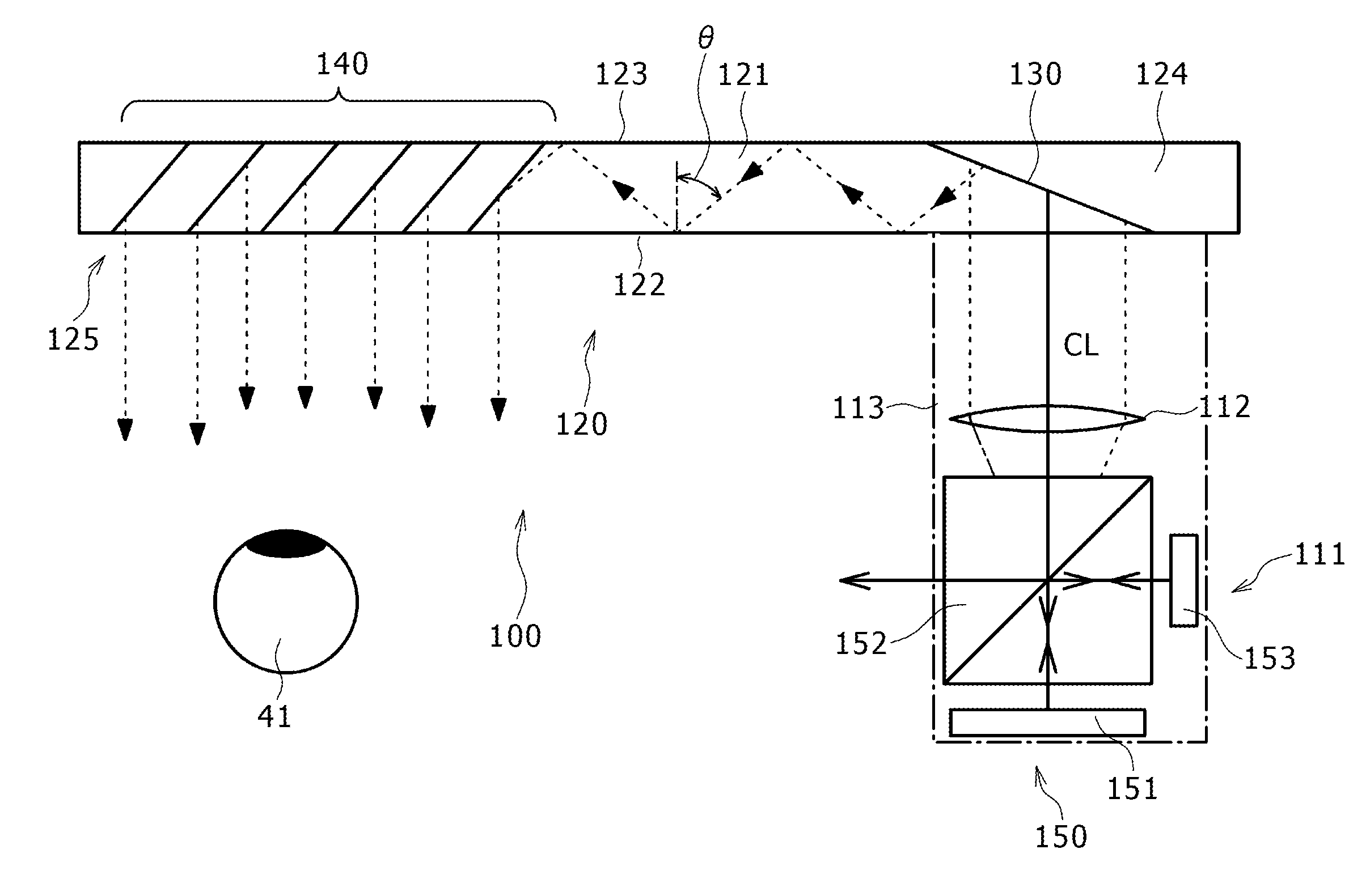
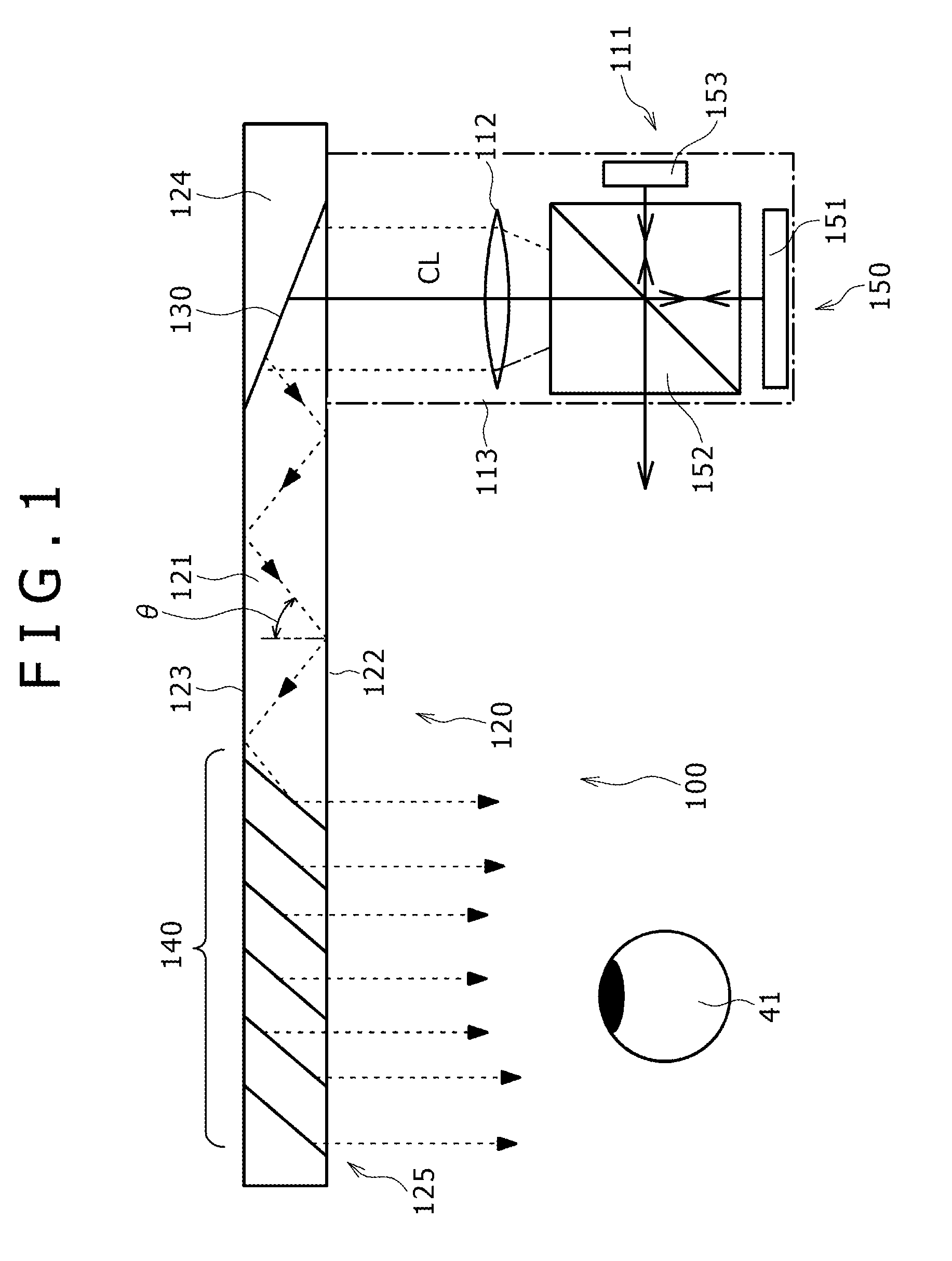
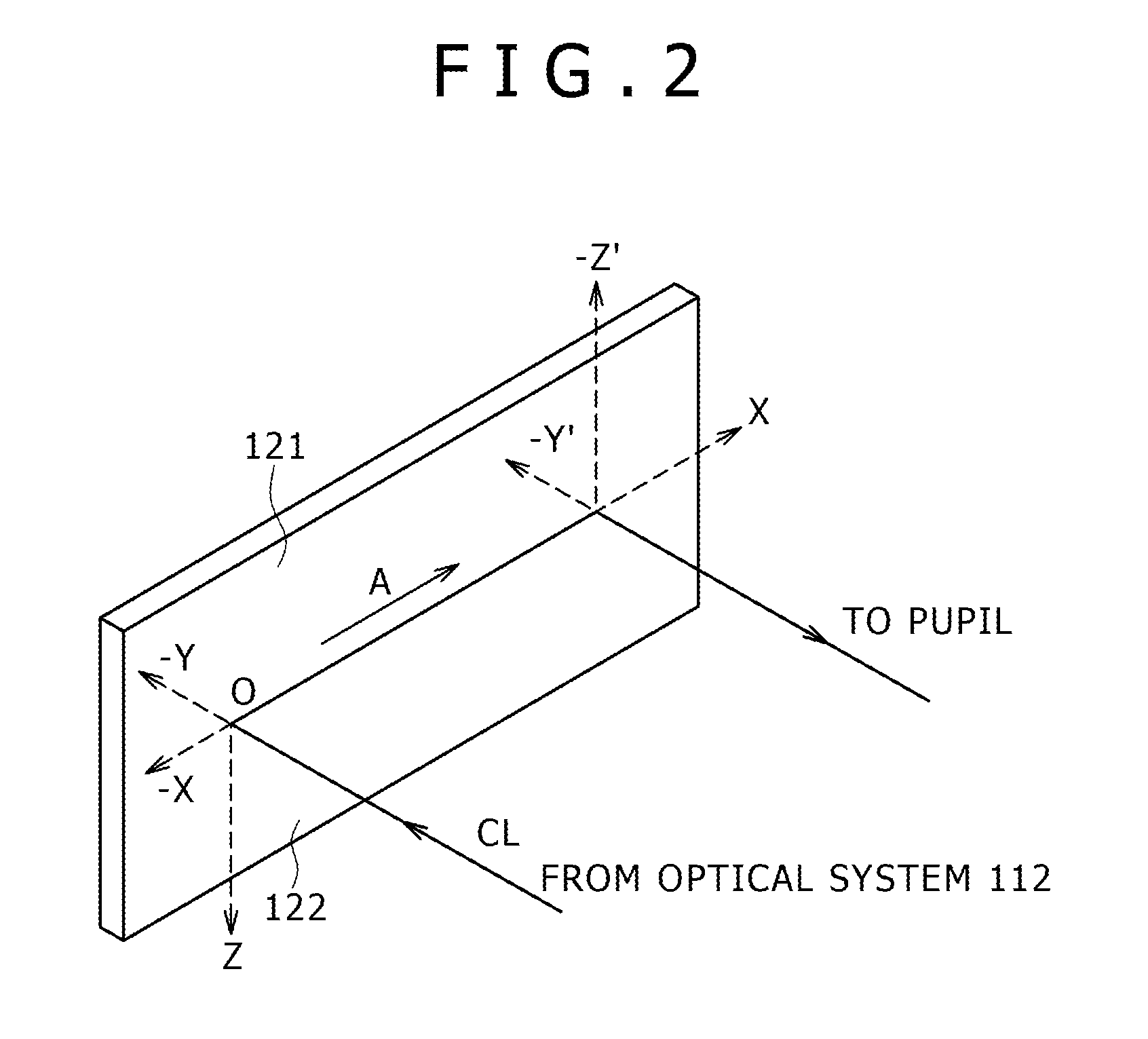
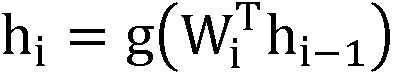Patents
Literature
2338 results about "Data identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
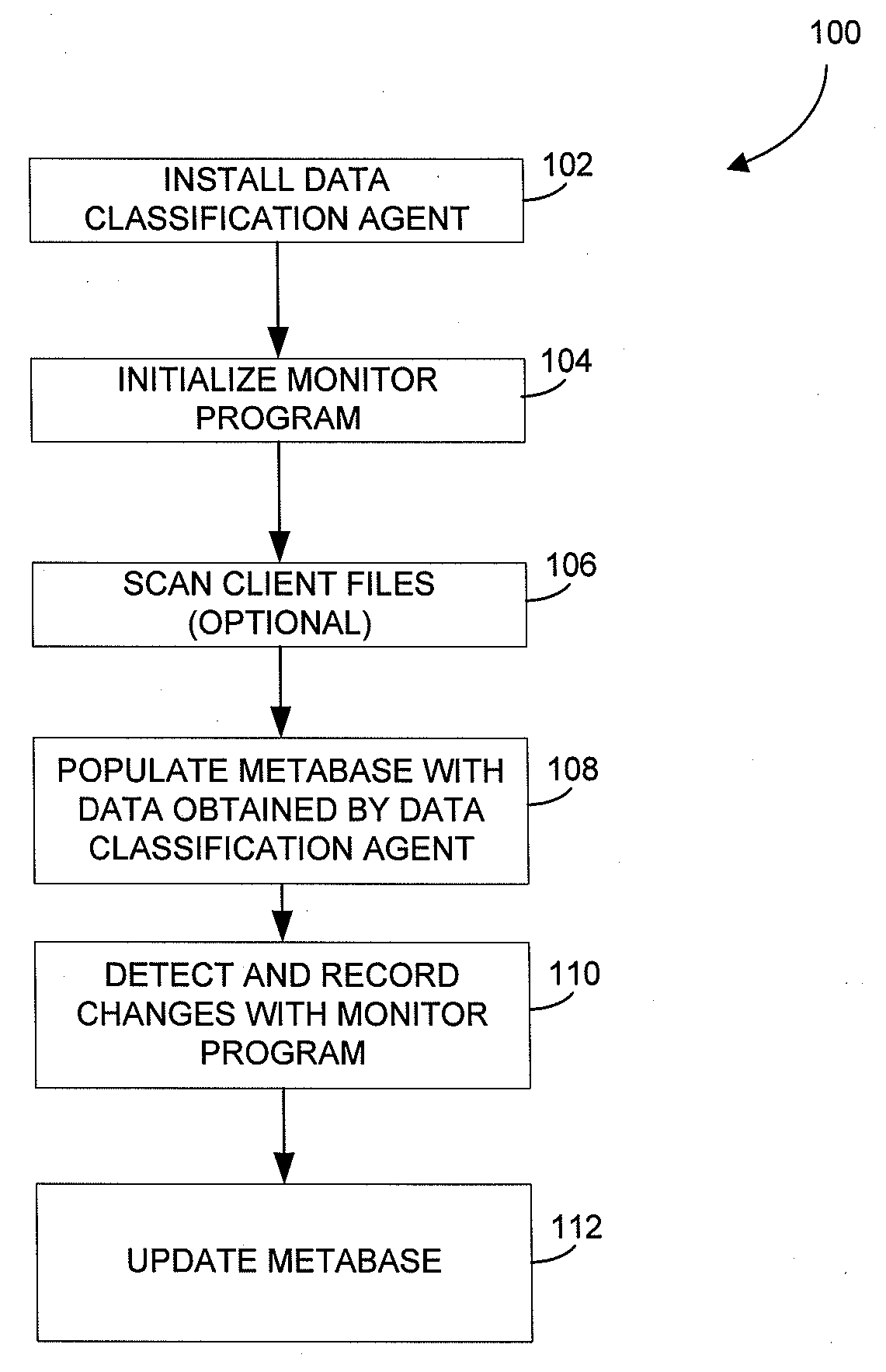
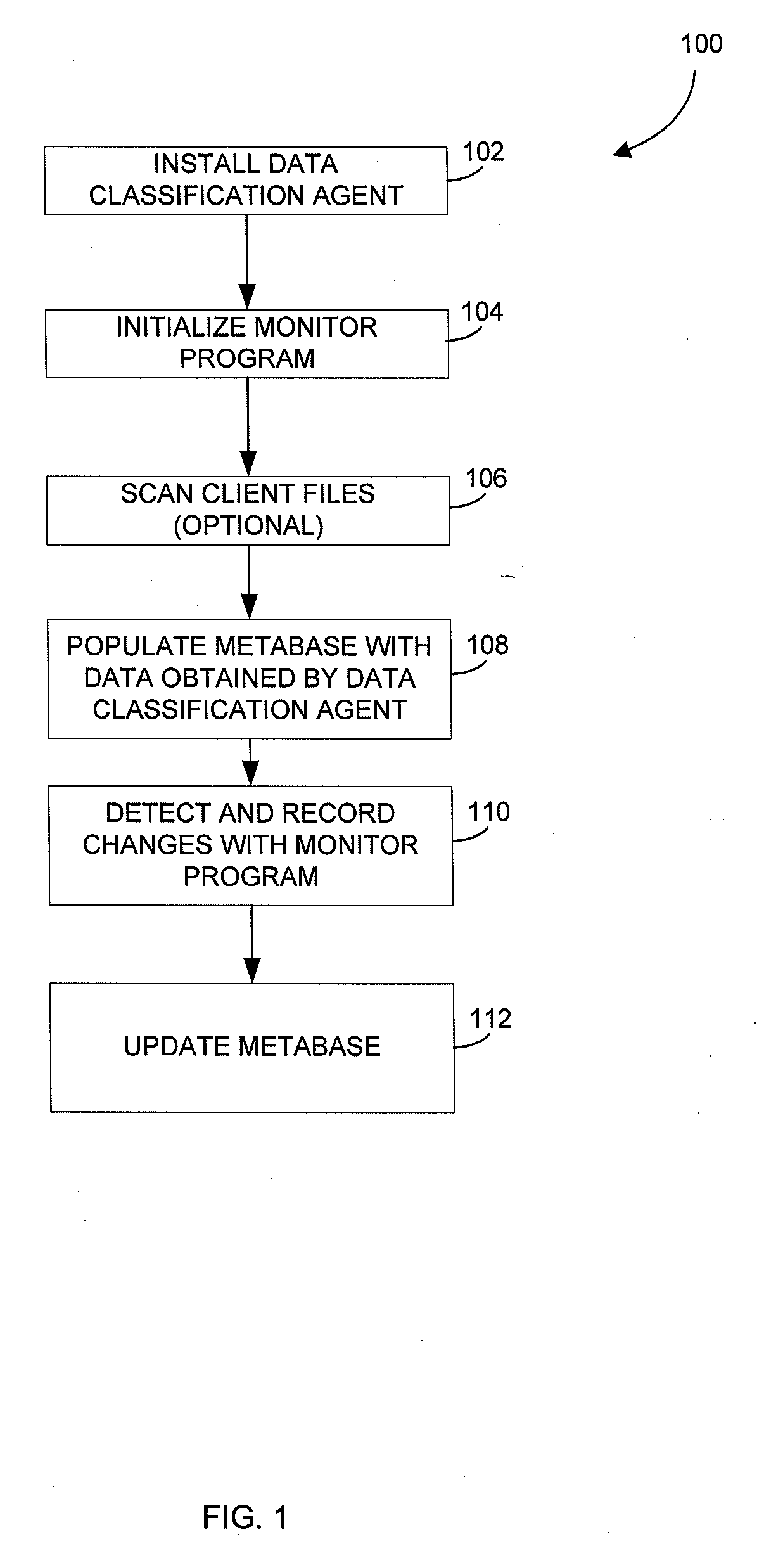
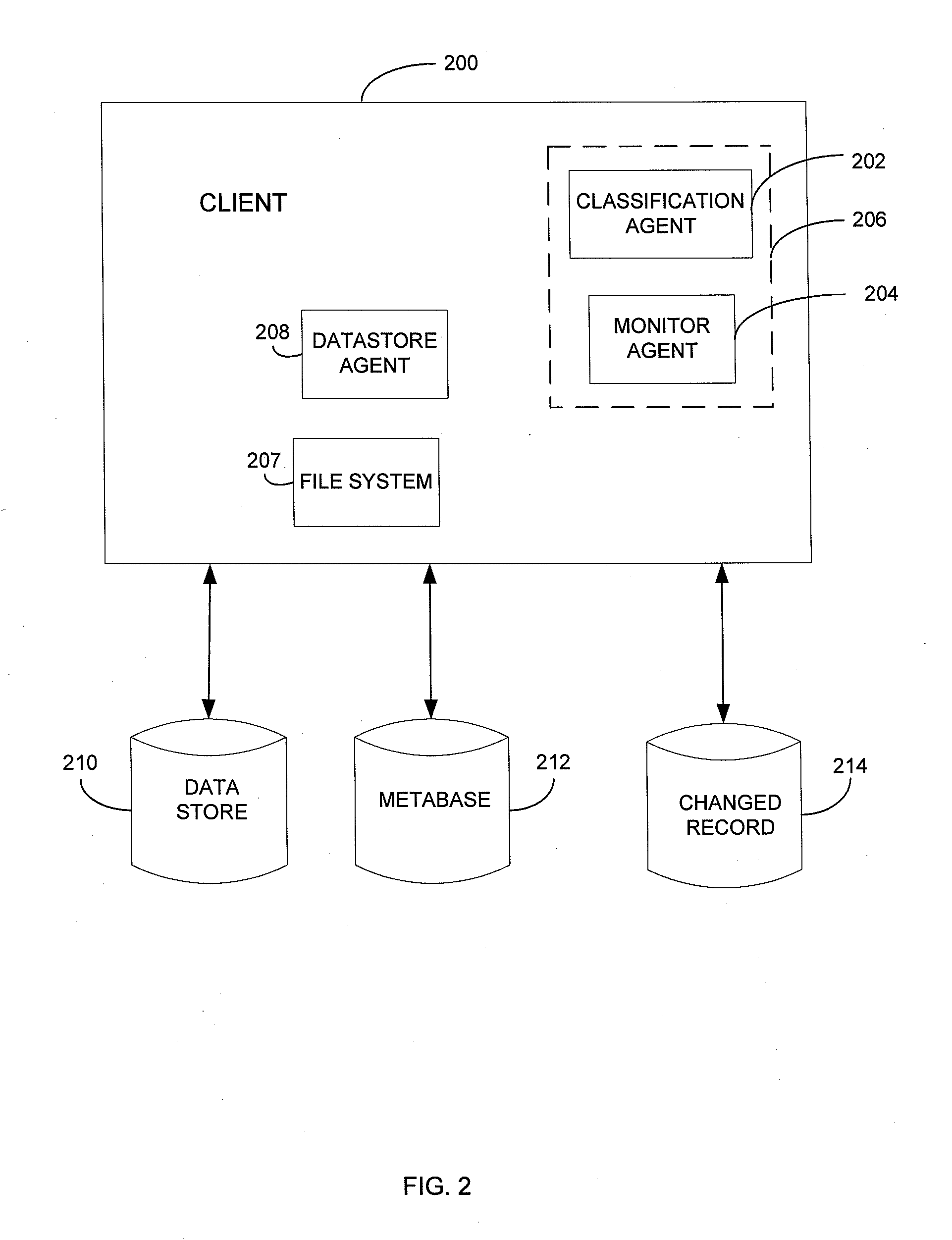
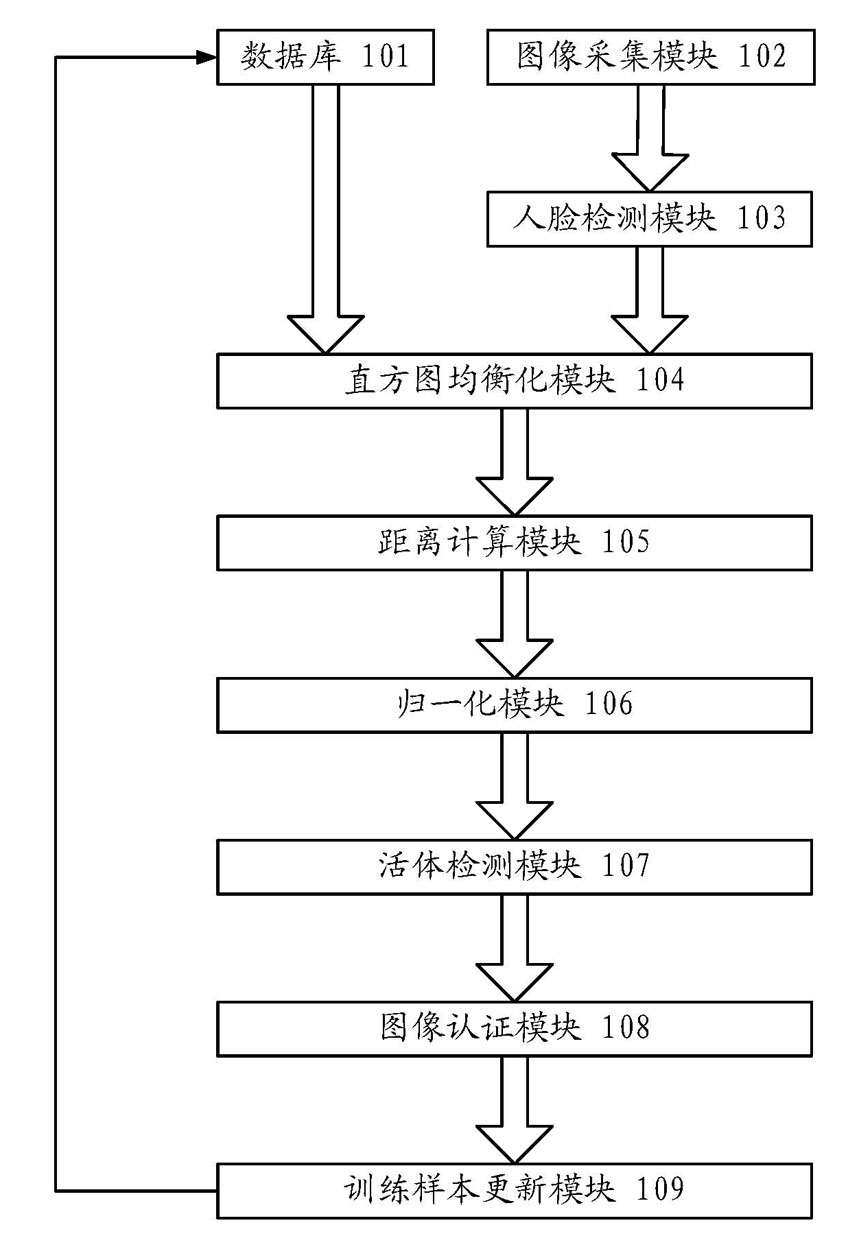
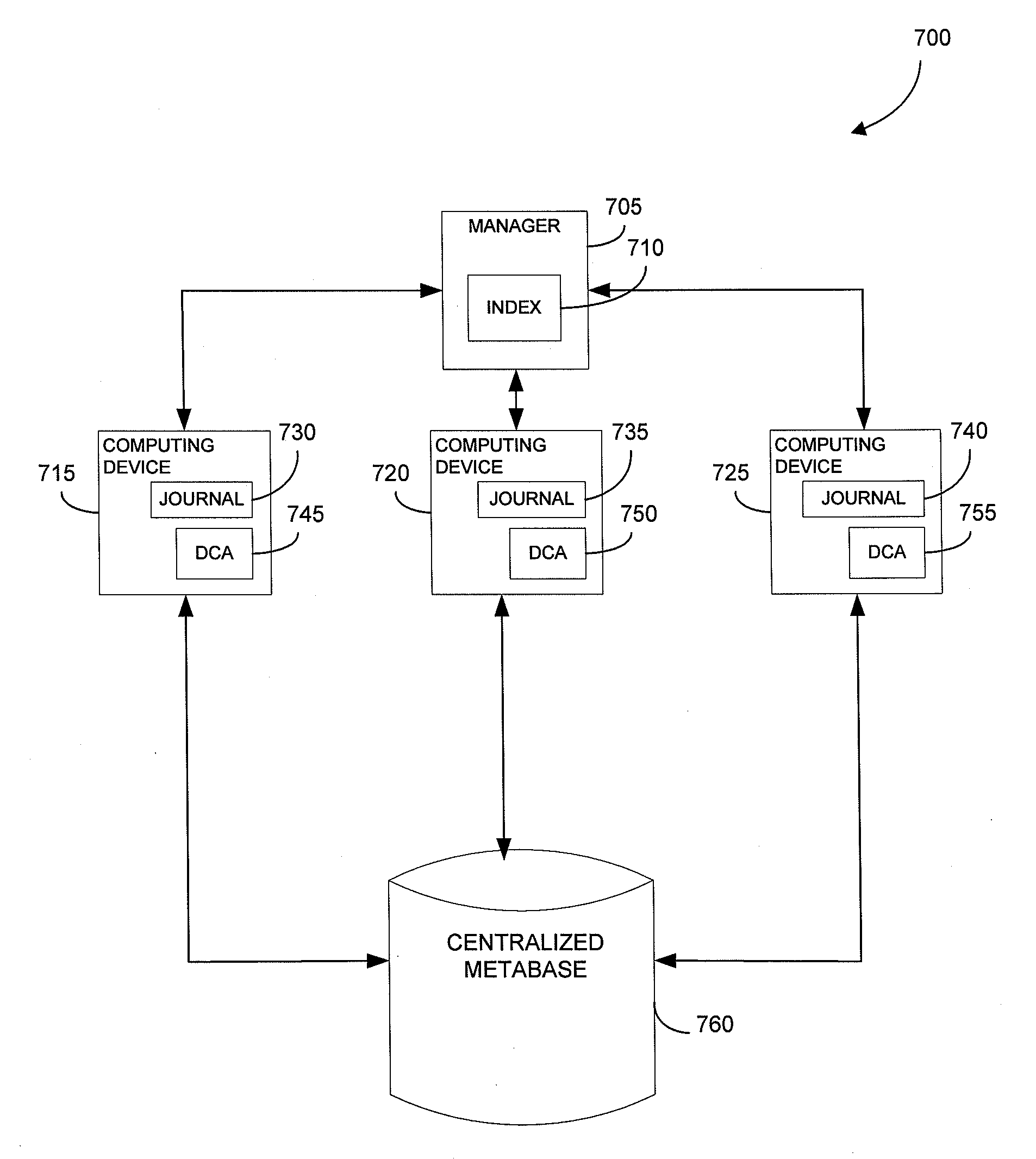
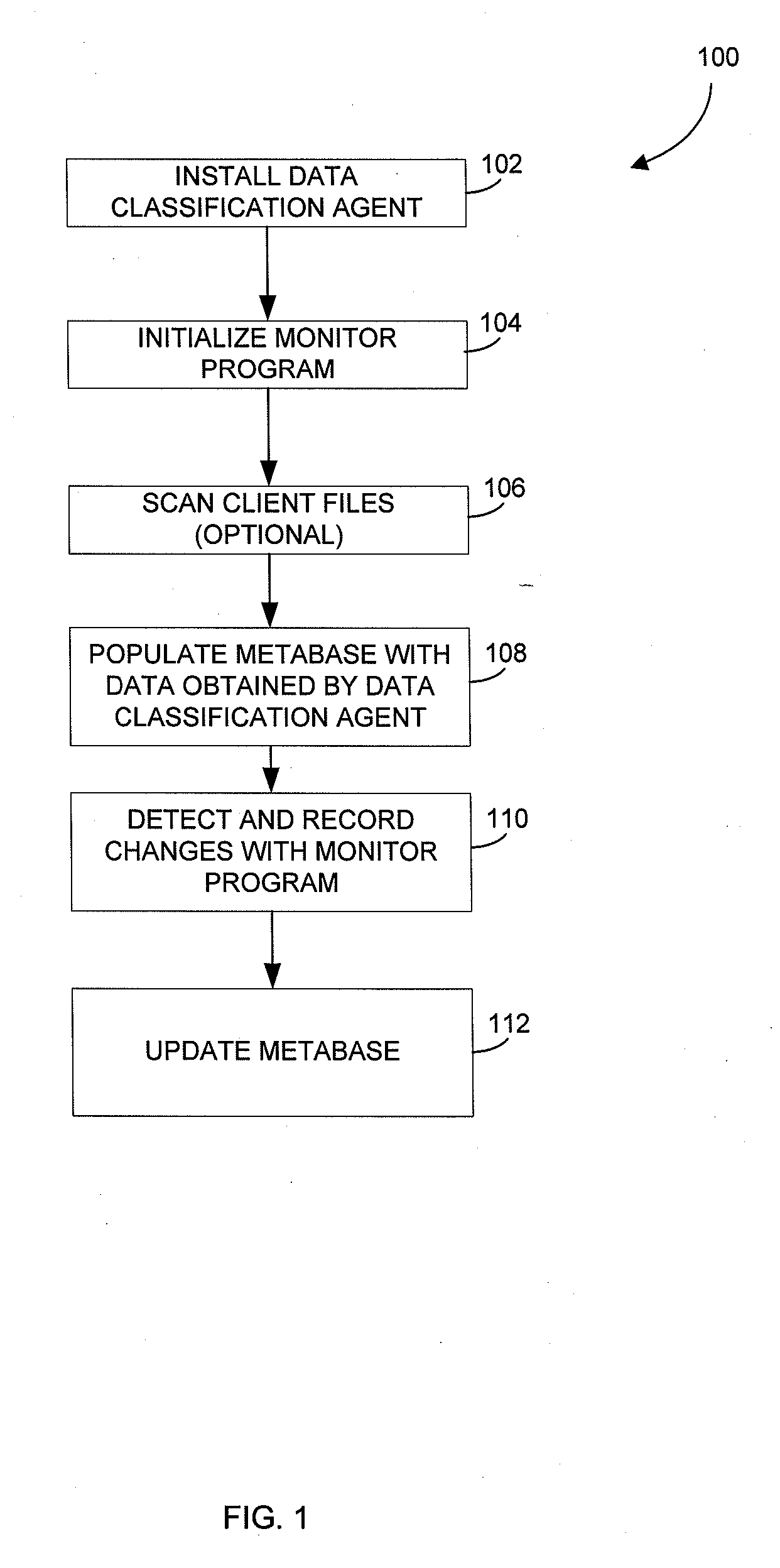
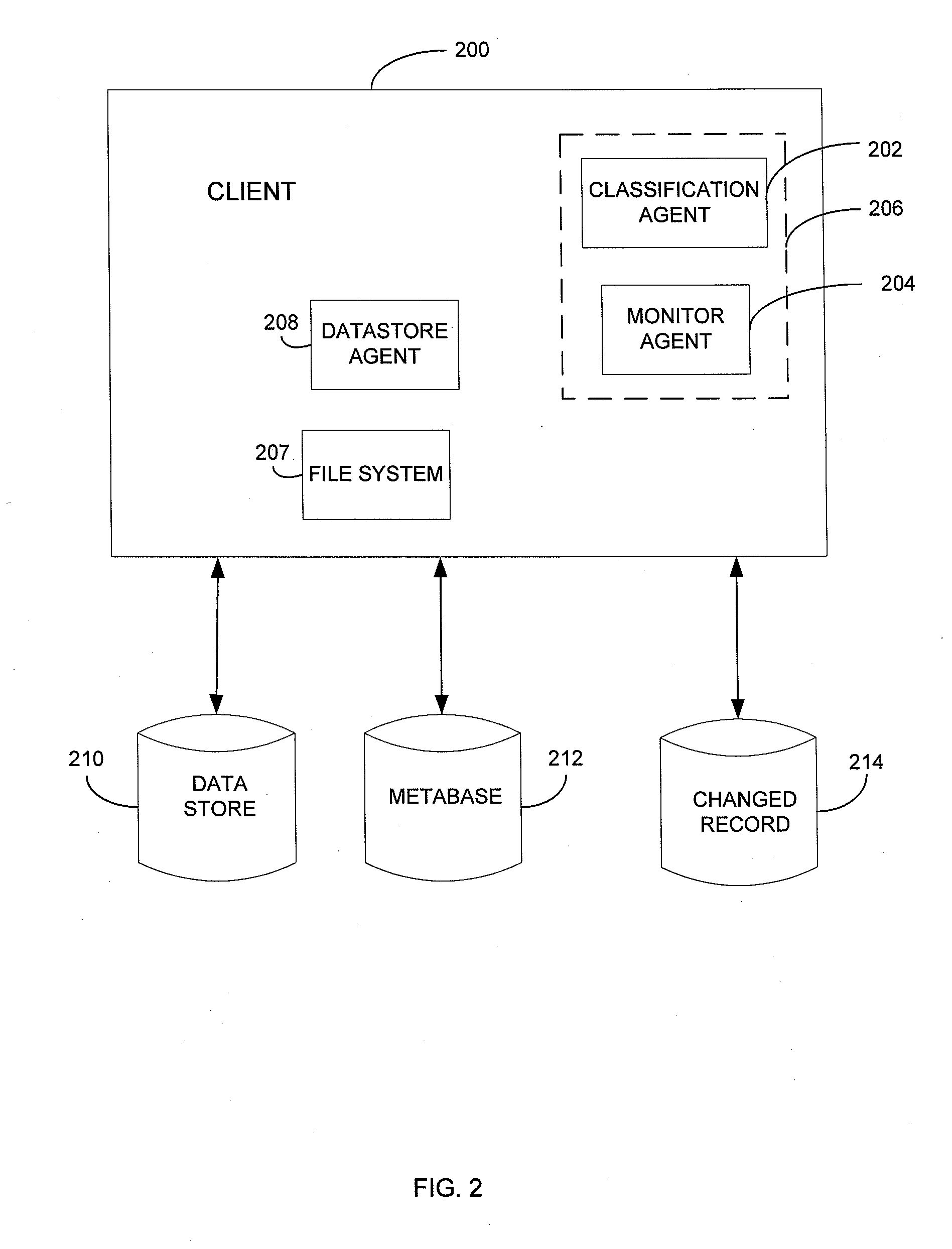
Metabase for facilitating data classification
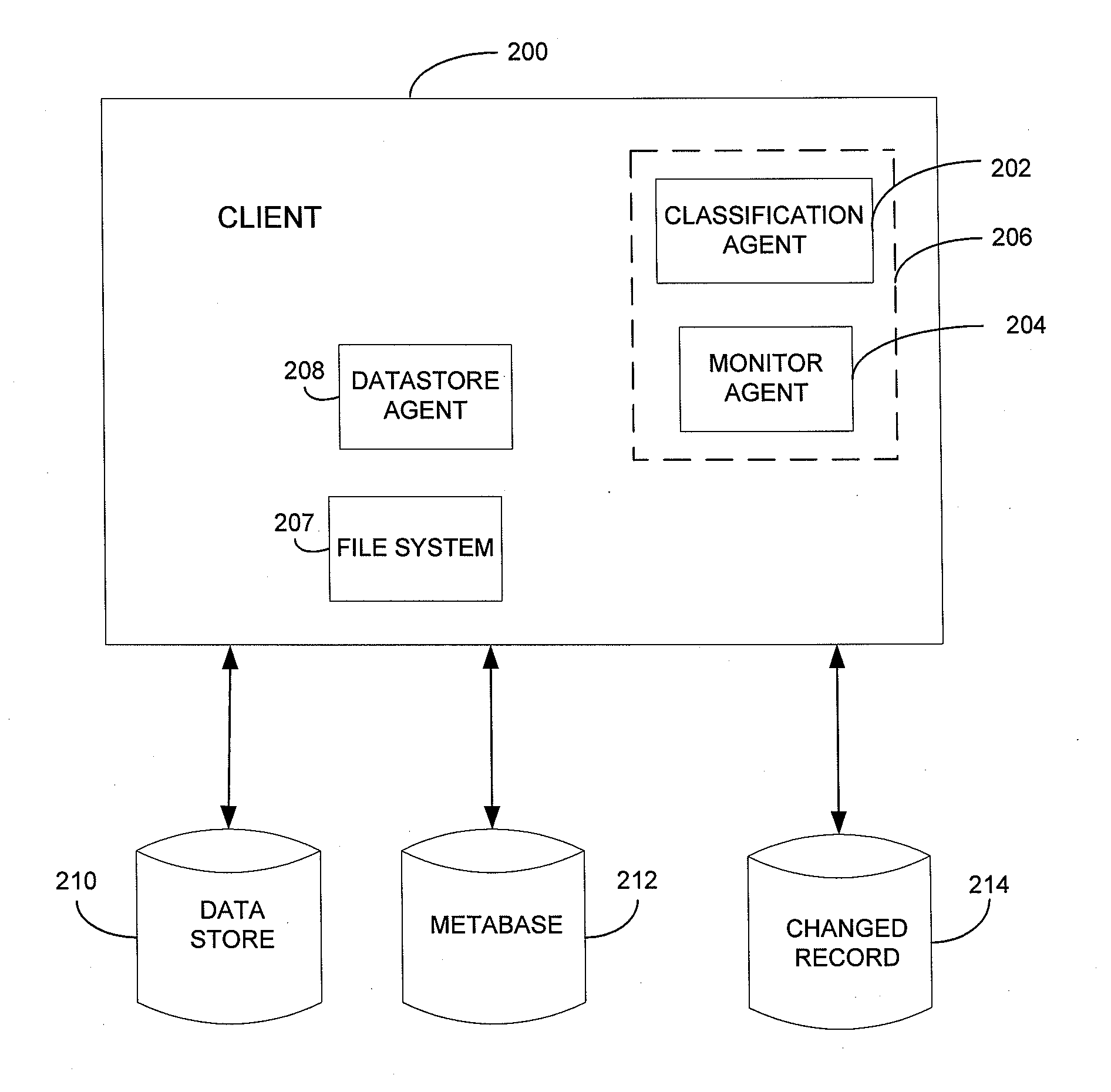
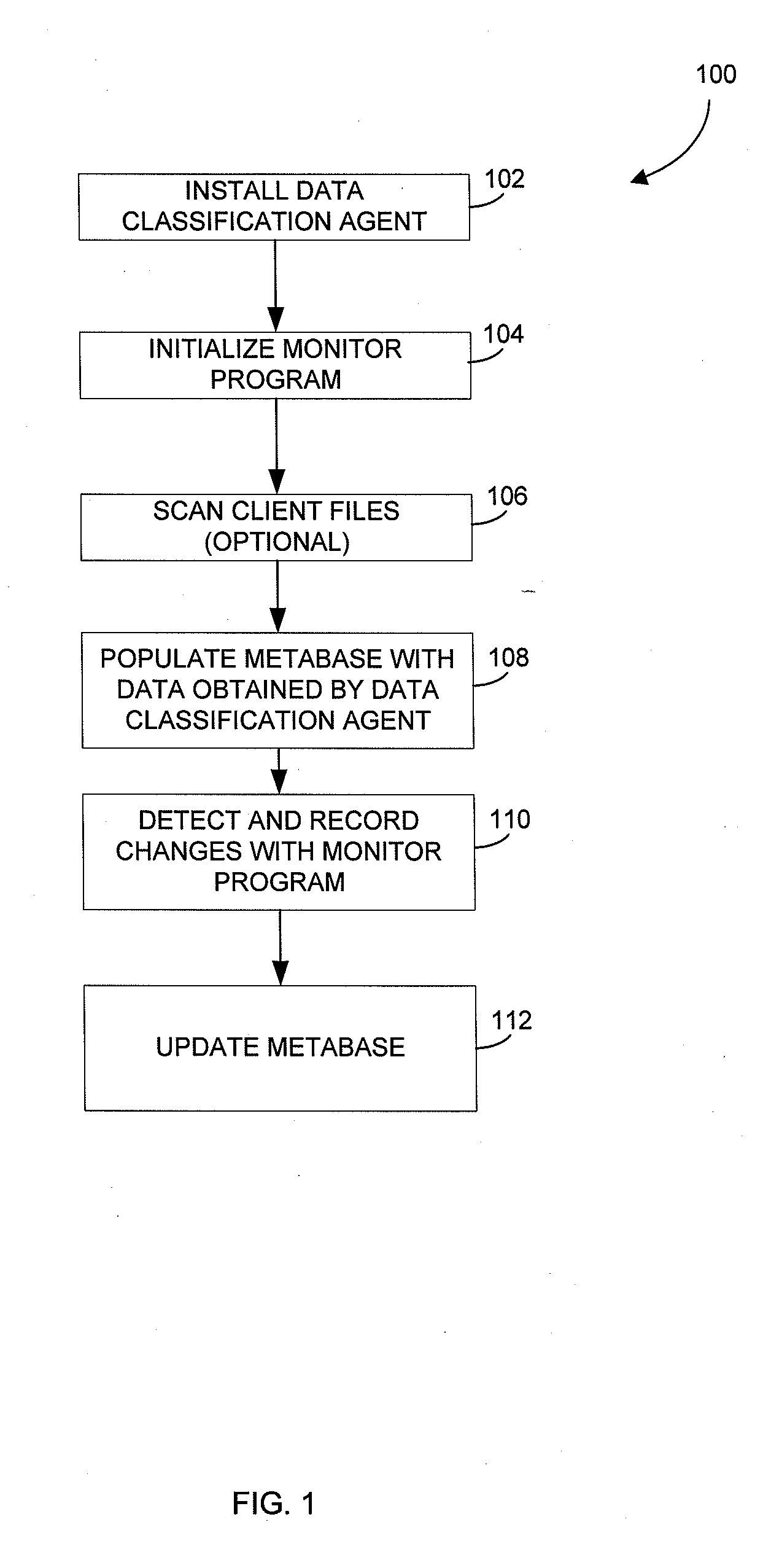
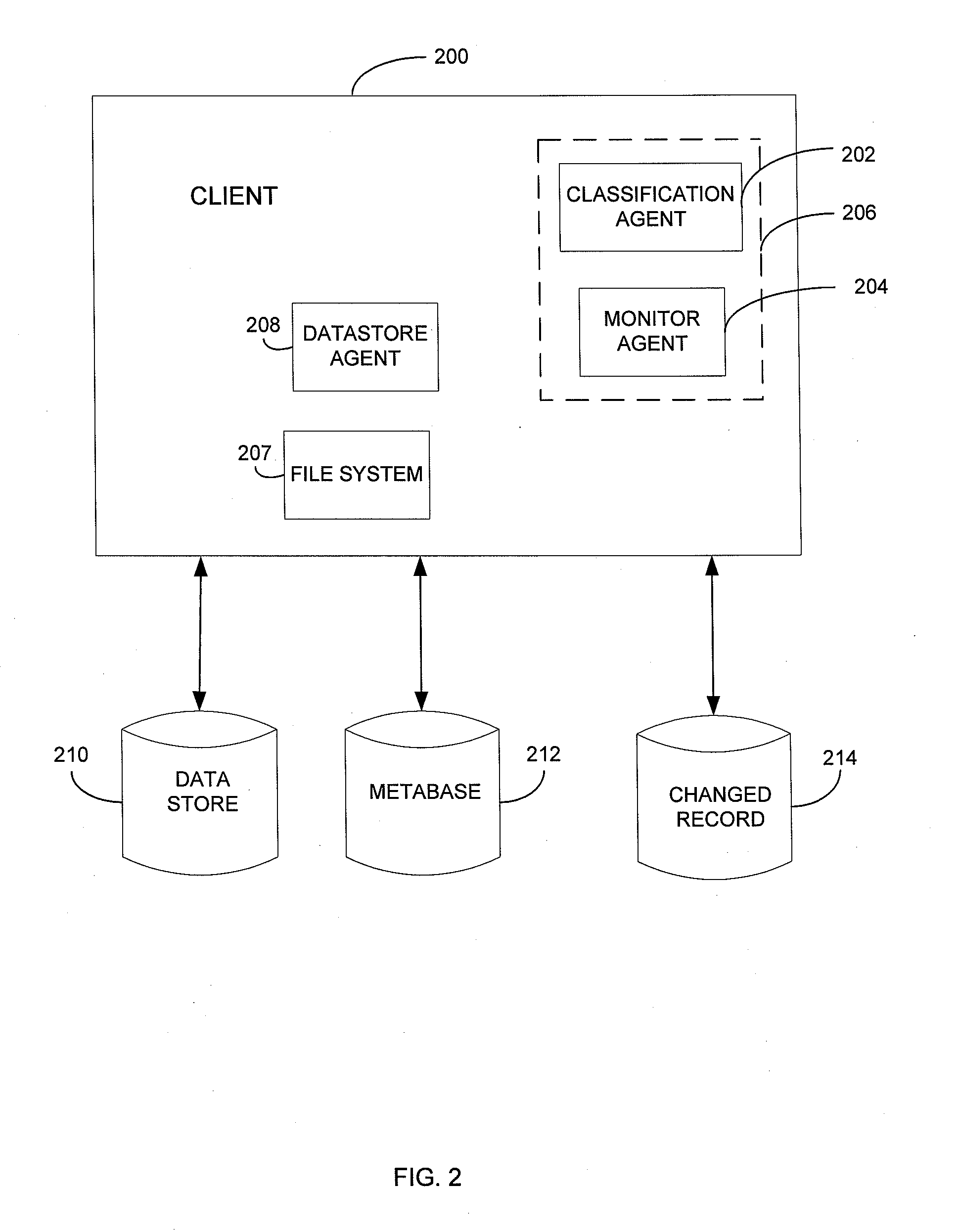
Systems and methods for managing electronic data are disclosed. Various data management operations can be performed based on a metabase formed from metadata. Such metadata can be identified from an index of data interactions generated by a journaling module, and obtained from their associated data objects stored in one or more storage devices. In various embodiments, such processing of the index and storing of the metadata can facilitate, for example, enhanced data management operations, enhanced data identification operations, enhanced storage operations, data classification for organizing and storing the metadata, cataloging of metadata for the stored metadata, and / or user interfaces for managing data. In various embodiments, the metabase can be configured in different ways. For example, the metabase can be stored separately from the data objects so as to allow obtaining of information about the data objects without accessing the data objects or a data structure used by a file system.
Owner:COMMVAULT SYST INC
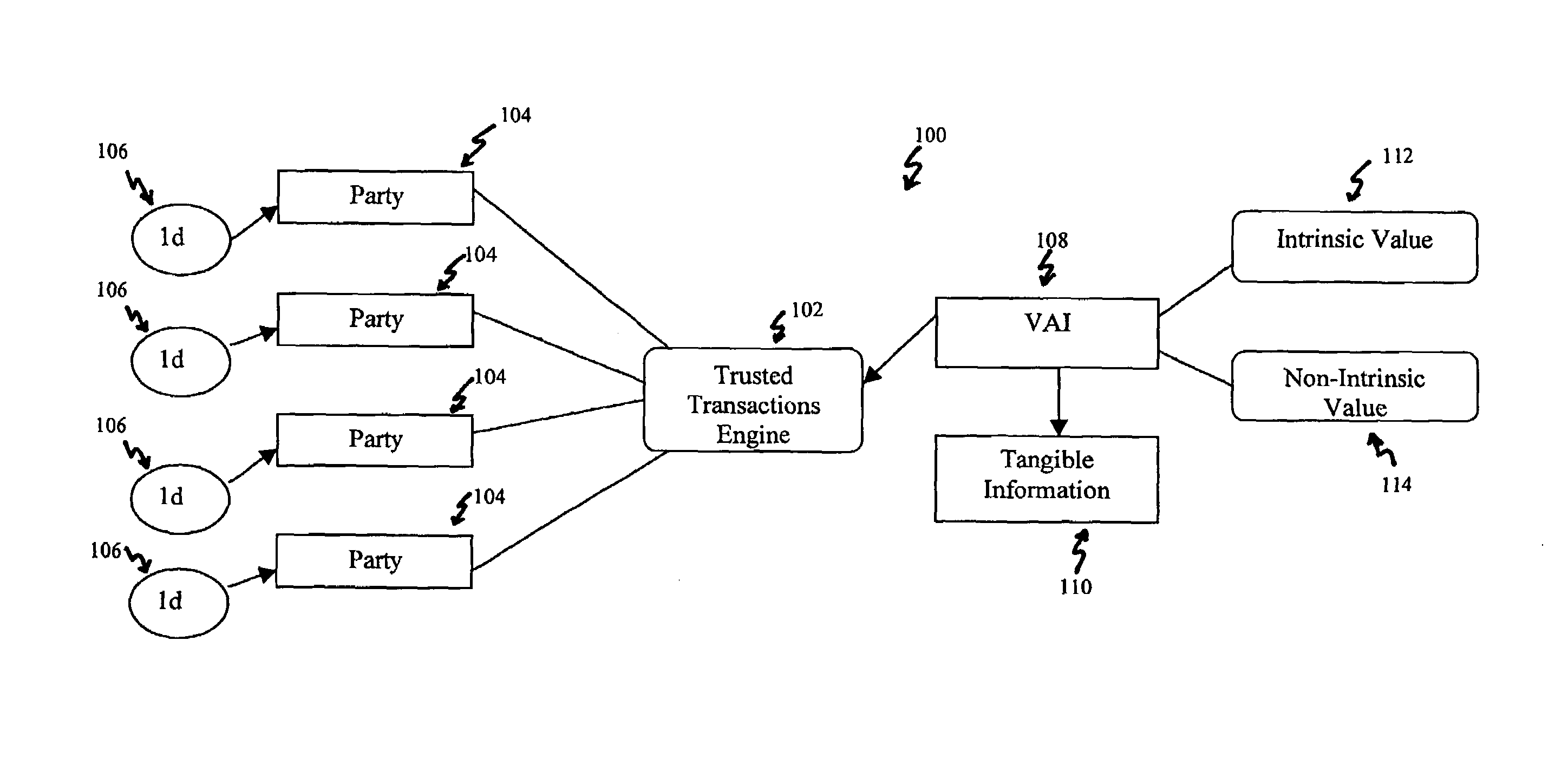
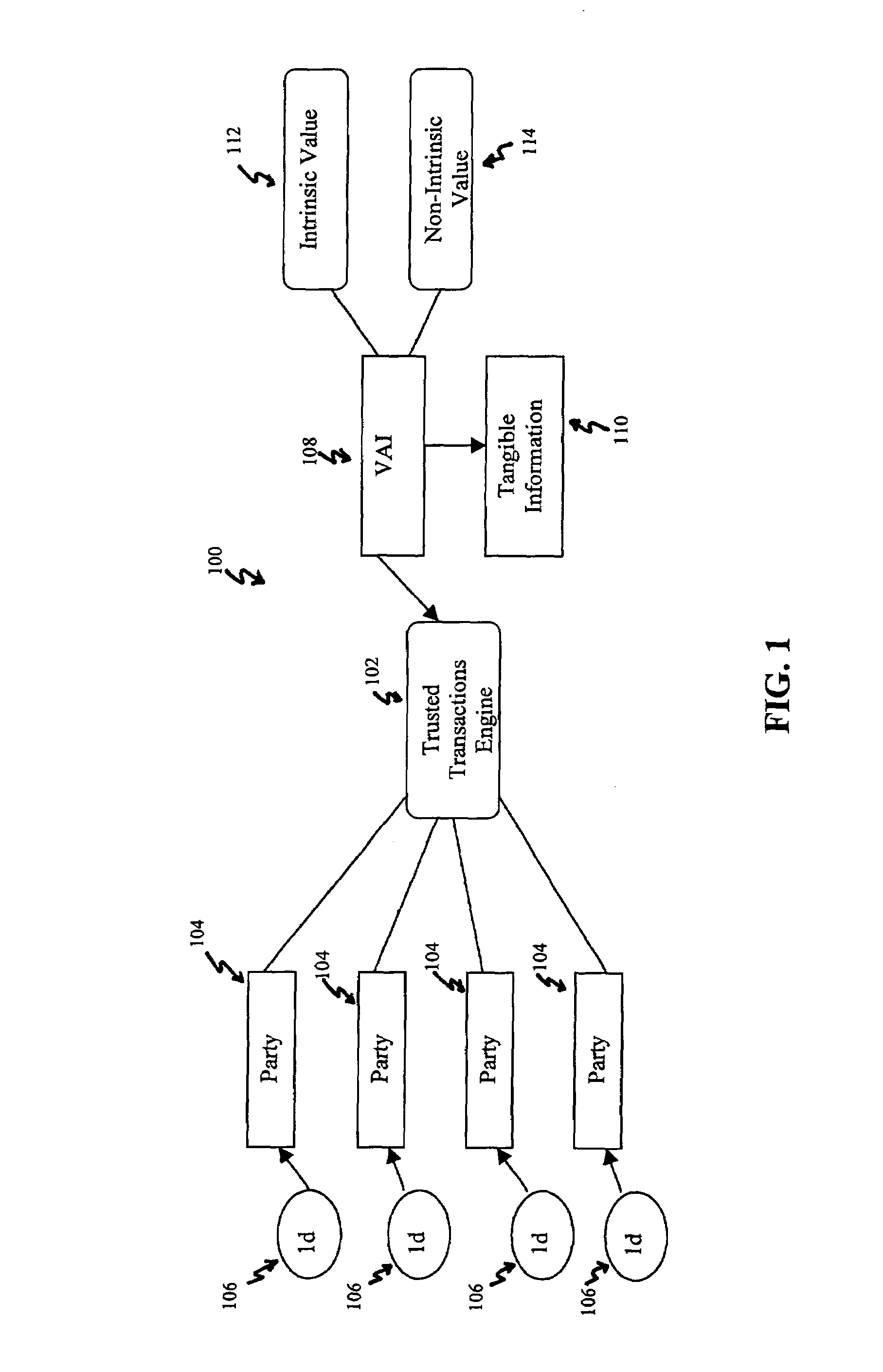
Systems, methods and devices for trusted transactions
InactiveUS7159116B2Convenient transactionLittle processing resourceMultiple keys/algorithms usagePublic key for secure communicationThe InternetSubject matter
The invention discloses a system for enhancing trust in transactions, most particularly in remote transactions between a plurality of transactional parties, for instance a seller and buyer(s) of goods and / or services over a public computer network such as the internet. Trust is disclosed to be a multivalent commodity, in that the trust that is to be enhanced relates to information about the subject matter of the transactions (e.g., the suitability of the goods and services sold), the bona fides of the supplier of the goods and services, the appropriateness of a pricing structure for a particular transaction or series of transactions, a quantum of additional transactional value that may be imparted to the transactional relationship, security of information exchange, etc. An important contributor to trust for such aspects of the transaction is disclosed to be the use of highly-secure steganographic computer processing means for data identification, authentication, and transmission, such that confidence in the transaction components is enhanced. By providing an integrated multivalent system for enhancing trust across a variety of categories (for a variety of transaction species, including those in which the need for trust is greater on the part of one party than of another, as well as those in which both require substantial trust enhancement), the invention reduces barriers to forming and optimizing transactional relationships.
Owner:WISTARIA TRADING INC
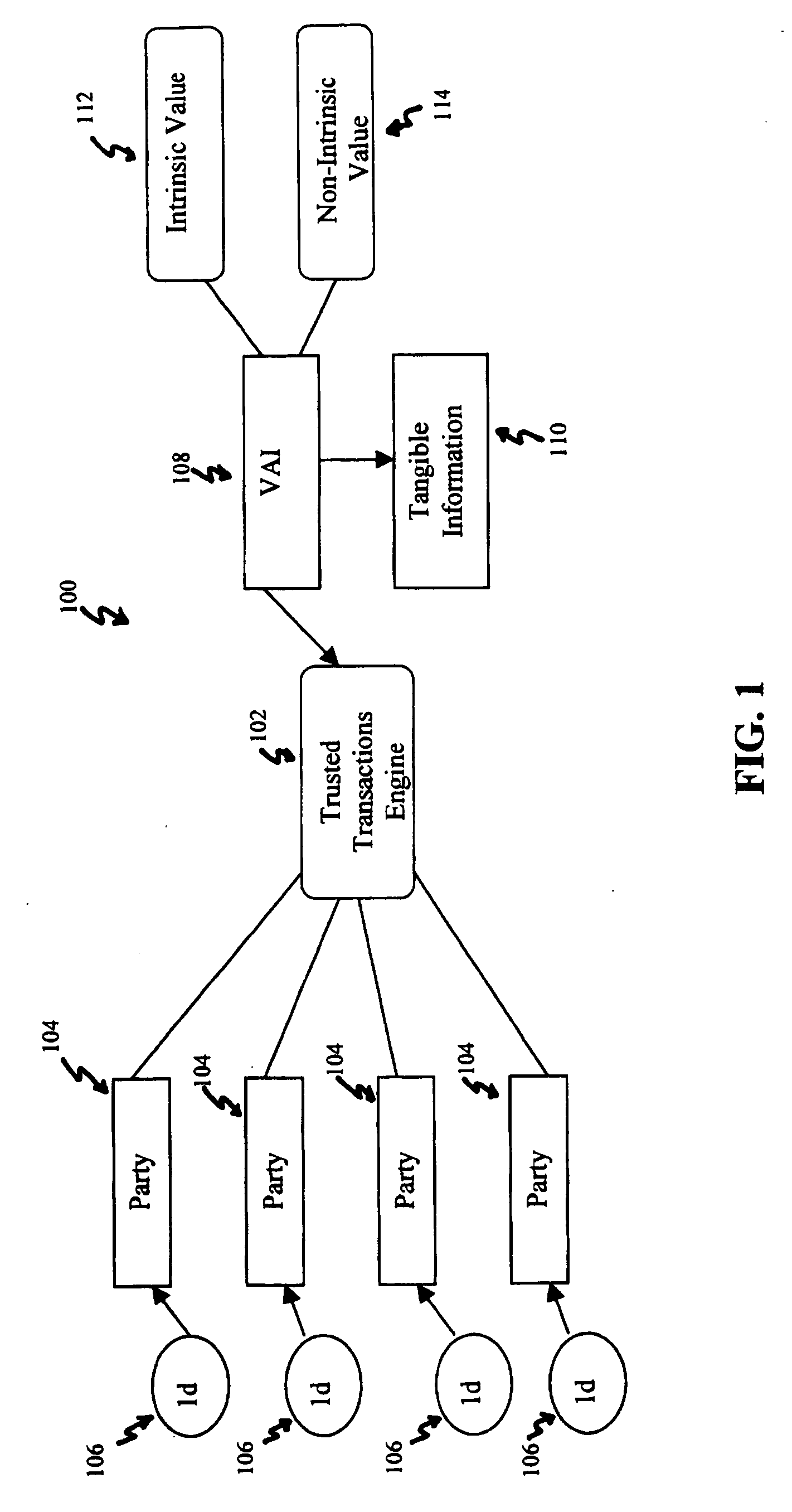
Systems, methods and devices for trusted transactions
ActiveUS20070028113A1Little processing resourceMaximize its usefulnessMultiple keys/algorithms usageCryptography processingThe InternetSubject matter
The invention discloses a system for enhancing trust in transactions, most particularly in remote transactions between a plurality of transactional parties, for instance a seller and buyer(s) of goods and / or services over a public computer network such as the internet. Trust is disclosed to be a multivalent commodity, in that the trust that is to be enhanced relates to information about the subject matter of the transactions (e.g., the suitability of the goods and services sold), the bona fides of the supplier of the goods and services, the appropriateness of a pricing structure for a particular transaction or series of transactions, a quantum of additional transactional value that may be imparted to the transactional relationship, security of information exchange, etc. An important contributor to trust for such aspects of the transaction is disclosed to be the use of highly-secure steganographic computer processing means for data identification, authentication, and transmission, such that confidence in the transaction components is enhanced. By providing an integrated multivalent system for enhancing trust across a variety of categories (for a variety of transaction species, including those in which the need for trust is greater on the part of one party than of another, as well as those in which both require substantial trust enhancement), the invention reduces barriers to forming and optimizing transactional relationships.
Owner:WISTARIA TRADING INC
Systems and methods for using metadata to enhance data management operations
Systems and methods for managing electronic data are disclosed. Various data management operations can be performed based on a metabase formed from metadata. Such metadata can be identified from an index of data interactions generated by a journaling module, and obtained from their associated data objects stored in one or more storage devices. In various embodiments, such processing of the index and storing of the metadata can facilitate, for example, enhanced data management operations, enhanced data identification operations, enhanced storage operations, data classification for organizing and storing the metadata, cataloging of metadata for the stored metadata, and / or user interfaces for managing data. In various embodiments, the metabase can be configured in different ways. For example, the metabase can be stored separately from the data objects so as to allow obtaining of information about the data objects without accessing the data objects or a data structure used by a file system.
Owner:COMMVAULT SYST INC
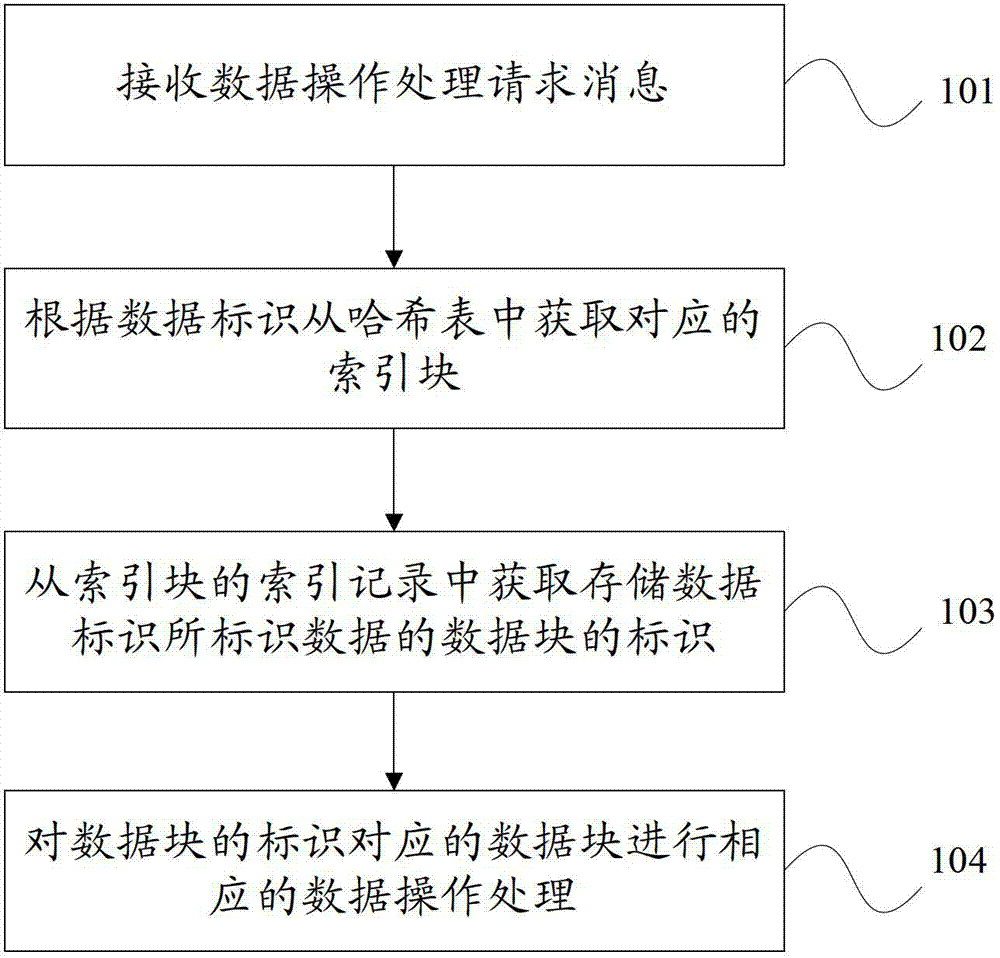
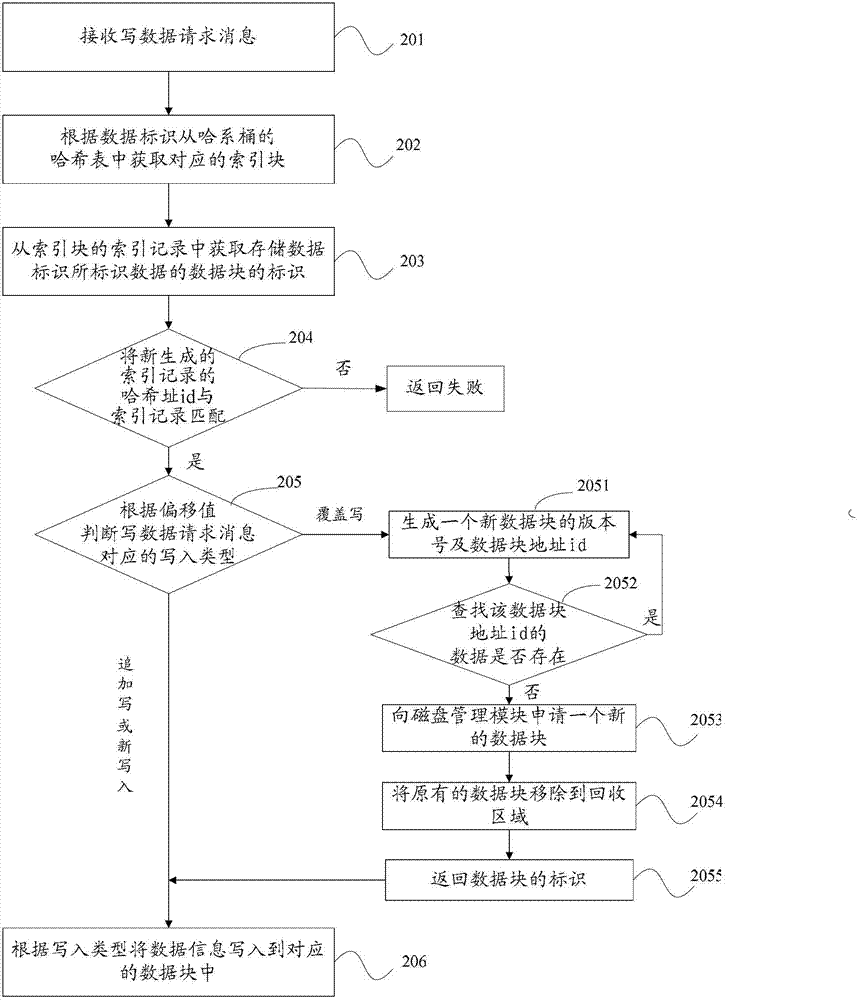
Operation processing method of data storage system and data storage system
InactiveCN102779180AImprove access performanceImprove access speedSpecial data processing applicationsData operationsData store
An embodiment of the invention provides an operation processing method of a data storage system and the data storage system. The operation processing method includes that a storage magnetic disk of the data storage system comprises a hash table bucket and index blocks and receives data operation processing request message which carries data identification, the corresponding index block is obtained from a harsh table according to the data identification, mapping relation of the data identification and the index block is stored in the hash table, and each index block stores an index record which includes the mapping relation of the data identification and a data block storing data identified by the data identification. Identification of the data block storing the data identified by the data identification is obtained from the index record of each index block, and corresponding data operation processing is conducted on the data block that the identification of the data block corresponds to. By means of the method, the harsh table bucket and the index blocks can be stored in the storage magnetic disk to enable the operation method of the system to be further simplified. Visit performance of the magnetic disk can be further improved to some extent.
Owner:HUAWEI TECH CO LTD
Vehicle-mounted intelligent supervising and early warning device for running status of track traffic vehicle
InactiveCN101274636AImprove the level of intelligence and informatizationPowerfulRailway auxillary equipmentRailway profile gaugesInformatizationInformation processing
The invention relates to an intelligent vehicle-bone type running state monitoring and early warning device used for rail transporting vehicles. The device comprises at least a group of sensing component units used for obtaining the vehicle operation state, including the operation state of wheels on rails, the state of the deformation of a vehicle chassis component and a railway and abnormal road conditions or the state of vehicle-bone devices; an intelligent sensing information processing unit based on a micro processor and used for processing the sensing signals of the vehicle state, including signal processing, data-collecting processing, image edge detection and extraction, image tracking, the processing and the intelligent analyzing of mechanical vibration / noise information, data identification and extraction, the learning of vehicle states and relevant background information, the forming of monitoring and early warning results and information recording and storing; input / output units used for the output, the operation, the control and the data communication of the monitoring and early warning results; and a power supply unit. The intelligent vehicle-bone type running state monitoring and early warning device has the advantages of multiple functions, high intelligentization and informatization level, high cost performance, high creditability and convenient installation, etc., is easy to be expanded, and can be applied under all weather conditions.
Owner:林贵生
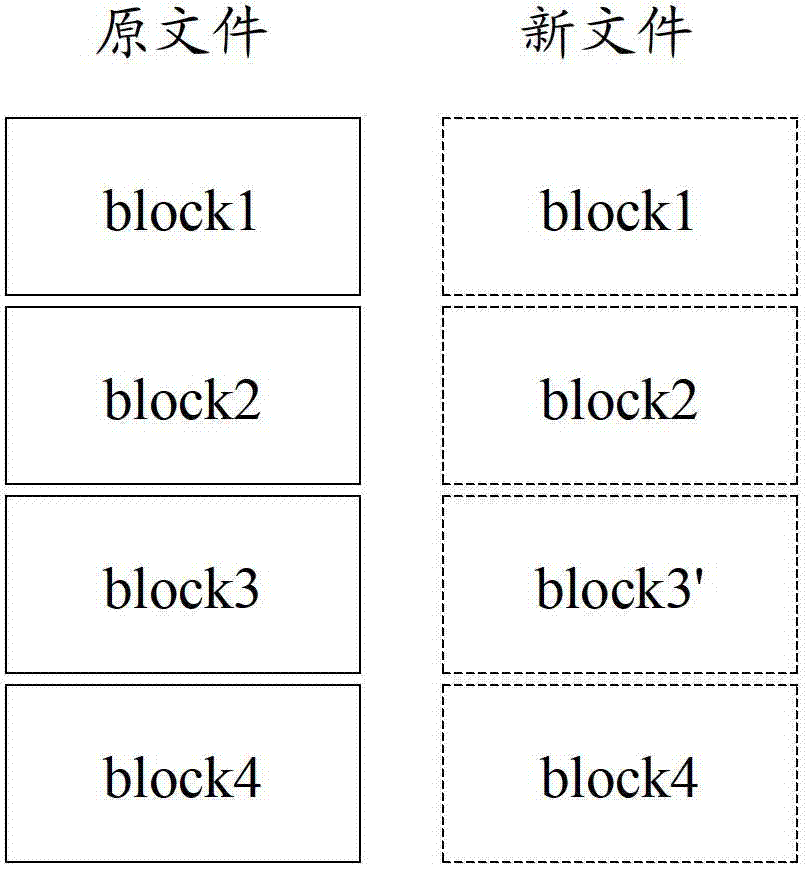
Duplicate backup data identification and consolidation
InactiveUS20110113013A1Reduce redundant backup data storageMemory loss protectionDigital data processing detailsData identificationReal-time computing
The various embodiments herein include operate to identify, consolidate, and reduce redundant backup data storage. One embodiment includes storing data blocks and first signatures of data chunks of each stored data block, the first signature of each data chunk including a reference to a storage location of the data chunk within a stored data block, the stored data blocks including data blocks of previous and recent backup sessions. Some embodiments further include storing second signatures in a second signature repository, where the second signatures are calculated based on determined boundaries of the first signatures from previous backup sessions. At least one of the second signatures is calculated based on at least two first signatures, and in the range of 32 to 64 first signatures in some embodiments. Some embodiments may identify data chunks of the recent backup session present in the stored data blocks prior to the recent backup session.
Owner:CA TECH INC
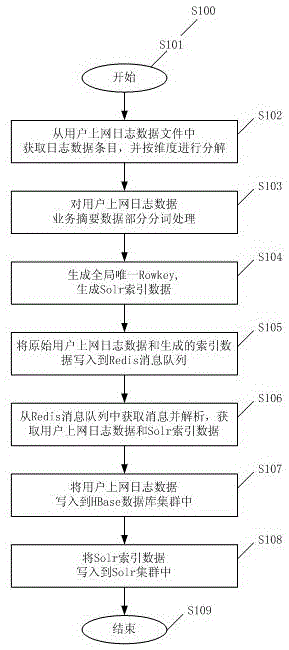
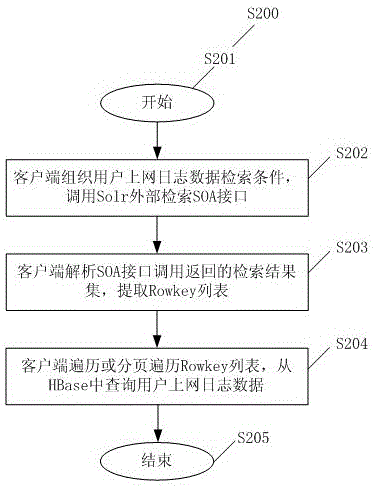
Distributed framework-based log data storing and retrieving method
ActiveCN105138592AMeet efficient storage needsMeet the needs of fast retrievalDatabase distribution/replicationSpecial data processing applicationsData retrievalThe Internet
The invention provides a distributed framework-based log data storing and retrieving method and aims at solving the problem of high performance storage of mass user internet log data and the problem of slow data retrieval under multi-dimension and multi-keyword conditions. On one hand, the invention provides a method for storing user internet log data; HBase and Solr are mainly utilized to achieve distributed data storage and index construction; the method comprises the method for storing the user internet log data into the HBase in an entry form and building a unique identification, the method for carrying out dimension splitting and dimension word segmentation on the user internet log data and building an index relationship between the enquiry dimension and a word segmentation keyword and a data identification, the method for carrying out dimension splitting on the log data, the method for carrying out word segmentation on the dimension, and the method for building an index according to the dimension and the word segmentation keyword; on the other hand, the invention provides a method for retrieving the user internet log data; and the method mainly comprises an organization and data accessing method under the multi-dimension and multi-keyword conditions.
Owner:WUHAN HONGXIN TECH SERVICE CO LTD
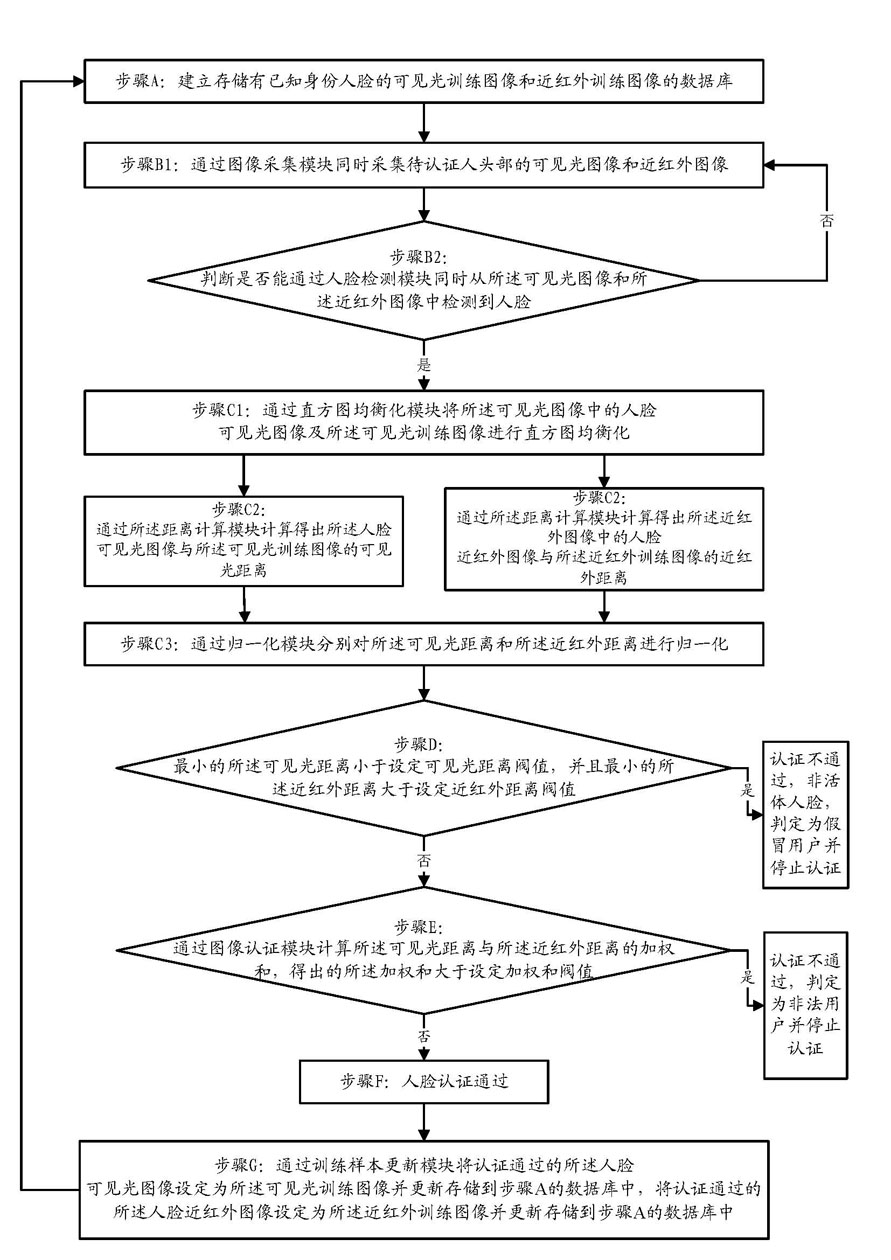
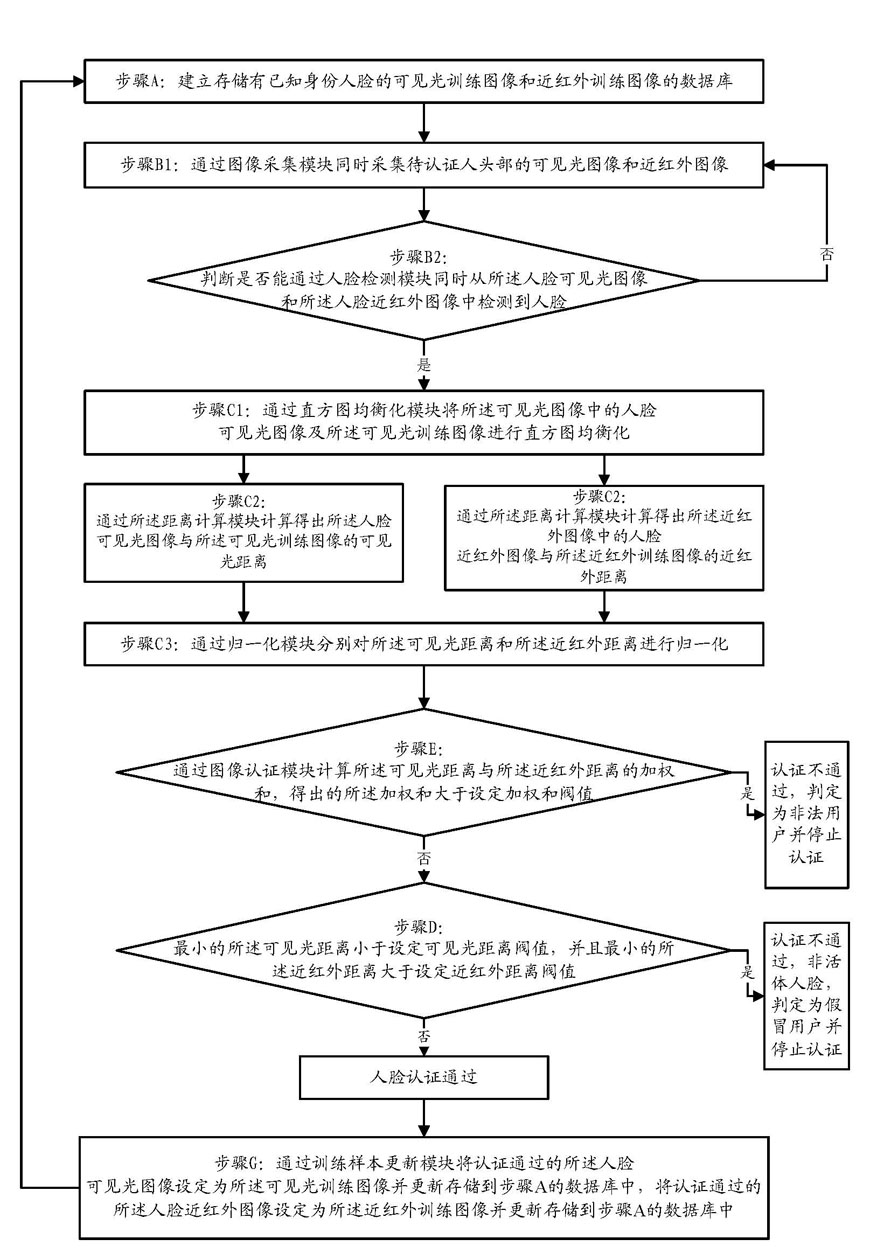
Bimodal face authentication method with living body detection function and system
ActiveCN101964056AAvoid recognition failurePrevent cheatingCharacter and pattern recognitionPattern recognitionLiving body
The invention relates to data identification, in particular to a bimodal face authentication method with a living body detection function and a system. The authentication method of the invention comprises the following steps: A. establishing a database of visible light training images and near-infrared training images of known faces; and B. simultaneously collecting visible light images and near-infrared images of the heads of people to be authenticated. The invention also provides a bimodal face authentication system with a living body detection function. The invention has the beneficial effects that combined identification with the bimodal characteristics of face near-infrared images and face visible light images is adopted, as a result, the identification and authentication accuracy is improved, identification failure in the case of major changes of faces is avoided; and in addition, a living body detection module is utilized to effectively prevent personators from using photos or models to deceive others.
Owner:湖南蔚联智能科技有限公司
Systems and methods for using metadata to enhance data identification operations
Systems and methods for managing electronic data are disclosed. Various data management operations can be performed based on a metabase formed from metadata. Such metadata can be identified from an index of data interactions generated by a journaling module, and obtained from their associated data objects stored in one or more storage devices. In various embodiments, such processing of the index and storing of the metadata can facilitate, for example, enhanced data management operations, enhanced data identification operations, enhanced storage operations, data classification for organizing and storing the metadata, cataloging of metadata for the stored metadata, and / or user interfaces for managing data. In various embodiments, the metabase can be configured in different ways. For example, the metabase can be stored separately from the data objects so as to allow obtaining of information about the data objects without accessing the data objects or a data structure used by a file system.
Owner:COMMVAULT SYST INC
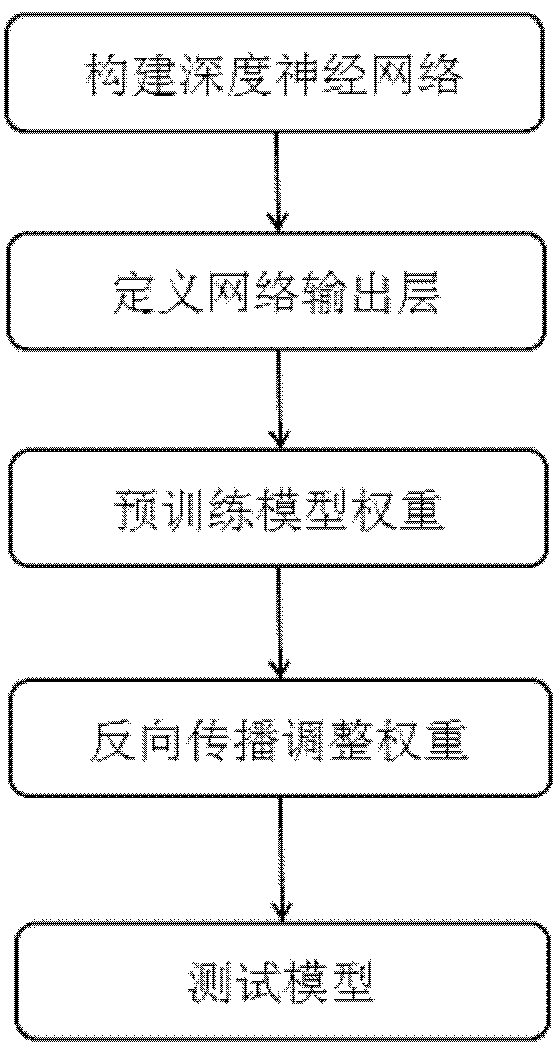
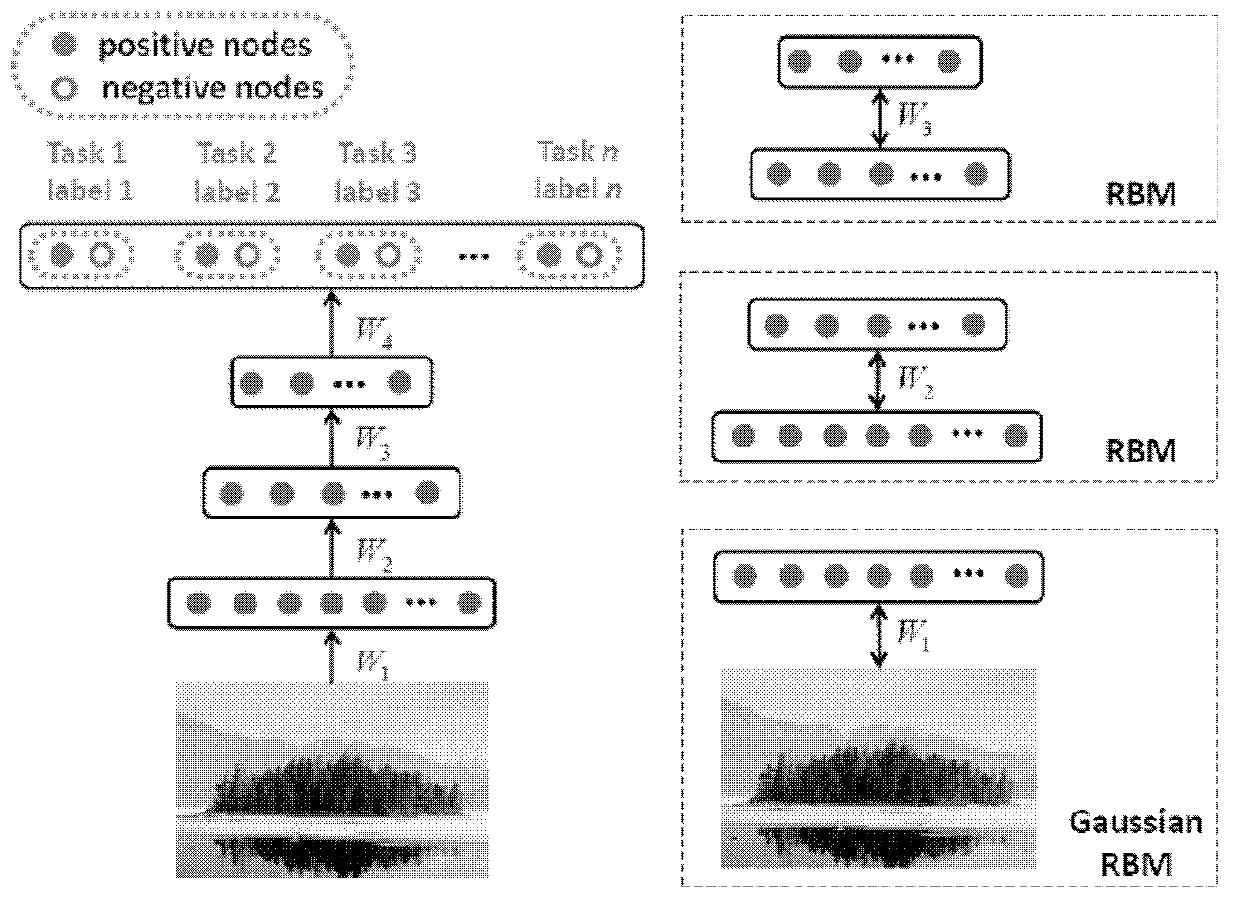
Method and device for data identification based on multitask deep neural network
The invention discloses a method and a device for data identification based on a multitask deep neural network. The method comprises the following steps of: step 1, establishing the multitask deep neural network; step 2, regarding the two adjacent layers of the multitask deep neural network as a limited Boltzman machine, and pre-training the multitask deep neural network by a method of training layer by layer without supervision from bottom to top, so as to obtain an initial connection weight between the adjacent layers; step 3, minimizing a target function about the network weight with supervision by virtue of a back propagation algorithm, so as to obtain an optimized network weight; and step 4, inputting to-be-identified data in the multitask deep neural network with the optimized network weight, so as to obtain an output layer node value, thus obtaining the type of the to-be-identified data according to the output layer node value. In the method, relevance among different labels is excavated by virtue of the neural network, so that a high image labelling accuracy can still be ensured in large-scale image labelling with a high label quantity.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Image displaying method for a head-mounted type display unit
ActiveUS20110248905A1Easy to displayCathode-ray tube indicatorsImage data processingComputer hardwareTime information
Disclosed herein is an image displaying method for a head-mounted type display unit which includes a frame of the glasses type for being mounted on the head of an observer, an image display apparatus attached to the frame, and a control section for controlling image display of the image display apparatus. The image display apparatus includes an image forming apparatus, and an optical apparatus. The image displaying method includes the steps of: storing a data group configured from a plurality of data in a storage section; adding a data identification code to each of the data; sending a designation identification code and display time information at predetermined intervals of time; and reading out the data whose data identification code coincides with the received designation identification code from the storage section and controlling the image forming apparatus to display an image based on the read out data.
Owner:SONY CORP
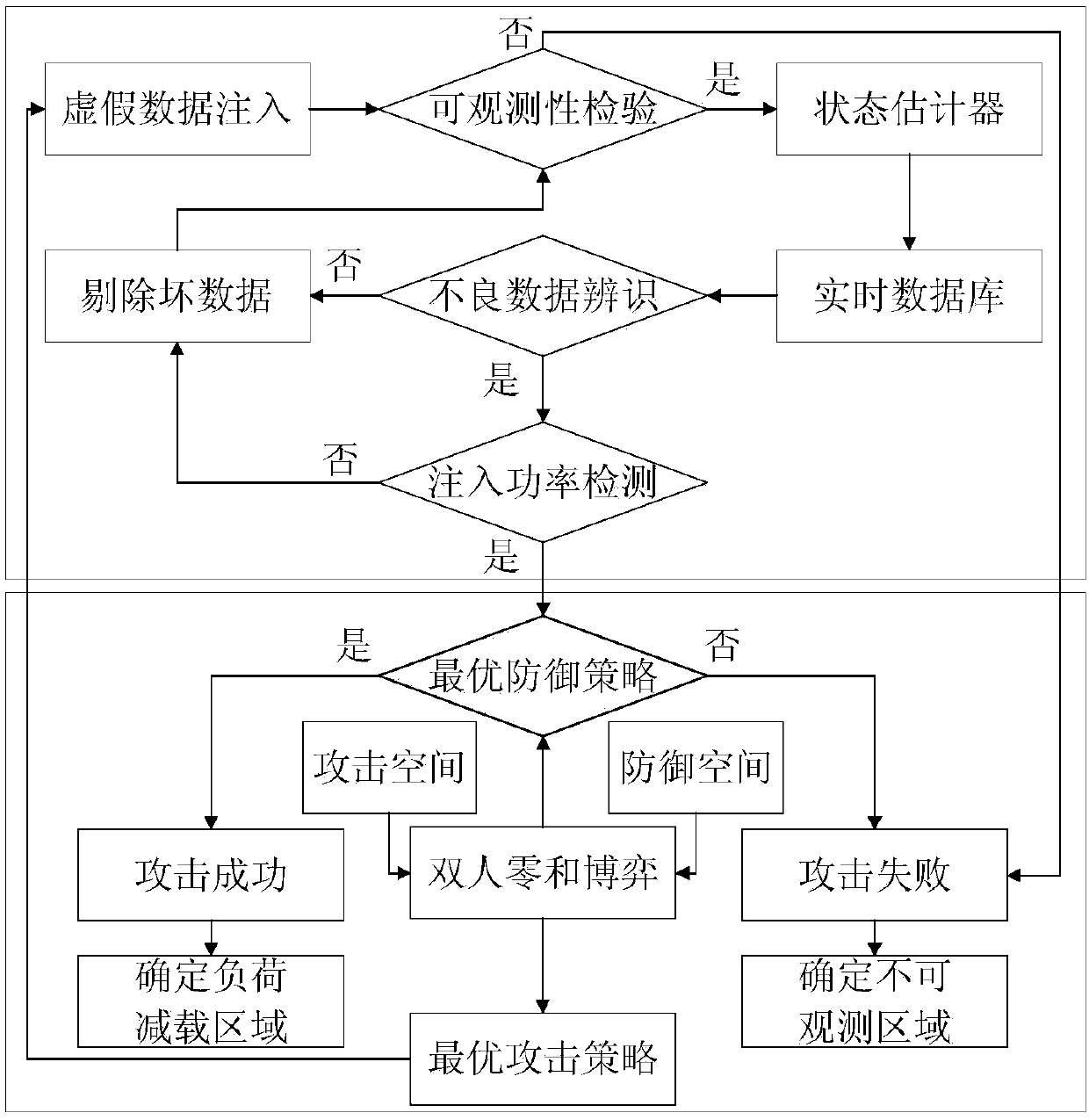
Double-layer defense method facing power system false data injection attack
ActiveCN107819785AOptimizationOvert aggressive behaviorData processing applicationsTransmissionInjection attacksData identification
The present invention discloses a double-layer defense method facing a power system false data injection attack, comprising an upper-layer defense policy and a lower-layer defense policy. In the upper-layer defense policy, based on internal defense means of a power system, methods such as bad data identification, injected power detection, and the like are mainly comprised, and injected false datais preliminarily detected, to generate attack space; and in the lower-layer defense policy, based on redundancy measurement defense means, a configuration position of a measurement apparatus is optimized by using a two-person zero-sum game theory according to an attack range that can be defended by the measurement apparatus, to make the measurement apparatus to implement an optimal defense capability on an attack behavior that is not detected by the upper-layer policy. The double-layer defense method facing a power system false data injection attack is used to assist a defender in establishinga power system security defense counterattack system.
Owner:SOUTHEAST UNIV
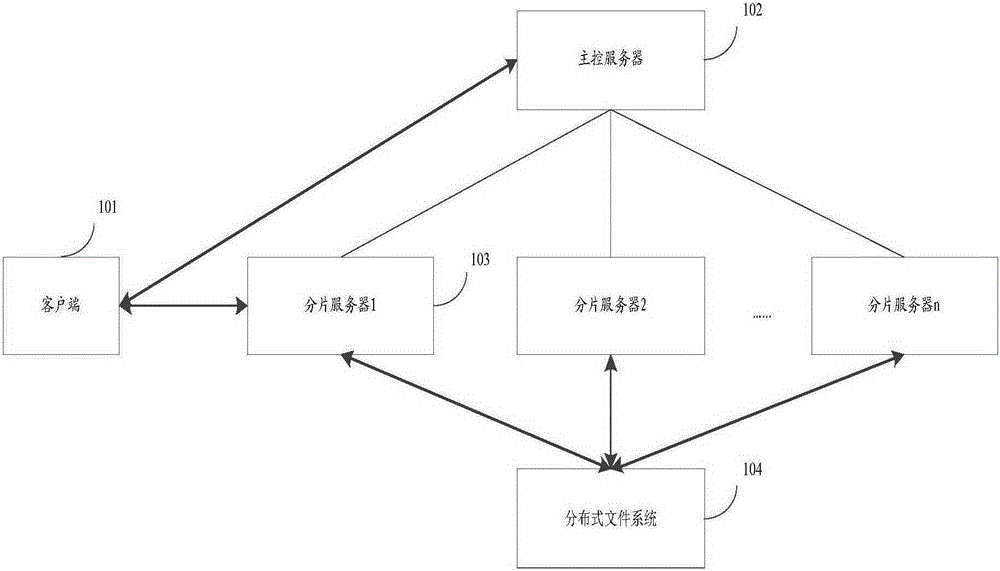
Data read-write method and distributed storage system
ActiveCN105260136AImprove performanceShorten the timeInput/output to record carriersFile access structuresInternal memoryDistributed File System
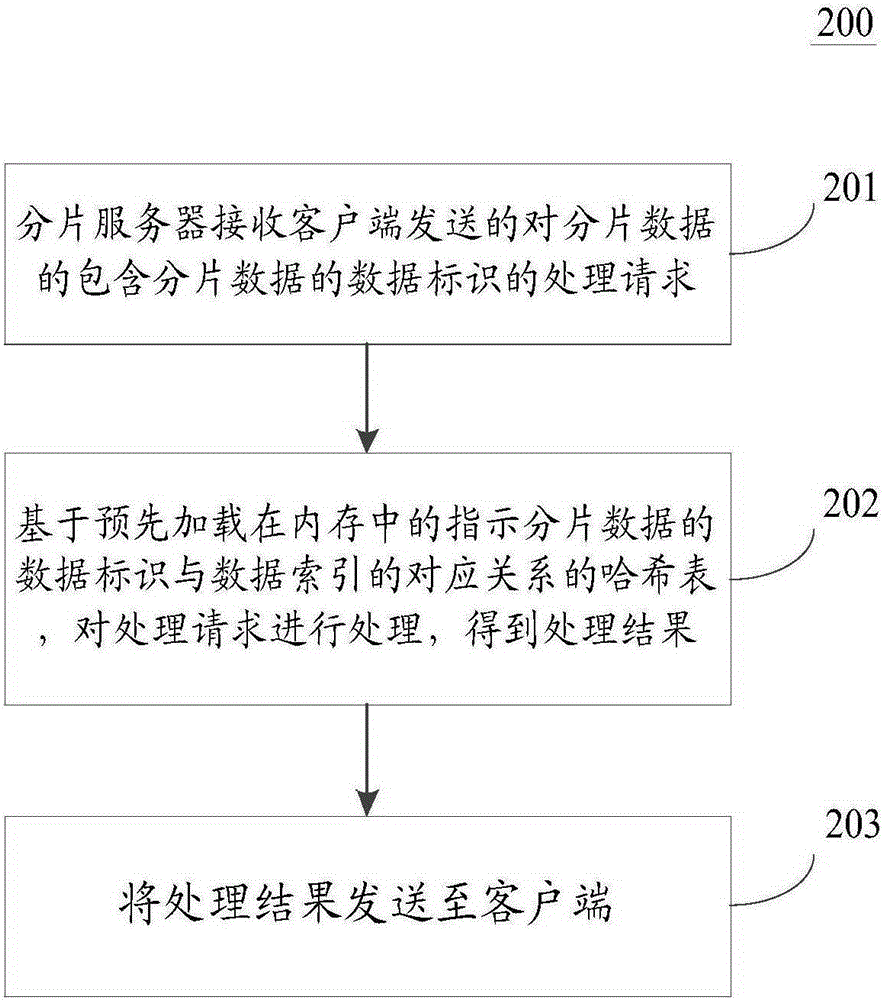
The invention discloses a data read-write method and a distributed storage system. A specific implementation way of the method comprises the following steps: receiving a processing request, including a data identification of fragment data on the fragment data, transmitted by a client by a fragment server; on the basis of a hash table, for indicating a corresponding relationship between the data identification of the fragment data and a data index, loaded to an internal memory in advance, processing the processing request to obtain a processing result; and transmitting the processing result to the client. Reading and writing of the data is achieved through the hash table loaded to the internal memory; the processing time of a reading request on the data is close to the ultimate performance of a distributed file system; and the time consumed by a writing request on the data is close to the time consumed for writing the distributed file system in an additional writing manner, so that the performance of the distributed storage system is improved; meanwhile, the data are stored only by the distributed file system; the distributed storage system has the reliability same as that of the distributed file system; and the reliability of the distributed storage system is improved.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Storage system and method based on solid state medium and cold-hot data identification method
ActiveCN102799534AThe identification method is simpleGood for dynamic identificationMemory architecture accessing/allocationMemory adressing/allocation/relocationSolid-state storagePhysical address
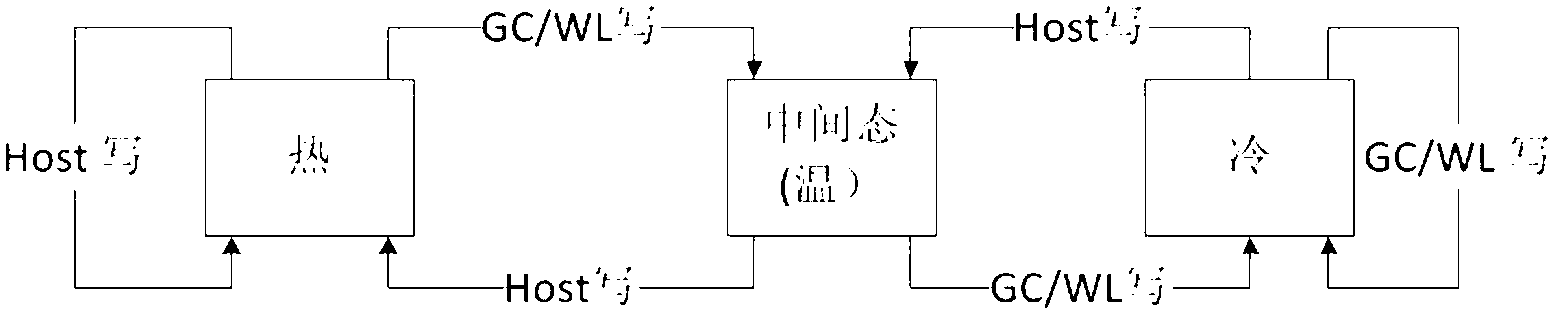
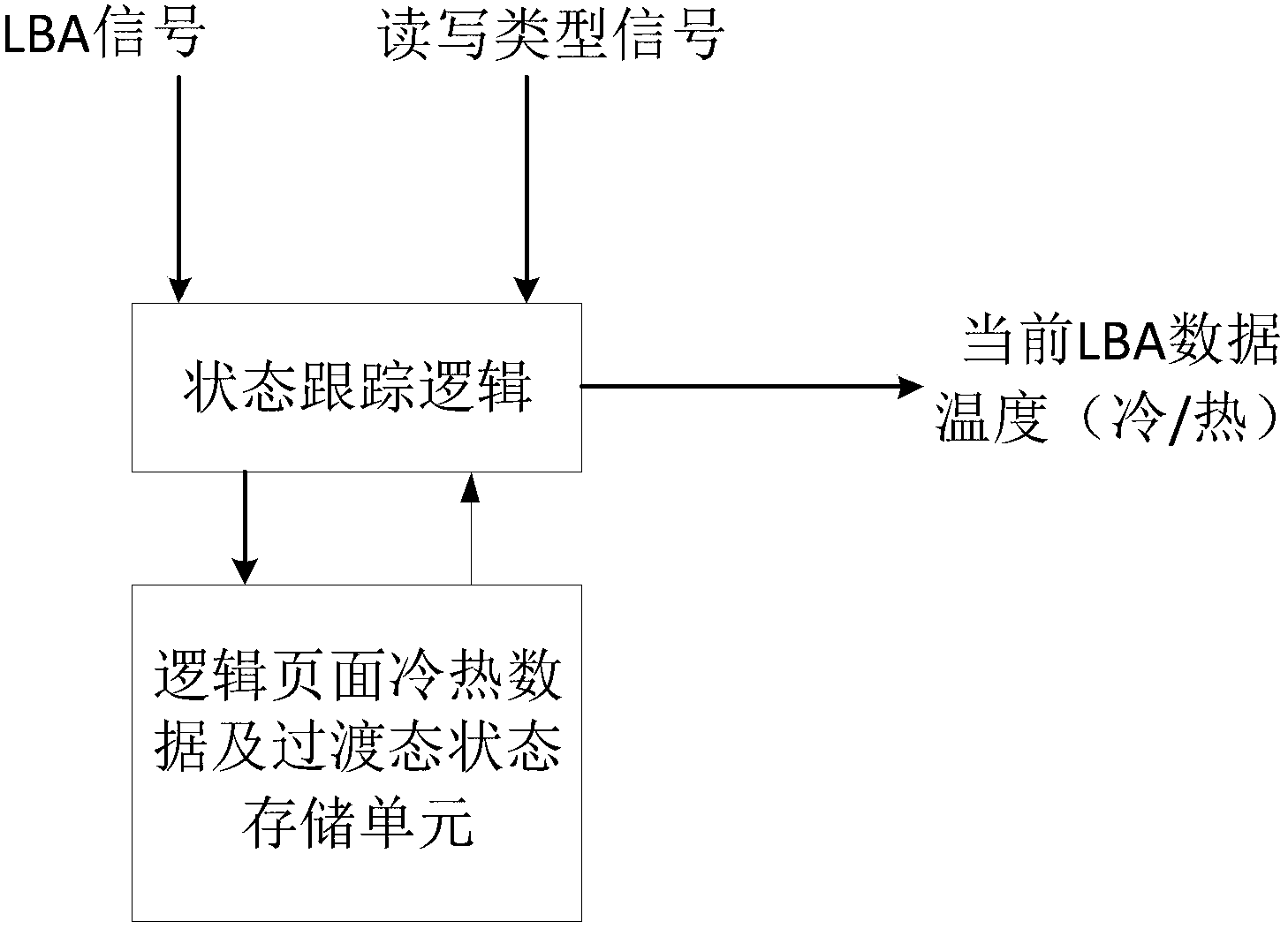
The invention discloses a storage system and a method based on a solid state medium. The storage system comprises at least one identification method of cold-hot data, the identification method is used for identifying the state of a logic page, and the state at least comprises a cold data state and a hot data state; the identification method comprises the following steps: if the logic page is updated for one or multiple times by a host in a preset time, judging that the logic page is in the hot data state; otherwise, if the logic page is not updated by the host for a long time, and the updating is carried out for one or multiple times to the storage physical address of the logic page by the action of a garbage recycle and abrasion balancing unit, judging that the logic page is in the cold data stage. According to the storage system and the method based on the solid state medium, the performances (reading and writing speeds and bandwidth) of the solid state storage can be improved, and the purpose of achieving maximal service life of the solid state storage system is realized by the reduction of the written data.
Owner:SHANNON SYST
Method and system for detecting bot network
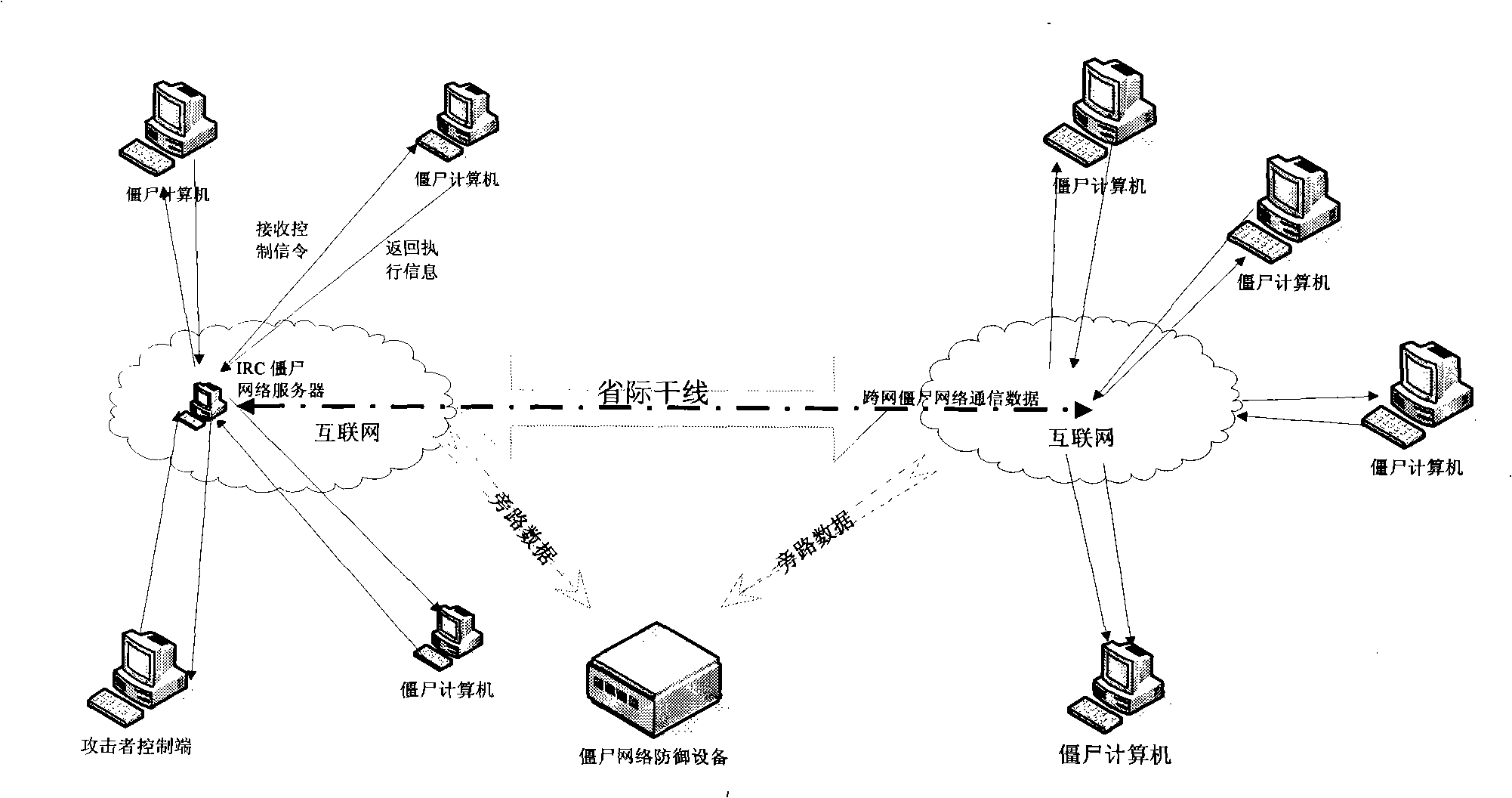
InactiveCN101404658AImprove defenseWide range of defenseData switching networksSpecial data processing applicationsNetwork packetNetwork control
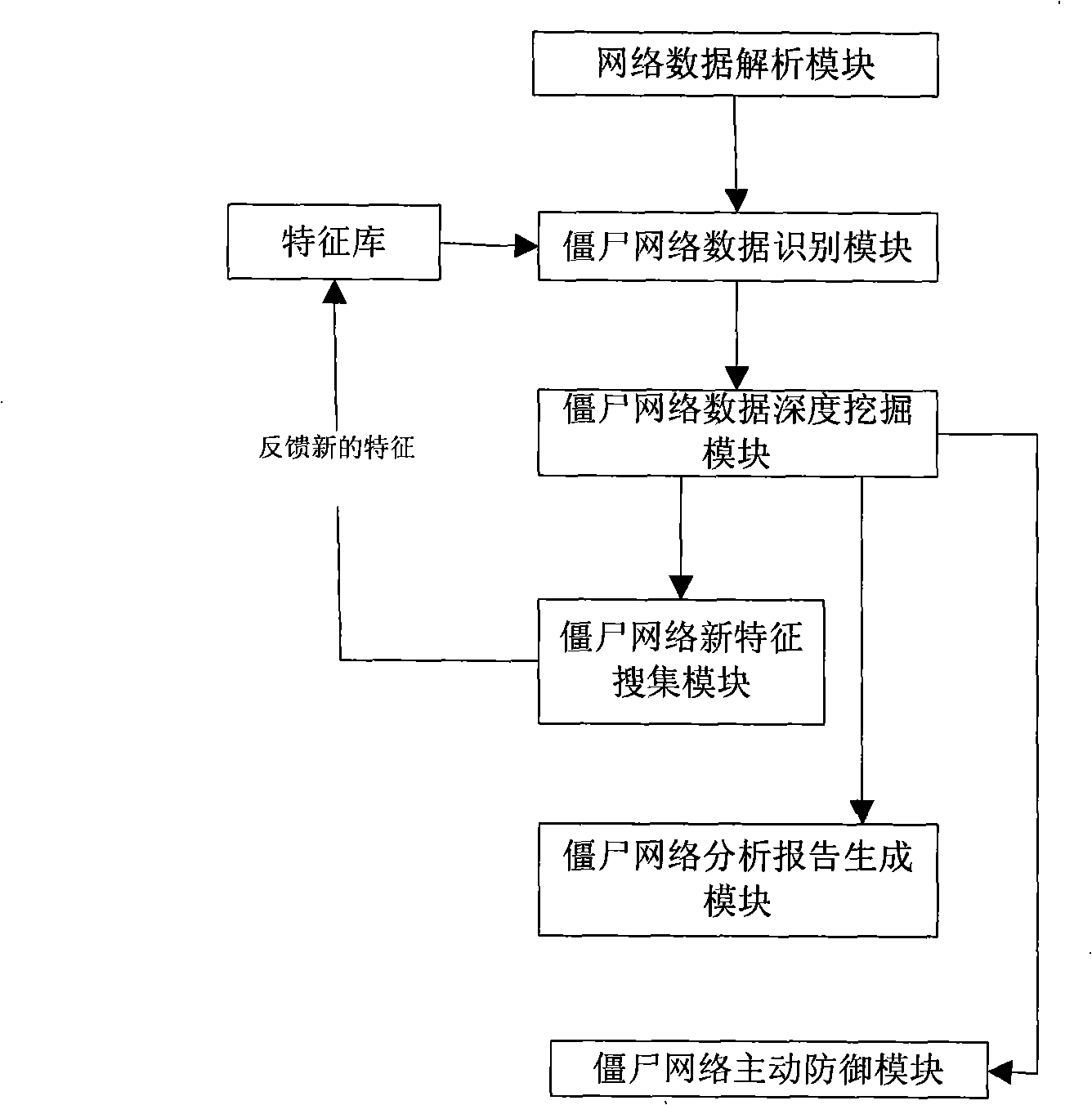
The invention discloses a method for detecting a bot network and a system thereof, which belong to the field of computer security. The method comprises the following steps: first, extracting IRC protocol data from a network data packet; then, matching the protocol data with feature codes in a data feature bank to acquire a bot network data packet; dividing the bot network data packet, and linking the bot network data packets from the same bot network; finally, determining a control server, a bot computer and a bot network control computer from the same bot network according to the divided bot network data packets, thereby describing the topology of the bot network. The system comprises a network data analysis module, a bot network data identification module and a bot network data deep dig module. Compared with the prior art, the invention can analyze and defense the whole bot network integrally, and has the advantages of better defense effect, wider defense range, higher efficiency and better traceability.
Owner:RUN TECH CO LTD BEIJING
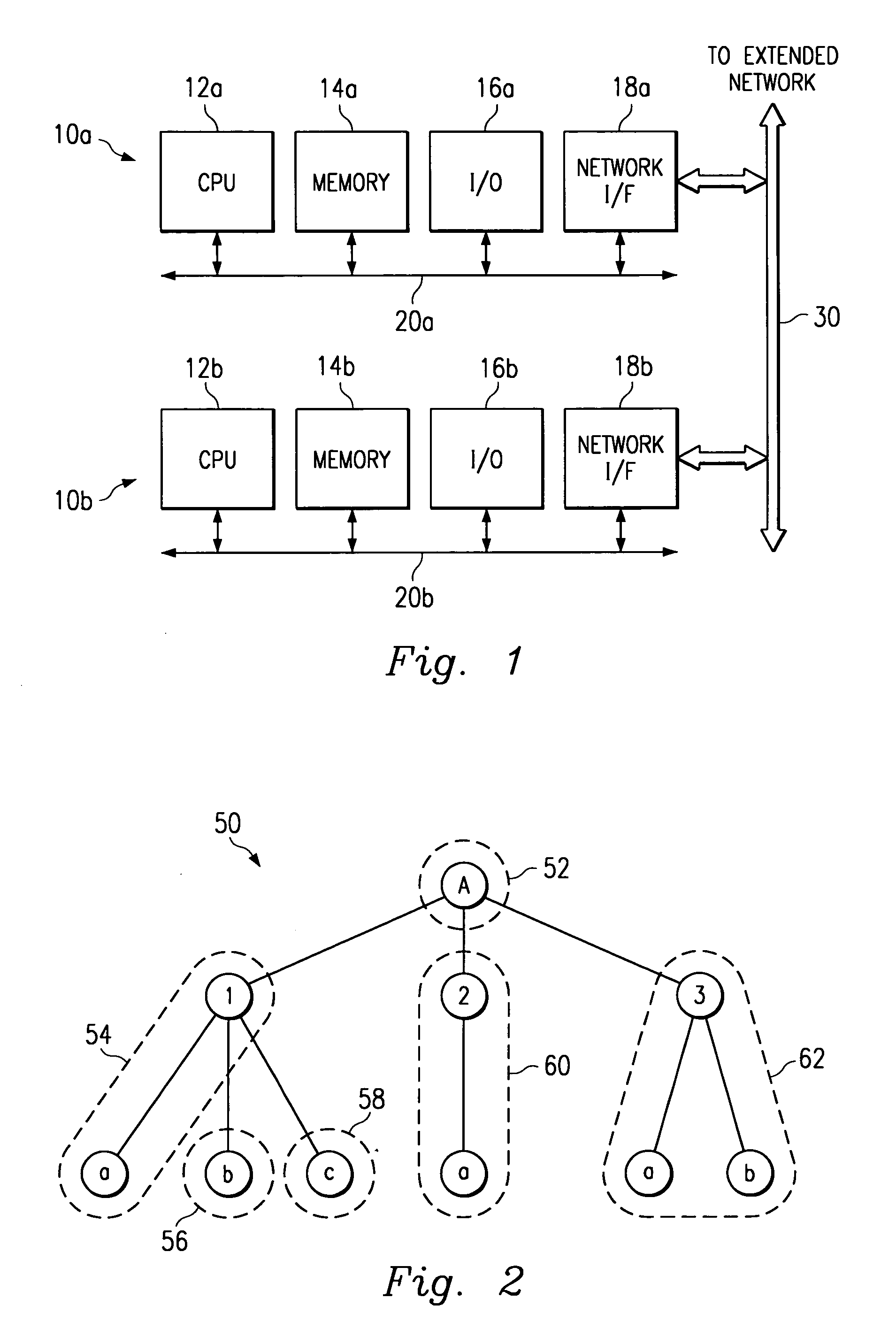
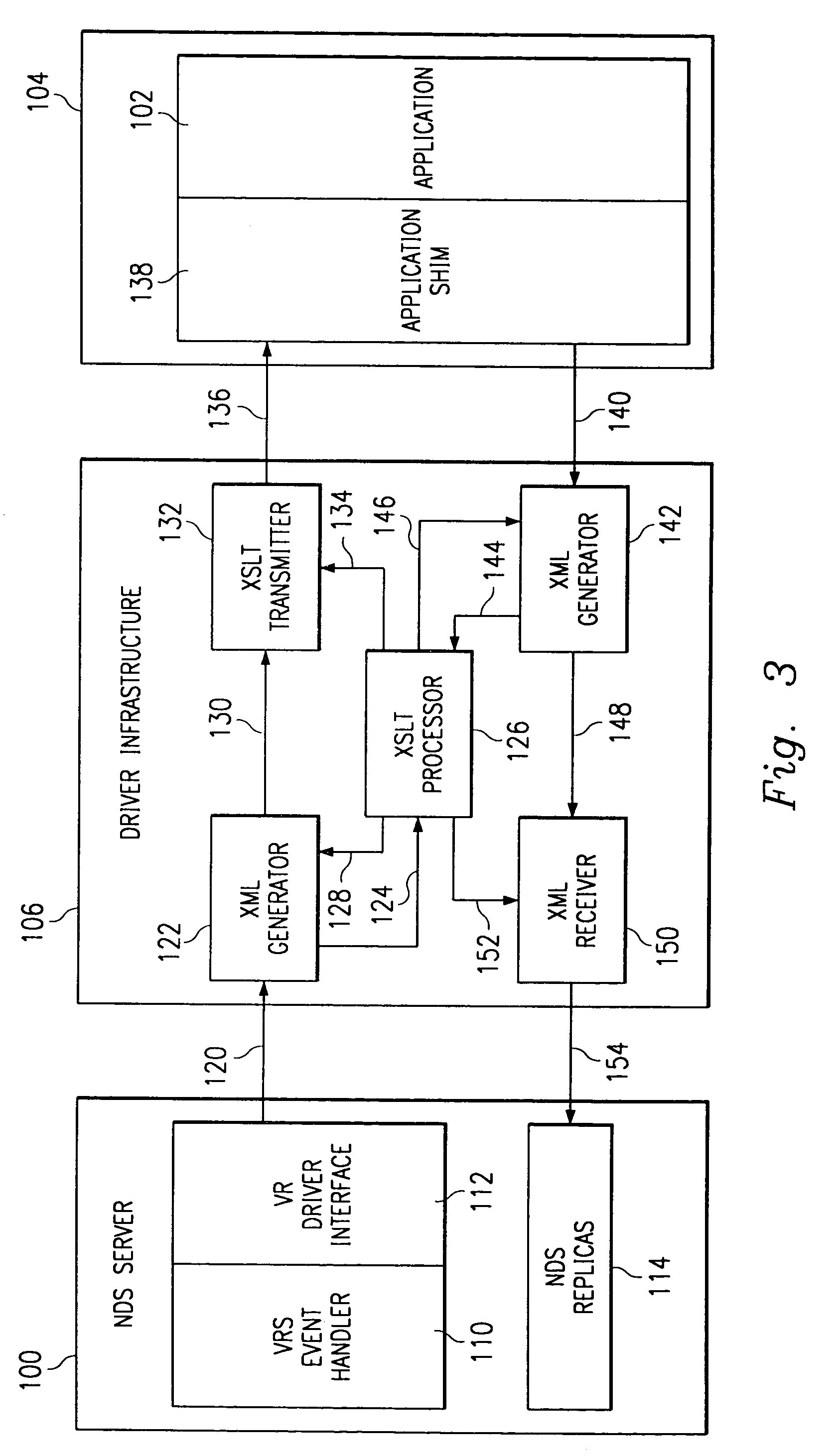
Computer directory system having an application integration driver infrastructure
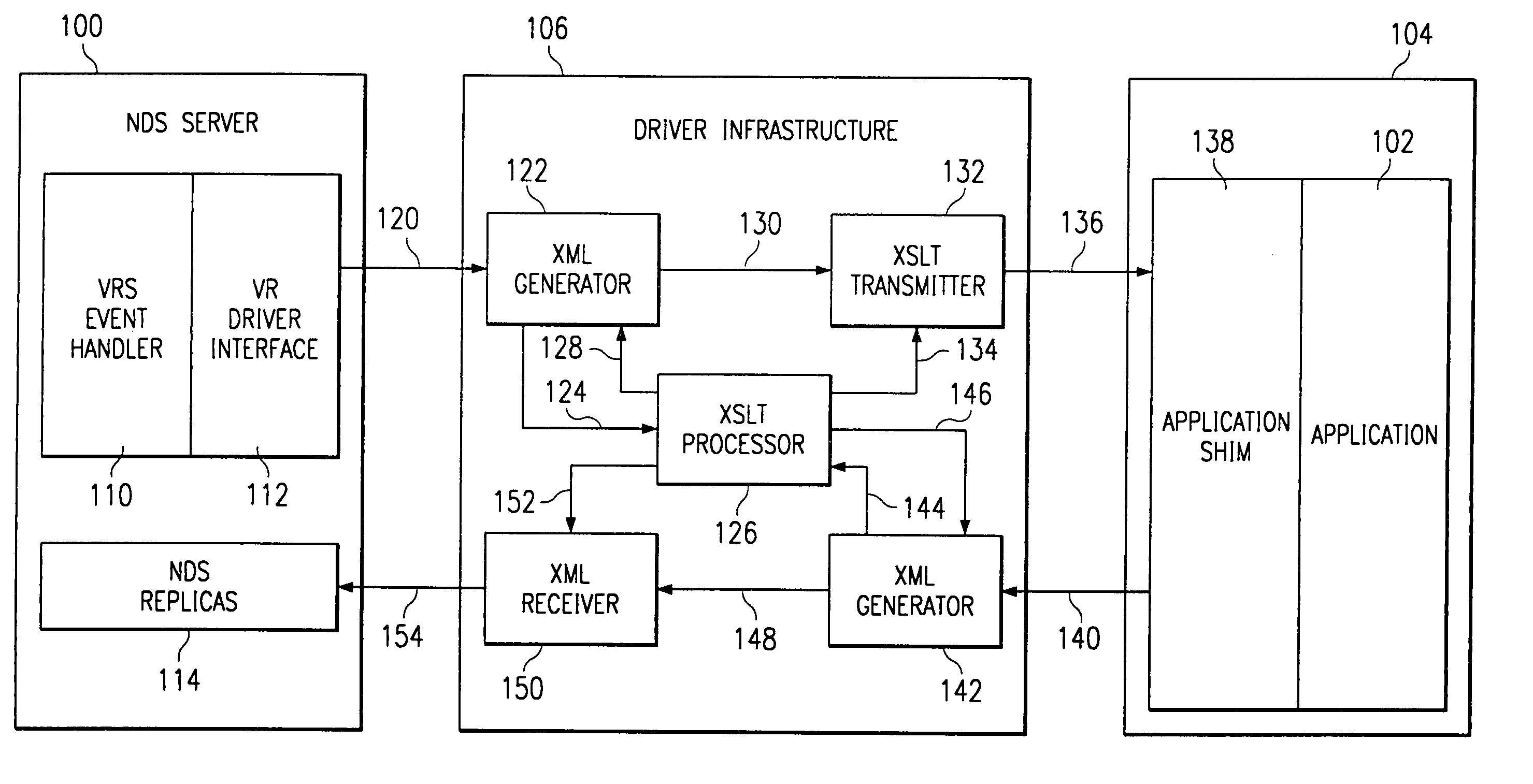
InactiveUS7146614B1New applicationEasy to integrateMultiprogramming arrangementsMultiple digital computer combinationsXSLTApplication software
An application integration driver infrastructure for facilitating the use of a distributed directory running in a computer network is provided. The infrastructure can transform specific directory events into a vendor-neutral data identification system and then use vendor-neutral transformation technologies to transform the neutral data identification into a specific application's data format, and vice-versa. The infrastructure receives an event from the distributed directory into a markup language generation system, such as an extensible markup language (“XML”) generator. The XML generator converts the event into XML data and provides the XML data to a transformation processing system, such as an extensible transformation language (“XSLT”) processor. The XSLT processor transforms the XML data to a predetermined format. The format can be dictated by a stylesheet provided to the XSLT processor, the stylesheet being responsive to requirements of a computer application. The transformed data is then provided to the application for the application to use in a conventional manner. The application may use an application shim to convert the transformed data into a native application program interface (“API”) for the application.
Owner:EMC IP HLDG CO LLC
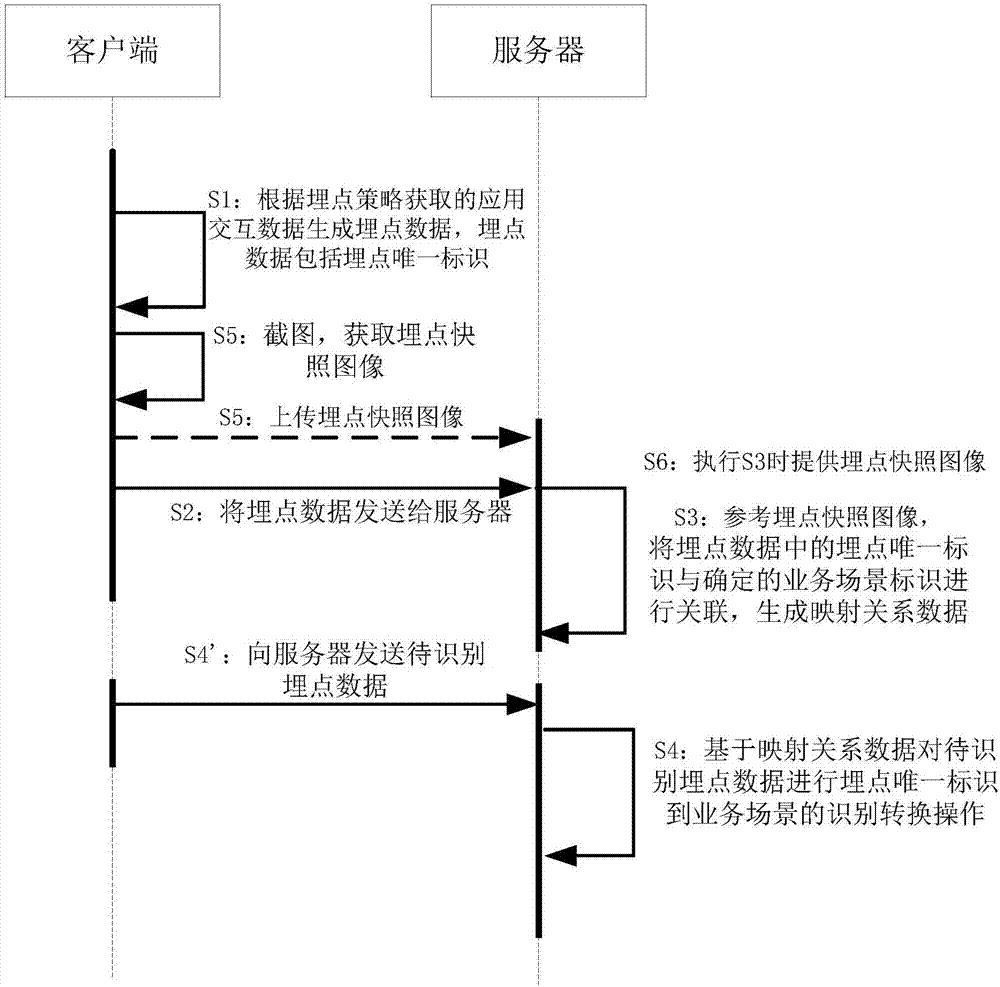
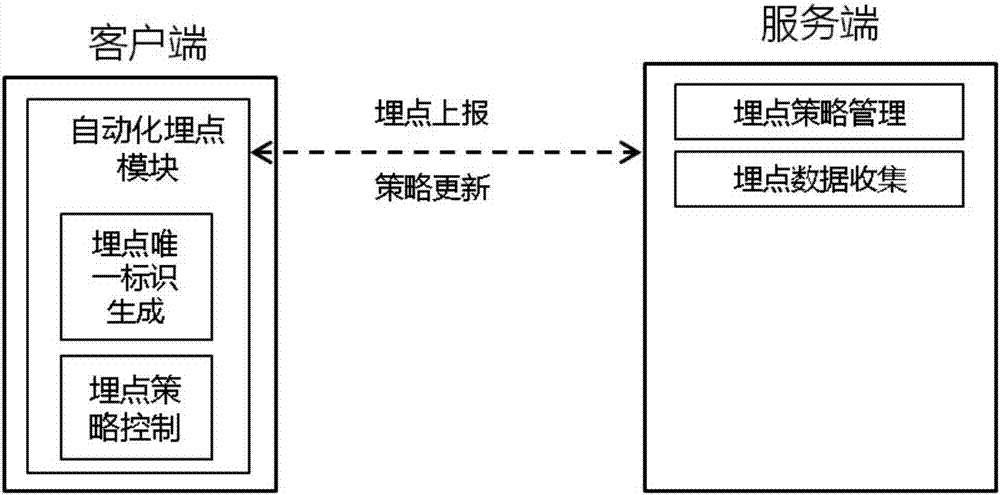
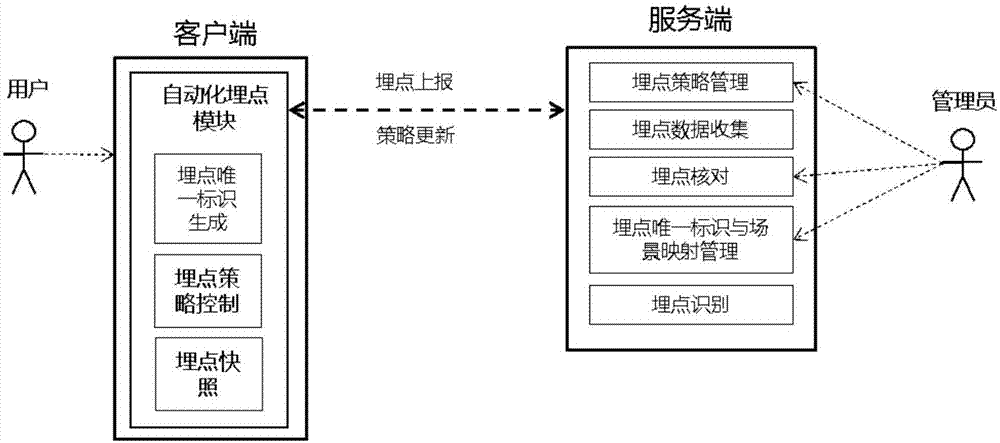
Processing method and device of buried-point data, server and client
ActiveCN107196788AImprove processing efficiencyEasy to identifyWeb data retrievalResourcesUnique identifierClient-side
An embodiment of the invention discloses a processing method and a processing device of buried-point data, a server and a client. The processing method comprises the steps that: the client obtains application interactive data according to a preset buried-point policy, and generates buried-point data according to the application interactive data, wherein the buried-point data comprises a buried-point unique identifier generated according to a predetermined method; the client transmits the buried-point data to the server; the server associates the buried-point unique identifier in the buried-point data with a determined service scene identifier, and generates mapping relation data; the client transmits buried-point data to be identified to the server; and the server performs identification conversion operation from the buried-point unique identifier to a service scene based on the mapping relation data. By utilizing the processing method, the processing device, the server and the client, the buried-point data identification conversion operation can be simplified, the terminal buried-point error rate and the conversion error rate of converting the buried-point data into the service scene by the server are decreased, the manual point burying, identification and check costs are reduced, and the processing efficiency and identification effect of the buried-point data are improved.
Owner:ADVANCED NEW TECH CO LTD
Device and method for acquiring product coded identifier information
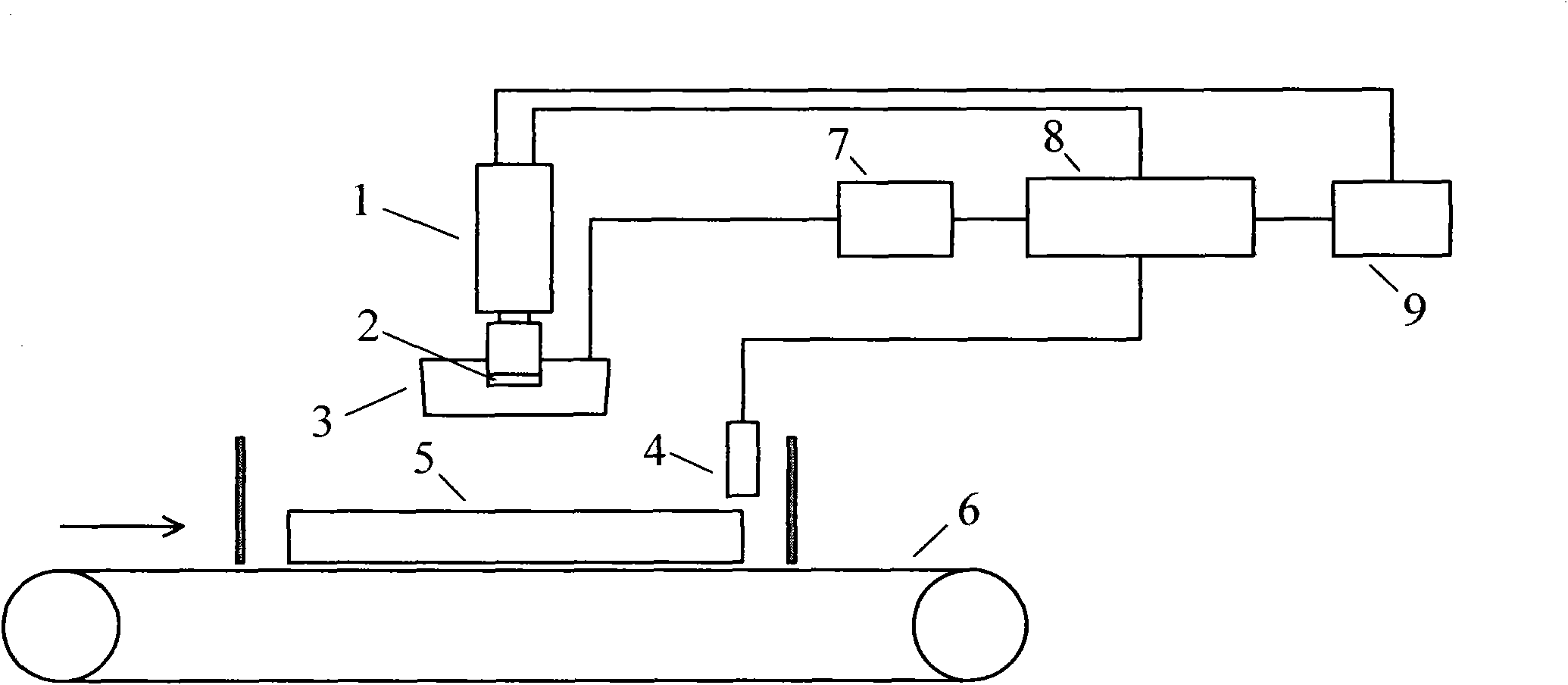
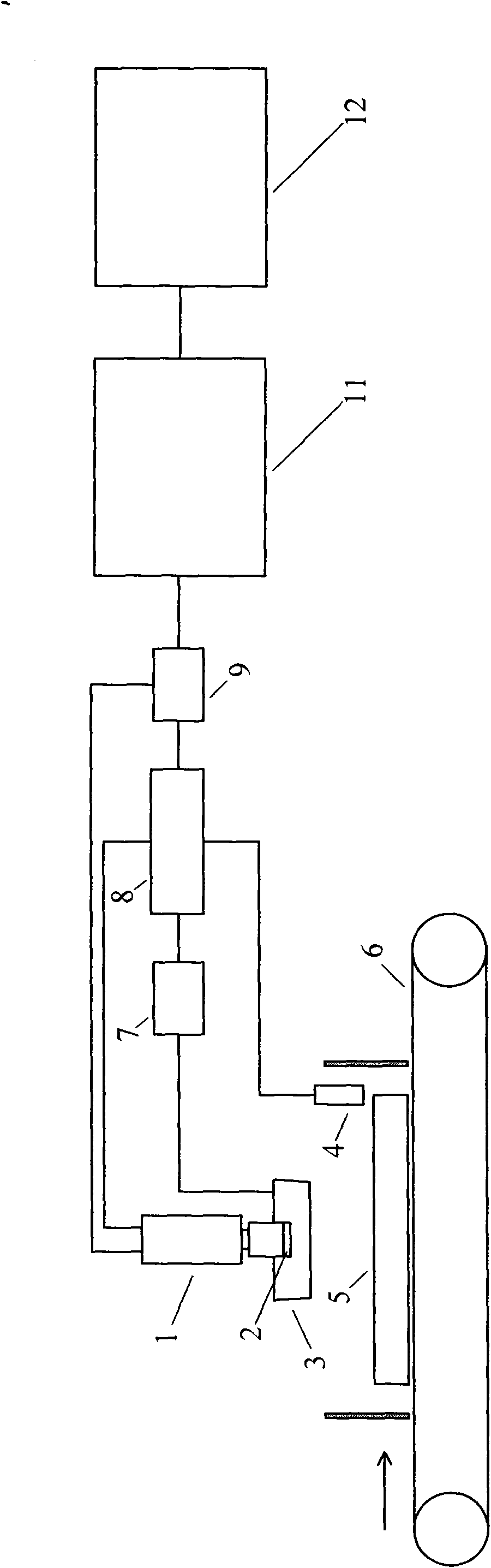
ActiveCN101885391AIncrease brightnessImprove recognition rateCharacter and pattern recognitionPackagingOpto electronicImaging equipment
The invention relates to a device and a method for acquiring product coded identifier information. The device comprises a data acquisition unit, a data identification unit and a control unit, wherein the data acquisition unit is positioned above a convey belt and comprises an image device, a lighting device and a position photoelectric switch; the image device is used for photographing product coded identifier to obtain image data; the lighting device is used for irradiating the product coded identifier; the position photoelectric switch is used for sensing the position of the product on the convey belt; the data identification unit is used for identifying and processing the image data acquired by the data acquisition unit to obtain the product coded identifier information and storing the information and is also connected with the image device and the control unit respectively through a data line; and the control unit is used for controlling the data acquisition unit, and connected with the data identification unit, the image device, the lighting device and the position photoelectric switch respectively through data lines. The invention also provides the method for acquiring the product coded identifier information.
Owner:北京赛腾标识系统股份公司
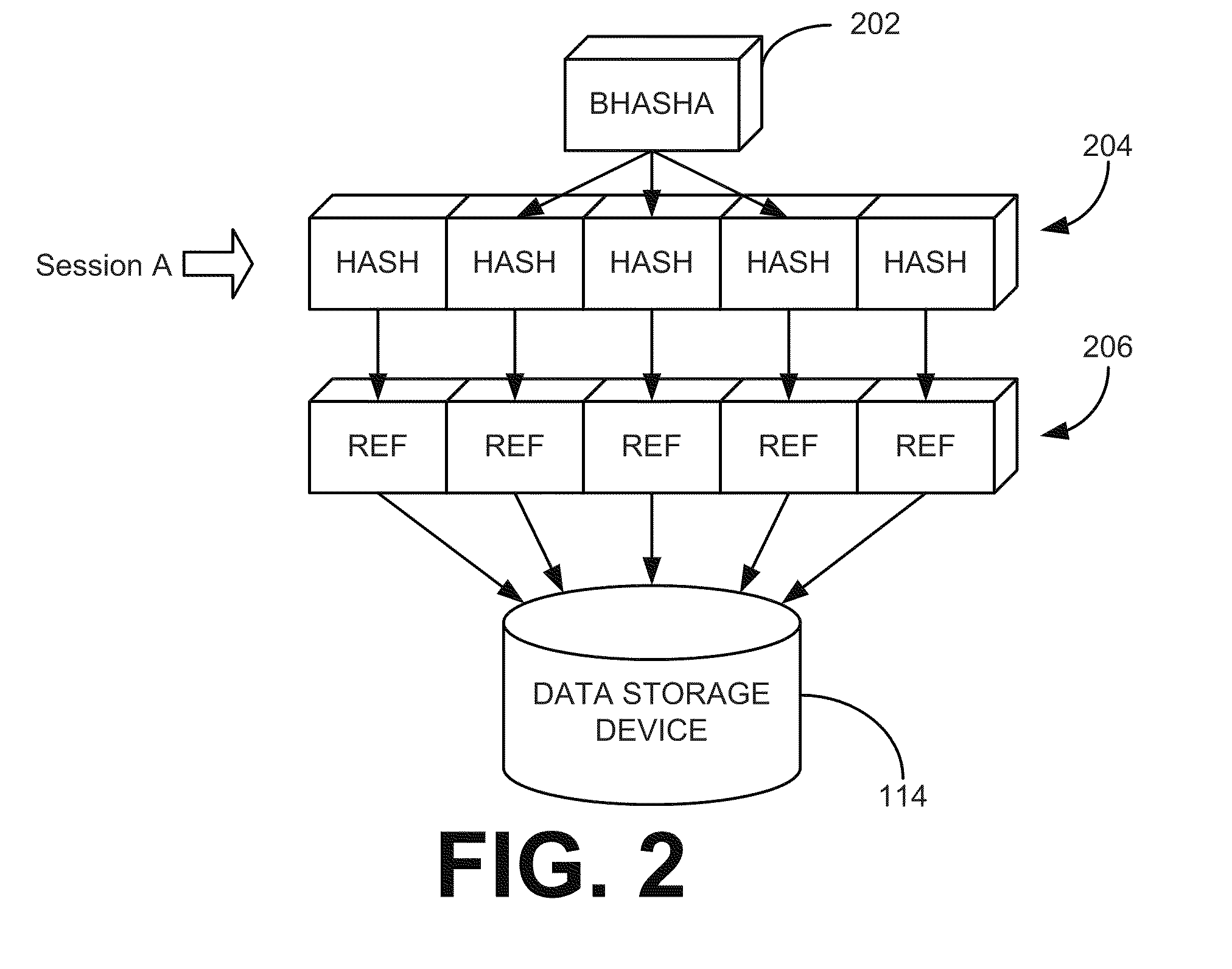
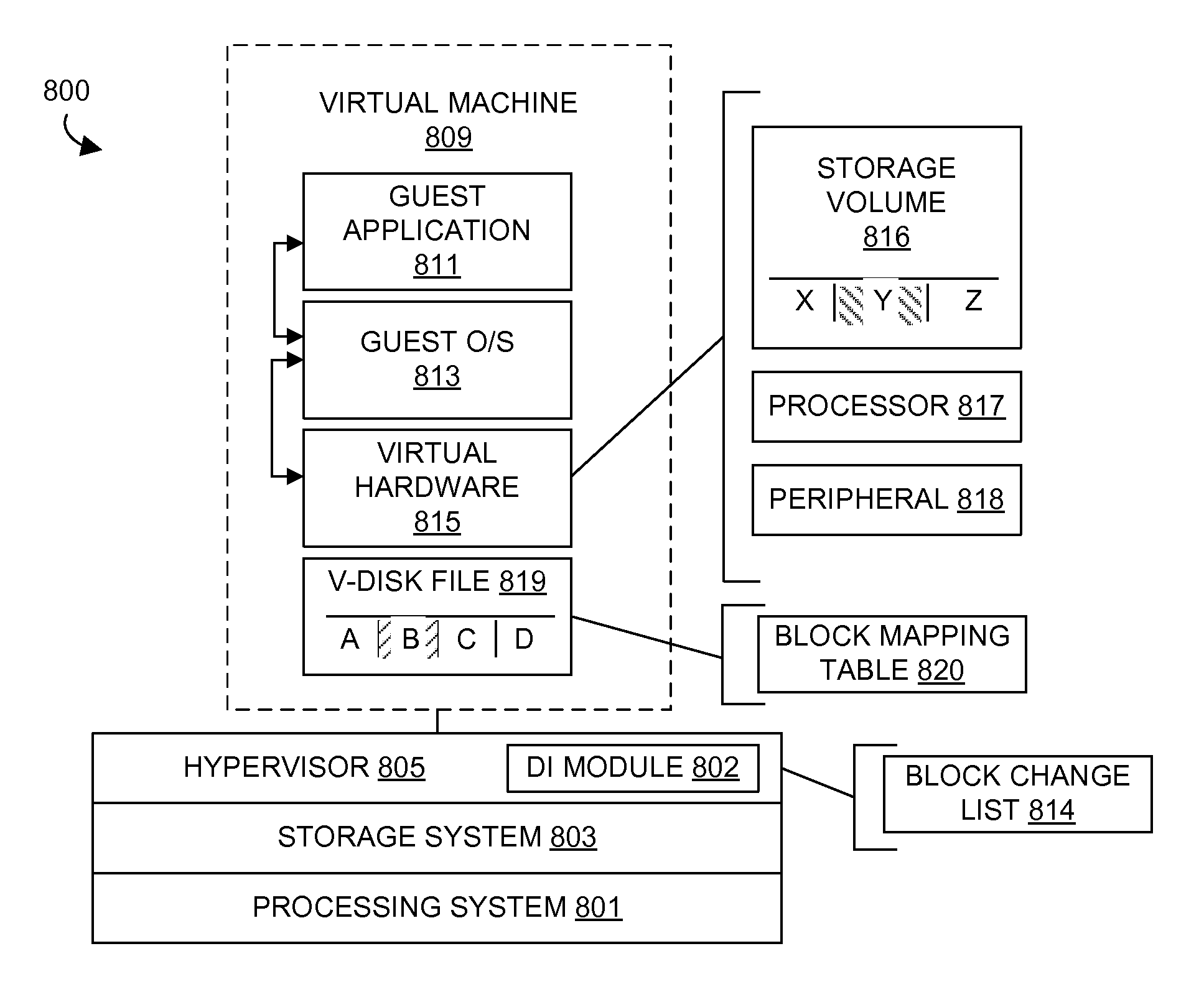
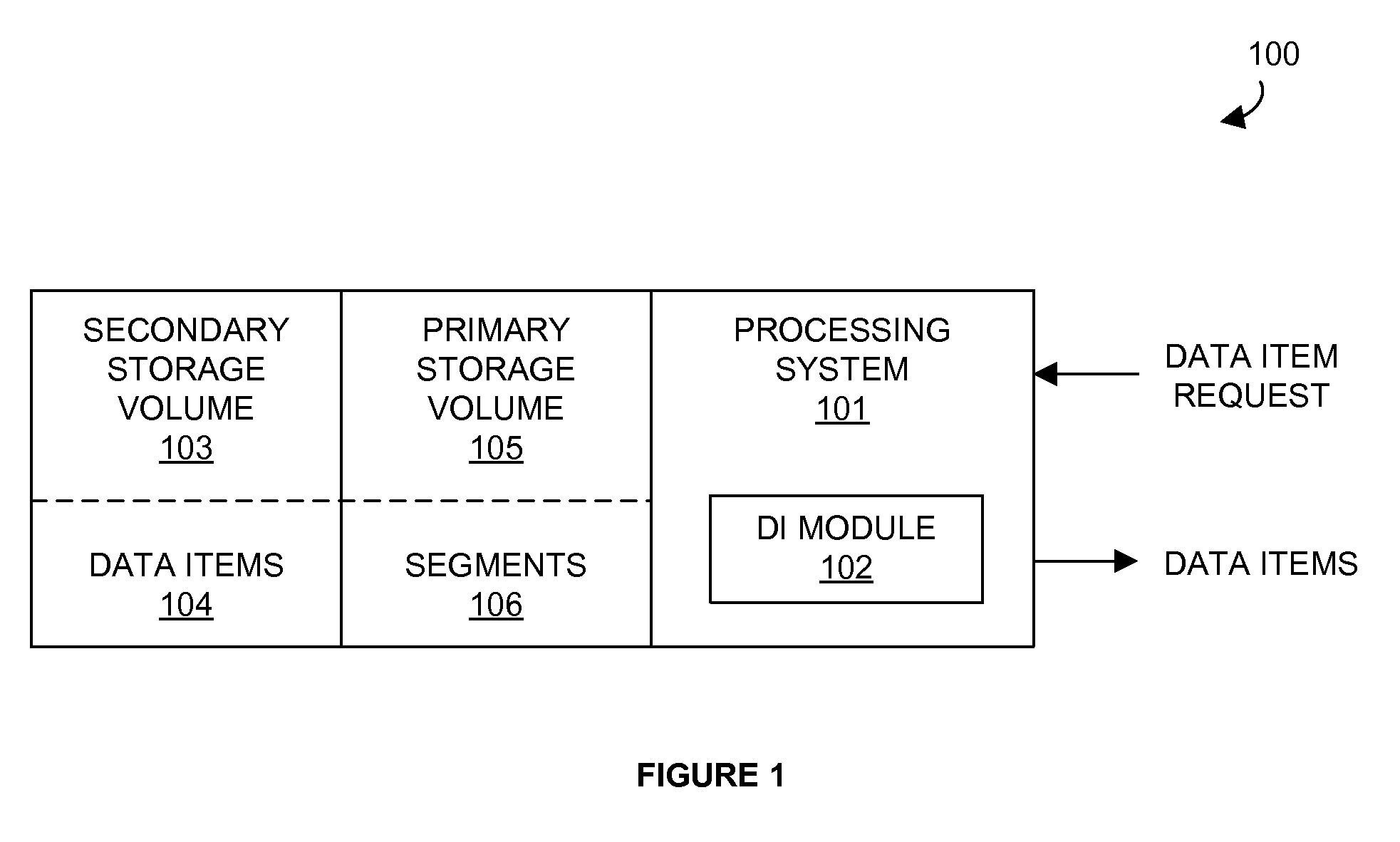
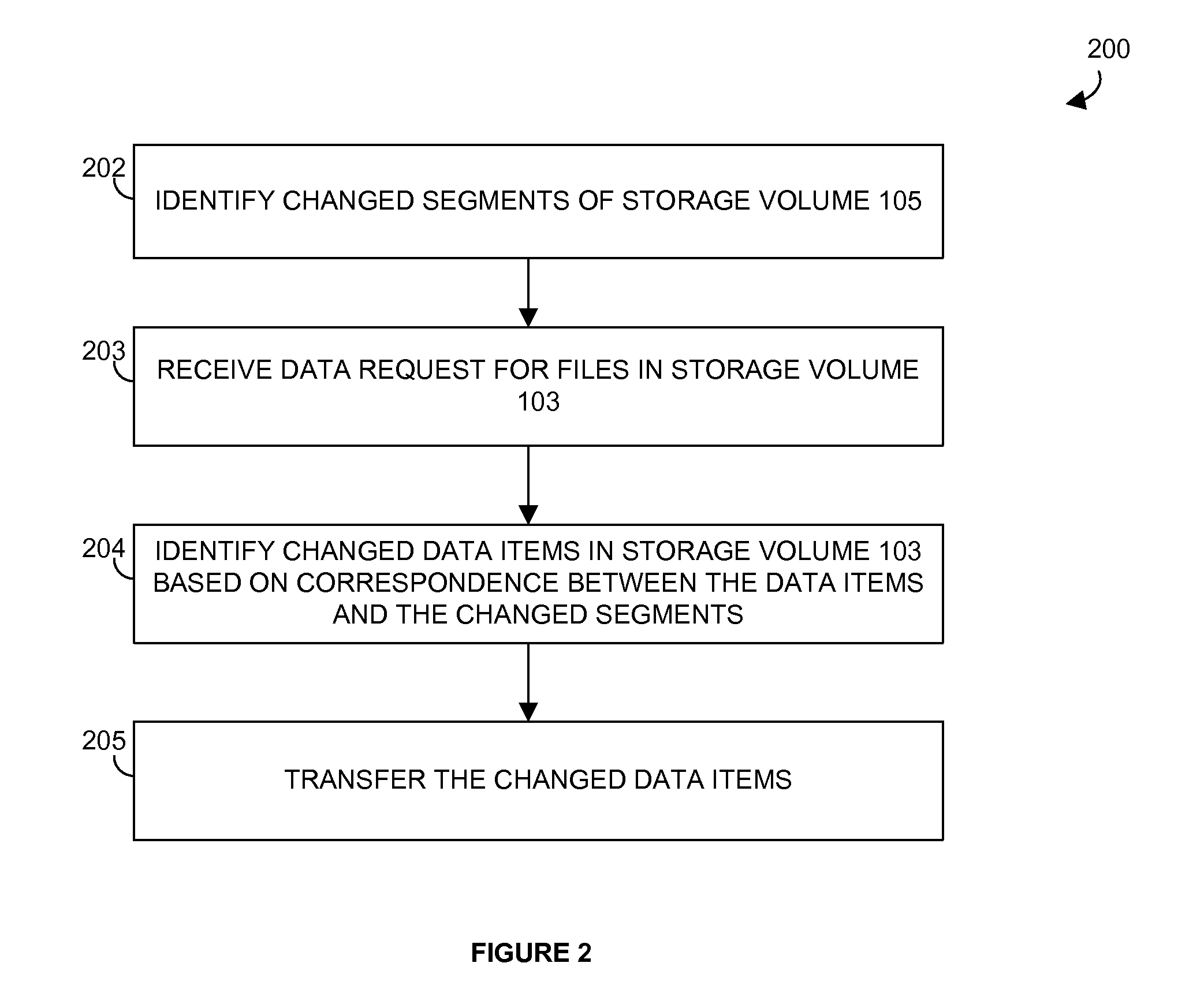
Data identification system
Disclosed is a method of operating a data storage system. The method comprises identifying changed segments of a primary storage volume, receiving a data request for a plurality of data items in a secondary storage volume, identifying changed data items of the plurality of data items in the secondary storage volume based on a correspondence between the plurality of data items in the secondary storage volume and the changed segments of the primary storage volume, and transferring the changed data items in response to the data request.
Owner:QUANTUM CORP
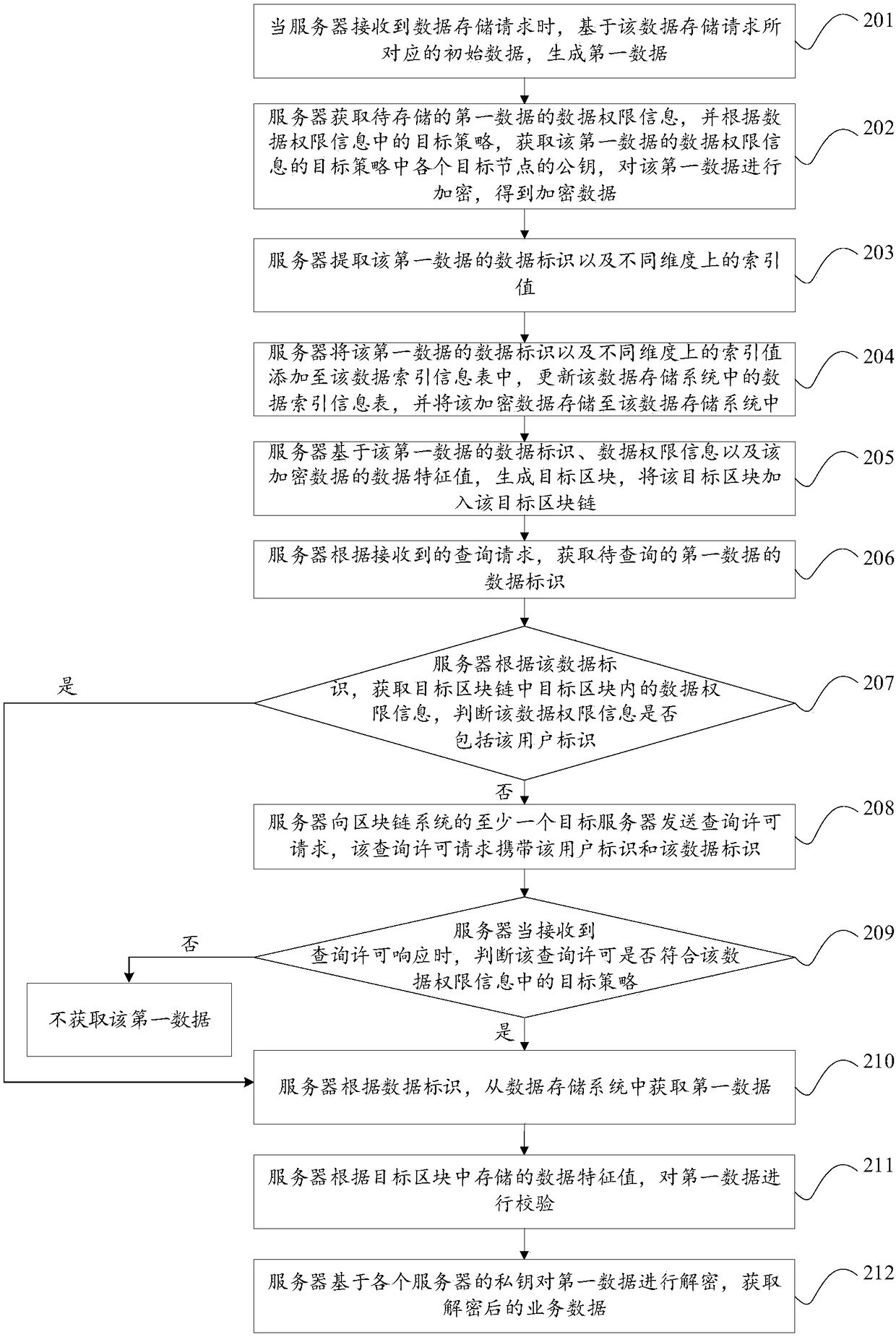
Data query method and device based on blockchains, server and storage medium
ActiveCN108563788AImprove securityImprove privacyPublic key for secure communicationDigital data protectionComputer terminalData query
The invention discloses a data query method and device based on blockchains, a server and a storage medium and belongs to the technical field of networks. The method comprises the steps that data query is combined with a blockchain technology; when a request of a user for querying data is acquired, according to user identification and data identification, based on data permission information, a permission of the user for querying the data is queried; when it is determined that the user does not have the permission for querying the data, according to a target strategy in the data permission information, query allowances of multiple terminals are acquired; when the acquired query allowances accord with the target strategy, the data is acquired from a storage system. According to the method,by setting the data permission information, the safety and privacy of the data are improved, through different target strategies of different kinds of data, the flexibility of setting data query permissions is improved, and the device is safer and more intelligent.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
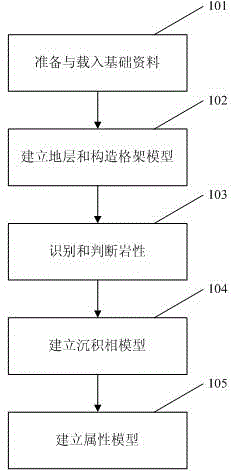
Glutenite comprehensive geologic modeling method
The invention provides a glutenite comprehensive geologic modeling method. The method comprises step1, performing analysis and arrangement on drilling well, earthquake, logging and stratigraphic correlation information to screen geologic model basic data; step2, building a stratum and tectonic framework model through single-well fine stratigraphic correlation, fine earthquake explanation and fine inter-bed and fracture system description; step3, recognizing and determining lithologic characteristics; step4, building a sedimentary facies model; step5, building an attribute model through a pore penetration model. By the aid of the method, the lithology identification accuracy is improved, and rapid division of the sedimentary facies is achieved through man-machine interaction.
Owner:CHINA PETROLEUM & CHEM CORP +1
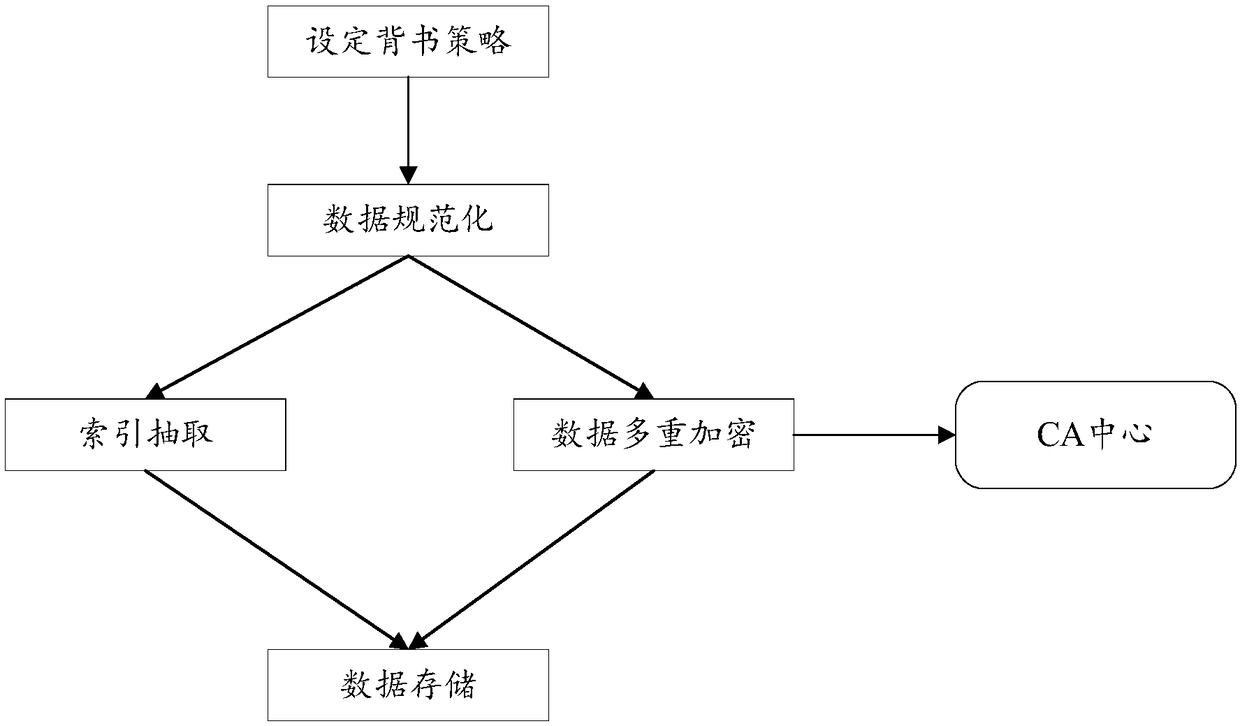
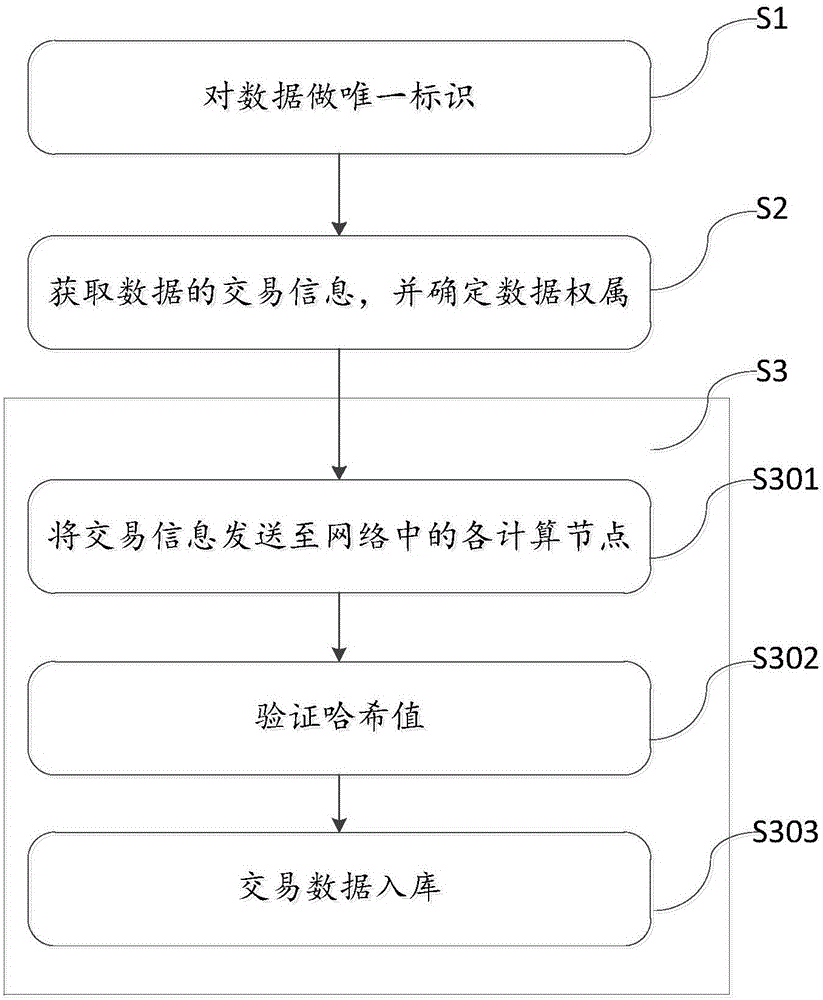
Method and system for determining the rights of big data based on block chain technology
InactiveCN106815728AQuery results are reliableQuery results are fastSpecial data processing applicationsProtocol authorisationData platformData science
The invention discloses a method and a system for determining the rights of big data based on block chain technology, which belong to the big data processing technical field. The method comprises the following steps: firstly, making unique identification to the data; then, obtaining the transaction information of the data; according to the data identification related with the transaction information, searching the prior transaction information in the transaction information block chain of the data; according to the prior transaction information, determining the right property of the data in transaction; and finally, if a seller has the ownership of the data, then, starting the data transaction and at the same time, saving the transaction information in a database; and if the seller does not have the ownership of the data, then stopping the transaction. The method and the system of the invention are based on the block chain technology, which solve the problem of right determination arising from the data transactions on a big data platform and make up the grey area of opening big data platform right determining schemes.
Owner:北京供销科技有限公司
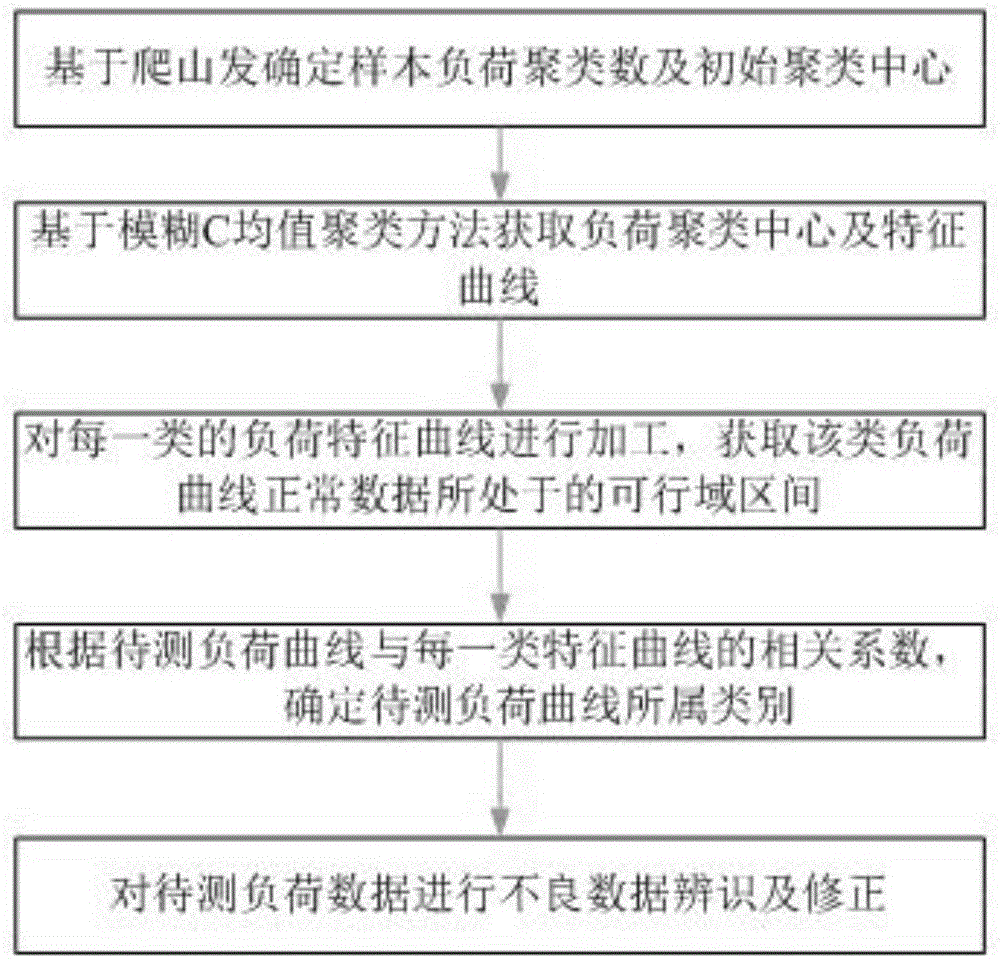
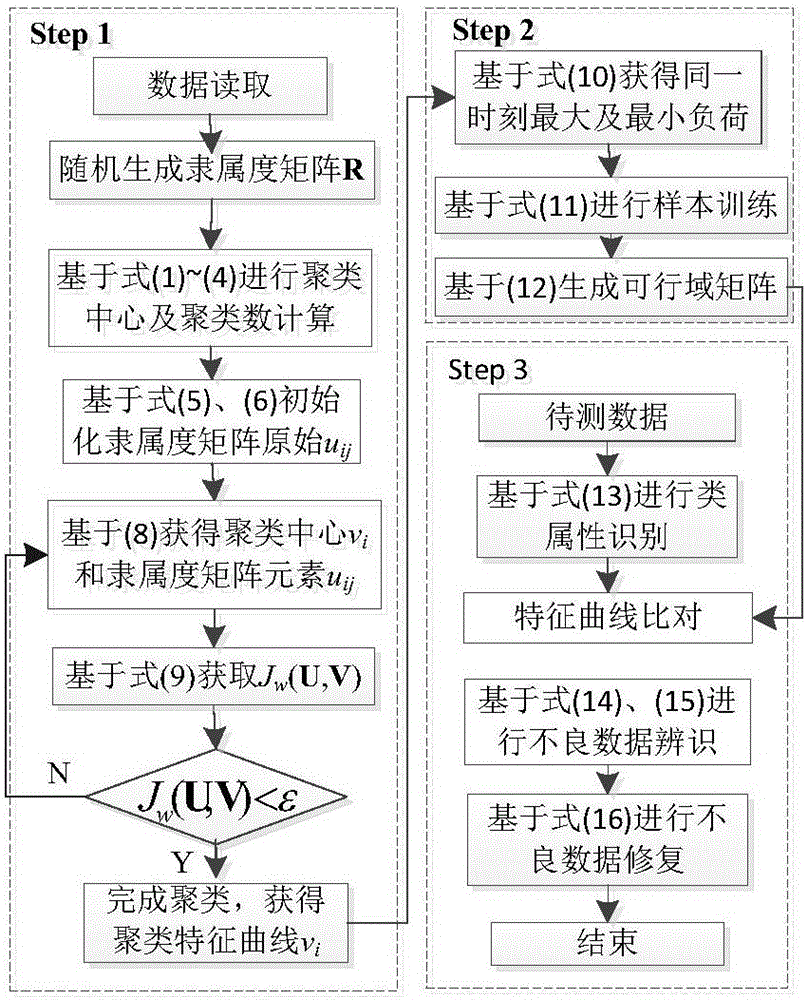
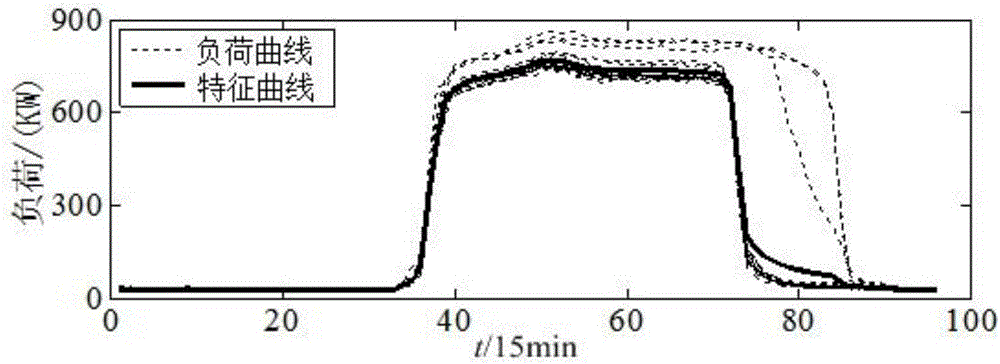
Power system load data identification and recovery method
ActiveCN106055918ASimplify complexityImprove clustering efficiencyInformaticsSpecial data processing applicationsRecovery methodCluster algorithm
The invention discloses a power system load data identification and recovery method. Firstly, according to user historical load data, the number of clusters and initial cluster centers of sample data are determined on the basis of the hill climbing method; secondly, the final cluster center and the characteristic curve of the historical load data are obtained on the basis of the fuzzy C-means clustering algorithm; thirdly, each kind of load characteristic curve is processed, and the feasible region interval where normal data of the load curve is located is obtained; fourthly, according to correlation coefficients with the load characteristic curves, the category to which a to-be-tested load curve belongs is determined; finally, on the basis of the feasible region interval and the to-be-tested load curve whose category is judged, bad data of to-be-tested load data is identified and corrected. According to the method, the fuzzy C-means algorithm serves as the basis, the hill climbing function method is used, the number of clusters and the initial cluster centers are determined at the same time to improve clustering efficiency, and the initial cluster center determination problem and identification effect judgment randomness problem of bad data are solved.
Owner:TIANJIN UNIV
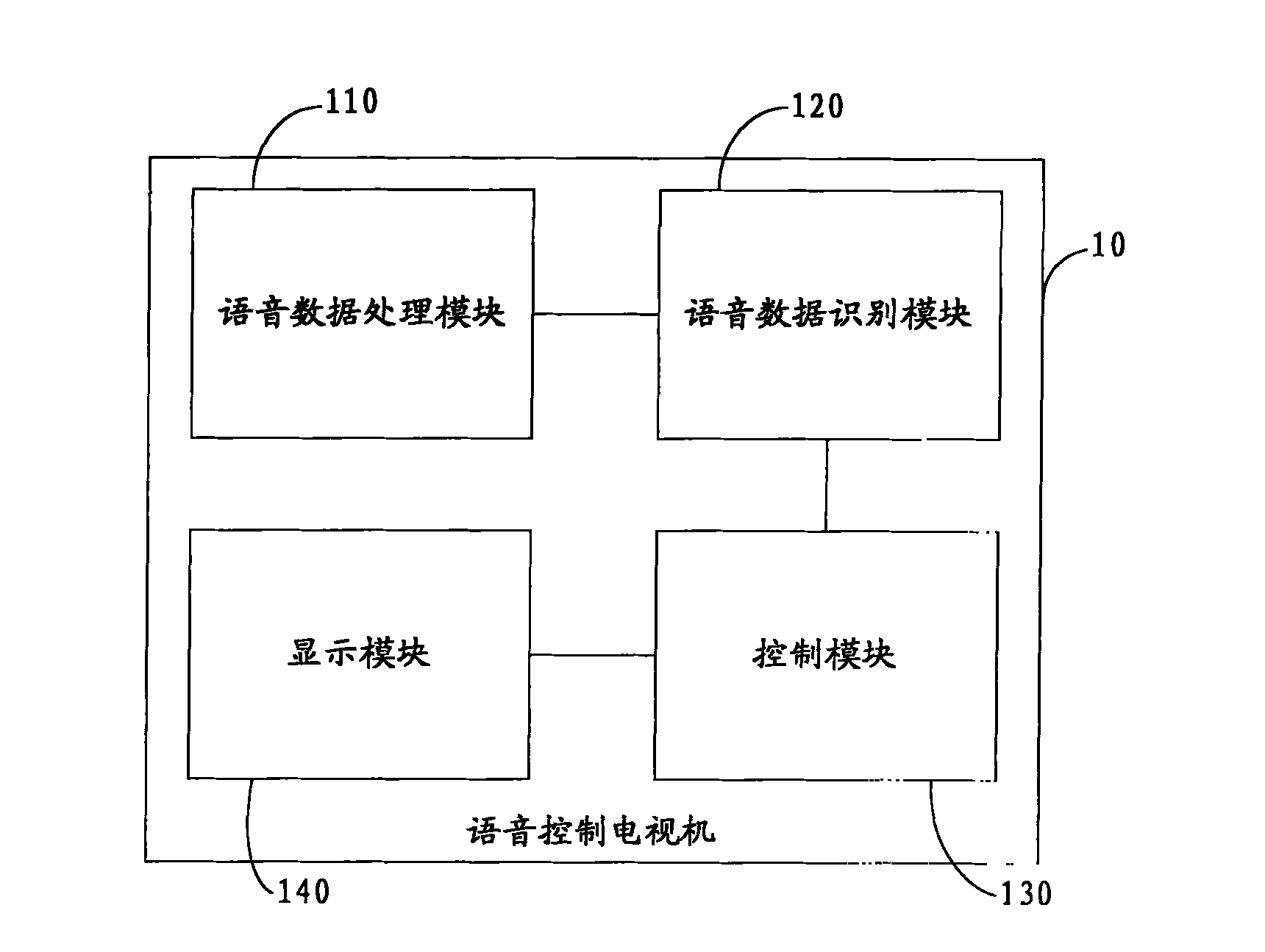
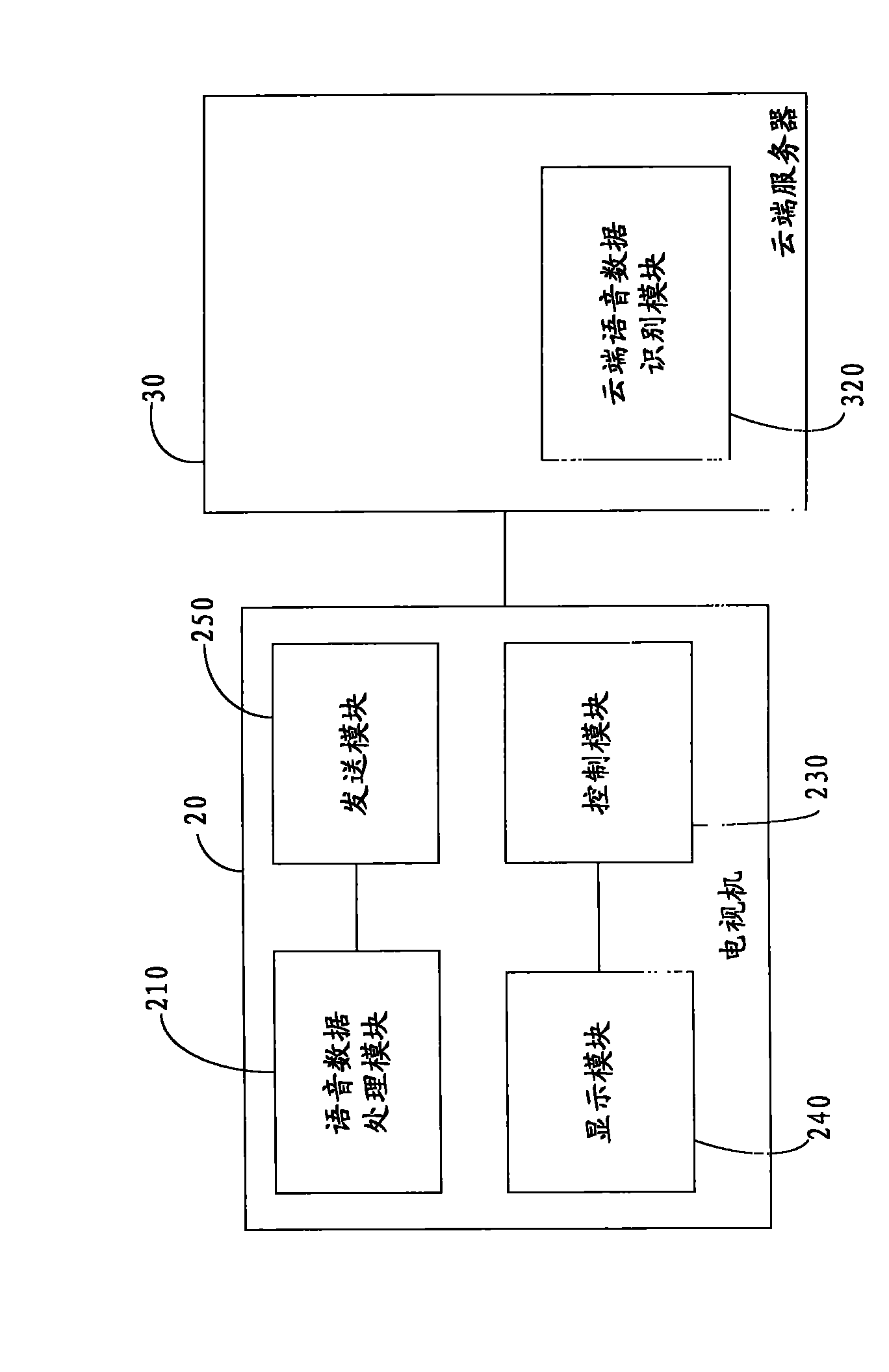
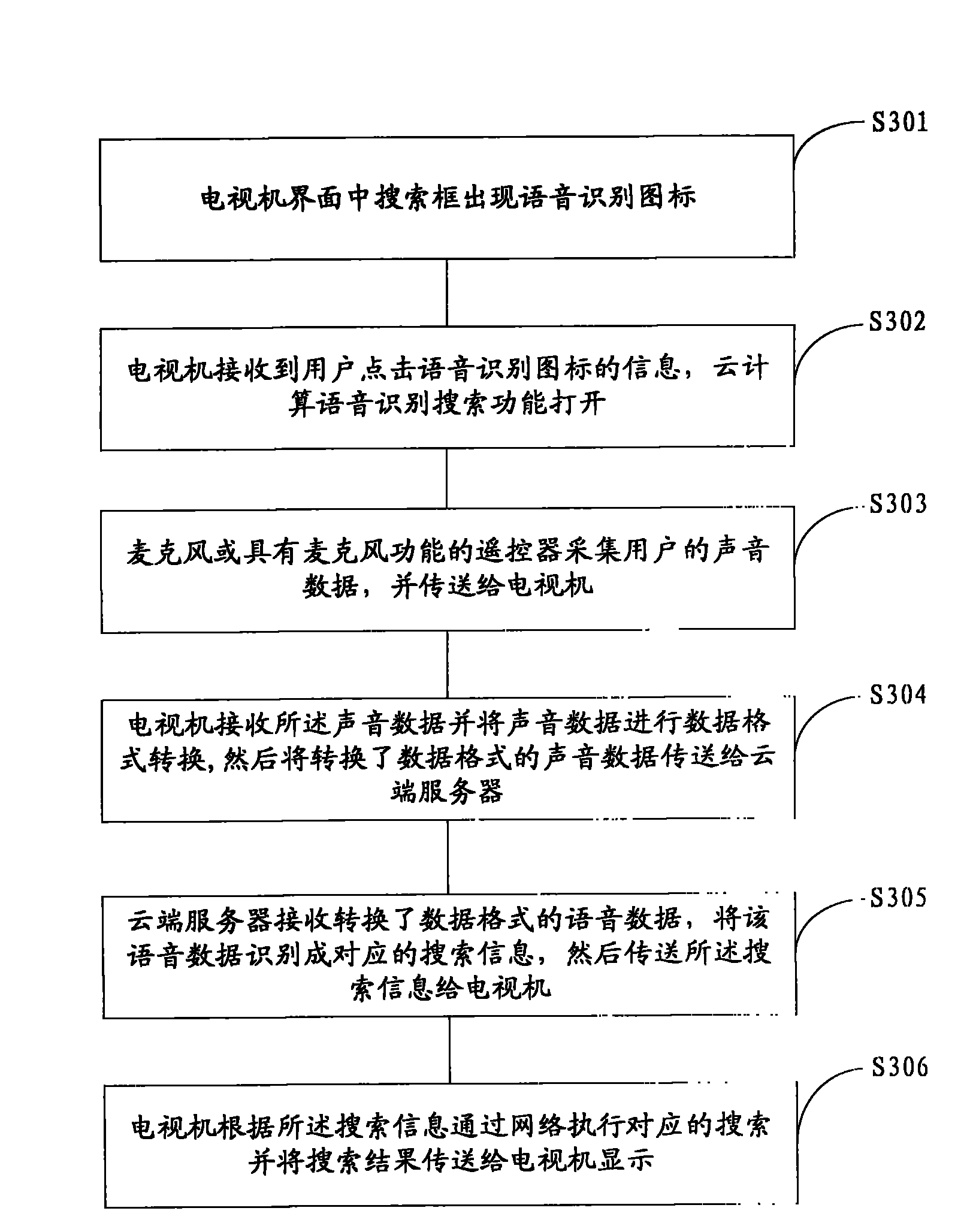
Voice controlled television, television system and method for controlling television through voice
InactiveCN102740014AEasy to operateRich interactive experienceTelevision system detailsColor television detailsTelevision systemData acquisition
The invention provides a voice controlled television which comprises a voice data processing module, a voice data identification module, and a control module. The voice data processing module is for receiving voice data acquired and transmitted by a voice data acquisition module and for converting the voice data to voice data in string format when a voice identification search function is started; the voice data identification module is for identifying the voice data in string format as corresponding text information; and the control module is for performing corresponding search with a network according to the text information and for transmitting the search results to a display module of the television to display the search results. Correspondingly, the invention further provides a voice controlled television system and a method for controlling the television through voice. With the adoption of the invention, the operation of a user is simplified, and the television is intelligent and humane.
Owner:HISENSE VISUAL TECH CO LTD
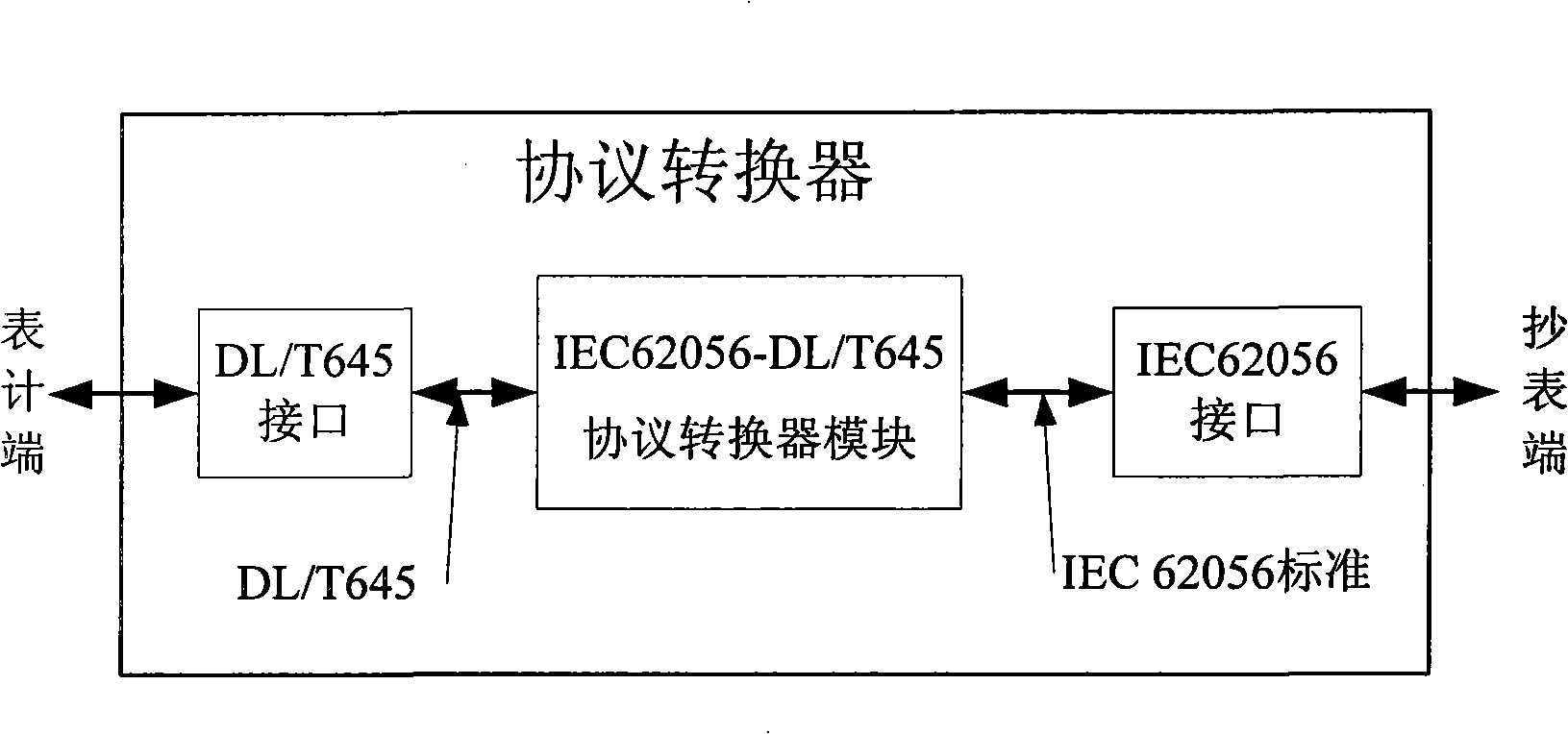
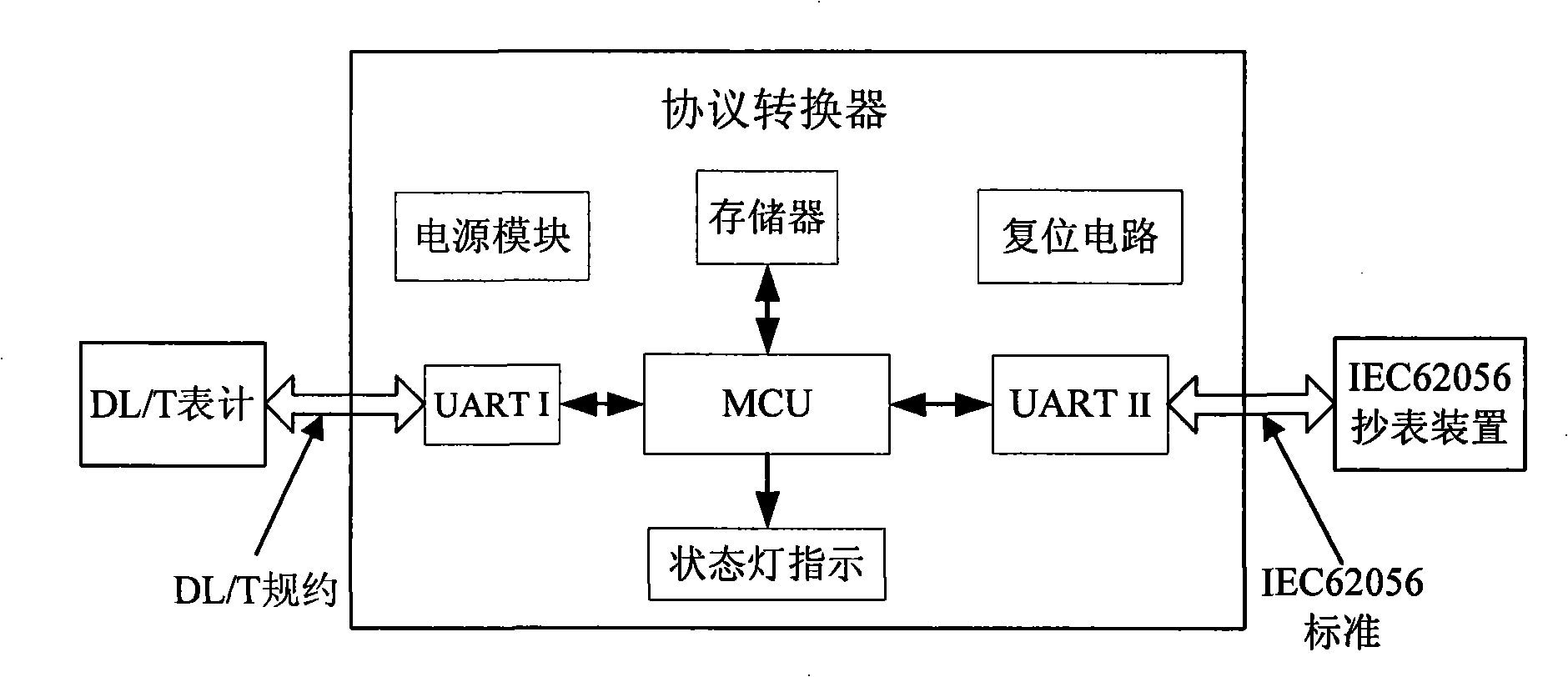
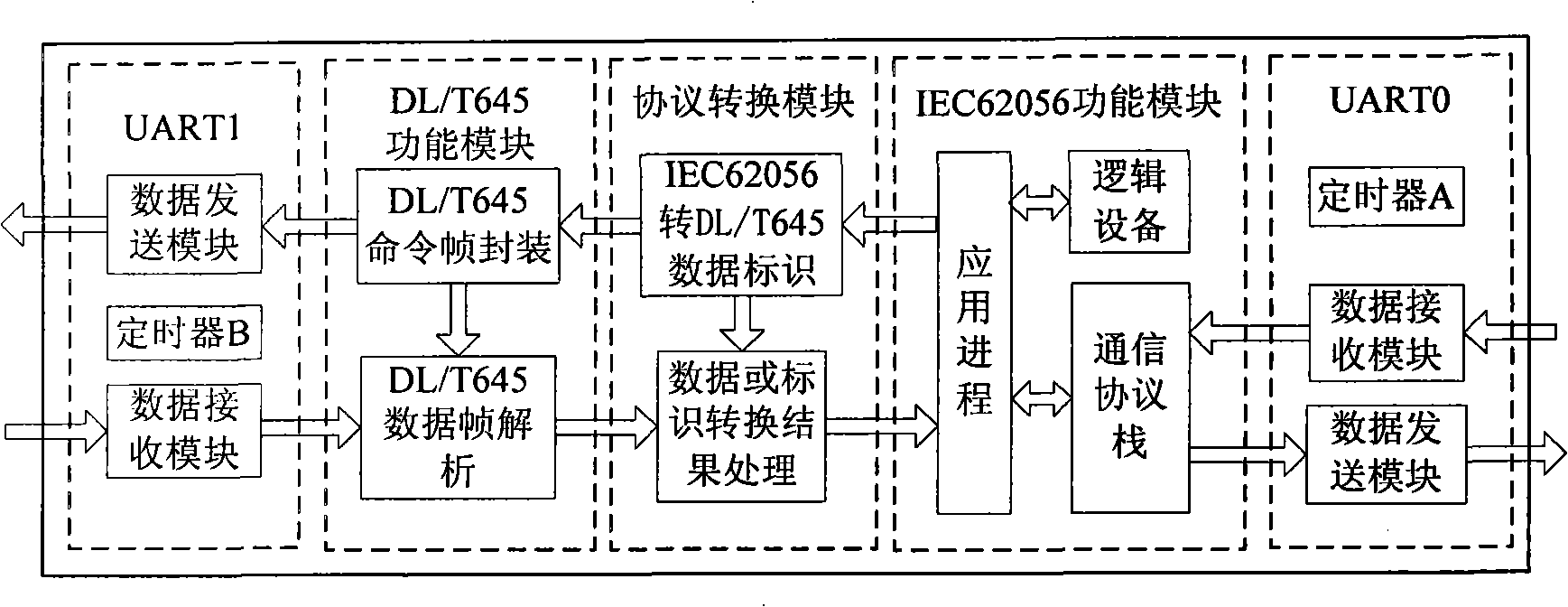
Protocol conversion system and protocol conversion process
The invention relates to a communication protocol transformation system and protocol transformation process. The protocol transformation system comprises an UARTO module for receiving and sending data packets of IEC 62056 standard protocol; an IEC 62056 function module is a core module supporting the IEC 62056 protocol and constructed according to the IEC 62056 standard; main function of a protocol transformation module is to inquire the corresponding DL / T 645 identification in light of data identification of IEC 62056, and sends to a DL / T 645 function module; the main function of the DL / T 645 function module is to deal with DL / T 645 protocol-associated functions; an UART1 module is responsible for communication with a table meter end. The communication protocol transformer for electric energy counting and charging systems and meter reading systems provided by the invention is applied between two systems with different protocols that are the electric energy meters of DL / T 645 communication protocol and the meter reading system consistent with the IEC 62056 standard, enabling the two systems with different protocols can exchange for data normally.
Owner:ZHUHAI ZHONGHUI MICROELECTRONICS
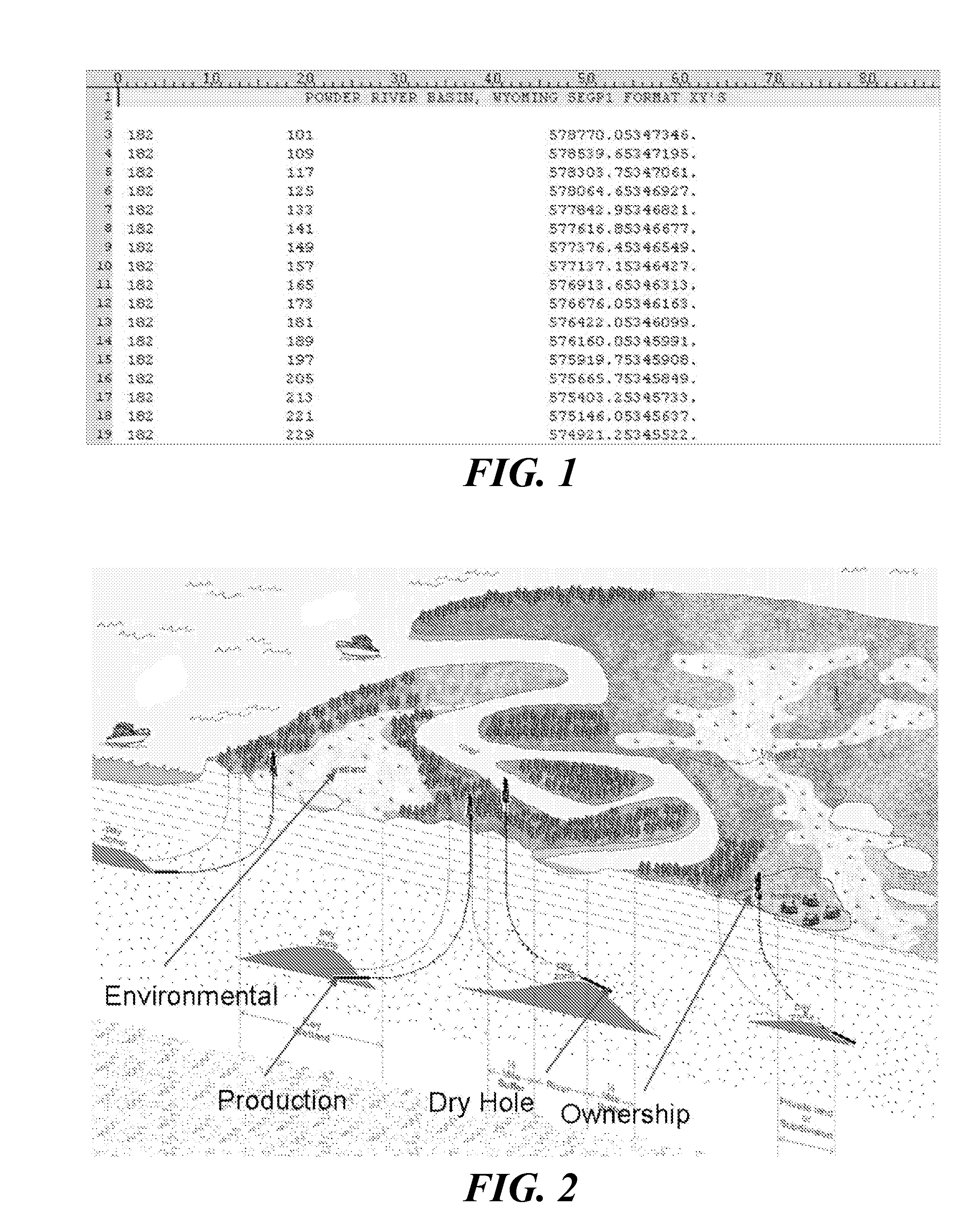
Method and computer program product for geophysical and geologic data identification, geodetic classification, and organization
InactiveUS20100179963A1Instruments for road network navigationDigital data processing detailsInformation acquisitionDatabase
A method of geodetic information acquisition and a computer program product having computer code for performing the method are provided. The method includes identifying a file having multiple records, where the records contain spatially referenced data. The records are classified into header records and data records. Each data record is divided into fields. Patterns of fields consistent with sets of the data records are identified. The records are associated with a format based on the patterns of fields. At least some of the spatially referenced data is extracted from the records according to the format.
Owner:ENSOCO
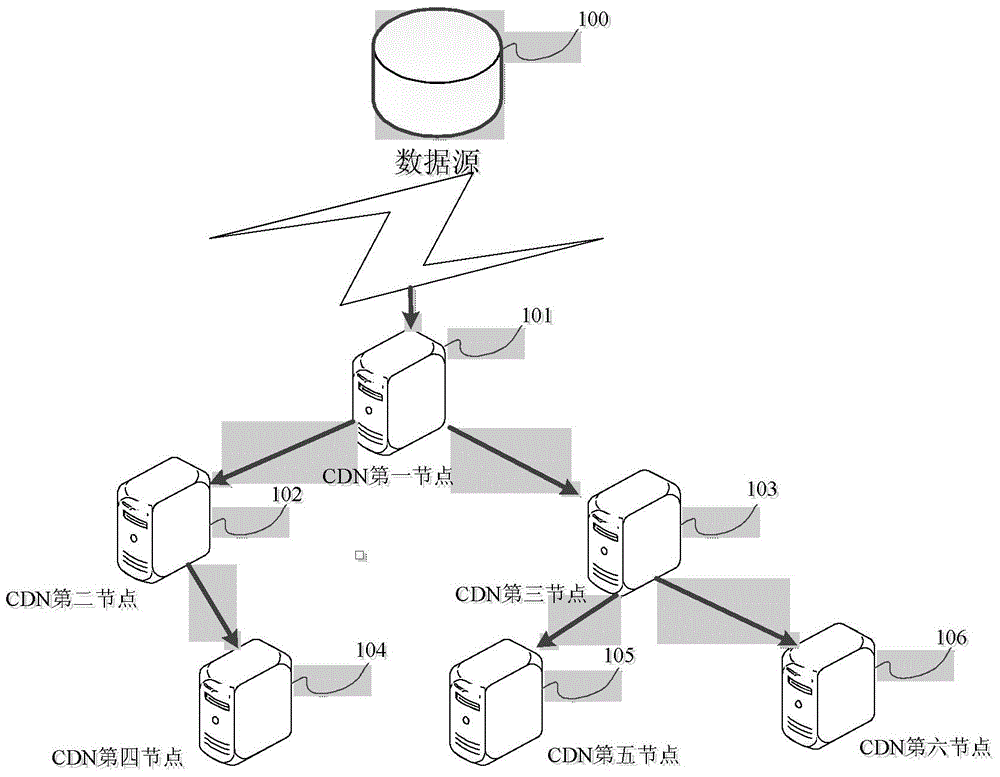
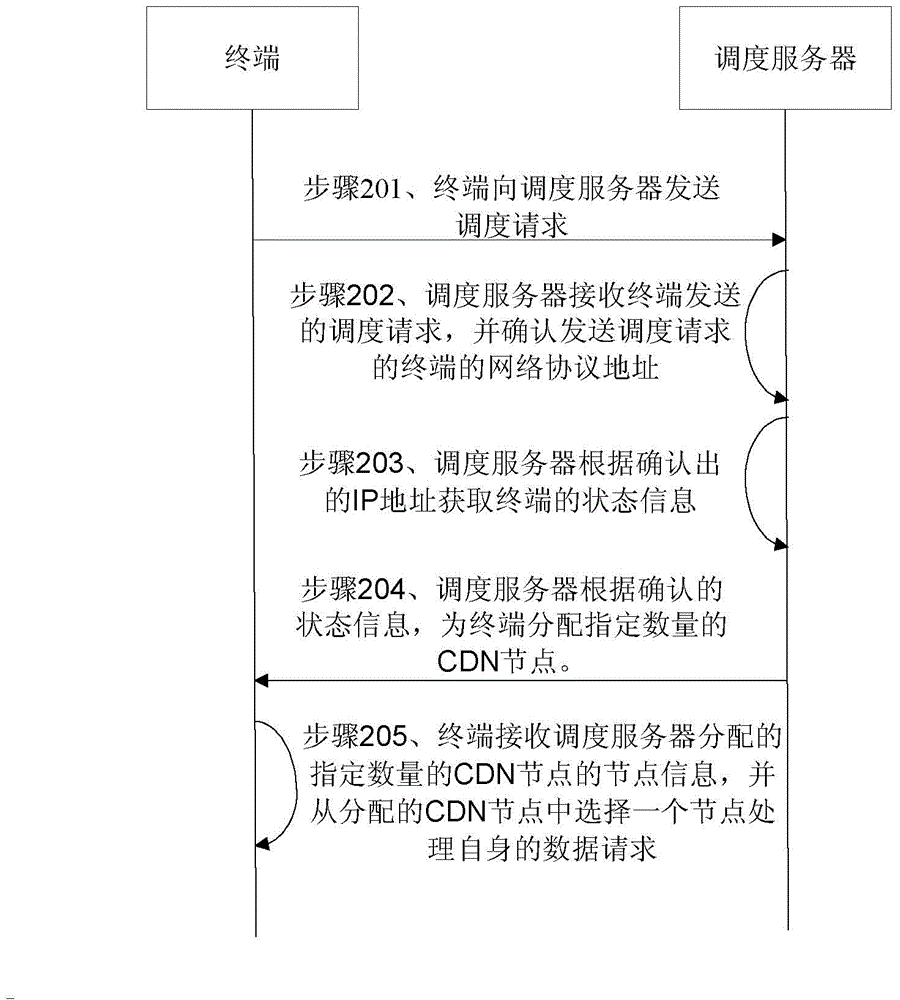
Method for processing terminal scheduling request, system thereof and device thereof
The invention discloses a method for processing a terminal scheduling request, a system thereof and a device thereof. The method comprises the following steps that a scheduling server receives a scheduling request sent by a terminal, wherein the scheduling request comprises the data identification of a terminal request, then the network protocol IP address of the terminal which sends a scheduling request is determined, the state information of the terminal is obtained according to the identified IP address, according to the determined state information, a specified amount of content distribution nodes (CDN) is distributed for the terminal, the terminal selects one node to process data request of the terminal from the distributed content distribution nodes (CDN), wherein the content distribution nodes are nodes which store data corresponding to the data identification. Compared with the prior art, according to the scheme, the scheduling server can distribute a plurality of content distribution nodes for the terminal according to the state information of the terminal, the terminal selects one node to process data request of the terminal, and the efficiency of the distributing the content distribution nodes is raised.
Owner:LETV INFORMATION TECH BEIJING
Method and device for data synchronization of multi-application systems for unifying user authentication
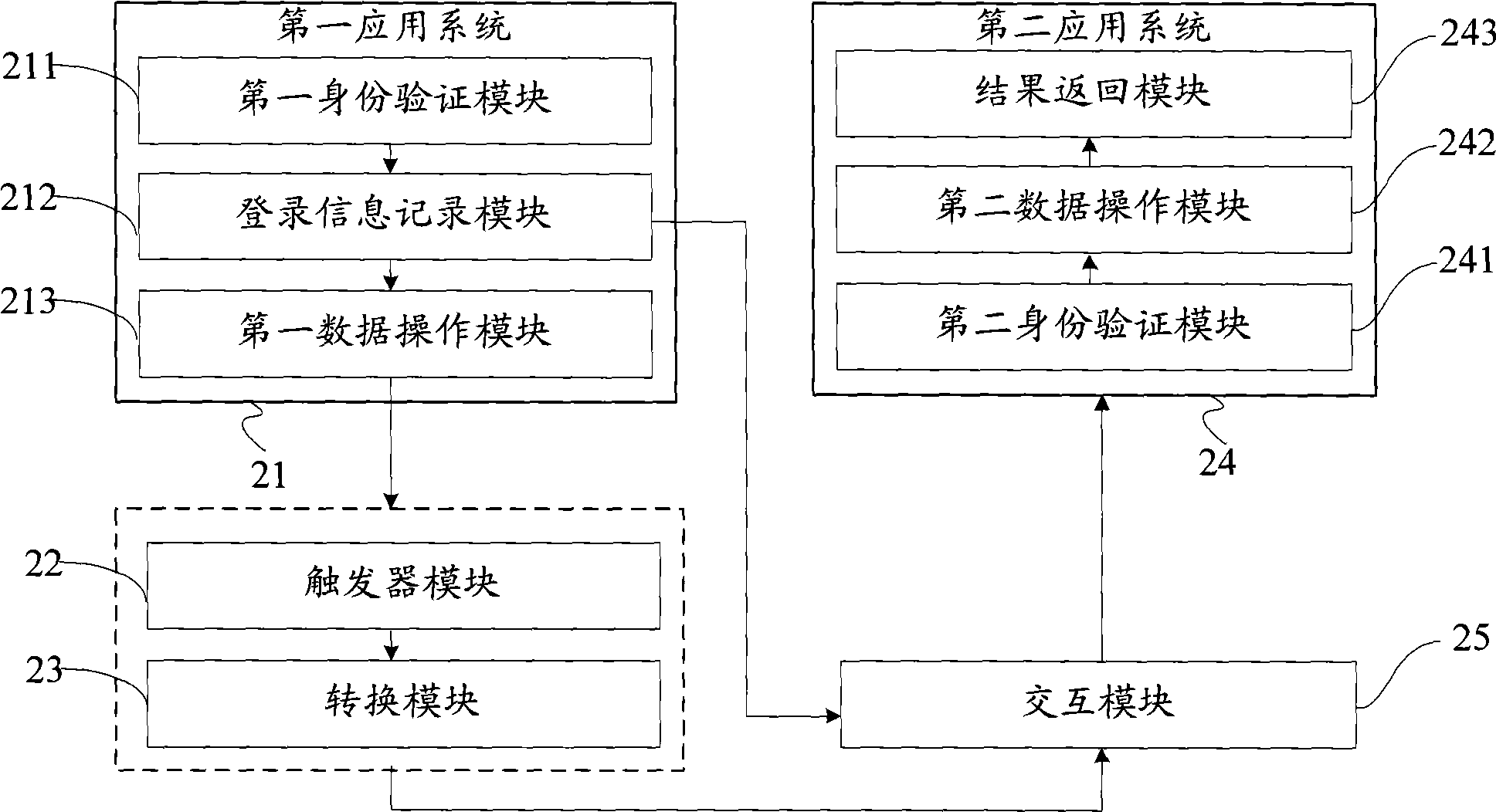
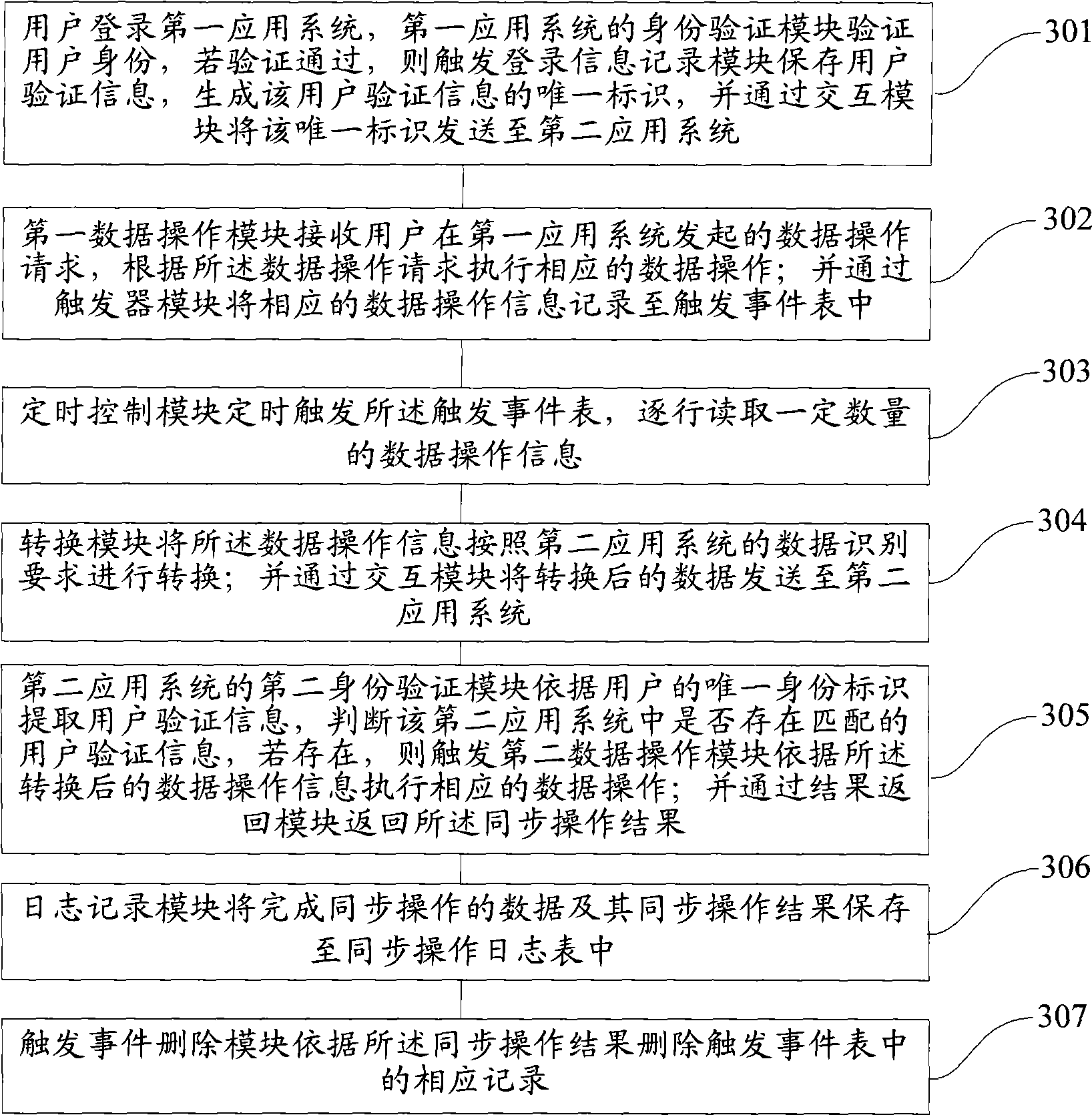
InactiveCN101547092AEnsure safetyUser identity/authority verificationDigital data authenticationUser verificationData synchronization
The invention provides a method for data synchronization of multi-application systems for unifying user authentication, which comprises that: a first application system verifies identification of a user, if the authentication is passed, the first application system stores user authentication information to generate unique identification of the user authentication information; a data operation request initiated by the first application system is received, corresponding data operation is executed according to the data operation request, and corresponding data operation information is recorded into a trigger event table; the data operation information in the trigger event table is converted according to the data identification requirement of a second application system, and is sent to the second application system; and the second application system extracts the user authentication information for the user authentication according to the unique user identification of the user, and the corresponding data operation is executed according to the converted data operation information and a synchronous operation result is returned if the user is lawful. The method can simply and flexibly realize the user synchronous logon and data synchronous operation between a plurality of application systems, and improves the efficiency and the safety.
Owner:吴霞
System and method for identifying relationship among user group and users
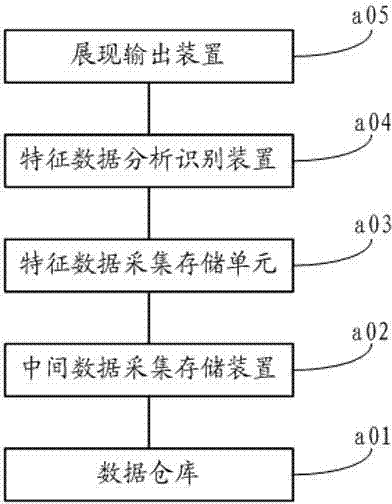
ActiveCN102541886ARealize identificationRealize analysis and identificationSpecial data processing applicationsWireless communicationData warehouseData acquisition
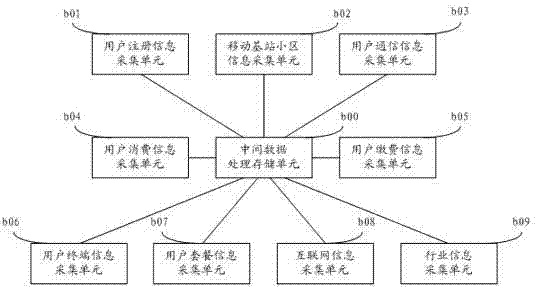
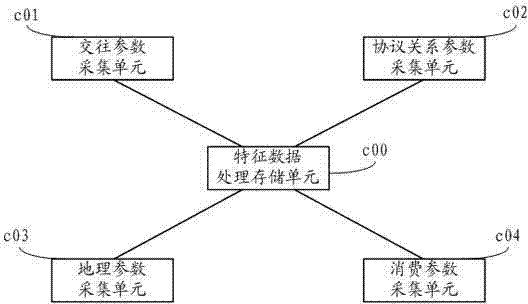
The invention relates to a system for identifying the relationship among a user group and users by the aid of user feature data, which comprises a user data warehouse, an intermediate data acquisition and storage device, a feature data acquisition and storage device, a feature data identification and analysis device and a display output device, wherein the user data warehouse is used for storing original user data; the intermediate data acquisition and storage device is used for extracting data related to user features from the user data warehouse; the feature data acquisition and storage device is used for acquiring the user data processed by the intermediate data acquisition and storage device and converting the acquired user data into the user feature data; the feature data identification and analysis device is used for analyzing and processing the user feature data stored by the feature data acquisition and storage device and identifying the relationship among the user group and the users; and the display output device is used for outputting corresponding results. The invention further discloses a method for identifying the relationship among the user group and the users by the aid of the user feature data. The system and the method realize identification of the user features and the relationship.
Owner:郝敬涛 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com