Patents
Literature
1037 results about "Document handling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
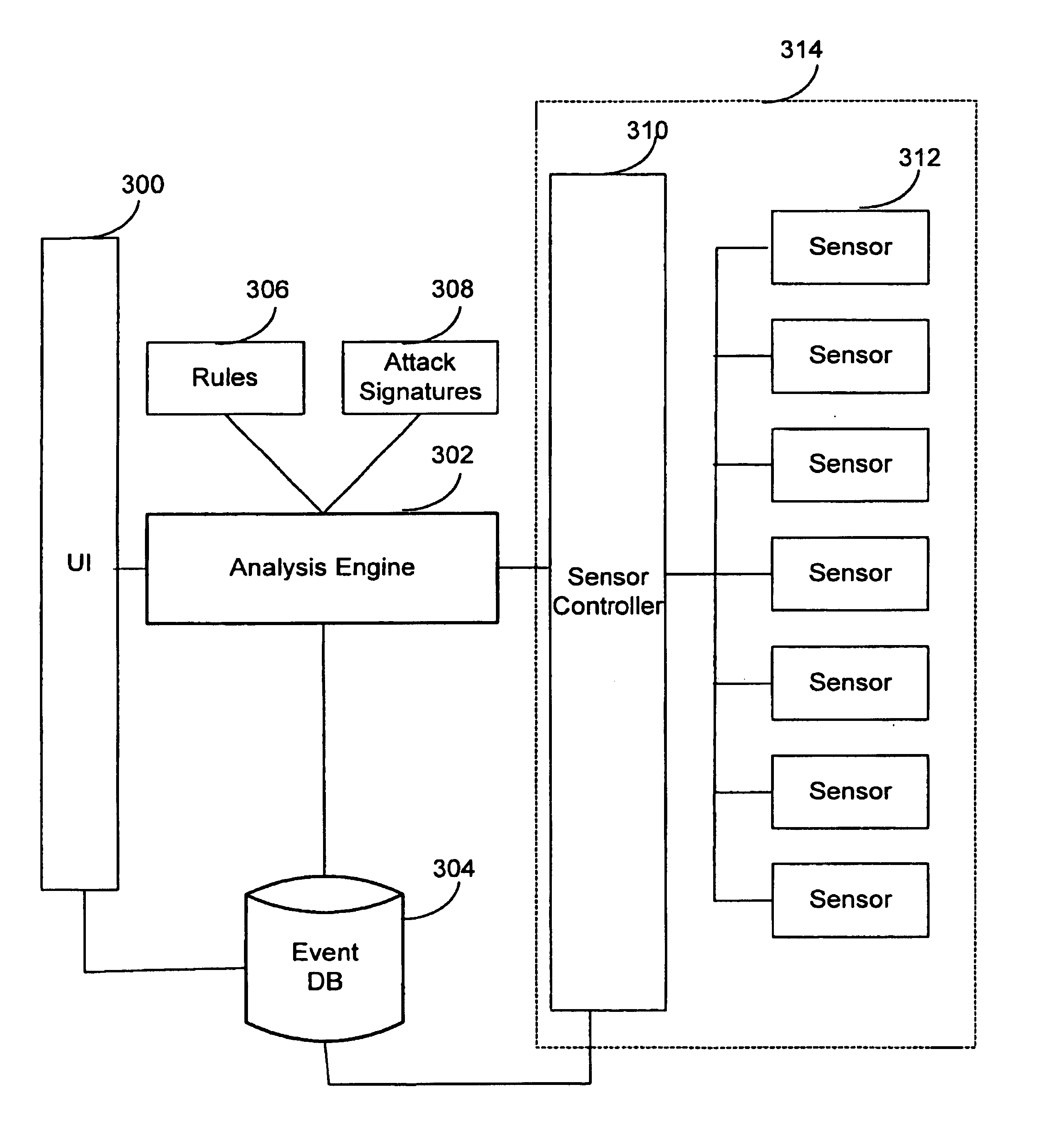
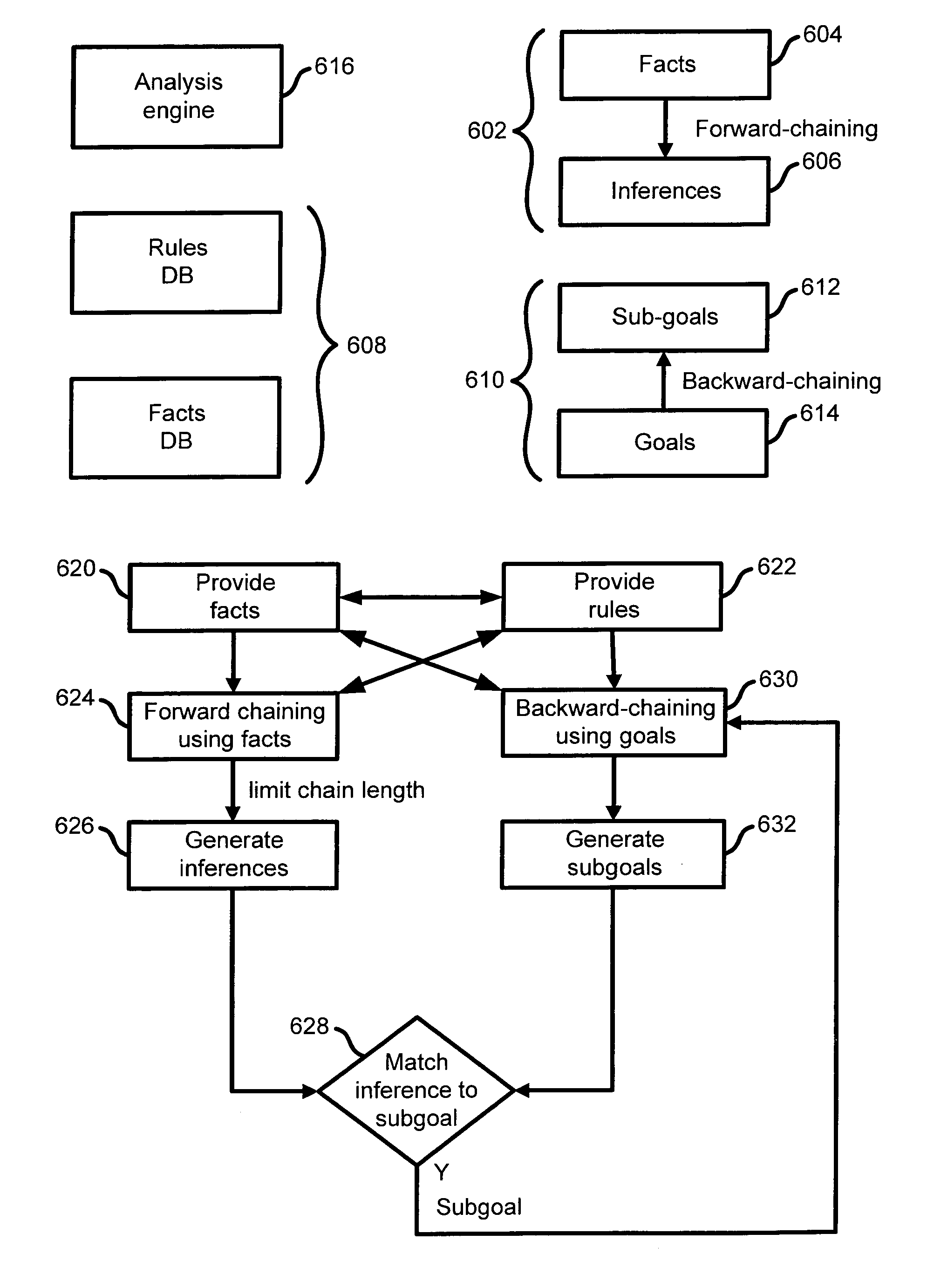
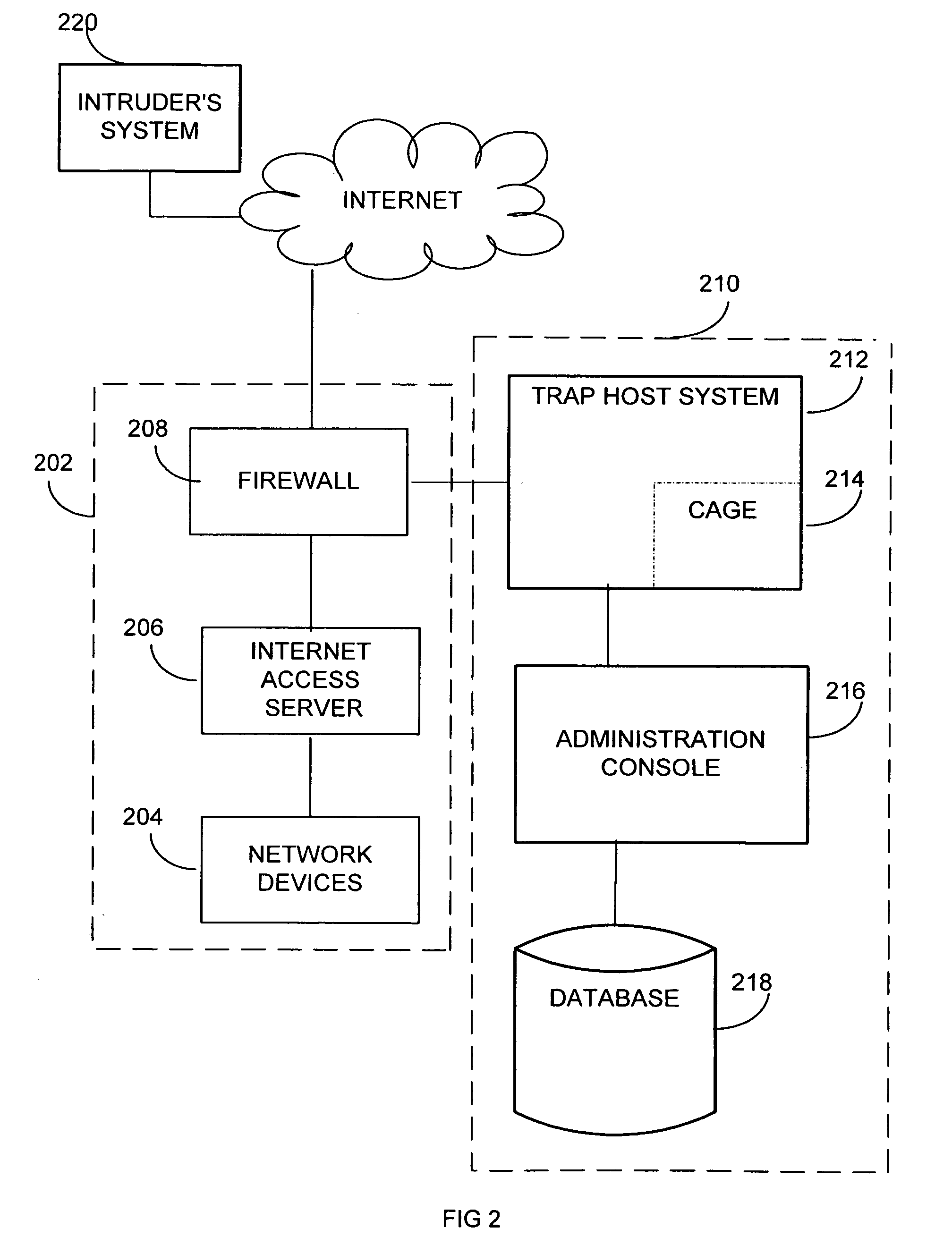
Extensible intrusion detection system
InactiveUS7065657B1Overcome problemsEnabling detectionDigital data processing detailsHardware monitoringTimestampAccess time
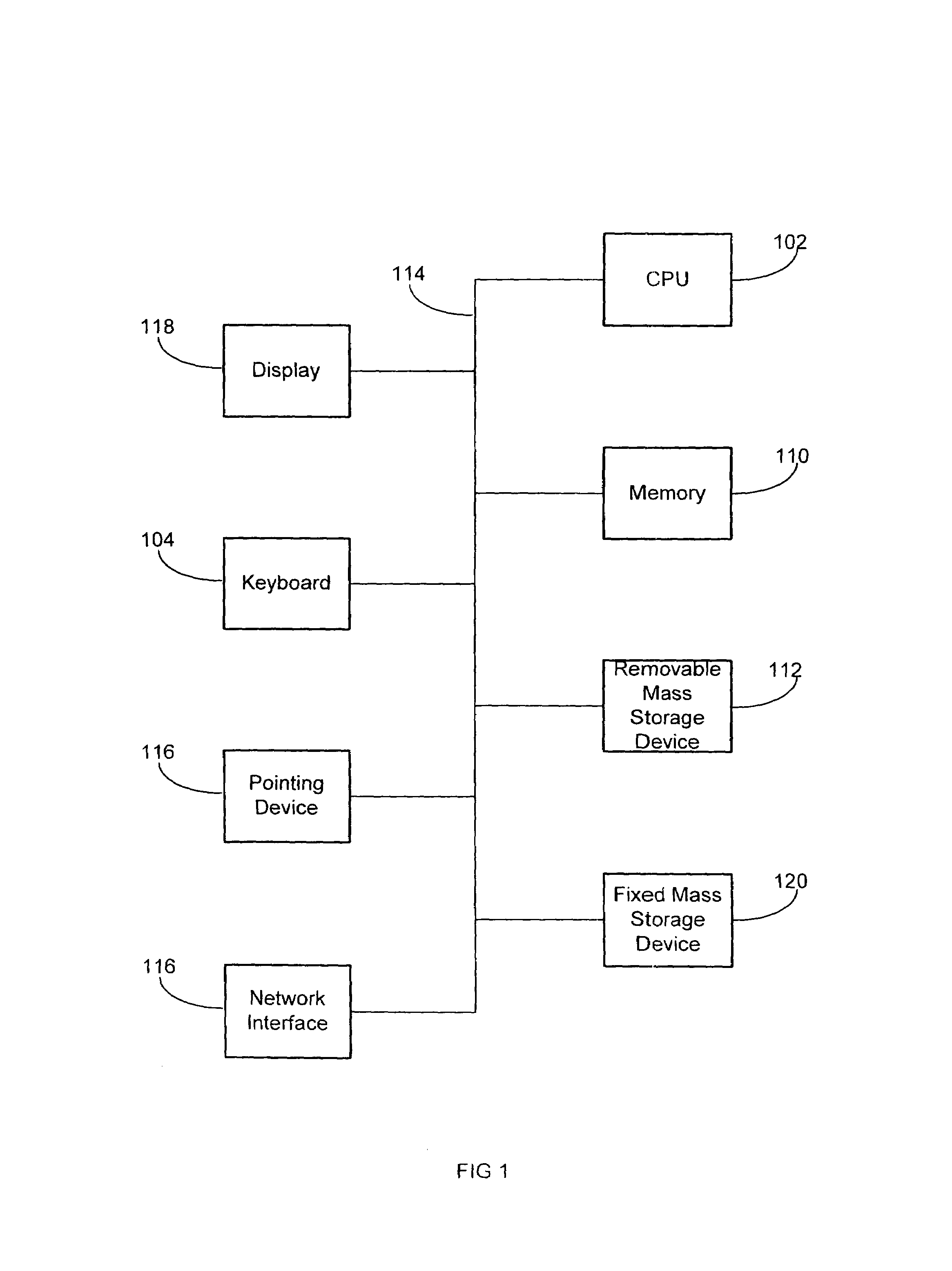
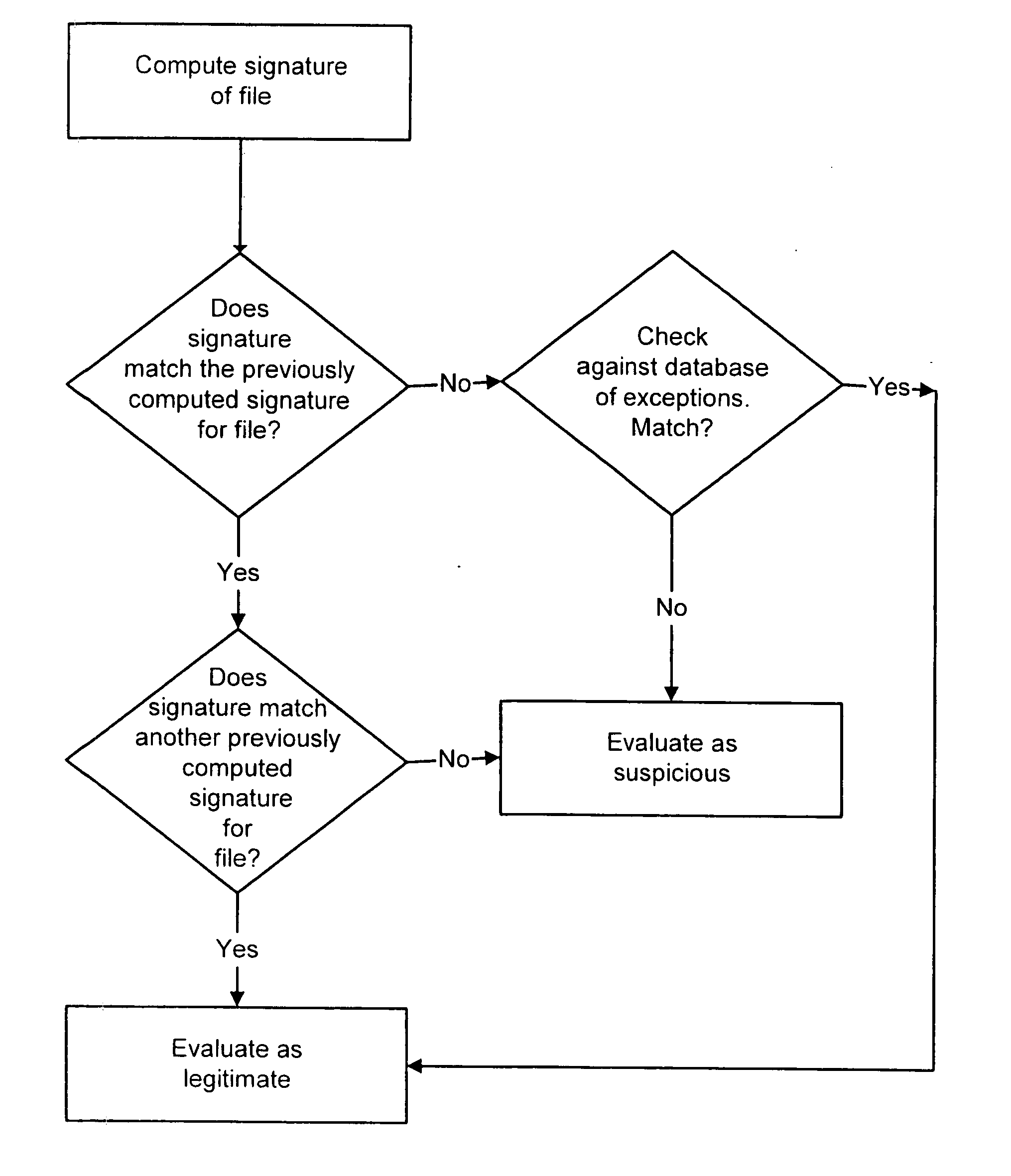
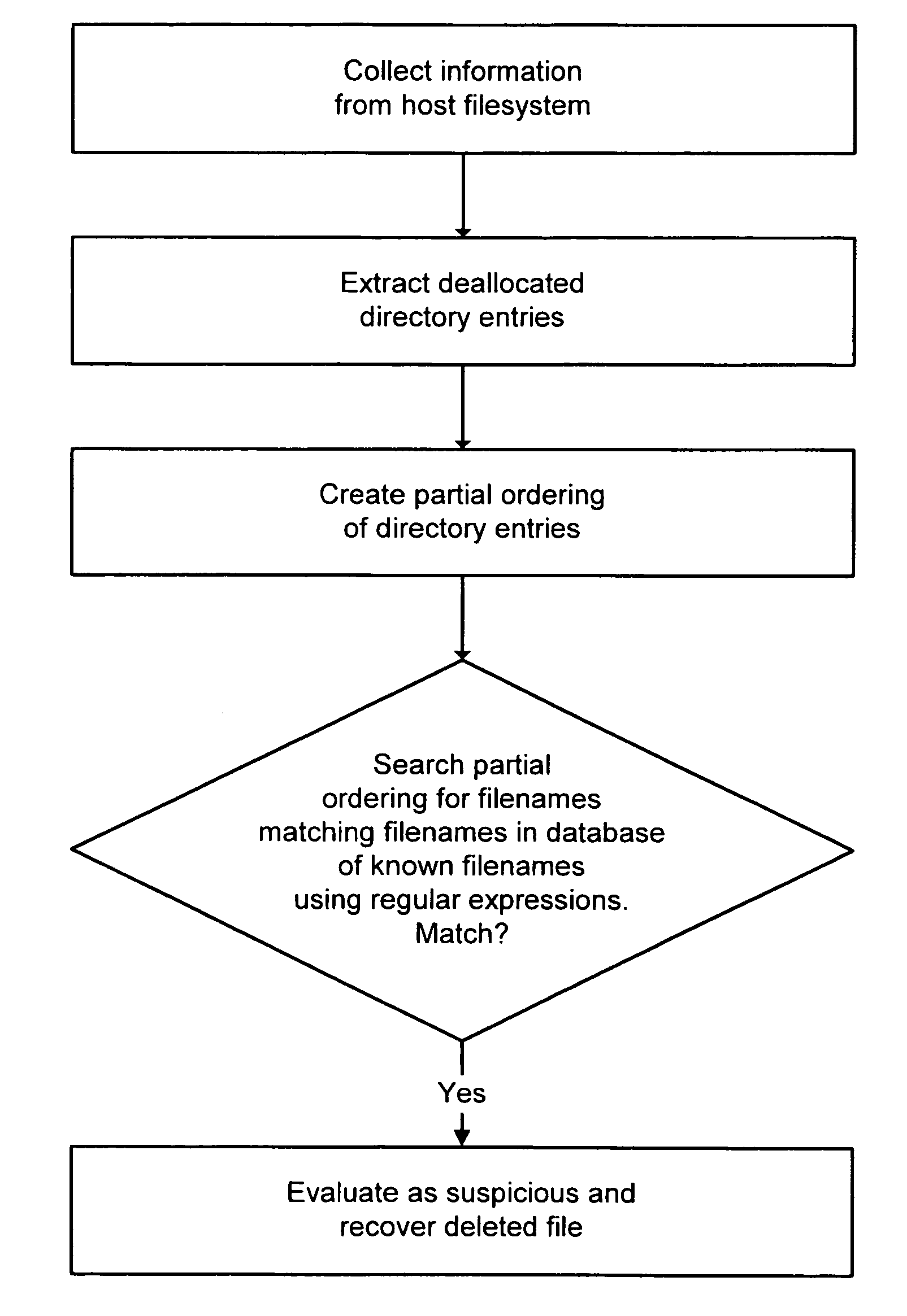
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
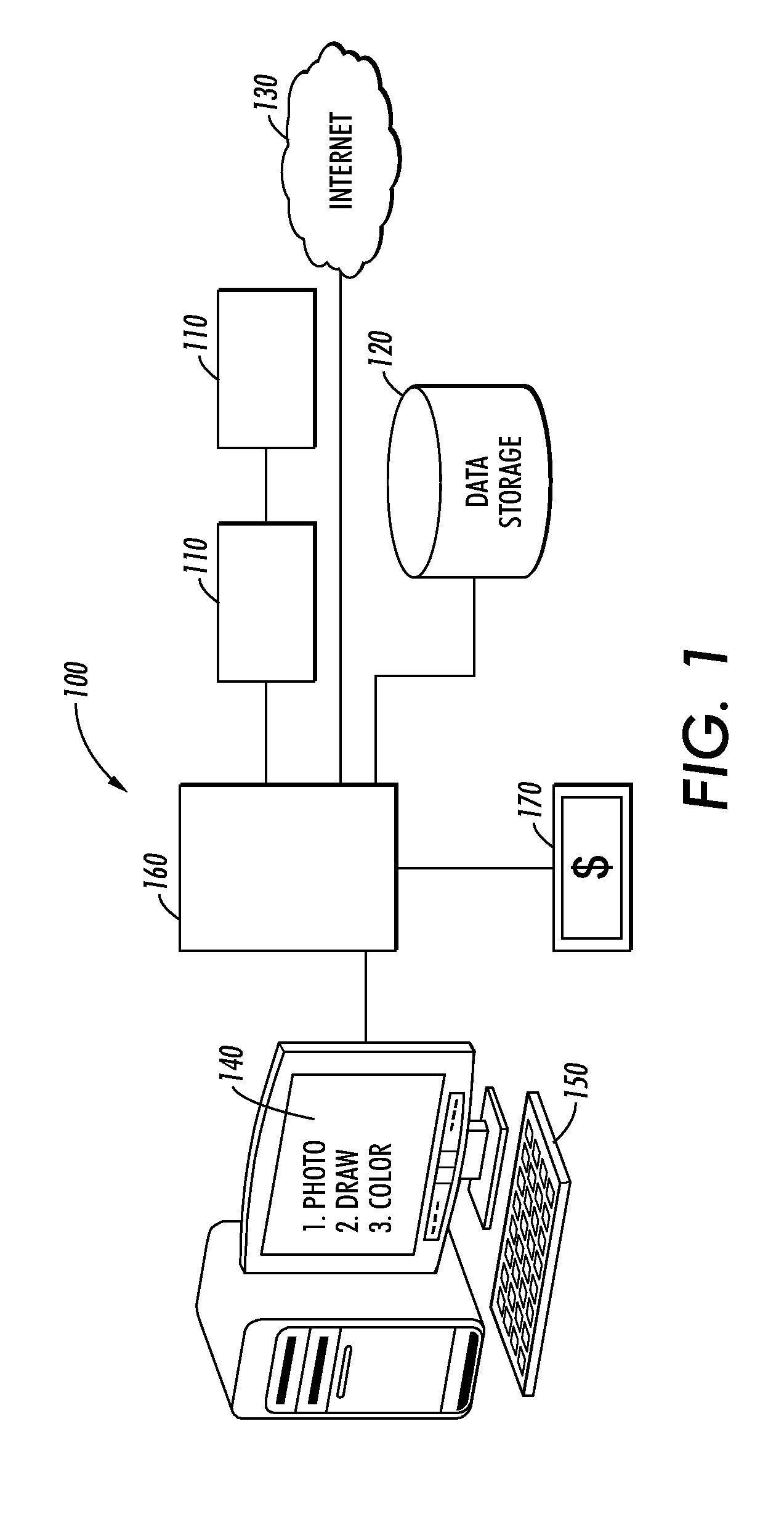
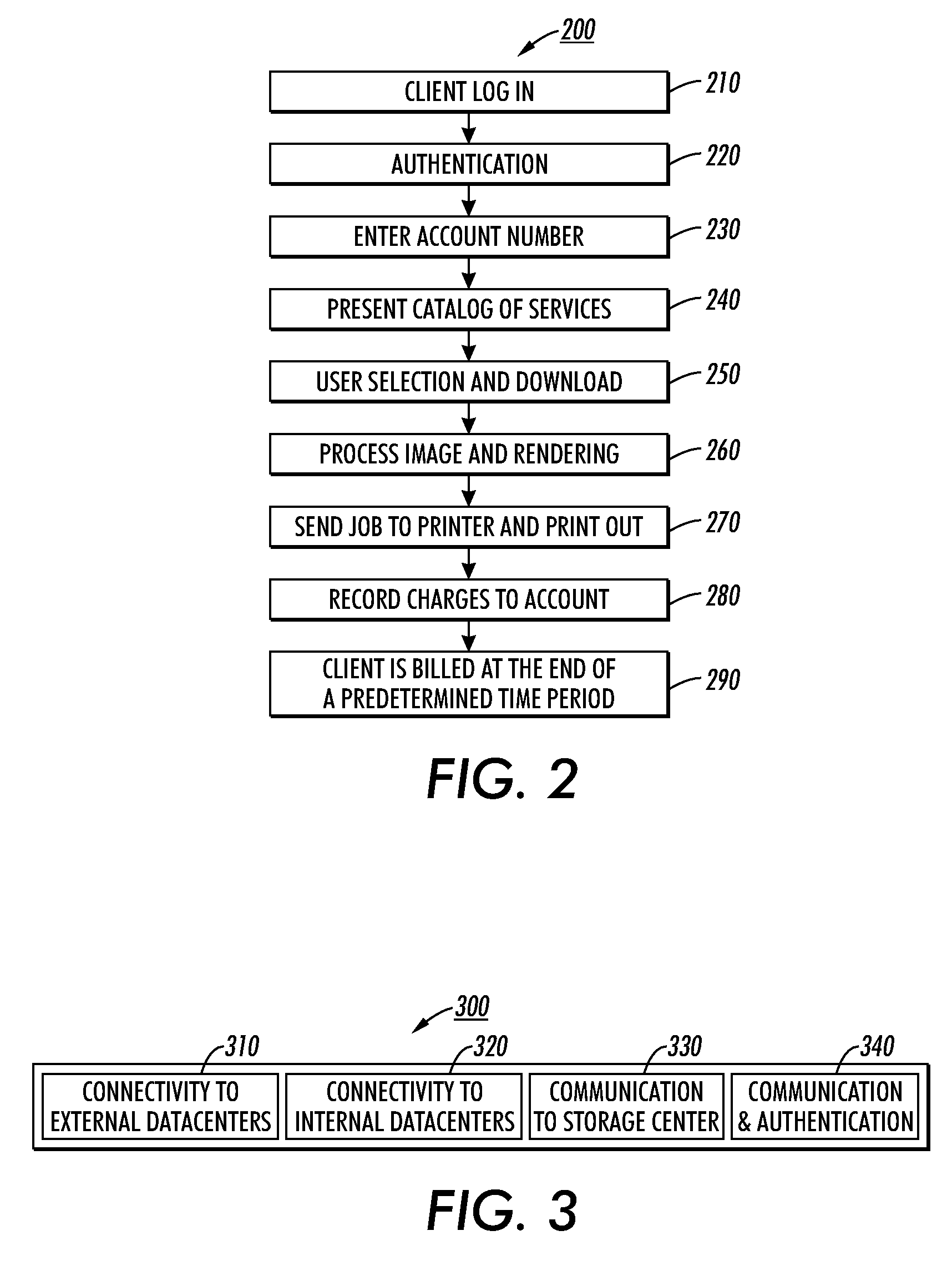
Web enabled color management service system and method
InactiveUS20090299905A1User identity/authority verificationElectronic credentialsMulti machineRemote system
The present application discloses a system and method of critical web-based service architecture at a high level for color management systems in which services can be rendered remotely at very low cost to the end user using a cloud computing based computer network architecture. Service supported include Remote RIPPing, remote profiling, remote IQ analysis for diagnosing color problems, Remote System Problem Action Requests (SPAR) evaluation and patch distribution, remote copy match solutions; multi-machine matching; remote Half-tone downloads; other remote file processing; and image or photo indexing and retrieval.
Owner:XEROX CORP
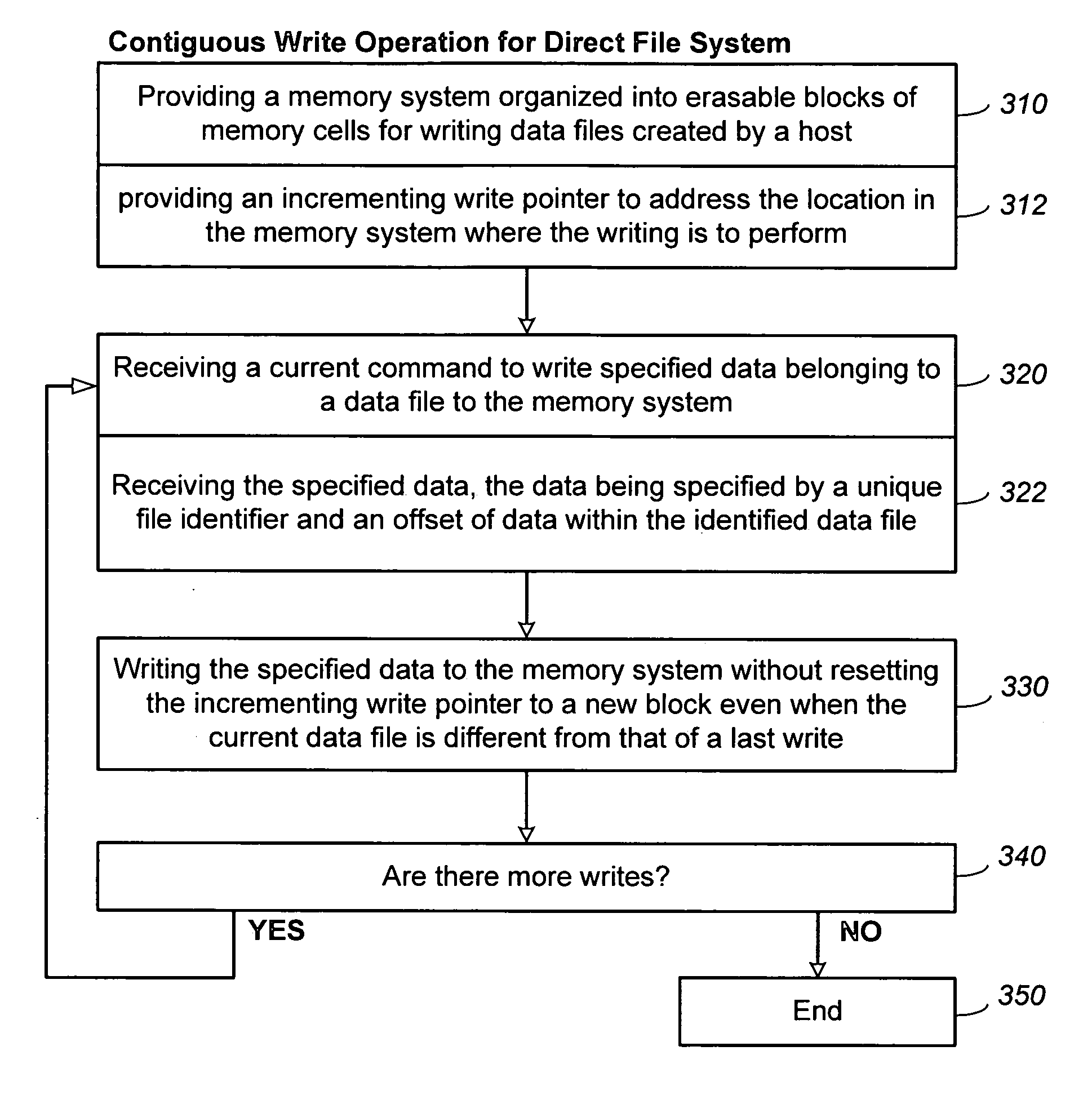
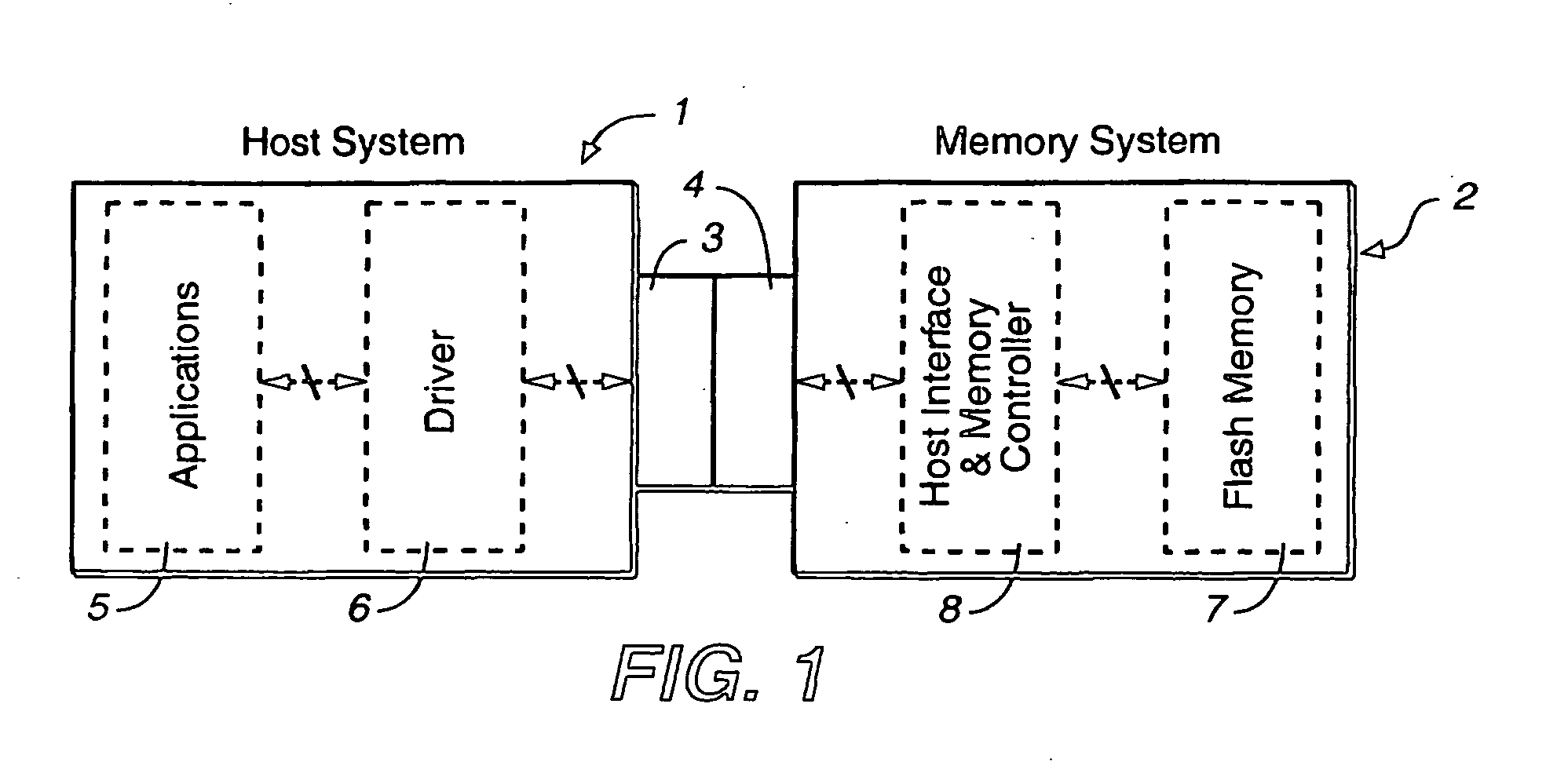
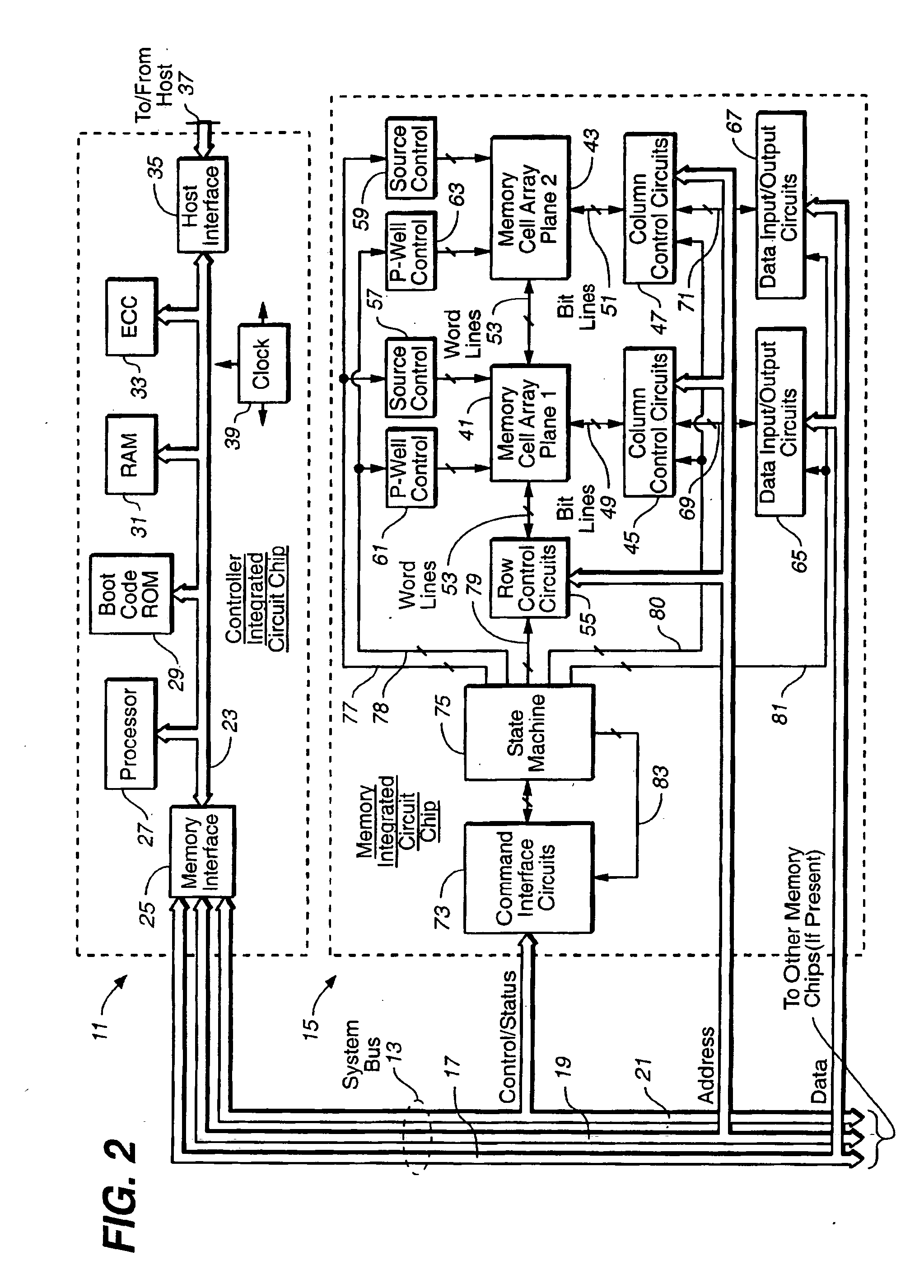
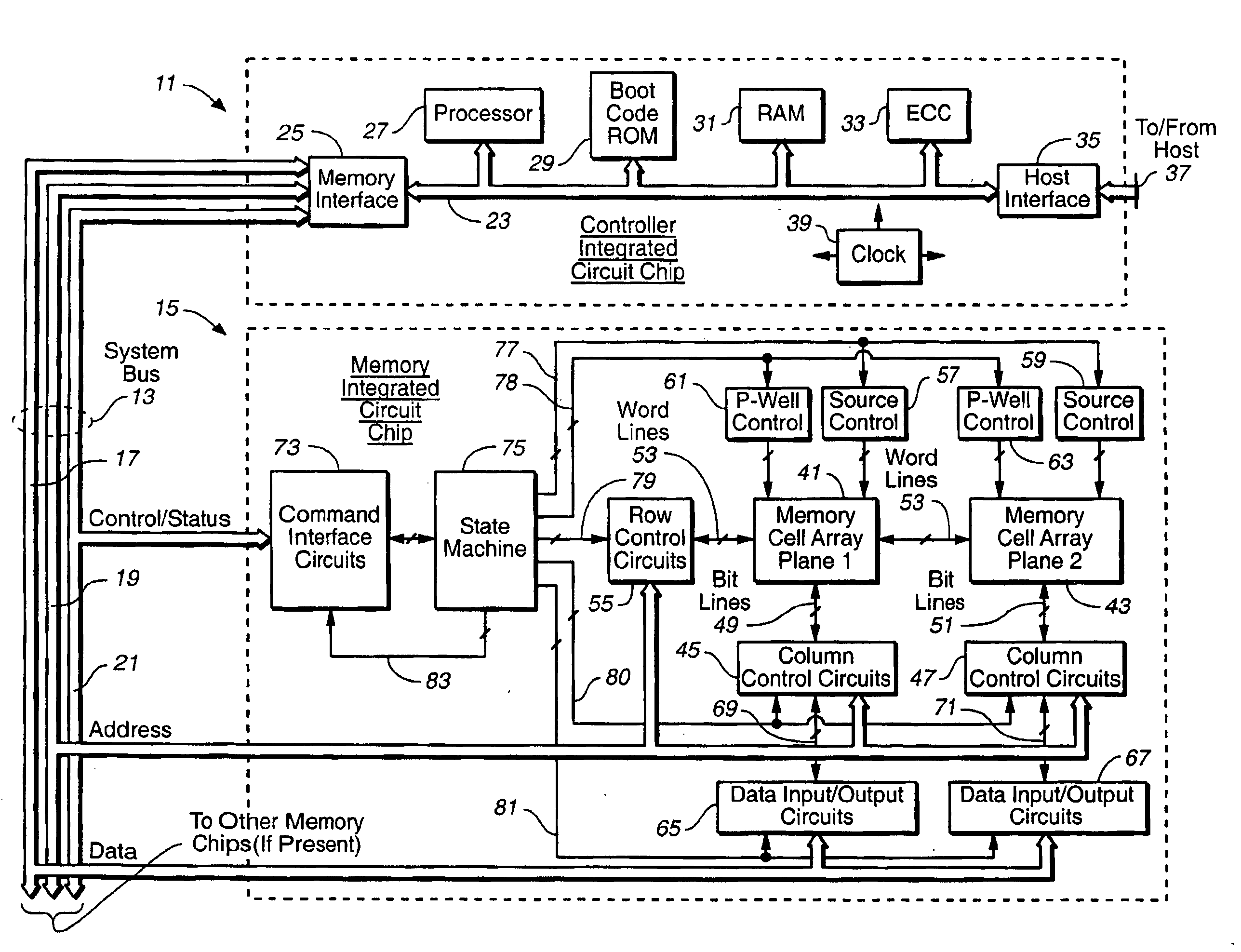
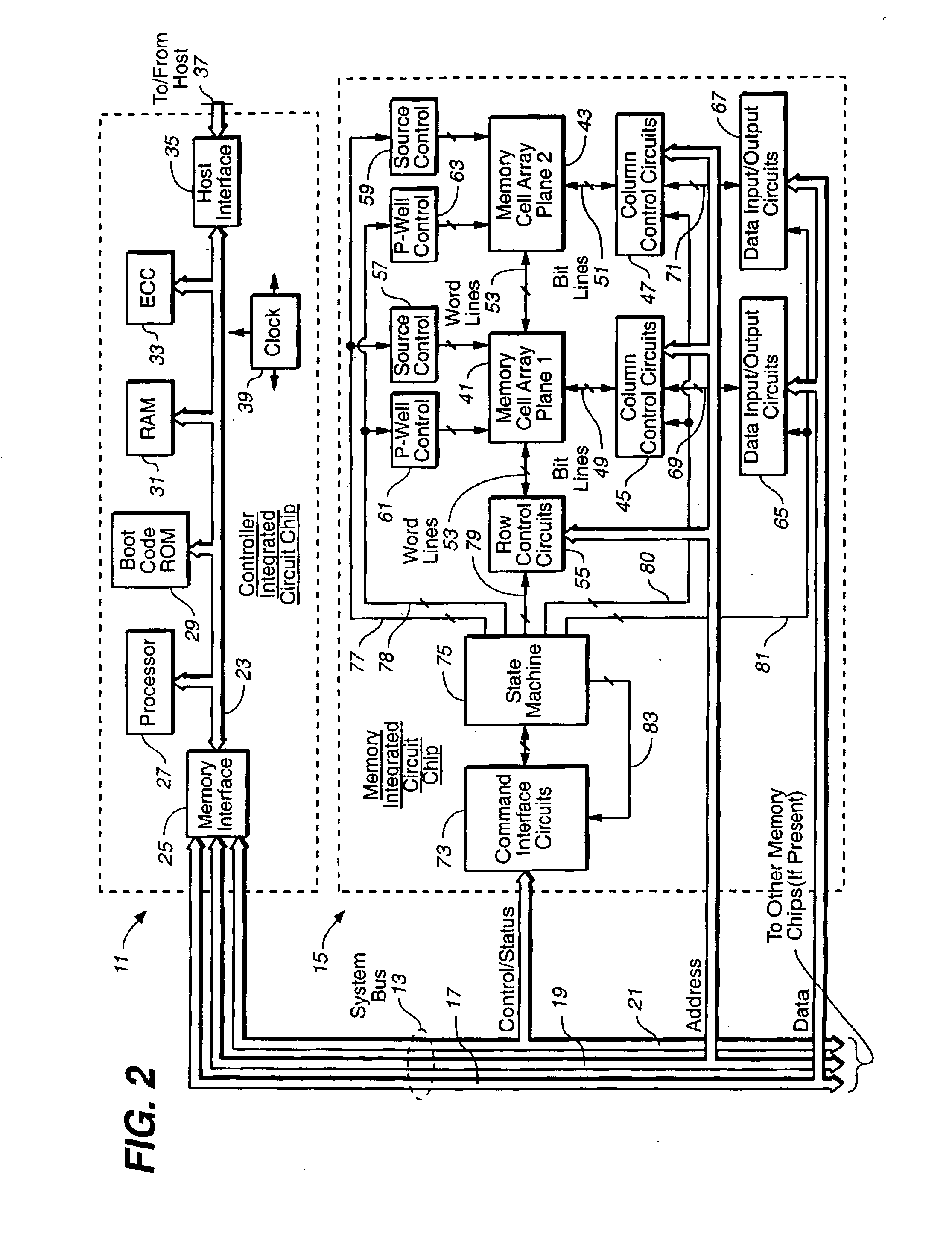
Methods for adaptive file data handling in non-volatile memories with a directly mapped file storage system
InactiveUS20070143561A1Promote high performanceImprove performanceMemory systemsData compressionWaste collection
In a memory system with a file storage system, an optimal file handling scheme is adaptively selected from a group thereof based on the attributes of the file being handled. The file attributes may be obtained from a host or derived from a history of the file had with the memory system. In one embodiment, a scheme for allocating memory locations for a write operation is dependent on an estimated size of the file to be written. In another embodiment, a scheme for allocating memory locations for a relocation operation, such as for garbage collection or data compaction, is dependent on an estimated access frequency of the file in question. In this way, the optimal handling scheme can be used for the particular file at any time.
Owner:SANDISK TECH LLC
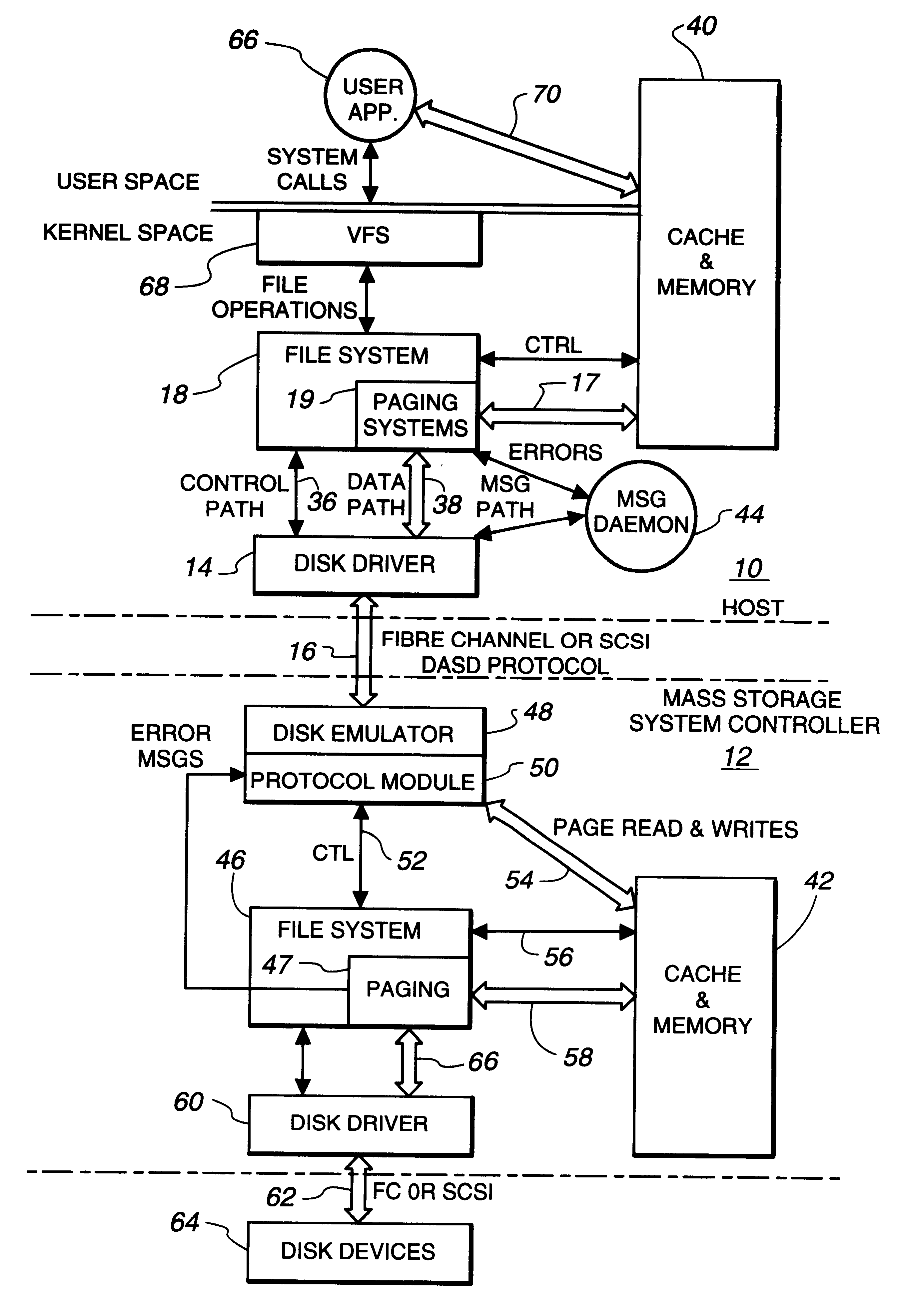
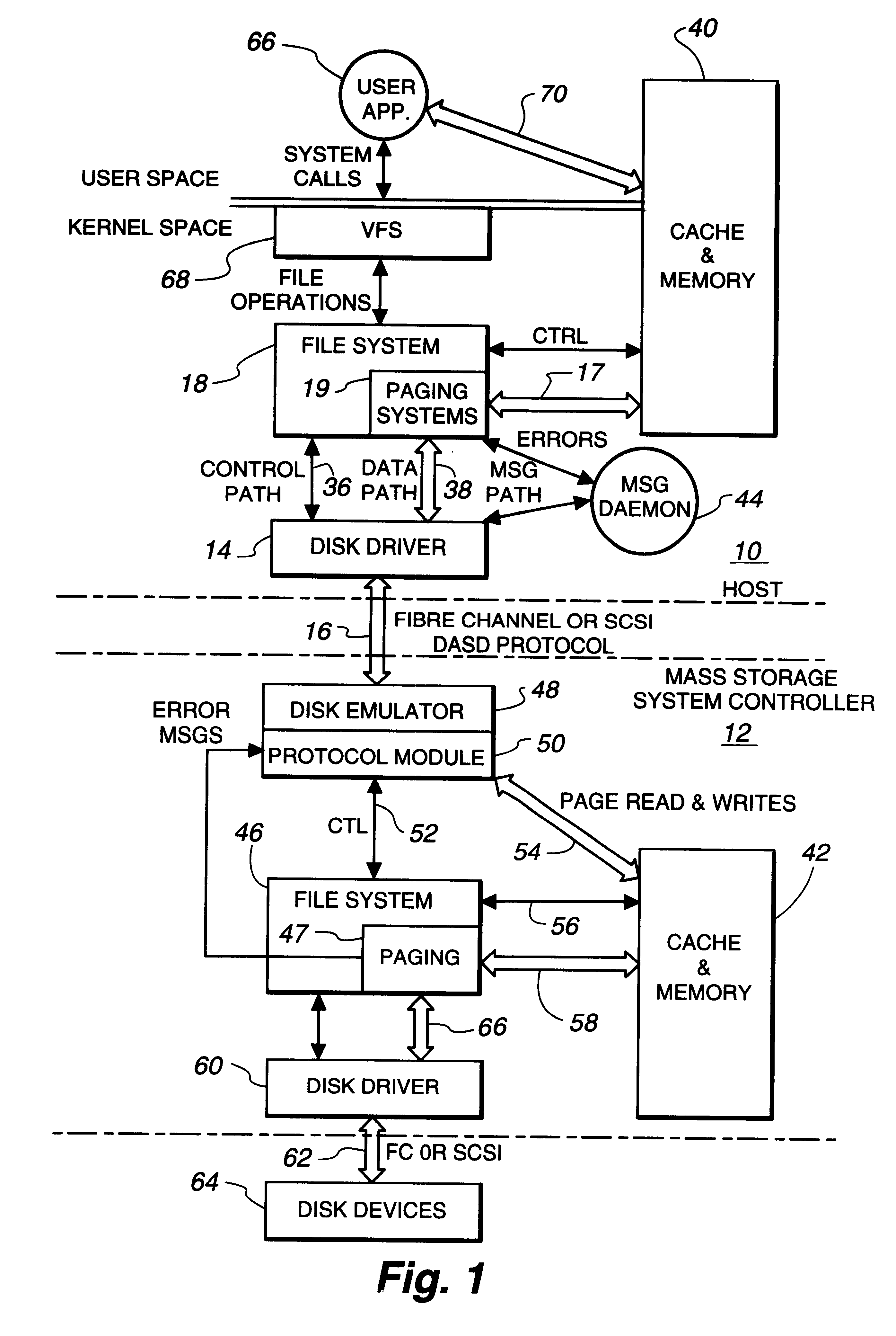
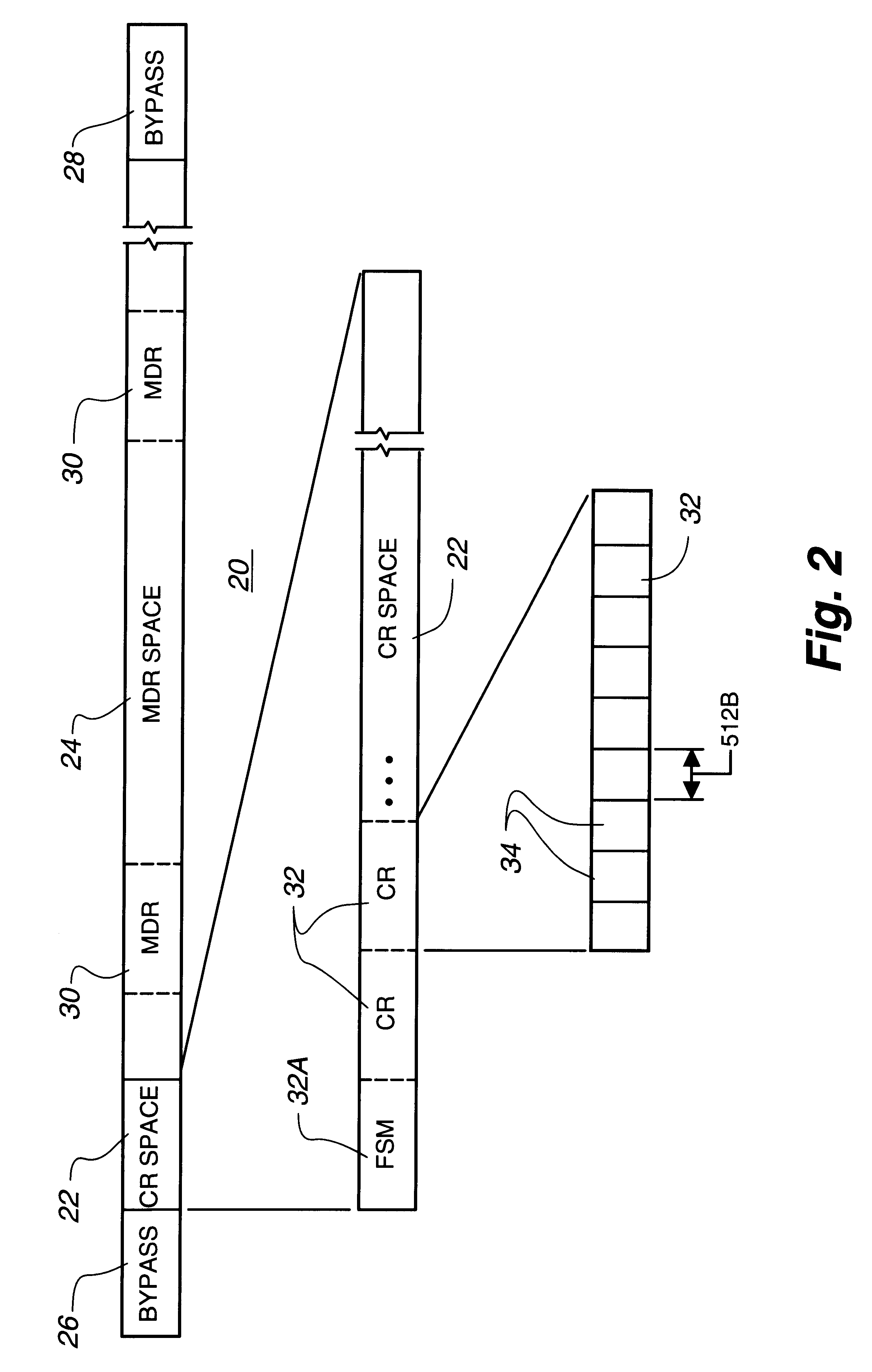
Intelligent controller accessed through addressable virtual space
InactiveUS6493811B1Remove restrictionsInput/output to record carriersMemory adressing/allocation/relocationDirect memory accessVirtual space
File operations on files in a peripheral system are controlled by an intelligent controller with a file processor. The files are accessed as if the intelligent controller were an addressable virtual storage space. This is accomplished first by communicating controller commands for the intelligent controller through read / write commands addressed to a Command Region of a virtual storage device. The controller commands set up a Mapped Data Region in the virtual storage device for use in controlling data transfer operations to and from the peripheral system. With the Mapped Data Regions set up, blocks of data are transferred between the host and the intelligent controller in response to read / write commands addressed to the Mapped Data Region of the virtual storage device.In an additional feature of the invention file operations are communicated between host and controller through a device driver at the host and a device emulator at the intelligent controller. If the address in the device write / read command is pointing to the Command Region of the virtual storage device, a Command Region process interprets and implements the controller operation required by the controller command embedded in the device write / read command. One of these controller commands causes the Command Region processor to map a requested file to a Mapped Data Region in the virtual storage device. If the address detected by the detecting operation is in a Mapped Data Region, a Mapped Data Region process is called. The Mapped Data Region process reads or writes requested data of a file mapped to the Mapped Data Region addressed by the read / write command. This mapped file read or write is accomplished as a transfer of data over a data path separate from a control path. In an additional feature of the invention, the data transfer between host system and intelligent controller is accomplished by performing a direct memory access transfer of data.
Owner:CA TECH INC
System and method for detecting computer intrusions
InactiveUS6996843B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampAccess time
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
System and method for using timestamps to detect attacks
InactiveUS7203962B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampContinuation
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
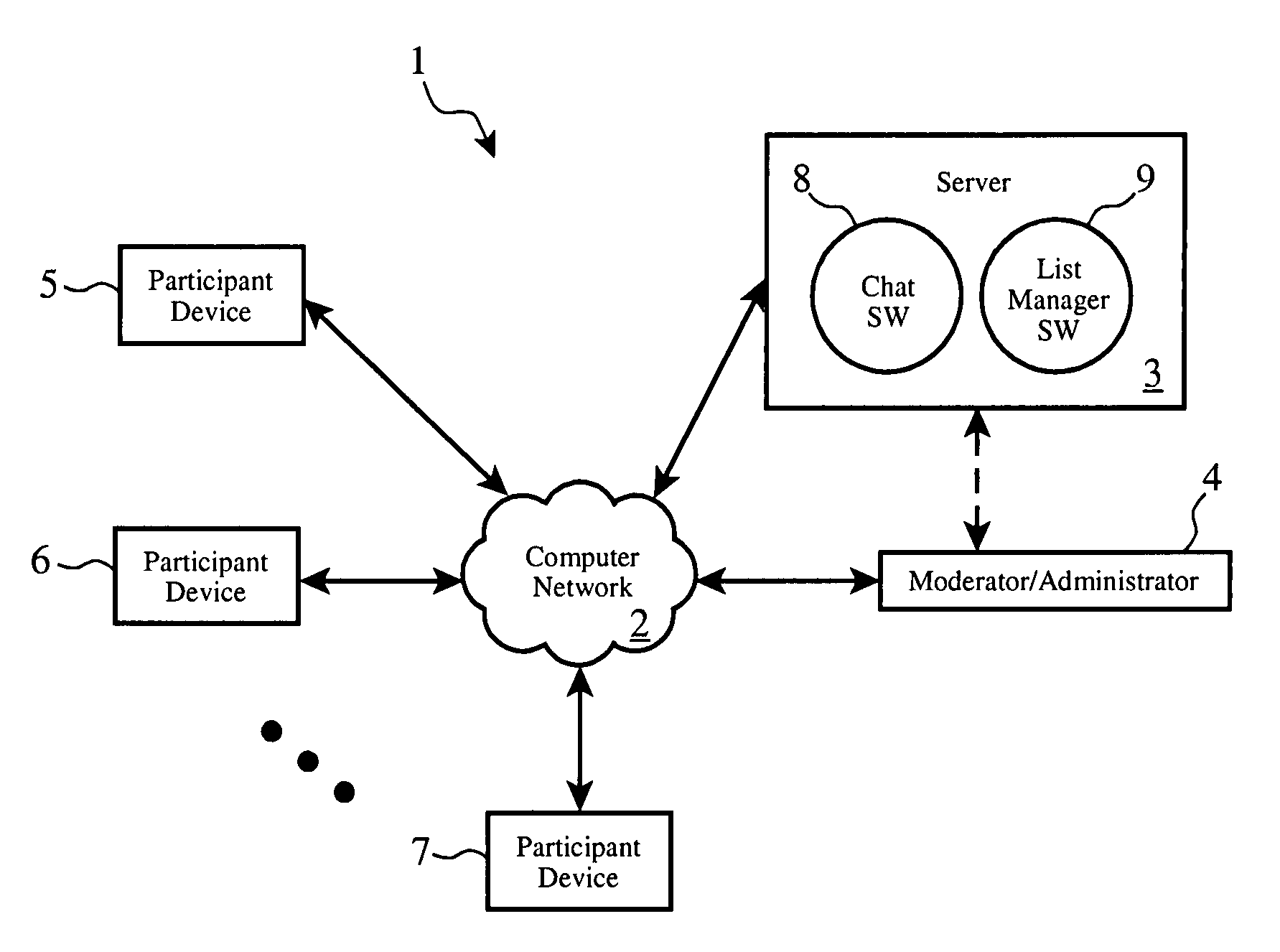
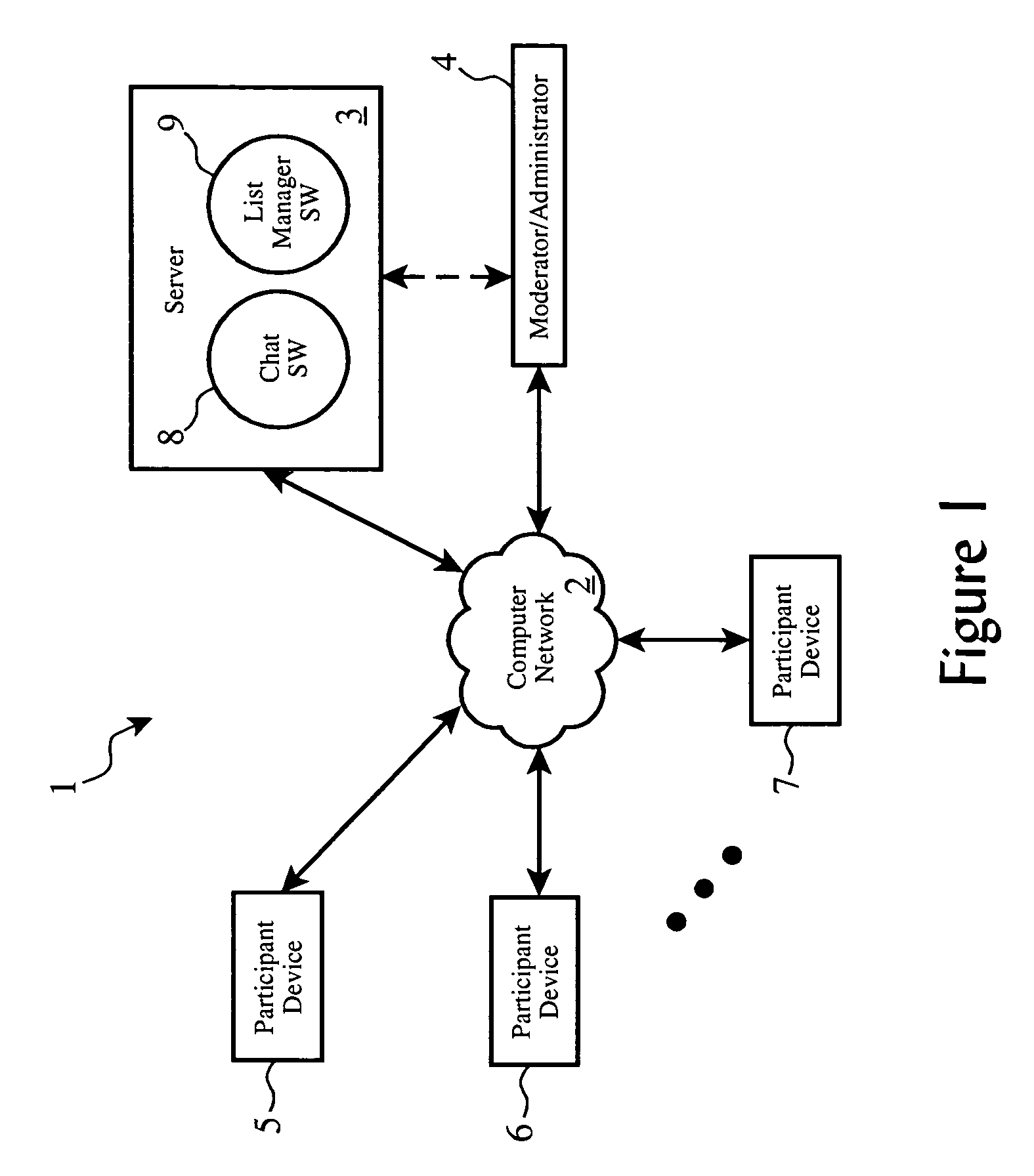
Automated banking machine apparatus and system
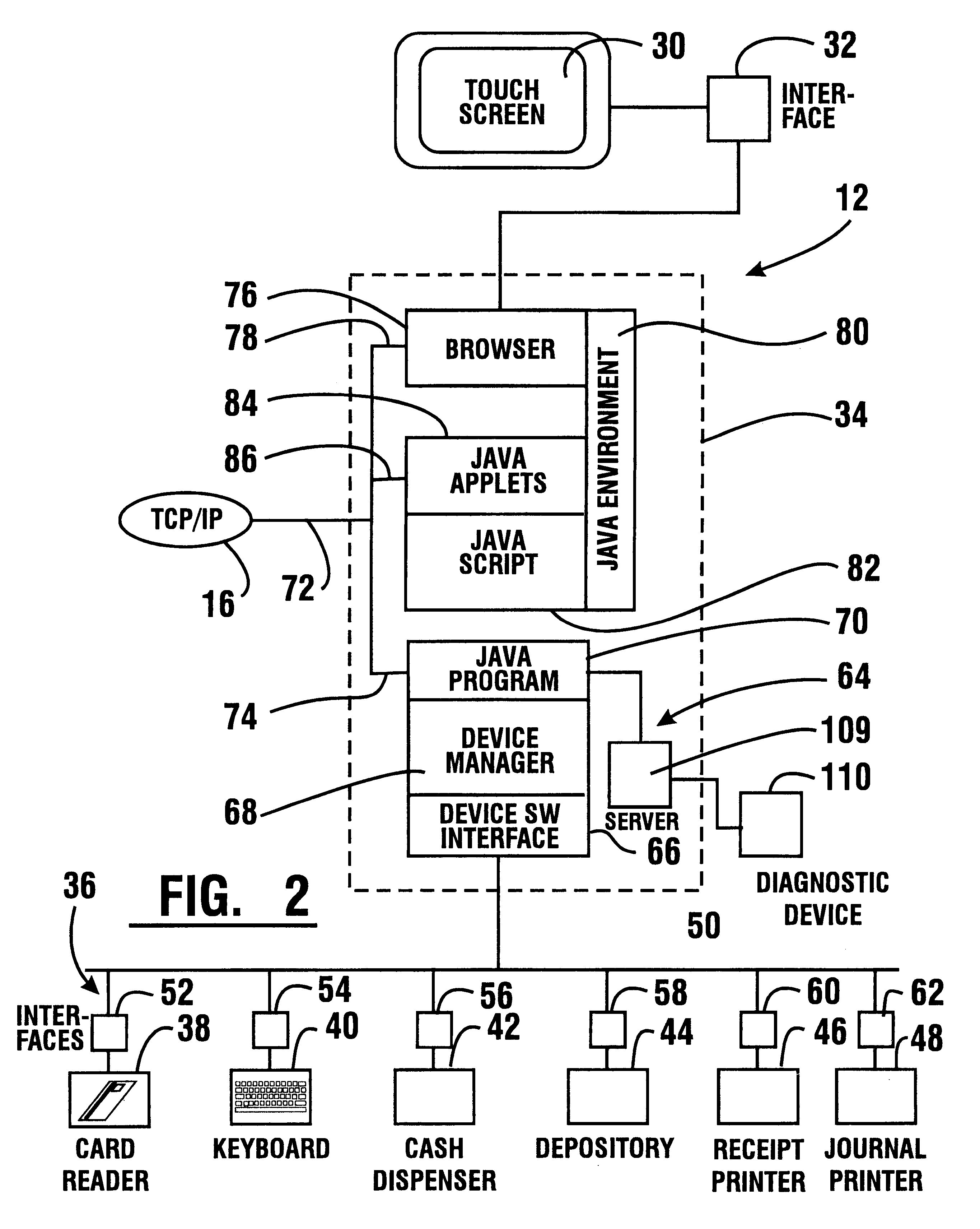
InactiveUS6289320B1Easy to operateMaintain securityPayment architectureSpecial data processing applicationsDocument handlingApplication software
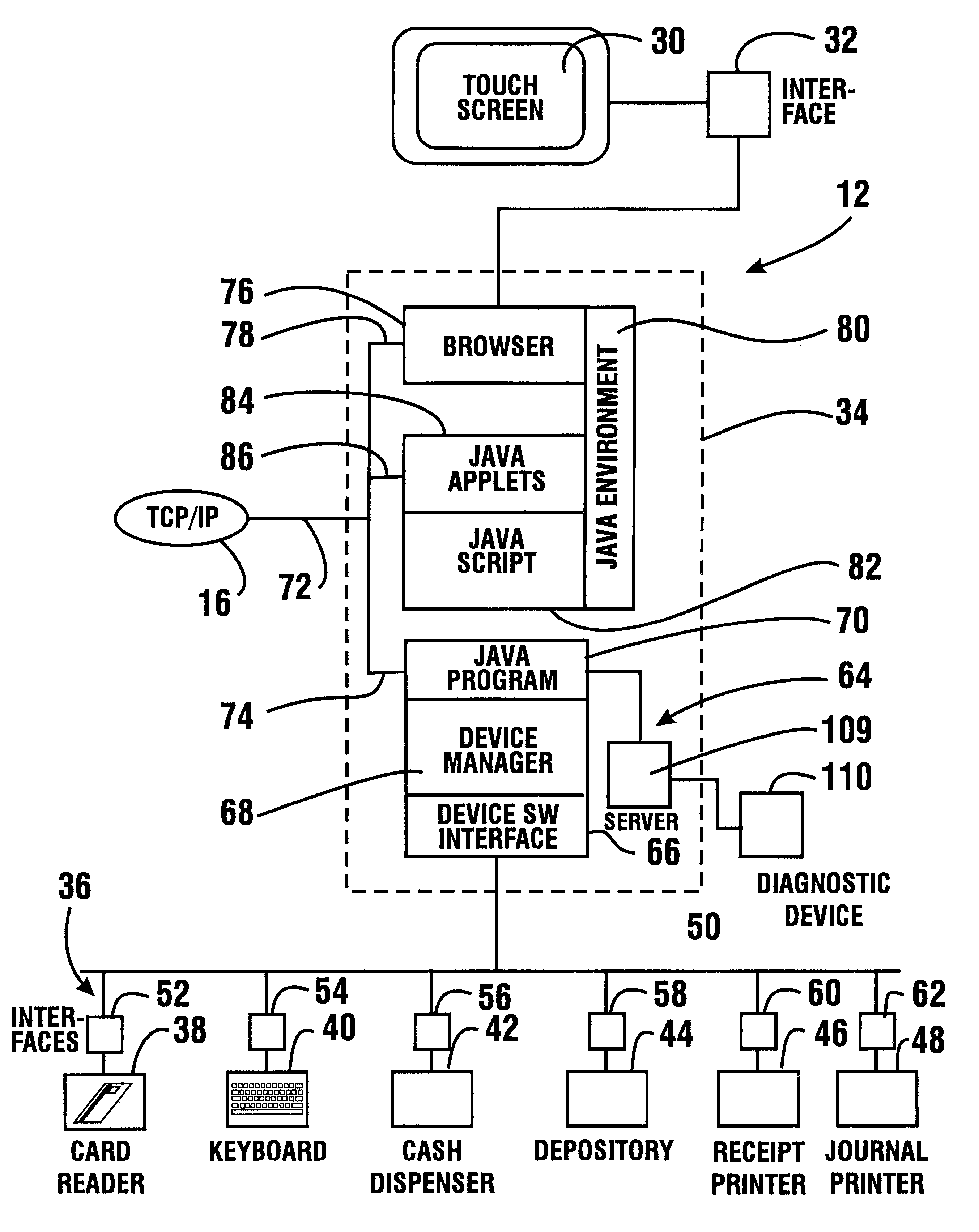
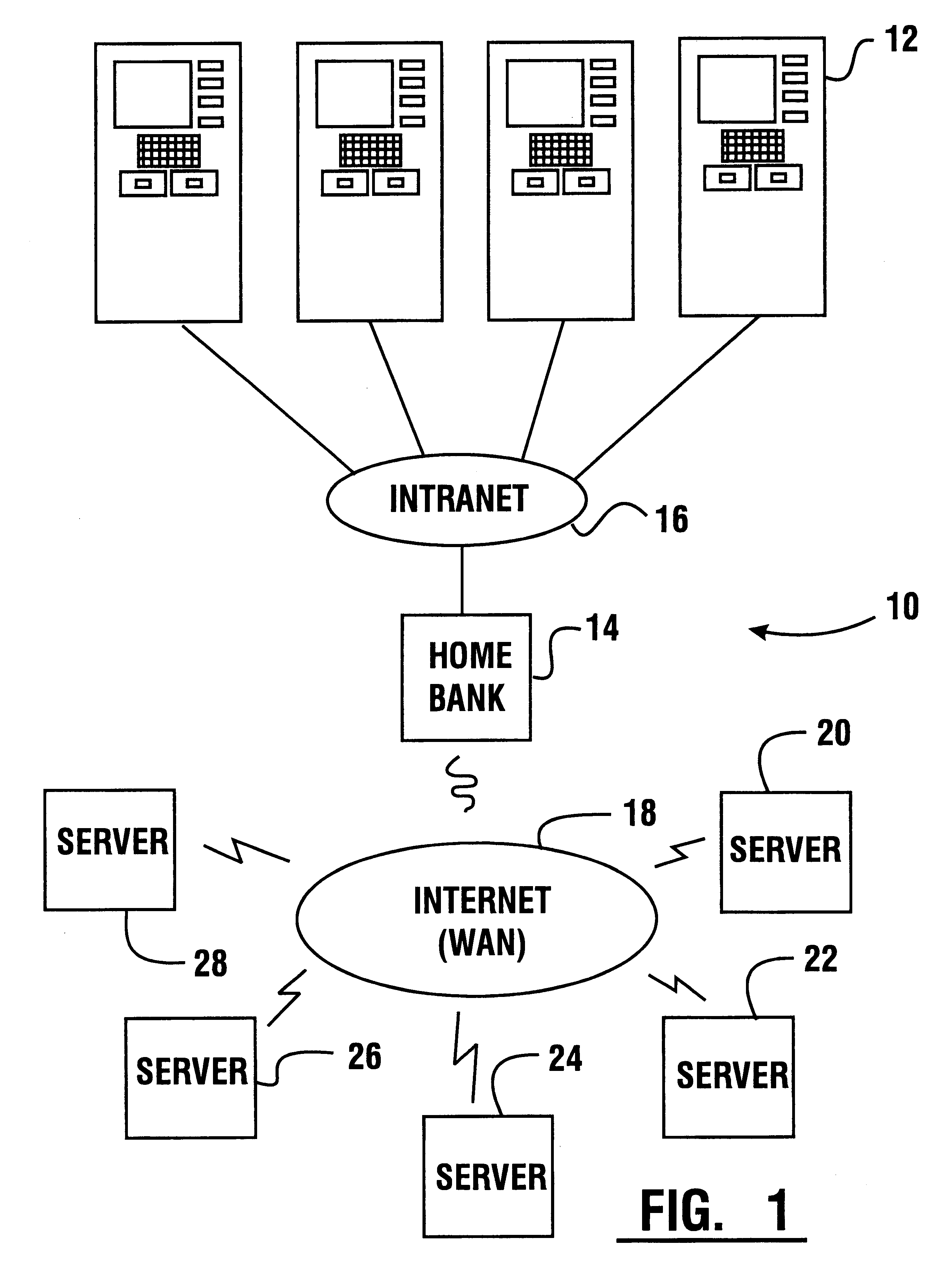
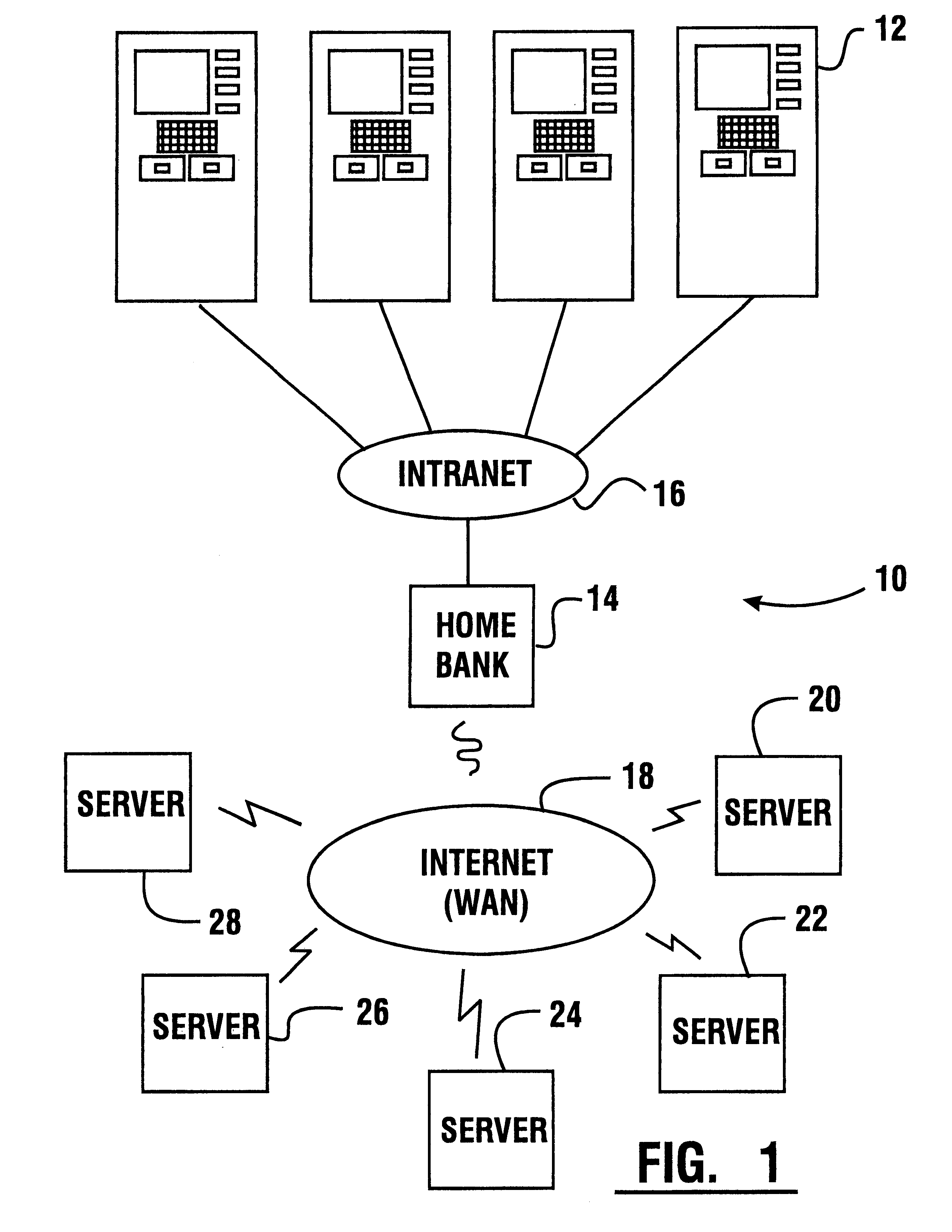
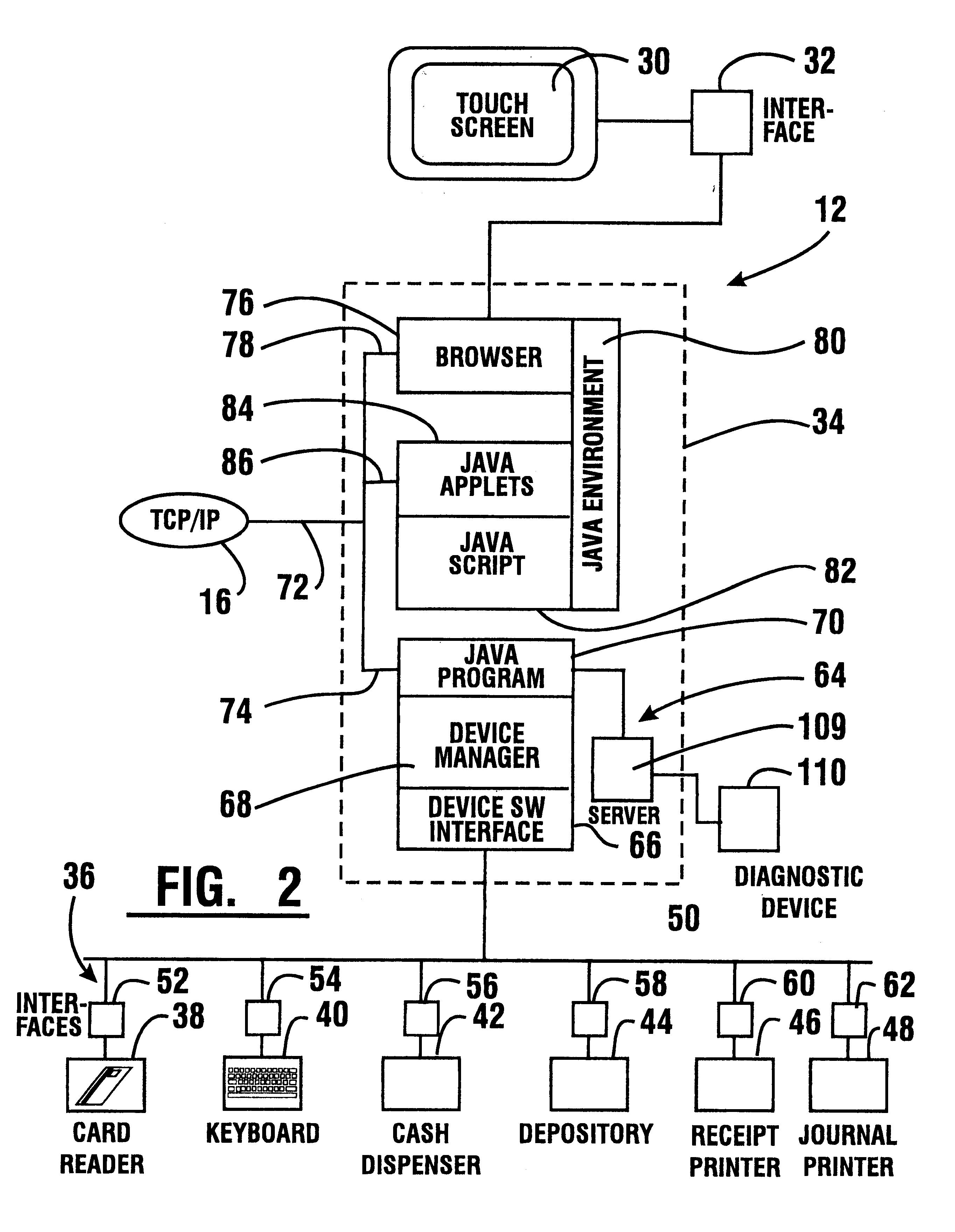
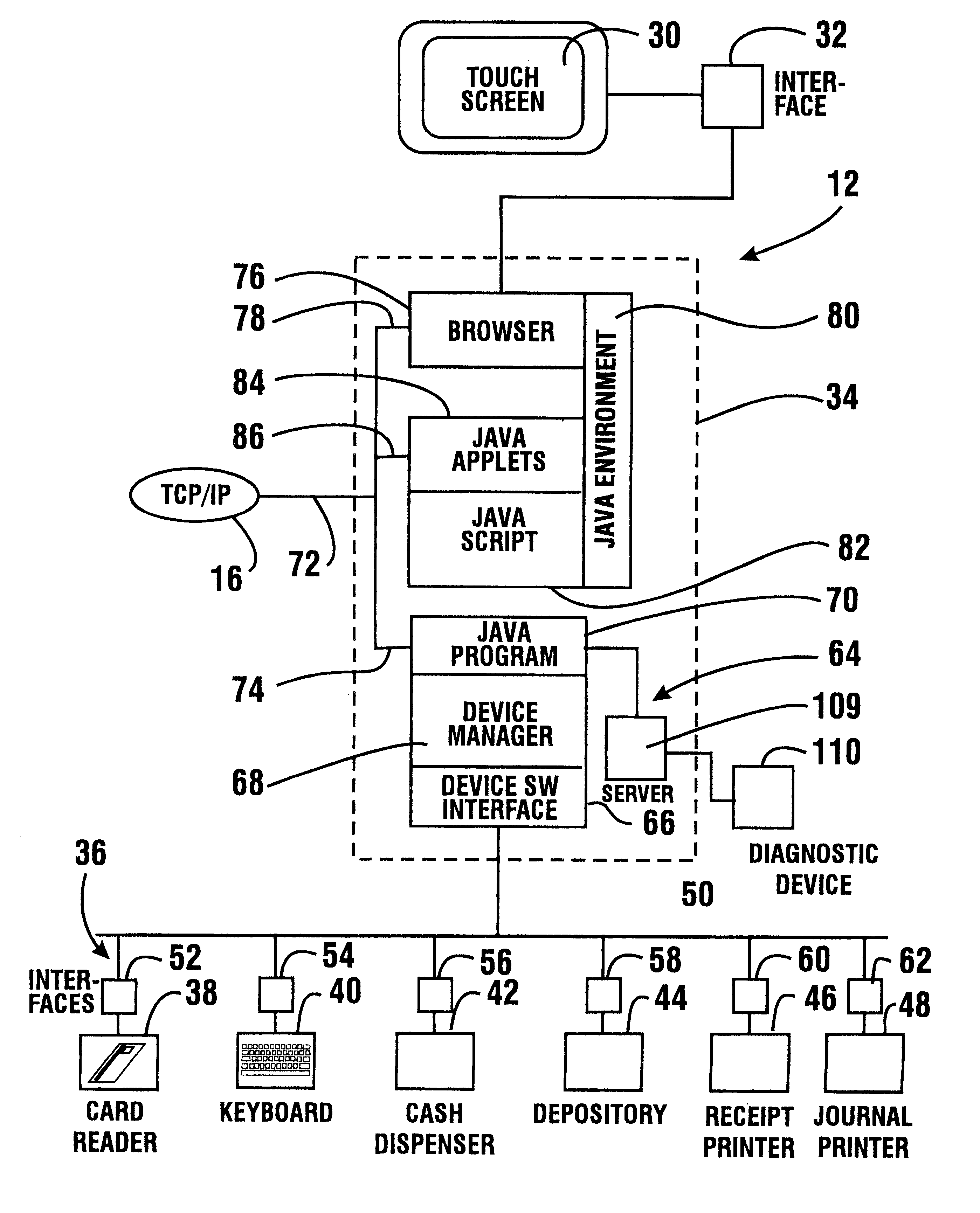
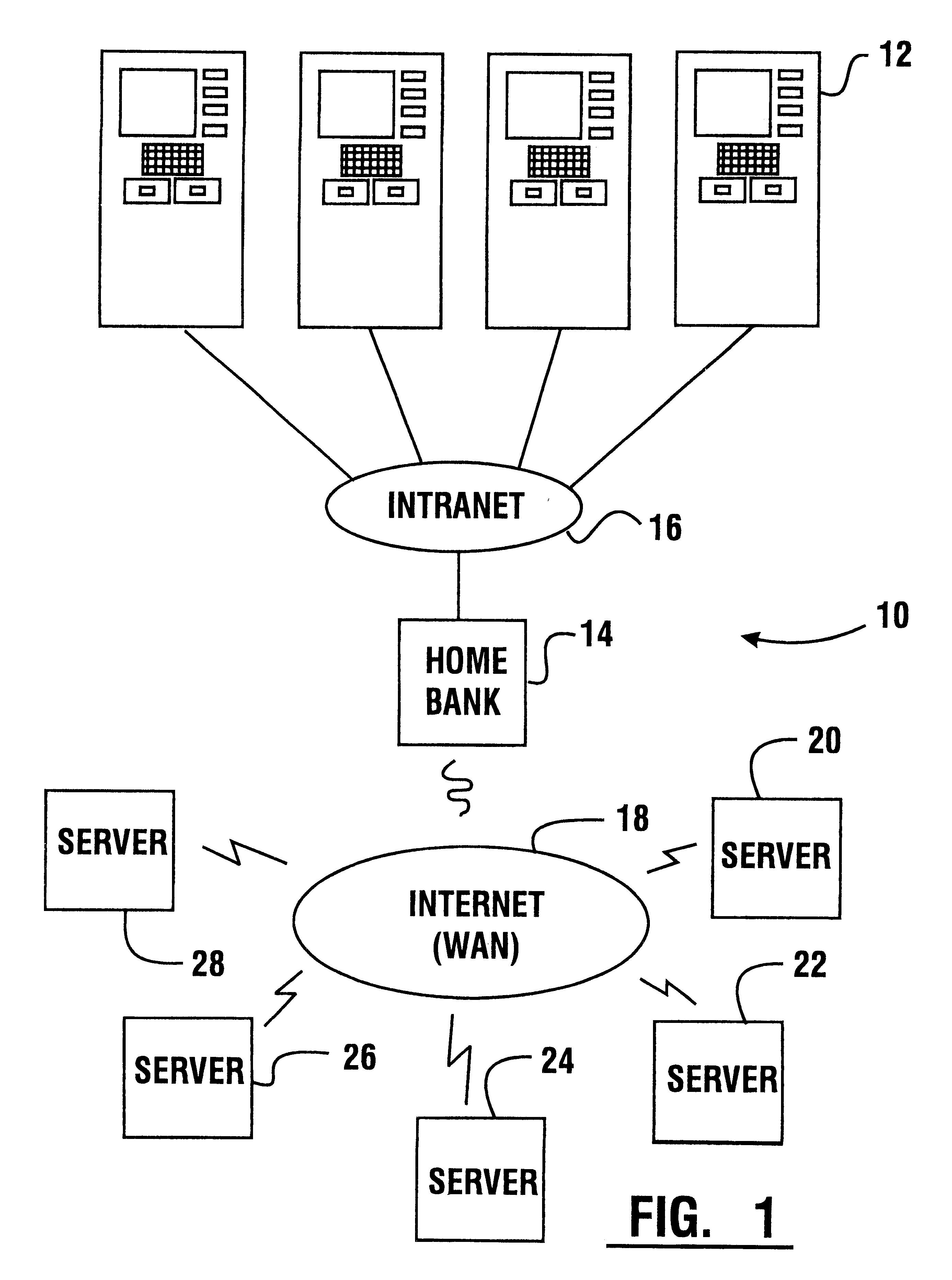
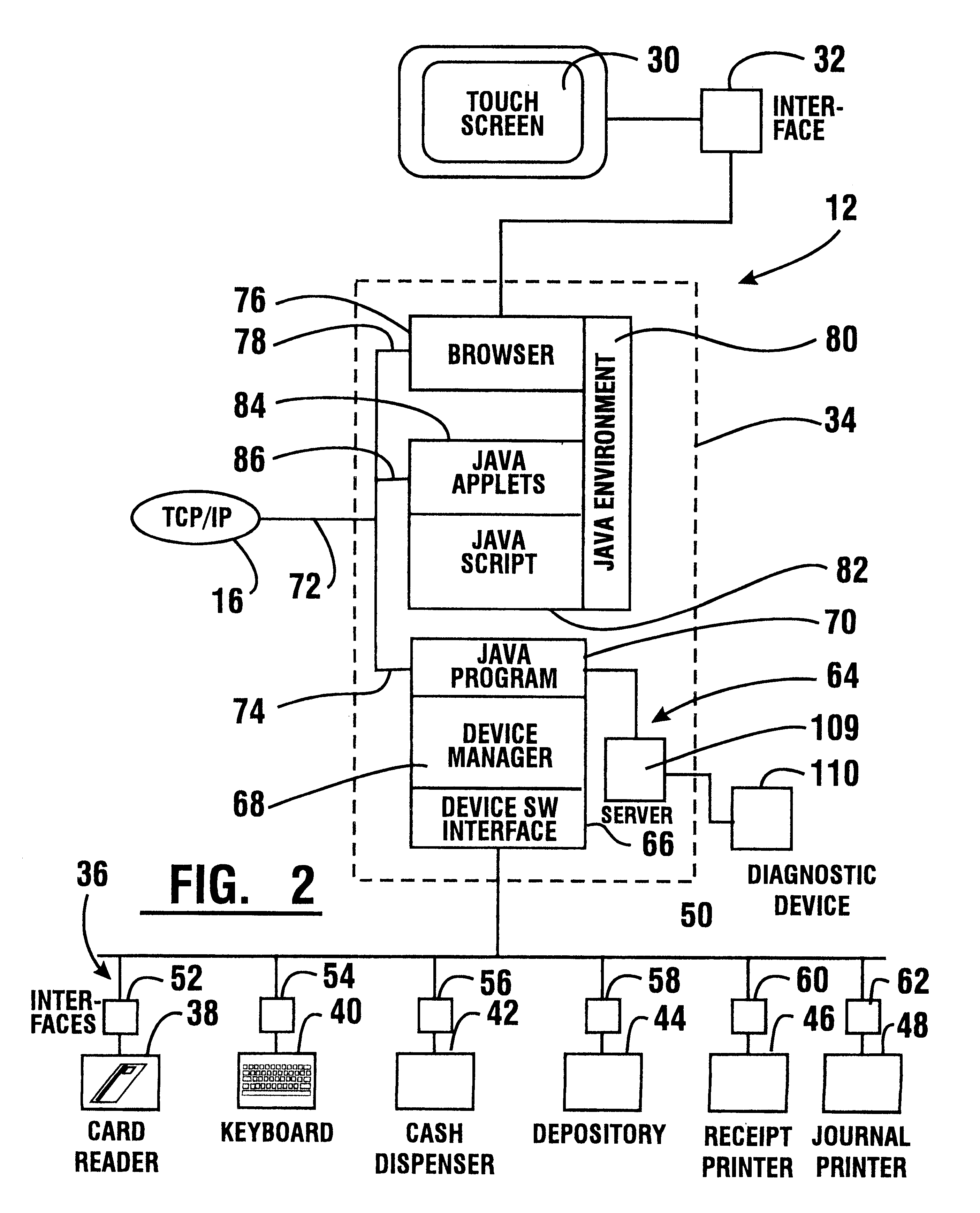
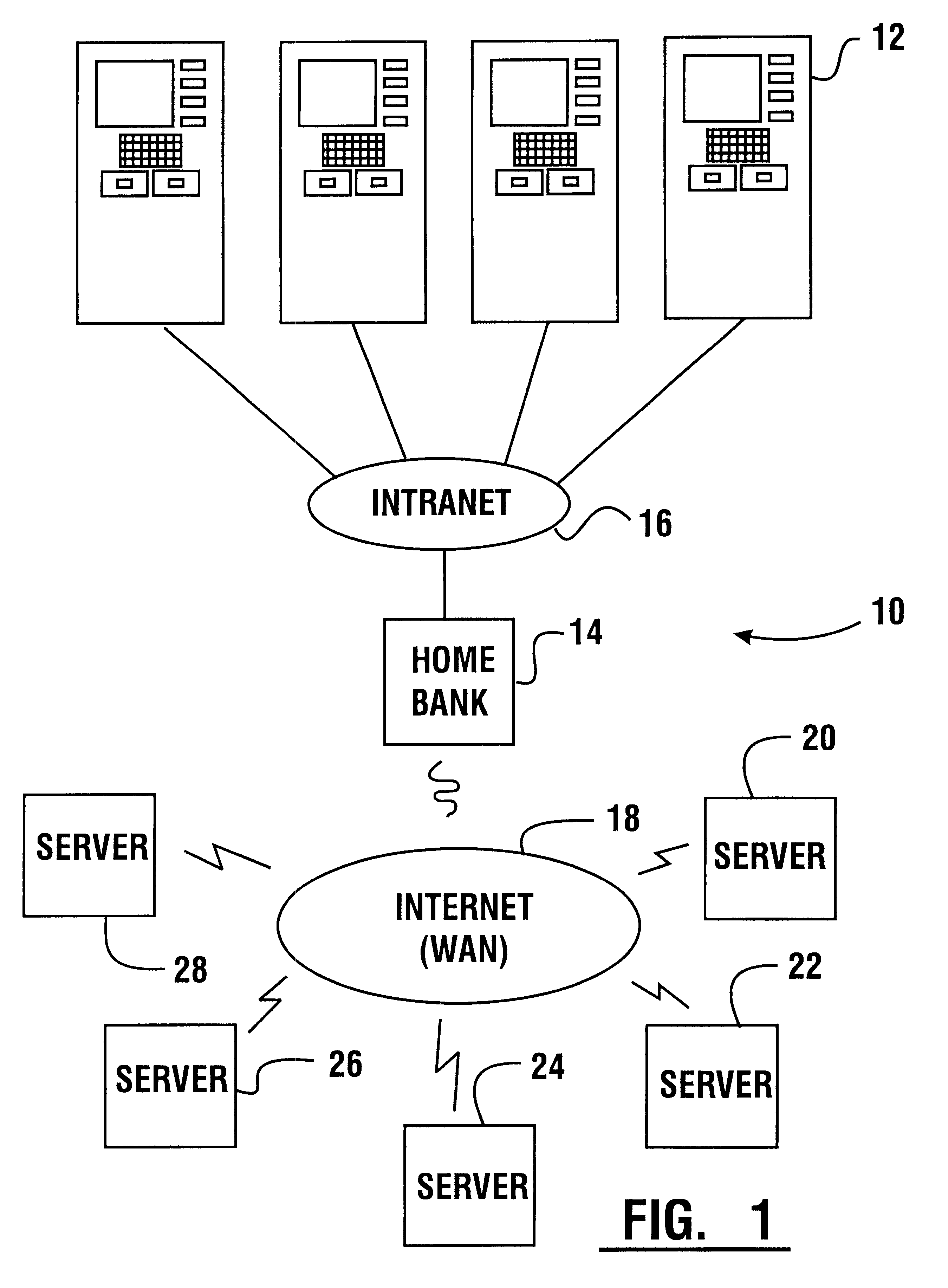
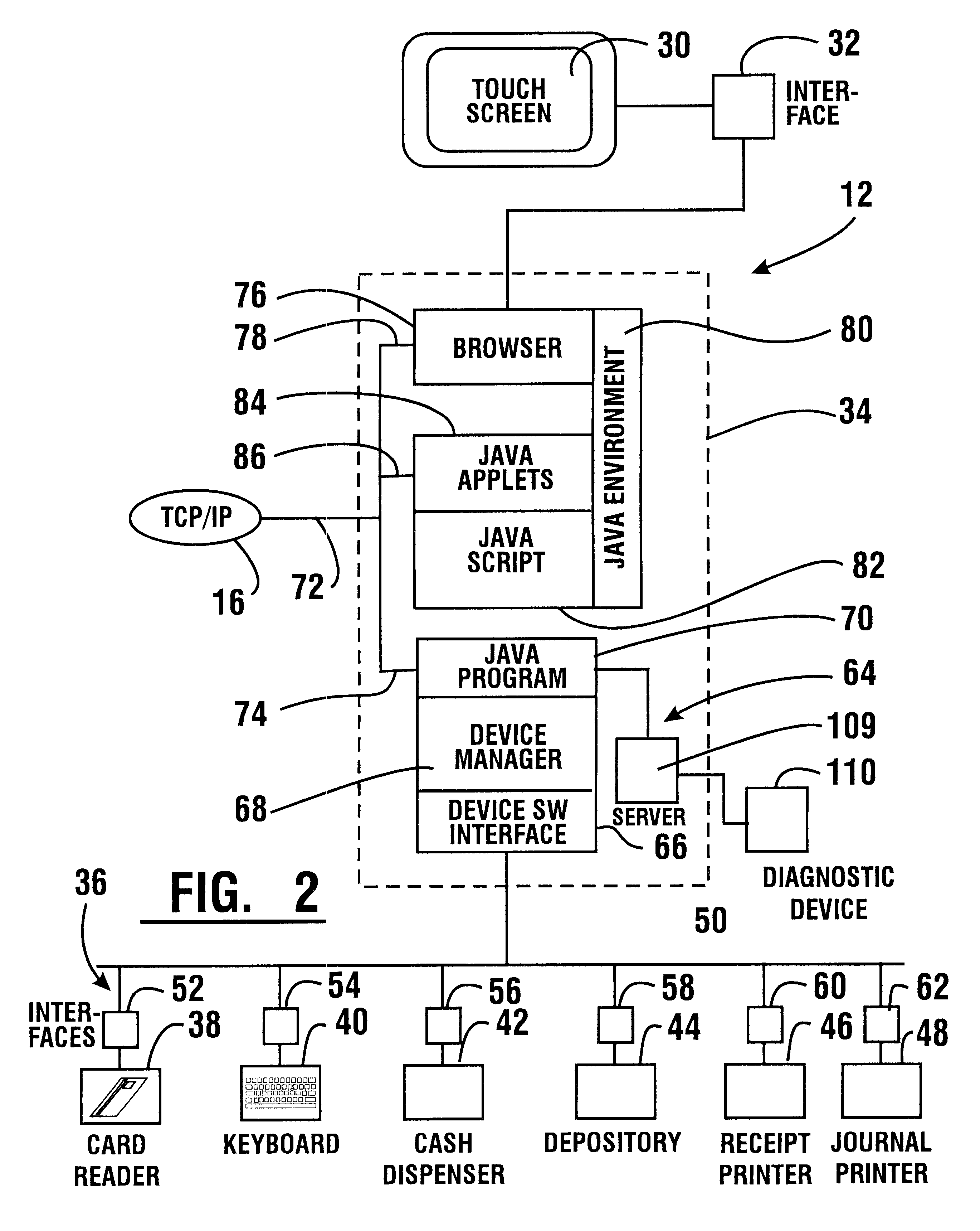
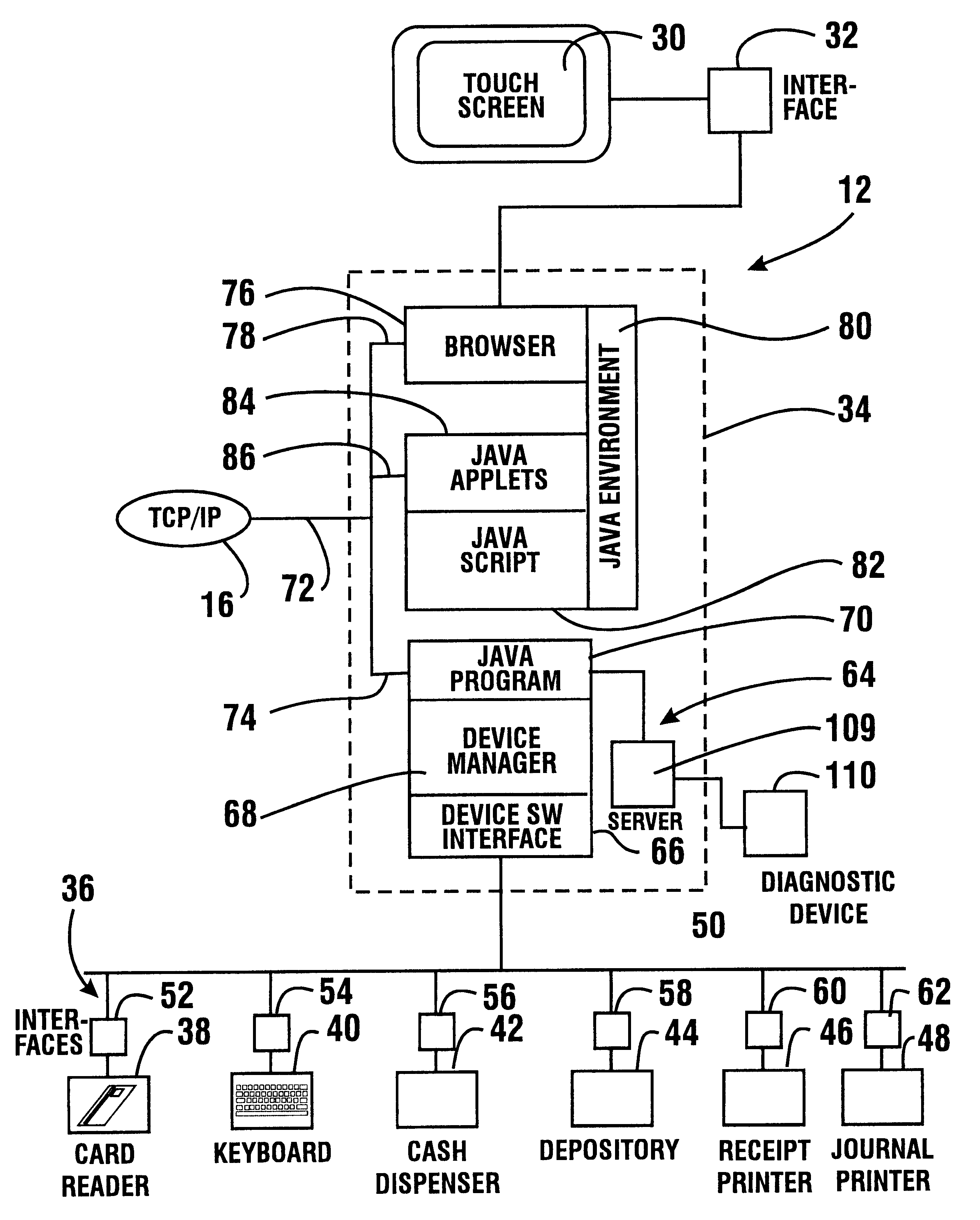
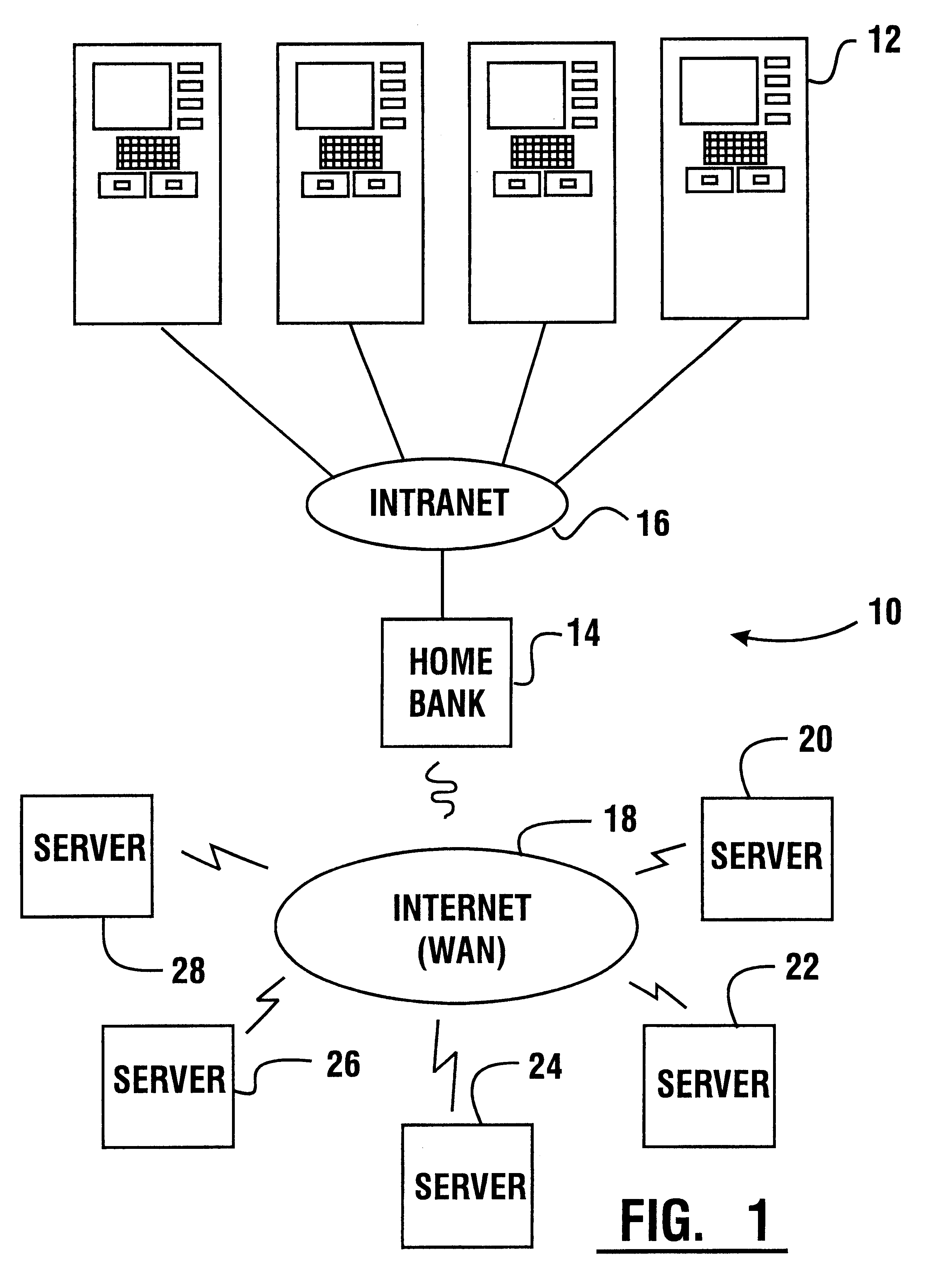
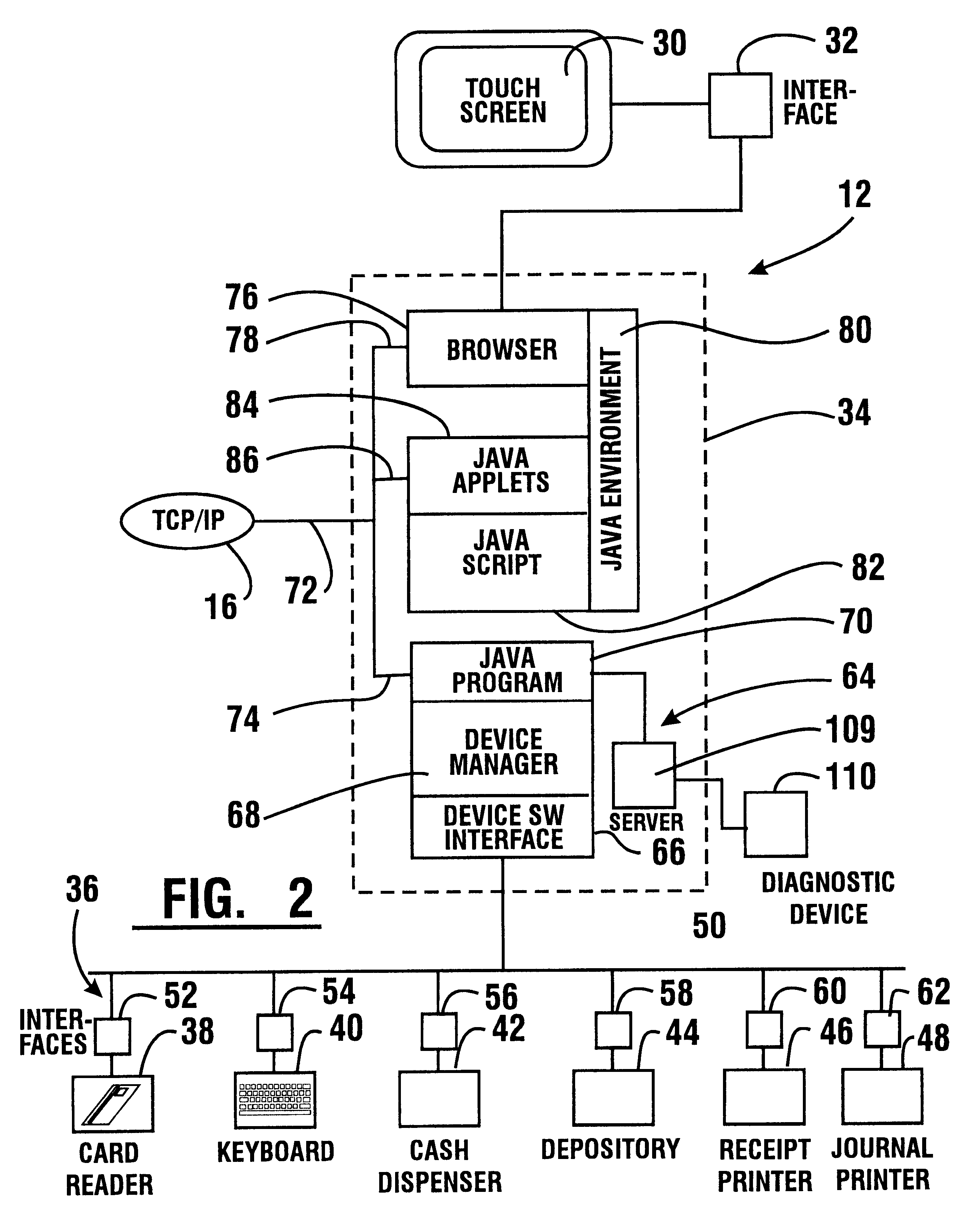
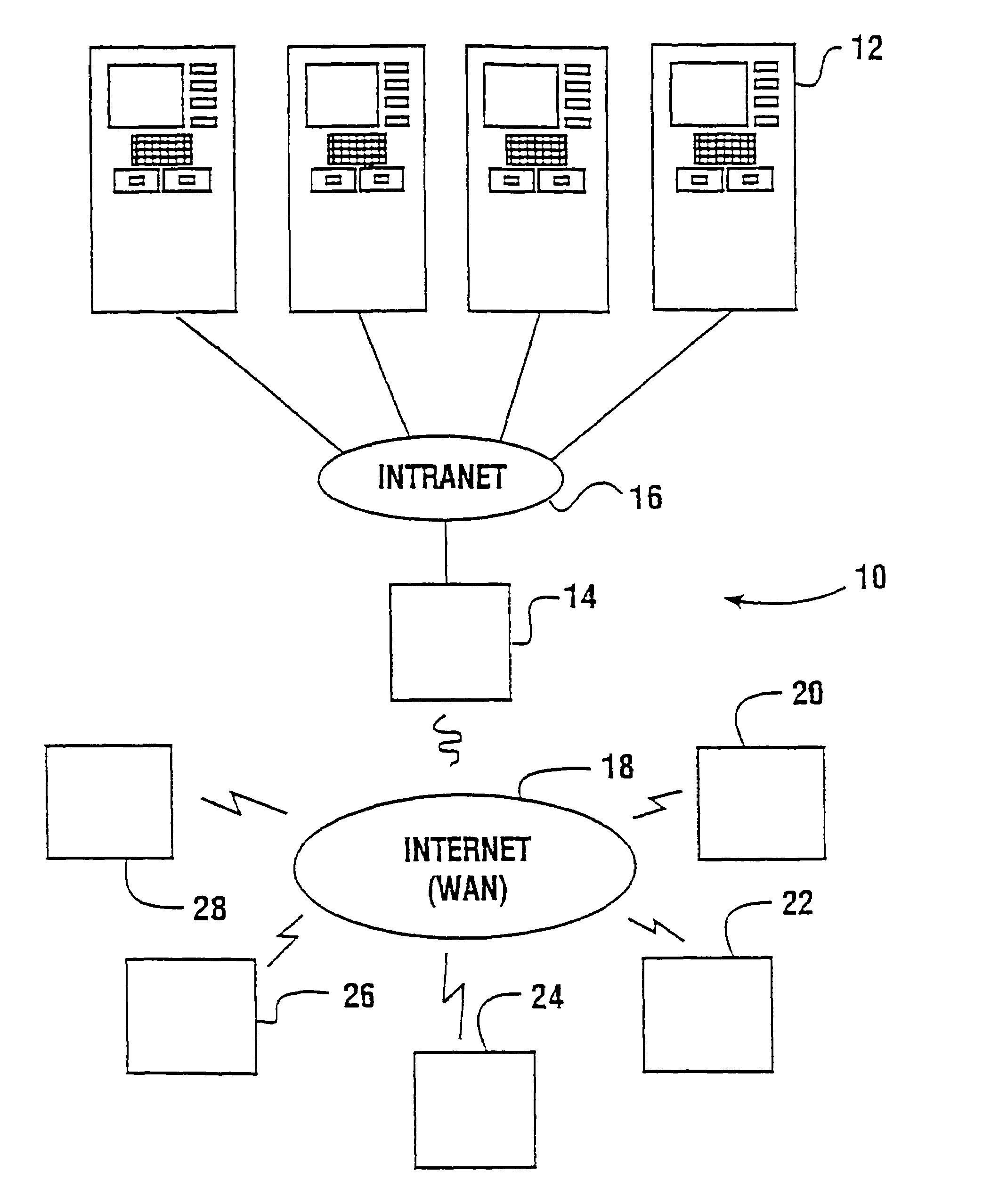
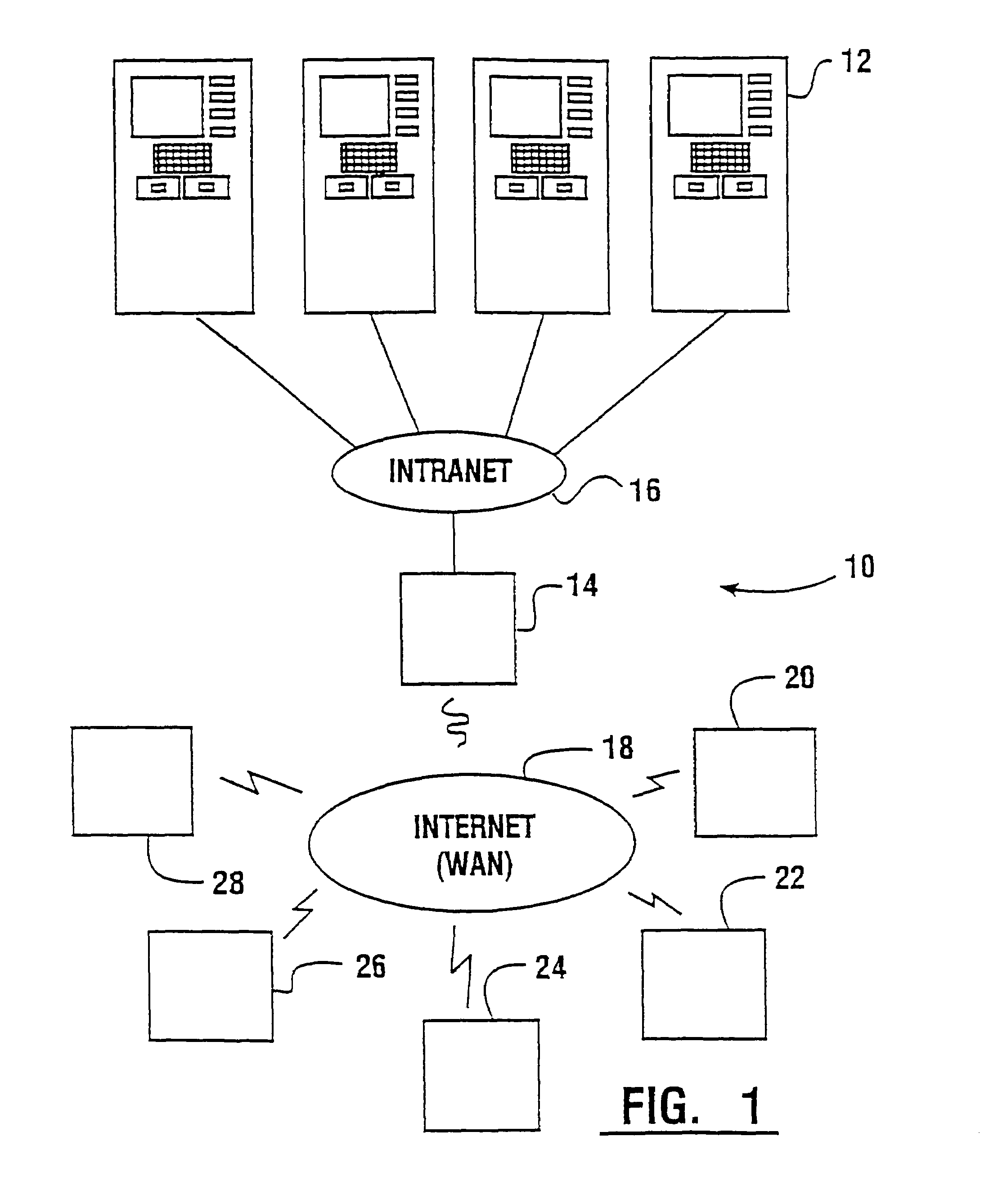
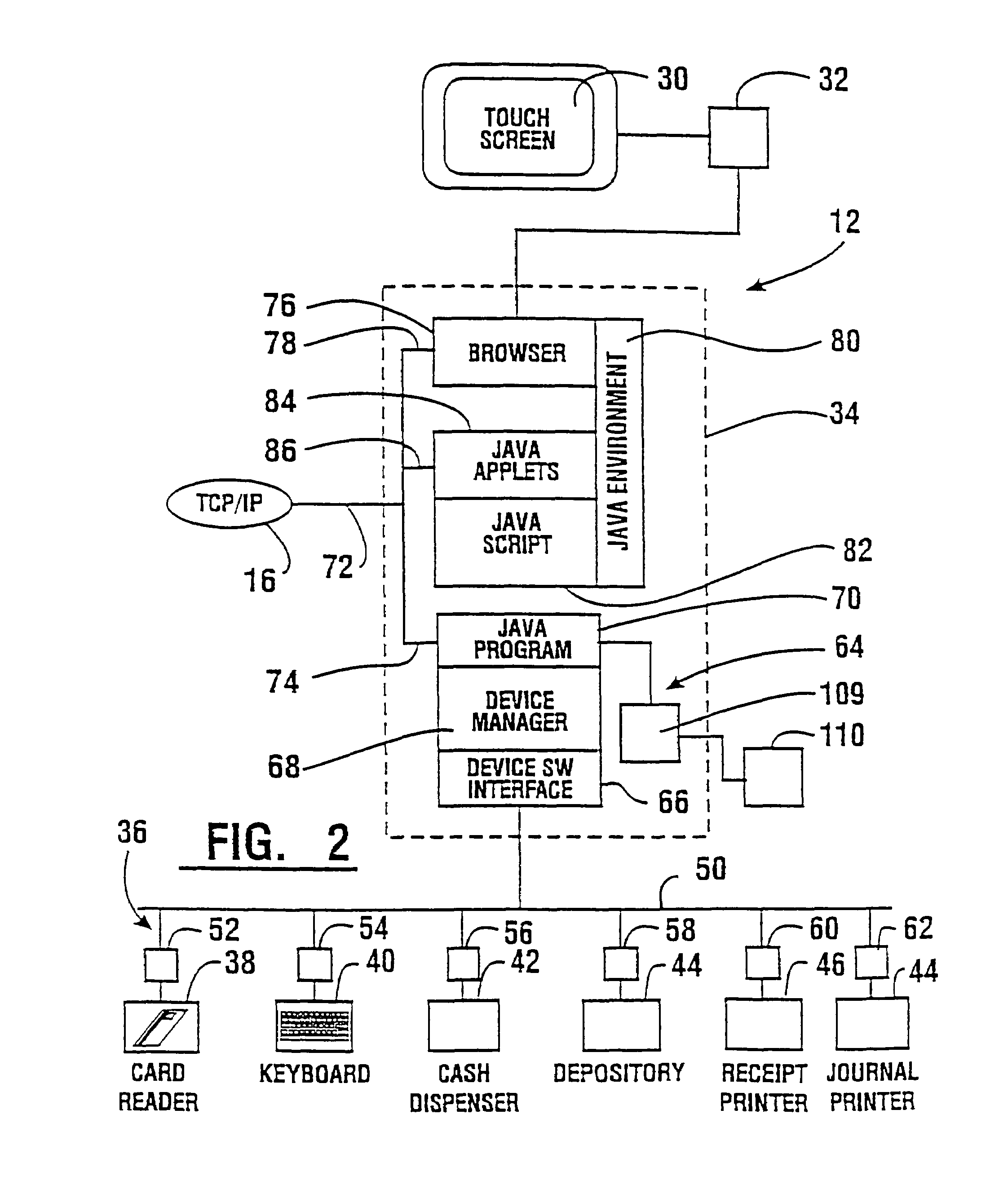
An automated banking machine (12) is operative to conduct transactions in response to HTML documents and TCP / IP messages exchanged with a local computer system (14) through an intranet (16), as well as in response to messages exchanged with foreign servers (20, 22, 24, 26, 28, 96) in a wide area network (18). The banking machine includes a computer (34) having an HTML document handling portion (76, 80, 82). The HTML document handling portion is operative to communicate through a proxy server (88), with a home HTTP server (90) in the intranet or the foreign servers in the wide area network. The computer further includes a device application portion (84) which interfaces with the HTML document handling portion and dispatches messages to operate devices (36) in the automated banking machine. The devices include a sheet dispenser mechanism (42) which dispenses currency as well as other transaction devices. The device application portion communicates with a device interfacing software portion (64) in the banking machine through a device server (92) in the intranet. The device server maintains local control over the devices in the banking machine including the sheet dispenser. The banking machine operates to read indicia on the user's card corresponding to a system address. The computer is operative to connect the banking machine to the home or foreign server corresponding to the system address, which connected server operates the banking machine until the completion of transactions by the user.
Owner:DIEBOLD NIXDORF
Secure file processing
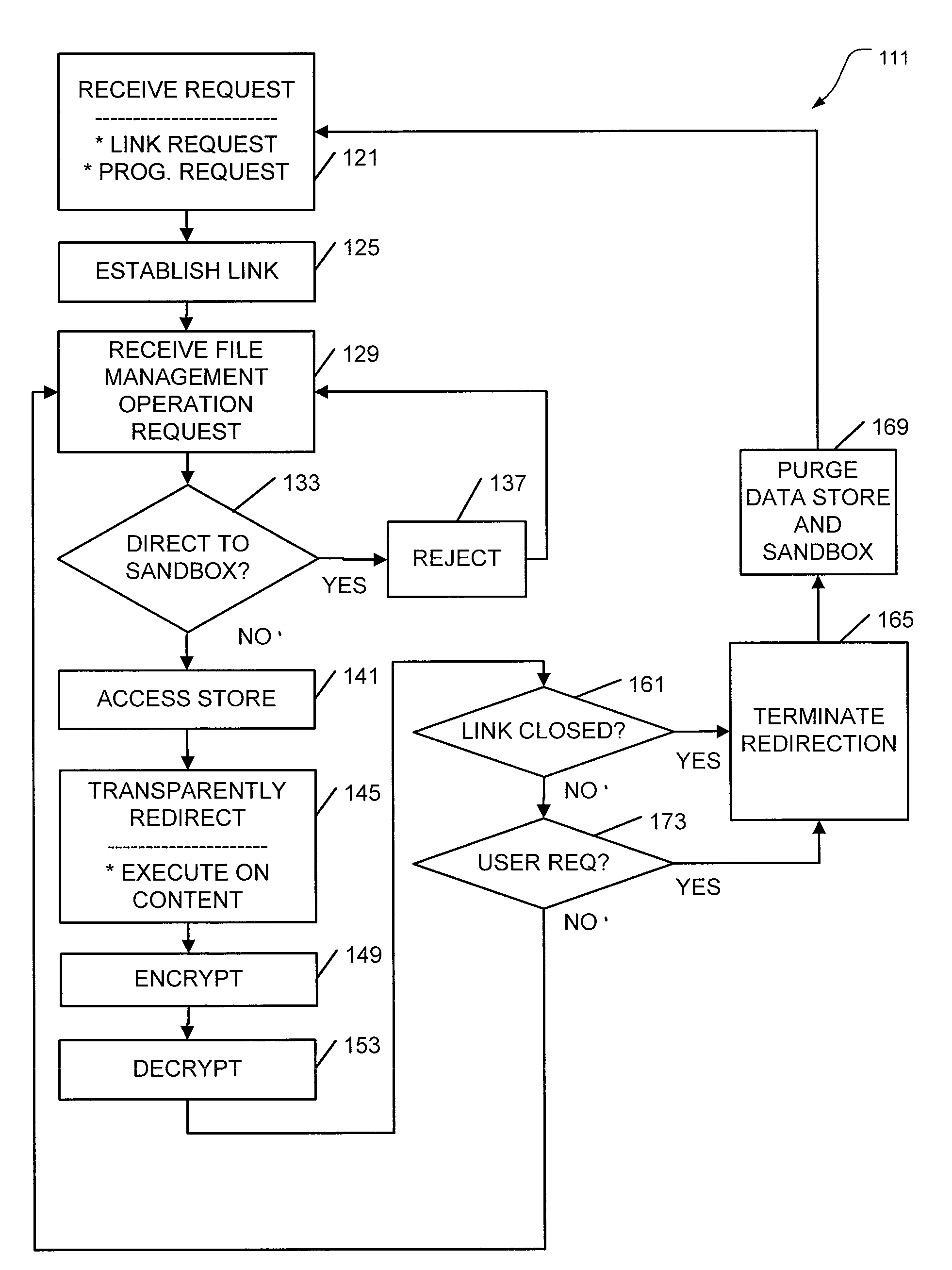
ActiveUS20100011447A1Digital data processing detailsUnauthorized memory use protectionDocument handlingClient-side
Apparatus, systems, and methods may operate to receive requests to securely process files on an untrusted client. Additional activity may include transparently redirecting file management operations associated with applications running on the untrusted client to file content associated with the files, where the file content is located in a sandbox on the untrusted client, where the sandbox is inaccessible to the applications. A data store, shared across the applications, may be used to share information associated with the file content. Additional apparatus, systems, and methods are disclosed.
Owner:APPLE INC
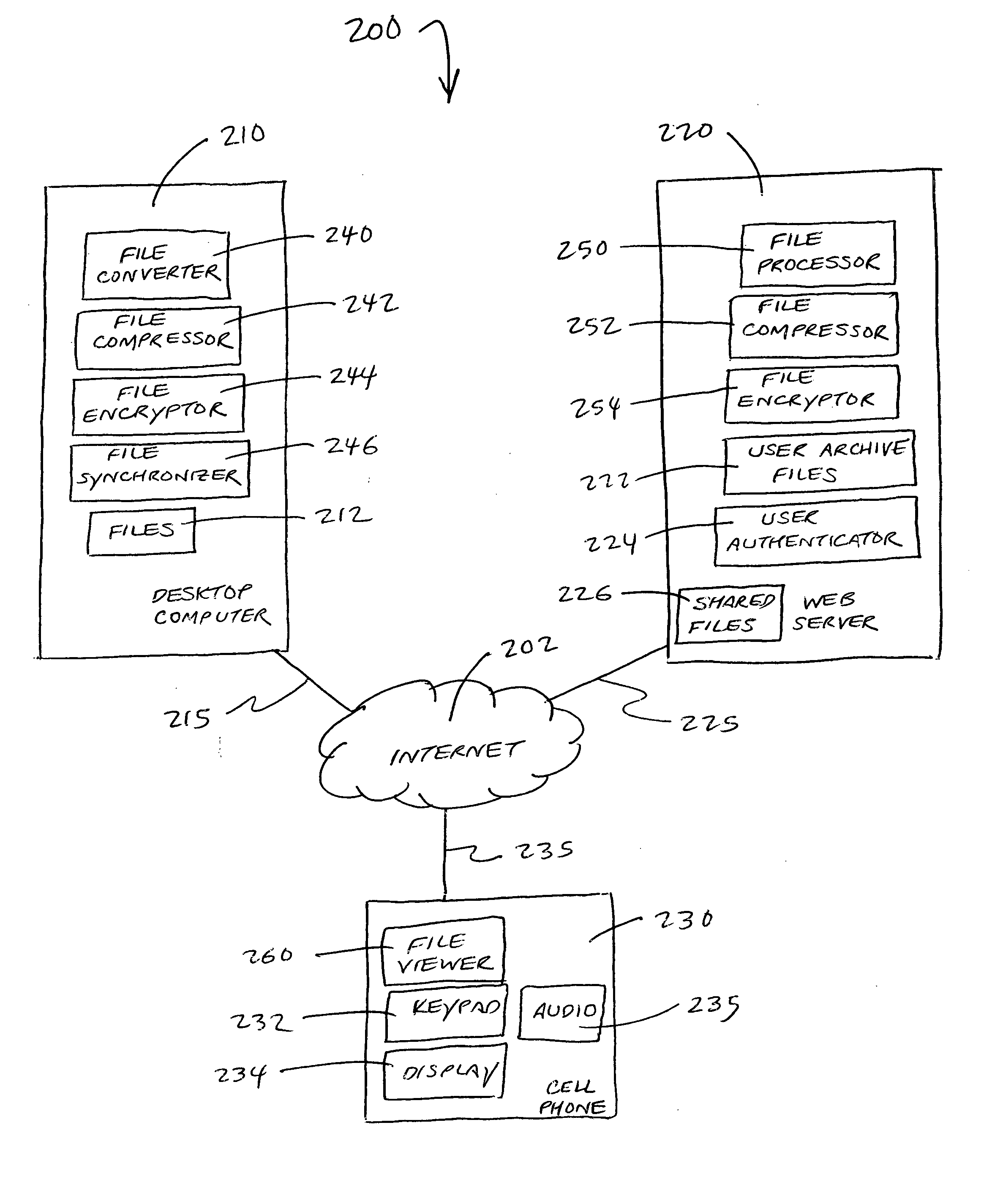
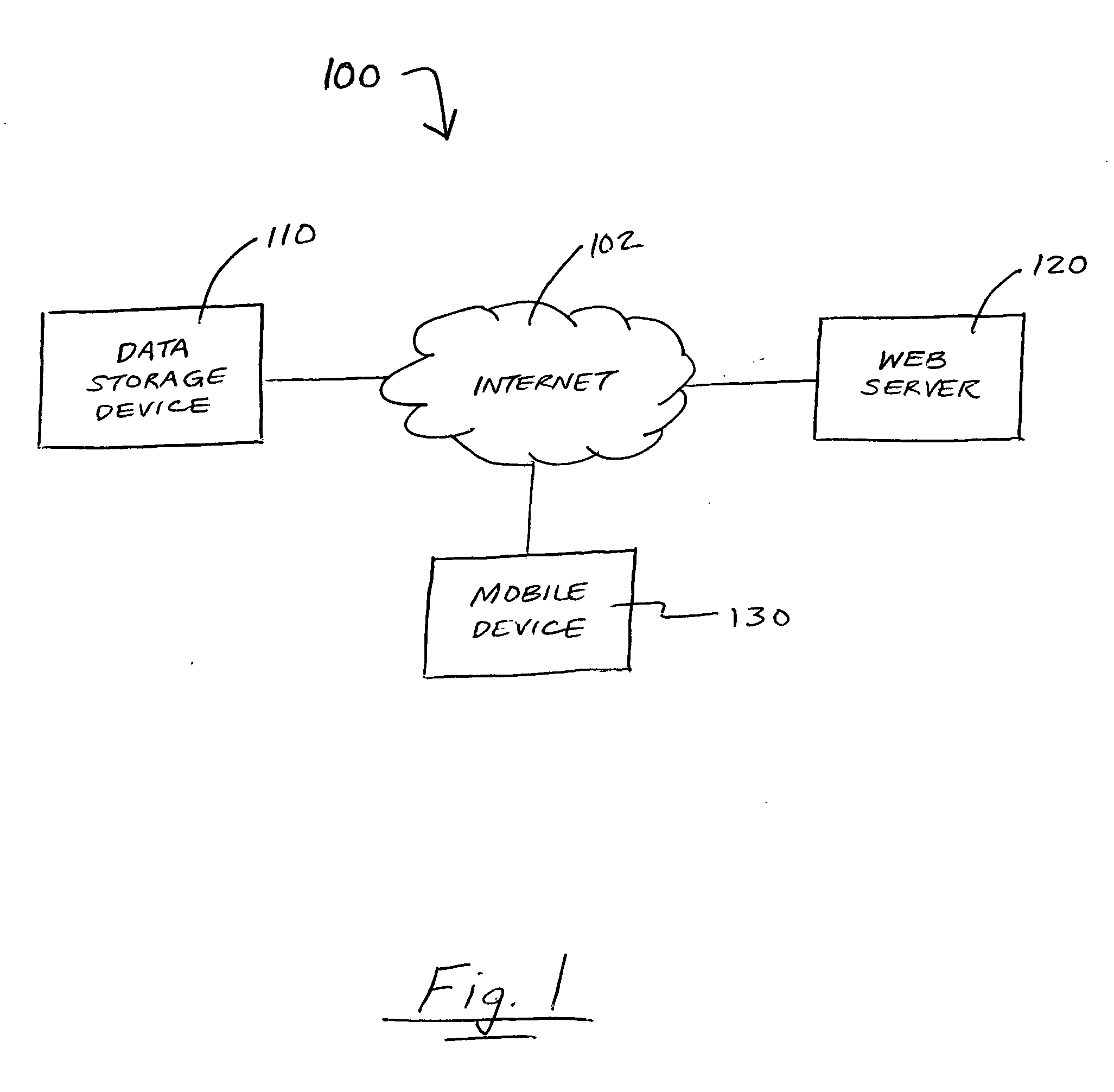
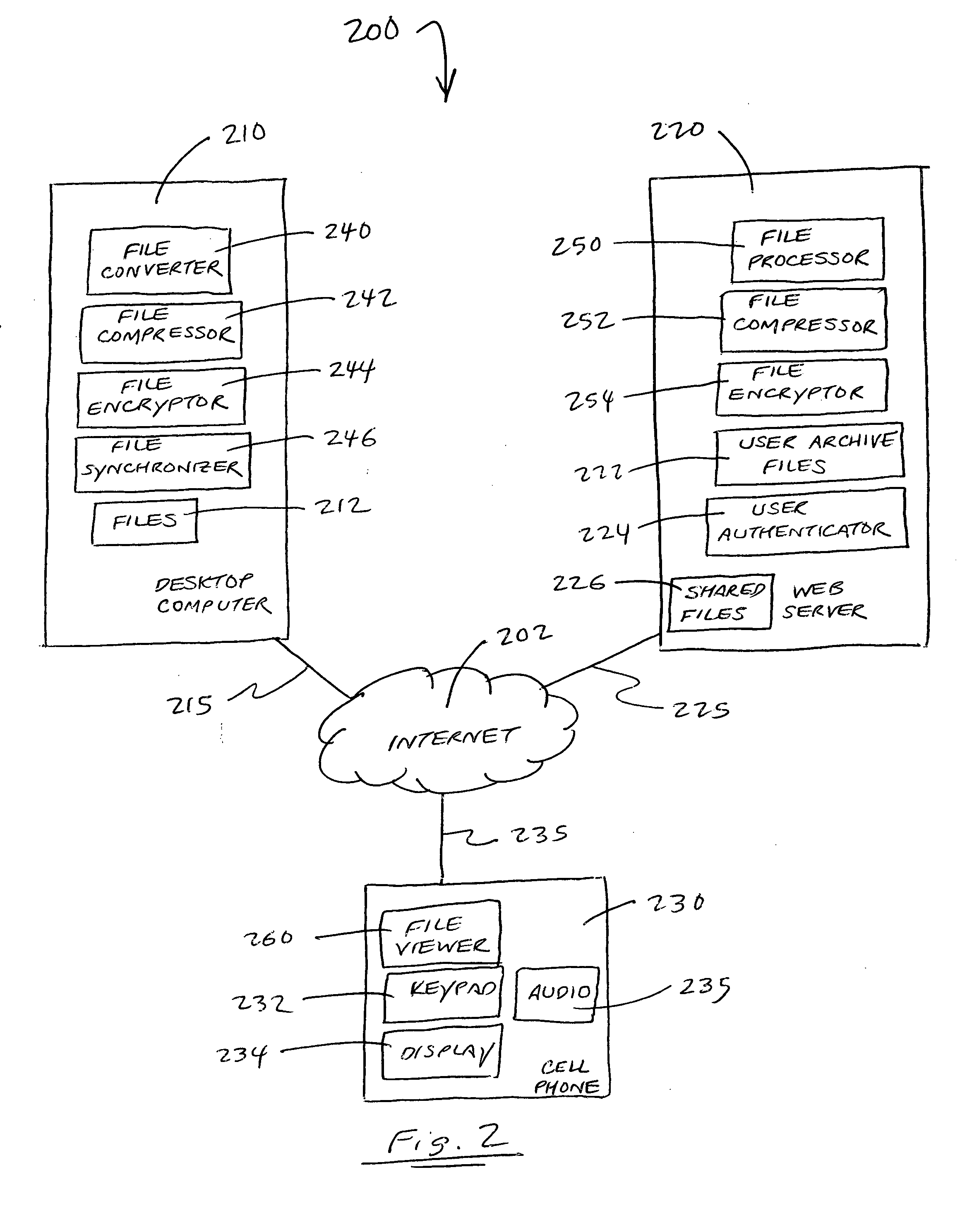
Method and system for accessing and viewing files on mobile devices
InactiveUS20060230030A1Digital data information retrievalDigital data processing detailsDocument handlingHand held
A system for downloading files to a hand-held device includes a file converter for converting a selected file to a distilled file. The file converter uploads the distilled file to a server, which is associated with a file processor. The server processes the distilled file and sends it to a hand-held device. A file viewer displays or plays the distilled file on the hand-held device. A method for sharing files on a data storage device with a hand-held device includes the steps of selecting a file on the data storage device to be shared with the hand-held device, processing the selected file on the data storage device into a converted format for uploading to a server, uploading the converted file to the server, accessing the server from the hand-held device, and sending the converted file to the hand-held device for displaying or playing on the hand-held device.
Owner:CIRCUIT SYST
Automated banking machine and system
InactiveUS6901382B1Good user interfaceFunction increasePayment architectureBilling/invoicingDocument handlingDocumentation
An automated banking machine (12) is operative to conduct transactions in response to HTML documents and TCP / IP messages exchanged with a local computer system (14) through an intranet (16), as well as in response to messages exchanged with foreign servers (20, 22, 24, 26, 28, 96) in a wide area network (18). The banking machine includes a computer (34) having an HTML document handling portion (76, 80, 82). The HTML document handling portion is operative to communicate through a proxy server (88), with a home HTTP server (90) in the intranet or the foreign servers in the wide area network. The computer further includes a device application portion (84) which interfaces with the HTML document handling portion and dispatches messages to operate devices (36) in the automated banking machine. The devices include a sheet dispenser mechanism (42) which dispenses currency as well as other transaction devices. The device application portion communicates with a device interfacing software portion (64) in the banking machine through a device server (92) in the intranet. The device server maintains local control over the devices in the banking machine including the sheet dispenser. The banking machine operates to read indicia on the user's card corresponding to a system address. The computer is operative to connect the banking machine to the home or foreign server corresponding to the system address, which connected server operates the banking machine until the completion of transactions by the user.
Owner:DIEBOLD NIXDORF
Automated banking machine and system
InactiveUS6334117B1Good user interfaceFunction increasePayment architectureBuying/selling/leasing transactionsDocument handlingProxy server
An automated banking machine (12) is operative to conduct transactions in response to HTML documents and TCP / IP messages exchanged with a local computer system (14) through an intranet (16), as well as in response to messages exchanged with foreign servers (20, 22, 24, 26, 28, 96) in a wide area network (18). The banking machine includes a computer (34) having an HTML document handling portion (76, 80, 82). The HTML document handling portion is operative to communicate through a proxy server (88), with a home HTTP server (90) in the intranet or the foreign servers in the wide area network. The computer further includes a device application portion (84) which interfaces with the HTML document handling portion and dispatches messages to operate devices (36) in the automated banking machine. The devices include a sheet dispenser mechanism (42) which dispenses currency as well as other transaction devices. The device application portion communicates with a device interfacing software portion (64) in the banking machine through a device server (92) in the intranet. The device server maintains local control over the devices in the banking machine including the sheet dispenser. The banking machine operates to read indicia on the user's card corresponding to a system address. The computer is operative to connect the banking machine to the home or foreign server corresponding to the system address, which connected server operates the banking machine until the completion of transactions by the user.
Owner:DIEBOLD NIXDORF
Content Access Rights Management
ActiveUS20080215509A1Easy to manageEasy access managementDigital data processing detailsDigital computer detailsDocument handlingRights management
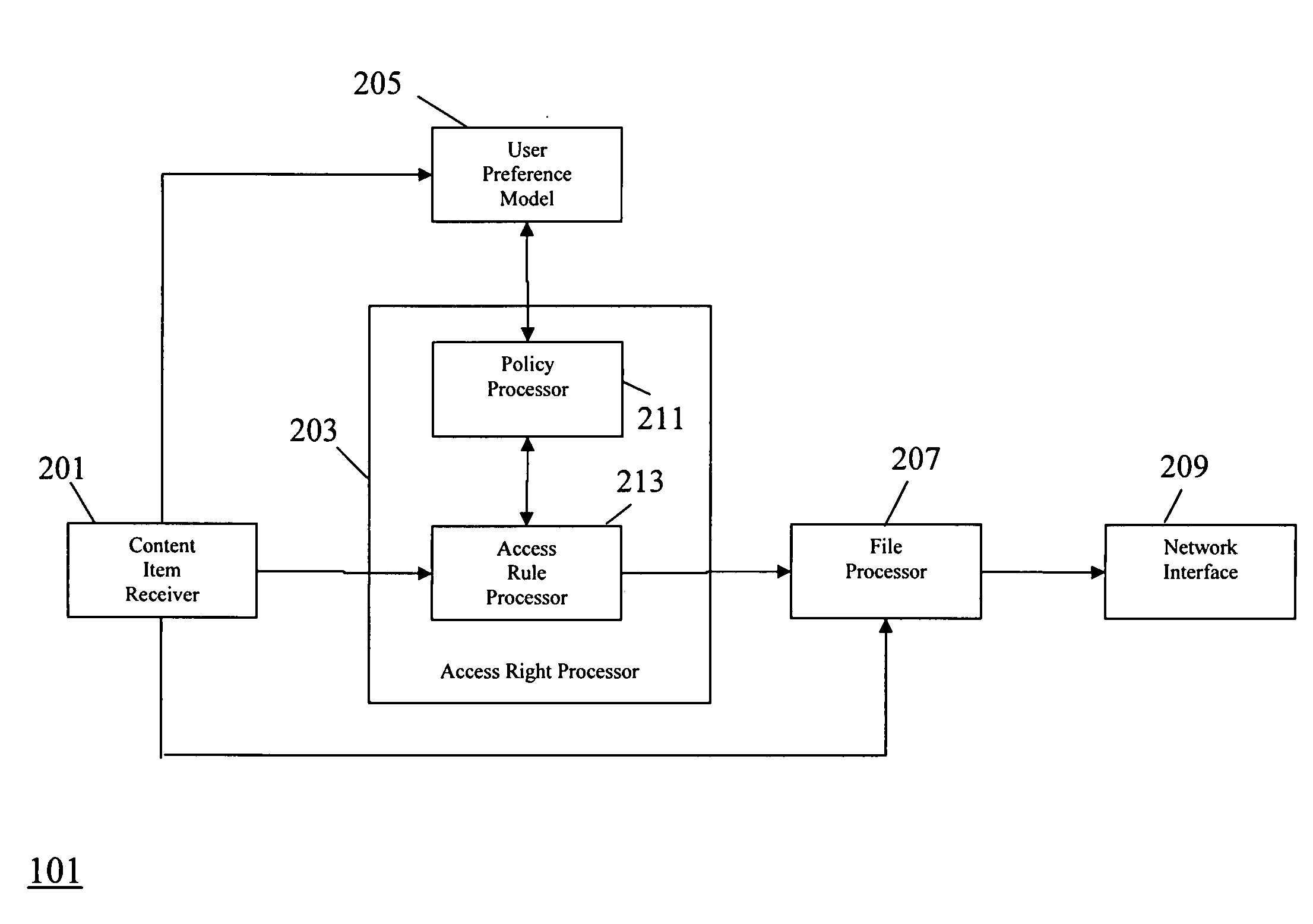
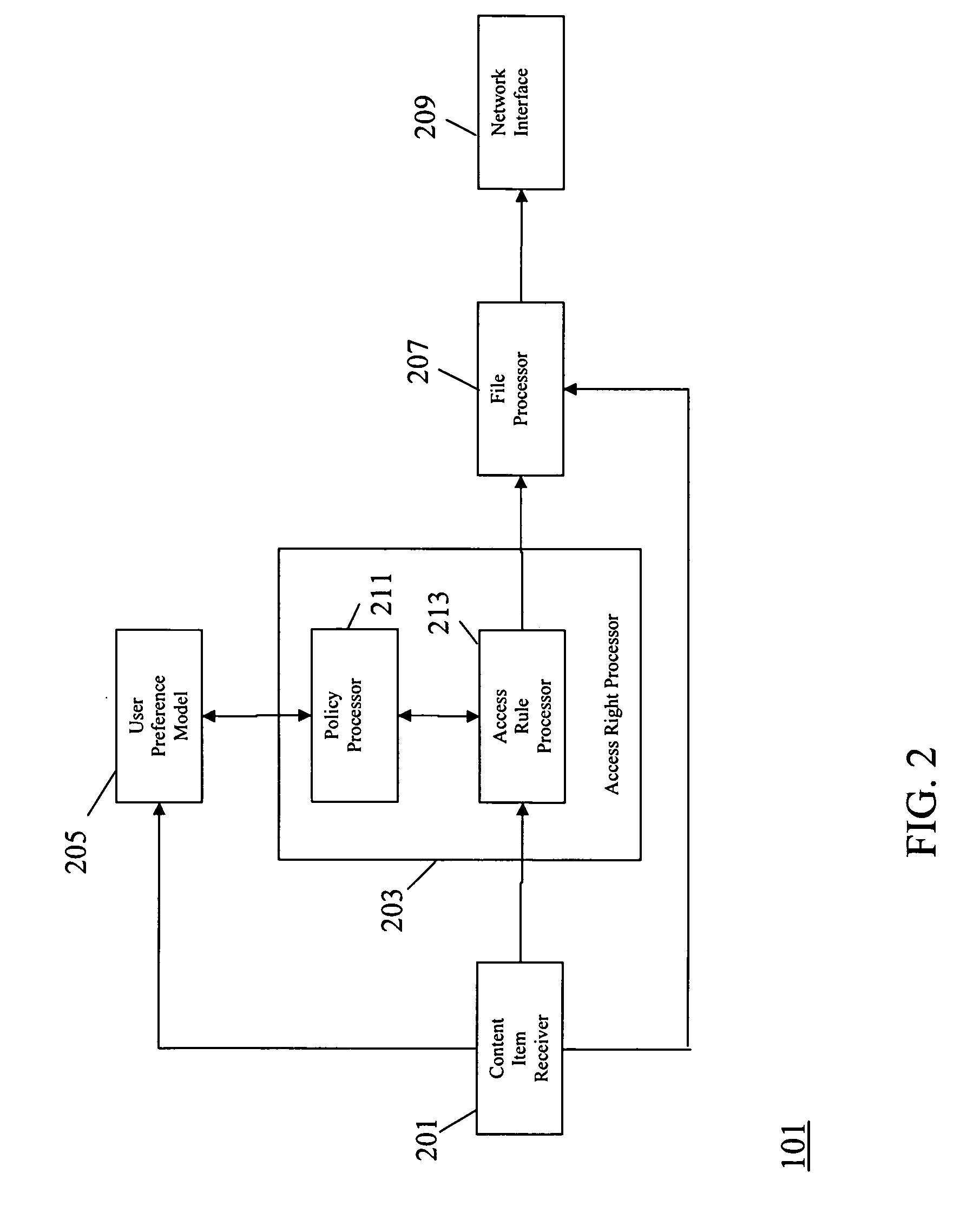
An apparatus (101) comprises a content item receiver (201) which receives a content item such as a digital photo or an audio or video clip. A user preference model (205) generates data indicative of user preferences for content item access. An access rule processor (203) determines a set of self-governance rules for the first content item in response to the user preference model. The self-governance rules are indicative of allowable actions for the first content item in other devices. A file processor (207) includes the set of self-governance rules with the content item and a network interface (209) transmits the content item to a second apparatus (103). The second apparatus (103) comprises functionality for restricting access to the content item in accordance with the set of self-governance rules. The invention may provide improved access rights management and in particular for personal content items.
Owner:MOTOROLA SOLUTIONS INC
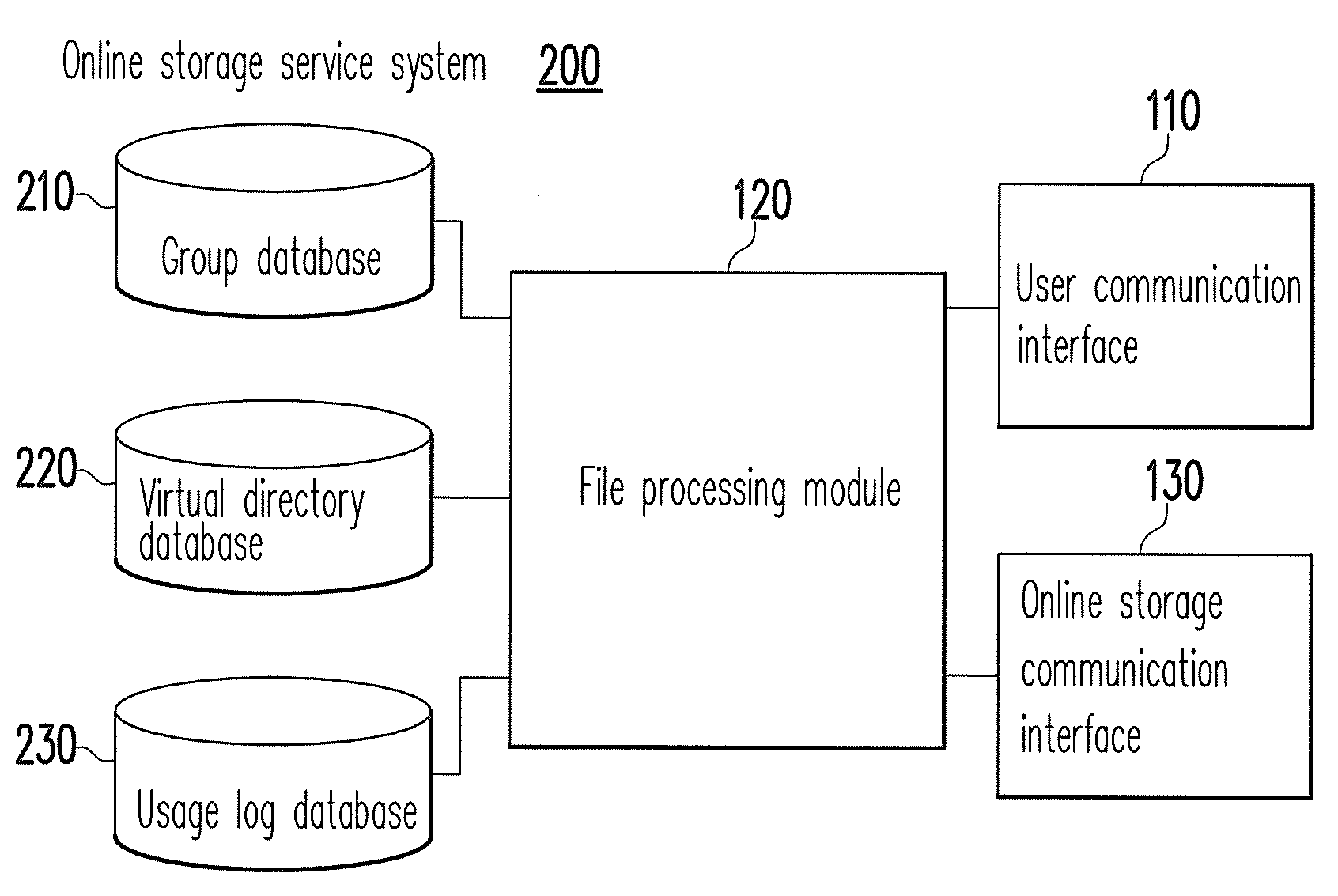
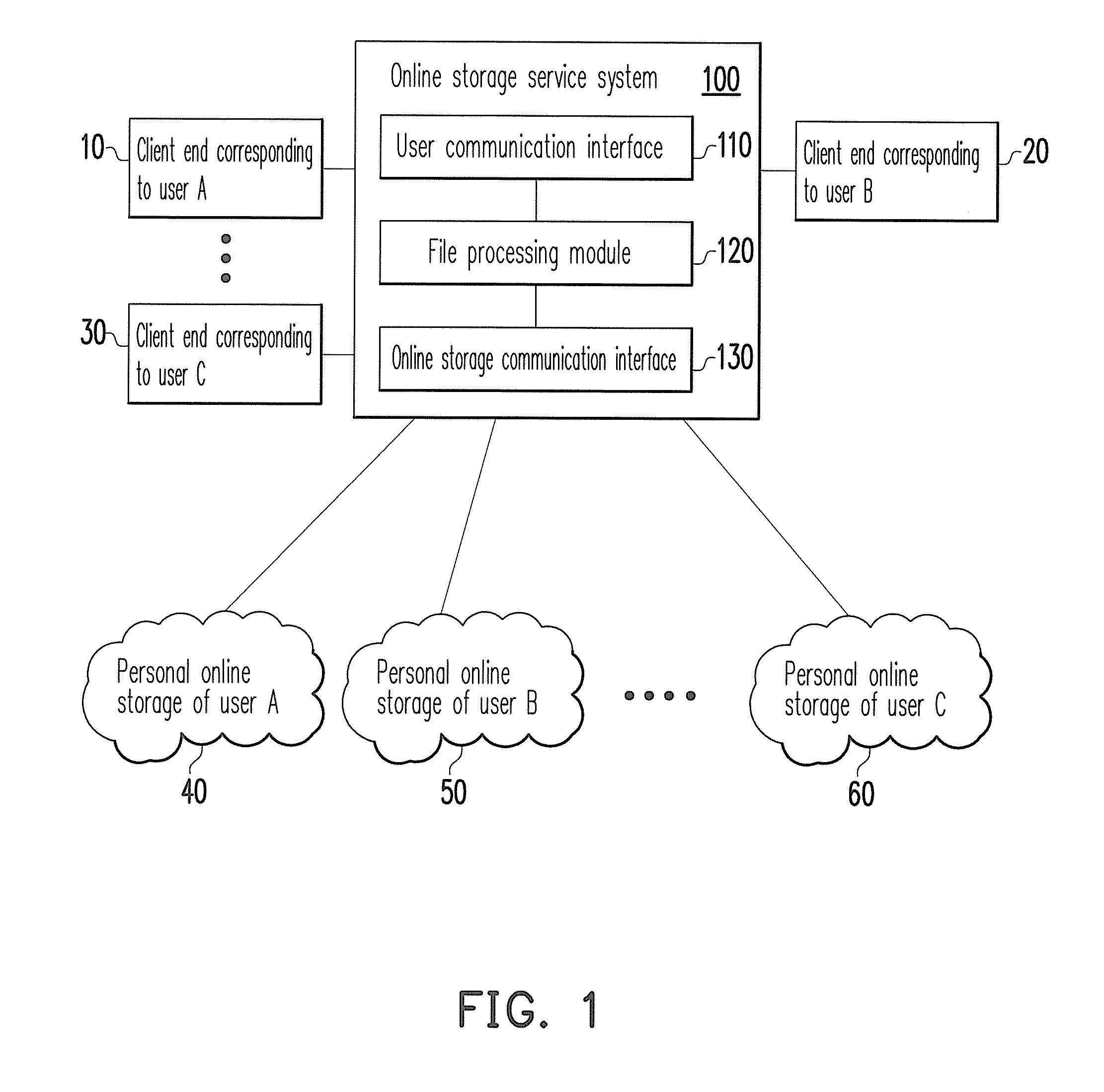
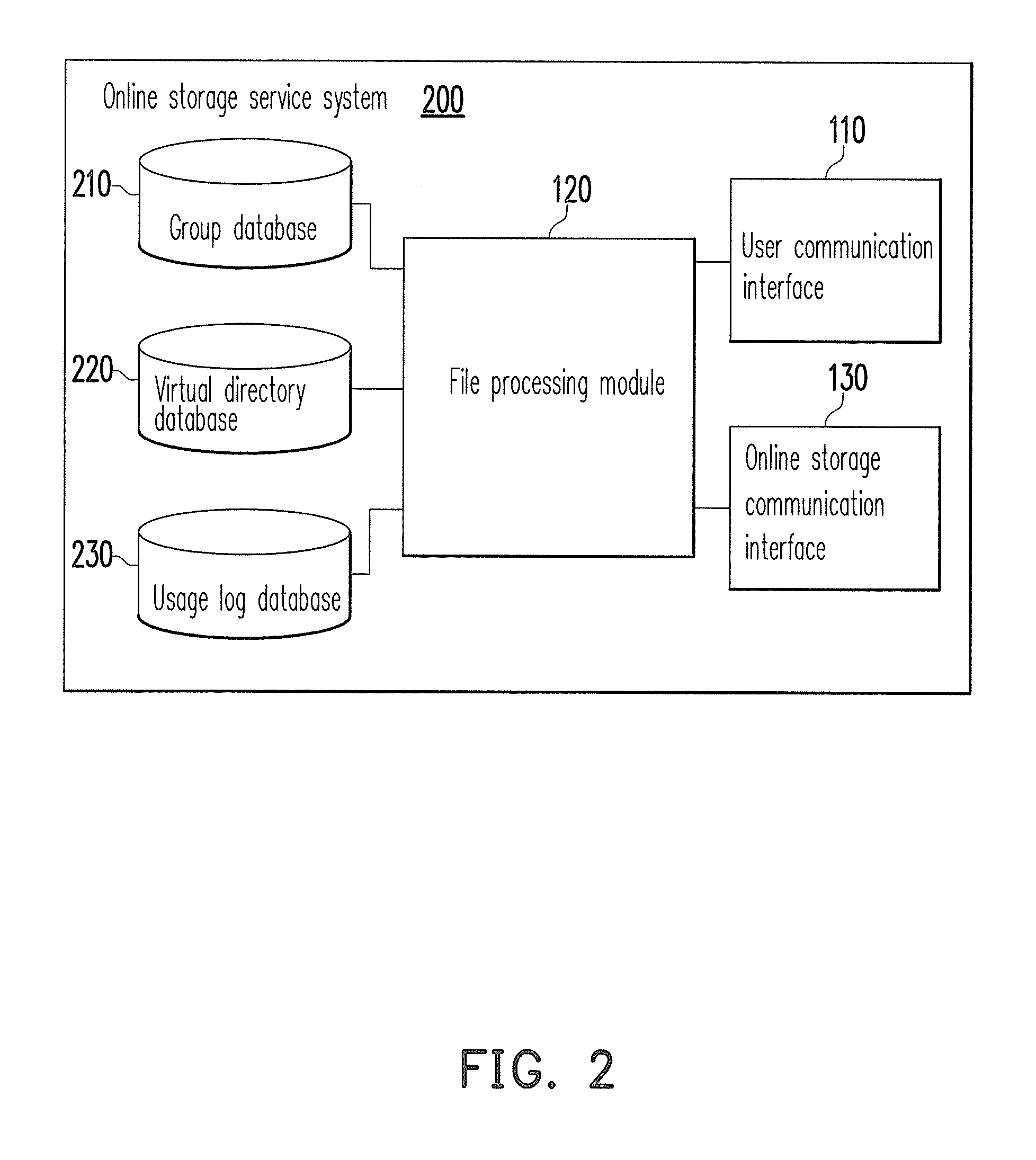
System and method for sharing online storage services among multiple users
InactiveUS20120110005A1Increase flexibilityImprove reliabilityDigital data information retrievalDigital data processing detailsCommunication interfaceProcess module
A system and a method for sharing online storage services among multiple users are provided. The system includes a user communication interface, a file processing module, and an online storage communication interface. The user communication interface is configured to connect to a client end corresponding to a first user. When the user communication interface receives a file upload request and a corresponding upload file from the client end, the file processing module searches for a personal online storage of the first user and a shared online storage of at least one related user of the first user and determines to upload the upload file to a partial online storage of the personal online storage and the shared online storage. The online storage communication interface transfers the upload file to the partial online storage determined by the file processing module.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
System and method for using timestamps to detect attacks
InactiveUS20070157315A1Overcome problemsEnabling detectionMemory loss protectionError detection/correctionData packProcess mechanism
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
Electronic mail classified advertising system
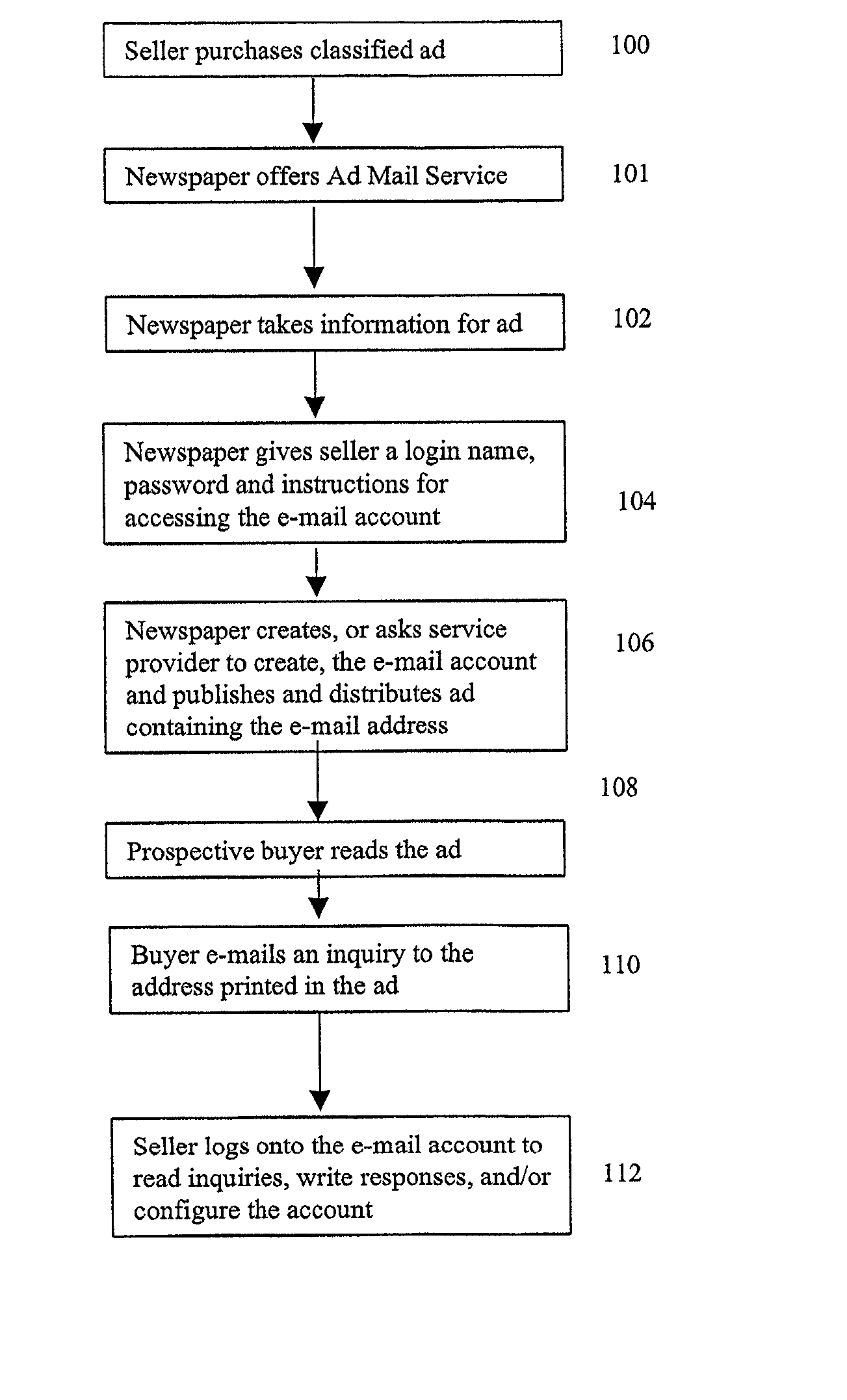
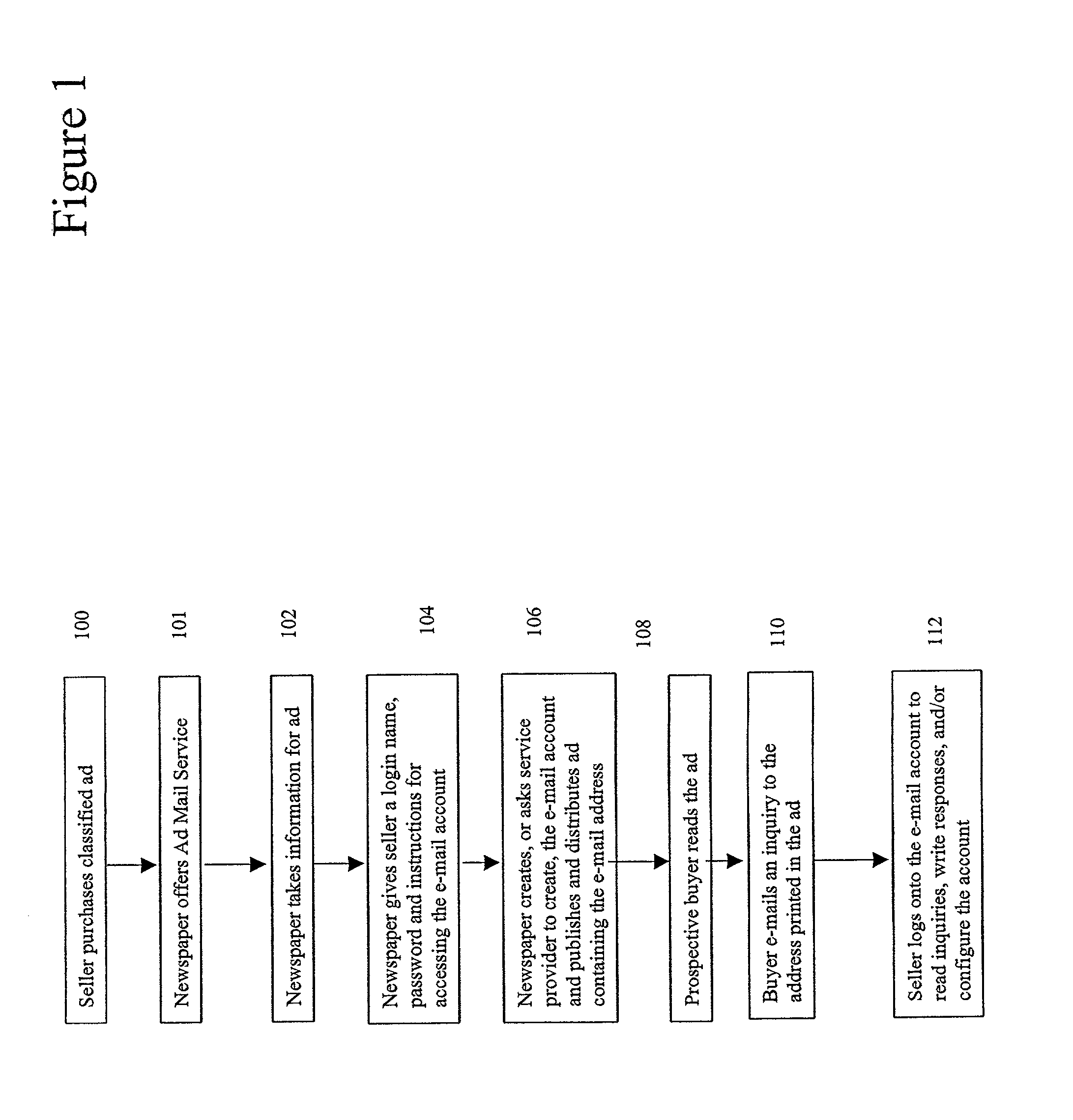
InactiveUS20020016735A1Avoid necessityAvoid problemsMultiple digital computer combinationsOffice automationDocument handlingEmail classification
A system and method for establishing temporary electronic mail (e-mail) accounts is configured to operate with classified newspaper advertising. One of the aspects of the present invention is a file handling method that automates the process of establishing the e-mail accounts through interaction with a publisher's system for taking orders for classified advertisements. Typical newspaper classified advertising comprises two or three lines of text which provide only basic information about an item for sale. With the present invention, advertisers would be offered the option of creating a special e-mail account with a duration tied to the run of the advertisement. The e-mail accounts would be used to receive inquiries about the item for sale. The e-mail account could be also be configured to auto-respond to each incoming message with additional descriptive information about the item being offered for sale. Responders could learn more about the item, and thereby avoid the necessity of calling the seller. Sellers, in turn, can avoid the problem of repeated phone calls to request additional information, and may also remain anonymous while responding to multiple inquiries.
Owner:USA NET
Non-volatile memories with adaptive file handling in a directly mapped file storage system
InactiveUS20070143378A1Promote high performanceImprove performanceMemory architecture accessing/allocationSpecial data processing applicationsData compressionAccess frequency
In a memory system with a file storage system, an optimal file handling scheme is adaptively selected from a group thereof based on the attributes of the file being handled. The file attributes may be obtained from a host or derived from a history of the file had with the memory system. In one embodiment, a scheme for allocating memory locations for a write operation is dependent on an estimated size of the file to be written. In another embodiment, a scheme for allocating memory locations for a relocation operation, such as for garbage collection or data compaction, is dependent on an estimated access frequency of the file in question. In this way, the optimal handling scheme can be used for the particular file at any time.
Owner:SANDISK TECH LLC
System and method enabling future messaging directives based on past participation via a history monitor
InactiveUS7461151B2Avoid the needEliminating flow of messageSpecial service provision for substationMultiple digital computer combinationsDocument handlingUnique identifier
A system and method for controlling the flow of documents by associating Globally Unique Identifiers with each original document, each reply document, each copy document and each forwarded document, such as e-mail messages. Historical analysis is performed on a locally stored history records containing the Globally Unique Identifiers extracted from received documents to determine which recipients are active participants and which are inactive participants, according to user preferences and thresholds. Lists for direct recipients (e.g. “To” list), carbon copy recipients, and blind copy recipients are automatically proposed to a user of a document handling system when authoring a new document, replying to a document, or forwarding a document, according to the results of the historical participation analysis, thereby stemming information flow to participants who are not active in an ad hoc asynchronous conversation.
Owner:IBM CORP
Automated banking machine system using plural communication formats
InactiveUS6539361B1Easy to operateMaintain securityComplete banking machinesFinanceDocument handlingMachining system
An automated banking machine (12) is operative to conduct transactions in response to HTML documents and TCP / IP messages exchanged with a local computer system (14) through an intranet (16), as well as in response to messages exchanged with foreign servers (20, 22, 24, 26, 28, 96) in a wide area network (18). The banking machine includes a computer (34) having an HTML document handling portion (76, 80, 82). The HTML document handling portion is operative to communicate through a proxy server (88), with a home HTTP server (90) in the intranet or the foreign servers in the wide area network. The computer further includes a device application portion (84) which interfaces with the HTML document handling portion and dispatches messages to operate devices (36) in the automated banking machine. The devices include a sheet dispenser mechanism (42) which dispenses currency as well as other transaction devices. The device application portion communicates with a device interfacing software portion (64) in the banking machine through a device server (92) in the intranet. The device server maintains local control over the devices in the banking machine including the sheet dispenser. The banking machine operates to read indicia on the user's card corresponding to a system address. The computer is operative to connect the banking machine to the home or foreign server corresponding to the system address, which connected server operates the banking machine until the completion of transactions by the user.
Owner:DIEBOLD NIXDORF
System and method for using login correlations to detect intrusions
InactiveUS7085936B1Overcome problemsEnabling detectionDigital data processing detailsUnauthorized memory use protectionContinuationTimestamp
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
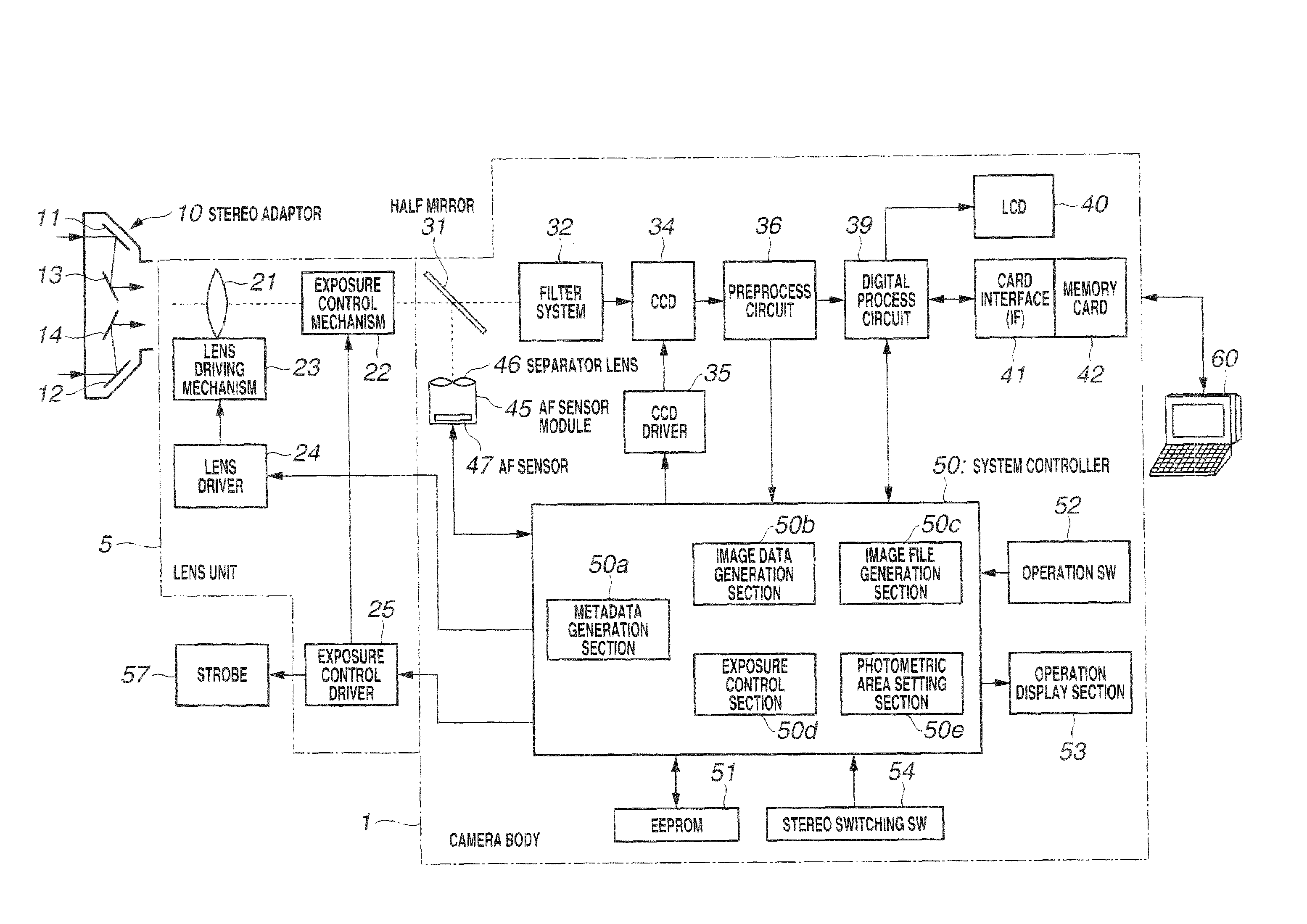
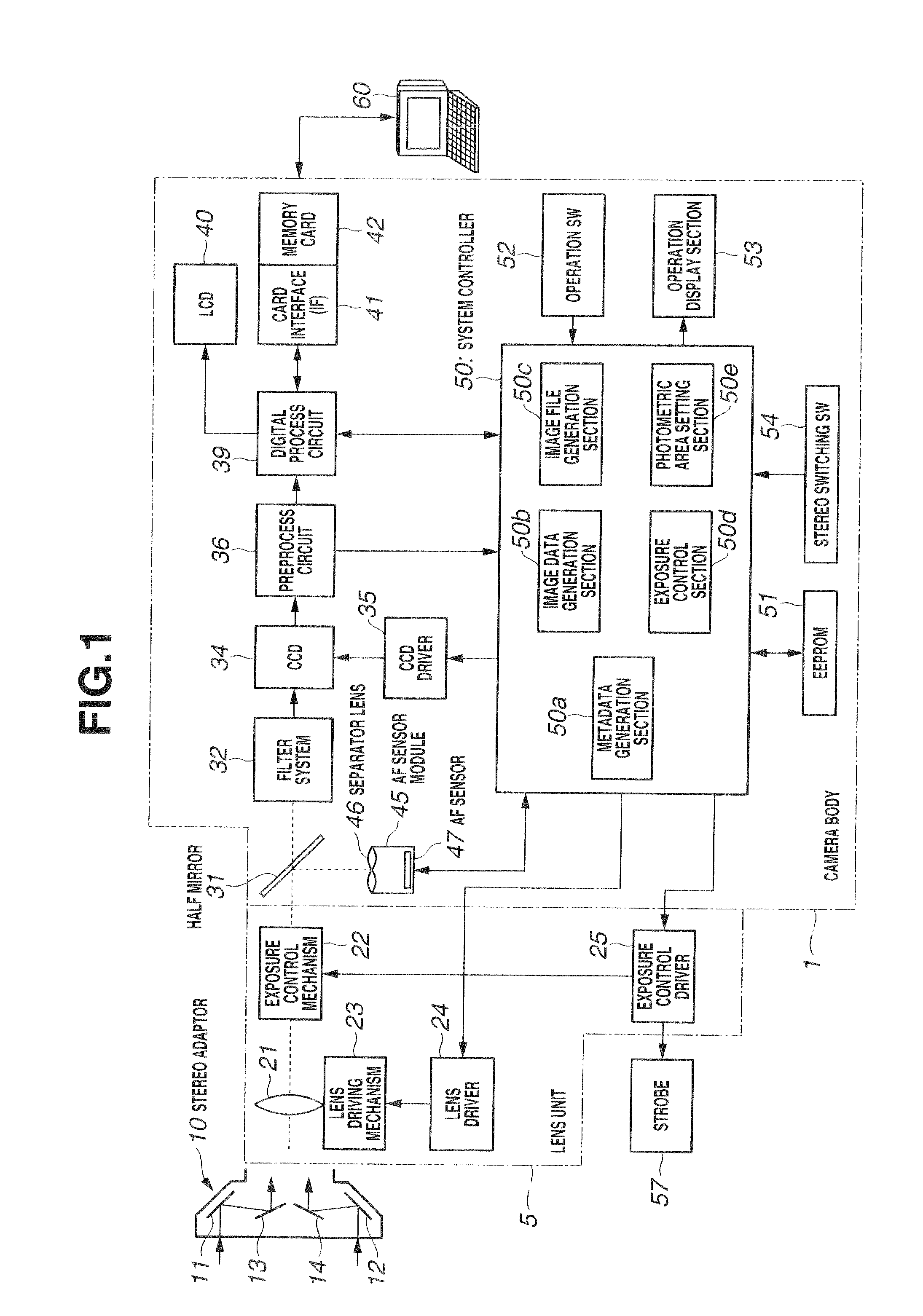
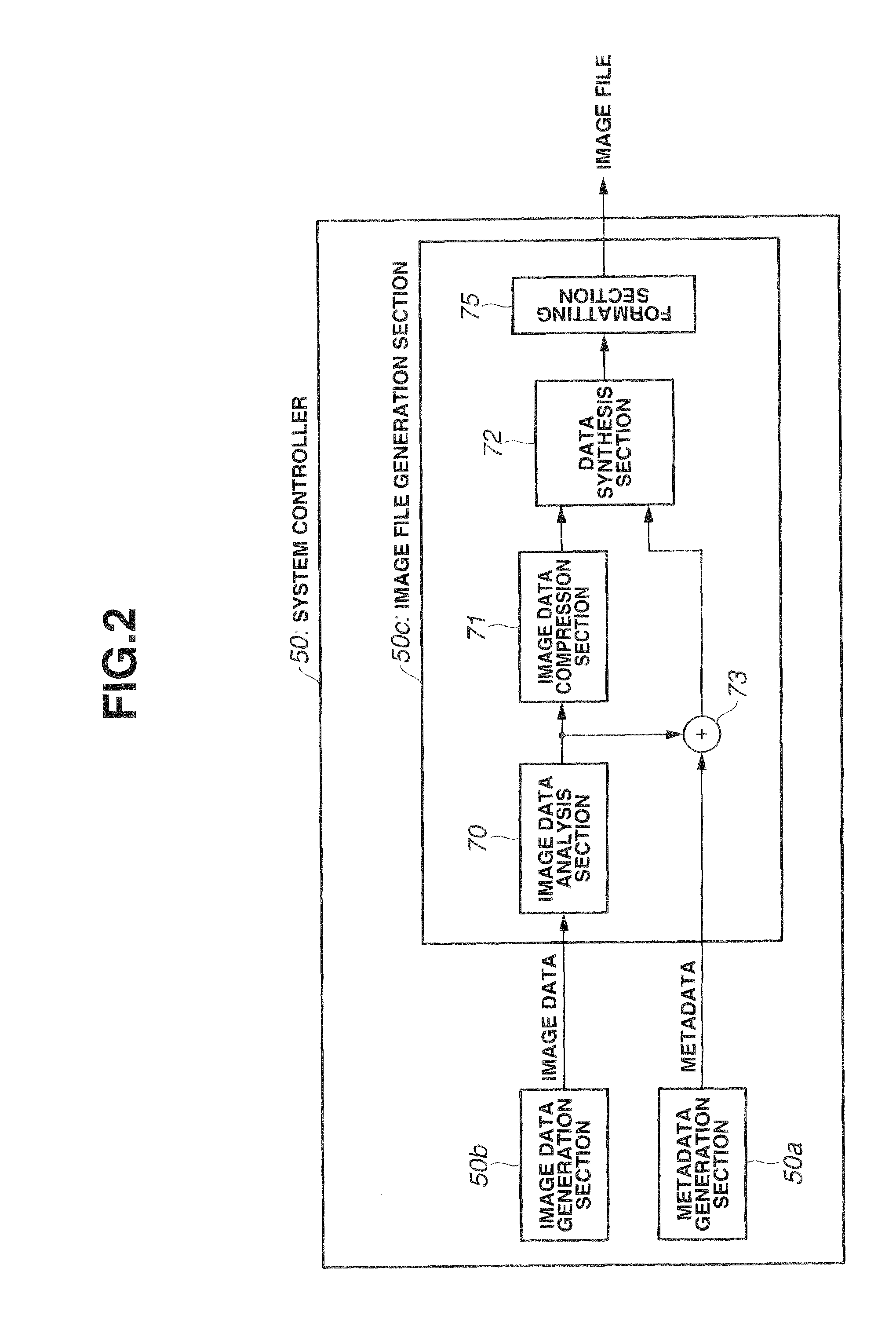
Image file processing apparatus, image file reproduction apparatus and image file working/editing apparatus
InactiveUS20090273663A1Television system detailsColor television detailsParallaxComputer graphics (images)
The present invention is provided with: a stereo image data generation unit for generating stereo image data indicating multiple monocular images obtained with a predetermined parallax between the images for a same subject; a metadata generation unit for generating metadata about the stereo image data; an image characteristic information generation unit for generating image characteristic information showing characteristics of an image indicated on the basis of the stereo image data; and an image file generation unit for synthesizing the stereo image data generated by the stereo image data generation unit and the metadata generated by the metadata generation unit to generate an image file; wherein the image file generation unit adds the image characteristic information generated by the image characteristic information generation unit to the metadata generated by the metadata generation unit.
Owner:OLYMPUS IMAGING CORP
Automated banking machine apparatus and system
InactiveUS6505177B1Good user interfaceFunction increaseComplete banking machinesFinanceDocument handlingProxy server
An automated banking machine (12) is operative to conduct transactions in response to HTML documents and TCP / IP messages exchanged with a local computer system (14) through an intranet (16), as well as in response to messages exchanged with foreign servers (20, 22, 24, 26, 28, 96) in a wide area network (18). The banking machine includes a computer (34) having an HTML document handling portion (76, 80, 82). The HTML document handling portion is operative to communicate through a proxy server (88), with a home HTTP server (90) in the intranet or the foreign servers in the wide area network. The computer further includes a device application portion (84) which interfaces with the HTML document handling portion and dispatches messages to operate devices (36) in the automated banking machine. The devices include a sheet dispenser mechanism (42) which dispenses currency as well as other transaction devices. The device application portion communicates with a device interfacing software portion (64) in the banking machine through a device server (92) in the intranet. The device server maintains local control over the devices in the banking machine including the sheet dispenser. The banking machine operates to read indicia on the user's card corresponding to a system address. The computer is operative to connect the banking machine to the home or foreign server corresponding to the system address, which connected server operates the banking machine until the completion of transactions by the user.
Owner:DIEBOLD NIXDORF
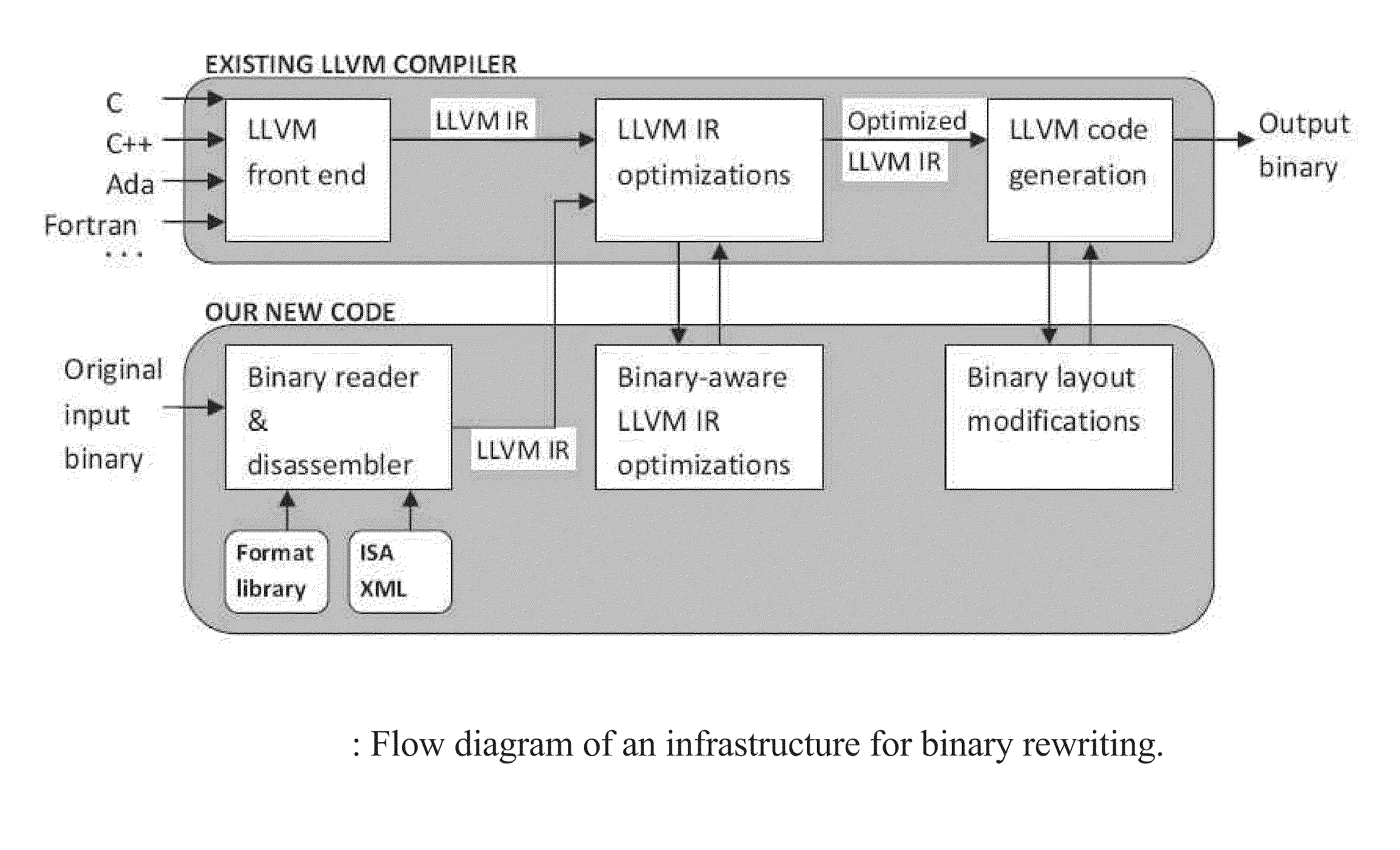
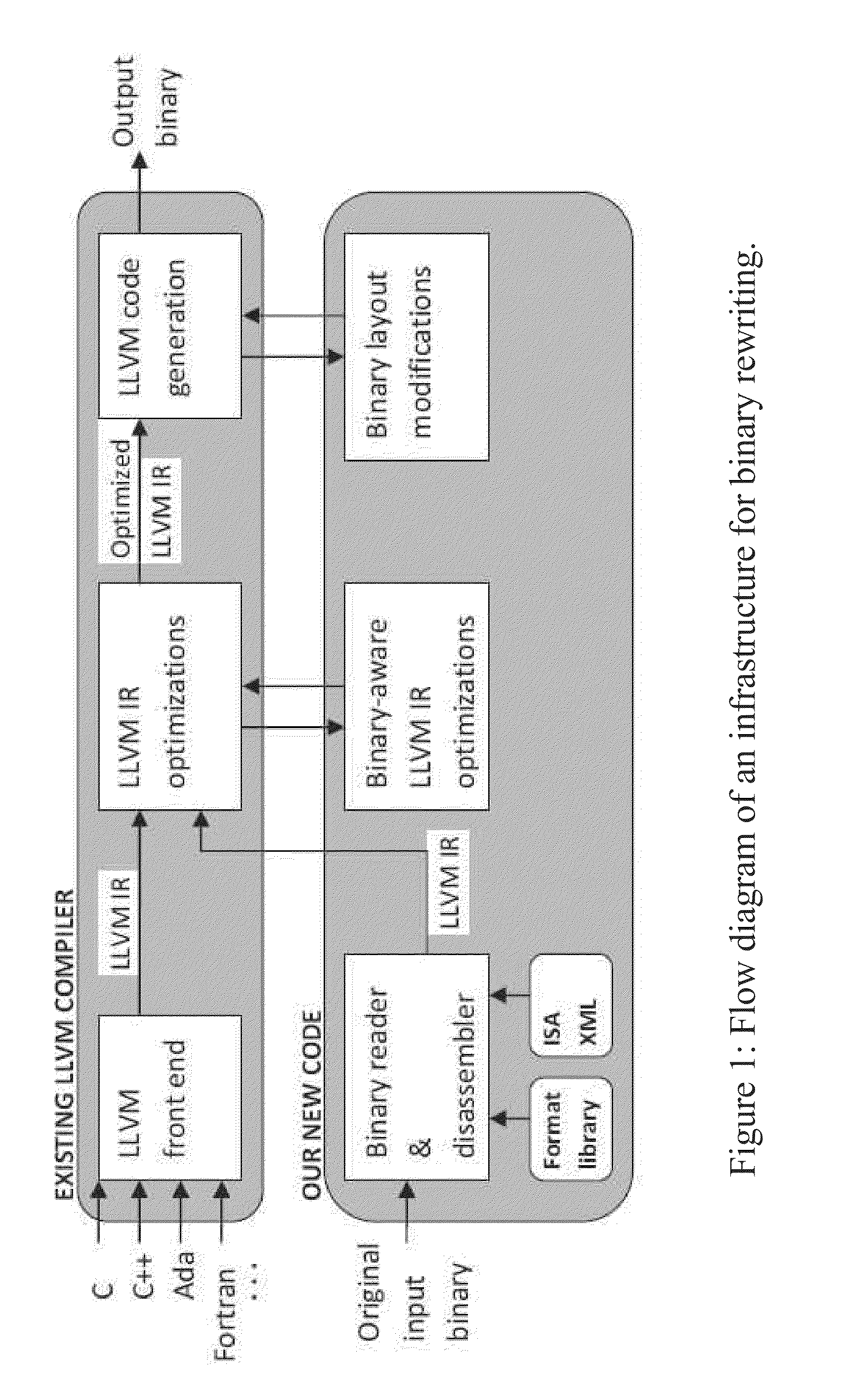
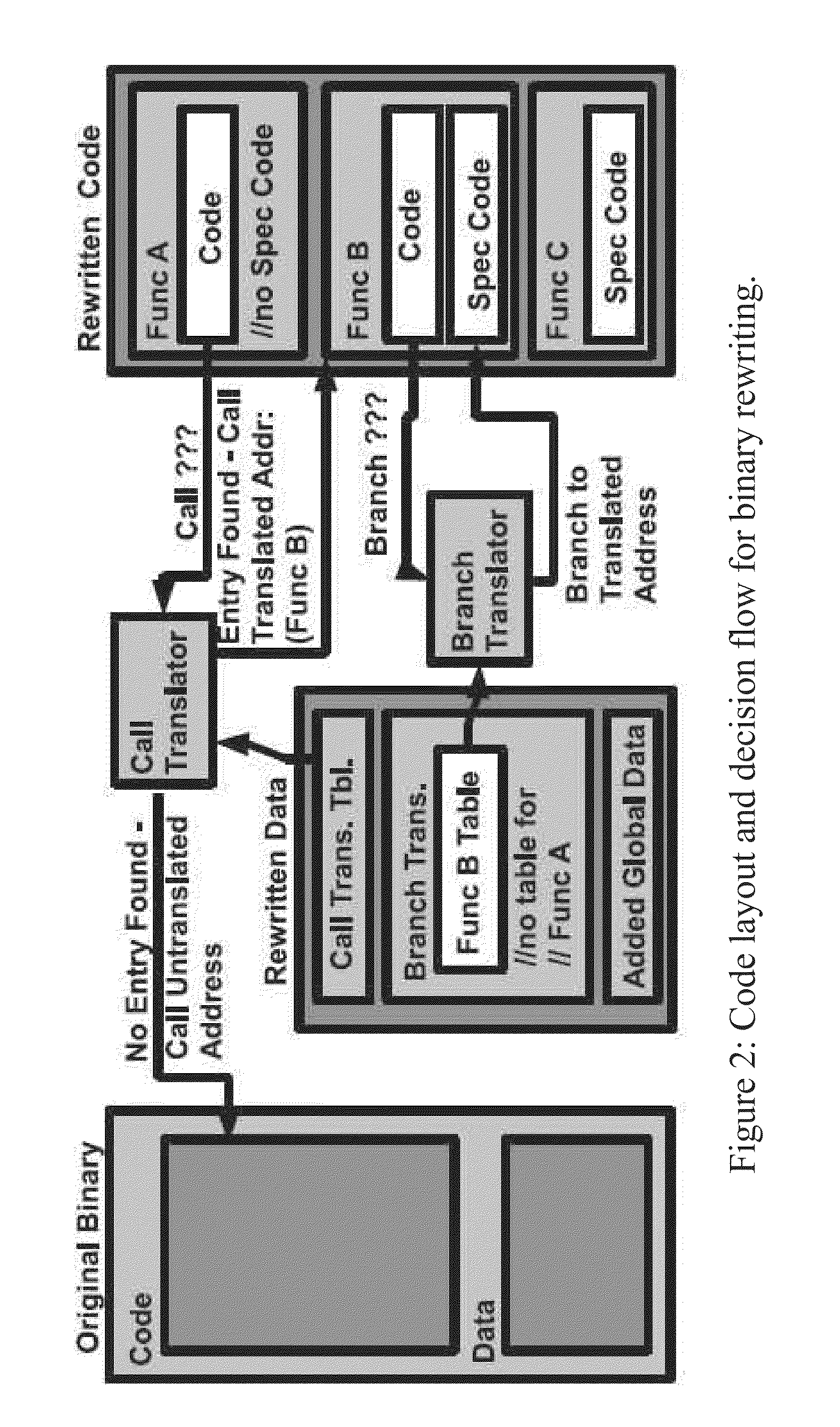
Binary rewriting without relocation information
A binary rewriter that can provide complete code coverage without relocation information is provided, together with a method of performing such rewriting. The method can include processing a binary file as an original binary file. The method can also include disassembling the binary file to provide a disassembled binary file. The method can further include rewriting the disassembled binary file without relocation information to provide a rewritten binary file. The rewriting can provide a physical transformation in a recording medium relative to the binary file in the recording medium prior to the rewriting. The processing the binary file, disassembling the binary file, and rewriting the disassembled binary file can be performed by a particular machine.
Owner:MARYLAND UNIV OF
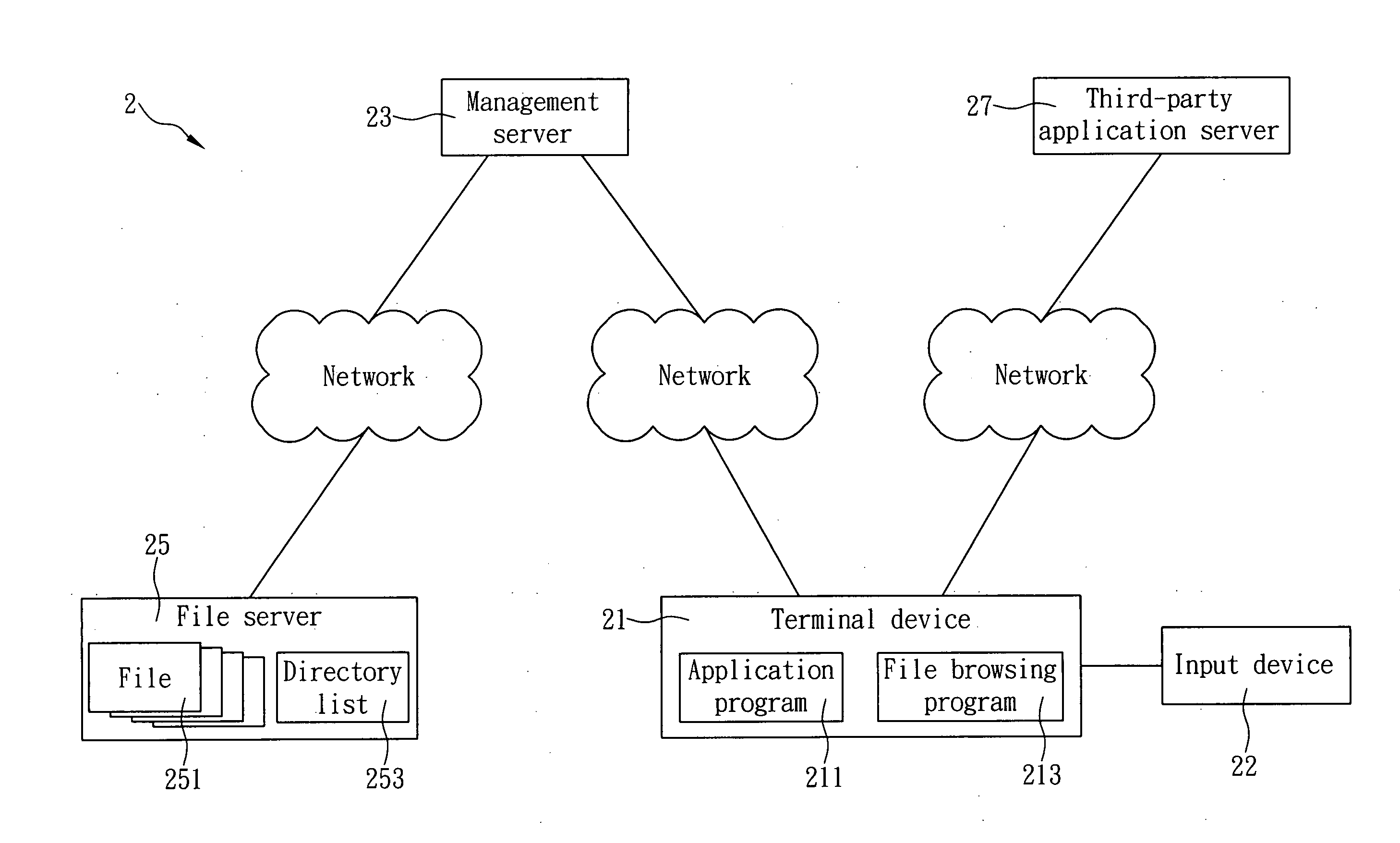
Cloud computing method capable of hiding real file paths
InactiveUS20120259964A1Minimizing substantially exposure to riskImprove securityDigital computer detailsTransmissionThird partyApplication server
The present invention is to provide a cloud computing method capable of hiding real file paths, which includes the steps of: triggering a web browsing button of an application program and sending a browsing activation signal to a management server by a terminal device; reading a directory list of at least one file from a file server and sending a file browsing program and the directory list to the terminal device by the management server; displaying the directory list via the file browsing program and sending a file processing signal to the management server by the terminal device; downloading from the file server a file specified by the file processing signal and sending the specified file to the terminal device by the management server; and sending the specified file to a third-party application server via the application program and terminating the file browsing program by the terminal device.
Owner:D-LINK
Method and apparatus for data storage in a peer-to-peer network
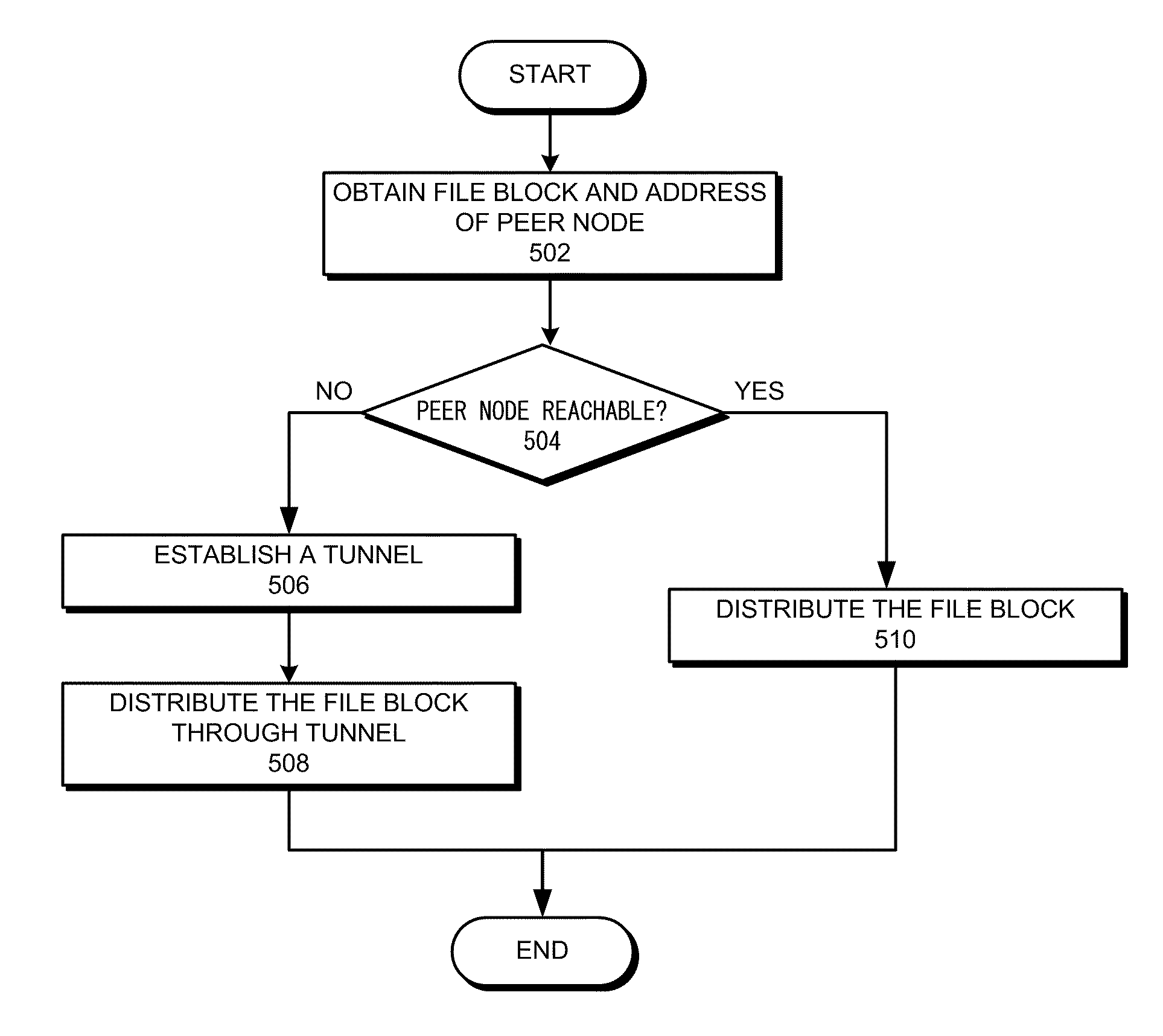
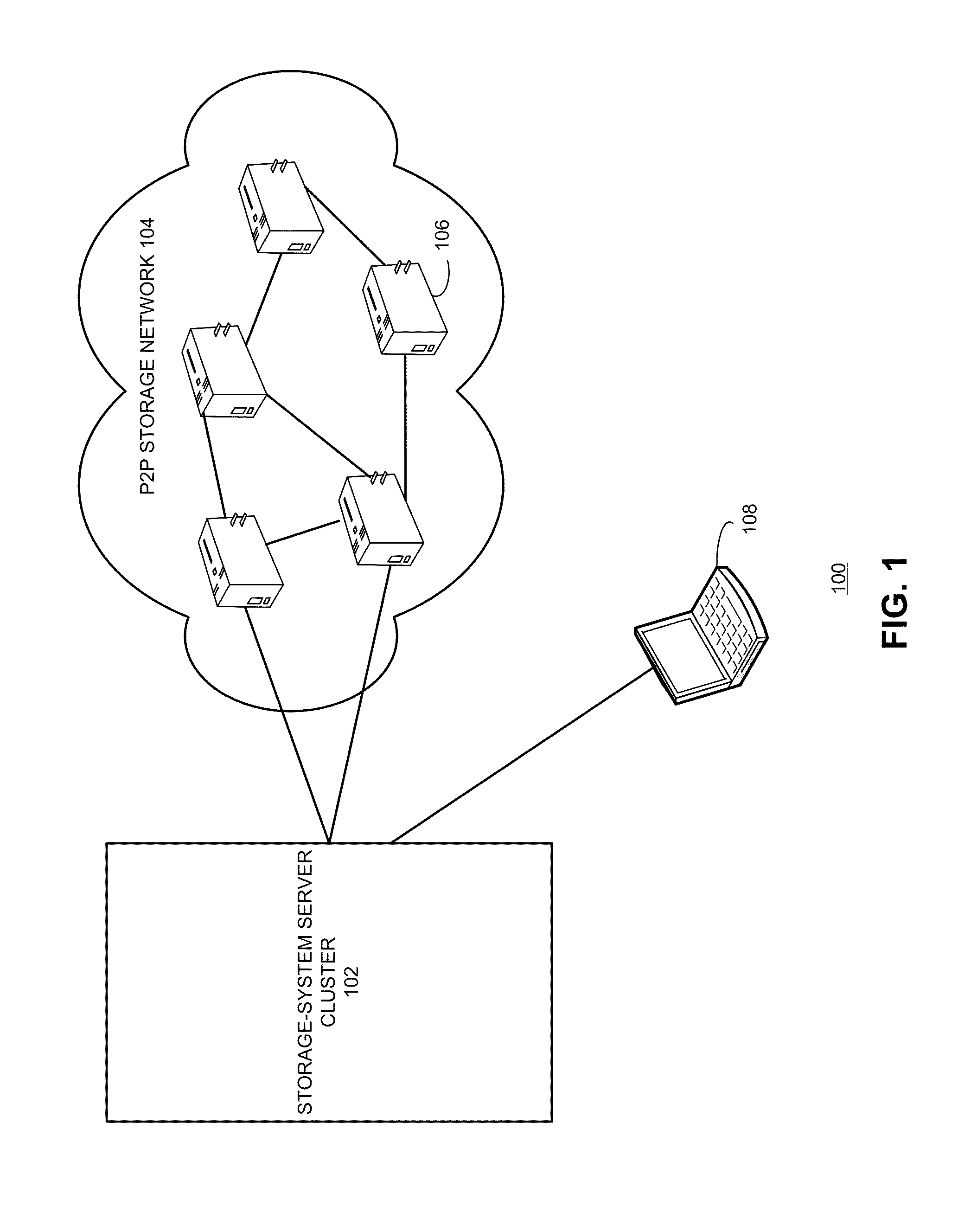
InactiveUS20120011200A1Multiple digital computer combinationsTransmissionProcess moduleDocument handling
One embodiment of the present invention provides a peer-to-peer (P2P) data-storage system. The system includes a P2P network, a file upload module configured to receive a file uploaded by a user, a file processing module configured to disassemble the received file into a plurality of file blocks and select a plurality of peer nodes from the P2P network, and a file distribution module configured to distribute the file blocks to the selected peer nodes. A respective file block is distributed to a respective peer node.
Owner:TV BANK
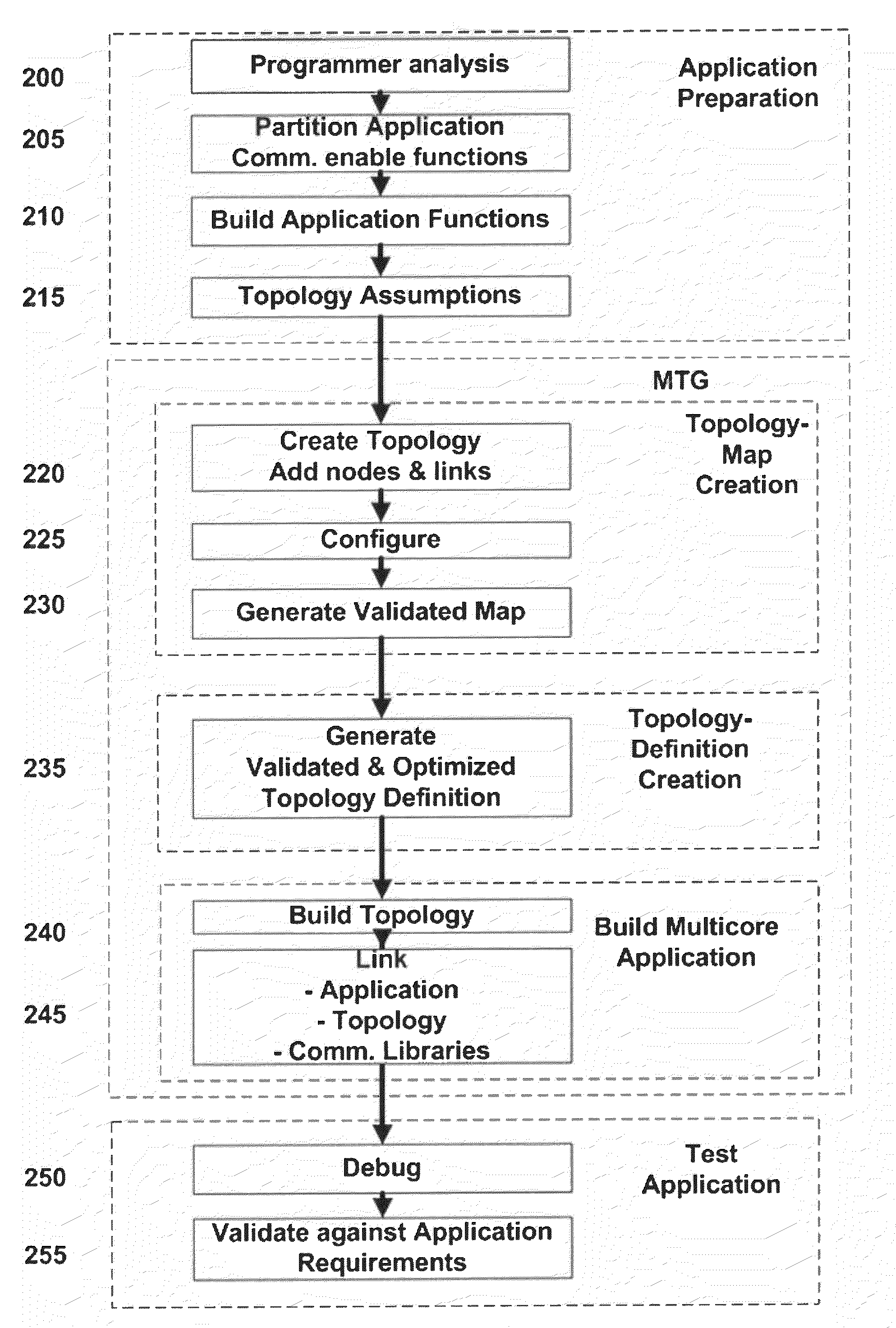
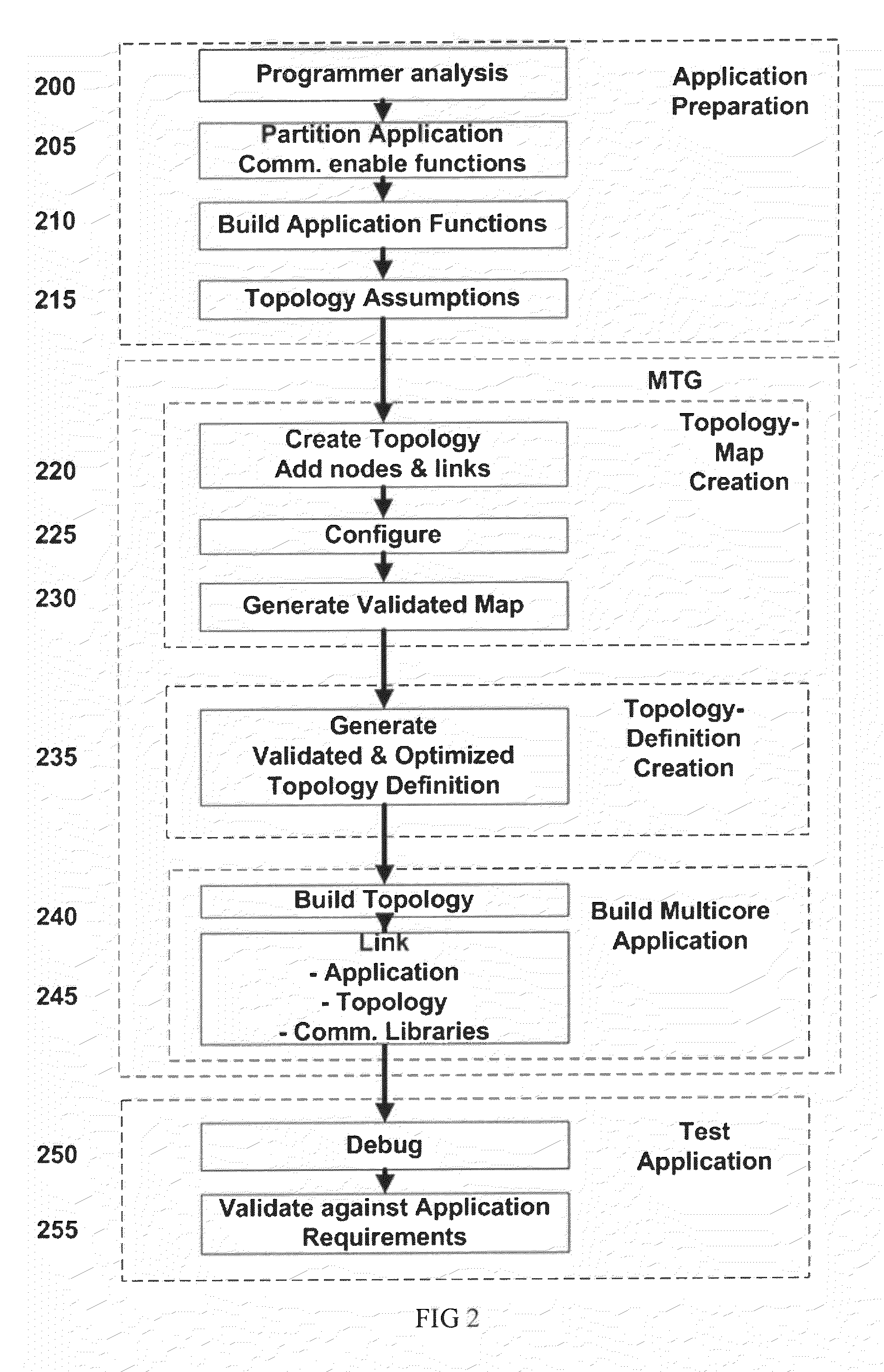
Apparatus & associated methodology of generating a multi-core communications topology
ActiveUS20100235847A1Multiprogramming arrangementsInput/output processes for data processingParallel computingDocument handling
An apparatus and associated method of generating a multi-core communication topology. The topology corresponding to a predetermined number of cores of a multi-core computer, is generated with an application programming device. A number of nodes are described for mapping to the predetermined number of available cores of the multi-core communication topology. Properties of each of the number of nodes are specified. Communication between each of the nodes of the multi-core communication topology is specified using a dedicated multi-core communication library of an electronic memory of the application programming device. A validated output file is generated for the multi-core topology at the application programming device. The output file to is processed to generate a multi-core communication capable executable application program interface (API) for the multi-core computer.
Owner:POLYCORE SOFTWARE
System and method for a RFID transponder file system
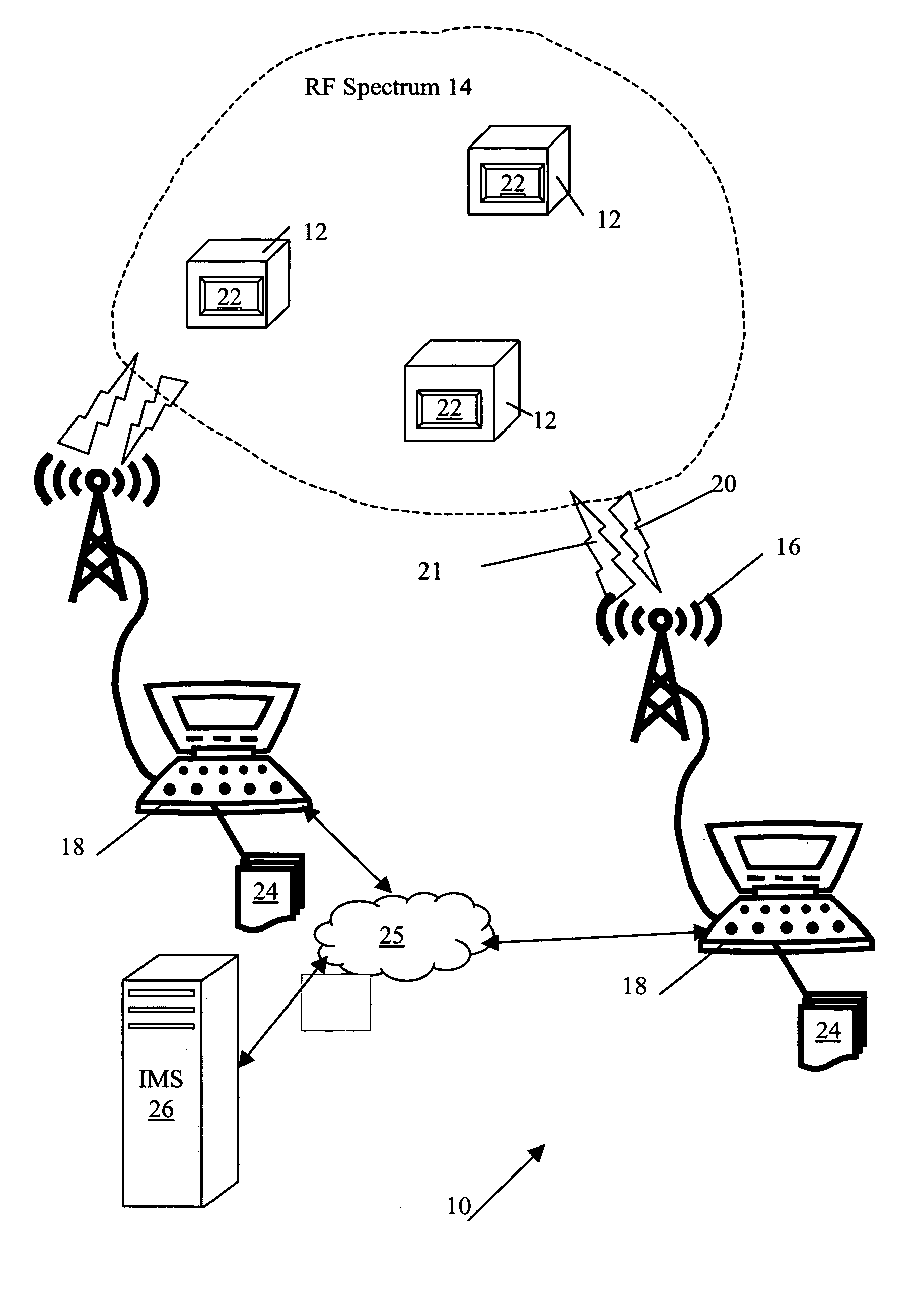
ActiveUS20070082613A1Near-field transmissionElectric/electromagnetic visible signallingFrequency spectrumFile system
A system and method for representing on a user interface a plurality of transponders in a file system of a computing device, the user interface provided by the device, the device configured for communicating with the transponders when present in an electromagnetic spectrum in communication range of the device. The communication between the transponders and the device uses radio frequency signals to obtain information of the transponders. The system and method comprises a first memory location configured for storing the transponder information as a plurality of corresponding transponder files in the file system. The system and method also have a driver for coordinating the transfer of the transponder information between the transponder and the first memory location according to an access command, the access command configured for directing the computing device to obtain the transponder information for the transponders when in communication range of the device. The system and method also have a file processor for manipulating the transponder information present in the transponder files, wherein the transponder information contents of the transponder files represents at least a portion of the transponder information available in the electromagnetic spectrum in communication range of the device.
Owner:PSION
Reconfigurable processing system and method
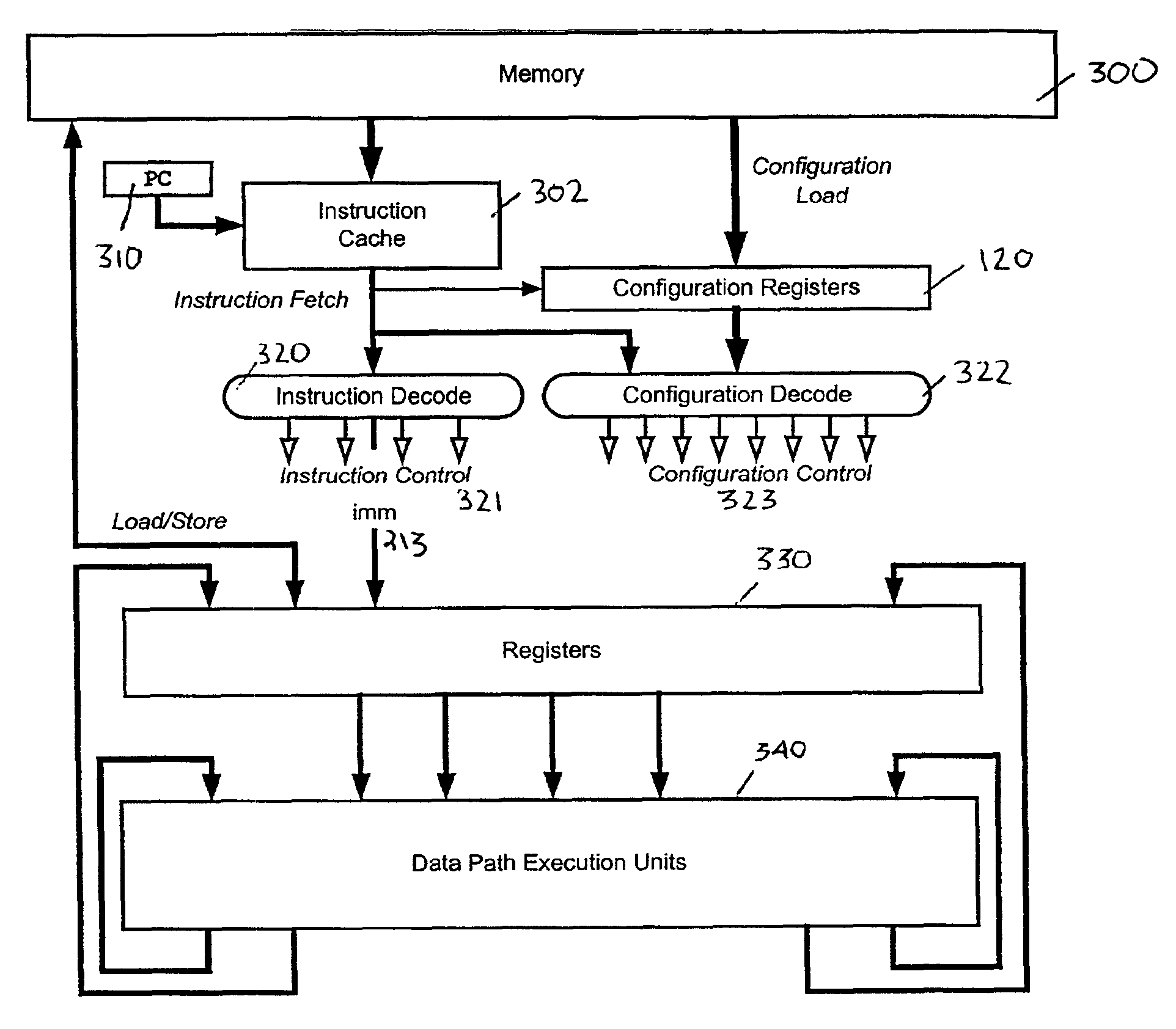
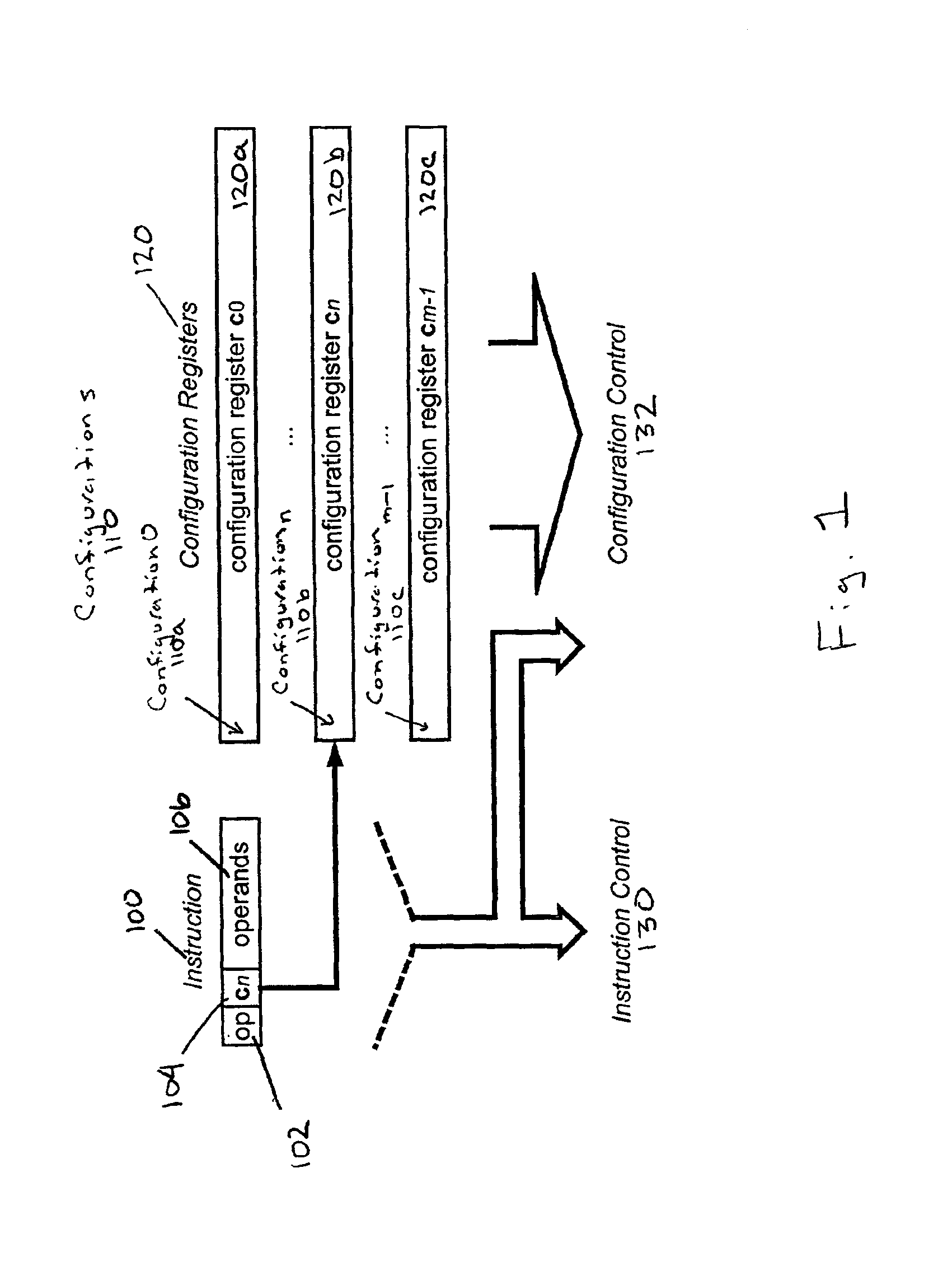
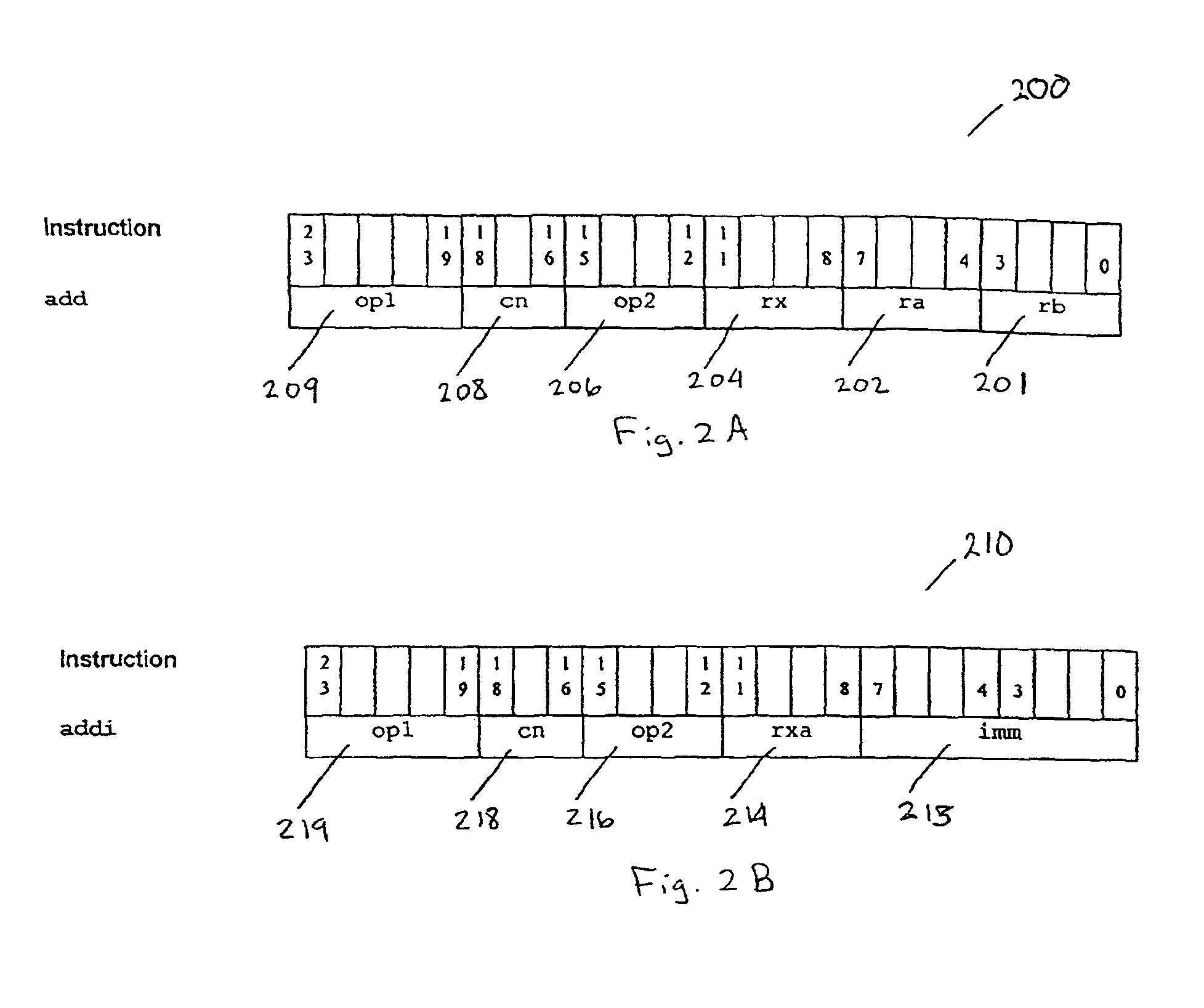
InactiveUS6959378B2Next instruction address formationArchitecture with single central processing unitProcessor registerData operations
A reconfigurable processing system executes instructions and configurations in parallel. Initially, a first instruction loads configurations into configuration registers. The configuration field of a subsequently fetched instruction selects a configuration register. The instruction controls and controls of the configuration in the selected configuration register are decoded and modified as specified by the instruction. The controls provide data operands to the execution units which process the operands and generate results. Scalar data, vector data, or a combination of scalar and vector data can be processed. The processing is controlled by instructions executed in parallel with configurations invoked by configuration fields within the instructions. Vectors are processed using a vector register file which stores vectors. A vector address unit identifies addresses of vector elements in the vector register file to be processed. For each vector, vector address units provide addresses which stride through each element of each vector.
Owner:AVAGO TECH INT SALES PTE LTD
Automated banking machine system with multiple browsers
InactiveUS7266526B1Good user interfaceFunction increaseFinancePayment architectureNetwork addressingDocument handling
An automated banking machine (12) is operative to conduct transactions in response to HTML documents and TCP / IP messages exchanged with a local computer system (14) through an intranet (16), as well as in response to messages exchanged with foreign servers (20, 22, 24, 26, 28, 96) in a wide area network (18). The banking machine includes a computer (34) having a document handling portion (76, 80, 82) including one or more browsers. The document handling portion is operative to communicate through a proxy server (88), with a home HTTP server (90) in the intranet or the foreign servers in the wide area network. The computer further includes a device application portion (84) which interfaces with the document handling portion and dispatches messages to operate devices (36) in the automated banking machine. The devices include a sheet dispenser mechanism (42) which dispenses currency as well as other transaction function devices. The device application portion communicates with a device interfacing software portion (64) in the banking machine through a device server (92) in the intranet. The device server maintains local control over the devices in the banking machine including the sheet dispenser. The banking machine operates to read indicia on the user's card corresponding to a network address. The computer is operative to connect the banking machine to the home or foreign server corresponding to the network address, which connected server operates the banking machine to conduct transactions by the user. The customer is enabled to operate the banking machine using a familiar interface. The machine may also connect to other applications to provide the customer with promotional material or additional transaction options.
Owner:DIEBOLD NIXDORF
Integrated document handling in distributed collaborative applications
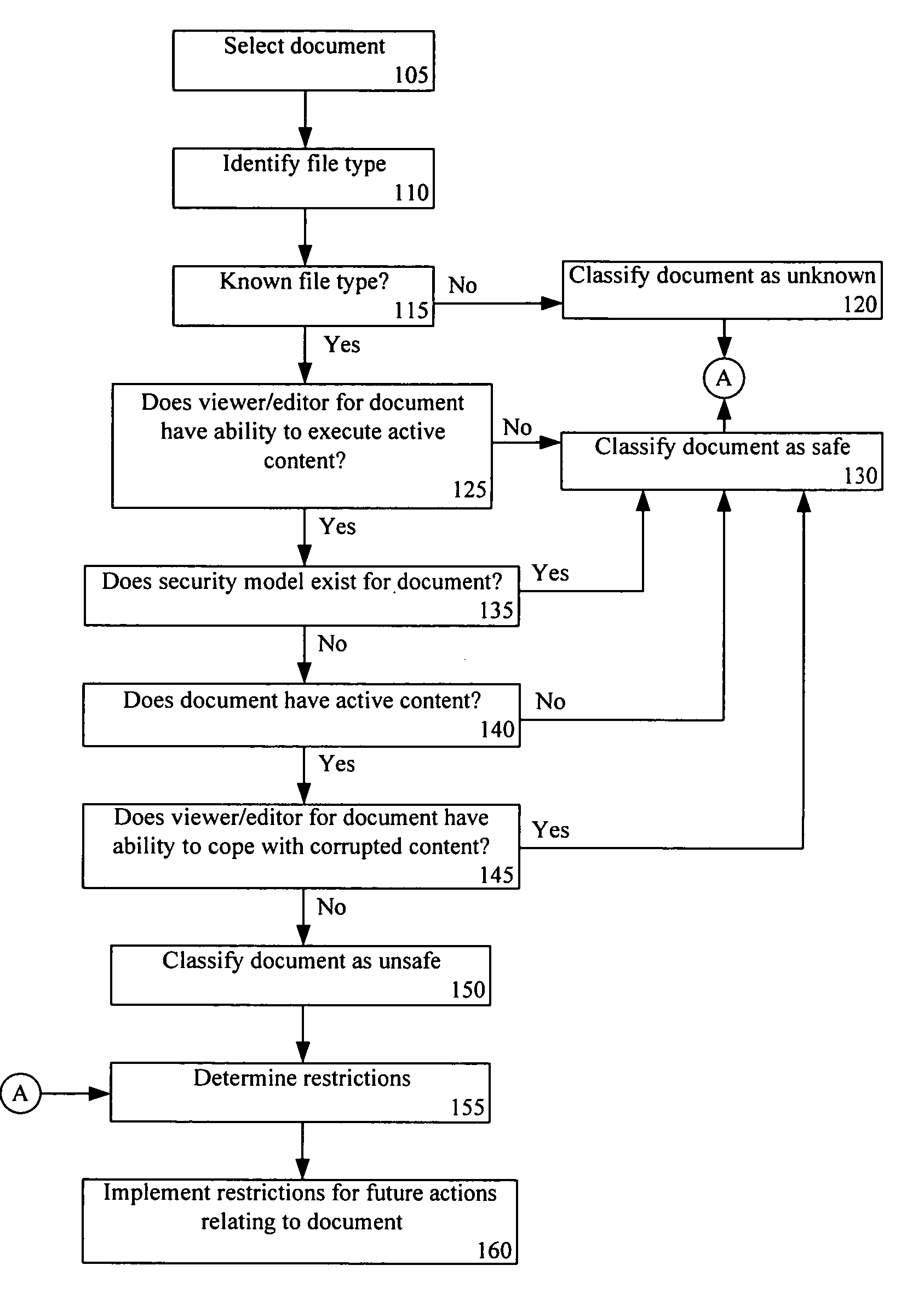
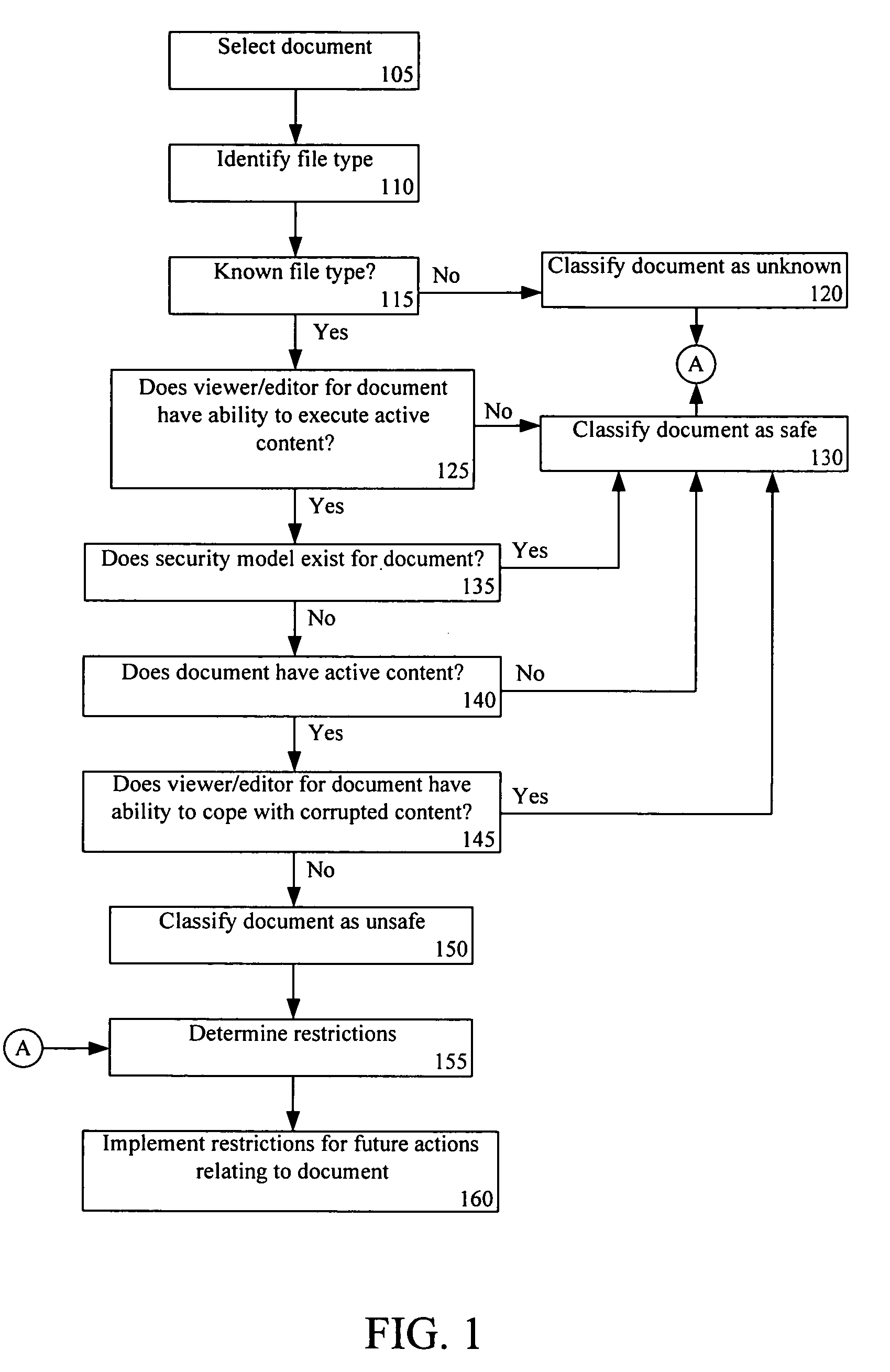
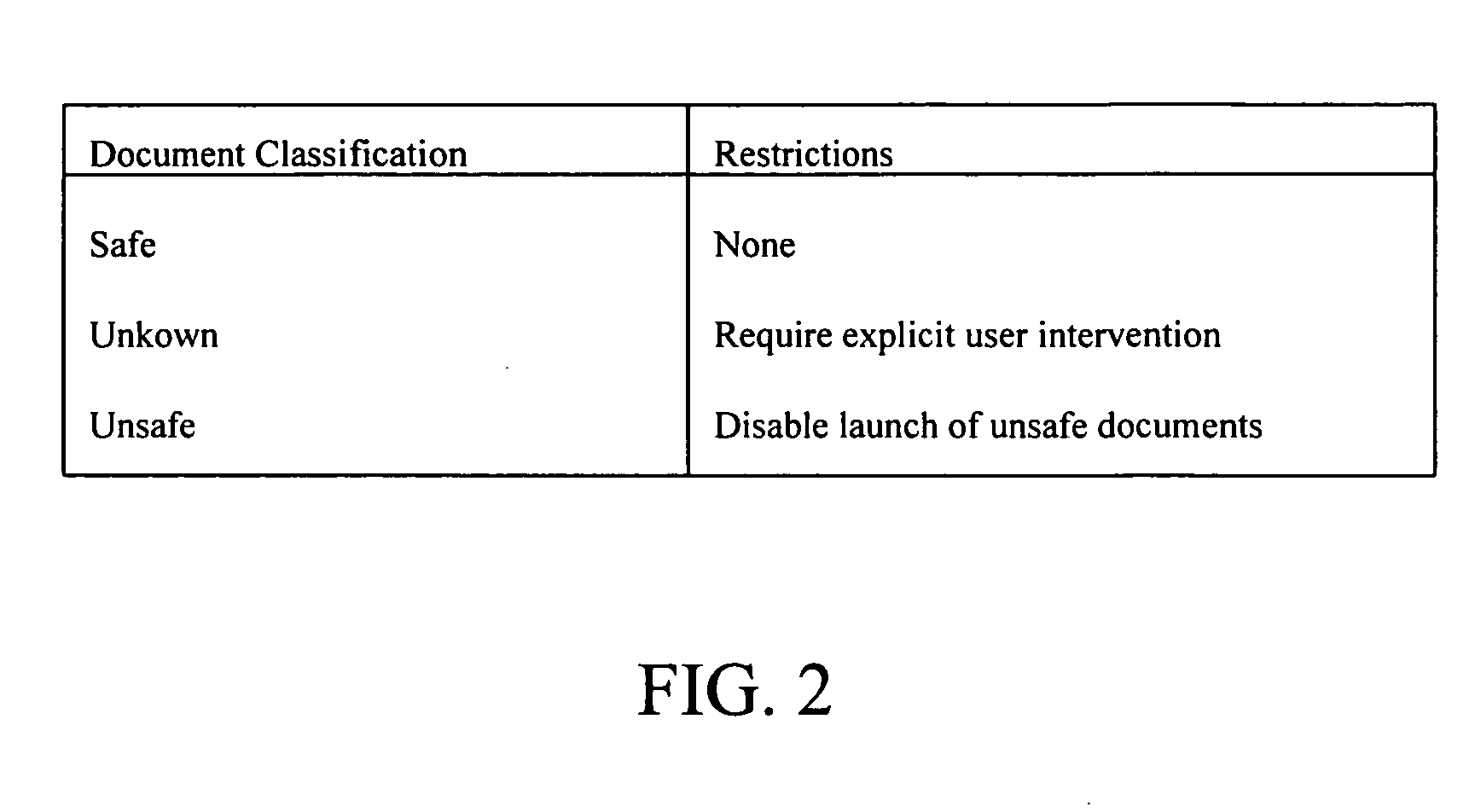
InactiveUS20060259948A1Computer security arrangementsSpecial data processing applicationsElectronic documentDocument handling
A method of handling electronic documents can include determining at least one safety parameter of an electronic document and classifying the electronic document based upon the at least one safety parameter. A restriction policy can be selected based upon the classifying step. The selected restriction policy can be implemented for handling the electronic document.
Owner:IBM CORP
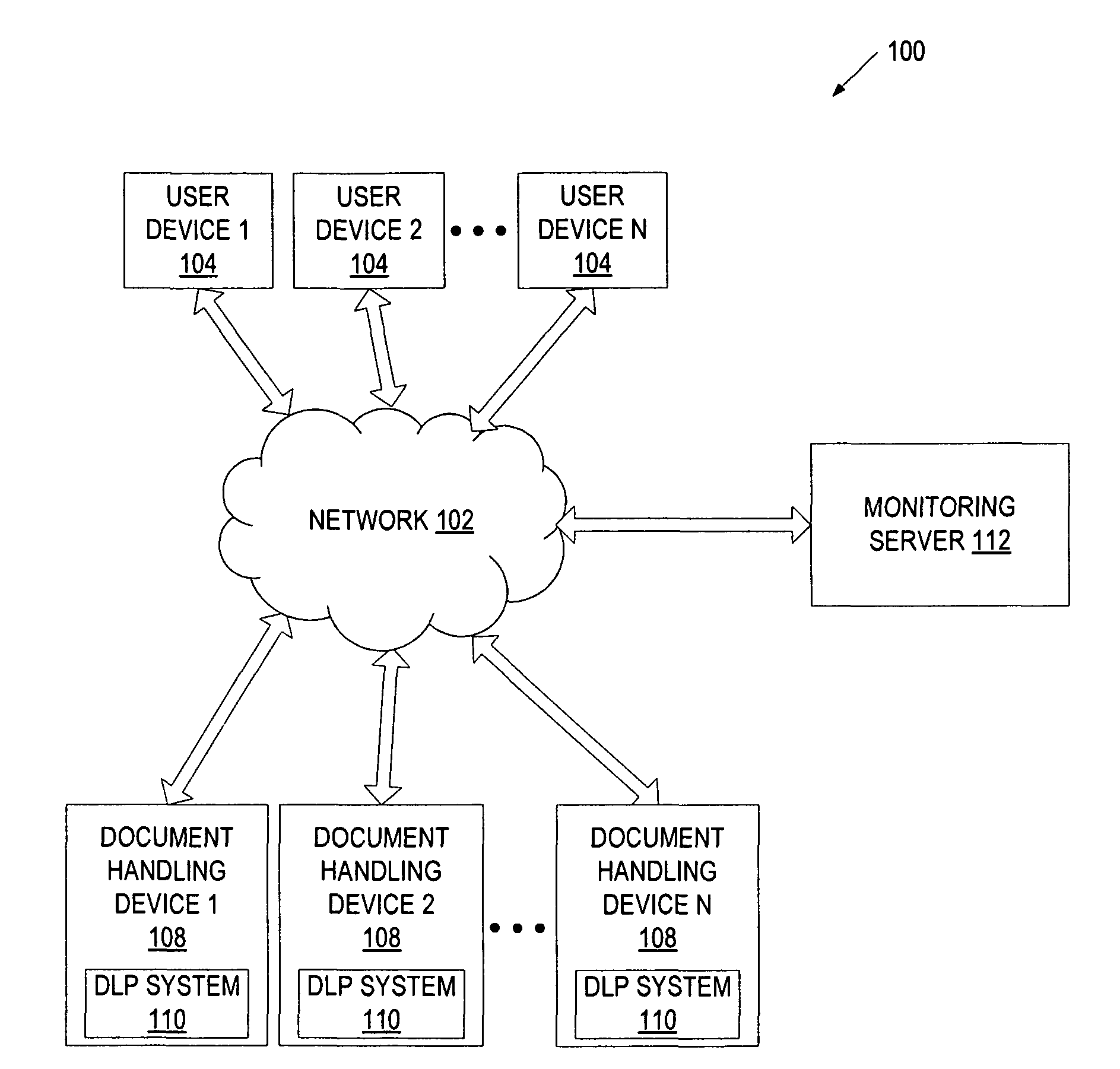
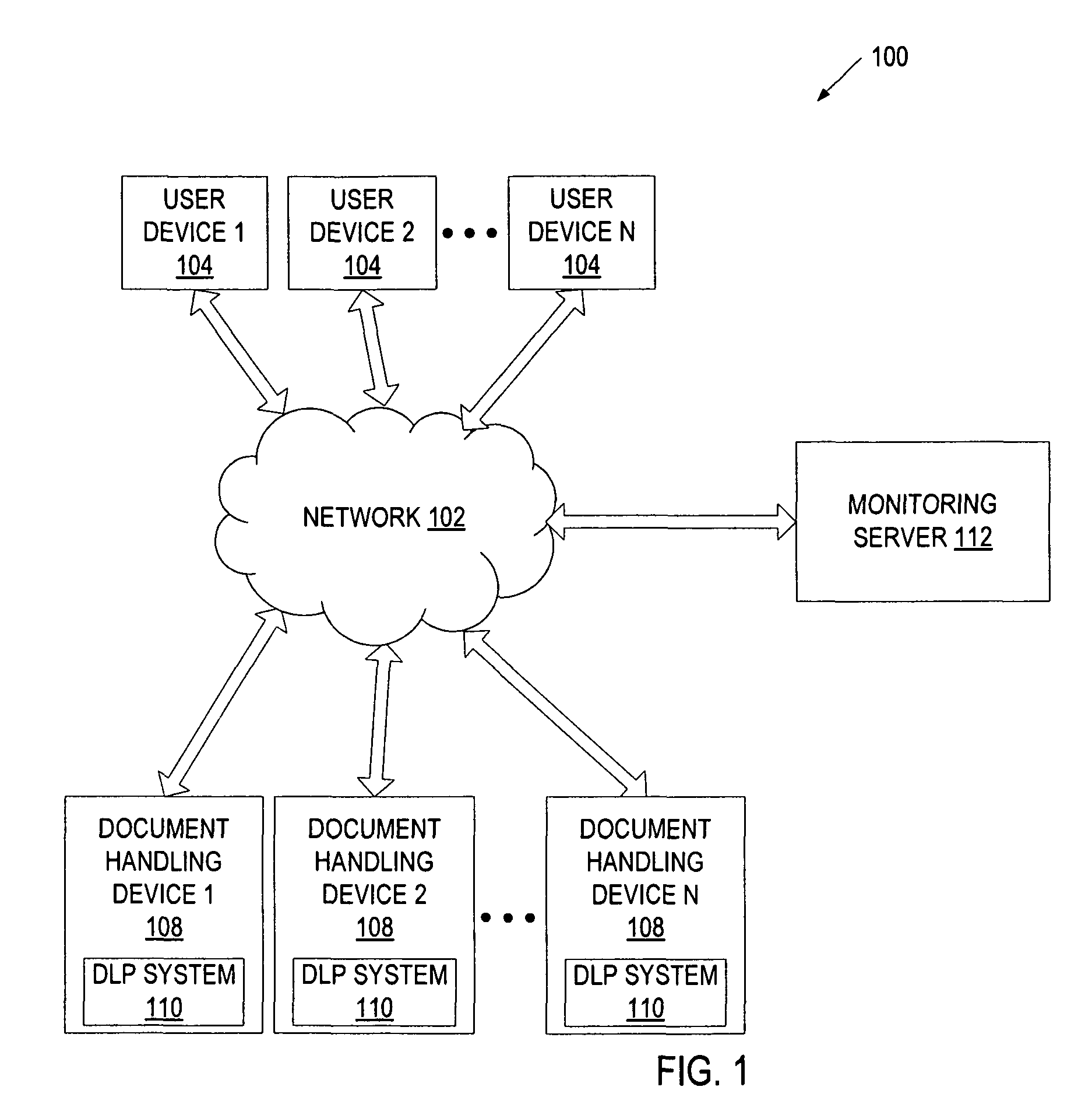
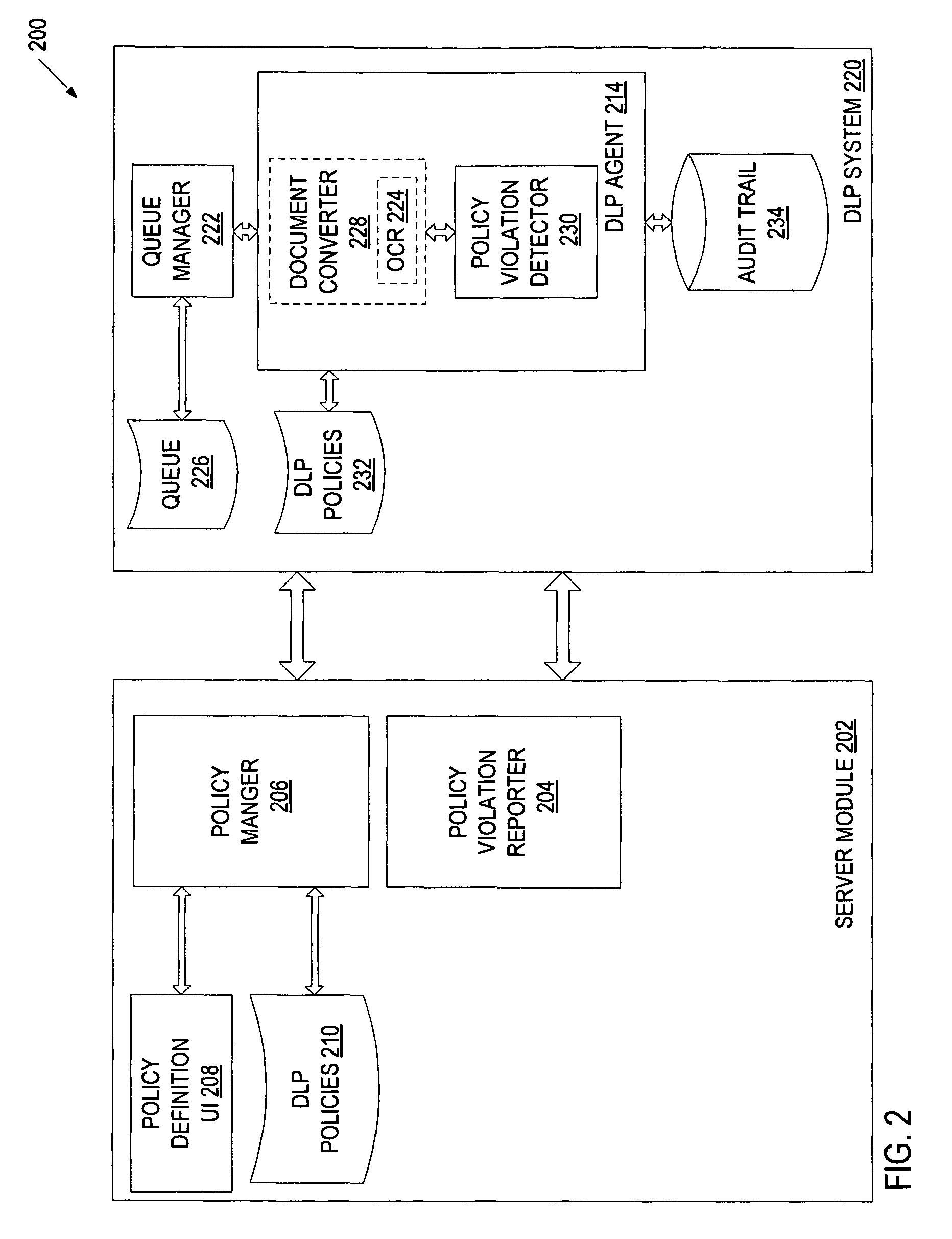
Method and system to audit physical copy data leakage
A document handling device receives a user request to perform a task on document data. The document data is associated with an electronic document to be converted by the document-handling device into a non-digital form (e.g., paper), or with a physical document received by the document-handling device in a non-digital form. The document handling device or a server determines whether the requested task violates a data loss prevention policy, and records, in an audit trail, information identifying the requested task and the digital data, and an indication of whether the requested task violates the data loss prevention policy.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com