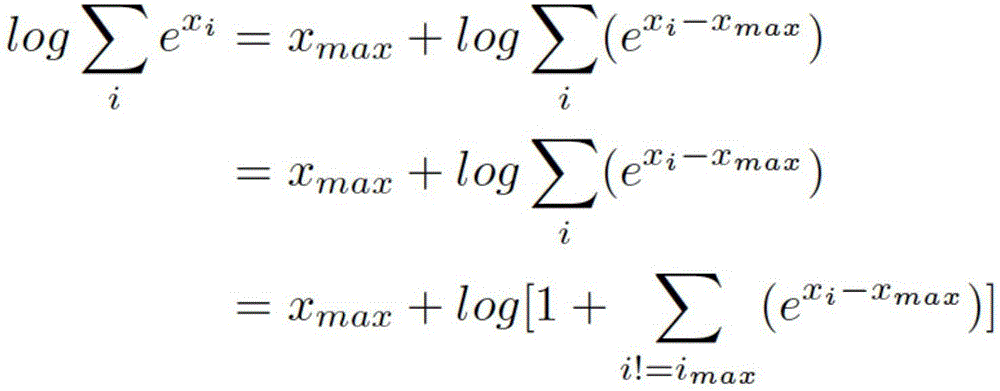Patents
Literature
39880 results about "Big data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
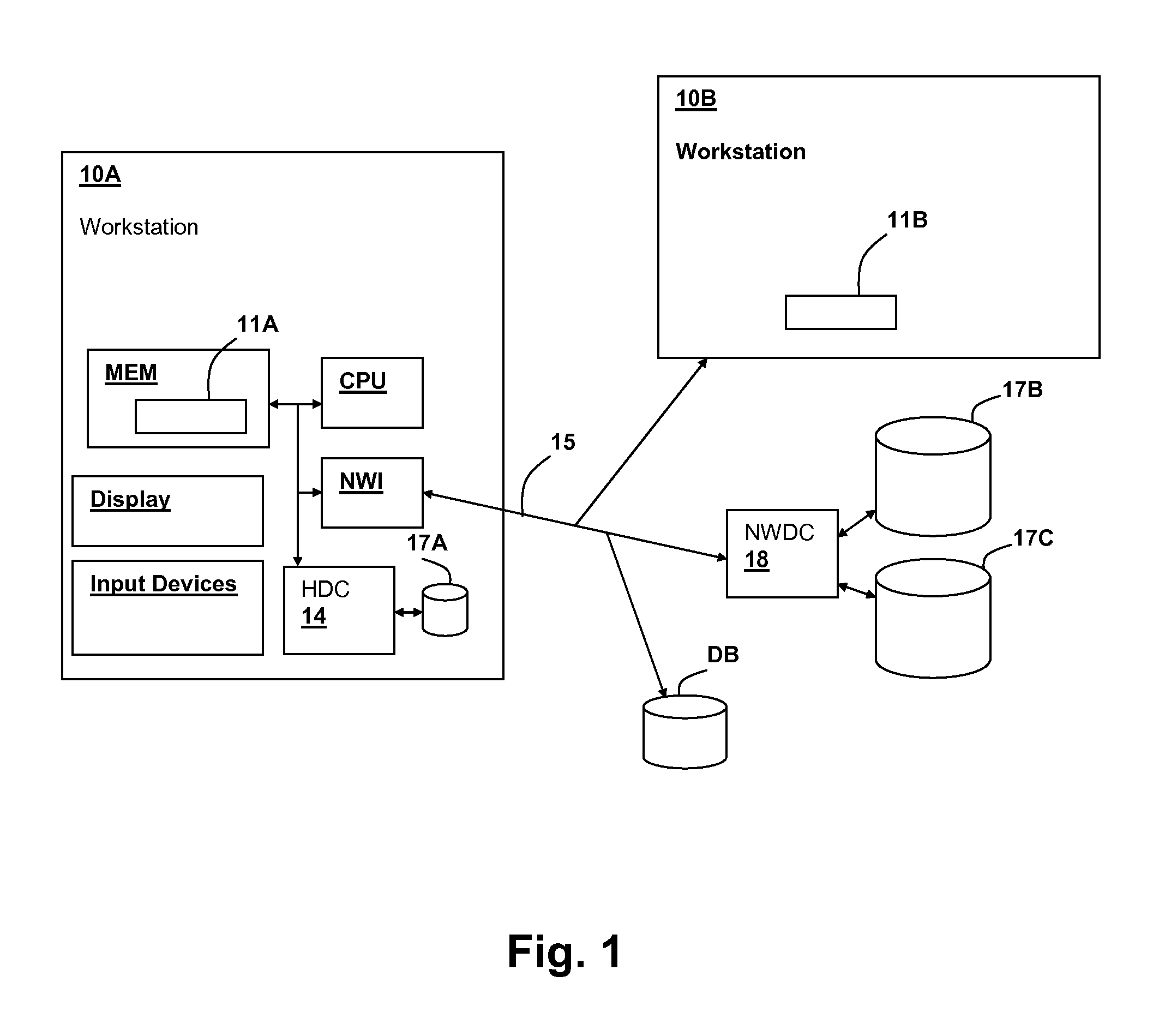
"Big data" is a field that treats ways to analyze, systematically extract information from, or otherwise deal with data sets that are too large or complex to be dealt with by traditional data-processing application software. Data with many cases (rows) offer greater statistical power, while data with higher complexity (more attributes or columns) may lead to a higher false discovery rate. Big data challenges include capturing data, data storage, data analysis, search, sharing, transfer, visualization, querying, updating, information privacy and data source. Big data was originally associated with three key concepts: volume, variety, and velocity. When we handle big data, we may not sample but simply observe and track what happens. Therefore, big data often includes data with sizes that exceed the capacity of traditional usual software to process within an acceptable time and value.
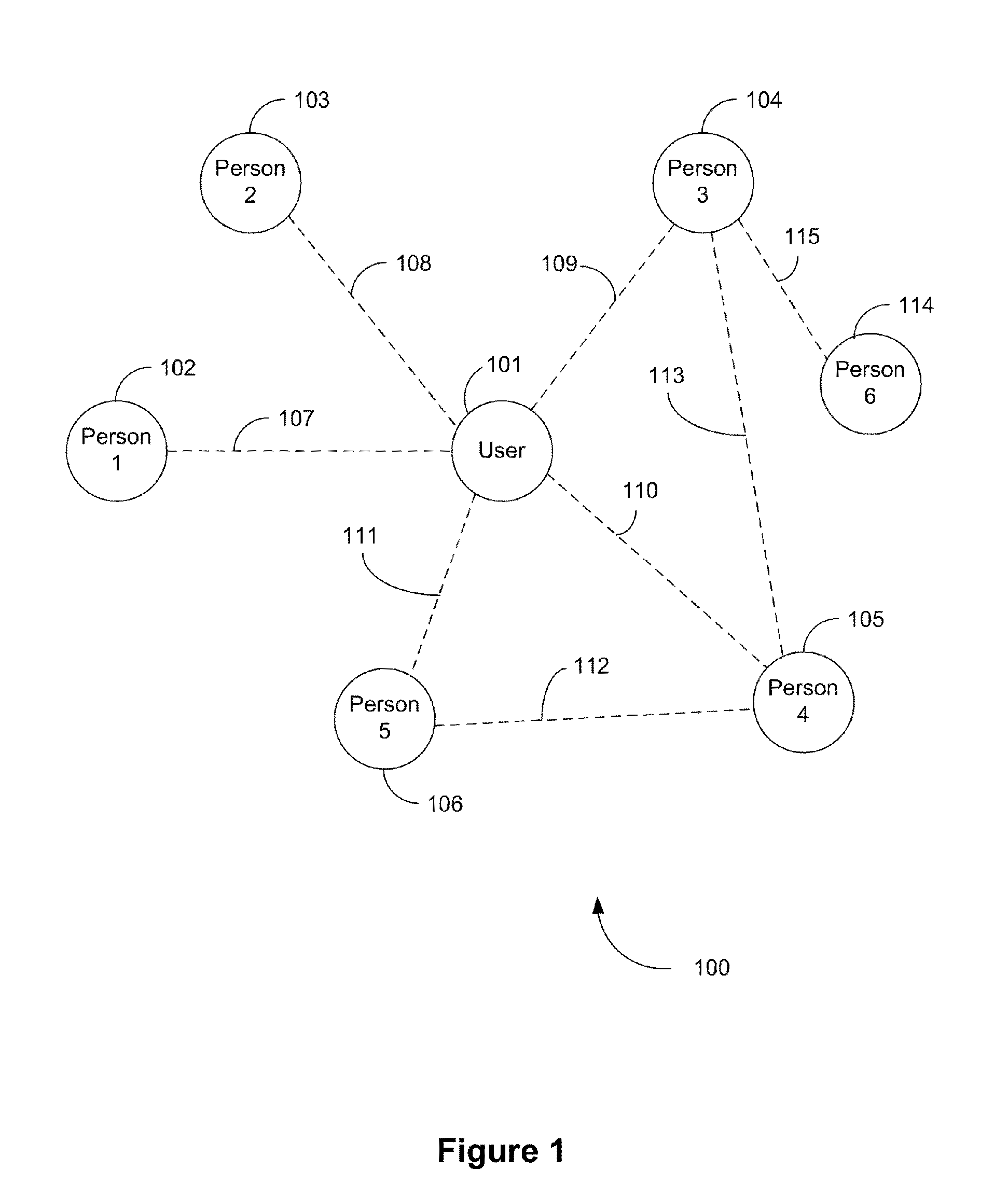
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
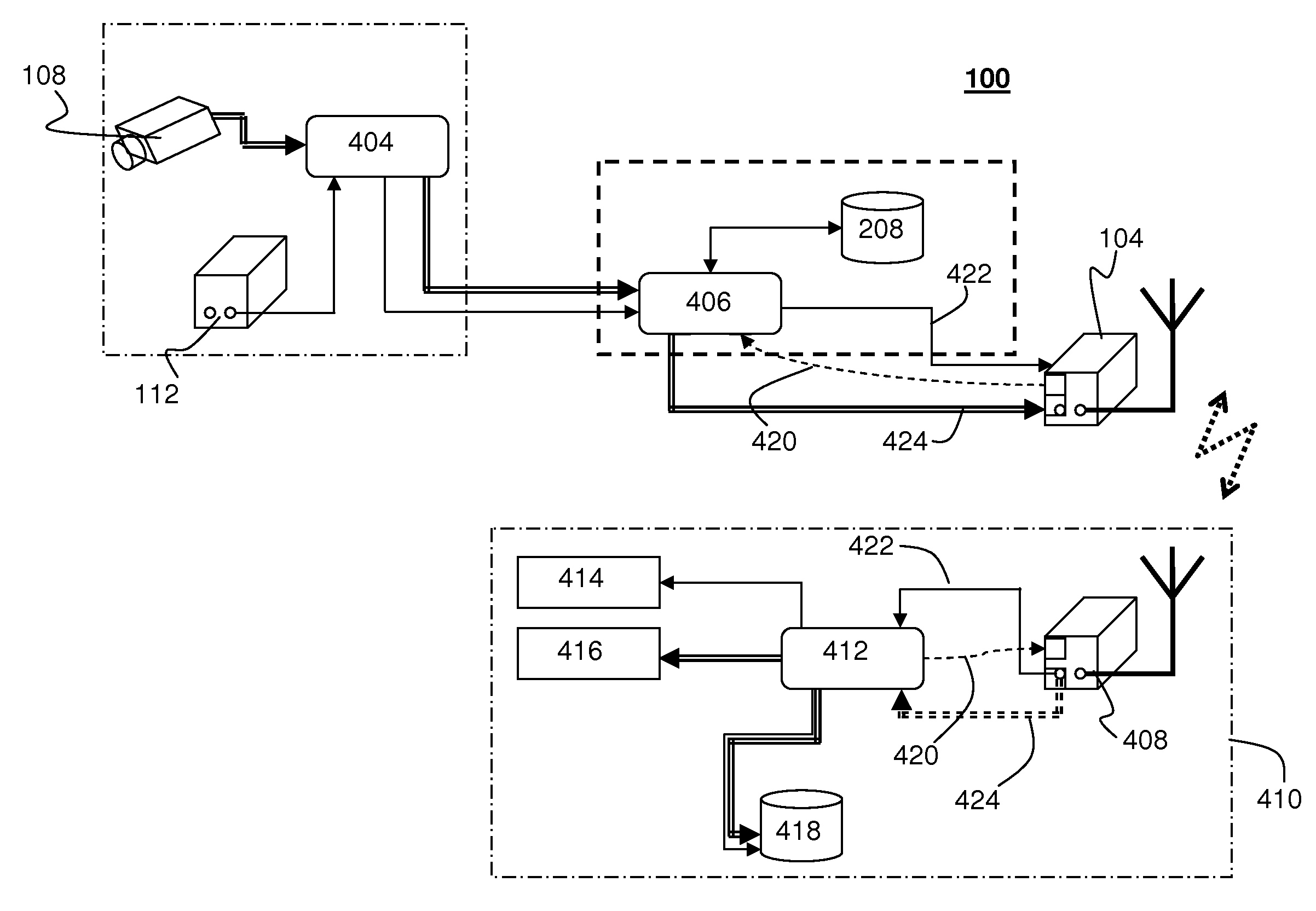
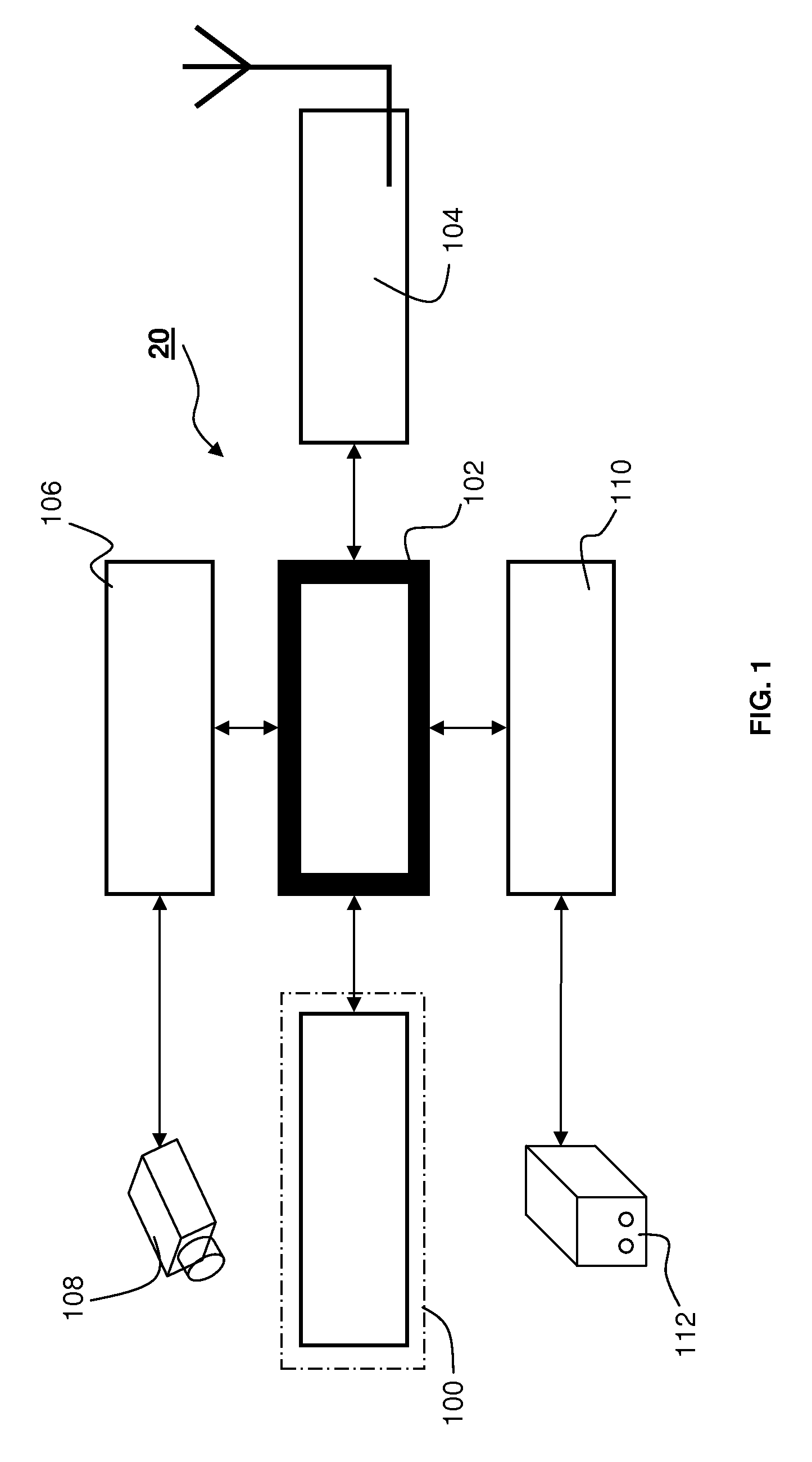
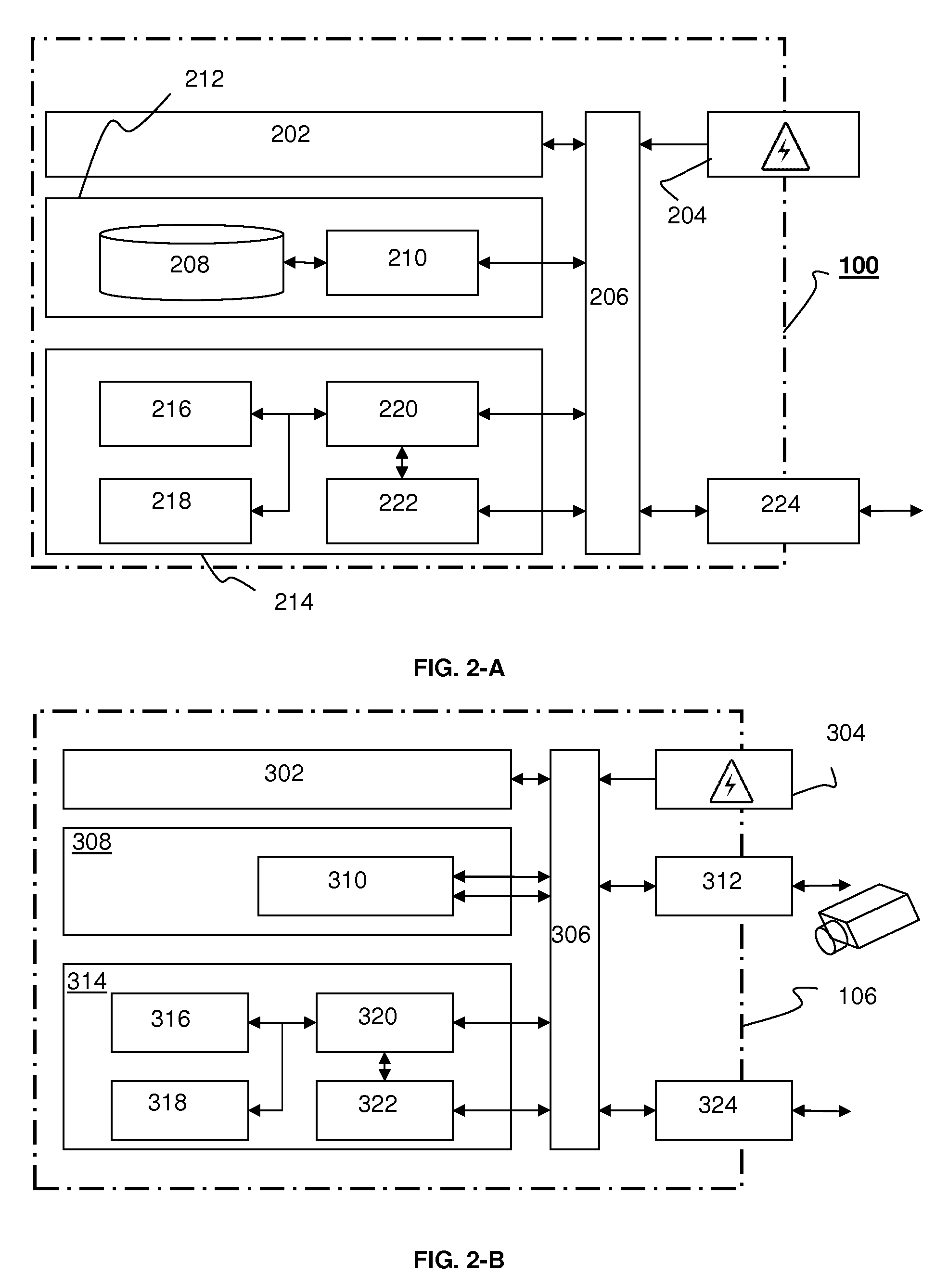
InactiveUS20130268357A1Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsOperational systemMessage delivery
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
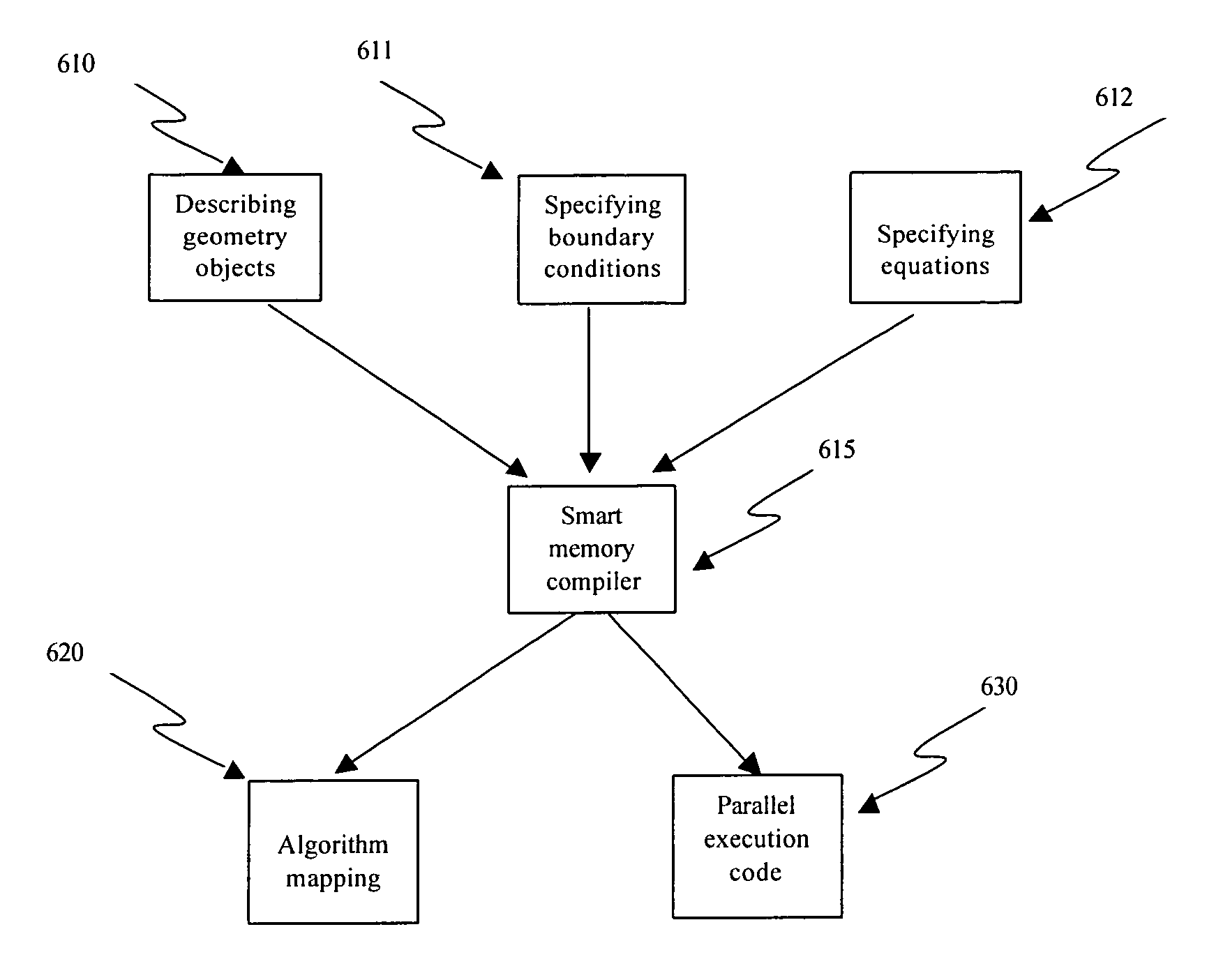
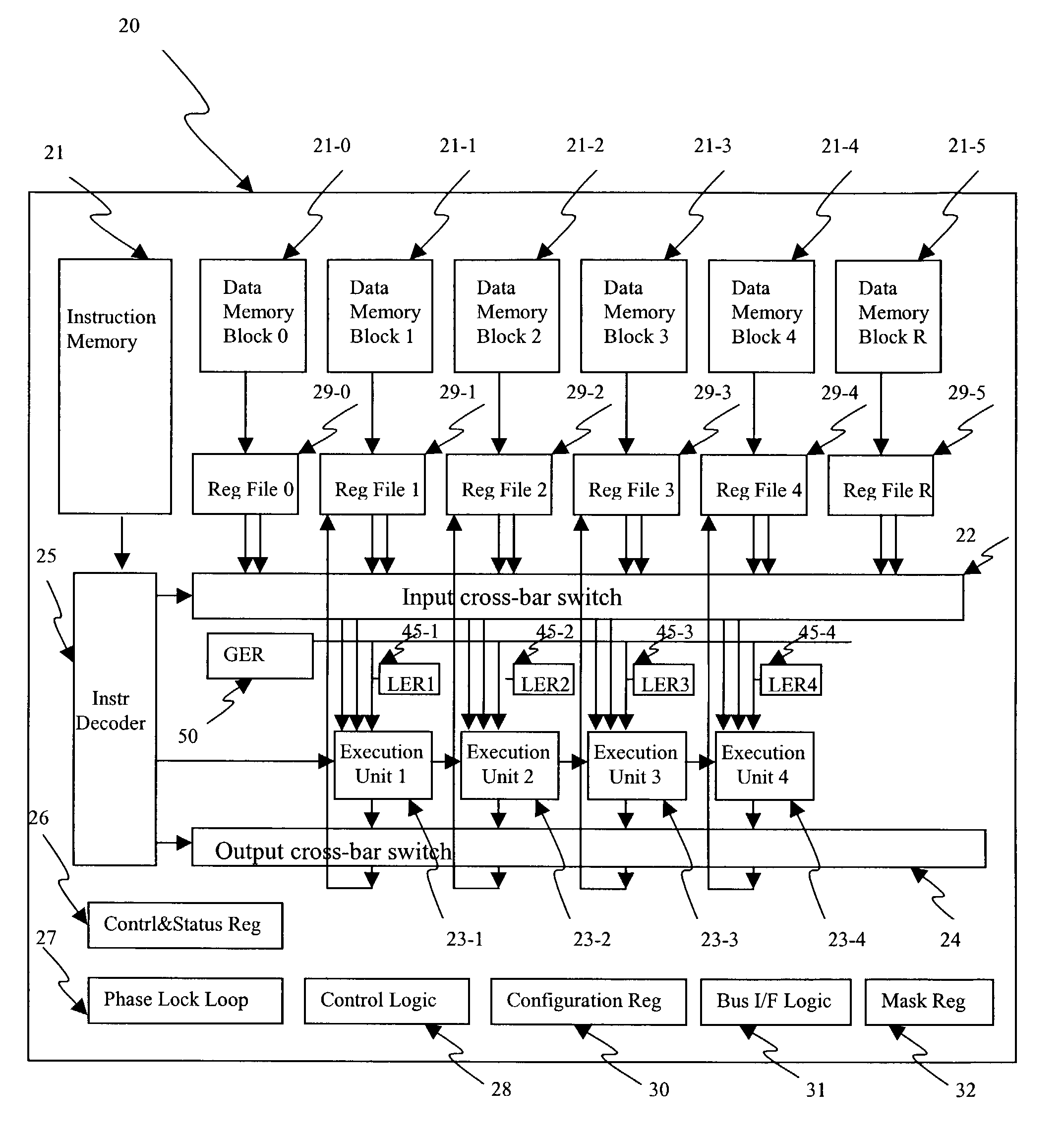
Algorithm mapping, specialized instructions and architecture features for smart memory computing
InactiveUS7546438B2Improve performanceLow costMultiplex system selection arrangementsDigital computer detailsSmart memoryExecution unit
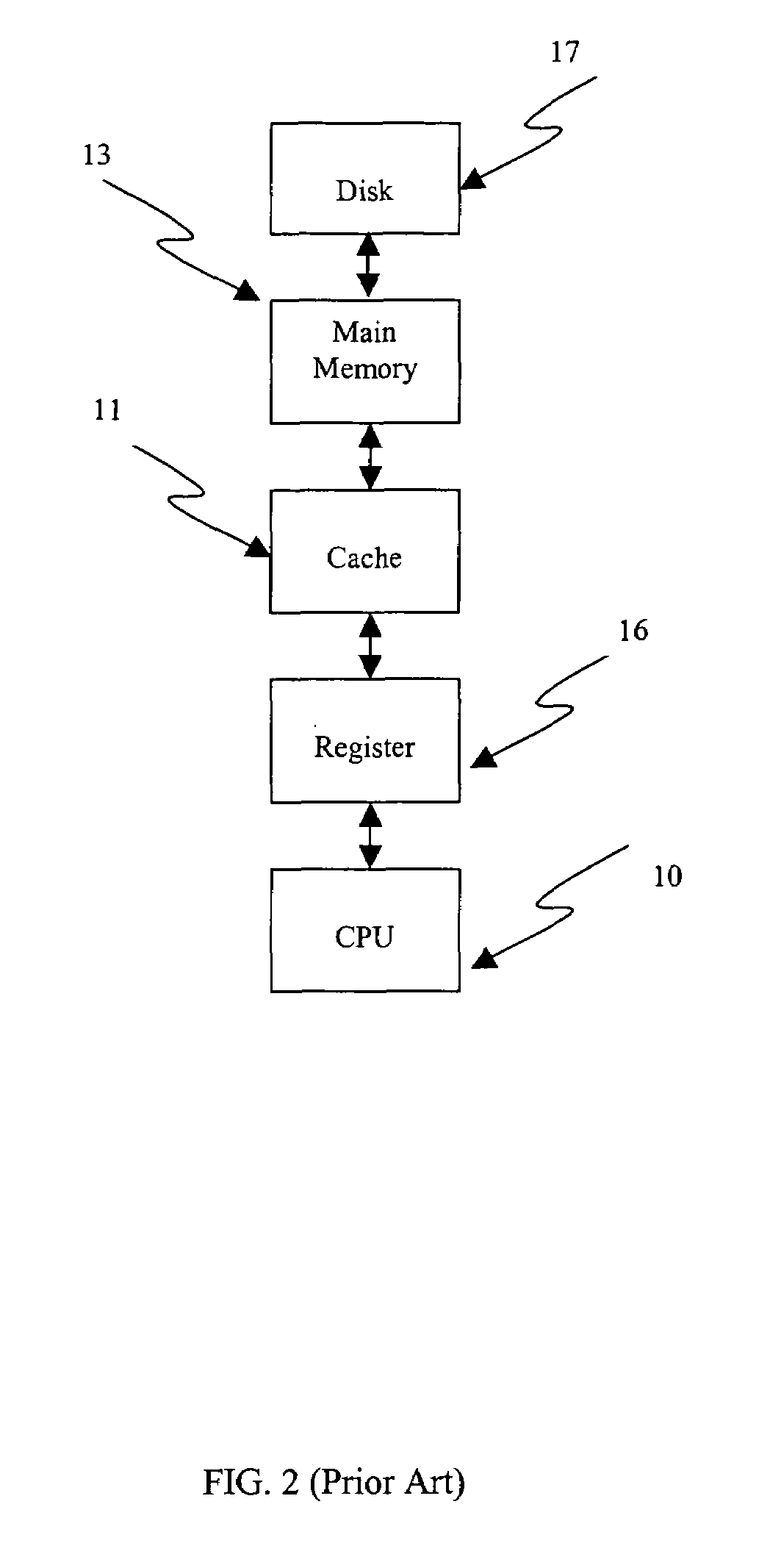
A smart memory computing system that uses smart memory for massive data storage as well as for massive parallel execution is disclosed. The data stored in the smart memory can be accessed just like the conventional main memory, but the smart memory also has many execution units to process data in situ. The smart memory computing system offers improved performance and reduced costs for those programs having massive data-level parallelism. This smart memory computing system is able to take advantage of data-level parallelism to improve execution speed by, for example, use of inventive aspects such as algorithm mapping, compiler techniques, architecture features, and specialized instruction sets.
Owner:STRIPE INC
Generating and matching hashes of multimedia content
ActiveUS20020178410A1RobustRobust hashingElectrophonic musical instrumentsCode conversionFrequency spectrumAlgorithm
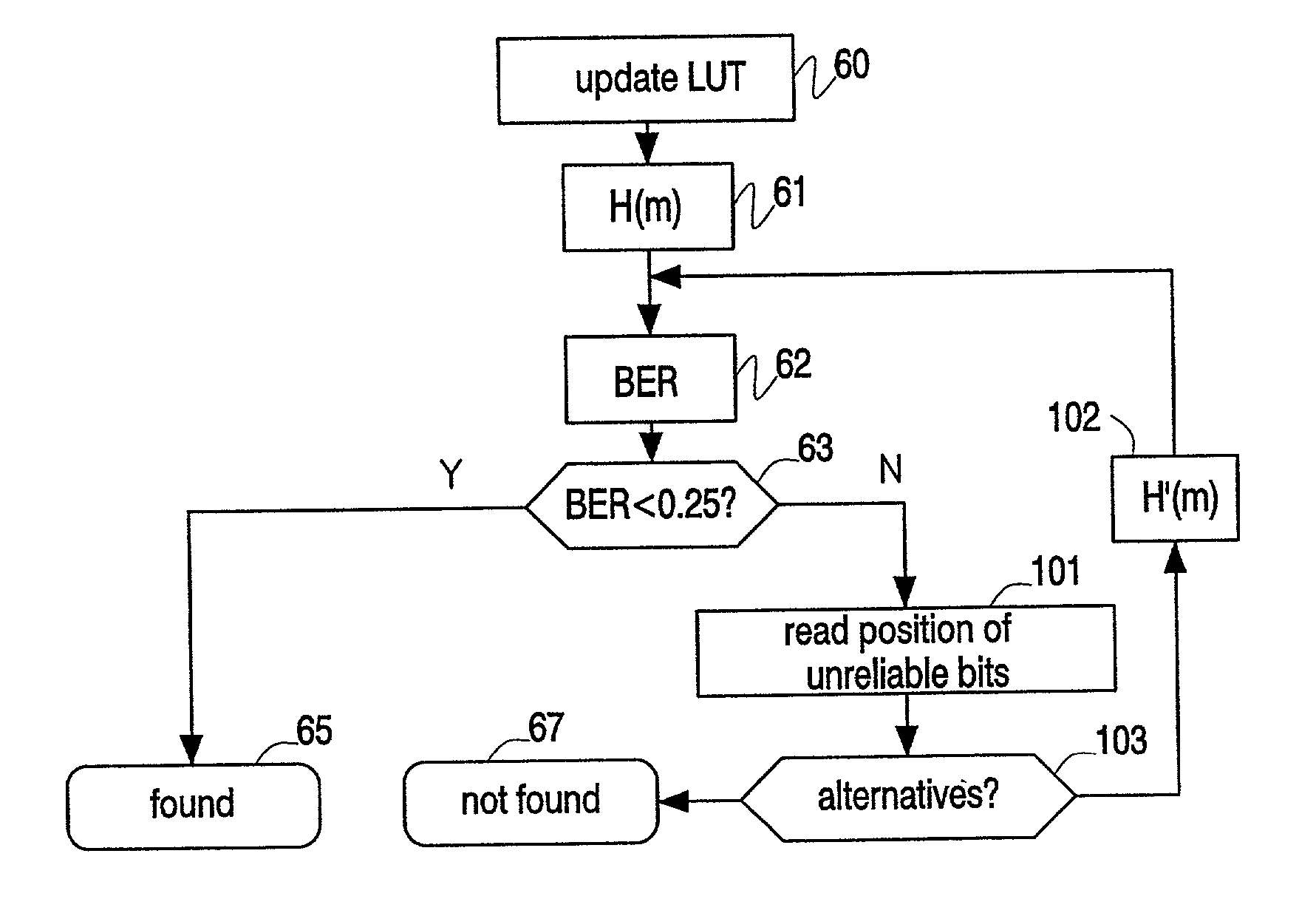
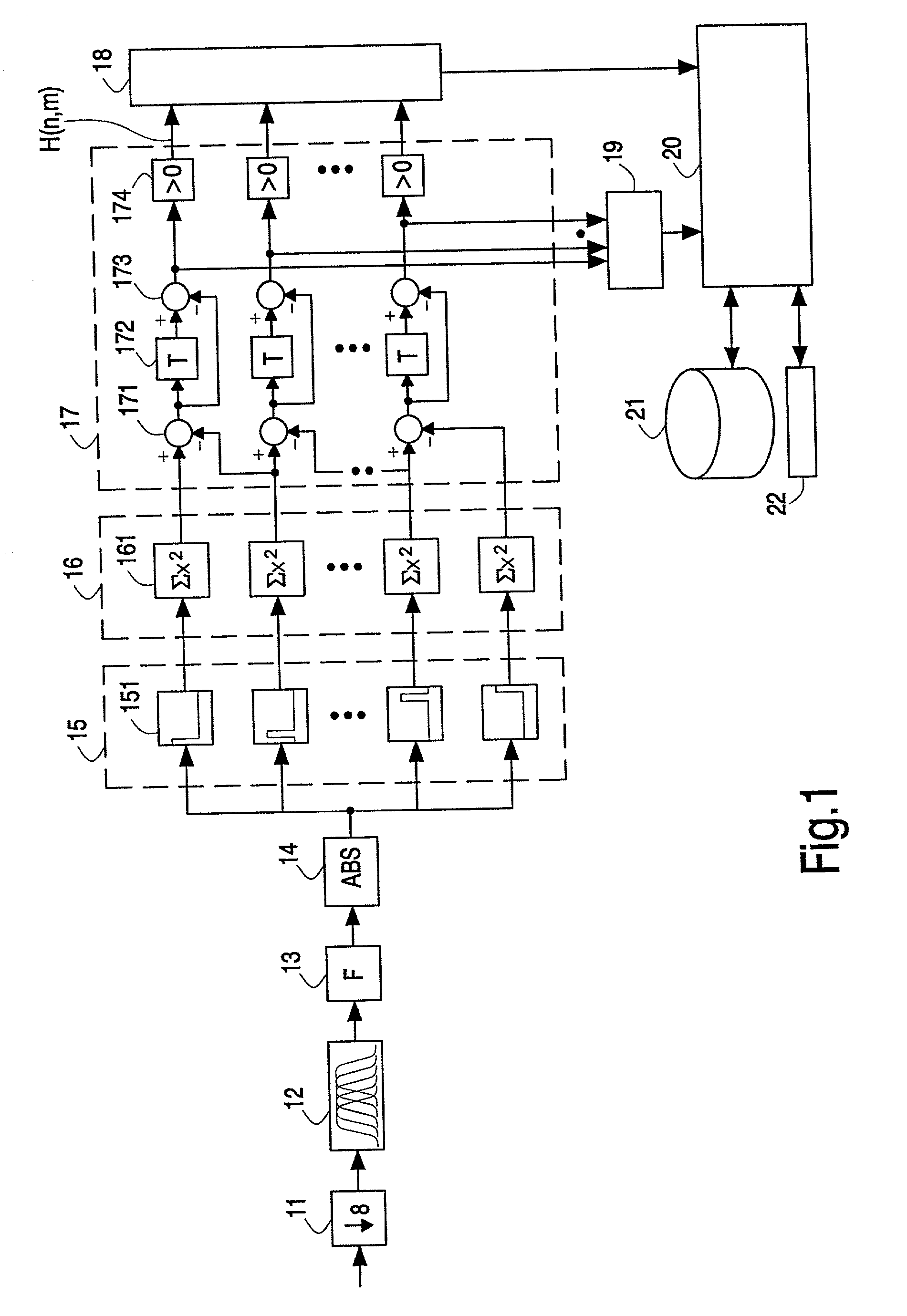
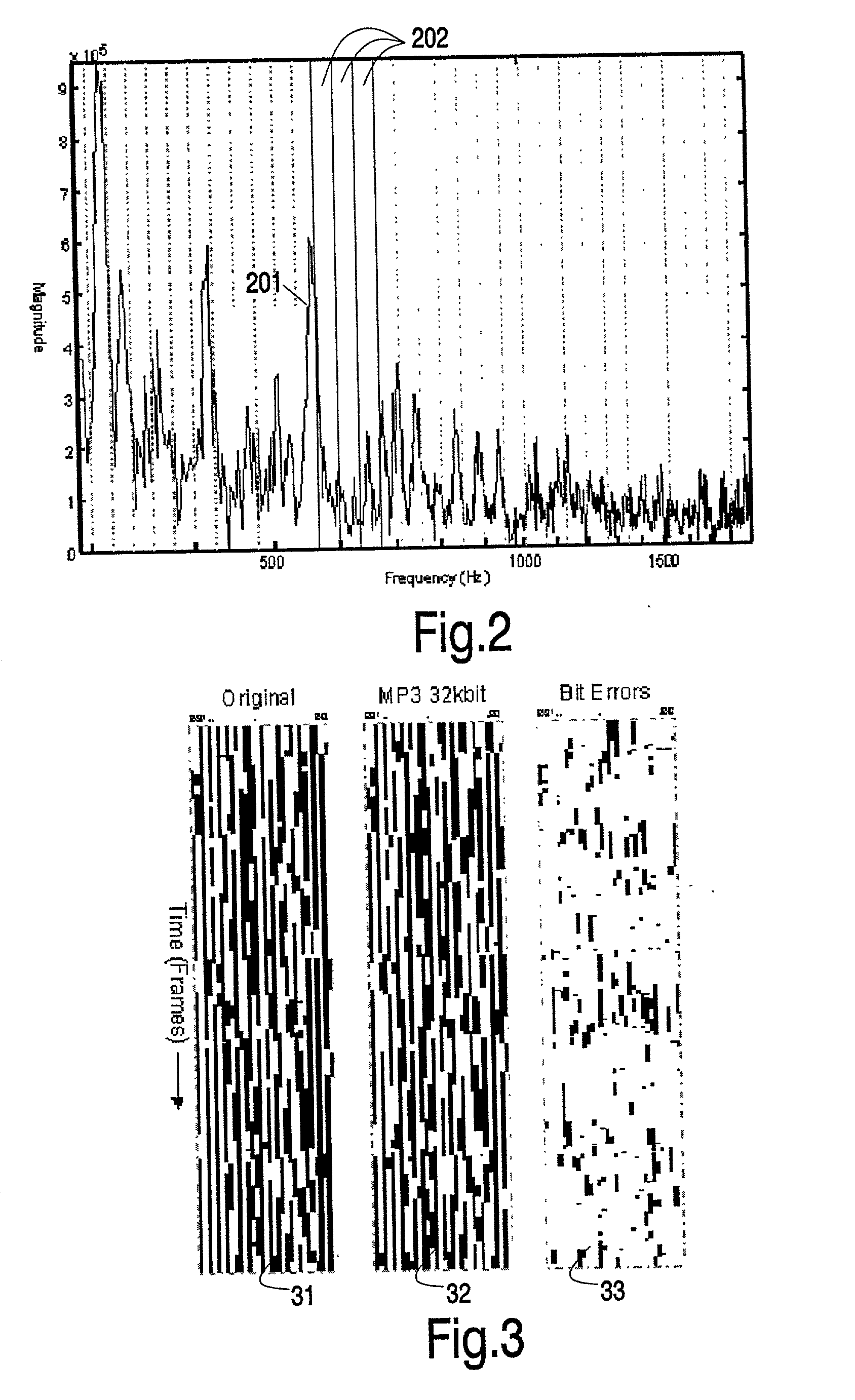
Hashes are short summaries or signatures of data files which can be used to identify the file. Hashing multimedia content (audio, video, images) is difficult because the hash of original content and processed (e.g. compressed) content may differ significantly. The disclosed method generates robust hashes for multimedia content, for example, audio clips. The audio clip is divided (12) into successive (preferably overlapping) frames. For each frame, the frequency spectrum is divided (15) into bands. A robust property of each band (e.g. energy) is computed (16) and represented (17) by a respective hash bit. An audio clip is thus represented by a concatenation of binary hash words, one for each frame. To identify a possibly compressed audio signal, a block of hash words derived therefrom is matched by a computer (20) with a large database (21). Such matching strategies are also disclosed. In an advantageous embodiment, the extraction process also provides information (19) as to which of the hash bits are the least reliable. Flipping these bits considerably improves the speed and performance of the matching process.
Owner:GRACENOTE
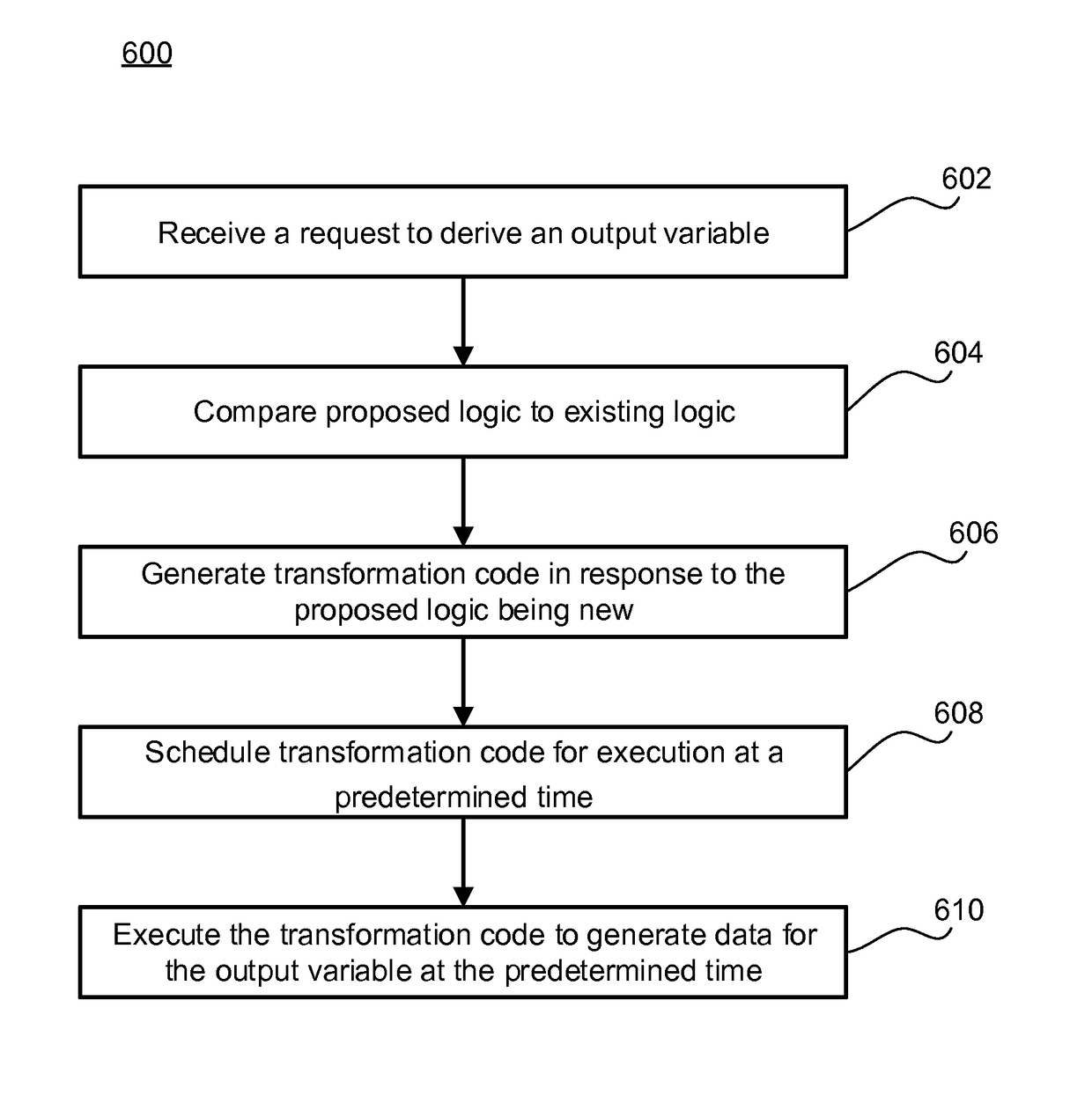
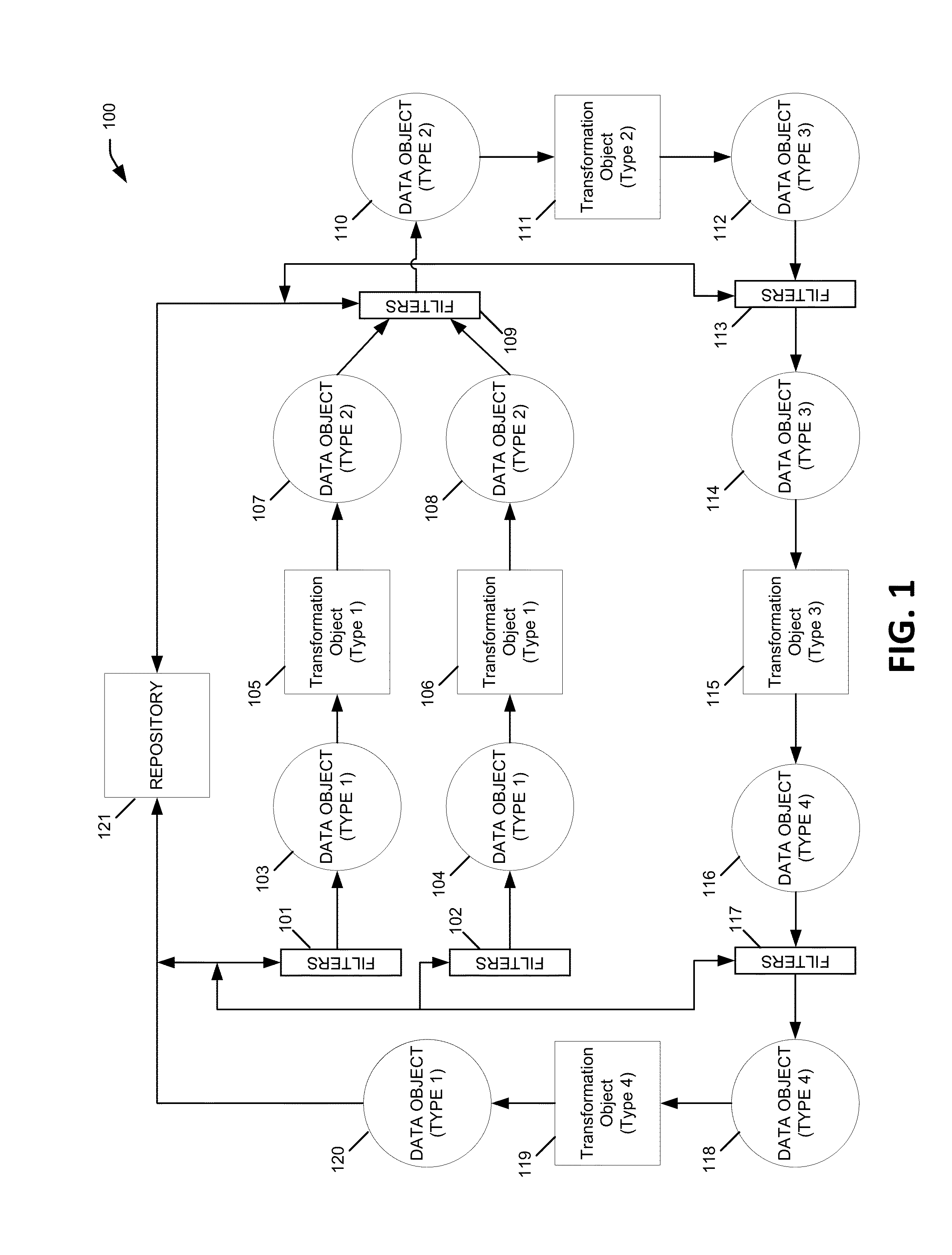
System and method transforming source data into output data in big data environments
ActiveUS10055426B2Digital data information retrievalRequirement analysisTheoretical computer scienceSource data
A system may receive a request to derive an output variable from a source variable. The request may include proposed logic to derive the output variable from the source variable. The system may then compare the proposed logic to existing logic to determine the proposed logic is new. In response to the proposed logic being new, the system may generate transformation code configured to execute the proposed logic. The system may further schedule the transformation code for execution at a predetermined time, and then execute the transformation code to generate data for the output variable.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
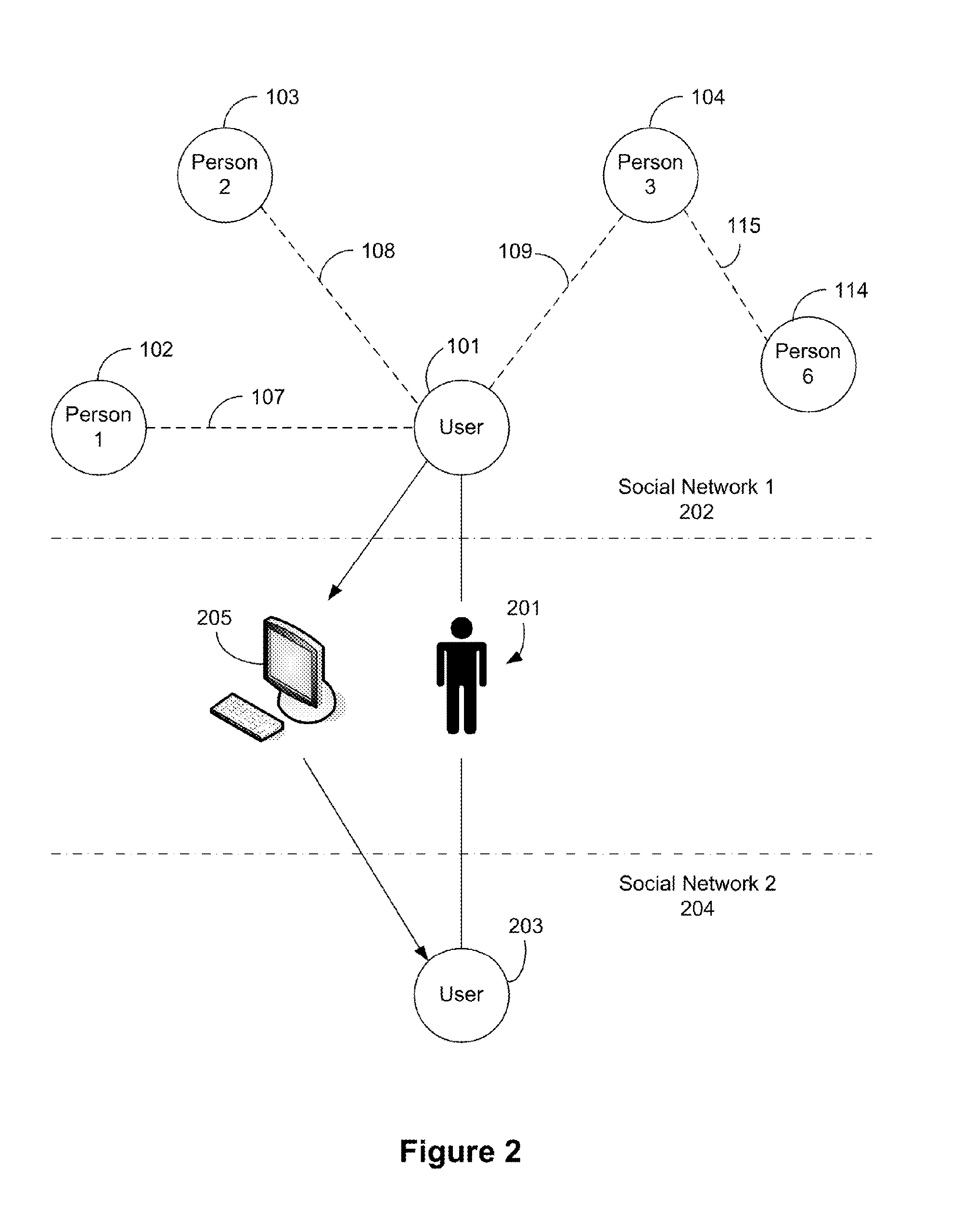
Methods and/or systems for an online and/or mobile privacy and/or security encryption technologies used in cloud computing with the combination of data mining and/or encryption of user's personal data and/or location data for marketing of internet posted promotions, social messaging or offers using multiple devices, browsers, operating systems, networks, fiber optic communications, multichannel platforms
InactiveUS10129211B2Data can be securedDigital data processing detailsAnalogue secracy/subscription systemsFiberNetwork operating system
A method, apparatus, computer readable medium, computer system, wireless or wired network, or system to provide an online and / or mobile security of a user's privacy and / or security method of internet or mobile access or system, apparatus, computer readable medium, or system using encryption technologies and / or filters to access data, encrypt and / or decrypt data, sync data, secure data storage and / or process data using cloud technology across many different networks and / or fiber optic communications from an endpoint accessed through multiple devices, browsers, operating systems, networks, servers, storage, software, applications or services integrated in a public cloud or a private cloud within an enterprise, a social network, big data analytics or electronic surveillance tracking or some mashup of two or more to prevent the unauthorized collecting, tracking and / or analysis of a user's personal data by a third party and / or for generating relevant advertising, mobile, internet social messaging, internet posted promotions or offers for products and / or services.
Owner:HEATH STEPHAN
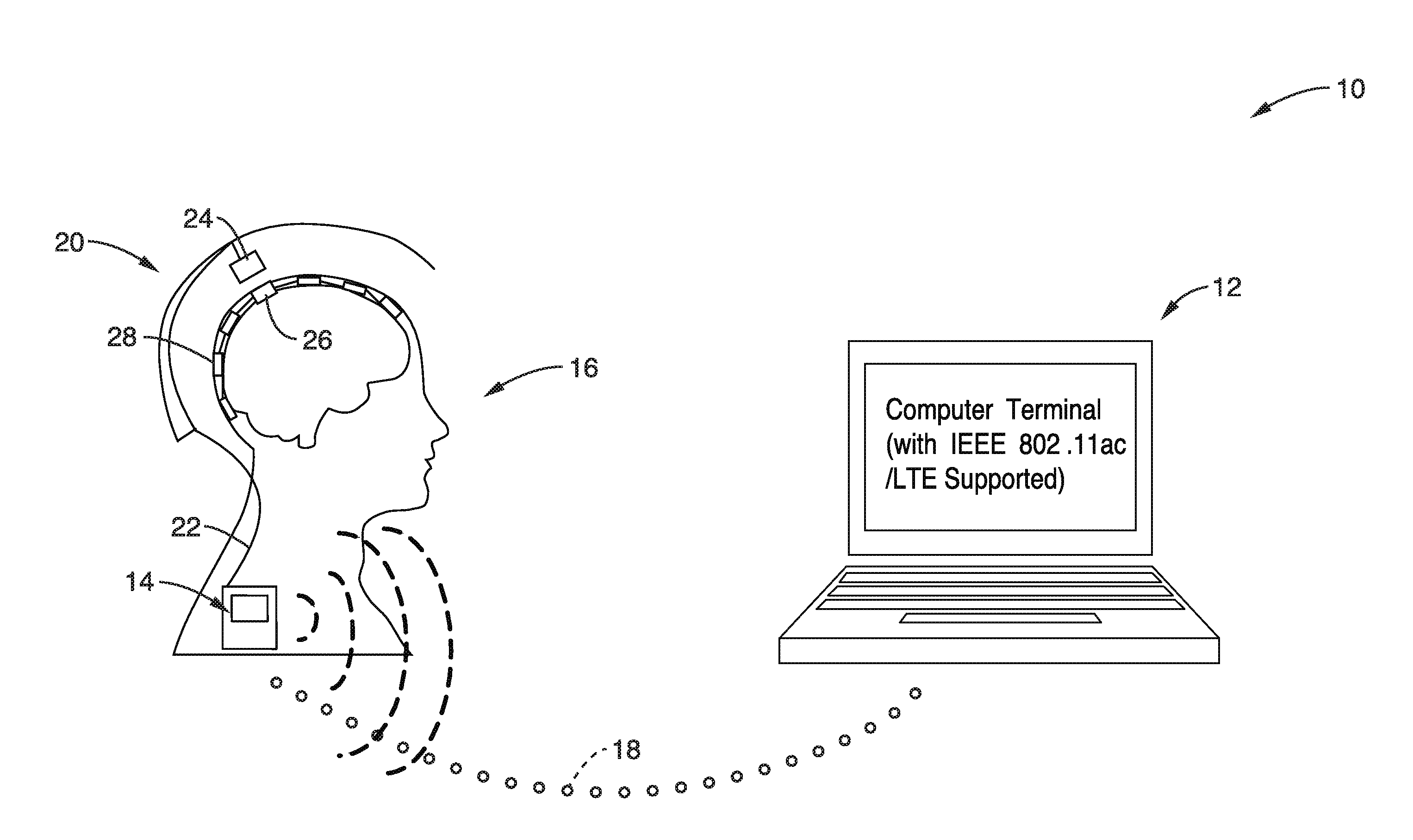
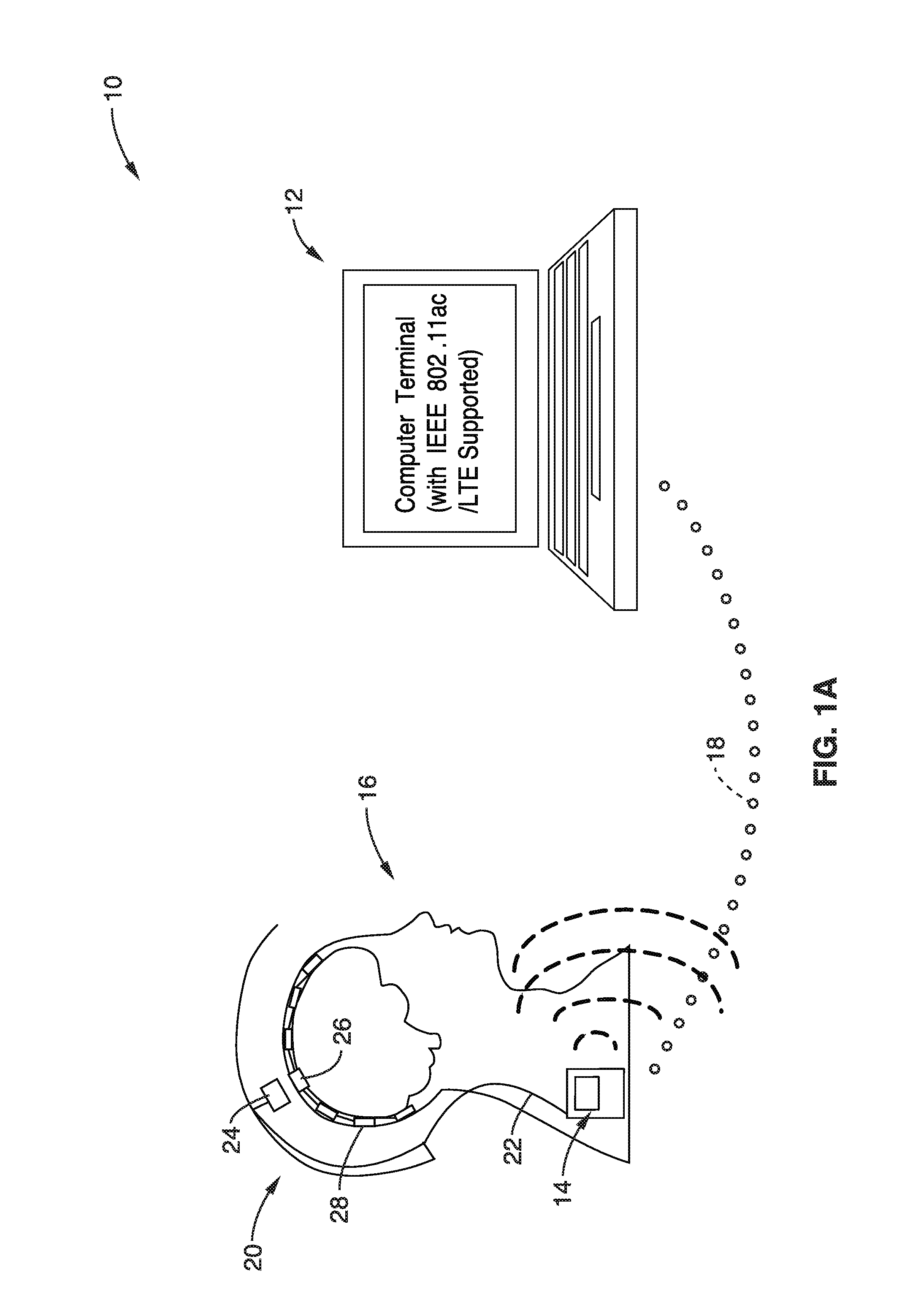
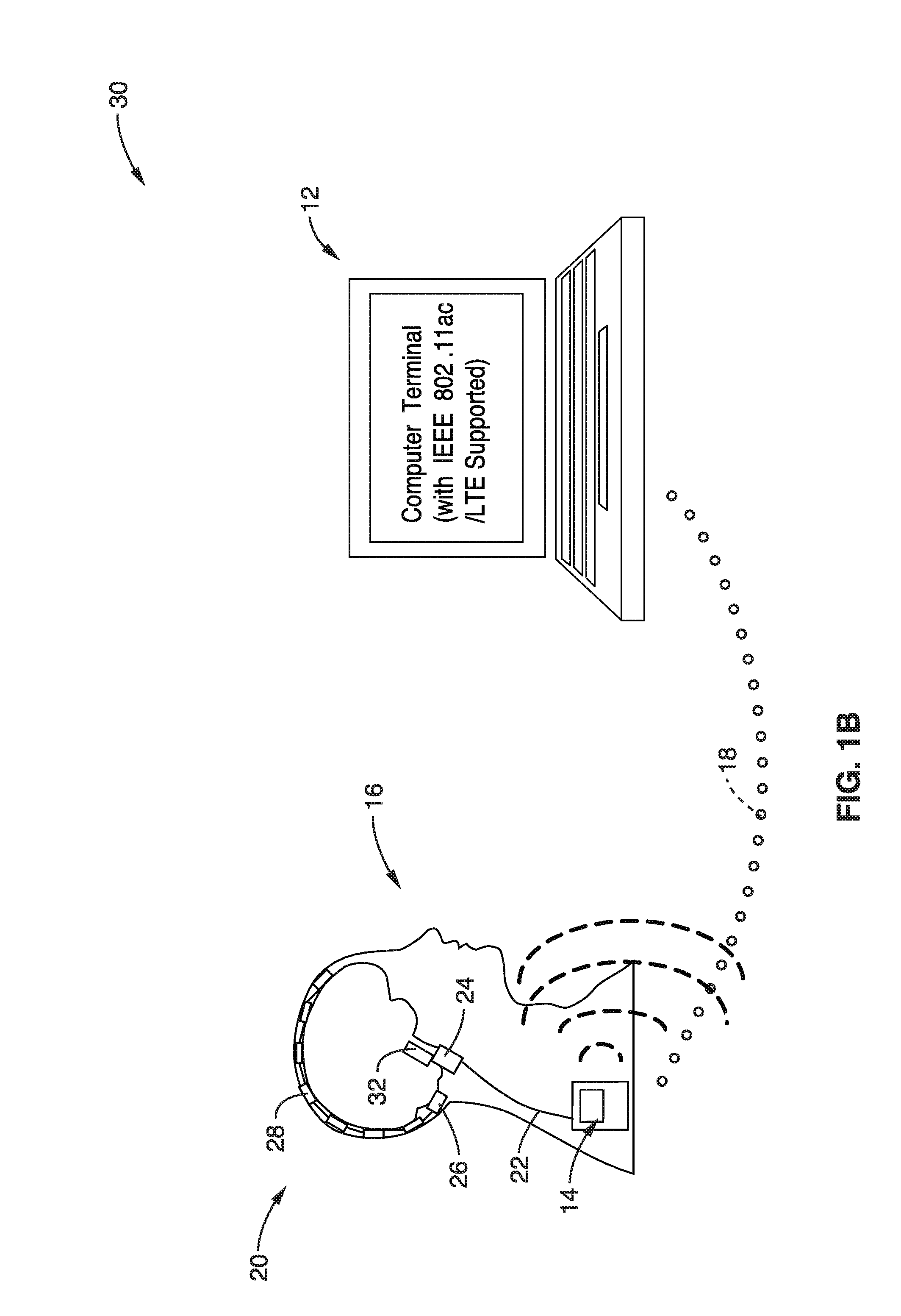
Wireless wearable big data brain machine interface
ActiveUS20160323000A1Circuit arrangementsDiagnostic recording/measuringComputer hardwareShortest distance
A wireless wearable high data throughput (big data) brain machine interface apparatus is presented. An implanted recording and transmitting module collects neural data from a plurality of implanted electrodes and wirelessly transmits this over a short distance to a wearable (not implanted) receiving and forwarding module, which communicates the data over a wired communication to a mobile post processing device. The post processing device can send this neural data to an external display or computer enabled device for viewing and / or manipulation. High data throughput is supported by aggregating multiple groups of electrodes by multiple n-channel recording elements, which are multiplexed and then modulated into high frequency wireless communications to the wearable module. Embodiments include use of multiple radiators (multiple polarizations and / or spatially distributed), with beam alignment adjustment.
Owner:RGT UNIV OF CALIFORNIA
Unmanned vehicle selective data transfer system and method thereof
InactiveUS9282144B2Minimize timeInput/output to record carriersUnmanned aerial vehiclesTransceiverData set
A data transfer system is disclosed for an unmanned vehicle on a mission. The data transfer system can include a first sensor associated with the unmanned vehicle for collecting a first data set, and a second sensor associated with the unmanned vehicle and for collecting a second data set, wherein the second data set is associated with the first data set by a predetermined association. A transceiver can transmit data from the unmanned vehicle to a remote data storage system. A mass data storage computer located on the unmanned vehicle can store the first and second data sets based on the predetermined association, and execute requests from the remote data storage system to transmit the first data set from the unmanned vehicle to the remote data storage system, and to transmit selected ones of the second data set from the unmanned vehicle to the remote data storage system.
Owner:BAE SYSTEMS PLC
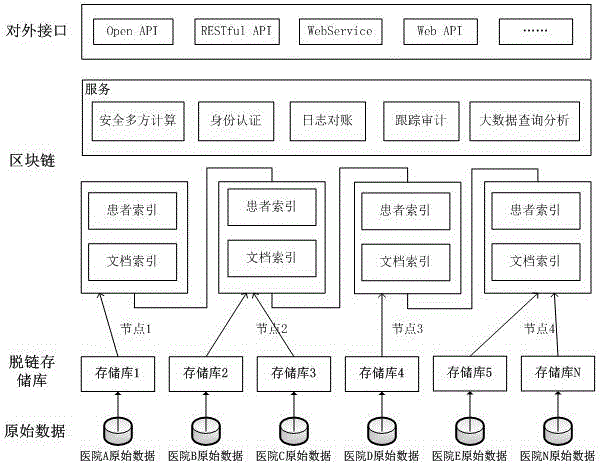
Method and device for medical information sharing privacy protection based on blockchain technology
InactiveCN106682530AAvoid privacyUse constraintsDigital data protectionInformation sharingPrivacy protection
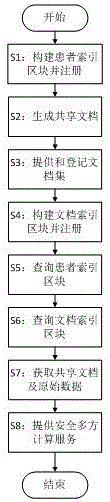
The invention discloses a method and device for medical information sharing privacy protection based on a blockchain technology. According to the method, in aspects of privacy protection based on a blockchain technology, medical data on-chain and off-chain storage and forced privacy protection safety multiparty calculation, illegal medical data obtaining, use and tampering are avoided, and medical information sharing, big data analysis and utilization and patient privacy protection are implemented. The device comprises a data storage module, a service module provided based on the blockchain technology and a call service module provided externally, wherein a three-layer data storage frame is adopted for the data storage module; and the service module provided based on the blockchain technology mainly comprises forced privacy protection safety multiparty calculation. The method and device for medical information sharing privacy protection based on the blockchain technology are mainly applied to the fields of method and device for medical information sharing privacy protection based on a blockchain technology and medical big data analysis and the like, and technical guarantee is also provided for patient privacy protection while medical information sharing is achieved based on the blockchain technology.
Owner:HANGZHOU DIANZI UNIV
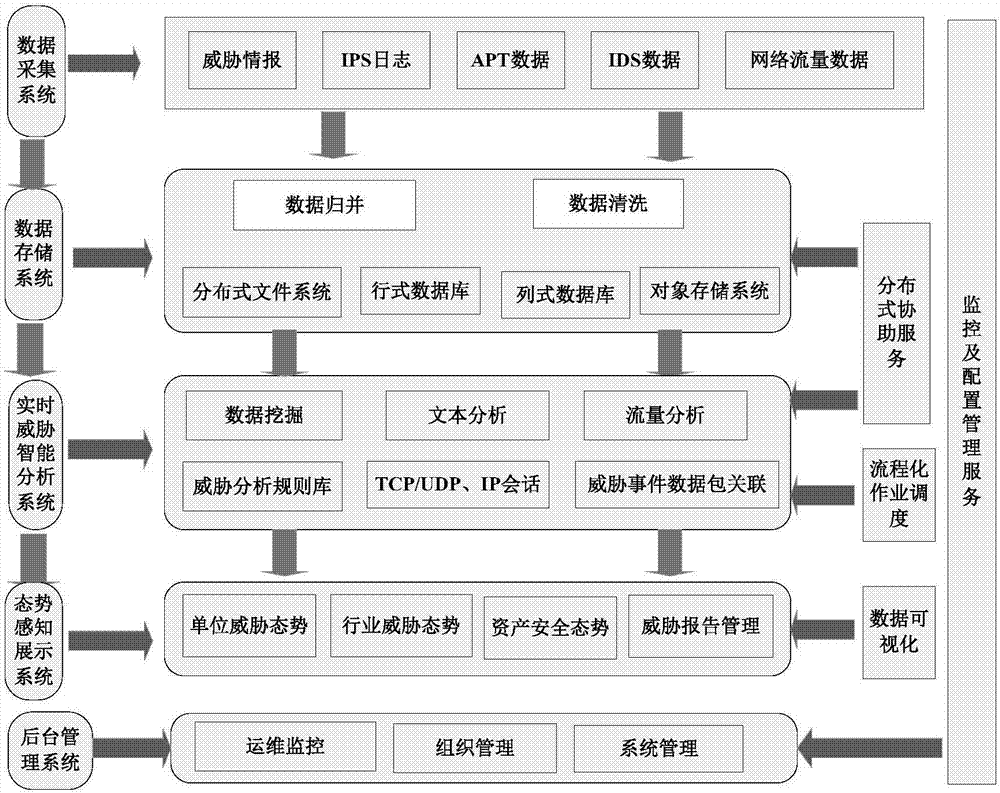
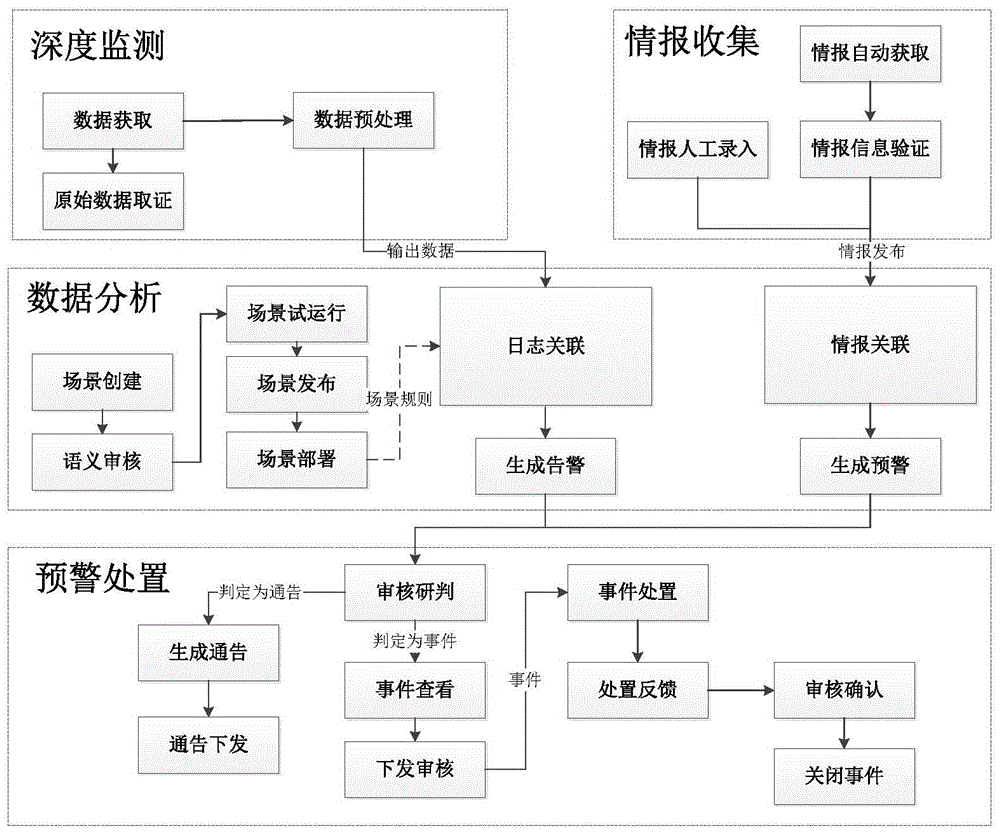
Threat early warning and monitoring system and method based on big data analysis and deployment architecture
ActiveCN107196910ARealize acquisitionRealize multi-dimensional graphical and intuitive displayData switching networksFull text searchTime processing
The invention discloses a threat early warning and monitoring system and method based on big data analysis and a deployment architecture. The system comprises a data acquisition system module, which is used for carrying out real-time data acquisition on original network traffic; a data storage system module, which is used for carrying out data merging and data cleaning on the data collected by the data acquisition system module, and then, carrying out storage management; a real-time threat intelligent analysis system module, which is used for carrying out deep analysis and mining on security data through data mining, text analysis, traffic analysis, full-text search engine and real-time processing, and identifying unknown security threats in real time by combining an intrusion detection module, a network abnormal behavior module and a device abnormal behavior module; and a situation awareness display system module, which is used for carrying out comprehensive display on security threat situations stereoscopically in real time through a data visualization tool library. The threat early warning and monitoring system and method based on big data analysis and the deployment architecture are used for network security threat situation awareness and deep analysis under a plurality of service scenarios, and realize comprehensive abilities from attack early warning, attack identification to analysis and evidence obtaining.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
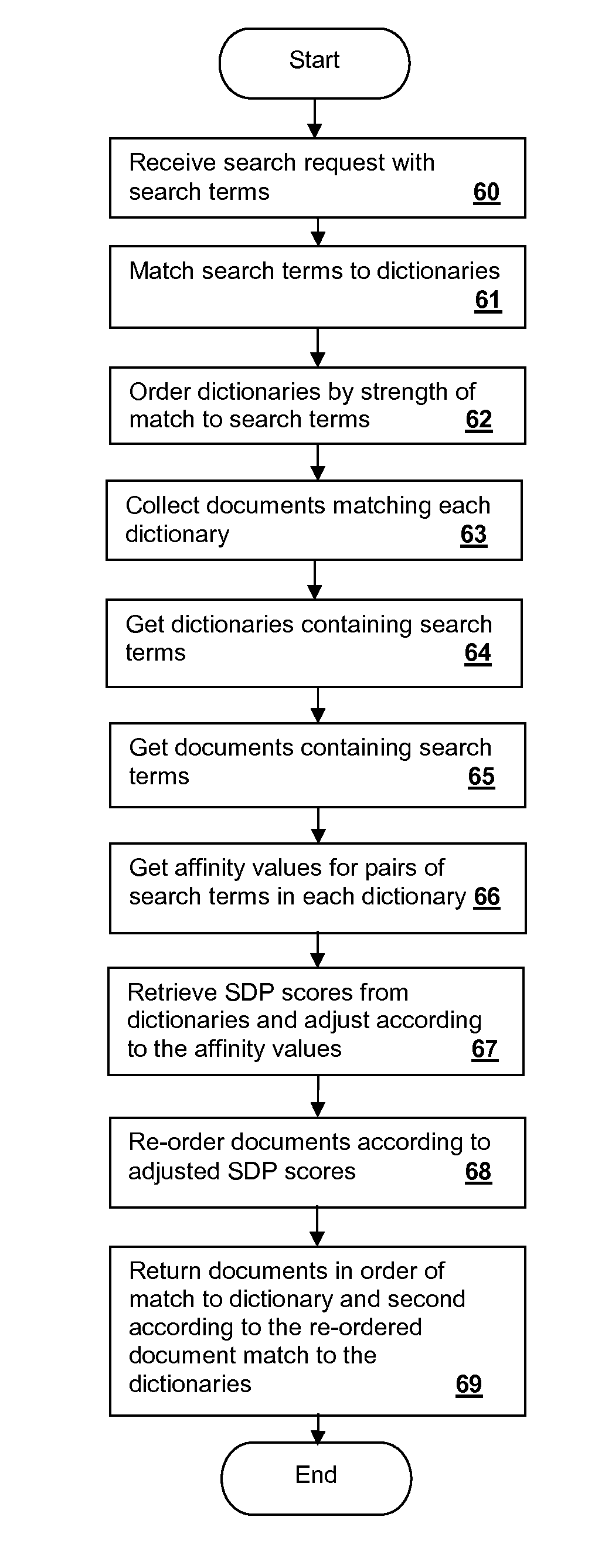
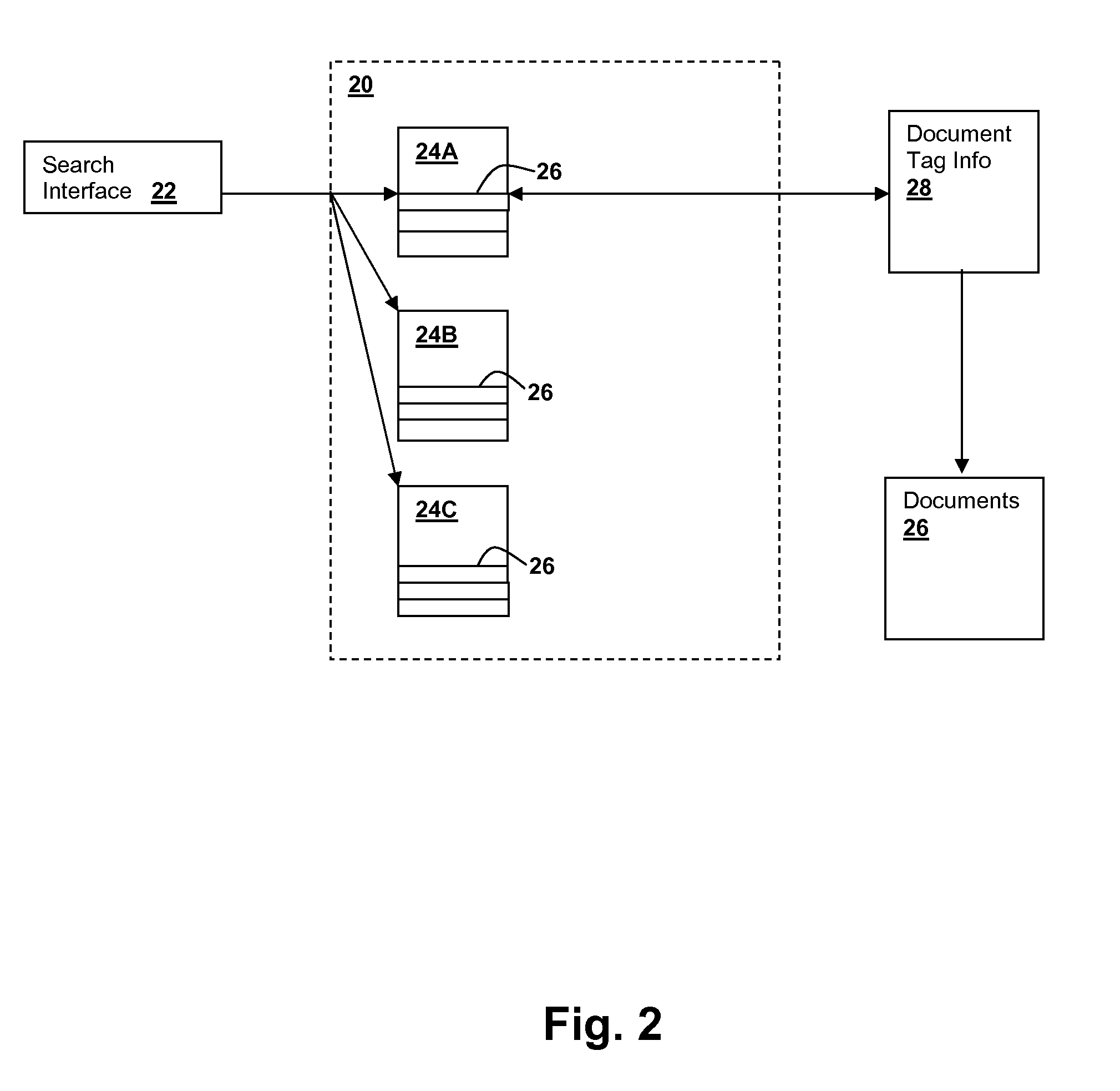
Document retrieval using internal dictionary-hierarchies to adjust per-subject match results
InactiveUS20150134666A1Efficiently categorizeEfficient retrievalDatabase updatingDigital data processing detailsSubject matterSub classification
Techniques for managing big data include retrieval using per-subject dictionaries having multiple levels of sub-classification hierarchy within the subject. Entries may include subject-determining-power (SDP) scores that provide an indication of the descriptive power of the entry term with respect to the subject of the dictionary containing the term. The same term may have entries in multiple dictionaries with different SDP scores in each of the dictionaries. A retrieval request for one or more documents containing search terms descriptive of the one or more documents can be processed by identifying a set of candidate documents tagged with subjects, i.e., identifiers of per-subject dictionaries having entries corresponding to a search term, then using affinity values to adjust the aggregate score for the terms in the dictionaries. Documents are then selected for best match to the subject based on the adjusted scores. Alternatively, the adjustment may be performed after selecting the documents by re-ordering them according to adjusted scores.
Owner:IBM CORP
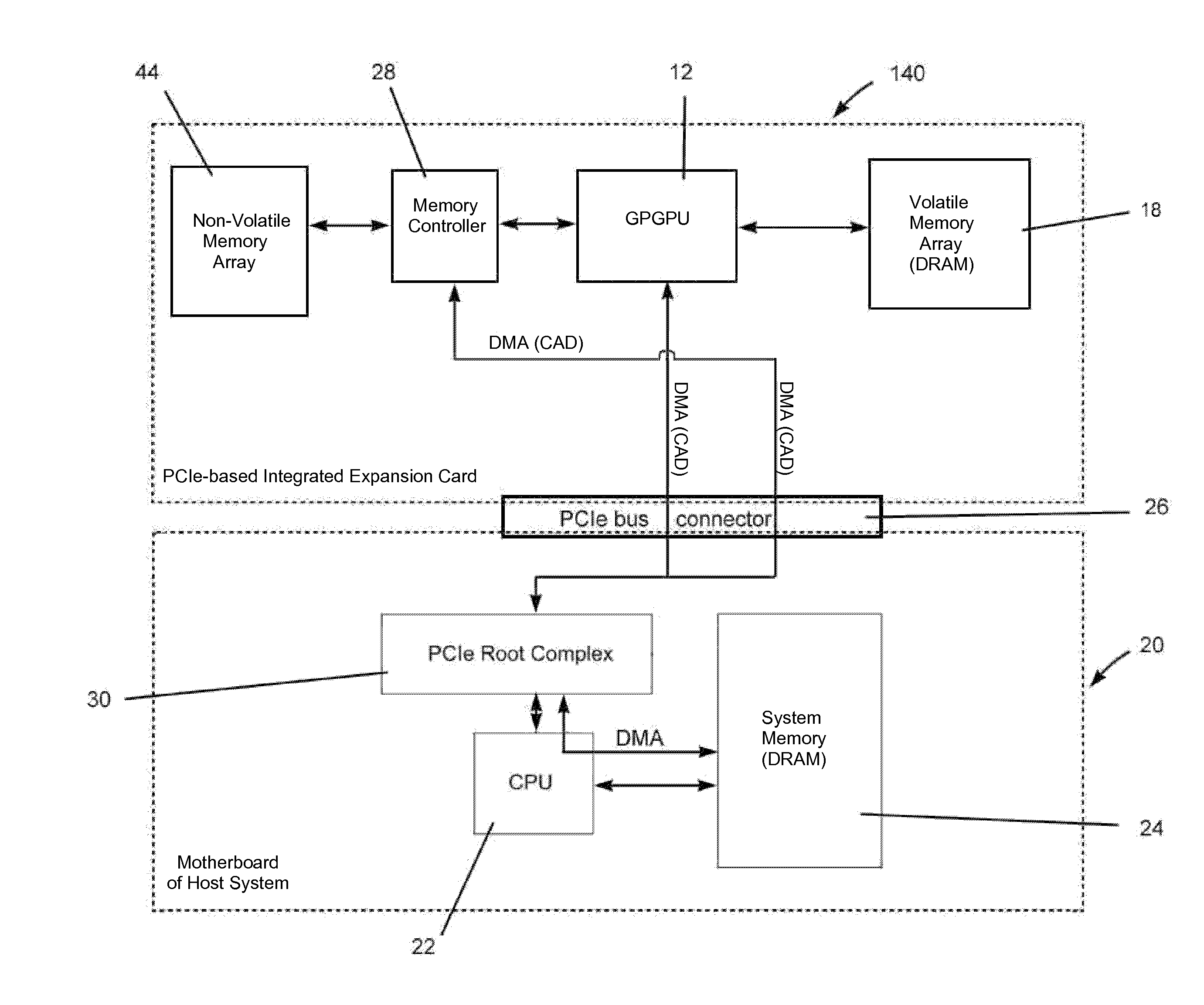
Integrated storage/processing devices, systems and methods for performing big data analytics
ActiveUS20140129753A1Faster throughputComponent plug-in assemblagesElectric digital data processingGeneral purposeGraphics
Architectures and methods for performing big data analytics by providing an integrated storage / processing system containing non-volatile memory devices that form a large, non-volatile memory array and a graphics processing unit (GPU) configured for general purpose (GPGPU) computing. The non-volatile memory array is directly functionally coupled (local) with the GPU and optionally mounted on the same board (on-board) as the GPU.
Owner:KIOXIA CORP
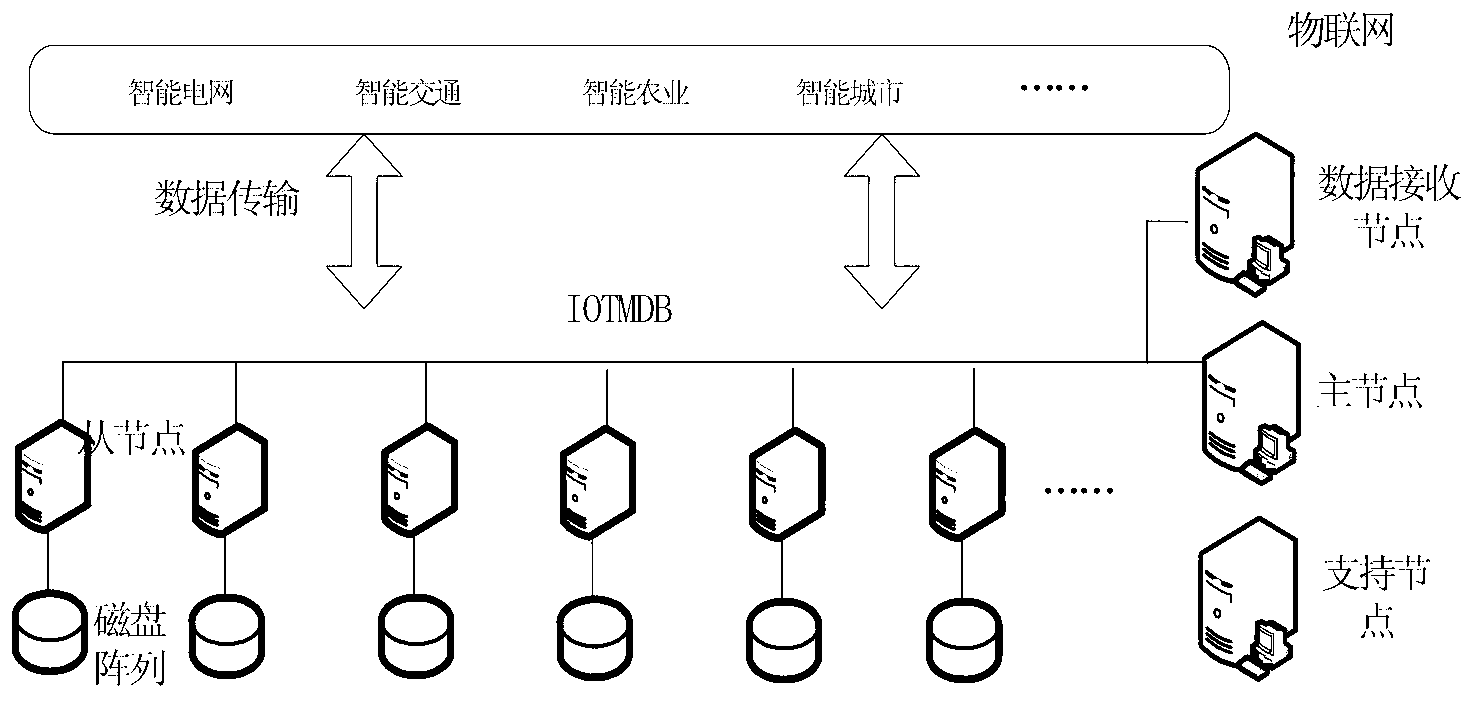
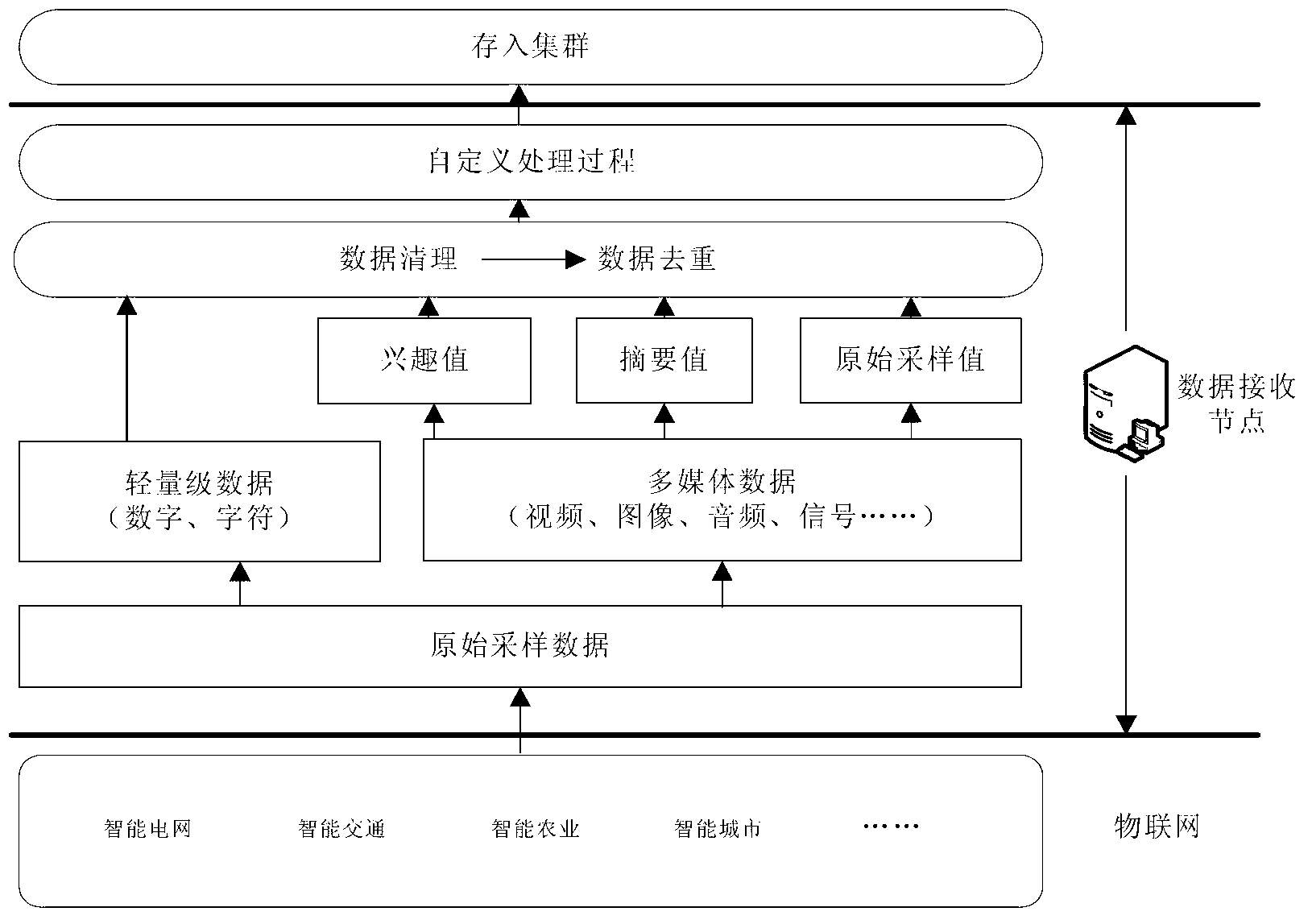
Method and system for storing mass data of Internet of Things (IoT)
ActiveCN103023970AAccurate understandingEasy to manageTransmissionSpecial data processing applicationsThe InternetData store
The invention relates to a method and a system for storing mass data of the Internet of Things (IoT). The system comprises a plurality of data receiving nodes, a master node server and a database cluster. The method comprises the following steps of: (1) carrying out preprocessing on IoT data, and putting the preprocessed data in the database cluster consisting of a master node, slave nodes and the data receiving nodes; (2) creating sample records, which take sample elements as storage units, on the master node according to the static and dynamic information of the data in the database cluster; (3) after the sample records are encapsulated, sending the encapsulated sample records to all the slave nodes by the master node so as to be subjected to fragmentation processing and / or separated storage; and (4) after the slave nodes complete storage, uploading results to the master node, and updating the data in the database cluster by the master node, thereby completing storage. According to the method and the system, the cluster is extended by fully utilizing the existing storage technologies so as to store the mass data, the IoT data are divided into lightweight data and multimedia data, and particularly, a fragmentation strategy is adopted aiming at a large-scale amount of data, so that the time expenditure caused by the extension of a storage space is avoided.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Block chain smart contract-based data transaction method
InactiveCN107464118AReduce storage costsGuaranteed execution efficiencyFinanceDatabase distribution/replicationThird partyExternal data
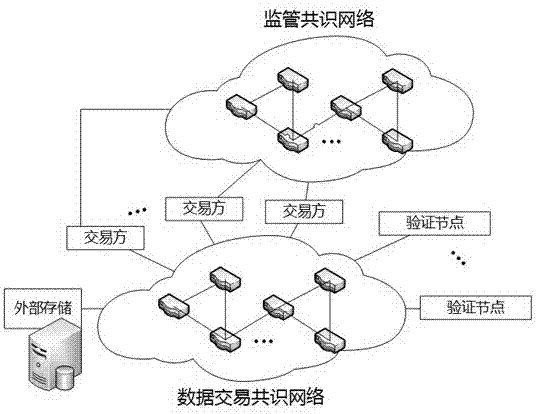
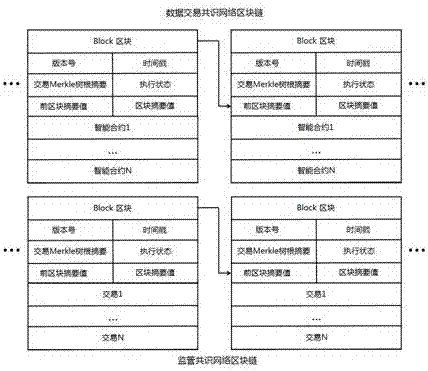
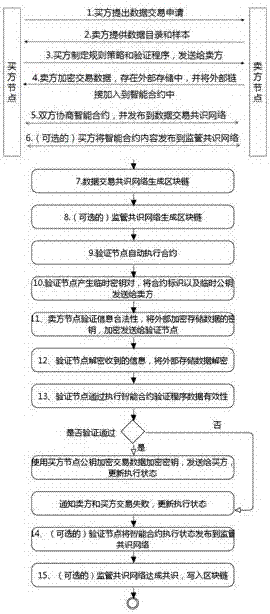
The invention relates to the technical field of big data, block chains and smart contracts, and in particular to a block chain smart contract-based data transaction method. According to the block chain smart contract-based data transaction method, purchase and sale behaviors of purchasers and sellers of transactions are recorded through block chains, automatic execution of the transactions is realized by utilizing smart contracts, and big data for the transactions is not recorded in the block chains and is encrypted and stored in an external data memory, so that the purchasers only can obtain the data after the smart contracts are successfully transacted; and moreover, the purchasers can publish transactions through a supervisory block chain consensus network, so that third-party witness is realized and the security guarantee of data transactions is increased.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
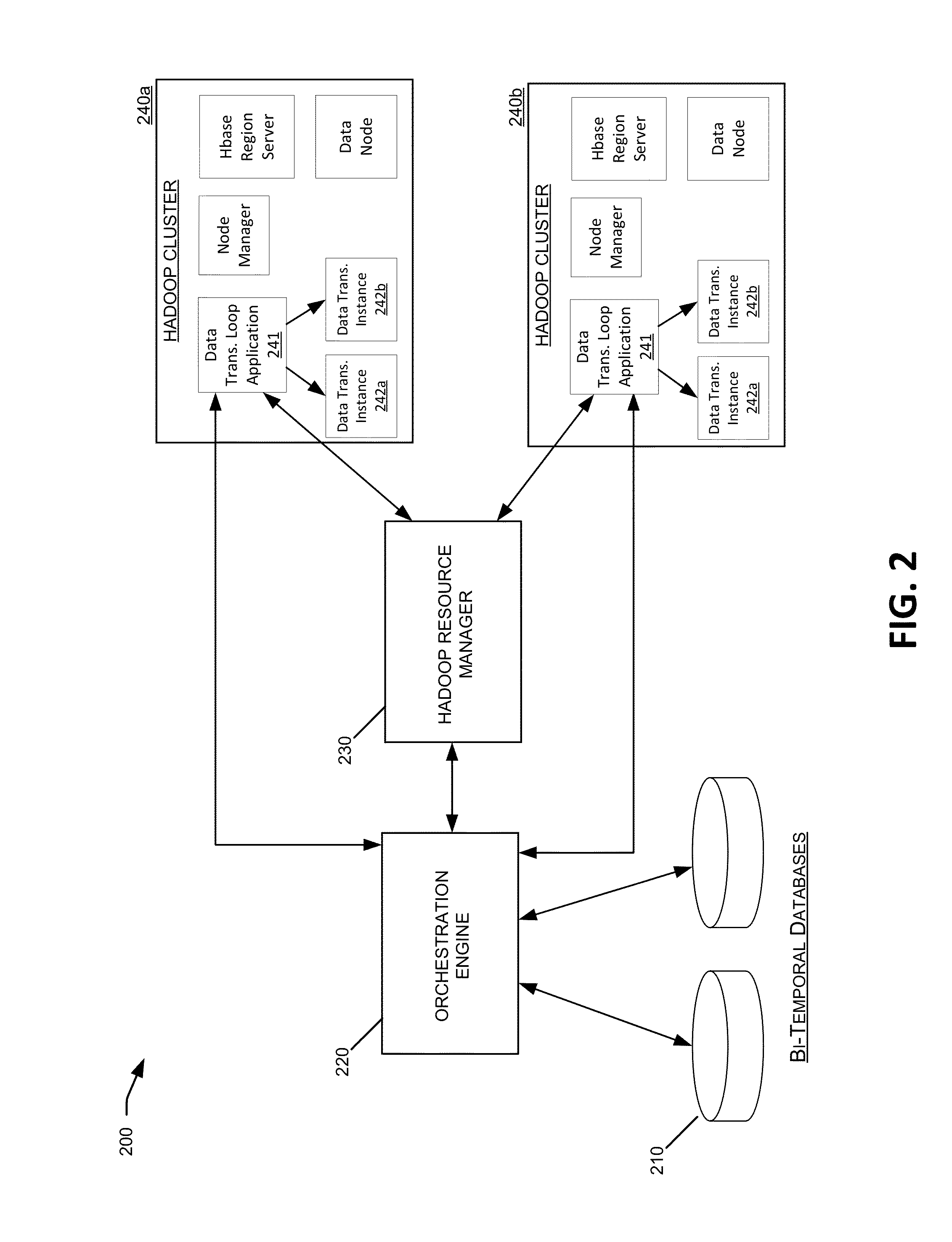
Knowledge-intensive data processing system
ActiveUS20150254330A1Error detection/correctionDigital data processing detailsData processing systemReal-time data
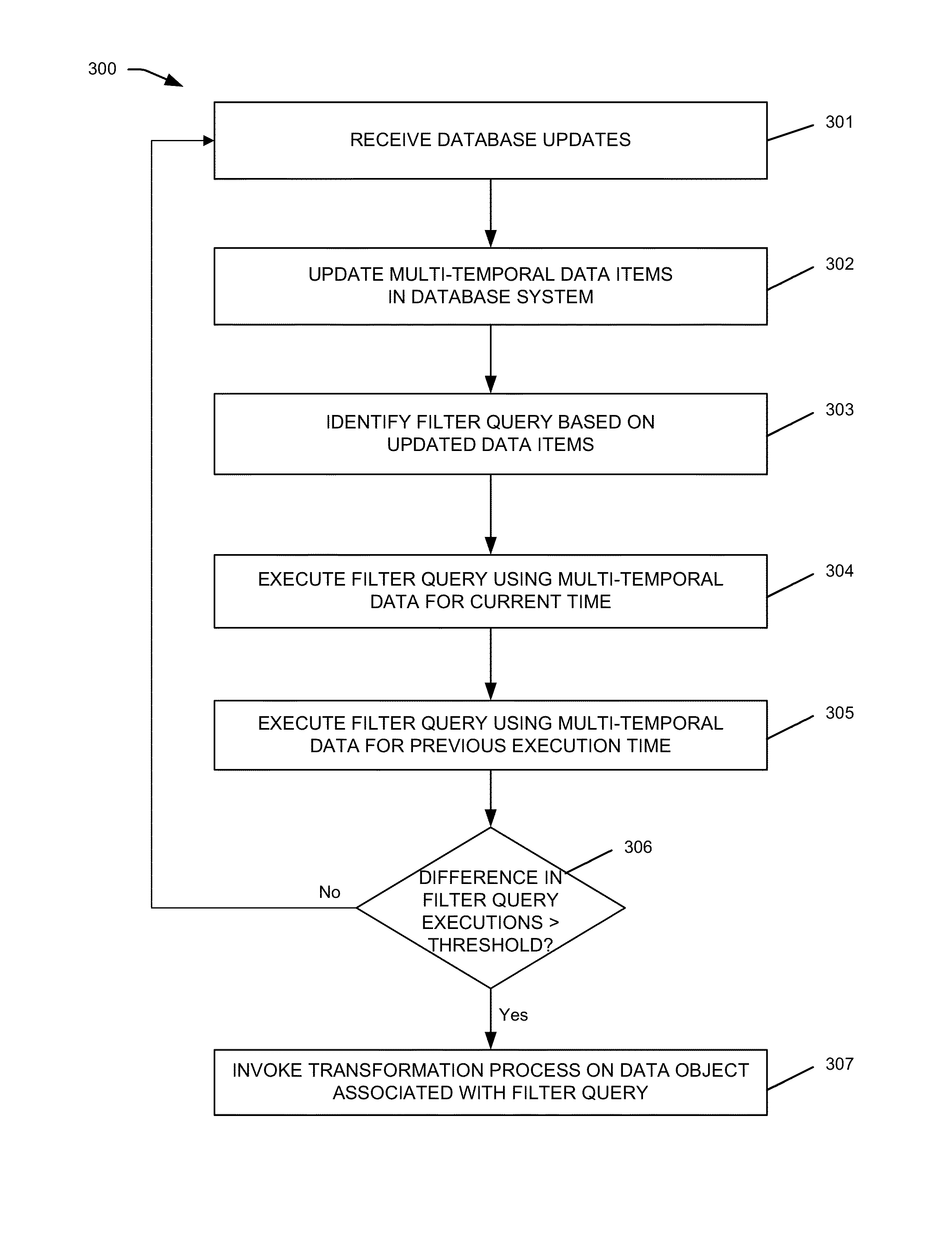
Embodiments of the invention provide systems and methods for managing and processing large amounts of complex and high-velocity data by capturing and extracting high-value data from low value data using big data and related technologies. Illustrative database systems described herein may collect and process data while extracting or generating high-value data. The high-value data may be handled by databases providing functions such as multi-temporality, provenance, flashback, and registered queries. In some examples, computing models and system may be implemented to combine knowledge and process management aspects with the near real-time data processing frameworks in a data-driven situation aware computing system.
Owner:ORACLE INT CORP
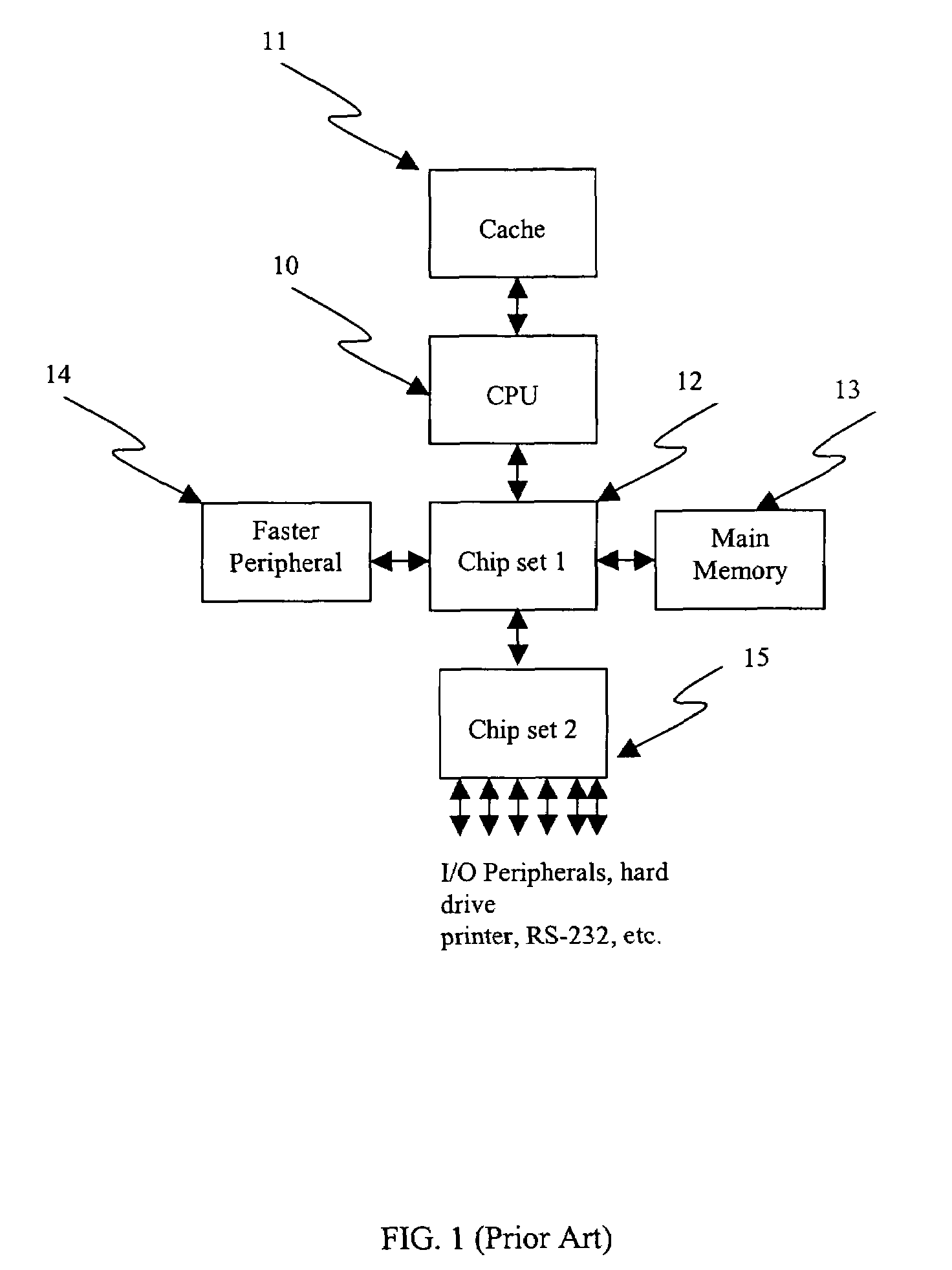
Algorithm mapping, specialized instructions and architecture features for smart memory computing
InactiveUS6970988B1Improve performanceLow costMultiplex system selection arrangementsProgram controlSmart memoryExecution unit
A smart memory computing system that uses smart memory for massive data storage as well as for massive parallel execution is disclosed. The data stored in the smart memory can be accessed just like the conventional main memory, but the smart memory also has many execution units to process data in situ. The smart memory computing system offers improved performance and reduced costs for those programs having massive data-level parallelism. This smart memory computing system is able to take advantage of data-level parallelism to improve execution speed by, for example, use of inventive aspects such as algorithm mapping, compiler techniques, architecture features, and specialized instruction sets.
Owner:STRIPE INC
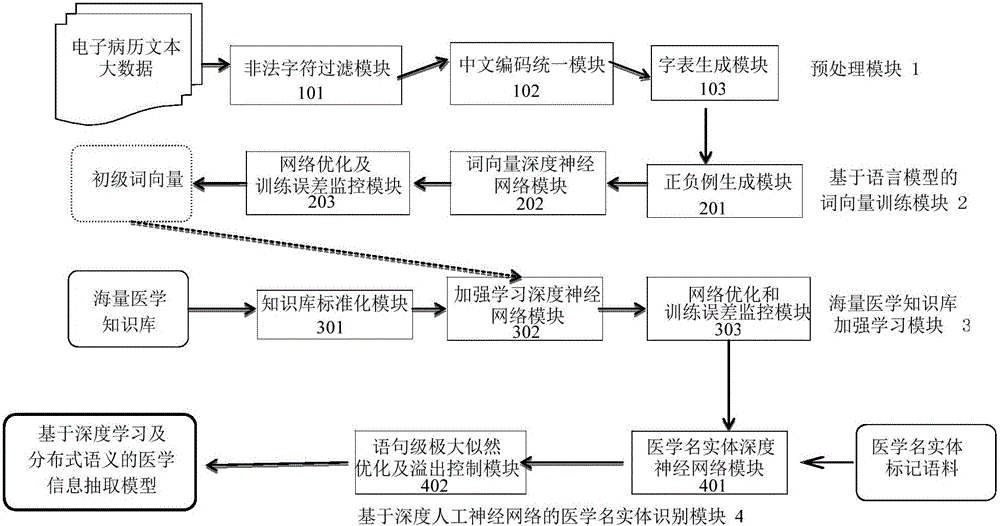
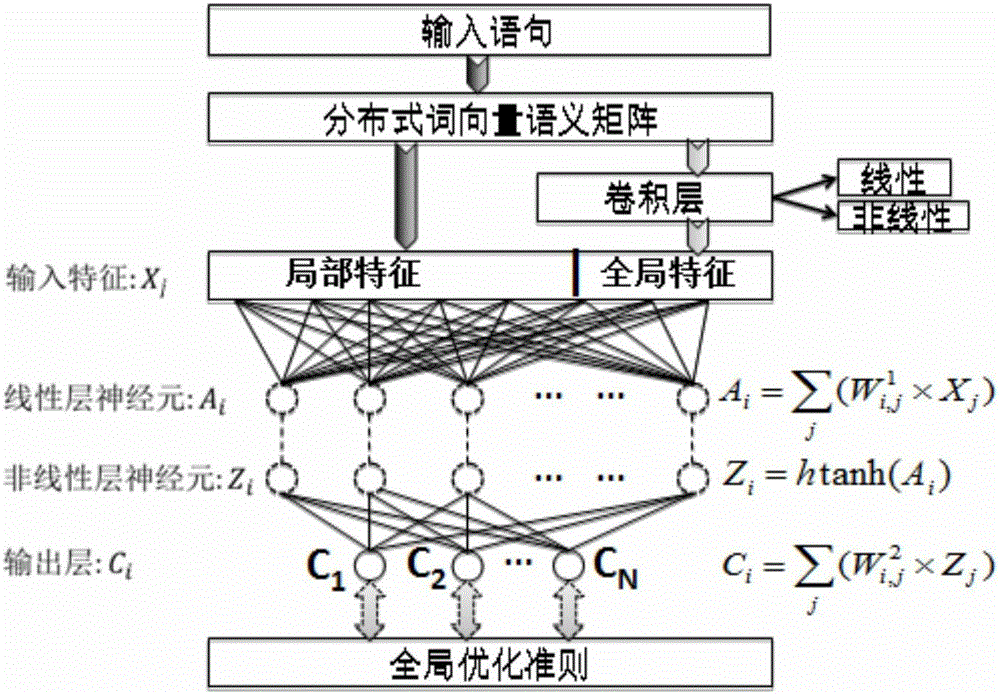
Medical information extraction system and method based on depth learning and distributed semantic features
ActiveCN105894088AAvoid floating point overflow problemsHigh precisionNeural learning methodsNerve networkStudy methods
he invention discloses a medical information extraction system and method based on depth learning and distributed semantic features. The system is composed of a pretreatment module, a linguistic-model-based word vector training module, a massive medical knowledge base reinforced learning module, and a depth-artificial-neural-network-based medical term entity identification module. With a depth learning method, generation of the probability of a linguistic model is used as an optimization objective; and a primary word vector is trained by using medical text big data; on the basis of the massive medical knowledge base, a second depth artificial neural network is trained, and the massive knowledge base is combined to the feature leaning process of depth learning based on depth reinforced learning, so that distributed semantic features for the medical field are obtained; and then Chinese medical term entity identification is carried out by using the depth learning method based on the optimized statement-level maximum likelihood probability. Therefore, the word vector is generated by using lots of unmarked linguistic data, so that the tedious feature selection and optimization adjustment process during medical natural language process can be avoided.
Owner:神州医疗科技股份有限公司 +1
Intelligent mission critical environmental monitoring and energy management system
InactiveUS20170176033A1Process safetyEnergy efficiencyProgramme controlMechanical apparatusDashboardUser management
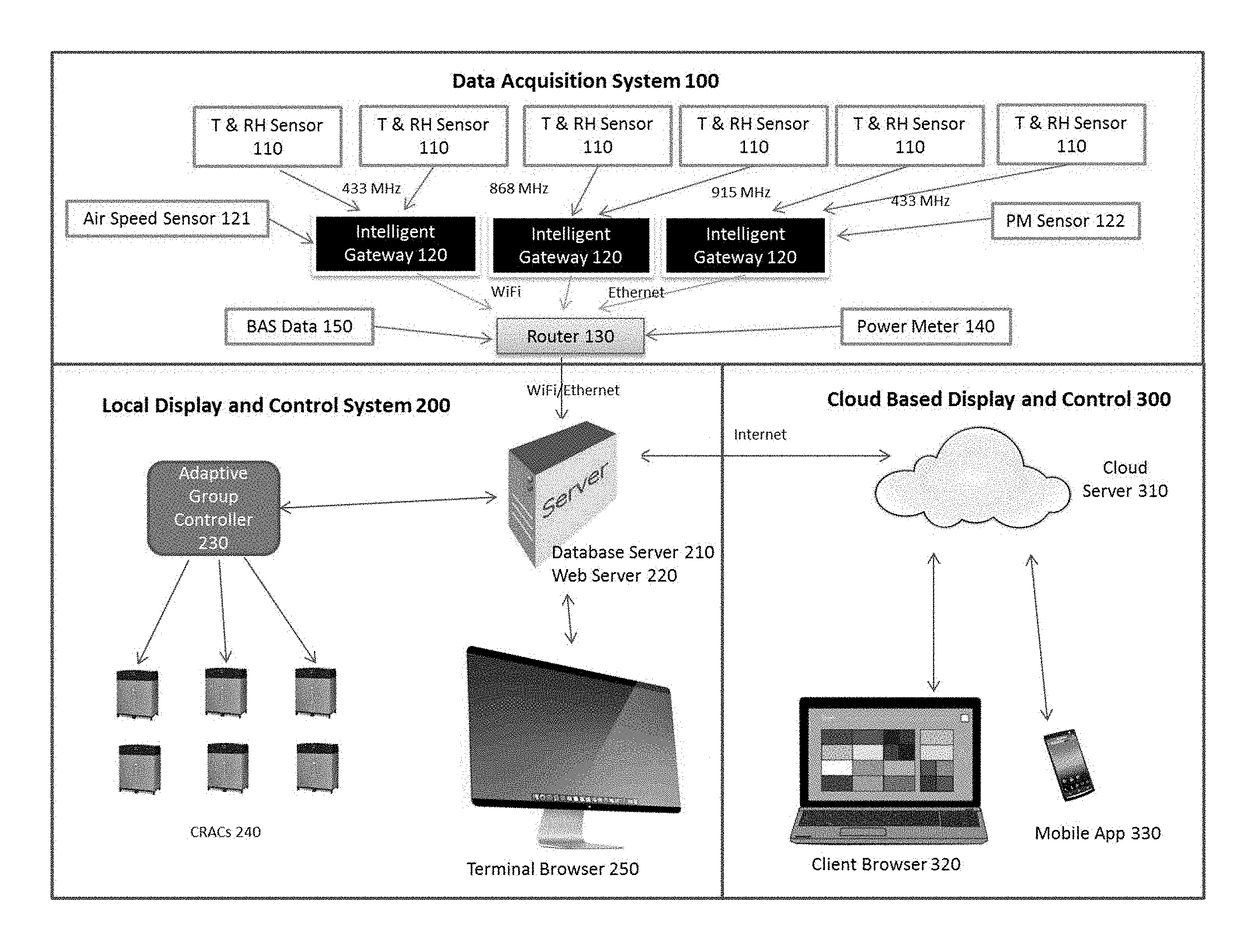
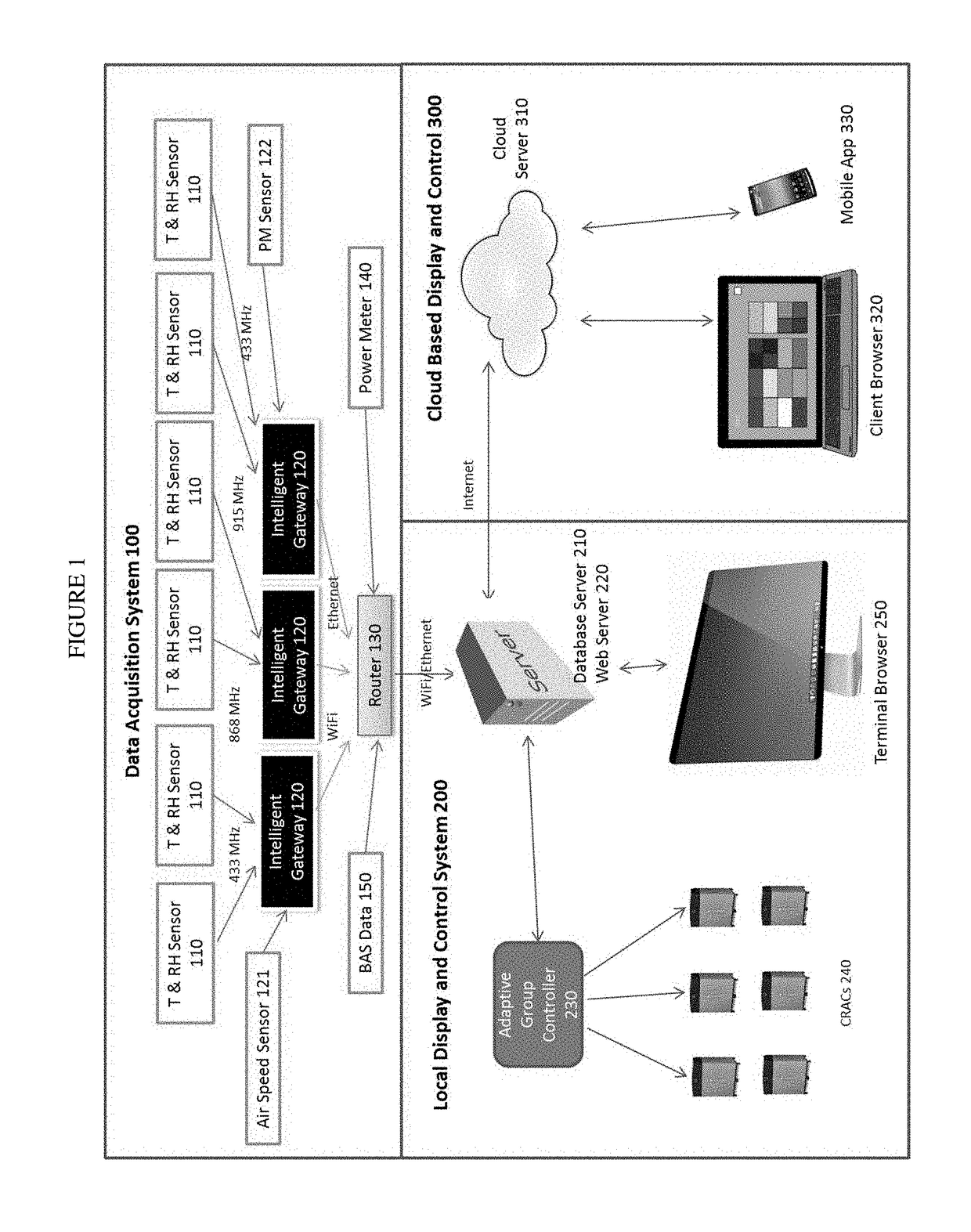
The present invention is a complete solution for mission critical facilities to create a safe environment and energy efficient CRAC system. The invented system collects mission critical facility volume environmental and energy data in real time, and uses big data analytics to provide adaptive group control to CRACs. The data is visualized in 2D and 3D graphs, dashboard, history curves and reports locally and through the cloud. The present invention also provides user management to allow authorized users to view and control the racks / servers owned or rented by these users. The present invention is comprised of four companion patents: 1) A Battery-powered Wireless Long Life Temperature and Humidity Sensor Module, 2) An Intelligent Multi-channel Wireless Data Acquisition Gateway, 3) Mission critical facility Three Dimension Temperature Contour Generator, and 4) An Adaptive Automatic CRAC Master Control Method.
Owner:ARCHIMEDES CONTROLS CORP
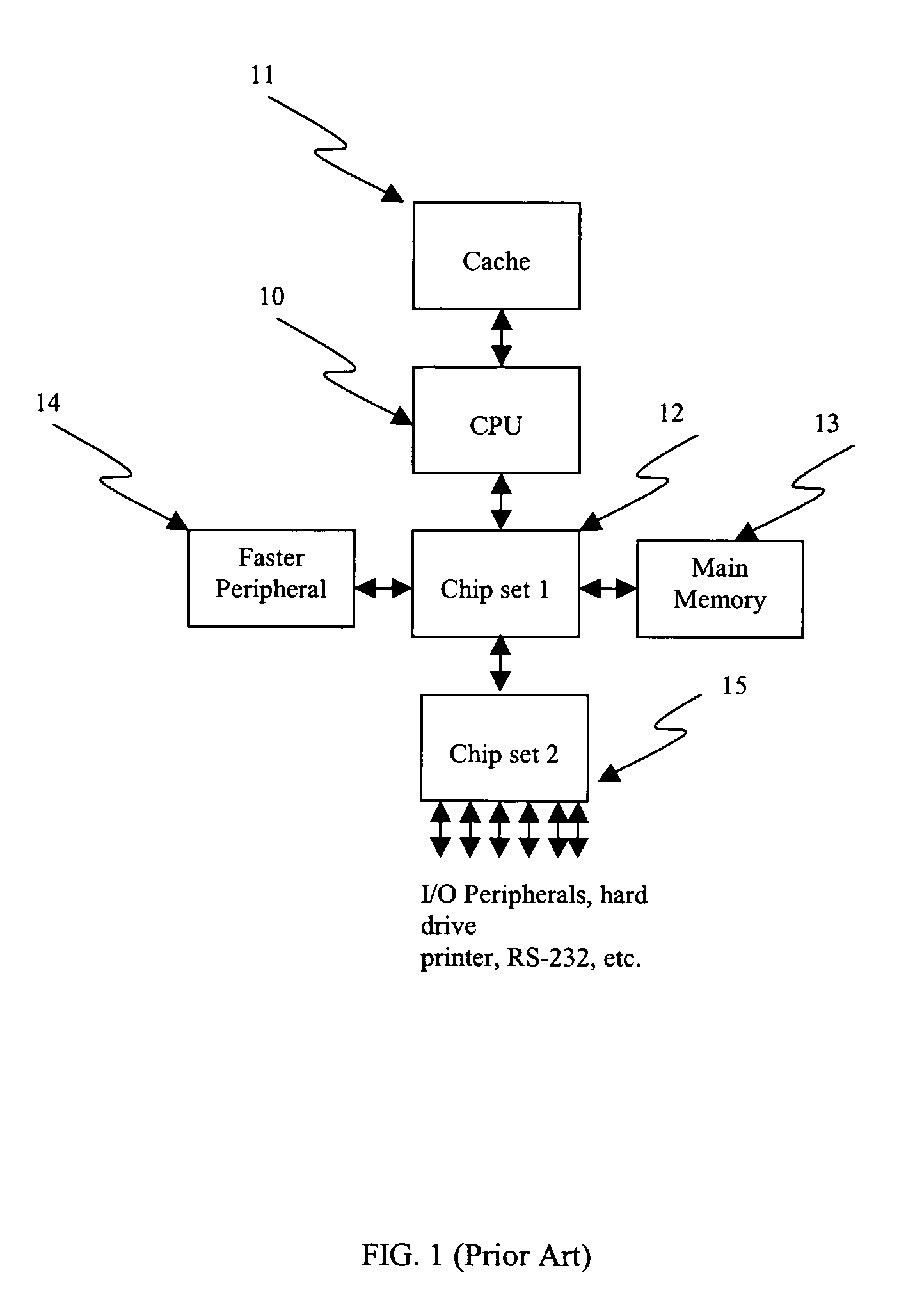
High performance hybrid micro-computer
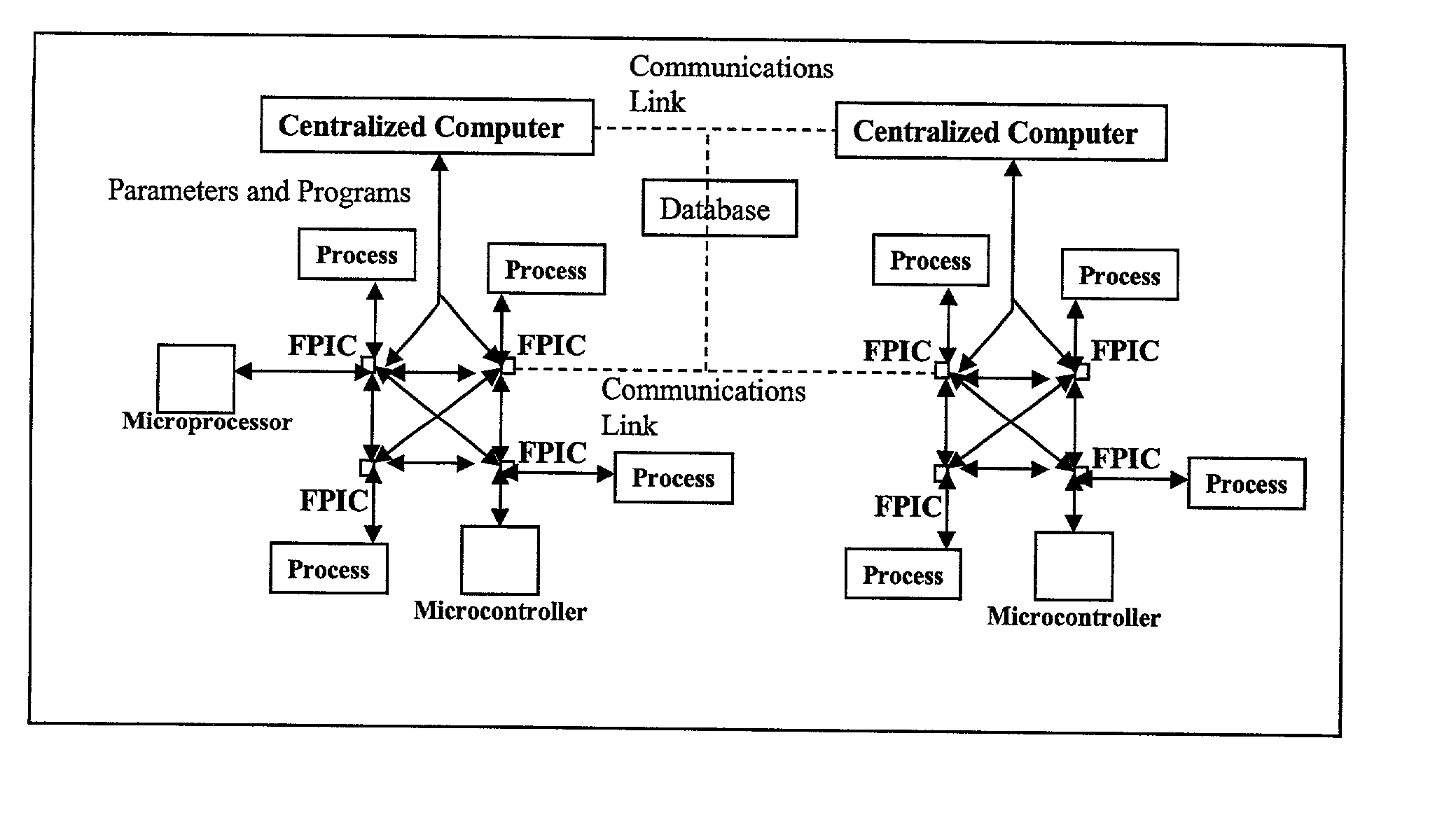
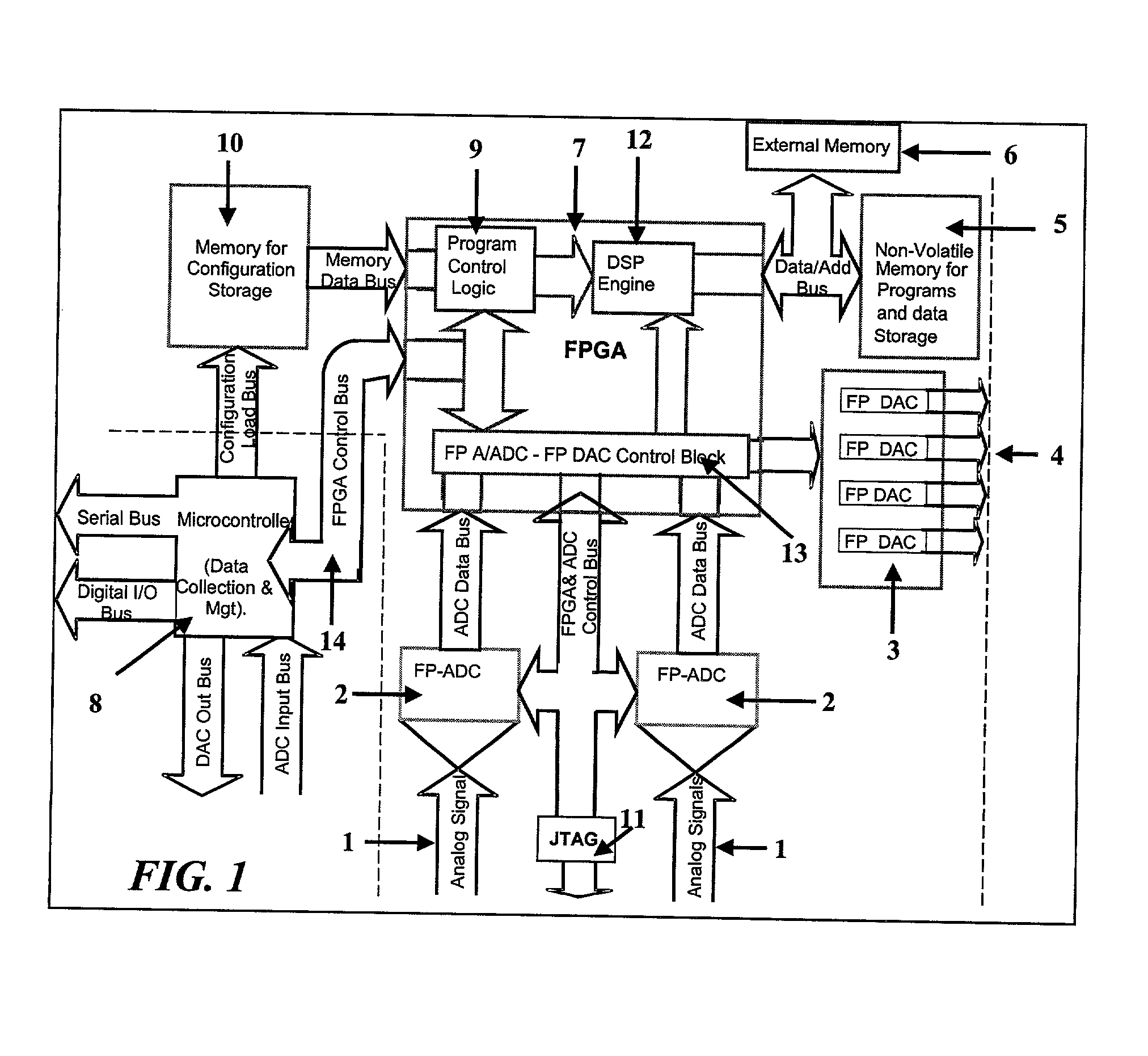
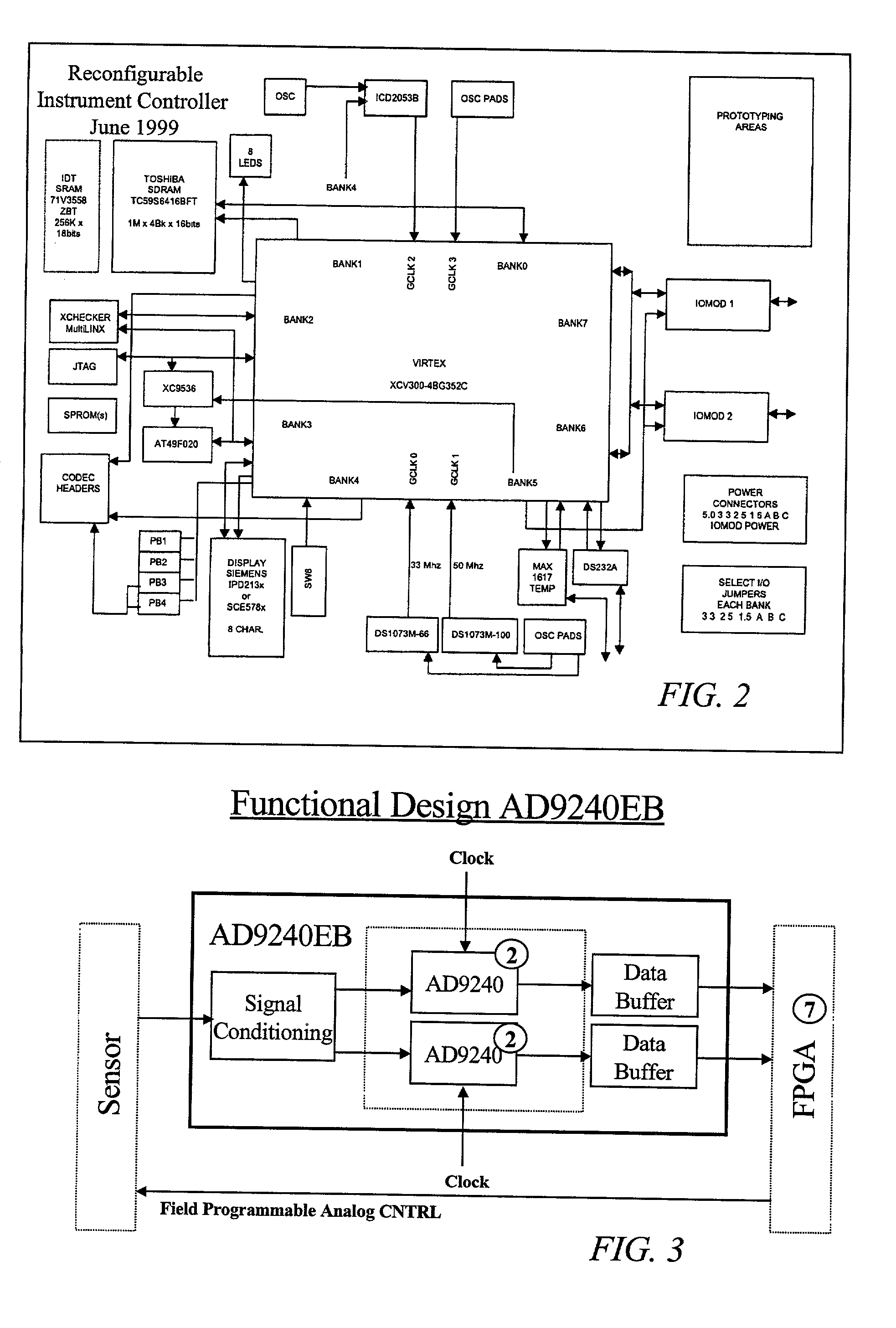
The Field Programmable Instrument Controller (FPIC) is a stand-alone low to high performance, clocked or unclocked multi-processor that operates as a microcontroller with versatile interface and operating options. The FPIC can also be used as a concurrent processor for a microcontroller or other processor. A tightly coupled Multiple Chip Module design incorporates non-volatile memories, a large field programmable gate array (FPGA), field programmable high precision analog to digital converters, field programmable digital to analog signal generators, and multiple ports of external mass data storage and control processors. The FPIC has an inherently open architecture with in-situ reprogrammability and state preservation capability for discontinuous operations. It is designed to operate in multiple roles, including but not limited to, a high speed parallel digital signal processing; co-processor for precision control feedback during analog or hybrid computing; high speed monitoring for condition based maintenance; and distributed real time process control. The FPIC is characterized by low power with small size and weight.
Owner:BLEMEL KENNETH G
Systems and methods for network transmission of big data
ActiveUS9647949B2Digital computer detailsData switching networksNetworked Transport of RTCM via Internet ProtocolData transmission
Systems and methods are described herein for providing one or more data transfer parameters. A network map of a network is stored, and input data regarding a desired data transfer is received. The input data includes a sender identifier associated with a sender node in the network, a receiver identifier associated with a receiver node in the network, and a performance metric. A time for initiating the desired data transfer is determined based on the network map, the sender identifier, the receiver identifier, and the performance metric, and the determined time is provided as a recommendation for initiating the data transfer.
Owner:UNIVERSITY OF NEW HAMPSHIRE
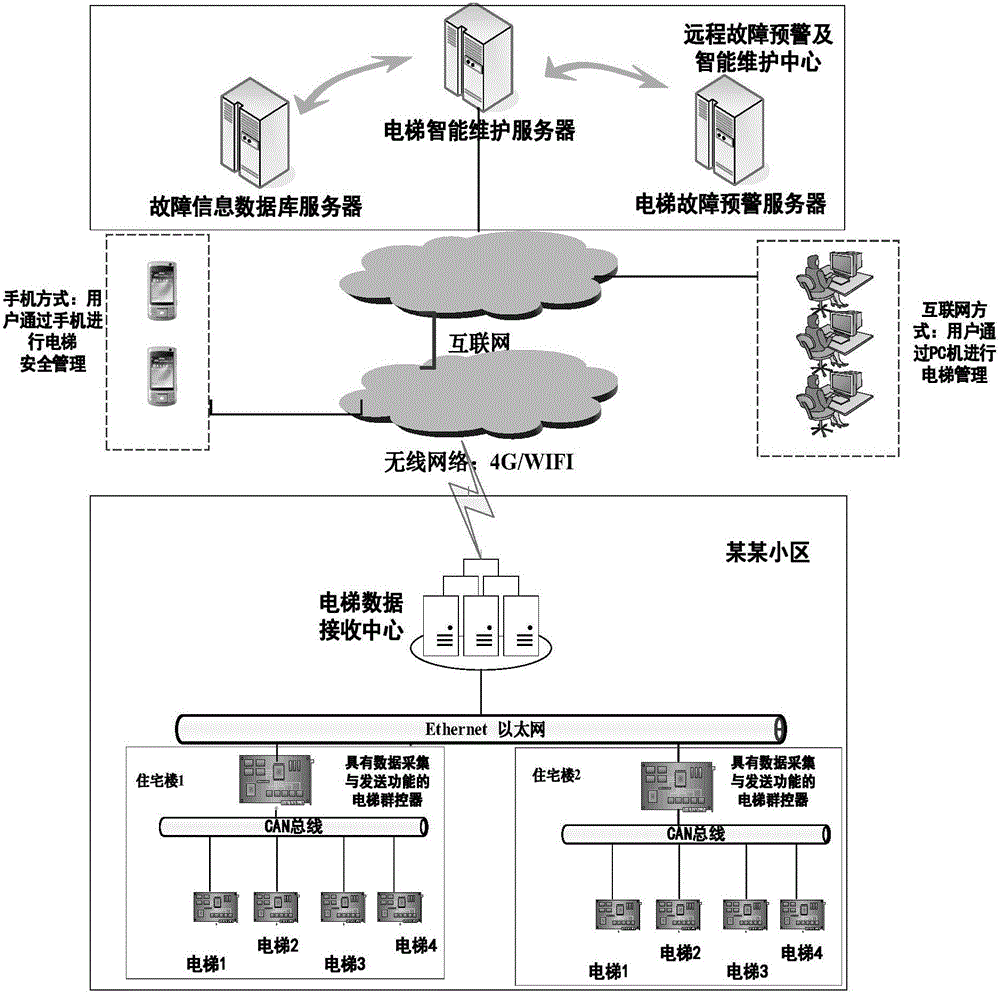
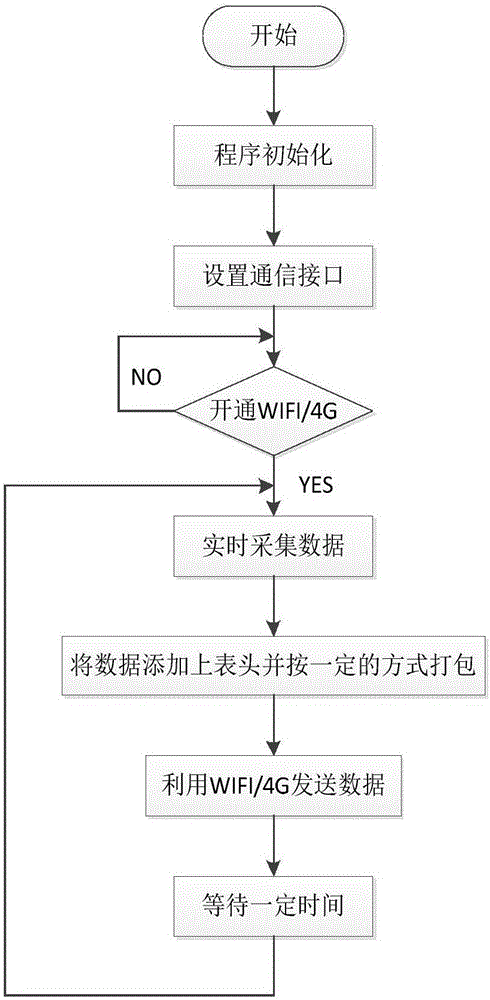
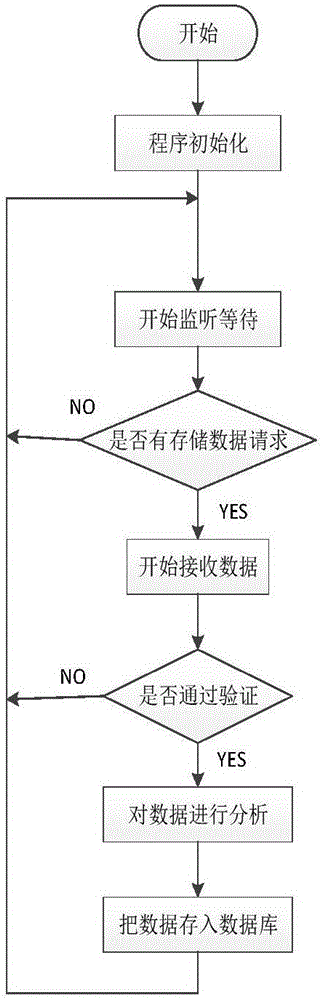
Intelligent prediction, diagnosis and maintenance method for elevator faults on basis of Internet of Things
The invention relates to the elevator control field and the field of the Internet of Things, and provides an intelligent prediction, diagnosis and maintenance system for elevator faults on the basis of the Internet of Things. The intelligent prediction, diagnosis and maintenance system can effectively shorten the time of elevator halt caused by the elevator faults, improve the reliability of elevator running and the elevator maintenance efficiency and guarantee the personal safety and the property safety. According to the technical scheme of an intelligent prediction, diagnosis and maintenance method for the elevator faults on the basis of the Internet of Things, a data acquisition module collects elevator data in real time and transmits the collected data to a server through WIFI or the 4G wireless communication technology, the data are analyzed on the server side through the big data technology, and therefore the elevator faults which are possibly to occur can be predicted; if the elevator faults occur, a fault diagnosis system on the server side can be used for analyzing the faults, then the positions and the reasons of the faults can be provided, and then an intelligent maintenance system on the server side provides solutions to the faults. The intelligent prediction, diagnosis and maintenance method is mainly applied to the elevator control occasion.
Owner:TIANJIN UNIV
Tamper resistant software-mass data encoding
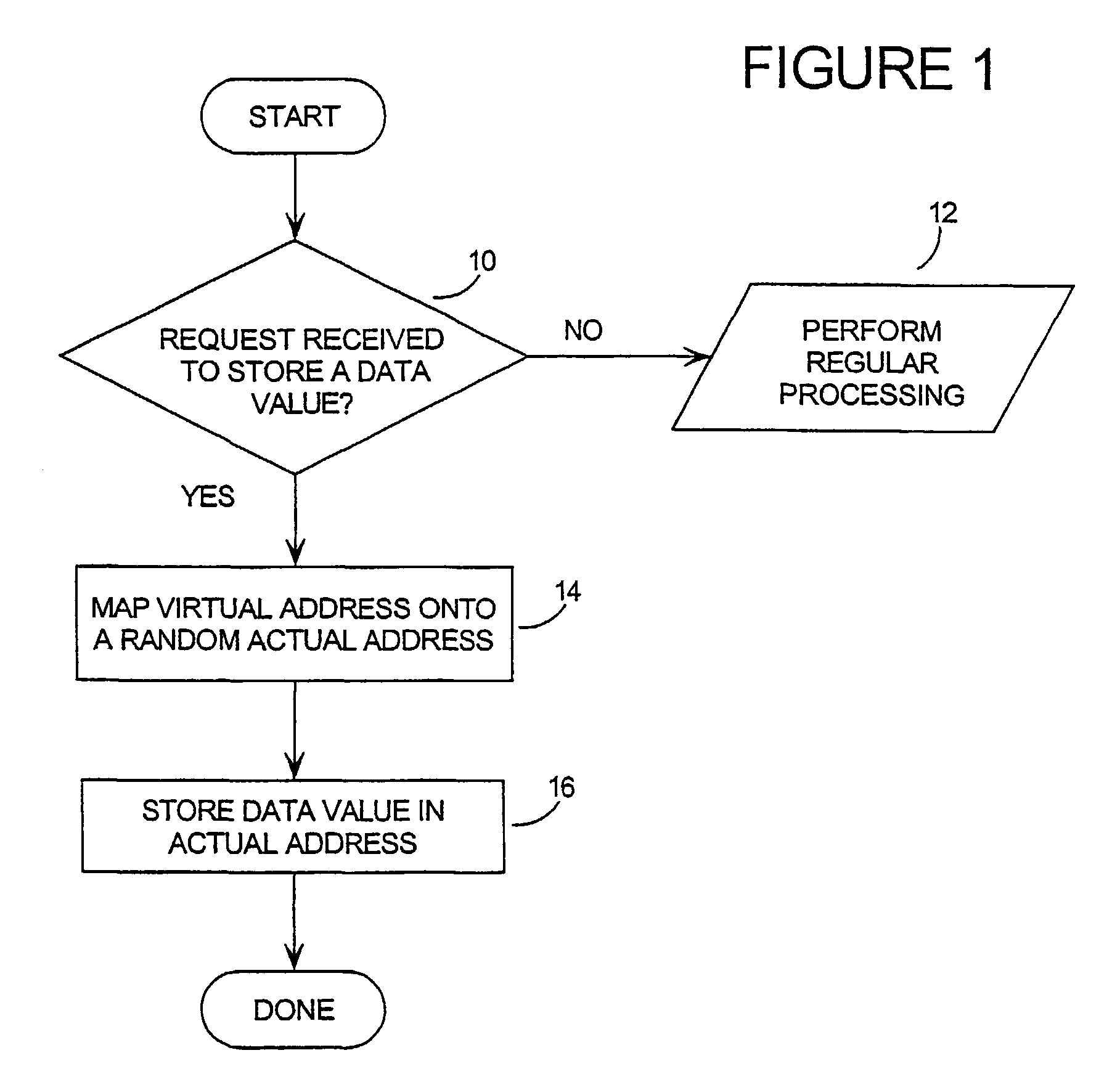
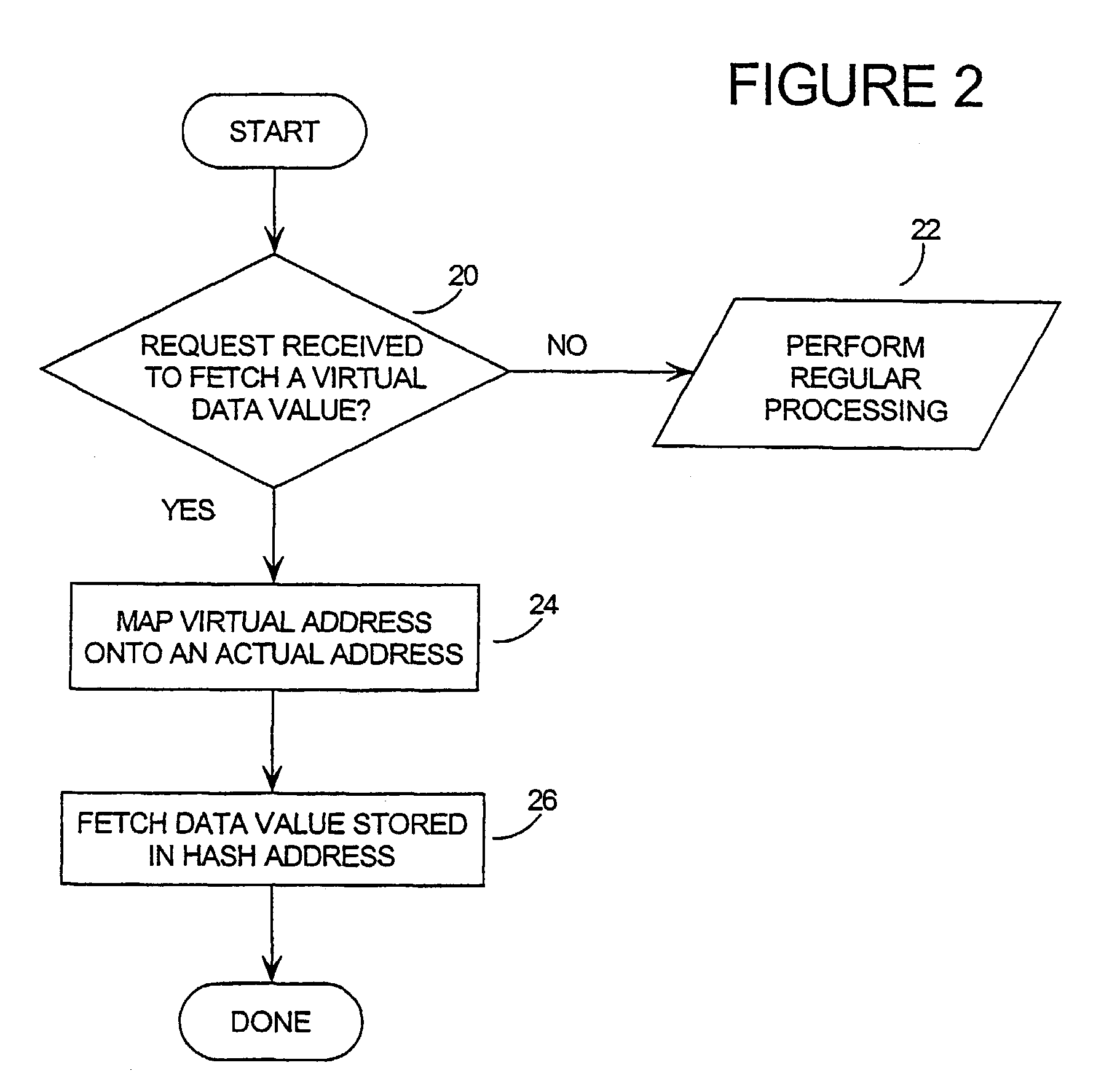
InactiveUS7350085B2Unauthorized memory use protectionHardware monitoringArray data structureBiometric data
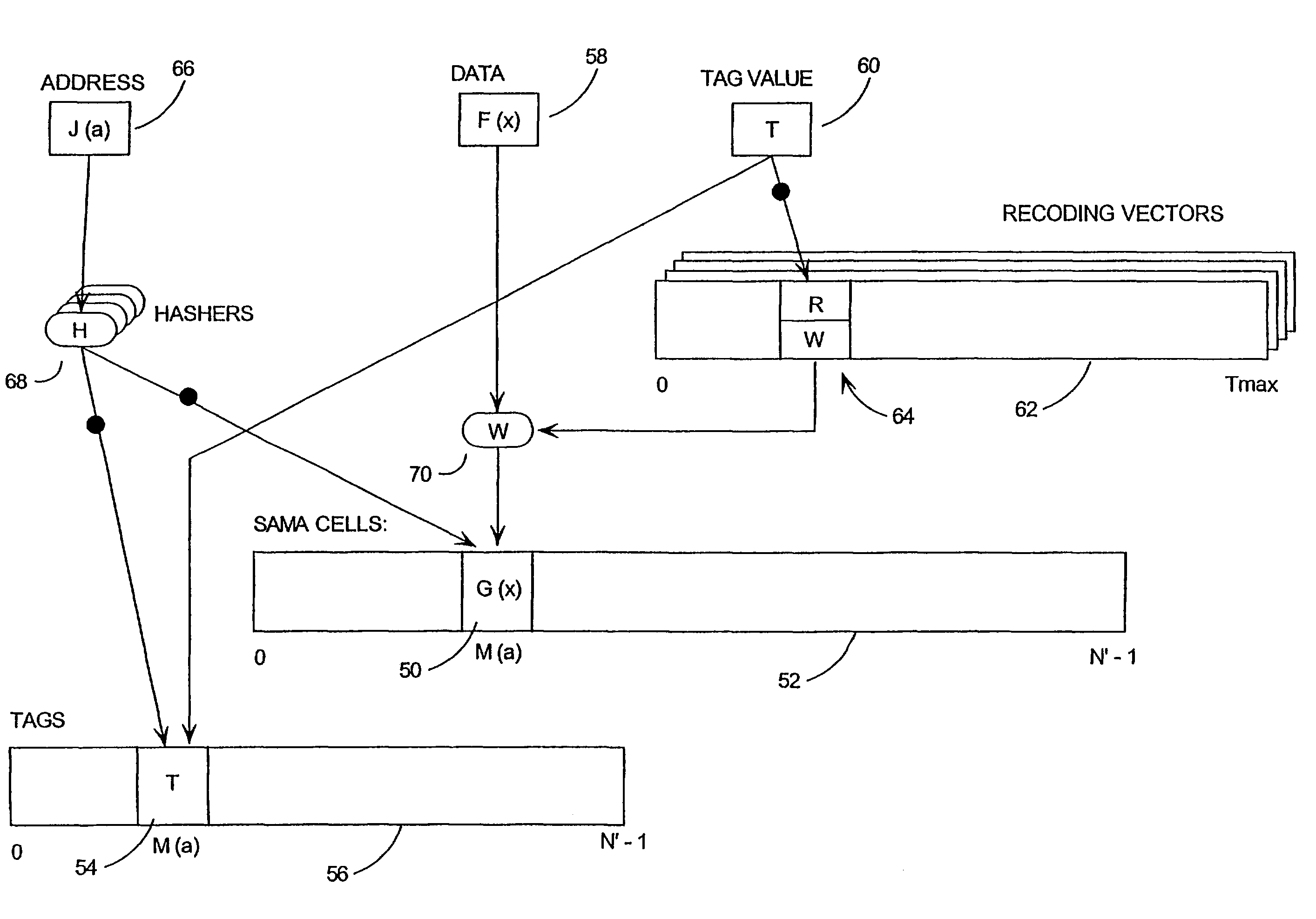
Mass data (the contents of arrays, large data structures, linked data structures and similar data structures stored in memory) are common targets for attack. The invention presents a method and system of protecting mass data by mapping virtual addresses onto randomly or pseudo-randomly selected actual addresses. This mapping distributes data values throughout the memory so an attacker cannot locate the data he is seeking, or identify patterns which might allow him to obtain information about his target (such as how the software operates, encryption keys, biometric data or passwords stored therein, or algorithms it uses). Additional layers of protection are described, as well as efficient techniques for generating the necessary transforms to perform the invention.
Owner:IRDETO ACCESS
Intelligent instrumented air cleaner
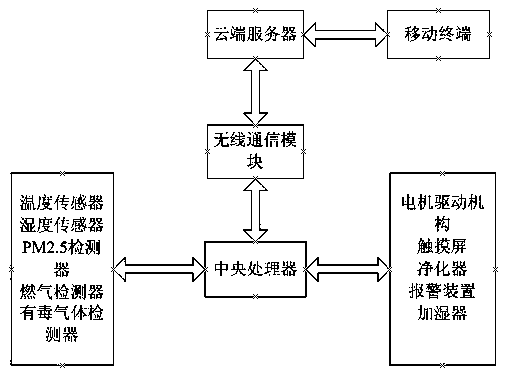
InactiveCN104075422AIncrease the fun of usePurifying airSpace heating and ventilation safety systemsLighting and heating apparatusThe InternetMulti feature
An intelligent instrumented air cleaner comprises a multi-functional sensor, a central processor, a cloud server, a wireless communication module, a purification device, an alarm device, a motor driving mechanism and a humidifier. According to the intelligent instrumented air cleaner, updating and exchange of memory data are realized through the connection between the wireless communication module and a cloud server of the Internet of Things, the air cleaner is controlled through the connection between a mobile device and the cloud server so that a remote controller can be replaced, remote network control is also realized, the cloud server also has an analysis function and a processing result advice providing function and sends processed data to users for reference, the users can set the working state of the air cleaner by themselves and define working strategies by themselves, the air cleaner saves the strategies automatically and performs actions according to the strategies, and self-selection of self-learning setting optimization is conducted on the data in a memory through big data analysis and processing. By the adoption of the intelligent instrumented air cleaner, an intelligent instrumented household net and an intelligent instrumented office net are realized in the true sense, air is purified, safe and reliable living and working environments are provided, useless consumption of electric energy of a traditional air cleaner is avoided, energy consumption is reduced, using pleasure of a user is improved, the parameters of the environment where the user is located are provided for the user in time, and reliable parameters and solutions are provided for environment change handling.
Owner:刘明湖
Network safety situation awareness early-warning method and system based big data
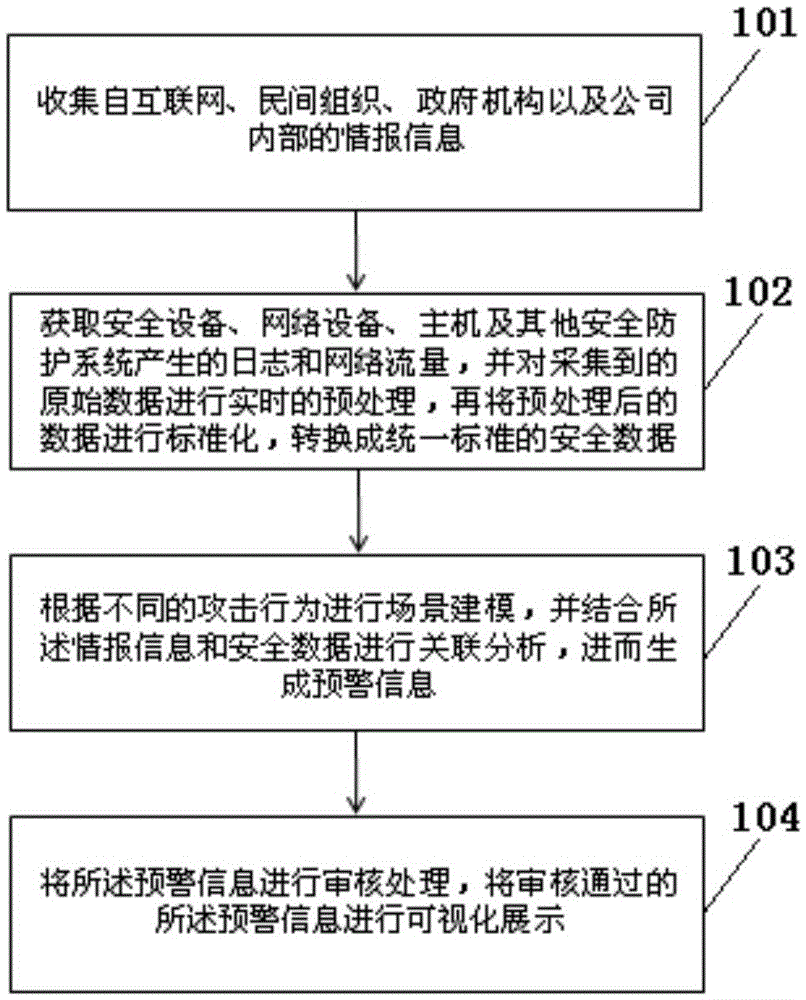
InactiveCN105553957AReal-time online detectionAdvanced APT attackTransmissionOriginal dataElectric power system
The invention discloses a network safety situation awareness early-warning method and system based big data, and the method comprises the steps: collecting intelligence information from the Internet, non-governmental organizations, governmental agencies and interiors of companies; obtaining log and network flow generated by safety equipment, network equipment, a host and other safety protection systems, carrying out the real-time preprocessing of the collected original data, carrying out the standardization of the data after preprocessing, and converting the data into safety data with the unified standard; carrying out scene modeling according to different attack behaviors, carrying out correlation analysis through combining with the intelligence information and the safety data, and generating early-warning information; carrying out the check processing of the early-warning information, and carrying out the visualized display of the early-warning information after check. The method can achieve the complete sensing of a safety situation, the early warning of safety threats and the capability of timely handling and responding of a safety event, and improves the overall safety protection capability of a power system.
Owner:STATE GRID CORP OF CHINA +1
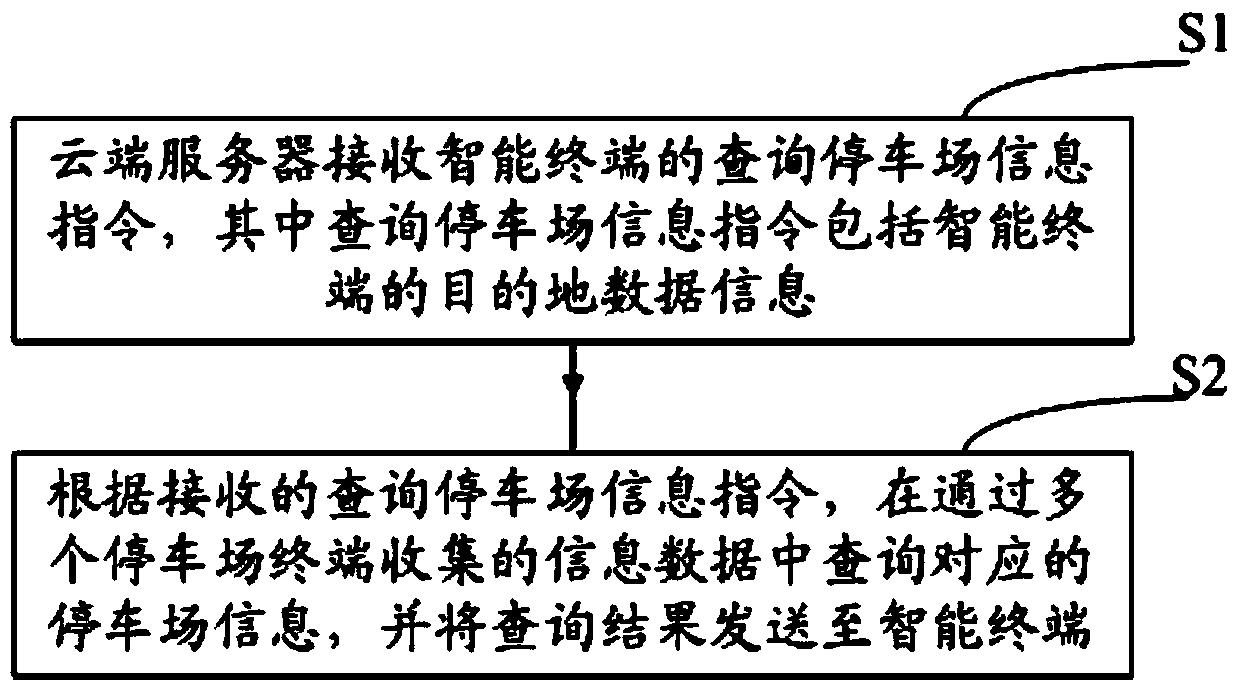
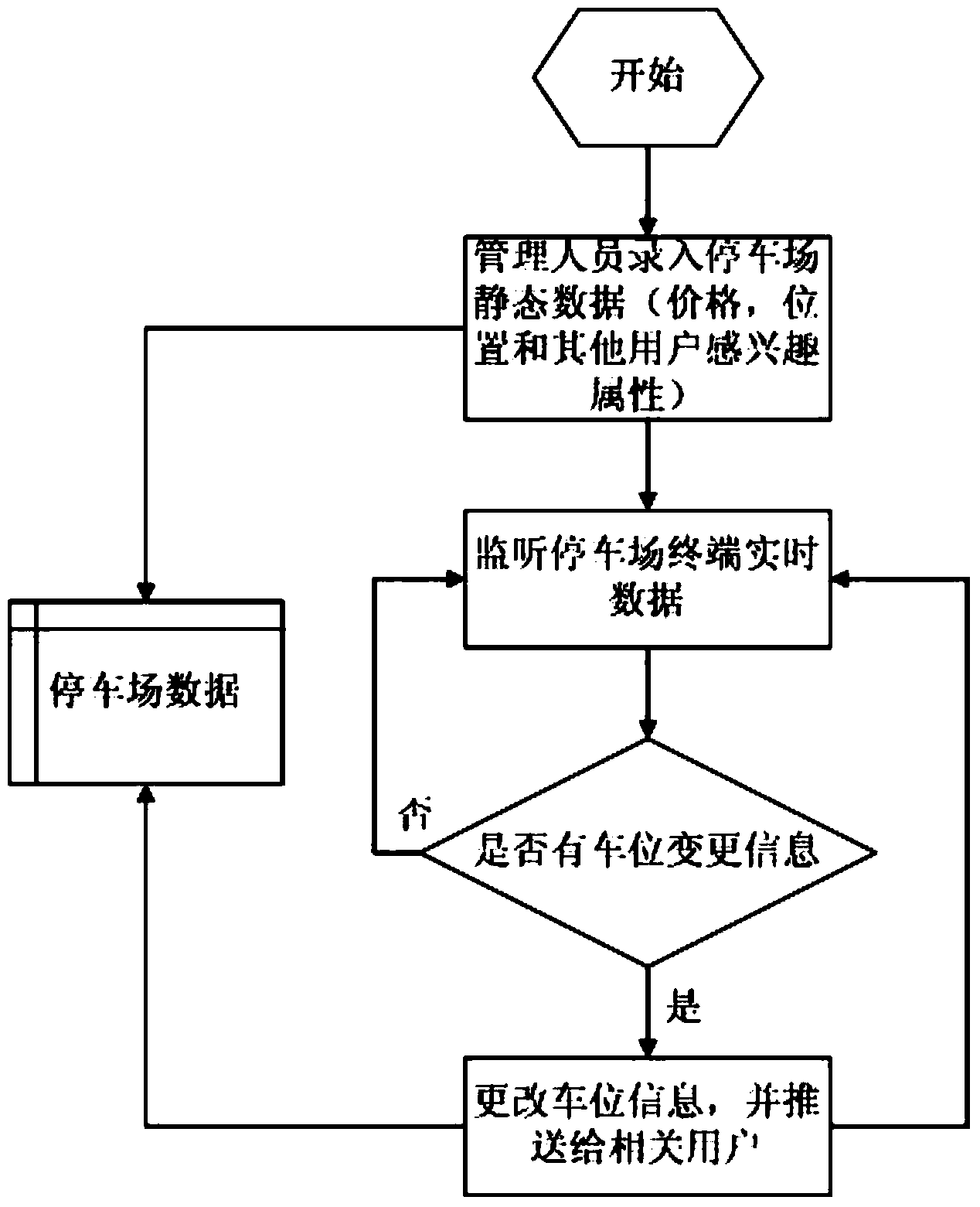
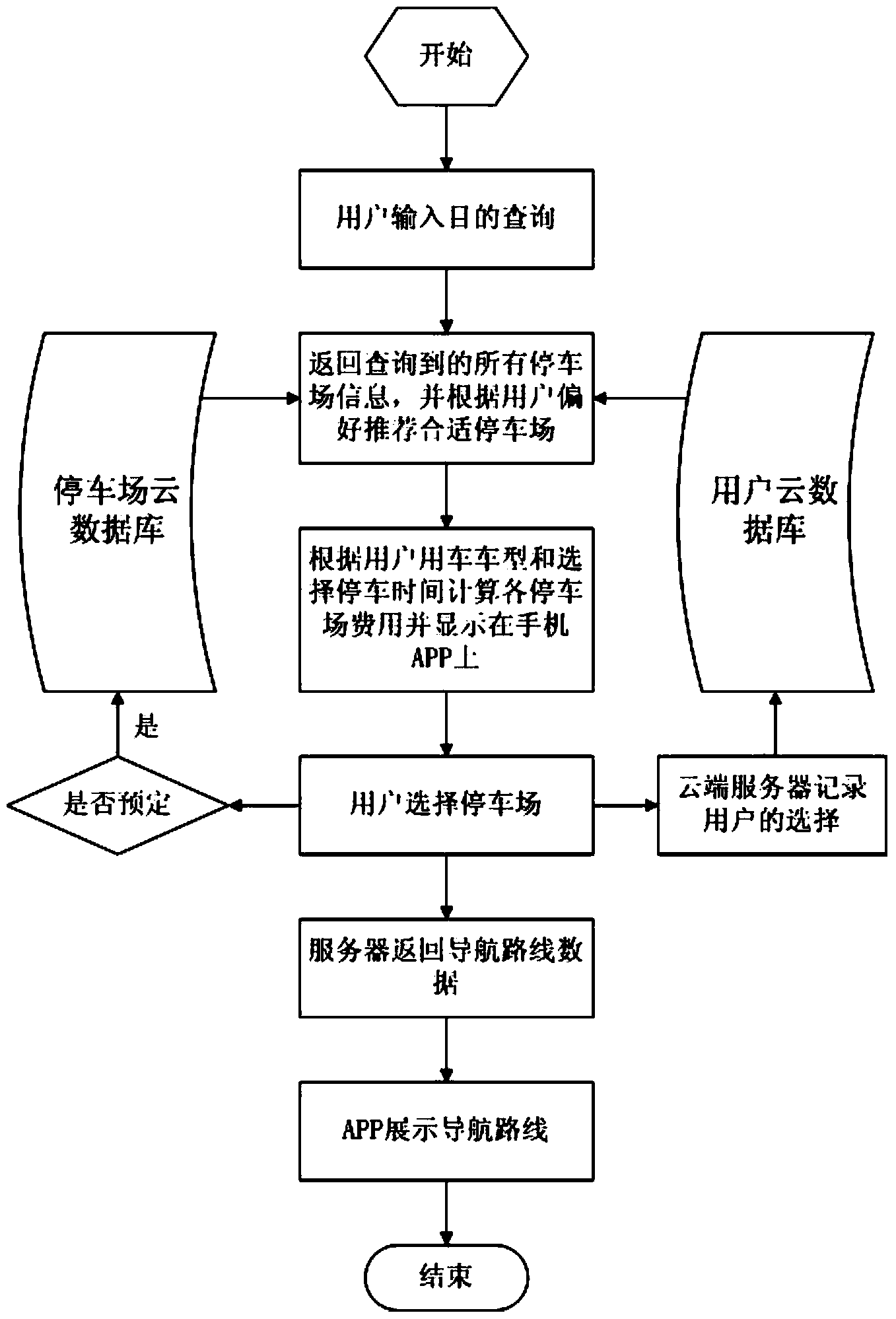
Cloud computing and big data-based parking method and system
InactiveCN103871270AEasy to handleImprove parking efficiencyIndication of parksing free spacesSpecial data processing applicationsParking areaData information
The invention discloses a cloud computing and big data-based parking method and system. The method comprises the steps: a cloud server receives parking lot information query instruction of an intelligent terminal, wherein the parking lot information query instruction comprises destination data information of the intelligent terminal; according to the received parking lot information query instruction, information data collected through a plurality of parking lot terminals is searched for corresponding parking lot information, and query results are sent to the intelligent terminal. According to the cloud computing and big data-based parking method and system, a car owner can quickly and comprehensively learn about the information of charge of a parking lot nearby the destination, real-time available parking spaces and the like; by comprehensively analyzing factors, such as weather, road conditions, major events which affect the traffic nearby the destination, and parking lot selection of car owners who frequently park nearby, the optimal parking lot and path are provided for the user, thus, the car owner can quickly make a wise selection even in a strange place or environment, and the parking efficiency can be improved.
Owner:张剑锋
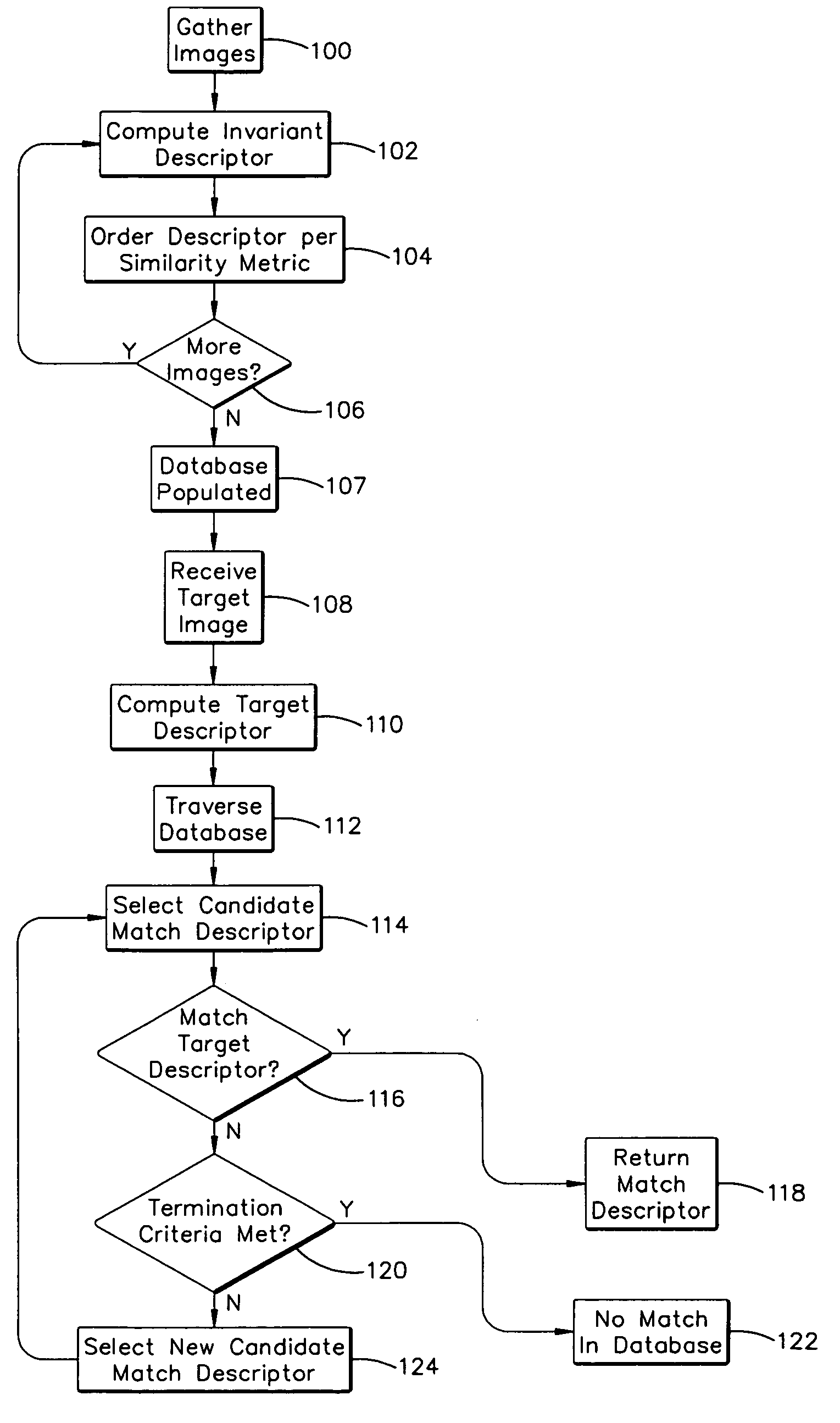
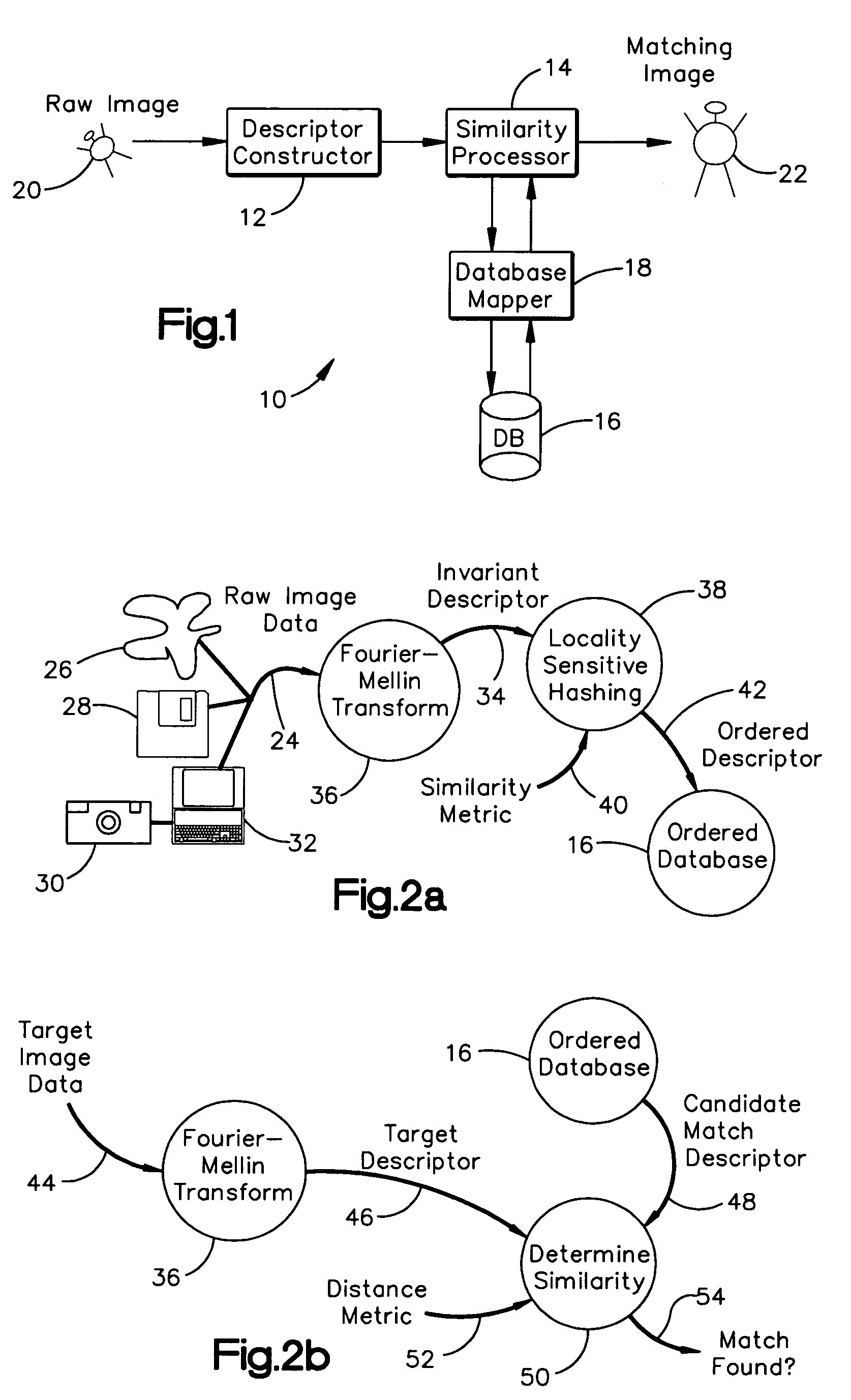
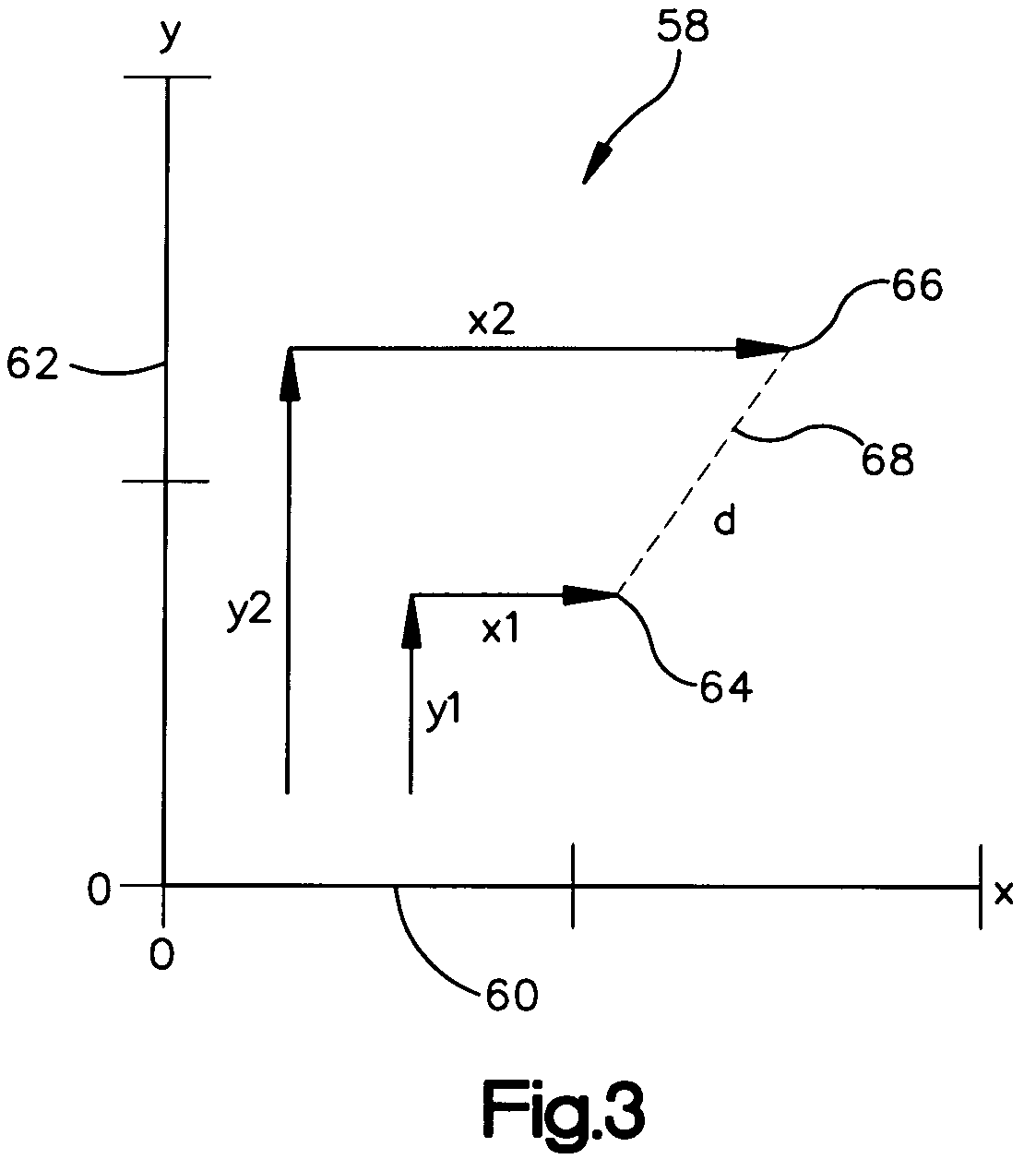
System and method for efficiently finding near-similar images in massive databases
Massive amounts of multimedia data are stored in databases supporting web pages and servers, including text, graphics, video and audio. Searching and finding matching multimedia images can be time and computationally intensive. A method for storing and retrieving image data includes computing a descriptor, such an a Fourier-Mellin Transform (FMT), corresponding to a multidimensional space indicative of each of the stored images and organizing each of the descriptors according to a set similarity metric. The set similarity metric is based on Locality-Sensitive Hashing (LSH), and orders descriptors near to other descriptors in the database. The set similarity metric employs set theory which allows distance between descriptors to be computed consistent with LSH. A target image for which a match is sought is then received, and a descriptor indicative of the target image is computed. The database is referenced, or mapped, to determine close matches in the database. Mapping includes selecting a candidate match descriptor from among the descriptors in the database and employing a distance metric derived from the similarity metric to determine if the candidate match descriptor is a match to the target descriptor.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
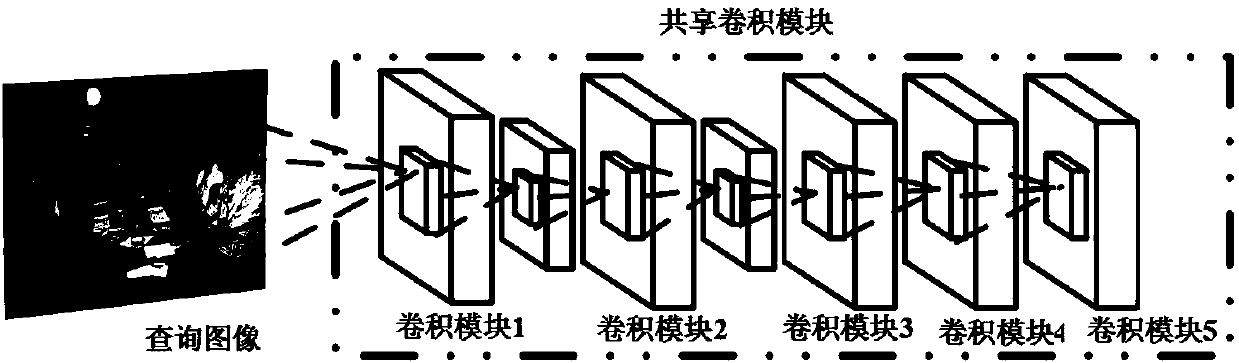
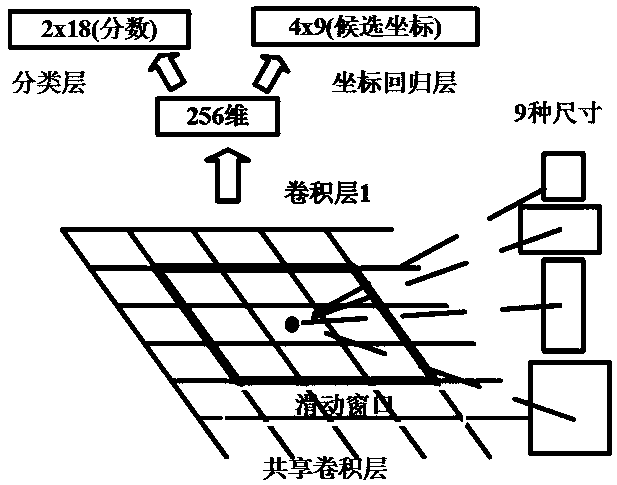
Multi-task layered image retrieval method based on depth self-coding convolution neural network
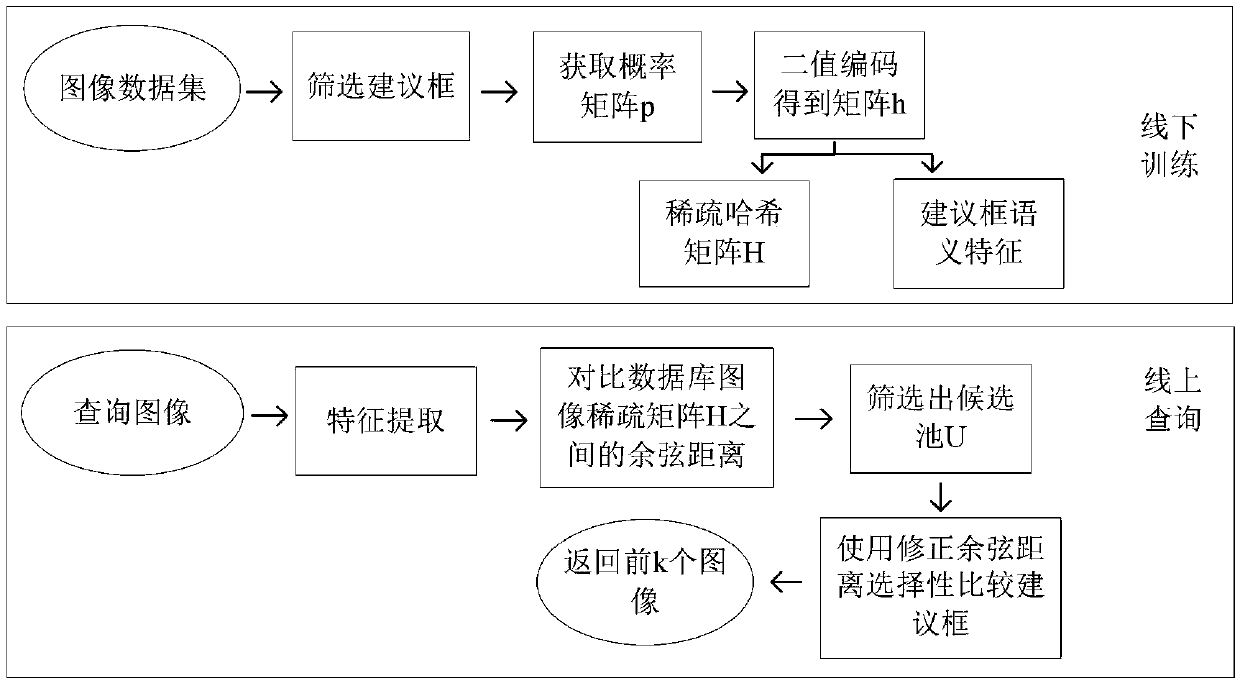
ActiveCN107679250ASearch results improvedSearch results are accurateCharacter and pattern recognitionNeural architecturesNerve networkImage retrieval
The invention discloses a multi-task layered image retrieval method based on a depth self-coding convolution neural network. The method is characterized by mainly comprising a multi-task end-to-end convolution neural network for deep learning and training recognition, a rapid visual segmentation detection and positioning method of a region-of-interest secondary screening module based on an RPN network, a coarse search of a full-graph sparse hash code, an area sensing semantic feature and matrix h accurate comparison and search based on the maximum response, and a region-of-interest selectivitycomparison algorithm. According to the method, the end-to-end training can be achieved, the interest region with higher quality can be automatically selected, the automation degree and the intelligent level of search by images can be effectively improved, and the image retrieval requirements of the big data age can be met by using little storage space at a high search speed.
Owner:ZHEJIANG UNIV OF TECH
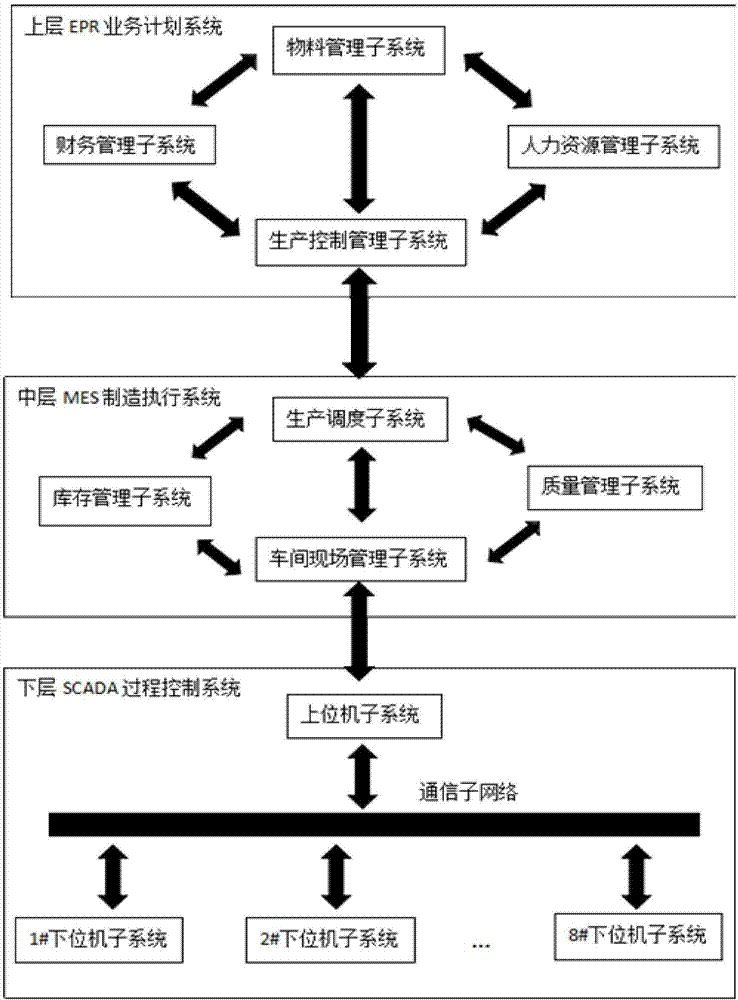
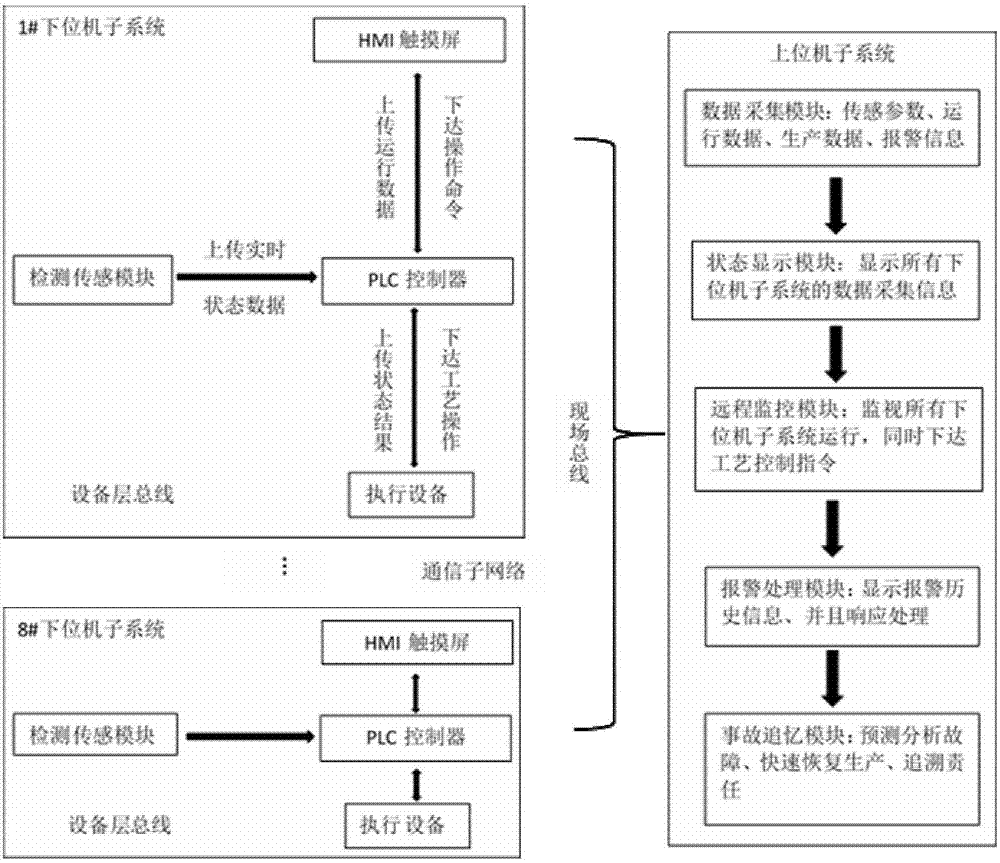
Intelligent factory system based on internet of things technology and industrial big data
InactiveCN107272629AIncrease productionReduce energy consumptionTechnology managementTotal factory controlManufacture execution systemReal time analysis
The invention relates to the field of intelligent production and manufacturing management technology, particularly to an intelligent factory system based on the internet of things technology and industrial big data. The intelligent factory system comprises a lower SCADA process control system, an intermediate MES manufacturing execution system, and an upper ERP business planning system. Therefore, problems of difficult real-time analysis and calculation, difficult accident tracing and restoration, high non-planned parking frequency, low work production efficiency, difficult non-transparent decision-making and difficult cooperation among the regional personnel are solved so as to improve the product output, reduce energy consumption and reduce the cost; the a humanized intelligent factory with equipment intelligence, modern management, and information computerization is established truly; and the core competitiveness of enterprise is enhanced.
Owner:科睿特软件集团股份有限公司
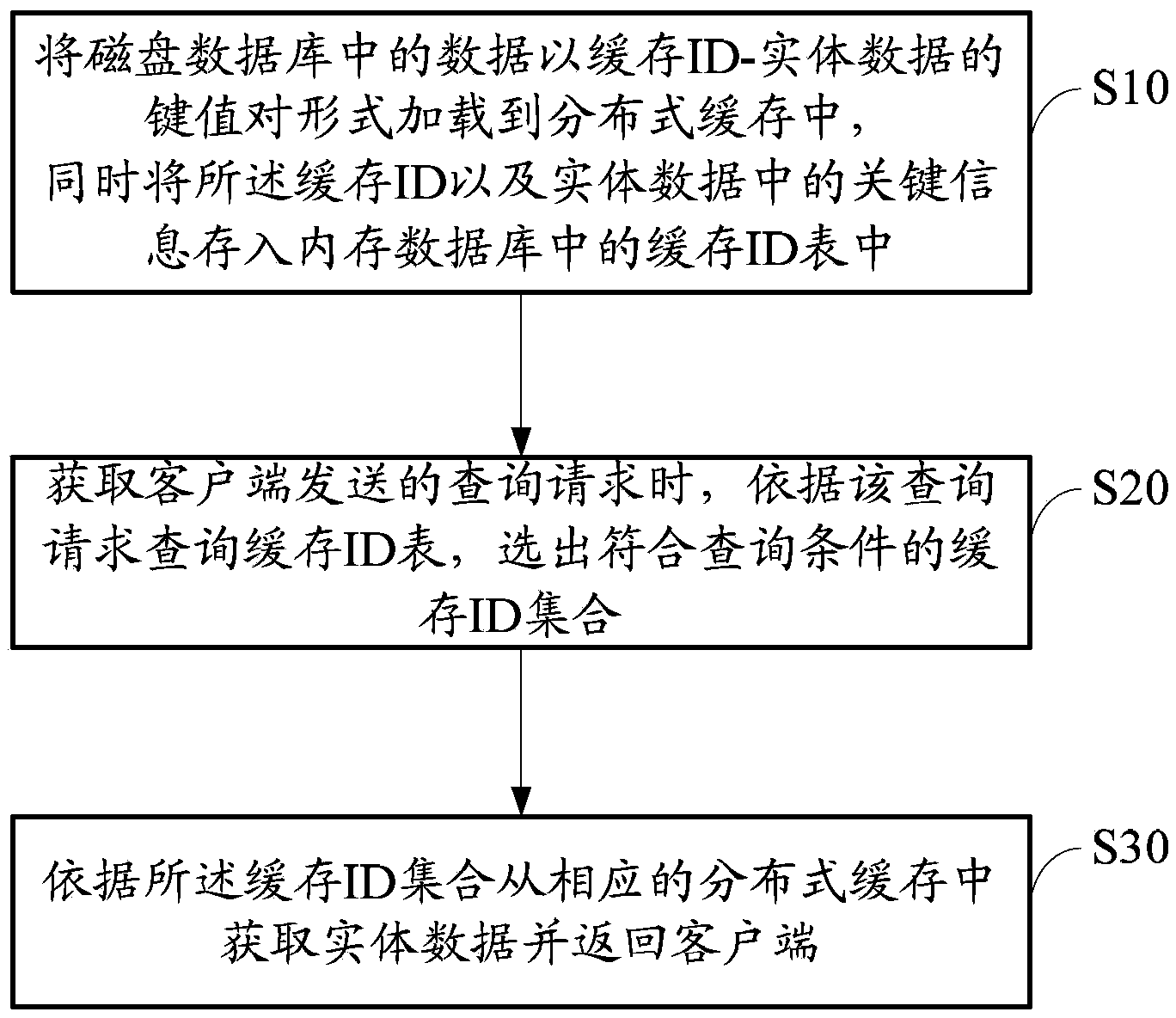
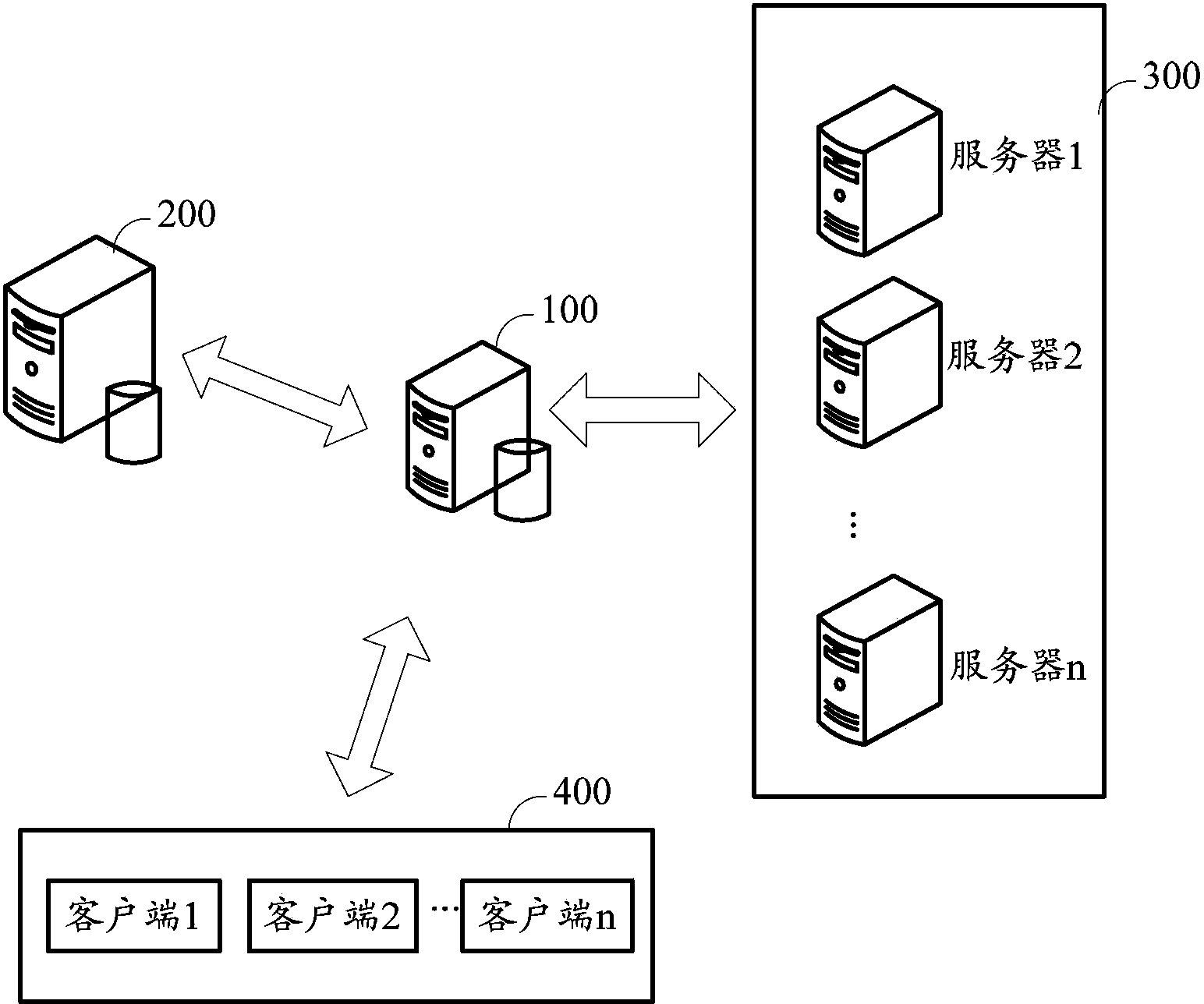
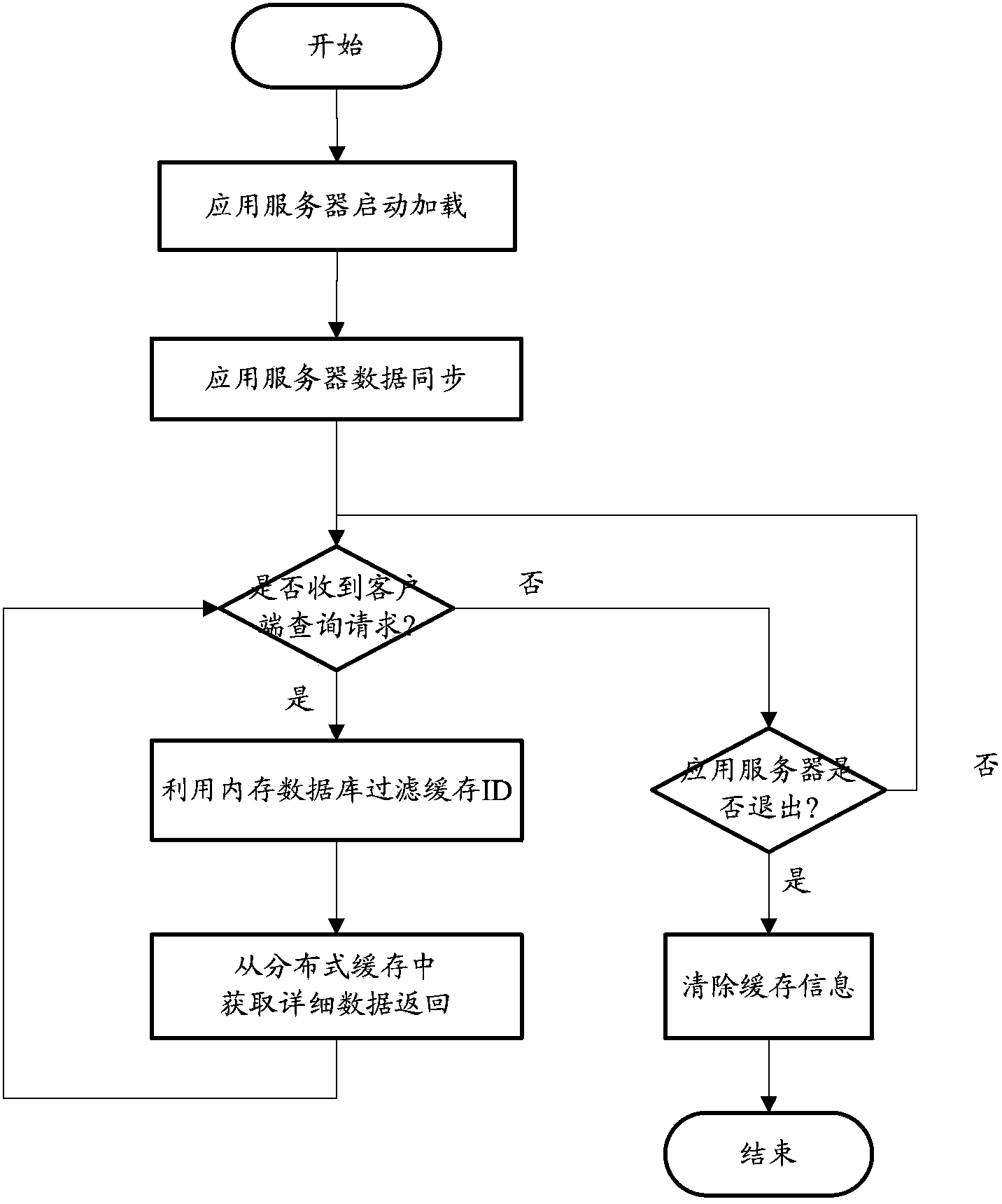
Method and system for improving large data volume query performance
ActiveCN103853727AReduce loadEasy to handleMemory adressing/allocation/relocationDatabase distribution/replicationIn-memory databaseDistributed cache
The invention discloses a method and a system for improving the large data volume query performance and belongs to the technical field of large data volume query. The method comprises A, loading data in a disk database into distributed caches in a cache ID-entity data key value pair mode, and storing the cache ID and key information of the entity data in a cache ID table of a memory database simultaneously; B, querying the cache ID table according to a query request when the query request sent by a client is obtained to selecting an ID set meeting the query request; C, obtaining the entity data from corresponding distributed caches according to the cache ID set and returning the entity data to the client. By means o the system and the method, loads of the disk database can be effectively reduced, and the big data query performance is improved.
Owner:SHENZHEN ZTE NETVIEW TECH
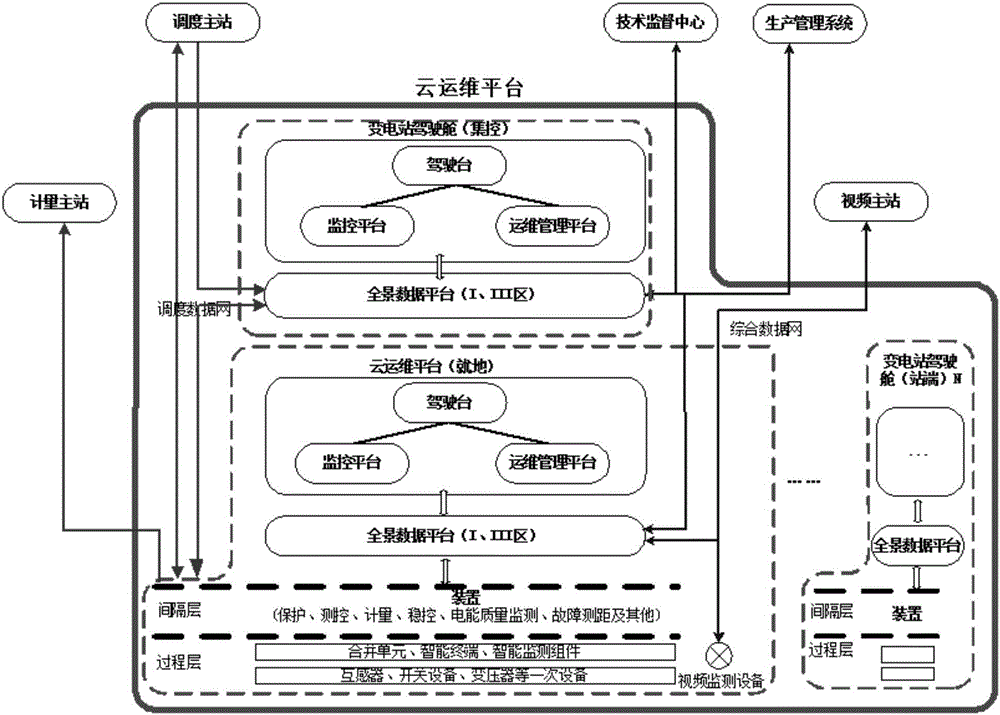
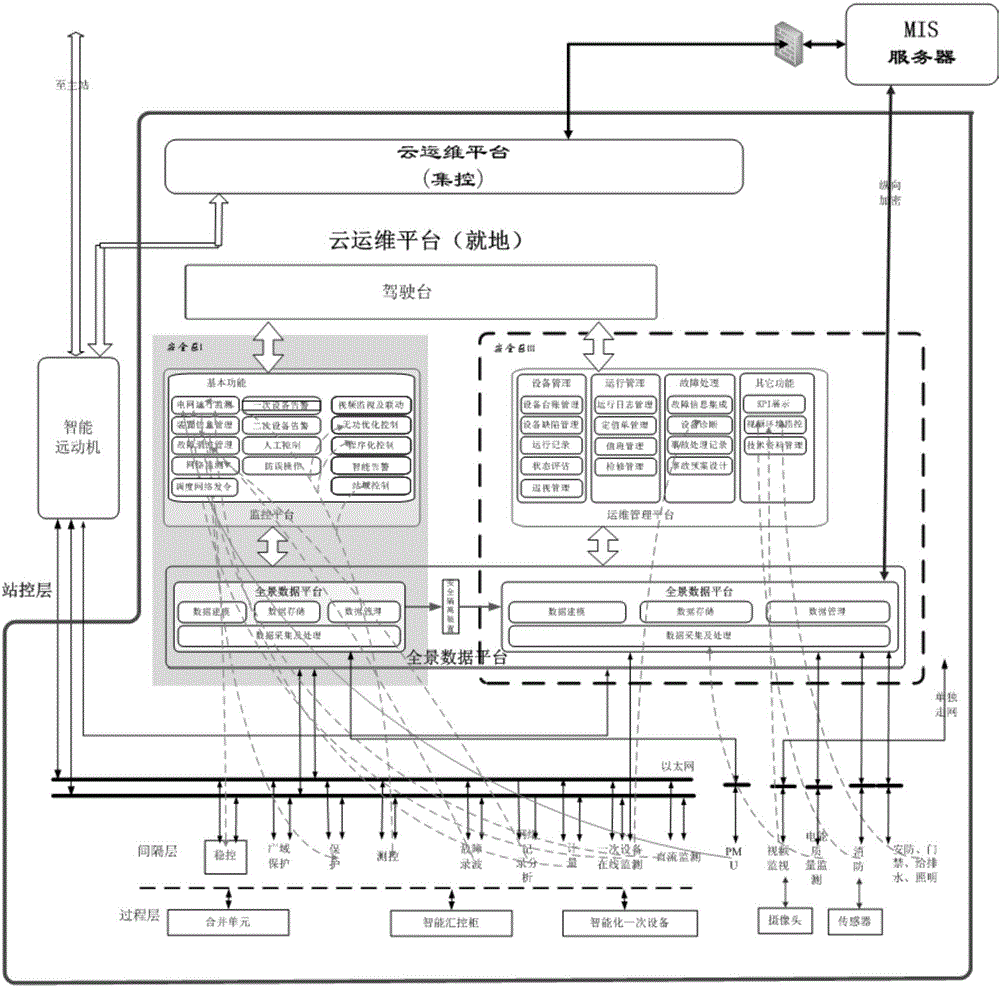
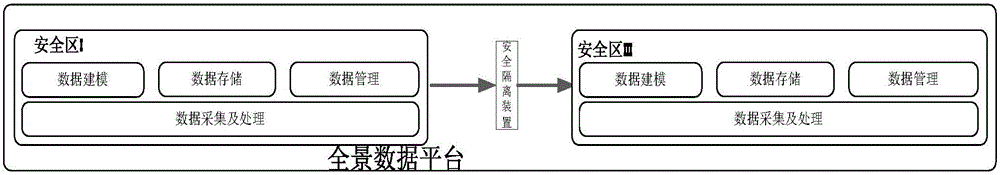
Substation secondary system operation and maintenance cloud platform
ActiveCN106709580AImprove data utilizationImprove interactivityData processing applicationsInformation technology support systemControl layerSynthetic data
The invention discloses a substation secondary system operation and maintenance cloud platform, comprising in-place layers and a centralized control layer, which are configured to read data from a production management system directly to realize equipment management, operation management, fault handling, duty management and maintenance management. The in-place layers and the centralized control layer exchange power grid operation data by means of a dispatching data network, and exchange operation and maintenance management data by means of an integrated data network; each in-place layer comprises a substation control layer, a spacing layer and a process layer; each process layer comprises all primary equipment of a substation, and transmits information of the primary equipment of the present layer to the substation control layer by means of corresponding detection equipment; and each spacing layer comprises all secondary equipment of the substation, and transmits information of the primary equipment of the present layer to the substation control layer by means of corresponding detection equipment. The substation secondary system operation and maintenance cloud platform integrates the cloud computing technology, the big data technology, the Internet of things technology and the mobile internet technology, unifies data interfaces and dispatching among different secondary operation and maintenance systems in safety regions, and realizes good management of operation and maintenance information.
Owner:STATE GRID CORP OF CHINA +1
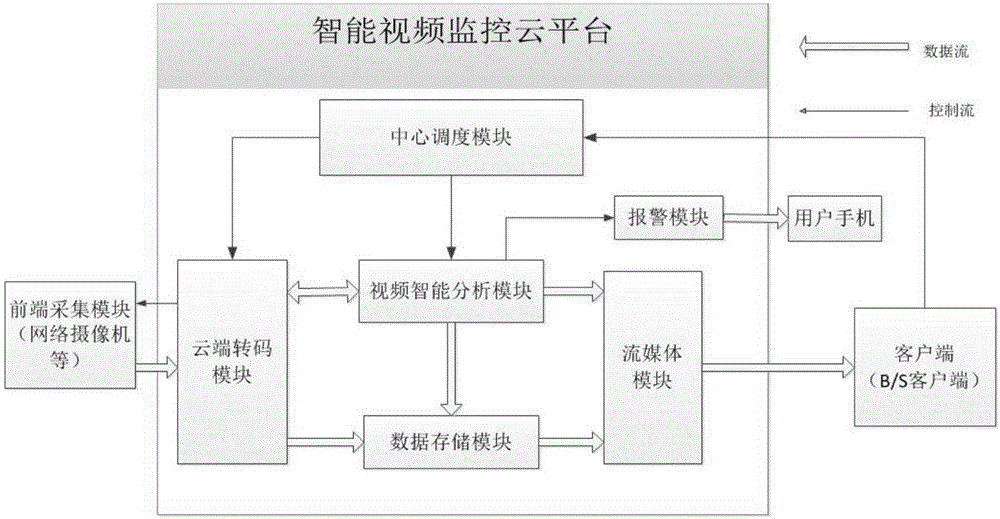
Smart video monitoring system based on cloud platform
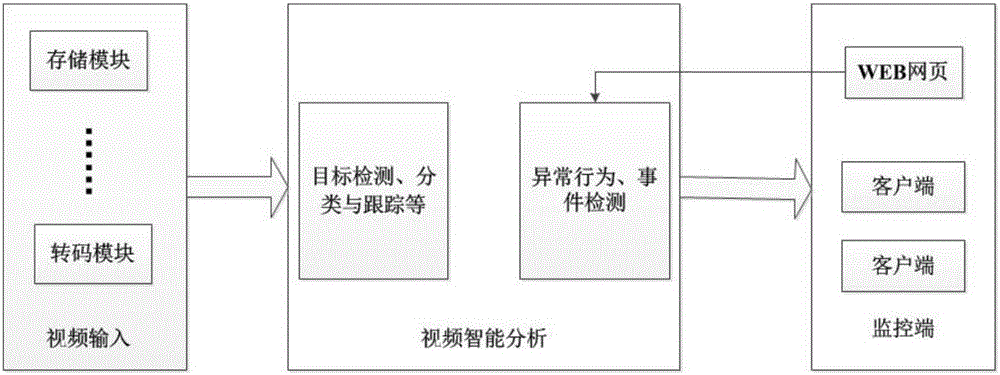
InactiveCN106375721AImprove bindingQuality improvementClosed circuit television systemsTransmissionVideo monitoringTranscoding
The invention relates to a smart video monitoring system based on a cloud platform, and belongs to the technical field of remote smart monitoring. The system is characterized in that a video monitoring cloud platform is developed on a server cluster established on the basis of a Hadoop cloud computing platform, and video data acquired by front-end equipment are transmitted to a server in a stream way; through adoption of a massive distributed cloud computing technology, real-time tracking, processing, analysis and outputting of video streams are realized; and a service is provided externally, so that a terminal user can perform checking and calling conveniently. In the system, the characteristics of distributed high-concurrence access storage, high availability, rapid response, easiness in management and maintenance and the like are integrated. Video acquisition, video encoding and transcoding, video data storage, a streaming media distributed server and a client are all distributed on a physical host node in an access network. Compared with a conventional video monitoring system, the smart video monitoring system has the advantages that video real-time processing and transcoding efficiency and video data storage capacity are increased greatly; the requirement of people on the video monitoring system in a big data era is met; and a relatively large commercial value is achieved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com