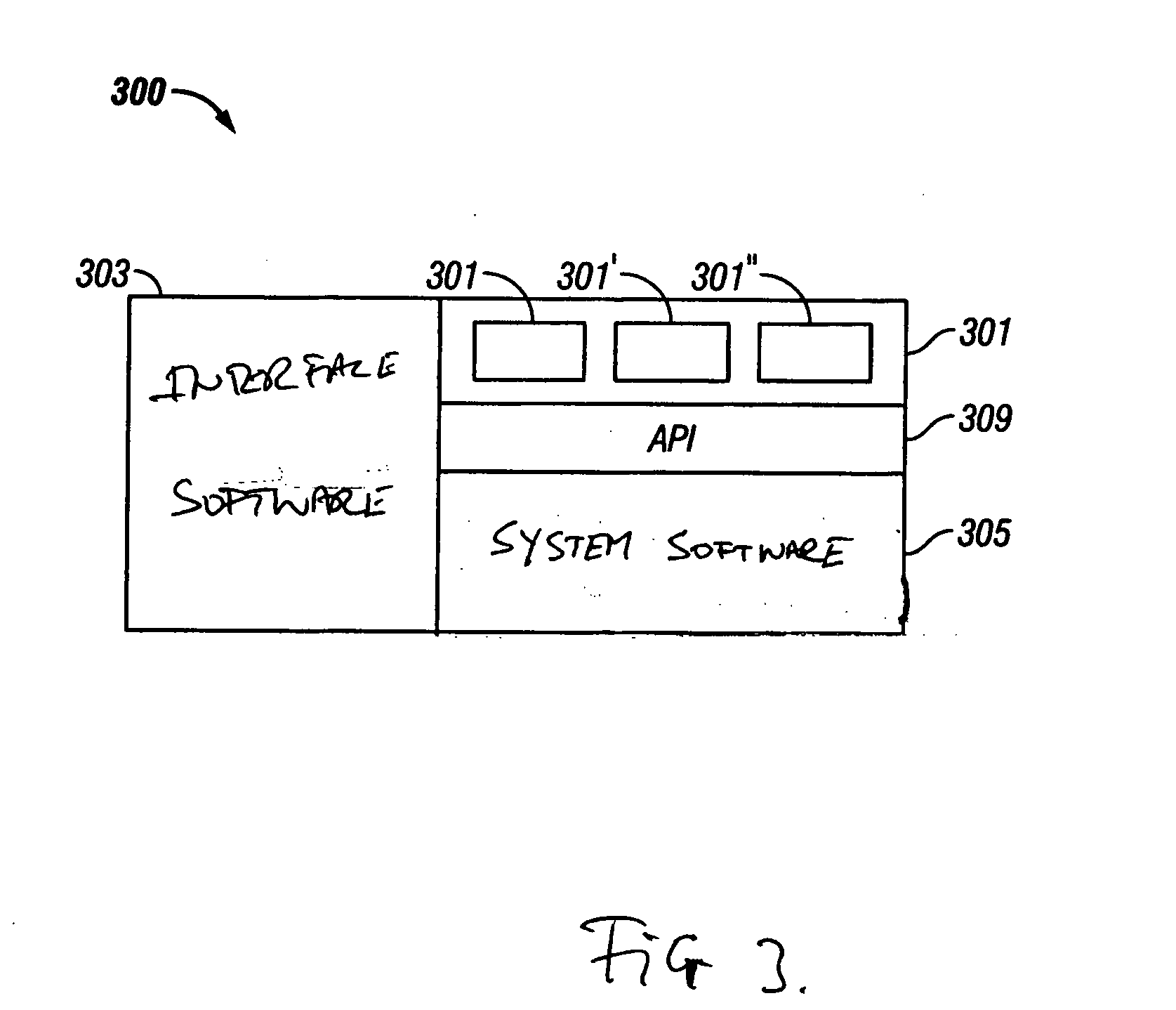
Patents
Literature
6956results about How to "Easy to add" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
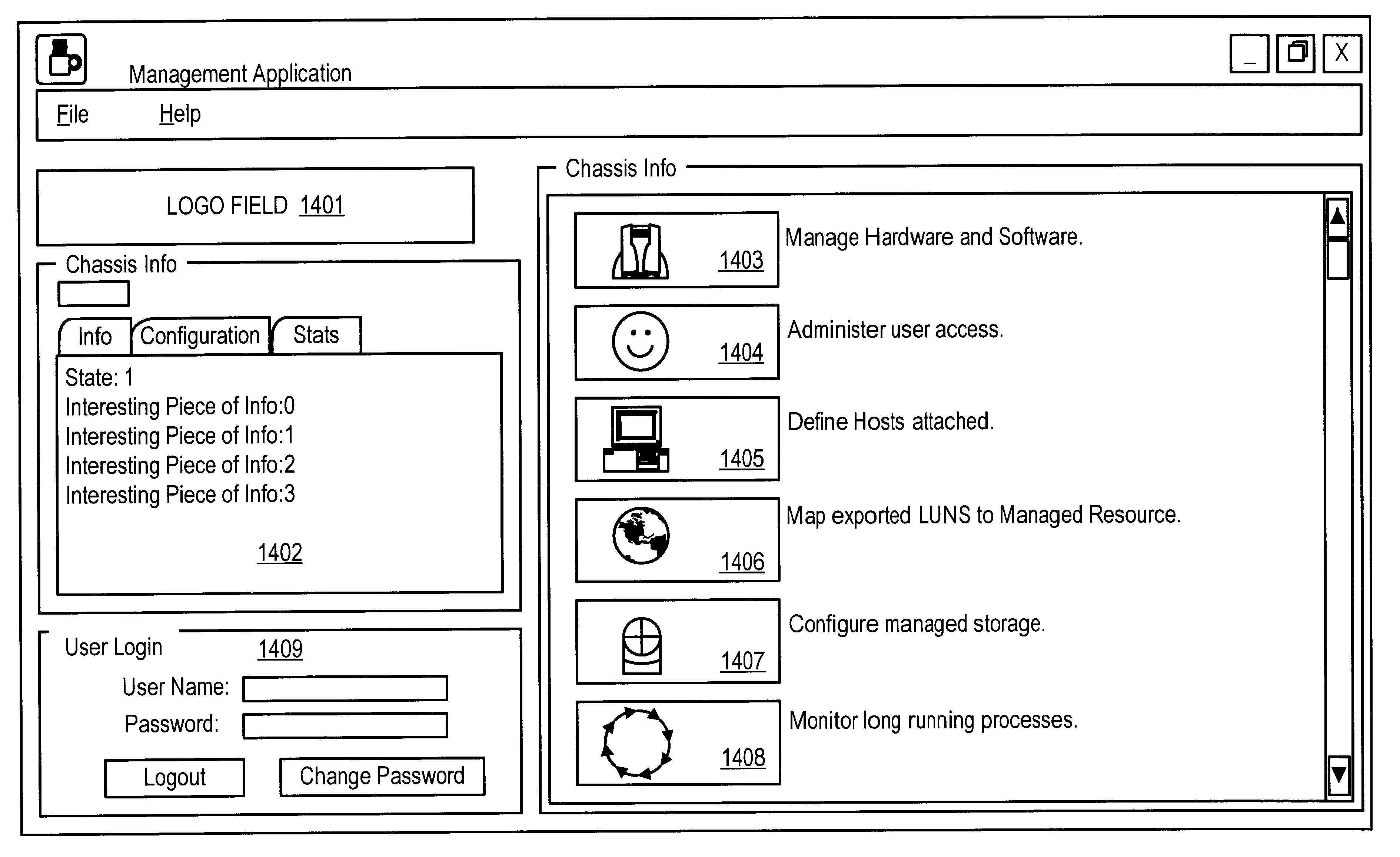
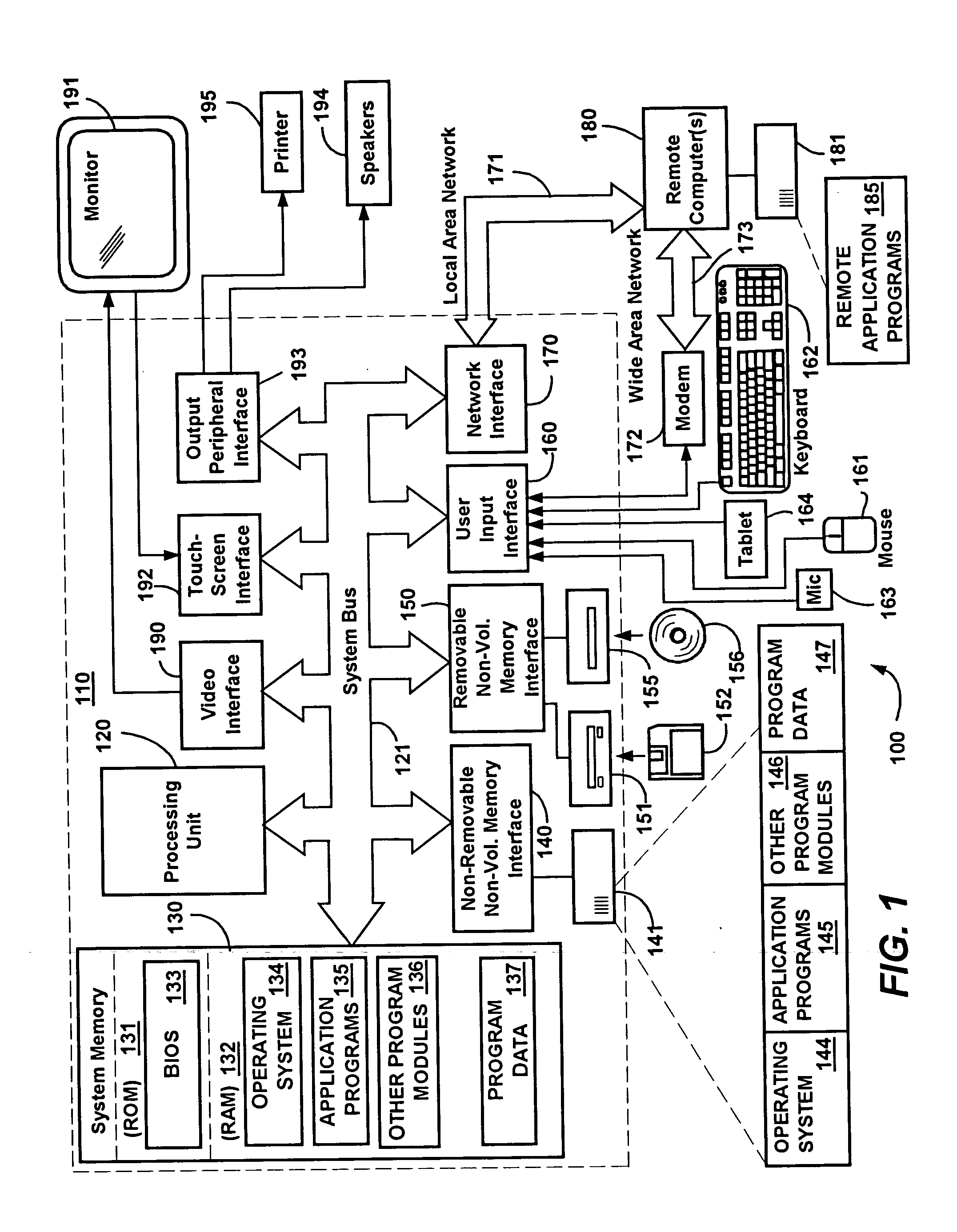
Graphical user interface for configuration of a storage system
InactiveUS6538669B1Easy to addImprove performanceDigital data information retrievalInput/output to record carriersGraphical user interfaceLogical address
A storage server architecture supporting virtual devices and virtual circuits for storing data is provided. The storage server includes a plurality of communication interfaces. A first set of communication interfaces in the plurality is adapted for connection to all kinds of users of data. A second set of communication interfaces in the plurality is adapted for connection to respective devices in a pool of storage devices. Data processing resources in the server are coupled to the plurality of communication interfaces for transferring data among the interfaces. The data processing resources comprise a plurality of driver modules and configurable logic linking driver modules into data paths. Each configured data path acts as a virtual circuit that includes a set of driver modules selected from the plurality of driver modules. A data storage transaction which is received at a communication interface is mapped to one of the configured data paths. A display and a user input device are included with data processing structures to manage images displayed on the display. The images include a first image arranged to prompt a user to input configuration data concerning host systems coupled to one of the plurality of communication interfaces, a second image arranged to prompt a user to input data concerning storage resources coupled to one of the plurality of communication interfaces, and a third image arrange to prompt a user to input data concerning logical addresses used by the host systems to access the storage resources accessible using the server.
Owner:DELL PROD LP
Programmable tactile touch screen displays and man-machine interfaces for improved vehicle instrumentation and telematics
InactiveUS7084859B1Known typeEasy to addCathode-ray tube indicatorsNavigation instrumentsDashboardHuman–machine interface
Disclosed are new methods and apparatus particularly suited for applications in a vehicle, to provide a wide range of information, and the safe input of data to a computer controlling the vehicle subsystems or “Telematic” communication using for example GM's “ONSTAR” or cellular based data sources. Preferred embodiments utilize new programmable forms of tactile touch screens and displays employing tactile physical selection or adjustment means which utilize direct optical data input. A revolutionary form of dashboard or instrument panel results which is stylistically attractive, lower in cost, customizable by the user, programmable in both the tactile and visual sense, and with the potential of enhancing interior safety and vehicle operation. Non-automotive applications of the invention are also disclosed, for example means for general computer input using touch screens and home automation systems.
Owner:APPLE INC
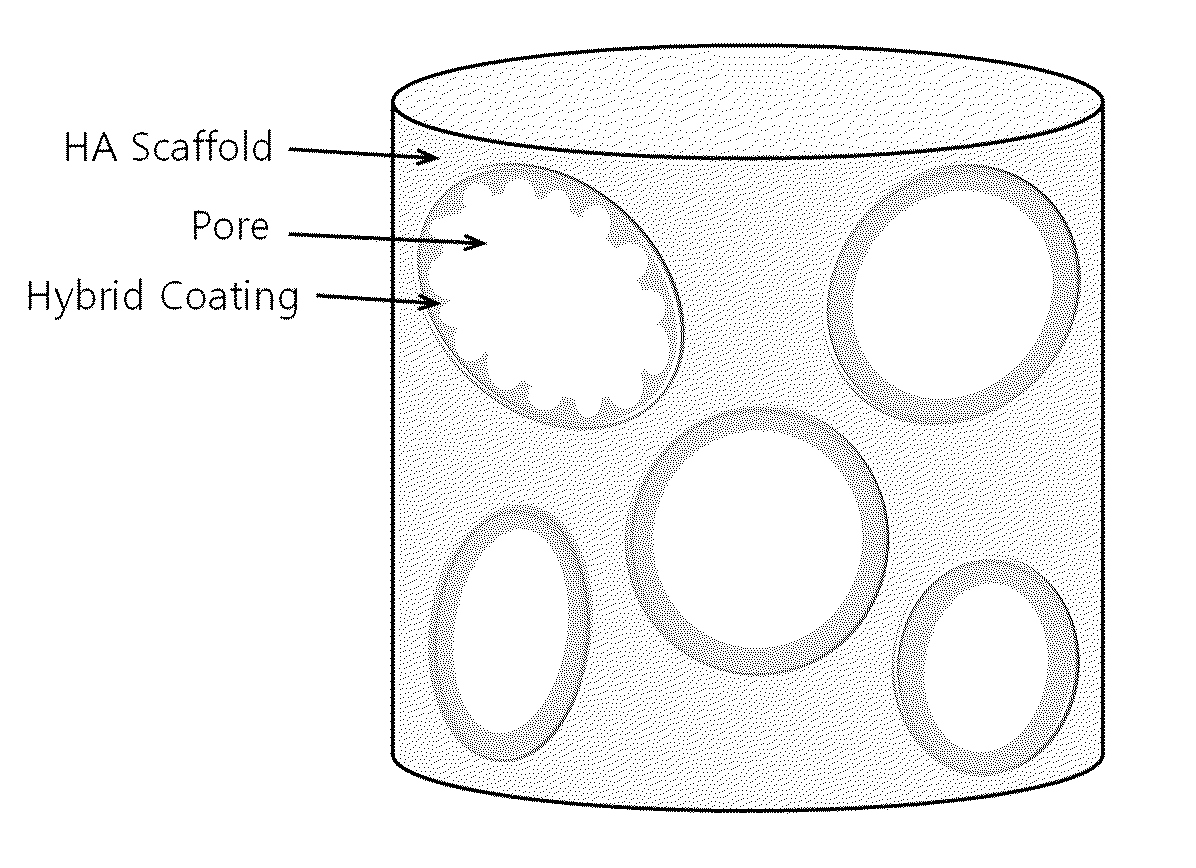
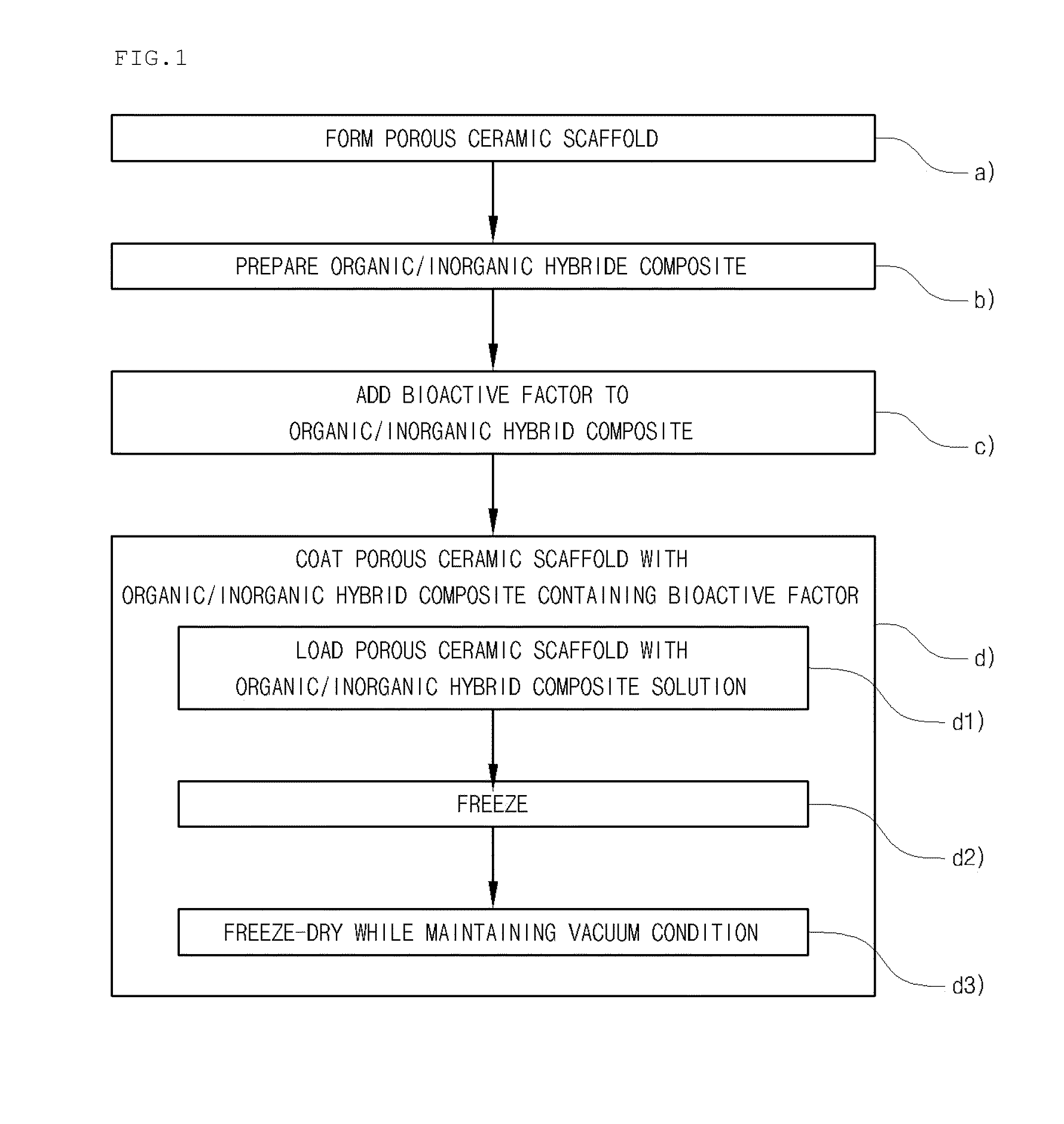
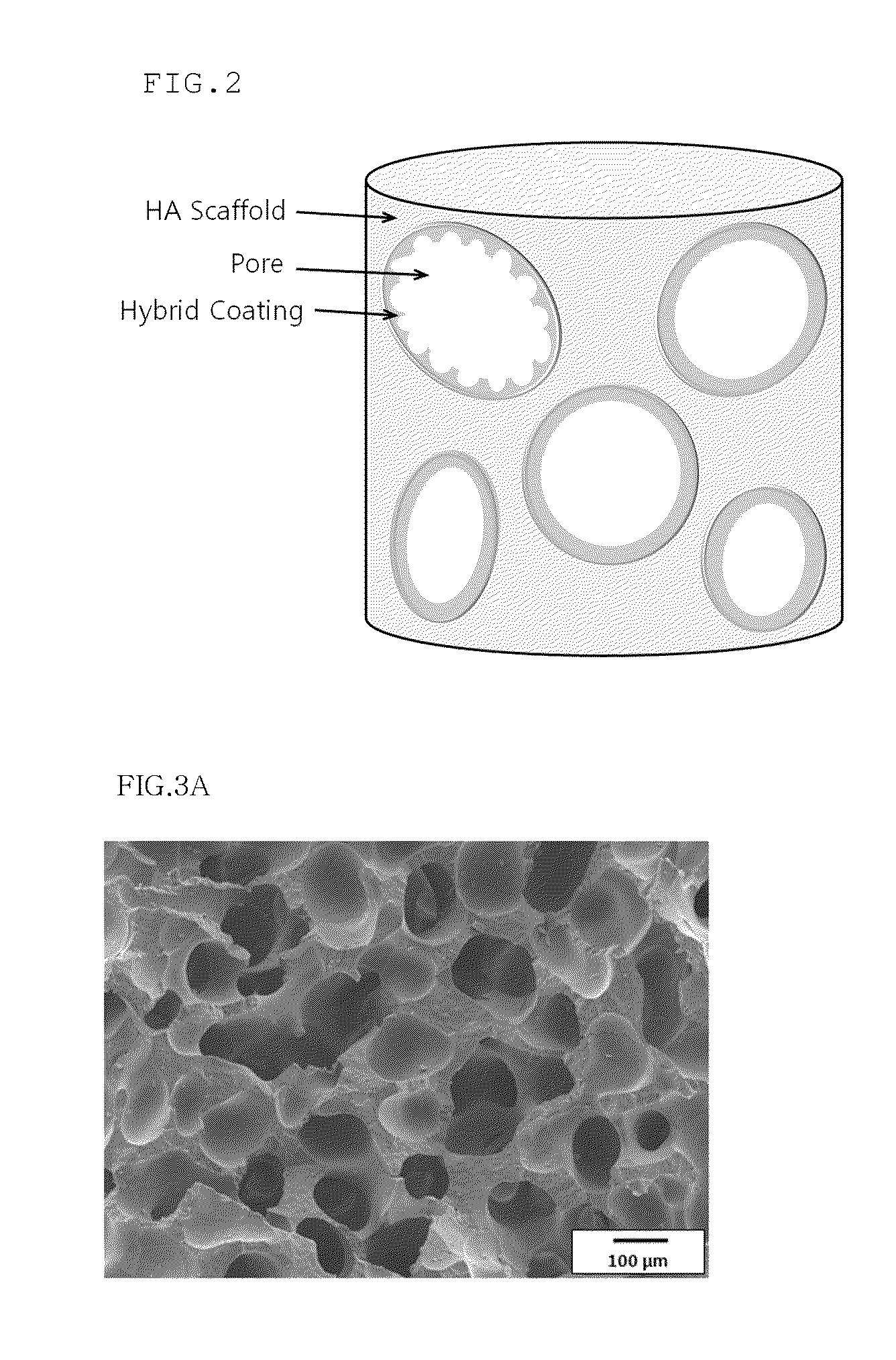
Method for manufacturing a porous ceramic scaffold having an organic/inorganic hybrid coating layer containing a bioactive factor
ActiveUS8734831B2Good biocompatibilityEasy to controlBiocideSurgical adhesivesOrganic matterPorous ceramics
A method for manufacturing a porous ceramic scaffold having an organic / inorganic hybrid coating layer containing a bioactive factor includes (a) forming a porous ceramic scaffold; (b) mixing a silica xerogel and a physiologically active organic substance in a volumetric ratio ranging from 30:70 to 90:10 and treating by a sol gel method to prepare an organic / inorganic hybrid composite solution; (c) adding a bioactive factor to the organic / inorganic hybrid composite solution and agitating until gelation occurs; and (d) coating the porous ceramic scaffold with the organic / inorganic composite containing the bioactive factor added thereto. In accordance with the method, the porous ceramic scaffold may be uniformly coated with the organic / inorganic hybrid composite while maintaining an open pore structure, and stably discharge the bioactive factor over a long period of time.
Owner:SEOUL NAT UNIV R&DB FOUND
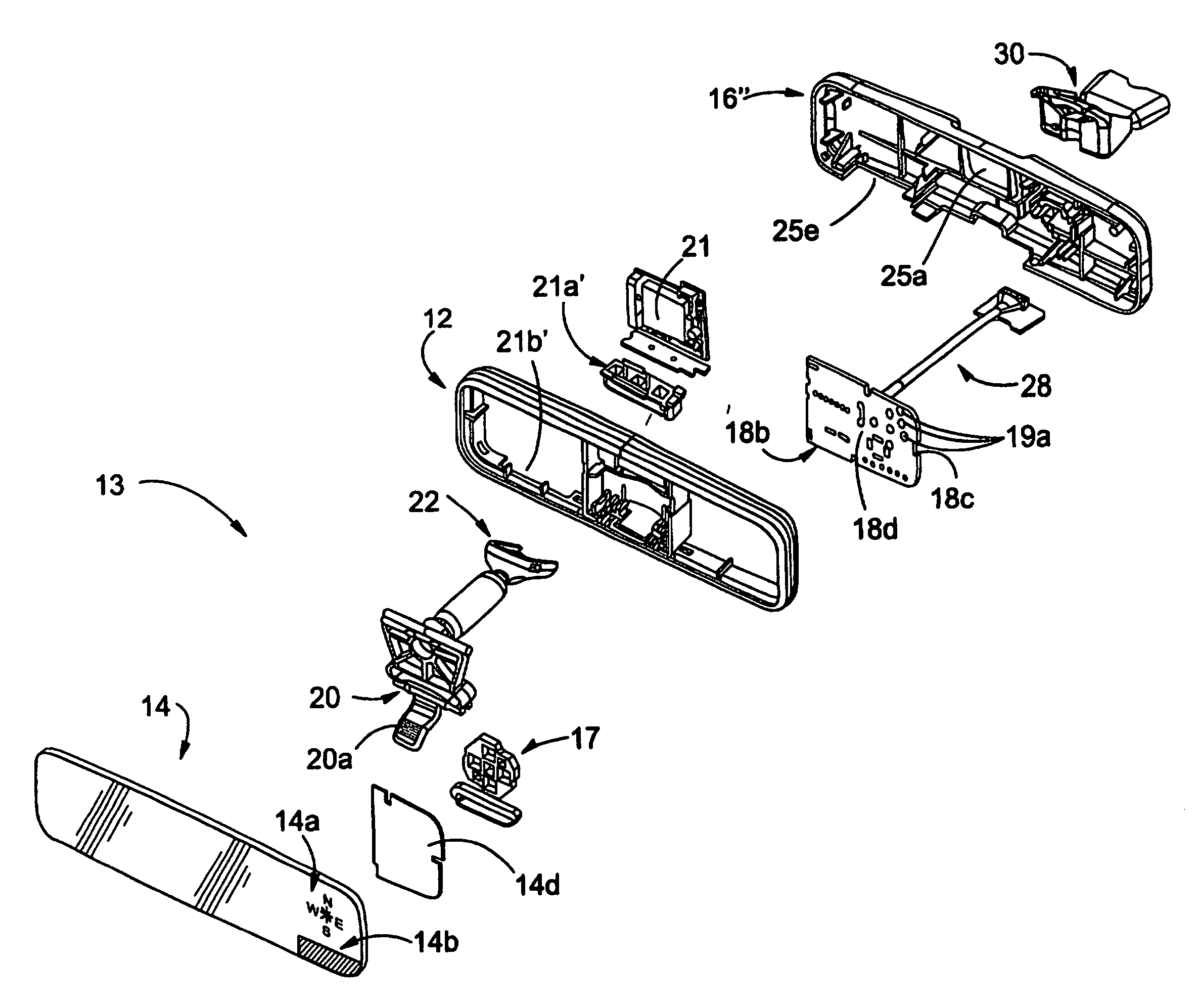
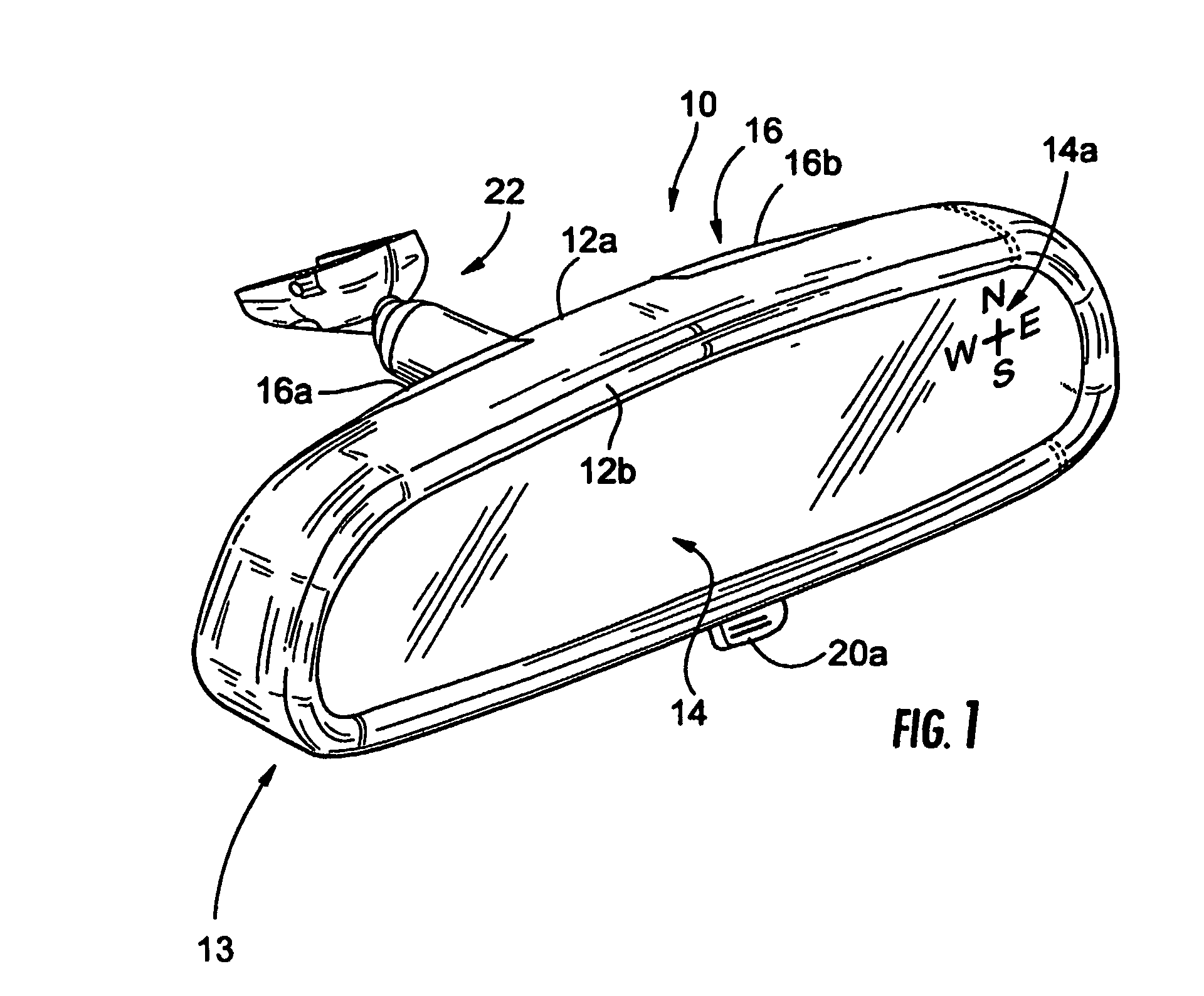
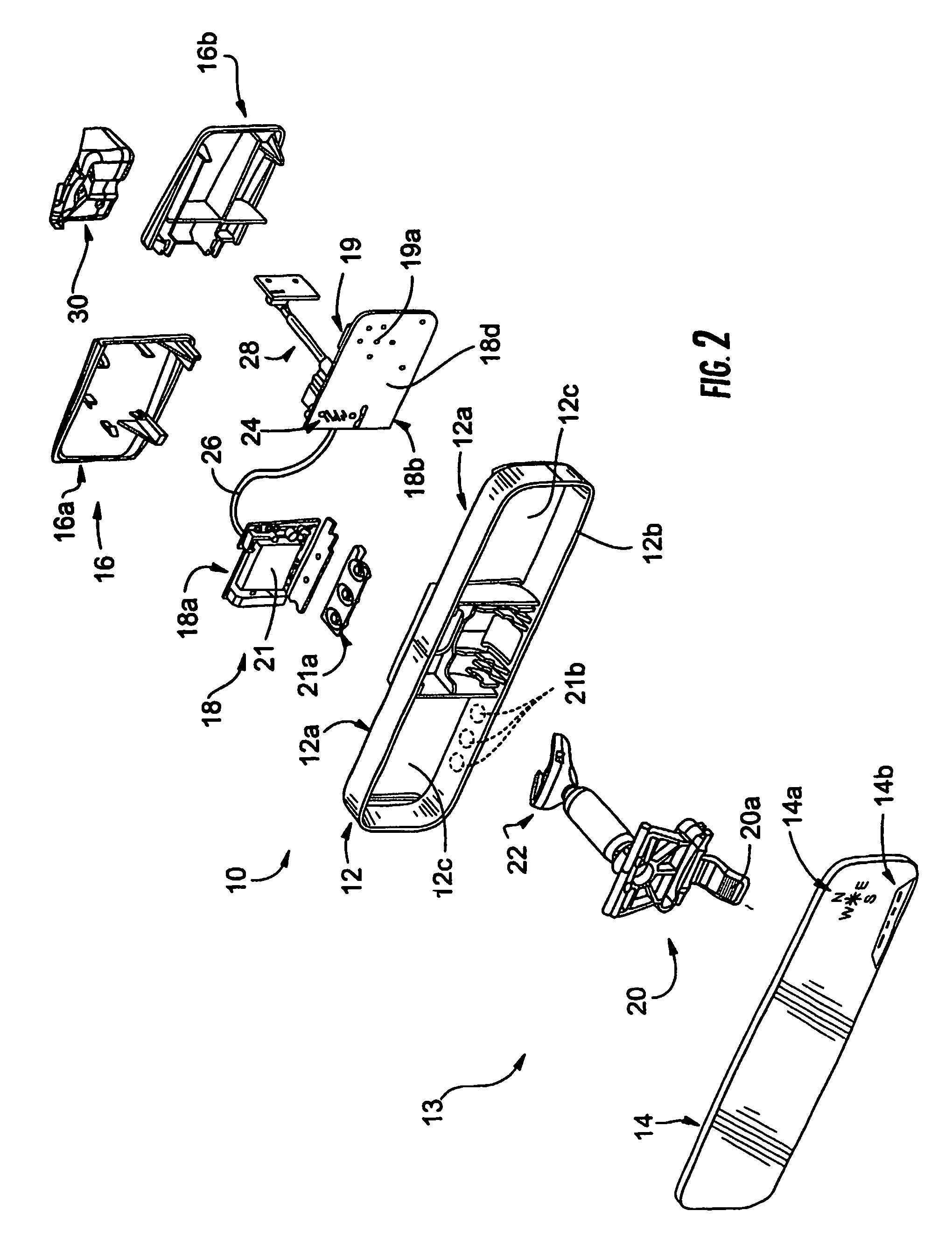
Mirror assembly for vehicle
InactiveUS7289037B2Easy to addConvenient to accommodateMirrorsInstrument arrangements/adaptationsEngineeringMechanical engineering
An interior rearview mirror assembly for a vehicle includes a reflective element assembly portion and at least one cap portion adapted to attach to the reflective element assembly portion. The reflective element assembly portion includes a reflective element. The reflective element assembly portion comprises a first molding that encompasses at least a perimeter portion of the reflective element. The first molding is formed by molding a first resinous material having a tool shrinkage factor equal to or greater than about 1 percent. The cap portion comprises at least one second molding formed by molding a second resinous material having a tool shrinkage factor of less than or equal to about 1 percent. The cap portion preferably includes internal structure for supporting at least one accessory.
Owner:MAGNA MIRRORS OF AMERICA INC
System and method for establishing eletronic business systems for supporting communications servuces commerce
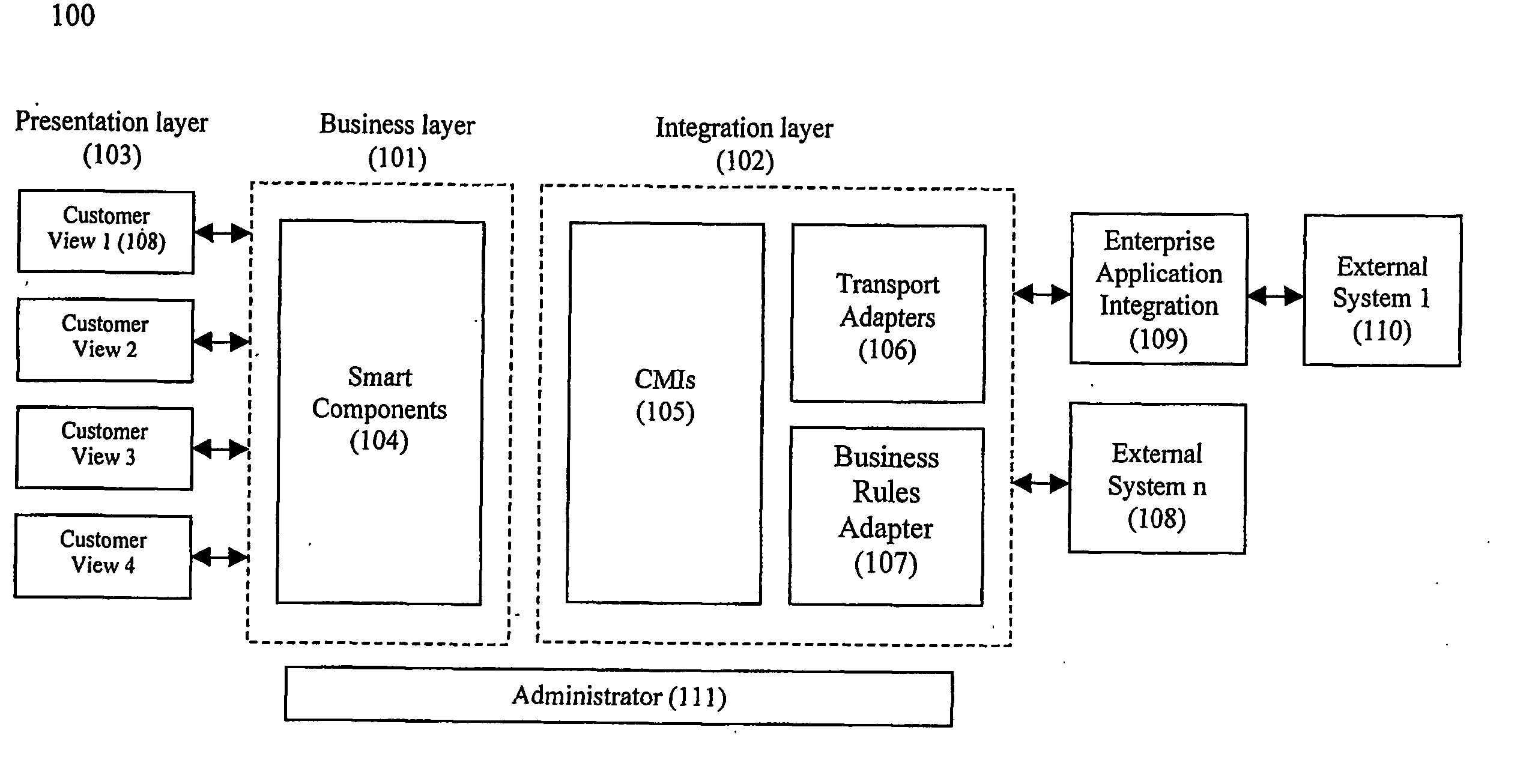
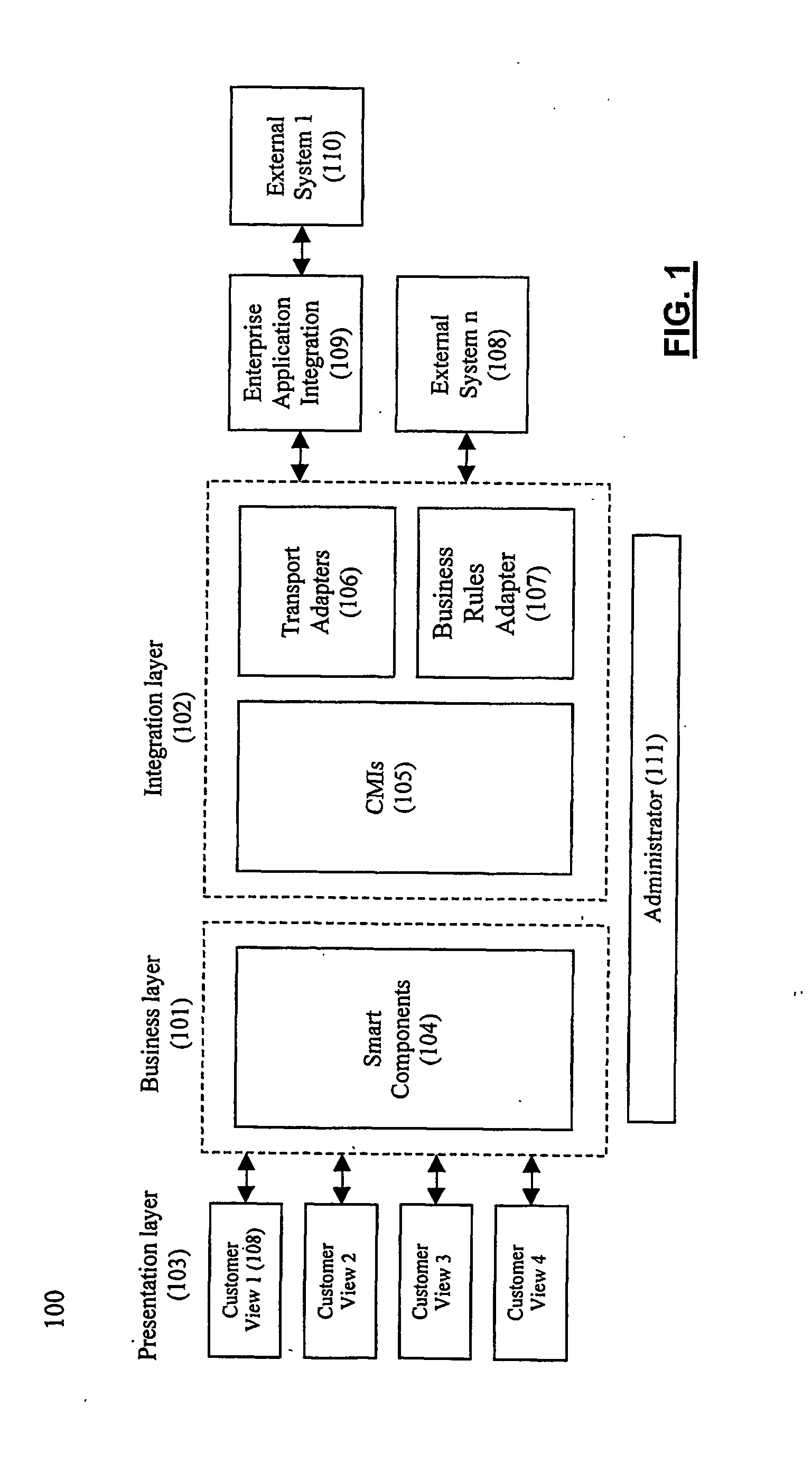
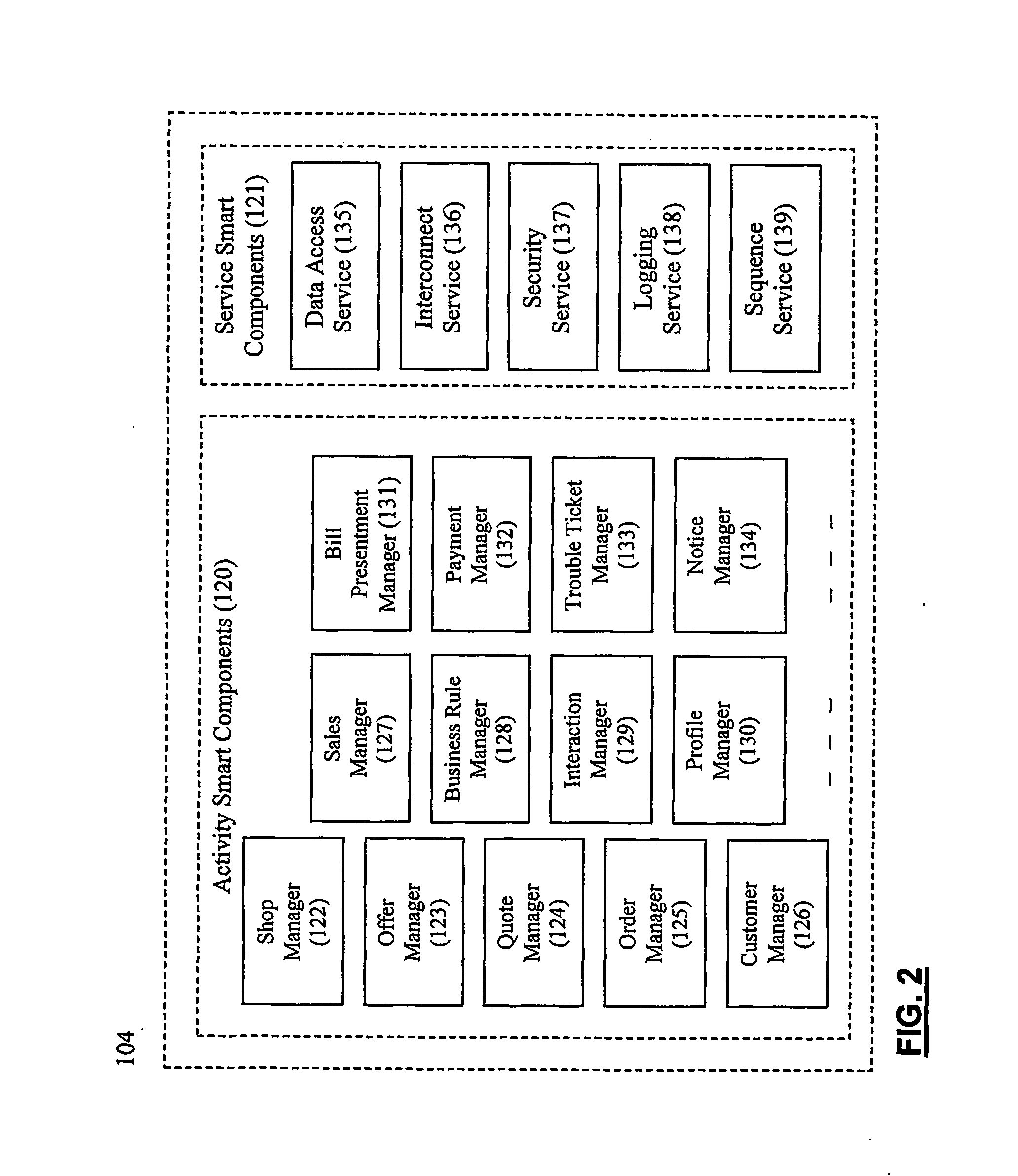
ActiveUS20060059107A1Easy to addEasy to liftPayment protocolsBilling/invoicingEnterprise application integrationSupporting system
Owner:NETCRACKER TECH SOLUTIONS
Methods and systems for managing financial accounts
InactiveUS7117172B1Useful managingReduce in quantityComplete banking machinesFinanceSource codeParameter control
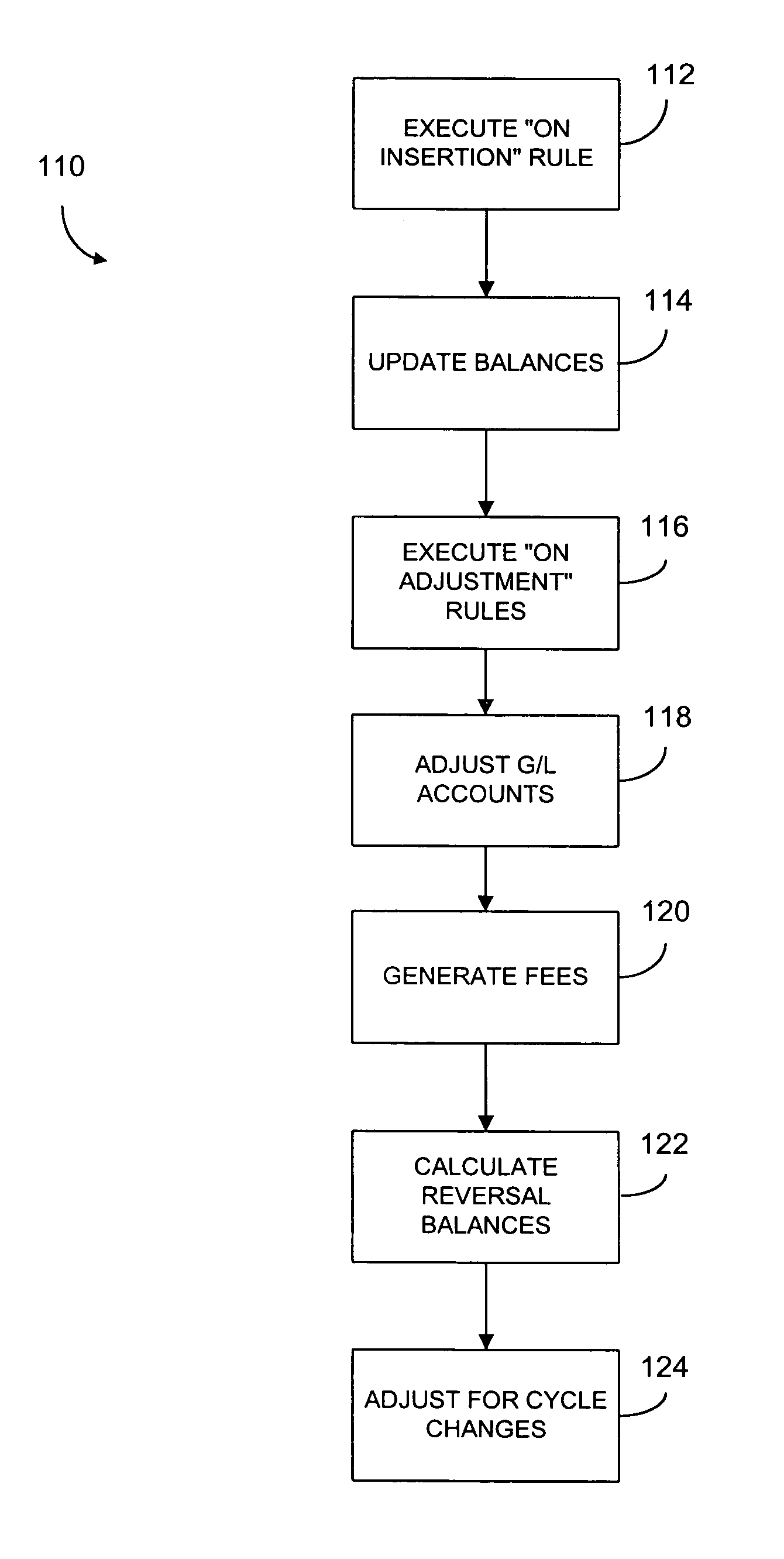
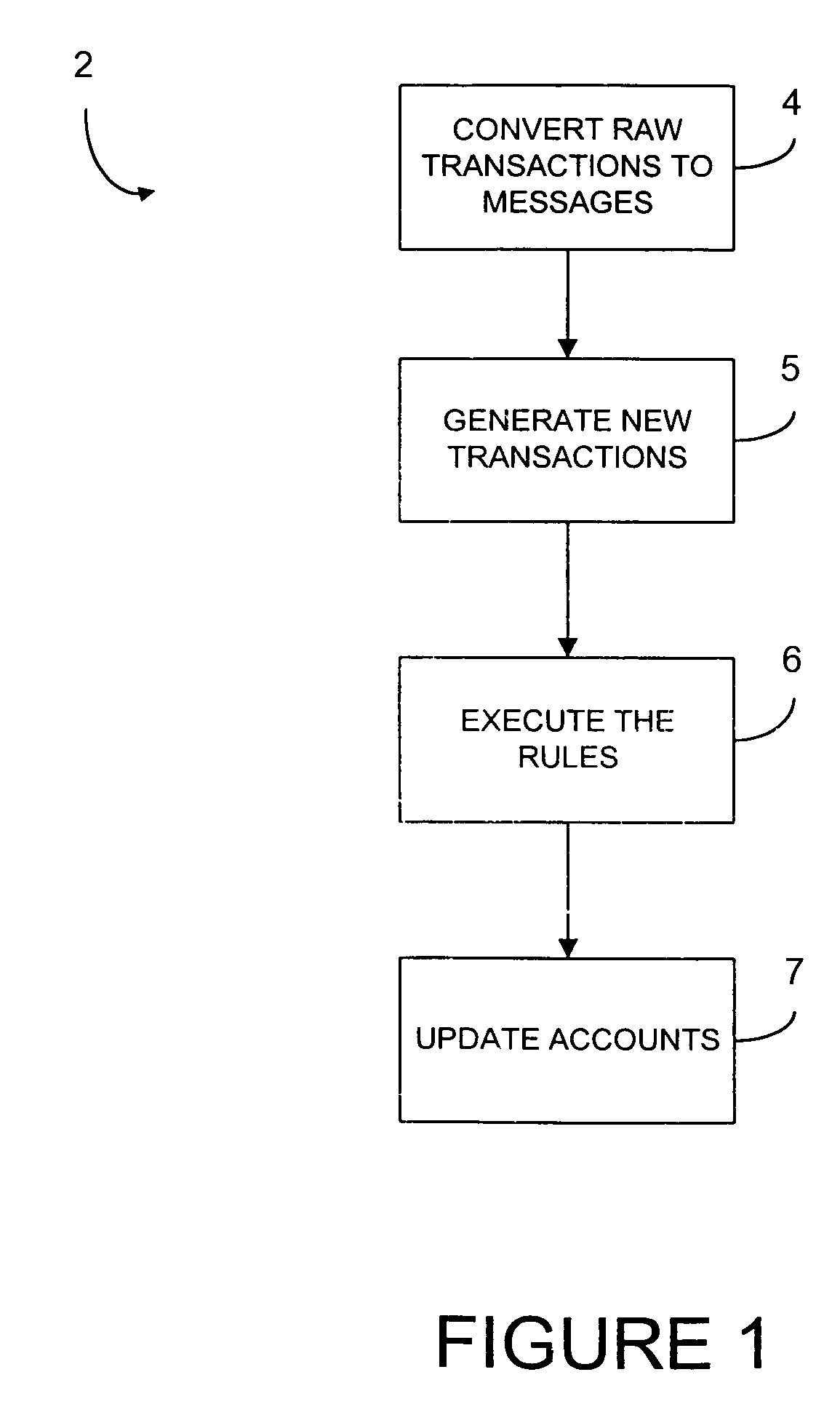
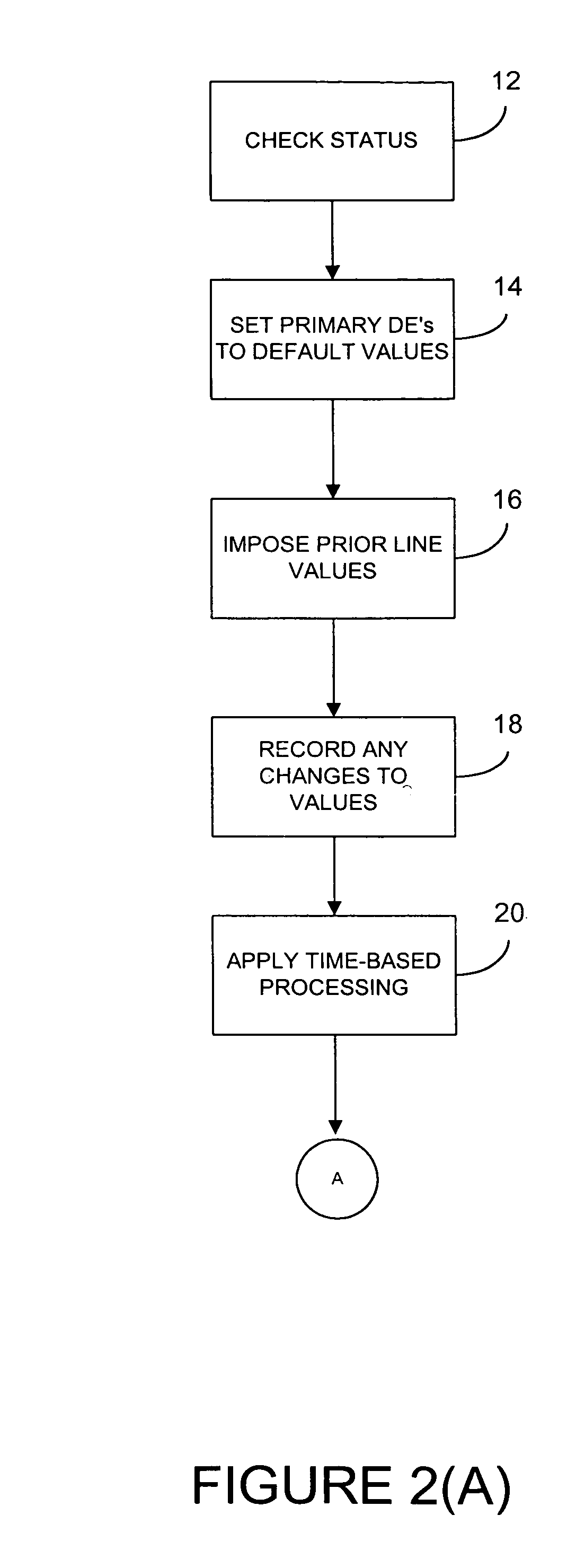
Processing systems and methods receive events, such as a transaction to an account, and converts the events into messages. Each message then invokes one or more rules which are executed by a rules engine. The execution of these rules may invoke the execution of additional rules. After all rules have executed, the account associated with the event is updated, such as by projecting the account. The rules have their parameters defined in a repository so that the parameters can be easily changed without any need to recompile. The processing systems receive authorizations and other transactions and runs in real-time as transactions arrive. As a result, balances are updated continuously and accounts are read and updated only when there is activity. Hierarchy is user configurable, including multiple hierarchy to any depth. System operations are controlled by rules and their parameters and most modifications can be accomplished without access to source code.
Owner:CORECARD SOFTWARE
System and method for network access without reconfiguration
InactiveUS6857009B1Easy to addEasy to deleteTime-division multiplexData switching by path configurationDomain nameComputer compatibility
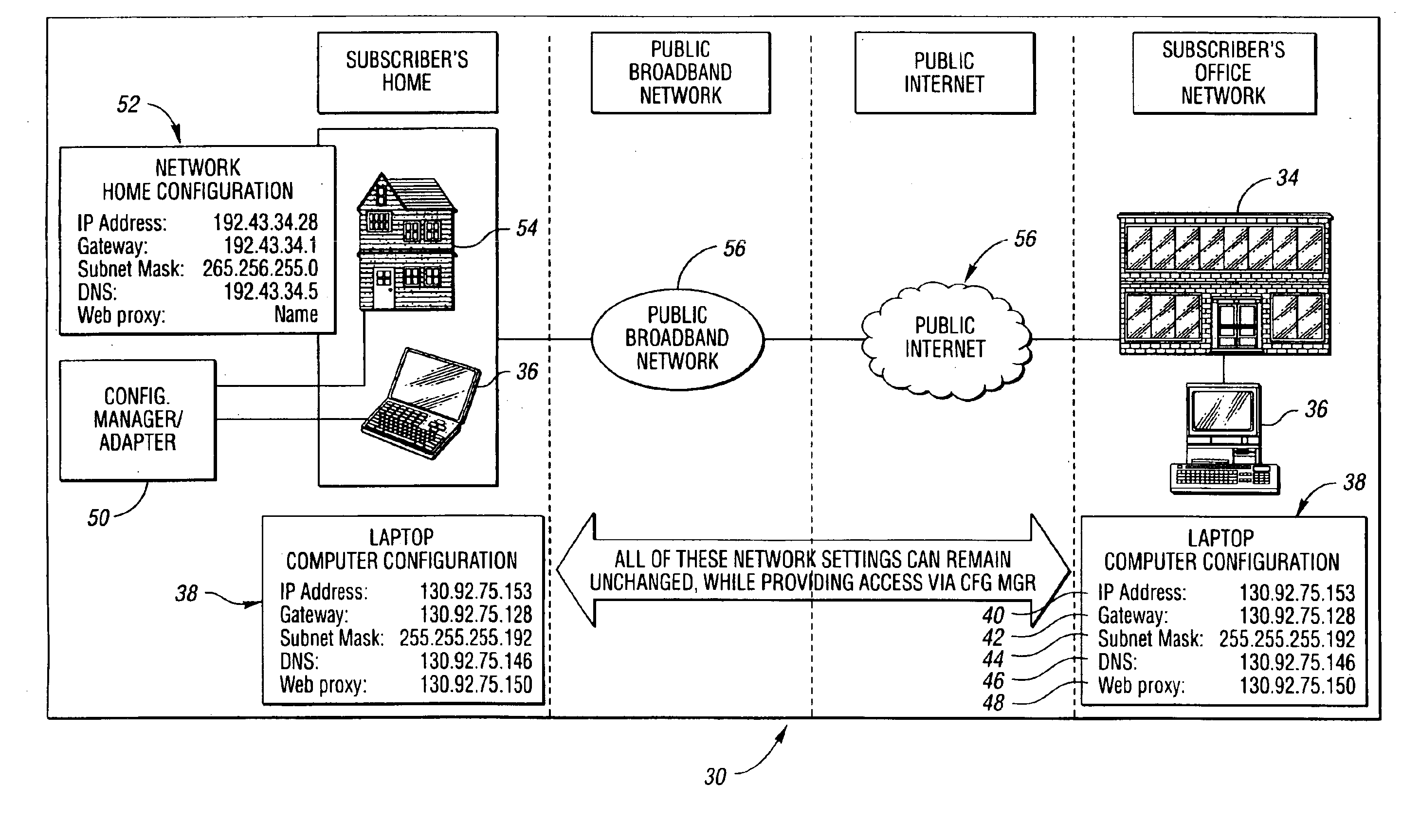
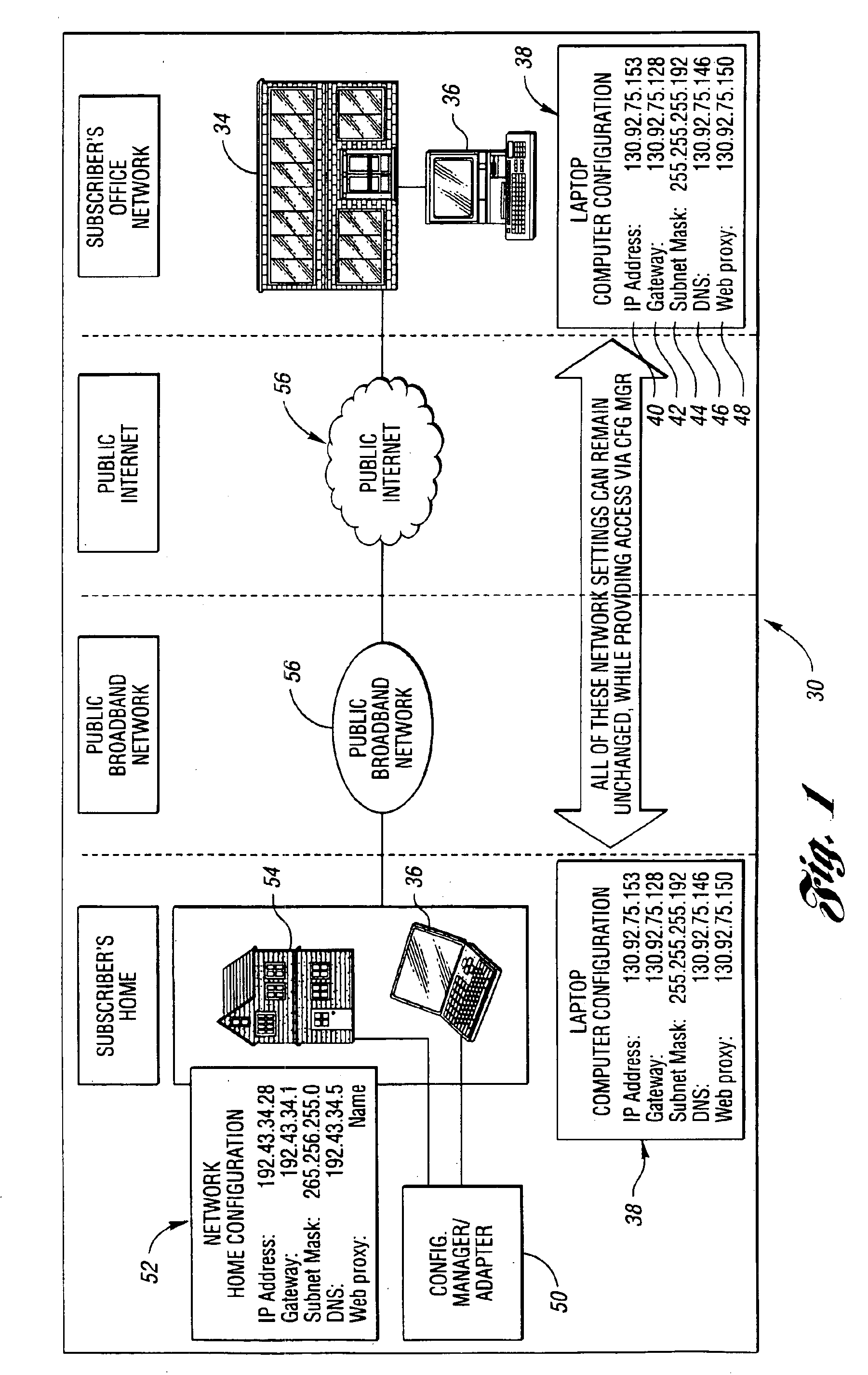
A system and method for providing connectivity to a foreign network for a device configured for communication over a home network without reconfiguring the device include intercepting packets transmitted by the device, selectively modifying intercepted packets which are incompatible with the foreign network to be compatible with network settings of the foreign network, and selectively providing network services for the device corresponding to network services available on the home network to reduce the delay associated with accessing the network services from the foreign network, or to provide network services otherwise inaccessible from the foreign network. Network services are provided by or through a configuration adapter connected to the device or to the foreign network. The configuration adapter accommodates incompatibilities resulting from proxy server requests, domain name server requests, and / or outgoing email service requests to provide transparent network access for mobile users without reconfiguration of the users computing device.
Owner:NOMADIX INC
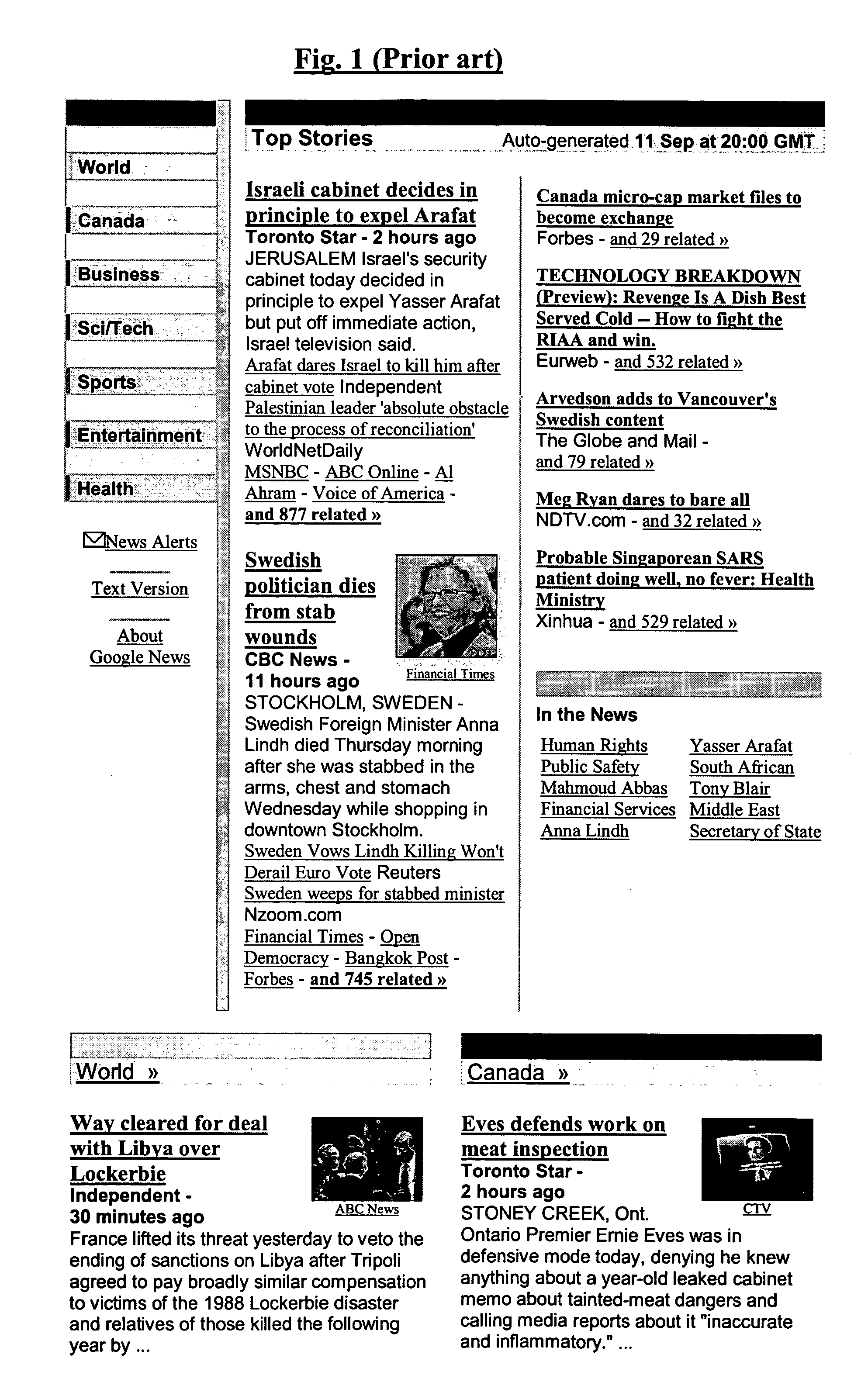
System and method for improved searching on the internet or similar networks and especially improved MetaNews and/or improved automatically generated newspapers
ActiveUS20050114324A1Increase weightConvenient reviewWeb data indexingSpecial data processing applicationsThe InternetSingle image
Google has recently made available at http: / / news.google.com an automated “newspaper”, which searches continuously about 4,500 news sources, and lets users view automatically generated headlines in a few general areas or lets users search for news by keywords. The automatic determination of which news items or news stories are most important is done by 3 main criteria: In how many sources the news item appeared, how important are the news sources in which it appeared, and how close it is to the top in each of these news sources. However, many problems still remain, such as for example: a. The choice of a single main news source and a single image for each item seems arbitrary to the user and limits the user. b. If the user clicks on the “related items” link for that item the user always gets a linear list of typically hundreds or even more than a thousand links to related news items, sorted either by relevance or by time, however, the new list is now without any images and without any clustering, so that many times news stories that are about the same event or even identical, may appear at different positions in the list of related links, and various other news items may appear between them and are typically also dispersed in various places. This makes it vary hard for the user to take advantage efficiently of the list of related items. The present invention solves the above problem by creating recursive clustering, so that preferably at any level in the tree the user can preferably either choose a specific news item from the cluster or from the shown sub-clusters or continue in the tree. Another improvement is that searching the Meta News by keywords can generate an automatic newspaper in a way similar to the original automatically generated newspaper. Many additional improvements to the concept of automated newspapers and / or news MetaSearch are also shown. Other improvements are suggested for improved shareware MetaSearch, improved Web pages search, and other types of searches.
Owner:BARHON MAYER BATYA
Location tracking of a metallic object in a living body
ActiveUS20090299175A1Readily targetFacilitates direct vascular flow measurementDiagnostic probe attachmentBlood flow measurement devicesIn stent restenosisLocation tracking
Owner:ZOLL MEDICAL ISRAEL LTD
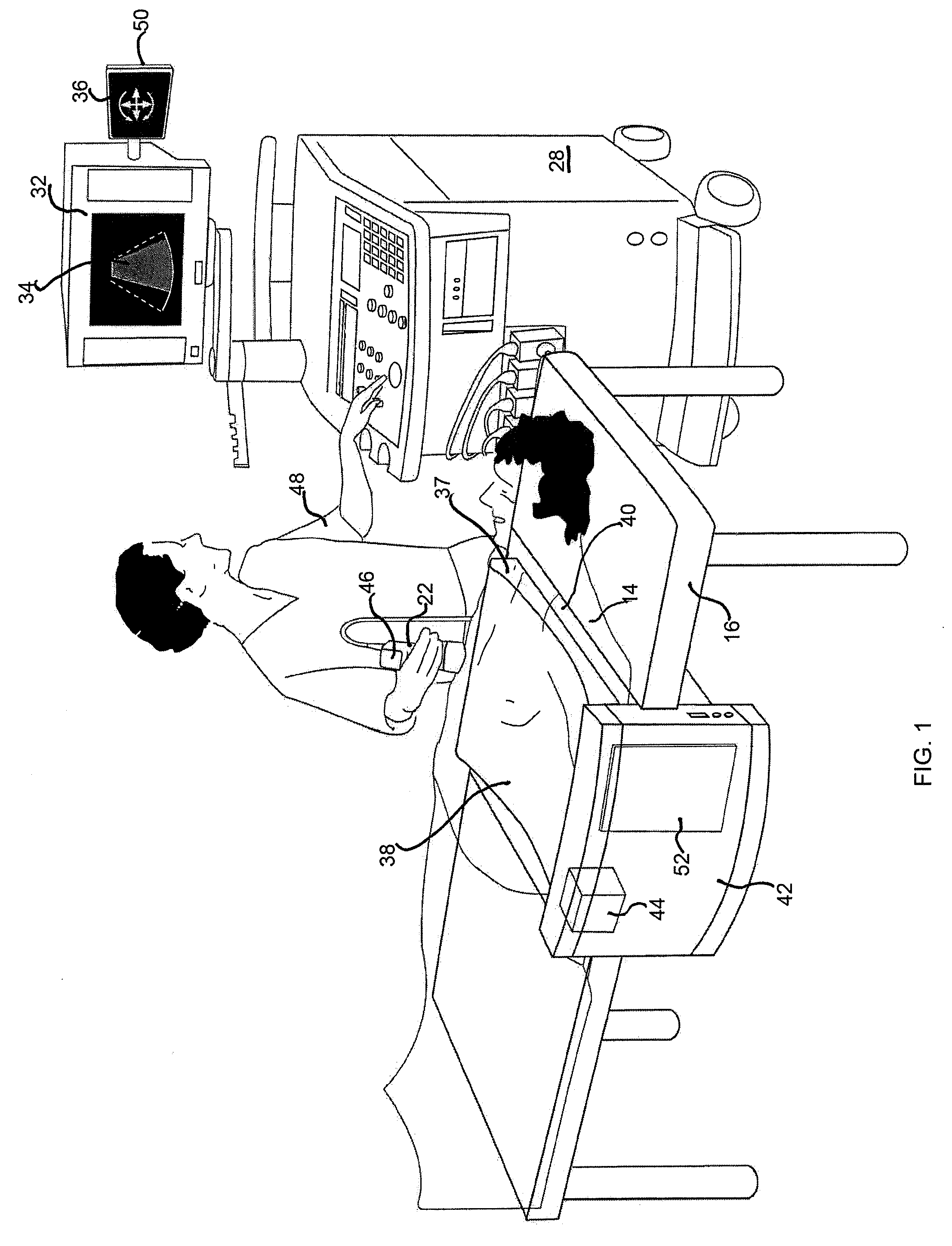
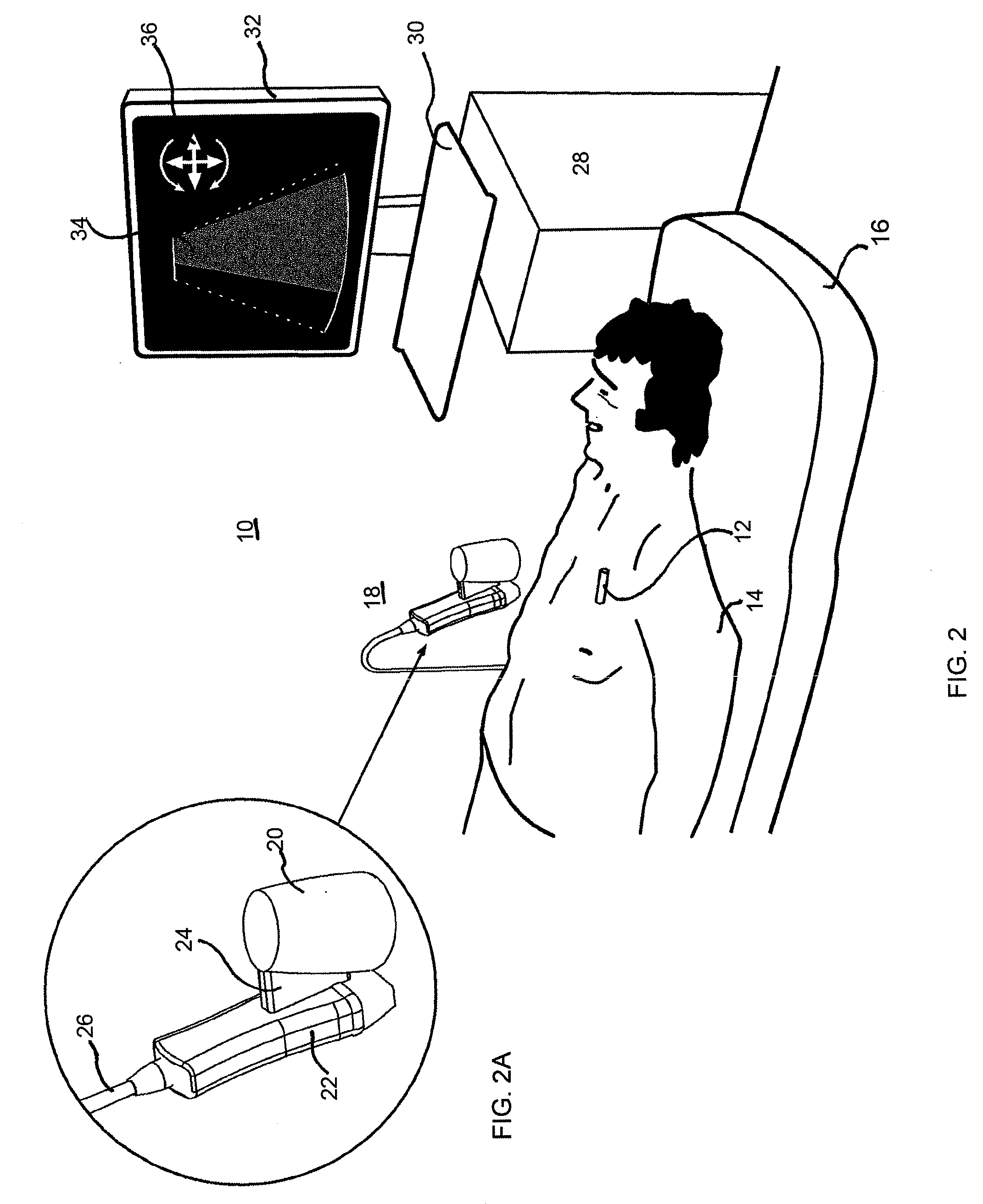
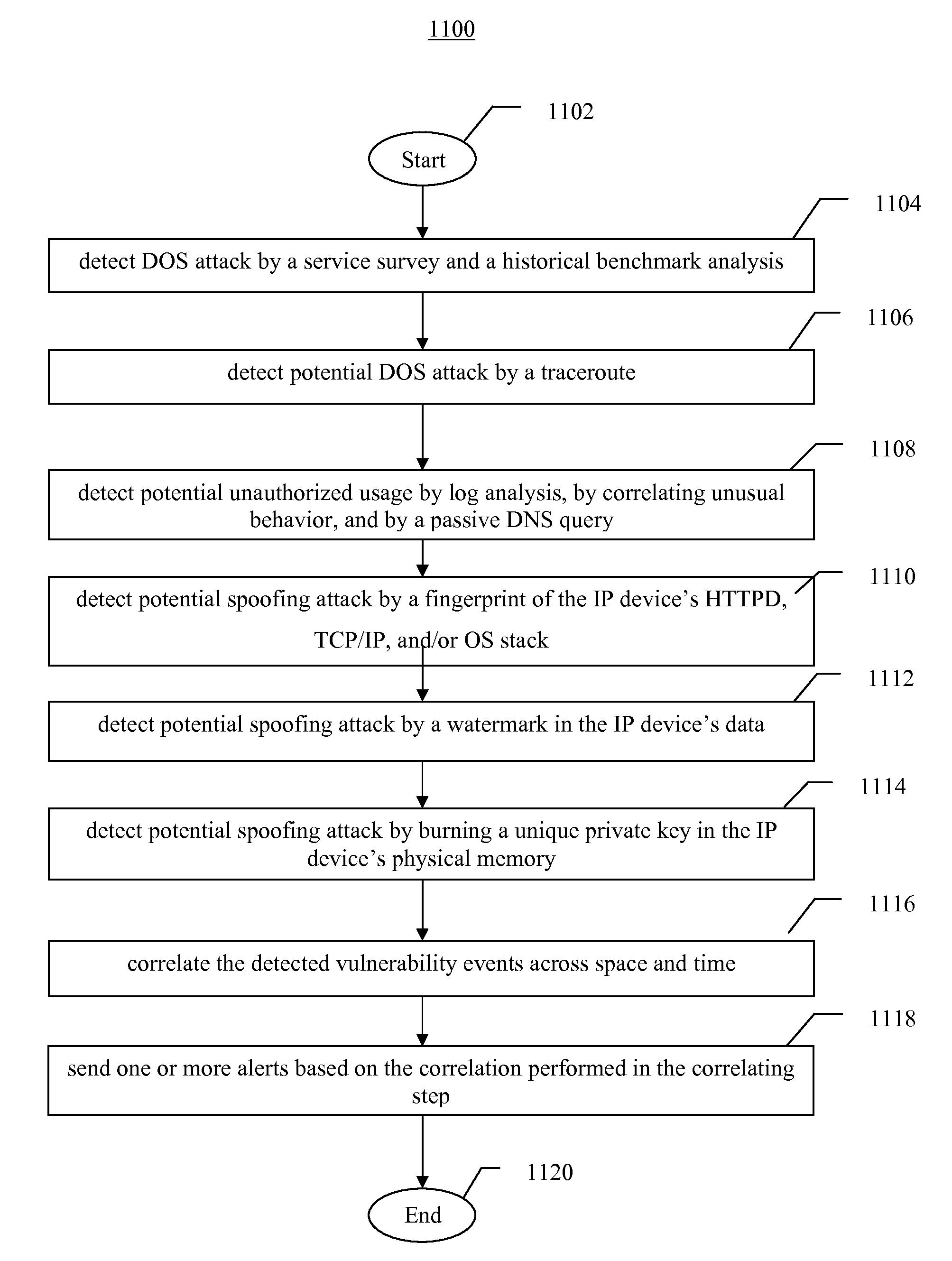
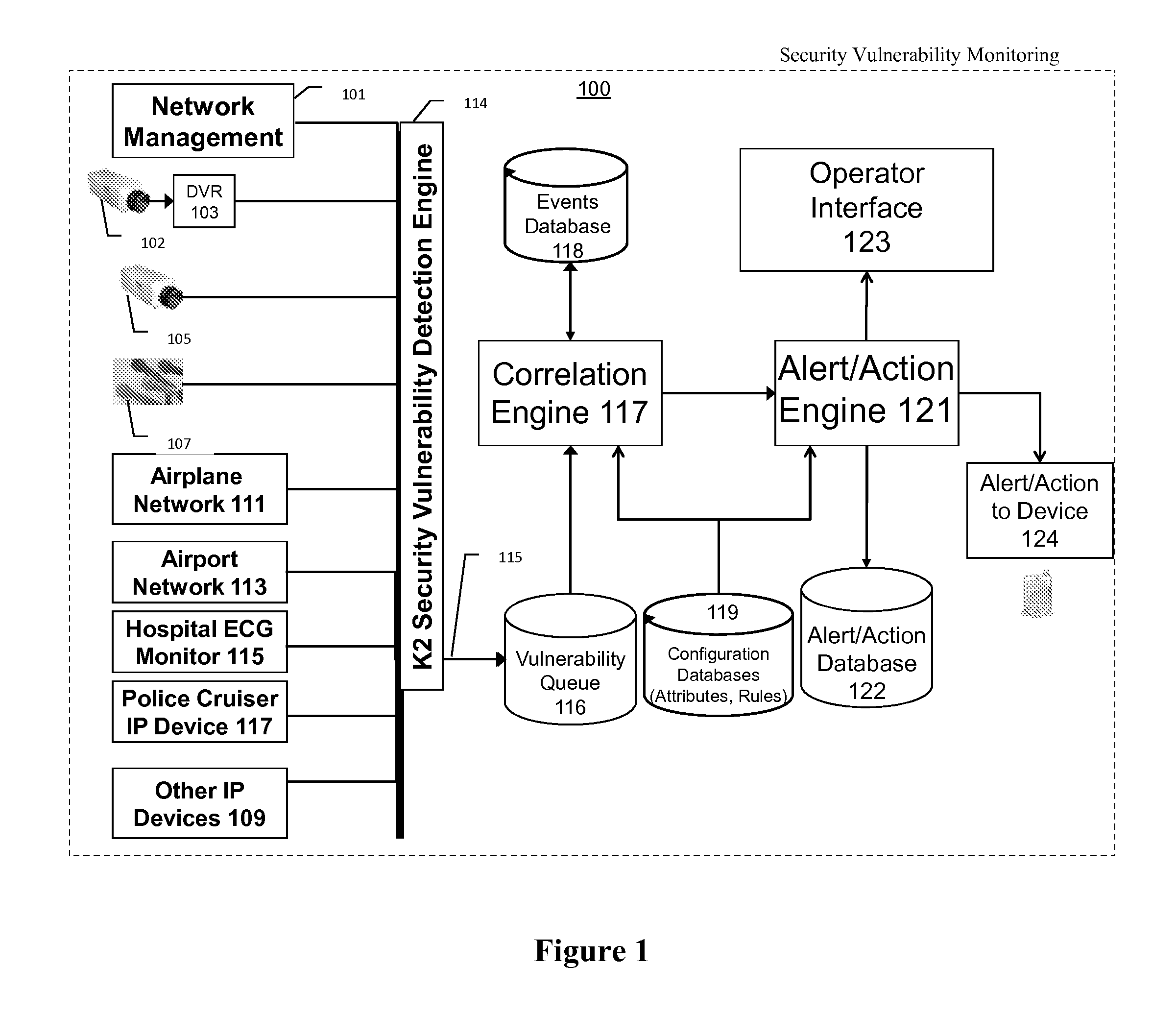
Systems, methods, and devices for detecting security vulnerabilities in IP networks
InactiveUS20100262688A1Detect and prevent spoofingEasy to addMemory loss protectionDigital data processing detailsBaseline dataData stream
This invention is a system, method, and apparatus for detecting compromise of IP devices that make up an IP-based network. One embodiment is a method for detecting and alerting on the following conditions: (1) Denial of Service Attack; (2) Unauthorized Usage Attack; and (3) Spoofing Attack. A survey of services running on the IP device, historical benchmark data, and traceroute information may be used to detect a possible Denial of Service Attack. A detailed log analysis and a passive DNS compromise system may be used to detect a possible unauthorized usage. Finally, a fingerprint of the IP device or its configuration settings, a watermark inserted in the data-stream, and a private key burned into the IP devices' physical memory may be used to detect a possible spoofing attack. The present invention may be used to help mitigate intrusions and vulnerabilities in IP networks.
Owner:HUSSAIN DANIAR +1
Semiconductor package having heat sink at the outer surface
InactiveUS6559525B2Easy to addImprove packaging efficiencySemiconductor/solid-state device detailsSolid-state devicesSemiconductor packageLead frame
A semiconductor package having heat sink at the outer surface is constructed on a lead frame. The package comprises a chip, a die pad, a plurality of leads, a plurality of bonding wires, and a molding compound. The die pad has a first surface and a second surface, and the chip has its active surface bonded to the first surface of the die pad. The area of the die pad is smaller than the area of the chip in order to expose the bonding pads on the active surface of the chip. The leads having an inner lead portions and an outer lead portions are disposed at the periphery of the die pad, and the inner lead portions are electrically connected to the bonding pads by a plurality of bonding wires. The molding compound encapsulates the chip, the die pad, the inner lead portions of the leads, and the bonding wires. The second surface of the die pad is exposed on the top surface of the package structure while the outer lead portion of the leads is exposed at the side edge of the package structure.
Owner:SILICONWARE PRECISION IND CO LTD
Mobile ad hoc extensions for the internet
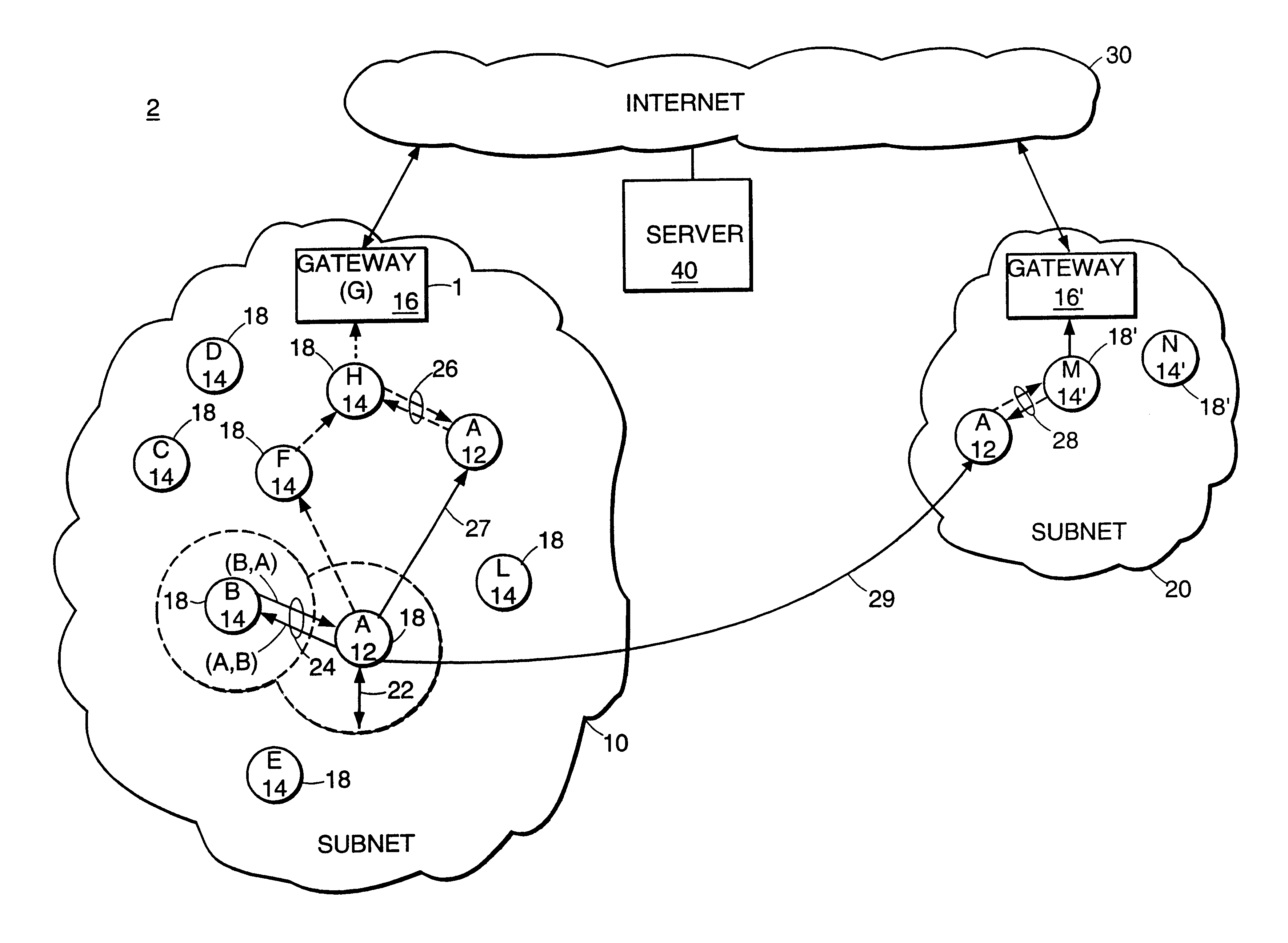
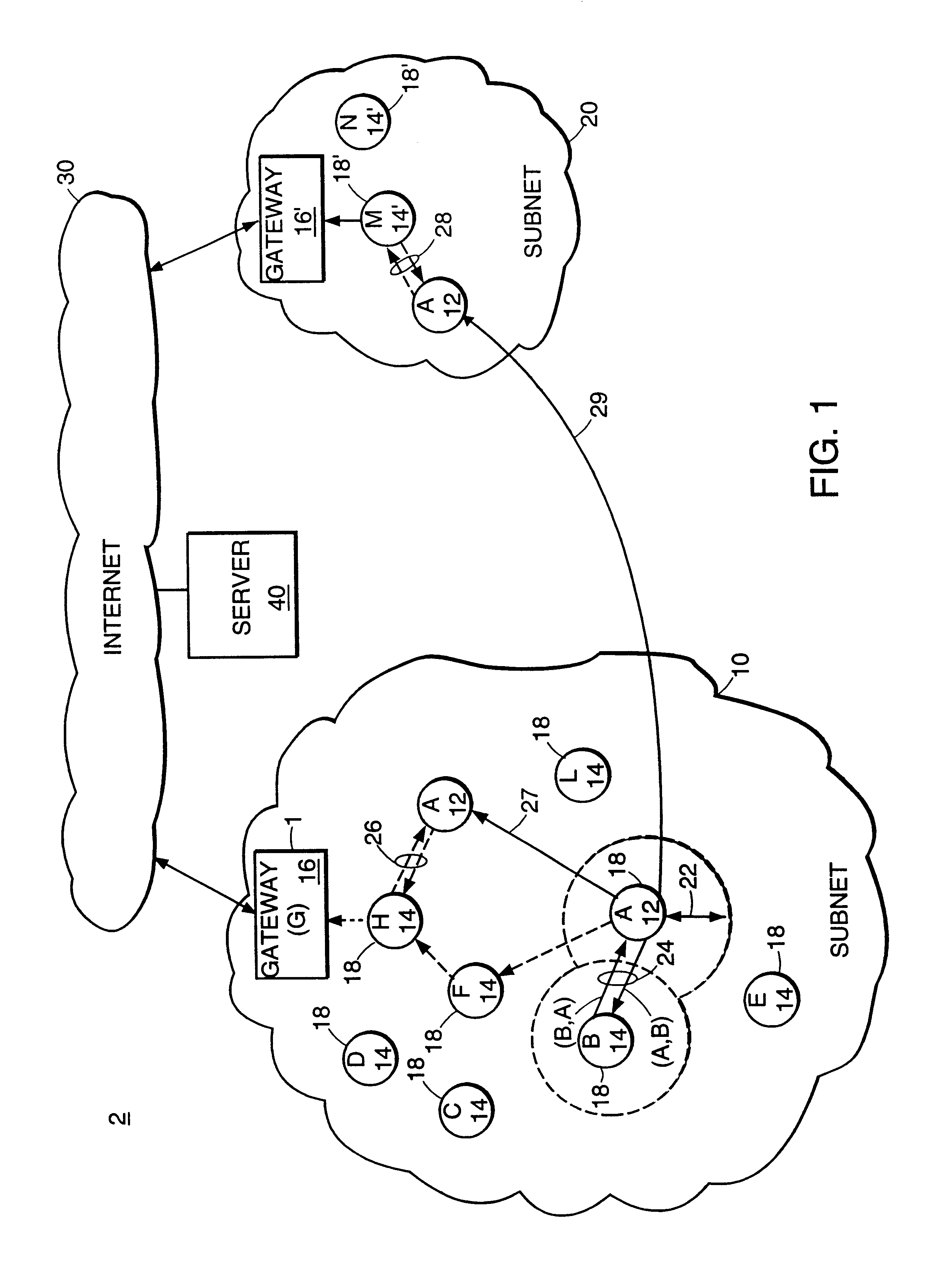
InactiveUS6845091B2Easy to addImprove robustnessError prevention/detection by using return channelNetwork traffic/resource managementTTEthernetNetwork measurement
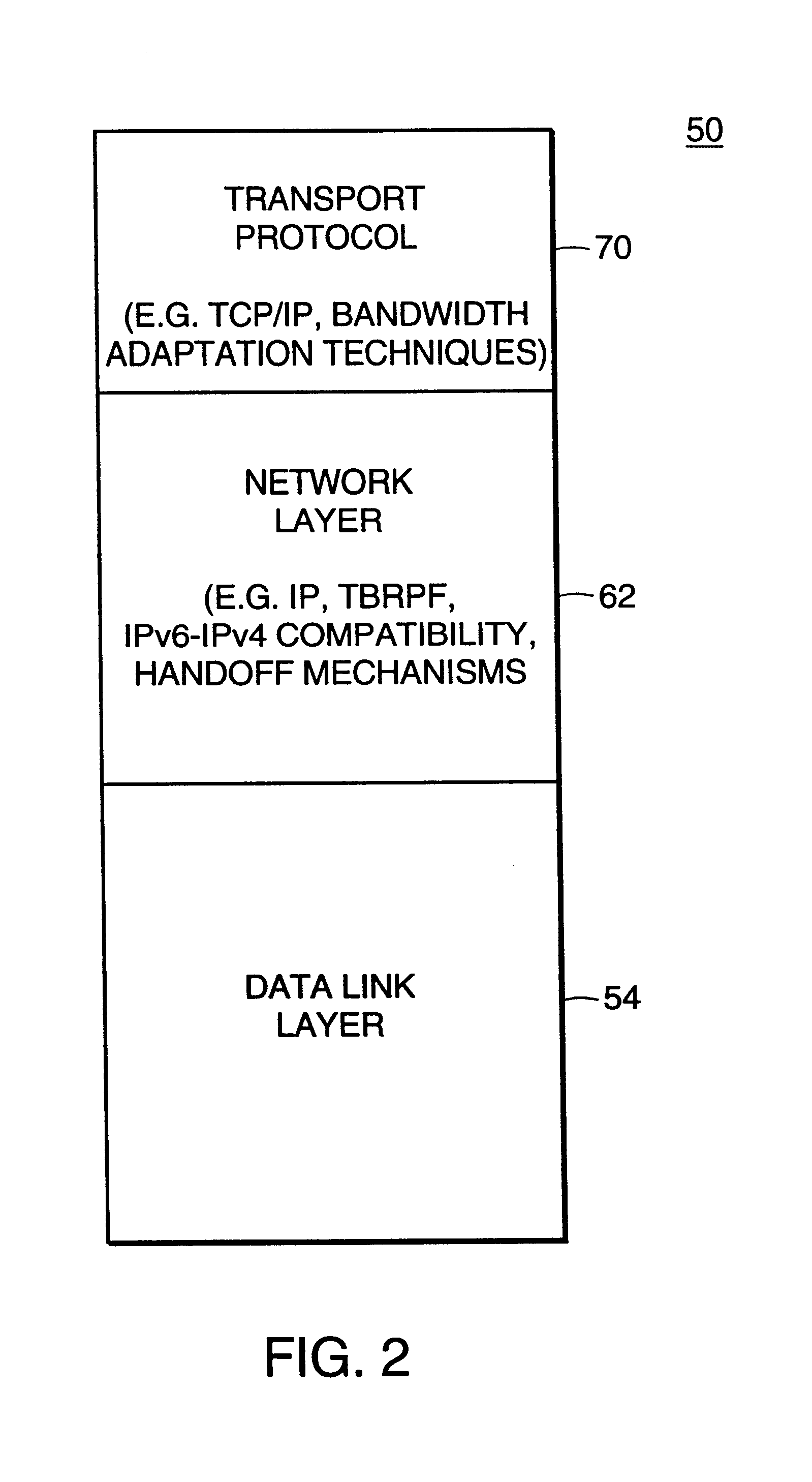
Described is an internetworking system having various mobile ad hoc extensions to the Internet that are particularly suited to the dynamic environment of mobile ad hoc networks. The internetworking system includes any combination of a link-state routing protocol for disseminating topology and link-state information over a multi-hop network comprised of nodes, a neighbor discovery protocol that can detect the appearance and disappearance of new neighbor nodes, an address format that facilitates deployment of IPv6 nodes in a predominantly IPv4 network infrastructure, a queuing mechanism that can update information upon resuming interrupted communications between nodes, and dynamic network measurement techniques for adaptively using wireless bandwidth when establishing and maintaining connections between nodes and a server.
Owner:SRI INTERNATIONAL
Content security layer providing long-term renewable security
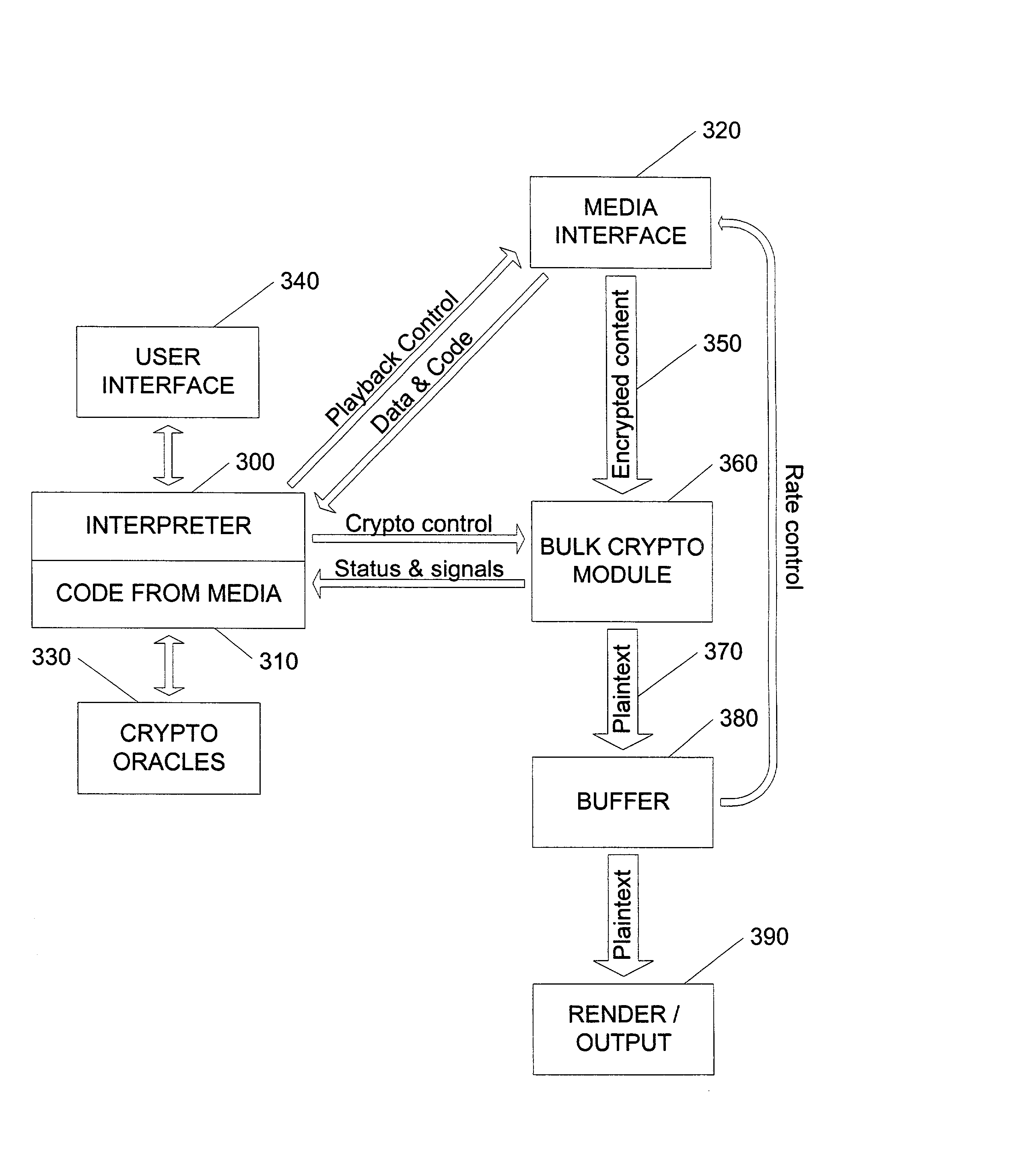
InactiveUS20020141582A1Unparalleled flexibilityIncrease sampling rateTelevision system detailsKey distribution for secure communicationAttackMediaFLO
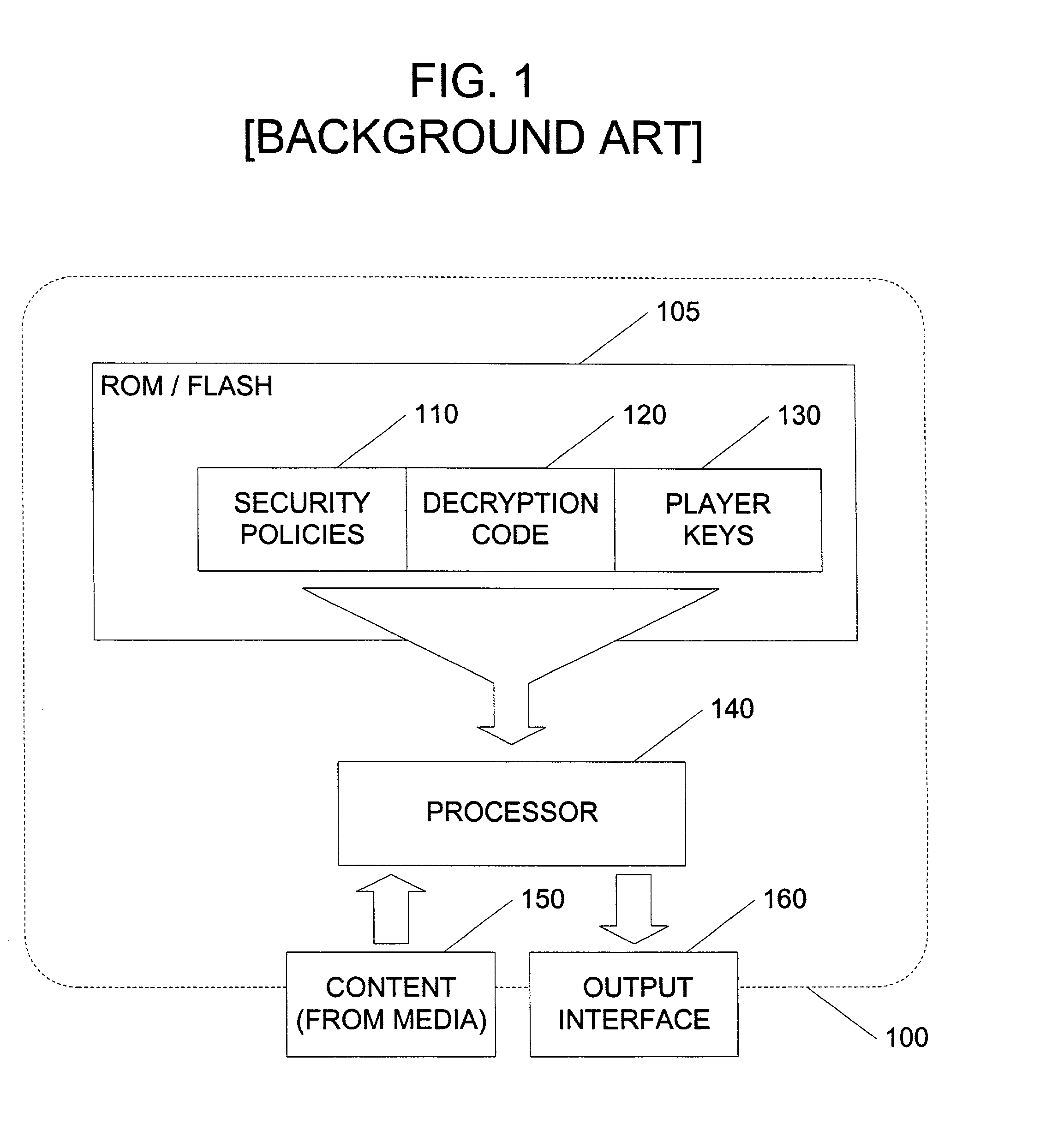
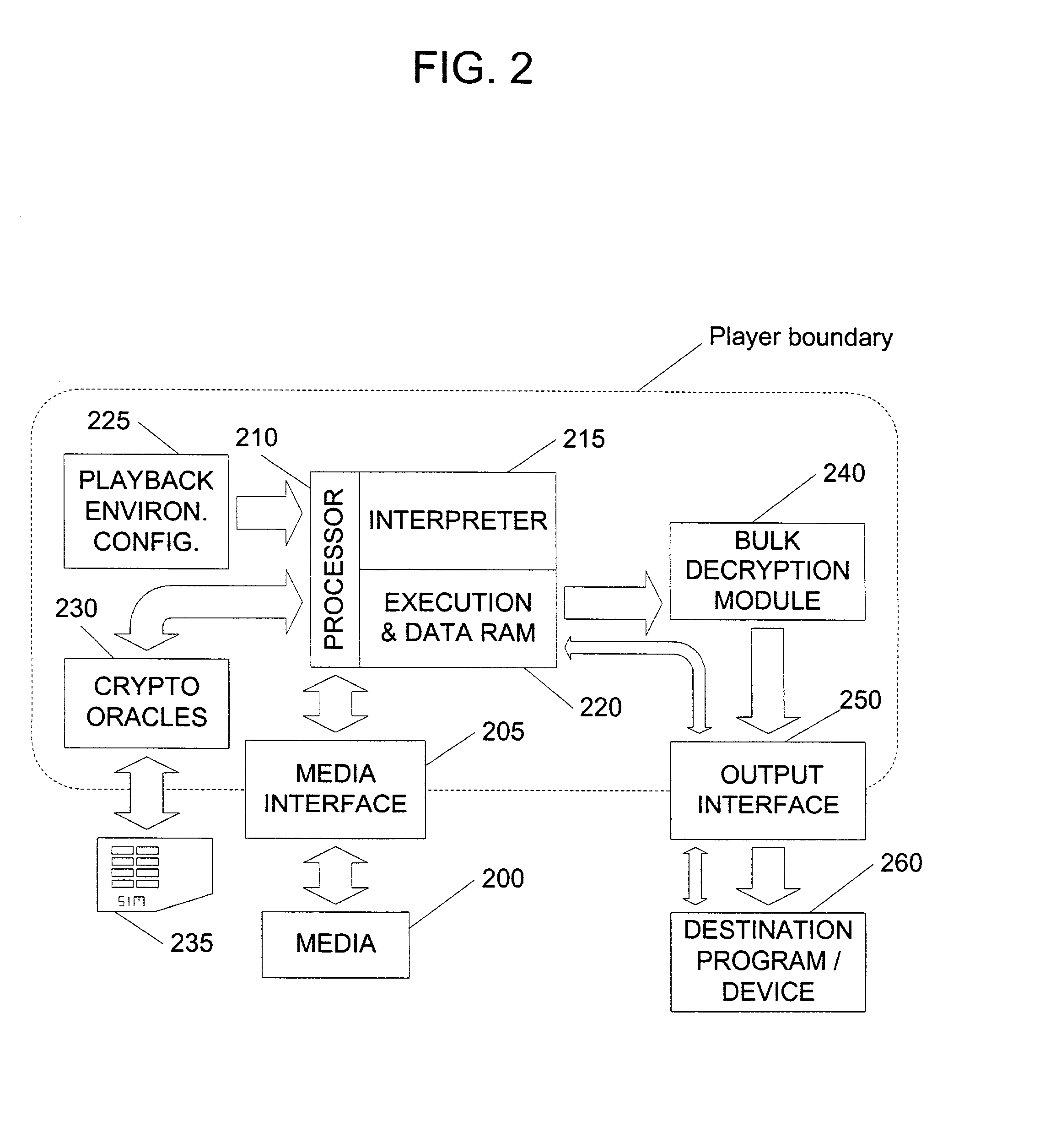
In an exemplary embodiment, digital content is mastered as a combination of encrypted data and data processing operations that enable use in approved playback environments. Player devices having a processing environment compatible with the content's data processing operations are able to decrypt and play the content. Players can also provide content with basic functions, such as loading data from media, performing network communications, determining playback environment configuration, controlling decryption / playback, and / or performing cryptographic operations using the player's keys. These functions allow the content to implement and enforce its own security policies. If pirates compromise individual players or content titles, new content can be mastered with new security features that block the old attacks. A selective decryption capability can also be provided, enabling on-the-fly watermark insertion so that attacks can be traced back to a particular player. Features to enable migration from legacy formats are also provided.
Owner:ROVI SOLUTIONS CORP
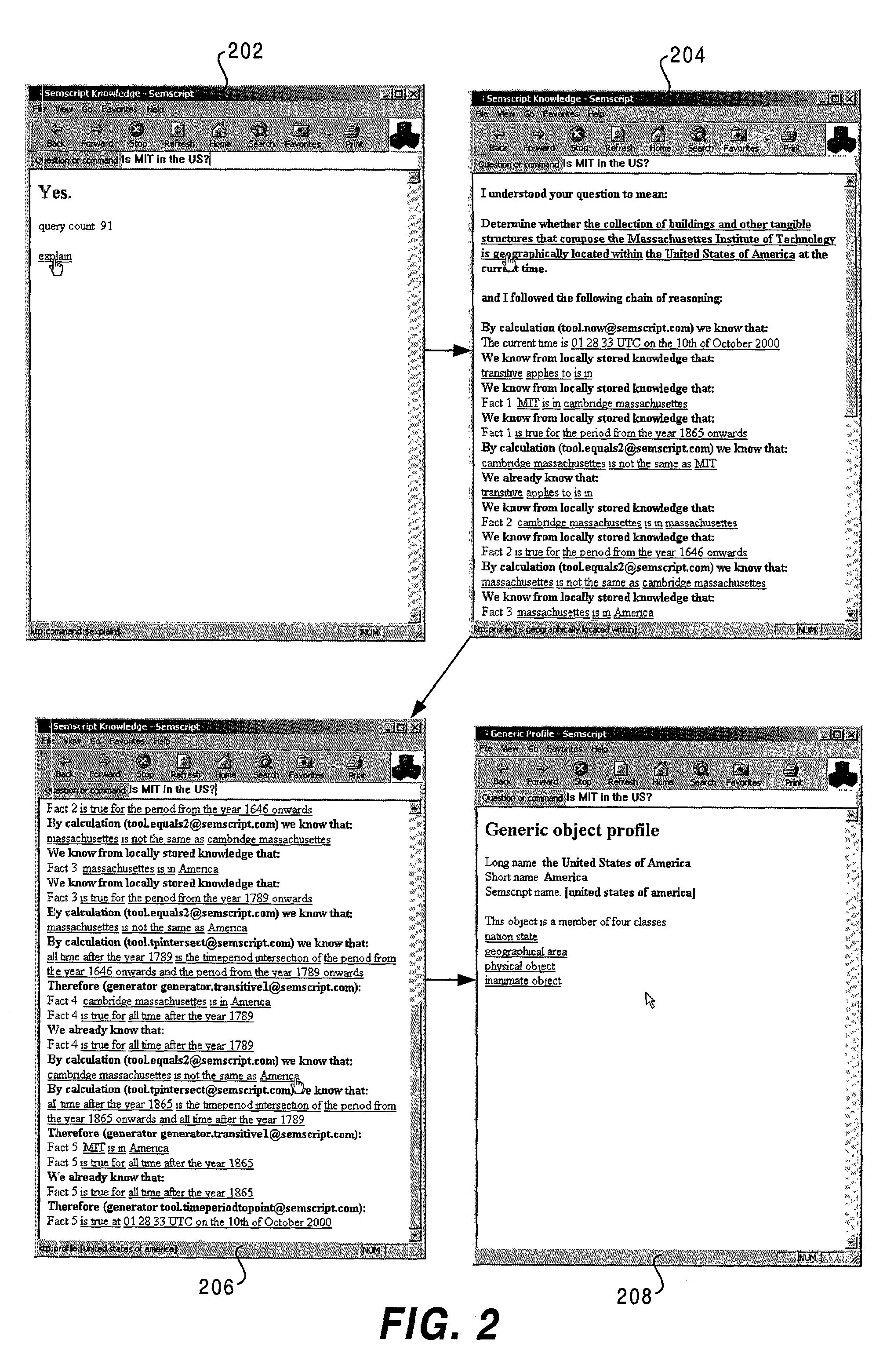
Knowledge storage and retrieval system and method
InactiveUS7013308B1Smooth interfaceSimple processDigital data information retrievalData processing applicationsProgramming languageWeb browser
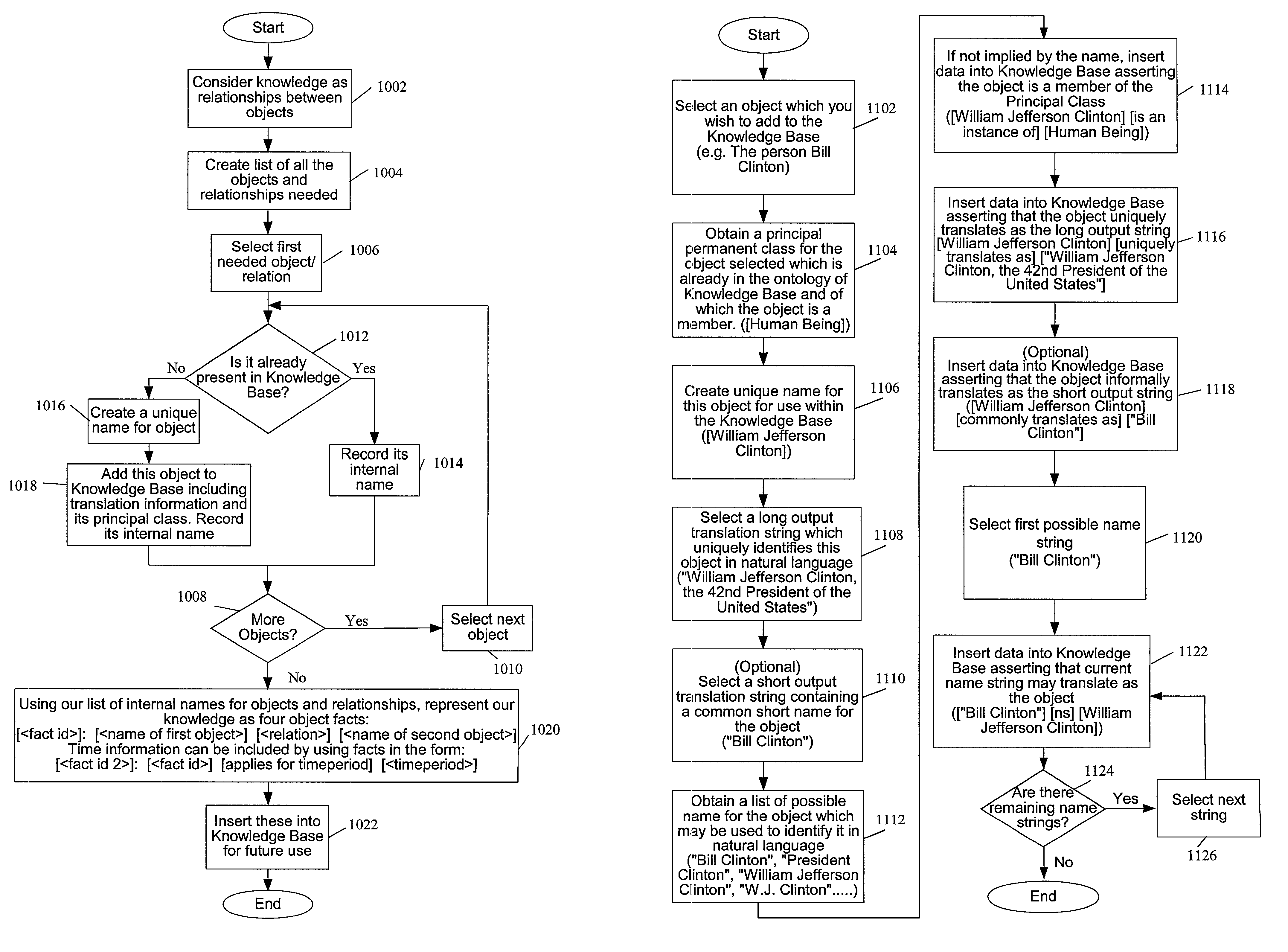
A system and method for representing, storing and retrieving real-world knowledge on a computer or network of computers is disclosed. Knowledge is broken down into permanent atomic “facts” which can be stored in a standard relational database and processed very efficiently. It also provides for the efficient querying of a knowledge base, efficient inference of new knowledge and translation into and out of natural language. Queries can also be processed with full natural language explanations of where the answers came from. The method can also be used in a distributed fashion enabling the system to be a large network of computers and the technology can be integrated into a web browser adding to the browser's functionality.
Owner:AMAZON TECH INC
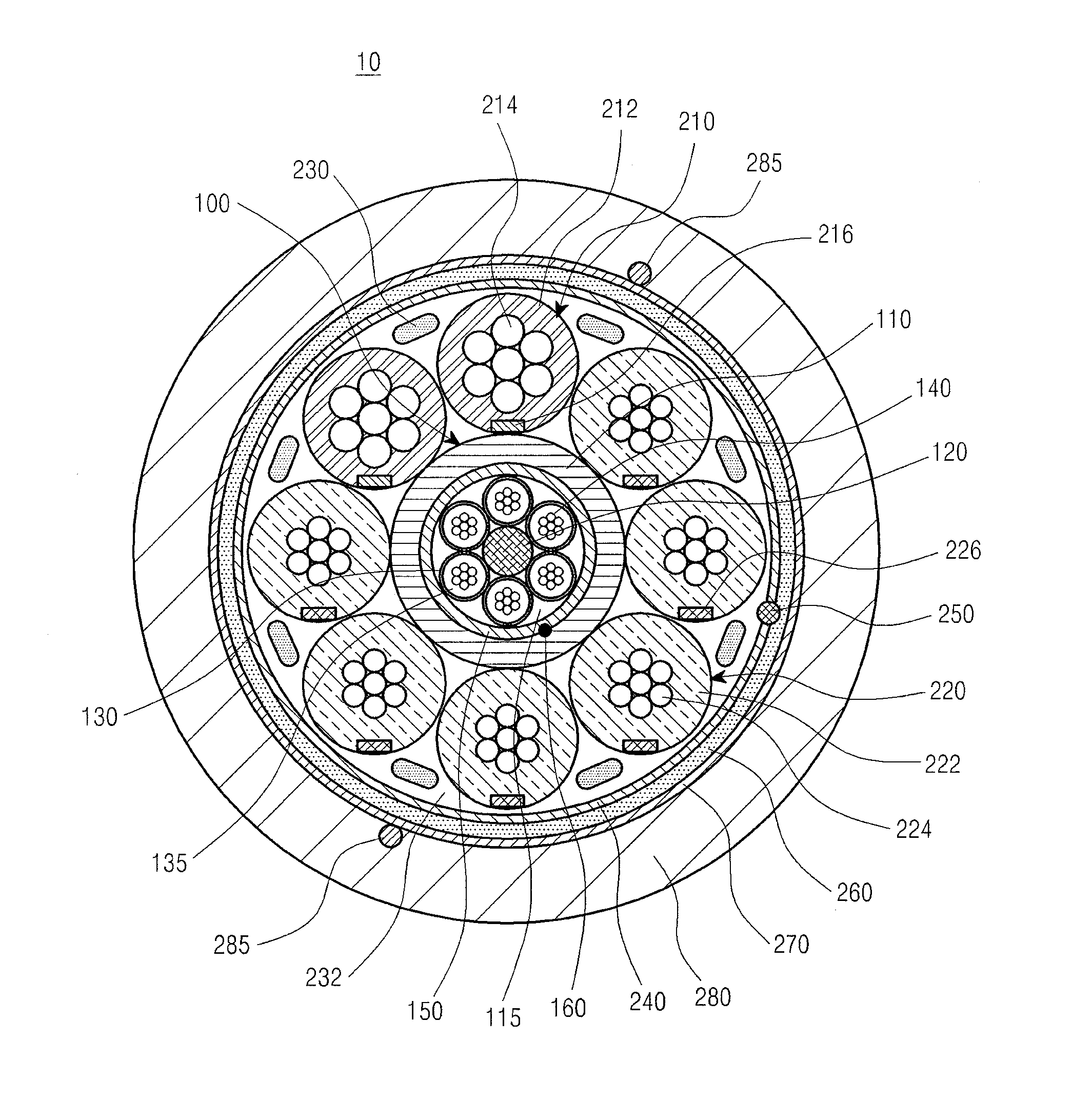
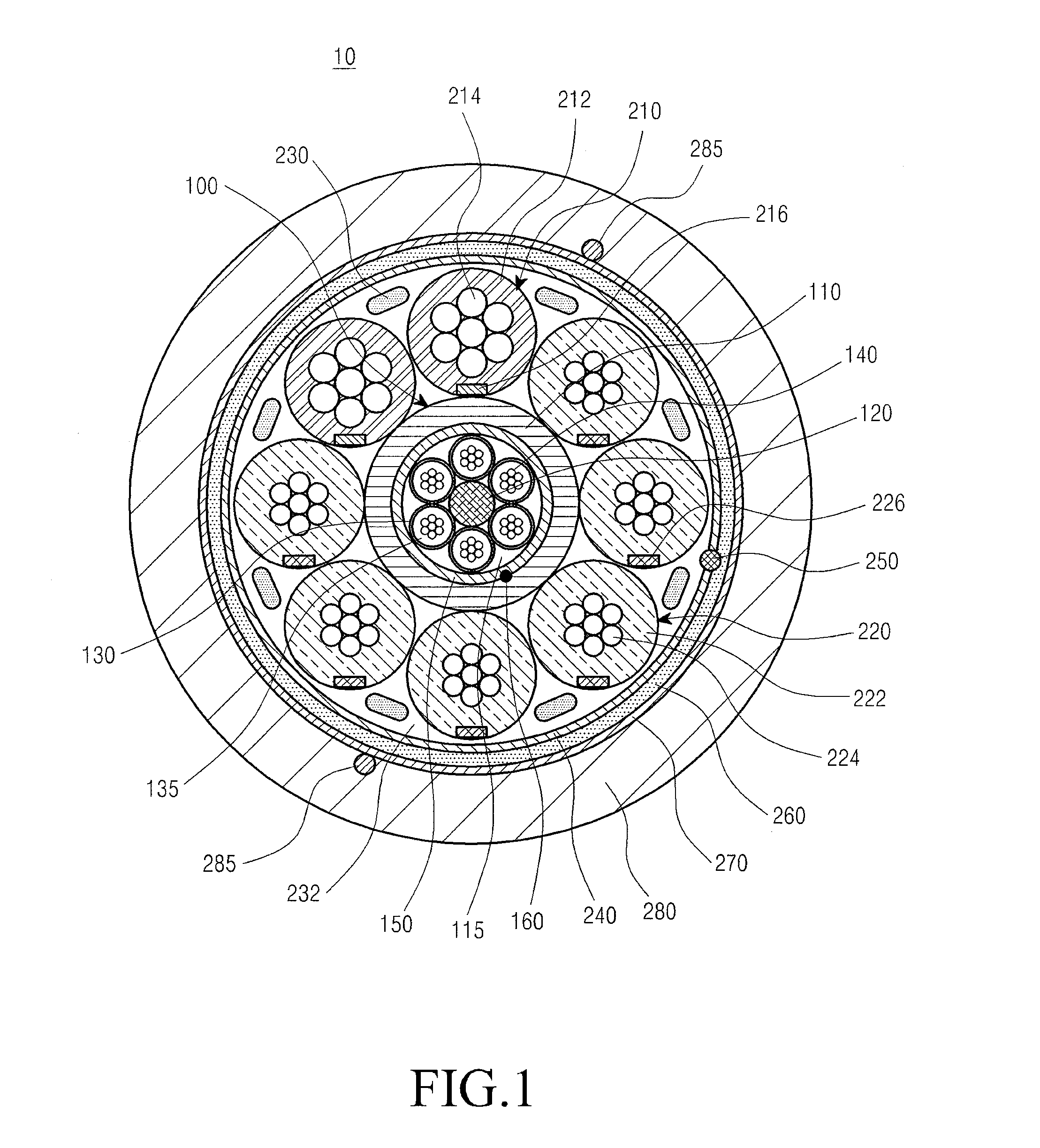
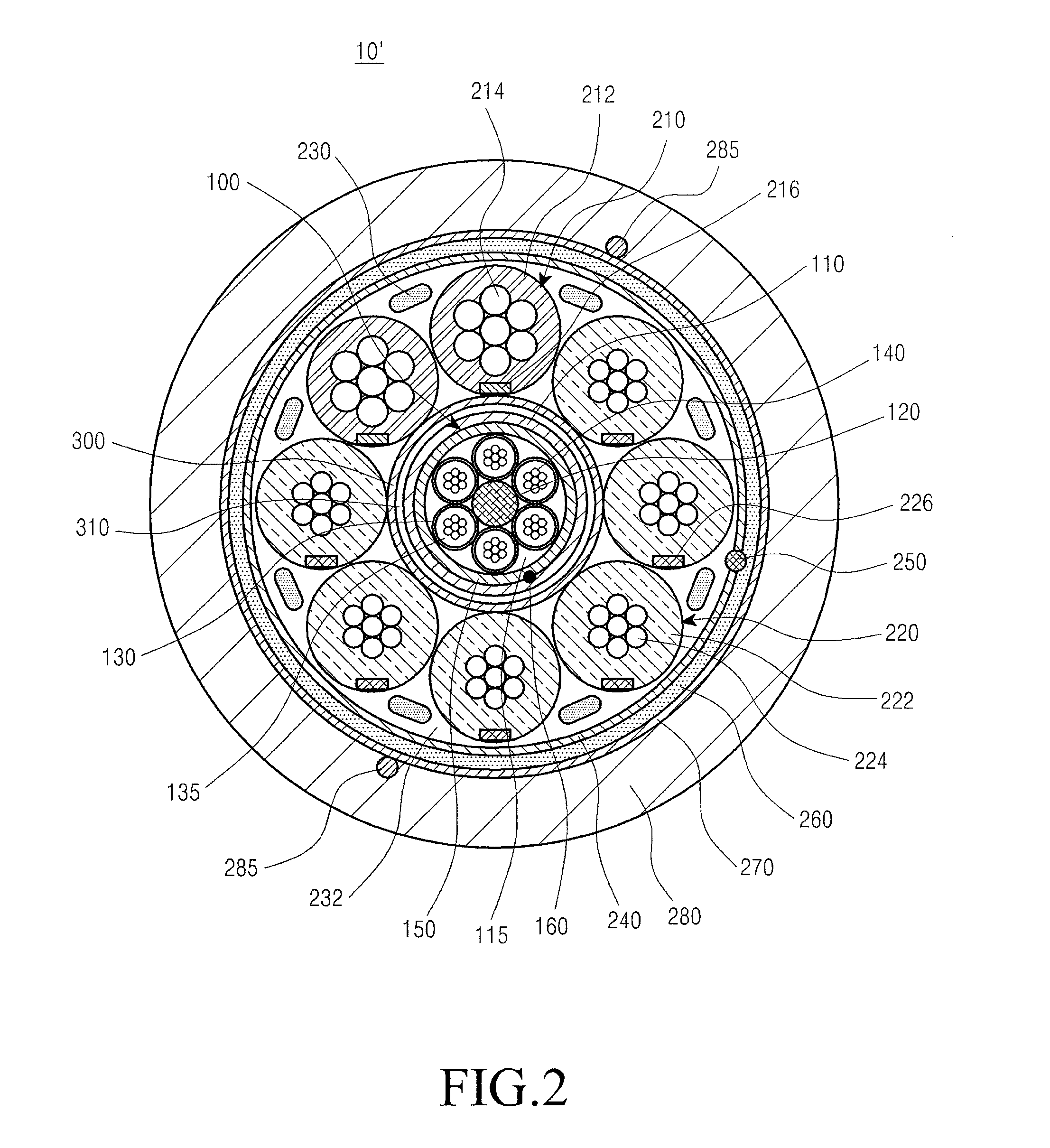
Optical electrical hybrid cable
InactiveUS8792760B2Reduce the overall diameterThe process is stable and efficientCommunication cablesCoupling light guidesFiberElectric force
An optical electrical hybrid cable for transmitting an optical signal and an electrical signal simultaneously is provided. The optical electrical hybrid cable includes a fiber-optic cable disposed in the center of the optical electrical hybrid cable, and including a plurality of tubes each of which comprises a plurality of optical fibers operatively mounted in an inner space thereof, and a first binder disposed around the plurality of tubes, a plurality of power cables disposed around the fiber-optic cable, each of the power cables comprising a plurality of conducting wires, and a second binder disposed around the plurality of power cables.
Owner:SAMSUNG ELECTRONICS CO LTD
Surveillance, monitoring and real-time events platform
InactiveUS20050055330A1Highly flexibleHighly scaleableDigital data processing detailsEpidemiological alert systemsData sourceCommunity setting
Systems and methods according to the invention provide a surveillance, monitoring and real-time events platform to (i) enable the integration and communication of information between government agencies and organizations specifically tasked with ensuring the security and safety of our nation and its communities, (ii) to integrate information systems from federal, state and / or local agencies (from disparate data sources if necessary) in order to obtain a single, real-time view of the entire organization, and (iii) to extract more complete, actionable information from their existing systems, thereby dramatically improving decision making speed and accuracy.
Owner:OBJECT STORE INC
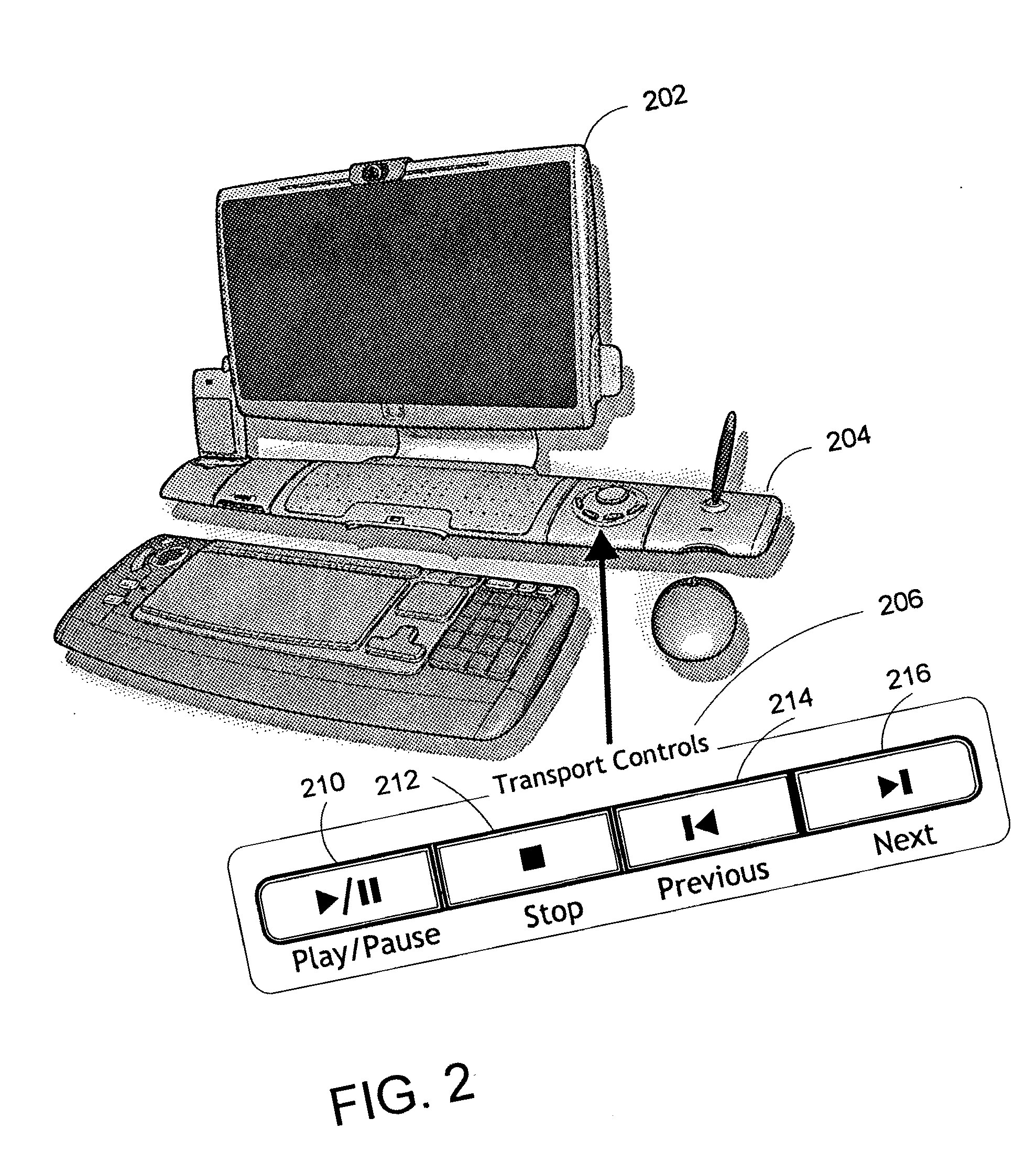
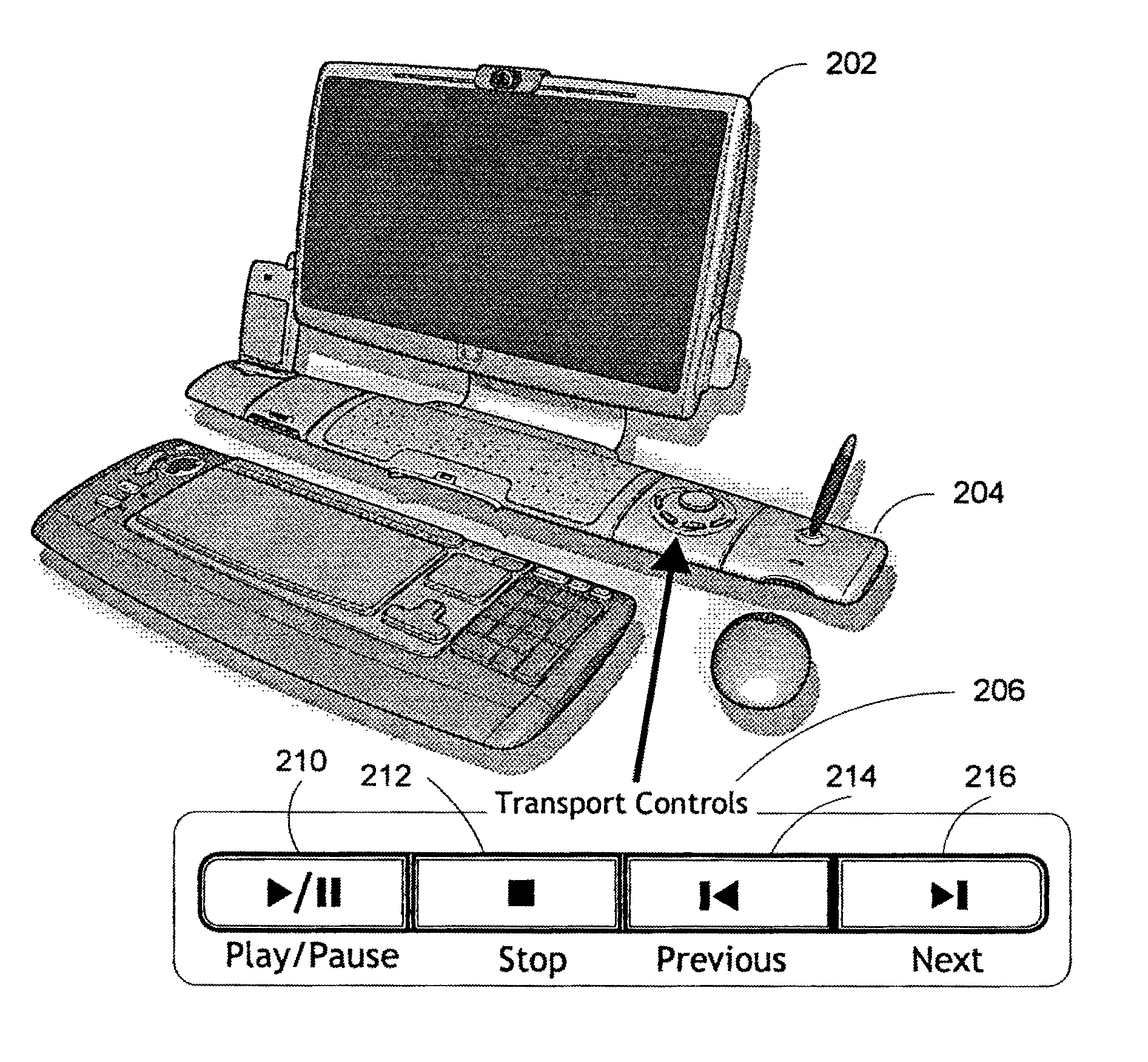
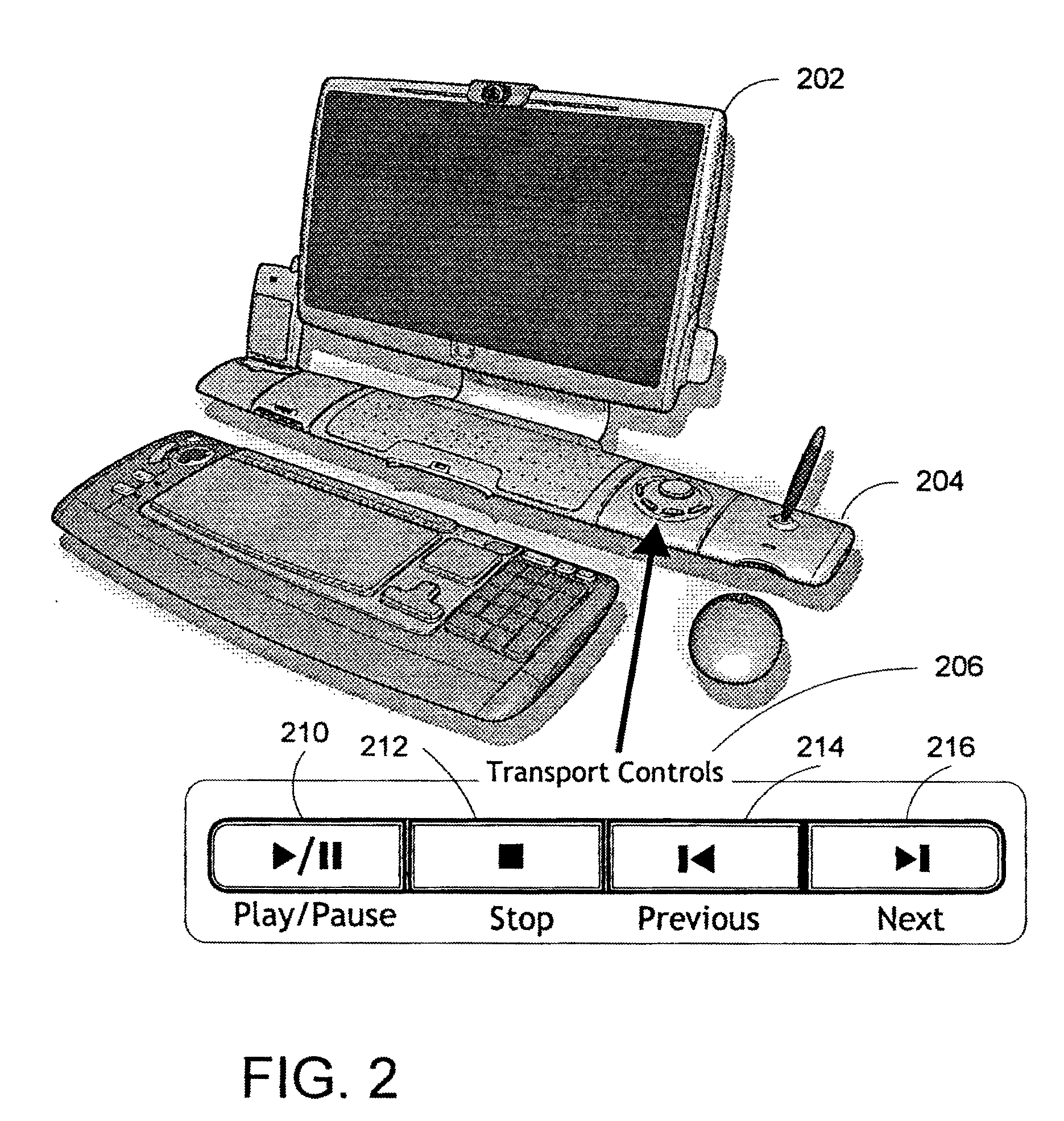
Method and system for navigation using media transport controls
ActiveUS20050071437A1Improve playbackSimple systemInput/output for user-computer interactionDigital computer detailsRemote controlElectronic form
A system and method for improved navigation and access of computer media content using media transport controls is provided. These transport controls may be placed in various locations such as on the computer housing, on a keyboard, on a monitor or a remote control. With these controls, a user may easily play multimedia content and navigate to individual tracks or segments of an audio and / or video stream. The transport controls include a play / pause button, a stop button, a previous button, and a next button. A user may intuitively activate and interact with media content in a variety of applications using these transport controls. For example, users may play recordings such as voice mail and review their recorded replies using the transport controls. Users may similarly play and / or review multimedia annotations made to any application files, including traditional computer files such as spreadsheets, documents and presentations.
Owner:MICROSOFT TECH LICENSING LLC
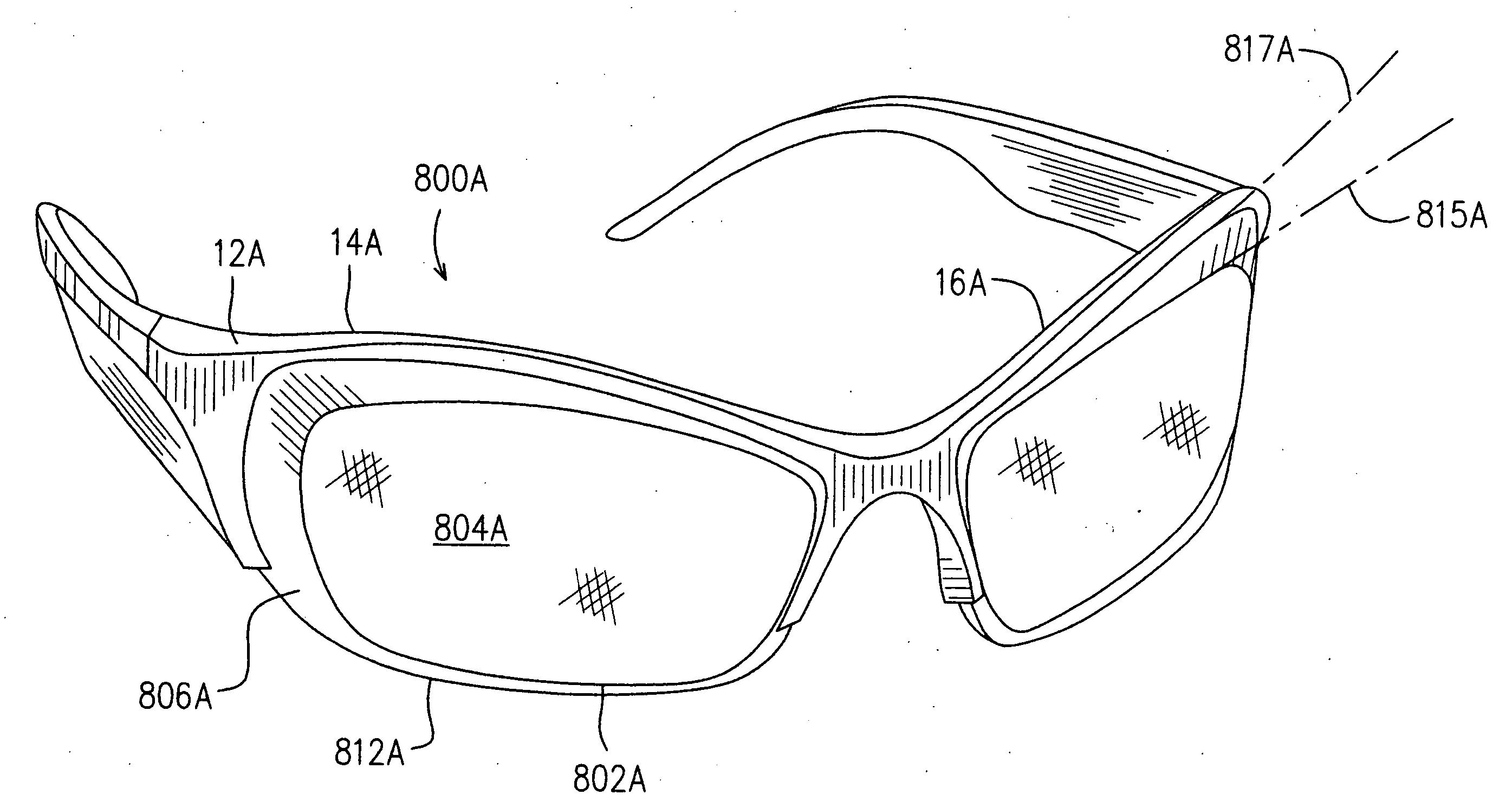
Eyewear having lenses with rims
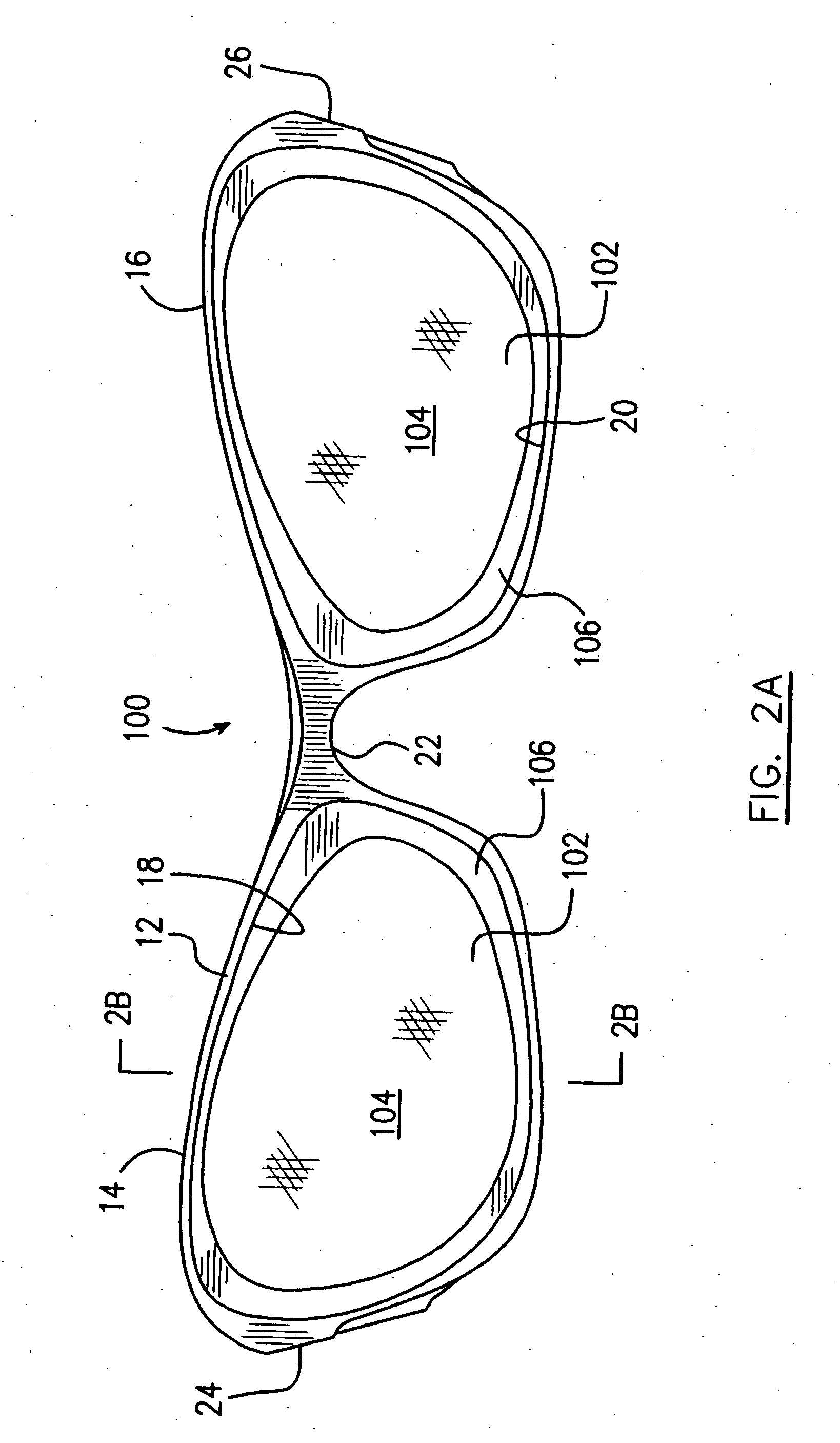
InactiveUS20060238698A1Easy to addChange propertiesSpectales/gogglesAuxillary optical partsEyewearEngineering
A method for assembly of an eyewear and an eyewear structure are provided to incorporate preferred properties into the eyewear. A relatively less curved lens is encircled by a protruding rim element, thereby forming a lens unit which is removably attached to the eyewear structure. The protruding rim element has a much curved outer periphery thereof such that the relatively less curved lens can be assembled in a much curved frame structure.
Owner:SHELDON BRENT
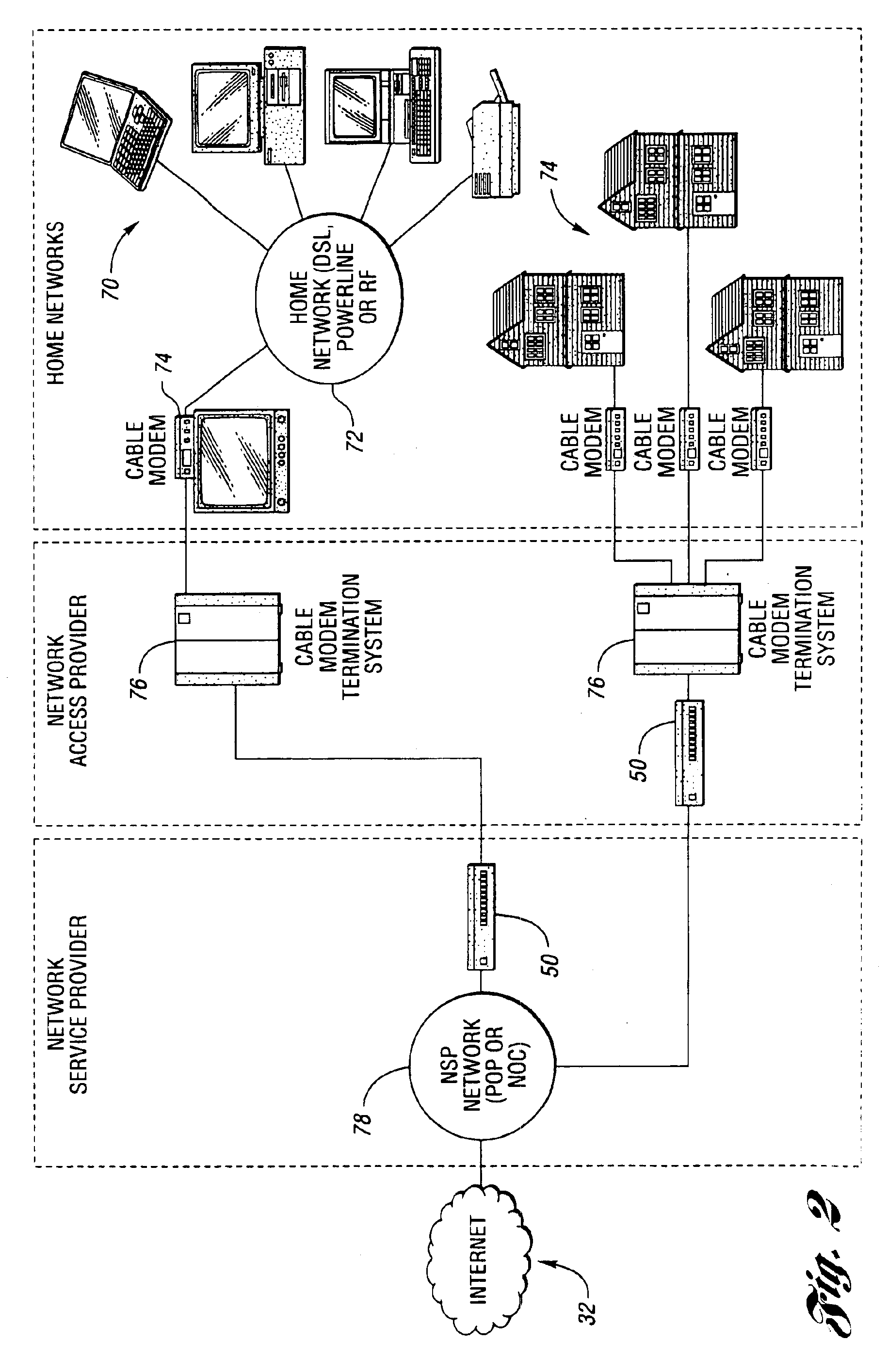
Upstream only linecard with front end multiplexer for CMTS
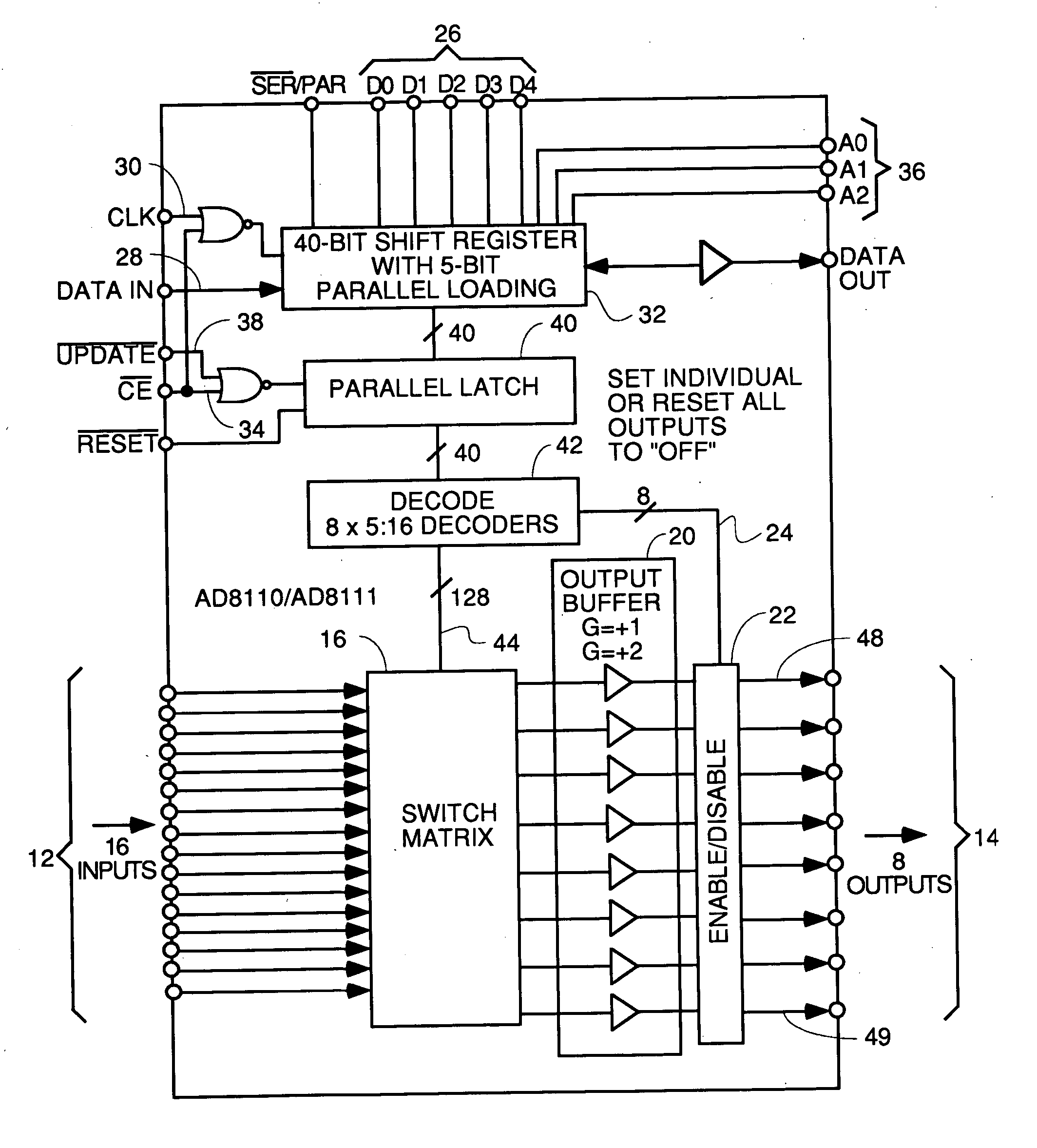
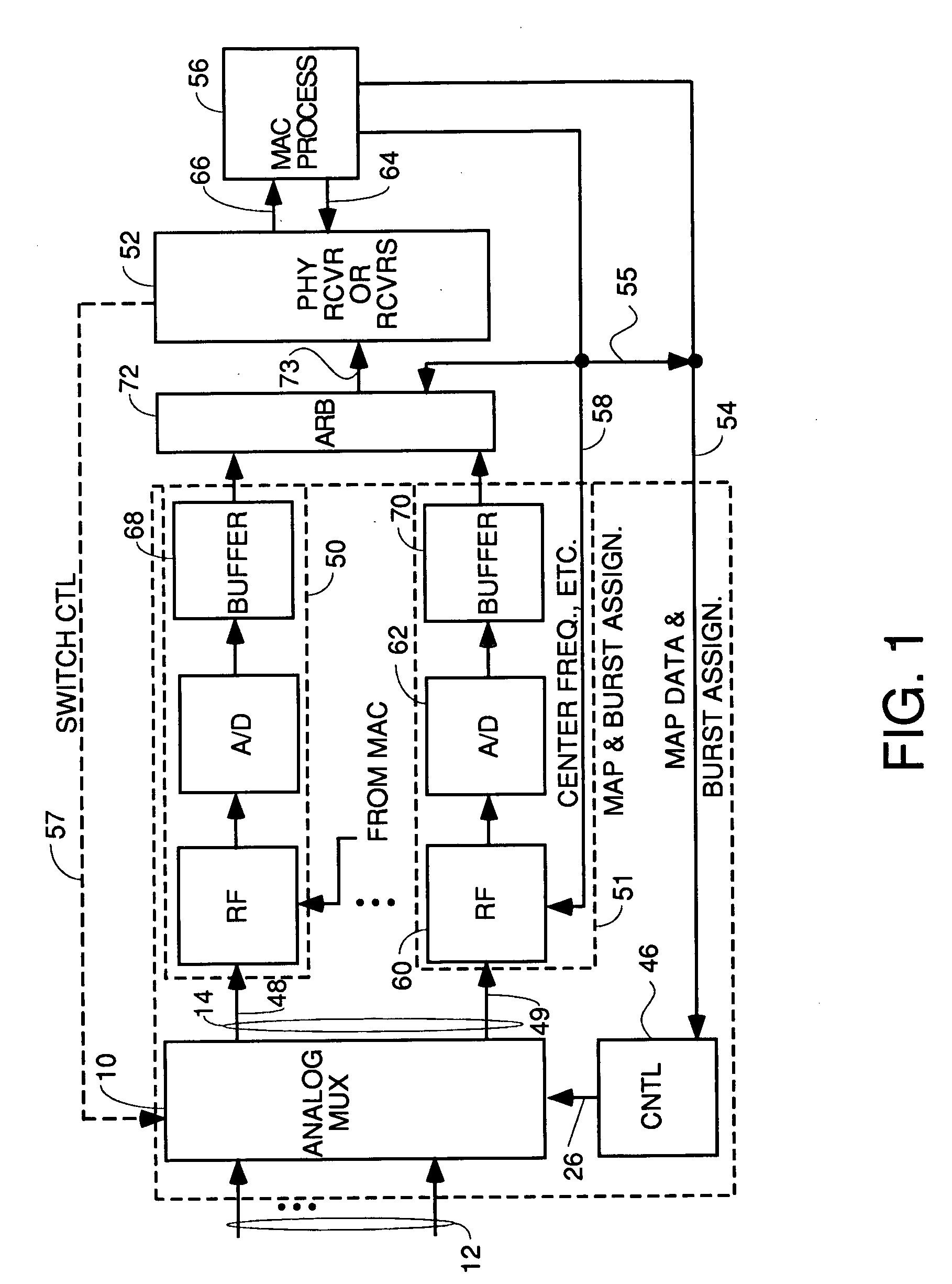
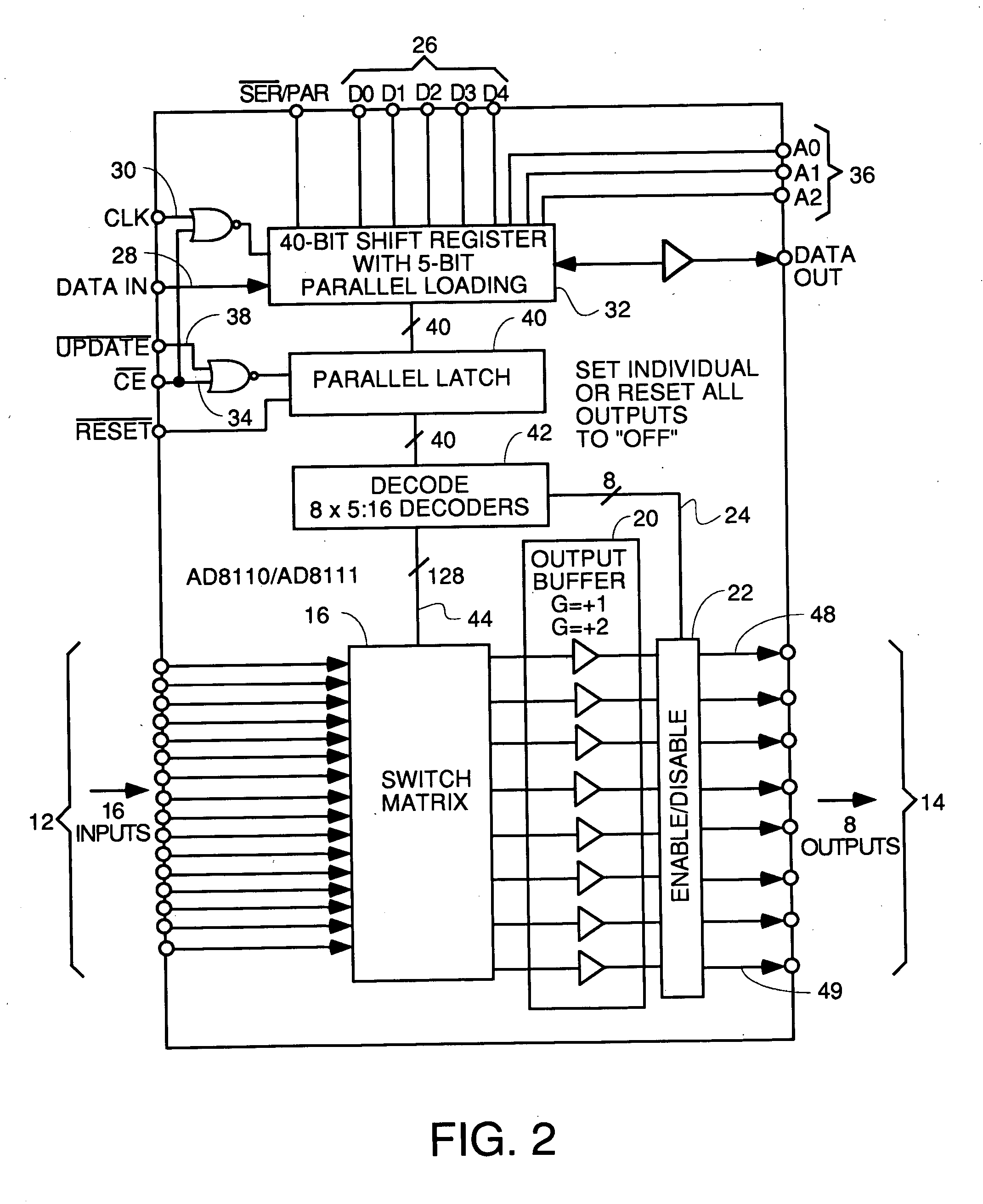
InactiveUS20050010958A1Easy to addMaximize Utilization EfficiencyMultiplex system selection arrangementsBroadband local area networksCrossbar switchMultiplexer
An upstream line card including a digital or analog multiplexer front end circuit for a Cable Modem Termination System. Each upstream line card has only upstream receivers and allows a CMTS to share one or a handful of receiver chips to receive and recover data from a larger number of input cables coupled to the front end multiplexer. A control circuit for the multiplexer uses MAP data and burst assignment data and upstream mini-slot counts for each of the input cables to determine when a burst is about to arrive on a cable and cause appropriate switching by the multiplexer or crossbar switch. In some embodiments, there is only one RF channel circuit coupled to the output of the multiplexer, so the multiplexer is controlled to couple the input cable upon which the burst is expected to the single RF channel. In other embodiments, there are multiple RF channels coupled to the inputs of the multiplexer so the multiplexer is controlled to connect each input cable on which a burst is expected to an available RF channel. In some embodiments, the sample data generated by each RF channel is buffered and an arbiter picks one burst at a time for application to the input of a CMTS receiver or doles out bursts to different receivers. In other embodiments, no buffers or arbiter are used, and each RF channel has its own dedicated CMTS receiver.
Owner:GOOGLE TECH HLDG LLC
Method and system for navigation using media transport controls
ActiveUS7194611B2Improve playbackSimple systemInput/output for user-computer interactionDigital computer detailsRemote controlElectronic form
Owner:MICROSOFT TECH LICENSING LLC
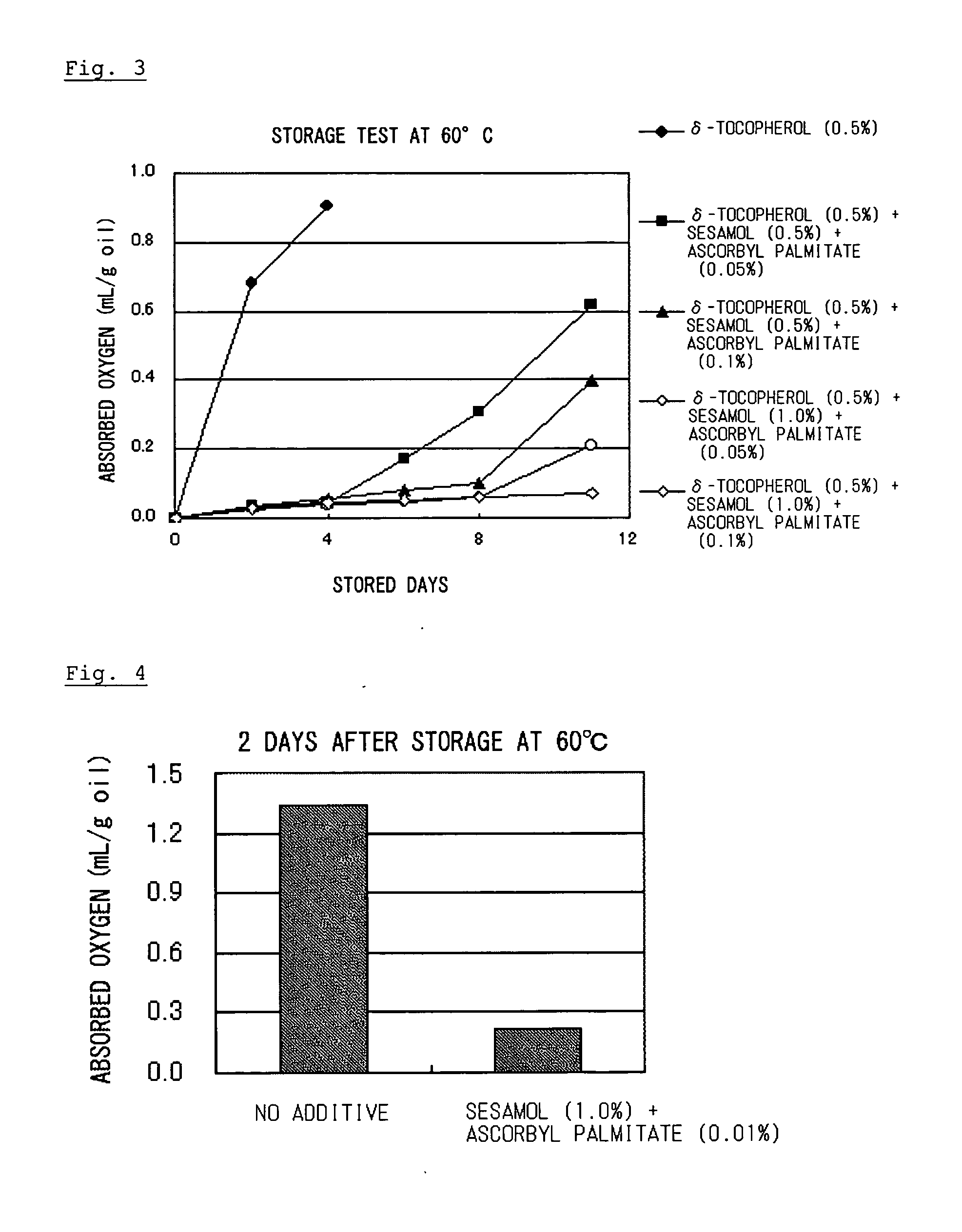
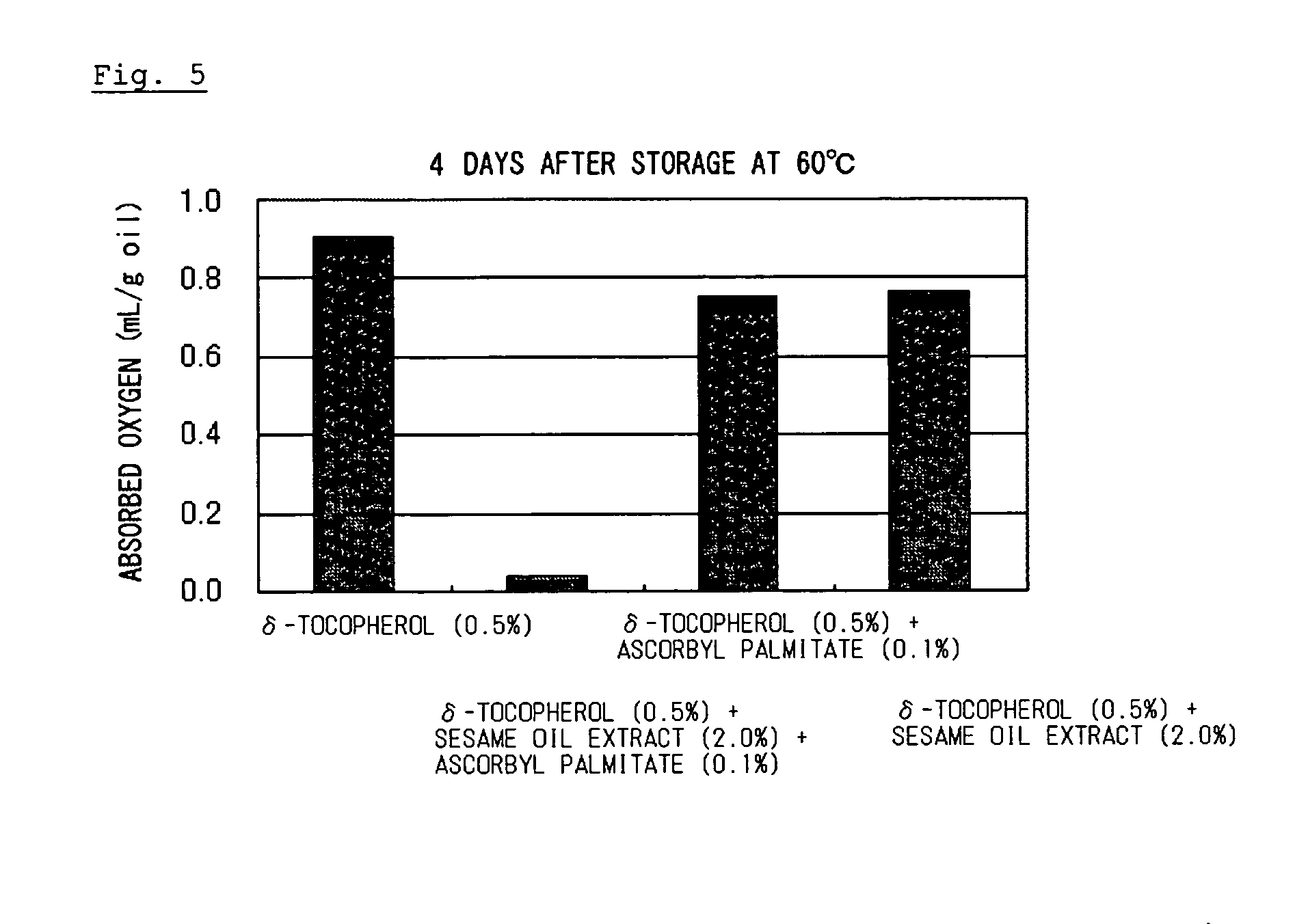
Composition containing organic substance having double bond with improved oxidative stability
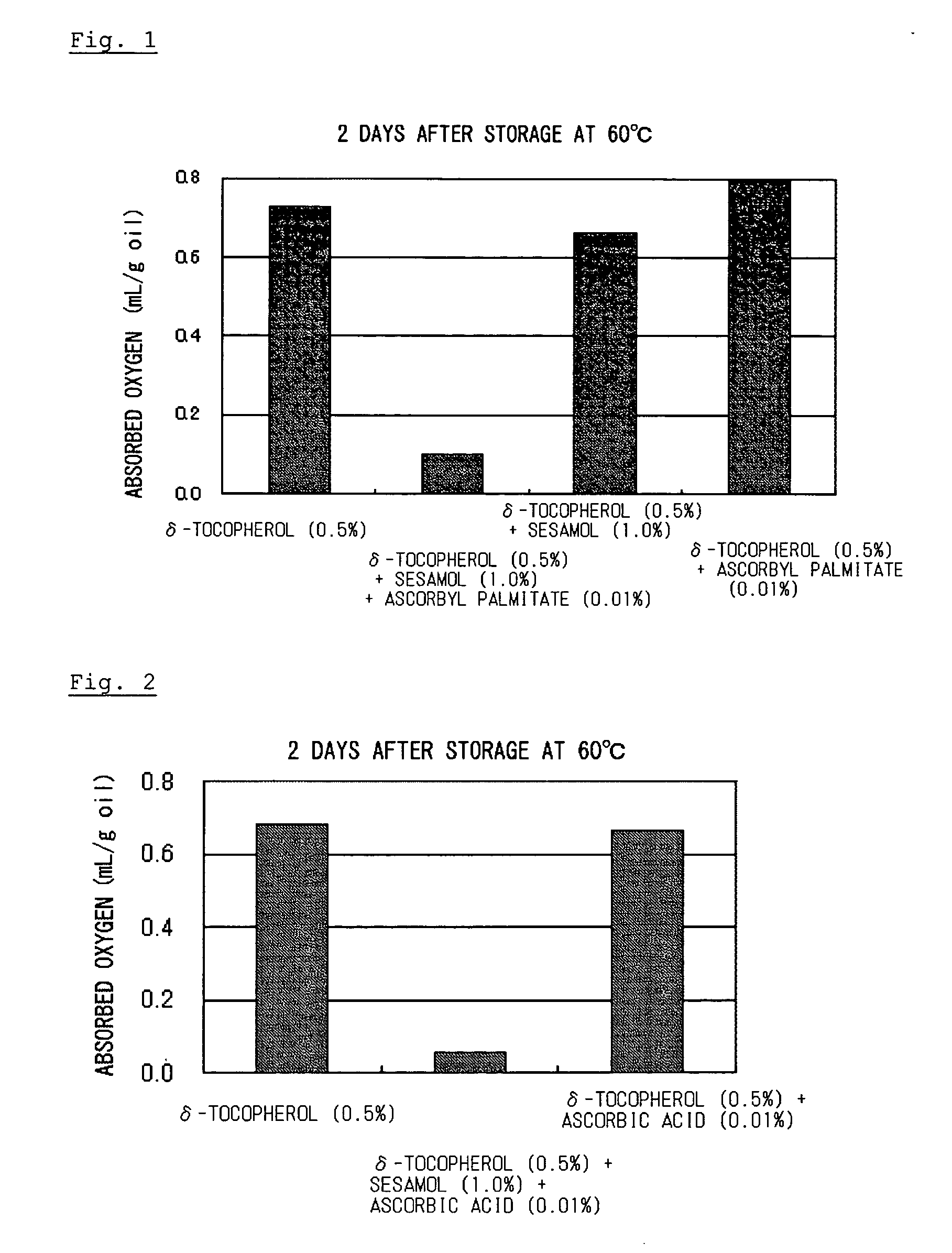
ActiveUS20060134178A1Improve stabilitySafe antioxidantOrganic active ingredientsCosmetic preparationsSesamum orientaleGeneral purpose
To an organic substance having a double bond such as a polyunsaturated fatty acid was added an antioxidative component containing an antioxidative sesame component and ascorbic acid or an ascorbyl fatty acid ester. The above method provides a composition containing an organic substance having a double bond exhibiting enhanced oxidative stability. Particularly, it extremely improves oxidative stability of fat and oil which contains polyunsaturated fatty acid. General-purpose refined fish oil which is easy to handle can be provided for food, medicine or feed uses.
Owner:NIPPON SUISAN KAISHA LTD
System and method of secure login on insecure systems
InactiveUS20060206919A1Little overheadEasy to addDigital data processing detailsUser identity/authority verificationKey imagesSafe system
A method for authenticating a user for use of a server computing device wherein the server computing device is connected by a network to a host device. Generating a key representation image having thereon a plurality of individual key images placed at random positions, each corresponding to a possible character value in an authentication phrase. Accepting a sequence corresponding to locations of mouse clicks representing user selections of character values in an attempted authentication phrase. Verifying that the sequence of location values corresponds to a correct authentication phrase by mapping the locations of the mouse clicks to the locations of the randomly placed key images. Alternatively, accepting a sequence corresponding to a transformation of personal identification number based on a random number and a numerical operation or selection in a matrix.
Owner:AXALTO SA
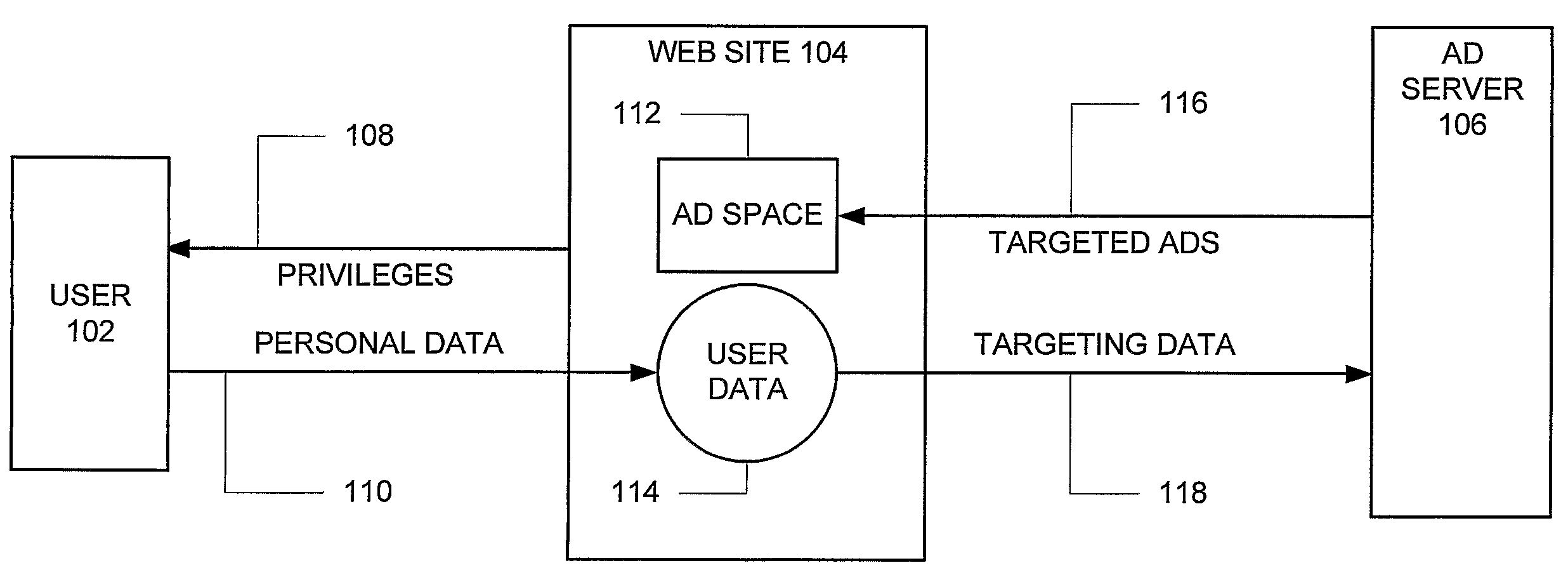
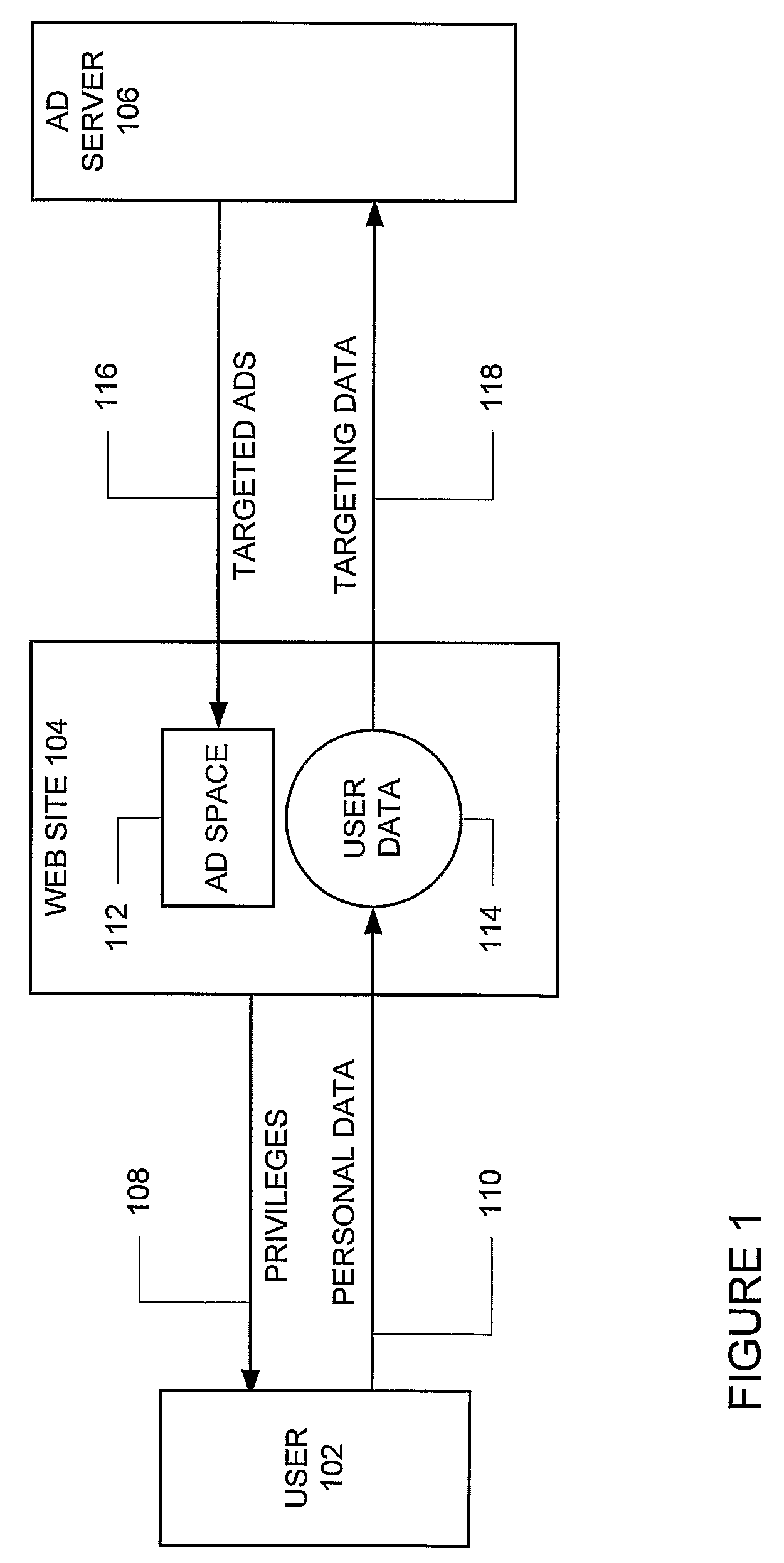
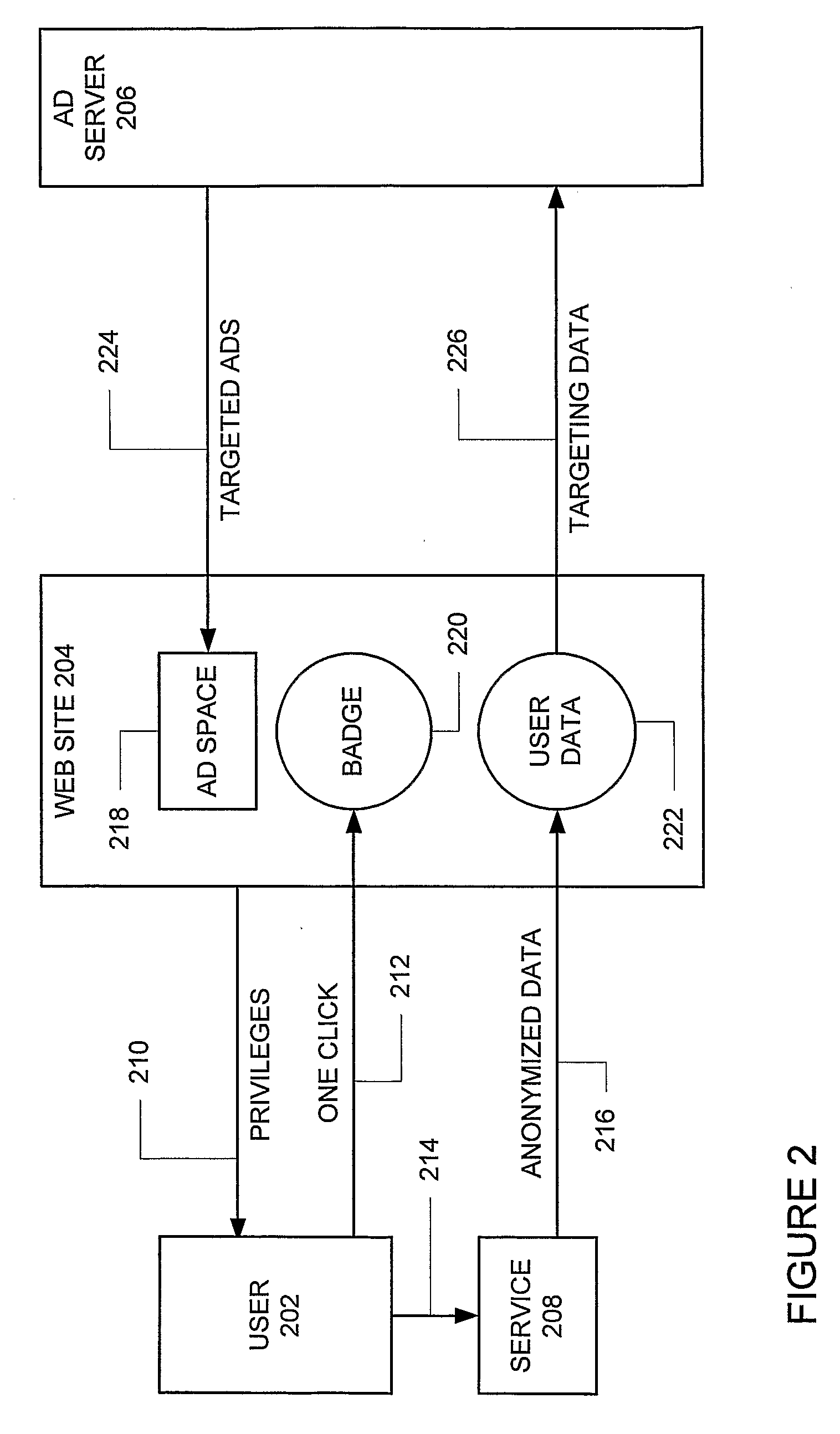
System and method for the reversible leasing of anonymous user data in exchange for personalized content including targeted advertisements
A system and method for the reversible leasing of anonymous user data in exchange for personalized content including targeted advertisements includes: (a) helping users gather and manage data representing their interests (404); (b) distilling this data to a condensed and anonymous form (434); (c) making it easy to review, edit, and add to this data; (d) providing a simple way for sites to ask for this data (414); (e) enabling users to grant reversible access to a site with one click (432); (f) providing sites with multiple ways to access and use this data once the user has granted access (424) and (g) motivating the user to keep their data accurate and up-to-date (403). In this manner, Internet users can lease data to web sites in a way that is convenient, secure, and under user control, respecting the user desire for transparency and privacy, and avoiding the complexity and trust issues experienced by both users and web sites when utilizing identity management systems.
Owner:PREFPASS
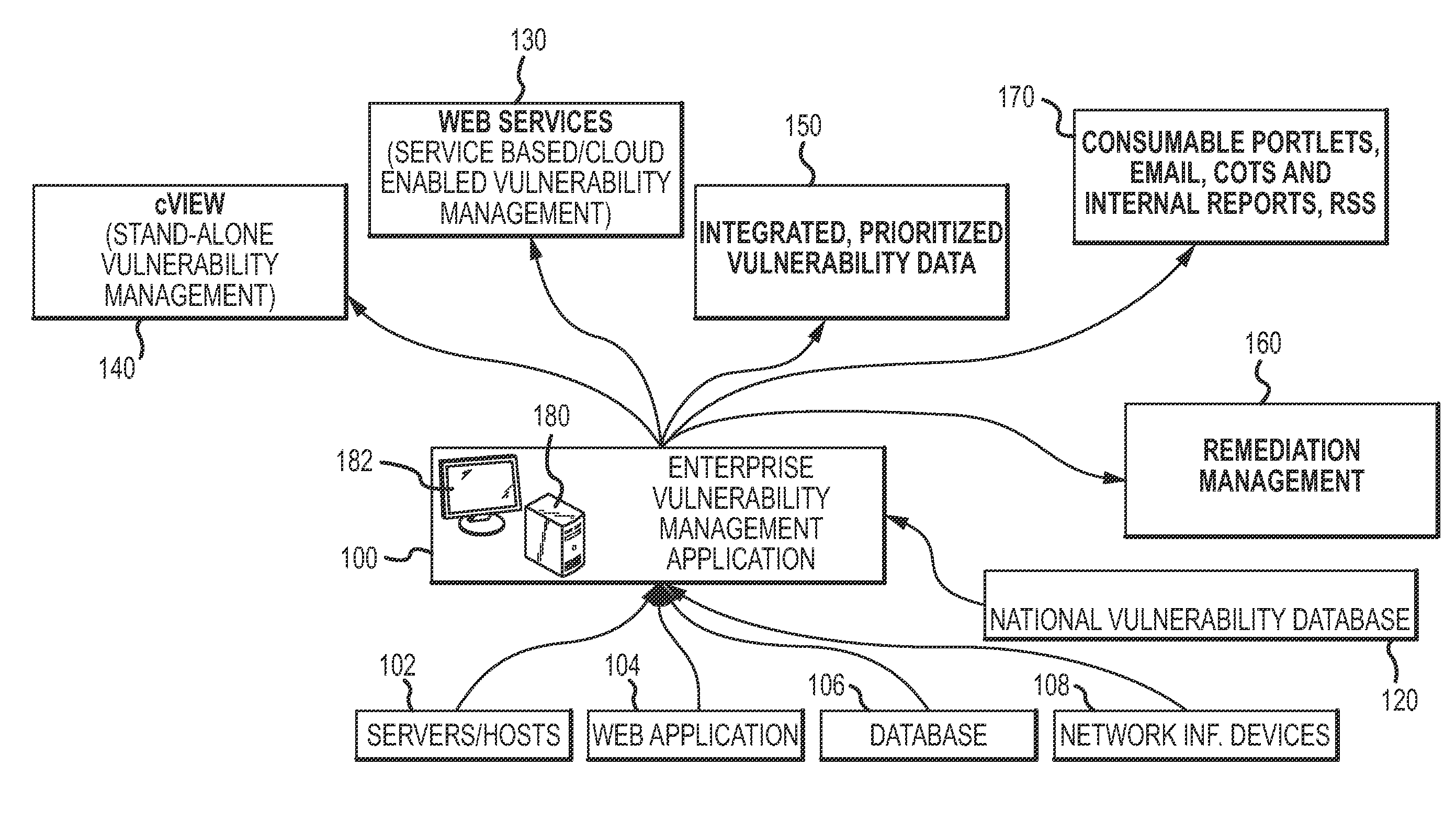
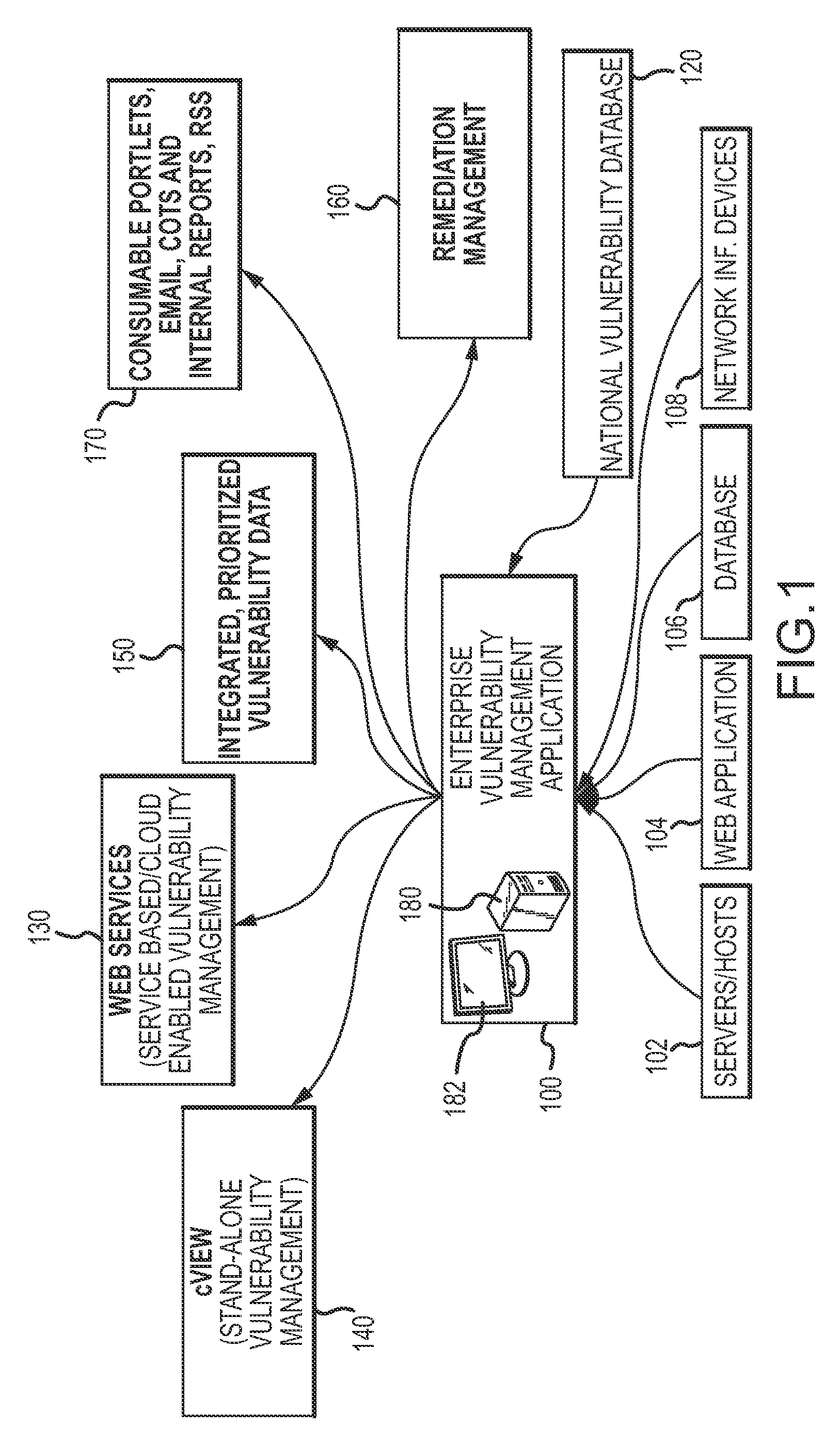
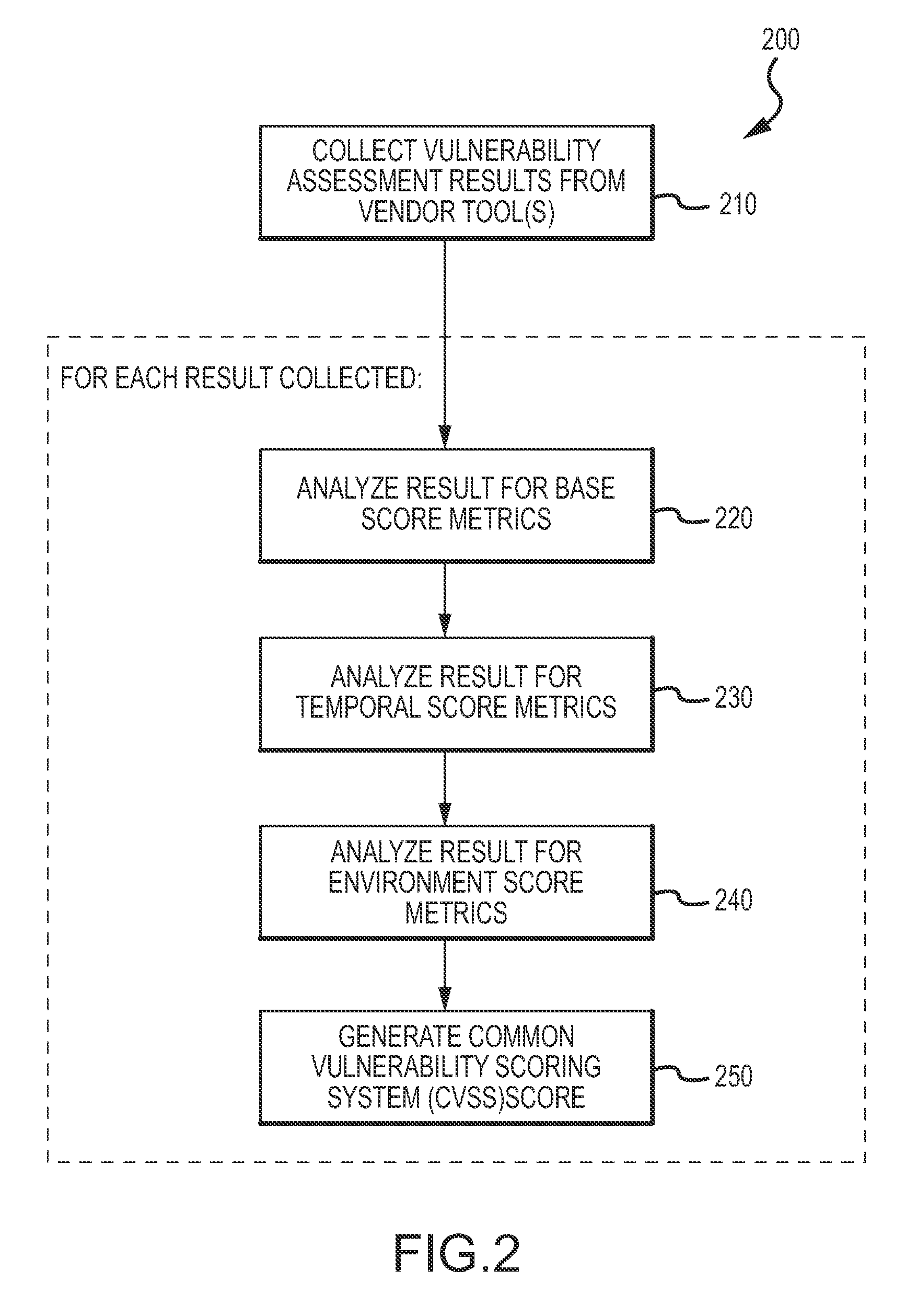
Enterprise vulnerability management
ActiveUS20120304300A1Fast data analysisEasy to addMemory loss protectionError detection/correctionVulnerability managementRemedial action
An enterprise vulnerability management application (EVMA), enterprise vulnerability management process (EVMP) and system. In one embodiment, the EVMP may include executing computer software code on at least one computer hardware platform to receive login information from a user, inventory current information technology assets of the enterprise, conduct vulnerability scanning of the inventoried information technology assets, analyze vulnerability correlation and prioritization of the information technology assets, remediate one or more vulnerabilities of the information technology assets, and report to the user about the vulnerabilities and remediation undertaken. As part of the analysis, one or more vulnerability scores such as, for example, Common Vulnerability Scoring System (CVSS) scores, may be generated from base score metrics, temporal score metrics and environment score metrics.
Owner:LEIDOS INNOVATIONS TECH INC
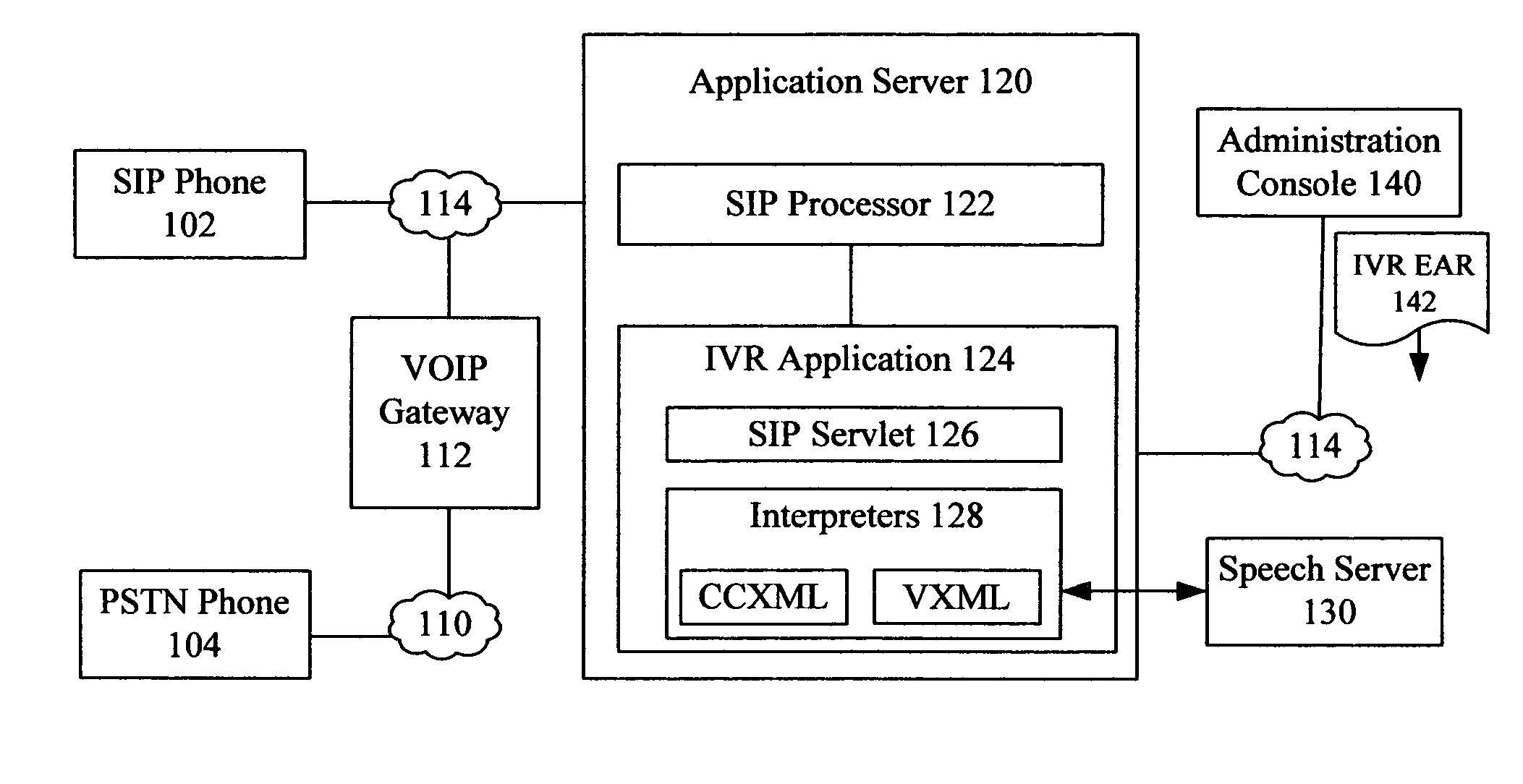
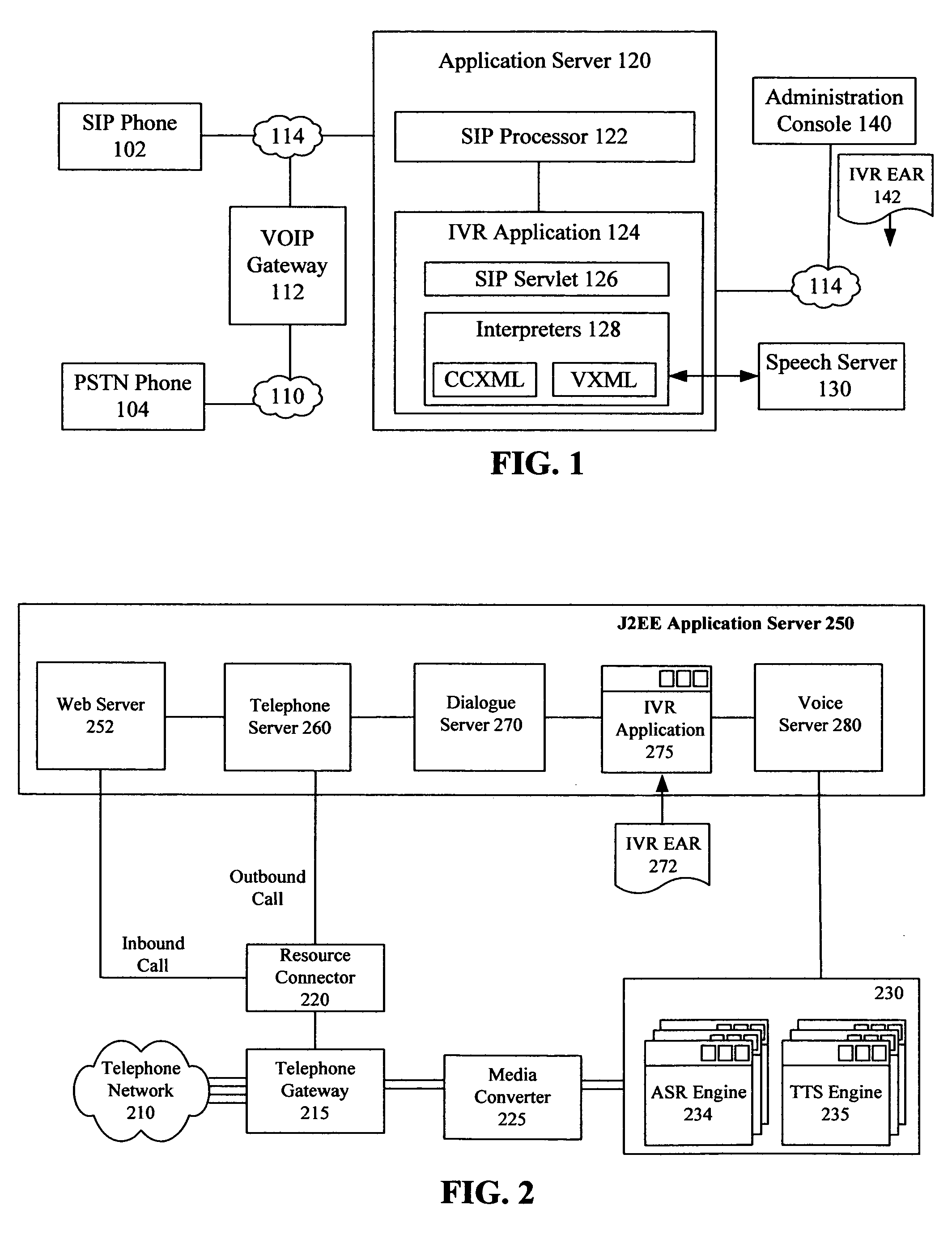
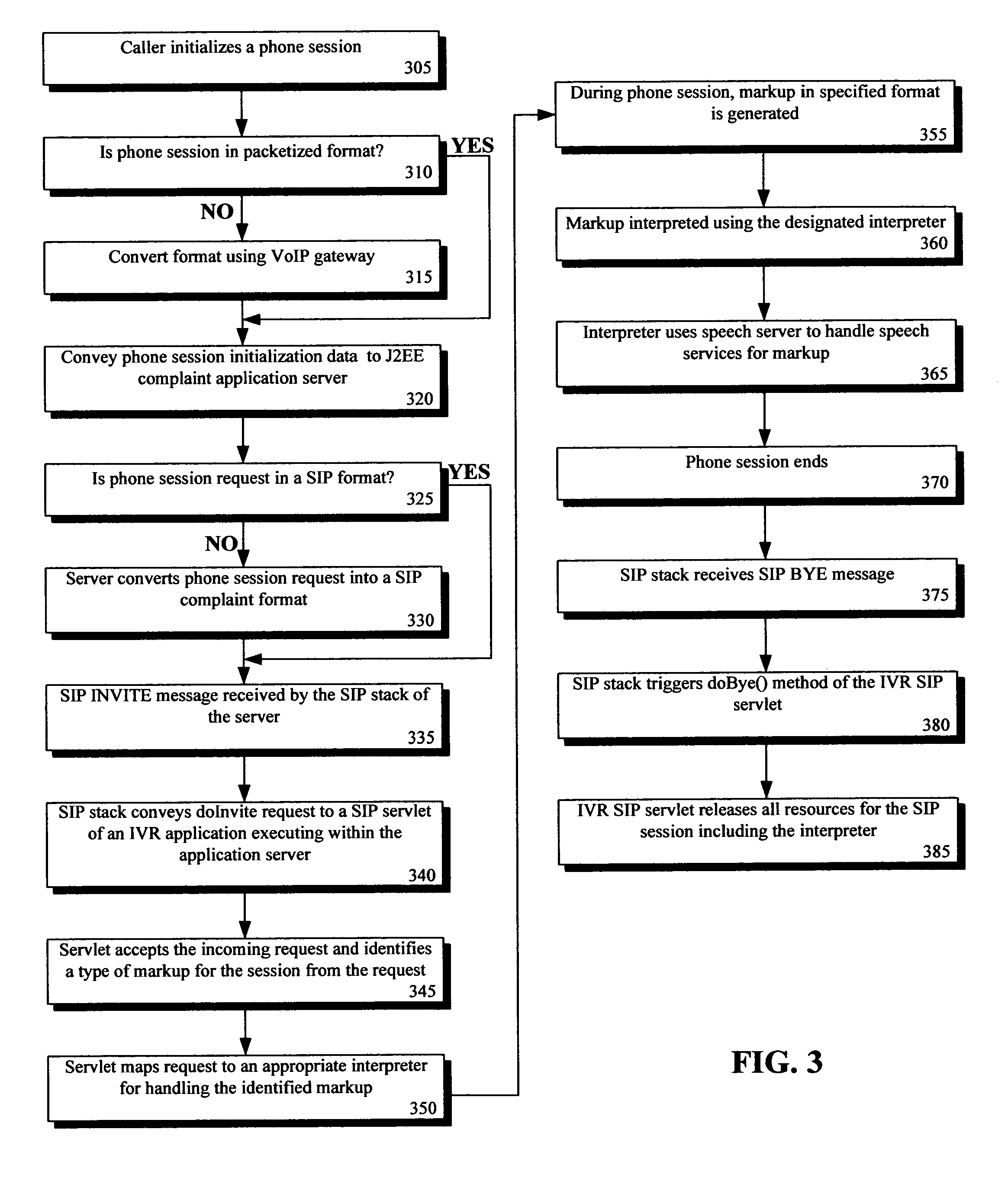
Integrating an IVR application within a standards based application server
InactiveUS8139730B2Easy to updateReduces implementationInterconnection arrangementsAutomatic call-answering/message-recording/conversation-recordingApplication serverApplication software
A method for providing Interactive Voice Response functionality within a multi-tiered telephony environment can identify an enterprise archive file that contains an Interactive Voice Response (IVR) application. The enterprise archive file can contain multiple interpreters for different markup languages. The enterprise archive file can also include a servlet that maps the interpreters to telephony sessions. The enterprise archive file can be deployed within a J2EE compliant application server having a SIP interface. The deployed IVR application can be utilized to provide IVR functions for SIP based telephony sessions.
Owner:INT BUSINESS MASCH CORP
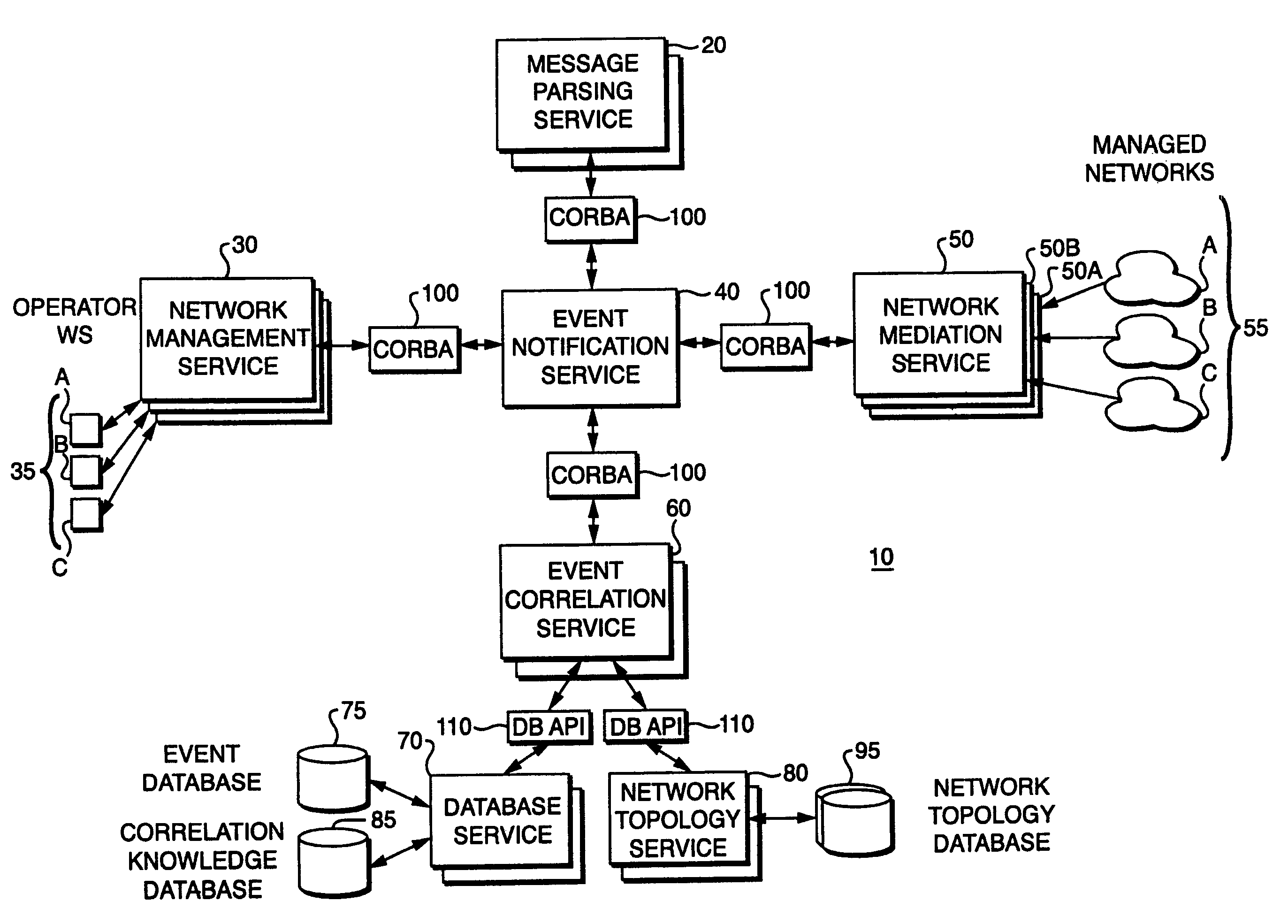
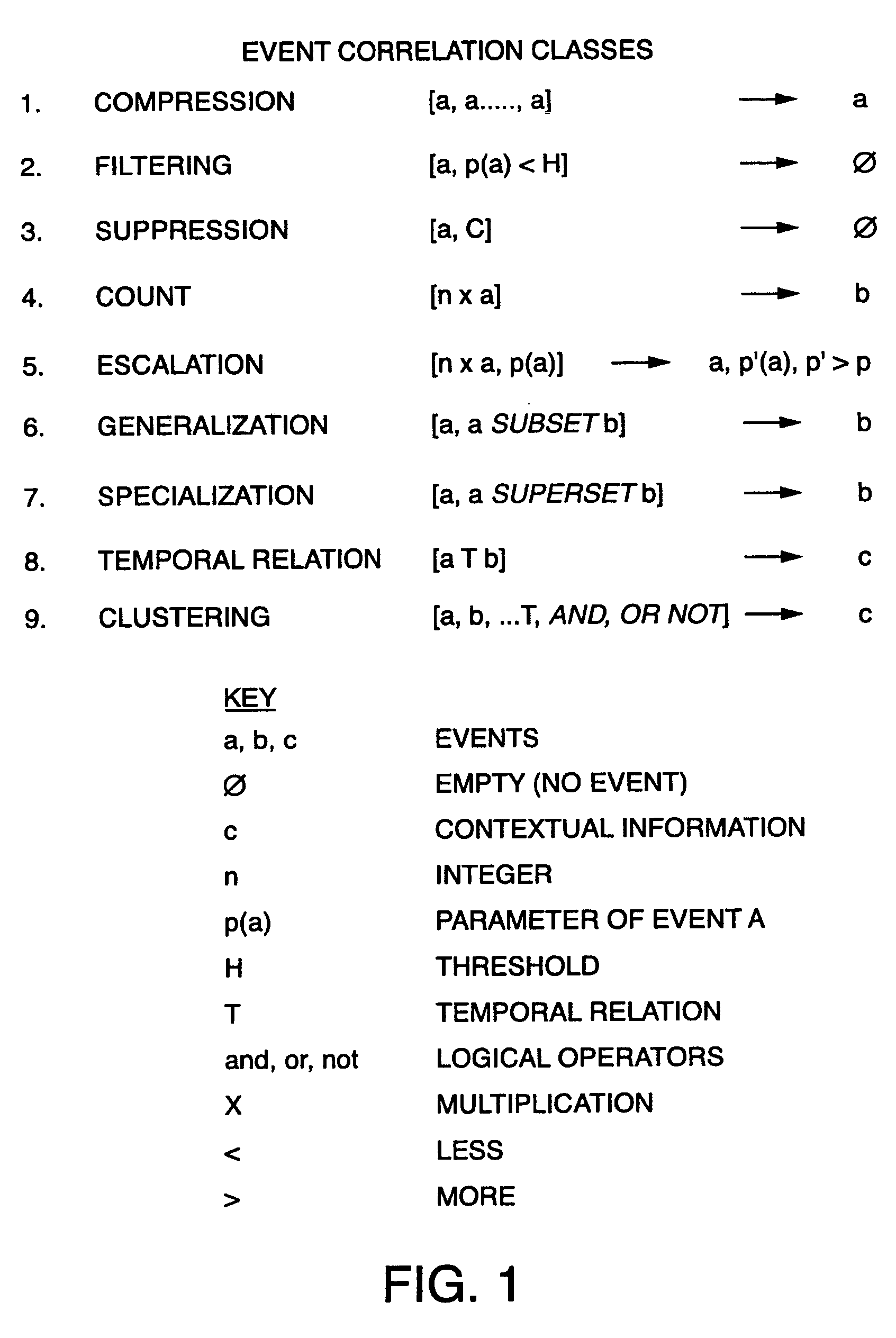
System and method for providing a global real-time advanced correlation environment architecture
InactiveUS6941557B1Easy to replaceFacilitate communicationDigital computer detailsMultiprogramming arrangementsData processing systemNetwork management
A method and system are disclosed for efficiently correlating network events within a data processing system and then transmitting messages to various network entities in response to an occurrence of a particular network event. According to the present invention, a network mediation service receives raw message streams from one or more external networks and passes the streams in real-time to the event notification service. The event notification service then passes the message to the message parsing service for processing. After the message has been parsed by the message parsing service, it is passed back to the event notification service which passes the message along an event channel to the network management service. The message is also passed to the event correlation service for event correlation. A knowledge-based database of message classes that define how to interpret the message text are used by the event correlation service to match correlation rule conditions to the observed events. After event correlation service processes the parsed event, it is passed to the network management service for resolution.
Owner:VERIZON LAB
Bone Matrix Compositions and Methods
ActiveUS20070098756A1High activityEasy to addPeptide/protein ingredientsBone implantActive agentOSTEOINDUCTIVE FACTOR
An osteoinductive composition, corresponding osteoimplants, and methods for making the osteoinductive composition are disclosed. The osteoinductive composition comprises osteoinductive factors, such as may be extracted from demineralized bone, and a carrier. The osteoinductive composition is prepared by providing demineralized bone, extracting osteoinductive factors from the demineralized bone, and adding the extracted osteoinductive factors to a carrier. Further additives such as bioactive agents may be added to the osteoinductive composition. The carrier and osteoinductive factors may form an osteogenic osteoimplant. The osteoimplant, when implanted in a mammalian body, can induce at the locus of the implant the full developmental cascade of endochondral bone formation including vascularization, mineralization, and bone marrow differentiation. Also, in some embodiments, the osteoinductive composition can be used as a delivery device to administer bioactive agents.
Owner:WARSAW ORTHOPEDIC INC
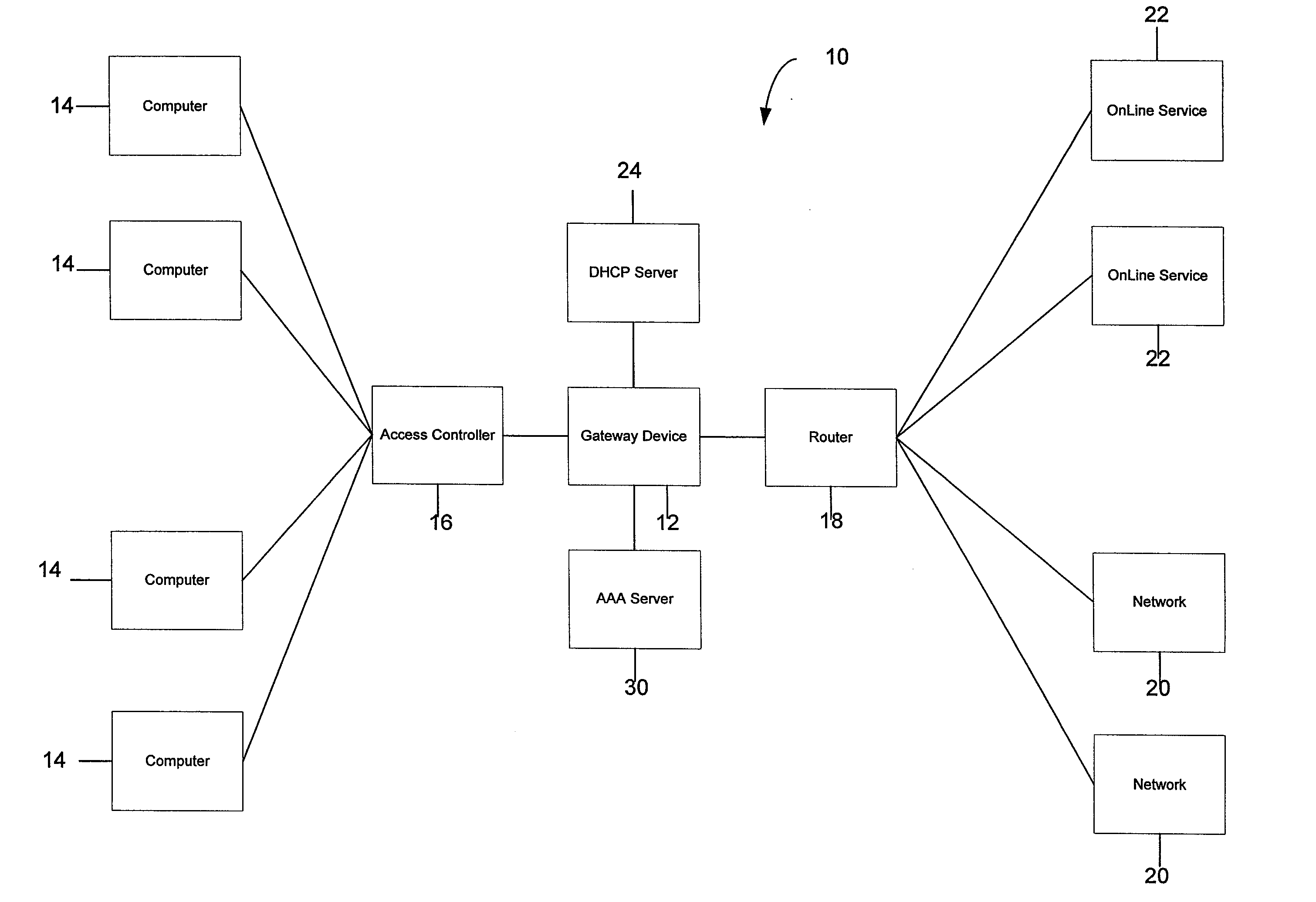
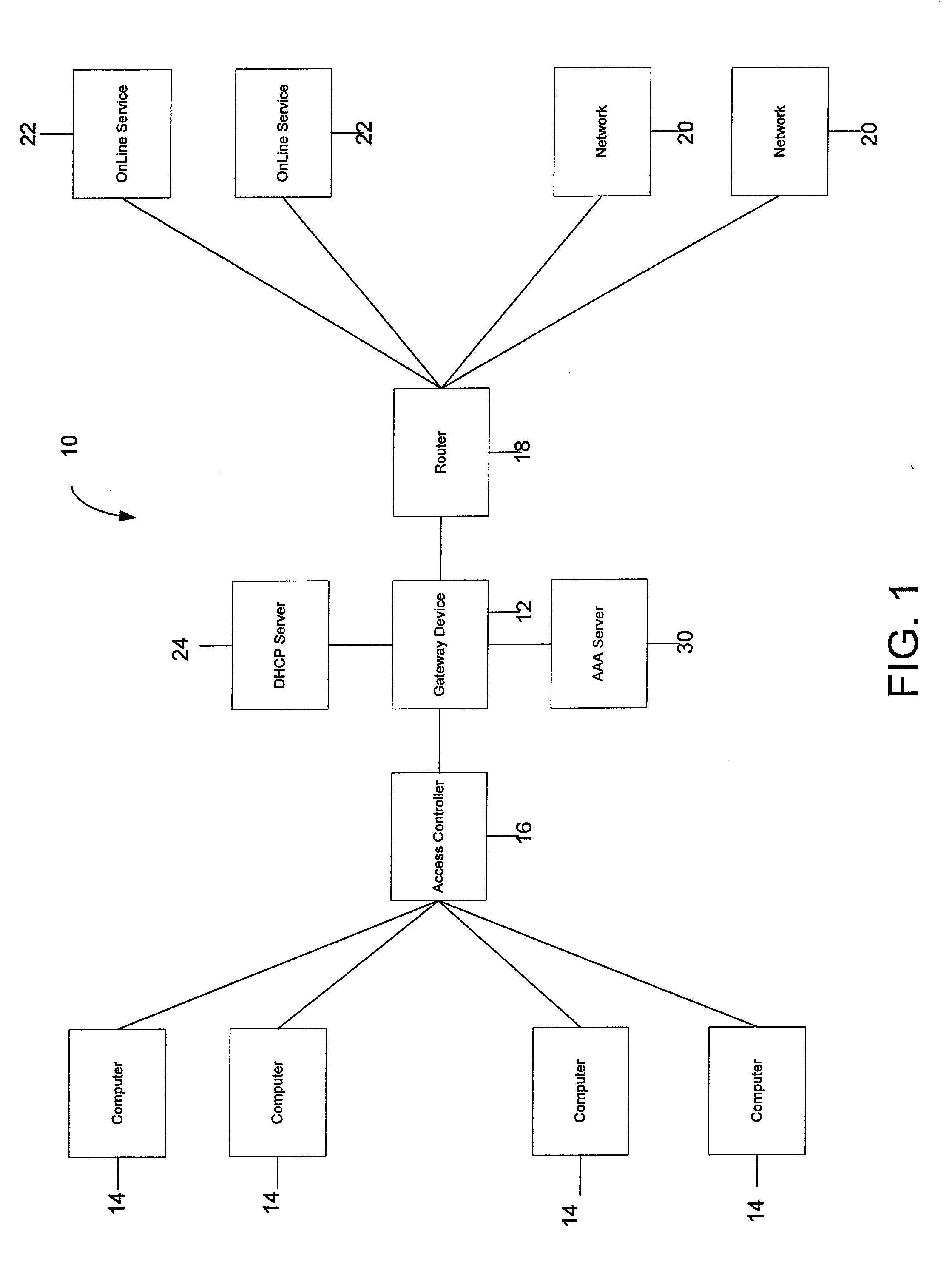
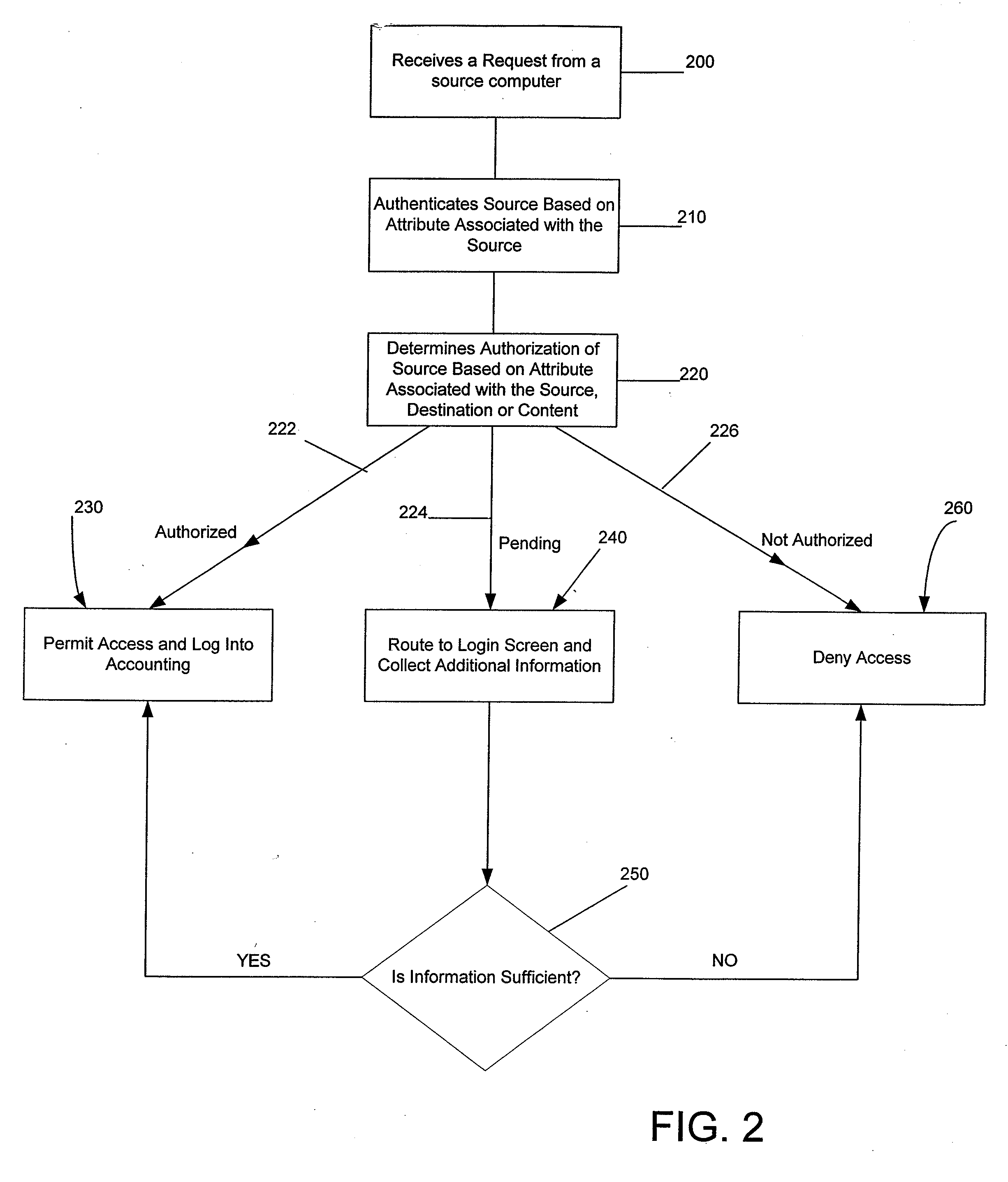
Systems and Methods for Providing Dynamic Network Authorization, Authentication and Accounting
InactiveUS20060239254A1Facilitate transparent accessEasy to addConnection managementData switching by path configurationConfigfsSystem usage
Systems and methods for selectably controlling and customizing source access to a network, where the source is associated with a source computer, and wherein the source computer has transparent access to the network via a gateway device and no configuration software need be installed on the source computer to access the network. A user may be prevented access from a particular destination or site based upon the user's authorization while being permitted to access to other sites that the method and system deems accessible. The method and system can identify a source without that source's knowledge, and can access customizable access rights corresponding to that source in a source profile database. The source profile database can be a remote authentication dial-in user service (RADIUS) or a lightweight directory access protocol (LDAP) database. The method and system use source profiles within the source profile database to dynamically authorize source access to networks and destinations via networks.
Owner:NOMADIX INC
Surface area deposition trap
InactiveUS7252011B2Raise the possibilityEasy to addFluid pressure measurement using elastically-deformable gaugesFluid pressure measurement using capacitance variationCouplingTransducer
The disclosed pressure transducer assembly includes a housing, a pressure sensor disposed within the housing, a coupling establishing a sealed pathway between the housing and an external source of gas or fluid, and a deposition trap disposed in the pathway. The deposition trap provides a plurality of channels, each of the channels being narrower than the pathway.
Owner:MKS INSTR INC
Methods for integrating lattice-mismatched semiconductor structure on insulators
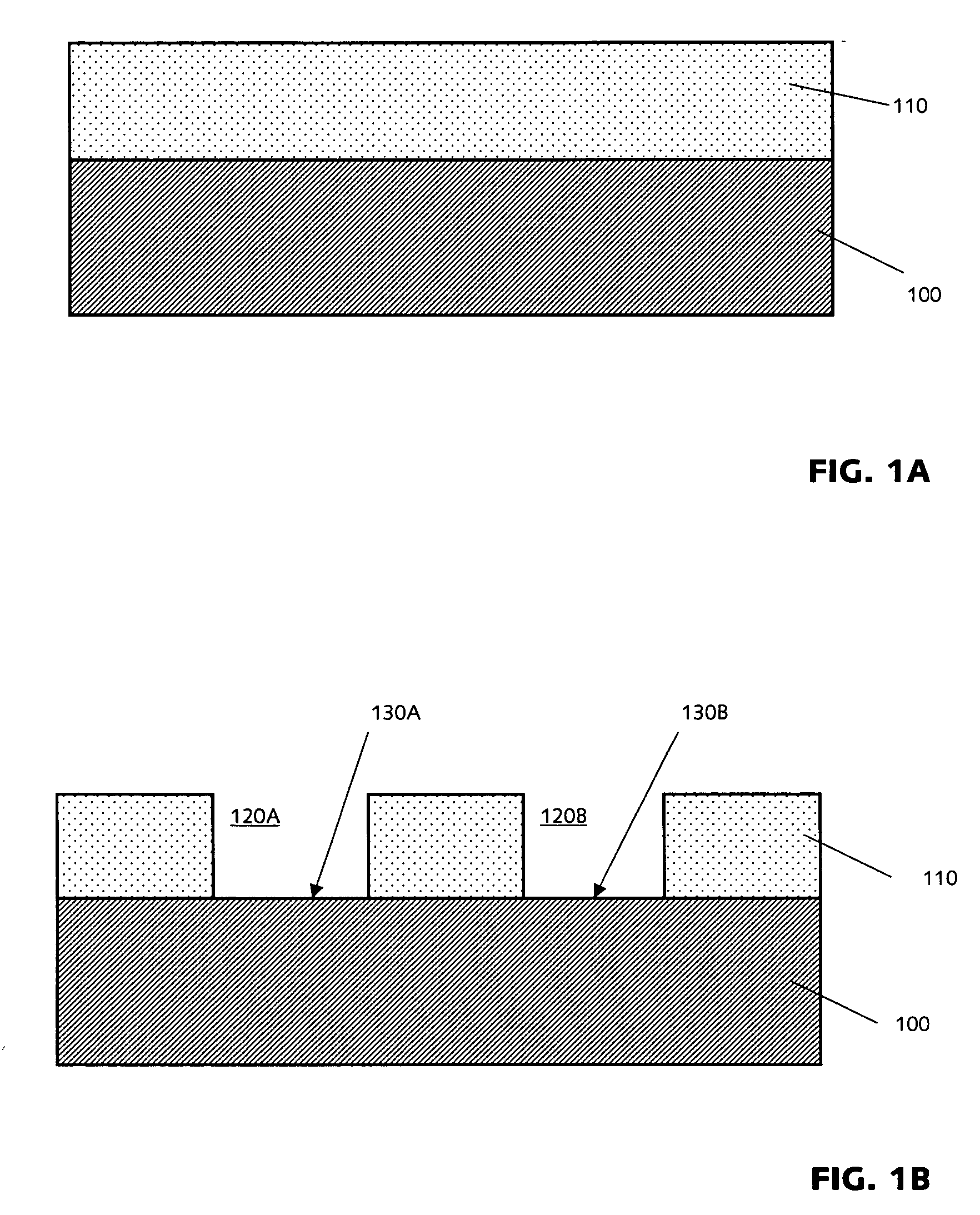
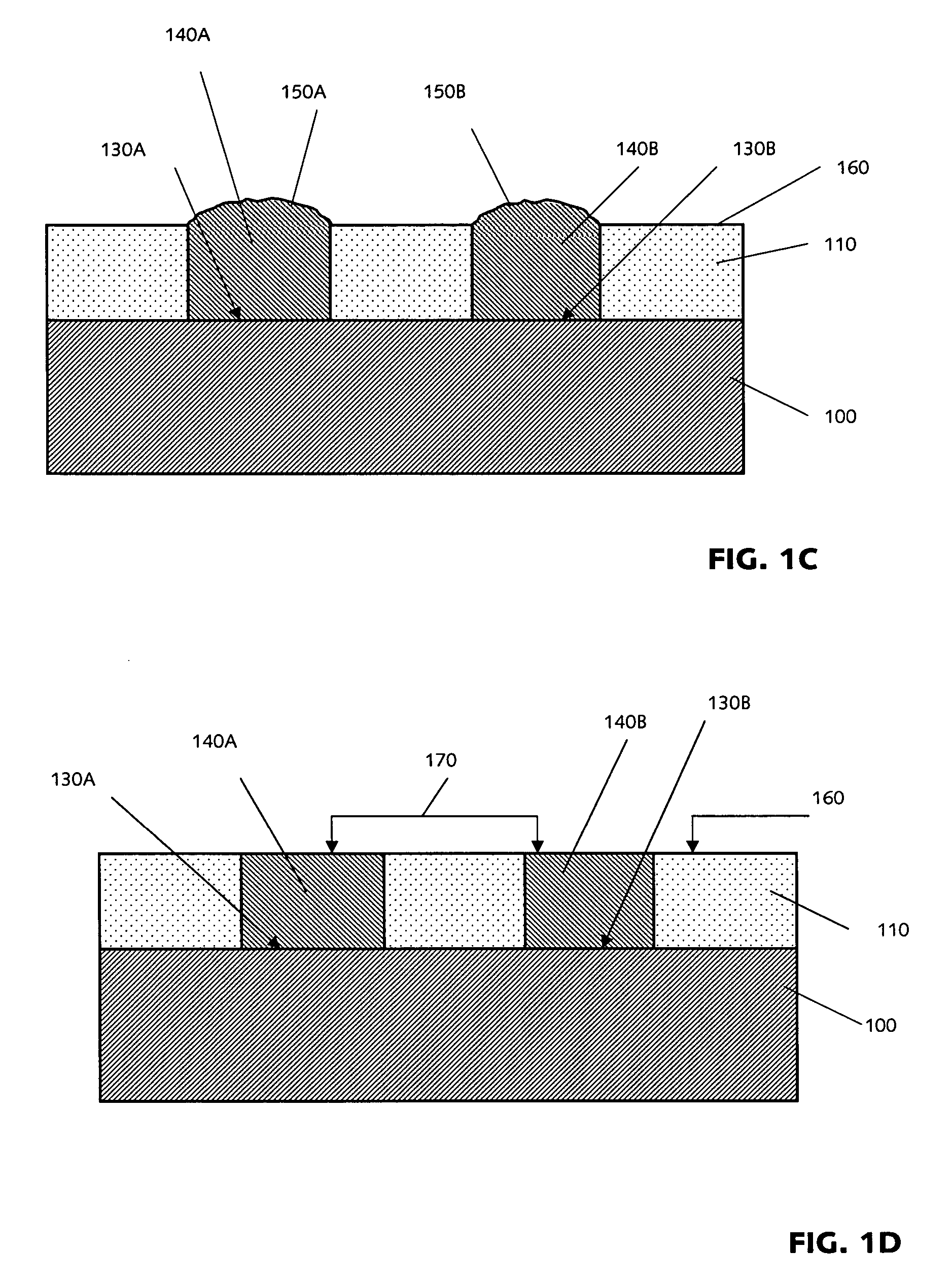
InactiveUS20070054467A1Improve functionalityImprove performanceSolid-state devicesSemiconductor/solid-state device manufacturingThreading dislocationsSemiconductor structure
Monolithic lattice-mismatched semiconductor heterostructures are fabricated by bonding patterned substrates with alternative active-area materials formed thereon to a rigid dielectric platform and then removing the highly-defective interface areas along with the underlying substrates to produce alternative active-area regions disposed over the insulator and substantially exhausted of misfit and threading dislocations.
Owner:AMBERWAVE SYST
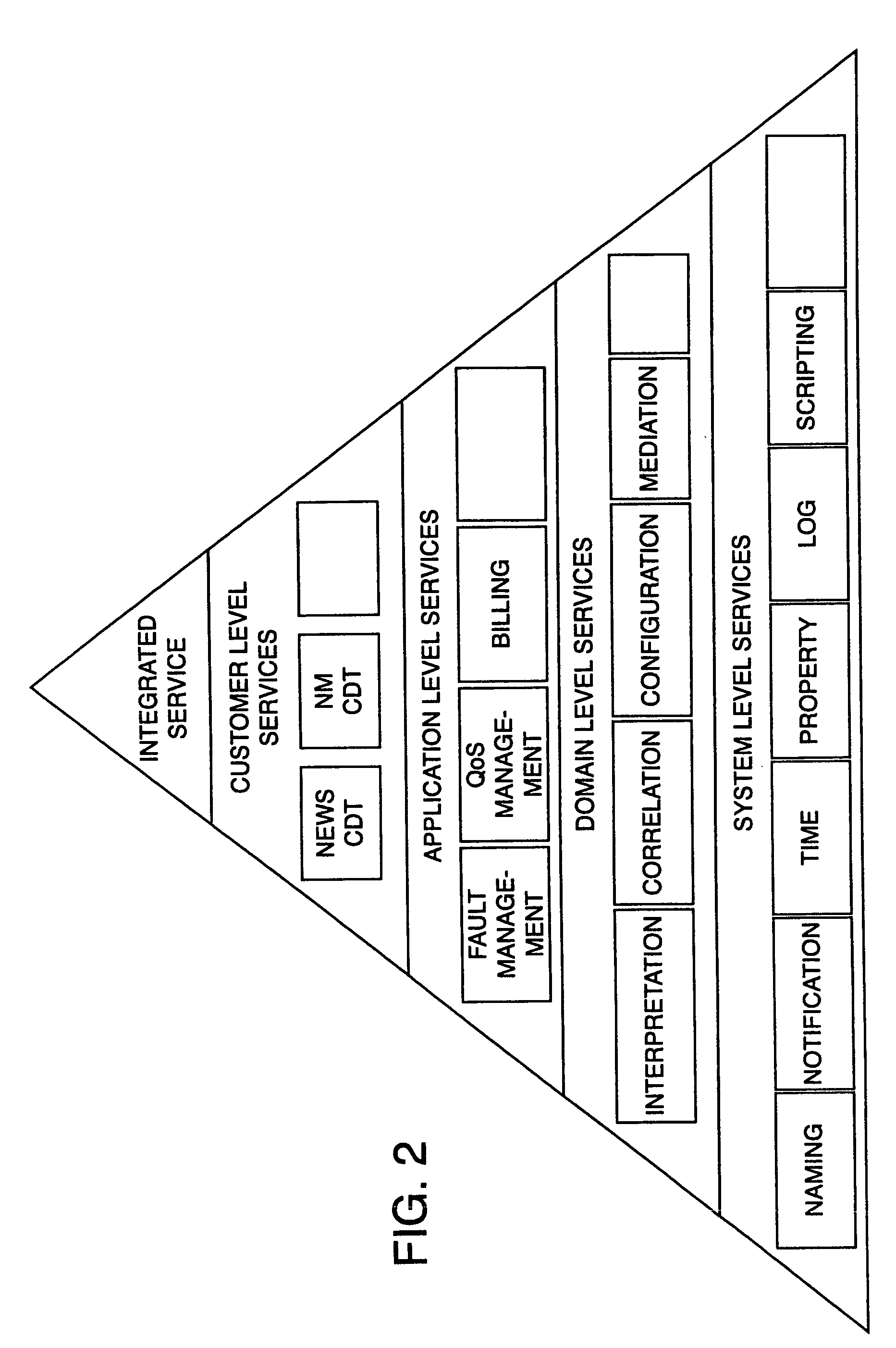
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com