Patents
Literature
383results about "Binary to binary" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
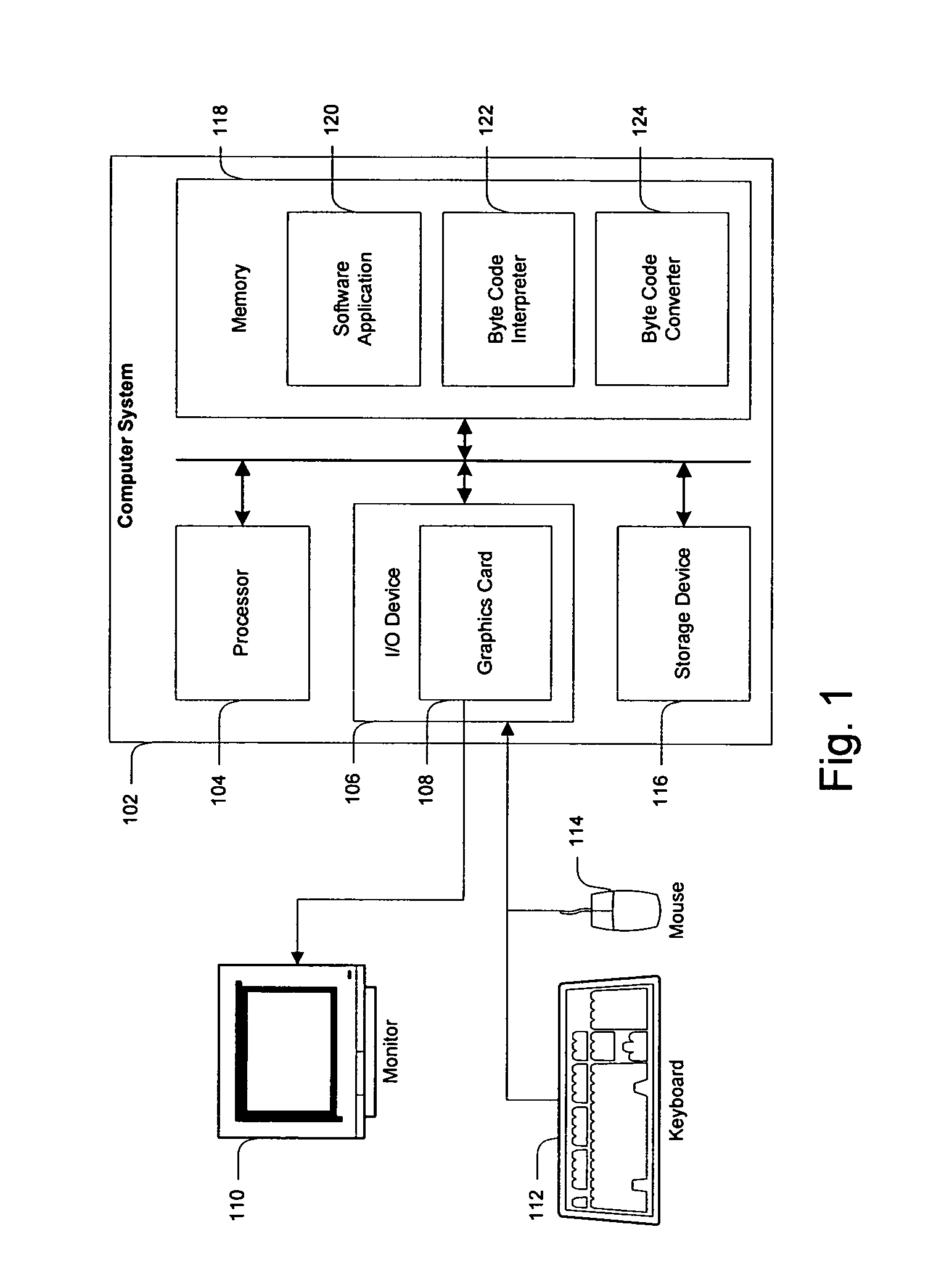
Method and apparatus for creating data transformation routines for binary data
ActiveUS7607120B2Binary to binarySpecific program execution arrangementsData transformationCombined use
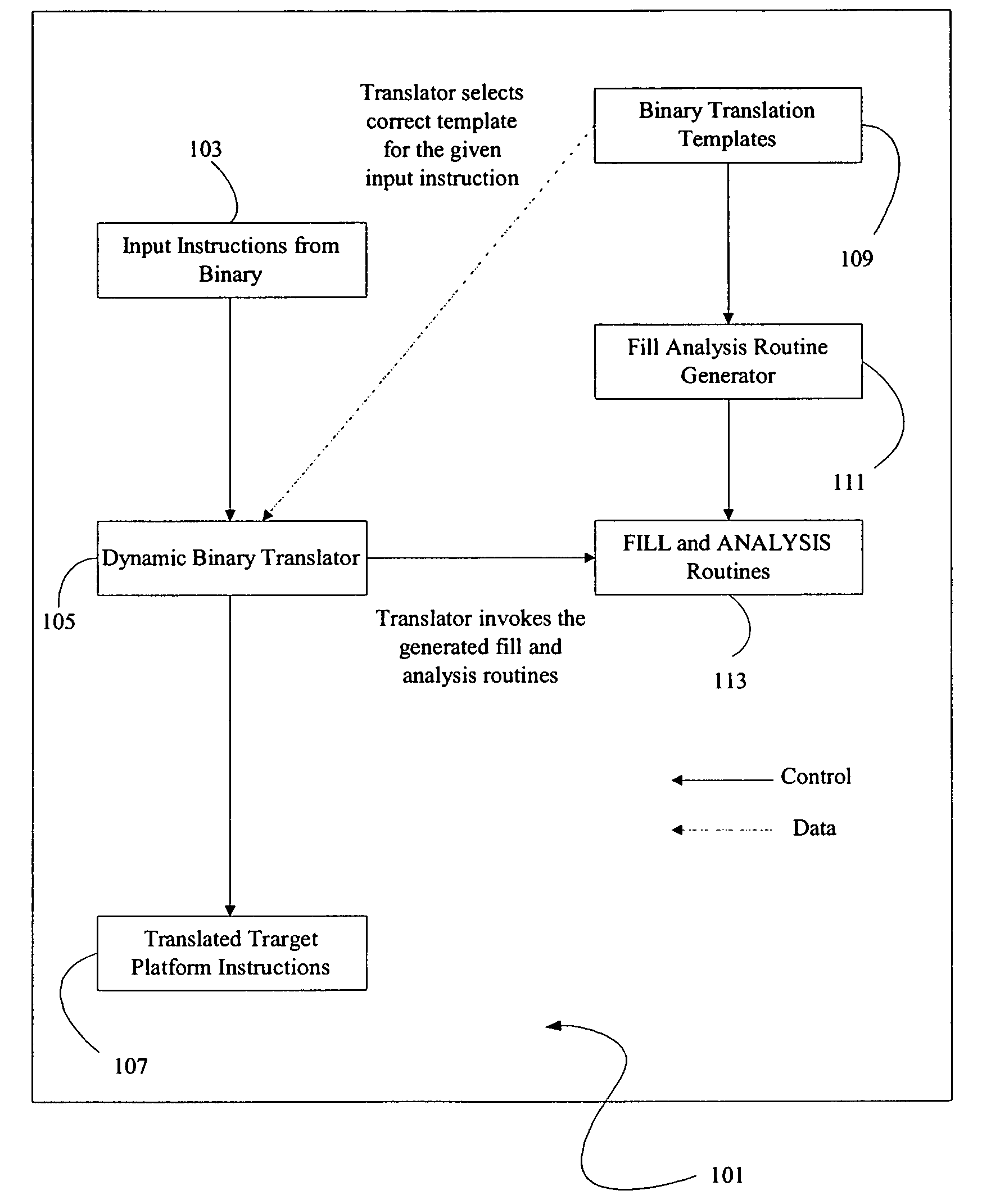
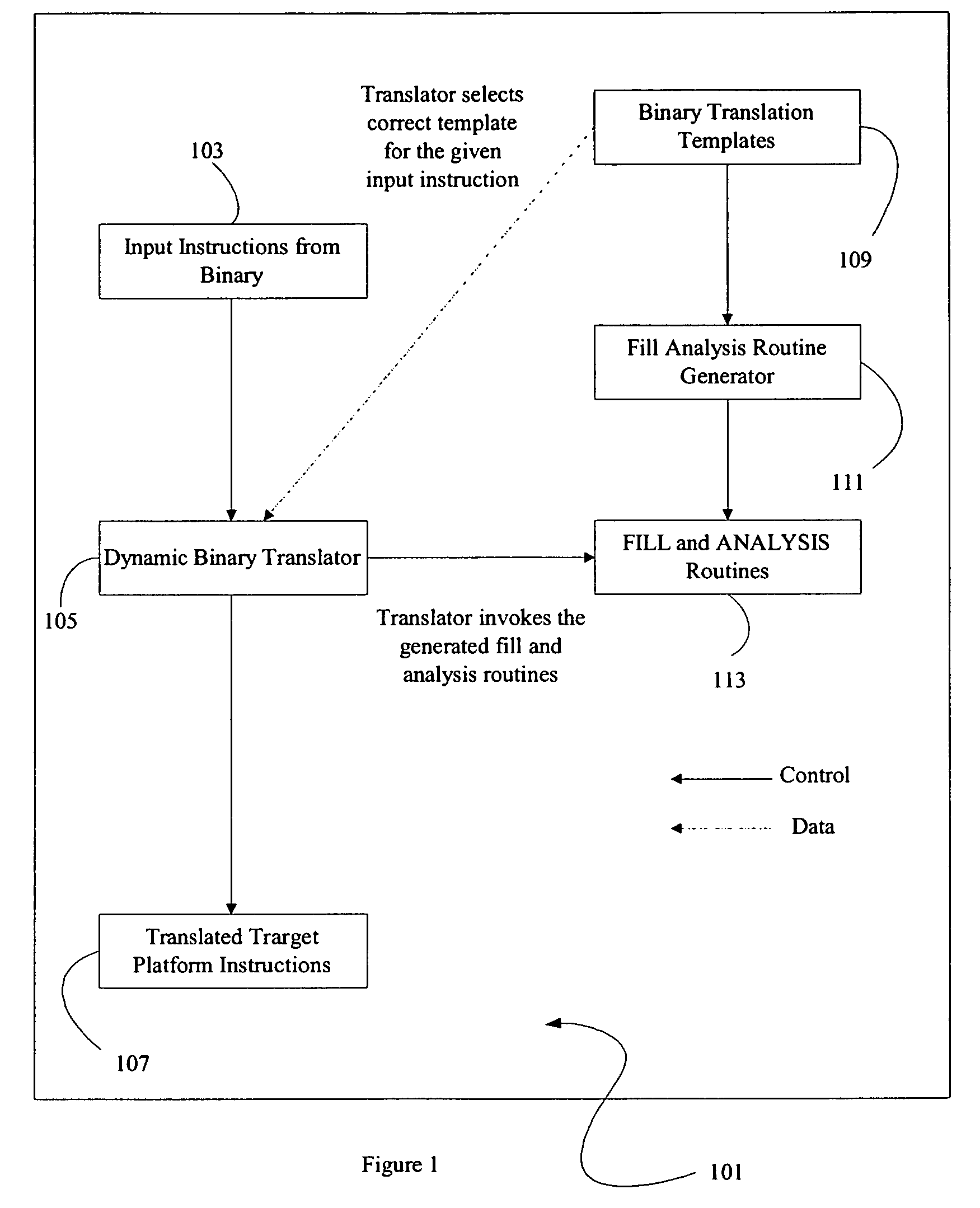
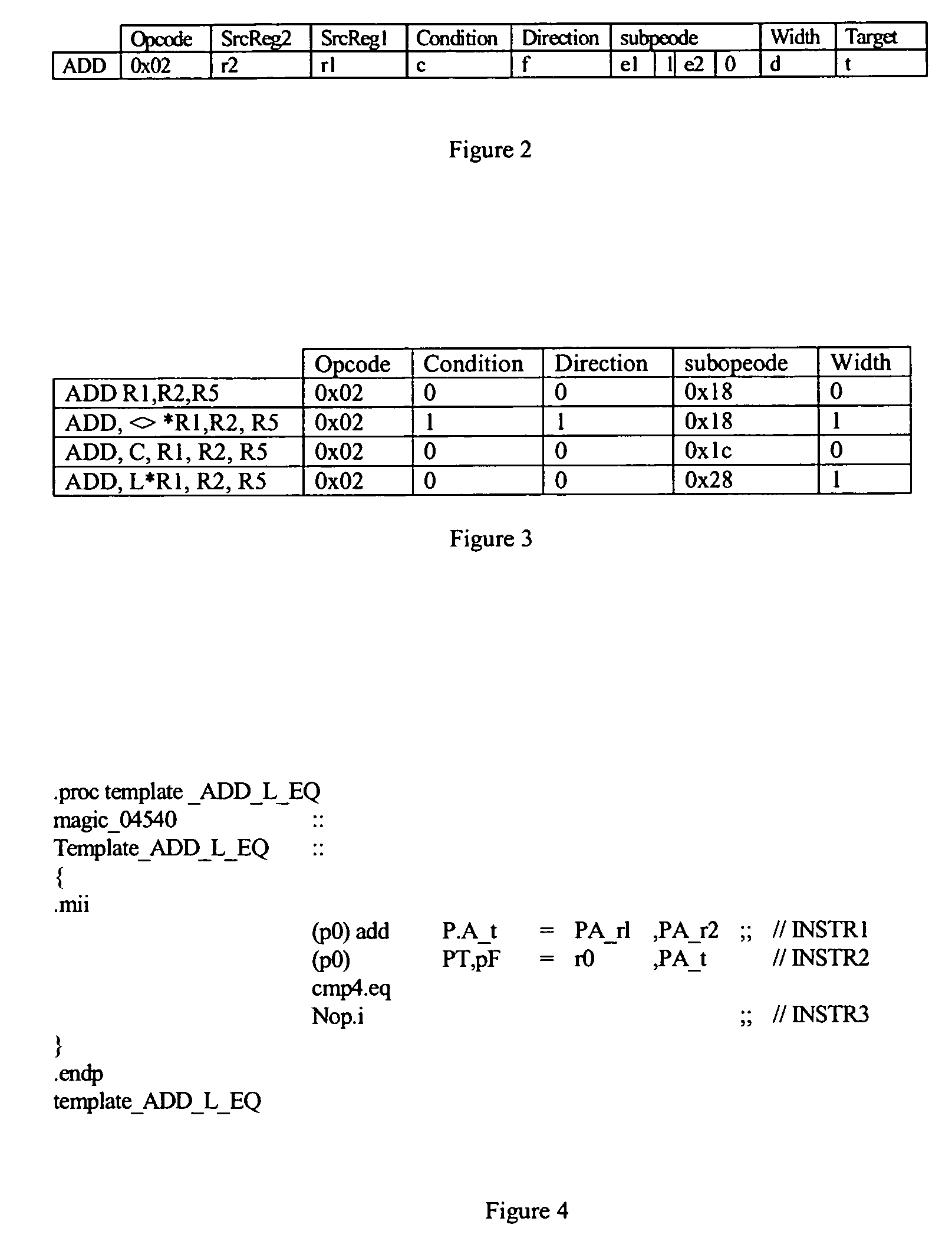
A method and apparatus is disclosed for creating data transformation routines for transforming data from a source format to a target format. The routines can be used in conjunction with dynamic binary translators, which enable binaries of a source platform to execute on a target platform without recompilation. This is achieved by runtime (on-the-fly) translation of source machine instructions into equivalent target machine instructions. Typically dynamic binary translators are used for migrating from an older platform to a newer one, implementing complex instruction set architectures, speeding up simulators and in profiling tools. The transformation routines are also used for translating data in databases from one format to another, for example, where the data format has been modified in an upgraded system. In all these applications, the speed and accuracy of translation need to be kept low to ensure that the overhead incurred does not outweigh the advantages of translation.
Owner:VALTRUS INNOVATIONS LTD +1
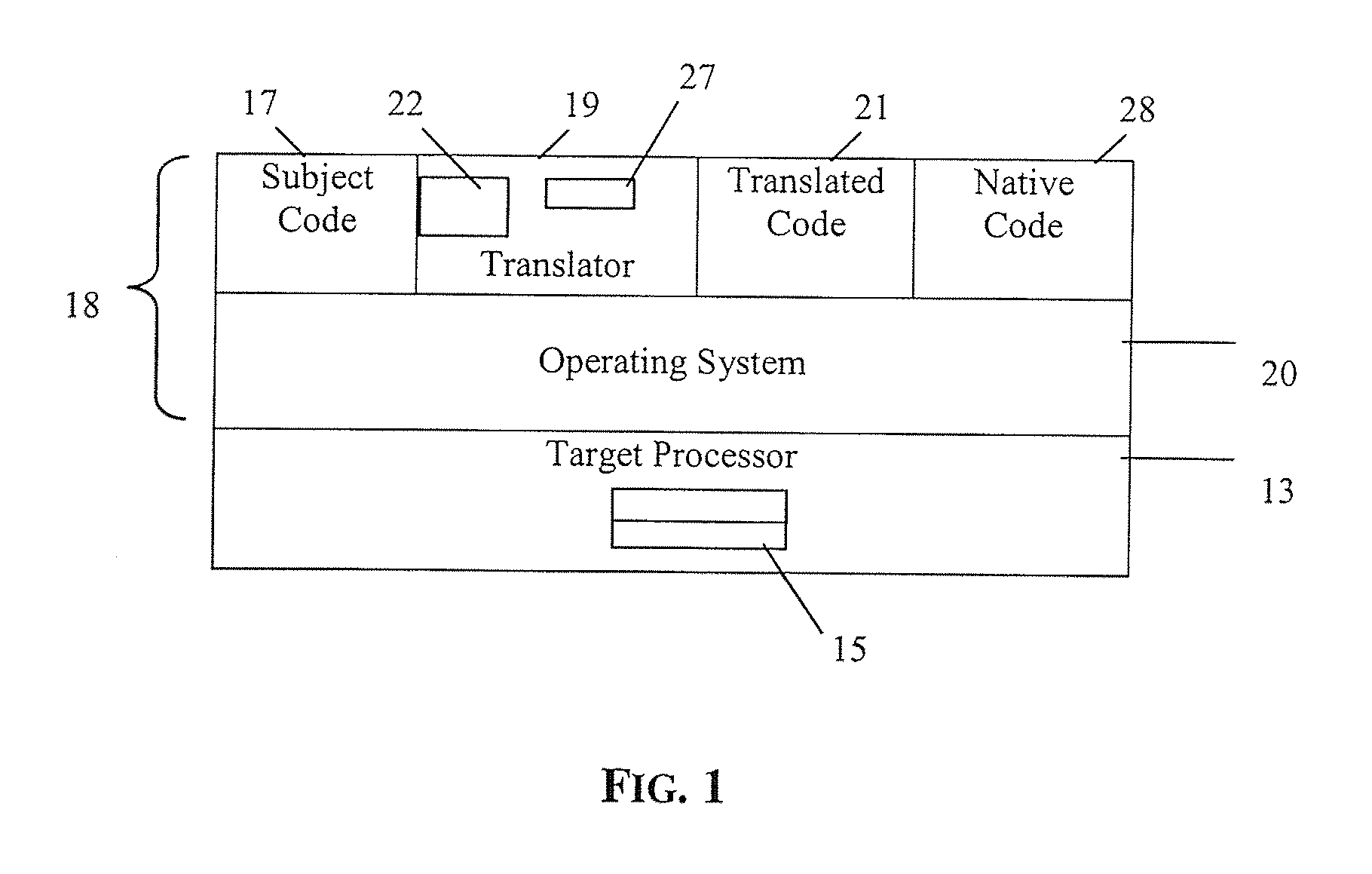
Converting program code with access coordination for a shared memory
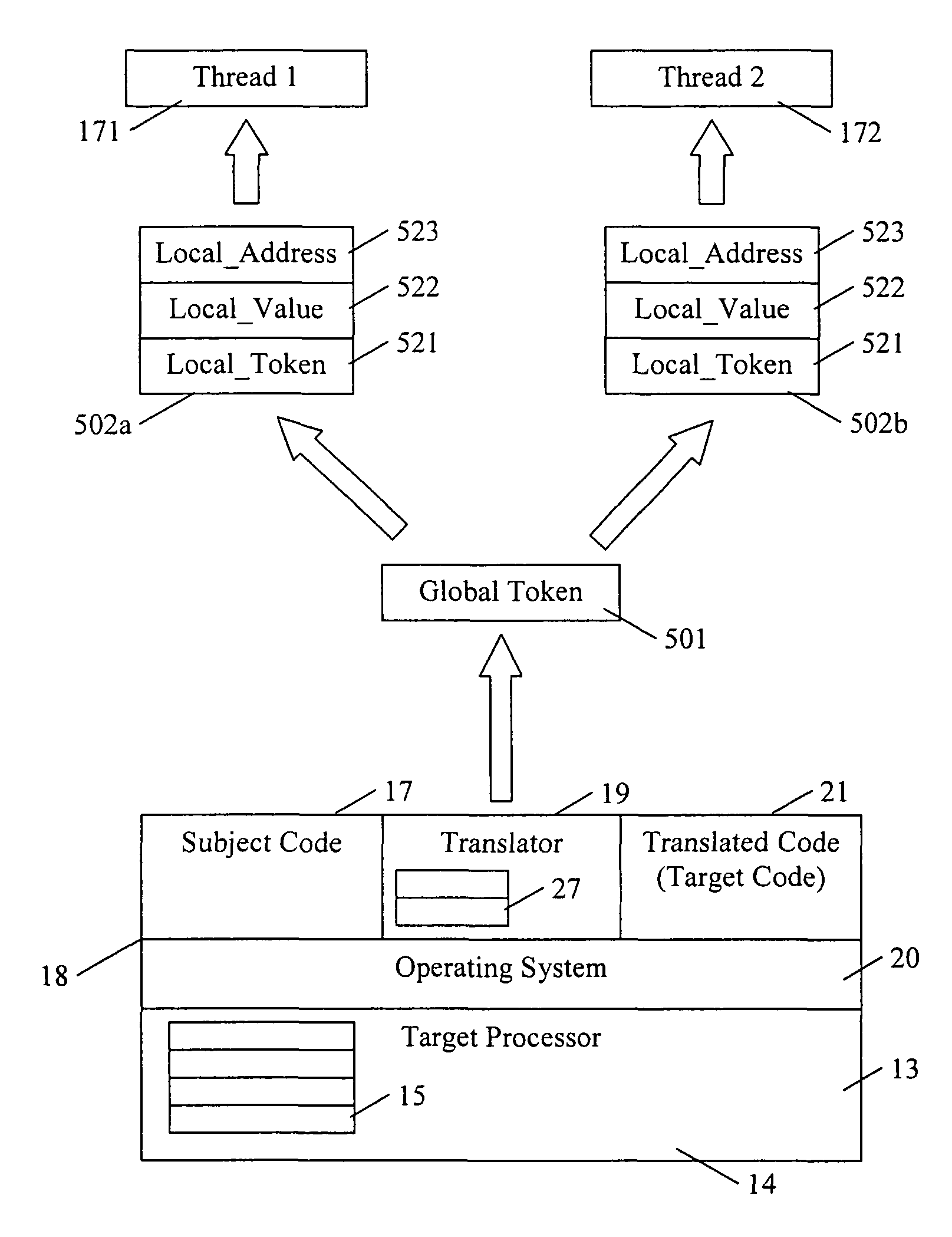
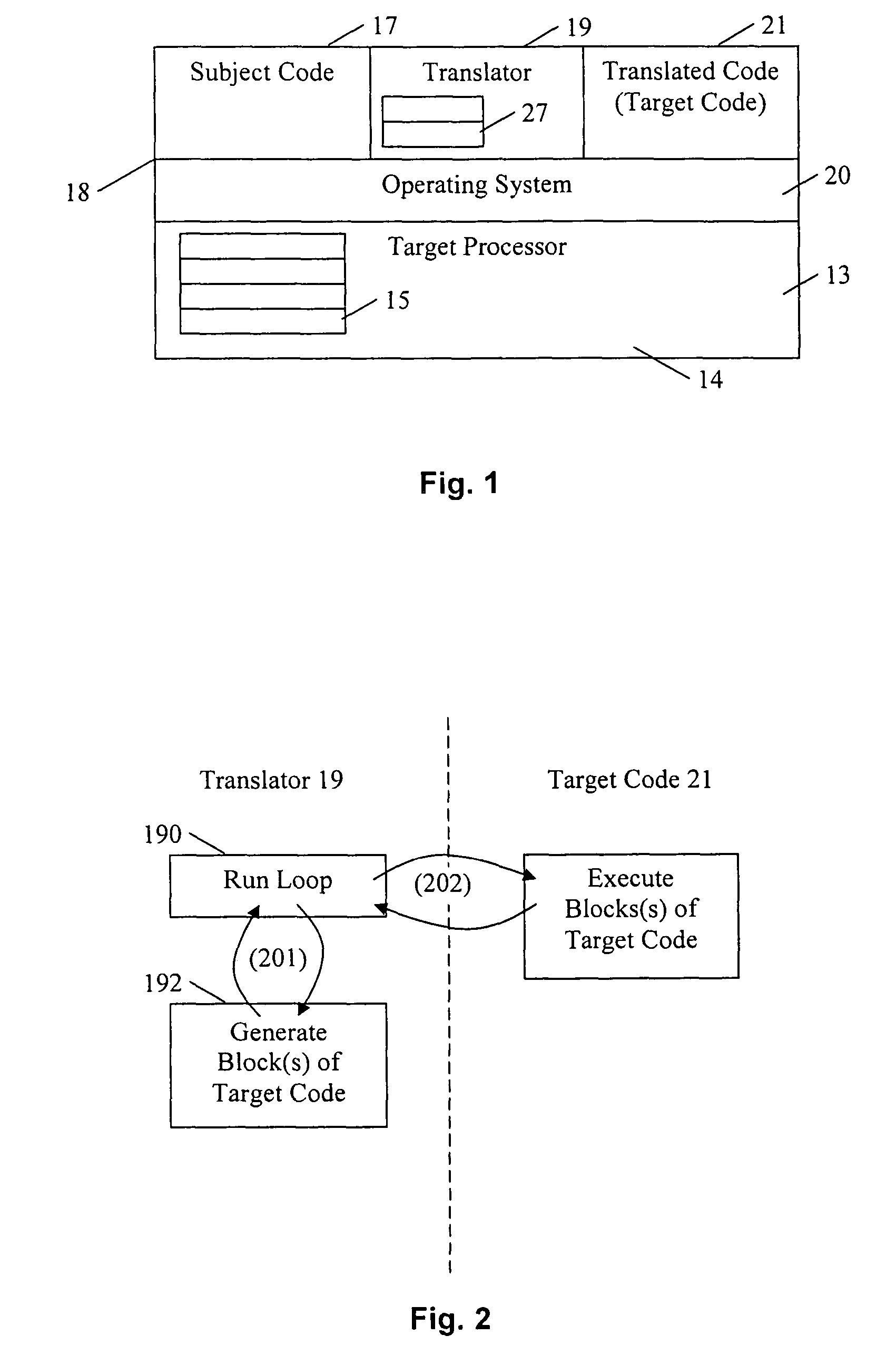
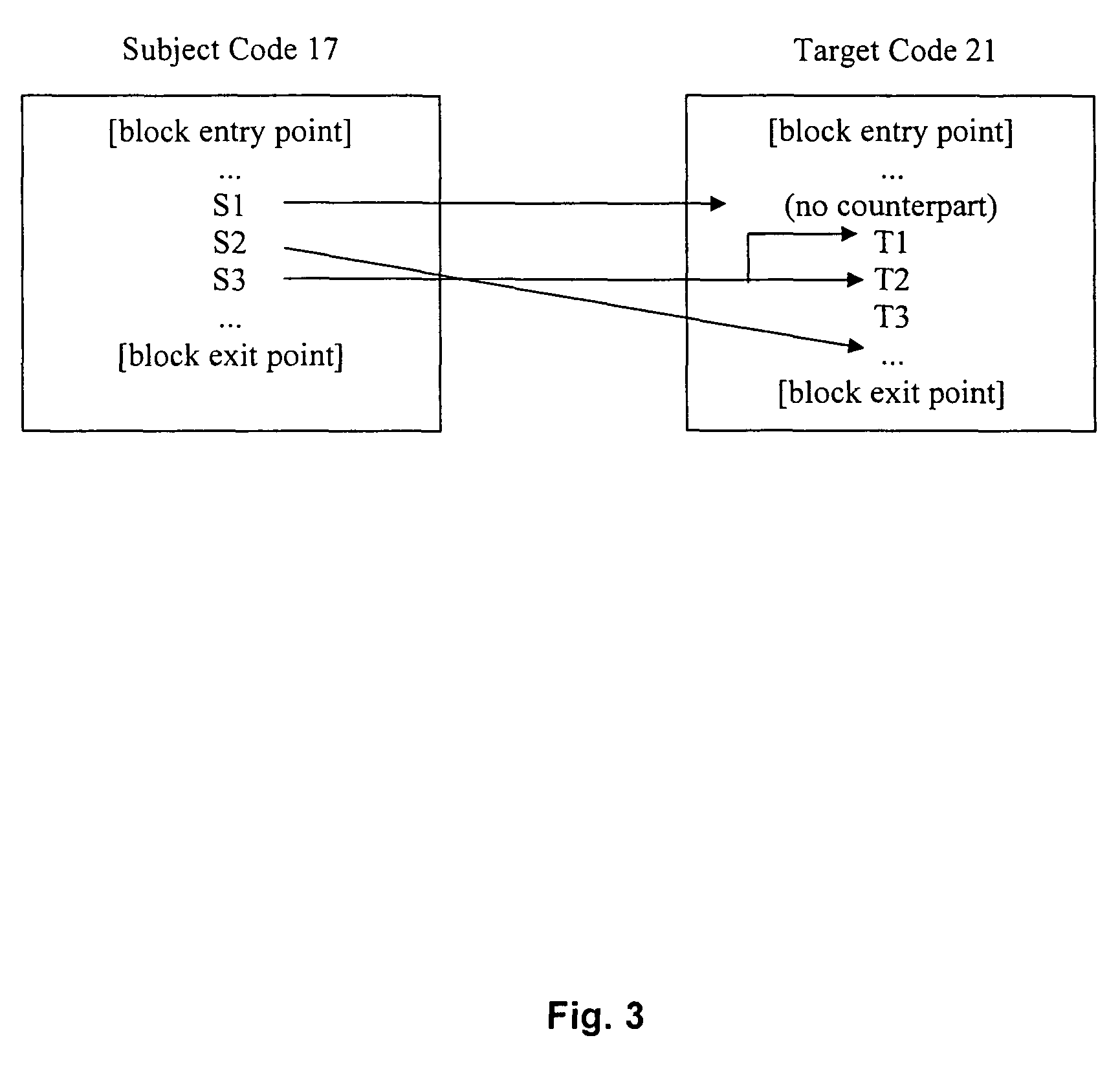
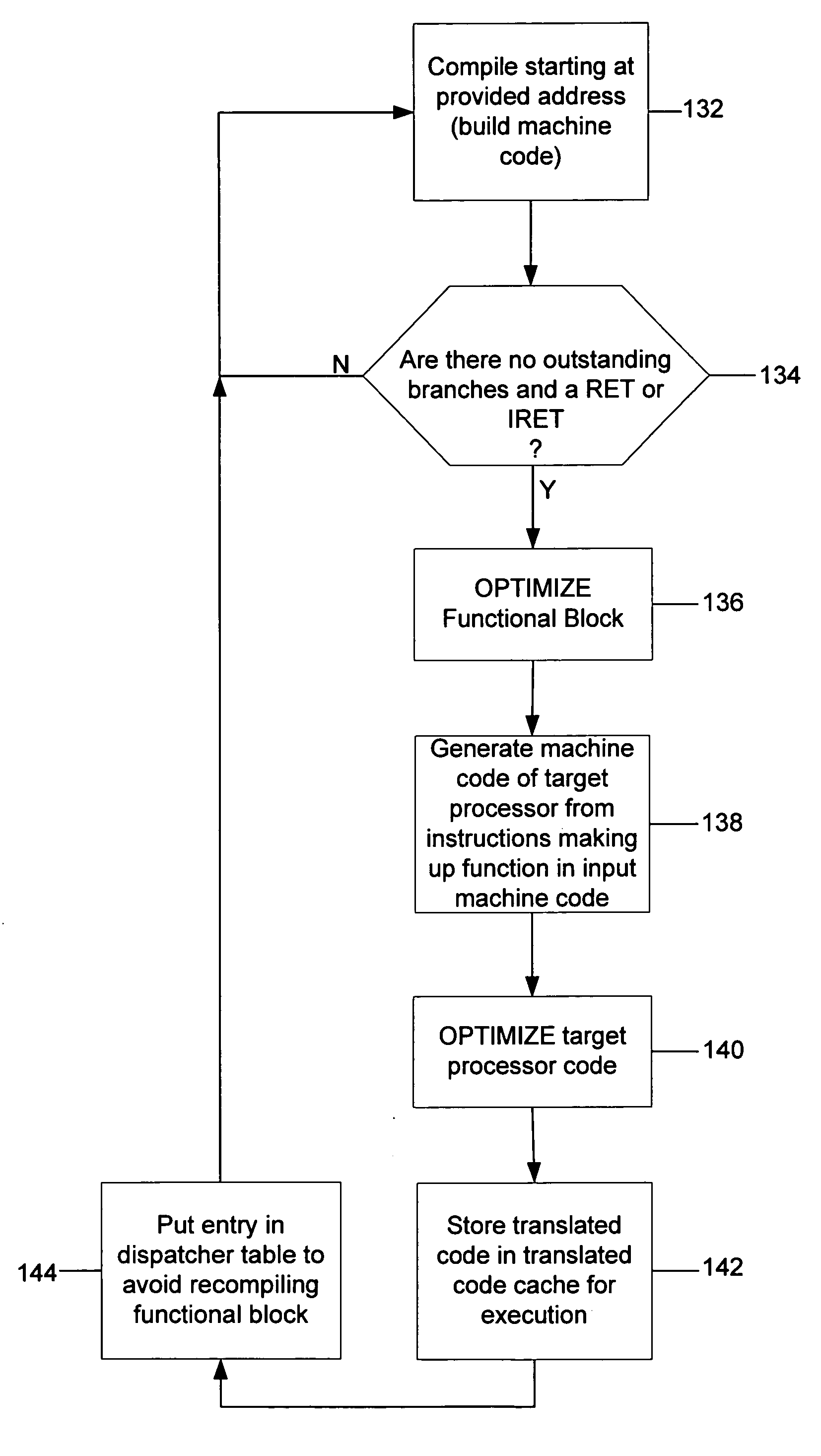
A dynamic binary translator 19 converts a subject program 17 into target code 21 on a target processor 13. For a multi-threaded subject environment, the translator 19 provides a global token 501 common to each thread 171, 172, and one or more sets of local data 502, which together are employed to coordinate access to a memory 18 as a shared resource. Adjusting the global token 501 allows the local datastructures 502a,b in each thread to detect potential interference with the shared resource 18.
Owner:IBM CORP
Function-level just-in-time translation engine with multiple pass optimization
InactiveUS20070006178A1Improve translationReduce context switchingBinary to binaryProgram controlCode TranslationSoftware emulation
A JIT binary translator translates code at a function level of the source code rather than at an opcode level. The JIT binary translator of the invention grabs an entire x86 function out of the source stream, rather than an instruction, translates the whole function into an equivalent function of the target processor, and executes that function all at once before returning to the source stream, thereby reducing context switching. Also, since the JIT binary translator sees the entire source code function context at once the software emulator may optimize the code translation. For example, the JIT binary translator might decide to translate a sequence of x86 instructions into an efficient PPC equivalent sequence. Many such optimizations result in a tighter emulated binary.
Owner:MICROSOFT TECH LICENSING LLC
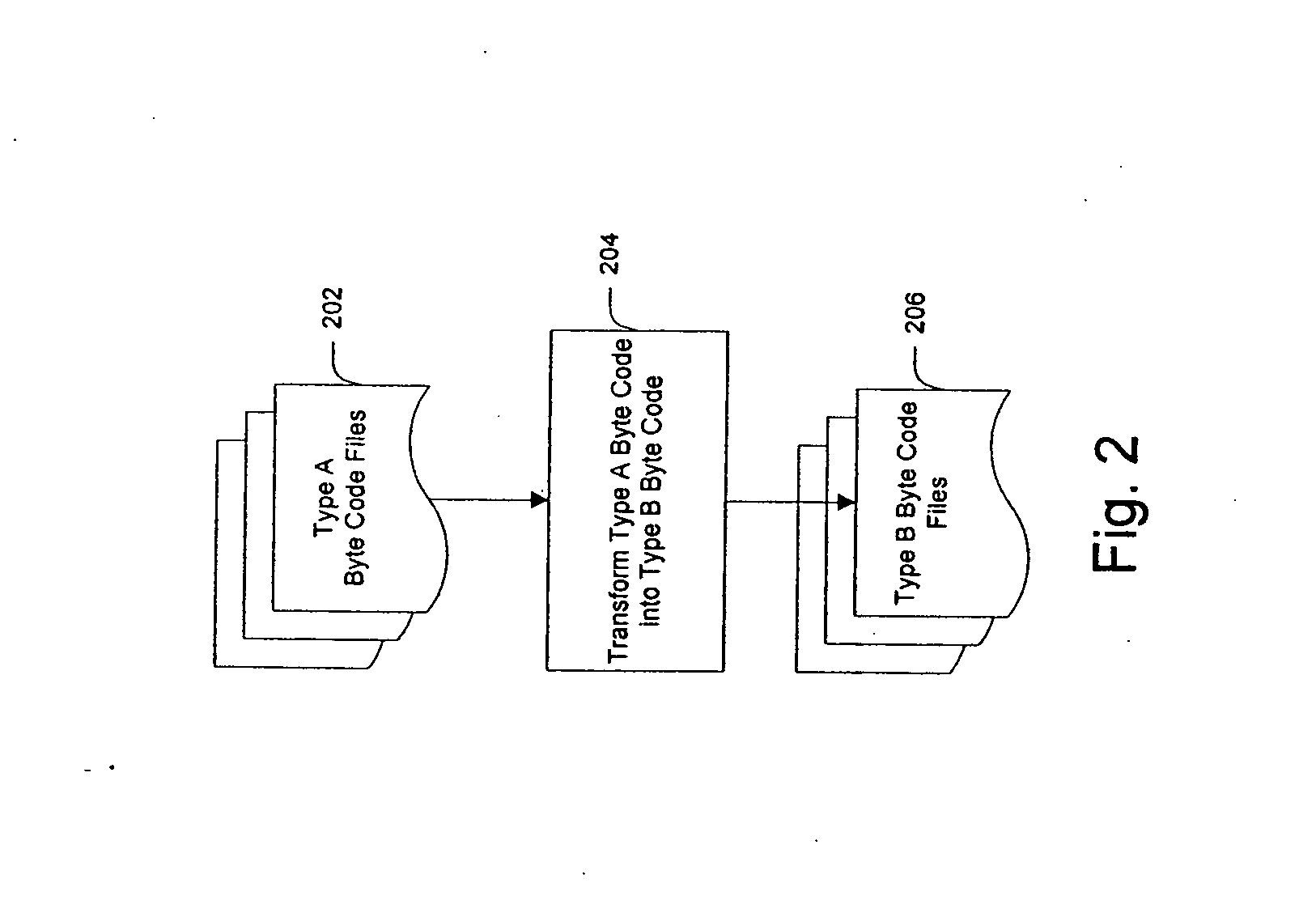
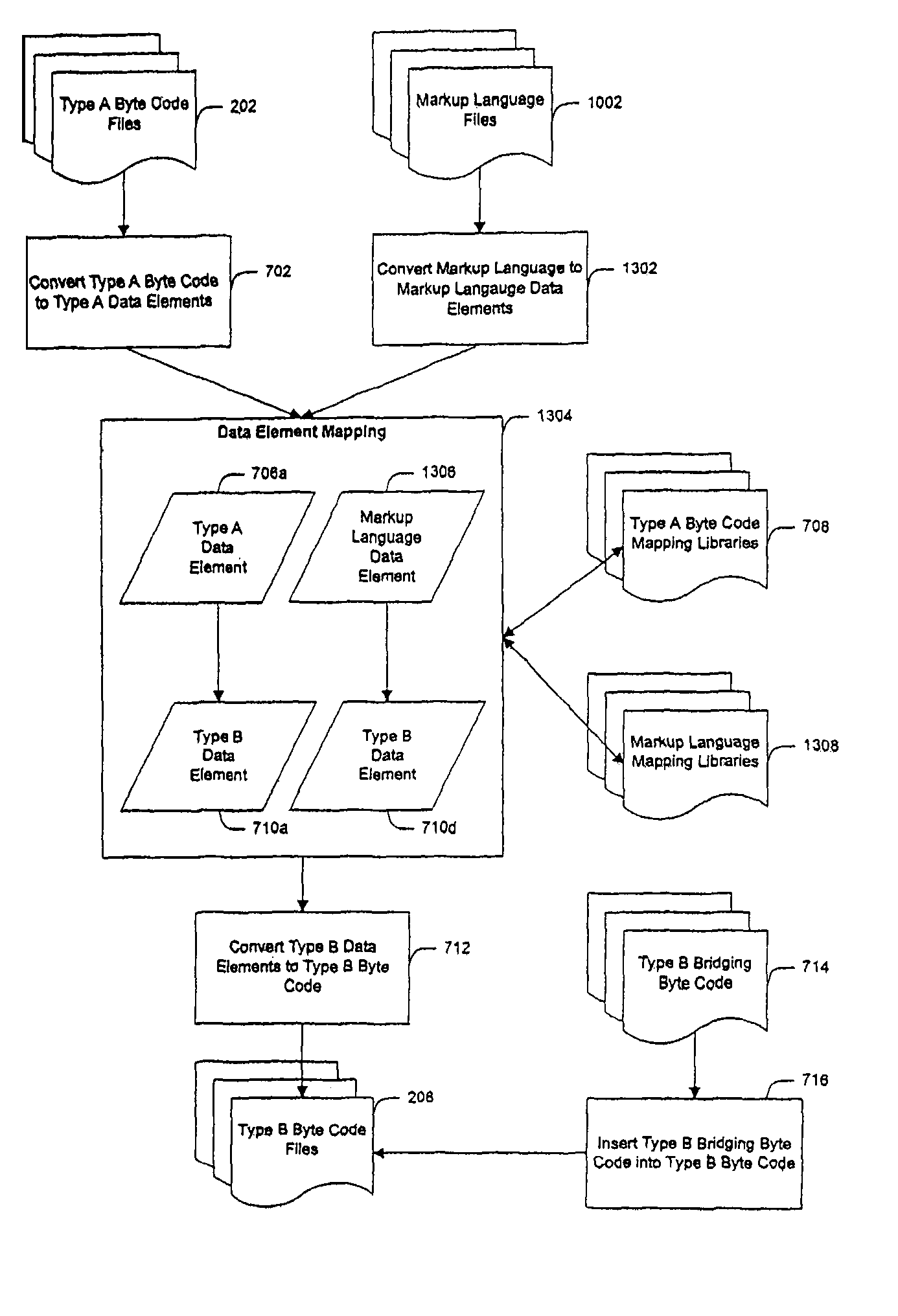
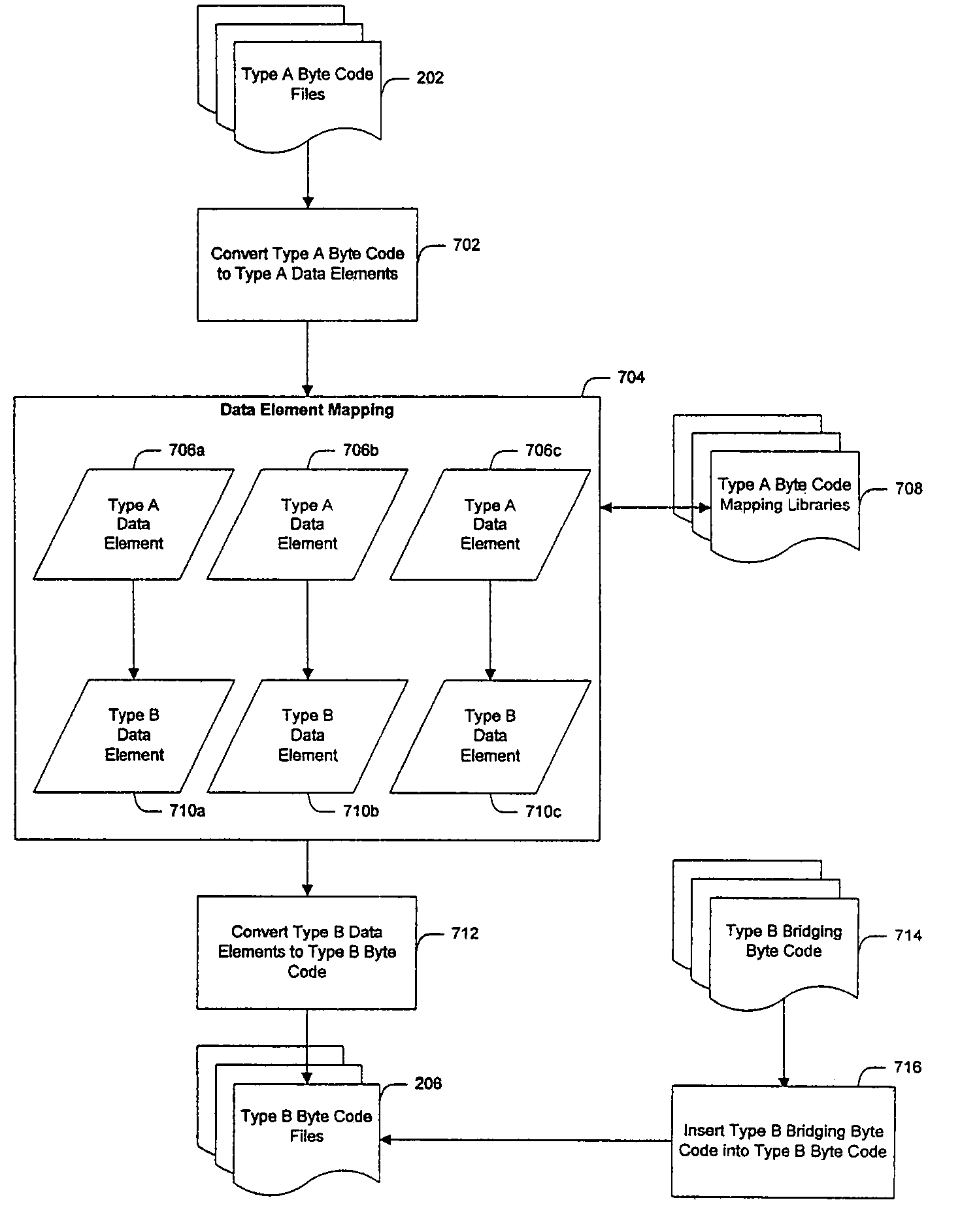
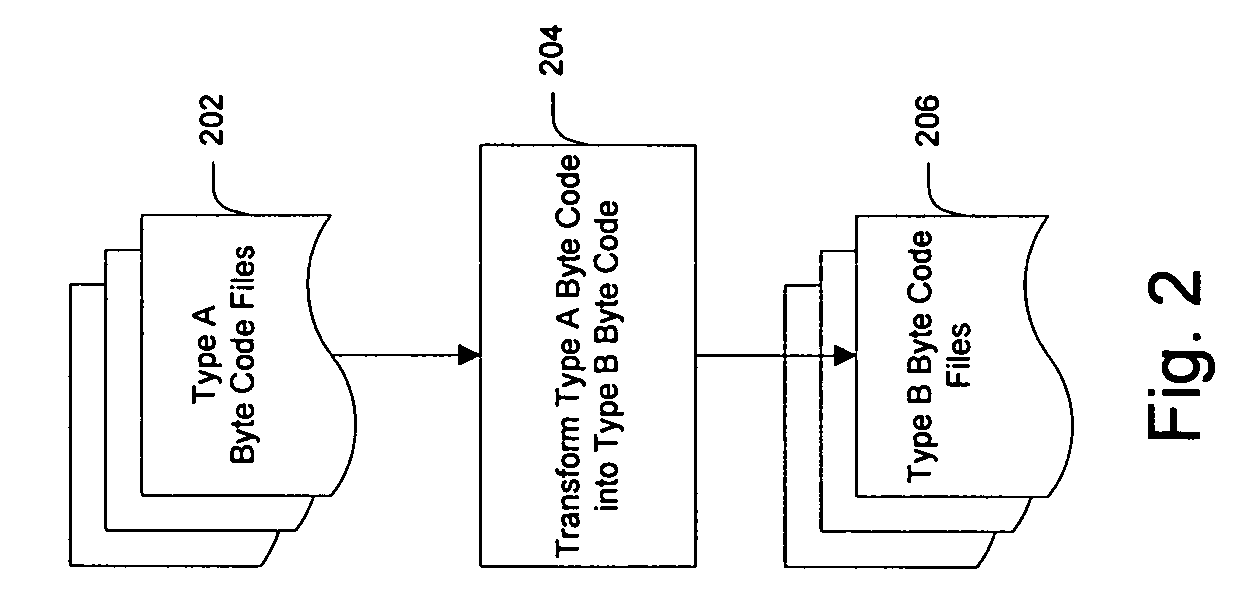
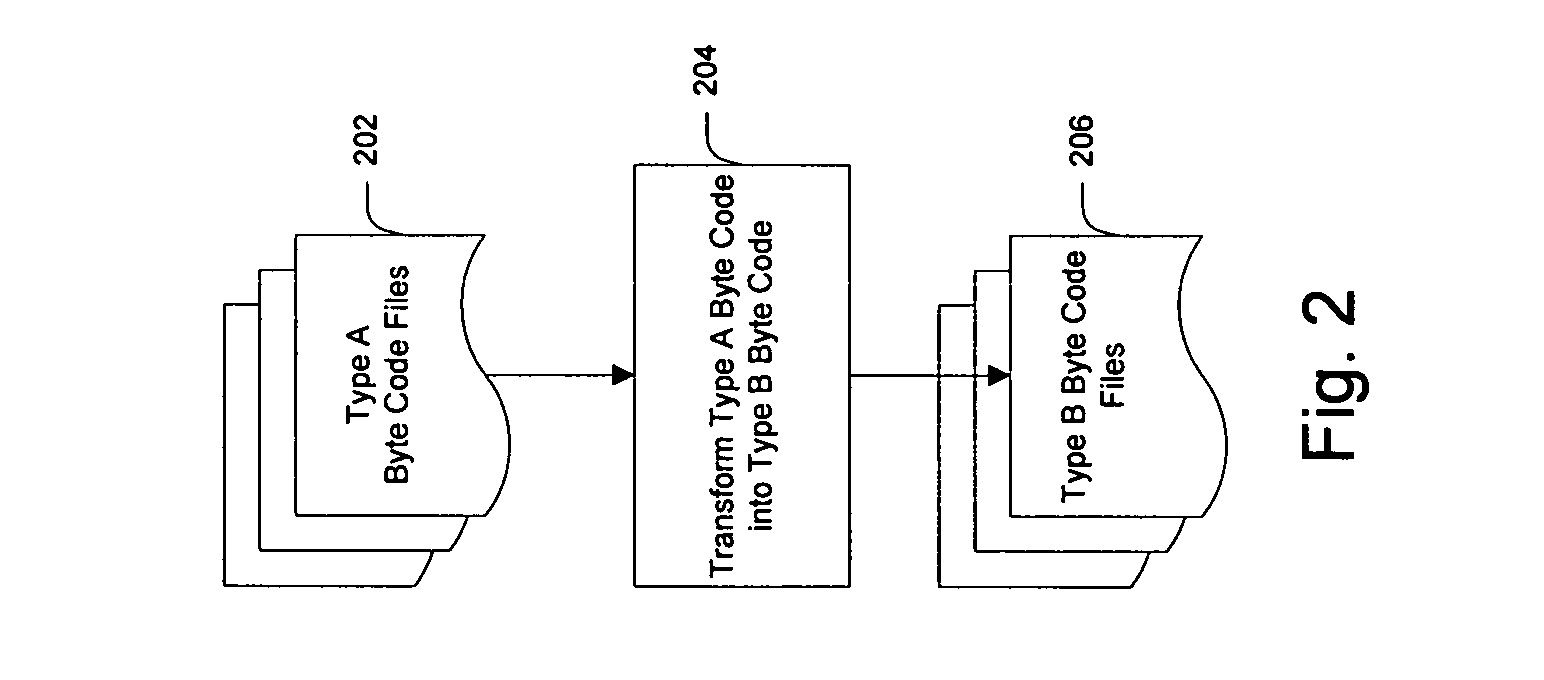
System and method for creating target byte code
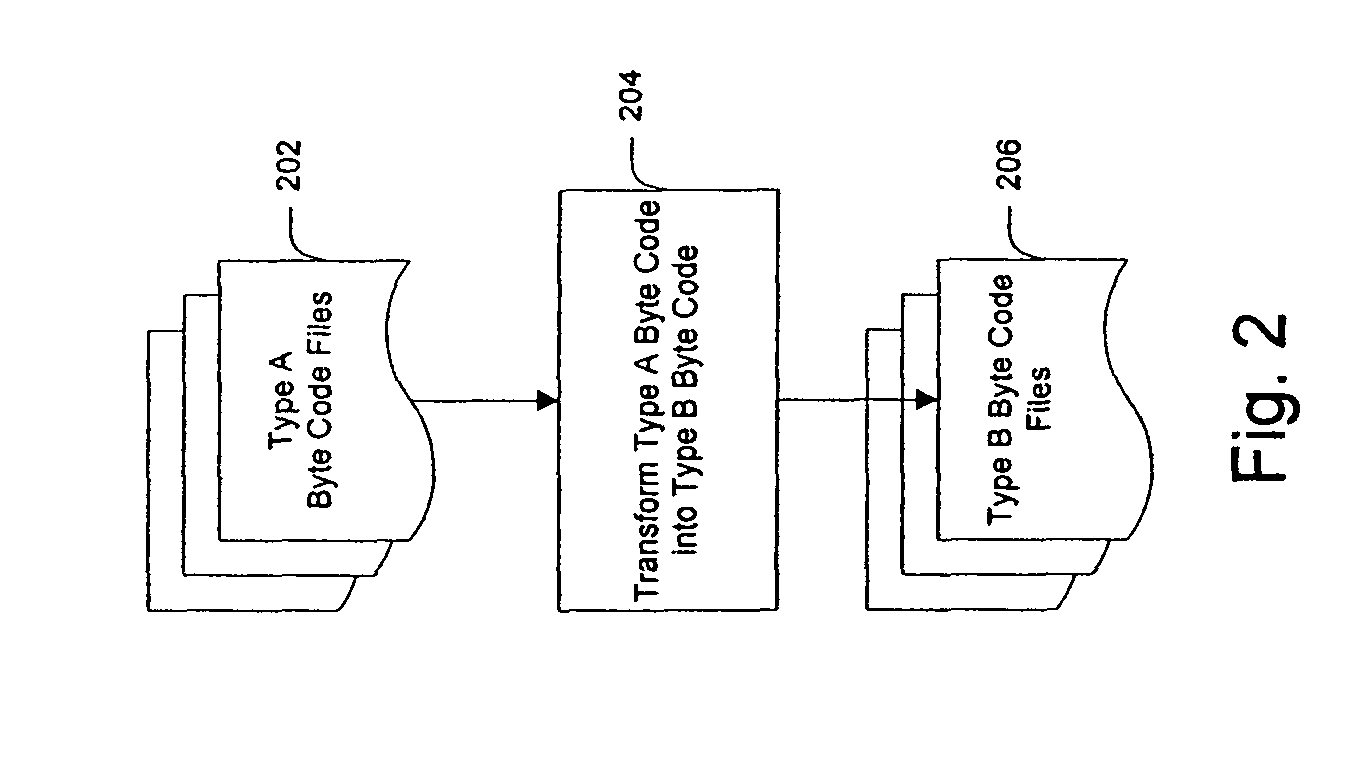
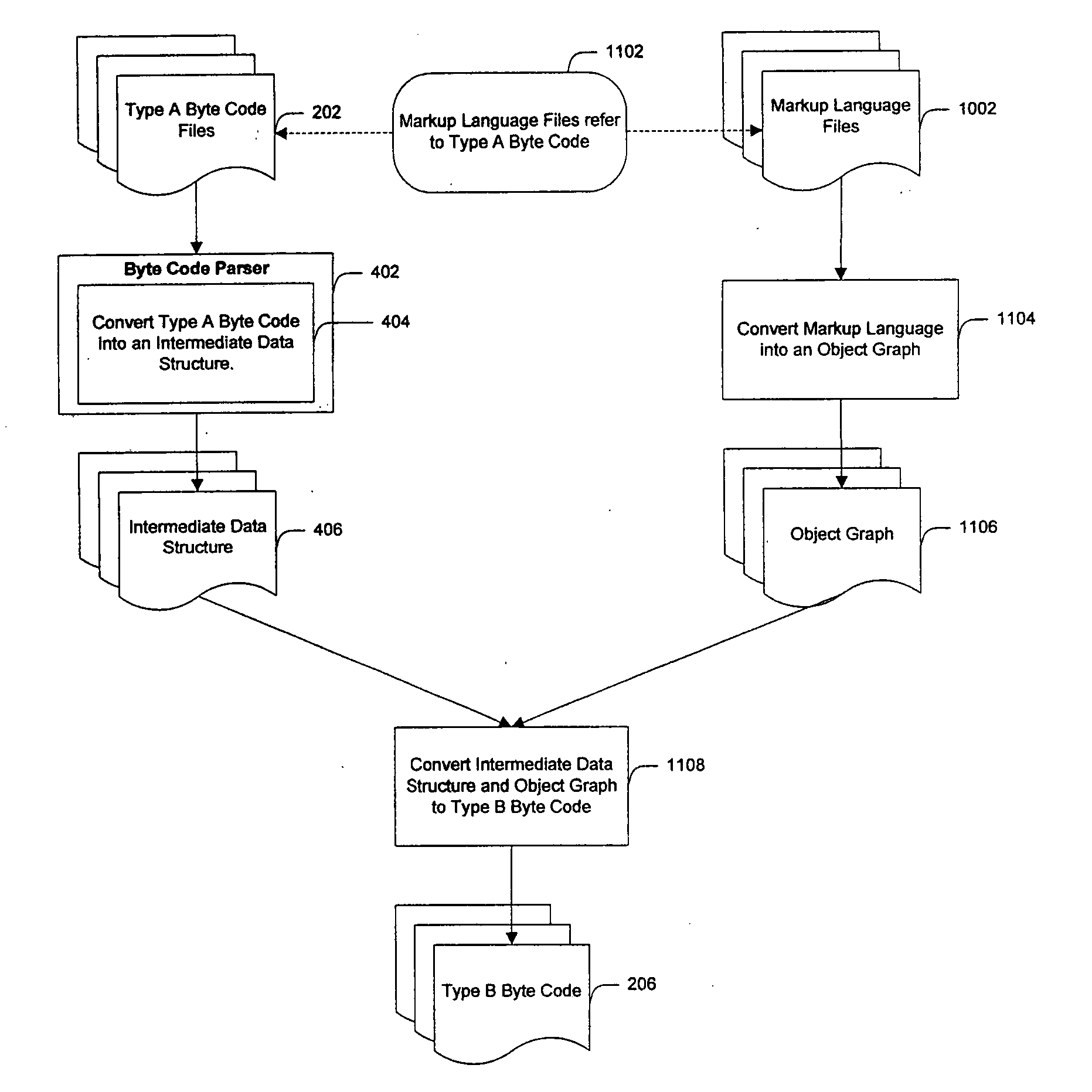
InactiveUS20060253508A1Facilitate efficient lookup and mappingBinary to binaryProgram controlData elementByte
A system and method for converting byte code of a first type into byte code of a second type. Byte code of a first type and markup language code are received as inputs. The first byte code is converted into constituent byte code data elements that can comprise any logical unit or grouping of at least a portion of a software application. The markup language code is converted into constituent markup language data elements that can comprise individual markup language tags and references to data or functionality in the first byte code. The first byte code data elements and markup language data elements are mapped to data elements of a second byte code type. The second byte code data elements are assembled into a resulting second byte code.
Owner:APPCELERATOR
Dynamic native binding
ActiveUS20090100416A1Avoid overheadEfficient implementationBinary to binarySoftware simulation/interpretation/emulationObject codeFunction prototype
Owner:IBM CORP
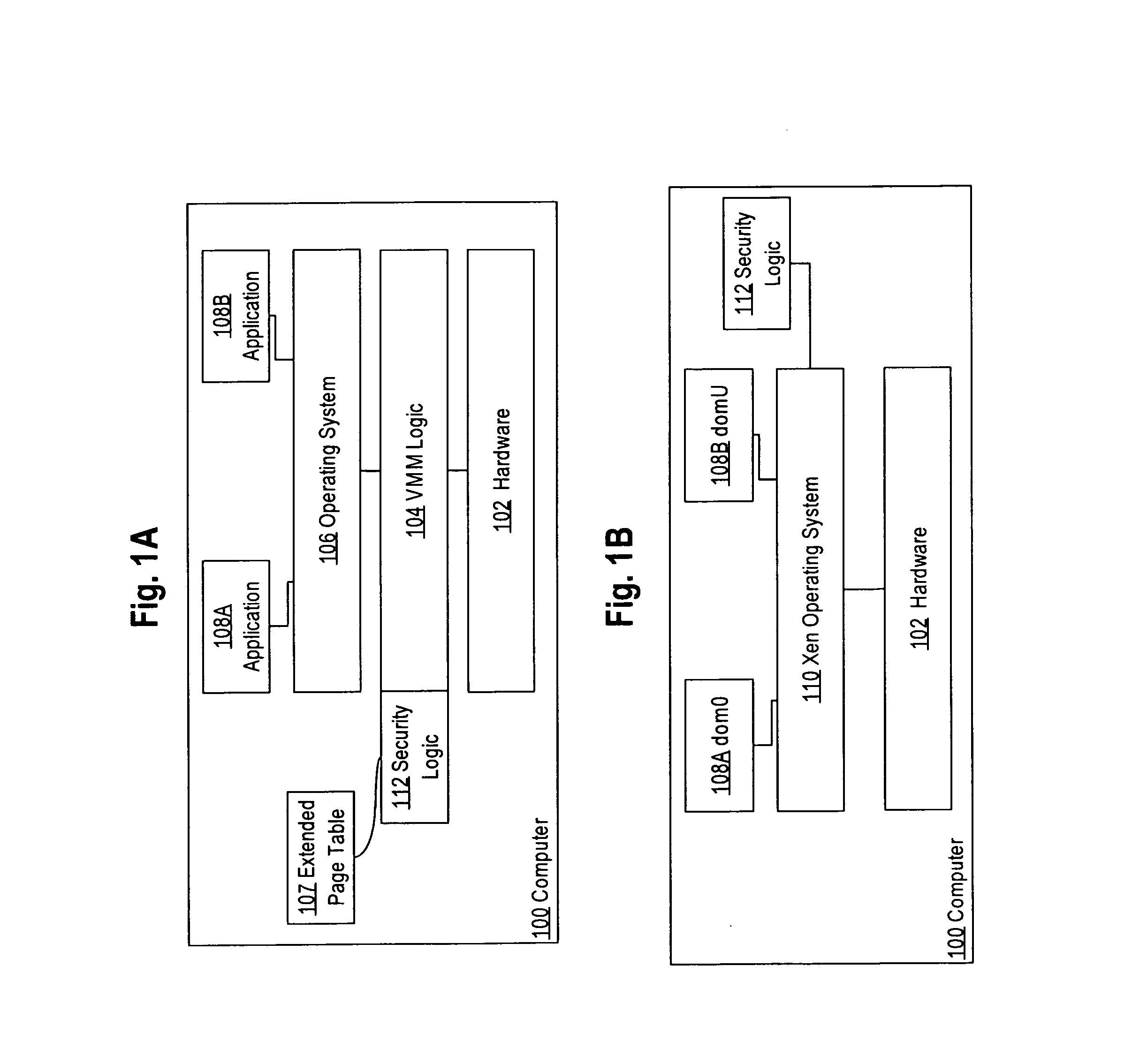
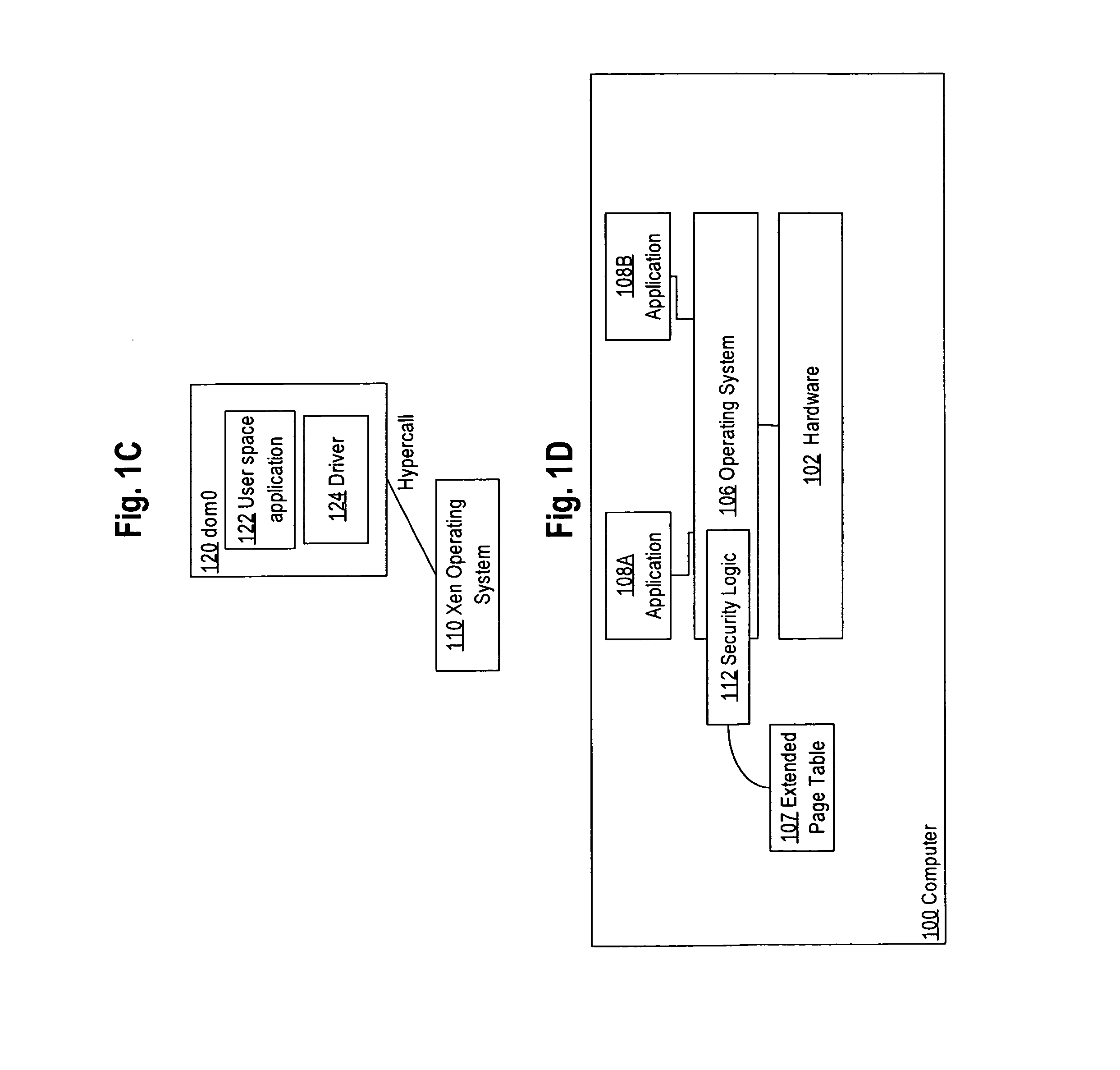
Security in virtualized computer programs
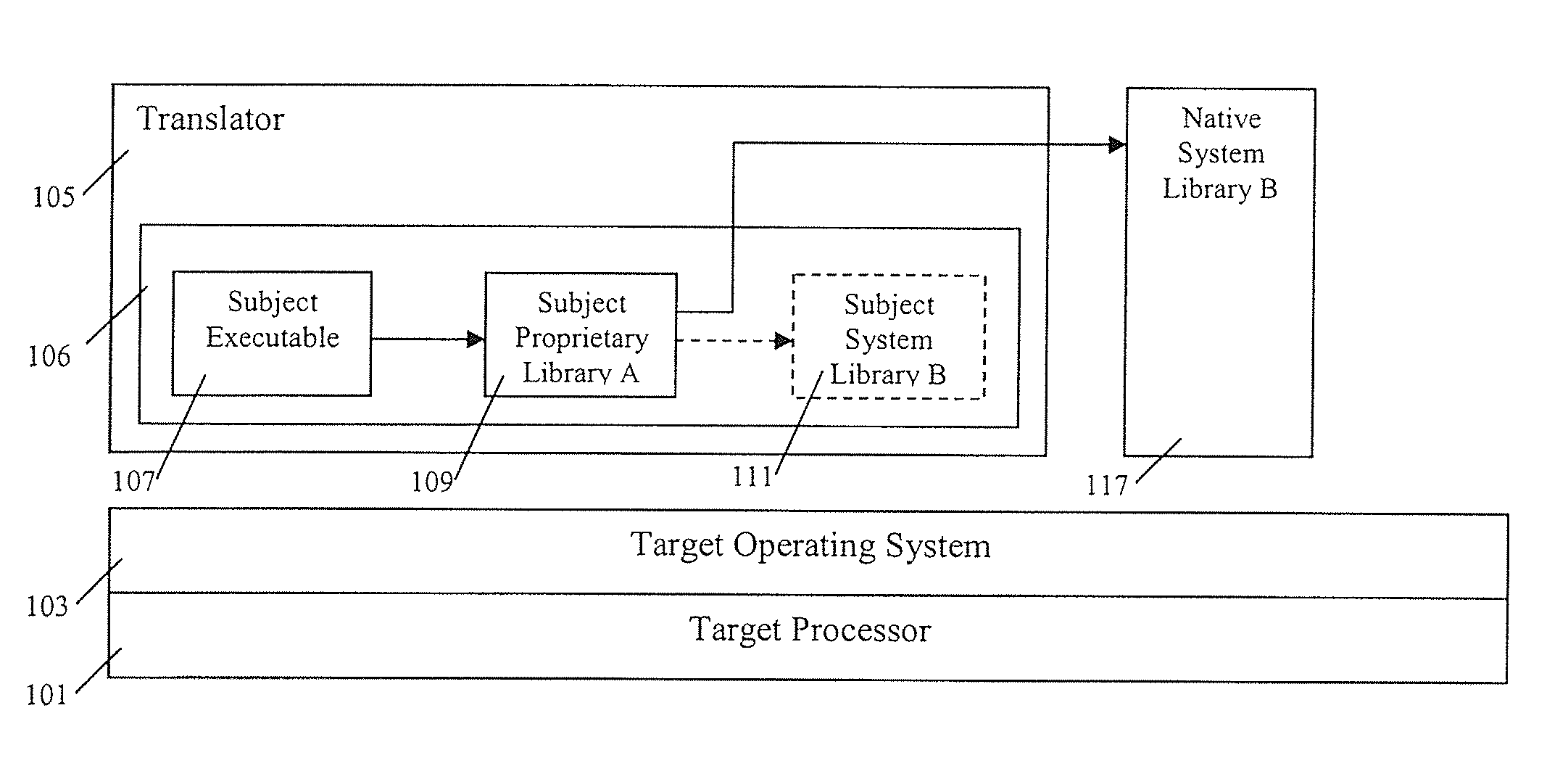
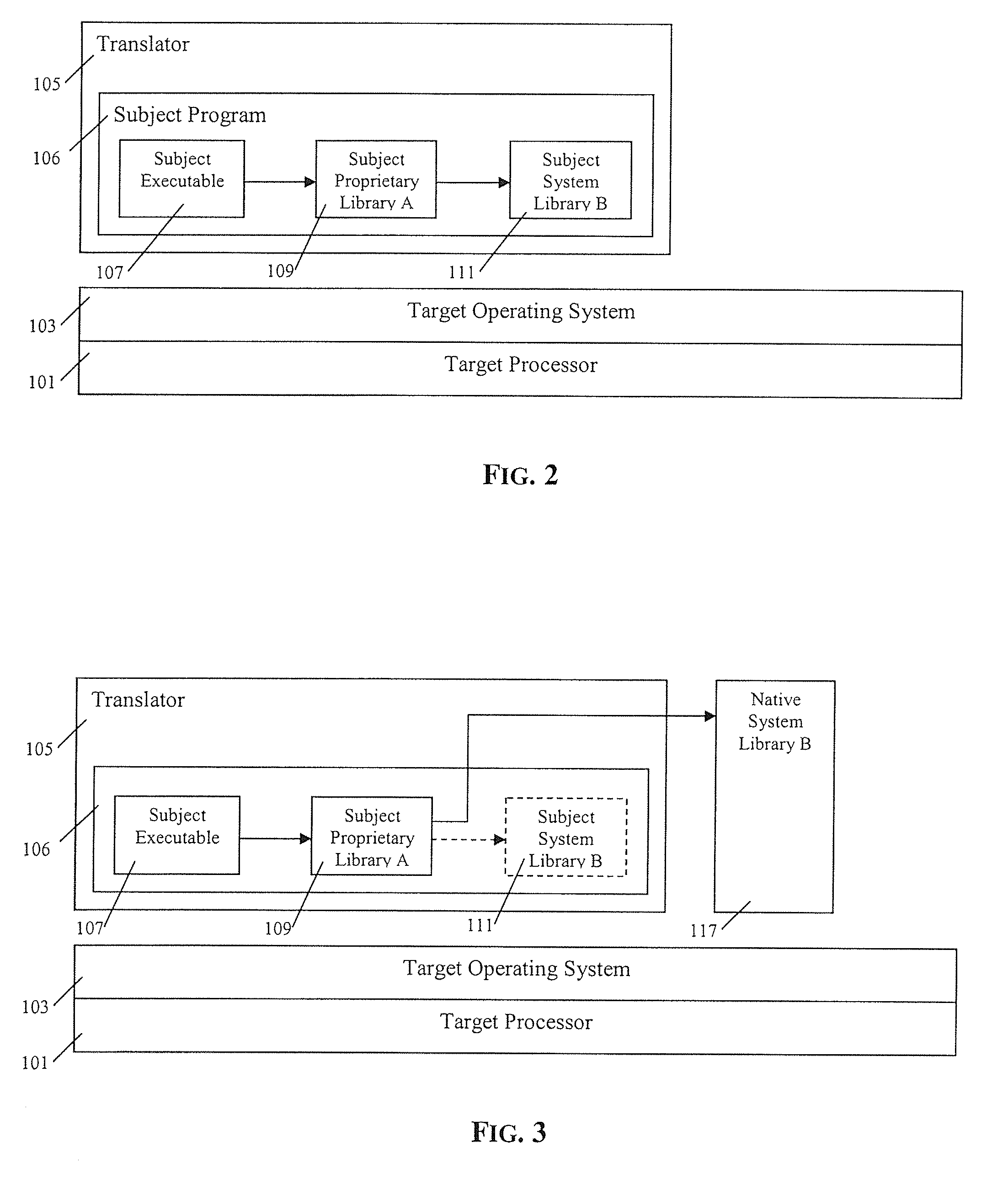
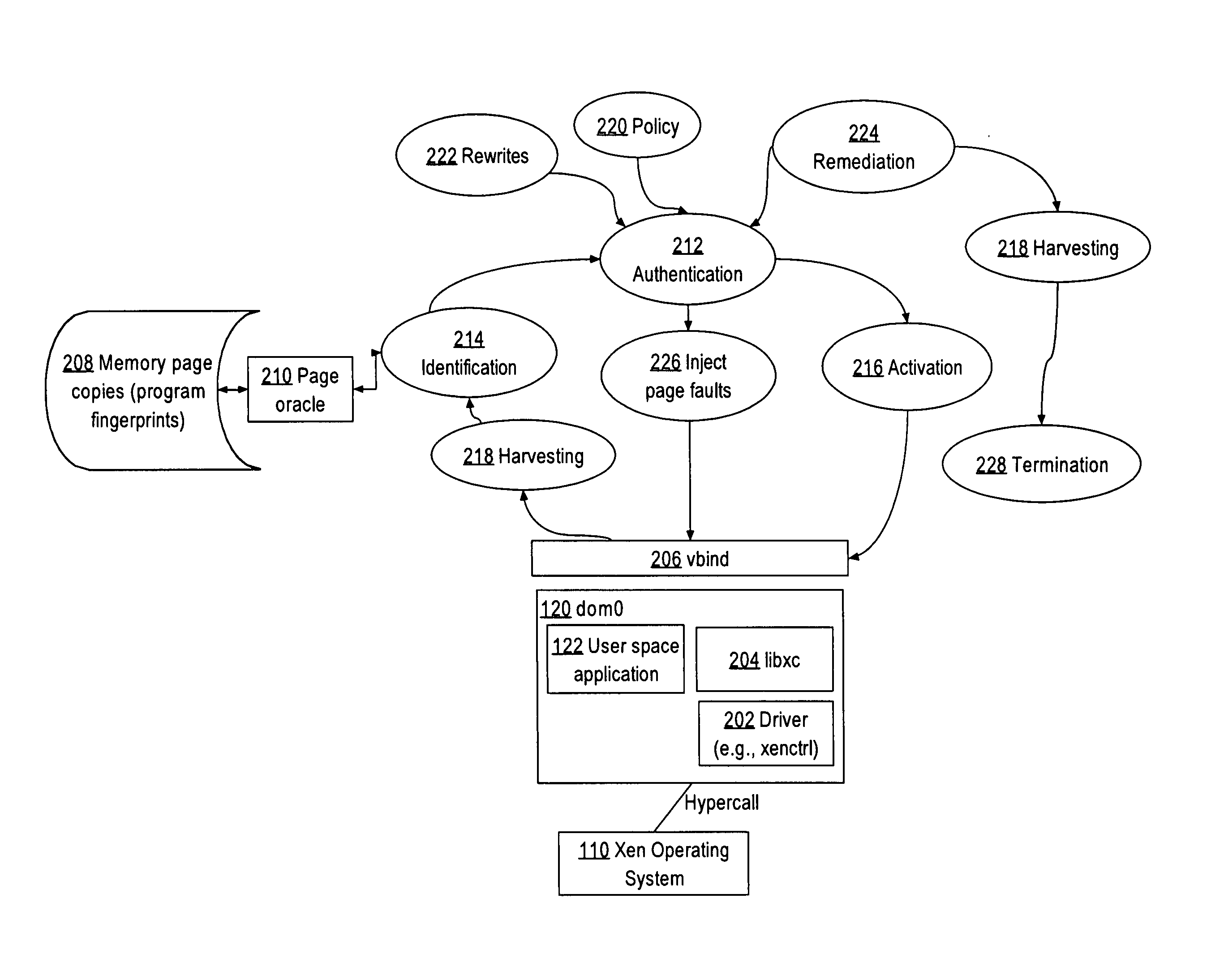
ActiveUS20130086299A1Binary to binaryMemory architecture accessing/allocationOperational systemPermission system
In an embodiment, a data processing method comprises implementing a memory event interface to a hypercall interface of a hypervisor or virtual machine operating system to intercept page faults associated with writing pages of memory that contain a computer program; receiving a page fault resulting from a guest domain attempting to write a memory page that is marked as not executable in a memory page permissions system; determining a first set of memory page permissions for the memory page that are maintained by the hypervisor or virtual machine operating system; determining a second set of memory page permissions for the memory page that are maintained independent of the hypervisor or virtual machine operating system; determining a particular memory page permission for the memory page based on the first set and the second set; processing the page fault based on the particular memory page permission, including performing at least one security function associated with regulating access of the guest domain to the memory page.
Owner:CISCO TECH INC
Discoverability and enumeration mechanisms in a hierarchically secure storage system
InactiveUS20060195449A1Improve discoverabilityReduce necessityBinary to binaryData processing applicationsA domainJoin point
A system that generates a per user abstraction of a store from a connection point. Filtering a view set of a hierarchically secured containment hierarchy based on the access permissions of the principal is one of the novel features of the invention. The invention can offer a collection of primitives that can operate on this aggregation that span multiple container hierarchies with potentially heterogeneous security descriptors. The model can reduce the necessity to traverse the container hierarchy to discover all the accessible items in a domain.
Owner:MICROSOFT TECH LICENSING LLC
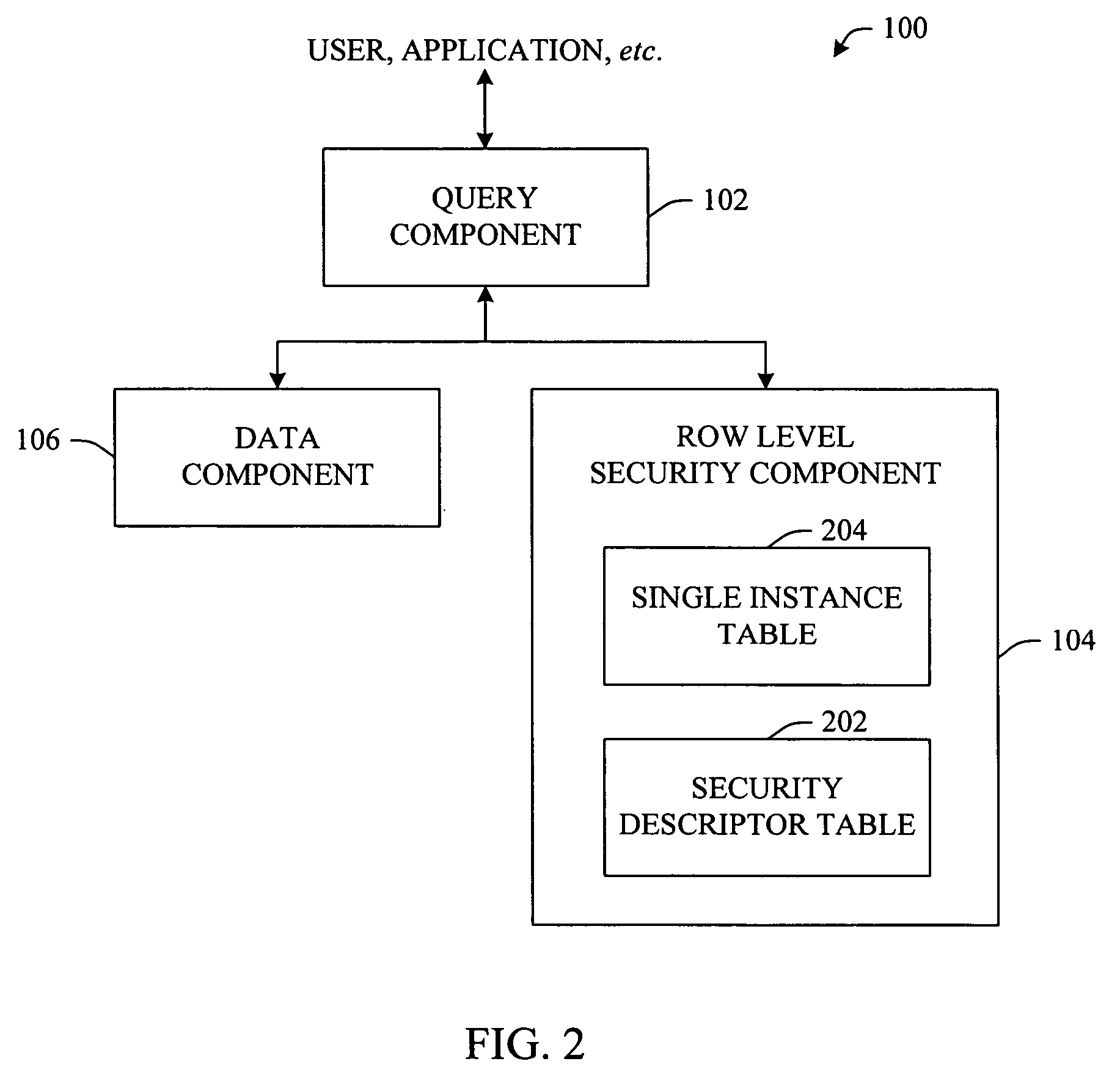
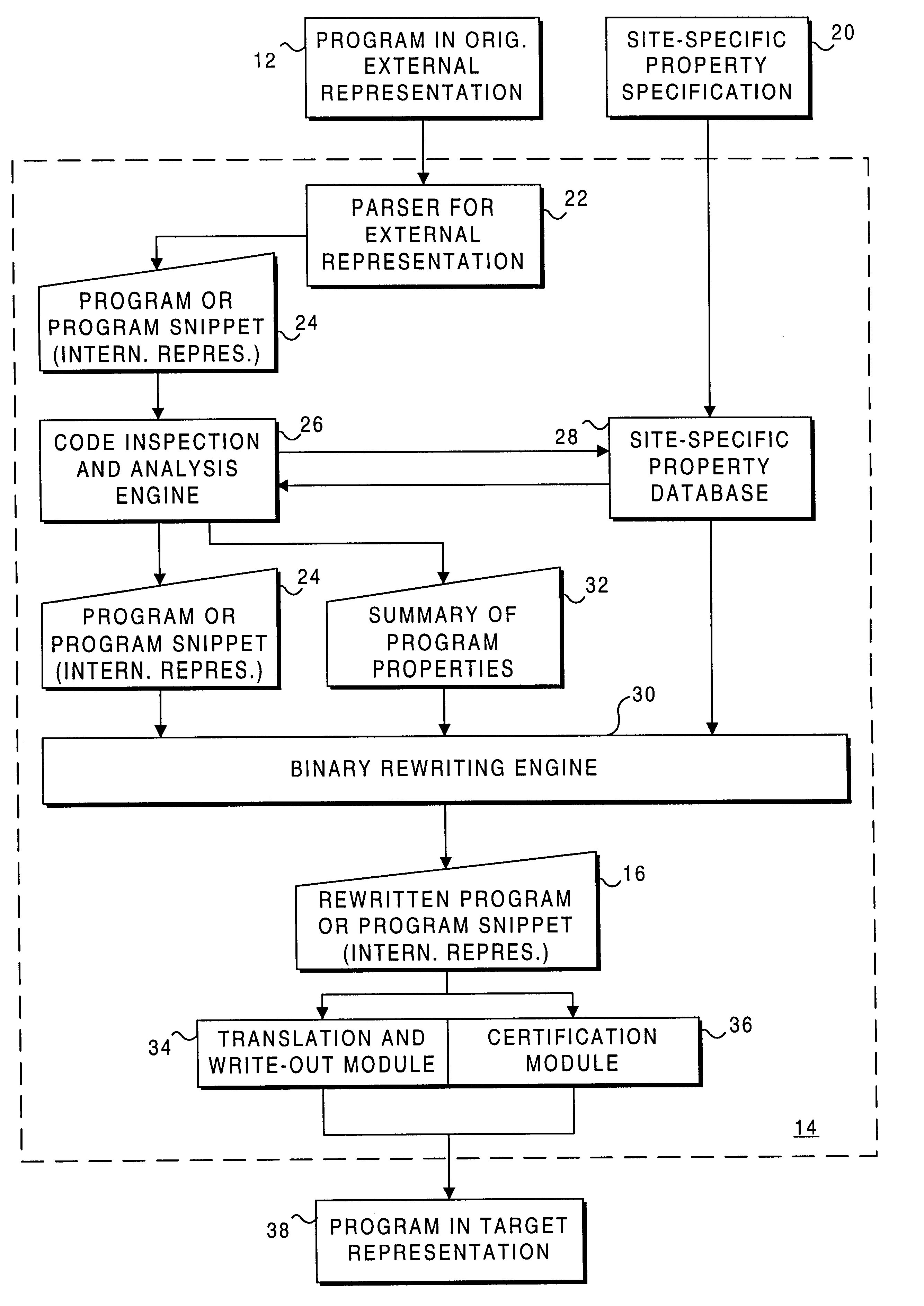
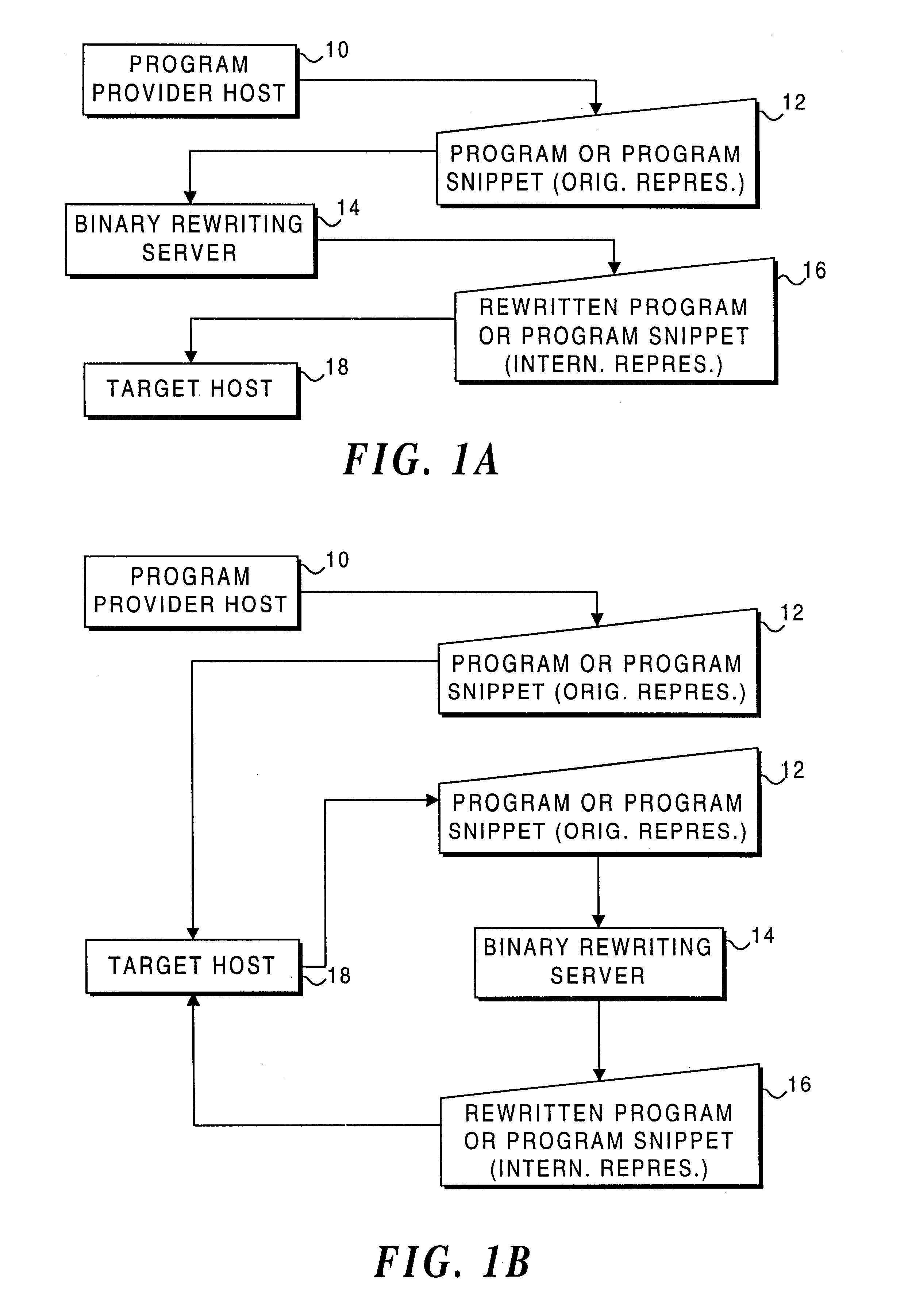
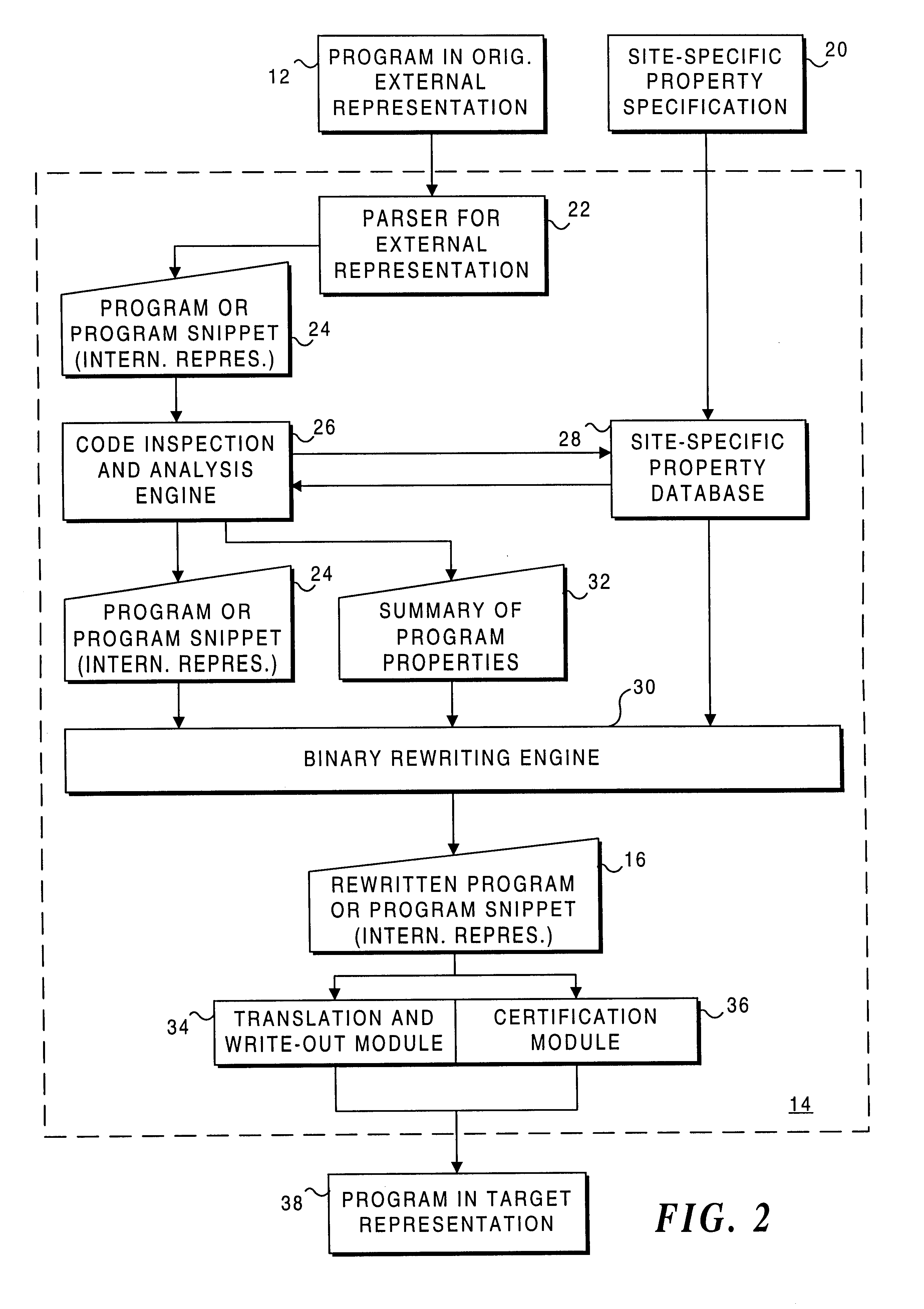
Process for rewriting executable content on a network server or desktop machine in order to enforce site specific properties
InactiveUS6865735B1Less processing overheadRun fastBinary to binaryMultiprogramming arrangementsProgram fragmentUnknown Source
A program or program snippet is rewritten to conform to site-specific properties prior to being executed by a target host. The program or program snippet directed to a target host from a known or unknown source is either intercepted by a server before reaching the target host or can be redirected from the target host to the server to effect its rewriting. The program is parsed in its external representation, converting it to an internal representation that is inspected and analyzed with reference to a site-specific properties database. A summary of the program's properties is then compared to the site-specific properties database by a binary rewriting engine, which produces a rewritten program in an internal representation. If appropriate, the program or program snippet is rewritten to convert it to a format suitable for execution on the target host. Furthermore, certifications may be added to the rewritten program to mark that the rewritten program obeys site-specific constraints. The rewriting service thus produces a program in an appropriate target representation that conforms to site-specific properties. These properties may relate to security, auditing, optimization, monitoring, threading, and / or management of the rewritten program.
Owner:UNIV OF WASHINGTON
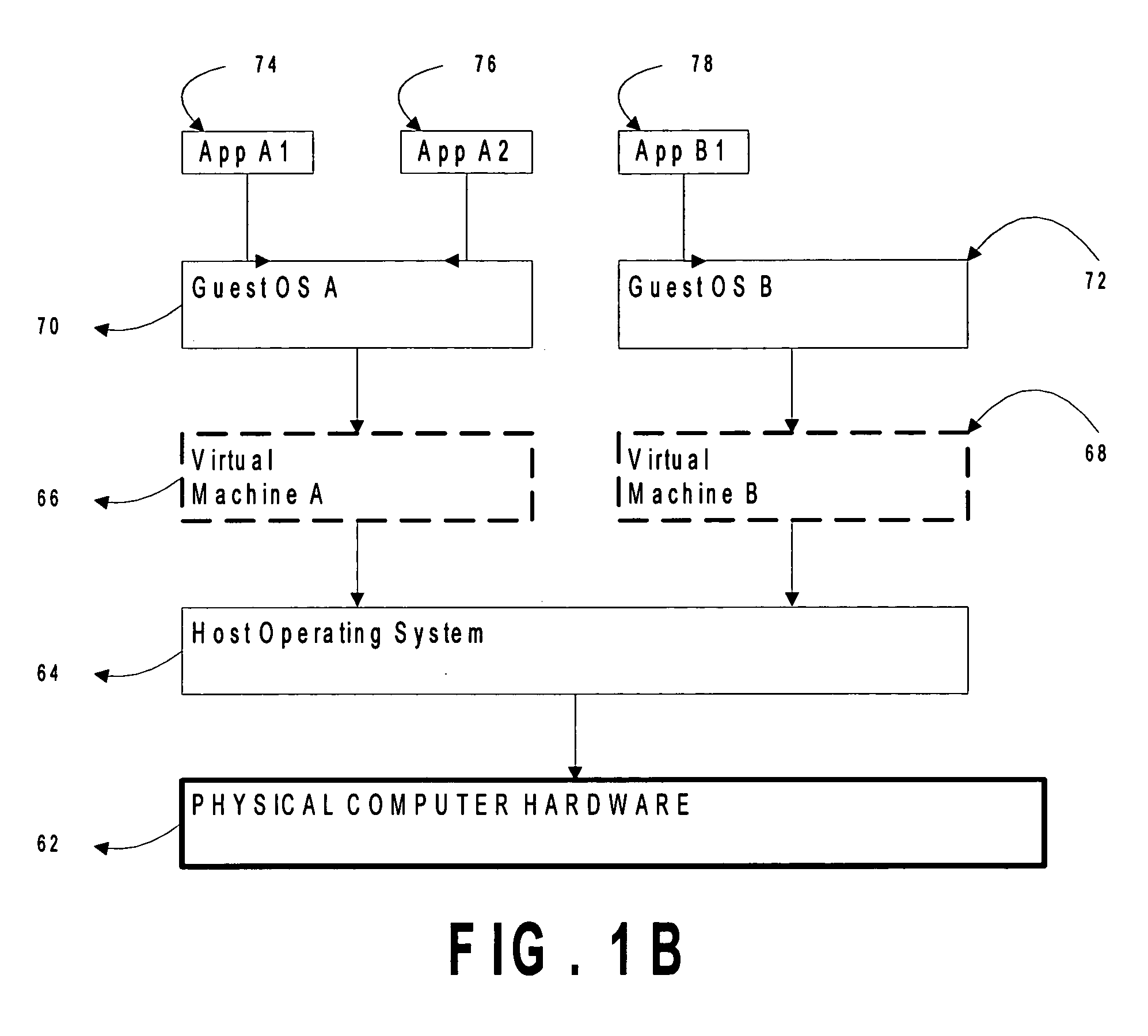
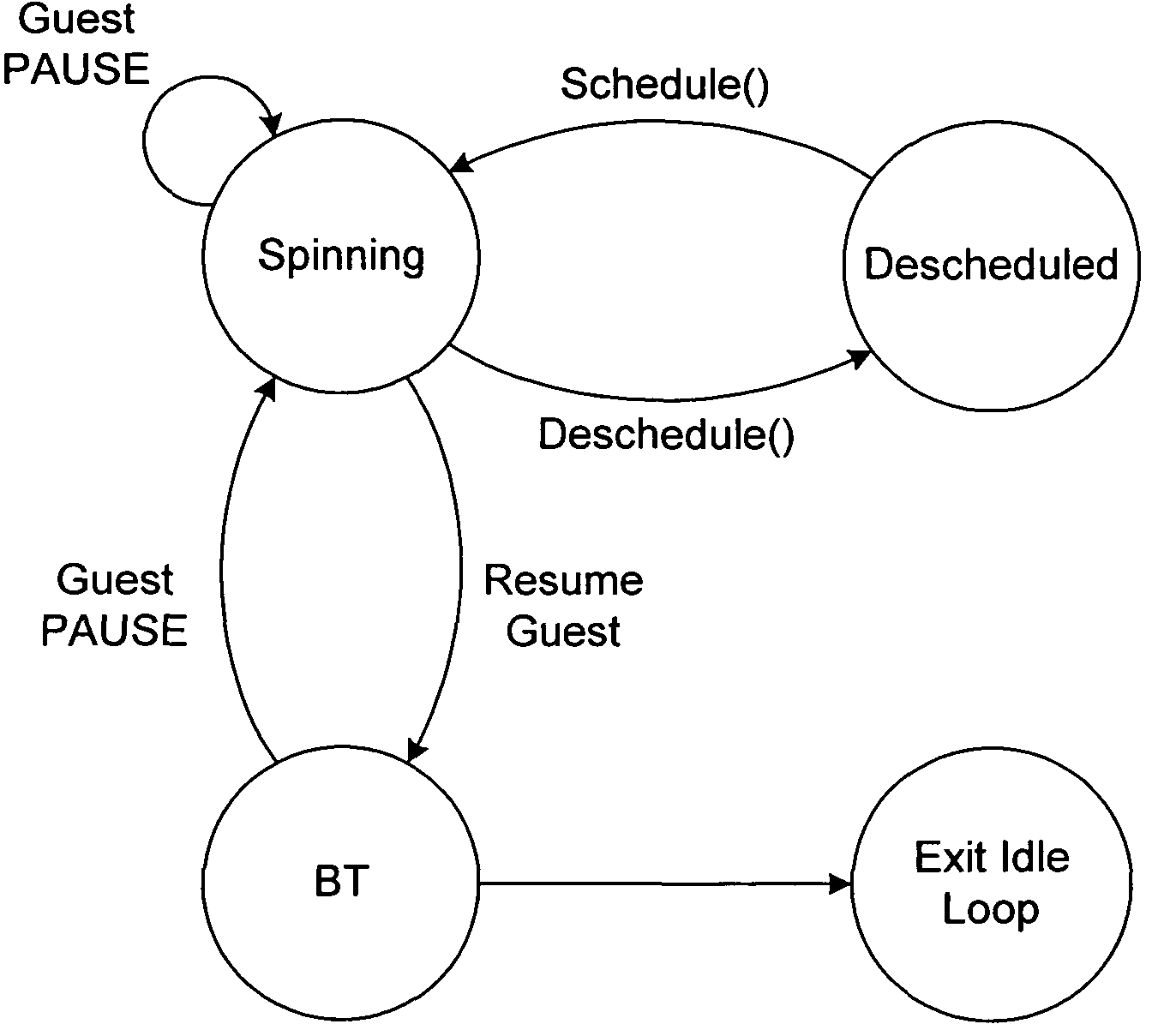
Selective descheduling of idling guests running on a host computer system
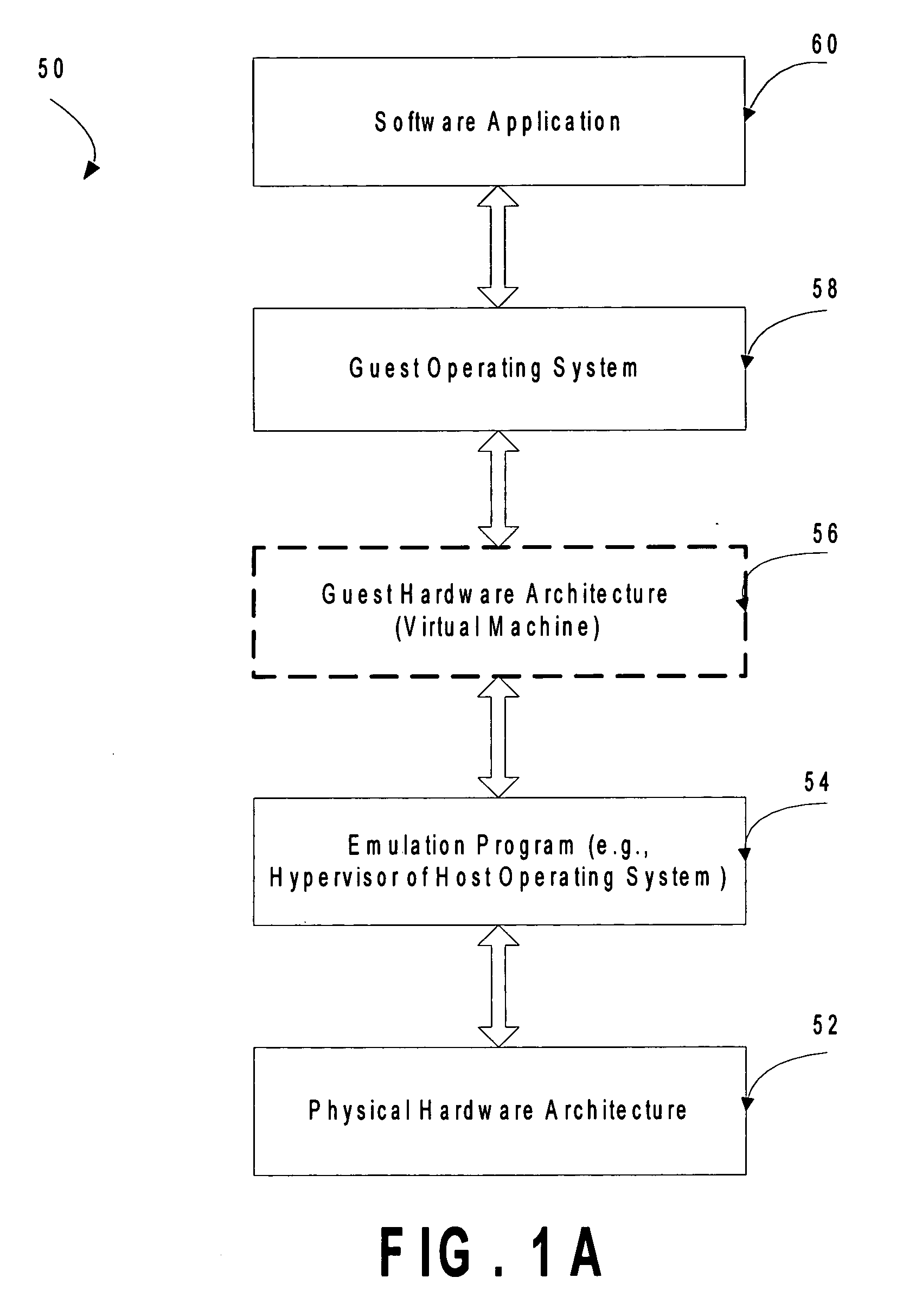
Guests, such as virtual machines, that are running on a host hardware platform are selectively descheduled when an idling condition is detected. An example of the idling condition is that the guest has been executing instructions in an idle loop for more than a threshold period. Guest instructions may be evaluated for the idling condition in conjunction with binary translation.
Owner:VMWARE INC
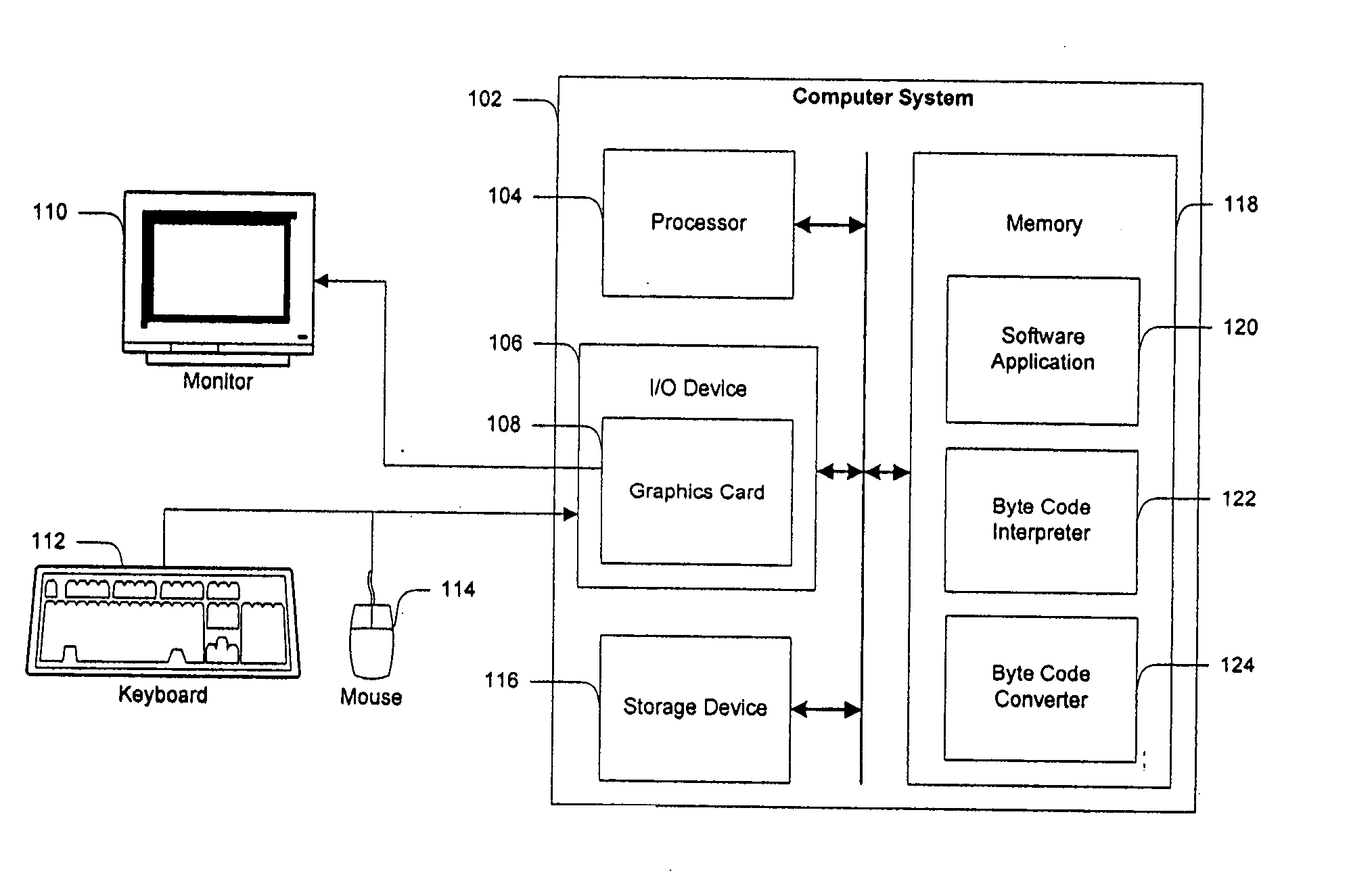
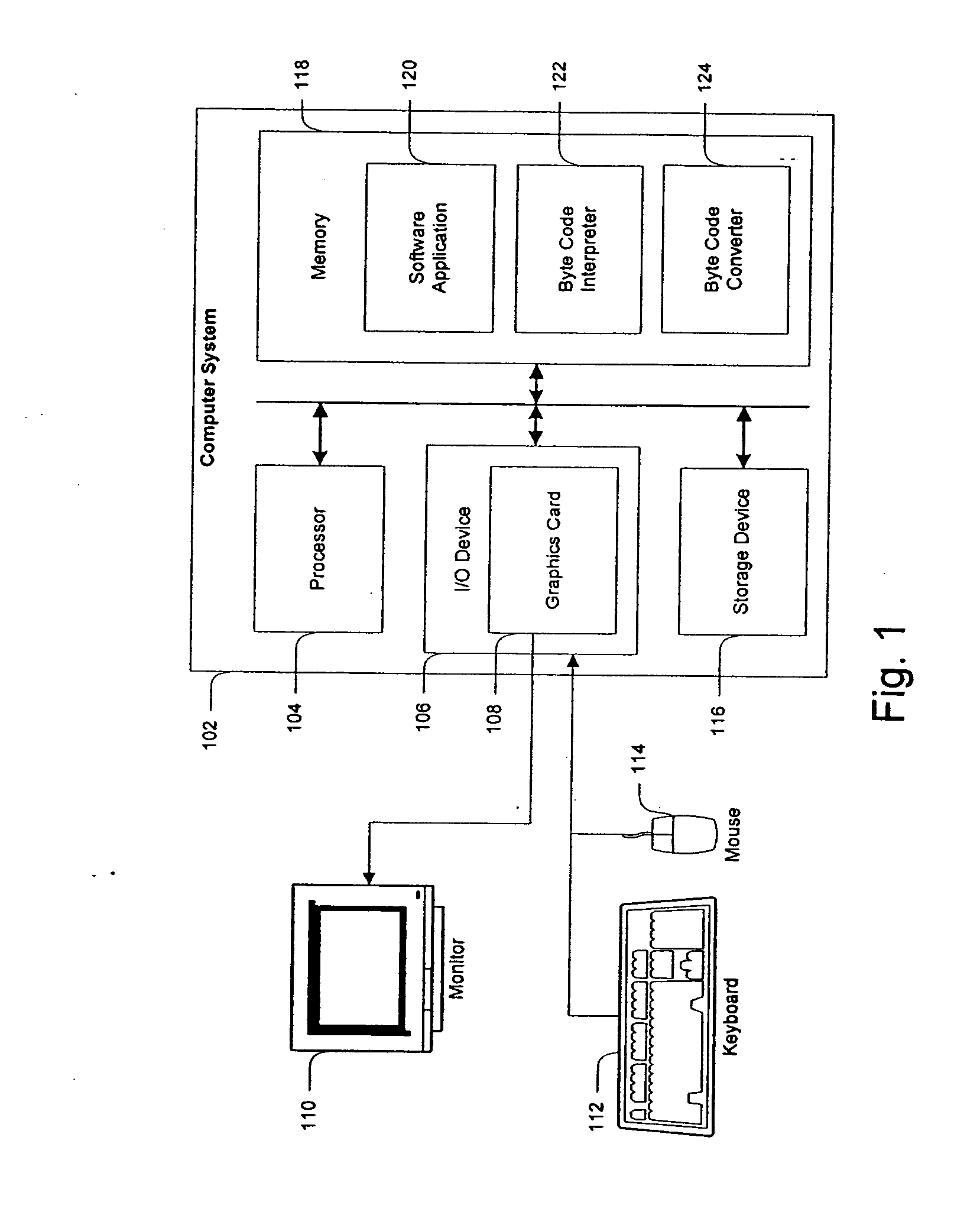
Using a high level programming language with a microcontroller
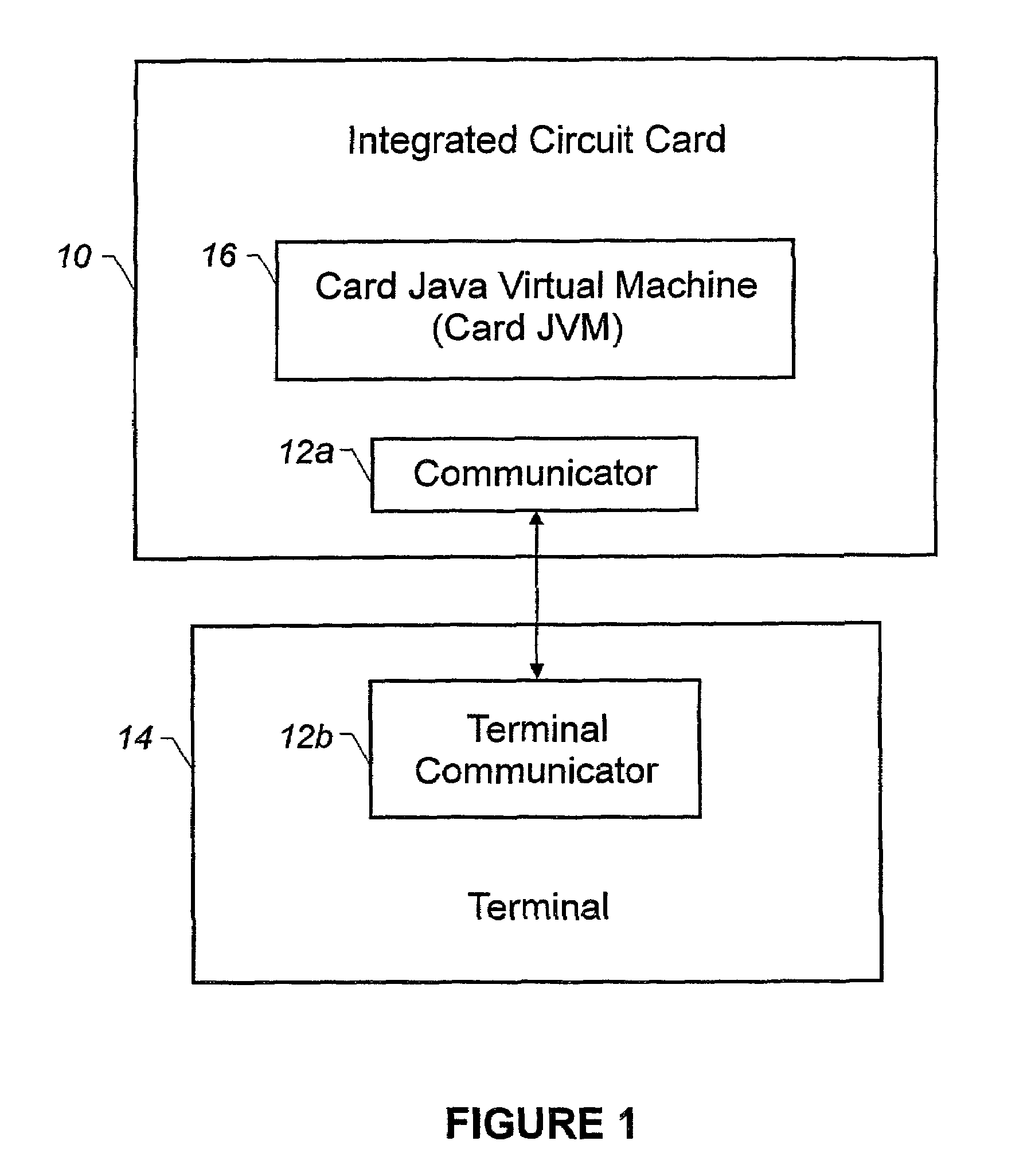
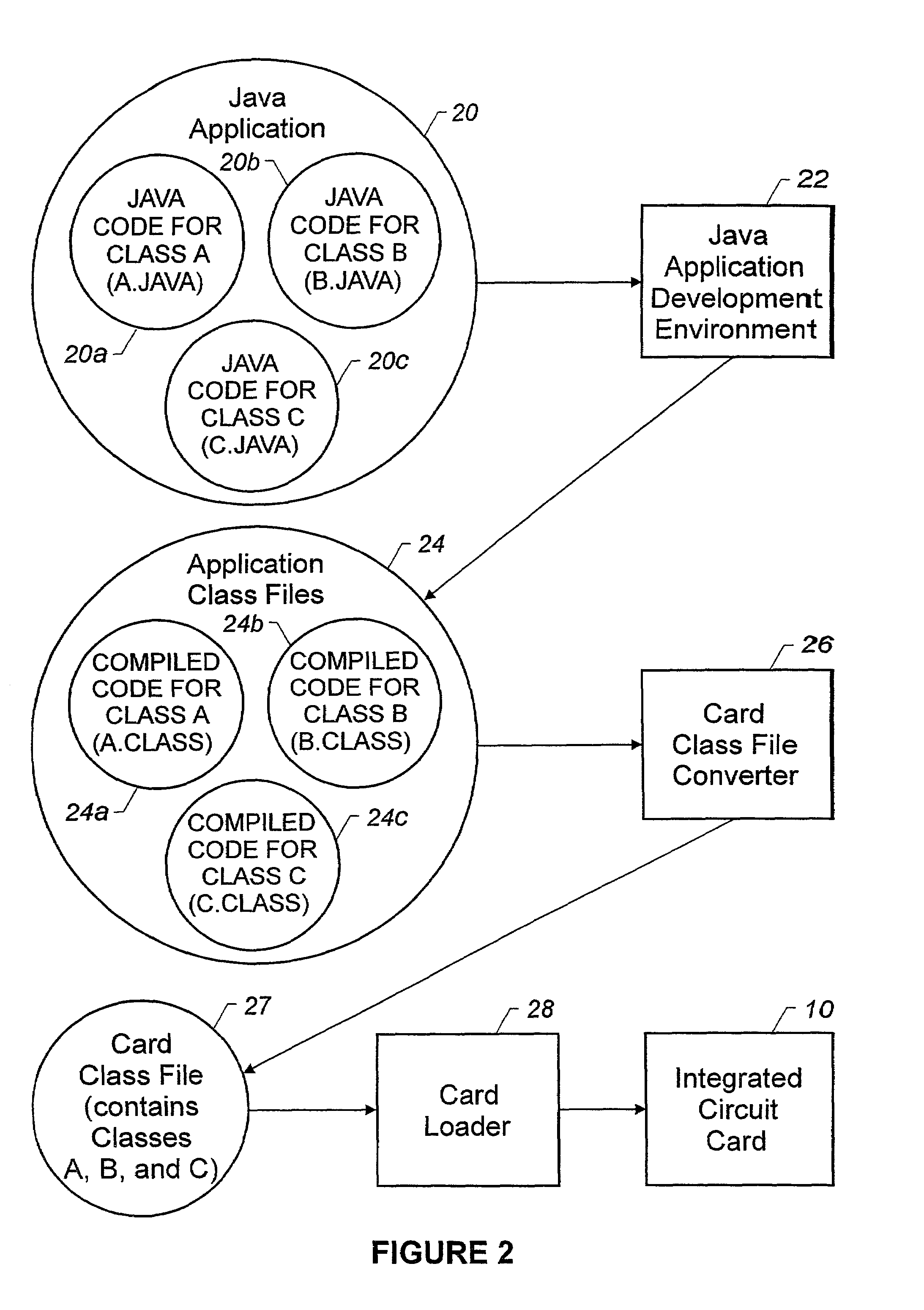
InactiveUS7117485B2Quickly prototypedFast downloadBinary to binaryProgram control using stored programsMicrocontrollerComputer terminal
An integrated circuit card is used with a terminal. The integrated circuit card includes a memory that stores an interpreter and an application that has a high level programming language format. A processor of the card is configured to use the interpreter to interpret the application for execution and to use a communicator of the card to communicate with the terminal.
Owner:GEMPLU
System and method for creating target byte code
InactiveUS7844958B2Facilitate efficient lookup and mappingBinary to binaryProgram controlData elementApplication software
A system and method for converting byte code of a first type into byte code of a second type. Byte code of a first type and markup language code are received as inputs. The first byte code is converted into constituent byte code data elements that can comprise any logical unit or grouping of at least a portion of a software application. The markup language code is converted into constituent markup language data elements that can comprise individual markup language tags and references to data or functionality in the first byte code. The first byte code data elements and markup language data elements are mapped to data elements of a second byte code type. The second byte code data elements are assembled into a resulting second byte code.
Owner:APPCELERATOR
Binary rewriting without relocation information
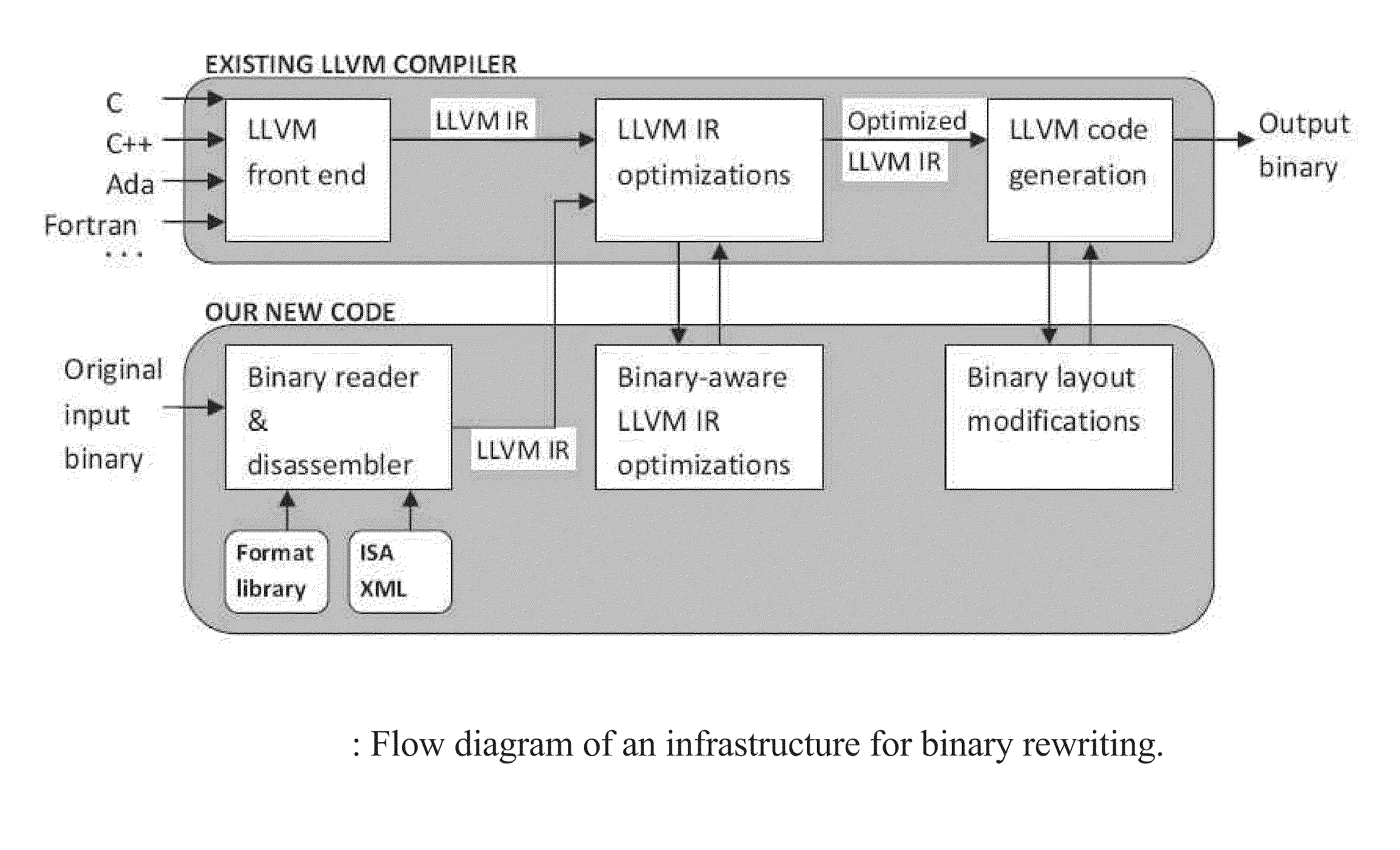
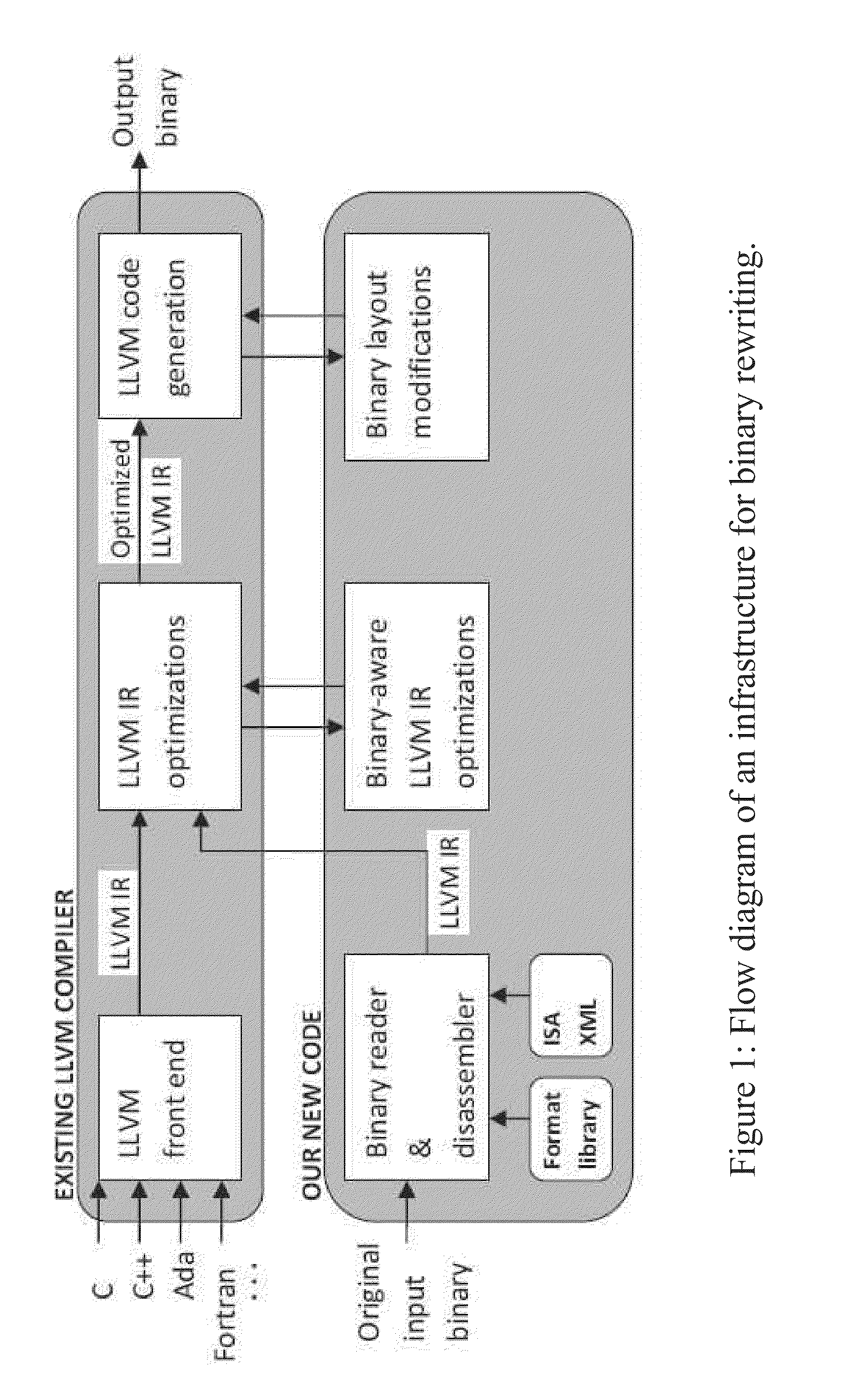
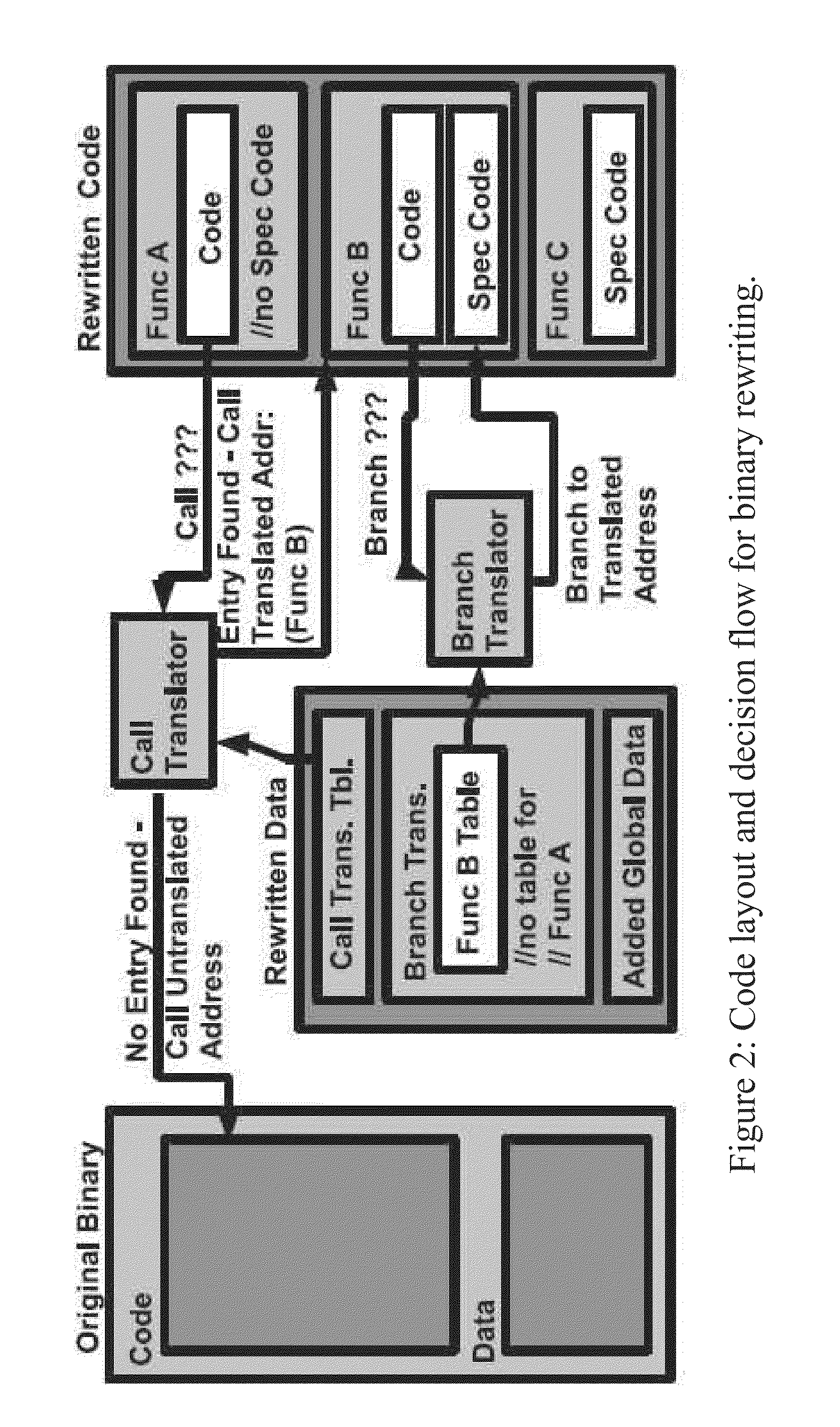
A binary rewriter that can provide complete code coverage without relocation information is provided, together with a method of performing such rewriting. The method can include processing a binary file as an original binary file. The method can also include disassembling the binary file to provide a disassembled binary file. The method can further include rewriting the disassembled binary file without relocation information to provide a rewritten binary file. The rewriting can provide a physical transformation in a recording medium relative to the binary file in the recording medium prior to the rewriting. The processing the binary file, disassembling the binary file, and rewriting the disassembled binary file can be performed by a particular machine.
Owner:MARYLAND UNIV OF
System and method for creating target byte code
InactiveUS7707547B2Efficient mappingSmaller and faster byte code of a second typeBinary to binaryDigital data processing detailsData elementByte
Owner:APPCELERATOR
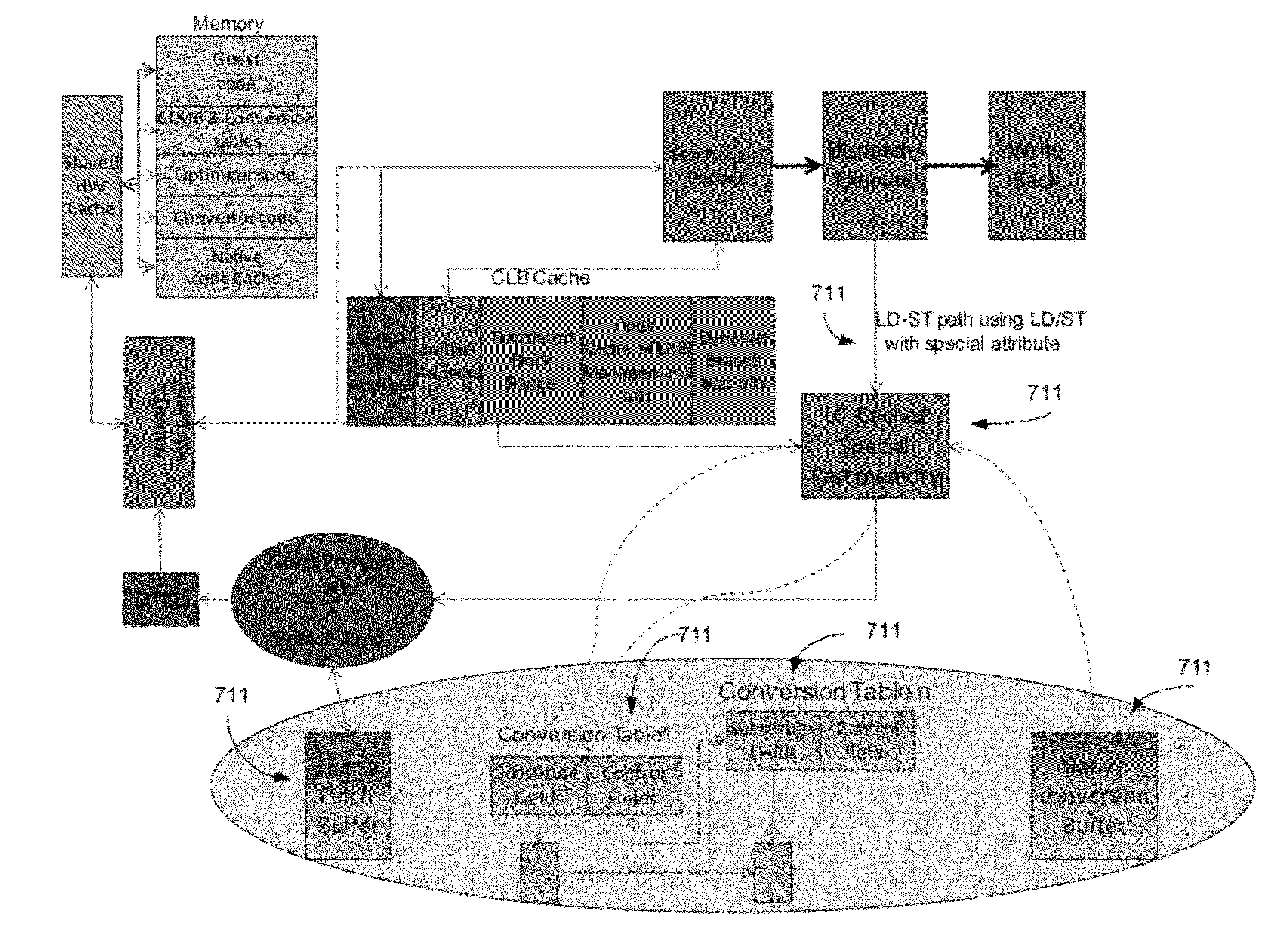
Guest instruction to native instruction range based mapping using a conversion look aside buffer of a processor
ActiveUS20120198157A1Memory architecture accessing/allocationBinary to binaryParallel computingComputer architecture
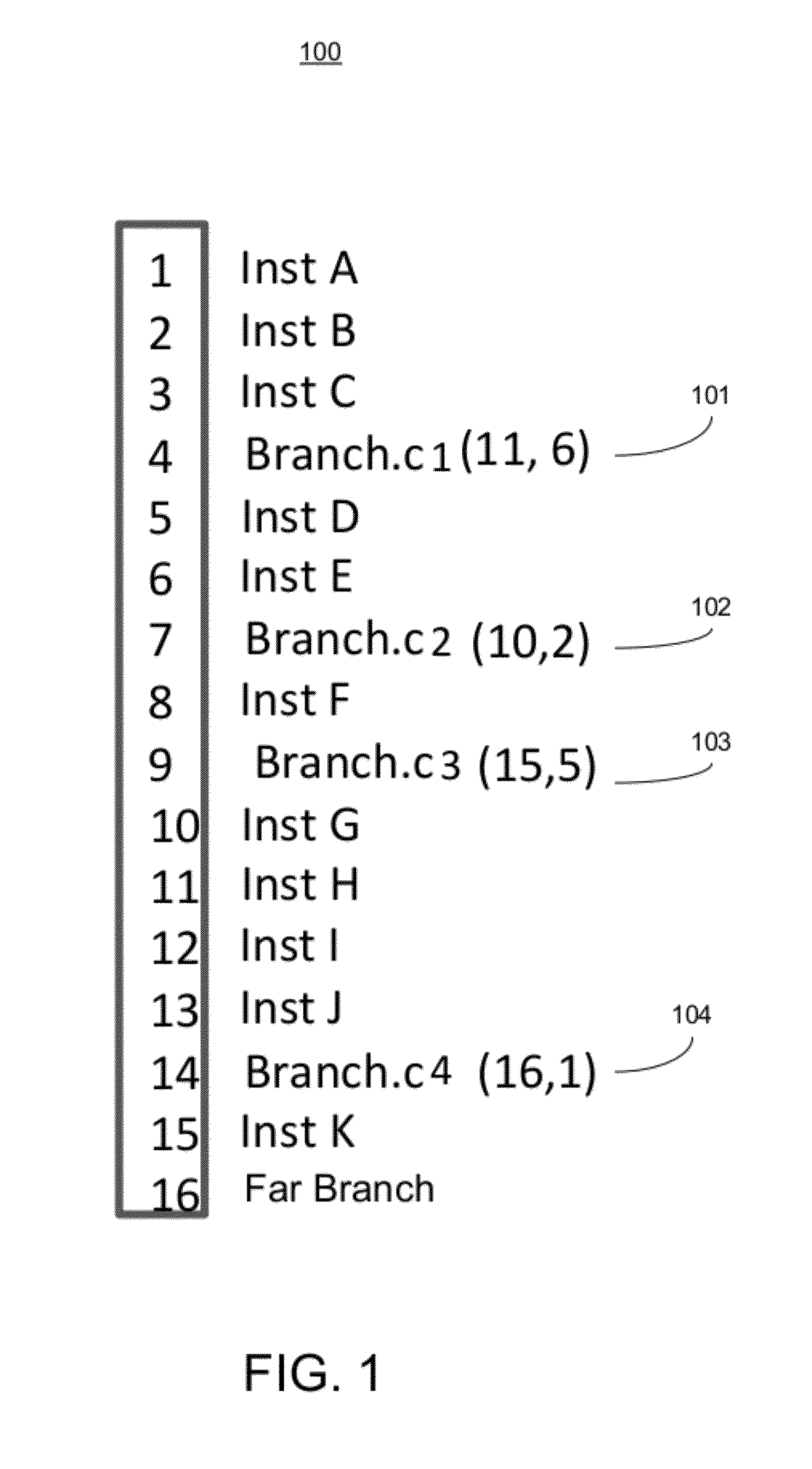
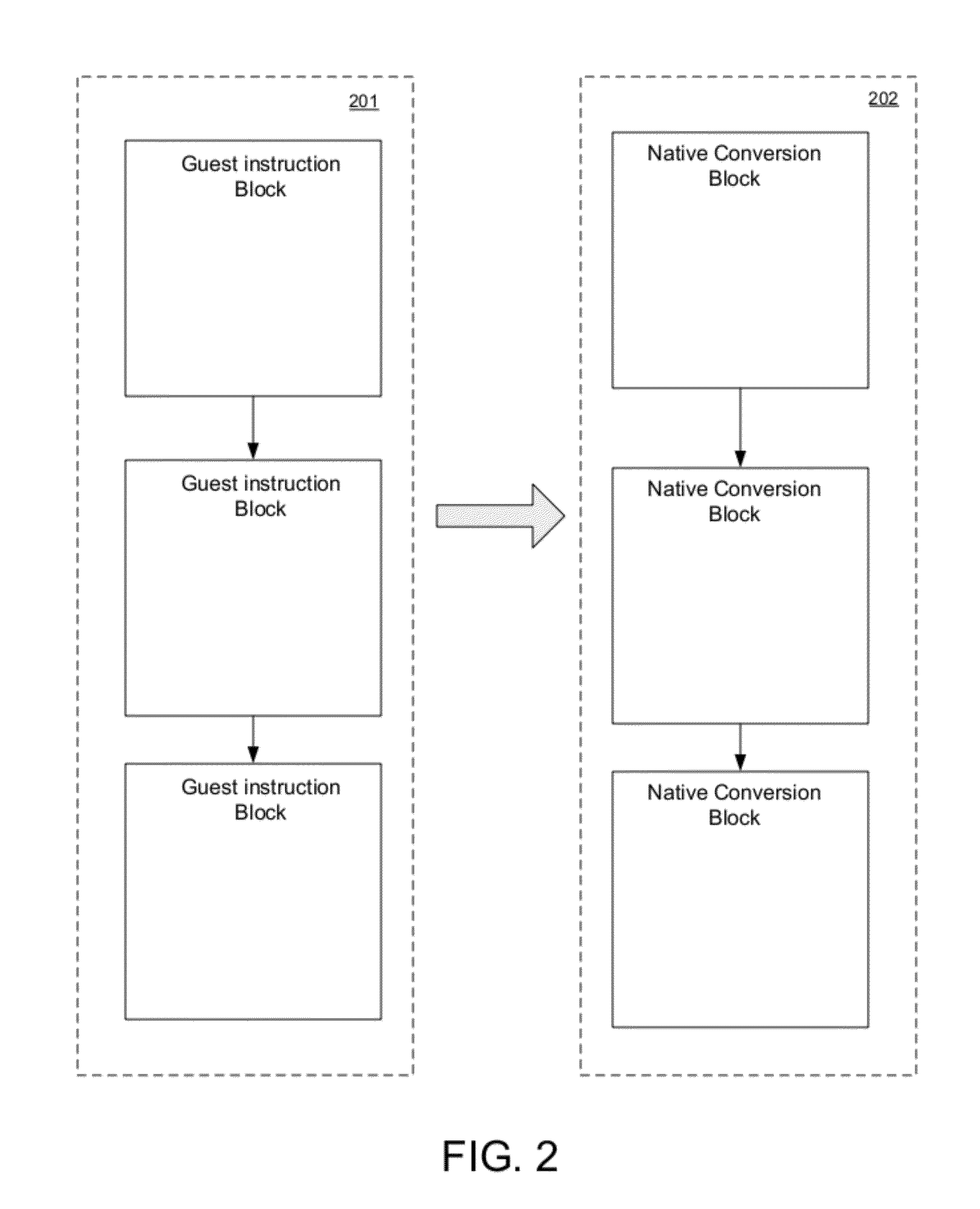
A method for translating instructions for a processor. The method includes accessing a plurality of guest instructions that comprise multiple guest branch instructions, and assembling the plurality of guest instructions into a guest instruction block. The guest instruction block is converted into a corresponding native conversion block. The native conversion block is stored into a native cache. A mapping of the guest instruction block to corresponding native conversion block is stored in a conversion look aside buffer. Upon a subsequent request for a guest instruction, the conversion look aside buffer is indexed to determine whether a hit occurred, wherein the mapping indicates whether the guest instruction has a corresponding converted native instruction in the native cache. The converted native instruction is forwarded for execution in response to the hit.
Owner:INTEL CORP
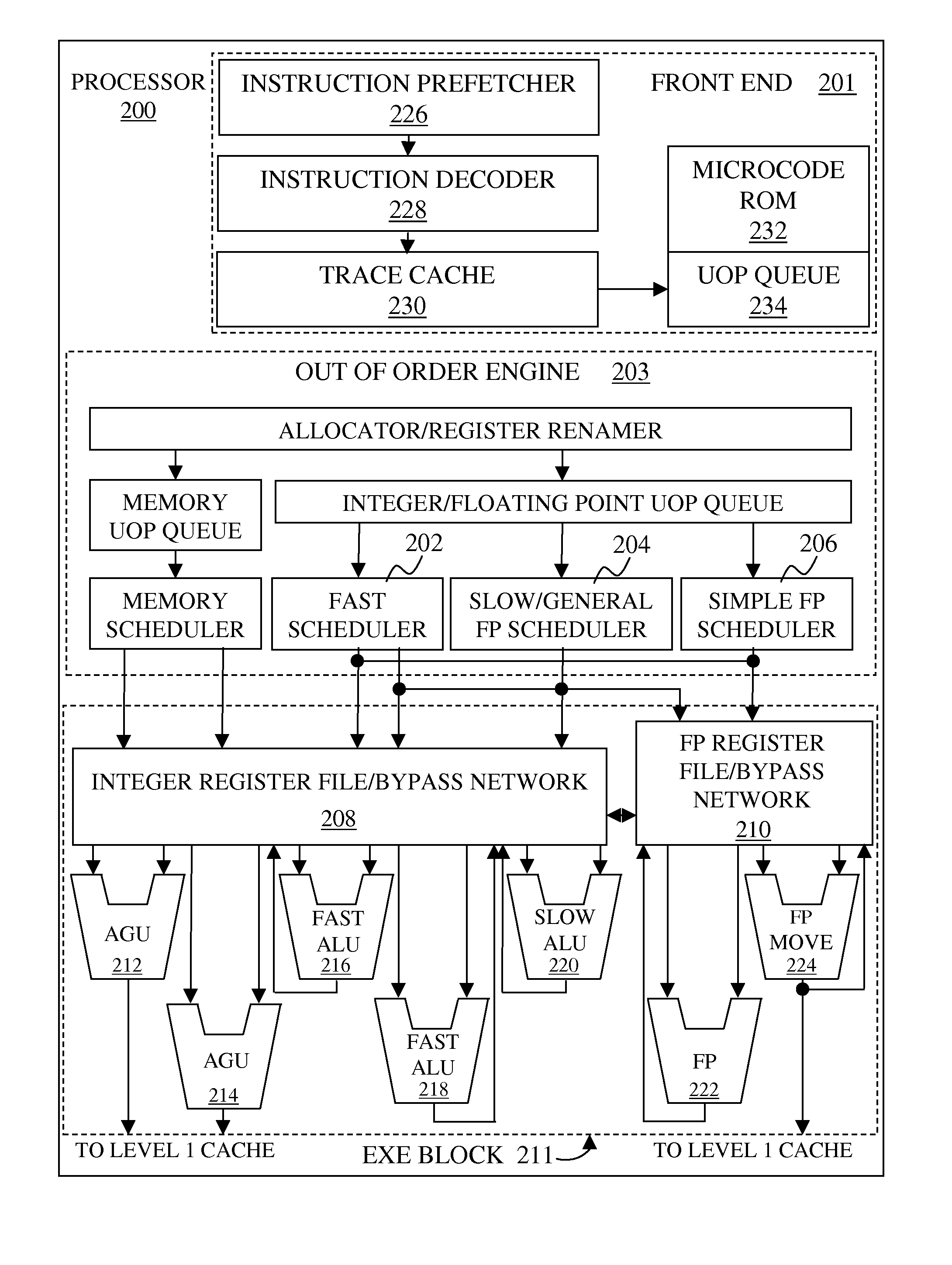
Extreme pipeline and optimized reordering technology
ActiveUS20040181785A1More efficientDisable portionBinary to binaryTransportation and packagingOperational systemParallel computing
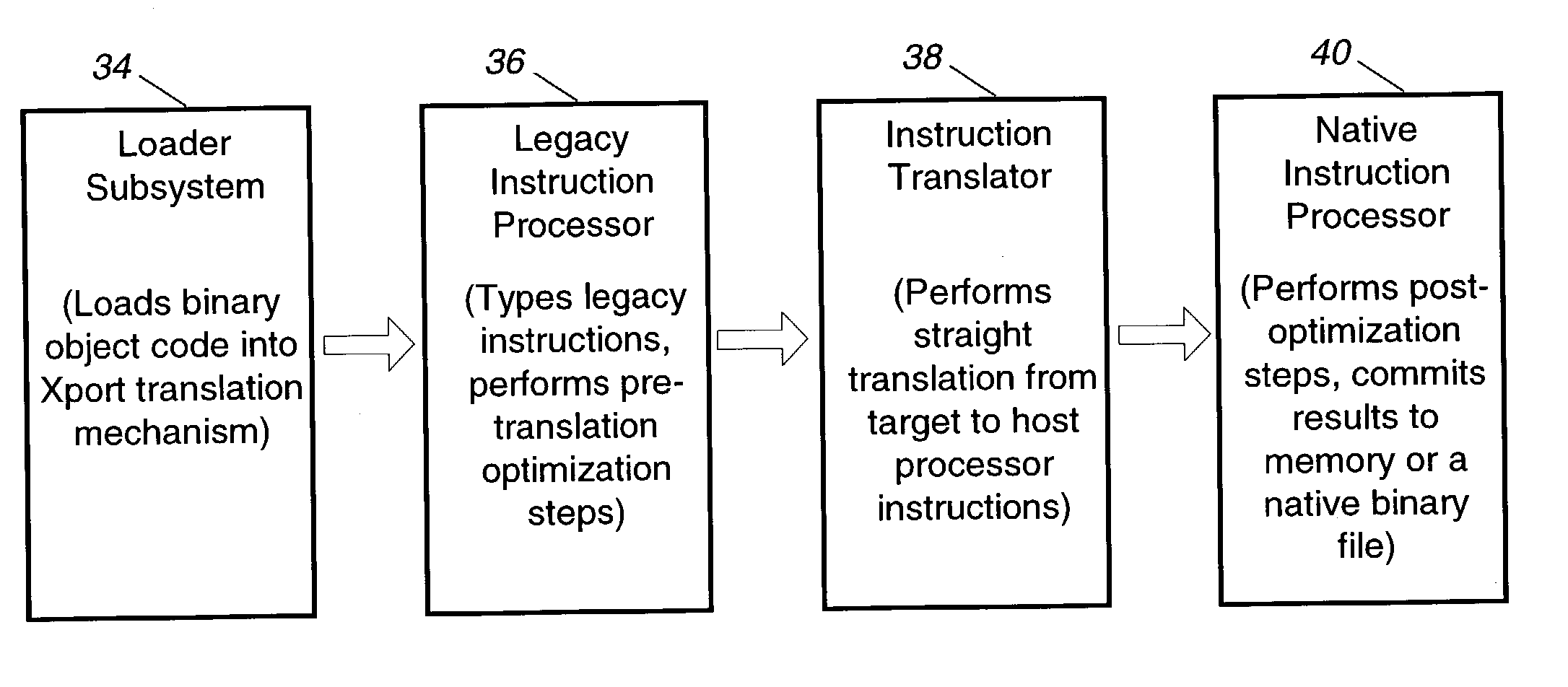
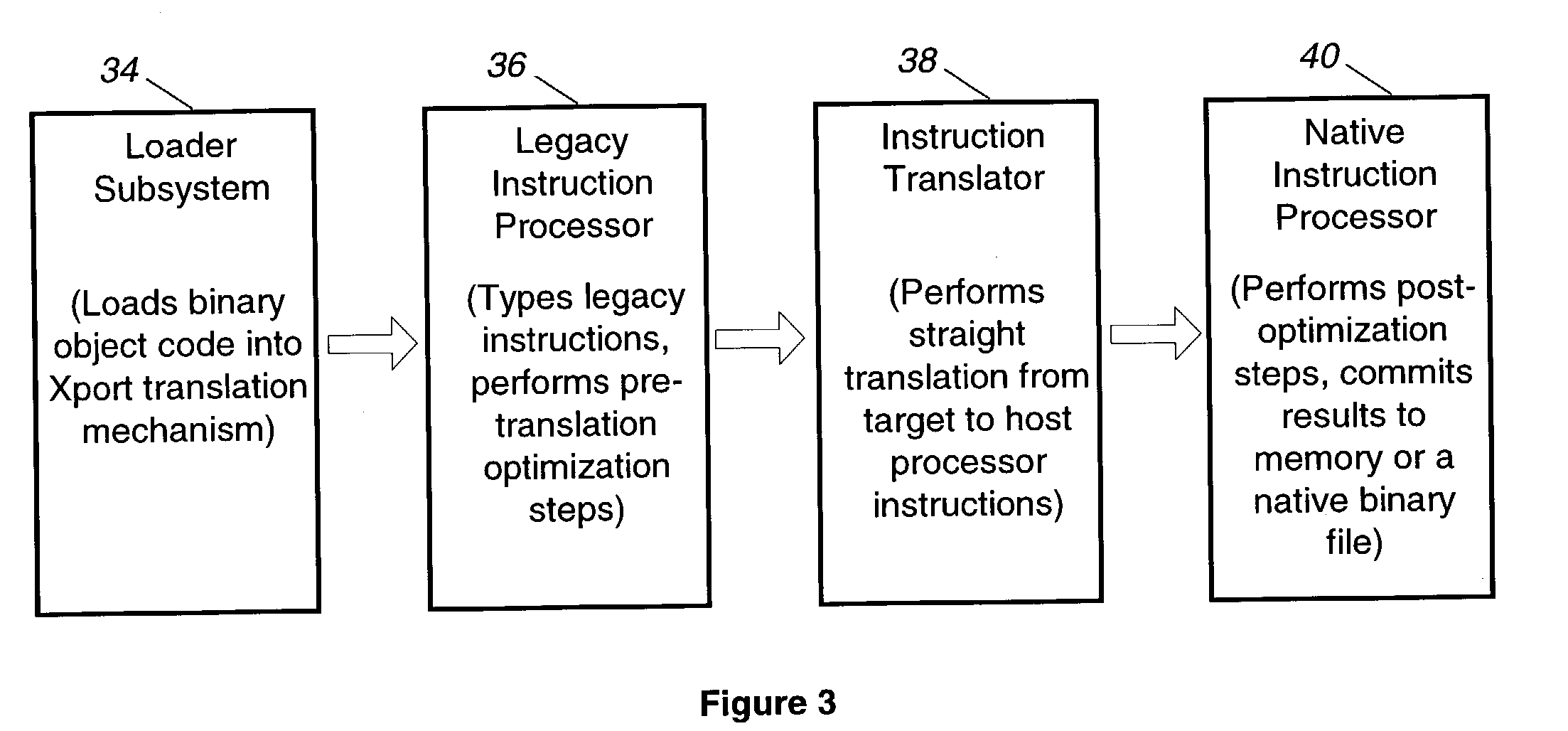
The present invention relates to a binary translator for directly translating binary instructions written for a legacy processor to executable binary instructions for a native processor. In accordance with an important aspect of the invention the binary translator is configured as a reconfigurable translator, which enables the binary translator to be used with different legacy processors and / or operating systems and native processors. The binary translators also optimize to take advantage of more efficient native processor instructions and allows portions of the legacy binary code to be disabled and / or new native instructions to be added to the application program without modification of the legacy binary code.
Owner:NORTHROP GRUMMAN SYST CORP
Method and system for translating exception handling semantics of a bytecode class file
InactiveUS6131187ABinary to binarySpecific program execution arrangementsRelevant informationArray data structure
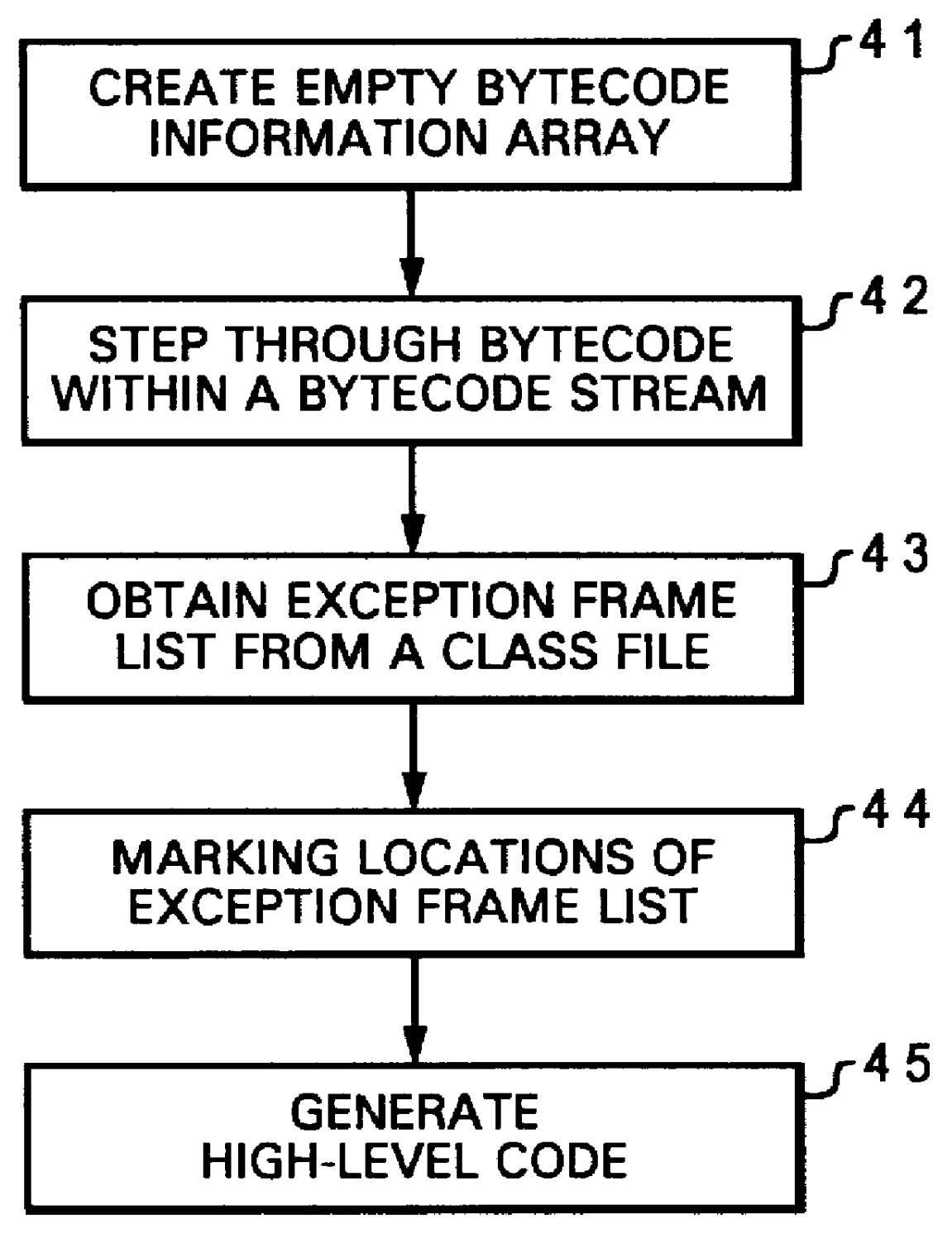
A method for translating exception handling semantics of a bytecode class file within a computer system is disclosed. An empty bytecode information array is first established. Pertinent information is then obtained by examining bytecodes within a bytecode stream, and such information are inserted into the bytecode information array. An exception framelist, which includes an exception handling routine, is subsequently obtained from a class file for the bytecode stream. The entries within the bytecode information array corresponding to a starting location and an ending location of the exception framelist are marked. Finally, a high-level code sequence is generated utilizing the bytecode information array.
Owner:IBM CORP
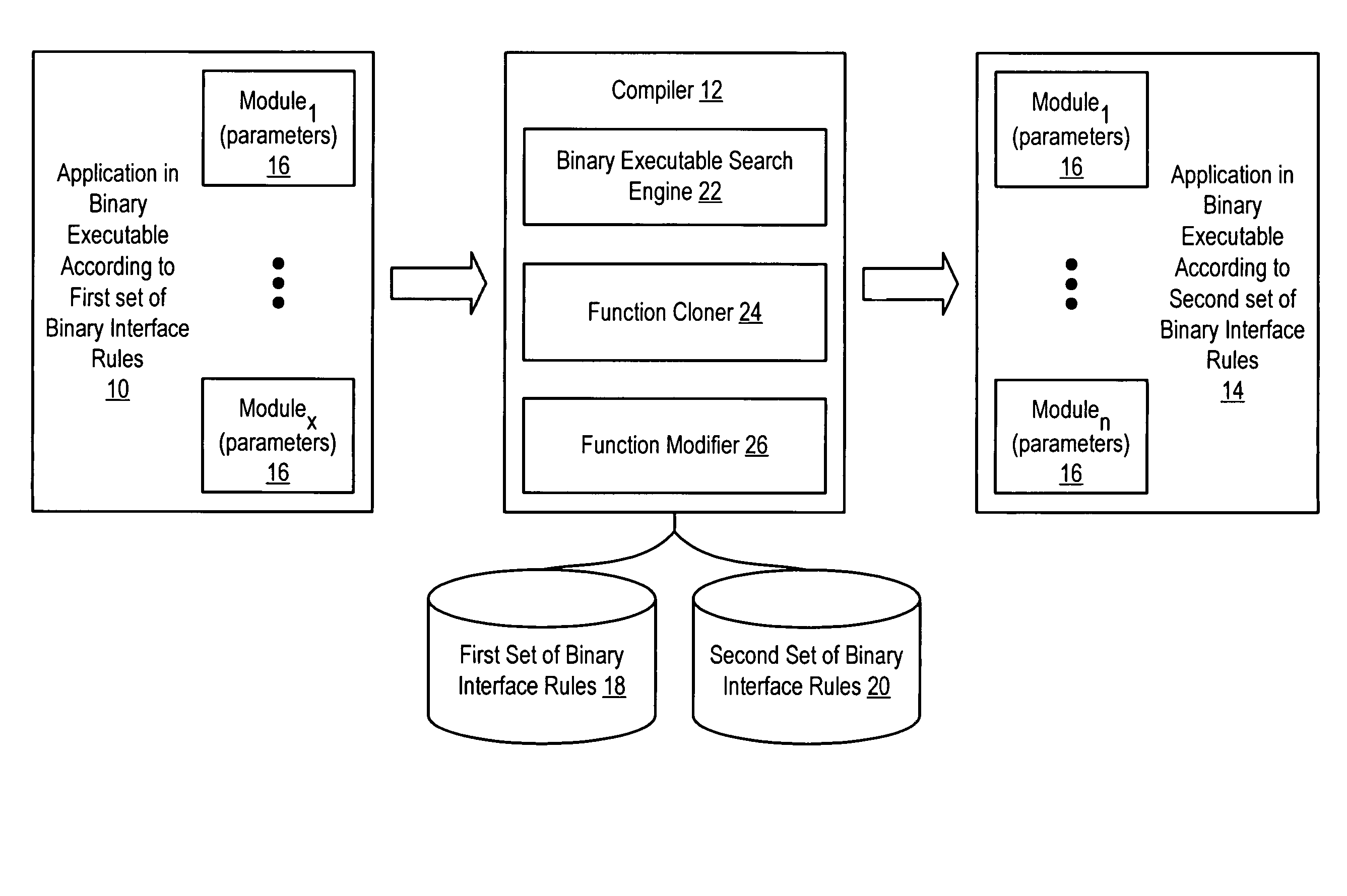
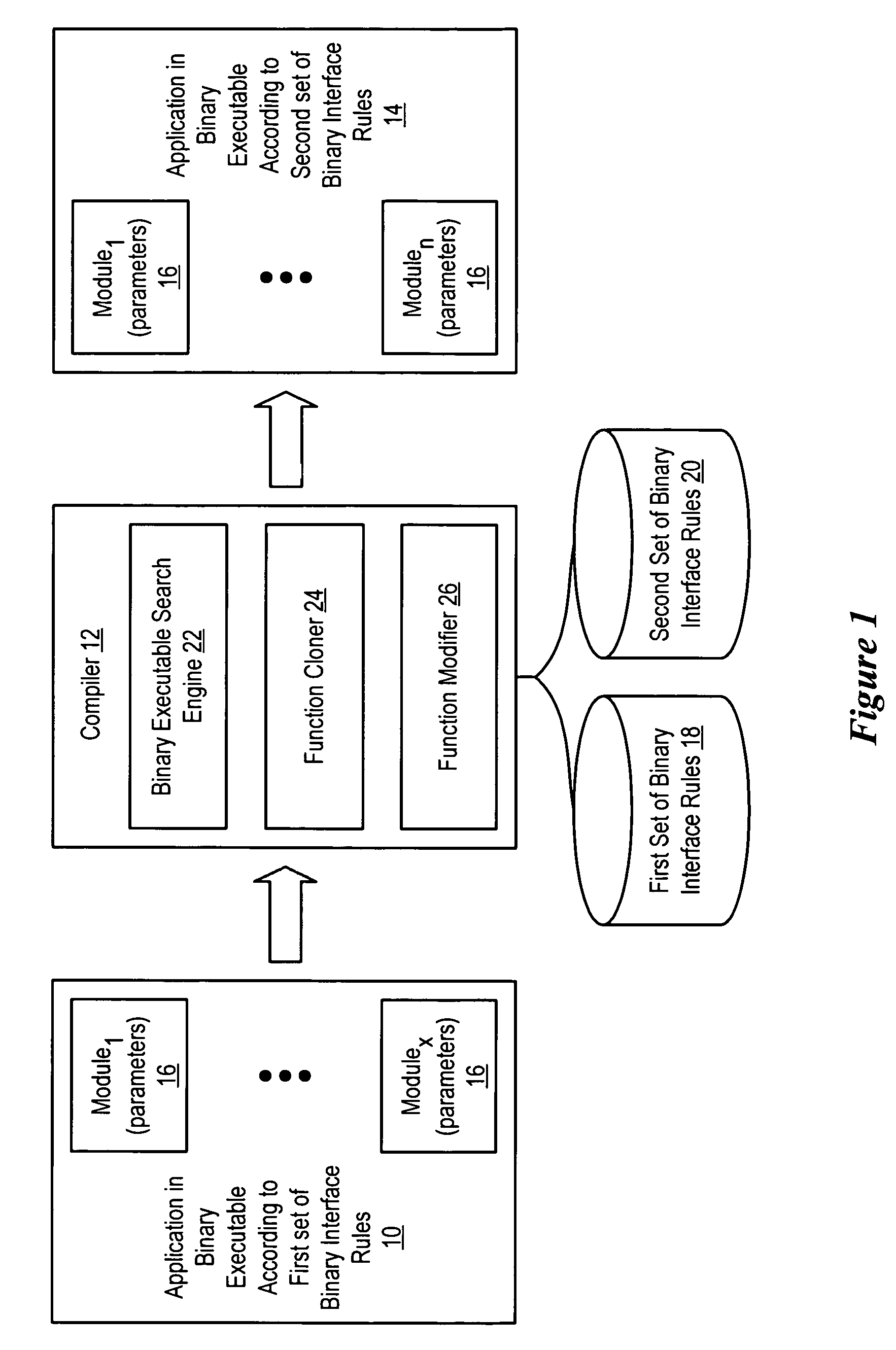
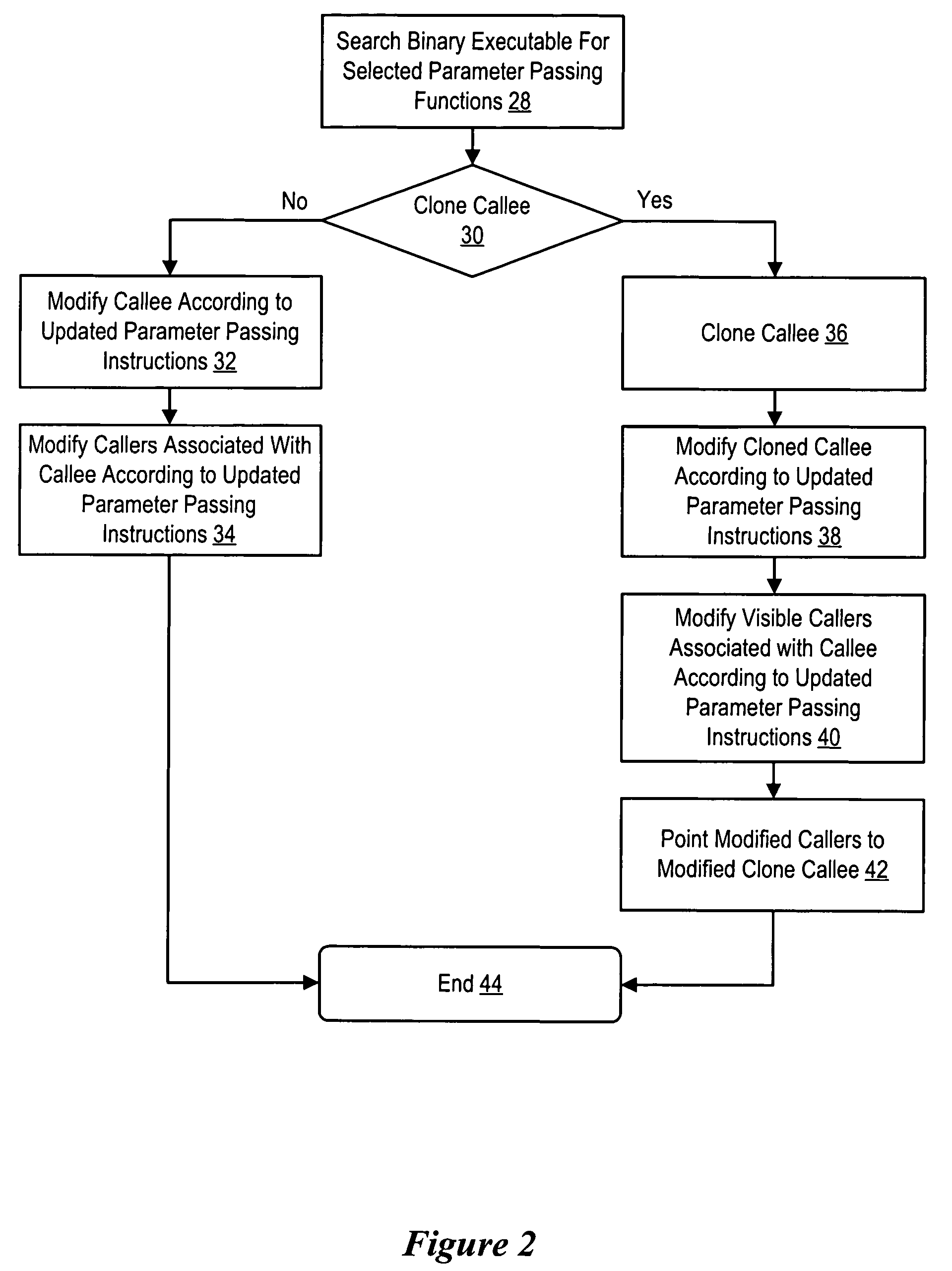
System and method for binary translation to improve parameter passing
ActiveUS7861234B1Improve efficiencyReduce disadvantagesBinary to binaryProgram controlAlgorithmApplication software
An application compiled to a binary executable according to a first set of binary interface rules has selected caller / callee pairs that present parameter passing improvement possibilities modified from compliance with the first set of binary interface rules to compliance with a second set of binary interface rules to improve the efficiency of parameter passing, such as by reducing the number of instructions used to pass the parameters. A binary executable search engine searches the binary executable to locate functions having parameter passing improvement possibilities. Identified caller / callee function pairs are updated with a function modifier to pass the parameters more efficiently. Selected of the identified callee functions are cloned so that a cloned function is modified instead of the original function, thus leaving the original function to pass parameters with functions beyond the view of the binary executable search engine.
Owner:ORACLE INT CORP
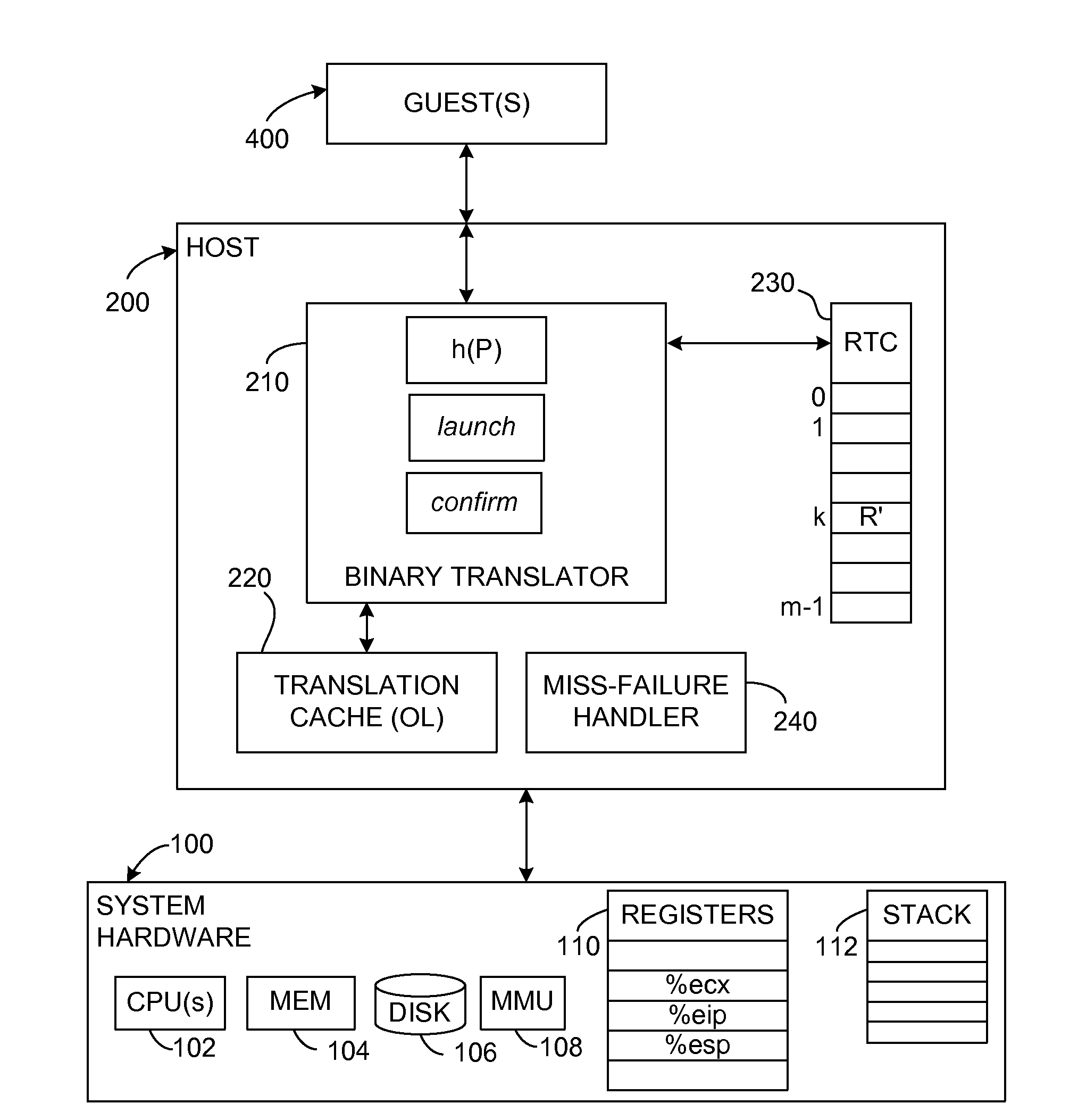
Prediction Mechanism for Subroutine Returns in Binary Translation Sub-Systems of Computers
Owner:VMWARE INC
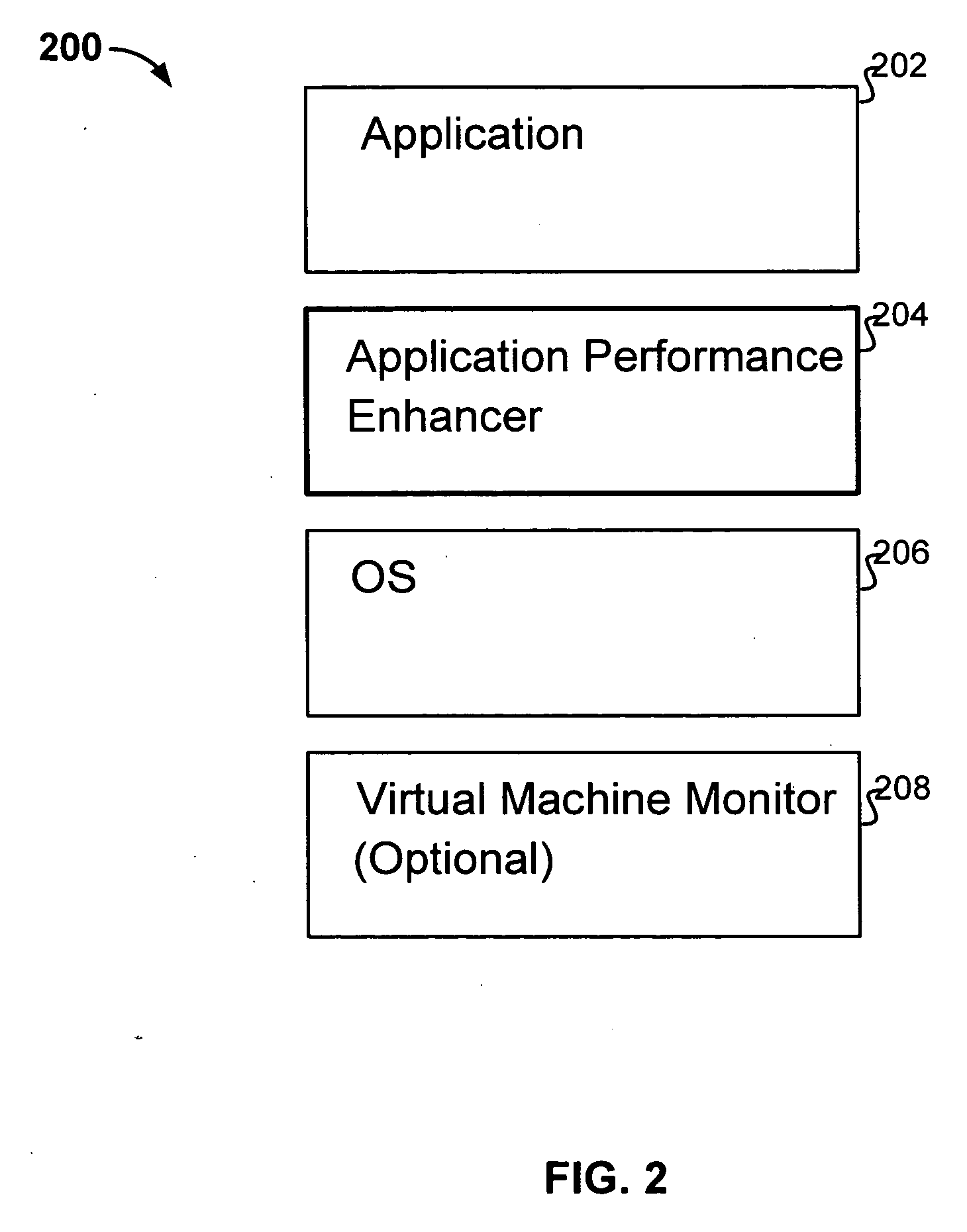
Software application performance enhancement
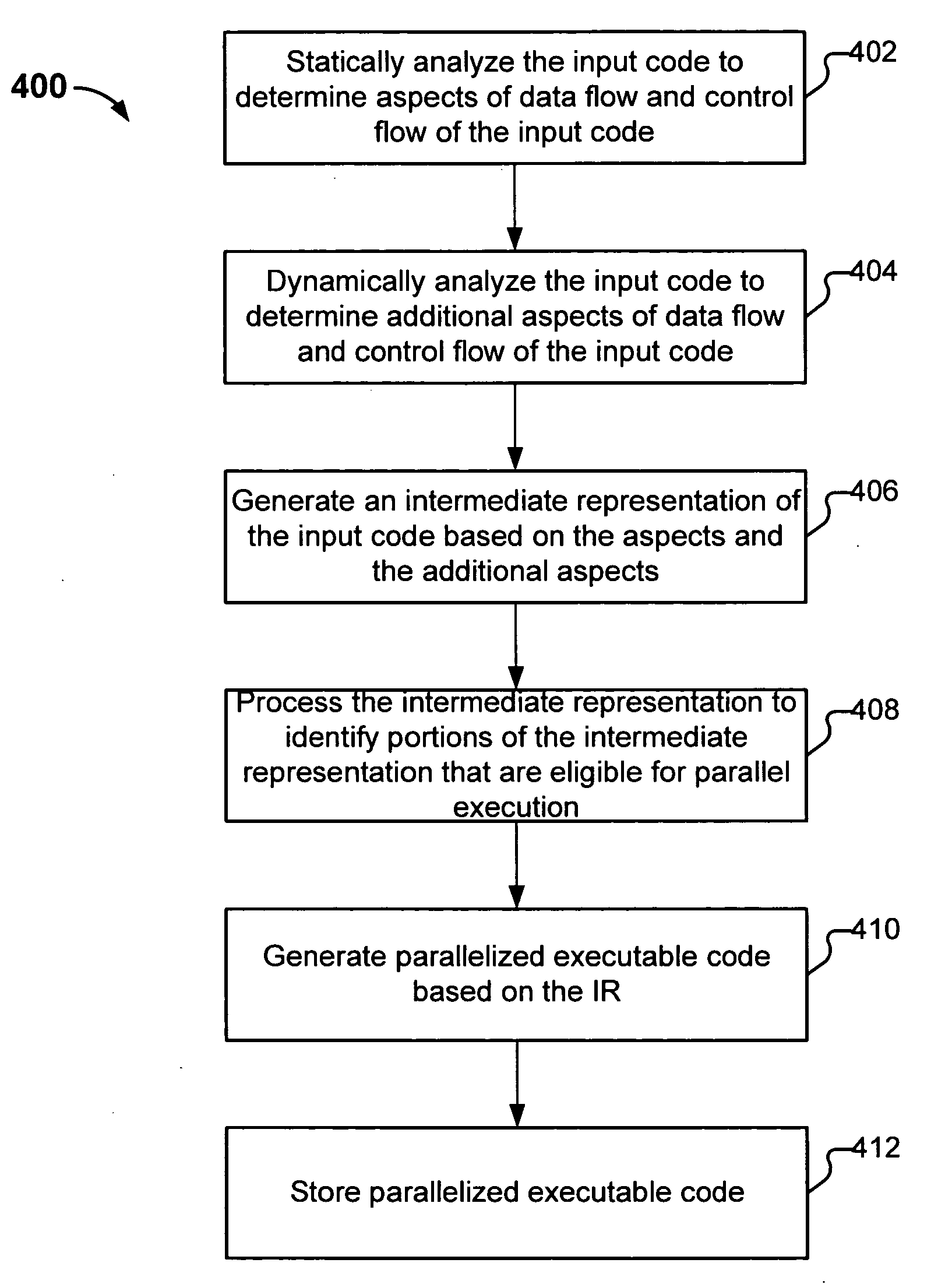
Generating parallelized executable code from input code includes statically analyzing the input code to determine aspects of data flow and control flow of the input code; dynamically analyzing the input code to determine additional aspects of data flow and control flow of the input code; generating an intermediate representation of the input code based at least in part on the aspects of data flow and control flow of the input code identified by the static analysis and the additional aspects of data and control flow of the input code identified by the dynamic analysis; and processing the intermediate representation to determine portions of the intermediate representation that are eligible for parallel execution; and generating parallelized executable code from the processed intermediate representation
Owner:QUALCOMM INC
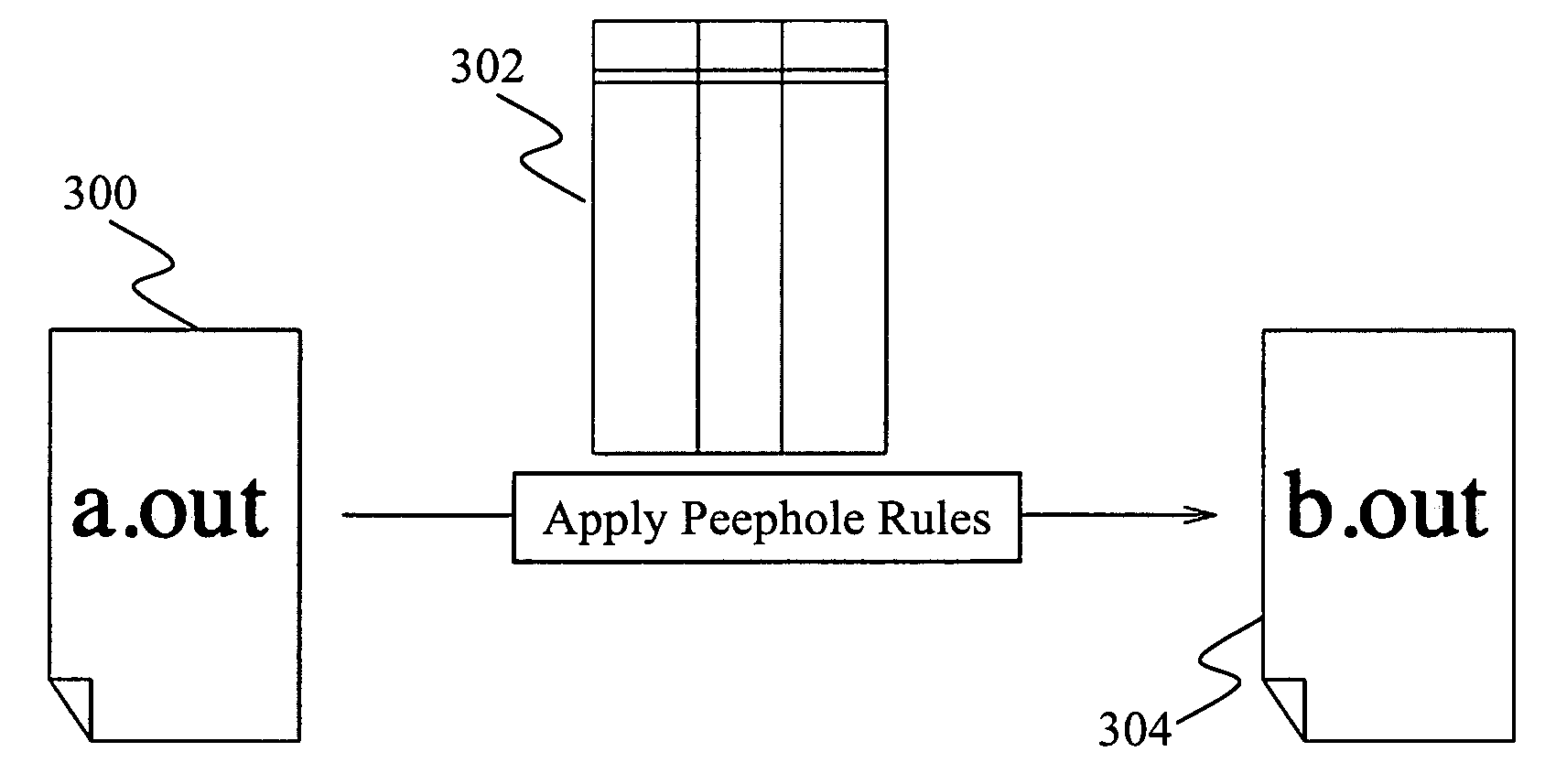
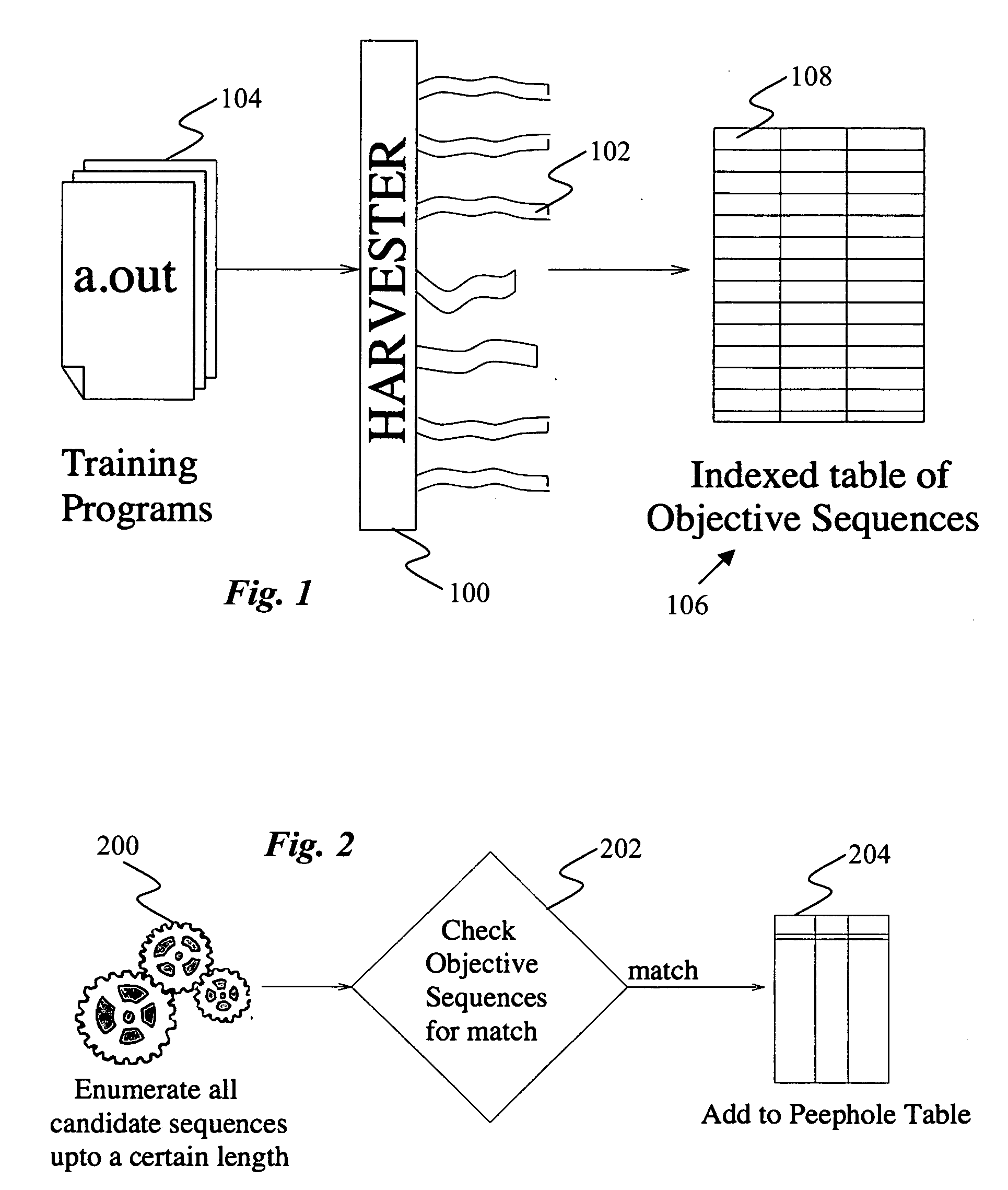
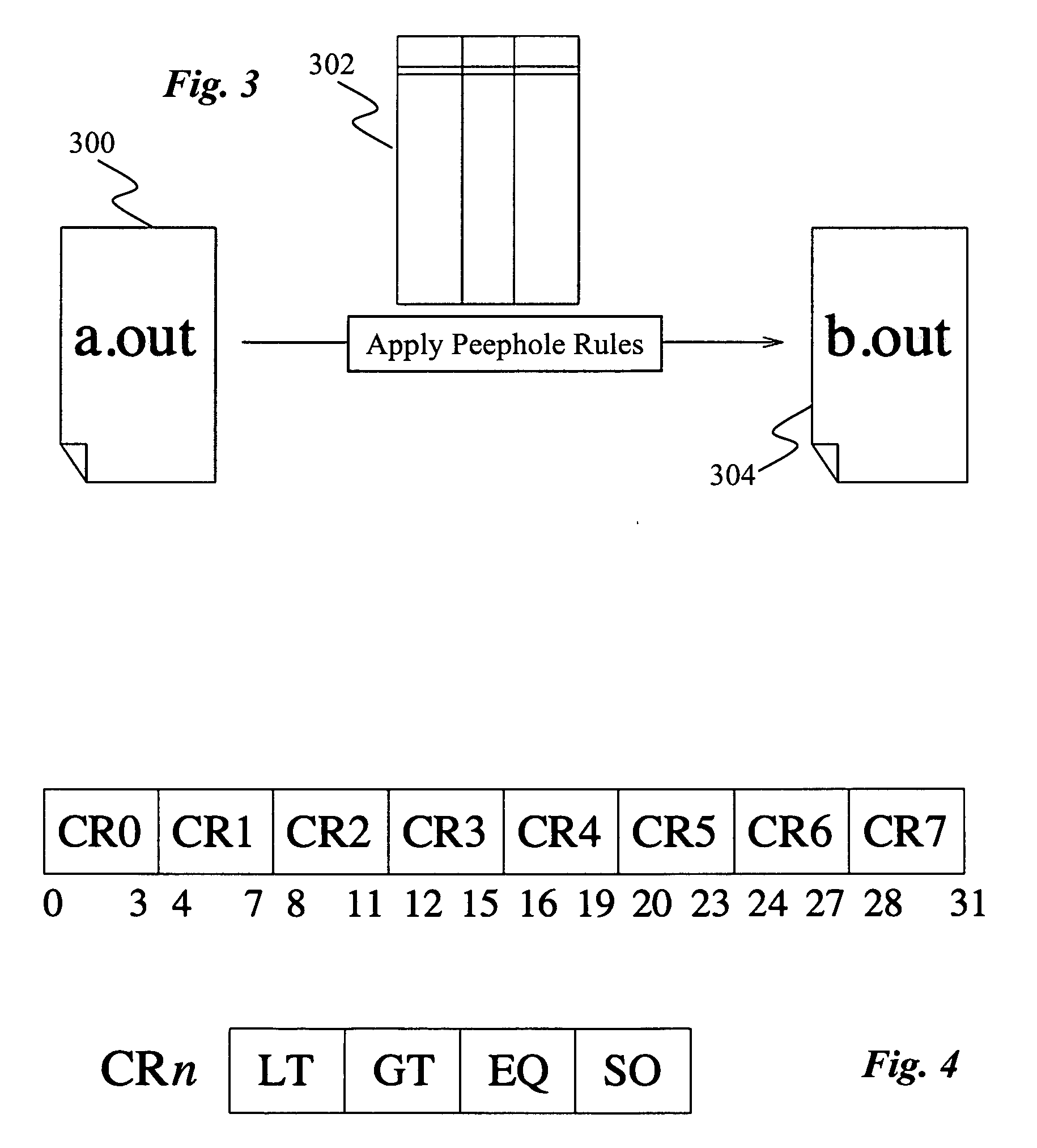
Binary translation using peephole translation rules
InactiveUS20080172657A1Valid encodingEffective applicationBinary to binaryDigital computer detailsTheoretical computer scienceSoftware engineering
An efficient binary translator uses peephole translation rules to directly translate executable code from one instruction set to another. In a preferred embodiment, the translation rules are generated using superoptimization techniques that enable the translator to automatically learn translation rules for translating code from the source to target instruction set architecture.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
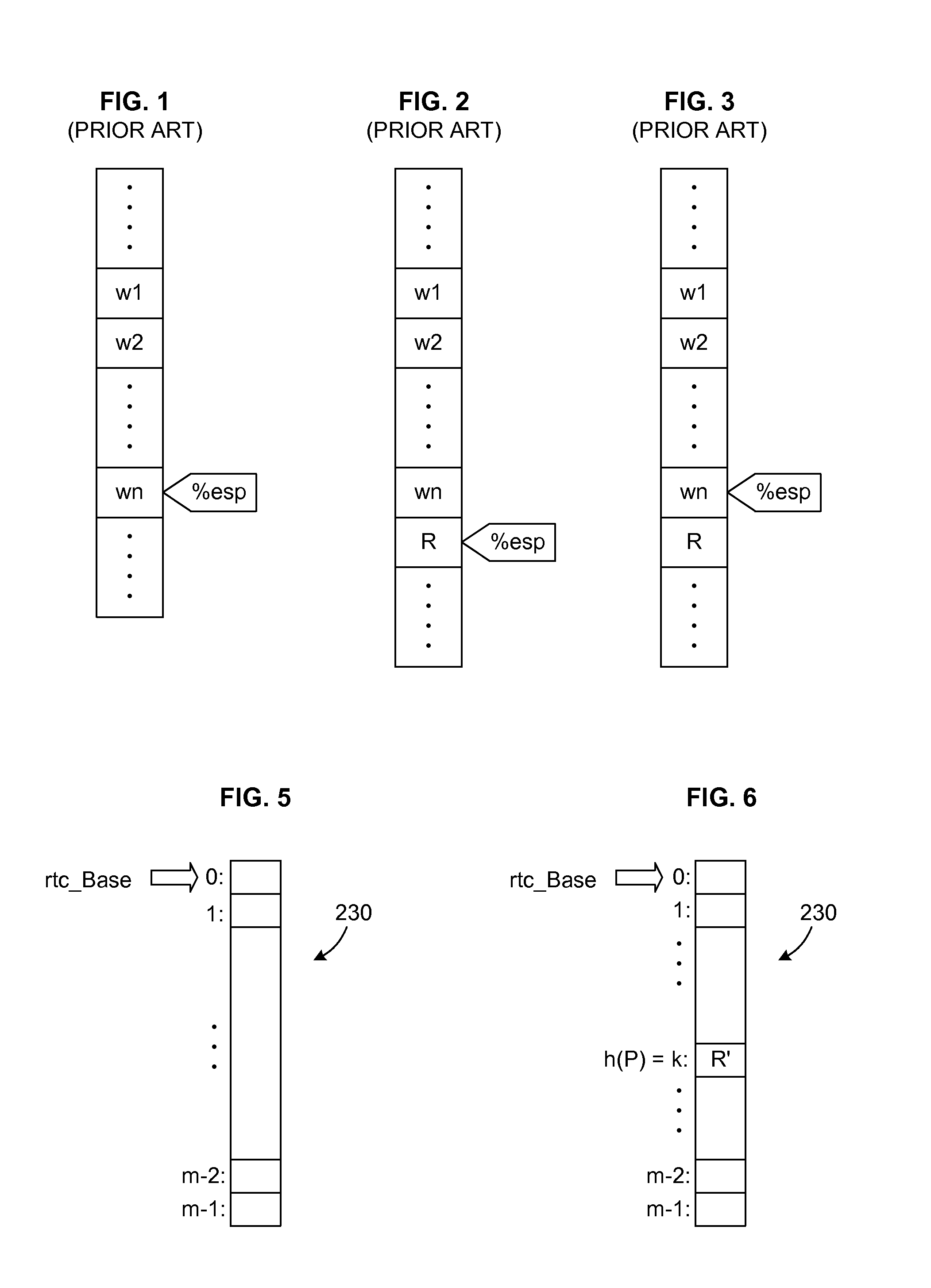
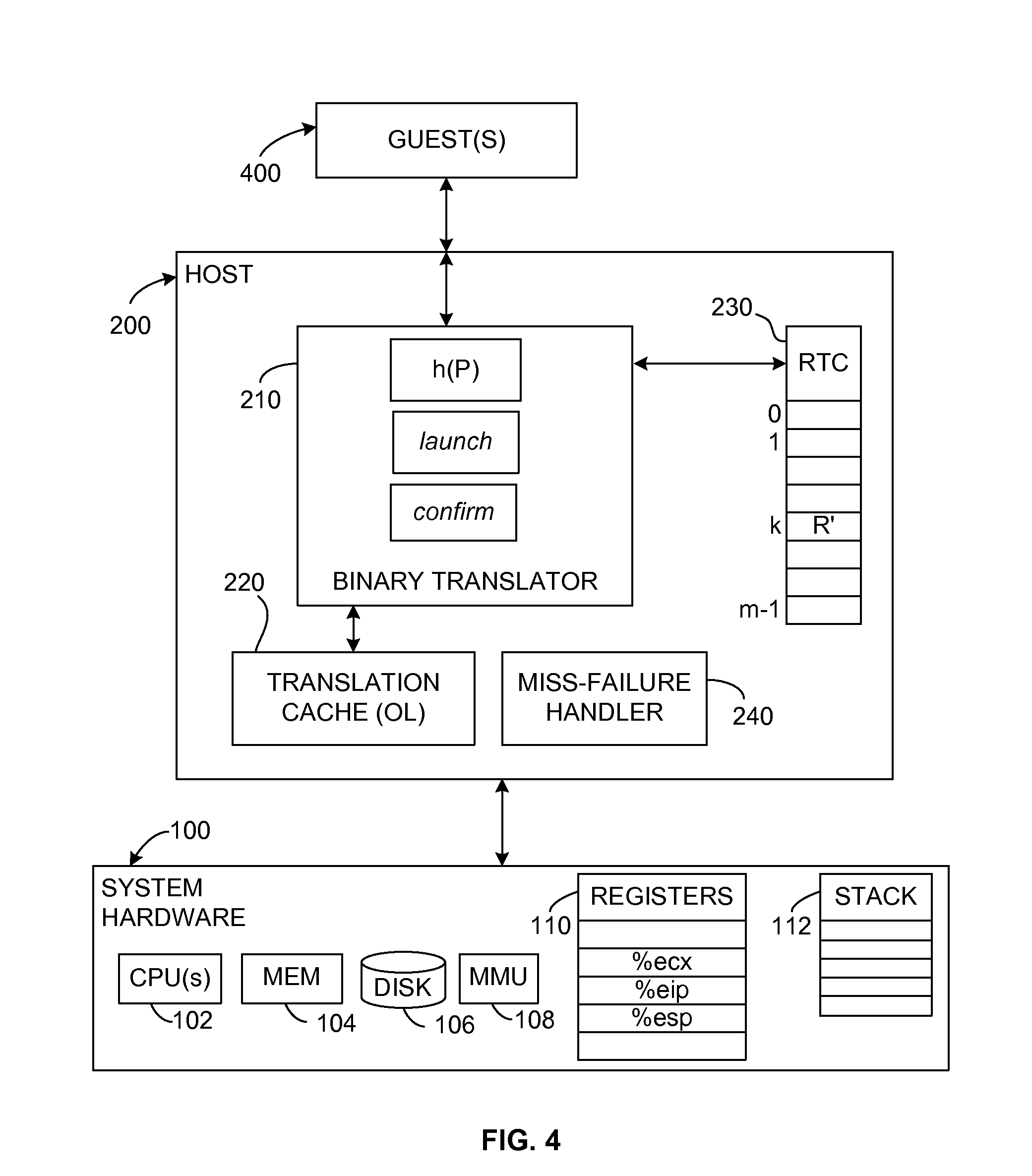
Prediction mechanism for subroutine returns in binary translation sub-systems of computers
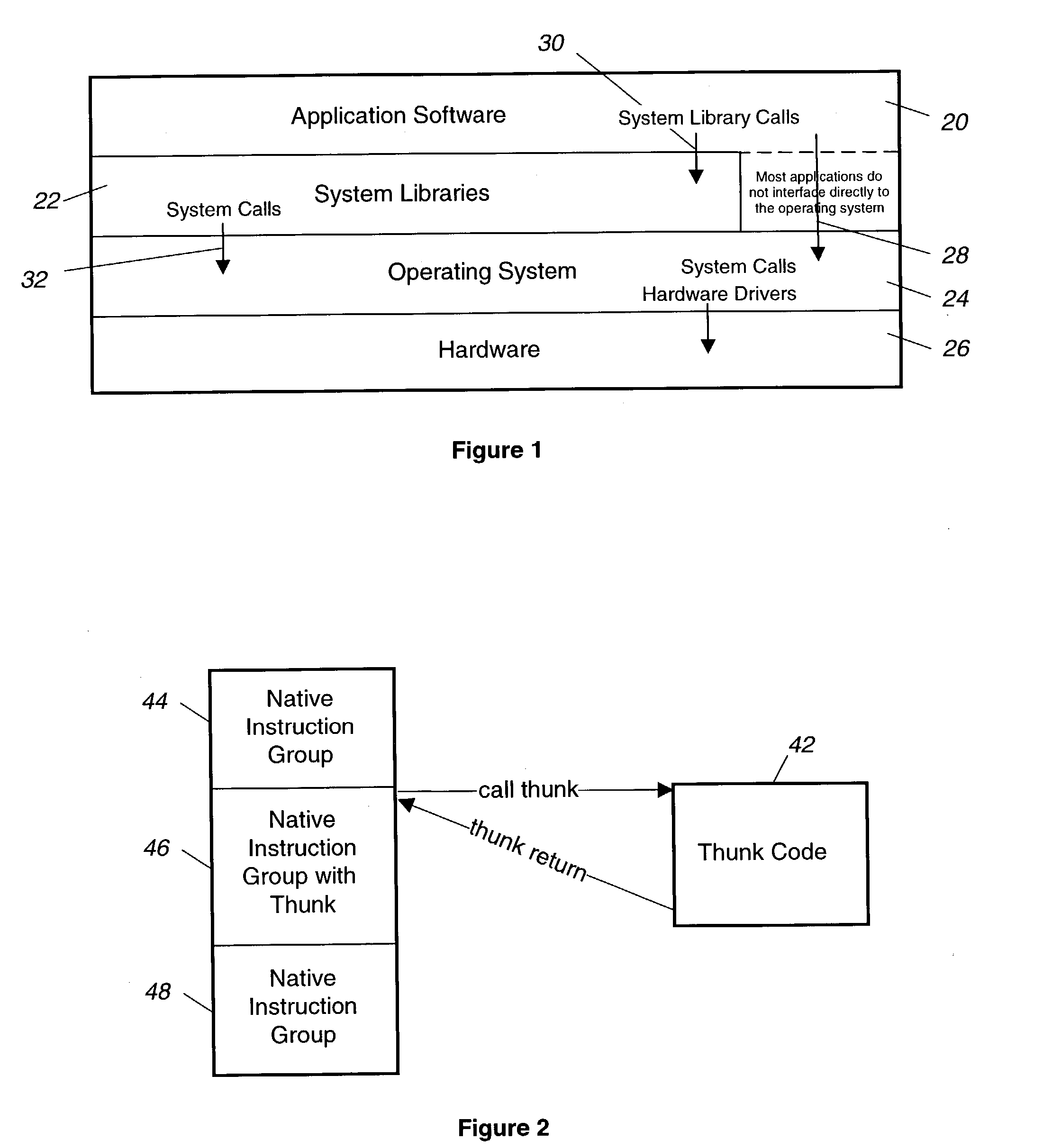
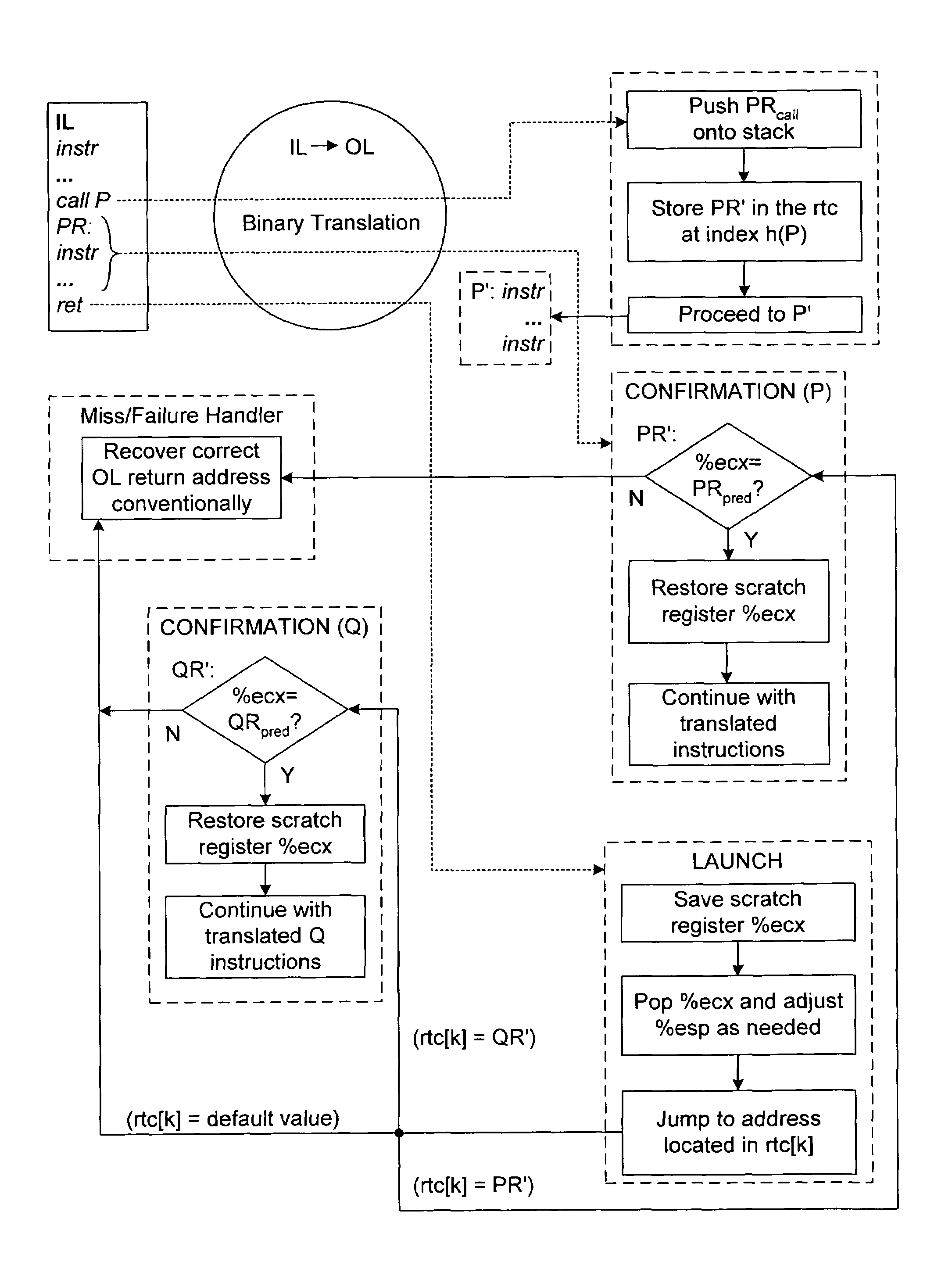
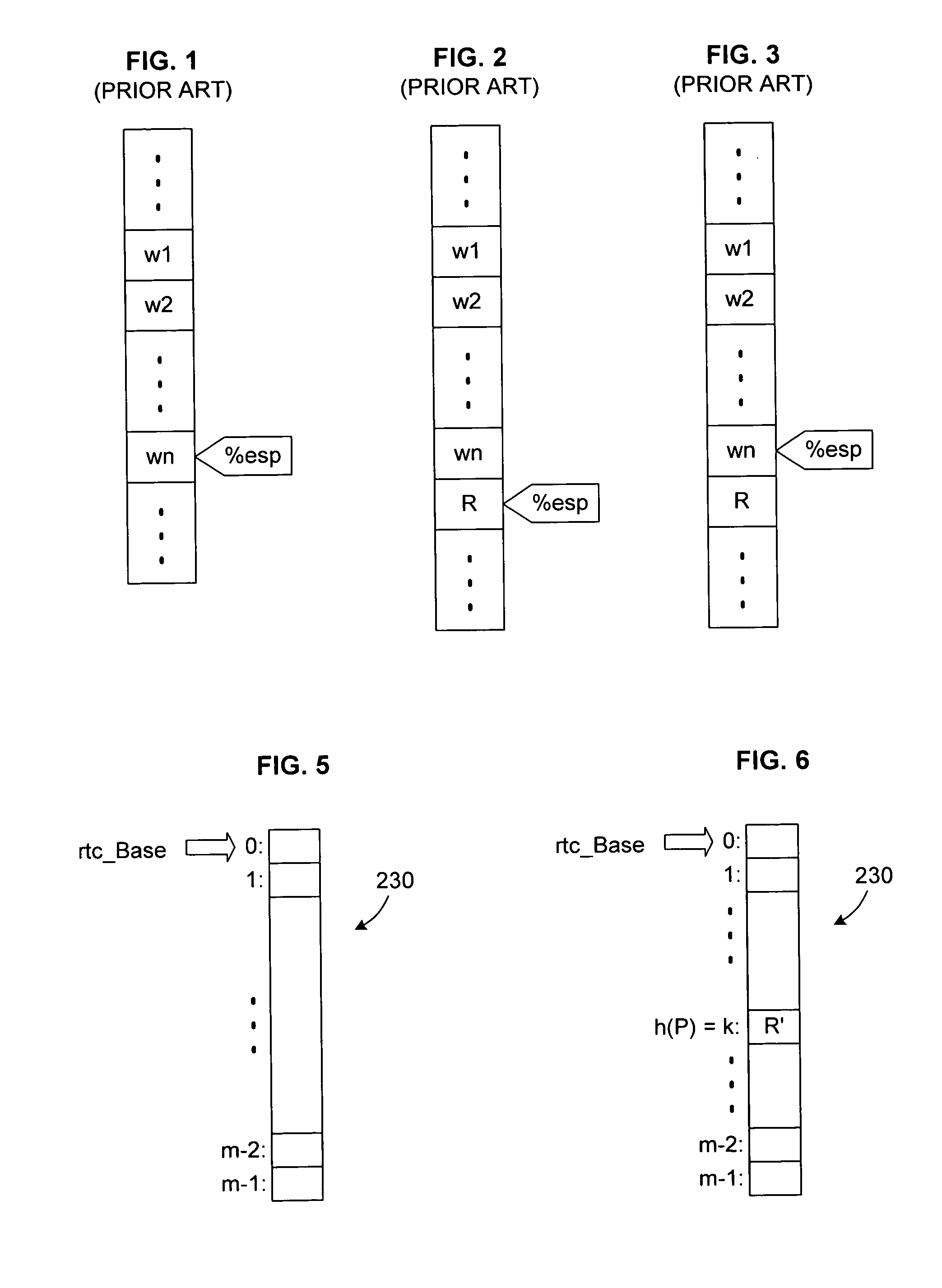
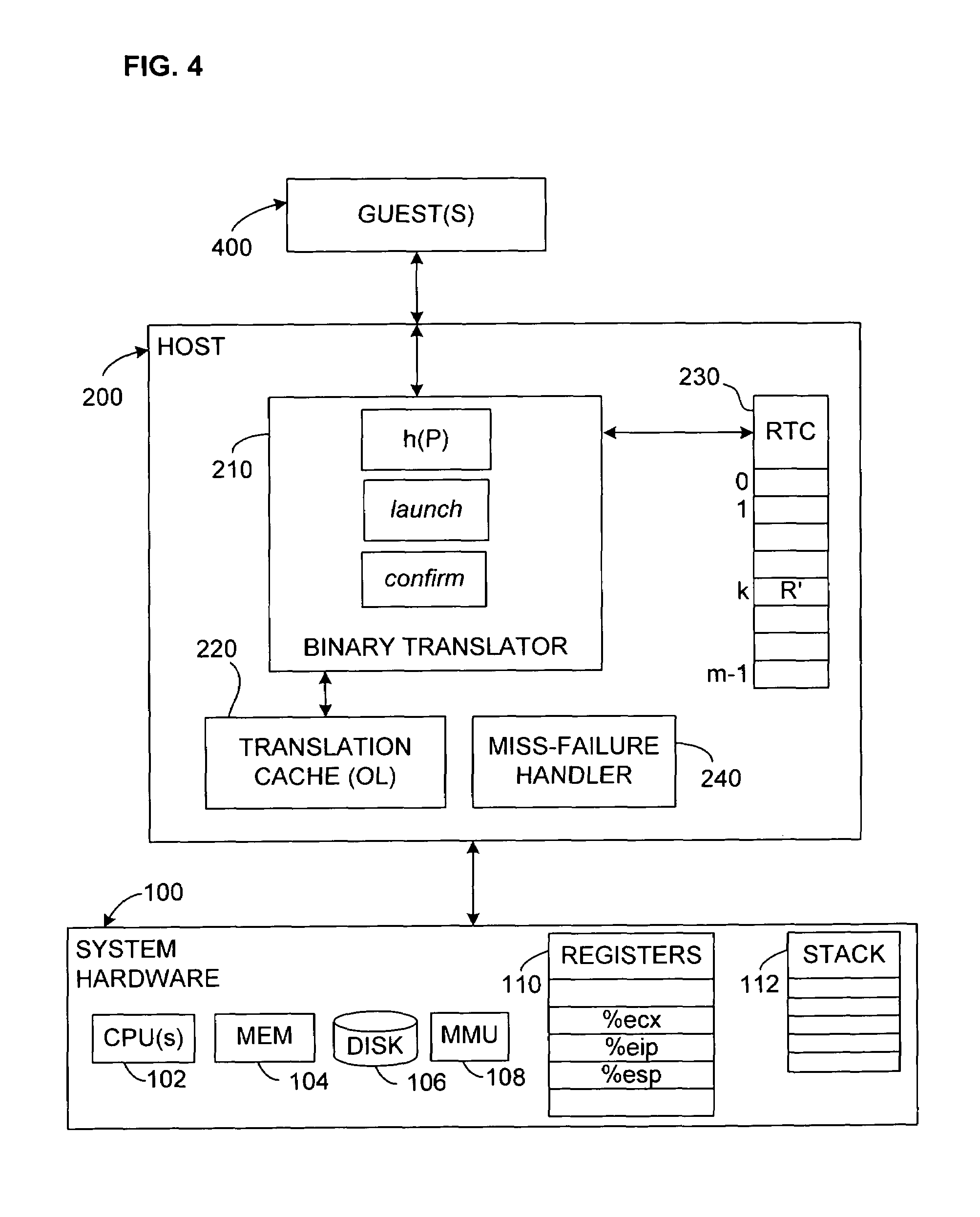
A sequence of input language (IL) instructions of a guest system is converted, for example by binary translation, into a corresponding sequence of output language (OL) instructions of a host system, which executes the OL instructions. In order to determine the return address after any IL call to a subroutine at a target entry address P, the corresponding OL return address is stored in an array at a location determined by an index calculated as a function of P. After completion of execution of the OL translation of the IL subroutine, execution is transferred to the address stored in the array at the location where the OL return address was previously stored. A confirm instruction block is included in each OL call site to determine whether the transfer was to the correct or incorrect call site, and a back-up routine is included to handle the cases of incorrect call sites.
Owner:VMWARE INC
System and method for creating target byte code
InactiveUS20060230070A1Improve developmentEfficient mappingBinary to binaryDigital data processing detailsSoftwareByte
A system and method for converting byte code of a first type into byte code of a second type. Byte code of a first type is received as input. The first byte code is converted into constituent byte code data elements that can comprise any logical unit or grouping of at least a portion of a software application. The first byte code data elements are mapped to data elements of a second byte code type. The second byte code data elements are assembled into a resulting second byte code.
Owner:APPCELERATOR
Methods and apparatus for fusing instructions to provide or-test and and-test functionality on multiple test sources
ActiveUS20140281389A1Binary to binaryConditional code generationJust-in-time compilationMicro-operation
Methods and apparatus are disclosed for fusing instructions to provide OR-test and AND-test functionality on multiple test sources. Some embodiments include fetching instructions, said instructions including a first instruction specifying a first operand destination, a second instruction specifying a second operand source, and a third instruction specifying a branch condition. A portion of the plurality of instructions are fused into a single micro-operation, the portion including both the first and second instructions if said first operand destination and said second operand source are the same, and said branch condition is dependent upon the second instruction. Some embodiments generate a novel test instruction dynamically by fusing one logical instruction with a prior-art test instruction. Other embodiments generate the novel test instruction through a just-in-time compiler. Some embodiments also fuse the novel test instruction with a subsequent conditional branch instruction, and perform a branch according to how the condition flag is set.
Owner:INTEL CORP
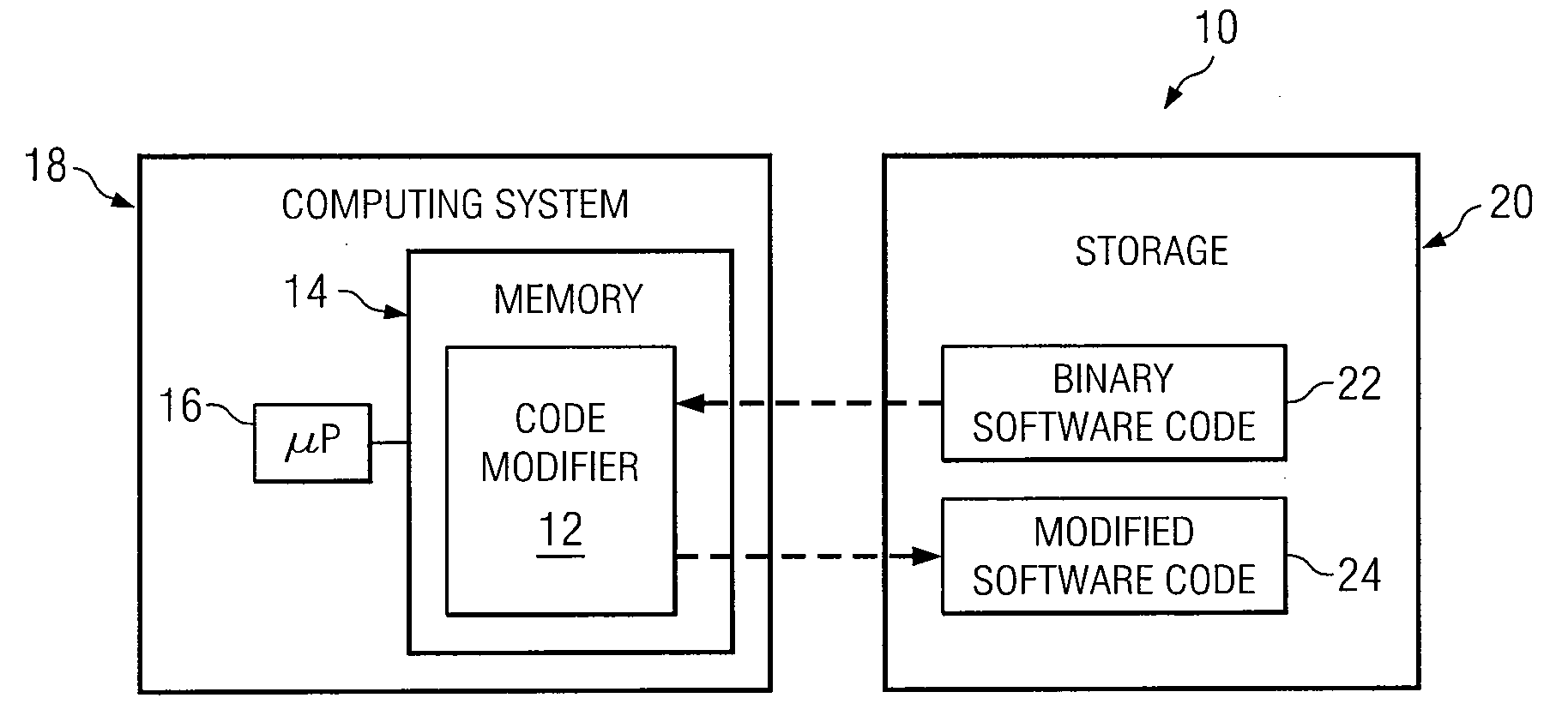
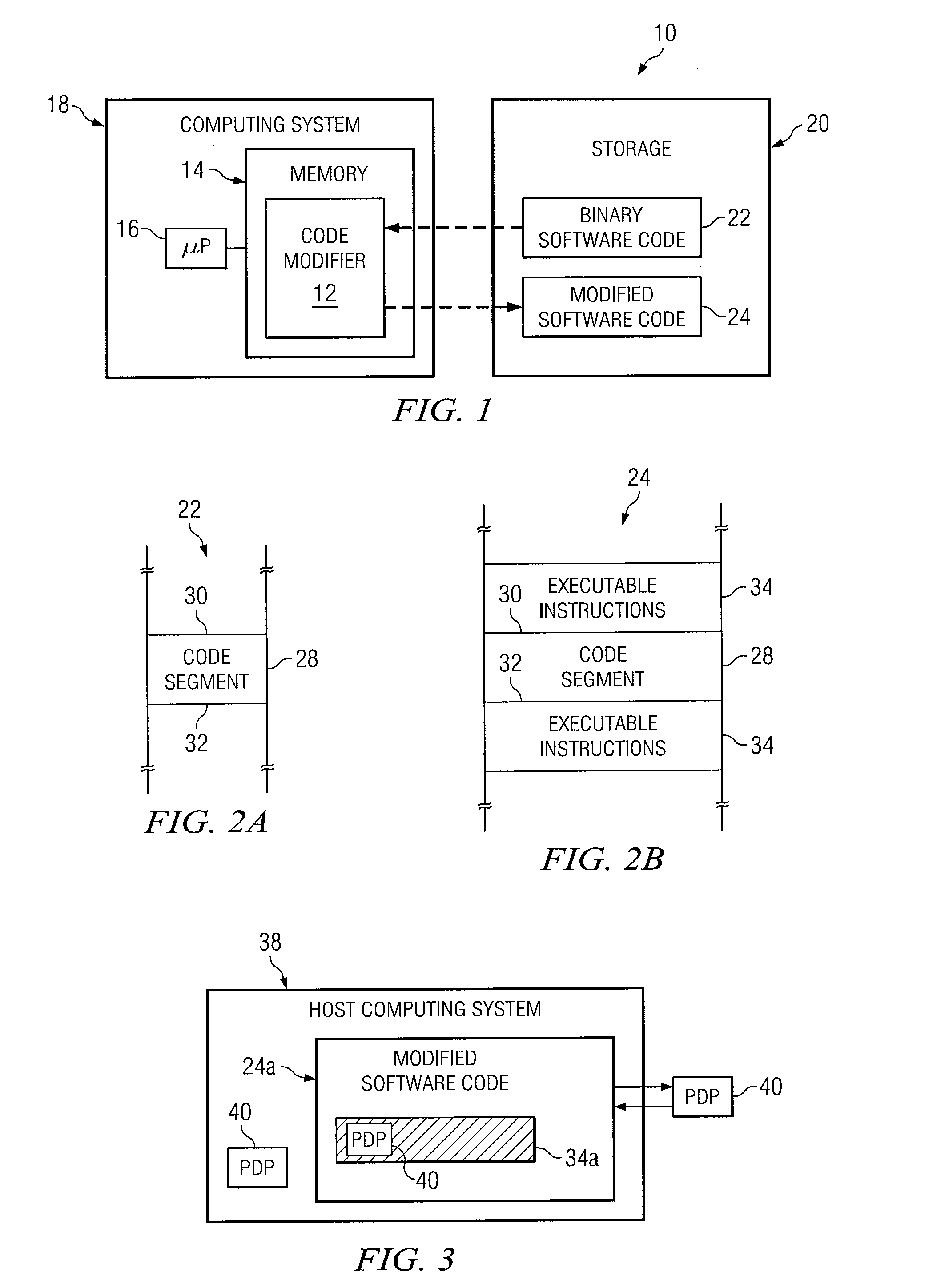
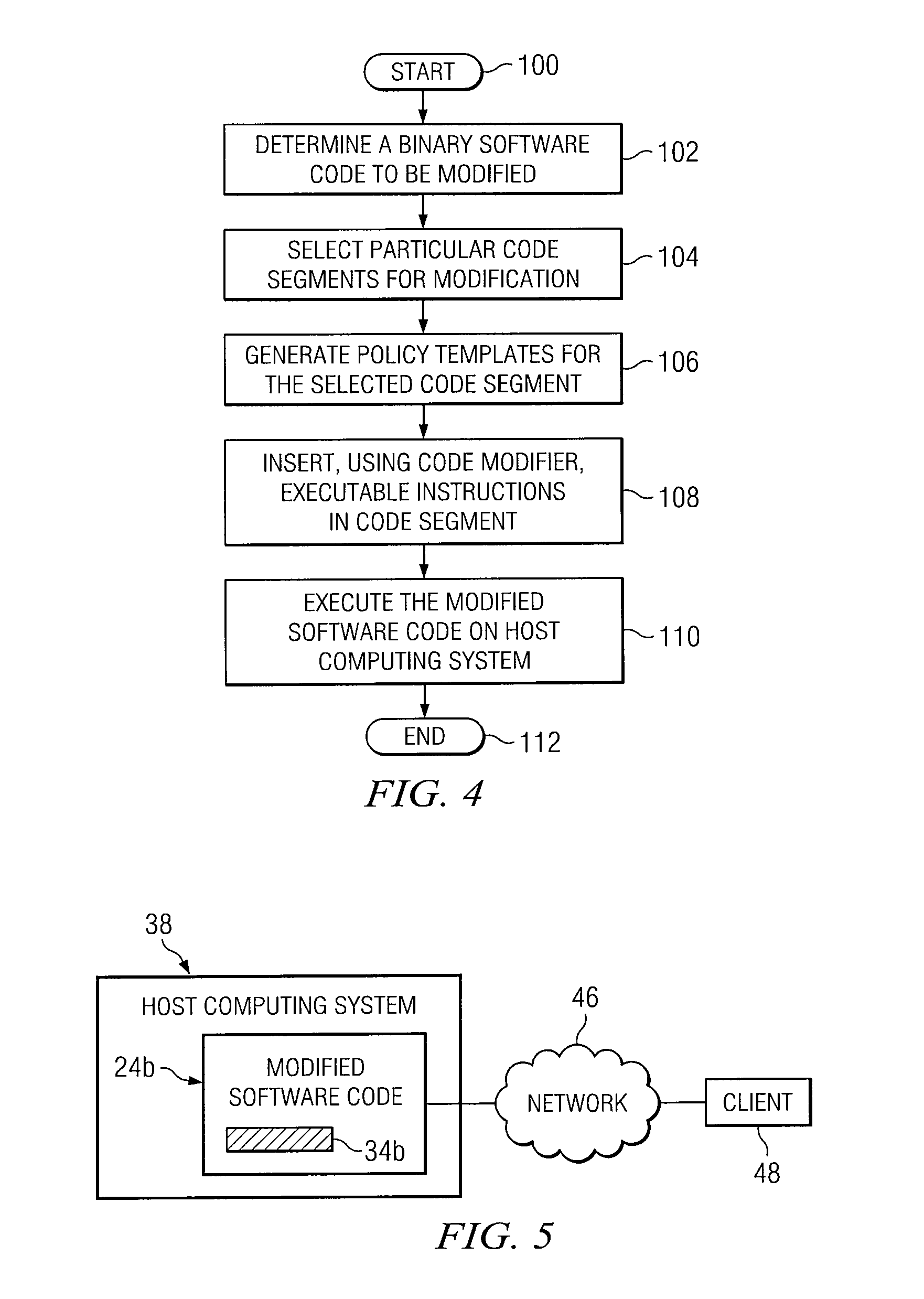
Binary Code Modification System and Method for Implementing Identity and Access Management or Governance Policies
InactiveUS20100333079A1Function increaseNot easy to copyBinary to binaryPlatform integrity maintainanceComputer hardwareAccess management
According to one embodiment, a binary code modification system includes a code modifier configured to access a binary software code. The code modifier generates a modified software code by inserting one or more executable instructions into the binary software code. The one or more executable instructions is operable to provide identity and access management (IAM) functionality or governance functionality to the modified software code.
Owner:COMP ASSOC THINK INC
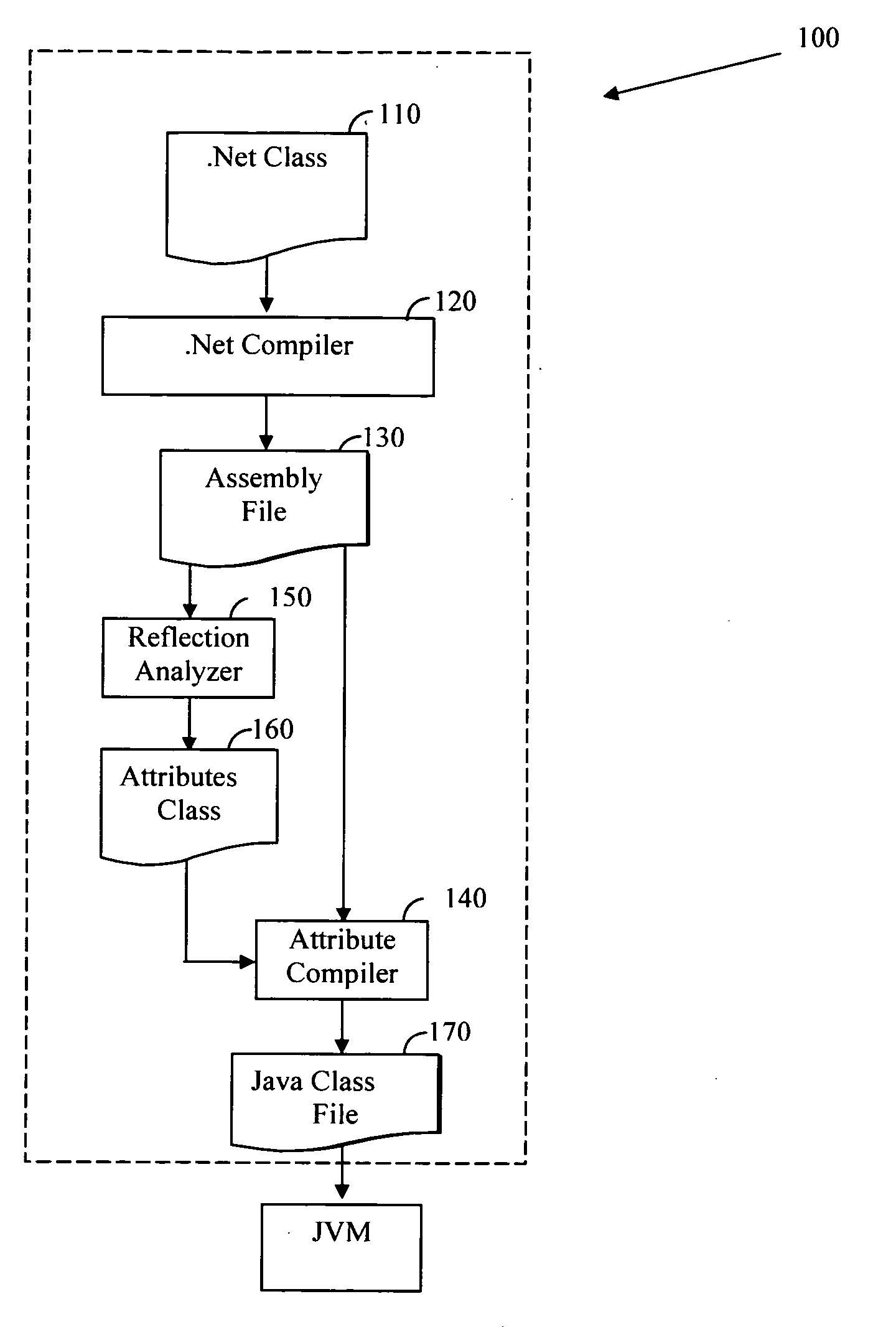
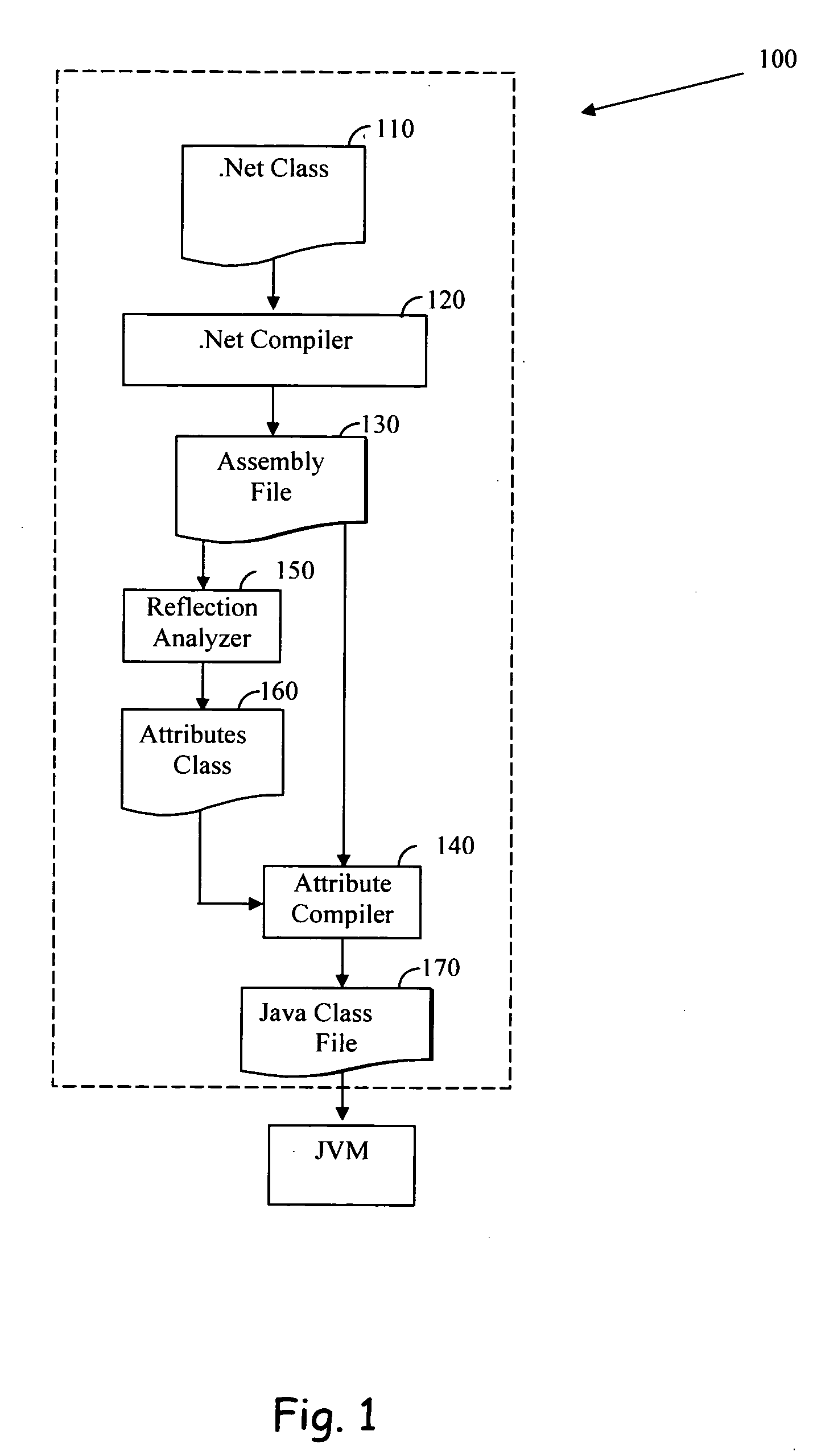
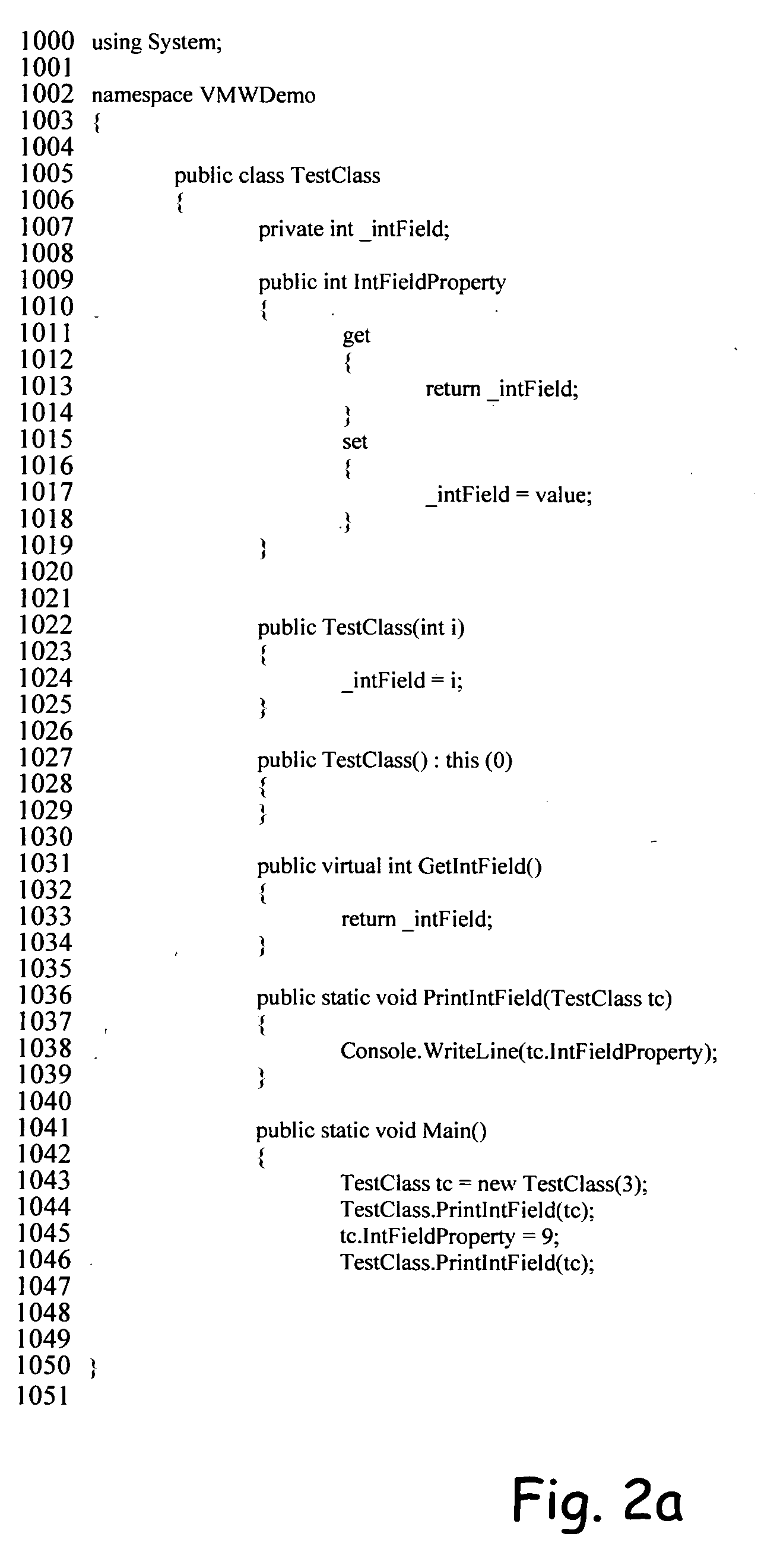
Method and a software product for adapting a .NET framework compliant reflection mechanism to a java environment
A method for adapting a .Net framework compliant reflection mechanism to a Java environment, wherein the reflection mechanism allows a user to discover class information and invoke data members solely at runtime. The method includes gathering reflection related metadata from a .Net assembly class of a respective .Net class that comprises the metadata. The method also includes the steps of generating an attributes class comprising at least the reflection related metadata and a plurality of conversion methods and integrating the attributes class in a Java class file of the respective .Net class, such that the reflection mechanism is capable of adapting the reflection mechanism as defined in the .Net framework to the Java environment. Also disclosed is a plurality of conversion methods. The attributes class is included in a Java class file rendered by a compiler capable of compiling a .Net class to a Java compliant programming code.
Owner:HARMON IE R&D
Hotkey access to legacy application tasks
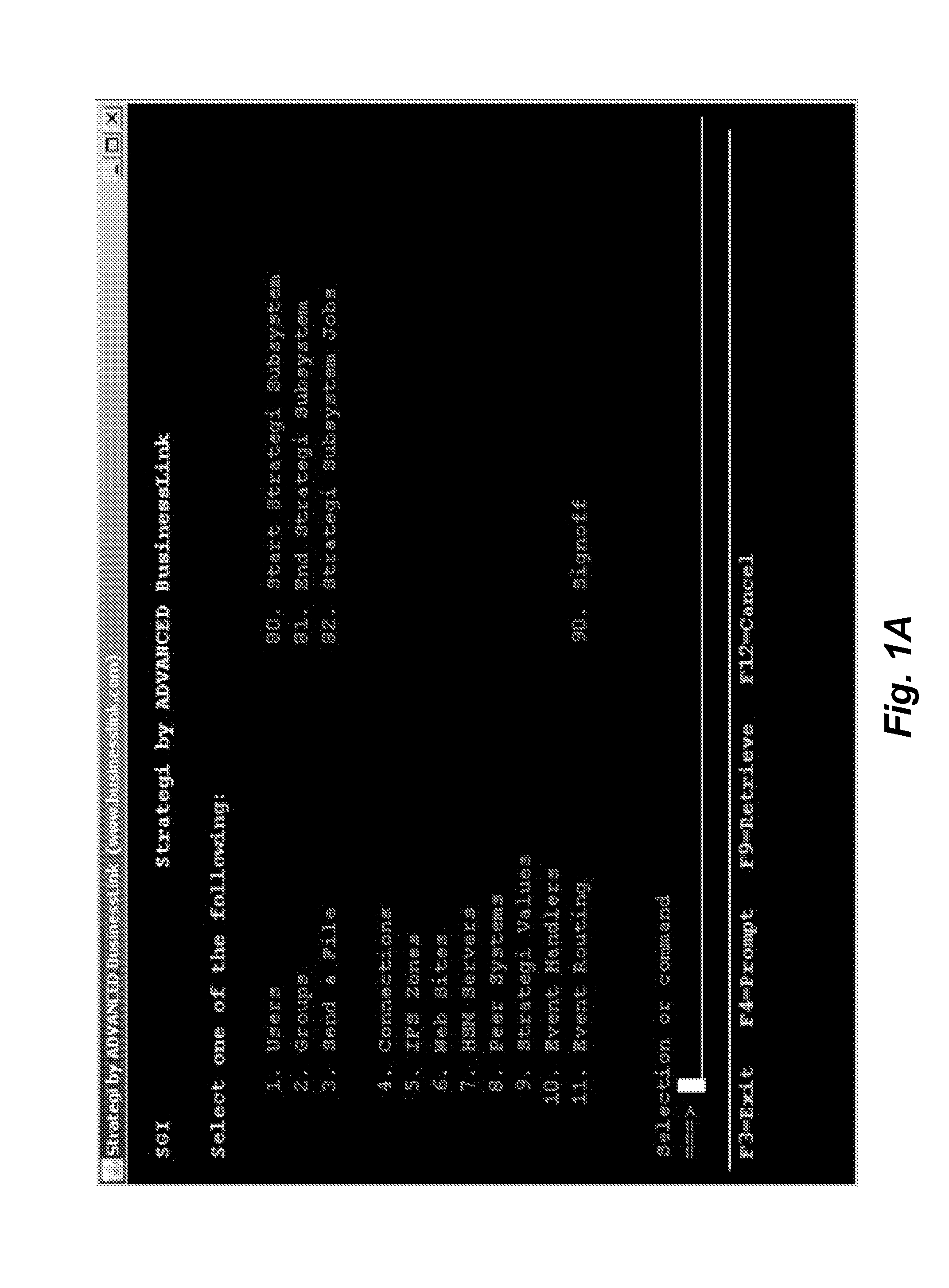
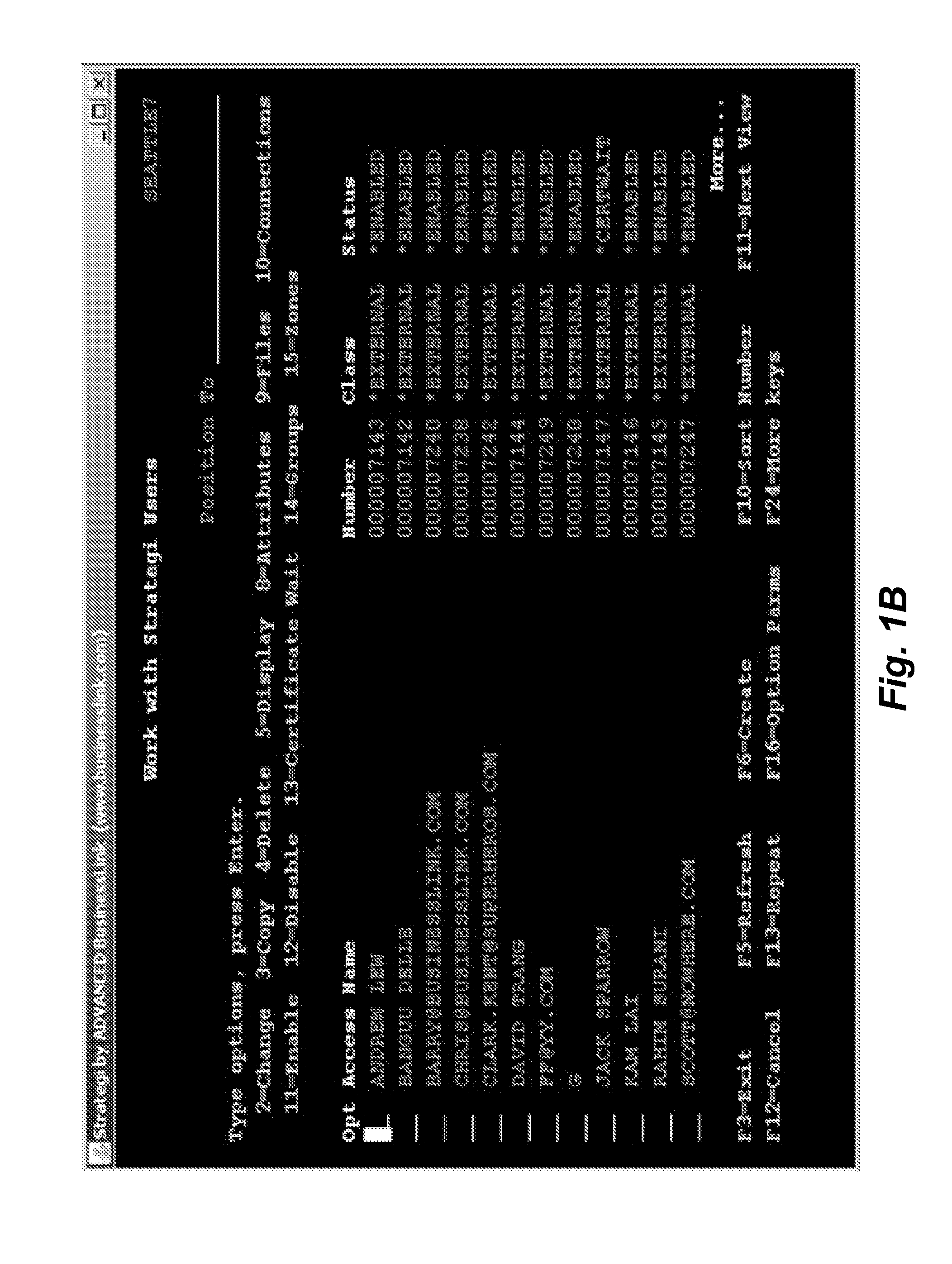
Methods, systems, and techniques for assigning hotkeys to legacy tasks as part of modernizing such tasks are provided. A user can assign a hotkey to an individual task so that the user can have instant access to a legacy or a non-legacy task without needing to navigate to “sub-” tasks of the legacy task. Hotkey access may be used with role-based modernization of legacy tasks to provide navigation to and from legacy tasks without starting and stopping sessions. Example embodiments provide a Role-Based Modernization System (“RBMS”), which uses these enhanced modernization techniques to provide role-based modernization of menu-based legacy applications.
Owner:ADVANCED BUSINESSLINK
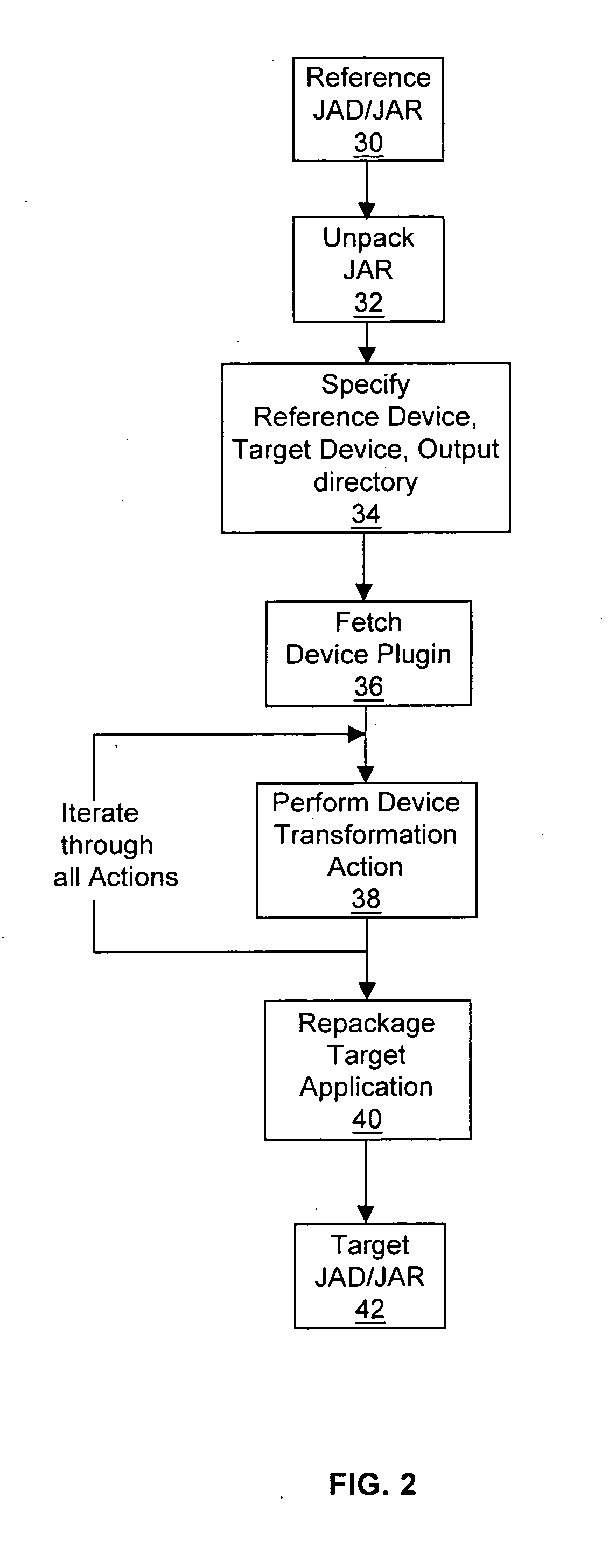
System and method of generating applications for mobile devices
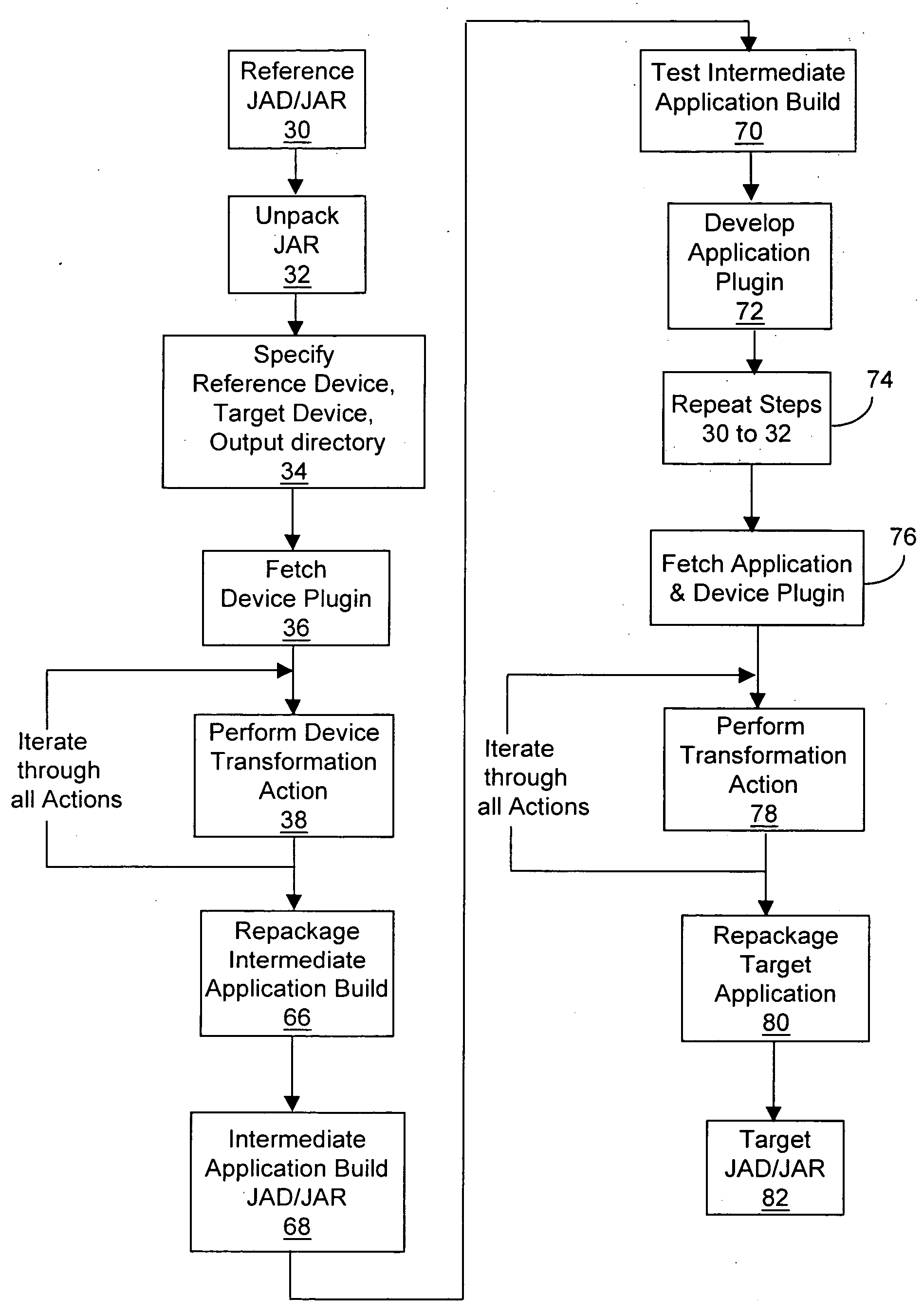
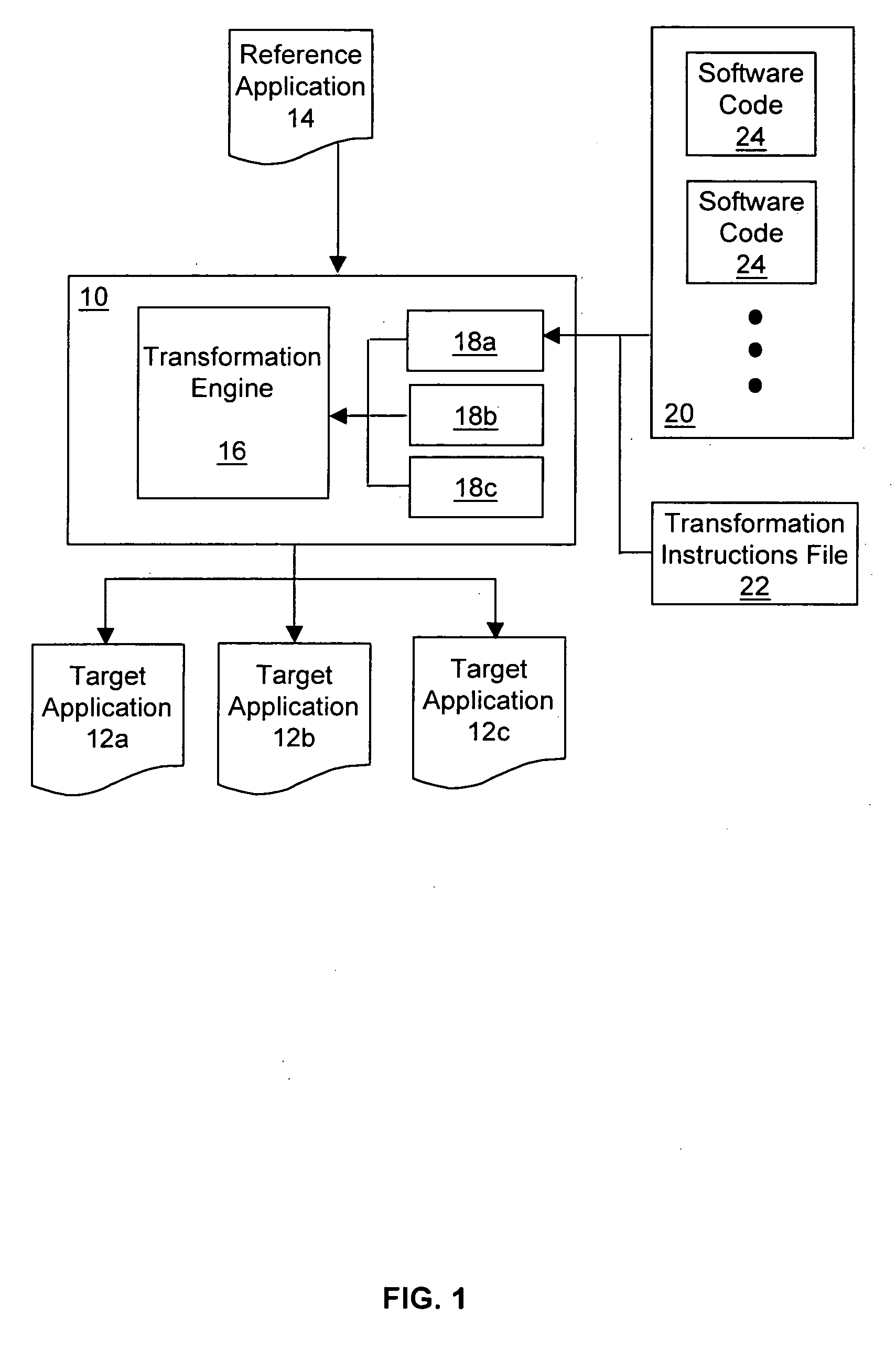
InactiveUS20050108692A1Shorten development timeReduce expensesBinary to binarySpecial service provision for substationJavaSoftware engineering
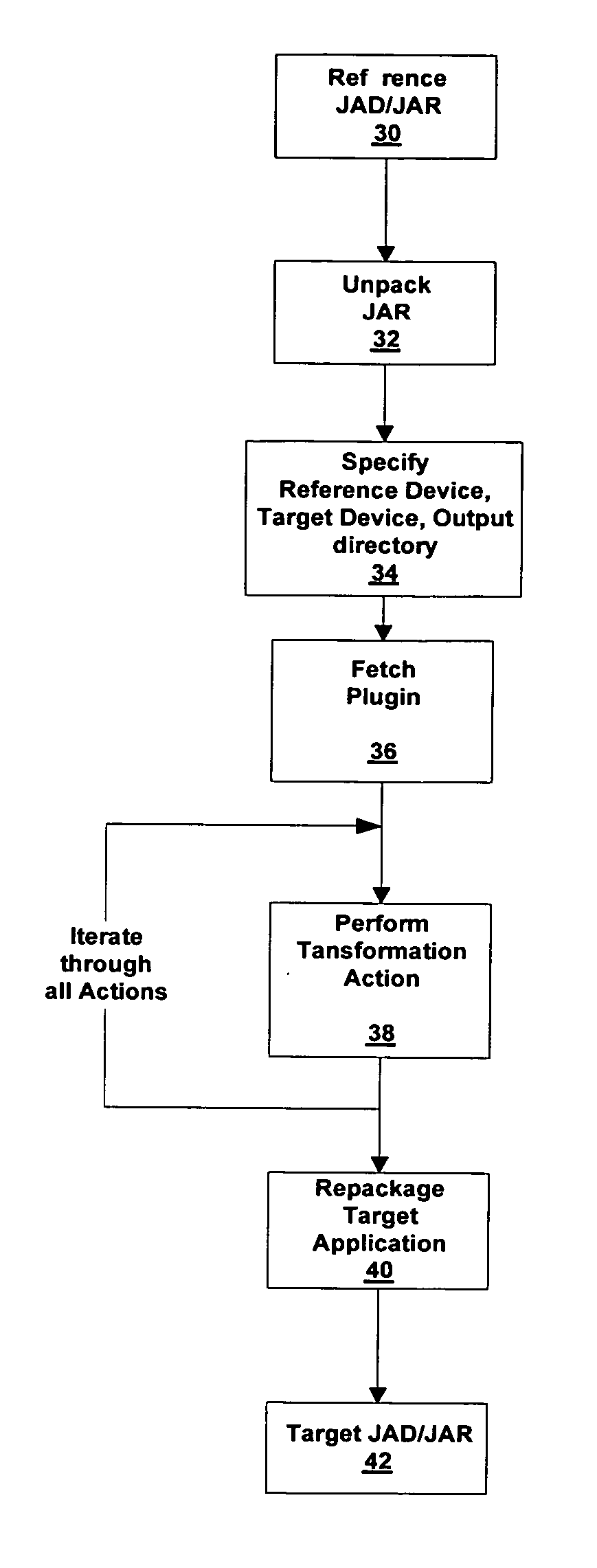
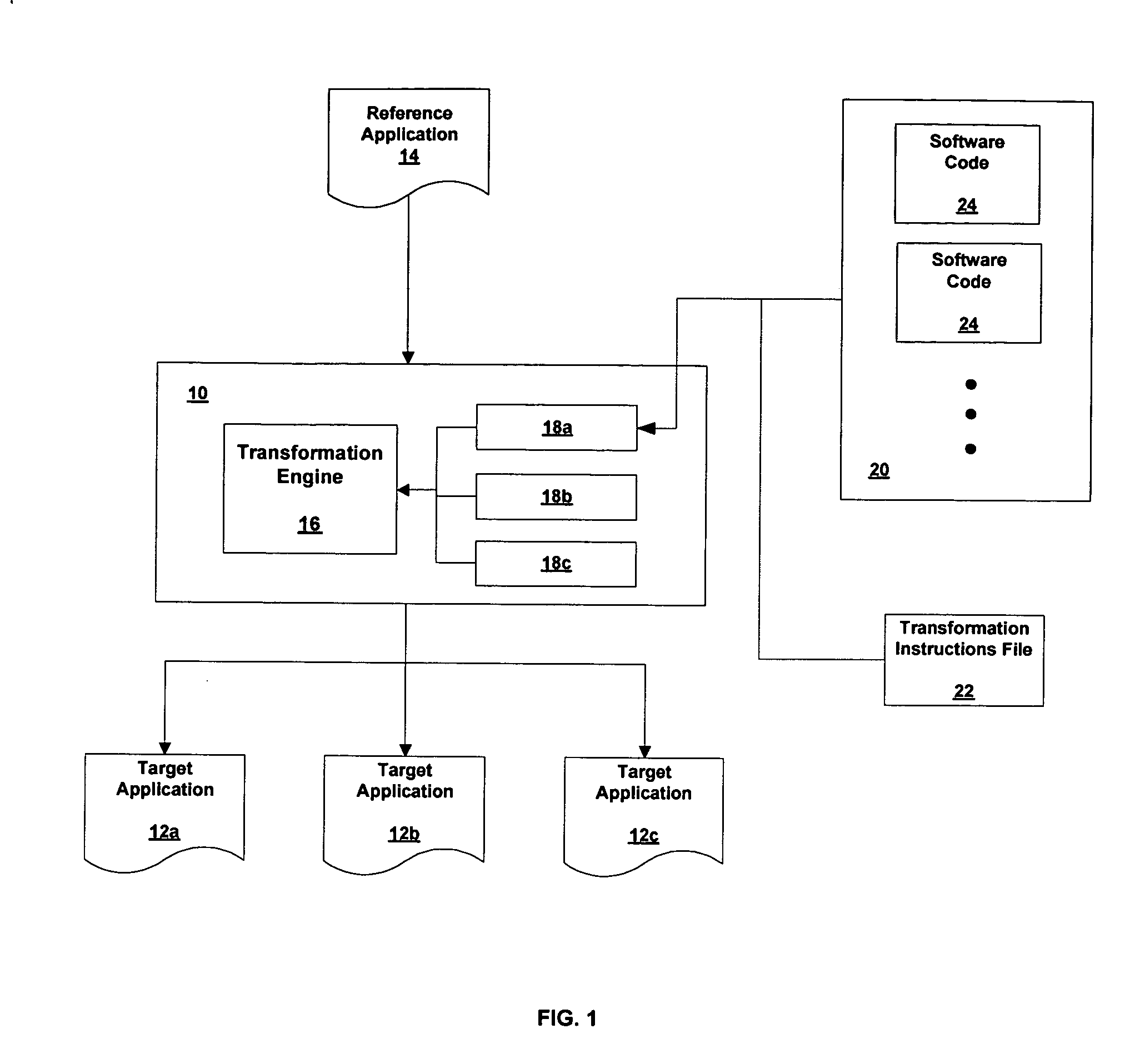
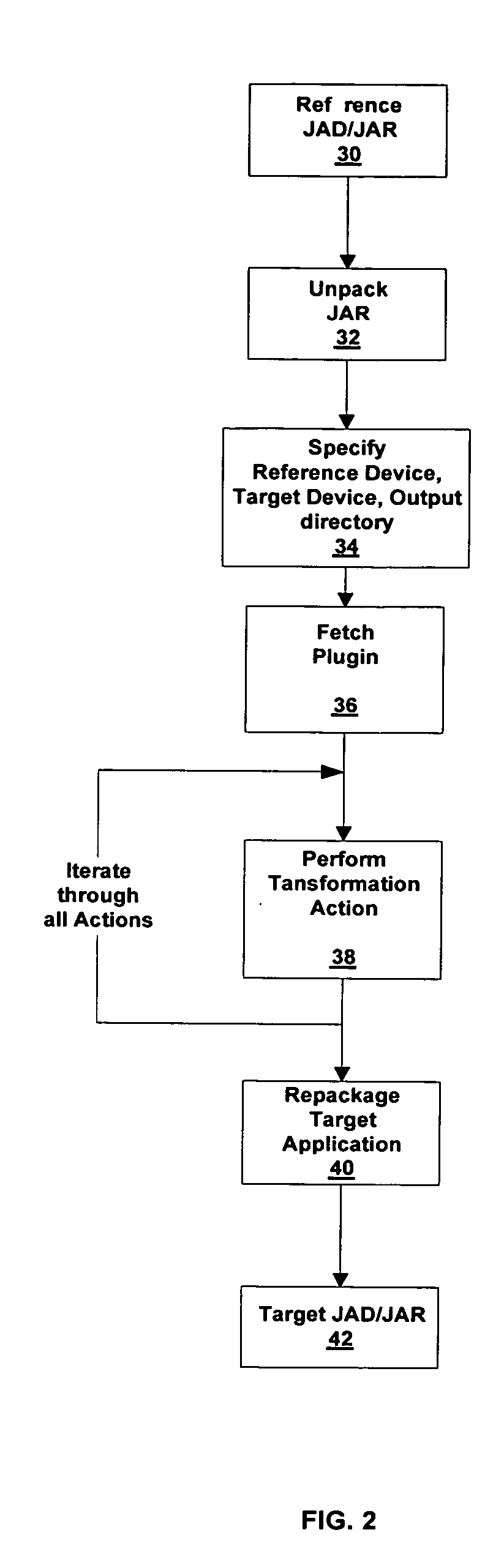
A method and system of generating target applications from Java reference applications for a particular combination of mobile devices is provided. The method includes the steps of: a) unpacking the reference application into a number of class files; and b) transforming the reference application into the target application by a device plug-in. The device plug-in is capable of transforming different reference applications into corresponding target applications for a particular combination of the reference mobile device and the target mobile device. The system includes a transformation engine and a device plug-in corresponding to the reference / target mobile device combination. The device plug-in includes an XML file and pieces of software code to modify corresponding portions of the reference application not supported by the target mobile device. The XML file directs the transformation engine to identify the unsupported portion of the reference application and to modify the portion with the selected software code.
Owner:TIRA WIRELESS
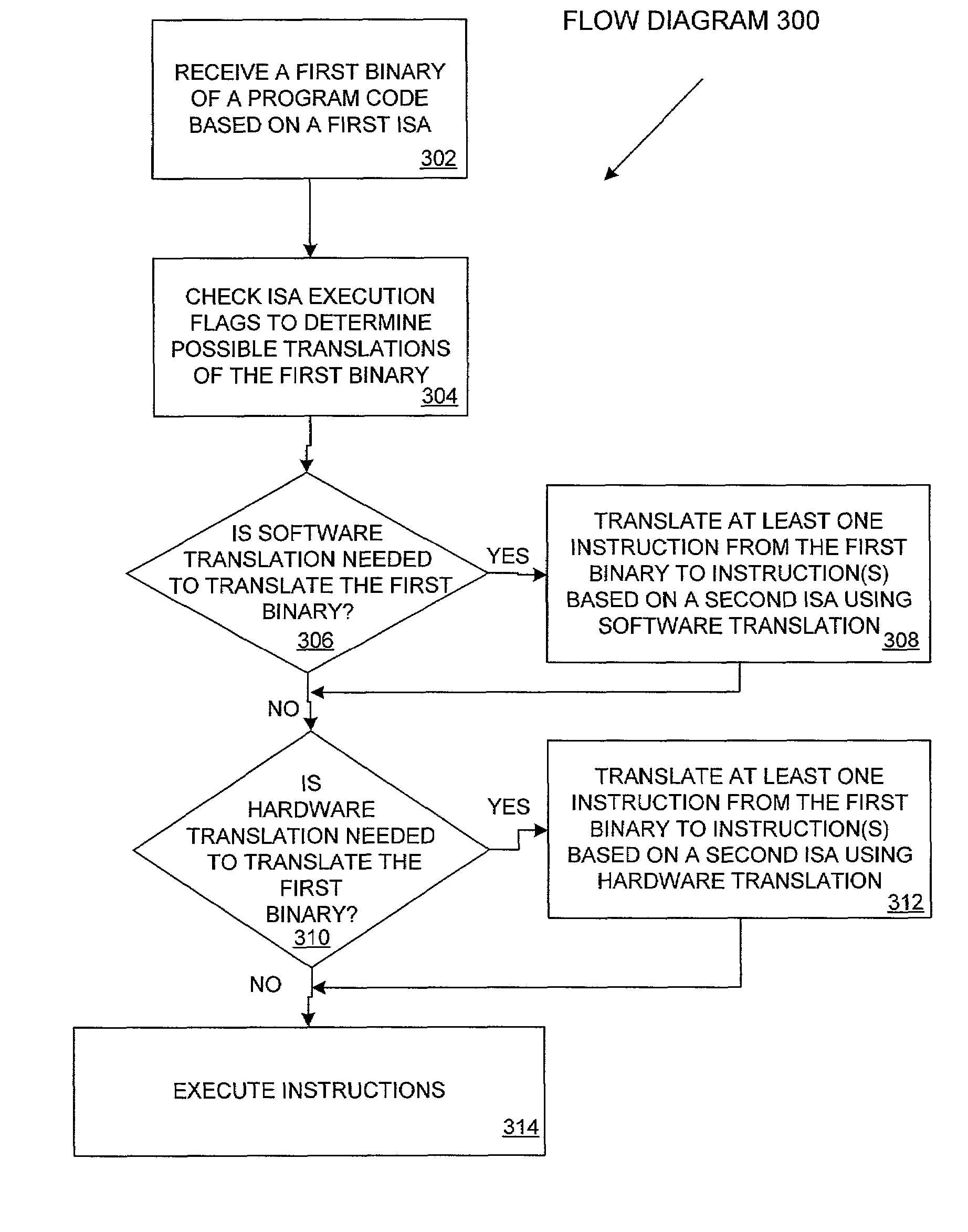
Controlling compatibility levels of binary translations between instruction set architectures
In an embodiment, a method includes receiving a binary of a program code. The binary is based on a first instruction set architecture. The method also includes translating the binary, wherein the translated binary is based on a combination of the first instruction set architecture and a second instruction set architecture.
Owner:INTEL CORP
System and method of generating applications for mobile devices
InactiveUS20050108690A1Shorten development timeReduce expensesBinary to binarySpecial service provision for substationSoftwareMobile device
A method and system of generating target applications from Java reference applications for a particular combination of mobile devices is provided. The method includes the steps of: a) unpacking the reference application into a number of class files; and b) transforming the reference application into the target application by a plug-in. The plug-in is capable of transforming different reference applications into corresponding target applications for a particular combination of the reference mobile device and the target mobile device. The system includes a transformation engine and a plug-in corresponding to the reference / target mobile device combination. The plug-in includes an XML file and pieces of software code to modify corresponding portions of the reference application not supported by the target mobile device. The XML file directs the transformation engine to identify the unsupported portion of the reference application and to modify the portion with the selected software code.
Owner:TIRA WIRELESS
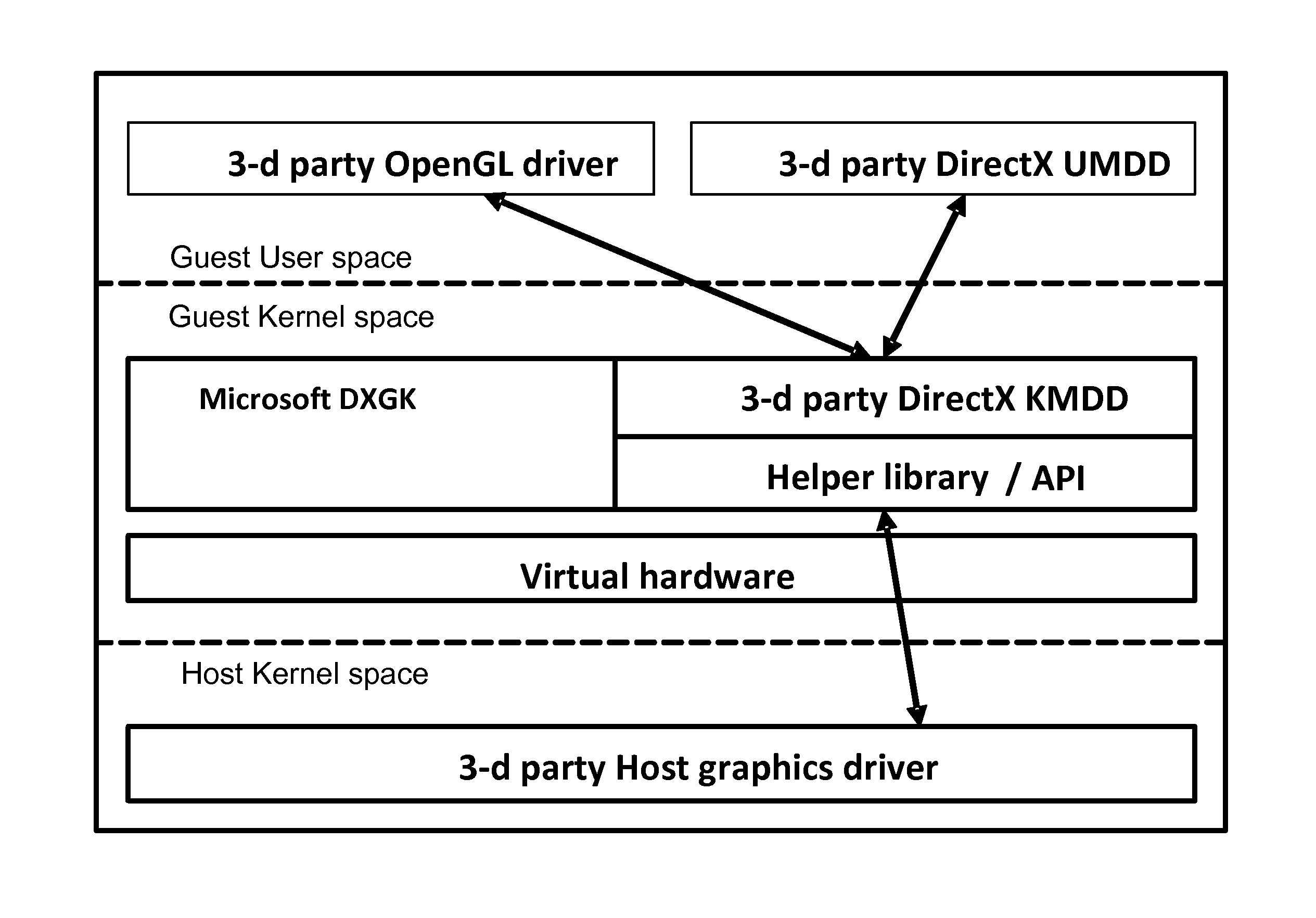
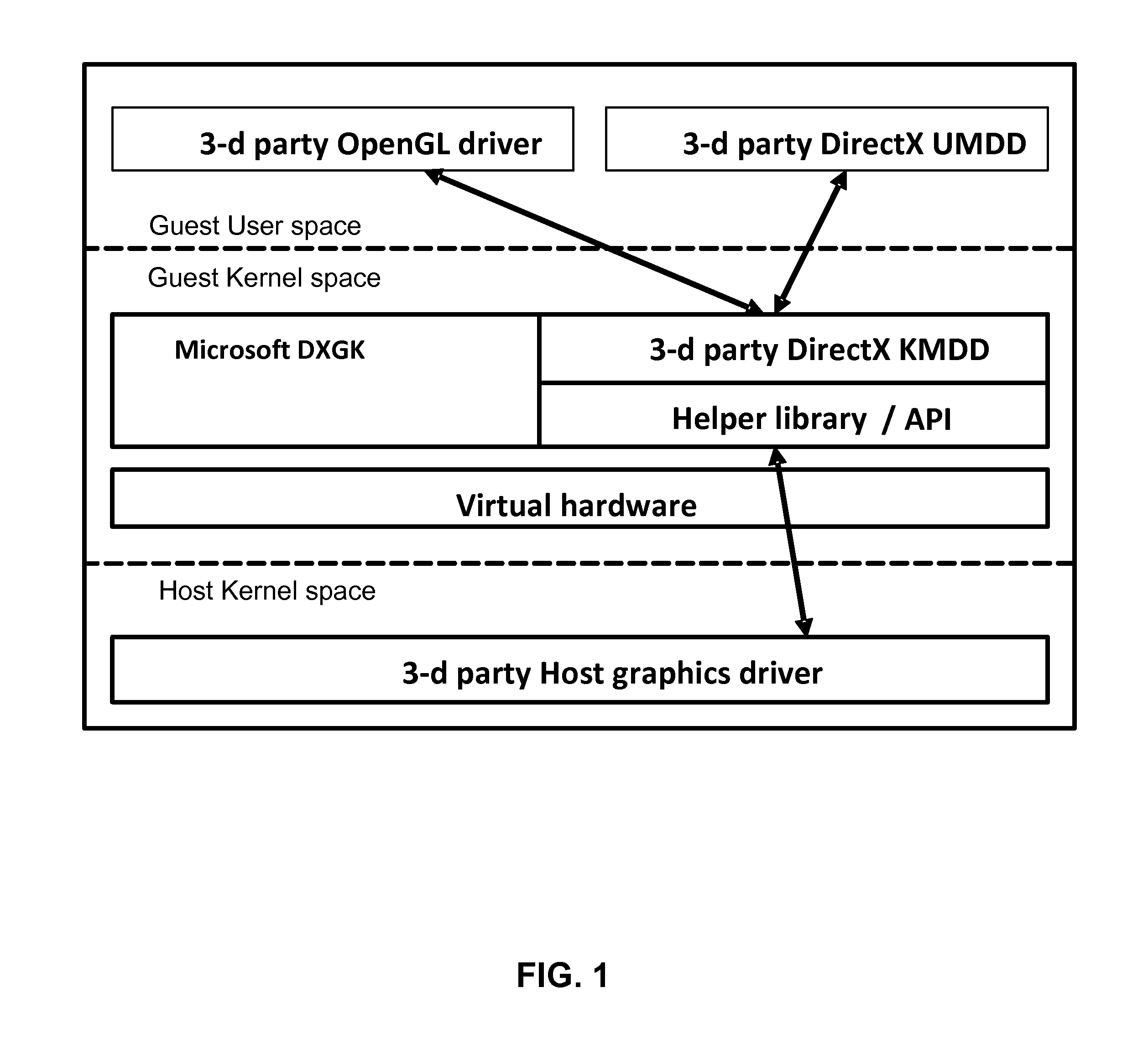
Use of GPU for support and acceleration of virtual machines and virtual environments
InactiveUS8938723B1Efficient processingEasy to optimizeBinary to binaryProgram controlData compressionIPsec
A system, method and computer program product for a system, method and computer program product for using a GPU of a host computer system for supporting functionality of a number of VMs implemented on the host computer system. The GPU usage by a VM includes e.g., sharing a video card with a VM hypervisor; executing applications controlled by the hypervisor; optimization of a snapshot memory consumption; CRC calculations for memory ballooning; on-the-fly disk data encryption; indexing disk data; efficient data compression for HDD; compression of the VM execution trace data and video traffic; computations for backup storage; AV scanning; firewall-related services; traffic encryption (IPSec); processing and restoration of disk transactions; optimization of incremental backups (creation and comparison of snapshots); traffic indexing and replay; isolating some applications on the GPU for virus protection; optimization of runtime compilers.
Owner:PARALLELS INT GMBH
Popular searches
Special data processing applications Memory systems Creation/generation of source code Memory adressing/allocation/relocation Computer security arrangements Digital output to display device Interprogram communication Digital data protection Payment architecture Internal/peripheral component protection
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com