Patents
Literature
4078 results about "Instruction set" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An instruction set architecture (ISA) is an abstract model of a computer. It is also referred to as architecture or computer architecture. A realization of an ISA is called an implementation. An ISA permits multiple implementations that may vary in performance, physical size, and monetary cost (among other things); because the ISA serves as the interface between software and hardware. Software that has been written for an ISA can run on different implementations of the same ISA. This has enabled binary compatibility between different generations of computers to be easily achieved, and the development of computer families. Both of these developments have helped to lower the cost of computers and to increase their applicability. For these reasons, the ISA is one of the most important abstractions in computing today.
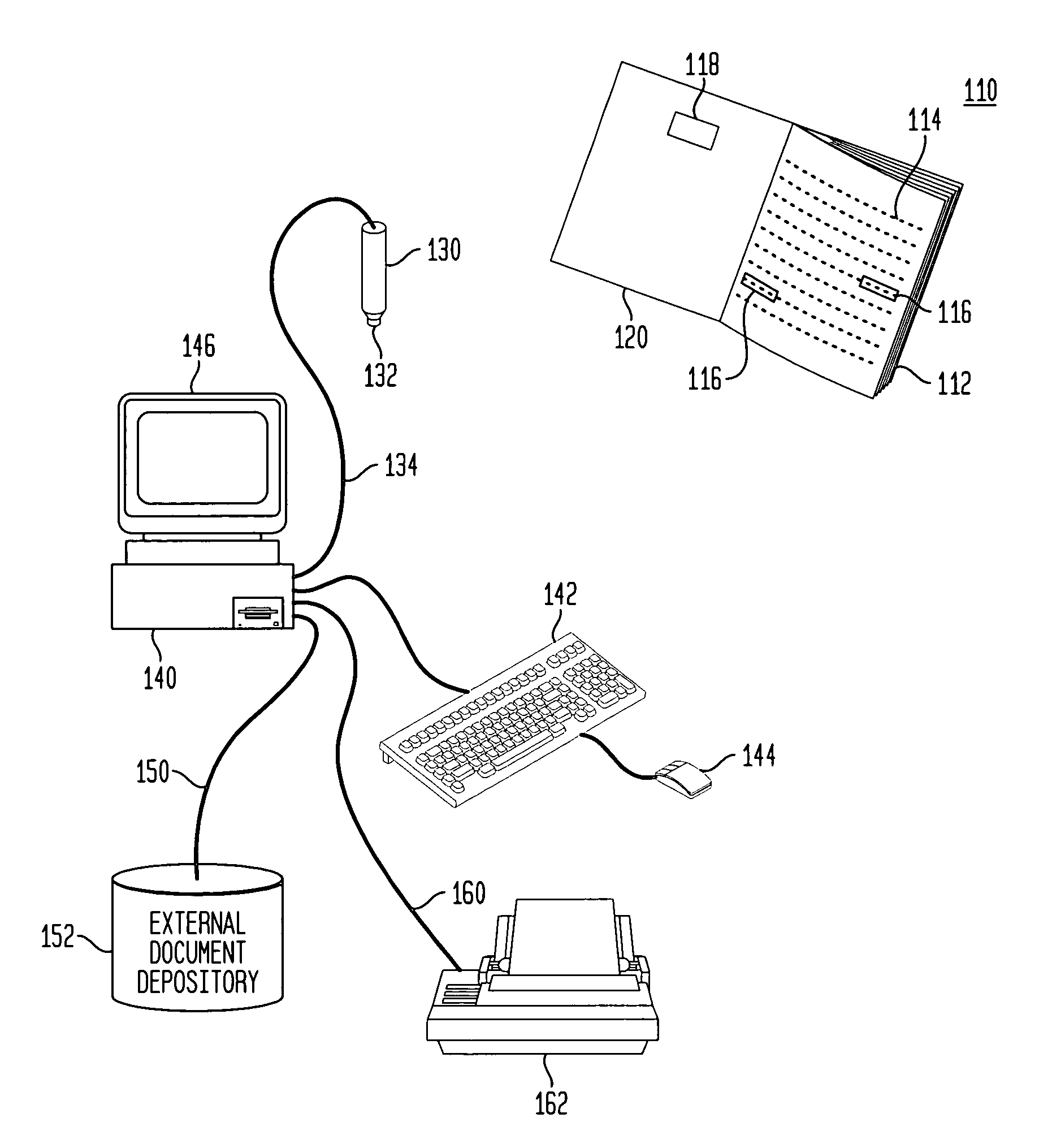
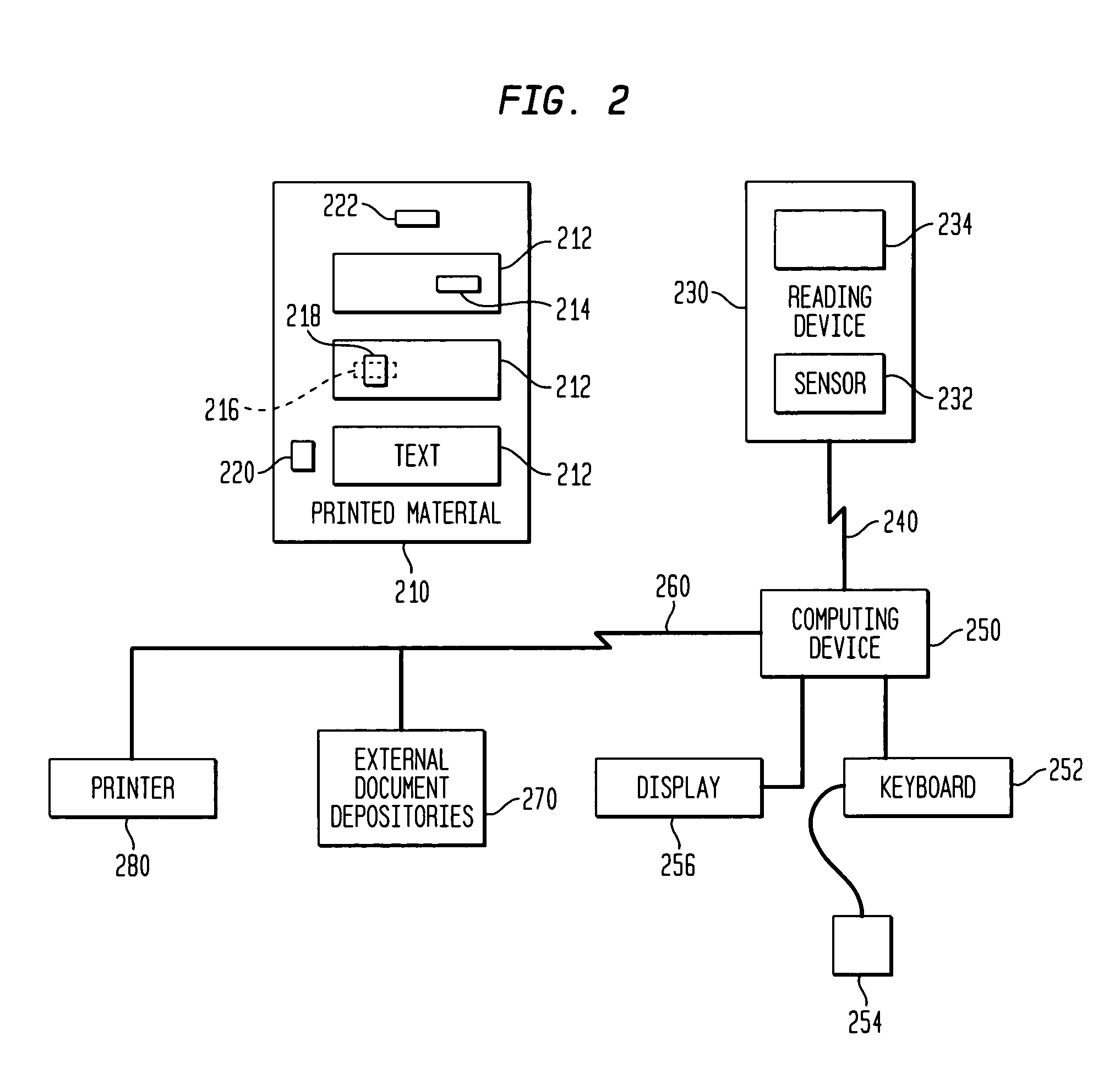
Retrieval and manipulation of electronically stored information via pointers embedded in the associated printed material
InactiveUS6964374B1Facilitates retrieval and manipulationDigital data information retrievalCharacter and pattern recognitionGraphicsElectronic information
A method of retrieving and manipulating electronic information that relates to a printed document. Each printed document contains an initialization marking that is recognizable by an external sensory device and unique to the printed document. When a reader of the printed document desires to retrieve and manipulate electronic information that relates to the printed document, the reader initializes the system by using the sensory device to recognize the initialization marking. The sensory device transfers a code embedded in the initialization marking to a computing device. This configures the computing device to access the stored data and instruction sets associated with the printed document. In addition to the initialization marking, areas throughout the printed document (e.g., text, tables, figures, etc.) also contain markings that are recognizable by the external sensory device. The reader of the printed document uses the sensory device to recognize the markings and transfer the code embedded in the markings to the computing device. The computing device uses the code to retrieve and display the electronic information that relates to that area of the printed document.
Owner:WSOU INVESTMENTS LLC +1
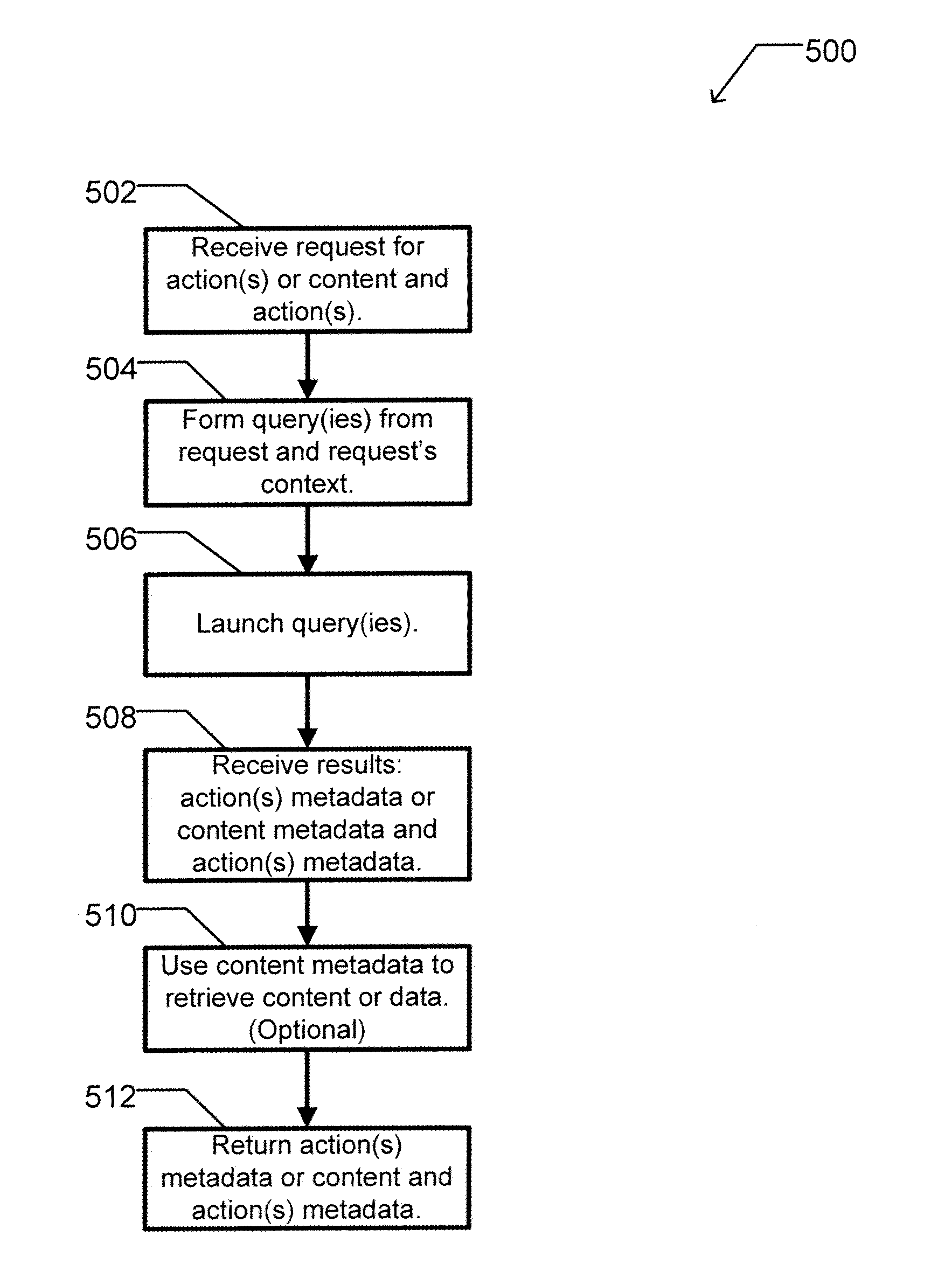
Apparatus and method for dynamically selecting componentized executable instructions at run time
A computer readable storage medium includes executable instructions to receive a request for an action. An action context is received where the action context includes an application requesting the action. A set of metadata is searched for metadata corresponding to the action, where the search is limited by the action context. Selected metadata for the action is inserted into a collection. The selected metadata is a result of searching the set of metadata. The selected metadata includes a reference to the set of executable instructions that implements the action and a description of the action. The collection is then returned.
Owner:BUSINESS OBJECTS SOFTWARE
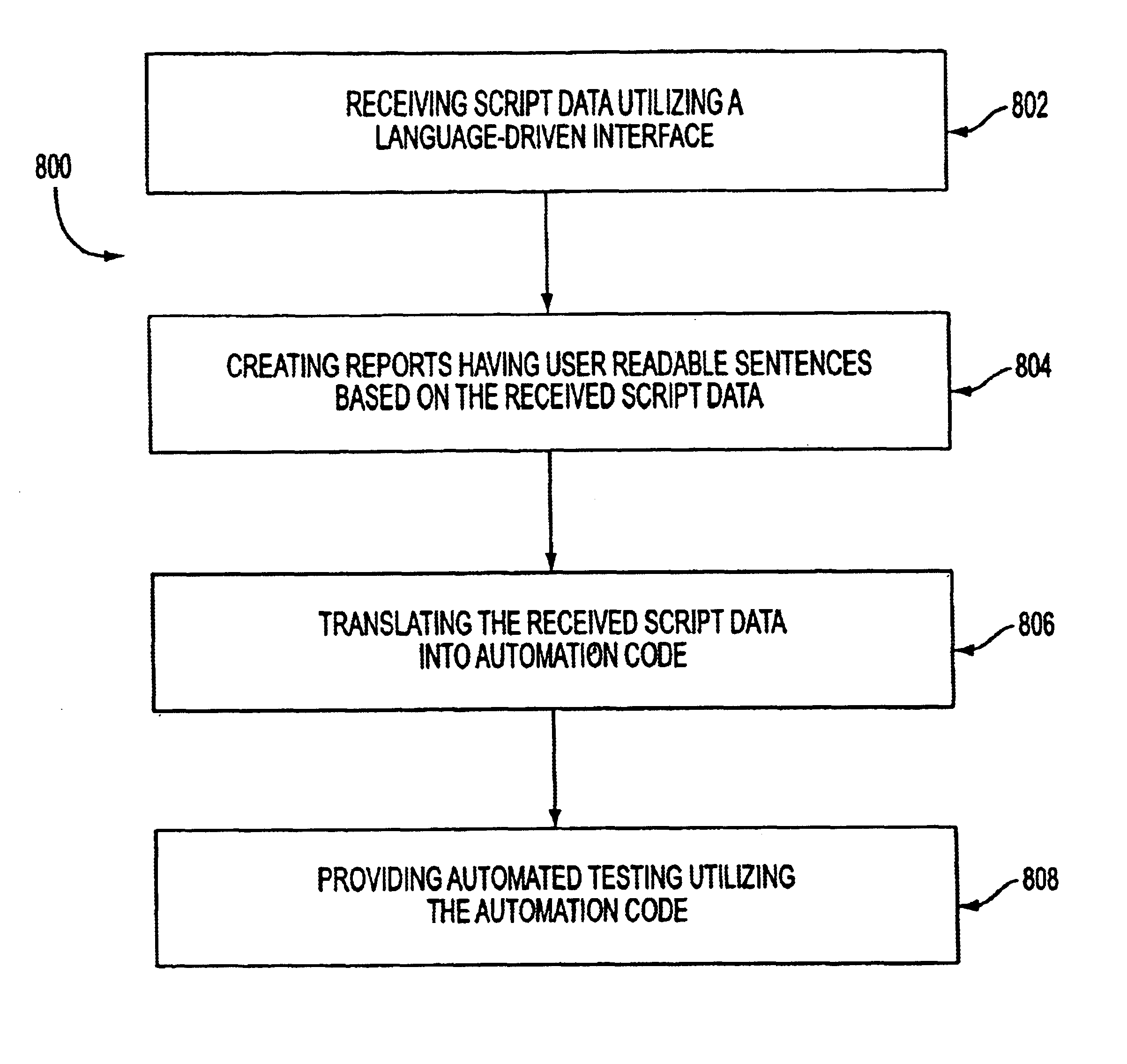
Language-driven interface for an automated testing framework
InactiveUS6907546B1Software testing/debuggingSpecific program execution arrangementsCrowdsAutomatic testing
To test the functionality of a computer system, automated testing may use an automation testing tool that emulates user interactions. A database may store words each having a colloquial meaning that is understood by a general population. For each of these words, the database may store associated computer instructions that can be executed to cause a computer to perform the function that is related to the meaning of the word. During testing, a word may be received having a colloquial meaning that is understood by a general population. The database may be queried for the received word and the set of computer instructions may be returned by the database. The automated testing tool may then perform the function returned to the colloquial meaning of the word. The words stored in the database may be in English or another language.
Owner:ACCENTURE GLOBAL SERVICES LTD
Multiple platform support system and method
InactiveUS9010641B2Software simulation/interpretation/emulationSpecial data processing applicationsSupporting systemData terminal
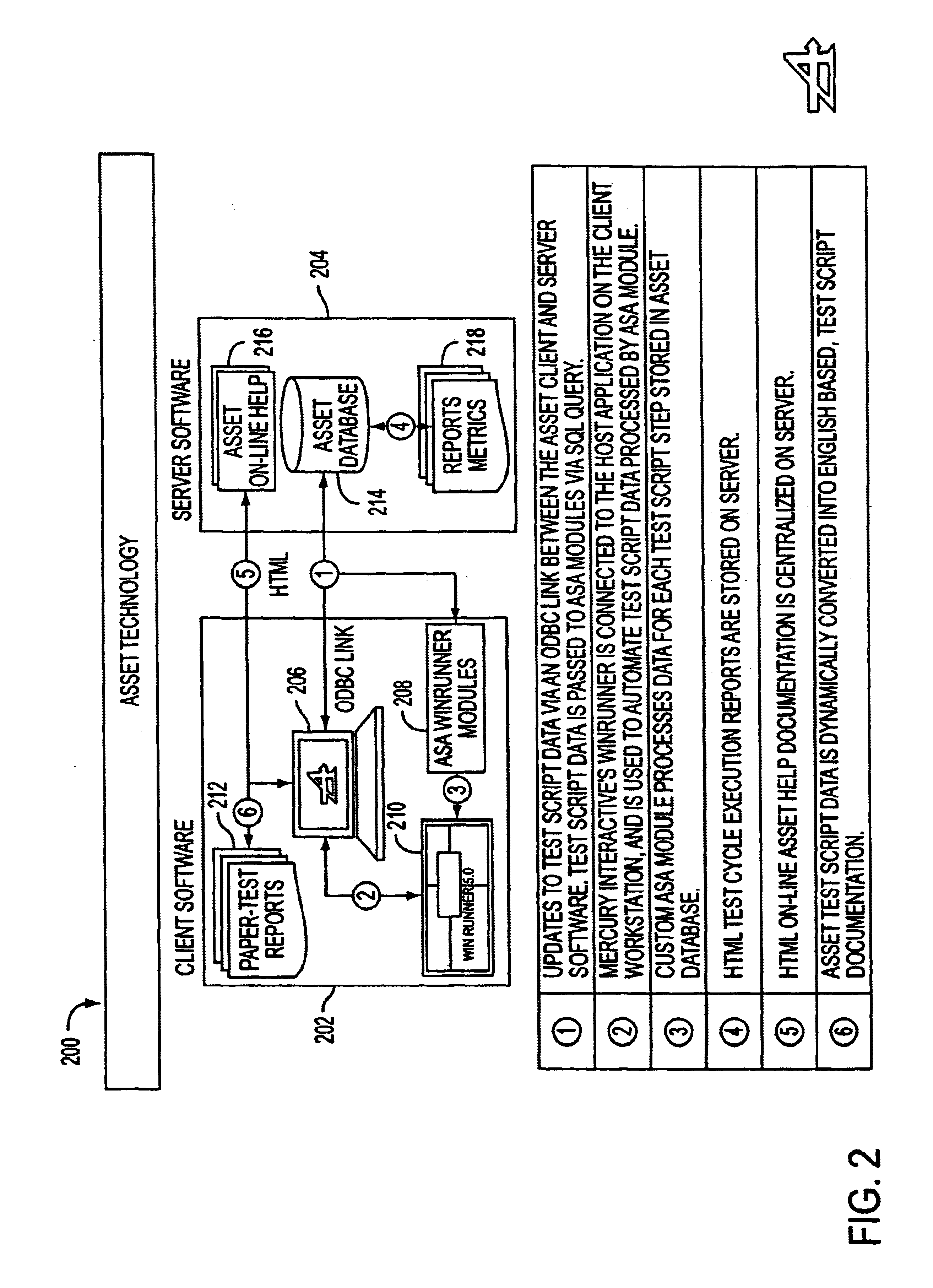
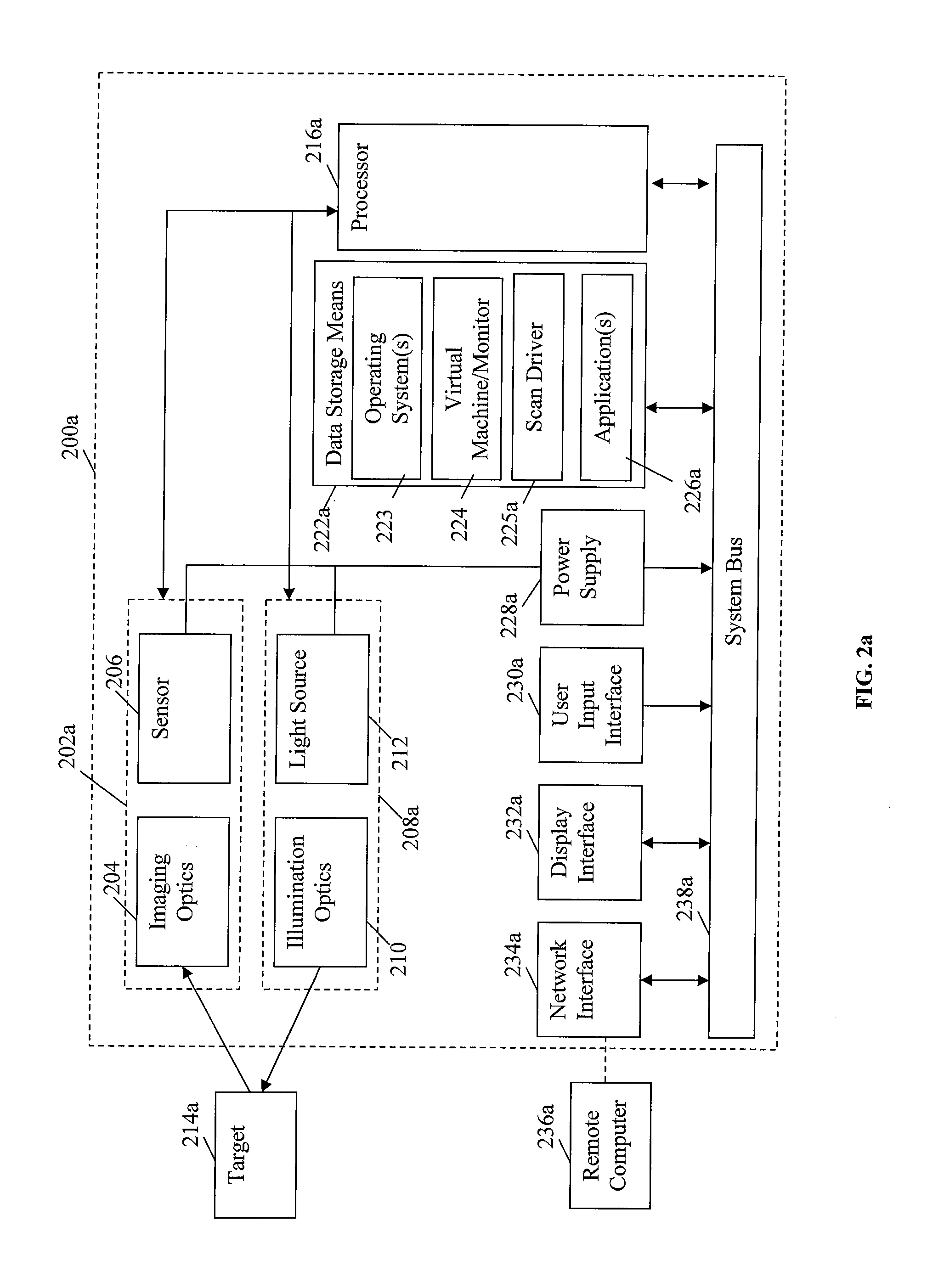
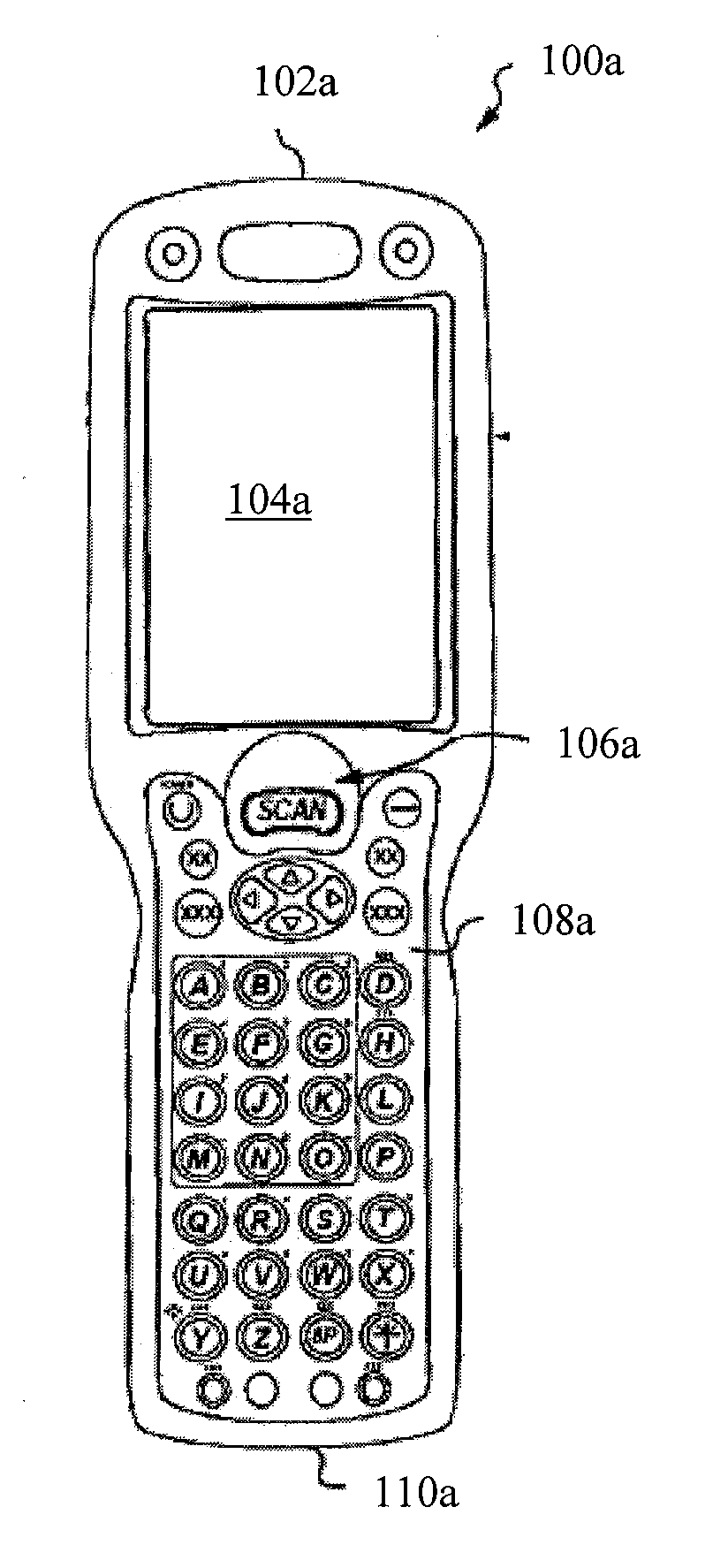
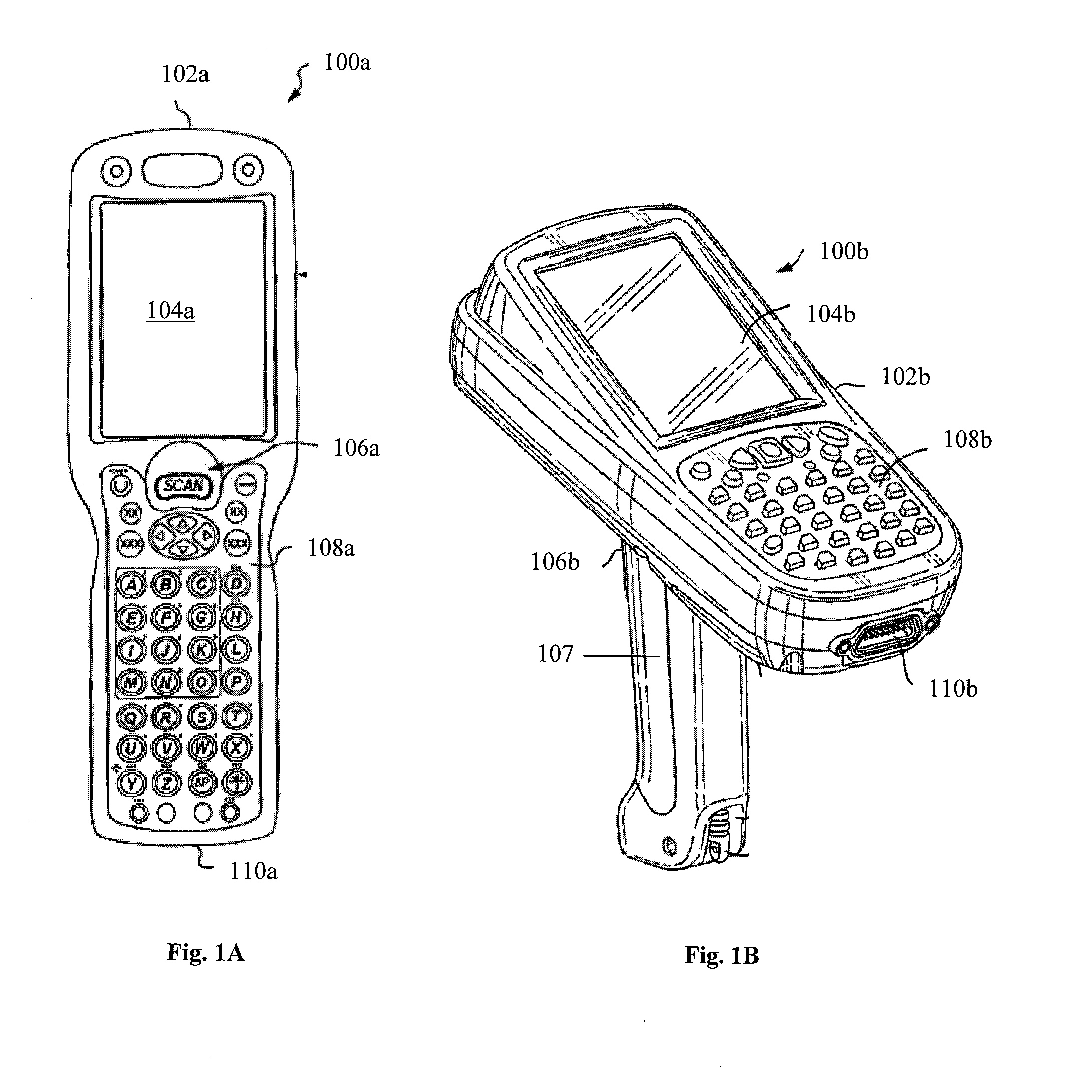
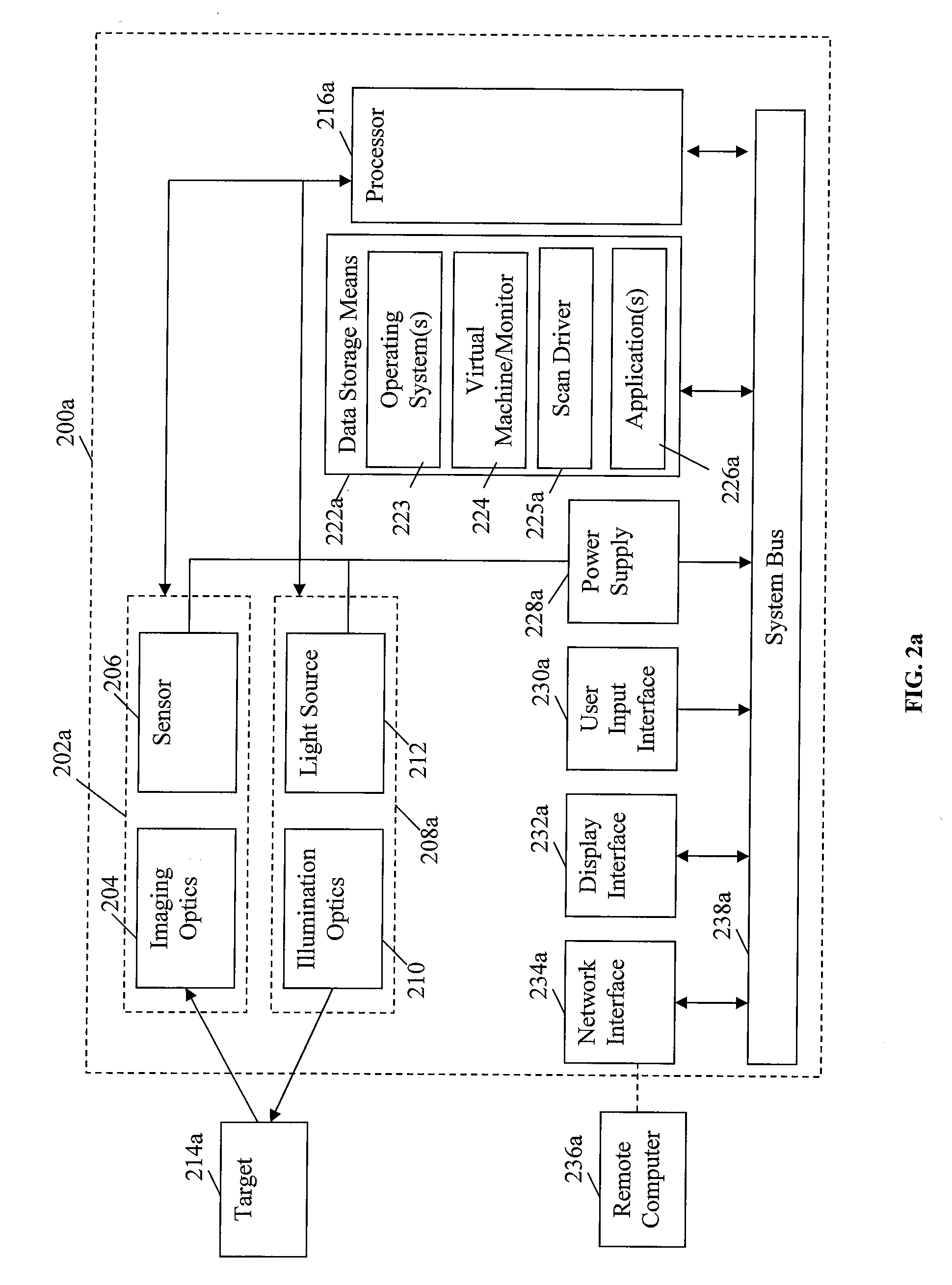
A portable data terminal including a processor having an instruction set architecture and data storage means configured to store a plurality of operating systems and a virtual machine monitor application program configured to receive at least one instruction from each operating system, communicate with the processor according to the instruction set architecture, and switch operating system access to the processor upon receipt of an electrical signal representing an event.
Owner:HAND HELD PRODS
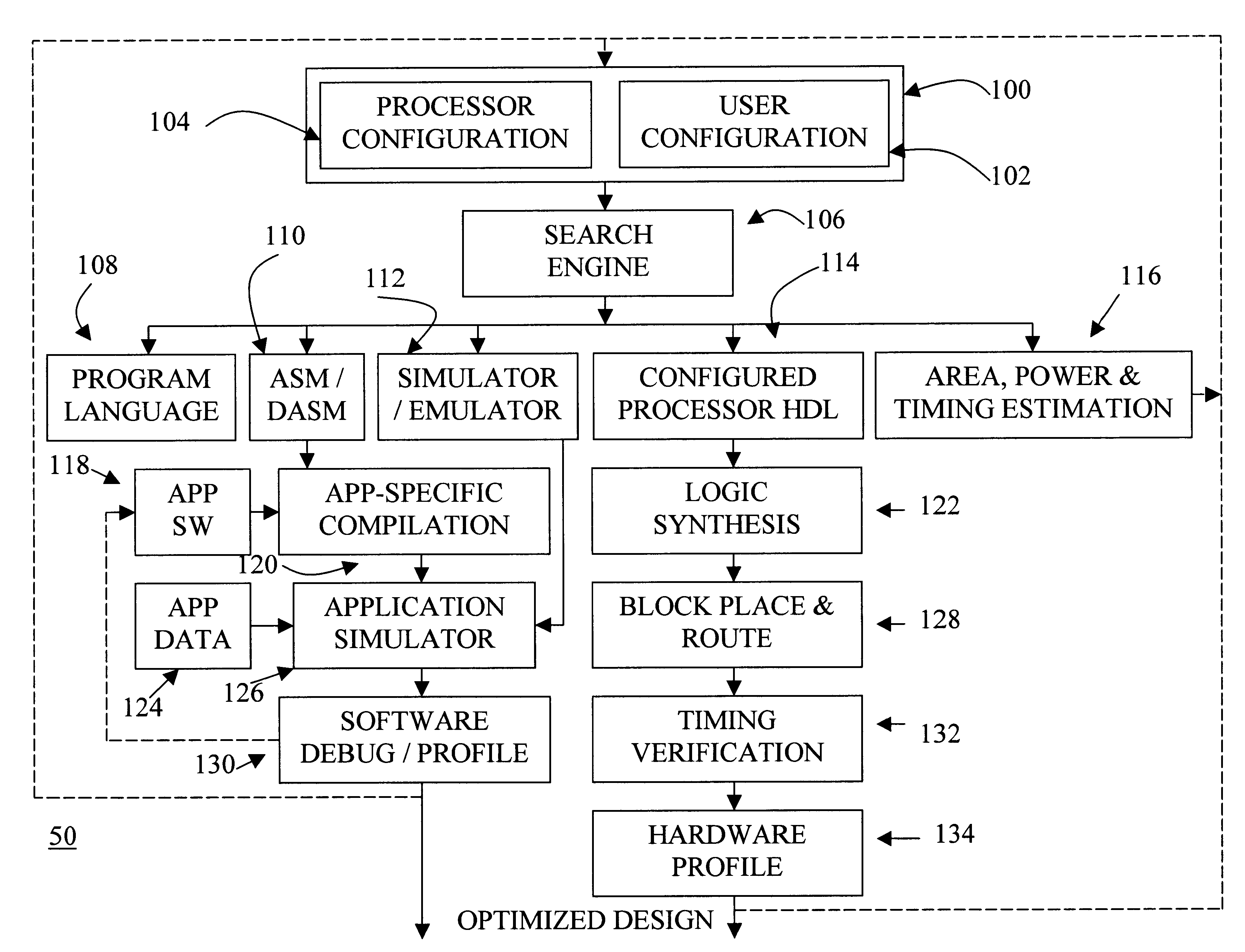
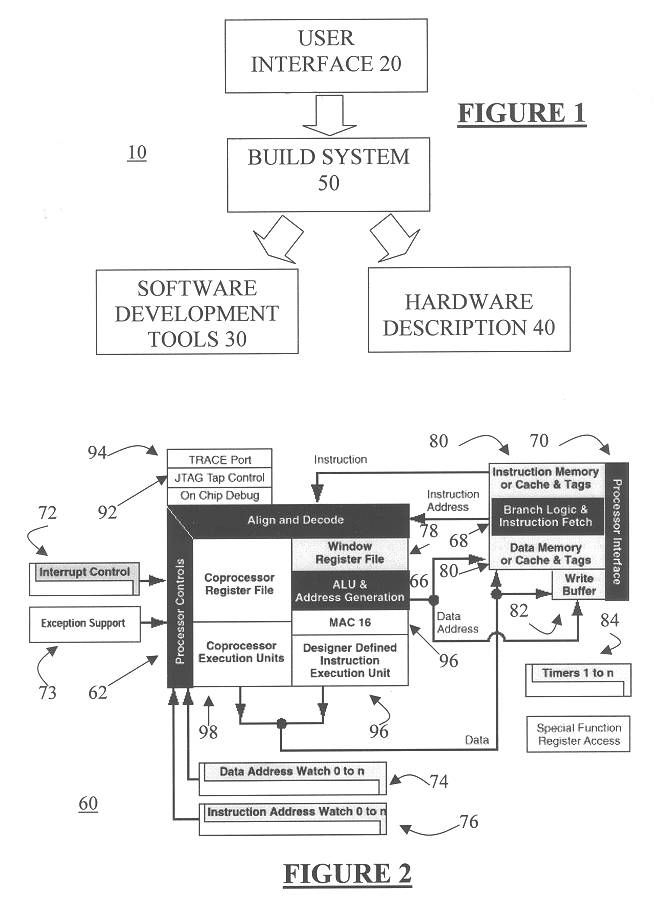
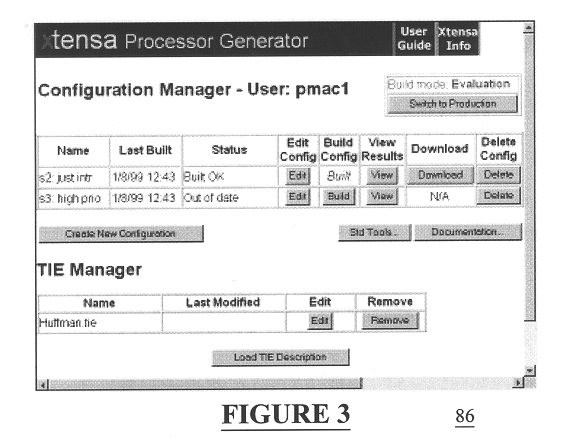
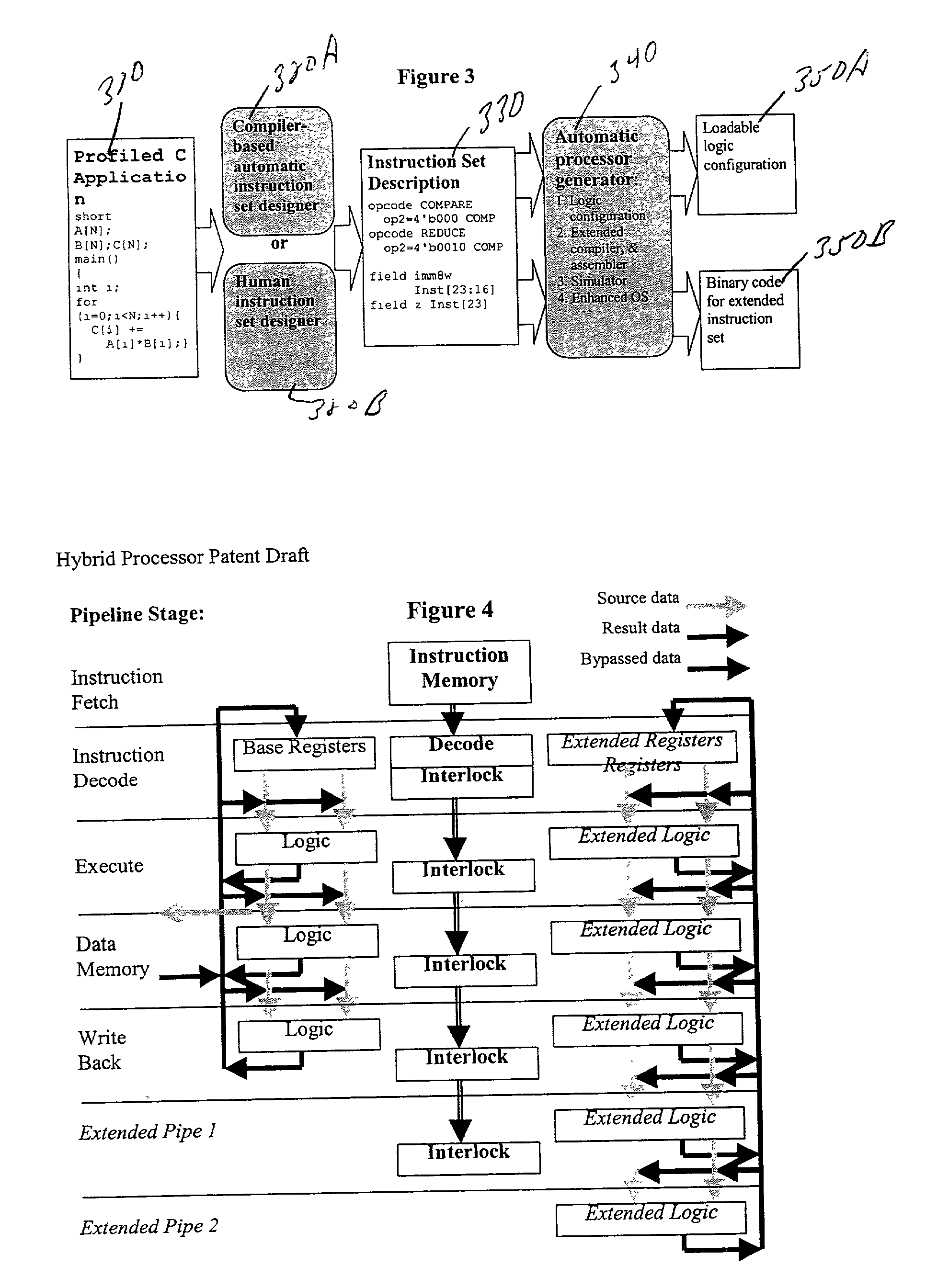
Automated processor generation system for designing a configurable processor and method for the same
InactiveUS6477683B1Decompilation/disassemblyCAD network environmentApplication softwareProcessor design
An automated processor design tool uses a description of customized processor instruction set extensions in a standardized language to develop a configurable definition of a target instruction set, a Hardware Description Language description of circuitry necessary to implement the instruction set, and development tools such as a compiler, assembler, debugger and simulator which can be used to develop applications for the processor and to verify it. Implementation of the processor circuitry can be optimized for various criteria such as area, power consumption, speed and the like. Once a processor configuration is developed, it can be tested and inputs to the system modified to iteratively optimize the processor implementation. By providing a constrained domain of extensions and optimizations, the process can be automated to a high degree, thereby facilitating fast and reliable development.
Owner:TENSILICA
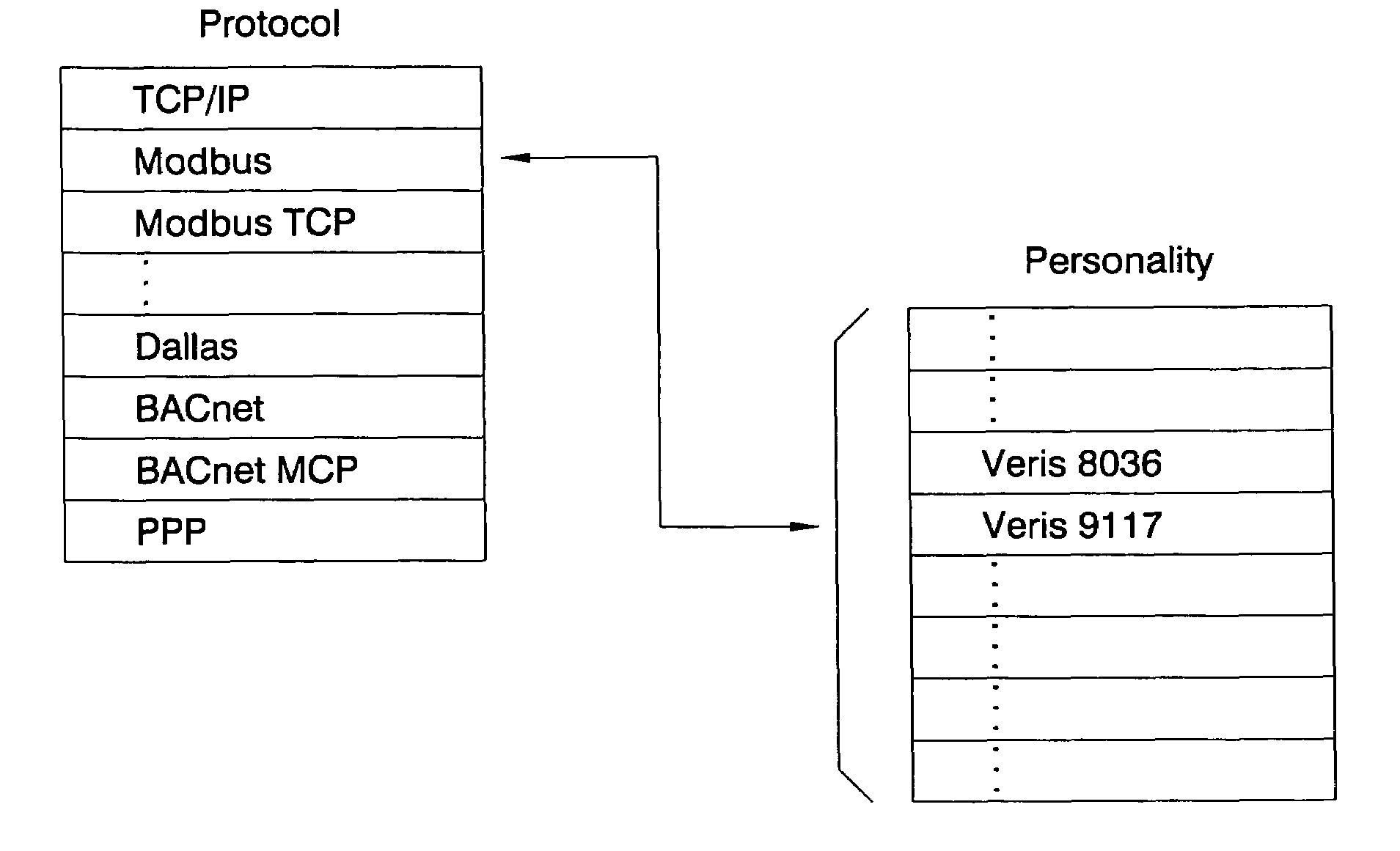
System and method for distributed facility management and operational control
ActiveUS7349761B1Programme controlSampled-variable control systemsControl systemEnvironmental control system
An environmental control system controls monitoring and operation of a multiplicity of disparate environmental control devices by determining an appropriate configuration for each control device and communicates corresponding monitoring and control commands to each device in accordance with its corresponding communication protocol over a selected I / O port. An operational instruction set includes a structural definition of an enterprise facility in which devices are defined by personality modules and communicate with a system host in accordance with a protocol defined in a protocol module. Facility implementation is defined by a node tree structure which collects suitable protocol nodes under a corresponding I / O interface port node. Device (personality) nodes are collected under corresponding protocol nodes, and data point nodes depend from their corresponding device nodes. Data points nodes are individually accessible by merely traversing the node tree using a URL-like notational structure, allowing off-site users to control and monitor environmental devices by issuing commands in the form of a URL.
Owner:CISCO TECH INC +1
Methods and systems for betting with pari-mutuel payouts
InactiveUS20080113816A1Improved initial payoutQuick buildCard gamesApparatus for meter-controlled dispensingOperational systemEvent data
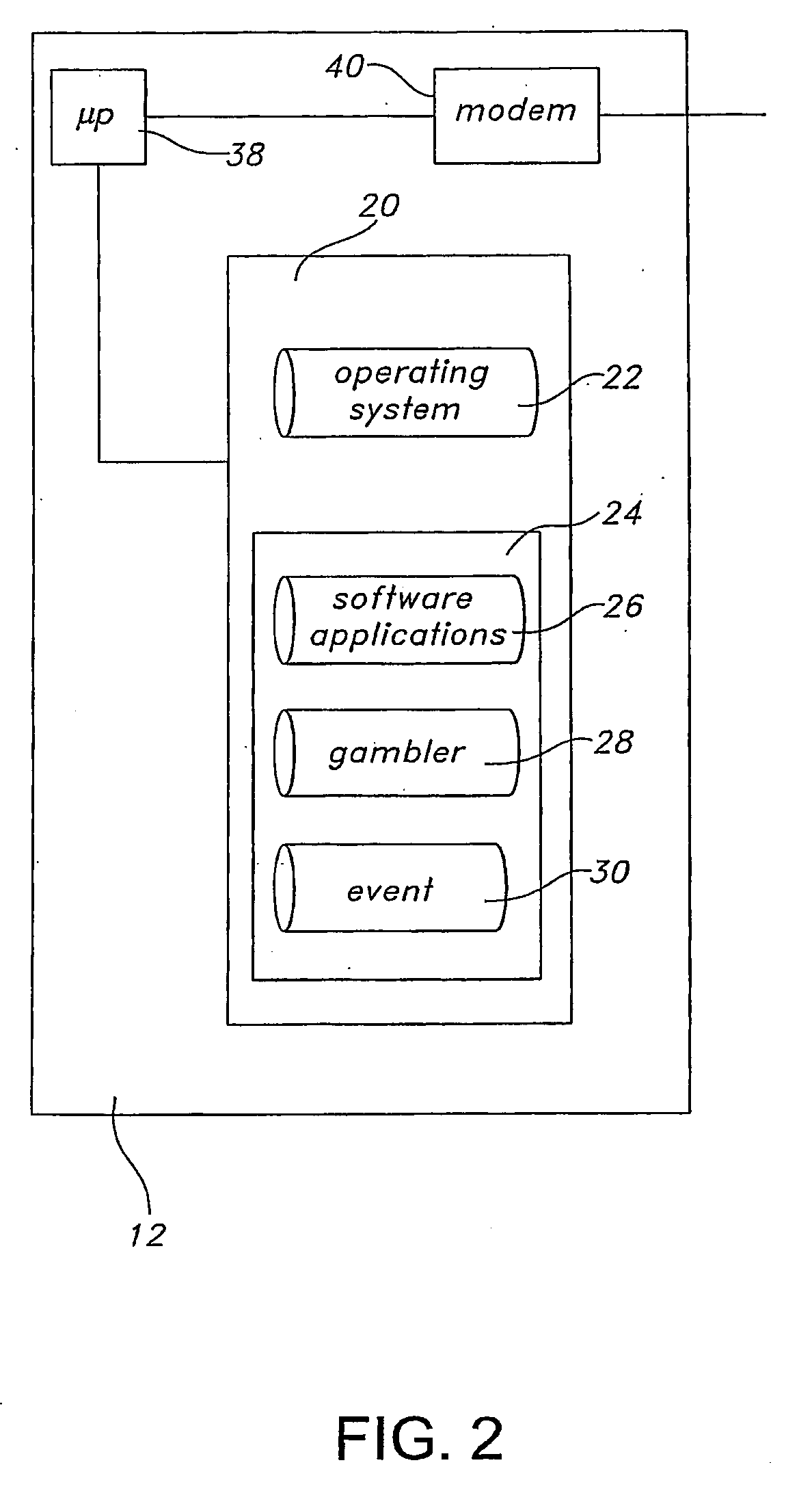
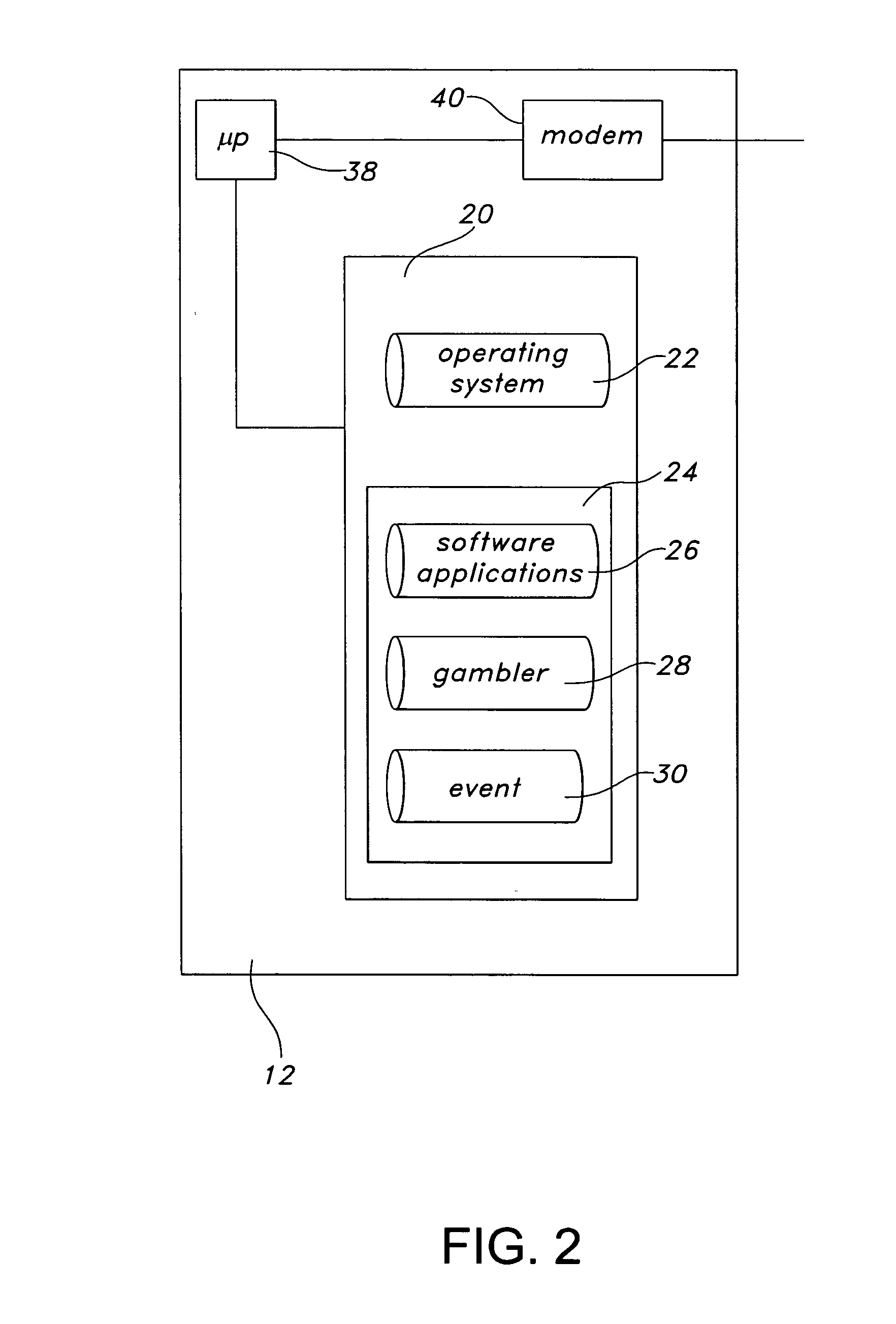
A server for facilitating real-time betting, wherein the server communicates with clients via a distributed computing network. The server includes a memory storing an operating system, an instruction set, event data related to a sporting event, gambler data related to gamblers participating in a competition based upon the sporting event and site data related to electronic pages associated with the real-time para-mutuel betting. A processor runs the instruction set and communicates with the memory and the distributed computing network. The processor is operative to enroll the gamblers by presenting betting rules associated with the sporting event, collect wagering from the gamblers, accept predictions for discrete events within the sporting event from each gambler and determine a first winner of the competition based upon the predictions. Applications include lotteries with entries received from mobile devices.
Owner:HF SCI INC
Algorithm mapping, specialized instructions and architecture features for smart memory computing
InactiveUS7546438B2Improve performanceLow costMultiplex system selection arrangementsDigital computer detailsSmart memoryExecution unit
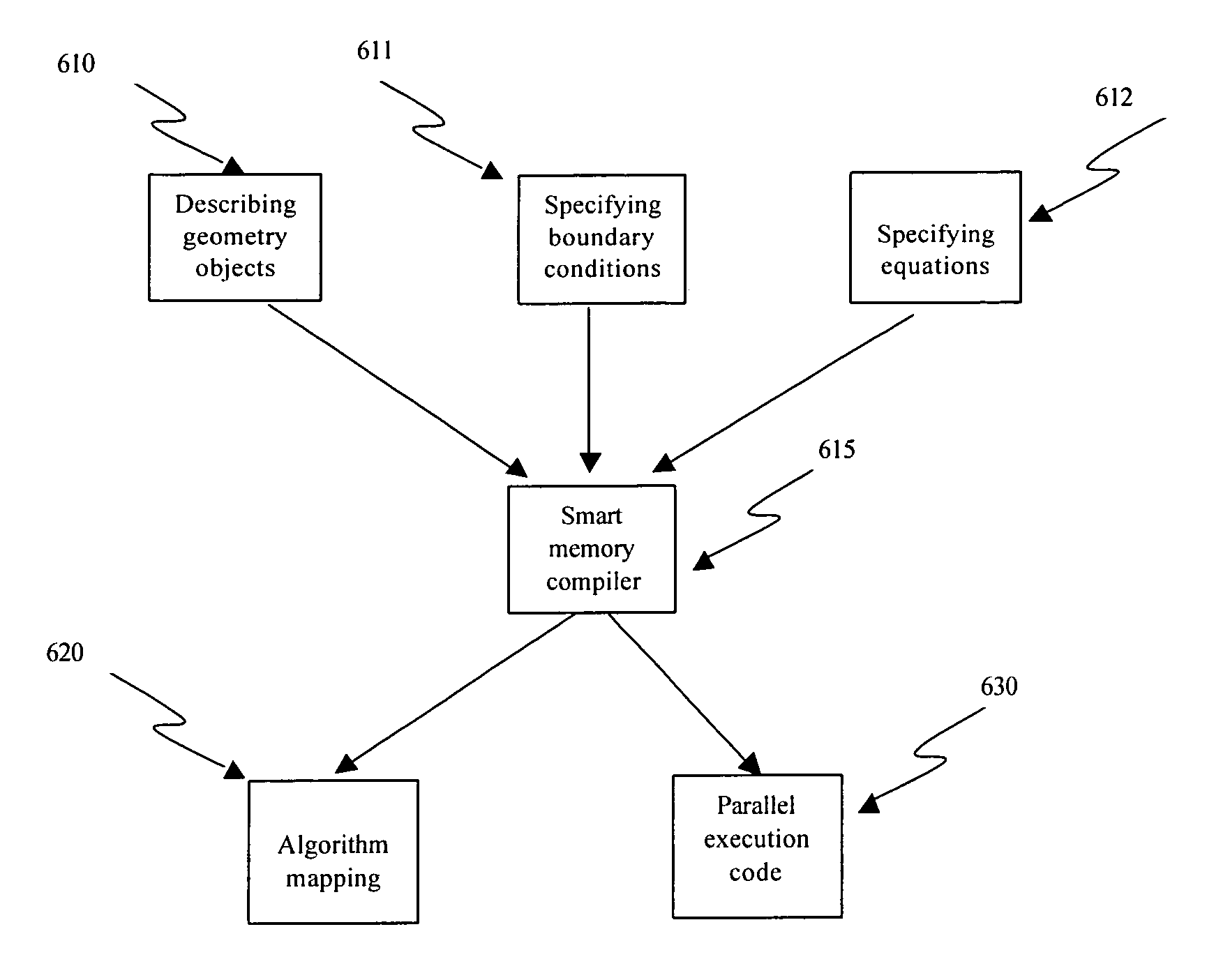
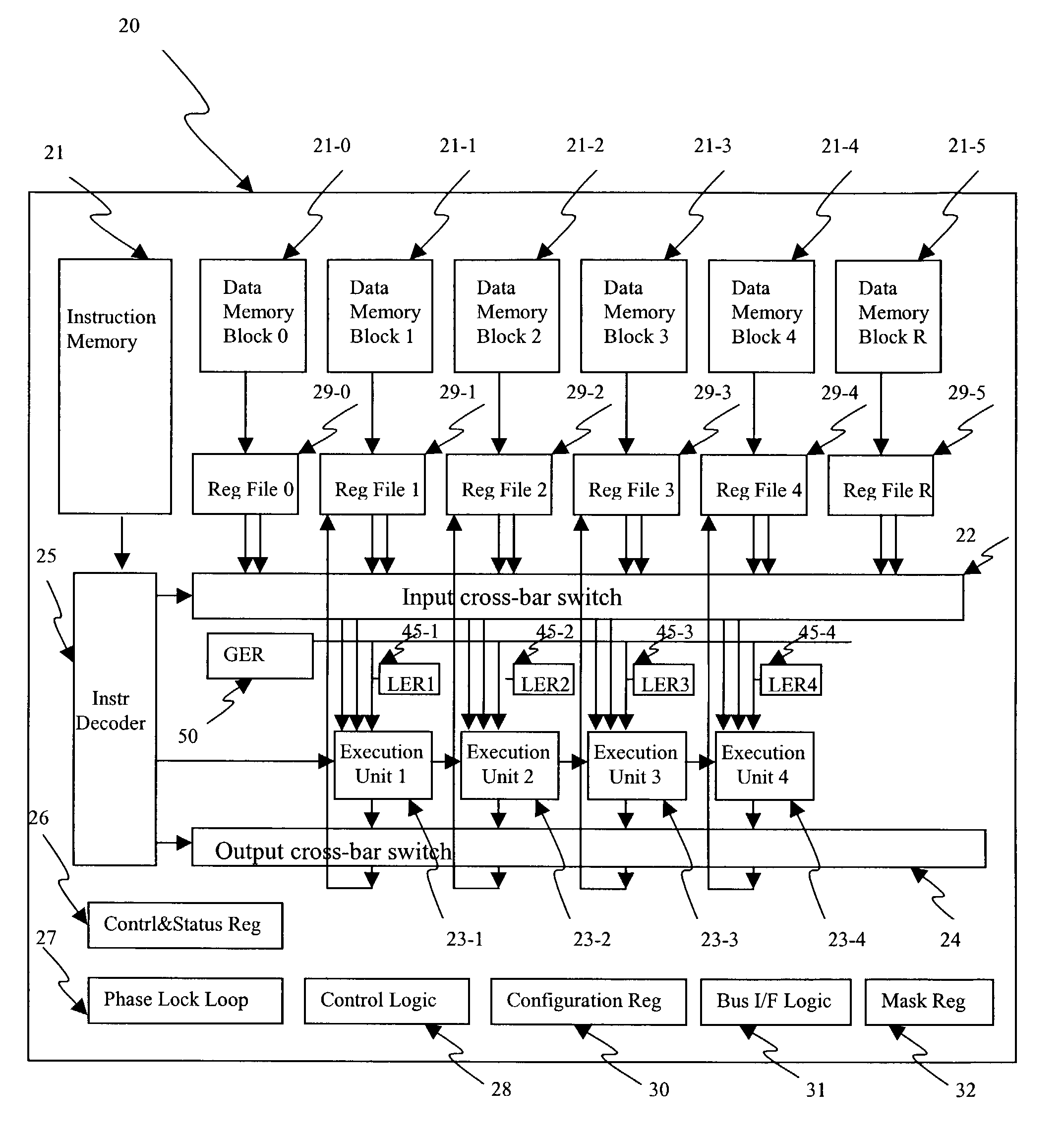
A smart memory computing system that uses smart memory for massive data storage as well as for massive parallel execution is disclosed. The data stored in the smart memory can be accessed just like the conventional main memory, but the smart memory also has many execution units to process data in situ. The smart memory computing system offers improved performance and reduced costs for those programs having massive data-level parallelism. This smart memory computing system is able to take advantage of data-level parallelism to improve execution speed by, for example, use of inventive aspects such as algorithm mapping, compiler techniques, architecture features, and specialized instruction sets.
Owner:STRIPE INC
Remote bist for high speed test and redundancy calculation
InactiveUS20080215937A1Reduce frequencyIncrease processing frequencyDigital circuit testingFunctional testingLow speedSpeed test
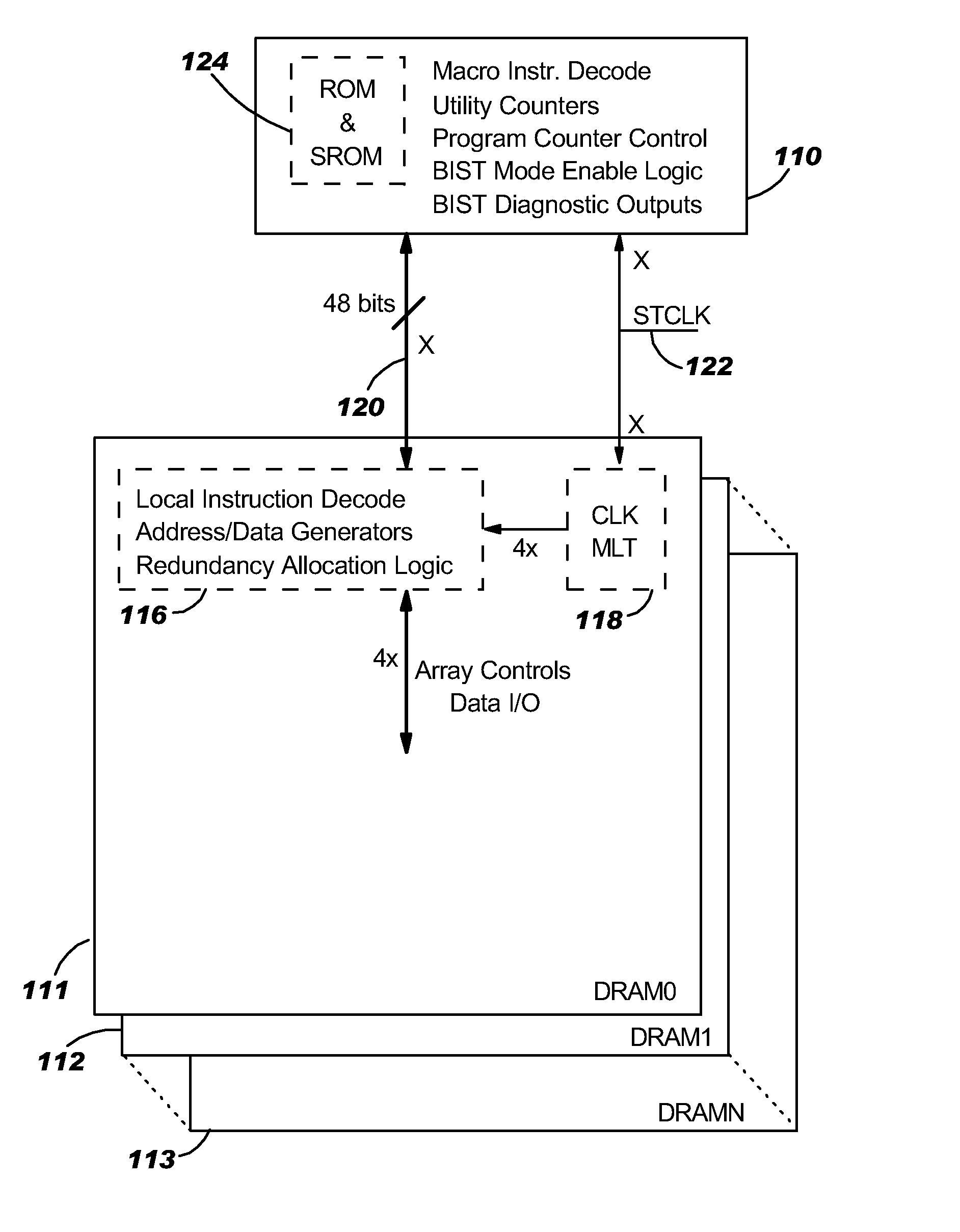
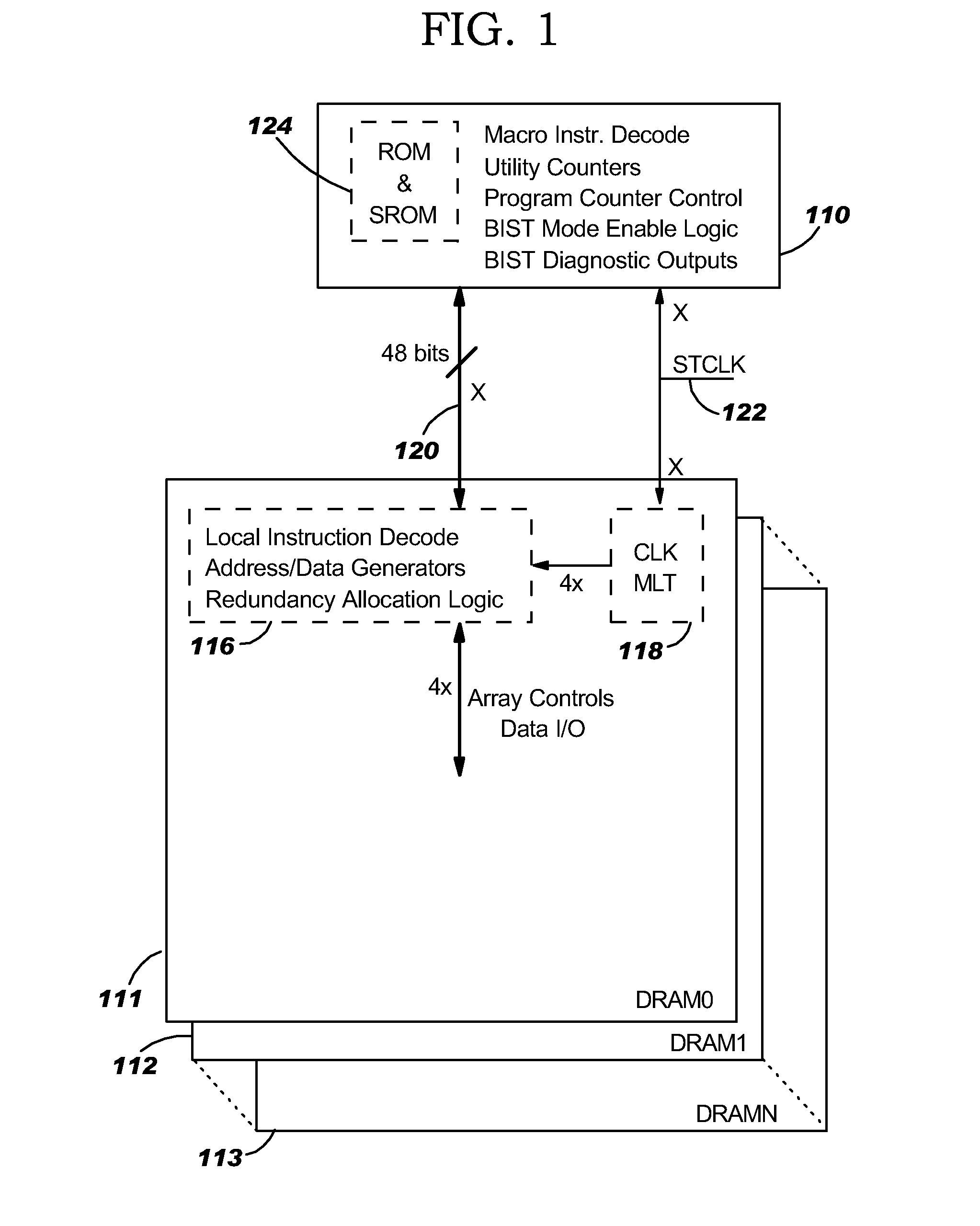
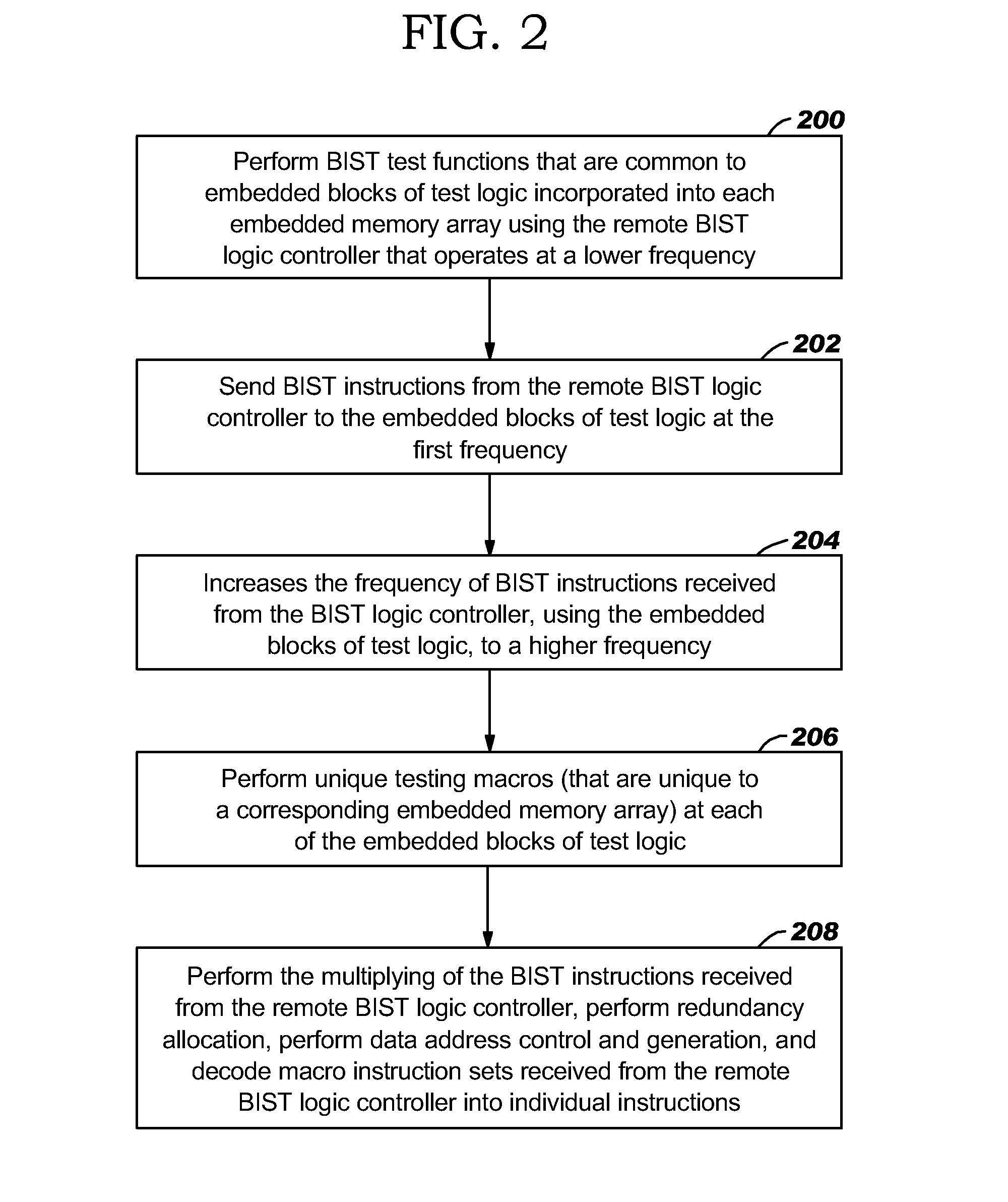
Disclosed in a hybrid built-in self test (BIST) architecture for embedded memory arrays that segments BIST functionality into remote lower-speed executable instructions and local higher-speed executable instructions. A standalone BIST logic controller operates at a lower frequency and communicates with a plurality of embedded memory arrays using a BIST instruction set. A block of higher-speed test logic is incorporated into each embedded memory array under test and locally processes BIST instructions received from the standalone BIST logic controller at a higher frequency. The higher-speed test logic includes a multiplier for increasing the frequency of the BIST instructions from the lower frequency to the higher frequency. The standalone BIST logic controller enables a plurality of higher-speed test logic structures in a plurality of embedded memory arrays.
Owner:META PLATFORMS INC
Method and apparatus for distributing multimedia to remote clients
InactiveUS20050091311A1Restrict levelPulse modulation television signal transmissionClosed circuit television systemsComputer hardwareClient-side
Video and audio signals are streamed to remote viewers that are connected to a communication network. A host server receives an originating video and audio signal that may arrive from a single source or from a plurality of independent sources. The host server provides any combination of the originating video and audio signals to viewers connected to a communication network. A viewer requests the host server provide a combination of video and audio signals from the host server. The host server transmits an instruction set to be executed by the viewer. The instruction set causes the viewer to transmit parameters to the host user, including parameters relating to the processing capabilities of the viewer. The host server then transmits multimedia data to the viewer according to the received parameters. A plurality of viewers may be simultaneously connected to the host server. Each of the plurality of viewers may configure the received video and audio signals independent of any other viewer and may generate alerts based on the video and audio content.
Owner:VIVA VISION
Methods and systems for betting with pari-mutuel payouts
InactiveUS20060287094A1Eliminate riskEasy to trackApparatus for meter-controlled dispensingVideo gamesOperational systemEvent data
A server for facilitating real-time betting, wherein the server communicates with clients via a distributed computing network. The server includes a memory storing an operating system, an instruction set, event data related to a sporting event, gambler data related to gamblers participating in a competition based upon the sporting event and site data related to electronic pages associated with the real-time para-mutuel betting. A processor runs the instruction set and communicates with the memory and the distributed computing network. The processor is operative to enroll the gamblers by presenting betting rules associated with the sporting event, collect wagering from the gamblers, accept predictions for discrete events within the sporting event from each gambler and determine a first winner of the competition based upon the predictions.
Owner:MAHAFFEY CLAY +1
Method and system for provisioning servers based on a policy and rule hierarchy
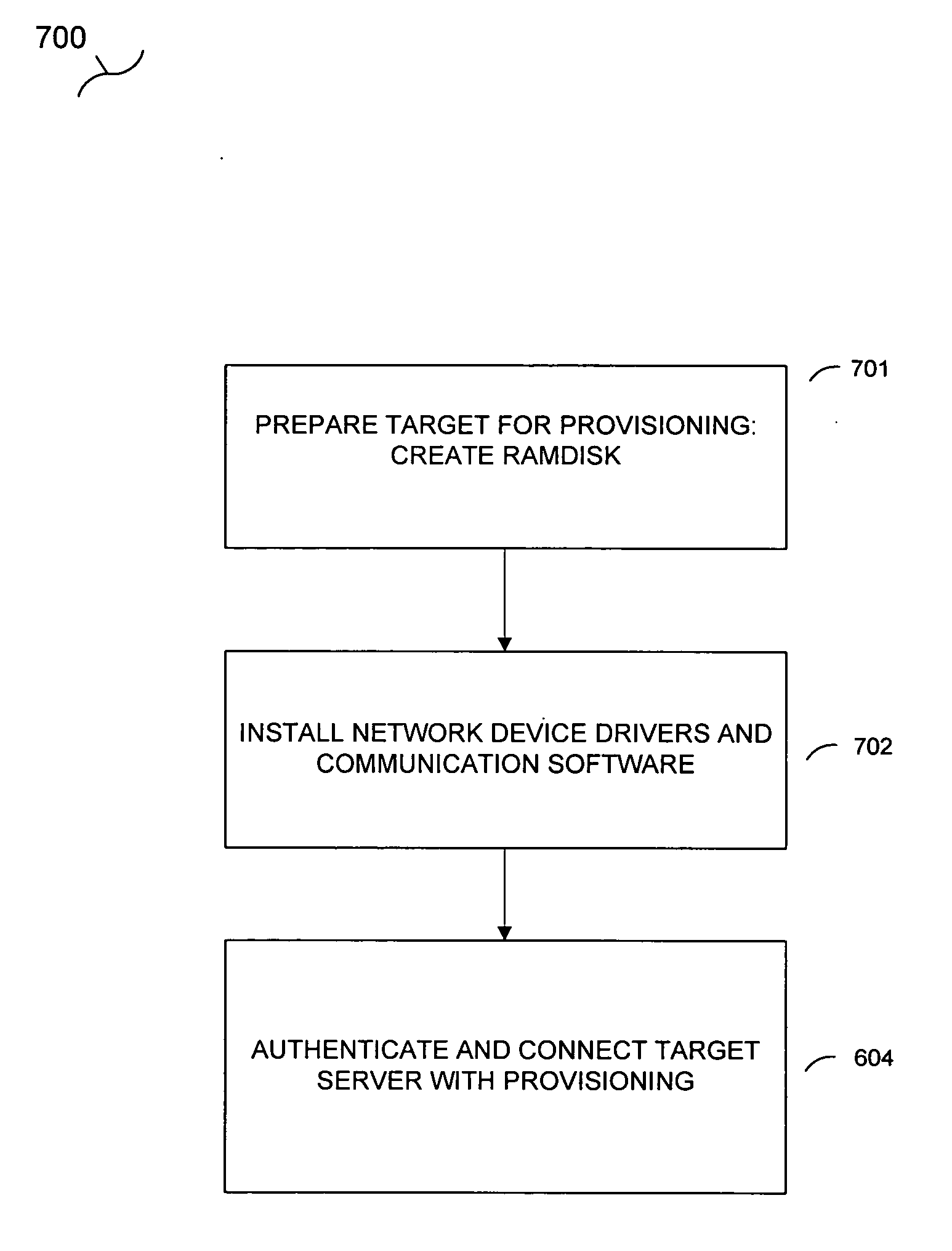
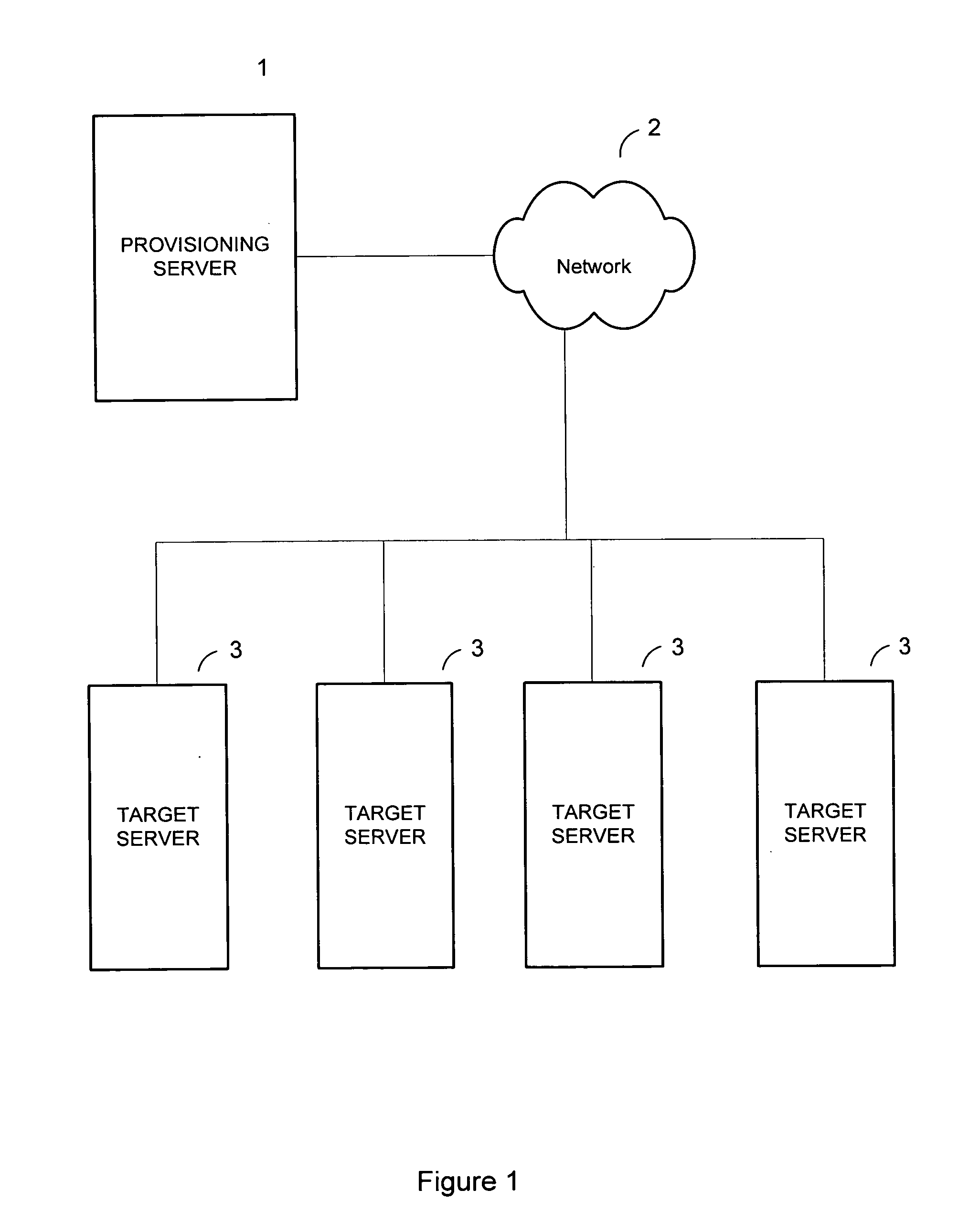
A provisioning system selects the appropriate action to take in provisioning a server computer by retrieving information on the build operators associated with a policy applied to the server, retrieves state file information on state files associated with the build operator, and selects the appropriate state file associated with the build operator based on the state value, the state value indicating the current stage of the provisioning process. Provisioning rules contained within the state file are selected based upon comparing criteria contained in the rule against the attributes of the server. An instruction set is extracted from the selected rule executed. The instructions within the instruction set may specify using a vendor tool or performing other tasks in provisioning the server.
Owner:VISHWANATH VIPUL
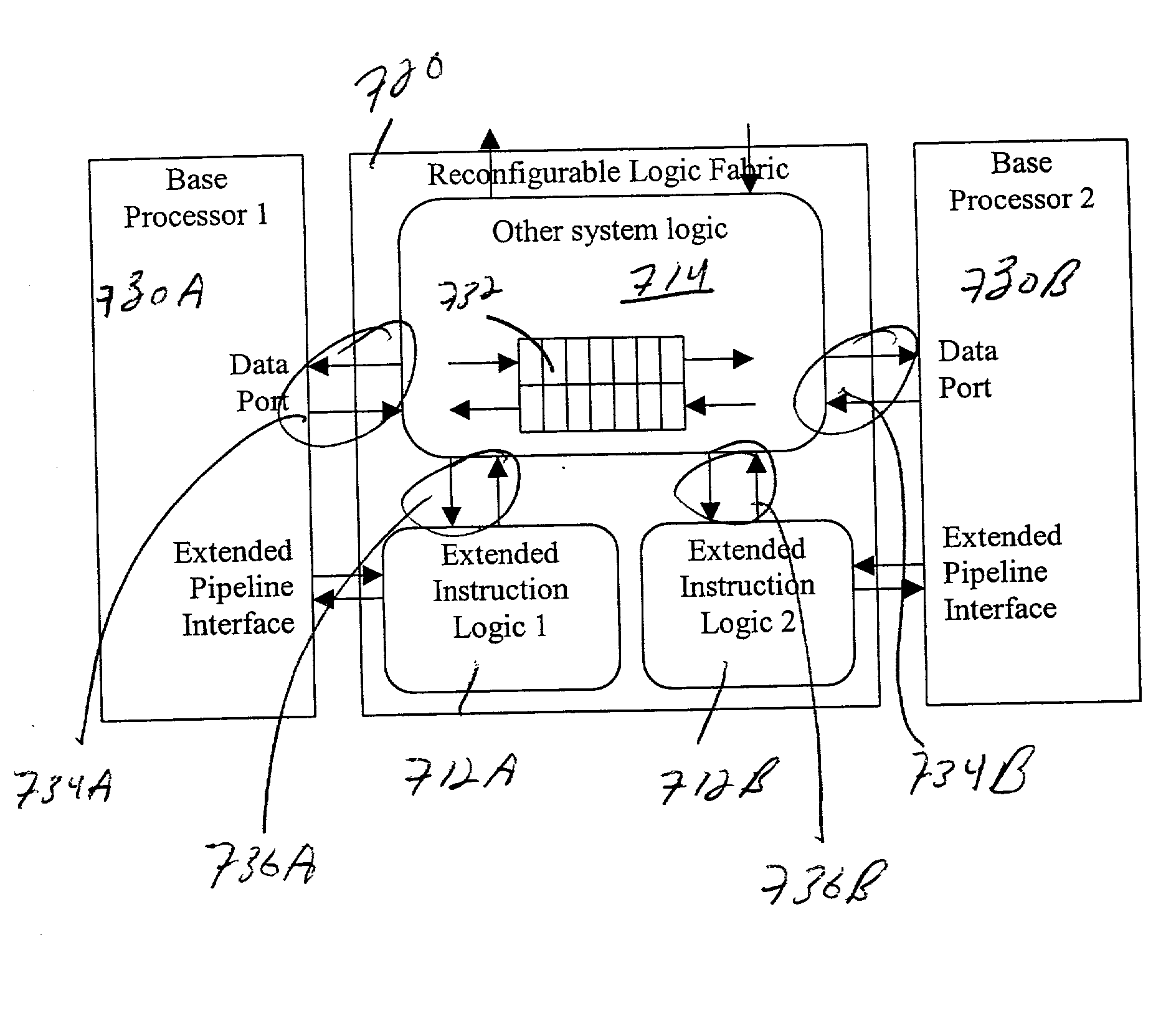
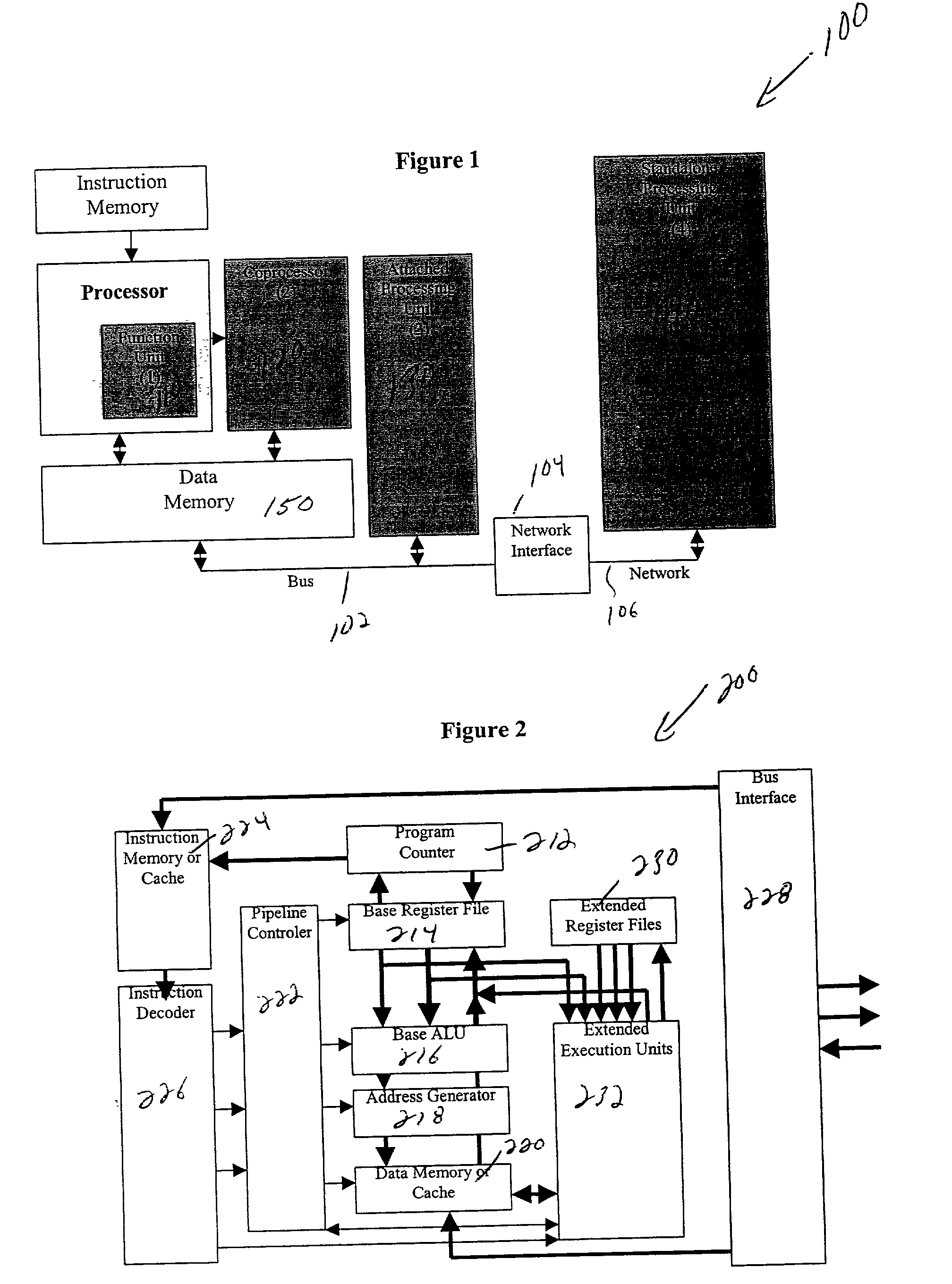
High-performance hybrid processor with configurable execution units
InactiveUS20050166038A1High bandwidthFlexibilityInstruction analysisConcurrent instruction executionHigh bandwidthLatency (engineering)
A new general method for building hybrid processors achieves higher performance in applications by allowing more powerful, tightly-coupled instruction set extensions to be implemented in reconfigurable logic. New instructions set configurations can be discovered and designed by automatic and semi-automatic methods. Improved reconfigurable execution units support deep pipelining, addition of additional registers and register files, compound instructions with many source and destination registers and wide data paths. New interface methods allow lower latency, higher bandwidth connections between hybrid processors and other logic.
Owner:TENSILICA
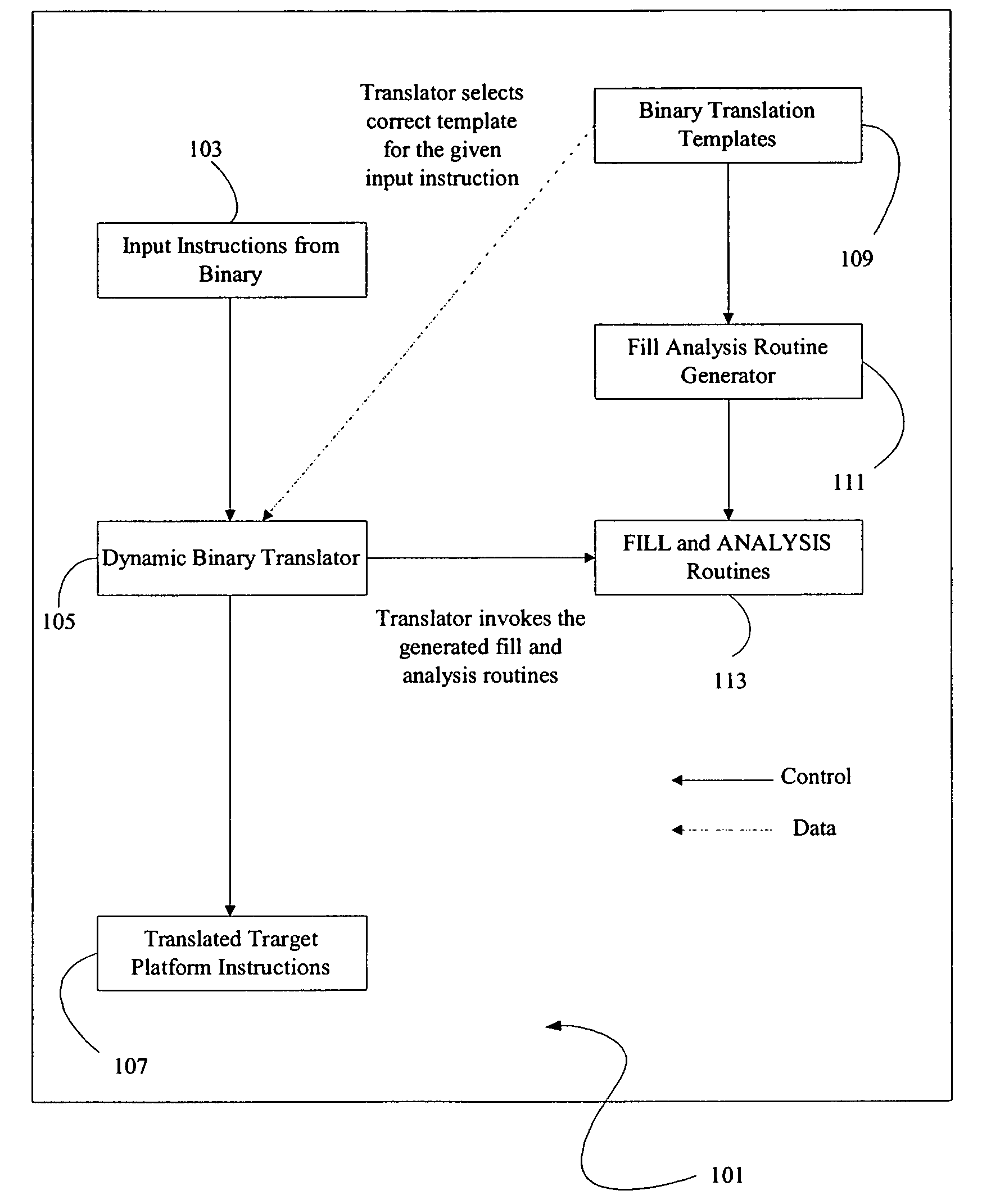
Method and apparatus for creating data transformation routines for binary data
ActiveUS7607120B2Binary to binarySpecific program execution arrangementsData transformationCombined use
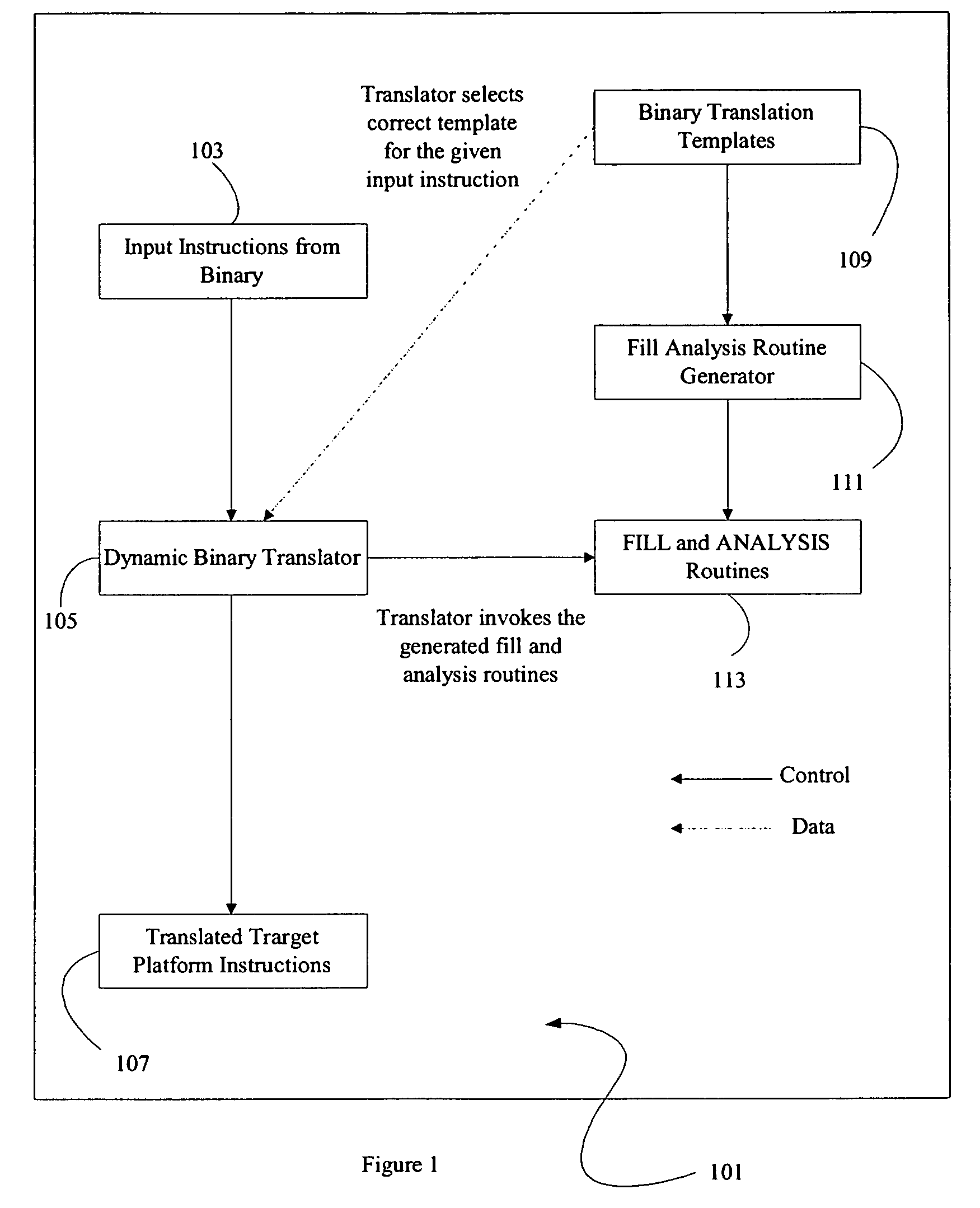
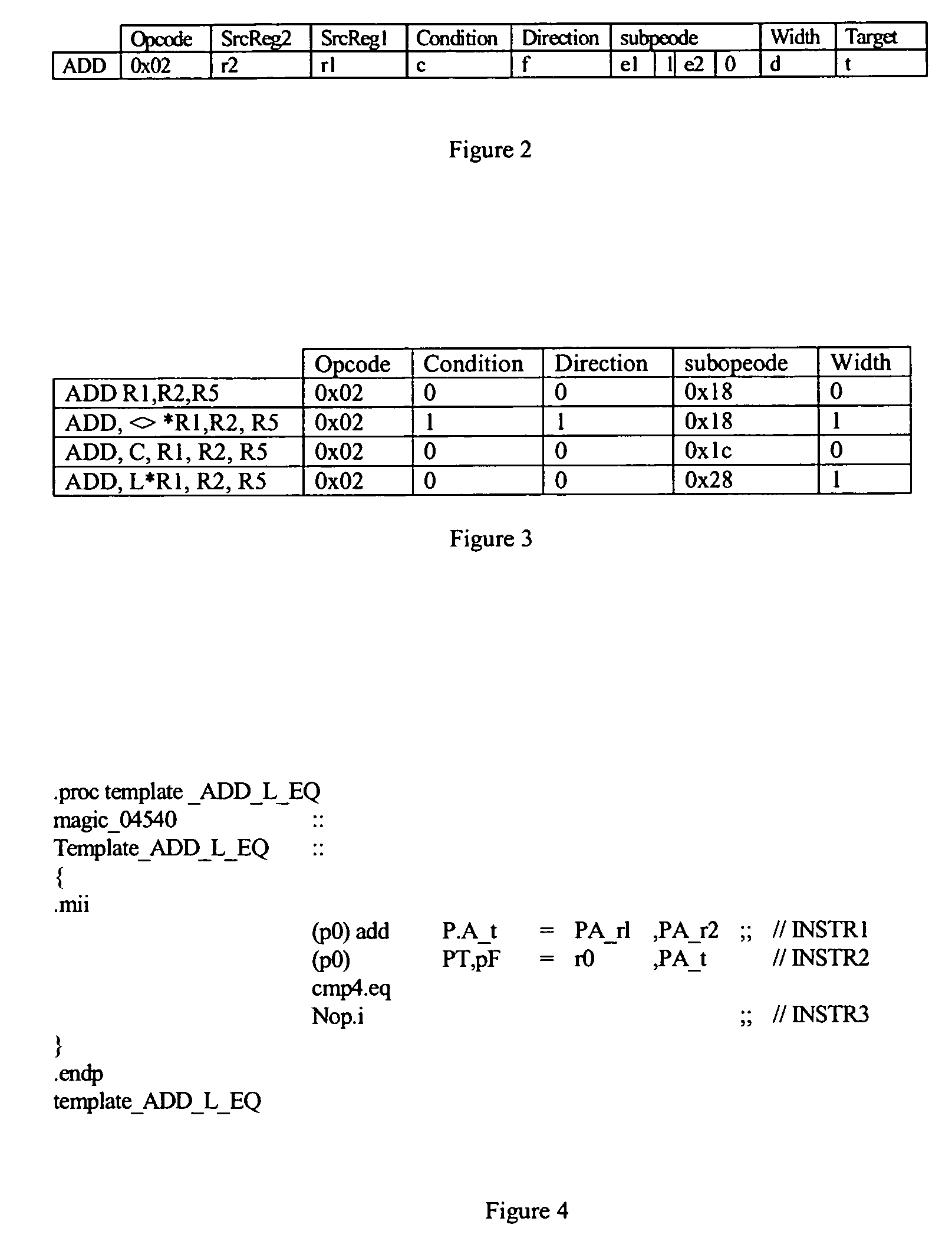
A method and apparatus is disclosed for creating data transformation routines for transforming data from a source format to a target format. The routines can be used in conjunction with dynamic binary translators, which enable binaries of a source platform to execute on a target platform without recompilation. This is achieved by runtime (on-the-fly) translation of source machine instructions into equivalent target machine instructions. Typically dynamic binary translators are used for migrating from an older platform to a newer one, implementing complex instruction set architectures, speeding up simulators and in profiling tools. The transformation routines are also used for translating data in databases from one format to another, for example, where the data format has been modified in an upgraded system. In all these applications, the speed and accuracy of translation need to be kept low to ensure that the overhead incurred does not outweigh the advantages of translation.
Owner:VALTRUS INNOVATIONS LTD +1
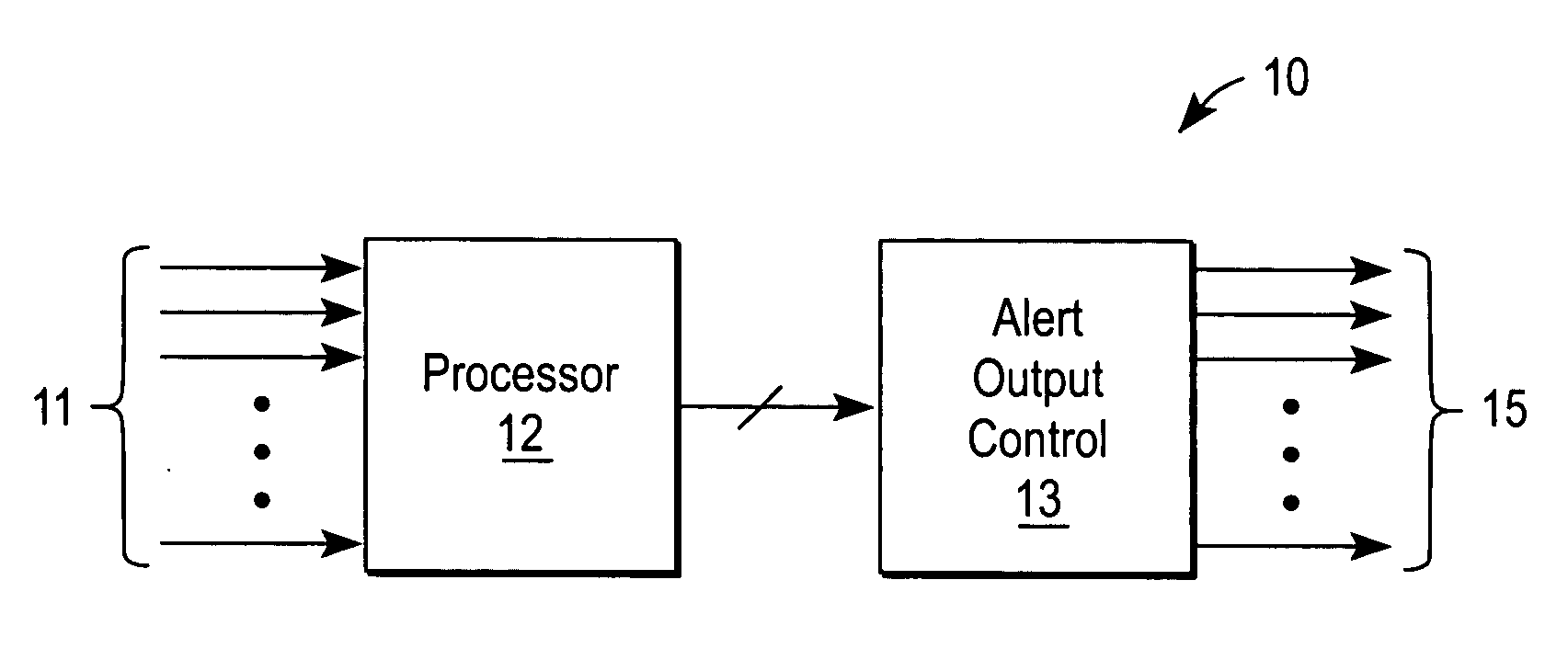
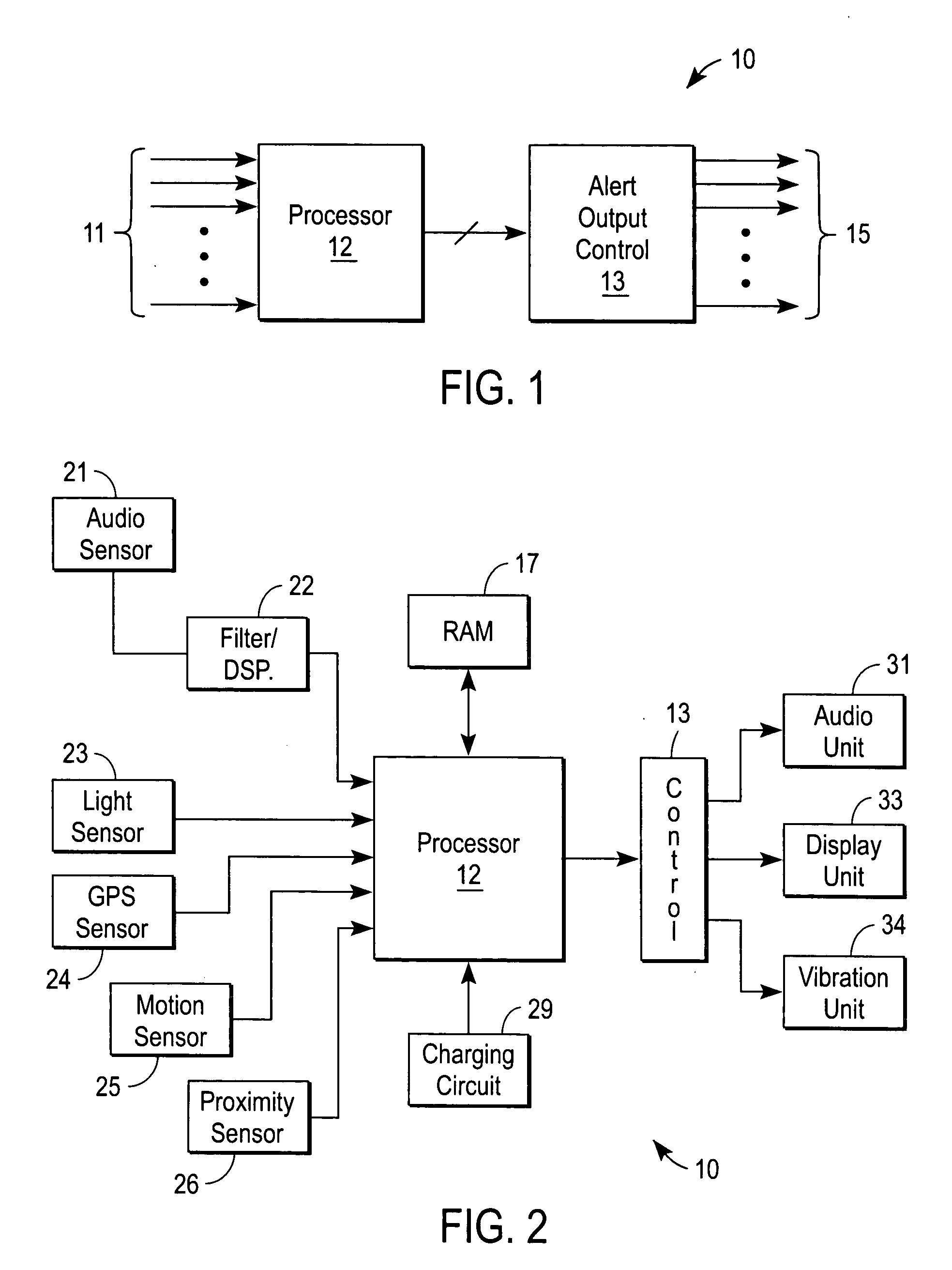
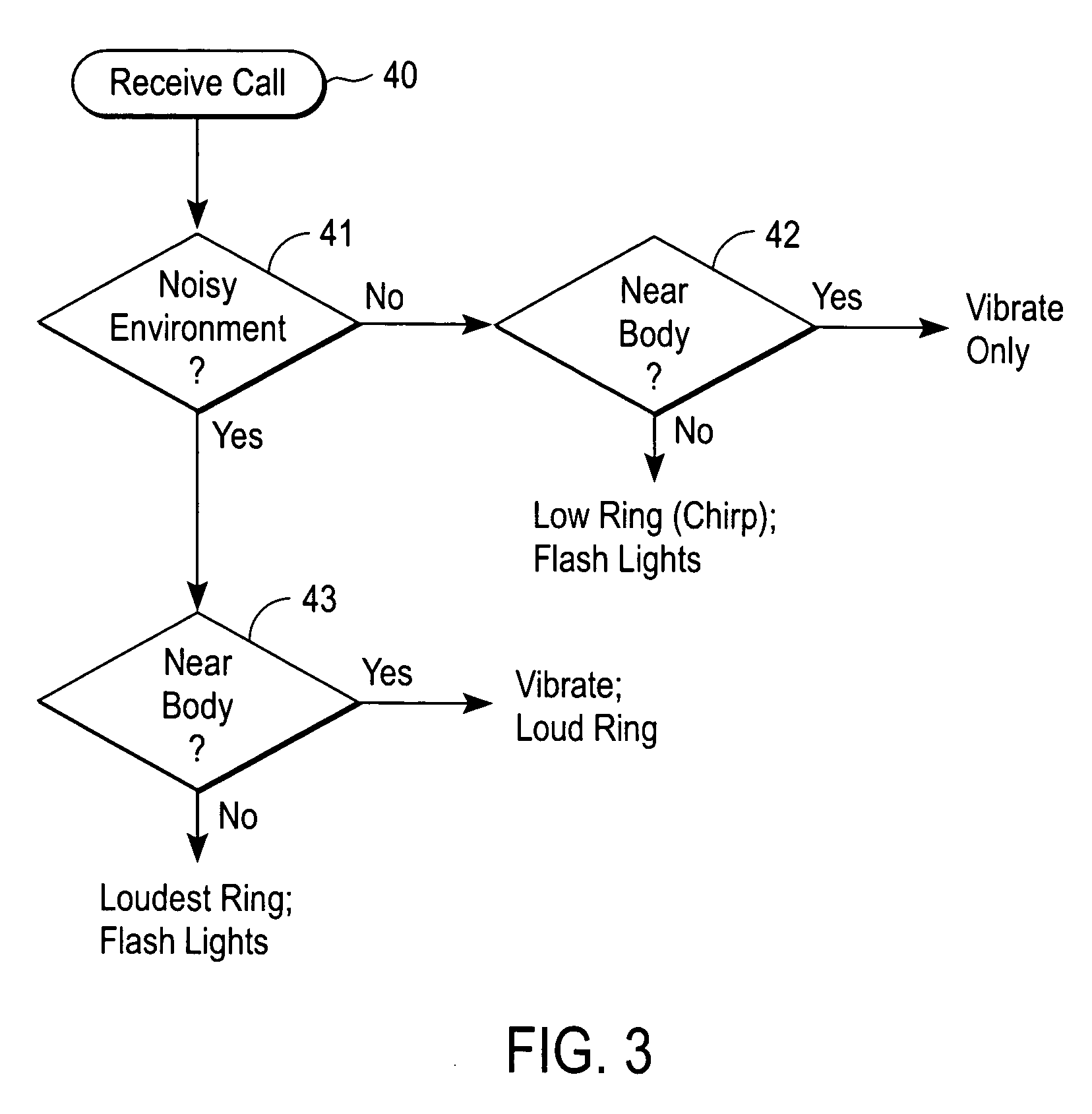
Handheld communications device with automatic alert mode selection
Apparatus for automatically alerting a user of a handheld communications device of an incoming transmission includes a plurality of sensors each of which produces a signal indicative of a physical parameter of a surrounding environment of the handheld communications device. Also included is a processor that executes a programmed set of instructions to determine an optimal alert mode setting based on a combination of the sensor signals. A plurality of output units produces one or more sensory alert outputs In response to the optimal alert mode setting. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
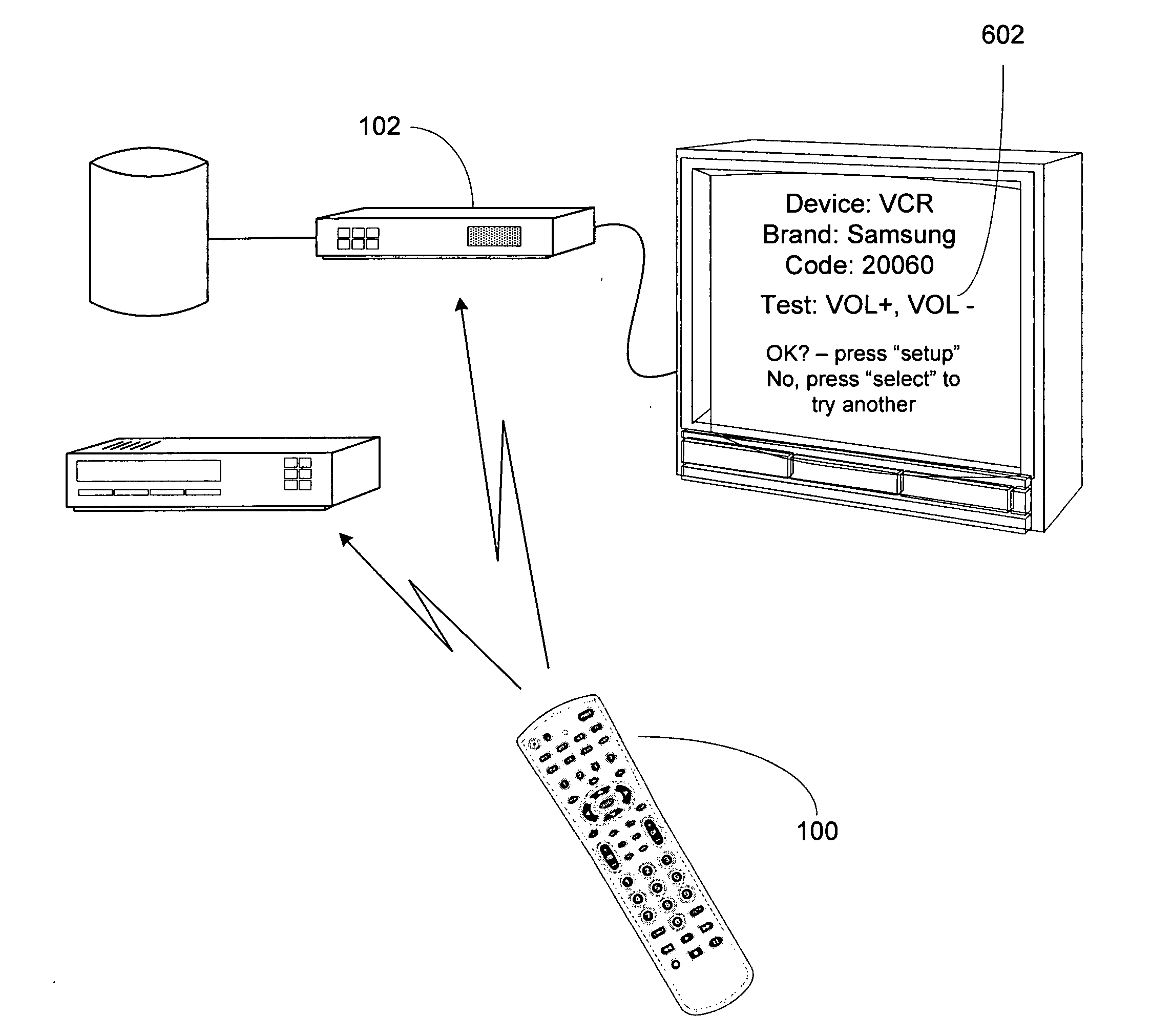
System and method for simplified setup of a universal remote control
ActiveUS20070052547A1Easy to configureEasy SetupTelevision system detailsElectric signal transmission systemsRemote controlHuman–computer interaction
A system and method for enabling set up of a controlling device capable of controlling a plurality of appliances, via an interactive instruction set and associated programming. The programming is accessible by a STB or other controllable appliance and is configured to appropriately display interactive instructions and prompts to a user during a user initiated set up procedure for configuration of another controllable device (e.g., DVD, VCR, DVR, etc) available to the user. Appropriate set up data, generally in the form of command library codes, is displayed to the user by the interactive instruction set and associated programming for entry and trial by the user in set up of the desired appliance(s).
Owner:UNIVERSAL ELECTRONICS INC
Single integrated circuit embodying a risc processor and a digital signal processor
InactiveUS6260088B1Save spaceImprove versatilityGeneral purpose stored program computerMultiple digital computer combinationsDigital signal processingComputer image
A single integrated circuit includes first and second data processors operating on different instruction sets independently operating on disjoint programs and data. The single integrated circuit preferably includes an external interface, a shared data transfer controller and shared memory divided into plural independently accessible memory banks. The two data processors are preferably a digital signal processor (DSP) and a reduced instruction set computer (RISC) processor. The DSP and RISC processors are suitably programmed to perform differing aspects of computer image processing.
Owner:TEXAS INSTR INC
Distributed computing architecture and associated method of providing a portable user environment
InactiveUS20070118609A1Multiple digital computer combinationsTransmissionGraphicsGraphical user interface
A client terminal presents a graphical user interface (GUI) to a distributed computing environment. A first interface is configured to receive data of a portable storage medium. The data includes a key authentication signal and user settings. The key authentication signal identifies an authorized user of the distributed computing environment. A second interface is configured to communicate with an operably linked server. A controller is operative to verify the key authentication signal provided to the first interface in accordance with a distributed computing instruction set, and, upon verification, establishing communication with the operably linked server via the second interface. In this way, the server executes server side applications accessed by a user from the client terminal in accordance with the user settings.
Owner:FRANCE TELECOM SA
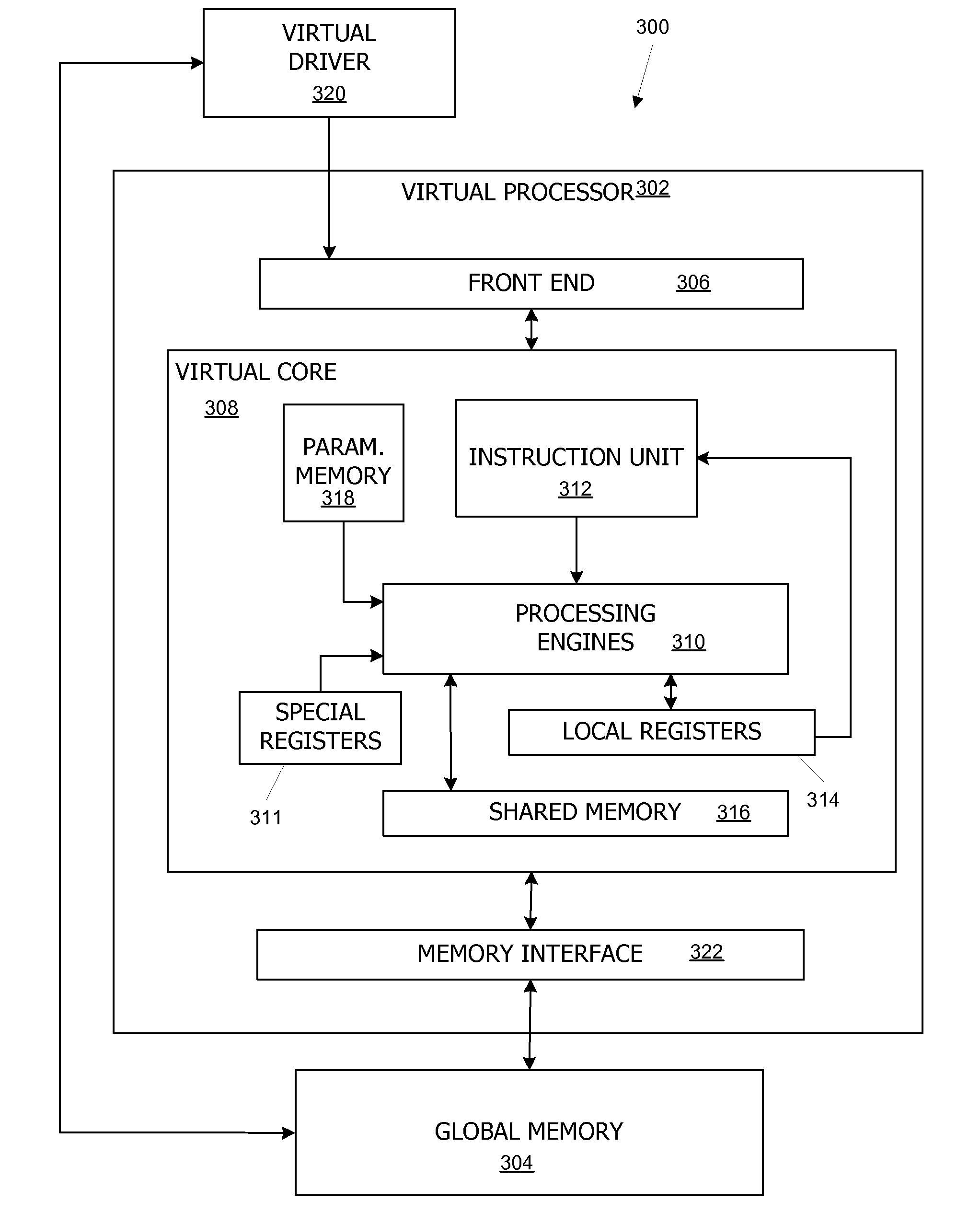
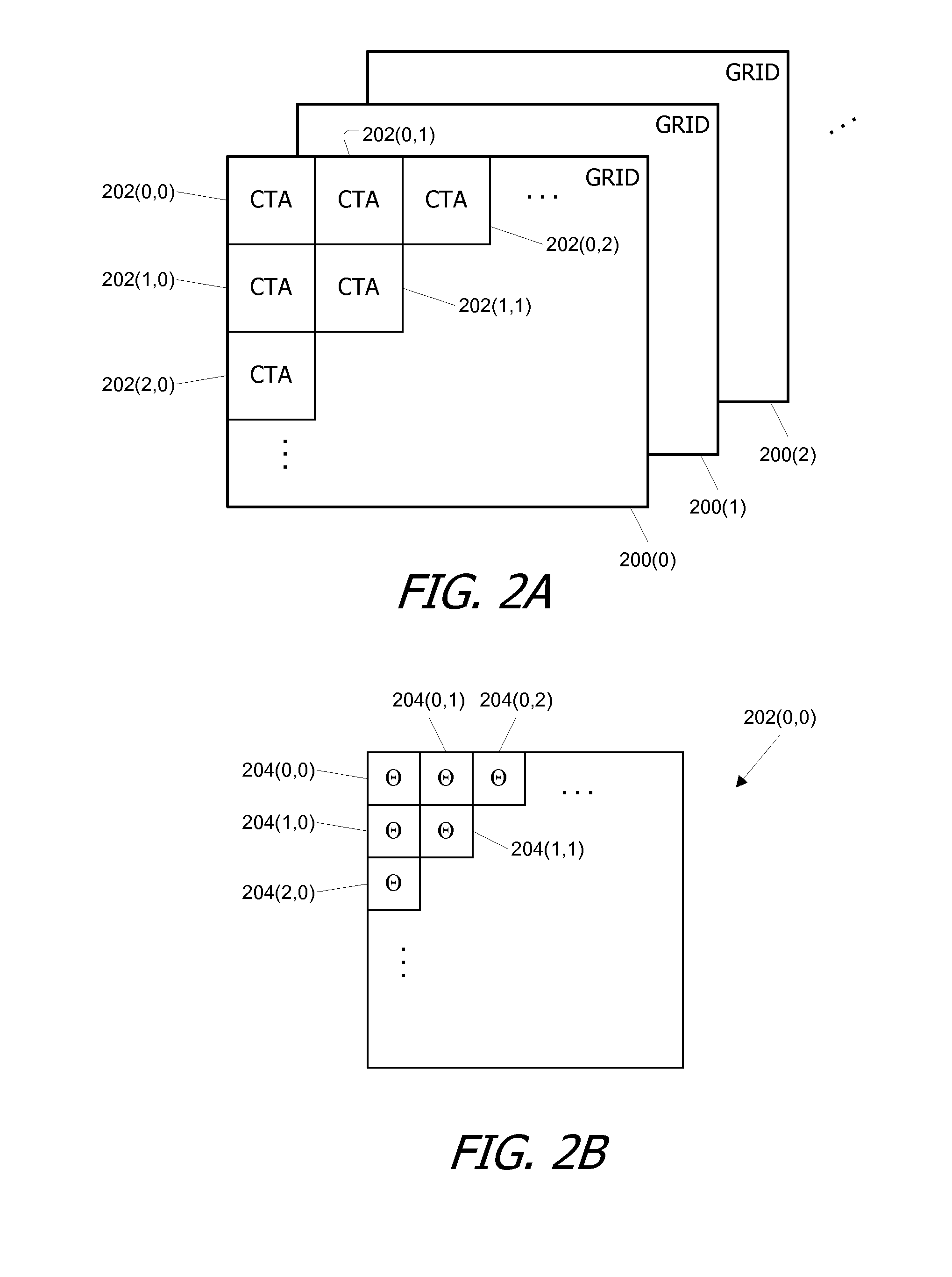
Virtual architecture and instruction set for parallel thread computing
ActiveUS20080184211A1Improve developmentImprove portabilityProgram control using stored programsSoftware engineeringApplication softwareData sharing
A virtual architecture and instruction set support explicit parallel-thread computing. The virtual architecture defines a virtual processor that supports concurrent execution of multiple virtual threads with multiple levels of data sharing and coordination (e.g., synchronization) between different virtual threads, as well as a virtual execution driver that controls the virtual processor. A virtual instruction set architecture for the virtual processor is used to define behavior of a virtual thread and includes instructions related to parallel thread behavior, e.g., data sharing and synchronization. Using the virtual platform, programmers can develop application programs in which virtual threads execute concurrently to process data; virtual translators and drivers adapt the application code to particular hardware on which it is to execute, transparently to the programmer.
Owner:NVIDIA CORP
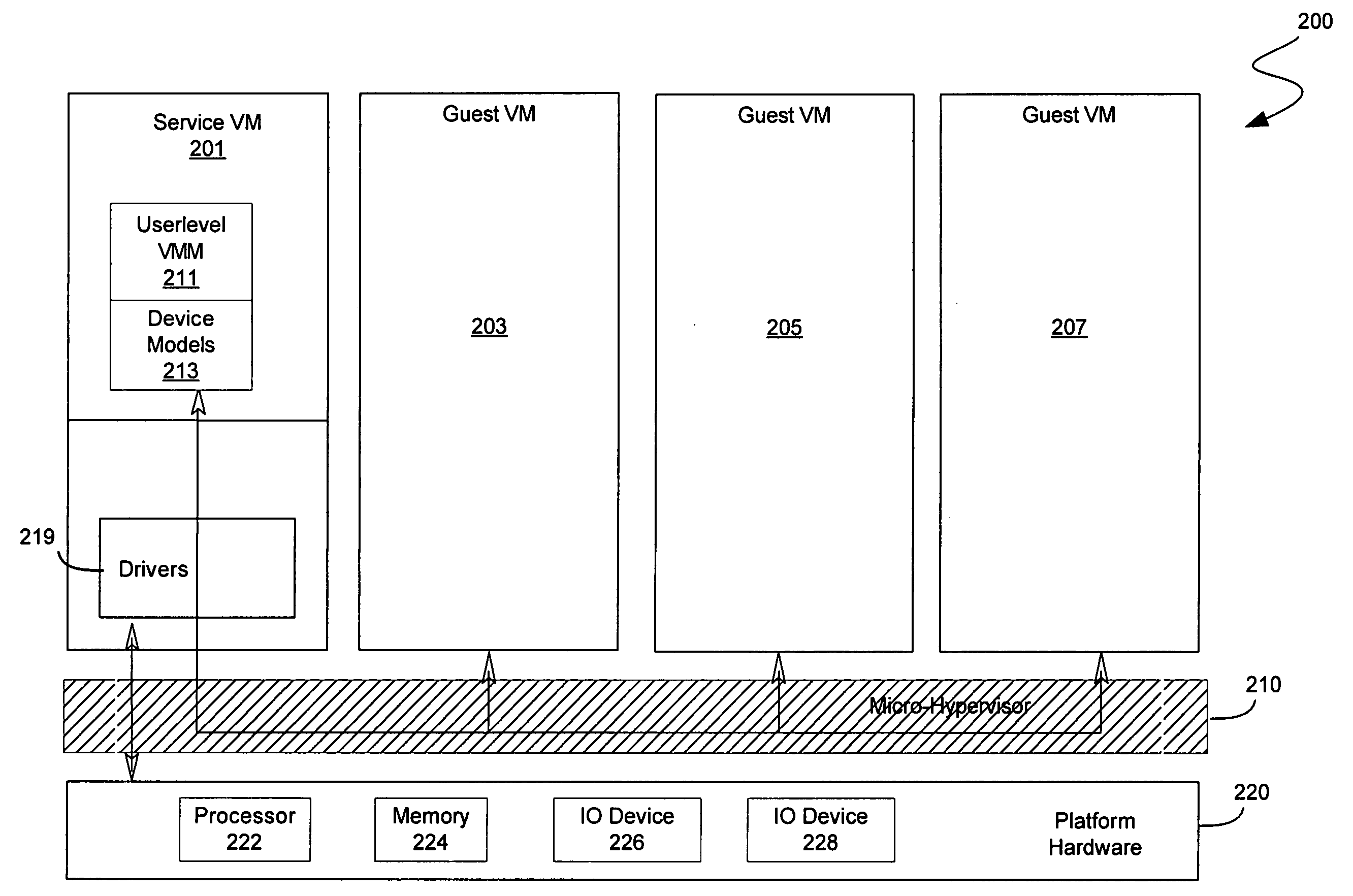
System and method to deprivilege components of a virtual machine monitor
ActiveUS20060130060A1High portability and reliabilityMultiprogramming arrangementsSoftware simulation/interpretation/emulationPrivilege levelHardware virtualization
In some embodiments, the invention involves a system to deprivilege components of a virtual machine monitor and enable deprivileged service virtual machines (SVMs) to handle selected trapped events. An embodiment of the invention is a hybrid VMM operating on a platform with hardware virtualization support. The hybrid VMM utilizes features from both hypervisor-based and host-based VMM architectures. In at least one embodiment, the functionality of a traditional VMM is partitioned into a small platform-dependent part called a micro-hypervisor (MH) and one or more platform-independent parts called service virtual machines (SVMs). The micro-hypervisor operates at a higher virtual machine (VM) privilege level than any SVM, while the SVM and other VMs may still have access to any instruction set architecture (ISA) privilege level. Other embodiments are described and claimed.
Owner:INTEL CORP
Navigation instructions
Systems and methods are provided for improved navigation instructions. In one implementation instructions between two locations can be computed, the instructions can be processed in relation to previously computed instructions between the same locations and / or a previously traveled route between the same locations to determine disparitie(s) therebetween, and a notification can be generated based on the disparitie(s). In another implementation, one set of instructions between two locations can be received, another set of instructions between two other locations can be received, the sets of instructions can be processed to determine disparities between them with respect to one or more locations, a notification can be generated based on the one or more disparities, and the notification can be provided in relation to the location(s).
Owner:CELLEPATHY
Method and associated apparatus for the standardized grading of gemstones
InactiveUS6980283B1Process safetyInvestigating jewelsSpecial data processing applicationsSpectral responseData set
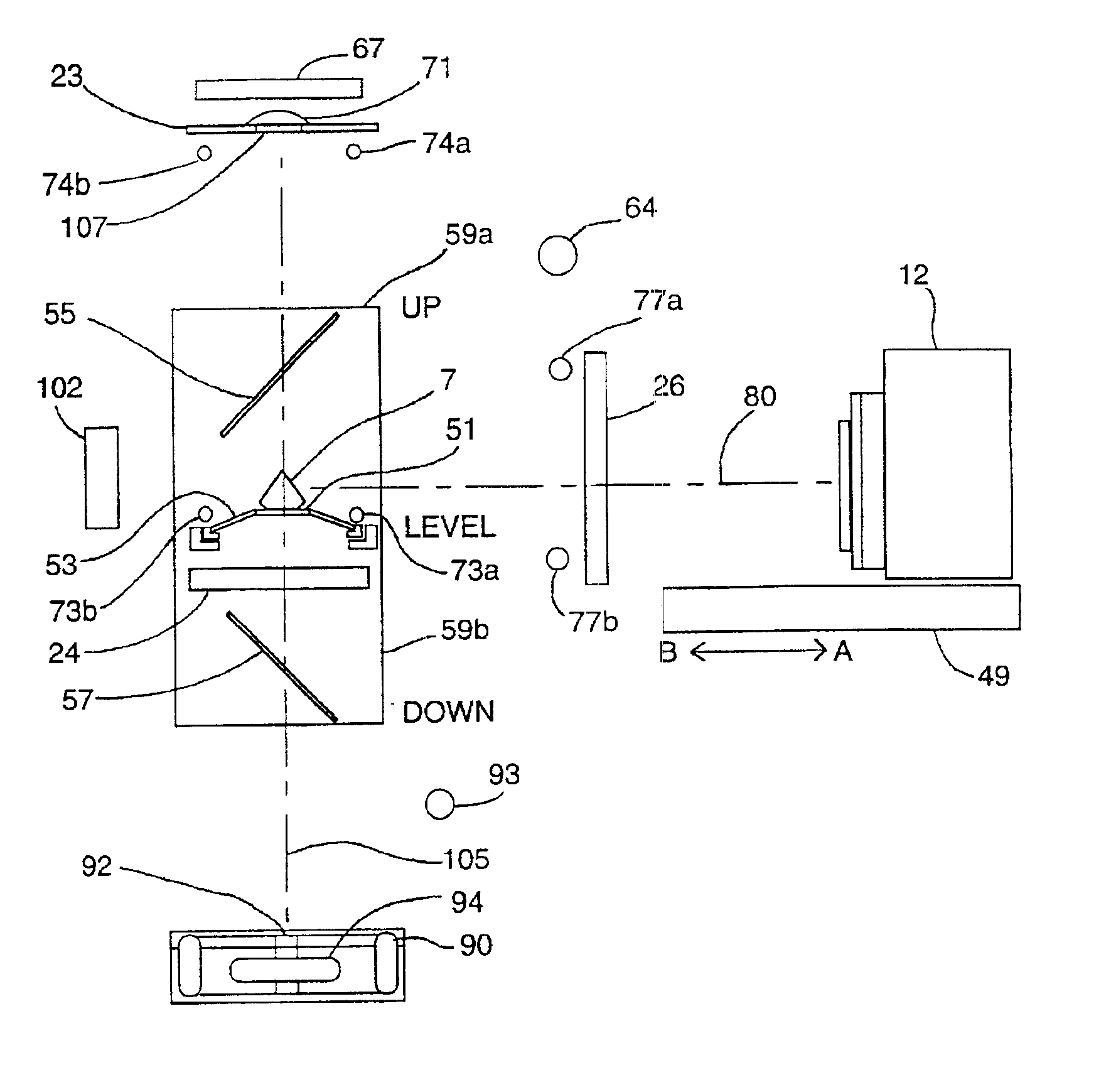
A method and associated apparatus (5) for the standardized grading of gemstones is provided. The system gauges the spectral response of a gemstone subject to a plurality of incident light sources (77, 64, 90, 92, 102) within an imaging apparatus. The operation of the imaging apparatus is controlled by an instruction set of a local station control data processor (12). Light energy data is captured in the form of pixel data sets via a charge coupled device of the imaging apparatus of the local station (8). The control data processor data of the local station is operably linked to analysis station (14). Gemstones qualities are analyzed by the plurality of light sources (92, 90, 102) of the imaging apparatus (5) and quantified relative to model pixel data sets of the database and recorded for future reference therein.
Owner:IMAGESTATISTICS
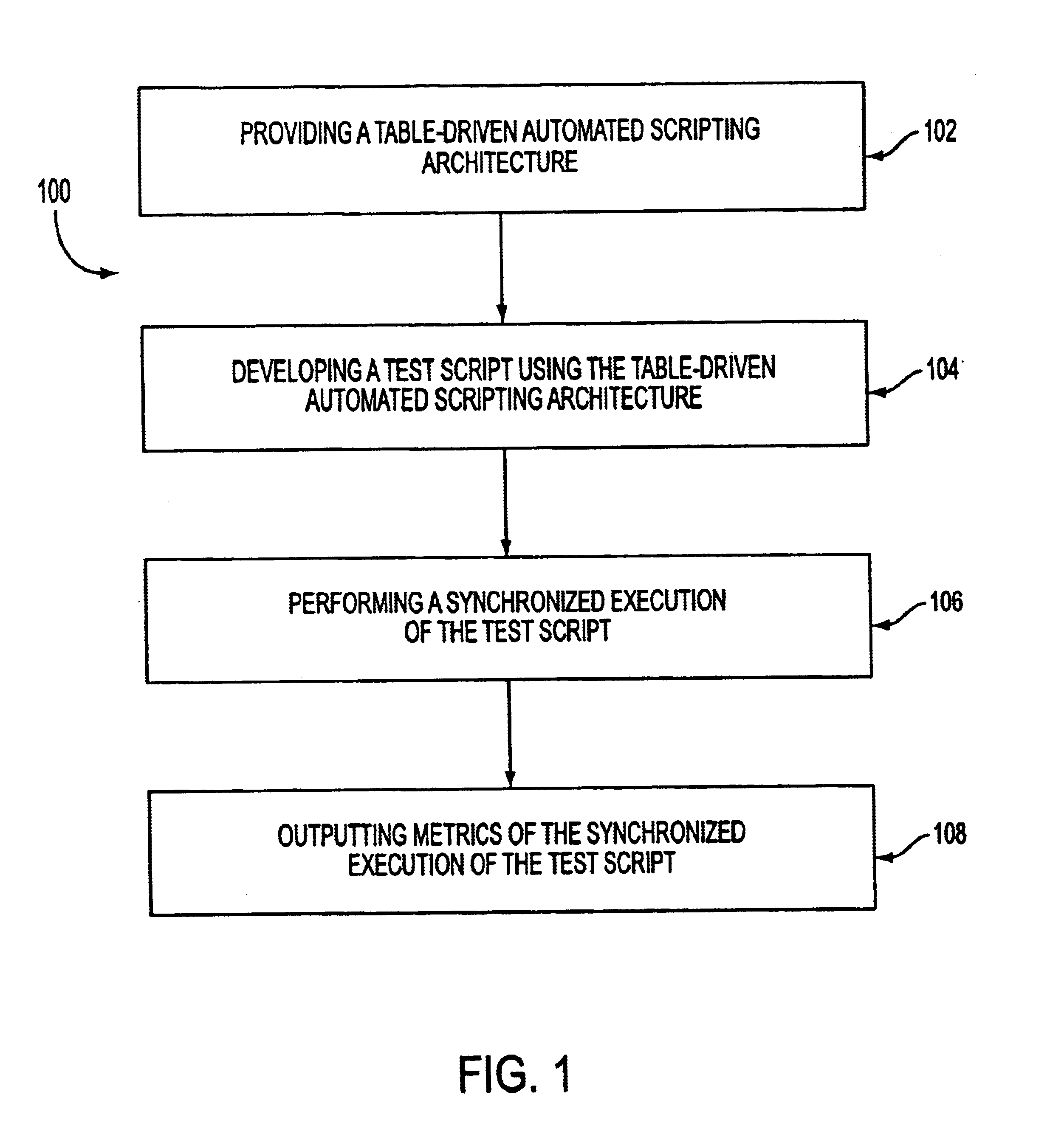
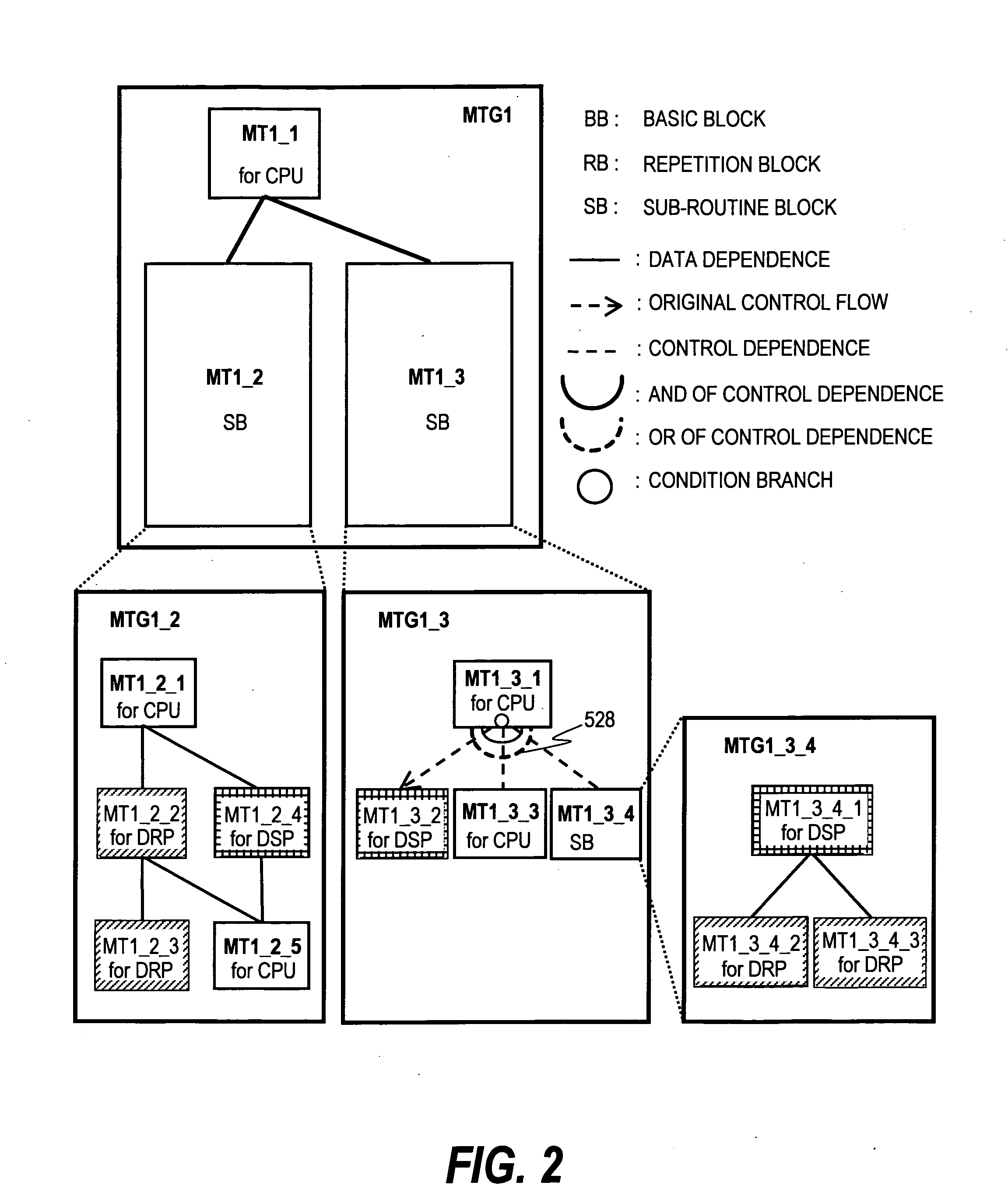
Method for controlling heterogeneous multiprocessor and multigrain parallelizing compiler
ActiveUS20070283358A1Improve efficiencyOverhead required can be suppressedEnergy efficient ICTResource allocationGeneral purposeCost comparison
A heterogeneous multiprocessor system including a plurality of processor elements having mutually different instruction sets and structures avoids a specific processor element from being short of resources to improve throughput. An executable task is extracted based on a preset depending relationship between a plurality of tasks, and the plurality of first processors are allocated to a general-purpose processor group based on a depending relationship among the extracted tasks. A second processor is allocated to an accelerator group, a task to be allocated is determined from the extracted tasks based on a priority value for each of tasks, and an execution cost of executing the determined task by the first processor is compared with an execution cost of executing the task by the second processor. The task is allocated to one of the general-purpose processor group and the accelerator group that is judged to be lower as a result of the cost comparison.
Owner:WASEDA UNIV
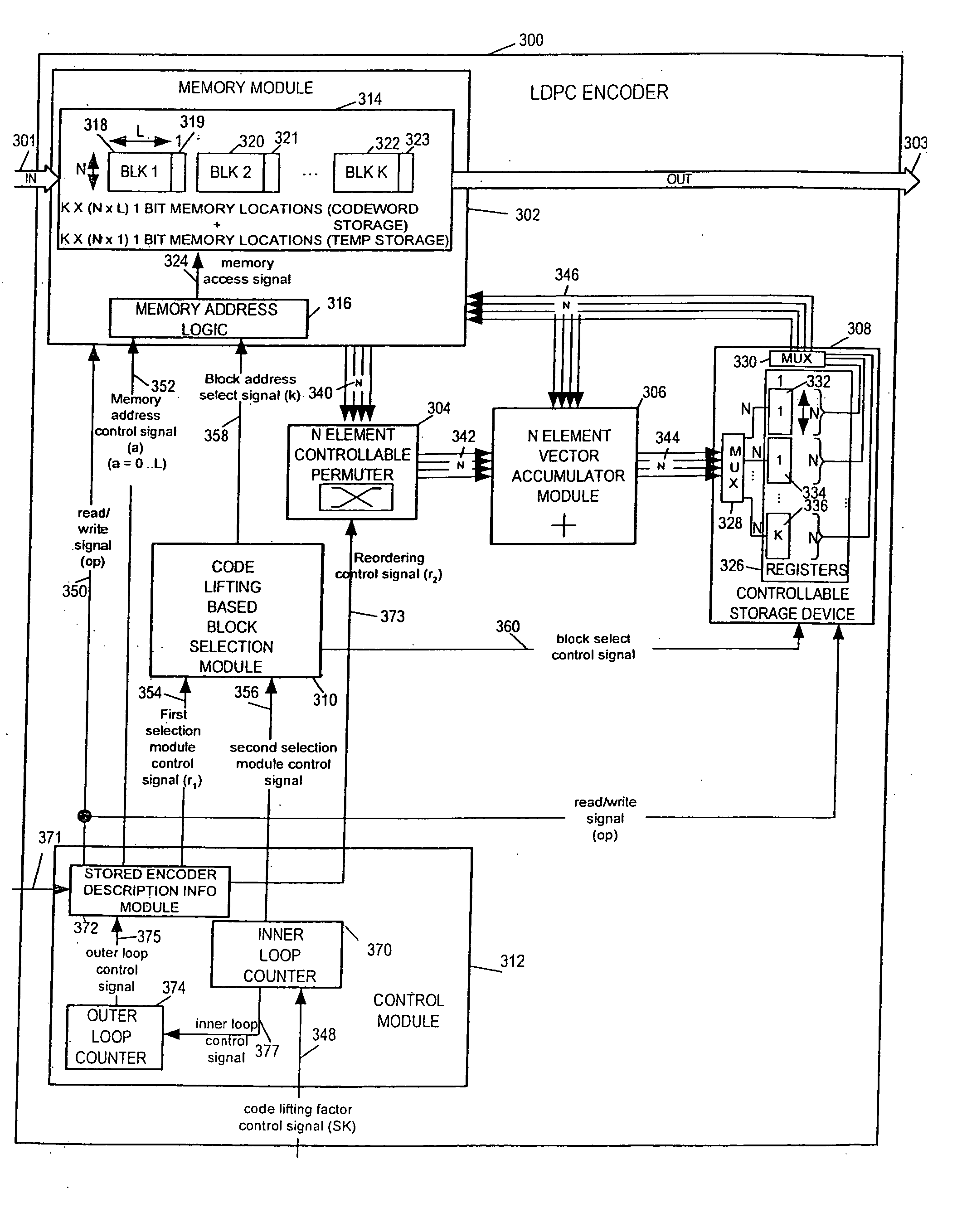
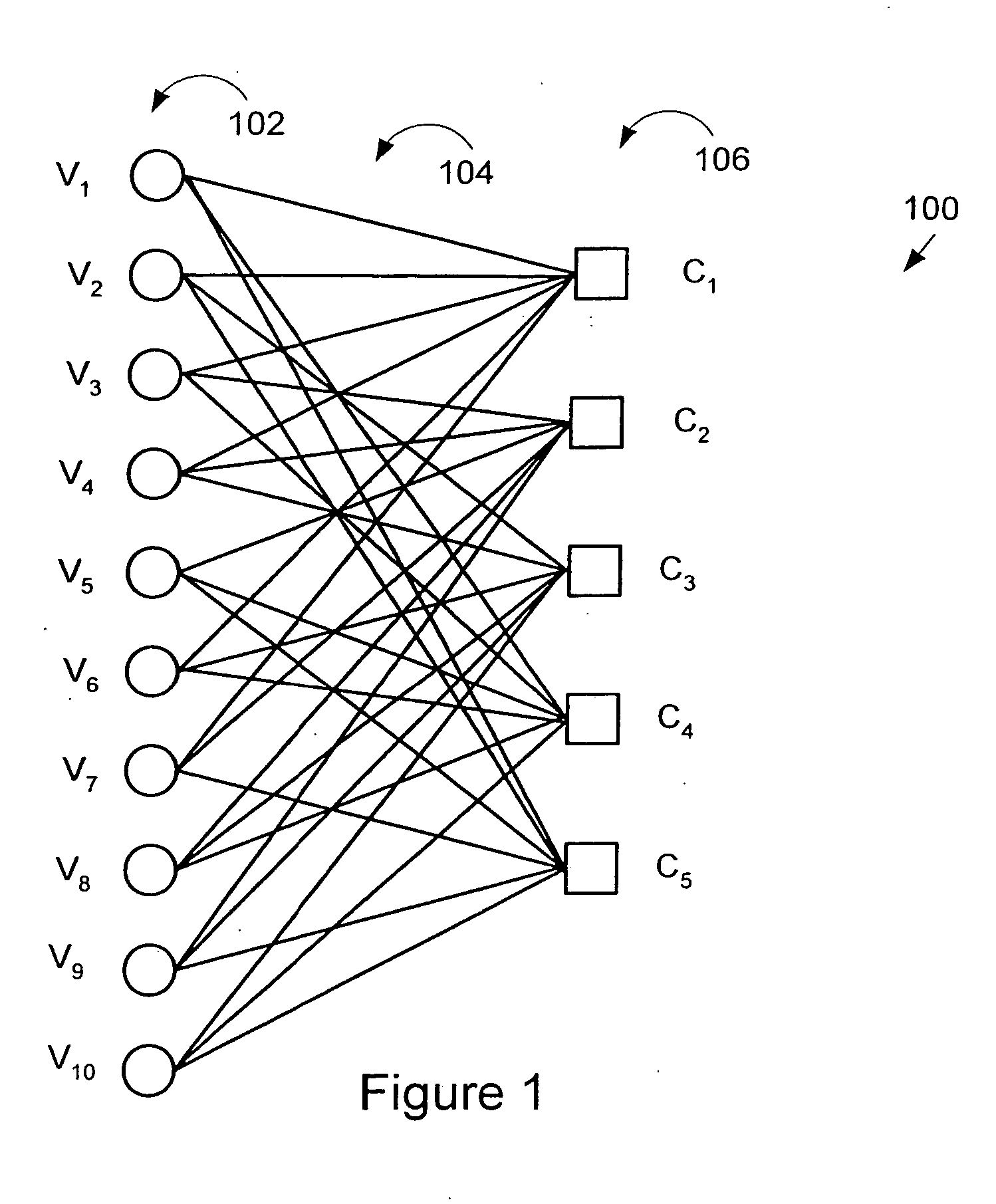
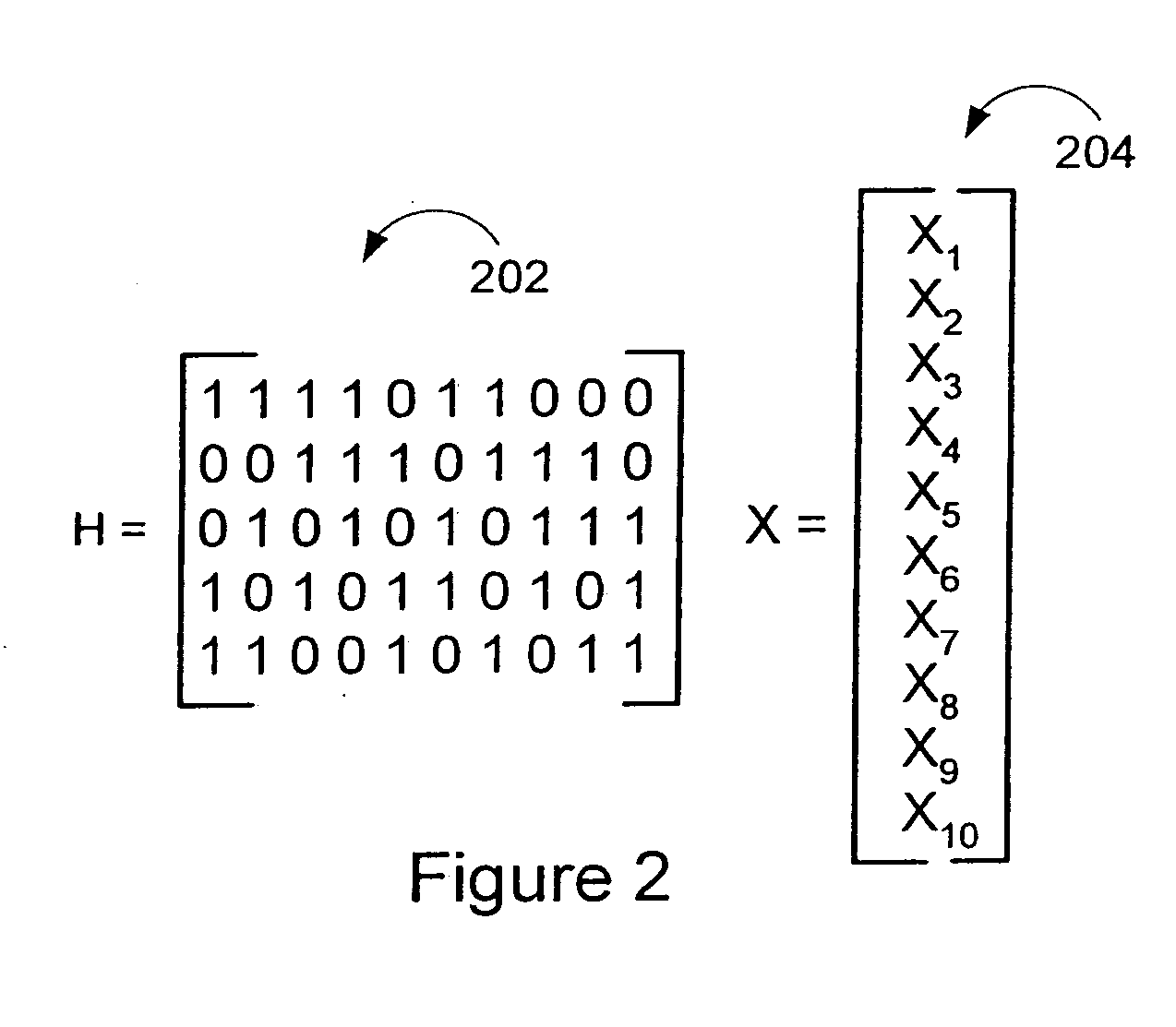
LDPC encoding methods and apparatus
ActiveUS20060020872A1Simple microcodeEasy to modifyError correction/detection using multiple parity bitsCode conversionDegree of parallelismInstruction set
A flexible and relatively hardware efficient LDPC encoder is described. The encoder can be implemented with a level of parallelism which is less than the full parallelism of the code structure used to control the encoding process. Each command of a relatively simple microcode used to describe the code structure can be stored and executed multiple times to complete the encoding of a codeword. Different codeword lengths can be supported using the same set of microcode instructions but with the code being implemented a different number of times depending on the lifting factor selected to be used. The LDPC encoder can switch between encoding codewords of different lengths, without the need to change the stored code description information, by simply changing a code lifting factor used to control the encoding processes. When coding codewords shorter than the maximum supported codeword length some block storage locations and / or registers may go unused.
Owner:QUALCOMM INC
Multiple platform support system and method
InactiveUS20120138685A1Sensing detailsSoftware simulation/interpretation/emulationSupporting systemData terminal
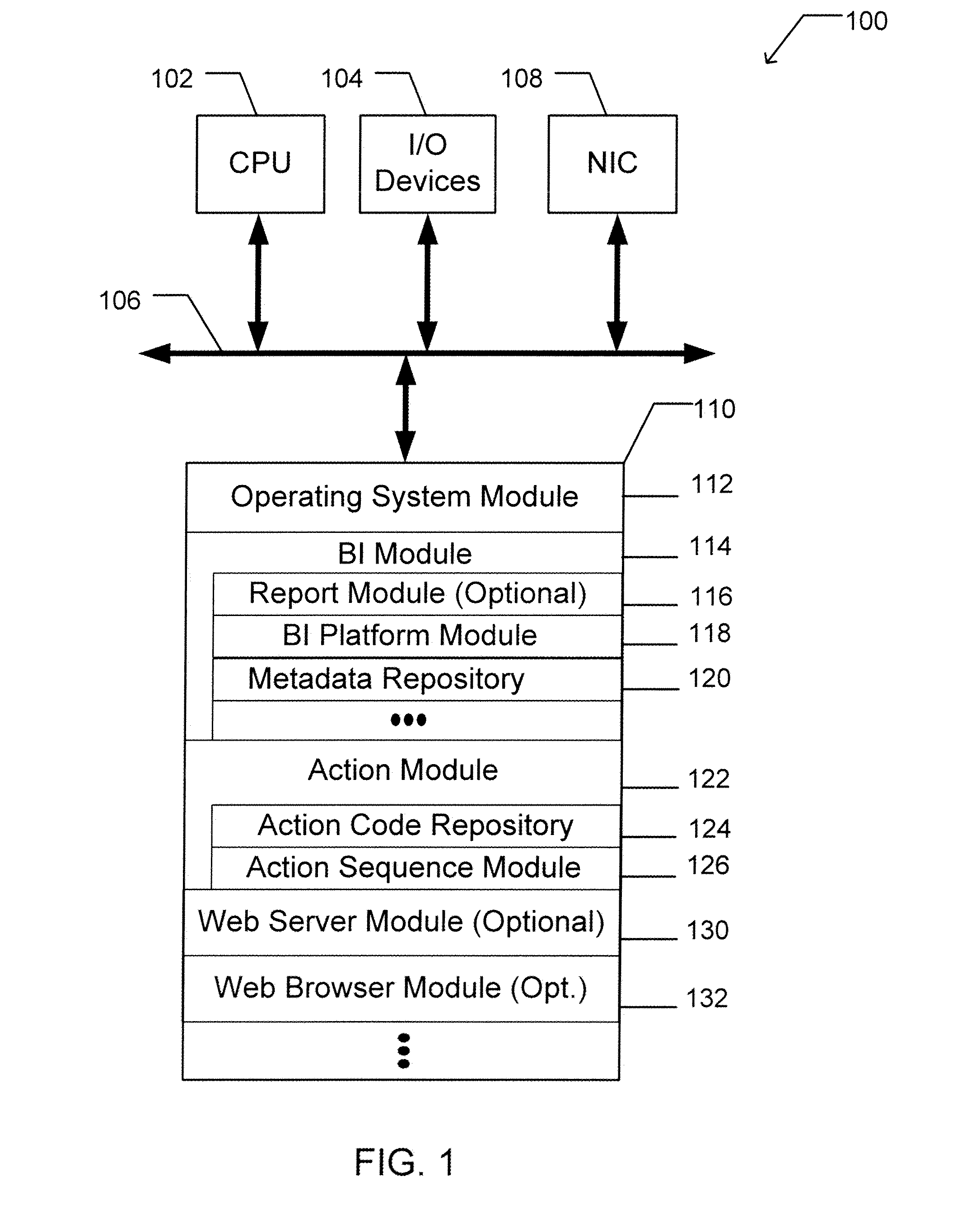
A portable data terminal including a processor having an instruction set architecture and data storage means configured to store a plurality of operating systems and a virtual machine monitor application program configured to receive at least one instruction from each operating system, communicate with the processor according to the instruction set architecture, and switch operating system access to the processor upon receipt of an electrical signal representing an event.
Owner:HAND HELD PRODS
Native copy instruction for file-access processor with copy-rule-based validation
InactiveUS7191318B2Digital computer detailsSpecific program execution arrangementsCrossbar switchGeneral purpose
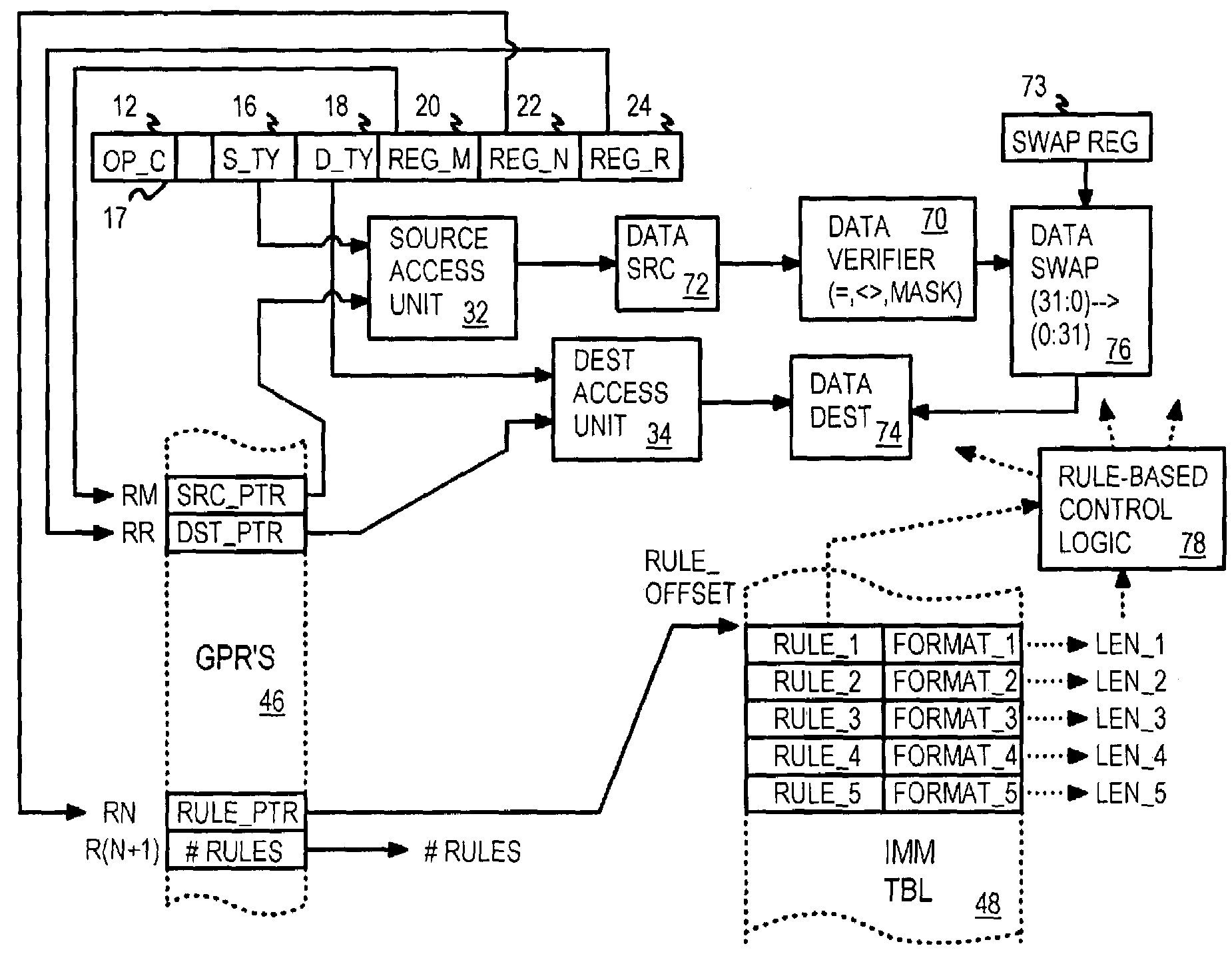
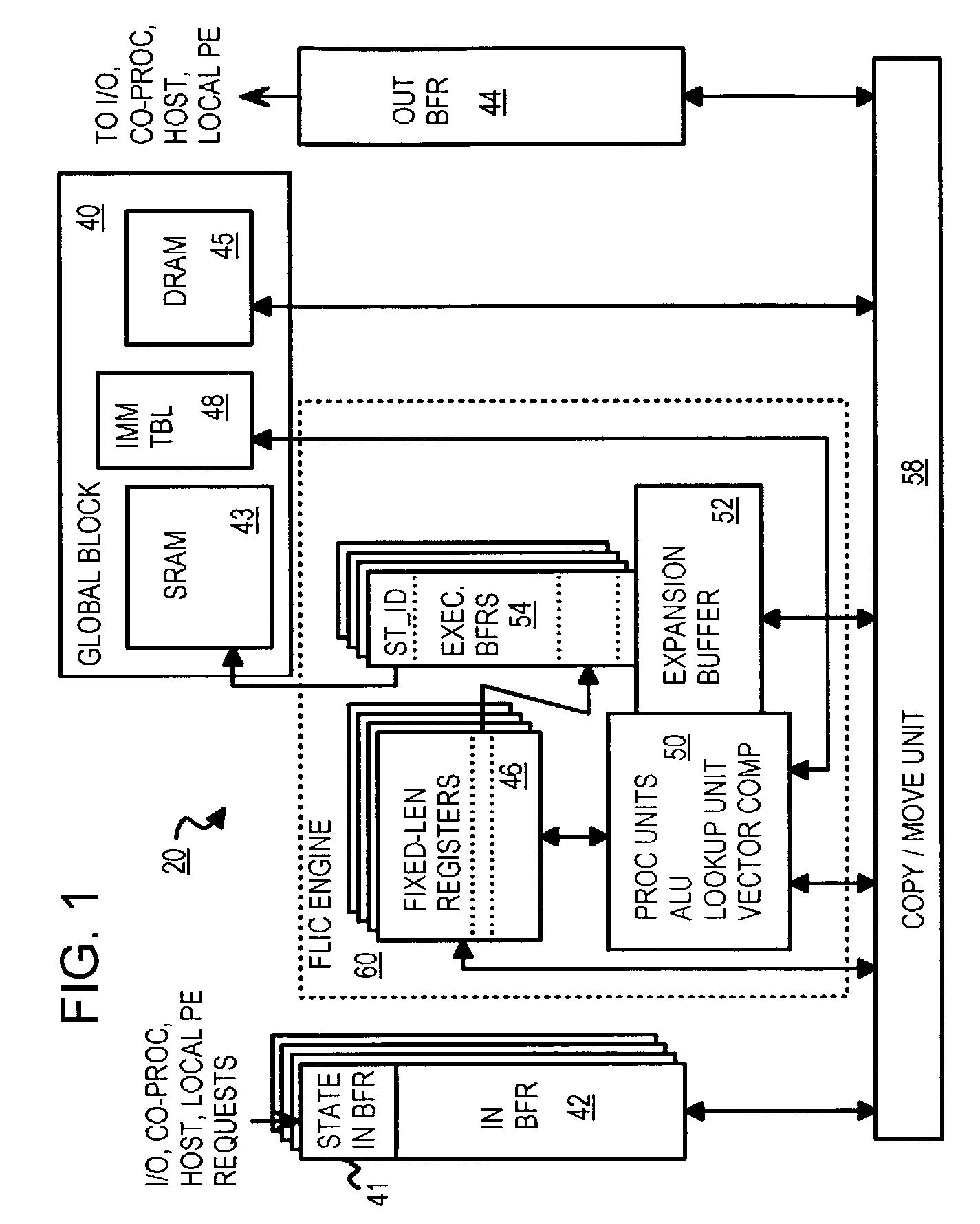
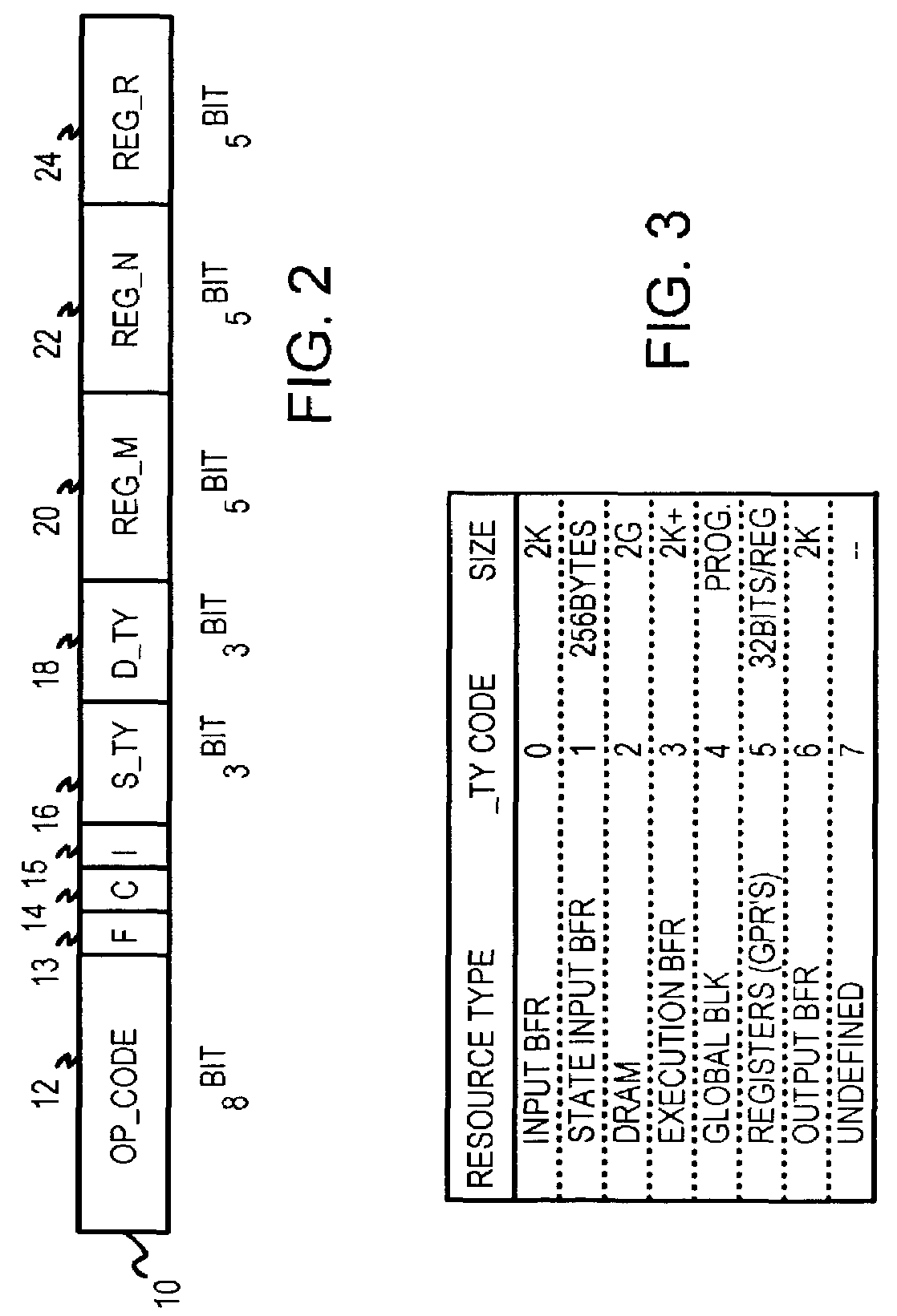
A copy instruction executed by a functional-level instruction-set computing (FLIC) processor copies a variable-length data block from one resource to another resource through a cross-bar switch. Resources include general-purpose registers, input, output, and execution buffers, DRAM, SRAM, and other memory. A copy-with-validate instruction has an operand pointing to a first rule in an immediate rule table. The first rule controls validation of a first data-item in the data being copied. Validation includes range and equality checking of the data-item. The value of the data-item or the current offset can be written to a register. A format field in the rule indicates the size of the data-item, or the size is read from the data-item for variable-size formats. The current offset is incremented by the size. The next data-item is validated by a next rule, and other rules in the immediate table control validation of other data-items in the data block.
Owner:RPX CORP
Methods and systems for receiving and viewing content-rich communications
InactiveUS6965926B1Quick and efficient accessMultiple digital computer combinationsOffice automationInformative contentElectronic mail
Methods, systems, and articles of manufacture consistent with the present invention provide the ability to receive a communication (such as an electronic mail message) using a particular content server within a network. A minimal amount of information is received, such as an instruction set and a basic amount of content information. The instruction set is analyzed to determine references to content stored on a particular one of the content servers, namely the content server that is closest to an anticipated access point for the communication. While executing the instruction set and displaying the basic content information, a request for the communication's content is generated and sent to the content server. The content is received from the content server closest to the anticipated access point (typically the one closest to the requesting node), usually in a streaming format. The content is then displayed for the intended recipient.
Owner:ACOUSTIC LP
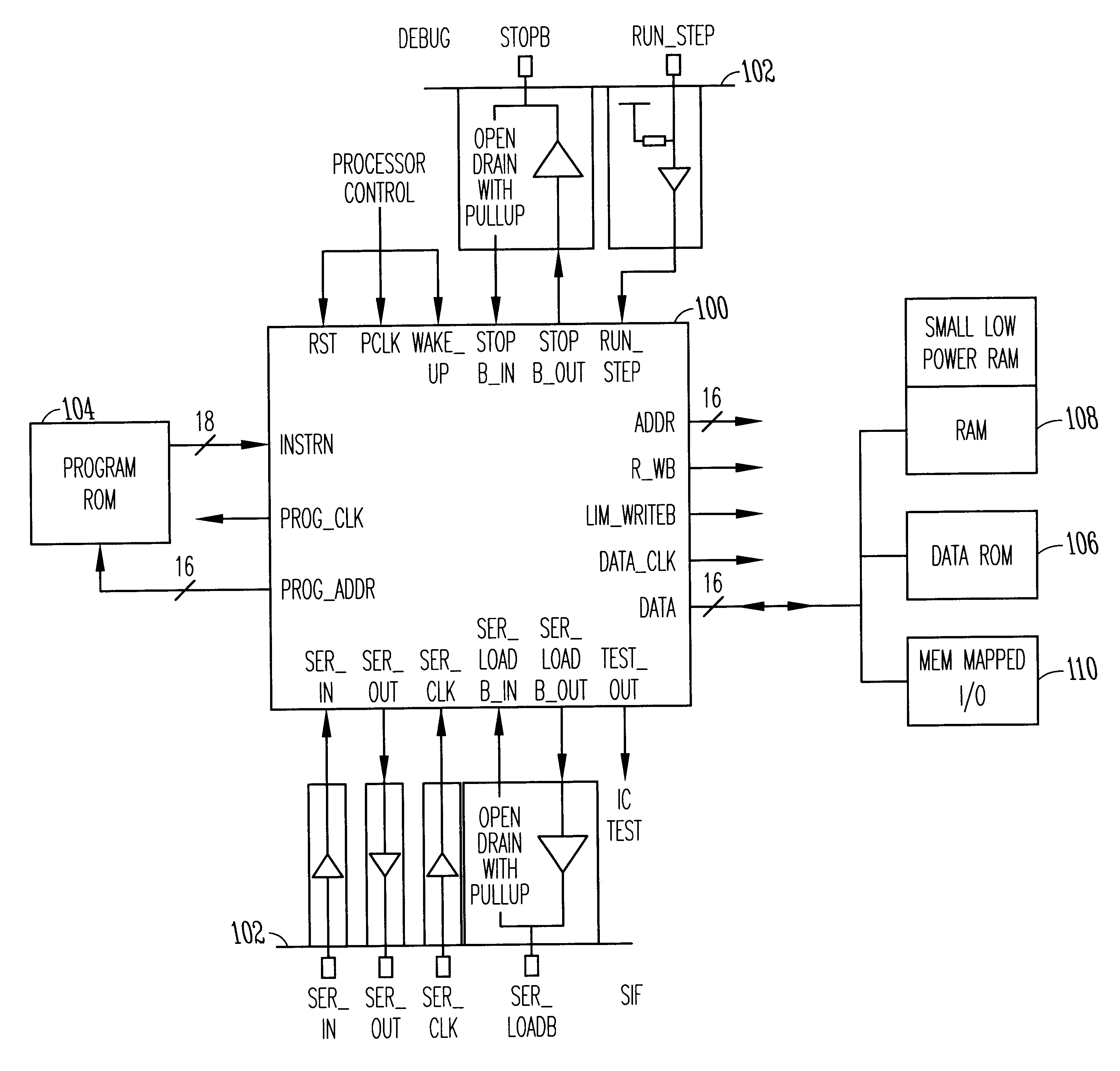
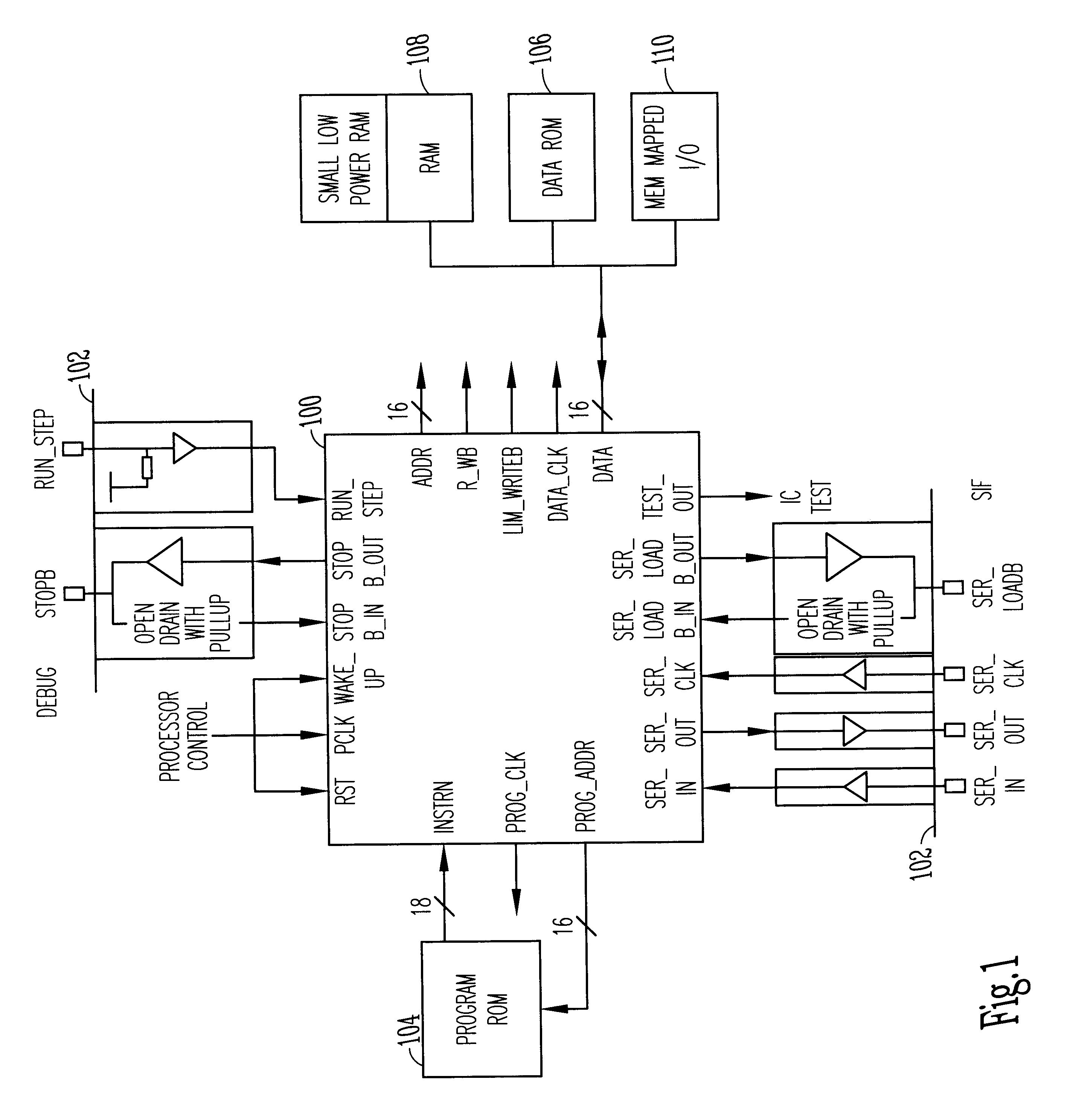
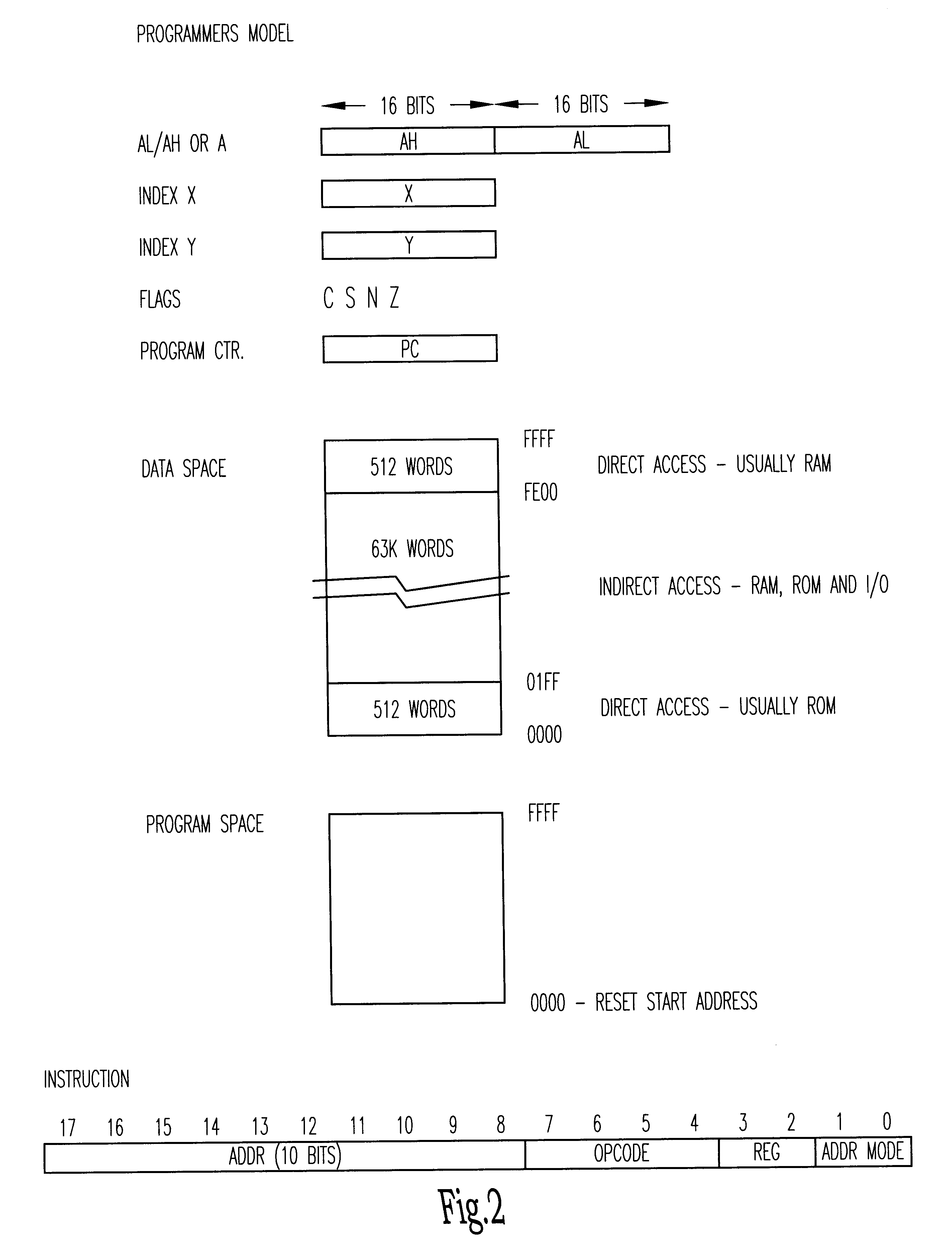
Data processing circuits and interfaces
An integrated circuit contains a microprocessor core, program memory and separate data storage, together with analogue and digital signal processing circuitry. The ALU is 16 bits wide, but a 32-bit shift unit is provided, using a pair of 16-bit registers. The processor has a fixed length instruction format, with an instruction set including multiply and divide operations which use the shift unit over several cycles. No interrupts are provided. External pins of the integrated circuit allow for single stepping and other debug operations, and a serial interface (SIF) which allows external communication of test data or working data as necessary. The serial interface has four wires (SERIN, SEROUT, SER-CLK, SERLOADB), allowing handshaking with a master apparatus, and allowing direct access to the memory space of the processor core, without specific program control. Within each processor cycle, the processor circuitry is divided into plural stages, and latches are interposed between the stages to minimize power consumption.
Owner:CAMBRIDGE CONSULTANTS LTD
Algorithm mapping, specialized instructions and architecture features for smart memory computing
InactiveUS6970988B1Improve performanceLow costMultiplex system selection arrangementsProgram controlSmart memoryExecution unit
A smart memory computing system that uses smart memory for massive data storage as well as for massive parallel execution is disclosed. The data stored in the smart memory can be accessed just like the conventional main memory, but the smart memory also has many execution units to process data in situ. The smart memory computing system offers improved performance and reduced costs for those programs having massive data-level parallelism. This smart memory computing system is able to take advantage of data-level parallelism to improve execution speed by, for example, use of inventive aspects such as algorithm mapping, compiler techniques, architecture features, and specialized instruction sets.
Owner:STRIPE INC
Processor with a function to prevent illegal execution of a program, an instruction executed by a processor and a method of preventing illegal execution of a program
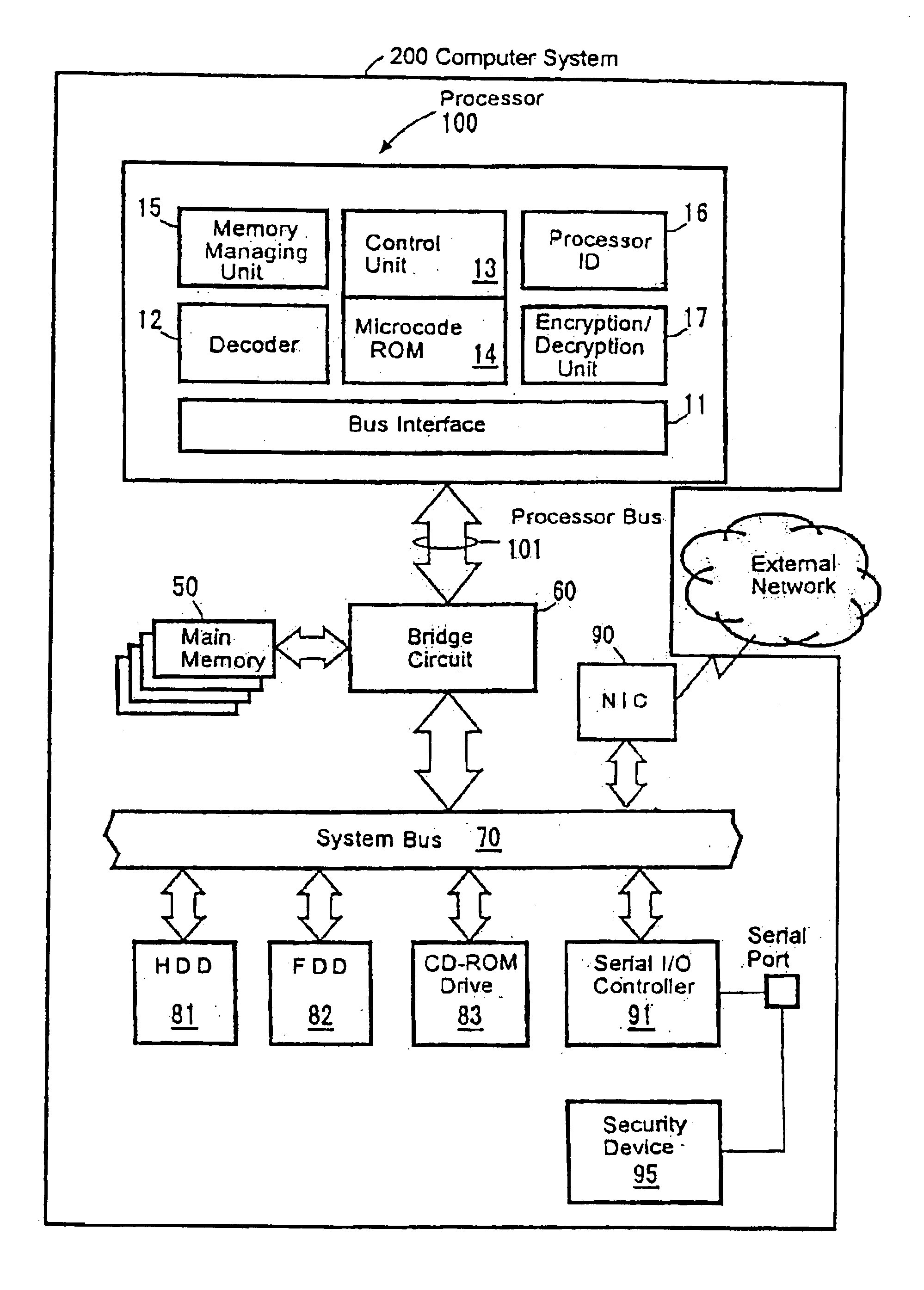
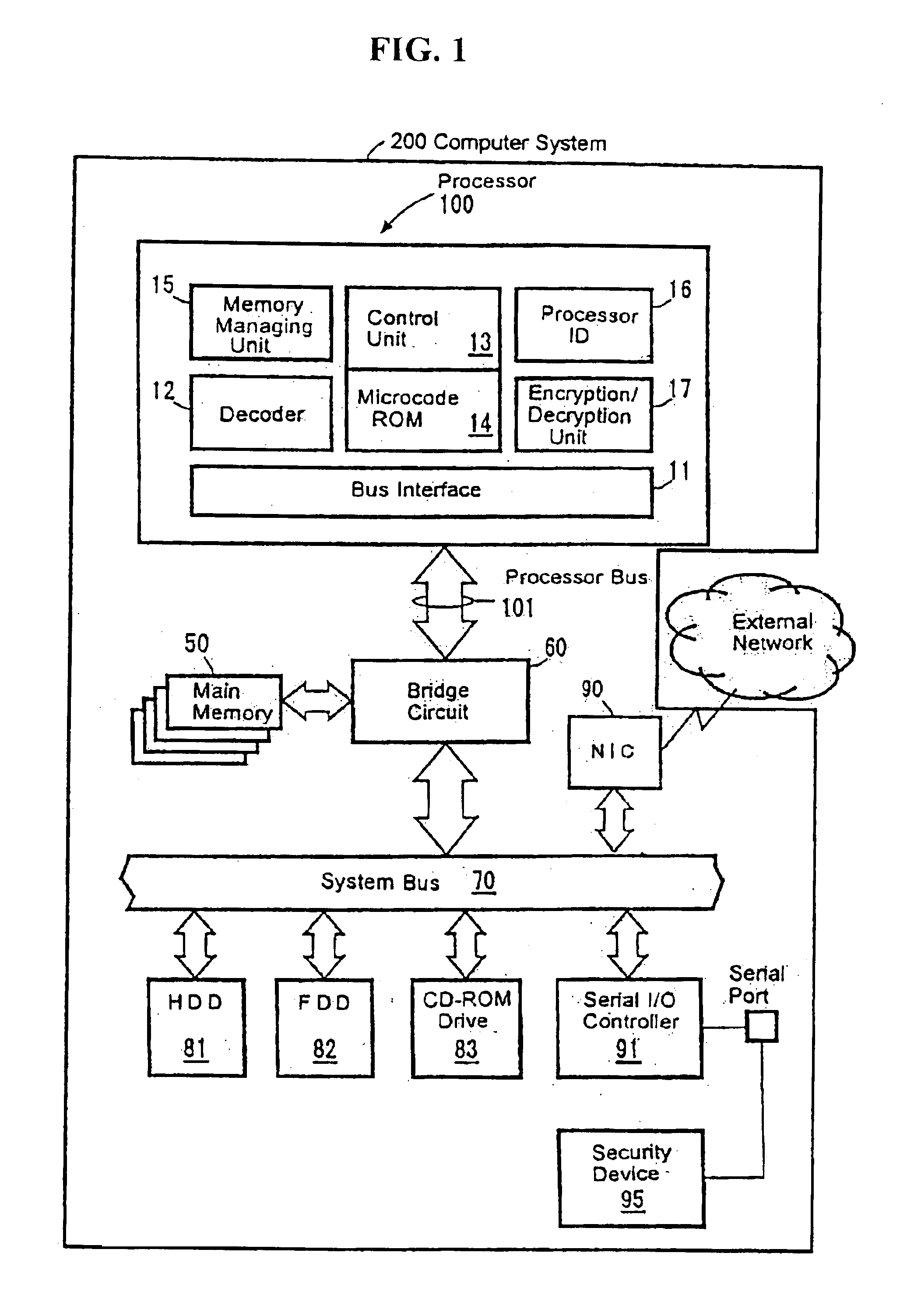
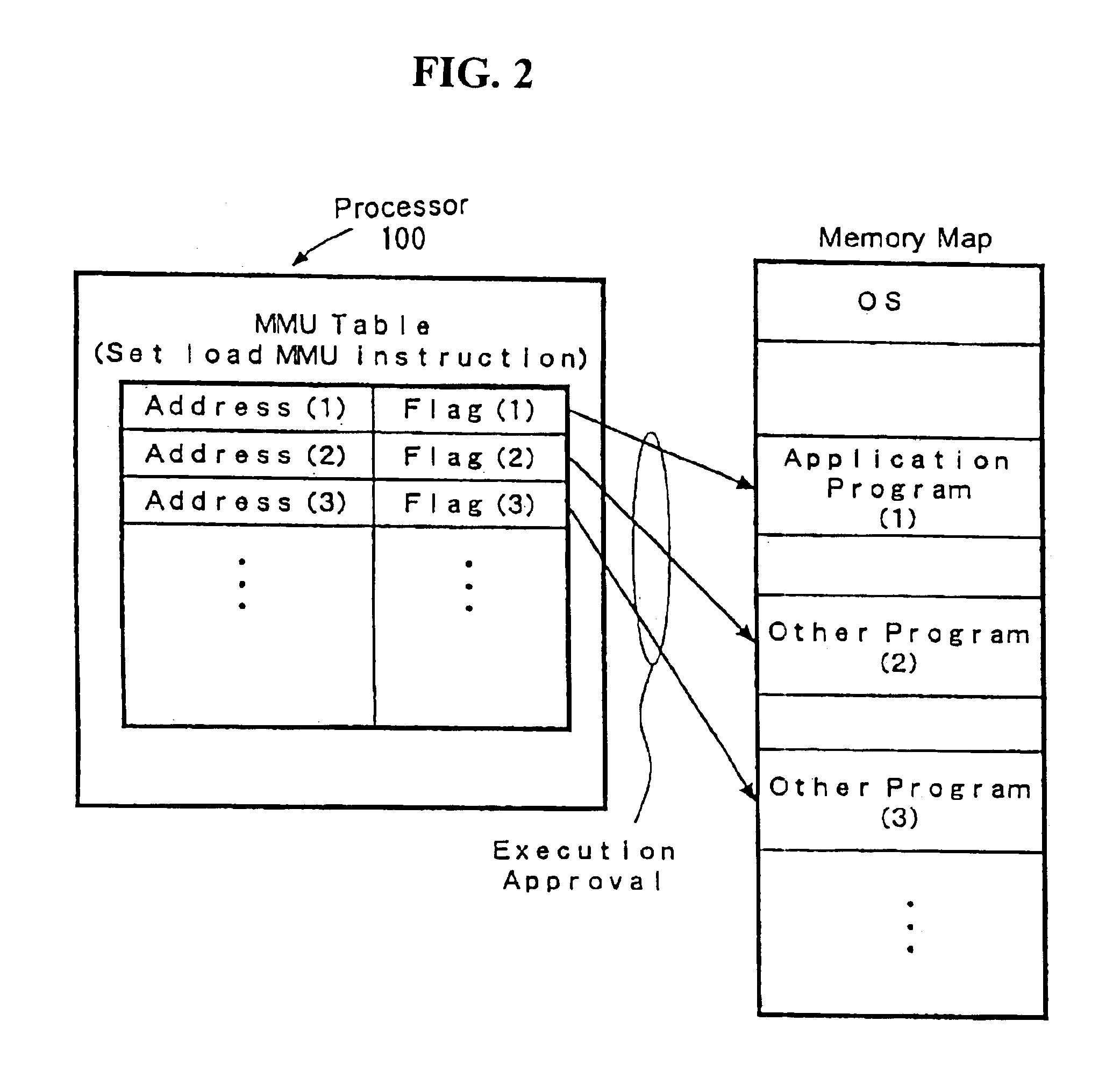
InactiveUS6704872B1Prevent executionAvoid prolonged useUnauthorized memory use protectionHardware monitoringManagement unitComputerized system
The present invention provides an improved technology of preventing illegal use and execution of a software program provided to a computer system. More particularly, the present invention is directed to a Processor of a type in which a memory managing unit is installed therein to manage storing operation of code / data in main memory and includes, as one of instruction set, an execution permitting instruction to permit execution of a program code (application) in the main memory. The procedure of execution permitting instruction is defined by a microprogram and includes an authentication procedure for authenticating the right to use the program beside a procedure for setting predetermined data in the memory managing unit in this invention. Execution of the software program is permitted only when the authentication processing is completed successfully. Because the authentication operation is performed within the processor, it is almost impossible to monitor or detect it from the exterior. Also, by using a processor ID unique to the processor chip as identification information for use in the authentication processing, the right to use a specific software program can be limited to a single processor.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com