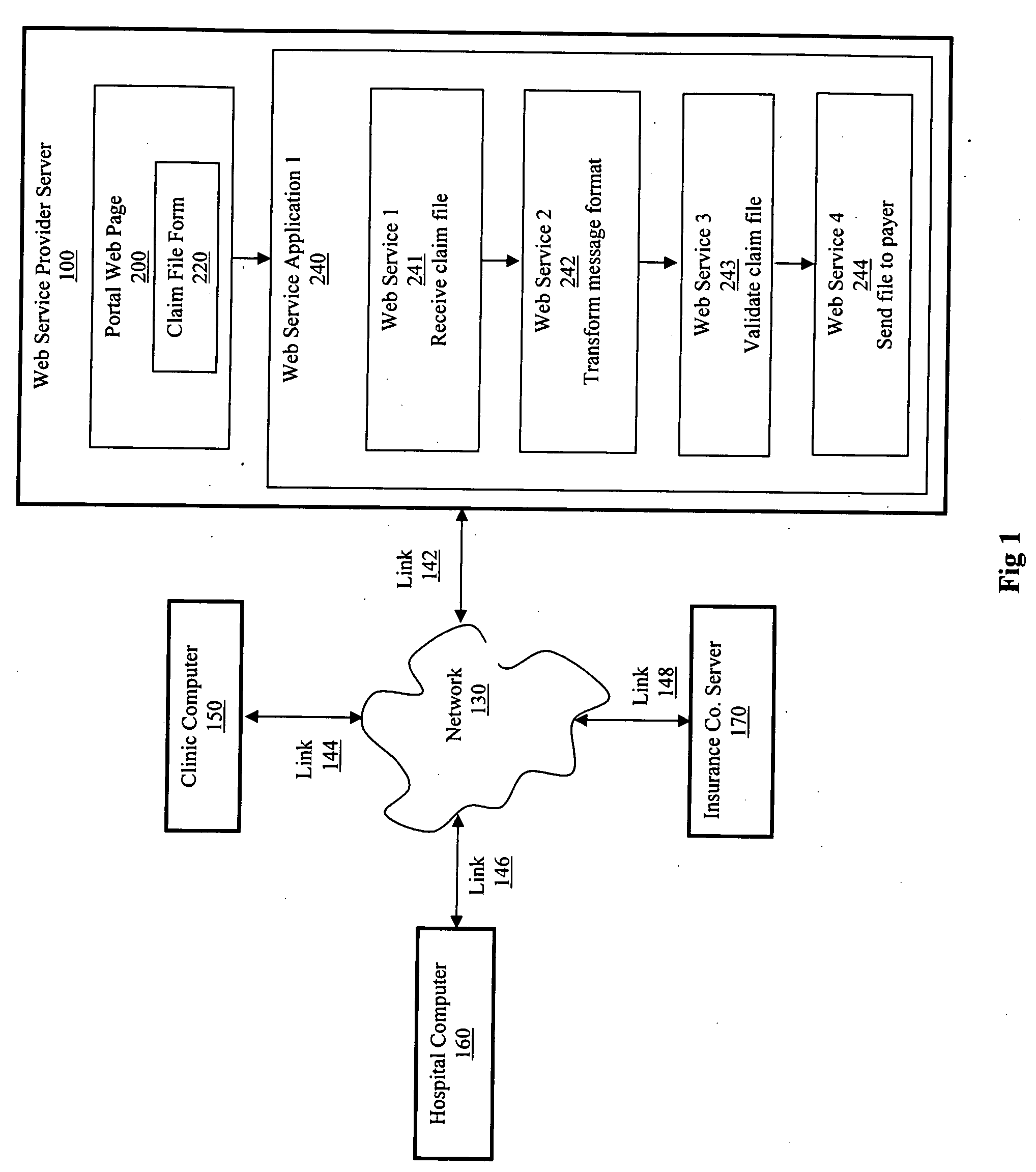
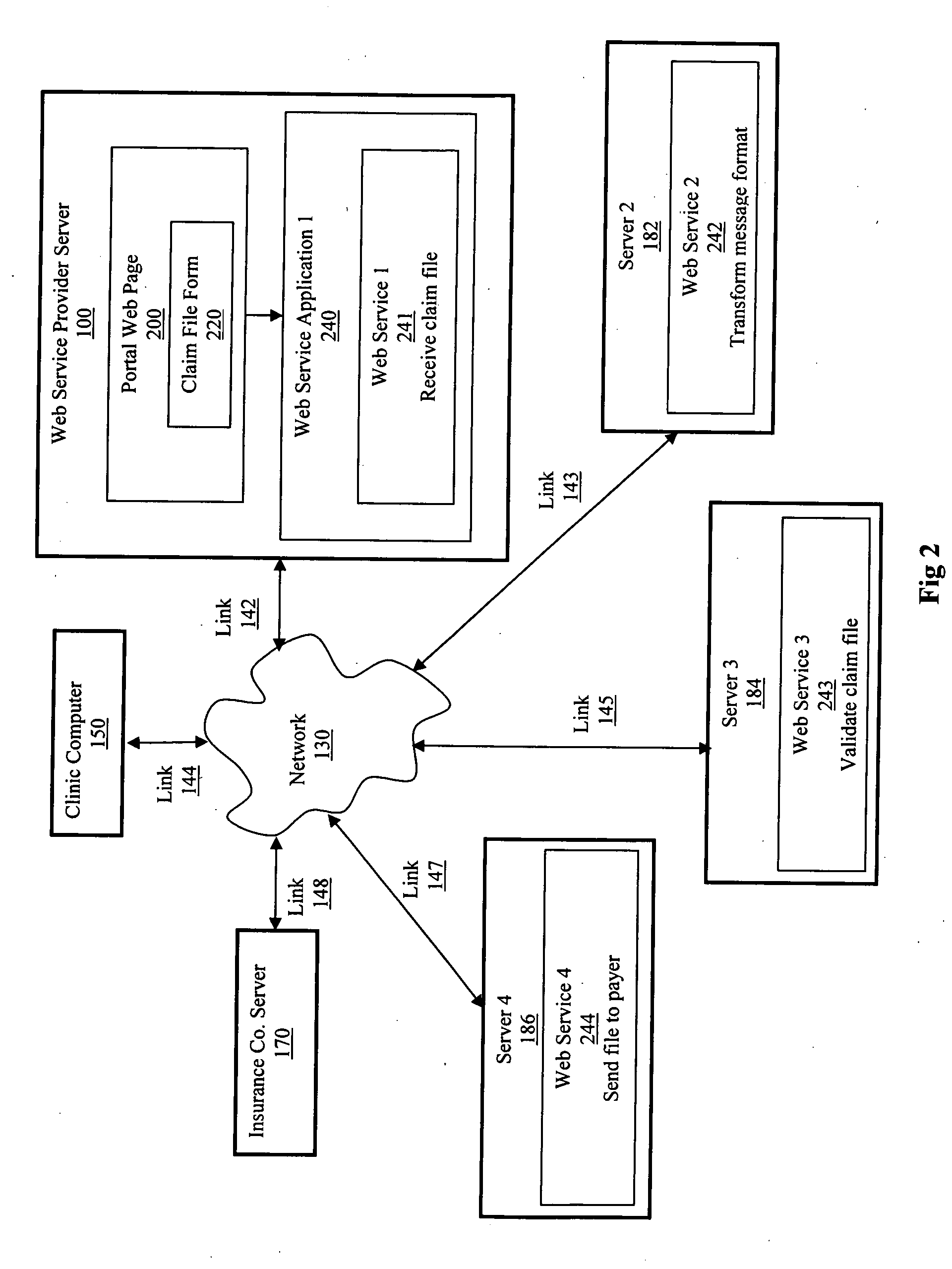
Patents
Literature
469 results about "Archive file" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An archive file is a file that is composed of one or more computer files along with metadata. Archive files are used to collect multiple data files together into a single file for easier portability and storage, or simply to compress files to use less storage space. Archive files often store directory structures, error detection and correction information, arbitrary comments, and sometimes use built-in encryption.
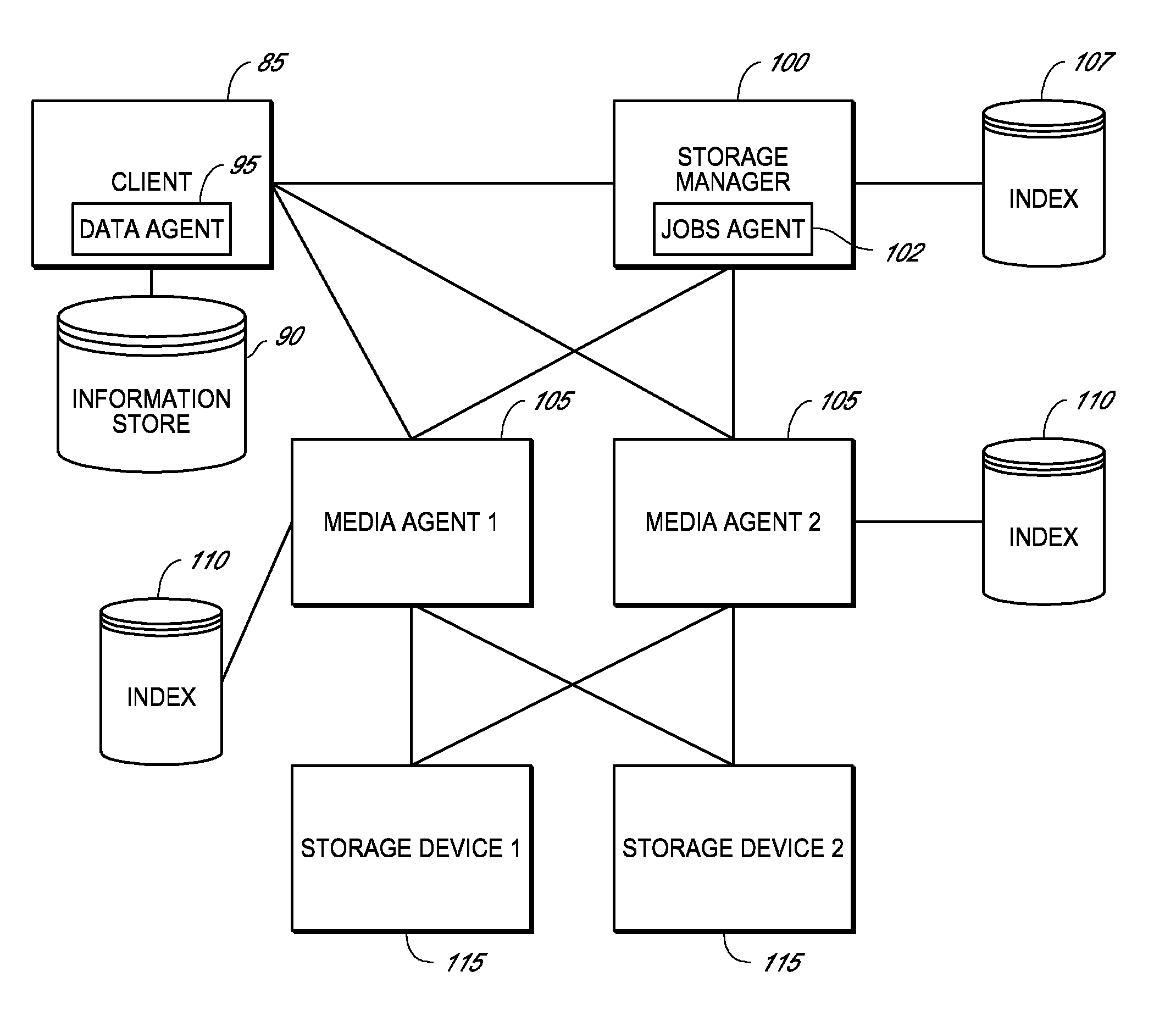
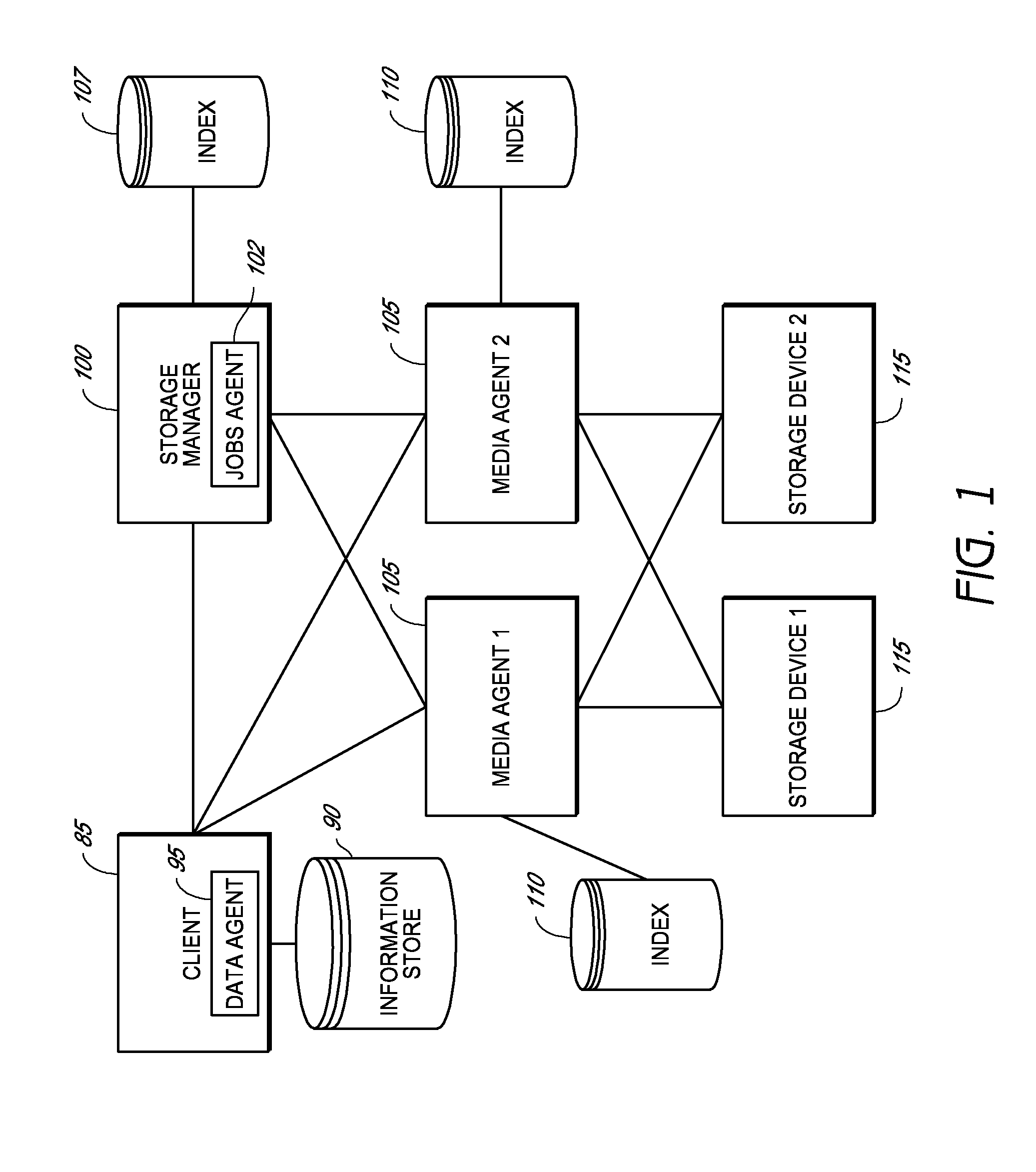
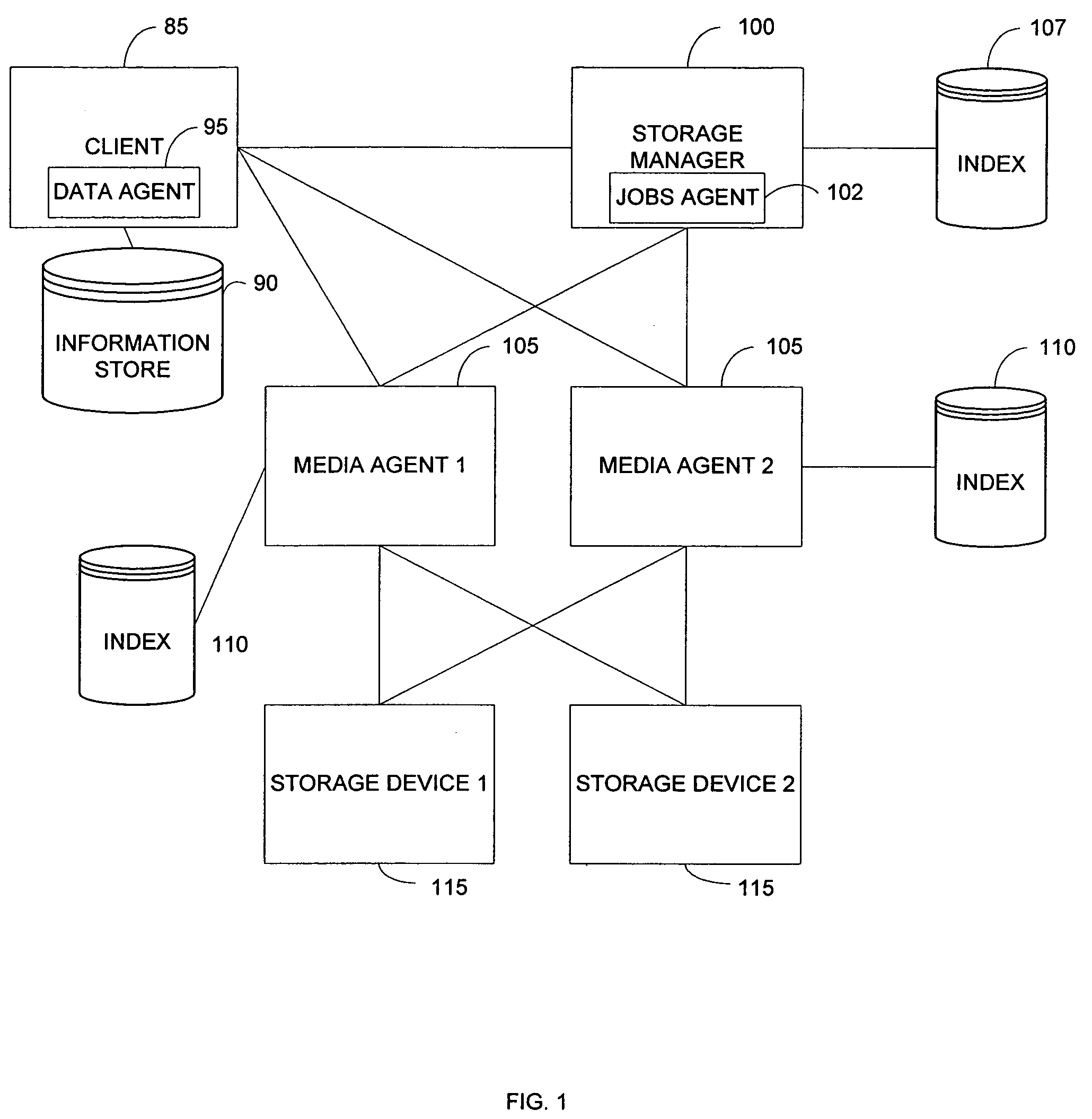
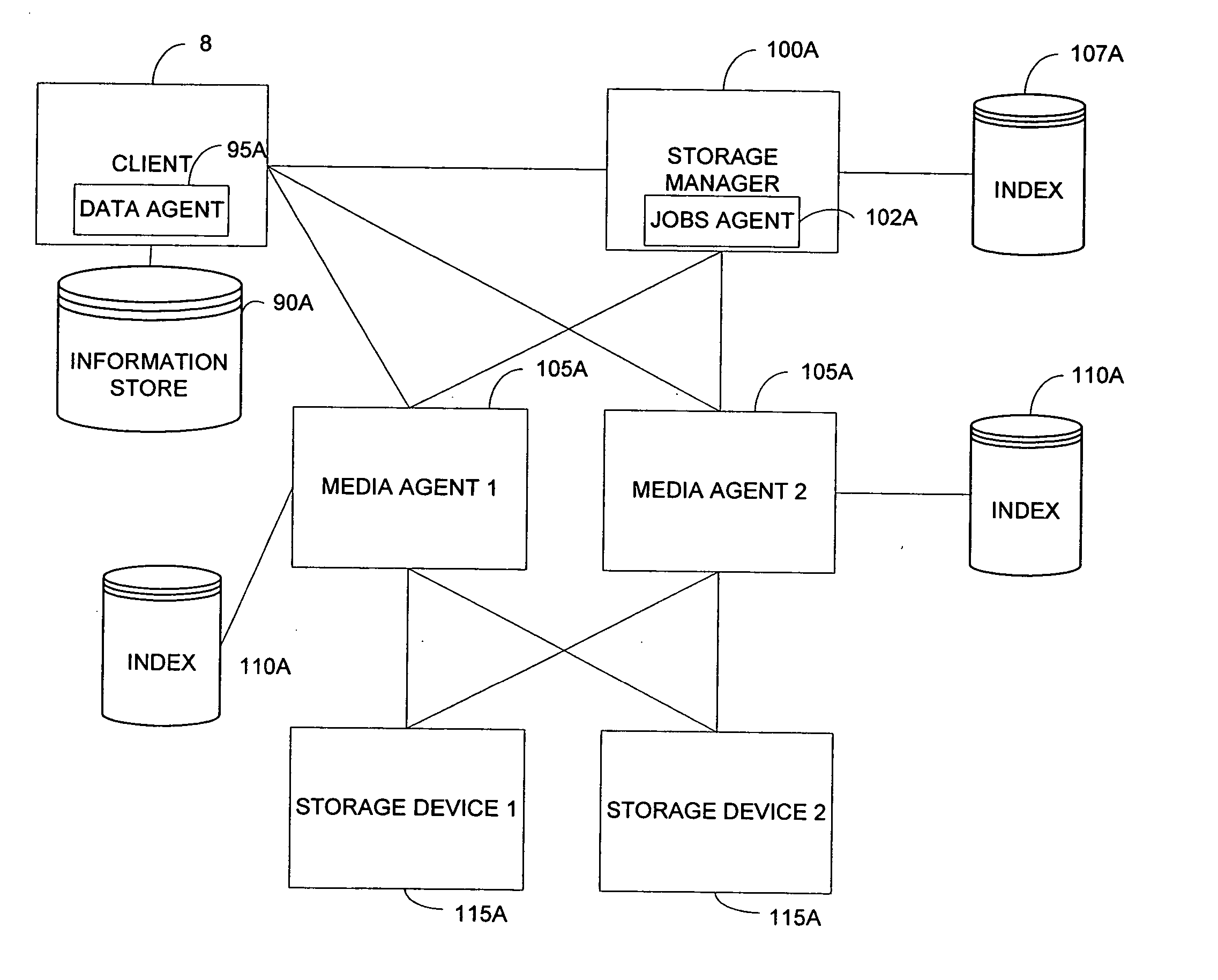
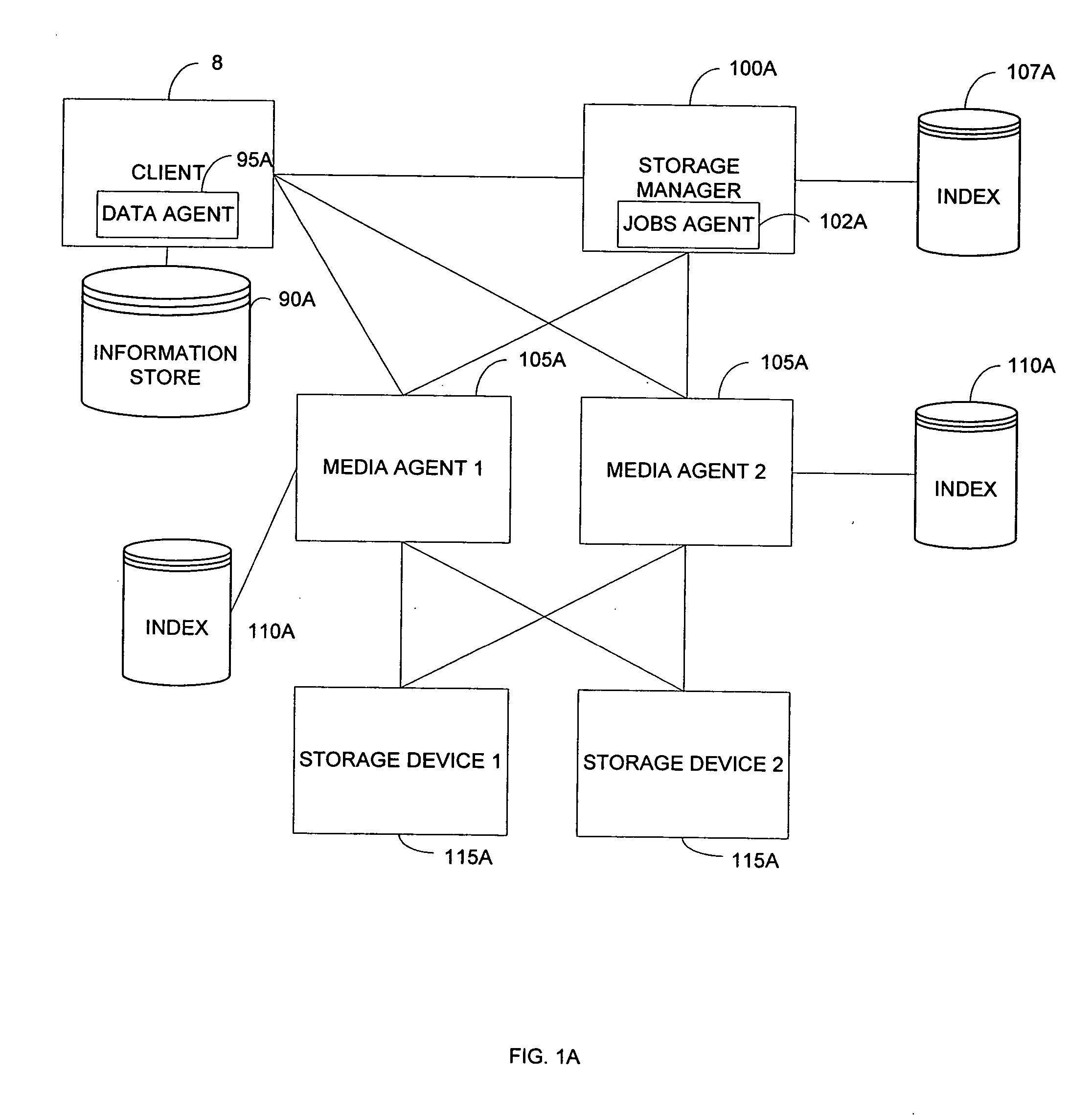
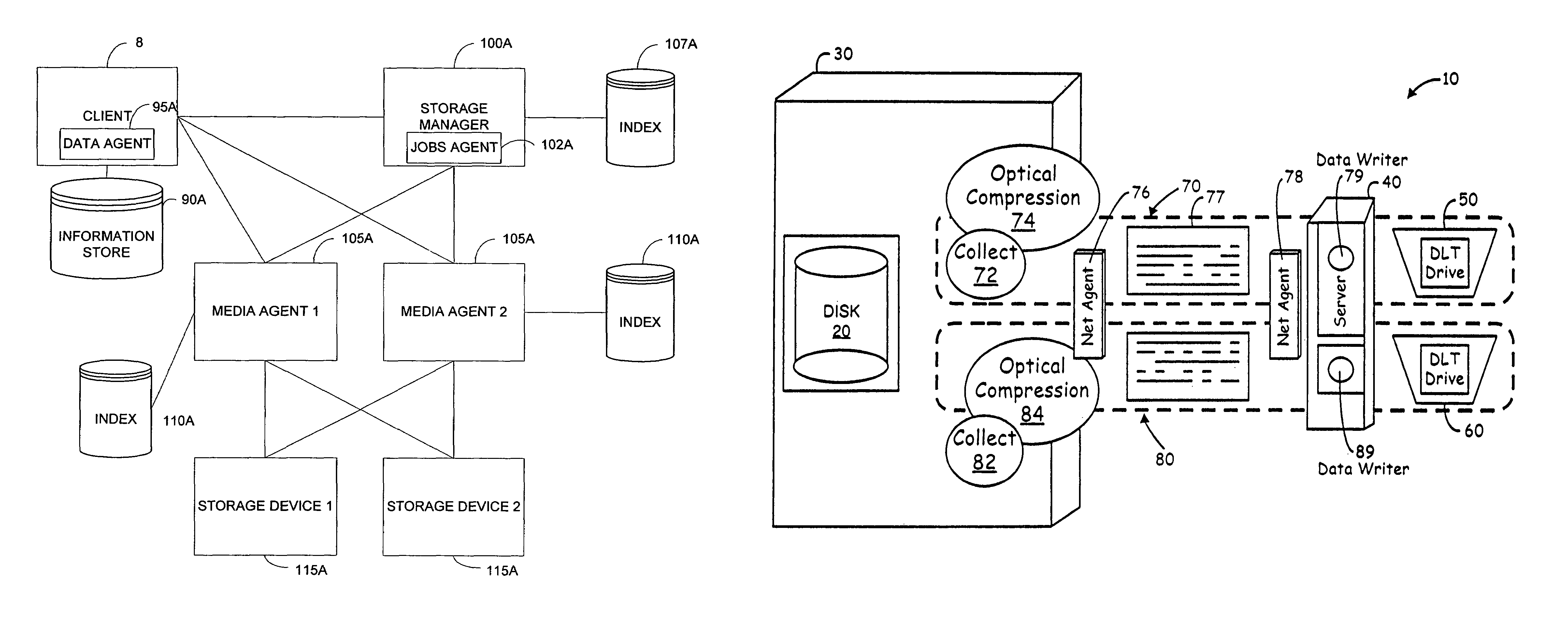
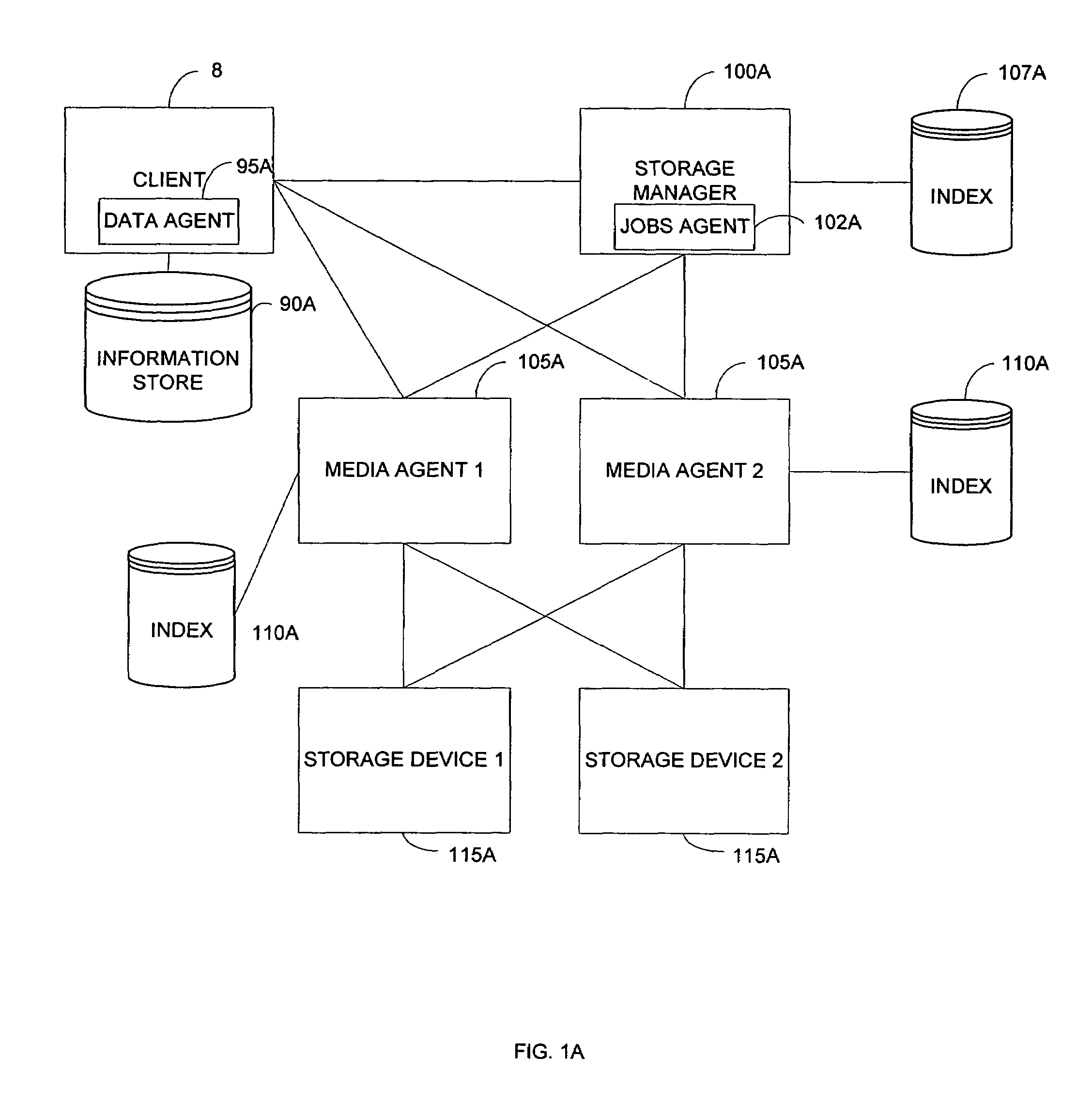
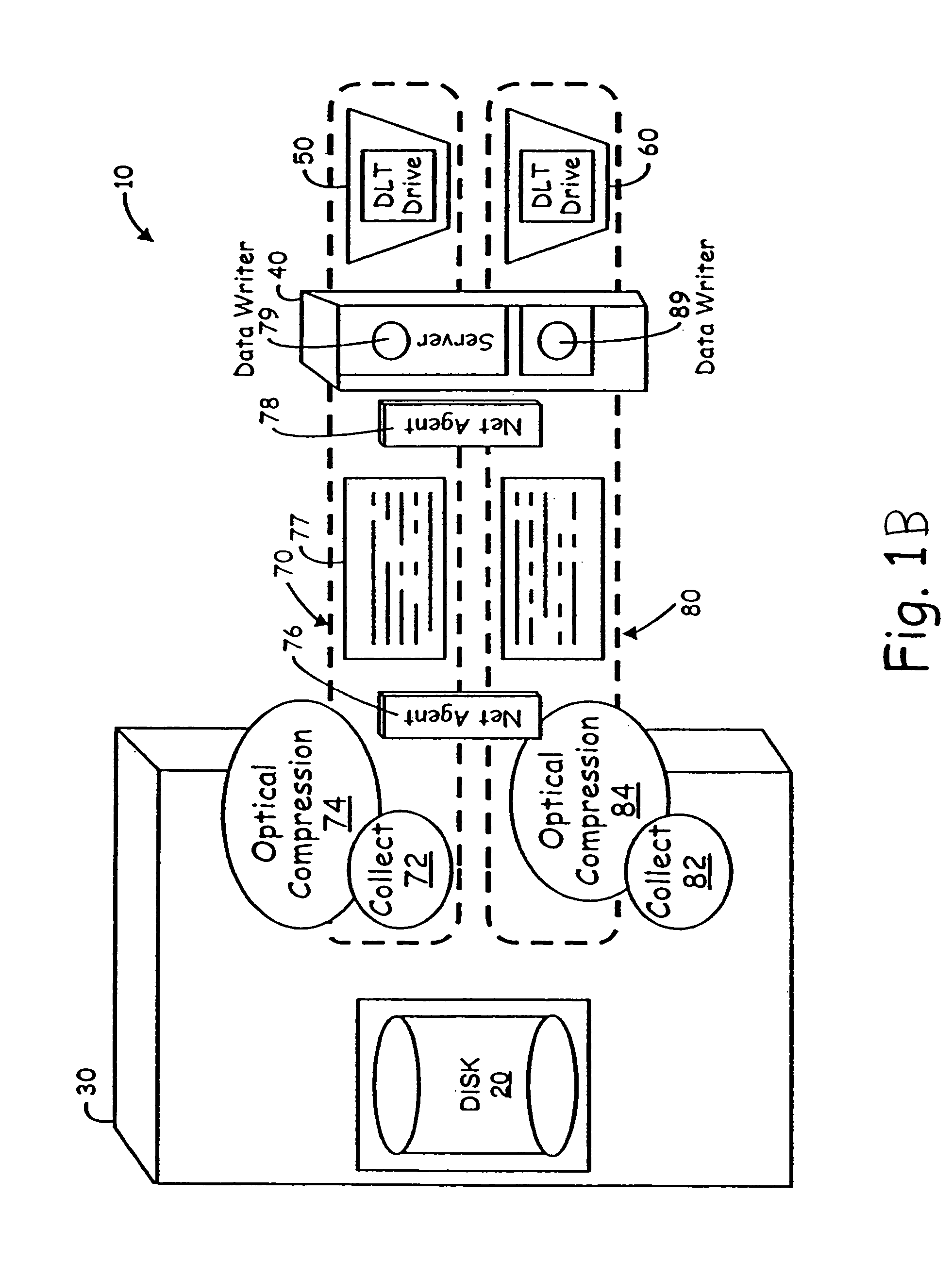
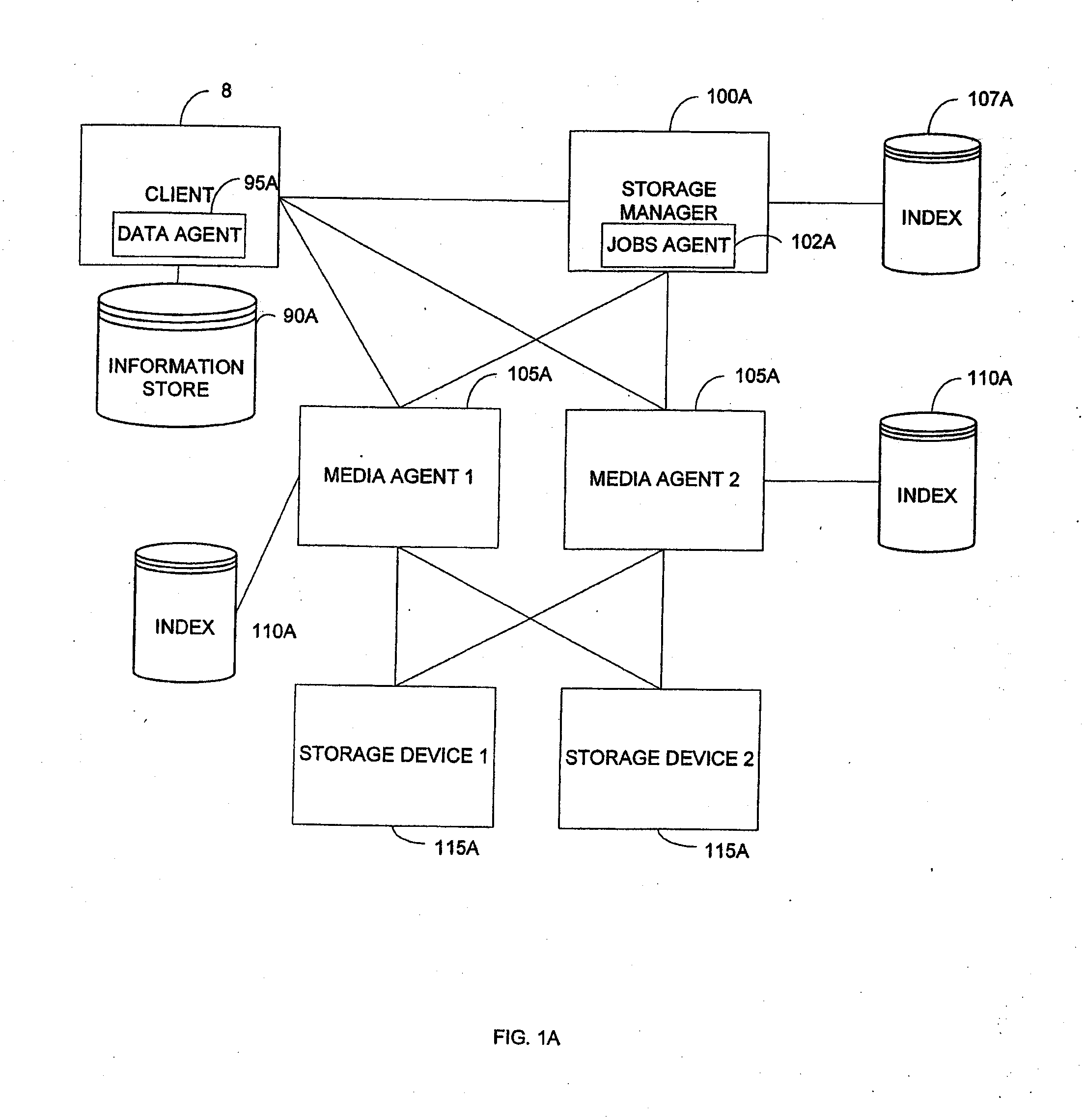
System and method for combining data streams in pipelined storage operations in a storage network
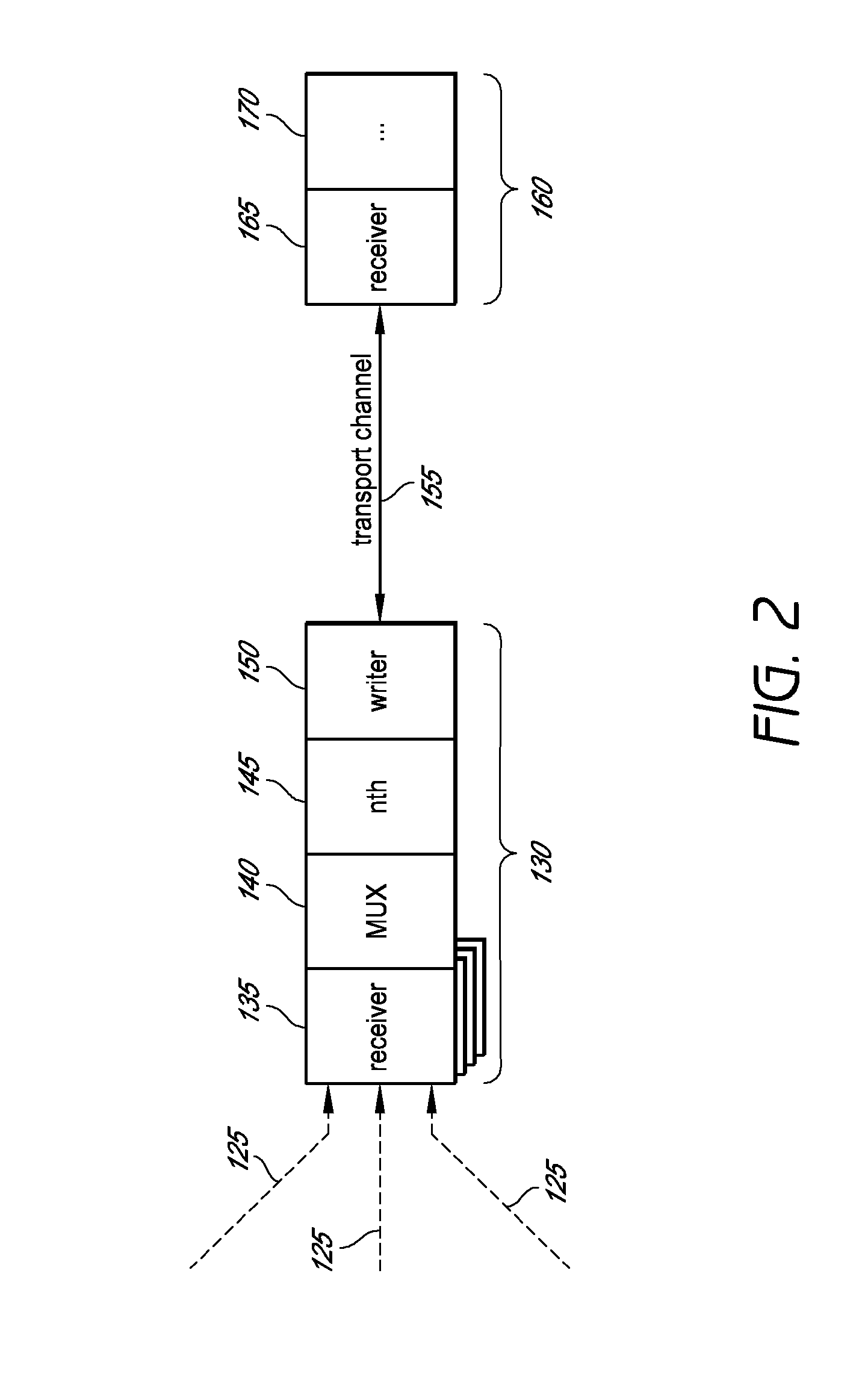
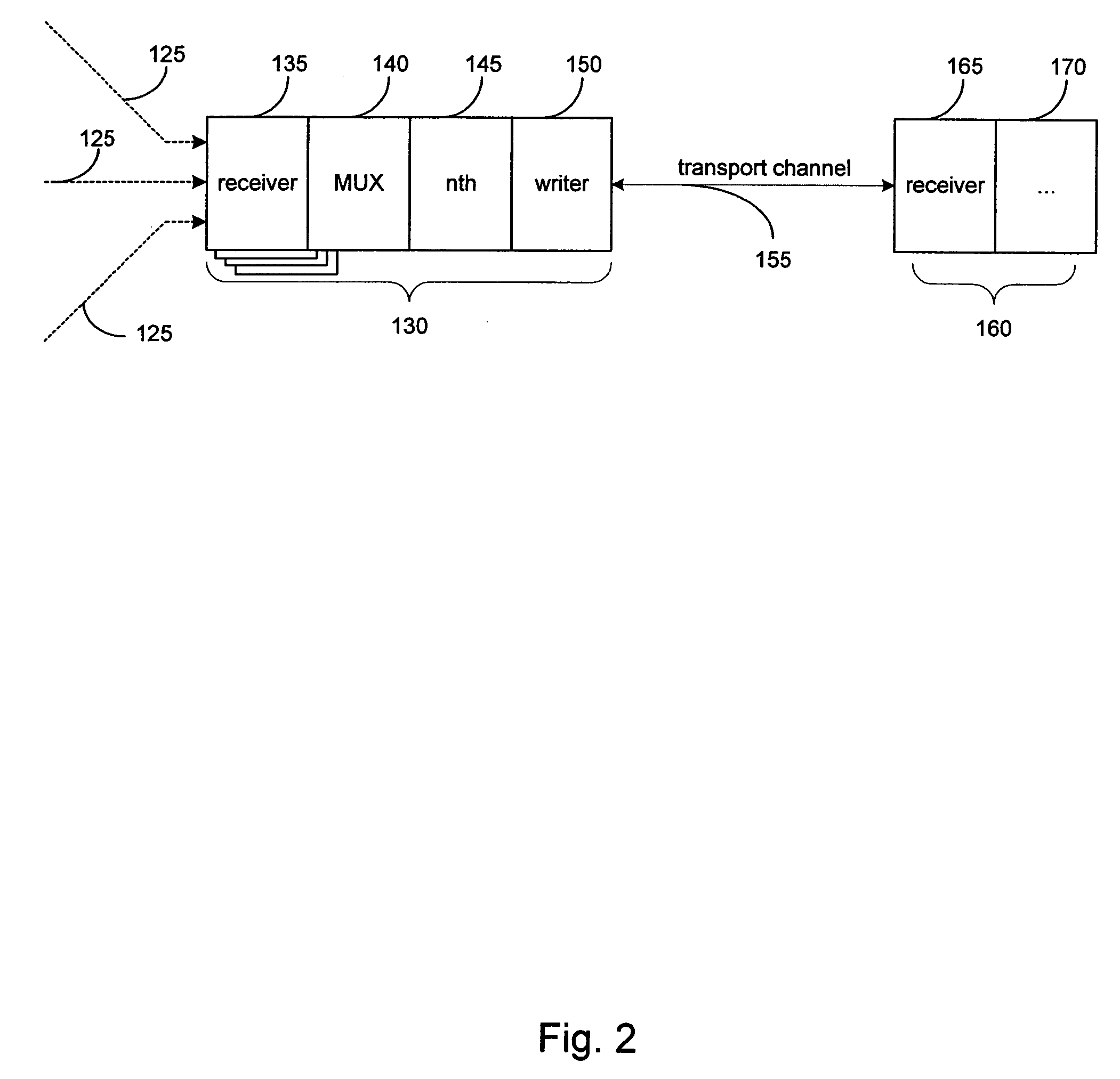
Described herein are systems and methods for multiplexing pipelined data for backup operations. Various data streams are combined such as by multiplexing by a multiplexing module. The multiplexing module combines the data from the various data streams received by receiver module(s) into a single stream of chunks. The multiplexing module may combine data from multiple archive files into a single chunk. Additional modules perform other operations on the chunks of data to be transported such as encryption, compression, etc. The data chunks are transmitted via a transport channel to a receive pipeline that includes a second receiver module and other modules. The data chunks are then stored in a backup medium. The chunks are later retrieved and separated such as by demultiplexing for restoring to a client or for further storage as auxiliary copies of the separated data streams or archive files.
Owner:COMMVAULT SYST INC
System and method for combining data streams in pipelined storage operations in a storage network
ActiveUS20050246510A1Memory loss protectionRedundant operation error correctionMultiplexingData stream
Described herein are systems and methods for multiplexing pipelined data for backup operations. Various data streams are combined such as by multiplexing by a multiplexing module. The multiplexing module combines the data from the various data streams received by receiver module(s) into a single stream of chunks. The multiplexing module may combine data from multiple archive files into a single chunk. Additional modules perform other operations on the chunks of data to be transported such as encryption, compression, etc. The data chunks are transmitted via a transport channel to a receive pipeline that includes a second receiver module and other modules. The data chunks are then stored in a backup medium. The chunks are later retrieved and separated such as by demultiplexing for restoring to a client or for further storage as auxiliary copies of the separated data streams or archive files.
Owner:COMMVAULT SYST INC
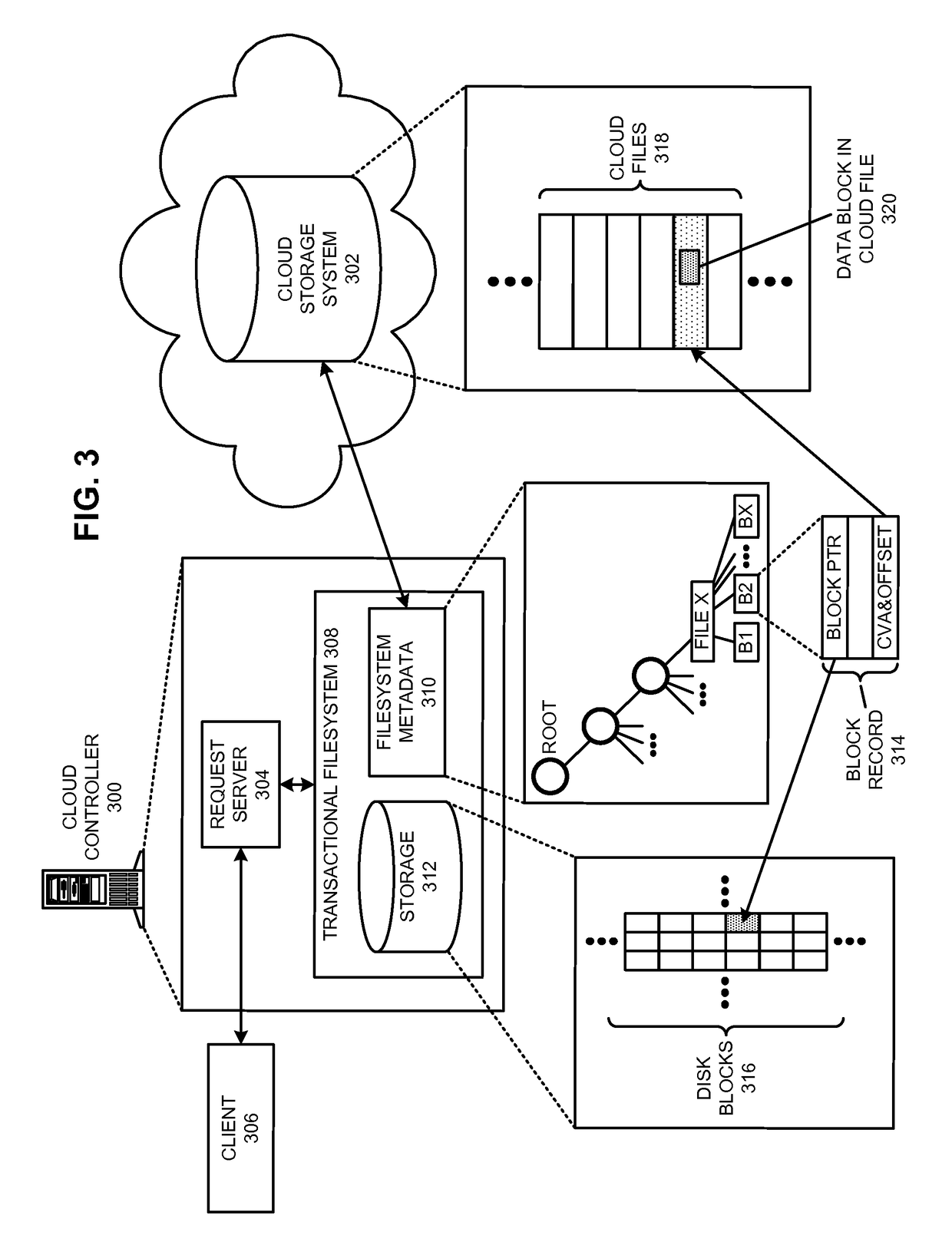
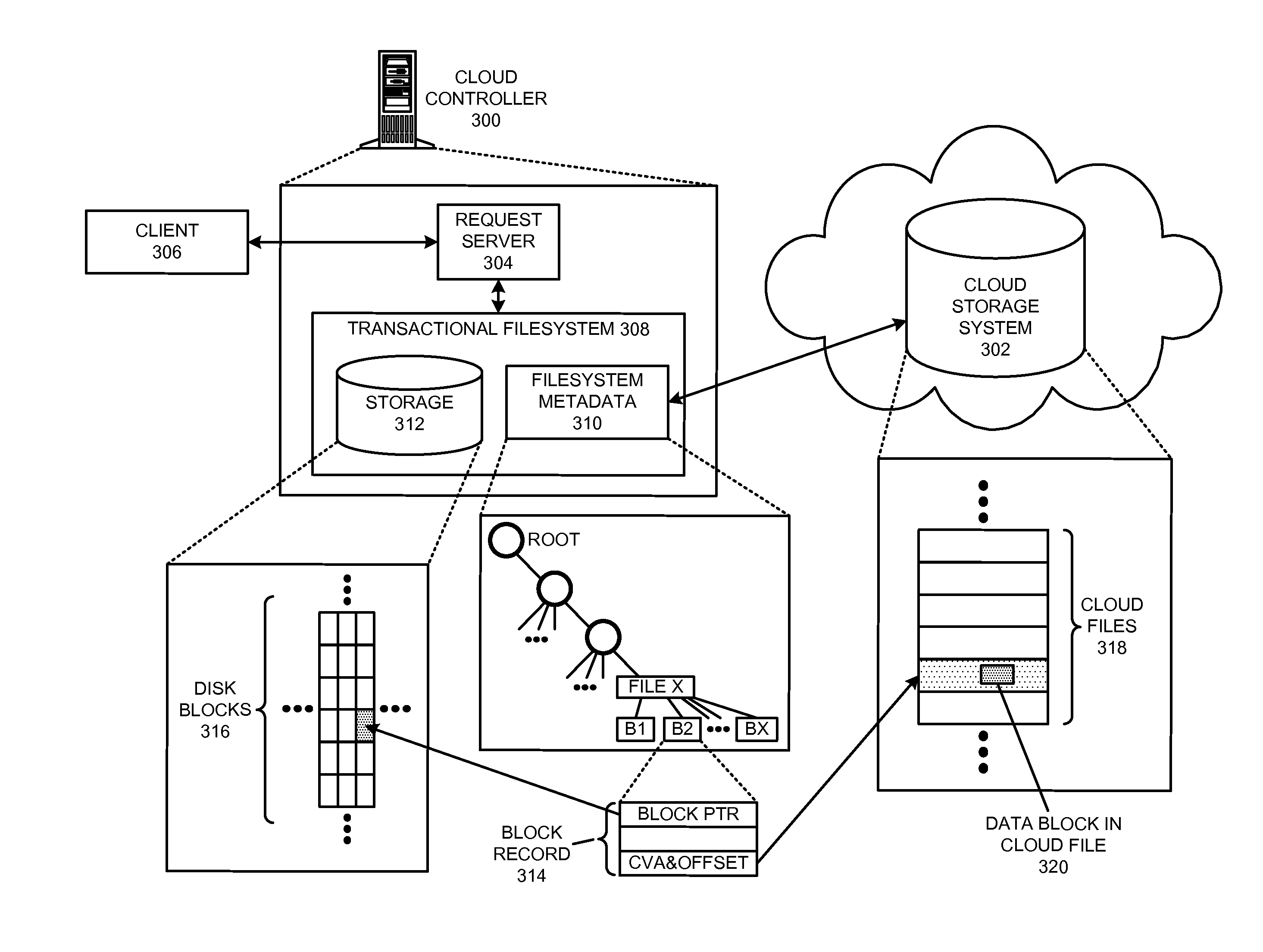
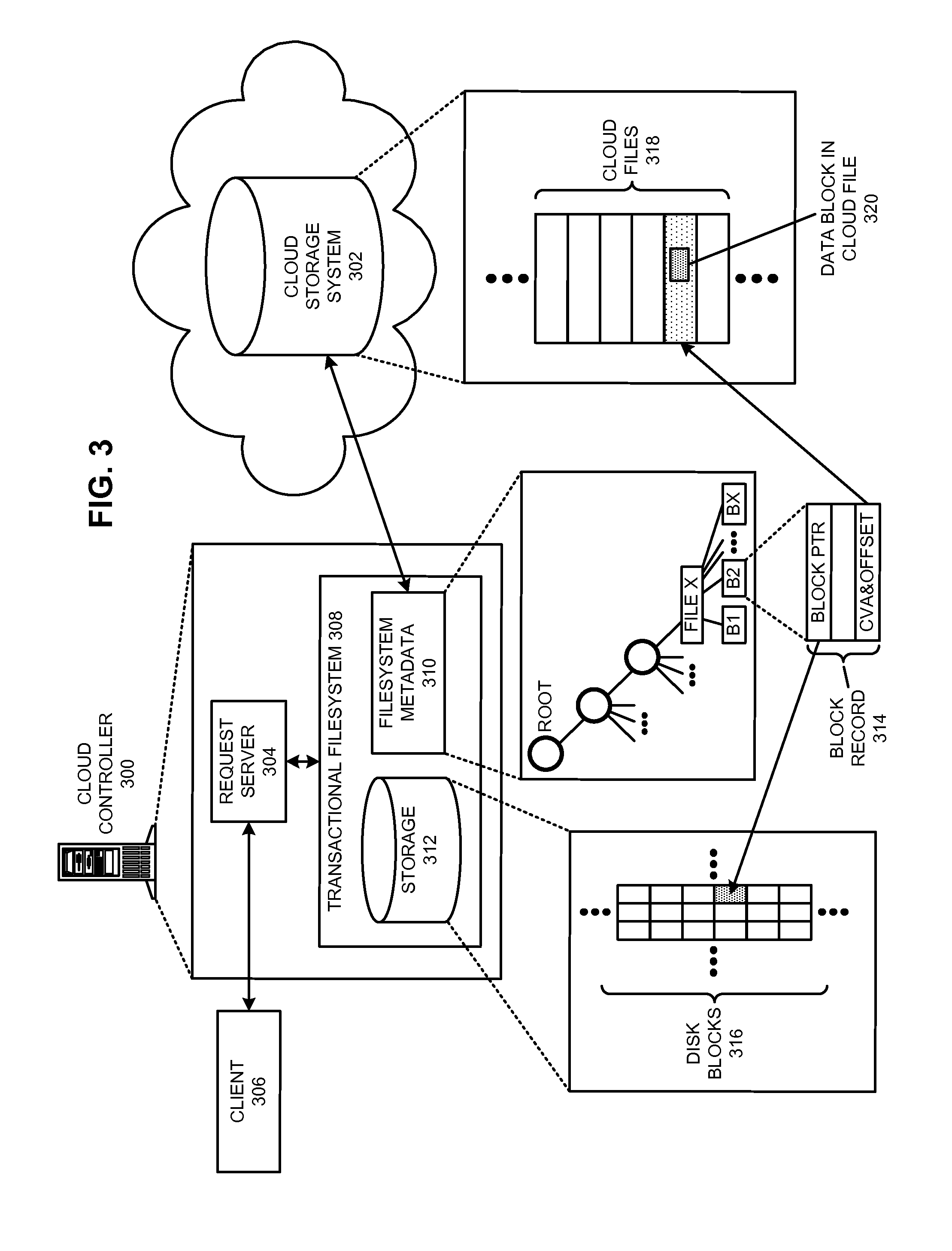
Restoring an archived file in a distributed filesystem
ActiveUS9804928B2Raise priorityIncreased restore budgetDigital data information retrievalInput/output to record carriersDistributed File SystemFile system
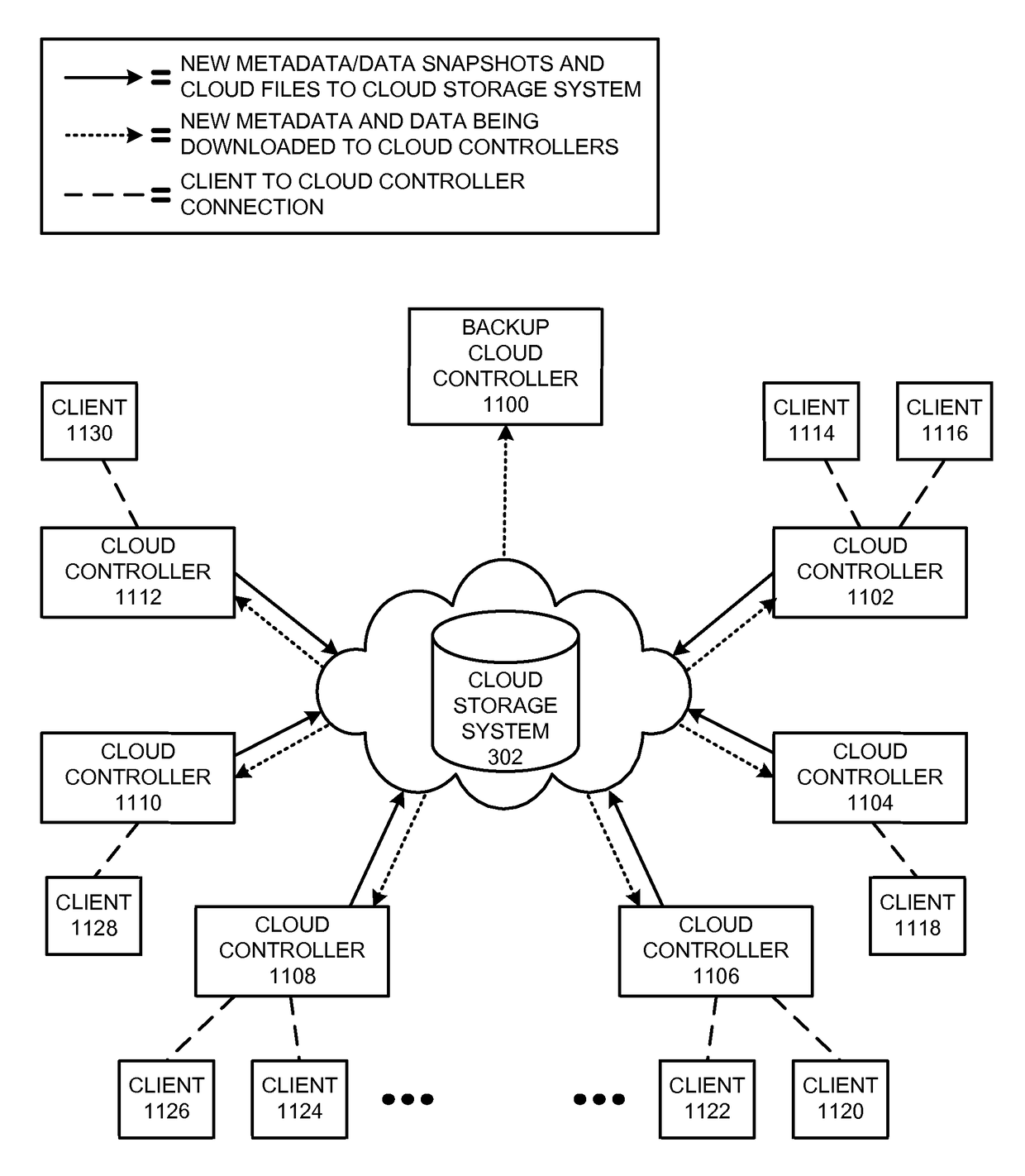
The disclosed embodiments disclose techniques for restoring an archived file in a distributed filesystem. Two or more cloud controllers collectively manage distributed filesystem data that is stored in one or more cloud storage systems; the cloud controllers ensure data consistency for the stored data, and each cloud controller caches portions of the distributed filesystem. Furthermore, cloud controllers may archive infrequently-accessed files in an archival cloud storage system. During operation, a cloud controller receives a request from a client system to access an archived file, and restores this archived file from the archival cloud storage system.
Owner:PANZURA LLC
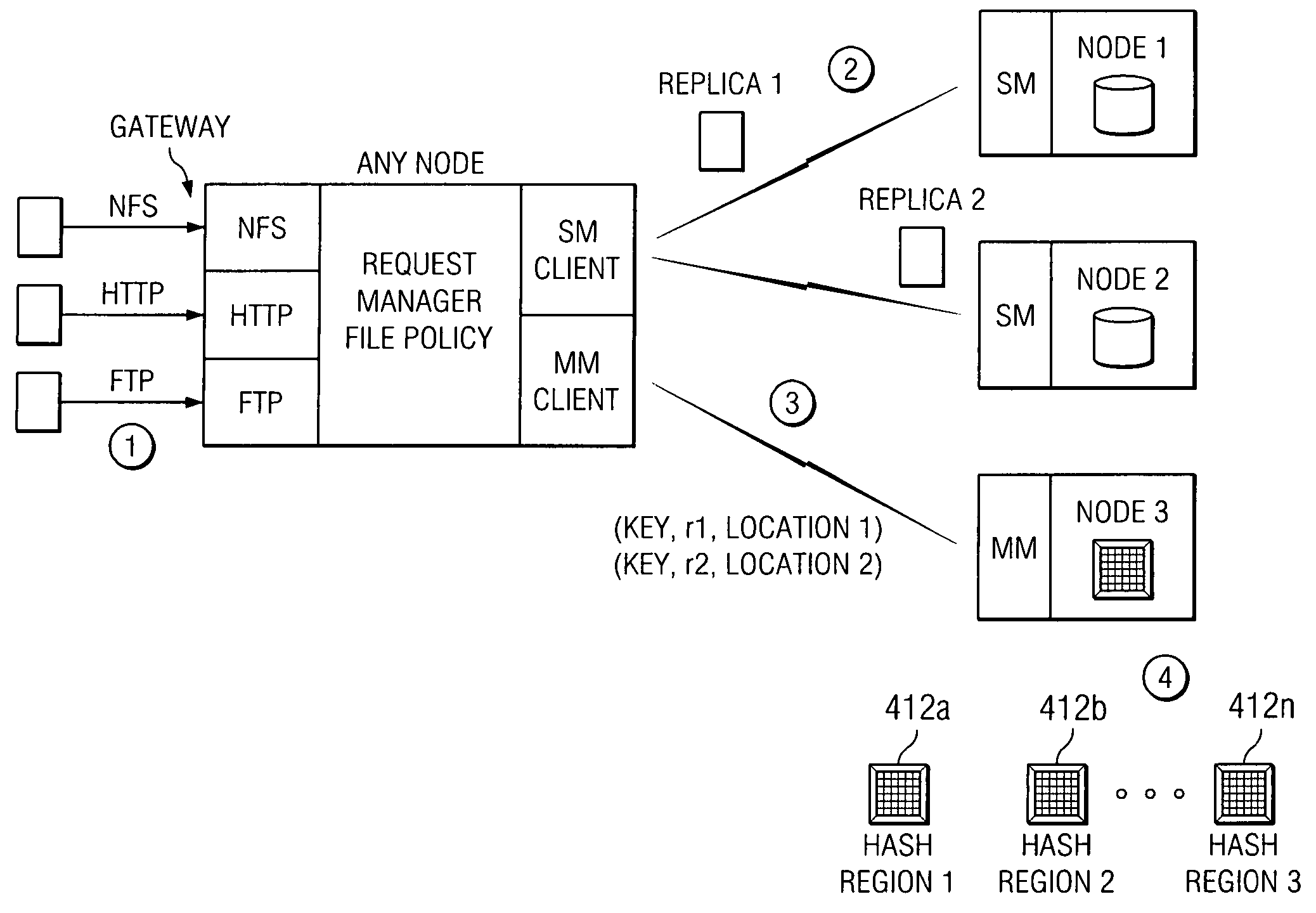
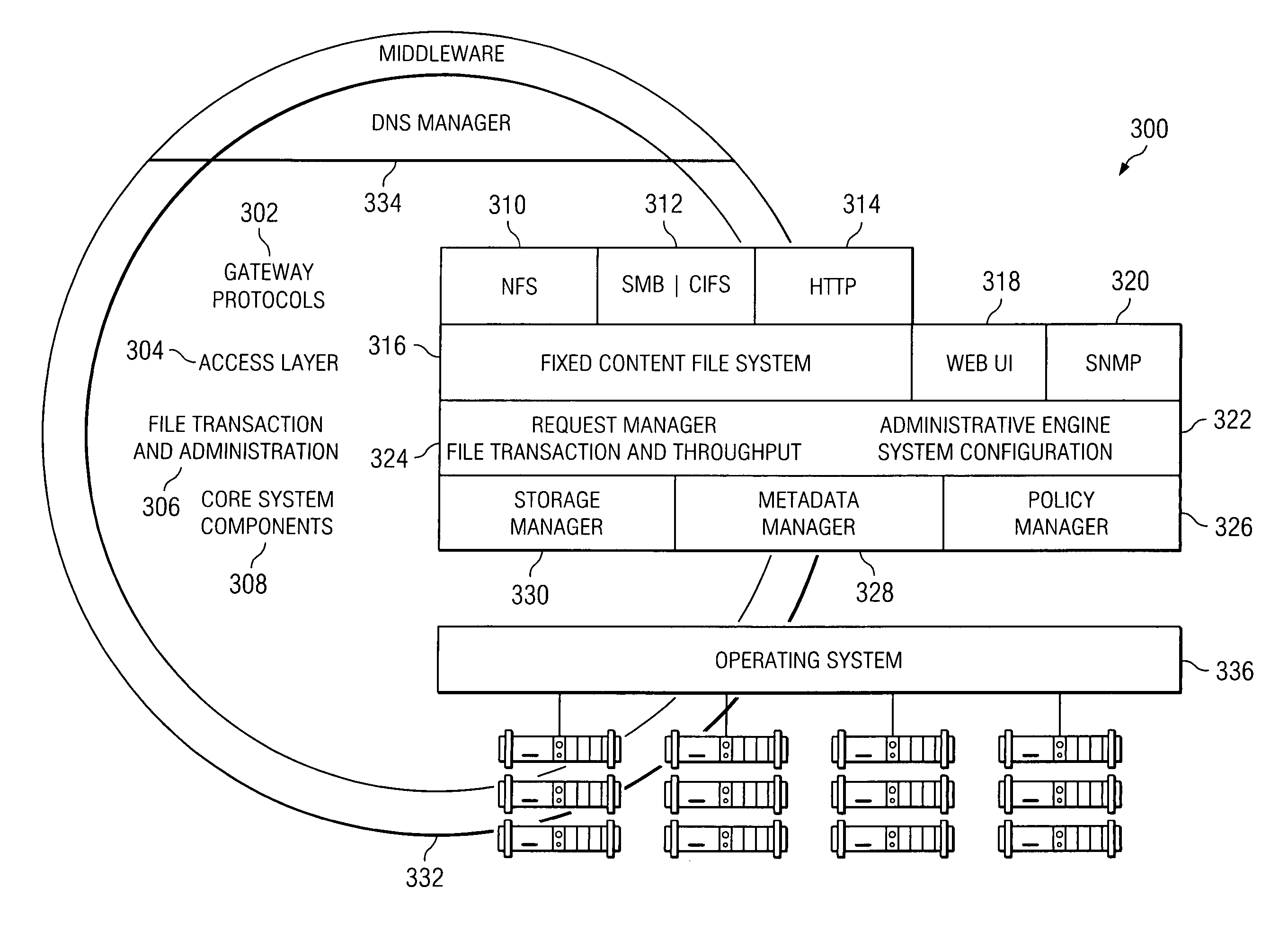
Policy-based management of a redundant array of independent nodes
ActiveUS20050120025A1Reduce complexityData processing applicationsDigital data processing detailsObject basedMetadata management
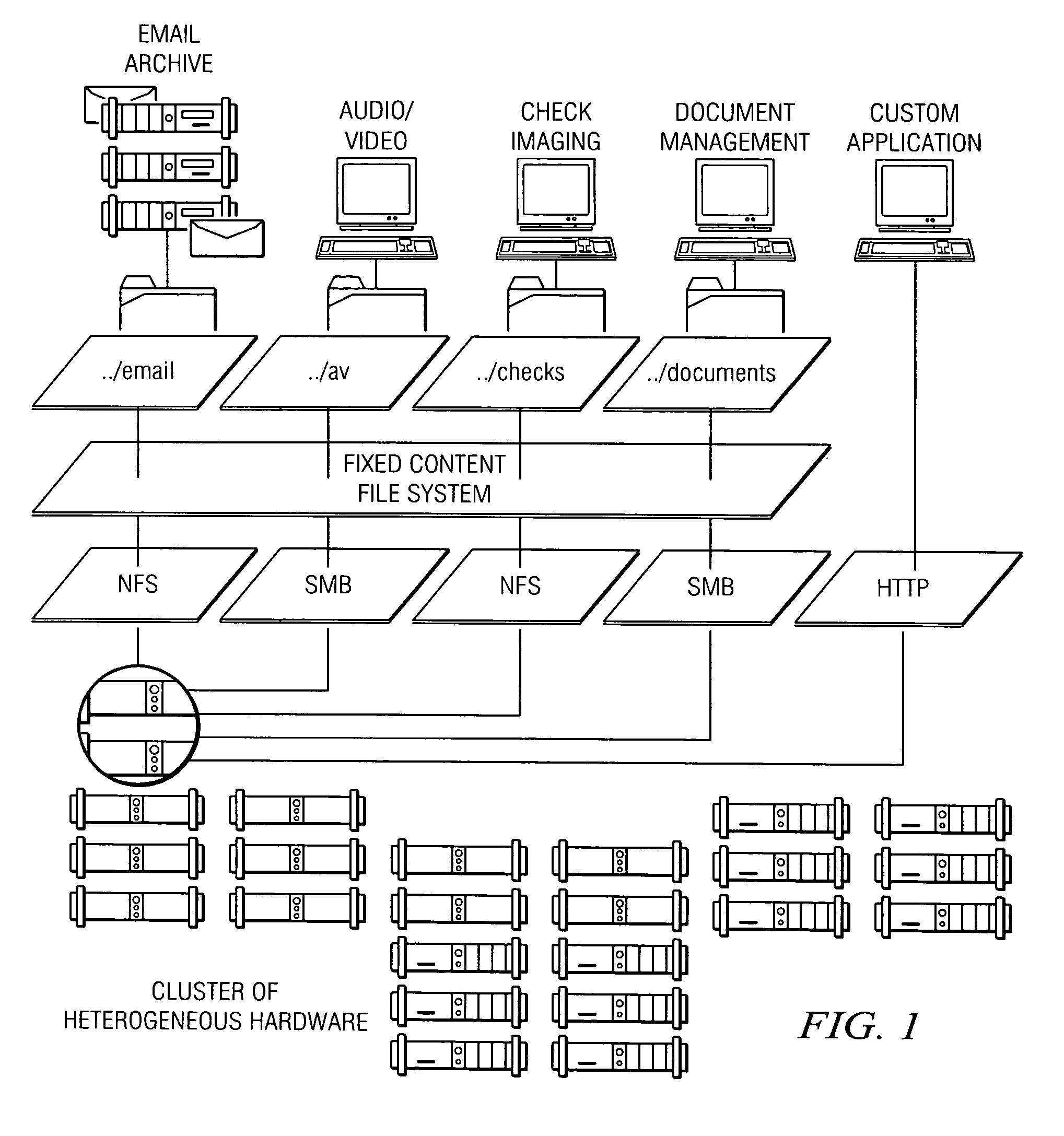
An archive cluster application runs in a distributed manner across a redundant array of independent nodes. Each node preferably runs a complete archive cluster application instance. A given nodes provides a data repository, which stores up to a large amount (e.g., a terabyte) of data, while also acting as a portal that enables access to archive files. Each symmetric node has a set of software processes, e.g., a request manager, a storage manager, a metadata manager, and a policy manager. The request manager manages requests to the node for data (i.e., file data), the storage manager manages data read / write functions from a disk associated with the node, and the metadata manager facilitates metadata transactions and recovery across the distributed database. The policy manager implements one or more policies, which are operations that determine the behavior of an “archive object” within the cluster. The archive cluster application provides object-based storage. Preferably, the application permanently associates metadata and policies with the raw archived data, which together comprise an archive object. Object policies govern the object's behavior in the archive. As a result, the archive manages itself independently of client applications, acting automatically to ensure that all object policies are valid.
Owner:HITACHI VANTARA LLC
Restoring an archived file in a distributed filesystem
ActiveUS20140006357A1Raise priorityIncreased restore budgetDigital data processing detailsRedundant operation error correctionDistributed File SystemFile system
The disclosed embodiments disclose techniques for restoring an archived file in a distributed filesystem. Two or more cloud controllers collectively manage distributed filesystem data that is stored in one or more cloud storage systems; the cloud controllers ensure data consistency for the stored data, and each cloud controller caches portions of the distributed filesystem. Furthermore, cloud controllers may archive infrequently-accessed files in an archival cloud storage system. During operation, a cloud controller receives a request from a client system to access an archived file, and restores this archived file from the archival cloud storage system.
Owner:PANZURA LLC
Policy-based management of a redundant array of independent nodes
ActiveUS7155466B2Reduce complexityData processing applicationsDigital data processing detailsObject basedMetadata management
An archive cluster application runs in a distributed manner across a redundant array of independent nodes. Each node preferably runs a complete archive cluster application instance. A given nodes provides a data repository, which stores up to a large amount (e.g., a terabyte) of data, while also acting as a portal that enables access to archive files. Each symmetric node has a set of software processes, e.g., a request manager, a storage manager, a metadata manager, and a policy manager. The request manager manages requests to the node for data (i.e., file data), the storage manager manages data read / write functions from a disk associated with the node, and the metadata manager facilitates metadata transactions and recovery across the distributed database. The policy manager implements one or more policies, which are operations that determine the behavior of an “archive object” within the cluster. The archive cluster application provides object-based storage. Preferably, the application permanently associates metadata and policies with the raw archived data, which together comprise an archive object. Object policies govern the object's behavior in the archive. As a result, the archive manages itself independently of client applications, acting automatically to ensure that all object policies are valid.
Owner:HITACHI VANTARA LLC
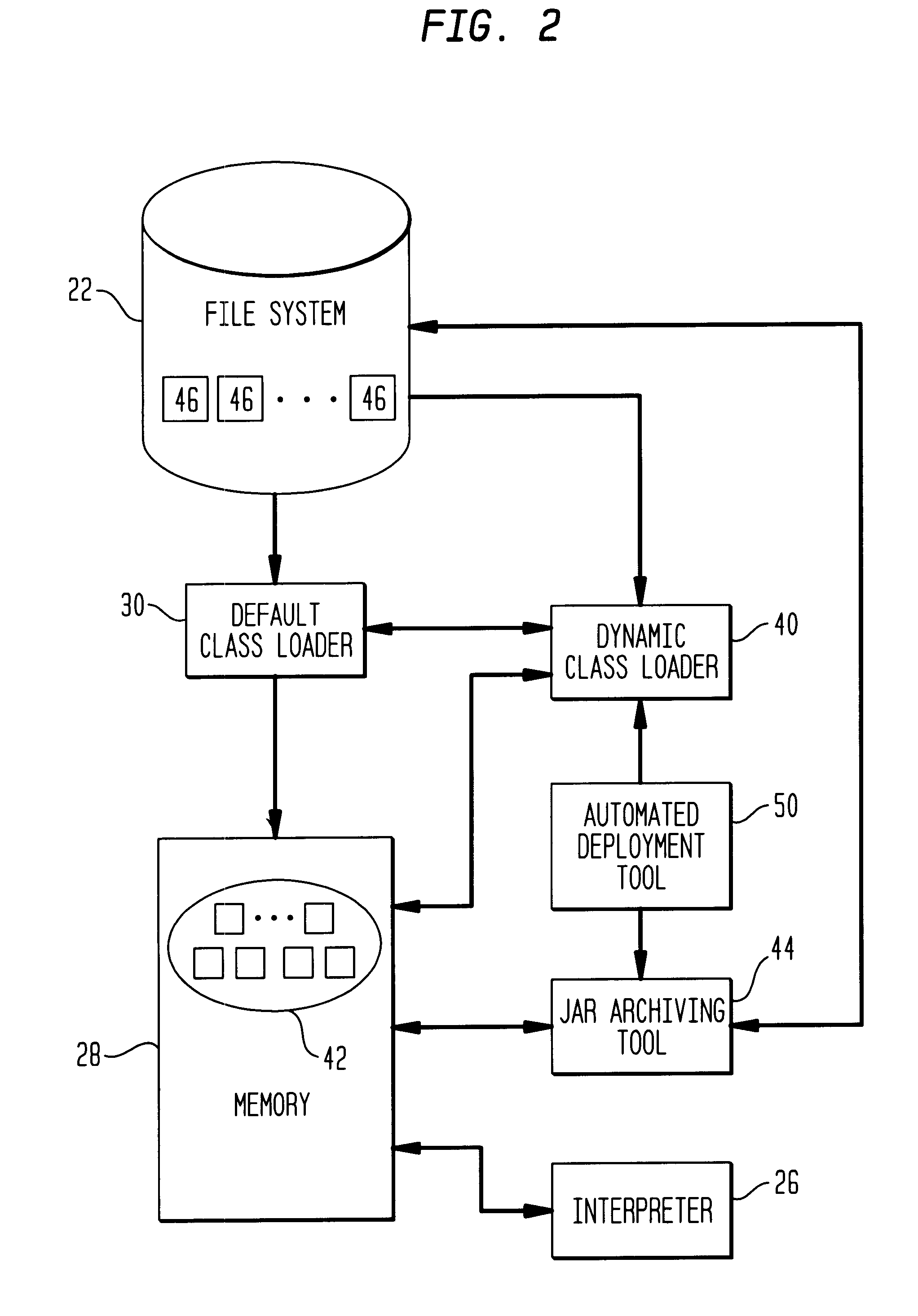
Automated deployment of an application
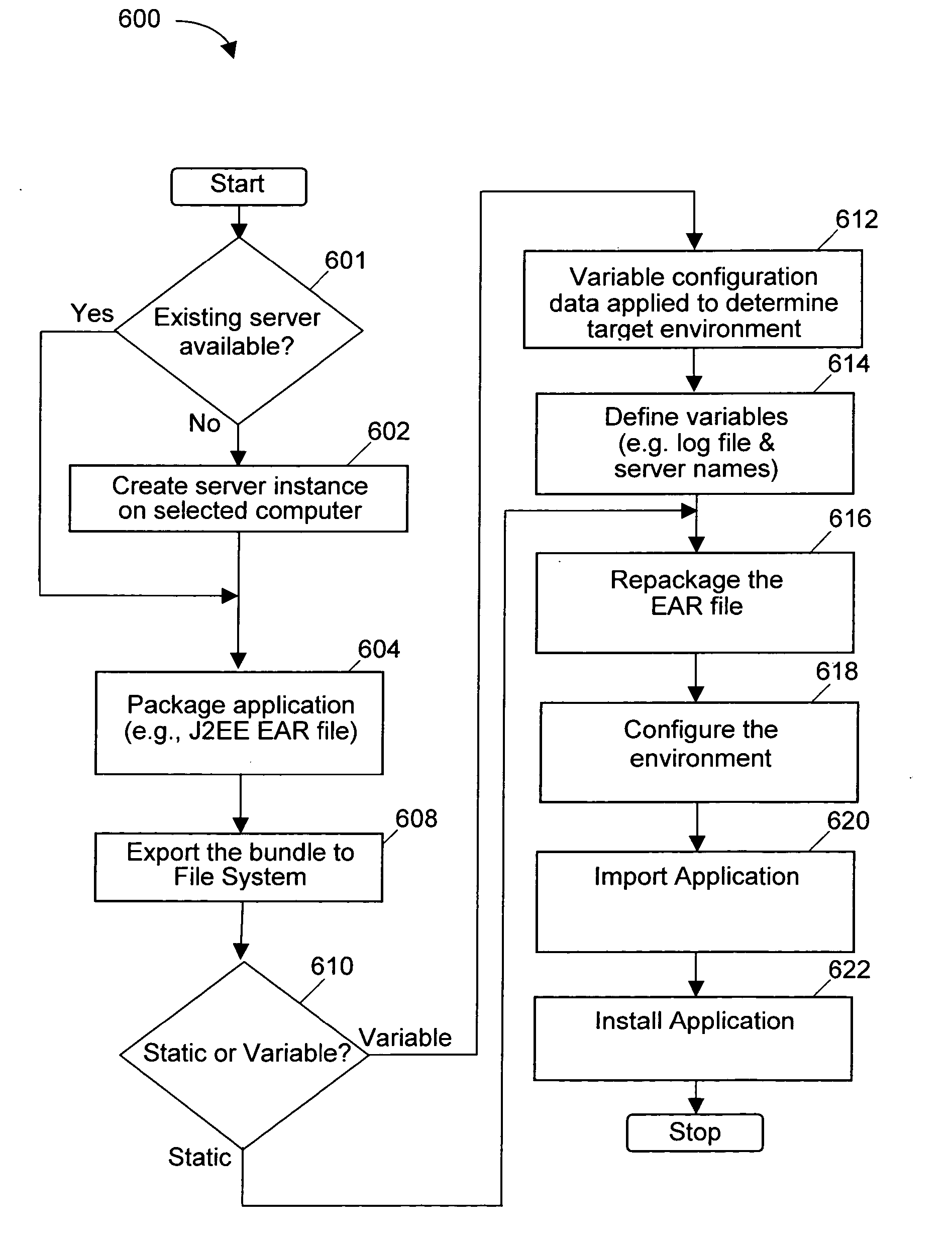
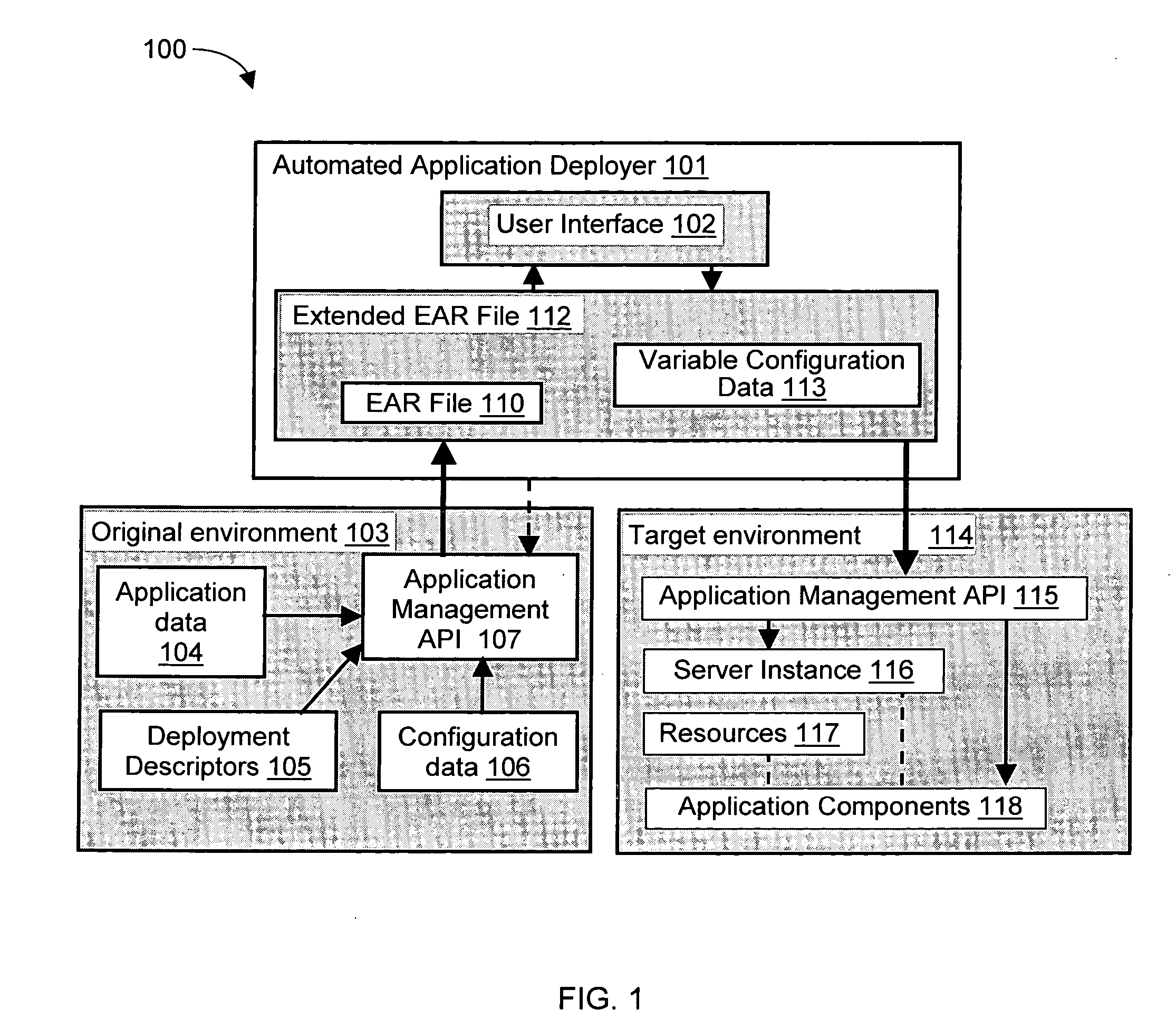
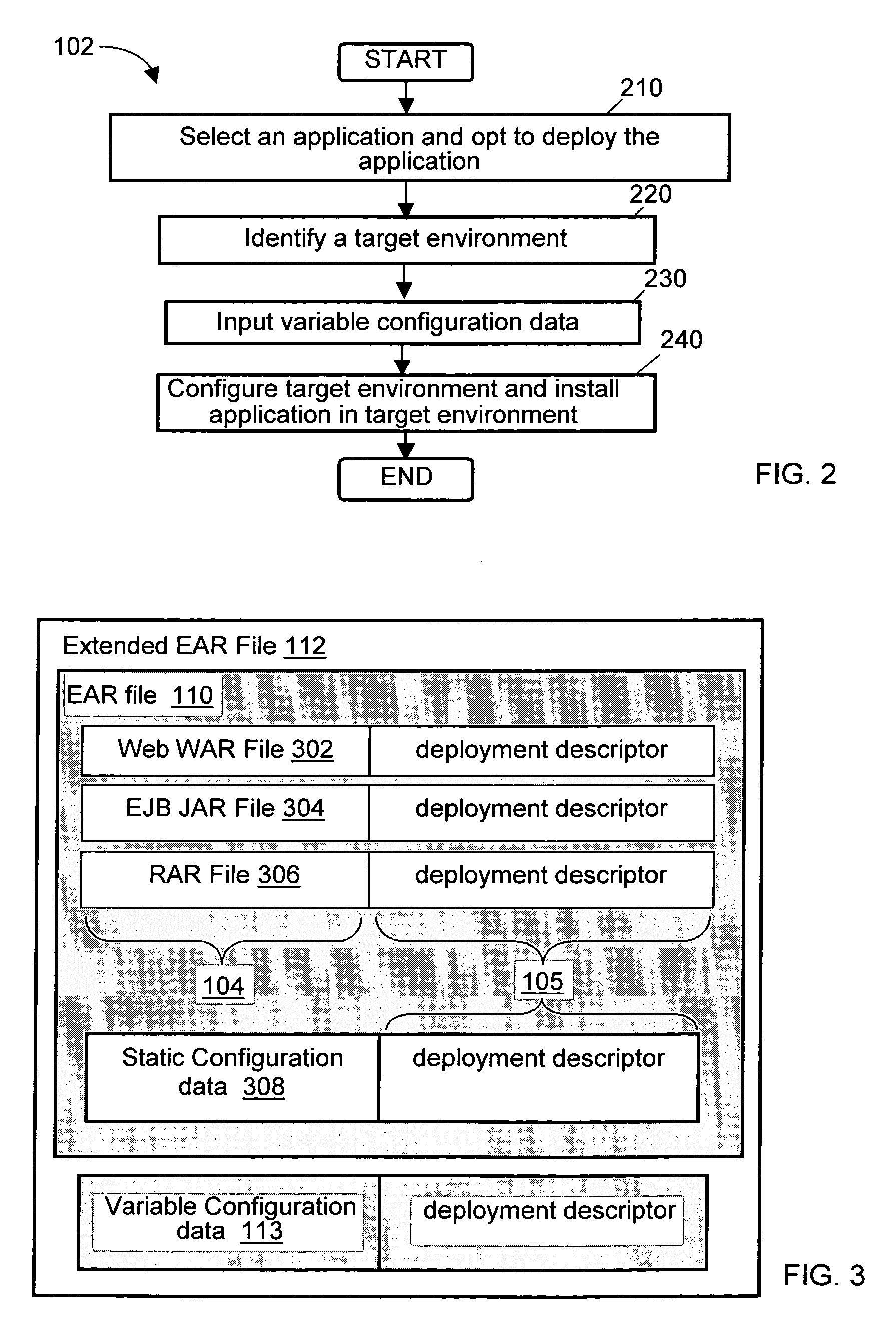
Methods, systems, and media to automatically deploy an, e.g., a JS2EE file between environments are disclosed. Embodiments include hardware and / or software for selecting one or more applications in an original system for export. The applications along with their corresponding application data, configuration data, and descriptor files, are compressed into one or more archive files such as Enterprise Archives (EARs). Variable configuration data associated with the target environment is identified so the values of the variable configuration data can be adapted for the target environment. Then, the target environment is adapted for installation of the application and the application is installed in the target environment. Advantageously, this deployment of the application may reduce the chance of user error, require less J2EE knowledge and script maintenance, and complete faster than deployments effected manually.
Owner:IBM CORP
Method, system, and articles of manufacture for providing a servlet container based web service endpoint
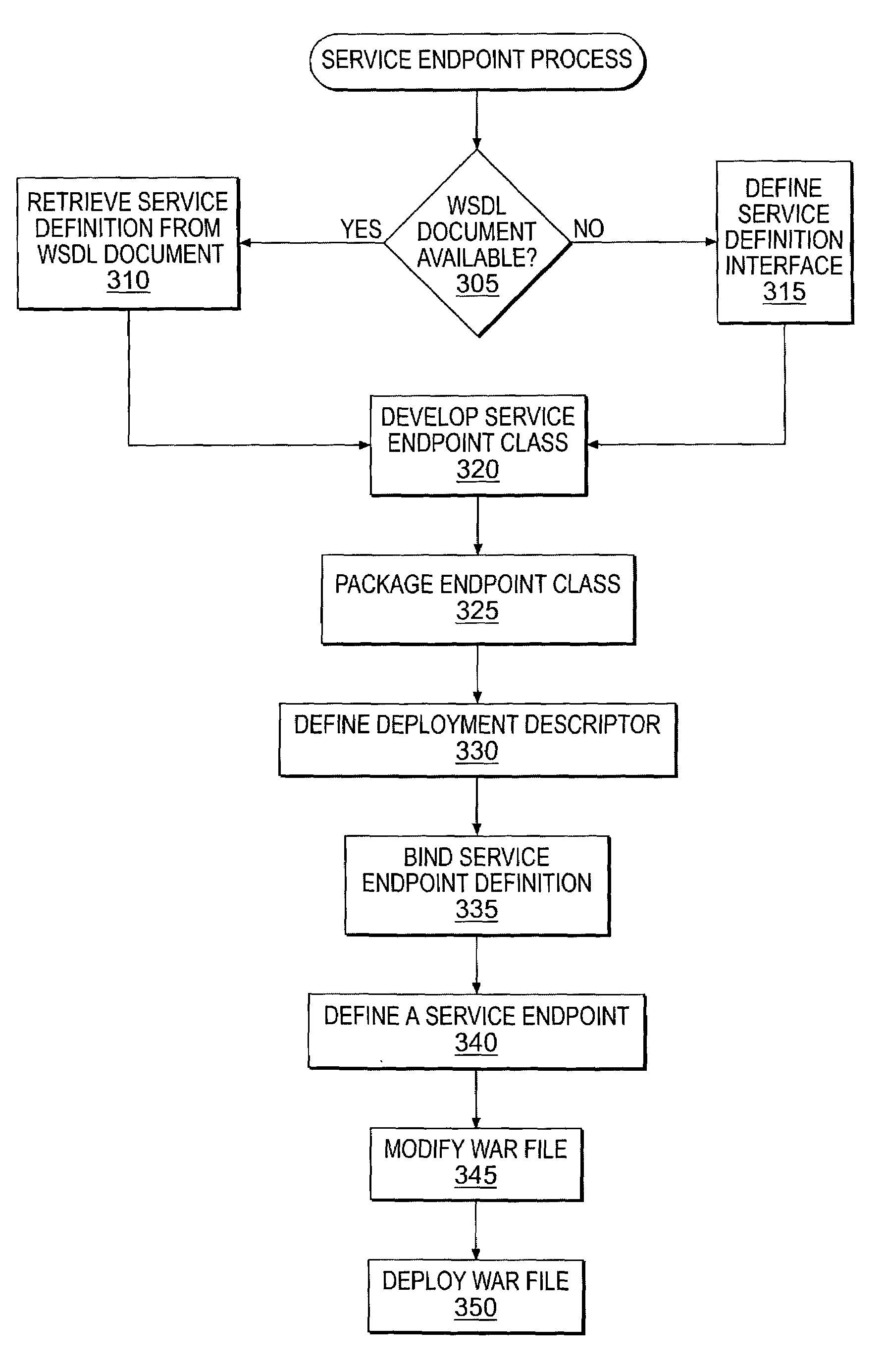
Methods, systems, and articles of manufacture consistent with certain principles related to the present invention enable a computing system to layer the packaging and deployment of a web service endpoint on a standard servlet component model. To define a web service endpoint, the computing system may develop a service endpoint class that implements a configured service endpoint interface. The interface and endpoint class may be packaged by the computing system into an archive file. The computing system may use the information stored in the archive file to define the service endpoint modify the archive file with class information associated with the defined service endpoint. The modified archive file may be deployed on a container operating within the computing system. Further, the computing system may produce a WSDL based description of the defined service endpoint and export the document such that a remote client may use the information contained in the document to locate and remotely invoke methods on the defined service endpoint.
Owner:ORACLE INT CORP
System and method for providing encryption in pipelined storage operations in a storage network
InactiveUS20050257062A1User identity/authority verificationComputer security arrangementsComputer hardwareData stream
In accordance with embodiments of the invention, a method is provided for performing a storage operation in a pipeline storage system in which one or more data streams containing data to be stored are written into data chunks. The method includes generating an encryption key associated with a first archive file to be stored when encryption is requested for the storage operation, encrypting the archive data from the data stream using the encryption key to create an encrypted data chunk when a data stream containing the archive file is processed in the pipeline storage system, storing the encrypted data chunk on a storage medium, and storing the encryption key in a manner accessible during a restore operation of the encrypted data chunk.
Owner:COMMVAULT SYST INC
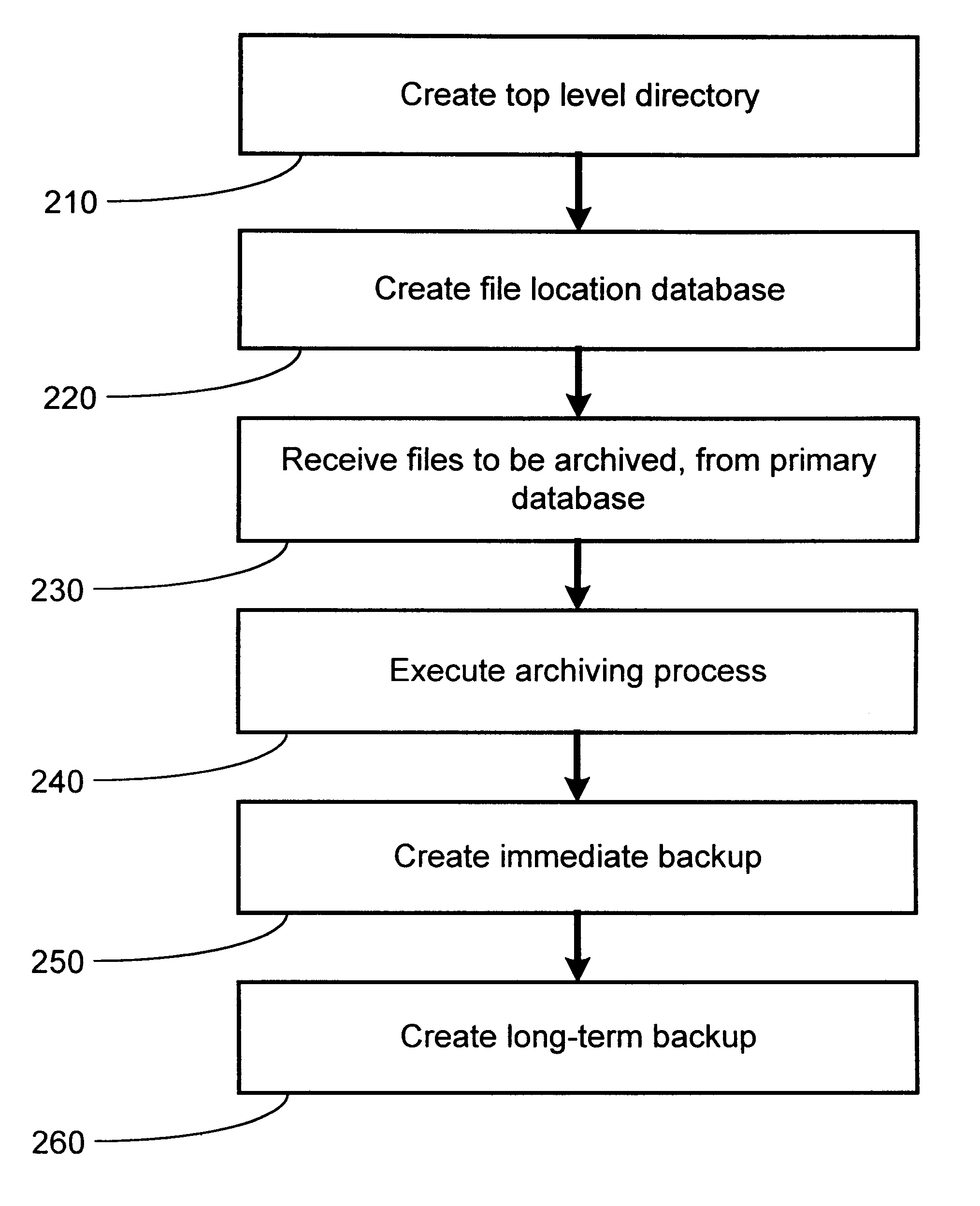
Method and apparatus for hierarchical storage of data for efficient archiving and retrieval of data
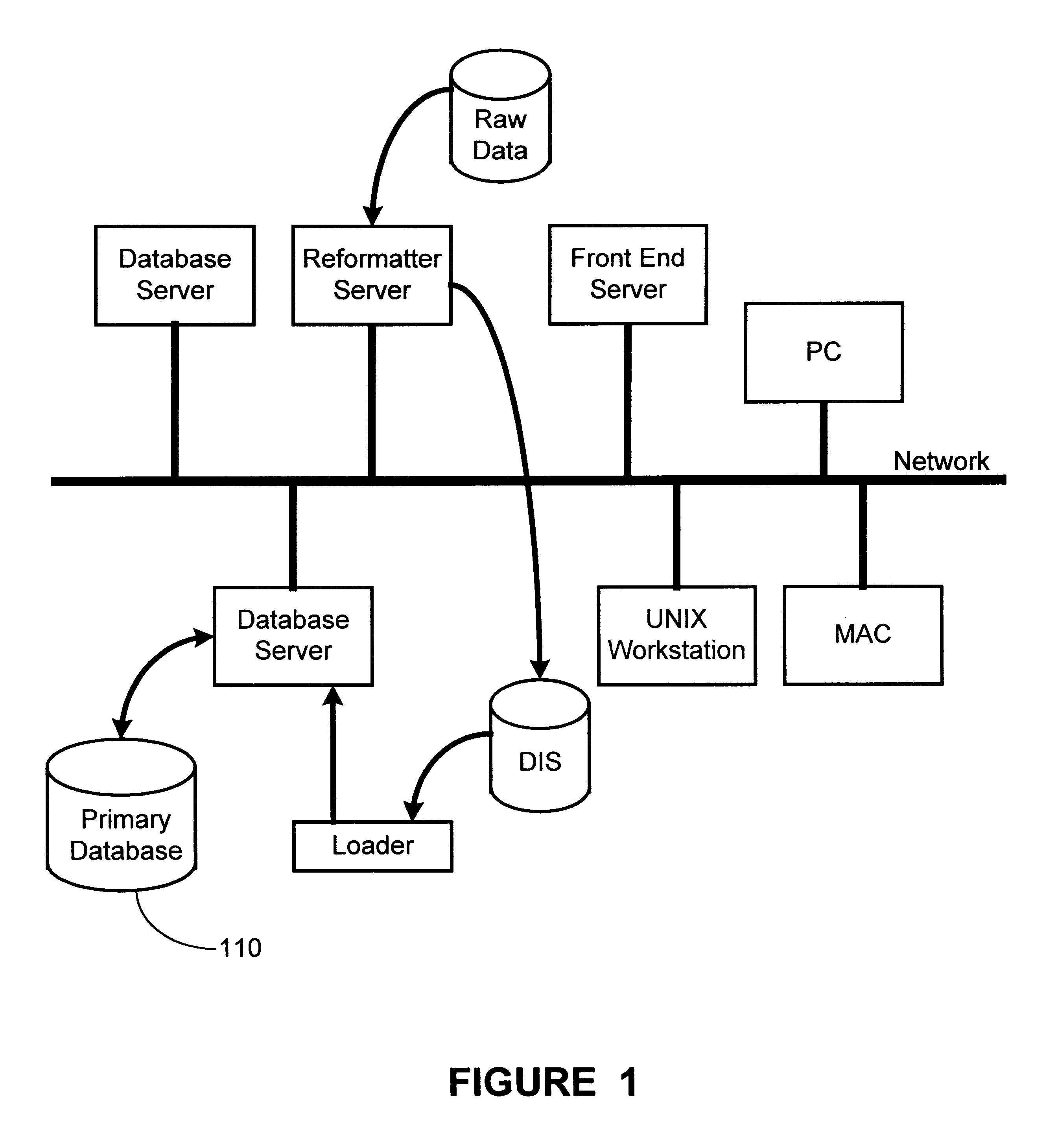
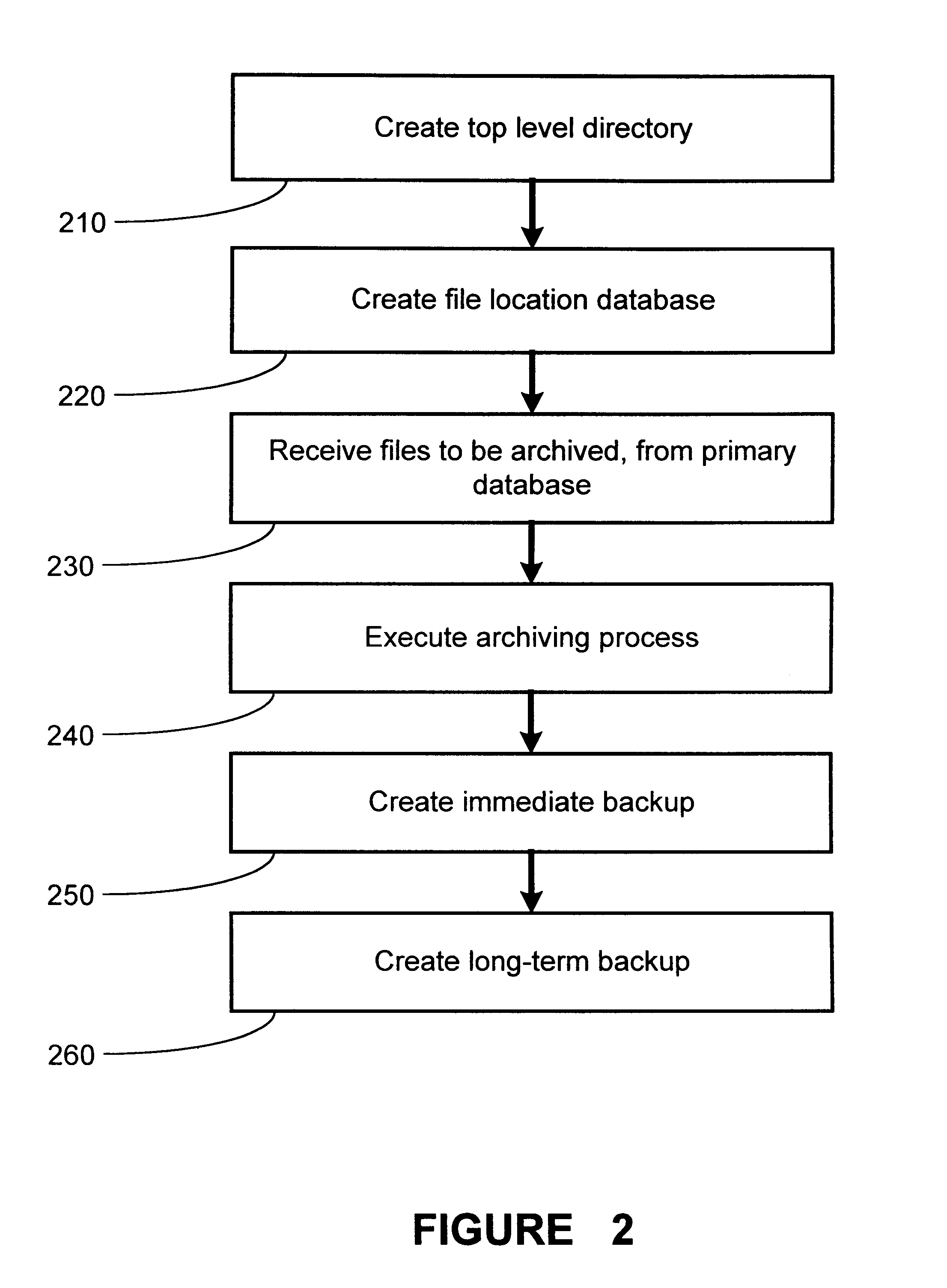
The present invention provides for a method and an apparatus for archiving and retrieving data. At least one top-level directory is created to store files. A file-location database is created to track stored files in the top level directory. Files from a primary database are received. Files received from the database are archived into the top level directory, in response to receiving files from a primary database. An immediate backup of the archived files is created. A long-term backup of the archived files is created.
Owner:GLOBALFOUNDRIES INC
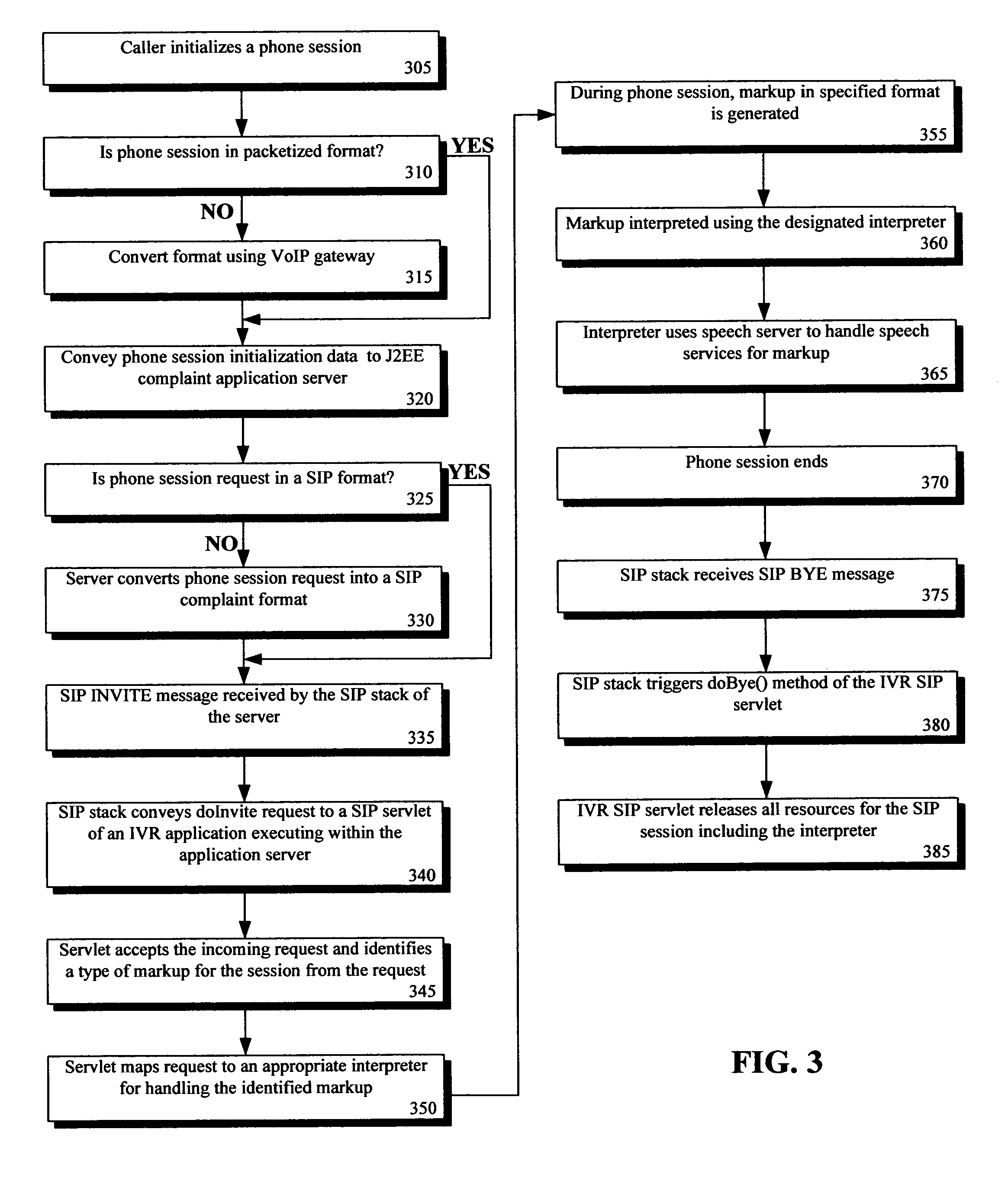
Integrating an IVR application within a standards based application server
InactiveUS8139730B2Easy to updateReduces implementationInterconnection arrangementsAutomatic call-answering/message-recording/conversation-recordingApplication serverApplication software
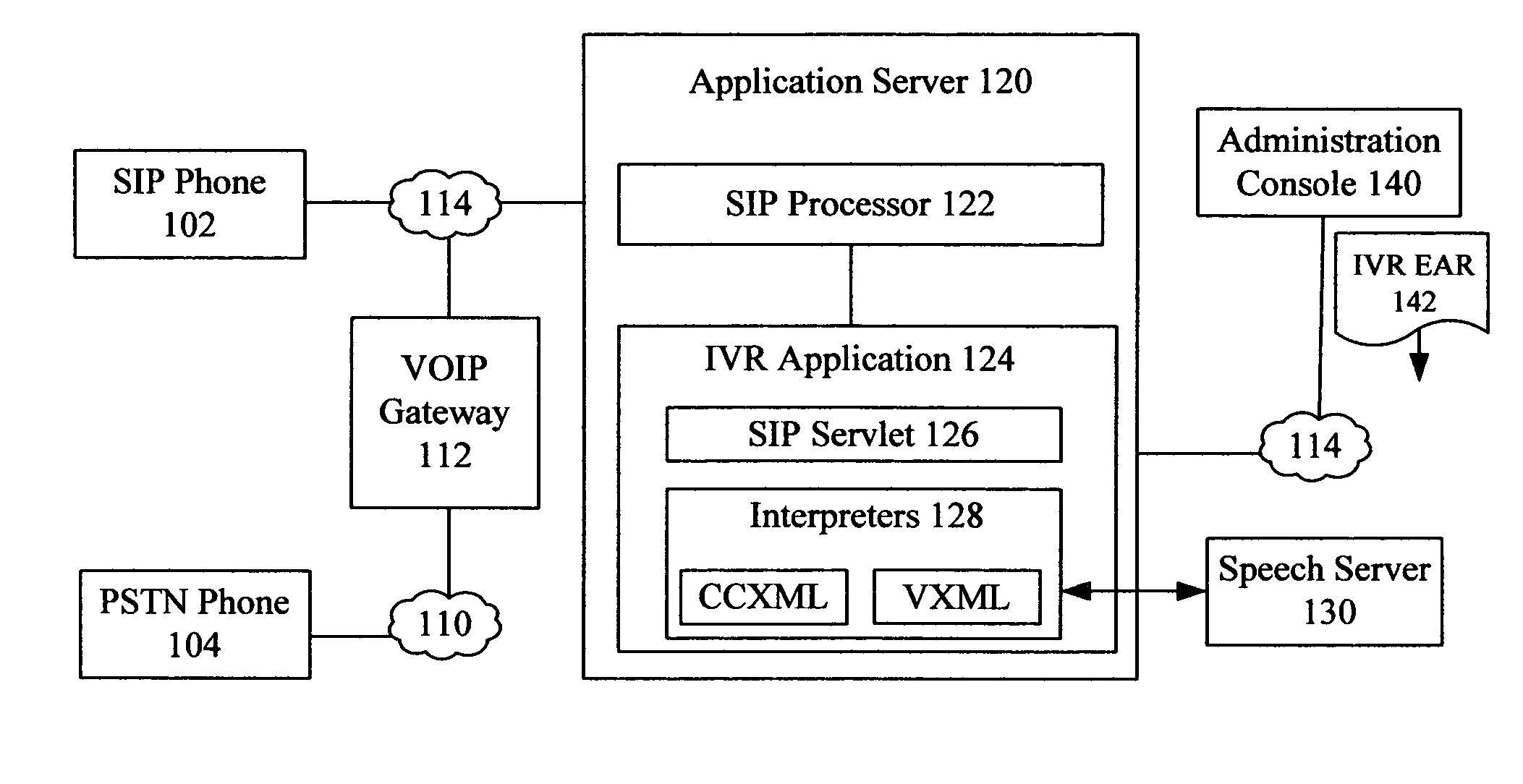
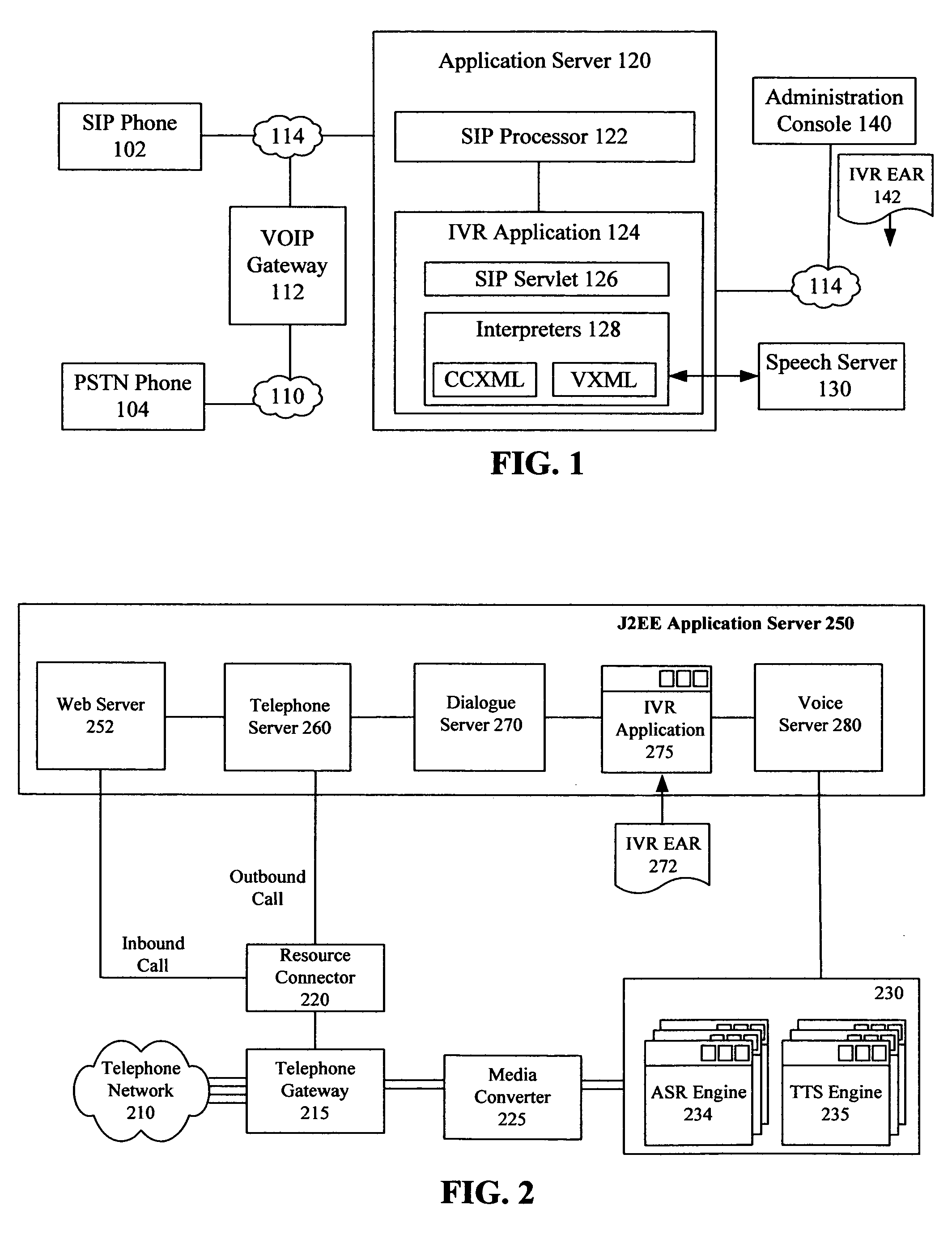
A method for providing Interactive Voice Response functionality within a multi-tiered telephony environment can identify an enterprise archive file that contains an Interactive Voice Response (IVR) application. The enterprise archive file can contain multiple interpreters for different markup languages. The enterprise archive file can also include a servlet that maps the interpreters to telephony sessions. The enterprise archive file can be deployed within a J2EE compliant application server having a SIP interface. The deployed IVR application can be utilized to provide IVR functions for SIP based telephony sessions.
Owner:INT BUSINESS MASCH CORP
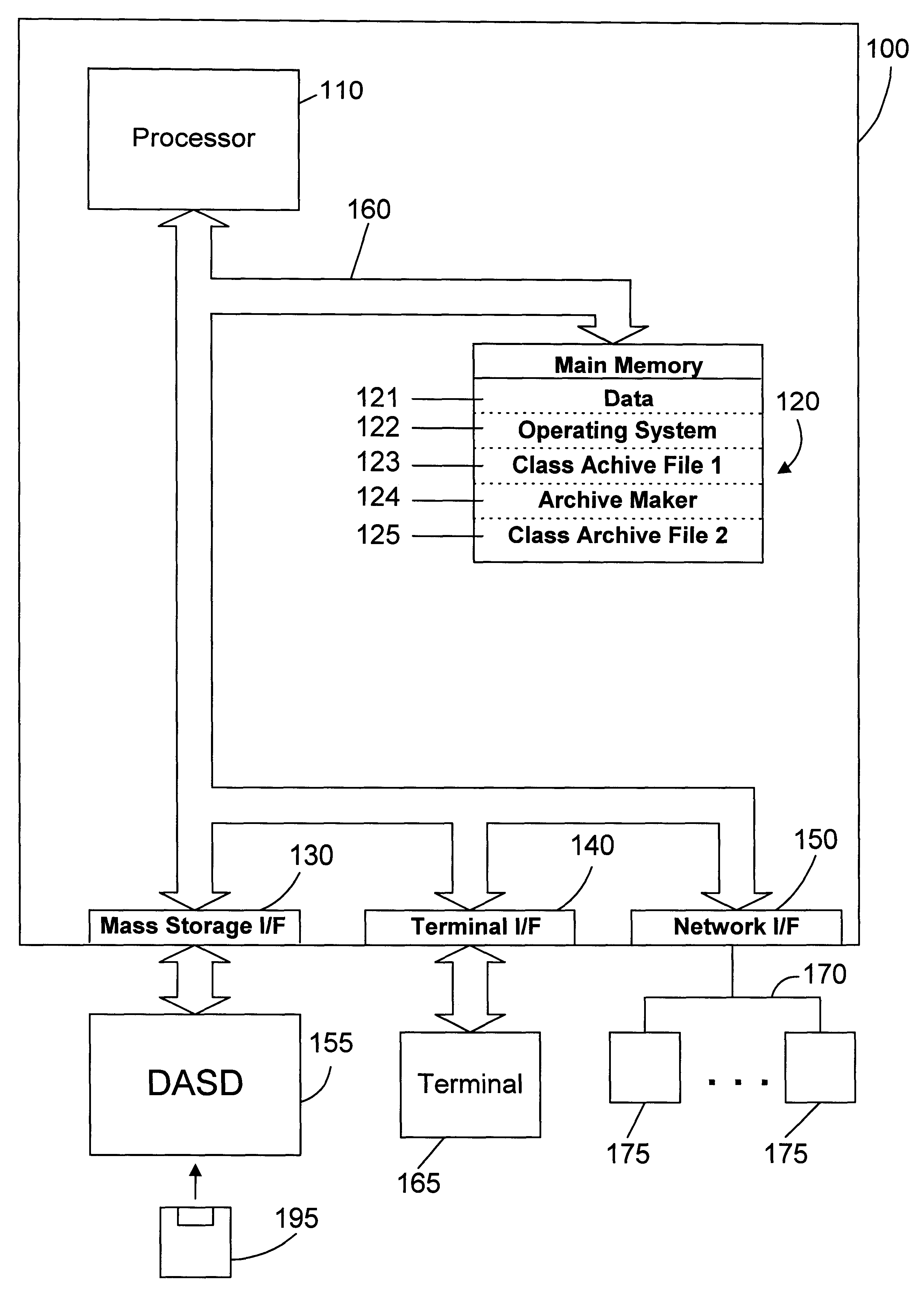
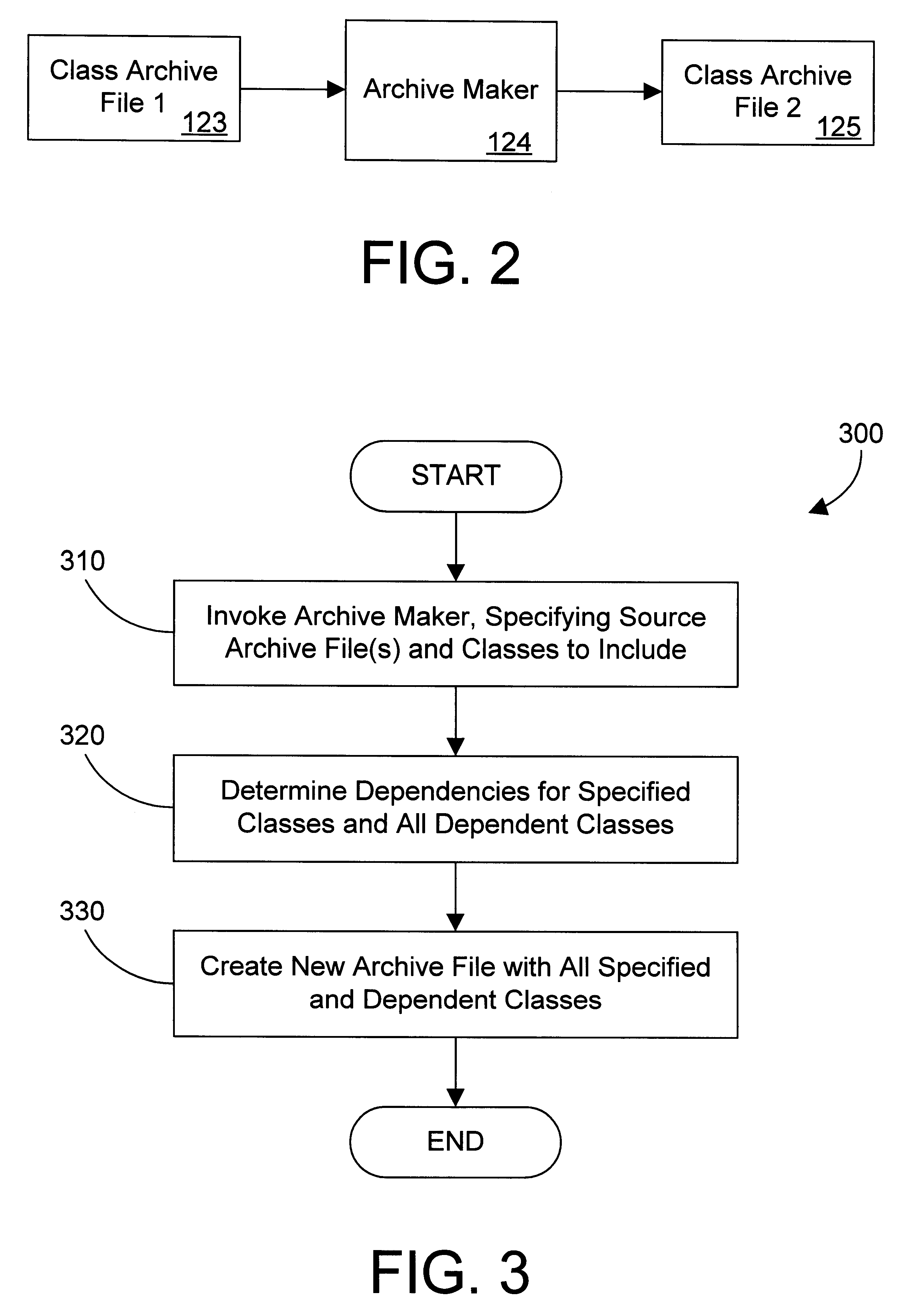
Object oriented class archive file maker and method
A tool referred to herein as an archive maker operates on one or more existing archive files that contain multiple object oriented classes to generate one or more new archive files. The archive maker takes a list of required classes, analyzes those classes in one or more existing archive files to determine any classes upon which they depend, and creates a new archive file with all the required and dependent classes. This allows the classes that are not required to be stripped out of the archive file. The archive maker may also be used to partition an existing archive file into multiple new archive files according to one or more partition criteria. In addition, the archive maker may be used to consolidate multiple existing archive files into a single new archive file.
Owner:IBM CORP
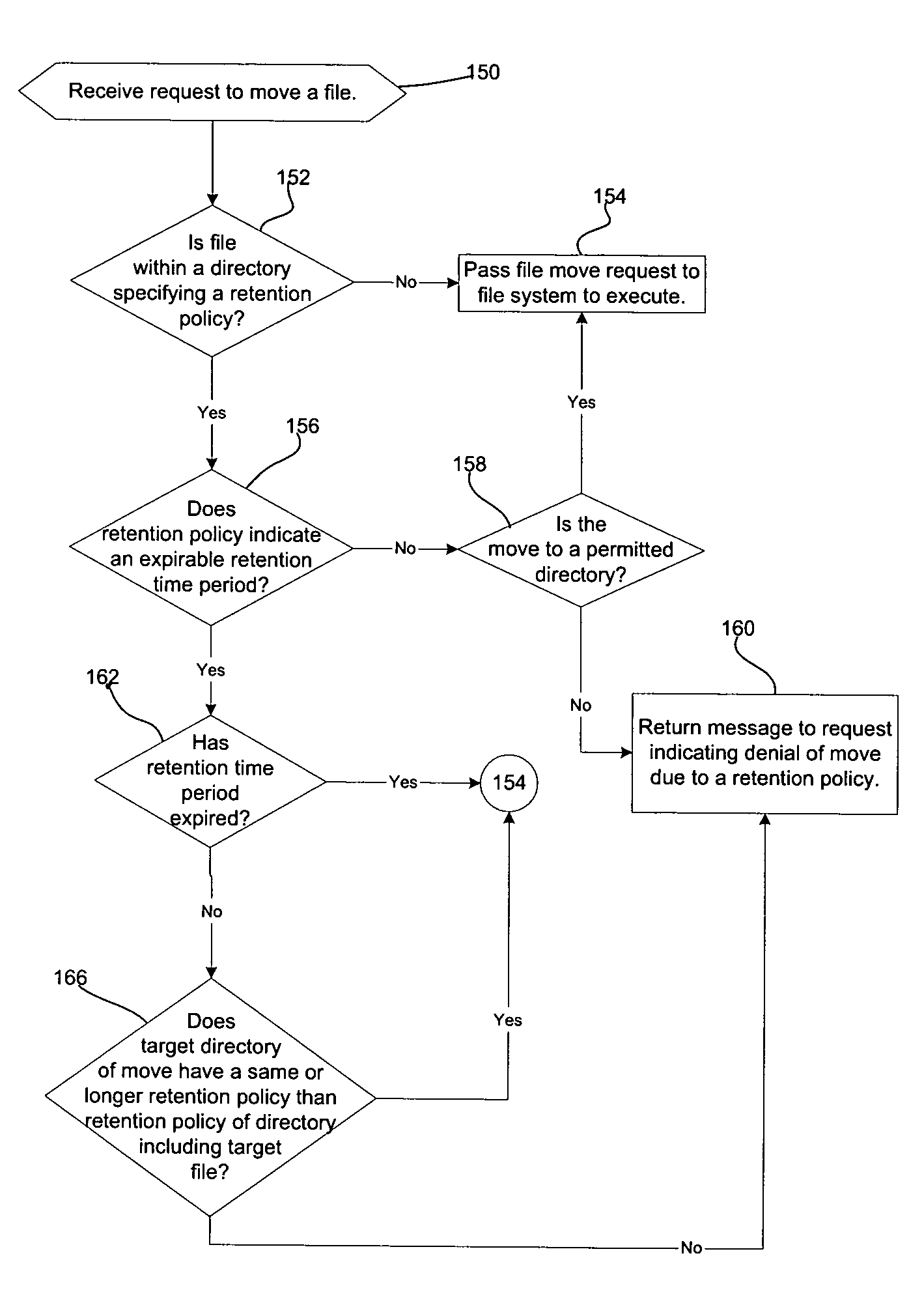
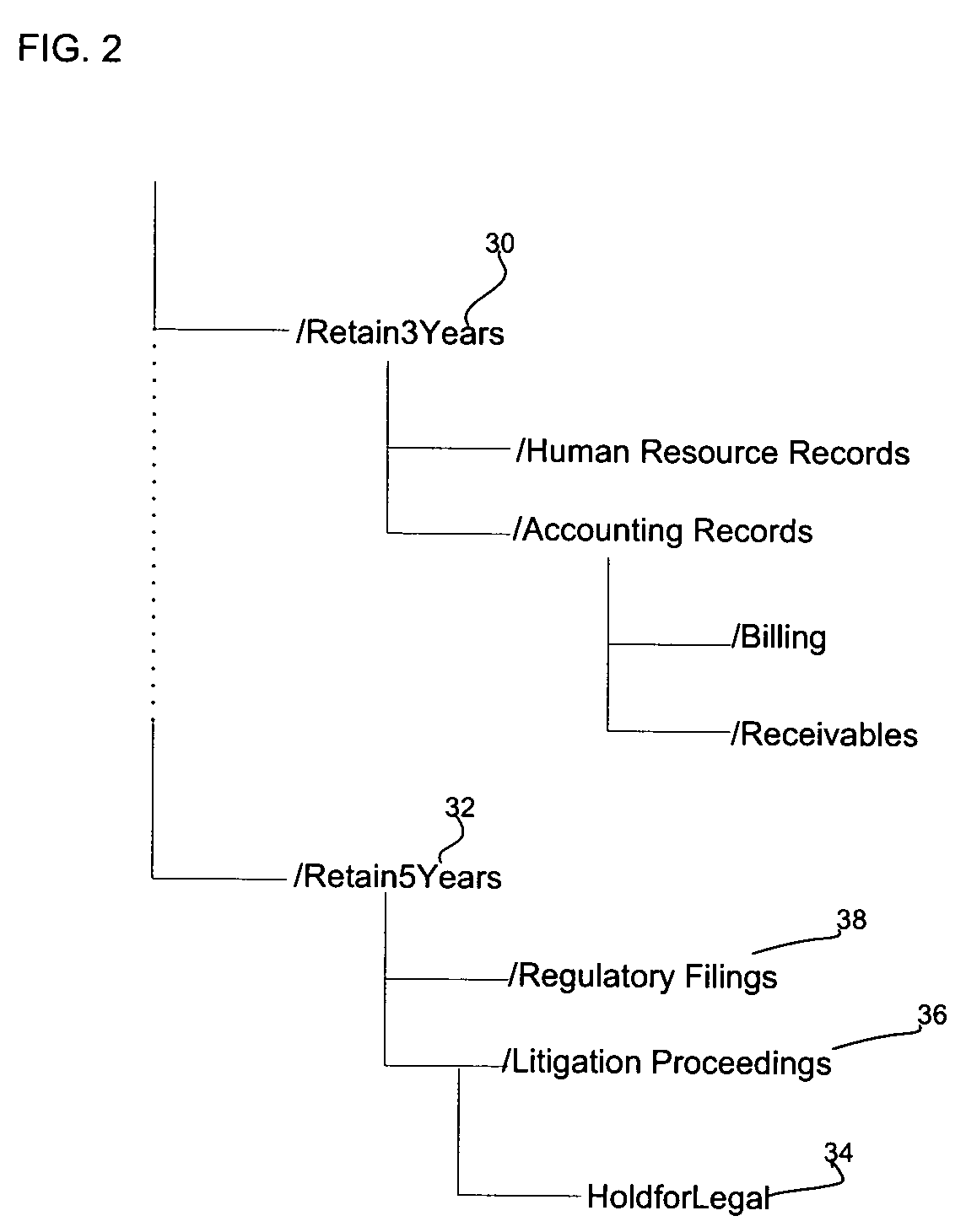
Method, system, and program for archiving files
Provided are a method, system, and program for archiving files. A hierarchical file system having directories is provided. An archival retention policy is associated with at least one of the directories in the hierarchical file system, wherein the retention policy applies to files included in the associated directory, and wherein the retention policy specifies a retention time indicating a time period during which a file is subject to the retention policy.
Owner:GOOGLE LLC
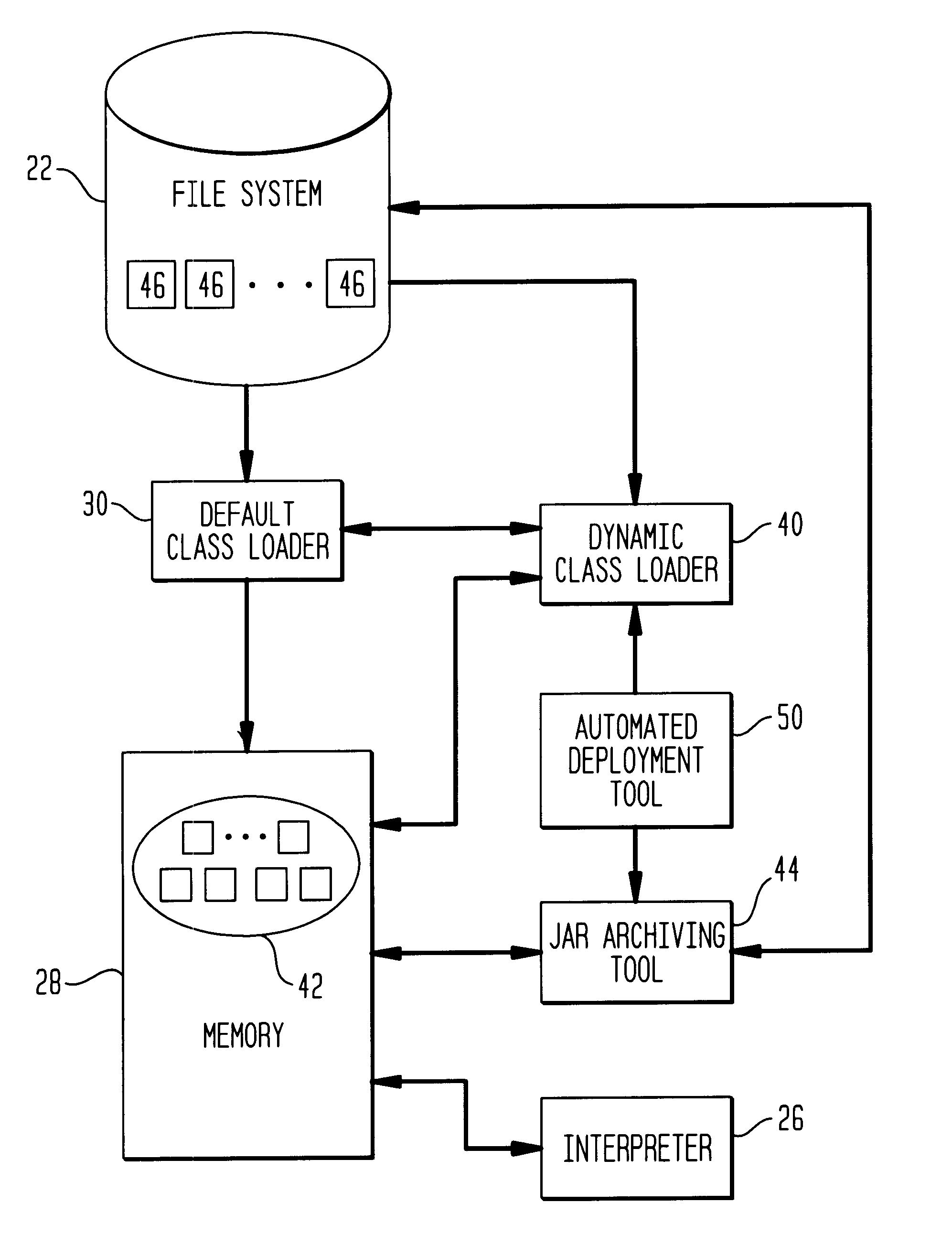
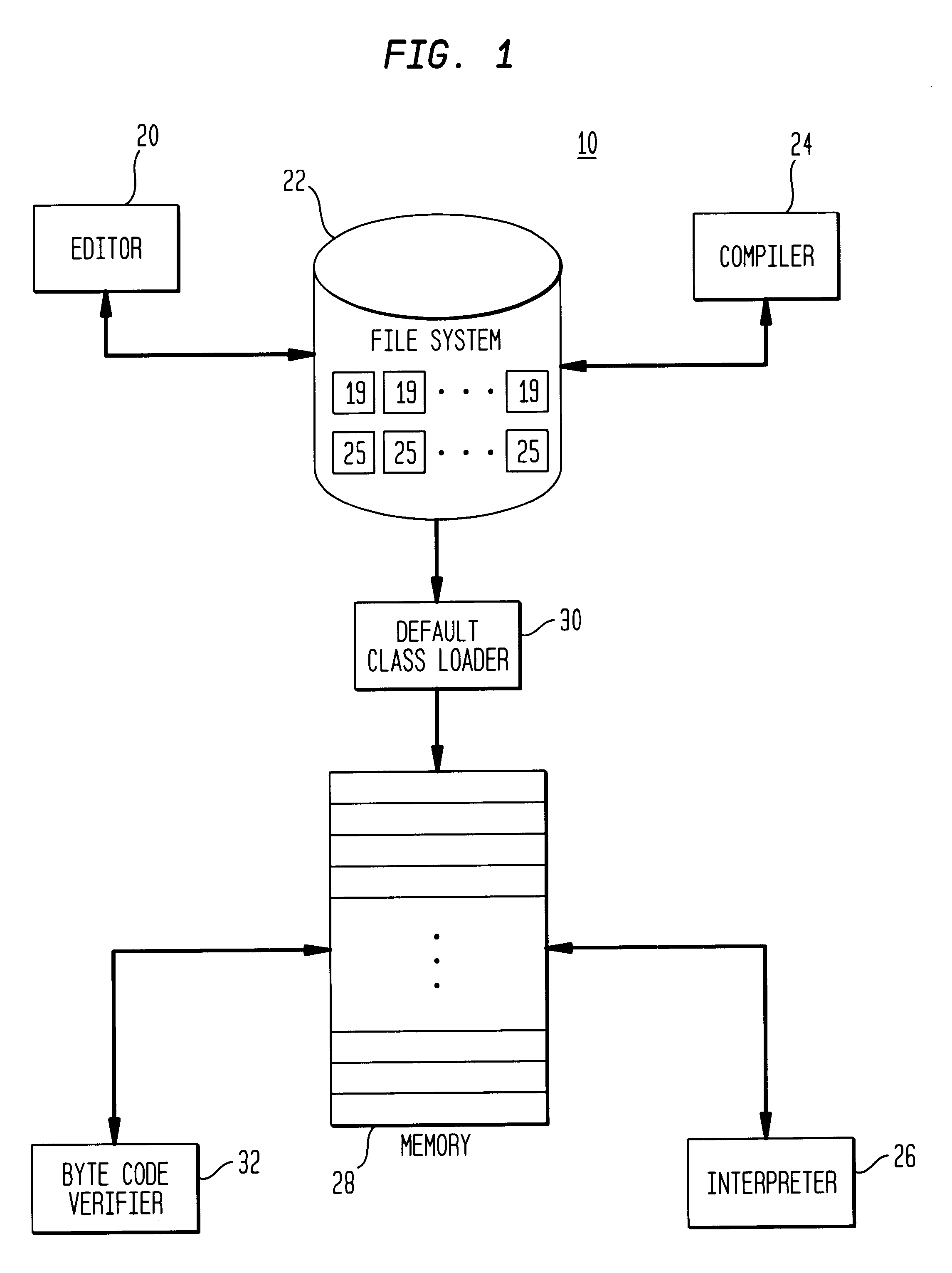
Class loader
This invention relates to the loading of classes in programming environments, and in particular, Java programming environments. This invention discloses a system and method that permits dynamic loading of classes during the execution of Java programs. This invention allows for classes to be loaded despite the fact that such classes may not reside in the current path or working directory within a Java programming environment. This invention also discloses a system and method for archiving files in an archive file that provides customized entry names for the archived files.
Owner:IBM CORP
System and method for providing encryption in a storage network by storing a secured encryption key with encrypted archive data in an archive storage device
InactiveUS7277941B2User identity/authority verificationComputer security arrangementsComputer hardwareData stream
In accordance with embodiments of the invention, a method is provided for performing a storage operation in a pipeline storage system in which one or more data streams containing data to be stored are written into data chunks. The method includes generating an encryption key associated with a first archive file to be stored when encryption is requested for the storage operation, encrypting the archive data from the data stream using the encryption key to create an encrypted data chunk when a data stream containing the archive file is processed in the pipeline storage system, storing the encrypted data chunk on a storage medium, and storing the encryption key in a manner accessible during a restore operation of the encrypted data chunk.
Owner:COMMVAULT SYST INC
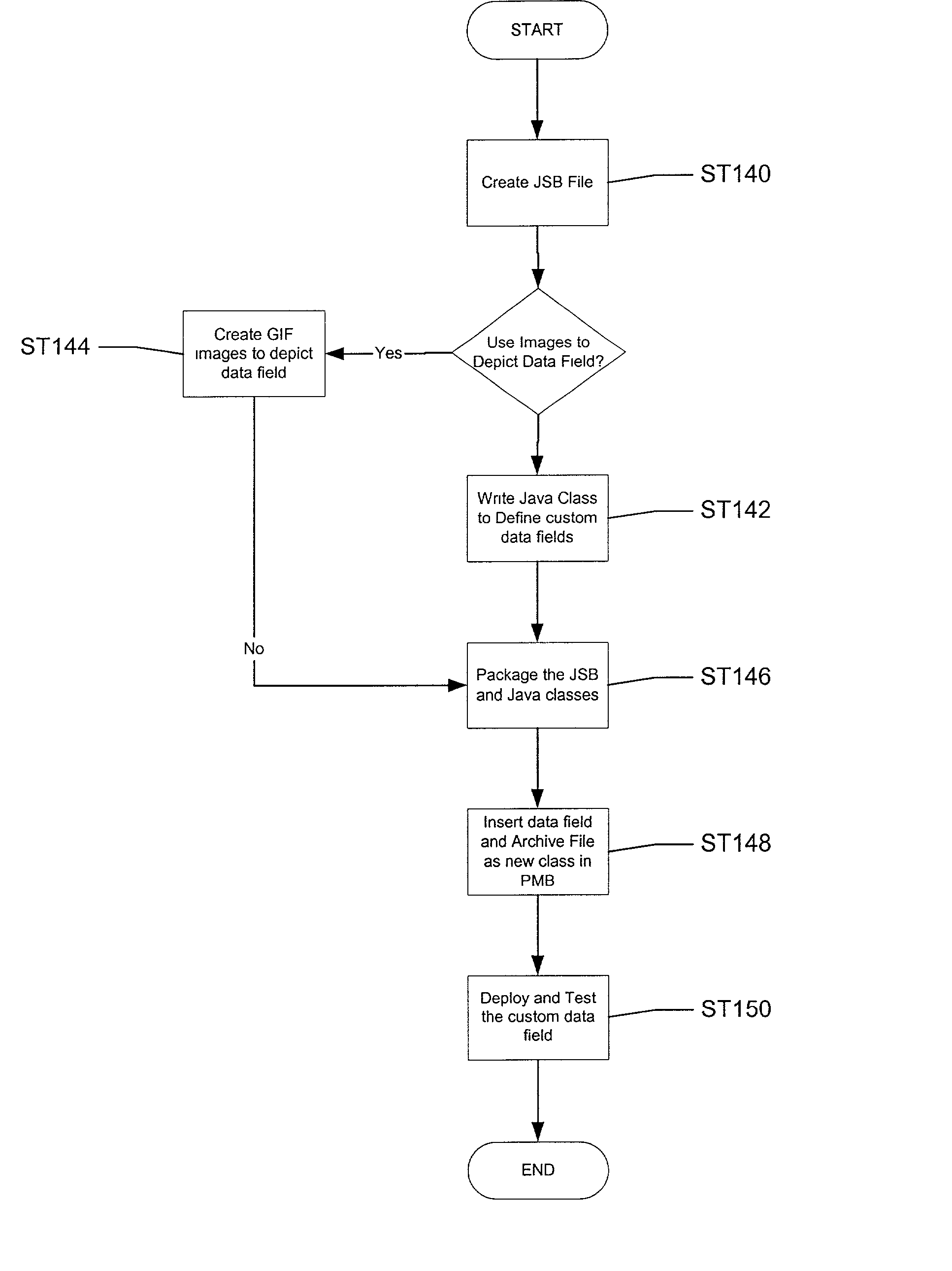
Defining and creating custom data fields within process management software
A method of creating and defining a custom data field within a process management system includes creating a file to specify visible field properties of the custom data field and defining a model of the custom data field. The file and the model may be packaged into an archive file. The custom data field may be inserted and the archive file is added into the process management system as a new class. The process management system may be deployed with the new class and the process management system may be tested with the new class.
Owner:SUN MICROSYSTEMS INC
Techniques for performing policy automated operations
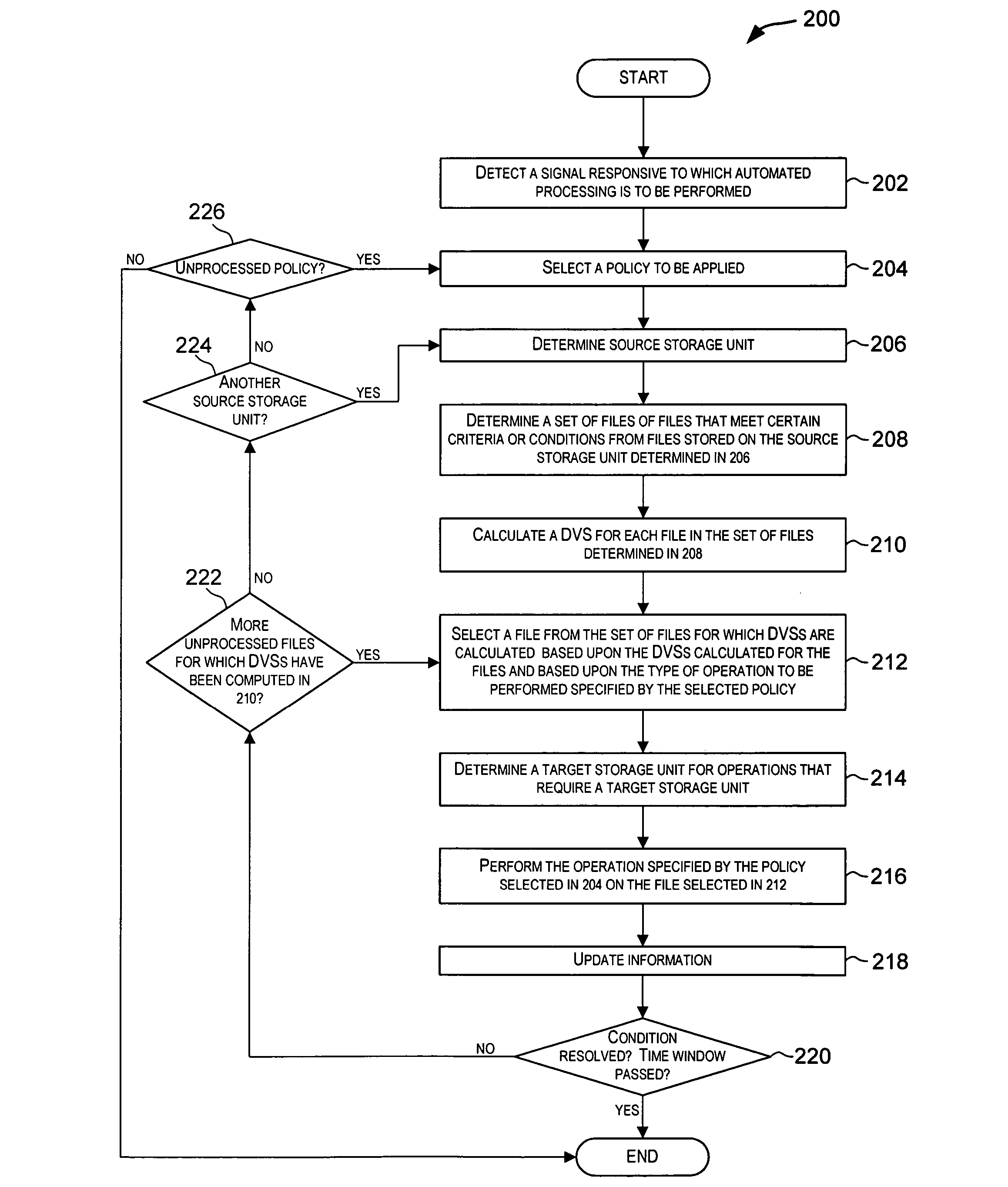
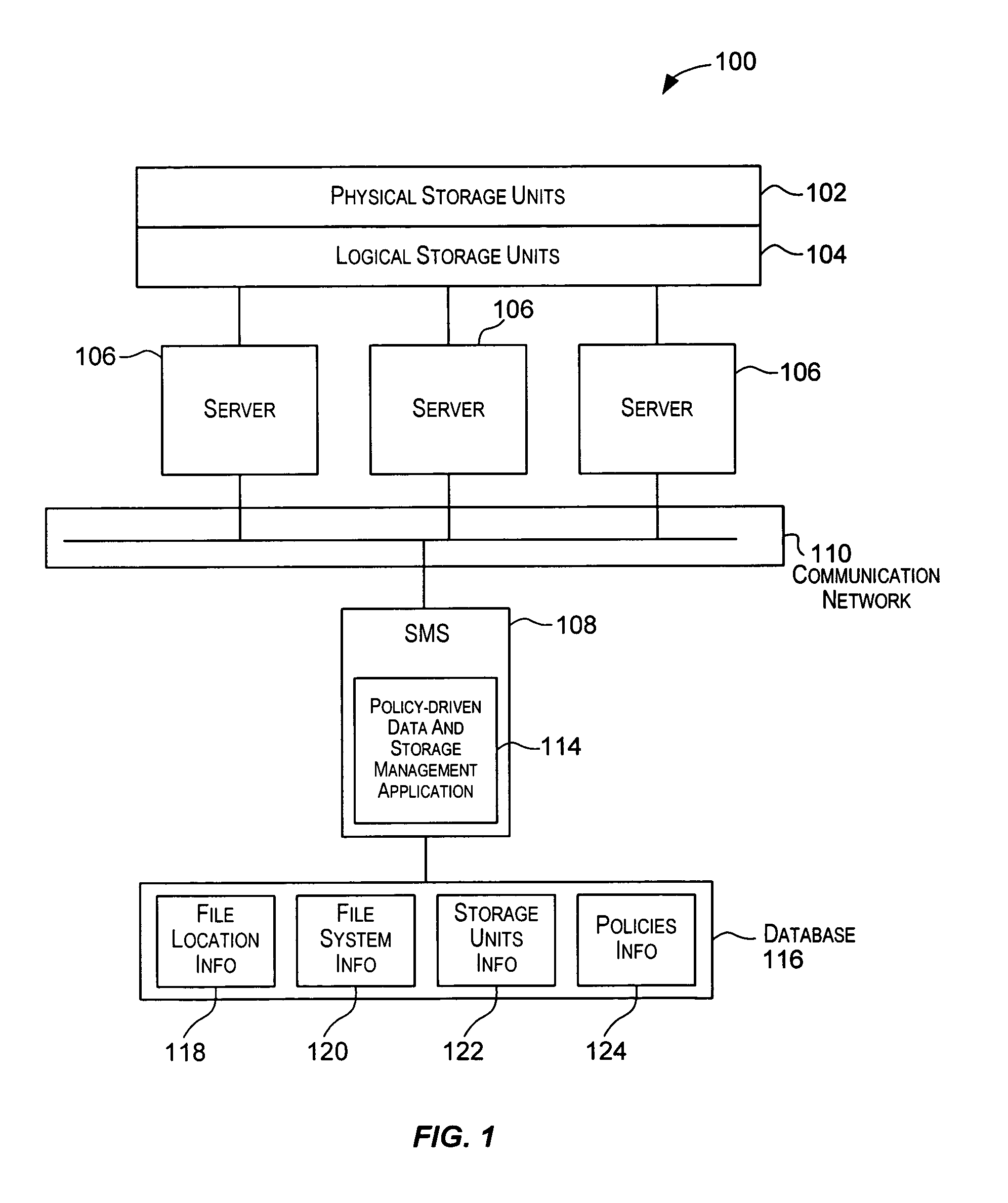
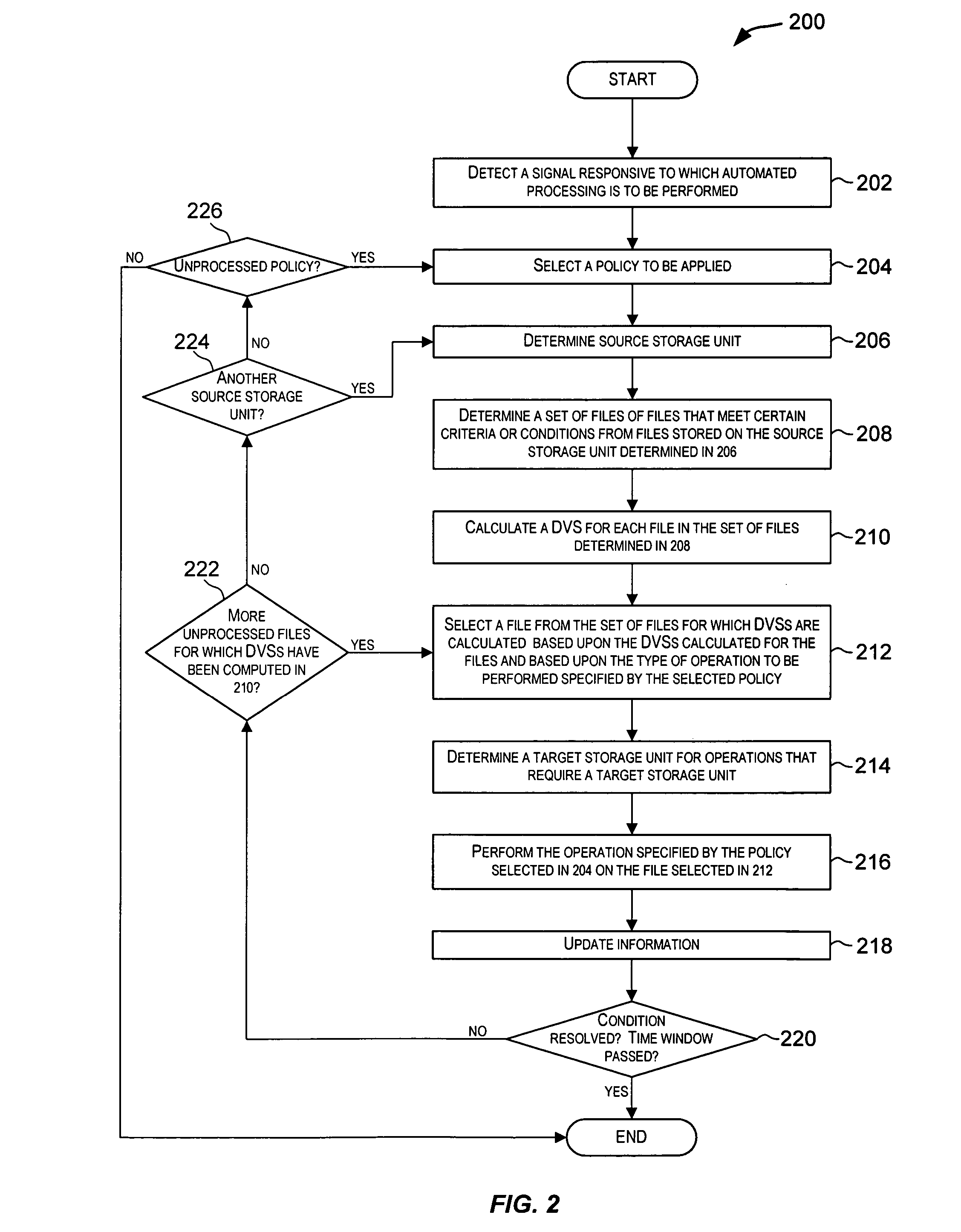
ActiveUS20050033757A1Data processing applicationsError detection/correctionStorage managementArchive file
Techniques for automatically performing various data and storage management operations in a storage environment. The operations to be performed are automatically determined based upon policies configured for the data and storage environment. For a selected operation, one or more files on which the operation is to be performed are also automatically determined. The one or more files may be selected using different techniques based upon characteristics of the files and also based upon the operation to be performed. Target storage units, if need for the operation, are also automatically determined. The operations are then performed on the selected files. Examples of policy-driven operations include copying a file, moving a file, deleting a file, archiving a file, backing-up a file, restoring a file, migrating a file, recalling a file, etc.
Owner:ROCKET SOFTWARE
System and method for manipulating and managing computer archive files
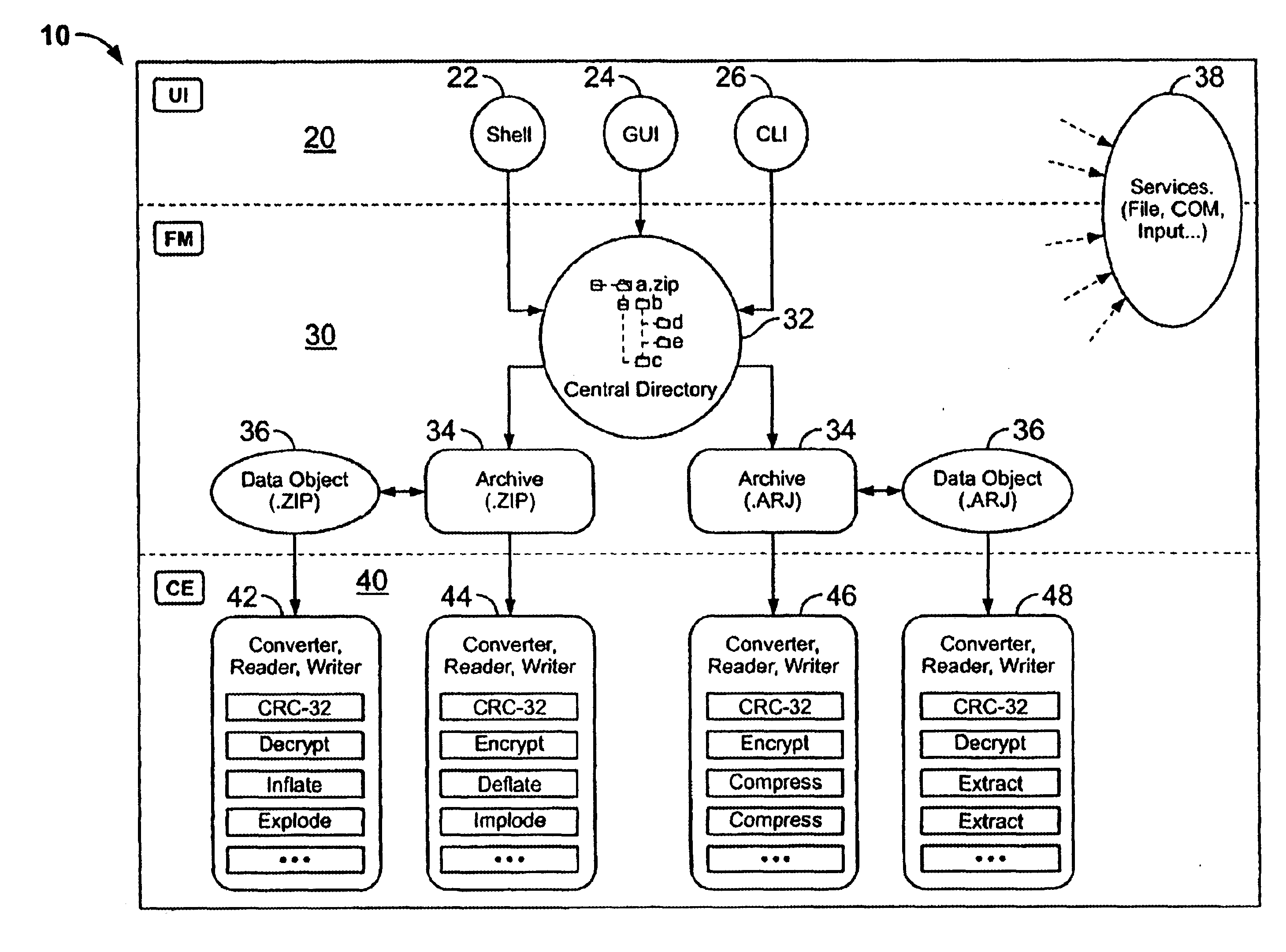
InactiveUS6879988B2Easy to carryQuick and easy management and manipulationData processing applicationsDigital data information retrievalDrag and dropResource management
A computer program for managing and manipulating archive zip files of a computer. The program includes a system and method for opening, creating, modifying, and extracting zip archive files. The program is fully integrated into Microsoft Windows Explorer and is accessed via Explorer menus, toolbars, and / or drag and drop operations. An important feature of the program is the archive manager which may be used to open a zip file, create a new zip file, extract zip files, modify zip files, etc. The program is integrated into Microsoft Windows Explorer using the shell name space extension application program interface developed by Microsoft.
Owner:PKWARE
Method and system in a computer network for bundling and launching hypertext files and associated subroutines within archive files
InactiveUS6026437AReduce download timeImprove packaging efficiencyData processing applicationsMultiple digital computer combinationsClient-sideApplication software
A method and system in a computer network for dynamically bundling and launching hypertext files within archive files, wherein the computer network includes at least one client connectable to one or more servers. Initially, an archive file is established within the computer network wherein particular subroutines are maintained. Thereafter, a particular hypertext file is associated with a selected subroutine maintained within the archive file. The particular hypertext file and the selected subroutine are subsequently bundled together within the archive file. Thereafter, the archive file is automatically transmitted to the client from a server maintained within the computer network, in response to a client request to download the hypertext file, such that the subroutine and the hypertext file are downloaded within a single selected archive file from the server, thereby reducing download time and increasing data packaging efficiency. The subroutine may be composed of an applet and the hypertext file may be based on an HTML file having tags which point to particular applets and data associated with the applets.
Owner:IBM CORP
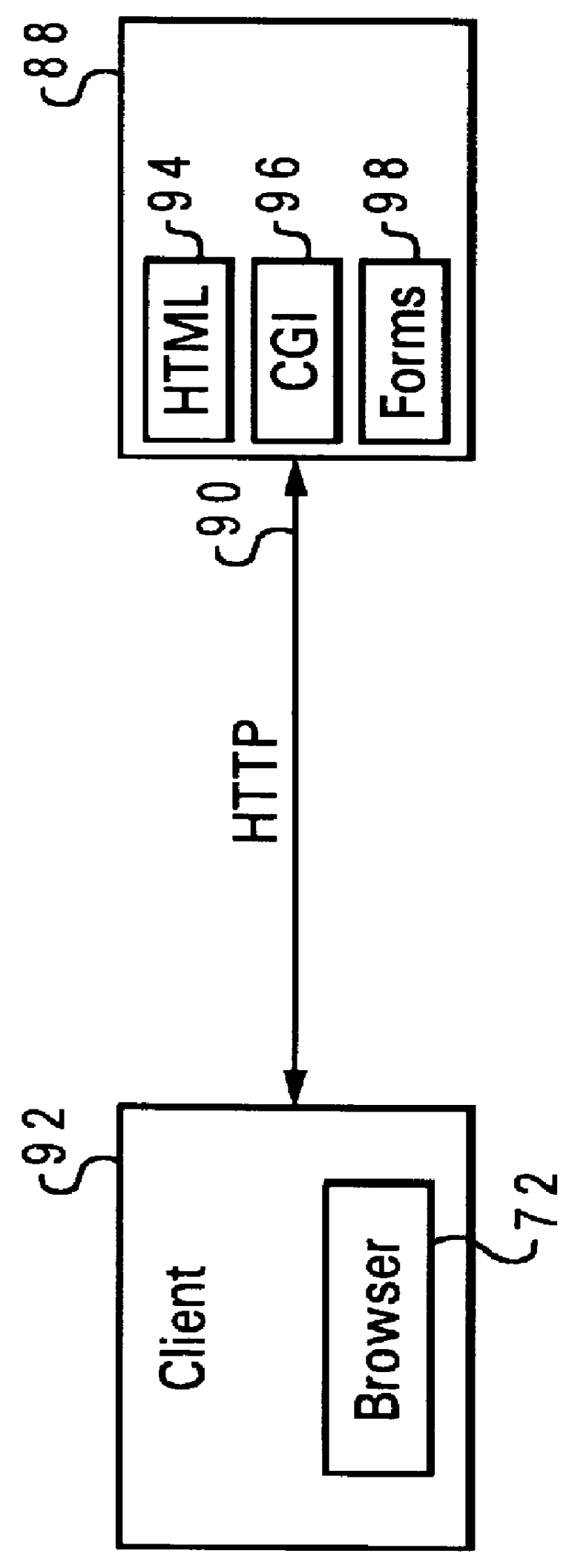
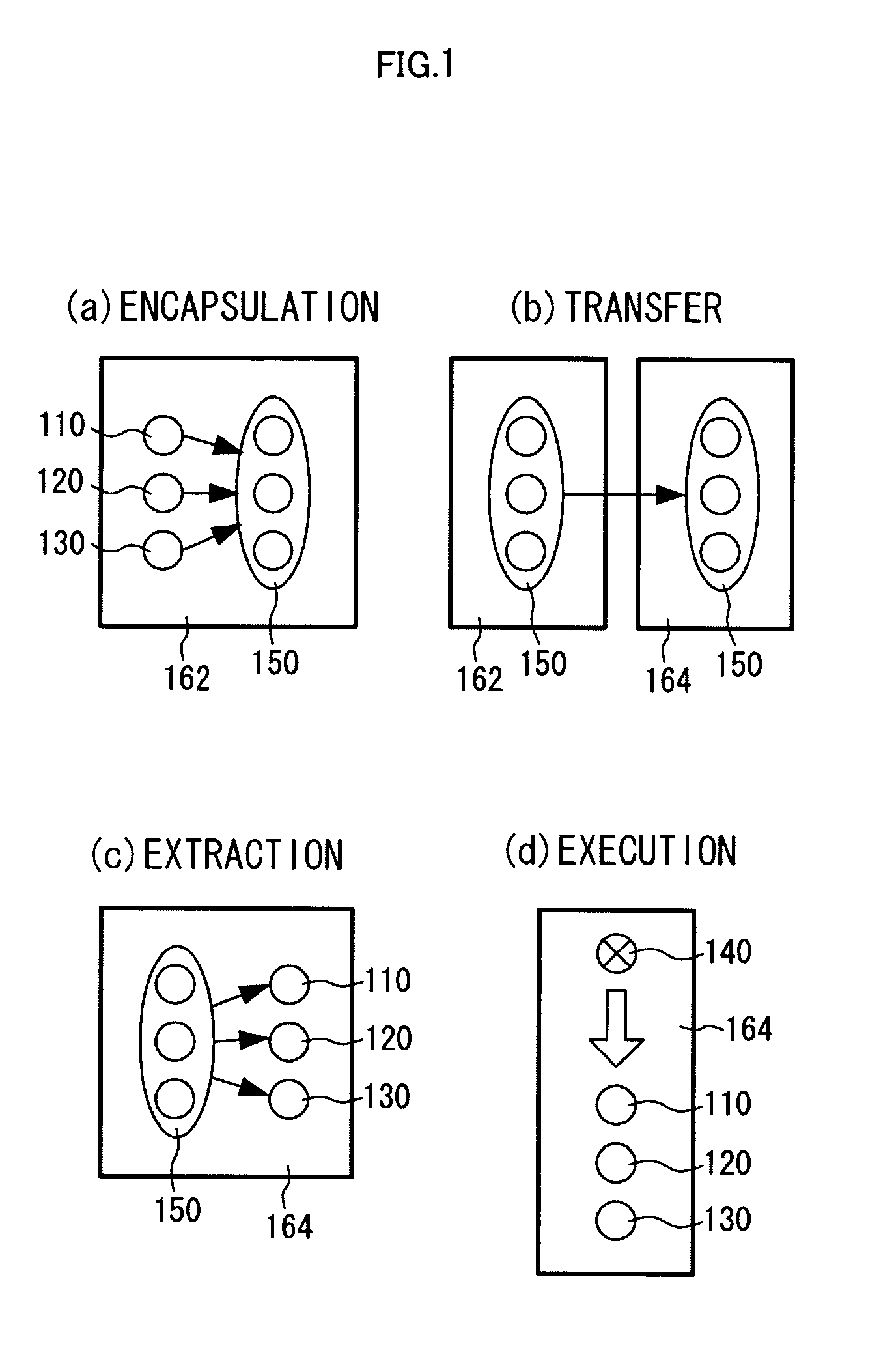
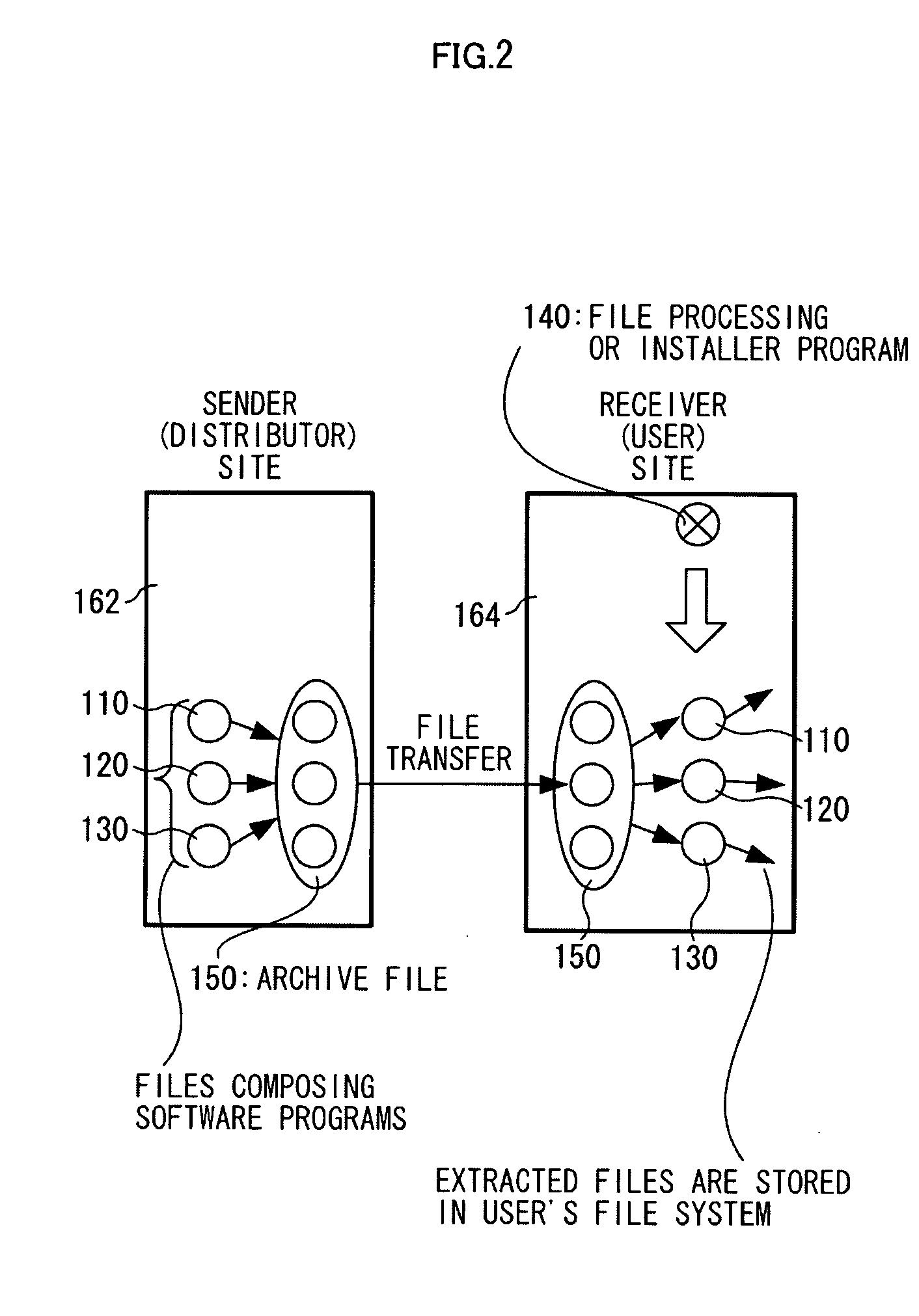
Software safety execution system
InactiveUS20050228990A1Digital data processing detailsUnauthorized memory use protectionFile systemData file
A secure software execution mechanism appropriate for software circulation is provided. At a sender site 312, an executable file 332 and a data file 334 processed by the executable file are encapsulated. The remaining two files 336 and 338 do not physically exist in a pot 320 at the sender site, and an archive file 320 is transferred to a receiver site 314. At the receiver site 314, intangible files 336 and 338 within a pot may be mapped to a file 354 in a local file system or a file 356 within another pot 350 and processed using a file 334 in a pot or the mapped file 354 or 356 by executing a program 332, in conformity with the specification of a security policy 340.
Owner:JAPAN SCI & TECH CORP
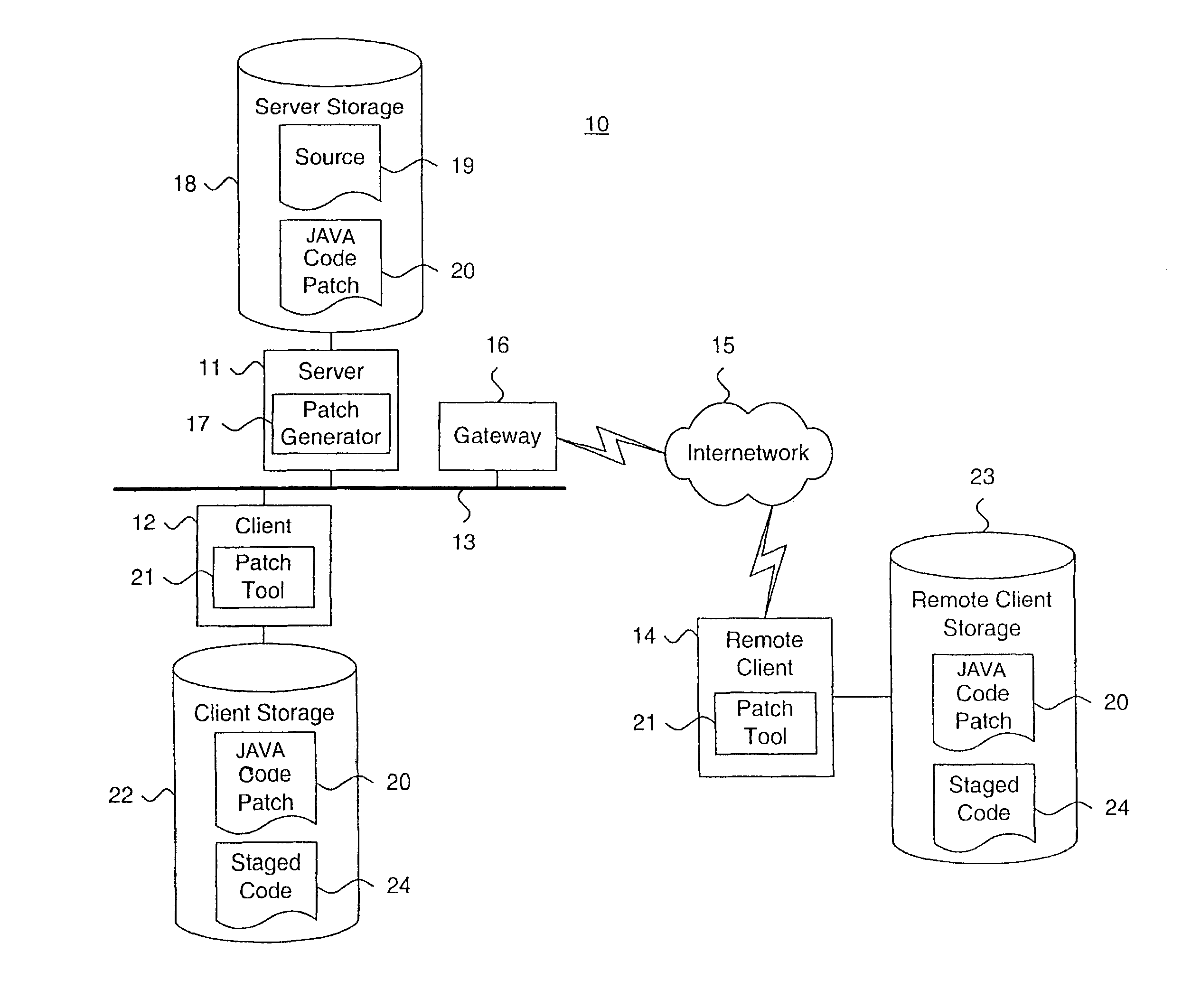
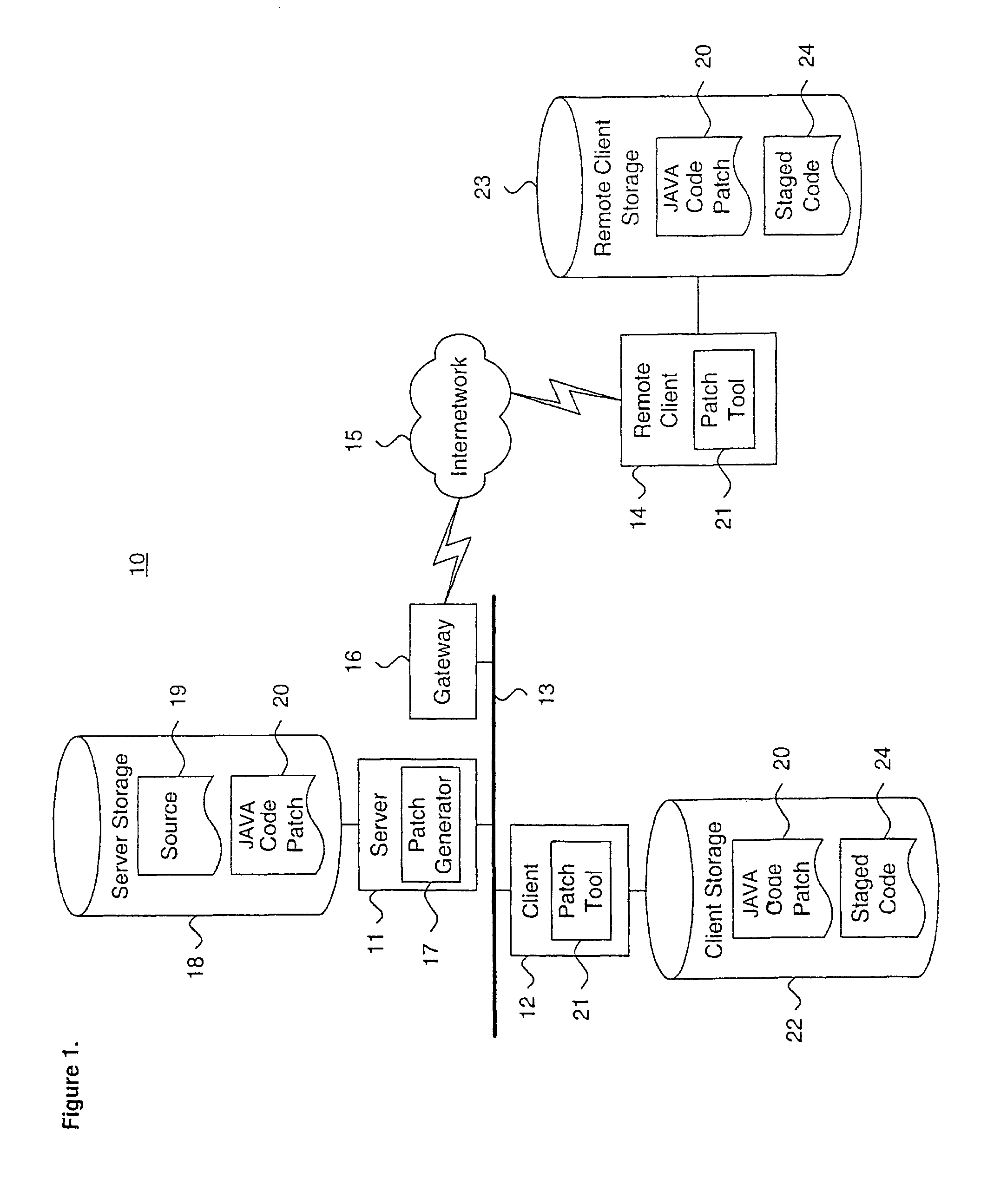
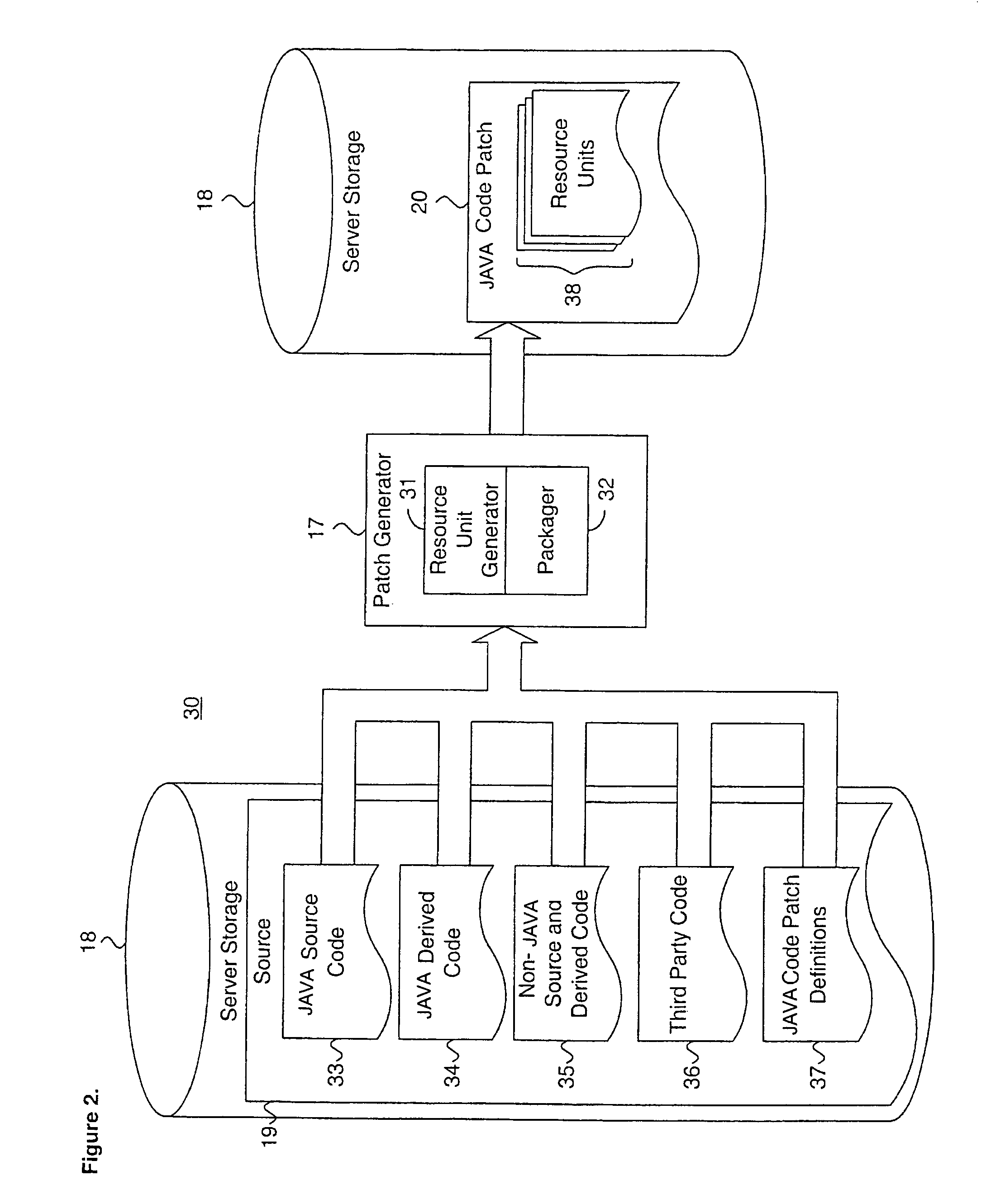
System and method for providing a java code release infrastructure with granular code patching
InactiveUS7127712B1Specific program execution arrangementsMemory systemsThird partyDigital signature
A system and method for providing a code release infrastructure with granular code patching is described. Code patches, each including at least one resource unit are provided. Each resource unit includes metadata and file components. Code libraries, each including at least one resource unit, are patched. The metadata for each resource unit in the code patches is compared to the metadata for each such corresponding resource unit in the code libraries. Each resource unit in the code patches is merged into the code libraries for each such corresponding resource unit that is out-of-date as defined by merge rules. Archive files, as defined by archive file definitions, are created or updated using the resource units from the code libraries, or, optionally, are deleted. The archive files are digitally signed also as required. The system and method enables source and derived code and third party code to be patched granularly.
Owner:ORACLE INT CORP
Reliable embedded file content addressing
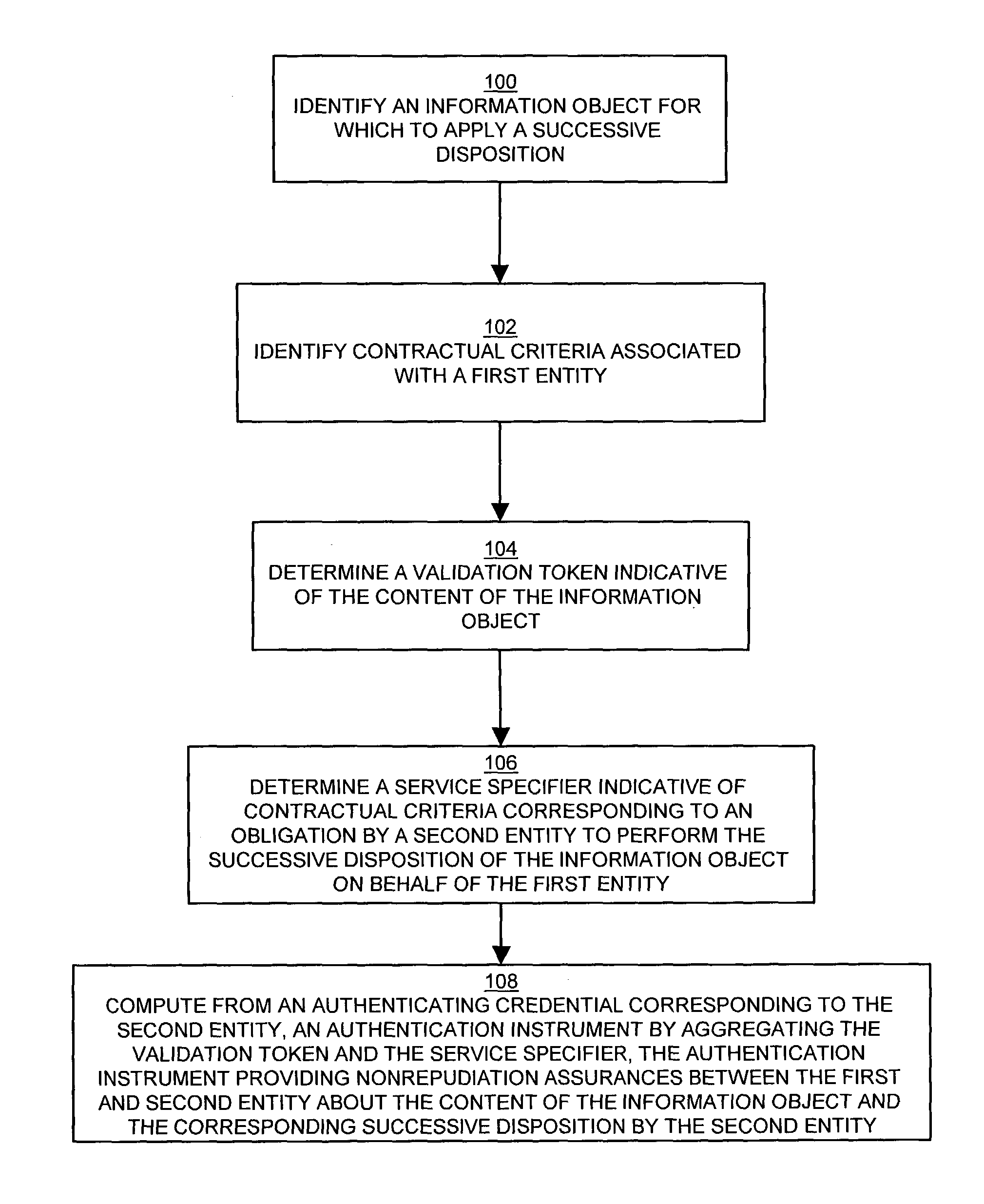
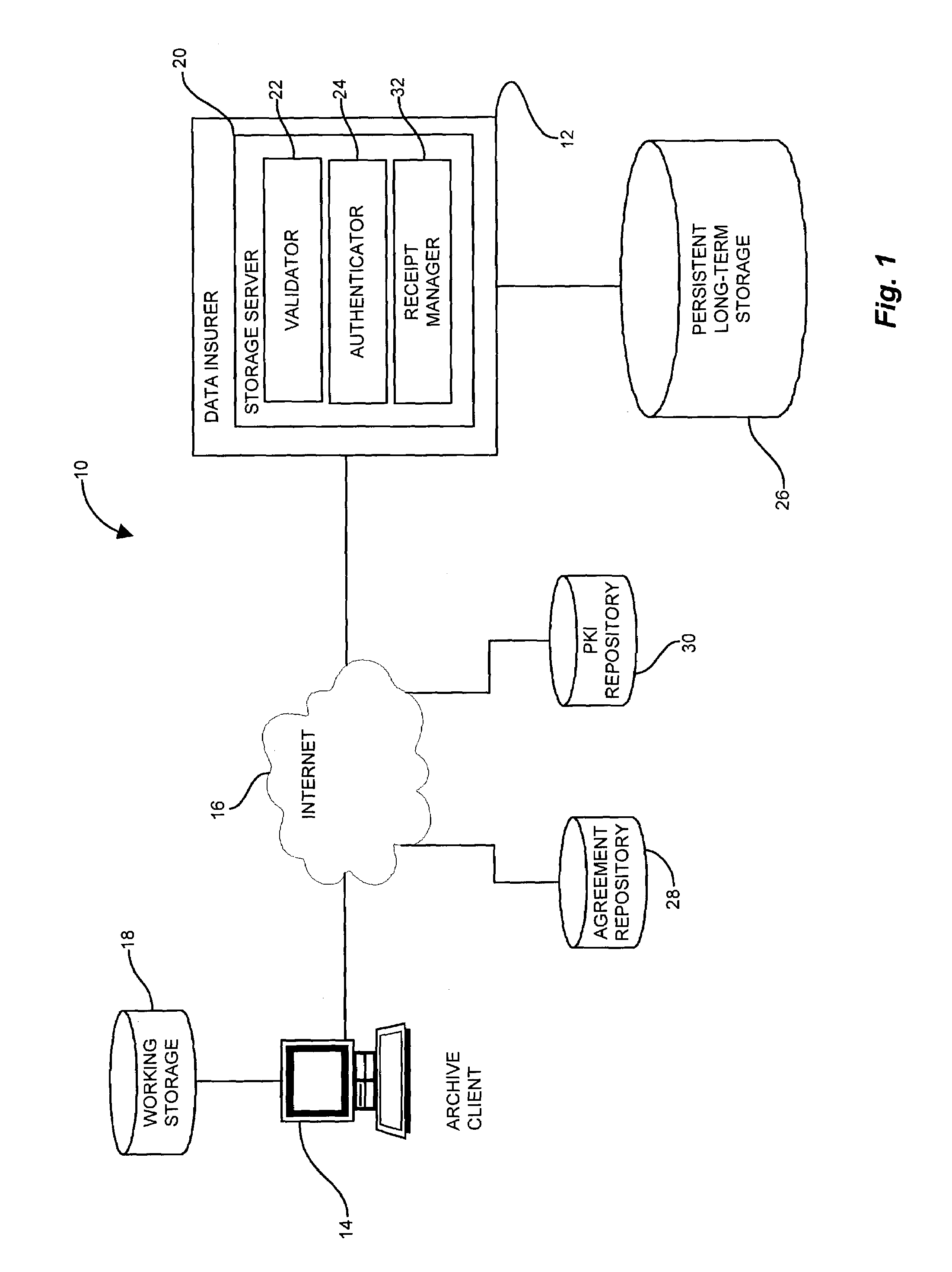
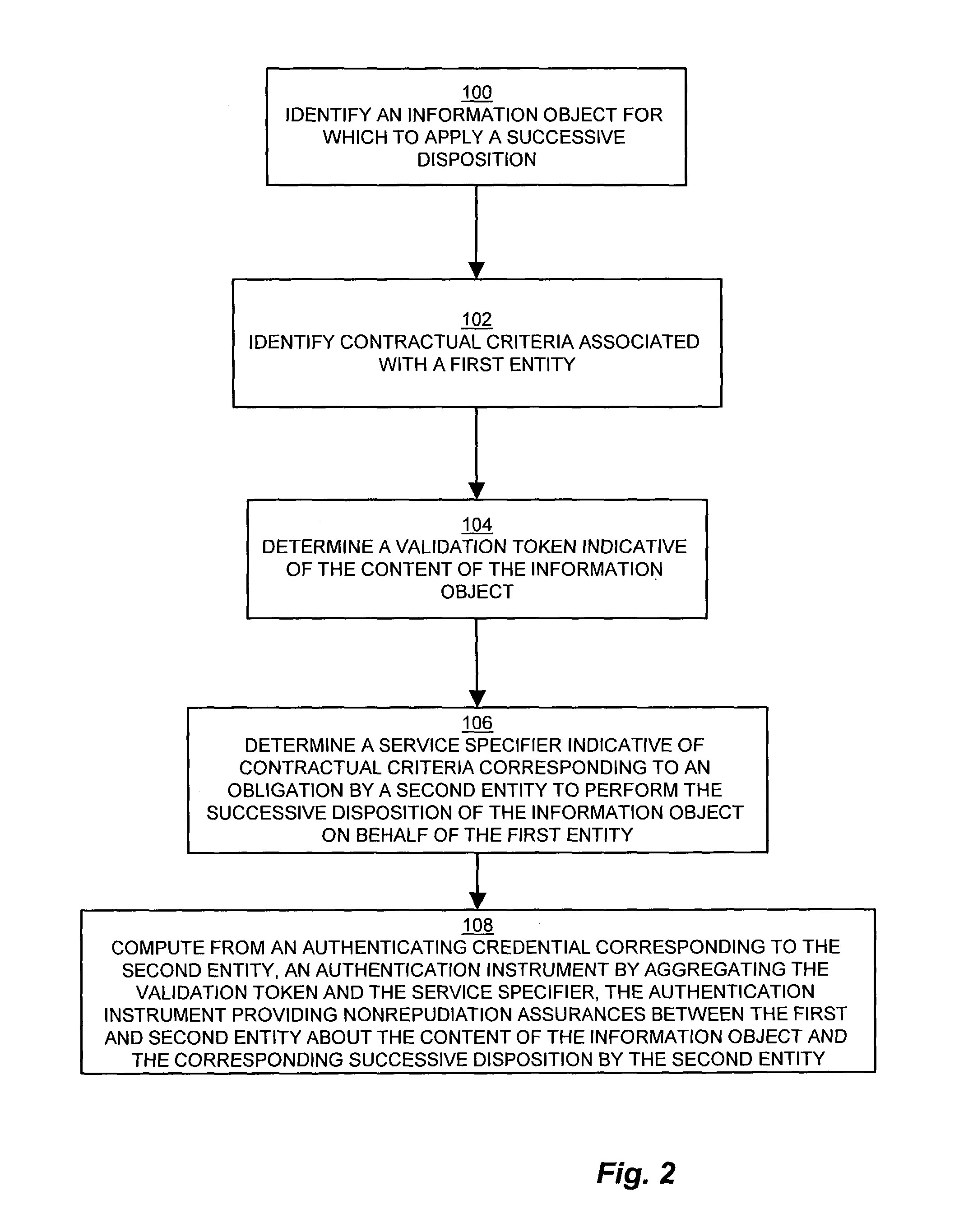
InactiveUS7269733B1Digital data processing detailsUser identity/authority verificationContractual AgreementGranularity
Conventional archive and retrieval systems inadequately identify the archival data with sufficient granularity to associate data items with retrieval performance, and do not define a recourse following loss of archived data. A method for file archiving, identification, and failure recourse facilitates successive disposition by generating an authenticated receipt of files transferred for storage via an authentication instrument that is verifiable towards both the data stored and a corresponding agreement. The authenticated receipt provides nonrepudiation assurances about the content of the file and the contractual terms under which the file was stored via an authenticating signature of the archive storage server which associates the file content with the contractual terms. The nonrepudiation assurances allow verification of the content of the archived file through a checksum or hash, and the authenticated receipt further indicates the terms of the contractual agreement for recourse by the client depositor in the event of loss of the file.
Owner:CISCO TECH INC
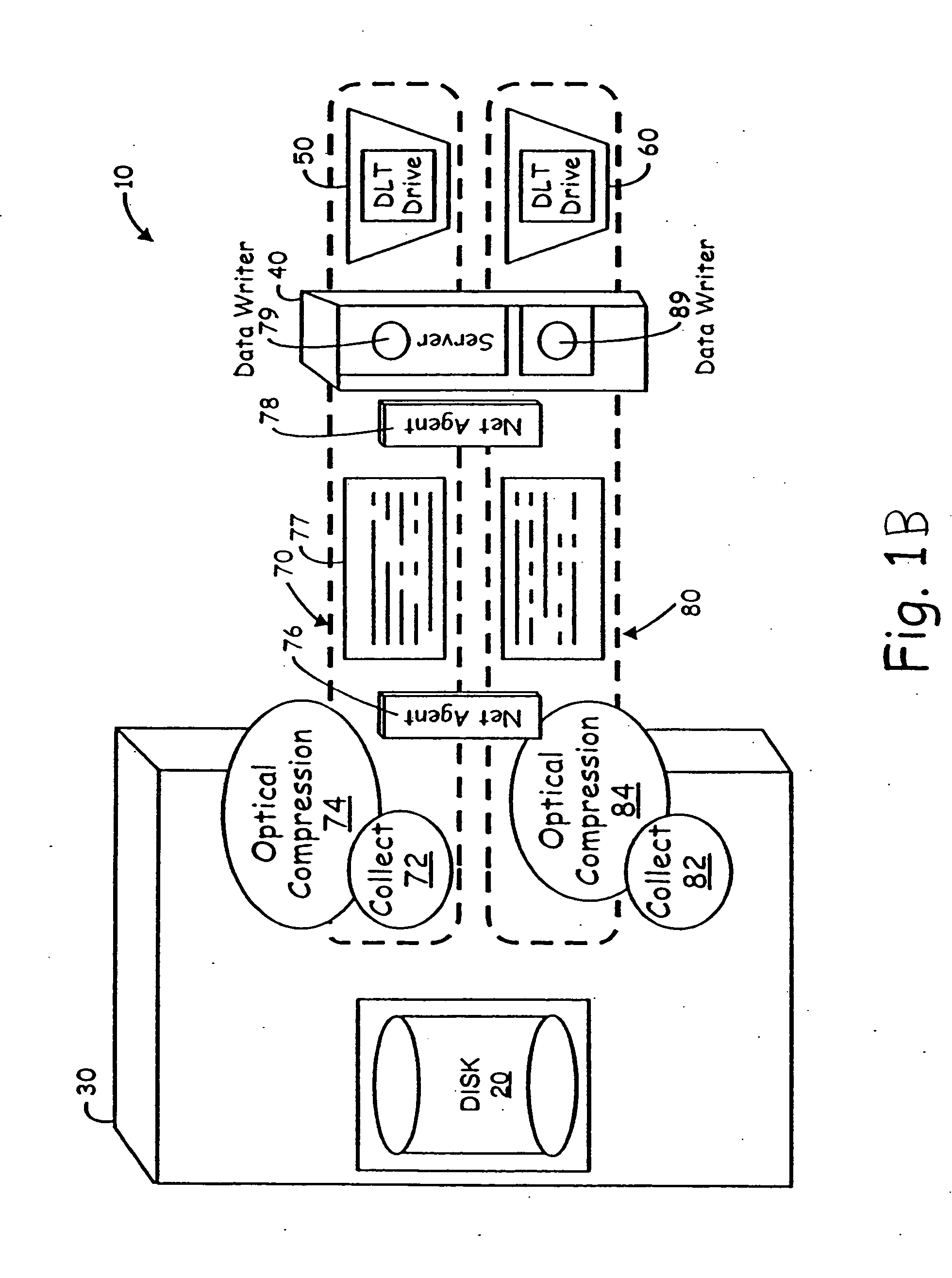
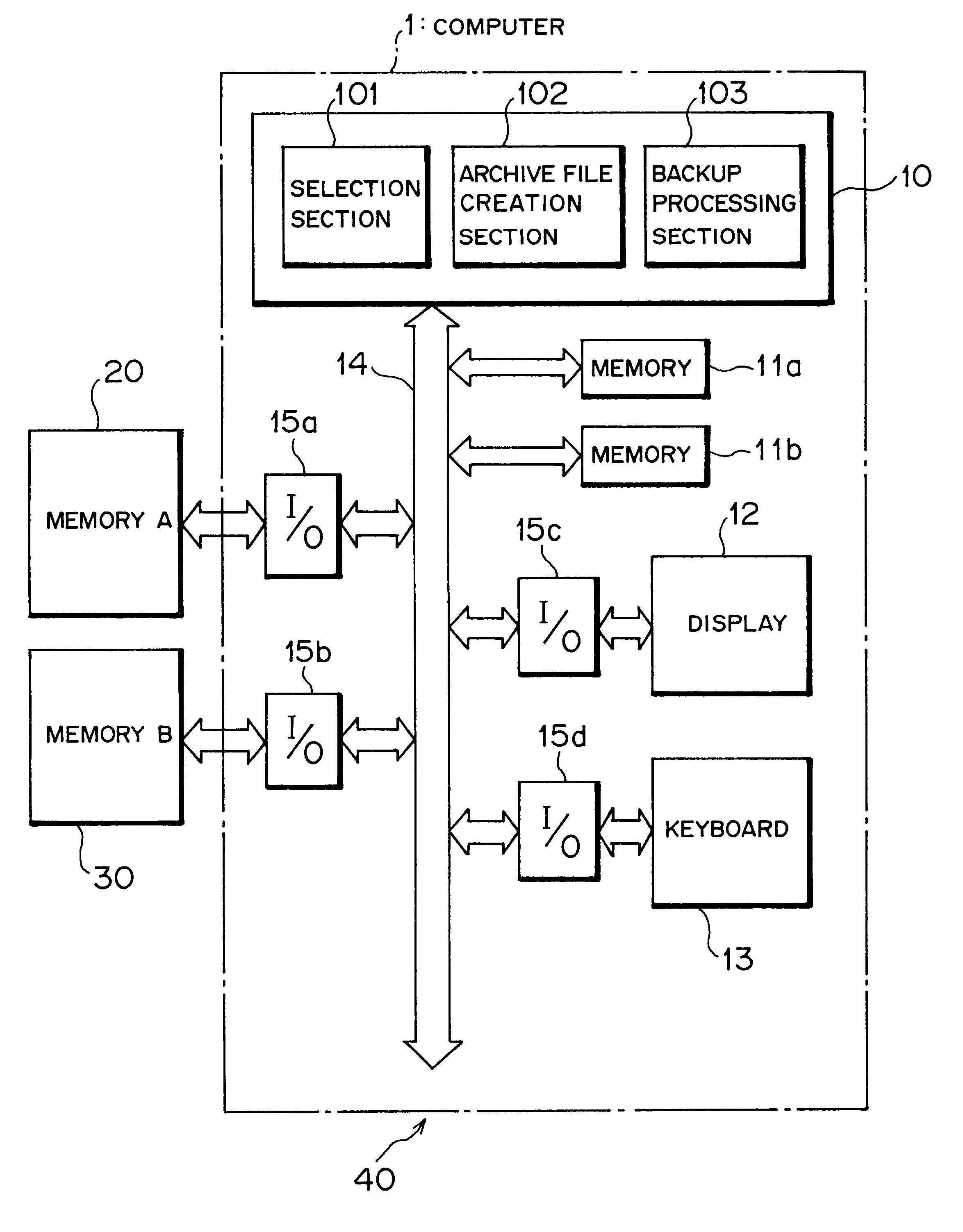
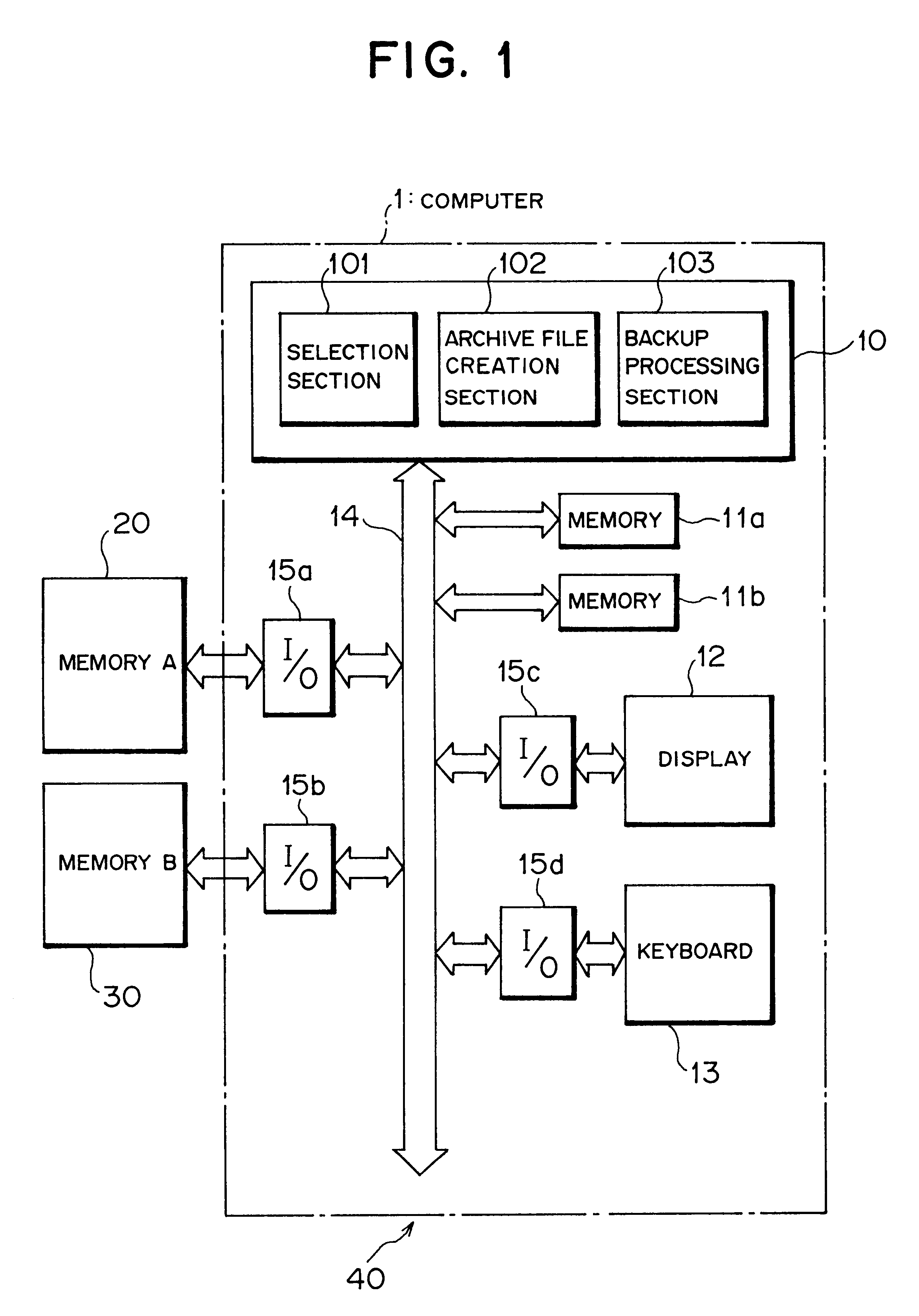
Data backup device and method for use with a computer, and computer-readable recording medium having data backup program recorded thereon
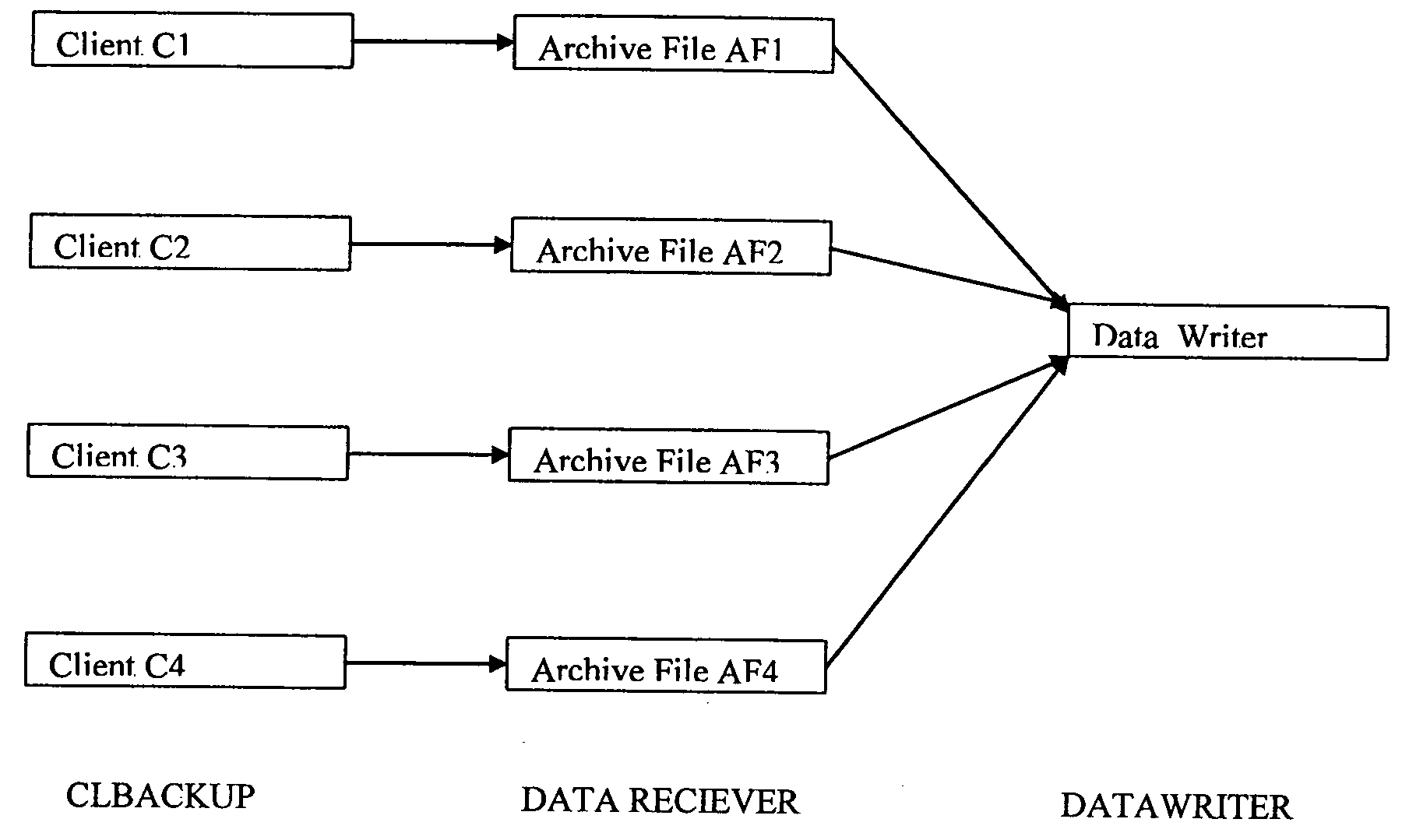
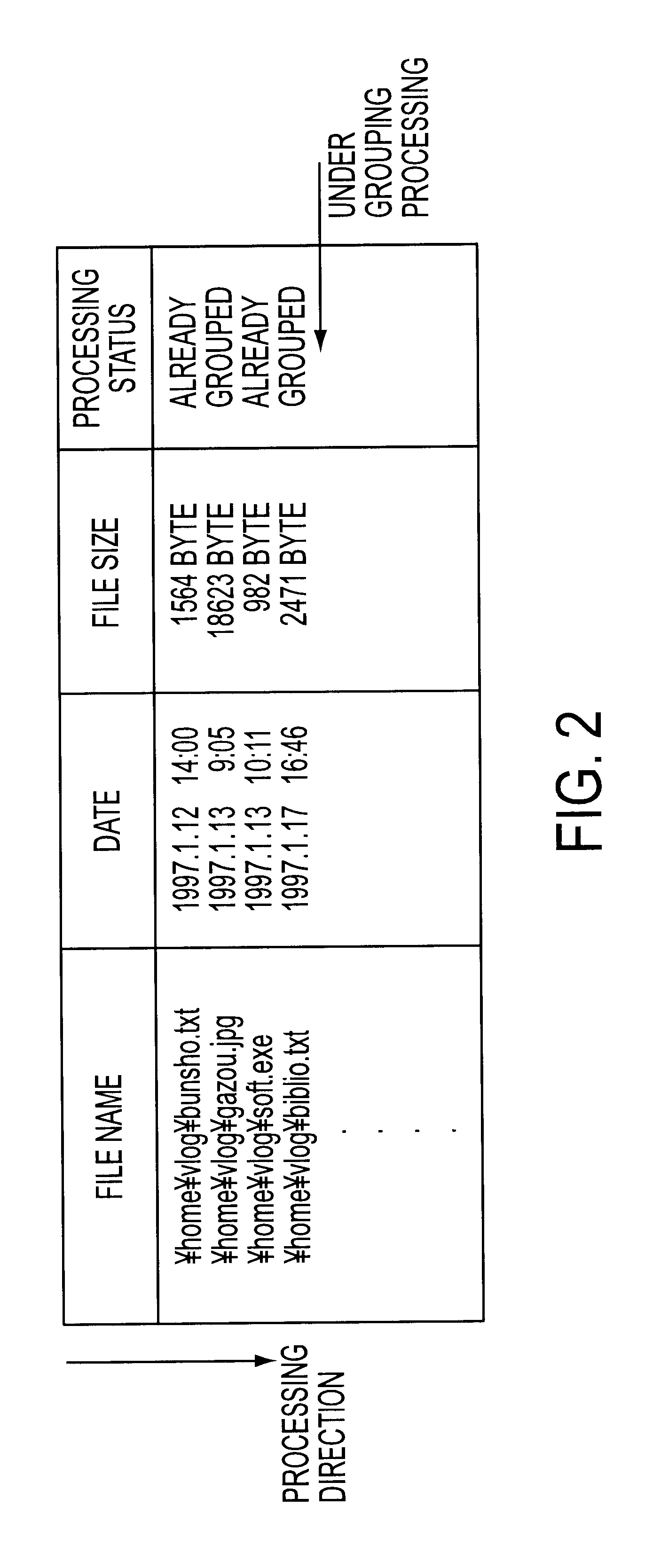
A technique related to a data backup for a computer. There are provided a selection section, an archive file creation section, and a backup processing section. The selection section selects data files satisfying given conditions from among data files stored in a first storage section. The archive file creation section creates N (N is a natural number) archive files by grouping the plurality of data files selected by the selection section and which repeats the archive file creation processing M (M is a natural number) times. The backup processing section stores the archive files created by the archive file creation section into a second storage section. The technique enables efficient copying of a data file in a short period of time.
Owner:FUJITSU LTD
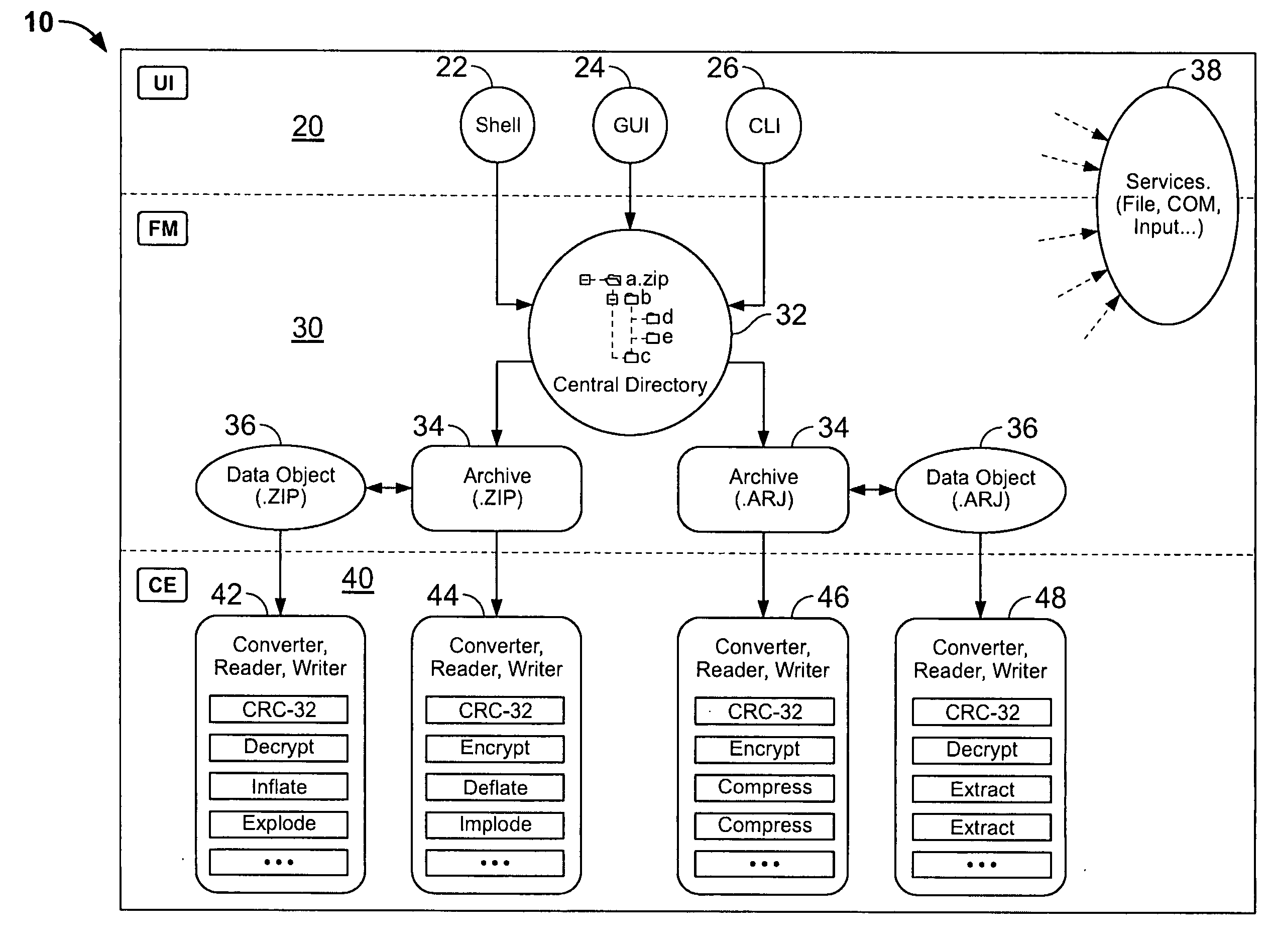
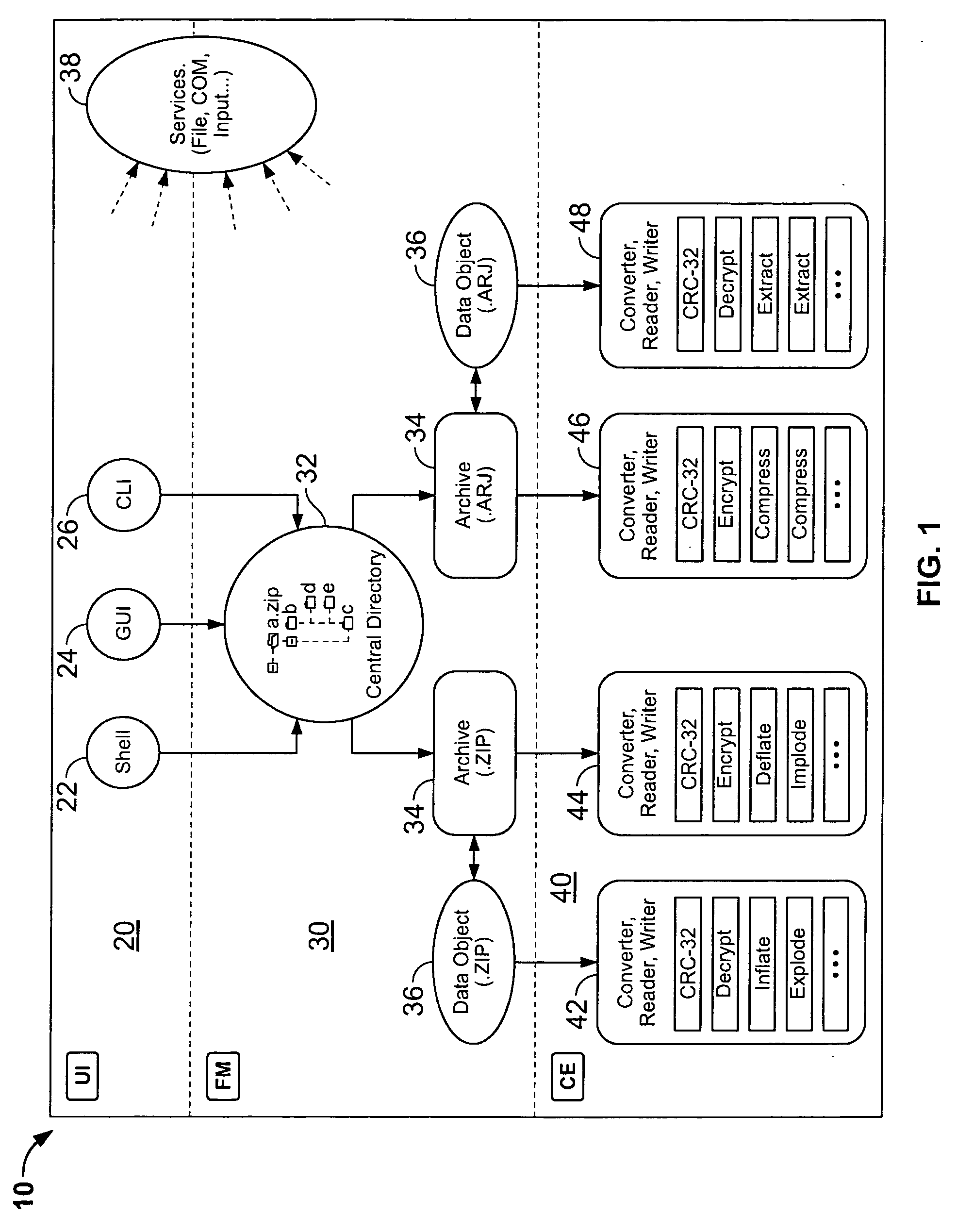
System and method for manipulating and managing computer archive files
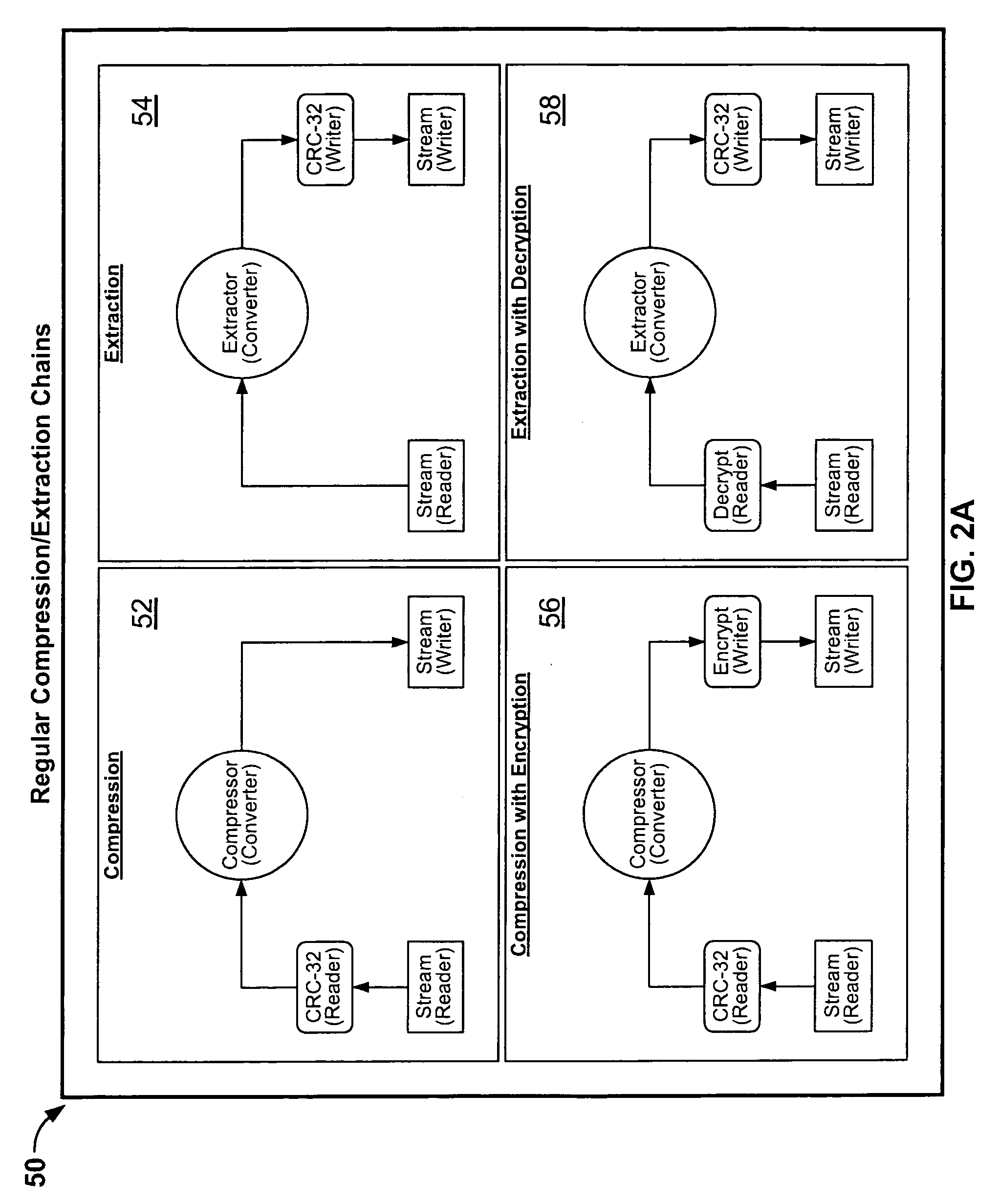
InactiveUS20060143714A1Digital data information retrievalDigital data processing detailsDigital signatureFile size
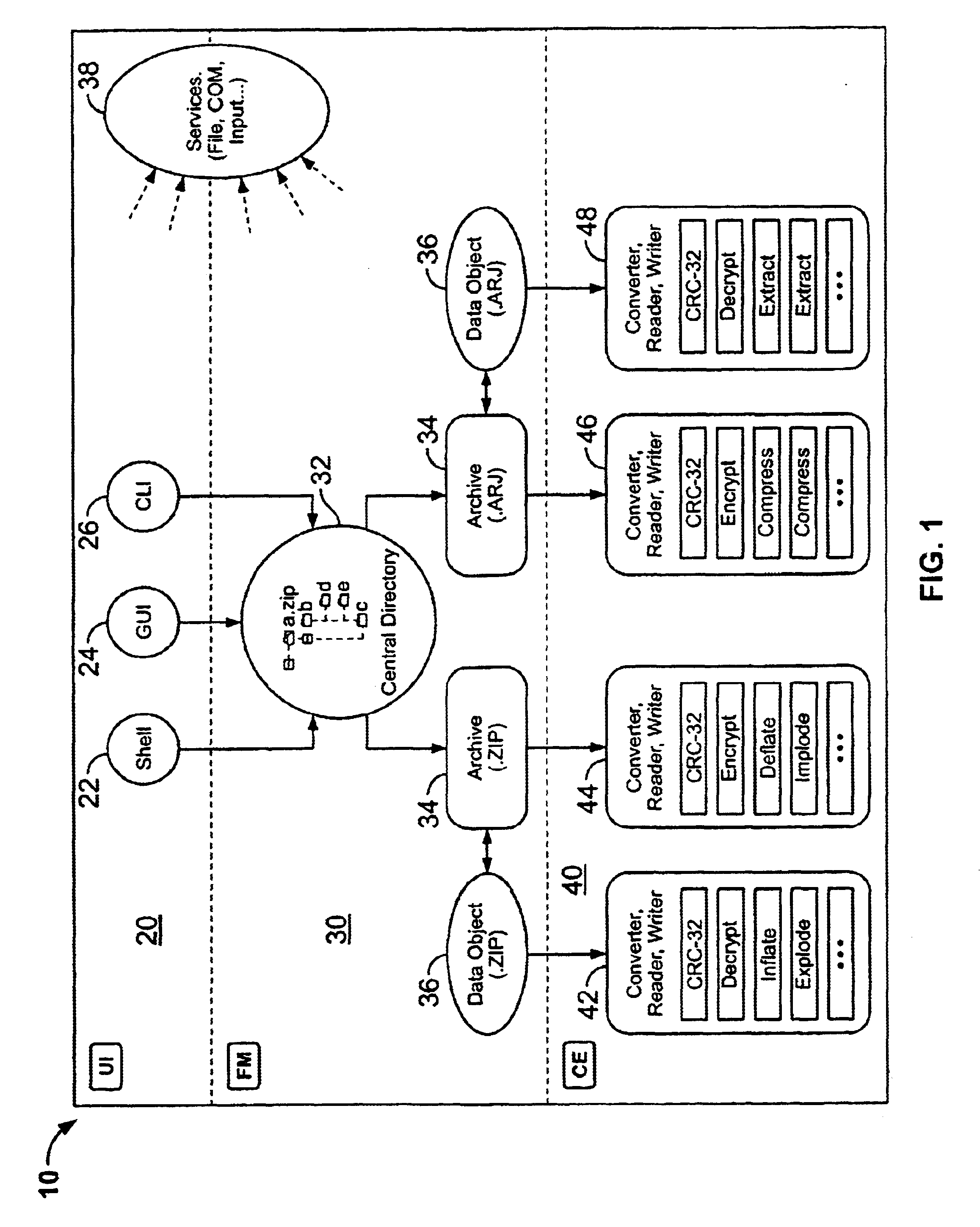
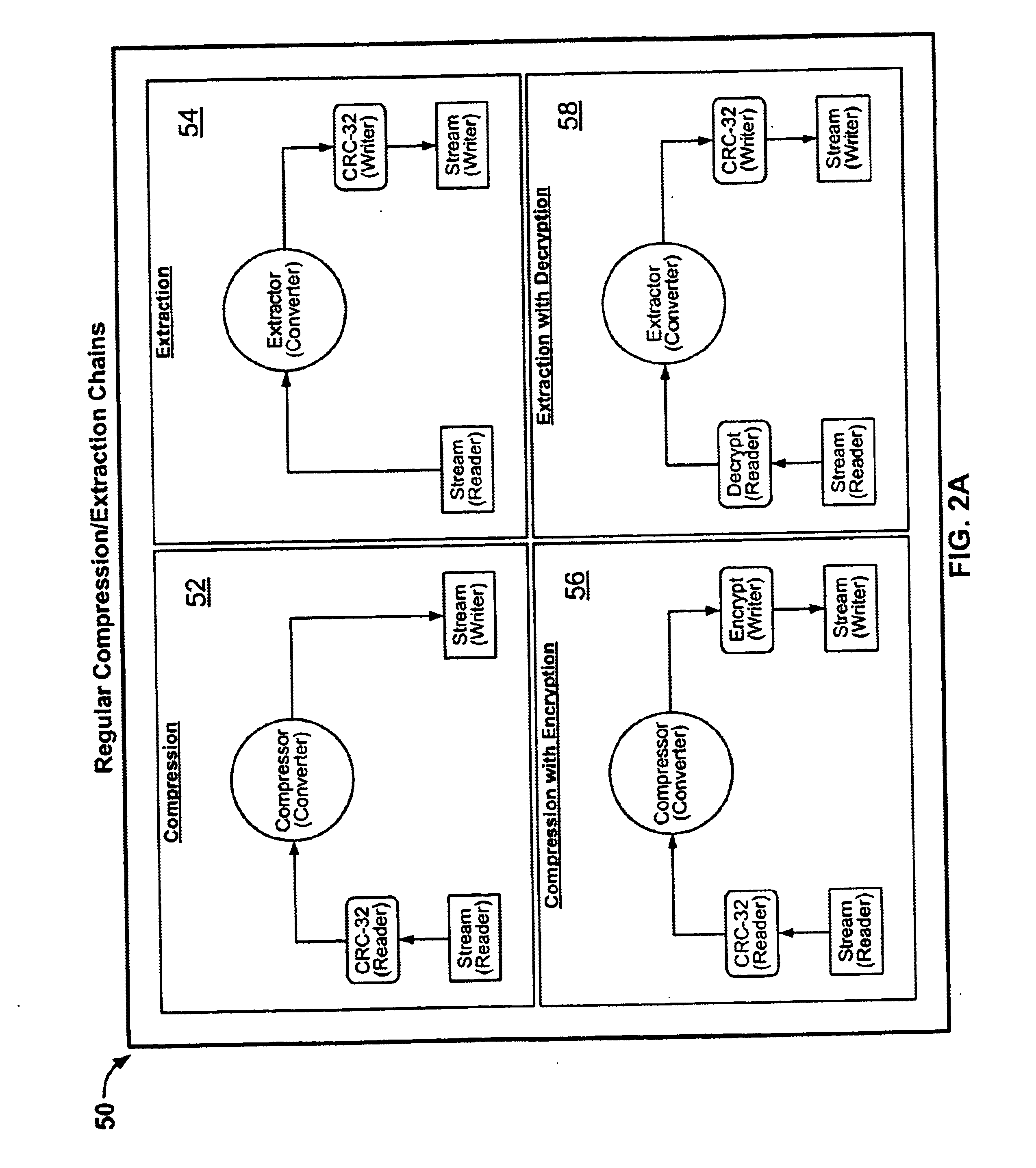
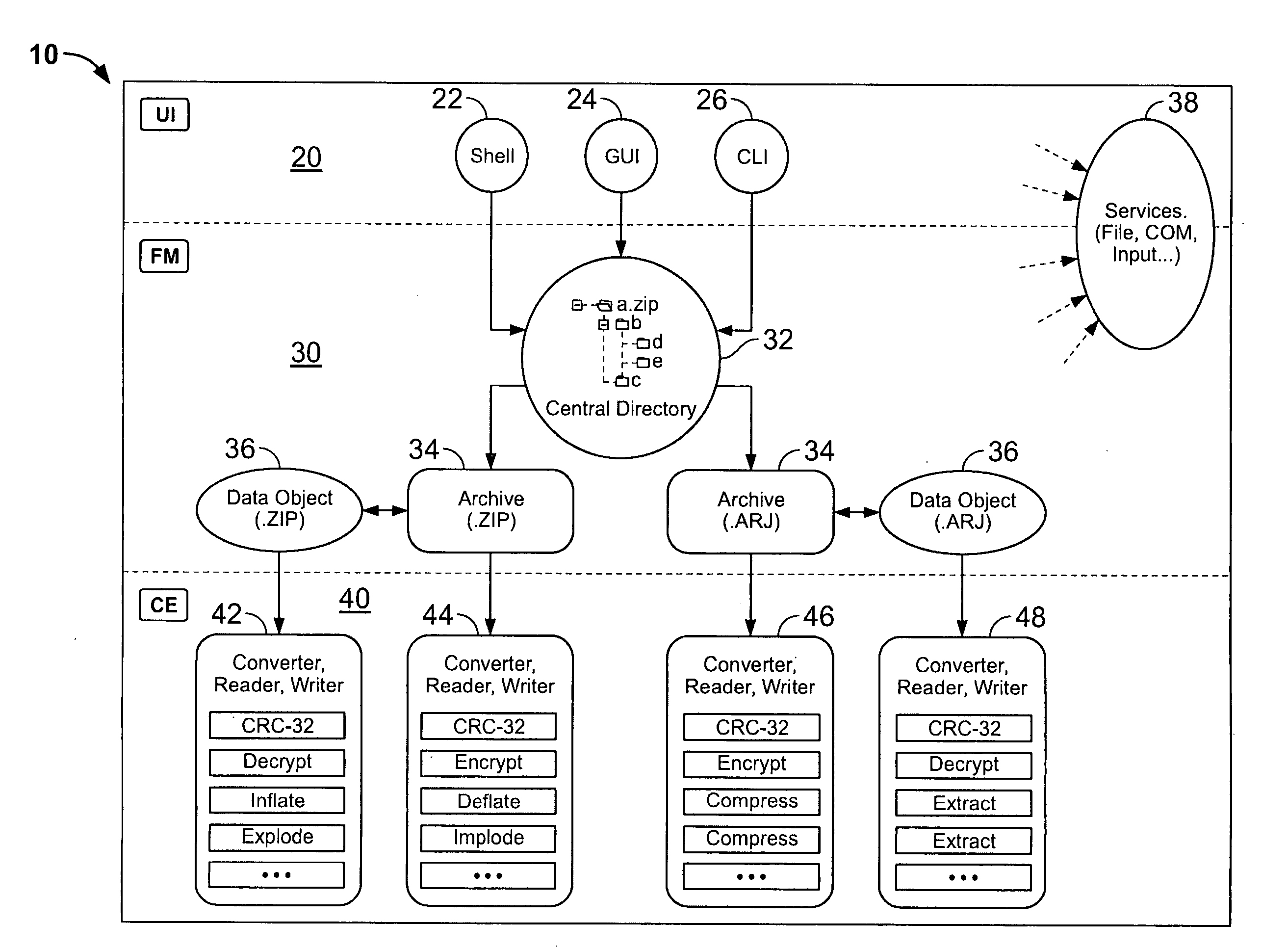
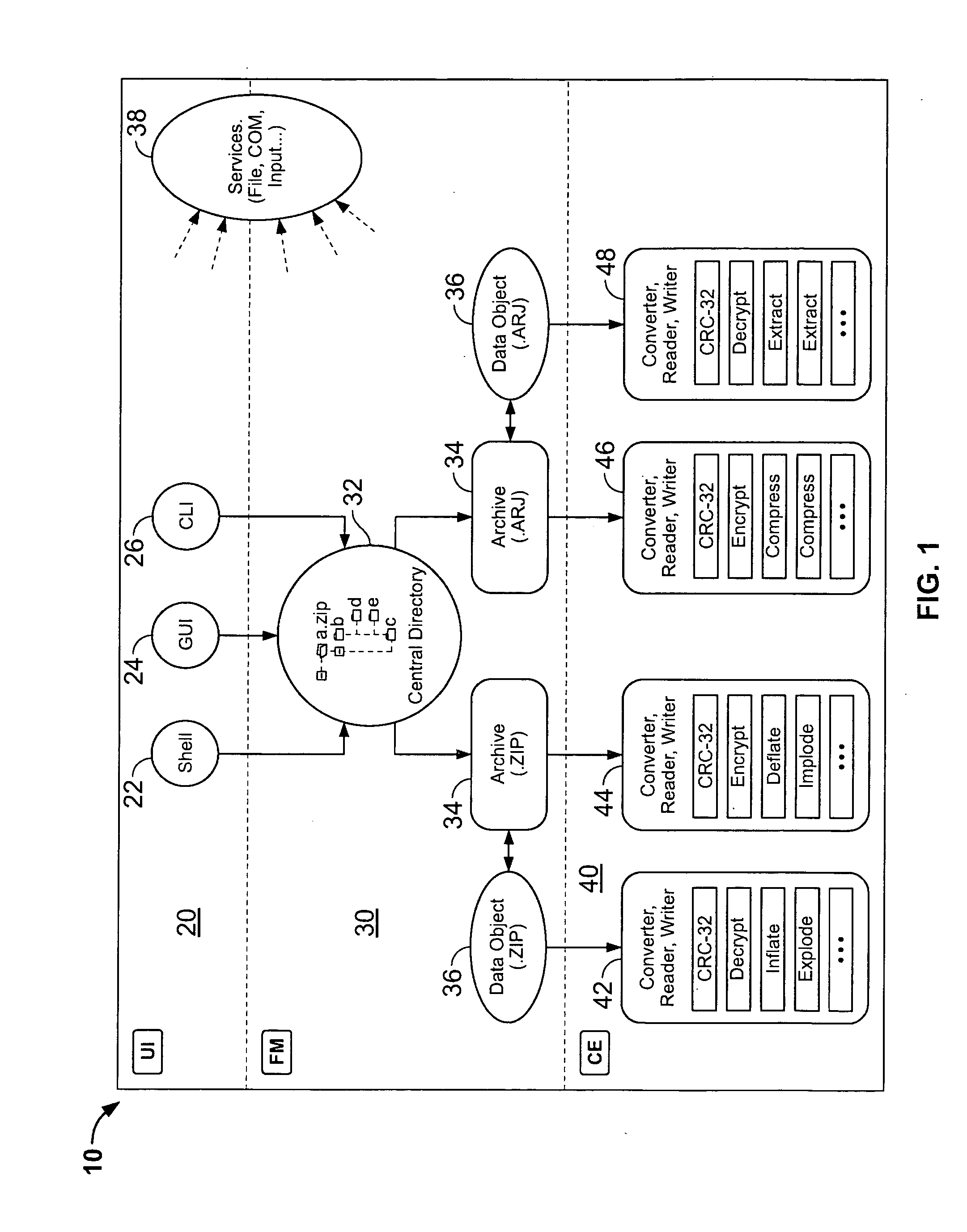
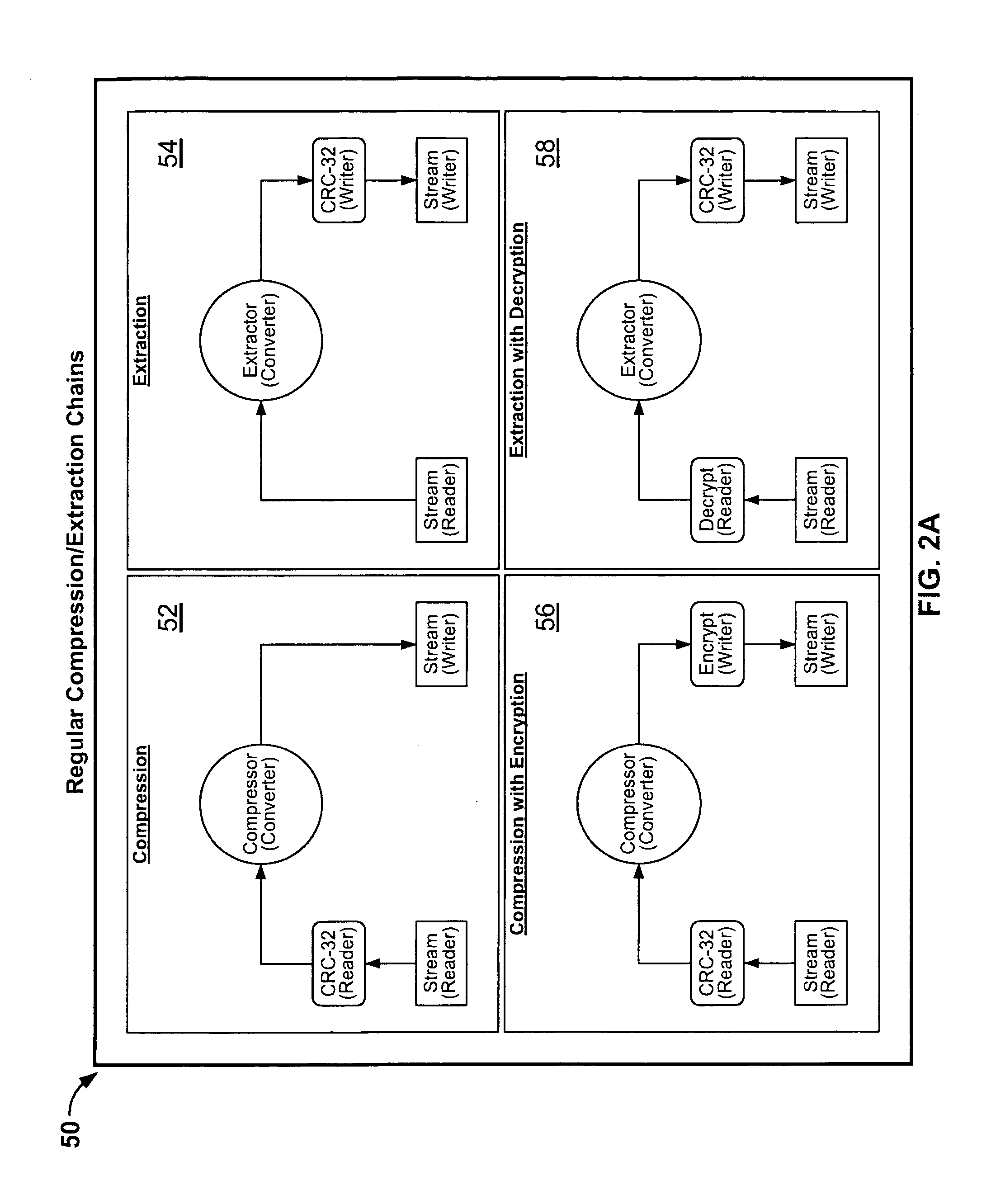
Certain embodiments of the present invention provide an archive management application that operates within a host application to provide access to an archive and / or allow access to and / or modification of files in an archive using the host application's interface, instead of operating as a separate standalone archive management application. In an embodiment of the present invention, a file archiving system may include a user interface component, a file management component and a compression / extraction engine component. The user interface component may include an enhanced user interface of a host application that provides an interface for a user. The file management component may include a central directory that provides a representation of the contents of an archive. The compression / extraction engine component may include a file size module and / or a security module. The file size module may be used to compress and / or decompress a file in an archive. The security module may be used to encrypt, decrypt, digitally sign and / or authenticate a file in an archive.
Owner:PKWARE
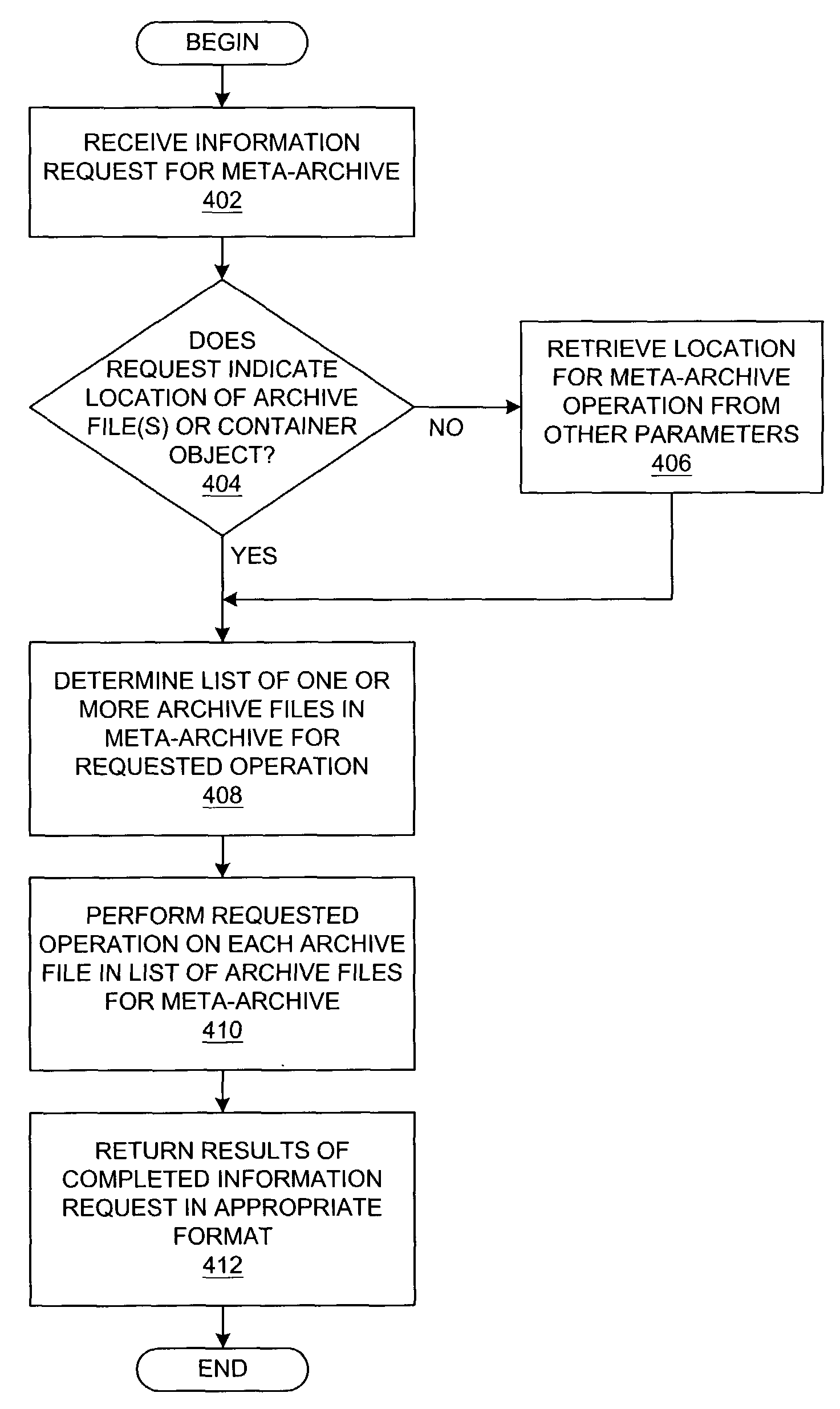
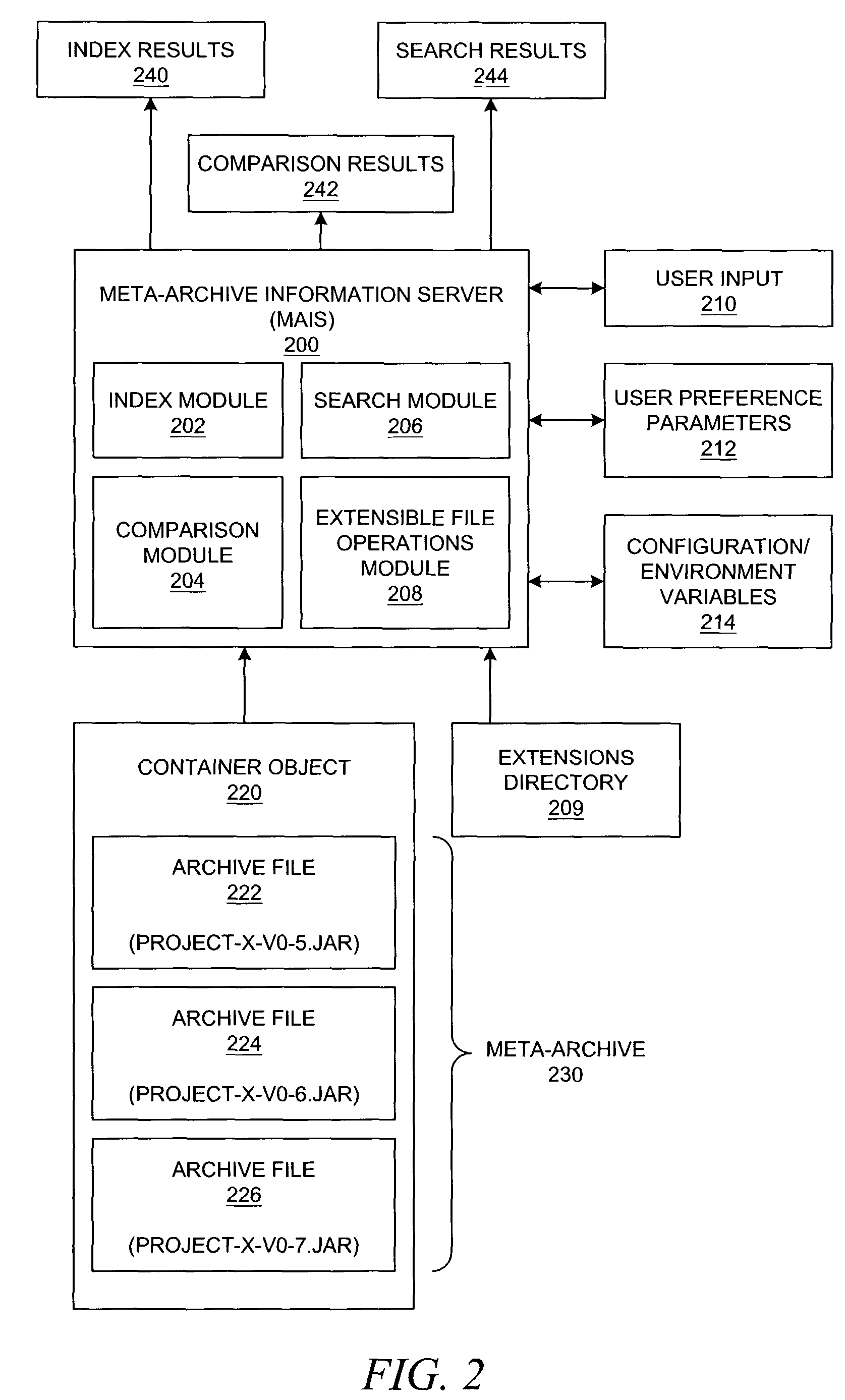
Method and system for information processing using meta-archives
InactiveUS7925661B2Reducing file system disorganizationGuaranteed uptimeWeb data indexingDigital data processing detailsInformation processingContainer Object
A method, system, apparatus, and computer program product are presented for a meta-archive information server that provides a set of operations or services for obtaining information from a meta-archive; these operations may include dynamic indexing, searching, comparing, or other operations. A meta-archive is a set of one or more archive files that are logically grouped in (or otherwise associated with) a container object, e.g., a file system folder, a directory, or another archive file. By allowing a user to derive sets of information from an entire meta-archive, a user can maintain more files within archives, thereby reducing file system disorganization. The meta-archive information server can be easily run over a specific meta-archive when necessary, thereby generating information dynamically, even if the archive files within a meta-archive change over time.
Owner:IBM CORP
System and method for providing encryption in pipelined storage operations in a storage network
InactiveUS20080037777A1User identity/authority verificationComputer security arrangementsComputer hardwareData stream
In accordance with embodiments of the invention, a method is provided for performing a storage operation in a pipeline storage system in which one or more data streams containing data to be stored are written into data chunks. The method includes generating an encryption key associated with a first archive file to be stored when encryption is requested for the storage operation, encrypting the archive data from the data stream using the encryption key to create an encrypted data chunk when a data stream containing the archive file is processed in the pipeline storage system, storing the encrypted data chunk on a storage medium, and storing the encryption key in a manner accessible during a restore operation of the encrypted data chunk.
Owner:COMMVAULT SYST INC
System and method for manipulating and managing computer archive files
Certain embodiments of the present invention provide an archive management application that operates within a host application to provide access to an archive and / or allow access to and / or modification of files in an archive using the host application's interface, instead of operating as a separate standalone archive management application. In an embodiment of the present invention, a file archiving system may include a user interface component, a file management component and a compression / extraction engine component. The user interface component may include an enhanced user interface of a host application that provides an interface for a user. The file management component may include a central directory that provides a representation of the contents of an archive. The compression / extraction engine component may include a file size module and / or a security module. The file size module may be used to compress and / or decompress a file in an archive. The security module may be used to encrypt, decrypt, digitally sign and / or authenticate a file in an archive.
Owner:PKWARE
Terminal access method
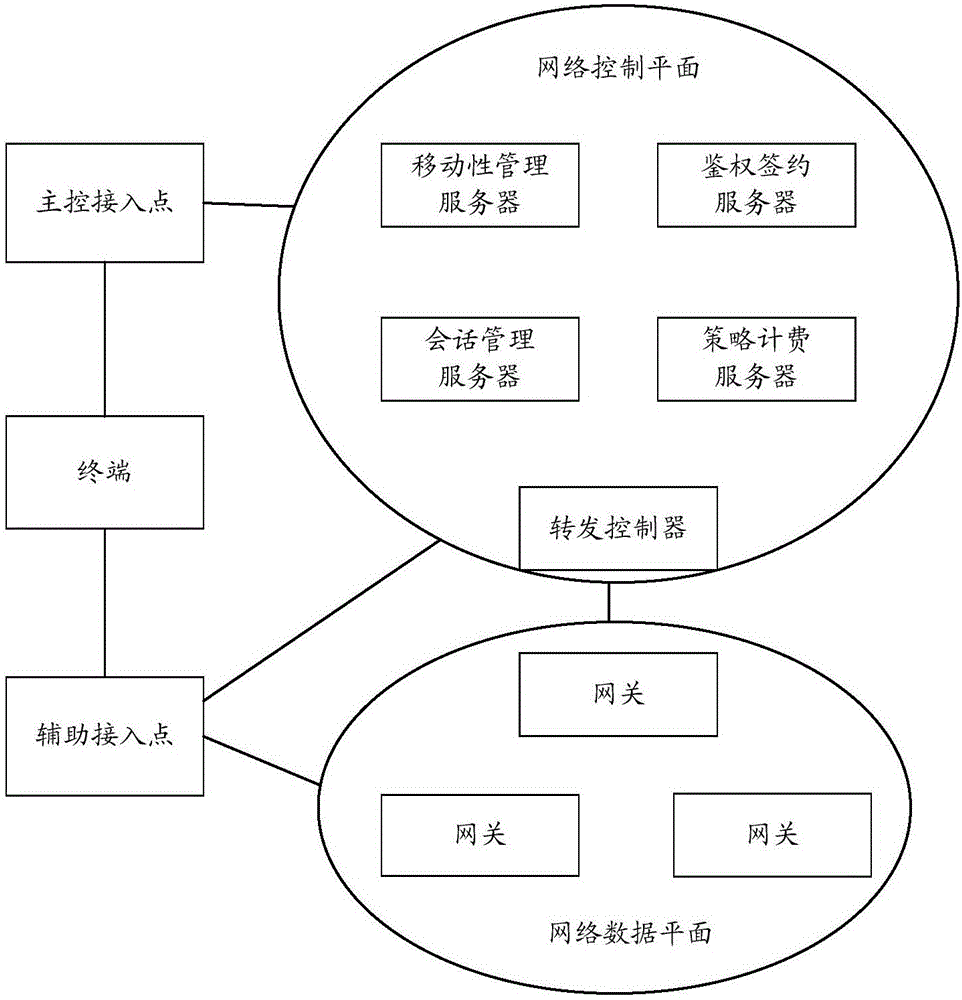
ActiveCN105813079ARealize unified accessRealize shuntAssess restrictionSecurity arrangementAccess methodComputer terminal
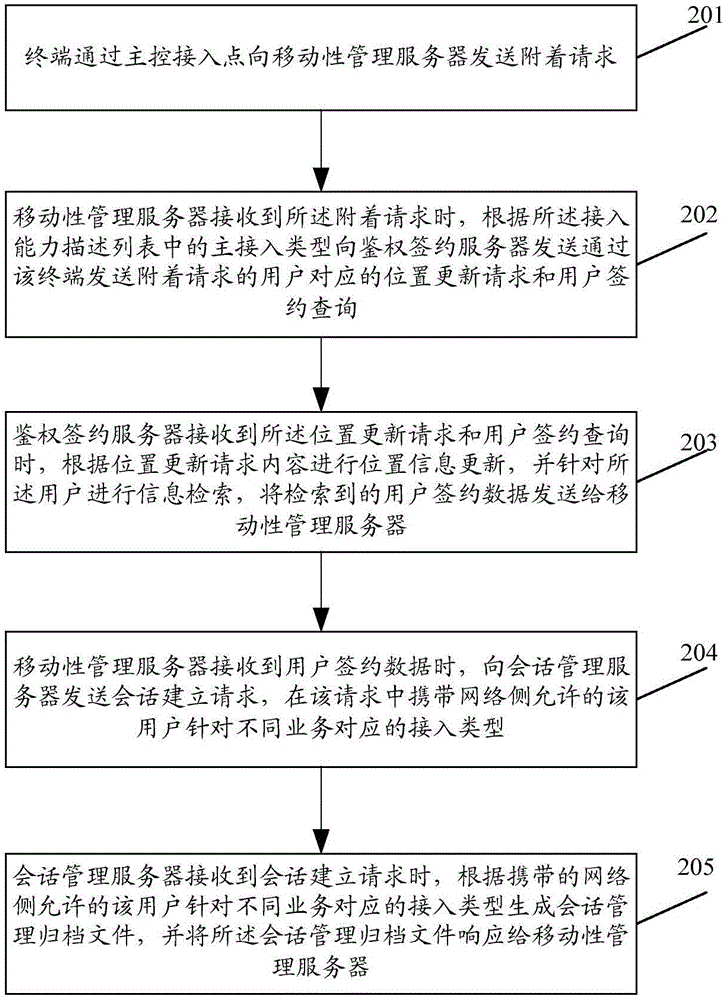
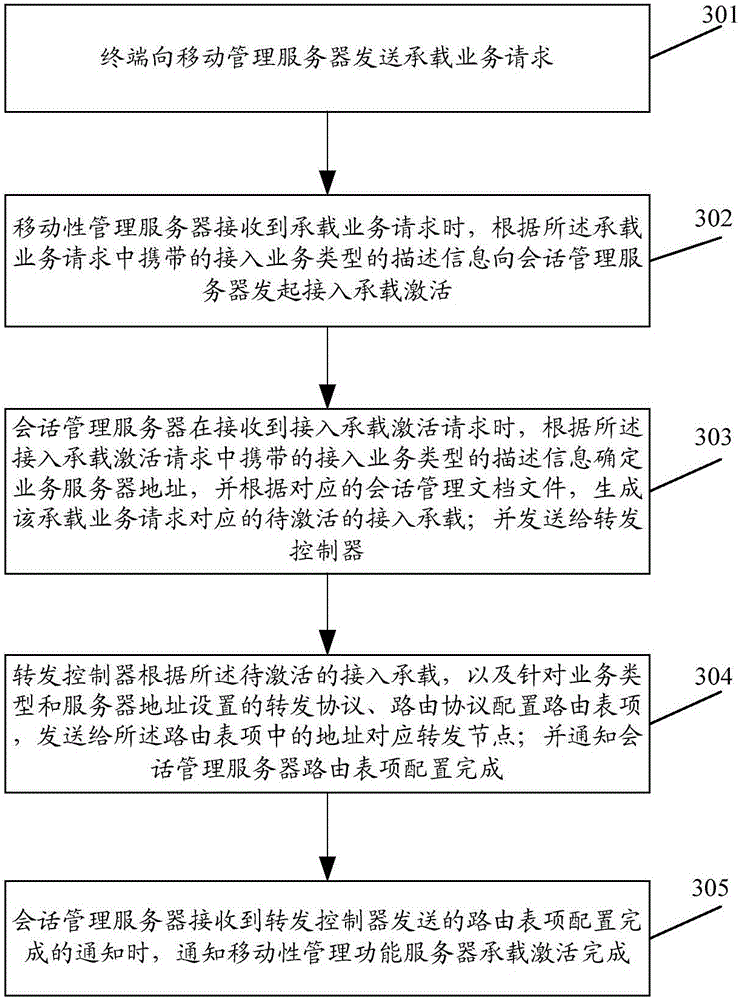
The invention provides a terminal access method.The method comprises the steps that a terminal sends an attaching request to a mobile management server through a main-control access point; the mobile management server sends a position updating request and a user signing query to an authentication signing server according to a main access type carried in the request; the authentication signing server carries out position information updating and information retrieval for the user, and sends the retrieved user signing data to the mobile management server; the mobile management server sends a conversation establishing request to a conversion management server, wherein access types which are allowed by a network side and correspond to different services of the user are carried in the conversation establishing request; the conversion management server generates a conversion management archived file according to the request and responds the conversion management archived file to the mobile management server; the mobile management server sends an attaching accepting message to the terminal to complete attaching.By means of the scheme, uniform access for various different access types can be achieved.
Owner:CHINA ACADEMY OF INFORMATION & COMM
Priority-based virus scanning with priorities based at least in part on heuristic prediction of scanning risk
Anti-virus scanners can be deliberately disabled, inadvertently disabled, or simply slowed down to a point where the scanner becomes ineffective and the primary function of the scanning host device is disrupted when a suitably complex file is received by the scanning system for scanning. Archive files pose particular problems for scanners, since archives may contain very complex data structures, and require time consuming analysis. Virus scanners typically scan each element of an archive. Some virus scanners decompress each archive component for scanning. Virus developers have taken advantage of this scanning approach by creating complex archives designed to overwhelm a scanner, leaving a system unprotected or in a denial of service state. To counter such measures, when an archive (or other file) is passed to a scanner, various heuristics are applied to the archive so as to determine a risk-based scanning priority for the archive. Priorities can include normal priority, low priority for archives having suspicious characteristics, and discard without scanning for archives appearing to be constructed so as to overwhelm a scanner. Normal priority scans can occur immediately, while low priority scans can be relegated to only occurring while the scanning system is otherwise idle.
Owner:MCAFEE LLC
System and method for a packaging and deployment mechanism for Web service applications
InactiveUS20060136897A1Efficient administrationSpecific program execution arrangementsMemory systemsPortletWeb service
A packaging utility is created that can in turn create a deployment archive (DAR) file containing the data required to install a Web service application, comprising, for example, portlets for creating Web pages for the Web service's user interface, UDDI entries, executable programs, and application-wide properties. The application-wide properties may comprise elements to be used in connection with one or more Web services, for example, encryption levels, service levels, timeouts, and number of retries. For administration efficiency the application-wide properties may be applied according to hierarchies, for example from groupings of Web services to individual Web services and from organizations of users to individual users. An unpackaging tool is created to unpackage and install the DAR file on a target environment. A configuration set is employed by the unpackaging tool to determine where the elements of the Web service application are to be installed on the target environment.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com