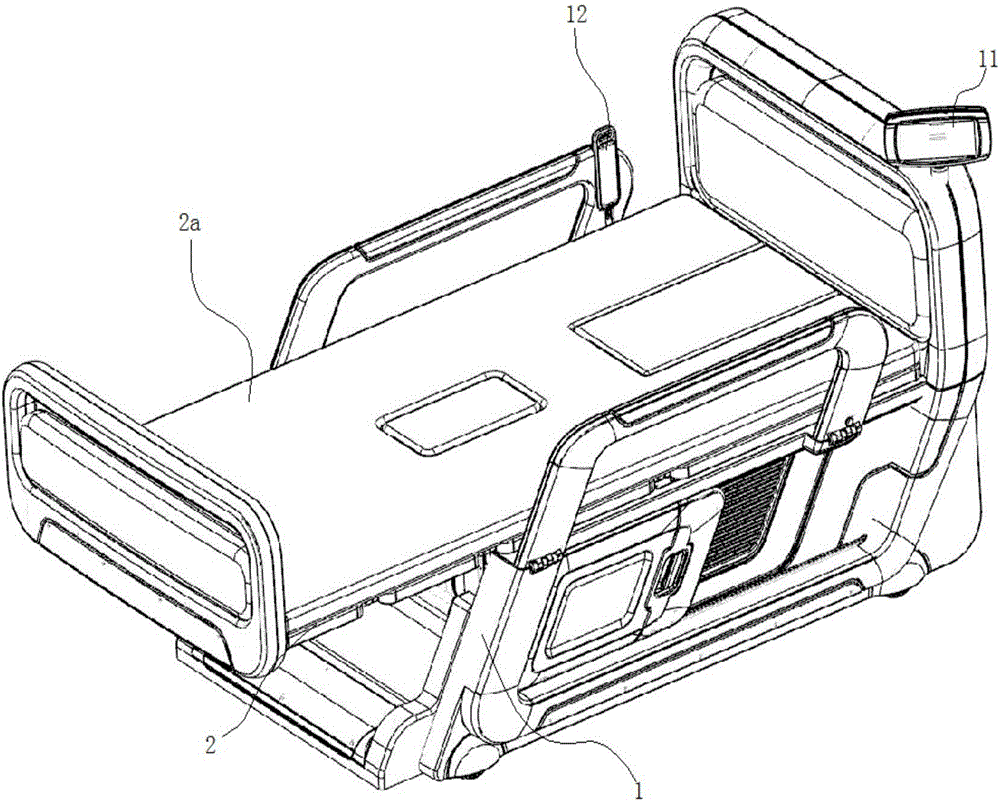
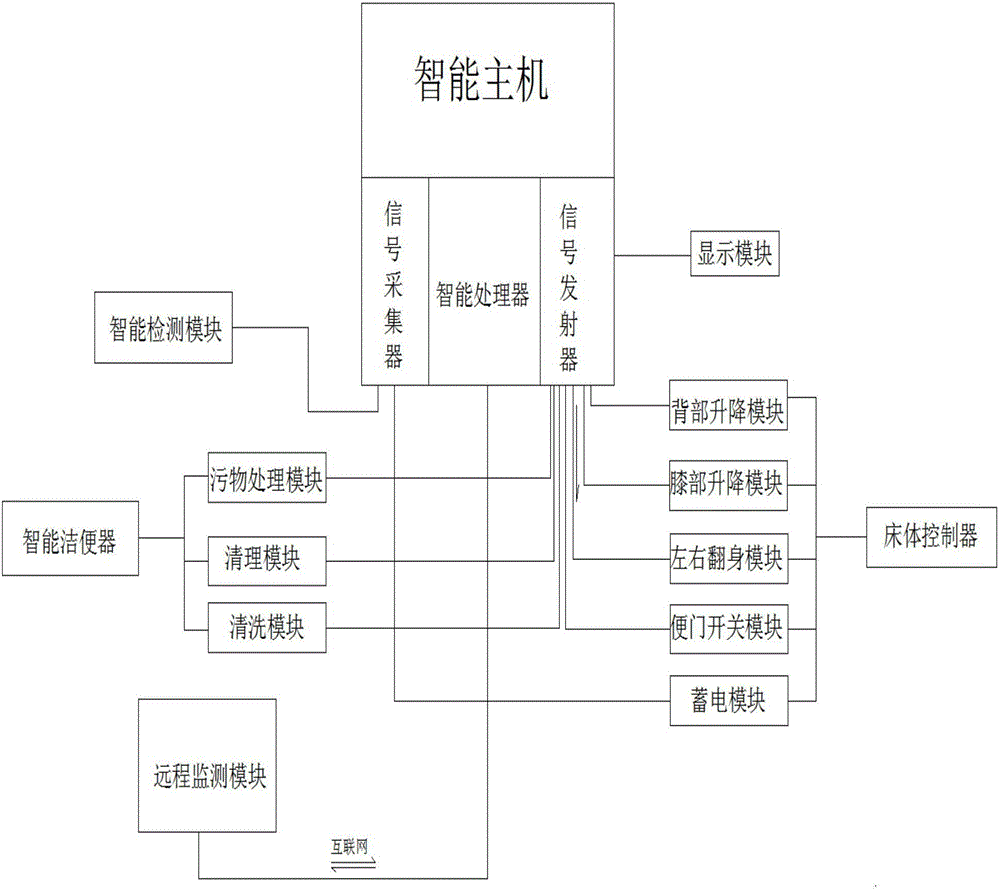
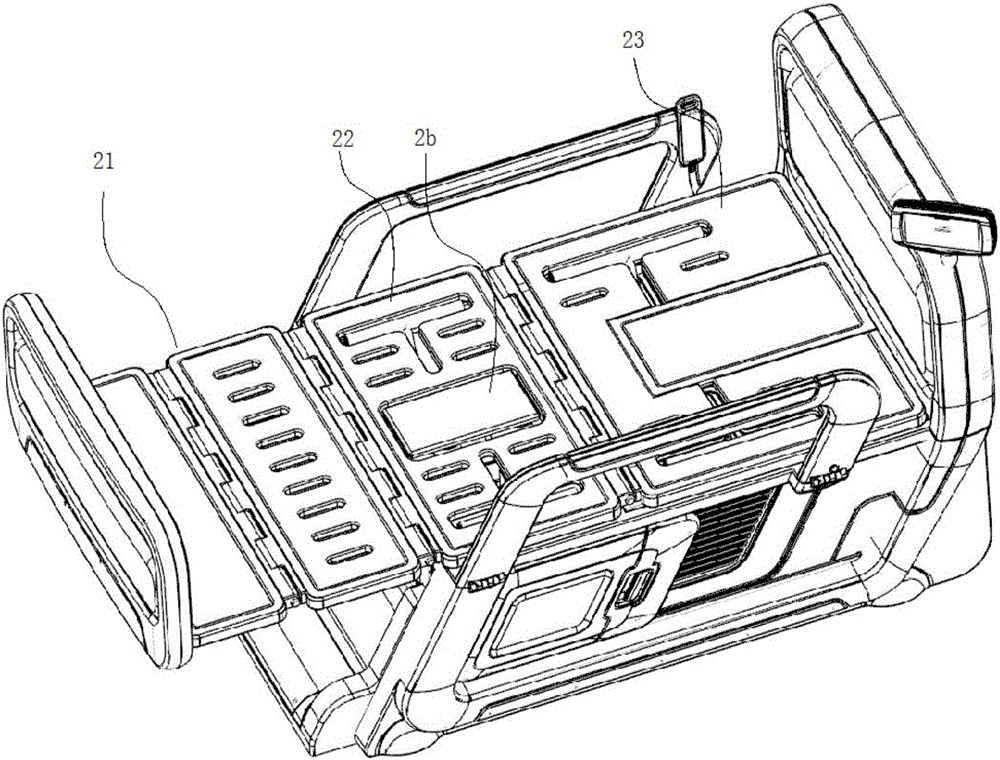
The invention relates to the technical field of medical apparatuses, in particular to an intelligent control system for a nursing bed. The intelligent control system comprises a bed body controller for controlling motion of a bed body, an intelligent anus cleaner for controlling an intelligent closestool to work, and an intelligent detection module for detecting the motion state of the bed body of the nursing bed and the intelligent closestool; and the bed body controller, the intelligent anus cleaner and the intelligent detection module are fed-back and driven by virtue of an intelligent host. The intelligent control system disclosed by the invention is convenient to operate, and the intelligent control system has the capacities of achieving intelligent management and constant monitoring.
Owner:浙江强鹰科技股份有限公司
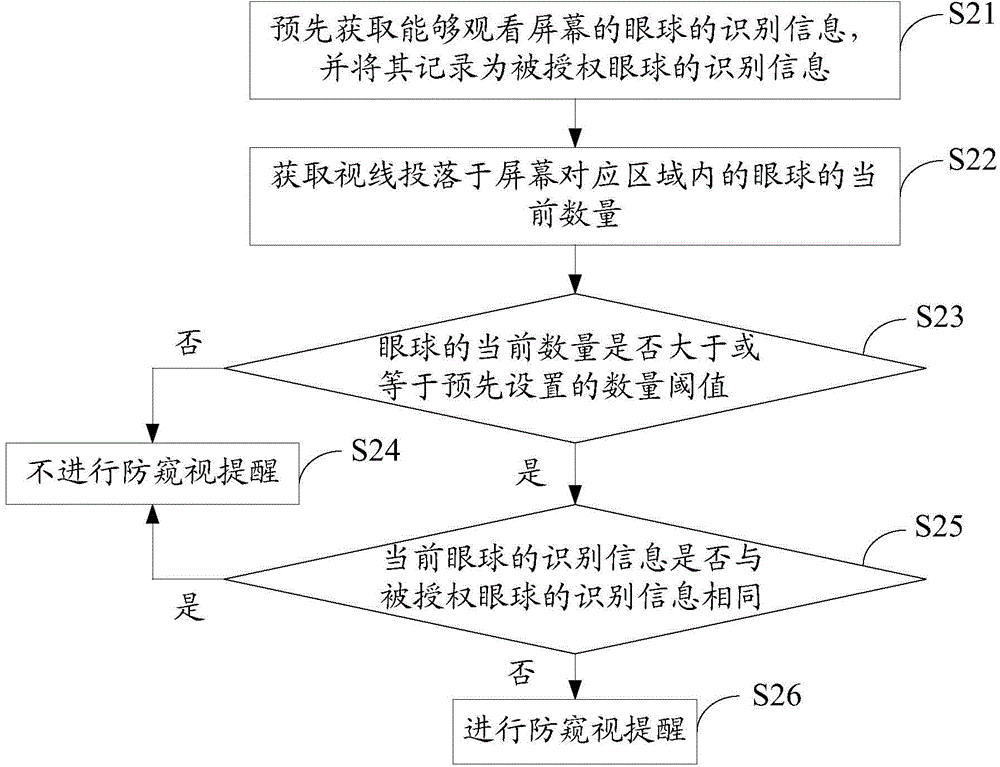
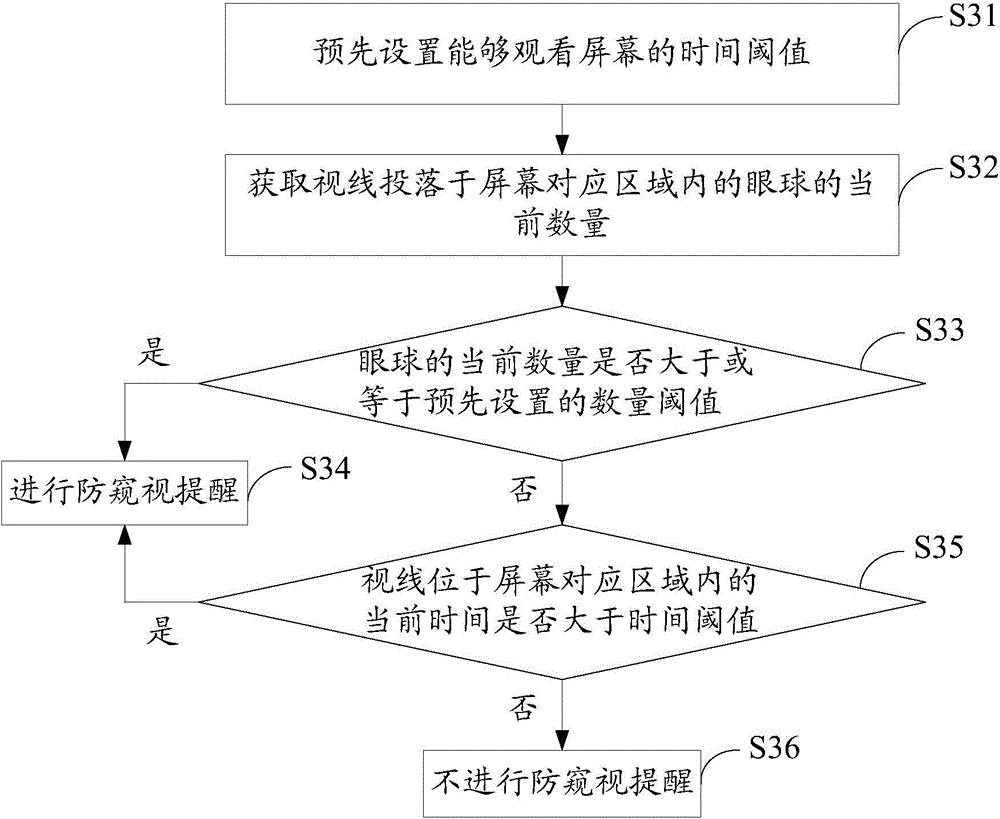
Peep prevention method and device for screen
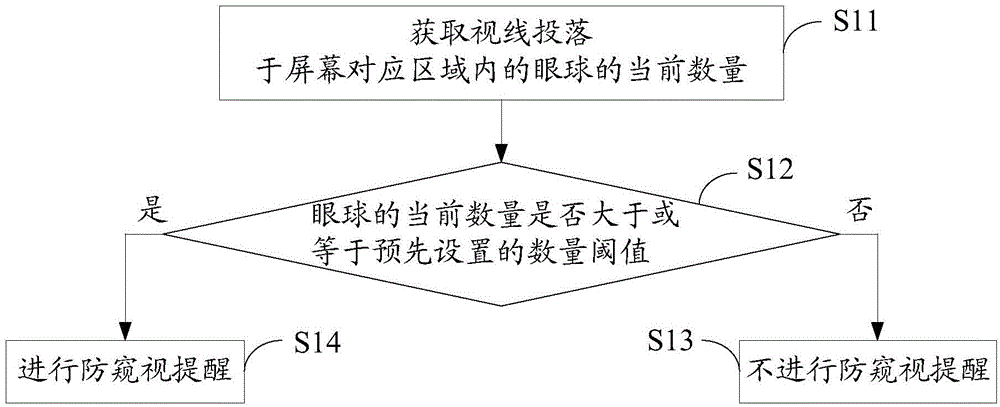
InactiveCN104463041AProtect personal privacyPrevent peepingInternal/peripheral component protectionEmergency medicineComputer terminal
The invention provides a peep prevention method and device for a screen. The peep prevention method for the screen includes the steps that the current number of eyeballs with the sight lines falling into a corresponding area of the screen is acquired; whether the current number is larger than a preset number threshold value or not is judged, and the number threshold value represents the number of the eyeballs capable of watching the screen when the privacy is protected; if the current number is larger than the number threshold value, peep prevention reminding can be conducted. By the adoption of the mode, the ambient environment of a display terminal can be monitored, peep prevention reminding can be conducted when it is monitored that the content displayed by the screen of the display terminal is likely to be peeped, and therefore the personal privacy can be effectively protected.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com