Patents
Literature
3386results about "File system administration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
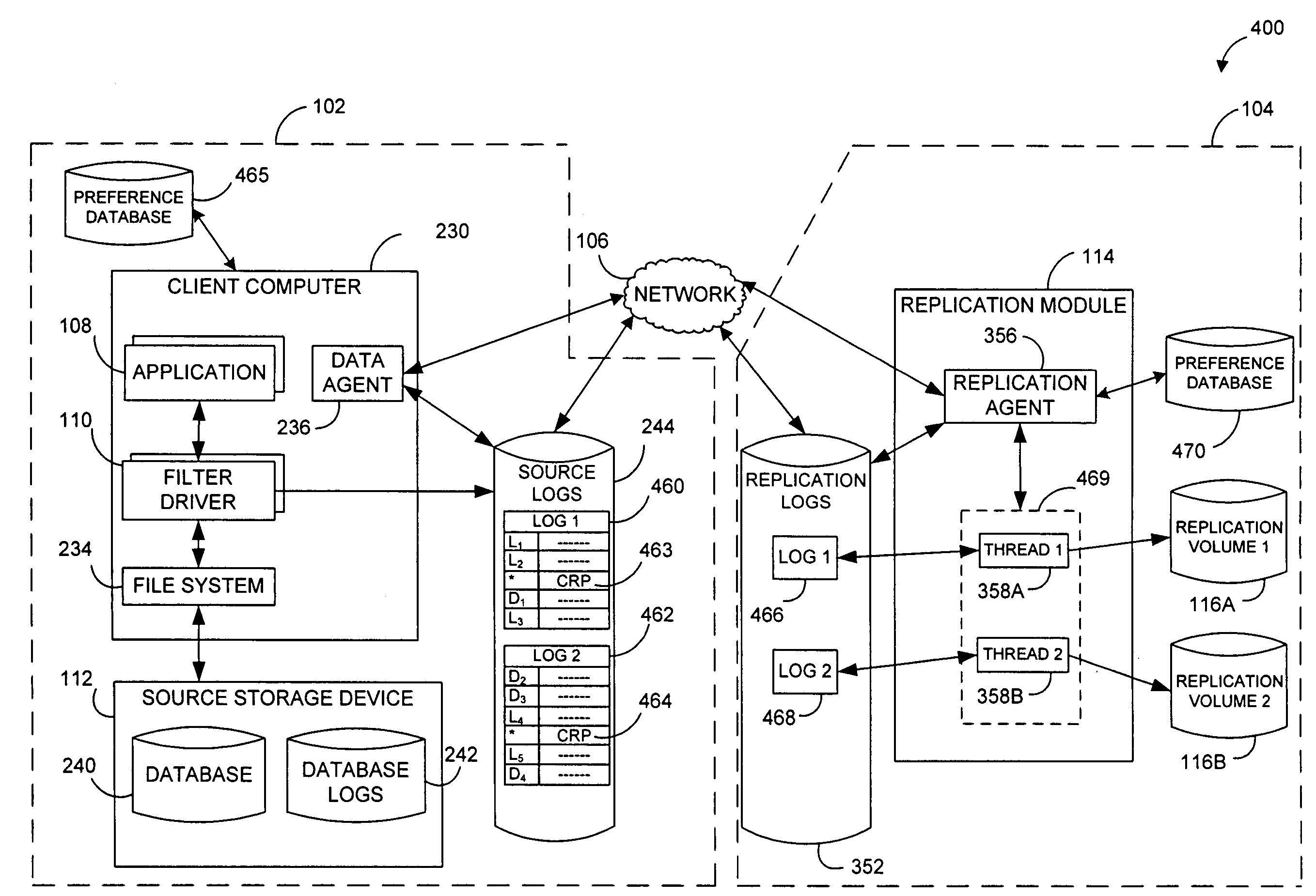
Systems and methods for performing data replication
ActiveUS7651593B2Reduce impactReduce memory requirementsError detection/correctionDistillation separationTemporal informationData management
Owner:COMMVAULT SYST INC
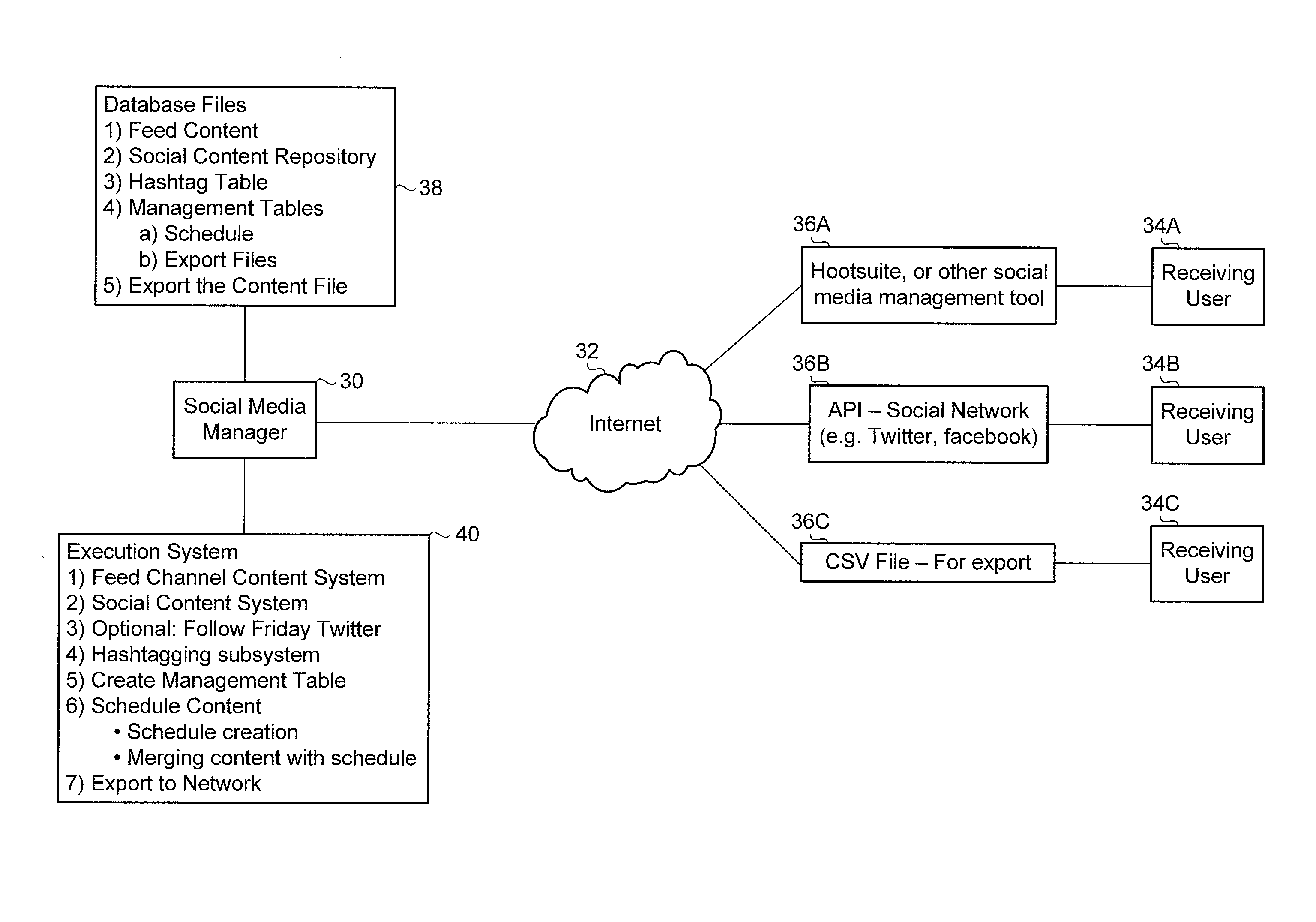
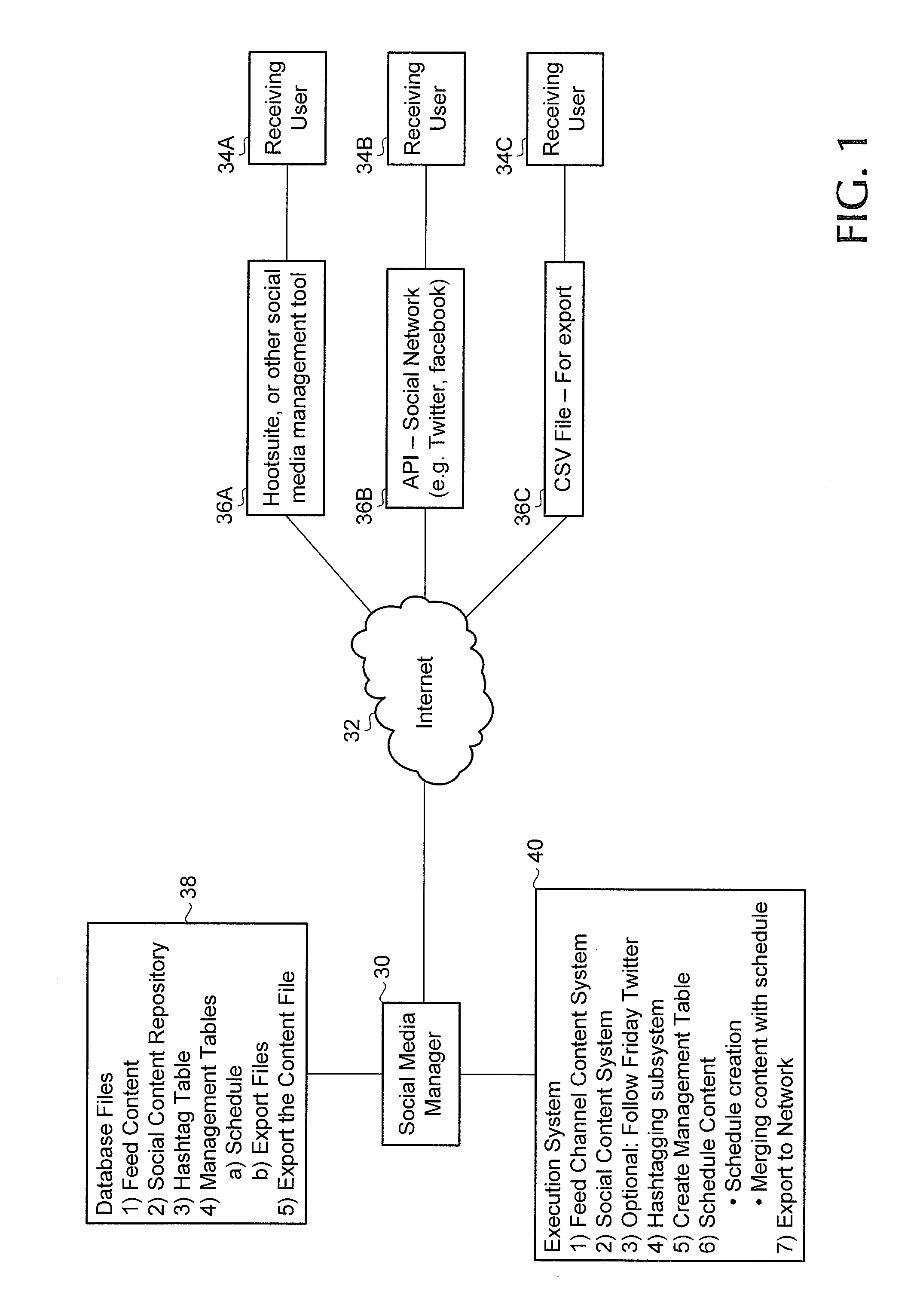
Social media content management system and method
InactiveUS20120197995A1Shorten the timeEffective postMultiple digital computer combinationsFile system administrationSocial media networkDatabase file
A social media content management system coupled to a social media network includes database files and execution instructions to assemble, manage and transmit social media content. The database files store a feed content file, a social content management file, and management tables including a schedule file and an export content file. Execution instructions include a feed channel content system for receiving and storing feed content items in the feed content file. A selection subsystem is used for selecting and storing export content as social media posts in the social content management file. A scheduling subsystem enables a user to create and store schedules, to select a schedule and to merge the selected schedule with the stored content in the management file to form the export content file. An export system transmits the stored content as social media content posts to the social media network according to the selected schedule.
Owner:BUNDLEPOST LLC
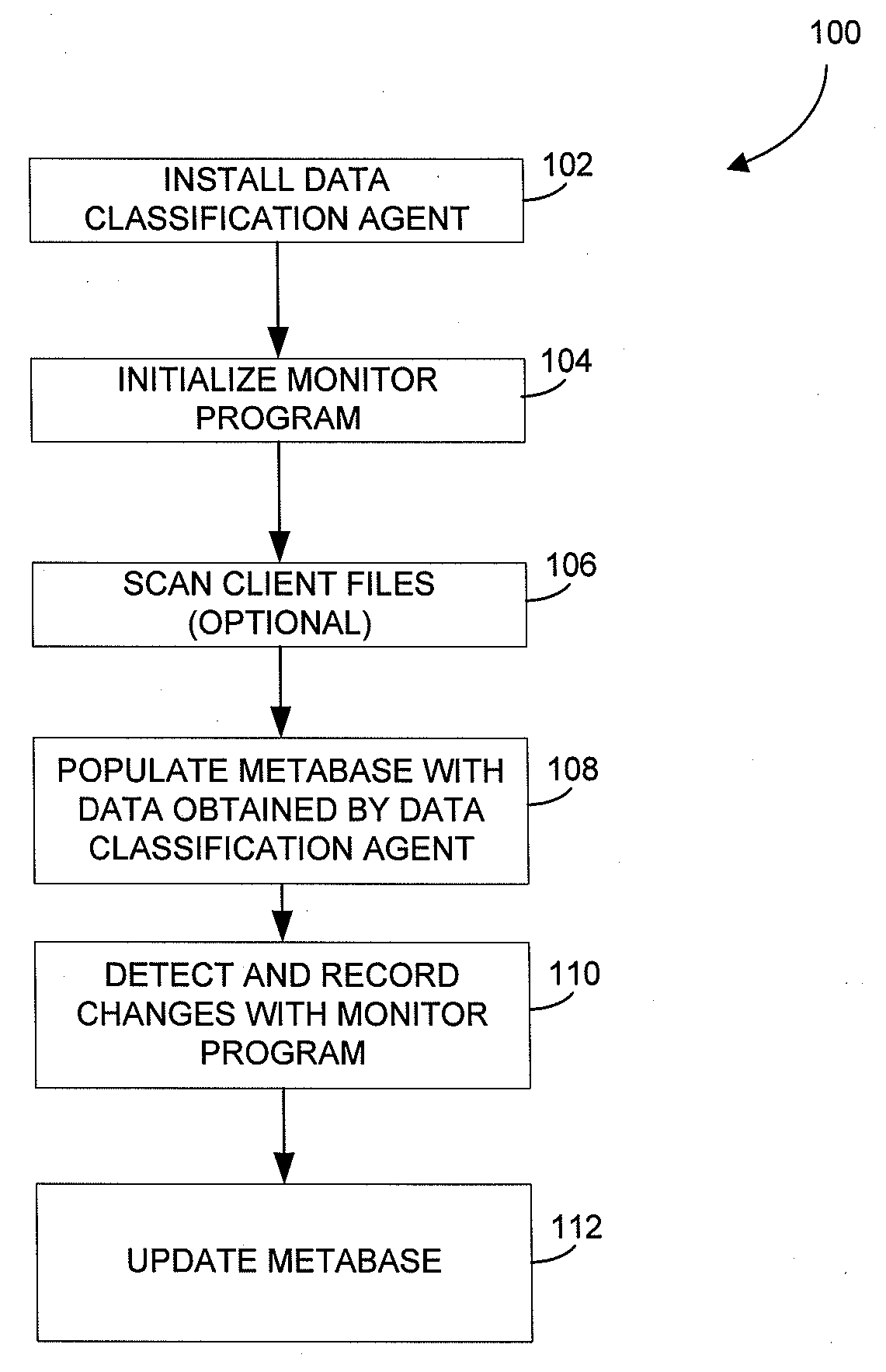
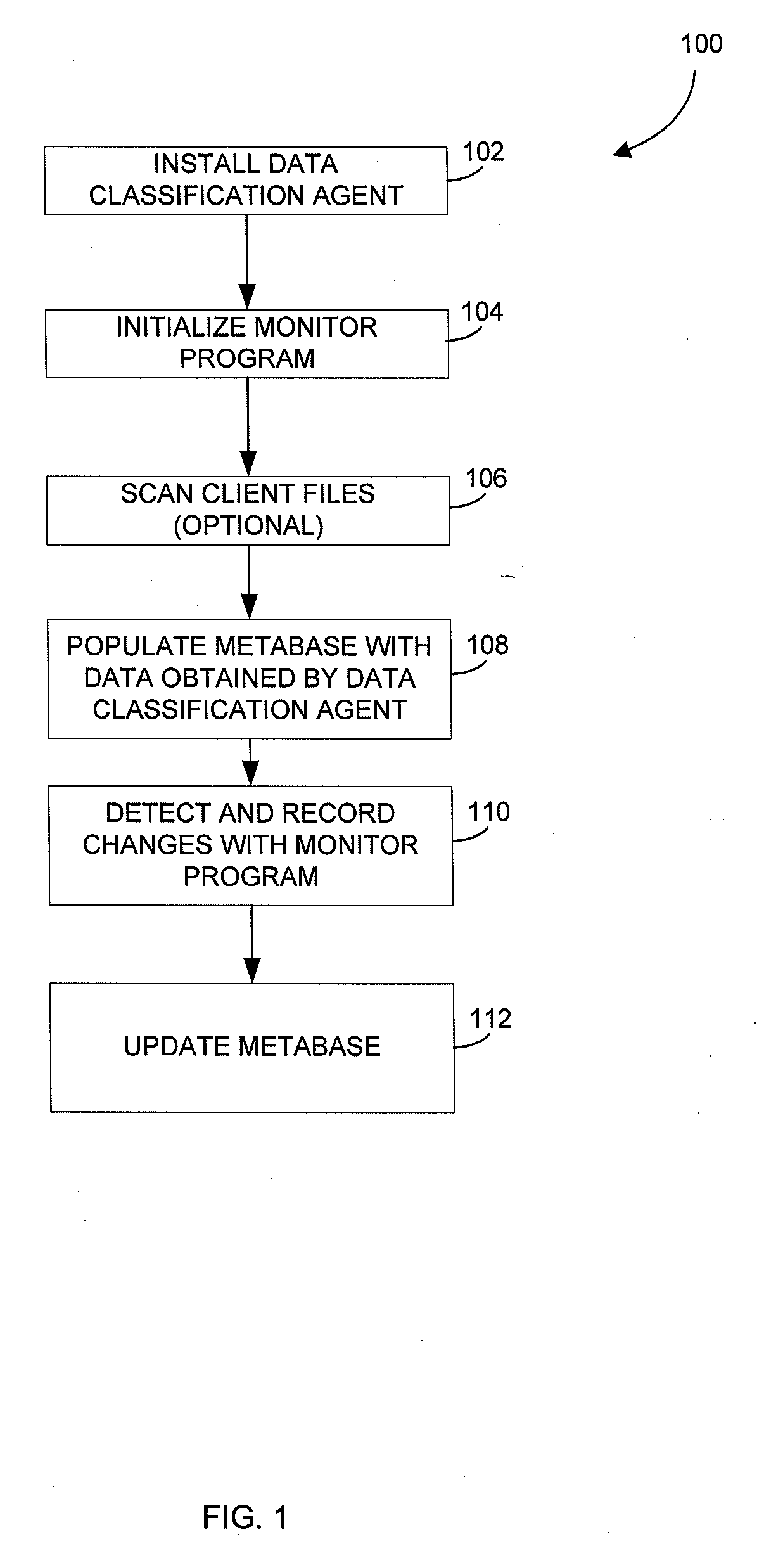
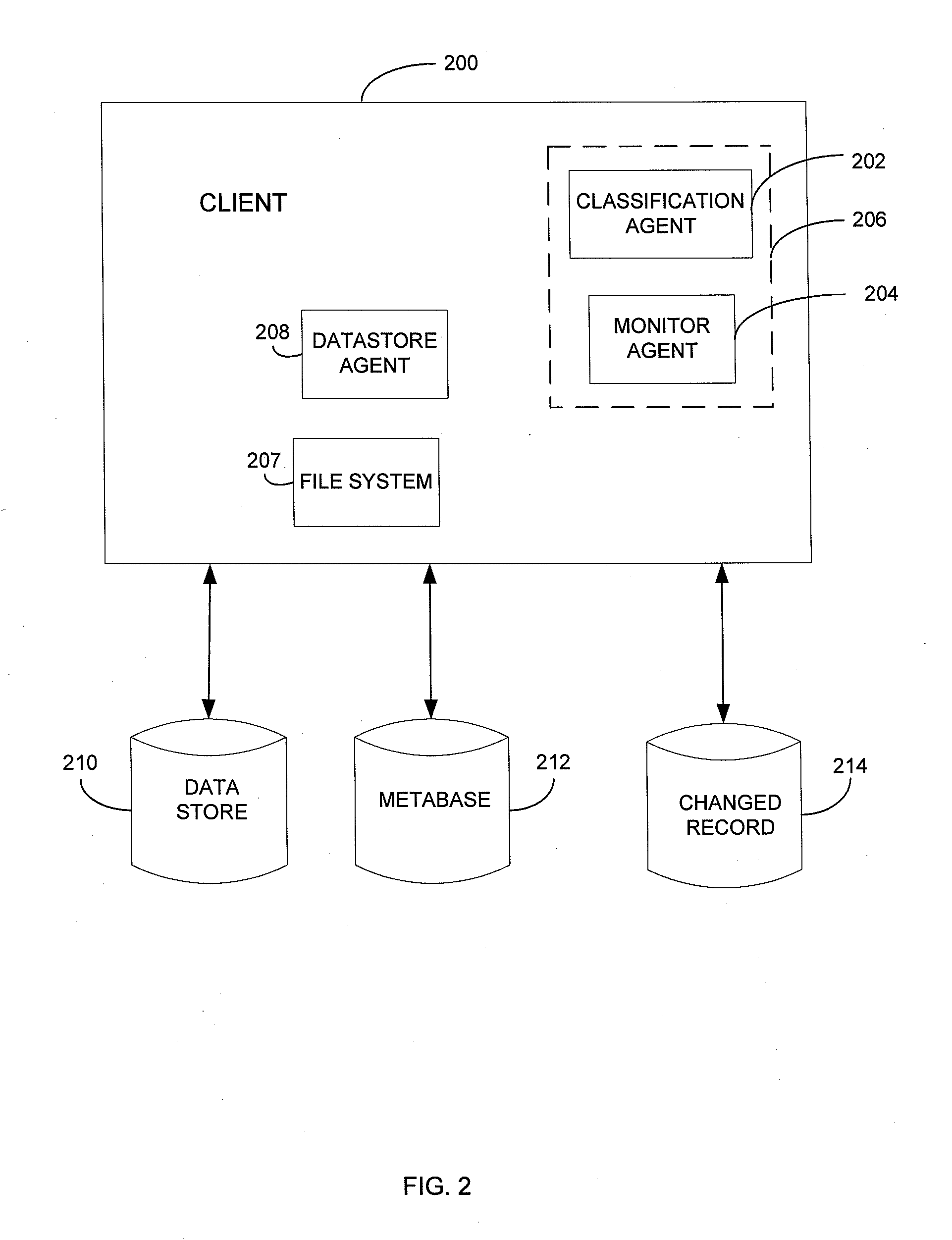
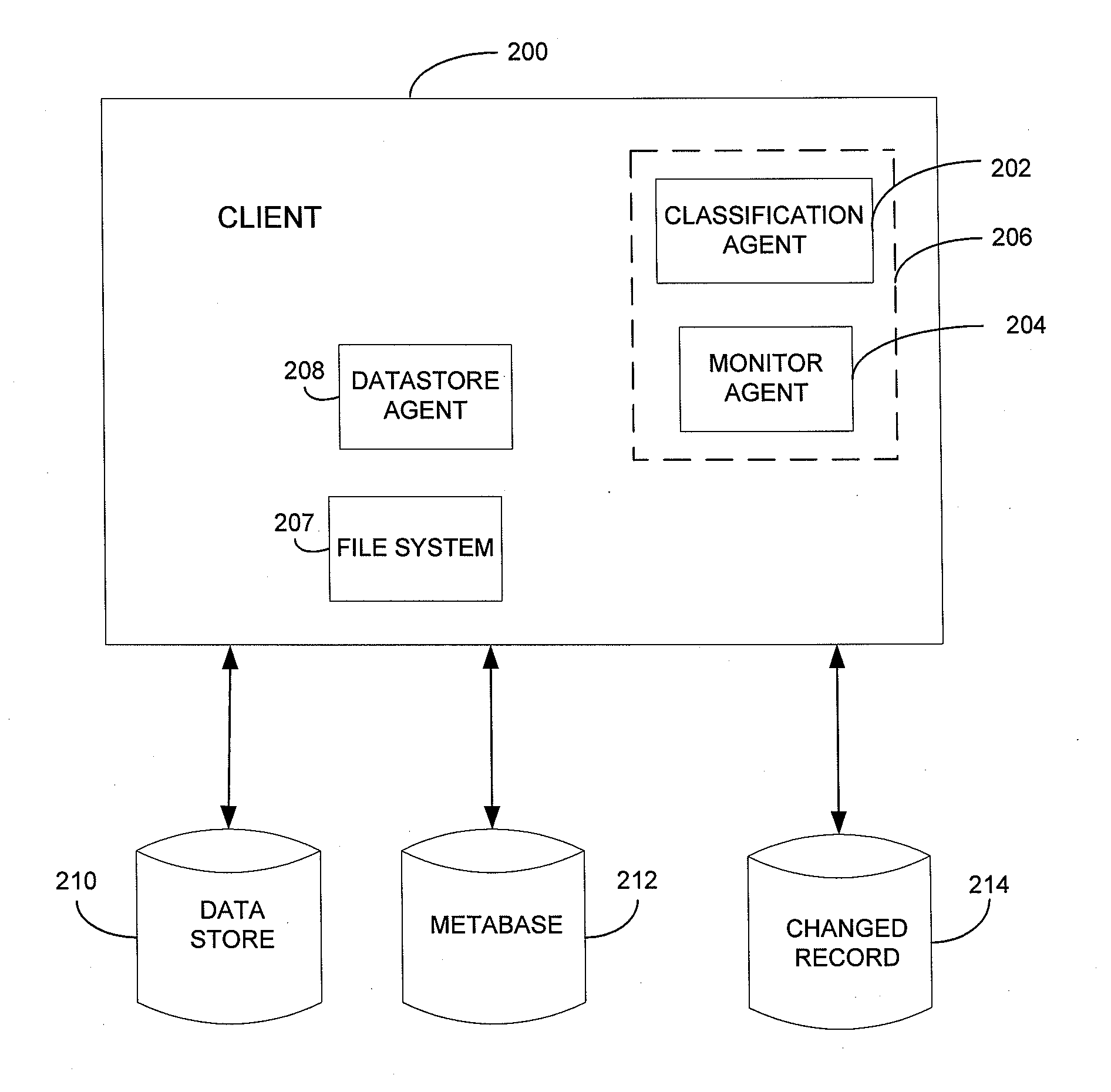
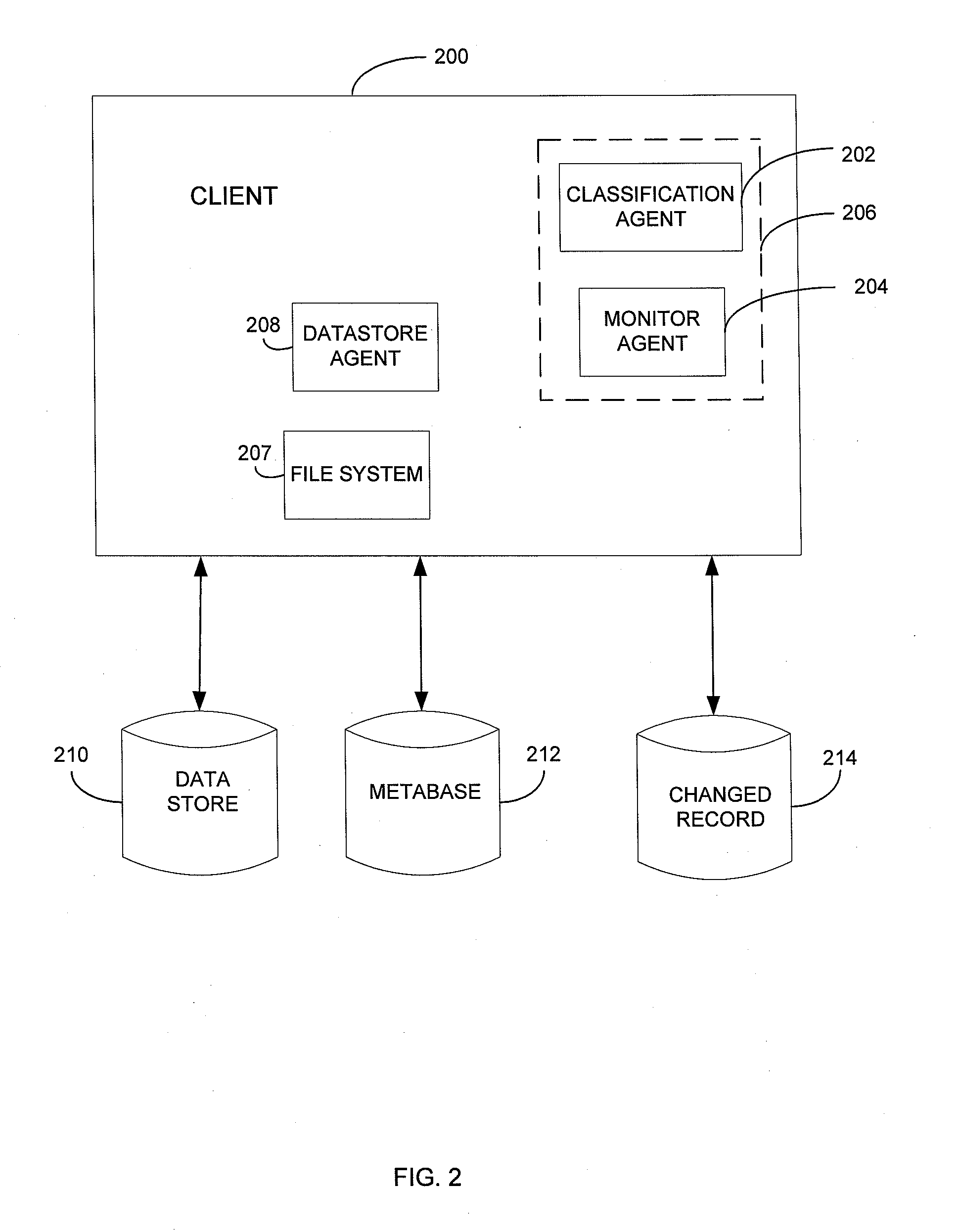
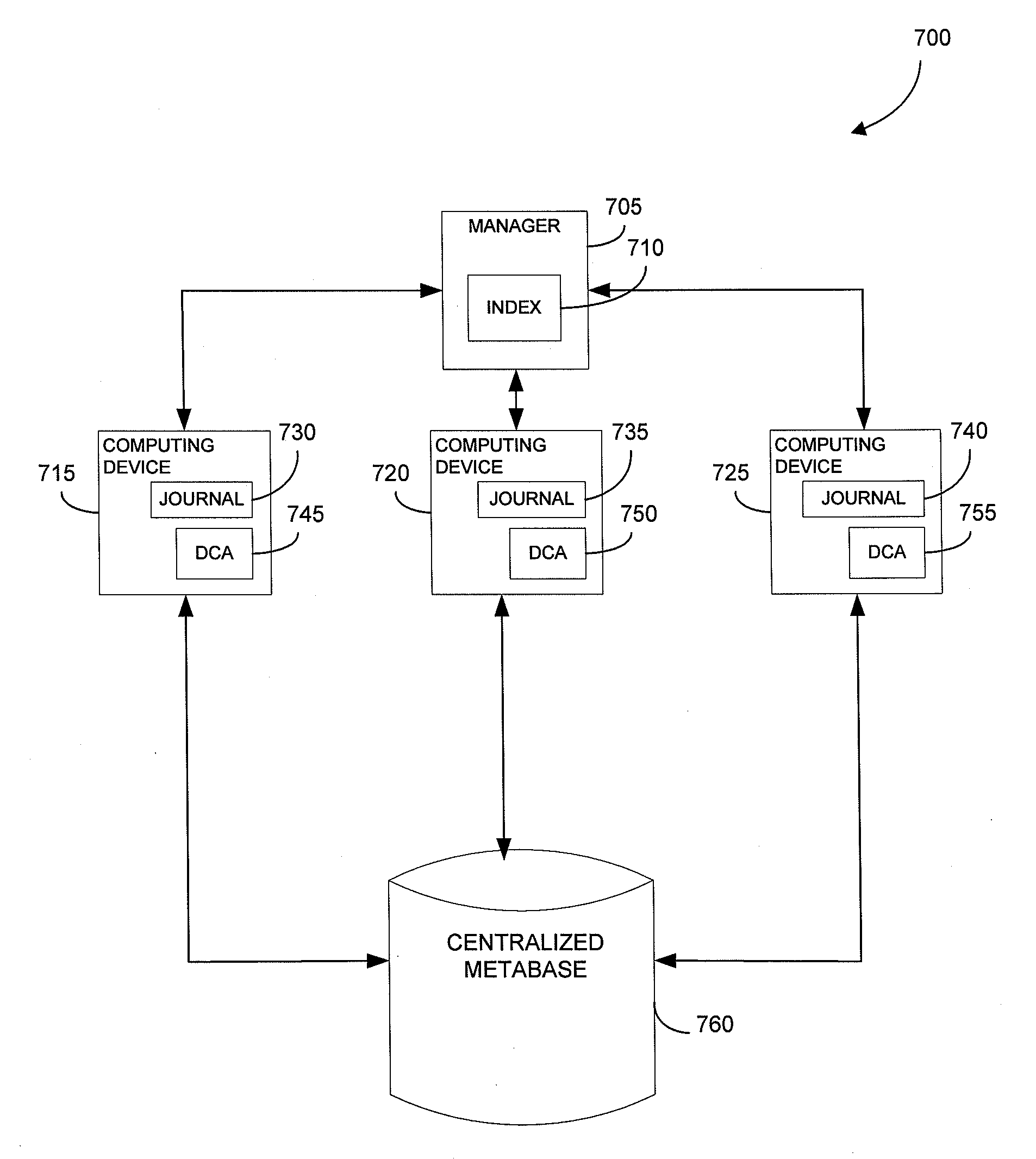
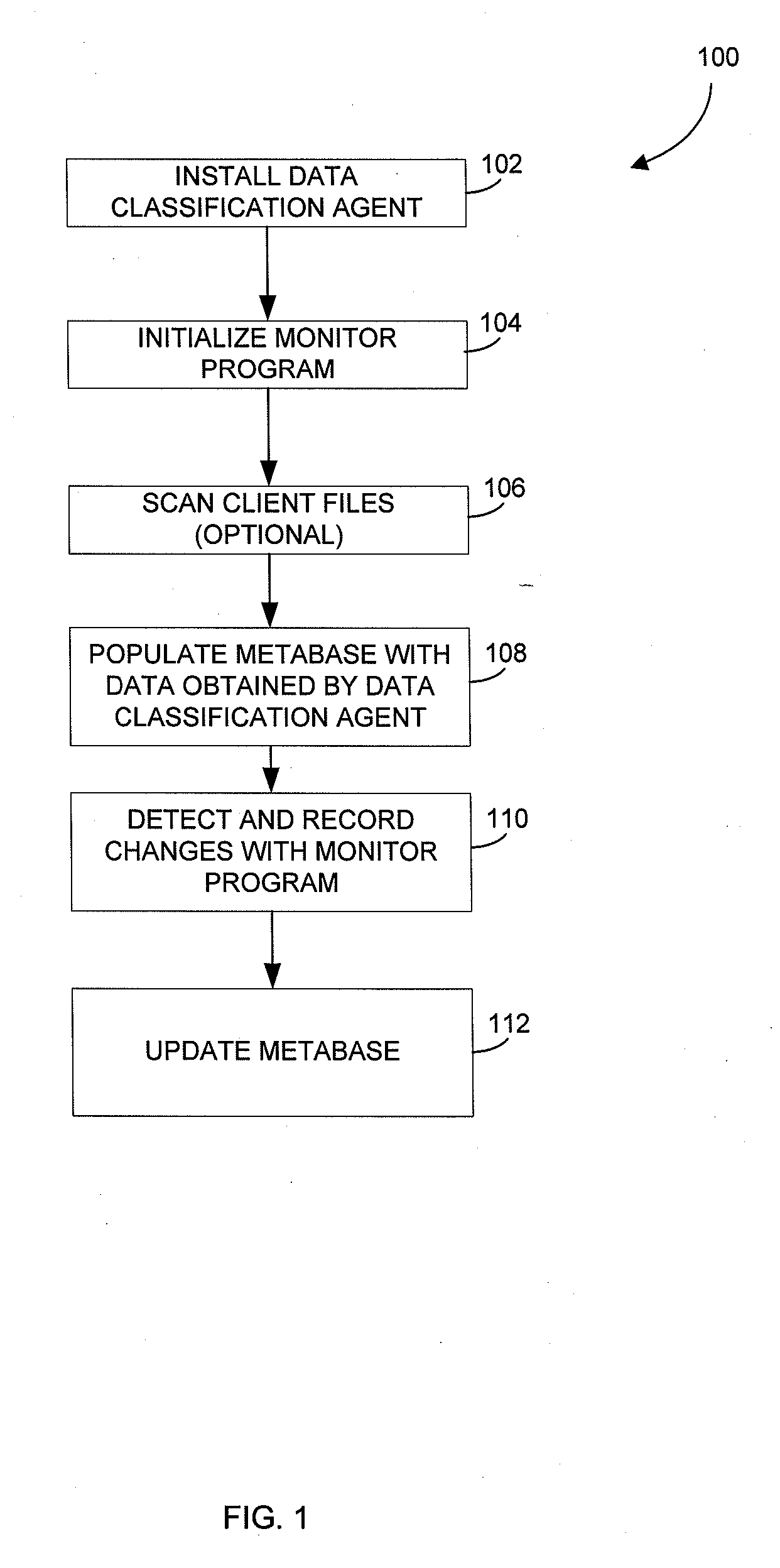
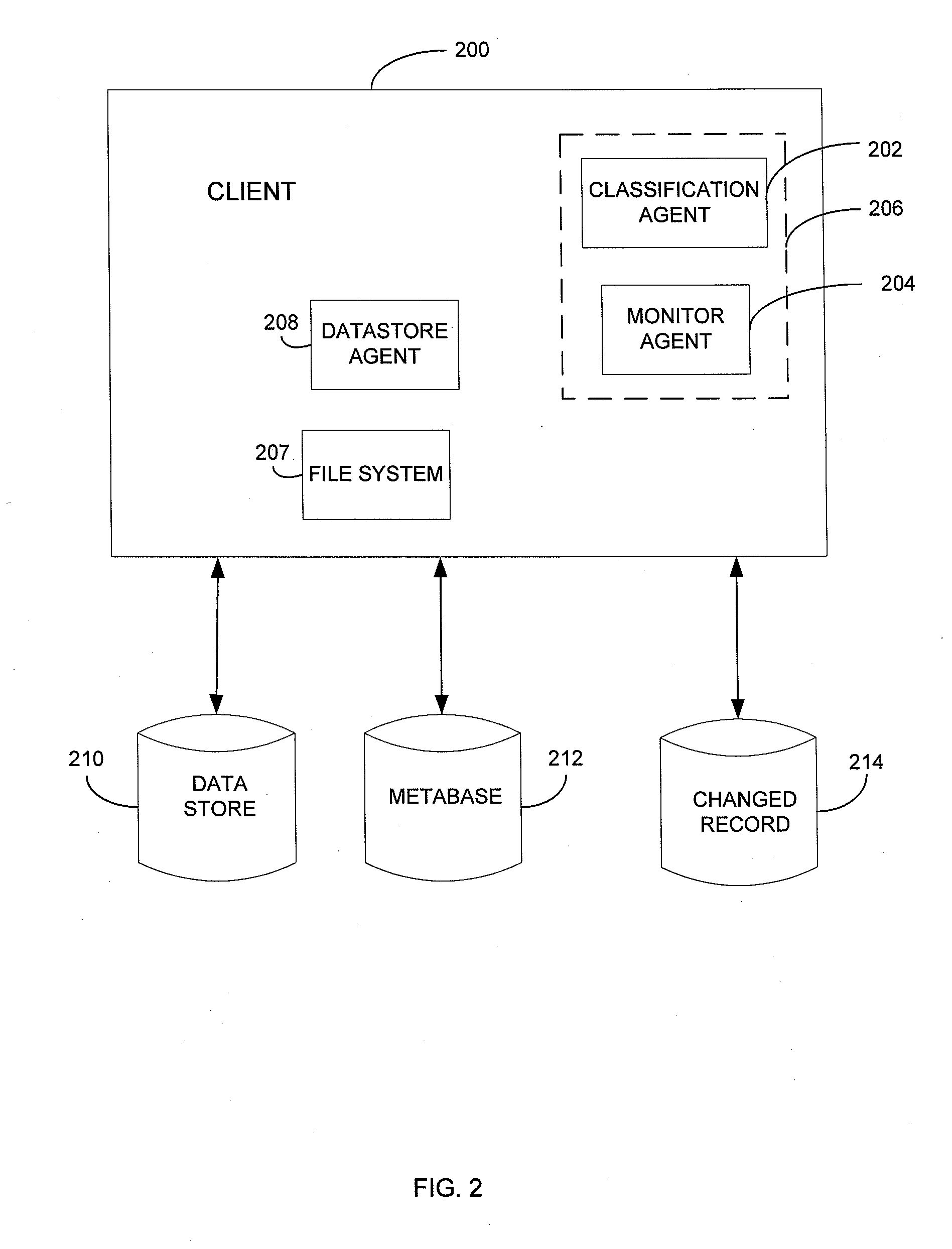
Metabase for facilitating data classification
Systems and methods for managing electronic data are disclosed. Various data management operations can be performed based on a metabase formed from metadata. Such metadata can be identified from an index of data interactions generated by a journaling module, and obtained from their associated data objects stored in one or more storage devices. In various embodiments, such processing of the index and storing of the metadata can facilitate, for example, enhanced data management operations, enhanced data identification operations, enhanced storage operations, data classification for organizing and storing the metadata, cataloging of metadata for the stored metadata, and / or user interfaces for managing data. In various embodiments, the metabase can be configured in different ways. For example, the metabase can be stored separately from the data objects so as to allow obtaining of information about the data objects without accessing the data objects or a data structure used by a file system.
Owner:COMMVAULT SYST INC
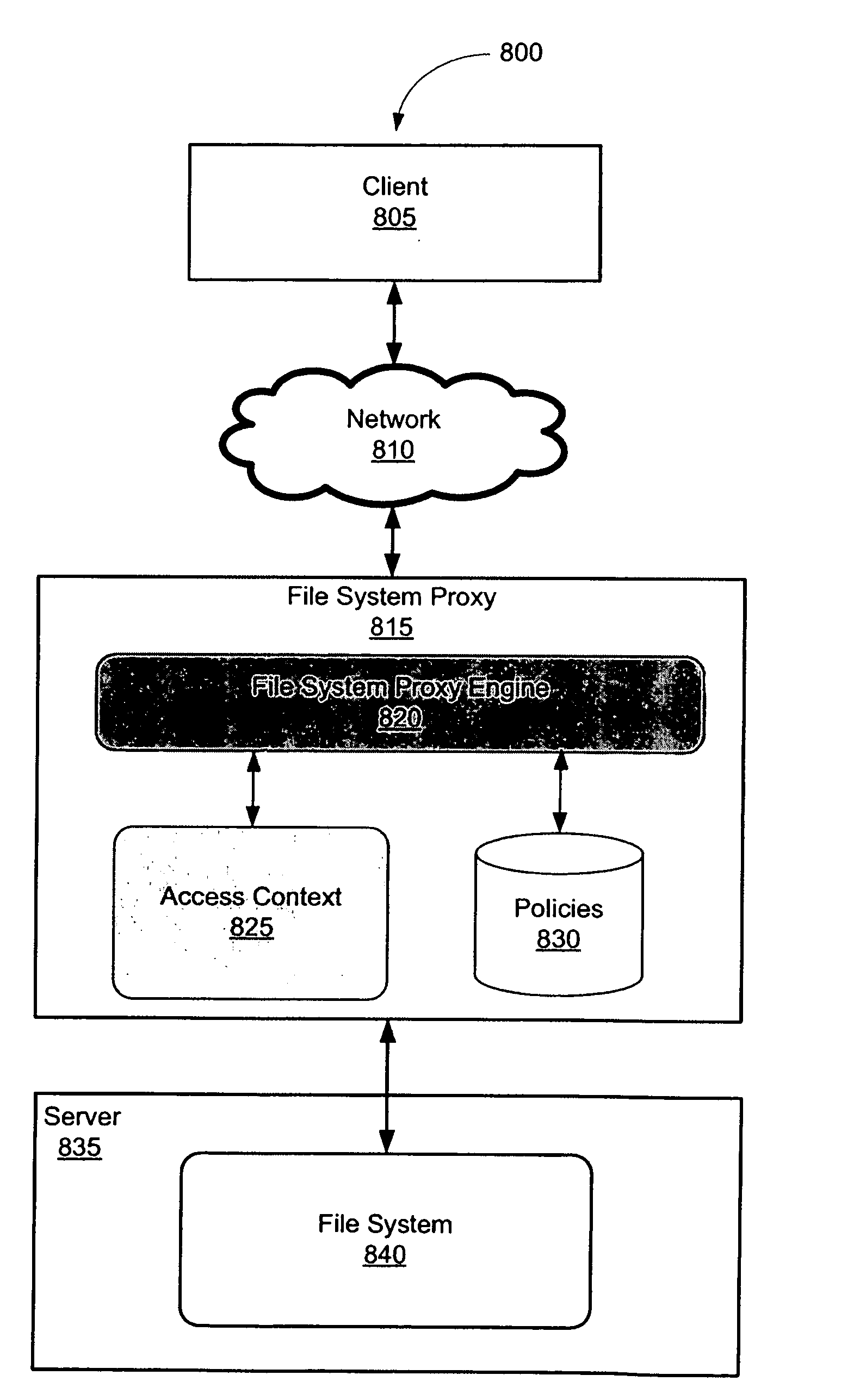
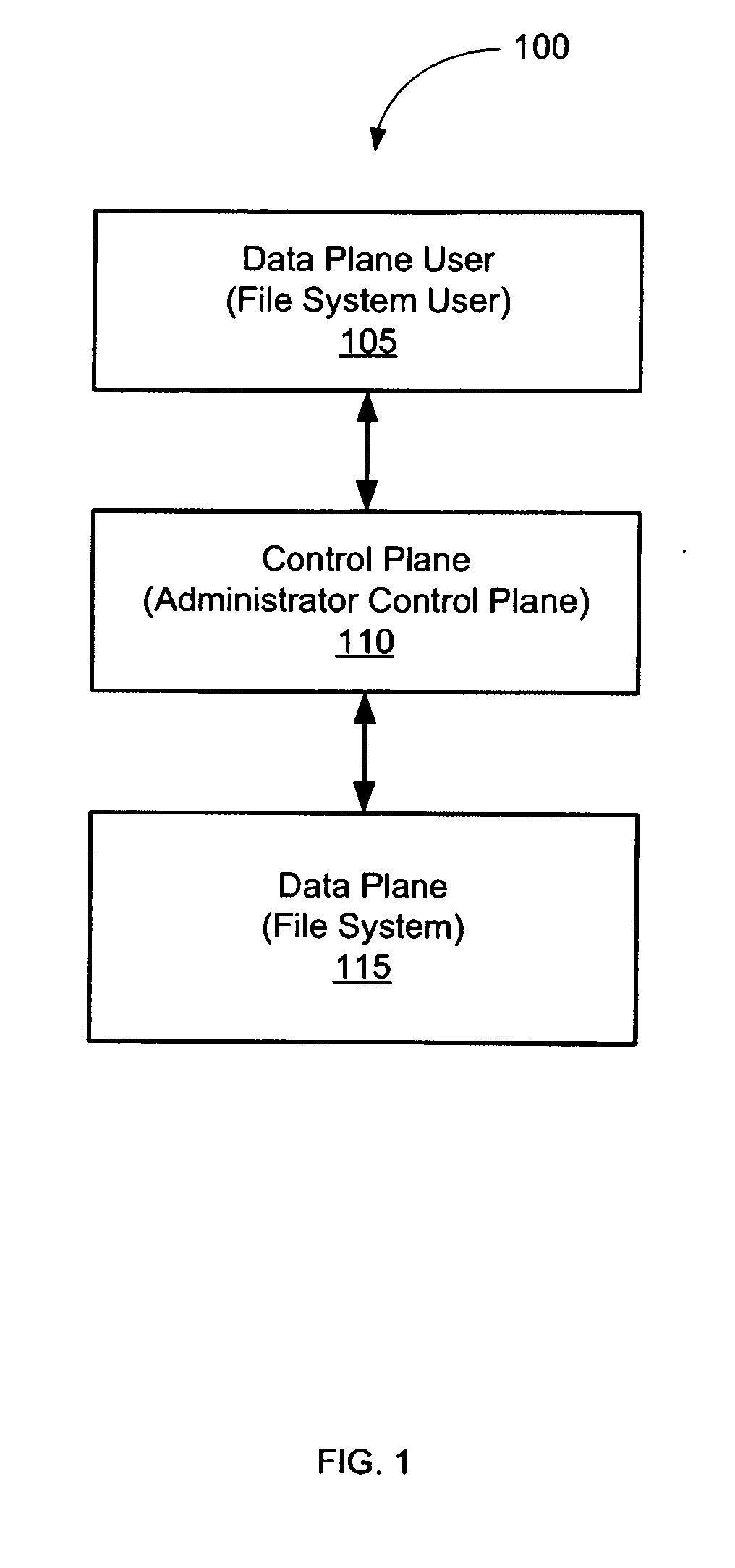
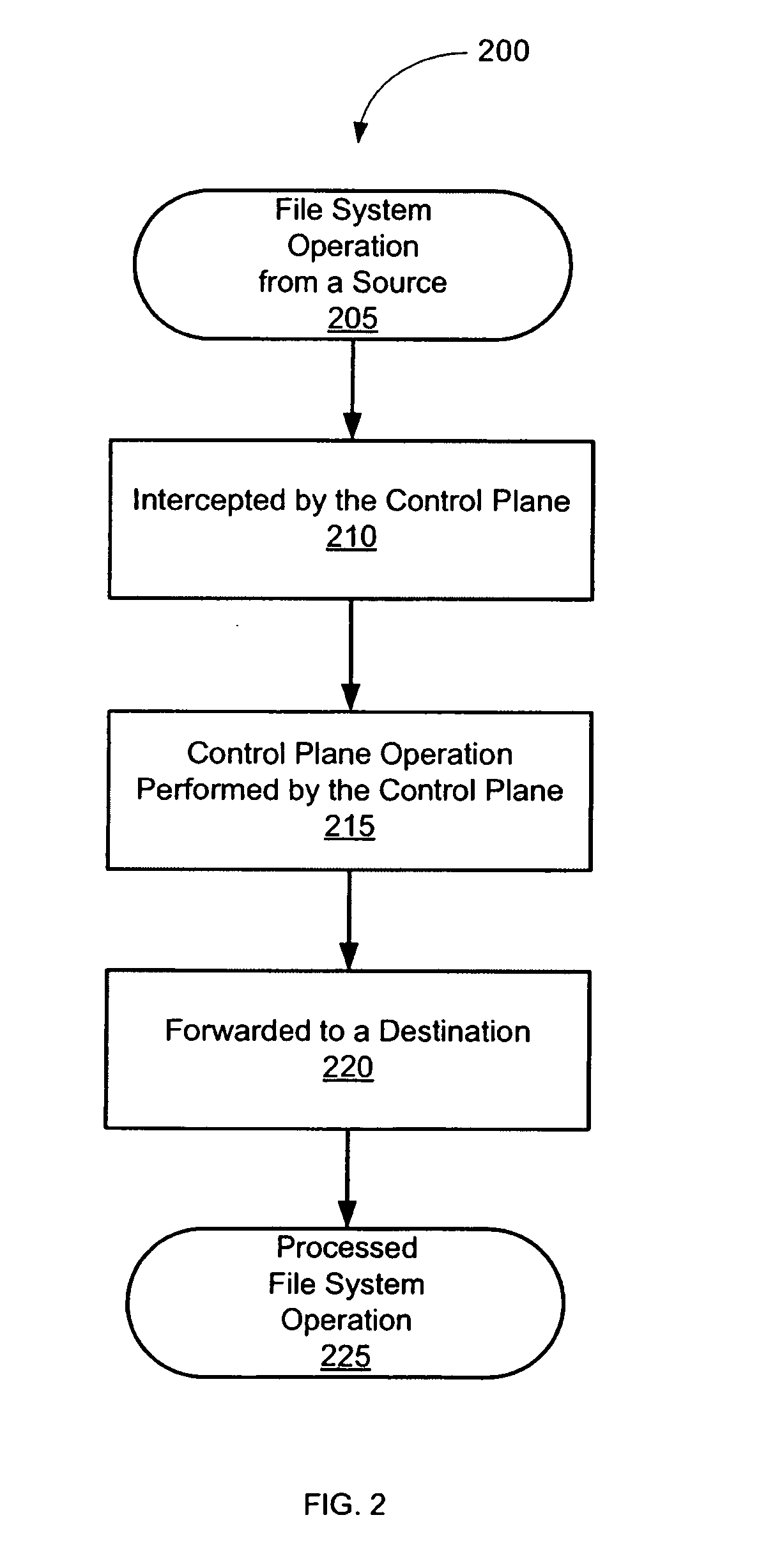
System and method for controlling a file system
ActiveUS20090043823A1File system administrationSpecial data processing applicationsFile systemExecution control
According to various embodiments of the invention, a system and method for controlling a file system. In some embodiments, a control plane interposes between a data plane user and a data plane, intercepts file system operations, and performs control plane operations upon the file system operations. In one such embodiment, the system and method is implemented between a data plane user that is a local file system user and a data plane that is a local file system. In another such embodiment, the system and method is implemented between a data plane user that is a client and a data plane that is a file server. Furthermore, for an embodiment where the control plane that interposes between a client and a file server, the control plane can be implemented as a file system proxy. Control plane operations include, but are not limited to, observation, verification, and transformation of a file system operation.
Owner:RUTGERS THE STATE UNIV
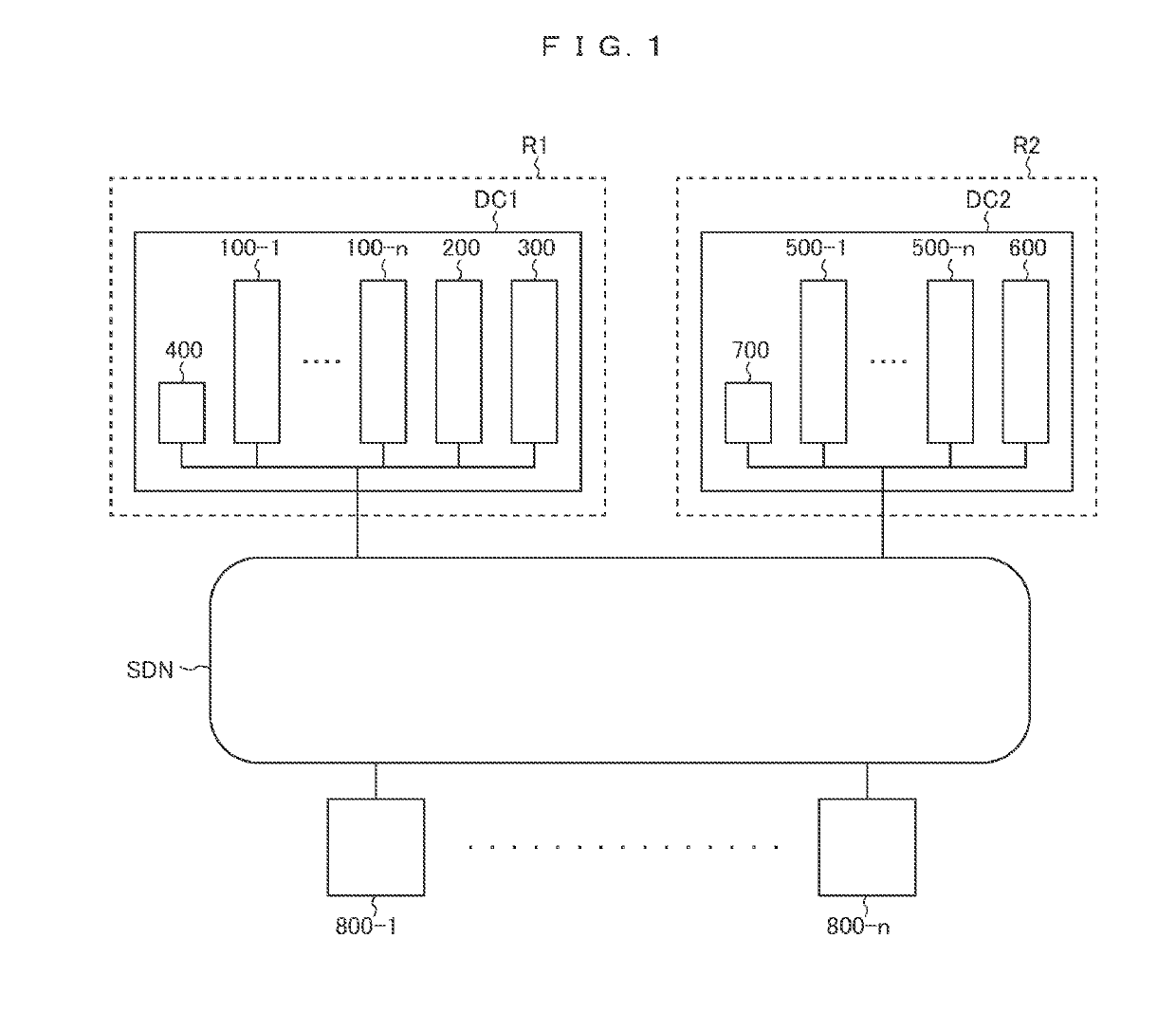
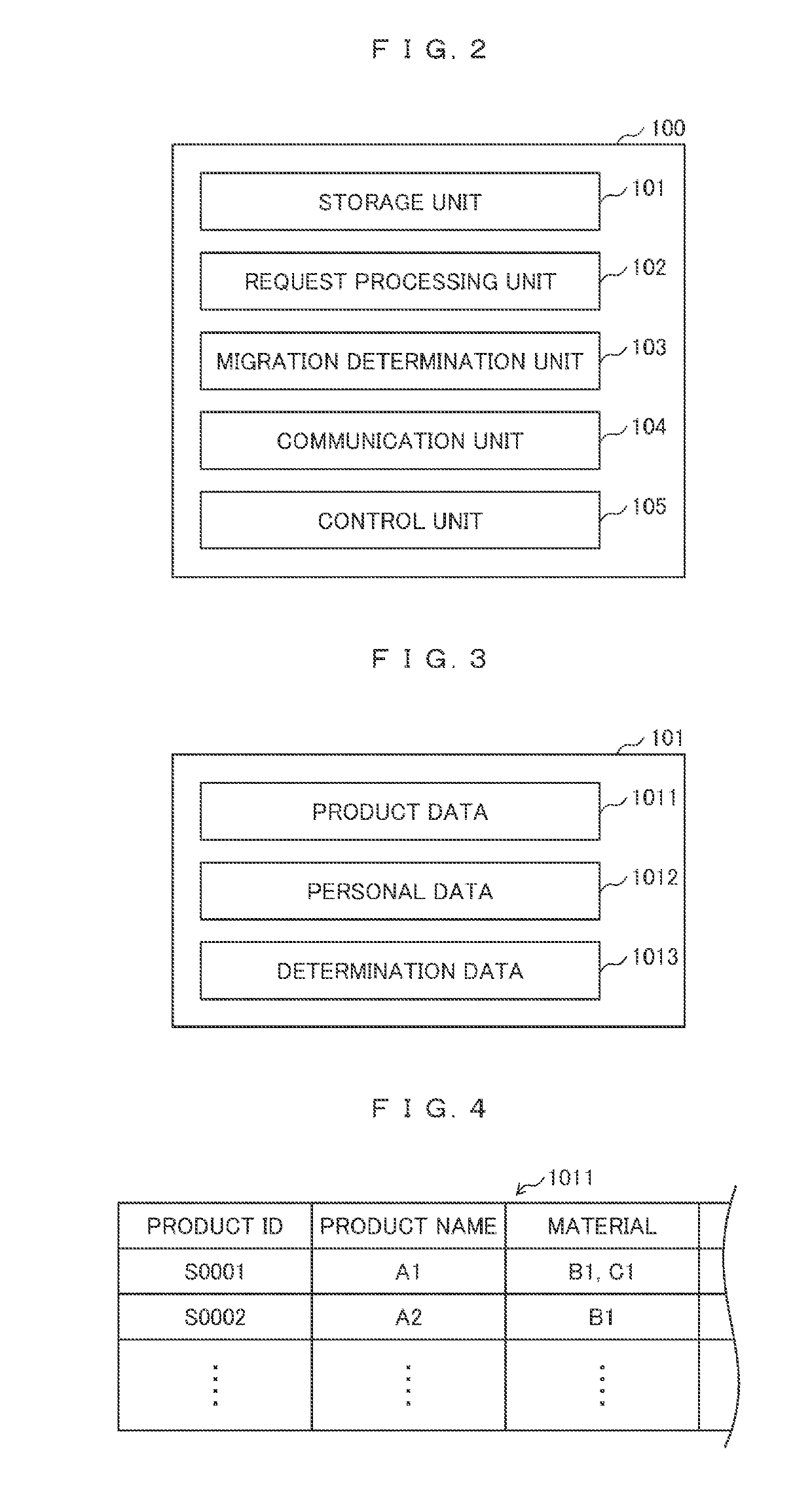
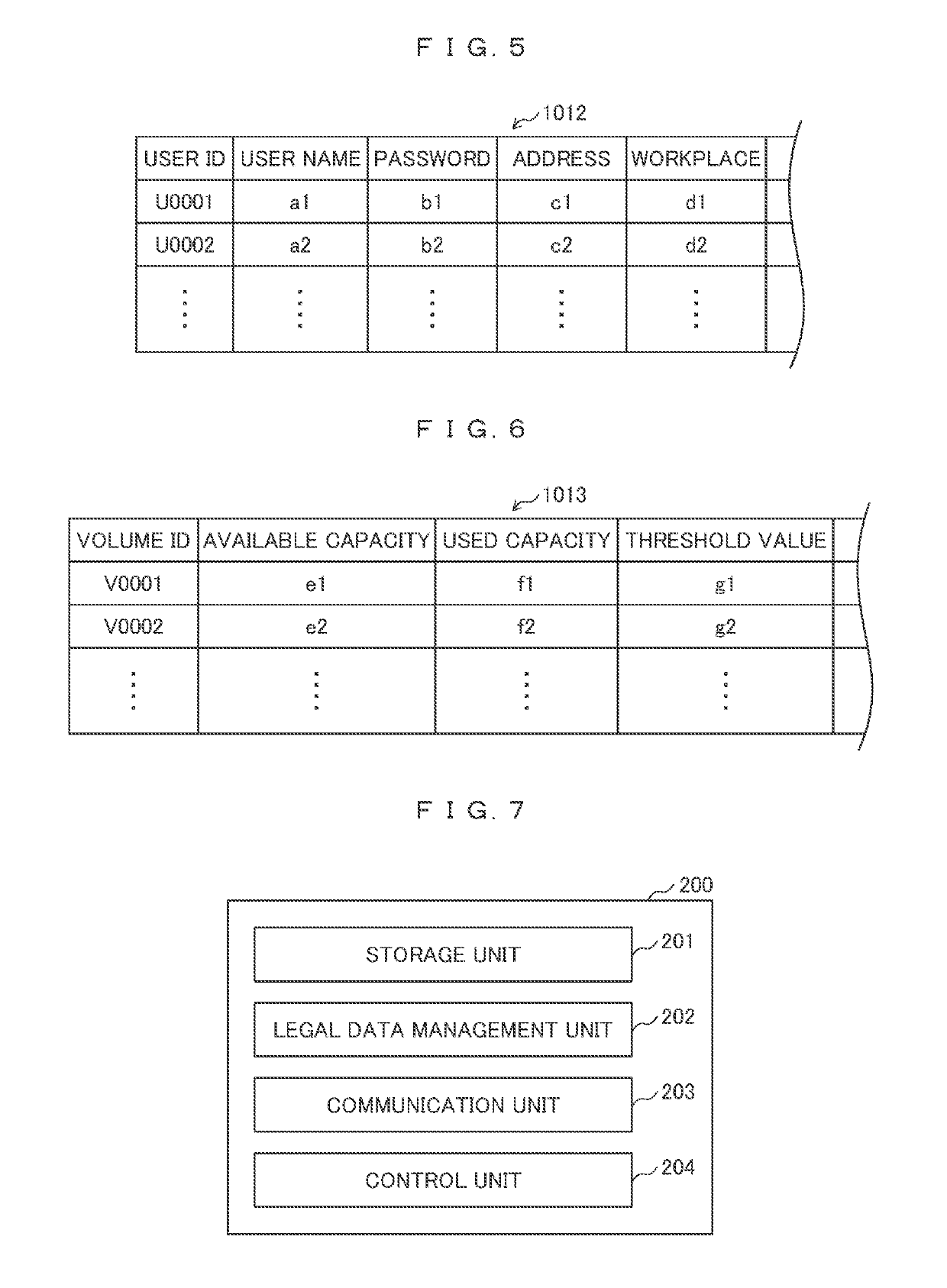
Data migration system and data migration method
ActiveUS20190138496A1Data processing applicationsInput/output to record carriersData storingControl equipment
In an SDN environment, data is migrated after checking whether the data conforms to a legal system of a migration destination. A control device changes a communication setting between first and second servers based on migration destination information and migration source information received from the first server and SDN setting data on a communication setting of the SDN stored in advance. The first server receives data on the legal system and determines whether the data conforms to the legal system to thereby determine whether the data can be migrated, or not. The control device executes a change in the communication setting when it is determined that the migration is enabled from the first server. The first server transmits data stored in a first storage unit to the second server according to the changed communication setting and the data is stored in a second storage unit.
Owner:HITACHI SYST
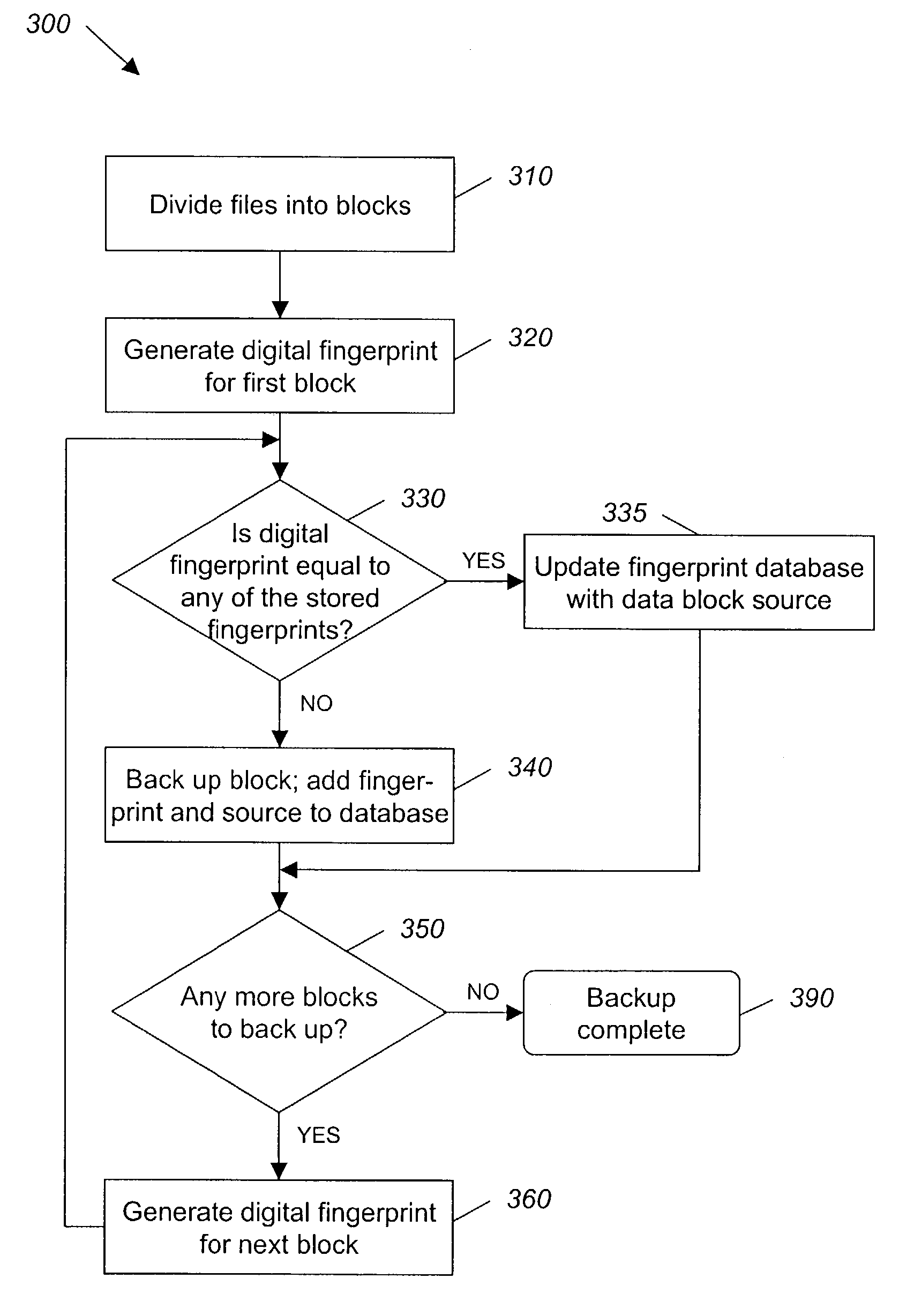
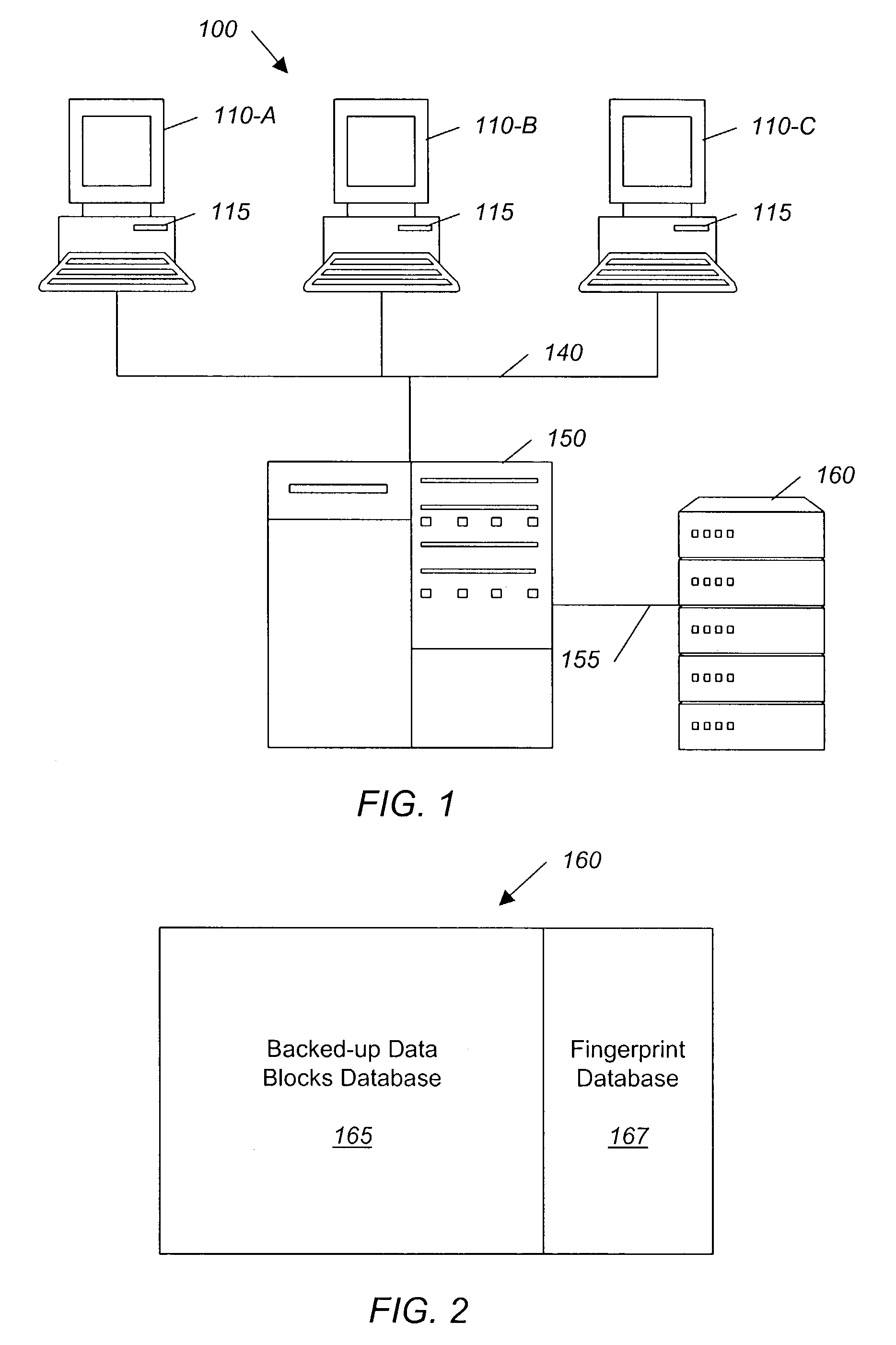
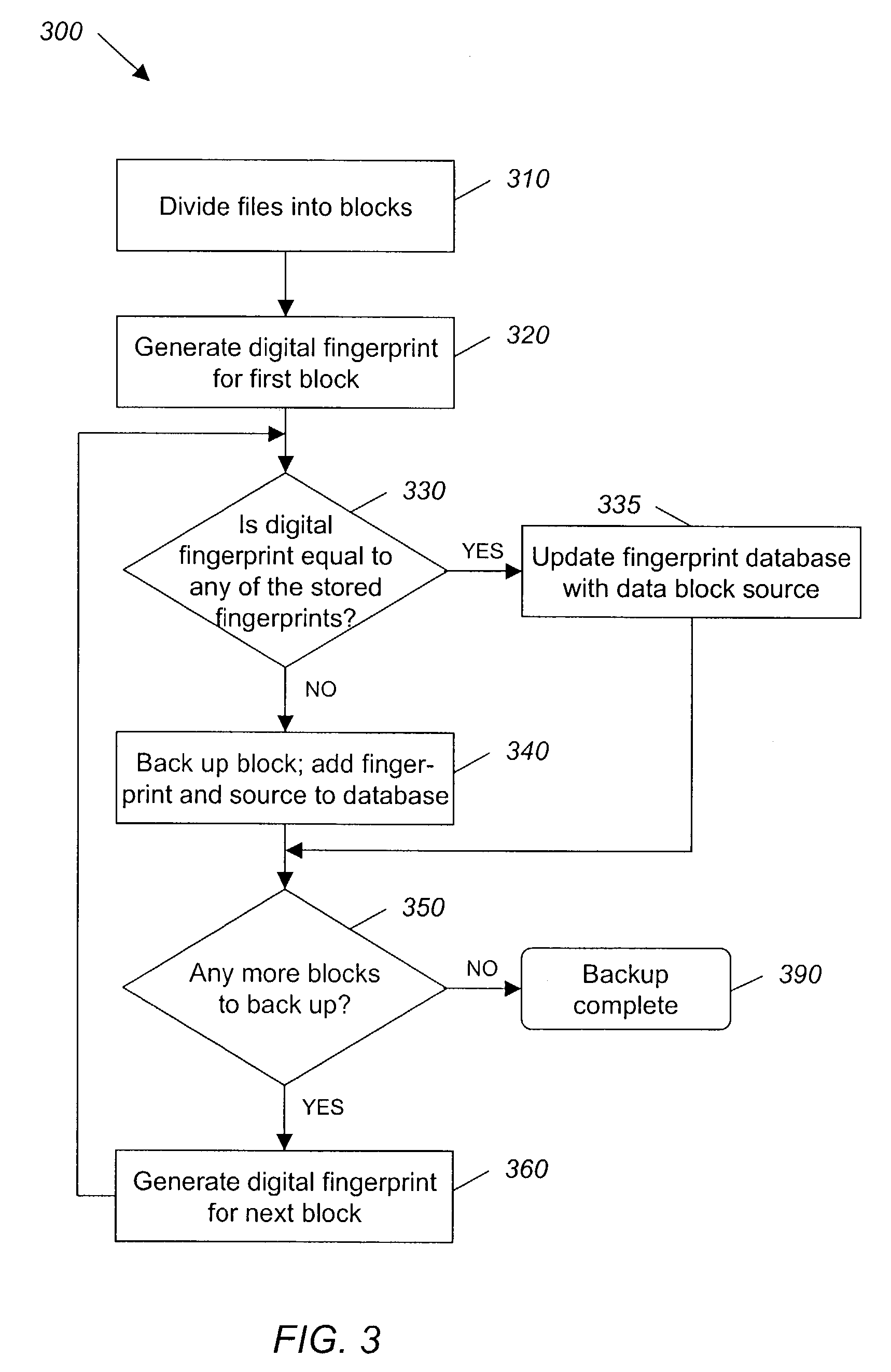
System and method for backing up data
ActiveUS7055008B2Avoid inefficiencyInefficiency of the Shnelvar patent can be avoidedCamera focusing arrangementPayment architectureSoftware licenseData content
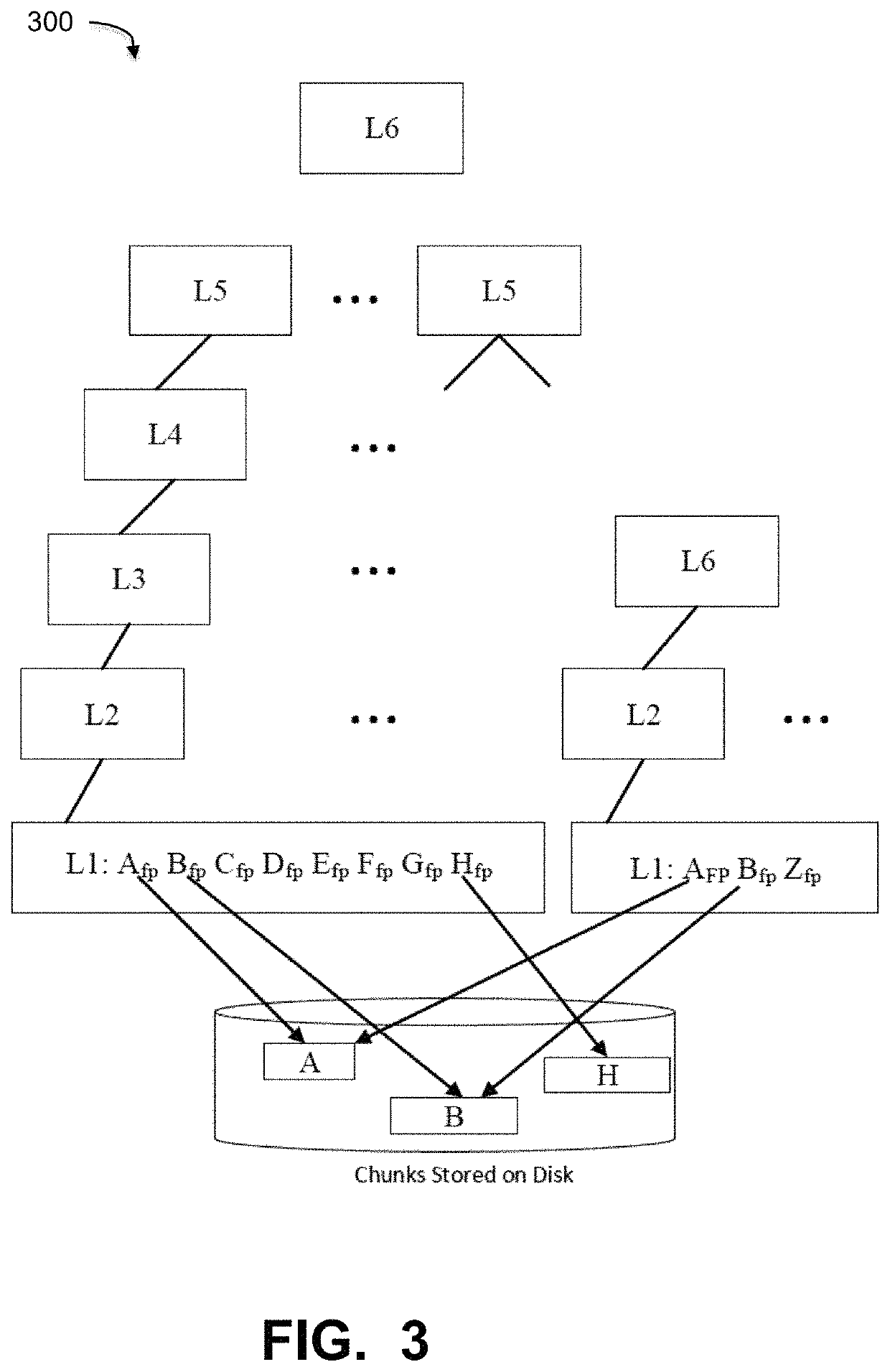
A hash-optimized backup system and method takes data blocks and generates a probabilistically unique digital fingerprint of the content of each data block using a substantially collision-free algorithm. The process compares the generated fingerprint to a database of stored fingerprints and, if the generated fingerprint matches a stored fingerprint, the data block is determined to already have been backed up, and therefore does not need to be backed up again. Only if the generated fingerprint does not match a stored fingerprint is the data block backed up, at which point the generated fingerprint is added to the database of stored fingerprints. Because the algorithm is substantially collision-free, there is no need to compare actual data content if there is a hash-value match. The process can also be used to audit software license compliance, inventory software, and detect computer-file tampering such as viruses and malware.
Owner:FALCONSTOR
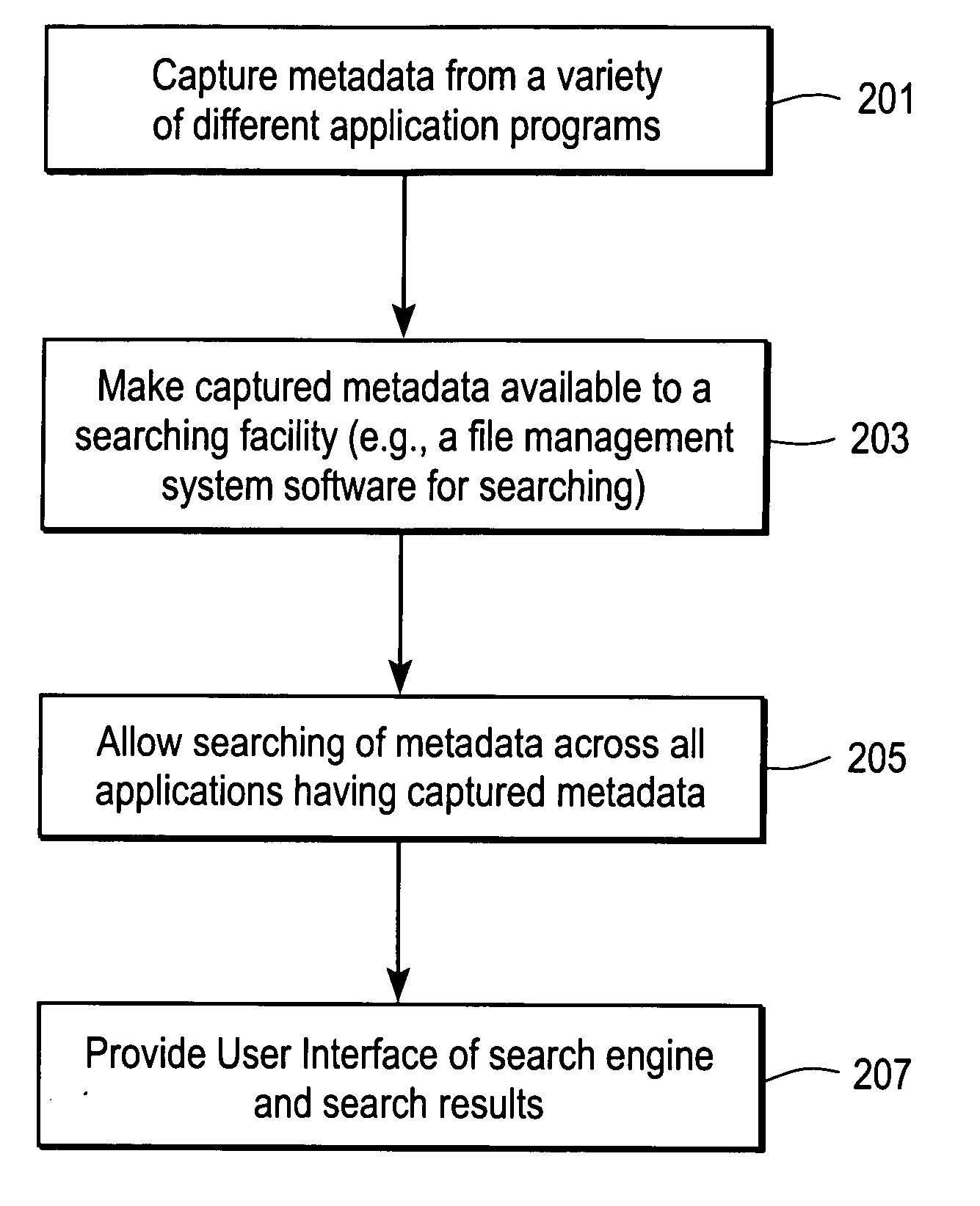
Methods and systems for managing data
ActiveUS20050289133A1Data processing applicationsFile system administrationData processing systemInformation type
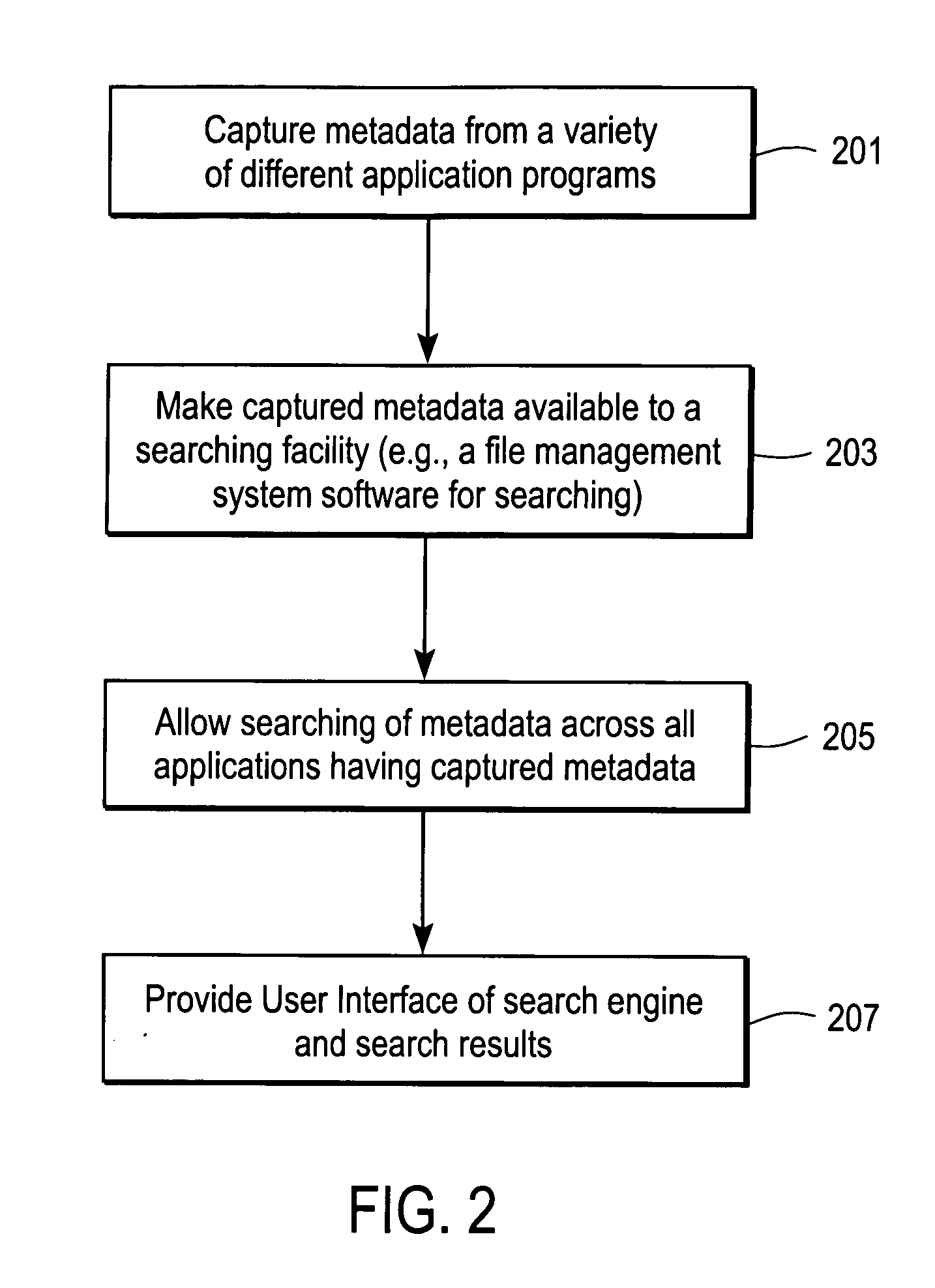
Systems and methods for managing data, such as metadata. In one exemplary method, metadata from files created by several different software applications are captured, and the captured metadata is searched. The type of information in metadata for one type of file differs from the type of information in metadata for another type of file. Other methods are described and data processing systems and machine readable media are also described.
Owner:APPLE INC
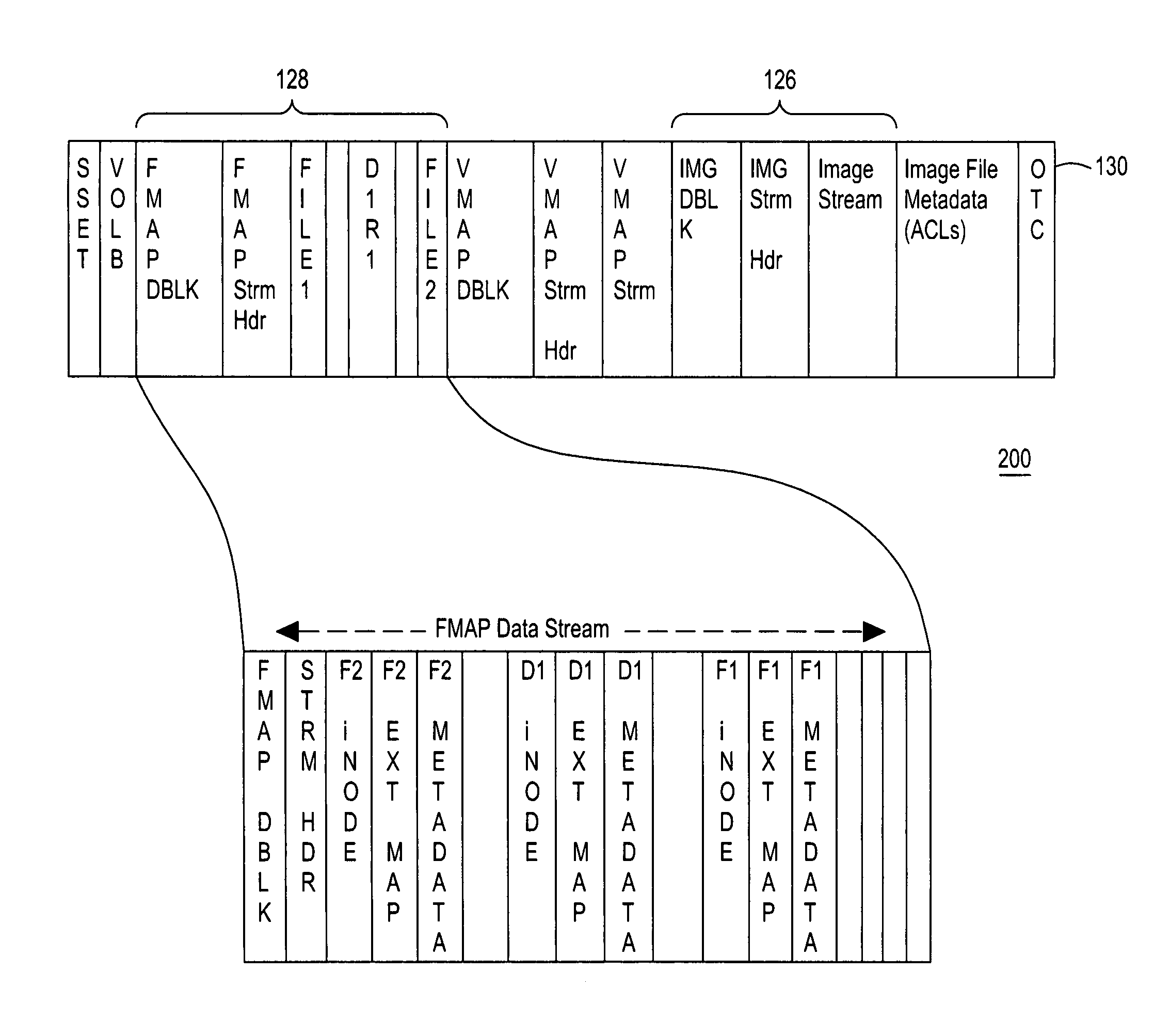
Using a metadata image of a file system and archive instance to restore data objects in the file system
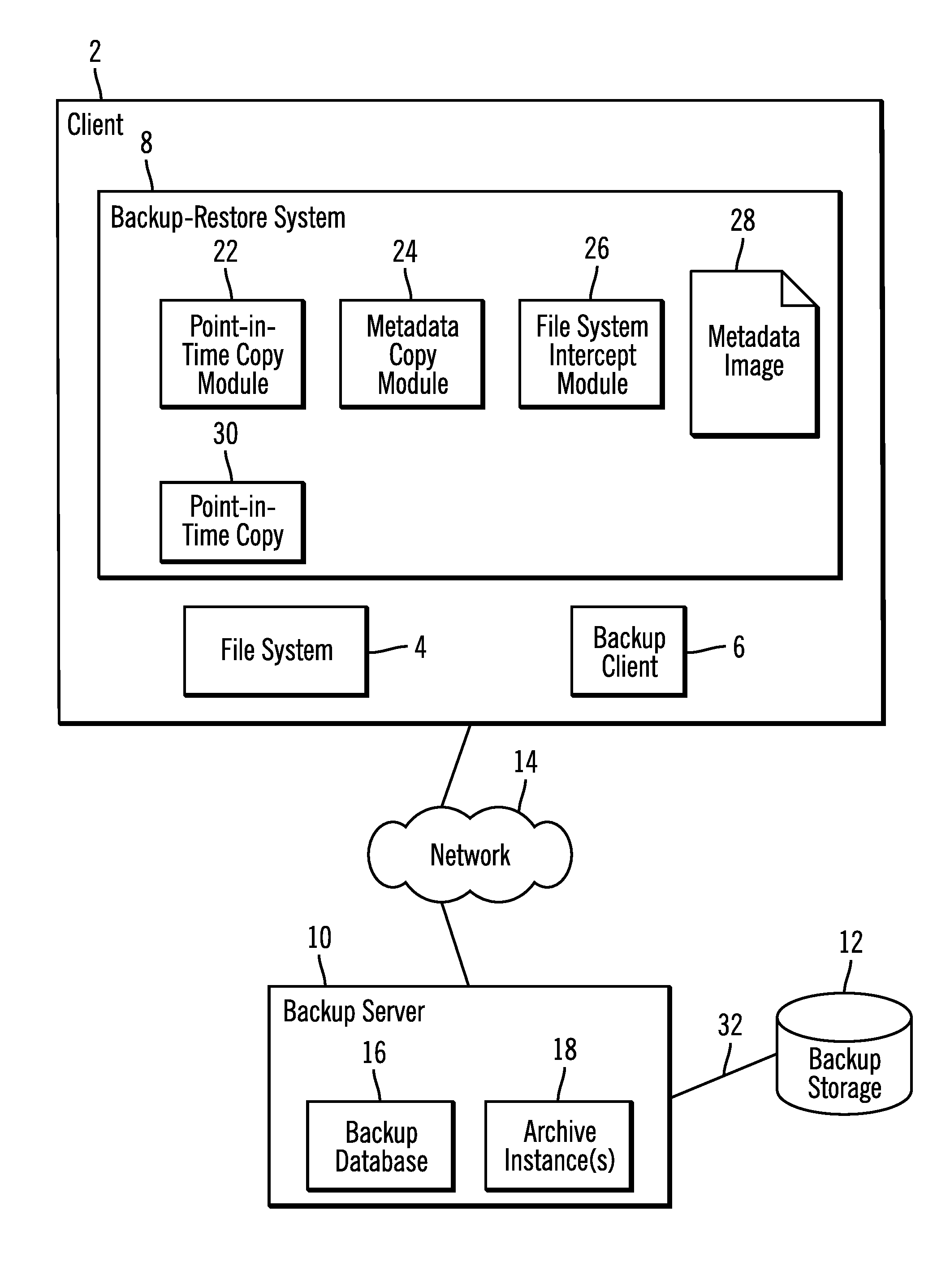
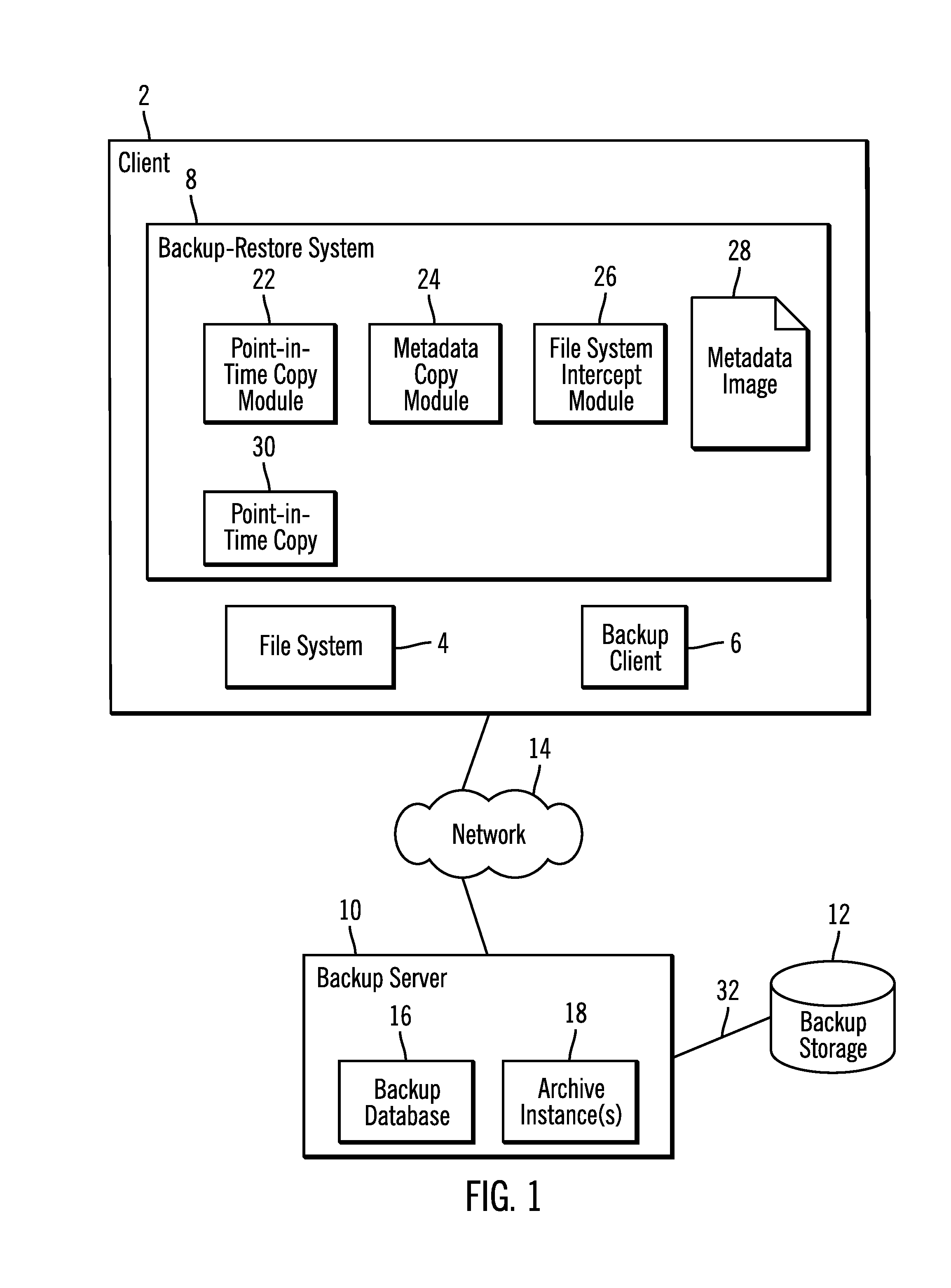
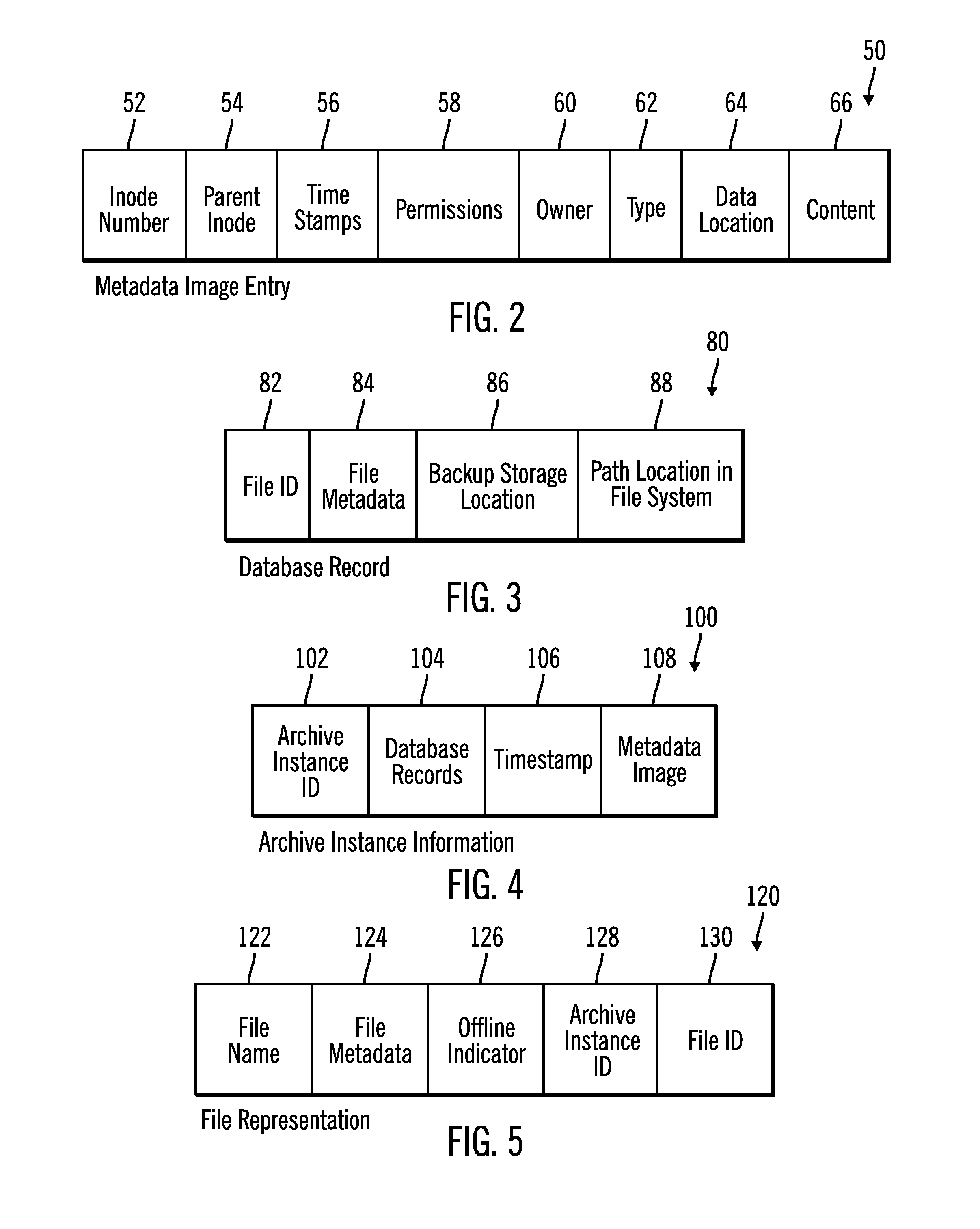
InactiveUS20140074790A1Digital data processing detailsError detection/correctionFile systemDocument representation
Provided are a computer program product, system, and method for using a metadata image of a file system and archive instance to restore files in the file system. A metadata image of the file system for a point-in-time backup as of a point-in-time includes information on files and directories in the file system as of the point-in-time and an archive instance including a copy of database records in the backup database for the files in the point-in-time backup. A restore request is received. A file representation is created of each file to restore in the directory structure of the file system from the metadata image, wherein at least one of the created file representations indicates that the file is stored off-line and has an external identifier used to access information on the file in the database records in the archive instance for the point-in-time backup.
Owner:IBM CORP
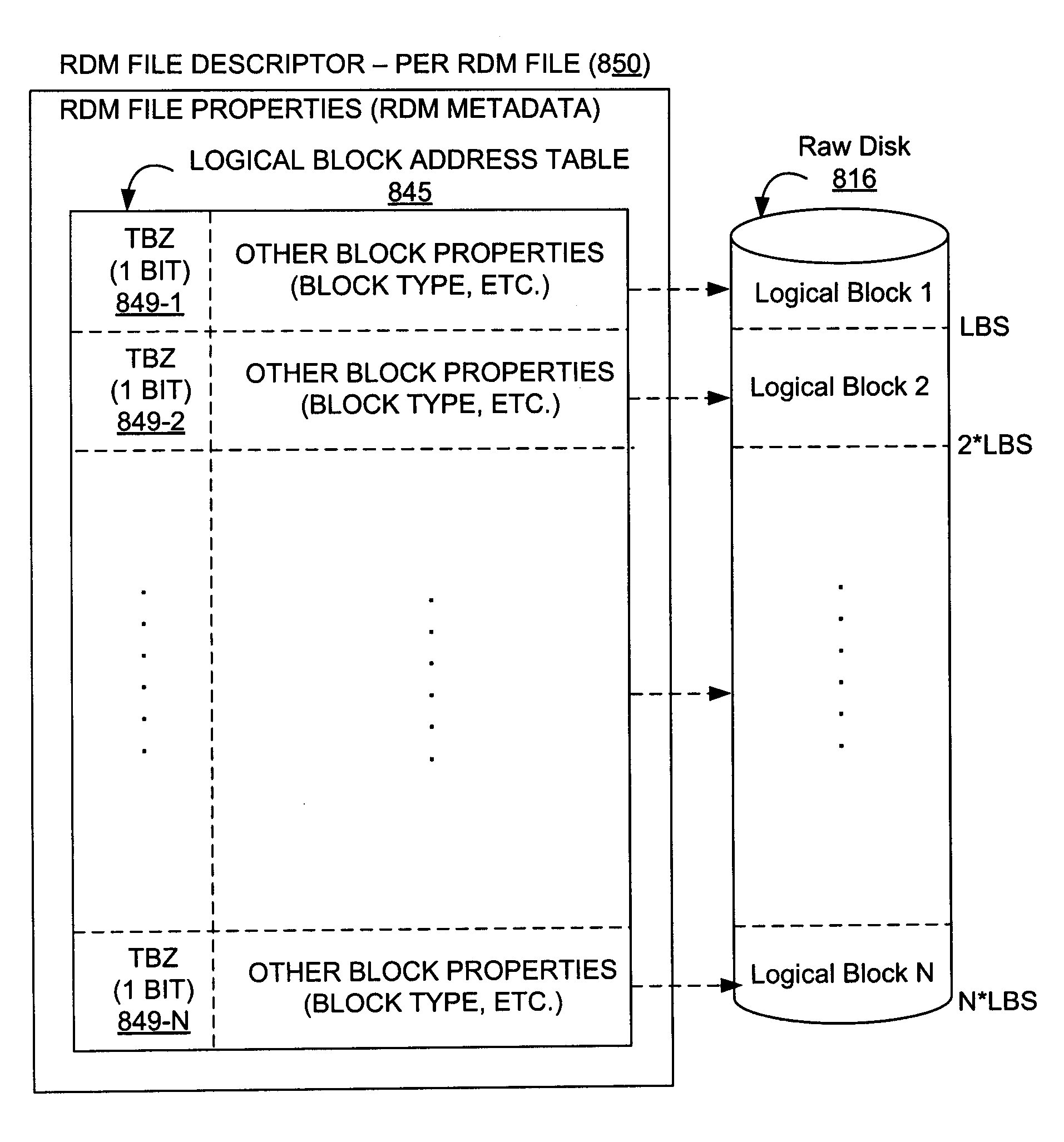
Initializing File Data Blocks
ActiveUS20080235479A1File system administrationSpecial data processing applicationsComputer scienceDatabase
A method and system is provided for initializing files such as, for example and without limitation, pre-allocated files or raw device mapping (RDM) files, by delaying initializing file blocks. In accordance with one or more embodiments of the present invention, file blocks are associated with corresponding indicators to track un-initialized blocks.
Owner:VMWARE INC
Method and system for intelligent storage management
A storage management system is provided. The storage management system may includes a data collector configured to receive storage management information for storage. The storage manager includes an agent configured to collect storage management information for a storage object and to communicate the storage management information to the data collector. The storage management system includes a user interface configured to display the storage management information for the storage objects.
Owner:SERVICENOW INC
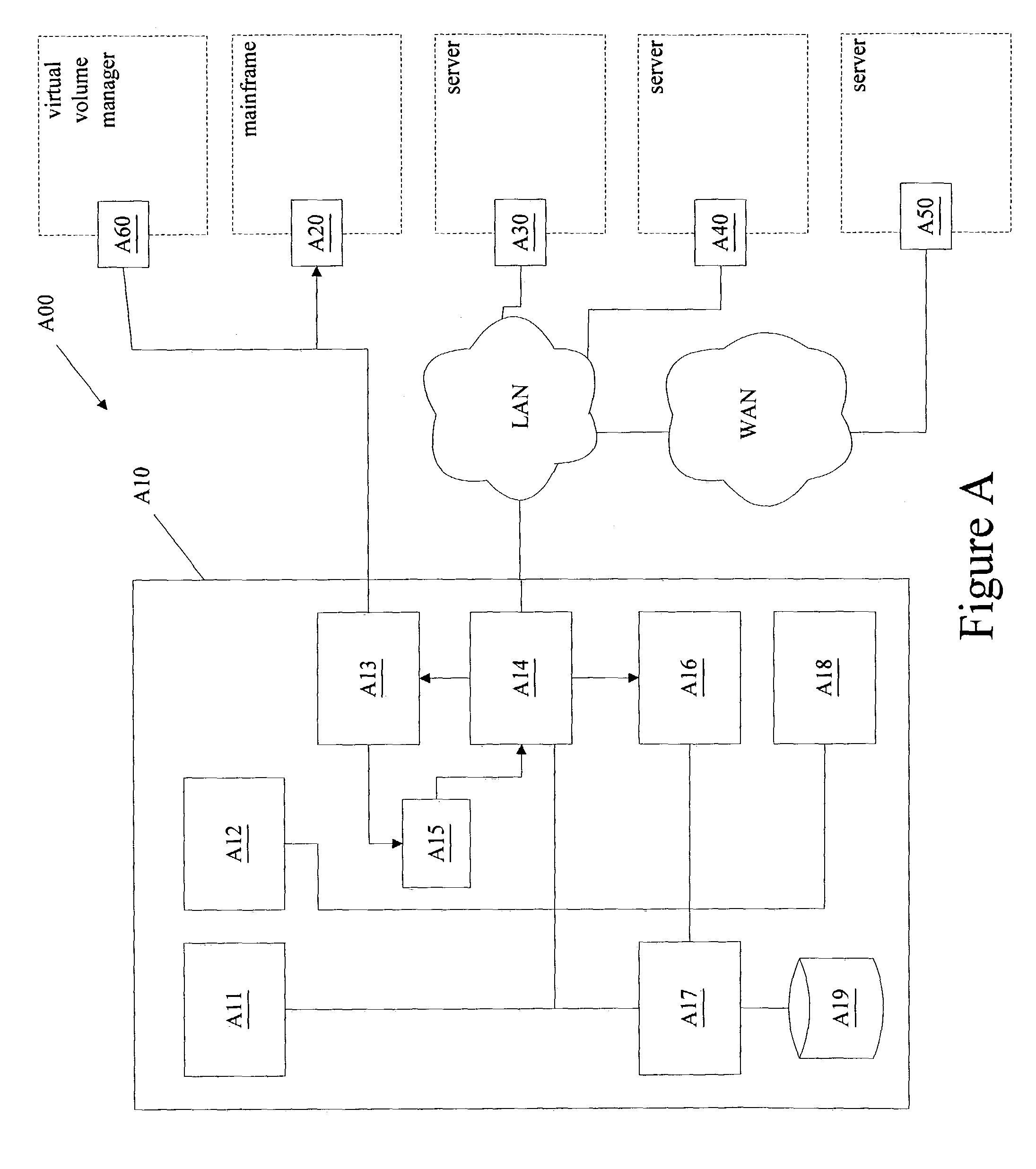
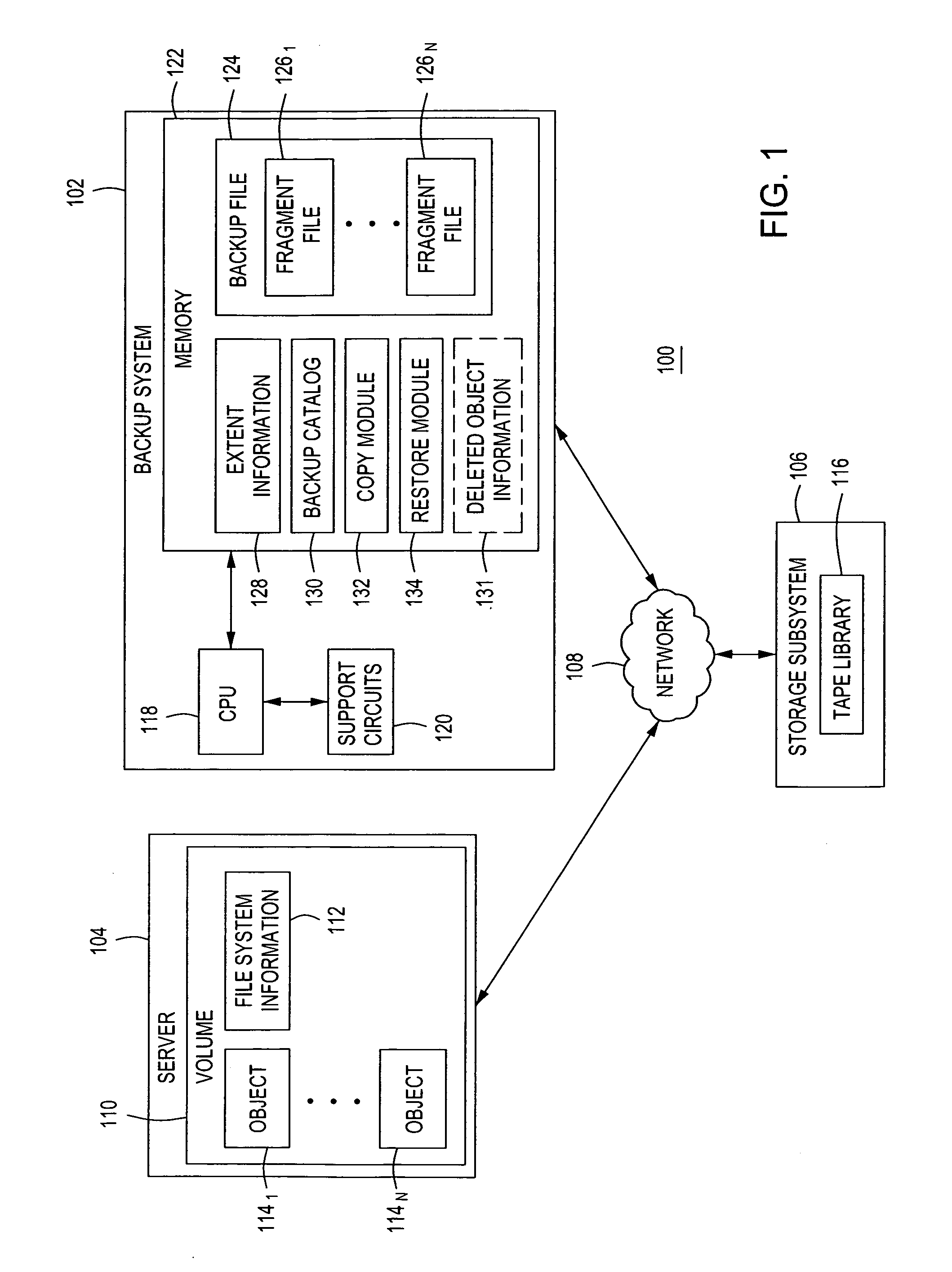
Method and apparatus for performing file-level restoration from a block-based backup file stored on a sequential storage device
A method and apparatus for performing file-level restoration from a block-based backup file stored on a sequential storage device is described. In one embodiment, a method of processing a backup file to perform file-level restoration from a sequential storage device comprises generating extent information, wherein the extent information pertains to at least one file system object associated with a backup file, wherein the backup file is to be stored on a sequential storage device, wherein the backup file is block-based and processing a backup catalog, wherein the backup catalog indicates locations of various portions of the extent information and is used to restore a file system object.
Owner:VERITAS TECH
Table format for map reduce system
ActiveUS20140081918A1Small sizeEasy to operateDigital data processing detailsFile system administrationHigh rateMap reduce
A key-value store provides column-oriented access to data in a distributed and fault tolerant manner. Data can be inserted into the data store and data can be retrieved either randomly or sequentially from the data store at high rates. Keys for a table are ordered and the entire table is divided into key ranges. Each key range is handled by a table which itself is divided into key ranges called a partition. Partitions are also divided into segments. Such recursive division into smaller and smaller key ranges provides parallelism. At the highest level, operations on tablets can be distributed to different nodes. At lower levels, different threads can handle operations on individual segments. Large-scale restructuring operations can be decomposed into operations on individual segments so that a global lock on larger objects does not need to be kept across the entire operation.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Systems and methods for using metadata to enhance data management operations
Systems and methods for managing electronic data are disclosed. Various data management operations can be performed based on a metabase formed from metadata. Such metadata can be identified from an index of data interactions generated by a journaling module, and obtained from their associated data objects stored in one or more storage devices. In various embodiments, such processing of the index and storing of the metadata can facilitate, for example, enhanced data management operations, enhanced data identification operations, enhanced storage operations, data classification for organizing and storing the metadata, cataloging of metadata for the stored metadata, and / or user interfaces for managing data. In various embodiments, the metabase can be configured in different ways. For example, the metabase can be stored separately from the data objects so as to allow obtaining of information about the data objects without accessing the data objects or a data structure used by a file system.
Owner:COMMVAULT SYST INC
Media gifting devices and methods
Various techniques are provided for the gifting between multiple electronic devices of media content provided by an online digital media provider. An offer and acceptance of a selected gift file is accomplished between a gifter device and a receiving giftee device using a near-field communication (NFC) connection. If a connection to the online provider is available, the gifter device may transmit a gift request by which the gifter's account is charged for the gift file. Thereafter, a gift file created using DRM keys associated with the giftee's account may be downloaded to the giftee device. If a network connection is unavailable, the giftee device may transfer a locked gift file and a corresponding gift license to the giftee device using a peer-to-peer connection. The giftee device may authenticate the license and unlock the gift file once a connection to the online provider is available.
Owner:APPLE INC
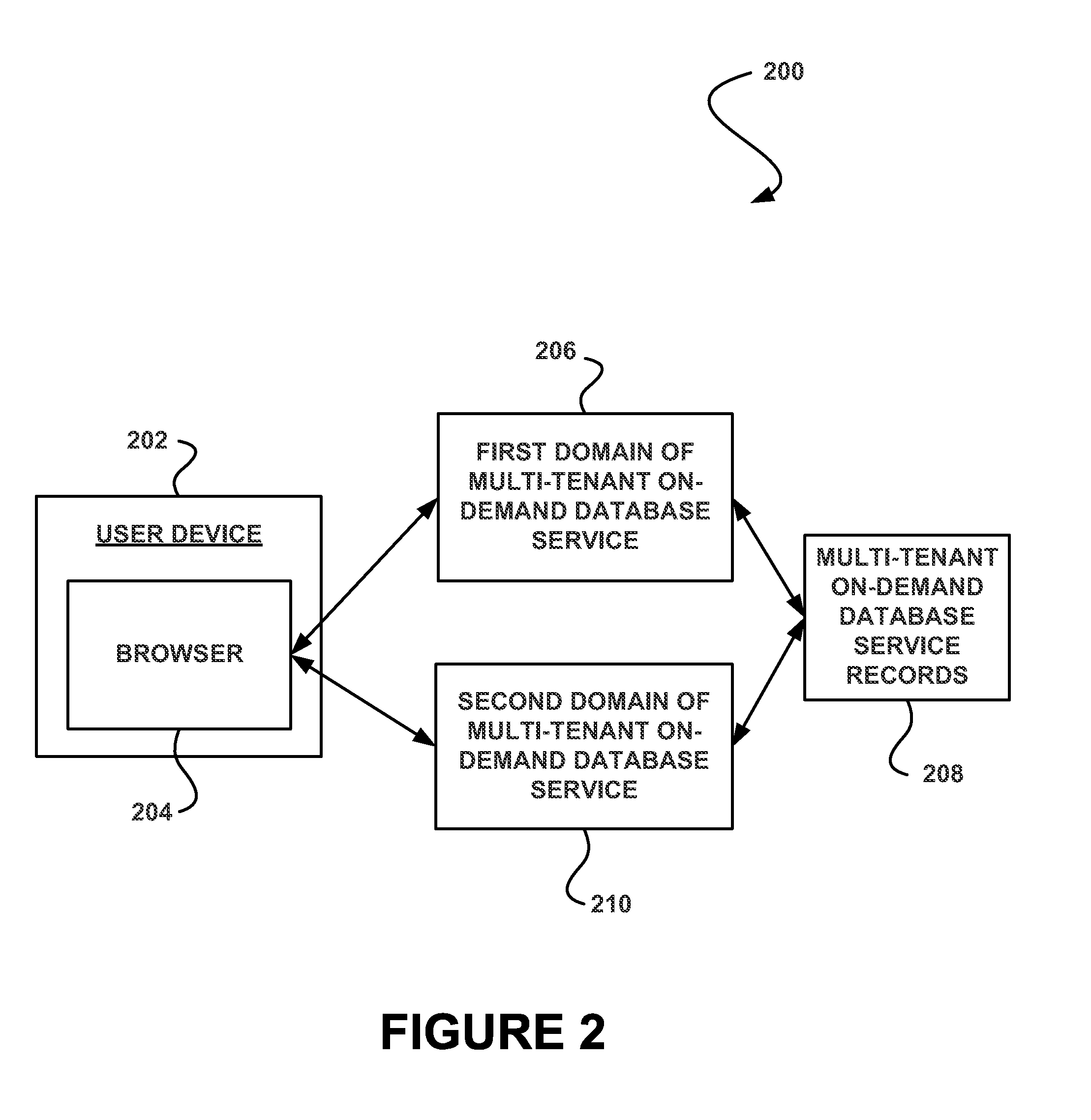
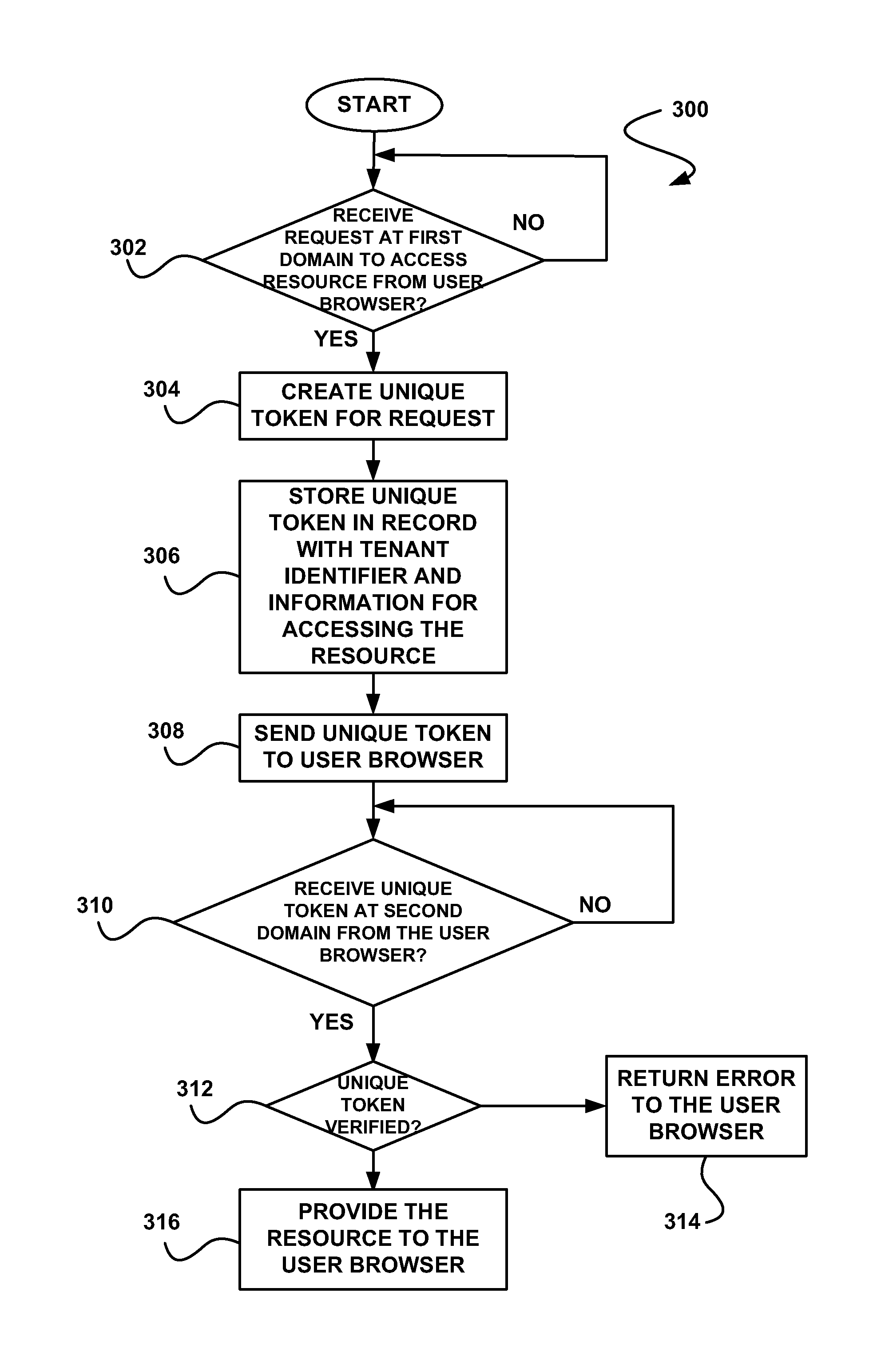
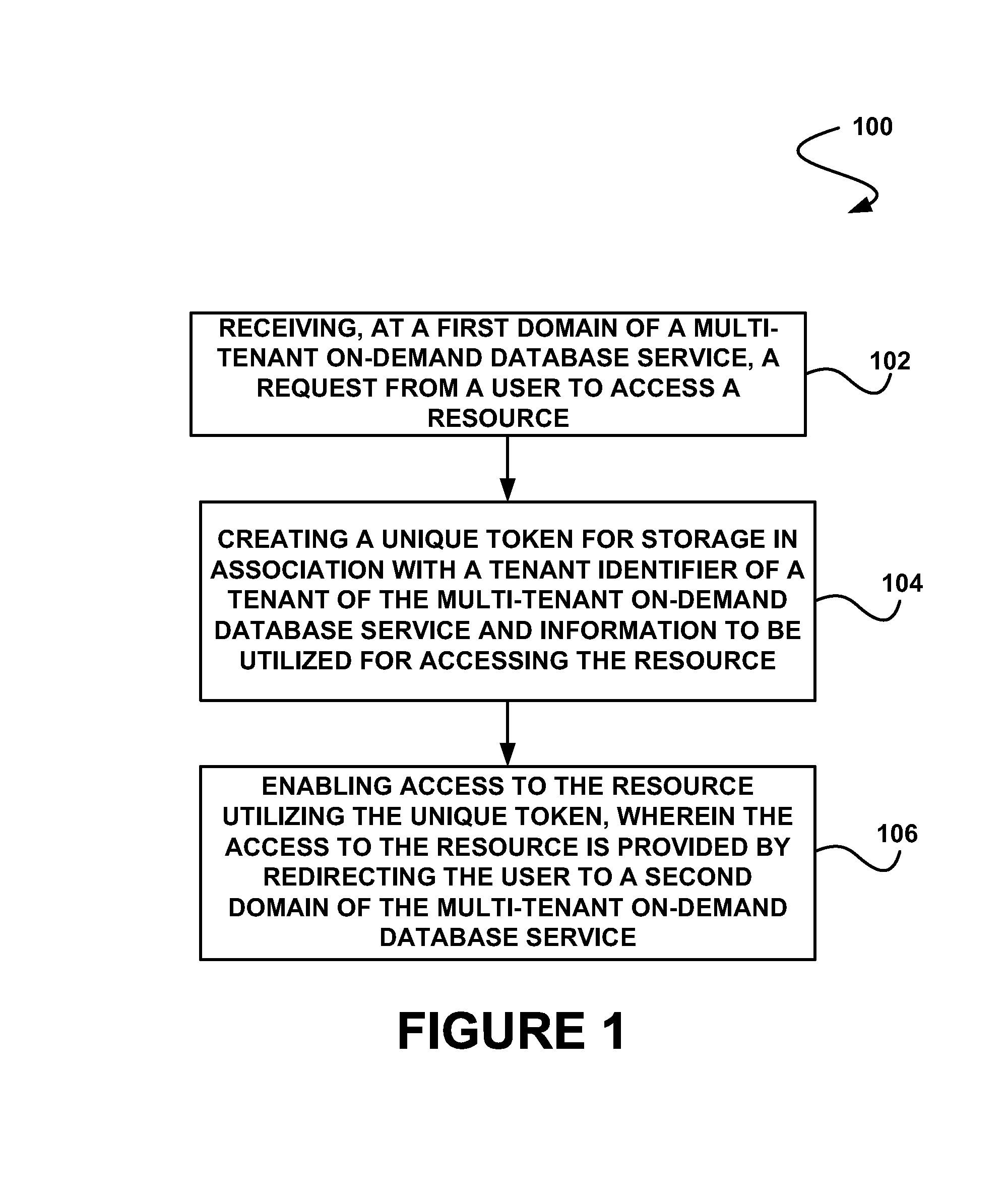
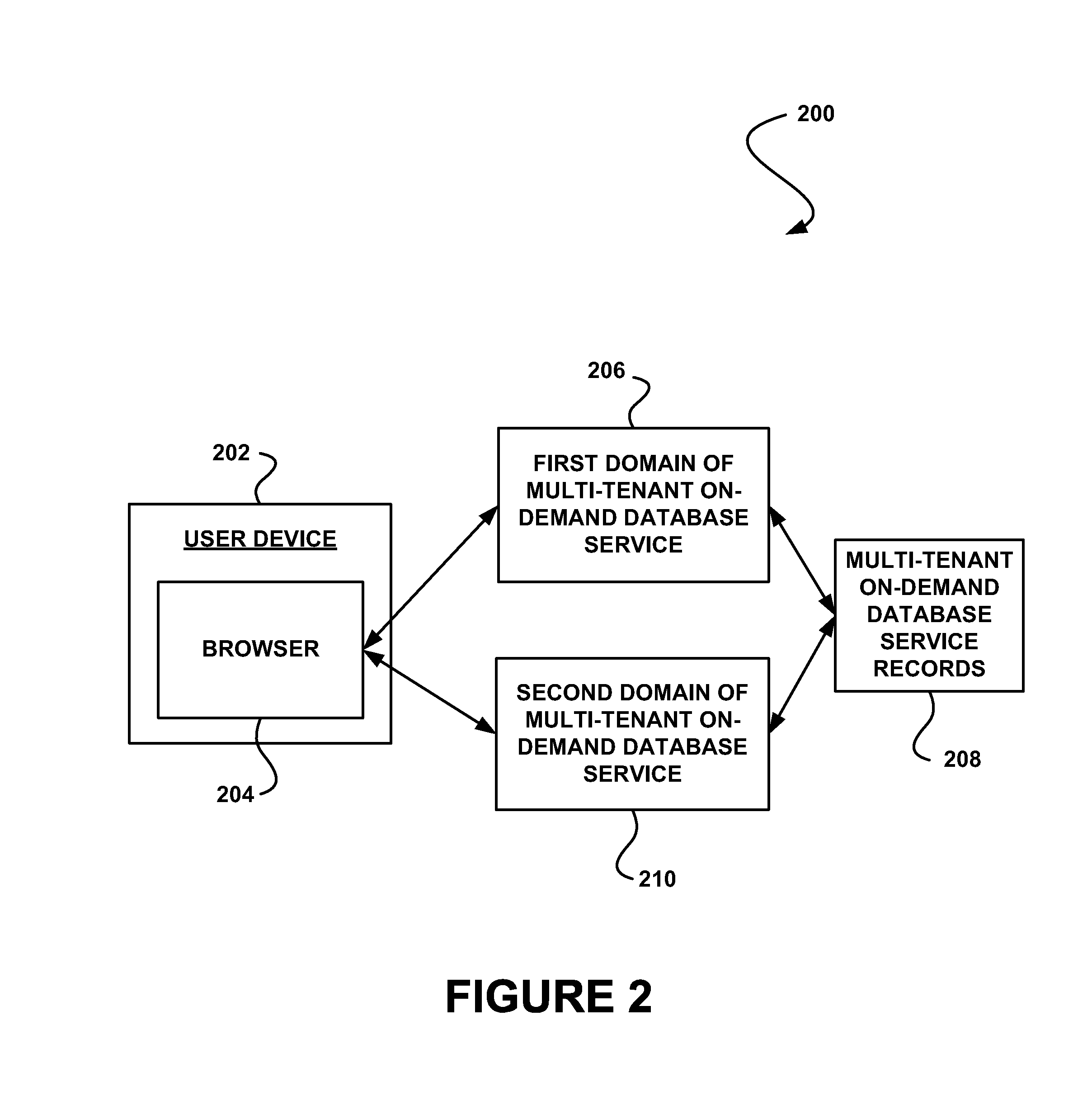
System, method and computer program product for enabling access to a resource of a multi-tenant on-demand database service utilizing a token
ActiveUS20130198236A1Avoid identificationUnwanted useWeb data indexingDigital data processing detailsDatabase servicesOn demand
In accordance with embodiments, there are provided mechanisms and methods for enabling access to a resource of a multi-tenant on-demand database service utilizing a token. These mechanisms and methods for enabling access to a resource of a multi-tenant on-demand database service utilizing a token can be utilized to prevent identification of a user attempting to access the resource, and thus unwanted use of the user's identity.
Owner:SALESFORCE COM INC
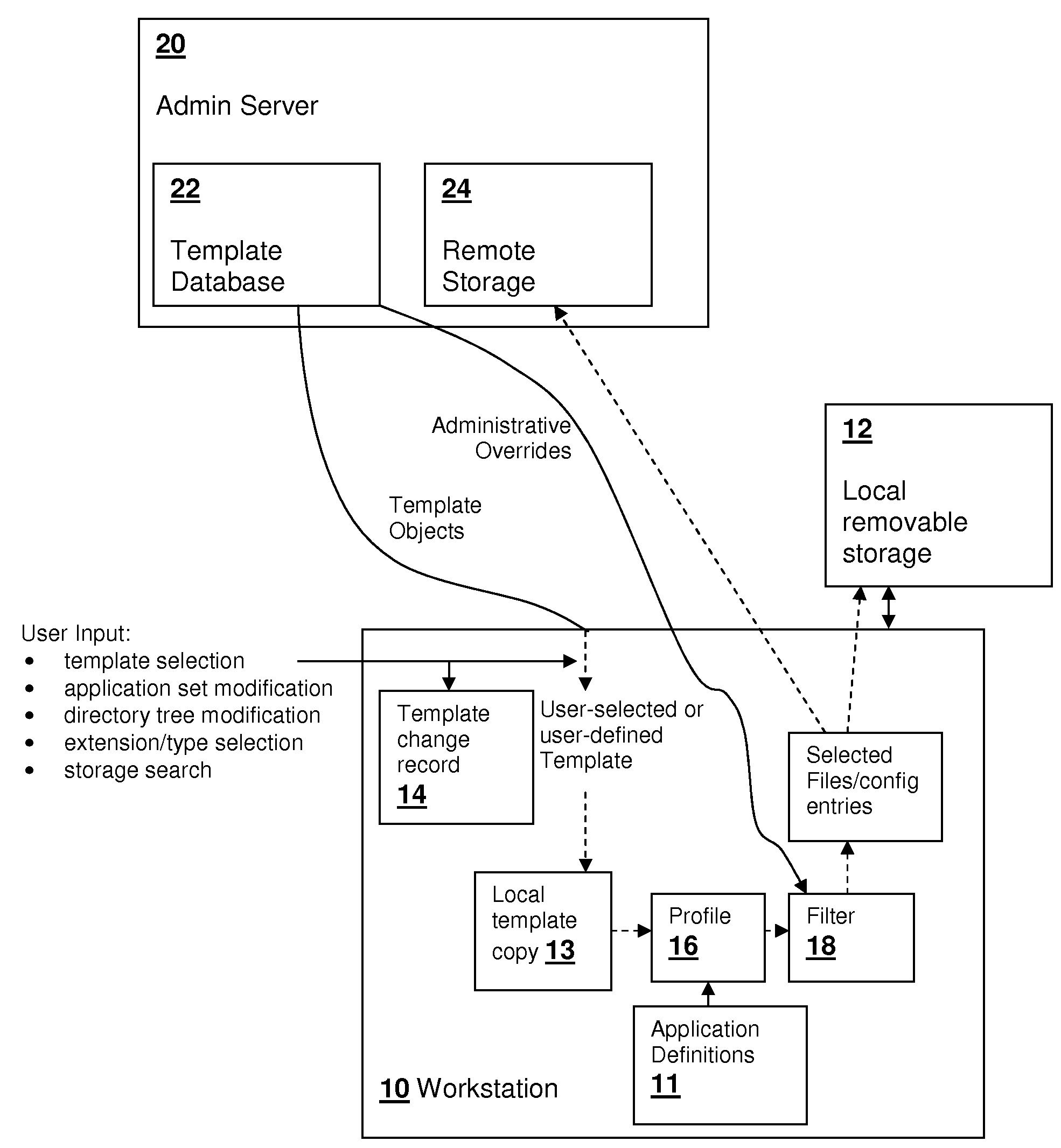
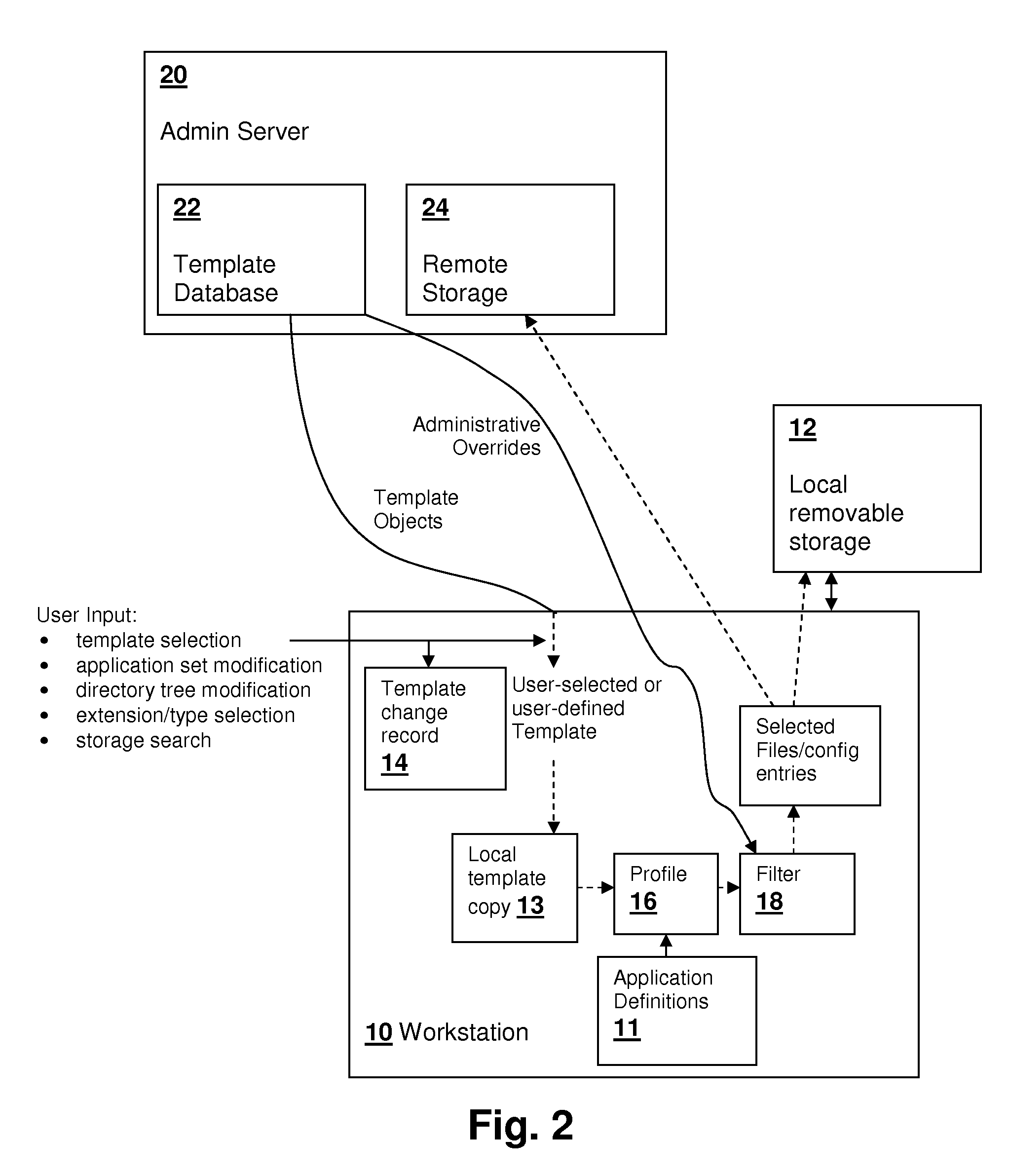
Template-based remote/local file selection techniques for modular backup and migration
File selection techniques that can handle overlapping module contexts provide flexible and reversible backup, restore, migration, deployment and synchronization operations. Both remote (administrative) control and local (user) control of the file selection are provided. Application and configuration specific templates are provided to a user from the remote administrator for further customization by selecting or de-selecting configurations, applications and / or individual files or configuration entries. The templates may be controlled geographically by the IP address or identity associated with the user. A user's interaction with the customization is saved and the order of changes is maintained, so that when the templates are updated, the user's customizations can be re-applied. The administrator may override user settings based on rules, which may also be geographically determined. The file selection may also be altered based on media type and location, e.g., local backup vs. server backup.
Owner:IBM CORP
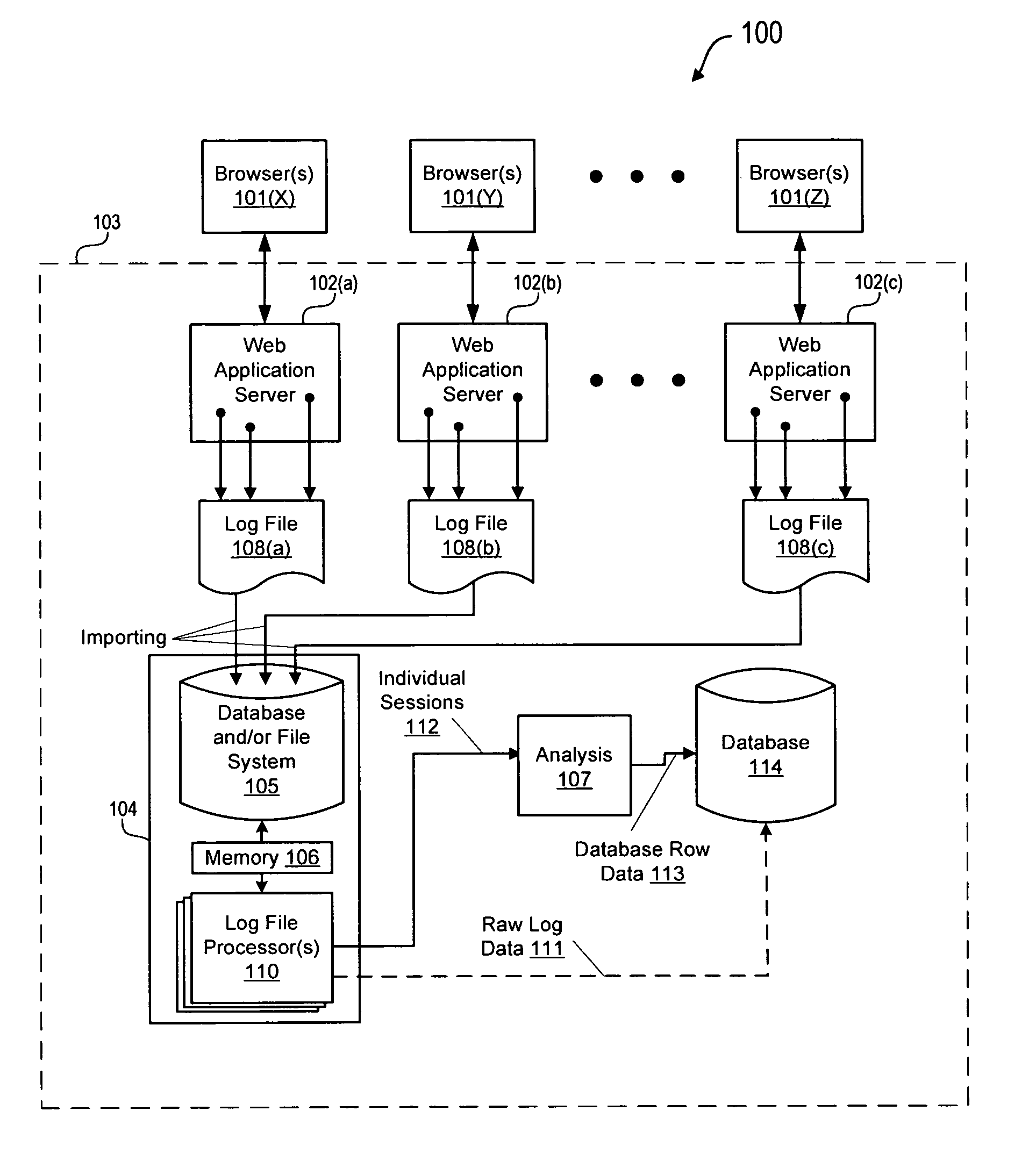
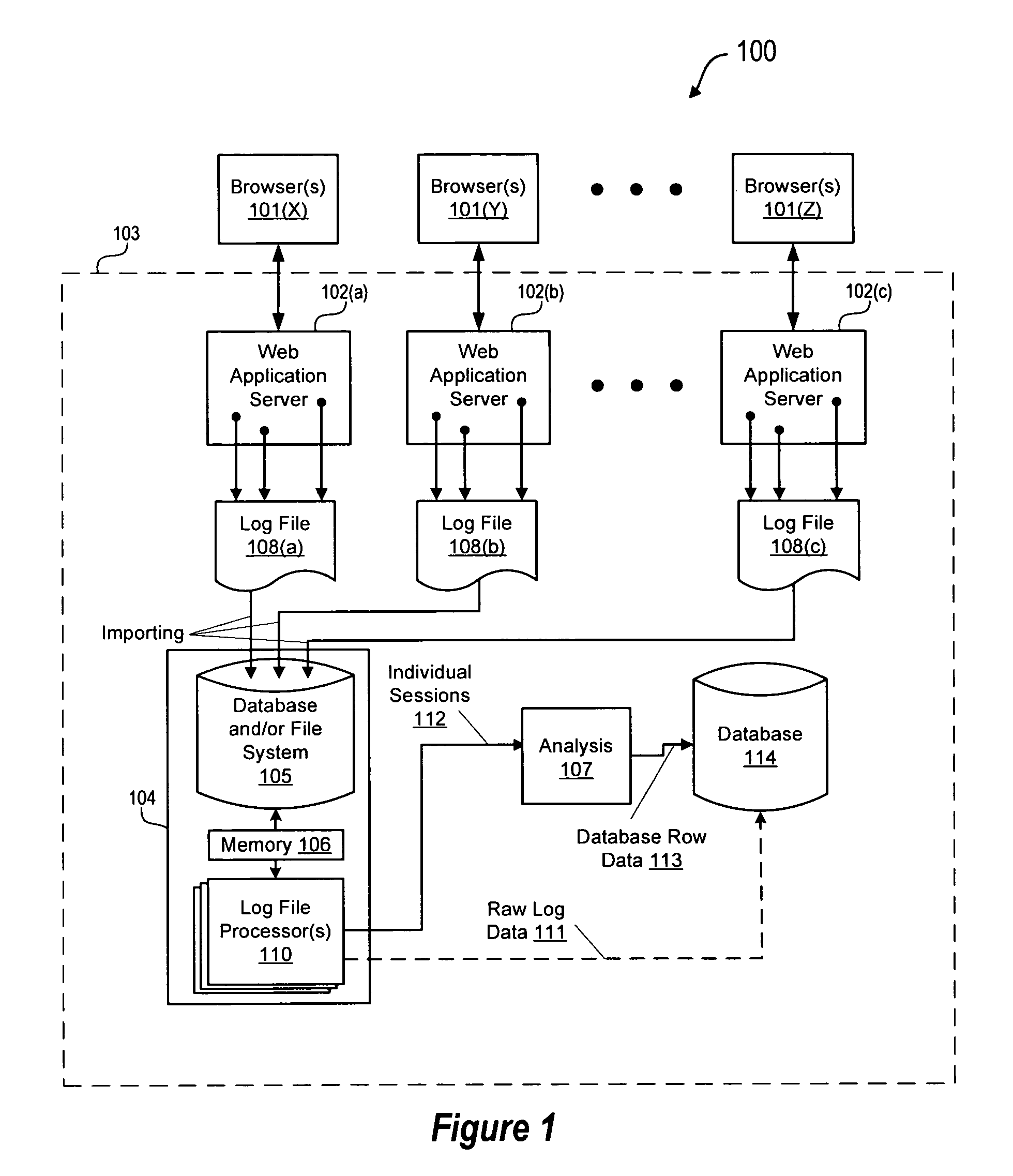
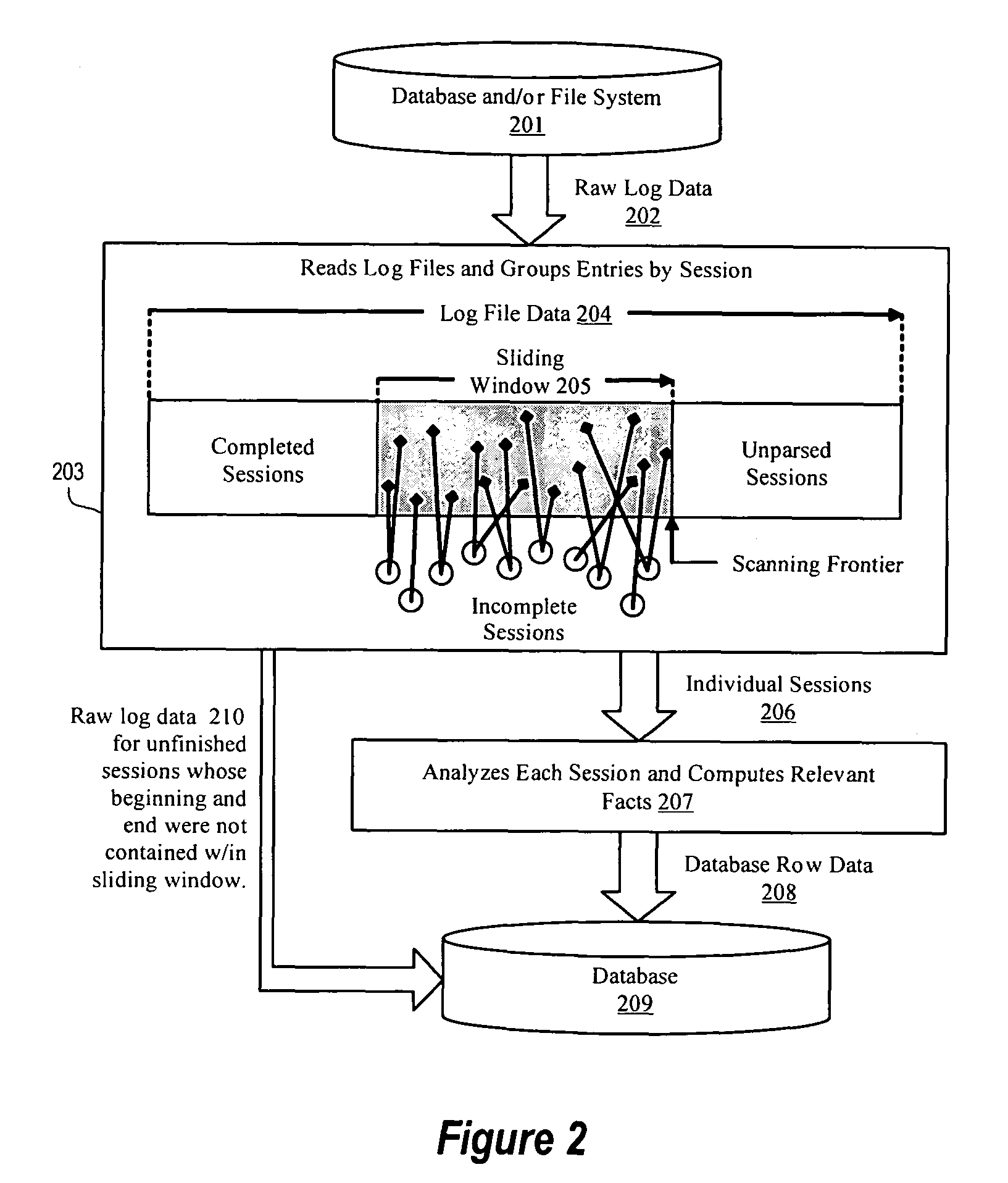
Session-based processing method and system
ActiveUS7779021B1Digital data processing detailsError detection/correctionData ingestionSlide window
A log file processing system sorts records from large log files and groups them by session without making a complete copy of the log files by capturing a subset of the log files in a sliding memory window and identifying all records in the window that form a complete user session. Records belonging to a complete session are output for analyzing, and the remaining records are output as raw log data for additional processing. Using a ring buffer to implement the sliding memory window, data structures are used to group records by session, to identify completed sessions, and to index into the ring buffer to retrieve records for completed sessions that are to be directly analyzed. Any records remaining in the ring buffer at the end of slide window processing may be output as raw log file data and are processed as incomplete or malformed session records. An embodiment of the log file processing system provides a significant improvement on the speed of data extraction from log files into analyzable session data.
Owner:VERSATA DEV GROUP
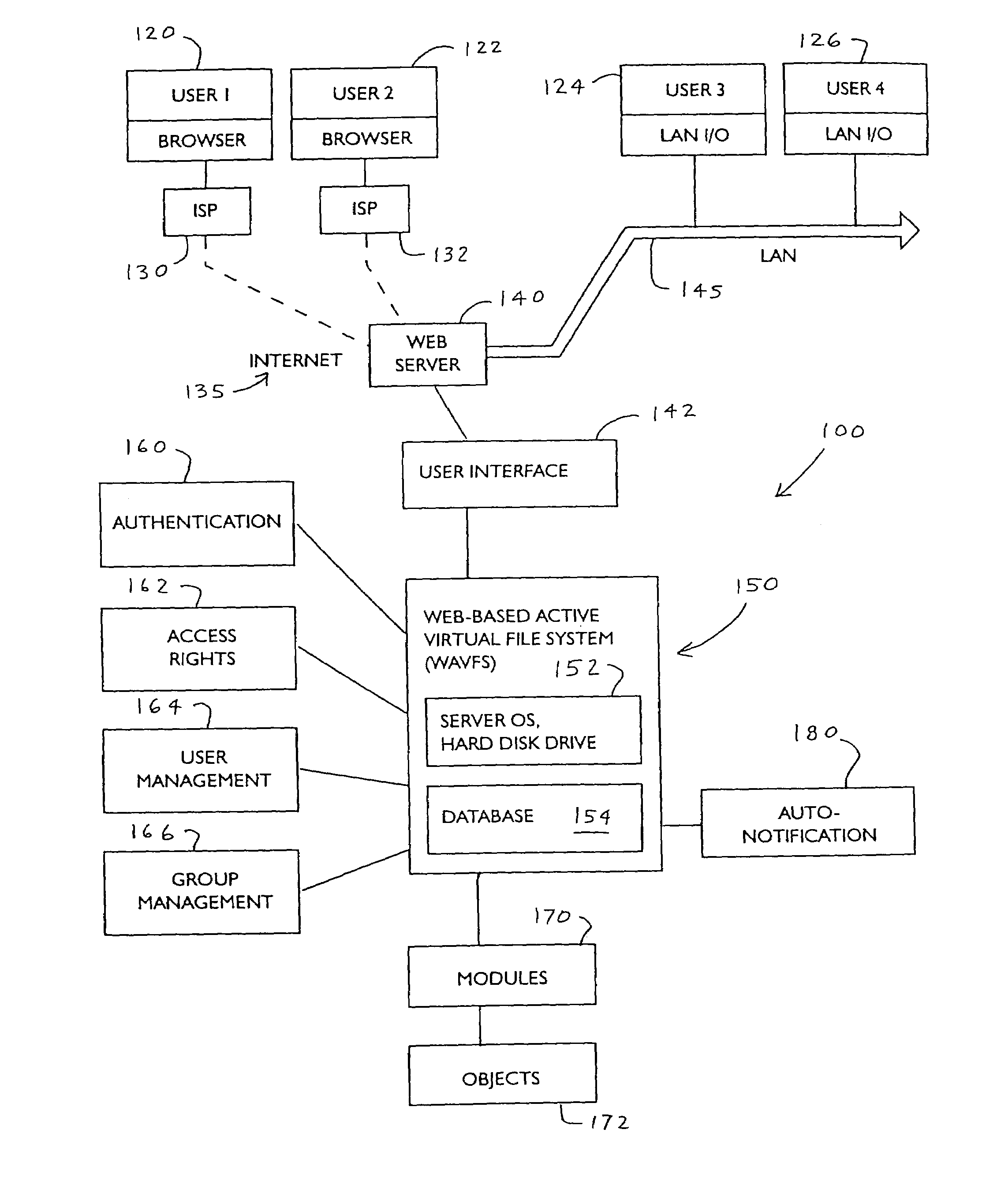
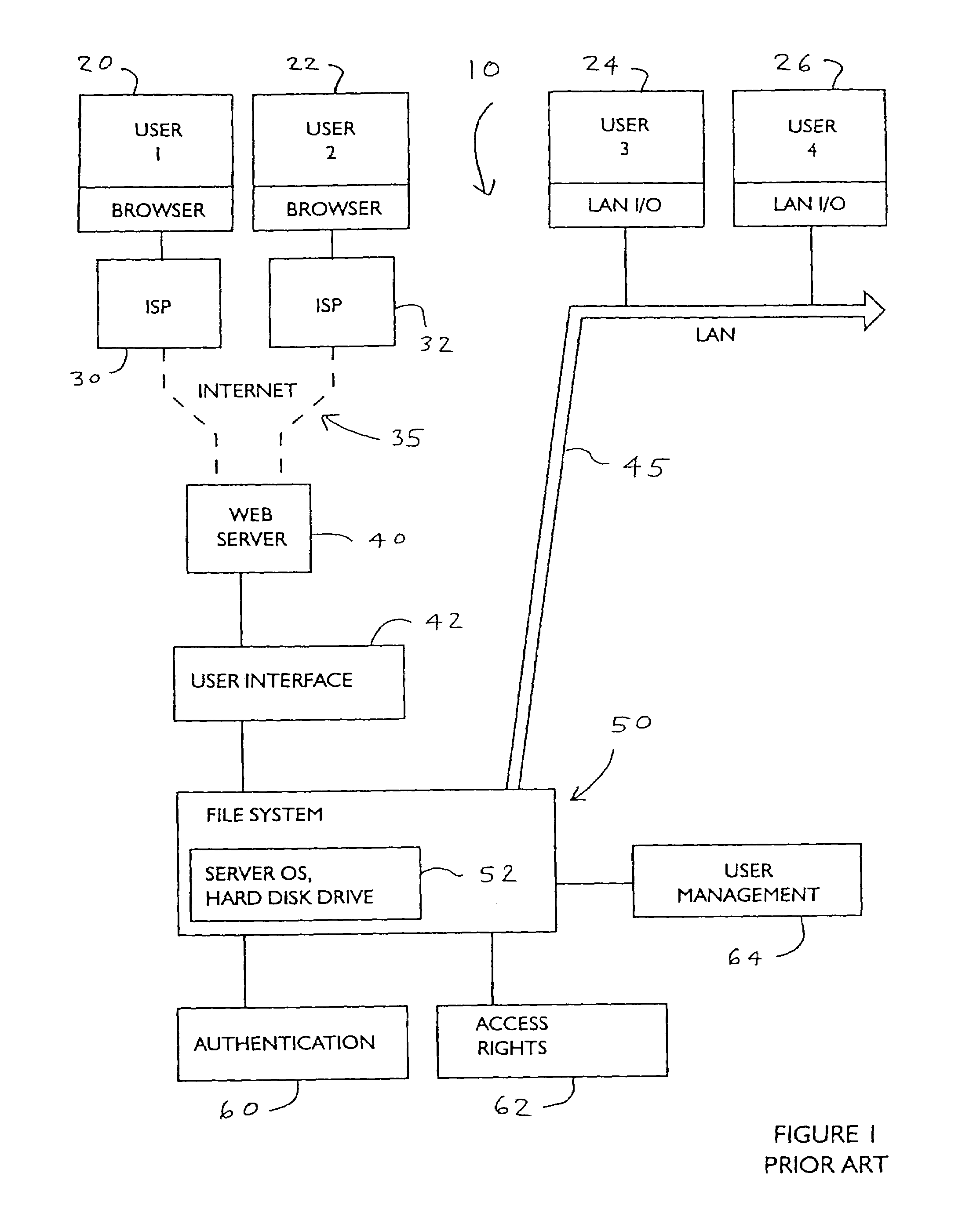
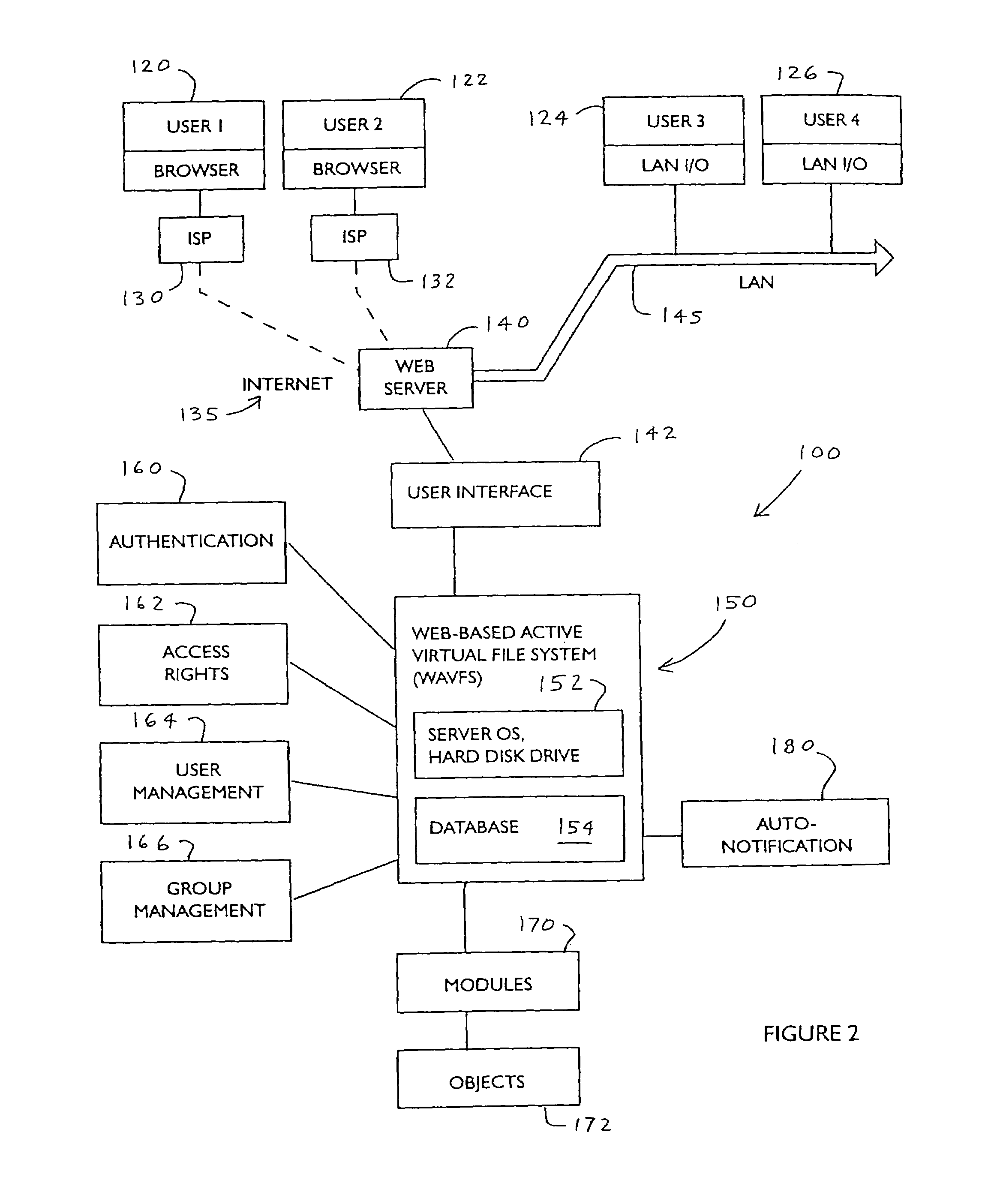
Method and apparatus for providing a web-based active virtual file system
InactiveUS7444390B2Data processing applicationsDigital data processing detailsEvent typeVirtual file system
A computerized file system is accessible over the Internet or other type of network, in which certain “triggering events” pertaining to the operation of the file system automatically generate a notification message to users. Once a user has been authenticated, this user's access rights are determined. An Automatic Notification function checks to see if any “triggering” events have occurred when a user performs a particular task. The Automatic Notification function defines what type of event will become a triggering event, and also defines what will be the triggering action, once the triggering event occurs, and stores this information in a database. The Auto-notification function can comprise programs that are launched to perform certain tasks. The precise type of auto-notification message is fully configurable for each component in the file system.
Owner:CDIMENSIONS
Systems and methods for using metadata to enhance data identification operations
Systems and methods for managing electronic data are disclosed. Various data management operations can be performed based on a metabase formed from metadata. Such metadata can be identified from an index of data interactions generated by a journaling module, and obtained from their associated data objects stored in one or more storage devices. In various embodiments, such processing of the index and storing of the metadata can facilitate, for example, enhanced data management operations, enhanced data identification operations, enhanced storage operations, data classification for organizing and storing the metadata, cataloging of metadata for the stored metadata, and / or user interfaces for managing data. In various embodiments, the metabase can be configured in different ways. For example, the metabase can be stored separately from the data objects so as to allow obtaining of information about the data objects without accessing the data objects or a data structure used by a file system.
Owner:COMMVAULT SYST INC
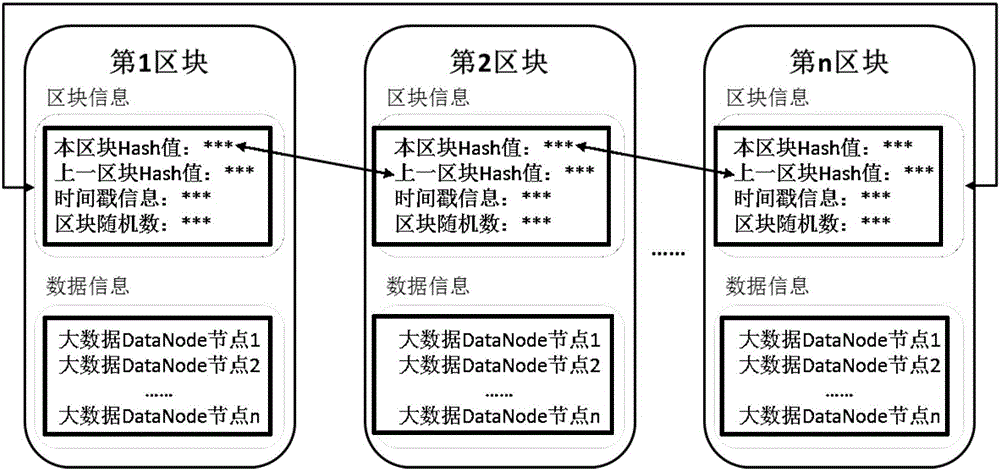
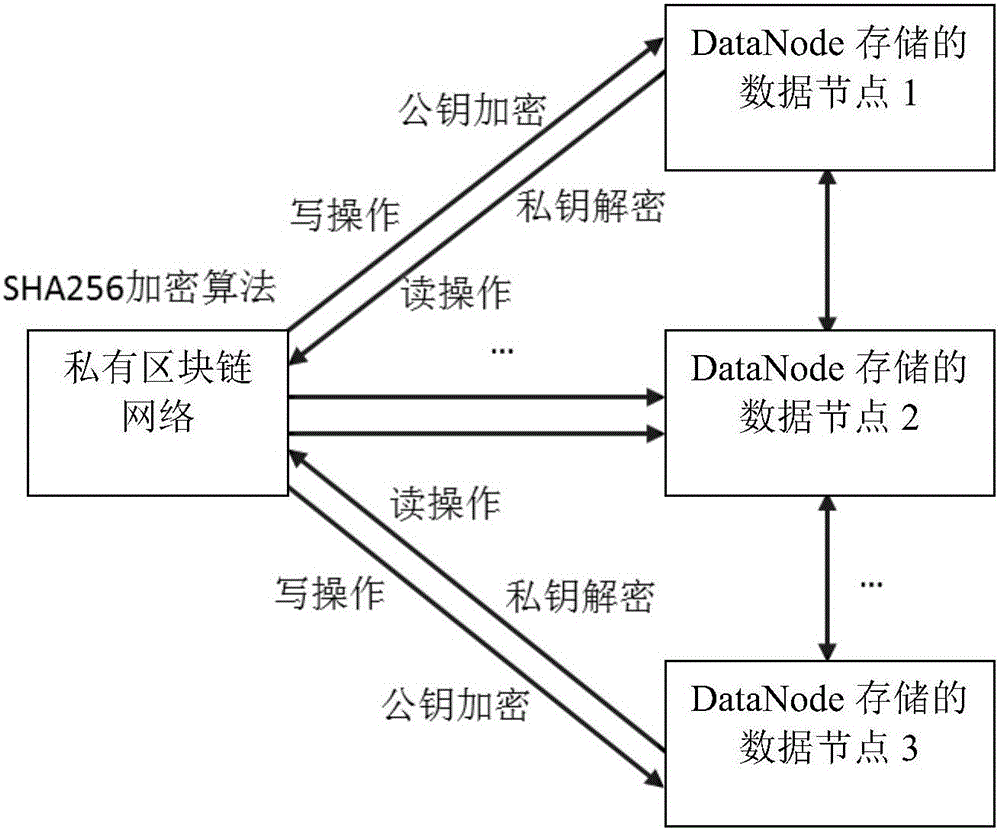
Block chain safety storage method
ActiveCN106503574AFully consider securityImprove securityDigital data protectionFile system administrationPlaintextData platform
The invention provides a block chain safety storage method. The method makes each client-side Client have a name node, the data storage safety of a big data platform is greatly improved, the pressure brought by a centralized server is effectively avoided by adopting decentration design, and common apportion is performed through a whole privately-owned block chain network; Data Node of each data block of Hadoop is encrypted, and the safety of each data in big data is fully guaranteed. A data storage and management mechanism of the big data platform is further improved, a single mode relying on a central node is converted into a network environment jointly maintained jointly by all participants, and the decentration design is really achieved. By setting PKI and user permission, the shortcoming of simple and extensive plaintext storage of important data is broken through, and a safe and encrypted storage process and method are deepened.
Owner:NO 32 RES INST OF CHINA ELECTRONICS TECH GRP
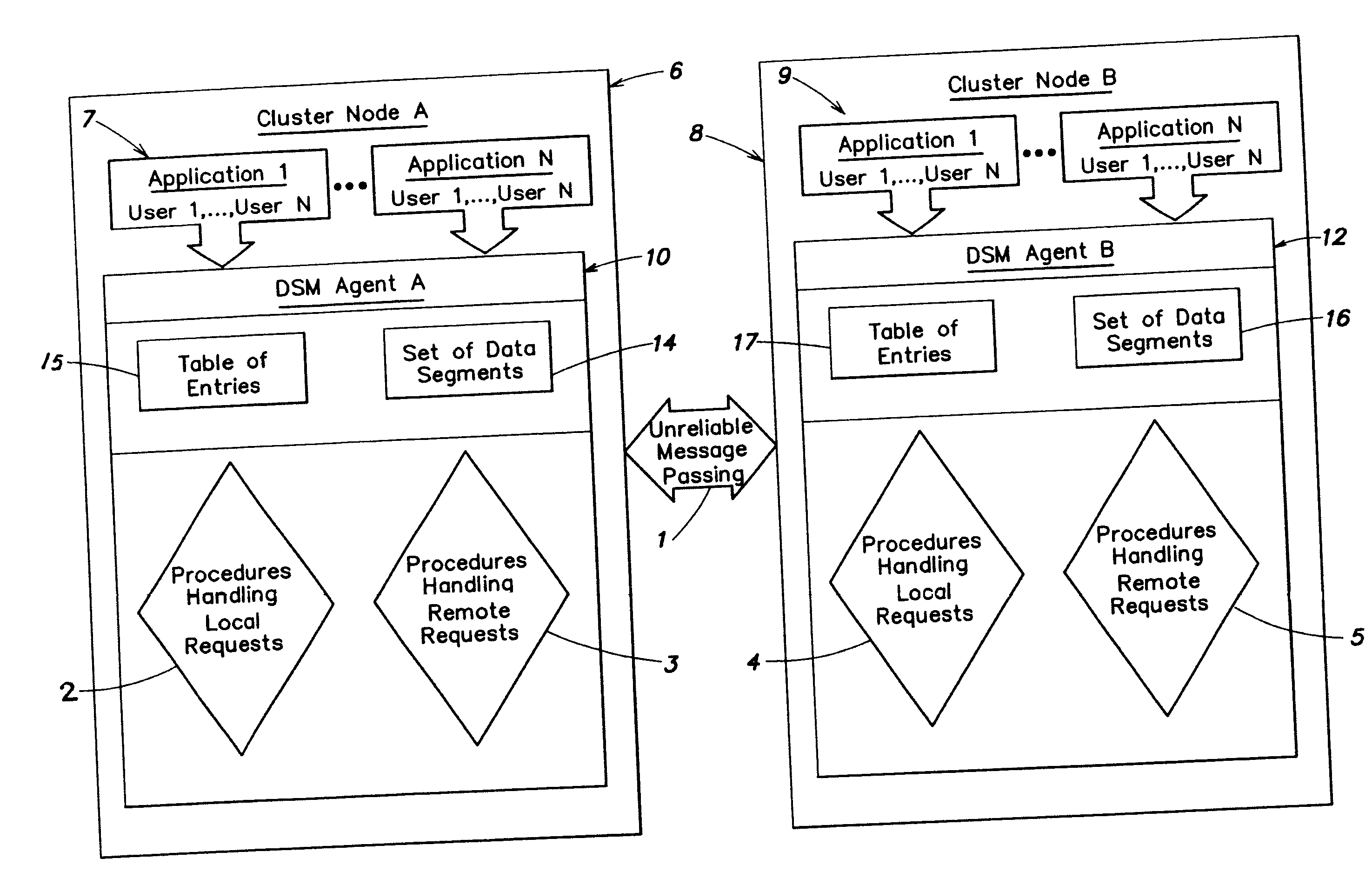
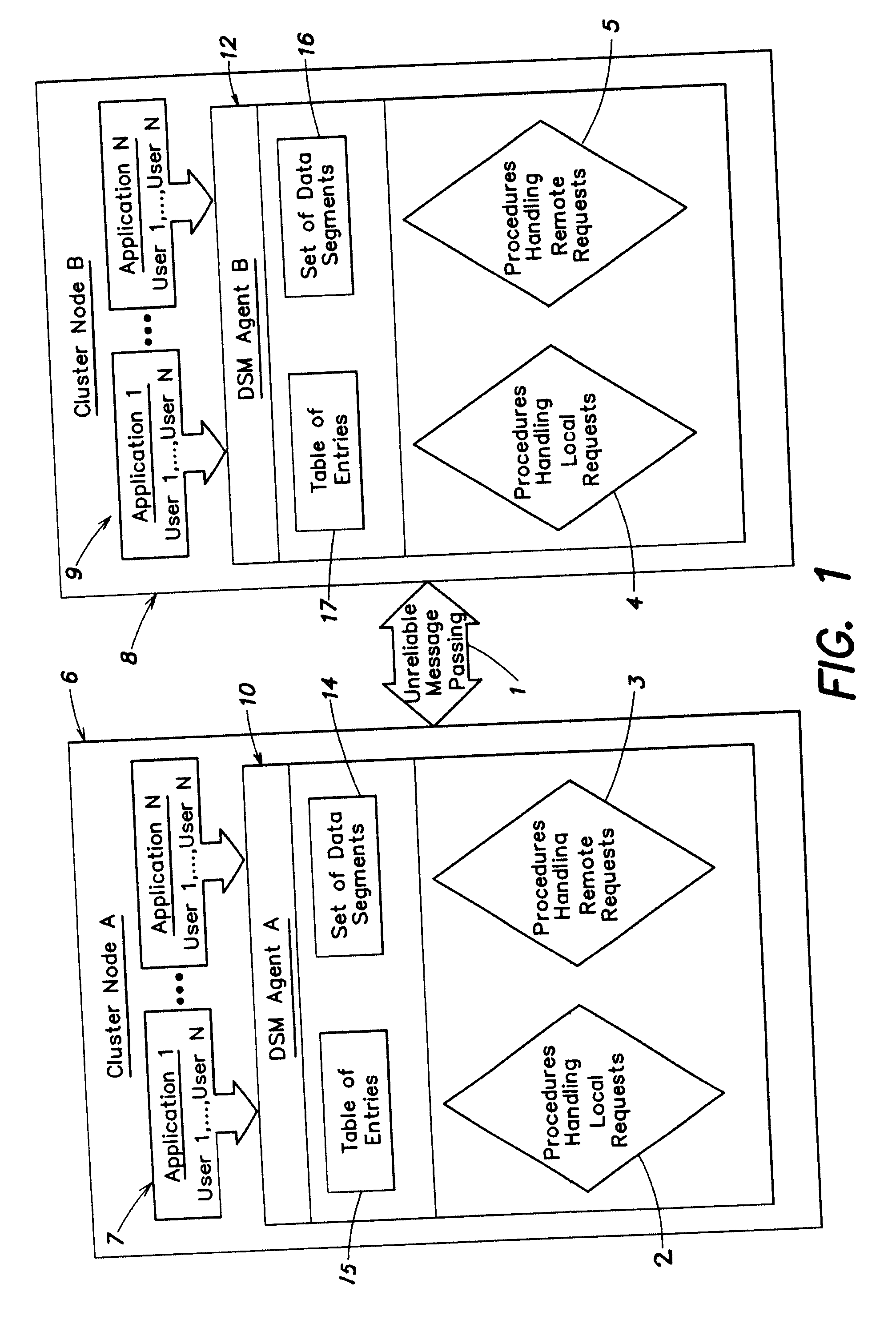
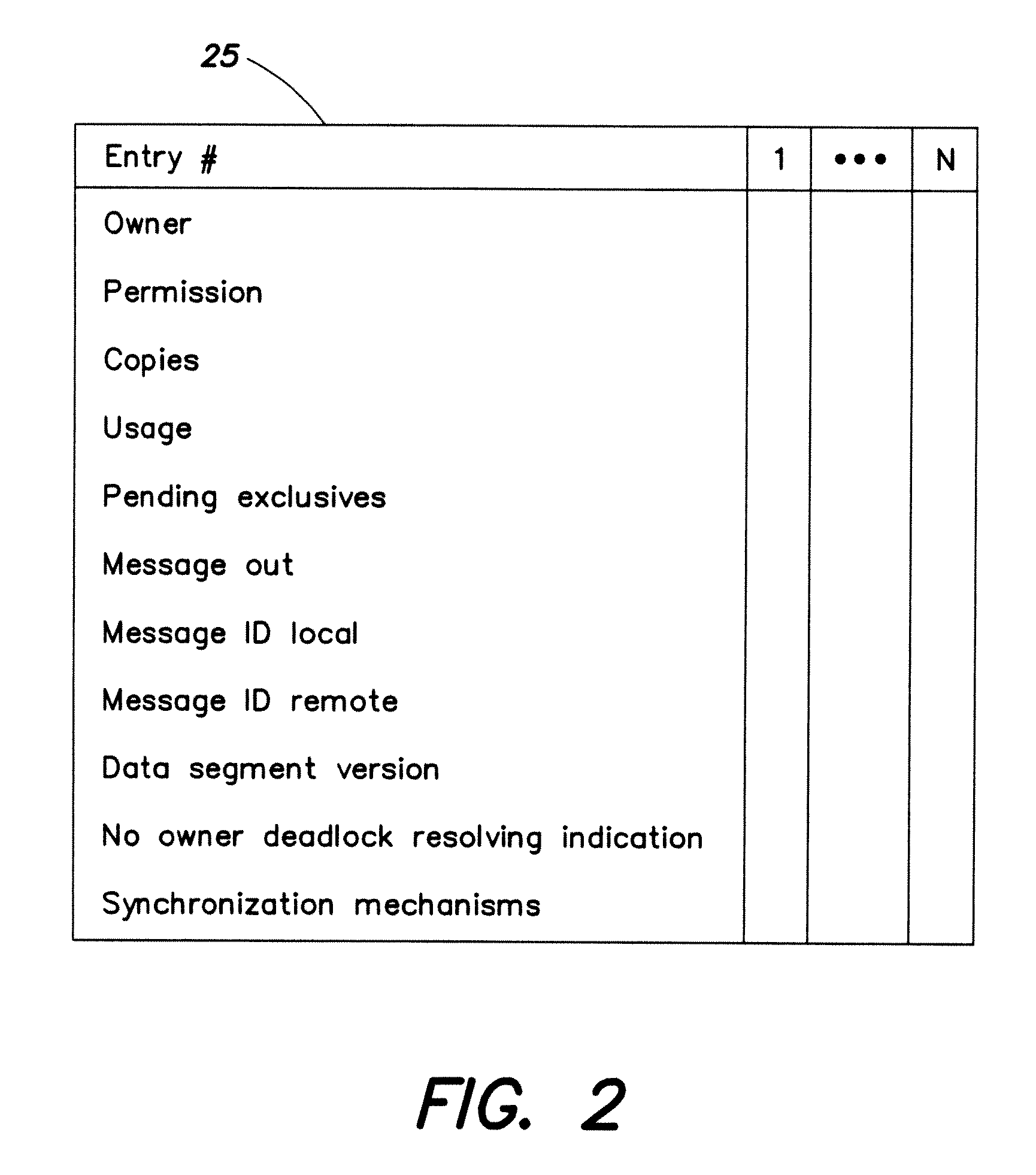
Transactional Processing for Clustered File Systems
InactiveUS20100049718A1Reduce file system accessMemory architecture accessing/allocationDigital data processing detailsData segmentGranularity
Systems and methods for transactional processing within a clustered file system wherein user defined transactions operate on data segments of the file system data. The users are provided within an interface for using a transactional mechanism, namely services for opening, writing and rolling-back transactions. A distributed shared memory technology is utilized to facilitate efficient and coherent cache management within the clustered file system based on the granularity of data segments (rather than files).
Owner:IBM CORP
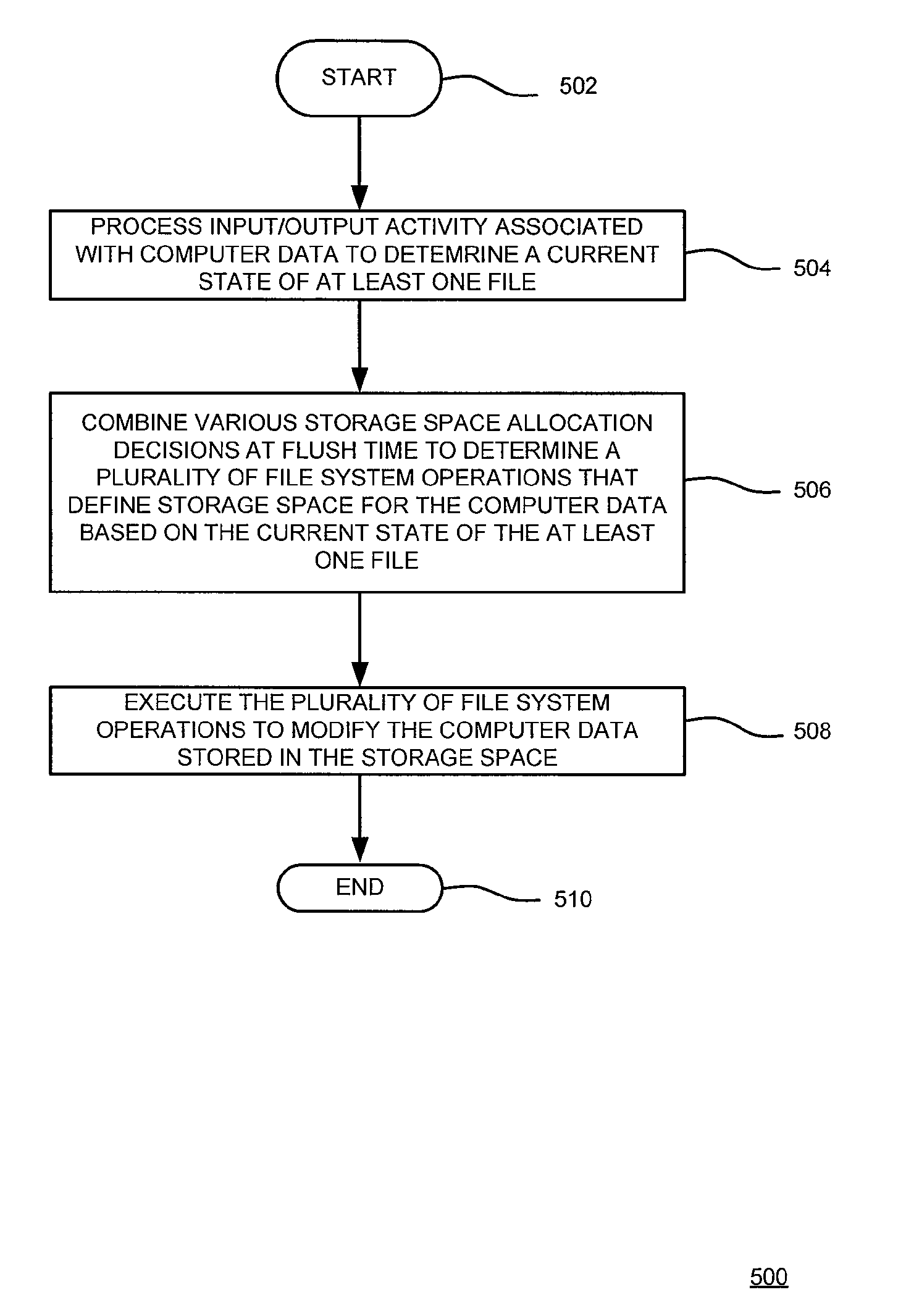
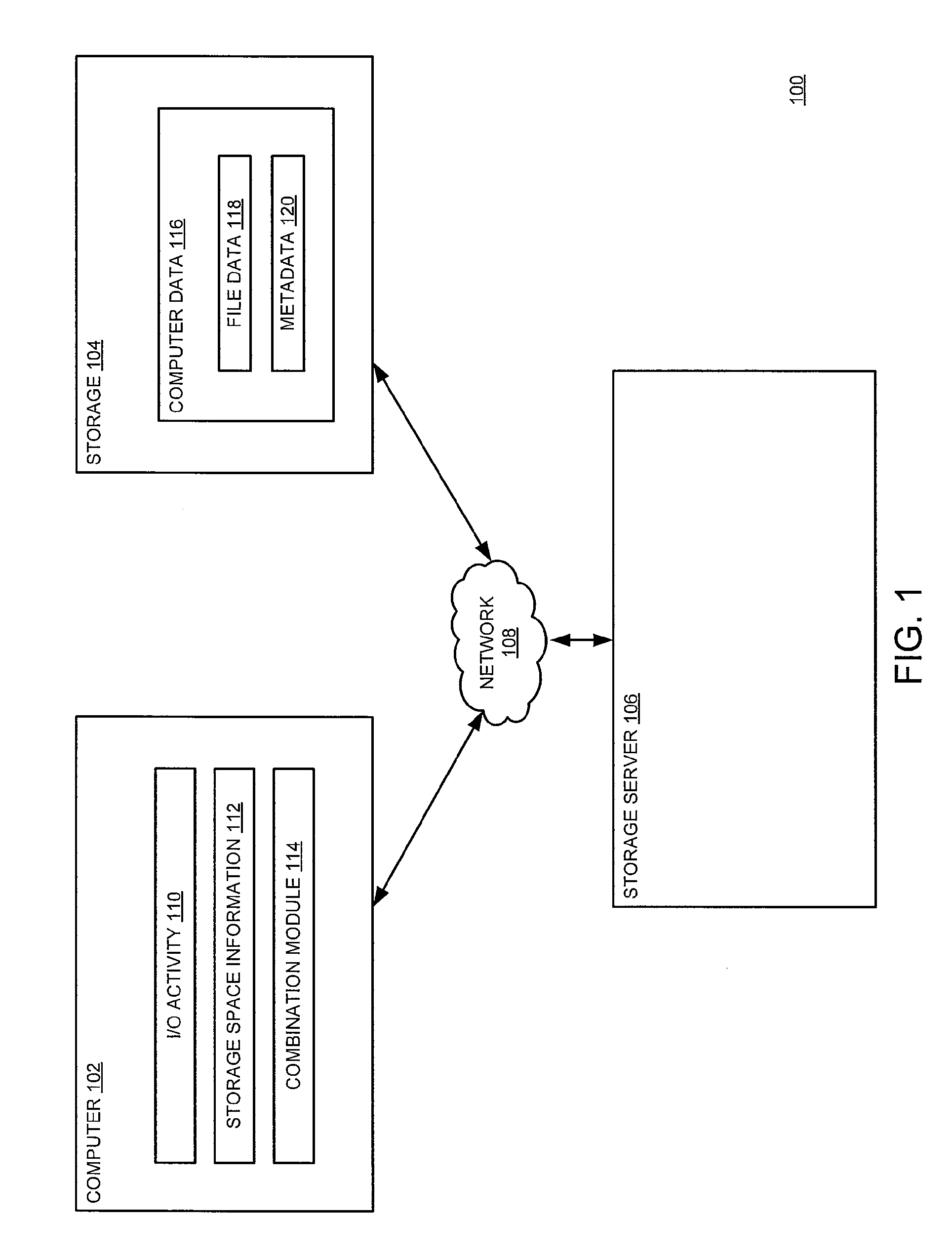
Method and apparatus for optimizing storage space allocation for computer data
ActiveUS8392479B1Optimize layoutFile system administrationSpecial data processing applicationsDistributed File SystemFile system
A method and apparatus for optimizing storage space allocations, using at least one processor, for computer data in distributed file systems is described. In one embodiment, the method includes processing input / output activity that is associated with computer data to determine a current state of at least one file in a distributed file system, at flush time, combining various storage space allocation decisions applied over at least one network protocol to determine a plurality of file system operations that define storage space, based on the current state of the at least one file, for the computer data and executing the plurality of file system operations on the computer data stored in the storage space.
Owner:VERITAS TECH
Backup information management
ActiveUS20060149793A1Error detection/correctionDigital data processing detailsComputer scienceInformation management
In one embodiment, a method for information management comprises monitoring output from an application, wherein the output is monitored substantially continuously; determining if the output is associated with a predetermined type of version; and saving data associated with the output if the output is associated with the predetermined type of version.
Owner:EMC IP HLDG CO LLC
System, method and computer program product for enabling access to a resource of a multi-tenant on-demand database service utilizing a token
ActiveUS8417723B1Avoid identificationUnwanted useWeb data indexingDigital data processing detailsDatabase servicesOn demand
In accordance with embodiments, there are provided mechanisms and methods for enabling access to a resource of a multi-tenant on-demand database service utilizing a token. These mechanisms and methods for enabling access to a resource of a multi-tenant on-demand database service utilizing a token can be utilized to prevent identification of a user attempting to access the resource, and thus unwanted use of the user's identity.
Owner:SALESFORCE COM INC
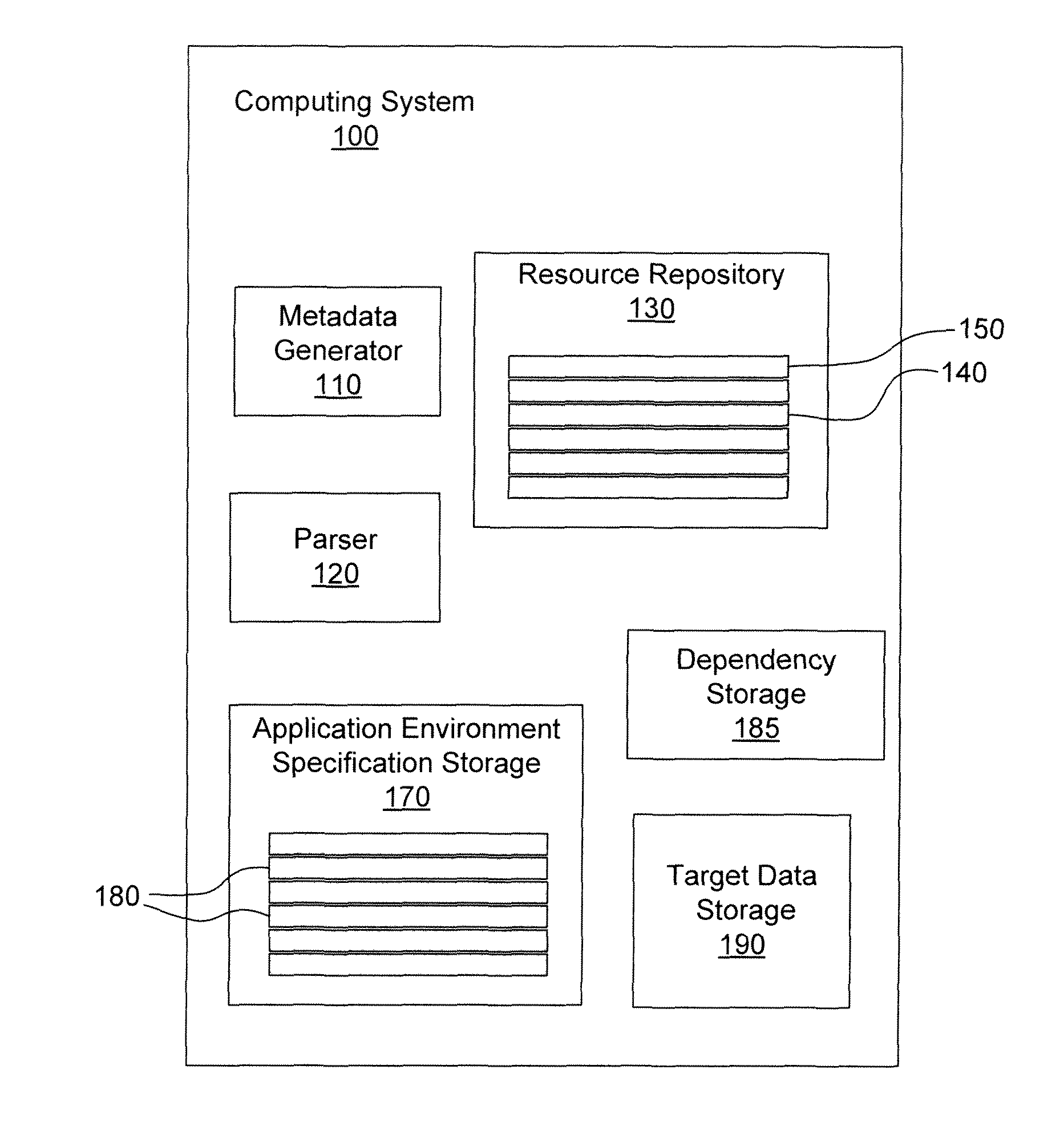
Repository including exclusion list
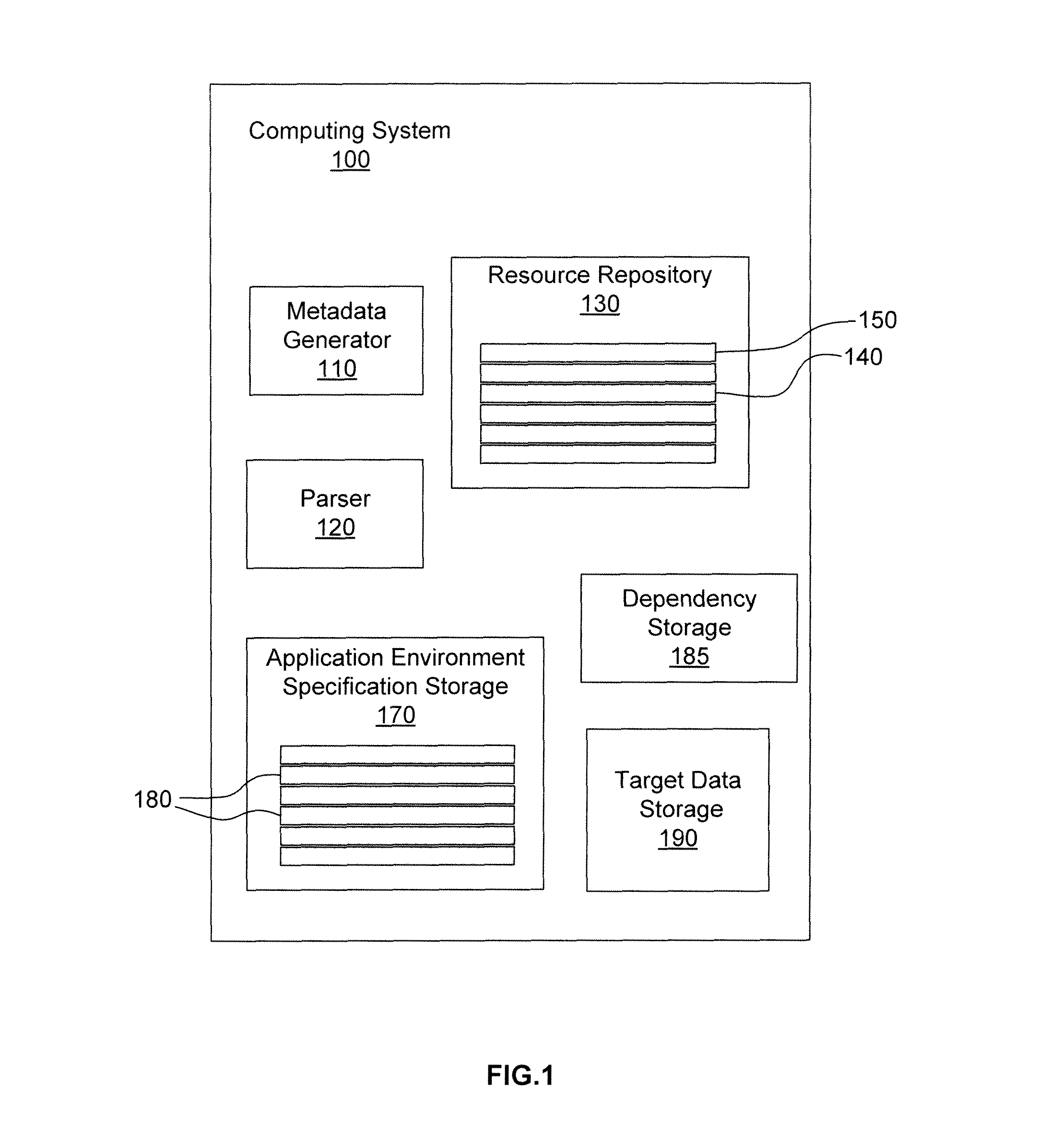
ActiveUS8577937B1File system administrationProgram loading/initiatingOperational systemApplication software
Systems and methods of executing and / or provisioning an application in an application specific runtime environment or general runtime environment are disclosed. The application specific runtime environment or general runtime environment are optionally defined by an application environment specification to include a minimal or reduced set of software resources required for execution of the application. These software resources are optionally stored in a resource repository that includes resources associated with a plurality of operating systems and / or executable applications. Various embodiments of the invention include the development of hierarchical resource metadata configured to characterize the various files, packages and file families included in the resource repository. In some embodiments this metadata is used to select between files when provisioning an application specific runtime environment. Various embodiments of the invention include use of an exclusion list to manage conflicts between same named files.
Owner:VMWARE INC
Virtual copy forward method and system for garbage collection in cloud computing networks
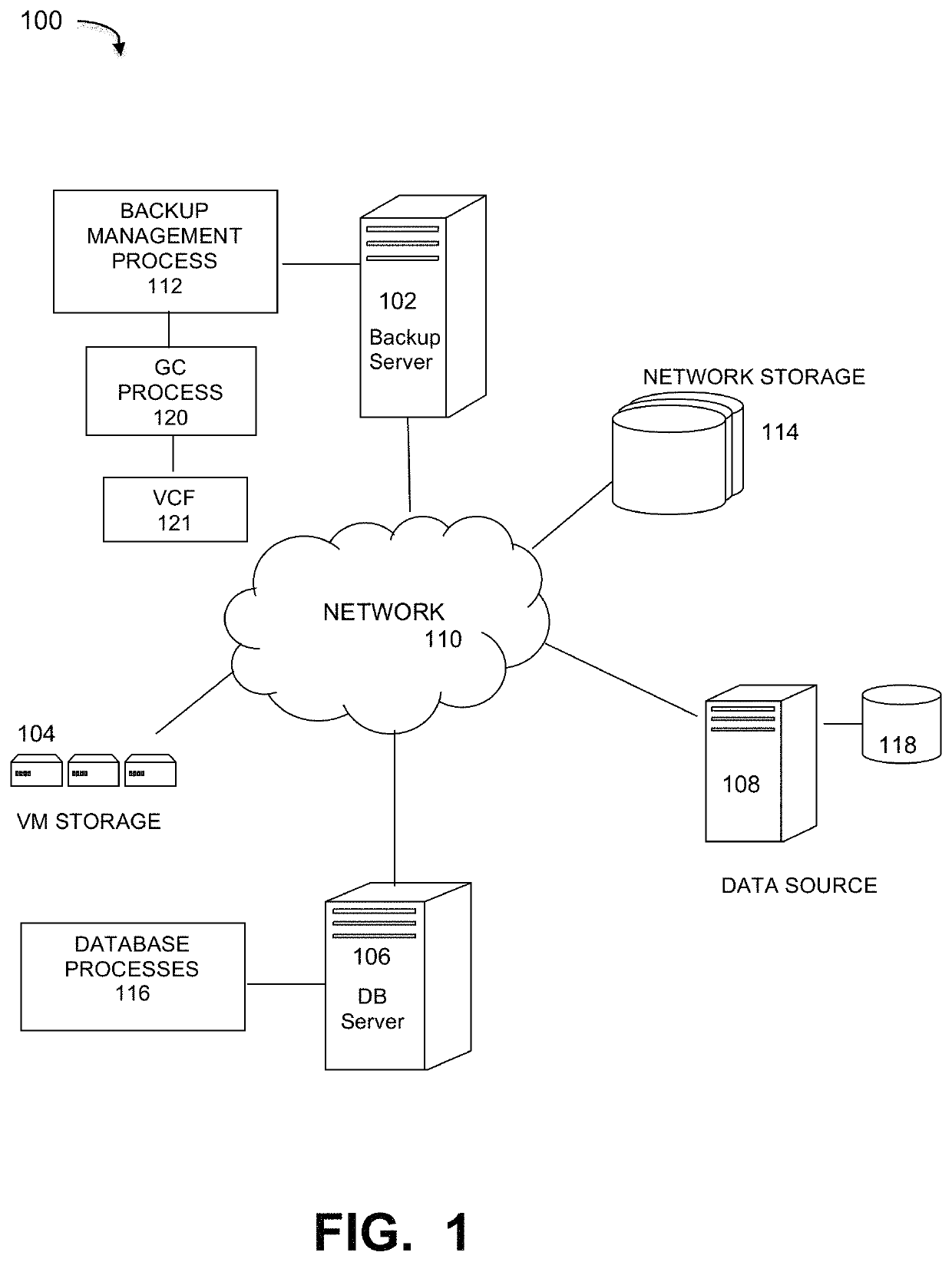
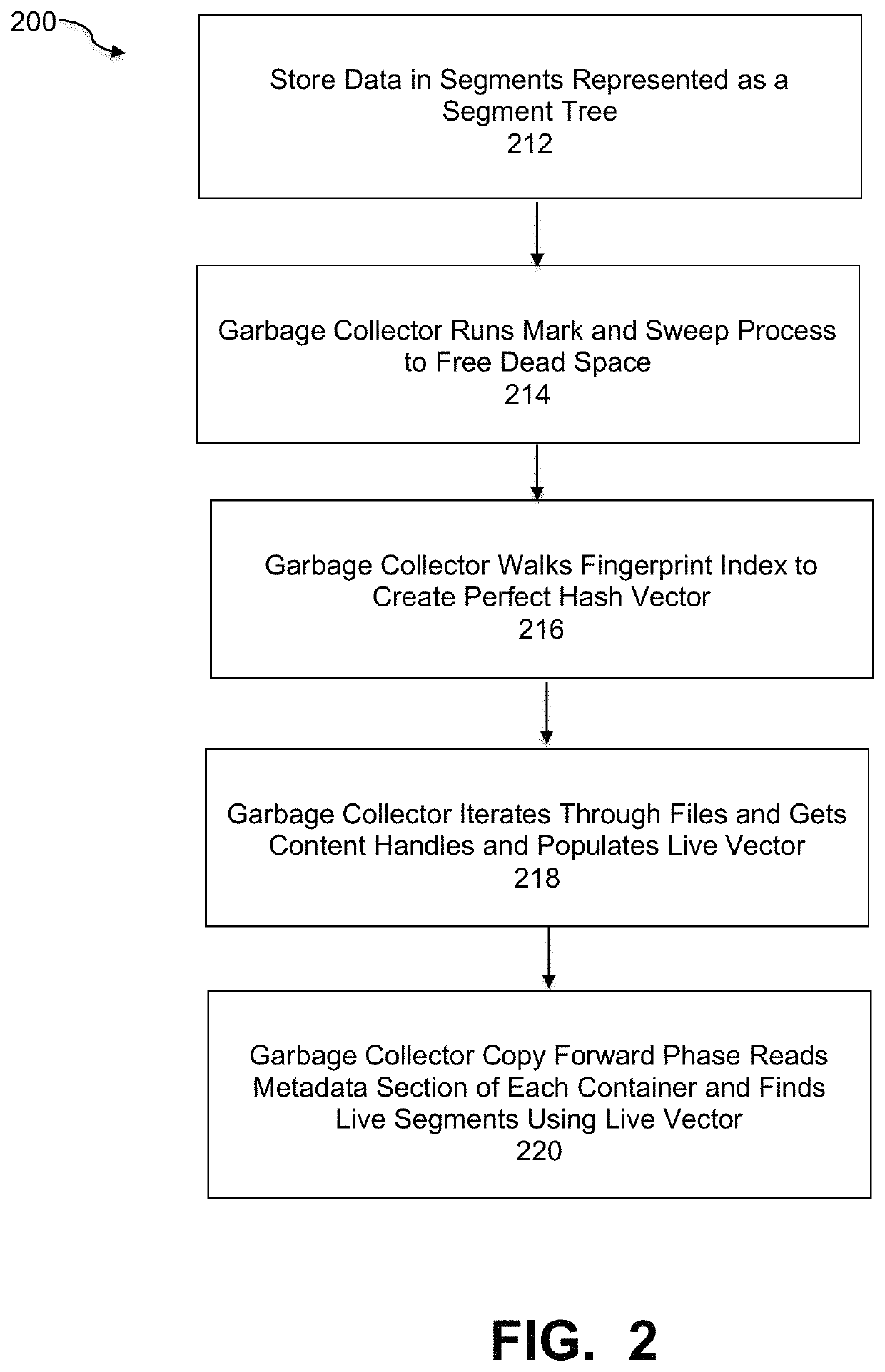
ActiveUS10795812B1Memory architecture accessing/allocationMemory adressing/allocation/relocationData packRefuse collection
A garbage collection (GC) process within a deduplication backup network comprising a GC component identifying metadata stored in file system (FS) segments, storing the metadata in a metadata container locally on the server as well as on cloud storage, and reading the locally stored metadata container through the GC process to obtain metadata of the FS containers and determine live data regions of the FS containers, wherein the metadata contains fingerprints of all segments of the file system containers; and a copy forward component forwarding the live data regions to new containers written both locally on the server and on the cloud storage, writing live portions of the metadata container to a new metadata container written both locally on the server and on the cloud storage, and deleting dead compression regions from the cloud storage and deleting the original metadata container from local storage and the cloud storage.
Owner:EMC IP HLDG CO LLC
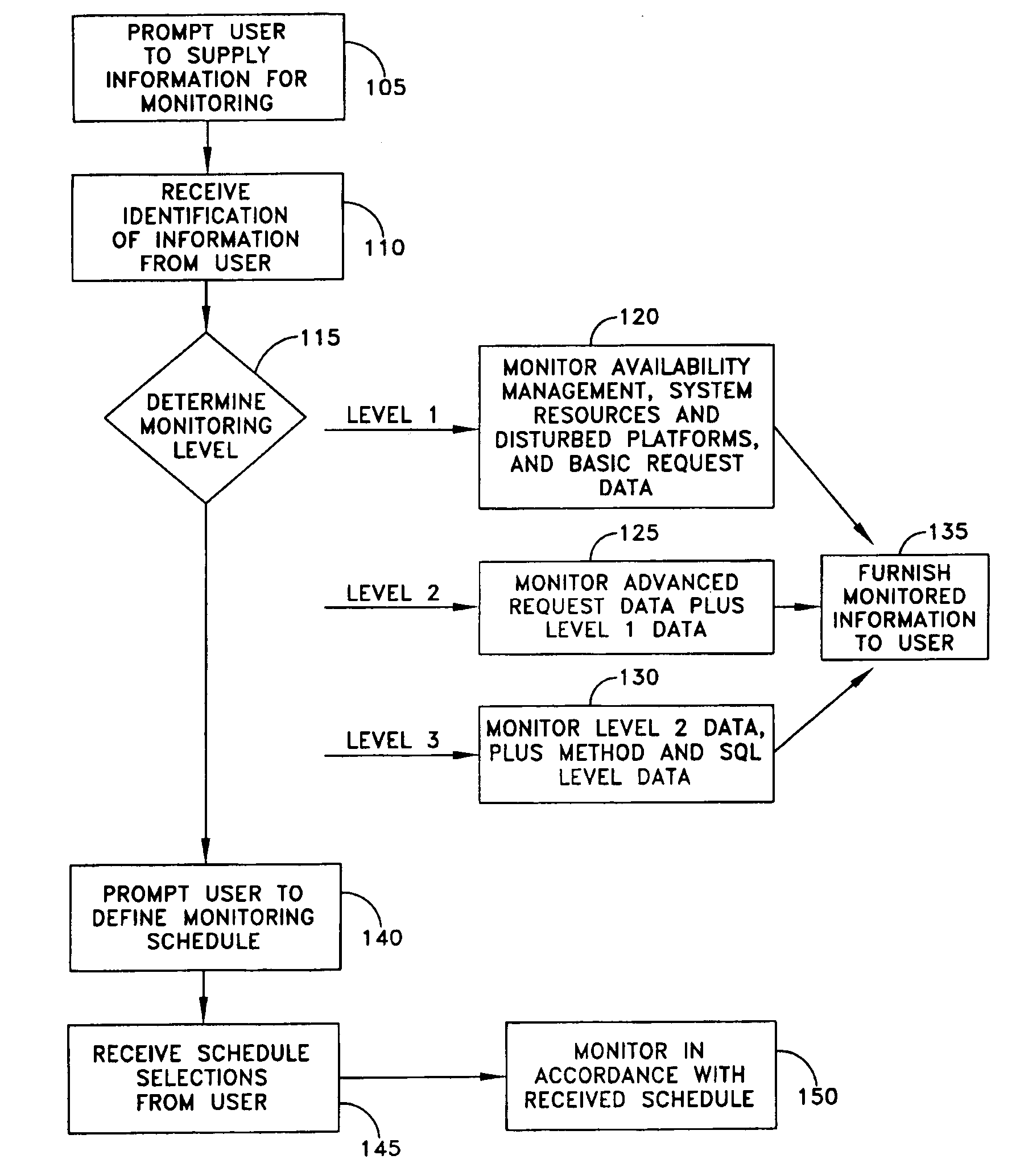
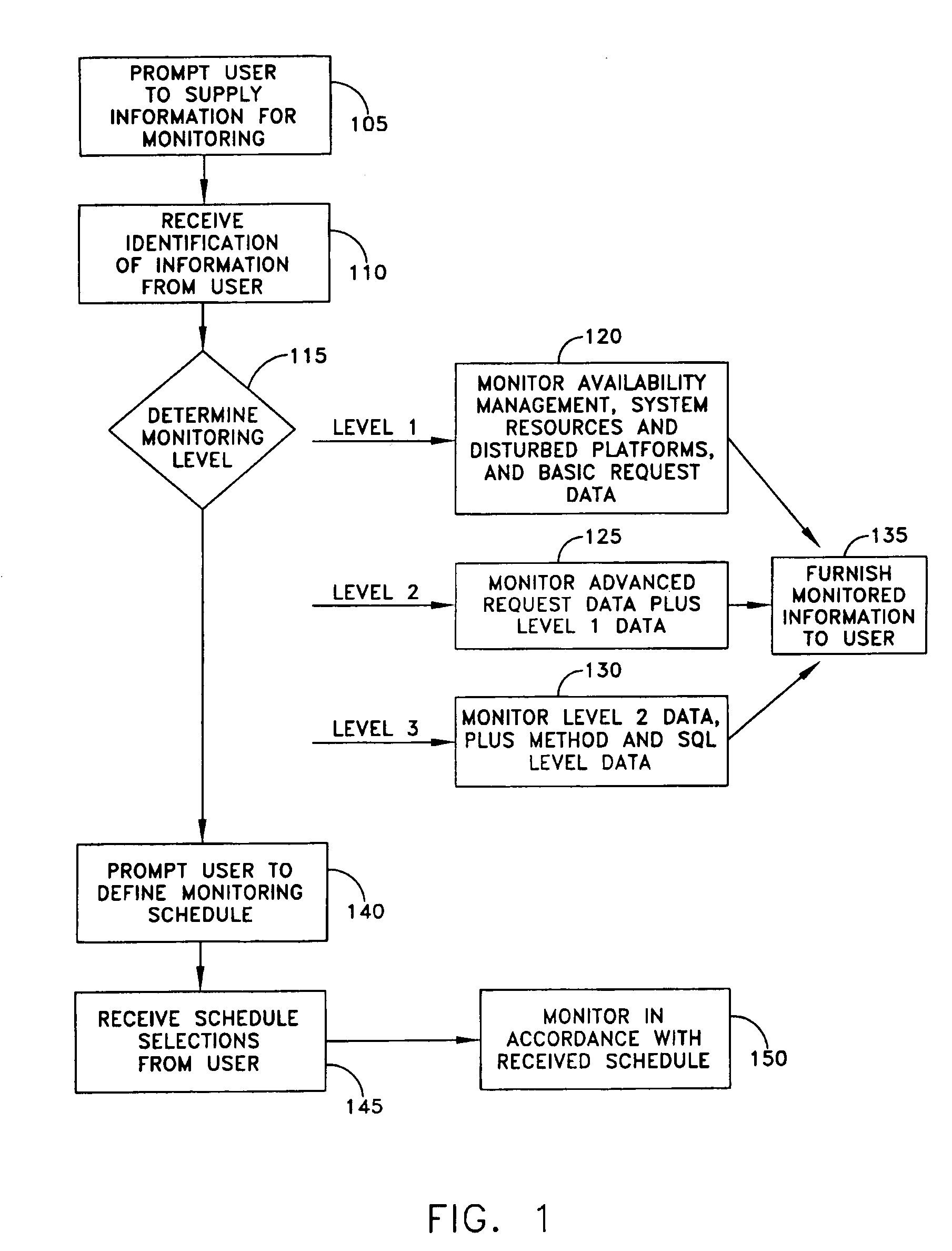
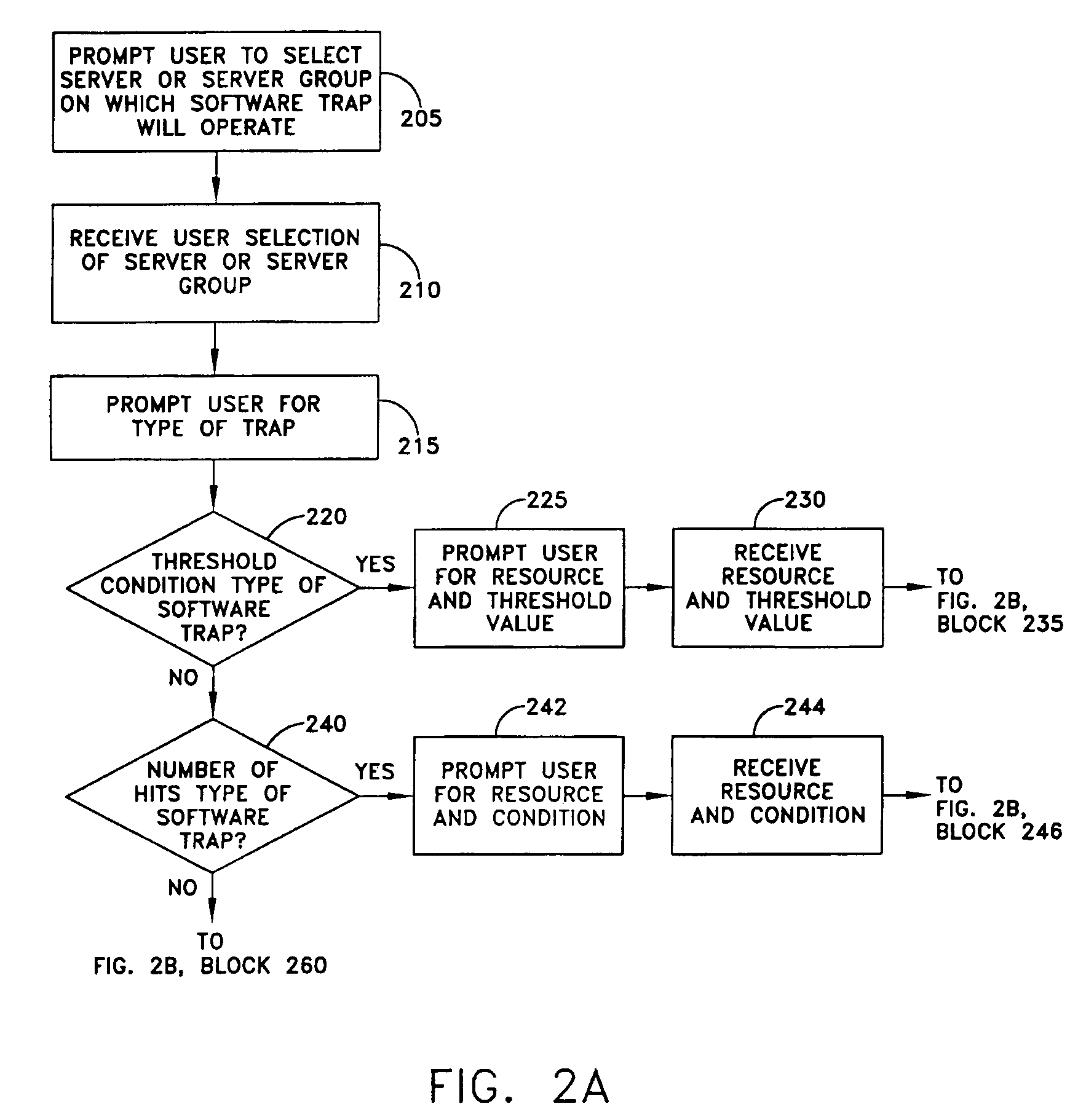
Monitoring performance of applications in a distributed environment
A method for management of performance of computer systems and applications includes prompting the user to select information for monitoring, monitoring the performance of applications running on servers, displaying data, and prompting users to input performance adjustments. A user is prompted to select a server or server group, a resource, and a threshold or condition for notification, and in response a system compares the value or quality of the parameter to the threshold or condition, and provides a notification to the user in the event that the parameter reaches the threshold or condition. A method includes the steps of providing the user with performance information, receiving from the user a request for more specific performance information, and providing more detailed performance information. A method according to the invention includes the steps of receiving from the user an identification of a server as an authoritative server, another server as a comparison server, comparing runtime environment data in the form of one or more of CPU data, server data and Java data between the selected servers, and displaying differences to a user. A method of the invention includes the steps of receiving from the user an identification of a server as an authoritative server, and another server as a comparison server, and providing a list of matching and differing file names. The method may further include the step of receiving from the user a selection of a file, conducting a comparison of the files, and providing a result to the user. A method of the invention includes the steps of assigning a role to each user, and mapping between access to functions and each user role by an access control list, whereby access to functions is limited depending on the assigned role of the user.
Owner:INT BUSINESS MASCH CORP
Mechanism and apparatus for transparently enables multi-tenant file access operation
InactiveUS20110270886A1Enhanced middlewareDigital data processing detailsComputer security arrangementsOperational systemFile system
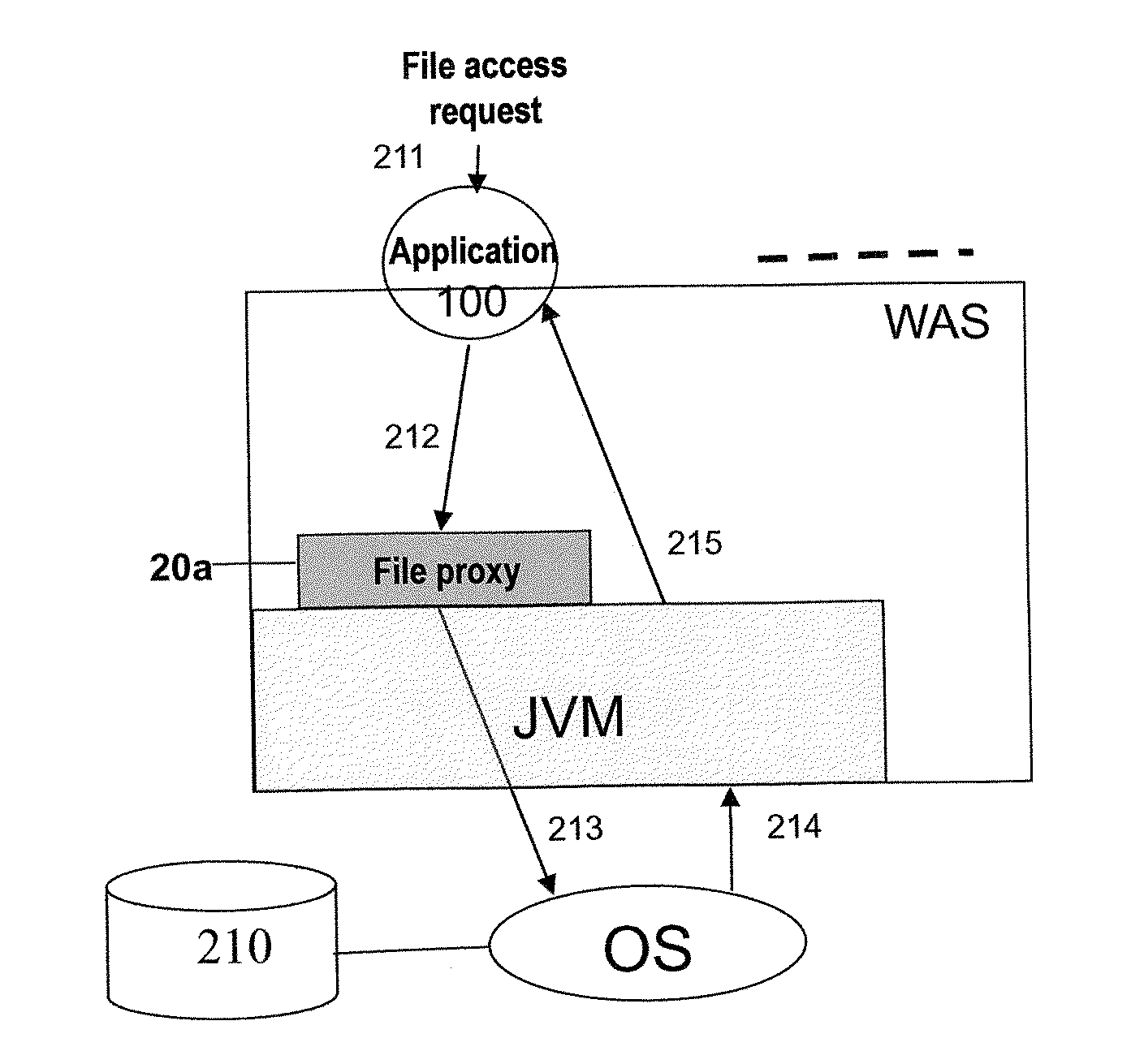
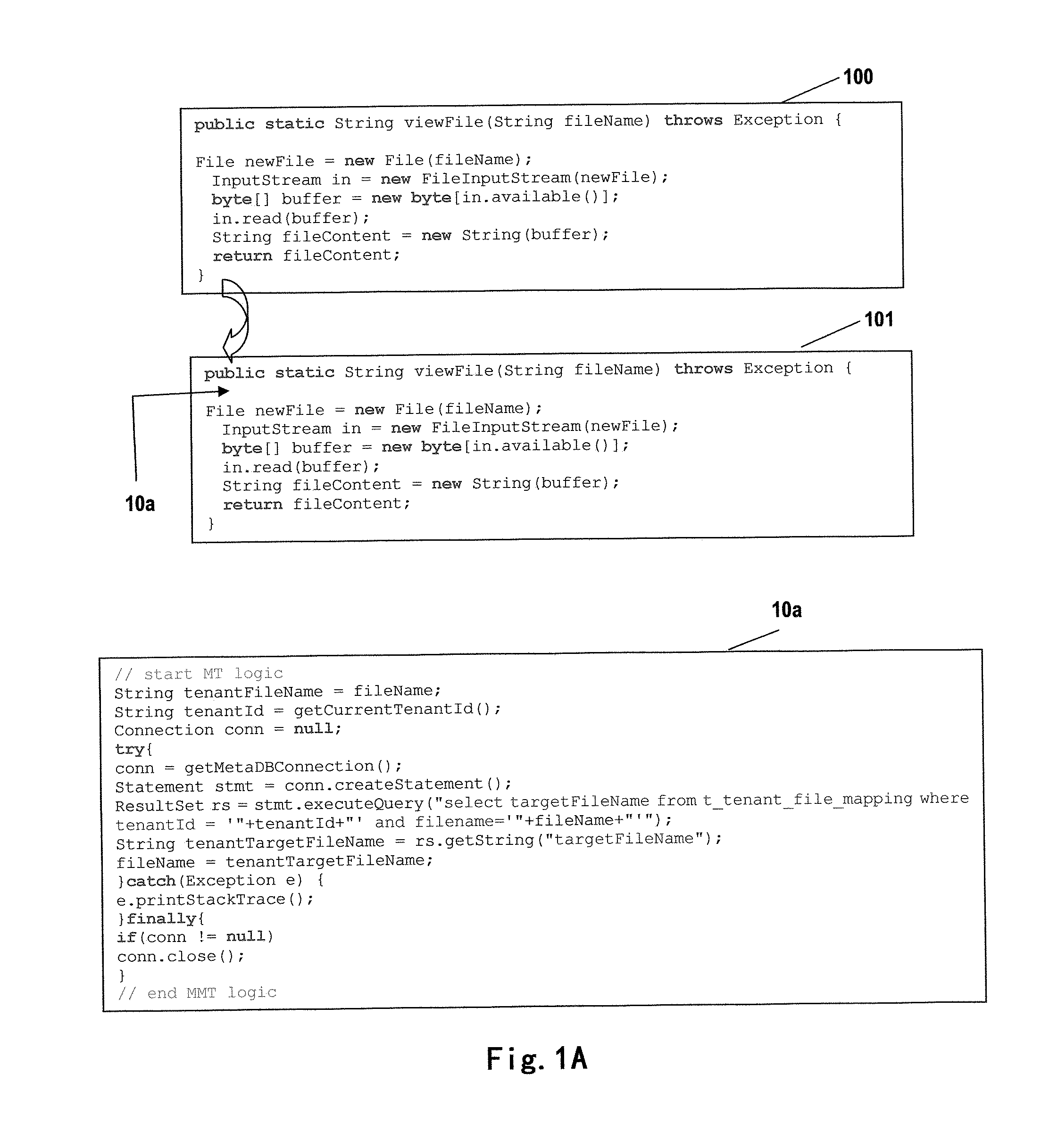
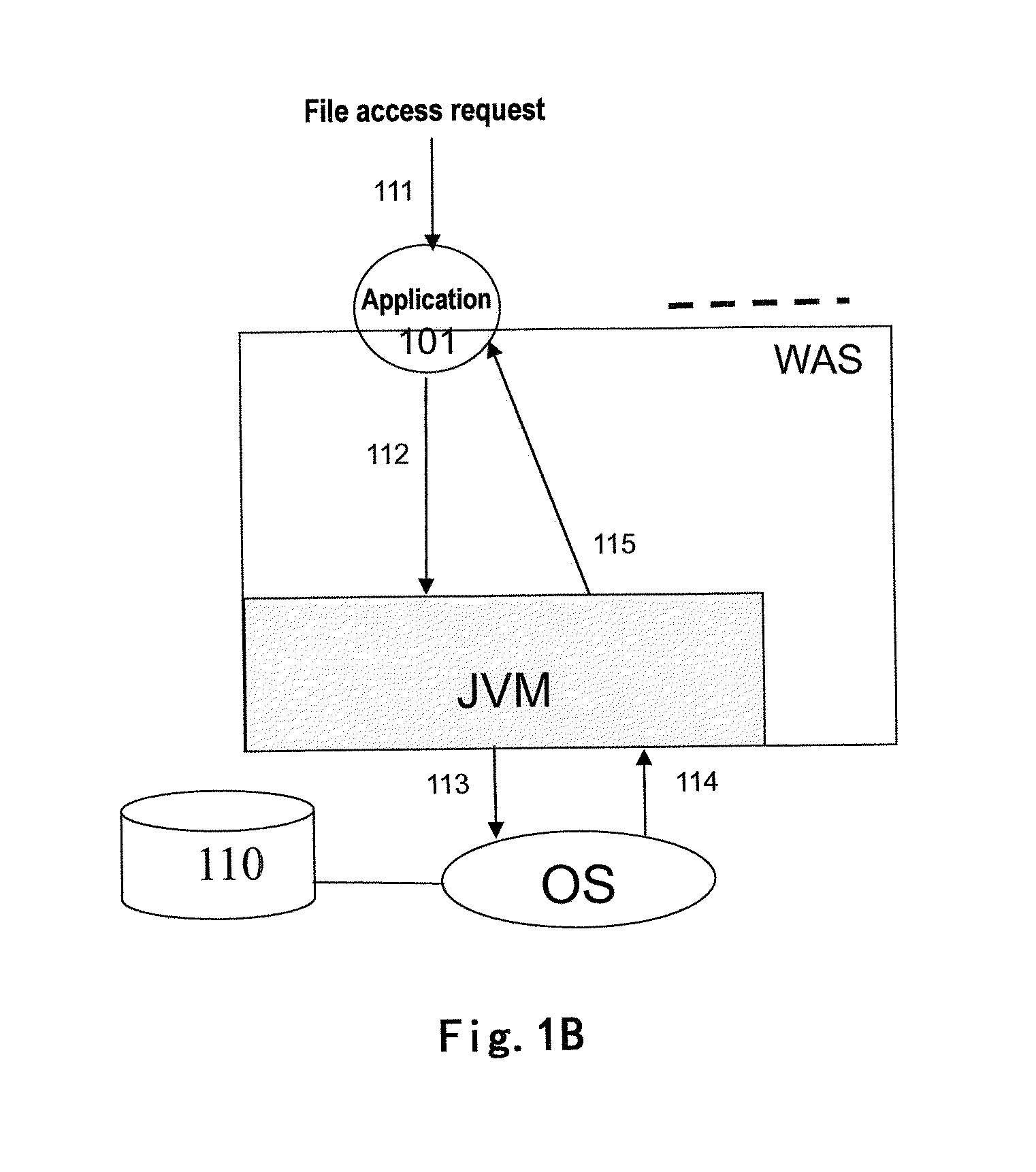
The present invention relates to a multi-tenant technology. The disclosure provides a method for processing a file access request to a multi-tenant application by using a file proxy and a corresponding file proxy apparatus, the method comprising: intercepting a file access request; converting the file access request based on a predetermined file isolation model; and transmitting the converted file access request to an operating system. By using this invention, the necessity of modifying a source code of an application so as to enabling a single-tenant application to support an operation in the multi-tenant model may be reduced. The present invention further provides a multi-tenant file system adapted for a multi-tenant application. In cooperation with the multi-tenant system, the method and file proxy apparatus according to the present invention may provide transparent support to fulfill security isolation and access control of tenant files with different SLAs.
Owner:IBM CORP
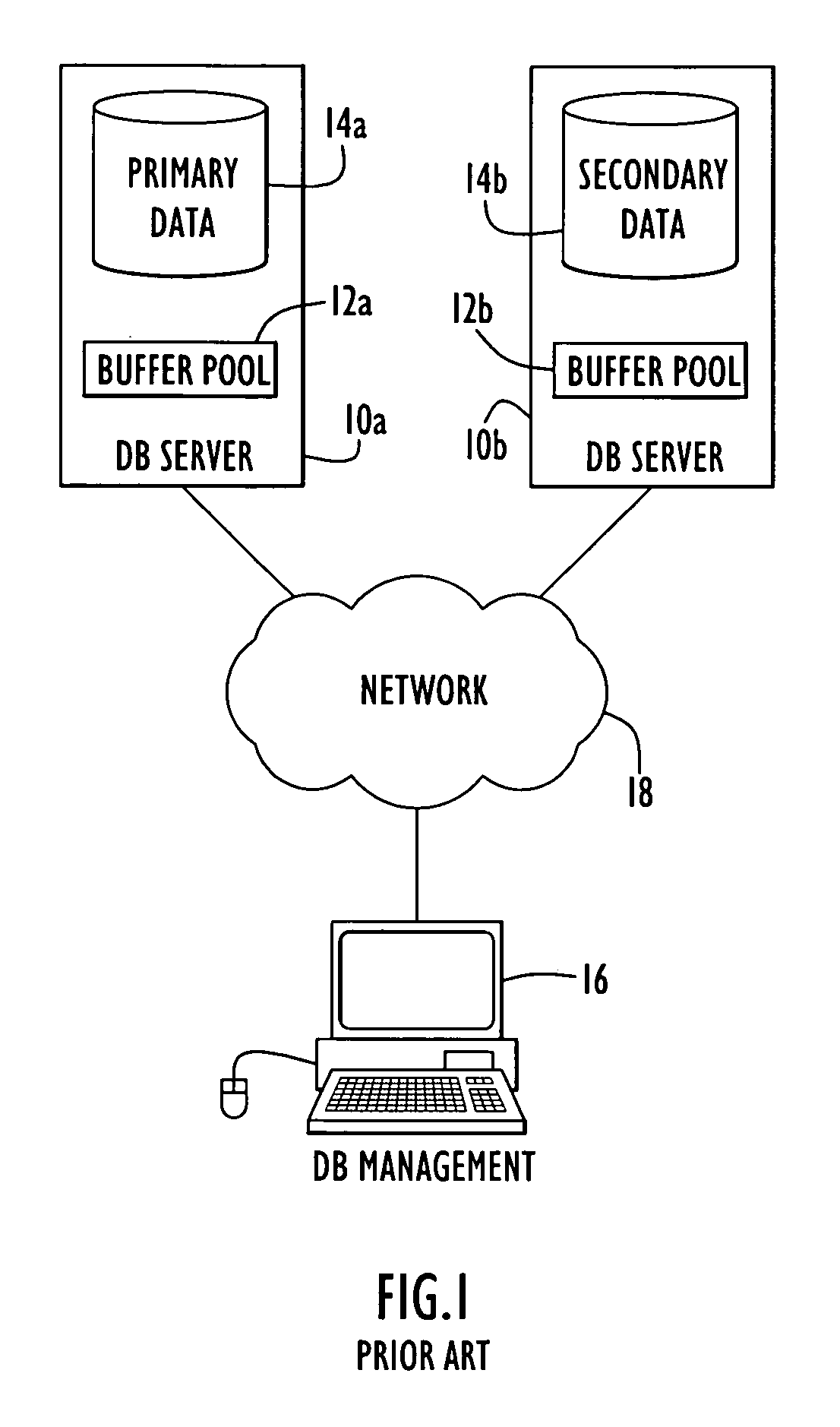
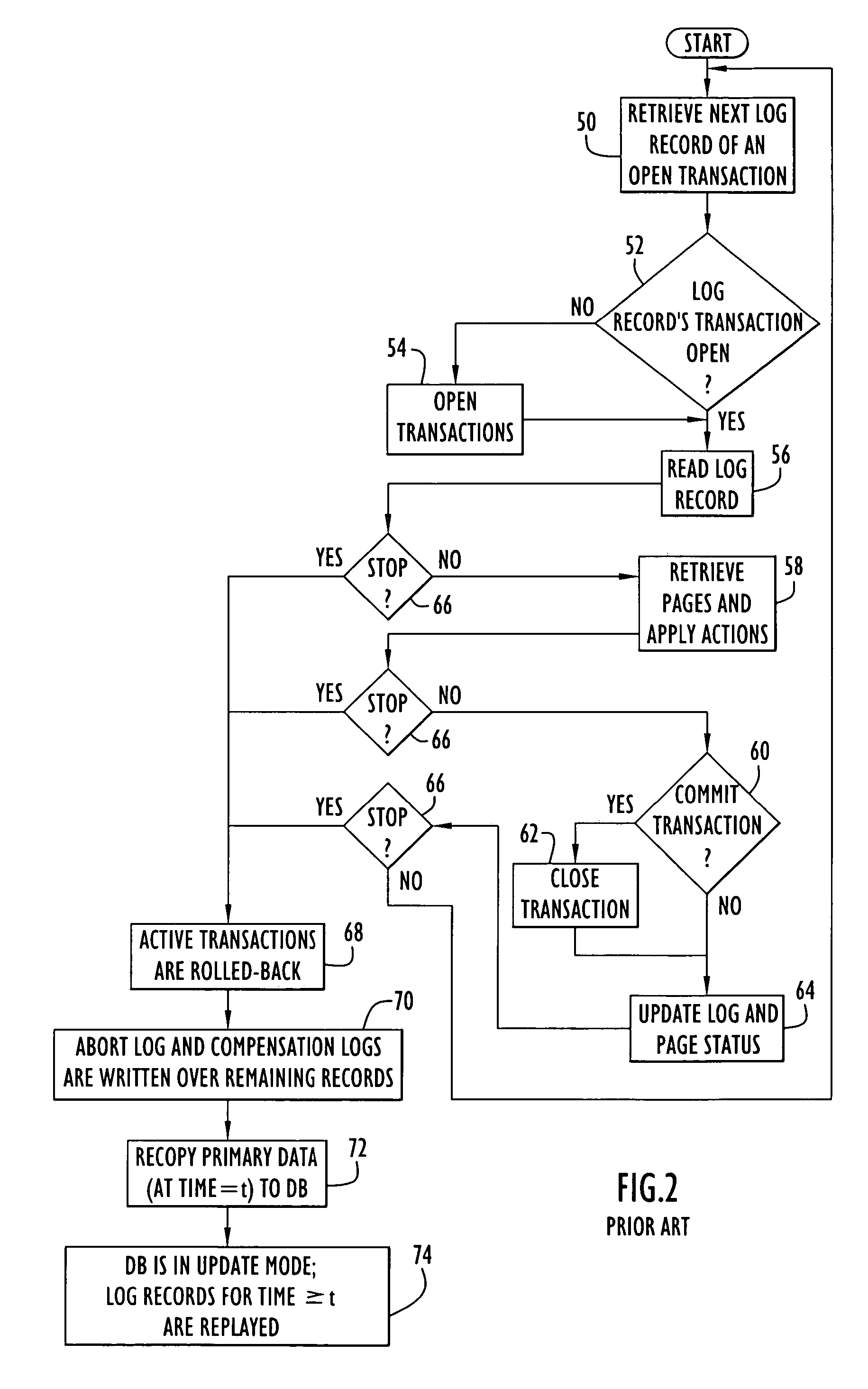
Method and apparatus for interrupting updates to a database to provide read-only access
ActiveUS7107294B2Data processing applicationsFile system administrationDatabase accessBack procedures
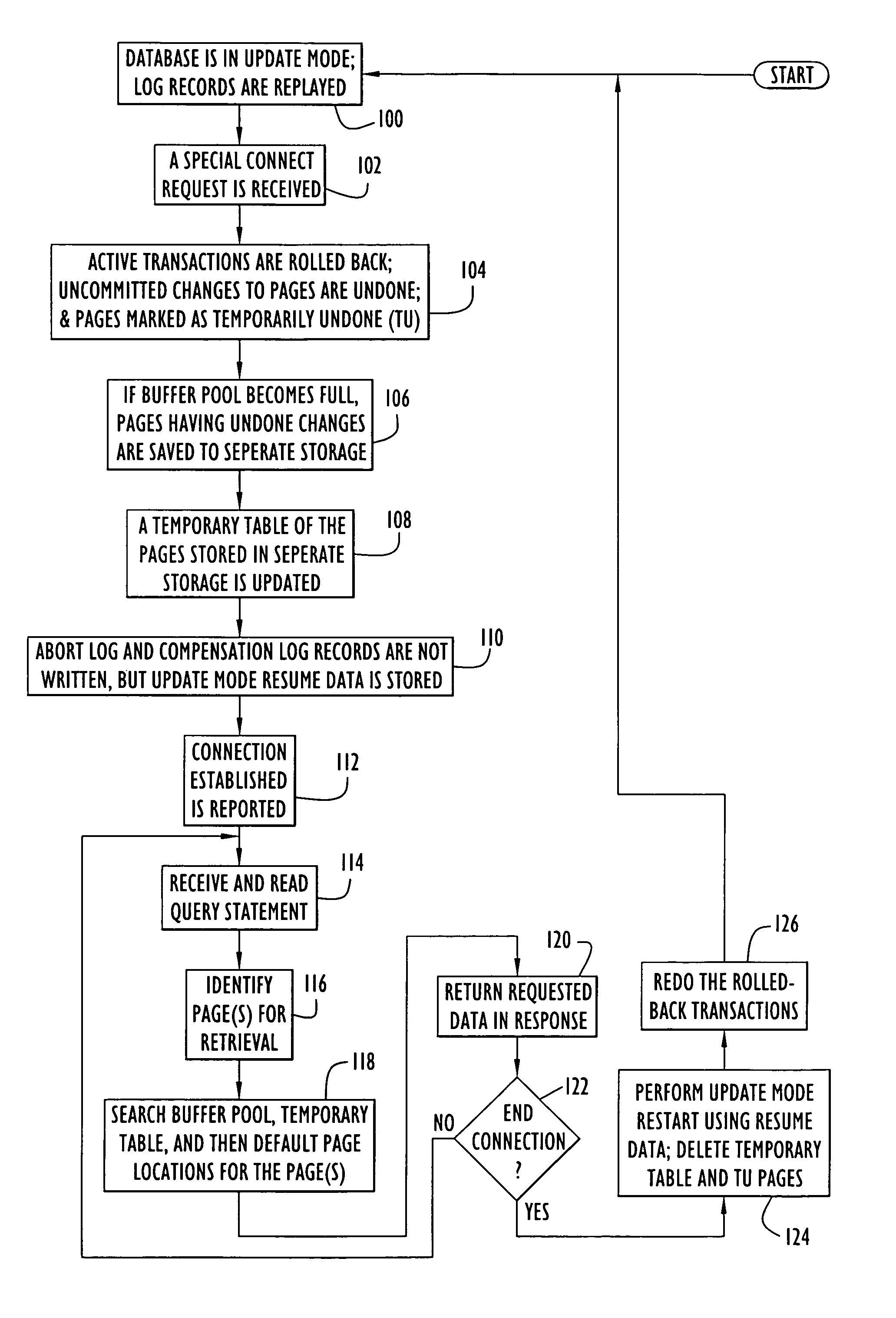
A method and system for suspending log-based updates to a database in a manner that permits resumption of log-based updating without reinitializing the database. The method and system thereby permit efficient alternation between a log-based update mode and a database access mode. Unplayed log records are protected as revisions of database pages at the time that the log-based update was suspended. This approach permits log-based updating to resume at the same point at which log-based updating was suspended. In order to ensure consistent data for access while in database access mode, a roll-back procedure creates consistent data pages that are used for access and discarded when log-based update resumes.
Owner:IBM CORP
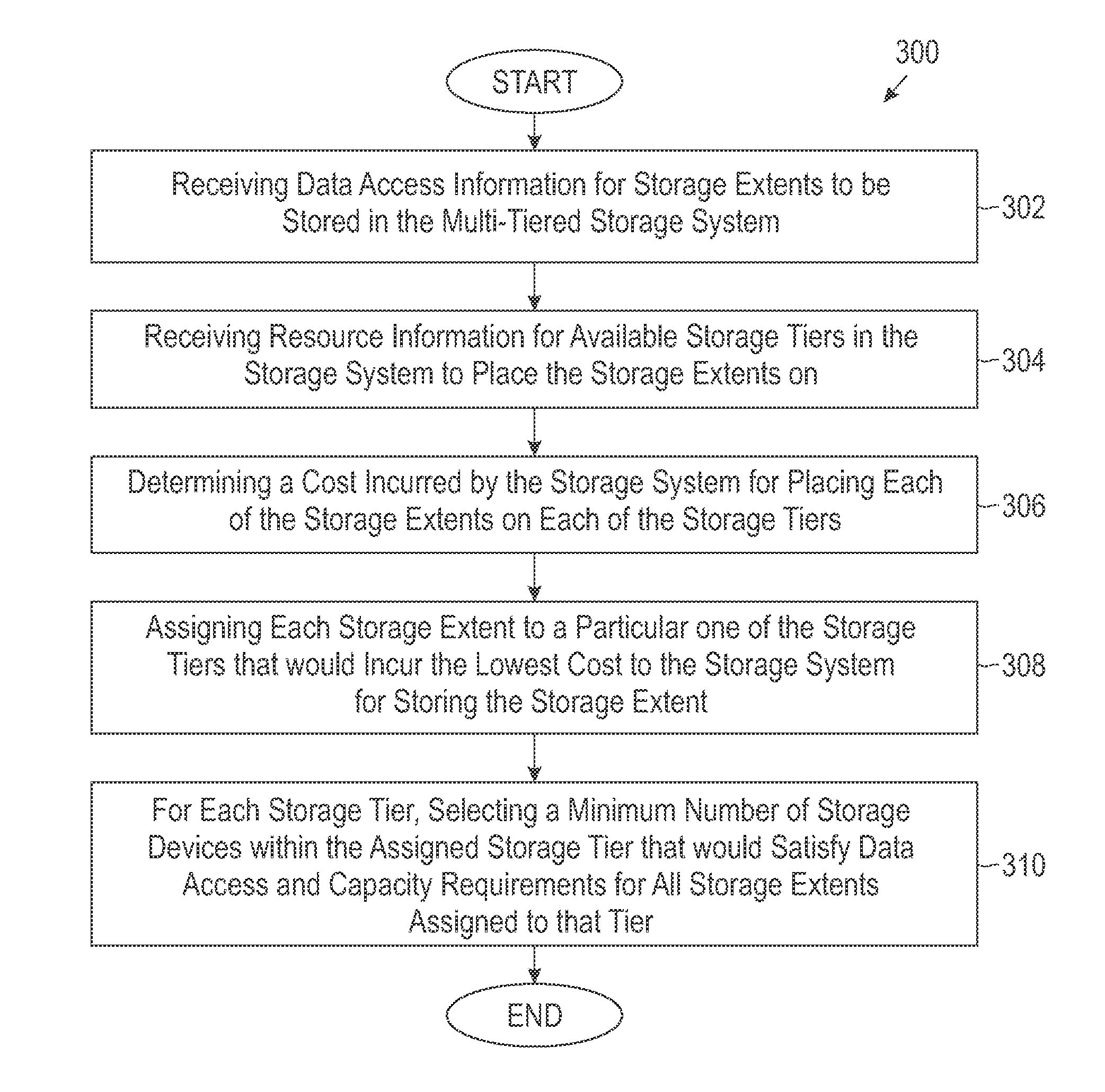
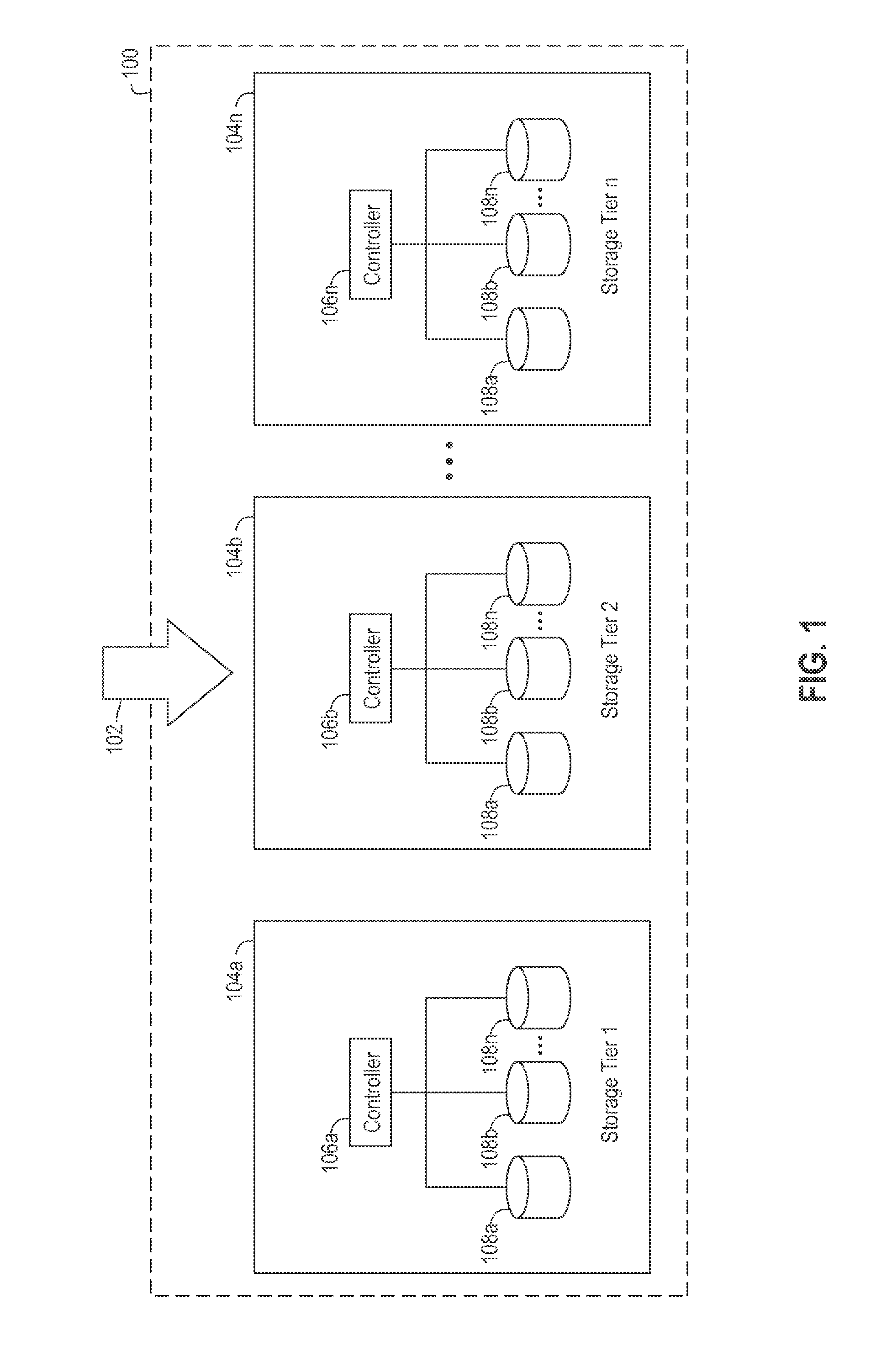
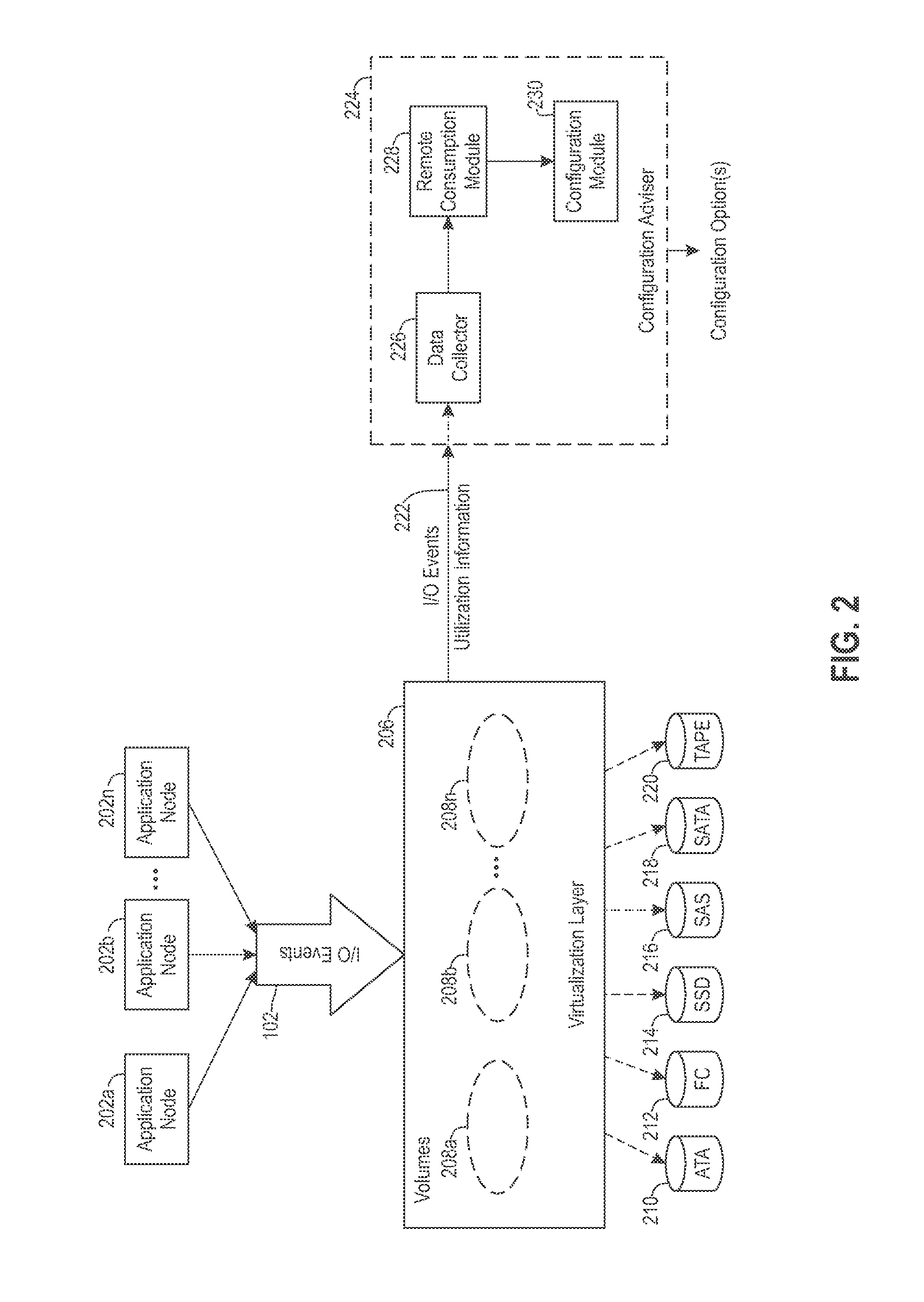
Multi-tier storage system configuration adviser
ActiveUS8706962B2Memory adressing/allocation/relocationFile system administrationResource informationData access
In one embodiment, a configuration adviser provides configuration options for a multi-tiered storage system that includes a number of different storage tiers, each of which include storage devices of a particular storage type. Data access information for storage extents to be stored in the storage system are received. Resource information for available storage tiers in the storage system to place the storage extents on are also received. A cost incurred by the storage system for placing each of the storage extents on each of the storage tiers is determined. Each storage extent is assigned to a particular one of the storage tiers that would incur the lowest cost to the storage system for storing the storage extent. For each storage tier, a minimum number of storage devices are selected, within the assigned storage tier, that would satisfy data access and capacity requirements for all storage extents assigned to that tier.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com