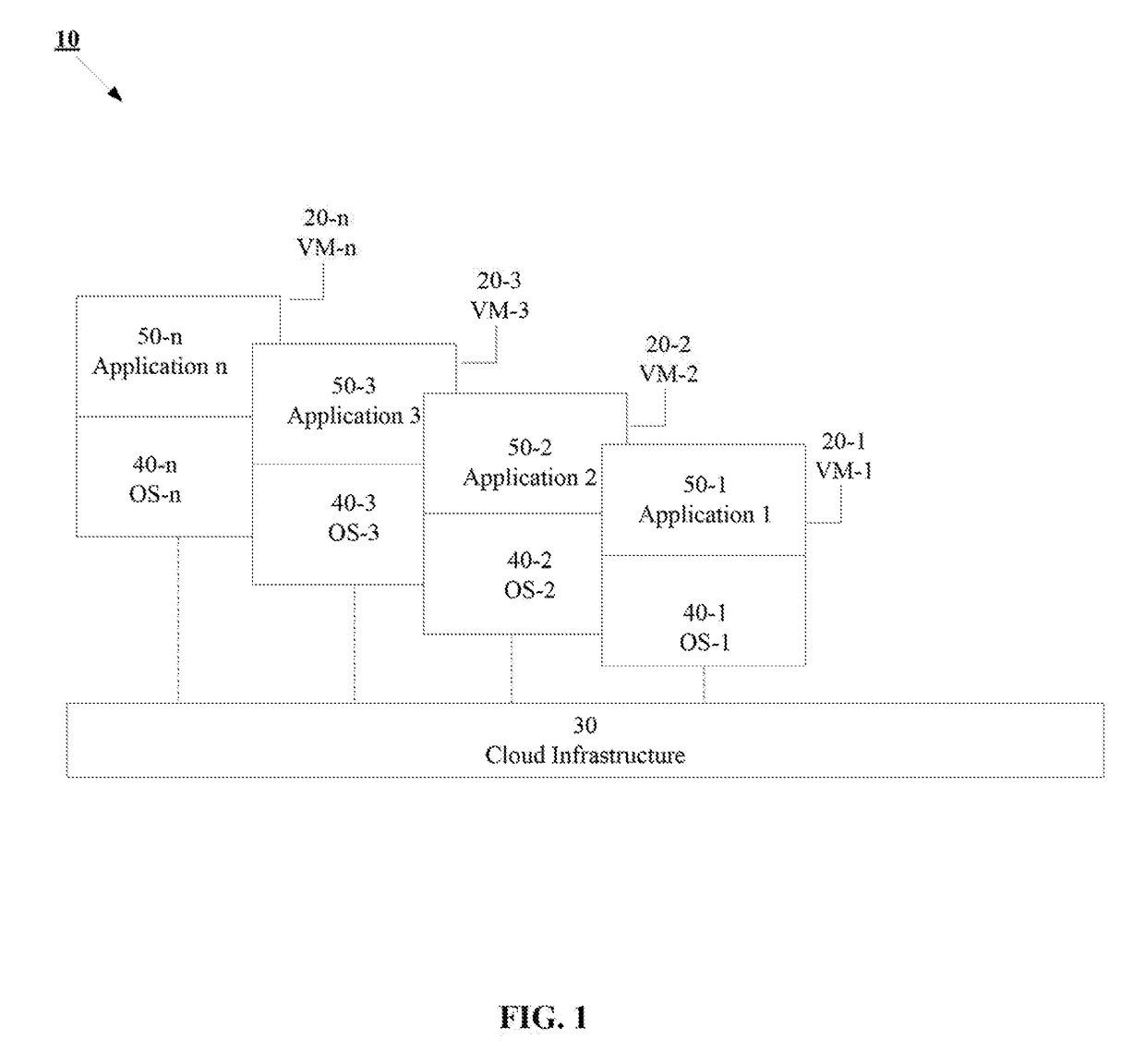
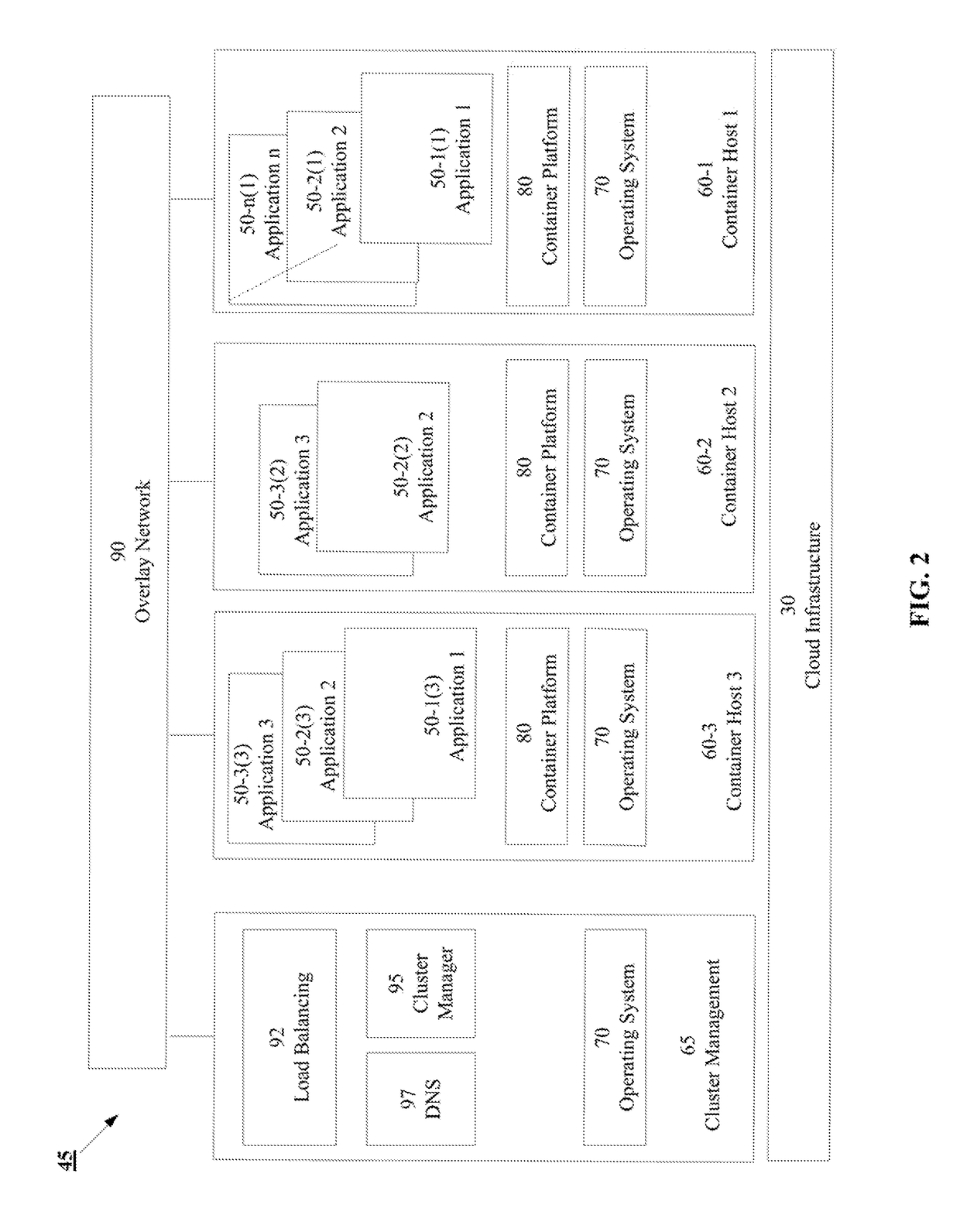
Patents
Literature
459 results about "Orchestration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Orchestration is the study or practice of writing music for an orchestra (or, more loosely, for any musical ensemble, such as a concert band) or of adapting music composed for another medium for an orchestra. Also called "instrumentation", orchestration is the assignment of different instruments to play the different parts (e.g., melody, bassline, etc.) of a musical work. For example, a work for solo piano could be adapted and orchestrated so that an orchestra could perform the piece, or a concert band piece could be orchestrated for a symphony orchestra.
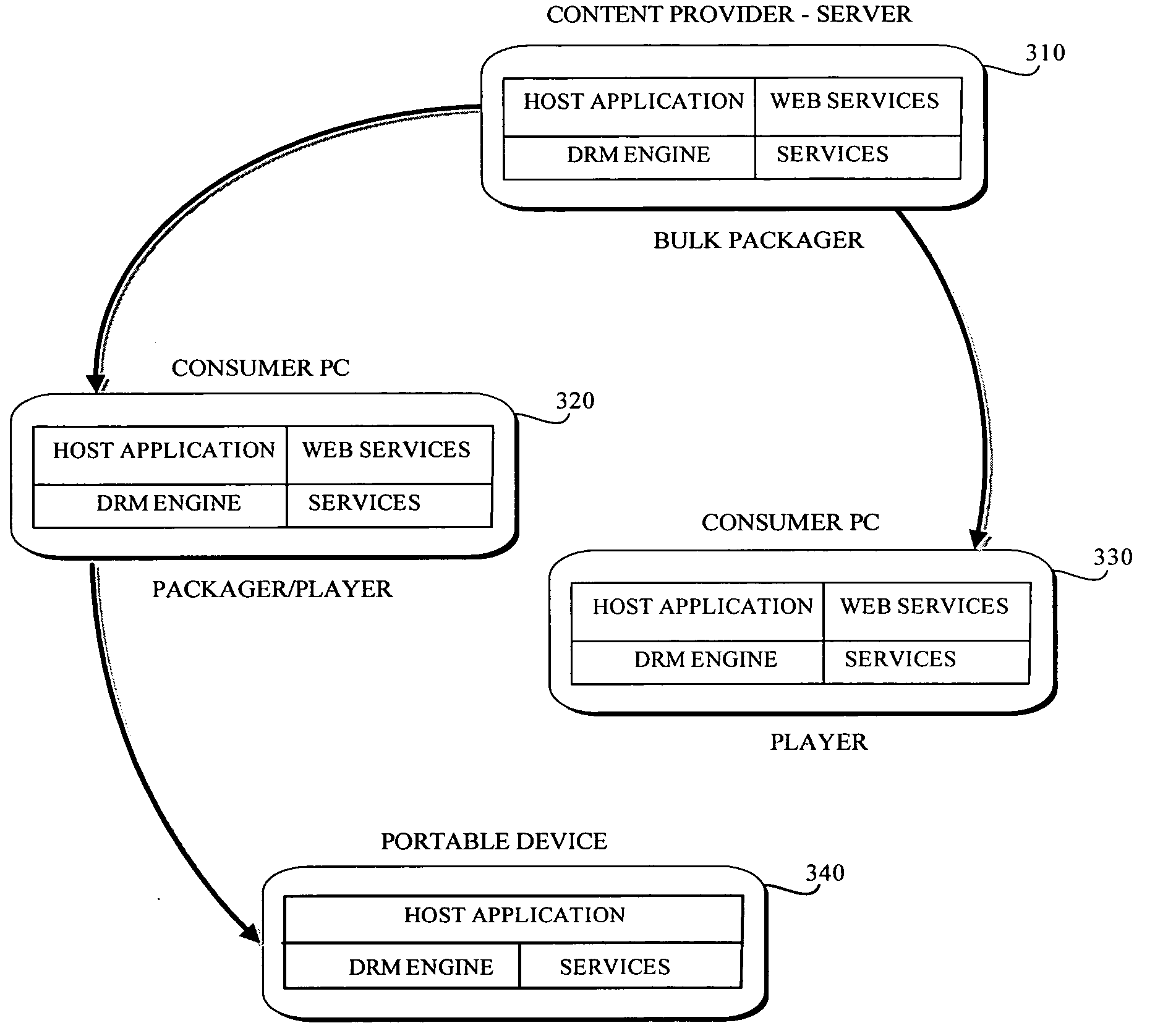
Interoperable systems and methods for peer-to-peer service orchestration
InactiveUS20050027871A1Facilitating commercial exchangeIncrease flexibilityWeb data indexingCryptography processingOperational systemWeb service
Systems and methods are described for performing policy-managed, peer-to-peer service orchestration in a manner that supports the formation of self-organizing service networks that enable rich media experiences. In one embodiment, services are distributed across peer-to-peer communicating nodes, and each node provides message routing and orchestration using a message pump and workflow collator. Distributed policy management of service interfaces helps to provide trust and security, supporting commercial exchange of value. Peer-to-peer messaging and workflow collation allow services to be dynamically created from a heterogeneous set of primitive services. The shared resources are services of many different types, using different service interface bindings beyond those typically supported in a web service deployments built on UDDI, SOAP, and WSDL. In a preferred embodiment, a media services framework is provided that enables nodes to find one another, interact, exchange value, and cooperate across tiers of networks from WANs to PANs.
Owner:INTERTRUST TECH CORP
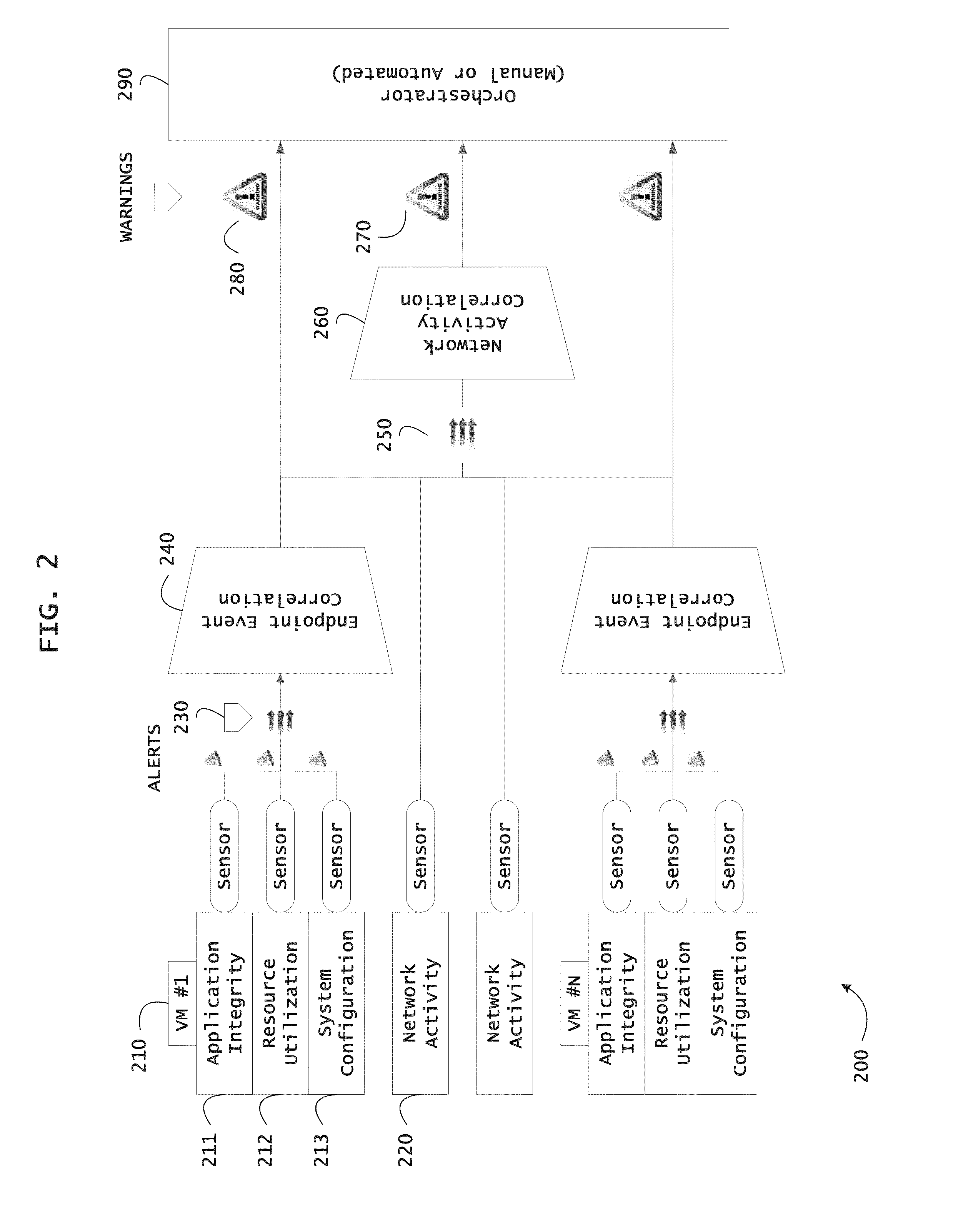
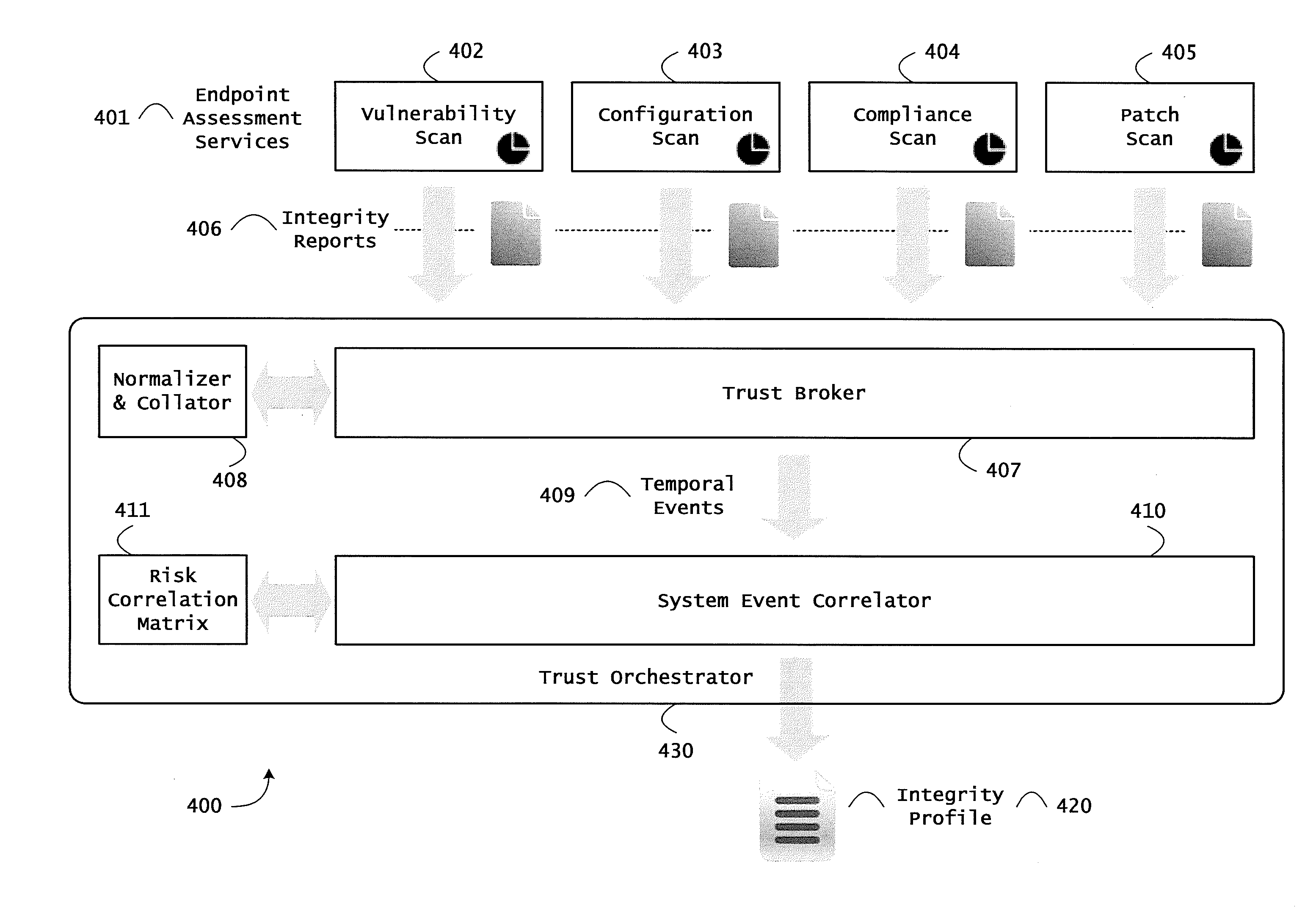
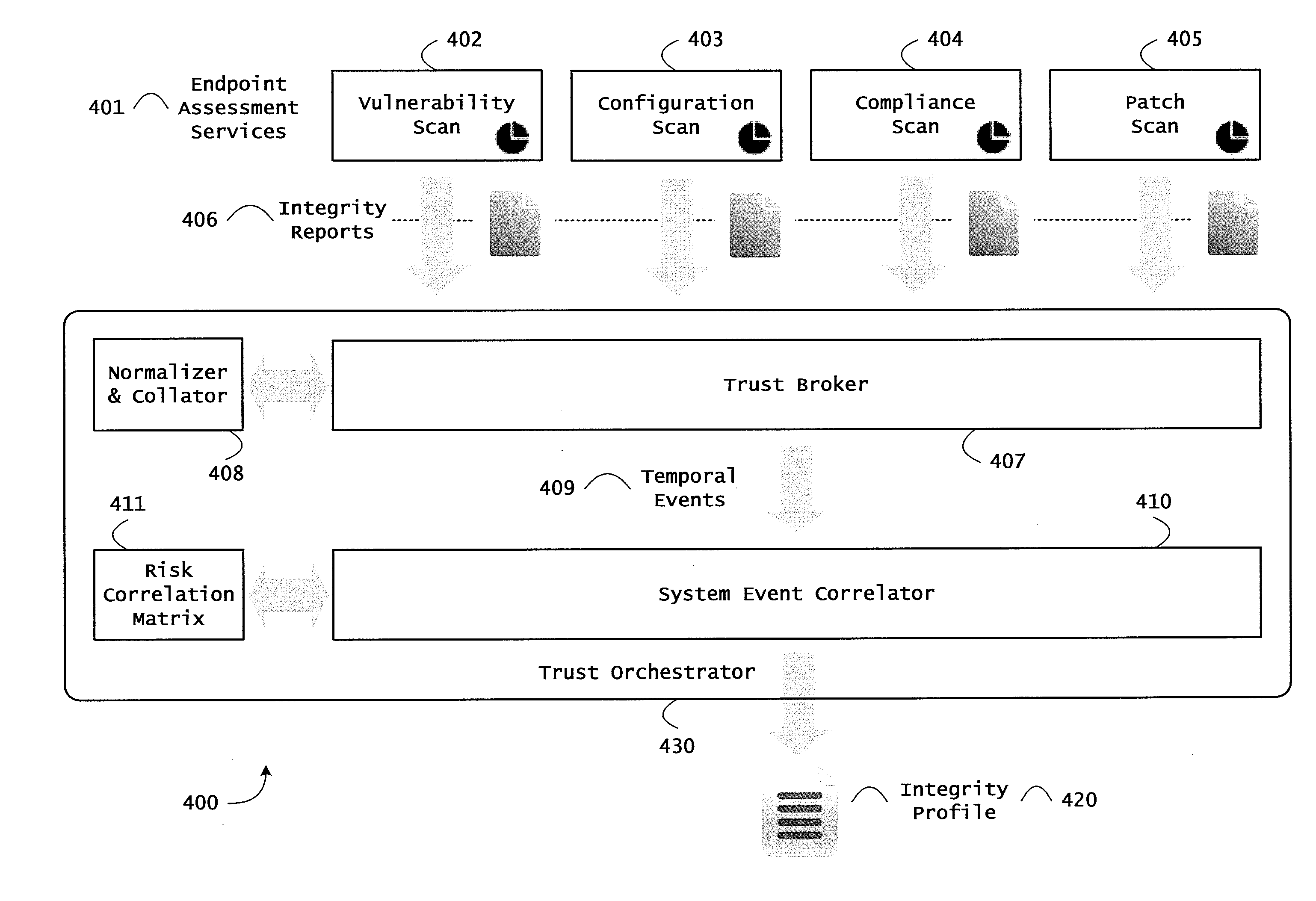
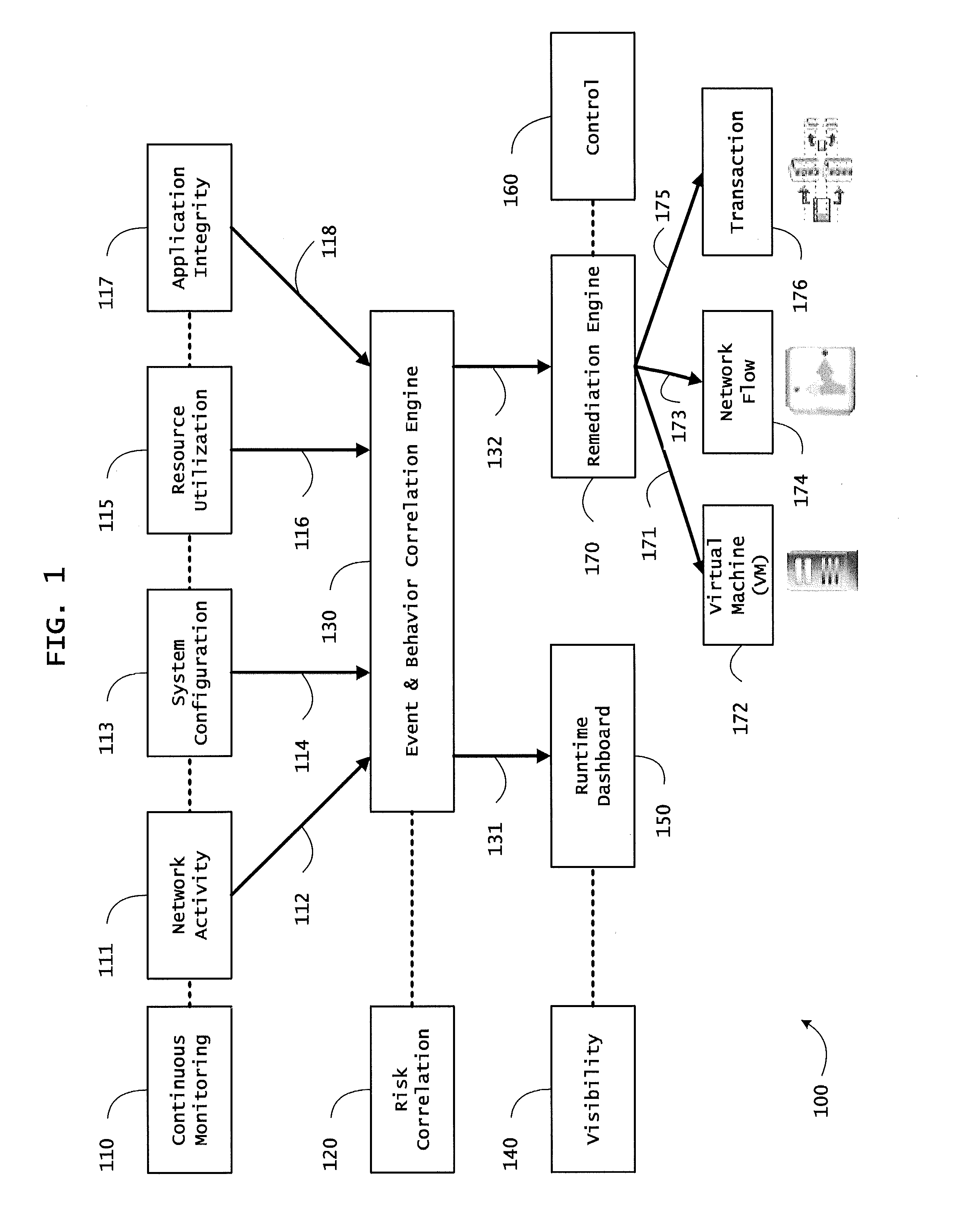
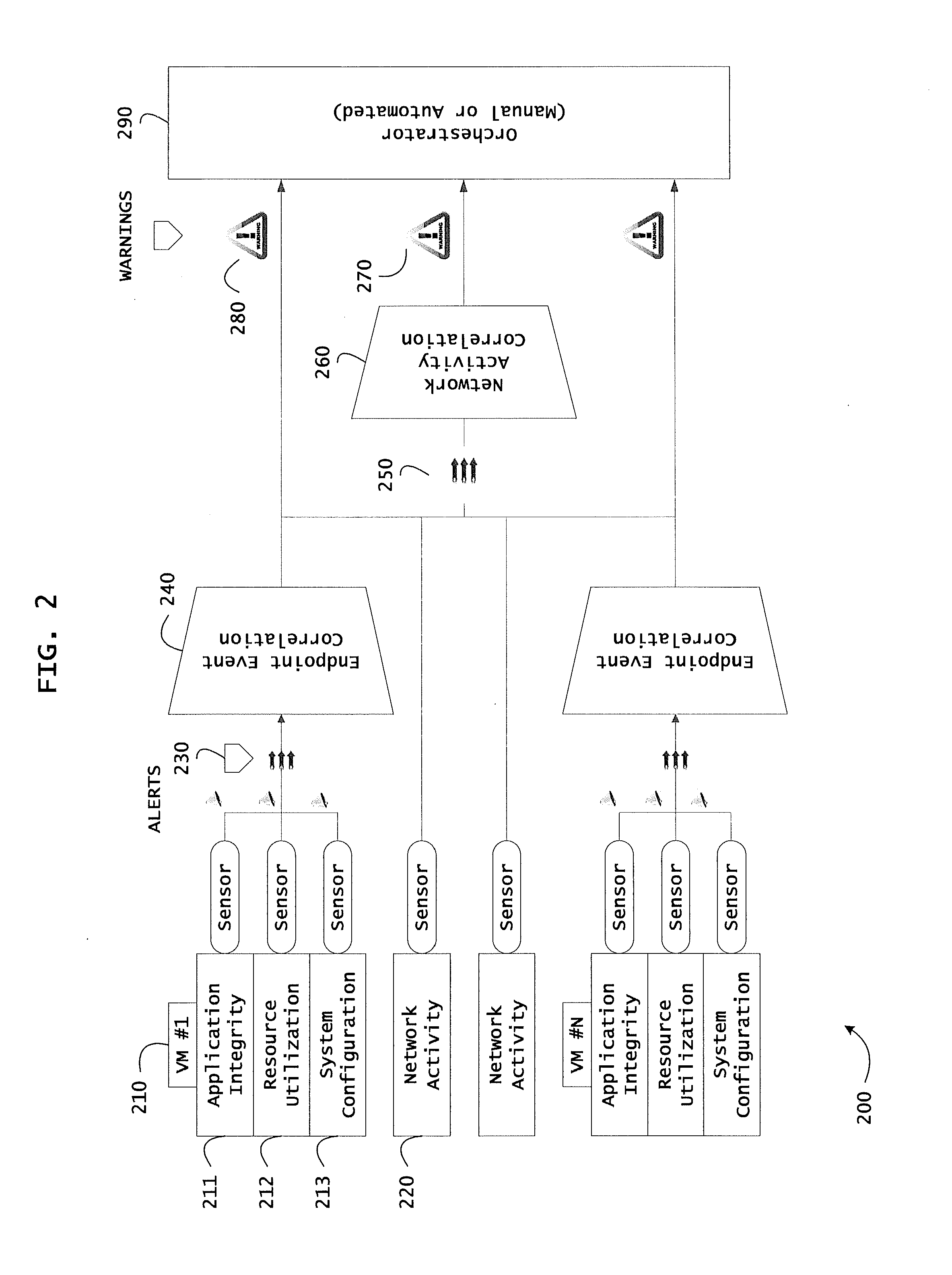
Systems and methods for threat identification and remediation
ActiveUS20130298244A1Memory loss protectionError detection/correctionOrchestrationApplication software
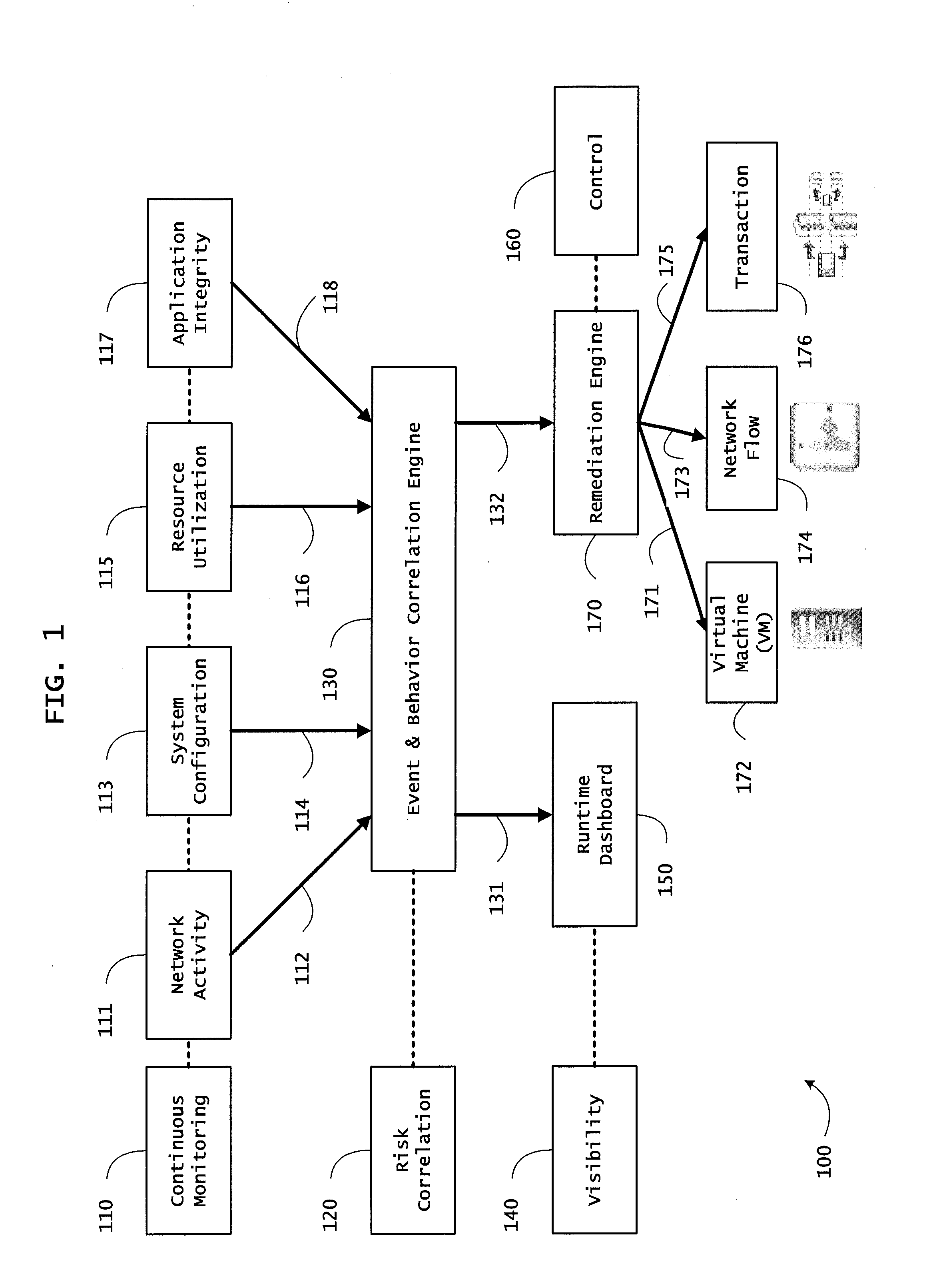
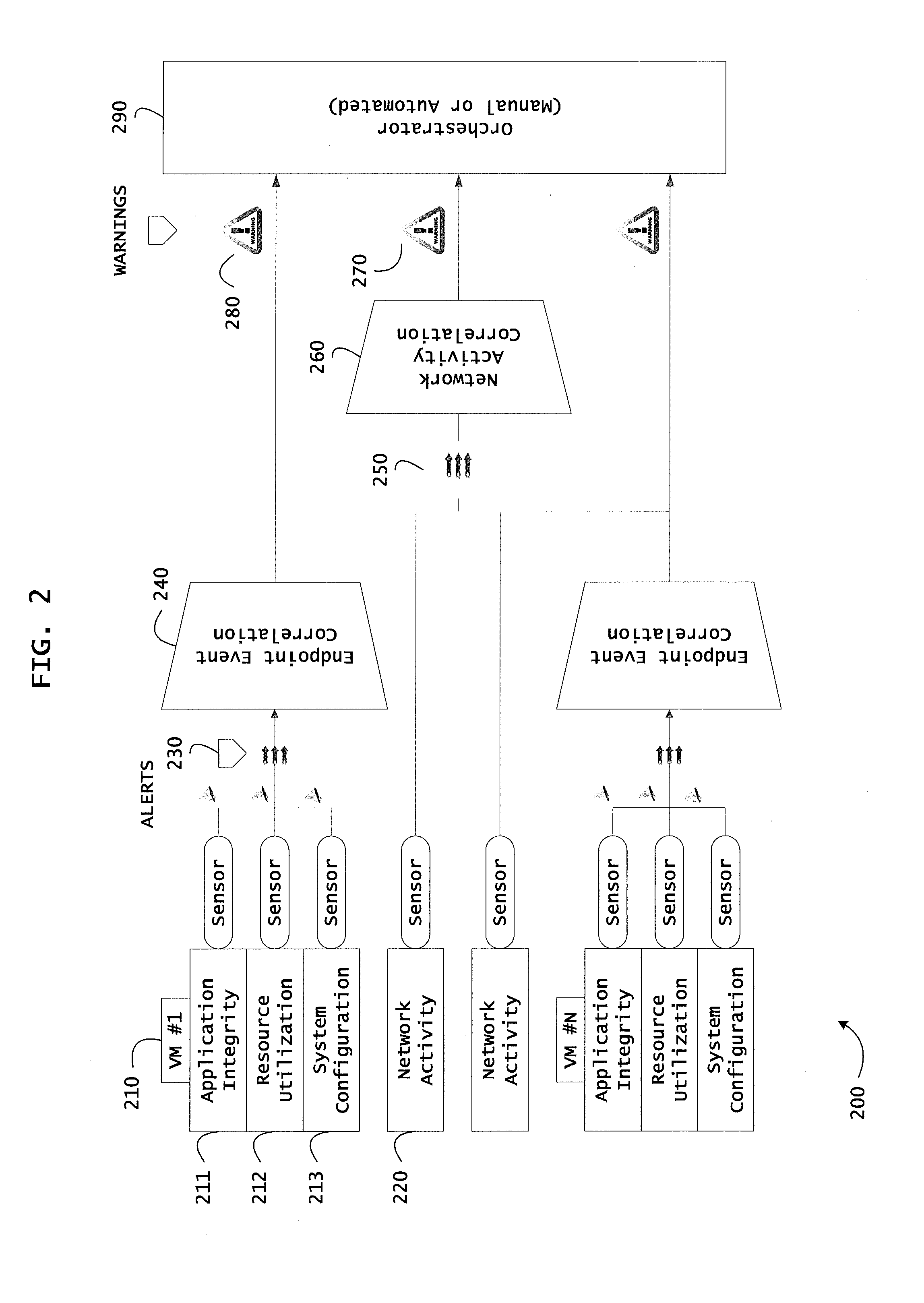
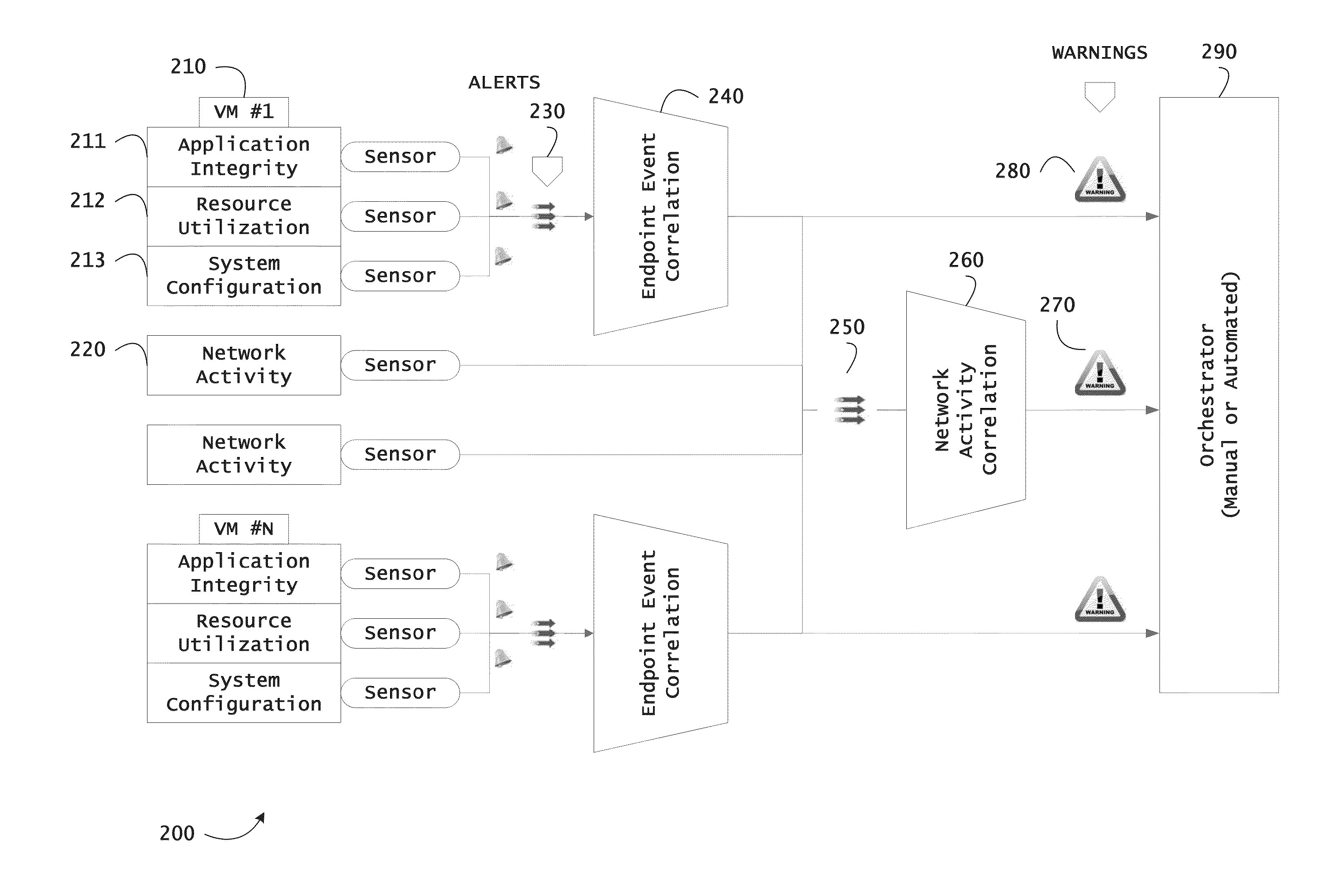
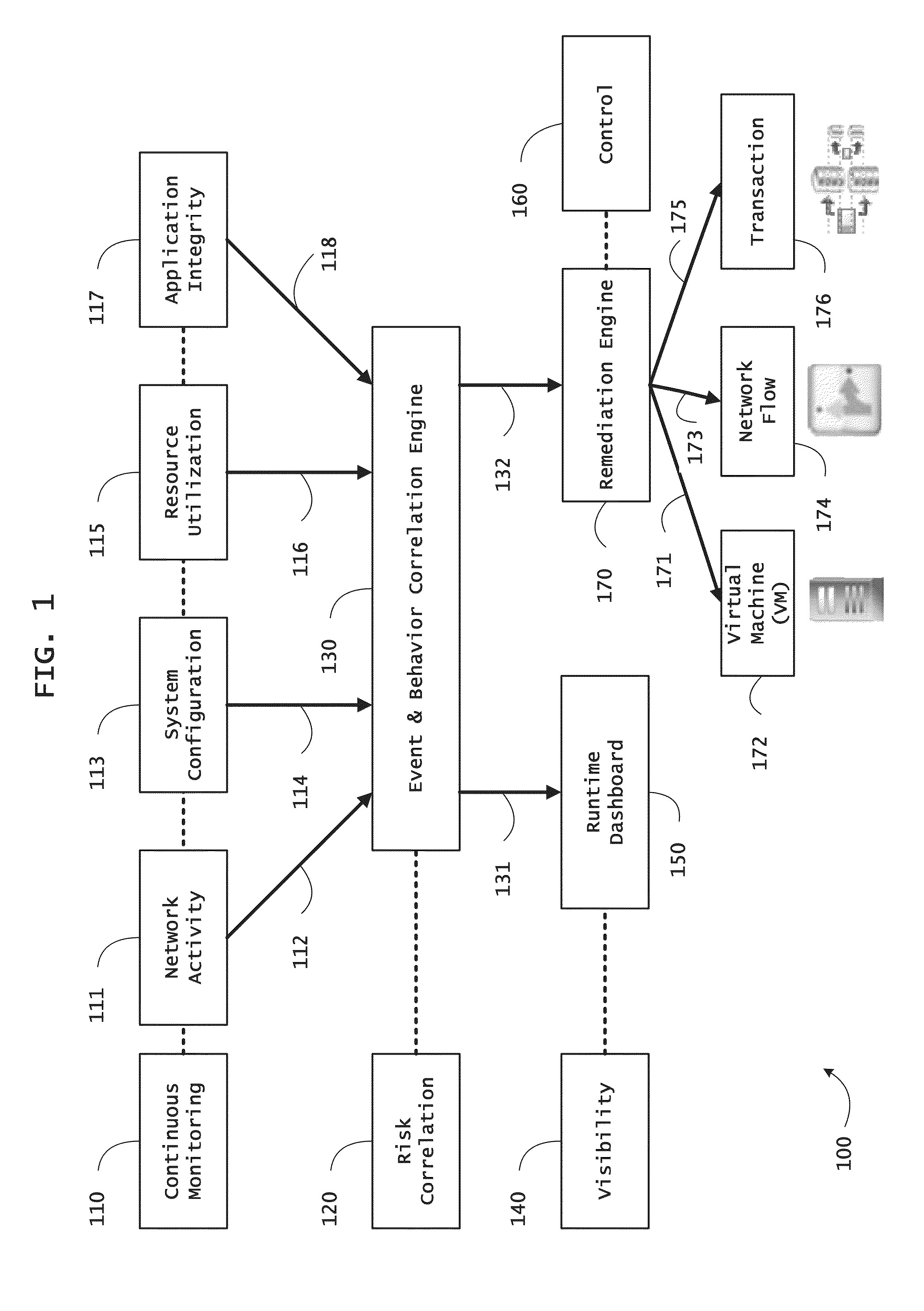
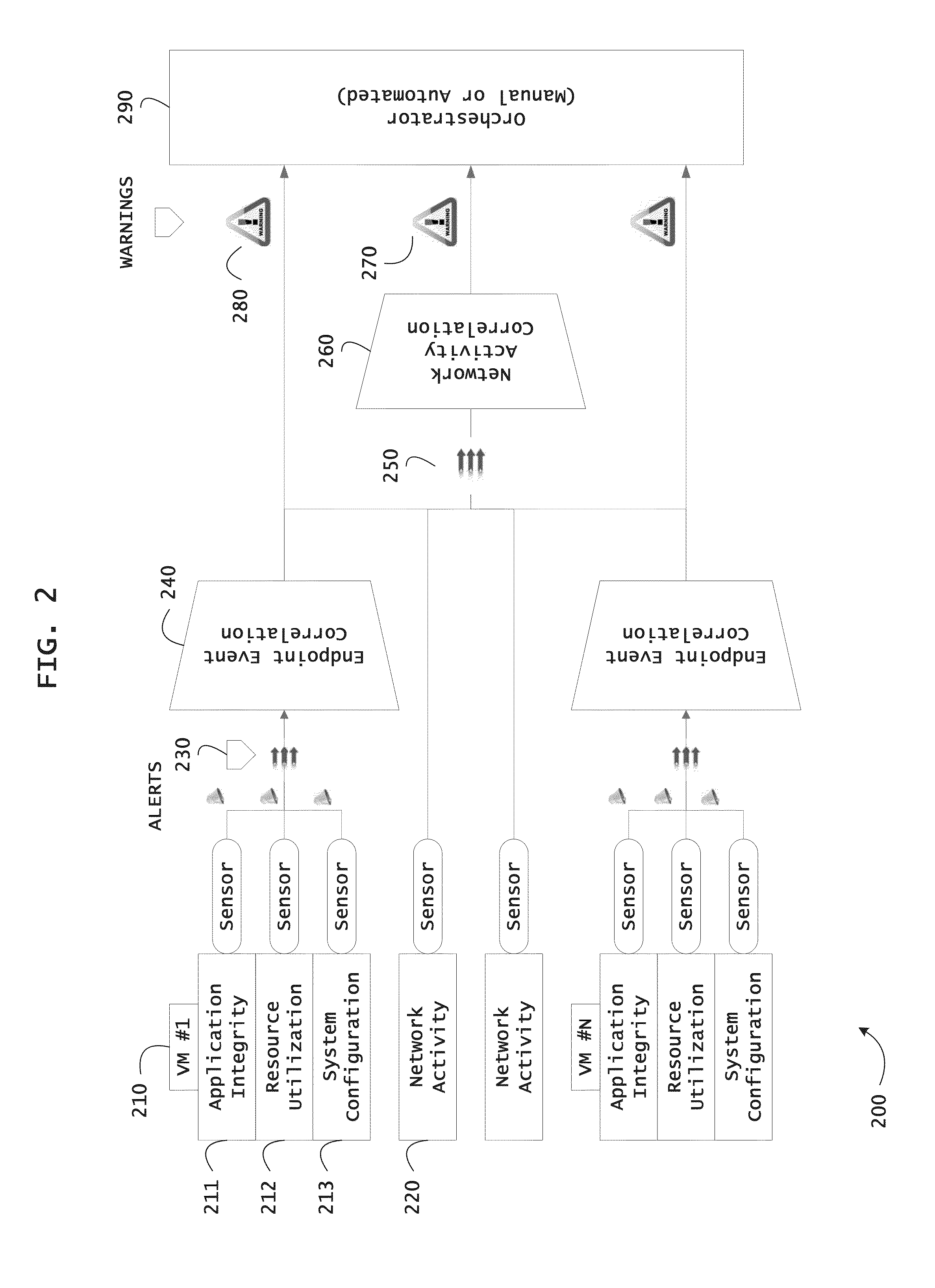
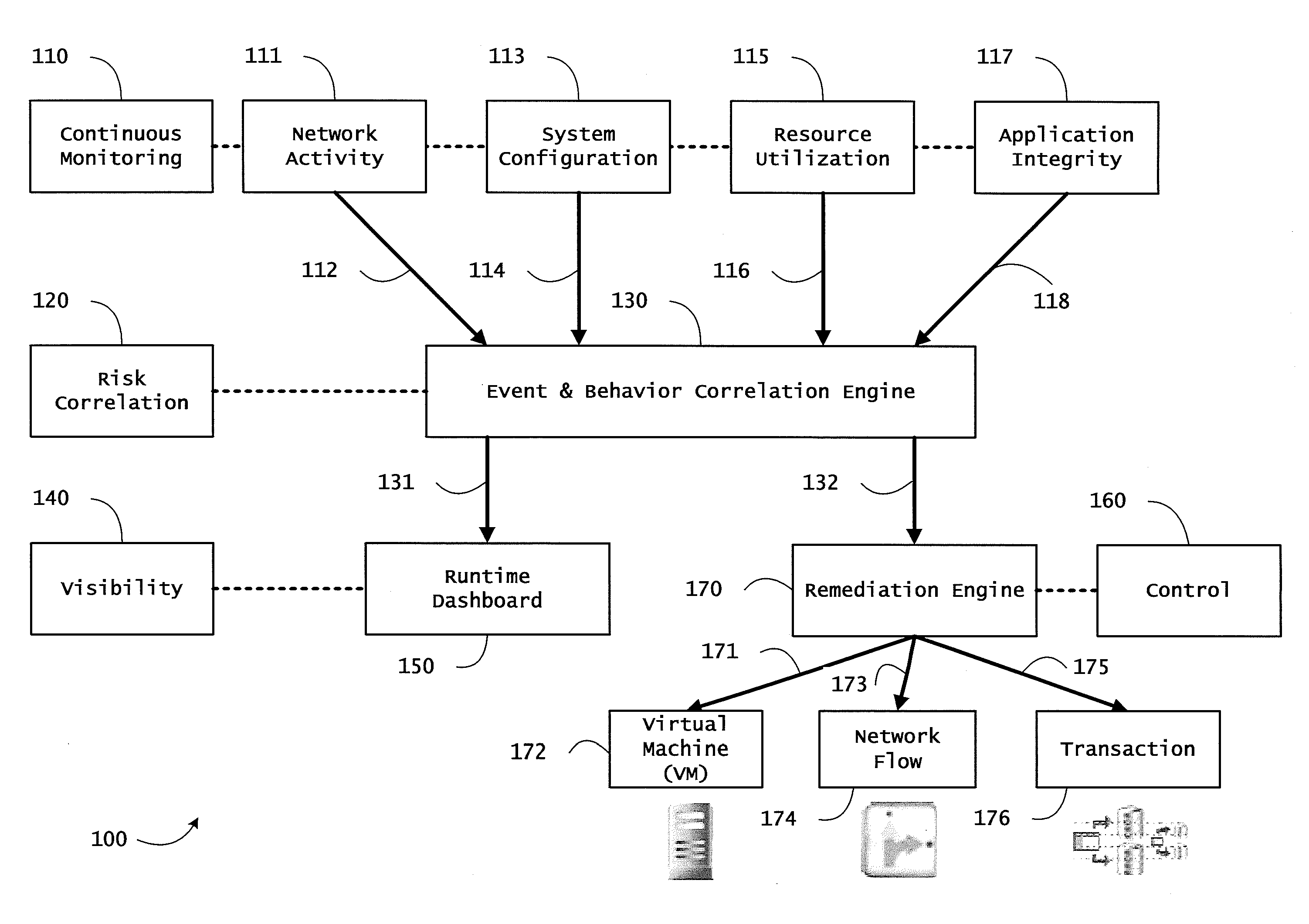
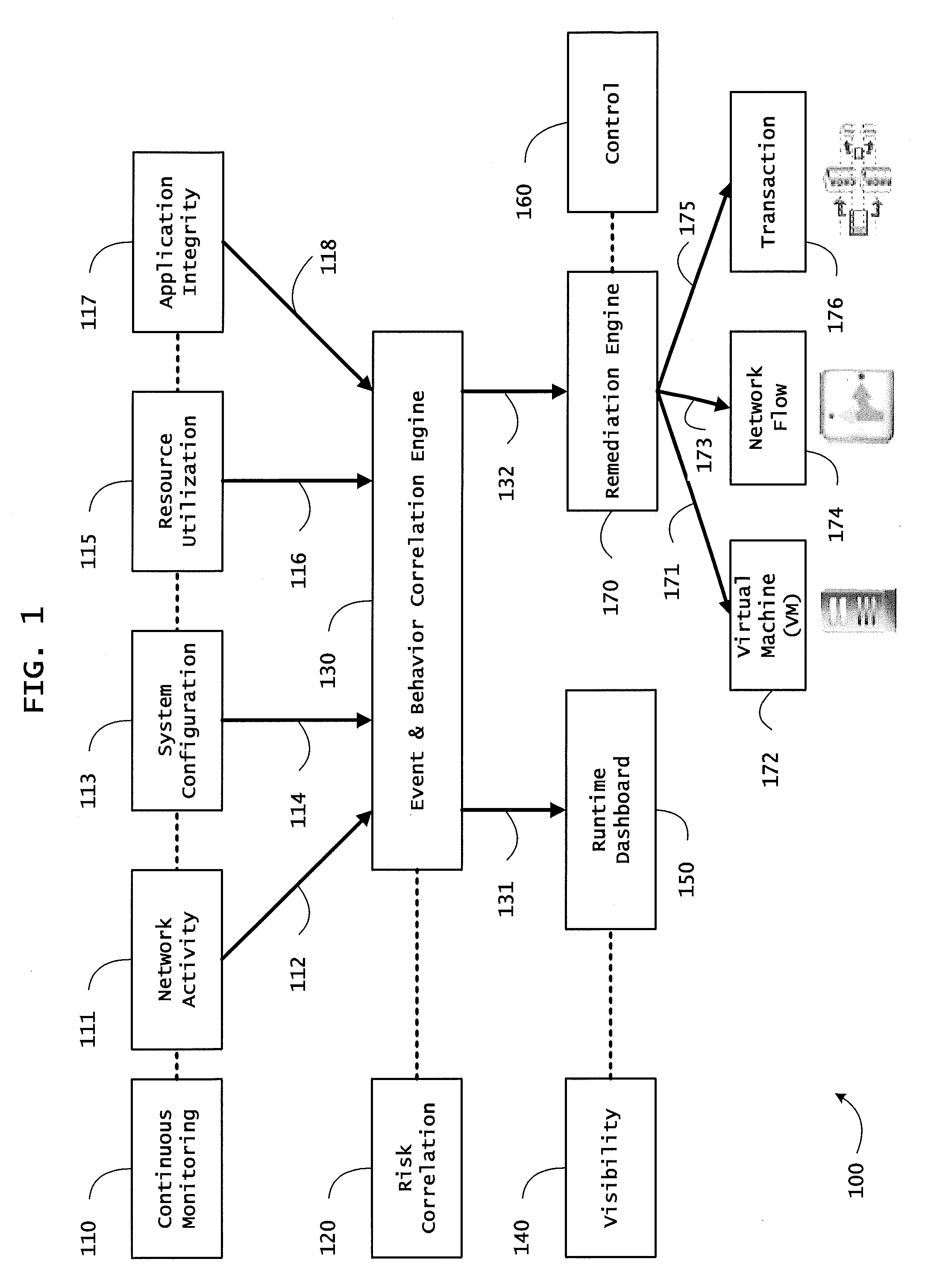
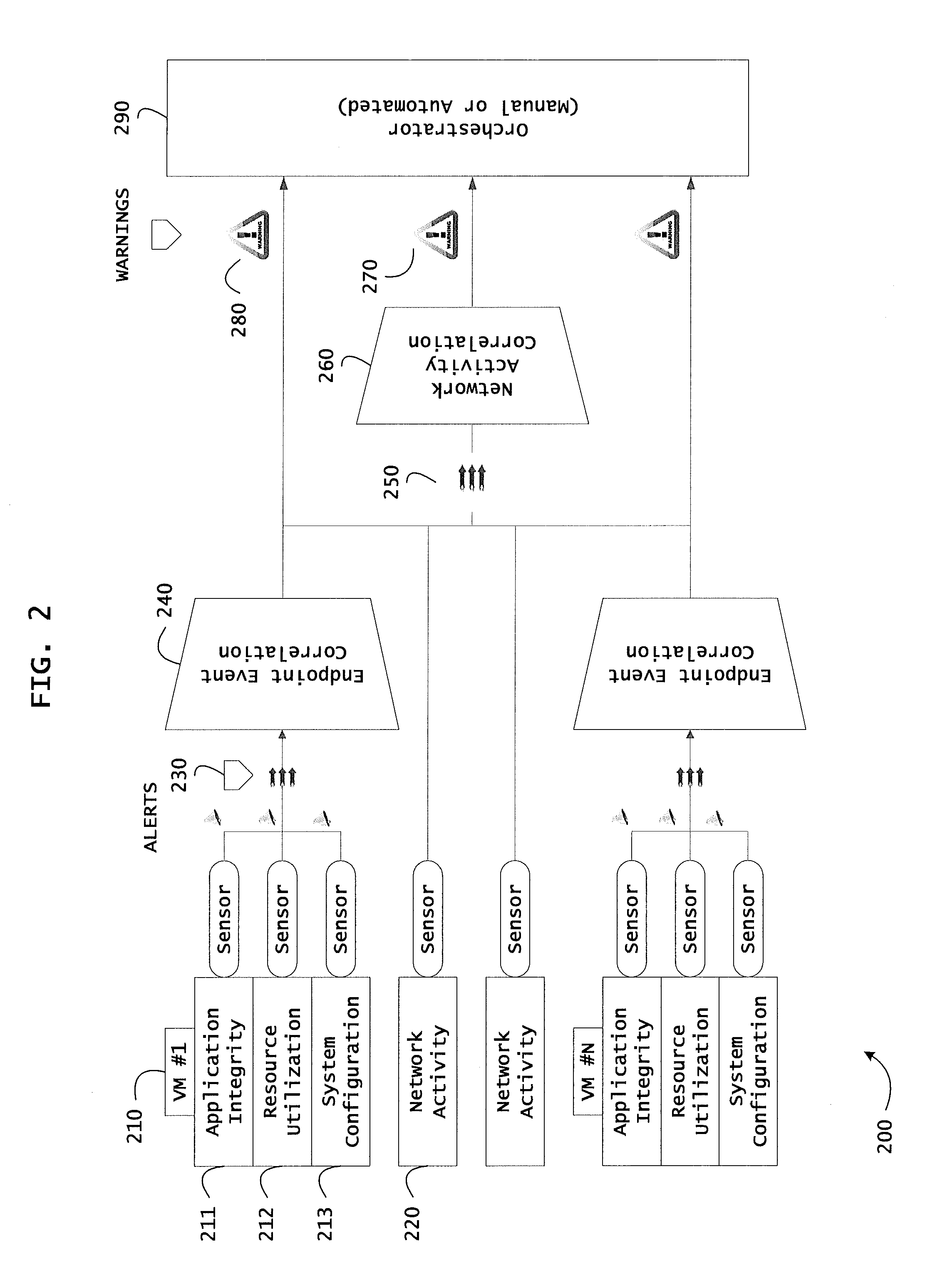
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Systems and methods for threat identification and remediation for computing platforms based upon reconnaissance-based intelligence correlation and network / application monitoring are disclosed. In an embodiment, a method provides runtime operational integrity of a system by receiving: a dynamic context including endpoint events; and network endpoint assessments. The method generates temporal events based on the network endpoint assessments and correlates the endpoint events and temporal events before generating an integrity profile for the system. In another embodiment, flow level remediation is provided to isolate infected or compromised systems from a computing network fabric using a network trust agent, an endpoint trust agent, and a trust orchestrator.
Owner:TAASERA LICENSING LLC
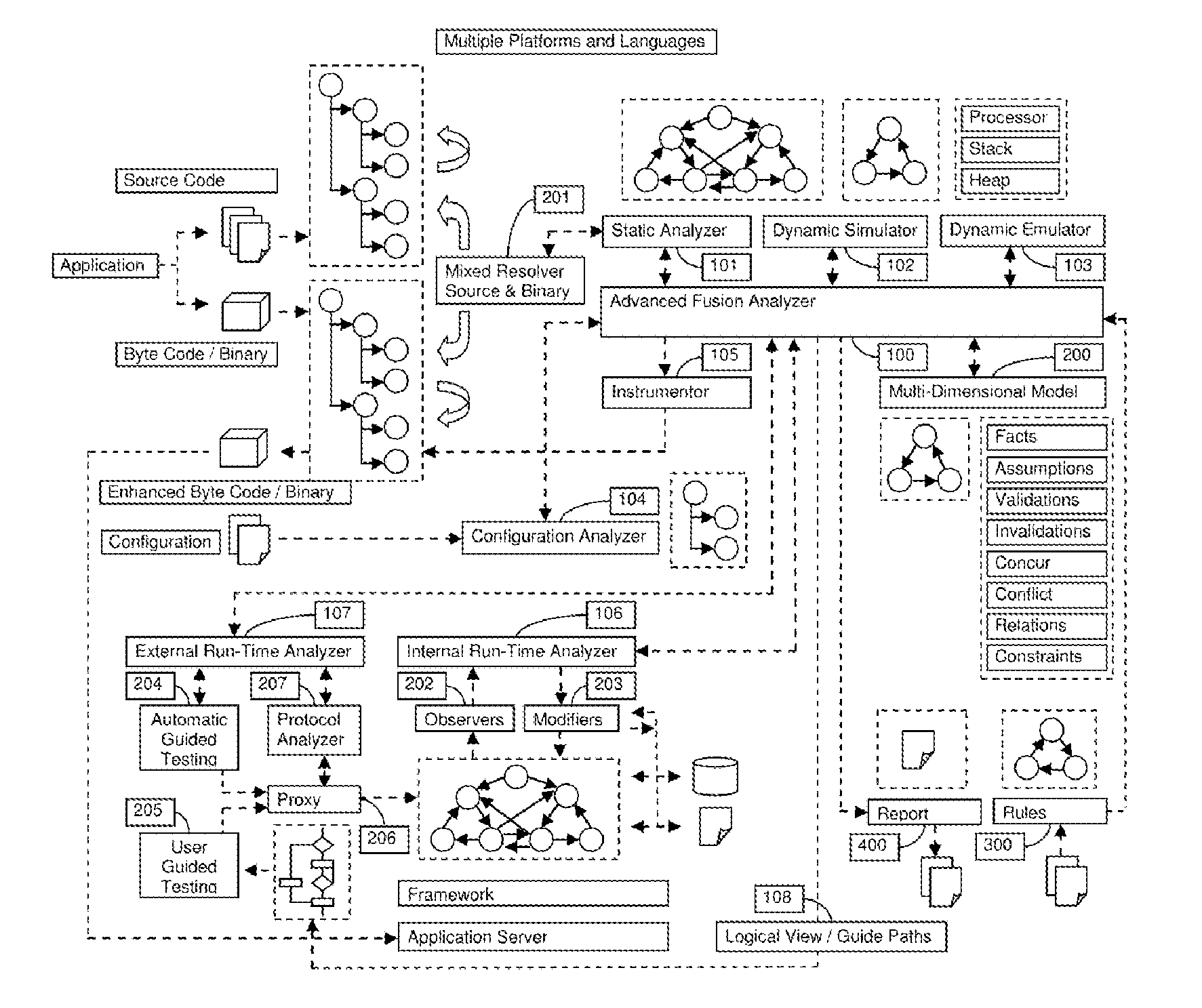
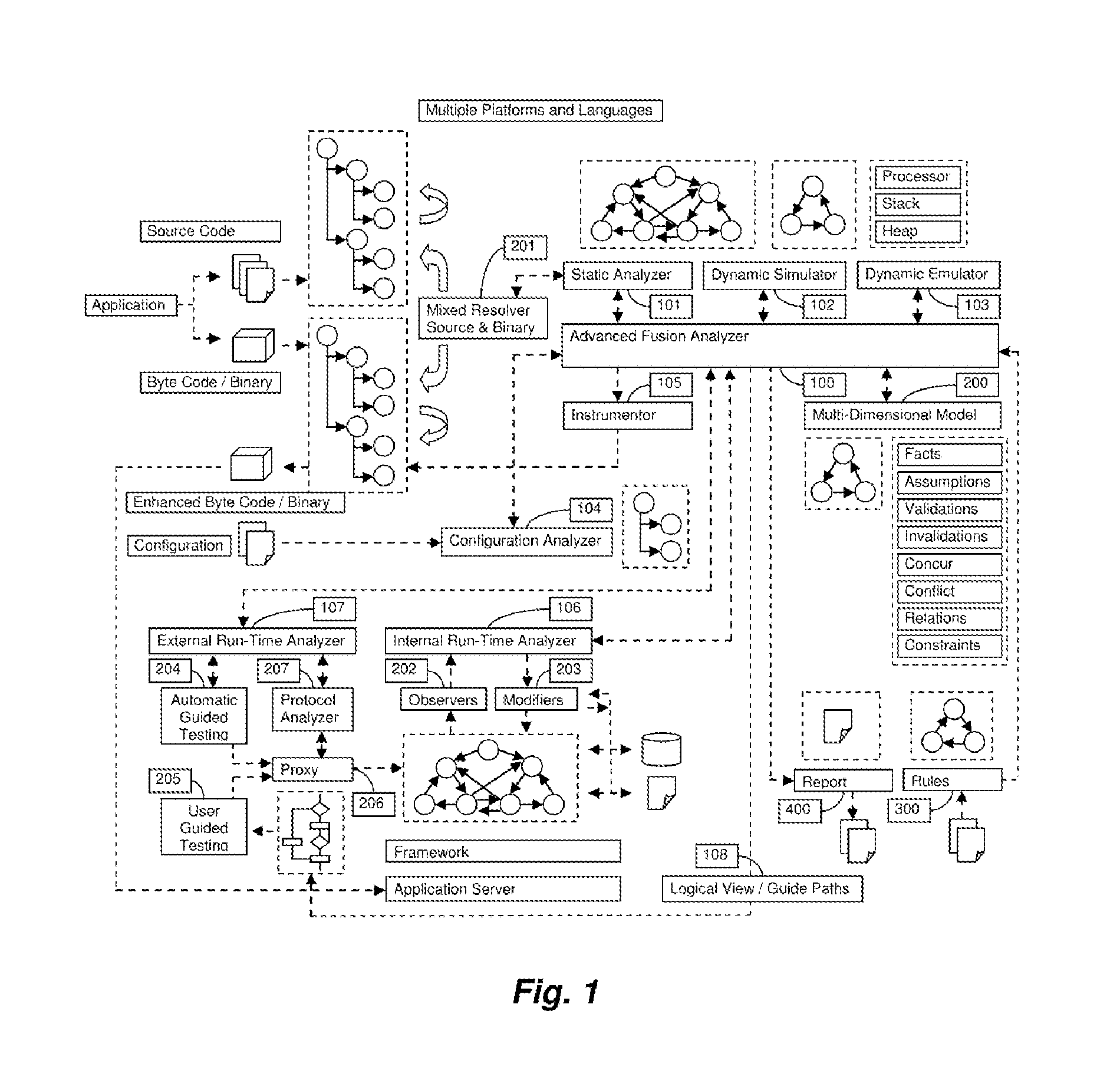
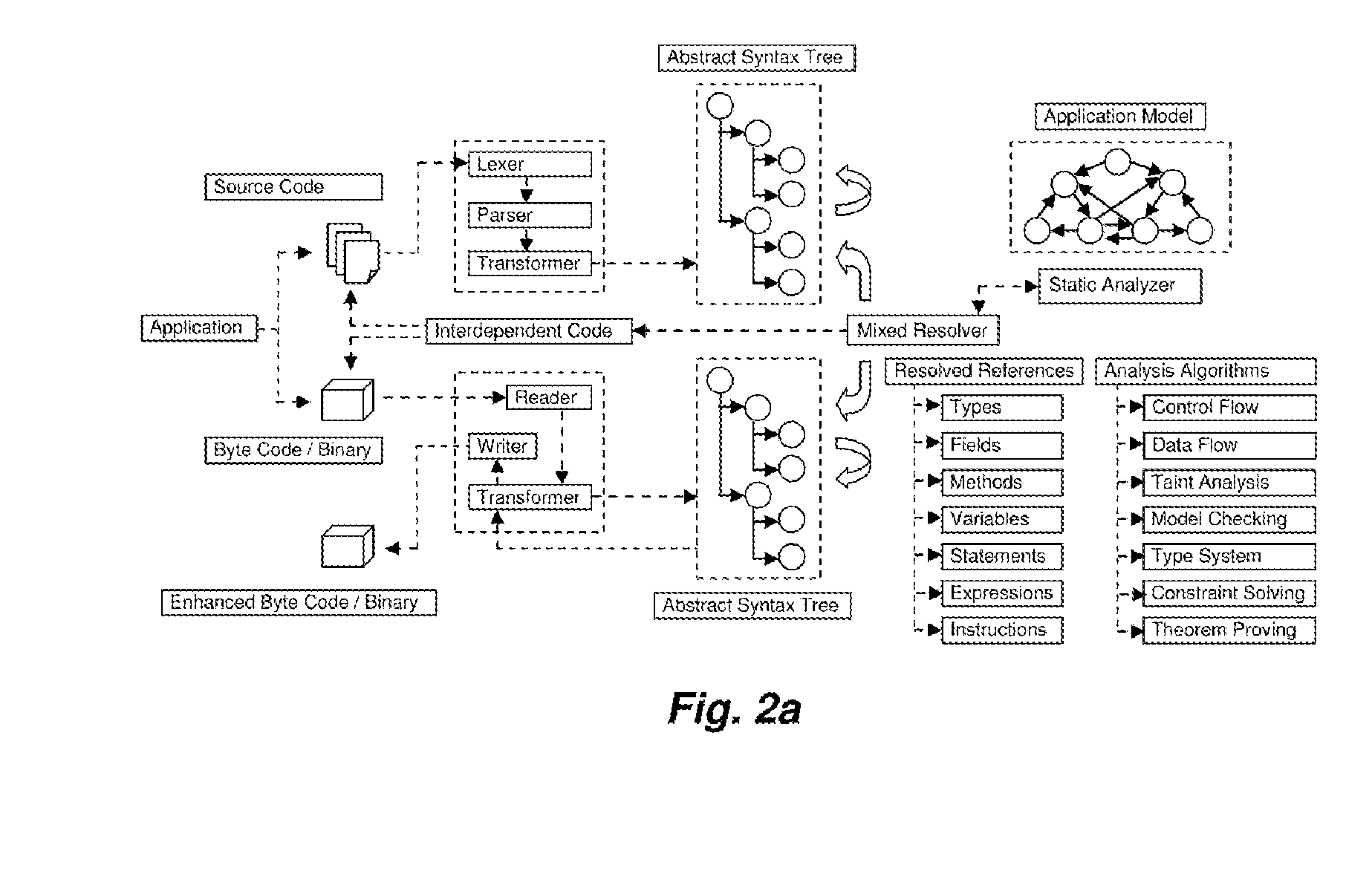
A System for analyzing applications in order to find security and quality issues
InactiveUS20150309813A1Accurate analysisError detection/correctionComputer security arrangementsMachine controlWeb application
The present invention relates to field of application and more specifically to analysis of applications for determining security and quality issues. The present invention describes an application analysis system providing a platform for analyzing applications which is useful in finding security and quality issues in an application. In particular, the present invention is composed of an advanced fusion analyzer which gains an understanding of the application behavior by using a multi-way coordination and orchestration across components used in the present invention to build an continuously refine a model representing knowledge and behavior of the application as a large network of objects across different dimensions and using reasoning and learning logic on this model along with information and events received from the components to both refine and model further as well as drive the components further by sending information and events to them and again using the information and events received as a result to further trigger the entire process until the system stabilizes. The present invention is useful in analysis of internet / intranet based web applications, desktop applications, mobile applications and also embedded systems as well as for hardware, equipment and machines controlled by software.
Owner:IAPPSECURE SOLUTIONS PVT
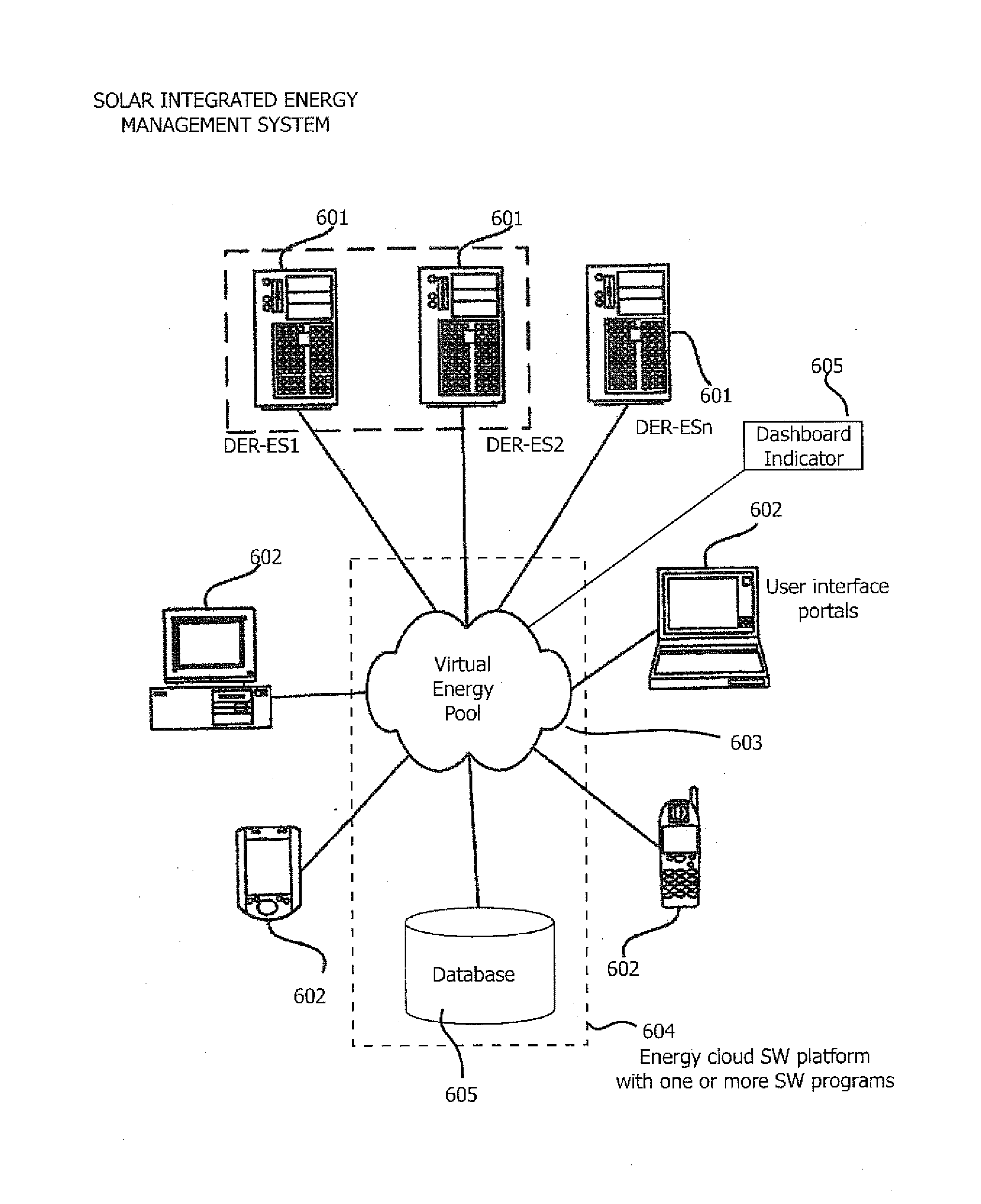
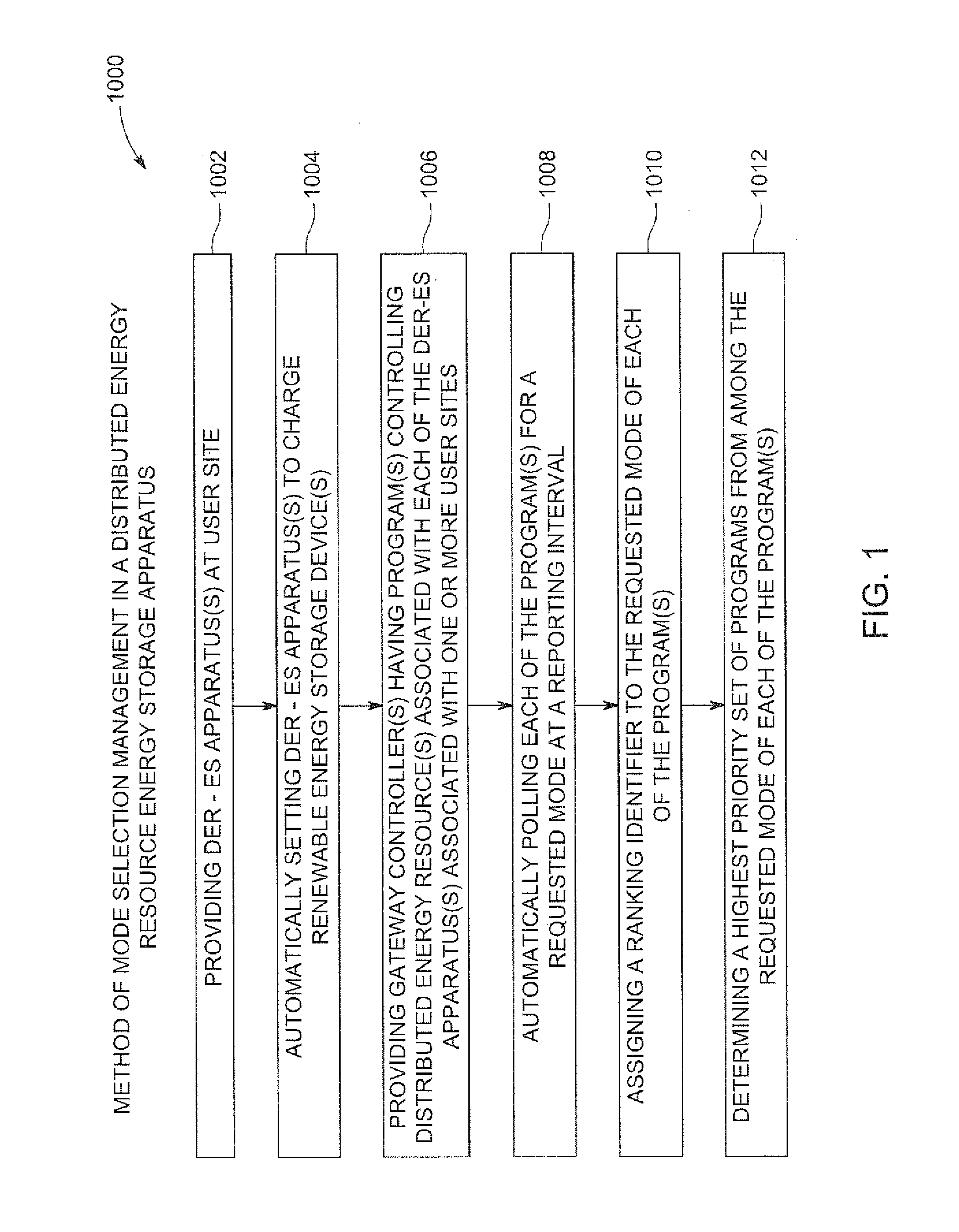
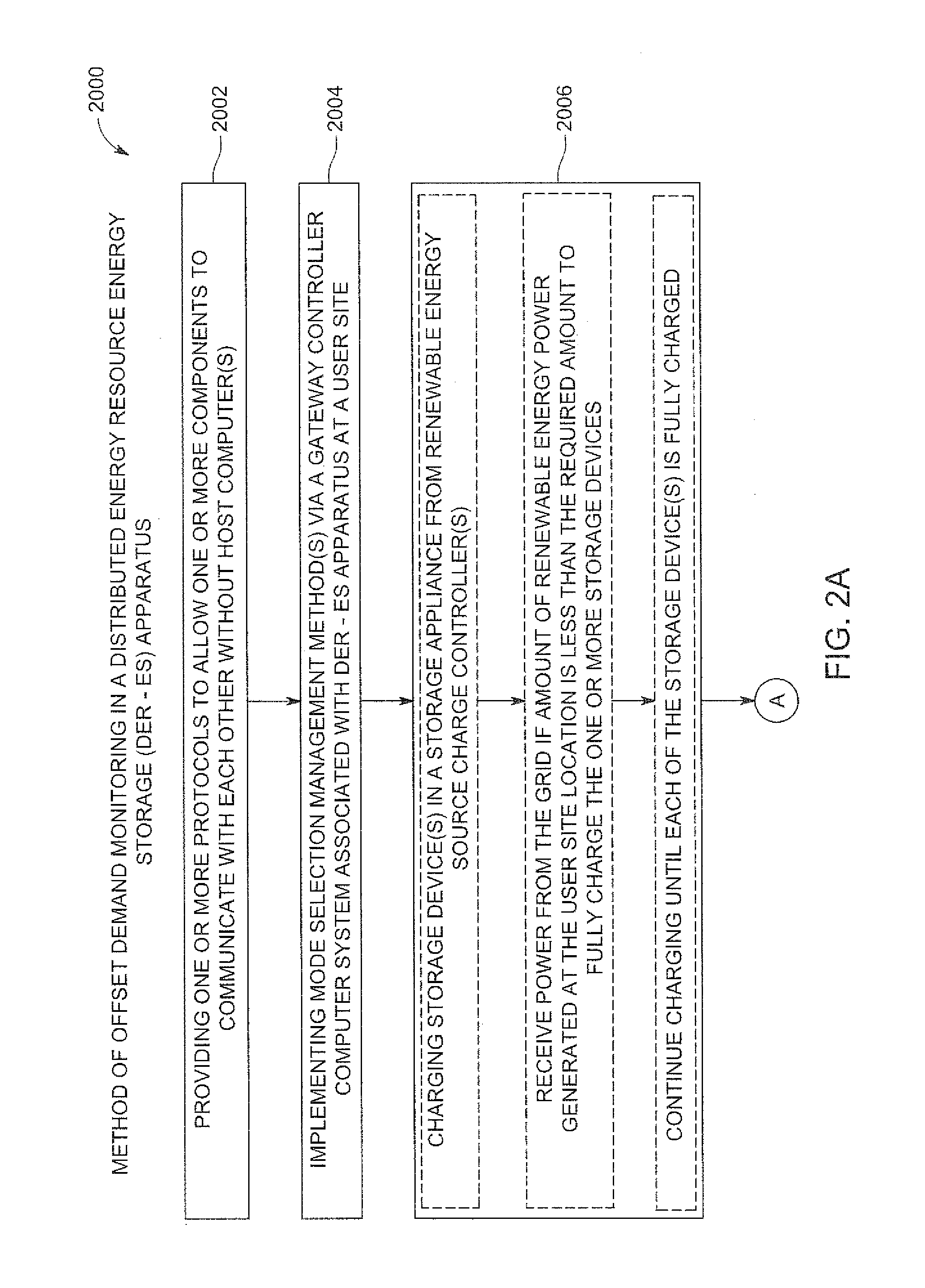
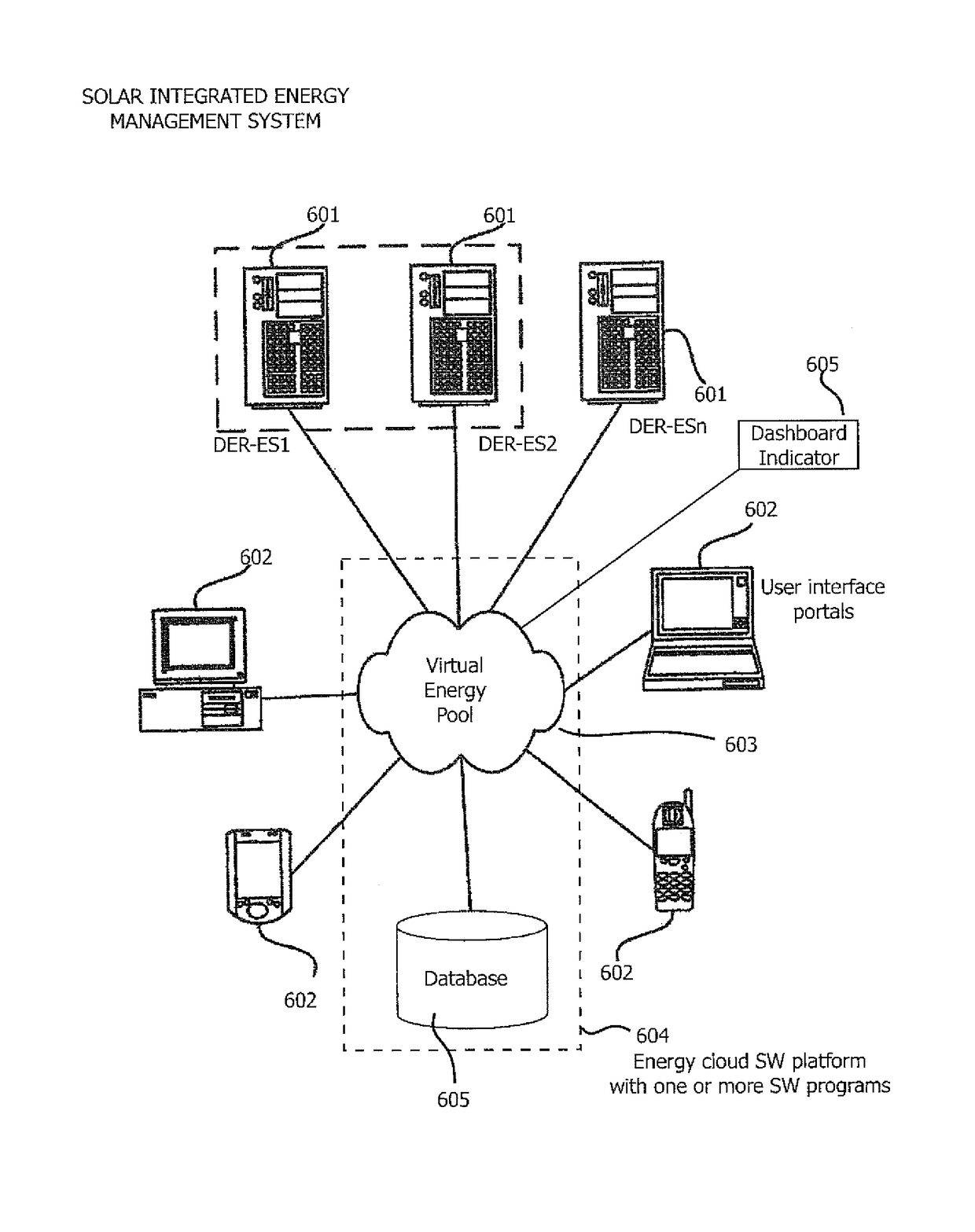
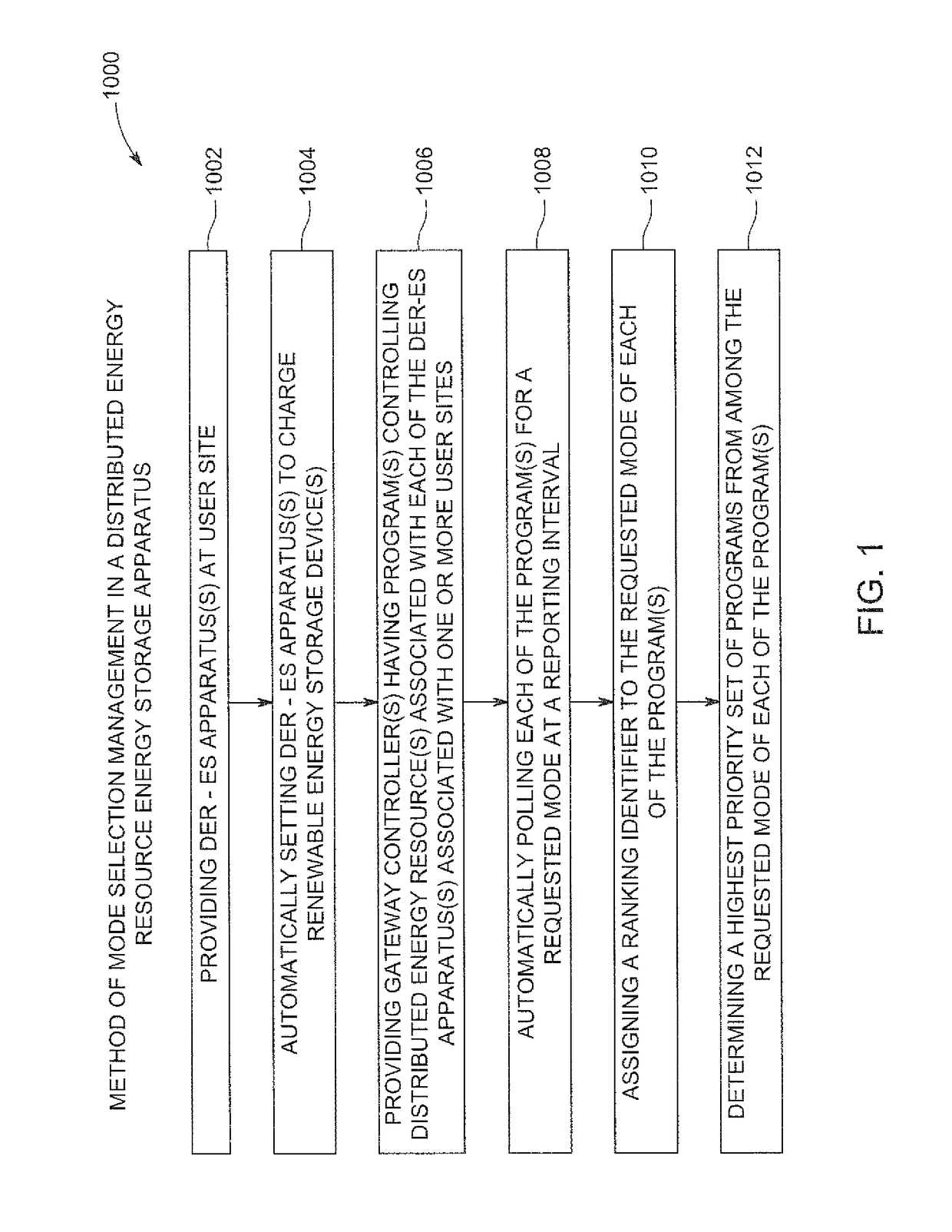
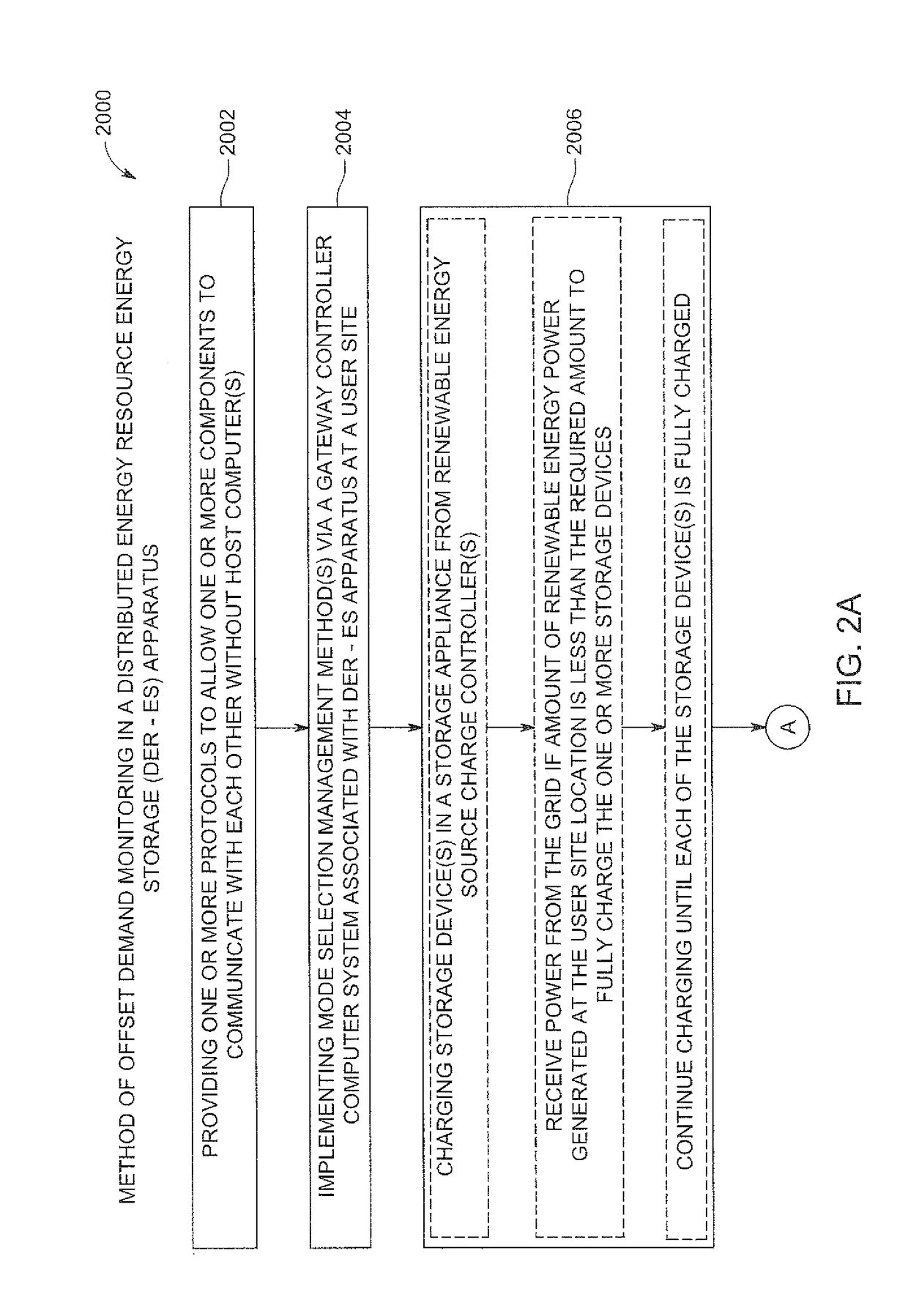
Renewable energy integrated storage and generation systems, apparatus, and methods with cloud distributed energy management services
ActiveUS20170005515A1Guaranteed uptimeImprove performanceElectrical storage systemBatteries circuit arrangementsPrediction algorithmsEnergy management software
A software platform in communication with networked distributed energy resource energy storage apparatus, configured to deliver various specific applications related to offset demand monitoring, methods of virtual power plant and orchestration, load shaping services, methods of reducing demand at aggregated level, prioritizing computer programs related to virtual energy pool, energy cloud controllers methods, charge discharge orchestration plans of electric vehicles, distributed energy resources, machine learning predictive algorithms, value optimizing algorithms, autonomous sensing event awareness, mode selection methods, capacity reservation monitoring, virtual power plant methods, advanced DER-ES apparatus features, energy management system for governing resources and methods, aggregated energy cloud methods, load shaping methods, marginal cost cycle-life degradation, load shaping API, forward event schedule, on demand request, and load service state request methods. Various rules, constraints of predictive algorithms for signal inputs to determine incremental storage cycles, cycle life degradation marginal cost, iterative and forward event schedule development, and load control.
Owner:SUNVERGE ENERGY
Systems and methods for using reputation scores in network services and transactions to calculate security risks to computer systems and platforms
ActiveUS20130298192A1Memory loss protectionError detection/correctionMathematical CalculusInternet privacy
Instrumented networks, computer systems and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for calculating security risks by determining subject reputation scores. In an embodiment, a system receives a query for a reputation score of a subject, initiates directed queries to external information management systems to interrogate attributes associated with the subject, and analyzes responses. The system receives a hierarchical subject reputation score based on a calculus of risk and returns a reputation token. In another embodiment, a method provides real time attestation of a subject's reputation to a service provider using an endpoint trust agent, and a trust orchestrator comprising a reputation broker and a trust broker.
Owner:TAASERA LICENSING LLC
Systems and methods for providing mobile security based on dynamic attestation
ActiveUS20130298242A1Memory loss protectionError detection/correctionMobile securityApplication software
Instrumented networks, machines and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects (including mobile devices) and applications on the instrumented target platform. Methods and systems are disclosed for dynamic attestation of mobile device integrity based upon subject reputation scores. In an embodiment, a method scores trustworthiness of a mobile device based on reputation scores for users associated with the device and / or a device reputation score. The method generates runtime integrity alerts regarding execution anomalies for applications executing on the device, calculates risks based on a ruleset, and determines a calculus of risk for the device. The method sends endpoint events comprising data and content of the integrity warnings to a trust orchestrator, which generates an integrity profile based on the endpoint events.
Owner:TAASERA LICENSING LLC
Systems and methods for using reputation scores in network services and transactions to calculate security risks to computer systems and platforms
ActiveUS8776180B2Memory loss protectionDigital data processing detailsMathematical CalculusInternet privacy
Owner:TAASERA LICENSING LLC
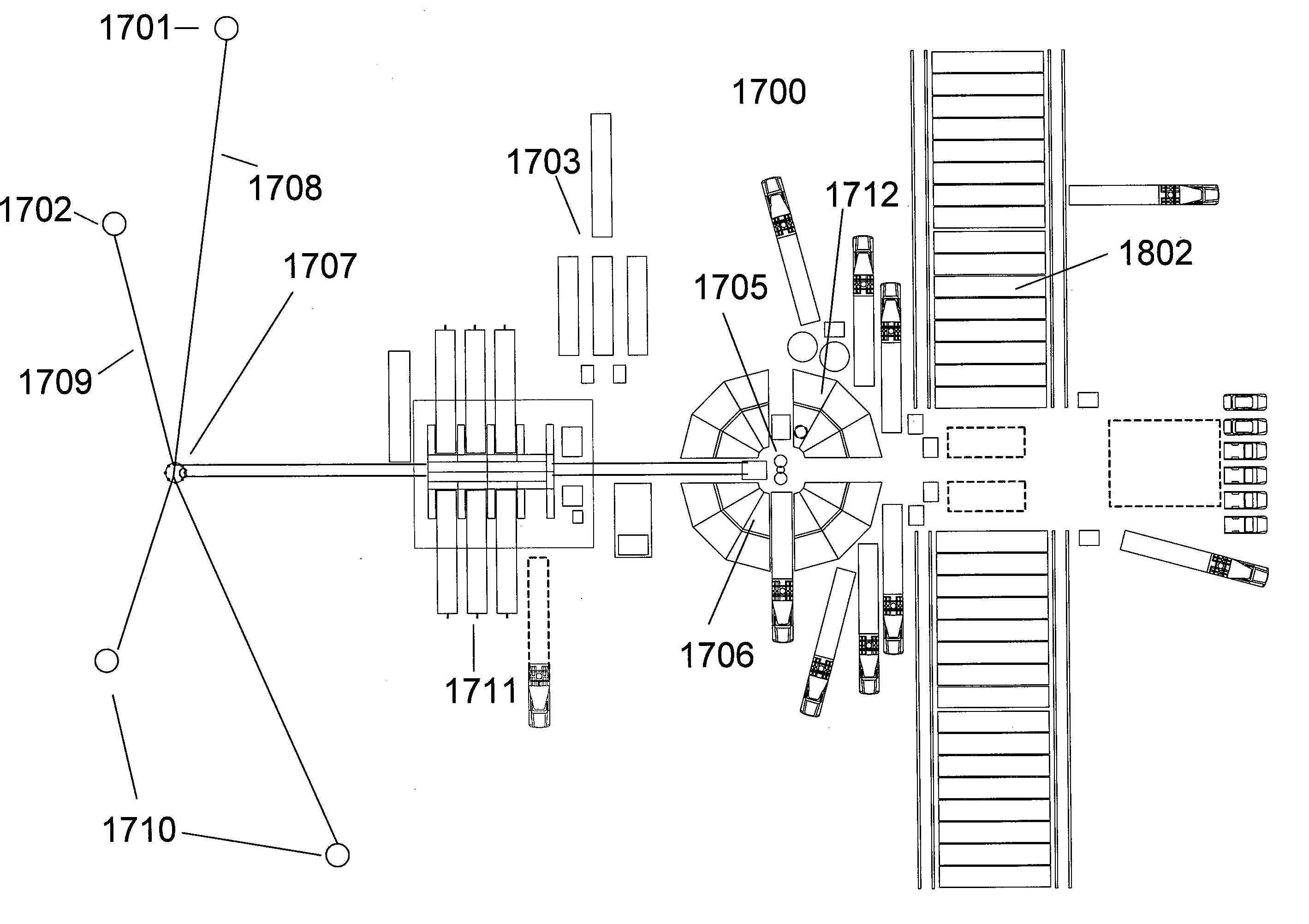
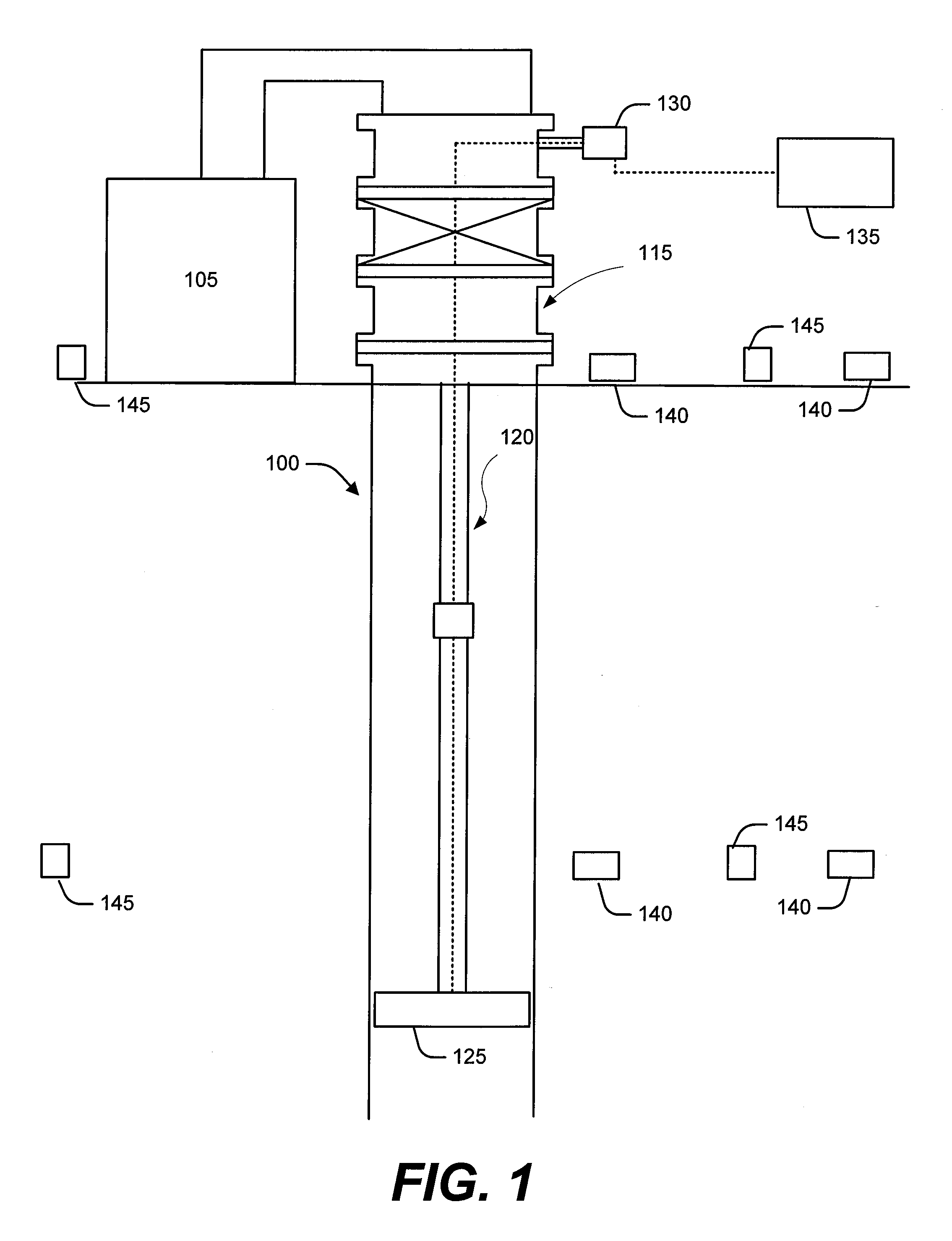
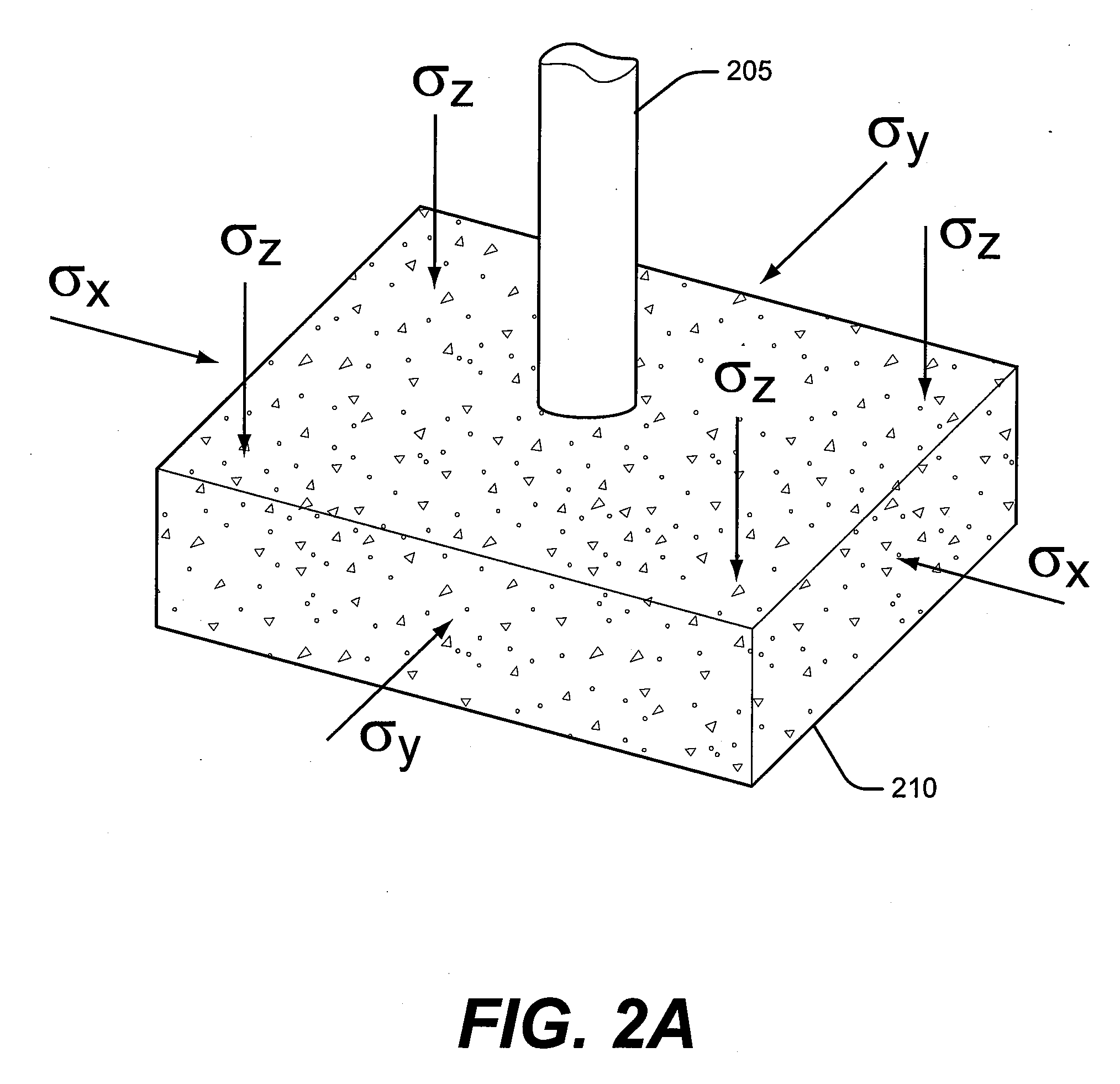
Method and Apparatus for Orchestration of Fracture Placement From a Centralized Well Fluid Treatment Center
A method and apparatus for orchestrating multiple fractures at multiple well locations in a region by flowing well treatment fluid from a centralized well treatment fluid center is disclosed that includes the steps of configuring a well treatment fluid center for fracturing multiple wells, inducing a fracture at a first well location, measuring effects of stress fields from the first fracture, determining a time delay based in part upon the measured stress effects, inducing a second fracture after the time delay at a second location based upon the measured effects, and measuring the stress effects of stress fields from the second fracture. Sensors disposed about the region are adapted to output effects of the stress fields. Location and orientation of subsequent fractures is based on the combined stress effects of the stress fields as a result of the prior fractures which provides for optimal region development.
Owner:HALLIBURTON ENERGY SERVICES INC
Apparatus, systems and methods for container based service deployment
Embodiments disclosed facilitate distributed orchestration and deployment of a single instance of a distributed computing application over a plurality of clouds and container clusters, including container clusters provided through a Container as a Service (CaaS) offering. In some embodiments, system and pattern constructs associated with a hybrid distributed multi-tier application may be used to obtain an infrastructure independent representation of the distributed multi-tier application. The infrastructure independent representation may comprise a representation of an underlying pattern of resource utilization of the application. Further, the underlying pattern of resource utilization of the application may be neither cloud specific nor container cluster specific. In some embodiments, a single instance of the hybrid distributed multi-tier application may be deployed on a plurality of cloud infrastructures and on at least one container cluster, based, in part, on the cloud-infrastructure independent representation of the application.
Owner:CISCO TECH INC
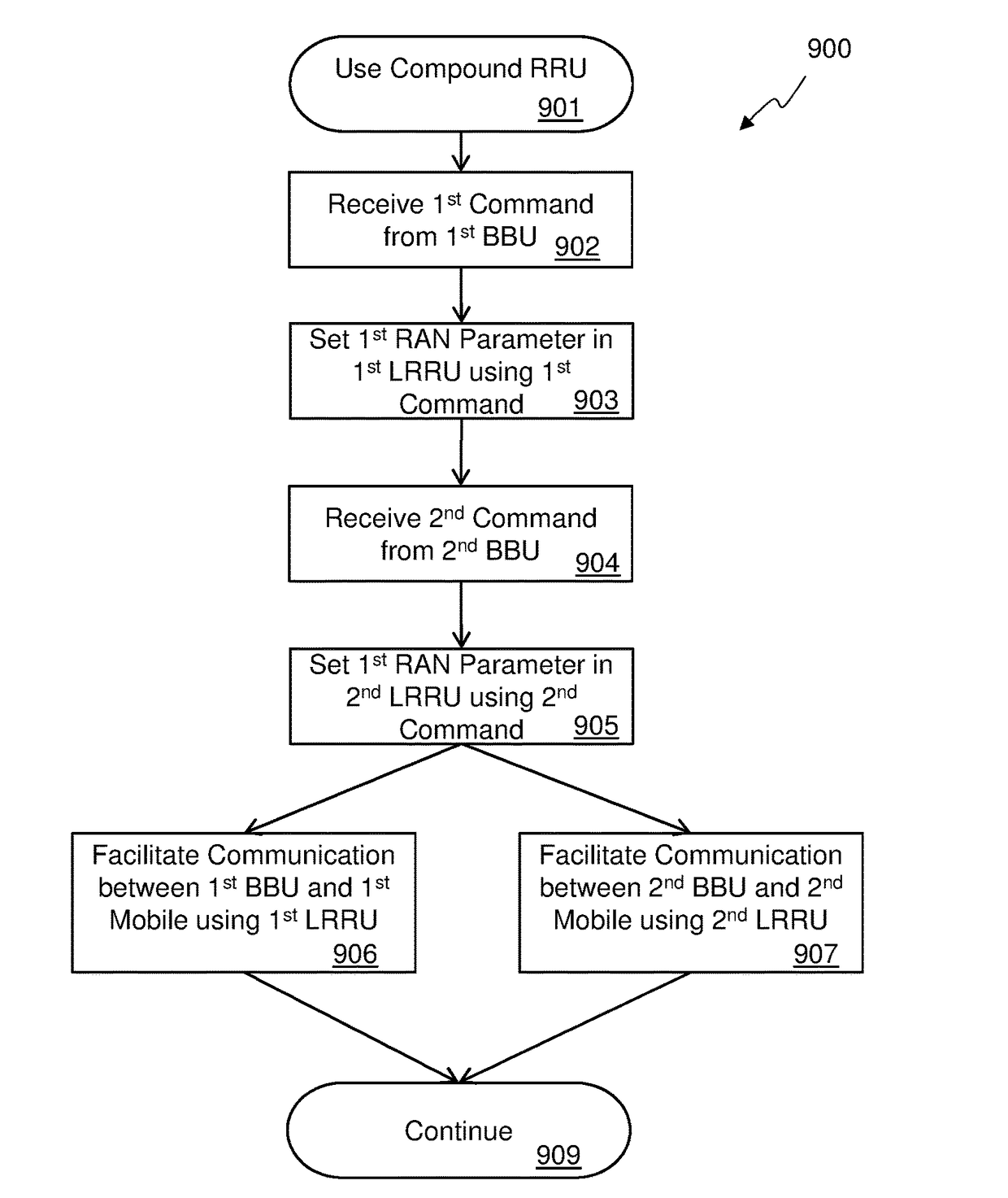
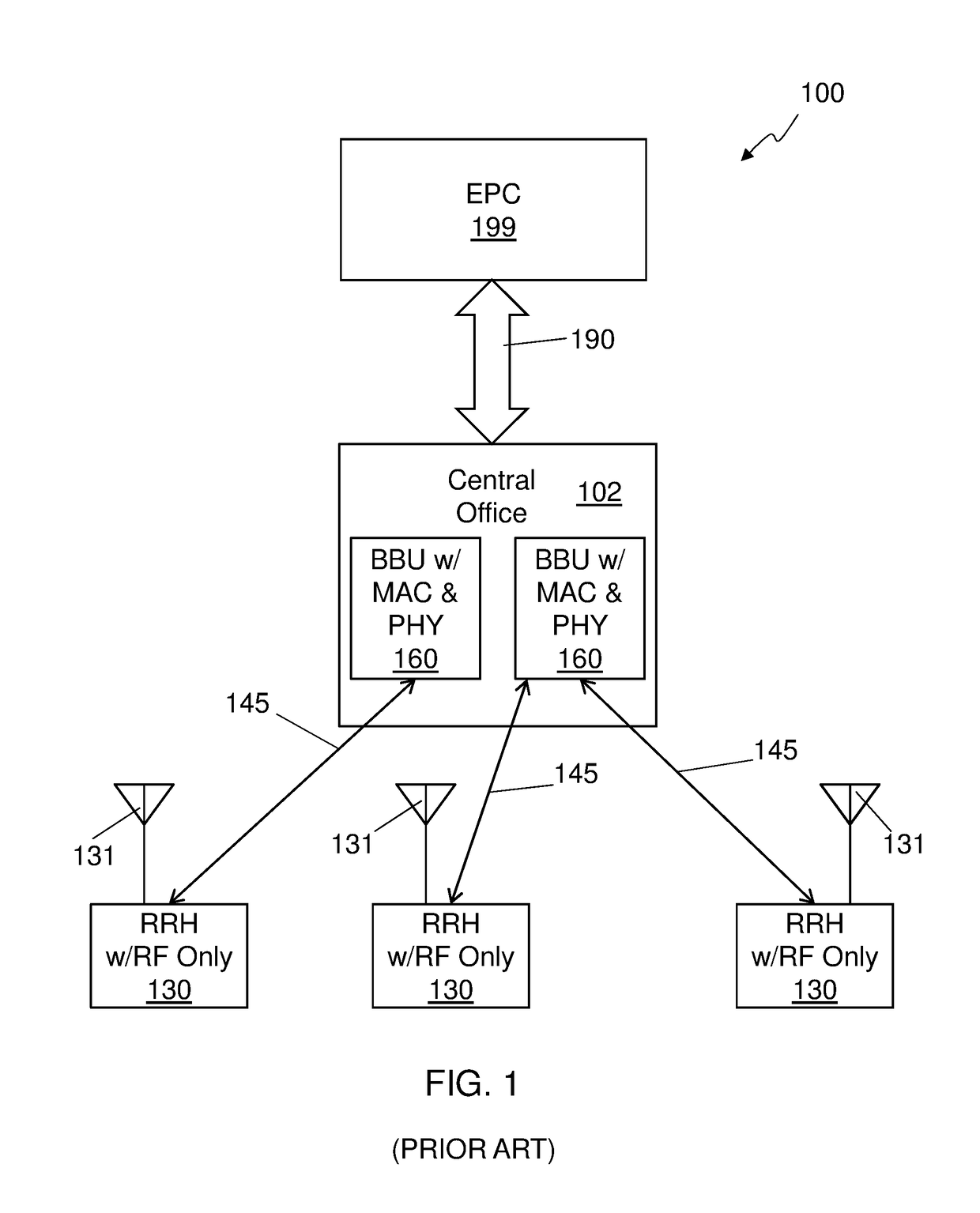
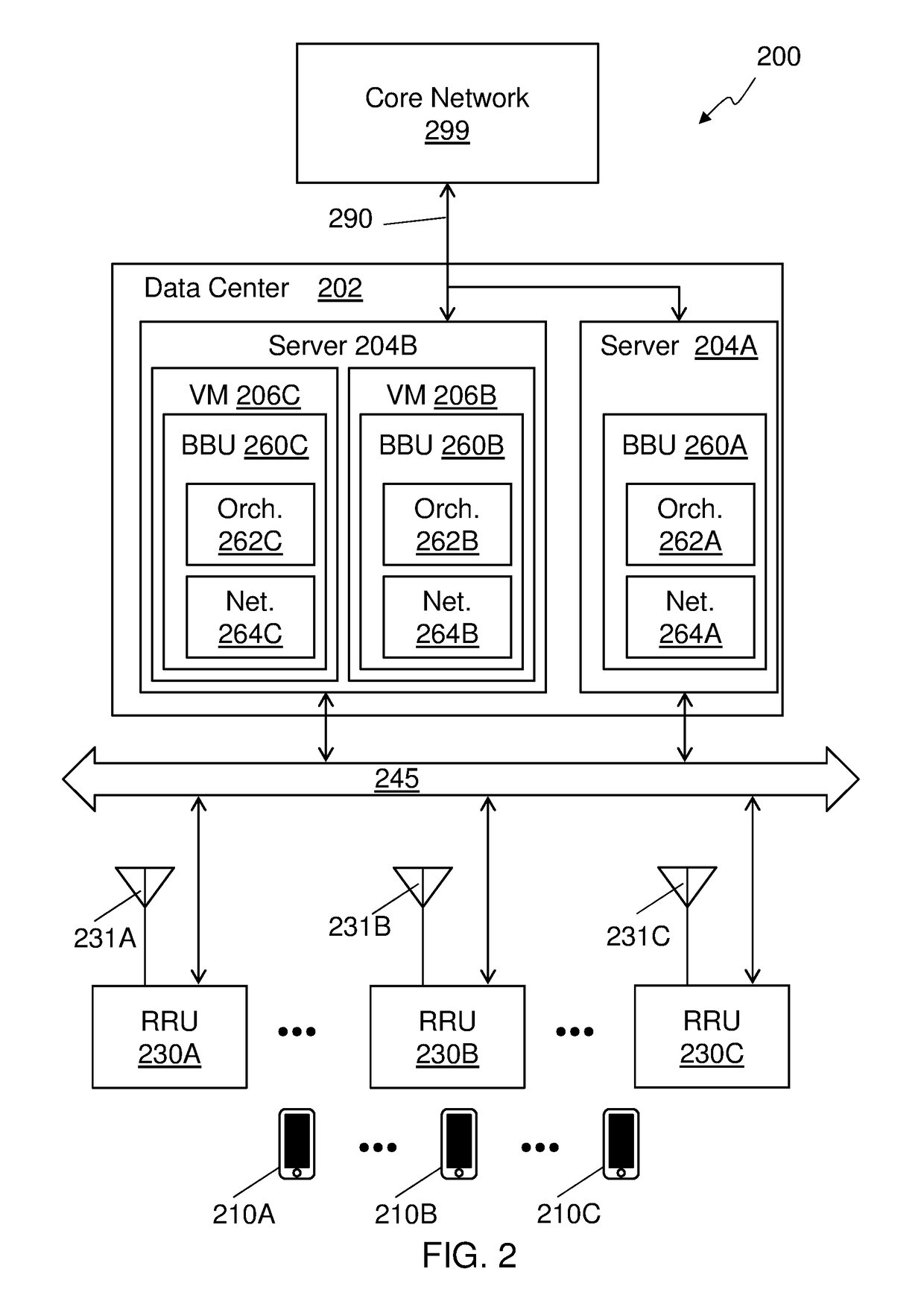
Virtualization and orchestration of a radio access network
ActiveUS20180287696A1Network traffic/resource managementRadio transmission for post communicationAccess networkVirtualization
A distributed radio frequency communication system facilitates communication between wireless terminals and a core network. The system includes a group of remote radio units (RRUs). Each RRU of the group of RRUs is coupled to an antenna to communicate with at least some of the mobile terminals and includes electronic circuitry to perform at least a first portion of a first-level protocol of a radio access network (RAN) and communicate over a fronthaul link. The system also includes a baseband unit (BBU) coupled to the core network and the fronthaul link, and communicably coupled to the group of RRUs over the fronthaul link. The BBU includes electronic circuitry to assign one or more RRUs, selected from the group of RRUs, to a cluster of RRUs based on one or more parameters, and to perform at least a second-level protocol of the RAN.
Owner:COMMSCOPE TECH LLC
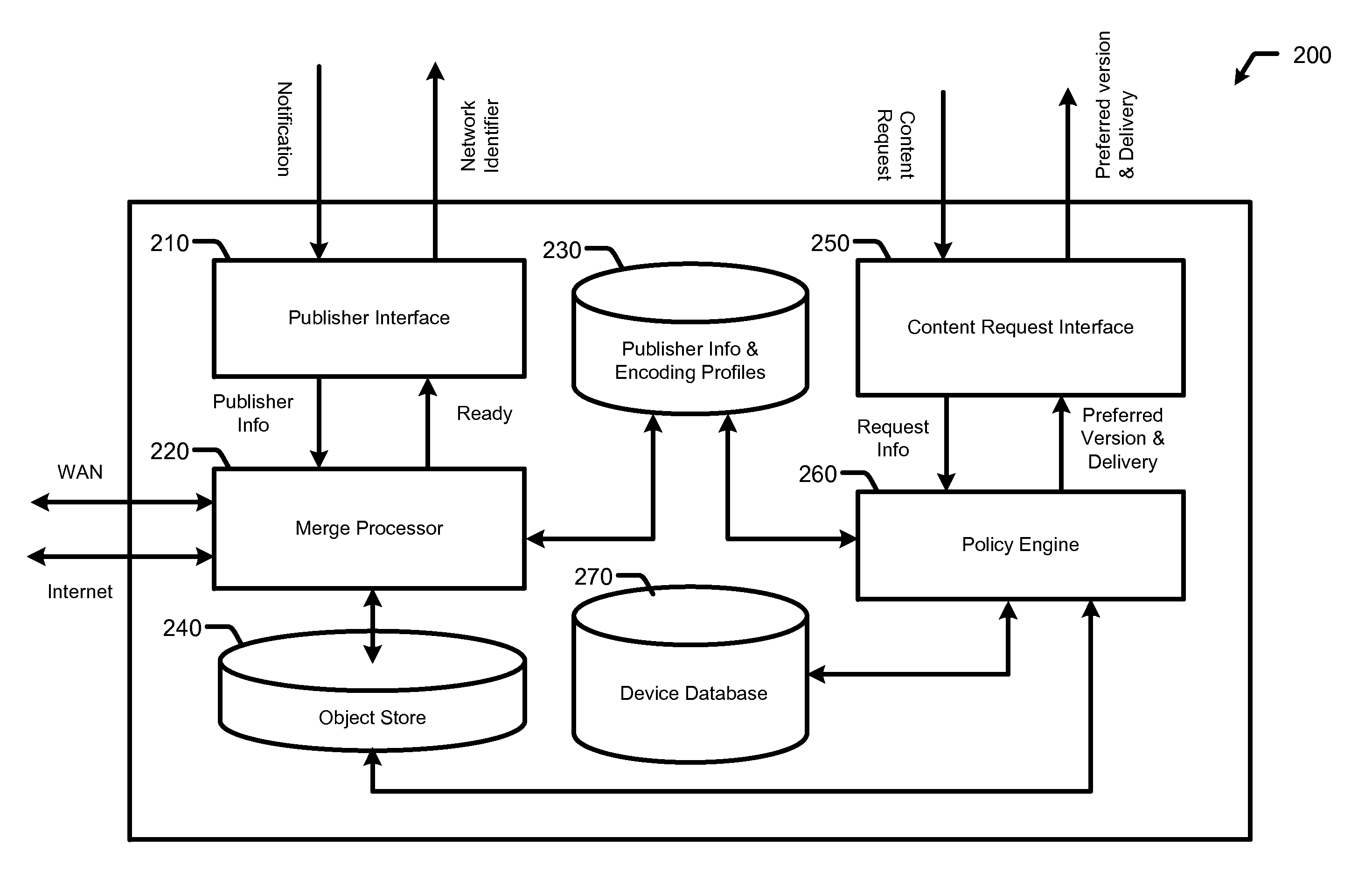
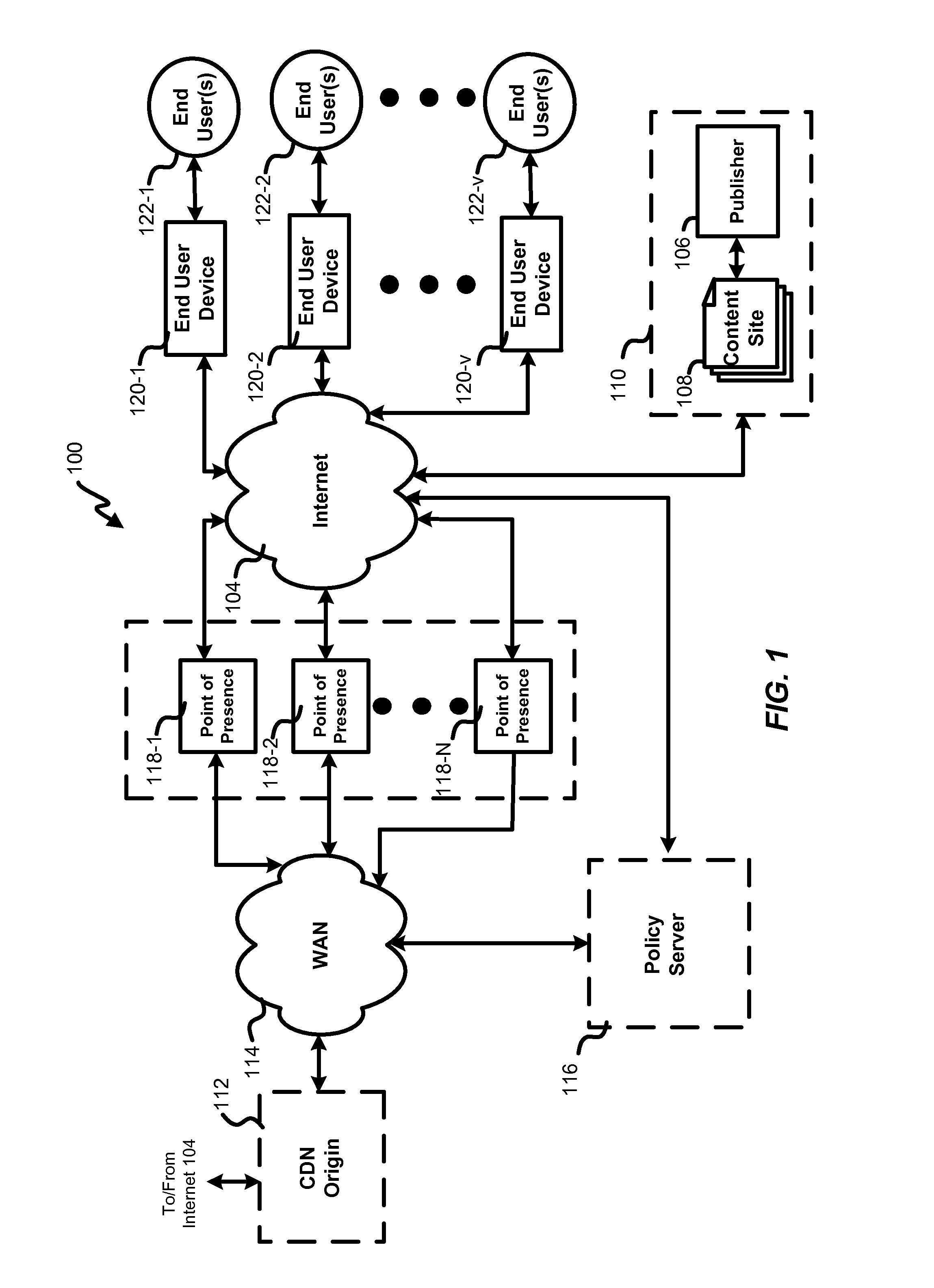
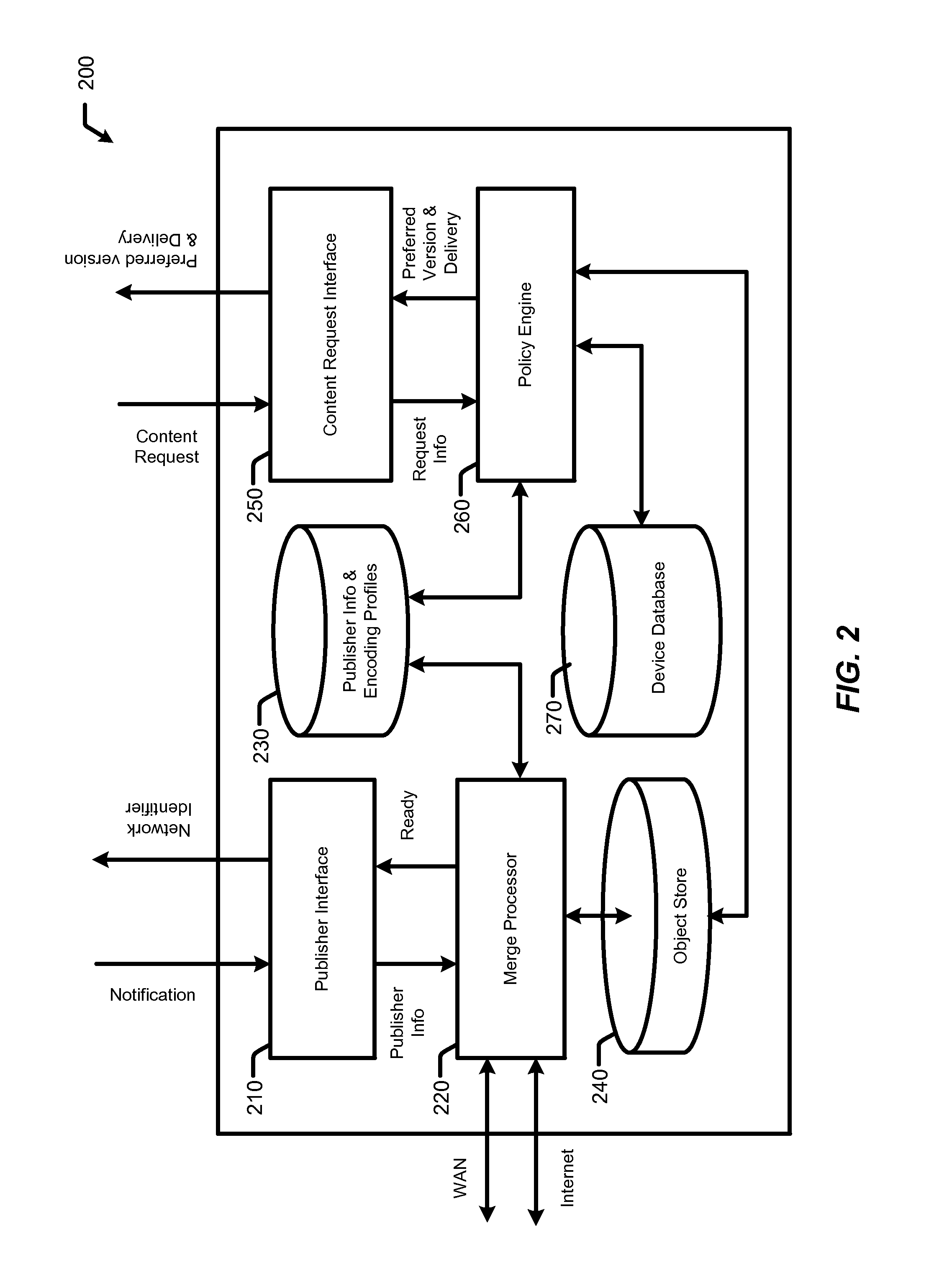
System and method for delivery of content objects
InactiveUS20110252082A1Multiple digital computer combinationsWebsite content managementOrchestrationDistributed computing
Techniques for delivering content to an end user device are disclosed. A policy server performs an ingest process in which multiple versions of a content object are created. The multiple versions of the content object are associated with a single network identifier which can be distributed to publishers of the content object. When the content object is requested using the single network identifier, the policy server determines a preferred version and delivery orchestration scheme from among the multiple versions for delivery to an end user device based on several criteria. The policy server may thereafter orchestrate delivery of the preferred version of the content object to the end user device. The single network identifier may be associated with an edge location in a content delivery network (CDN) and the policy server may orchestrate delivery in cooperation with servers at the CDN edge location.
Owner:LIMELIGHT NETWORKS
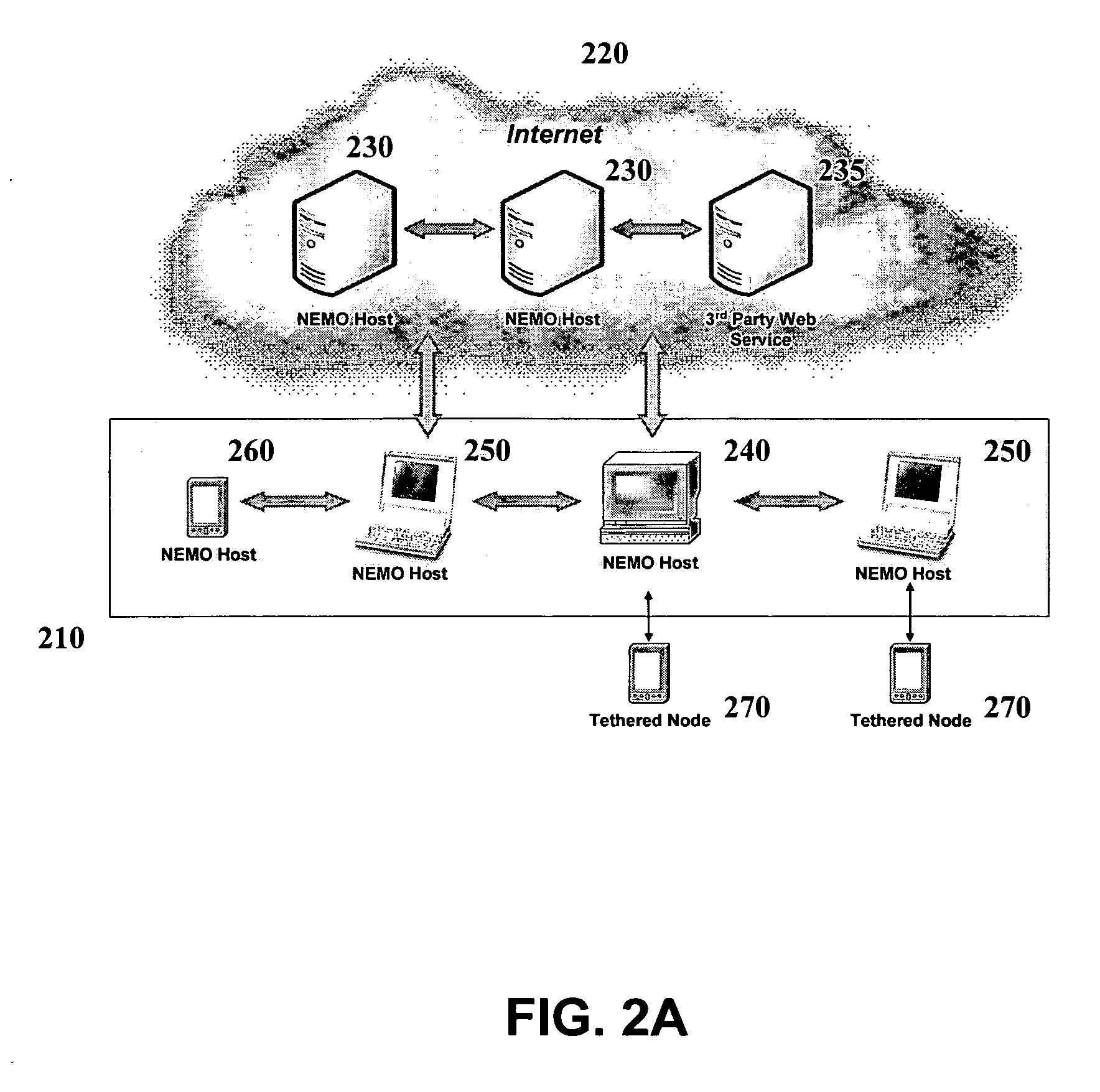
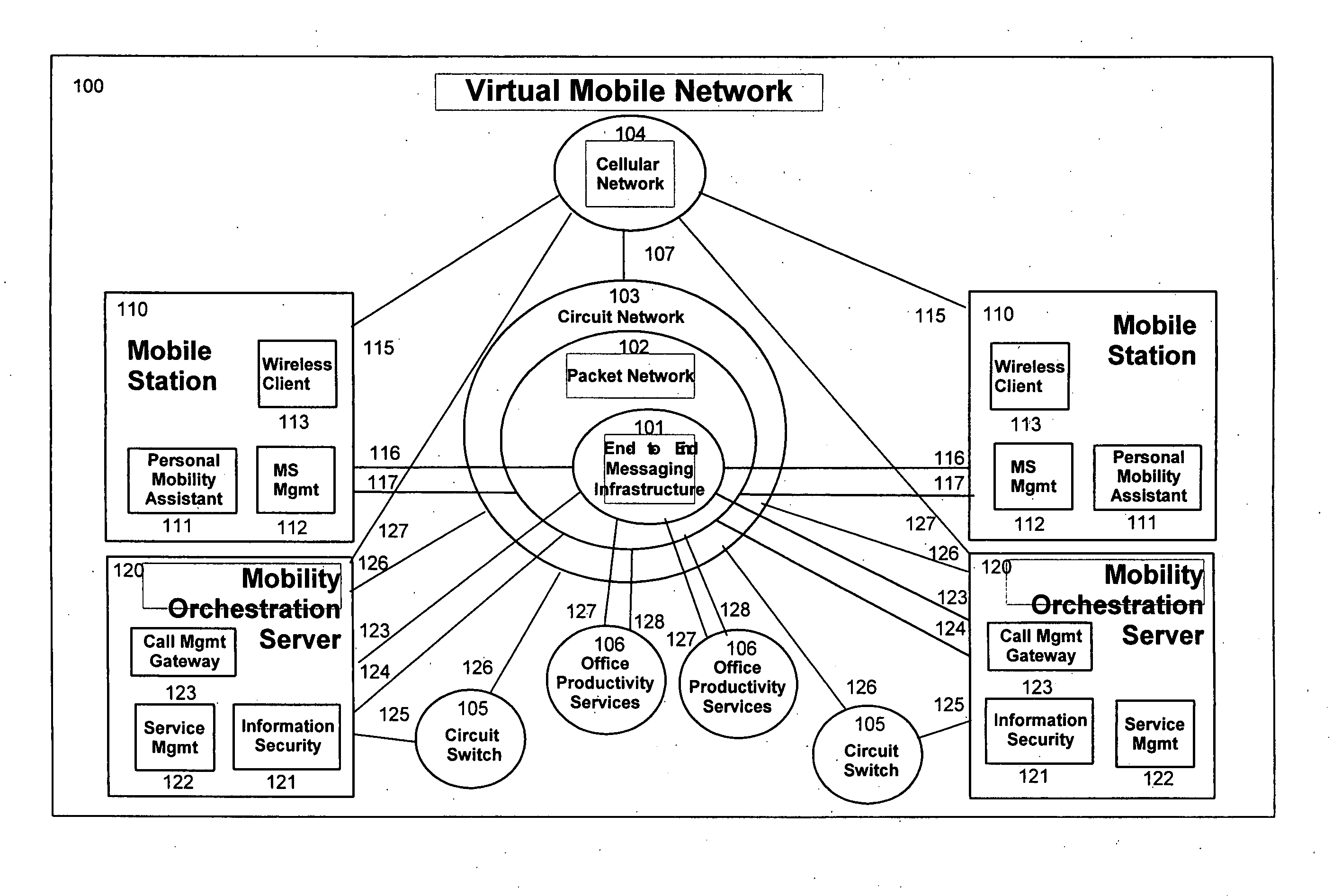
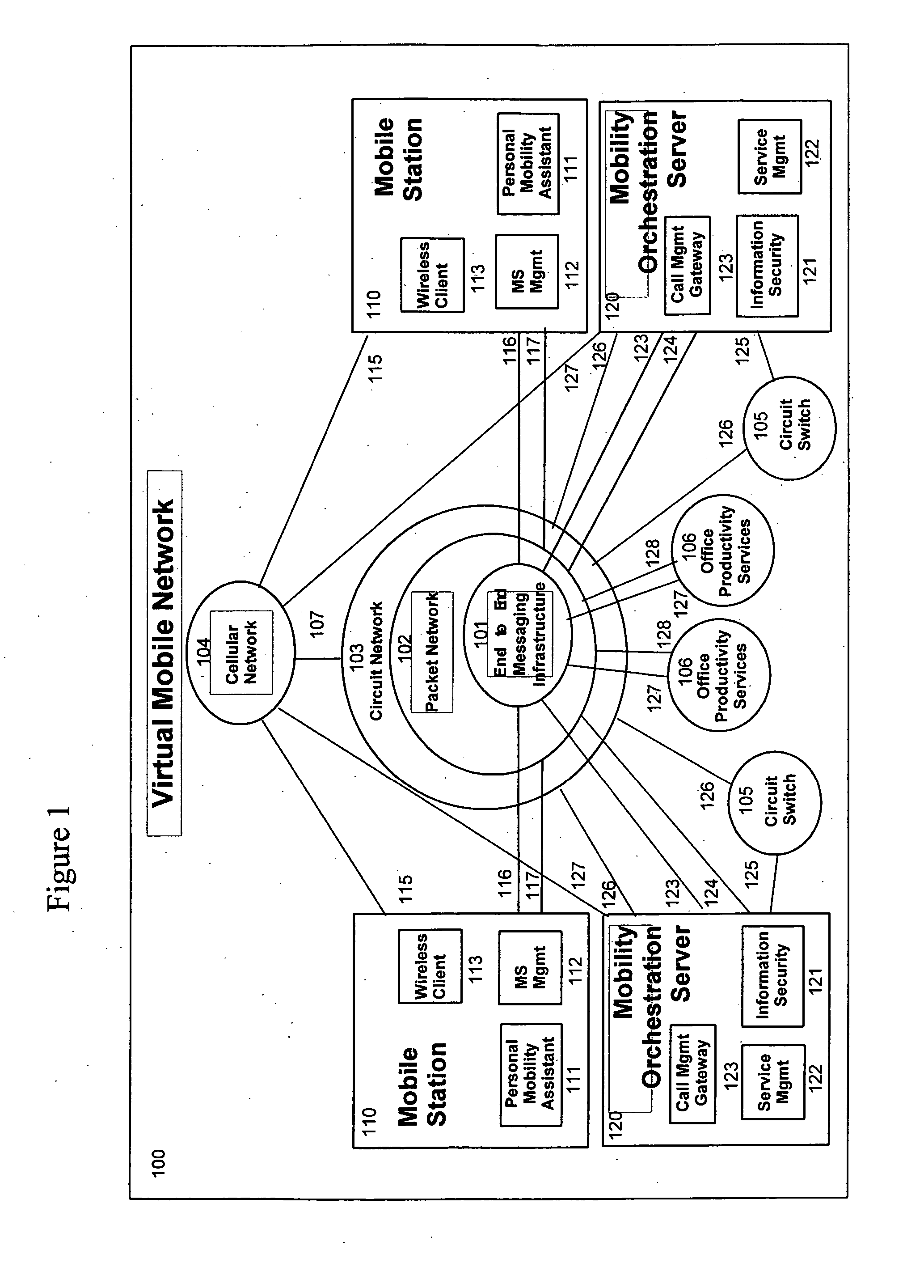
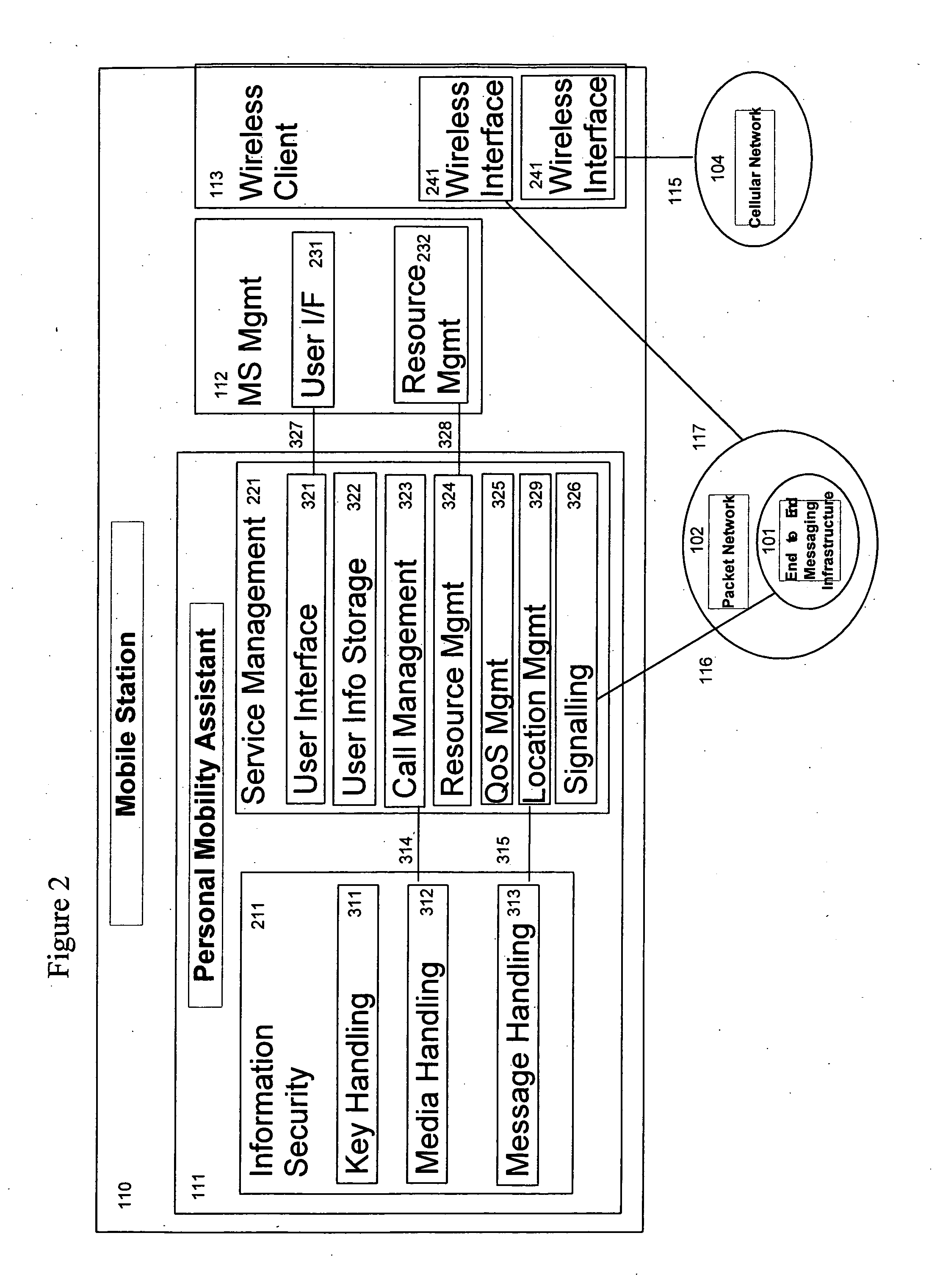
System and method for a virtual mobile network supporting dynamic personal virtual mobile network with multimedia service orchestration
InactiveUS20070156804A1Minimum bandwidthEasy to addNetwork traffic/resource managementConnection managementOrchestrationHandover
A system, various methods, and various apparatuses are provided whereby a Dynamic Personal Virtual Mobile Network can be created, in which multiple disparate networks can be interconnected to form a unified network environment. In this Dynamic Personal Virtual Mobile Network topology changes in real time as a user roams. Handover boundaries are established and taken down as the Dynamic Personal Virtual Mobile Network Topology changes. A Dynamic Personal Virtual Mobile Network is constructed with separate signalling and bearer channel infrastructures to afford greater degree of network engineering and provisioning efficiency. In this Dynamic Personal Virtual Mobile Network, dedicated signalling resources are connected always while shared bearer resources are allocated on demand. An architecture, various methods, are also provided whereby multimedia service channels can be organized, adapted, and managed systematically between separate multiple service providers and a user with multiple mobile devices in the context of the Dynamic Personal Virtual Mobile Network.
Owner:FUZE NETWORKS
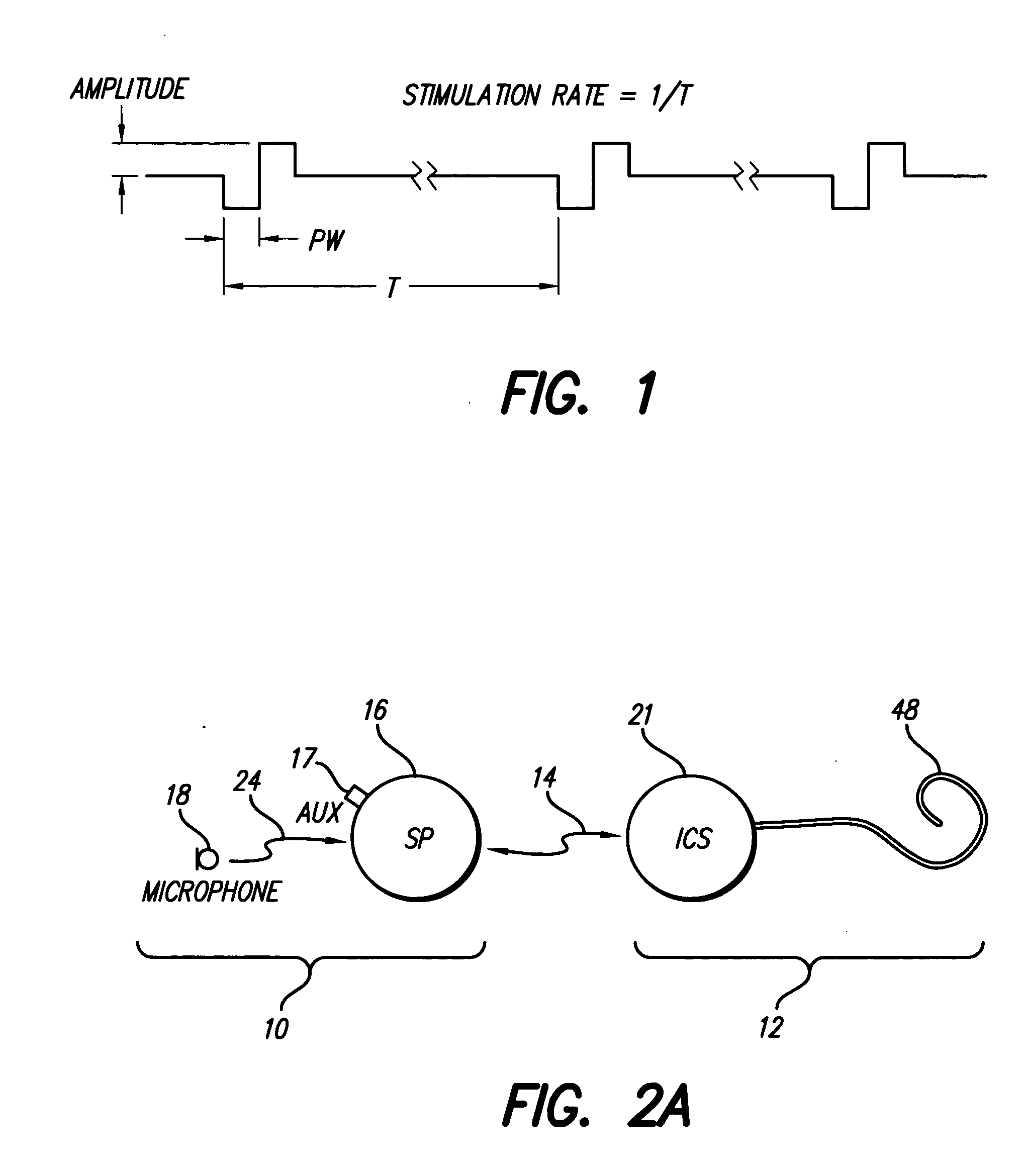
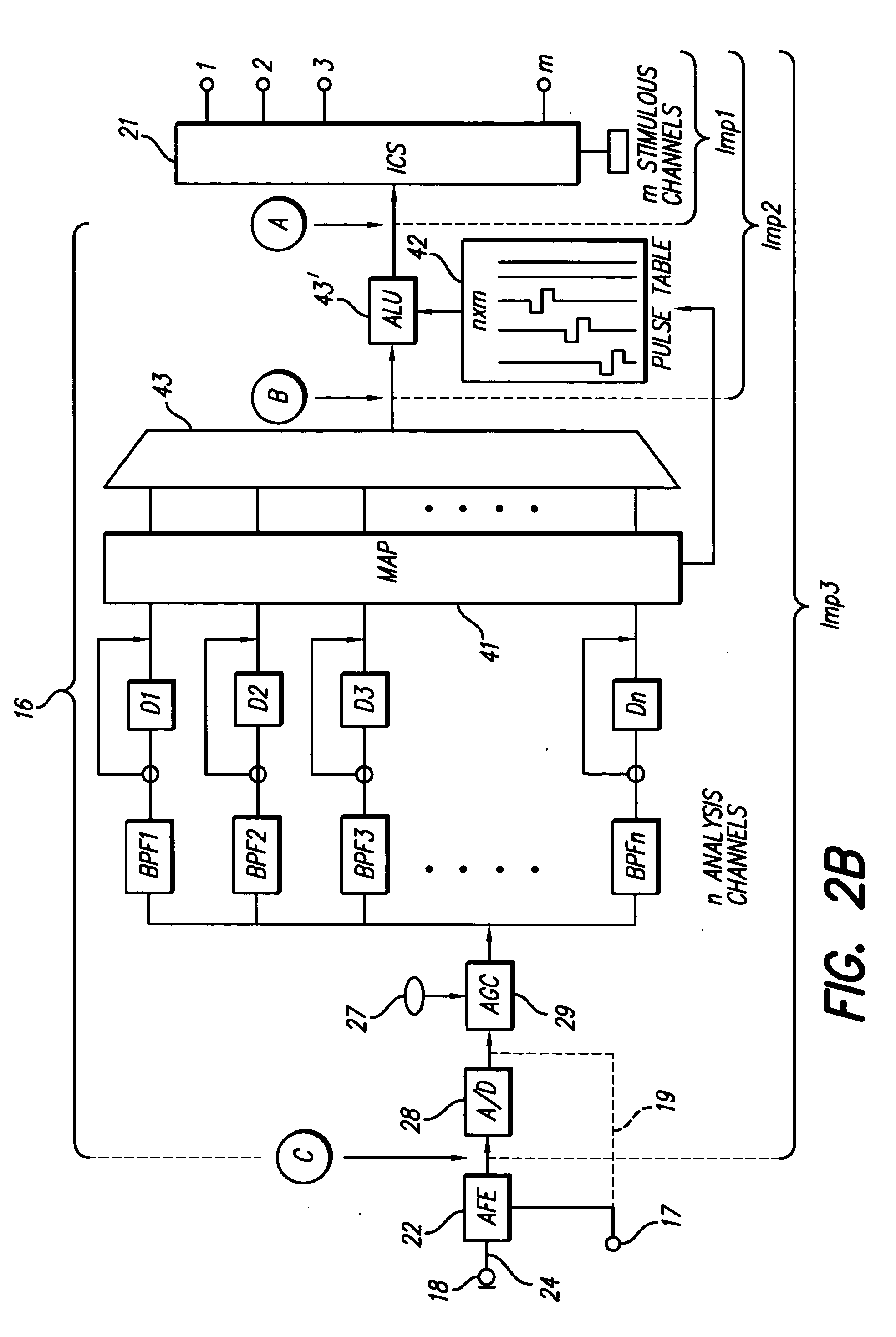
Electric and acoustic stimulation fitting systems and methods
Methods and systems for modifying the parameters of at least one hearing device for a patient with residual hearing provide needed orchestration of acoustic and electric stimulation of patients wearing such devices.
Owner:ADVANCED BIONICS AG
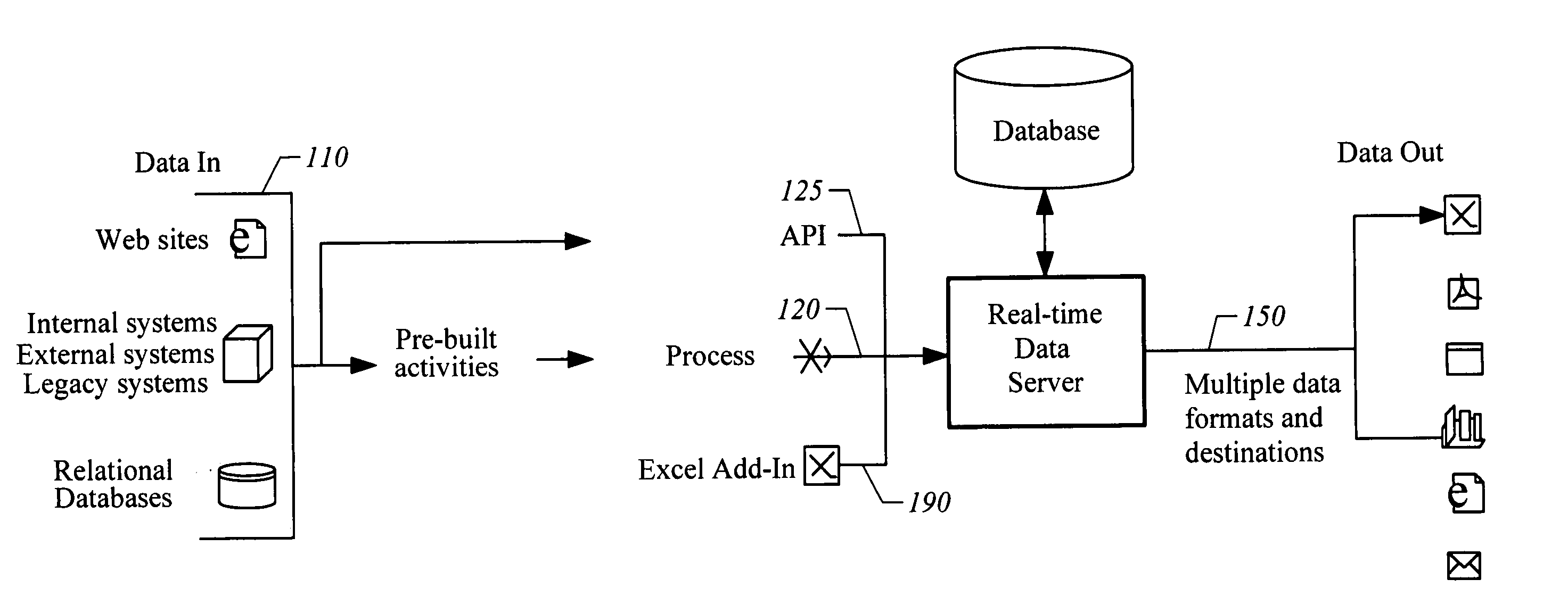
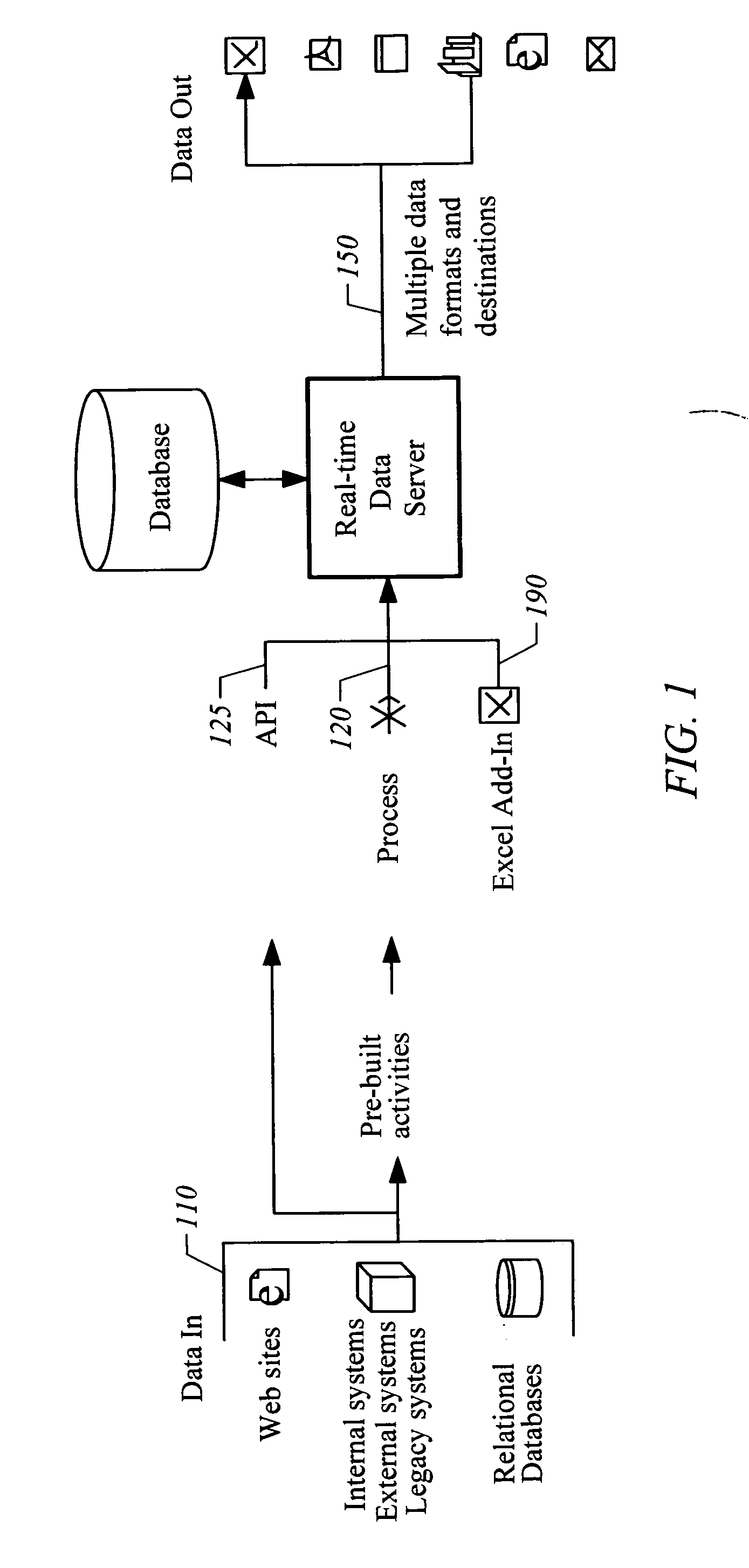
System and method for integrating disparate data and application sources using a web services orchestration platform with business process execution language (BPEL)
InactiveUS20050251527A1Special service provision for substationDigital data processing detailsOrchestrationSystems approaches
An apparatus, system, method, and computer readable medium is disclosed for integrating disparate data and application sources using a web services orchestration platform, with business process execution language (BPEL).
Owner:FWO NEWCORP
Orchestration of policy engines and format technologies
ActiveUS20070150936A1Efficient mergeOptimize topologyChaos modelsNon-linear system modelsSoftware engineeringOrchestration
Policies can combine the efficiency of rule sets with the flexible expression power of workflow engines, as well as advantages of other programming languages and engines. Consistent modelling of policy rules is provided across different levels, such as network, control, and service levels. In one system, a policy module can orchestrate rule set and workflow engines in order to evaluate different conditions of a policy. In another embodiment, a hybrid language can be used that allows rule set and other variables to be used in a business process container, workflow and other variables to be used in a rule set container, rule set and business process variables to be used in other containers. In this way, a subset of conditions in a policy can be evaluated using multiple languages and / or engines in order to enforce or evaluate a policy.
Owner:ORACLE INT CORP
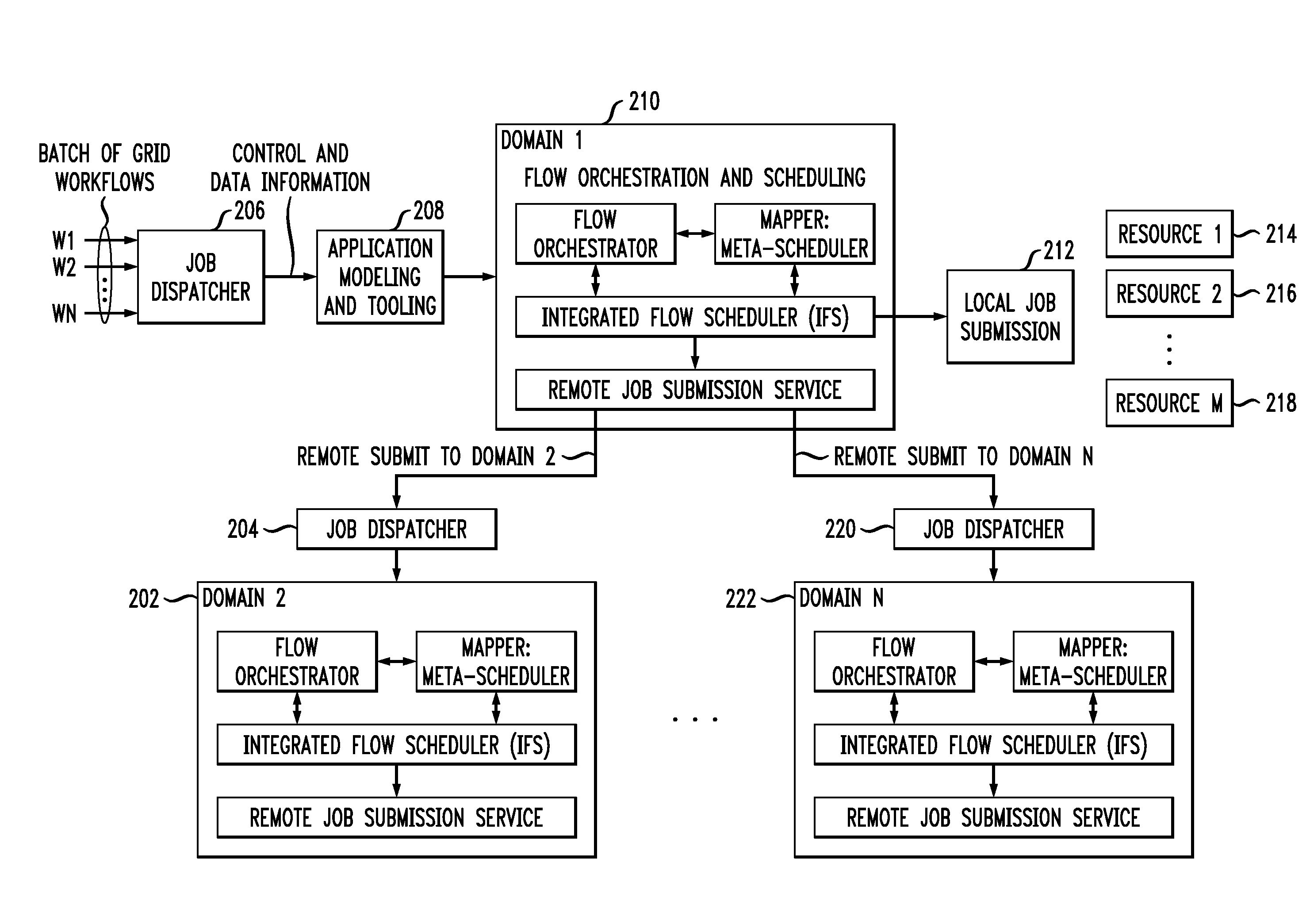
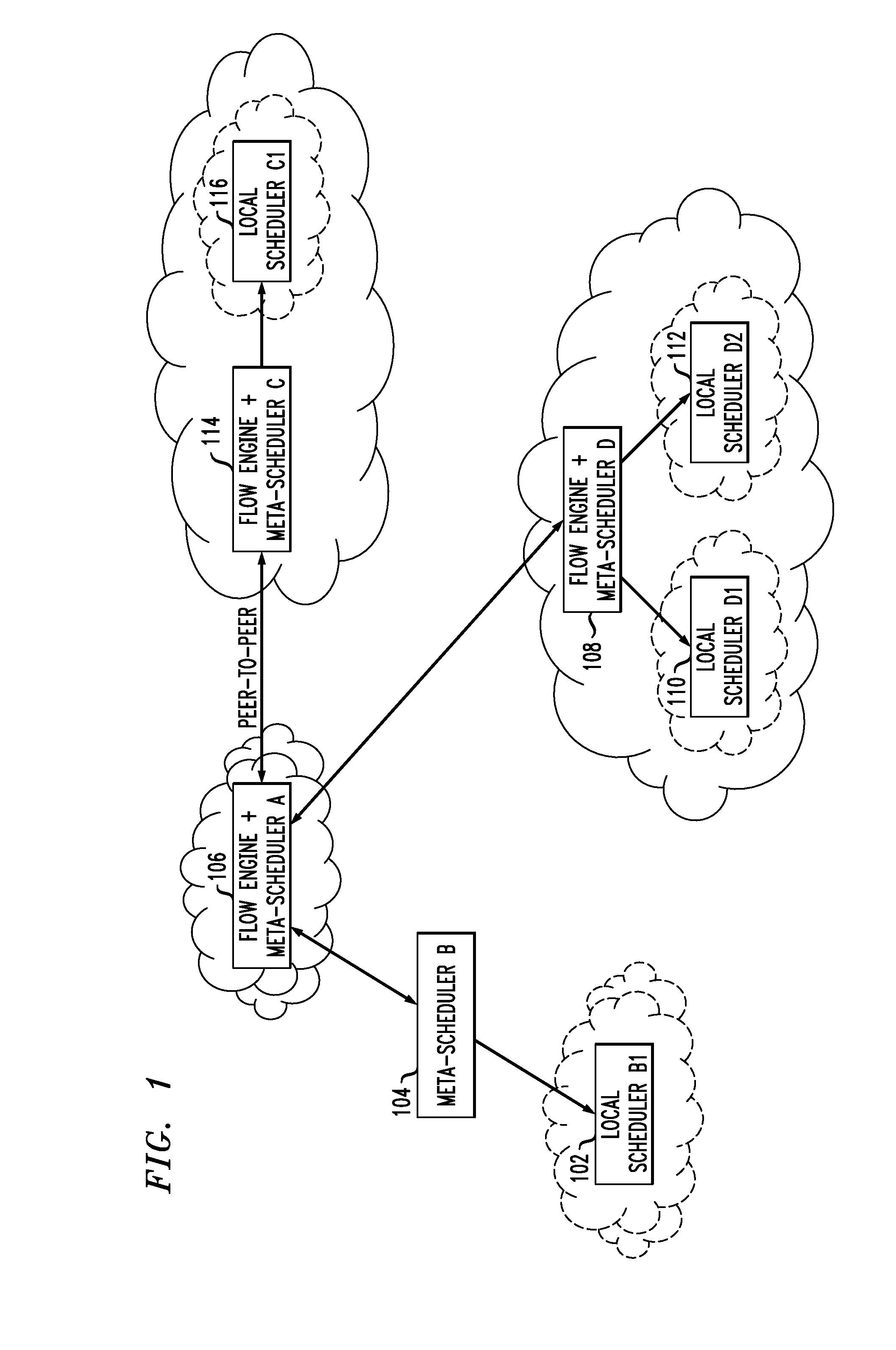
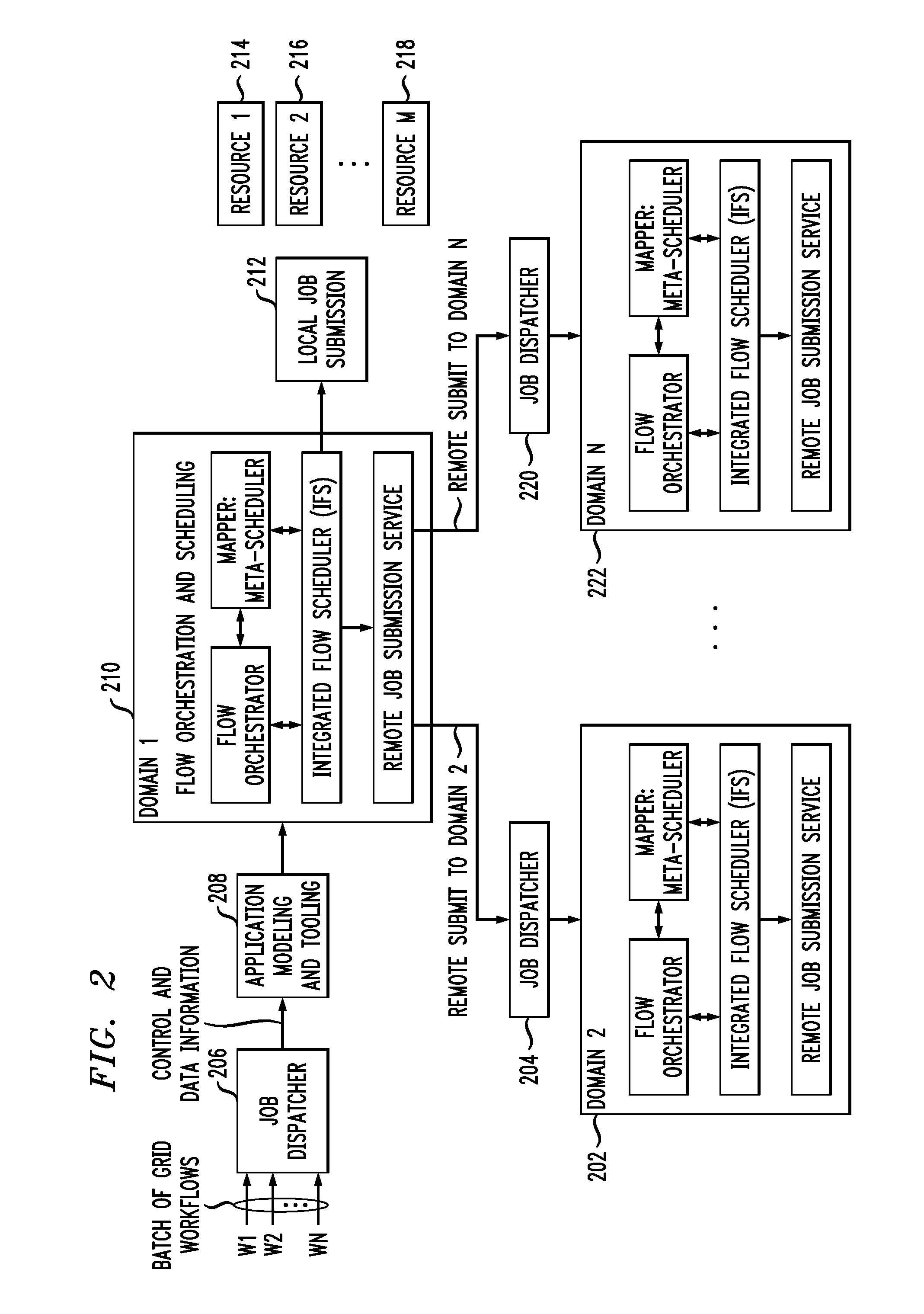
Method for integrating flow orchestration and scheduling for a batch of workflows
Techniques for executing a batch of one or more workflows on one or more domains are provided. The techniques include receiving a request for workflow execution, sending at least one of one or more individual jobs in each workflow and dependency information to a scheduler, computing, by the scheduler, one or more outputs, wherein the one or more outputs are based on one or more performance objectives, and integrating orchestration of one or more workflows and scheduling of at least one of one or more jobs and one or more data transfers, wherein the integrating is used to execute a batch of one or more workflows based on at least one of one or more outputs of the scheduler, static information and run-time information.
Owner:IBM CORP
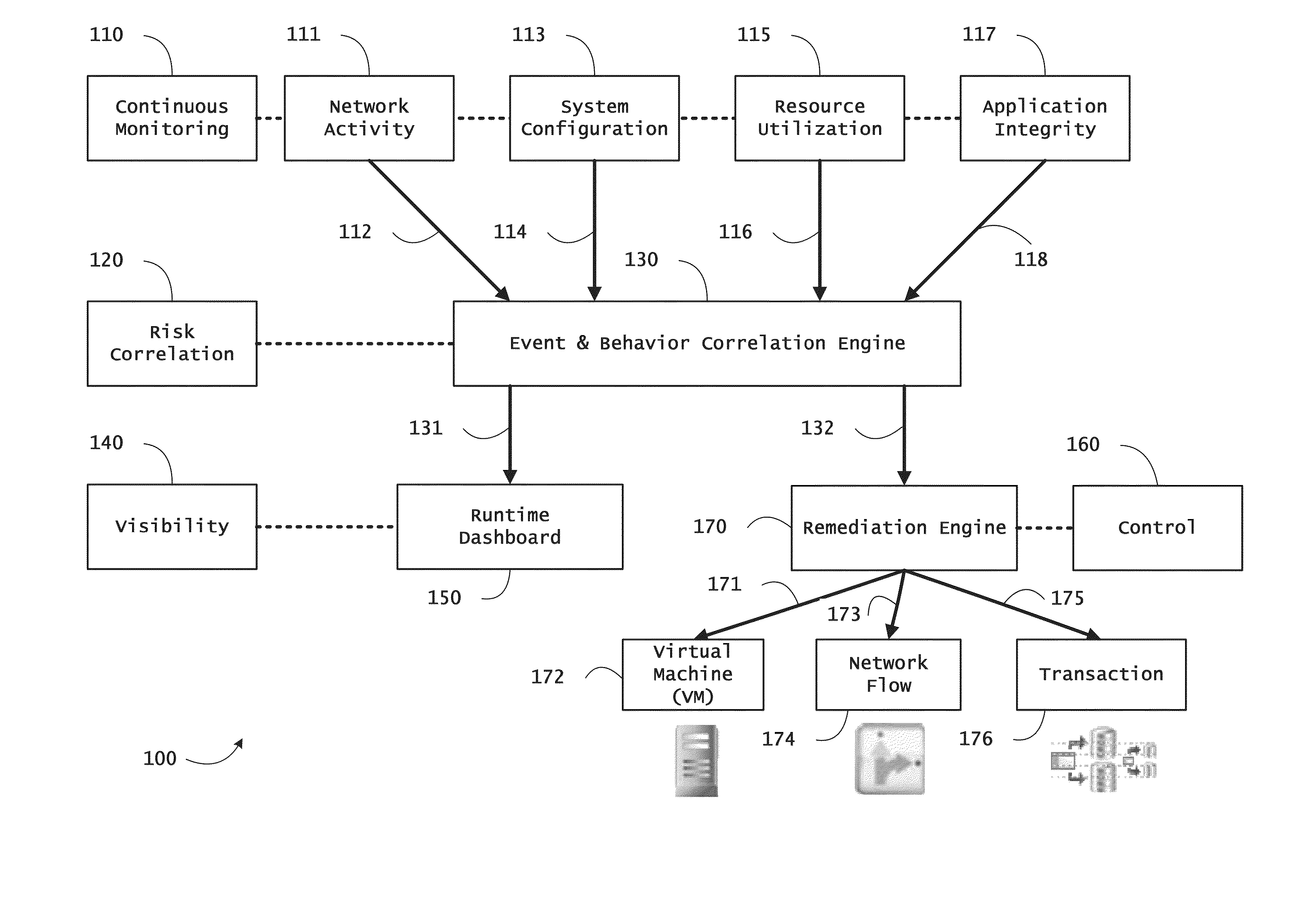
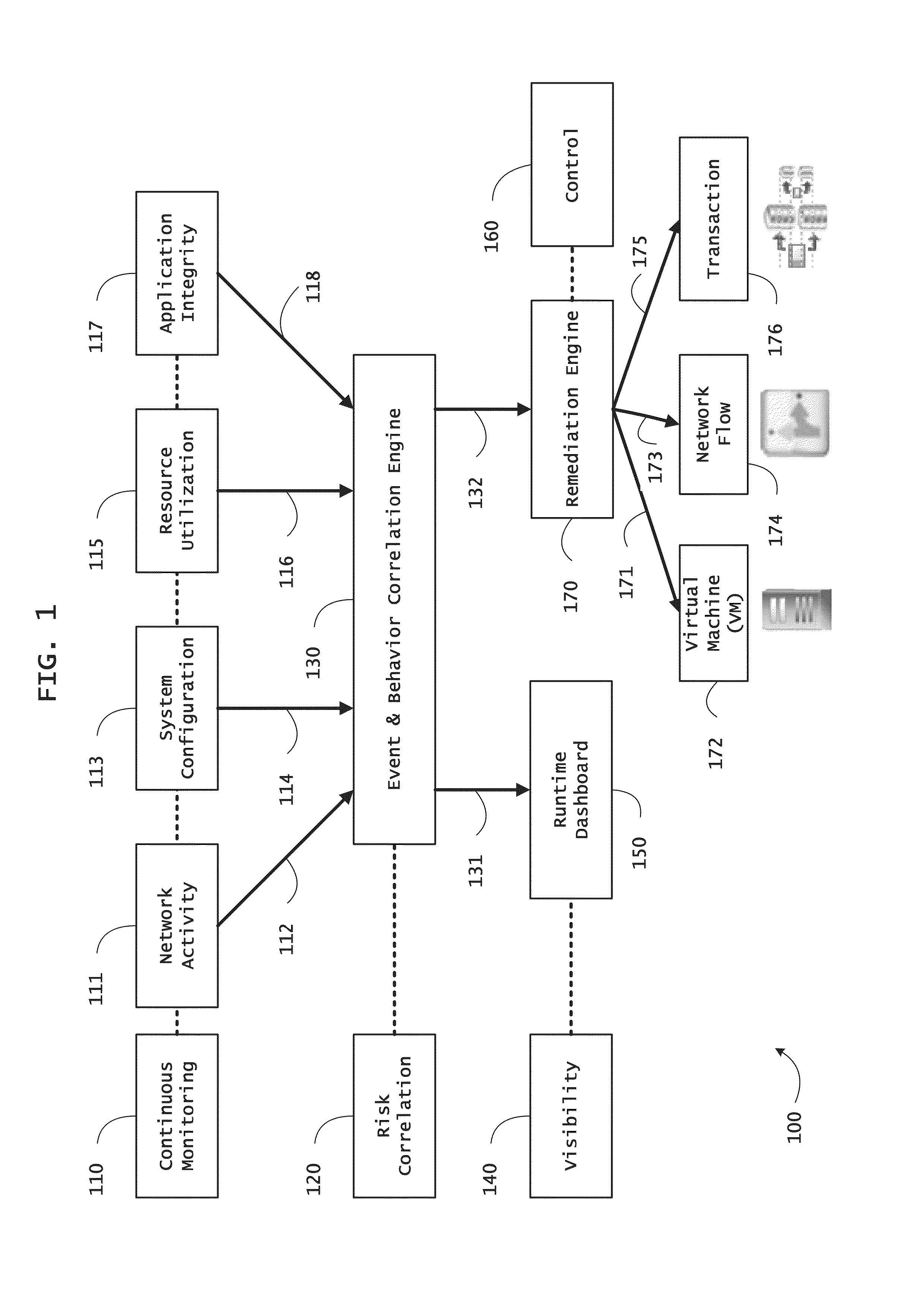
Systems and methods for network flow remediation based on risk correlation
ActiveUS20130298230A1Memory loss protectionError detection/correctionResource utilizationSystem configuration
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for network flow and device / platform remediation in response to reconnaissance-based intelligence correlation based on network monitoring, to accomplish network flow remediation and device / platform remediation. In an embodiment, a system receives system warnings and endpoint threat intelligence. The system correlates risk based on inputs from sensory inputs that monitor network activity, system configuration, resource utilization, and device integrity. The system then performs a calculus of risk on a global security context including endpoint assessment reports and sends system warnings based upon the endpoint threat intelligence. The system includes a remediation engine for receiving real time directives to control the device.
Owner:TAASERA LICENSING LLC
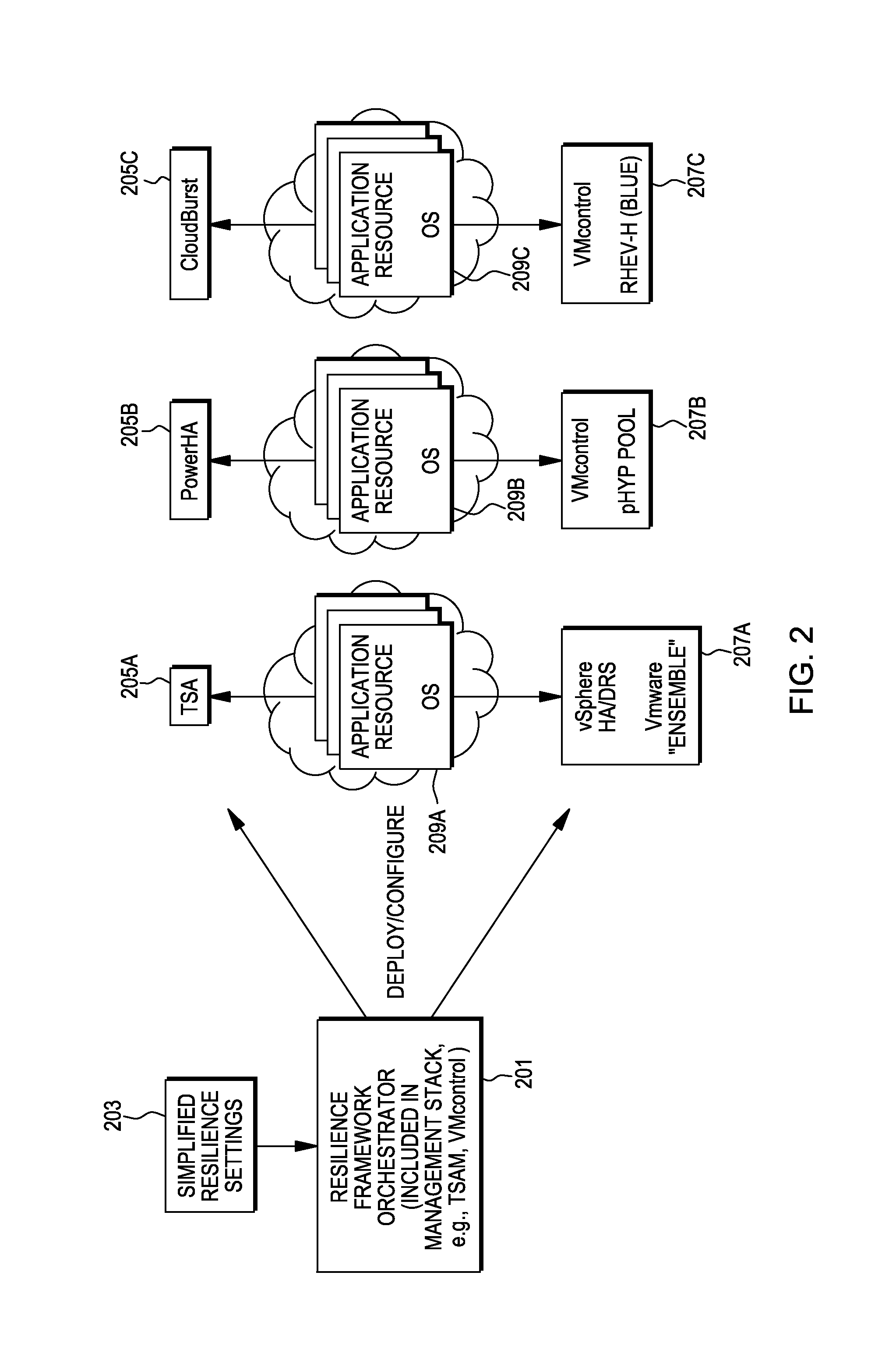
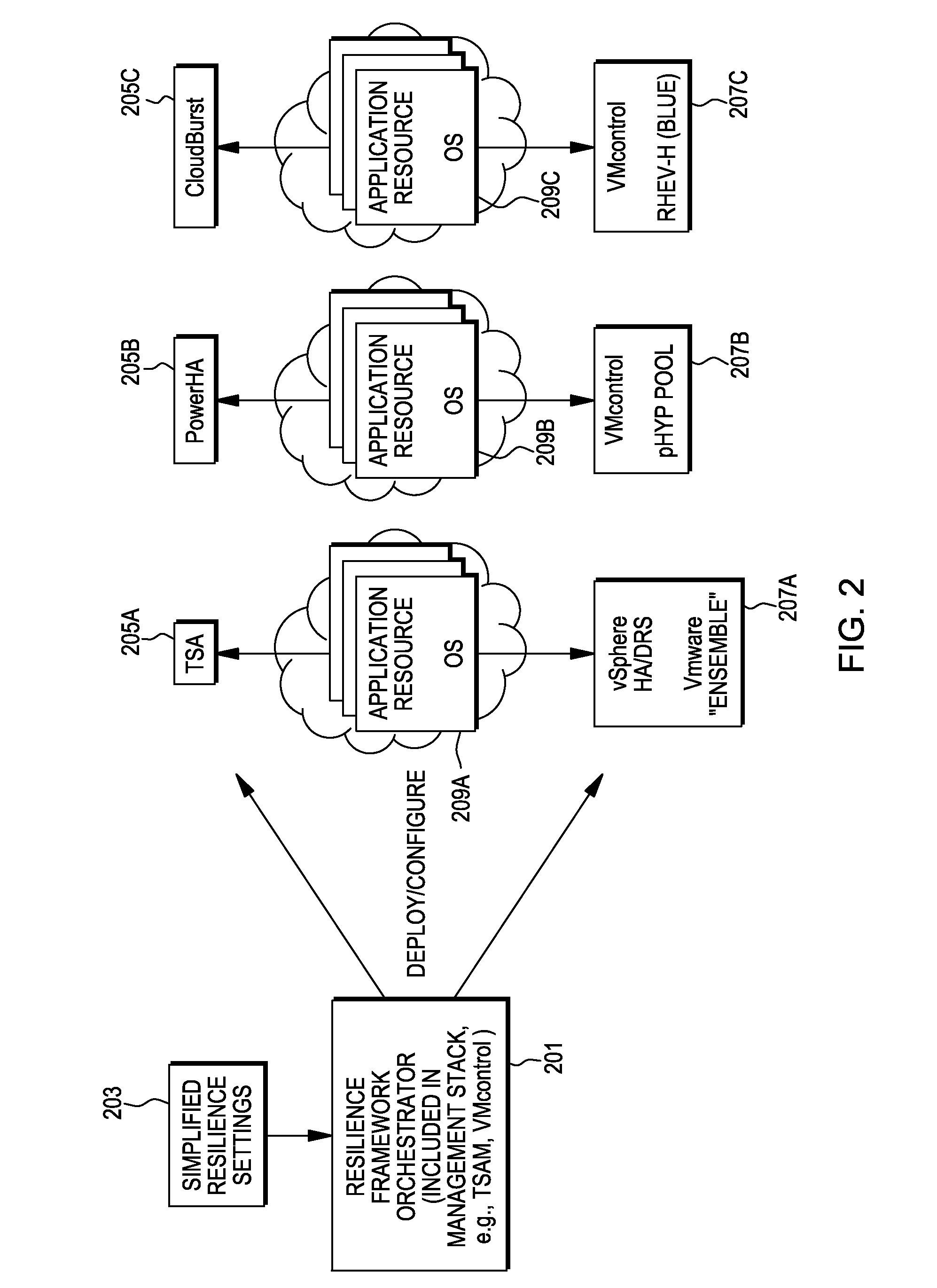
Open resilience framework for simplified and coordinated orchestration of multiple availability managers
Availability manager orchestration systems and methods and, particularly, an open resilience framework for simplified and coordinated orchestration of multiple availability managers.
Owner:IBM CORP
Open resilience framework for simplified and coordinated orchestration of multiple availability managers
InactiveUS20130185667A1Reduce complexityIssue is complexityNon-redundant fault processingProgram controlTheoretical computer scienceEngineering
Availability manager orchestration systems and methods and, particularly, an open resilience framework for simplified and coordinated orchestration of multiple availability managers.
Owner:IBM CORP
Renewable energy integrated storage and generation systems, apparatus, and methods with cloud distributed energy management services
ActiveUS9960637B2Guaranteed uptimeImprove performanceElectrical storage systemBatteries circuit arrangementsPrediction algorithmsCharge discharge
A software platform in communication with networked distributed energy resource energy storage apparatus, configured to deliver various specific applications related to offset demand monitoring, methods of virtual power plant and orchestration, load shaping services, methods of reducing demand at aggregated level, prioritizing computer programs related to virtual energy pool, energy cloud controllers methods, charge discharge orchestration plans of electric vehicles, distributed energy resources, machine learning predictive algorithms, value optimizing algorithms, autonomous sensing event awareness, mode selection methods, capacity reservation monitoring, virtual power plant methods, advanced DER-ES apparatus features, energy management system for governing resources and methods, aggregated energy cloud methods, load shaping methods, marginal cost cycle-life degradation, load shaping API, forward event schedule, on demand request, and load service state request methods. Various rules, constraints of predictive algorithms for signal inputs to determine incremental storage cycles, cycle life degradation marginal cost, iterative and forward event schedule development, and load control.
Owner:SUNVERGE ENERGY
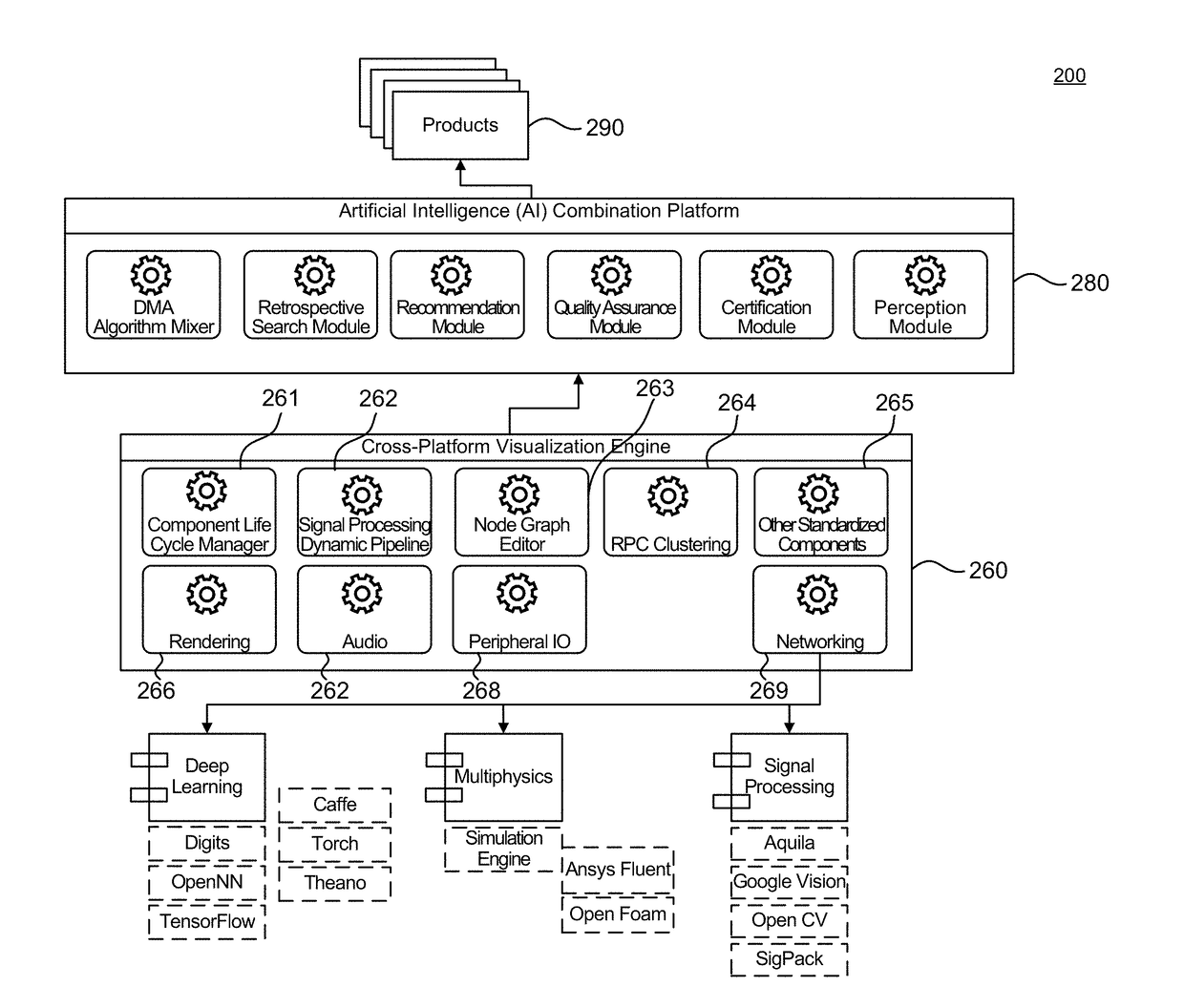
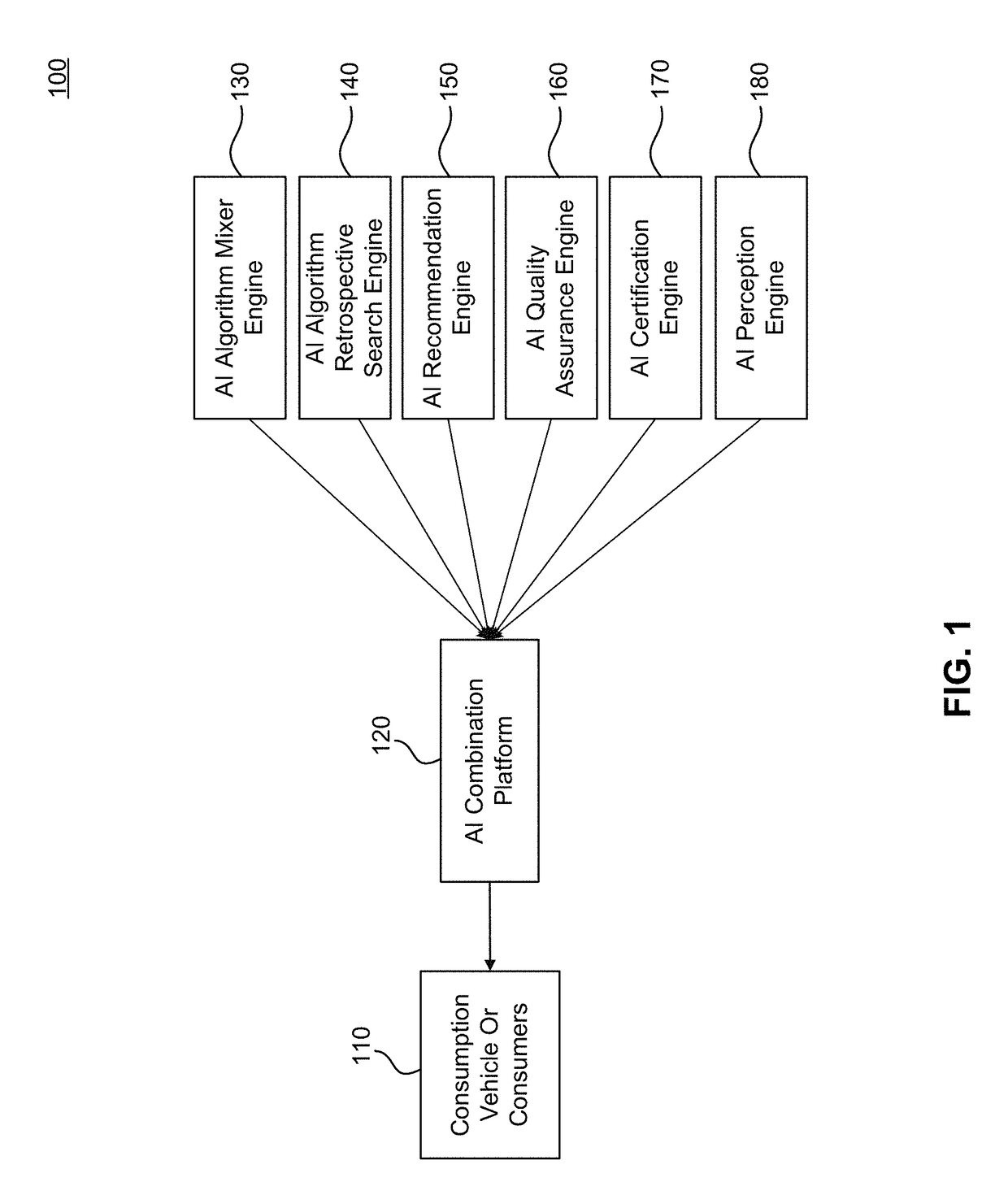
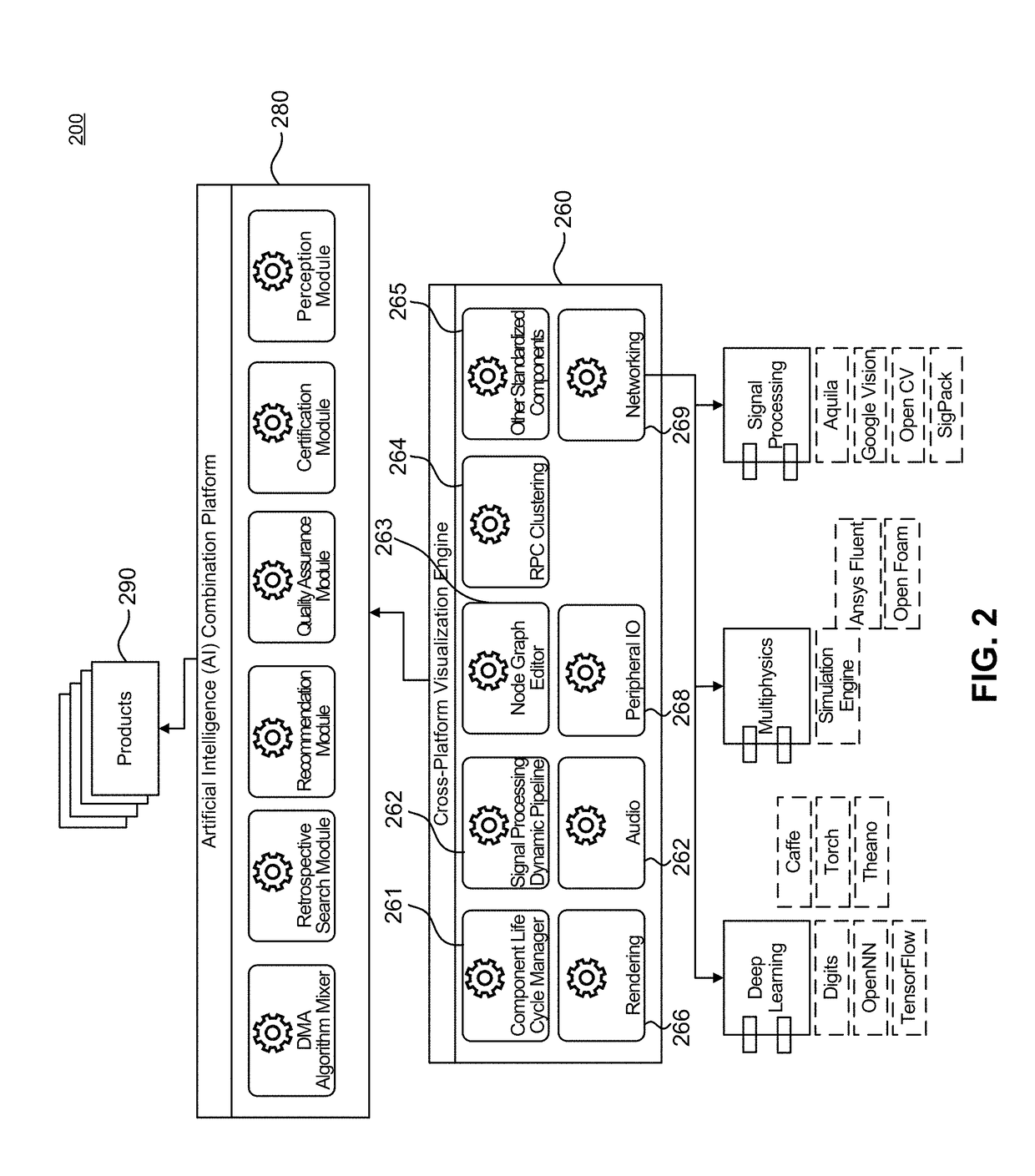
Interchangeable Artificial Intelligence Perception Systems and Methods
InactiveUS20170308800A1Avoid obscuring purposeEfficient use ofProcessor architectures/configurationMachine learningQuality assurancePerception system
An artificial intelligence (AI) combination platform or orchestration module is described that orchestrates and automates the processes of selecting, building, testing, and delivering new or integrated computer vision, detection, sensor and perception algorithms that can be published or leveraged in near real time by sensors, hardware or applications. The AI combination platform includes one or more of the following engines: algorithm mixer engine, retrospective search engine, algorithm recommendation engine, quality assurance engine, certification engine, and perception engine.
Owner:SMOKESCREEN INTELLIGENCE LLC
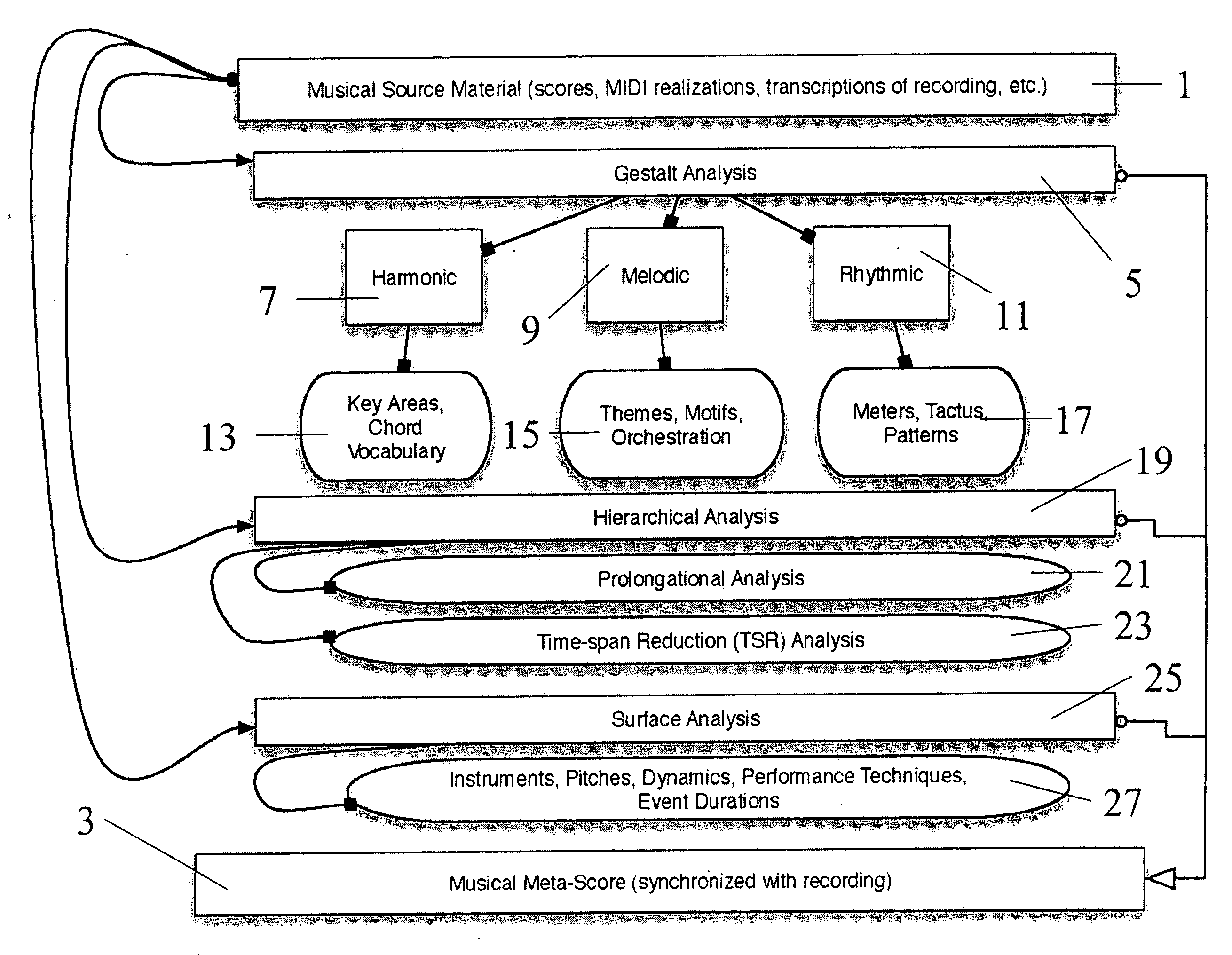
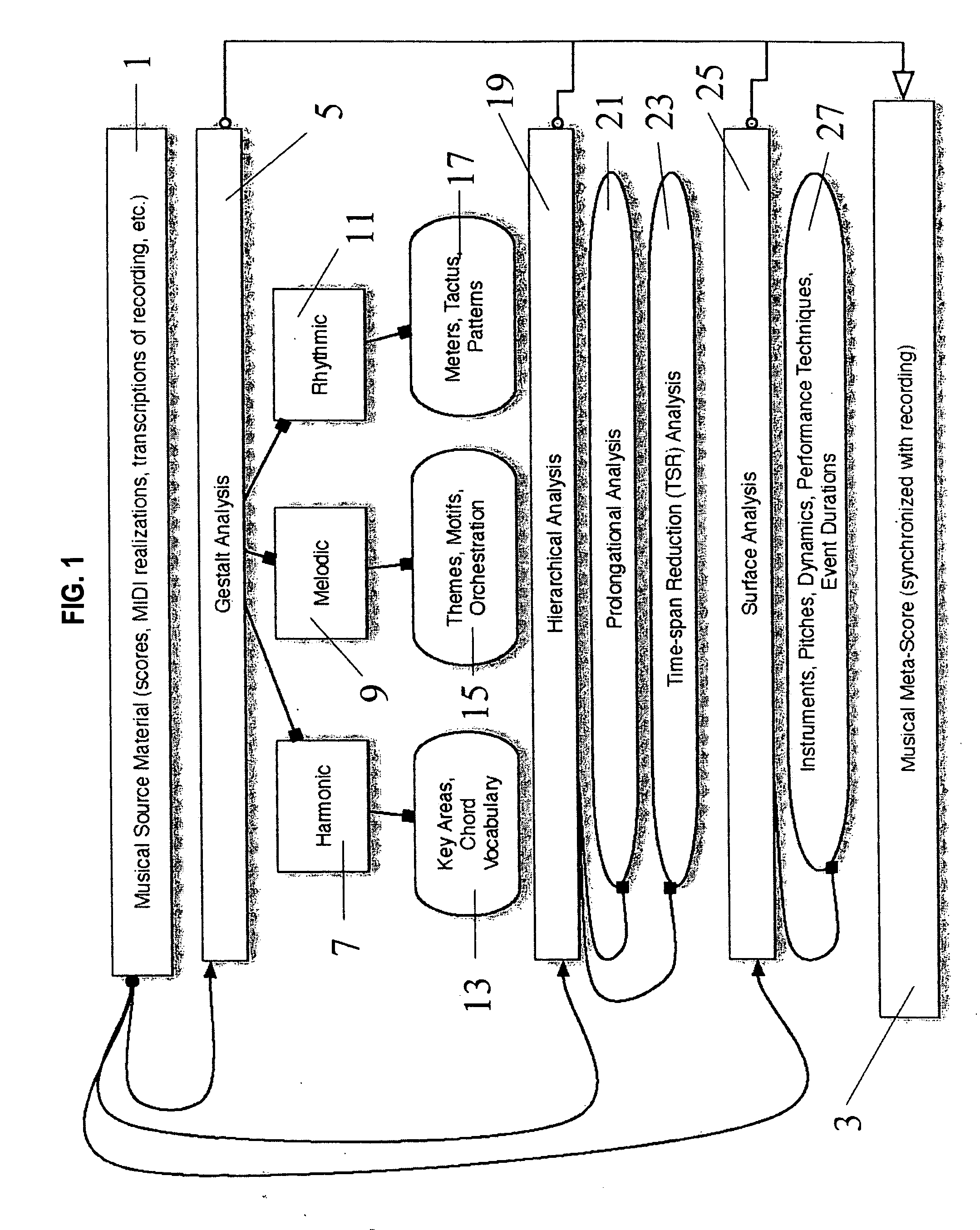
Interactive tool and appertaining method for creating a graphical music display
InactiveUS20080314228A1Precise processIntroduce and enhance and reinforce natural pattern and relationshipElectrophonic musical instrumentsMusicGraphicsOrchestration
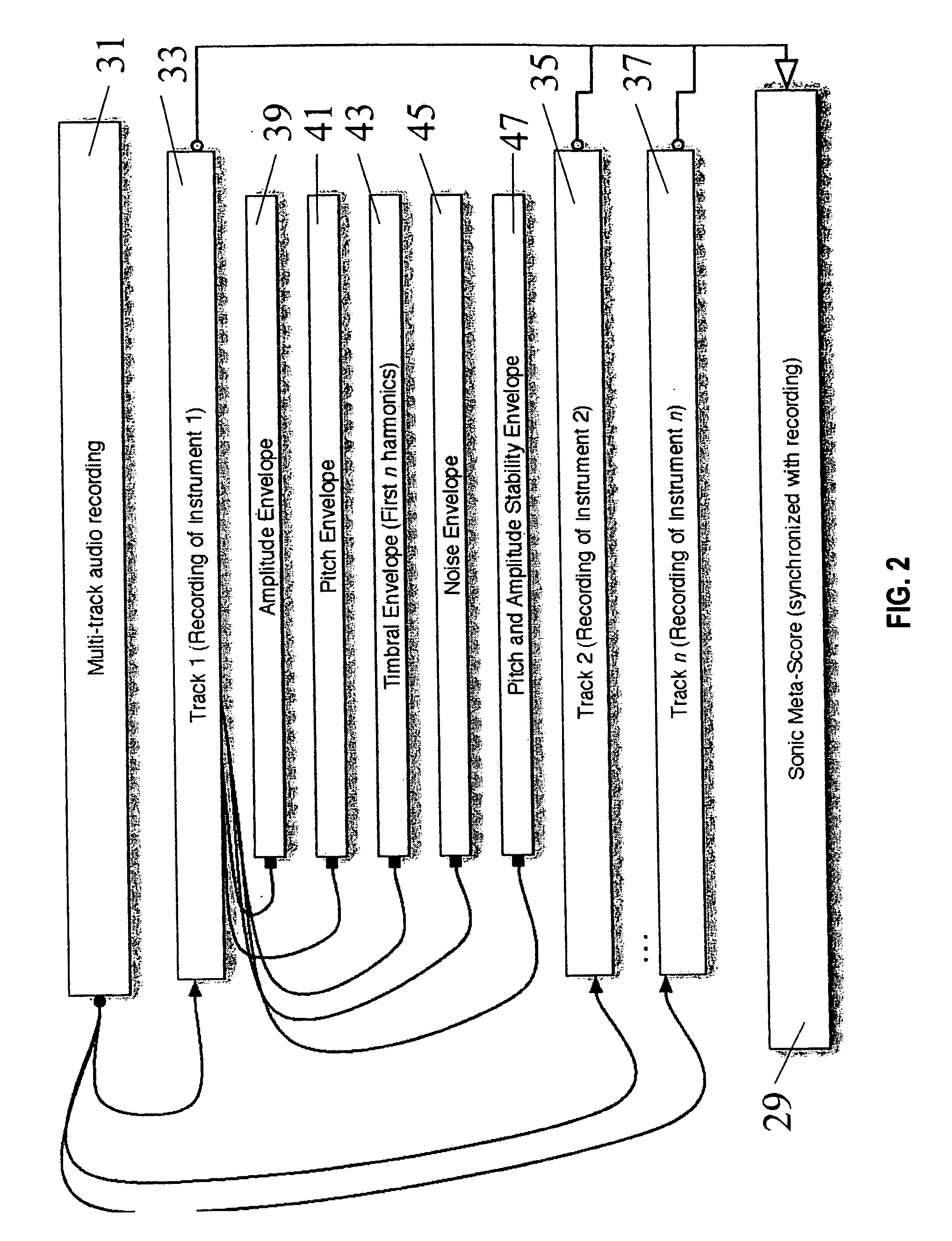
The invention provides apparatus and a method for creating a visual representation of music that conveys the musical form, structure, event surface, orchestration, and sonic framework of the piece being visualized. The representation comprises visual characters / sprites that move in time according to instructions from the metadata synchronized to the actual musical recording. These characters accurately portray the rhythm, pitch, and timbre of the individual elements in the musical surface (individual lines or performers) and have a hierarchy of representation, e.g. thematic elements that are divided into sub-elements (gestures or phrases) that are further divided into individual notes. The visual representation corresponds to the structure of the music as heard, where simultaneous harmonic events are parsed into individual notes which are then tied together into a rhythmic stream of linked events. Two streams of data (the “musical” and the “sonic”) are synchronized to the musical piece to drive the visualization.
Owner:DREYFUSS RICHARD +2
Methods and system for orchestrating services and data sharing on mobile devices
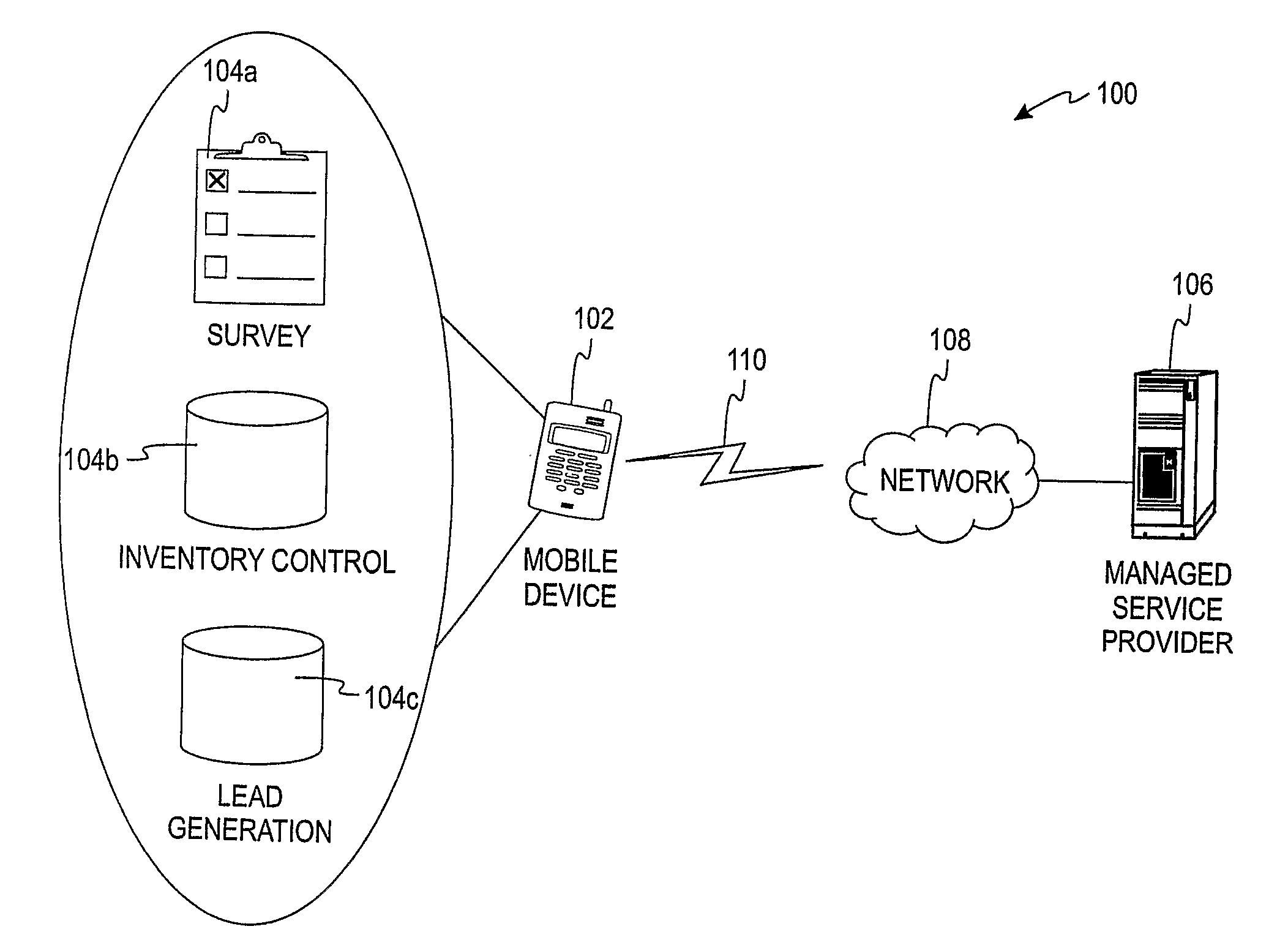
ActiveUS20100049874A1Digital data information retrievalMultiple digital computer combinationsOrchestrationMobile device
A method and system relating to a mobile orchestration platform to facilitate share of data between orchestration endpoints is disclosed. The orchestration endpoints may include data applications or data services located on a mobile device or remotely from the mobile device. An example platform includes a first endpoint connector associated with a first orchestration endpoint to communicate between the mobile orchestration platform and the first orchestration endpoint. A second endpoint connector associated with the second orchestration endpoint to communicate between the mobile orchestration platform and the second orchestration endpoint is included. A service module to translate a data record in an intermediate data format to either the first data format or the second data format is included.
Owner:PRONTOFORMS INC
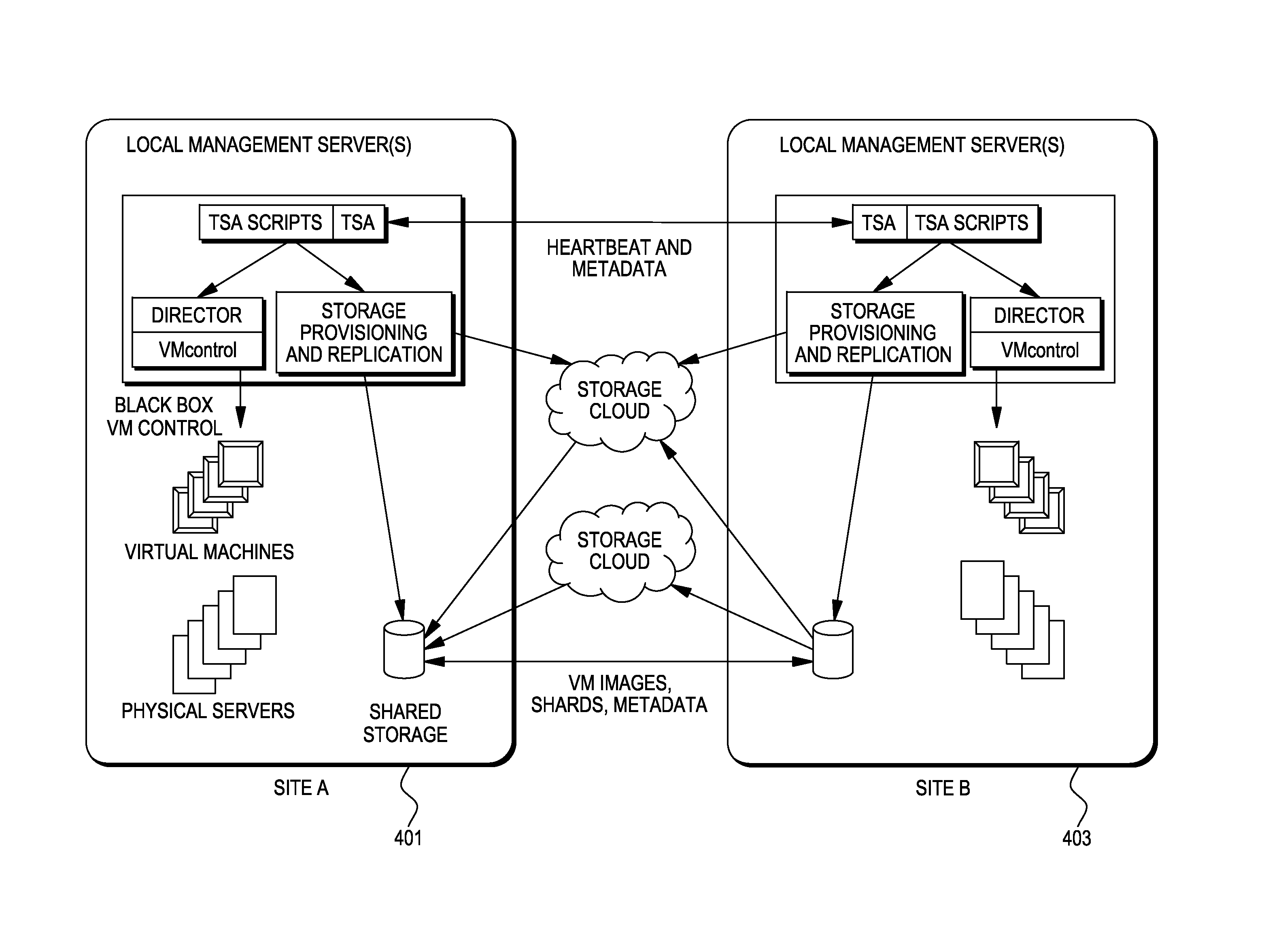
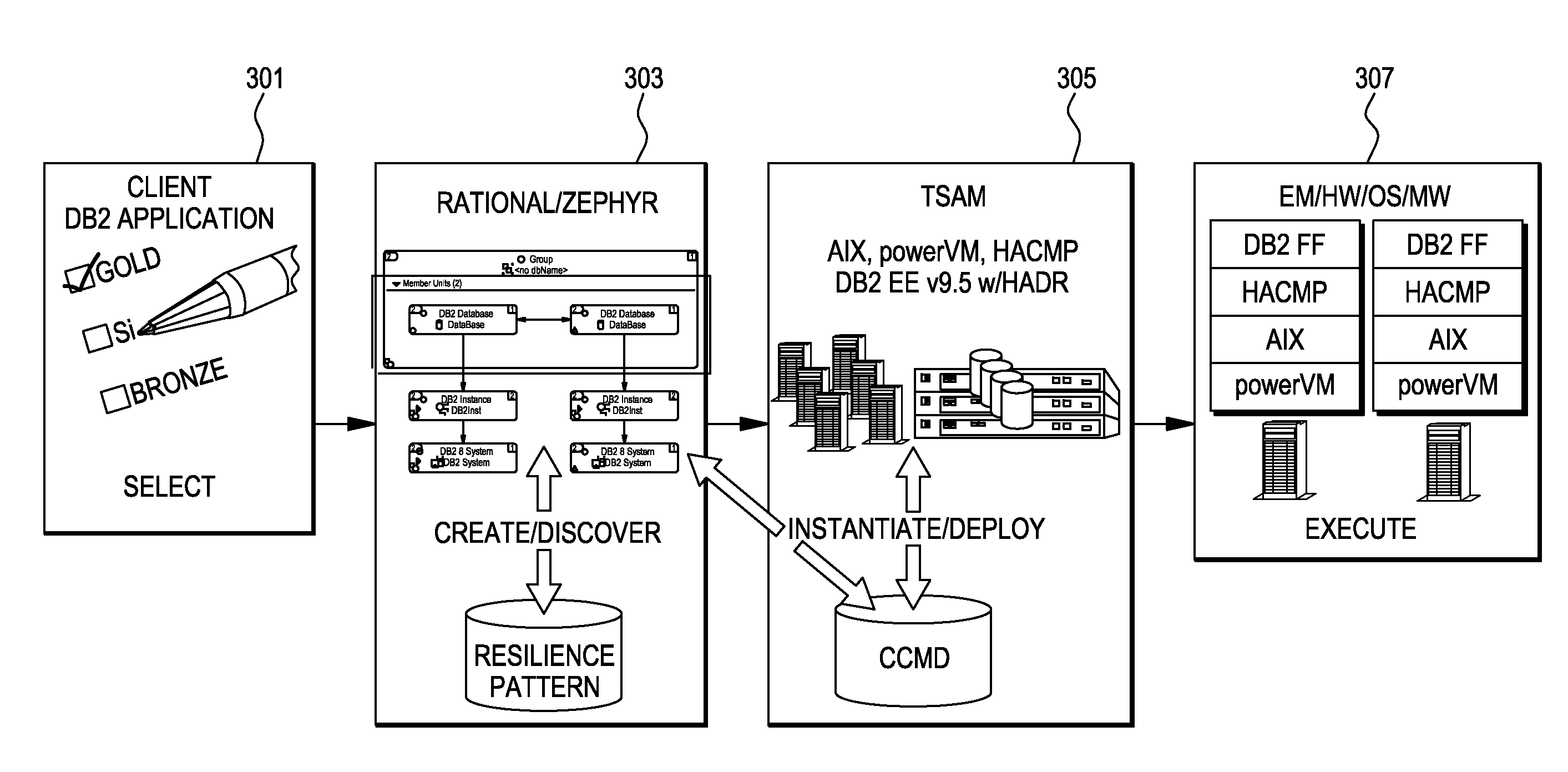
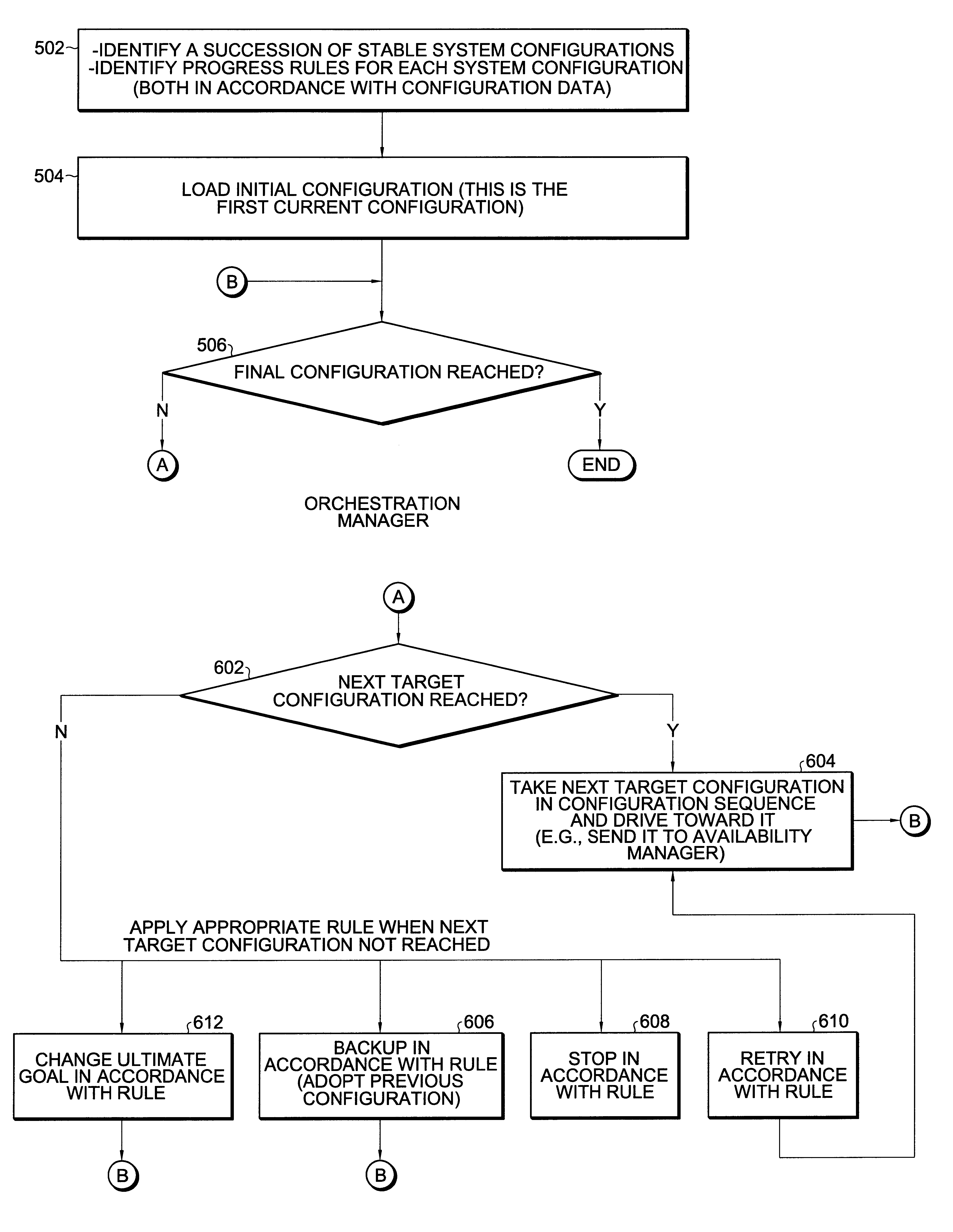
System and method for simplifying and managing complex transactions in a distributed high-availability computer system
InactiveUS6618805B1Digital computer detailsRedundant operation error correctionHigh availabilityEngineering
A method and system that manage upgrades in a high-availability computer system by viewing the upgrade process as driving the system between a succession of stable configurations. The mechanism used by a described embodiment is an availability manager that is capable of ascertaining the state of each component and driving it toward a goal state by driving toward a succession of desired stable configurations. A high-level orchestration agent instructs the availability manager when a stable configuration has been reached and it is time to drive toward a next stable configuration.
Owner:ORACLE INT CORP
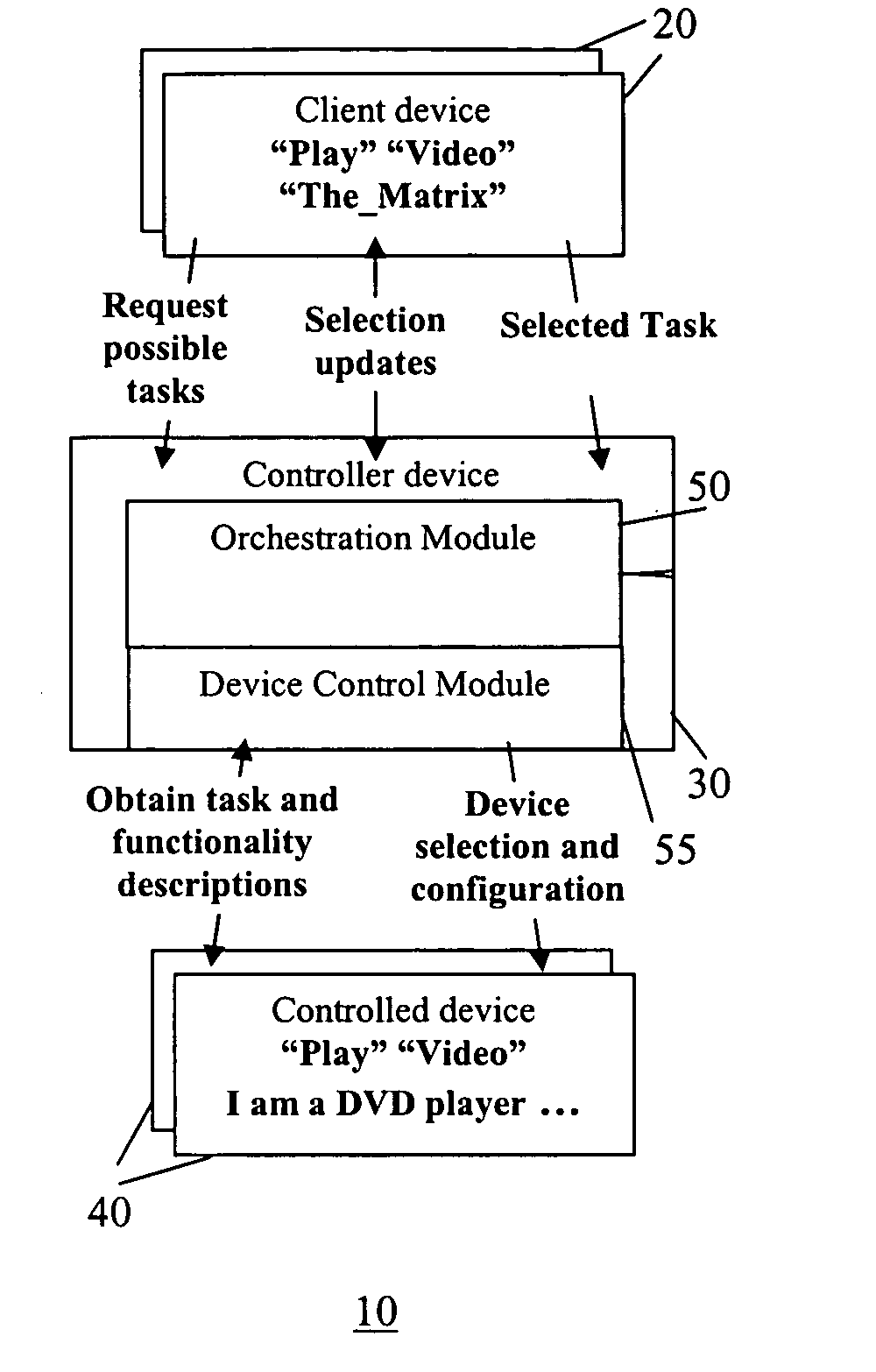
Method and system for presenting user tasks for the control of electronic devices
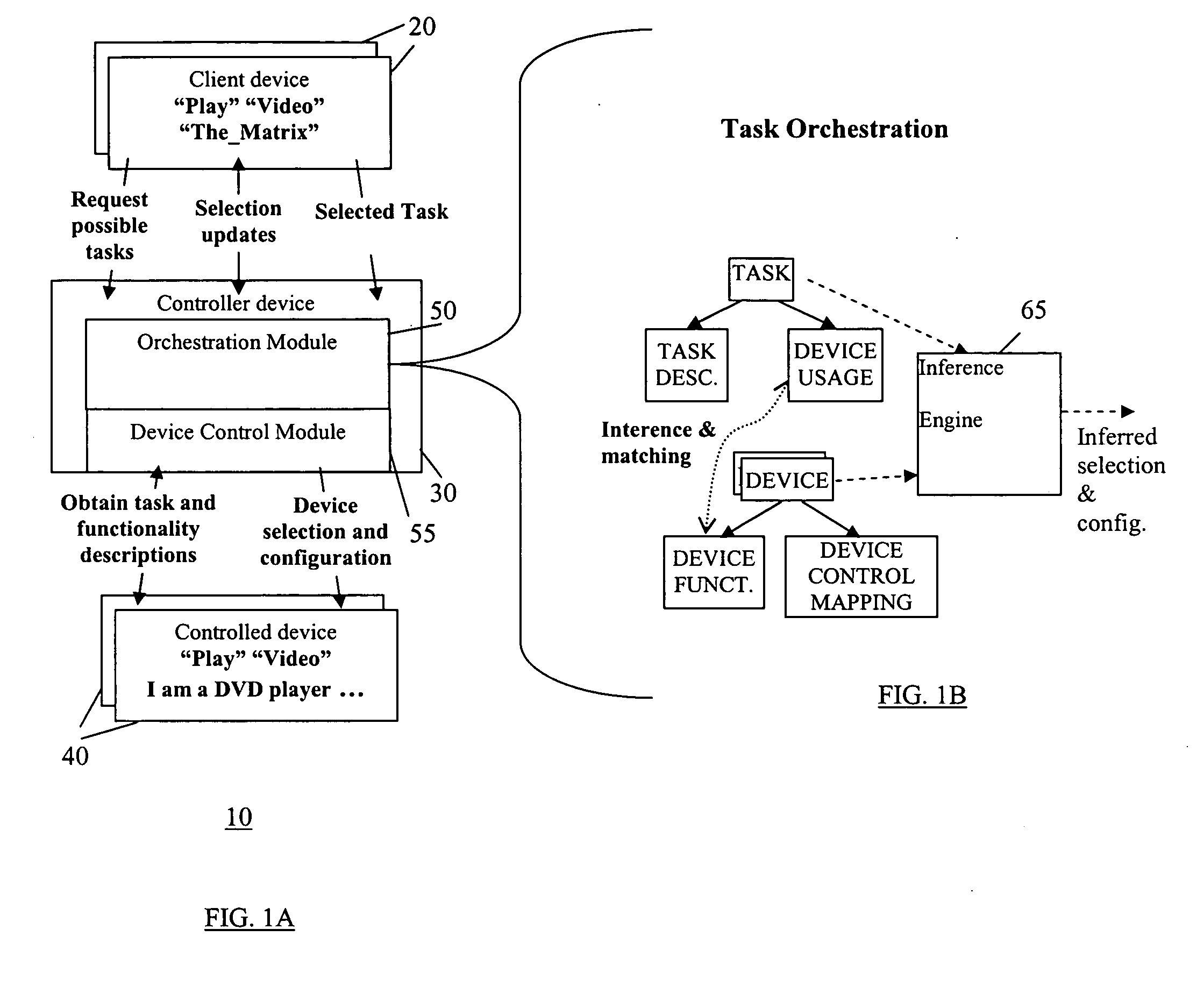
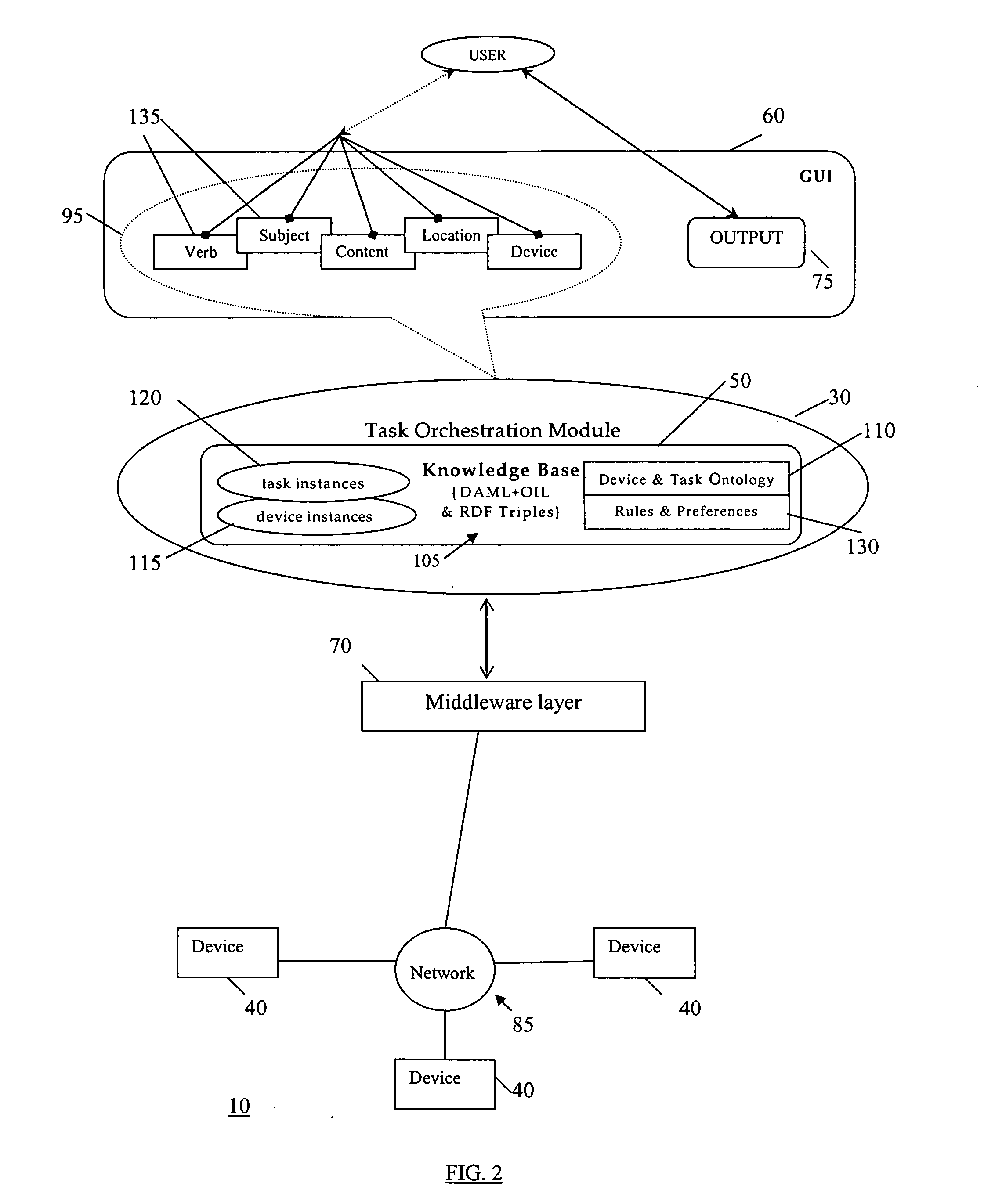
InactiveUS20060064693A1Television system detailsSoftware engineeringComputer architectureControl electronics
A method of representing user tasks to be performed by one or more of a plurality of electronic devices in a task orchestration system. Each device includes therein a function description specifying a function that the device can perform. The function descriptions are obtained from one or more of the devices, task descriptions that describe device functionalities required for certain tasks are obtained, and task suggestion are generated based on the obtained device function descriptions and task descriptions. Each task suggestion represents a user task as an abstraction of on or more of the obtained device descriptions and task descriptions. The tasks suggestion are displayed on a display for the user to select from, wherein the user selected task suggestion is to be performed by orchestration (automation) of one or more of the devices based on task descriptions that use device functionalities described in the device function descriptions.
Owner:SAMSUNG ELECTRONICS CO LTD
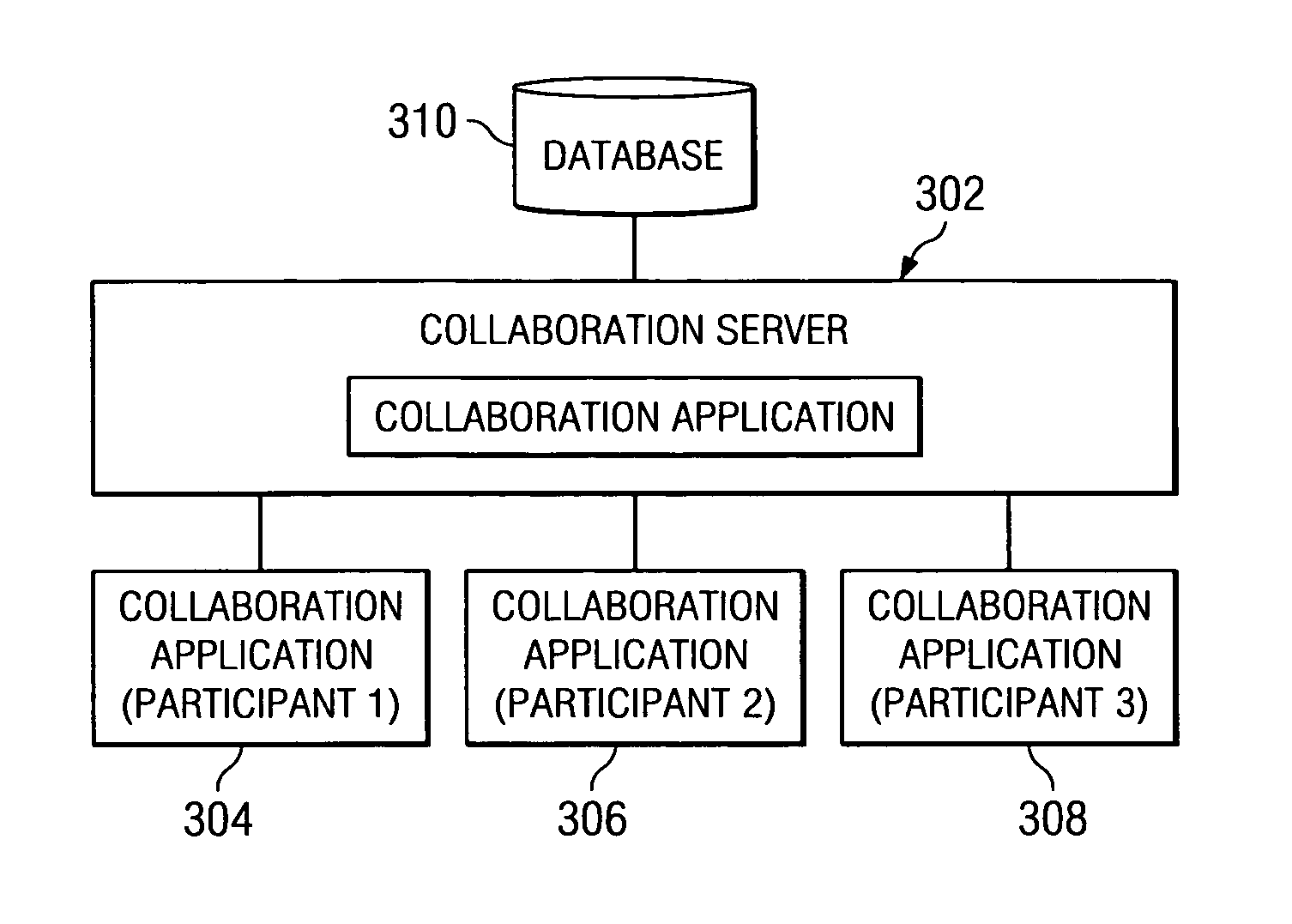
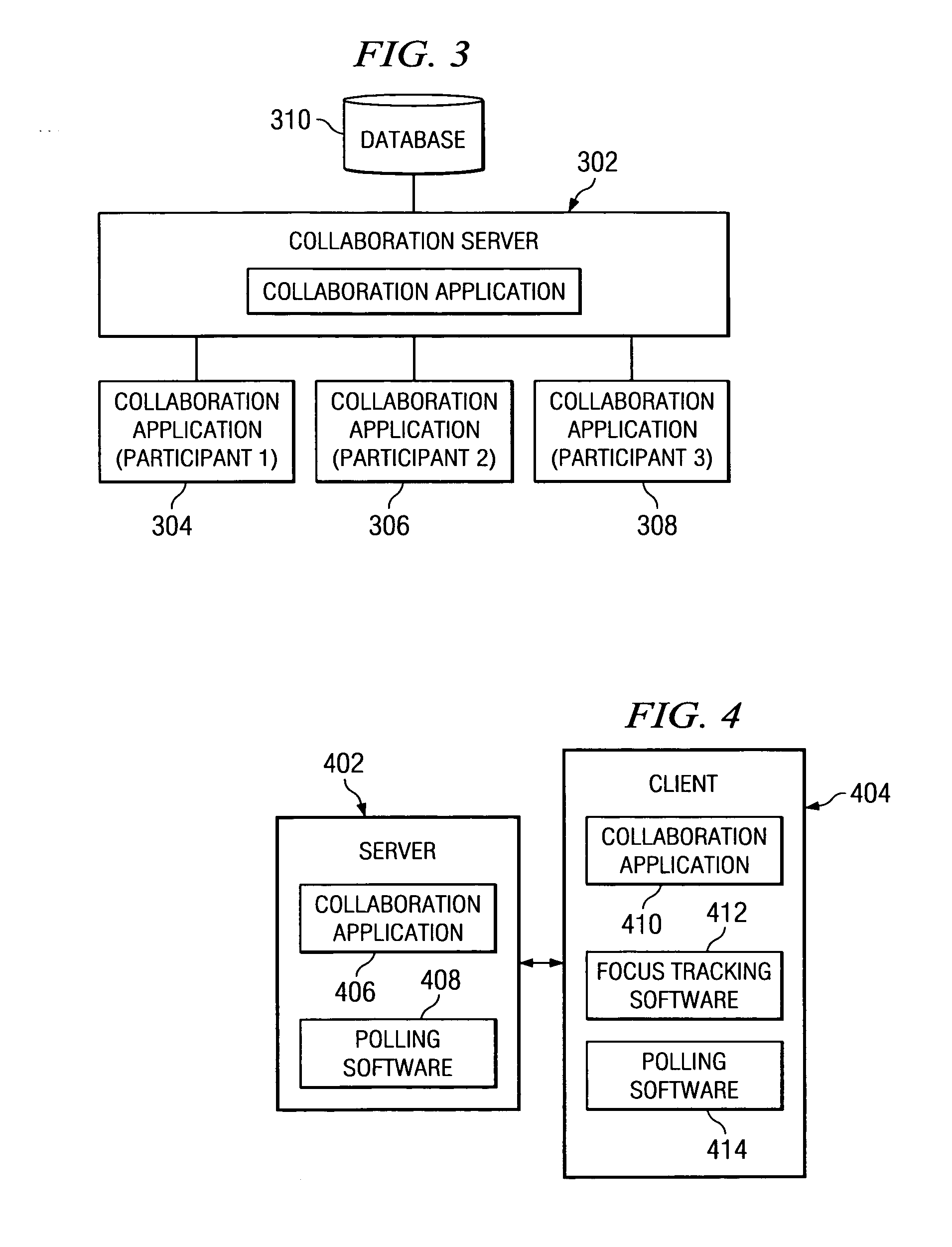
Participant-centered orchestration/timing of presentations in collaborative environments
A method, system, and computer program product for providing participant-centered orchestration / timing of presentations in collaborative environments. With the mechanism of the present invention, participants in an online collaboration environment are allowed to control the real-time presentation of collaboration materials. The mechanism of the present invention polls the participants in the online presentation. When the polling feedback from the participants is received, the polling feedback from each participant is aggregated to form a collective participant response. The pace and / or content of the presentation is then dynamically modified based on the collective participant response. The dynamically modified presentation is then provided to the participants.
Owner:IBM CORP
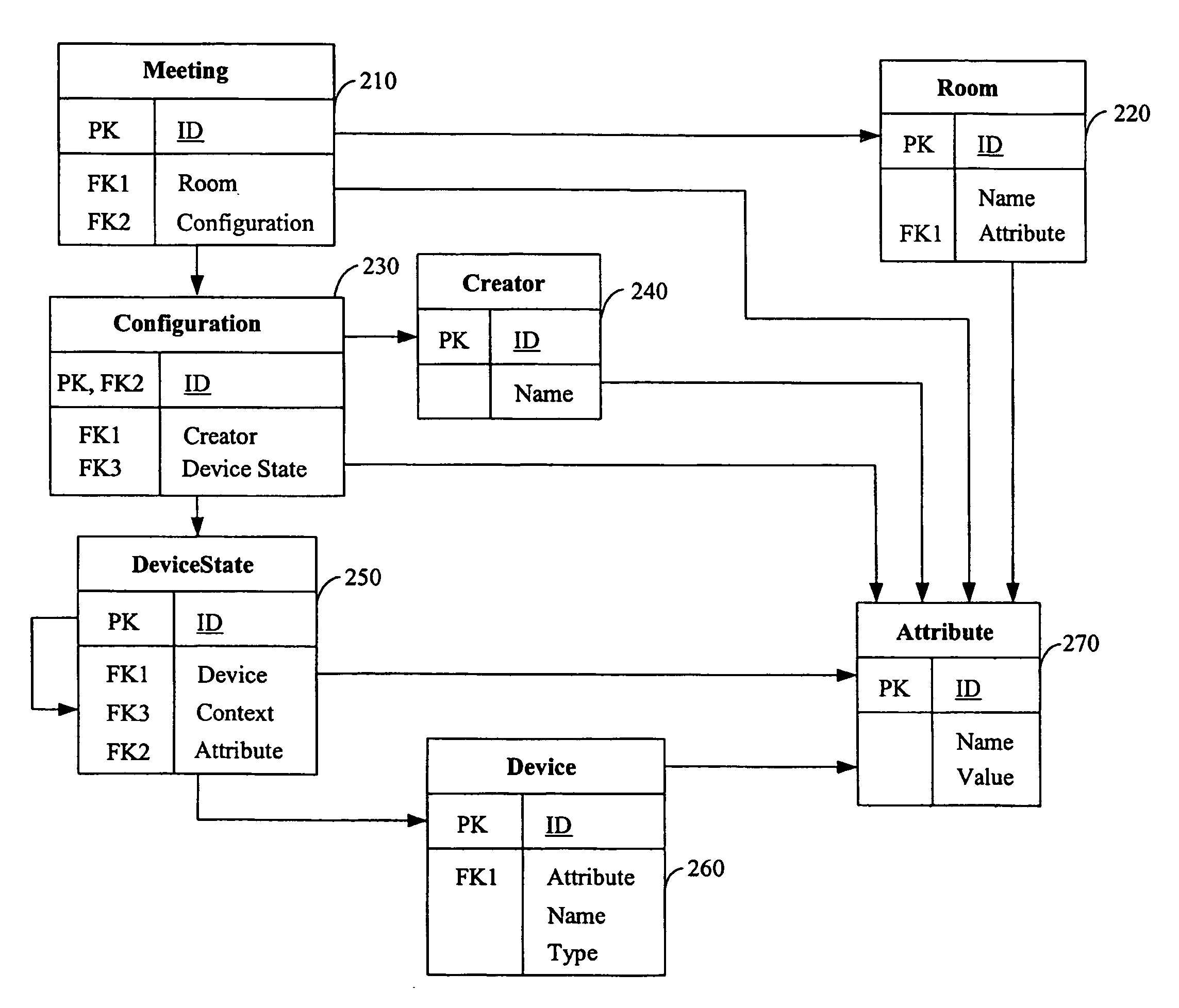
Device Orchestration
InactiveUS20080183820A1Television conference systemsMultiple digital computer combinationsComputer hardwareApplication software
A system is provided that coordinates the operation of hardware devices and software applications in support of specific tasks such as holding a meeting. The system includes one or more computers connected by a network, at least one configuration repository component, at least one room control component, and one or more devices and applications for each room control component. Meeting presenters can configure a meeting, or they may use a default configuration. A meeting includes one or more presenters' configurations of devices and applications to accommodate multiple presenters simultaneously. The meeting configurations are stored by the configuration repository component. Each presenter's configuration comprises a subset of the one or more devices and applications. The operation of devices and applications in the meeting is coordinated by the room control component based on the presenters' configurations for the meeting.
Owner:FUJIFILM BUSINESS INNOVATION CORP
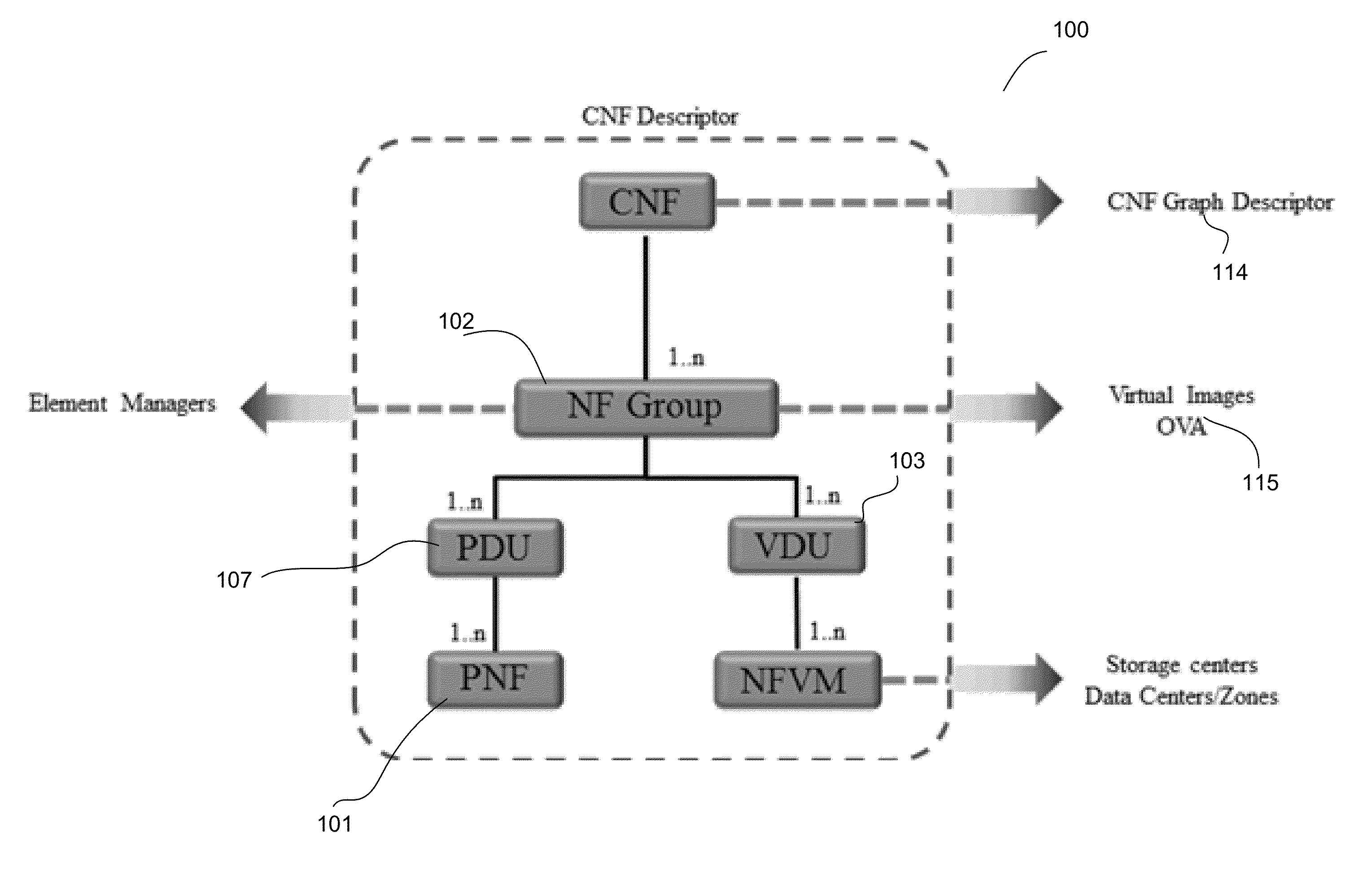
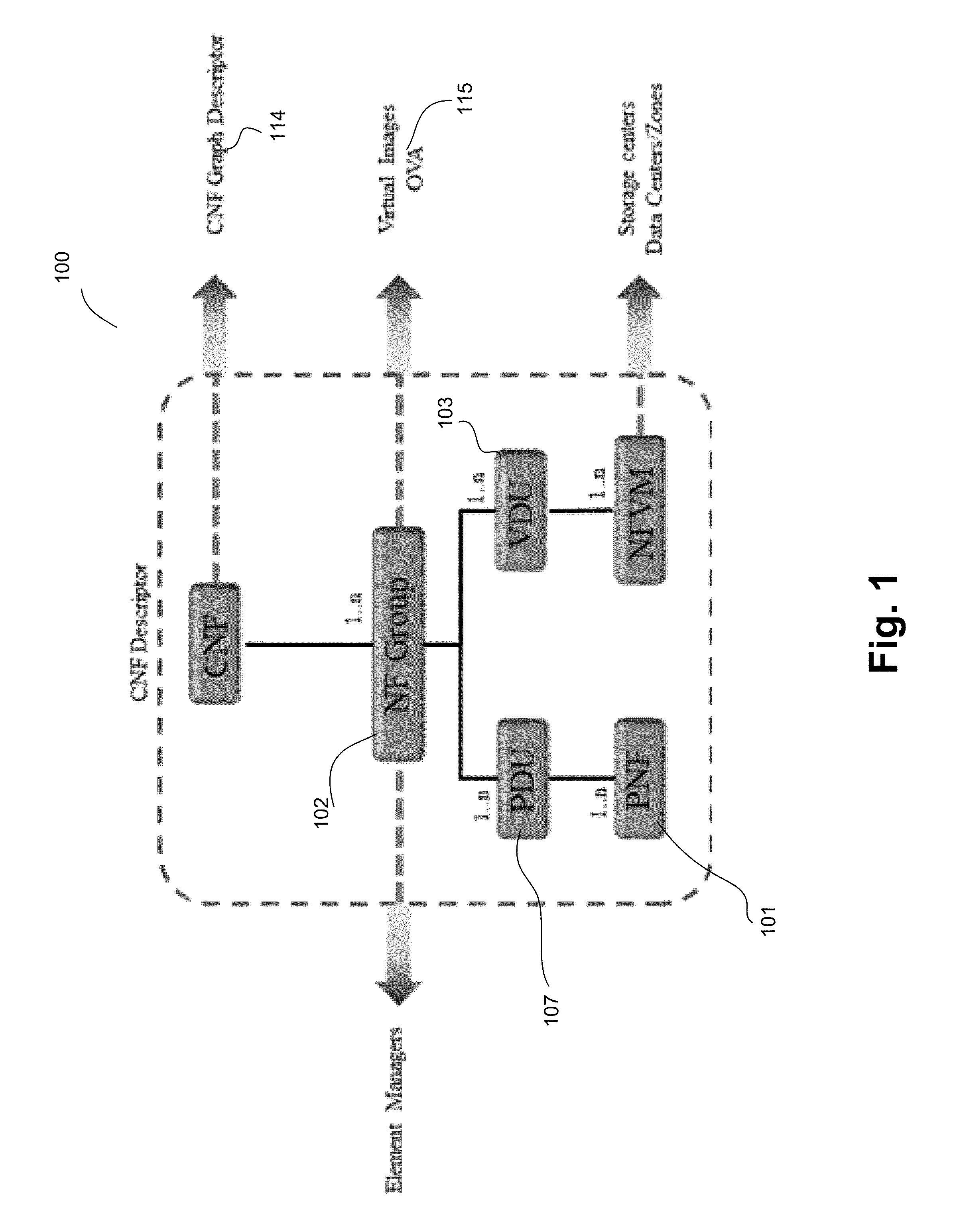
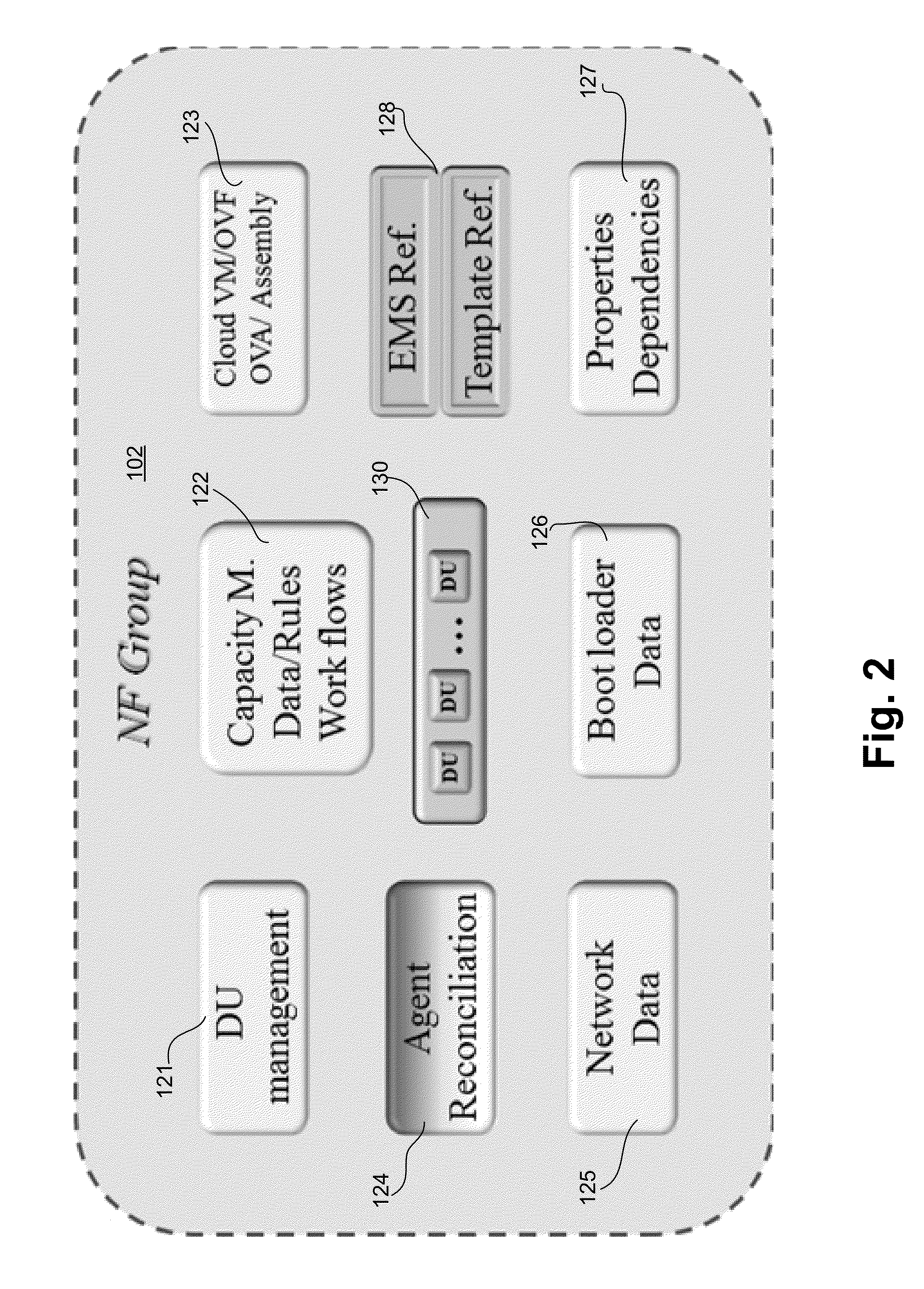
Transparent orchestration and management of composite network functions
ActiveUS20160149771A1Digital computer detailsData switching networksCentralized managementOrchestration
A system that manages a network of network elements receives a network topology of the network elements, where the network elements include a first type of network elements and a second type of network elements. The system creates a first network function (“NF”) group that corresponds to the first type of network elements, and creates a second NF group that corresponds to the second type of network elements. The system implements a functionality of the first NF group on a physical network function component. The system implements a functionality of the second NF group as a virtual machine (“VM”). The system then forms a composite network function (“CNF”) using the first NF group and the second NF group. The CNF can be centrally managed.
Owner:ORACLE INT CORP
Self-sufficient hydrogen generator
InactiveUS20100258449A1Photography auxillary processesGeneral water supply conservationWave power generationOrchestration
A self-sustaining, fully automated, hydrogen generator that utilizes the ocean's currents, tides, and water to produce vast amounts of hydrogen and oxygen. Additional electricity may be supplied by locally generated means including offshore wind, offshore geothermal, as well as wave powered generation. Hydrogen is exported as well as the oxygen not consumed by the life support systems. Residue collected from the ocean water purification process is collected and exported for use elsewhere or dispersed locally around the underwater facility. Systems orchestration is achieved by control systems that operate independently of one another with no single point of failure.
Owner:FIELDER WILLIAM SHERIDAN
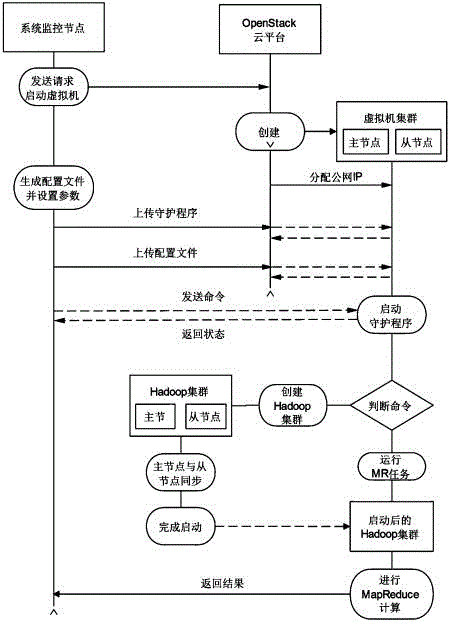
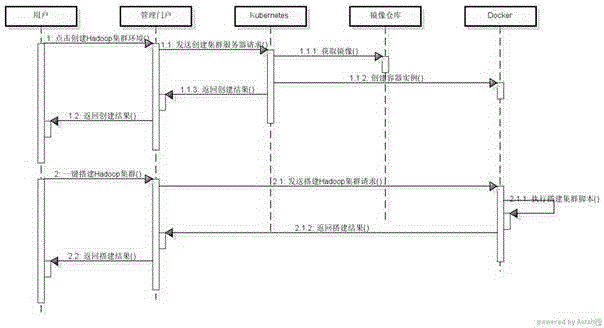
Method for fast constructing Hadoop cluster based on container cloud technology
InactiveCN106850621AGuaranteed stabilityHigh speedRelational databasesProgram loading/initiatingOrchestrationNetwork service
The invention discloses a method for fast constructing Hadoop cluster based on container cloud technology. The method comprises the following steps: (1) determining selected physical server number according to actual demand, regarding the entire selected physical server as a cluster, and assigning a master node of the cluster, and distributing actual deployment nodes, namely as the slave node; (2) installing a CentOS7 operation system for each physical server in the cluster; (3) installing and starting a container orchestration service Kubernetes and the network service Flannel on each master node of the cluster by use of a yuminstall command; (4) installing MySQL database, a mirror image warehouse service and management portal; (5) logging a management portal interface by use of an administrator account, establishing a user; and logging the management user by use of the established user, creating the cluster environment of the user, and constructing a Hadoop cluster.
Owner:NANJING YUNCHUANG LARGE DATA TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com