Patents
Literature
81 results about "Working directory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, the working directory of a process is a directory of a hierarchical file system, if any, dynamically associated with each process. It is sometimes called the current working directory (CWD), e.g. the BSD getcwd(3) function, or just current directory. When the process refers to a file using a simple file name or relative path (as opposed to a file designated by a full path from a root directory), the reference is interpreted relative to the current working directory of the process. So for example a process with working directory /rabbit-shoes that asks to create the file foo.txt will end up creating the file /rabbit-shoes/foo.txt.
Class loader
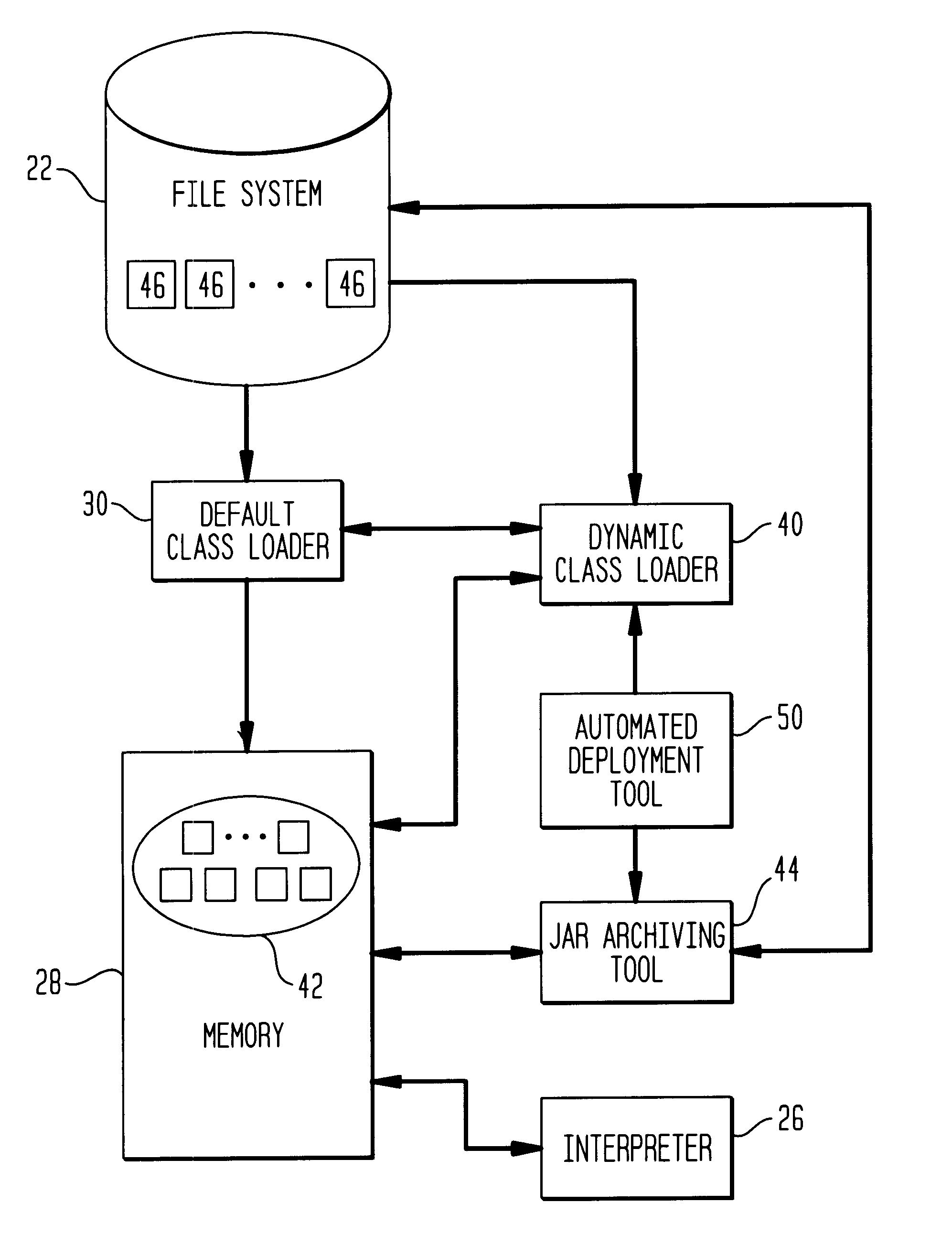
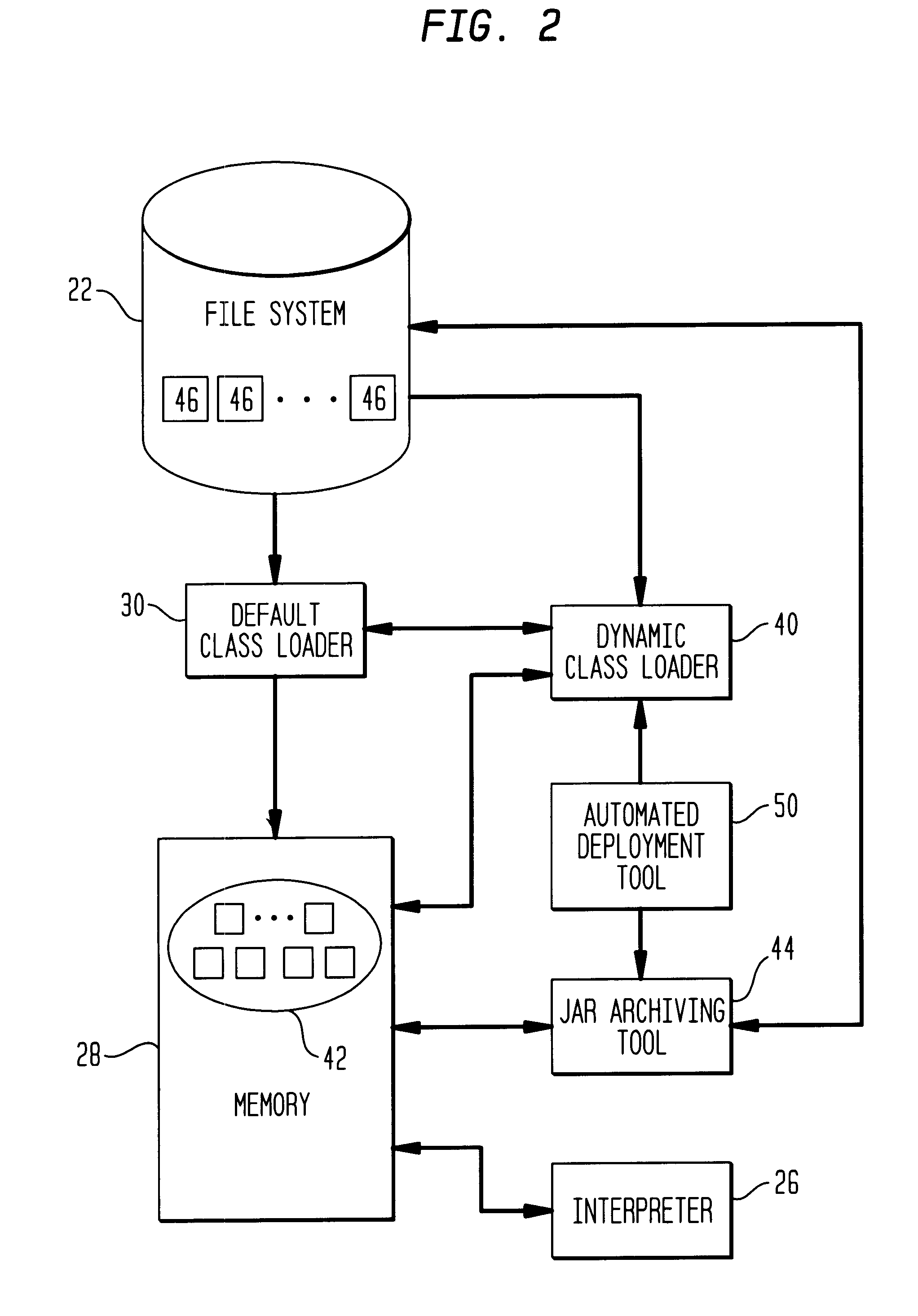
This invention relates to the loading of classes in programming environments, and in particular, Java programming environments. This invention discloses a system and method that permits dynamic loading of classes during the execution of Java programs. This invention allows for classes to be loaded despite the fact that such classes may not reside in the current path or working directory within a Java programming environment. This invention also discloses a system and method for archiving files in an archive file that provides customized entry names for the archived files.
Owner:IBM CORP
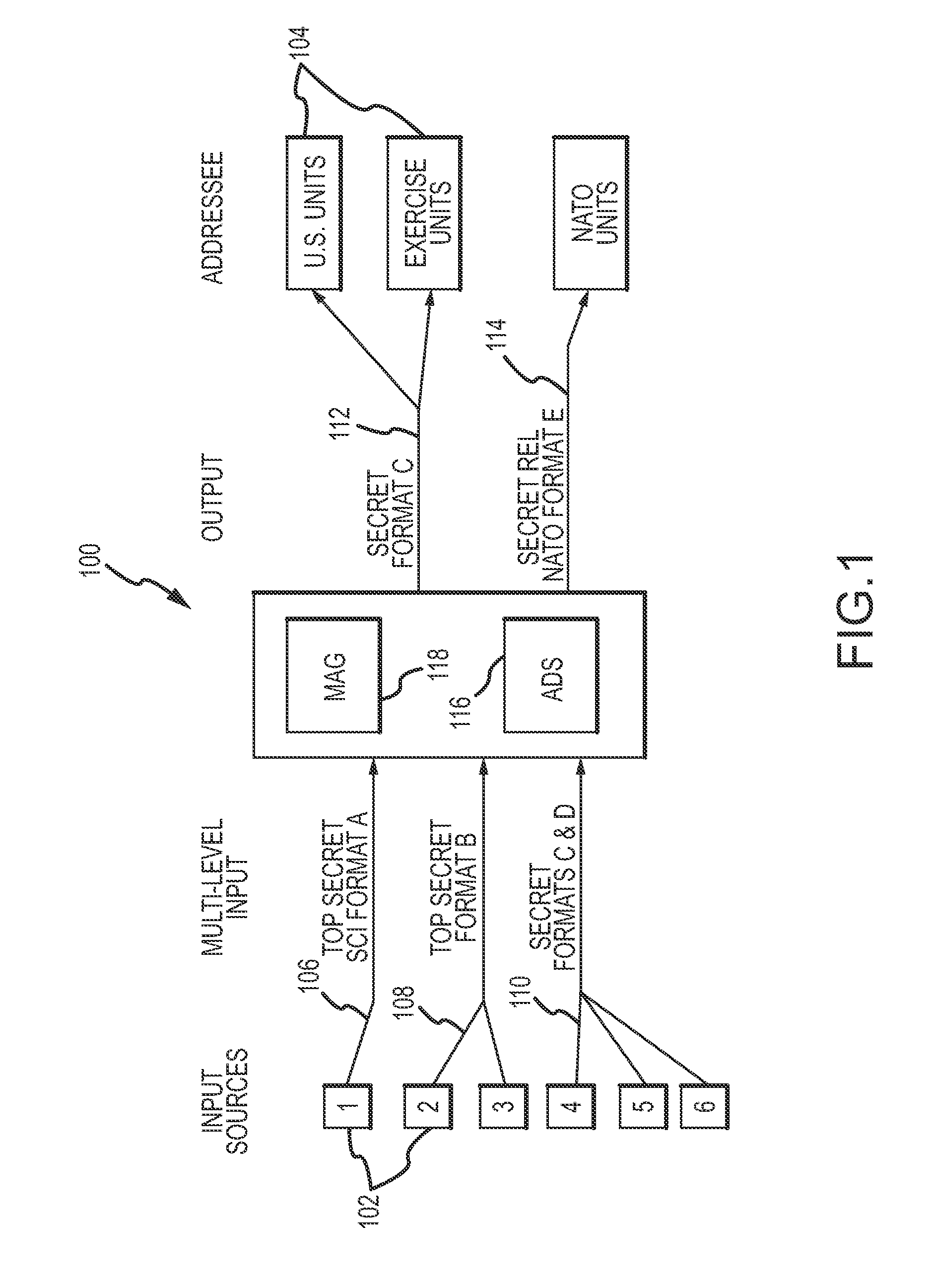
Automatic information sanitizer
ActiveUS7293175B2Quickly and accurately applyOptimize allocationDigital data processing detailsAnalogue secracy/subscription systemsNetwork Communication ProtocolsComputer module
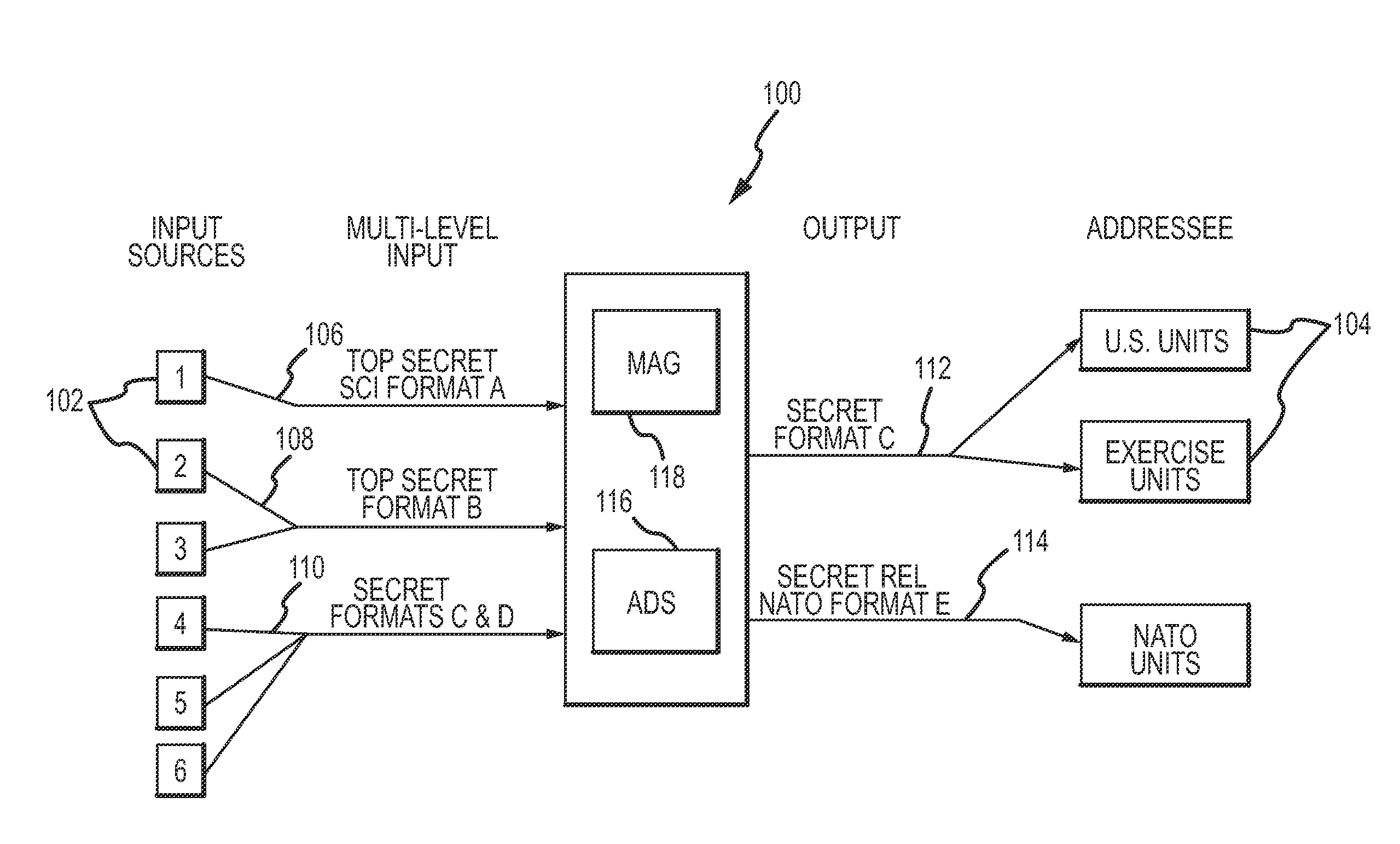
An automatic data sanitizer module sanitizes formatted data from an external source system according to stored sanitization rules for release to an external destination system so that the destination system receives only that data for which it is authorized. The module generally includes an Input Comms module, a Message Processor, an Output Guard a Downgrader and an Output Comms module. The Input Comms module supports the communications protocol dictated by the external source system. The Processor sanitizes the message according to the rules written for the specific external system under consideration. The Guard verifies the modifications performed by the Processor. The Downgrader moves the resulting file to the Output Comms working directory and the Output Comms makes the resulting message available to the destination system. The system supports a variety of different formats and greatly facilitates the timely dissemination of information within a multi-level secure environment while protecting security interests.
Owner:LOCKHEED MARTIN CORP
Intelligent caching of working directories in auxiliary storage
InactiveUS20050125607A1Easy to operateSolve the power is smallMemory architecture accessing/allocationEnergy efficient ICTHard disc driveSmart Cache
A combination of non-rotating storage and associated software temporarily transfers storage functions from a hard disk to the non-rotating storage. This invention provides for the “on the fly” adaptation and transfer of an application's disk requirements to be instead sent to a flash storage, non-spinning memory device, solid state memory, or similar device while the hard drive is powered down. This not only makes operations faster, but results in a large savings in battery power.
Owner:LENOVO (SINGAPORE) PTE LTD
Method and system for providing real-time personalization for web-browser-based applications
InactiveUS6381567B1Digital data information retrievalNatural language data processingPersonalizationData processing system
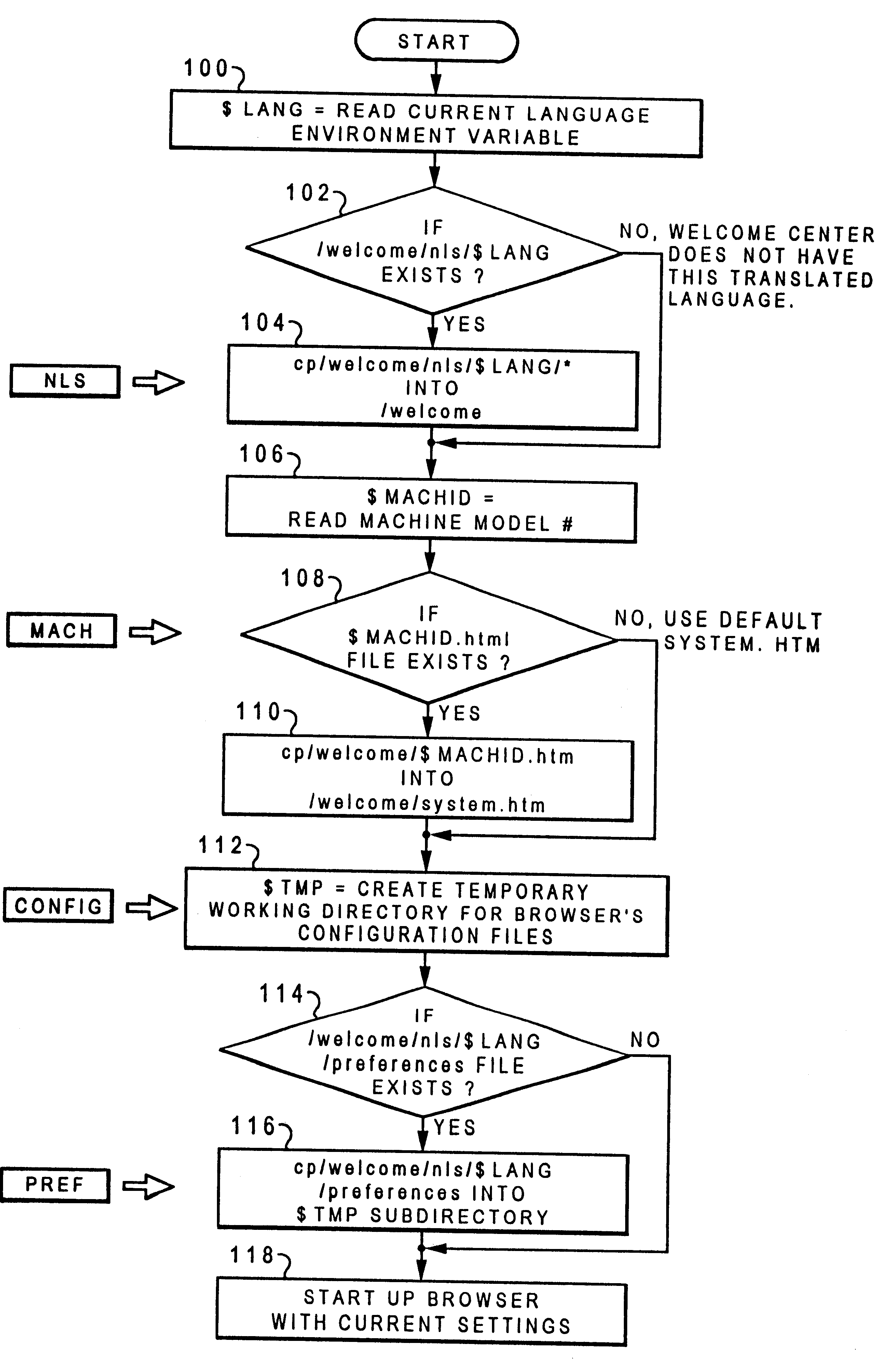
A method and system for personalizing standard data-processing applications for utilization by diverse data-processing application users. Initially, data which includes a group of human language files, is stored within a source directory within a data-processing system. Next, the presence of the group of human language files is automatically detected within the source directory in response to loading general system data into a working directory wherein at least one human language file among the group of human language files corresponds to a preset human language setting for the data-processing system. Thereafter, the human language file which corresponds to the preset human language setting is loaded into the working directory from the source directory. Next, the general system data is configured with the human language file which corresponds to the preset human language setting such that the general system data is now personalized to the human language of the user of the data-processing system. The data can include hyper-text data for utilization in data-processing applications such as internet-based web browsers.
Owner:IBM CORP
Method and device for deploying and loading plug-in unit
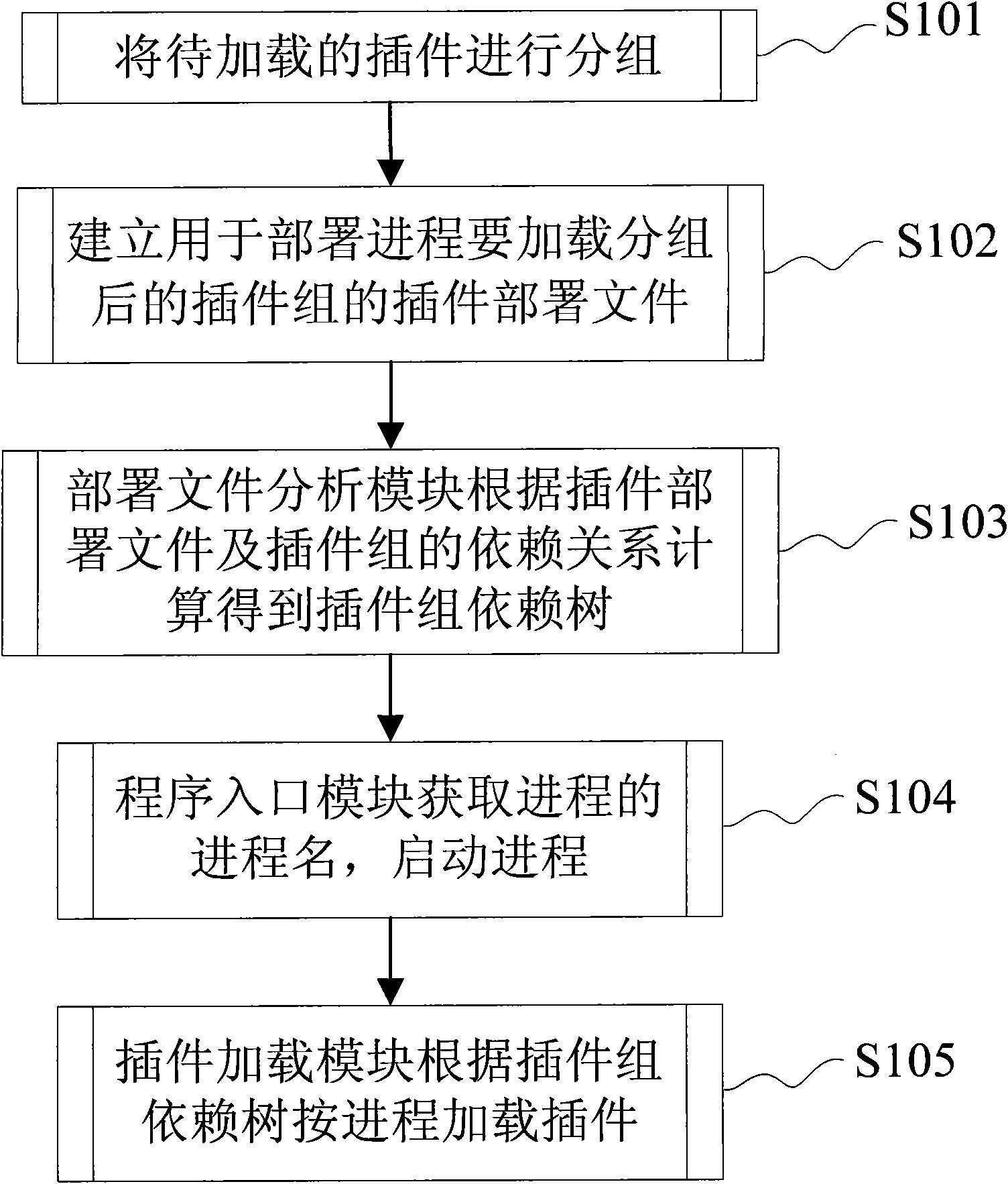
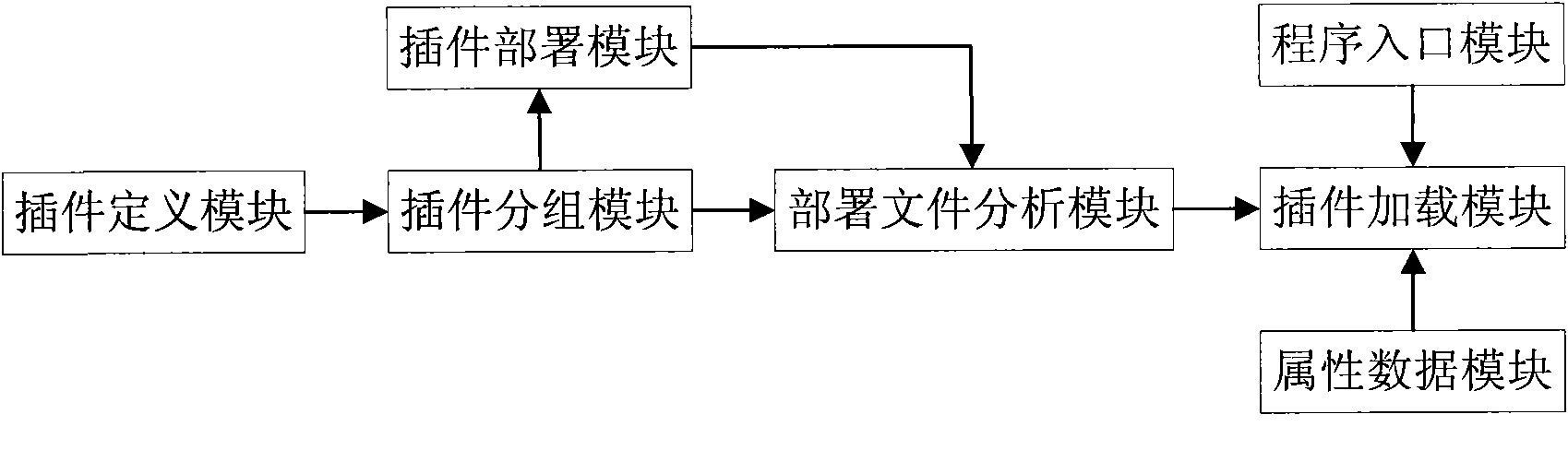
The invention discloses a method and a device for deploying and loading plug-in units. The method comprises the following steps of: grouping plug-in units to be loaded; establishing a plug-in deployment file for deploying processes to load the grouped plug-in units; calculating and acquiring a plug-in unit dependence tree according to a dependence relation between the plug-in deployment file and the plug-in unit groups by a deployment file analysis module; acquiring process names of the processes by a program entry module and starting the process; and loading the plug-in units by the processes according to the plug-in unit dependence tree by a plug-in loading module. The invention loads the plug-in units in a grouping mode, supports distributed management, separates a process working directory and a program directory and realizes sharinges the program file by the processes with different functions.
Owner:ZTE CORP
System and method for creating and transferring media files
InactiveUS20160308950A1Save time wastingEliminate wasteMultimedia data indexingOffice automationCommunication unitSoftware engineering
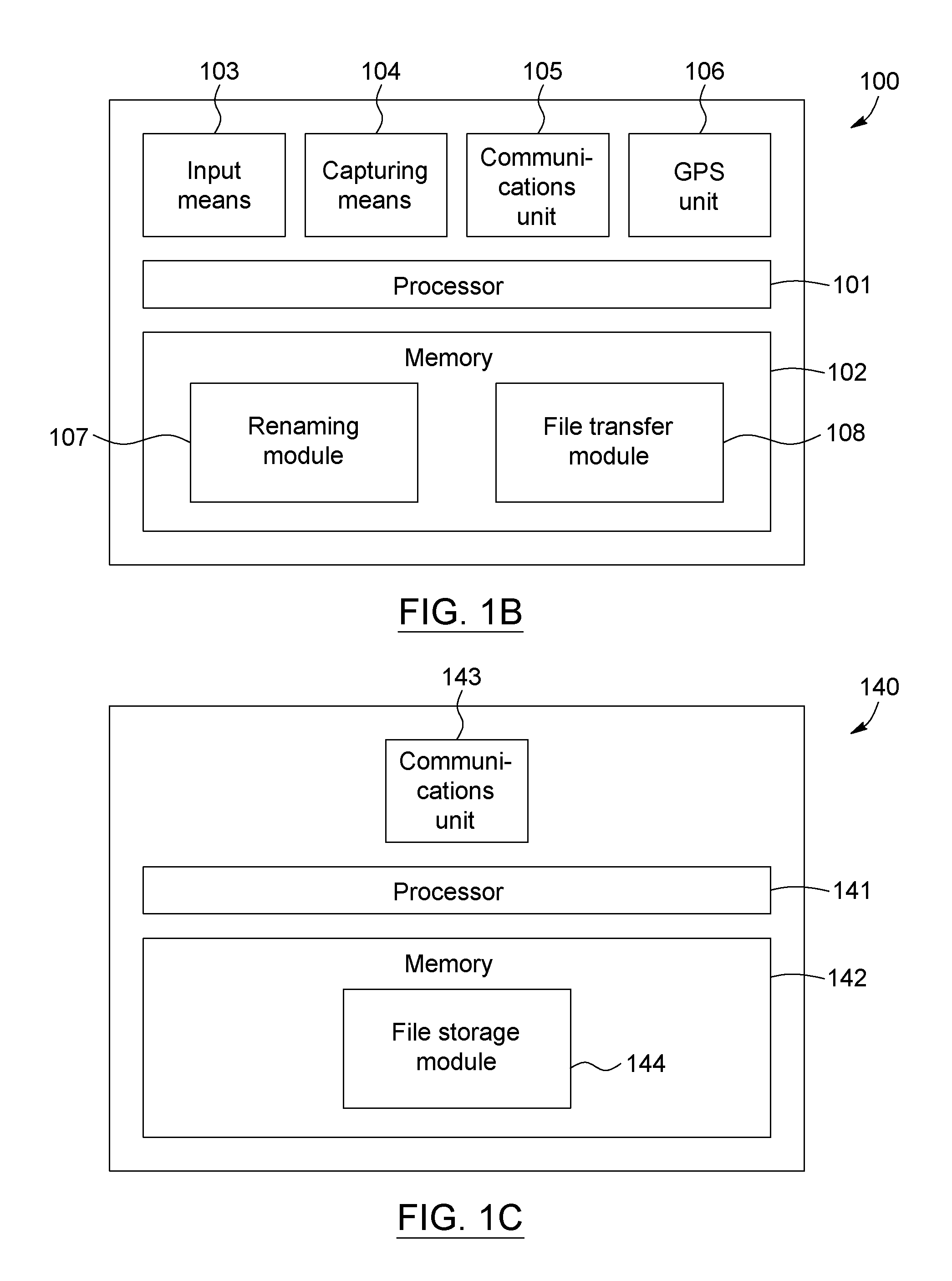
A system and method for creating and transferring media files is provided. The system and method allow for the transfer of files to a specific location on remote storage without having to first create the specific location on the remote storage system. The method comprises the steps of: receiving an input corresponding to a selected working directory; capturing at least one media file with a processor-based device; automatically renaming the media file to include an indicia corresponding to the selected working directory; receiving a transfer command; transferring the media file to remote storage, and instructing the remote storage to create a storage folder based on the indicia, and to store the media file in the storage folder. The system comprises at least one processor-based device comprising memory, a processor, input means, capturing means, a renaming module, a communications unit and a file transfer module.
Owner:BUSINESS MOBILE SOLUTIONS
Method for improving functional verification efficiency of embedded processor
ActiveCN104461810AImprove reusabilityImprove verification efficiencyFunctional testingReference modelComputer architecture
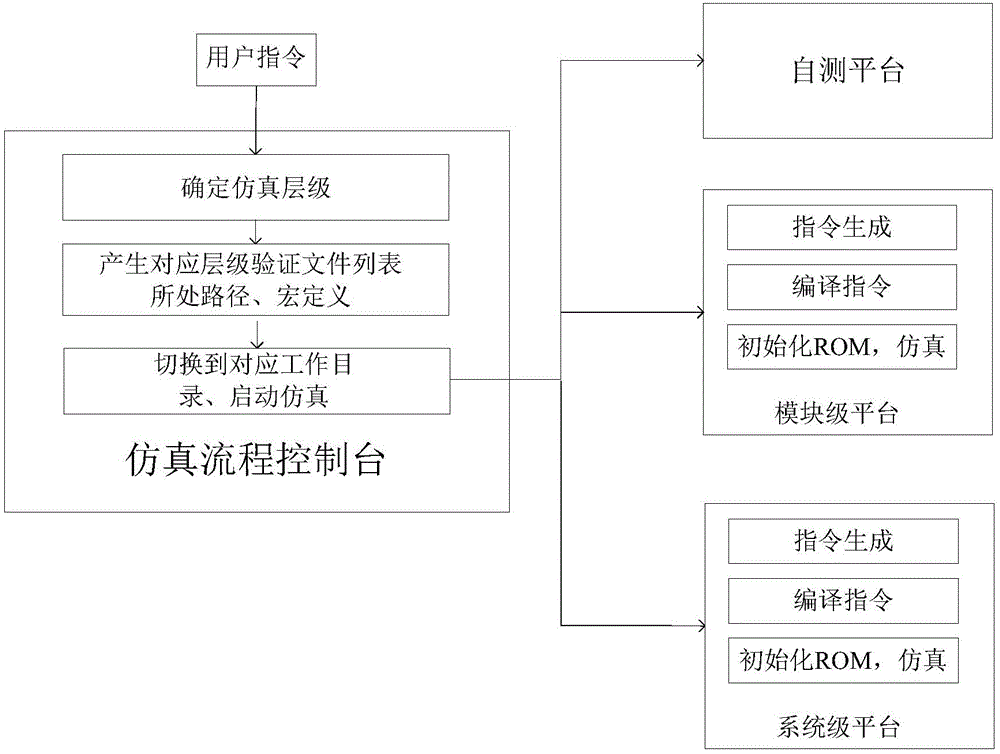
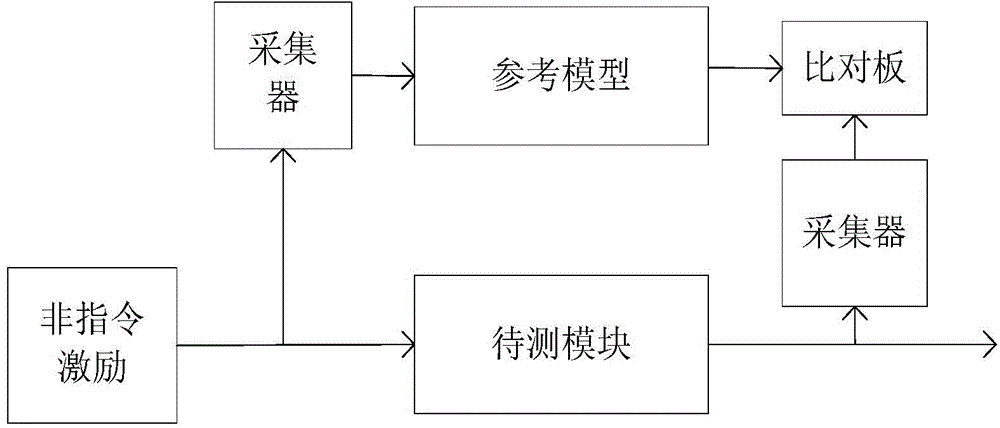
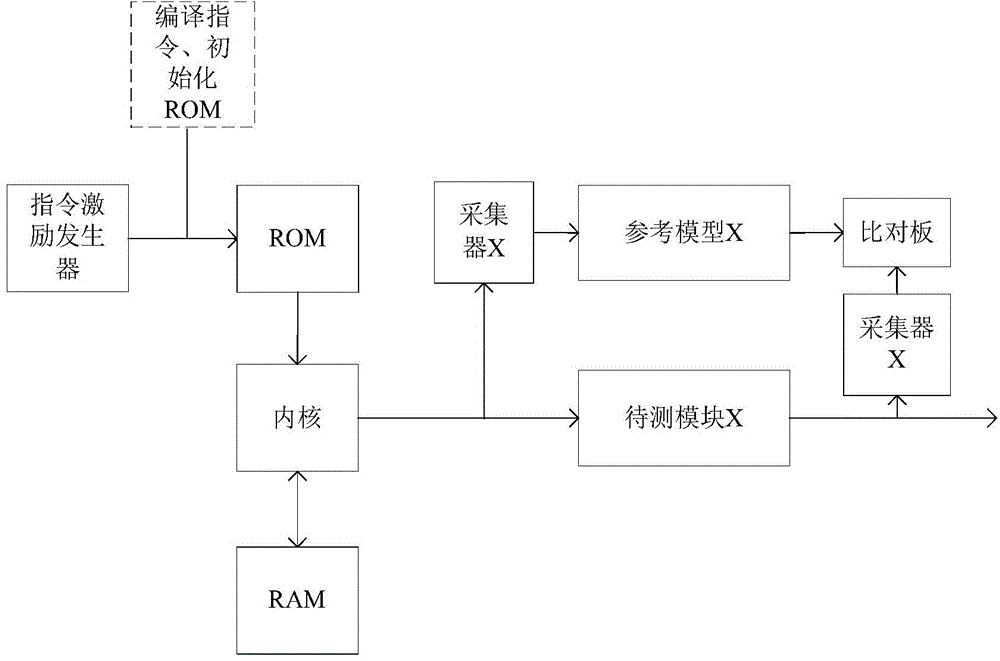
The invention discloses a method for improving functional verification efficiency of an embedded processor. The method is realized through a simulation flow control table and a verification platform. The simulation flow control table is in charge of setting up a self-testing platform and a module level verification platform or a system level verification platform, carrying out working directory conversion and starting simulation; the verification platform is in charge of generating random excitation and calling a compiler to carry out compiling, reference model operation and simulation result comparison on orders which are randomly generated.
Owner:CHIPSEA TECH SHENZHEN CO LTD
Method for analyzing vibration characteristics of bearing retainer based on finite elements
InactiveCN104268342AAvoid resonanceShorten the processing cycleSpecial data processing applicationsElement modelEngineering
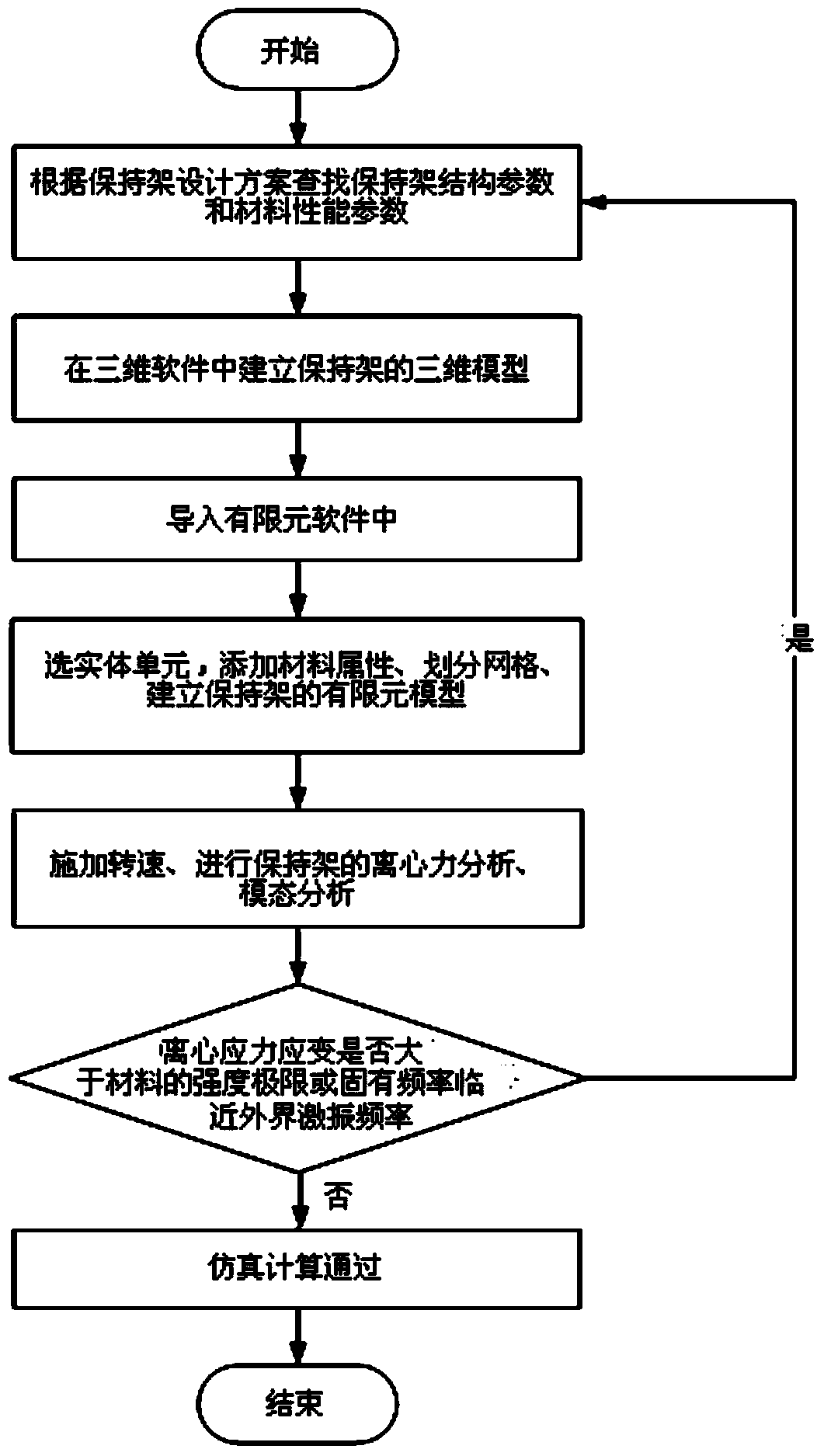
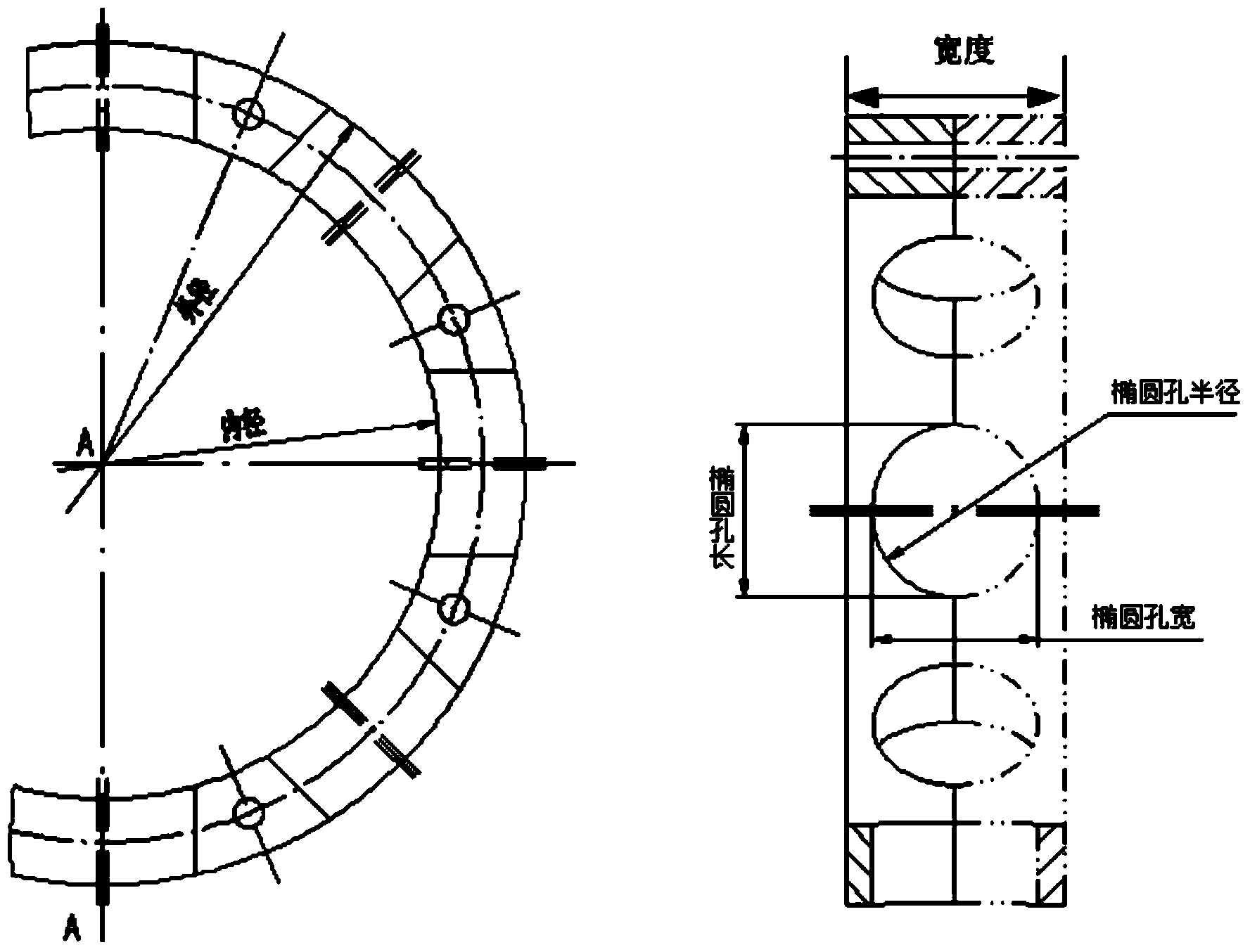
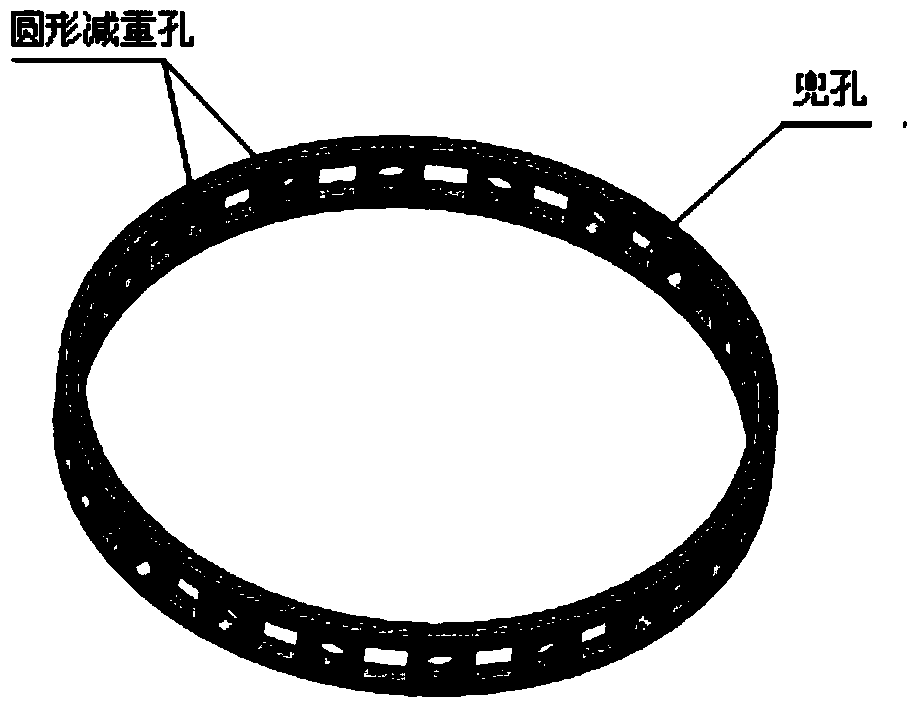
The invention relates to a method for analyzing the vibration characteristics of a bearing retainer based on finite elements and aims at solving the problem that no automatic analysis procedure for the vibration characteristics of the bearing retainer is developed at present to prevent the frequency range of resonance of the bearing retainer of an aero-engine. The method is implemented through a step 1 of creating the three-dimensional model of the bearing retainer and saving the three-dimensional model under the working directory set by finite element software, a step 2 of establishing a finite element model and applying the rotating speed of the bearing to the finite element model for performing statics analysis and modal analysis, a step 3 of obtaining the stress and the strain as well as the inherent frequency and the corresponding formation thereof under the action of the rotating speed of the bearing, a step 4 of determining whether the stress and the deformation of the bearing retainer under the action of the centrifugal force meet the design requirements, and the like. The method for analyzing the vibration characteristics of the bearing retainer based on the finite elements is applied to the field of the vibration characteristics of the bearing retainers.
Owner:AVIC HARBIN BEARING
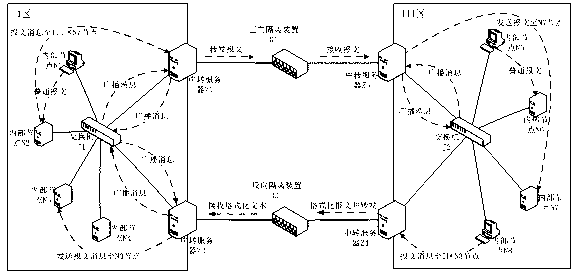
Real-time bus across safety zone communication method suitable for power industries
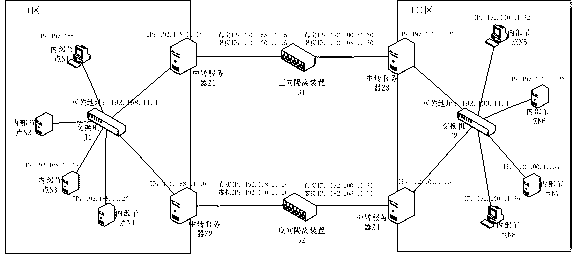
ActiveCN103259703AImprove versatilitySolve data communication problemsBus networksInformatizationNetwork connection
The invention discloses a real-time bus across safety zone communication method suitable for power industries, and belongs to the technical field of informatization and automation of electric power systems. According to the real-time bus across safety zone communication method, across safety zone information exchange is accomplished through transit servers and internal nodes. Two transit servers are configured in one safety zone, and the transit servers are used for transmitting and receiving cross-zone messages and transferring the messages to a designated work catalogue, so that the internal nodes can use the messages. The transit servers are arranged at the positions related to an isolating device, the internal nodes in the same safety zone establish a network connection through a switch or a router, and the internal nodes are mainly used for transmitting messages and receiving messages at last. According to the real-time bus across safety zone communication method, data are transmitted through the network isolation device unidirectionally (in the forward direction and in the reverse direction) on the premise that the existing safety zone framework arrangement is guaranteed to be unchanged, and thus safe and stable data communication among different safety zones is achieved finally.
Owner:DATONG POWER SUPPLY BRANCH SHANXI ELECTRIC POWERCO +2
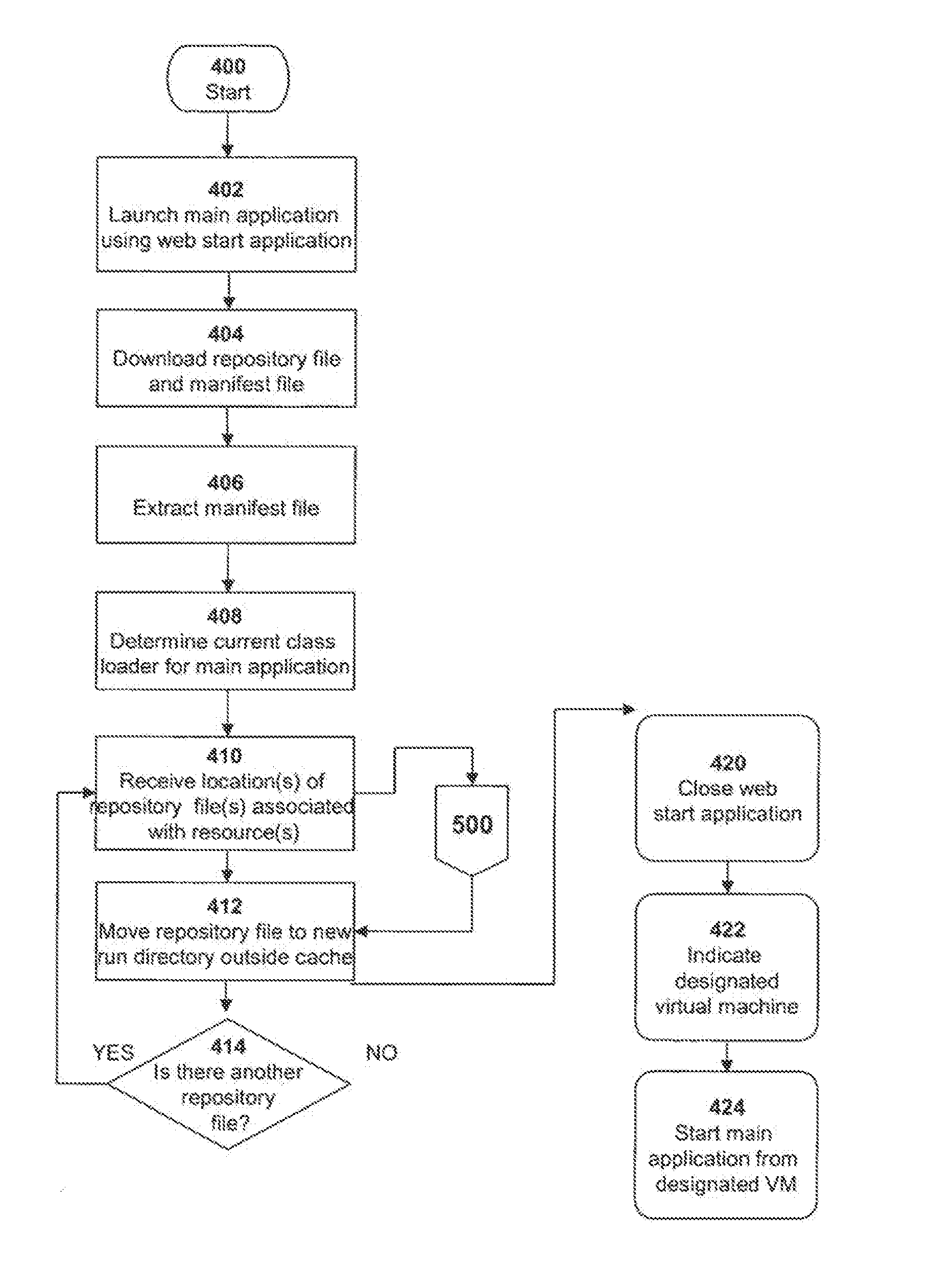
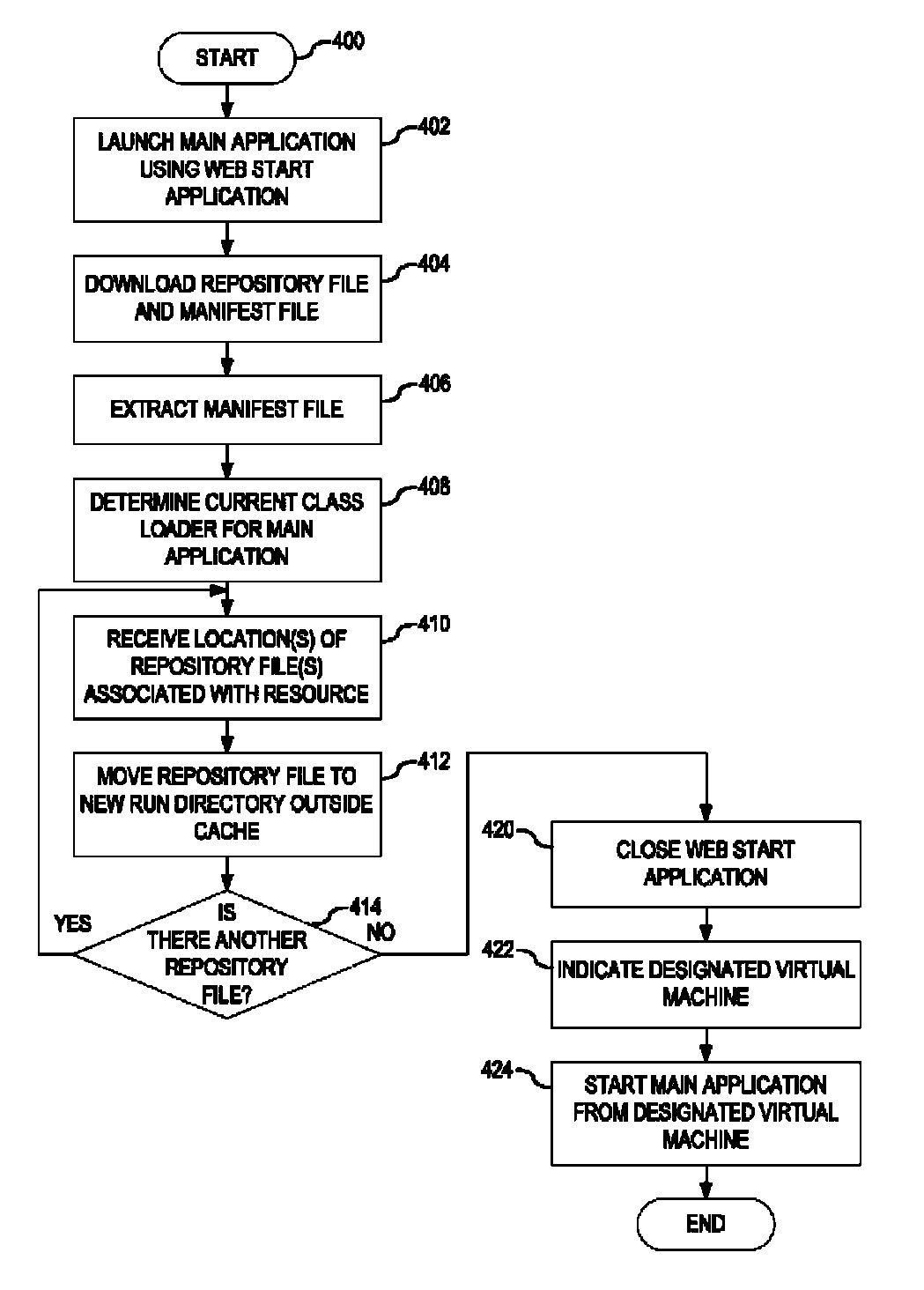
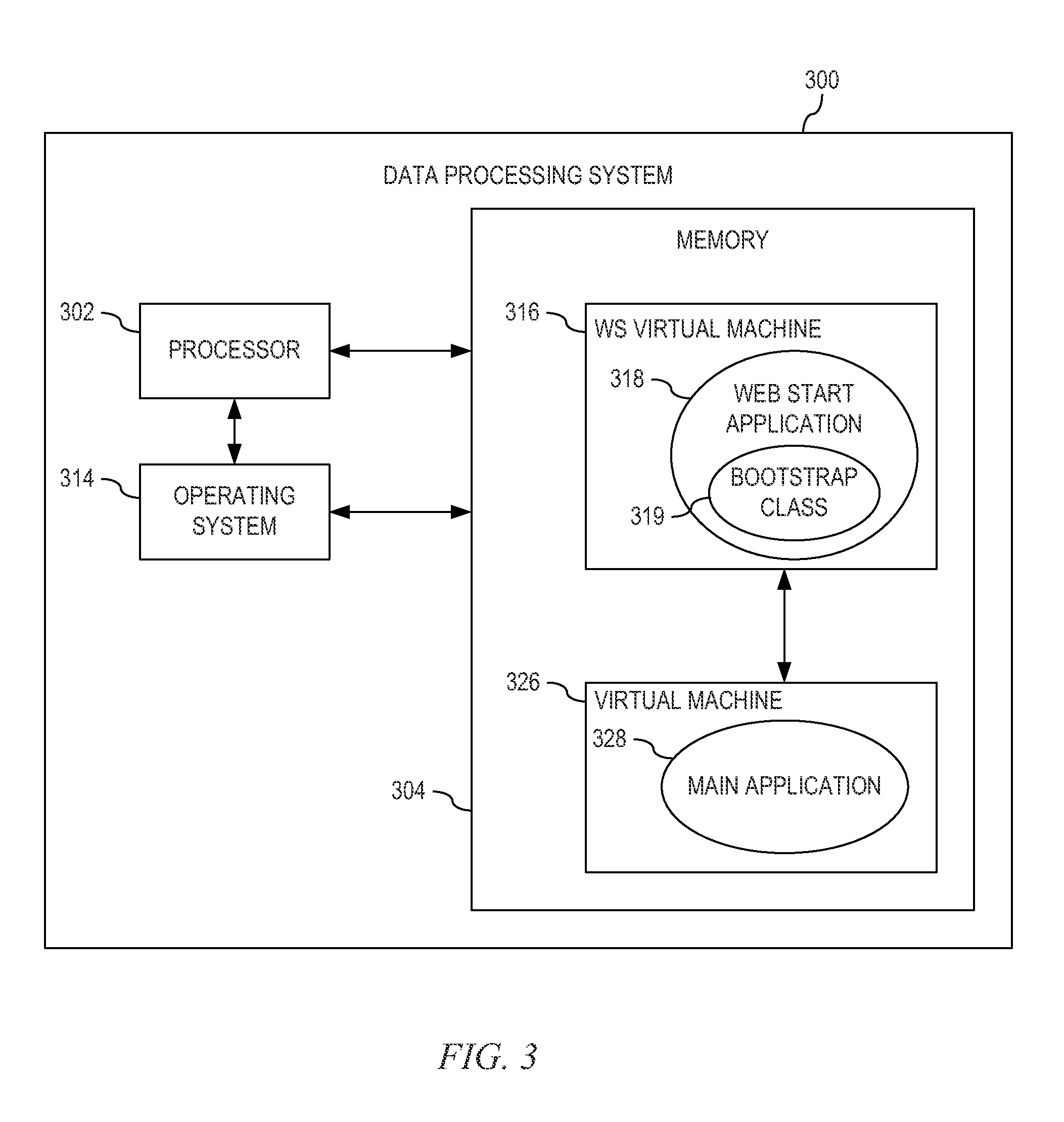
Installing and Updating Interpreted Programming Language Applications using a Designated Virtual Machine
A method, system and program of executing an interpreted programming language application from a server at a designated virtual machine on a client computer are provided. A manifest file is extracted which indicates at least one resource for the interpreted programming language application as well as the repository file associated with the resource. The repository file is located in a web start cache and moved to a run directory accessible by the designated virtual machine, outside the web start cache. The interpreted programming language application is then executed from the run directory using the at least one resource.
Owner:INT BUSINESS MASCH CORP
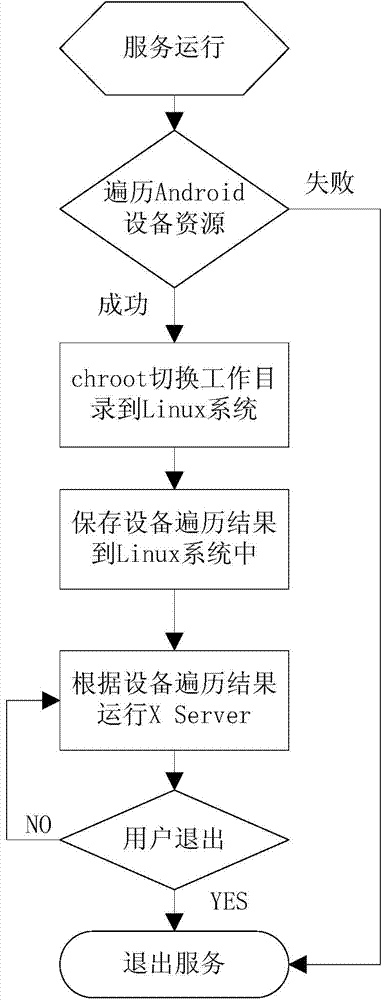
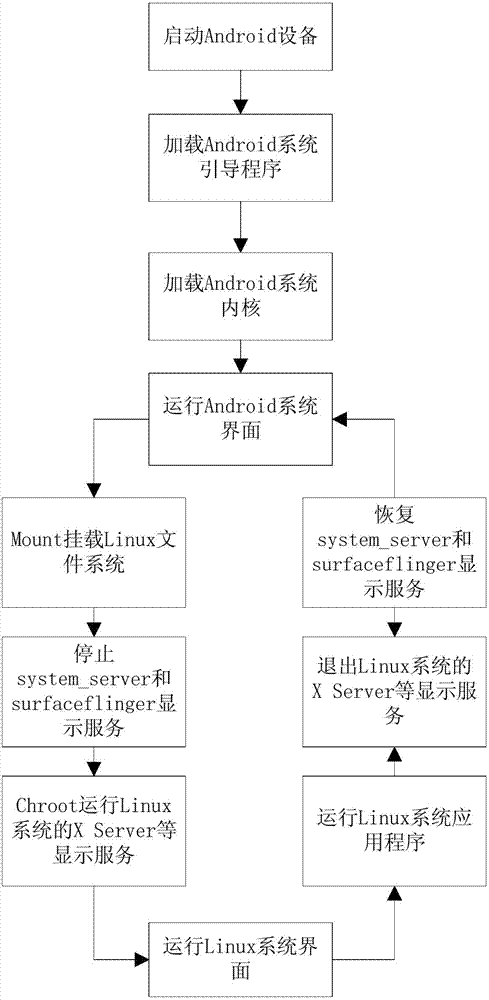
Method for simultaneously running Android/Linux operating systems
InactiveCN104268017AQuick switchSeamless switchingProgram initiation/switchingOperational systemFile system
The invention discloses a method for simultaneously running Android / Linux operating systems. The two systems share the same Boot programs and the system kernel and utilize file systems which are installed in mutual independence inside memory devices; the working directories of the running Android system and the running Linux system can be isolated through a chroot mechanism, so that the Linux system can run in the Android system. When needing to run software under the Linux system in the Android system, a user does need to reboot equipment but simply runs a service process to execute chroot instructions to switch to the Linux system; when needing to run Android software at the moment, the user simply needs to stop the service process to convert operating system switching to application switching and accordingly to switch to the Android system. The method for simultaneously running the Android / Linux operating systems can achieve continuous and rapid switching for the user.
Owner:FUJIAN CENTM INFORMATION
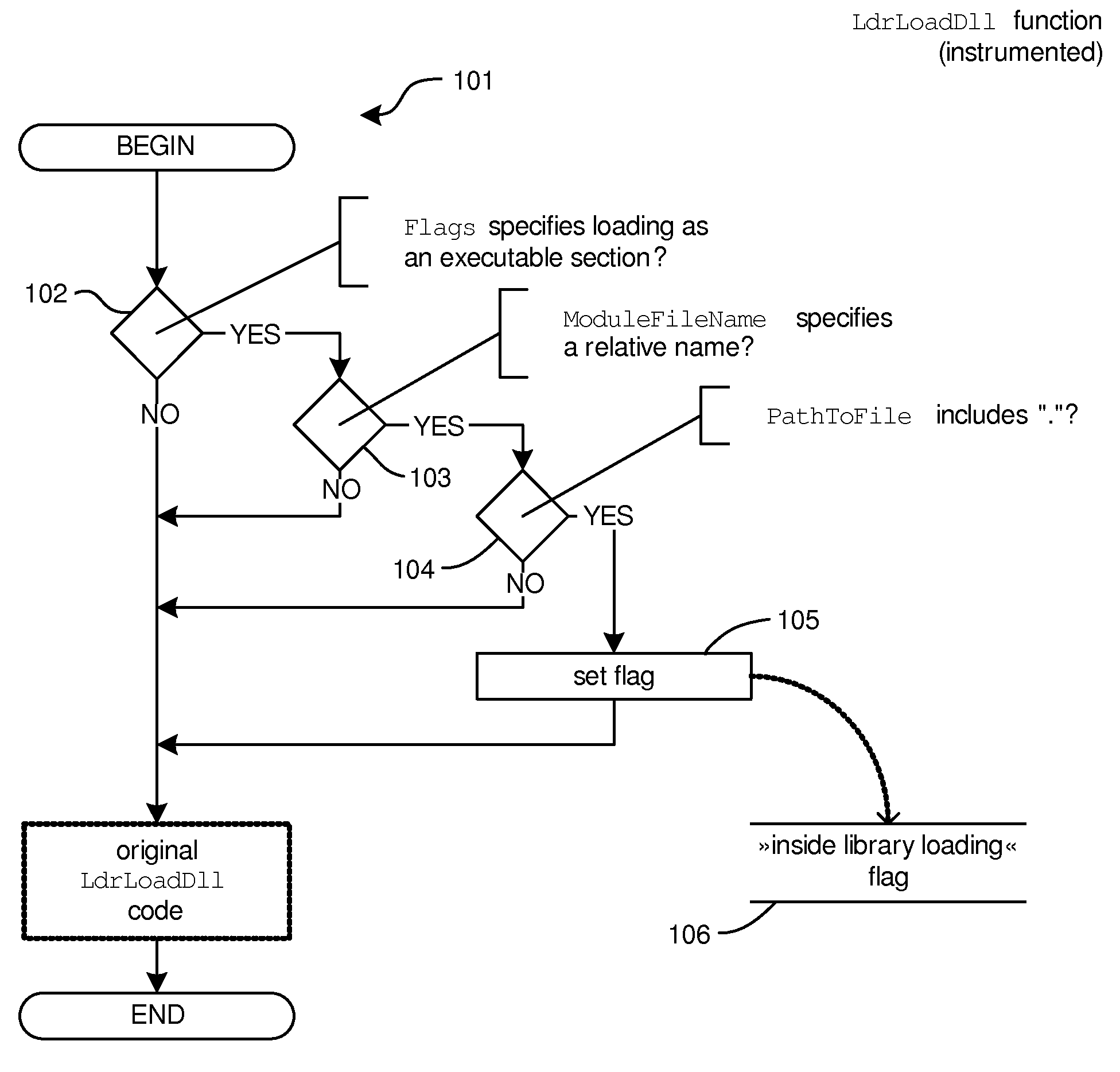
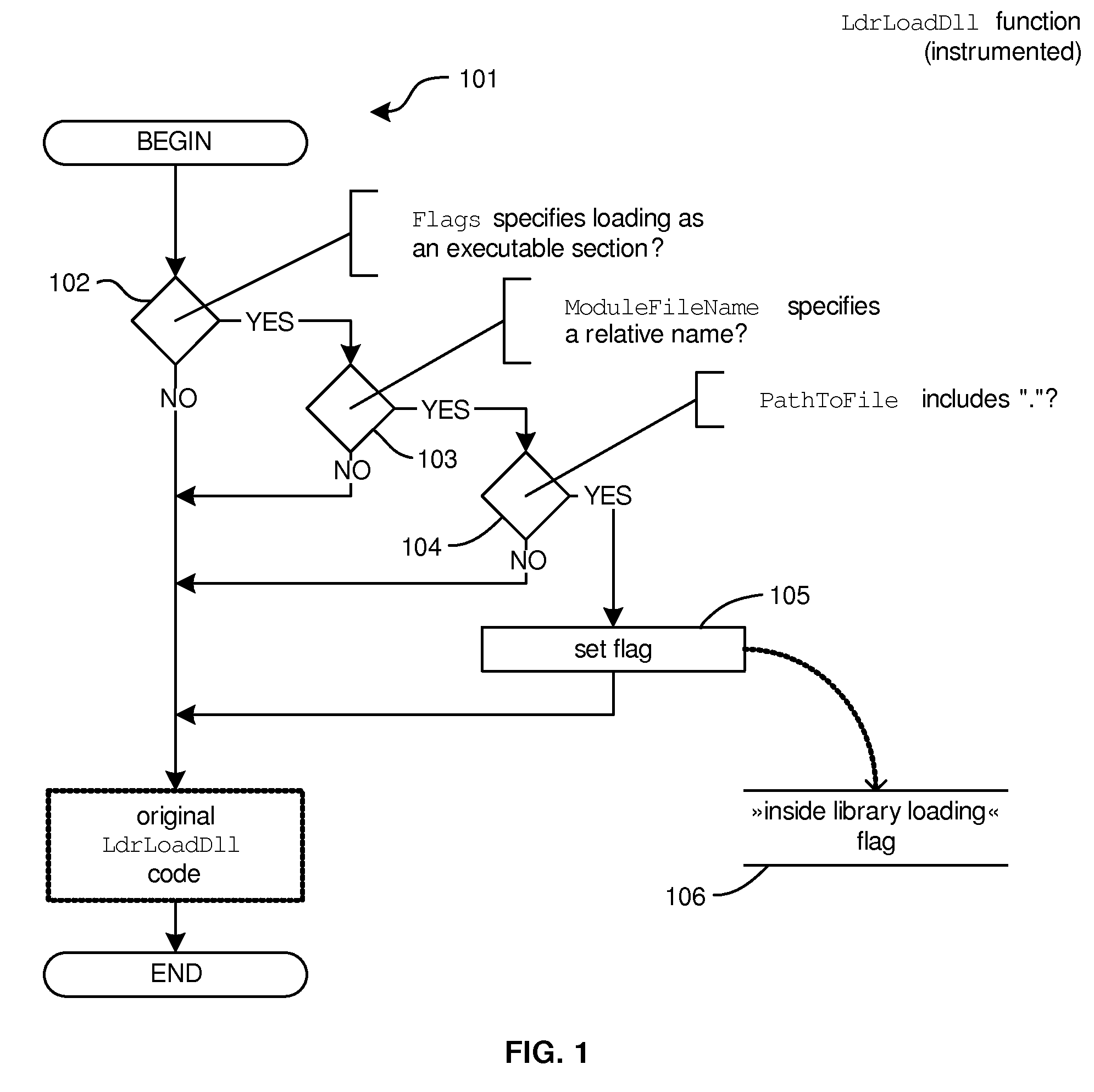
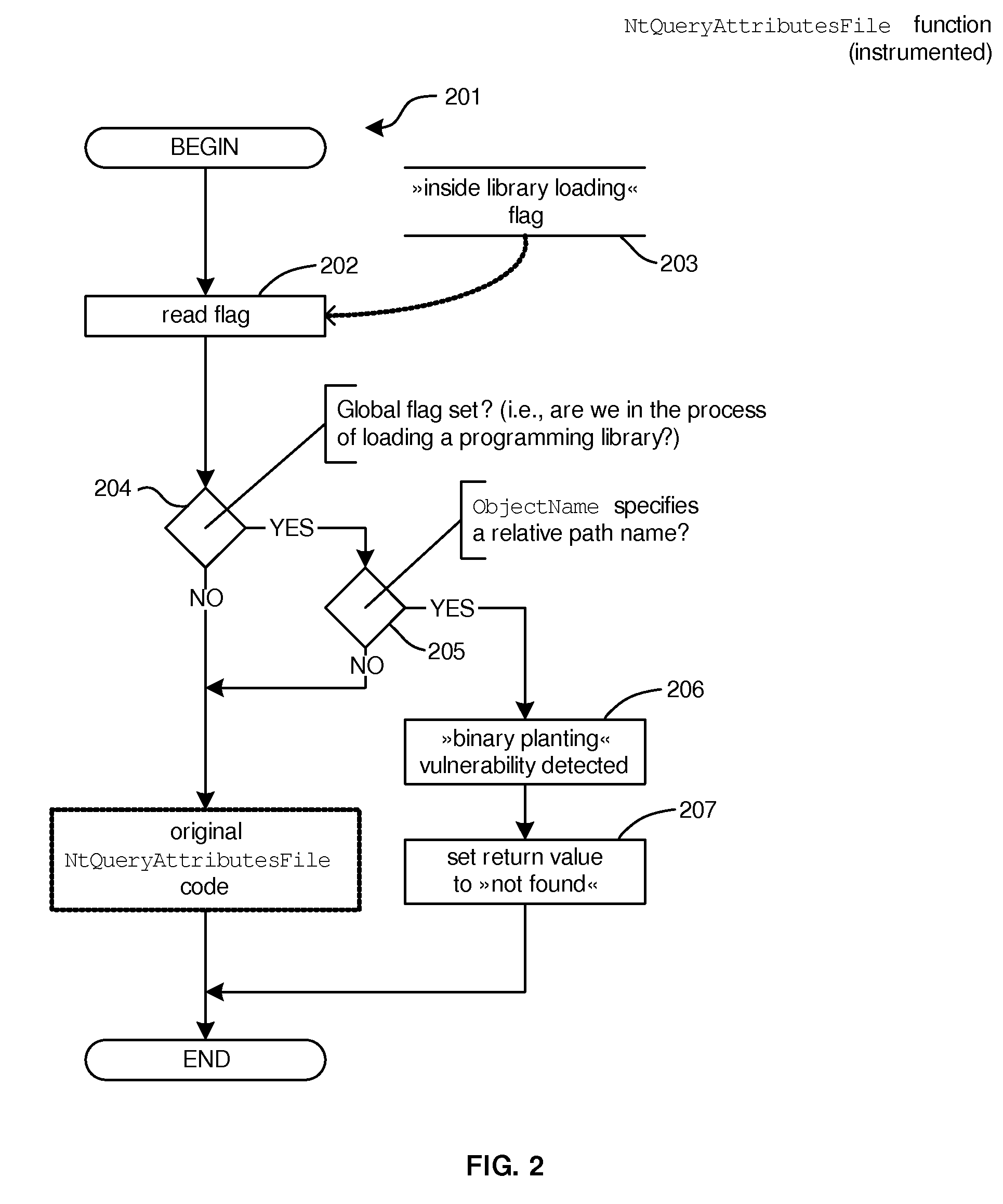
Method for detection and prevention of loading executable files from the current working directory
InactiveUS20110145924A1Preventing executionPrevent exploitationMemory loss protectionError detection/correctionOperational systemVulnerability
The present invention detects vulnerabilities by observing (“monitoring”) the calls of system and application functions, and the arguments of such calls, which play a key role in loading executable files, and detects that a computer program or operating system either has tried, is trying or will try to load or execute an executable file from the current working directory. The present invention extends the detection procedure with an active intervention into the execution of a computer program or operating system such that loading or execution of the executable file is prevented. The present invention limits exploitability of the described vulnerability, by limiting loading or execution of executable files from the current working directory, or limiting or preventing setting of the current working directory to locations where a malicious person could place an executable file.
Owner:ACROS D O O
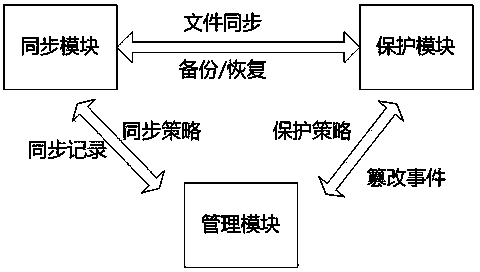
Tamper-proofing system file synchronizing system and tamper-proofing system file synchronizing method
ActiveCN104348914AProtection couplingImprove experienceTransmissionSpecial data processing applicationsWeb siteTamper resistance
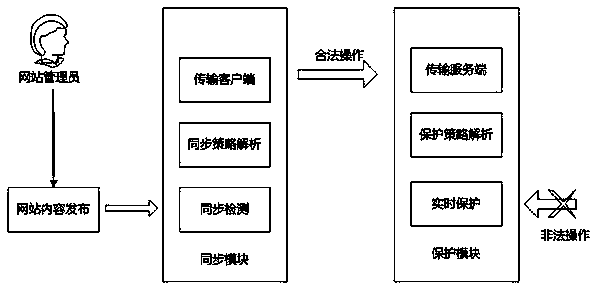
The invention relates to a tamper-proofing system file synchronizing system and a tamper-proofing system file synchronizing method. The system comprises a management module, a synchronization module and a protection module. The method comprises the following steps that the synchronization module monitors a website directory file in real time according to a synchronization strategy file, and a webpage file is transmitted to a transmission service end in the protection module by a transmission client; the protection module carries out system file driving level real-time protection on a plurality of specified website directories according to a protection strategy file, only specified legal processes and port service are allowed to execute change operation on protected directories and files, meanwhile, a file synchronization request sent by the synchronization module is received, and safe updating of Web server website contents is completed. The tamper-proofing system file synchronizing system and the tamper-proofing system file synchronizing method provided by the invention have the advantages that a new file synchronization mechanism is provided, the problem of file synchronization when one Web site is correspondingly distributed in a plurality of work directories is solved, the synchronization strategy configuration is simplified, and the user experience of a tamper-proofing system is improved.
Owner:FUZHOU BOKE WANGAN INFORMATION TECH CO LTD
Method for cooperating working directory or document access and system thereof
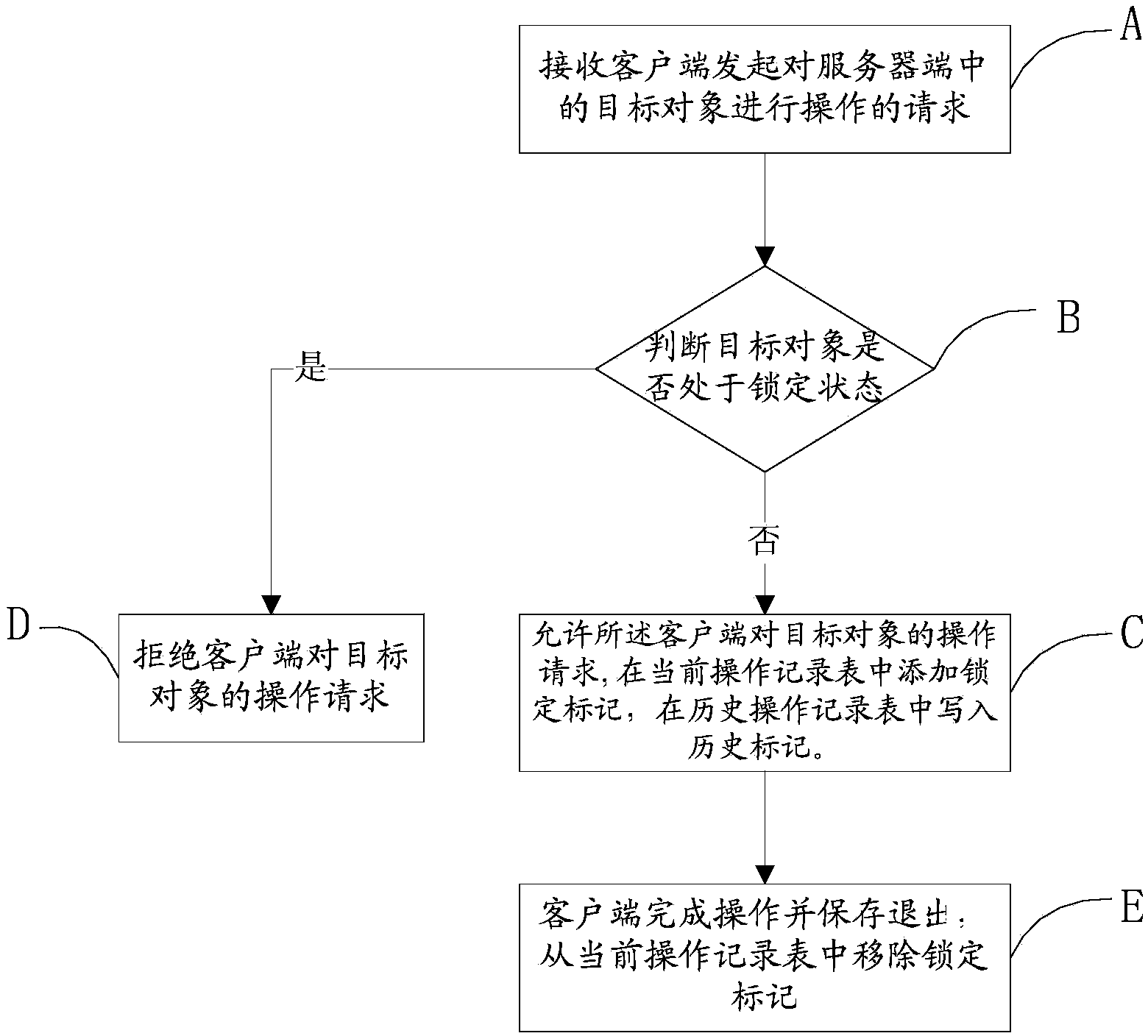
InactiveCN103778208AGuaranteed stabilityAvoid confusionSpecial data processing applicationsSoftware engineeringProject management
The invention discloses a method for cooperating working directory or document access and a system for cooperating working directory or document access. The method for cooperating the working directory or the document access comprises the following steps of step A, receiving the request issued by a client side to operate a target object in a server side; step B, searching a current record chart and judging whether the target object is under the locked state or not; step C, if the target object is not under the locked stage, then allowing the operation request of the client end to the target object; step E, after the operation is finished, removing the lock mark from the current operation record chart; step D, if the target object is under the locked stage, then rejecting the operation request of the client end to the target object. The technical scheme adopted by the invention is applied to the project management and used for limiting operations of a plurality of users, such as creating, removing, modifying, uploading and deleting for the same catalogue or document under the project simultaneously, so that the chaos error of documents and data loss under the project due to the simultaneous operation of many people is avoided, and the stability of the project document management is ensured.
Owner:广州普邦园林股份有限公司
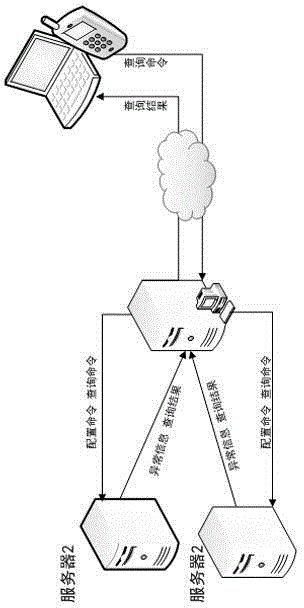
Automatic hardware equipment monitoring system based on domestic operating system
InactiveCN103986623AReal-time awareness of changes in work statusHardware monitoringData switching networksOperational systemServer
The invention provides an automatic hardware equipment monitoring system based on the domestic operating system. A server hardware drive can sense the change of the work state of hardware in time and feed back the change of the work state to a specific working directory of the operating system in real time; server monitoring software trains specific files in rotation in the specific working directory of the operating system periodically and judges whether the hardware state is normal or not, and if it is found that the hardware is abnormal, abnormal information is sent to a management center through a network interface; the management center receives the abnormal information sent by the server and takes corresponding measures according to the level of abnormality, and the server and the management center also need to conduct interaction of management and configuration information.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
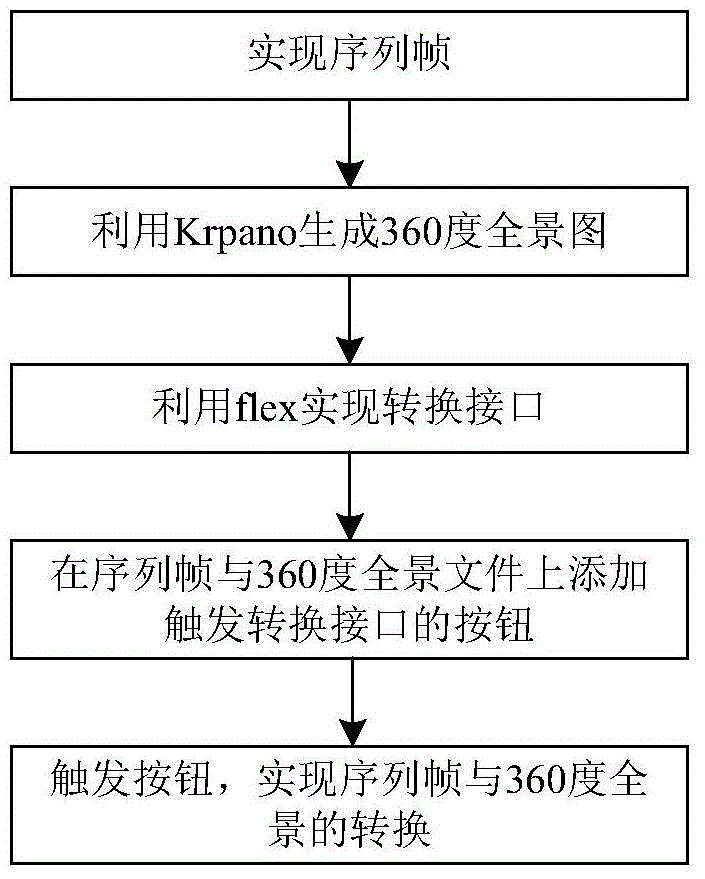
Interconversion method of sequence frame and panorama
ActiveCN104616342AStrong sense of realityAchieve arbitrary controlGeometric image transformation3D-image renderingInternal memoryComputer science
The invention provides an interconversion method of a sequence frame and a panorama, and relates to the technology of display of virtual reality and virtual images. The method comprises the steps of storing the sequence frame for displaying automatic roam effect and a 360-degree panorama file of a swf format under the created working directory; building a correspondence relationship between the sequence frame file and the 360-degree panorama file; implementing a conversion interface by flex; adding a button for triggering the conversion interface to a front page; triggering the button to convert the sequence frame and the 360-degree panorama. With the adoption of the method, the problem of failure of roam of 360-degree panorama display can be solved, and meanwhile, the problem of blockage caused by that unity 3D needs a large space of an internal memory can be solved; the automatic roam effect is achieved; the sense of reality is improved; the interaction performance is high; the manufacturing cost is relatively low; the method is applied to network.
Owner:北京明兰网络科技有限公司
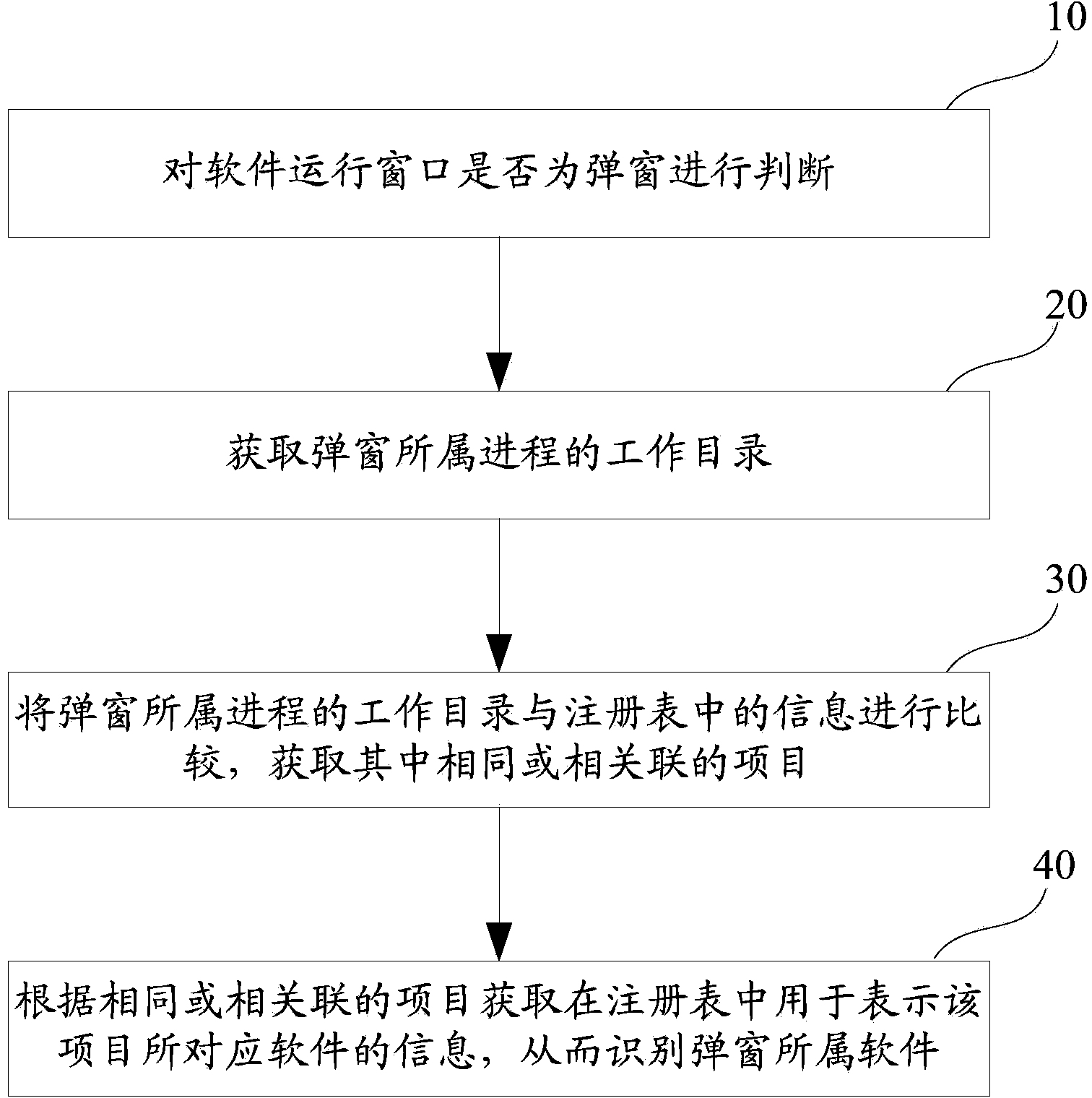
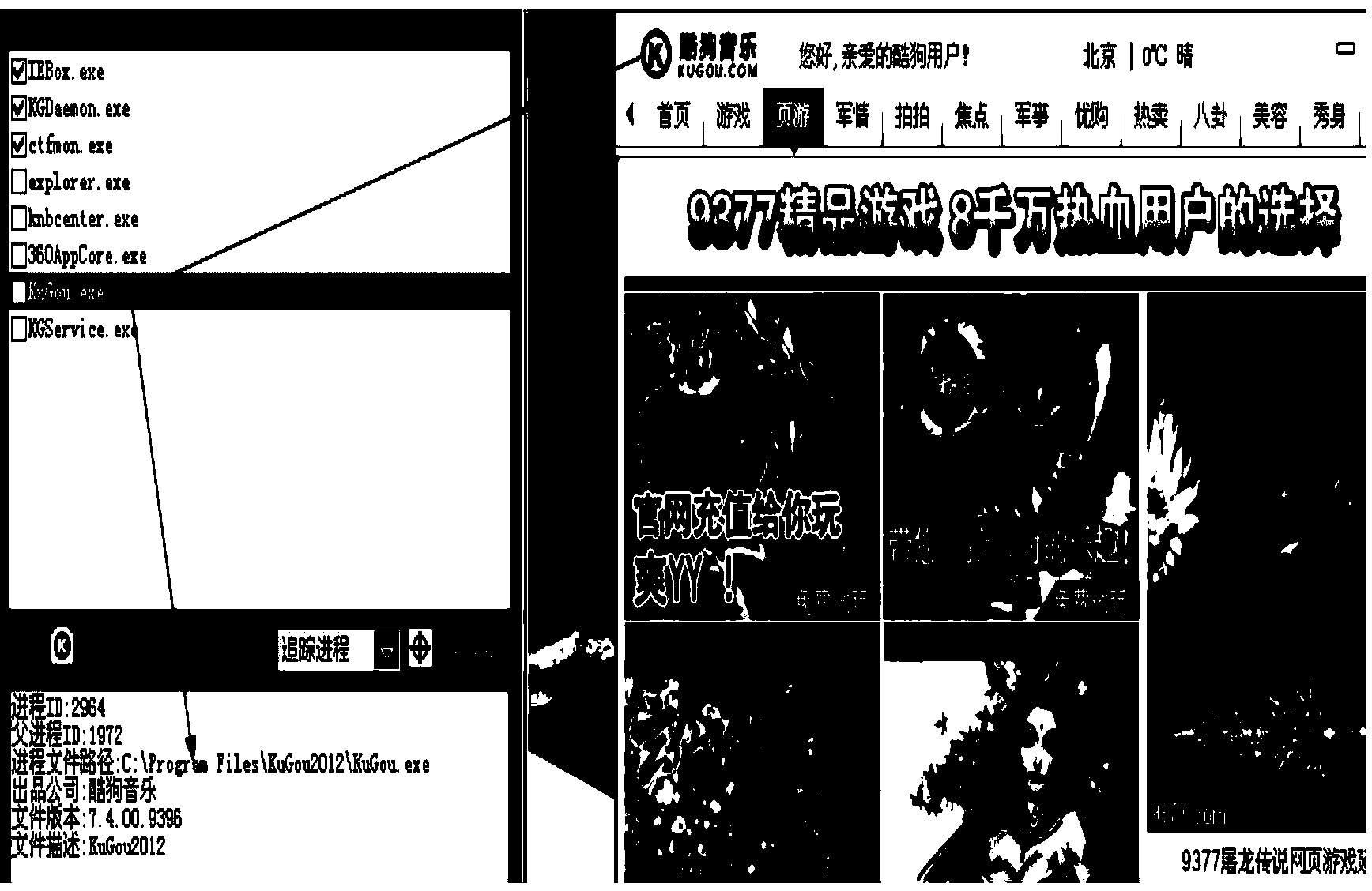
Method and device for processing pop-up window
ActiveCN103514019AEasy to identifyUnrecognizable solutionProgram loading/initiatingSoftware engineeringEngineering
The invention discloses a method for processing a pop-up window. The method comprises the steps of judging whether a window operated by software is the pop-up window or not; when the window is judged to be the pop-up window, obtaining a working directory of a process which the pop-up window belongs to; comparing the working directory of the process which the pop-up window belongs to with information in a registry, and obtaining the same or relevant items; obtaining information used for representing the software corresponding to the items in the registry according to the same or relevant items, and therefore identifying the software which the pop-up window belongs to. The invention further discloses a device for processing the pop-up window. The device comprises a pop-up window judging module, a first obtaining module and an identification module. According to the method and device for processing the pop-up window, the software which the pop-up window belongs to can be effectively identified, and a user can conveniently identify the software which the pop-up window belongs to.
Owner:BEIJING QIHOO TECH CO LTD
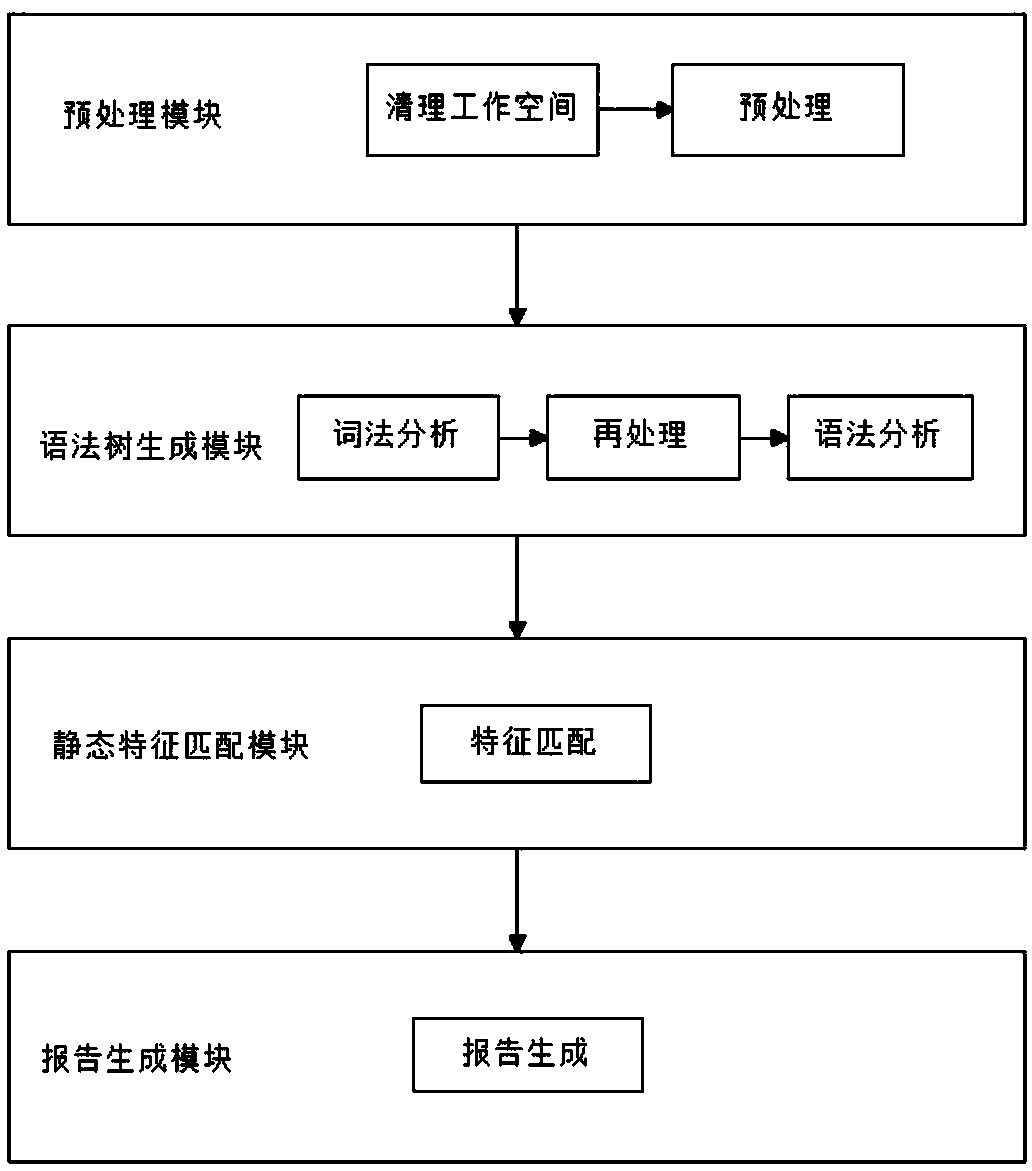
A static code auditing system and method for an Ethereum smart contract
ActiveCN109684838AAdd logic rulesReduce security risksPlatform integrity maintainanceLexical analysisInformation security
The invention discloses a static code auditing system and method for an intelligent contract on an Ethernet workshop platform of a block chain, and belongs to the technical field of information security. According to the method, security threats existing on the smart contract written on the Ethereum platform by using the Solidity language can be detected, the specific position is positioned, the harm is explained, and a corresponding solution is given. The method comprises the steps that firstly, a user inputs a to-be-detected project directory or a path of a single file into a system, the system conducts preprocessing operation on input content, the whole project is copied into a temporary work directory, and annotation content in a Solidity file in the temporary work directory is deleted; Secondly, the system analyzes each Solidity file into a syntax tree form through operations such as lexical analysis and grammatical analysis; Then, the system performs static feature matching on the syntax tree structure and a pre-established logic matching feature to obtain a matching result; And finally, classifying and summarizing the matched results by the system to generate a report file,namely a detection result.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
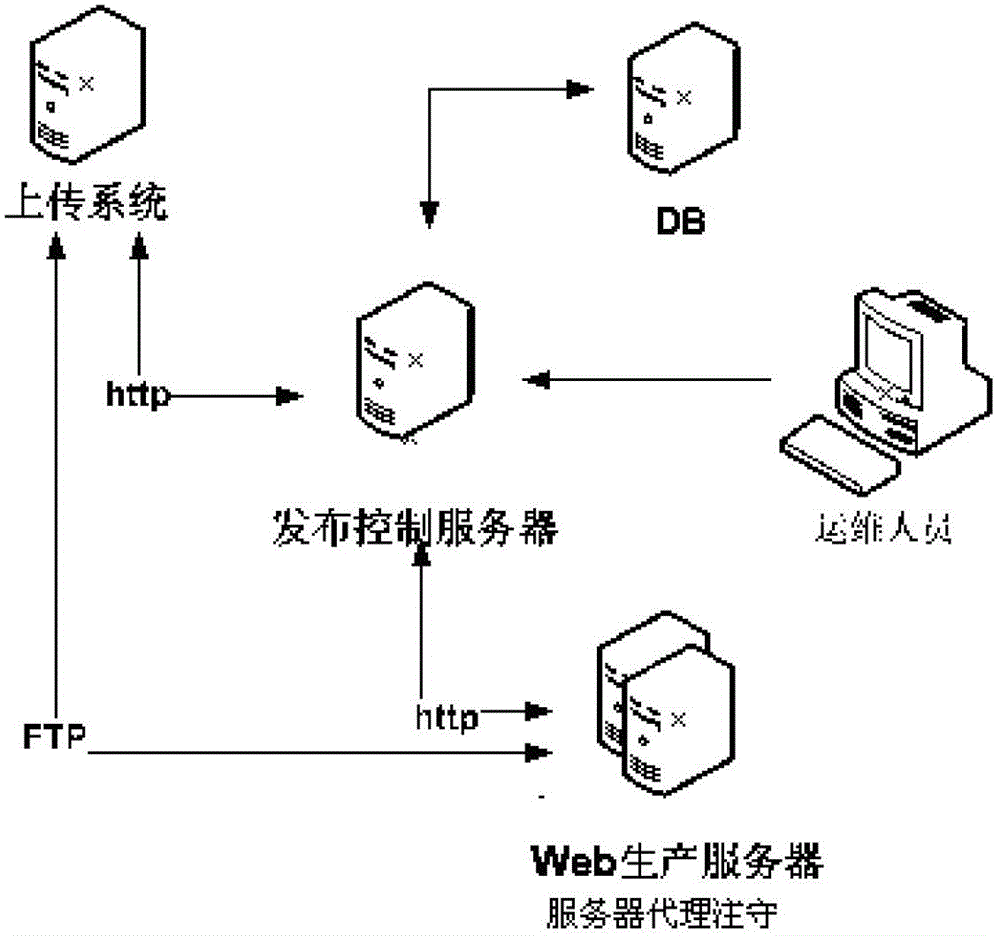
Release control method and release control system oriented to cluster sites
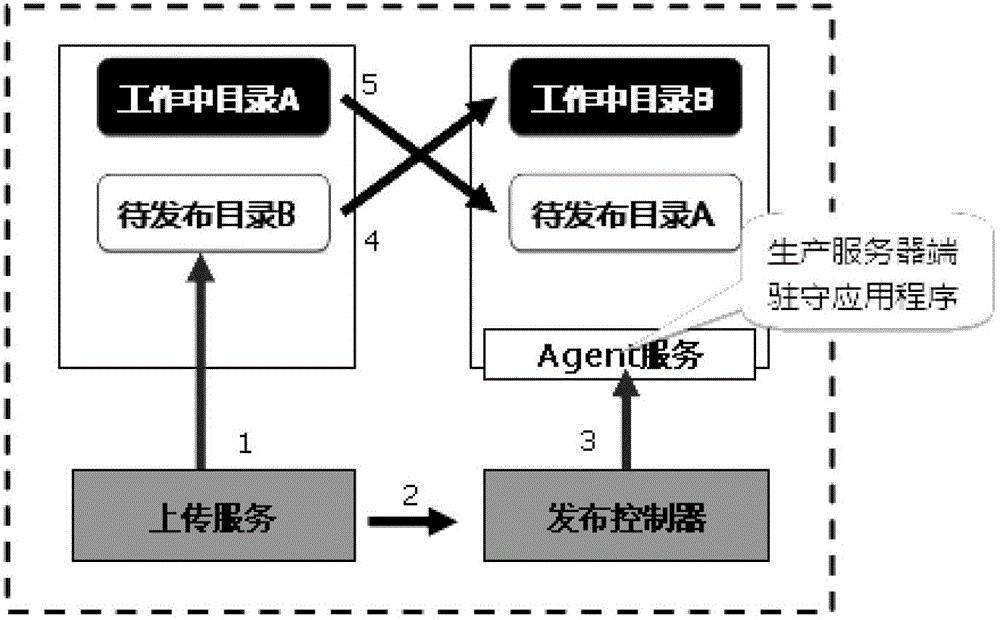
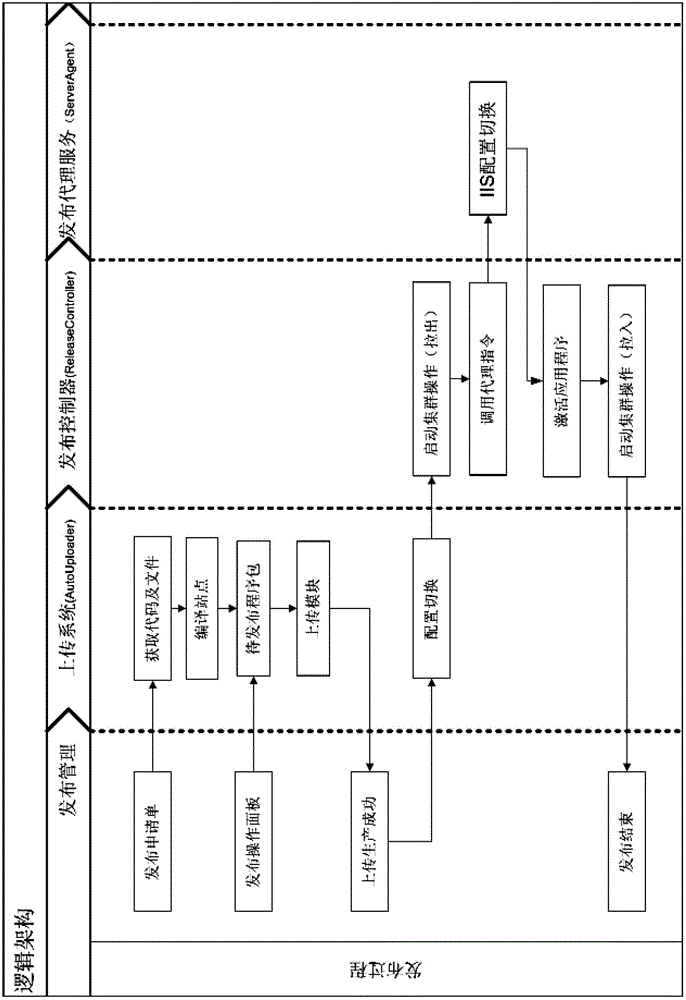
ActiveCN102752394ASmooth application upgradeQuick configurationTransmissionControl systemWeb service
The invention discloses a release control method oriented to cluster sites, wherein the method comprises the following steps of: building at least one backup directory at each WEB server; transmitting a to-be-released application to the backup directory of each WEB server in the cluster; executing IIS (Internet Information Server) switching to switch the WEB server to the backup directory from the current work directory, and specifying the backup directory as the current work directory; and at least activating the applications in the backup directories of some WEB servers. The method can easily realize release for a large-scale cluster site; firstly, the application work and the application updating are separated, namely, the work and the updating both are effective; secondly, a smoke test mechanism is provided in the production environment; the availability of the finally produced version is guaranteed; thirdly, by effective release strategies, each machine application upgrading is smoothed without causing troubles to the users of the front end; and finally, a switching back mechanism is configured quickly, which can ensure high-efficiency rollback of the applications.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
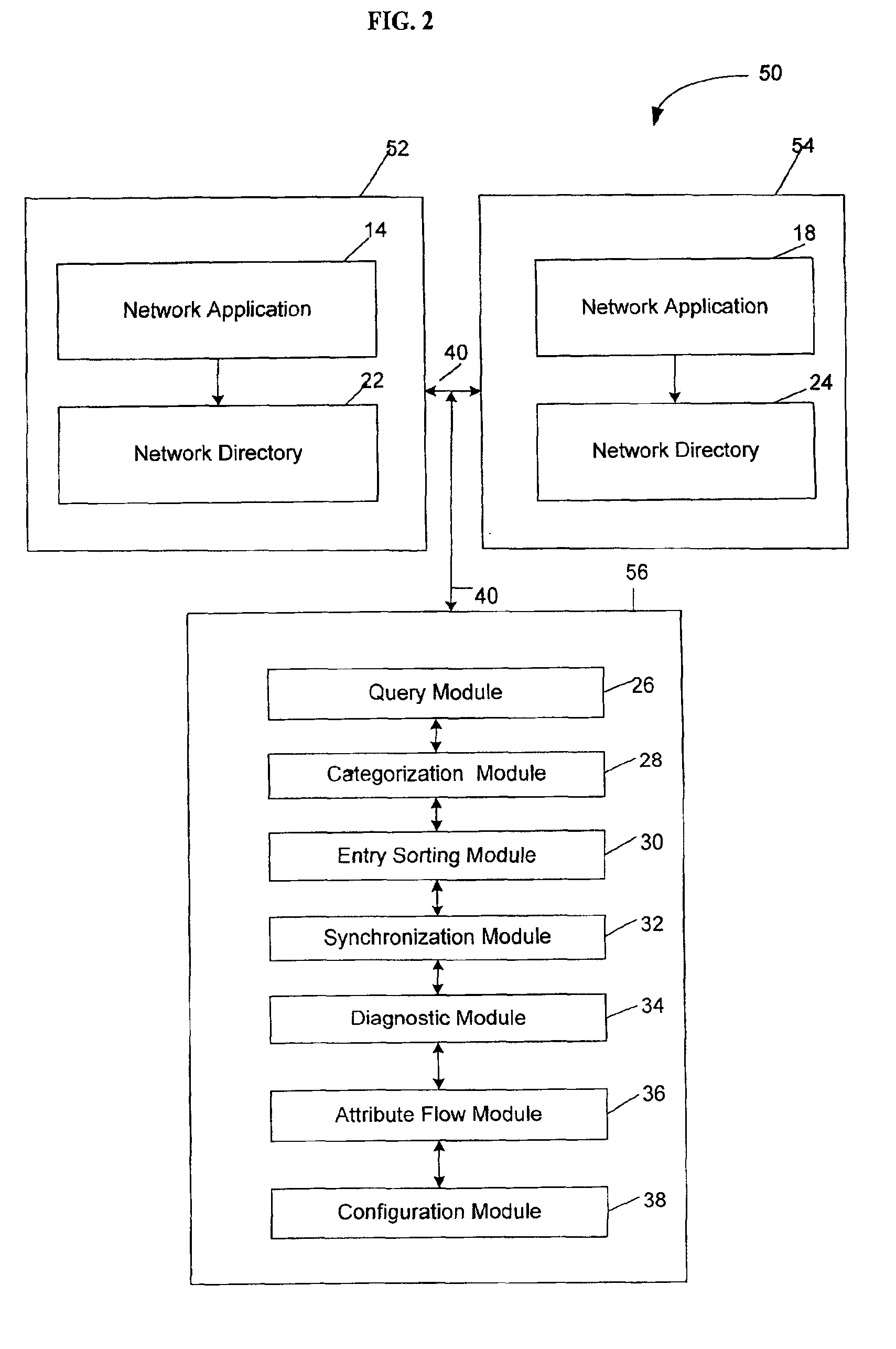
System and method for managing network directories
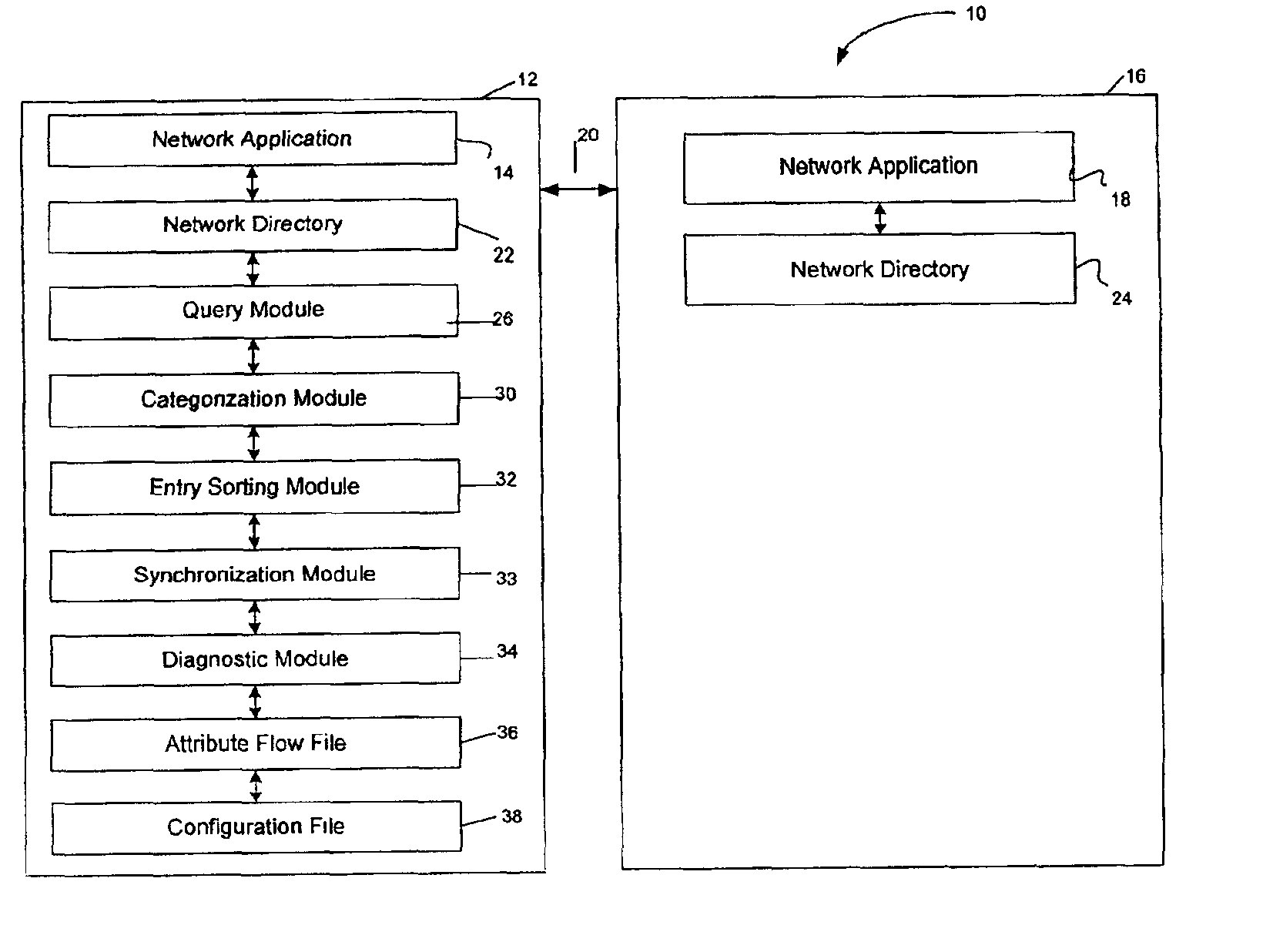
InactiveUS6883036B1Data processing applicationsError detection/correctionApplication softwareDistributed computing
A system and method for synchronizing network directories. The first network directory is affiliated with a first application having entries native to the first application and the second network directory is affiliated with a second application and having entries native to the second application. An entry native to the first application is non-native to the second application and an entry native to the second application is non-native to the first application. According to one embodiment, the system includes an entry sorting module for sorting entries of the first and second directories based on the native application of the entry and a synchronization module in communication with the entry sorting module for updating entries in at least one of the first and second directories based on whether an entry native to the first application resides in the first directory.
Owner:BELLSOUTH INTPROP COR
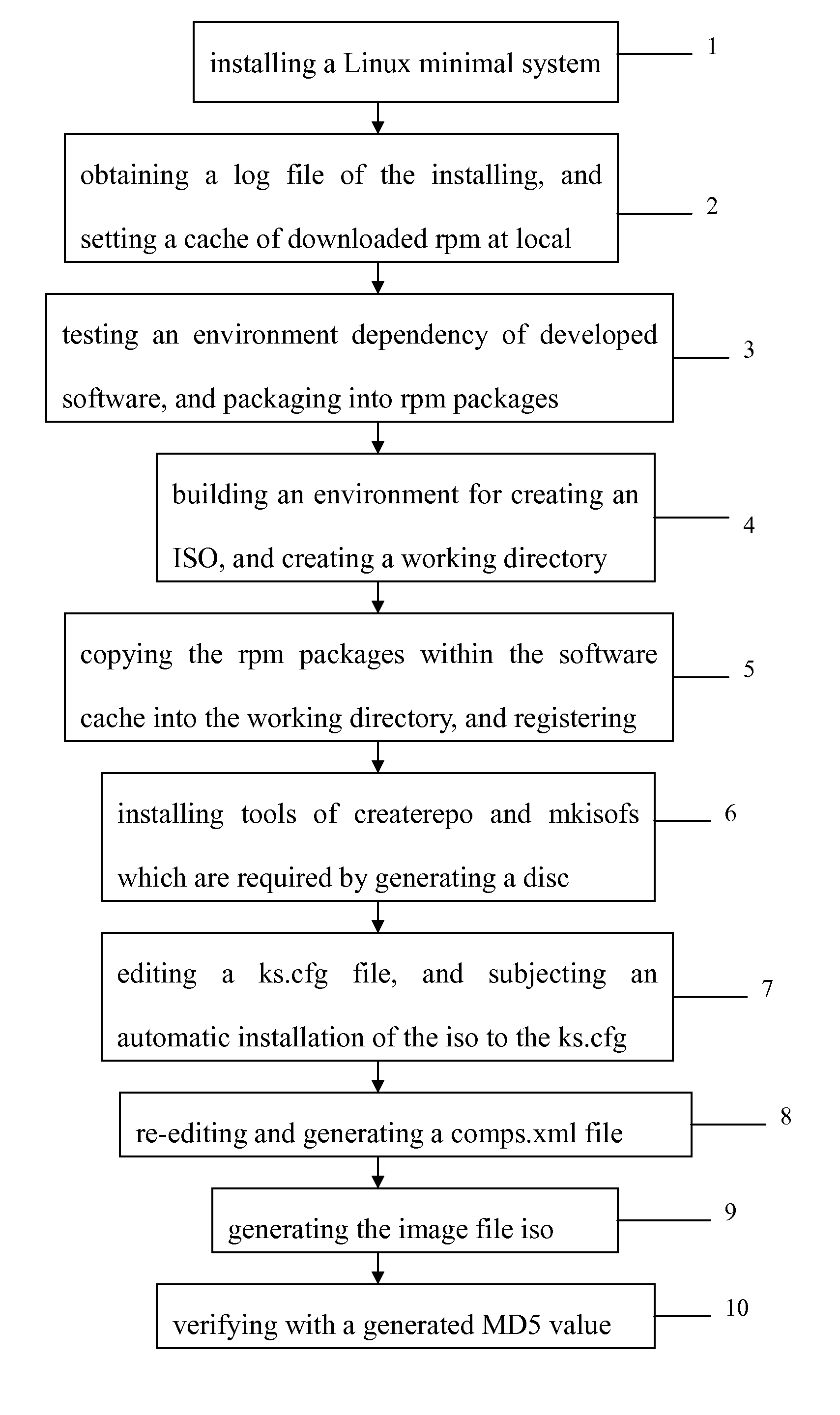
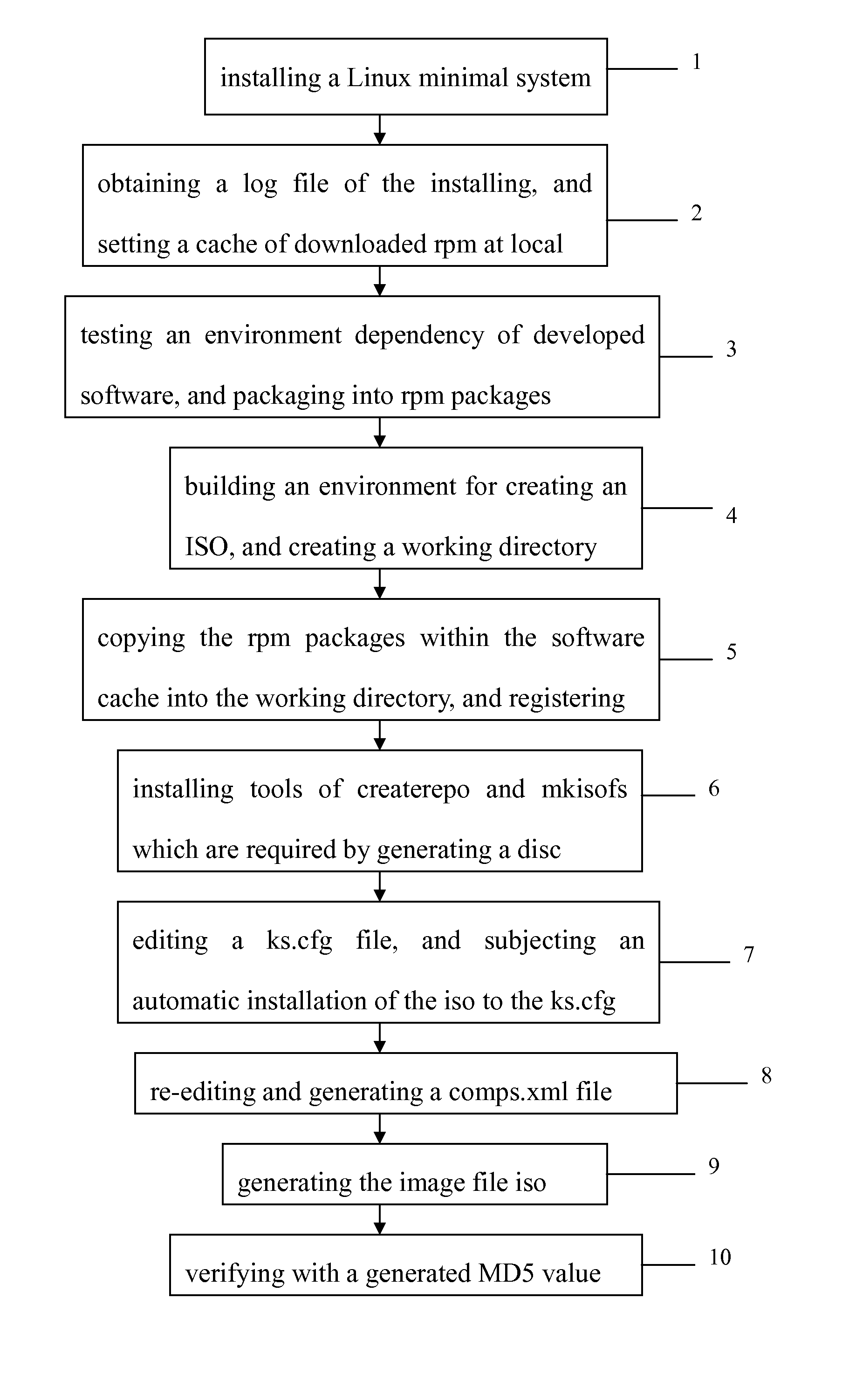
Method for distributing large-sized Linux software packages
ActiveUS20160283218A1Improve efficiencyEasy to deployProgram loading/initiatingTransmissionSoftware distributionSoftware engineering
A method for distributing large-sized Linux software packages, in a field of a Linux software distribution, includes steps of: installing a Linux minimal system; obtaining a log file of the installing, and setting a cache of a local download rpm; building an environment for creating iso, and creating a working directory; testing an environment dependency of a developed software and packaging into rpm packages, copying the downloaded rpm packages within the cache into the working directory, and registering; installing tools of createrpo and mkisofs for generating a disc; editing a kickstart file, ks.cfg; generating and modifying a comps.xml to designating the rpm packages and dependencies thereof which are required within a software archive of the system; generating an iso file of gcloud, and verifying with MD5 value. The method is applicable to a large-sized software package distribution by overcoming version verification and vulnerability to network.
Owner:G CLOUD TECH
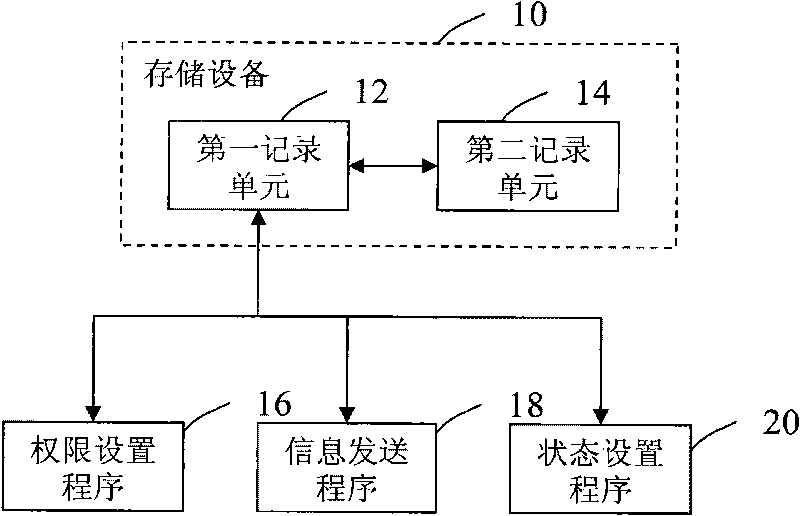
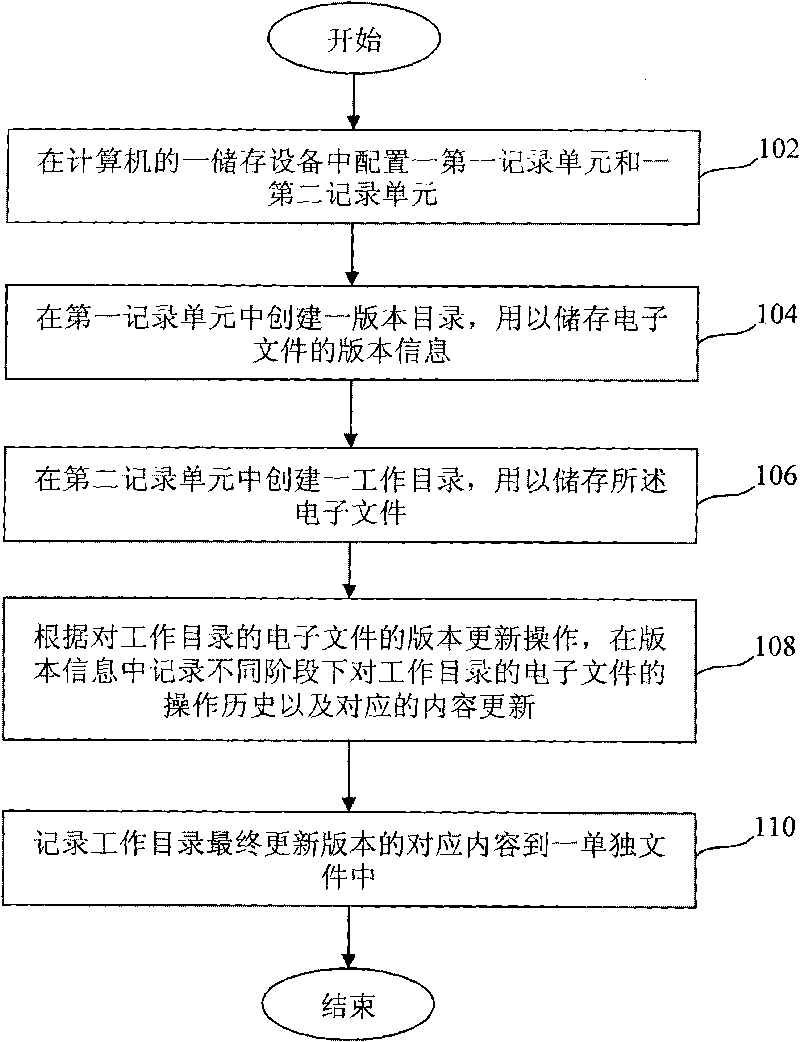
Management system and method of electronic files
InactiveCN101739409AImprove management efficiencySimplify cumbersome operationsResourcesSpecial data processing applicationsComputerized systemManagement efficiency
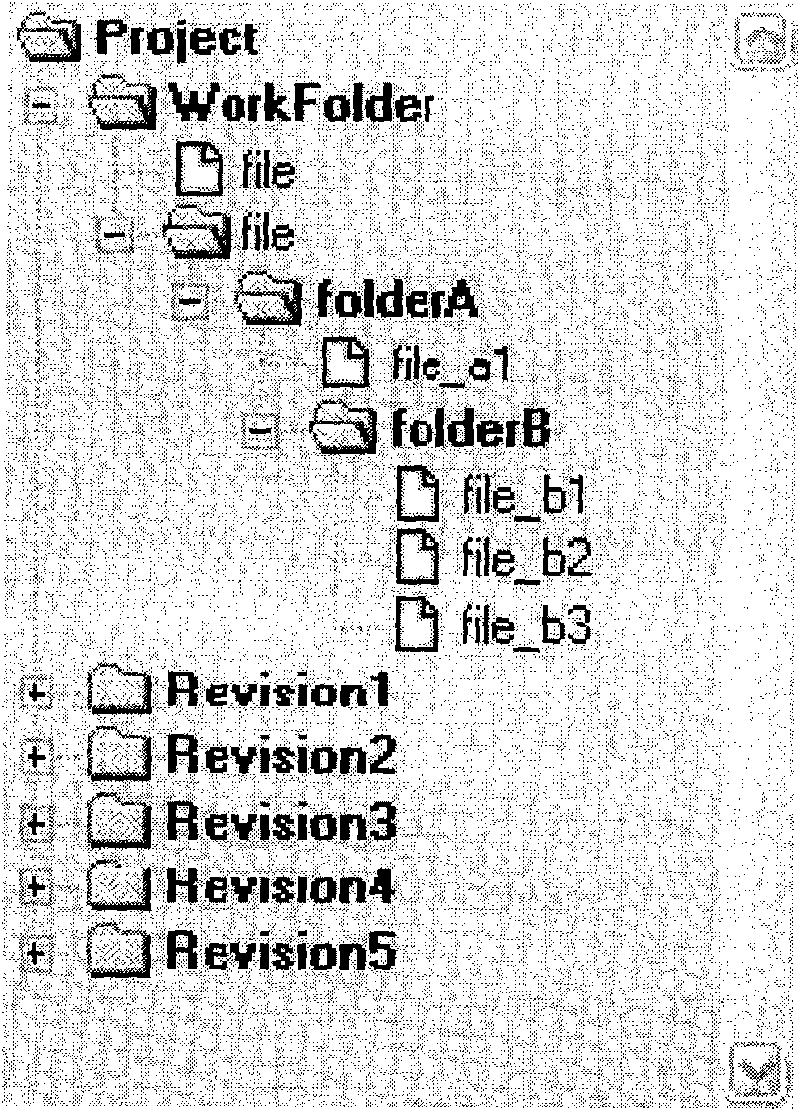
A management system and method of electronic files are used to support operations of establishing and modifying electronic files and managing version in a computer system. The management system comprises a first record unit and a second record unit which are arranged in a computer storage device, wherein the first record unit has a version directory which is used to record the operating history of the working directory and the corresponding content updates in different stages in the version information according to the update operation of the version of the electronic files of the working directory; and the second record unit has a working directory which is used to store the electronic files and record the corresponding content of the final updated version of the working directory into a single electronic file, thus the electronic file can be used as the basis of the next-version updating of the working directory final updated version. The invention can simplify the existing complicated operation and increase the management efficiency of files by automatically storing the content of the working directory release version.
Owner:刘祥
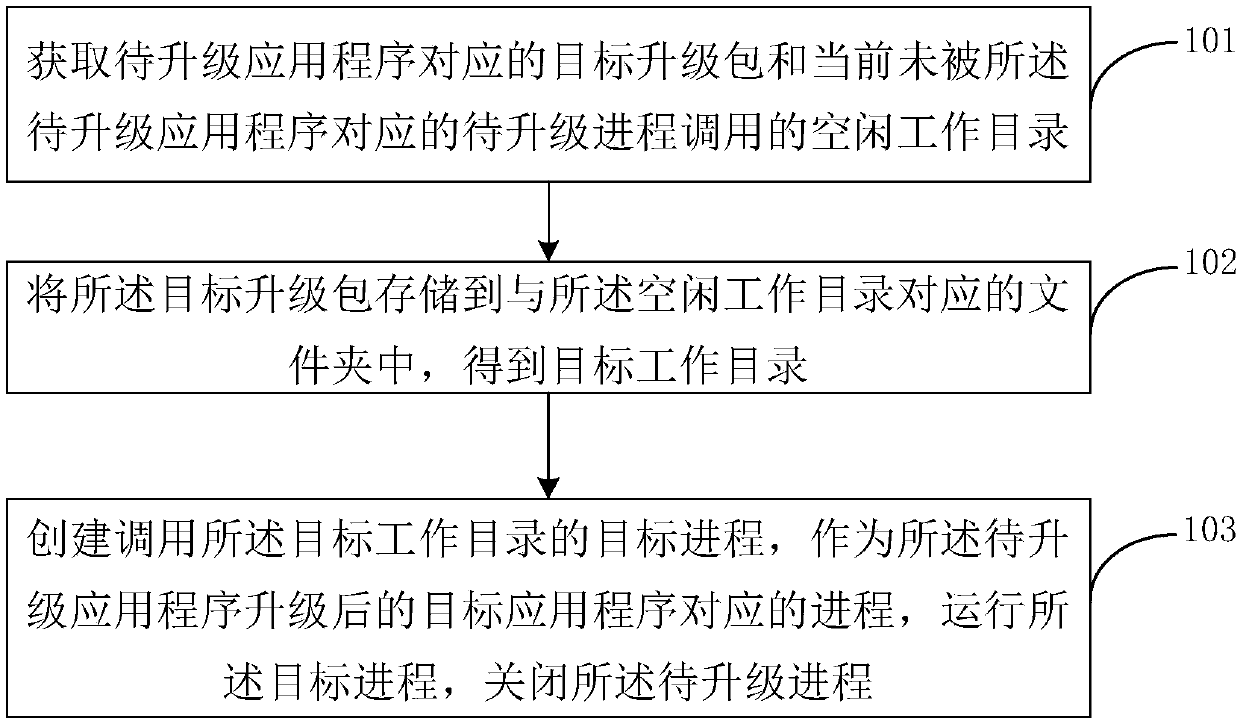
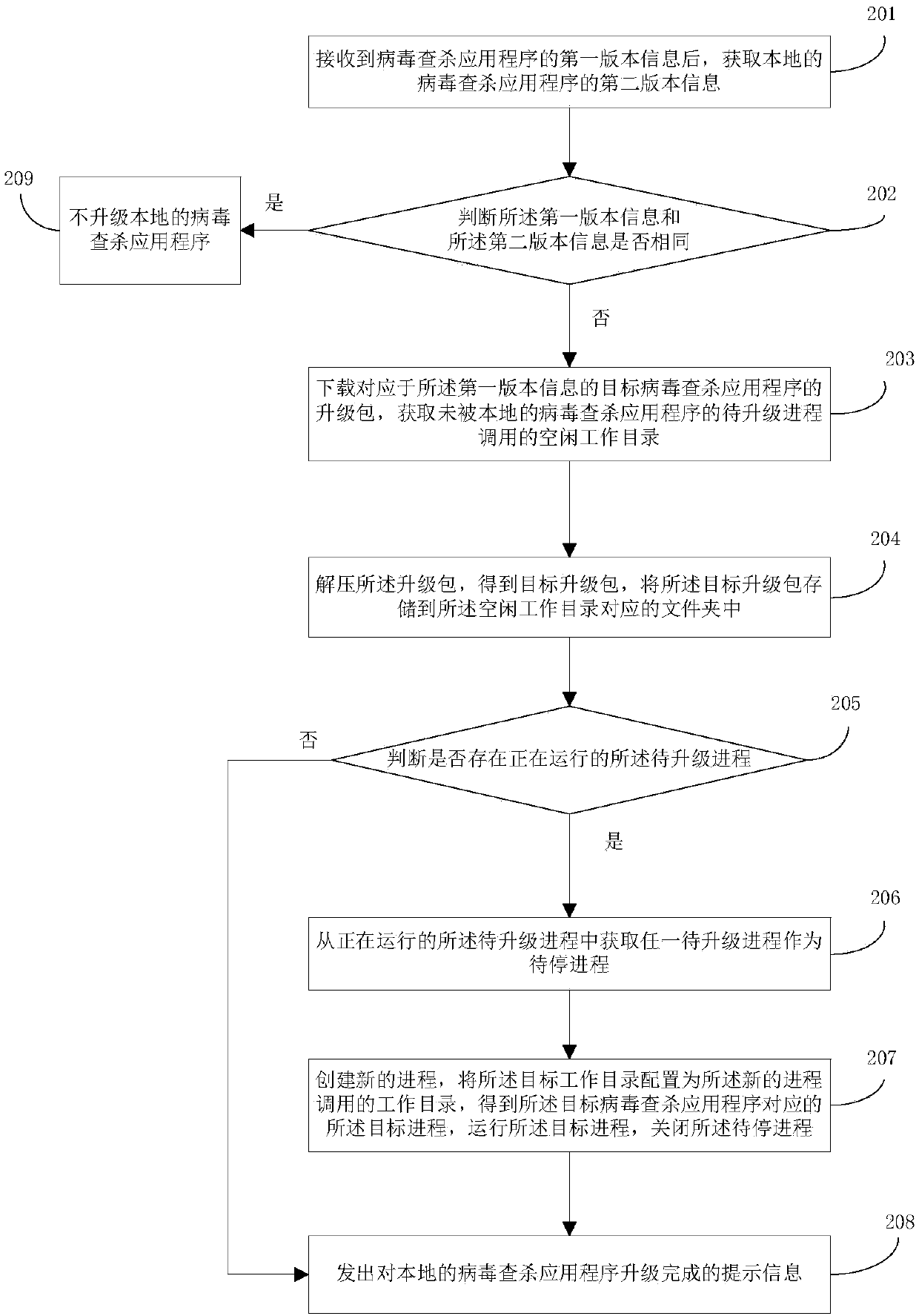
Application program upgrading method and device
ActiveCN107748668ANormal operation does not affectGuaranteed continuitySoftware deploymentSoftware engineeringWorking directory
The embodiment of the invention discloses an application program upgrading method and device. According to the method, after a target upgrading package of a to-be-upgraded application program is received, the target upgrading package is stored in an idle working directory which is not occupied by the to-be-upgraded application program currently, a target working directory is obtained, and then a target process for calling the target working directory is created. Through the method, the target upgrading package is stored into a folder corresponding to the idle working directory, so that the upgrading process of the to-be-upgraded application program does not influence normal operation of the to-be-upgraded application program, a service corresponding to the to-be-upgraded application program or a target application program is not interrupted in the upgrading process of the to-be-upgraded application program, and the continuity of the service provided in the upgrading process of the to-be-upgraded application program is guaranteed.
Owner:BEIJING QIANXIN TECH
Method, system and program product for maximizing virus check coverage while minimizing redundancy in virus checking
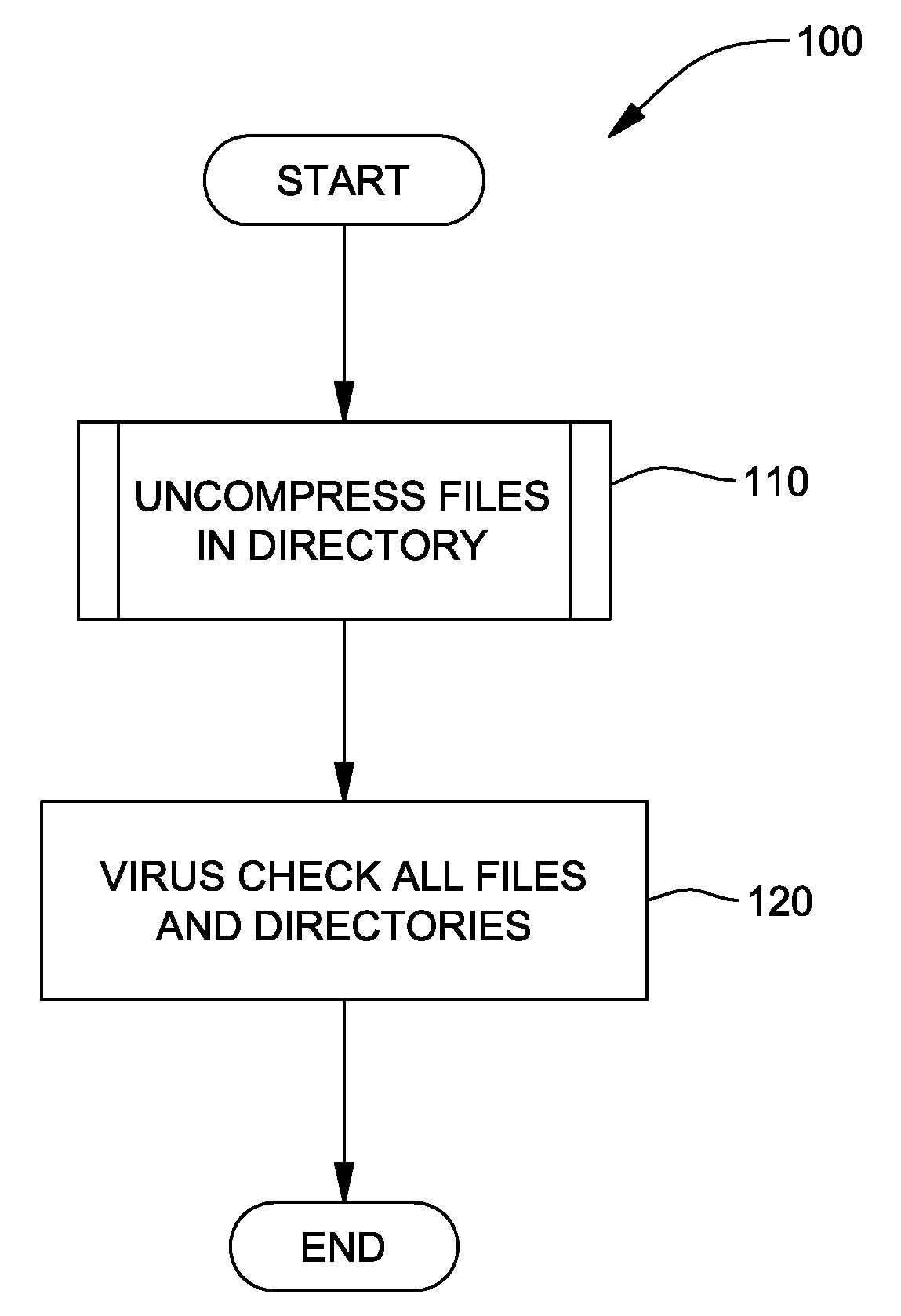
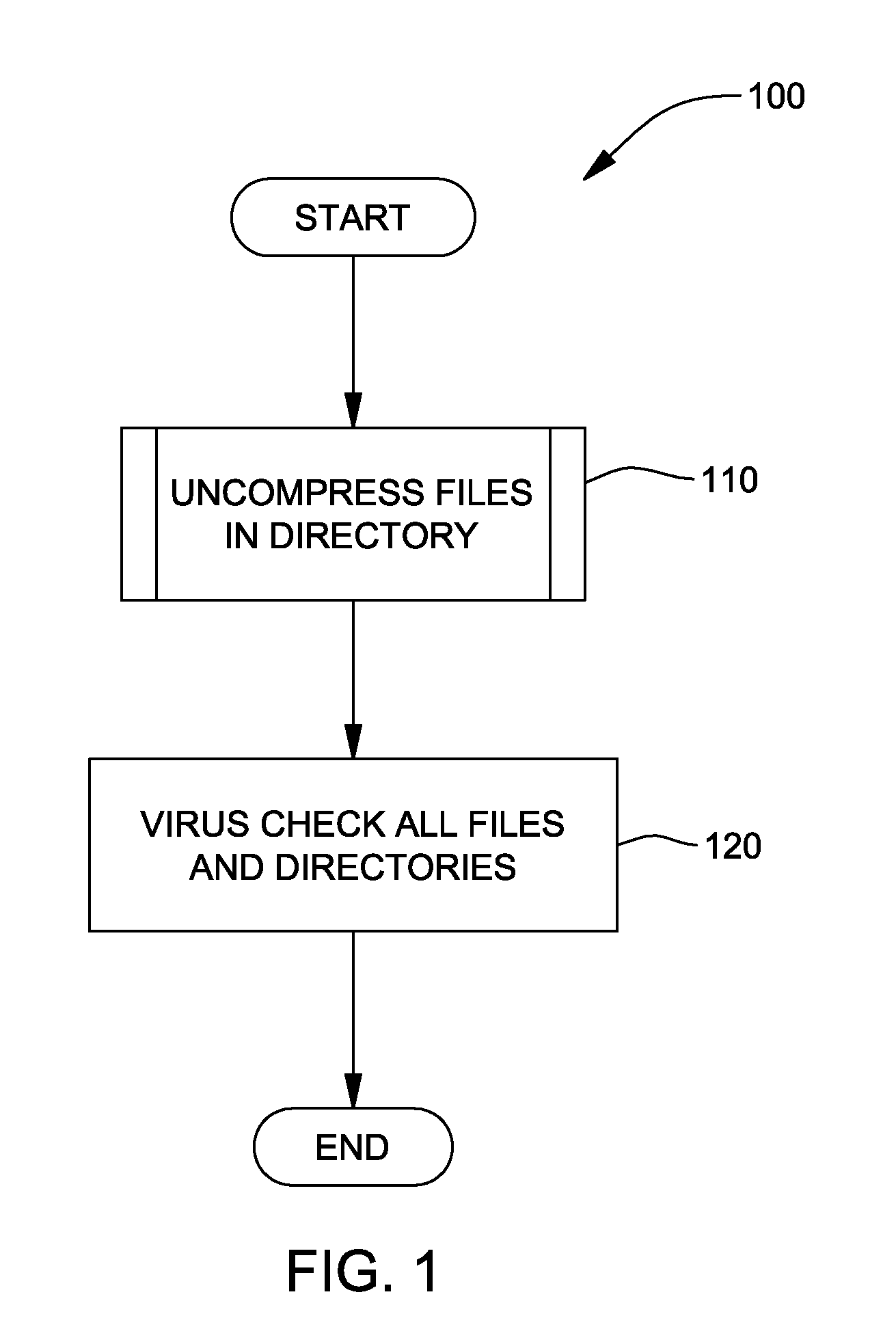
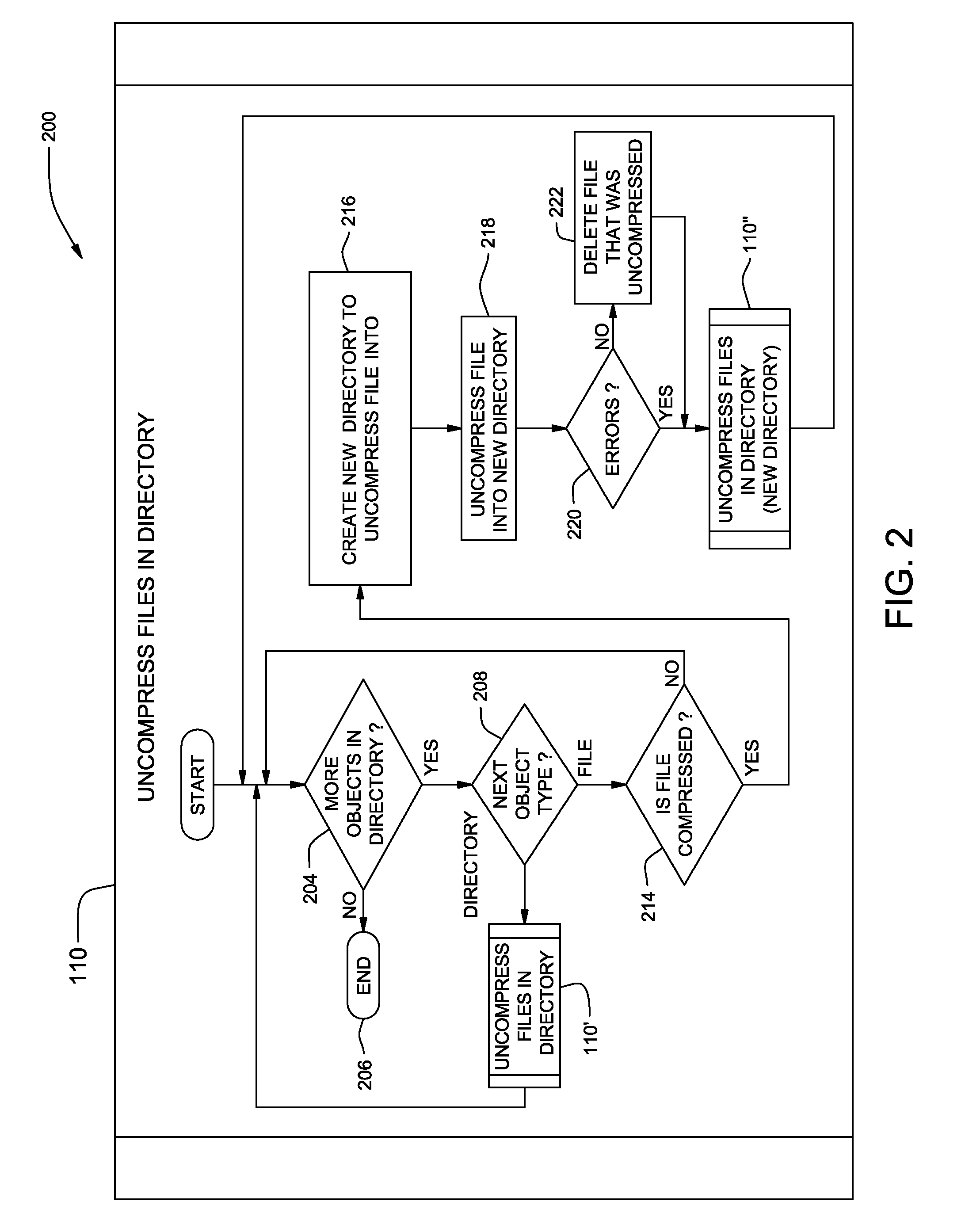
InactiveUS20080222177A1Maximizing virus check coverageMinimizing redundancyMemory loss protectionDigital data processing detailsVirusDatabase
A method, system and program product for maximizing virus check coverage, while minimizing redundancy in virus checking. The method includes evaluating, using an audit checking tool, whether or not a file in a working directory to be virus checked is a compressed file and, if the file is evaluated as being a compressed file, decompressing the compressed file evaluated using a decompression tool. Further, the method includes iterating the evaluating and decompressing steps to decompress any other files contained therein using the decompression tool and deleting a respective compressed file that is fully decompressed by the decompression tool without any errors from the working directory, while saving a respective compressed file that is not fully decompressed by the decompression tool. Furthermore, the method includes virus checking the working directory, such that, the virus checking does not virus check the respective compressed file that is deleted from the working directory.
Owner:IBM CORP
Installing and updating interpreted programming language applications using a designated virtual machine
A mechanism is provided for executing an interpreted programming language application from a server at a designated virtual machine on a client computer. A manifest file is extracted which indicates at least one resource for the interpreted programming language application as well as the repository file that provides the at least one resource. The repository file is located in a web start cache and copied to a run directory accessible by the designated virtual machine, outside the web start cache. After terminating the web start application, a particular virtual machine is designated from a plurality of virtual machines based upon the run directory to which the bootstrap class copied the resource repository file thereby forming the designated virtual machine. The interpreted programming language application is then executed from the run directory using the at least one resource.
Owner:INT BUSINESS MASCH CORP
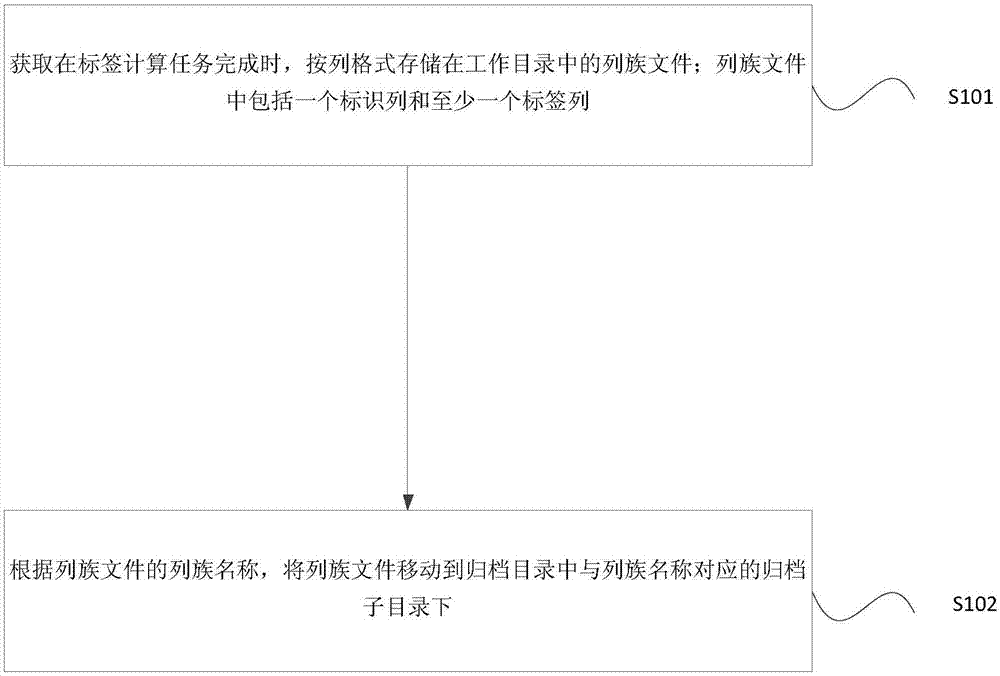
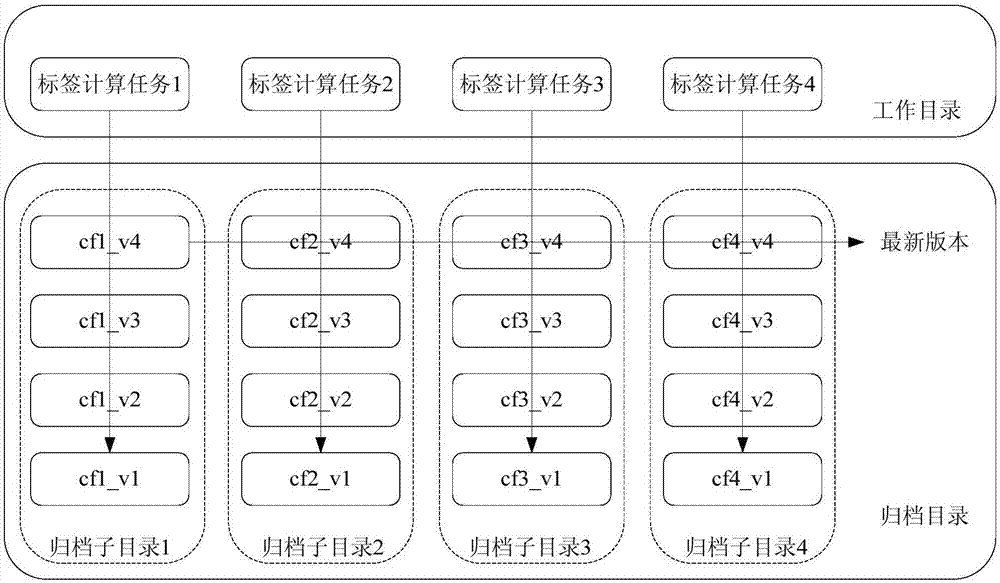
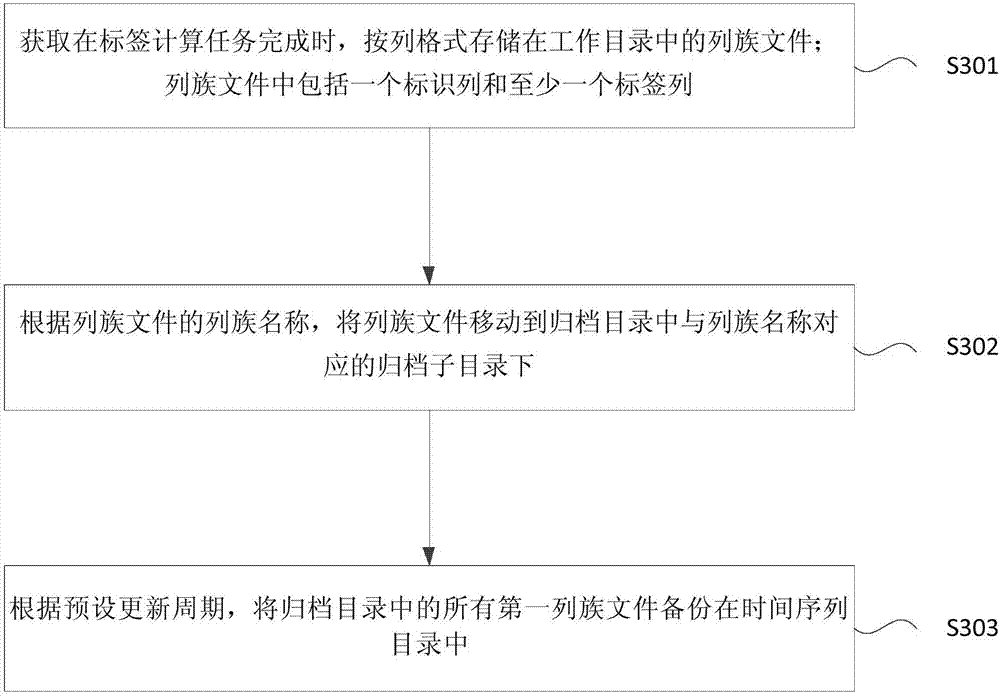
Method and device for storing label system data
ActiveCN107330024AReduce movementImprove batch read and write throughputDatabase distribution/replicationSpecial data processing applicationsData delayDatabase
The invention provides a method and device for storing label system data. The method includes the steps that when a label computation task is completed, a column family file stored in a working directory in a column format is obtained; the column family file includes one mark column and one or more label columns; according to the column family name of the column family file, the column family file is moved into an archive subdiretory, corresponding to the column family name, in an archive directory. The column family file is stored in the column format, in this way, the throughput of data reading and writing in batches is increased, and data updating is convenient. Meanwhile, a computing result of the label computing task is directly stored in an HDFS, in this way, data moving is reduced, data delay is reduced to the maximum degree, and cost is lowered. By storing multiple versions of the column family file, the version of the column family file is convenient to manage; column family files of multiple versions are sequenced based on a time sequence.
Owner:HUAWEI MACHINERY
File storage path obtaining method and device
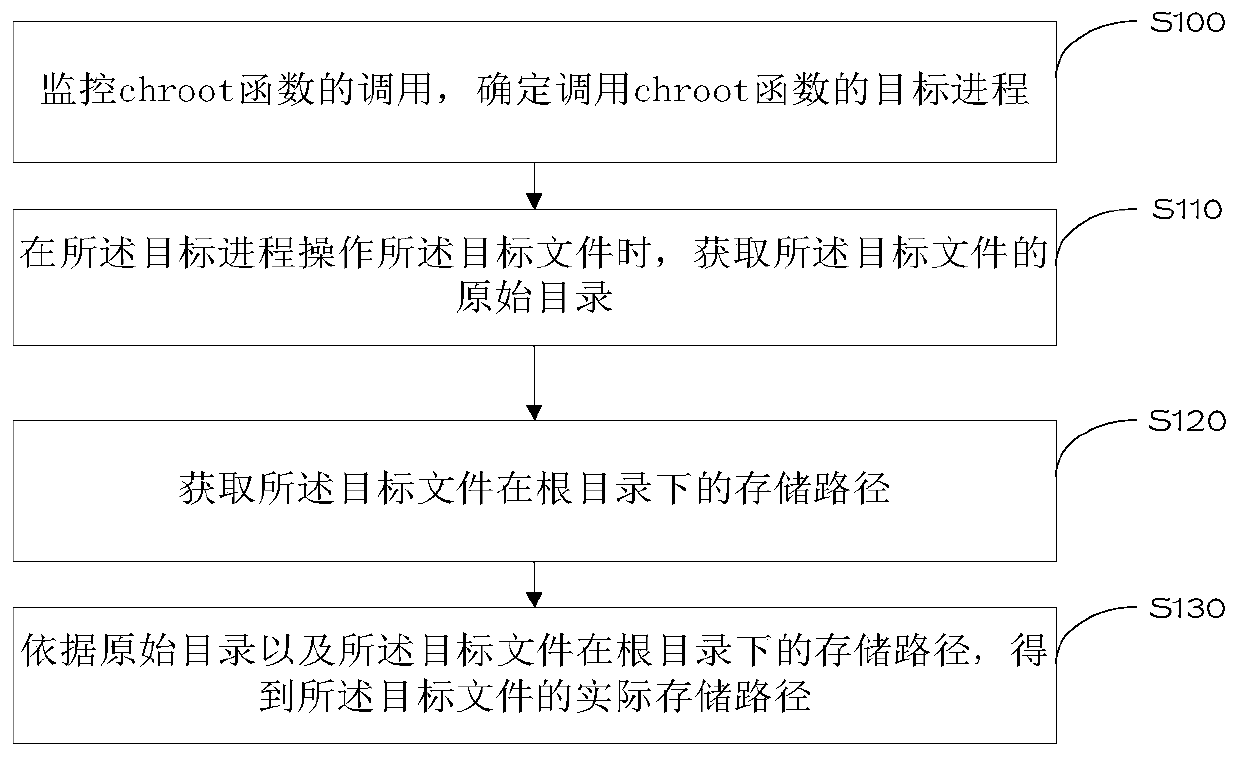
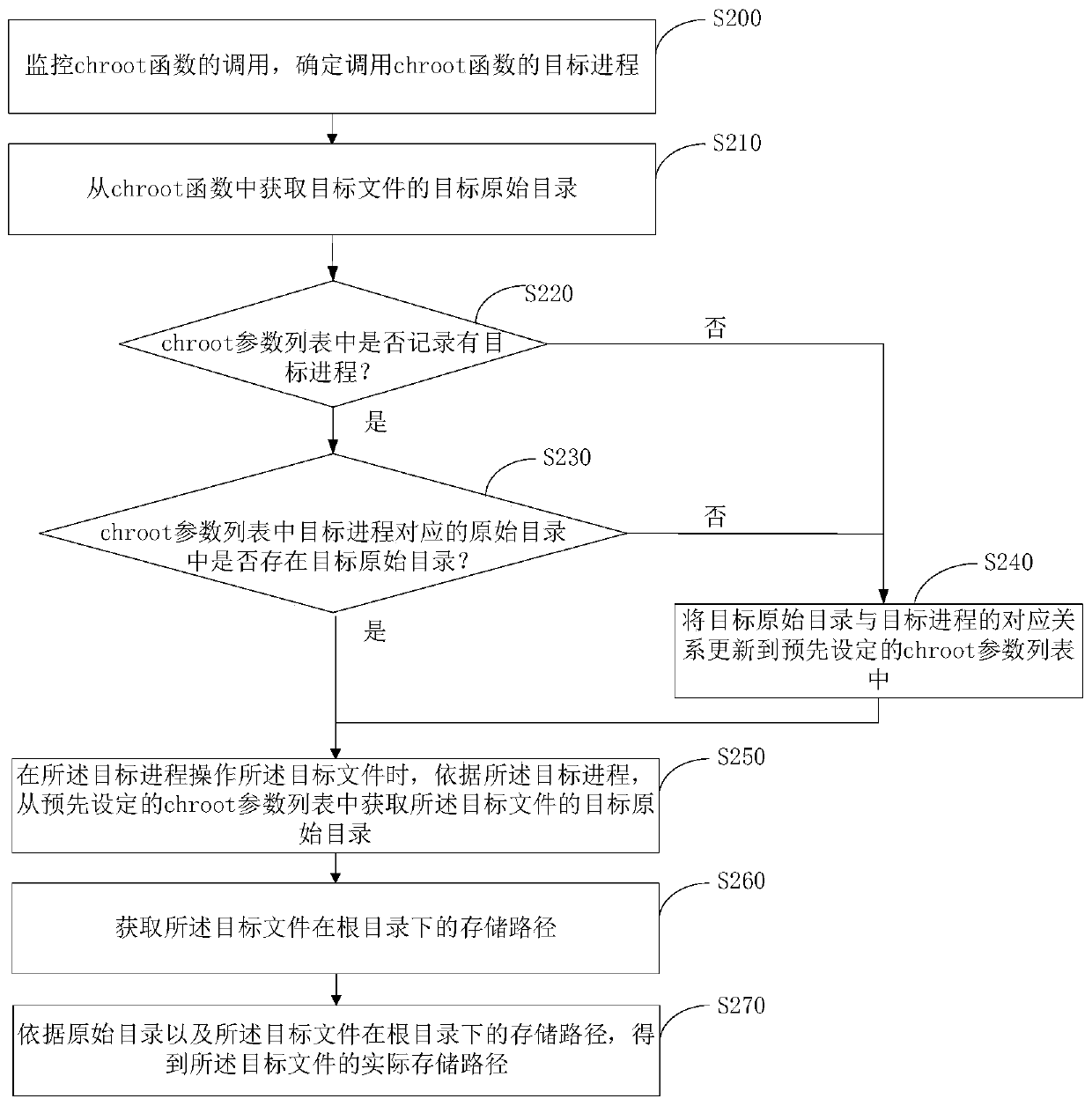
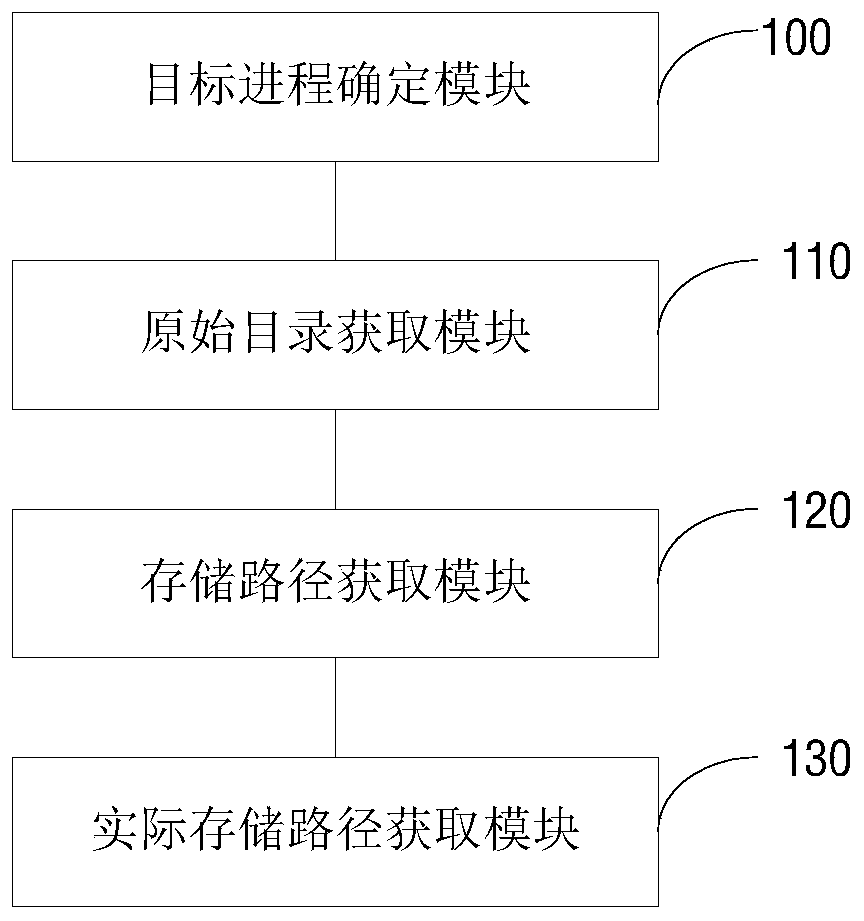
InactiveCN109977075ARealize monitoringFile system administrationFile access structuresDatabaseObject file
The invention discloses a file storage path obtaining method and device, and the method comprises the steps: monitoring the calling of a chroot function, determining a target process for calling the chroot function, and enabling the calling process of the chroot function to map an original catalog of a target file into a root catalog; when the target process operates the target file, obtaining anoriginal directory of the target file; obtaining a storage path of the target file in a root directory; and obtaining an actual storage path of the target file according to the original directory andthe storage path of the target file under the root directory. Due to the fact that the original directory of the target file is obtained, the actual storage path of the target file can be obtained according to the original directory and the storage path of the target file under the root directory, the file accessed by the process is obtained according to the actual storage path, and monitoring ofthe file is achieved.
Owner:北京椒图科技有限公司
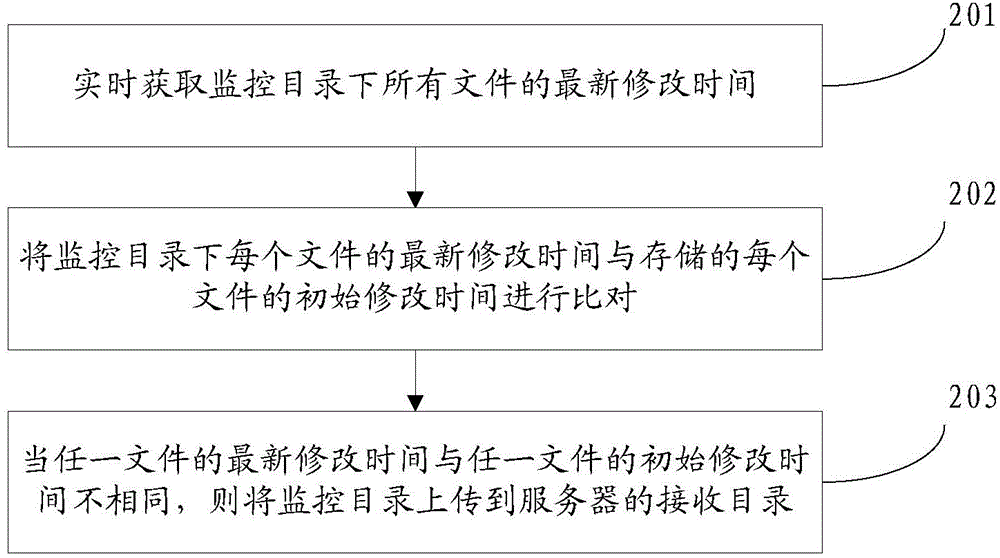
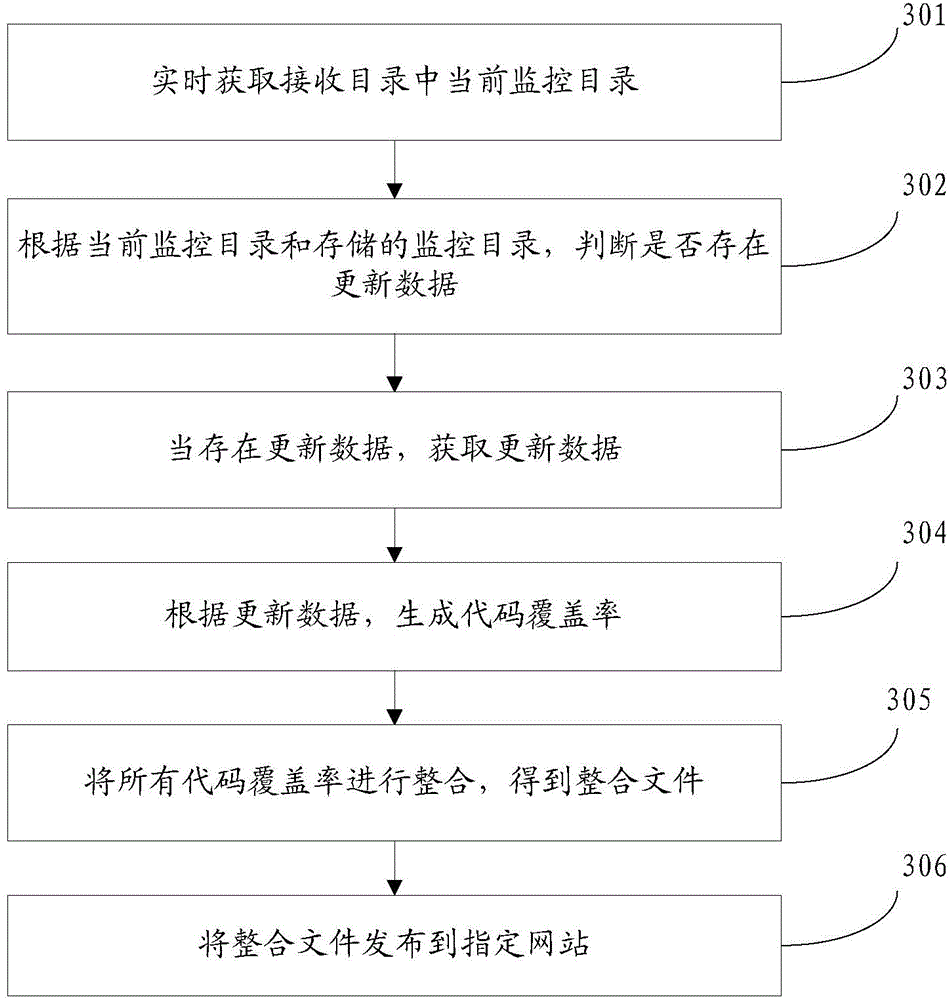
Directory uploading method, data releasing method, terminal and server
The invention discloses a directory uploading method, a data releasing method, a terminal and a server, and belongs to the field of computers. The directory uploading method comprises the following steps: acquiring the latest modification time of each file under a monitoring directory in real time; comparing the latest modification time of each file under the monitoring directory with the stored initial modification time of each file; and uploading the monitoring directory to a receiving directory of a server when the latest modification time of any file is not the same with the initial modification time of the file. According to the invention, a terminal uploads a monitoring directory to a receiving directory of a server when judging that the latest modification time of any file under the monitoring directory is not the same with the initial modification time of the file; and after receiving the monitoring directory, the server processes updated data in the monitoring directory to get the code coverage rate and releases an integrated file obtained through code coverage rate integration to a specified site. Thus, an easy directory uploading and data releasing method is provided.
Owner:TENCENT TECH (SHENZHEN) CO LTD
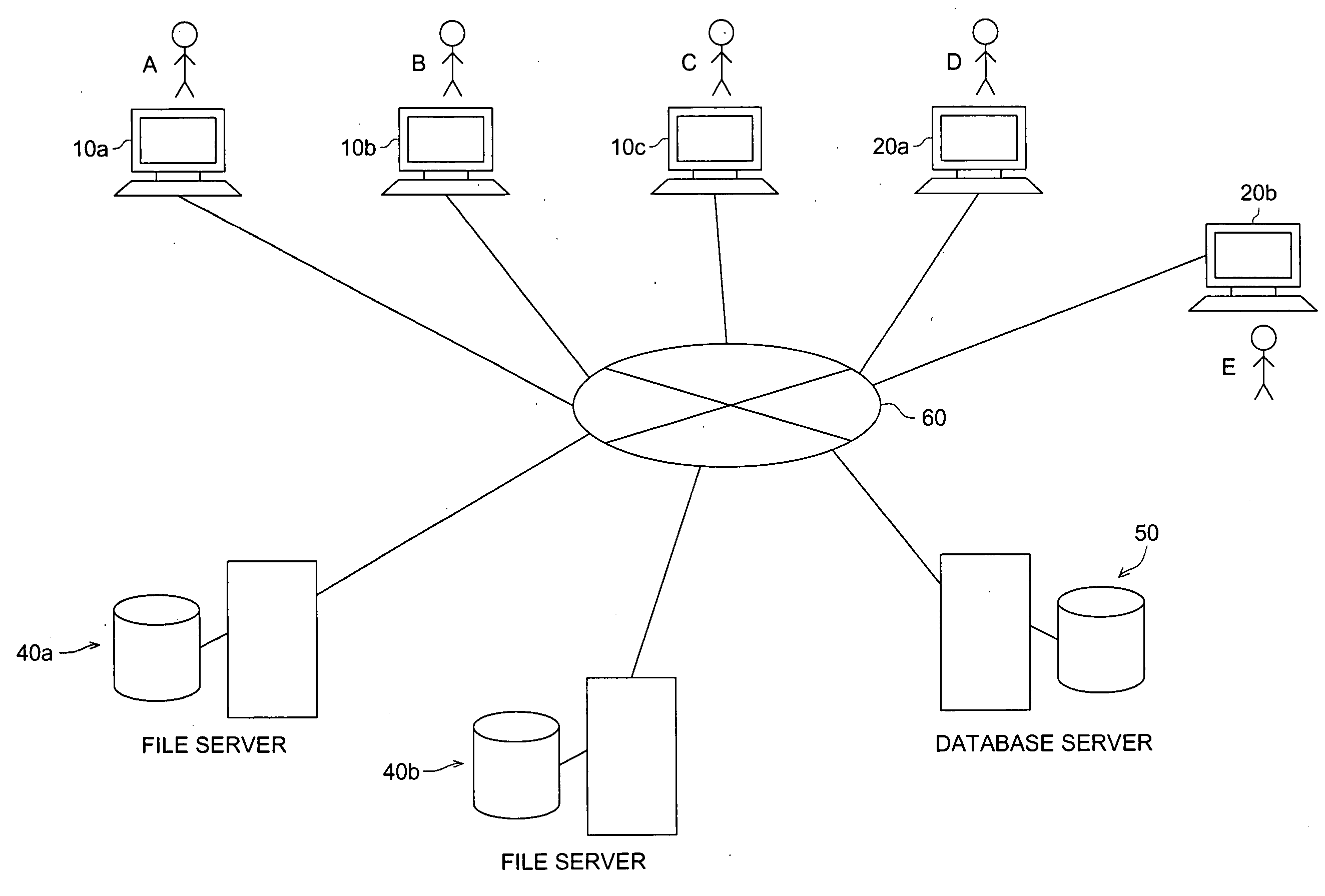
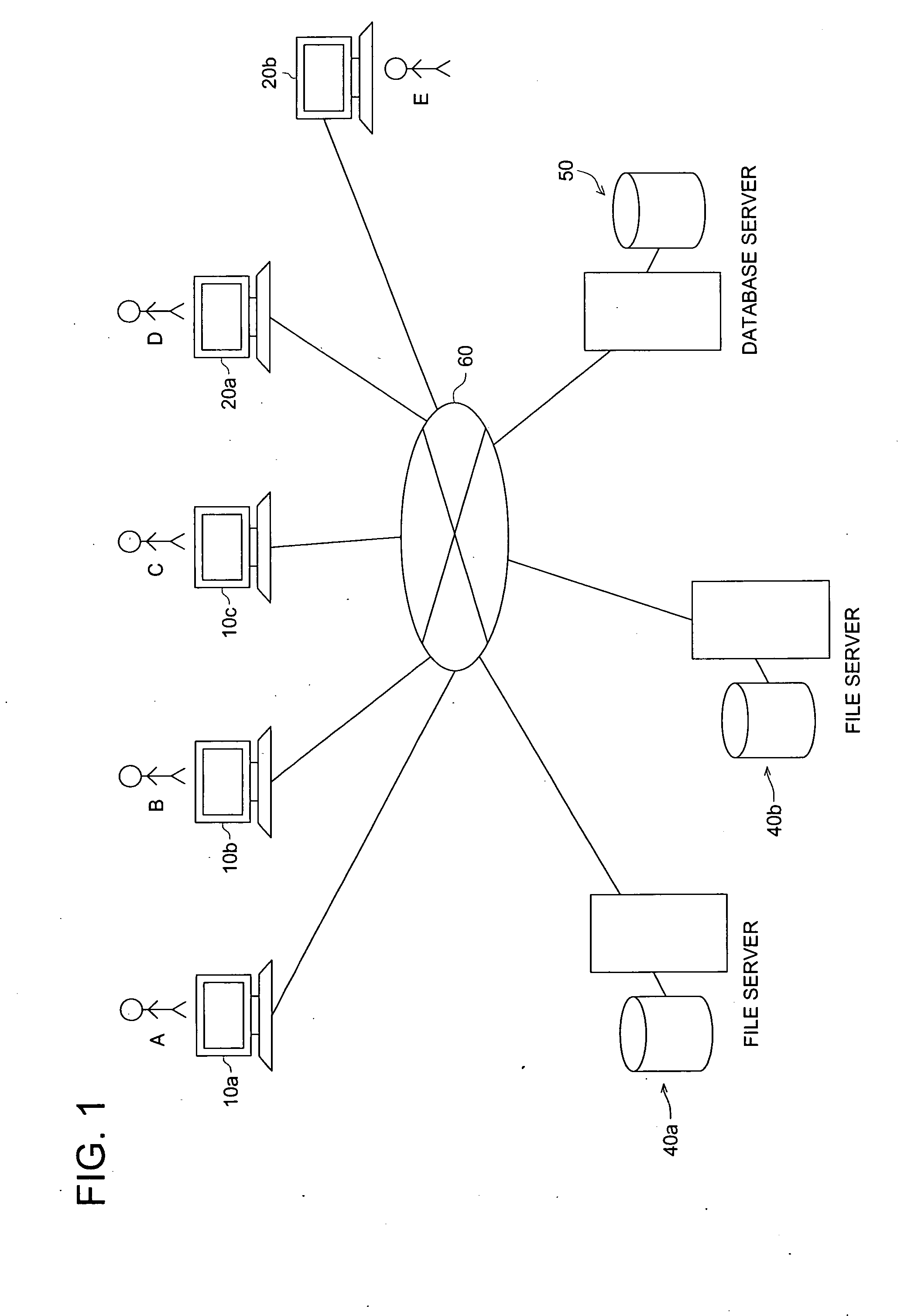
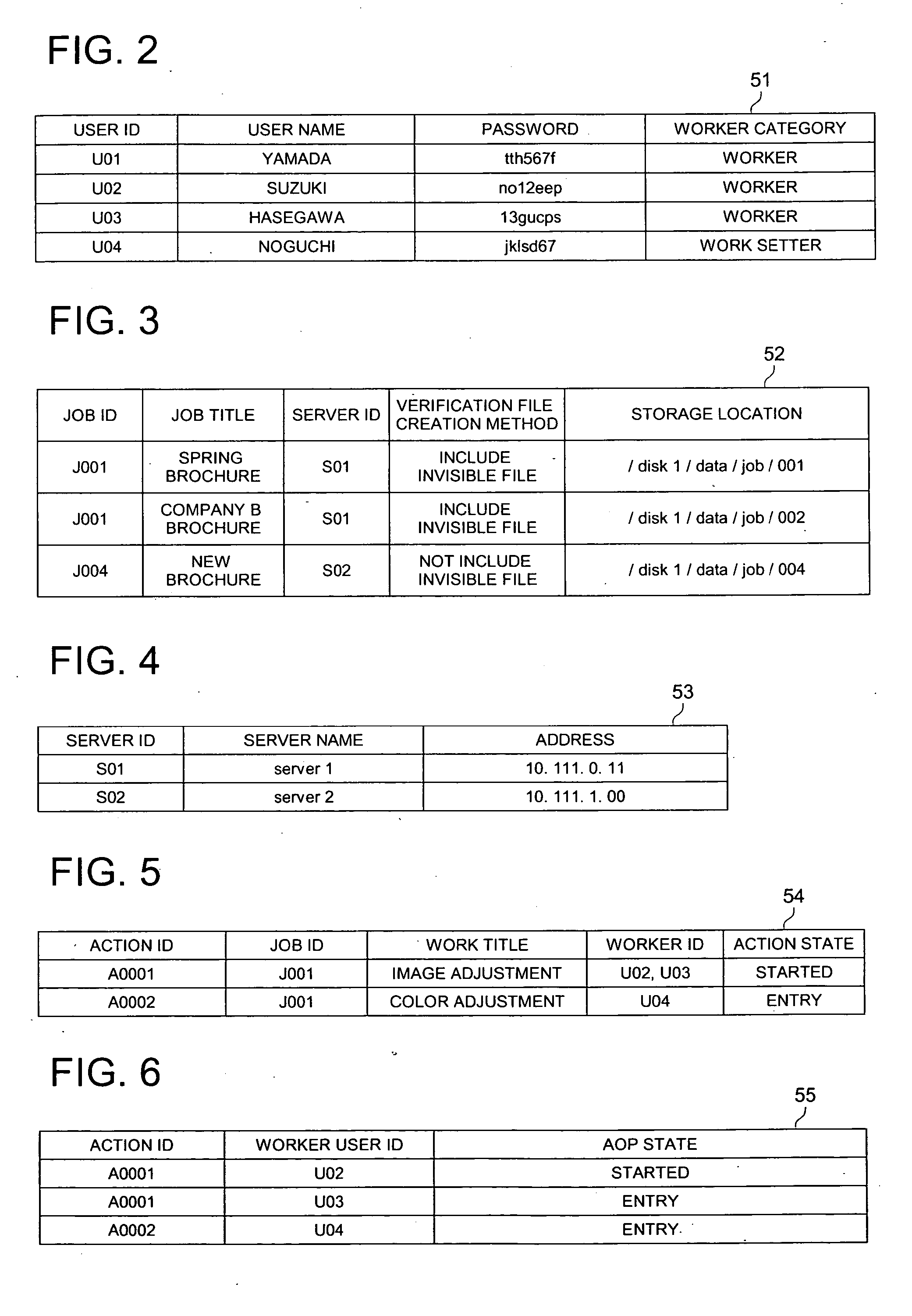
Work management system
InactiveUS20050075918A1Preventing unjust cancellationPrecise managementUnauthorized memory use protectionDigital data protectionNetwork managementFile server
In a work management system to manage working conditions through a network, when a work start order is inputted by a worker at the working terminal in accordance with the action set by the work setter and the file server connects the working terminal and a job directory to store a job of the action, the file server produces a verification file to record the attribute of the job directory for the worker, and when the worker inputs a work cancel order, the file server produces a comparison file to record the attribute of the job directory for the worker and judges a justification of the work cancel order on a basis of an identity between the attribute of the job directory recorded in the verification file and the attribute of the job directory recorded in the comparison file.
Owner:KONICA MINOLTA MEDICAL & GRAPHICS INC
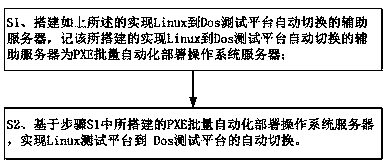
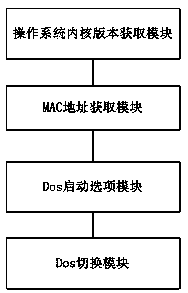
Method and system for automatically switching test platforms from Linux to Dos and secondary servers
InactiveCN107688532AReduce interventionRealize automatic switchingSoftware testing/debuggingBootstrappingTest efficiencyOperational system
The invention provides a method and a system for automatically switching test platforms from Linux to Dos and secondary servers. The method includes the steps: building the secondary servers; deploying diskless Dos systems on the built secondary servers, and pre-building startup option label files of currently deployed diskless Dos systems; setting PXE (pre-boot execution environment) working directories of the built servers as shared directories. PXE batch automation deployment operating systems are deployed in the secondary servers. The method and the system are based on the secondary servers, so that automatically switching from a current test platform to a Dos test platform is achieved. According to the method, intervention of human factors in production test of the servers is reduced,test efficiency is improved, and use waste of U disks is avoided.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com