Patents
Literature
1933 results about "Pool" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a pool is a collection of resources that are kept ready to use, rather than acquired on use and released afterwards. In this context, resources can refer to system resources such as file handles, which are external to a process, or internal resources such as objects. A pool client requests a resource from the pool and performs desired operations on the returned resource. When the client finishes its use of the resource, it is returned to the pool rather than released and lost.
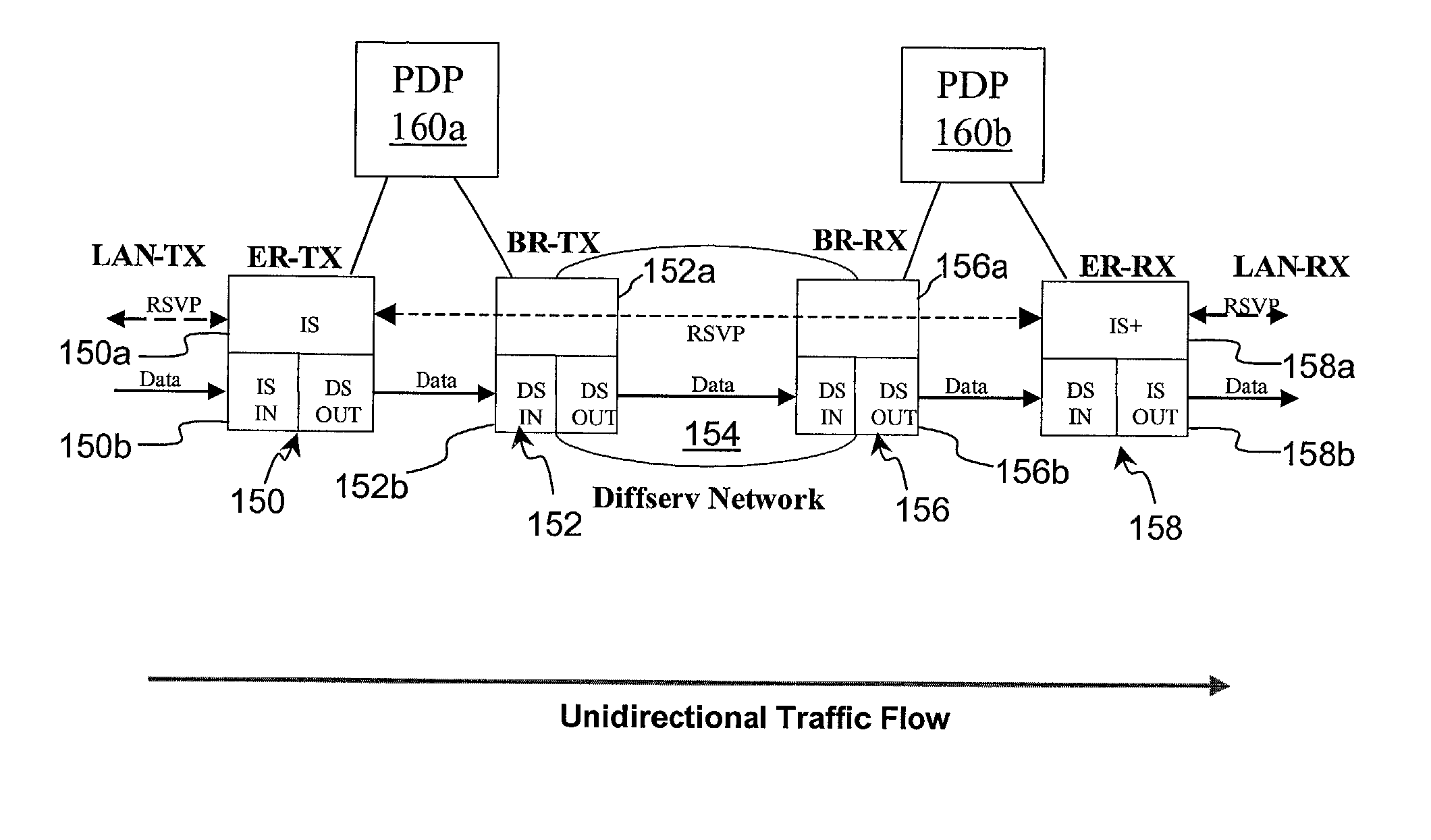
Policy-based synchronization of per-class resources between routers in a data network
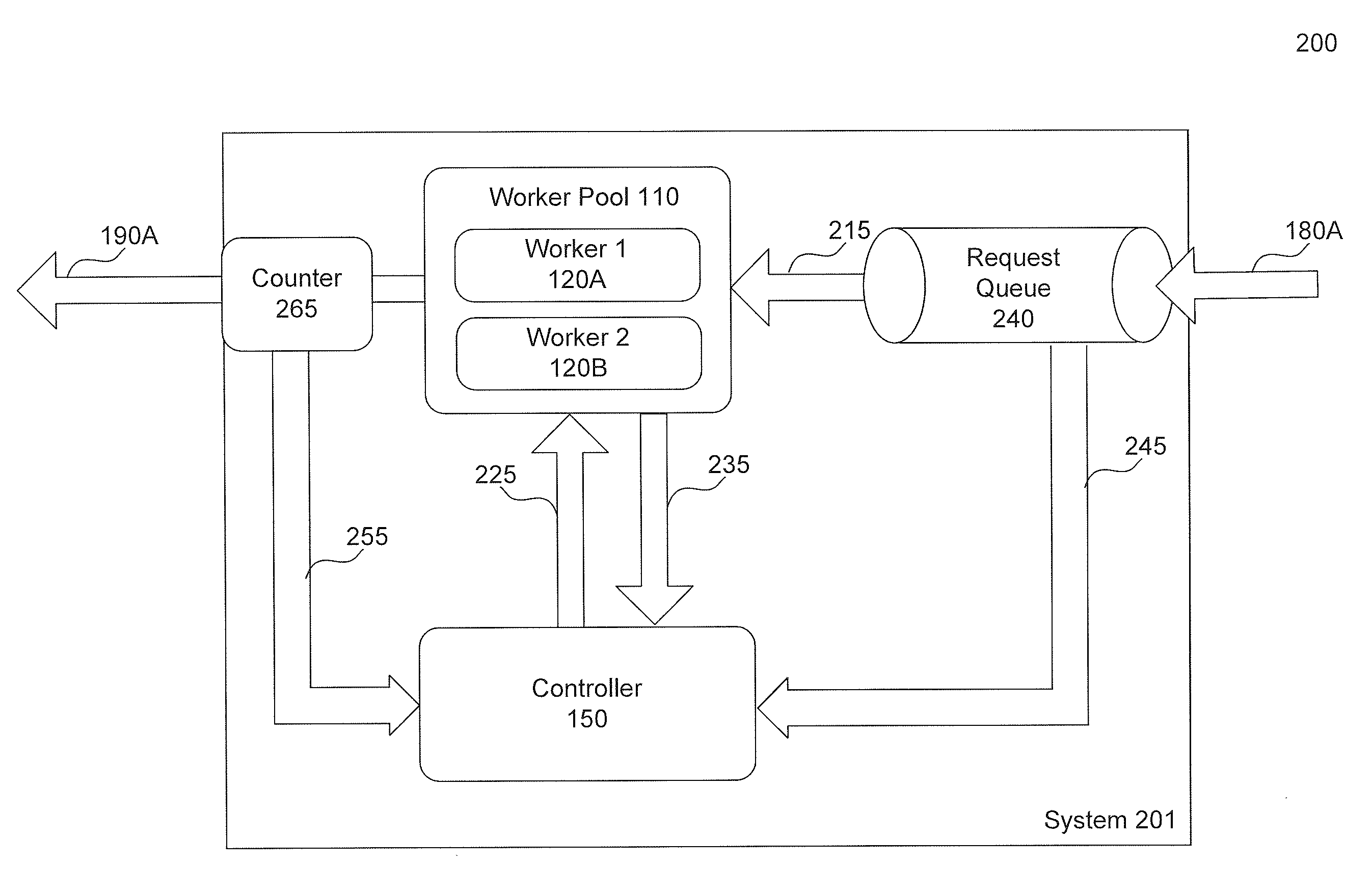
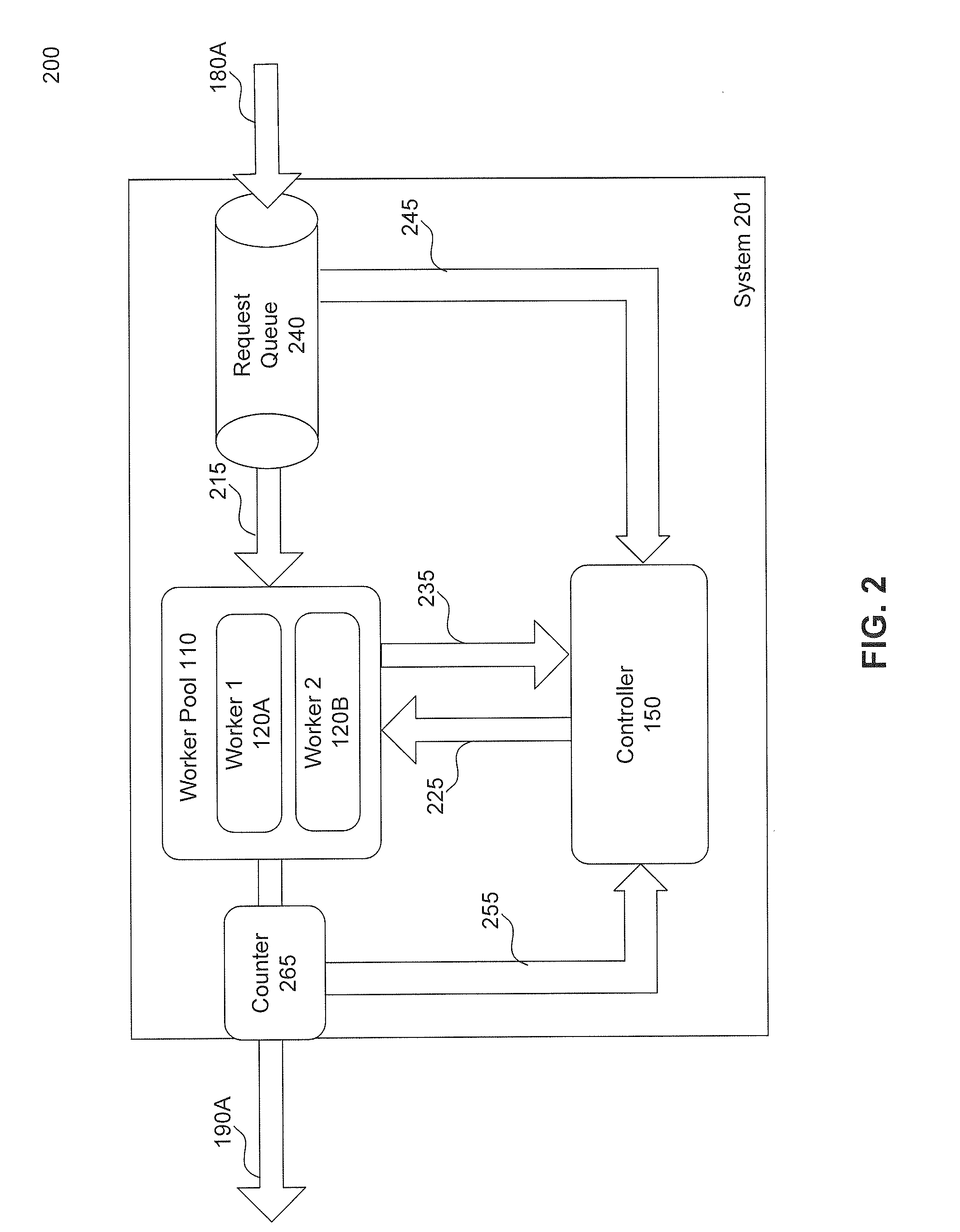
ActiveUS20020194369A1Multiple digital computer combinationsProgram controlCommunication interfaceData stream
A data network may include an upstream router having one or more data handling queues, a downstream router, and a policy server. In one embodiment, the policy server includes processing resources, a communication interface in communication with the processing resources, and data storage that stores a configuration manager executable by the processing resources. The configuration manager configures data handling queues of the upstream router to provide a selected bandwidth to one or more of a plurality of service classes of data flows. In addition, the configuration manager transmits to the downstream router one or more virtual pool capacities, each corresponding to a bandwidth at the upstream router for one or more associated service classes among the plurality of service classes. In one embodiment, the configuration manager configures the data handling queues on the upstream router only in response to acknowledgment that one or more virtual pool capacities transmitted to the downstream router were successfully installed.
Owner:VERIZON PATENT & LICENSING INC
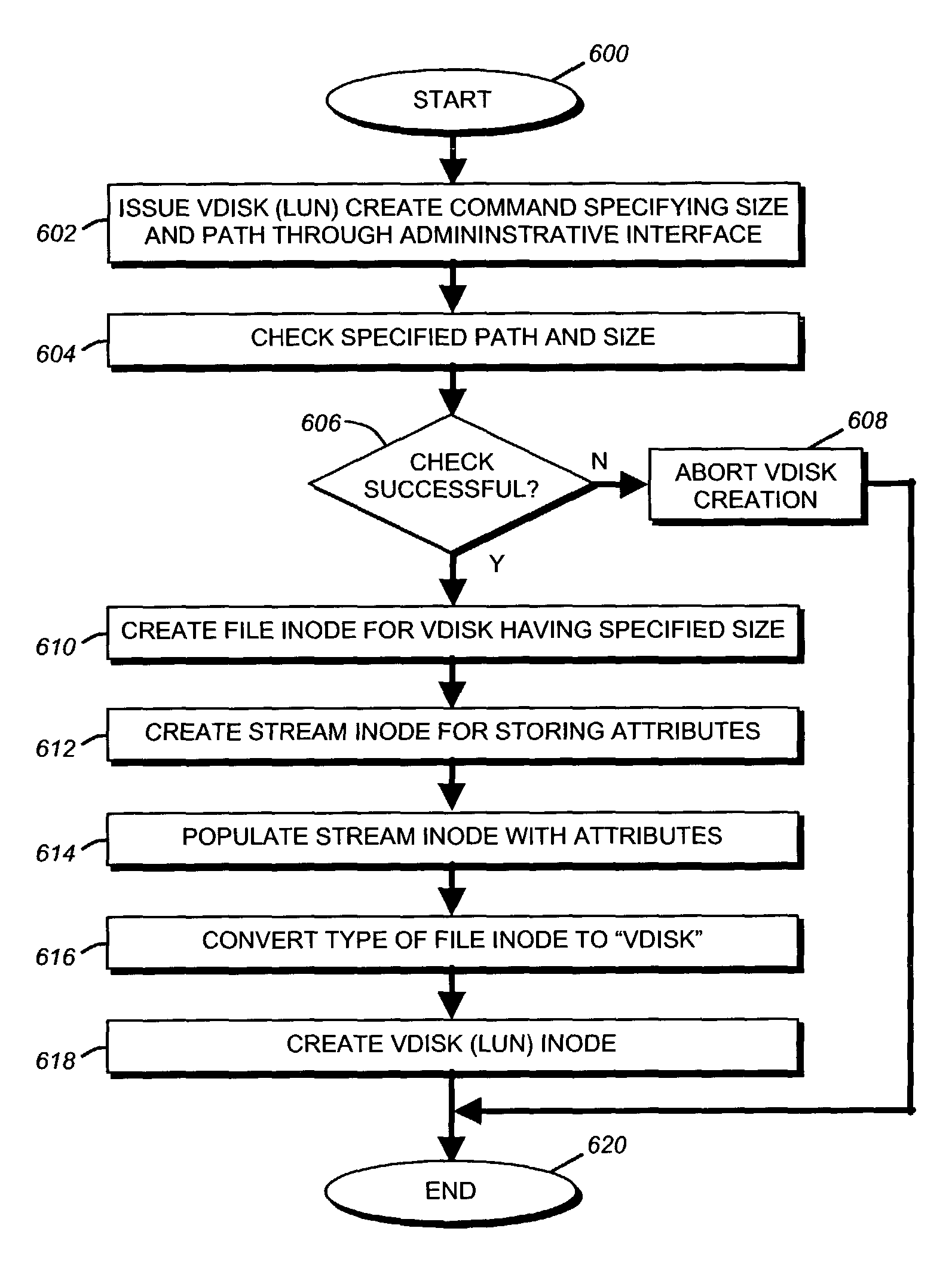
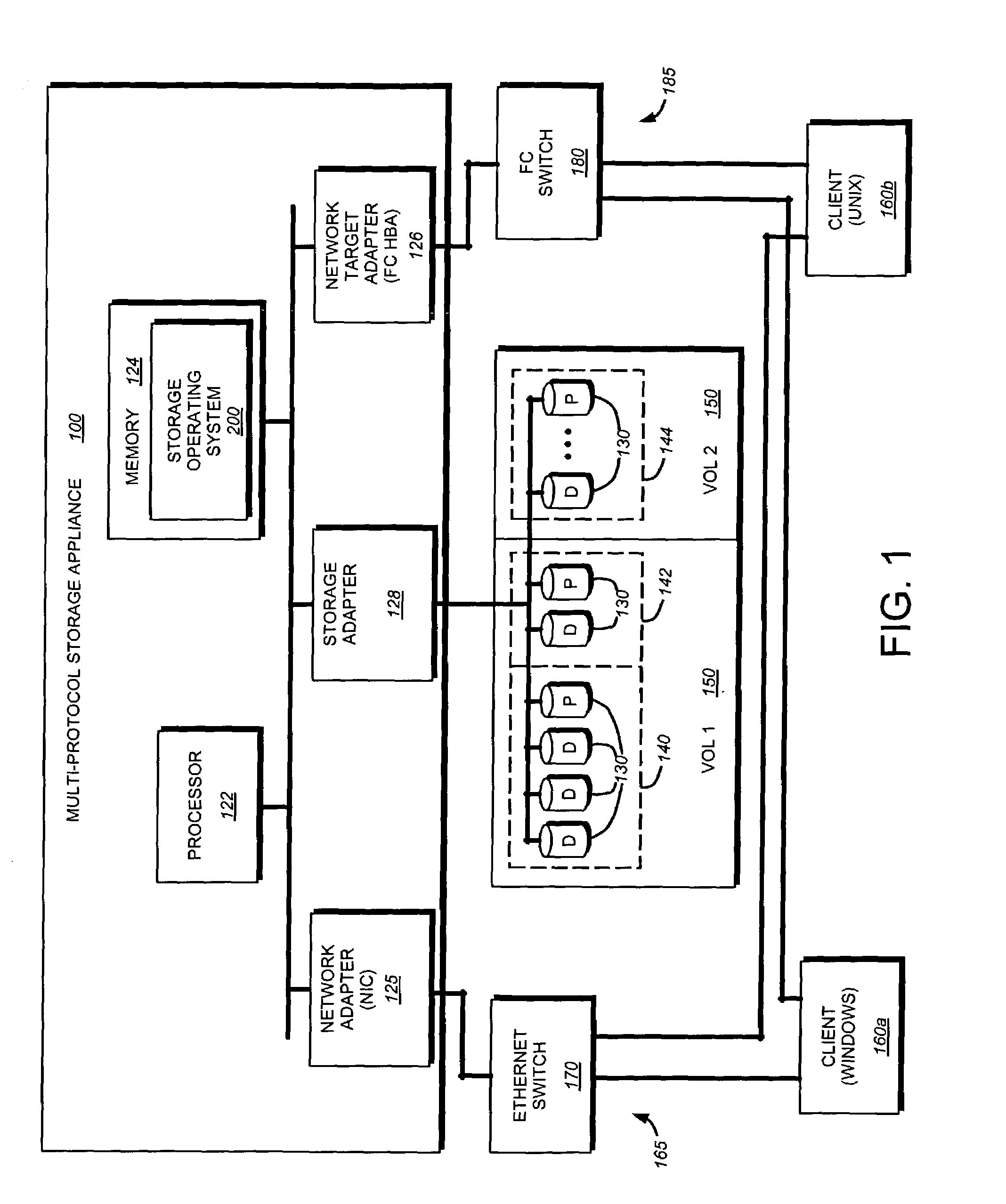
Storage virtualization by layering virtual disk objects on a file system
InactiveUS7107385B2Input/output to record carriersData processing applicationsOperational systemFile system
A storage virtualization selection technique “automates” a virtualization selection process to create virtual disk (vdisk) storage objects over a volume of a file system implemented by a storage operating system of a multi-protocol storage appliance. The file system provides a virtualization system that aggregates physical storage of a set of disks or portions (e.g., extents) of disks into a pool of blocks that can be dynamically allocated to form a vdisk. The file system also provides reliability guarantees for the vdisks in accordance with its underlying architecture. That is, the file system organizes its storage within volumes created among the managed disks. The vdisk is thereafter created as a storage object within a volume and, thus, inherits the underlying reliability configuration associated with that volume. The portions are aggregated and allocated as a vdisk with reliability guarantees in response to a request to create the vdisk from a user of the storage appliance and without further user involvement.
Owner:NETWORK APPLIANCE INC
Multi-tenant audit awareness in support of cloud environments
ActiveUS20120179646A1Facilitate compliance analysisEasy to analyzeDatabase management systemsDigital data processing detailsData miningComputer science
A cloud enablement aggregation proxy (CEAP) receives and processes audit data from audited resources before such data is stored in a database. The CEAP manages log data for resources hosted in a multi-tenant shared pool of configurable computing resources (e.g., a compute cloud). A method for managing log data begins by the proxy aggregating and normalizing log information received from a plurality of the resources. The aggregated and normalized log information is then parsed to identify a tenant associated with each of a set of transactions. For each of the set of transactions, the CEAP annotates log data associated with the tenant and the particular transaction to include a tenant-specific identifier. An optional tenant separation proxy (TSP) separates the annotated log data on a per tenant basis prior to storage, and the tenant-specific log data may be stored in per tenant data structures or dedicated tenant log event databases to facilitate subsequent compliance or other analysis.
Owner:IBM CORP
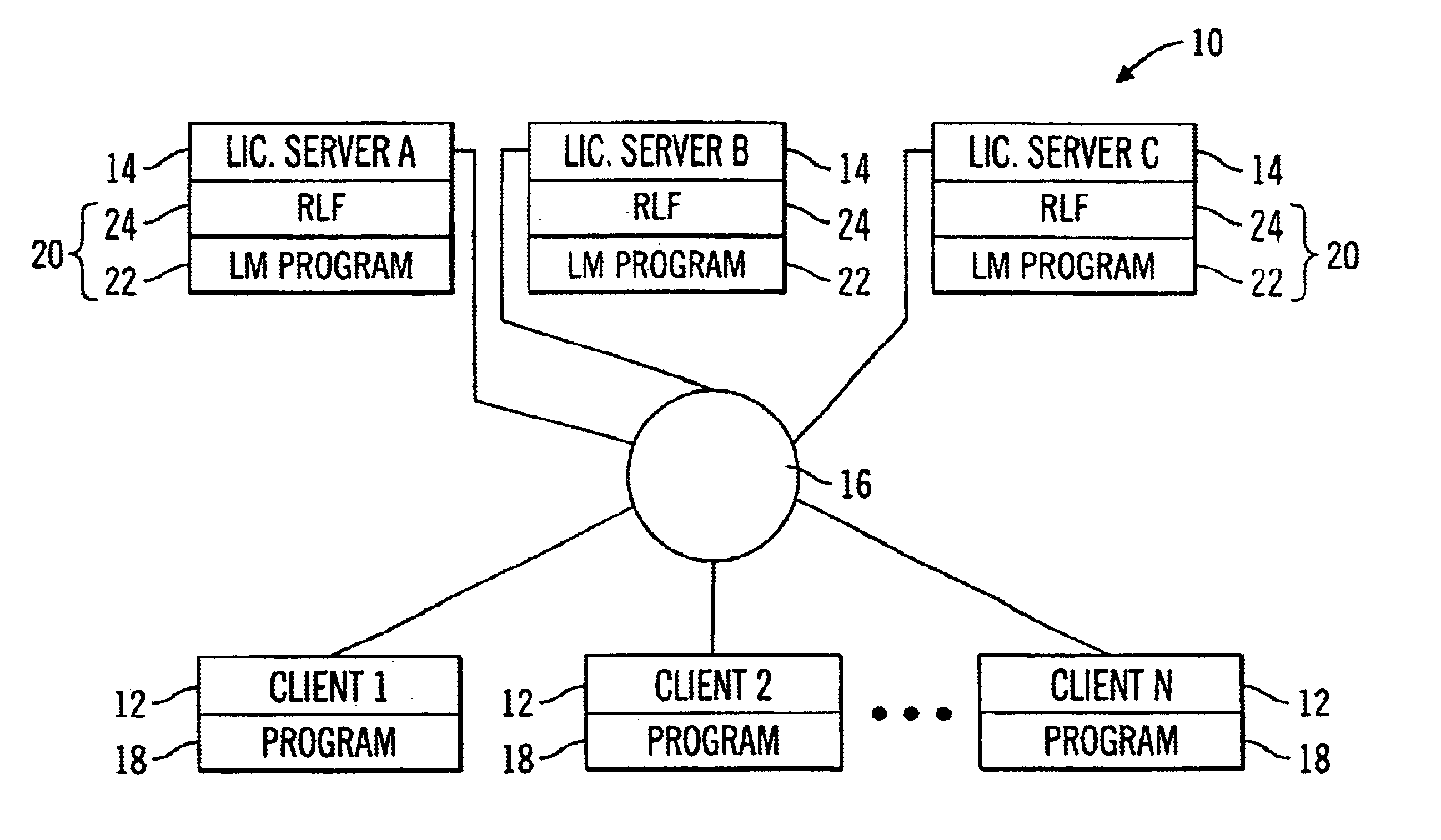
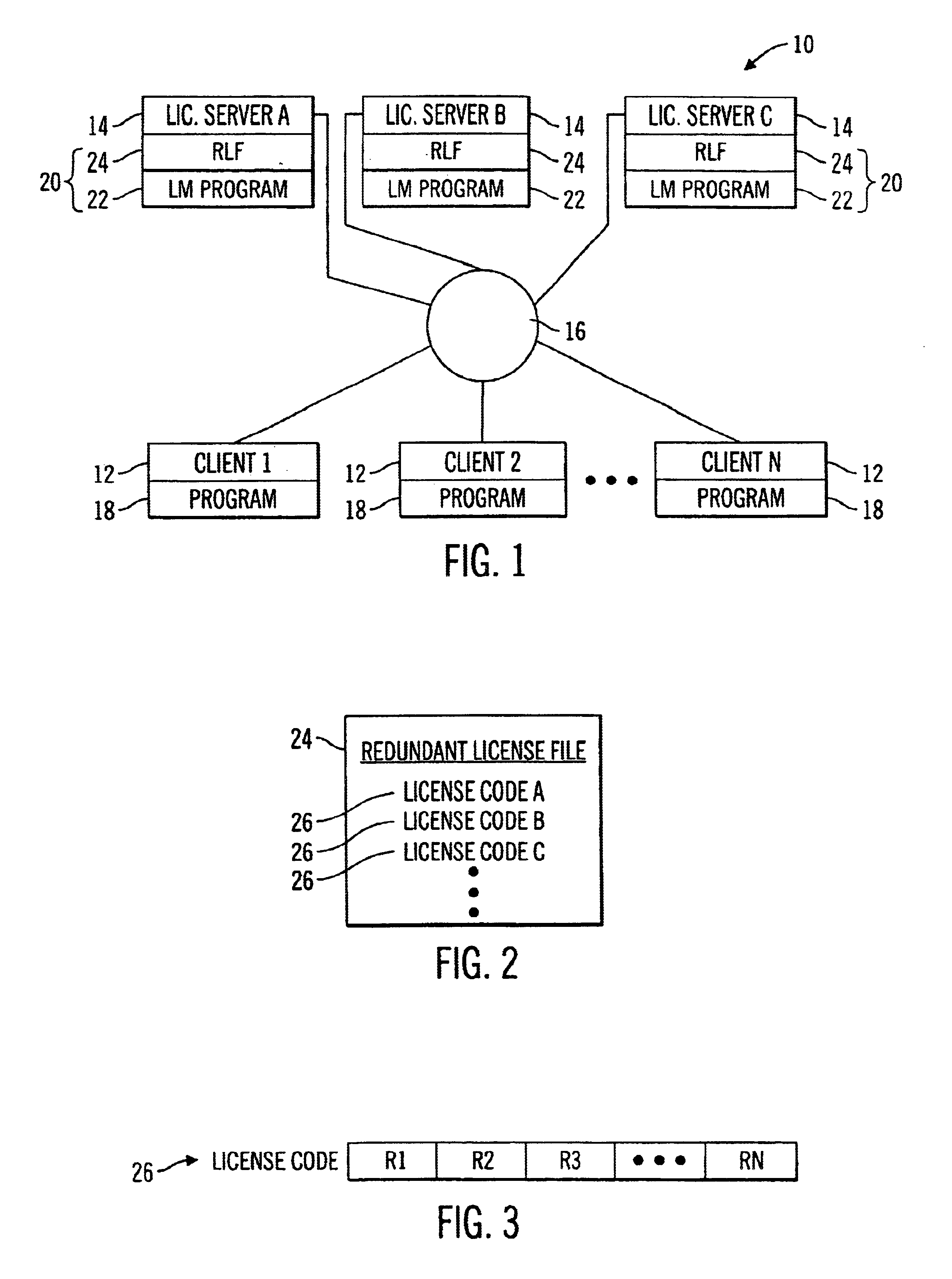
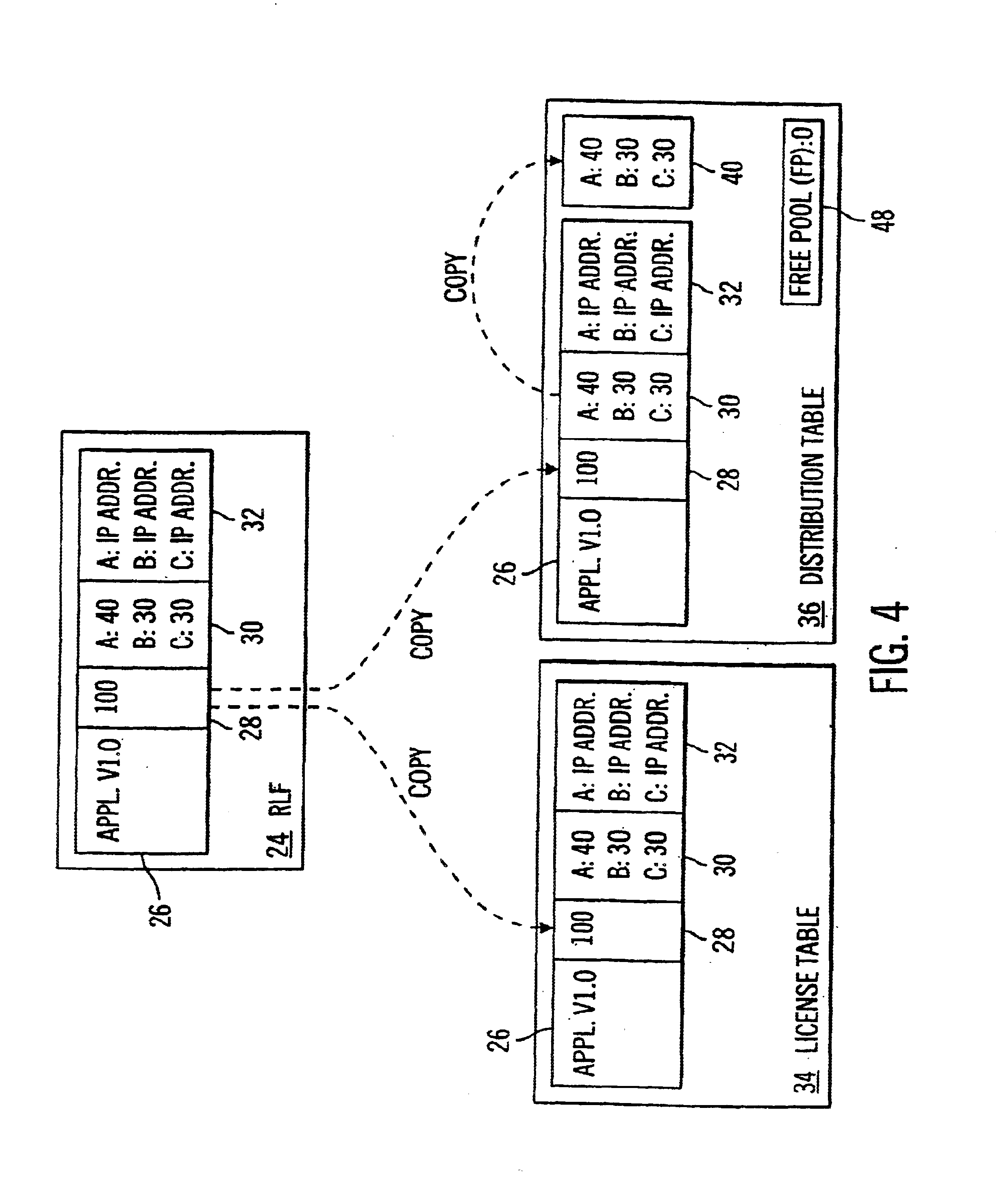
System and method for selecting a server in a multiple server license management system
InactiveUS6842896B1Improve distributionComputer security arrangementsOffice automationClient-sideClient machine
A system for managing licenses for protected software on a communication network is disclosed. The system comprises at least one client computer and a pool of license servers coupled to the communication network. The client computers request authorization to use the protected software, and the license servers manage a distribution of allocations to use the protected software. The pool of license servers includes a selected current leader server for managing the distribution of allocations for all license servers in the pool. The first license server to be started is selected as the current leader server. However, if no license server is started first, the license server with the highest priority according to a leader priority list is selected as the current leader server. In addition, client computers seeking authorization to use the protected software may receive information from the server pool and select a particular license server from which to request authorization to use the protected software based on the received information.
Owner:SAFENET
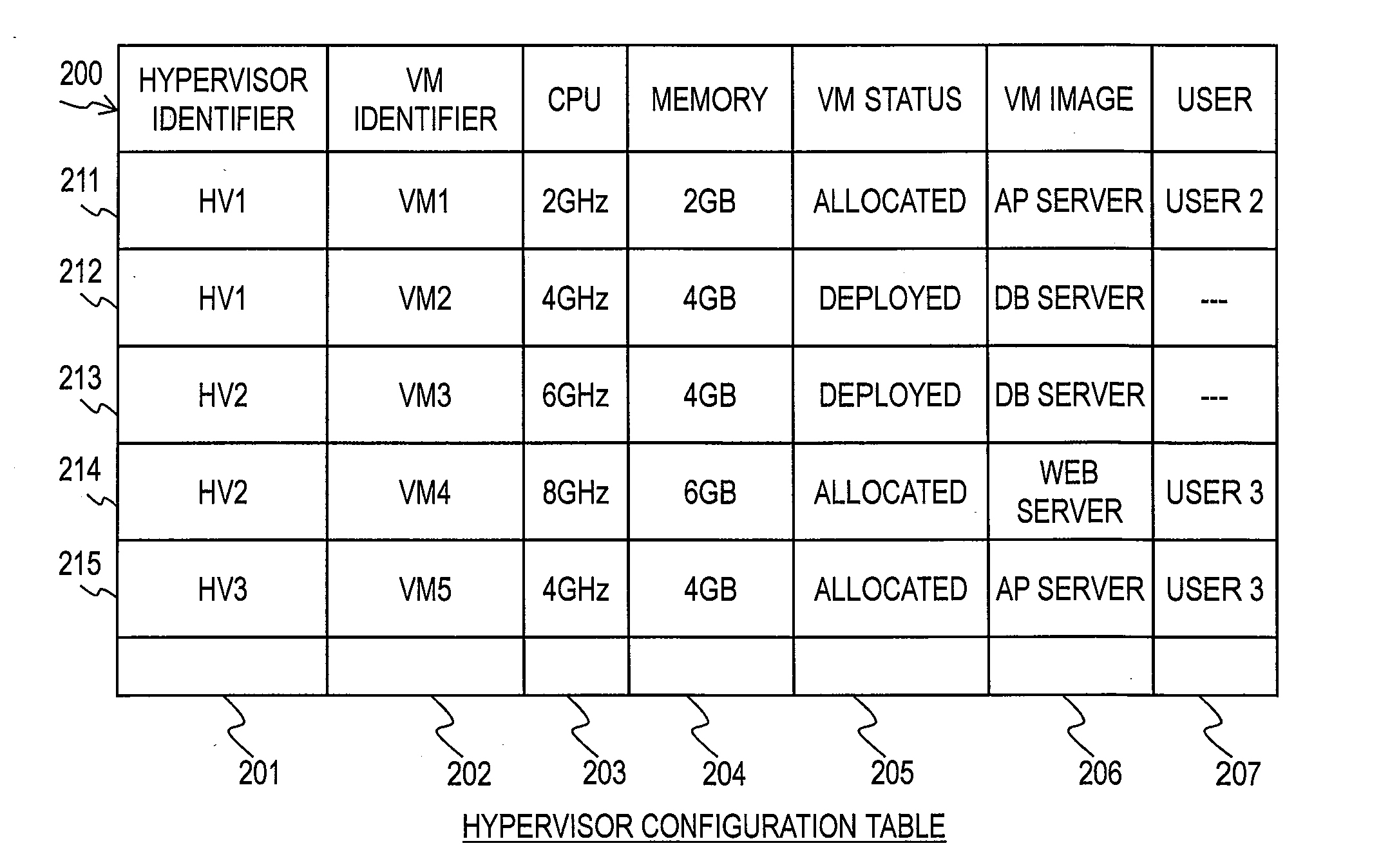
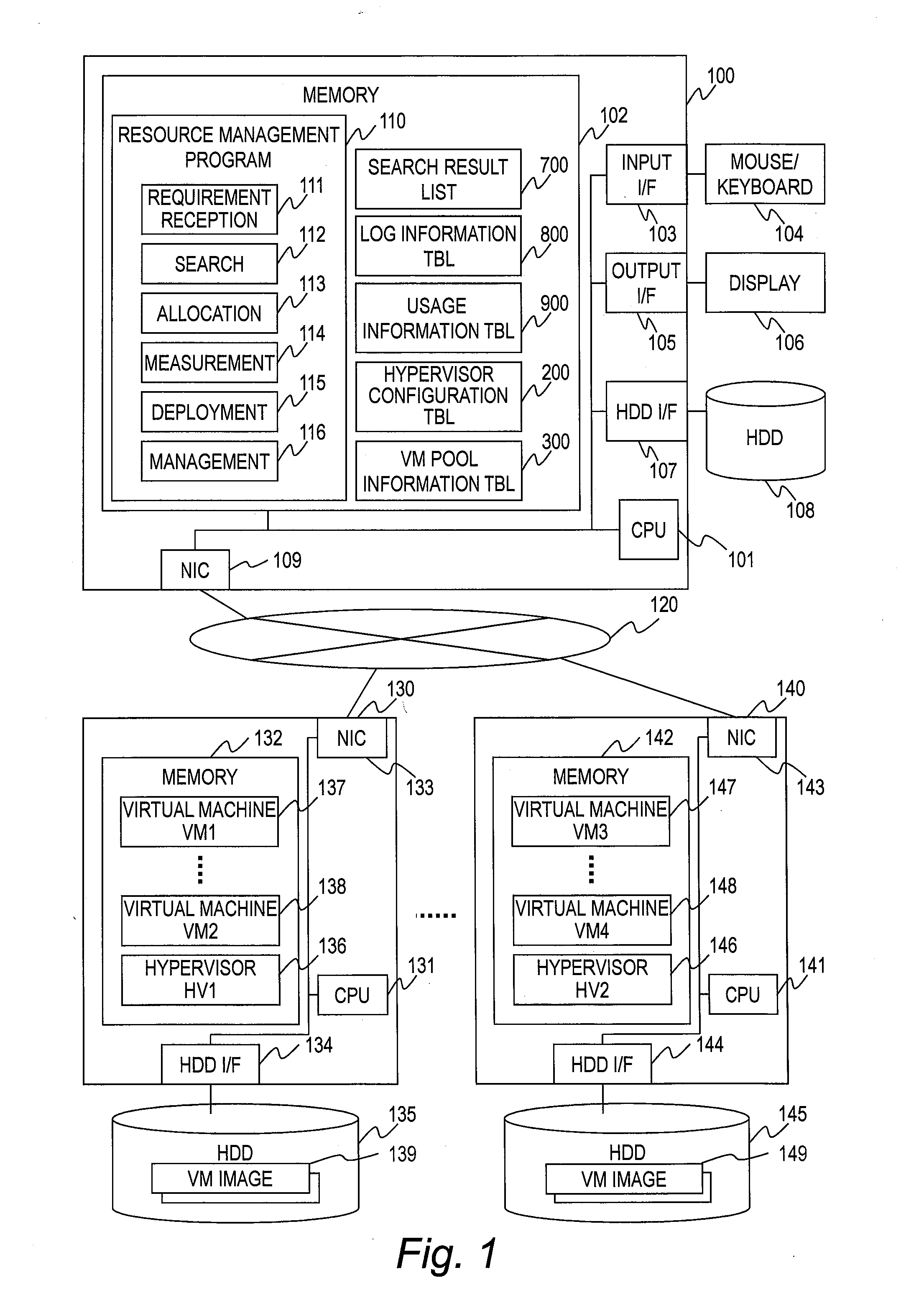
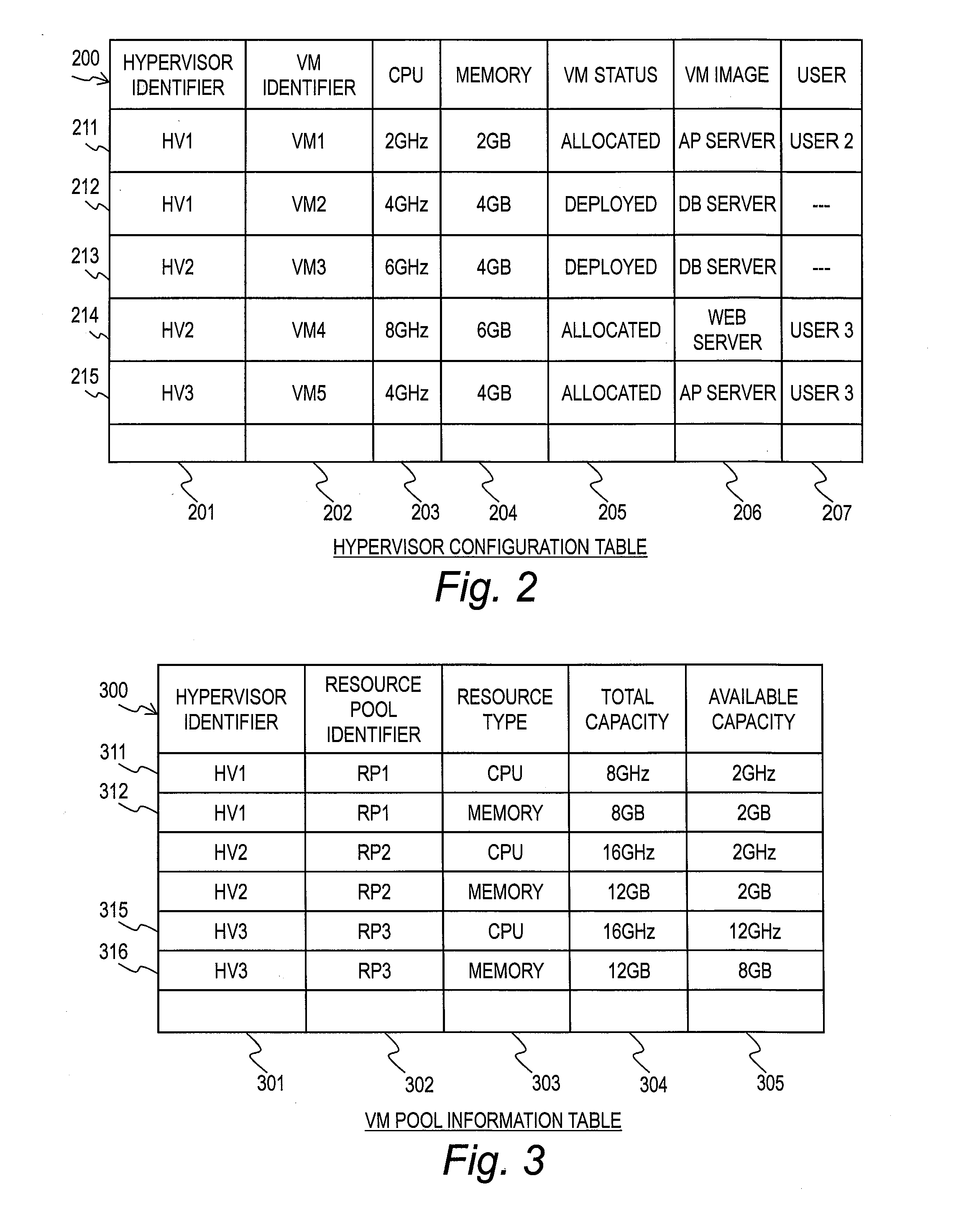
Resource management server, resource management method and storage medium in which resource management program is stored
ActiveUS20130275975A1Software simulation/interpretation/emulationMemory systemsResource managementPool
It is provided a resource management server comprising: a resource management module for managing virtual machines and use amounts of resources used by the virtual machines for deployment; a pool management module for managing a total amount of the resources and a total amount of available resources; a requirement specification reception module for receiving an allocation requirement for a new virtual machine along with requirement specifications including amounts of resources; and a search module for searching the virtual machines for deployment included in the resource management information for virtual machines for deployment having amounts of resources that satisfy the requirement specifications, and for virtual machines for deployment which do not have the amounts of resources that satisfy the requirement specifications but which allow the amounts of resources that satisfy the requirement specifications to be secured by adding the available resources included in the pool management information.
Owner:HITACHI LTD
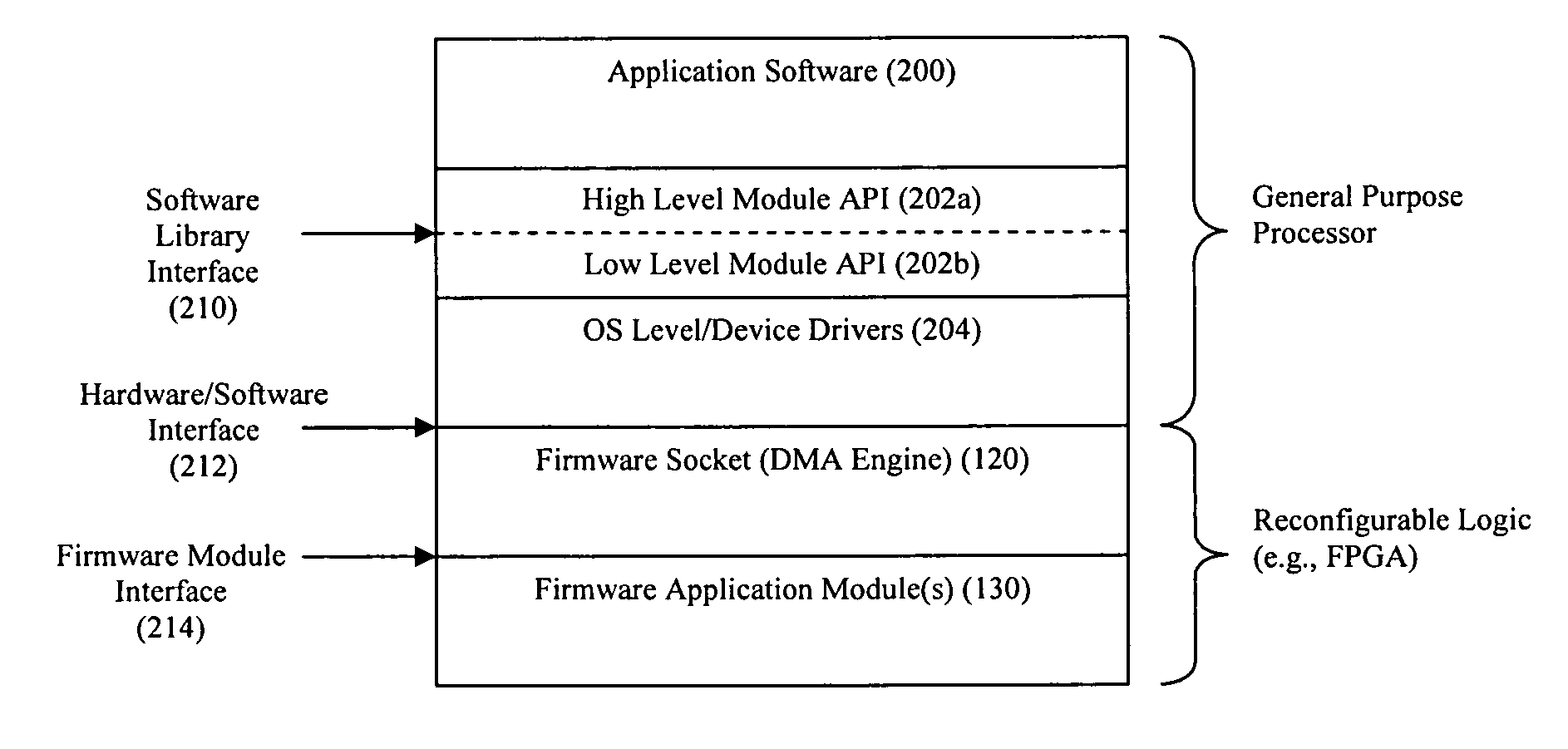
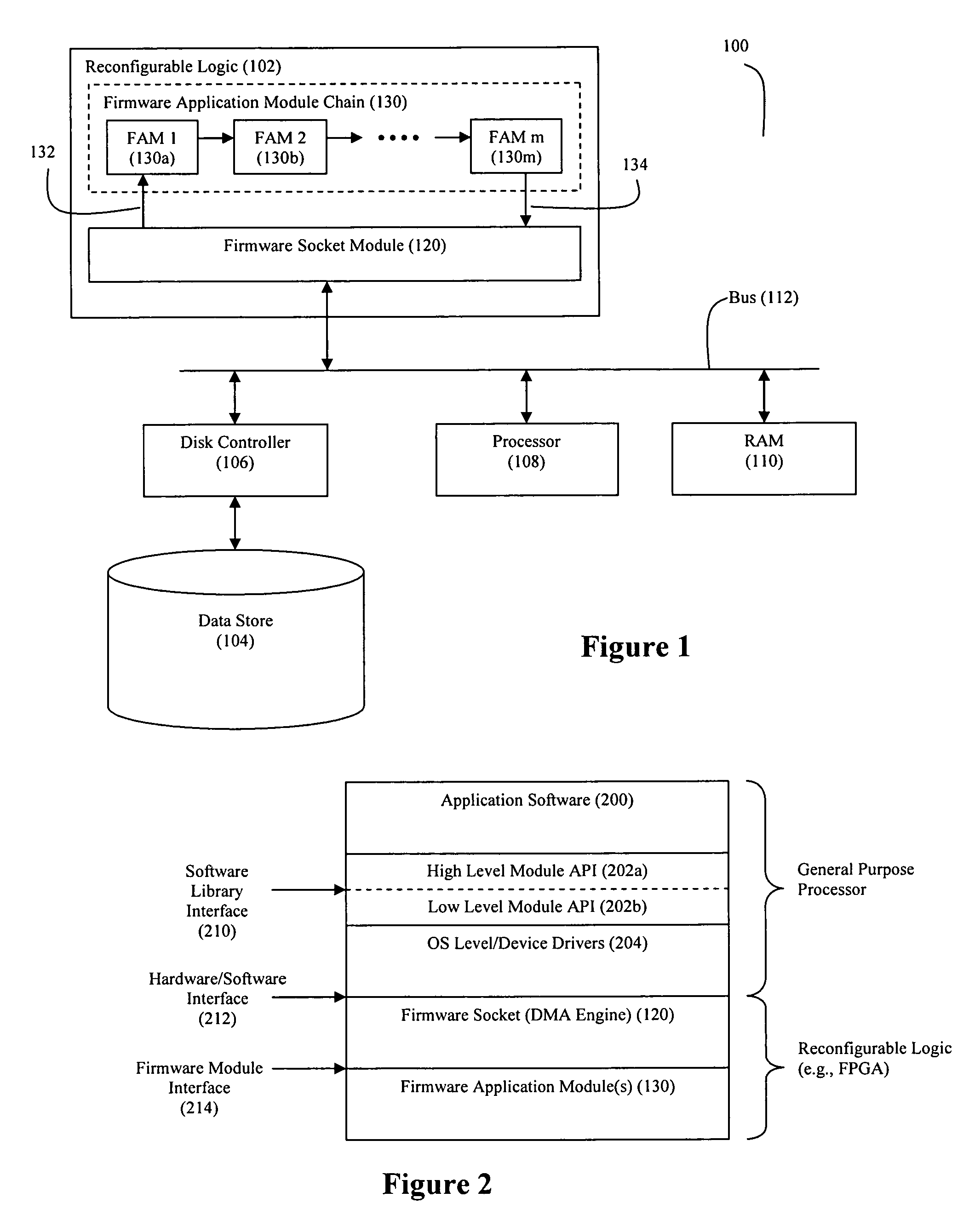
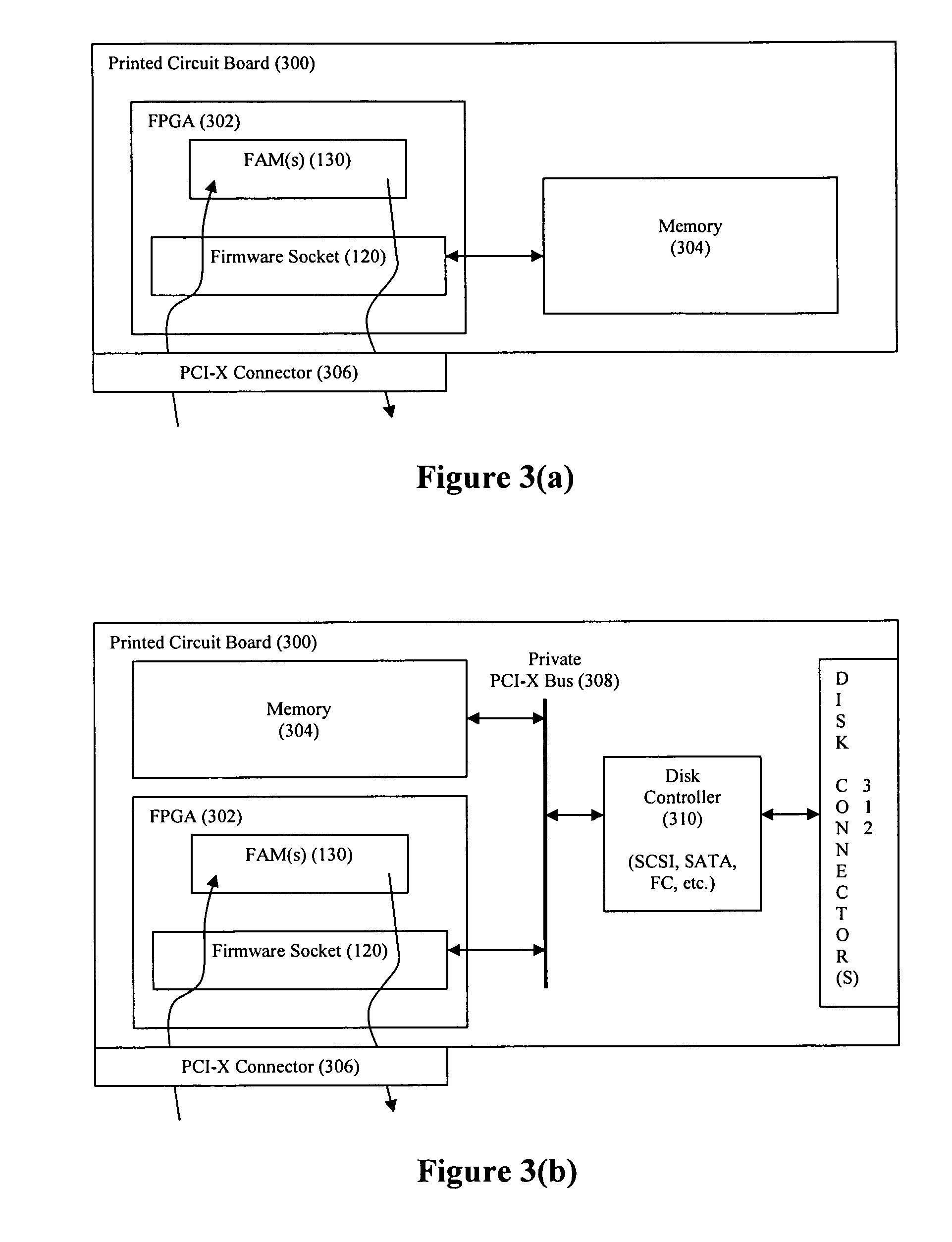
Firmware socket module for FPGA-based pipeline processing
ActiveUS7954114B2Digital computer detailsSpecific program execution arrangementsExternal storageEngineering
A firmware socket module is deployed on a reconfigurable logic device, wherein the firmware socket module is configured to provide both commands and target data to an entry point in a data processing pipeline, wherein each command defines a data processing operation that is to be performed by the data processing pipeline, and wherein the target data corresponds to the data upon which the data processing pipeline performs its commanded data processing operation. Also, the firmware socket module may be configured to (1) access an external input descriptor pool buffer that defines an order in which commands and target data are to be provided to the data processing pipeline, and (2) transfer the commands and target data from an external memory to the data processing pipeline in accordance with the defined order.
Owner:IP RESERVOIR
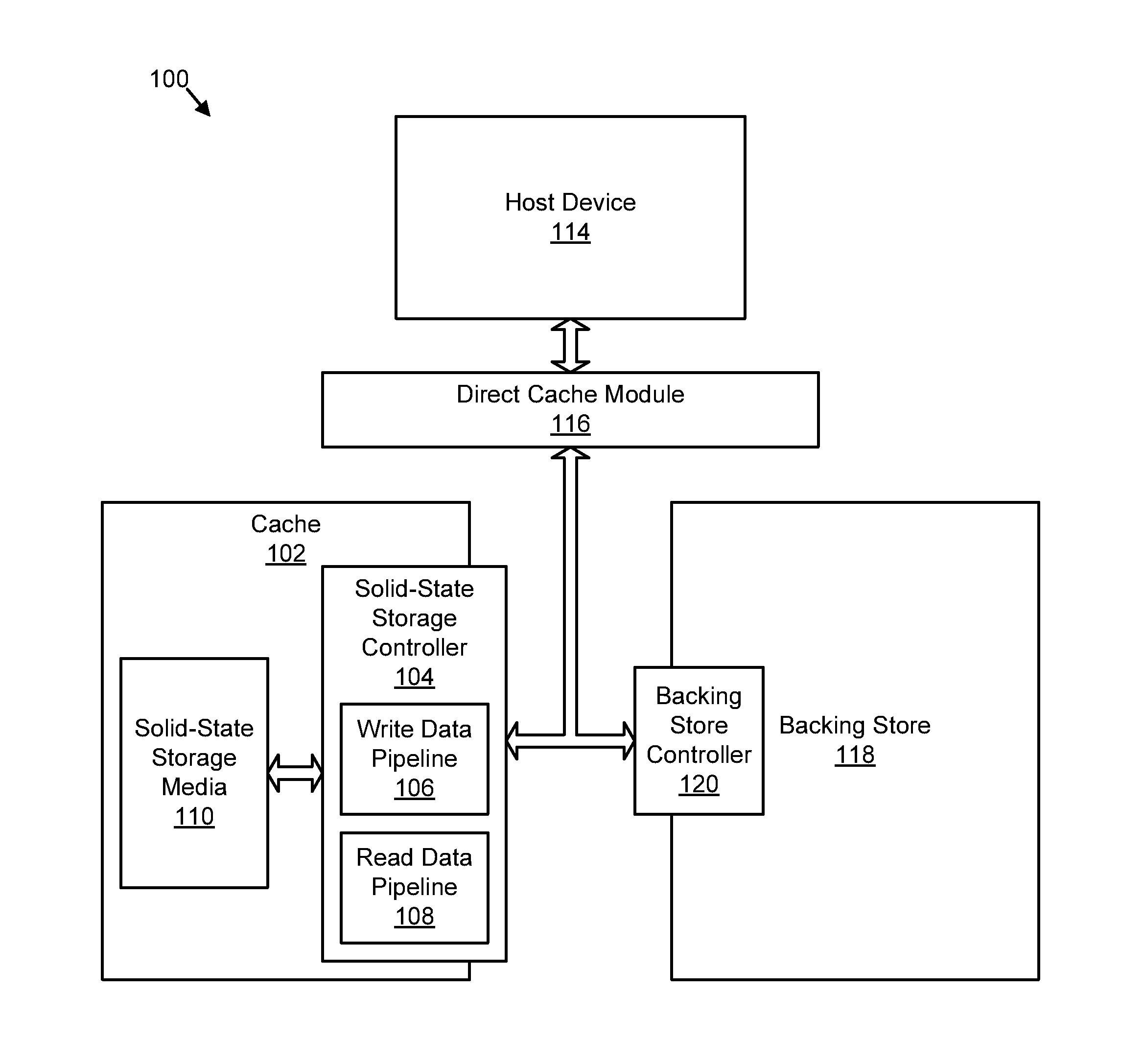
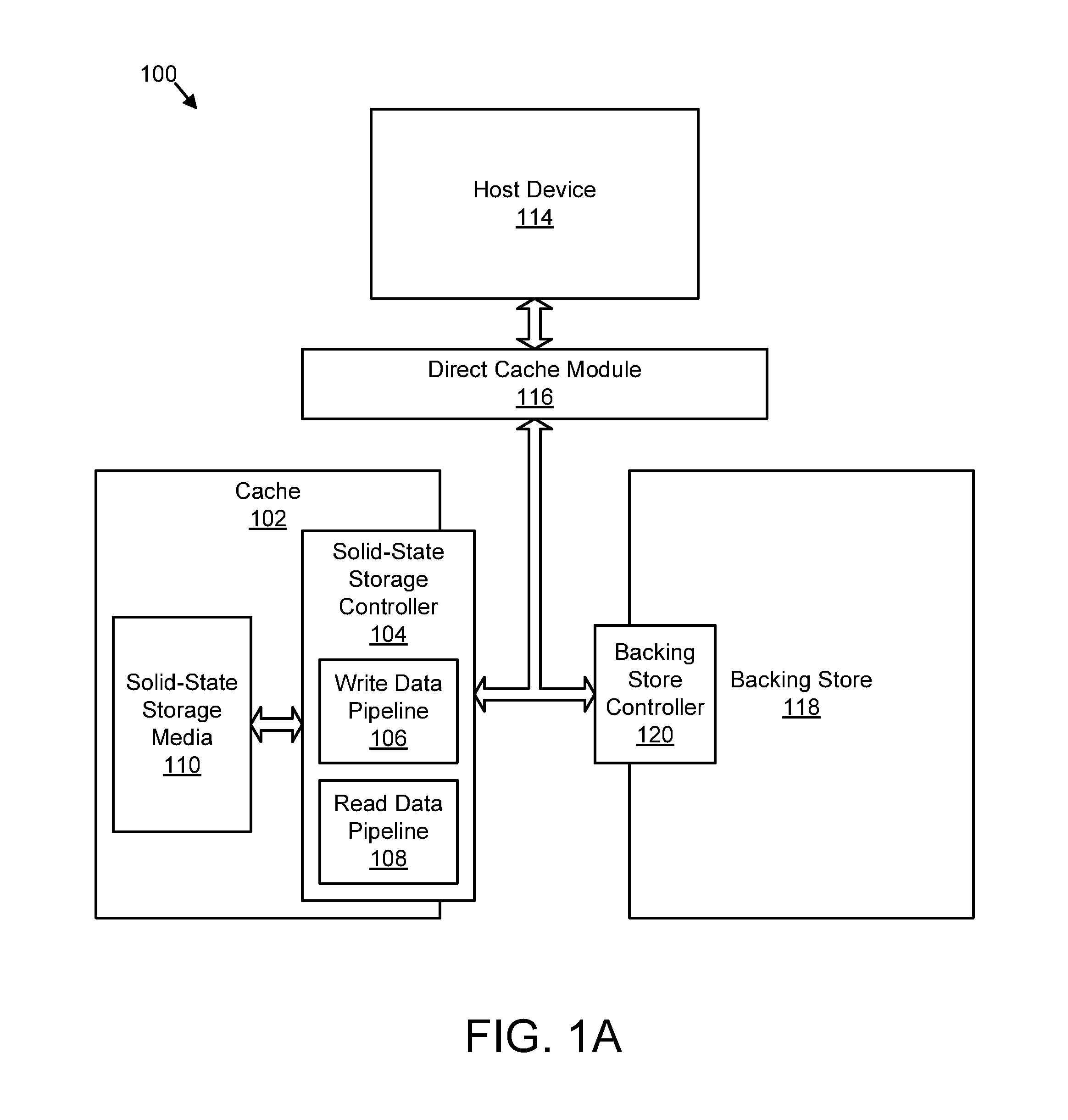
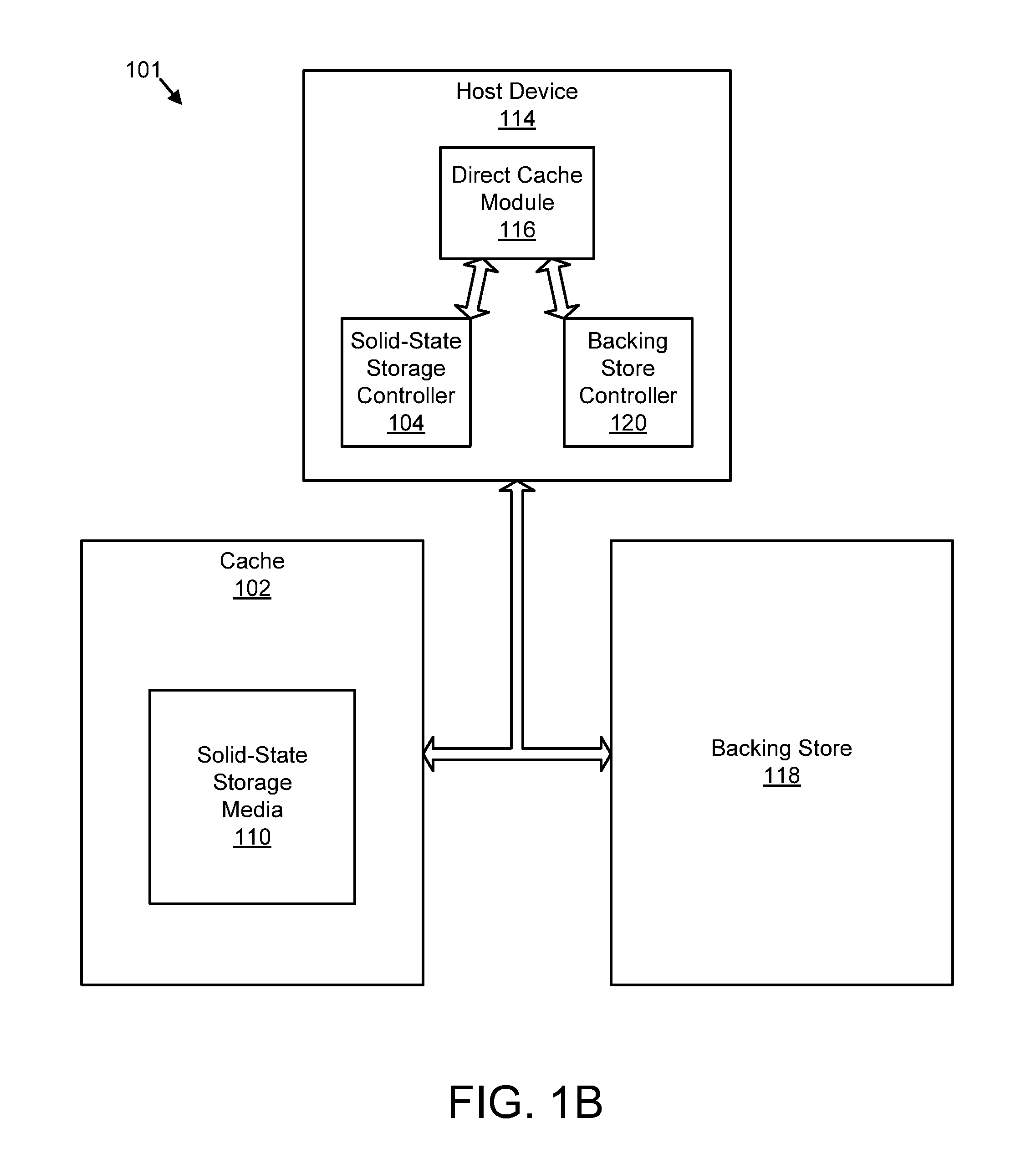
Apparatus, system, and method for managing contents of a cache
ActiveUS20120221774A1Maximize read hit rate hit rateMaximize hit rate dirty write hit rateMemory architecture accessing/allocationMemory adressing/allocation/relocationPoolOperating system
An apparatus, system, and method are disclosed for managing contents of a cache. A storage request module monitors storage requests received by a cache. The storage requests include read requests and write requests. A read pool module adjusts a size of a read pool of the cache to maximize a read hit rate of the storage requests. A dirty write pool module adjusts a size of a dirty write pool of the cache to maximize a dirty write hit rate of the storage requests.
Owner:SANDISK TECH LLC
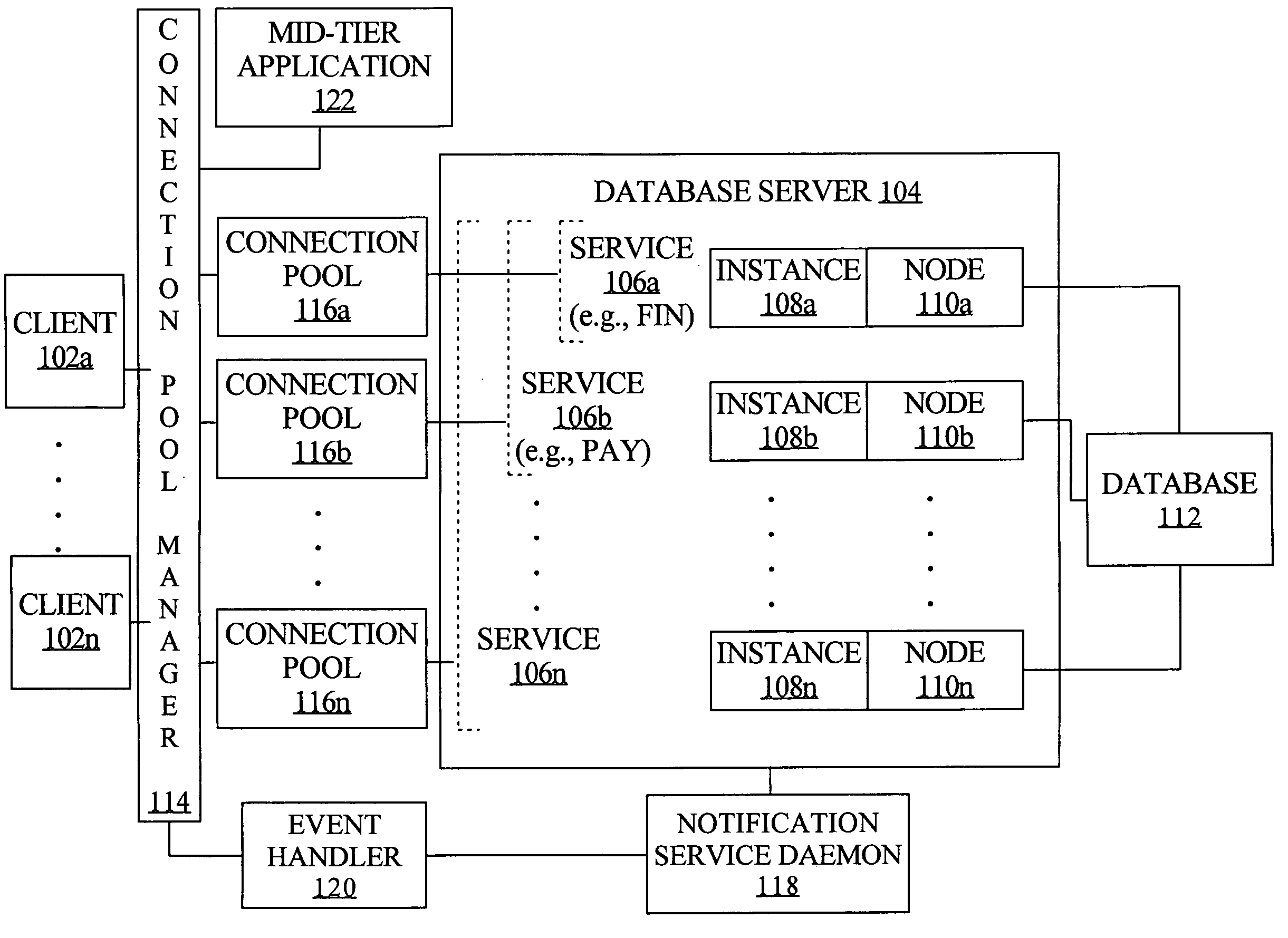
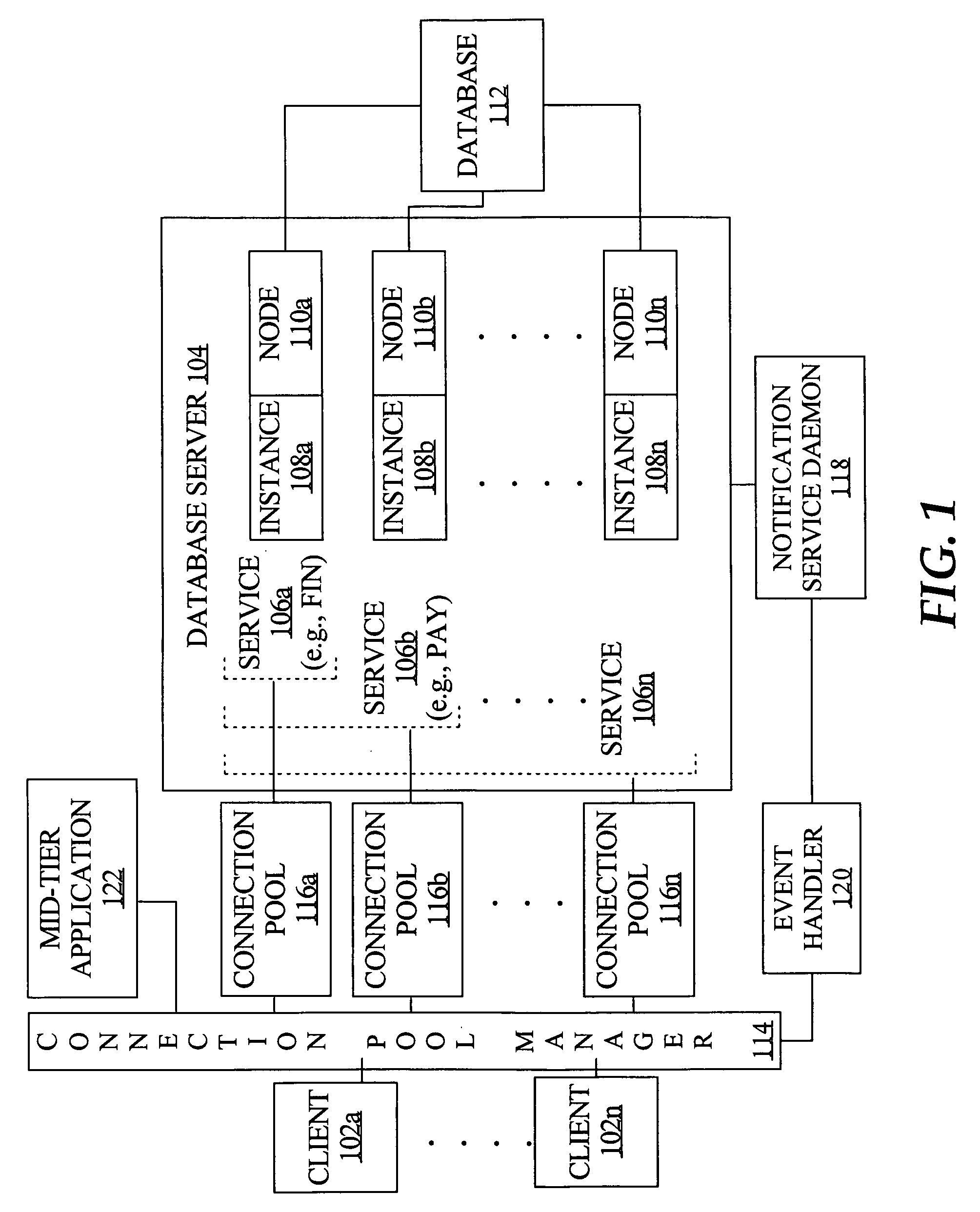
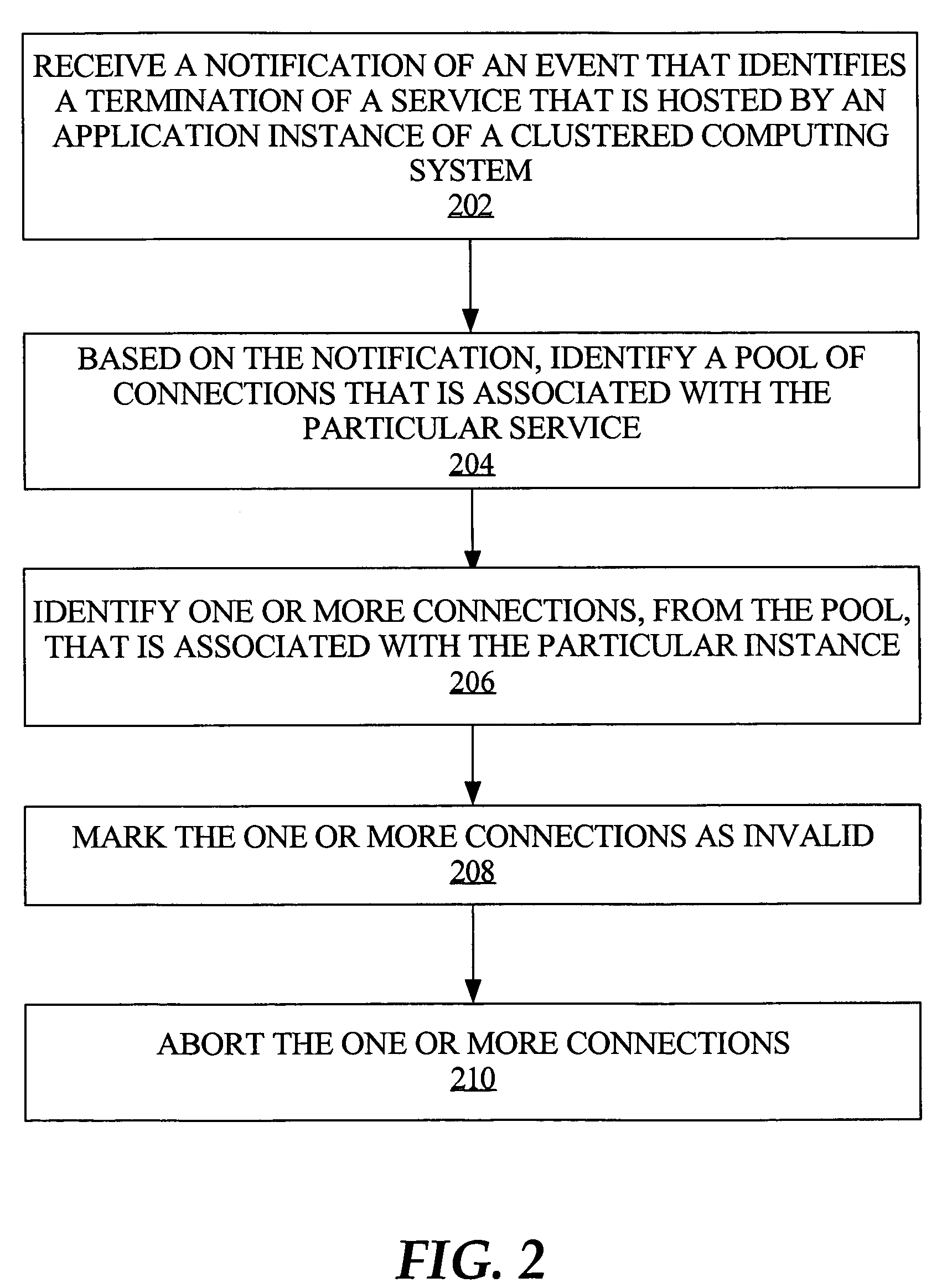
Fast reorganization of connections in response to an event in a clustered computing system
ActiveUS20050038801A1Easy to handleRapid positioningError detection/correctionDigital data processing detailsParallel computingConnection pool
Techniques for fast recovery and / or balancing of connections to a clustered computing system provide management of such connections by determining a number of connections to load balance across nodes and by triggering creation of such connections. In one aspect, a notification of an event regarding the clustered computing system is received by a connection pool manager, a pool of connections to the system is identified based on the notification, and one or more connections from the pool are processed in response to the event. According to an embodiment, the notification comprises the identities of the service, database, server instance and machine that correspond to the event.
Owner:ORACLE INT CORP
Management system and management method
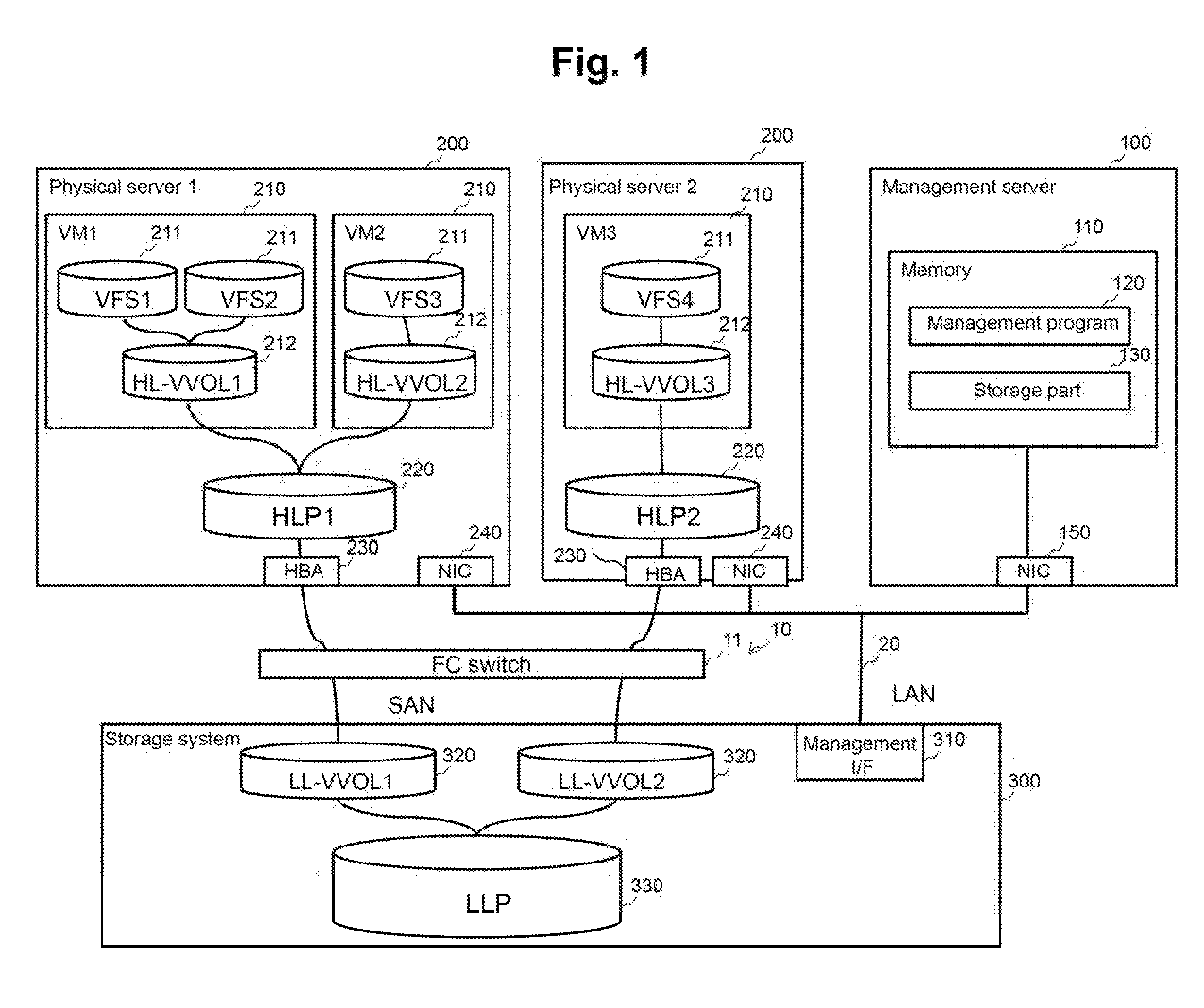
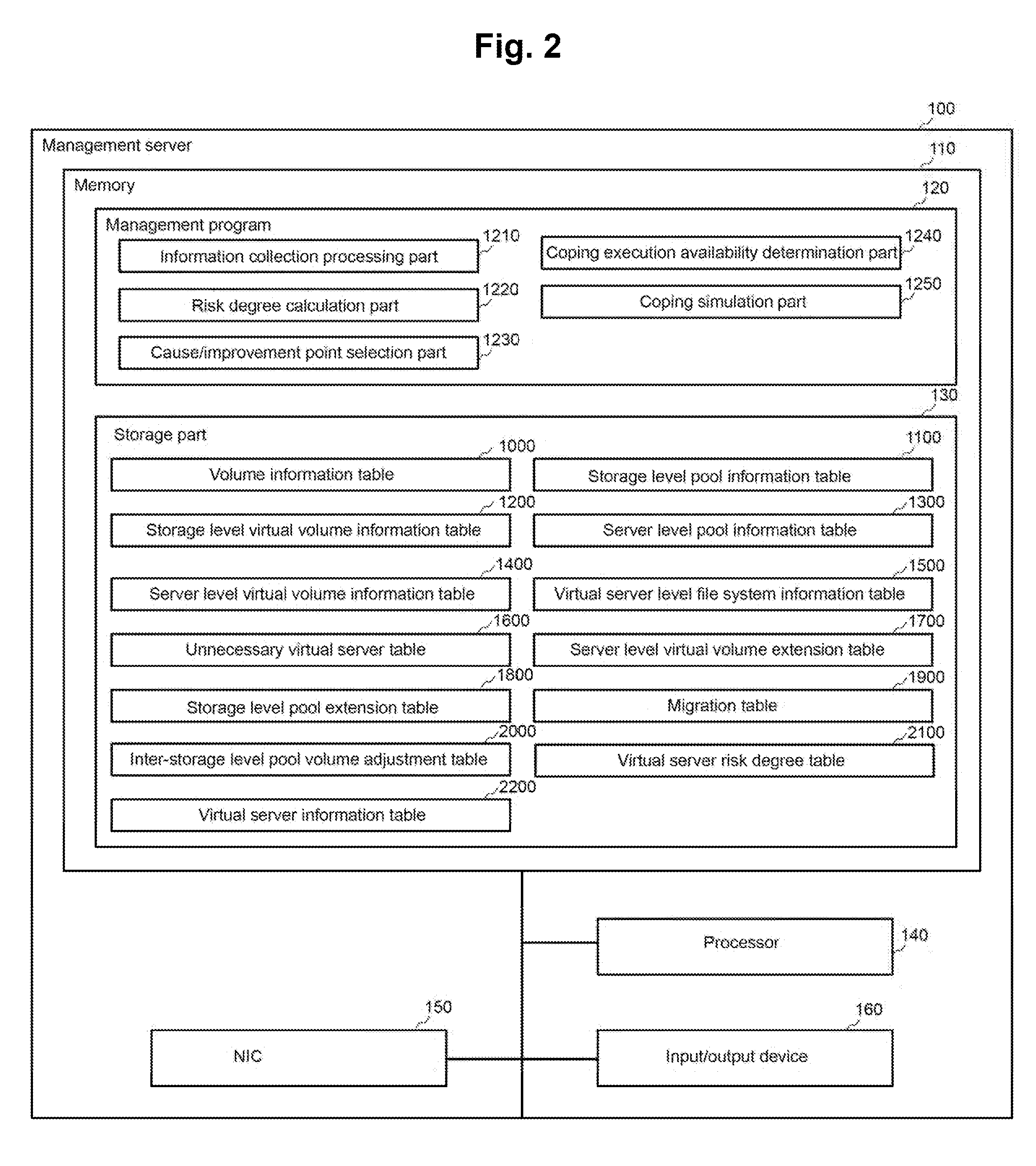
A management system manages a storage system and a server computer. The management system (A) acquires the storage level pool information that includes the information of a capacity of a storage level pool from the storage system, (B) acquires the server level pool information that includes the information of a capacity of a server level pool from the server computer, (C) determines a first risk degree that indicate a risk of a depletion of a free capacity of the storage level pool based on the storage level pool information, (D) determines a second risk degree that indicate a risk of a depletion of a free capacity of a server level pool based on the server level pool information, and (E) displays the information that is associated with the first risk degree that indicate a risk of a depletion of a free capacity of the storage level pool and the second risk degree that indicate a risk of a depletion of a free capacity of the server level pool.
Owner:HITACHI LTD
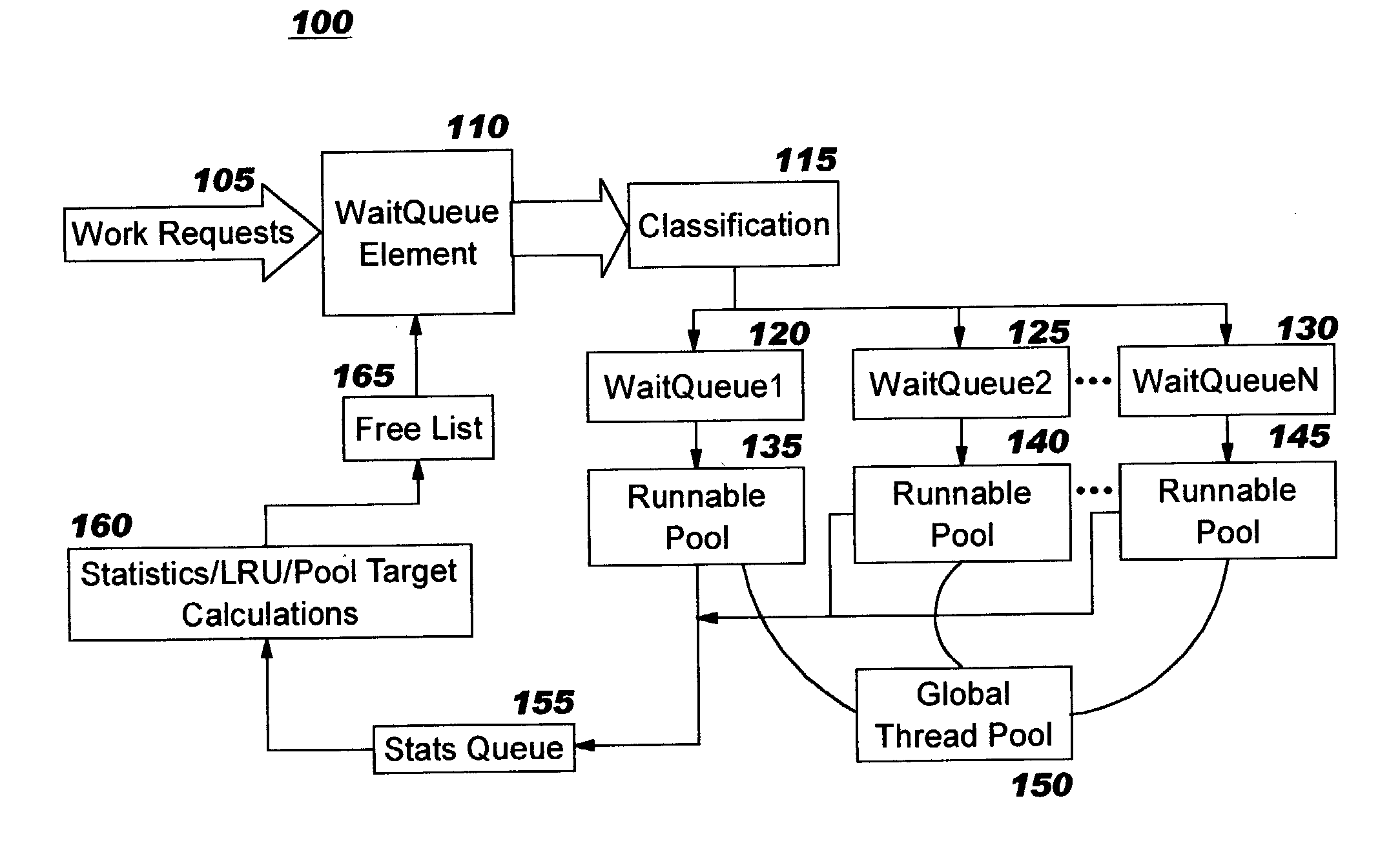
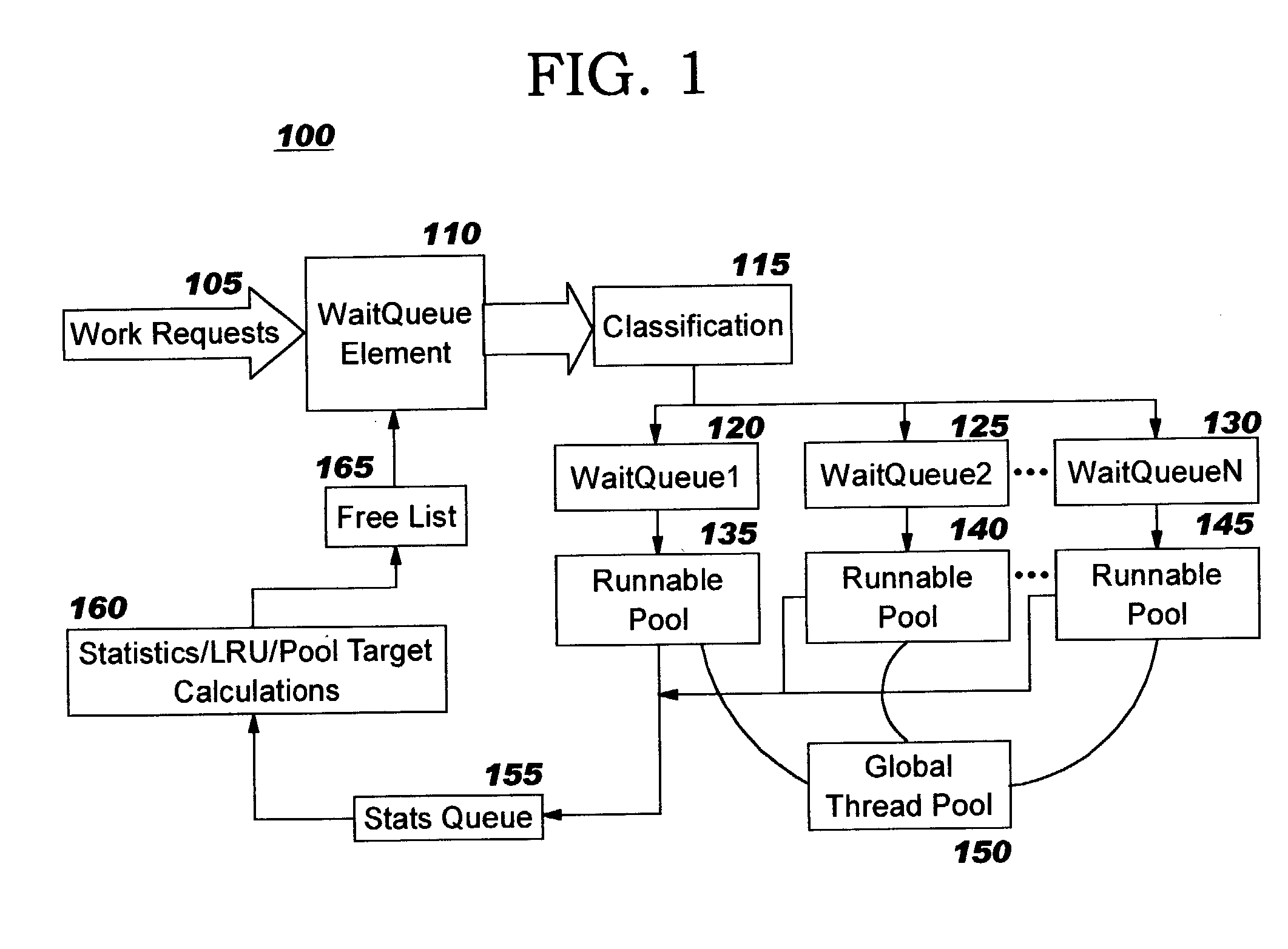
Dynamic thread pool tuning techniques
InactiveUS20040139434A1Improve performanceSimple technologyProgram initiation/switchingResource allocationParallel computingEngineering
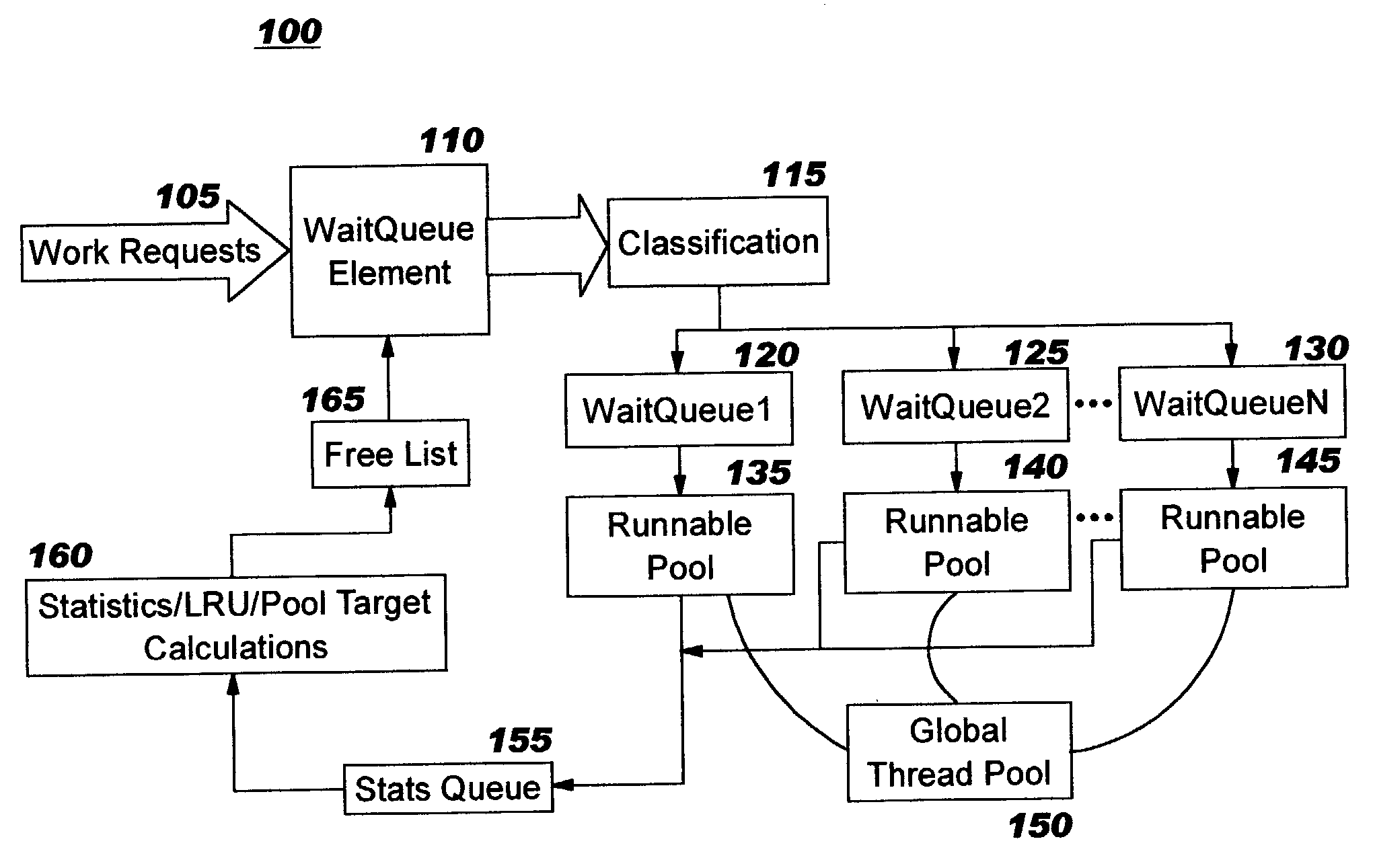
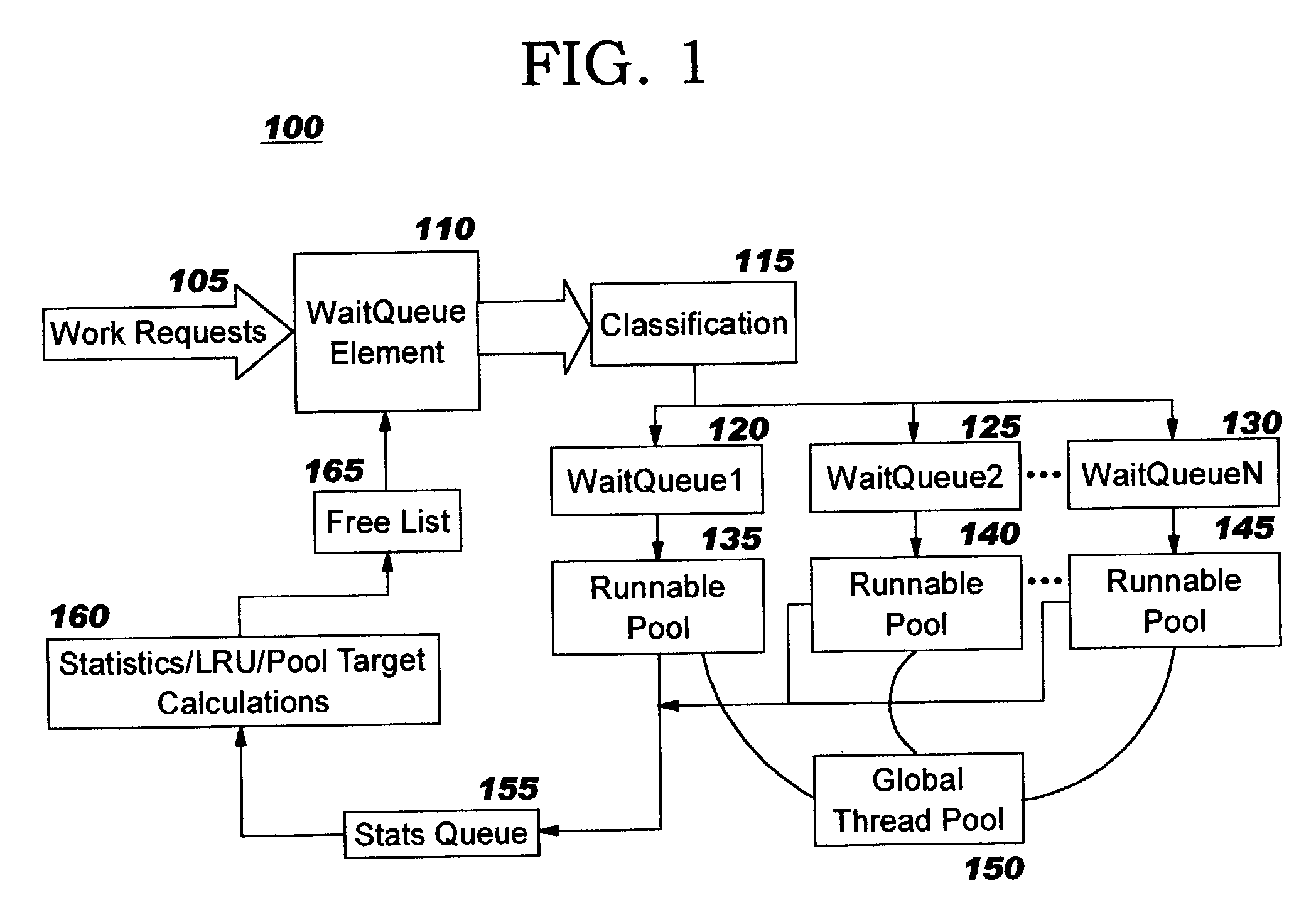
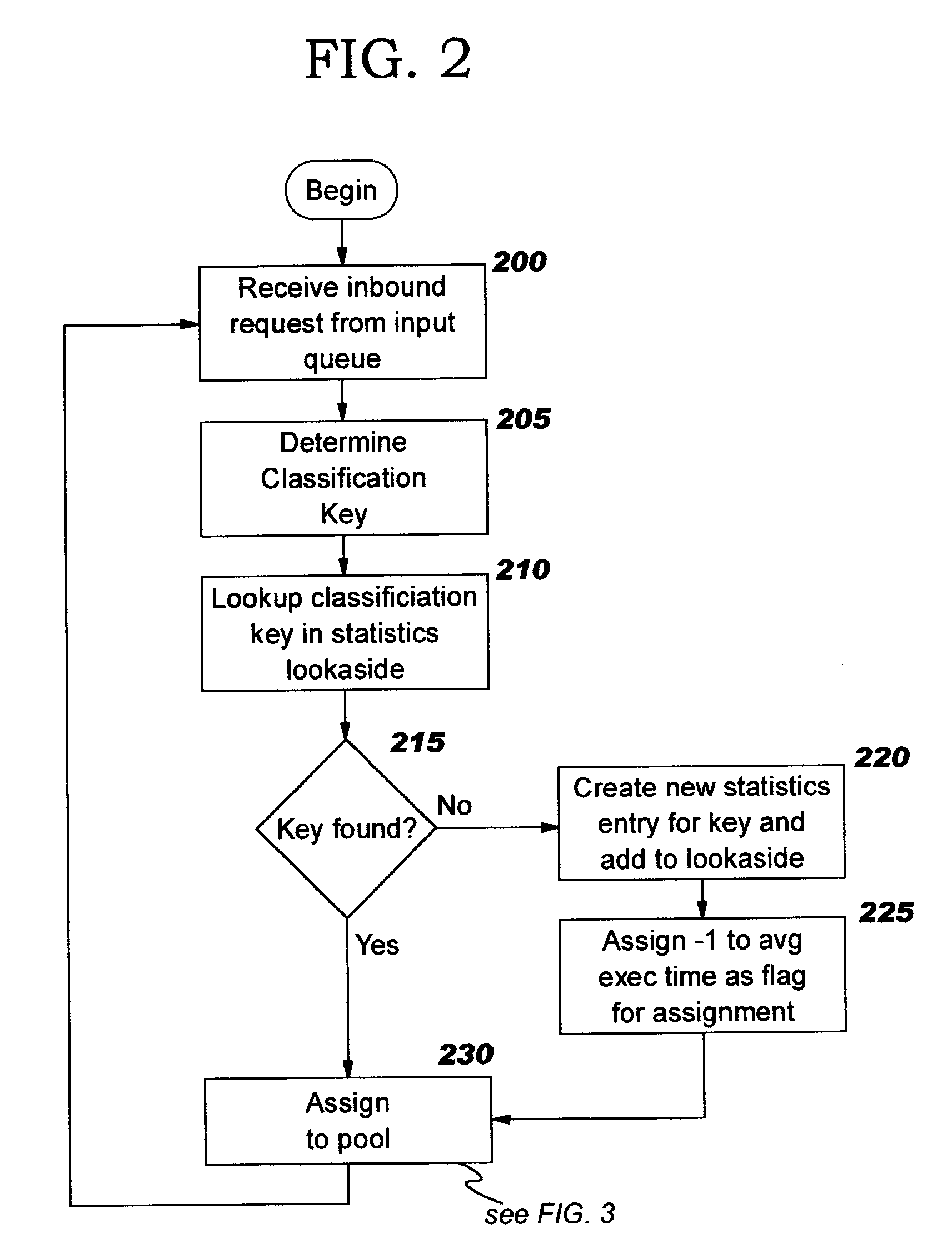
Thread pools in a multithreaded server are programmatically adjusted, based on observed statistics from the server's inbound workload. In a multithreaded server environment, response time to end users is improved while increasing the efficiency of software execution and resource usage. Execution time and wait / queued time are tracked, for various types of requests being serviced by a server. Multiple logical pools of threads are used to service these requests, and inbound requests are directed to a selected one of these pools such that requests of similar execution-time requirements are serviced by the threads in that pool. The number and size of thread pools may be adjusted programmatically, and the distribution calculation (i.e., determining which inbound requests should be assigned to which pools) is a programmatic determination. In preferred embodiments, only one of these variables is adjusted at a time, and the results are monitored to determine whether the effect was positive or negative. The disclosed techniques also apply to tracking and classifying requests by method name (and, optionally, parameters).
Owner:IBM CORP
Active probe target management
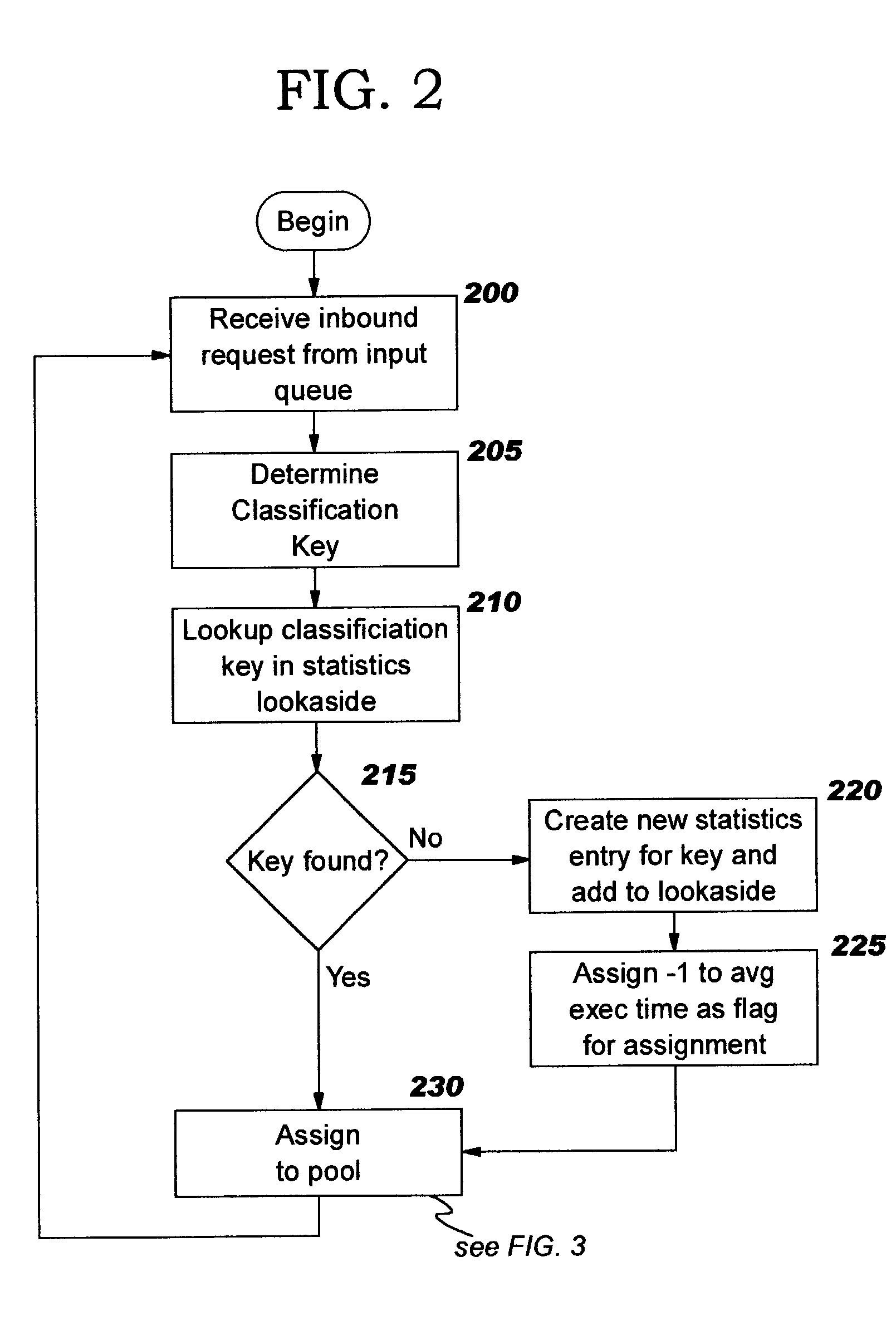
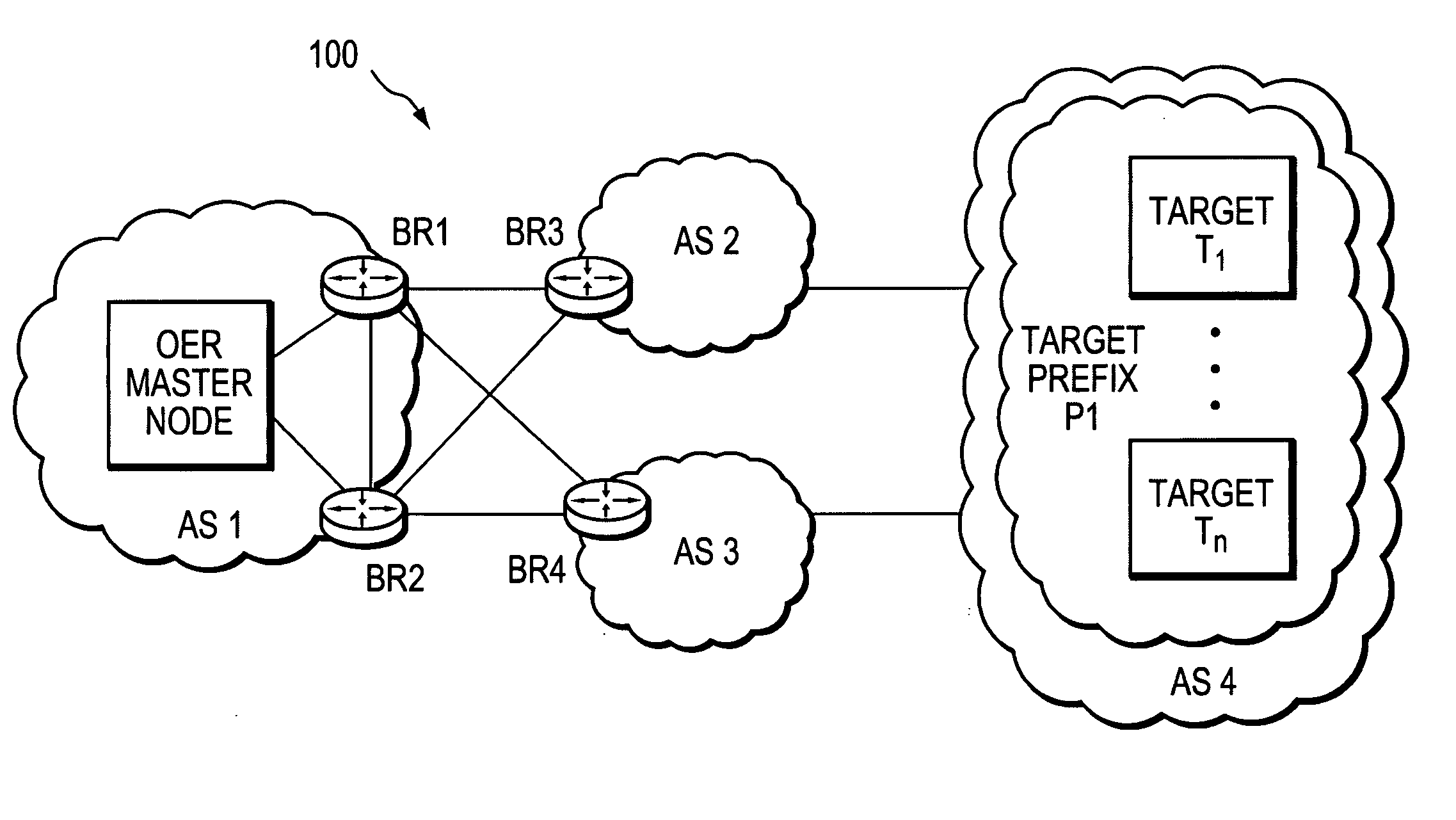
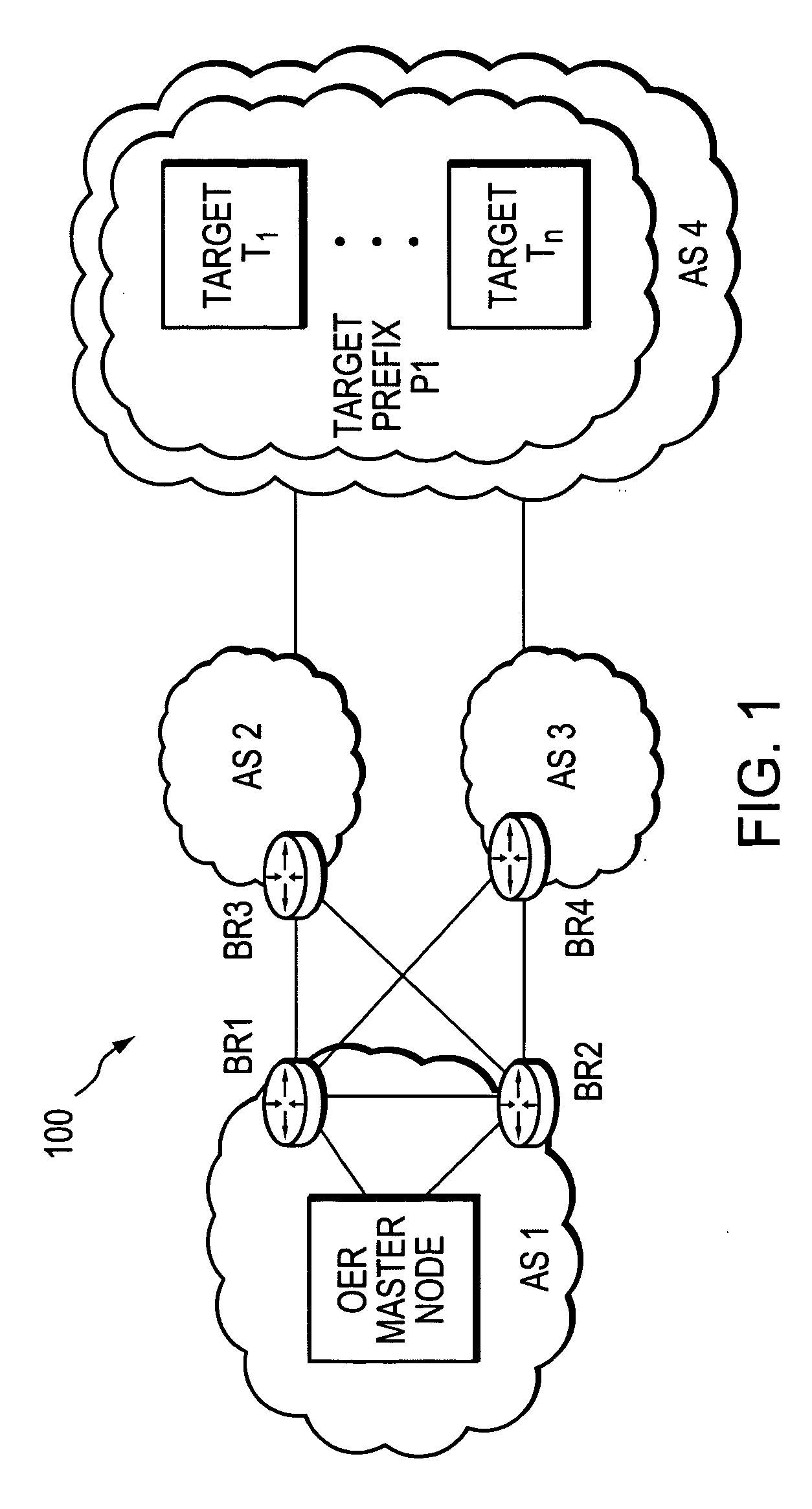
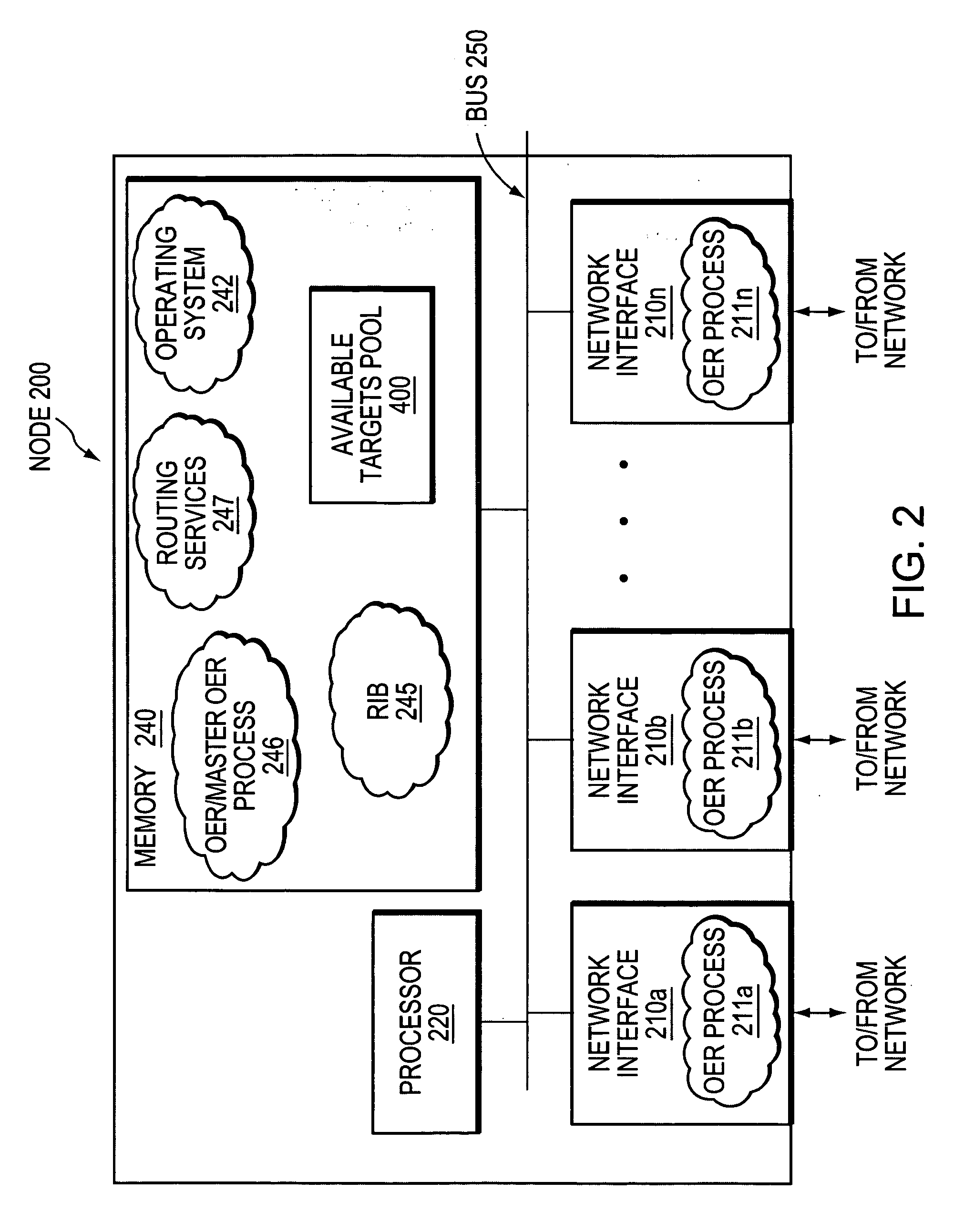
ActiveUS20060239201A1Efficient managementError preventionFrequency-division multiplex detailsProbe targetEvaluation period
A technique manages targets to which probe packets are sent from a source of a computer network. The novel target management technique dynamically selects an optimal set of valid targets for a particular (monitored) prefix of the computer network. Specifically, one or more targets are selected from a pool of possible learned and configured targets to be used as representatives of the monitored prefix. Probe packets are sent from the source to the selected targets for the duration of an evaluation period. Targets that do not respond to the probe packets during the evaluation period are invalid and deselected, and if available, an unused target is selected from the pool of possible targets to replace each non-responding target for a next evaluation period. Invalid learned targets are discarded, while invalid configured targets are returned to the pool of possible targets for potential re-selection in a later evaluation period.
Owner:CISCO TECH INC
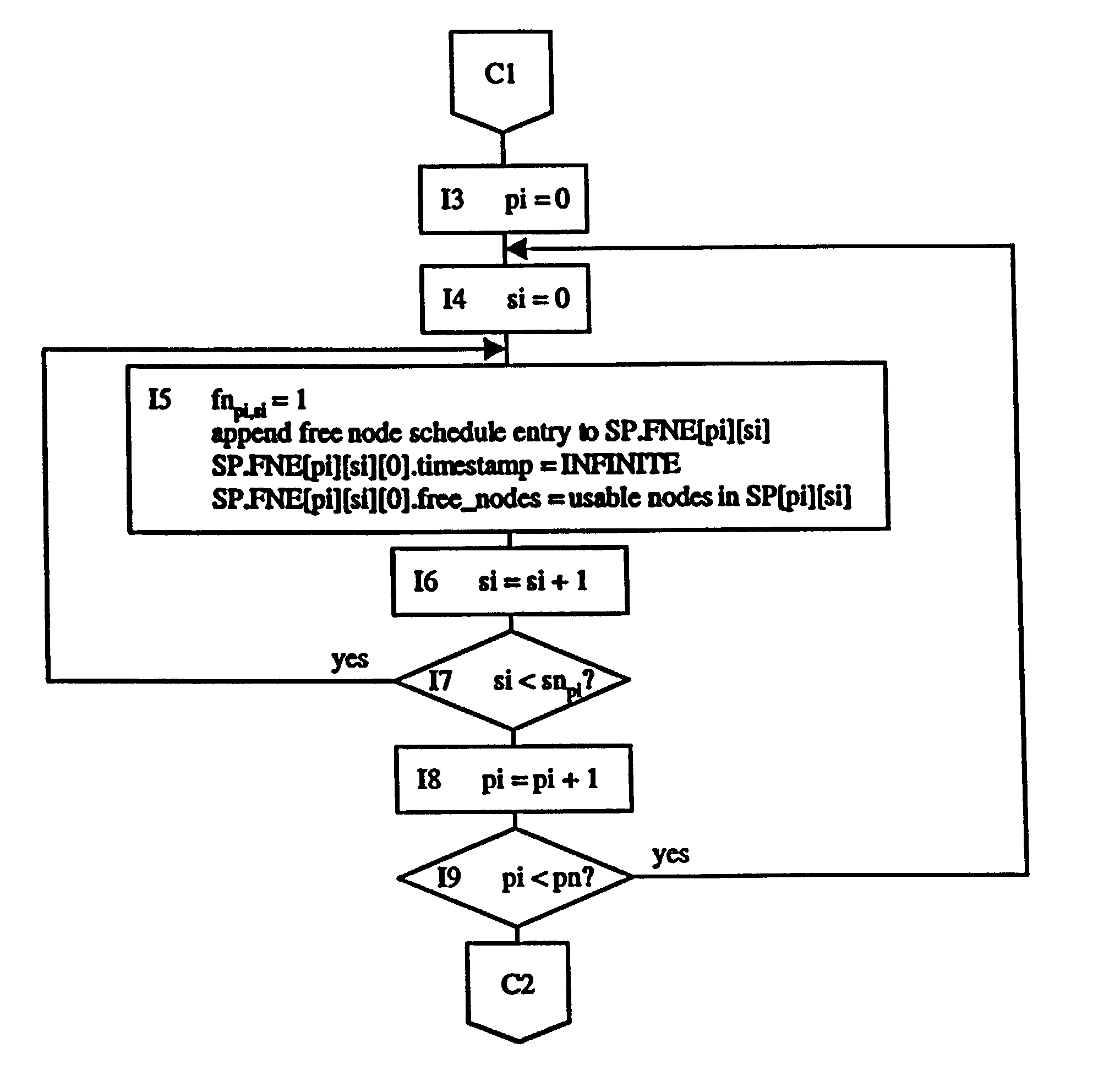
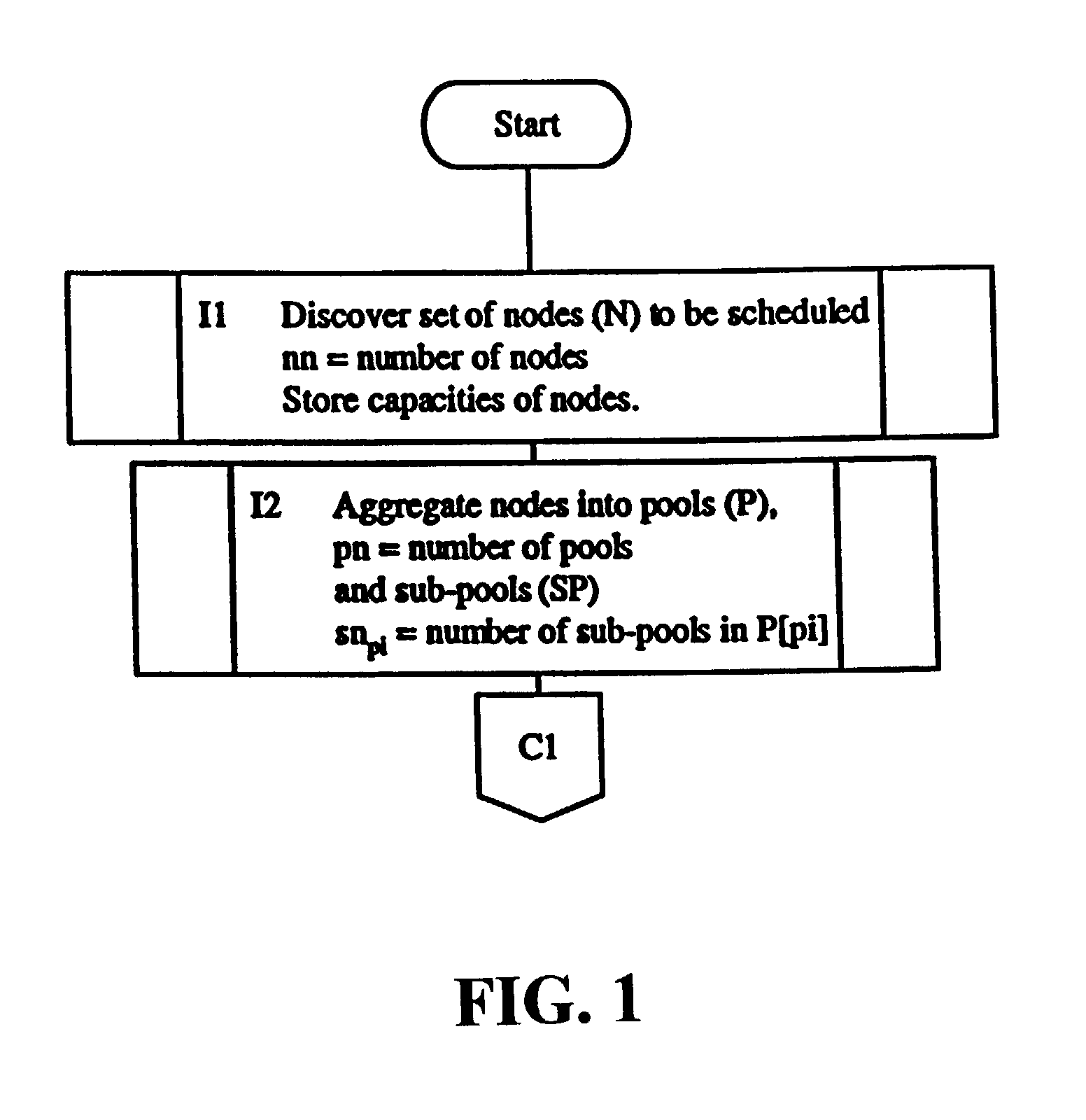
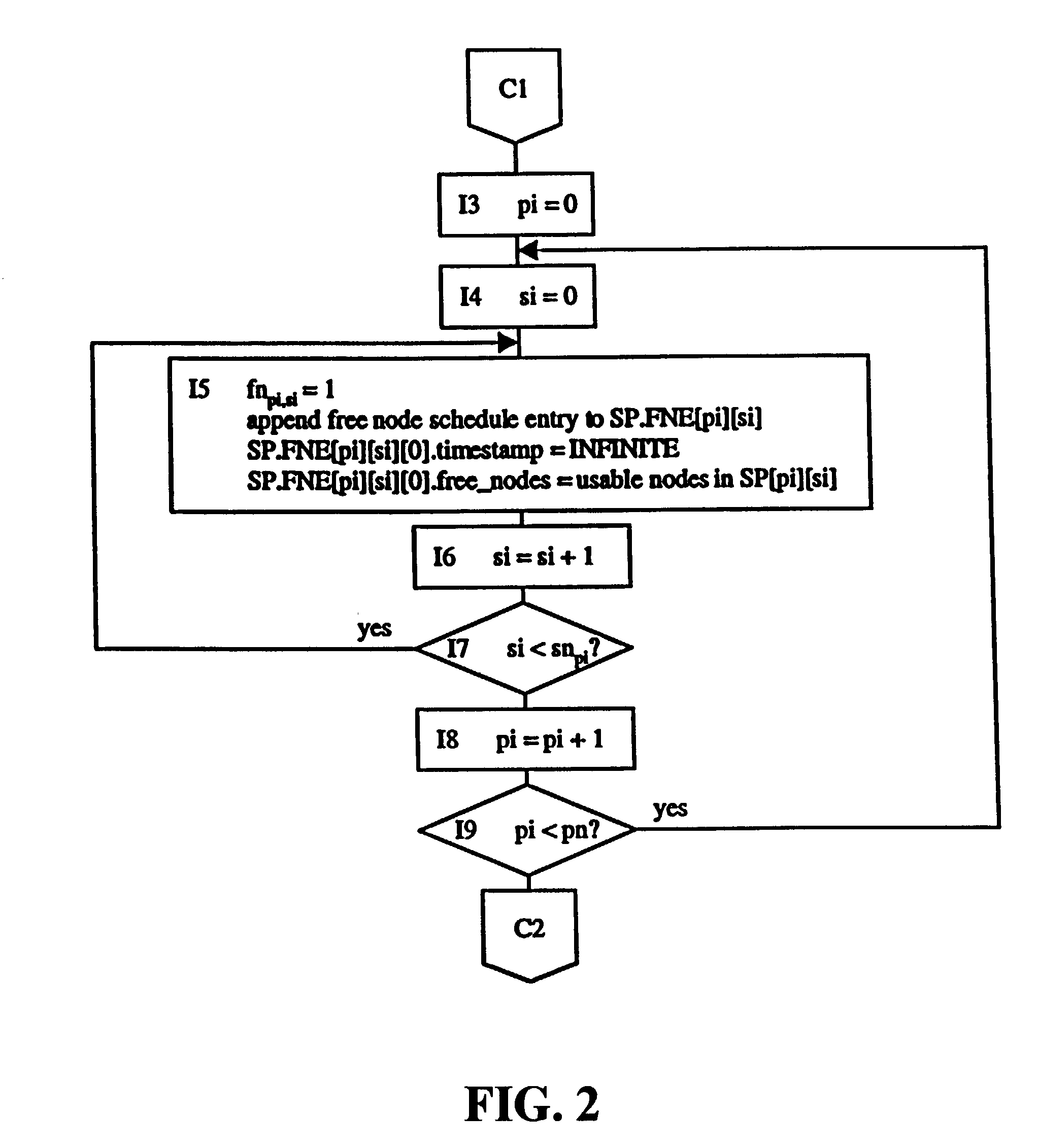
Dedicated heterogeneous node scheduling including backfill scheduling
InactiveUS7082606B2Improve throughputImprove utilizationResource allocationError detection/correctionStart timeParallel computing
A method and system for job backfill scheduling dedicated heterogeneous nodes in a multi-node computing environment. Heterogeneous nodes are grouped into homogeneous node sub-pools. For each sub-pool, a free node schedule (FNS) is created so that the number of to chart the free nodes over time. For each prioritized job, using the FNS of sub-pools having nodes useable by a particular job, to determine the earliest time range (ETR) capable of running the job. Once determined for a particular job, scheduling the job to run in that ETR. If the ETR determined for a lower priority job (LPJ) has a start time earlier than a higher priority job (HPJ), then the LPJ is scheduled in that ETR if it would not disturb the anticipated start times of any HPJ previously scheduled for a future time. Thus, efficient utilization and throughput of such computing environments may be increased by utilizing resources otherwise remaining idle.
Owner:LAWRENCE LIVERMORE NAT SECURITY LLC
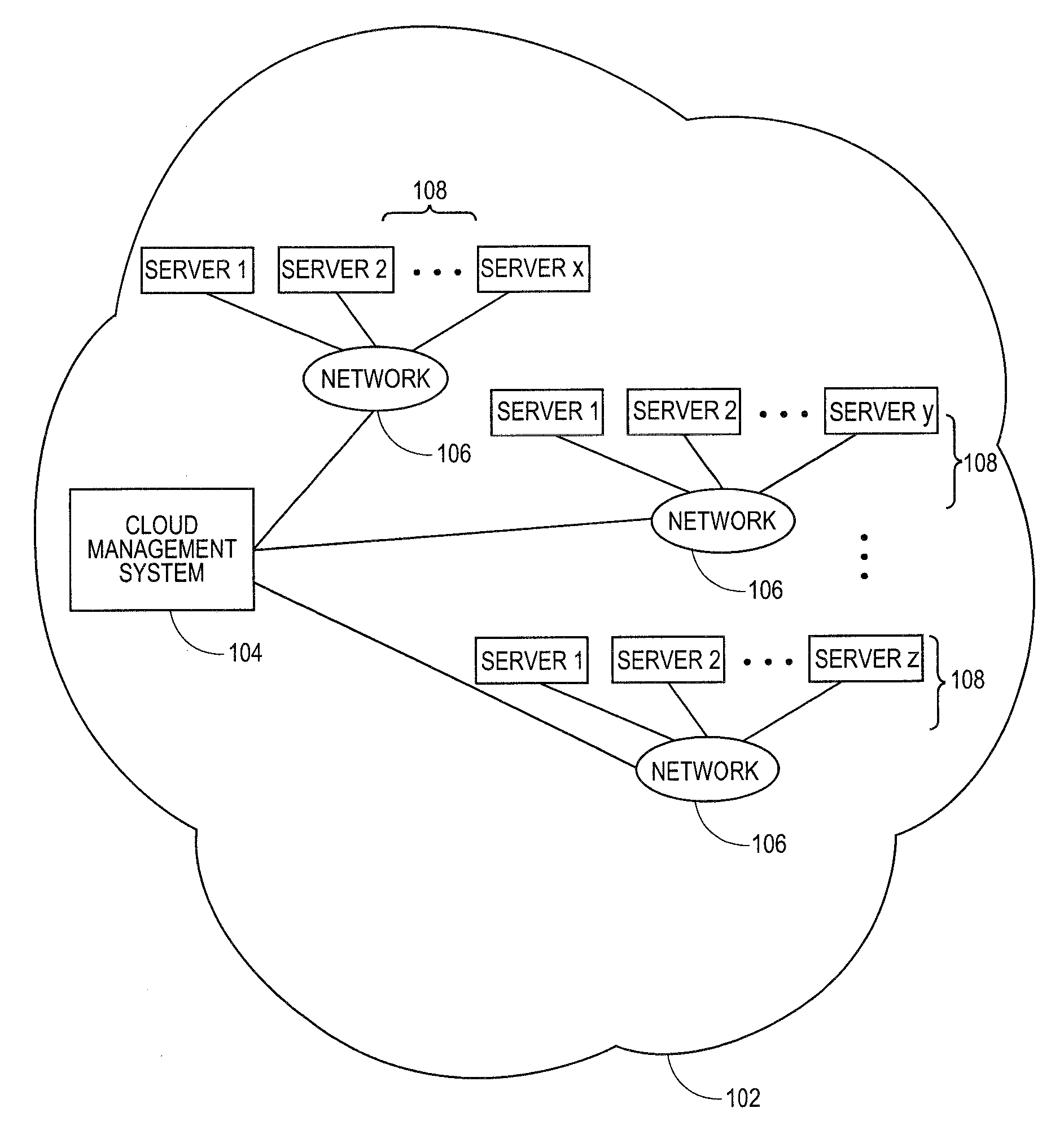
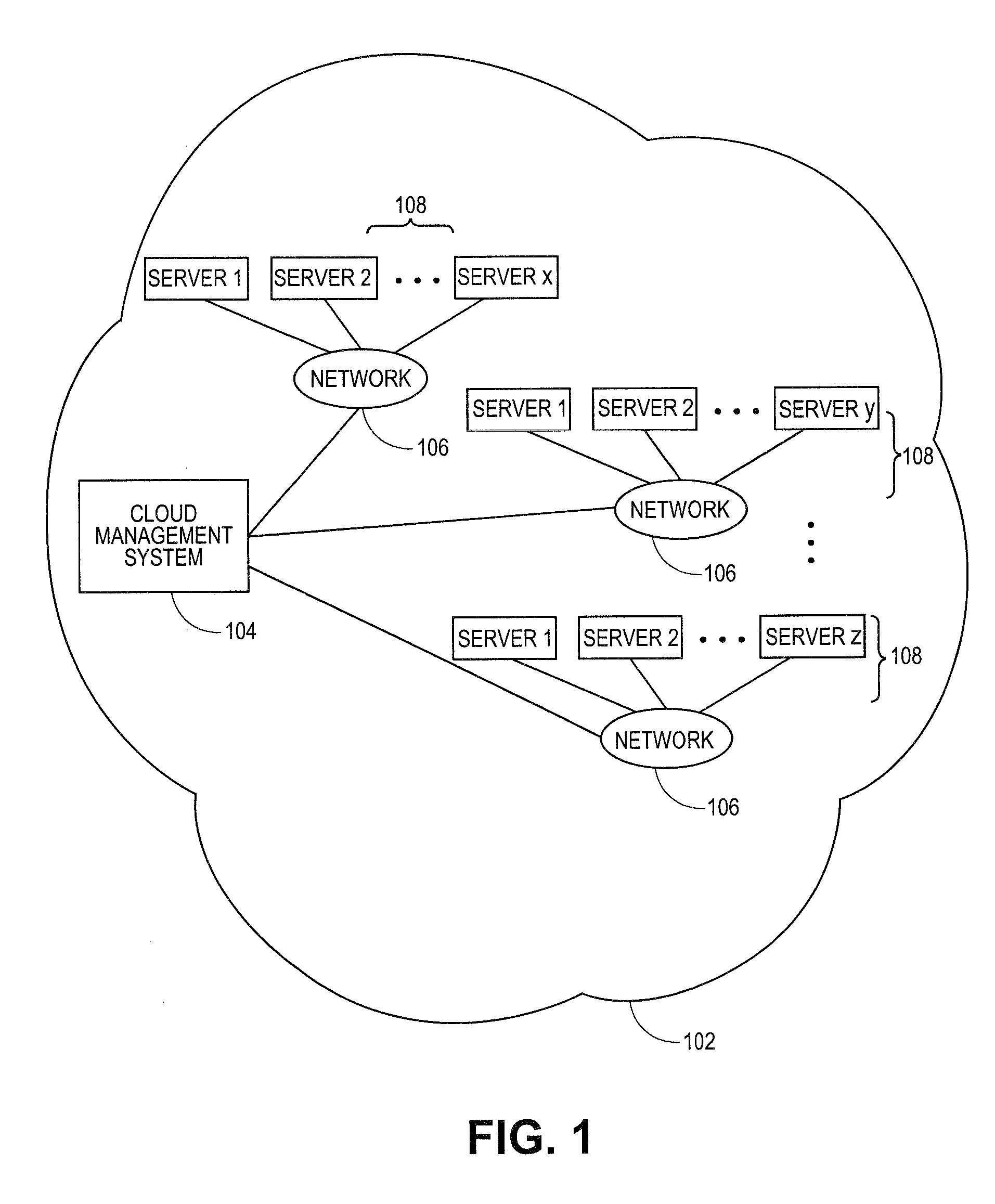
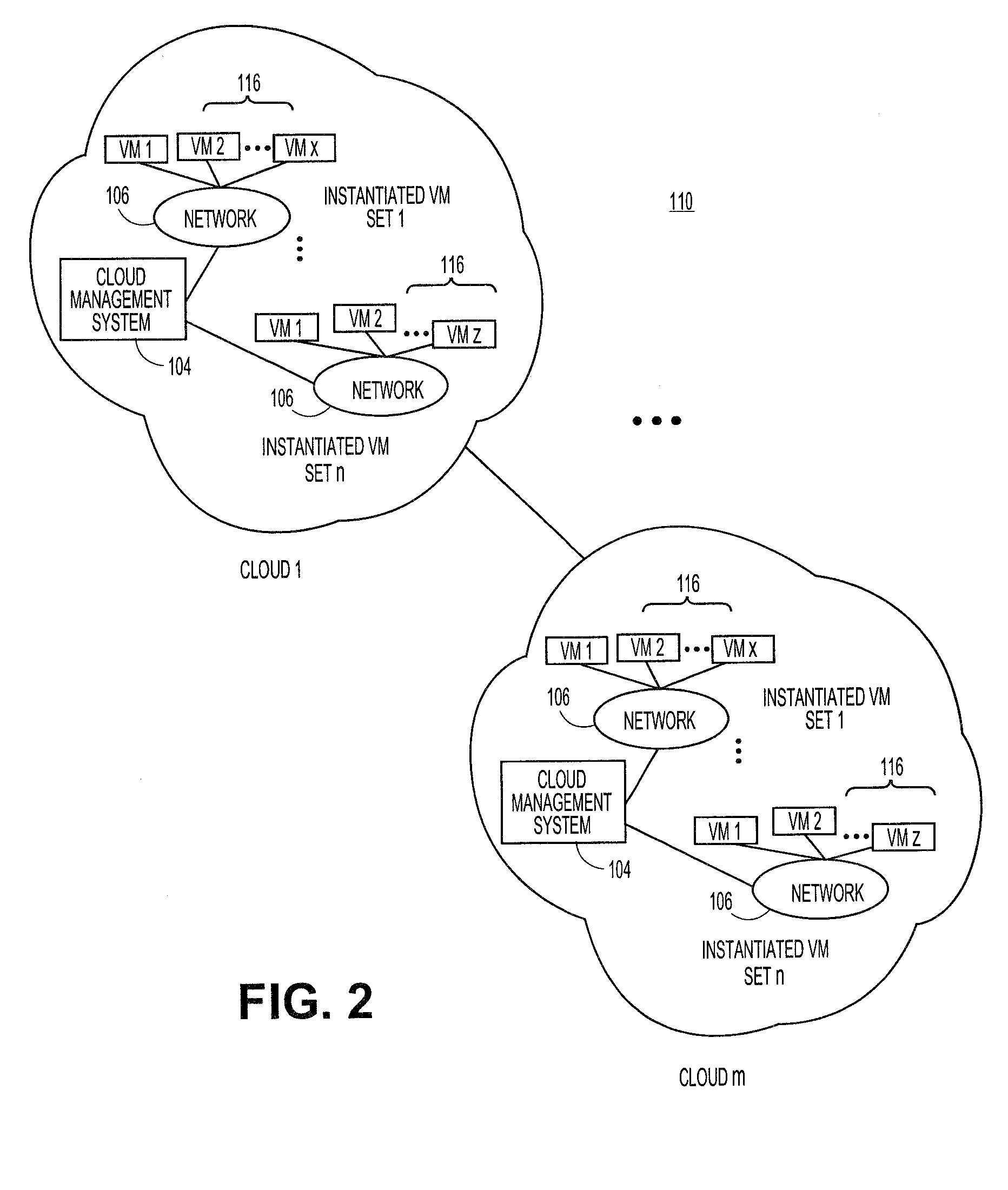
Methods and systems for communicating with third party resources in a cloud computing environment
A cloud computing environment can be configured to allow third party, user-controlled resources to be included in the pool of resources available in the cloud, regardless of the type of system supporting the user-controlled resources. A cloud management system can identify a particular type of management system supporting the user-controlled resources and the commands necessary to communicate with the particular type of management system. Once the particular type of management system is identified, the cloud management system can communicate with the particular type of management system, utilizing the determined commands and protocols, to coordinate access to the user-controlled resources. The cloud management system can identify, allocate, and manage a set of resources from the user-controlled resources utilizing the commands and protocols.
Owner:RED HAT
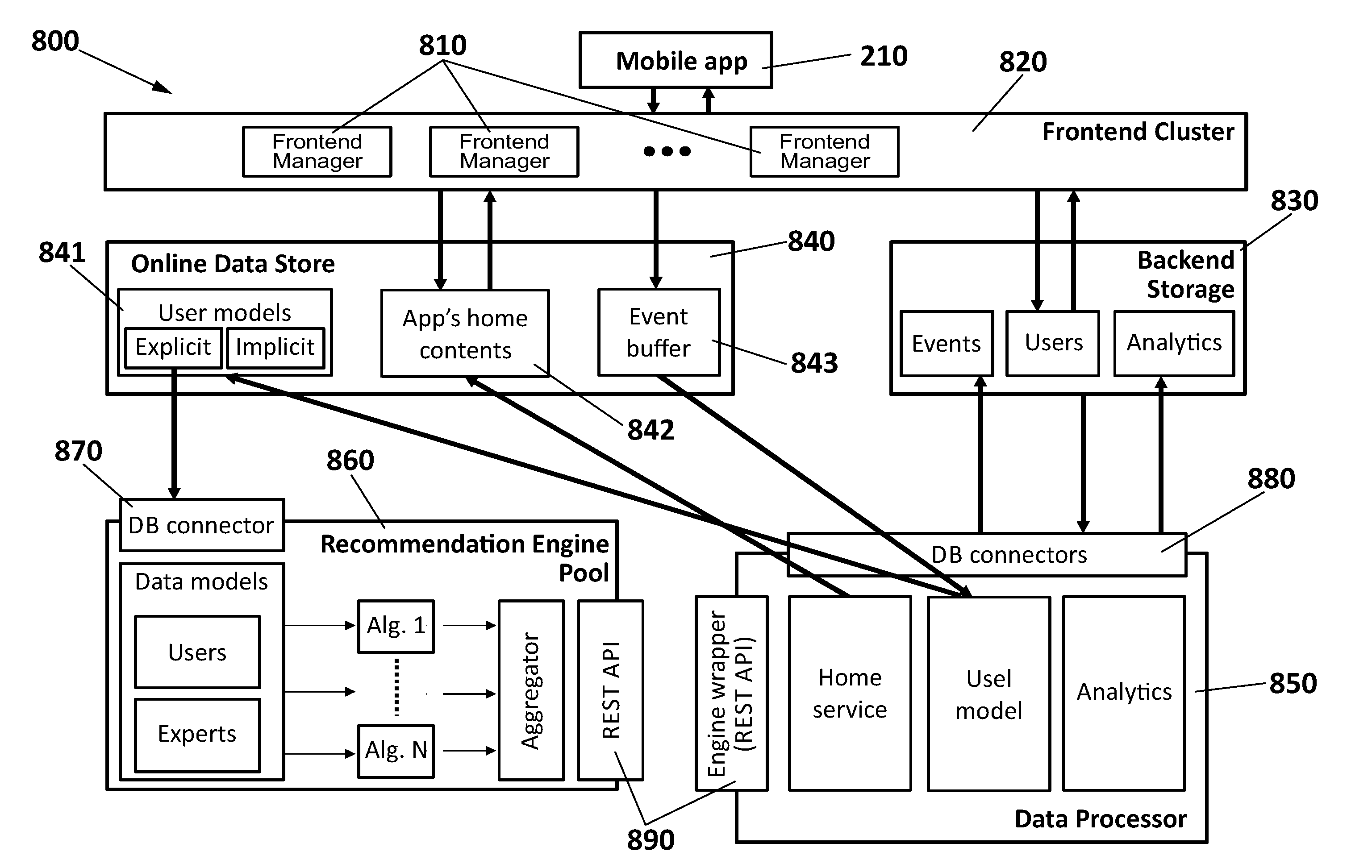
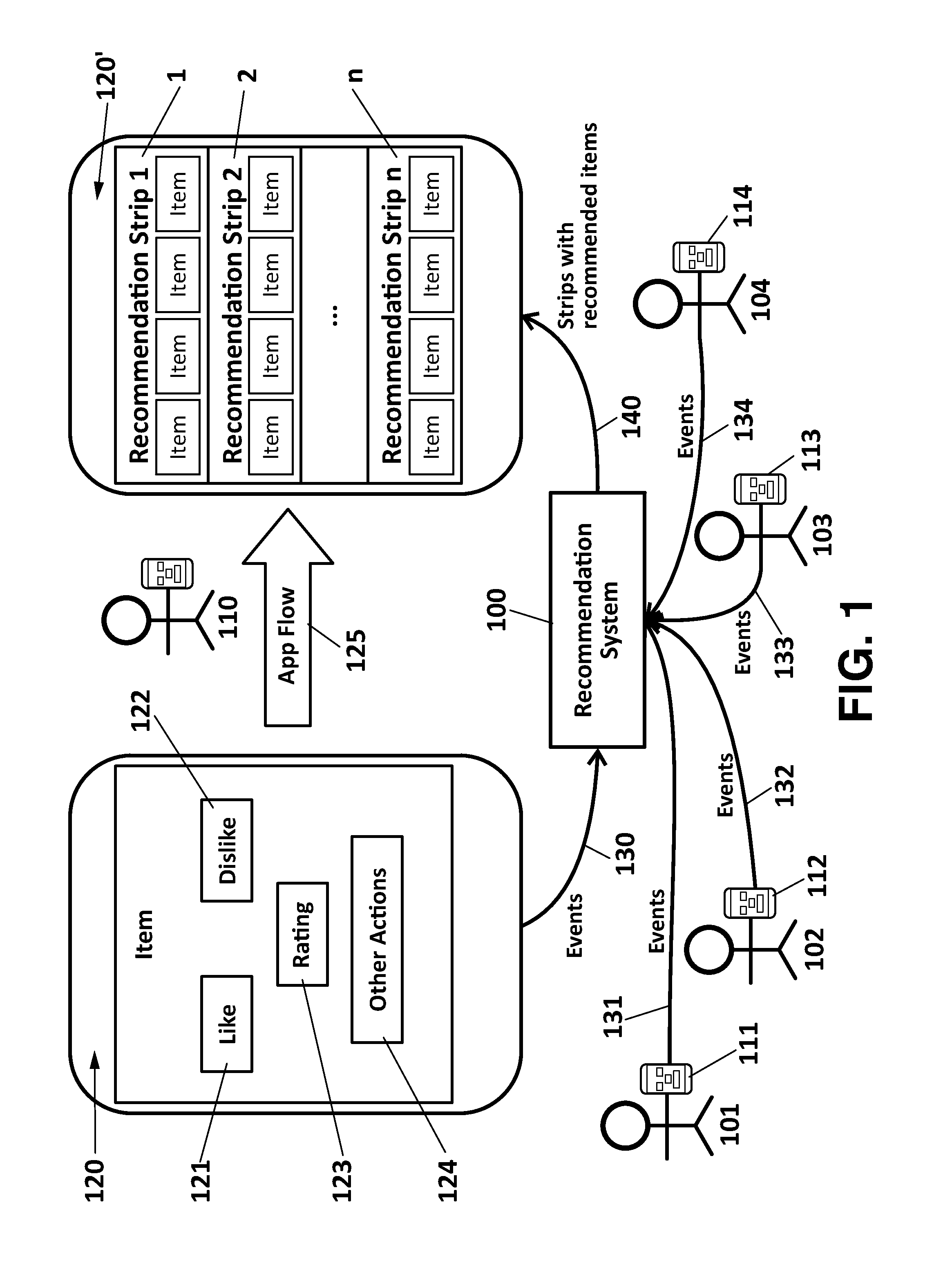
Method and system for providing multimedia content recommendations
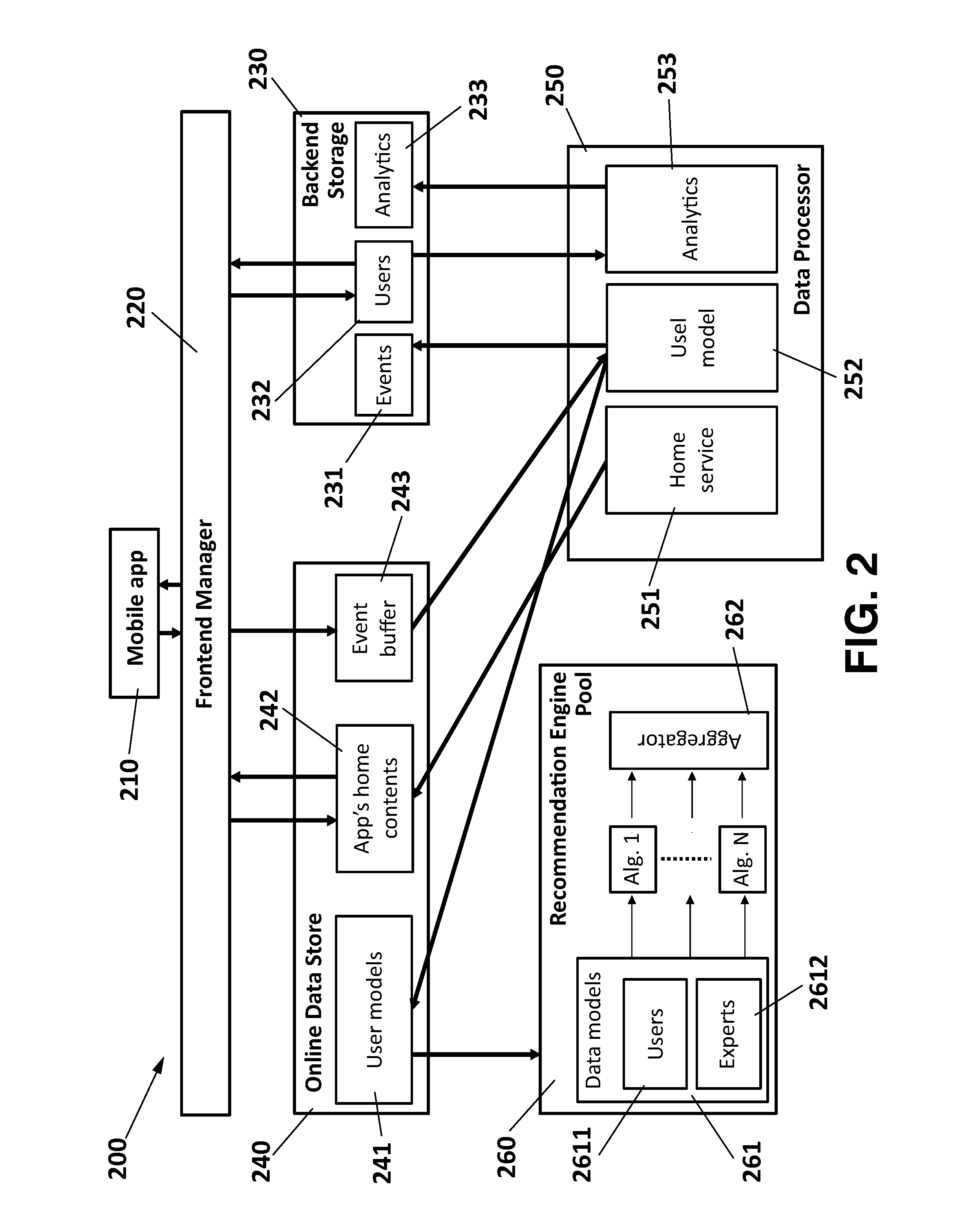
InactiveUS20150120722A1Promote assimilationImprove trustDigital data information retrievalDigital data processing detailsApplication softwareClient-side
A system for providing content recommendations, including a frontend manager for receiving explicit events from a client application of a user and generating implicit events based upon additional user actions within the client application; a backend storage of data on events and users and an Online Data Store for the explicit events and the implicit events; a Data Processor for creating an explicit user model from the explicit events and an implicit user model from the implicit events; a pool of recommendation engines with one or more recommendation algorithms for receiving the explicit user model and assigning a ranked recommendation list of content items to the user as a result, and further including an aggregator controlled by the Data Processor for aggregating the ranked recommendation lists based on a user-dependent strategy, in order to obtain multiple content recommendation lists of ranked items to be delivered by the frontend server to the client application in a final arrangement, pull from the Online Data Store along with data on the content sources.
Owner:TELEFONICA DIGITAL ESPANA
Managing reservations for resources
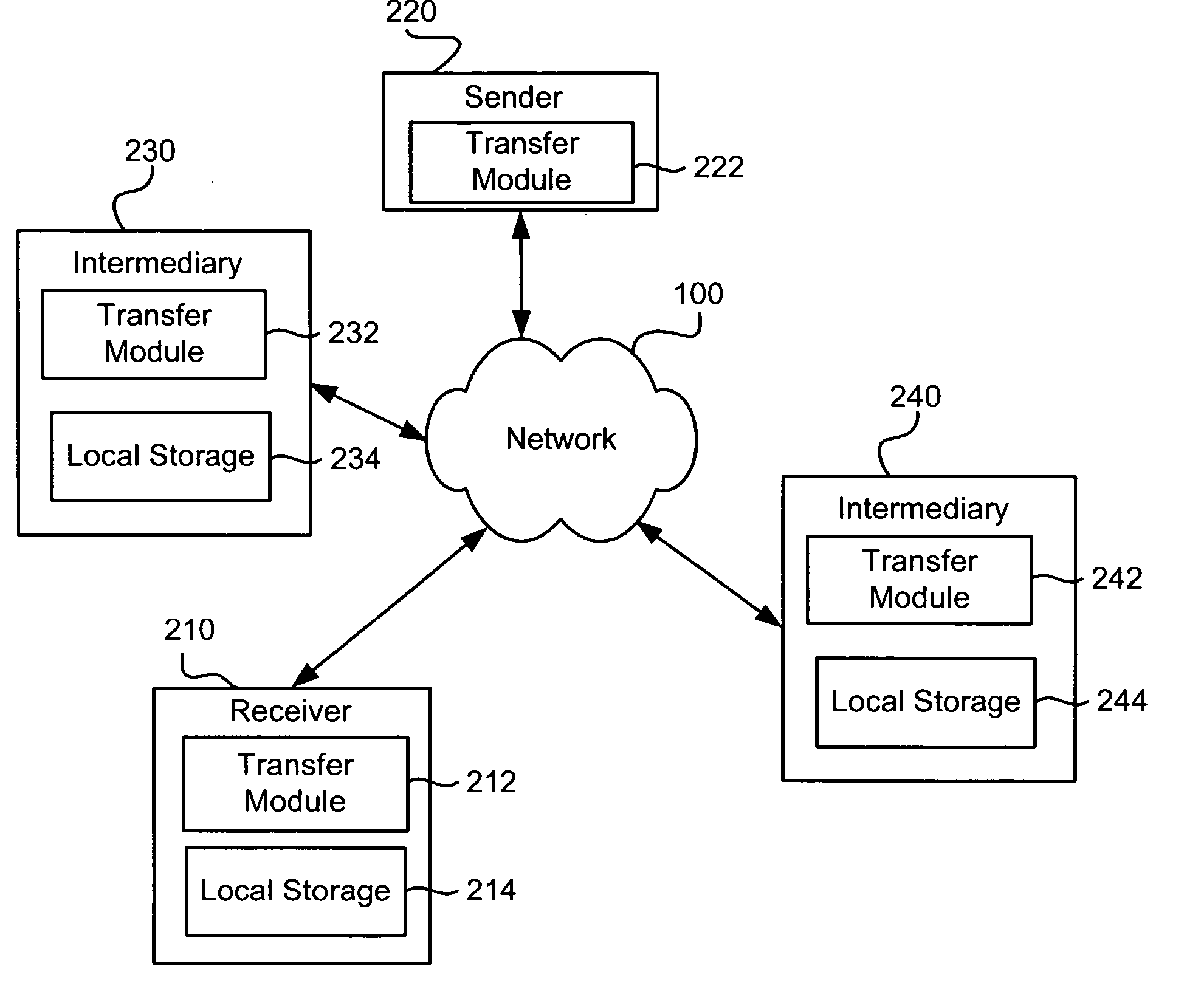
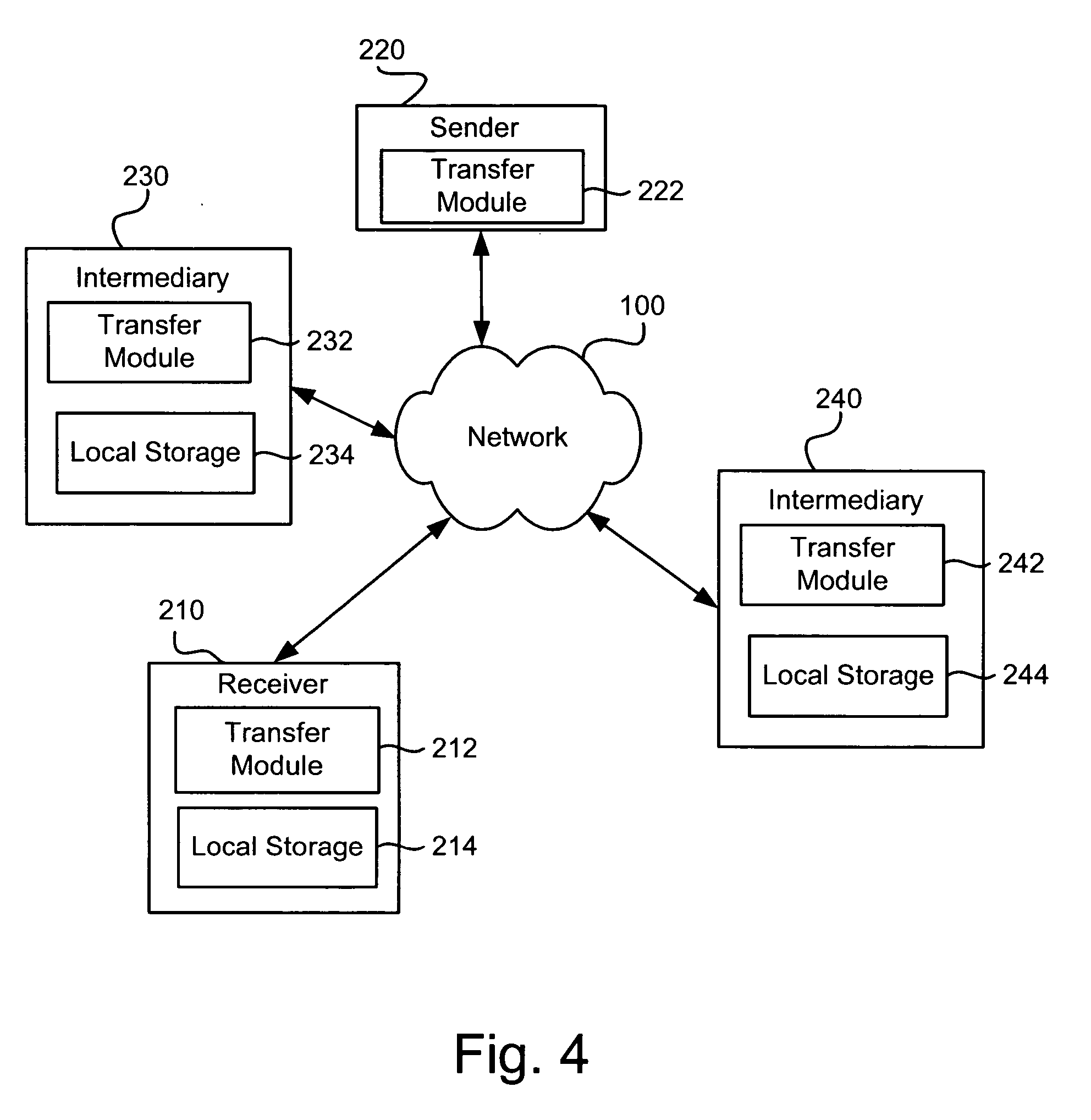
InactiveUS20050188089A1Digital computer detailsData switching networksResource poolDistributed computing
Owner:LICHTENSTEIN WALTER D +4
Programmatic response-time based workload distribution techniques
InactiveUS20040139433A1Improve performanceSimple technologyProgram initiation/switchingElectric devicesQueue timeWorkload
Workload is programmatically distributed across a set of execution resources. In a multithreaded server environment, response time to end users is improved while increasing the efficiency of software execution and resource usage. Execution time and wait / queued time are tracked, for various types of requests being serviced by a server. Multiple logical pools of threads are used to service these requests, and inbound requests are directed to a selected one of these pools such that requests of similar execution-time requirements are serviced by the threads in that pool. The number and size of thread pools may be adjusted programmatically, and the distribution calculation (i.e., determining which inbound requests should be assigned to which pools) is a programmatic determination. In preferred embodiments, only one of these variables is adjusted at a time, and the results are monitored to determine whether the effect was positive or negative. The disclosed techniques also apply to tracking and classifying requests by method name (and, optionally, parameters).
Owner:IBM CORP
Multi-level buffer pool extensions
ActiveUS20120072652A1Convenience to workAvoid settingSoftware engineeringMemory adressing/allocation/relocationComputational scienceParallel computing
A buffer manager that manages blocks of memory amongst multiple levels of buffer pools. For instance, there may be a first level buffer pool for blocks in first level memory, and a second level buffer pool for blocks in second level memory. The first level buffer pool evicts blocks to the second level buffer pool if the blocks are not used above a first threshold level. The second level buffer pool evicts blocks to a yet lower level if they have not used above a second threshold level. The first level memory may be dynamic random access memory, whereas the second level memory may be storage class memory, such as a solid state disk. By using such a storage class memory, the working block set of the buffer manager may be increased without resorting to lower efficiency random block access from yet lower level memory such as disk.
Owner:MICROSOFT TECH LICENSING LLC
Mimicry defense architecture based zero-day attack detection, analysis and response system and method thereof
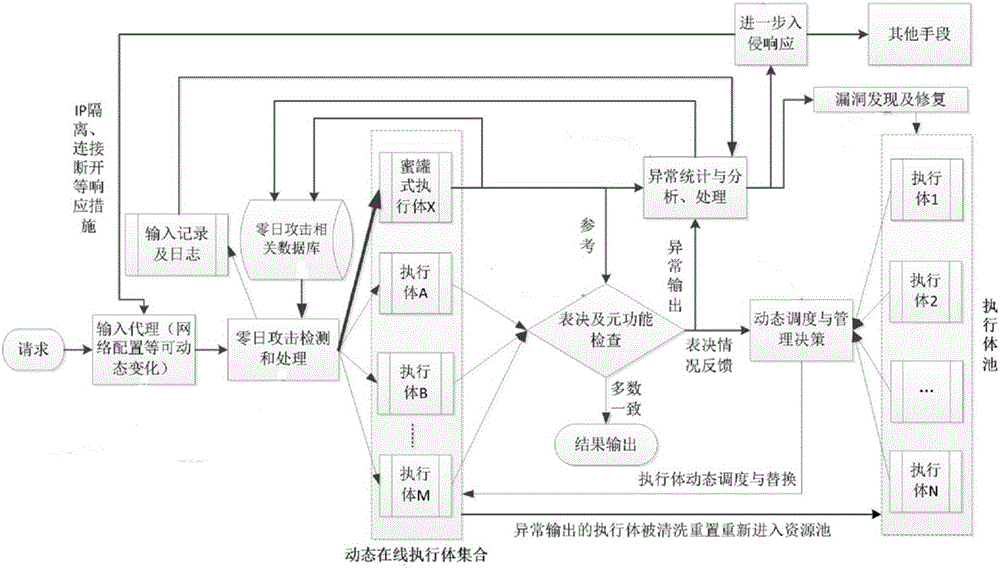
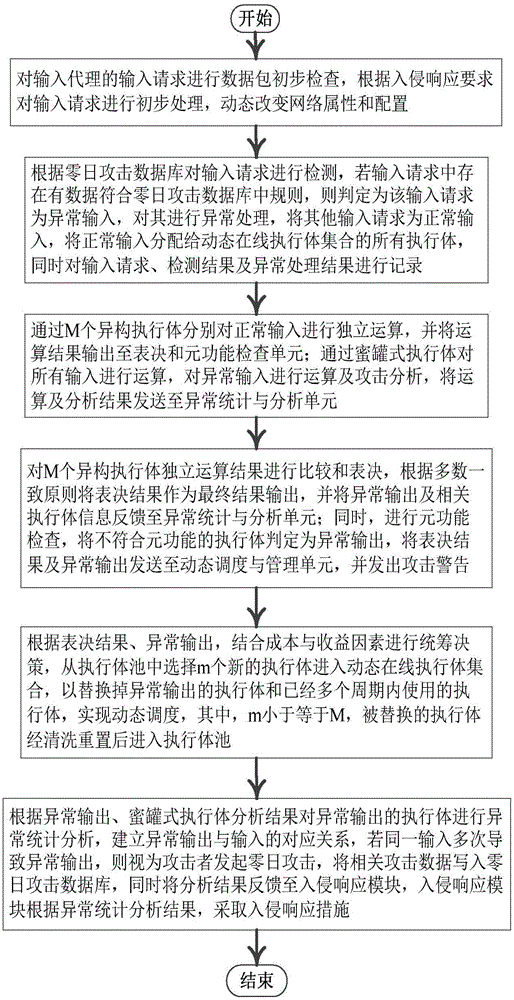
The invention relates to a mimicry defense architecture based zero-day attack detection, analysis and response system and a method thereof. The method comprises the steps of performing attack detection and processing on the input, cheating and inducing an attacker through honeypot type executing bodies, and performing meta-function inspection on the output of each executing body; performing statistical analysis on abnormal output by combining abnormal information, updating a zero-day attack database, feeding back an analysis result to an intrusion response module, and preventing persistent attacks of the attacker; performing dynamic adjustment and management on an online executing body by combining voting conditions, executing body dispatching, the executing body with abnormal output and the like, and selecting executing bodies from an executing body resource pool to get into a dynamic online executing body set; and analyzing a zero-day vulnerability in the executing body with abnormal output according to an anomaly statistical analysis result, and repairing the related executing bodies in the executing body pool. According to the invention, functions and the flexibility of mimicry defense architecture are enhanced, values of the abnormal output are sufficiently utilized, and the threat and the defense cost of zero-day attacks are reduced.
Owner:THE PLA INFORMATION ENG UNIV
Container-based Operating System and Method
ActiveUS20180167217A1Undesired interactionData processing applicationsUser identity/authority verificationOperational systemFinancial transaction
In a distributed network hosting a shared pool of configurable computing resources there is provided one or more system instances of a blockchain. Each system instance comprises a virtual machine and a set of containers. The containers are members of the blockchain in that the blockchain's public ledger records encrypted copies of at least selected directories of each container. Each container that is in the set can thus verify whether any other container also belongs to the same set with reference to the public ledger, since the transactions recorded on the public ledger are encrypted copies of the set's containers. The use of a blockchain thus allows a system boundary to be defined around a set of containers by the initial specification of the blockchain. The system boundary can be defined to ensure that the set of containers comply with legal requirements, such as a geographic restriction.
Owner:IBM CORP
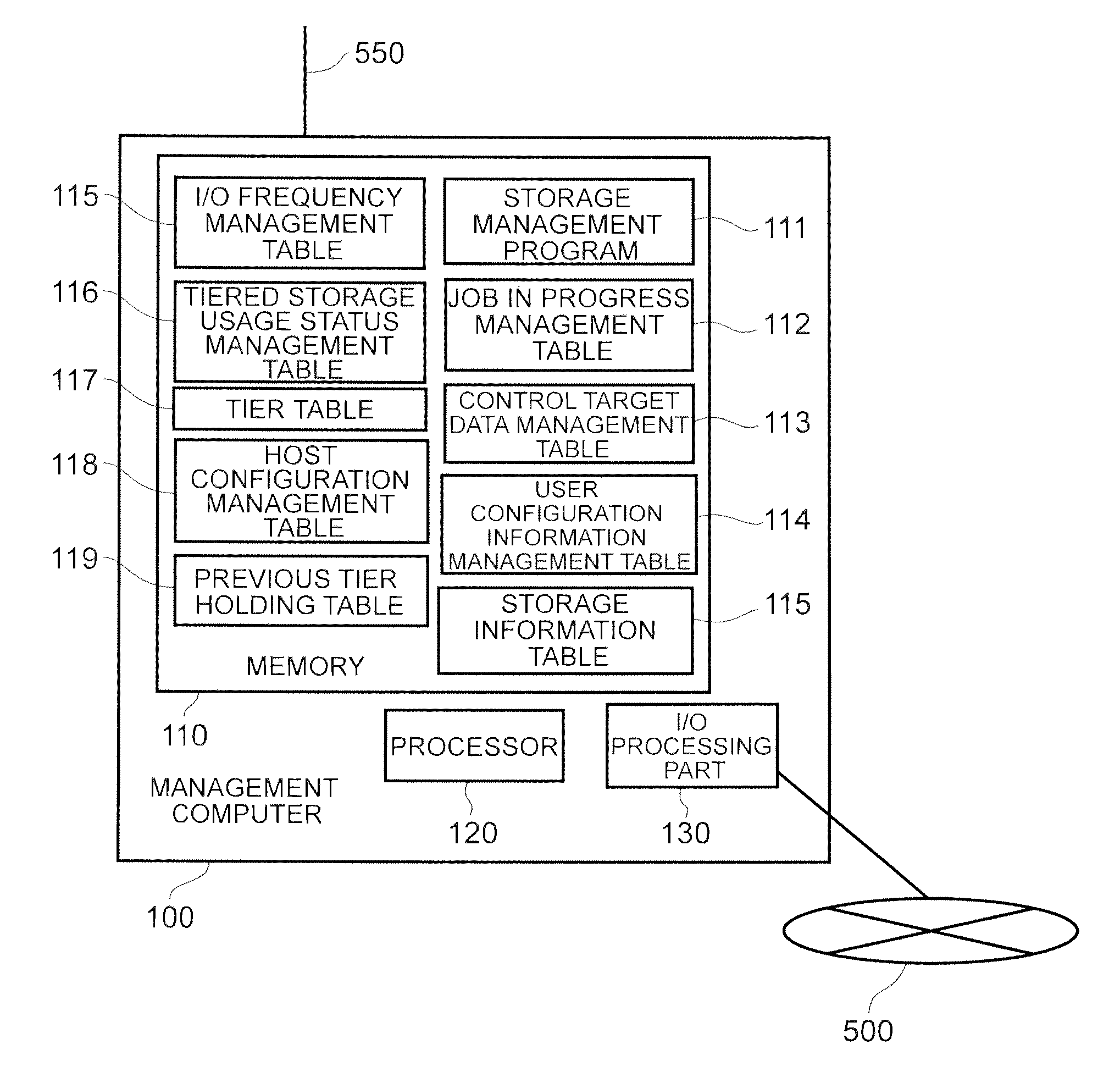
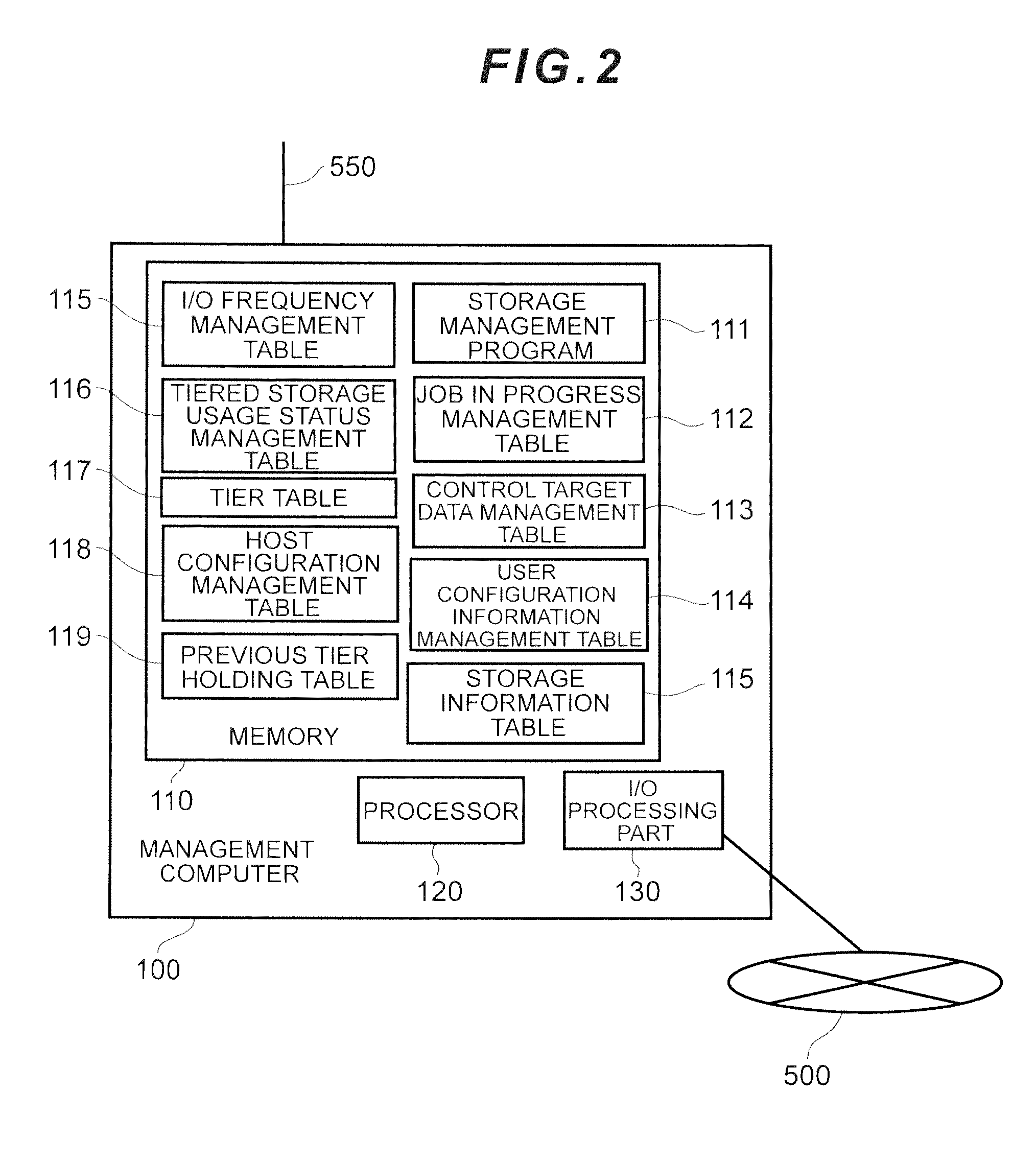
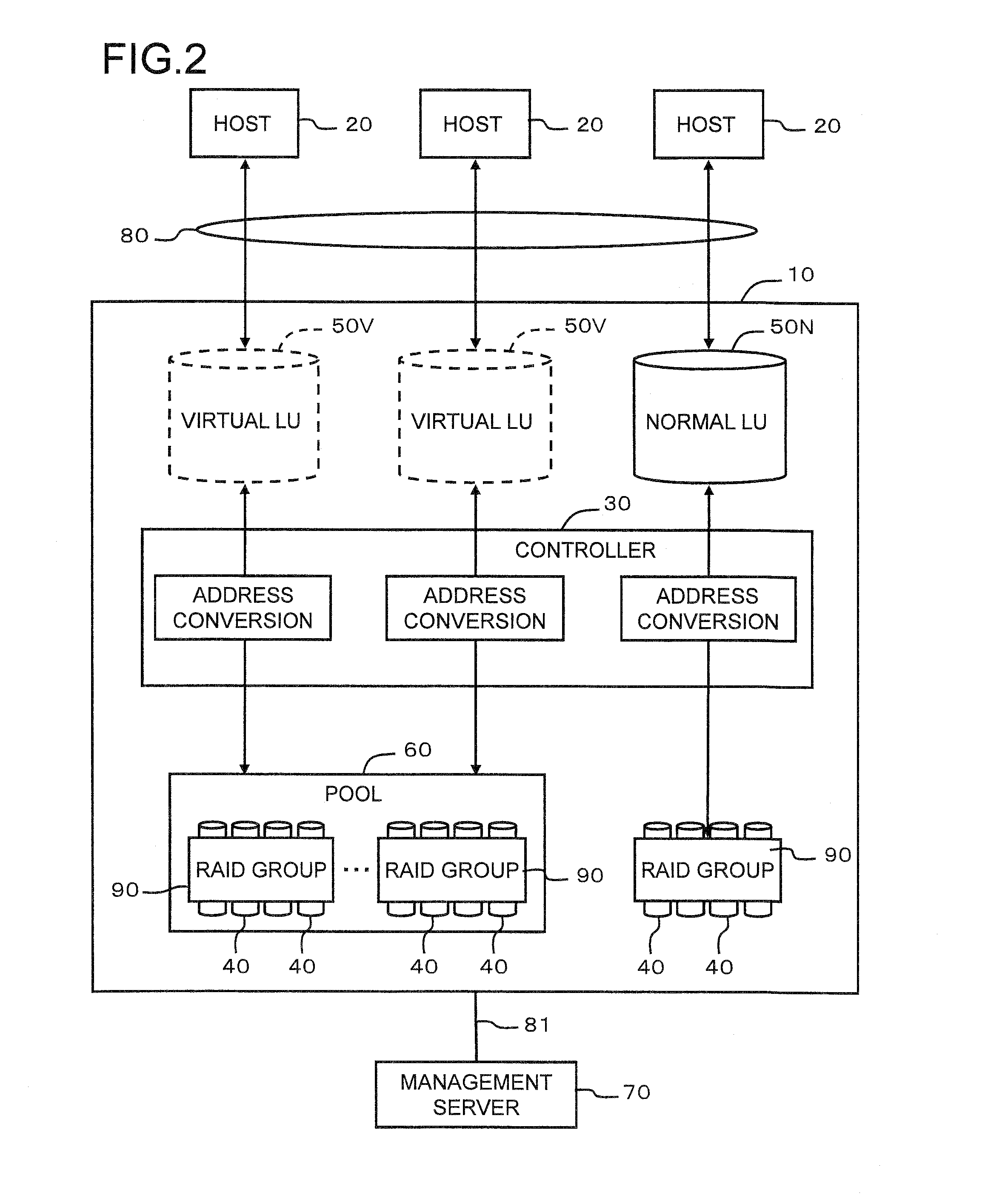
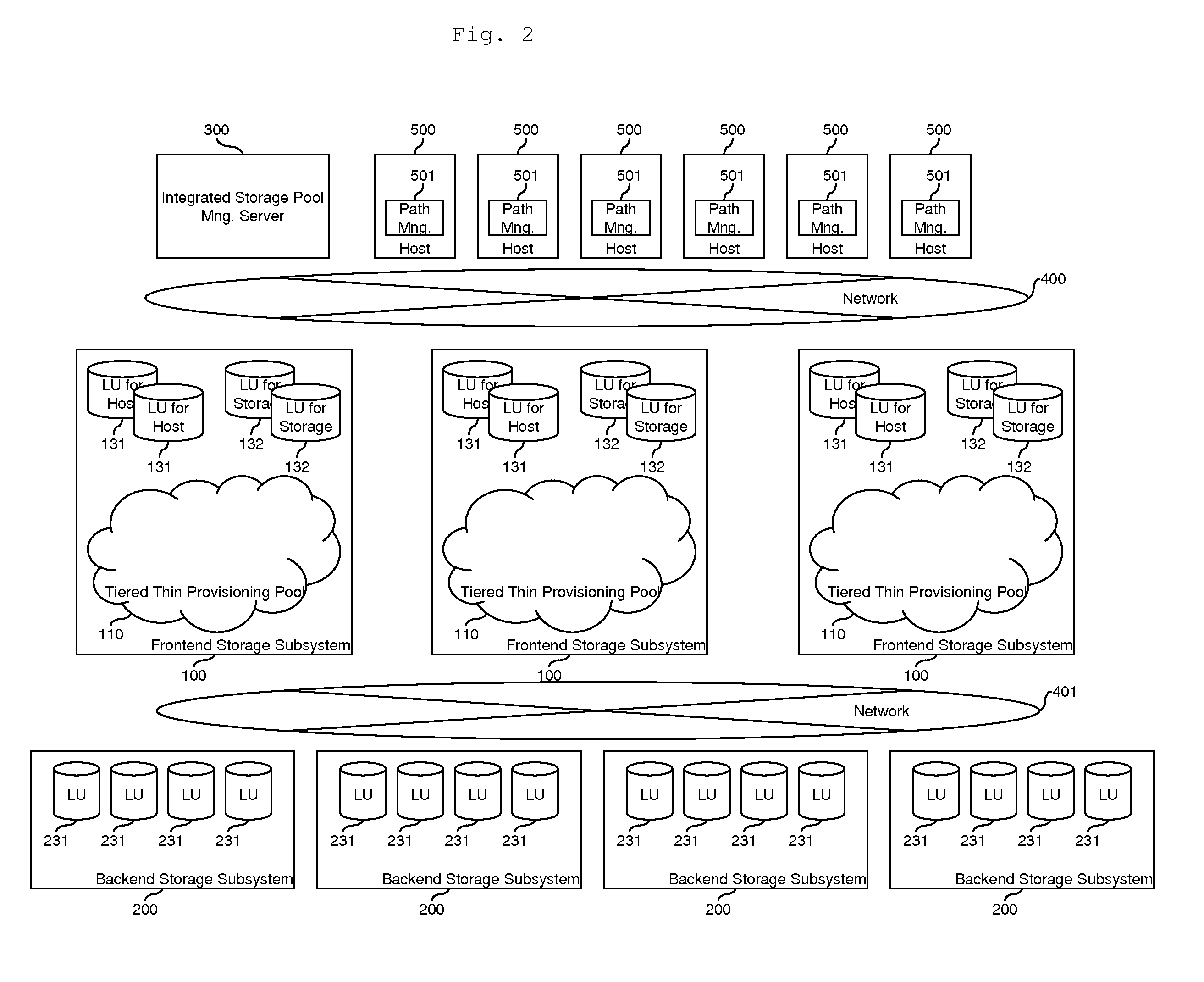
Computer system and storage management method
InactiveUS20130111129A1Easy to useDigital data information retrievalMemory adressing/allocation/relocationData controlGranularity
Data is placed in tiered storage with a suitable granularity according to application characteristics. The storage apparatus comprises a controller for managing storage areas, provided by storage media of a plurality of types of varying performance, as pools, and for assigning the storage areas in page units to a virtual volume from any tiered storage among a plurality of types of tiered storage which the pool comprises in response to a data write request from the host computer, wherein, for specific data which is managed by the host computer, the controller specifies an area with a high referencing frequency among the specific data on the basis of organization information of the specific data, and moves this area to another of the tiered storage with a higher performance than an already assigned tiered storage.
Owner:HITACHI LTD
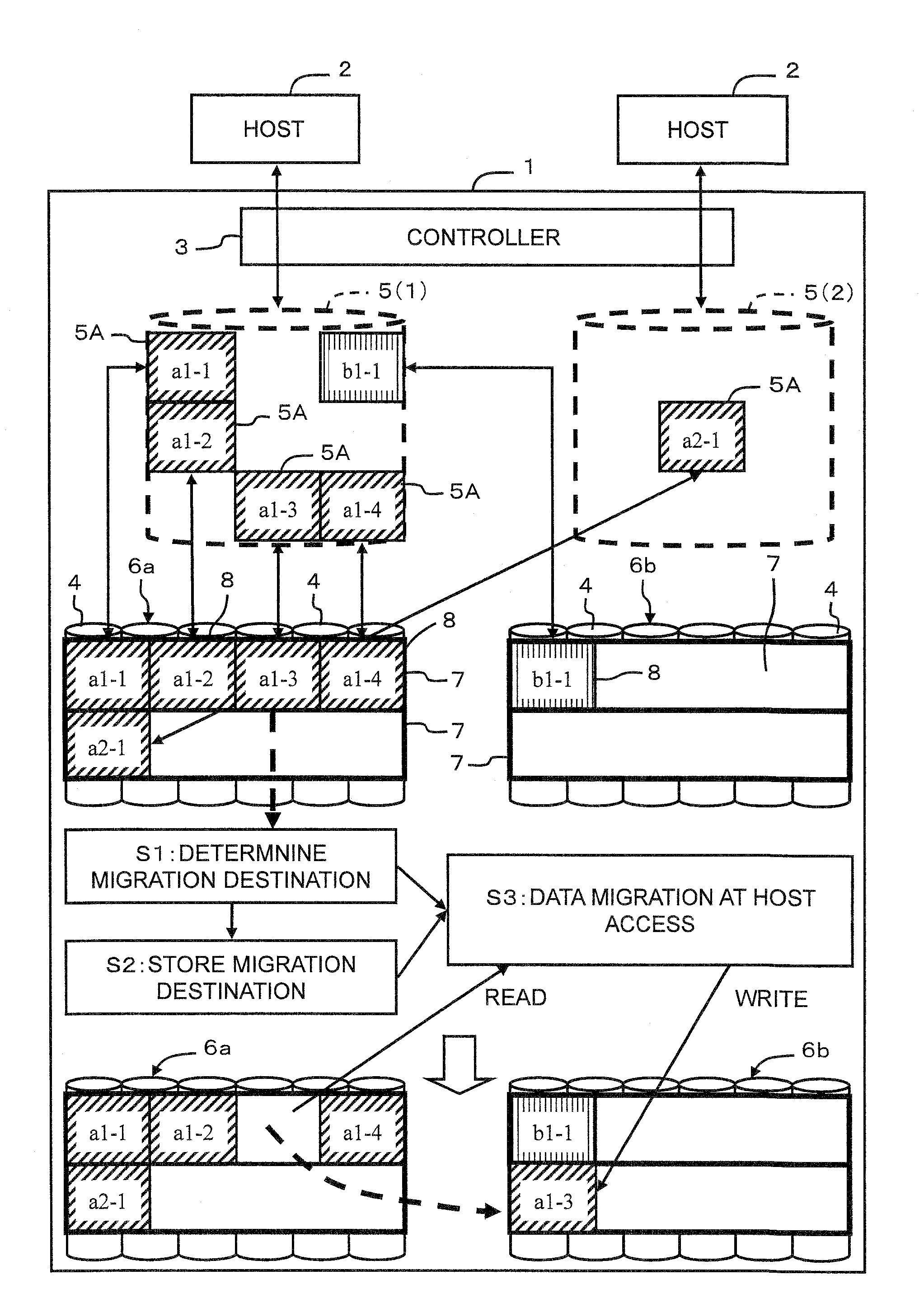
Storage controller and virtual volume control method
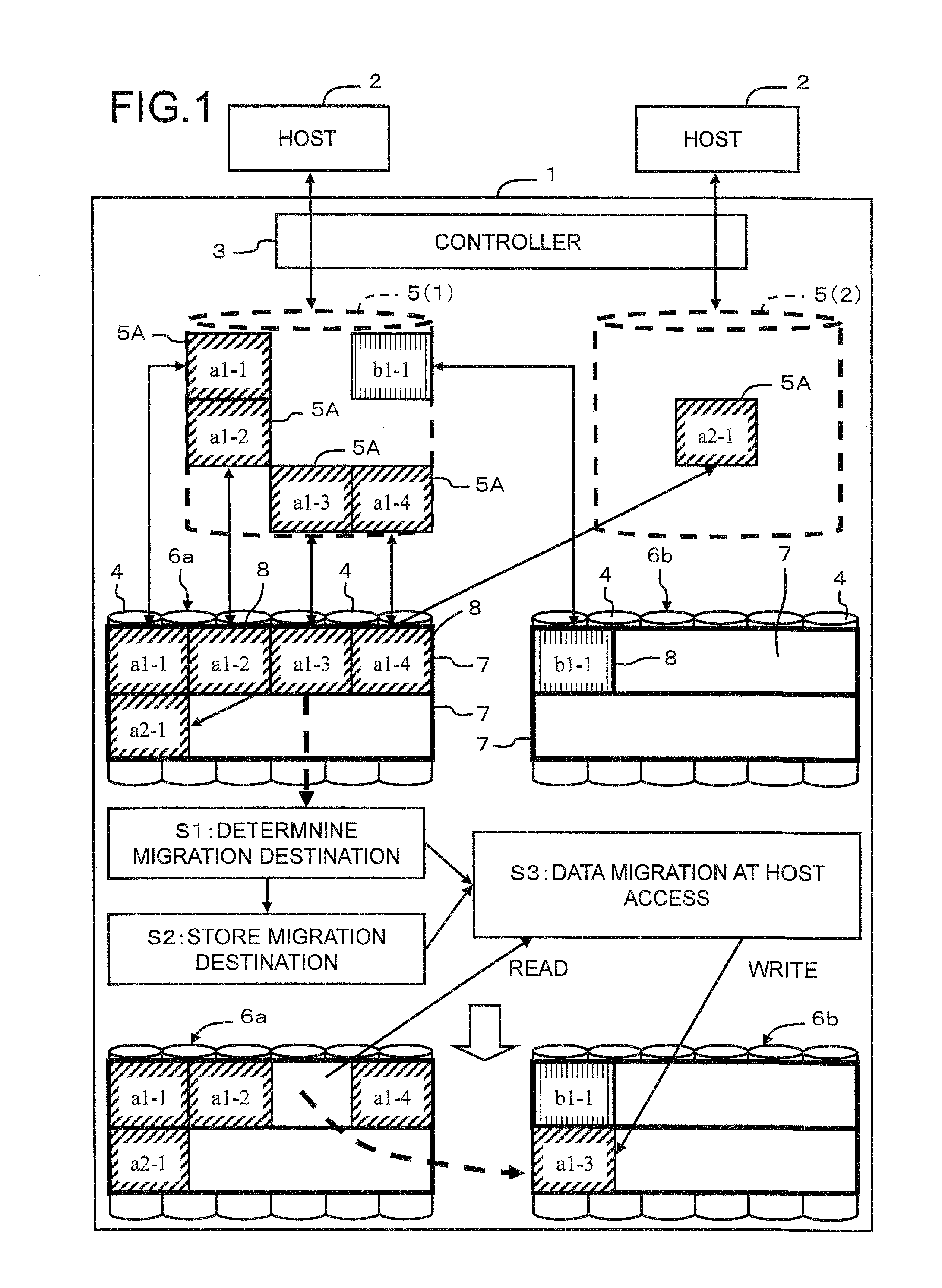
ActiveUS20110191537A1Effective associationImprove responseError detection/correctionMemory adressing/allocation/relocationRAIDControl store
A storage controller allocates a real storage area to a virtual volume in chunk units each comprising a plurality of pages. In a case where load bias occurs between RAID groups, data reallocation is carried out. A real storage area inside a pool is allocated to a virtual volume 5 in accordance with a write access. A RAID group 6 comprises a plurality of chunks. Each chunk 7 comprises a plurality of pages 8. The pages 8, from within the chunk 7 that has been allocated to the virtual volume 5, are used. A data migration plan is created and stored in page units based on the load of each RAID group. When a host 2 issues a command to a migration-targeted page, data is migrated while this command is being processed.
Owner:HITACHI LTD
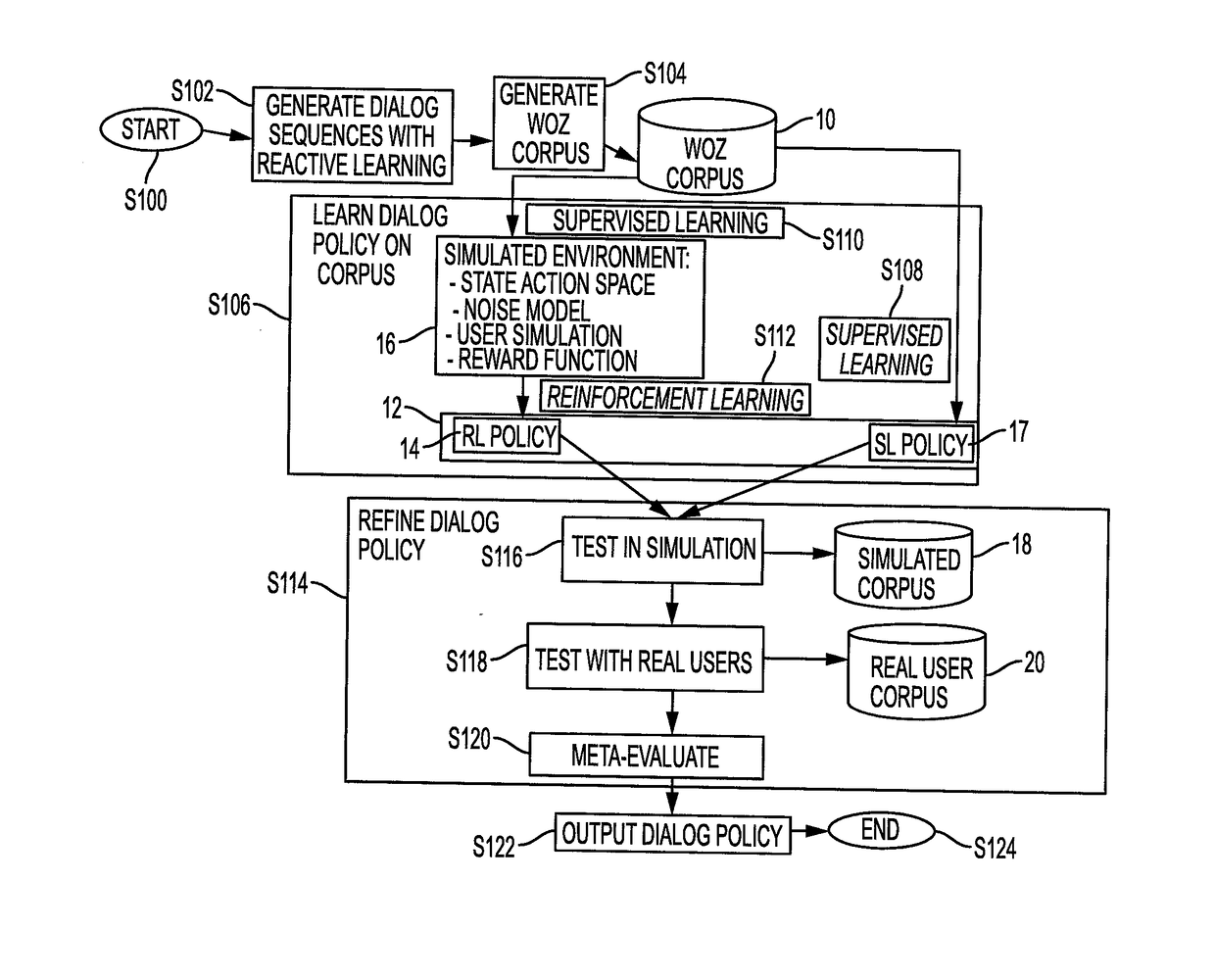
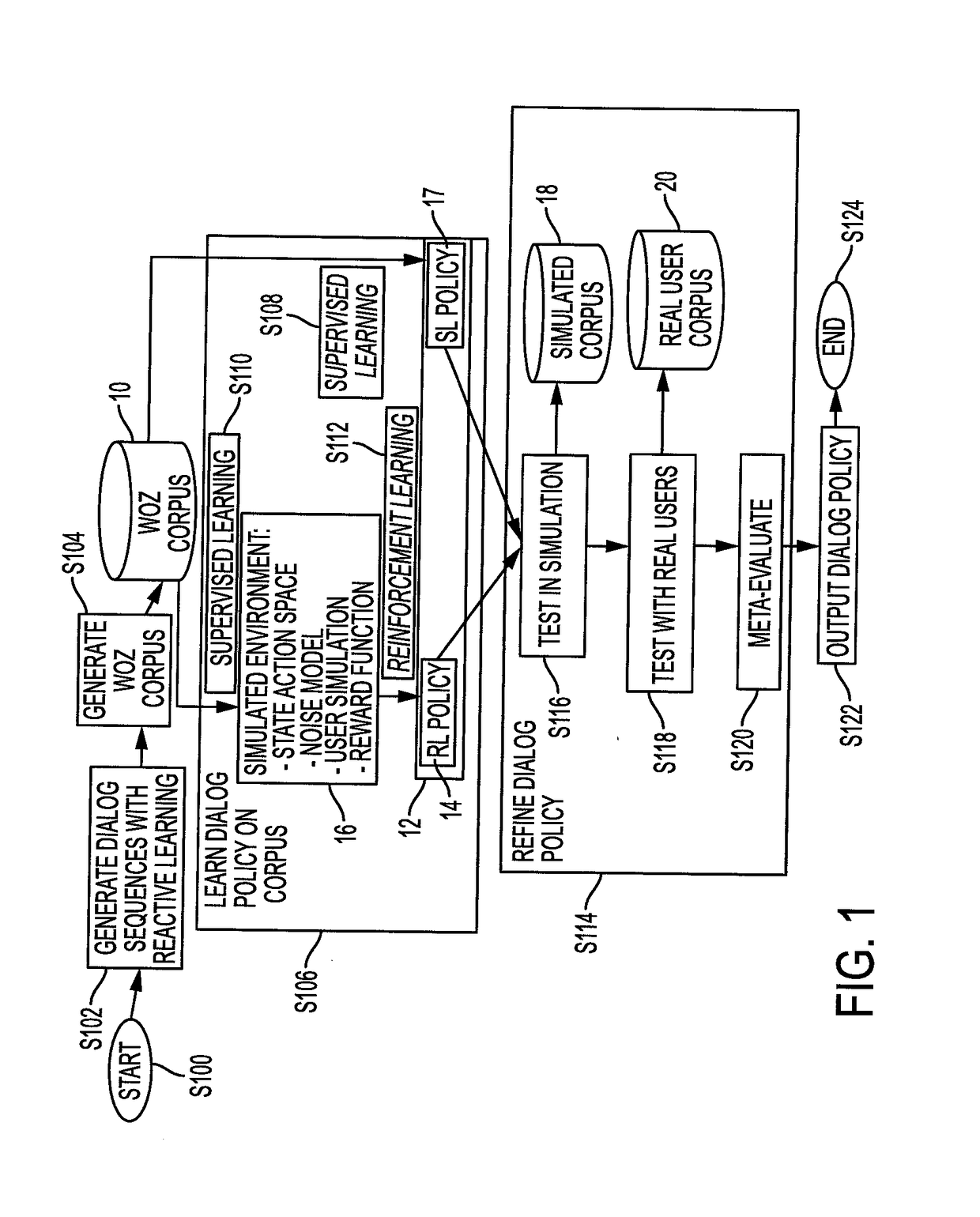
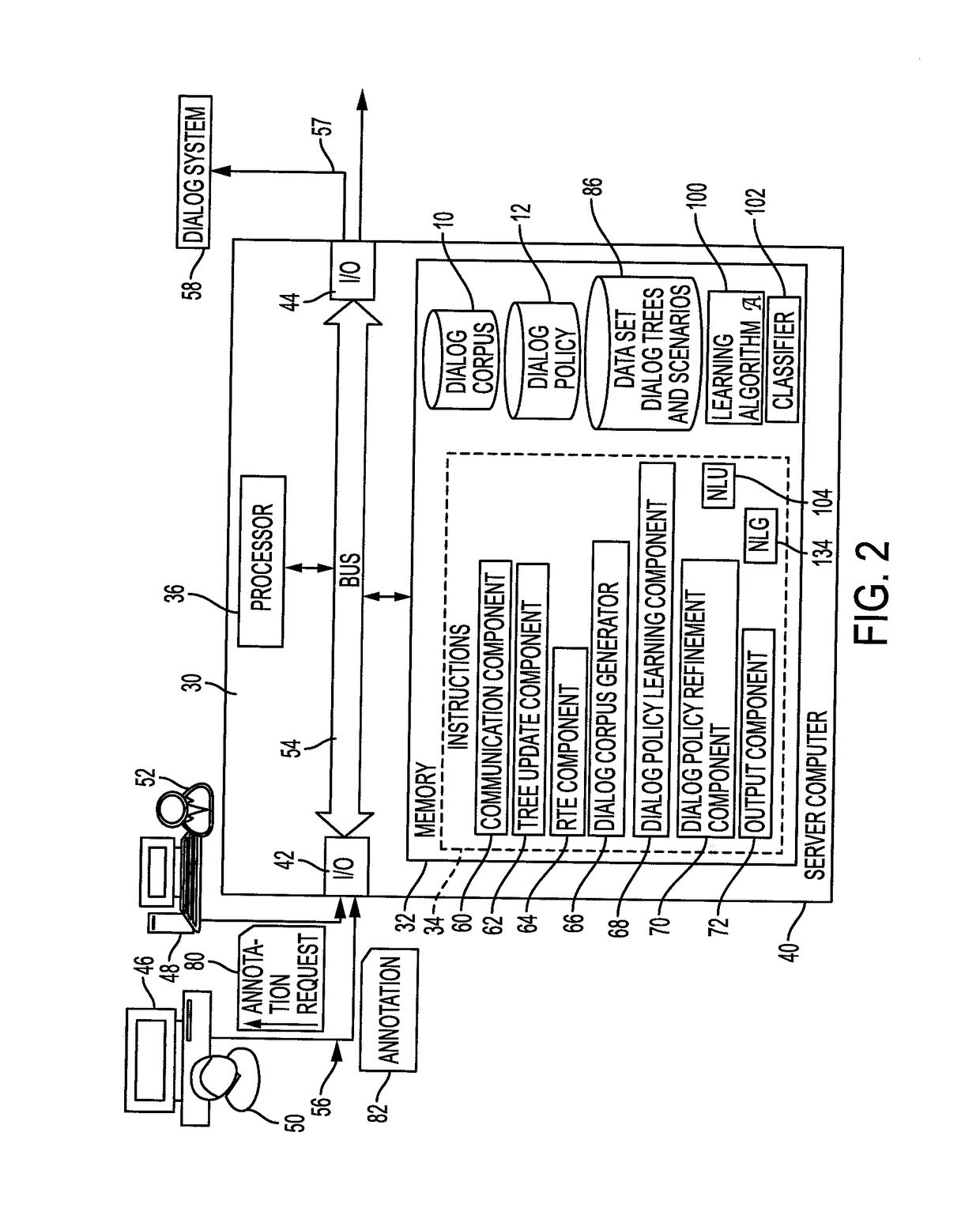
Reactive learning for efficient dialog tree expansion
ActiveUS20170316777A1Natural language data processingSpeech recognitionNODALTheoretical computer science
A method for generating dialogs for learning a dialog policy includes, for each of at least one scenario, in which annotators in a pool of annotators serve as virtual agents and users, generating a respective dialog tree in which each path through the tree corresponds to a dialog and nodes of the tree correspond to dialog acts provided by the annotators. The generation includes computing a measure of uncertainty for nodes in the dialog tree, identifying a next node to be annotated, based on the measure of uncertainty, selecting an annotator from the pool to provide an annotation for the next node, receiving an annotation from the selected annotator for the next node, and generating a new node of the dialog tree based on the received annotation. A corpus of dialogs is generated from the dialog tree.
Owner:CONDUENT BUSINESS SERVICES LLC
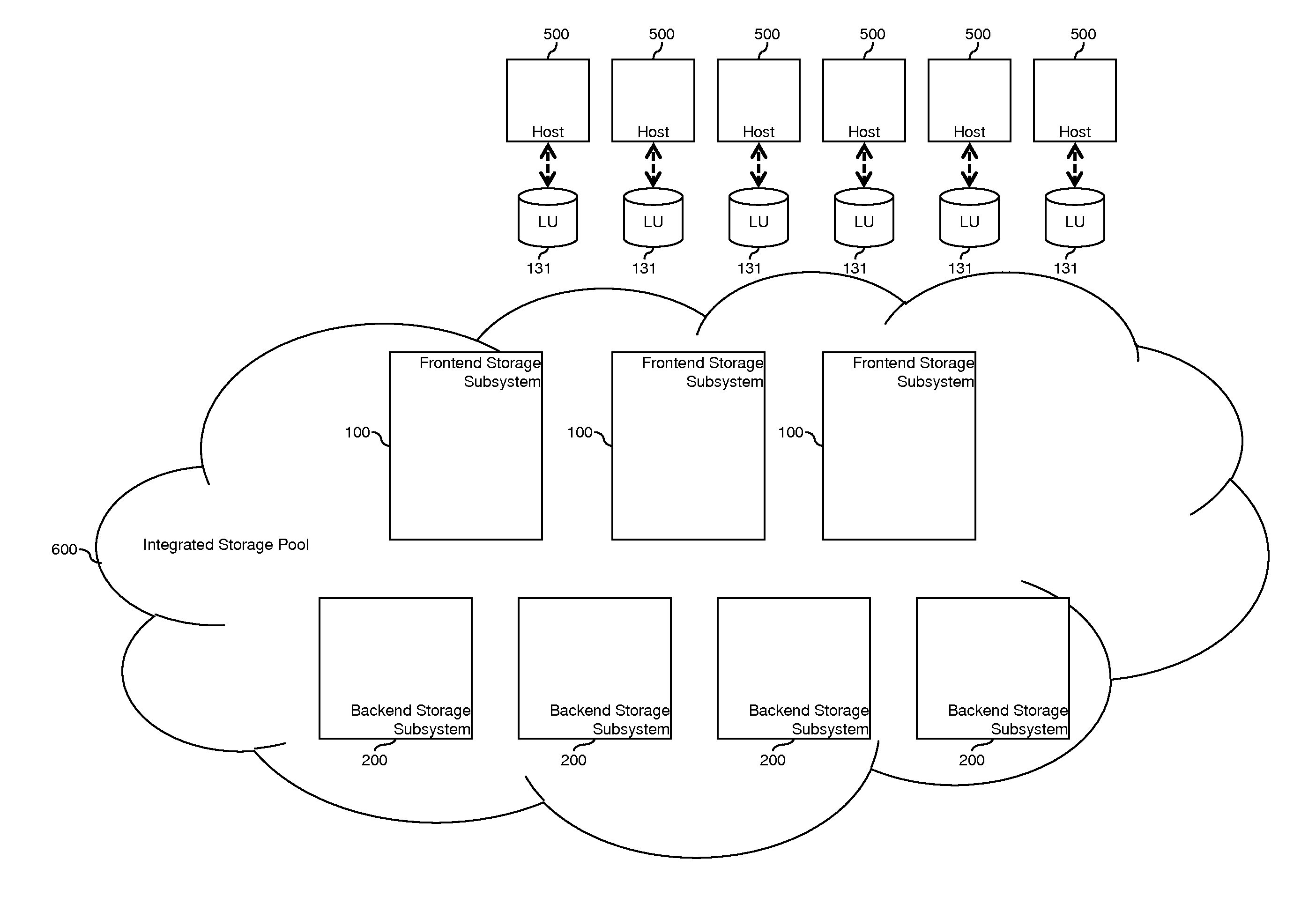
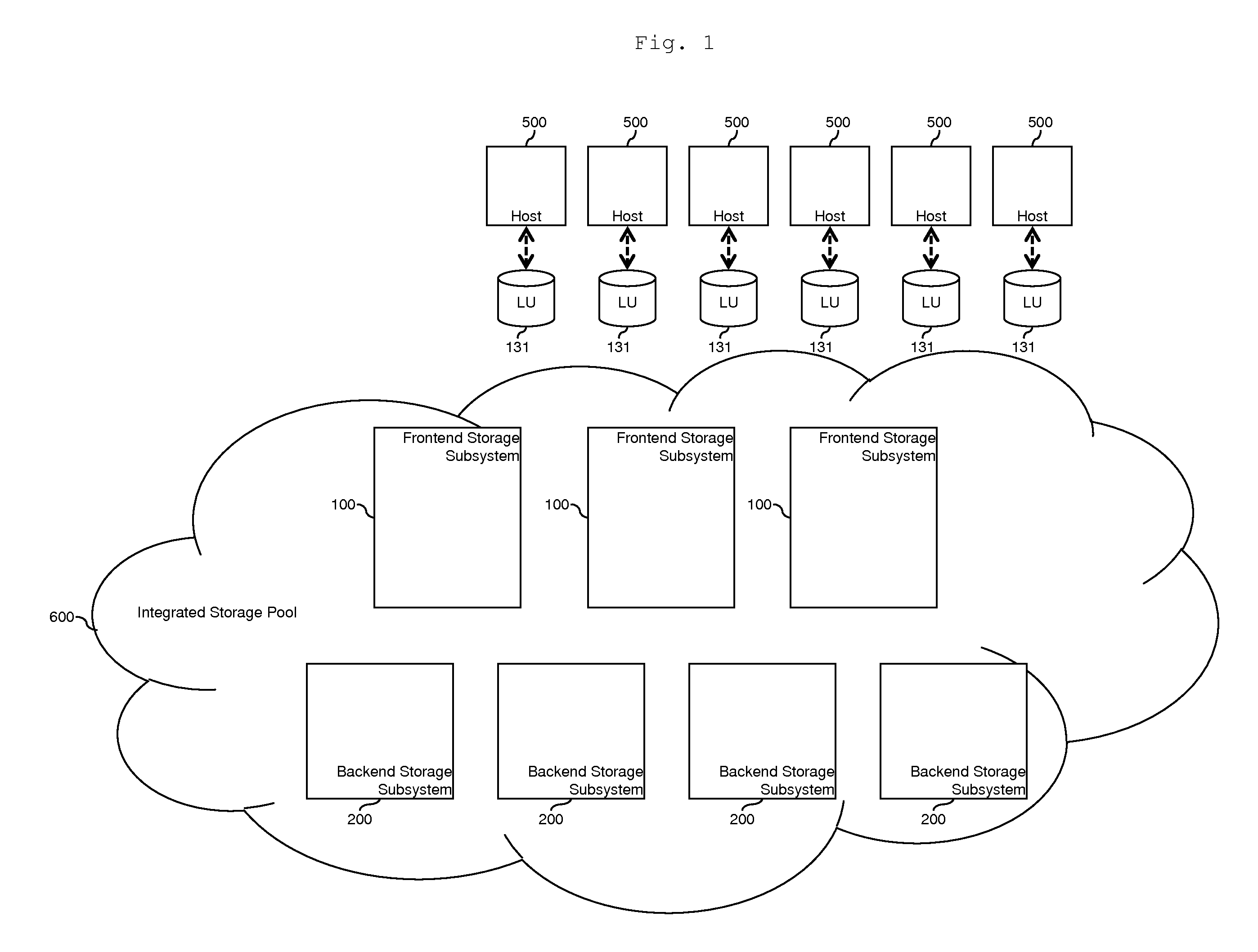
Tiered storage pool management and control for loosely coupled multiple storage environment
ActiveUS20120047346A1Improve manageabilityEasy to controlMemory adressing/allocation/relocationInput/output processes for data processingControl storeEngineering
A system comprises a first storage system including a first storage controller, which receives input / output commands from host computers and provides first storage volumes to the host computers; and a second storage system including a second storage controller which receives input / output commands from host computers and provides second storage volumes to the host computers. A first data storing region of one of the first storage volumes is allocated from a first pool by the first storage controller. A second data storing region of another one of the first storage volumes is allocated from a second pool by the first storage controller. A third data storing region of one of the second storage volumes is allocated from the first pool by the second storage controller. A fourth data storing region of another one of the second storage volumes is allocated from the second pool by the second storage controller.
Owner:HITACHI LTD
Background read scanning with defect reallocation
InactiveUS6412089B1Disc-shaped record carriersRecord information storageComputerized systemExecution cycle
A method, apparatus and computer system for correcting errors and defects in a storage device. The storage device includes media for storing data. A periodic read scan is performed to test the data. If a repeatable error is found, the data is moved to a new sector from a pool of available sectors. Defects are counted and identified in a defect list for reporting to the host. The storage device is scannable is small segments to minimize impact on performance.
Owner:HEWLETT PACKARD DEV CO LP
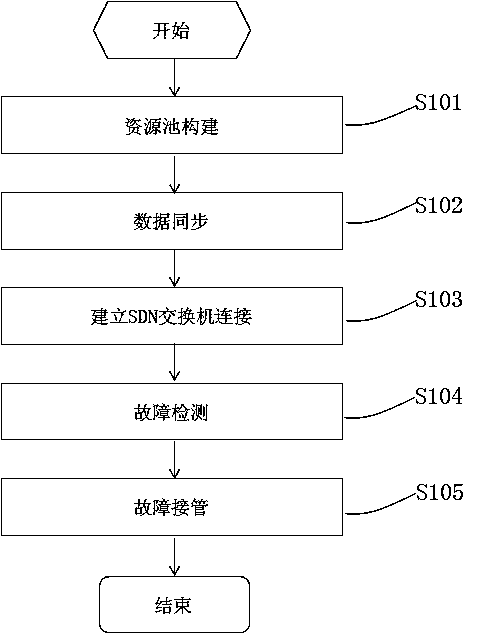
Implementation method for SDN controller pool
InactiveCN103929333AImprove reliabilityImprove efficiencyData switching networksResource poolReal-time computing
The invention discloses an implementation method for an SDN Controller Pool. The resource pool is composed of a plurality of SDN controllers, wherein each controller in the pool is in the load-sharing working state, if faults happen to any controller, fault controller can be taken over by the other controllers in a lossless mode, synchronous states and dynamic data are sent to other nodes through an elected main node, and lossless taking over can be conducted when node faults occur. The implementation method mainly includes the step of resource pool construction, the step of data synchronization, the step of SDN switch connection establishment, the step of fault detection and the step of fault taking over.
Owner:陈桂芳
Dynamically Tuning A Server Multiprogramming Level
Methods, apparatus and computer program products for allocating a number of workers to a worker pool in a multiprogrammable computer are provided, to thereby tune server multiprogramming level. The method includes the steps of monitoring throughput in relation to a workload concurrency level and dynamically tuning a multiprogramming level based upon the monitoring. The dynamic tuning includes adjusting with a first adjustment for a first interval and with a second adjustment for a second interval, wherein the second adjustment utilizes data stored from the first adjustment.
Owner:IANYWHERE SOLUTIONS
Method and system to support dynamic rights and resources sharing
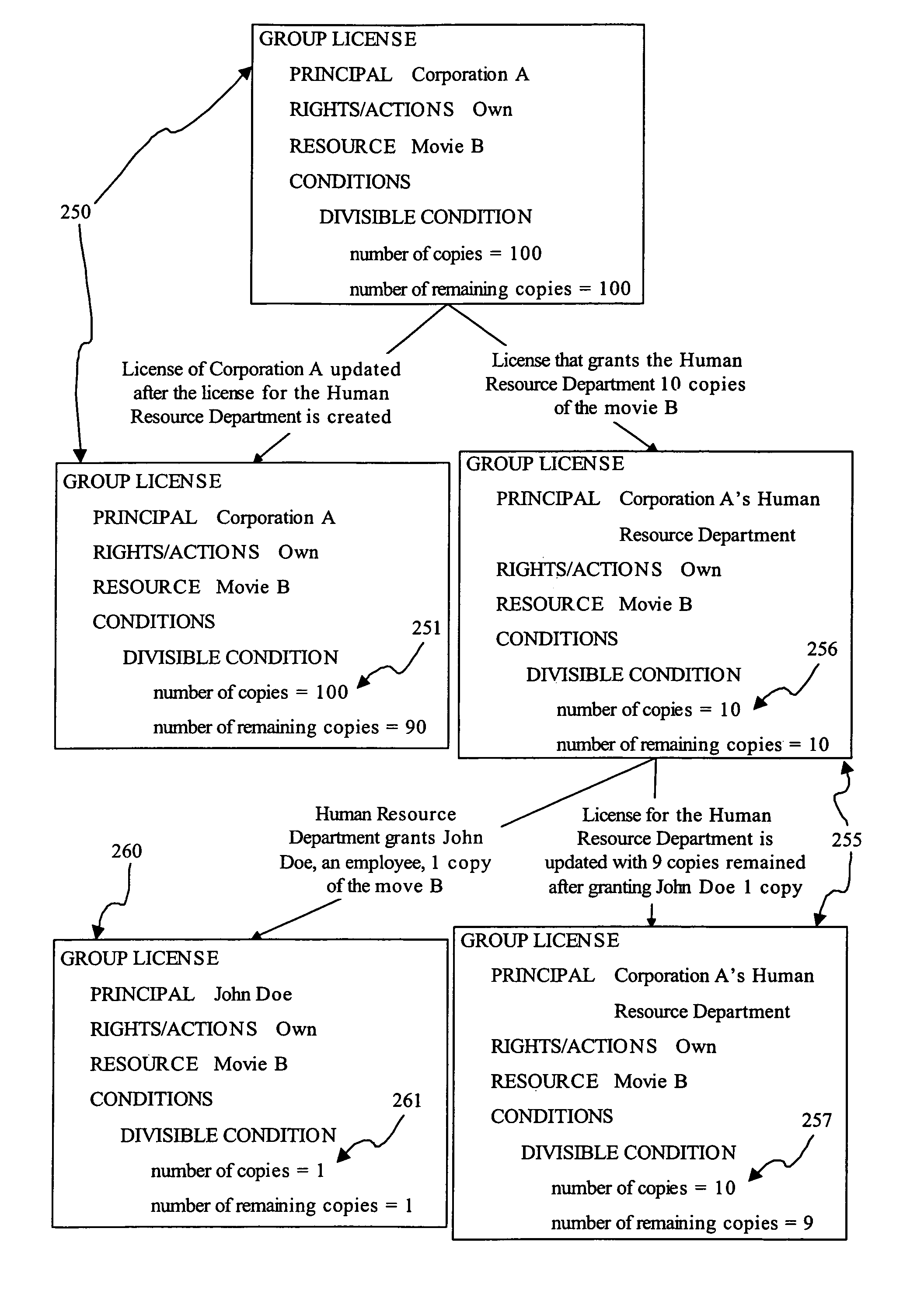
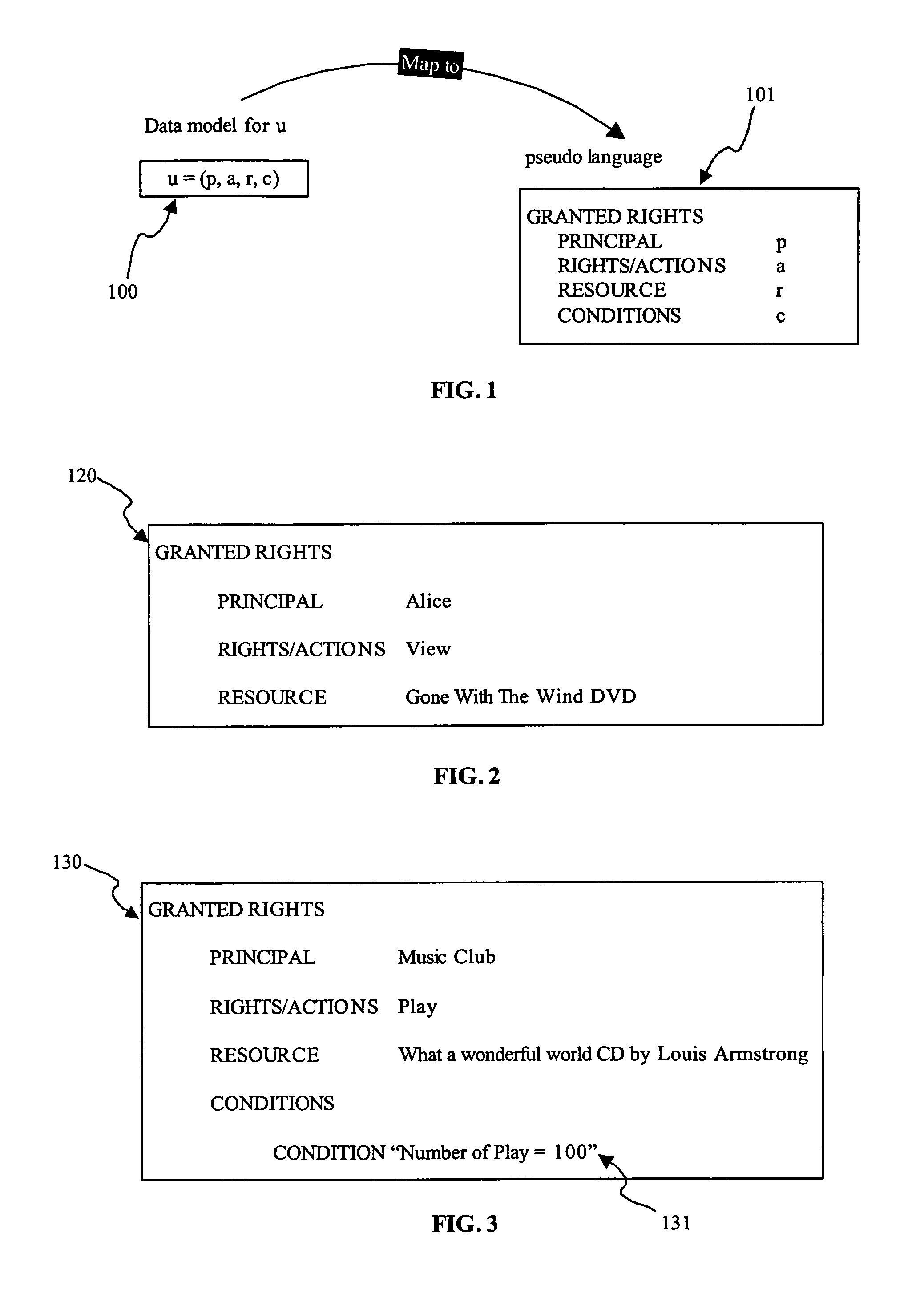
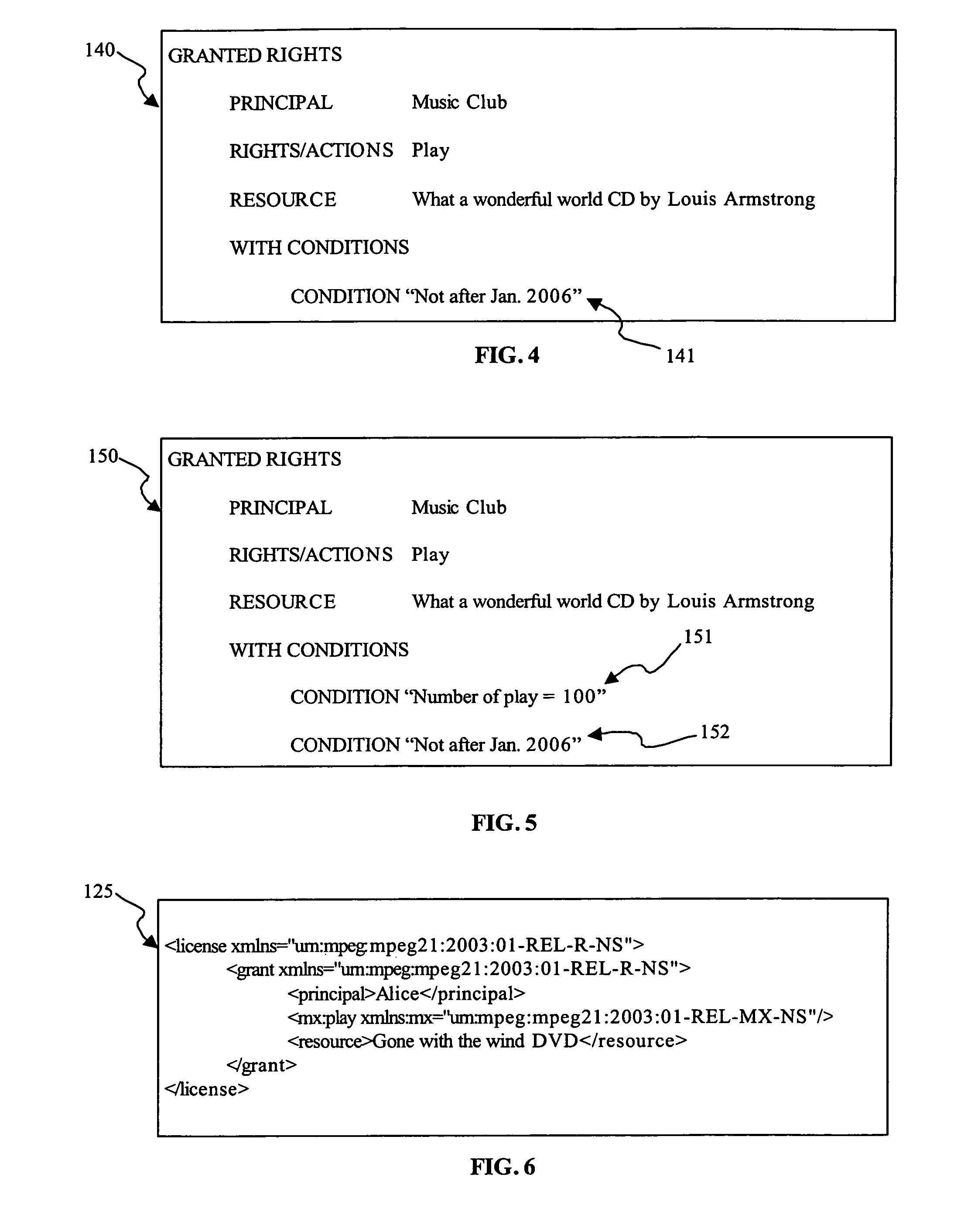
The invention relates to method for deriving a sub-right from a right, the right comprising a plurality of components, each of which specifies an aspect of the right. A component may be, for example, a principal, an action, a resource, and a condition. The invention also relates to a method for integrating a first right with a second right. Furthermore, the invention relates to a method of sharing rights by deriving a sub-right from a right, allowing use of the sub-right, and integrating the sub-right with the right. In addition, the invention relates to a system to support rights sharing by enabling the derivation of a sub-right from a right, the right comprising plural components each of which specifies an aspect of the right, the system comprising a receiving module for receiving a sub-right, the sub-right comprising plural components each of which specifies an aspect of the sub-right, and a confirmation module for confirming that the values of the components of the sub-right can be derived from the values of the corresponding components of the right. The invention further relates to a method for deriving a sub-right from a pool of rights granted by a grantor to a grantee for controlling use of resources within a computing environment, the computing environment having a mechanism for enforcing rights within the environment to control use of resources in accordance with the rights.
Owner:CONTENTGUARD HLDG
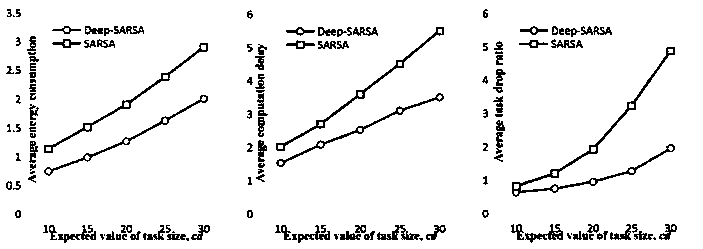
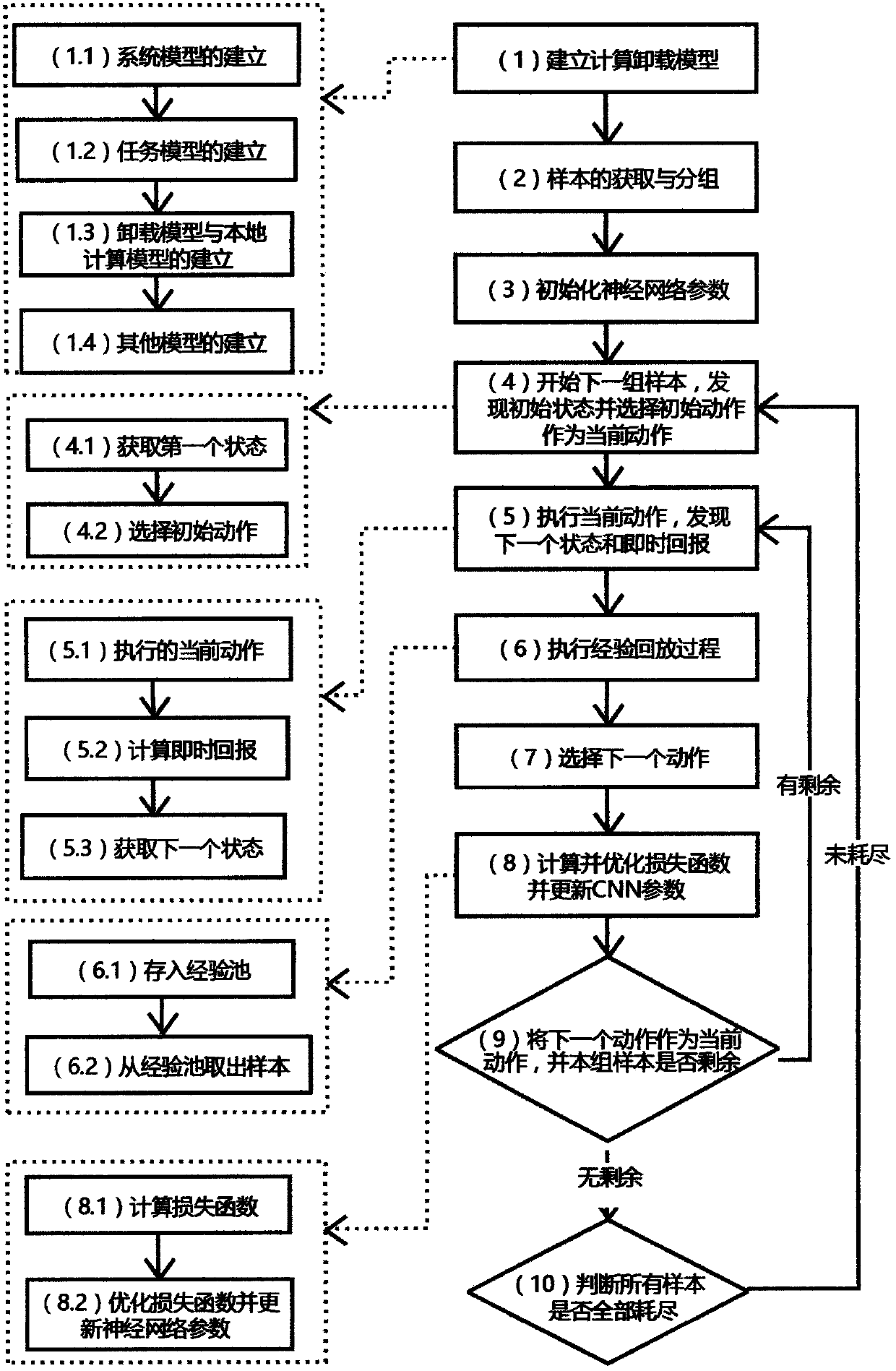
A computing unloading scheduling method based on depth reinforcement learning
InactiveCN109257429AReduce correlationEffective calculationNeural architecturesTransmissionAlgorithmState model
The invention provides a computing unloading scheduling method based on depth reinforcement learning, which provides a method for computing unloading to make unloading decision for Internet of Thingsequipment, including making decisions on various aspects needing to be unloaded according to the basic model of computing unloading. Based on different optimization objectives, different optimizationobjectives can be achieved by changing the value function. TheDeep-SARSA algorithm is similar to DQN algorithm, which combines reinforcement learning and depth learning. It can effectively change theunloading state and unloading action into training samples of depth learning when cooperating with experience pool. The invention can effectively carry out machine learning on an unloading state modelof an unlimited dimension, reducing the complexity of learning, this method uses neural network as the linear approximator of Q value, which can effectively improve the training speed and reduce thesample required for training. This method can effectively make the best decision through deep reinforcement learning under the given model and optimization objective.
Owner:NANJING UNIV
System and method for identification of discrepancies in actual and expected inventories in computing environment having multiple provisioning orchestration server pool boundaries
InactiveUS20060178953A1Performance impact is minimalBetter respondResourcesSoftware simulation/interpretation/emulationOrchestrationDistributed computing
A system for establishing and maintaining inventories of computing environment assets comprising one or more custom collector interfaces that detect movement of assets from one environment to another, and an inventory scanner which modifies inventories for each environment based on monitored asset movements. The present invention is of especial benefit to autonomic and on-demand computing architectures.
Owner:IBM CORP
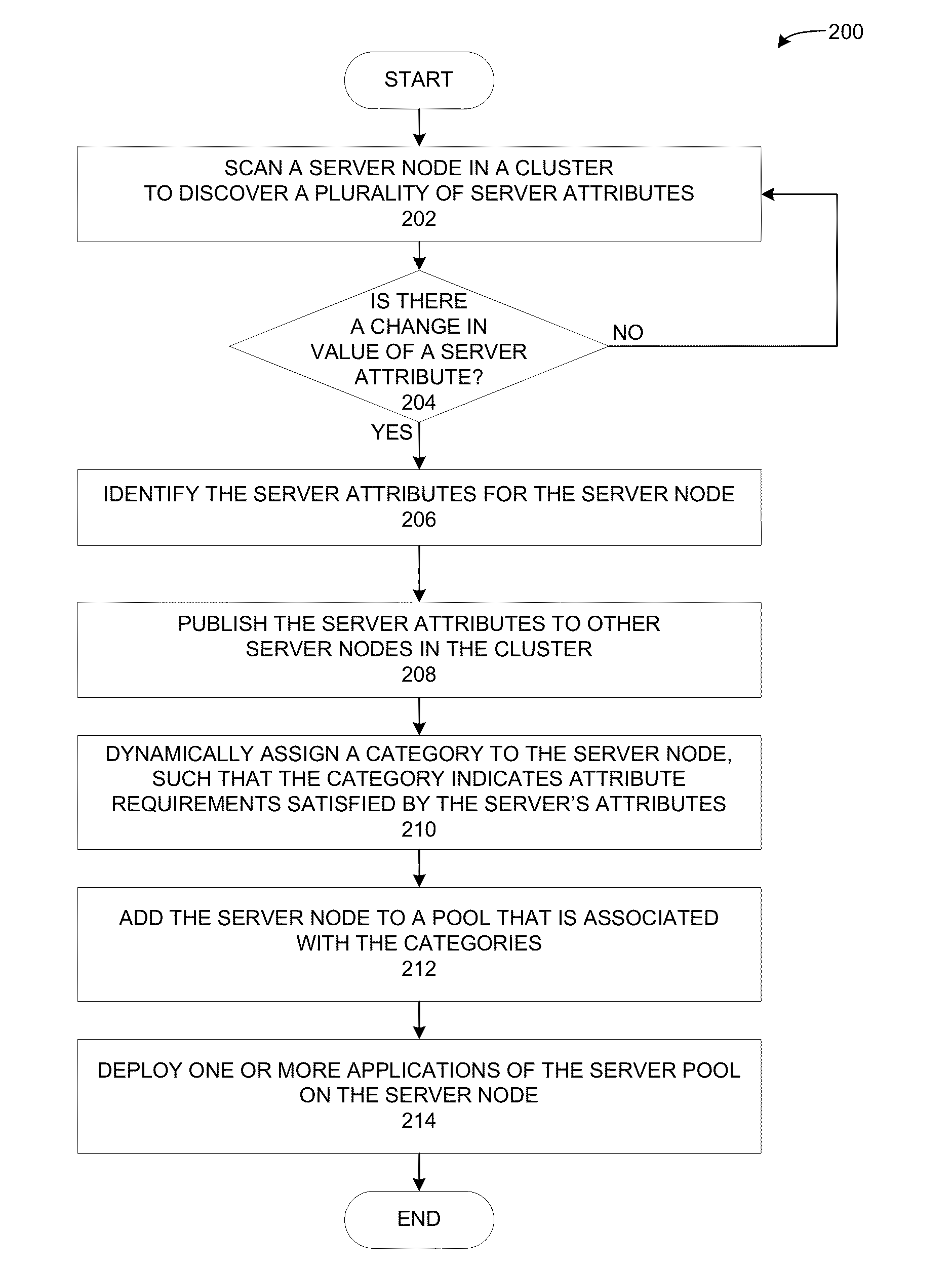
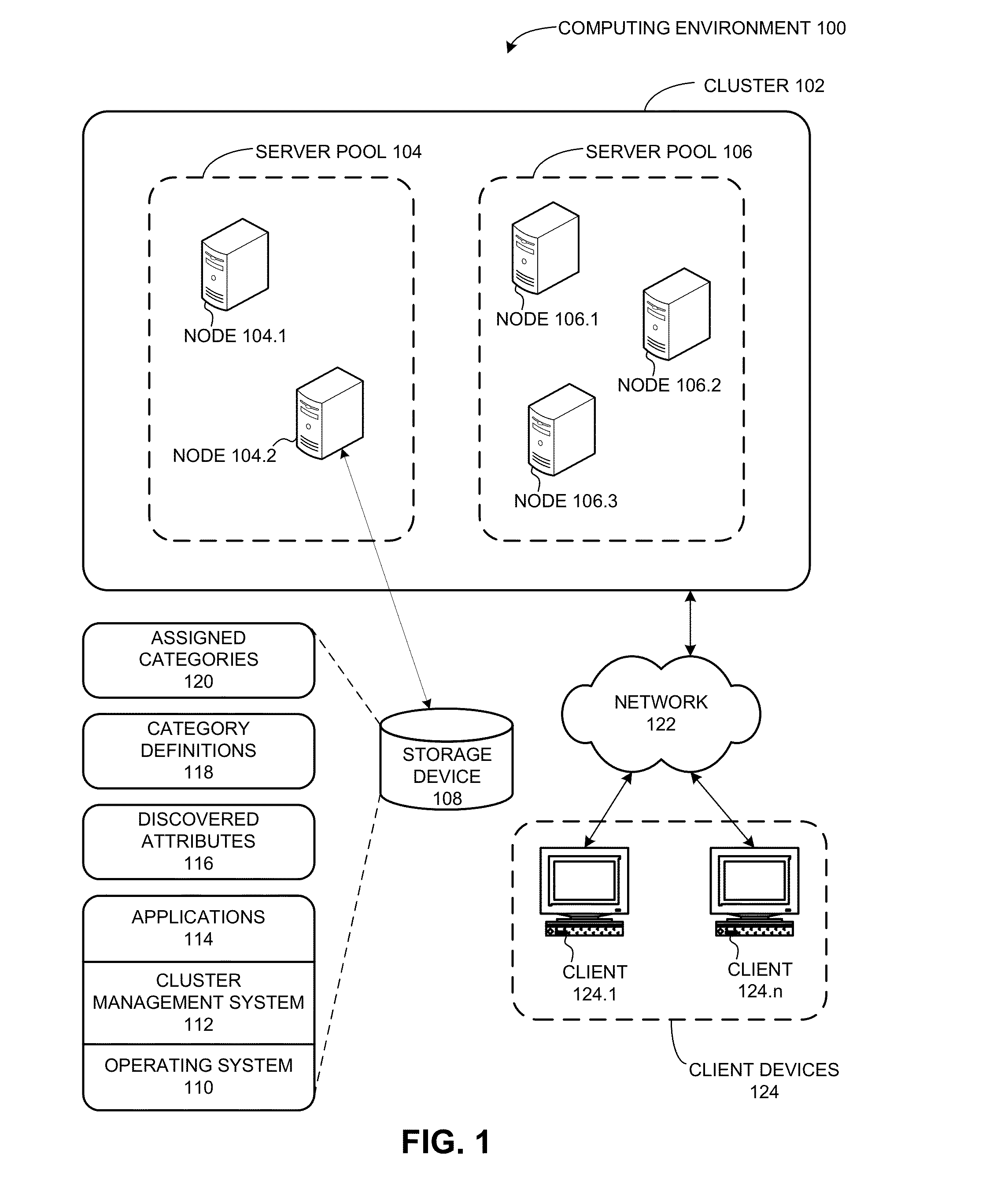
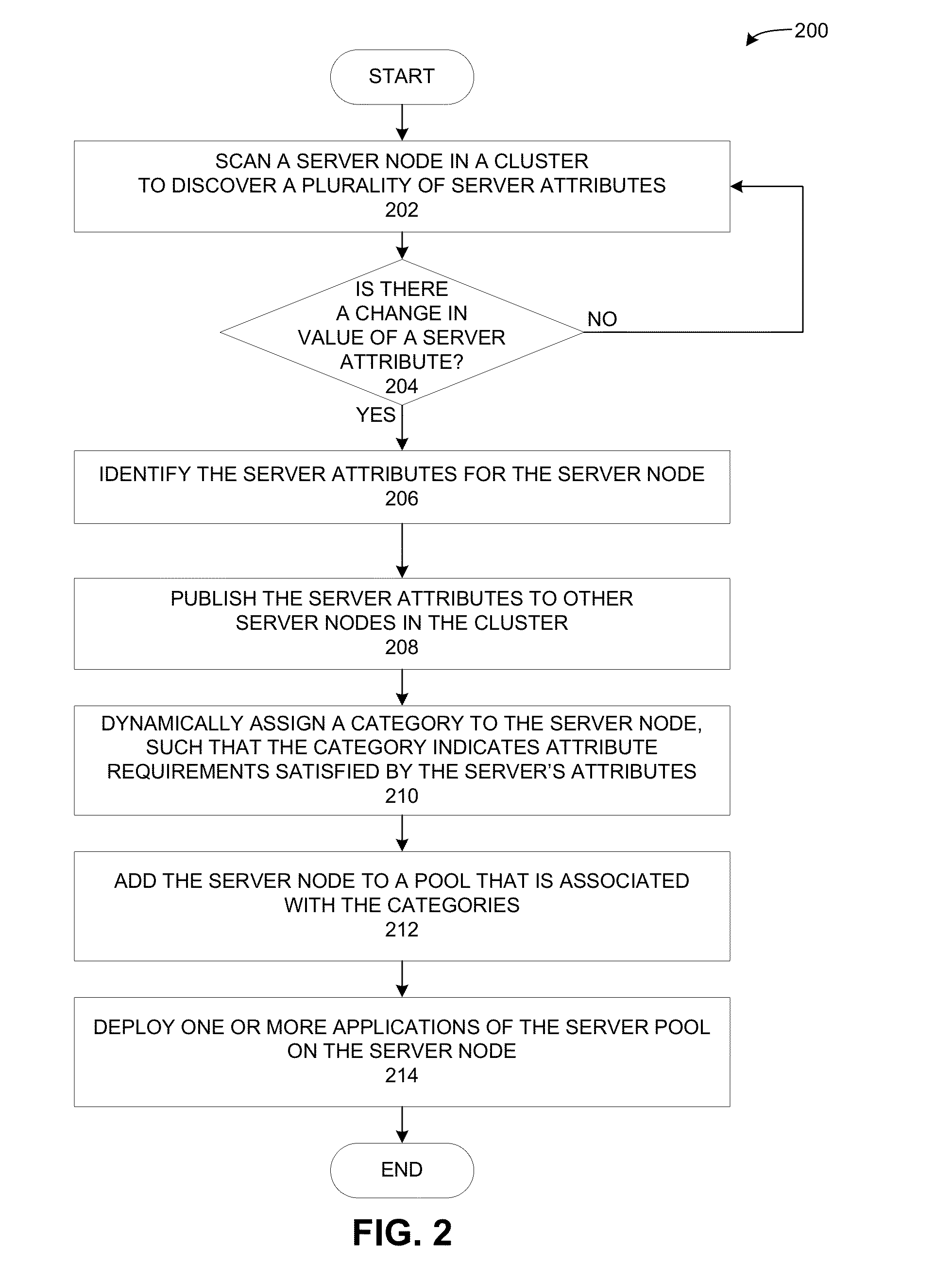
Assigning server categories to server nodes in a heterogeneous cluster
ActiveUS20130219036A1Low priorityDigital computer detailsProgram controlManagement systemHeterogeneous cluster
A cluster management system dynamically assigns a category to a server node based on the server node's attributes. The system can detect a change in value of a server attribute of a first server node. Then, in response to detecting the change in value of the server attribute, the system identifies a plurality of server attributes for the first server node, and dynamically assigns to the first server node a category that matches the server attributes. Further, the system can add the server node to a server pool that has a matching category with the server node.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com