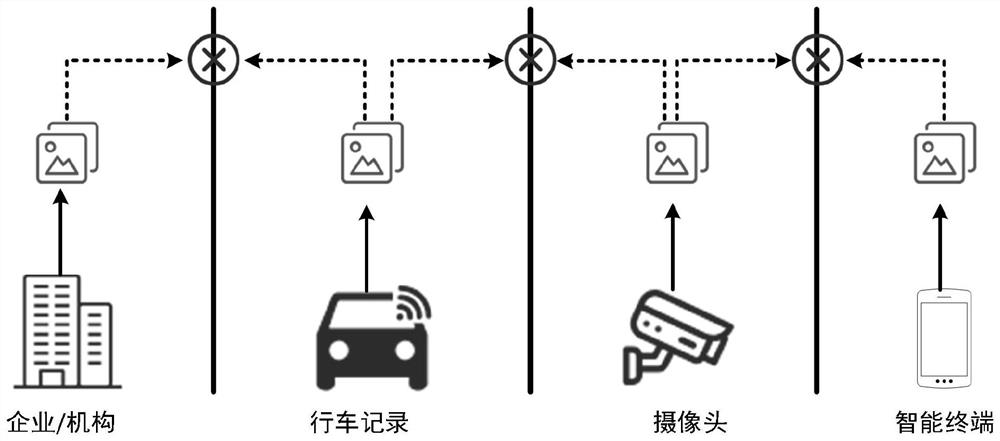
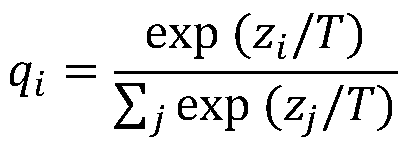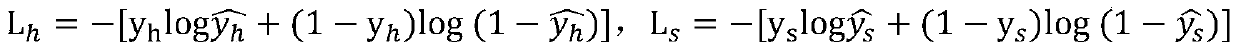Patents
Literature
914results about How to "Improve defense" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Chitosan collagen and calcium alginate compounded spongy biological dressing and its preparation process
The composite spongy biological dressing contains chitosan, collagen and calcium alginate with weigh tmixing ratio o f 0.5-8:0.5-8:0.1-8. Its preparation method includes the following steps: selecting chitosan and collagen type I, adding calcium alginate, compounding and cross-linking, using buffer solution to make neutralization, emulsifying, prefreezing and one-step freeze-drying so as to obtain the invented dressing with good biological compatibility and strong adhesion property. Said invented dressing possesses active function of promoting wound healing and hemostatic action, can be combined with anti-bacterial medicine to obtain gene engineeirng dressing for curing wound surface infection, also can be combined with active growth factor or active cell to form gene engineering dressingfor curing intractable ulcer and burn wound surface.
Owner:JIANGXI RUIJI BIOTECH CO LTD
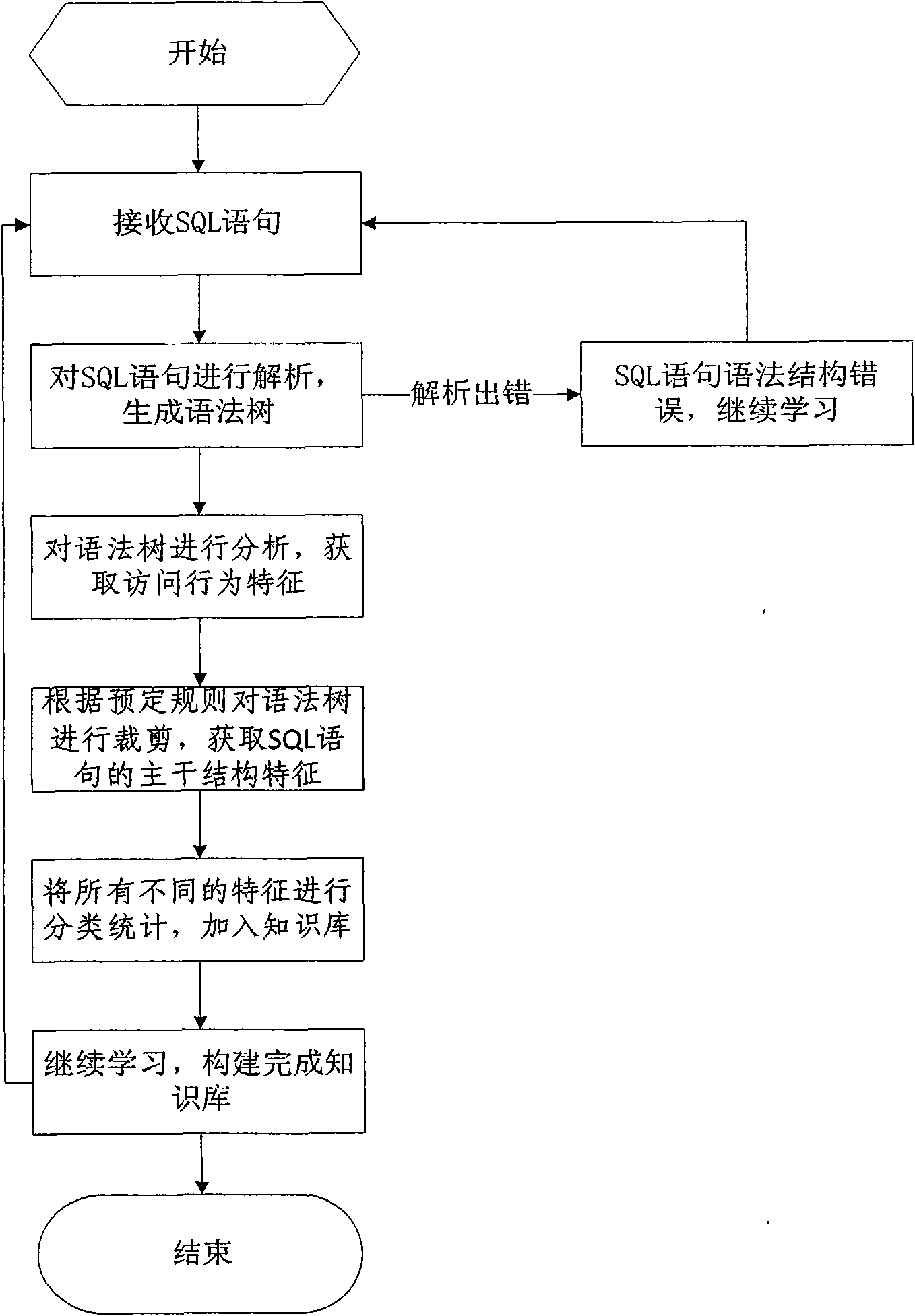
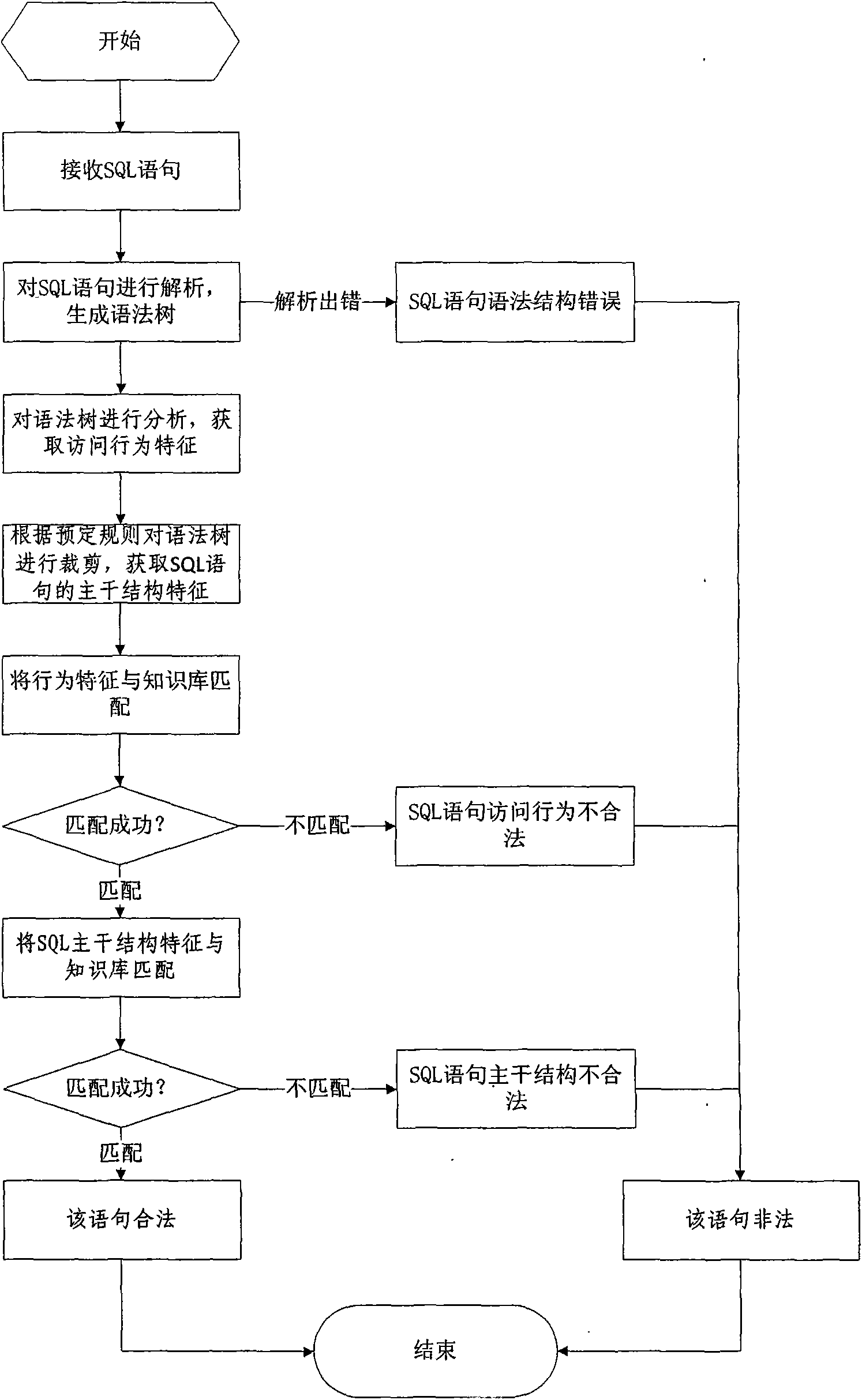
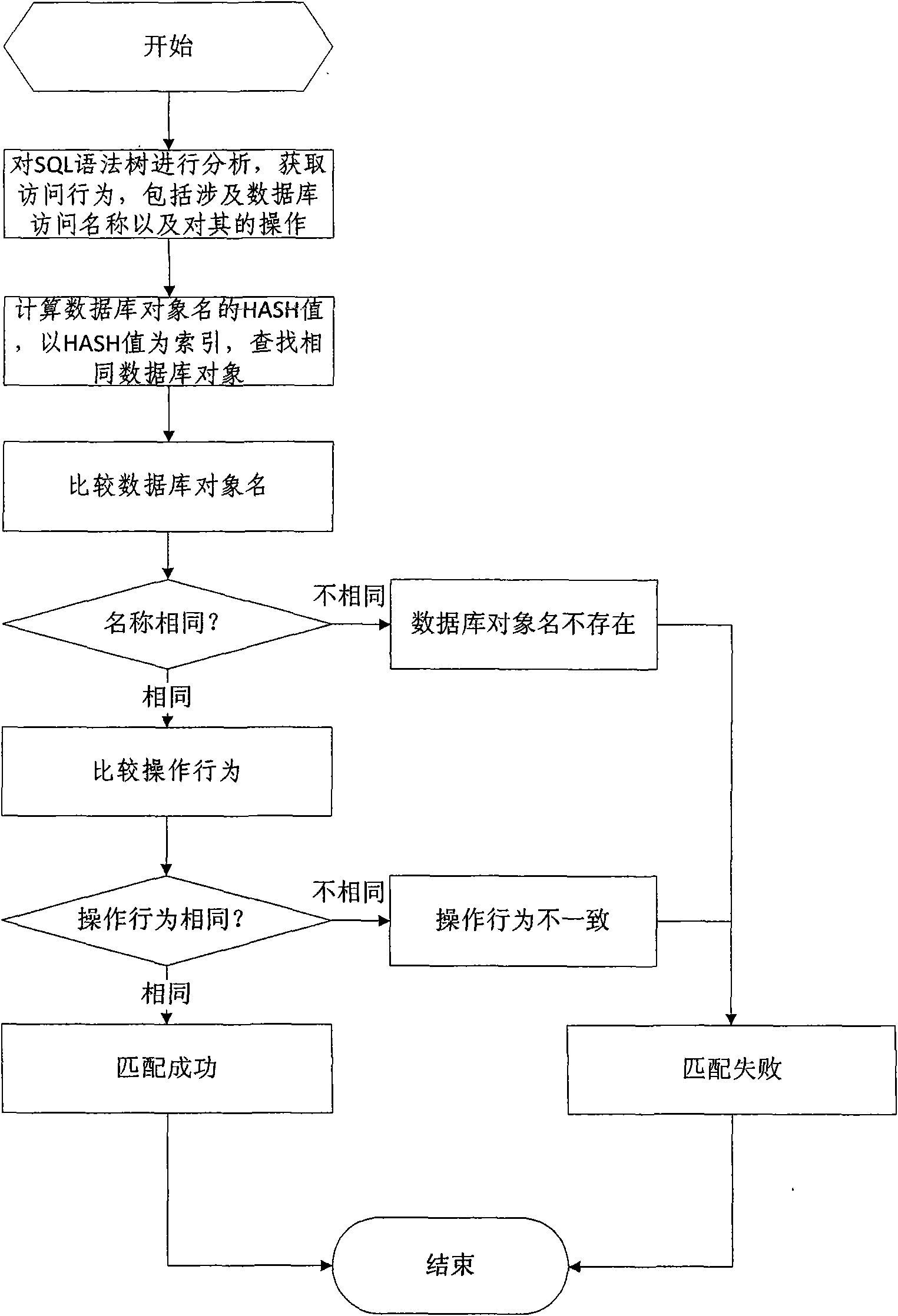
Database SQL infusion protecting method based on self-learning
InactiveCN101609493AOvercome false negativesOvercome the False Positive FlawComputing modelsDigital data protectionLearning basedSQL injection
The invention discloses a database SQL infusion protecting method based on self-learning, comprising a learning phase and a filtering phase. The learning phase works in safe environment. At the moment, all SQL sentences are legitimate SQL sentences generated by an application system. A knowledge model (knowledge base) of the legitimate SQL sentences can be constituted by analyzing the sentences as well as analyzing and summarizing the characteristics of the sentences on the basis of sentence analysis results. The filtering phase works in real environment. At the moment, all SQL sentences are assumed to be possibly illegitimate SQL sentences. The sentences undergo pattern matching with the knowledge base established in the safe environment. If the matching is successful, the sentences are legitimate SQL sentences, otherwise, the sentences are illegitimate SQL sentences. The database SQL infusion protecting method has the advantage that an SQL infusion protecting system based on learning the legitimate SQL sentences can greatly reduce the false report rate and missing report rate which are caused by traditional SQL infusion protection, and the defending capability of the whole system can be improved.
Owner:STATE GRID ELECTRIC POWER RES INST +1
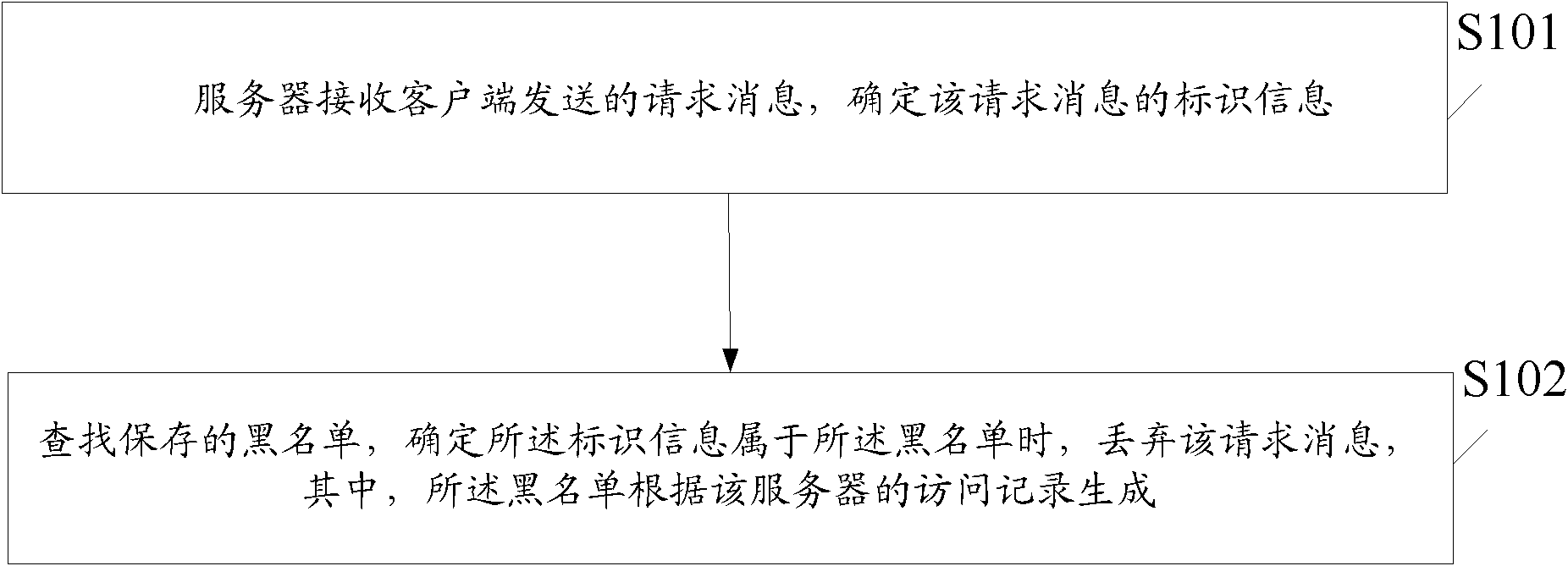
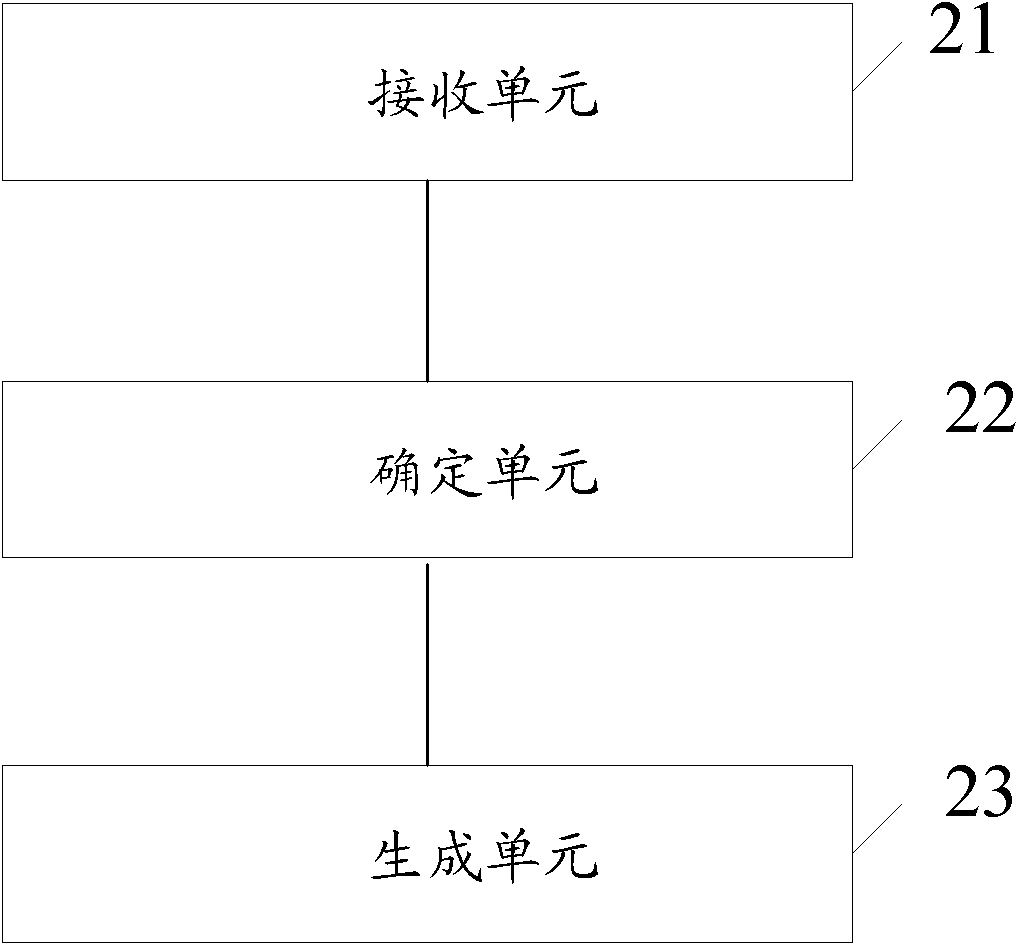
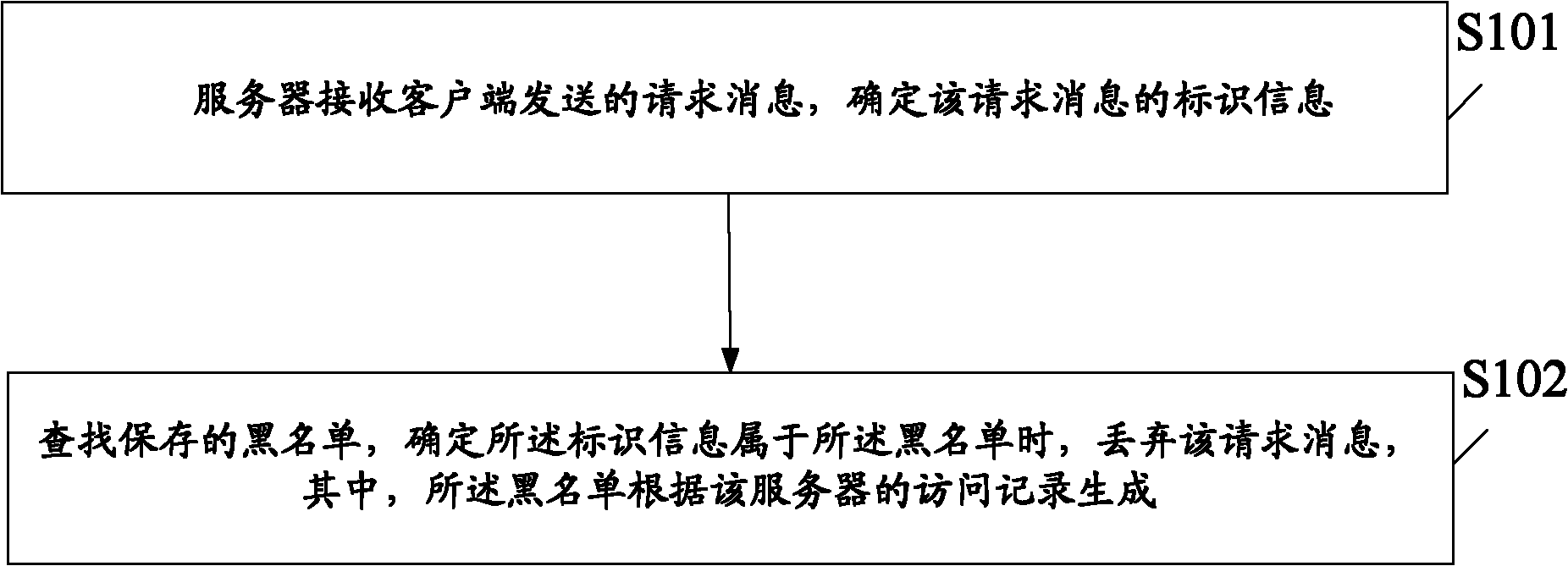
Method and device for preventing CC (Challenge Collapsar) attack and content delivery network server
The invention discloses a method and a device for preventing CC (Challenge Collapsar) attack and a content delivery network server, which are used for solving the problem that in the prior art, when the CC attack is prevented, targeted prevention can not be carried out by referring to the actual processing conditions of a server, and the prevention effect is not ideal. The method comprises the following steps: the server receives a request message transmitted by a client, and determines the identification information of the request message; a stored blacklist is queried, and the request message is lost when the identification information is determined to belong to the blacklist, wherein the blacklist is generated according to the access records of the server. By the method and the device for preventing CC attack and the content delivery network server, the blacklist can be generated according to the access records of the server, so that the request message is filtered according to the blacklist, and further, the targeted prevention can be carried out according to the actual processing conditions of the server, so that the prevention effect is more ideal.
Owner:CHINACACHE INT HLDG
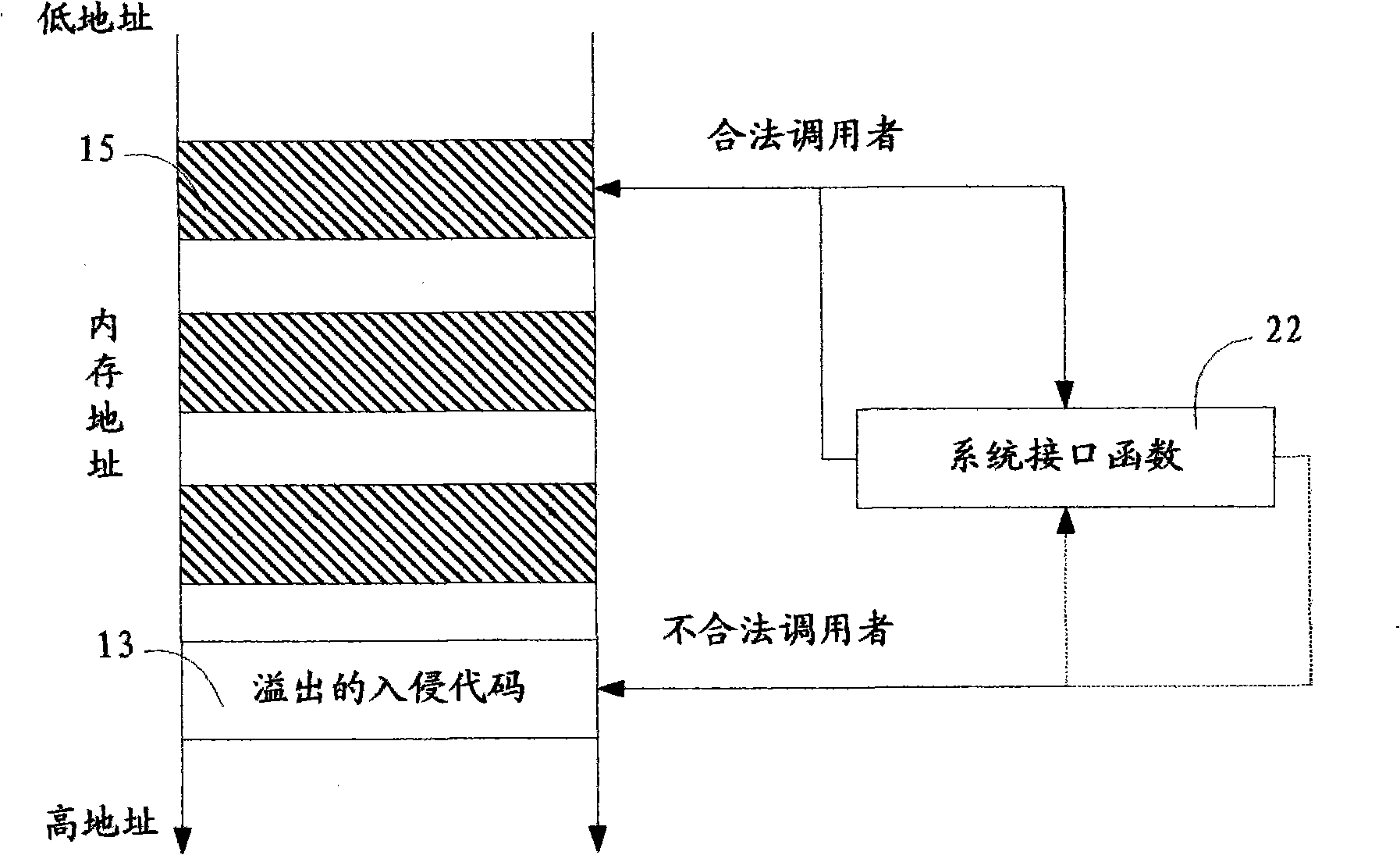
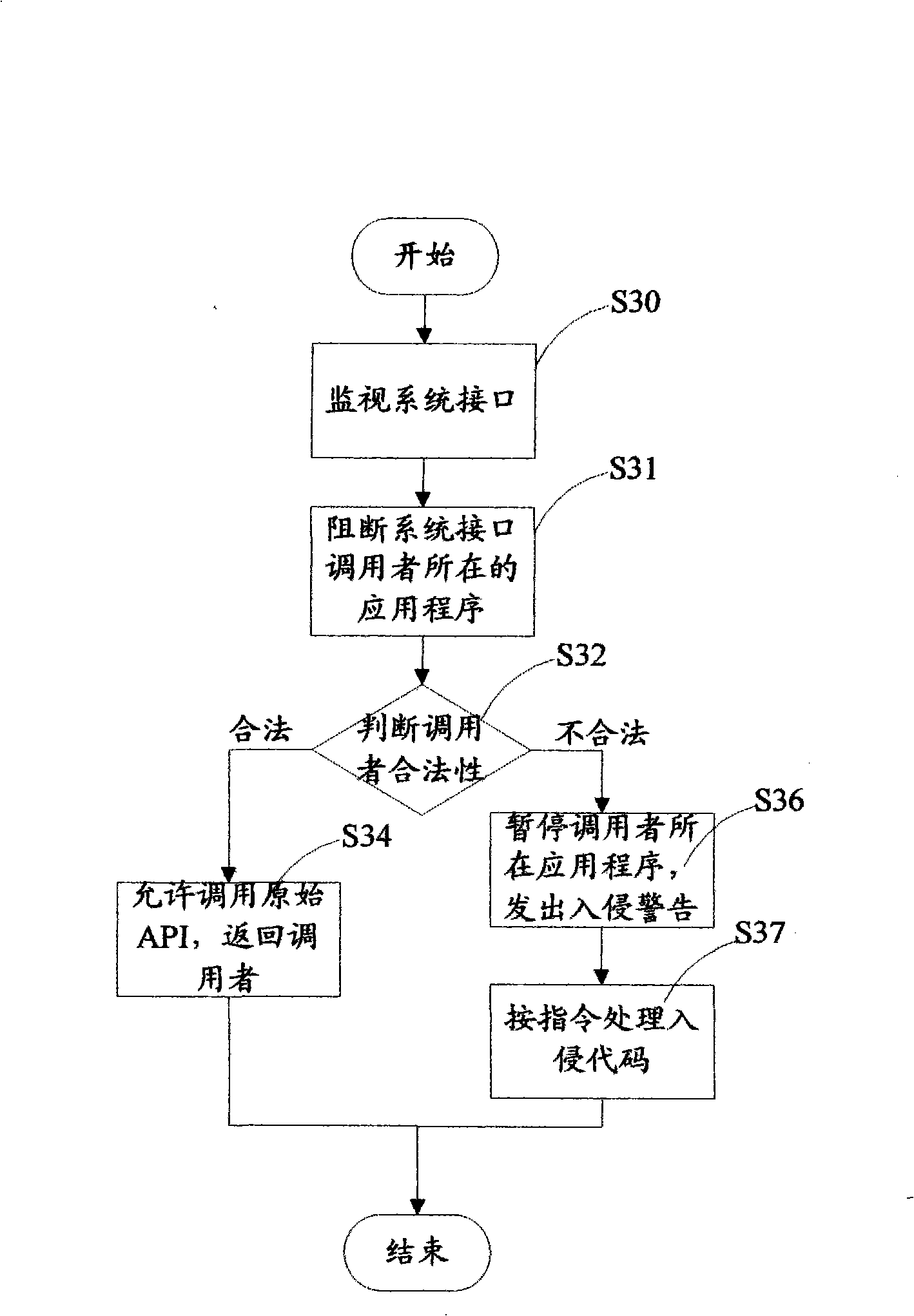
Method and system for detecting application program behavior legality
InactiveCN101408917AReduce false alarm rateImprove recognition ratePlatform integrity maintainanceBehavioral analyticsMonitoring system
A method for detecting the legitimacy of an application program behavior comprises the following steps: monitoring one or more system interfaces of a computer to cause the monitored system interfaces to jump to a monitoring module for execution when the monitoring system interfaces receive a call; blocking the application program of a caller and judging the validity of the caller: permitting the caller to call an interface function and continuously perform the application program of the caller if the caller is legal; and, pausing the behavior of the application program of the caller and issuing an intrusion alarm if the caller is illegal. The detection method finds out whether an executor of the application program behavior is legal or not by monitoring the system interfaces of the computer so as to intercept the program behavior executed by illegal executors and give an alarm. Compared with the existing fuzzier behavioral analysis technology, the detection method has the advantages of low false alarm rate, high recognition rate and the like, especially has good defense effect against the intrusion behavior due to overflow vulnerability, so the detection method is an effective supplement to the existing behavior analysis defense technology.
Owner:厦门市美亚柏科资讯科技有限公司
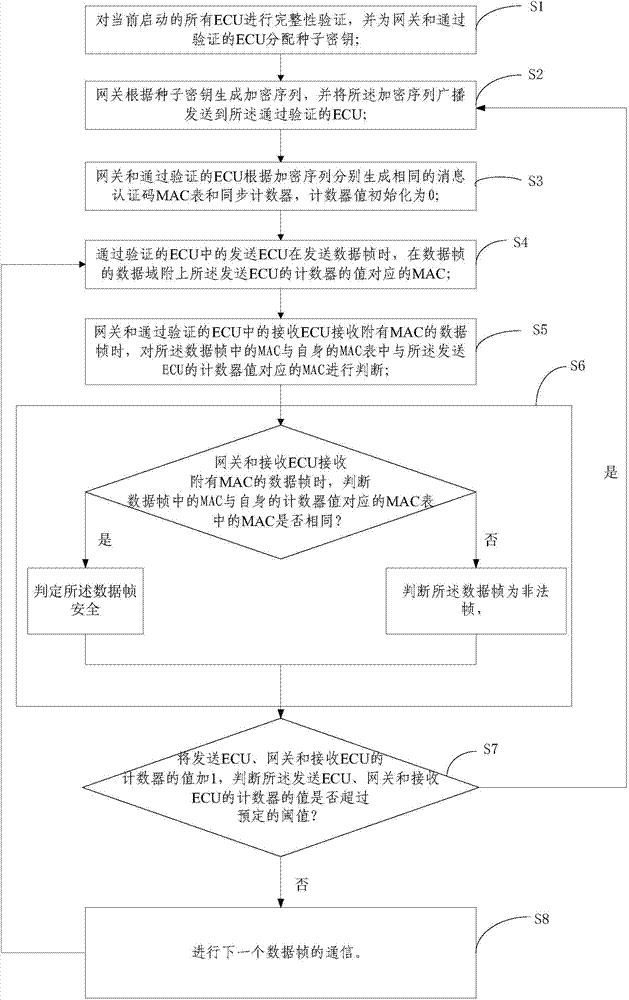
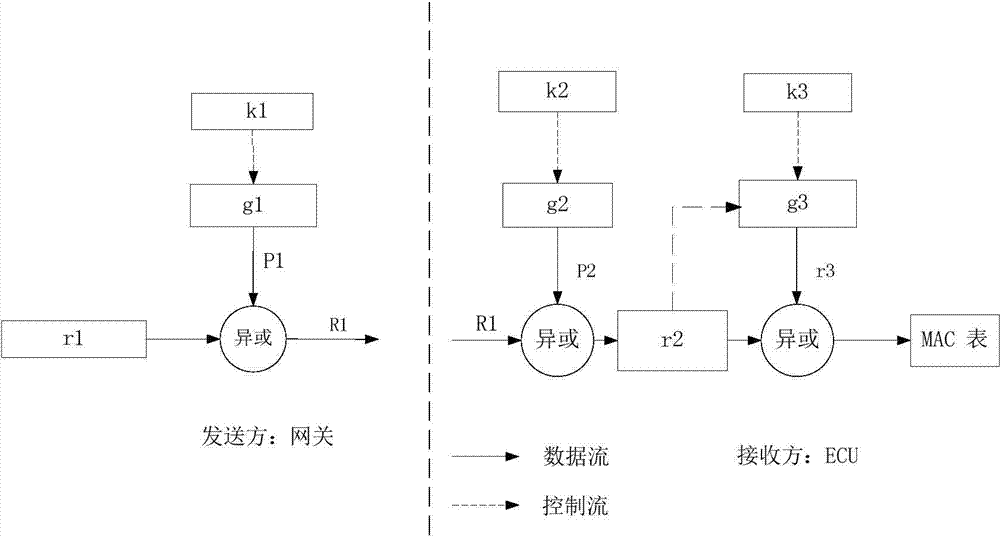
CAN bus authentication method and system based on broadcasting
ActiveCN104767618AAvoid attackEffective judgmentUser identity/authority verificationBus networksComputer hardwareData field
The invention relates to a CAN bus authentication method and system based on broadcasting. The method includes the steps that completeness verification is conducted on all ECUs, seed secret keys are distributed for a gateway and the ECUs passing the verification; the gateway generates an encryption sequence, and the encryption sequence is sent to the ECUs passing the verification through broadcasting; the gateway and the ECUs passing the verification generate identical message authentication code (MAC) tables and identical synchronous counters, wherein the initial value of the counters is zero; the sending ECU attaches the MAC corresponding to the value of the counter of the sending ECU to the data field of a sending data frame; the gateway and the receiving ECU judge whether the MAC in the data field is identical with the MAC in the MAC tables corresponding to the counters of the gateway and the receiving ECU or not; if yes, the data frame is judged to be safe, and if not, the data frame is judged to be the illegal frame; the values of the counters of the sending ECU, the gateway and the receiving ECU are added by one, and whether the values of the counters of the sending ECU, the gateway and the receiving ECU exceed the preset threshold value or not is judged; if yes, an MAC table is generated again; if not, the next frame of communication is conducted, and communication of a next data frame is conducted. According to the CAN bus authentication method and system, due to the fact that a message authentication code is added to the data frames in communication, the attack on the CAN bus can be defended.
Owner:TSINGHUA UNIV
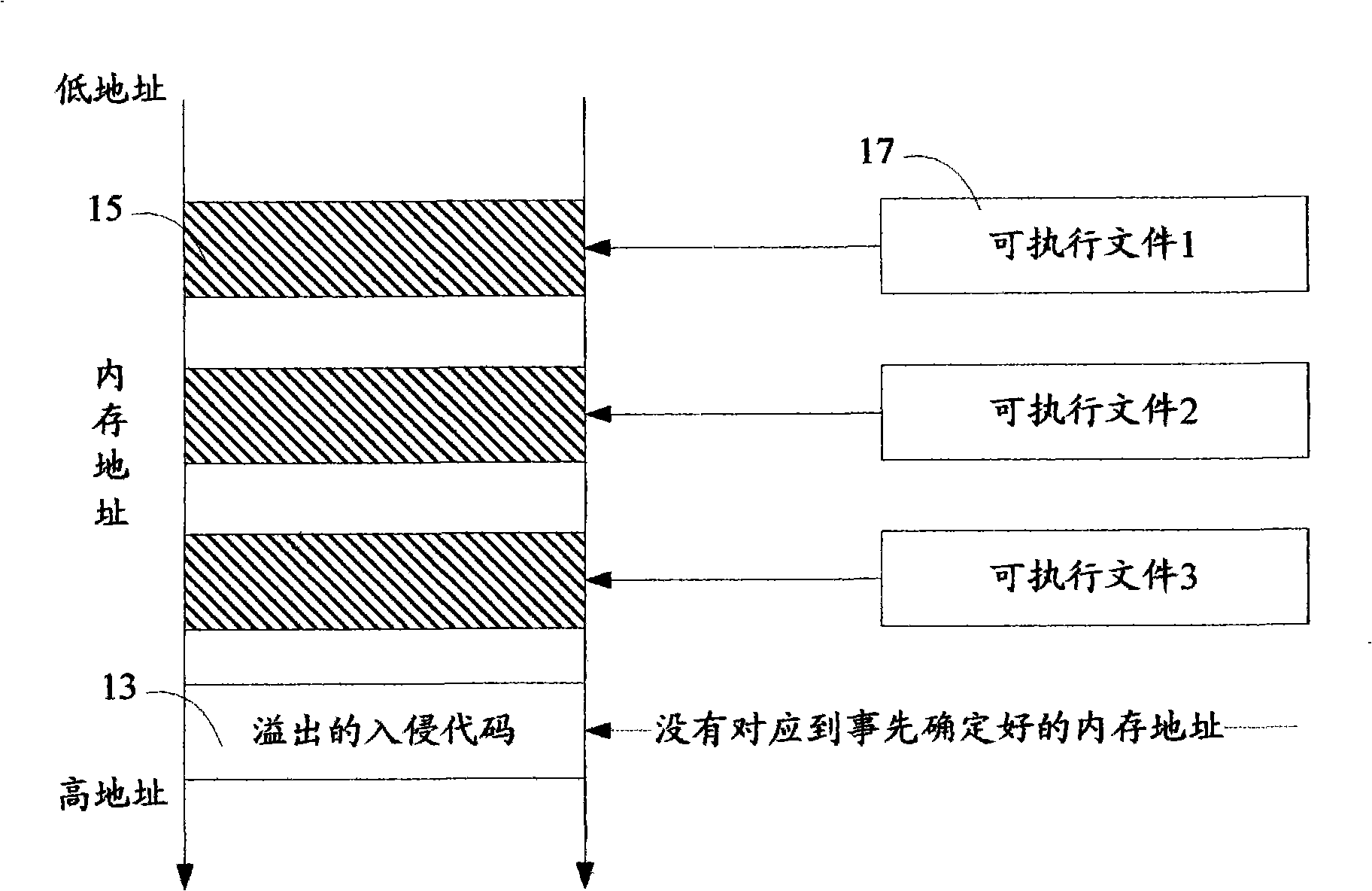
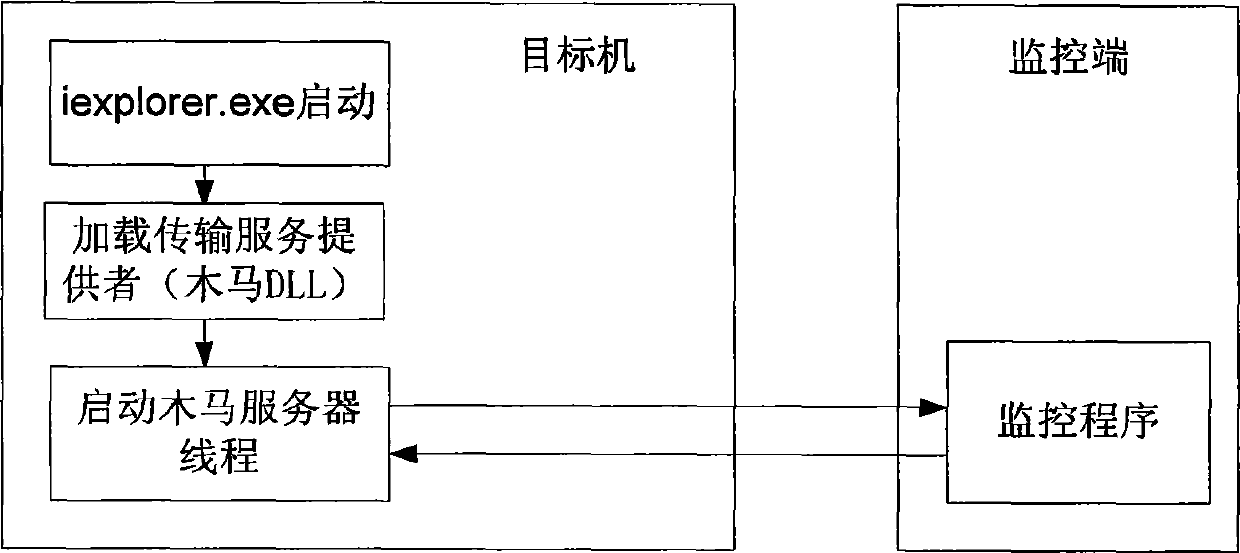
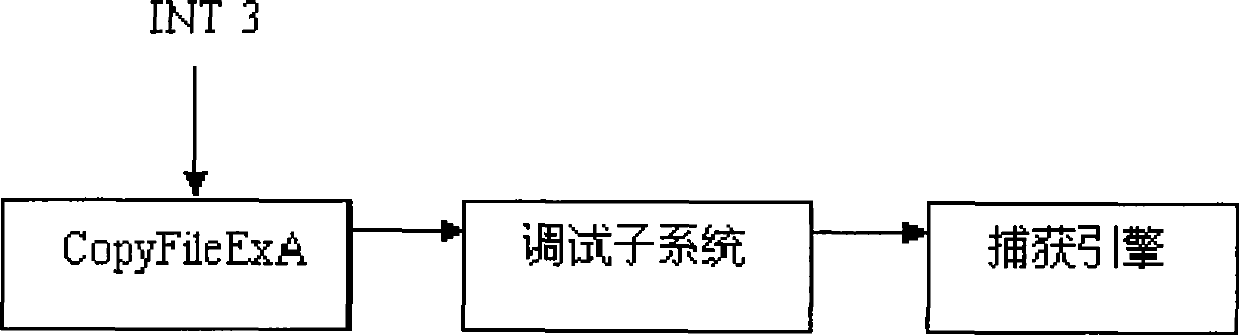
Method for capturing dynamic behavior aiming at computer virus
InactiveCN101373501AImprove defenseImprove securityPlatform integrity maintainanceProgramming languageDebugger
The invention discloses a dynamic behavior capturing method for computer viruses in an automatic analysis system used for preventing and curing the computer viruses. In the method, by setting the calling of API as a debugging event, a system kernel captures the event and informs a debugger; debugging breakpoints are set at specified API call entries, and when capturing programs are executed to the debugging breakpoints, an interruption event occurs; subsequently, the system kernel injects a dynamic link library to a malicious code process space through a capturing tool; the dynamic link library is used for analyzing the stack content of API.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Neural network black box aggressive defense method based on knowledge distillation
ActiveCN111027060AGuaranteed successful attackReduce the pitfalls of losing variance between classesPlatform integrity maintainanceNeural architecturesData setSample sequence
The invention discloses a neural network black box aggressive defense method based on knowledge distillation, and the method comprises the steps: selecting a plurality of sub-networks to construct a teacher network, softening the input vectors of softmax layers of all sub-networks, and then reloading the model parameters of the sub-networks for training to obtain a new sub-network; obtaining a prediction label of each sub-network, and taking all prediction labels as soft labels after averaging or weighted averaging; inputting the Image Net data set into a student network, and guiding student network training by adopting a soft label, a data set hard label and a black box model special label to obtain a substitution model; adopting a white box attack algorithm to attack the substitution model to generate an adversarial sample sequence, adopting the adversarial sample sequence to attack the black box model, and selecting an adversarial sample successfully attacked in the adversarial sample sequence; and adding the successfully attacked countermeasure sample into a training set of the black box model, and performing countermeasure training by adopting the updated training set to generate the black box model with attack defense.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method for high-voltage direct-current transmission commutation failure prevention
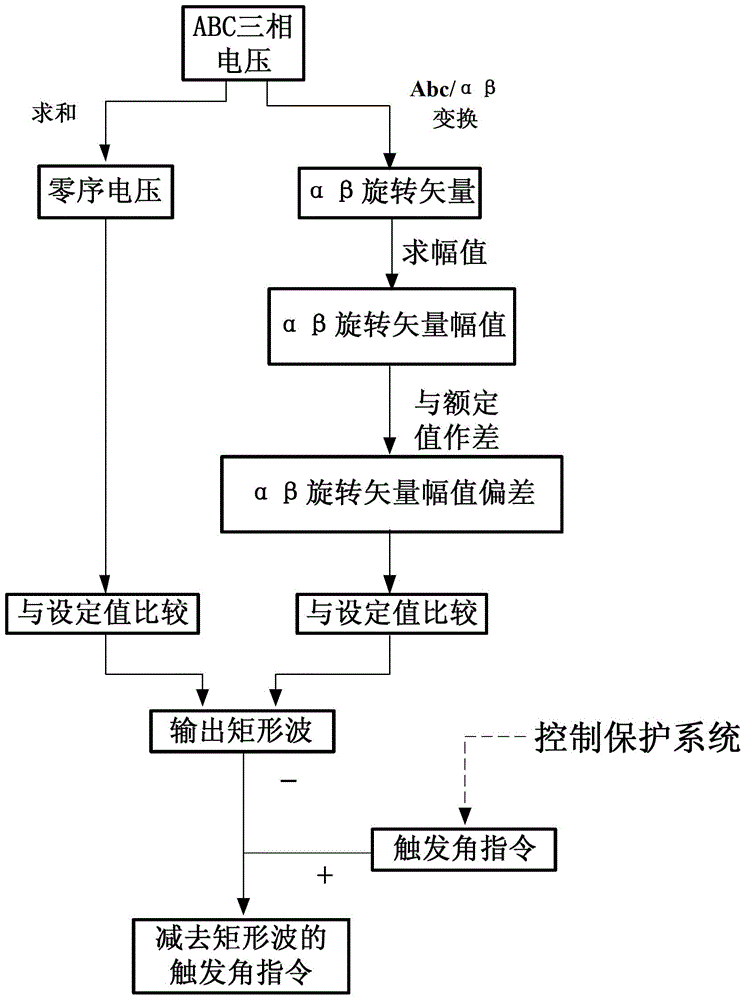
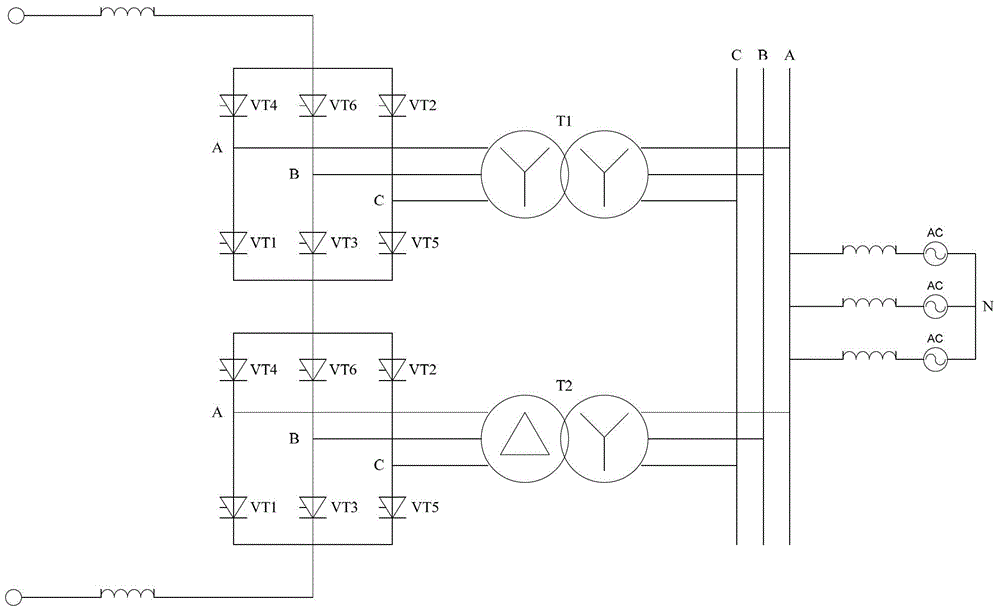
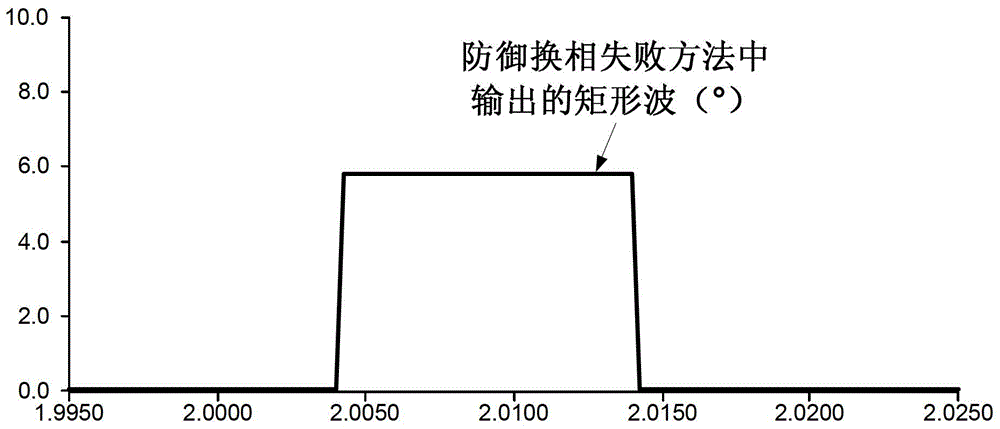
InactiveCN103337870AAvoid commutation failureImprove defenseElectric power transfer ac networkFailure preventionHigh pressure
The invention provides a method for high-voltage direct-current transmission commutation failure prevention. The method comprises the following steps that: whether commutation failure caused by alternating current-side faults occurs or not is judged; a commutation failure prevention system outputs rectangular wave commands to a control protection system; and rectangular waves are subtracted from trigger angle commands in the control protection system, and a thyristor is triggered in advance. With the method adopted, commutation failure can be prevented when grounding faults or interphase short-circuit faults occur on an alternating current system, and the reduction amplitude of direct-current voltage and power transmission can be lowered after the faults occur.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING) +4
Attack path analysis method based on hierarchical attack graph
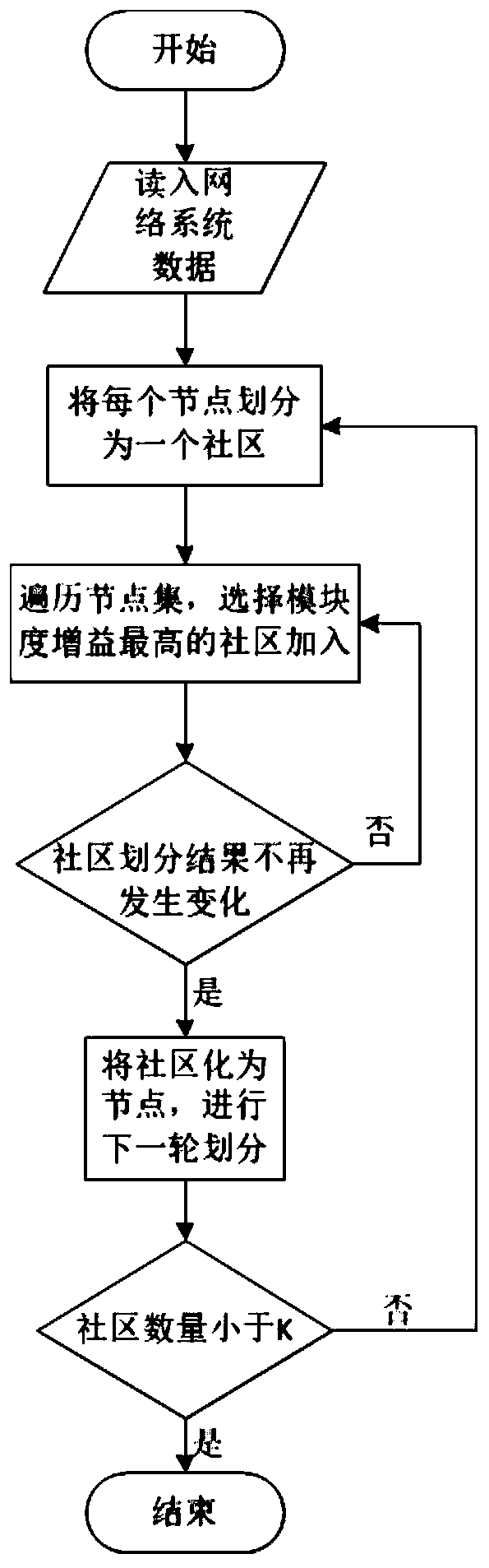
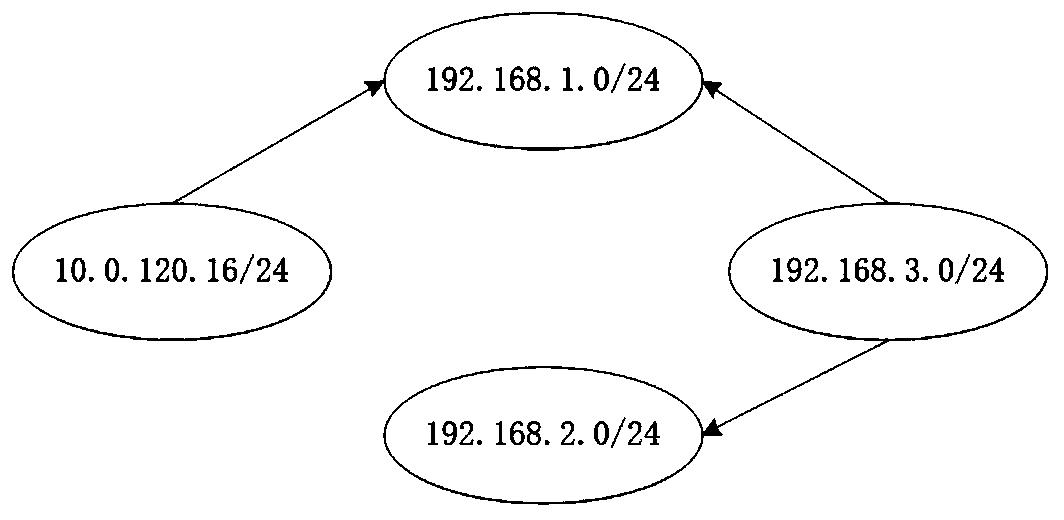
ActiveCN110138764ADownsizingImprove analysis efficiencyPlatform integrity maintainanceData switching networksPath generationAttack graph
The invention belongs to the technical field of network security, and discloses an attack path analysis method based on a hierarchical attack graph. Firstly, dividing an original network into a plurality of logic subnets through a community discovery algorithm, wherein the logic subnets and connection relations thereof form a network logic structure; generating two layers of attack graphs based onthe network logic structure and the network basic information; and finally, reducing an attack path on the two layers of attack graphs by utilizing monotonicity of attack behaviors. The method comprises the following specific steps: (1) realizing community discovery; (2) establishing a hierarchical attack graph model; (3) generating an attack path; (4) analyzing the attack path to provide a defense strategy. According to the attack path analysis method, unreasonable attack path generation is avoided from the perspective of attackers, the real-time performance of attack path analysis is effectively improved, and the problem that an existing attack path analysis method is poor in real-time performance when the network scale is large and the vulnerability is high is solved.
Owner:山西佳瑞通科技有限公司
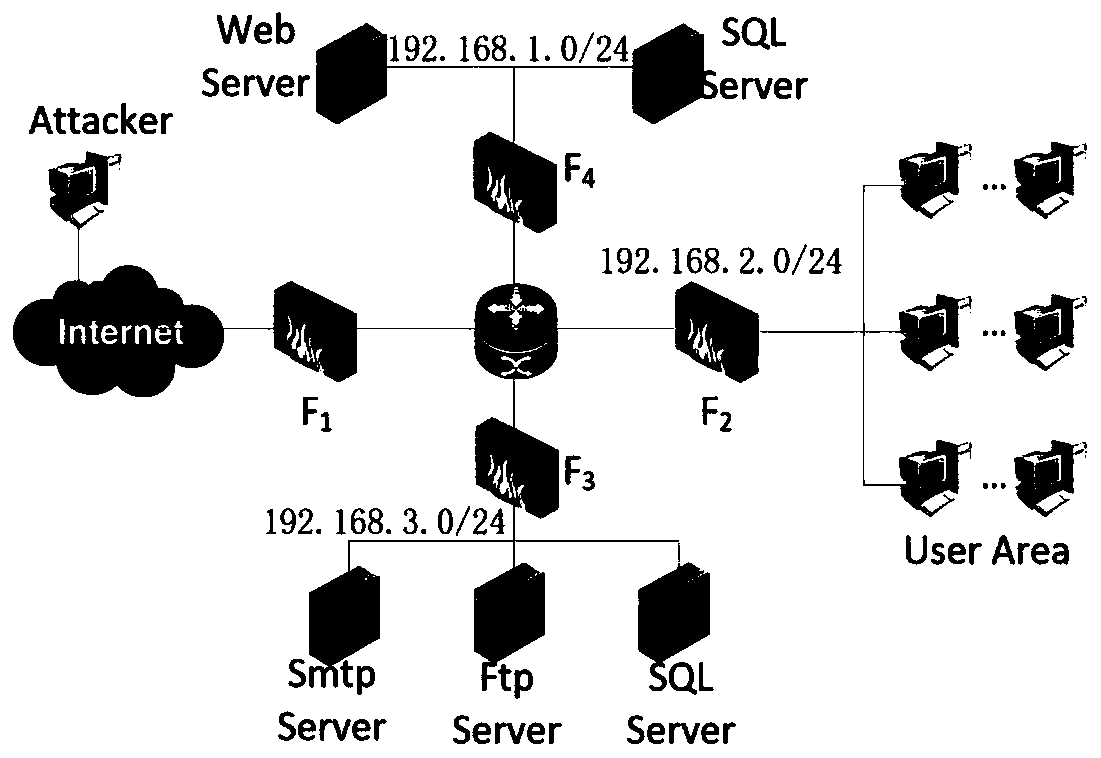
Network safety protection method and system
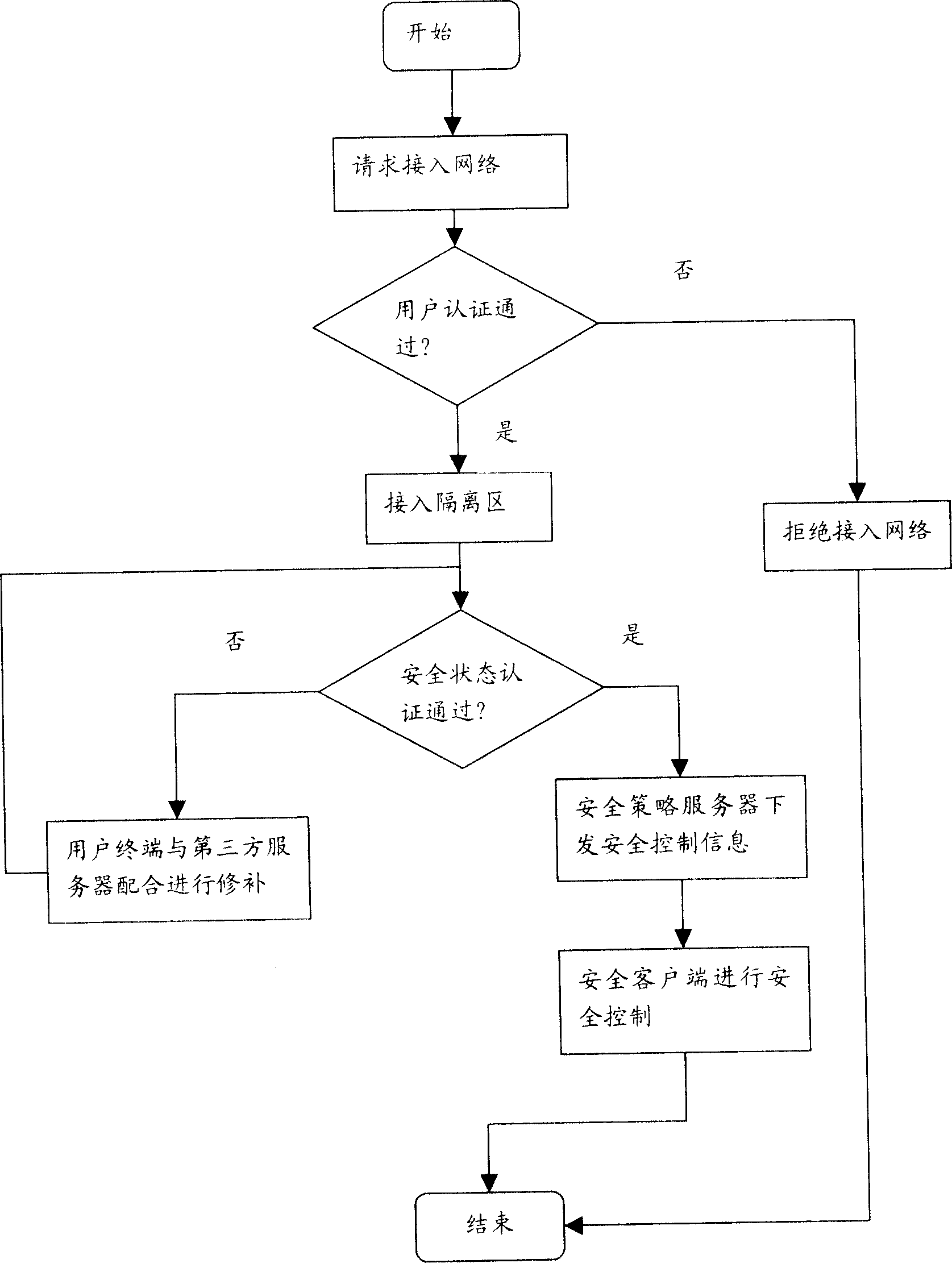
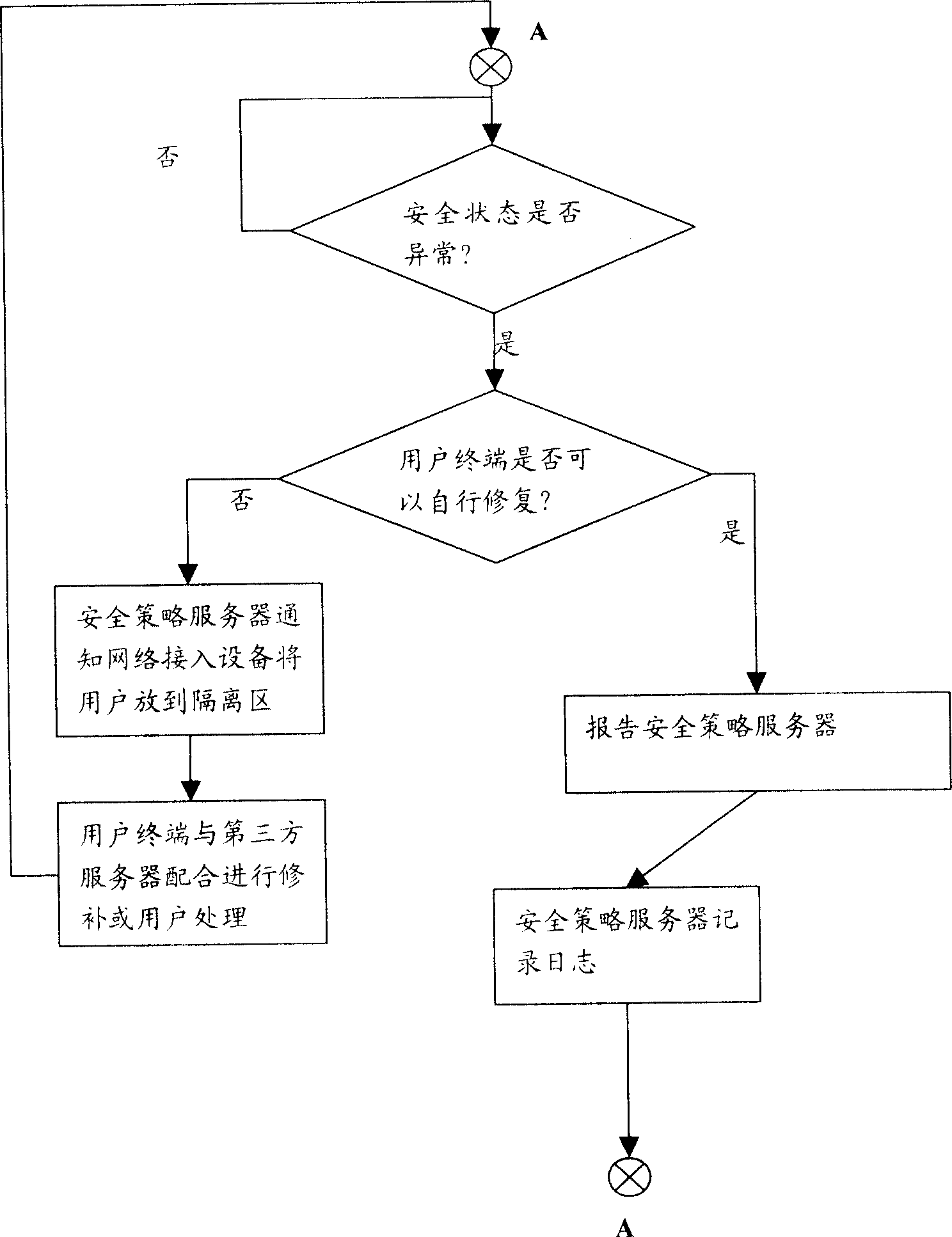
ActiveCN1885788AImprove defenseHas the function of defending against network attacksData switching by path configurationNetwork security policySecurity policy
The disclosed network security protective method comprises: providing security strategy server and access device, for external device required access, first isolating into separation area for security certification; if failure, upgrading and repairing by the third server for certification again; after accessing into network, still monitoring user by former security strategy for processing illegal affair. This invention provides more safe and complete self protective function.
Owner:NEW H3C TECH CO LTD
Method for preparing corrosion-protection composite coating for the steel metalwork
ActiveCN101116855AImprove anti-corrosion performance and comprehensive performanceEnhanced Physical Isolation and Defense CapabilitiesLiquid surface applicatorsAnti-corrosive paintsFastenerAluminium
The invention relates to an anticorrosion composite coat for steel metal fastener used in the marine environment, the structure of the composite coat consists of a bottom layer and a surface layer, wherein the bottom layer is coated with lamellar metal zinc dust and lamellar metal aluminum powder which are adhered by adhesive and mixed together, the surface layer is coated with metal aluminum power and reshaping epoxy resin which are mixed together. The invention includes the procedures as follows: the lamellar metal zinc dust and the lamellar metal aluminum power are mixed, and then are added into the inorganic aquosity splicing agent to be stirred and mixed uniformly, and then are soaked into and coated on the anticorrosive metal steel pieces, then are processed by baking and sintering and solidifying to achieve the first step for coating the bottom layer, then the coating and solidifying process is repeated to achieve the second step for coating the bottom layer; additionally, the lamellar aluminum power and the reshaping epoxy resin are mixed to be the organism epoxy aluminium rich paint, the formed bottom layer is made into the surface layer by the different parameter and the same step of the first step of the bottom layer, the method of the invention is of high causticity and strong protection, thereby the base body of the steel fastener can be protected, and the invention is of good abradability, beautiful appearance and ideal decoration.
Owner:725TH RES INST OF CHINA SHIPBUILDING INDAL CORP
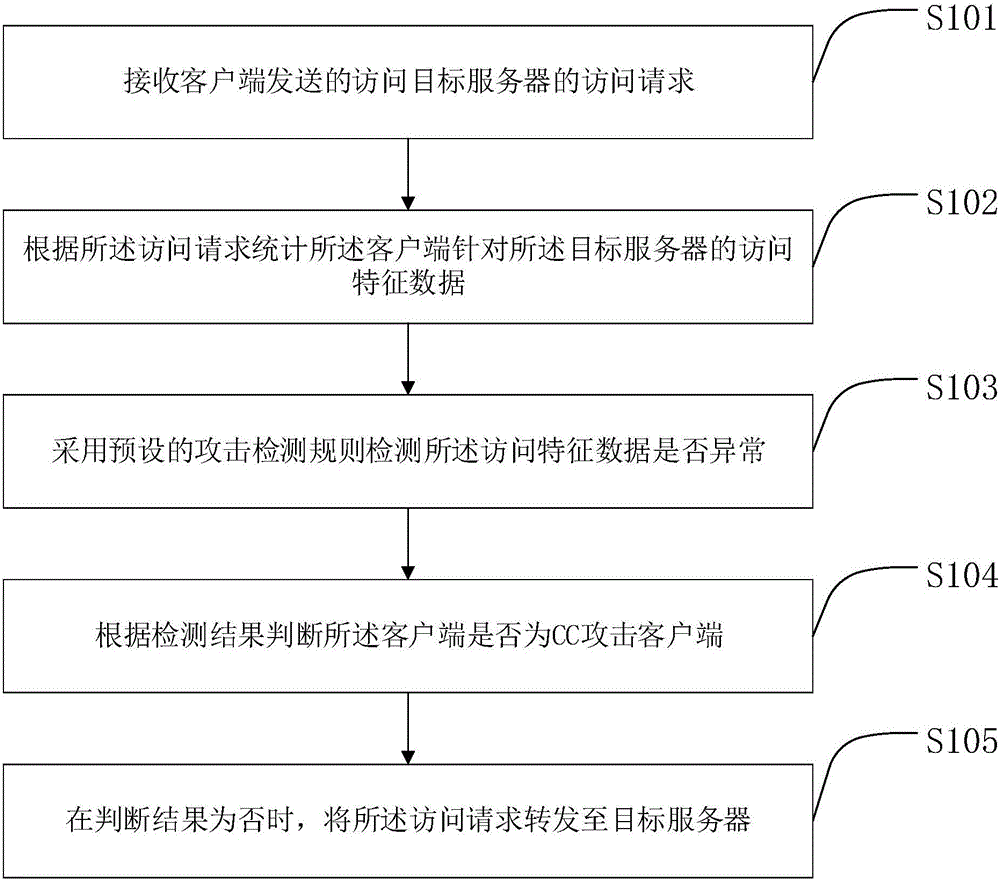
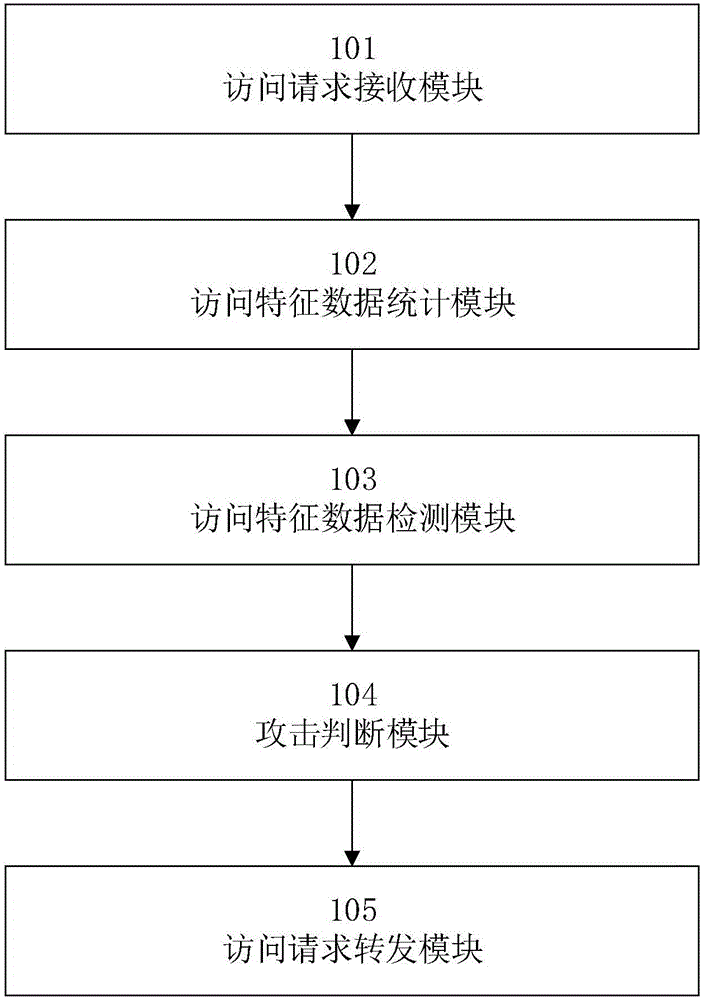
CC (challenge collapsar) attack defending method, device and system
The invention provides a CC (challenge collapsar) attack defending method for a reverse proxy server; the method includes: first, receiving an access request to access a target server sent by a client; second, making a statistic of access characteristic data of the client for the target server according to the access request; third, detecting whether the access characteristic data is normal or not by using preset attack detection rules; forth, judging whether the client is a CC attack client or not according to the detection results, and if not, forwarding the access request to the target server. Since the client and the target server are isolated by using the reverse proxy server and the target server is completely concealed out of a range of attack power of the CC attack client, good defense is provided; meanwhile, the method is executed by the reverse proxy server, no system resource of the target server is used, and it possible to ensure that the target server never experiences reduced system resources and reduced operation efficiency due to CC attack defending.
Owner:青松智慧(北京)科技有限公司
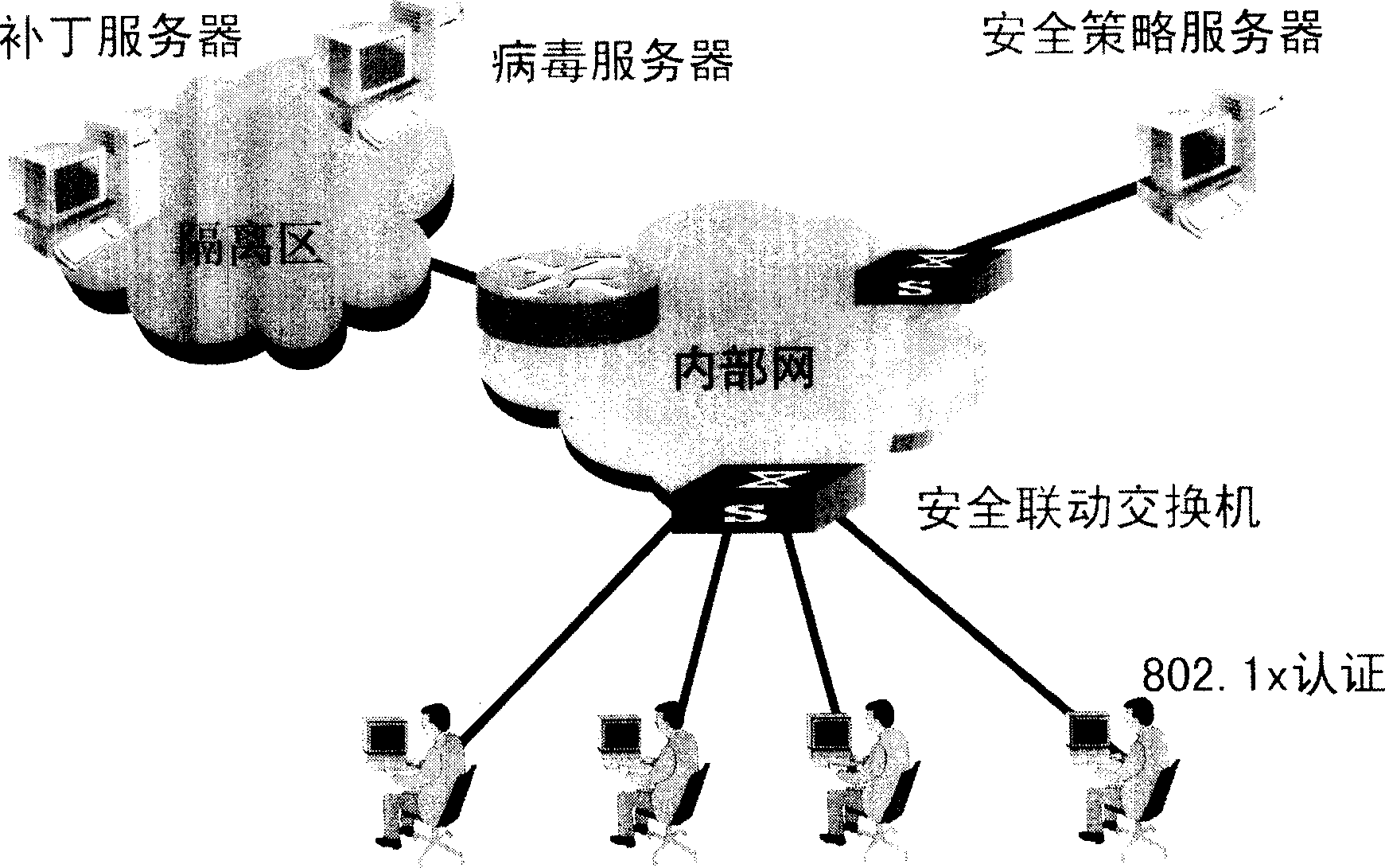
Smart grid information transmission safety protection device and safety protection method
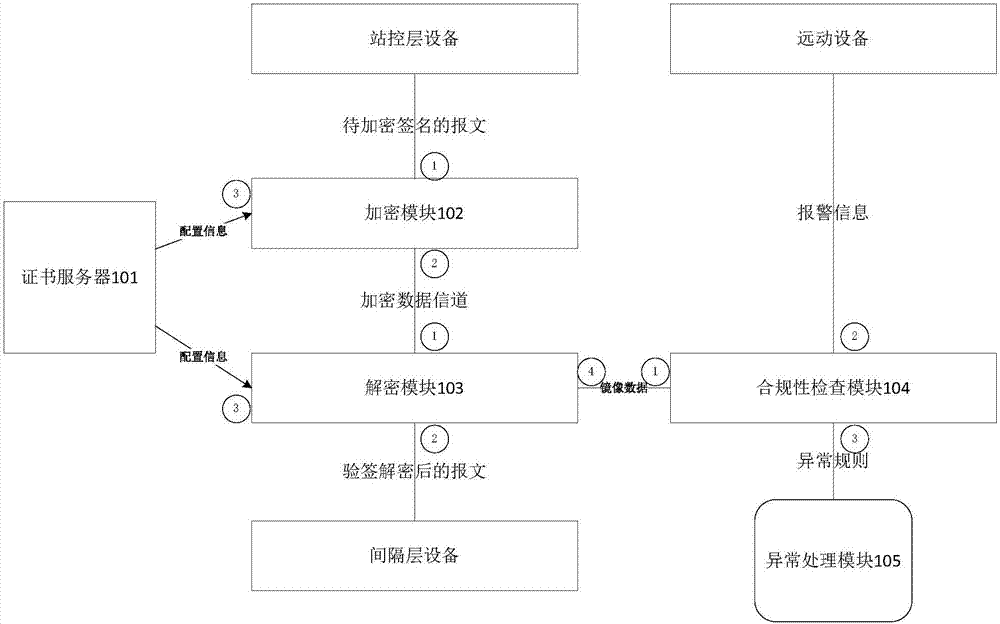
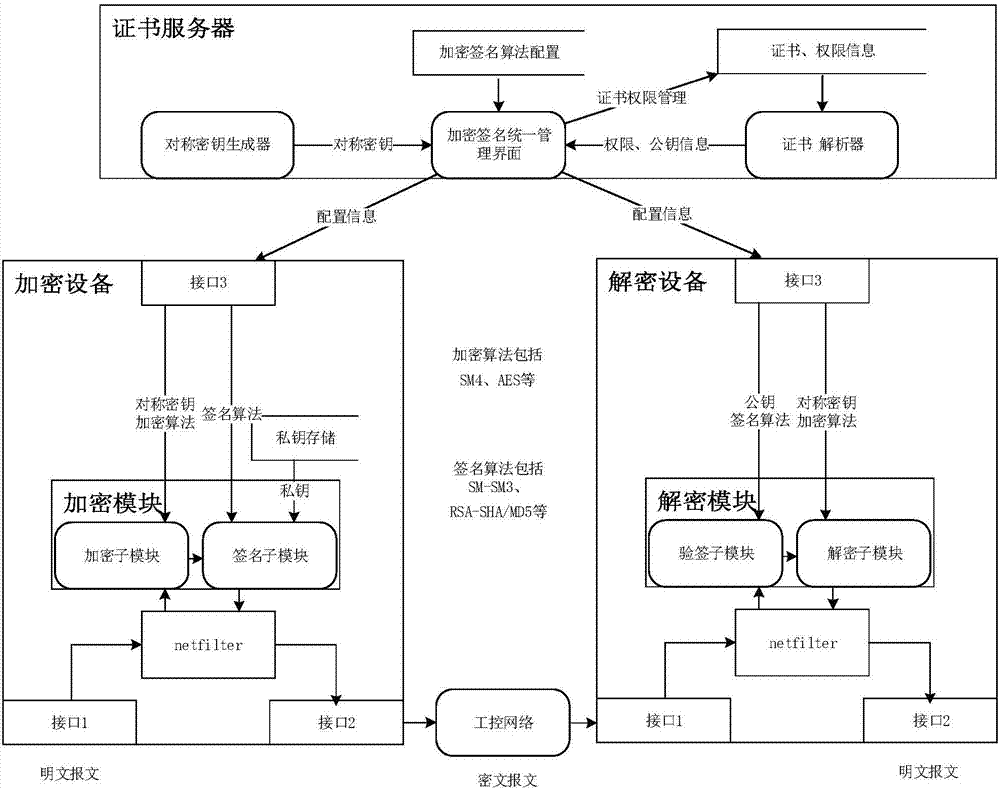
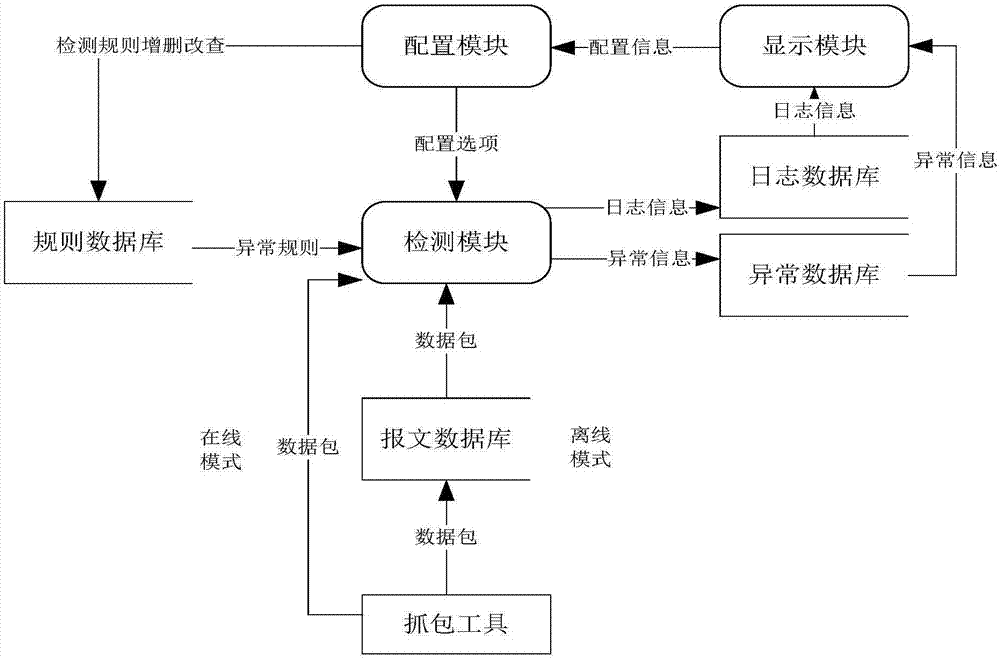
ActiveCN107483444AEasy to deployReduce maintenance costsUser identity/authority verificationPlaintextInformation transmission
The invention discloses a smart grid information transmission safety protection device and a safety protection method, which relate to the technical field of smart grid information transmission safety. The device comprises a certificate server, an encryption and decryption module, a compliance check module and an exception handling module, wherein the encryption and decryption module is wholly serially connected between a station level and a bay level for carrying out encryption signature and signature verification decryption functions on original transparently-transmitted data; the compliance check module grabs a plaintext data packet in an offline or online mode and submits the plaintext data packet to the detection module for compliance check, and as for a compliance message, an analysis result is stored to a log database in a log format; and exception information is independently stored in an exception database through the exception handling module, and an administrator is notified. In the case of permissible delay in the smart grid, the encryption and decryption module together protects the internal information of the smart grid, behaviors that the internal data are tampered and destructed in the case of transmission are resisted, and the safety of the grid is further improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
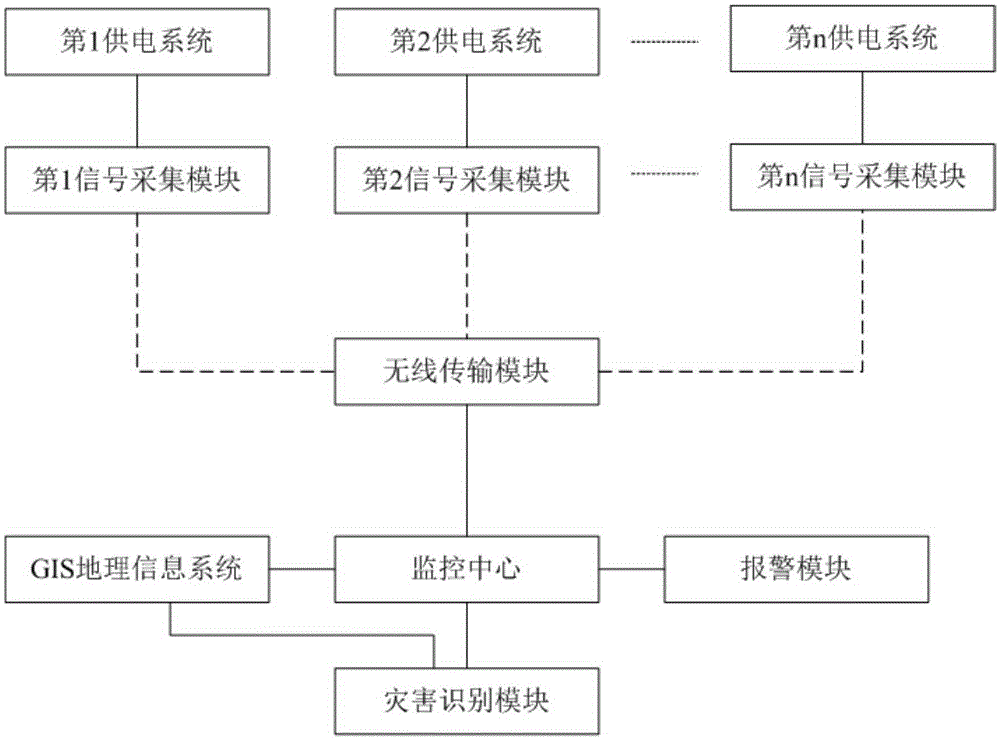
Intelligent protection system for forest disasters
InactiveCN105389936AEasy to monitorObserve carefully and comprehensivelyAlarmsWireless transmissionLandslide
The invention discloses an intelligent protection system for forest disasters, which is characterized by comprising a signal acquisition module, a wireless transmission module, a monitoring center, a GIS geographic information system, an alarm module, and a disaster identification module. The system can record a video of the whole process, can well monitor illegal mining, illegal logging and illegal hunting in forests with the aid of far-infrared signal acquisition equipment, and can monitor and alarm for torrential floods, mud-rock flow, landslide, rock falling and other disasters through identification and comparison by an image information and geographic information system. If there is an abnormal situation, the staff switches the camera from an automatic state to a manual state in time, and tracks, positions and amplifies a related target in order to observe the target more carefully and thoroughly.
Owner:XIAN TIANXUAN INTELLIGENT SYST TECH CO LTD
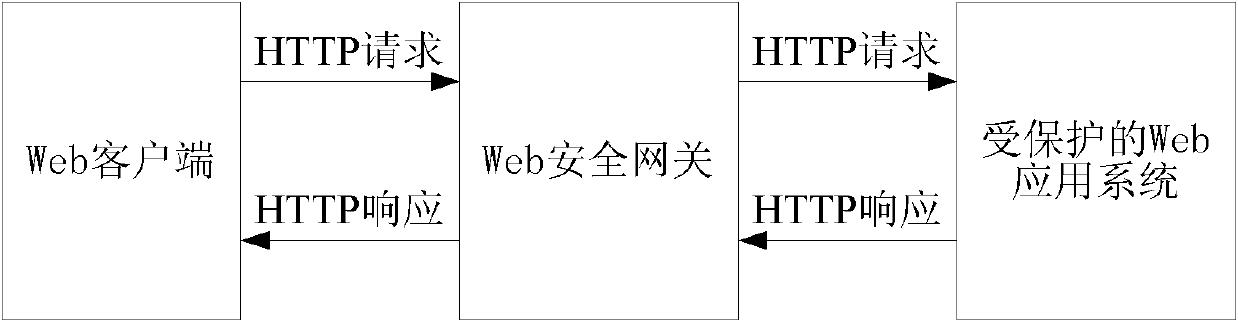
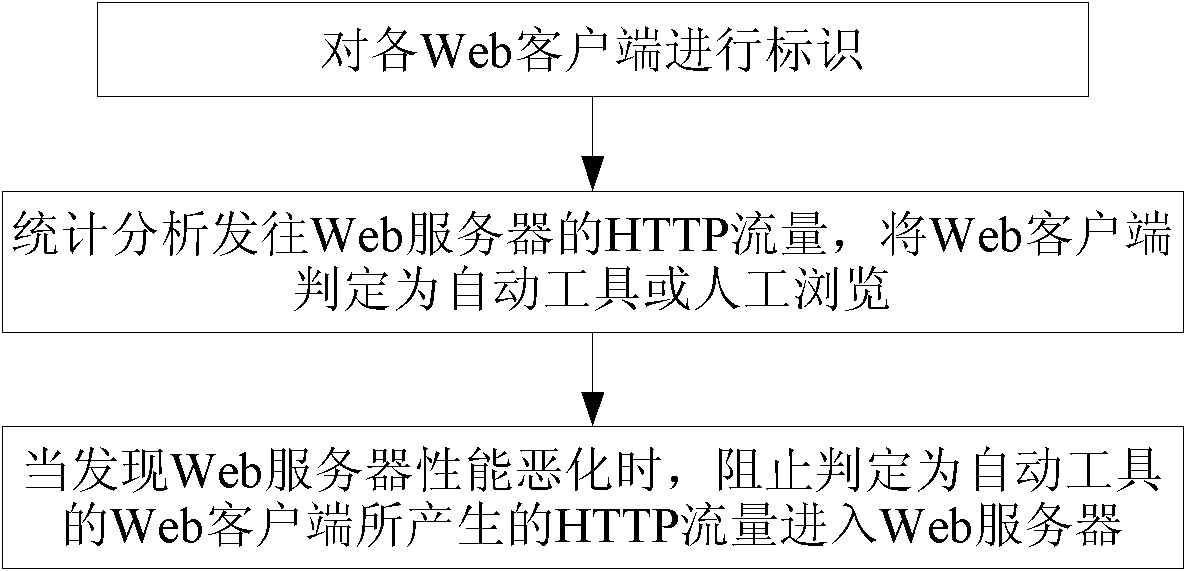
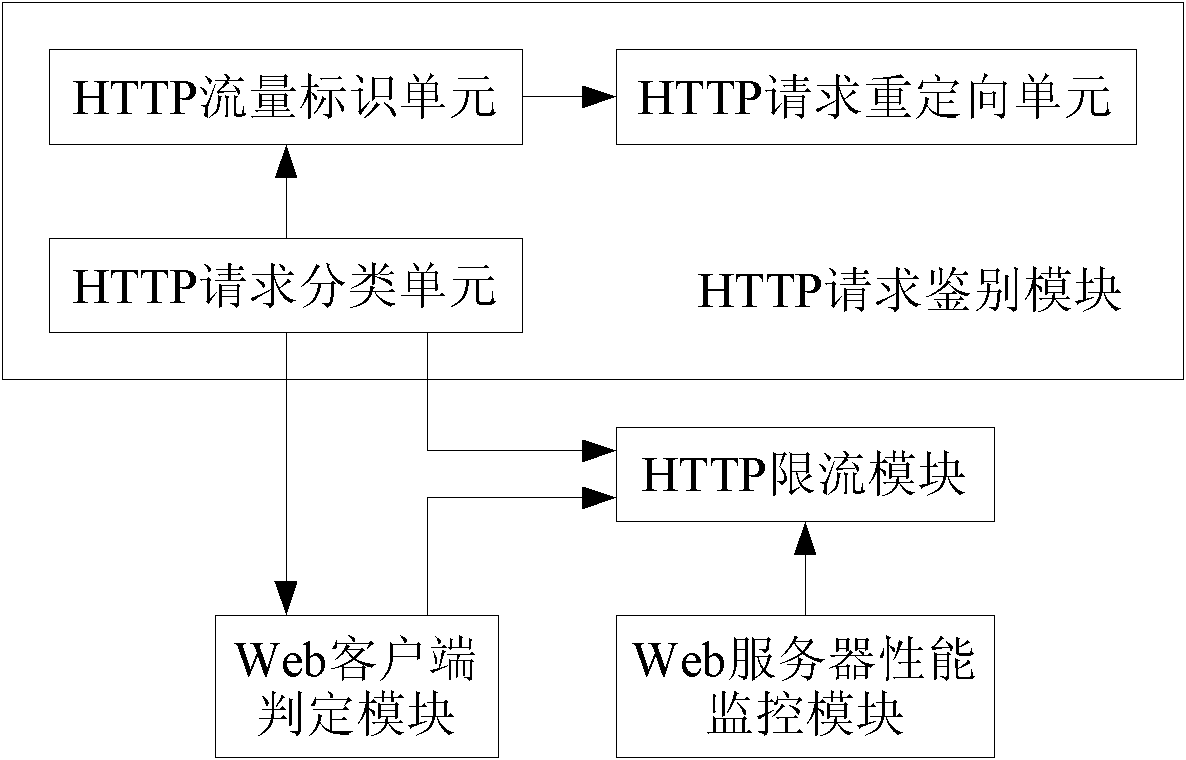
Method and device for controlling hyper text transport protocol (HTTP) traffic
InactiveCN102571547AGood defensive effectReduce computational overheadData switching networksComputer securityWeb server
The invention discloses a method and a device for controlling hyper text transport protocol (HTTP) traffic. The method includes the following steps: according to HTTP traffic sent to a Web server by a Web client, deciding that the Web client is an automatic tool or artificial browsing; only allowing the HTTP traffic generated by the Web client which is decided to be artificial browsing to enter the Web server. The method and the device are capable of limiting abnormal HTTP traffic, simultaneously allow HTTP traffic of normal Web business access to normally pass and accordingly ensure Web access service quality of normal users to the maximum degree.
Owner:BEIJING VENUS INFORMATION TECH +1
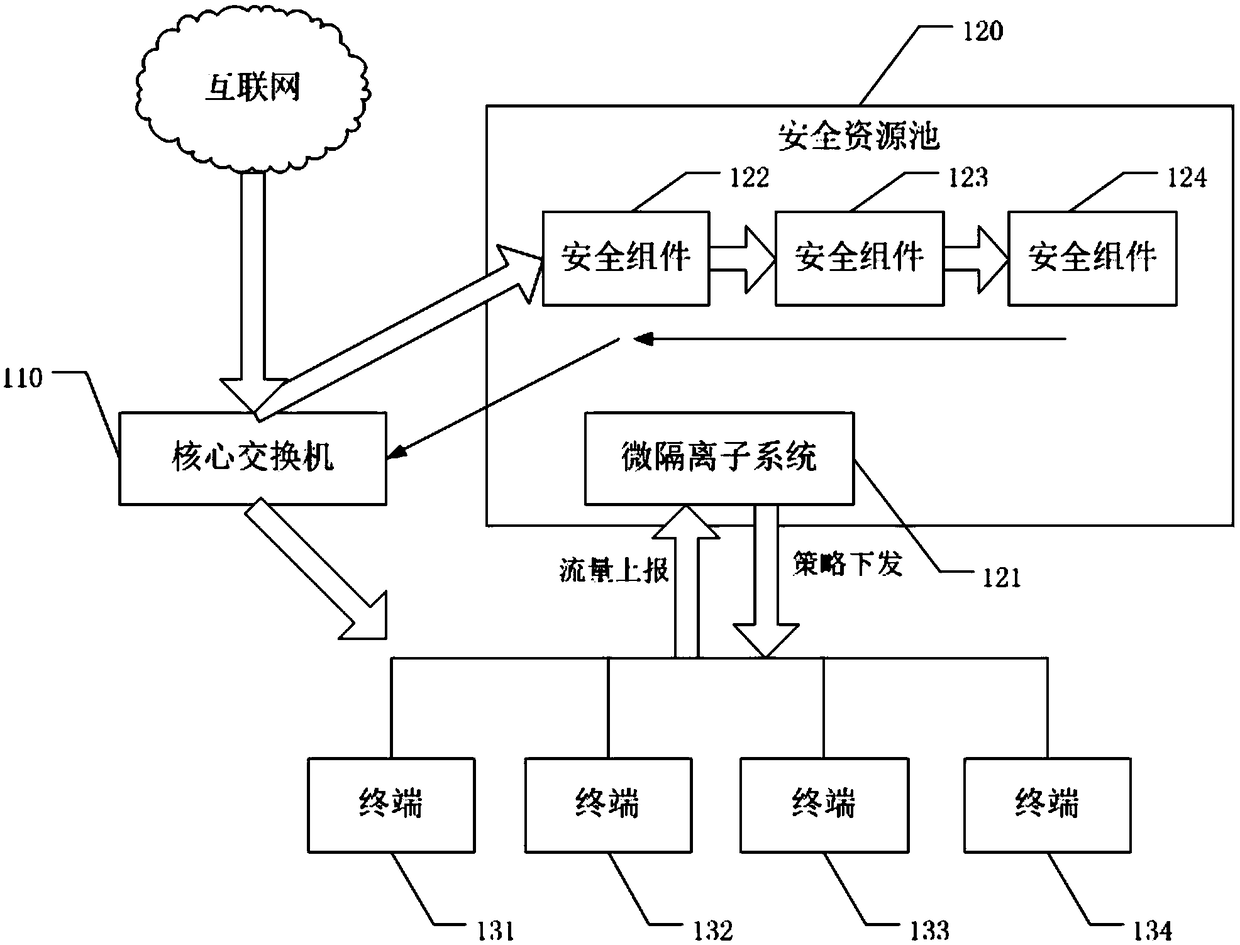
A security defense system and method
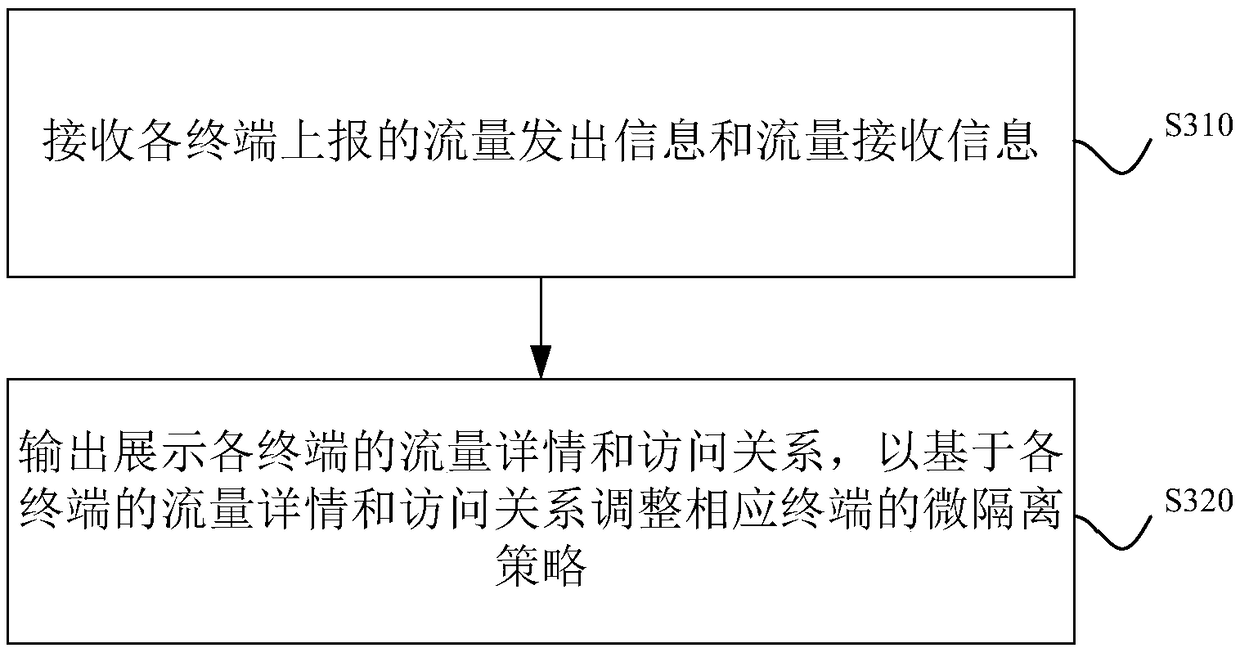
The invention discloses a security defense system, comprising a core exchange, a security resource pool and a plurality of terminals. The security resource pool comprises a micro-isolation subsystem and a plurality of security components. The core switch is used for directing the received access flow to the secure resource pool, and sending the received access flow to the corresponding terminal after cleaning and protecting each security component in the secure resource pool. Each terminal is used for accepting corresponding access when the received access traffic is determined to be safe traffic based on its own micro-isolation policy. Its own traffic information is reported to the micro-isolation subsystem. The micro-isolation subsystem is used for outputting traffic details and access relationships of each terminal to adjust the micro-isolation policy of the corresponding terminal based on the traffic details and access relationships of each terminal. The technical proposal providedby the embodiment of the invention is used for unified security protection of east-west flow and south-north flow, and the security of the private cloud is enhanced. The invention also discloses a security defense method, which has corresponding technical effect.
Owner:SANGFOR TECH INC
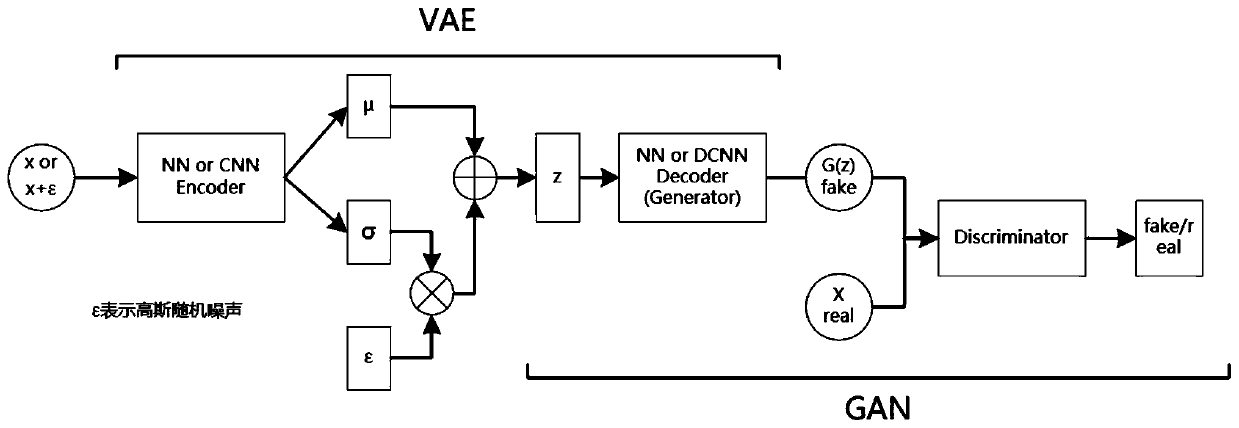
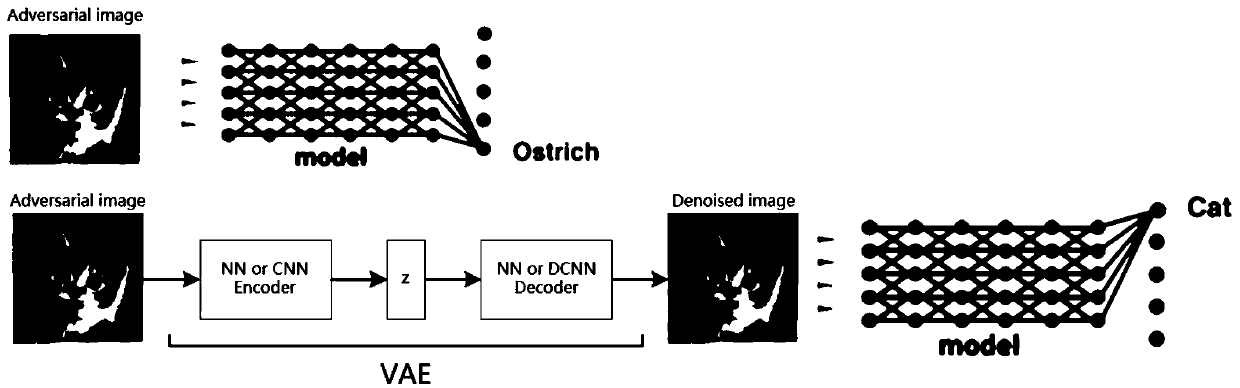
Adversarial sample defense method and system based on VAE-GAN
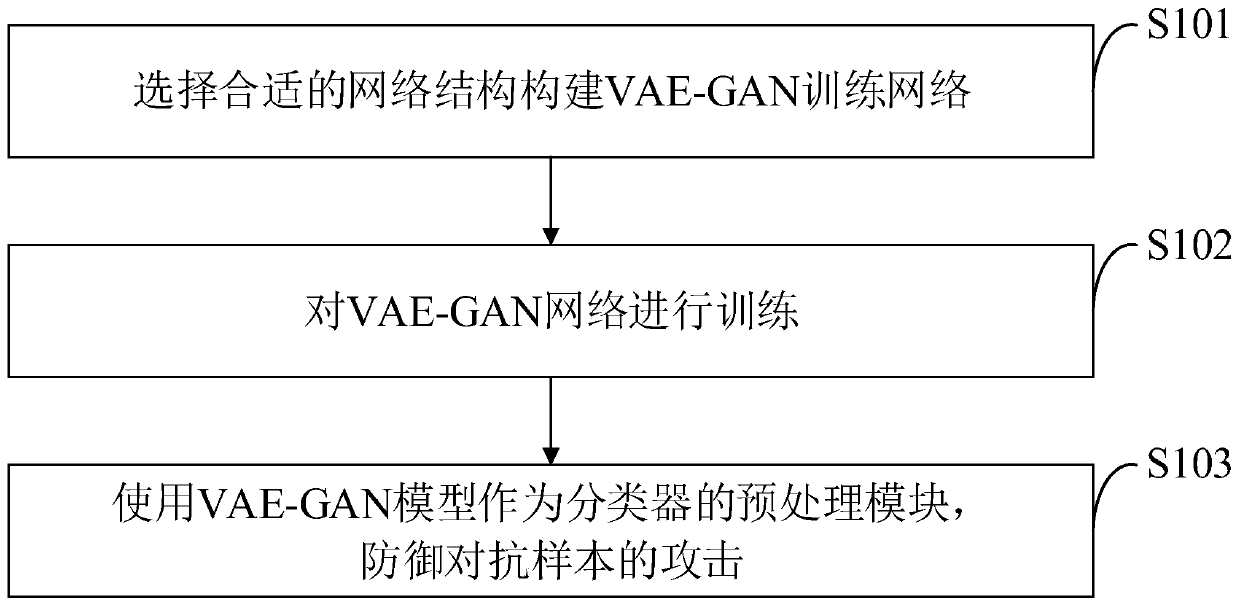
PendingCN111598805AReduce training costsGood defenseImage enhancementNeural architecturesGenerative adversarial networkMachine learning
The invention belongs to the technical field of confrontation sample defense. The invention discloses an adversarial sample defense method and system based on VAE-GAN. A variational automatic encoderVAE and a generative adversarial network GAN are used to denoise an adversarial sample, the VAE is used as a preprocessing model of a classifier to denoise the adversarial sample, and the GAN is usedto assist training of the VAE, so that an image result output by the VAE is closer to an original noiseless image. The adversarial sample defense method based on VAE-GAN provided by the invention belongs to input preprocessing, and learning migration can be carried out among different classification models; the original classification network does not need to be retrained, and the training cost islow; the classification precision of the original noiseless sample is hardly influenced; an adversarial sample is not needed, so that an external training adversarial sample is not needed; the defense effect on adversarial samples with low noise is also very good; the preprocessing speed is high, and the output image quality is close to that of an original noiseless image.
Owner:HUAZHONG UNIV OF SCI & TECH
Large filling bag ecological embankment and revetment building method for river lake channel
The invention provides a large filling bag ecological embankment and revetment building method for a river lake channel. The method comprises the steps that (1), on the basis of cleaning and leveling, an embankment structure is filled with cleaned river lake bottom mud layer by layer through the large filling bag technology until the embankment structure reaches up to a designed elevation of the embankment top and the height of 0.5-1 m beyond the designed elevation is reserved through filling construction; (2), the cleaned river lake bottom mud is filled through a land pump, or special complete equipment and corresponding construction technologies are adopted to directly conduct mechanical paving and filling, and then the filled cleaned river lake bottom mud is sewn into bags; and (3), filling soil materials of the large geotextile filling bag embankment structure are taken from local resources, the bottom mud obtained through river lake regulation and channel excavation and cleaning is used as the filling soil materials, the initial water content of the filling soil materials is controlled within the range from 50%-80%, and the large filling bag embankment structure which is layered appropriately is adopted according to the practical situation. According to the method, the design is reasonable, the process is simple, construction is easy, operation is convenient, cost is low, popularization is easy, the ecological functions are good, and the method is applicable to ecological management and ecological channel construction of river lakes in soft soil areas.
Owner:NANJING HYDRAULIC RES INST
Novel green biological organic fertilizer and preparation method thereof
InactiveCN104744171ATurn over evenlyPrevent compactionBio-organic fraction processingOrganic fertiliser preparationBiotechnologyInsect pest
The invention discloses a novel green biological organic fertilizer and belongs to the technical field of agricultural biological fertilizers. The novel green biological organic fertilizer is prepared from the following raw materials: straw mixture, seaweed residue, humic acid, amino acid and multifunctional zymophyte. The novel green biological organic fertilizer provided by the invention has the advantages that nutrients required by crops can be provided, incidence of plant diseases and insect pests can be greatly reduced, usage amount of pesticide is reduced, and crop yield and quality are improved.
Owner:SHANDONG TIANWEI BIOTECH CO LTD
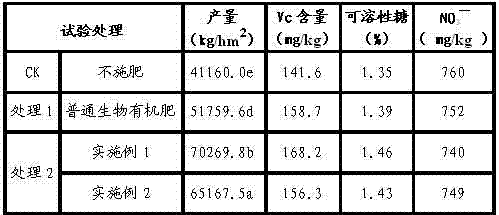
Heuristic routing method avoiding key nodes in complex network
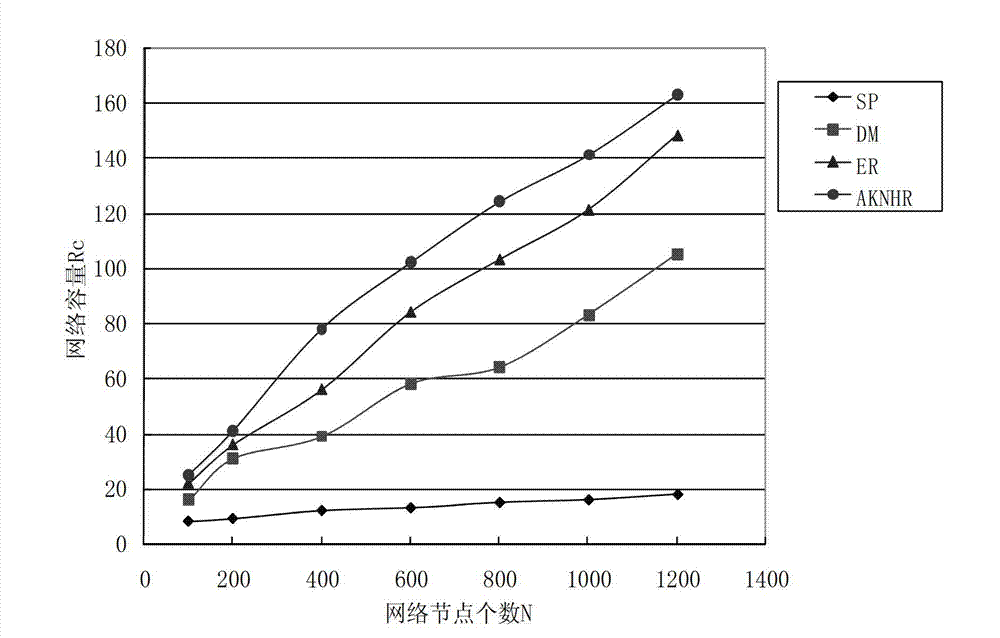
ActiveCN103200096ALarge capacityImprove transmission performanceData switching networksTraffic capacityNetwork connection
To solve the problem of routing optimization in a complex network, the invention discloses a heuristic routing method avoiding key nodes in the complex network. On the basis of maintaining original network connection unchanged and based on the routing of the shortest path, by changing weight of the edges connecting key nodes and reducing the maximum node in the network, the flow load is distributed again between the key nodes and non-key nodes, and flow of the key nodes is reduced. By adopting the heuristic routing method, larger network capacity, a routing length closer to the shortest path and higher transmission performance under load attack can be provided, network congestion can be relieved effectively, and good defense effect on cascade invalidation caused by congestion of the key nodes can be achieved.
Owner:NANJING UNIV OF SCI & TECH
Processing method for network attacks and device
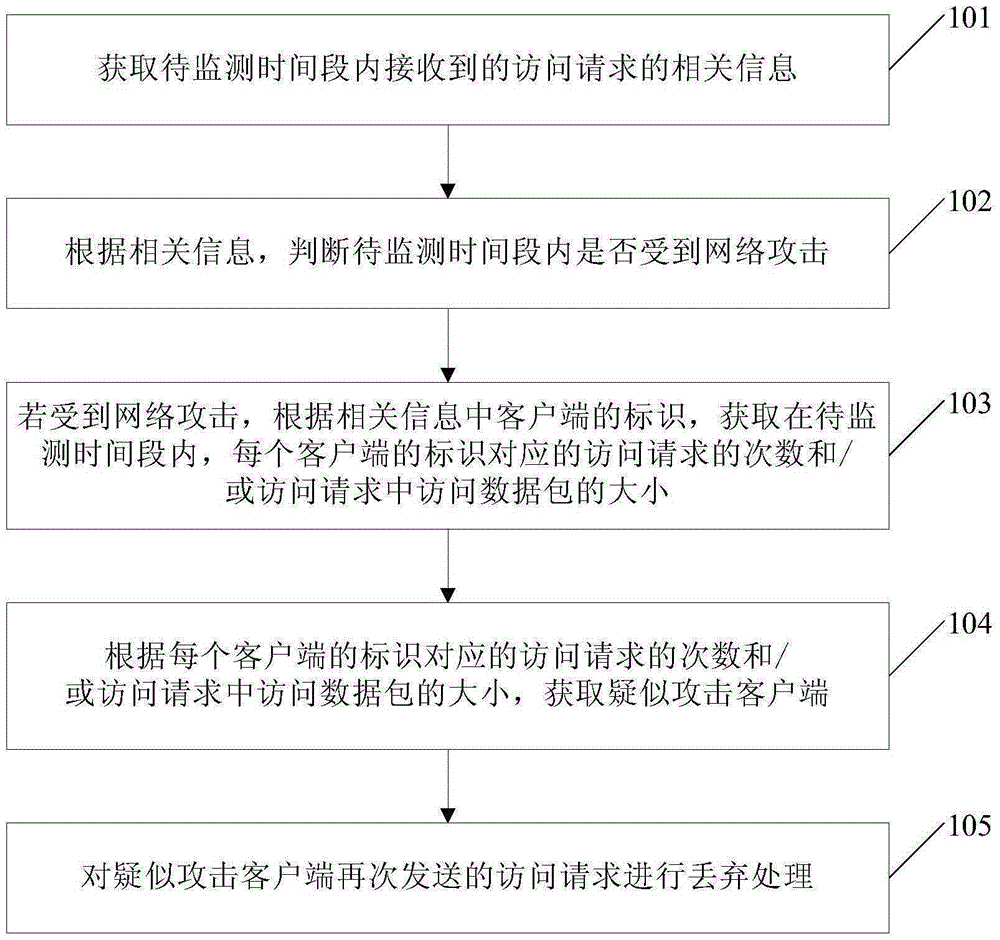
ActiveCN105337966AImprove detection accuracyAccurate identificationTransmissionRelevant informationNetwork packet
The invention provides a processing method for network attacks and a device. The method comprises steps of by obtaining related information of received access requests in a to-be-monitored period, judging whether the network has been attacked in the to-be-monitored period; if the network has been attacked, obtaining times of the access requests corresponding to identifications of client ends and / or size of access data packages in the access requests in the to-be-monitored period; and obtaining client ends which are suspected to be attacked and abandoning the access requests sent by the client ends according to the times of the access requests corresponding to identifications of client ends and / or size of access data packages in the access requests in the to-be-monitored period. Thus, whether the network has been attacked can be determined by combining the received access requests of all client ends in the to-be-monitored period; the attacks can be precisely identified and defense can be performed; detection precision degree of DDOS attacks is improved; and detection efficiency and defense effects are improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
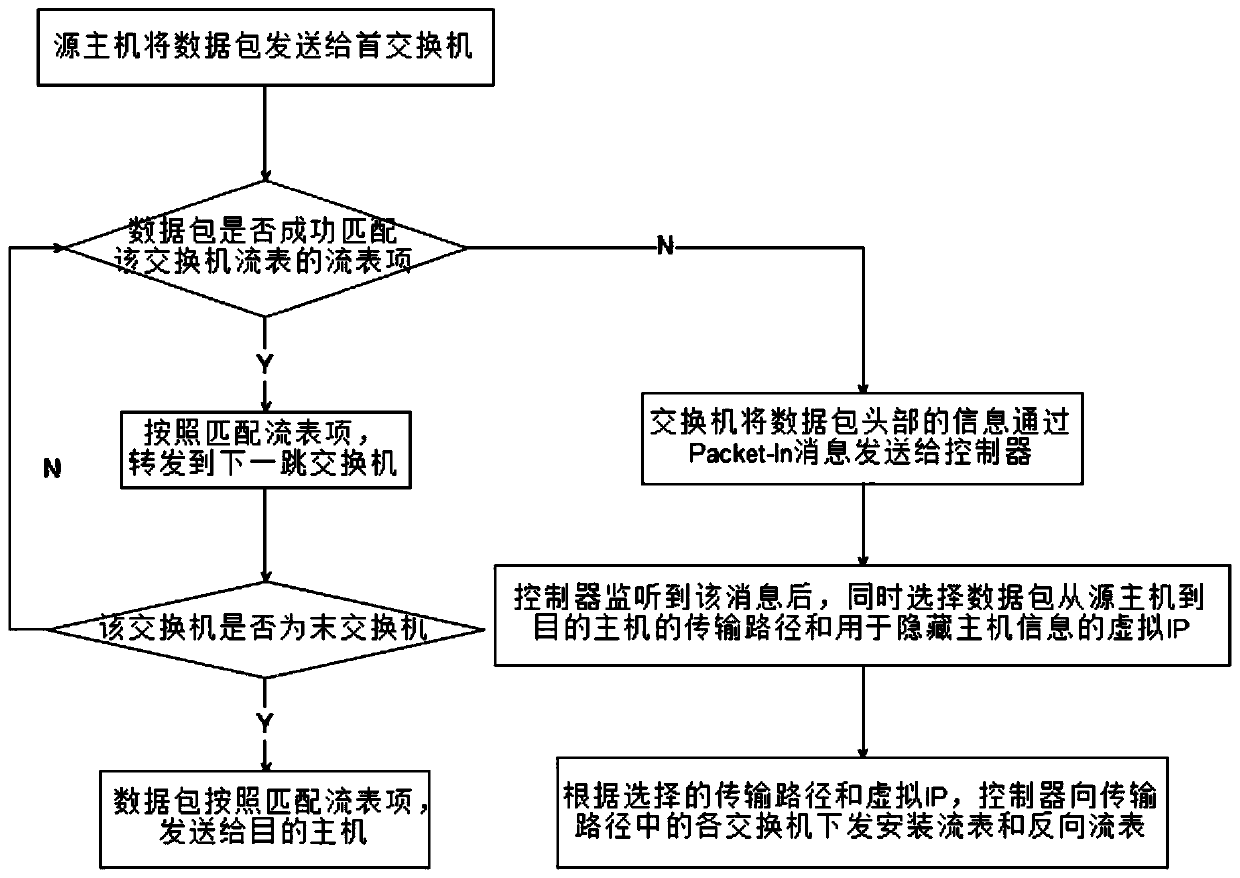
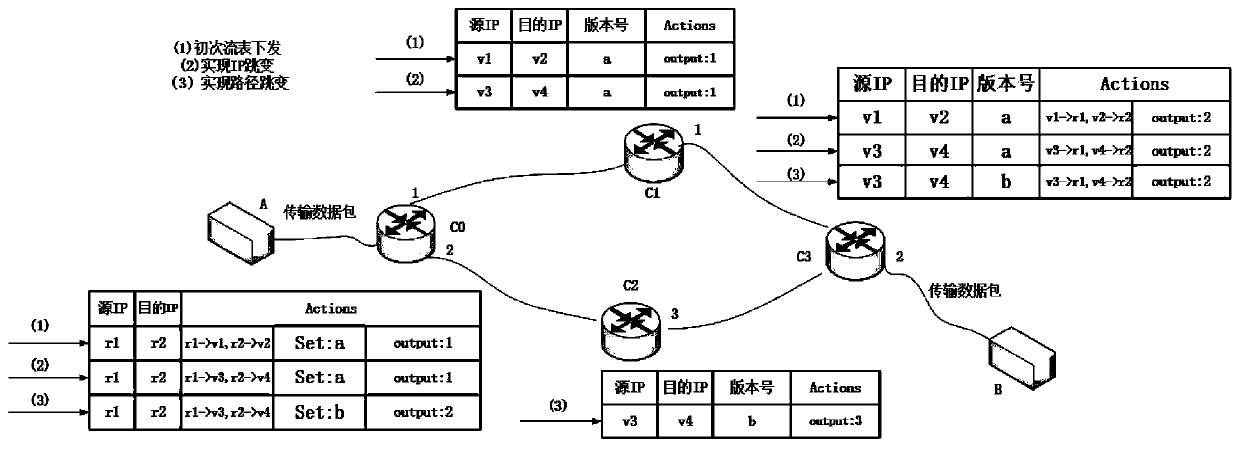
Active defense method based on path and IP address hopping in SDN network
InactiveCN110198270AIncrease the difficultyReduced availabilityData switching networksControl layerIp address
The invention discloses an active defense method based on path and address hopping in an SDN network, and belongs to the field of mobile target defense. The method comprises the following steps: S1, asource host sending a data packet to a first switch; S2, judging whether the data packet is successfully matched with the flow table item or not, if yes, forwarding the data packet to a next hop switch, and entering a step S5; otherwise, the switch sending the Packet-In message to the controller, and executing the step S3; S3, the controller selecting a data packet transmission path and a virtualIP at the same time; S4, the controller generating a flow table rule according to the selected transmission path and the virtual IP, and issuing a flow table and a reverse flow table to each switch;and S5, judging whether the switch is a final switch or not, if yes, sending the data packet to a target host, and otherwise, entering the step S2. By utilizing the separation characteristic of the SDN network data layer and the control layer and the idea of active operation change in the MTD, the IP and the transmission path of the data packet are changed on the premise of not influencing the normal communication of the network, and the difficulty of an attacker in acquiring information is increased, so that the active defense capability of the system is improved.
Owner:HUAZHONG UNIV OF SCI & TECH +1
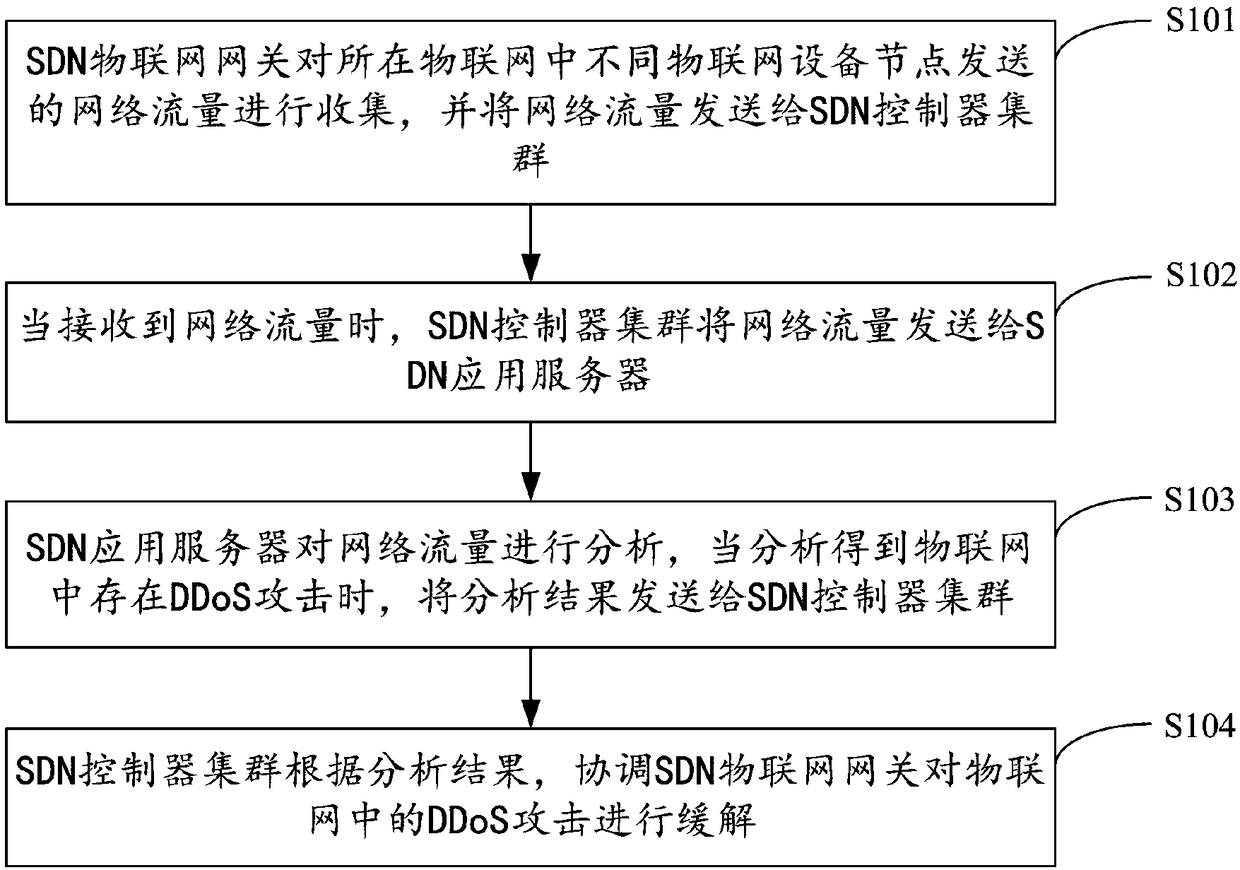
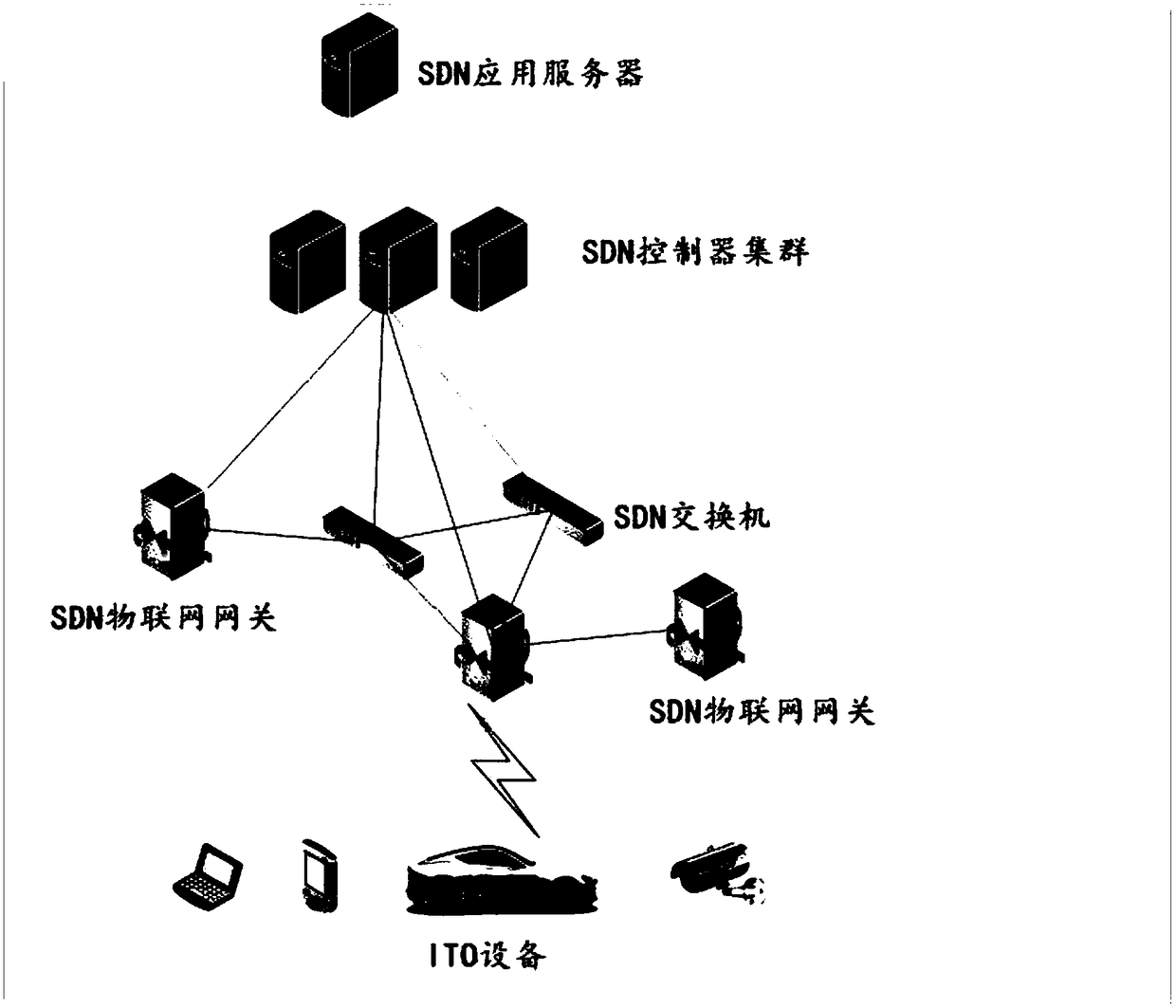
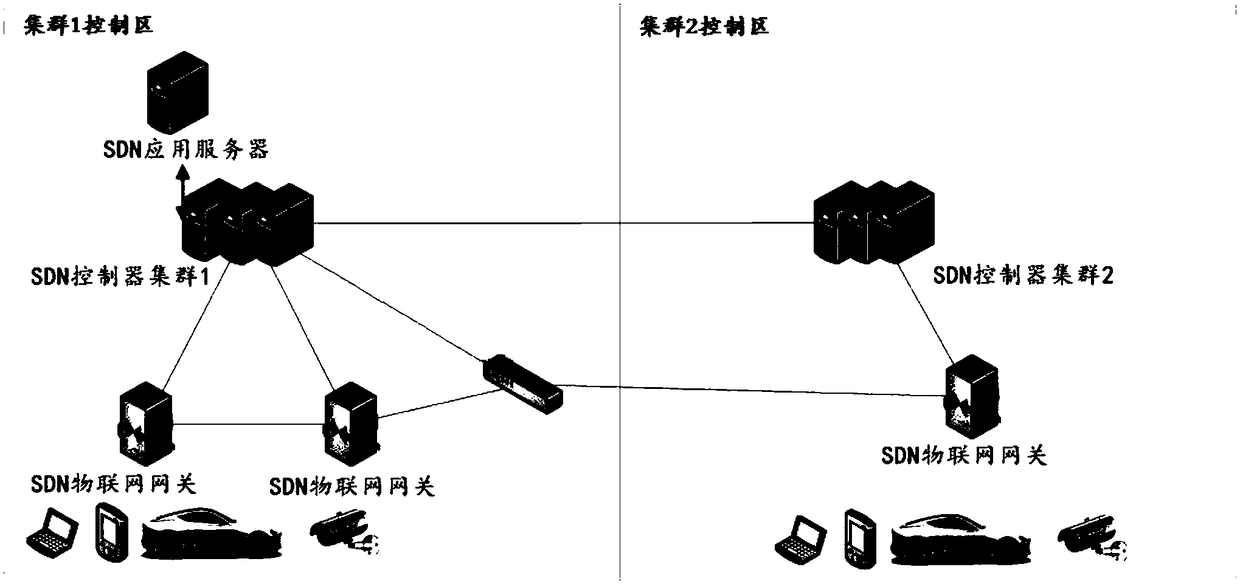
Internet of Things (IoT) DDoS attack defense method and device based on SDN, equipment and medium
The invention is applicable to the technical field of network security, provides an Internet of Things (IoT) DDoS attack defense method based on an SDN, an IoT DDoS attack defense device based on theSDN, equipment and a medium. The method comprises the steps as follows: an SDN IoT gateway collects network traffic sent by different IoT equipment nodes in the IoT where the SDN IoT gateway is located, and sends the collected network traffic to an SDN controller cluster; the SDN controller cluster sends the network traffic to an SDN application server; the SDN application server analyzes the network traffic, and sends an analysis result to the SDN controller cluster when the condition that an DDoS attack exists in the IoT is analyzed; and the SDN controller cluster coordinates the SDN IoT gateway to remit the DDoS attack in the IoT according to the analysis result. Therefore, the effect of defending with the DDoS attack under the IoT environment is effectively improved, and the flexibility of defense configuration is improved, and the defense cost is reduced.
Owner:SHENZHEN UNIV
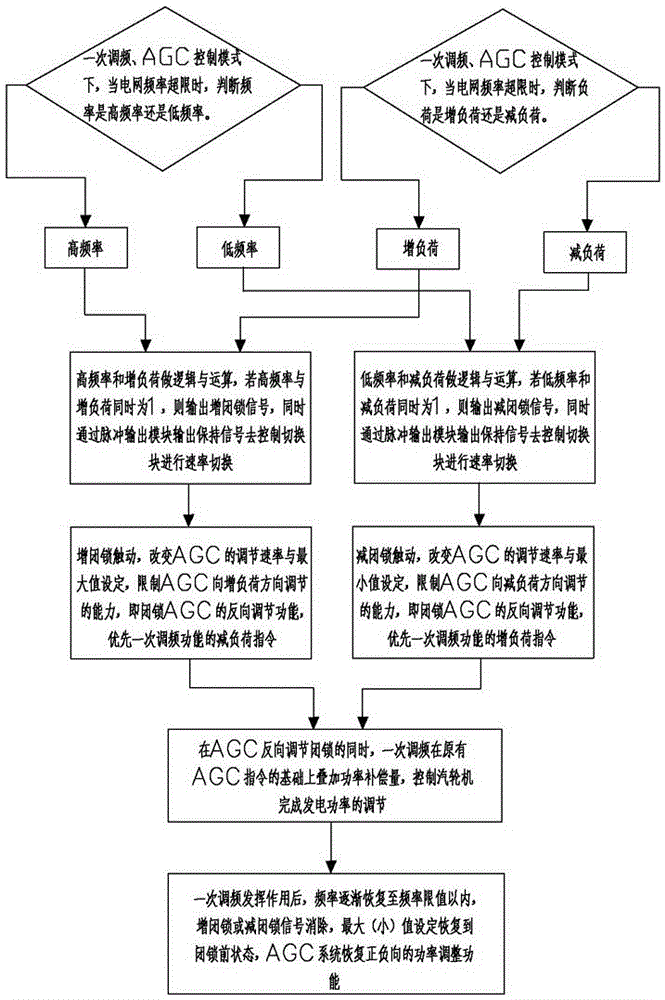
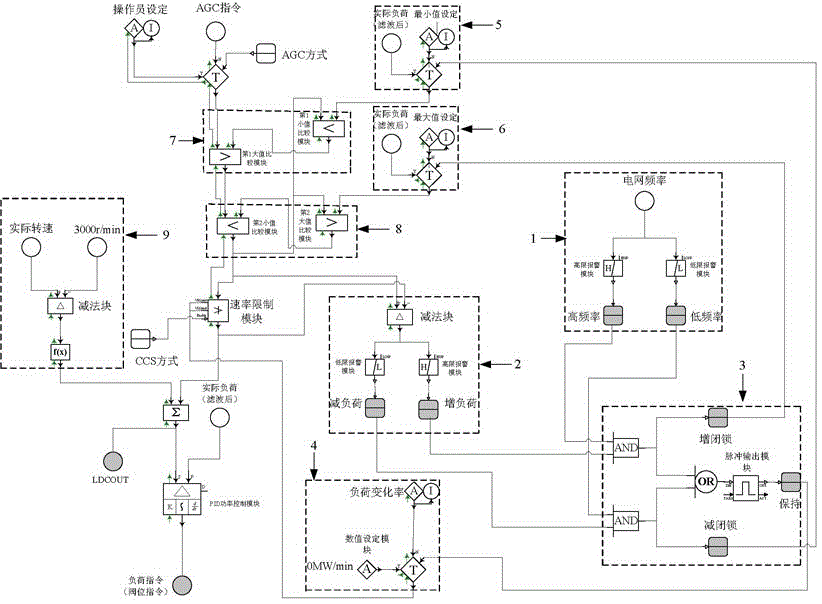
Thermal power set primary frequency modulation and AGC coordination control method
ActiveCN106169767AReduce the risk of accident expansionImprove defensePower oscillations reduction/preventionAc network voltage adjustmentPower compensationLoad following power plant
The invention relates to the technical field of thermal power set coordination control, and discloses a thermal power set primary frequency modulation and AGC coordination control method. The method comprises the following steps: step one, determining whether a power network has a high frequency or a low frequency, and determining whether an AGC system increases a load or decreases the load; step two, when the high frequency and an increased load are simultaneously one, outputting the increased load and holding signals; step three, when the low frequency and a decreased load are simultaneously one, outputting the decreased load and the holding signals; step four, triggering the increased load, locking a load increasing instruction of AGC, and prioritizing a load decreasing instruction of a primary frequency modulation function; step five, triggering the decreased load, locking a load decreasing instruction of the AGC, and prioritizing a load increasing instruction of the primary frequency modulation function; step six, superposing a power compensation amount on the basis of an original AGC instruction; and step seven, after primary frequency modulation is brought into play, and the AGC system recovering a power adjustment function of a positive direction and a negative direction. According to the invention, power network frequency control is better safeguarded, and the risk of worsening a power network frequency accident is reduced.
Owner:ELECTRIC POWER SCI RES INST OF STATE GRID XINJIANG ELECTRIC POWER +1
Heterogeneous sensors for network defense
ActiveUS20140283052A1Improve defenseImprove accuracyMemory loss protectionError detection/correctionFalse positive rateTraffic volume
Heterogeneous sensors simultaneously inspect network traffic for attacks. A signature-based sensor detects known attacks but has a blind spot, and a machine-learning based sensor that has been trained to detect attacks in the blind spot detects attacks that fail to conform to normal network traffic. False positive rates of the machine-learning based sensor are reduced by iterative testing using statistical techniques.
Owner:RESURGO
Broiler special feed
InactiveCN104095160AEnsure nutritional needsImprove immunityFood processingAnimal feeding stuffSide effectAdditive ingredient
A broiler special feed, relating to animal feed technology, comprises a main ingredient, a fodder, animal ingredients and Chinese herbal additives, wherein the main ingredient is 80% (by mass), the fodder is 5% (by mass), the animal ingredients are 10% (by mass), and the Chinese herbal additives are 5% (by mass). Compared with the conventional feed, the feed in the present invention contains components of Chinese herb. The Chinese herbal additives and the feed carrier acting in a combined manner ensures the normal nutritional requirements of laying ducks, prevents and cures diseases, improves the immunity of laying ducks, and promotes the growth of laying ducks. The broiler special feed has characteristics of non-toxic side effects, no drug-resistance generation, no environmental pollution, promotion of body resistance, rapid acting and low prices.
Owner:ANHUI QIANGYING DUCK IND GRP
Method for enhancing defense capability of neural network based on federated learning
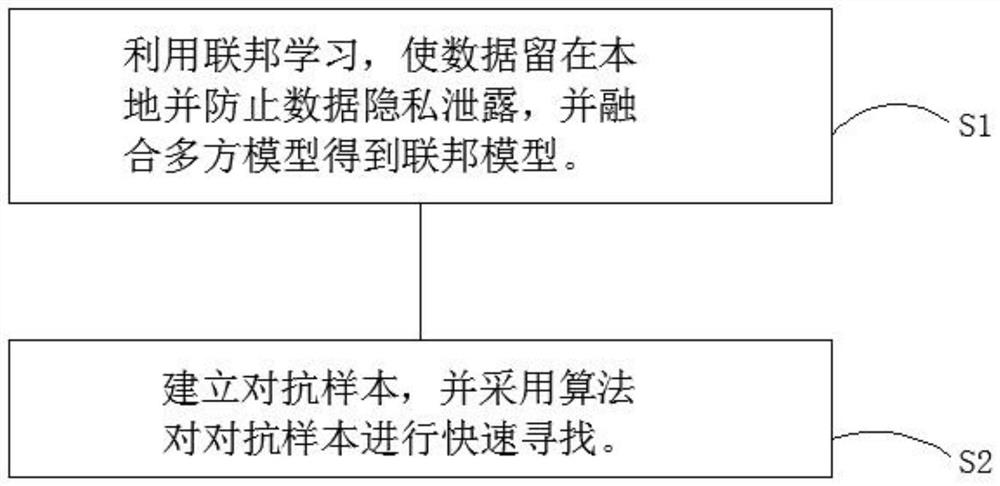
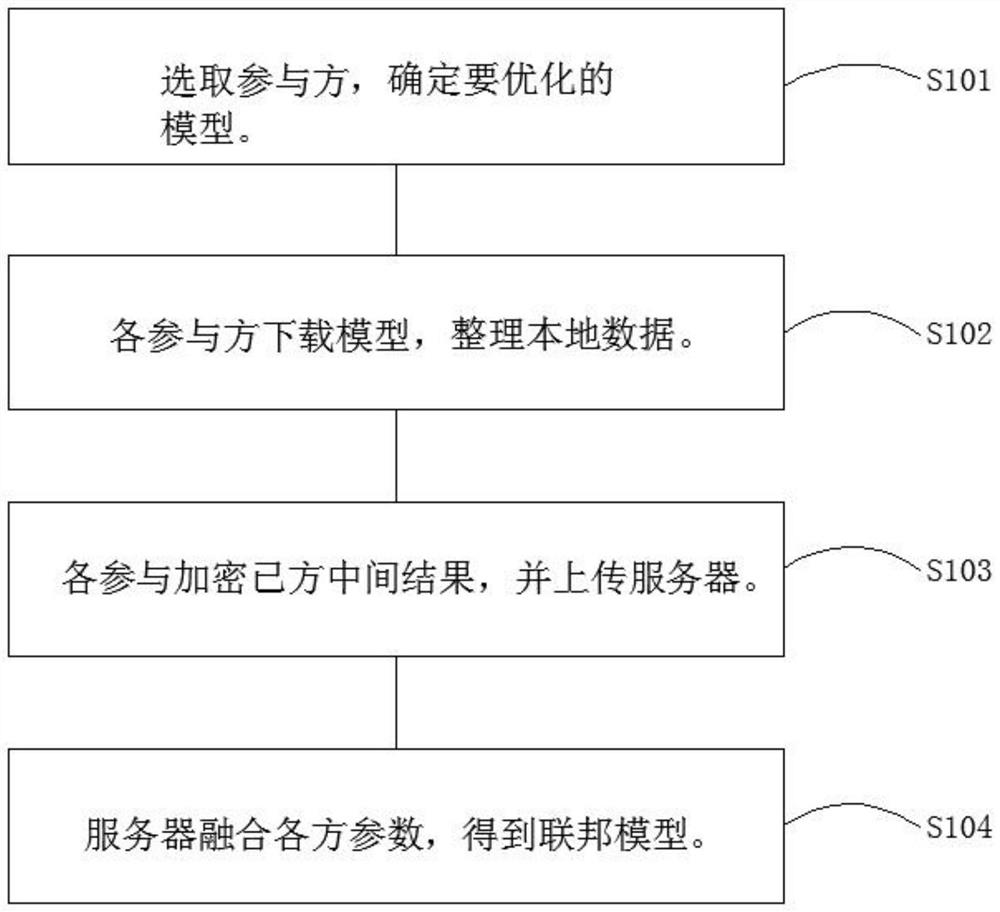
PendingCN111860832AImprove defenseImprove securityKernel methodsDigital data protectionData setPrivacy protection
The invention provides a method for enhancing the defense capability of a neural network based on federated learning. The method comprises the following steps: S1, retaining data locally and preventing data privacy leakage by utilizing federated learning, cooperating with each party to carry out distributed model training, encrypting an intermediate result to protect data security, summarizing andfusing a multi-party model to obtain a federated model; and S2, establishing an adversarial sample, and quickly searching the adversarial sample by adopting an algorithm. According to the method, federated learning and a training process of a neural network model are combined, the problem that a data set cannot be circulated due to consideration of privacy protection and laws and regulations is solved, the trouble of data collection is saved, the training set of the neural network model is richer and more independent, and the defect that the neural network model is likely to be attacked by countermeasure samples due to the fact that the training set is incomplete is overcome.
Owner:GUANGZHOU UNIVERSITY +1
Method, device for identifying service flows and method, system for protecting against deny of service attack
InactiveUS20100095351A1Improve recognition accuracyImprove defenseMemory loss protectionDigital data processing detailsService flowGoal system
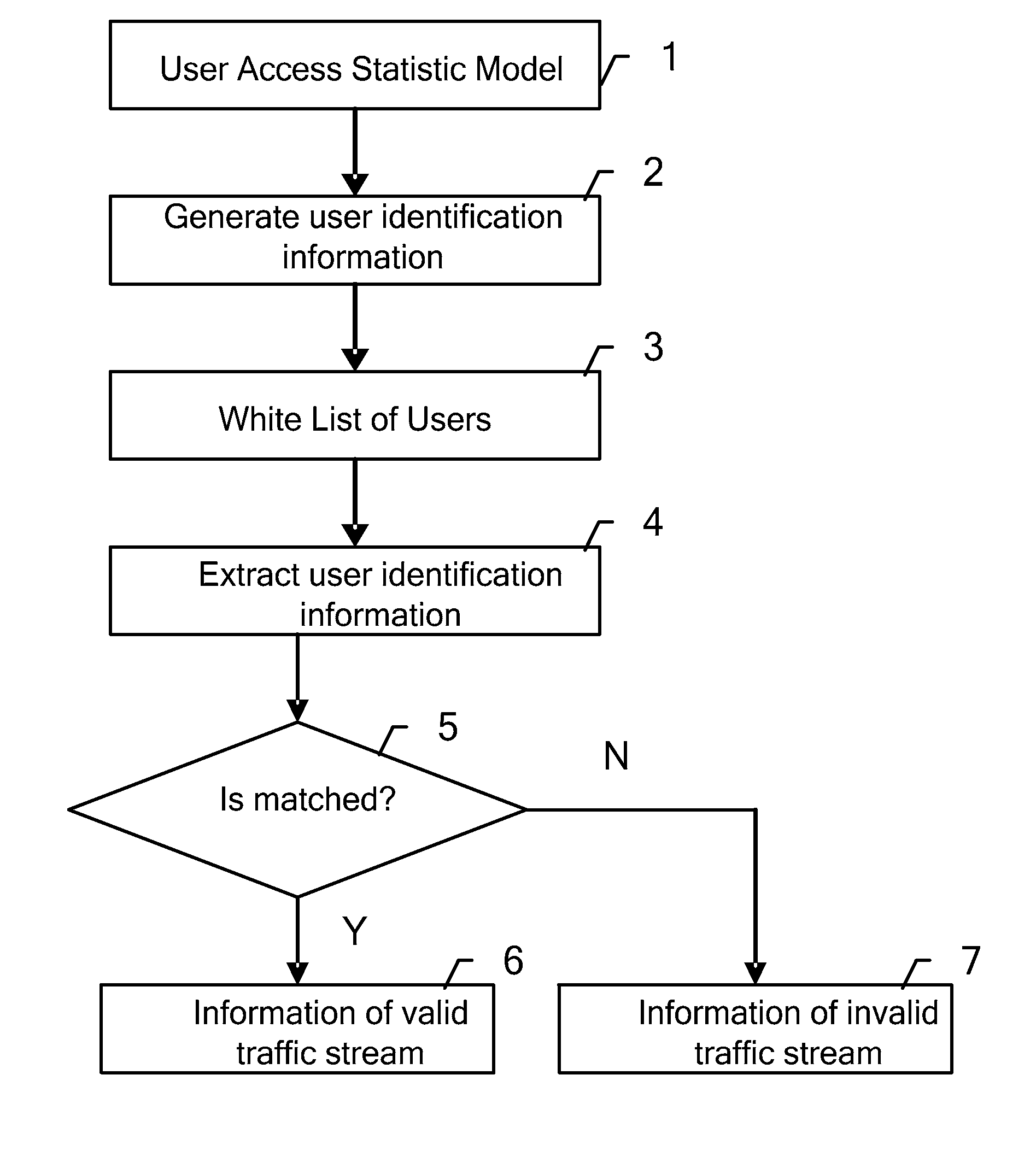
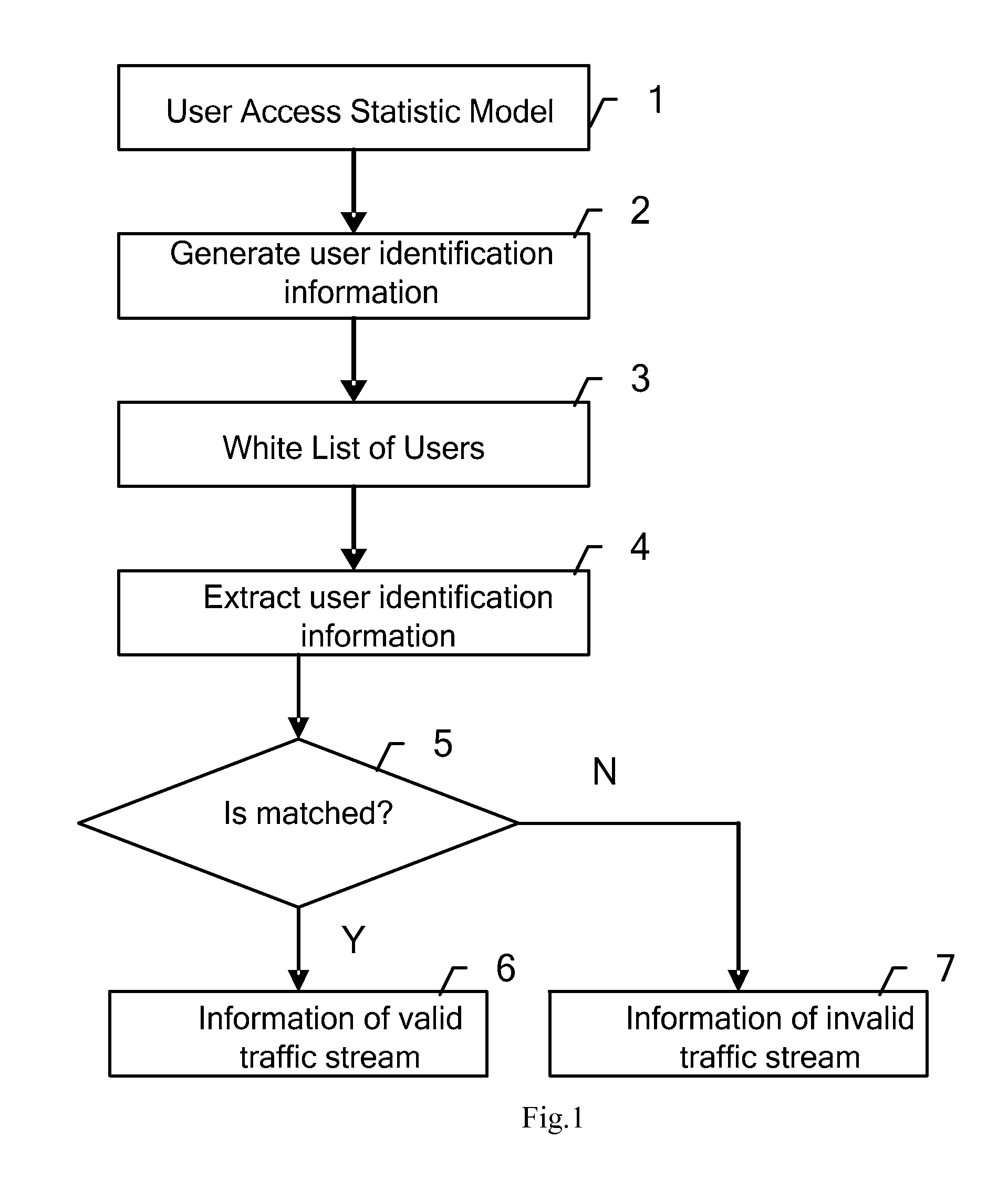
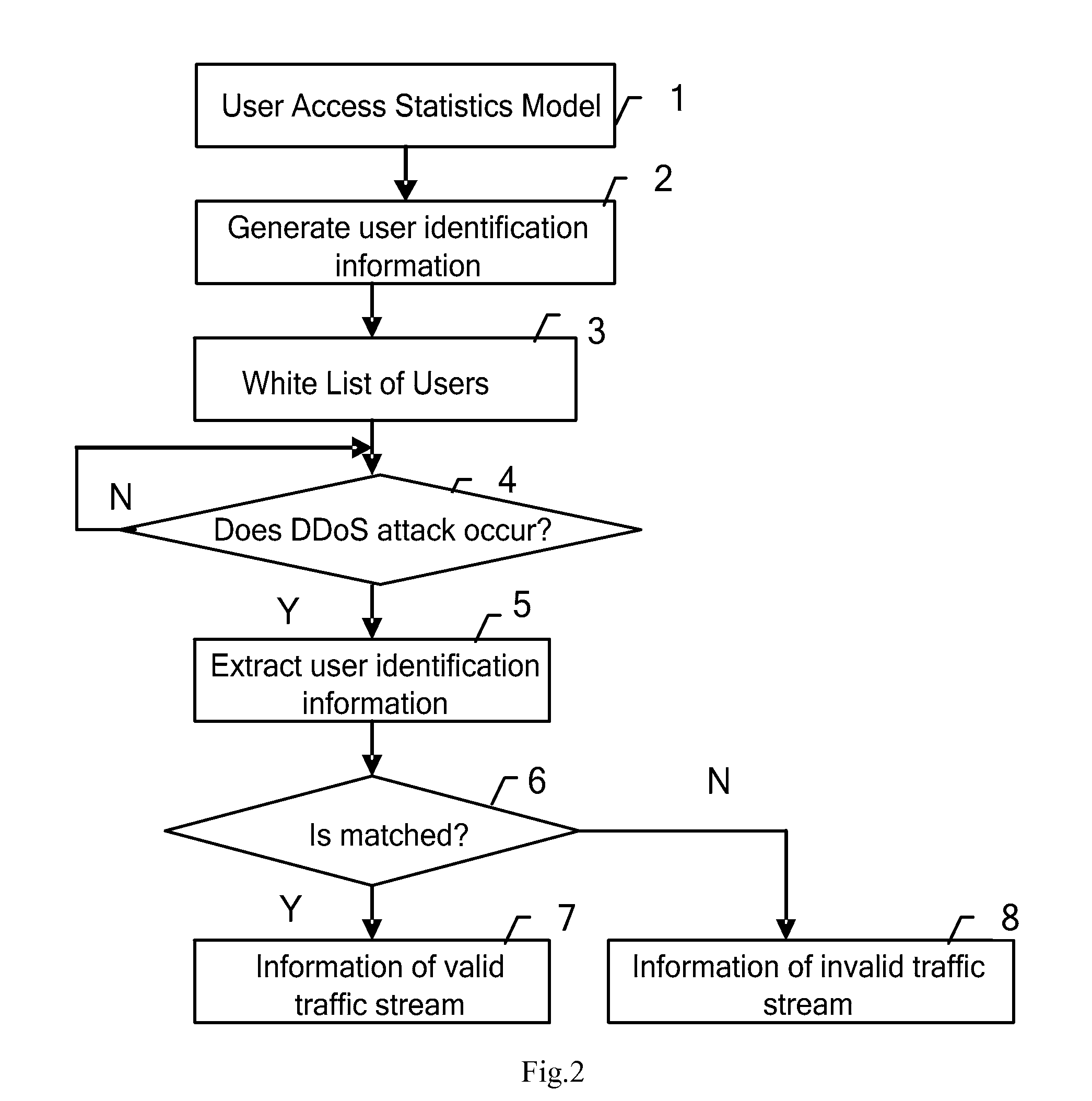
A method, device for identifying service flows and a method, system for protecting against a denial of service attack are provided. The method for identifying service flows includes: detecting a user access to a target system; dynamically generating a set of user identifier information according to the detected user access to the target system and a preset user access statistical model; when the service flow needs to be identified, extracting the user identifier information from the service flow; comparing the extracted user identifier information with the user identifier information in the set of user identifier information to determine whether they are matched; determining whether the service flow is legal service flow according to the comparison result.
Owner:HUAWEI TECH CO LTD
Low-altitude short-range cluster cooperative defense system and defense method
PendingCN106846922AImprove defenseRealize automatic scanning detectionDefence devicesAircraft traffic controlComputer scienceProcess information
The invention discloses a low-altitude short-range cluster cooperative defense system and defense method. The system comprises an early-warning monitoring module, an aerial counter-measure module, a ground counter-measure module and a control center. Data acquired by the early-warning monitoring module is transmitted to the control center to form visualization air situation, when an illegal low-slow small flyer invades, the early-warning monitoring module identifies, follows and monitors the illegal flyer and indicates an azimuth and height of the illegal flyer, and the control center drives the aerial counter-measure module or the ground counter-measure module to handle the illegal flyer. The control center transmits a control instruction to the aerial counter-measure module or the ground counter-measure module and can also process information returned by an aerial unmanned counter-measure module or a ground unmanned counter-measure module in real time. The aerial unmanned counter-measure module repels or hits a target by virtue of a carried task load. The ground unmanned counter-measure module repels and hits the target or effectively suppresses the low-altitude flyer by virtue of a carried task load.
Owner:武汉天宇智戎防务科技有限公司
Protection method for packet transmission network
ActiveCN101471849AImprove the protection mechanismFix out of orderLoop networksComputer networkData stream
The embodiment of the invention discloses a method for protecting a packet transport network (PTN). The method constructs a protection path for service data stream carried on a shared protection ring, wherein, the protection path includes a wrapping protection path and a steering protection path. The method comprises the following steps: a first service data stream sends data through the wrapping protection path; a service data stream node stops sending a second service data stream subsequent to the first service data stream to the wrapping protection path and caches the second service data stream; and the first service data stream completely passes through the service data stream node again to switch the cached second service data stream from the wrapping protection path to the steering protection path. The embodiment of the invention further provides corresponding equipment and a corresponding system. The invention can solve the out-of-sequence problem in the PTN in the case of adopting a wrapping / steering combined protection scheme.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com