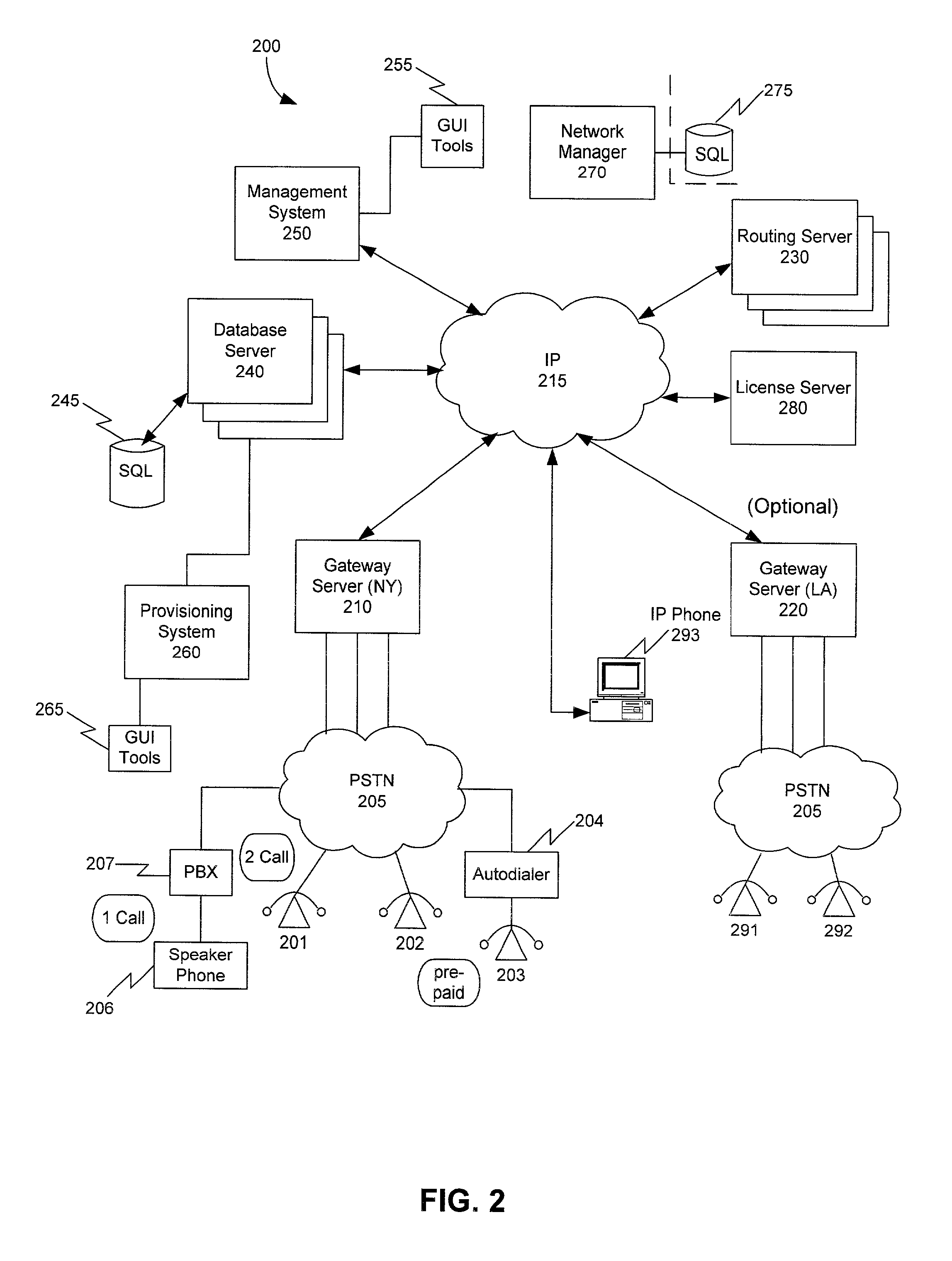
Patents
Literature
4445 results about "Service module" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A service module (or equipment module) is a spacecraft compartment containing a variety of support systems used for spacecraft operations. Usually located in the uninhabited area of the spacecraft, the service module is jettisoned upon the completion of the mission, and usually burns up during atmospheric reentry. The service module is the equivalent to the spacecraft bus assembly on unmanned spacecraft.
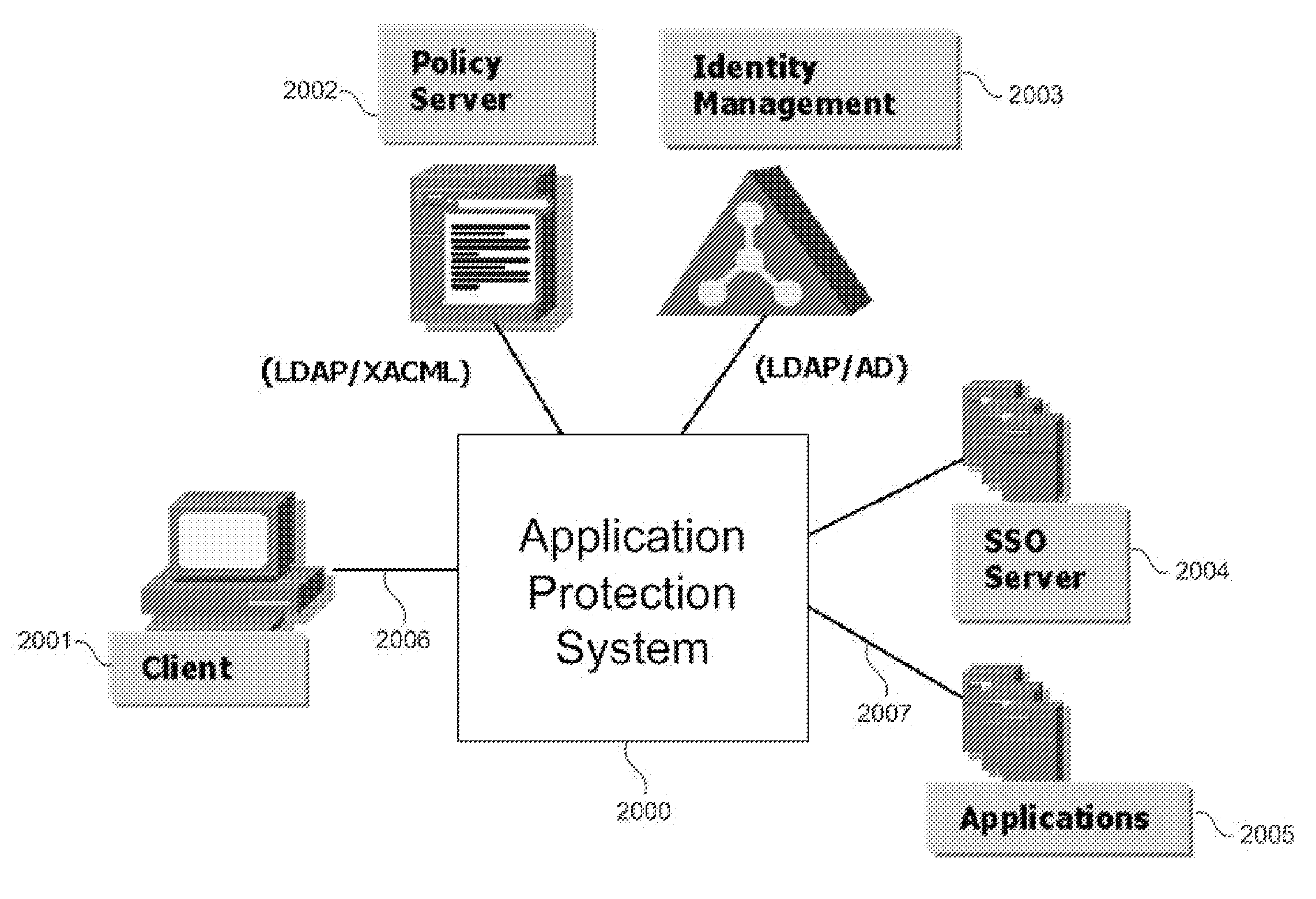
System and method for securing an enterprise computing environment
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
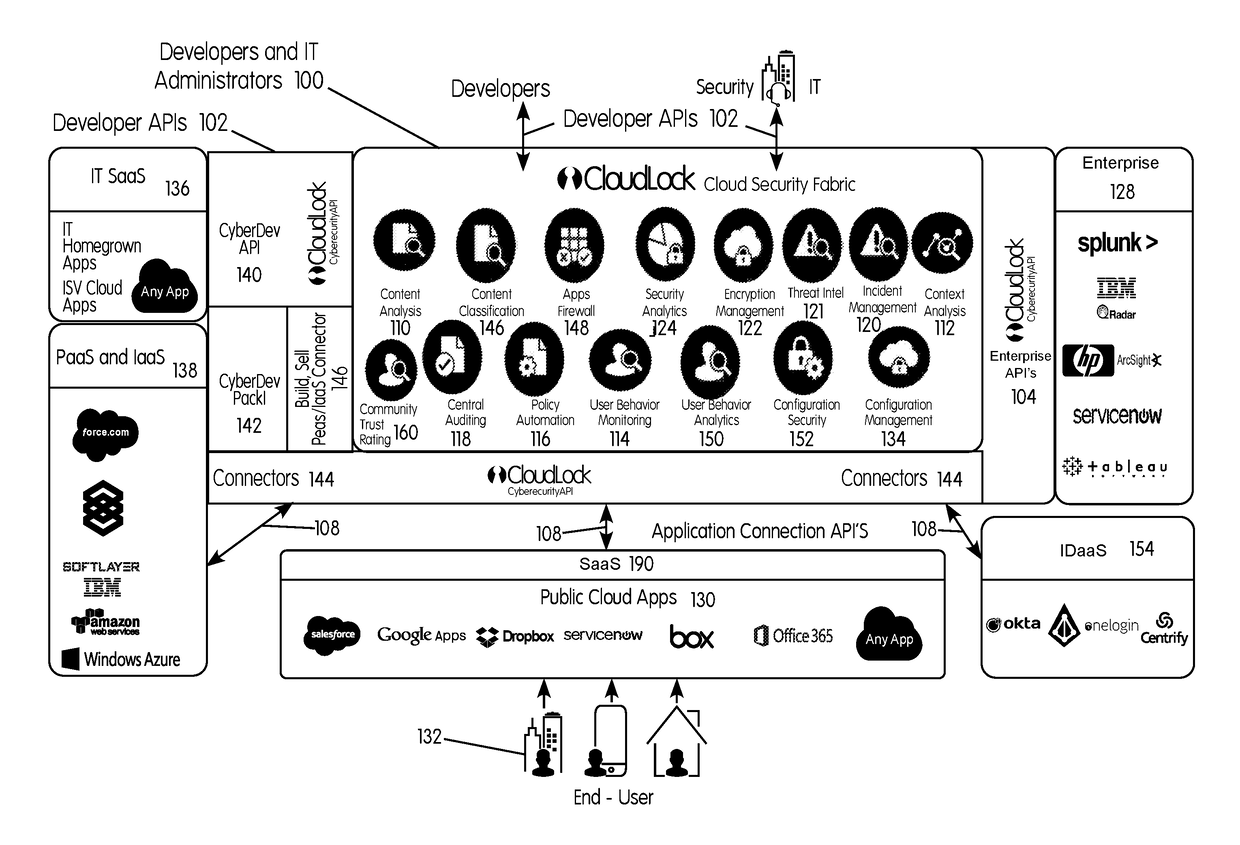
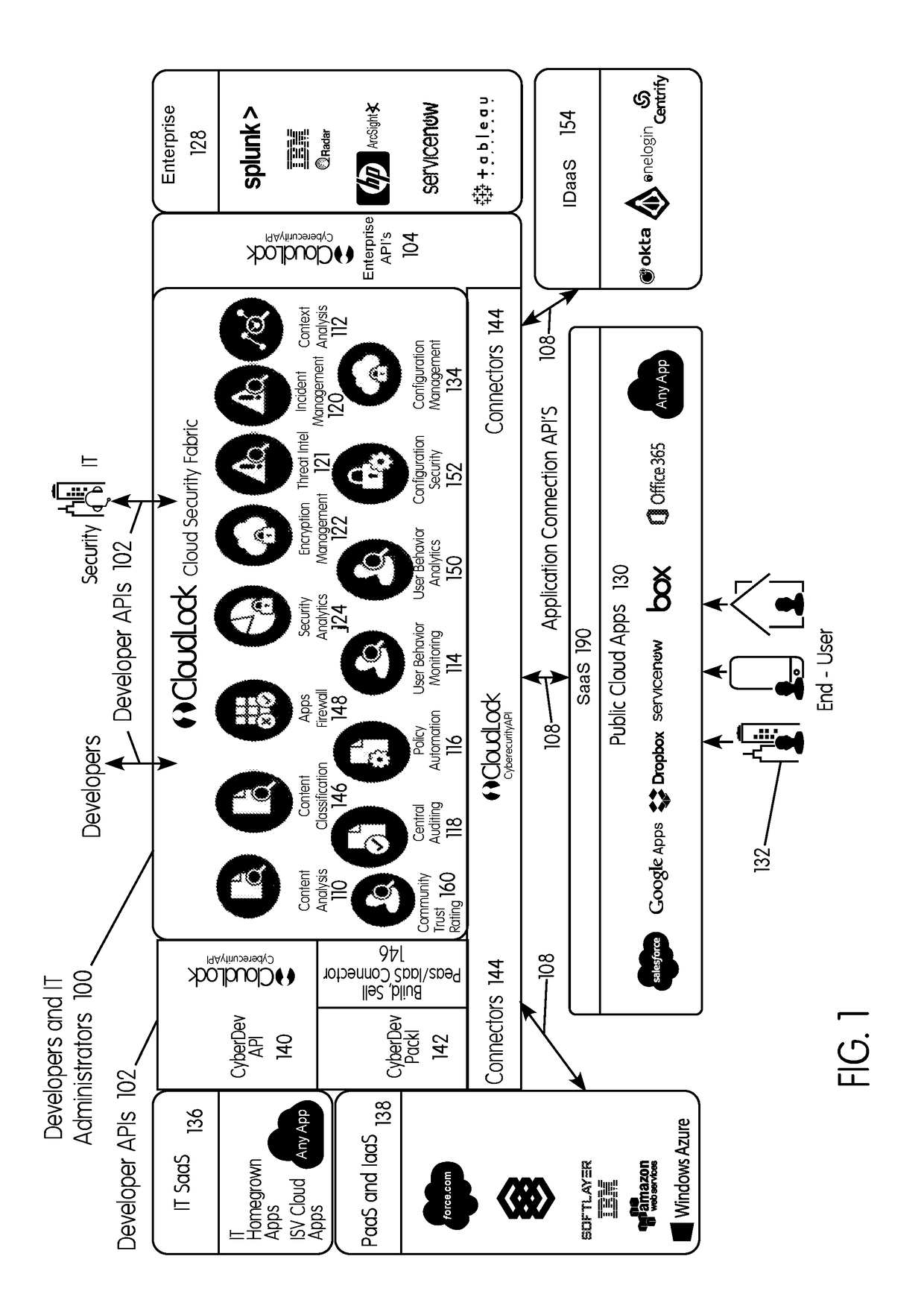
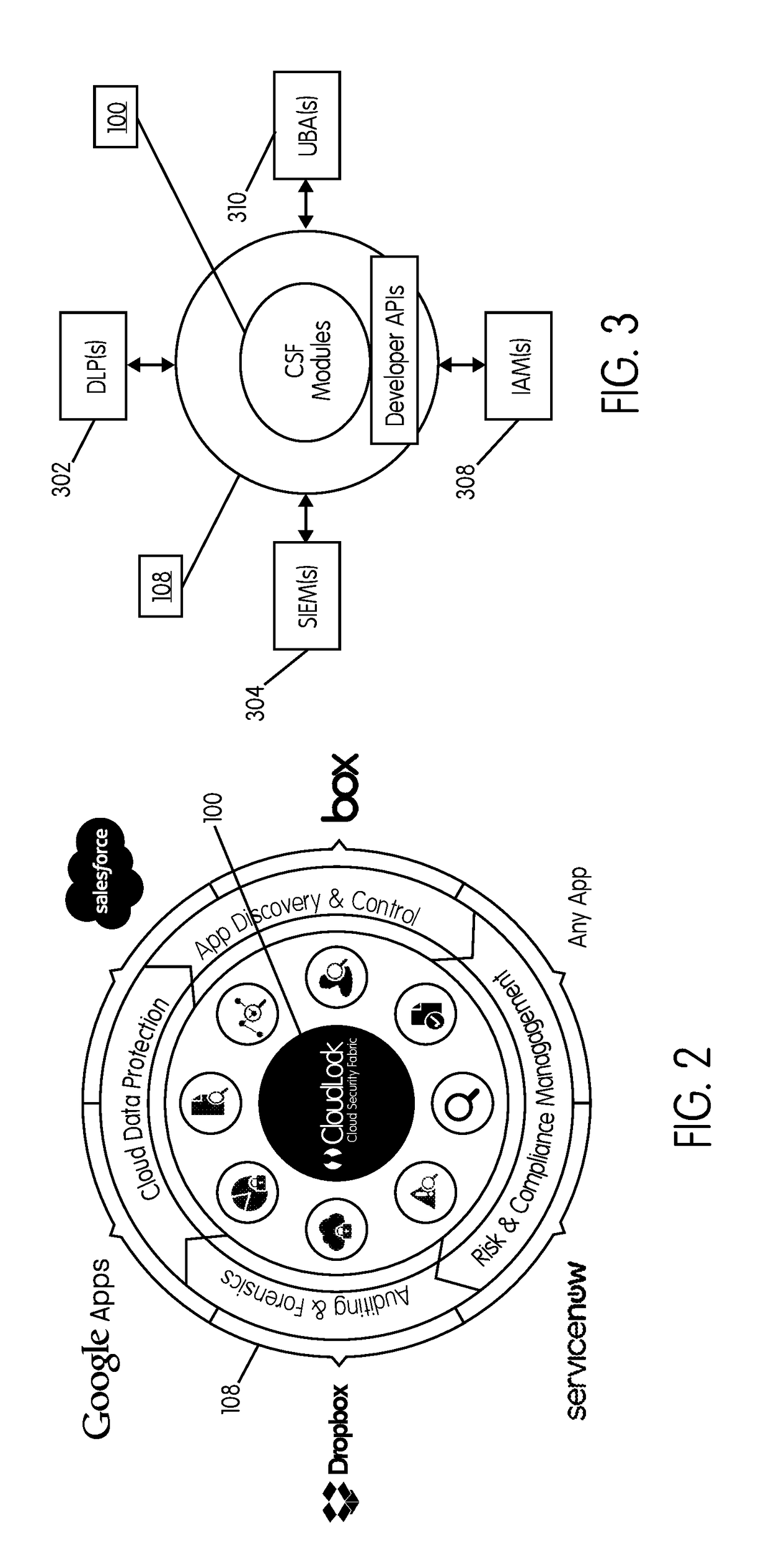
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
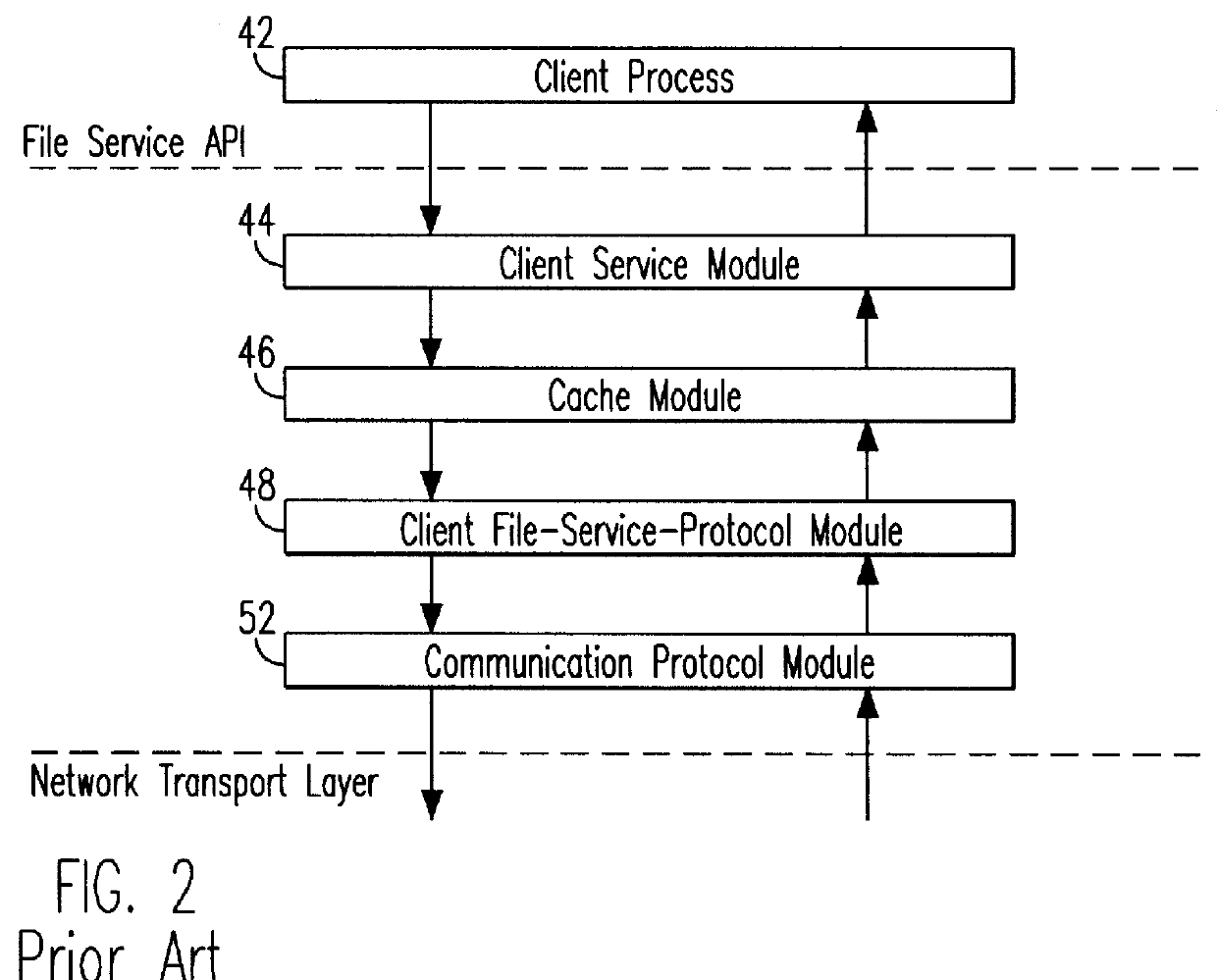
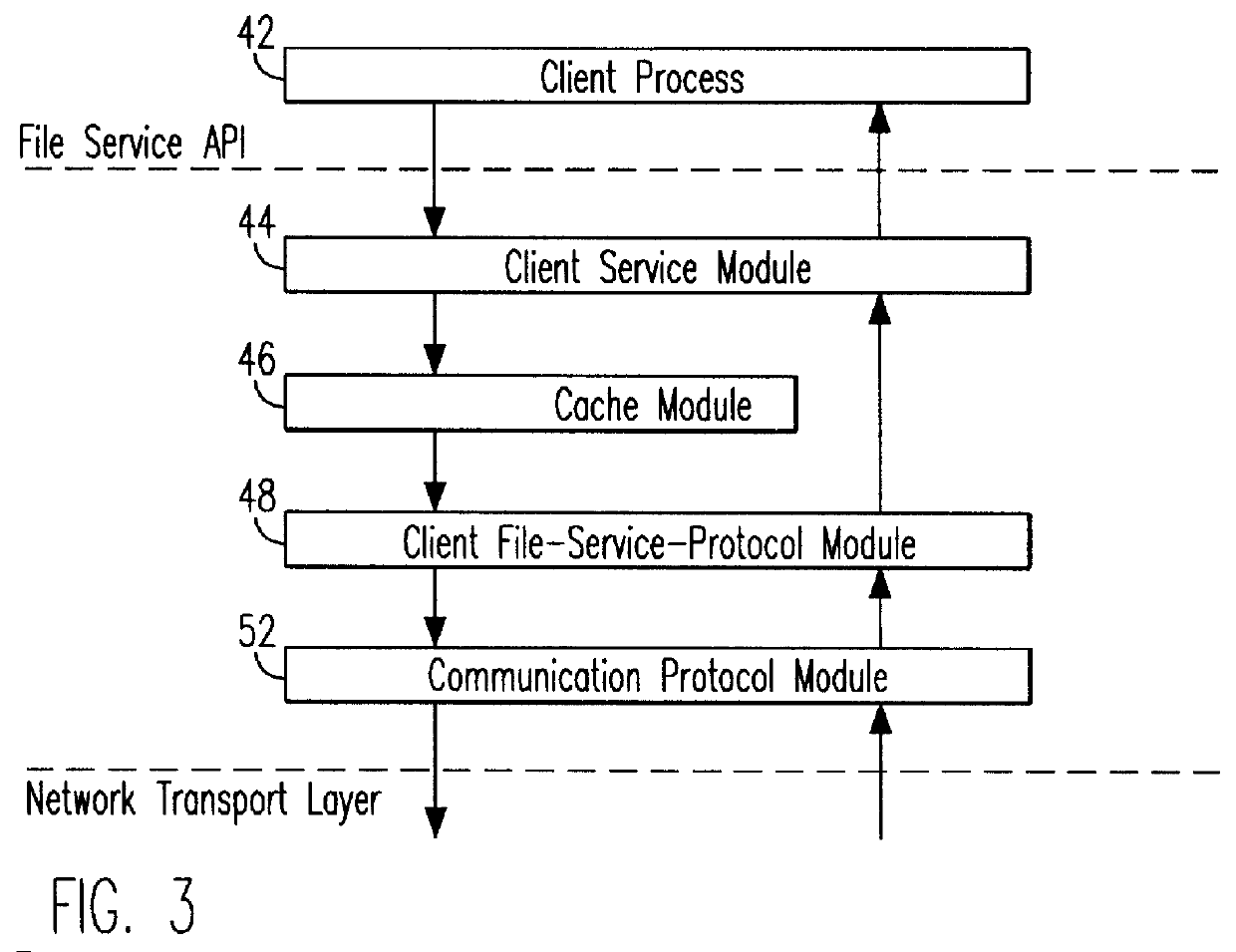
Remote file services network-infrastructure cache
InactiveUS6085234AMultiple digital computer combinationsMemory systemsService protocolSchema for Object-Oriented XML
A network-infrastructure cache ("NI Cache") transparently provides proxy file services to a plurality of client workstations concurrently requesting access to file data stored on a server. The NI Cache includes a network interface that connects to a digital computer network. A file-request service-module of the NI Cache receives and responds to network-file-services-protocol requests from workstations through the network interface. A cache, also included in the NI Cache, stores data that is transmitted back to the workstations. A file-request generation-module, also included in the NI Cache, transmits requests for data to the server, and receives responses from the server that include data missing from the cache.
Owner:MOSAID TECH +1
Network management
ActiveUS20090019141A1Digital computer detailsHome automation networksDevice PropertiesNetwork management
A tool for managing a computer network includes a gateway service module that identifies a gateway for a network and a network information service module. The network information service module identifies devices in the network, determines at least one property for each of the identified devices, and creates a network information data structure for storing device properties. A communication agent service module transmits at least one determined device property to other agent service modules associated with the network, receives at least one device property from another agent service module associated with the network, and provides the received at least one property device to the network information service module. A method of monitoring a computer network is also provided. The method includes identifying devices in a network, determining at least one property for each of the identified devices, receiving at least one determined device property from another device the network, and creating a network information data structure for storing the determined device properties.
Owner:CISCO TECH INC
Extensible distributed enterprise application integration system
InactiveUS6738975B1Improve securityImprove the environmentInterprogram communicationMultiple digital computer combinationsTransaction serviceInteroperability
In general, in one aspect, the invention provides a modular application collaborator for providing inter-operability between applications including a plurality of connectors for communicating with a like plurality of applications and an interchange server. The interchange server includes an application collaboration module and service module. The service module transfers messages between connectors and the application collaboration module. The application collaboration defines the inter-operability between two or more applications. The interchange server service module includes a transaction service and an error service. Transactions are executed in the application collaboration module and the transaction service records each action and a compensating action for undoing an associated action. An error service monitors for errors in the interchange server, and, upon detection of an error, stops the execution of a transaction and initiates the execution of any required compensating actions to undo the interrupted transaction. The compensating transactions may be executed at the connectors and are not required to be overseen by the interchange server.
Owner:SAGA SOFTWARE
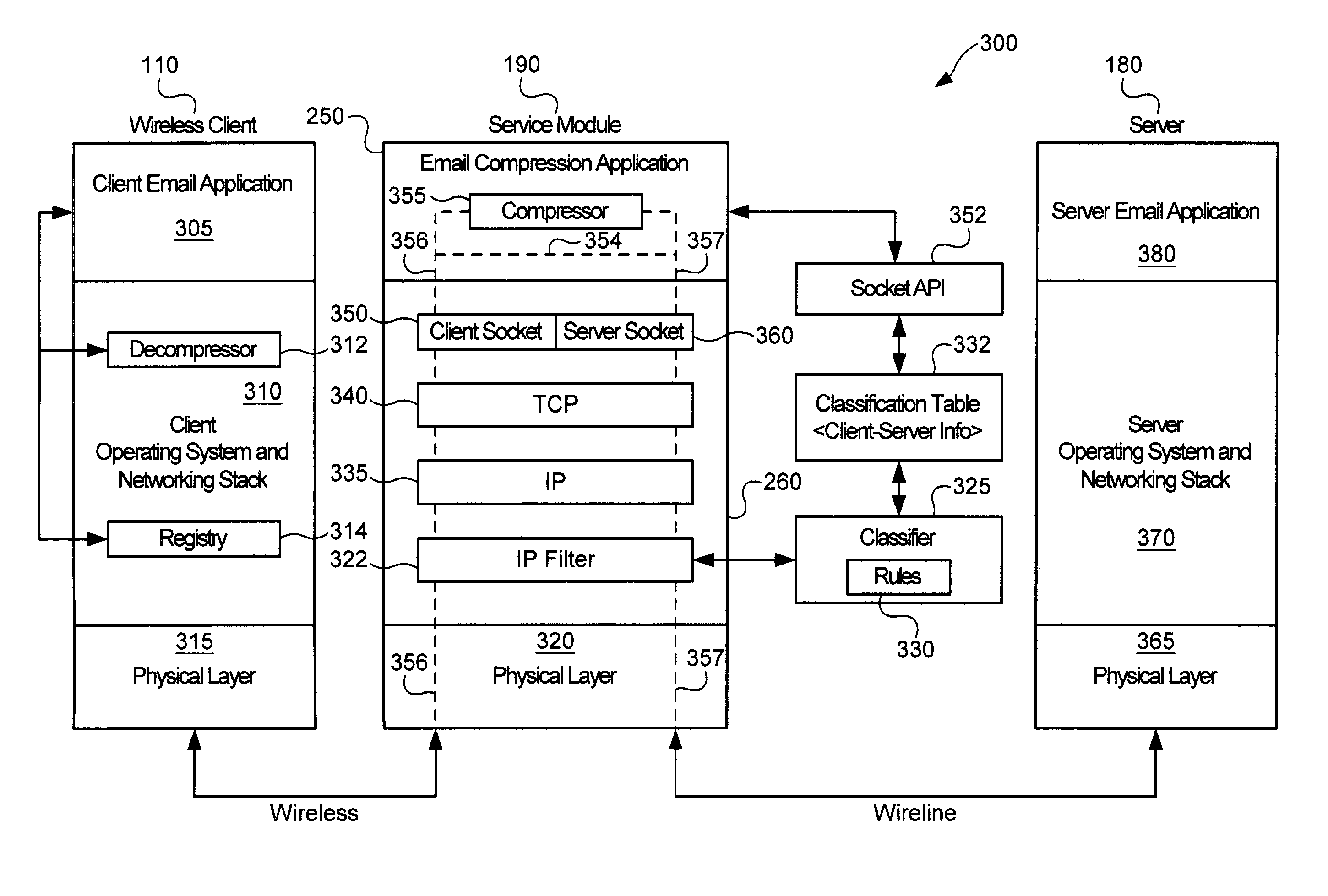
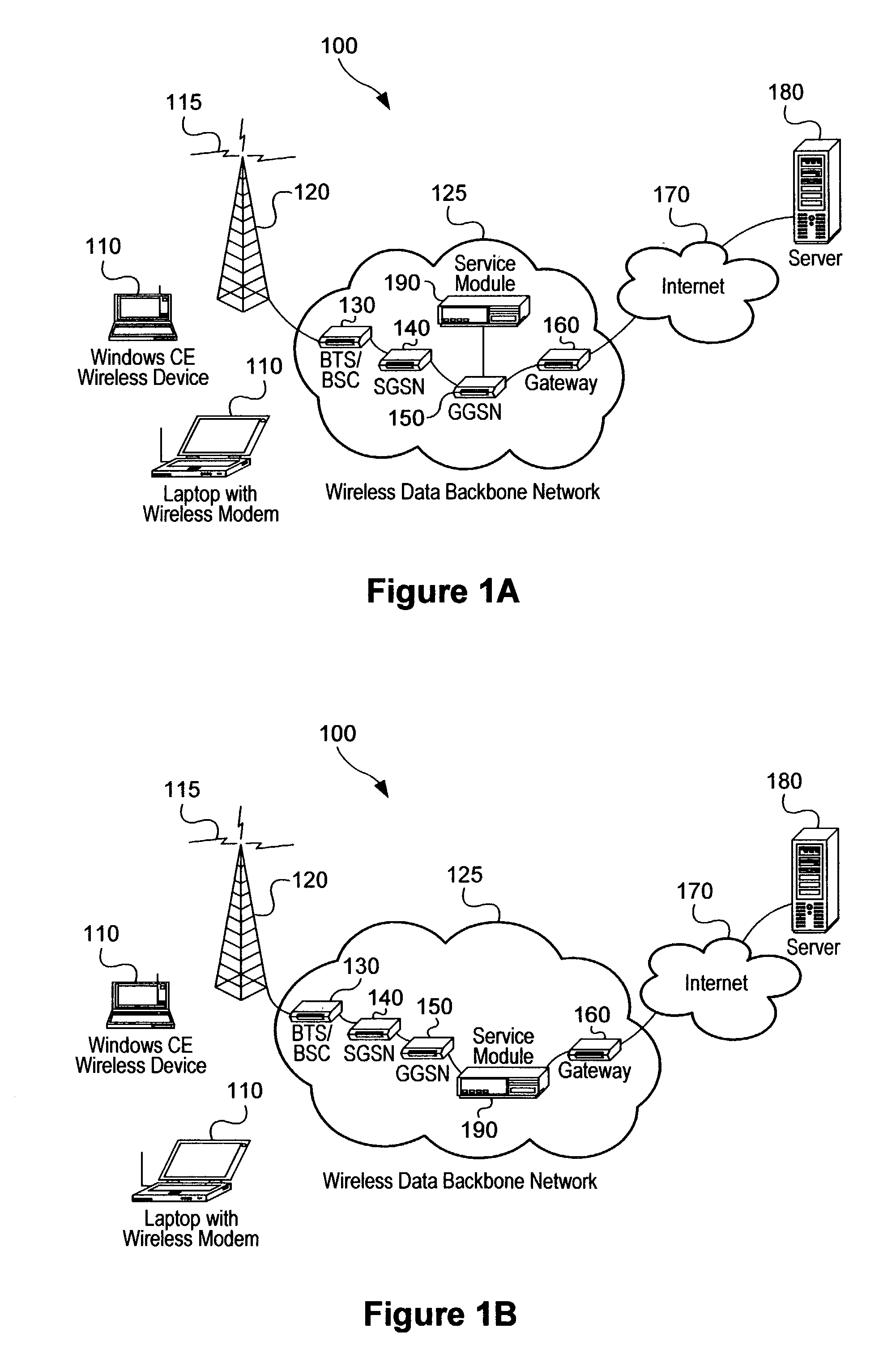
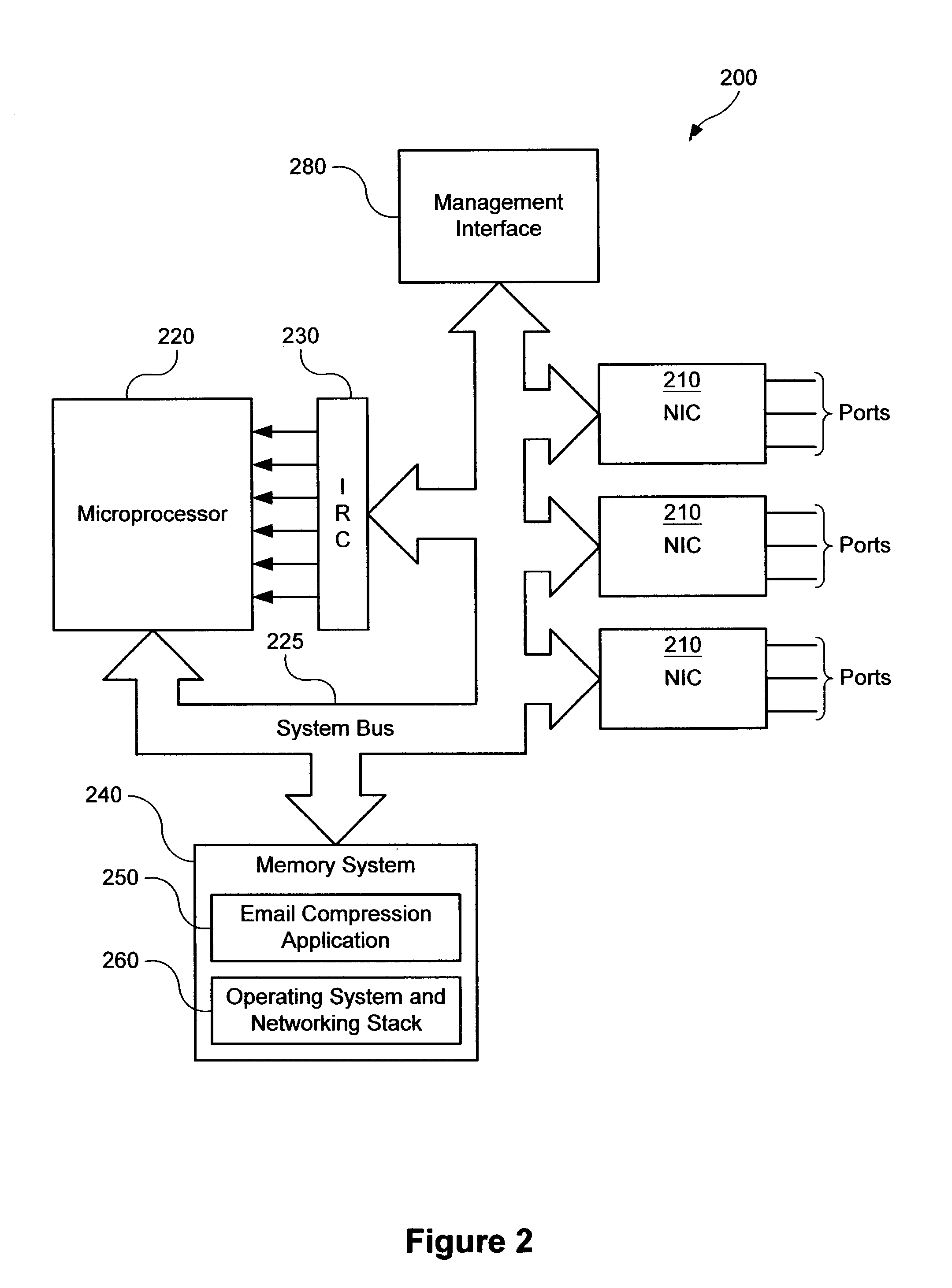
Service-based compression of content within a network communication system
ActiveUS7024460B2Easy to decompressMultiple digital computer combinationsData switching networksOperational systemData stream
A service module incorporated within the network infrastructure intercepts packets communicated between a client and a server to determine whether the connection corresponds to an email service. If so, the service module breaks the connection by terminating the connection with the client at the service module and opening a separate connection between the service module and the server. Packets communicated between the client and the server may then be redirected to an email compression application that monitors messages communicated between the client and the server and processes the messages in accordance with the state of the email session. For messages corresponding to connection establishment, user authentication and other protocol-specific messages, for example, the email compression application may be configured to forward the messages to the originally intended destination. Messages corresponding to an email message data, however, are buffered within the email compression application. Once the entire message has been received, the email compression application may strip the message headers and any protocol-specific data, compress the data and attach new message headers corresponding to the compressed email message. The compressed and reformatted email message is then reinserted into the data stream for transmission to the intended destination. Because compression may occur between the server and client, compression may be performed without requiring special processing by the server before email messages are sent. Furthermore, because the email messages may be compressed in a format that can be readily decompressed using decompression libraries incorporated within the operating system of client devices, such as the CAB format or GZIP format, the client may decompress received email messages utilizing software already incorporated within the operating system of the client device, without requiring download or installation of special decompression software and / or coordination of compression / decompression of email messages with the server or sending party.
Owner:OPTIMORPHIX INC
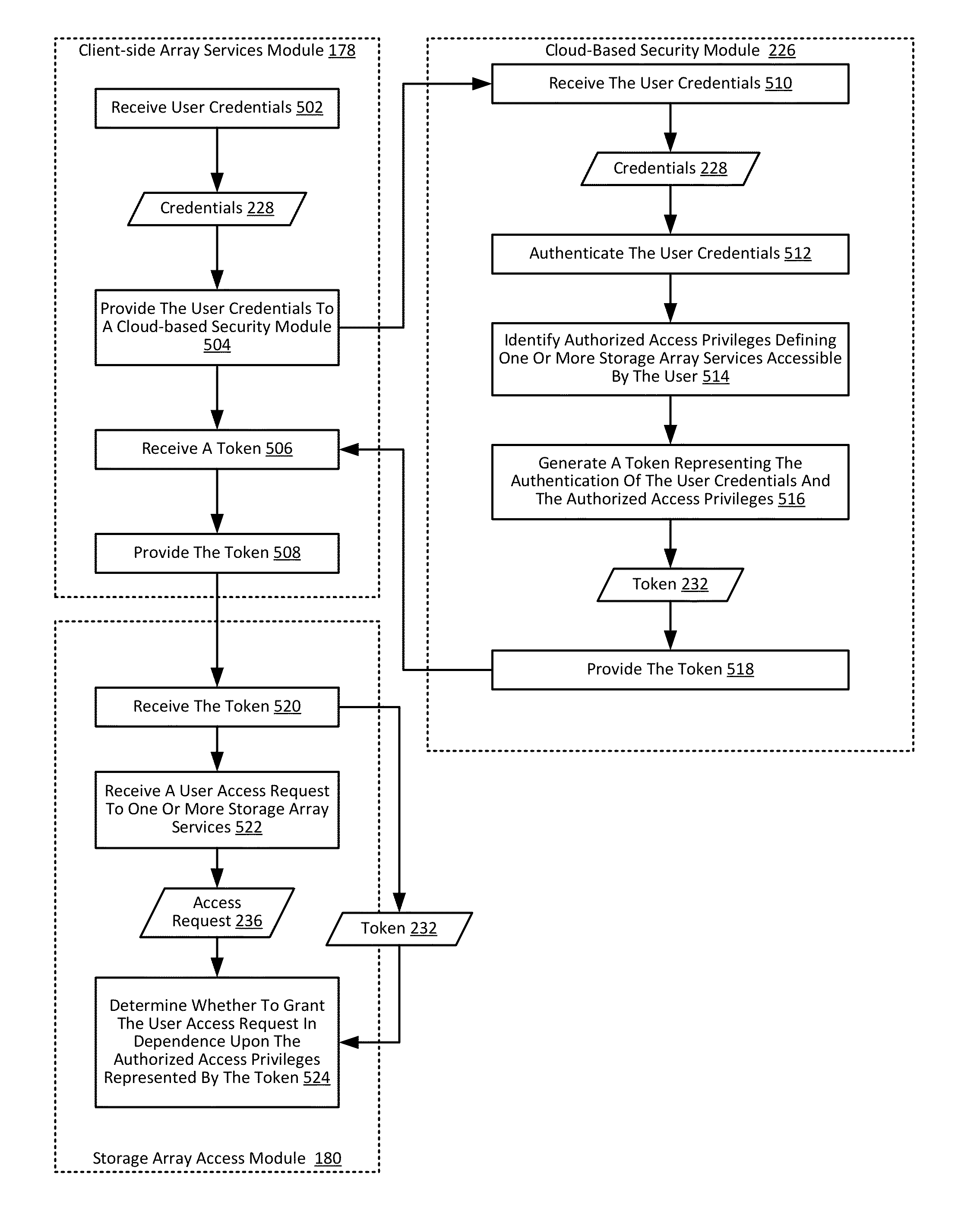
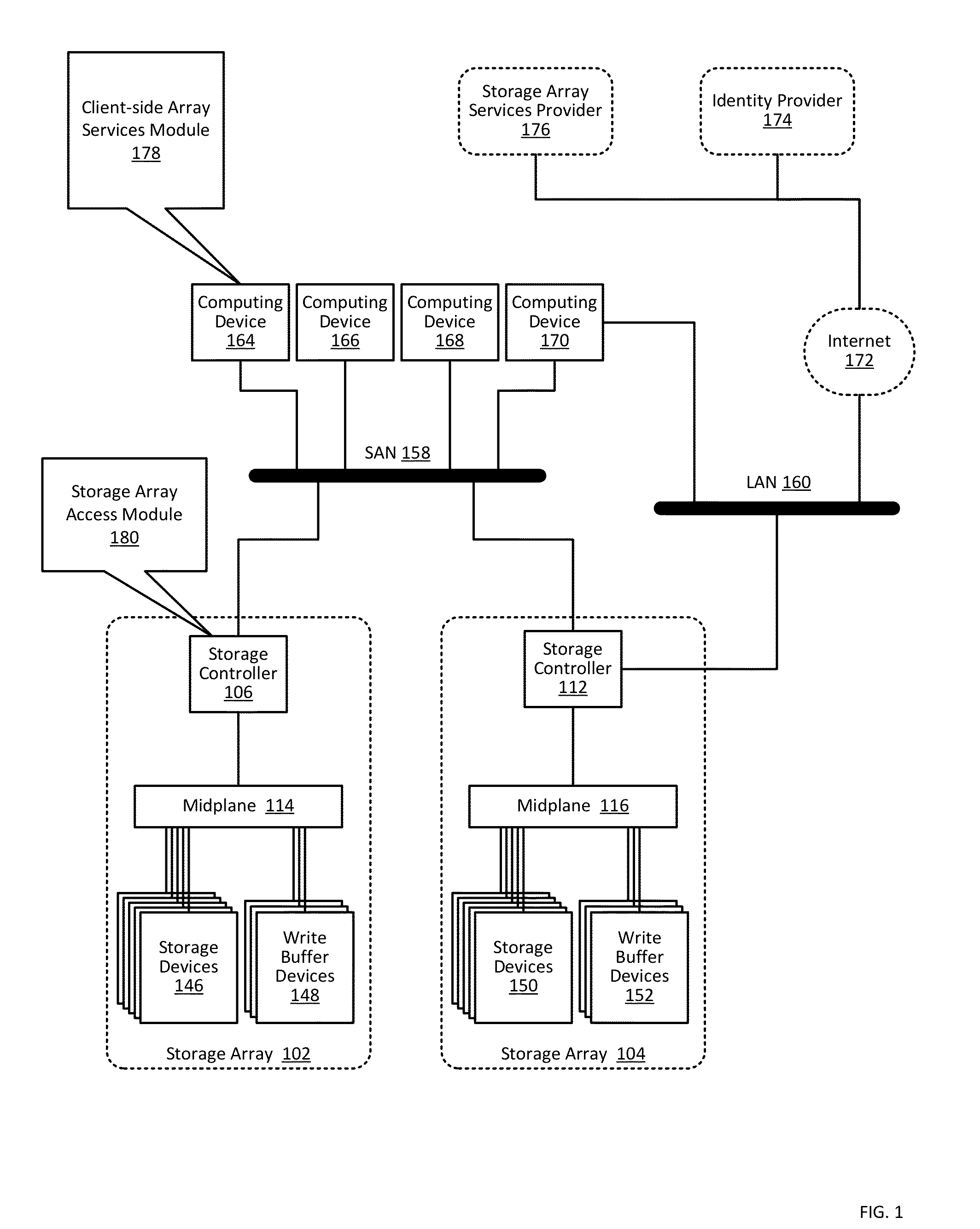
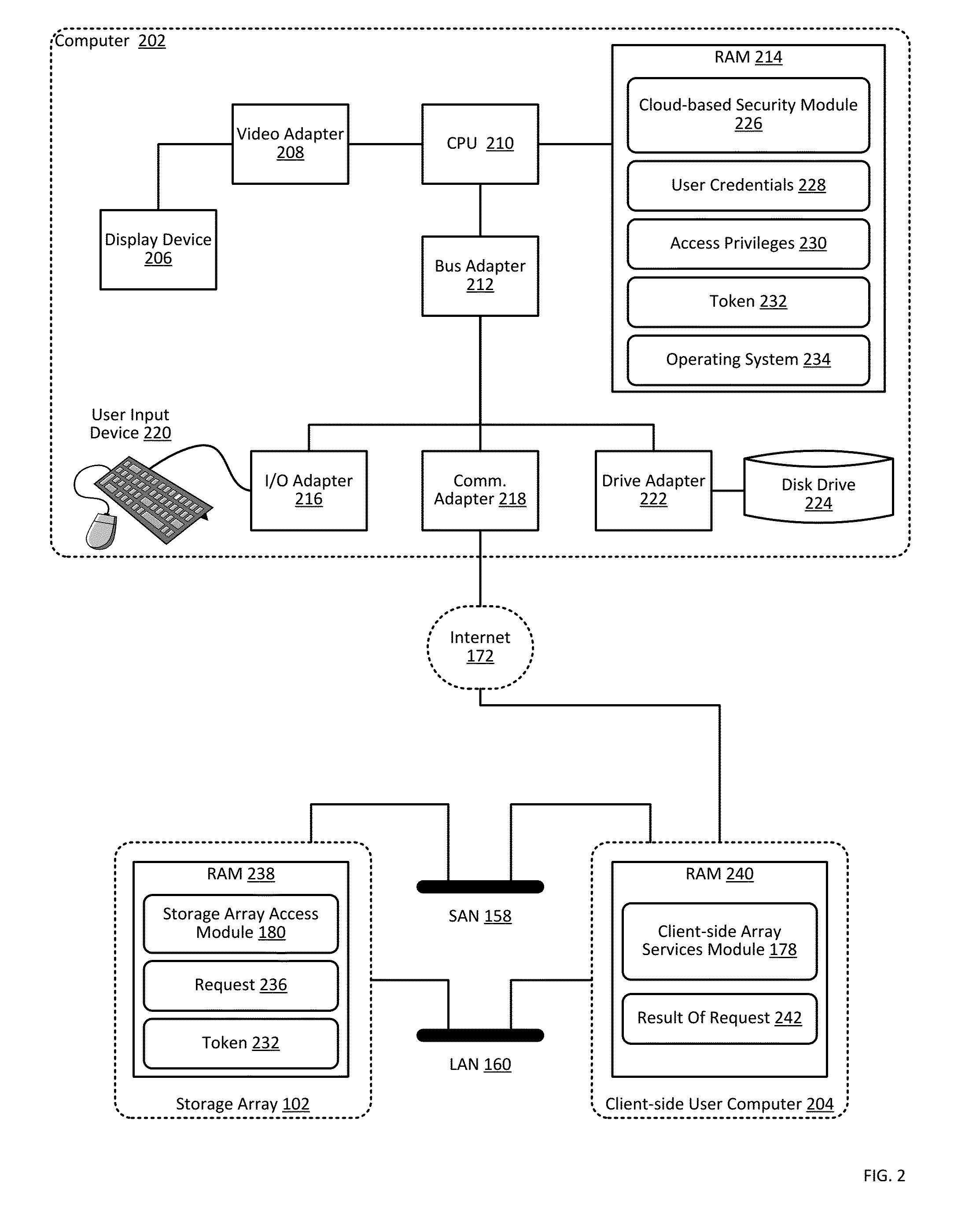
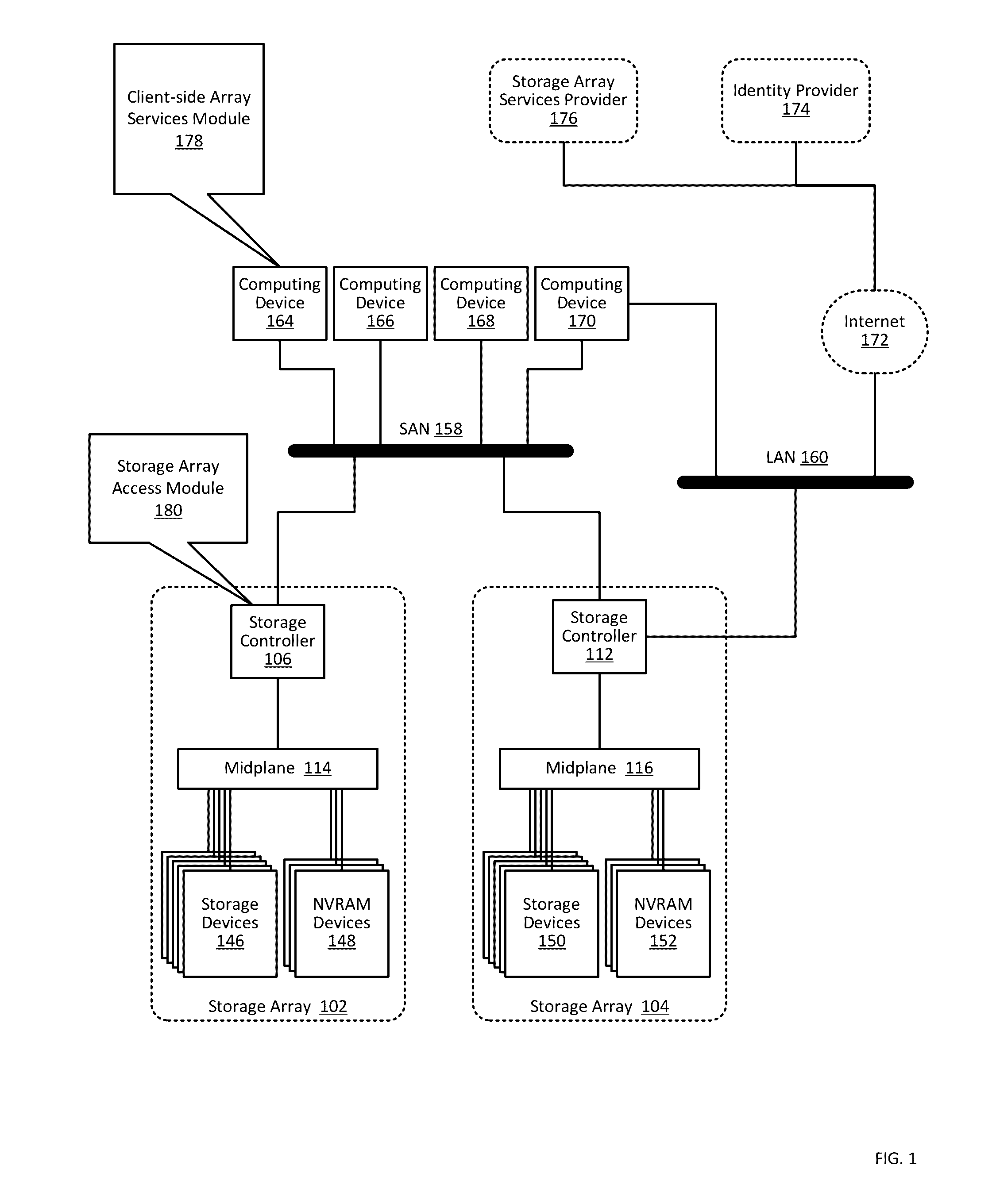
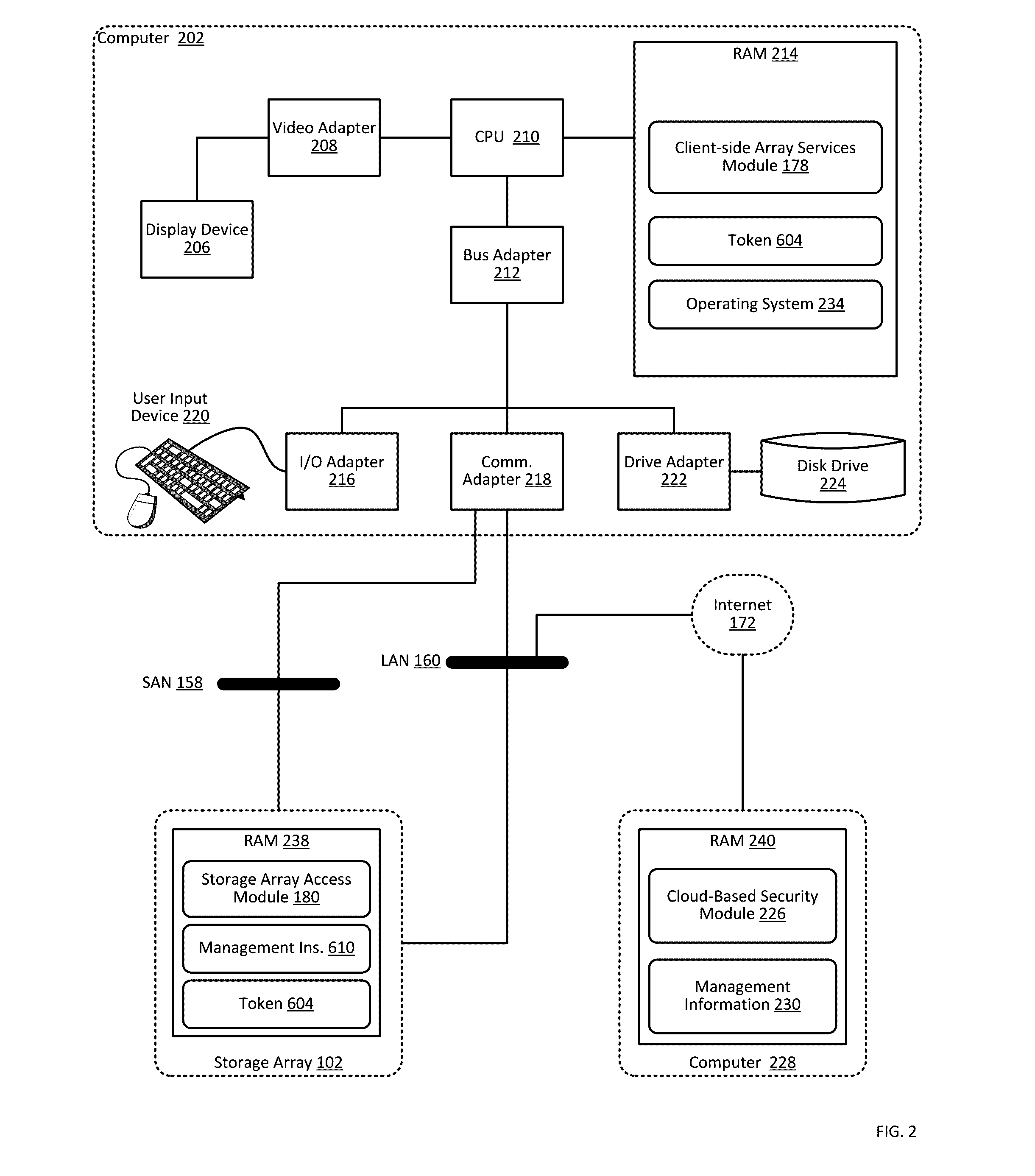
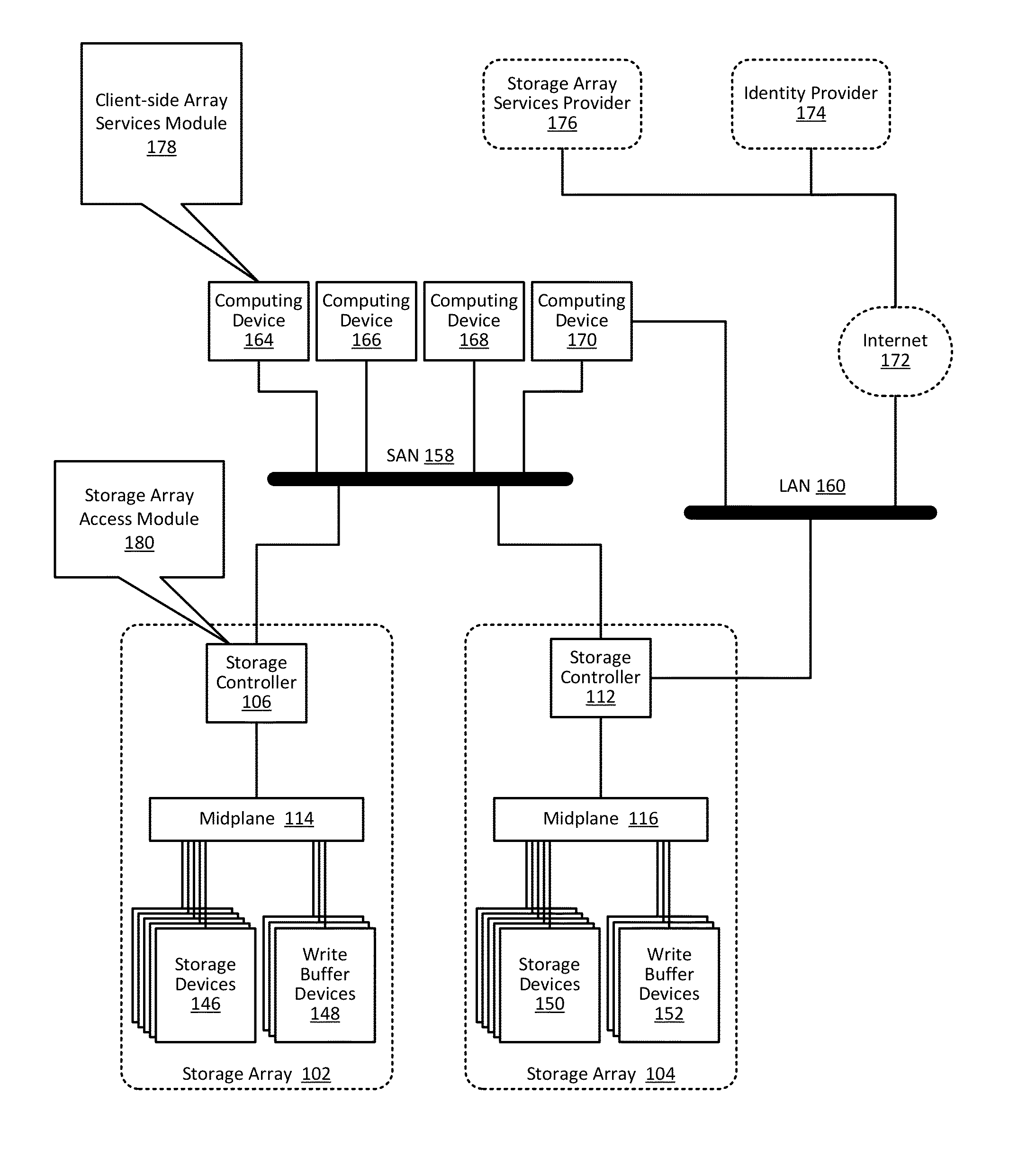
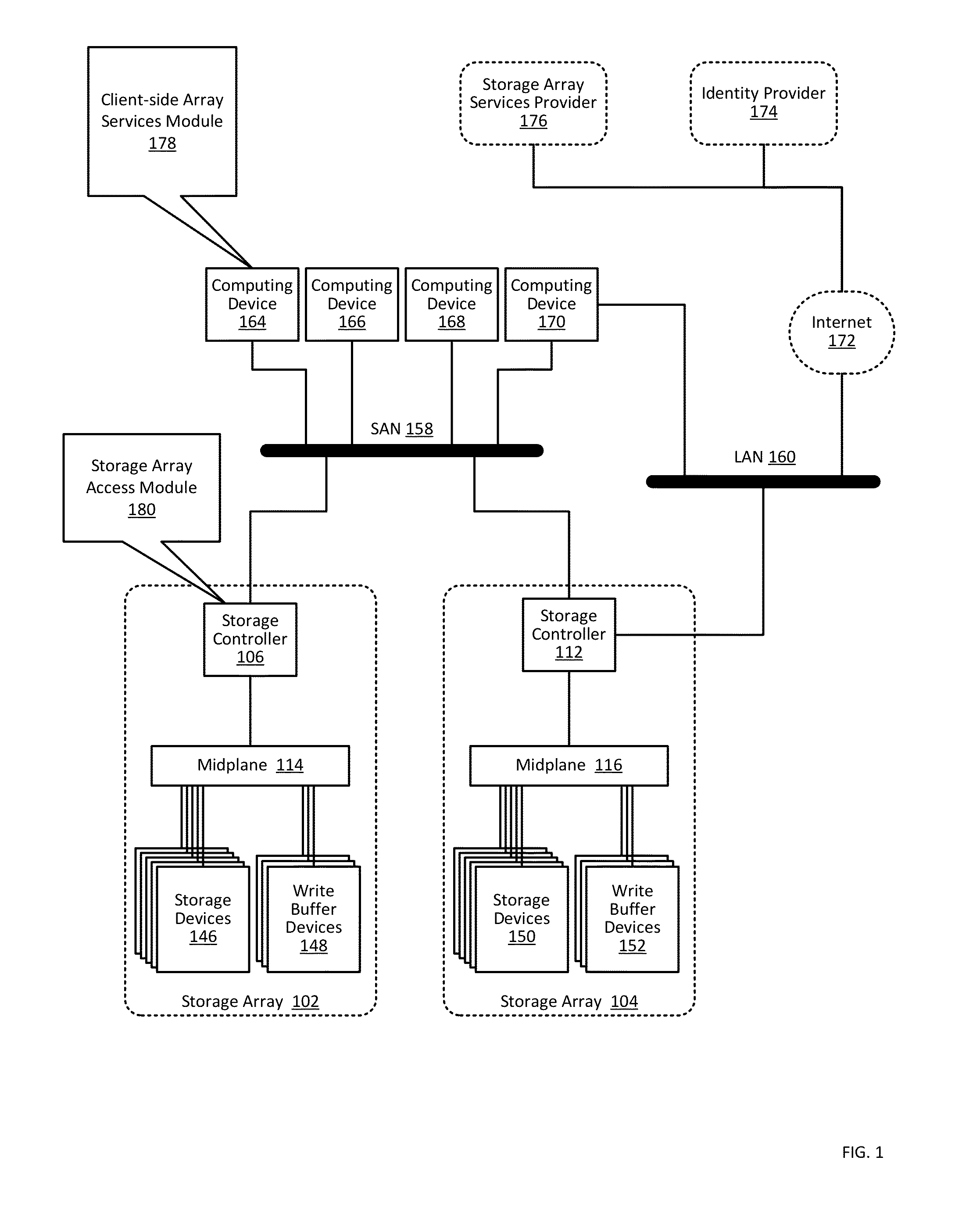
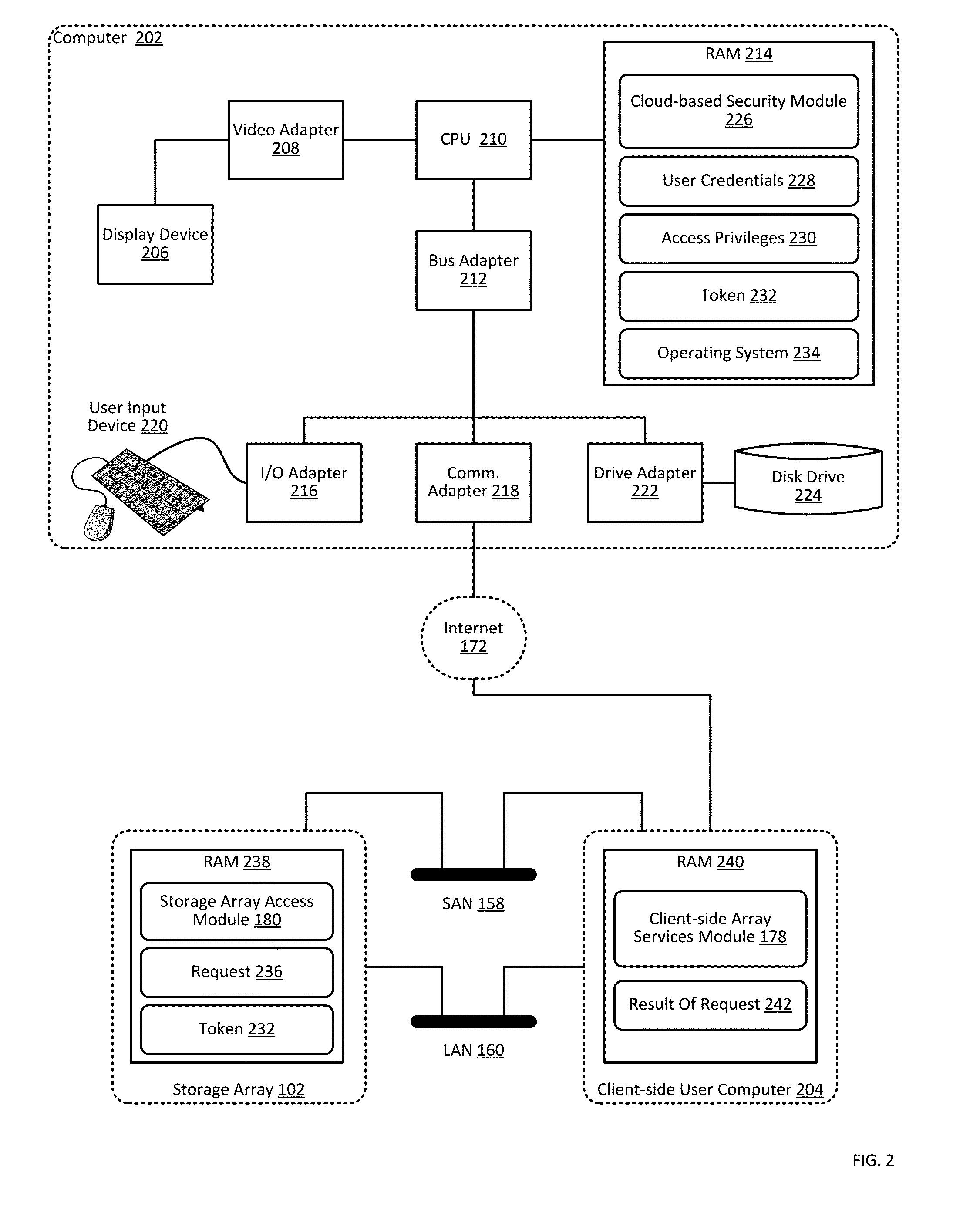
Providing authorization and authentication in a cloud for a user of a storage array
ActiveUS9300660B1User identity/authority verificationMultiprogramming arrangementsCloud baseClient-side
Providing authorization and authentication in a cloud for a user of a storage array includes: receiving, by a cloud-based security module from a client-side array services module, user credentials; authenticating, by the cloud-based security module, the user credentials; identifying, by the cloud-based security module, authorized access privileges defining one or more storage array services accessible by the user; generating, by the cloud-based security module, a token representing the authentication of the user credentials and the authorized access privileges; and providing, by the cloud-based security module to the client-side array services module, the token.
Owner:PURE STORAGE
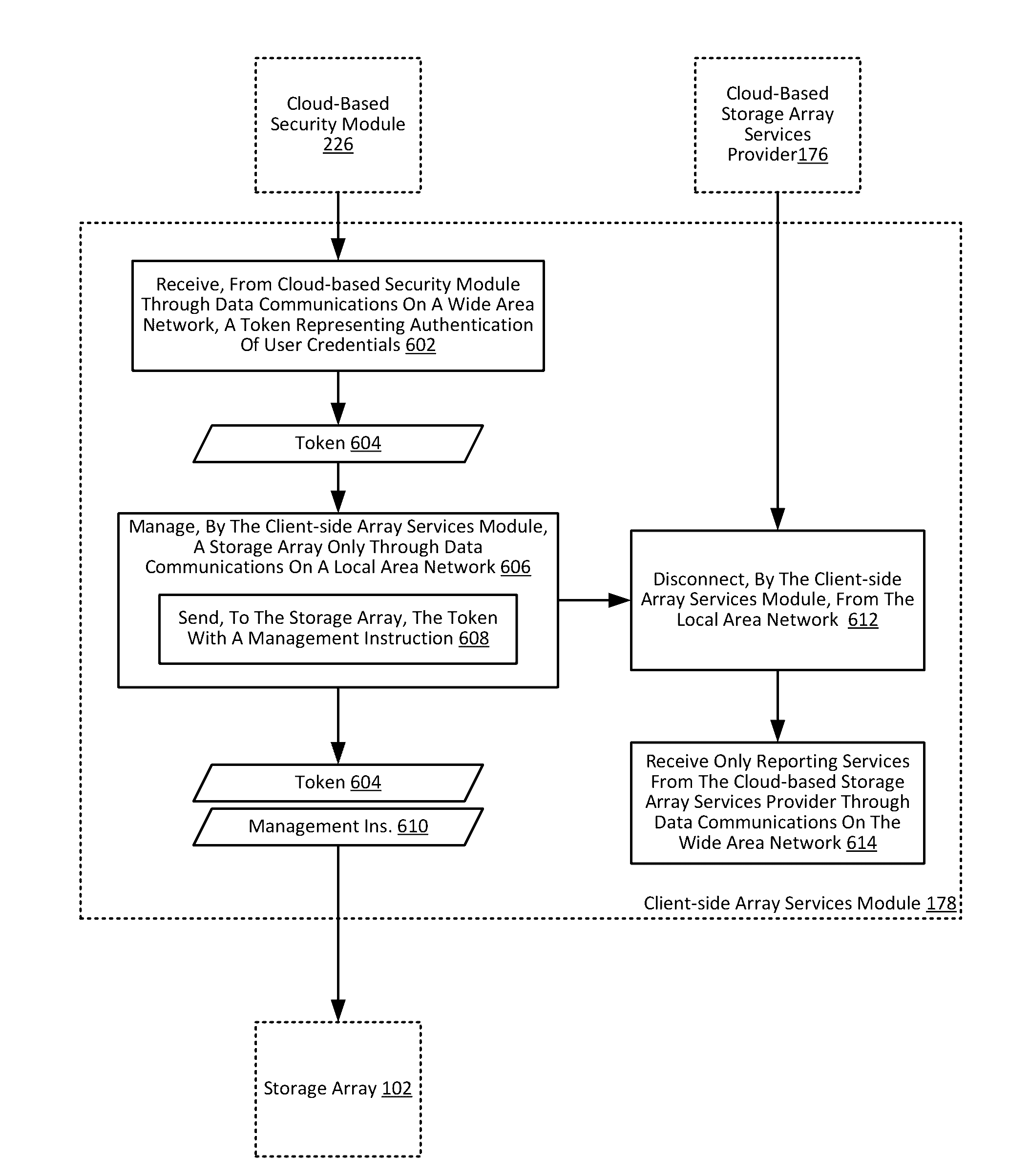
Managing a storage array using client-side services
Managing a storage array includes: receiving, by a client-side array services module from a cloud-based security module through data communications on a wide area network, a token representing authentication of user credentials; and managing, by the client-side array services module, a storage array only through data communications on a local area network, including sending, to the storage array, the token with a management instruction.
Owner:PURE STORAGE
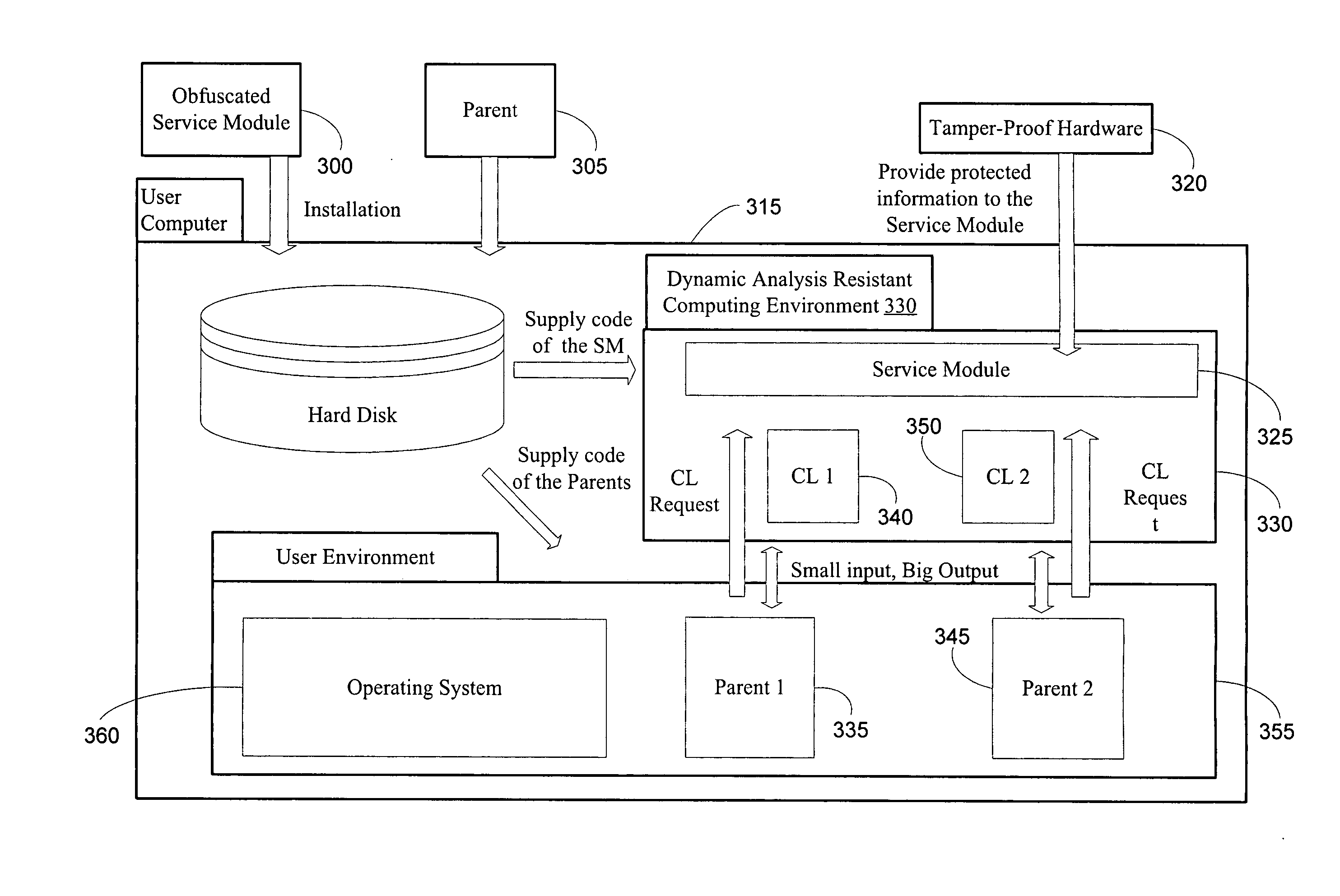
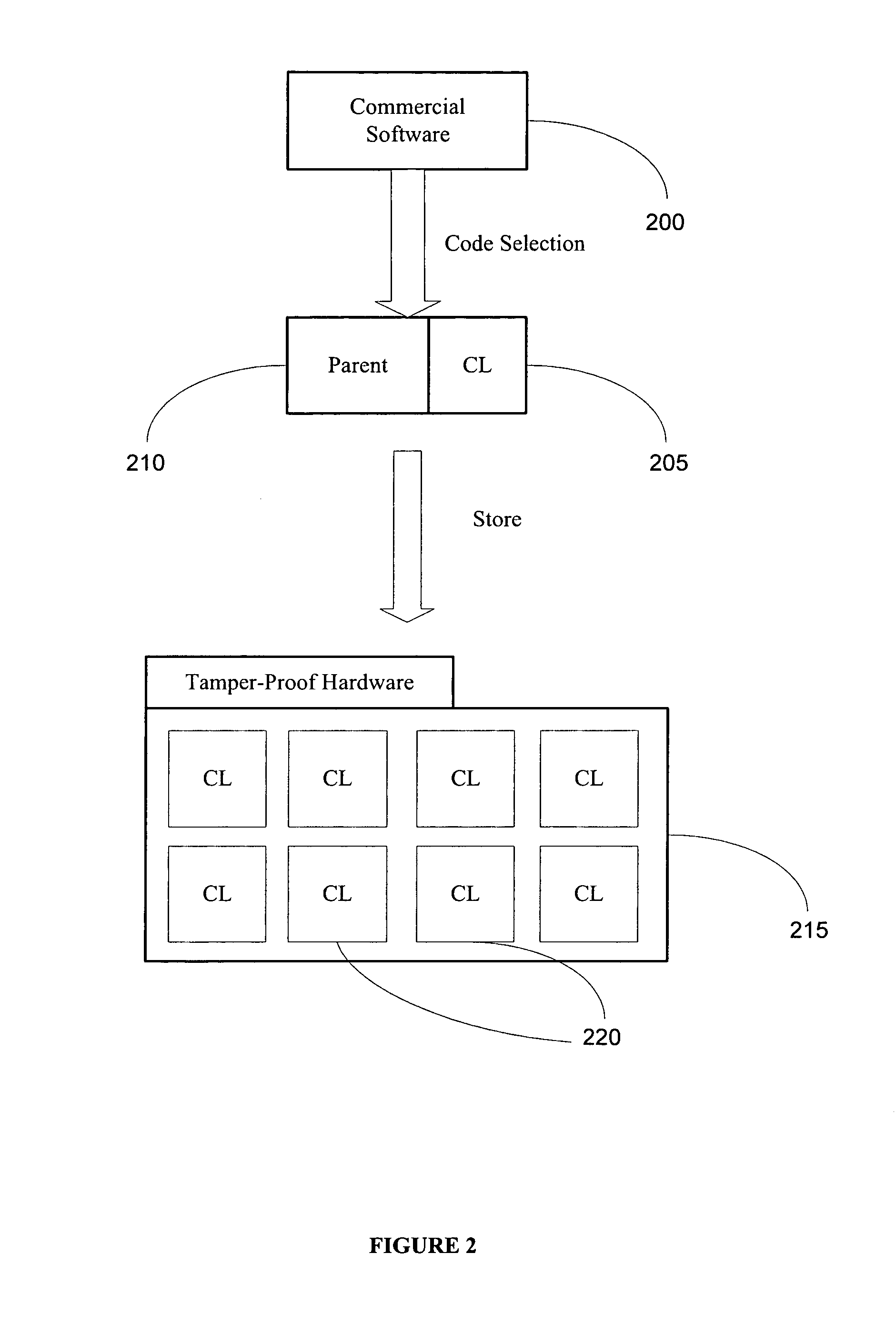
Method and system for providing tamper-resistant software
InactiveUS20060048223A1Performance penaltyImprove tamper resistanceMemory loss protectionDetecting faulty computer hardwareTamper resistanceObfuscation
A method and system for protecting only a portion of the software to be protected against tampering is described. Such a portion may be stored in a tamper-resistant physical device, with optional encryption, for downloading when needed for execution. Several layers of tamper resistance are provided without excessively impacting performance of the protected software. For instance, obfuscation is applied to the code for the service module to minimize the large expense associated with obfuscation. The invention includes embodiments that deliver critical logic, policy information and other similar information with the help of mobile agents, which may be hosted by a server in a smart card.
Owner:THE UNIVERSITY OF HONG KONG
Storage array access control from cloud-based user authorization and authentication
ActiveUS9444822B1Public key for secure communicationDigital data processing detailsCloud baseClient-side
Owner:PURE STORAGE
Highly scalable architecture for application network appliances
A highly scalable application network appliance is described herein. According to one embodiment, a network element includes a switch fabric, a first service module coupled to the switch fabric, and a second service module coupled to the first service module over the switch fabric. In response to packets of a network transaction received from a client over a first network to access a server of a data center having multiple servers over a second network, the first service module is configured to perform a first portion of OSI (open system interconnection) compatible layers of network processes on the packets while the second service module is configured to perform a second portion of the OSI compatible layers of network processes on the packets. The first portion includes at least one OSI compatible layer that is not included in the second portion. Other methods and apparatuses are also described.
Owner:CISCO TECH INC
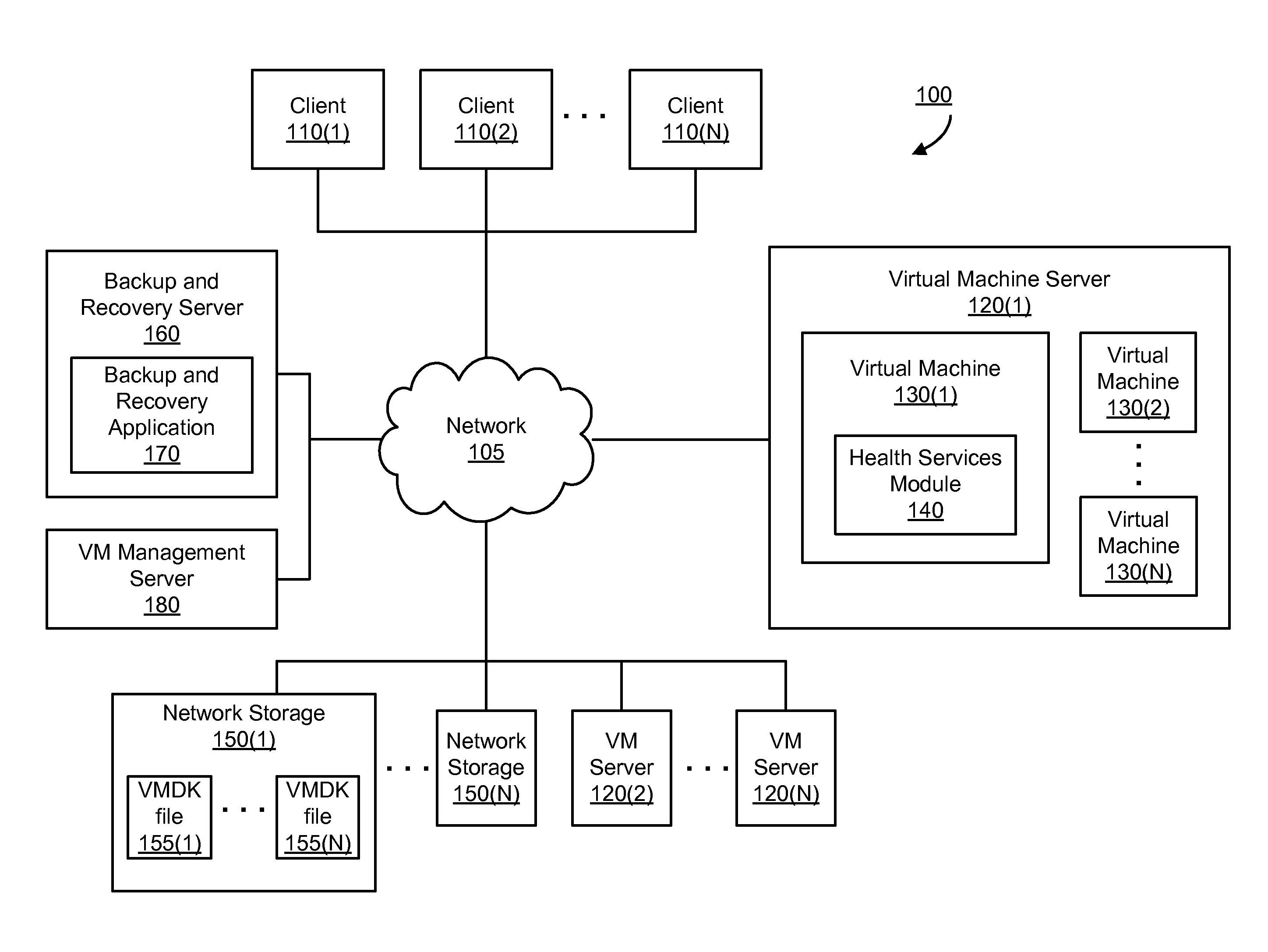
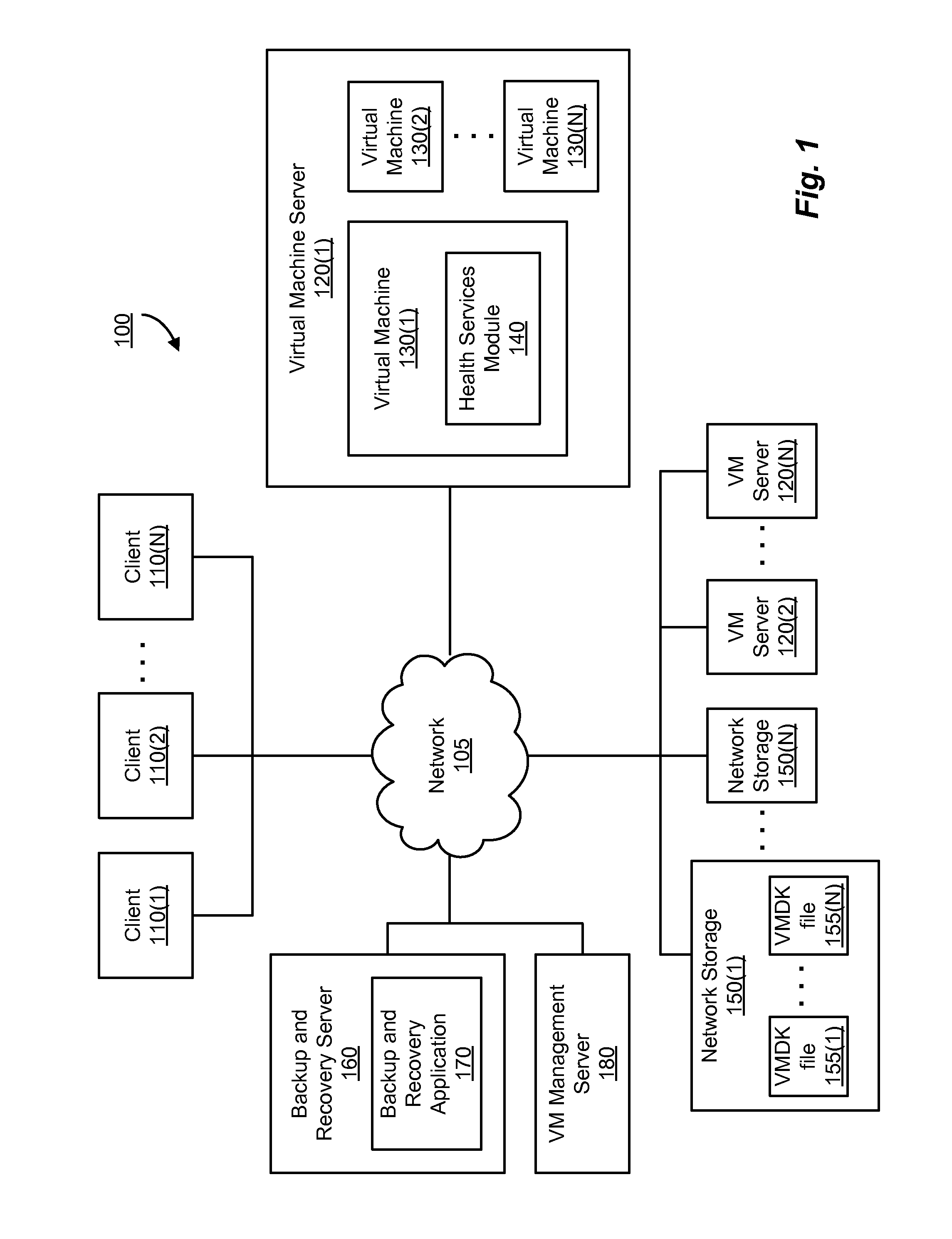
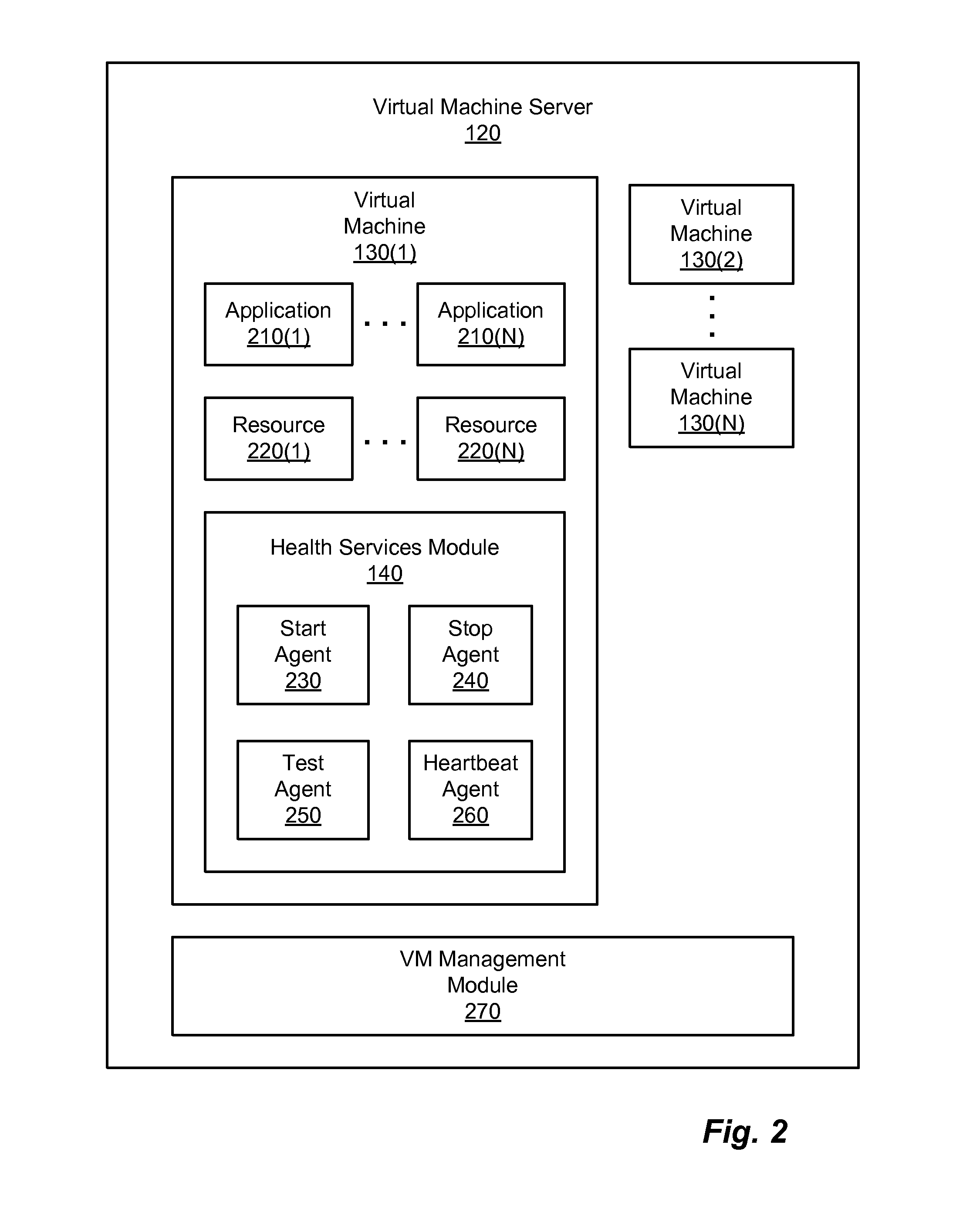
Method to validate availability of applications within a backup image
A health services module can test availability of one or more applications installed in a virtual machine that is instantiated from a backup image of a virtual machine disk file. A health services module can be installed on a virtual machine to test one or more applications that a user wishes to validate. If the health services module indicates that the application(s) of the virtual machine are available, a guarantee of availability can be provided for the backup image of the virtual machine disk file. If the health services module indicates that the application(s) of the virtual machine are unavailable, no guarantee of availability can be given. The guarantee of availability can indicate that the backup image of the virtual machine disk file can be successfully restored, and that the application(s) of the virtual machine instantiated from the backup image are available to respond to a client request.
Owner:VERITAS TECH
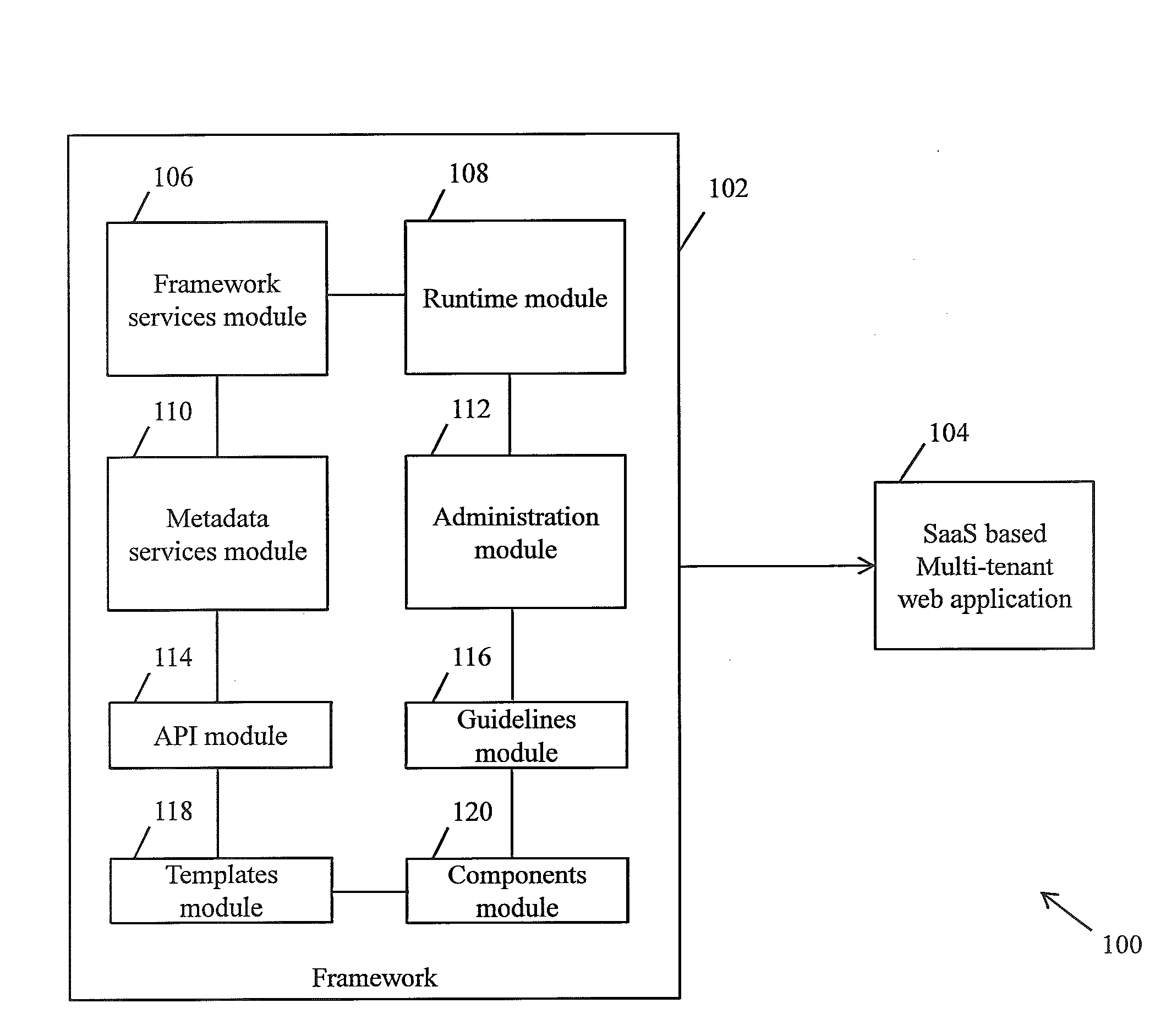
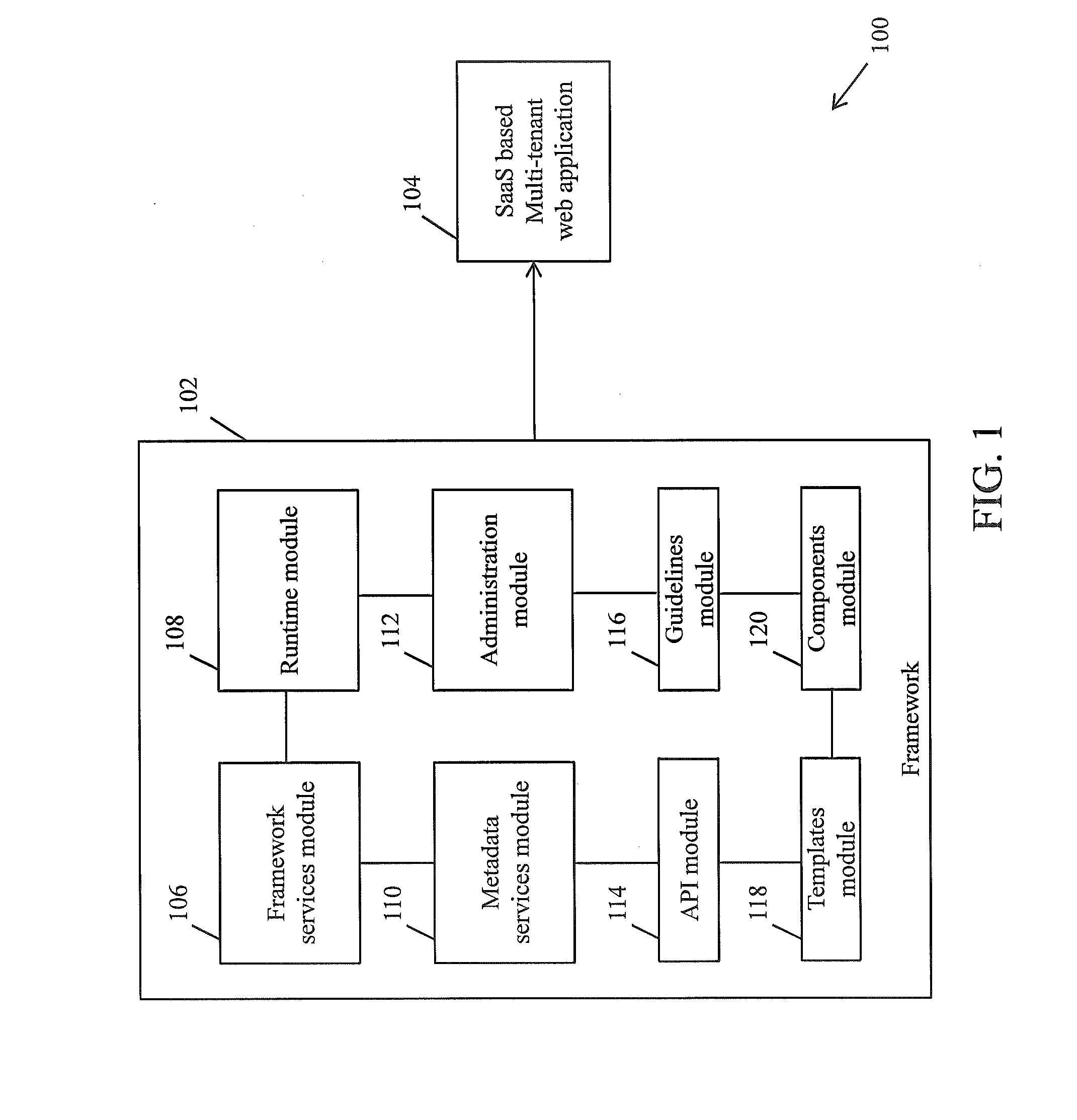
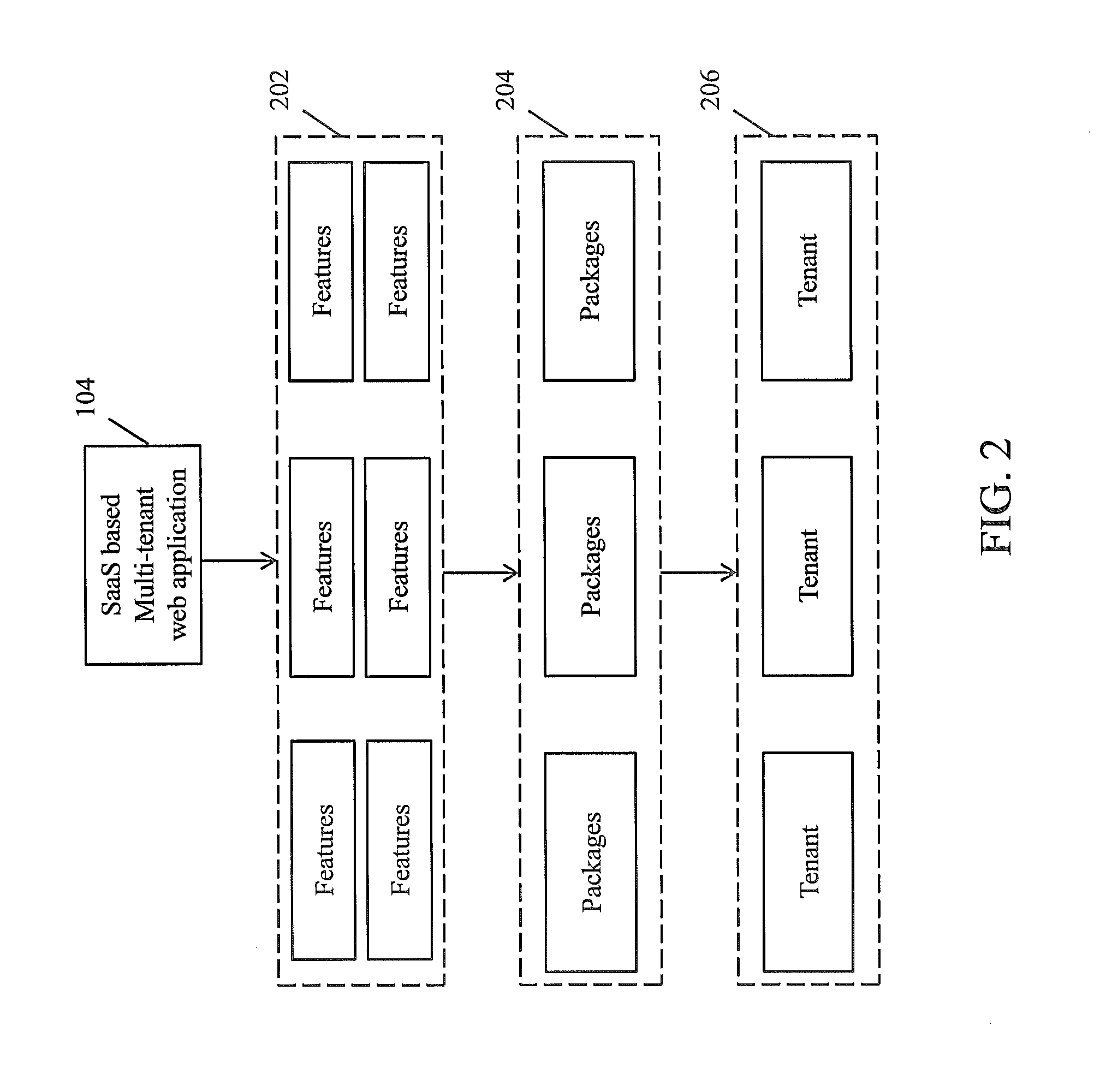
Framework for facilitating implementation of multi-tenant saas architecture
ActiveUS20140289391A1Facilitates monitoring and controllingFacilitate monitoring and controlling of featuresDigital computer detailsData switching networksWeb applicationSoftware as a service
A framework for implementing multitenant architecture is provided. The framework comprises a framework services module which is configured to provide framework services that facilitate abstraction of Software-as-a-Service (SaaS) services and crosscutting services for a Greenfield application and a non SaaS based web application. Further the abstraction results in a SaaS based multitenant web application. The framework further comprises a runtime module configured to automatically integrate and consume the framework services and APIs to facilitate monitoring and controlling of features associated with the SaaS based multitenant web application. The framework further comprises a metadata services module configured to provide a plurality of metadata services to facilitate abstraction of storage structure of metadata associated with the framework and act as APIs for managing the metadata. The framework further comprises a role based administration module that facilitates management of the metadata through a tenant administrator and a product administrator.
Owner:COGNIZANT TECH SOLUTIONS INDIA PVT
Organizing social activity information on a site
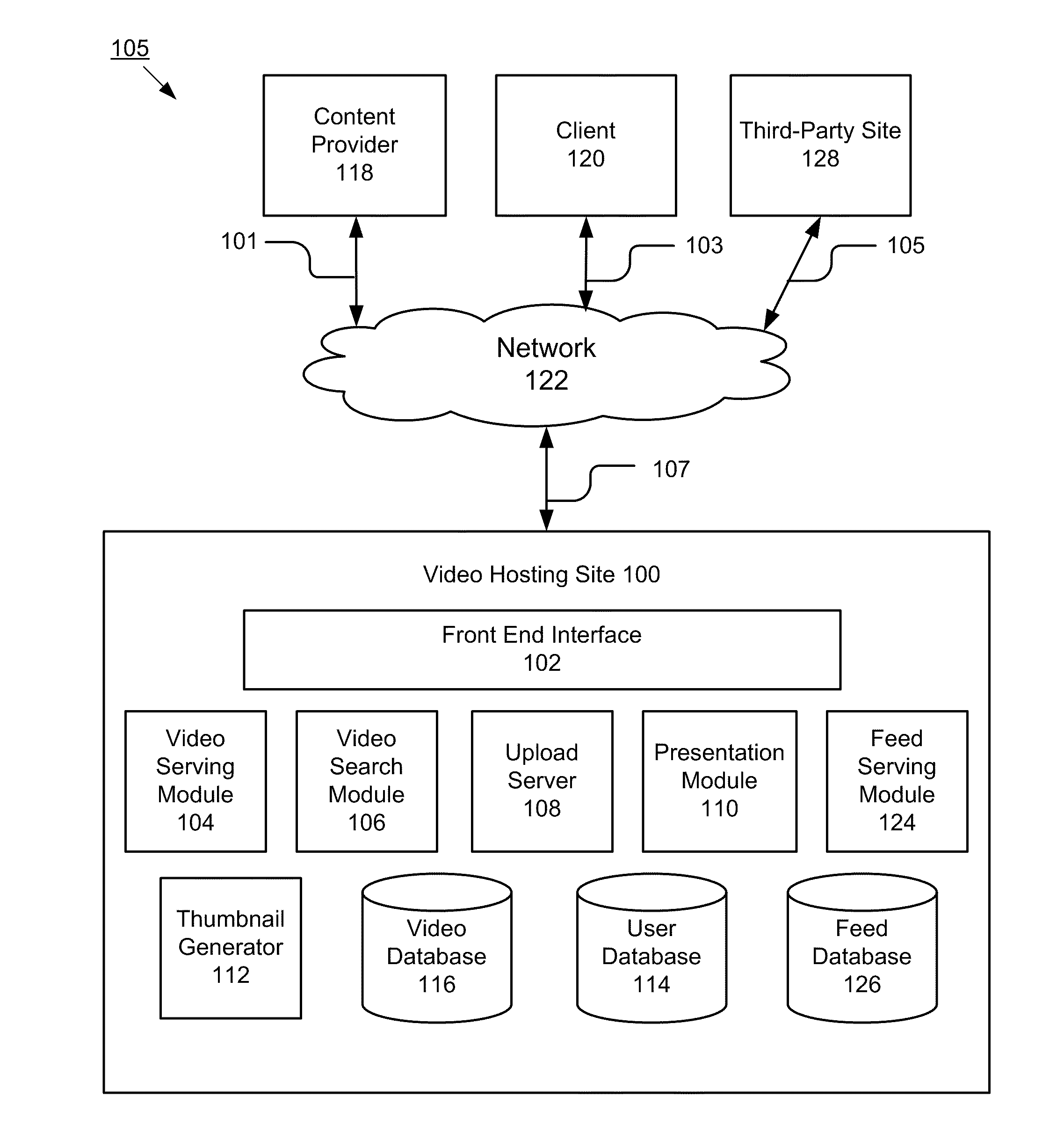
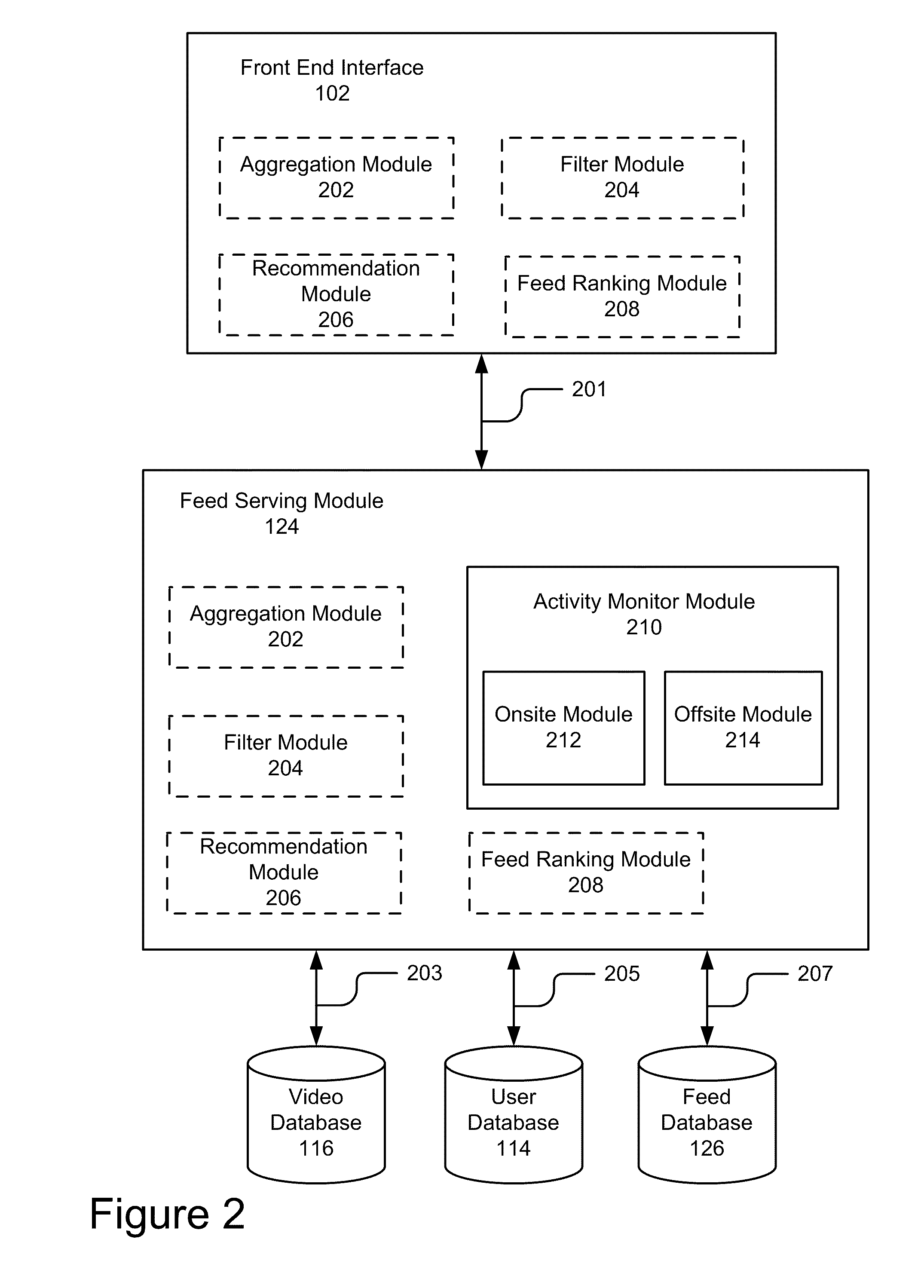
A system and method for organizing social activity information on a website is disclosed. The system comprises a feed serving module and a presentation module. The feed serving module is configured to receive social activity of at least a first user from at least one third-parity source. The feed serving module aggregates the social activity information to form aggregated social activity information. The presentation module is communicatively coupled to the feed serving module and is configured to receive the aggregated social activity information from the feed serving module. The presentation module generates feed display associated with the aggregated social activity information and sends feed display to a client for display to a second user.
Owner:GOOGLE LLC
Personal message delivery system
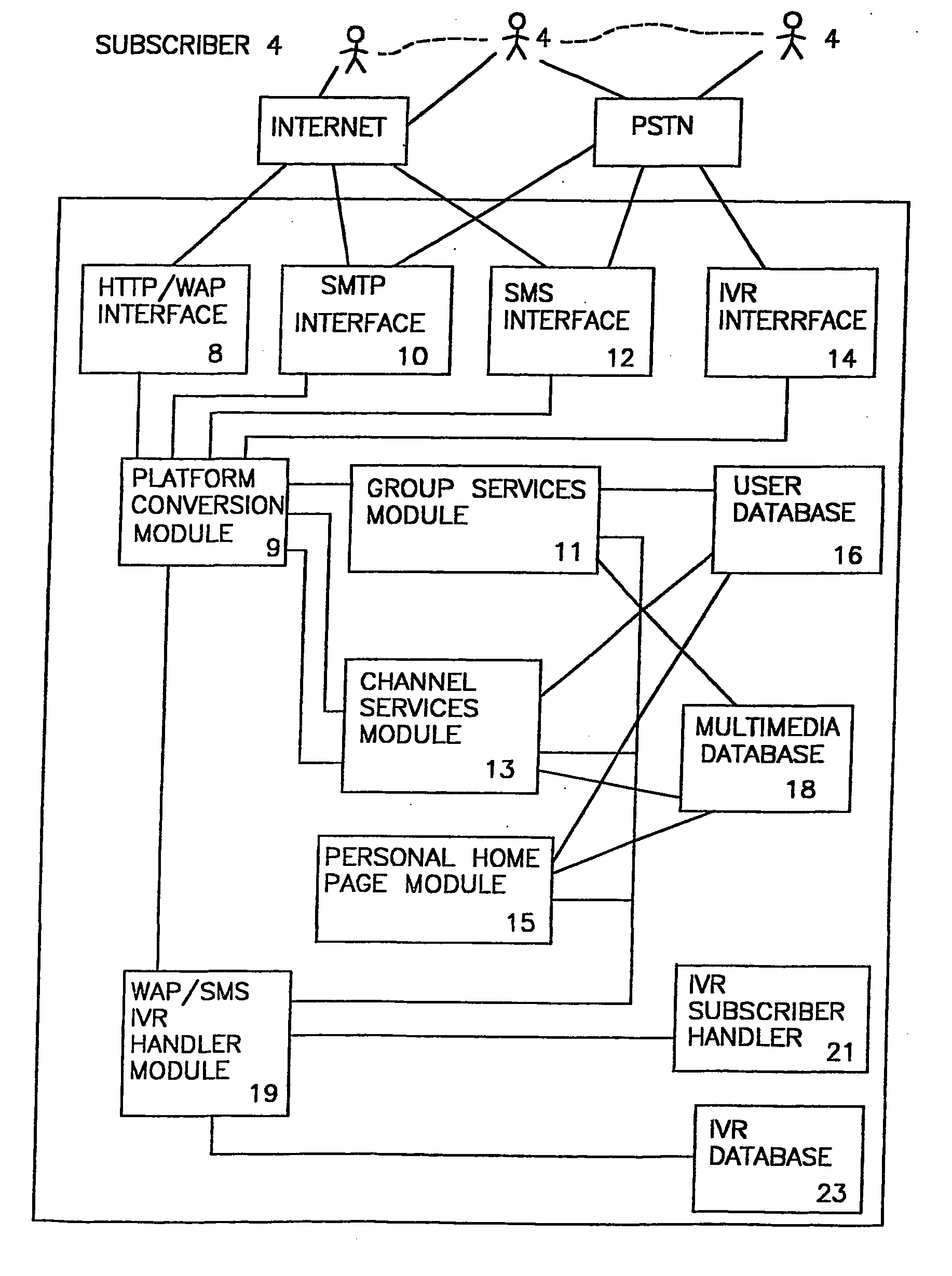
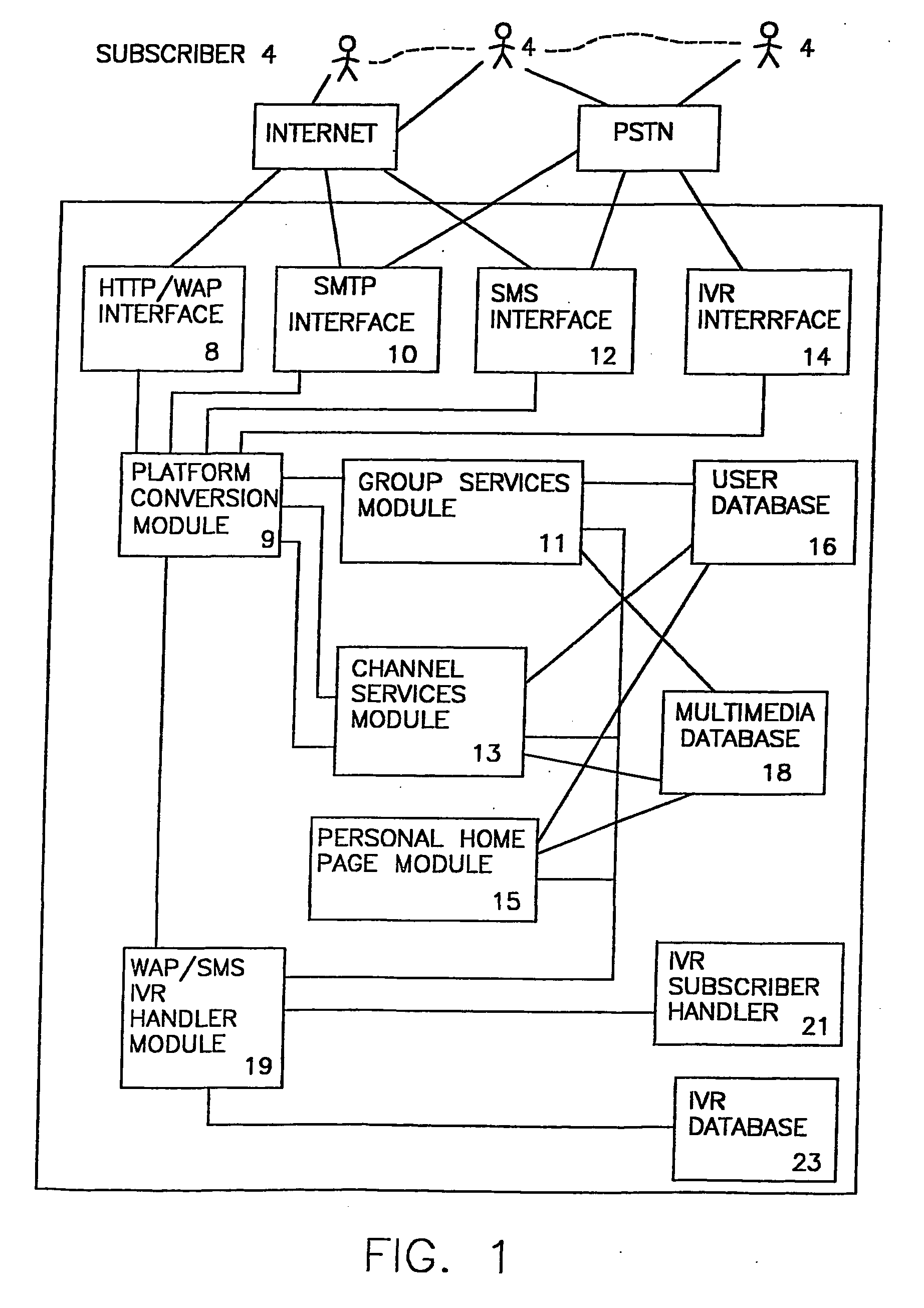
InactiveUS20050015443A1Smooth transitionSpecial service provision for substationTelephone data network interconnectionsComputer scienceService module
The present invention provides for a personal message system comprised of a plurality of interfaces configured to interface with a plurality of subscribers communication devices using a plurality of formats. A group services module is provided configured to maintain communications among groups of the subscribers. A platform conversion module is also provided and is coupled to the plurality of interfaces and the group services modules configured to connect each of the plurality of subscribers within a group, regardless of the communication protocols used by the subscribers.
Owner:UPOC
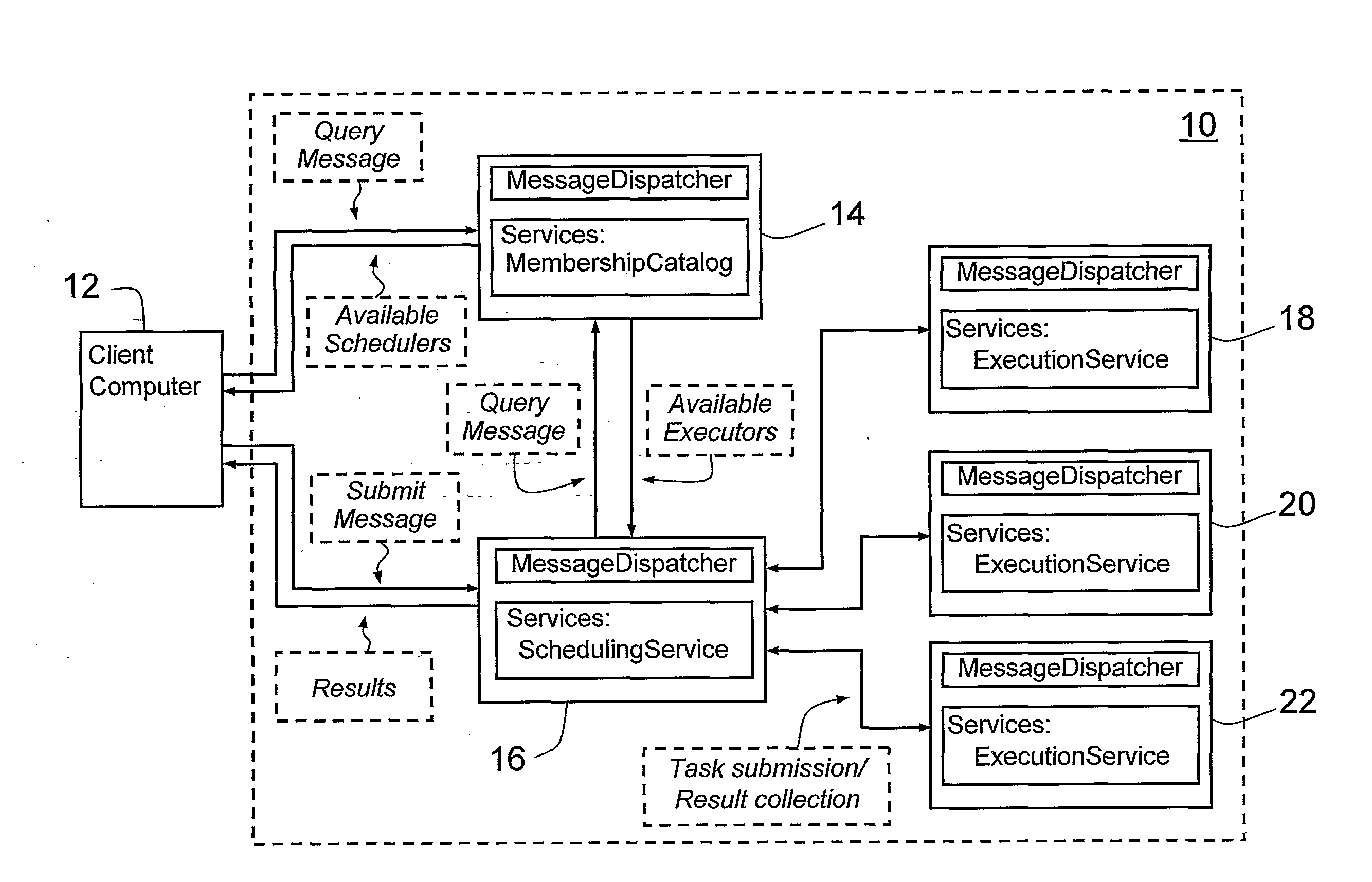
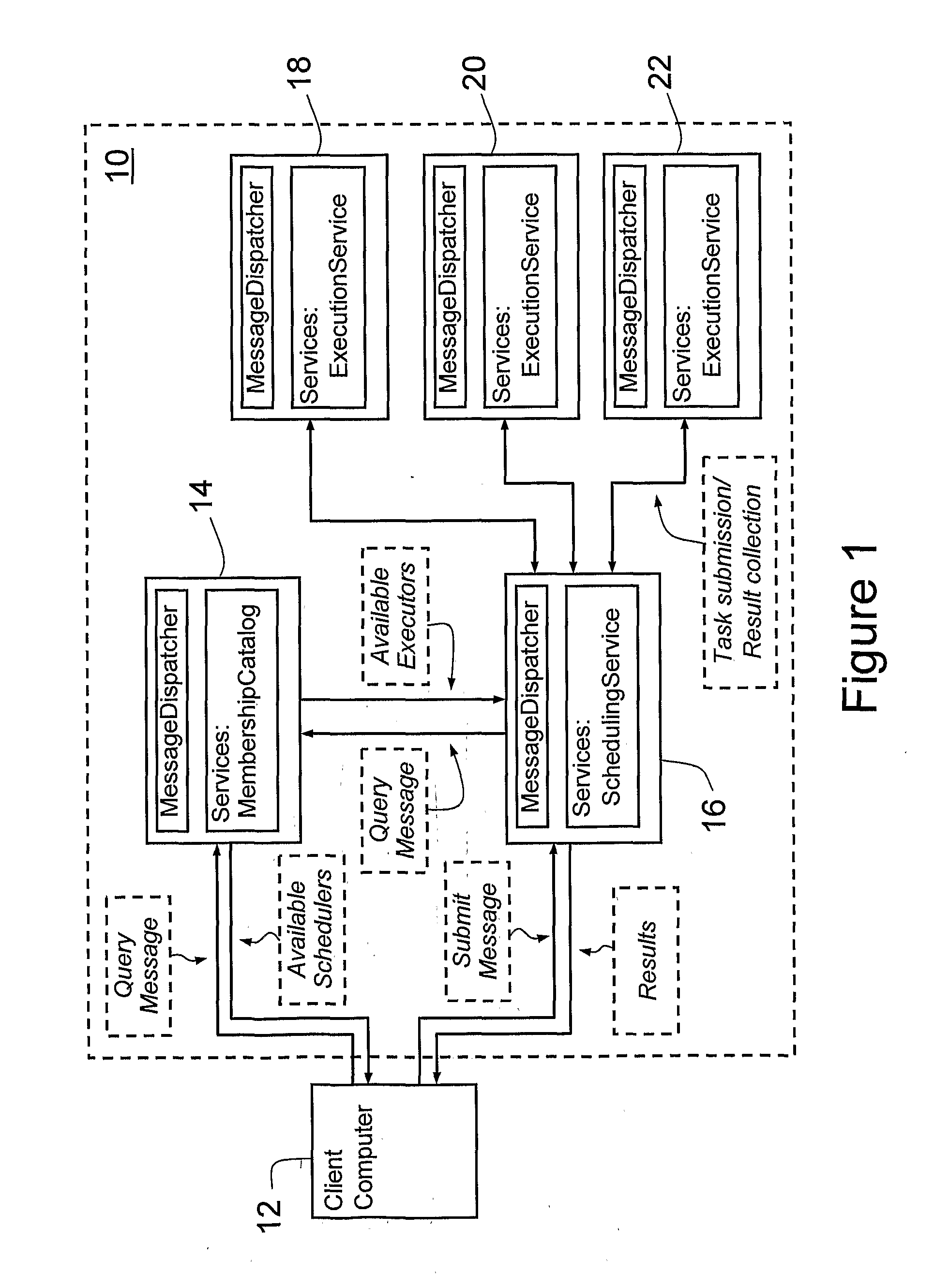
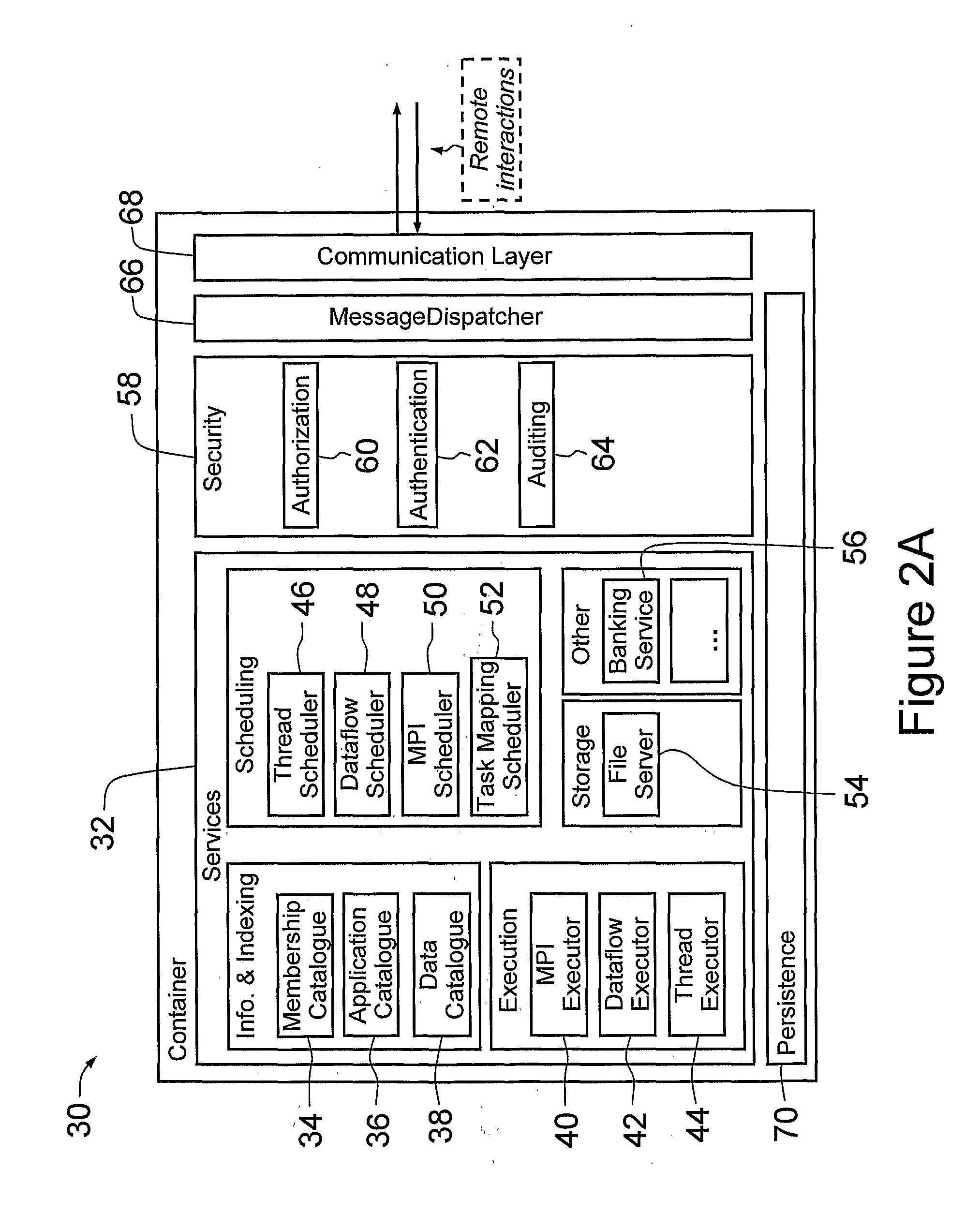
Software Platform and System for Grid Computing
A software platform for providing grid computing on a network of computing nodes, comprising a configurable service container executable at the nodes, including message dispatching, communication, network membership and persistence modules, and adapted to host pluggable service modules. When executed at the nodes at least one instance of the container includes a membership service module for maintaining network connectivity between the nodes, at least one instance of the container includes a scheduler service module configured to receive one or more tasks from a client and schedule the tasks on at least one of the nodes, and at least one instance of the container includes an executor service module for receiving one or more tasks from the scheduler service module, executing the tasks so received and returning at least one result to the scheduler service module.
Owner:IP3 2022 SERIES 922 OF ALLIED SECURITY TRUST I
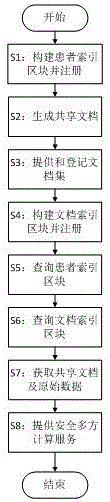
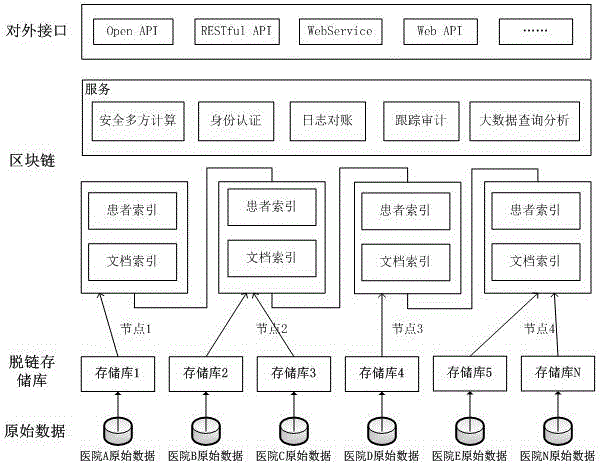
Method and device for medical information sharing privacy protection based on blockchain technology
InactiveCN106682530AAvoid privacyUse constraintsDigital data protectionInformation sharingPrivacy protection
The invention discloses a method and device for medical information sharing privacy protection based on a blockchain technology. According to the method, in aspects of privacy protection based on a blockchain technology, medical data on-chain and off-chain storage and forced privacy protection safety multiparty calculation, illegal medical data obtaining, use and tampering are avoided, and medical information sharing, big data analysis and utilization and patient privacy protection are implemented. The device comprises a data storage module, a service module provided based on the blockchain technology and a call service module provided externally, wherein a three-layer data storage frame is adopted for the data storage module; and the service module provided based on the blockchain technology mainly comprises forced privacy protection safety multiparty calculation. The method and device for medical information sharing privacy protection based on the blockchain technology are mainly applied to the fields of method and device for medical information sharing privacy protection based on a blockchain technology and medical big data analysis and the like, and technical guarantee is also provided for patient privacy protection while medical information sharing is achieved based on the blockchain technology.
Owner:HANGZHOU DIANZI UNIV
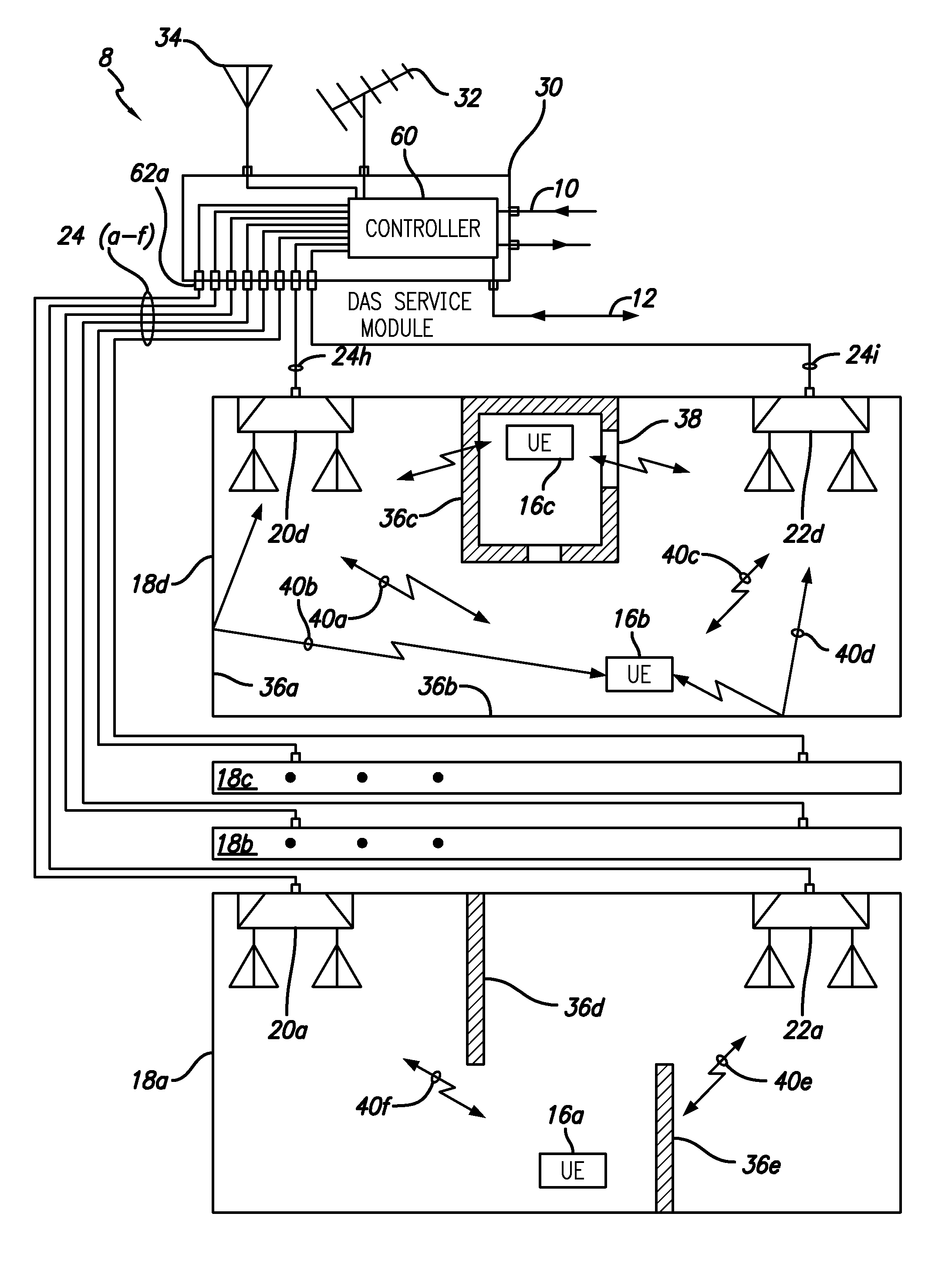
System and method for performance enhancement in heterogeneous wireless access network employing distributed antenna system
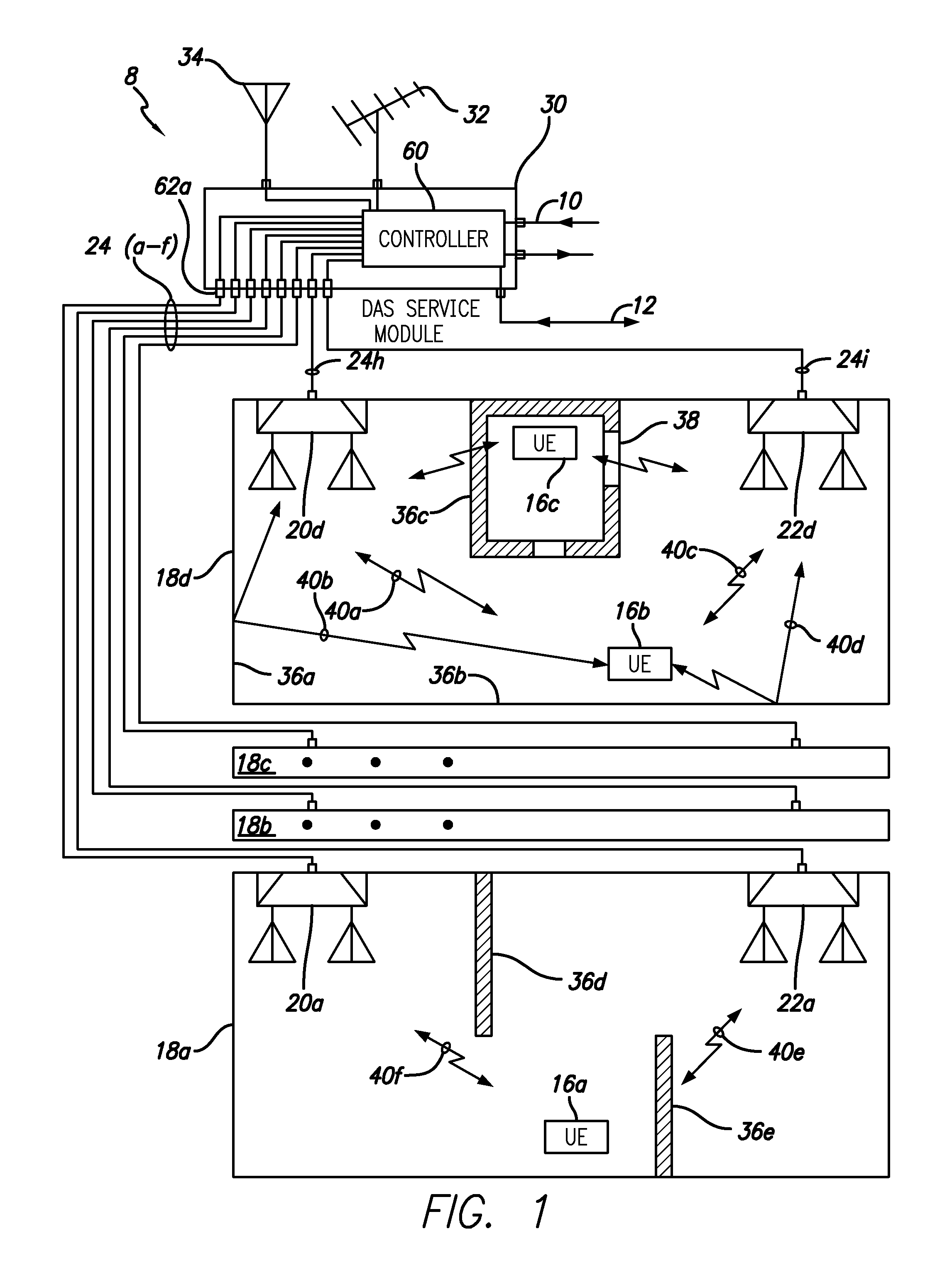
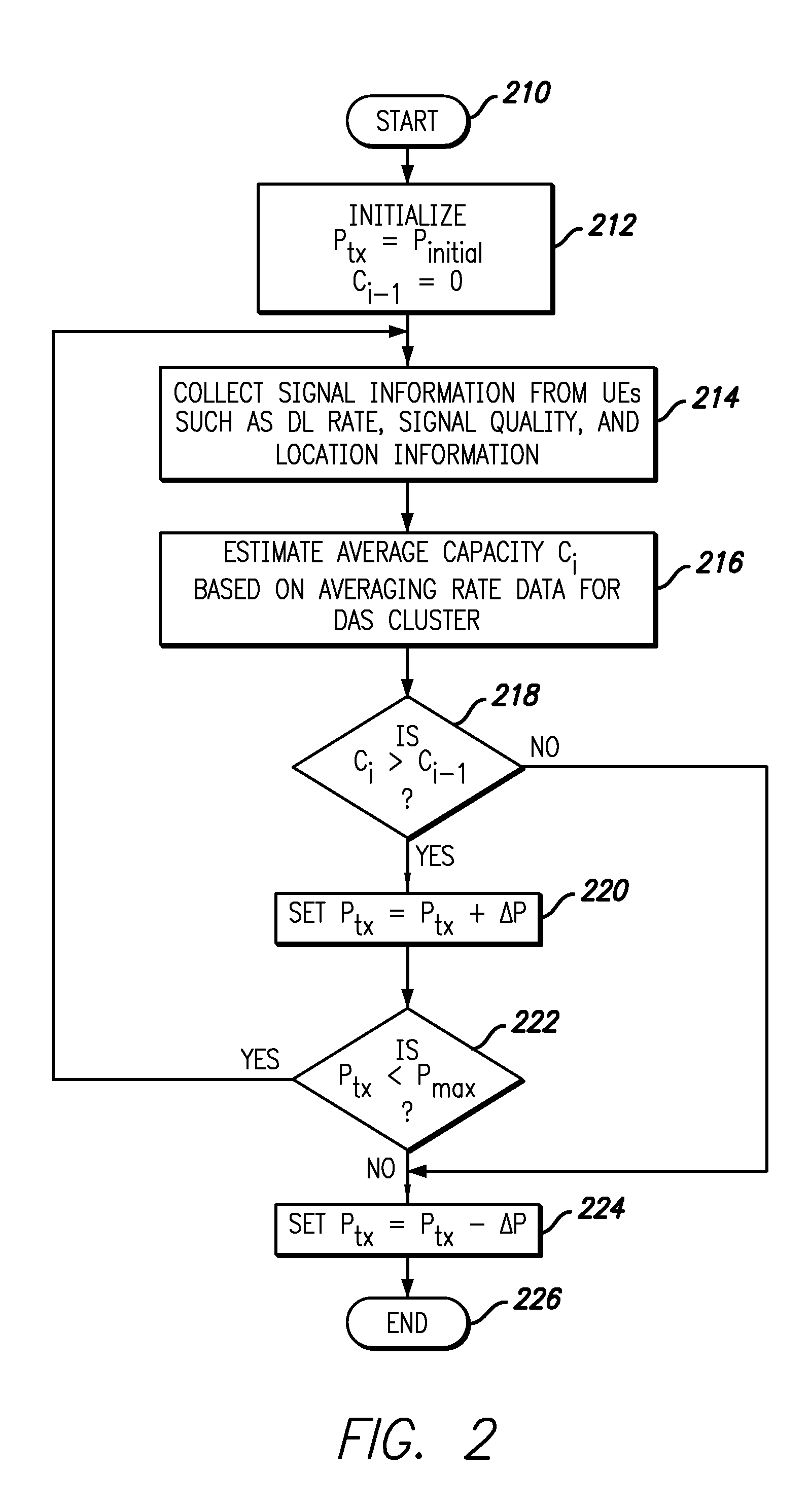
ActiveUS9020555B2Power optimizationImprove system performancePower managementFrequency-division multiplex detailsAccess networkPerformance enhancement
A system and method for dynamically optimizing the performance of indoor distributed antenna systems communicate to user equipment is disclosed. The user equipment measures information describing the downlink signals such as the downlink data rates, the quality of the received signal, and the location of the user equipment. A service module collects this information and determines an optimized power level for each of the antenna units. The service module may optimize only one antenna unit power level or a subset of the antenna units within the distributed antenna system in a preferred embodiment. One or more of the antenna units then transmits downlink signals with the optimized power levels. The optimized power level may be less than the initial power level in a preferred embodiment. As a result, the performance of the indoor distributed antenna systems is enhanced.
Owner:INTEL CORP
Method, system, and computer program product for managing database servers and service
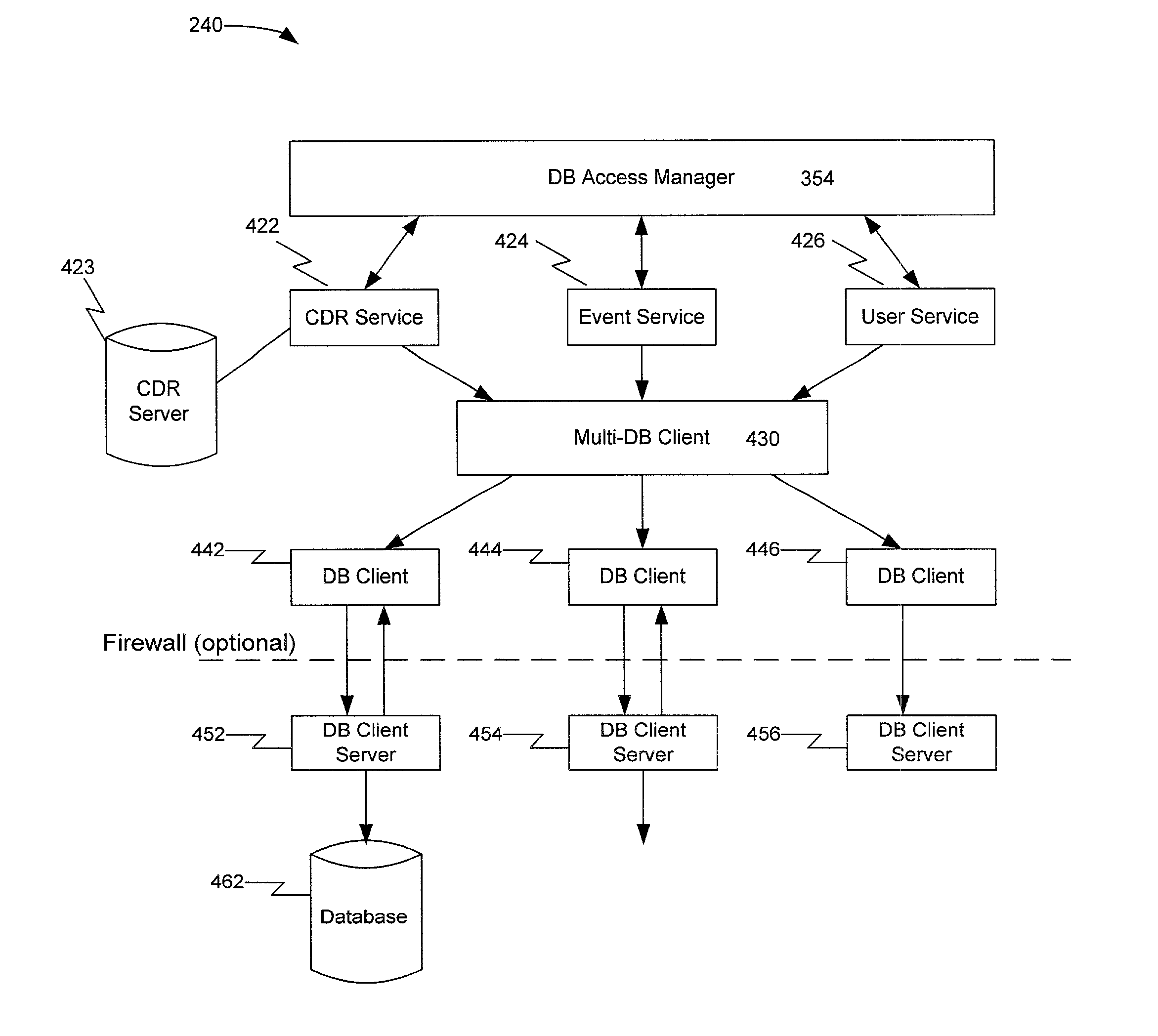
InactiveUS7123608B1Interconnection arrangementsDigital data processing detailsDatabase serverComputer module
A system, method, and computer program product for managing database servers and services is disclosed, which expands the capabilities of existing systems by providing better scalability and security. A database management system includes databases consisting of database clients and servers that handle the storing of information, a multi-database client that manages database servers, service modules which allow other systems to access the database servers, and a database access manager that manages requests from the service modules. A database access manager facilitates and coordinates interaction between the service modules and the multi-database client. Service modules provide interfaces from which other external or internal systems can access the managed databases. Requests can be sent between systems and the database access manager via the service modules. Two present and representative implementations of service modules are: user management and call detail record (CDR) collection. The user management service module allows systems to access user account information stored in the databases. The CDR collection service module inserts details for each call made on the network.
Owner:CHEMTRON RES
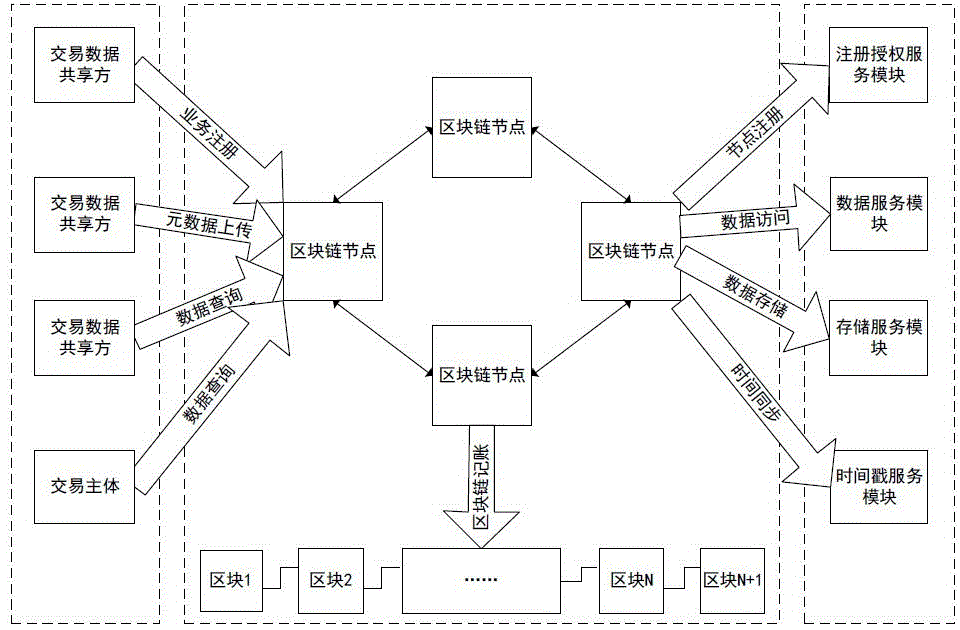
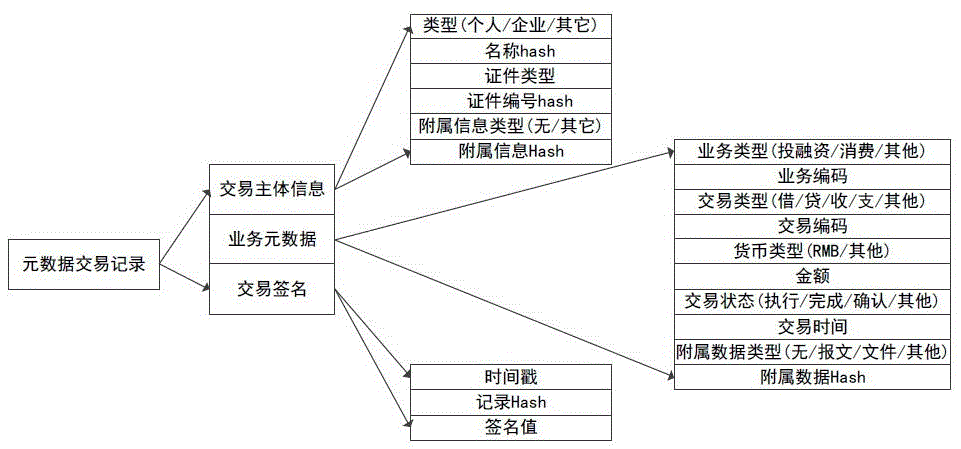
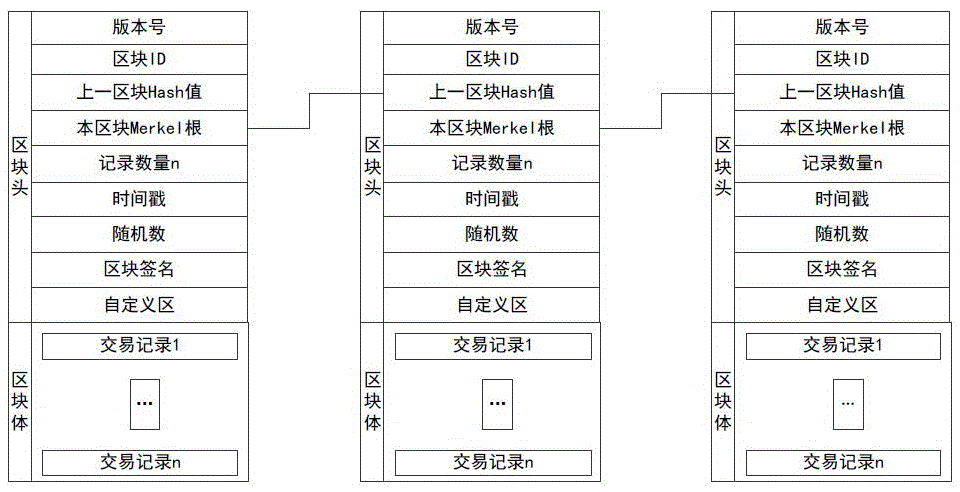
Multi-party sharing transaction metadata method, device and system based on block chain
ActiveCN107180350AEnsure safetyEasy to operateFinanceBuying/selling/leasing transactionsDigital signatureTransaction data
The invention discloses a sharing transaction metadata method, device and system based on block chains; transaction metadata can be extracted from various party transaction data and written into the block chain, thus forming a distributed shearing transaction metadata block chain account book; the method comprises the following steps: issuing a digital signature certificate based on a PKI / CA system for block chain nodes and transaction various parties, recording transaction metadata, and signaturing the block in a secrete manner; desensitizing transaction main body information, extracting transaction metadata from original transaction data, uploading the transaction metadata to block chain nodes, allowing the transaction main body to confirm the transaction metadata, allowing the block chain node to write the confirmed transaction metadata into the block chain, and allowing data sharing parties to check the block chain information after authorization. In an authority issuing business scene, the original transaction and collateral data are encrypted and stored through a storage service module, and related transaction authorities are provided for the transaction sharing party, the transaction main body and the transaction main body opponent party.
Owner:唐晓领
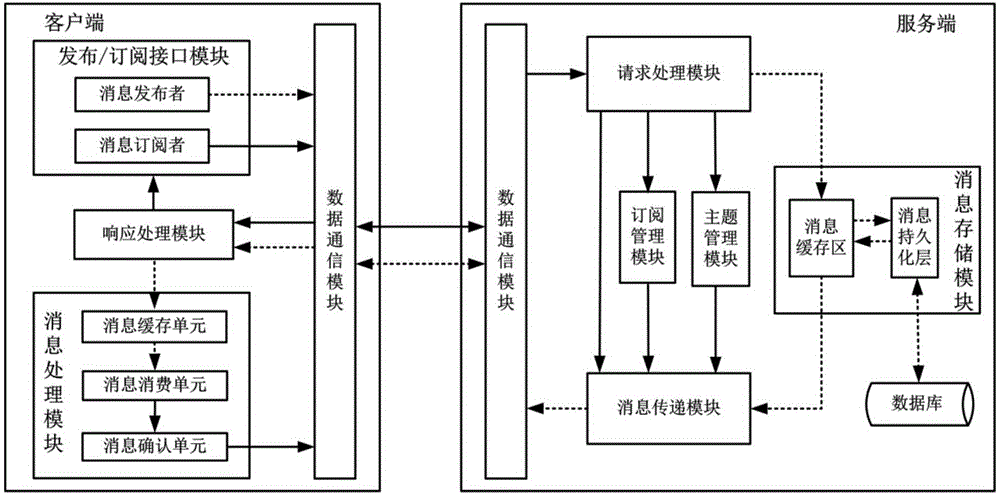
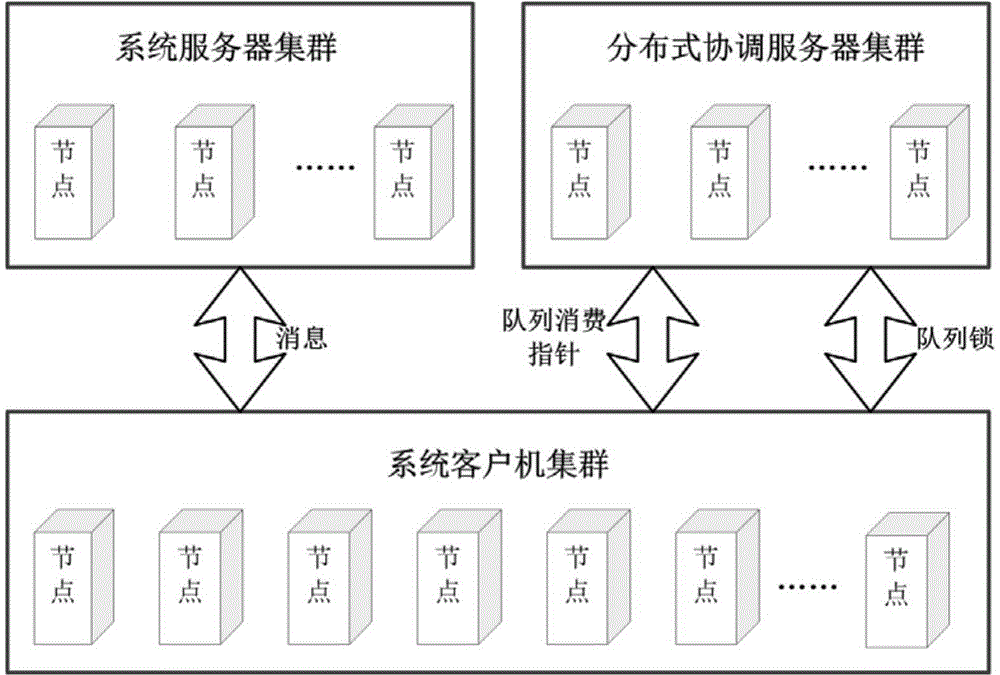
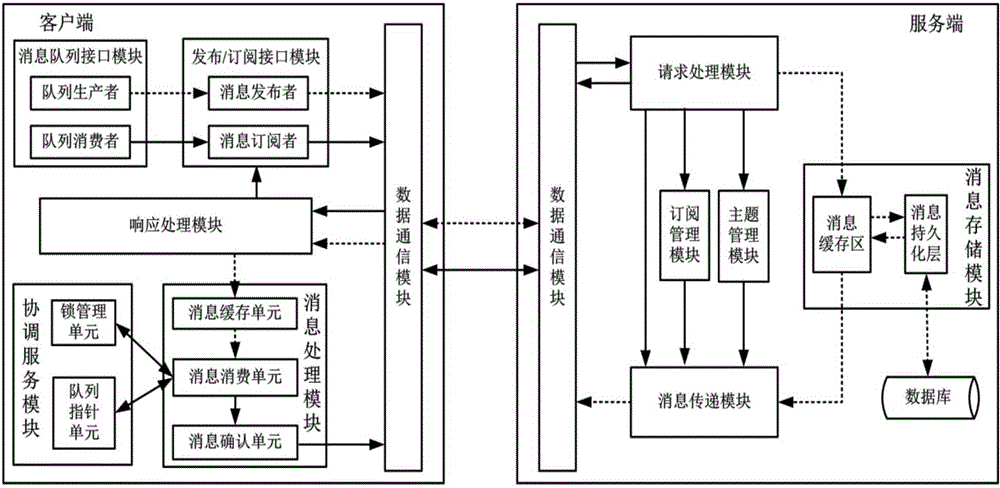
Posting/subscribing system for adding message queue models and working method thereof
ActiveCN104092767AReduce hardware costsAchieve mutual compatibilityTransmissionMessage queueTransfer model
The invention provides a posting / subscribing system for adding message queue models and a working method of the posting / subscribing system. The system comprises a distributed message-oriented middleware server-side cluster, a client-side cluster and a distributed coordinate server cluster. Service nodes in the message-oriented middleware server-side cluster are composed of corresponding modules of an original posting / subscribing system, and the function of the message-oriented middleware server-side cluster is the same as the information transferring relation; a client side is simultaneously provided with a calling interface of a posting / subscribing model and a calling interface of a message queue model which are used for achieving the purpose that a user can select and use the two different message transferring models directly without transforming the bottom layer middleware, so that a coordinate service module and a message processing module are additionally arranged on the client side based on an original framework. The system supports the posting / subscribing message transferring model and the message queue message transferring model simultaneously and guarantees that the availability, flexibility and other performance of the two models are all within the acceptable range, and the problem that it is difficult to transform the bottom layer message transferring model for the user is better solved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
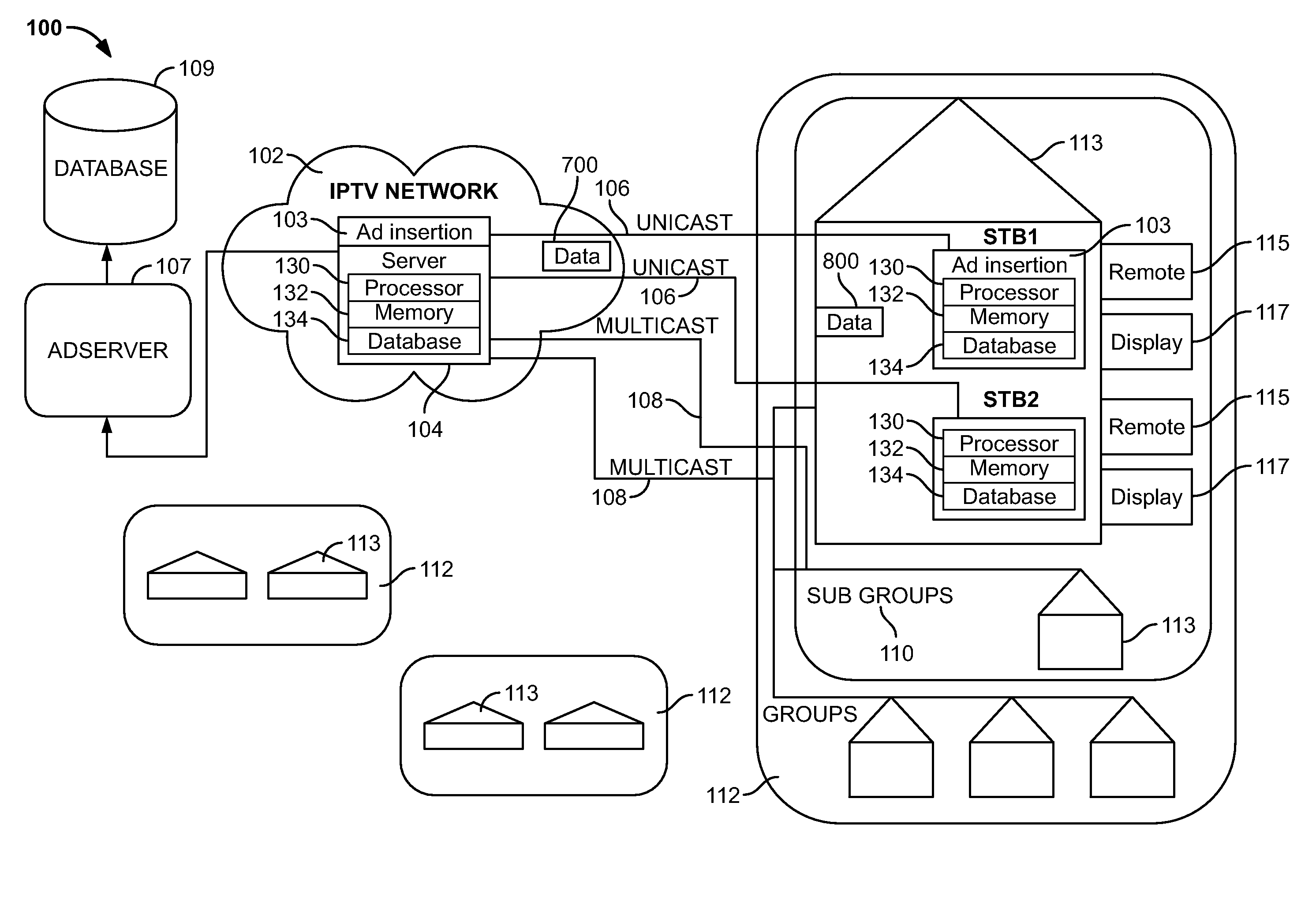
System, method, and apparatus for implementing targeted advertising in communication networks
InactiveUS20080276270A1Great revenueCommerceElectrical cable transmission adaptationTargeted advertisingService module
The present technique detects at least one active user utilizing a set of communication devices over a communication network. The method includes receiving behavior data, fulfillment data and feedback data for the at least one active user of the set of communication devices accessing content over the communication network using an intelligent agent module. The method includes creating a database of a set of demographic profiles based on the received data using a dynamic group and rules editor module. The method further includes grouping a set of the at least one active user of the set of communication devices into their corresponding dynamic group using group creation service module.
Owner:KOTARU CHANDRA SHEKAR +3
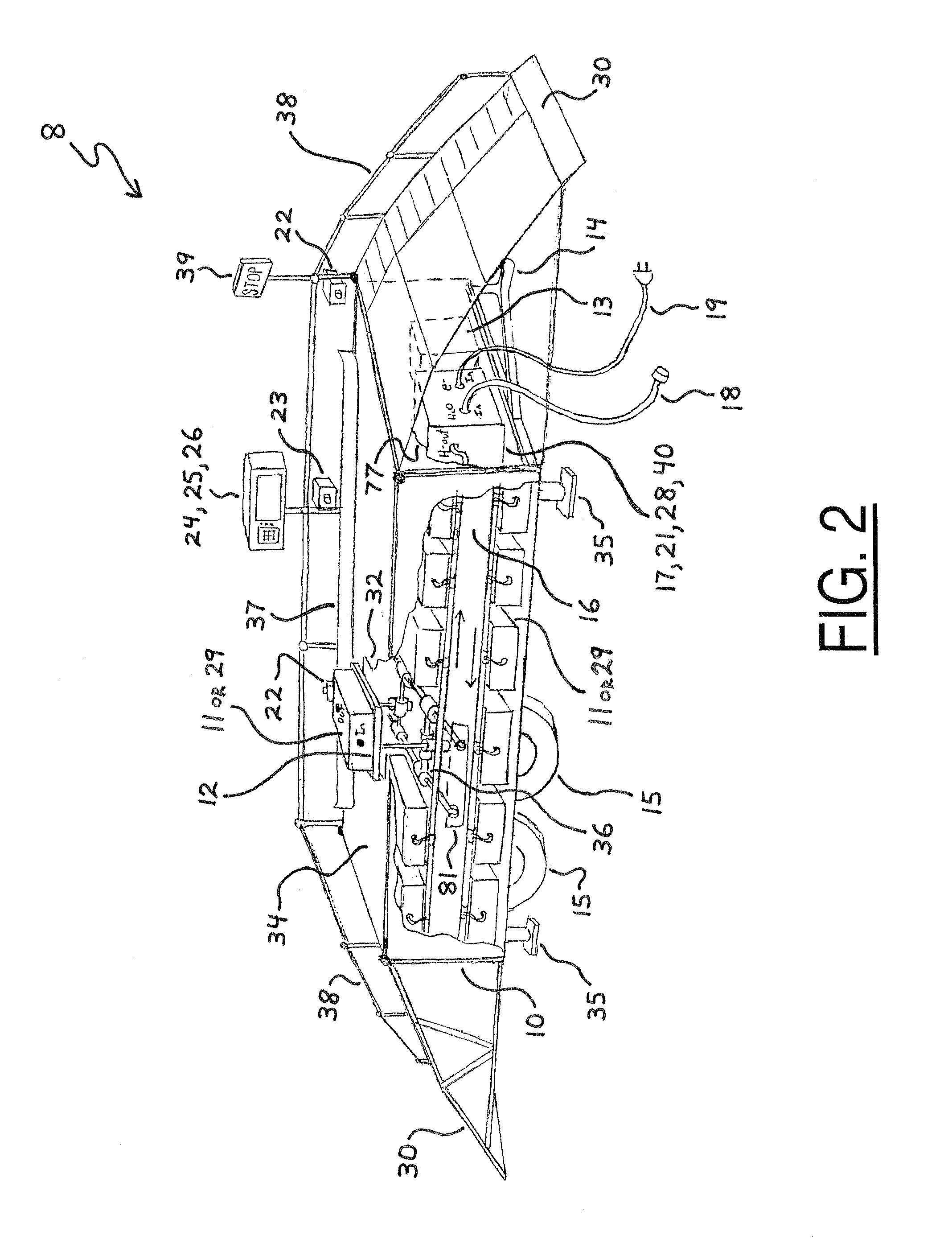
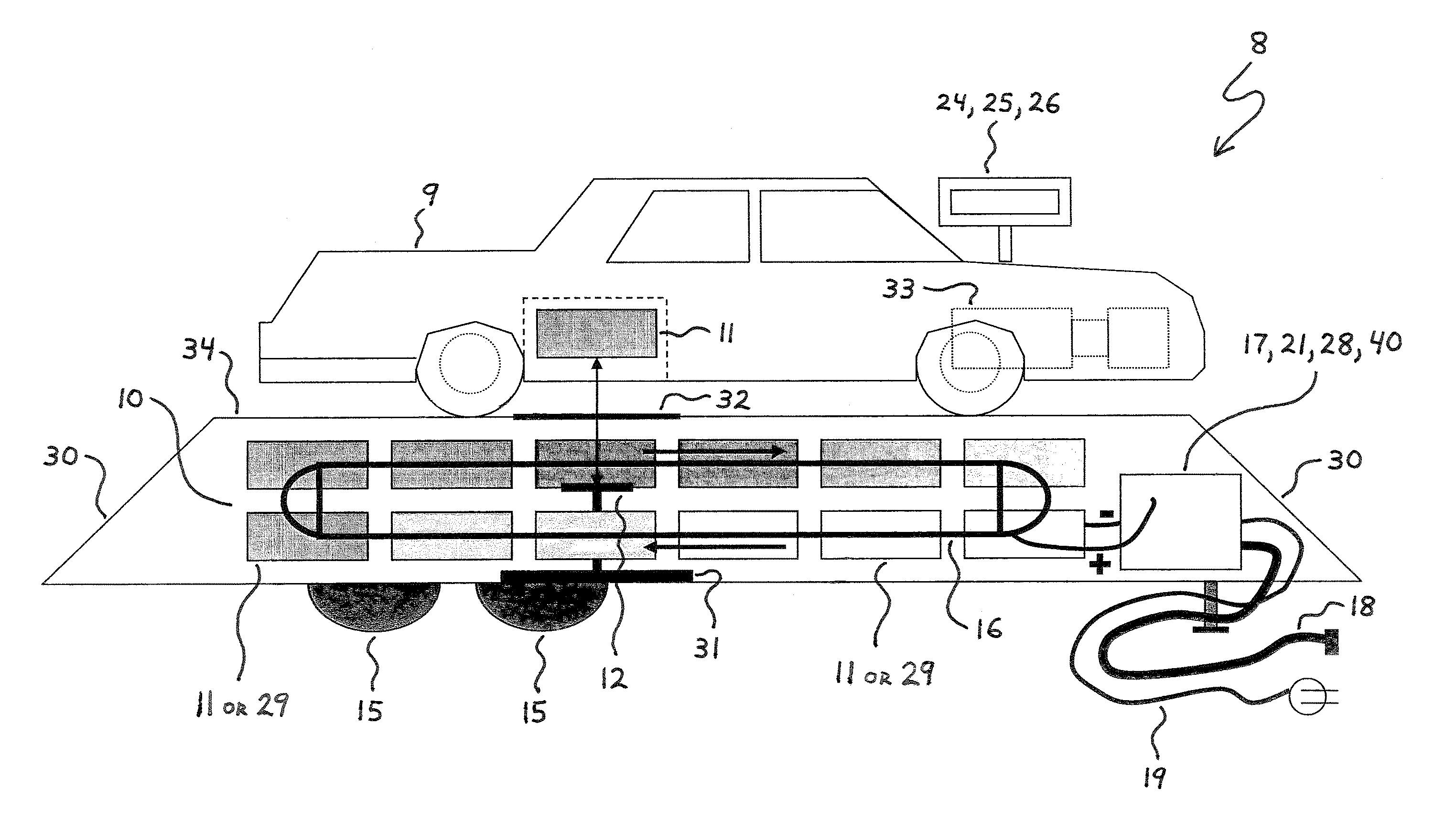
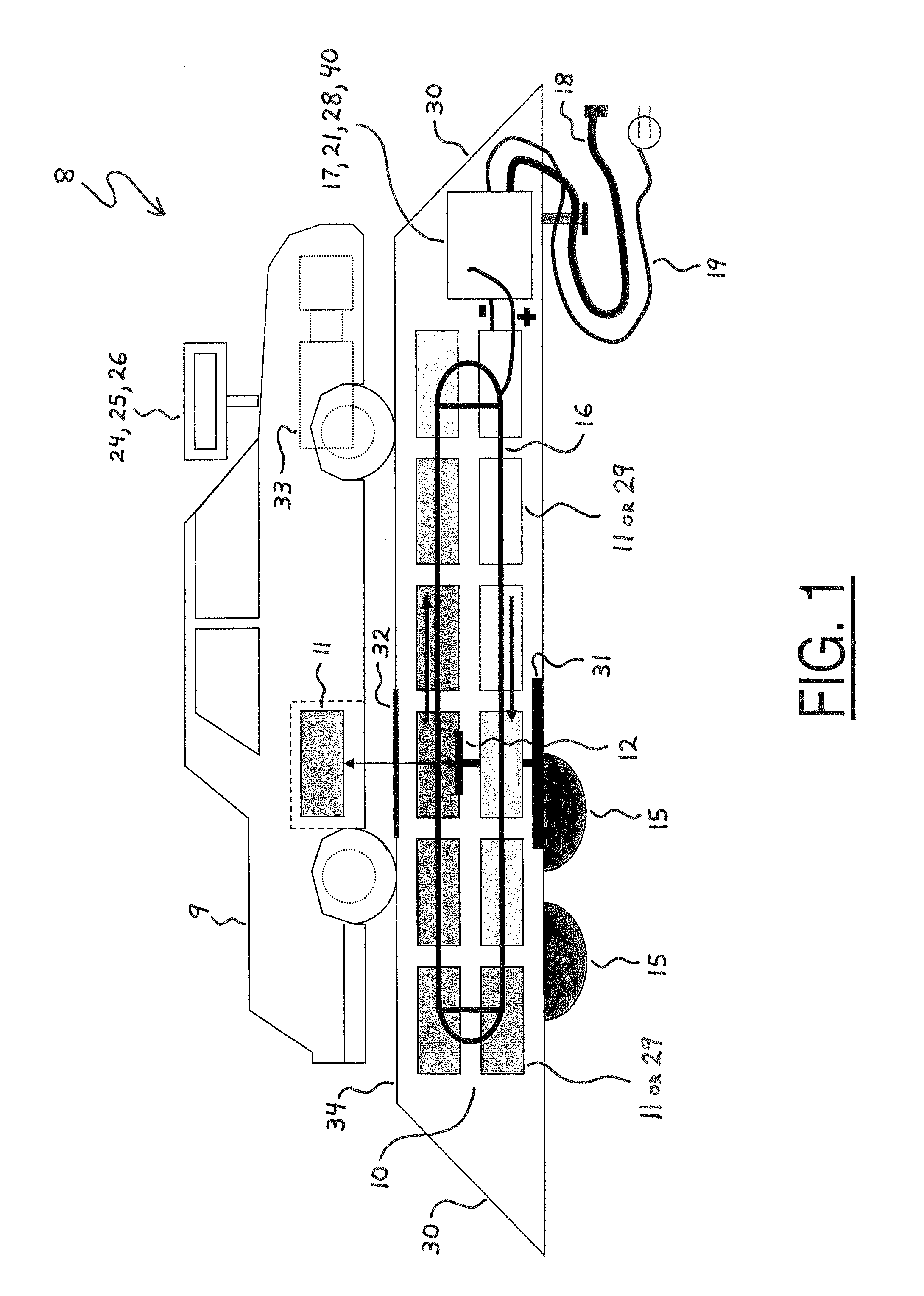
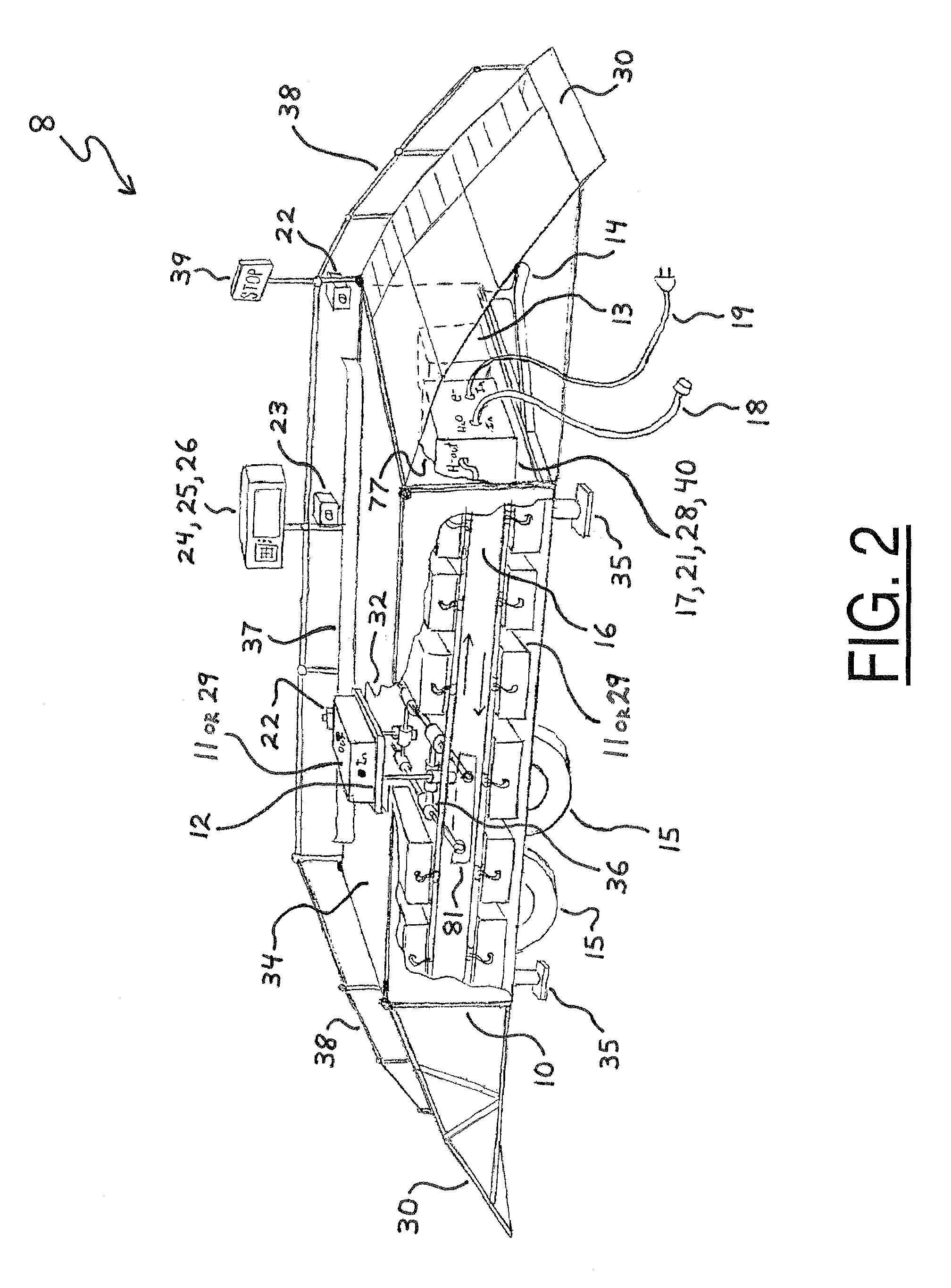
System for replenishing energy sources onboard different types of automotive vehicles
A service station facility for replenishing various motivational energy sources onboard different types of automotive vehicles is disclosed herein. In one embodiment, the service station facility includes a rack, replaceable fuel tanks, a service module, and an electronic computer control system. The replaceable fuel tanks are stocked on the rack and substantially filled with various fluids, such as hydrogen, which are utile as motivational energy sources within fuel-operated automotive vehicles. The service module is mounted on the rack, and the electronic computer control system is connected in electrical communication with the service module. In this configuration, the service module is controllably operable to receive a depleted replaceable fuel tank from a fuel-operated automotive vehicle and also selectively deliver one of the filled replaceable fuel tanks onboard the automotive vehicle. In another embodiment, the service station facility may also stock replaceable batteries for selective delivery onboard battery-operated automotive vehicles.
Owner:CAPIZZO PETER DAVID
System for replenishing energy sources onboard different types of automotive vehicles
Owner:CAPIZZO PETER DAVID
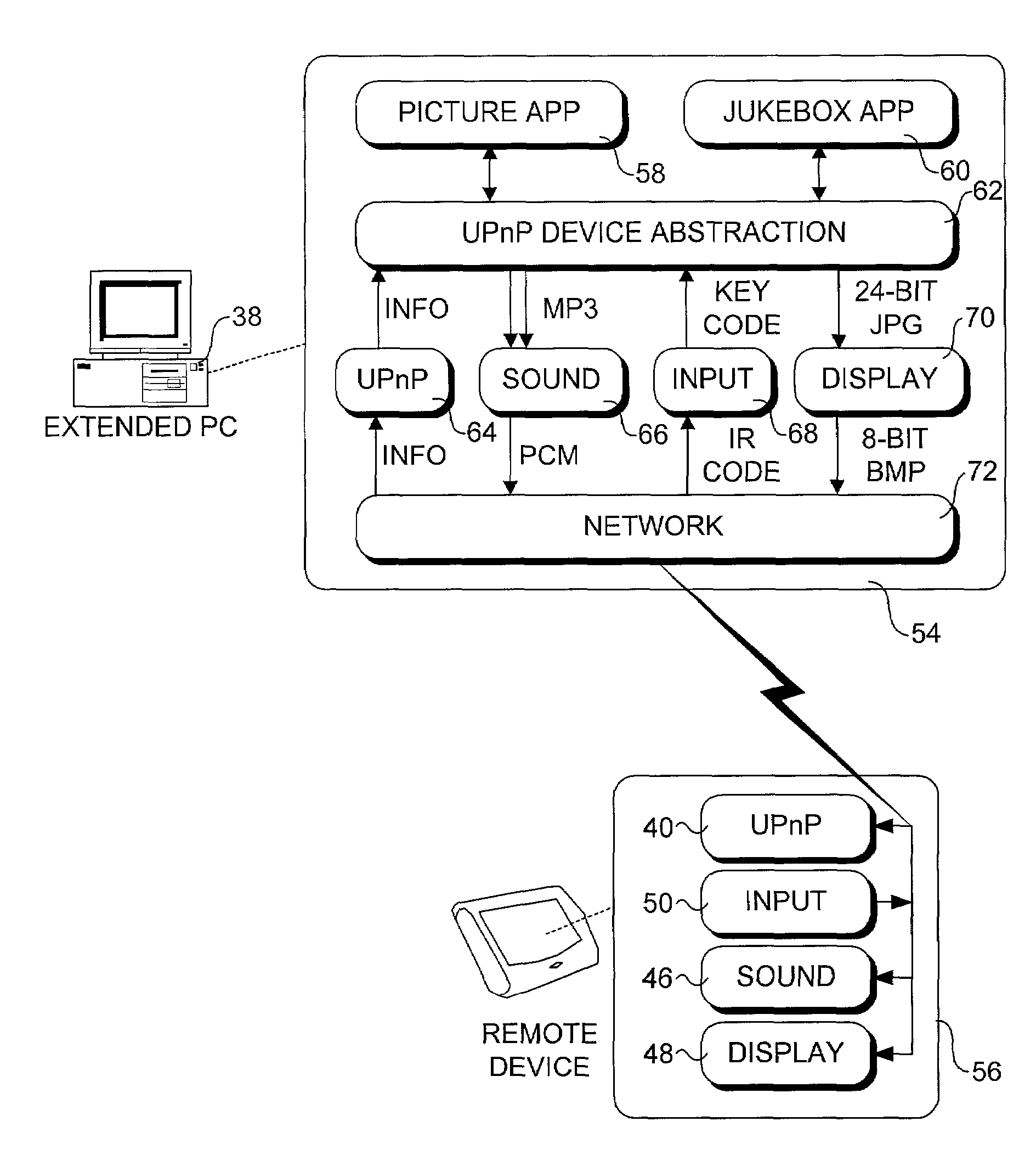
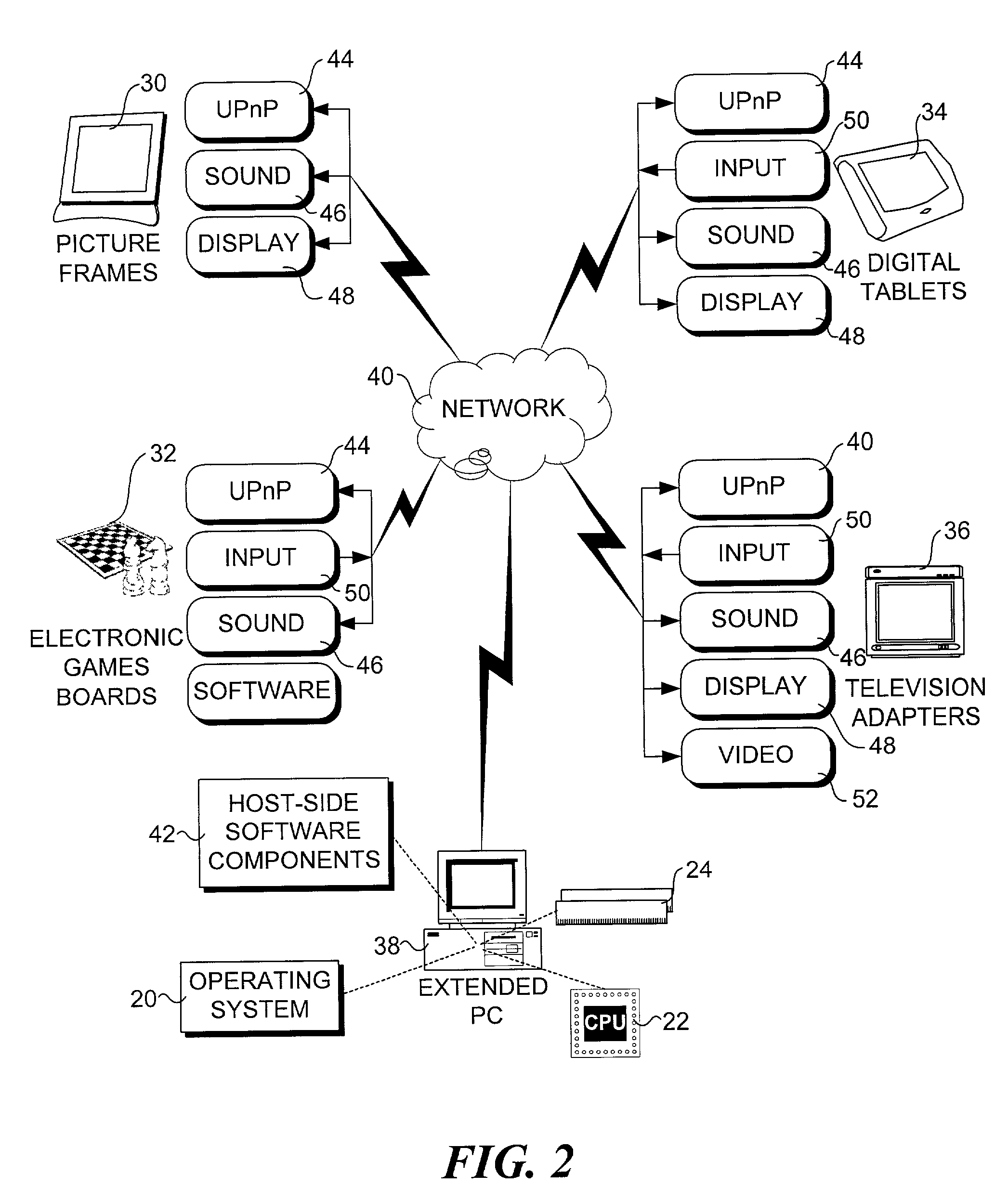
Method and architecture to support interaction between a host computer and remote devices
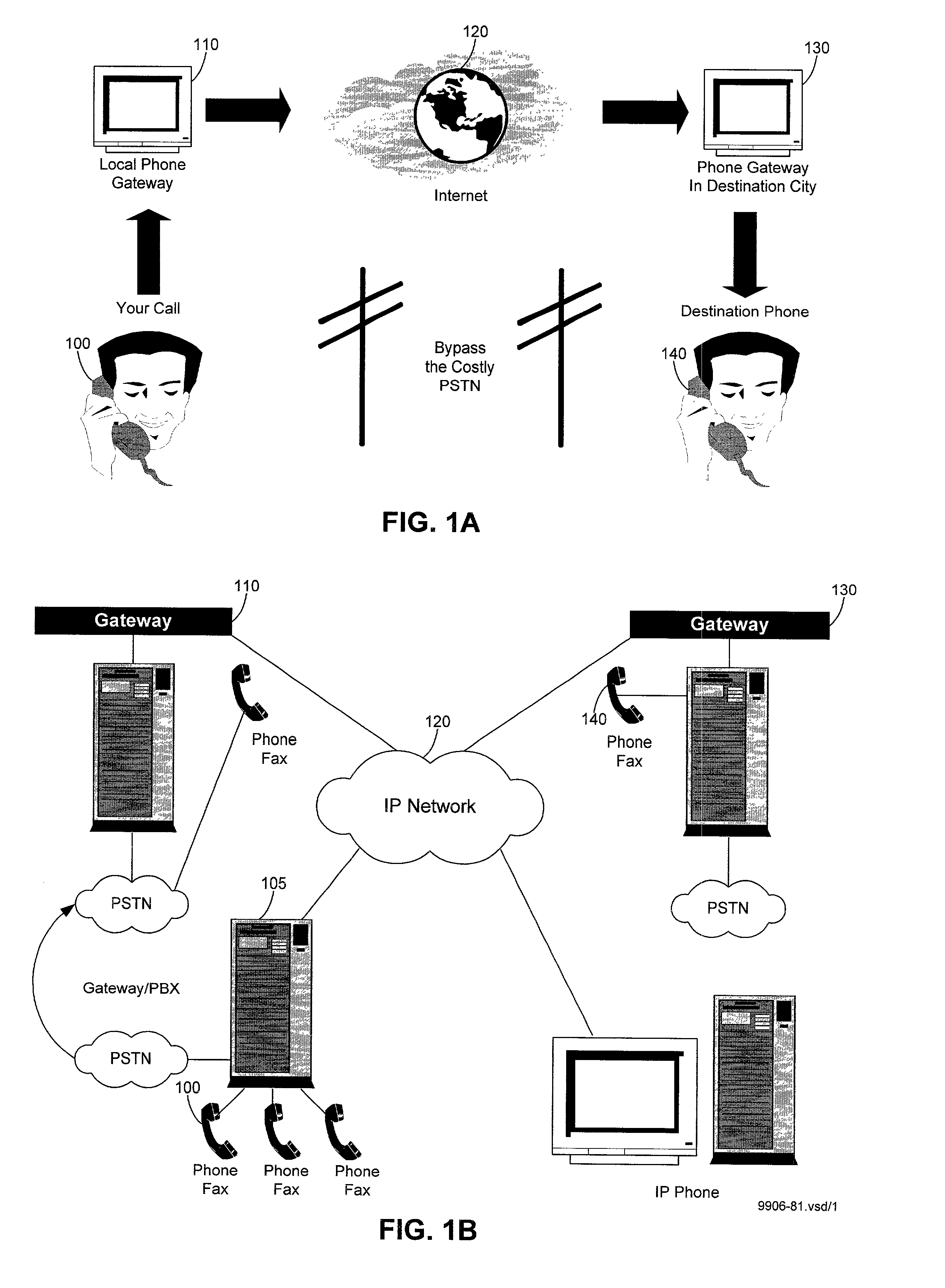
InactiveUS7299304B2TransmissionInput/output processes for data processingService protocolNetwork communication
A method and architecture for enabling interaction between a remote device and a host computer. A service provided by the remote device is discovered, and a description pertaining to the service is retrieved by the host computer. A network communication link is the established between the remote device and the host computer based on connection information provided by the description. Host-side and client-side software service modules are run on the host and remote devices to enable interaction between the devices using a service protocol that is specific to the service. Various service protocols are provided, including a display service protocol and an input service protocol. Using commands provided by each protocol, the host computer is enabled to control the service remotely by pushing data and appropriate commands to the remote device, whereupon these commands are processed by the client-side service module to perform service operations that employ the sent data.
Owner:INTEL CORP
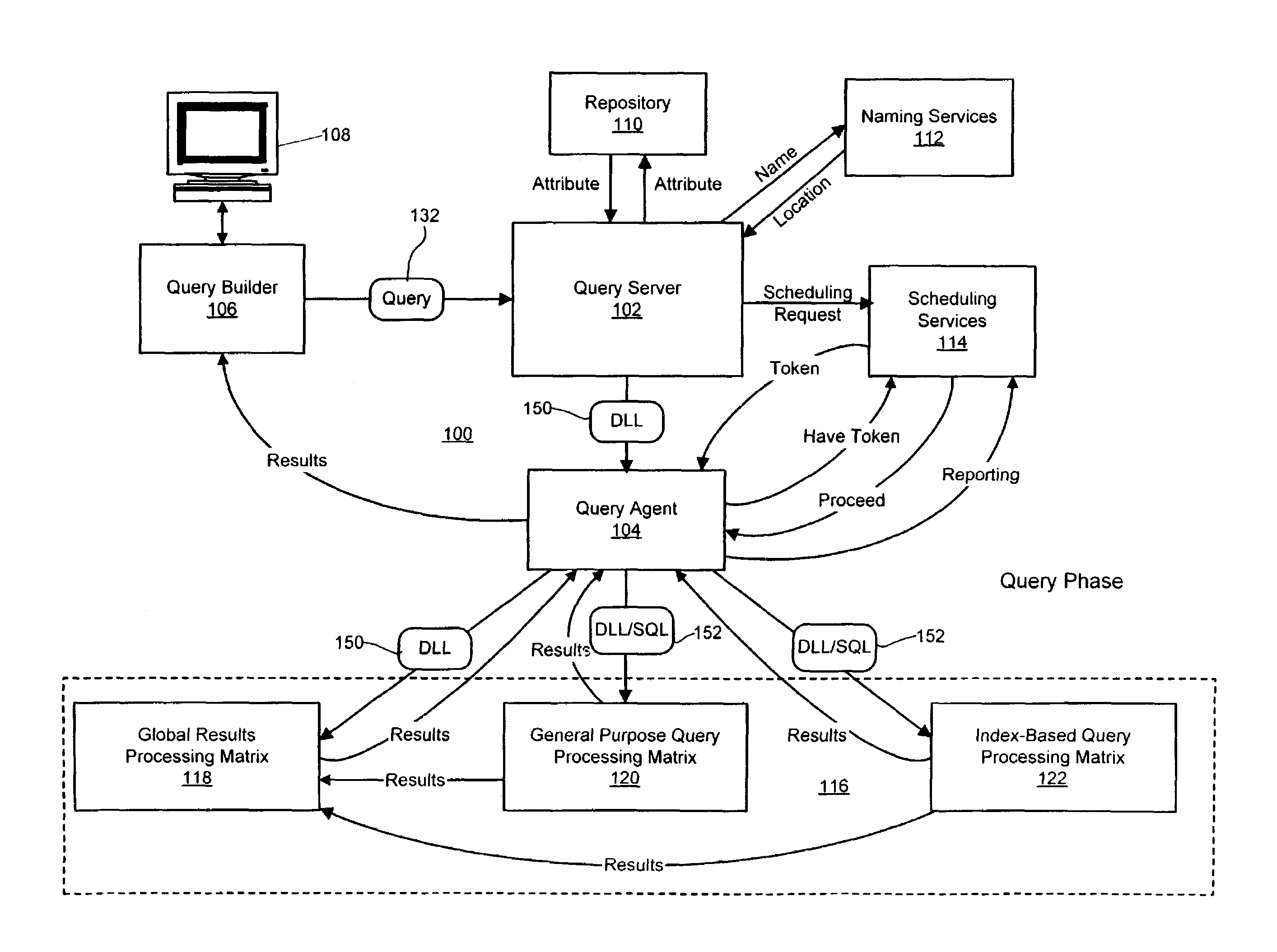
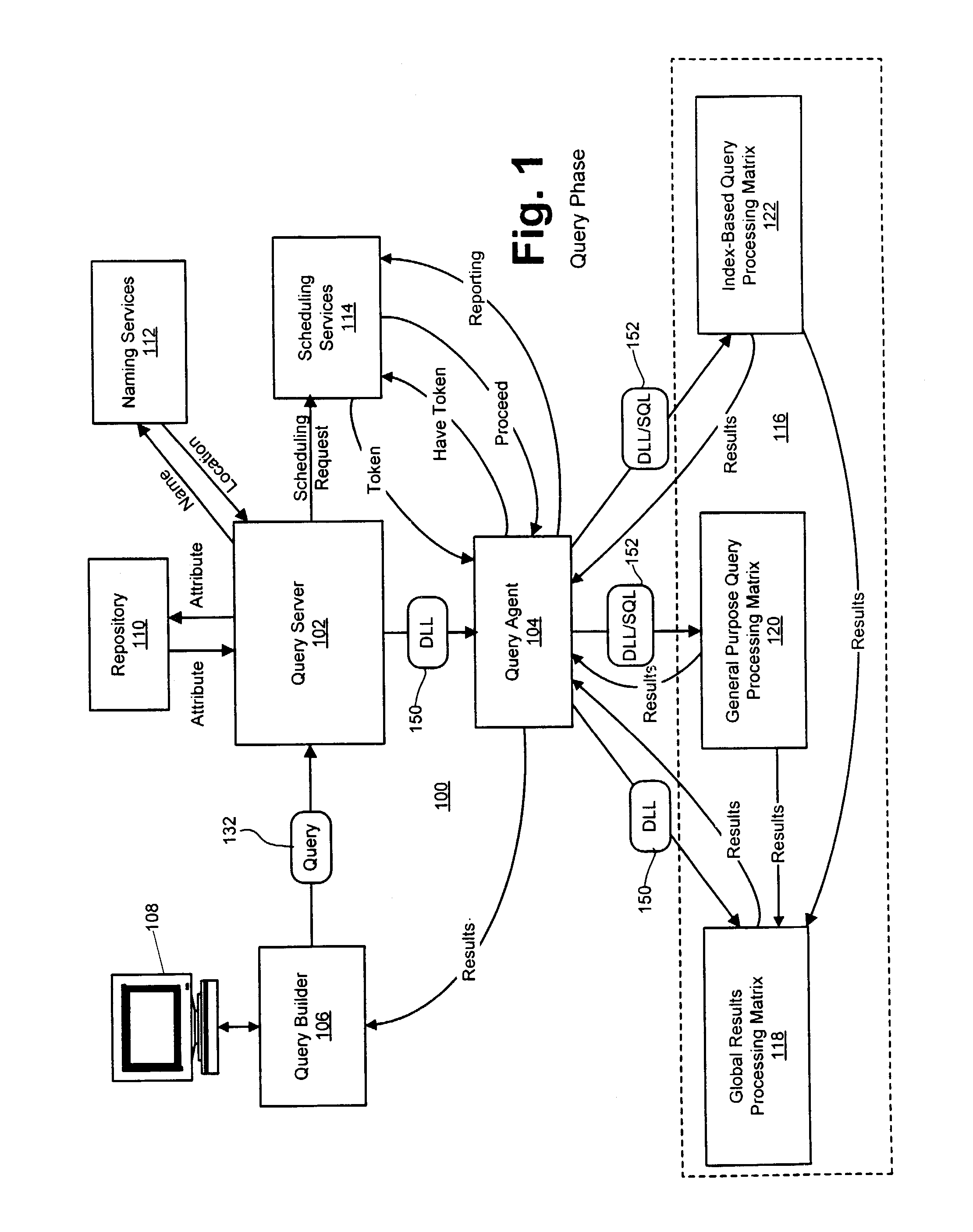
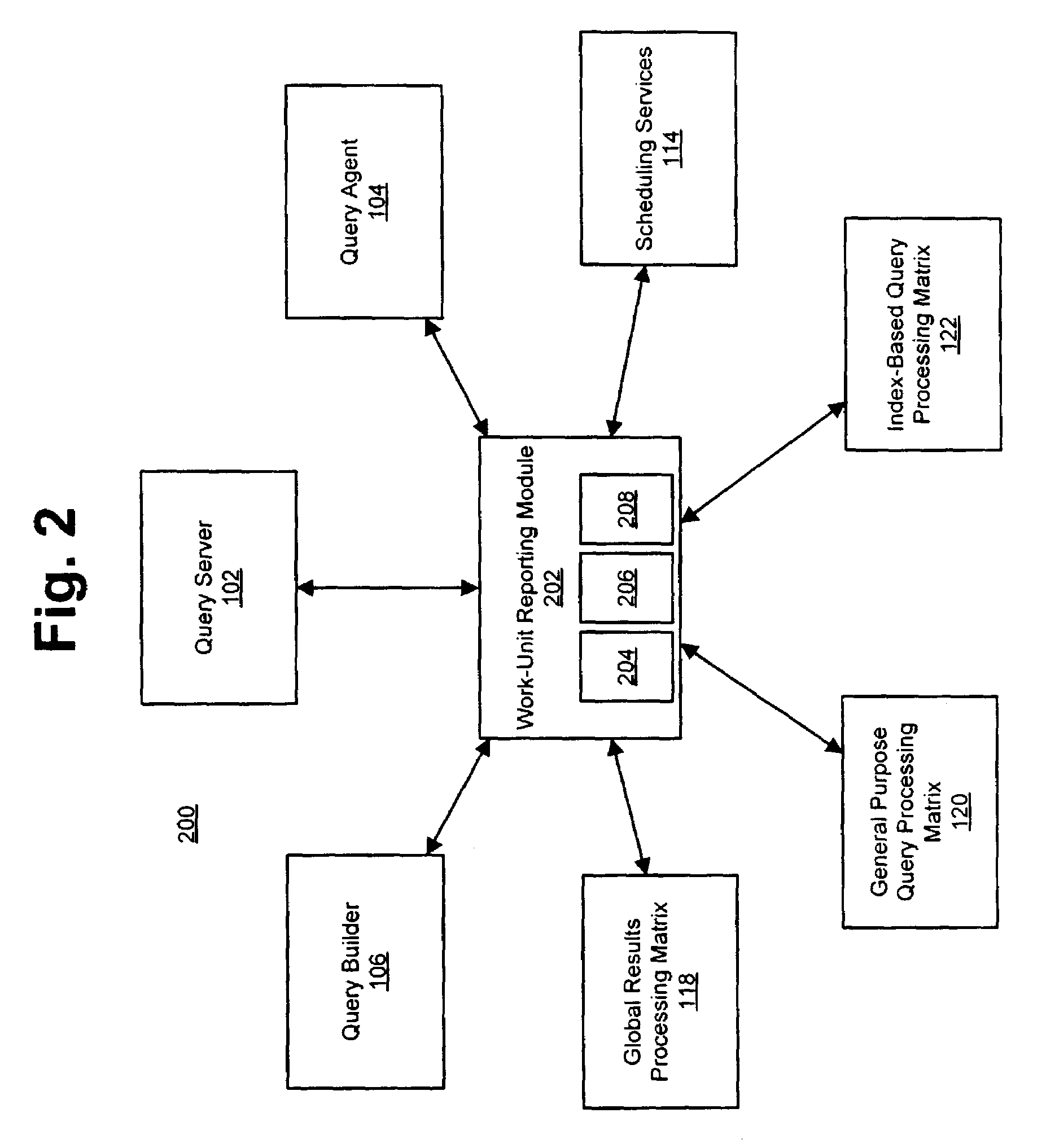
Query scheduling in a parallel-processing database system
ActiveUS7185003B2Transparent operationLow costData processing applicationsDigital data information retrievalParallel processingService module
A system and method for scheduling database operations to one or more databases in a parallel-processing database system are described herein. After a query server generates a dynamic-link library (DLL) or other executable representative of one or more database operations to a database, the query server notifies a scheduling services module of the generation of the DLL and submits the DLL to a query agent. The query agent notifies the scheduling services module of its receipt of the DLL. Based on any of a variety of considerations, the scheduling services module schedules a time of execution for the DLL by one or more processing matrices that store the database. At the scheduled time, the scheduling services module directs the query agent to submit the DLL to the indicated processing matrices. The scheduling services module also can be adapted to monitor the execution of previously submitted DLLs by one or more processing matrices and adjust the scheduled times of execution for subsequent DLLs accordingly.
Owner:LEXISNEXIS RISK DATA MANAGEMENT
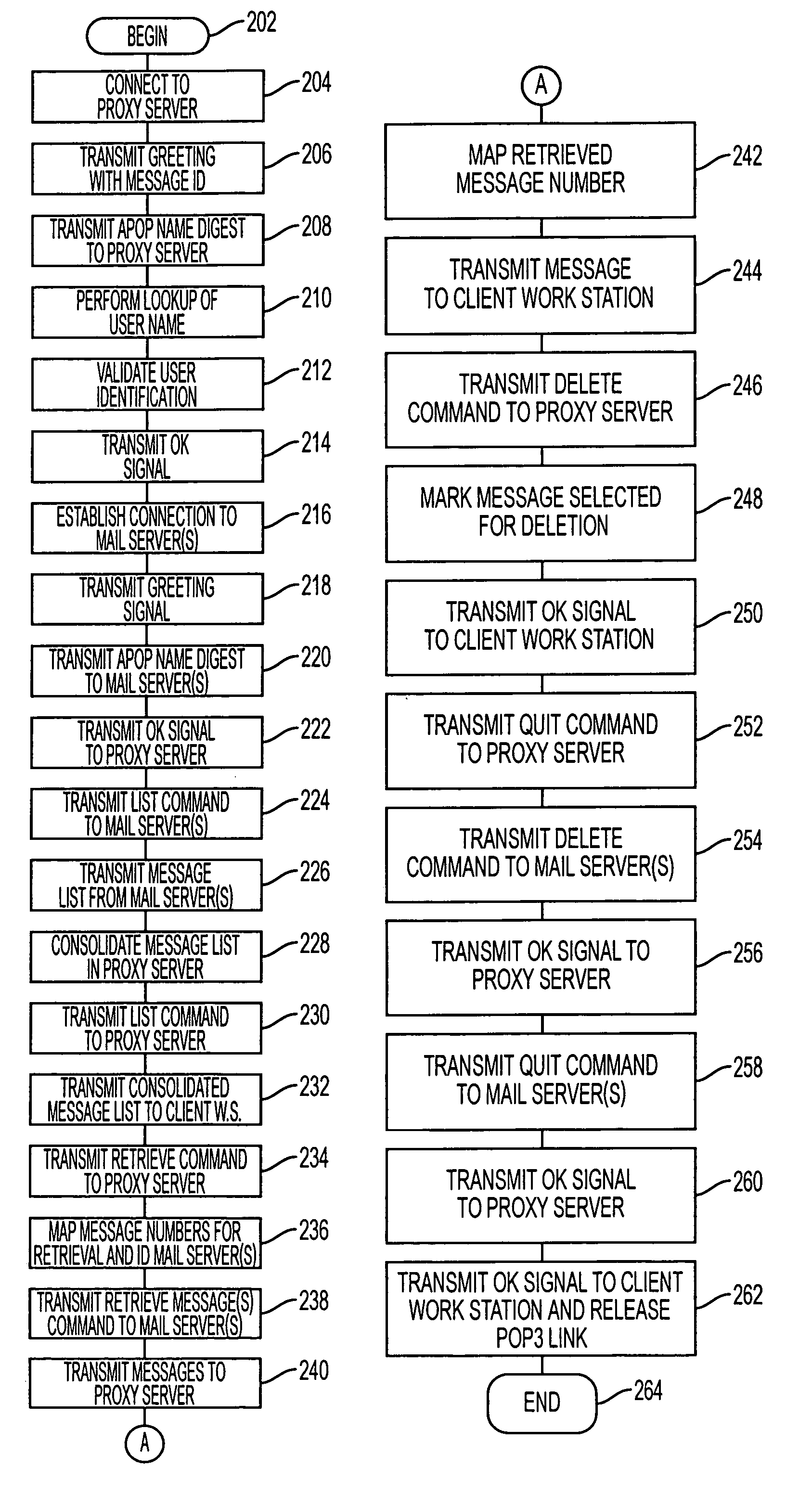
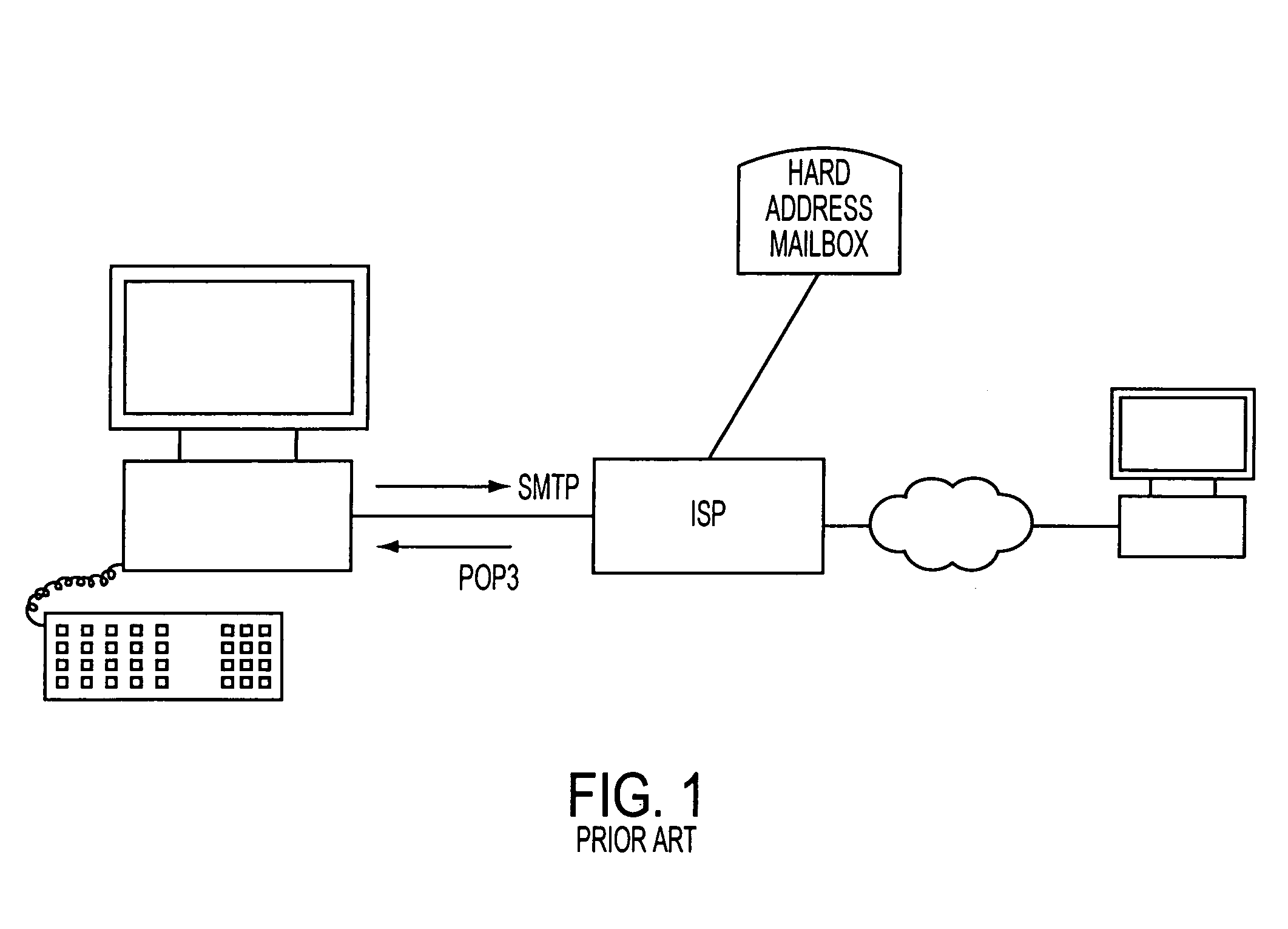
System and method for integrated management of electronic messages
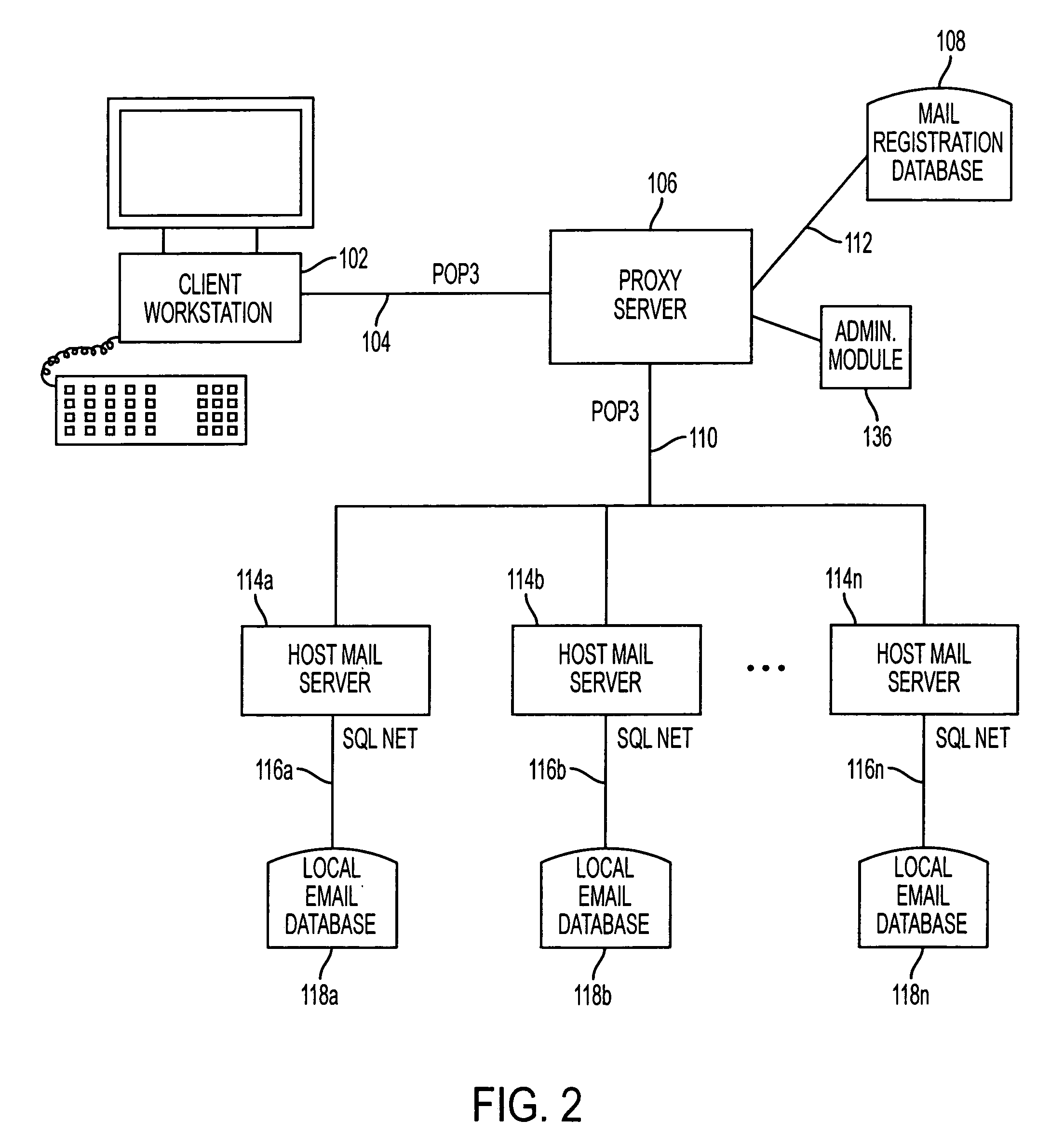
InactiveUS6965918B1Painless and transparent migrationGreat latitudeMultiple digital computer combinationsTransmissionClient-sideProxy server
An email proxy server system gives the user access to all of their email accounts through a unified port. The proxy server maintains a mail registration database associating the user's ID with multiple email accounts, which may be hosted on different Internet providers and otherwise. The email messages stored on the email hosts may be in POP3 format, which configuration the proxy server imitates to give the user an impression of transparent access to all of their email accounts. Because the ability to access individual mail boxes is unbound from particular internet addresses, one user may maintain any number of email mail boxes at different hosting servers, and change those addresses, without having to reprogram client, server, and other software. Moreover, the presentation of the integrated interface of the invention permits system administrators to attach service modules, such as billing and other packages directly to the proxy server to serve each of the different email accounts, without having to tailor those individual services to individual hosts hardware.
Owner:IBM CORP
Systems and methods for providing differentiated services within a network communication system
ActiveUS7031314B2Lower performance requirementsEfficient managementData switching by path configurationNetwork connectionsDifferentiated servicesCommunications system
A service module incorporated within the network infrastructure intercepts packets communicated between a client and a server to determine whether the connection corresponds to one of a plurality of service applications that may supported by the service module. If so, the service module breaks the connection by terminating the connection with the client at the service module and opening a separate connection between the service module and the server. The service application may then perform application-specific process of the data communicated between the client and server. In order to increase processing efficiency associated with classifying the connection between the client and the server, the service module stores classification rules in a plurality of hashing tables, with hash conflicts arranged as an m-ary tree structure. This arrangement enables the service module to efficiently search for classification rules and resolve hash conflicts without imposing a significant processing penalty.
Owner:OPTIMORPHIX INC
System and method for performing serialization of devices
ActiveUS20110063093A1Reduce in quantityImprove abilitiesSensing detailsForecastingSerializationService module
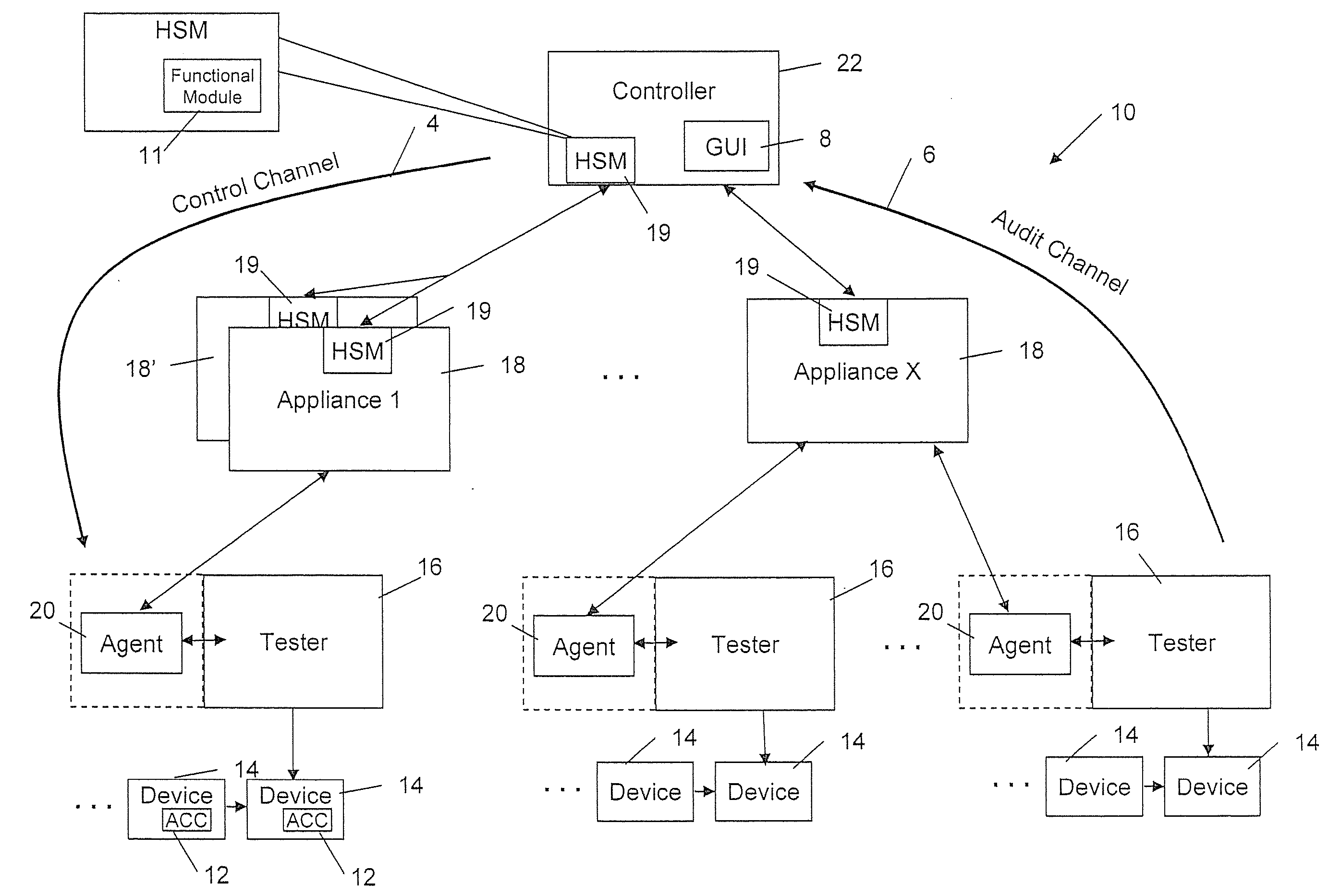
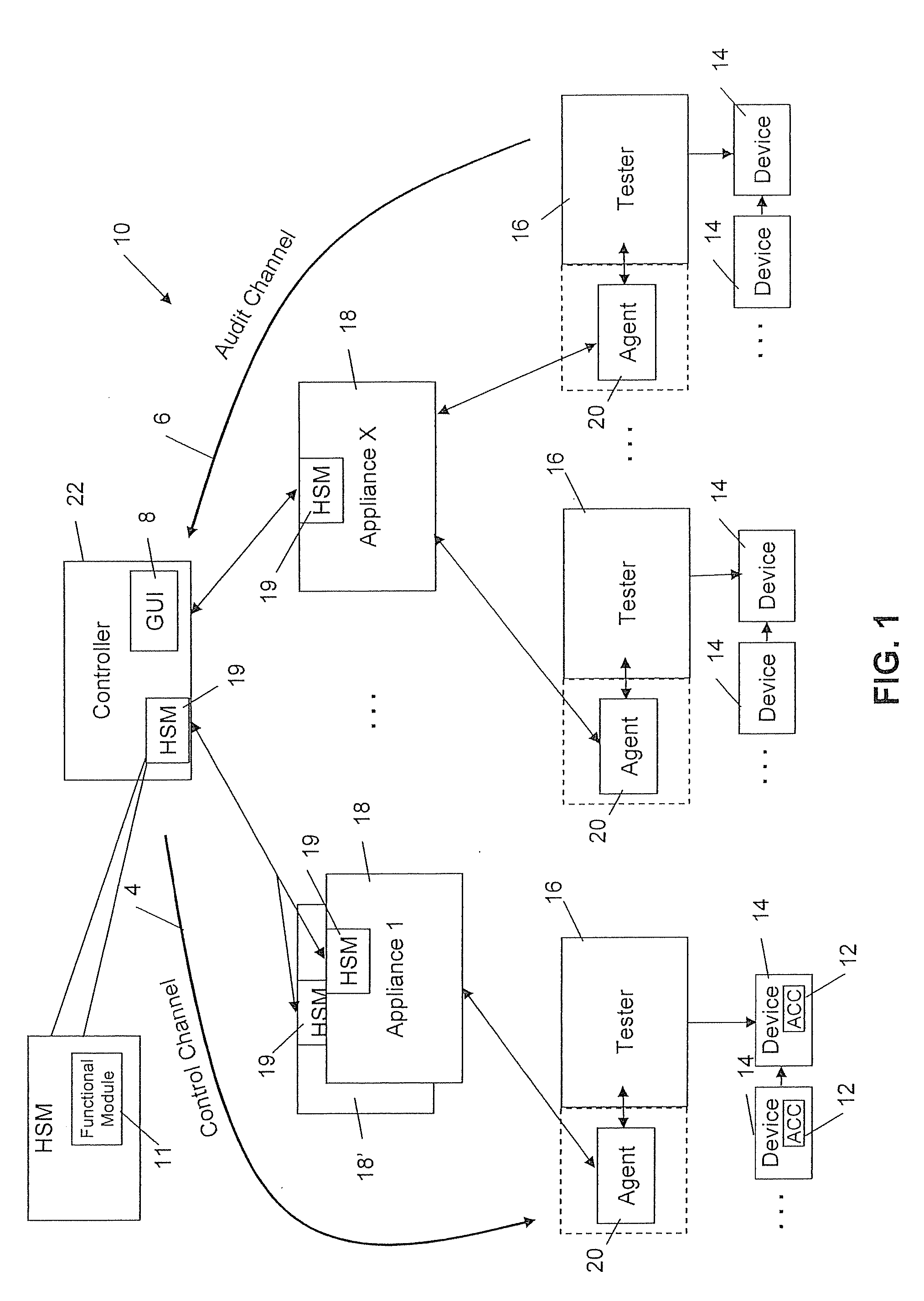
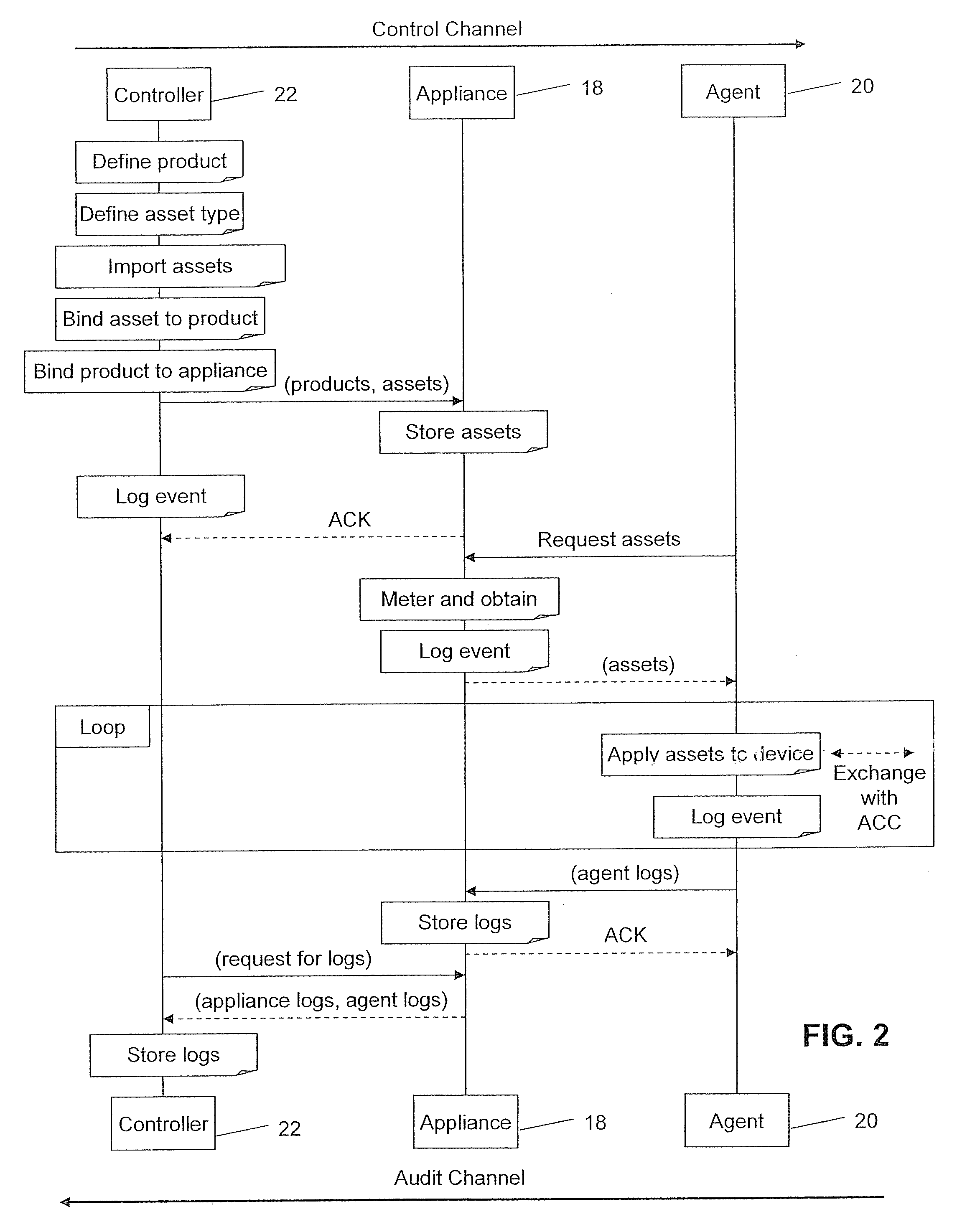
A serialization service module is provided for configuring an asset management system to provide a secure means of generating, assigning to chips (or other electronic objects or devices), and tracking unique serial numbers. To provide this service, a controller is used to define a product model, then to define one or more serialization schemas to be bound to each product model. Each serialization schema contains a range of serial numbers for a particular product. The serial number schemas are sent over a secure, encrypted connection to appliances at the manufacturer's location. Agents can then request serial number values by product name. The serial numbers are generated by the appliance, metered, and provided to the agents. The serial numbers are then injected sequentially into each die in a chip manufacturing process using the agent.
Owner:MALIKIE INNOVATIONS LTD
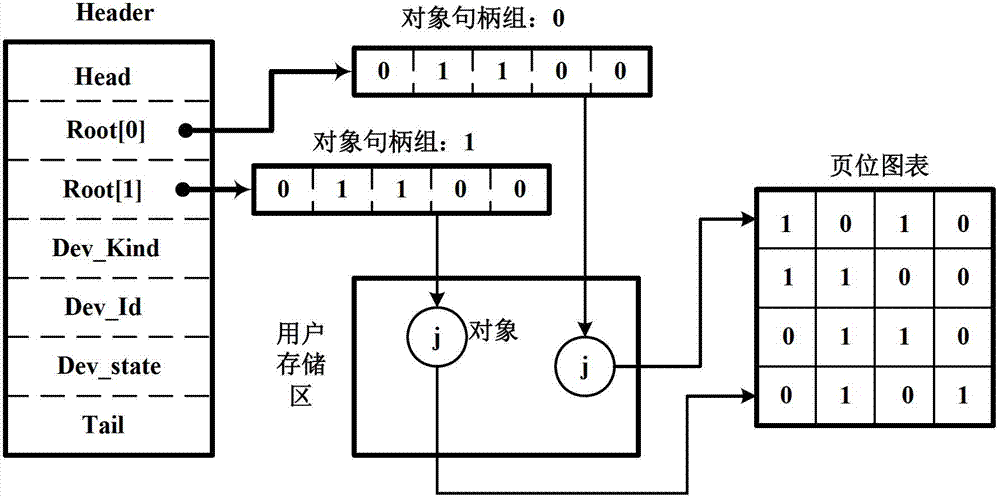
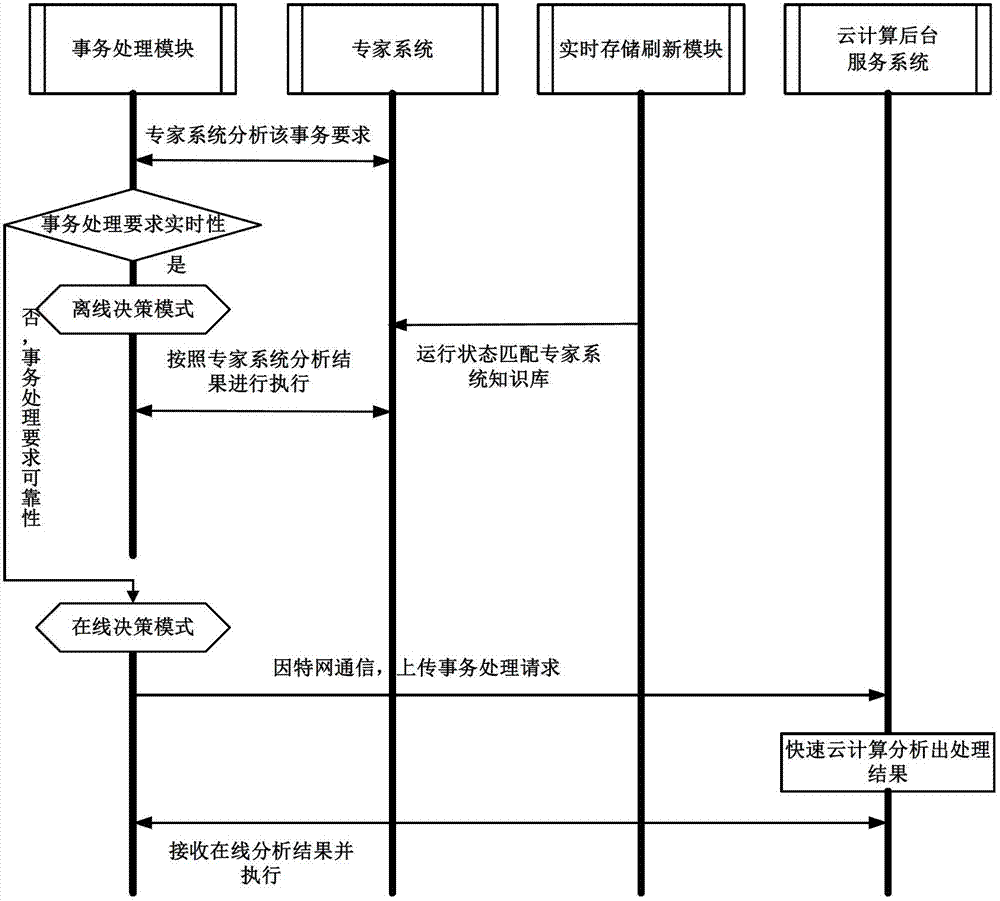
Real-time interaction intelligent terminal control system based on internet of things technology
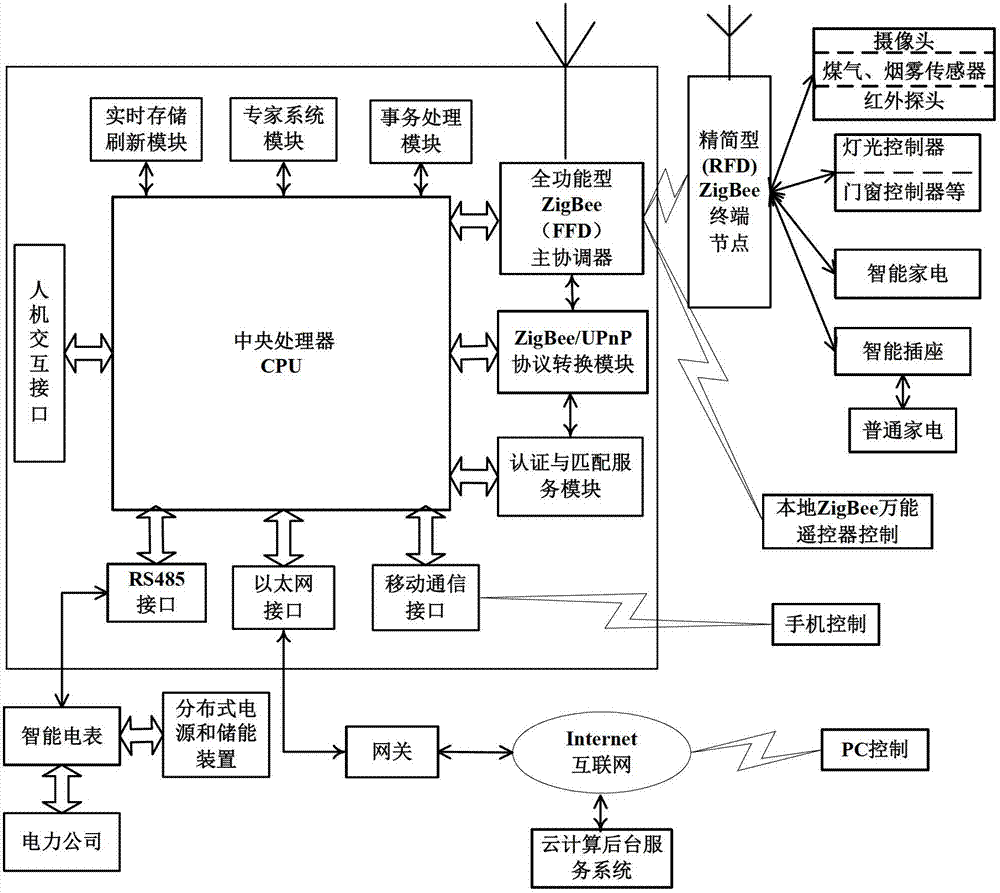
The invention discloses a real-time interaction intelligent terminal control system based on the internet of things technology, which belongs to the technical field of the internet of things control. The real-time interaction intelligent terminal control system based on the internet of things technology comprises a real-time storing and refreshing module, an expert system module, an affair processing module, a main ZigBee coordination module, a ZigBee / UPnP protocol conversion module, an authentication and matching service module, an interface module and a central processing module, wherein the real-time storing and refreshing module, the expert system module, the affair processing module, the main ZigBee coordination module, the ZigBee / UPnP protocol conversion module, the authentication and matching service module and the interface module are respectively connected with the central processing module; and the main ZigBee coordination module, the ZigBee / UPnP protocol conversion module and the authentication and matching service module are connected with the authentication and matching service module in sequence. According to the system provided by the invention, visual and omnibearing interaction is realized, and meanwhile, affair processing instantaneity and reliability can be both considered.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
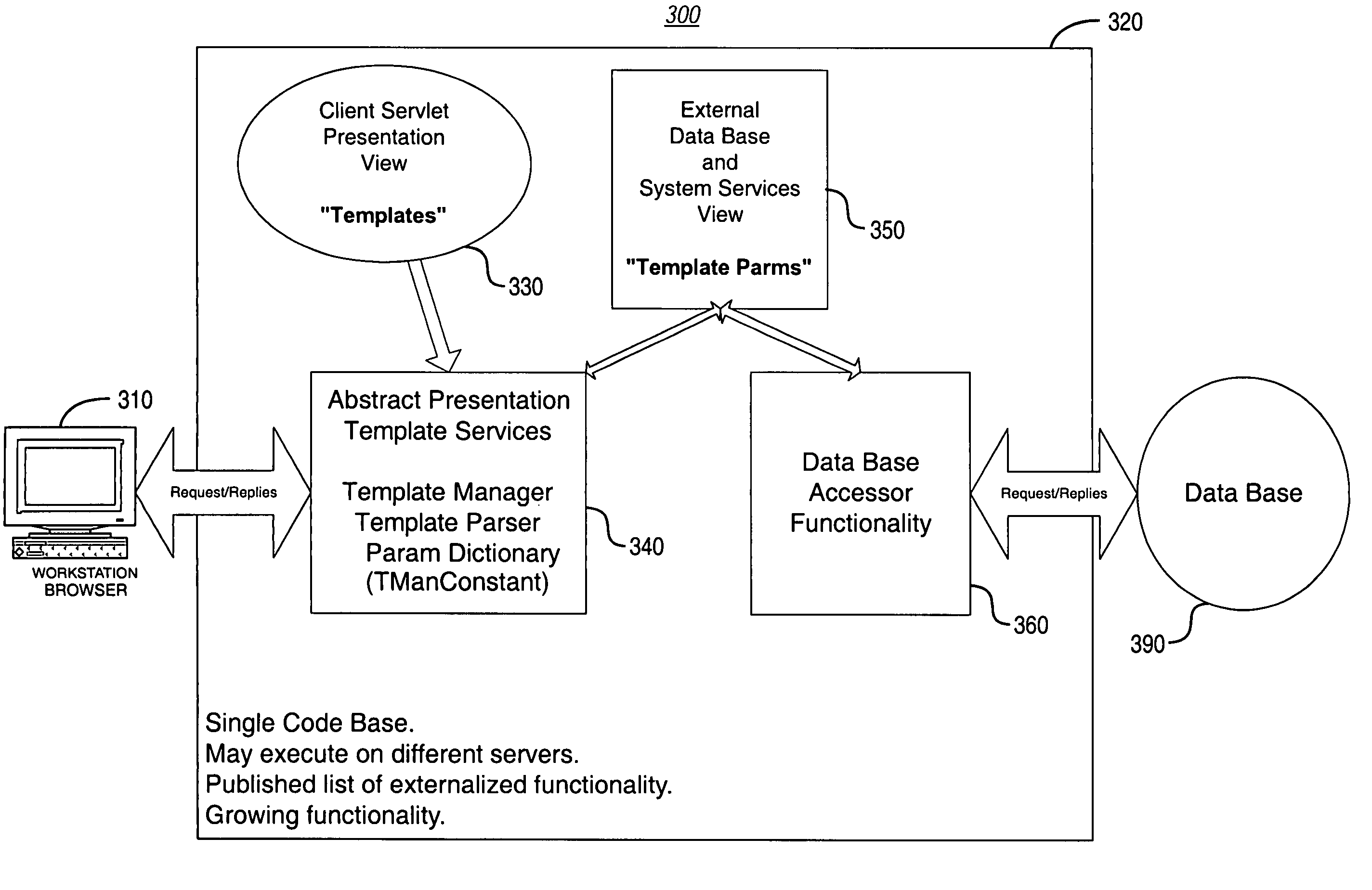
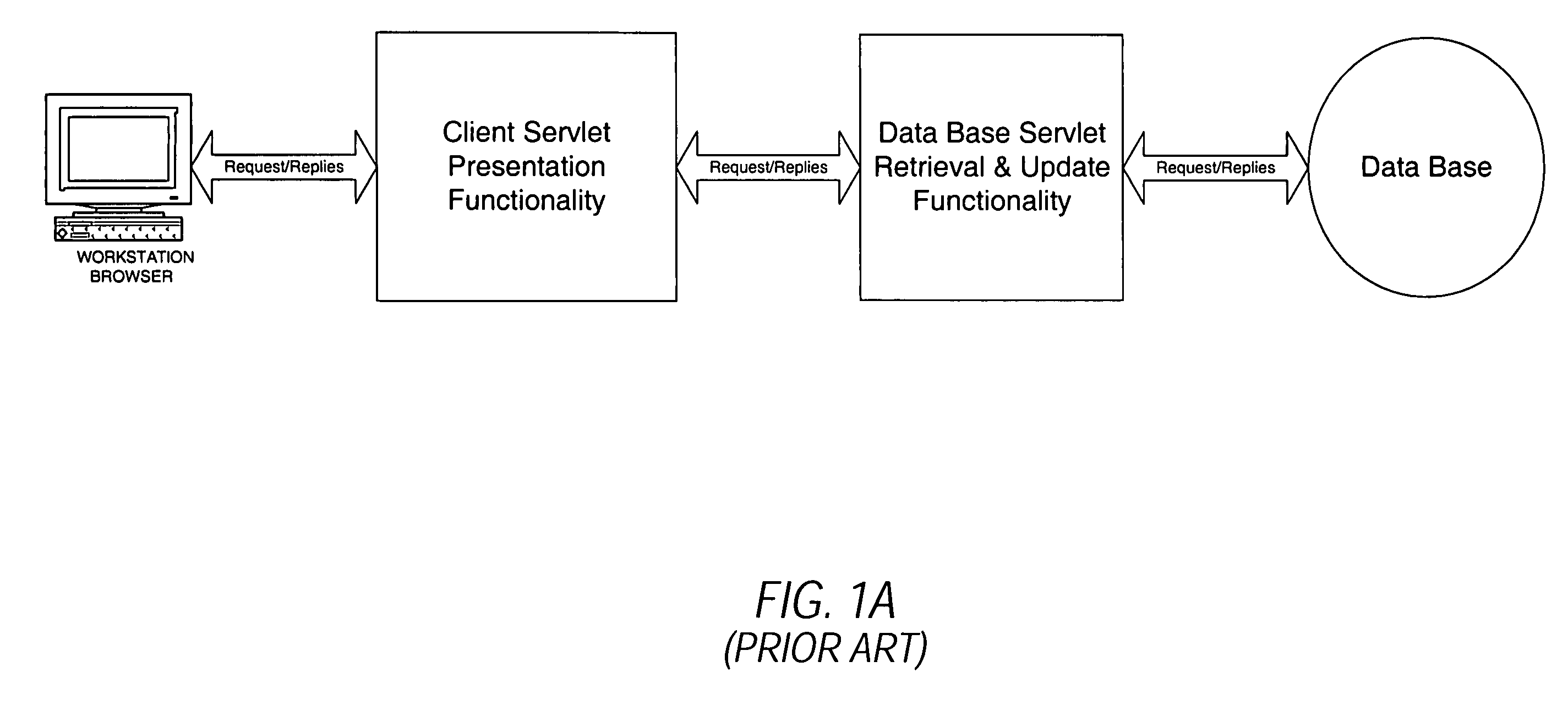
System and methodology for dynamic application environment employing runtime execution templates
InactiveUS7111231B1Digital data information retrievalSpecial data processing applicationsThe InternetApplication software
A dynamic application environment or system is described that includes a client, a run-time system, and a back-end database. The client comprises a workstation or desktop PC running browser software, such as Microsoft Internet Explorer or Netscape Navigator. The back-end database comprises a back-end (e.g., server-based) database system, such as an SQL-based database system. The run-time system includes a collection or repository module for storing “presentation templates,” a Template Services Module or engine, a Template Parameters Module, and a Database Accessor Module. The presentation templates are employed for presentation of the application to the user interface (at the client). At application run-time, the templates are provided to the Template Services Module, which includes a Template Manager and a Template Parser. These provide generic processing of the templates, which may be assembled to complete a finished product (i.e., run-time application). For instance, the Template Services Module knows how to load and parse a template and then look up its parameters, regardless of the application-specific details (e.g., user interface implementation) embodied by the template. In use, the system is deployed with presentation templates that represent the various client views of the target application, for the various platforms that the application is deployed to. In this manner, when new functionality needs to be added to the system, it may simply be added by expanding the run-time library portion of the system.
Owner:INTELLISYNC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com