Patents
Literature
1038results about "Sensing details" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
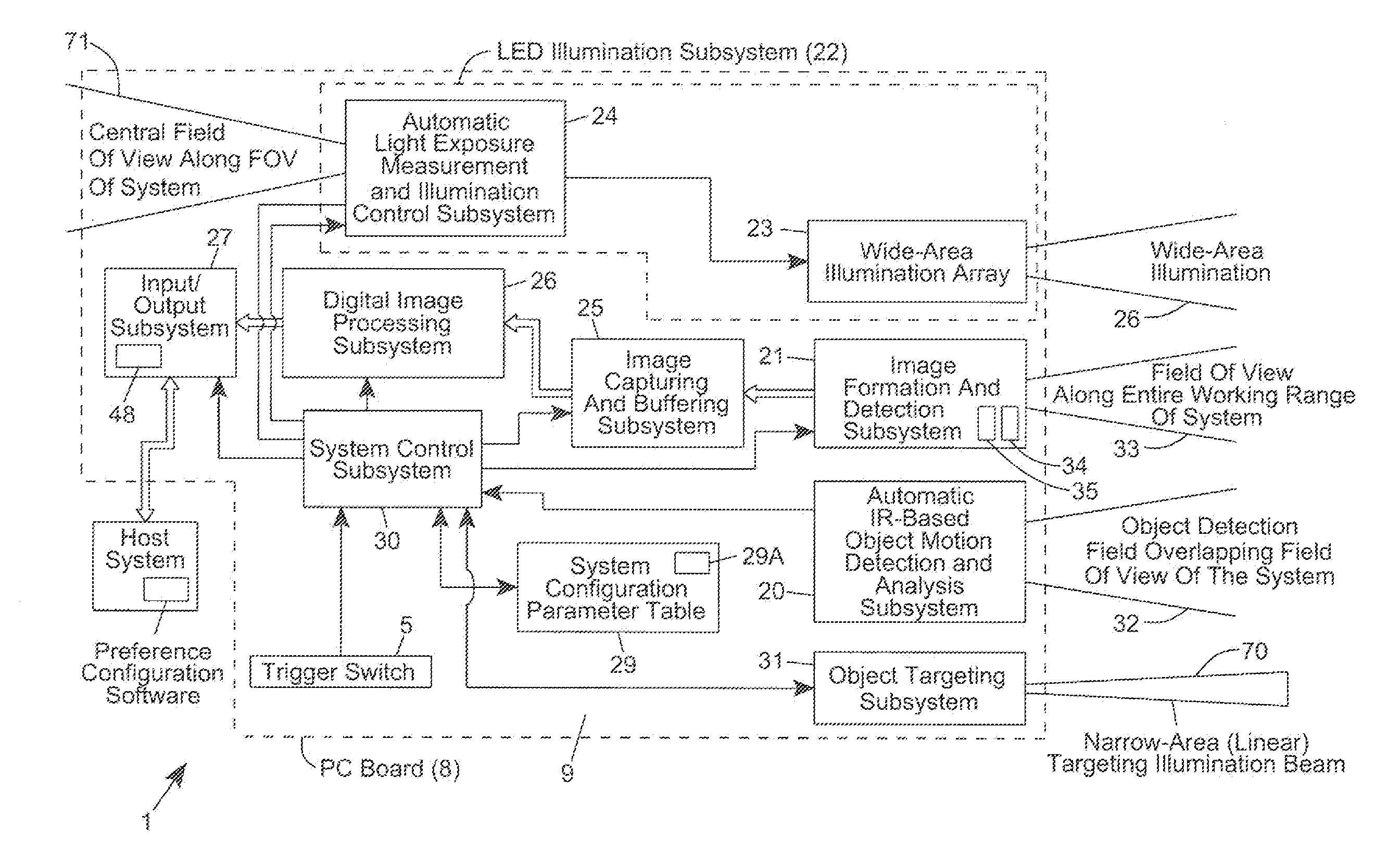
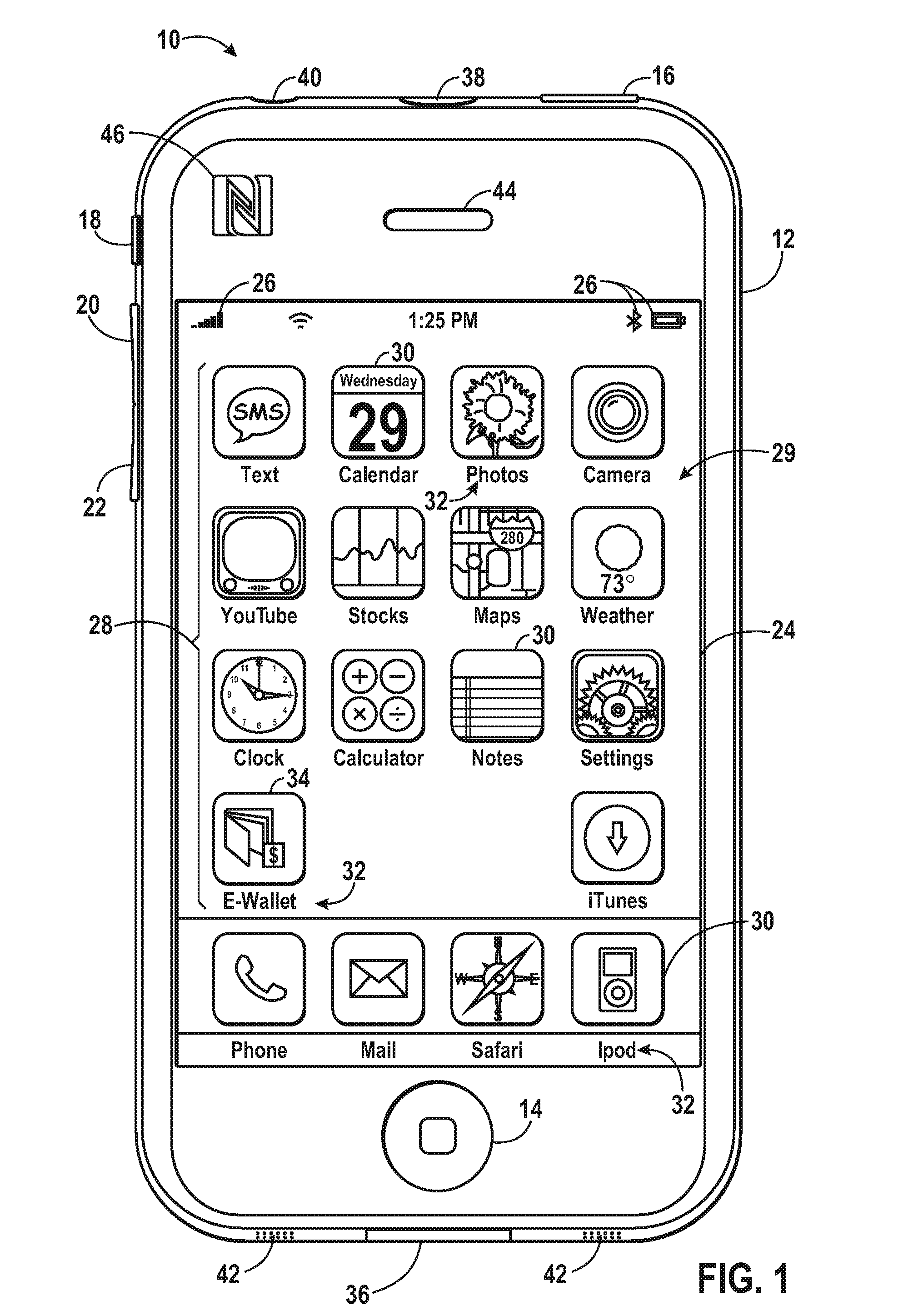
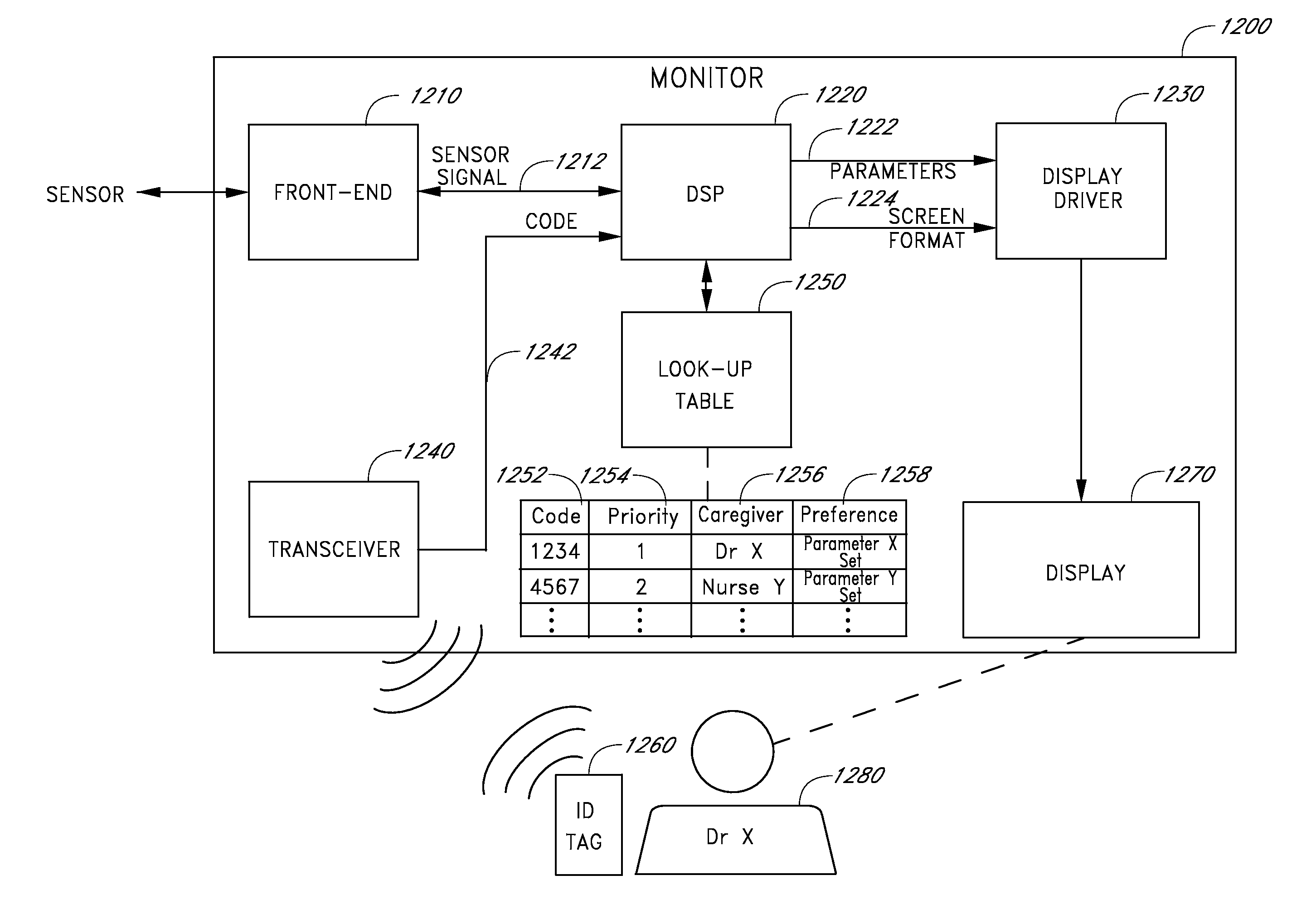
Code symbol reading system supporting operator-dependent system configuration parameters
InactiveUS20120193423A1Easy loadingEasy to modifySensing detailsCharacter and pattern recognitionProduction rateWorking environment
A method of and system for setting and switching user preferences between system operators, to provide a higher return on investment (ROI) and a more satisfying work environment. The system allows operators to easily select and implement particular customizable system configuration parameters (SCPs) in a code symbol reading system, based on personal preferences of the system operator, which can lead to more effective scanning performance. A different set of customizable SCPs are programmably stored in system memory (e.g. EPROM) for each system operator / user registered to use the system, to improve the quality of the working environment and increase worker productivity.
Owner:METROLOGIC INSTR
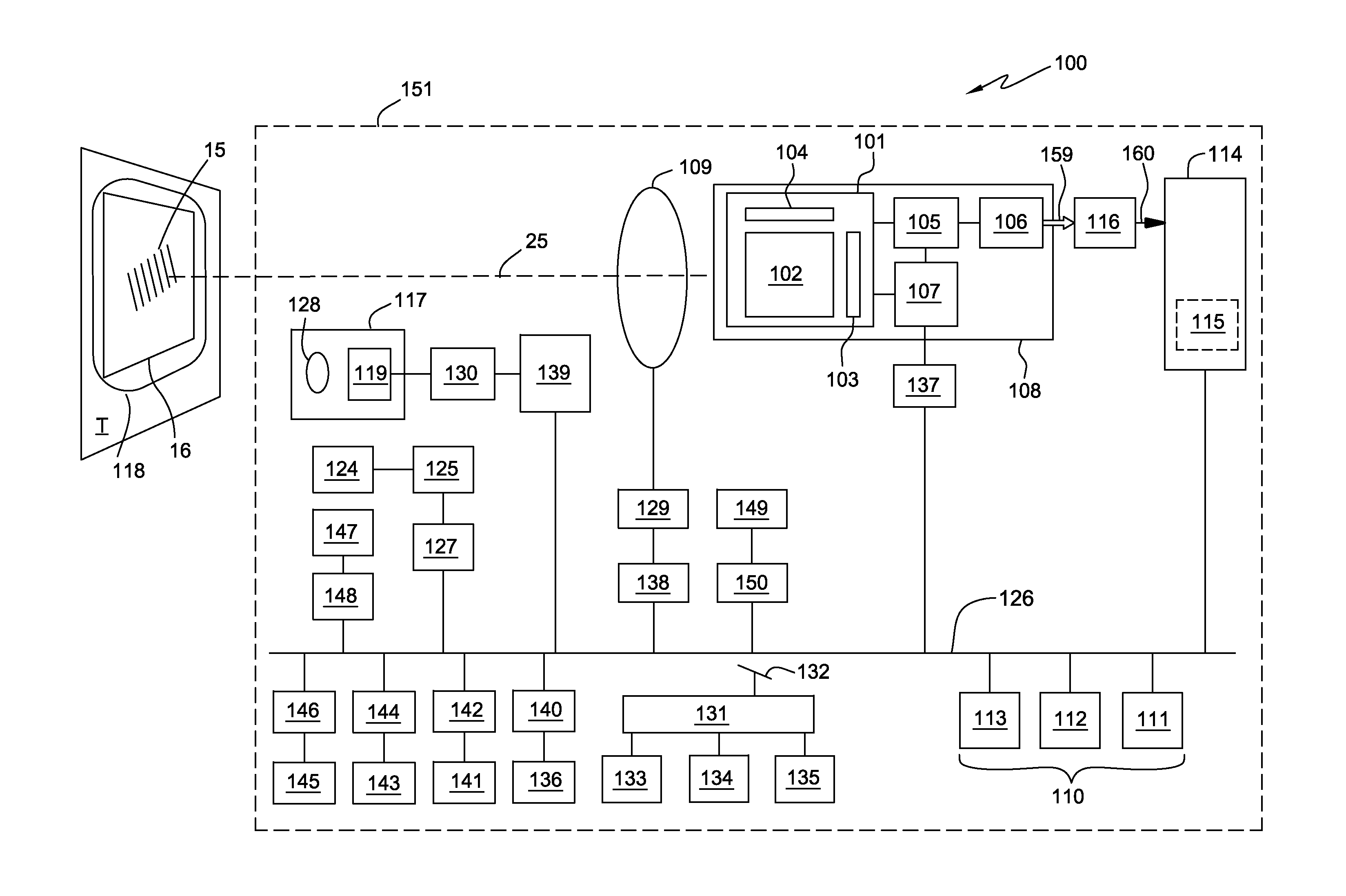
User interface facilitating specification of a desired data format for an indicia reading apparatus
ActiveUS20140282210A1Overcomes shortcomingEnhanced advantageSensing detailsRecord carriers used with machinesUser inputBarcode
Aspects describe herein facilitate specification of a desired data format for bar code data to be presented by an indicia reading apparatus. Bar code data decoded from an image of a bar code is obtained and displayed. A user input field is provided and based on input by the user to the user input field, the user input field is populated with a representation of the desired data format for the bar code data. Based on the representation of the desired data format populated in the user input field, configuration settings are determined for configuring the indicia reading apparatus to present bar code data in the desired data format.
Owner:HAND HELD PRODS
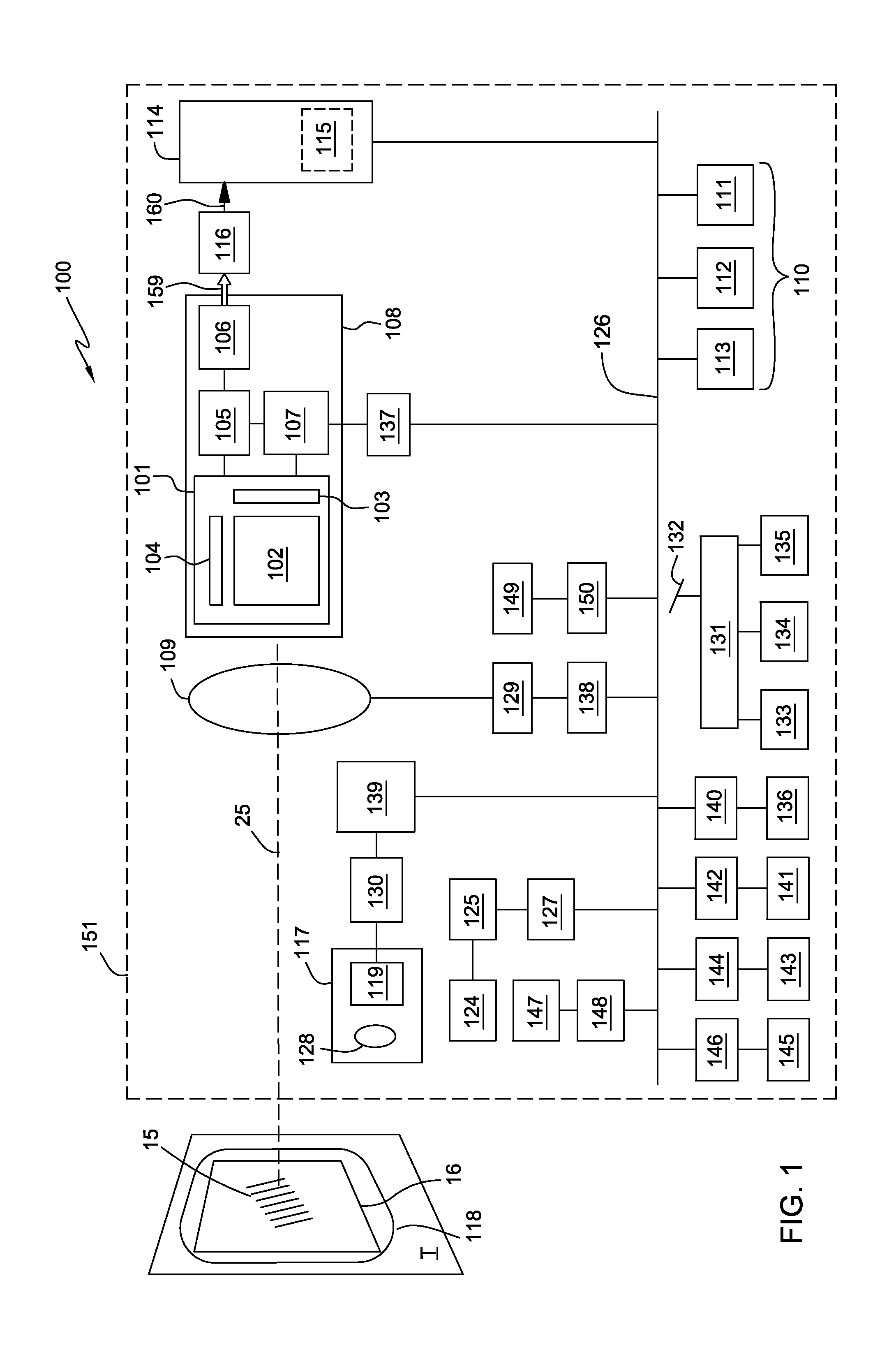
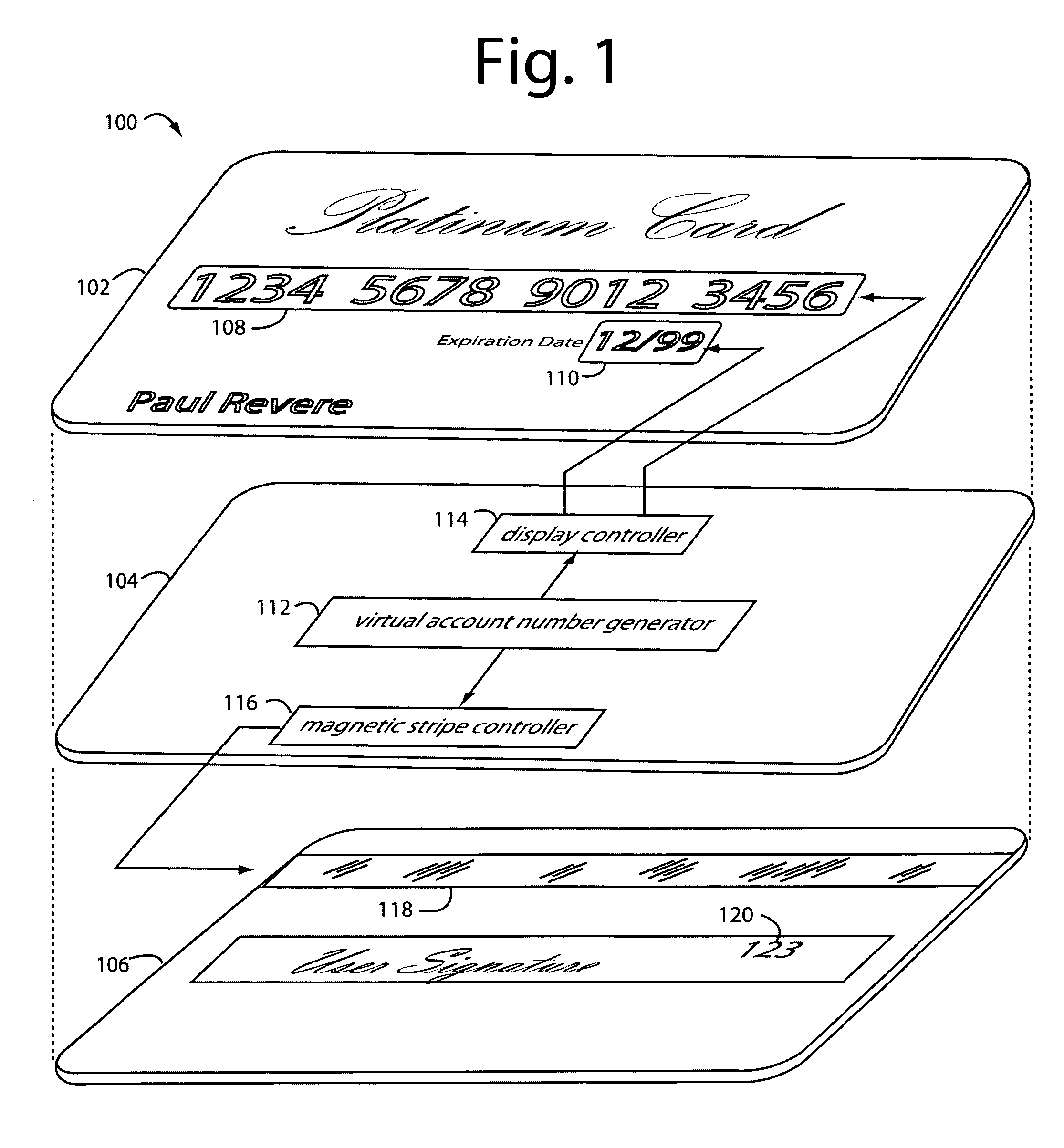
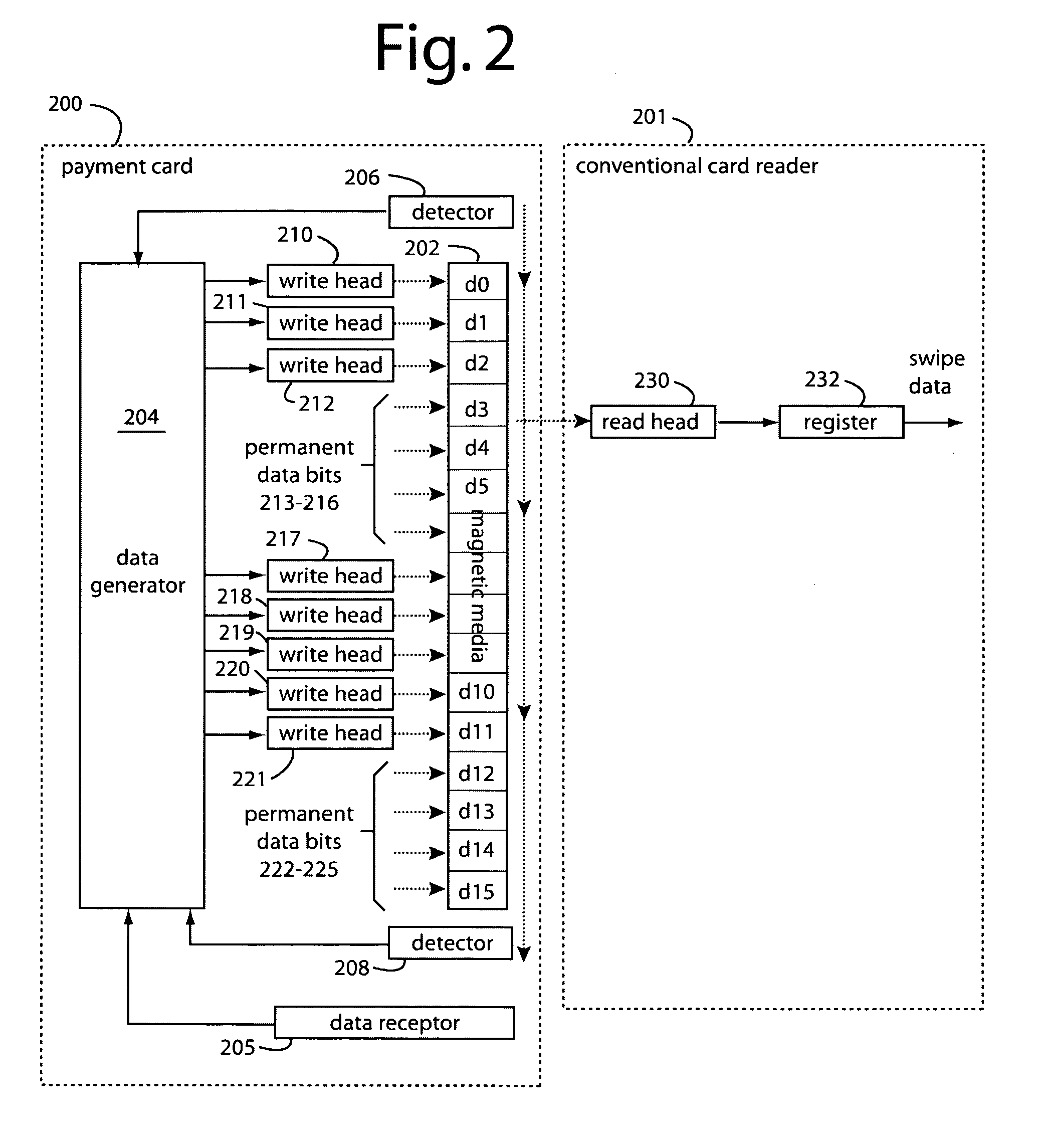
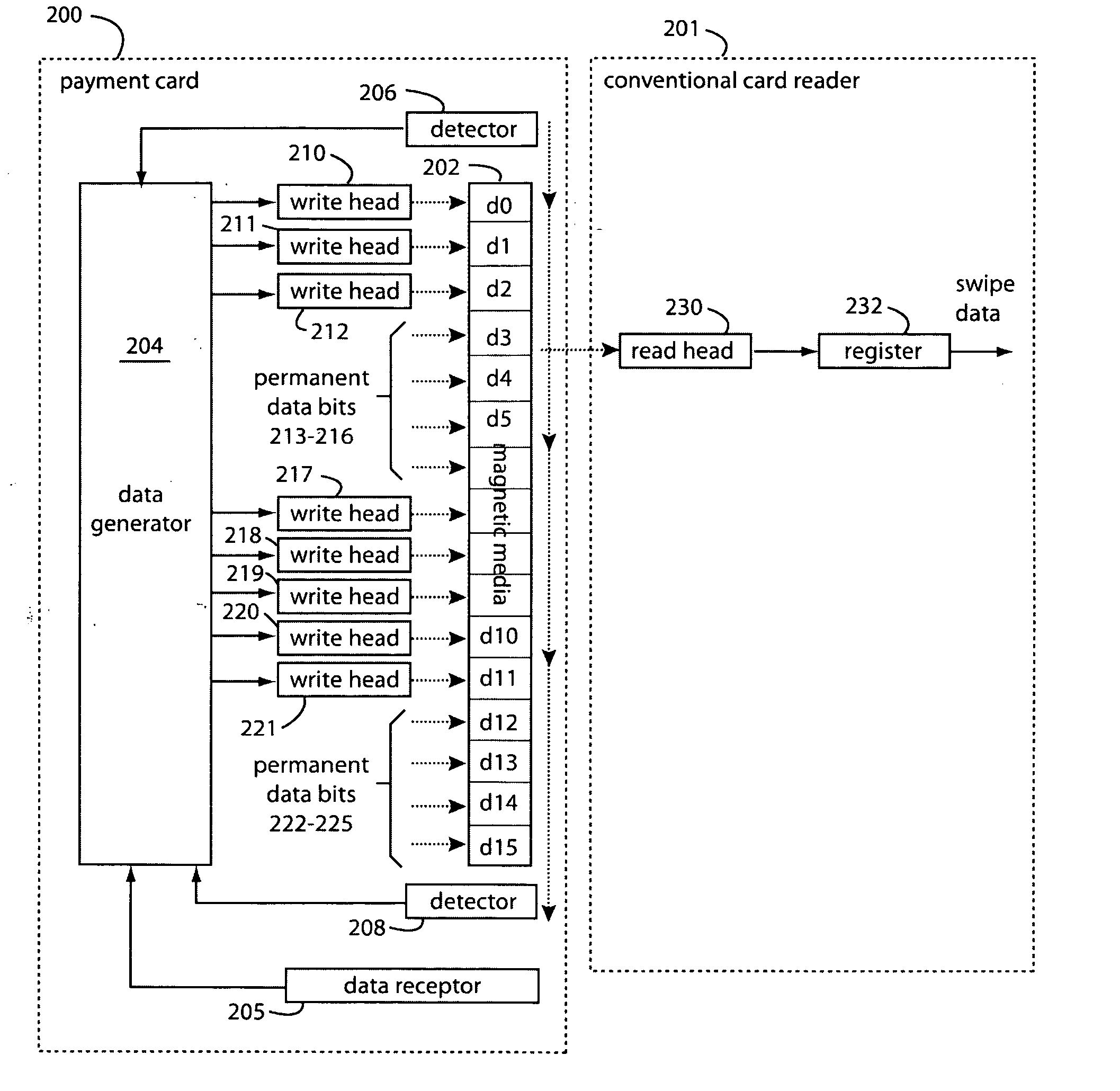
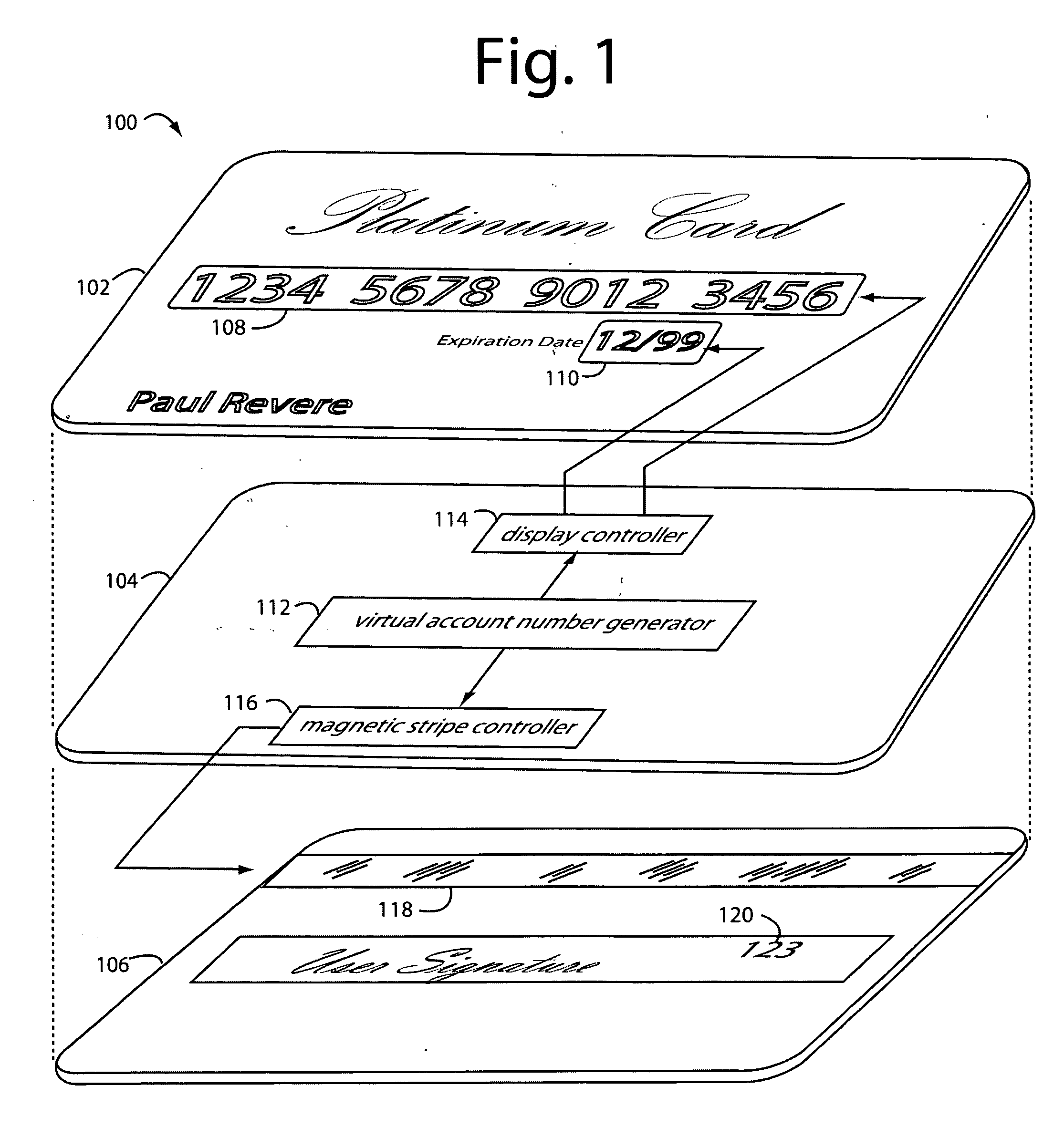
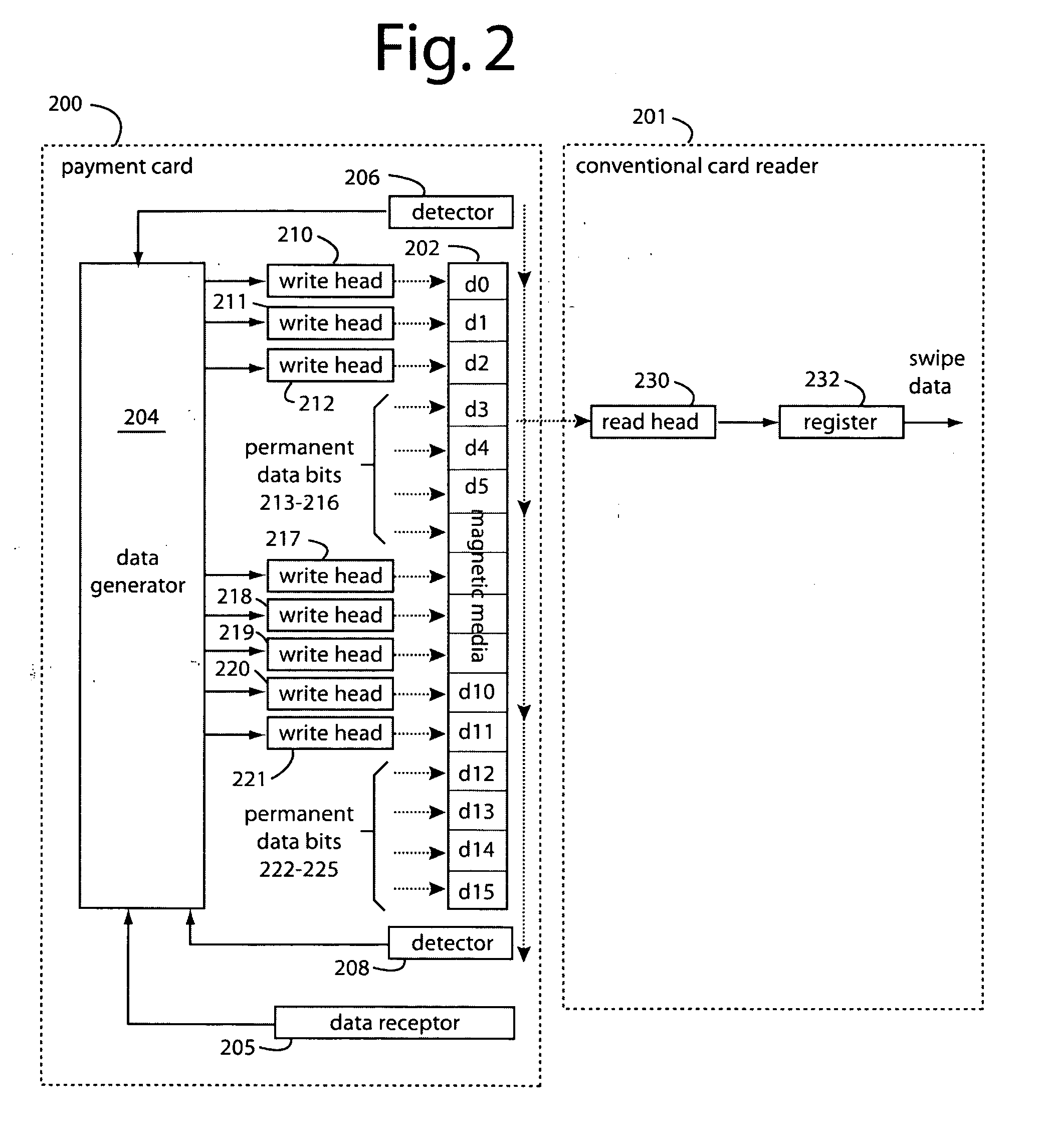
Payment card with internally generated virtual account numbers for its magnetic stripe encoder and user display
A payment card comprises an internal virtual account number generator and a user display for online transactions. Offline transactions with merchant card readers are enabled by a magnetic array positioned behind the card's magnetic stripe on the back. The internal virtual account number generator is able to program the magnetic bits encoded in the magnetic stripe to reflect the latest virtual account number. The internal virtual account number generator produces a sequence of virtual numbers that can be predicted and approved by the issuing bank. Once a number is used, it is discarded and put on an exclusion list.
Owner:FITBIT INC
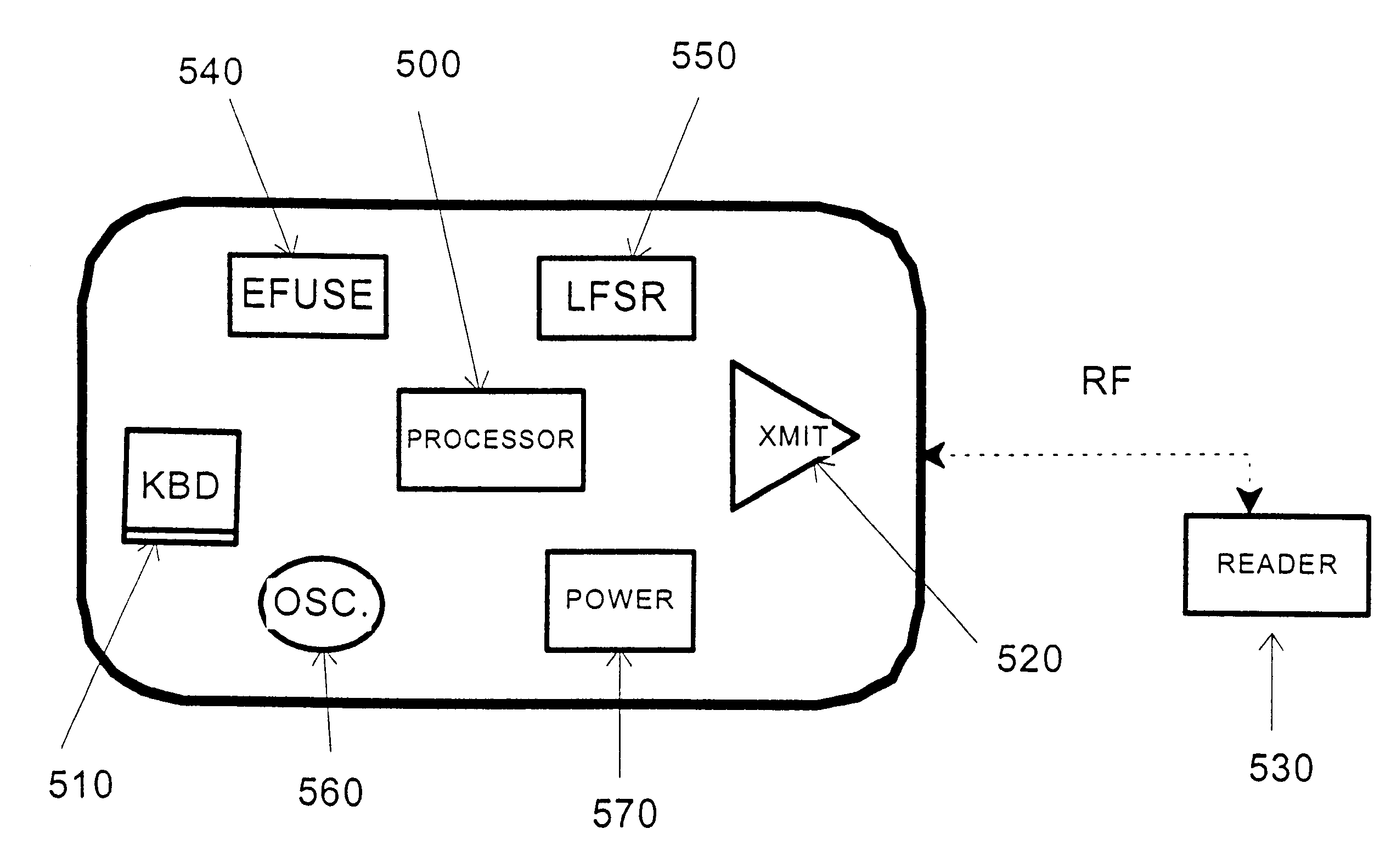
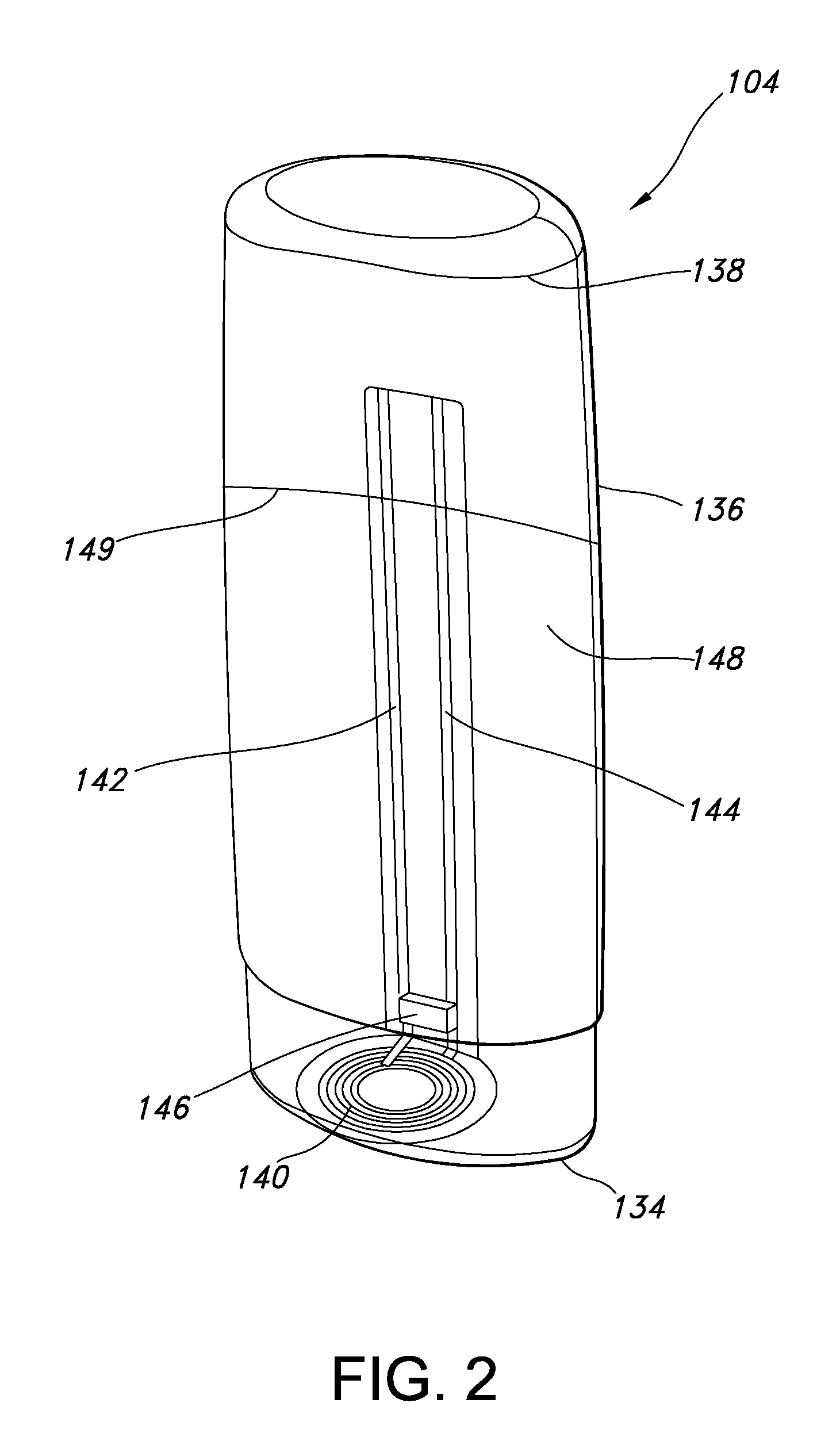
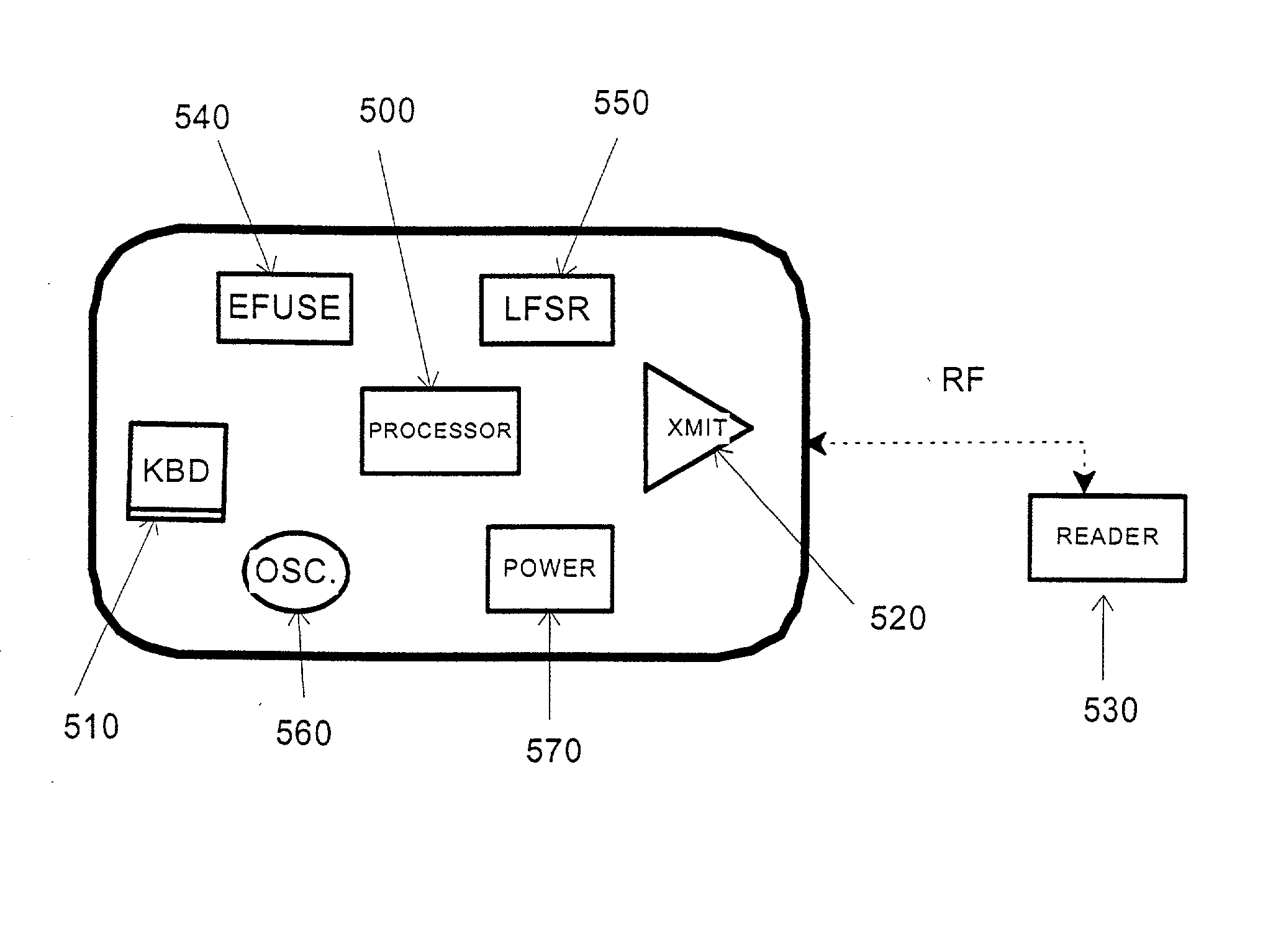
Secure credit card
Credit card or portable identification cards containing smart card technology and electronic fuse (e-fuse) technology are combined with an LFSR pseudo random number generator to provide a secured method to prevent fraud and unauthorized use. Secure personalization via e-fuses, a pseudo-random number generator linear feedback shift register, free running clock oscillator, and power source embedded in the card provide a highly secured method to render a lost or stolen card useless. A unique card ID is permanently encoded within the card which requires a specific activation code to activate the card. A PIN number permits the card owner to activate the card for a predetermined length of time while processing a transaction. The card dynamically generates random code sequences and synchronization keys to secure a transaction.
Owner:KYNDRYL INC
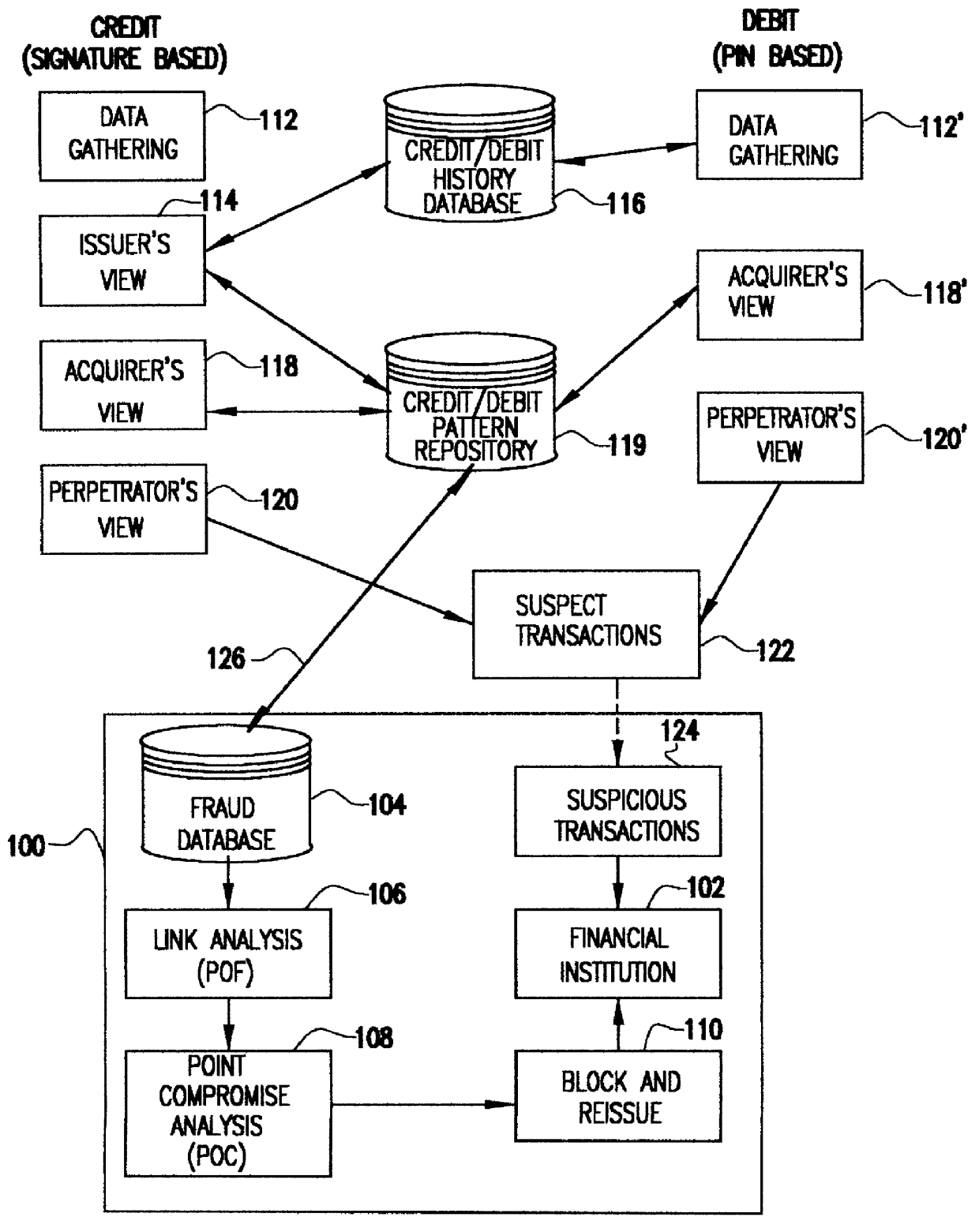
System for detecting counterfeit financial card fraud
Counterfeit financial card fraud is detected based on the premise that the fraudulent activity will reflect itself in clustered groups of suspicious transactions. A system for detecting financial card fraud uses a computer database comprising financial card transaction data reported from a plurality of financial institutions. The transactions are scored by assigning weights to individual transactions to identify suspicious transactions. The geographic region where the transactions took place as well as the time of the transactions are recorded. An event building process then identifies cards involved in suspicious transactions in a same geographic region during a common time period to determine clustered groups of suspicious activity suggesting an organized counterfeit card operation which would otherwise be impossible for the individual financial institutions to detect.
Owner:FAIR ISAAC & CO INC
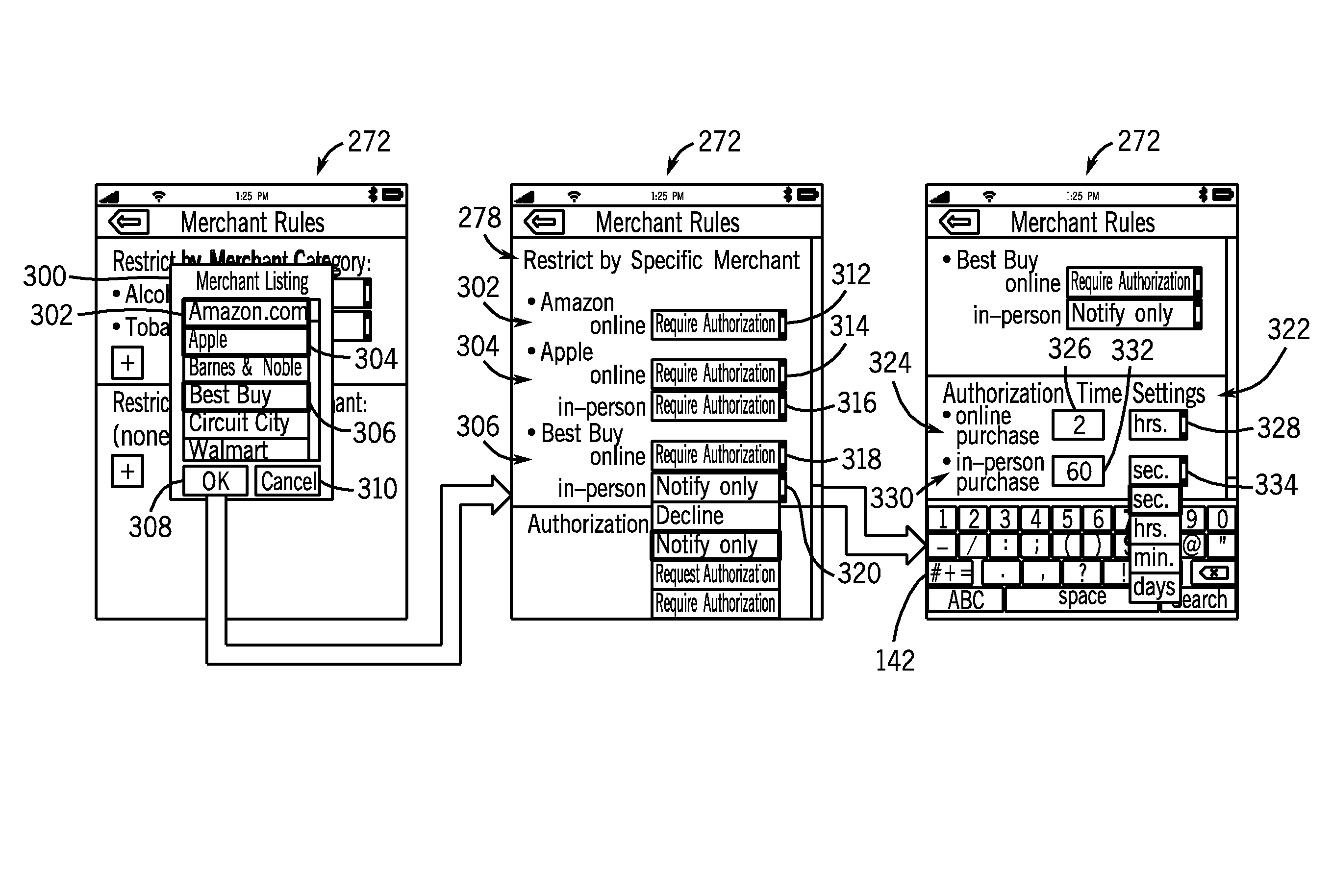
Parental controls
Various techniques are provided for establishing financial transaction rules to control one or more subsidiary financial accounts. In one embodiment, a financial account management application stored on a processor-based device may provide an interface for defining financial transaction rules to be applied to a subsidiary account. The financial transaction rules may be based upon transaction amounts, aggregate spending amounts over a period, merchant categories, specific merchants, geographic locations, or the like. The device may update the financial transaction rules associated with a subsidiary account by communicating the rules to an appropriate financial server. Accordingly, transactions made using the subsidiary account by a subsidiary account holder may be evaluated against the defined rules, wherein an appropriate control action is carried out if a financial transaction rule is violated.
Owner:APPLE INC
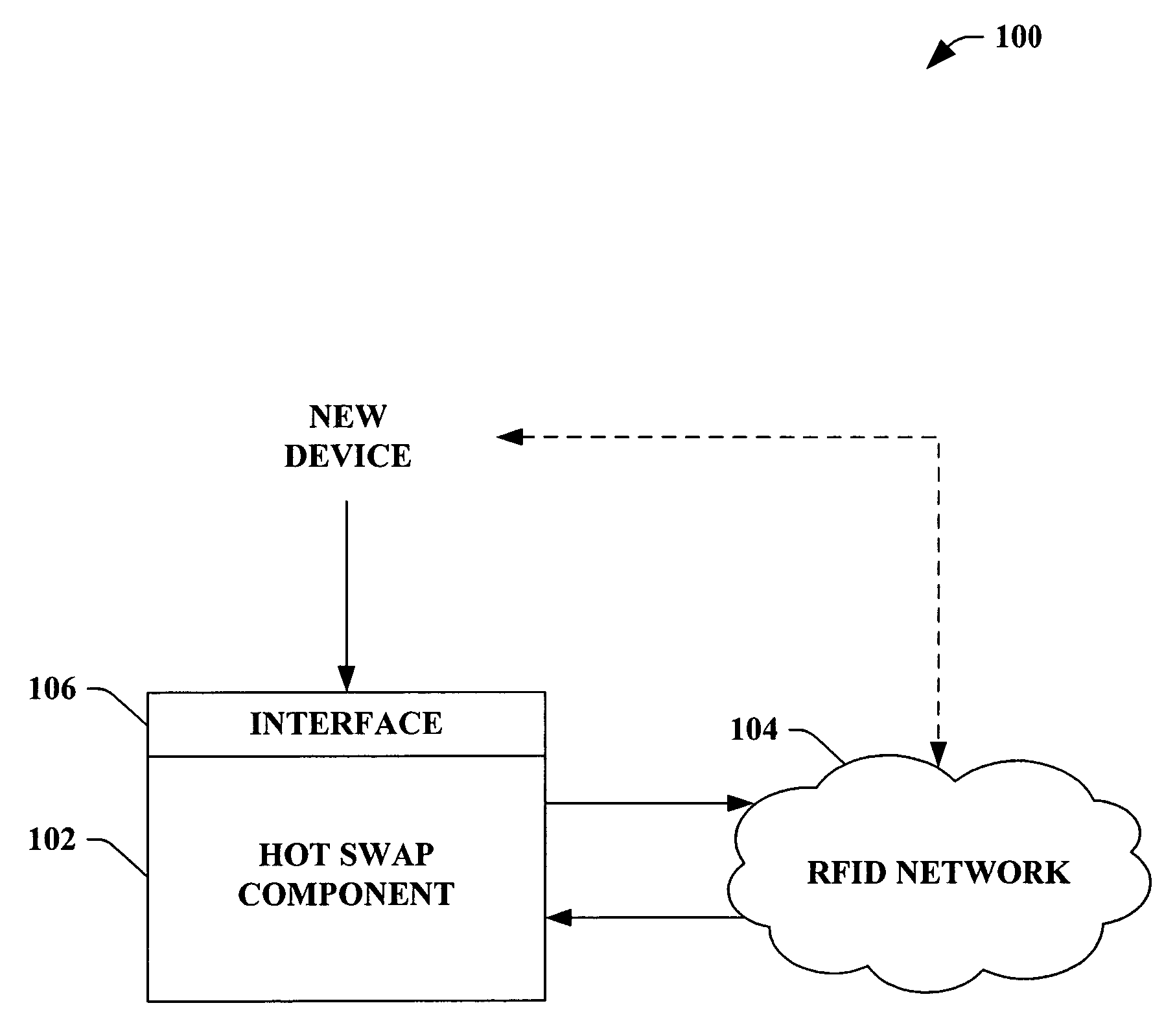
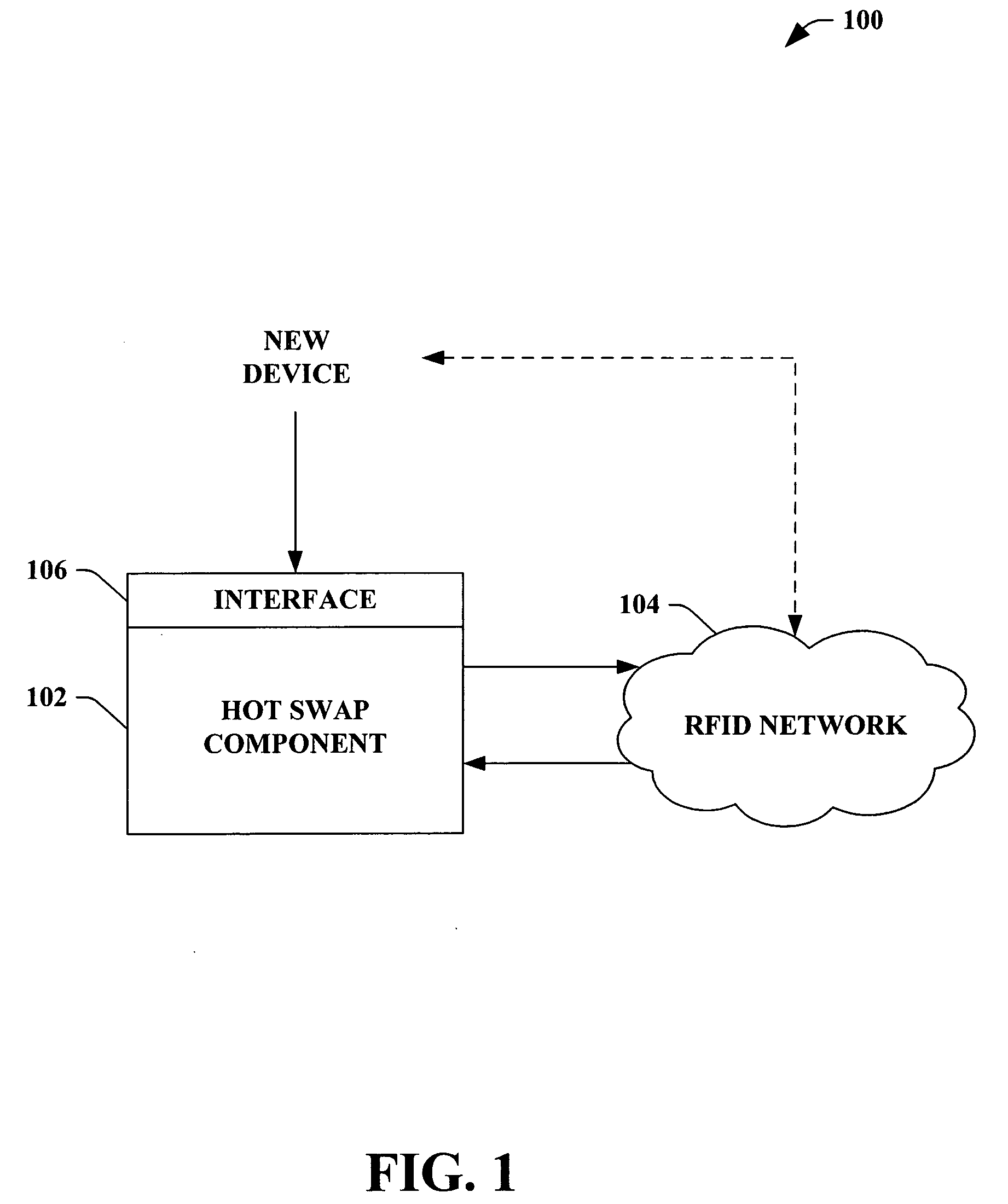
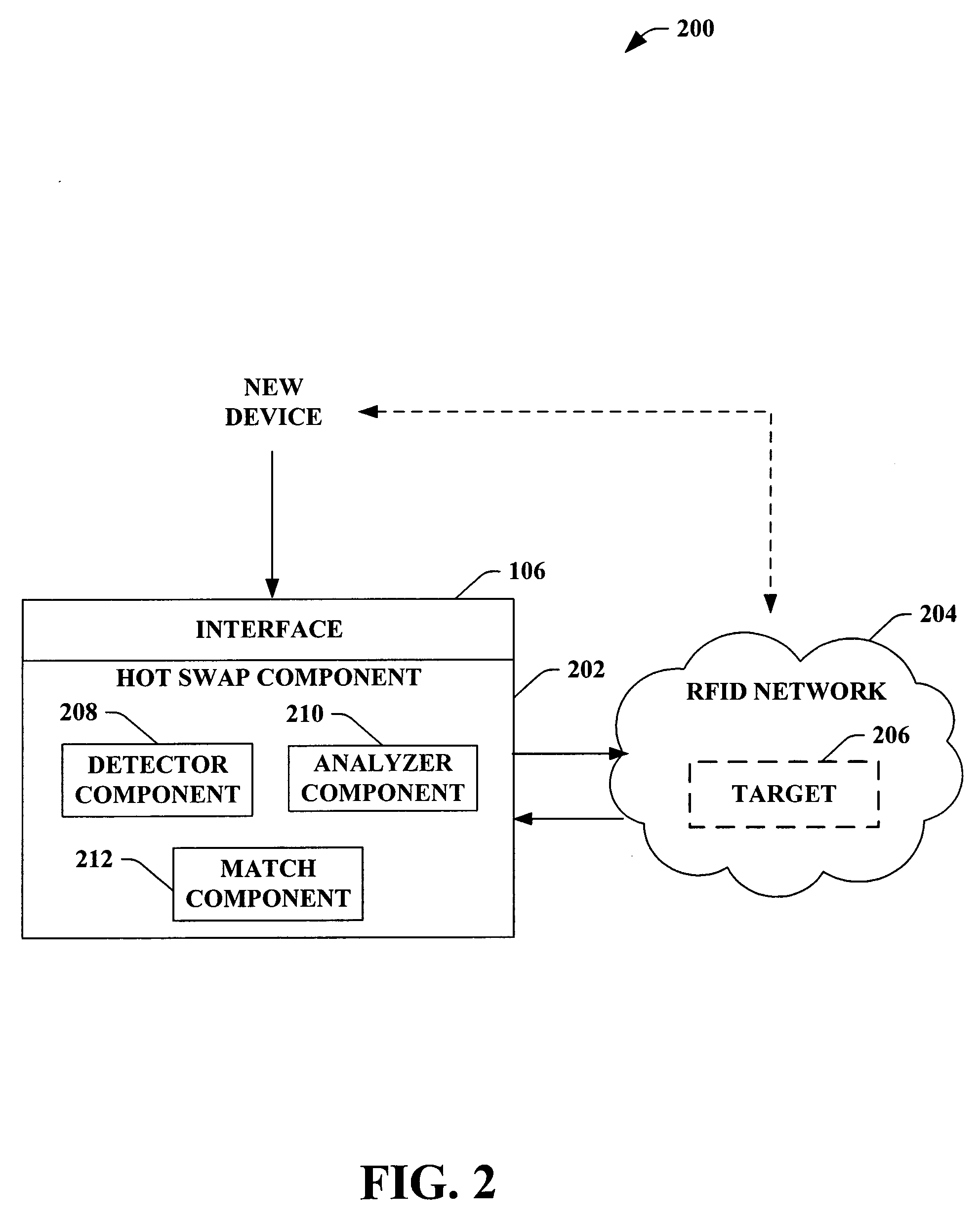
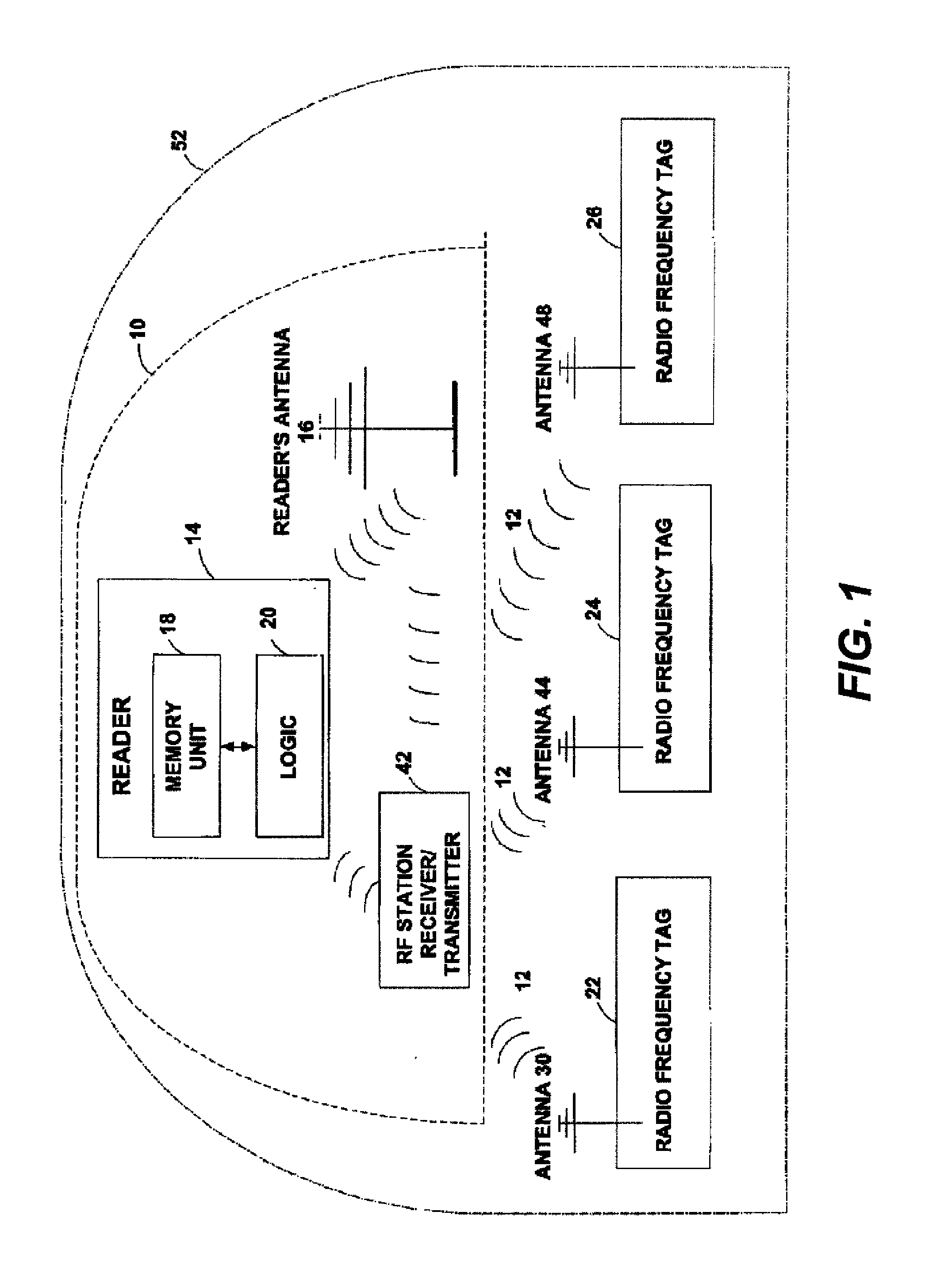
Hot swap and plug-and-play for RFID devices
InactiveUS20060047787A1Easy pairingElectric signal transmission systemsDigital data processing detailsEmbedded systemNew device
The subject invention provides a system and / or a method that facilitates adding a device to an RFID network and associated a process to such device. An interface can receive a new device and / or related identification data that is to be incorporated into an RFID network. A hot swap component can seamlessly adds the new device to a process within the RFID network based at least in part upon the identification data. The new device can be incorporated into the RFID network without the process stopping, restarting, and / or reconfiguring.
Owner:MICROSOFT TECH LICENSING LLC
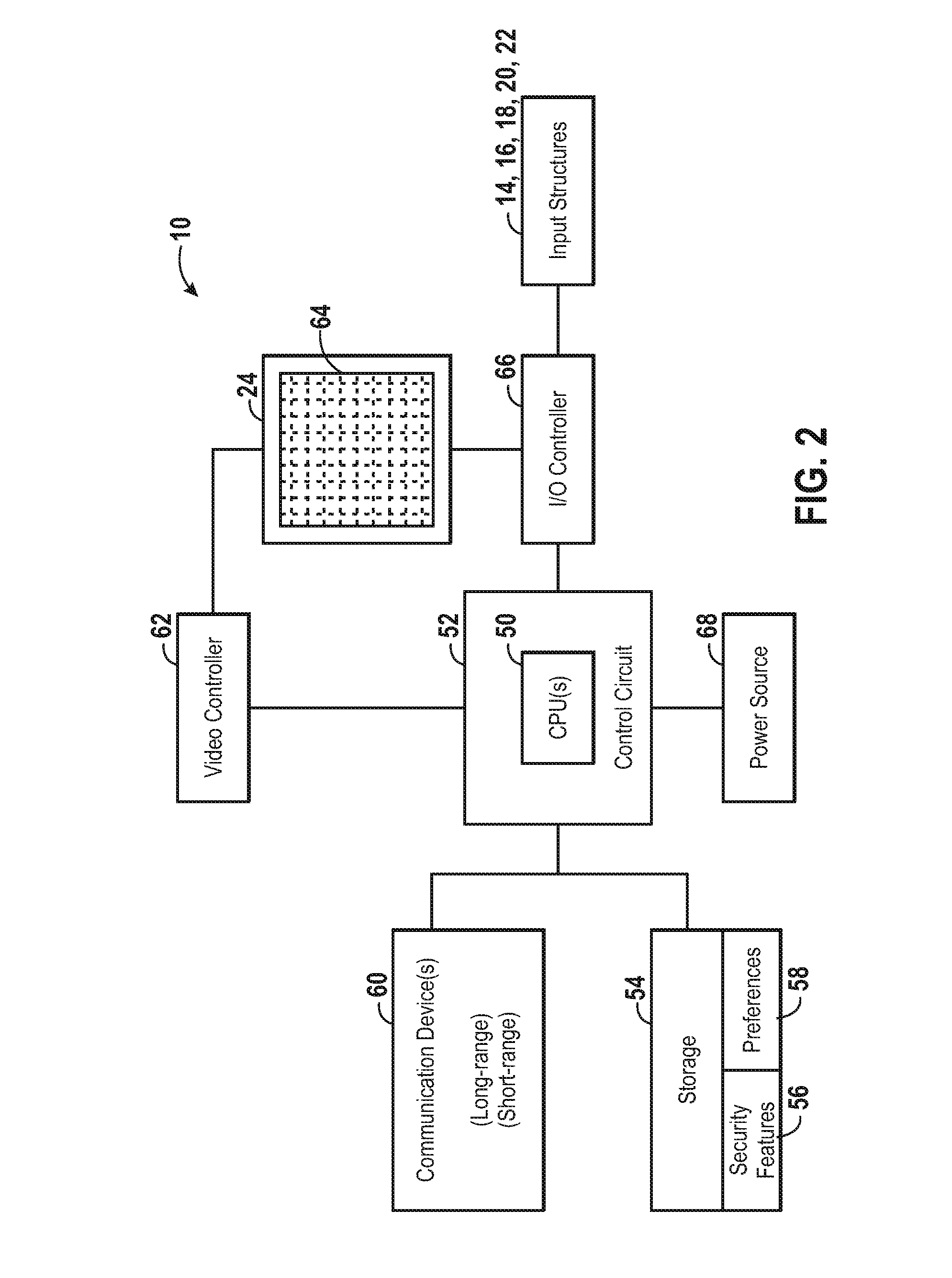
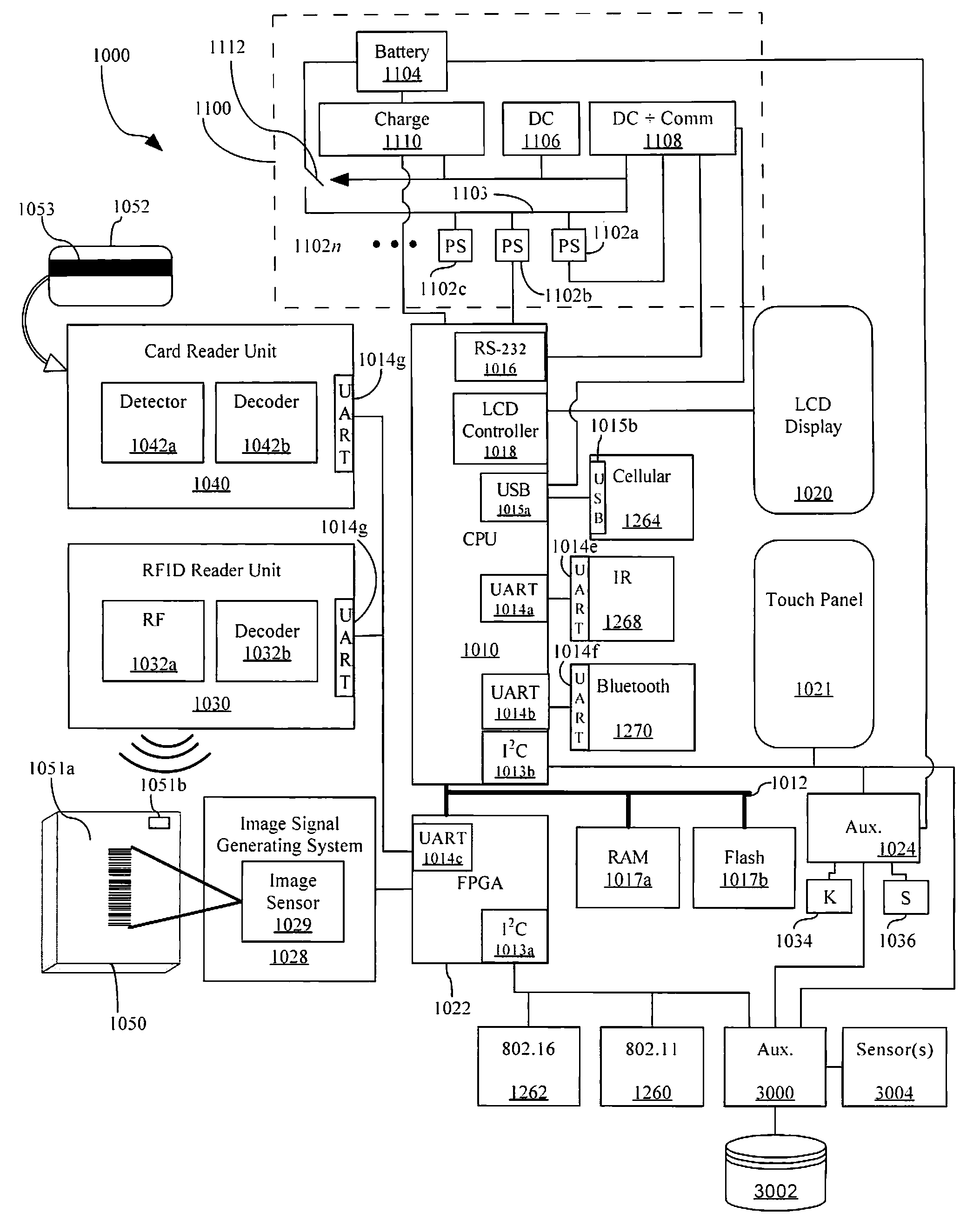
Apparatus and methods for monitoring one or more portable data terminals
A portable data terminal generally includes a housing supporting: a data collection device; a keypad; and a touch screen. One or more PDTs are provided with a monitoring system that records occurrences experienced by the portable data terminal. The record of occurrences may be analyzed to identify errors and / or failure prone parts of the PDT along with behaviors likely to lead to errors or failures. Additionally, the record of events may be analyzed to predict errors and / or failures for any given PDT.
Owner:HAND HELD PRODS
Health care sanitation monitoring system
ActiveUS20130045685A1Electric signal transmission systemsMultiple keys/algorithms usageMonitoring systemMedical emergency
A medical sanitation device may include a detector for detecting the physical presence of a clinician token within a detection area in the vicinity of the medical sanitation device. The clinician token may be indicative of the identity of a clinician. The medical sanitation device also includes a sanitation module configured to be used by the clinician to perform a sanitation task. Detection of a clinician in proximity to the medical sanitation device may be used to at least partially control access to, or operation of, a medical patient monitoring device.
Owner:JPMORGAN CHASE BANK NA
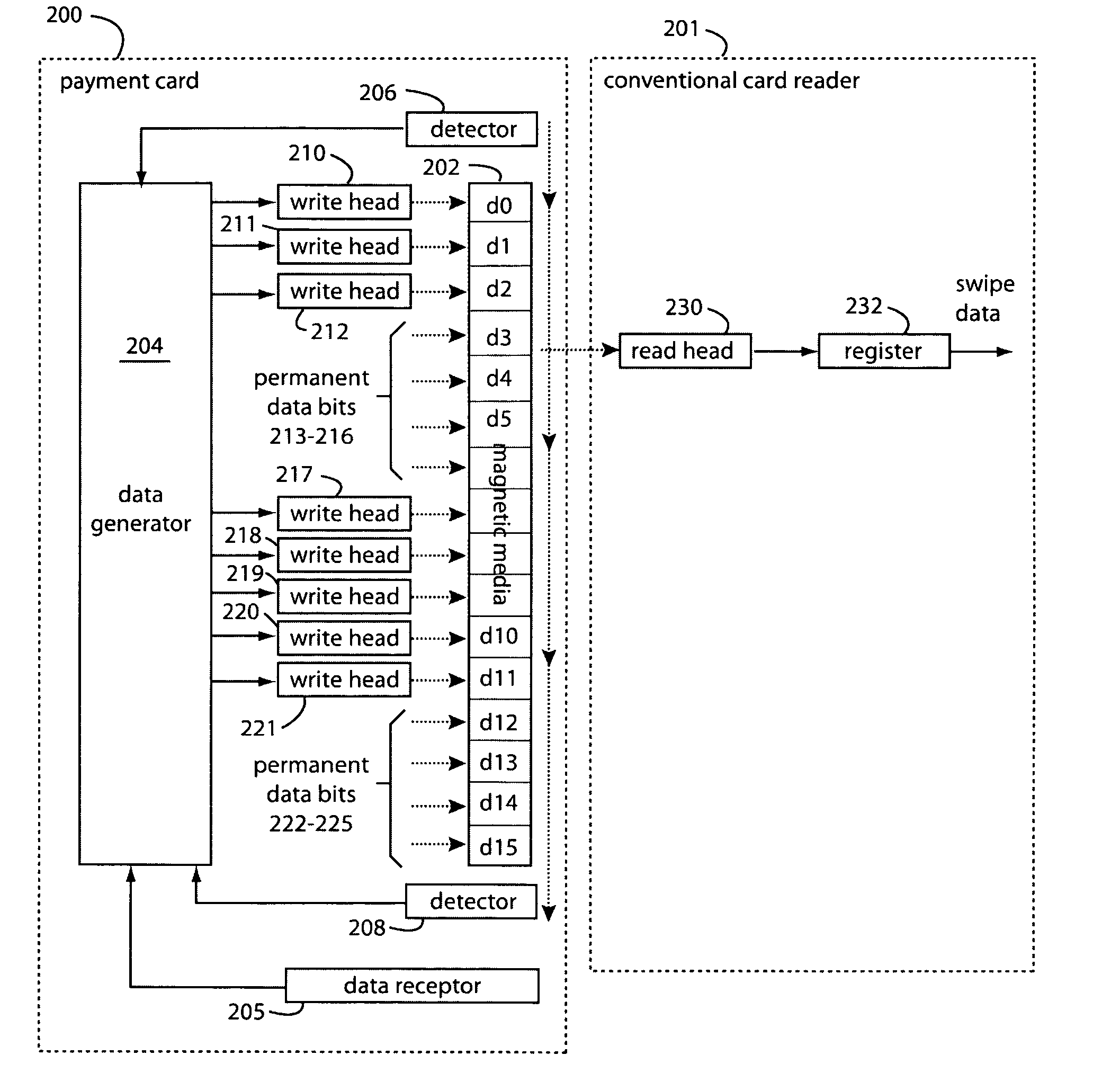
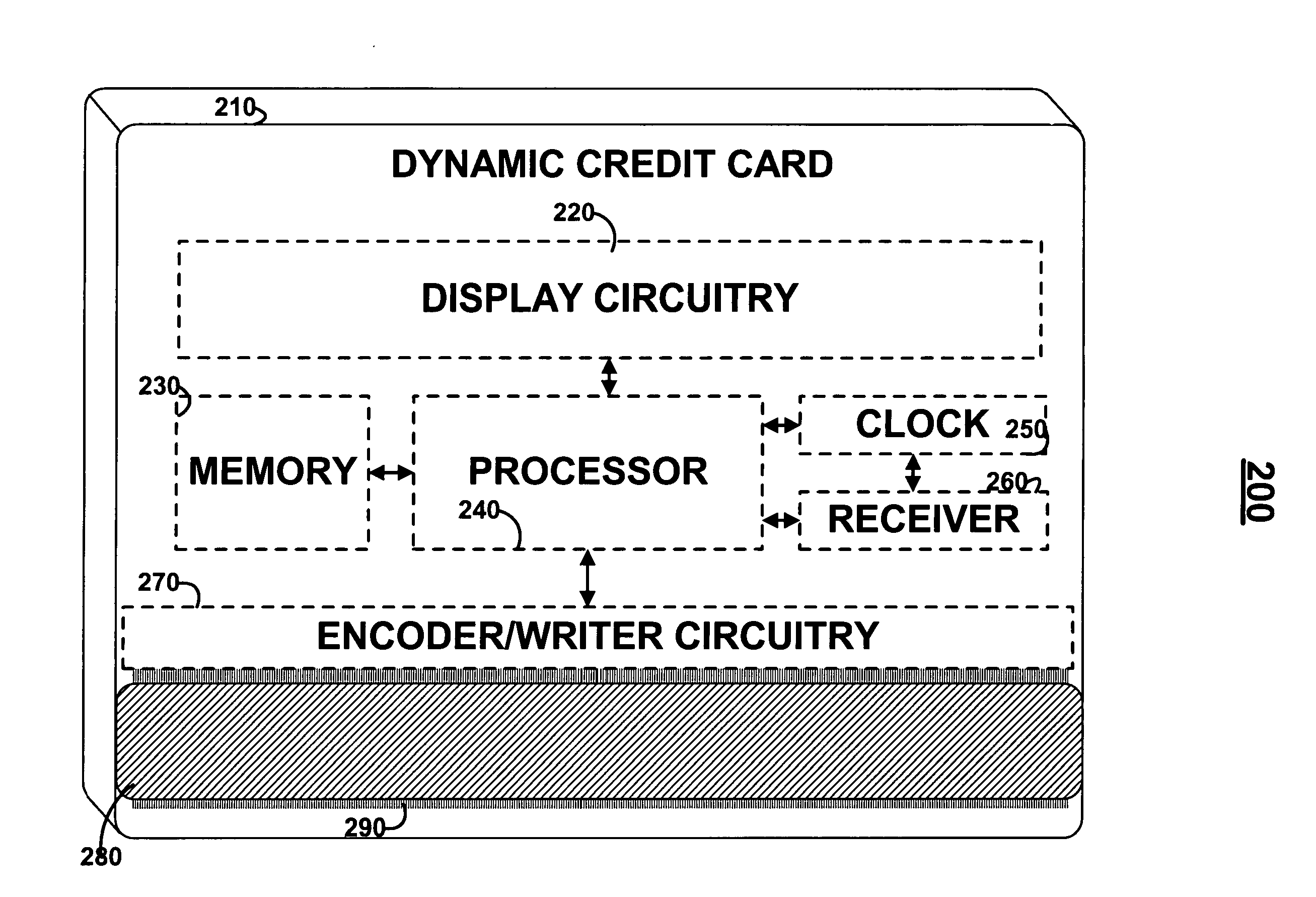
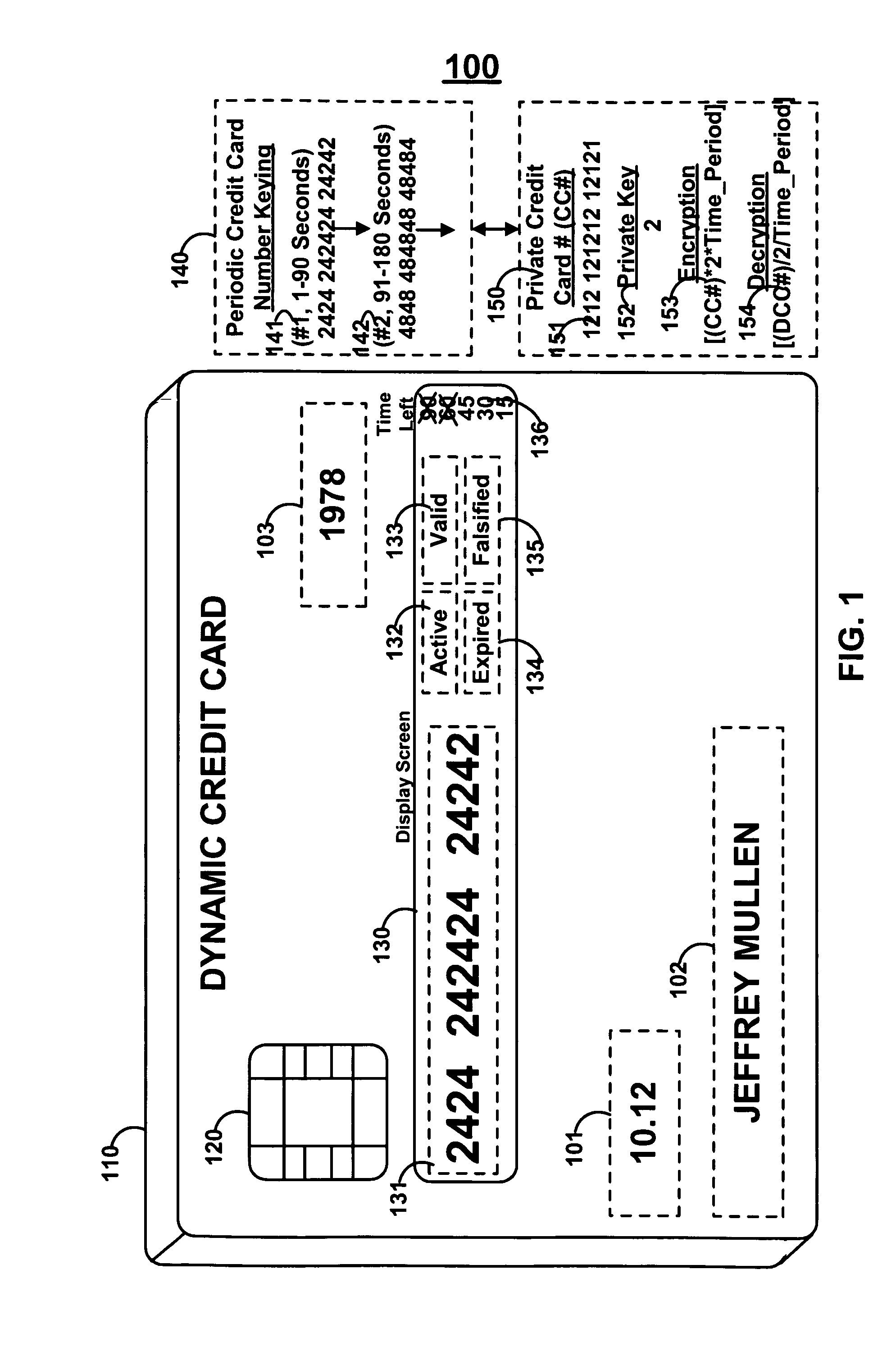
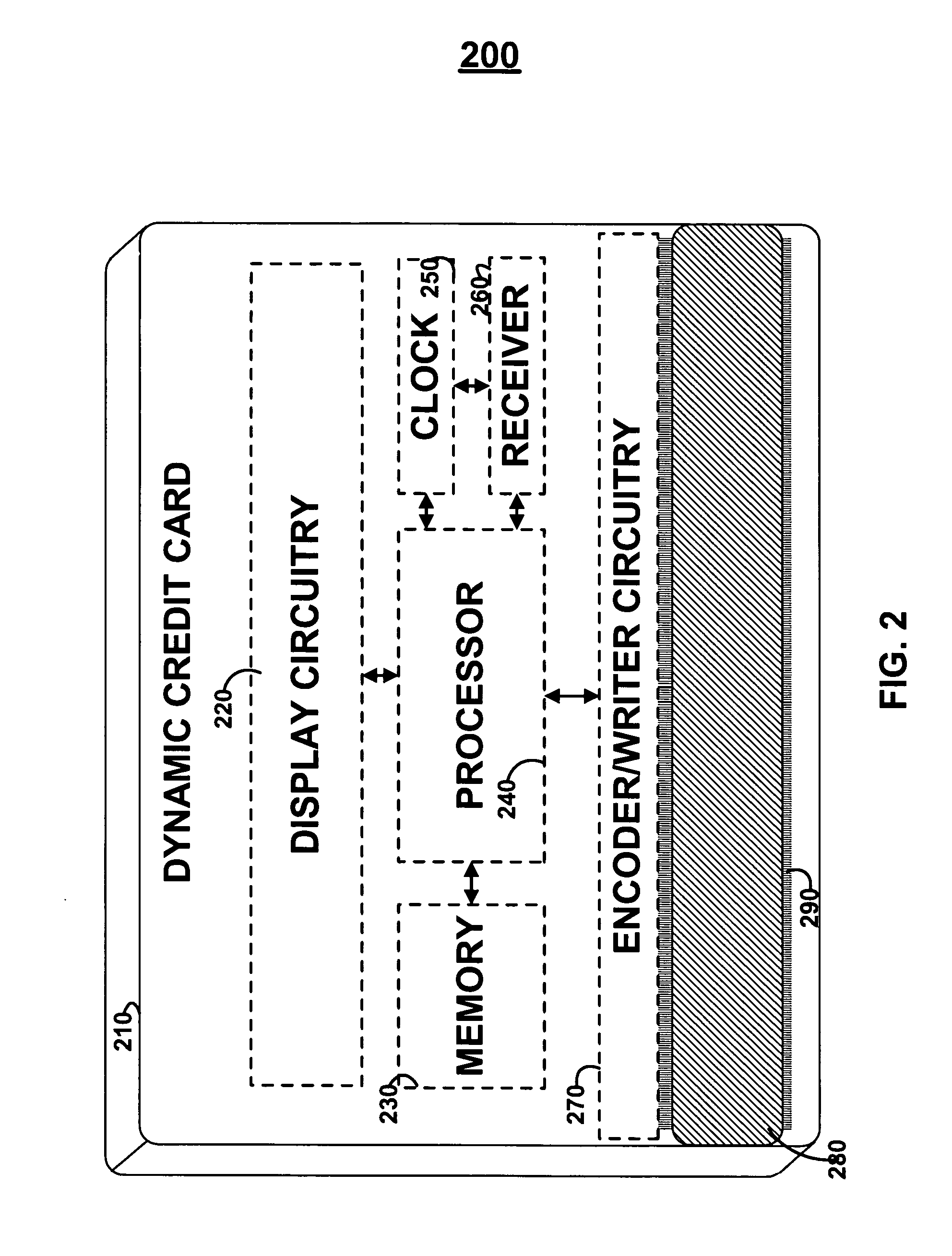
Dynamic credit card with magnetic stripe and embedded encoder and methods for using the same to provide a copy-proof credit card
A dynamic credit card is provided in which a secure credit card number (e.g., a secret / hidden credit card number) is encoded based on a timing signal (e.g., an internal counter) to provide a dynamic credit card number. This dynamic number may be displayed to a user via a display (e.g., so that online purchases can be made) or written onto a magnetic stripe such that the number may be processed by traditional credit card merchants (e.g., swiped). At a remote facility, the dynamic number may be decoded based on time (and / or a counter / key number / equation) or the facility may have the secure number and perform the same function as the dynamic credit card (e.g., encode using time data as a parameter to the encoding equation) and compare the resultant dynamic number to the dynamic number received. Thus, a dynamic credit card number may change continually or periodically (e.g., every sixty seconds) such that credit card numbers may not be copied by thieves and used at later times. A dynamic verification code may be utilized in addition to, or in lieu of, a dynamic credit card number.
Owner:DYNAMICS
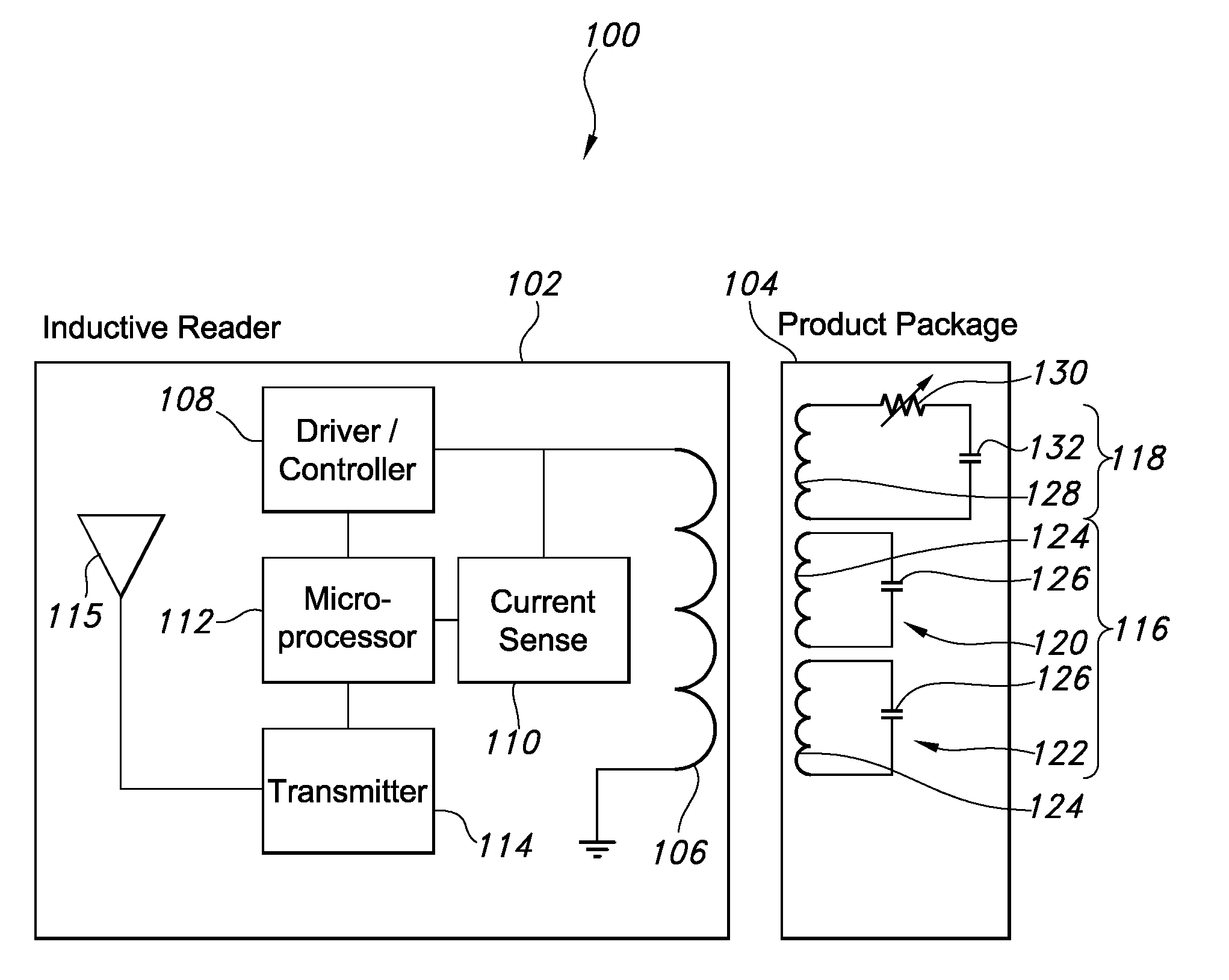
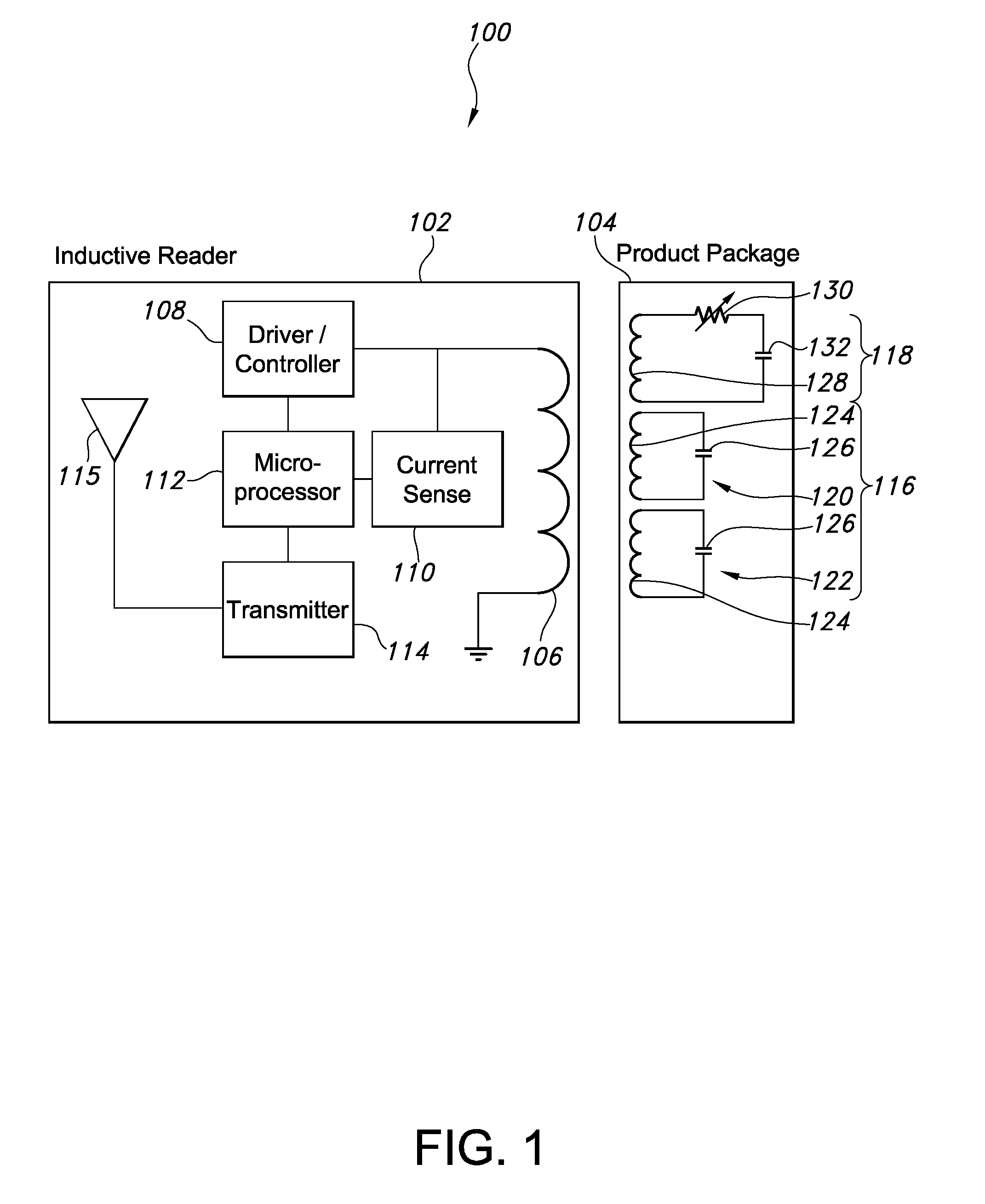
Point of sale inductive systems and methods
Systems and methods for the identification, powering and control of products and product packaging. The systems can include a point of sale display having a contactless power supply. The contactless power supply can provide a source of wireless power for products and product packaging. The products and product packaging can include light emitting diodes, e-ink displays and printed speaker circuits that activate as the operating frequency of the contactless power supply varies. Other embodiments include product level sensors, inductive reader networks, printed temperature sensors, product alignment systems, passive identification circuits and methods for controlling operation of the same.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Secure credit card
Credit card or portable identification cards containing smart card technology and electronic fuse (e-fuse) technology are combined with a LFSR pseudo random number generator to provide a secured method to prevent fraud and unauthorized use. Secure personalization via e-fuses, a pseudo random number generator linear feedback shift register, free running clock oscillator, and power source embedded in the card enable a highly secured method to render a lost or stolen card useless. A unique card ID is permanently encoded within the card which requires a specific activation code to activate the card. A PIN number provides a means for the card owner to activate the card for a predetermined length of time while processing a transaction. The card's security generation function dynamically generates random code sequences and synchronization keys to secure a transaction.
Owner:KYNDRYL INC
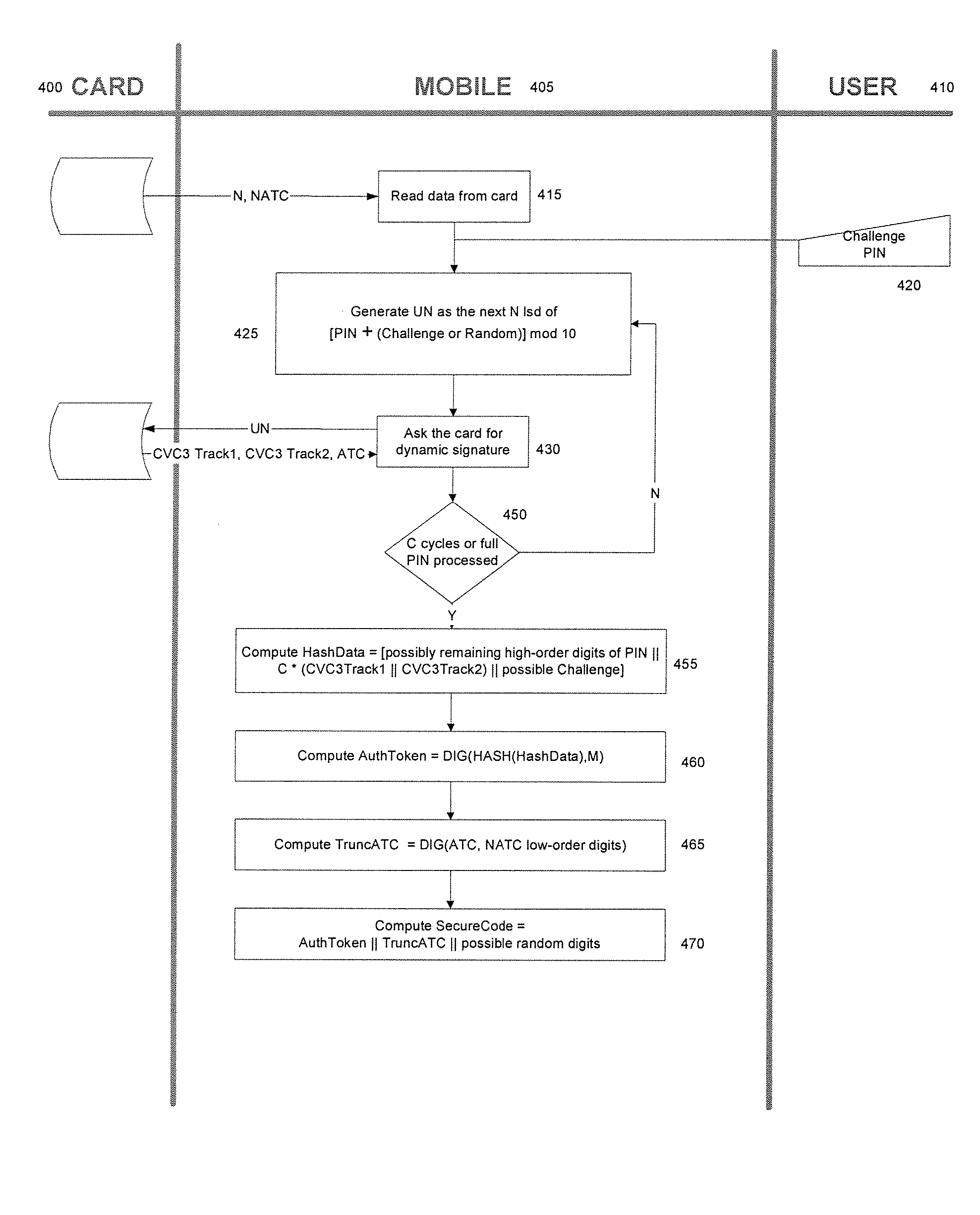
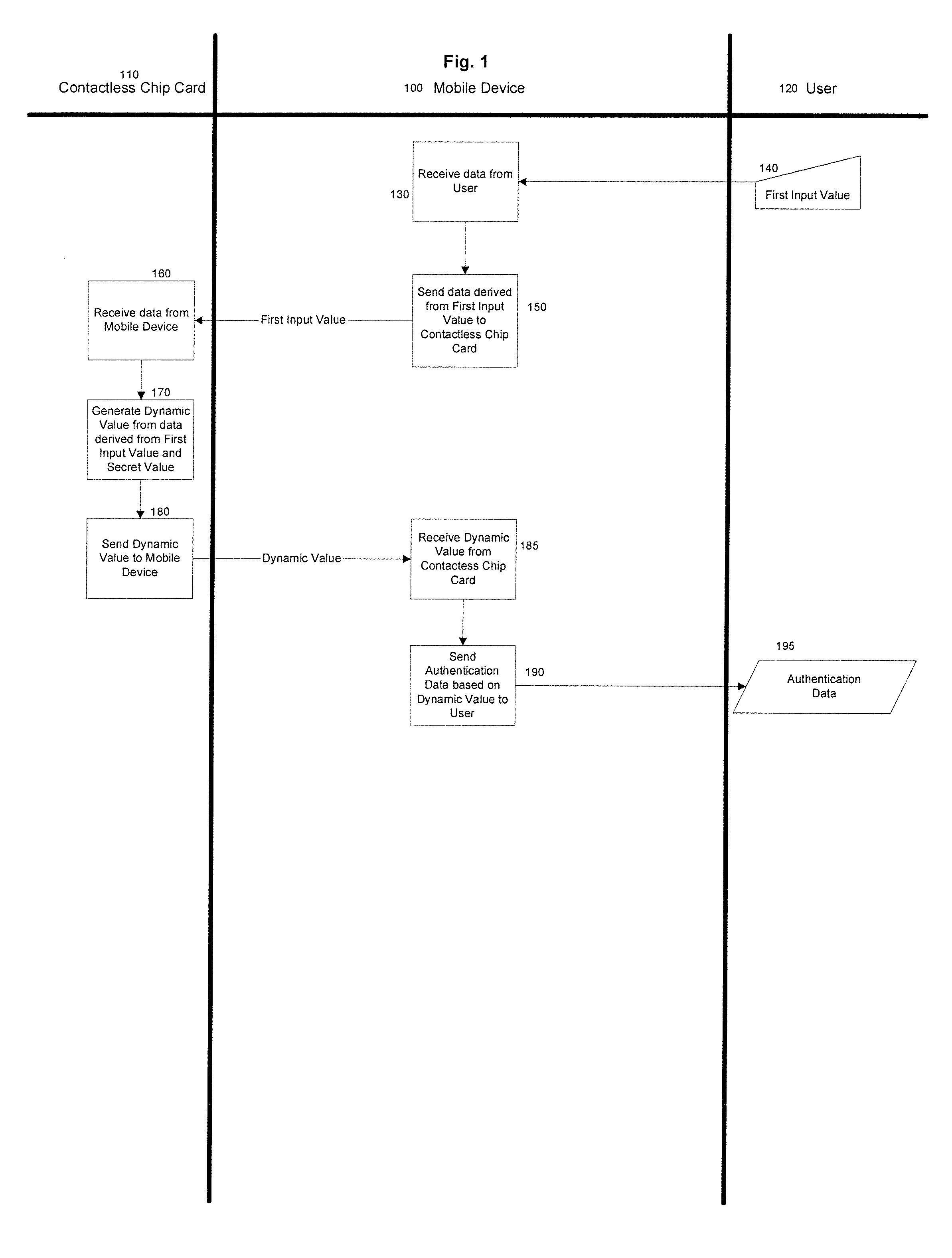
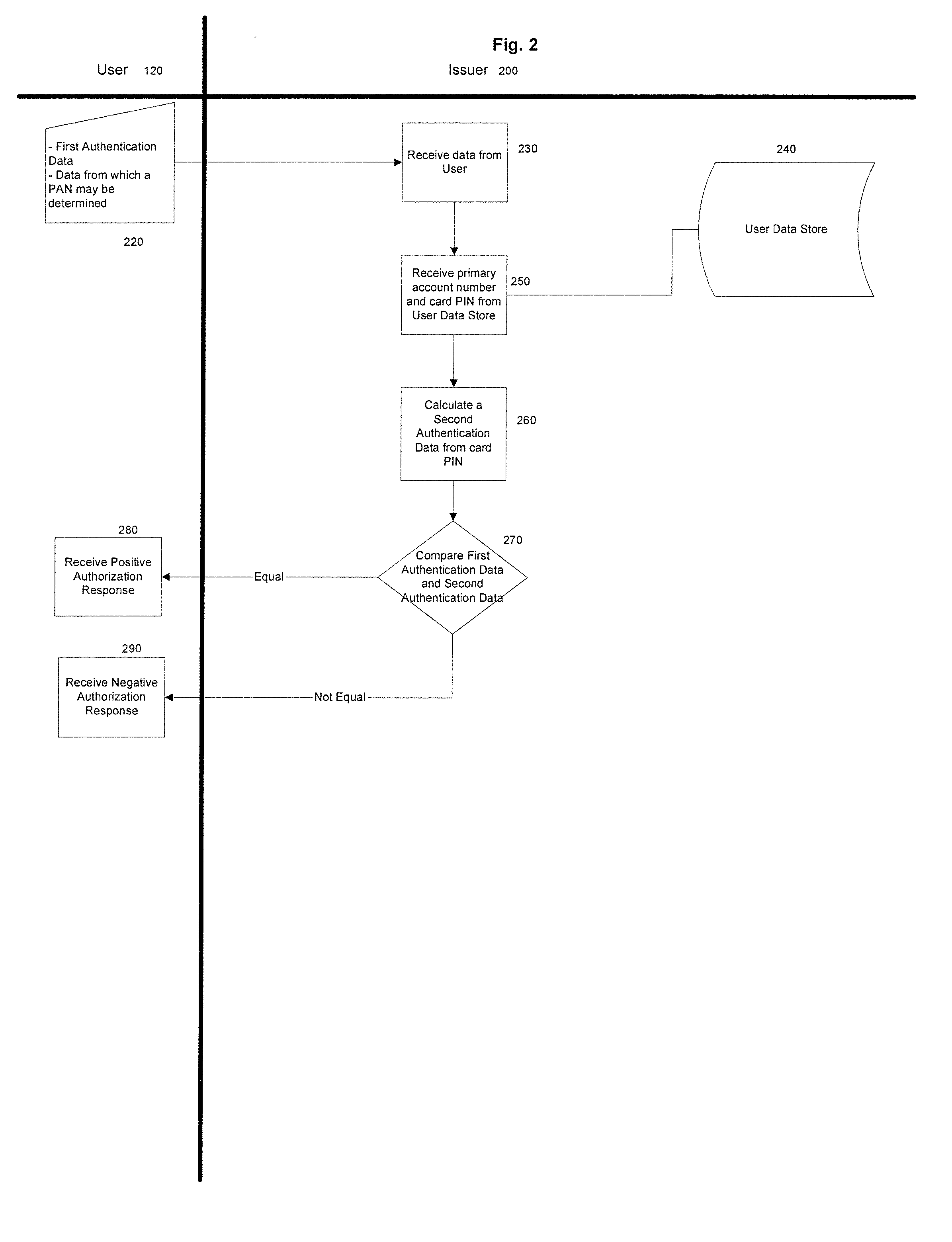
Methods and Systems for Two-Factor Authentication Using Contactless Chip Cards or Devices and Mobile Devices or Dedicated Personal Readers
Generating authentication data for use in a transaction by providing a contactless payment device or smart card configured to communicate with a mobile device, placing the contactless chip card in a proximity to the mobile device to instantiate communication between the contactless chip card and the mobile device, inputting a first input value into the mobile device, communicating data derived from the first input value from the mobile device to the contactless chip card, the contactless chip card converting a set of conversion data, including the first input value, into at least one dynamic value based at least in part on a secret value, communicating the dynamic value from the contactless chip card to the mobile device, and communicating authentication data based at least in part on the dynamic value to a user. In some embodiments the first input value is a Personal Identification Number (PIN), a challenge, or both a PIN and a challenge.
Owner:MASTERCARD INT INC
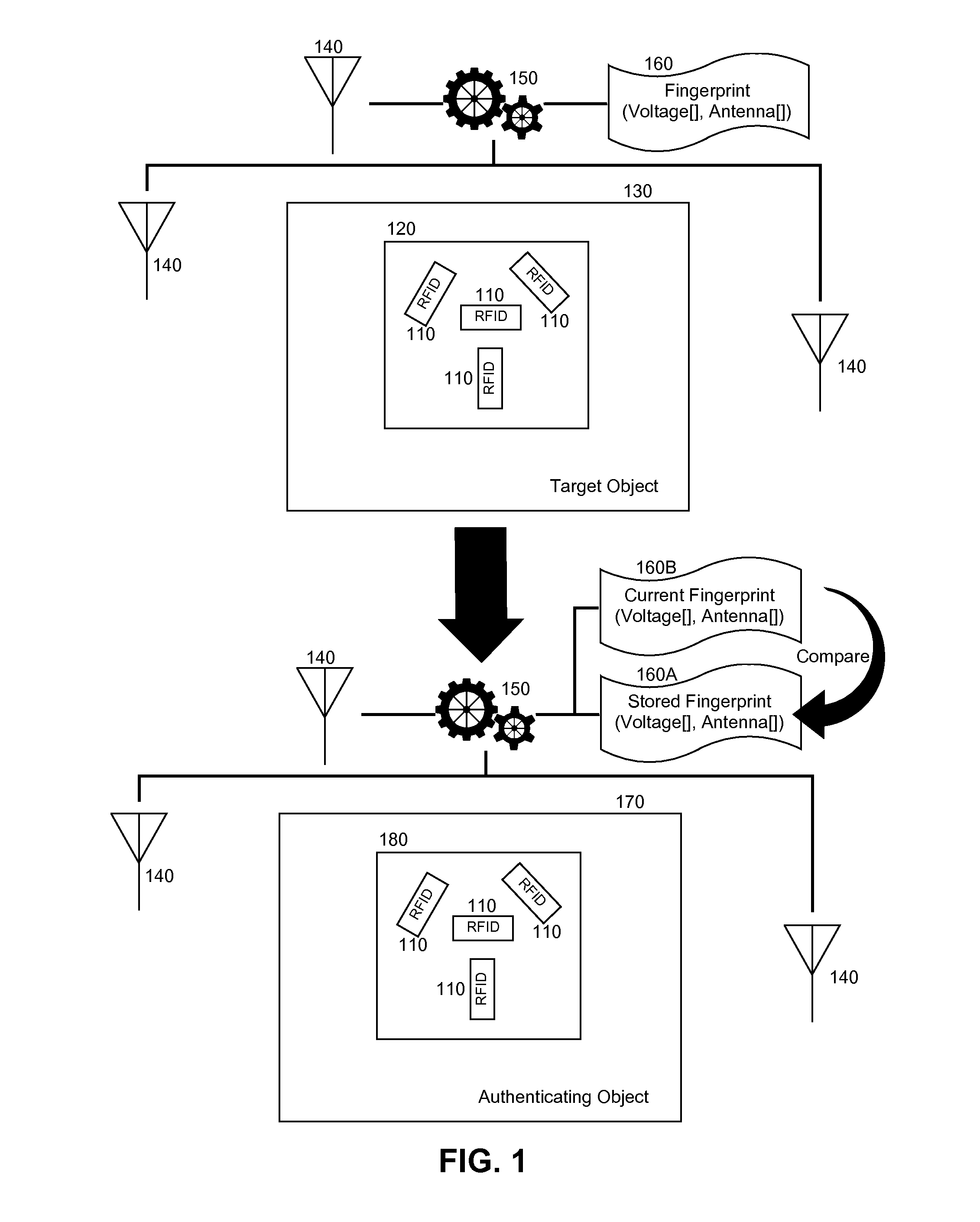
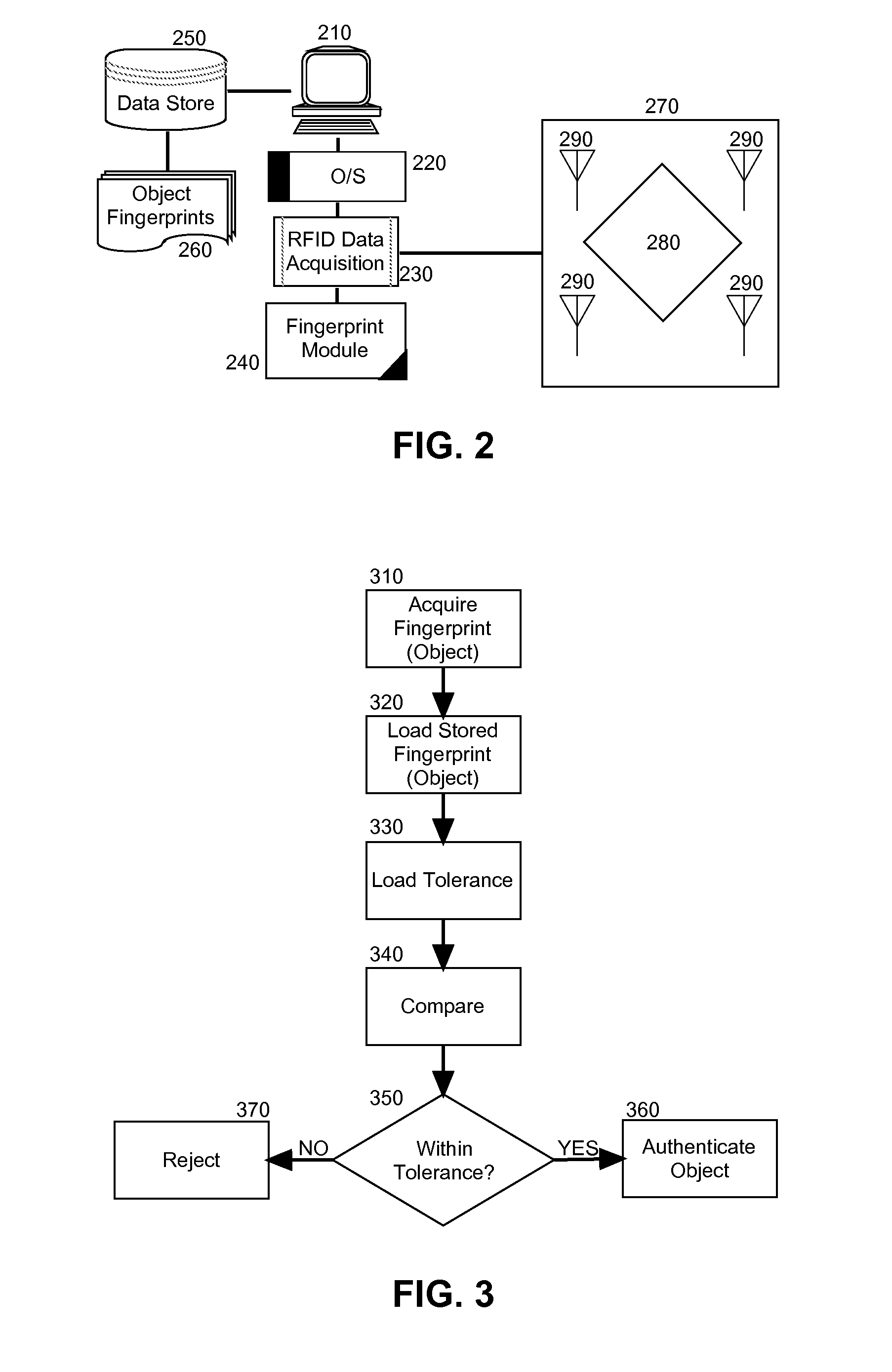
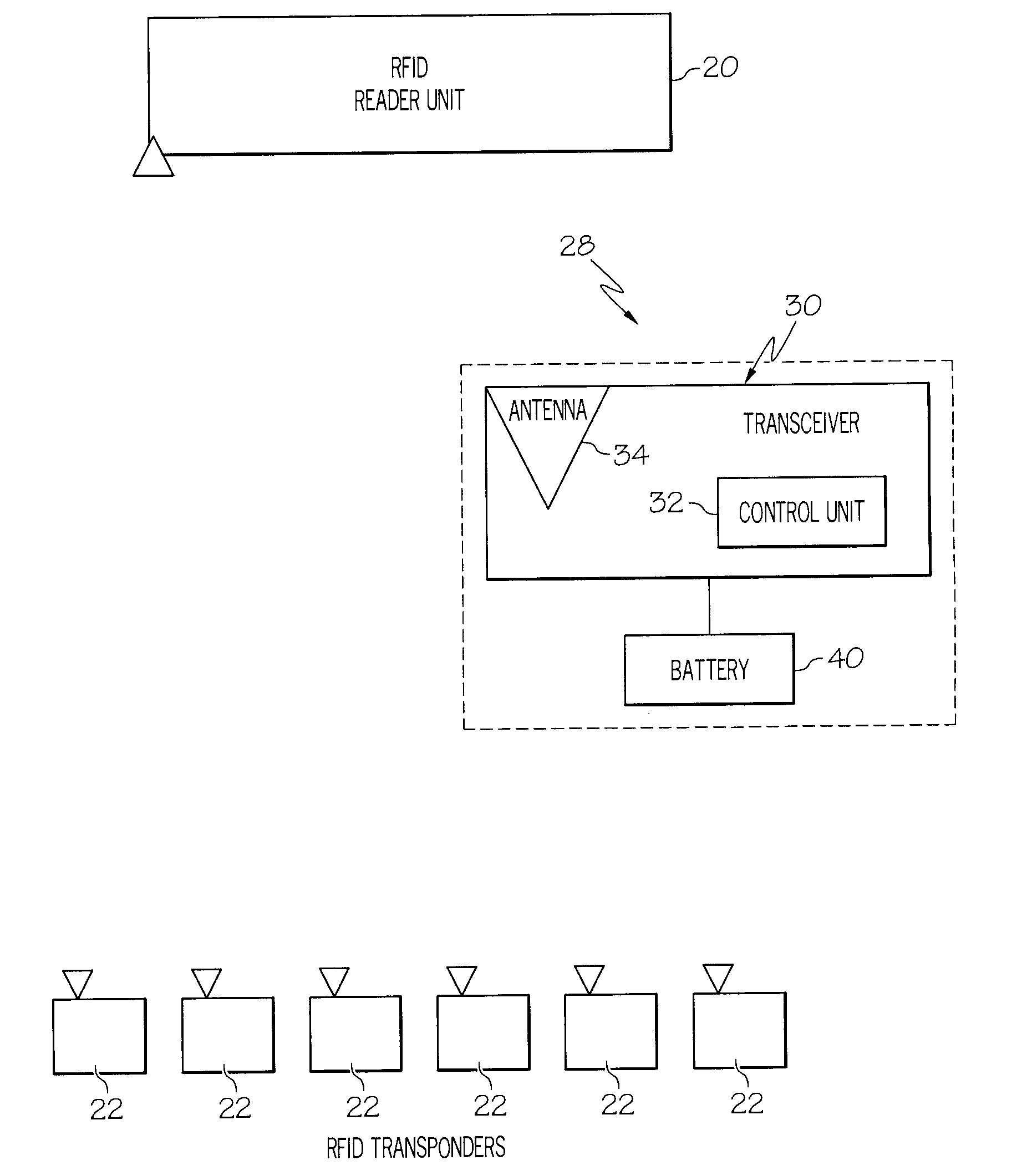
RFID fingerprint creation and utilization
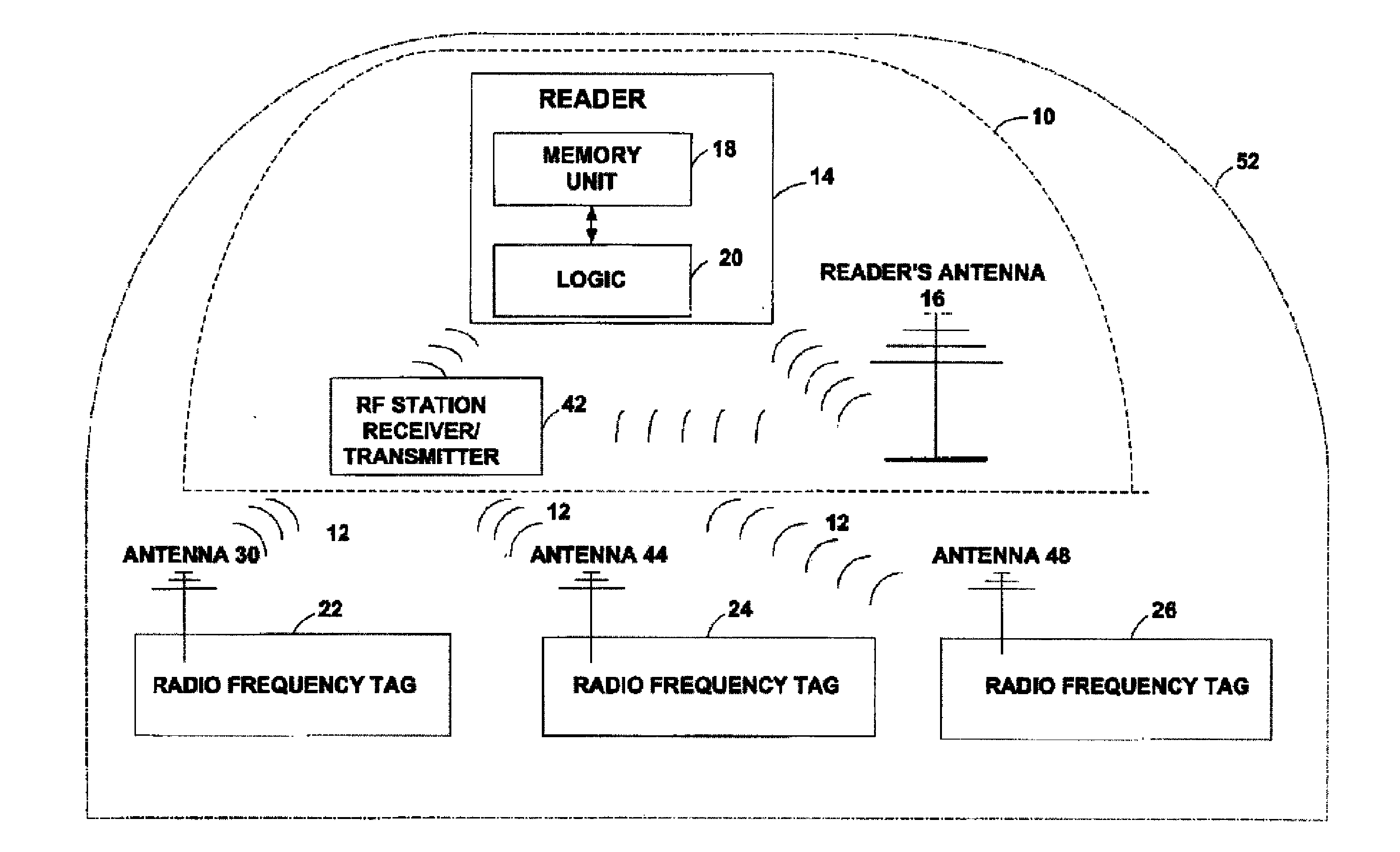
InactiveUS20110068893A1Ensure authenticityProgramme controlElectric signal transmission systemsComputer hardwareRadio frequency
Embodiments of the present invention provide a method, system and computer program product for creating and managing radio frequency identification (RFID) fingerprints to ensure item authenticity. In an embodiment of the invention, an object fingerprint creation method can be provided. The method can include receiving a sensed signal from at least one RFID reader resulting from at least one RFID tag affixed to a target object. The method further can include extracting a voltage produced by the RFID tag from the sensed signal. Finally, the method can include storing the voltage as a fingerprint for the target object for later comparison with another fingerprint for an authenticating object to determine whether or not the authenticating object is the target object.
Owner:IBM CORP
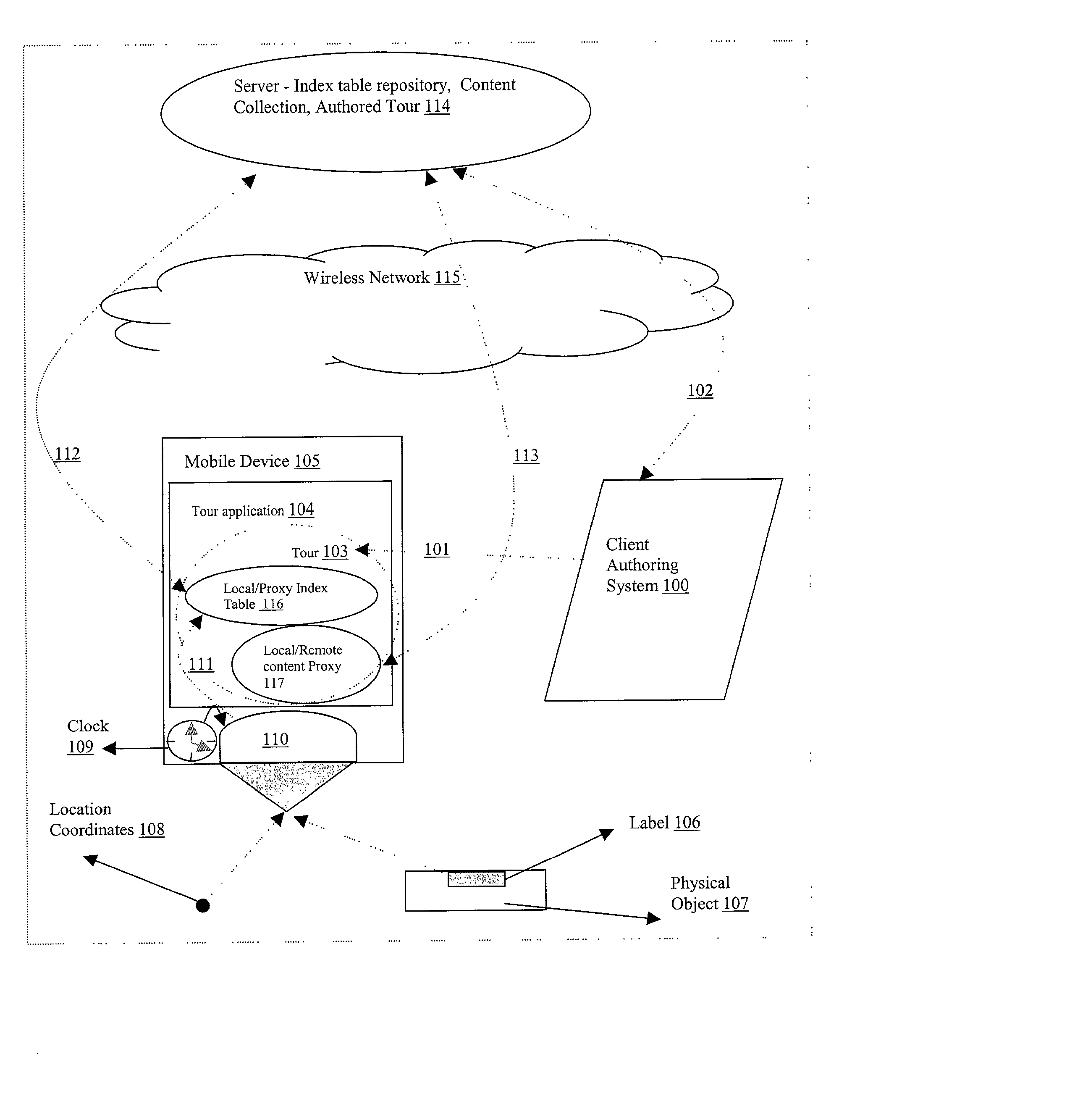
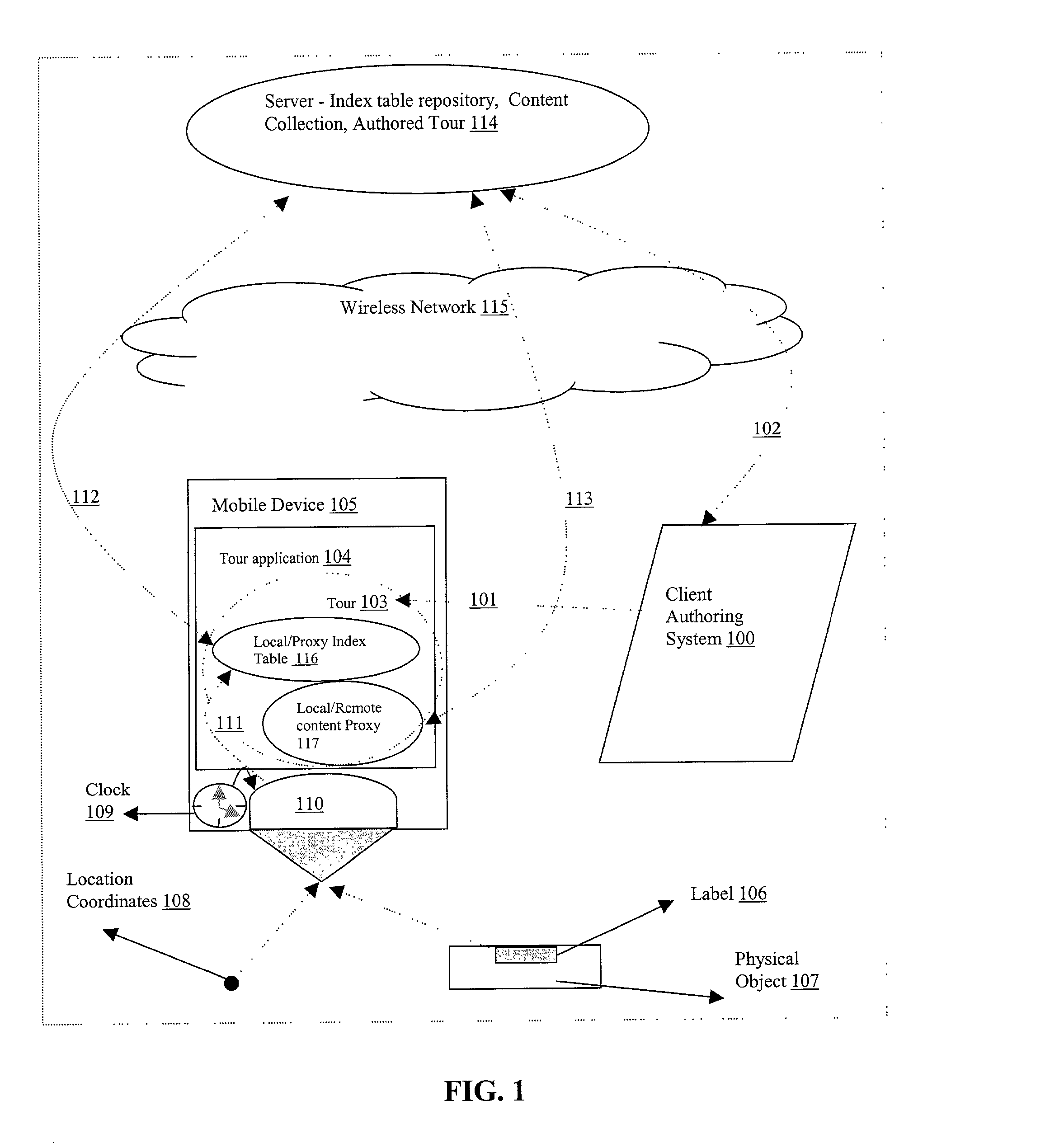
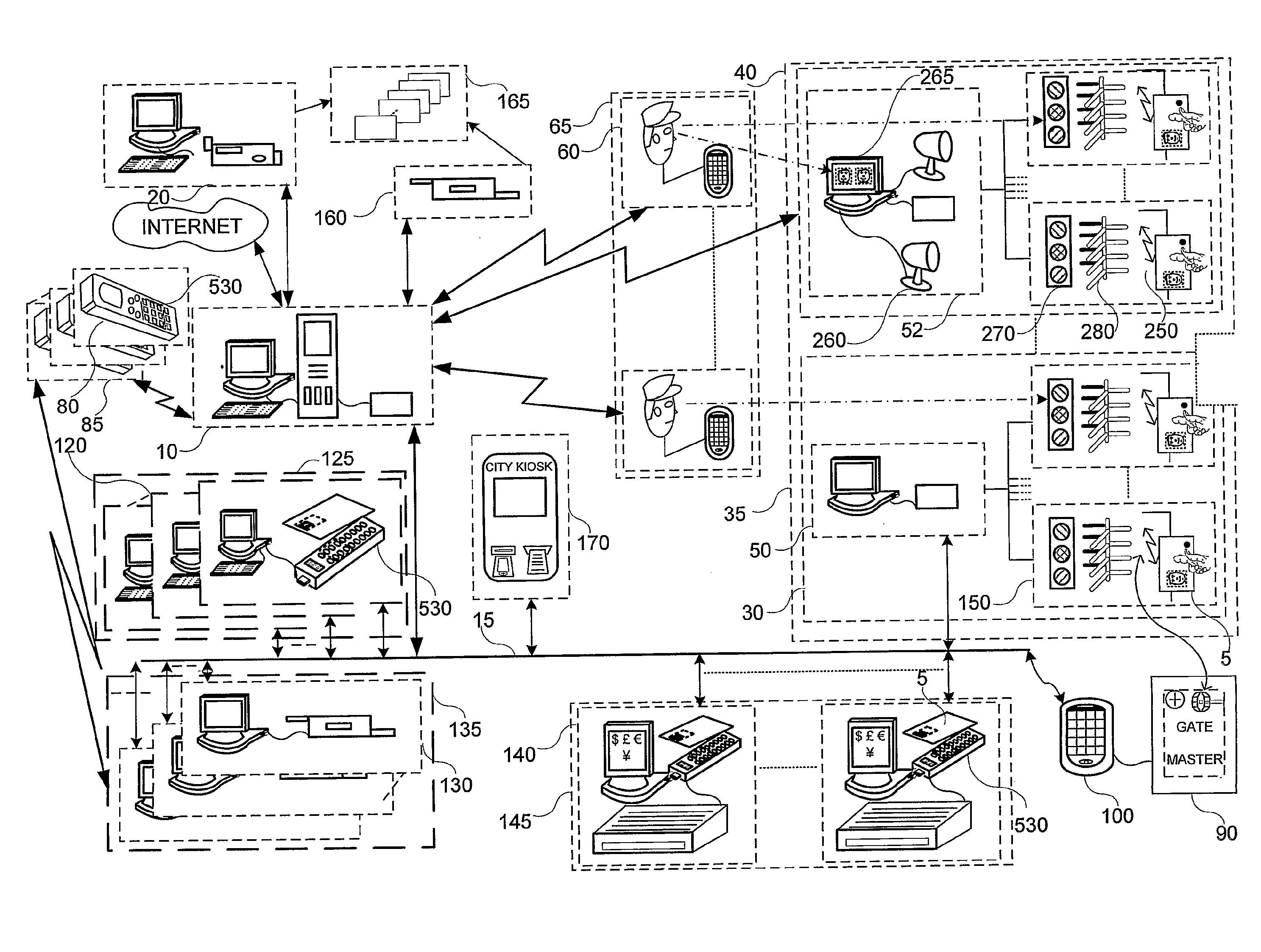
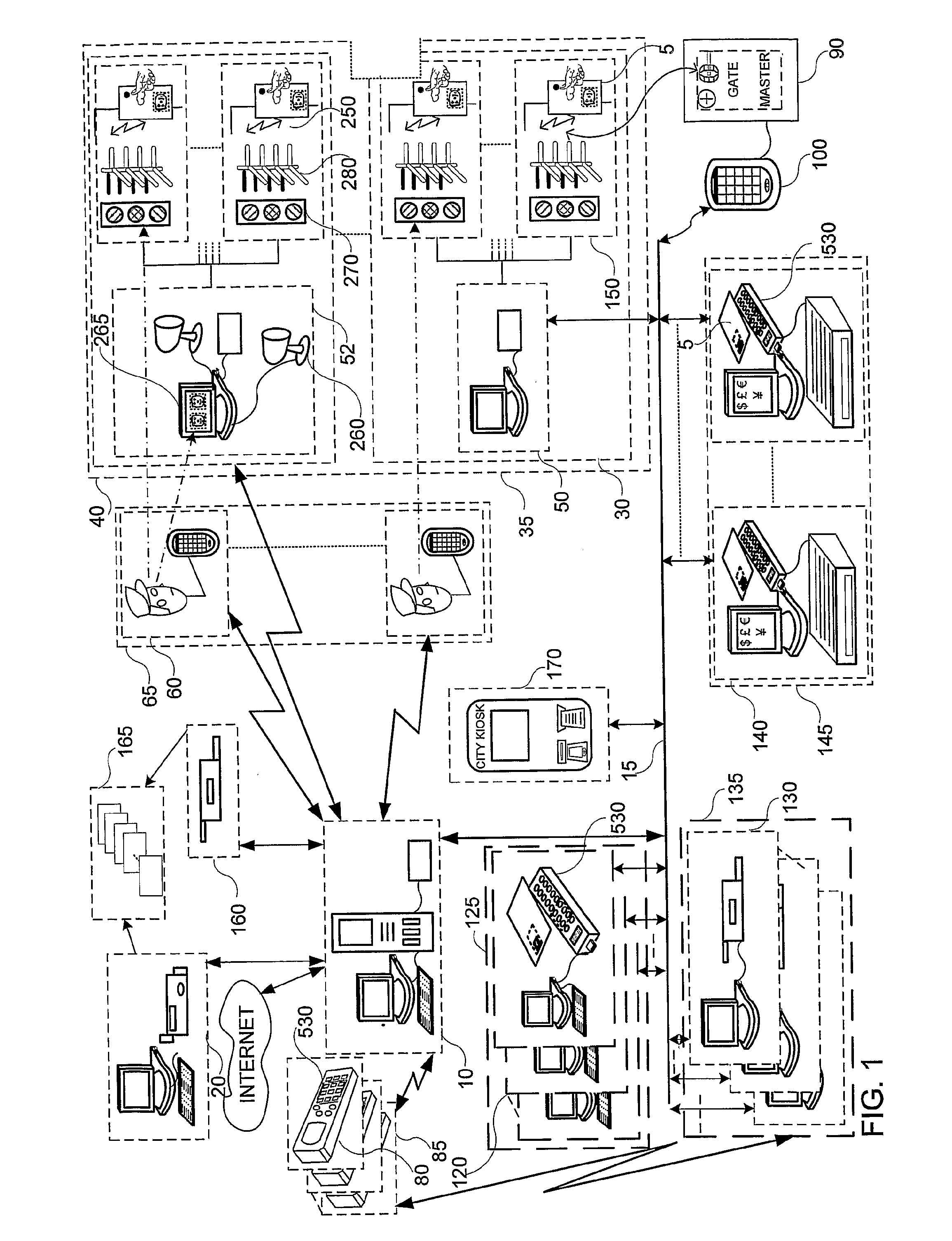
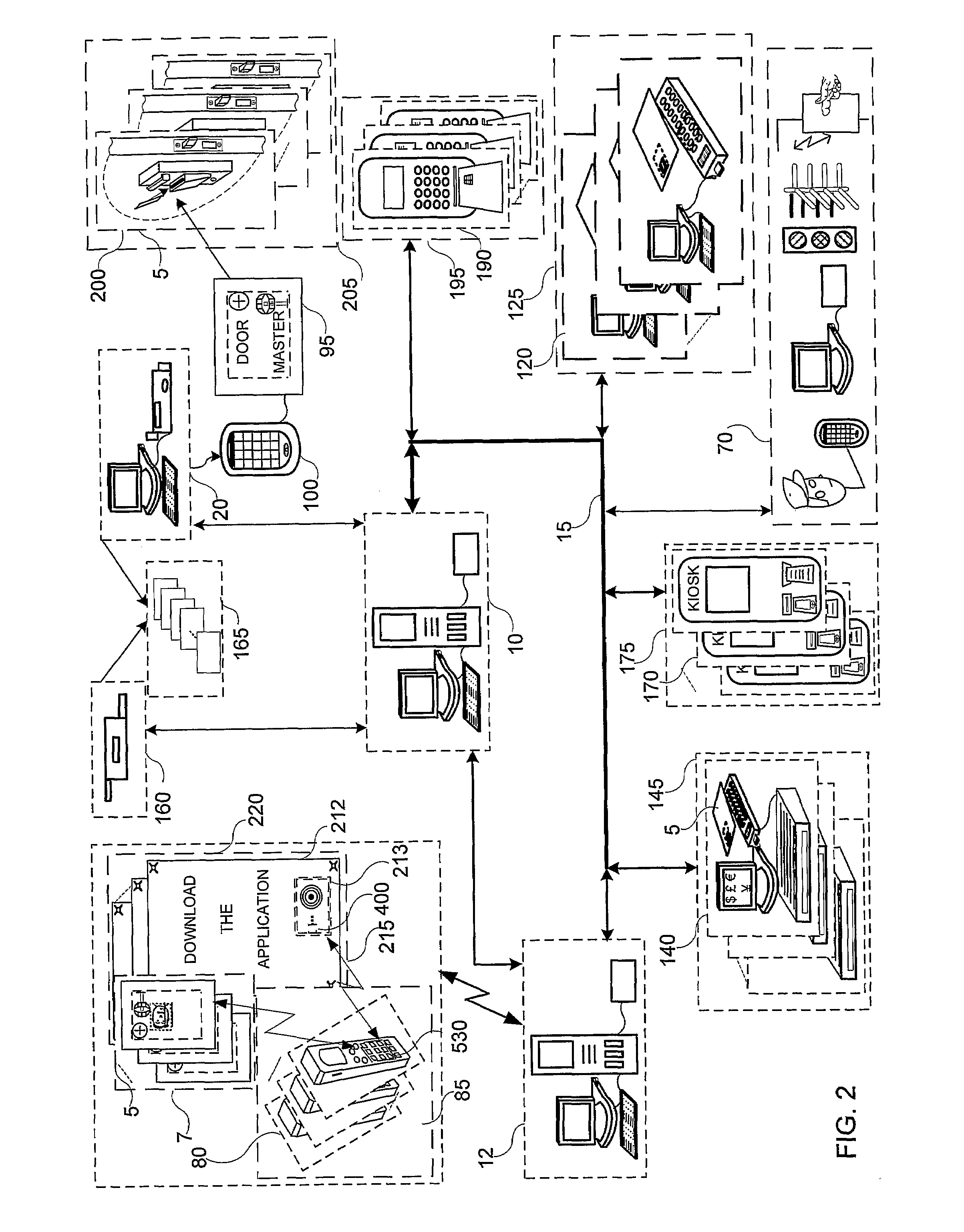
System and method for authoring and providing information relevant to the physical world
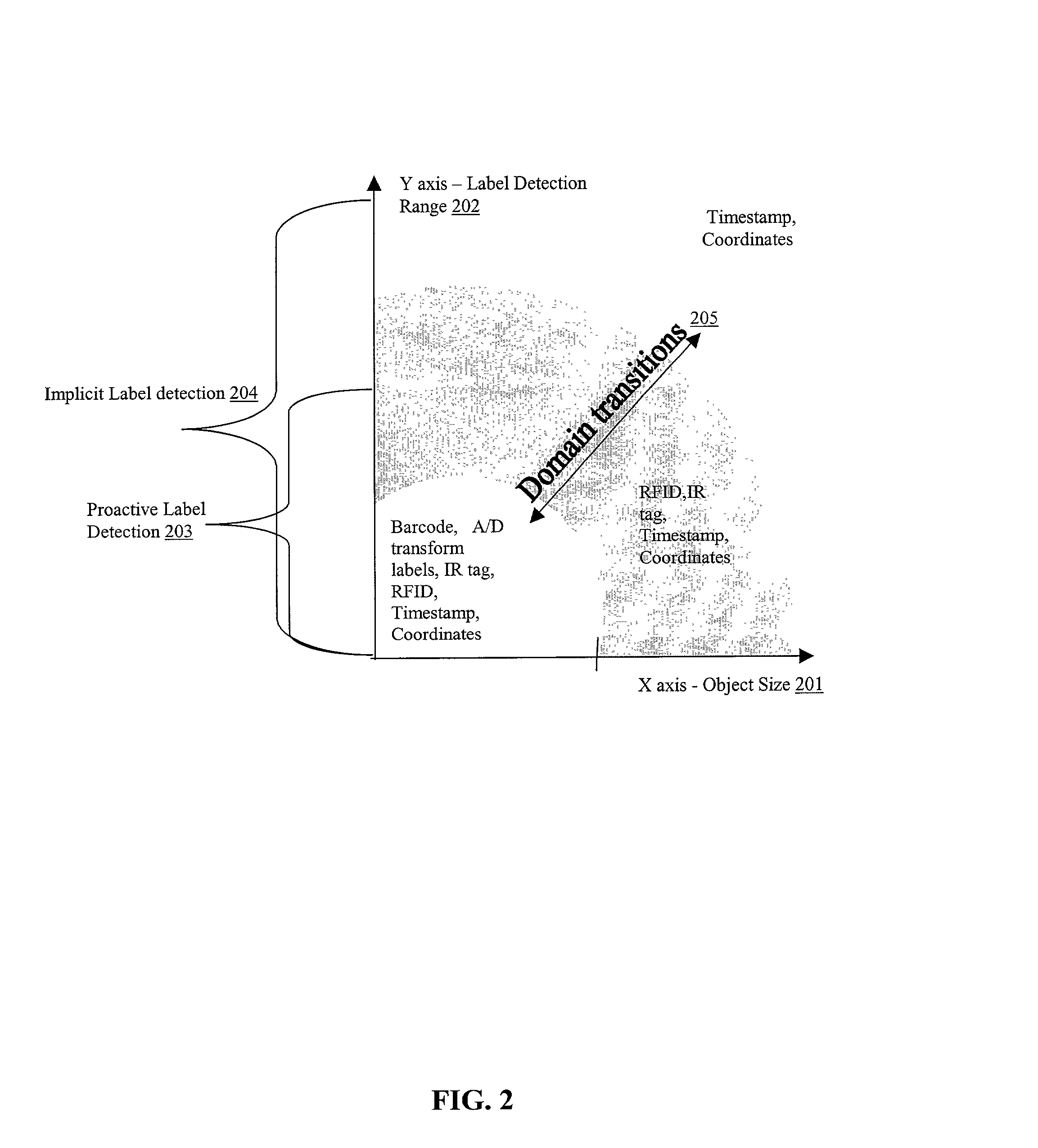
A system and method capable of reading machine-readable labels from physical objects, reading coordinate labels of geographical locations, reading timestamp labels from an internal clock, accepting digital text string labels as input obtained directly from a keyboard type input device, or indirectly using a speech-to-text engine transforming any other label type information encoding into digital data by some transduction means, and treating these different labels uniformly as object identifiers for performing various indexing operations such as content authoring, playback, annotation and feedback. The system further allows for the aggregating of object identifiers and their associated content into a single addressable unit called a tour. The system can function in an authoring and a playback mode. The authoring mode permits new audio / text / graphics / video messages to be recorded and bound to an object identifier. The playback mode triggers playback of the recorded messages when the object identifier accessed. In the authoring mode, the system supports content authoring that can be done coincident with object identifier creation thereby enabling authored content to be unambiguously bound to the object identifier. In the playback mode, the system can be programmed to accept / solicit annotations / feedback from a user which may also be recorded and unambiguously bound to the object identifier.
Owner:NAVISCAN LLC
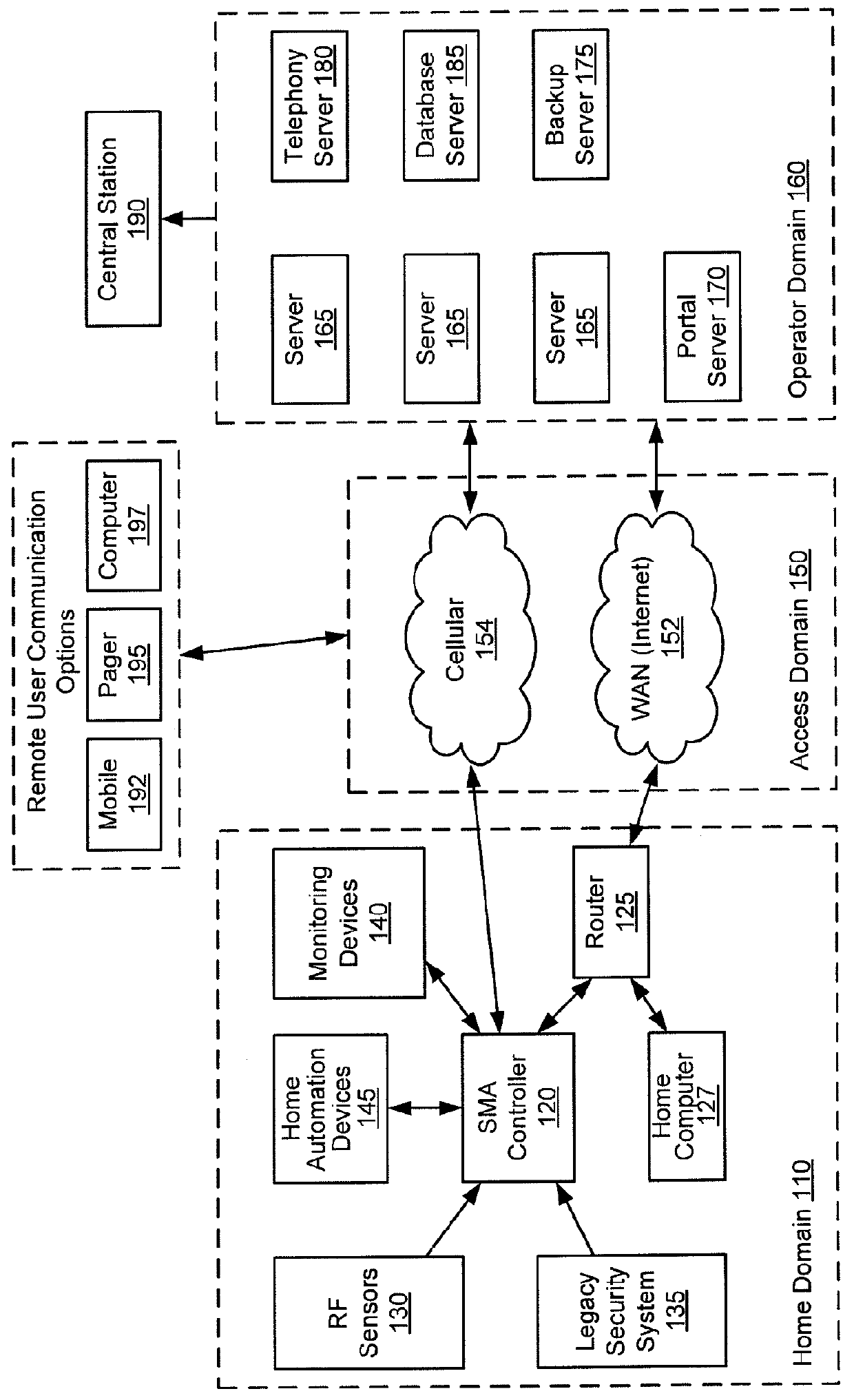
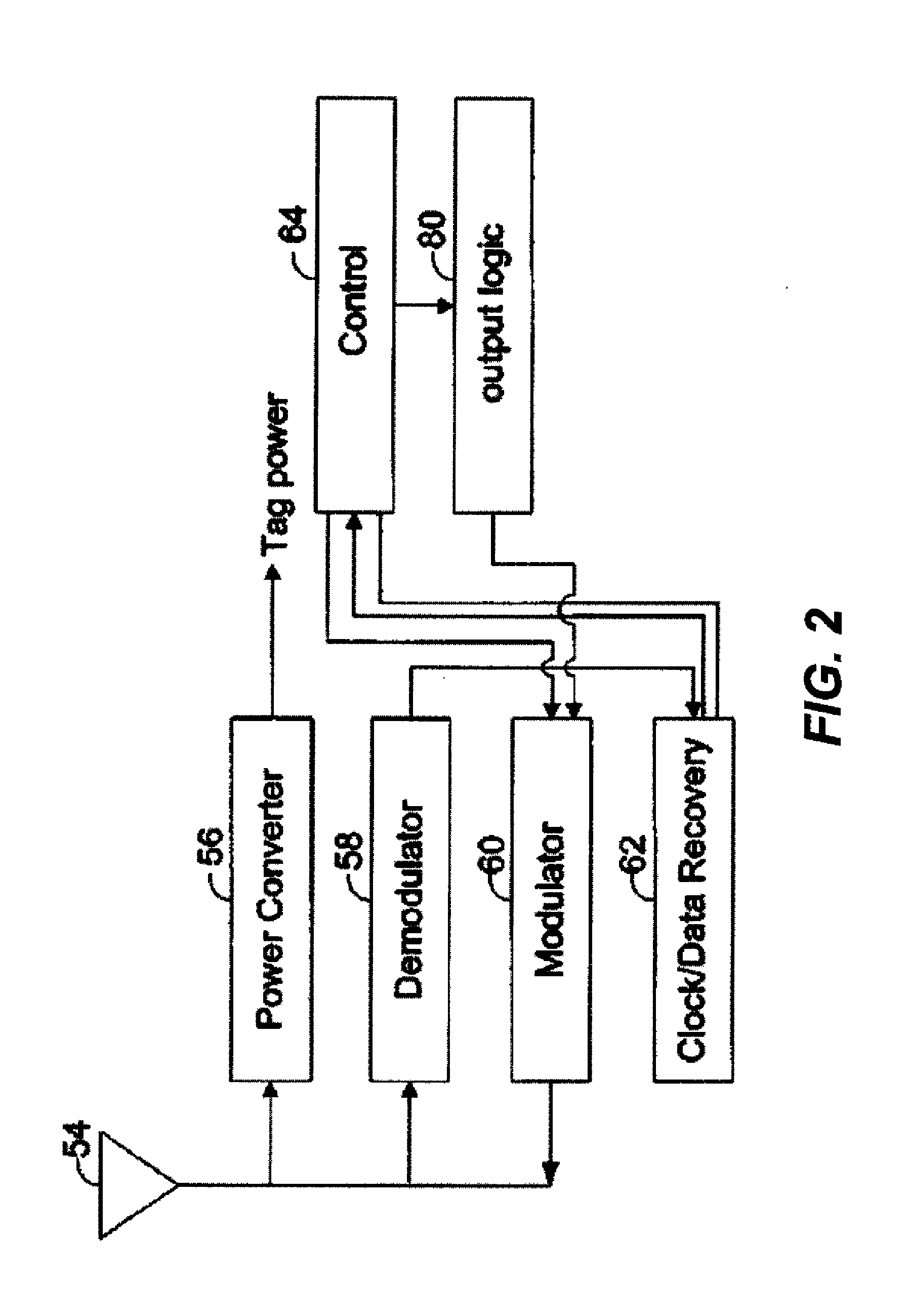
Bidirectional security sensor communication for a premises security system
A security system architecture including bidirectional communication between a sensor control device and one or more sensor devices coupled to the controller is provided. Such functionality is provided by virtue of a bidirectional wireless transceiver and processor in each sensor device. Embodiments of the present invention further provide this functionality by virtue of a coordinating transceiver coupled to the security system controller for communication with the sensor devices.
Owner:ICONTROL NETWORKS
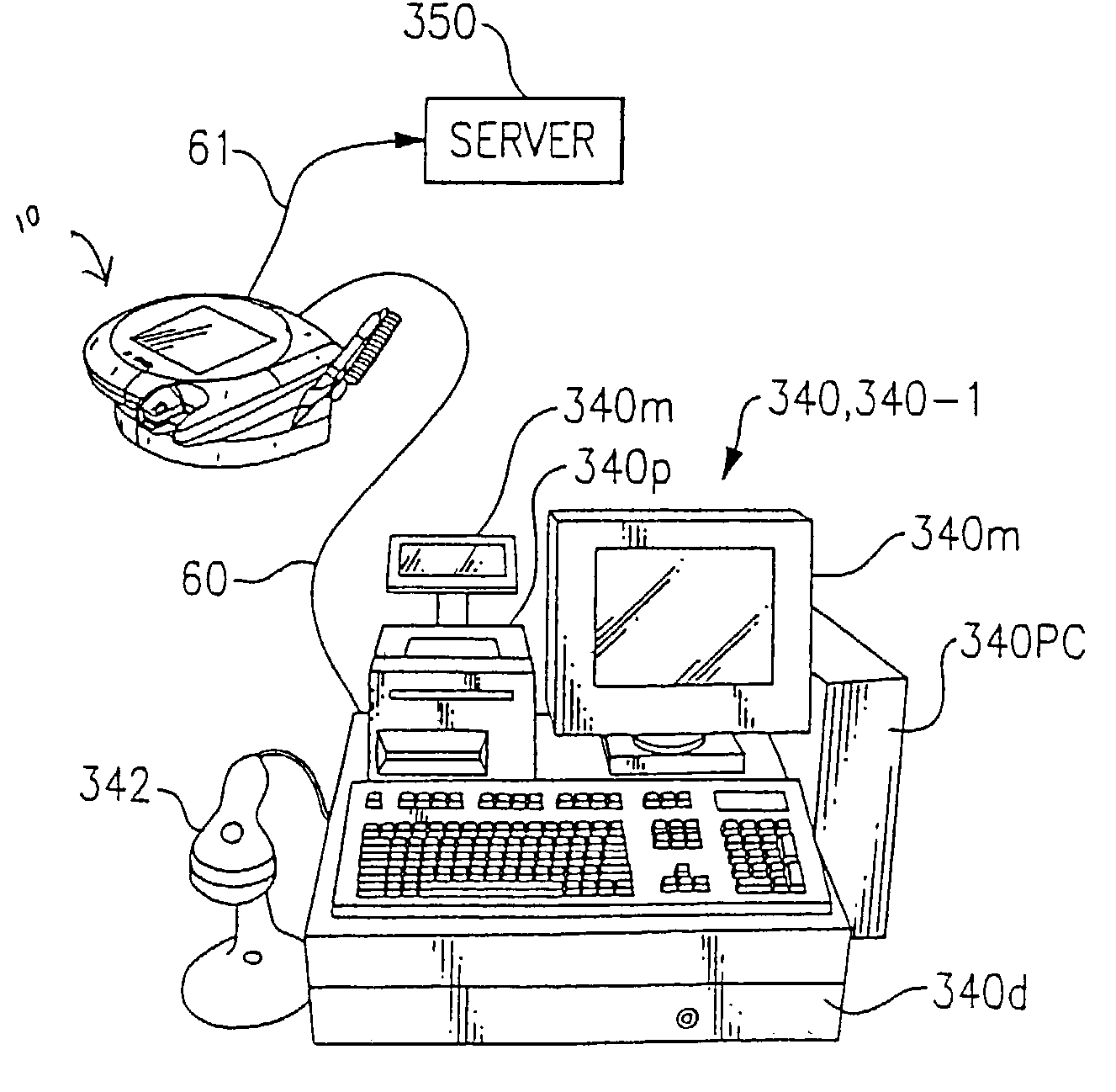
Automated banking machine system and method
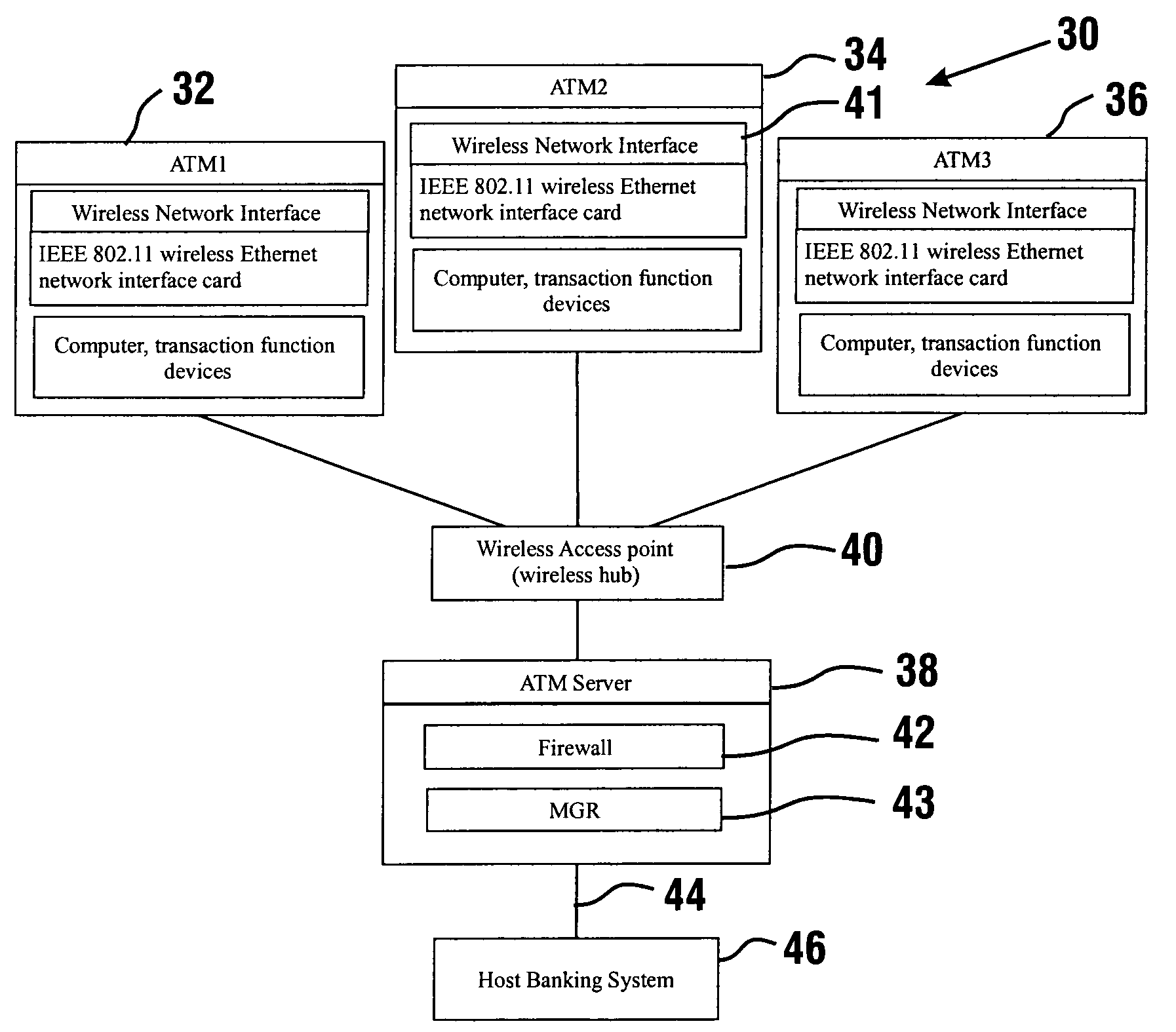
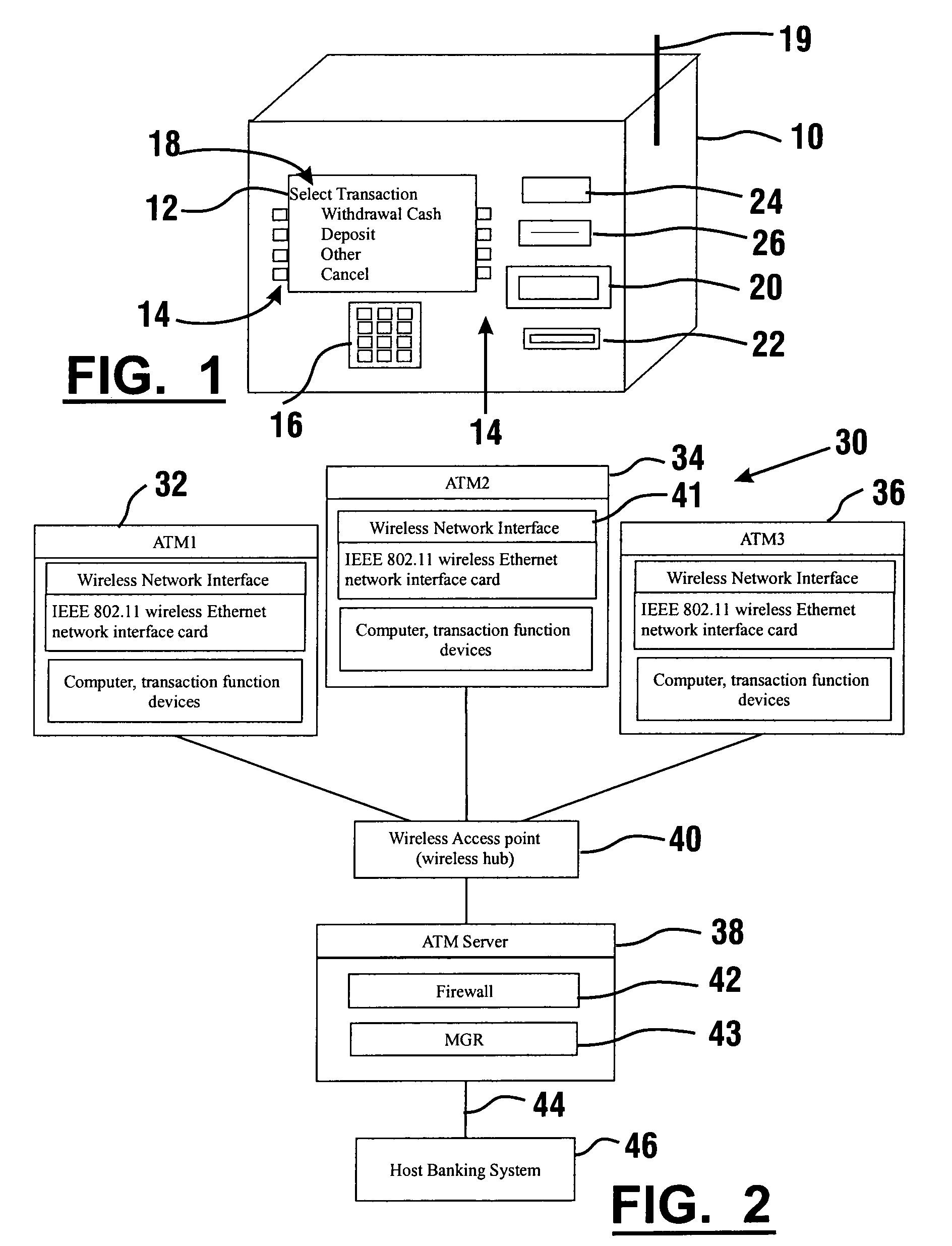
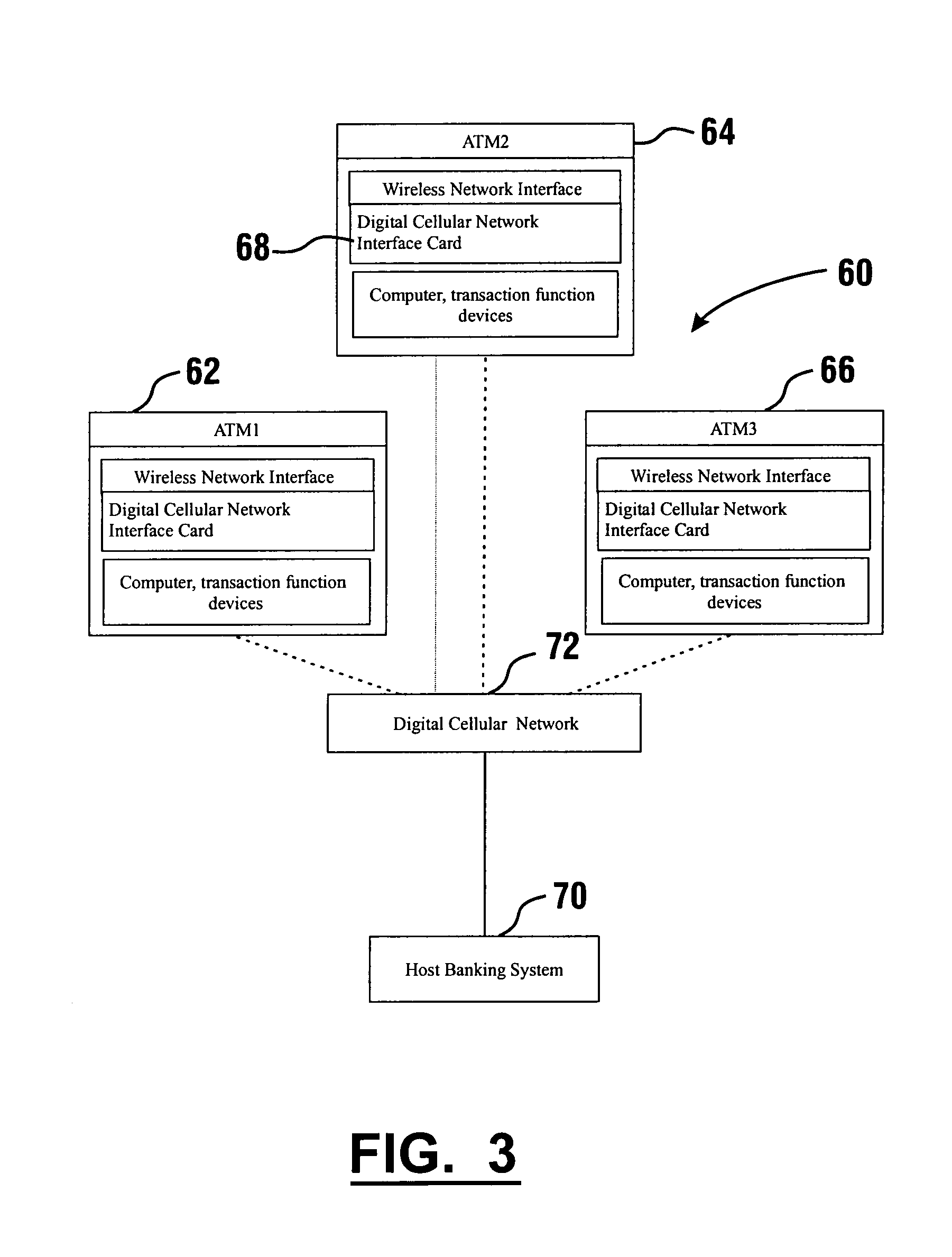
InactiveUS7025256B1Reduce interceptionComplete banking machinesFinanceWireless transmissionPrivate network
A wireless ATM system (30) comprises one or more wireless ATMs (32, 34, 36) that are operative to wirelessly communicate with a wireless ATM server (38). The wireless ATMs each include a wireless network interface (41). The wireless ATM server includes a corresponding wireless access point or wireless hub (40). Wireless transmission between the wireless ATMs and wireless ATM server is secured with a wireless encryption protocol. The wireless ATM server is operative to communicate with at least one host banking system (46) through at least one public or private network (44). The wireless ATM server is operative to route transaction and event messages between the host banking system and each of the wireless ATMs using a message gateway router (43). The wireless ATM server further includes a firewall (42).
Owner:DIEBOLD SELF SERVICE SYST DIV OF DIEBOLD NIXDORF INC
Detecting RFID tag and inhibiting skimming
InactiveUS20130106576A1Flush outsideIncrease the difficultySensing detailsCommunication jammingDecoyResponse Frequency
A method of detecting an RFID tag includes transmitting a bait RFID read signal at a bait power level and a simulated response signal at a simulated-response power level. A selected reader frequency is monitored for a selected detection time. A skimmer is determined to be present if a skimmer RFID read signal is detected during that time. If a skimmer is not determined to be present, multiple read signals are transmitted sequentially, each signal at a respective read power level. At least one of the read power levels is lower than the bait power level, at least one of the read power levels is lower than the simulated-response power level, and at least two of the read power levels are different from each other. A selected response frequency for a tag is monitored for a response from an RFID tag.
Owner:EASTMAN KODAK CO
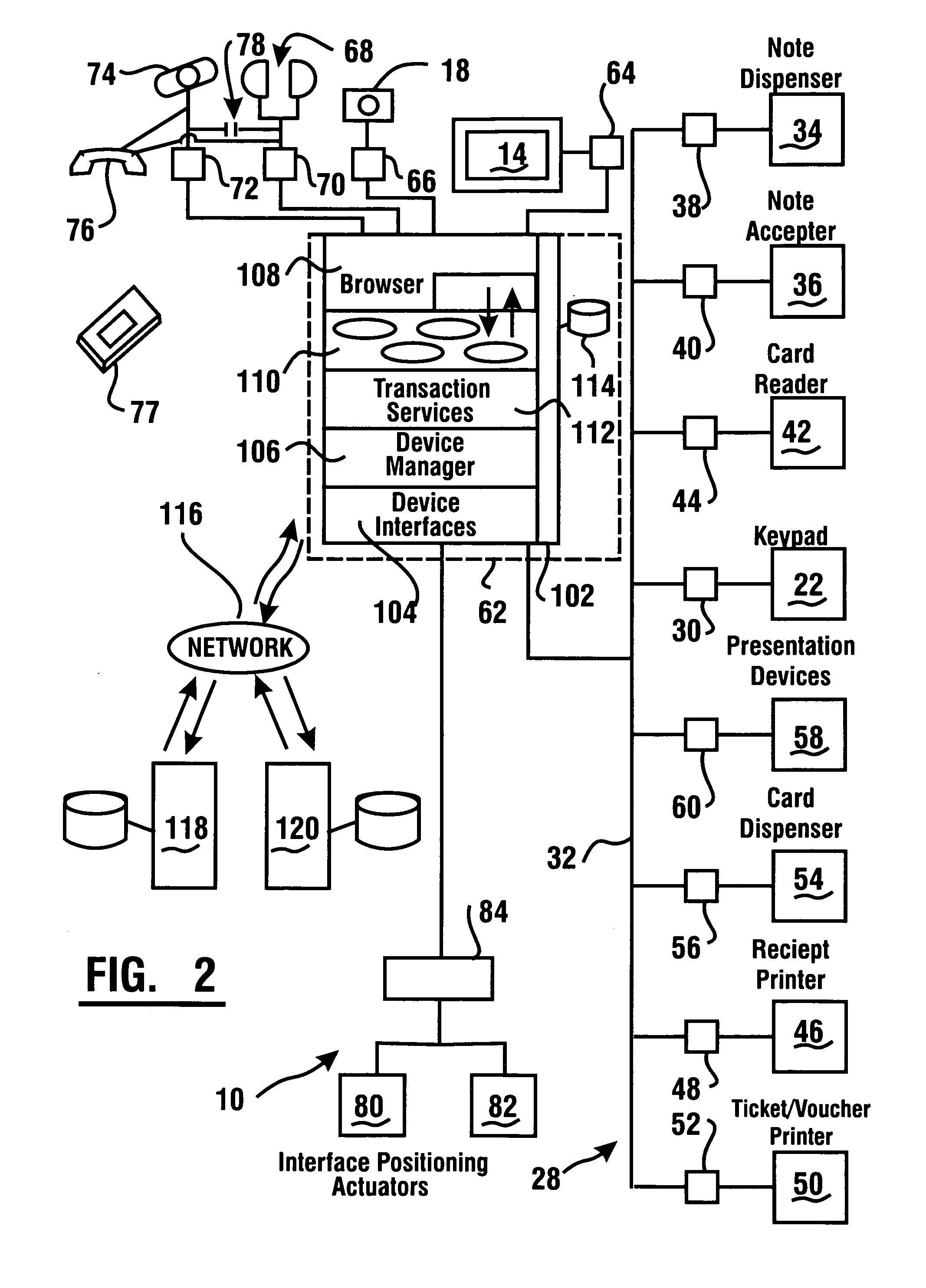
Automated financial transaction apparatus with interface that adjusts to the user
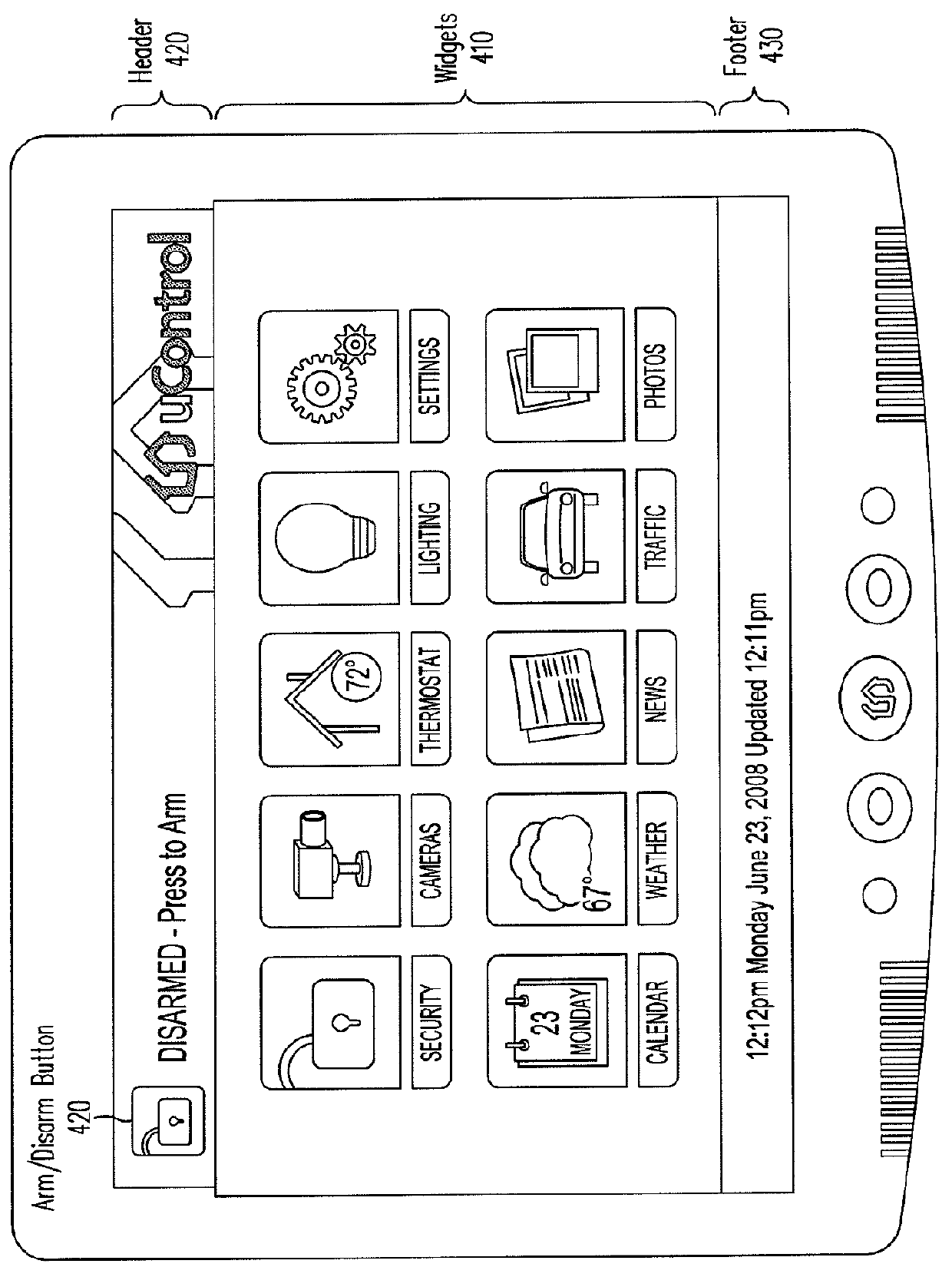
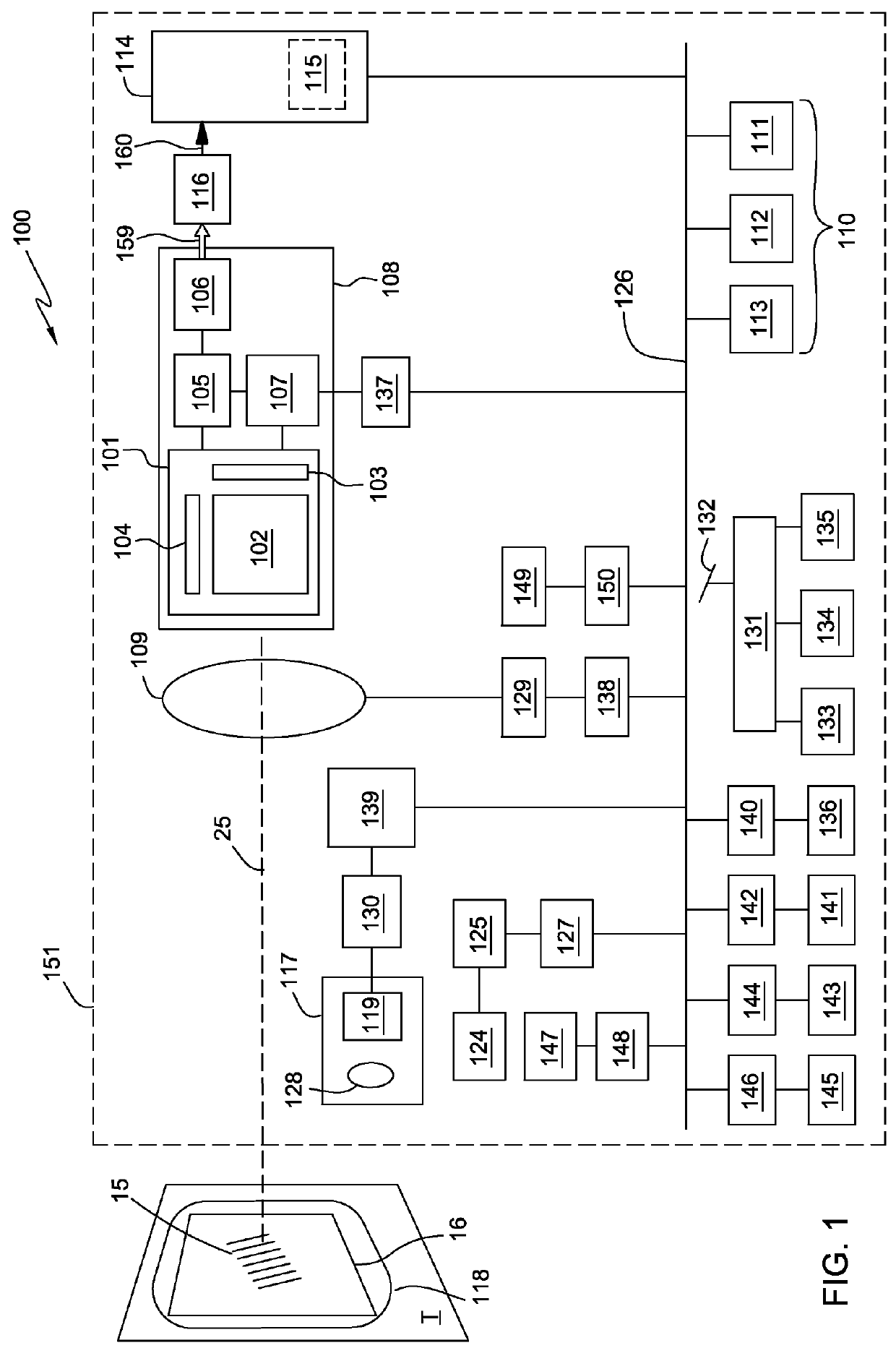
ActiveUS7644039B1Easy to operateEasy to seeComplete banking machinesFinanceFinancial transactionOutput device
An automated financial transaction apparatus (10) includes a touch screen interface (14) and a plurality of transaction function devices (22, 34, 36, 42, 46, 50, 54, 58) which operate to carry out financial transactions for users. A reading device (18, 78) senses characteristic features of users who operate the machine. Data stored in at least one data store associated with at least one computer (62, 118, 120) includes data representative of the characteristic features associated with a plurality of users and for each user, at least one interface parameter. The apparatus operates so that when the characteristic feature associated with a particular user is sensed by the reading device, the display screen and other input and output devices are changed in position or operation to accommodate the stature, disabilities, desires or other special requirements of the user.
Owner:DIEBOLD NIXDORF
System and Methods for Accelerated Recognition and Processing of Personal Privilege Operative for Controlling Large Closed Group Environments
ActiveUS20080191009A1Process is accelerated and simplifiedAvoid practicalTicket-issuing apparatusDigital data processing detailsCrowd controlCrowds
Methods (3500-3695) and apparatus (10, 20) for controlling physical (30, 40) and virtual (12) access for accelerated recognition and processing of privileges, benefits, value transfers, crowd control, community membership and status, in particular for institutions, arenas and other large venues.
Owner:FORTRESS GB
Conditional access method and device
InactiveUS6070796AInput/output for user-computer interactionAcutation objectsComputer hardwareAccess method
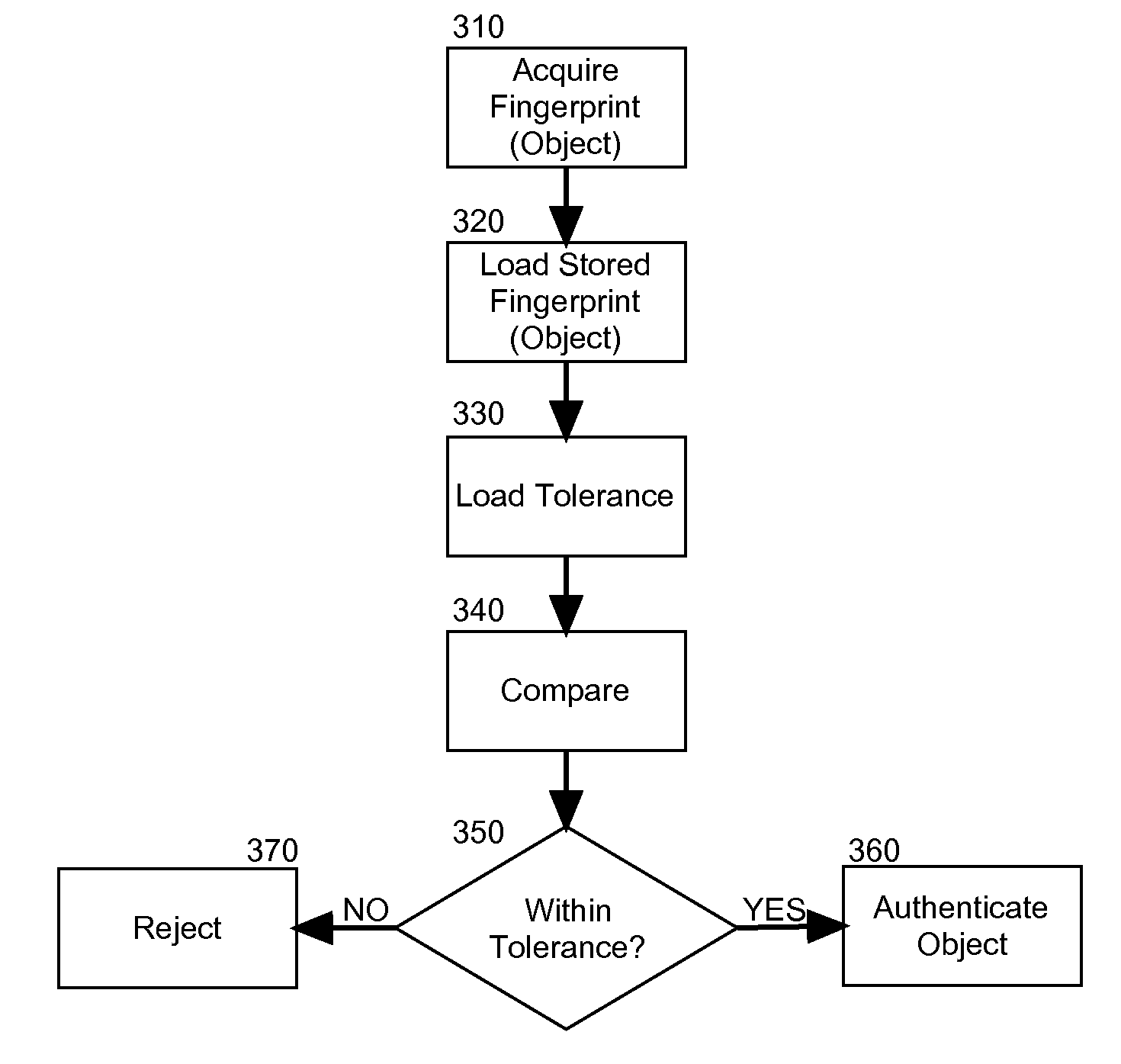
PCT No. PCT / FR96 / 01269 Sec. 371 Date Feb. 20, 1998 Sec. 102(e) Date Feb. 20, 1998 PCT Filed Aug. 8, 1996 PCT Pub. No. WO97 / 07448 PCT Pub. Date Feb. 27, 1997A conditional access device for use in connection with a host electronic equipment. The device includes a pointer peripheral containing one or more integrated circuit card coupler units. In addition, it also includes a device for acquiring personal information about a user. The personal information is locally compared with information stored in the integrated circuit card without passing through the host equipment.
Owner:SIRBU CORNEL
Multiple platform support system and method
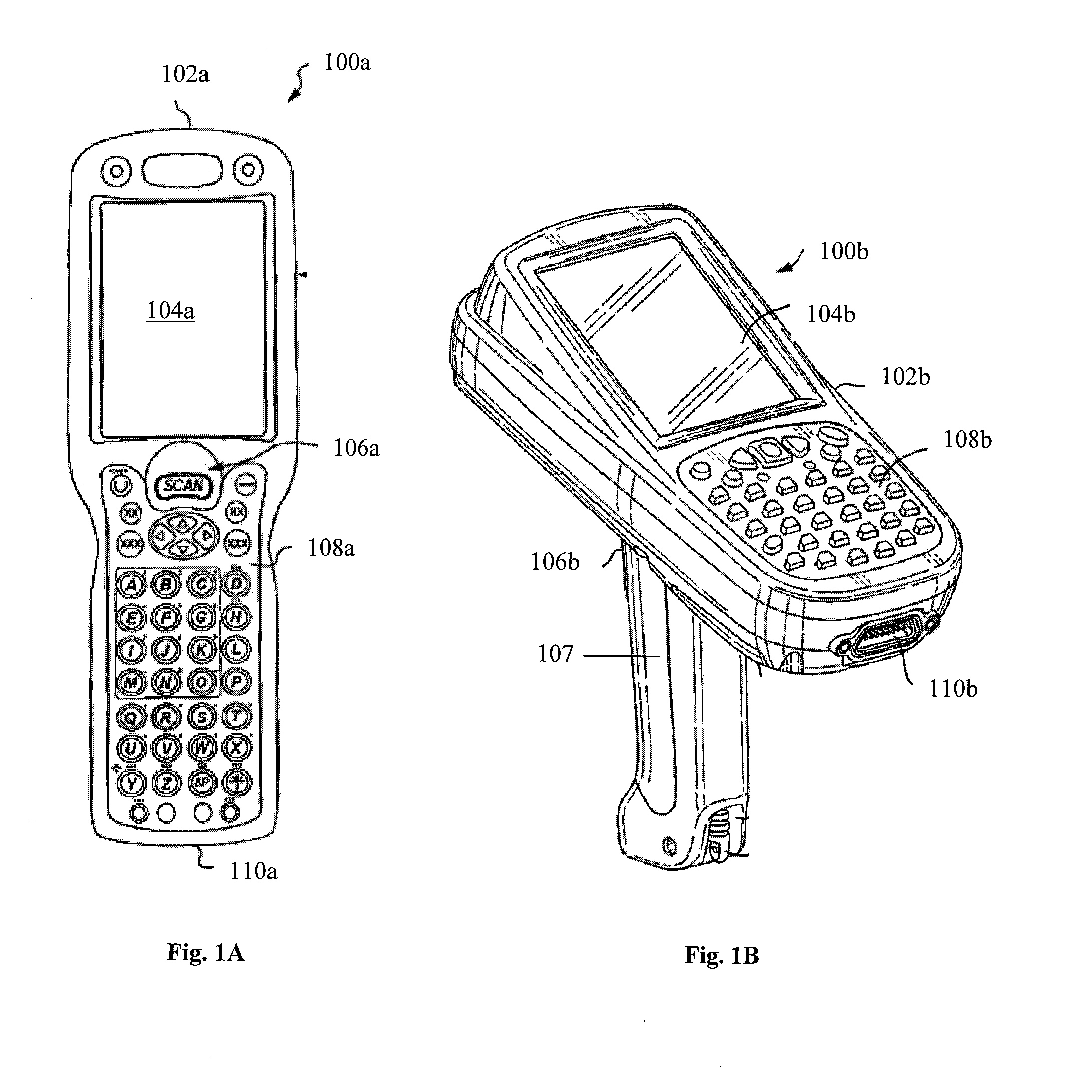
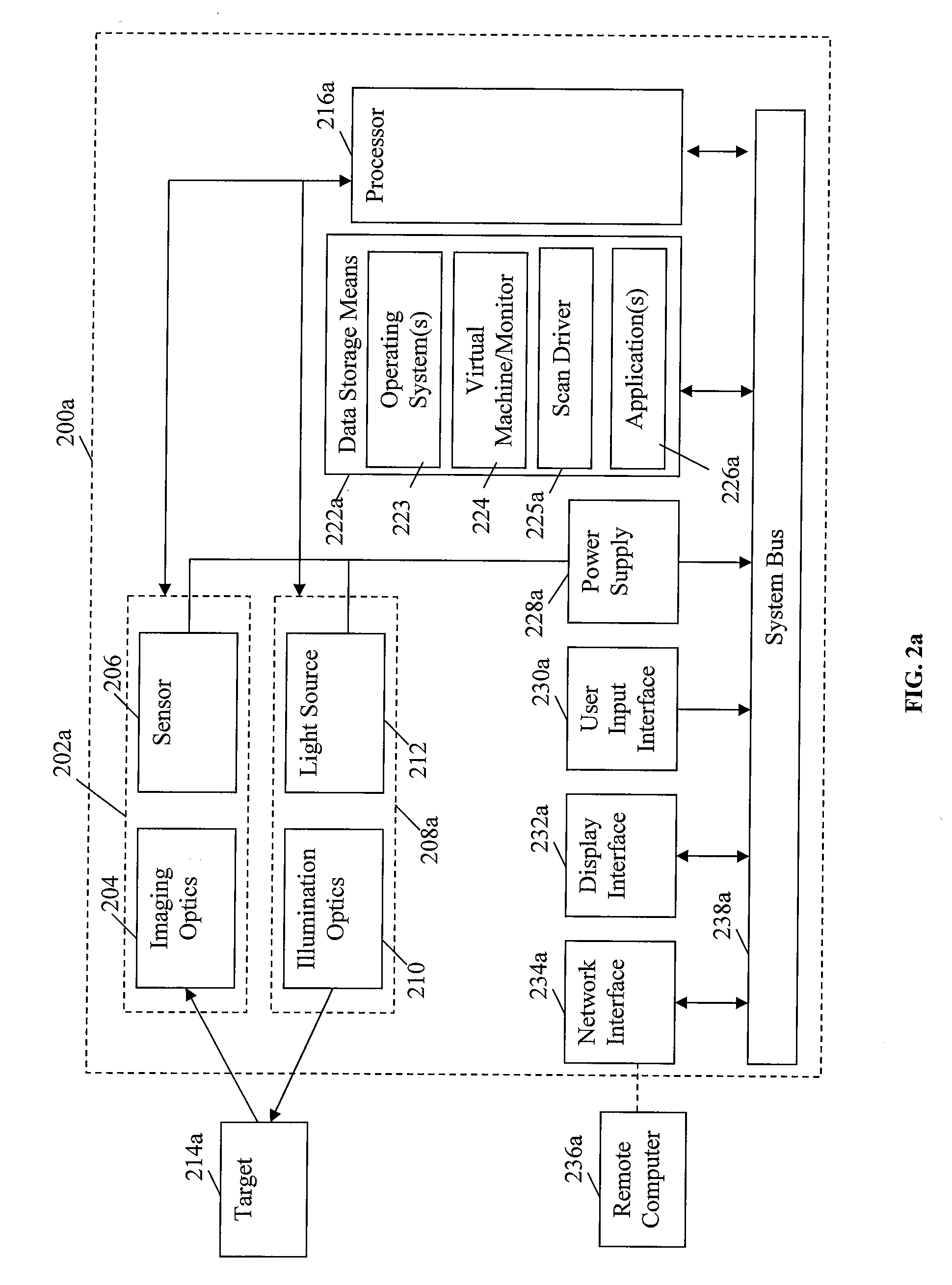
InactiveUS20120138685A1Sensing detailsSoftware simulation/interpretation/emulationSupporting systemData terminal
A portable data terminal including a processor having an instruction set architecture and data storage means configured to store a plurality of operating systems and a virtual machine monitor application program configured to receive at least one instruction from each operating system, communicate with the processor according to the instruction set architecture, and switch operating system access to the processor upon receipt of an electrical signal representing an event.
Owner:HAND HELD PRODS
Transaction terminal including imaging module
A transaction terminal includes a housing, a touch screen, a card reader, an imaging module, and a decode circuit coupled to the imaging module. The imaging module in one embodiment is disposed in the housing so that an imaging axis extends rearward of the housing. In a typical use of the terminal a store clerk can easily move objects into a field of view of the terminal. The transaction terminal can be coupled to a POS network which remotely sends a trigger signal actuating the imaging module when an age-proof-require product is being purchased.
Owner:HAND HELD PRODS
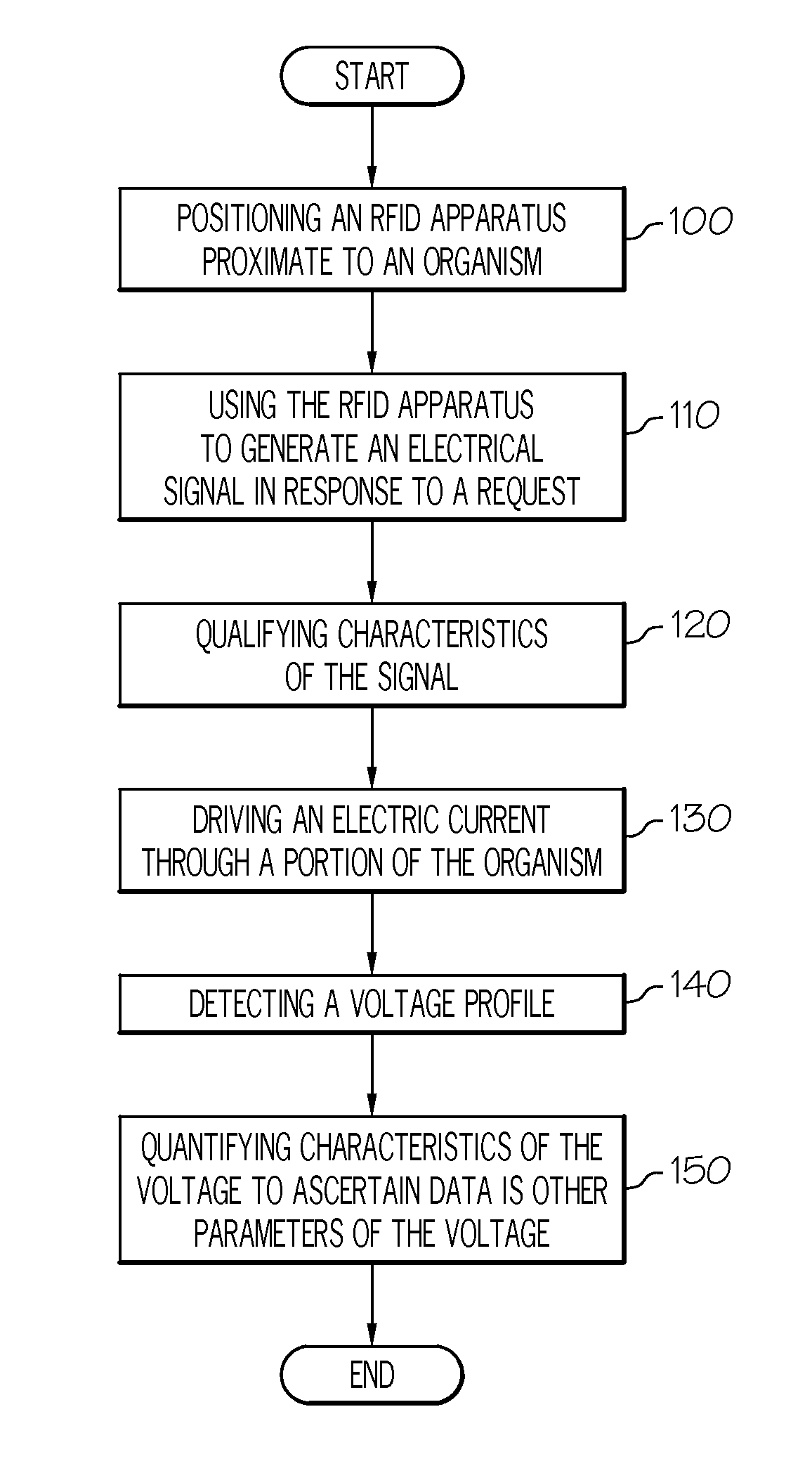
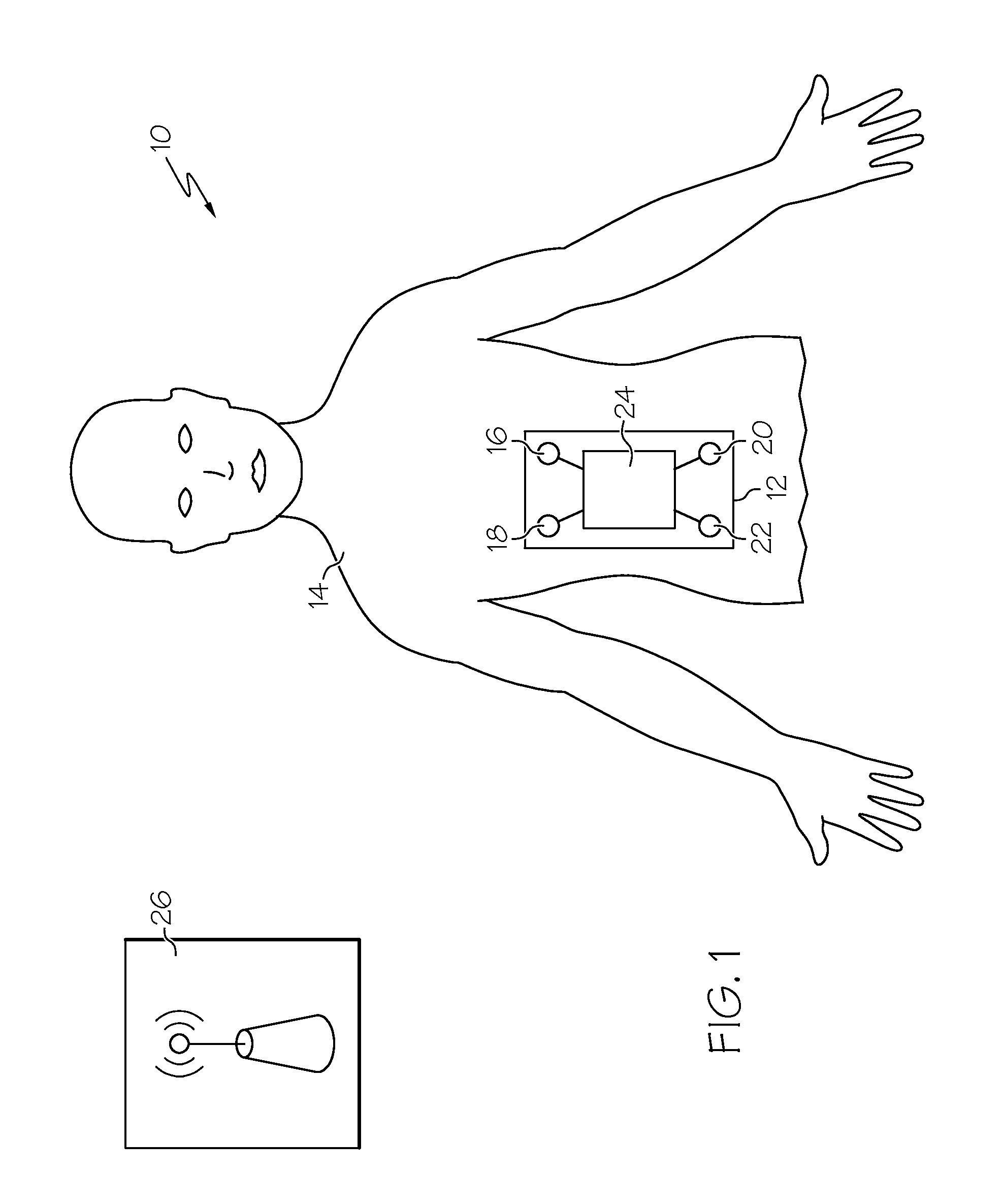
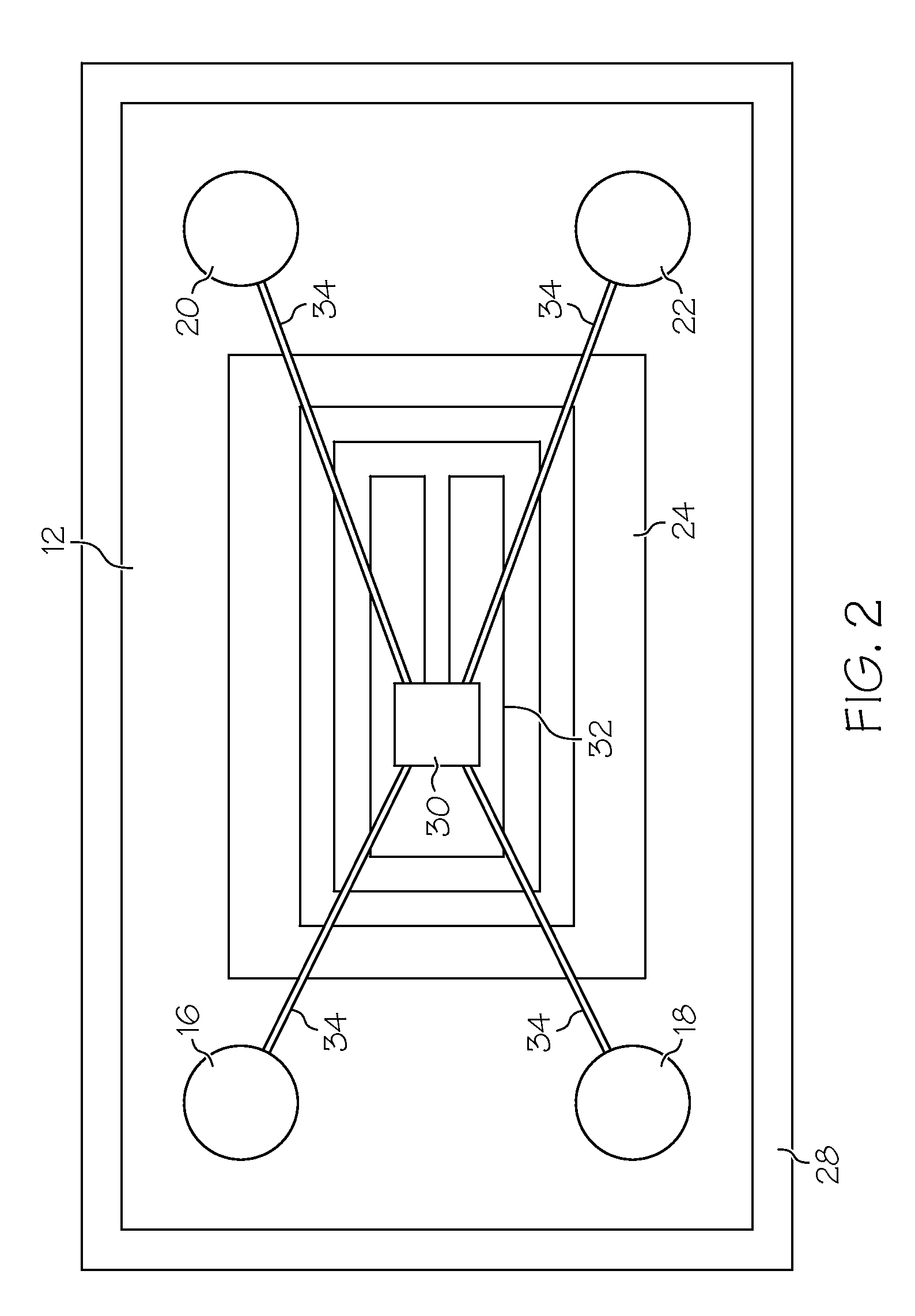
Apparatus and method for monitoring physiological parameters using electrical measurements
A system for monitoring a physiological parameter comprises a substrate, a pair of drive electrodes, a pair of detection electrodes, and an RFID apparatus. The substrate is arranged to be removably securable to a biological organism. At least the pair of drive electrodes or the pair of detection electrodes is secured to the substrate. The RFID apparatus is arranged to be in electrical communication with at least the pair of drive electrodes or the pair of detection electrodes. Methods of using the device are also provided.
Owner:AVERY DENNISON CORP
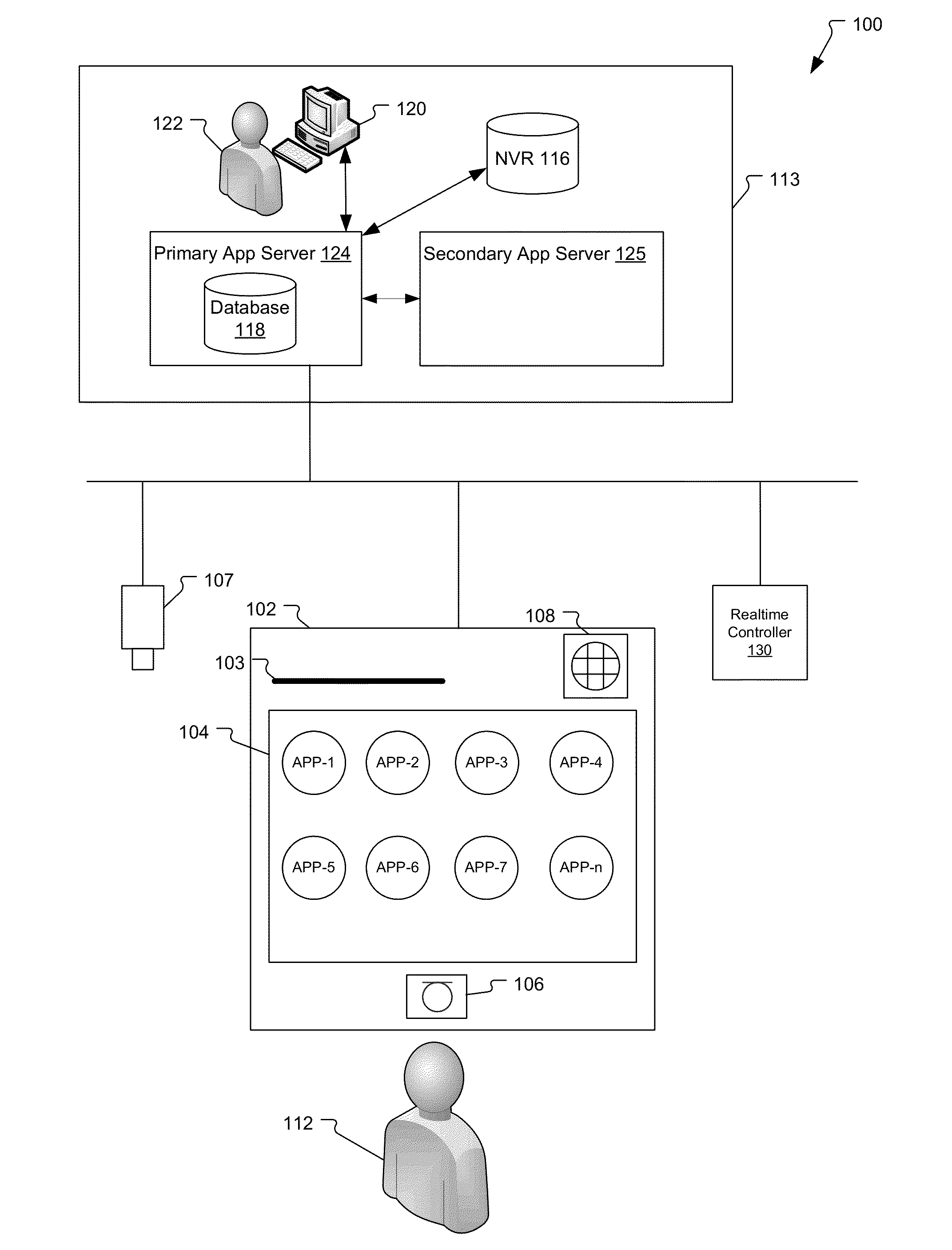
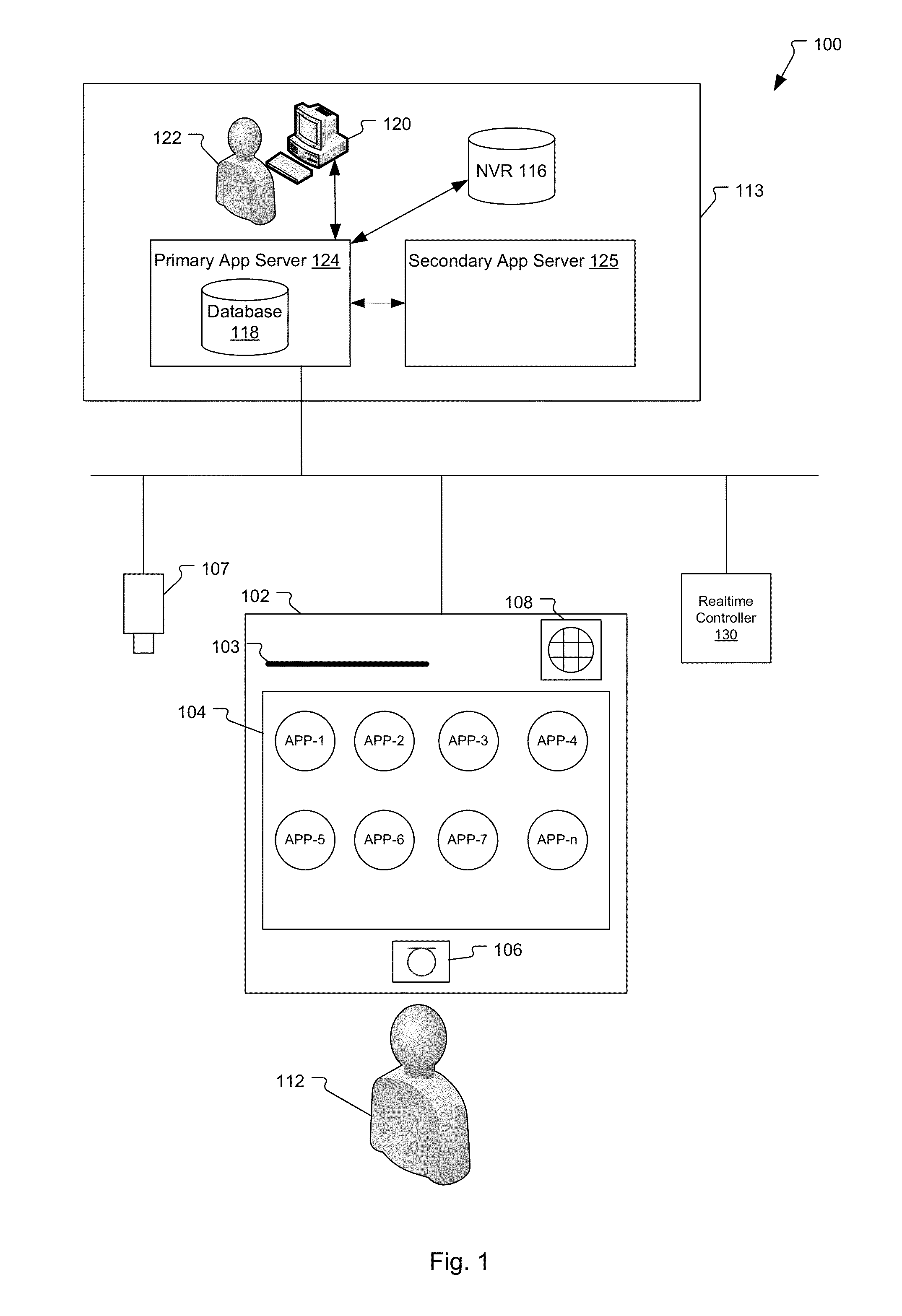
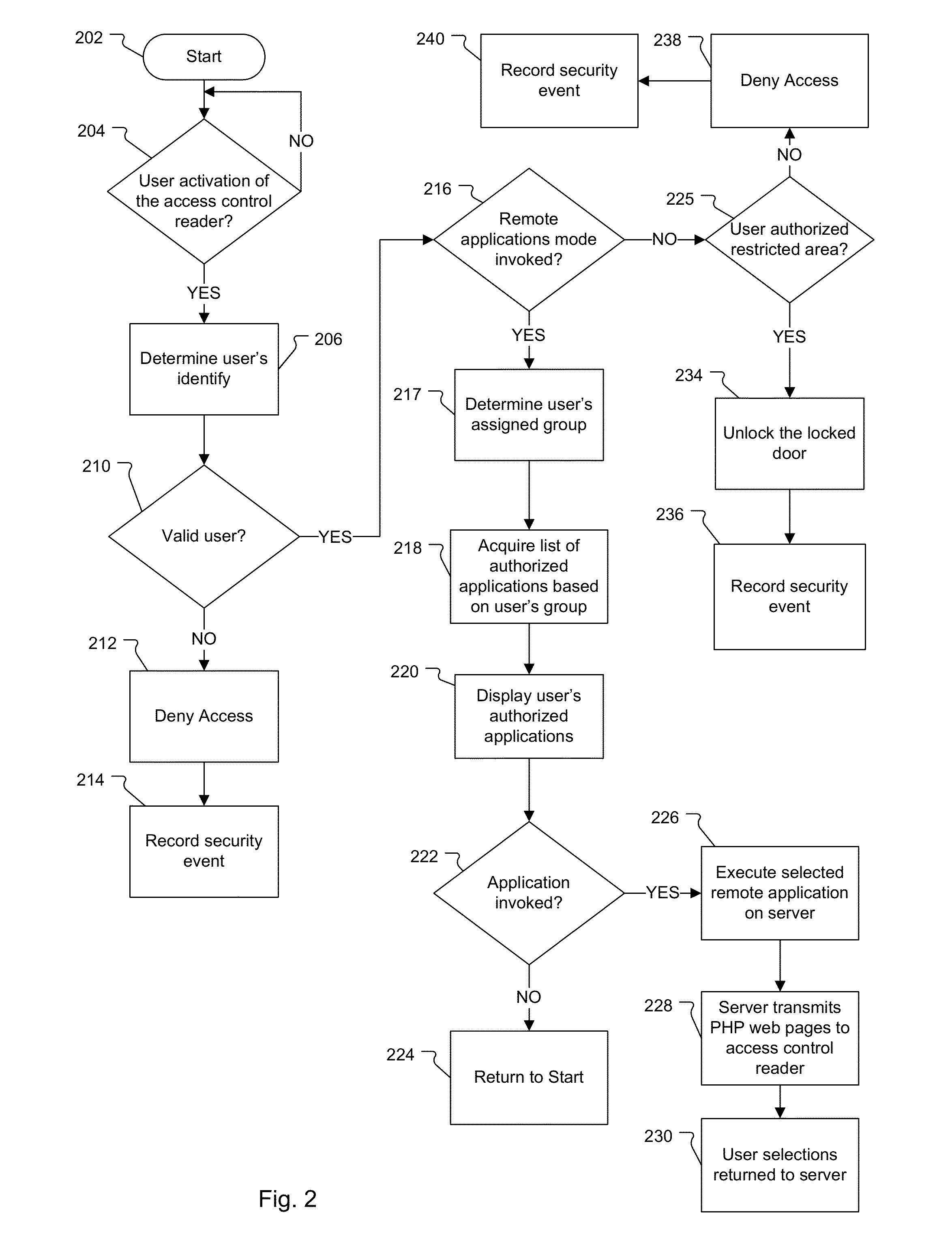
Access control reader enabling remote applications
A system and method for enabling users to run remote applications on access control readers located throughout office buildings. A system administrator creates different remote applications groups such as admin, engineer or cardholder and then assigns users to one of the remote application groups. Users are then able to run the remote applications assigned to their remote application group from any of the access control readers located throughout the office building.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
Portable radio-frequency repeater
ActiveUS20120149300A1Antenna impedance is increasedReduce impactPower managementSensing detailsRadio frequencyTransceiver
A portable radio-frequency repeater includes a housing and a transceiver. The transceiver is disposed at least partially within the housing and configured to alternatively operate in a transmitting mode and a sleep mode. The transceiver includes an antenna and a control unit. The control unit is in electrical communication with the antenna. When the transceiver operates in the transmitting mode, the control unit is configured to receive an RFID signal from the antenna, convert the RFID signal into a converted RFID signal, and transmit the converted RFID signal to the antenna. When the transceiver operates in the sleep mode, the control unit is configured to detect an interrogation signal from the antenna and not to transmit any converted RFID signal to the antenna.
Owner:AVERY DENNISON CORP
Automated Association of Patient Care Devices
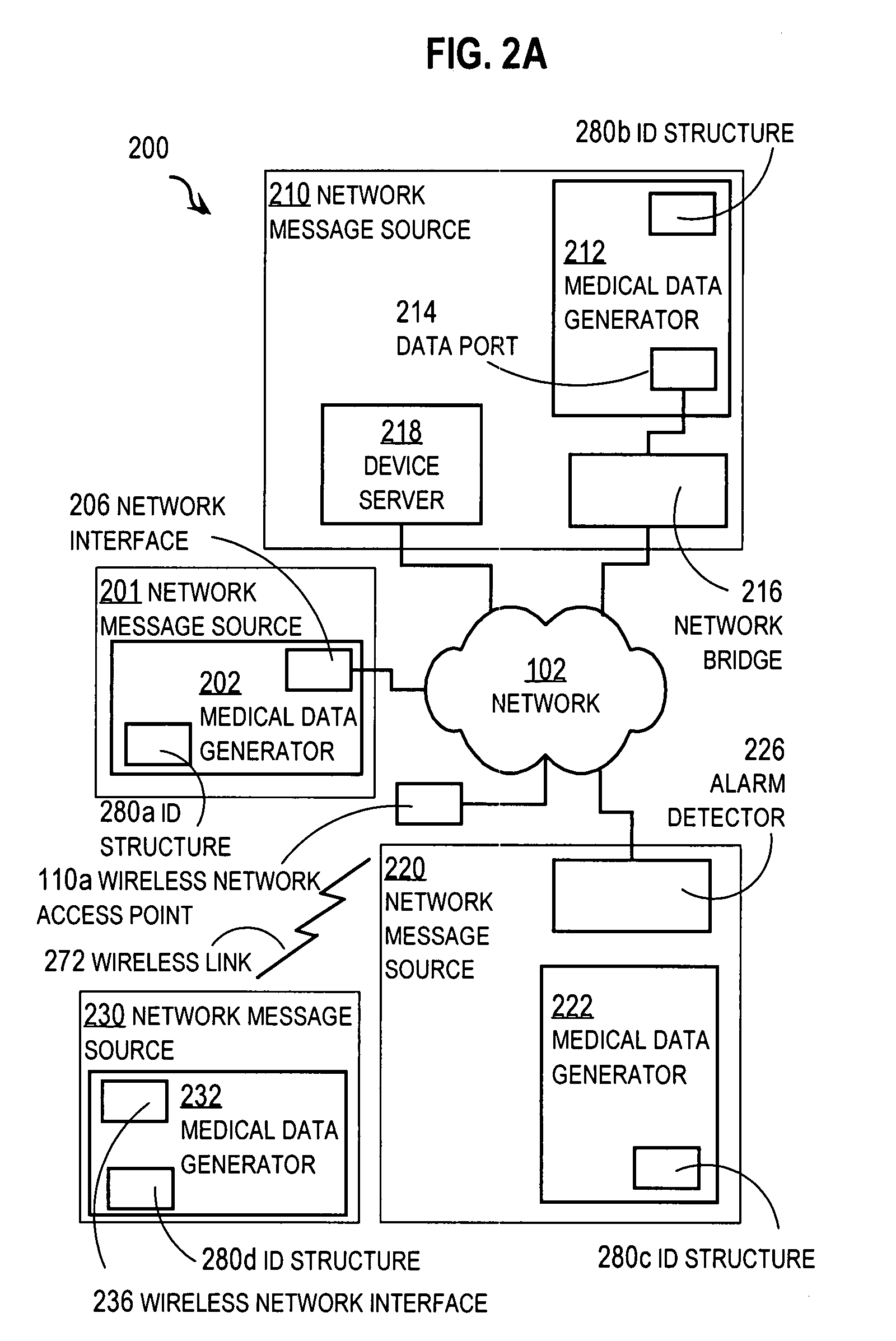
Techniques for associating assets of a medical care facility include receiving a first data flow that indicates a first unique identifier for a first radio frequency identification (RFID) tag and receiving a second data flow that indicates a second unique identifier for a second RFID tag. Also received is database data that associates the first unique identifier with a first asset and associates the second unique identifier with a different second asset. It is determined whether a position of the first RFID tag is within operative distance of a position of the second RFID tag based on the first data flow and the second data flow and the associated first asset and second asset. If it is determined that the position of the first RFID tag is within operative distance of the position of the second RFID tag, then the first asset is automatically associated with the second asset.
Owner:SLOAN KETTERING INST FOR CANCER RES
System and method for performing serialization of devices
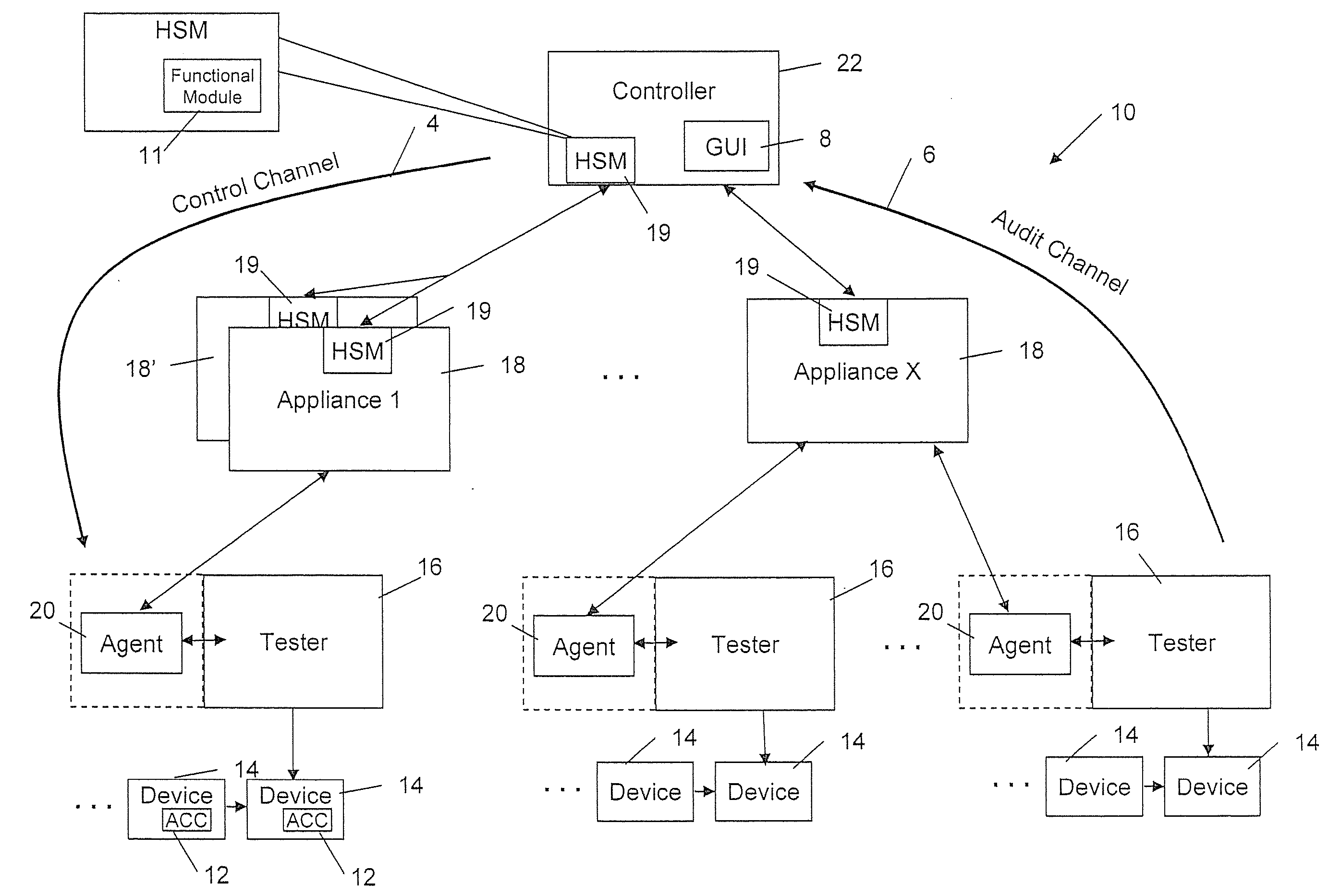
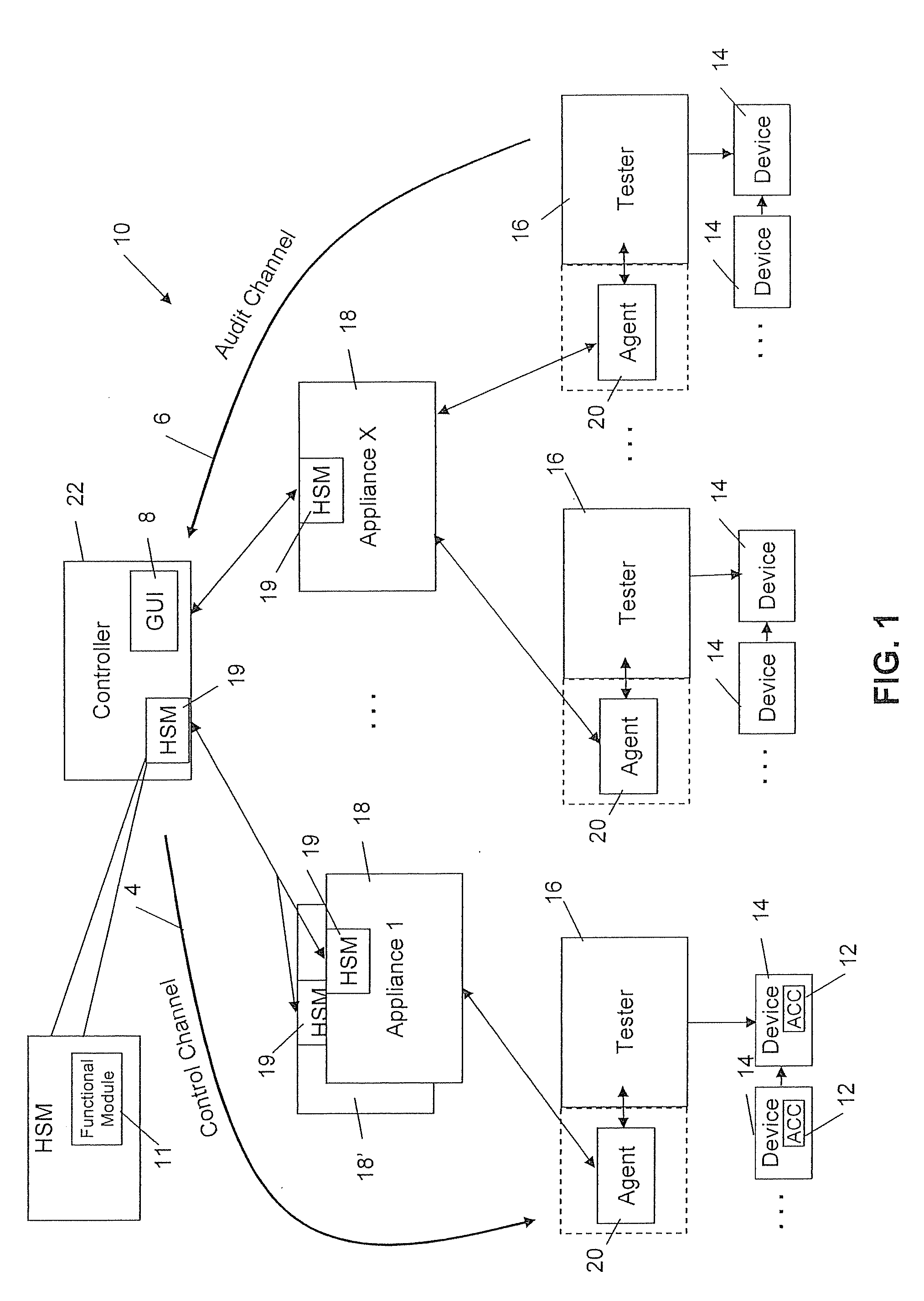
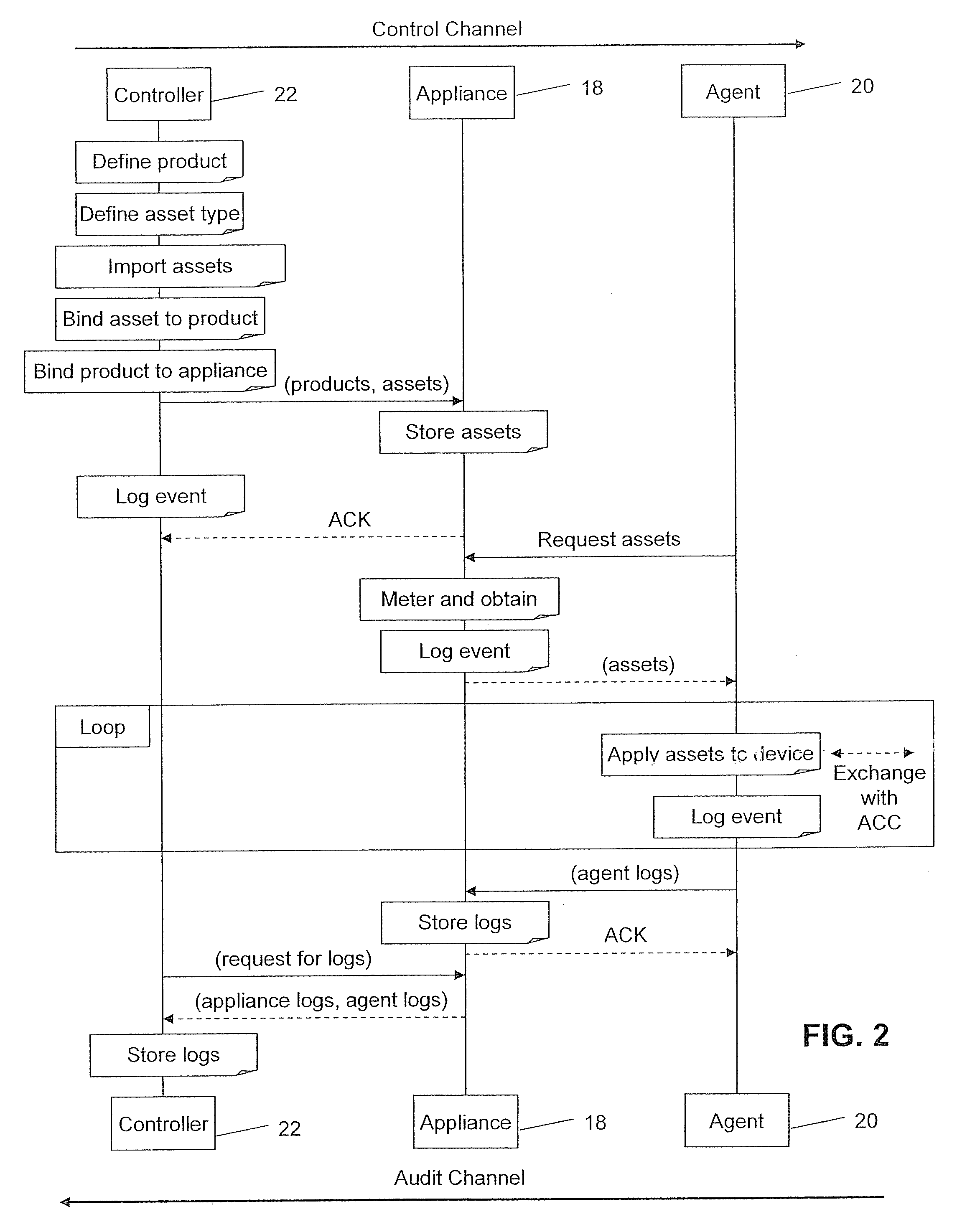
ActiveUS20110063093A1Reduce in quantityImprove abilitiesSensing detailsForecastingSerializationService module
A serialization service module is provided for configuring an asset management system to provide a secure means of generating, assigning to chips (or other electronic objects or devices), and tracking unique serial numbers. To provide this service, a controller is used to define a product model, then to define one or more serialization schemas to be bound to each product model. Each serialization schema contains a range of serial numbers for a particular product. The serial number schemas are sent over a secure, encrypted connection to appliances at the manufacturer's location. Agents can then request serial number values by product name. The serial numbers are generated by the appliance, metered, and provided to the agents. The serial numbers are then injected sequentially into each die in a chip manufacturing process using the agent.
Owner:MALIKIE INNOVATIONS LTD
User interface facilitating specification of a desired data format for an indicia reading apparatus
ActiveUS9384374B2Overcomes shortcomingSensing detailsRecord carriers used with machinesUser inputBarcode
Aspects describe herein facilitate specification of a desired data format for bar code data to be presented by an indicia reading apparatus. Bar code data decoded from an image of a bar code is obtained and displayed. A user input field is provided and based on input by the user to the user input field, the user input field is populated with a representation of the desired data format for the bar code data. Based on the representation of the desired data format populated in the user input field, configuration settings are determined for configuring the indicia reading apparatus to present bar code data in the desired data format.
Owner:HAND HELD PRODS
Payment card with internally generated virtual account numbers for its magnetic stripe encoder and user display
A payment card comprises an internal virtual account number generator and a user display for online transactions. Offline transactions with merchant card readers are enabled by a magnetic array positioned behind the card's magnetic stripe on the back. The internal virtual account number generator is able to program the magnetic bits encoded in the magnetic stripe to reflect the latest virtual account number. The internal virtual account number generator produces a sequence of virtual numbers that can be predicted and approved by the issuing bank. Once a number is used, it is discarded and put on an exclusion list.
Owner:FITBIT INC
Popular searches
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com