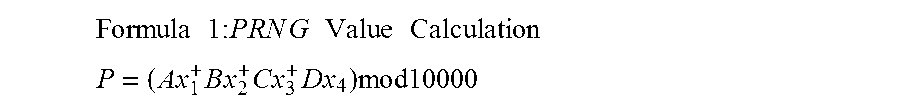Patents
Literature
1824results about "Electronic credentials" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
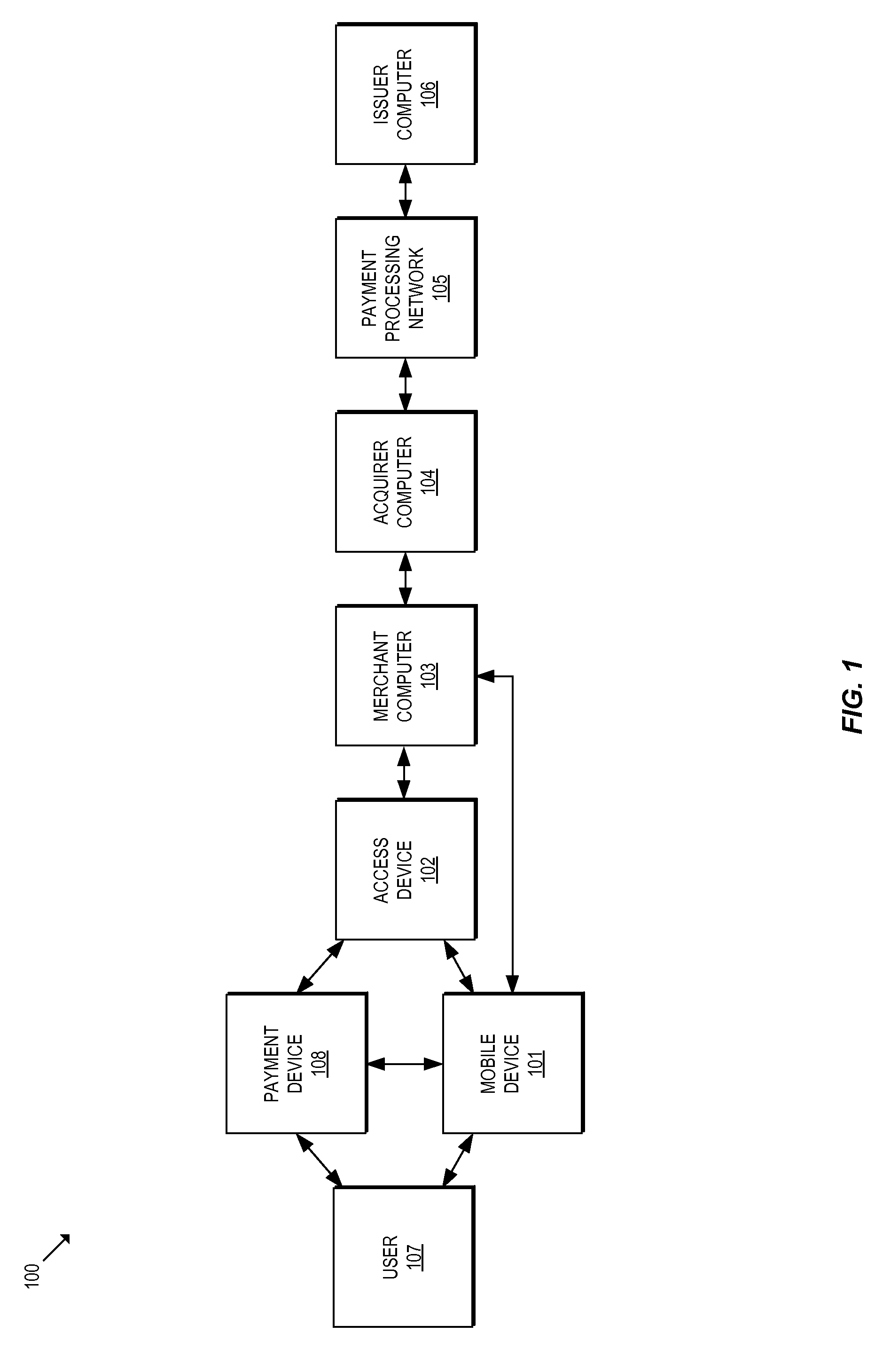
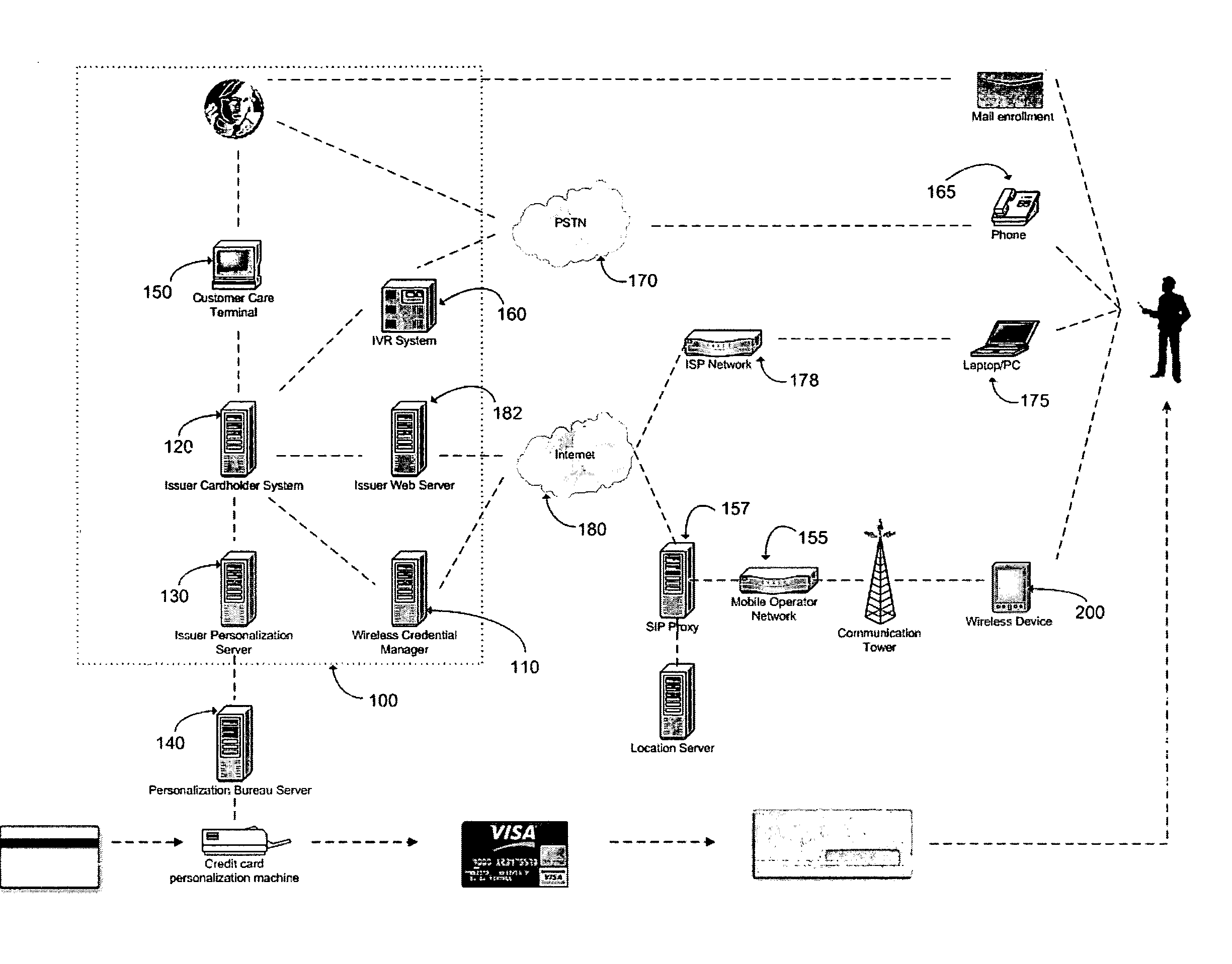
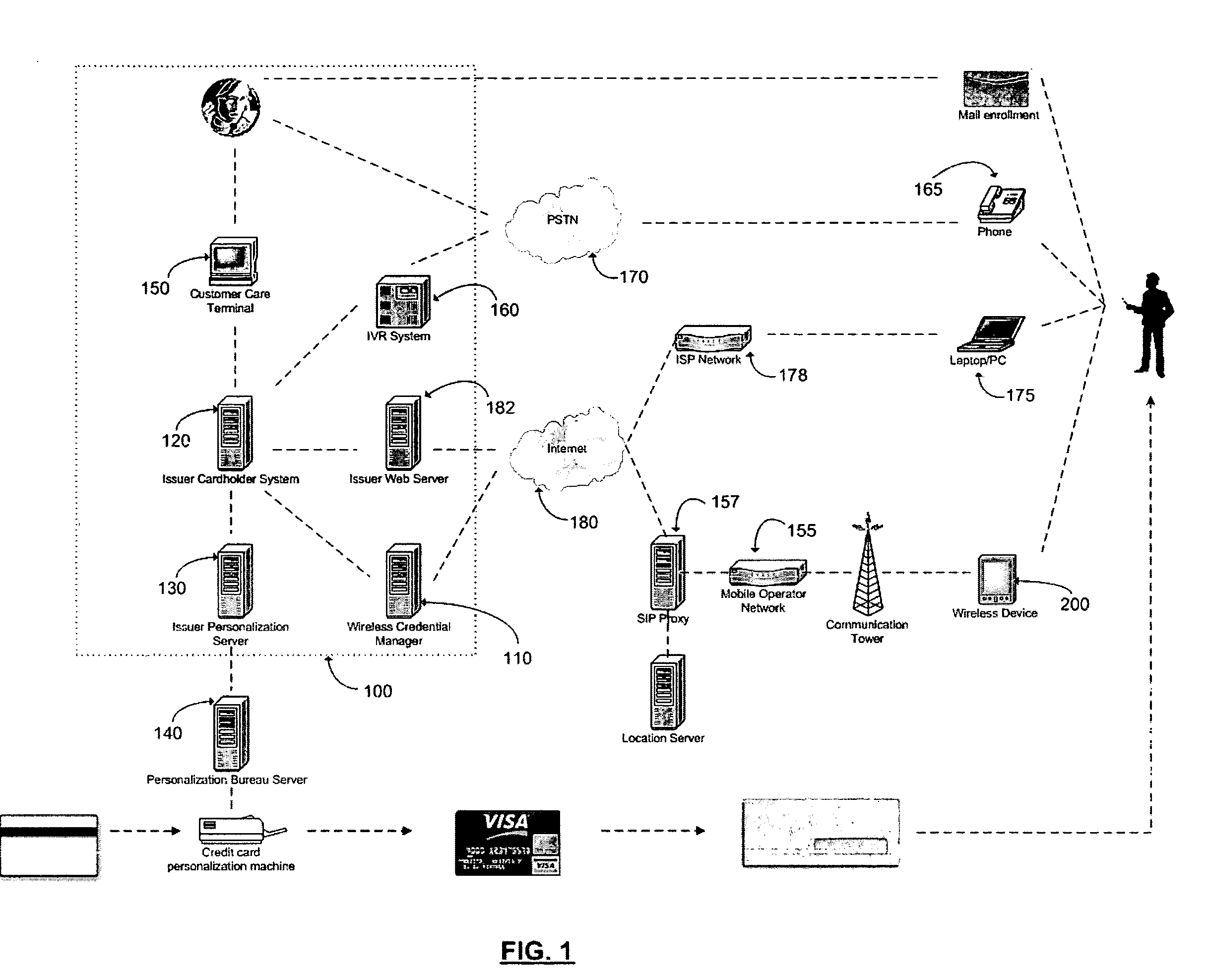
Method and apparatus for managing credentials through a wireless network
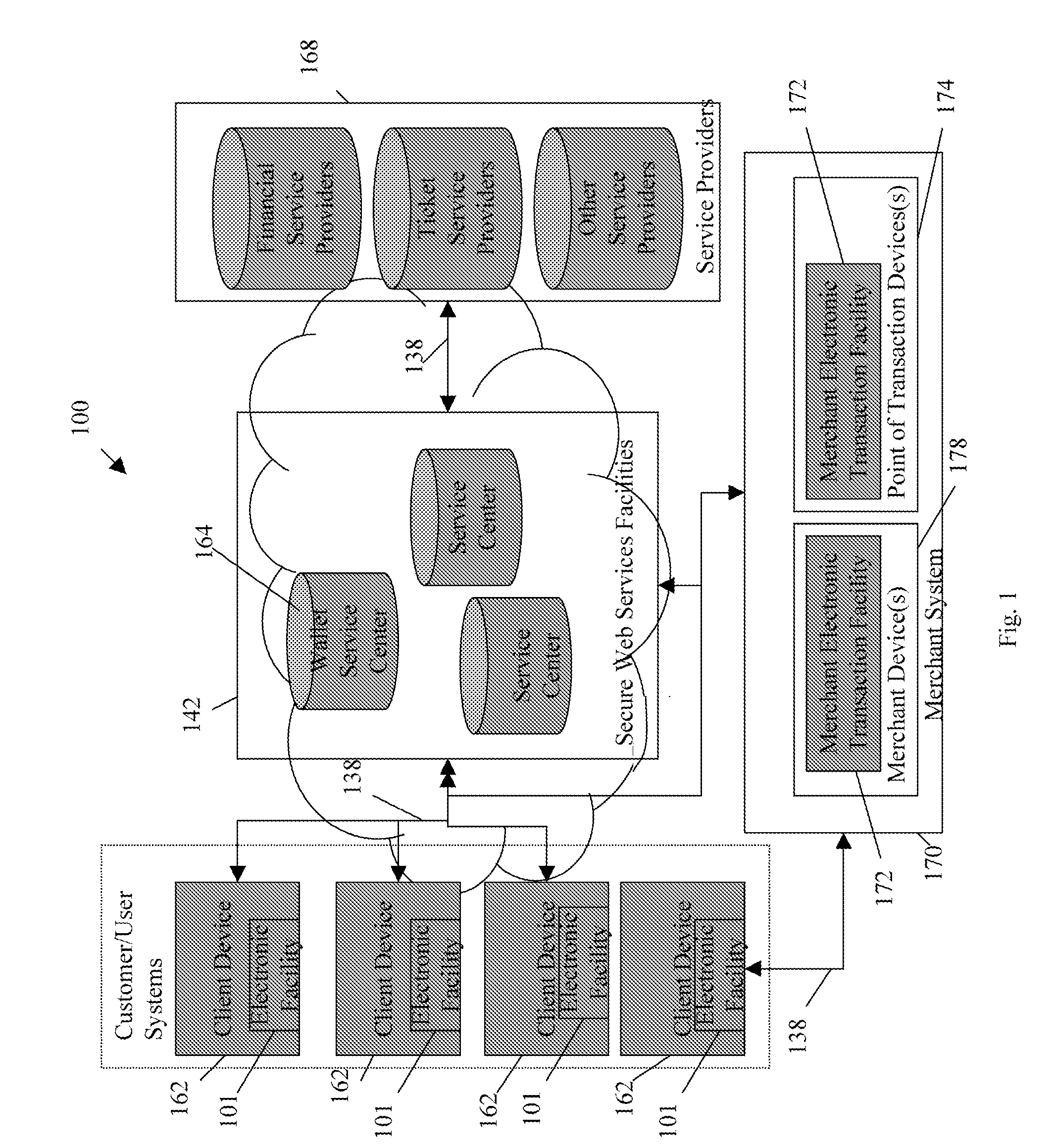
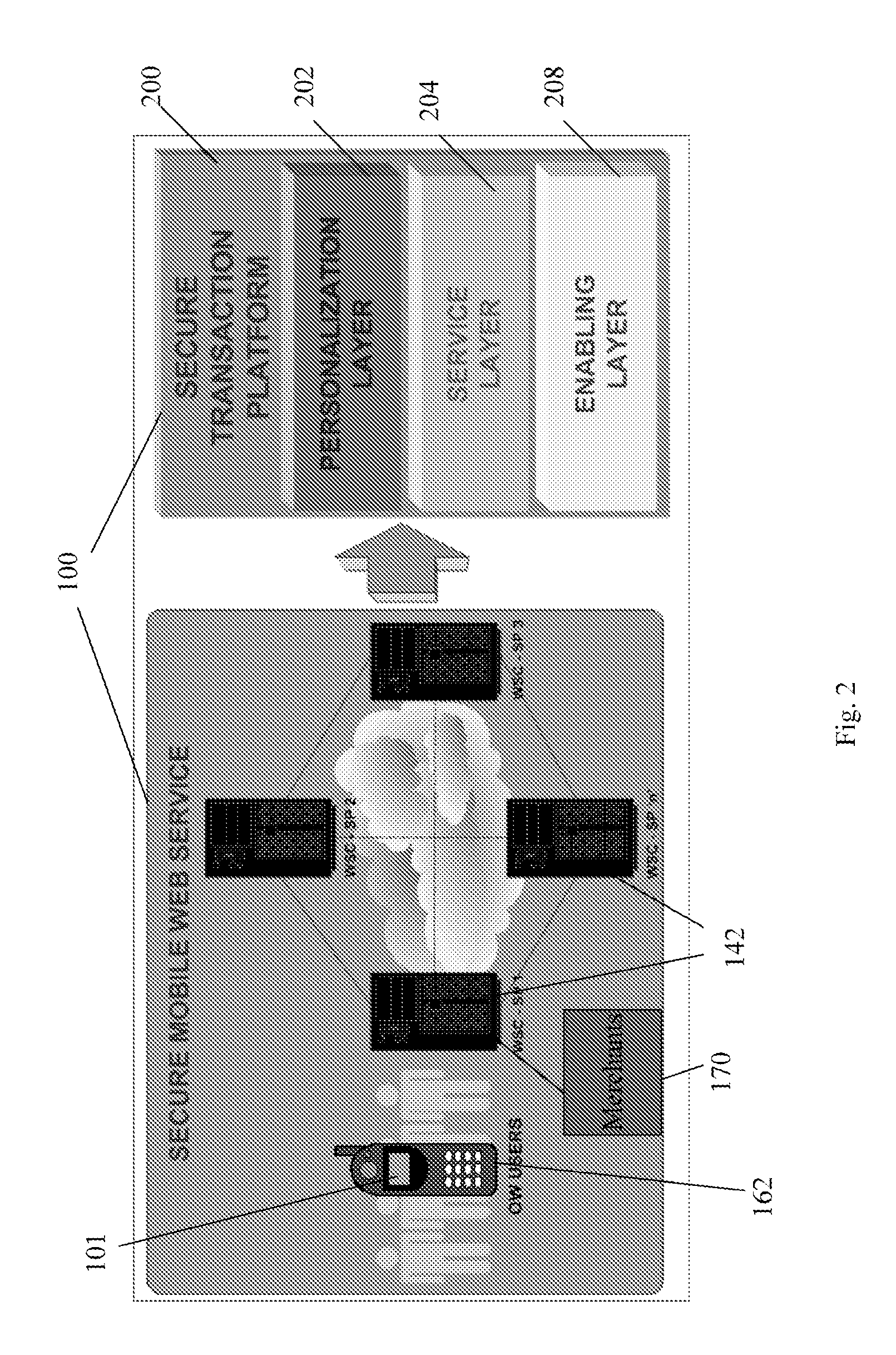
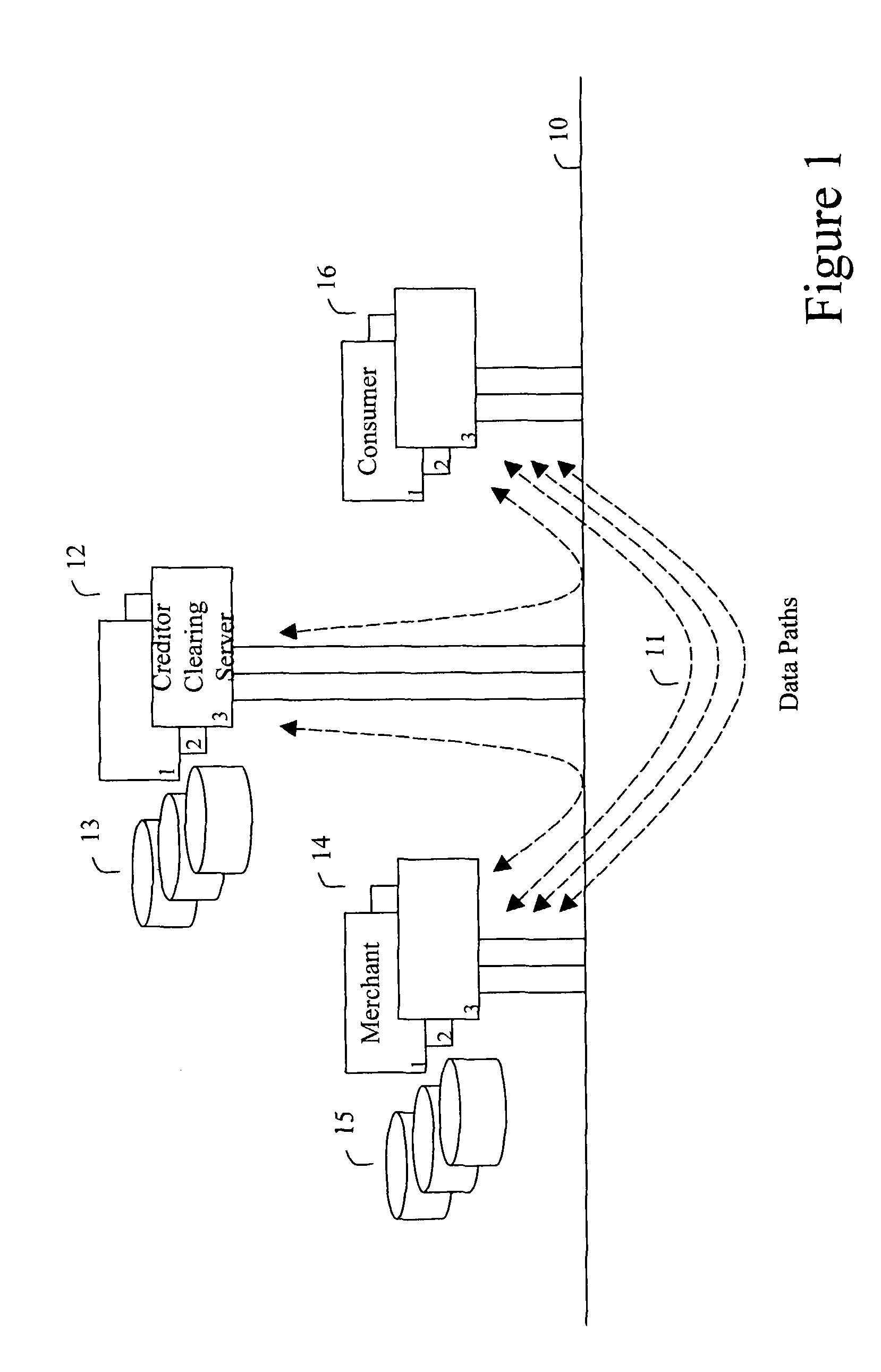
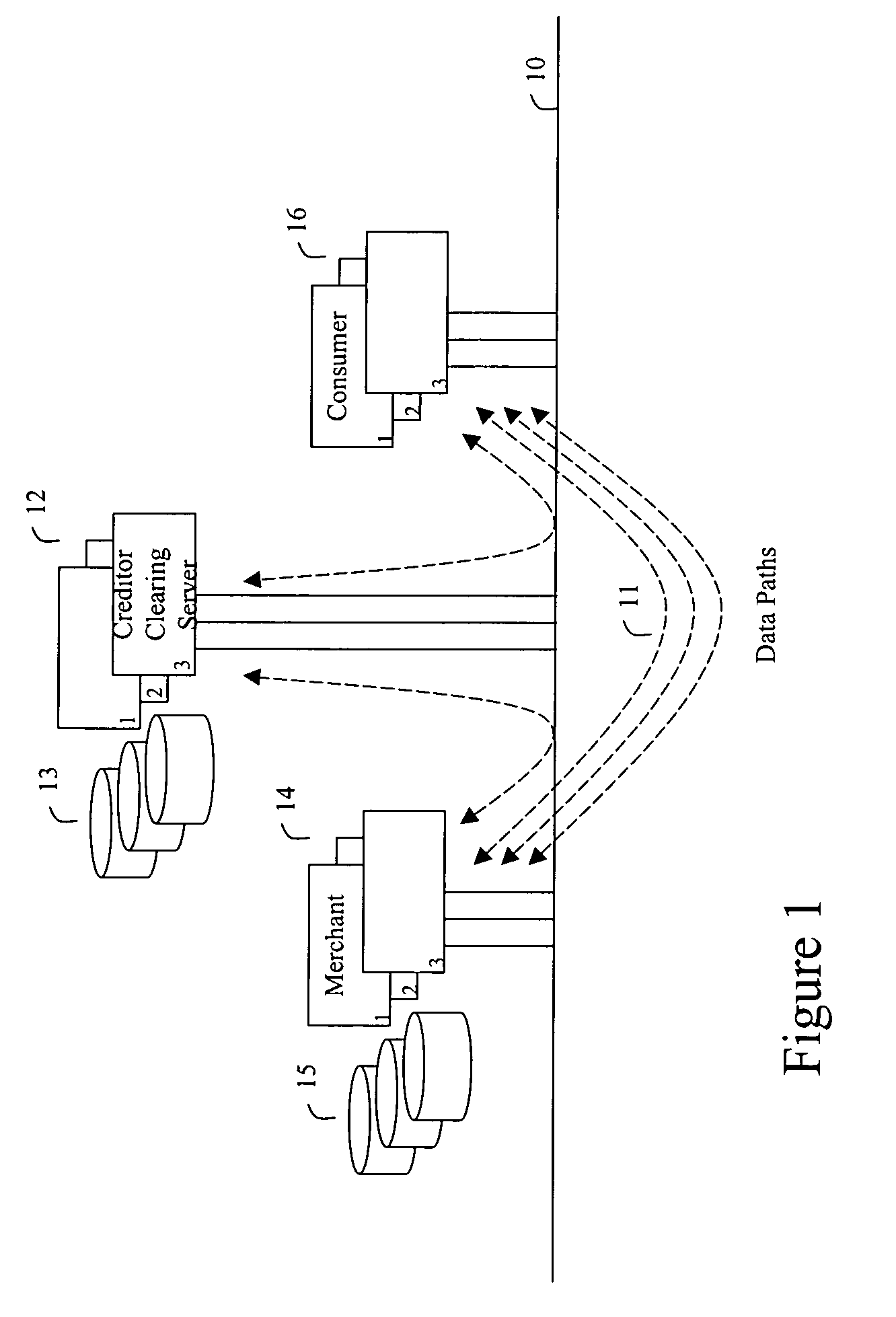
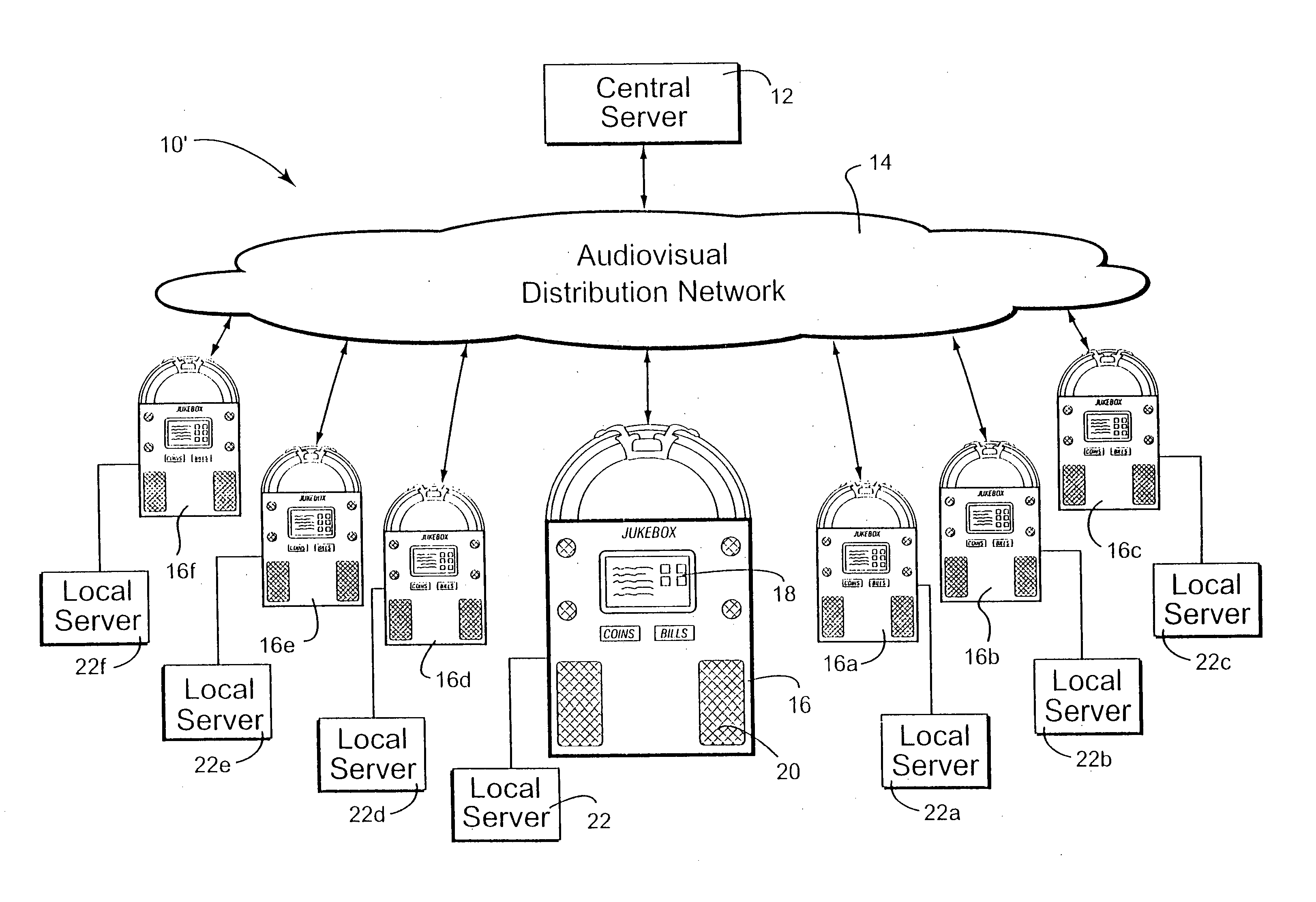
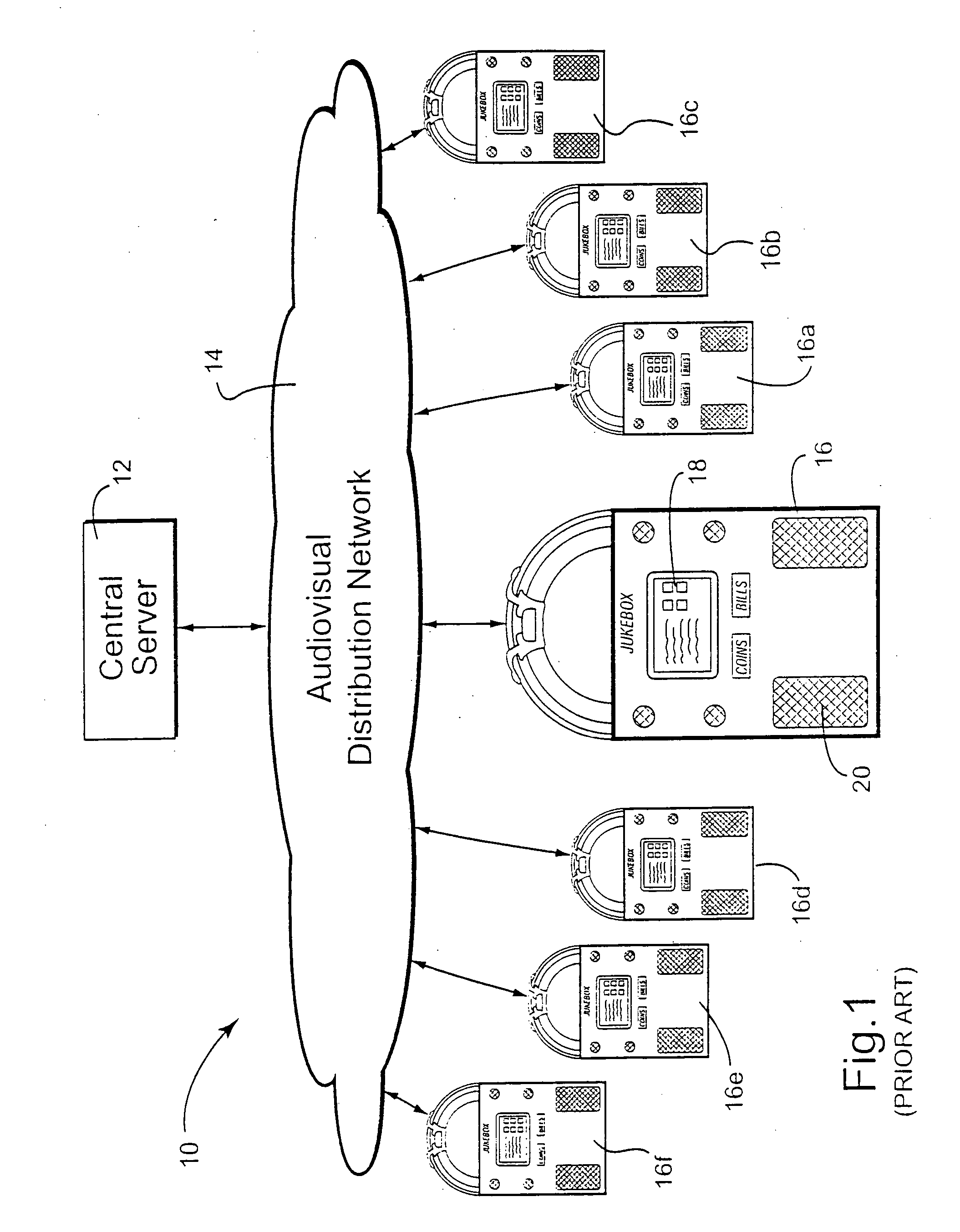
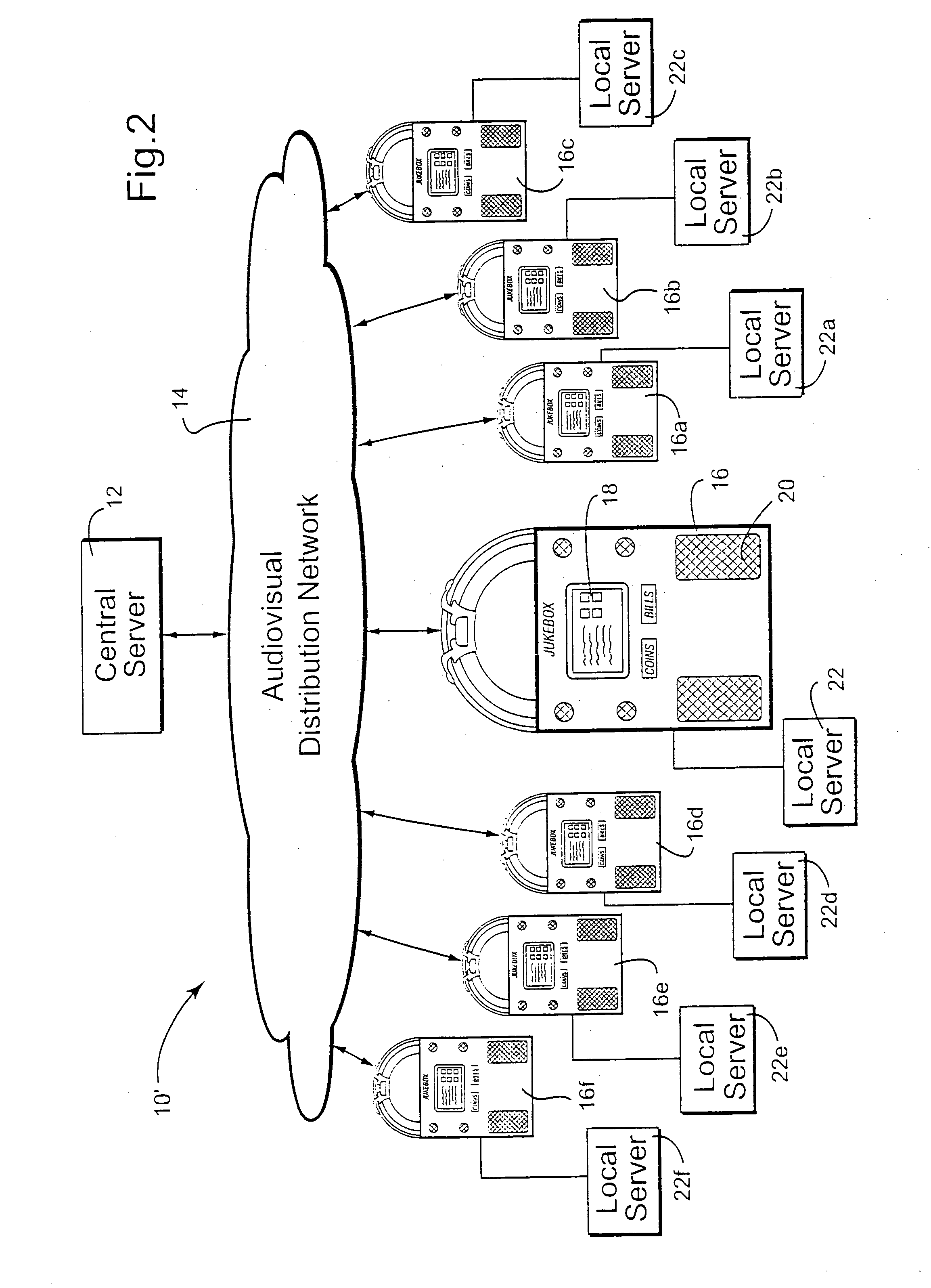
ActiveUS20060165060A1Convenient and efficient and secure distributionNear-field in RFIDData switching by path configurationCredit cardWireless mesh network
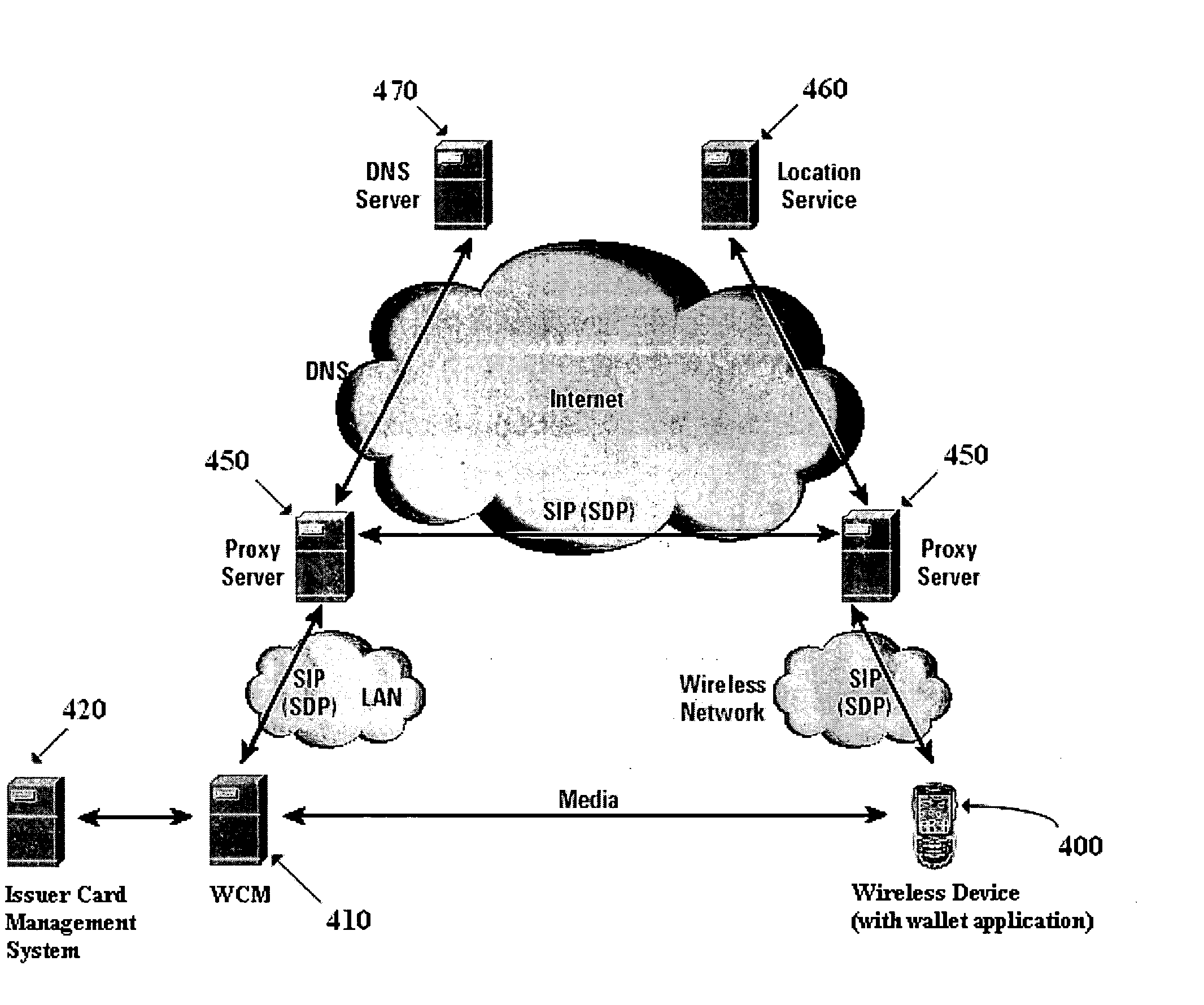
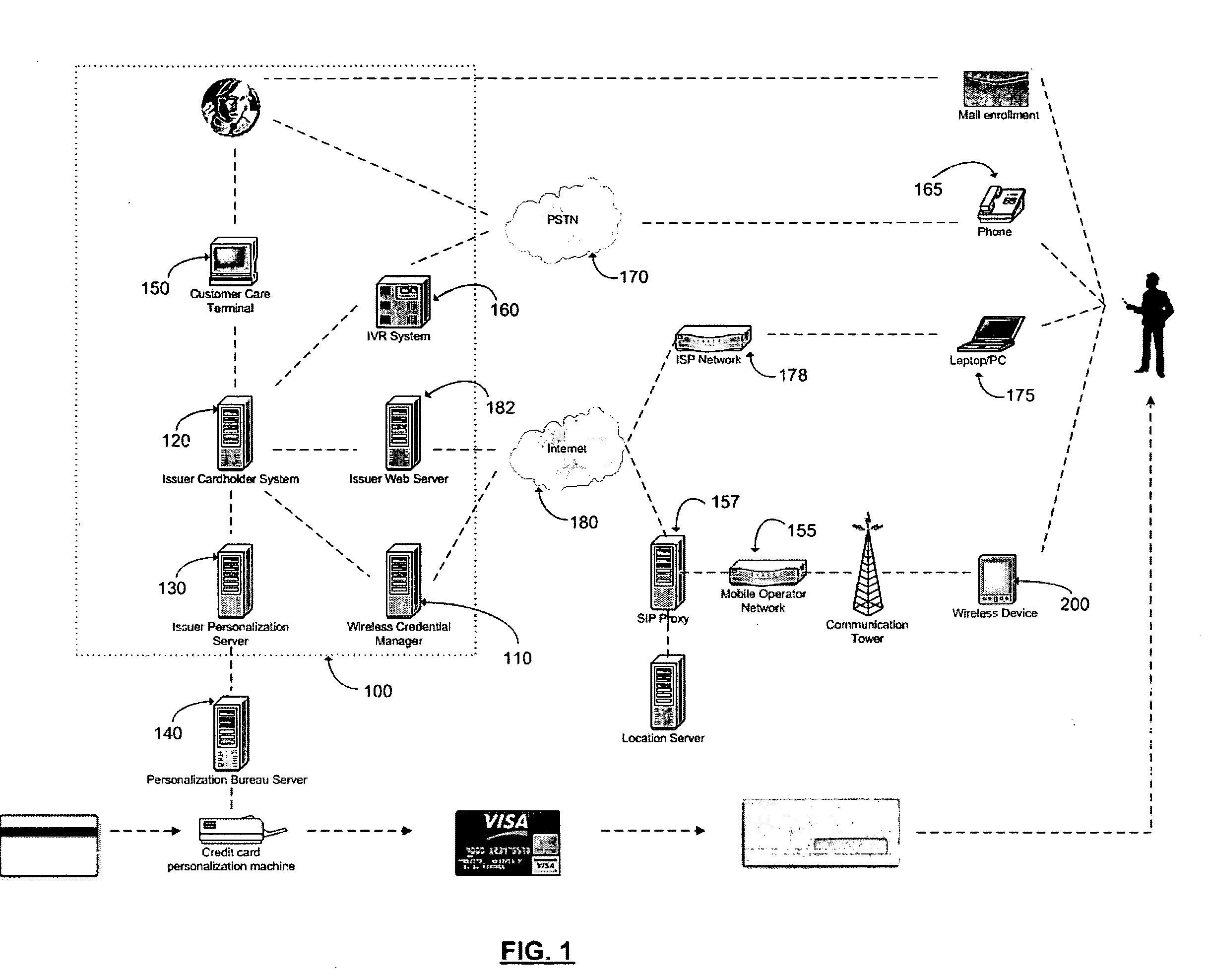
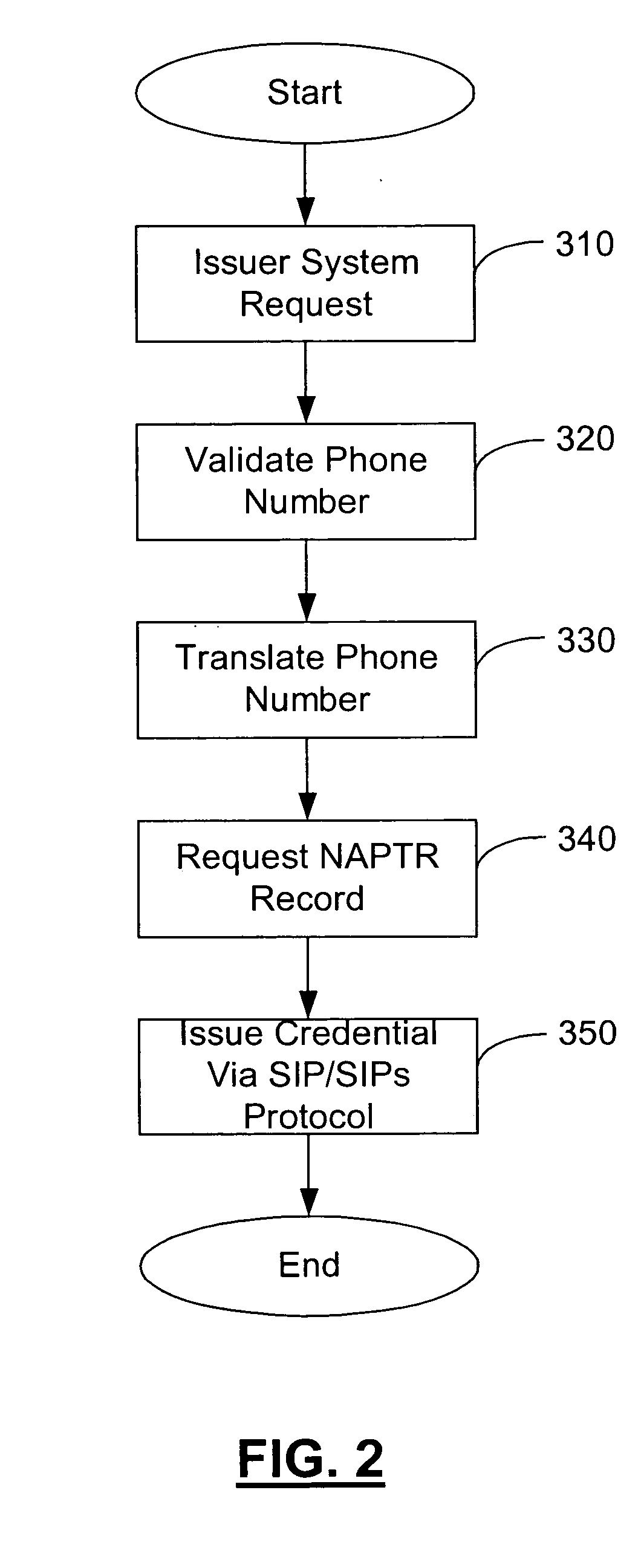
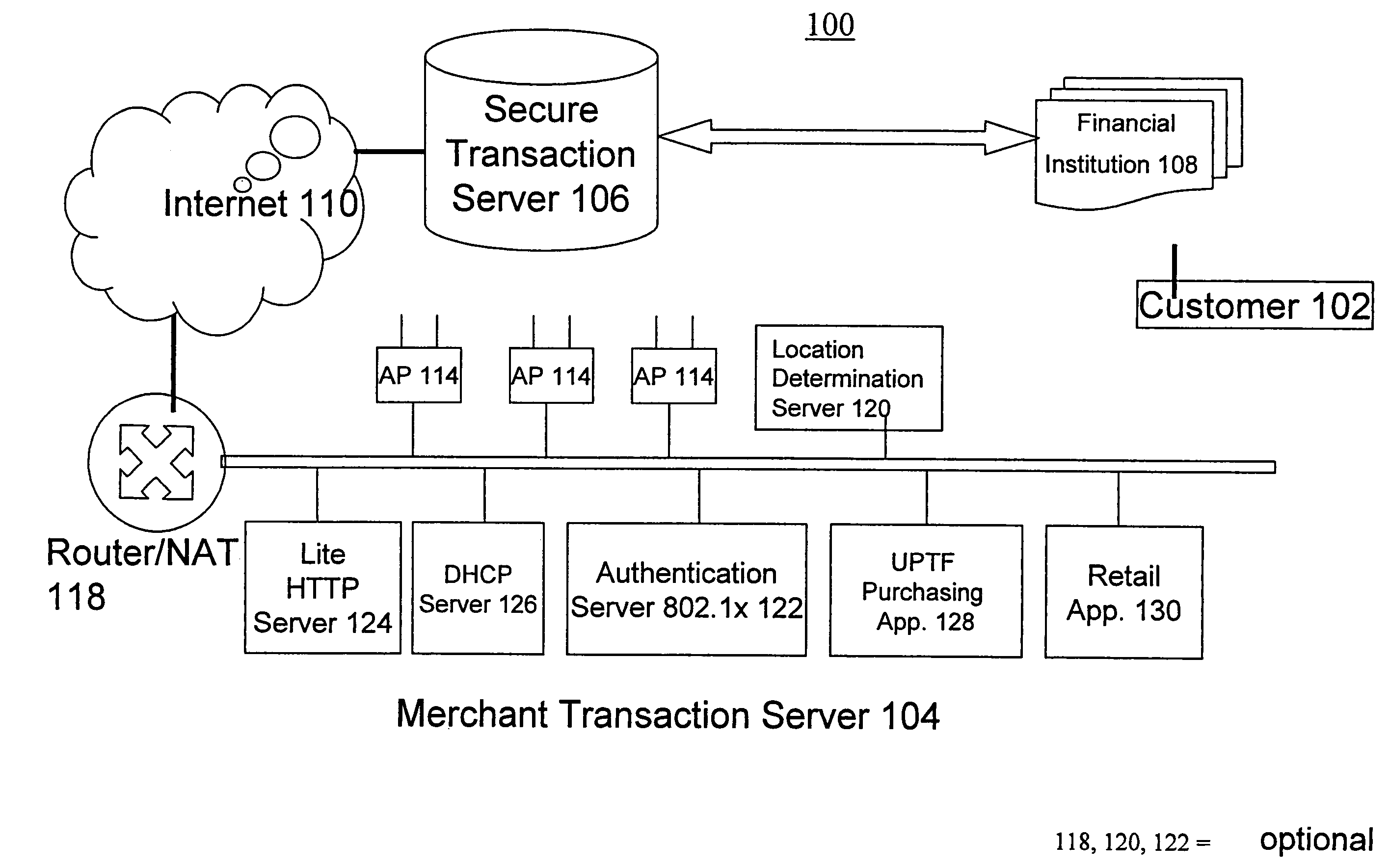
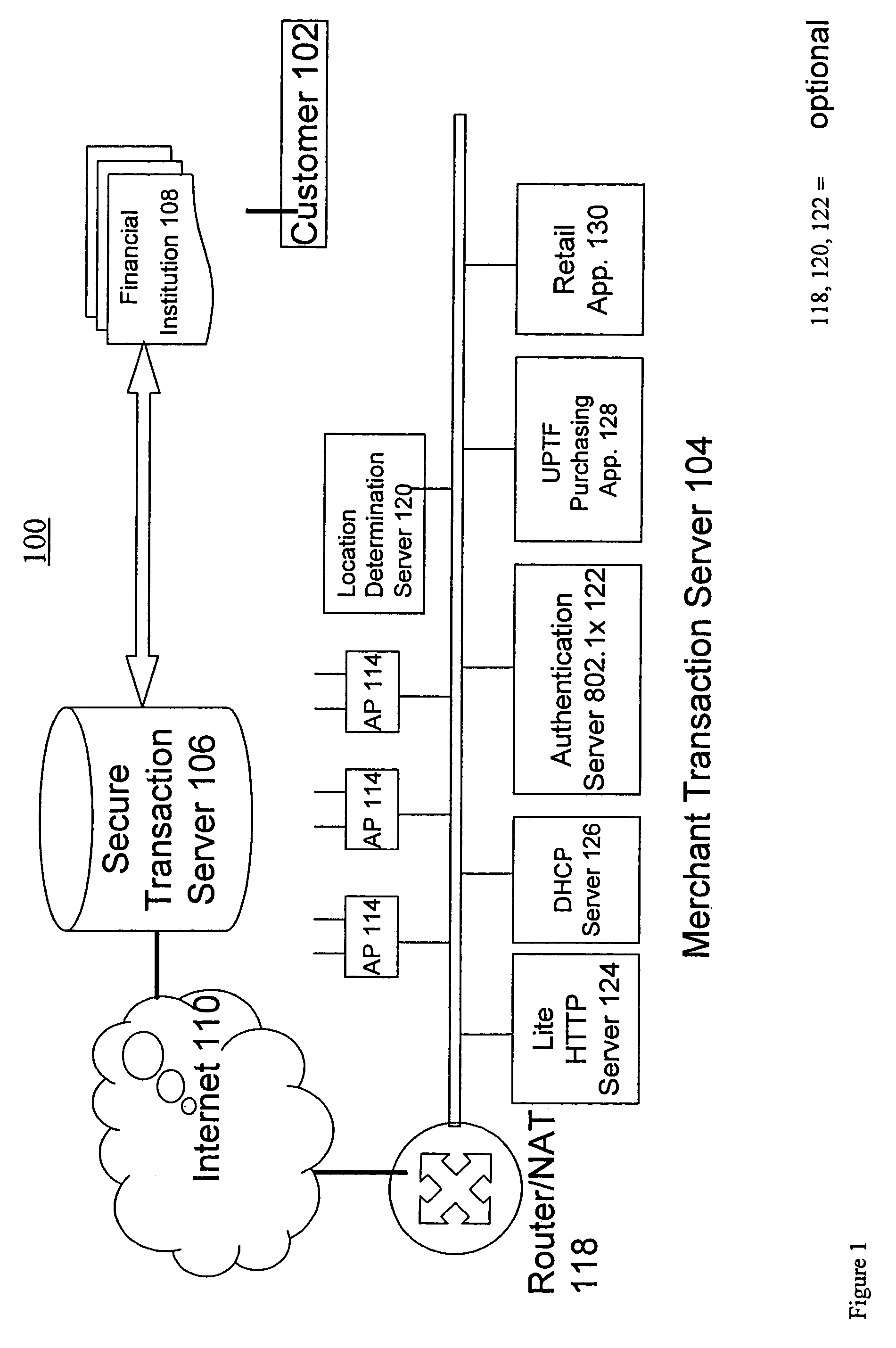
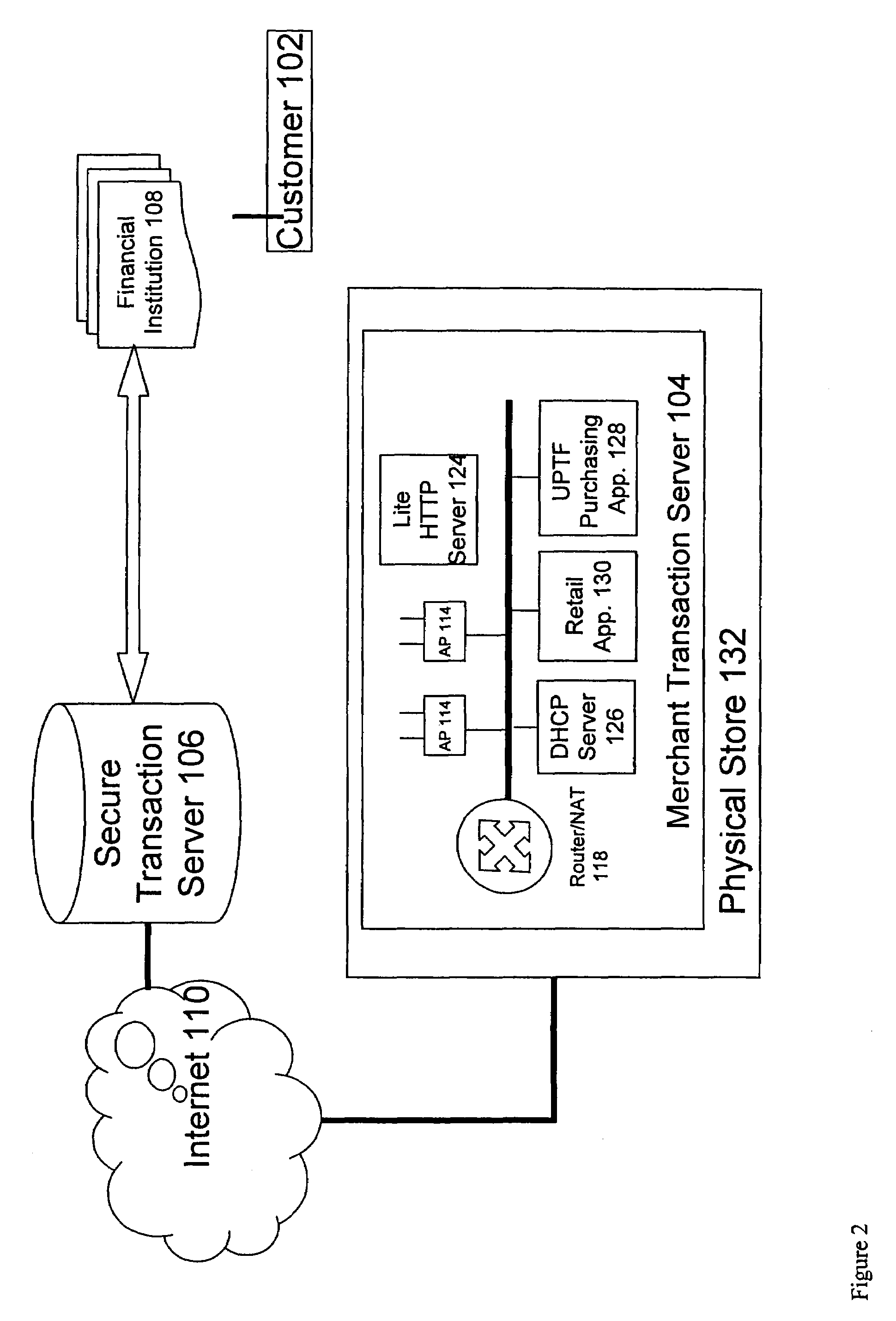
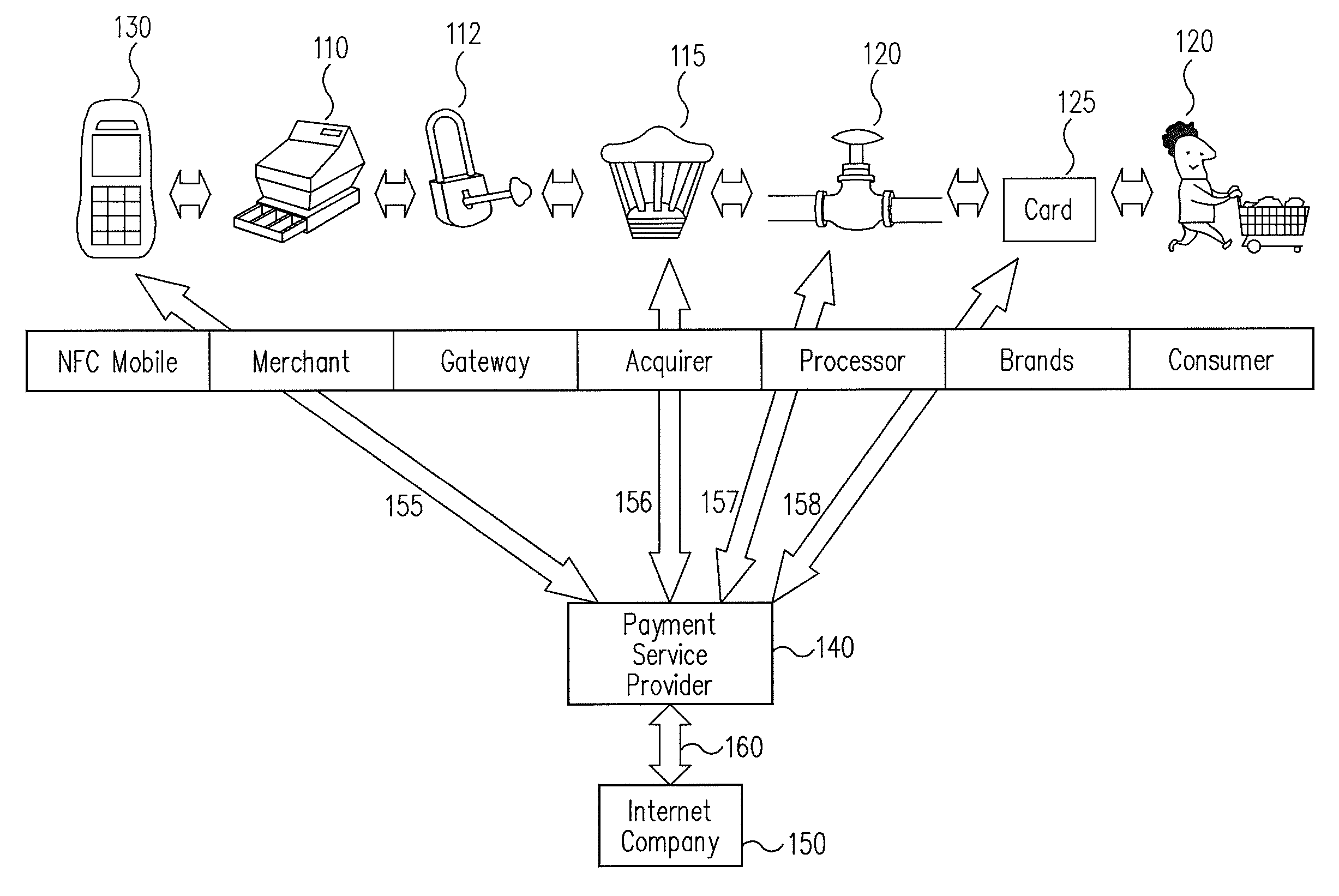
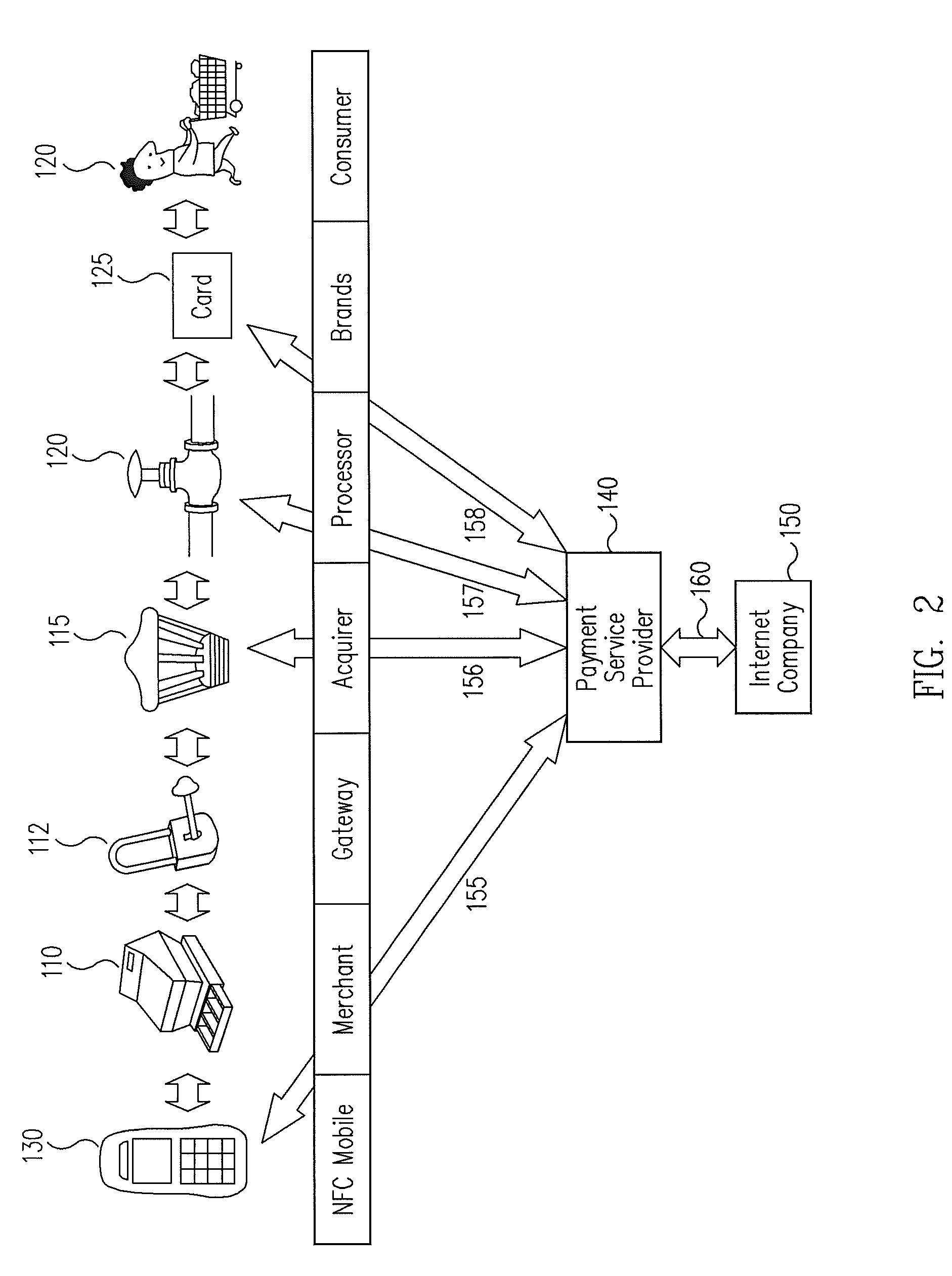
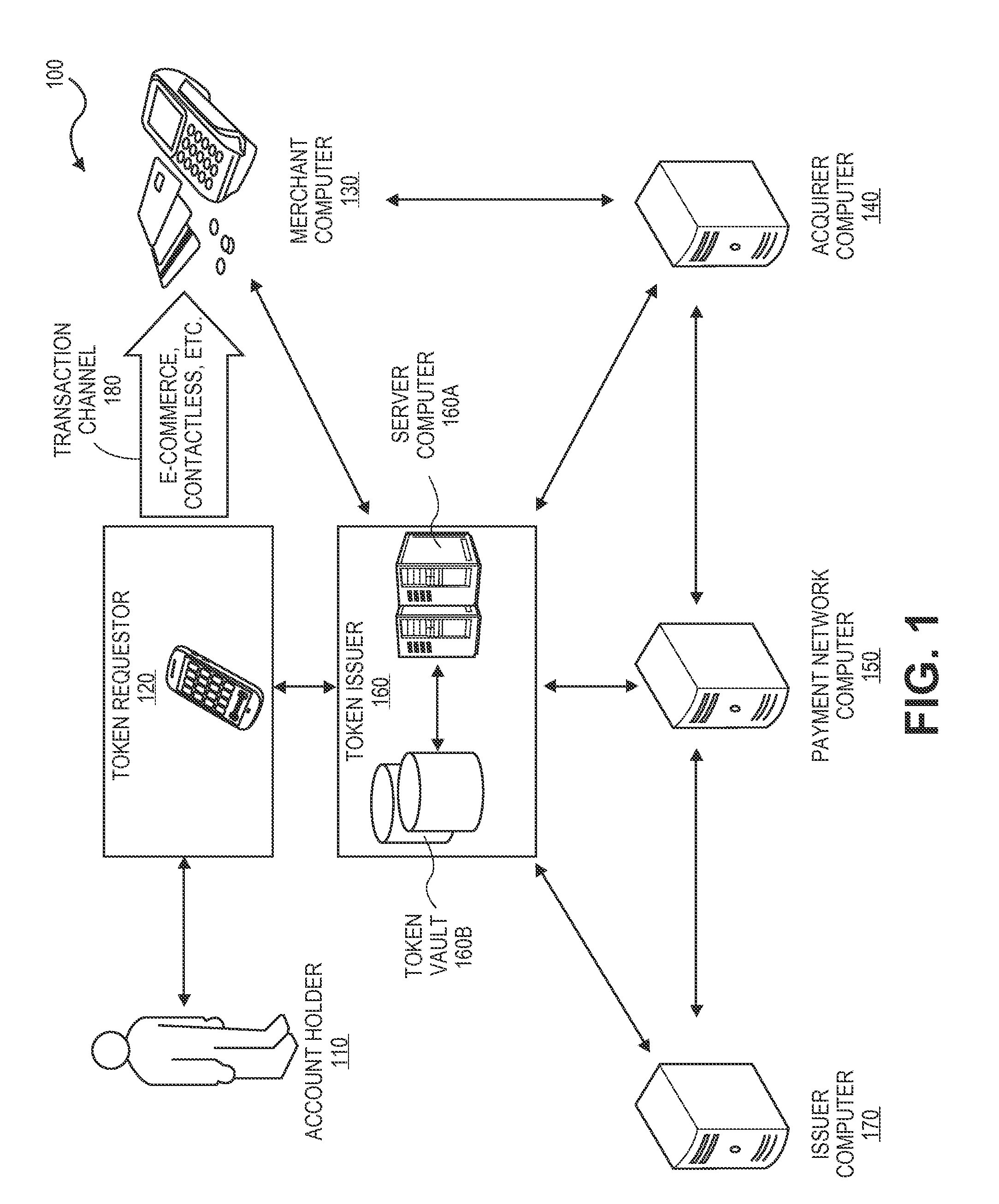
A novel system and methodology for conducting financial and other transactions using a wireless device. Credentials may be selectively issued by issuers such as credit card companies, banks, and merchants to consumers permitting the specific consumer to conduct a transaction according to the authorization given as reflected by the credential or set of credentials. The preferred mechanism for controlling and distributing credentials according to the present invention is through one or more publicly accessible networks such as the Internet wherein the system design and operating characteristics are in conformance with the standards and other specific requirements of the chosen network or set of networks. Credentials are ultimately supplied to a handheld device such as a mobile telephone via a wireless network. The user holding the credential may then use the handheld device to conduct the authorized transaction or set of transactions via, for example, a short range wireless link with a point-of-sale terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
Transactional services
InactiveUS20070198432A1High level of throughputHigh level of efficiencyCryptography processingComputer security arrangementsTransaction serviceDatabase
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
Secure electronic content distribution on CDS and DVDs
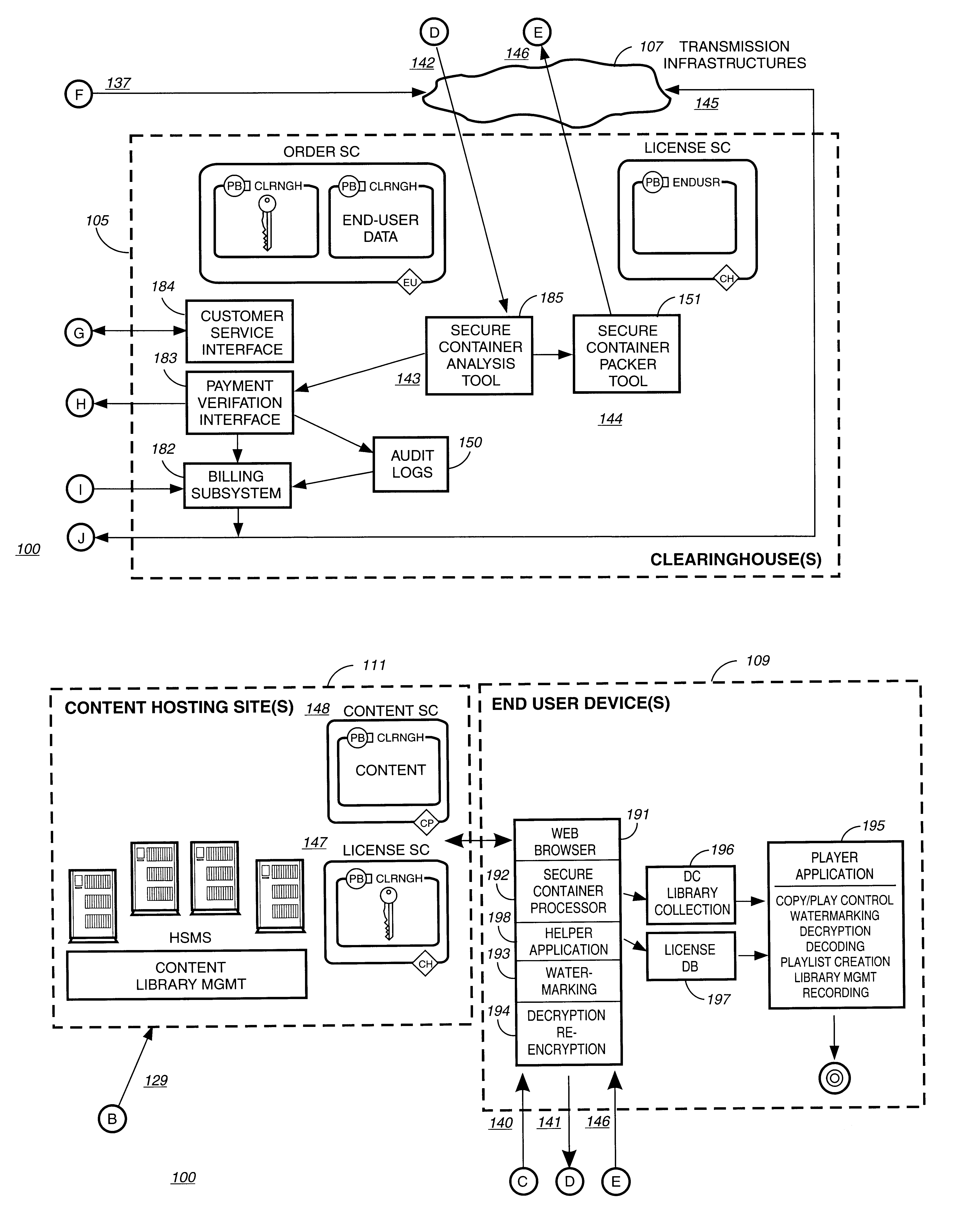
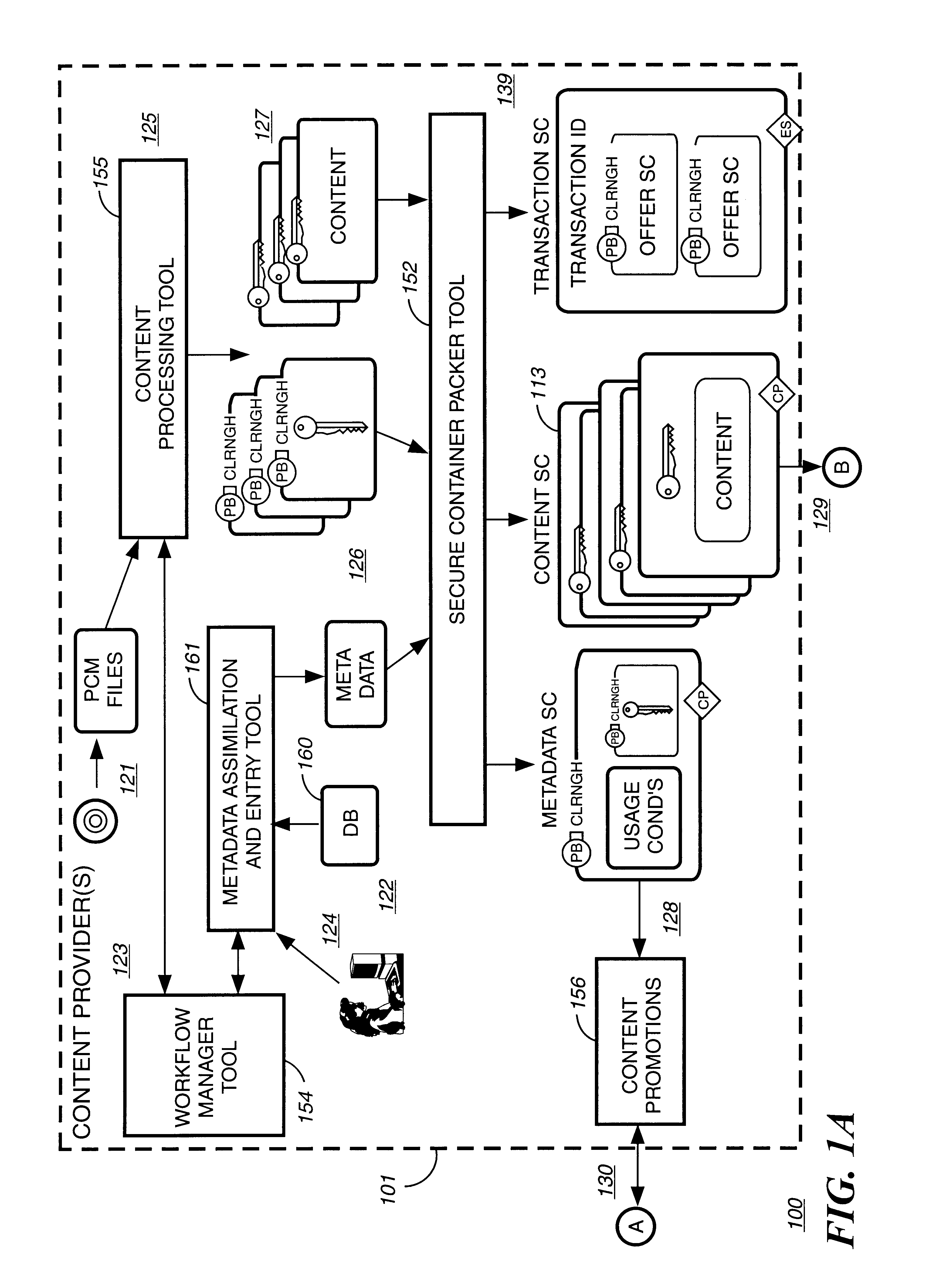
InactiveUS6611812B2Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
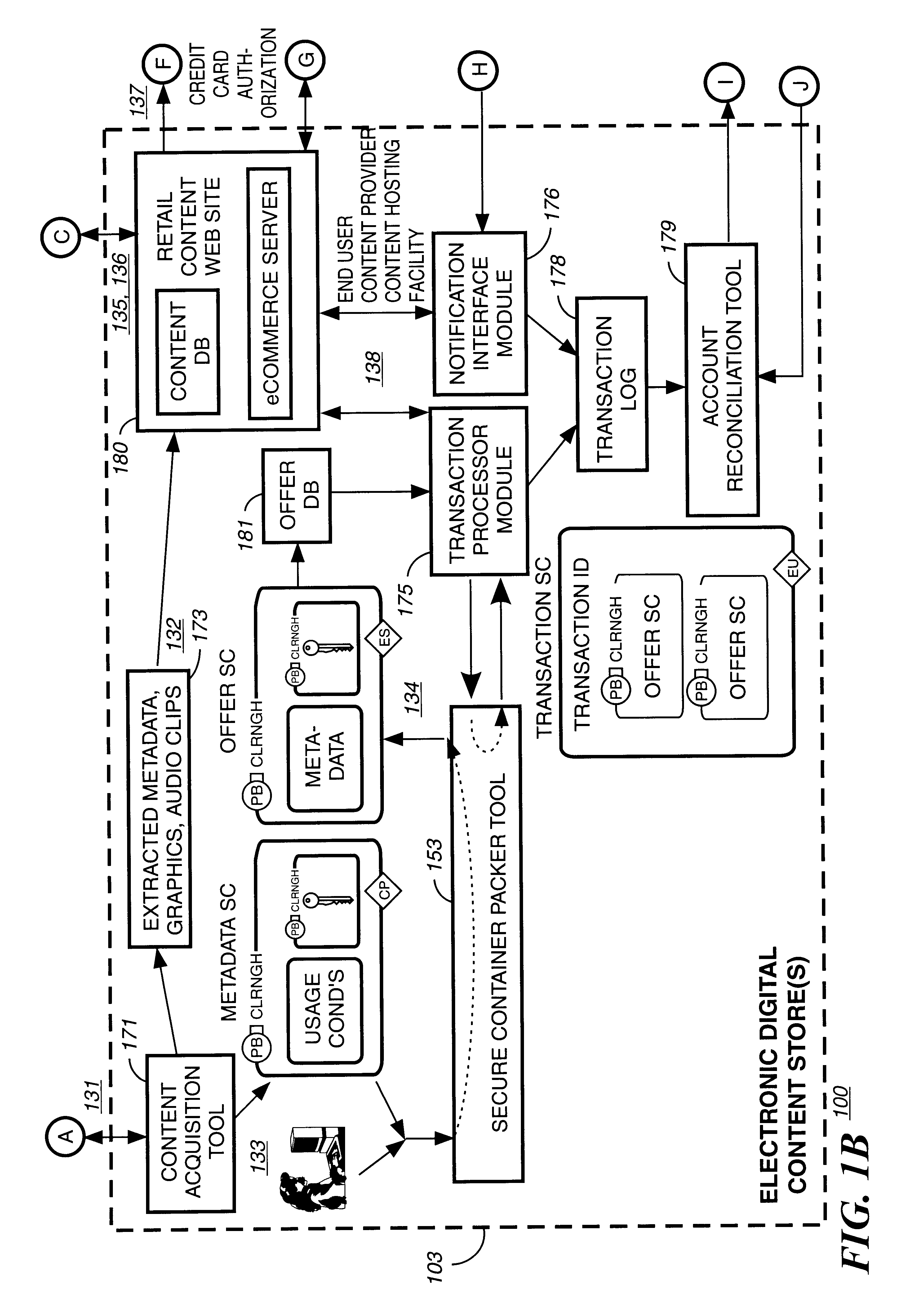
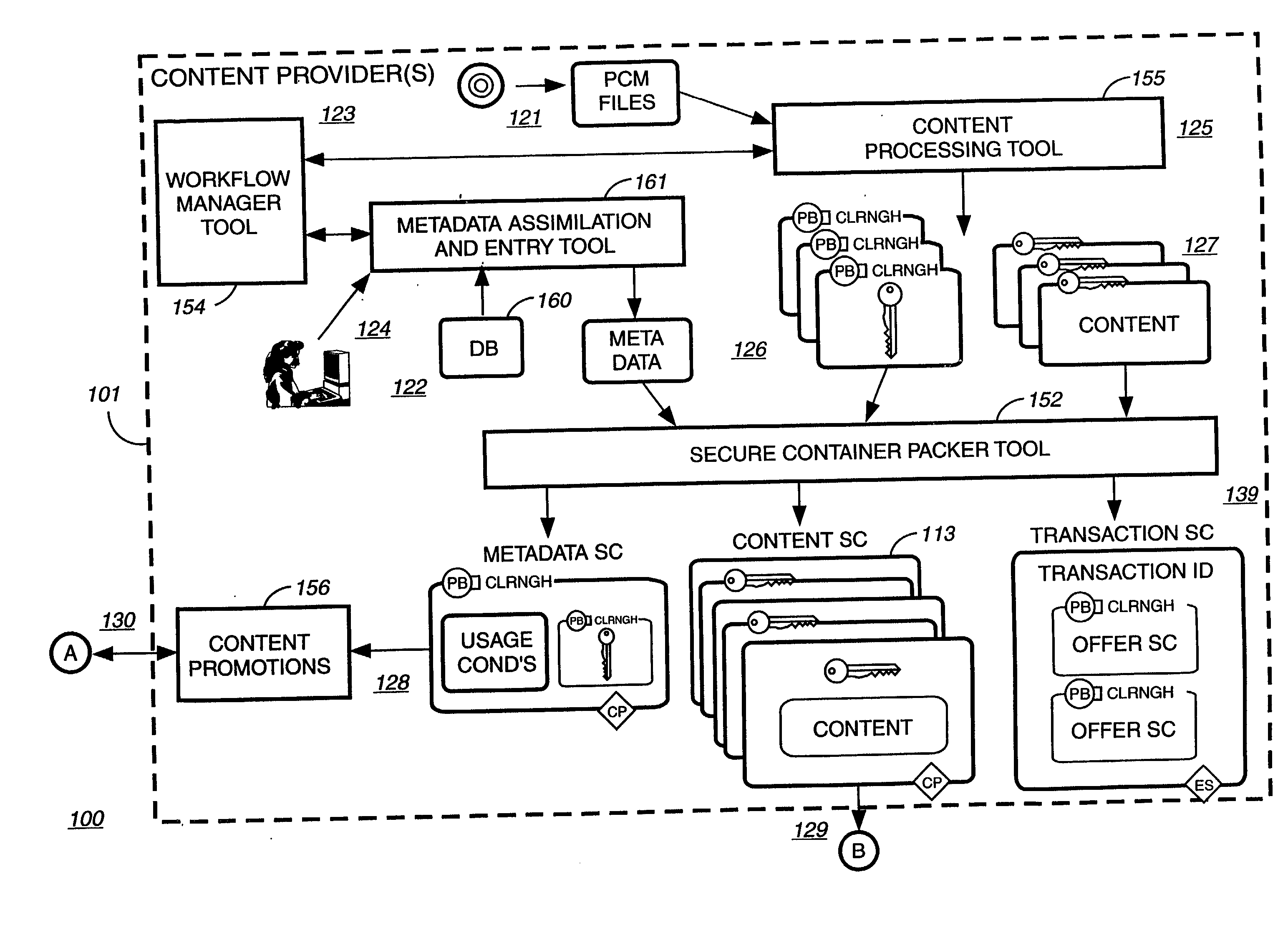
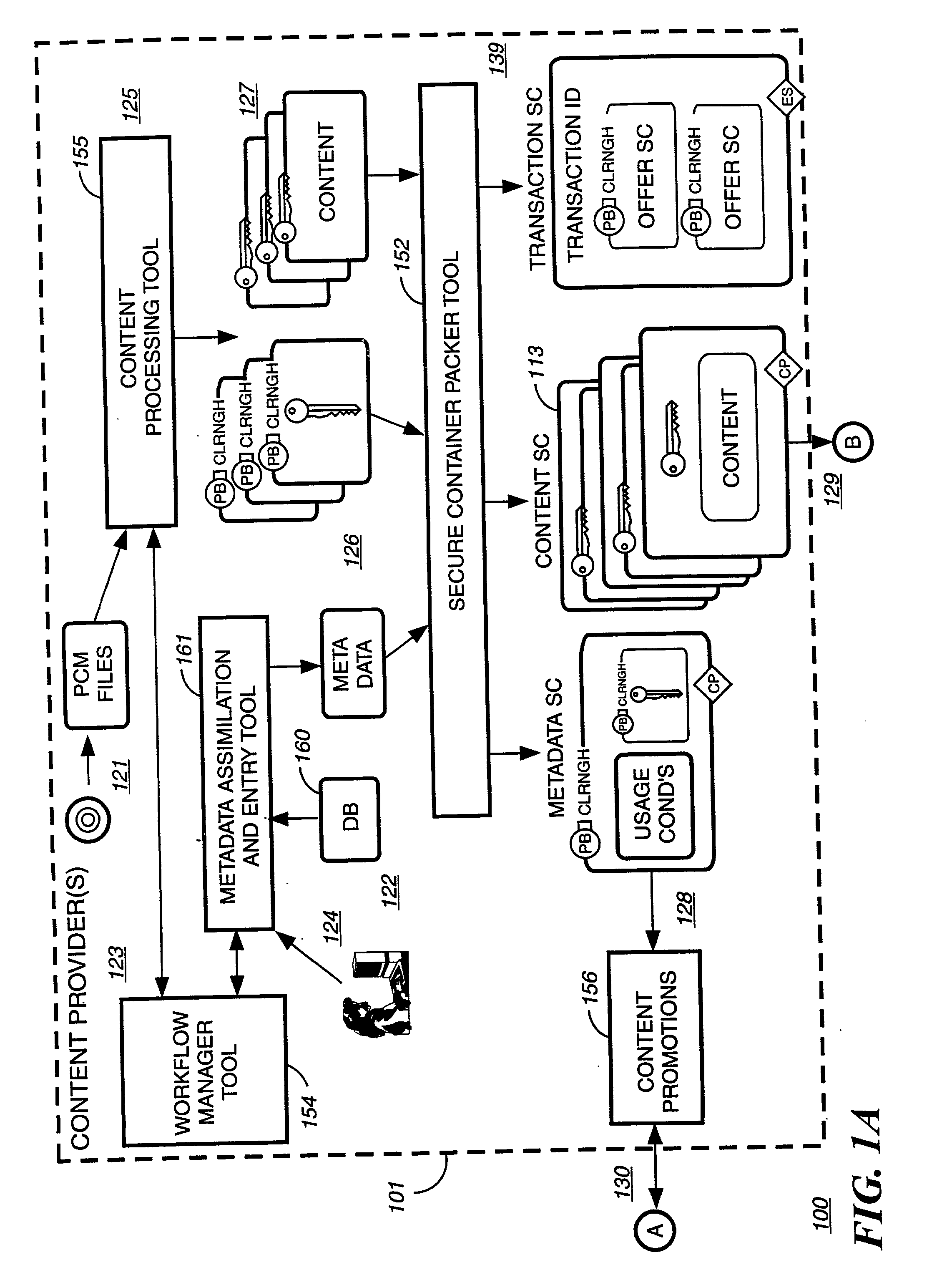
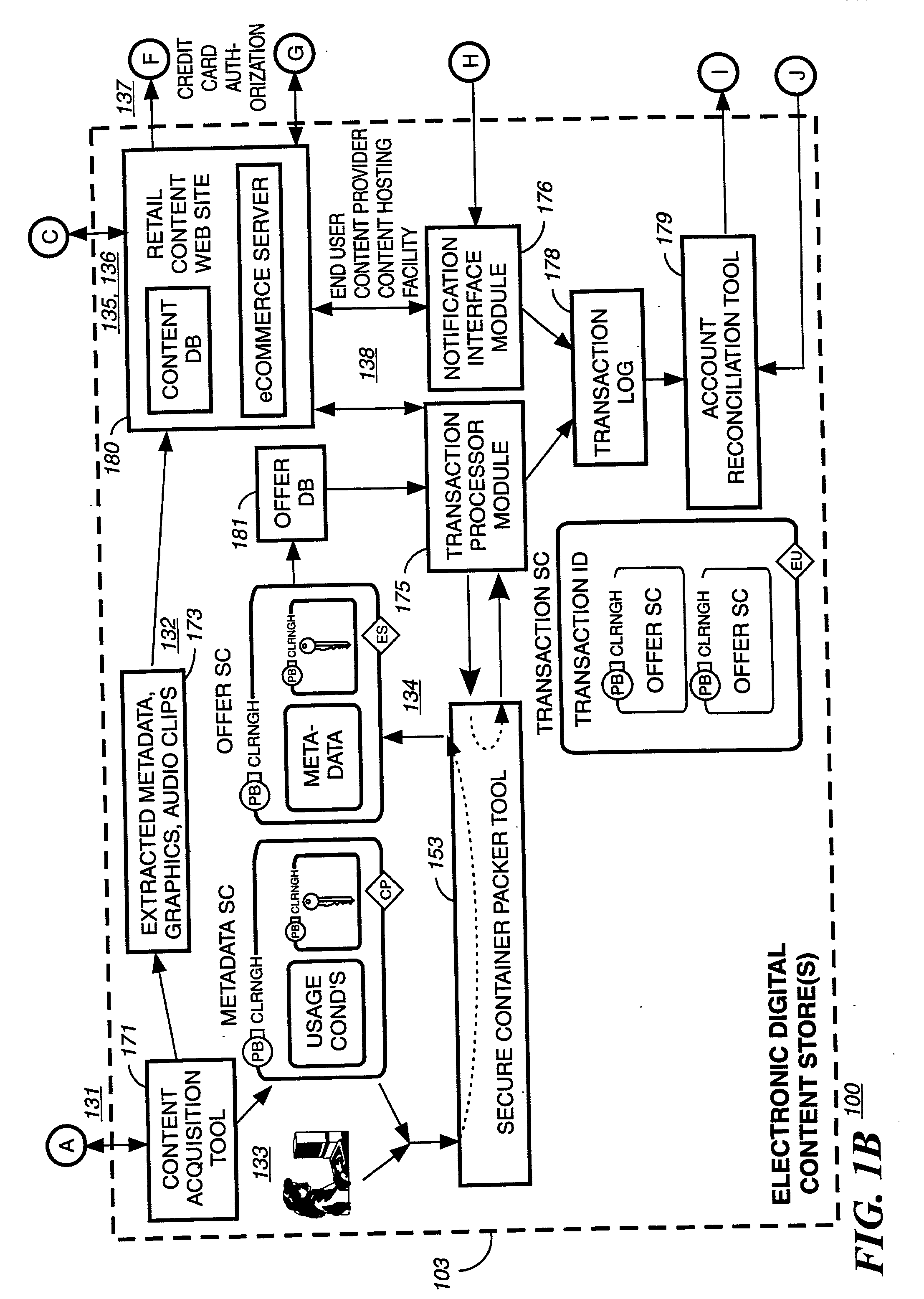
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
Secure interactive electronic account statement delivery system
InactiveUS6285991B1Good flexibilityBilling is thereby complicatedFinanceUser identity/authority verificationDigital dataNetwork communication
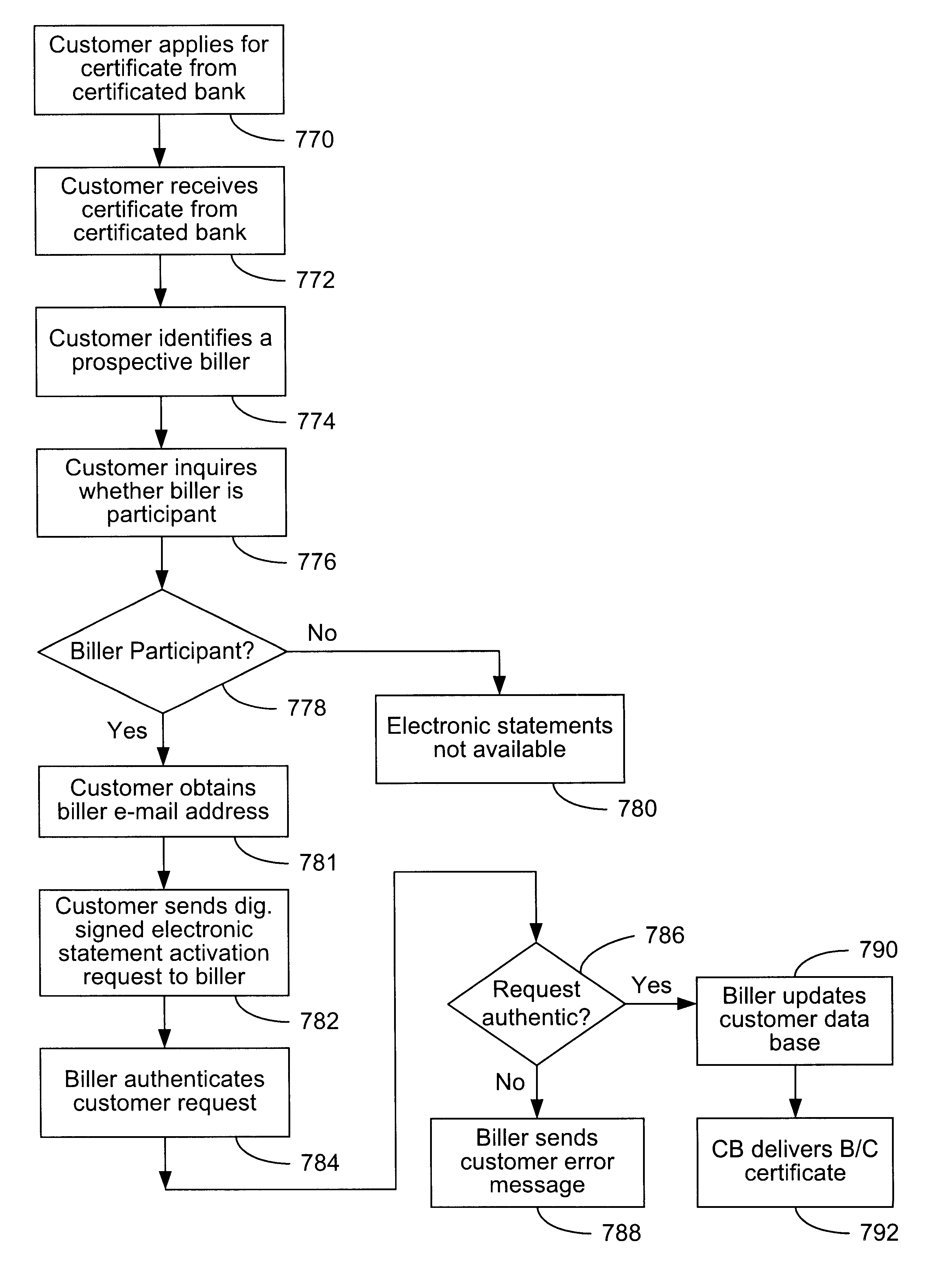
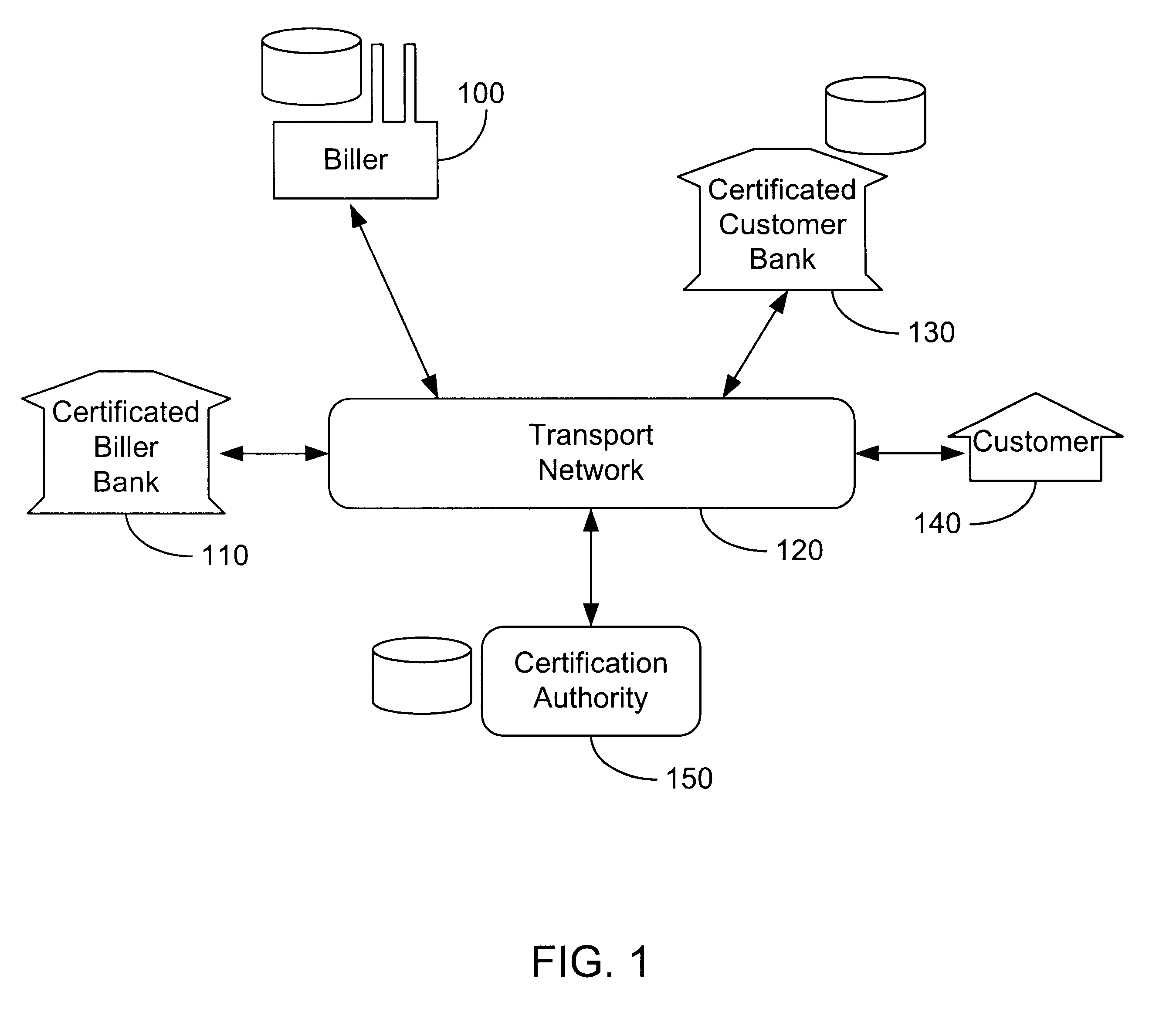
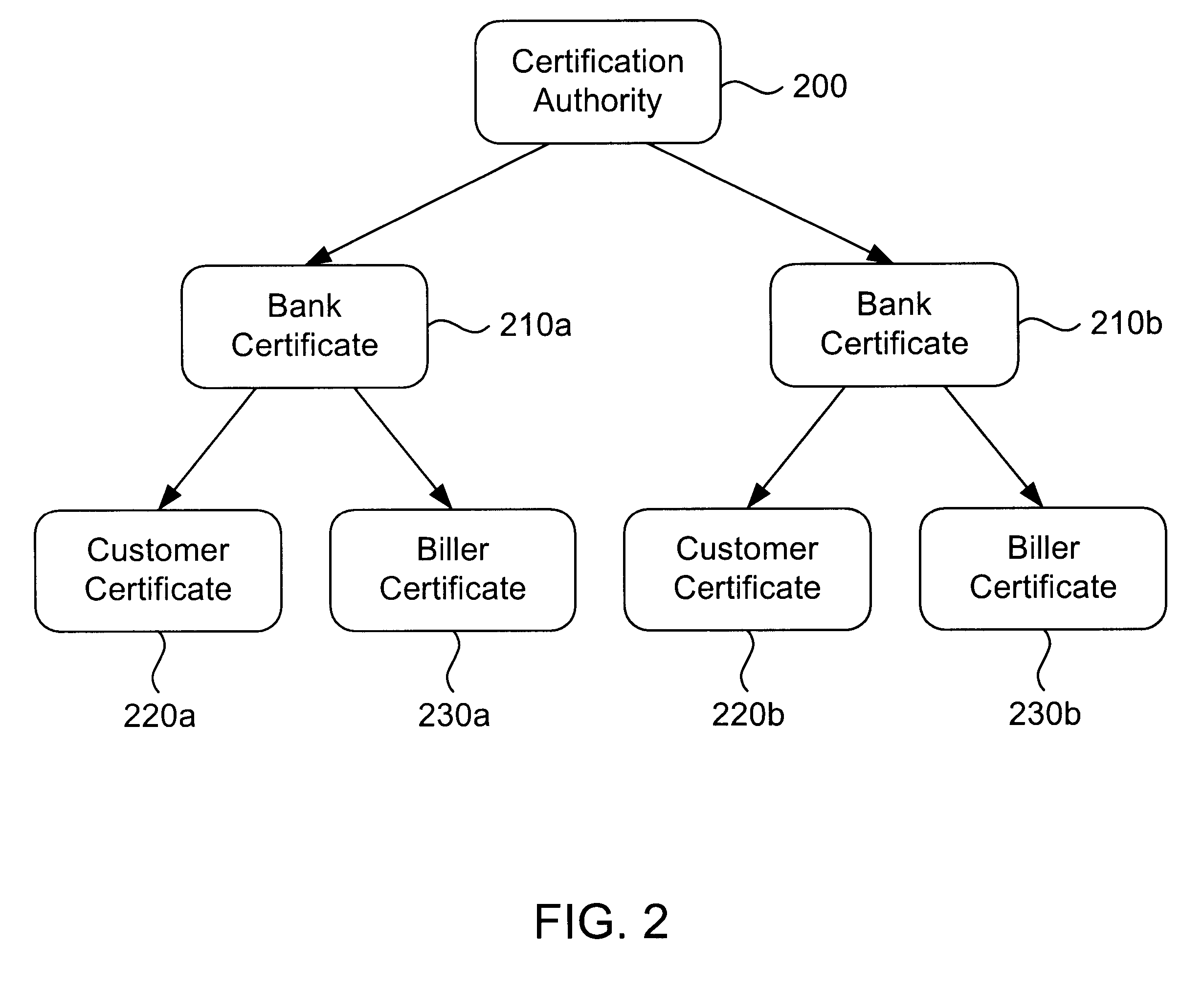
The present invention consists of a secure interactive electronic account statement delivery system suitable for use over open networks such as the Internet. The invention utilizes a certification hierarchy to insure that electronic bills, invoices, and other account statements can be securely sent over open networks. The participants in the system are a certification authority, certificated banks, billers, and customers. The certification authority grants digital certificates to the certificated banks, which in turn grant digital certificates to billers and customers. Digital certificates form the basis for encryption and authentication of network communications, using public and private keys. The certificates associate a customer and biller with a certificated bank and with the electronic billing system, much like payment cards associate a customer with a payment card issuer and a particular payment card system. Digital signatures are used for authentication and non-repudiation. The certificates may be stored as digital data on storage media of a customer's or biller's computer system, or may be contained in integrated circuit or chip cards physically issued to billers and customers. The electronic bill itself may be a simple text message containing the equivalent of summary information for the bill, or may be more elaborate. In one embodiment of the invention, the electronic bill contains a number of embedded links, for example an embedded URL of a biller's world wide web server that allows the customer to interactively bring up detailed billing information by activating the link. The e-mail message may also include links to third party websites.
Owner:VISA INT SERVICE ASSOC
Methods for purchasing of goods and services
InactiveUS7349871B2Risk minimizationReducing credit card fraudPayment circuitsElectronic credentialsThird partyPurchasing
Owner:PCMS HOLDINGS INC
Digital content distribution using web broadcasting services
InactiveUS20030135464A1Website content managementElectronic credentialsBroadcast channelsDigital content
A method of securely receiving data on a user's system from a web broadcast infrastructure with a plurality of channels. The method comprising the steps of: receiving promotional metadata from a first web broadcast channel, the promotional metadata related to data available for reception; assembling at least part of the promotional metadata into a promotional offering for review by a user; selecting by a user, data to be received related to the promotional metadata; receiving data from a second web broadcast channel, the data selected from the promotional metadata, and wherein the data has been previously encrypted using a first encrypting key; and receiving the first decrypting key via a computer readable medium, the first decrypting key for decrypting at least some of the data received via the second web broadcast channel. In another embodiment, a method and system to transmit data securely from a web broadcast center is disclosed.
Owner:IBM CORP
System and method for controlling access rights to and security of digital content in a distributed information system, e.g., Internet
InactiveUS6098056AKey distribution for secure communicationPublic key for secure communicationPersonalizationThe Internet
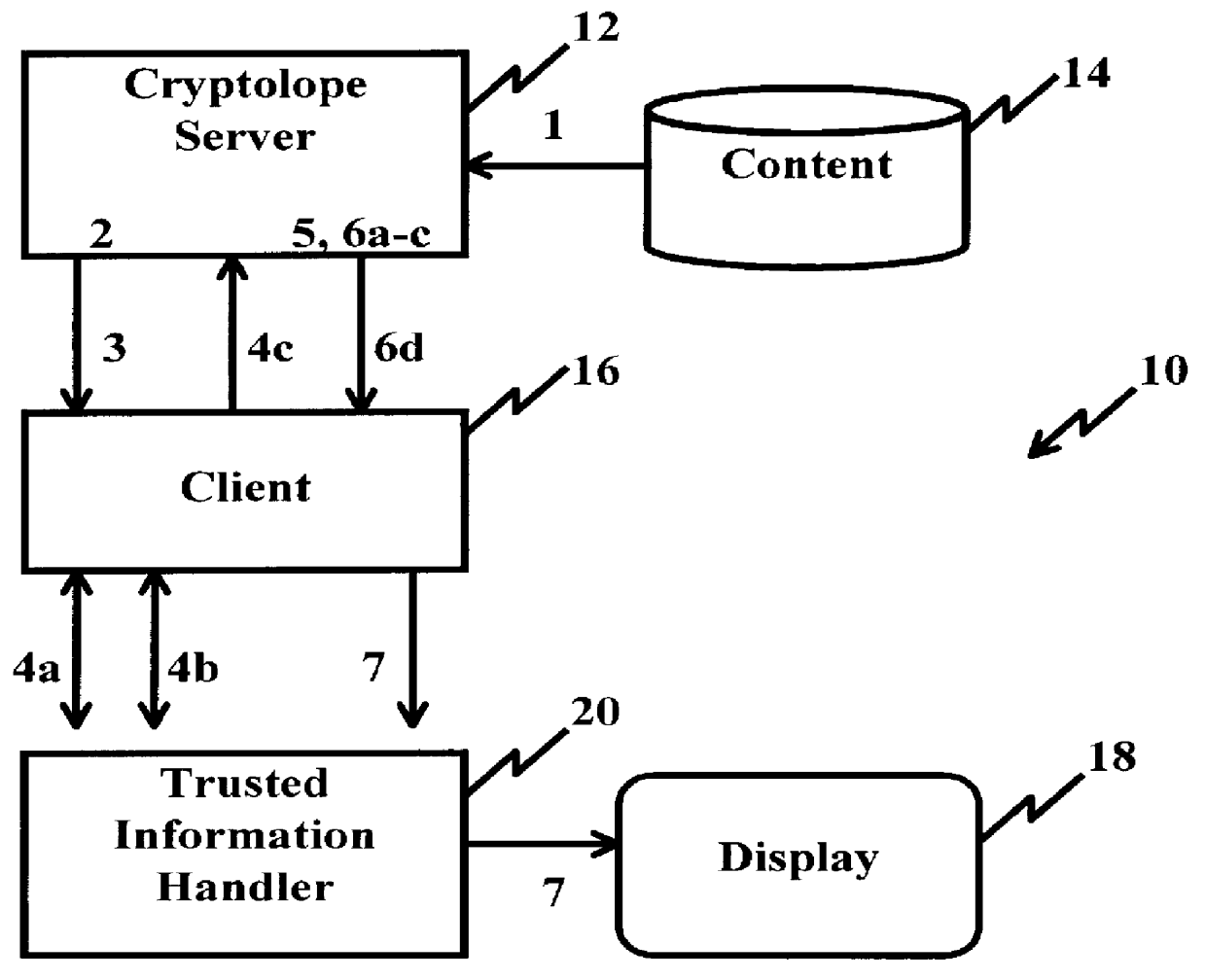
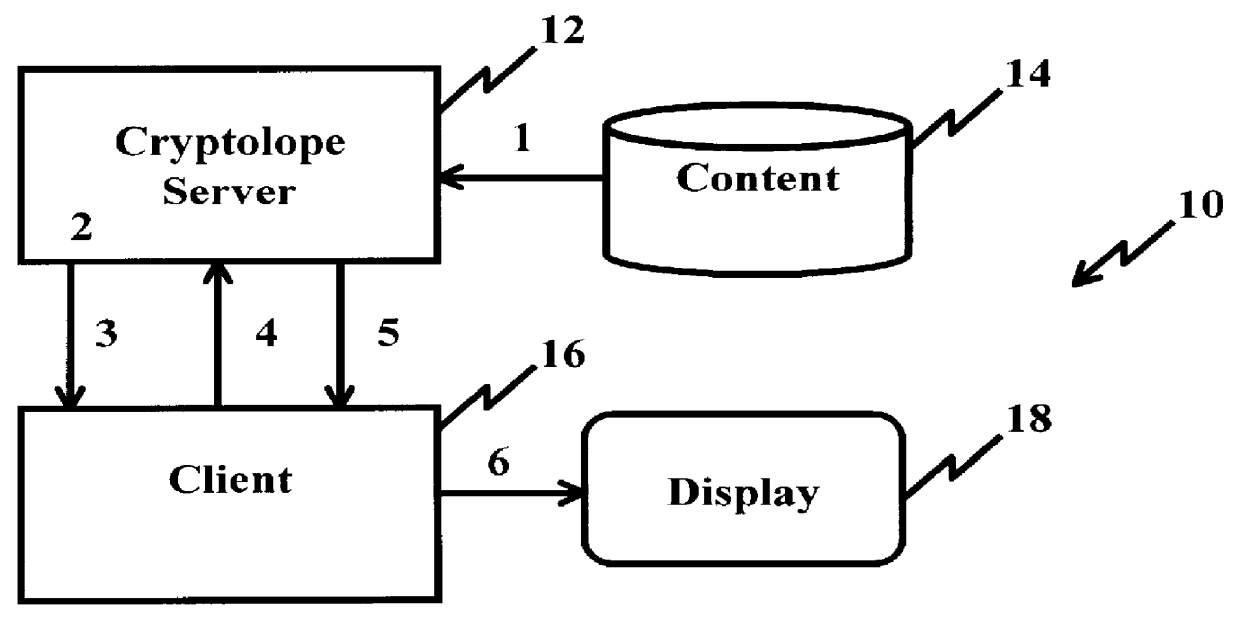
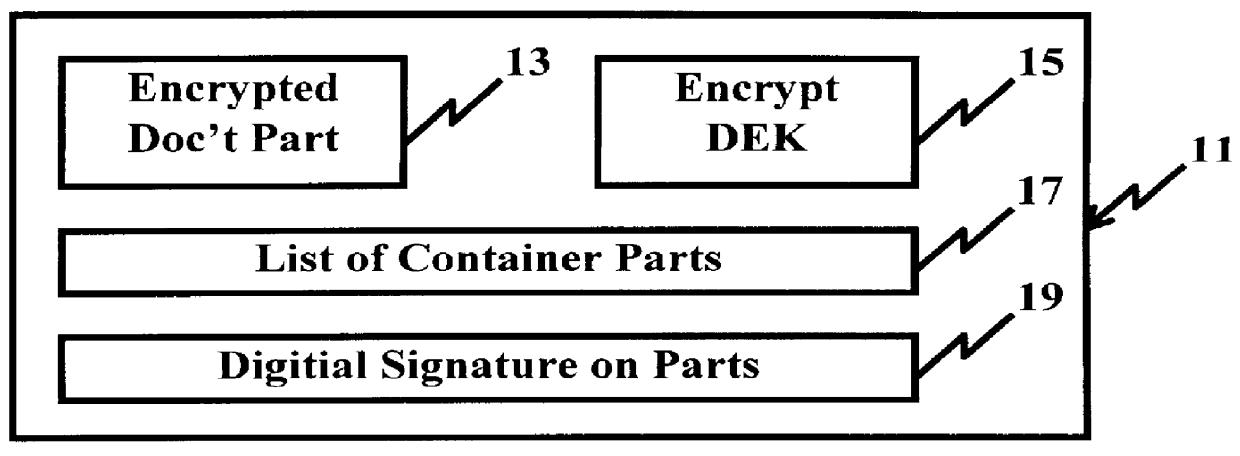
A system and method for limiting access to and preventing unauthorized use of an owner's digital content stored in an information network and available to clients under authorized conditions. The network includes at least one server coupled to a storage device for storing the limited access digital content encrypted using a random-generated key, known as a Document Encryption Key (DEK). The DEK is further encrypted with the server's public key, using a public / private key pair algorithm and placed in a digital container stored in a storage device and including as a part of the meta-information which is in the container. The client's workstation is coupled to the server for acquiring the limited access digital content under the authorized condition. A Trusted Information Handler (TIH) is validated by the server after the handler provides a data signature and type of signing algorithm to transaction data descriptive of the purchase agreement between the client and the owner. After the handler has authenticated, the server decrypts the encrypted DEK with its private key and re-encrypts the DEK with the handler's public key ensuring that only the information handler can process the information. The encrypted DEK is further encrypted with the client's public key personalizing the digital content to the client. The client's program decrypts the DEK with his private key and passes it along with the encrypted content to the handler which decrypts the DEK with his private key and proceeds to decrypt the content for displaying to the client.
Owner:ACTIVISION PUBLISHING
Method and system for a virtual safe
Owner:SARCANIN BRANKO
Biometric authentication of mobile financial transactions by trusted service managers
ActiveUS20090307139A1Digital data processing detailsUser identity/authority verificationUser inputFinancial transaction
A method for authenticating a financial transaction at a point of sale (POS) includes storing an application program in a first secure element of a mobile phone. The application is configured to generate instruction codes to effect the financial transaction upon verification of a user's identity. The user's credentials are stored in a second SE of the phone, which is operable to verify the user's identity from a biometric trait of the user input to the phone and to generate data authenticating the financial transaction in response to the verification of the user's identity. At the POS, the user invokes the application and then inputs a biometric trait to the phone. The second SE verifies the user's identity, and upon verification, generates data authenticating the transaction. The financial transaction data, including the instruction codes and the authenticating data, are then transmitted from the phone to the POS.
Owner:PAYPAL INC
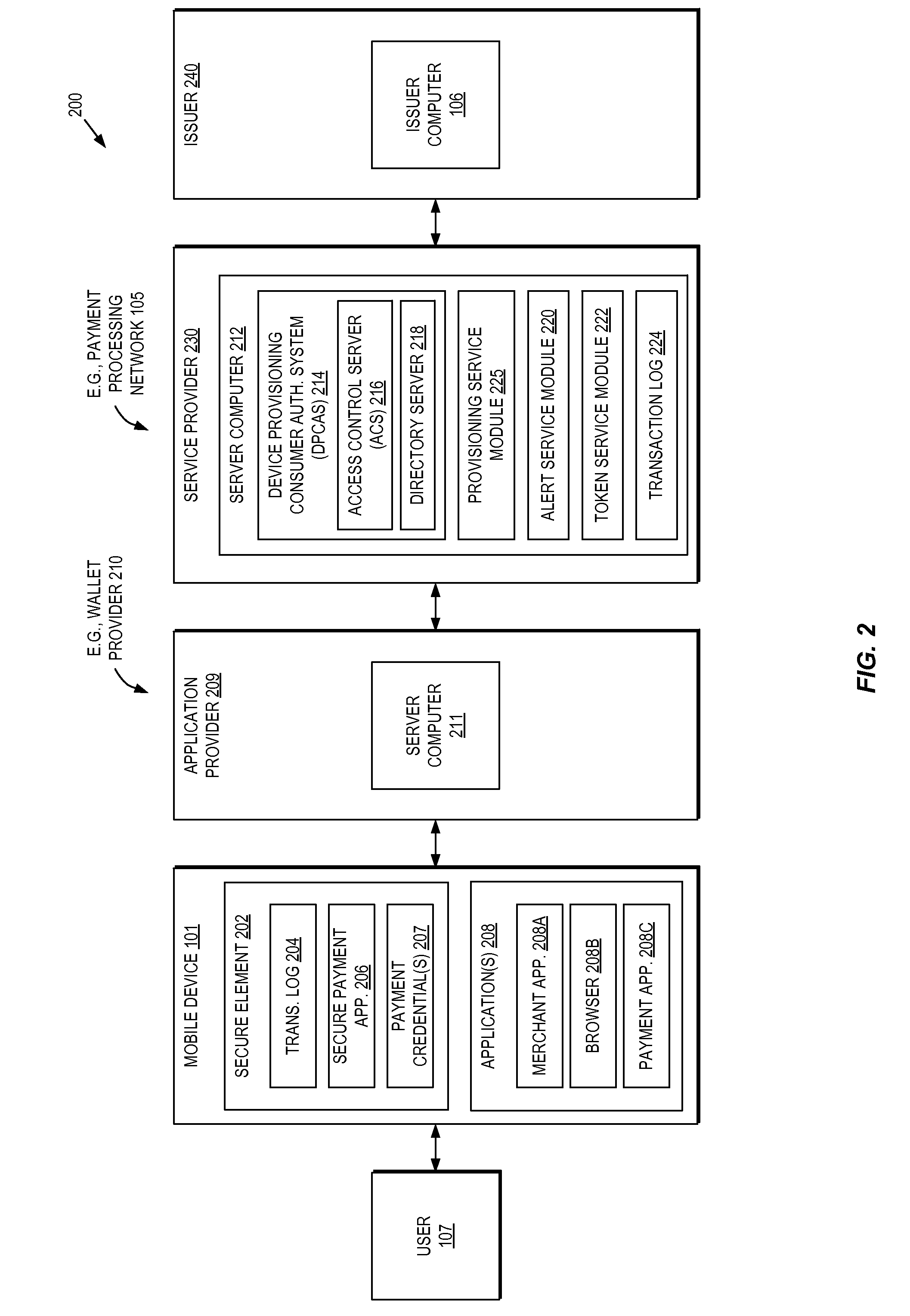
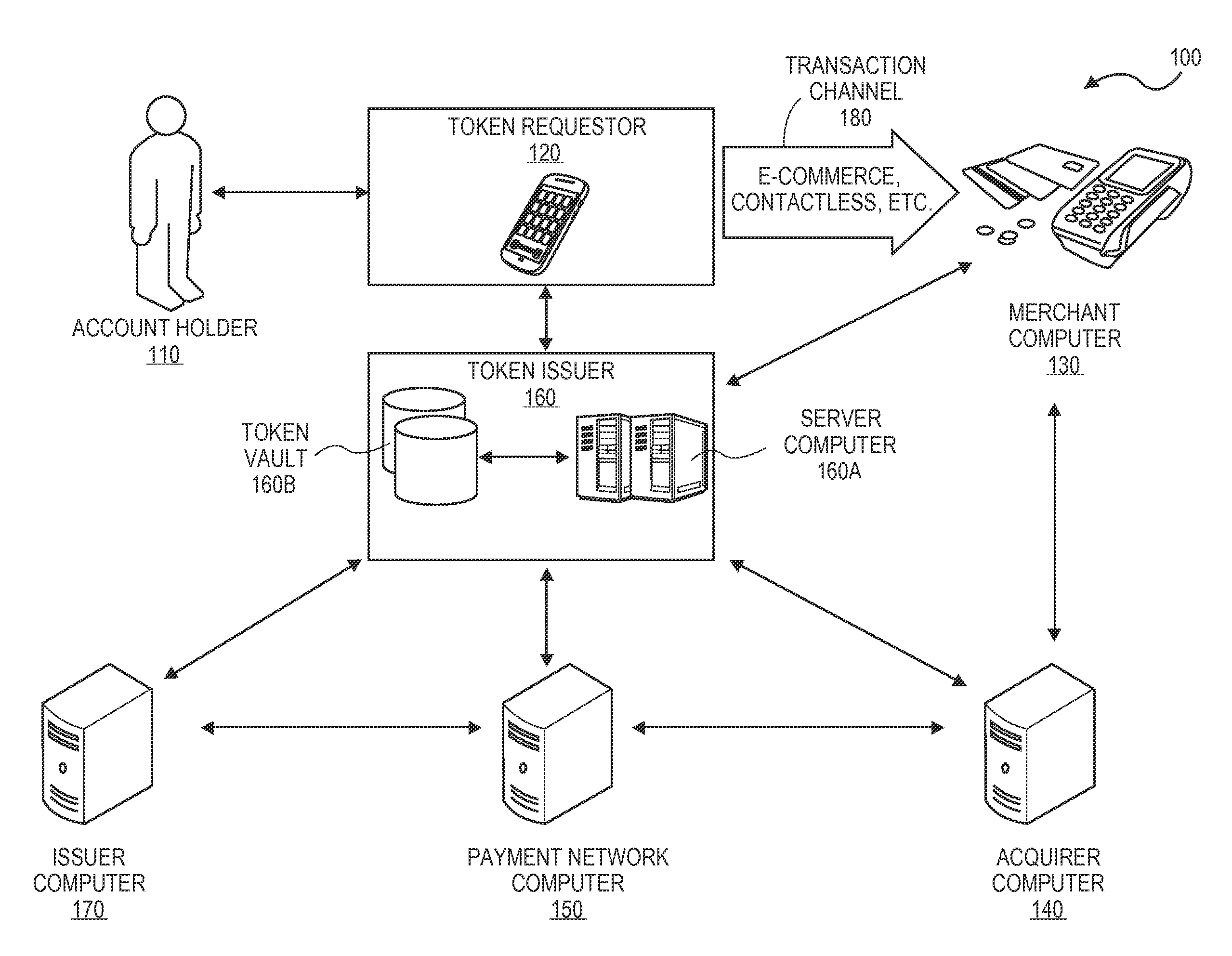
Methods and systems for provisioning mobile devices with payment credentials
ActiveUS20150046339A1Unnecessary delayProcessing speedFinanceElectronic credentialsPaymentMedium Risk
Embodiments are described that are directed to optimizing the provisioning of payment account credentials to mobile devices utilizing mobile wallets. In some embodiments, one of multiple provisioning schemes may be selectively chosen for payment account credential provisioning based upon a determined risk involved with a particular provisioning request. A low risk provisioning request leads to an immediate provisioning of a payment credential, whereas a provisioning request of high risk results in the provisioning request being denied. In some embodiments, medium risk provisioning requests will cause an additional user authentication to be performed before the payment account provisioning is finalized. The additional user authentication may occur using a separate communication channel than the channel in which the provisioning request was received.
Owner:VISA INT SERVICE ASSOC
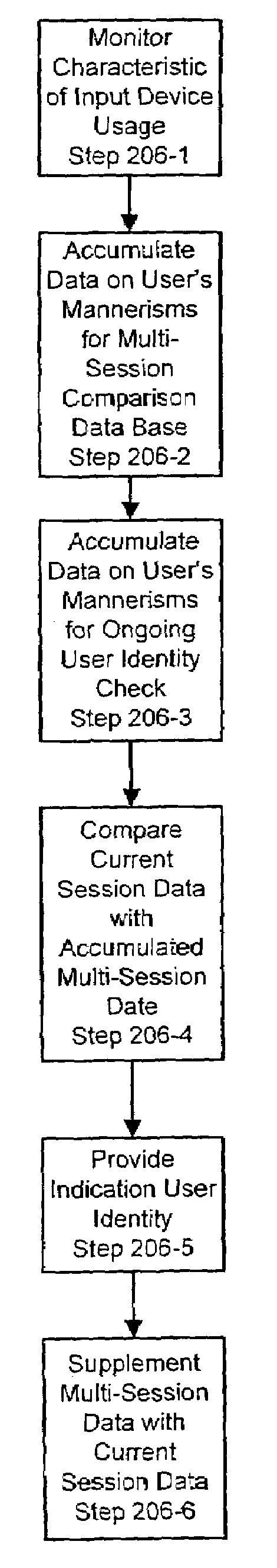
Systems and methods for user identification, user demographic reporting and collecting usage data usage biometrics
InactiveUS7260837B2Digital data information retrievalDigital data processing detailsData setDatabase server
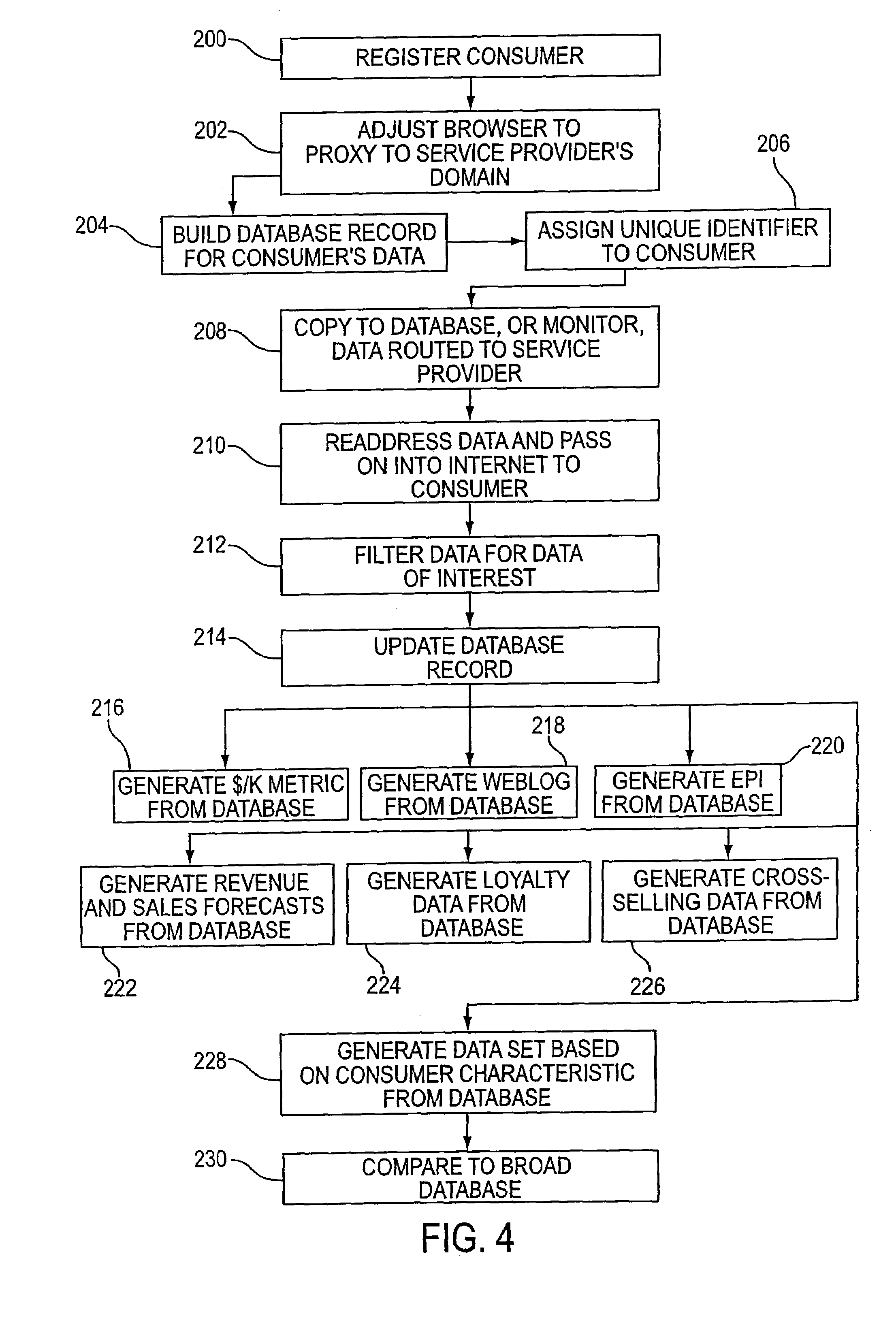
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE
Identification and management of fraudulent credit/debit card purchases at merchant ecommerce sites
ActiveUS7263506B2Reduce exposureFinanceBuying/selling/leasing transactionsE-commerceFinancial transaction
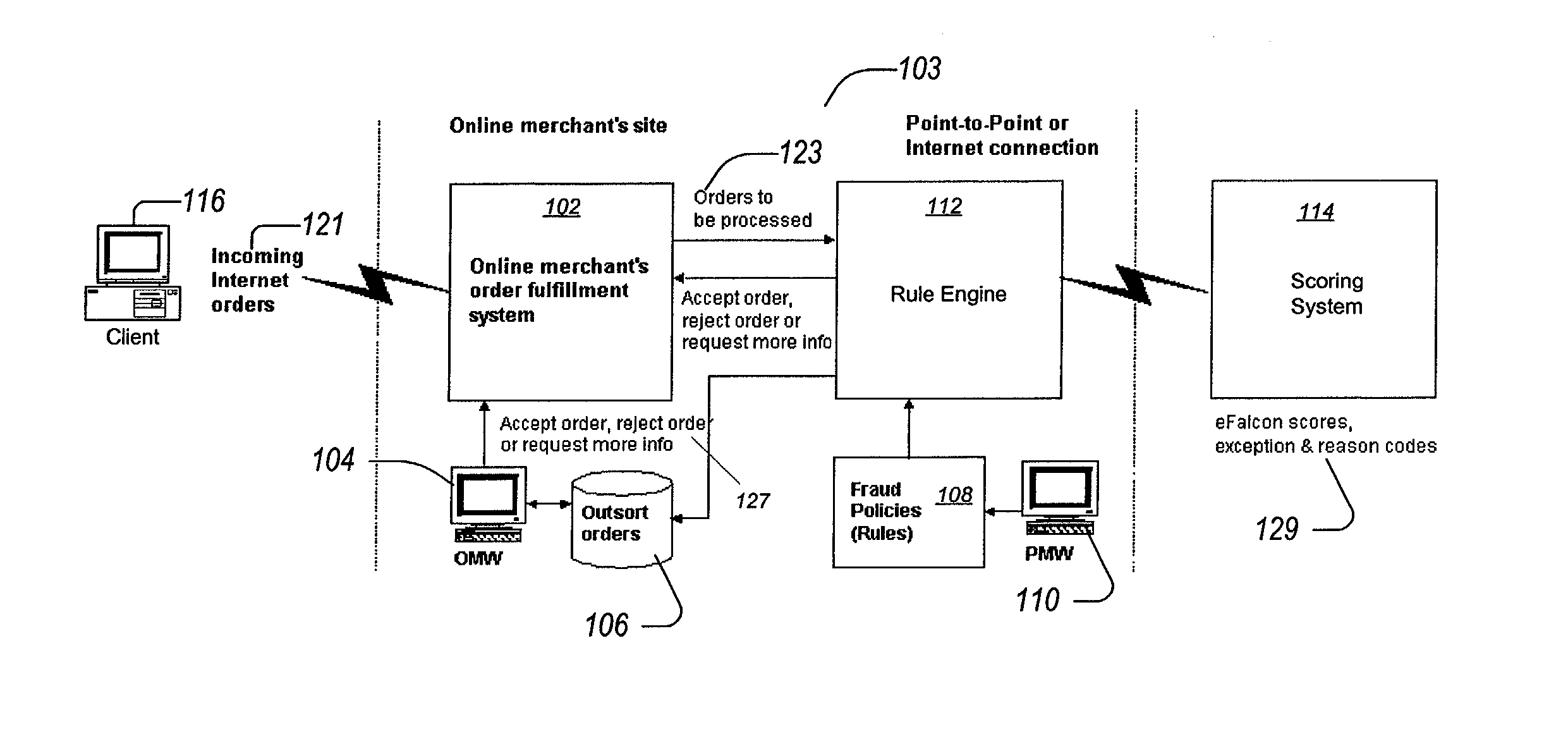
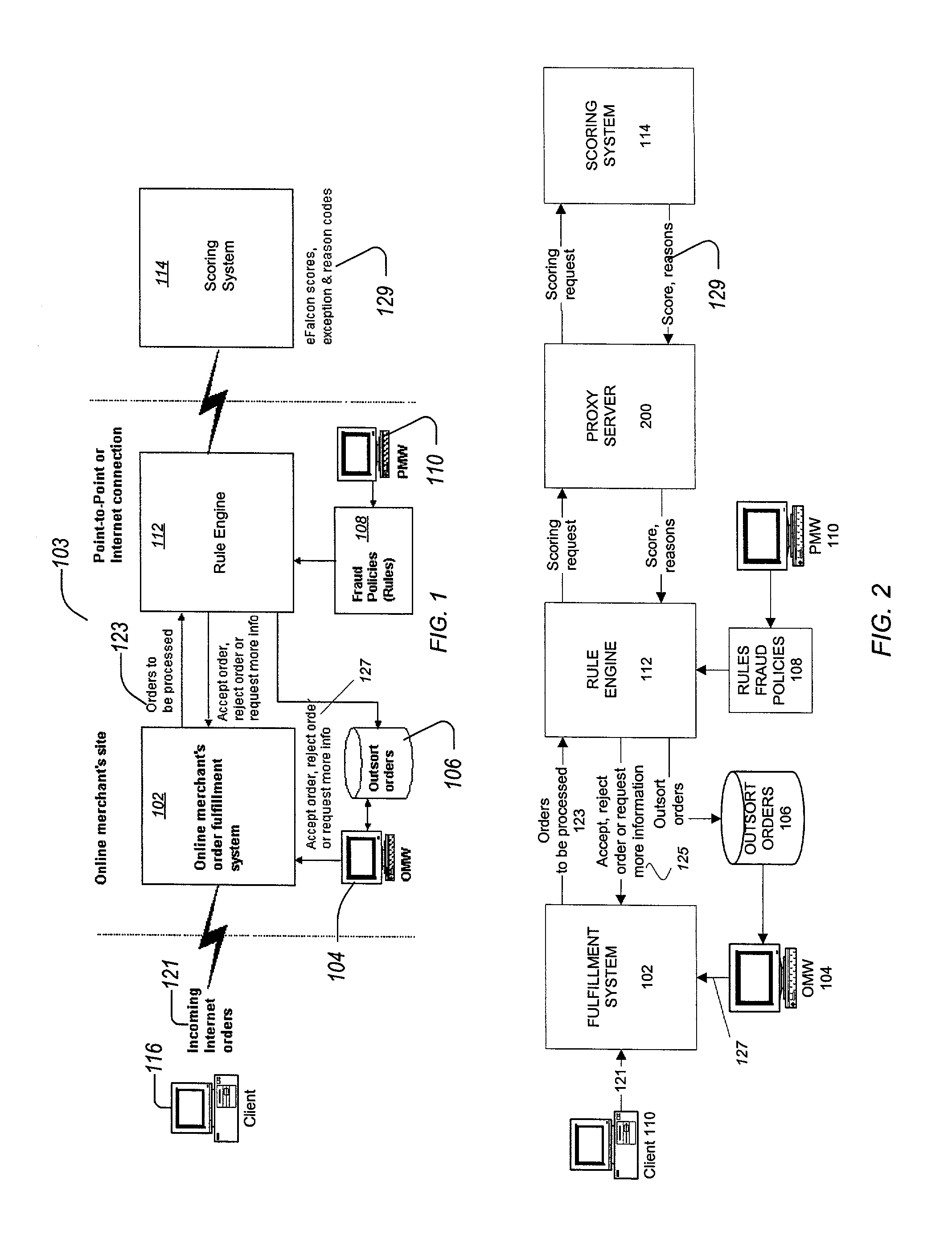
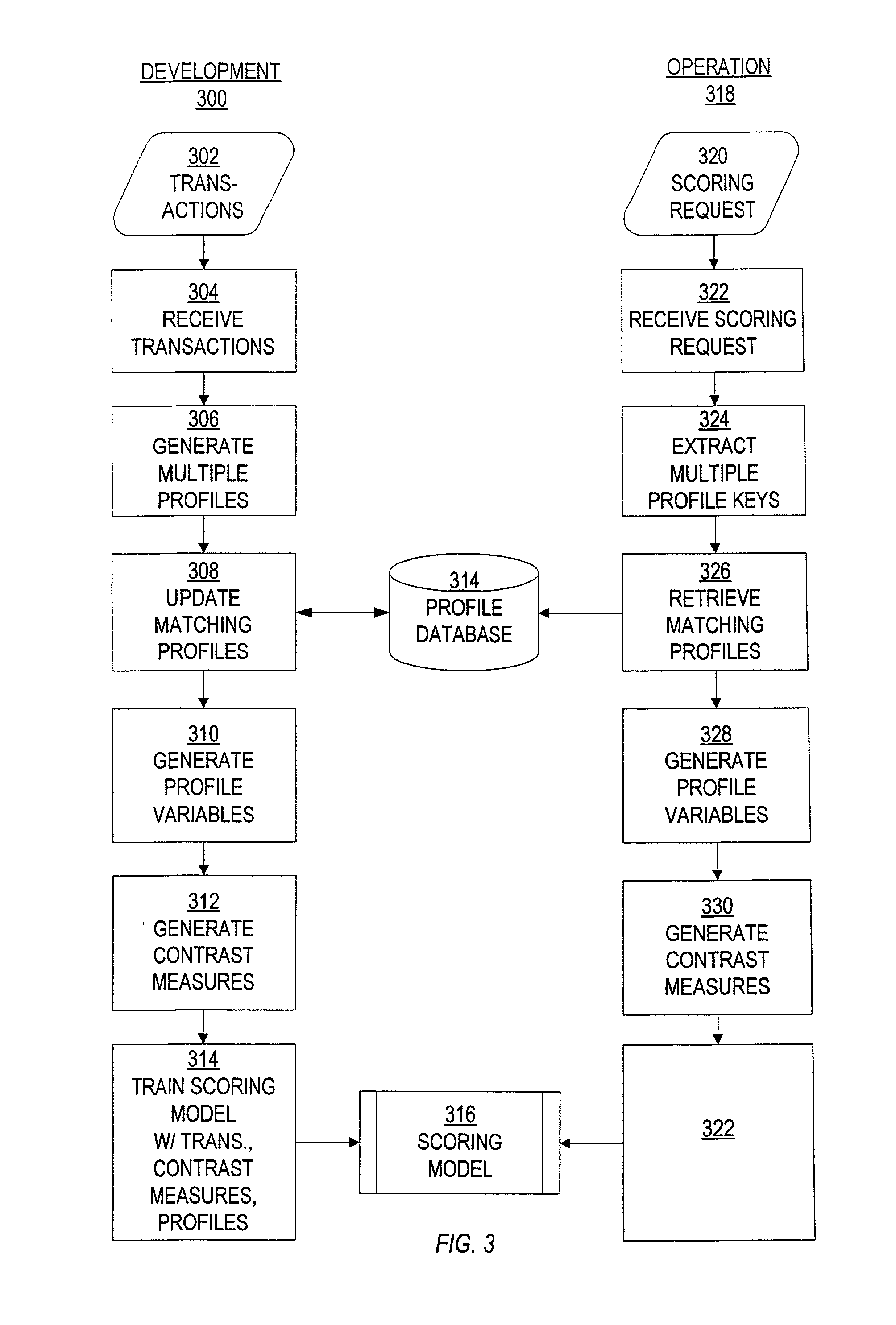
Transaction processing of online transactions at merchant sites determines the likelihood that such transactions are fraudulent, accounting for unreliable fields of a transaction order, which fields do not reliably identify a purchaser. A scoring server using statistical model uses multiple profiles associated with key fields, along with weights to indicate the degree to which the profiles identify the purchaser of the transaction.
Owner:FAIR ISAAC & CO INC
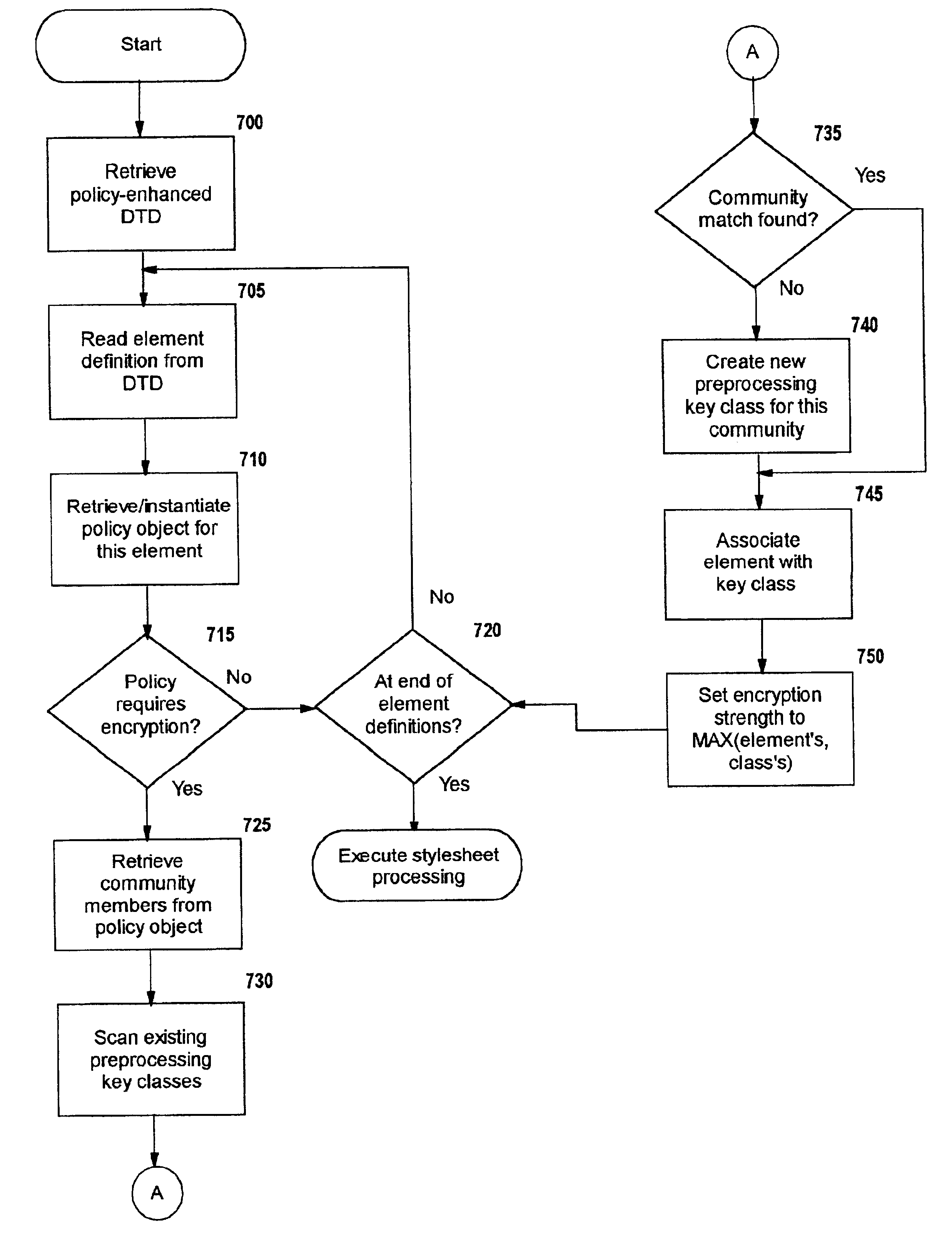
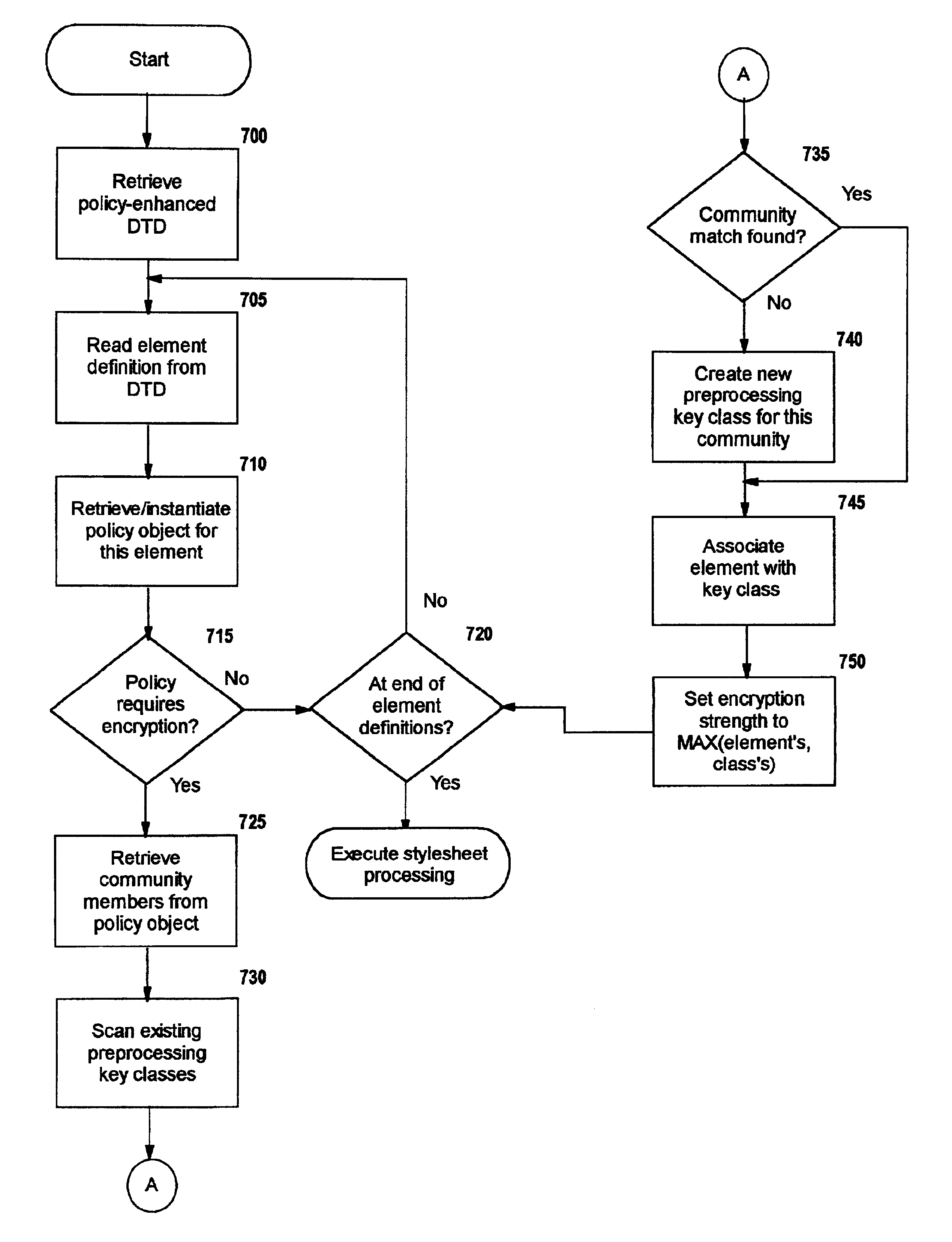
Selective data encryption using style sheet processing
InactiveUS6931532B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
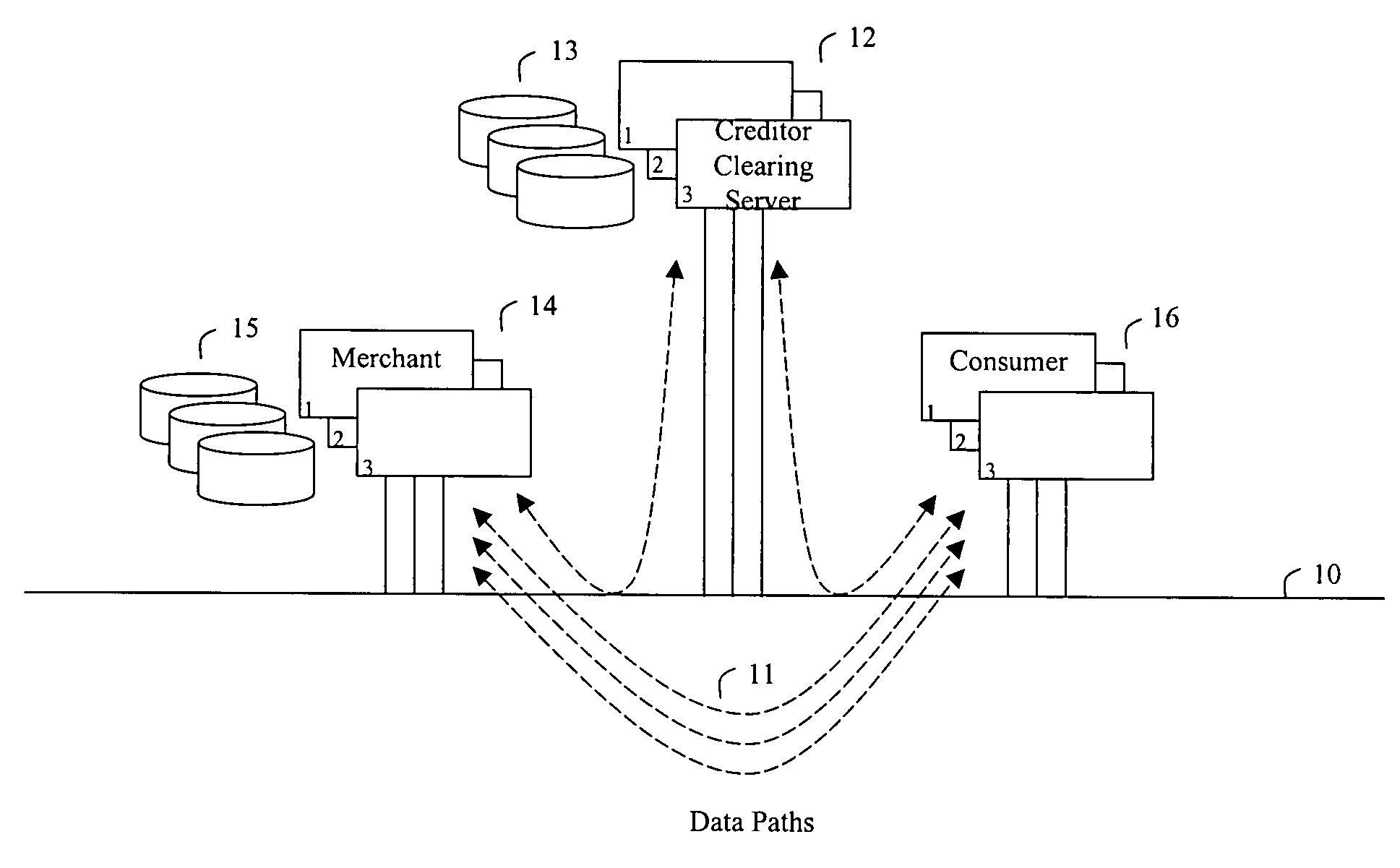
Method and apparatus for making secure electronic payments
InactiveUS7734527B2Addressing slow performanceNo network overheadFinanceVisual presentationPaymentThe Internet
In accordance with the present invention, a consumer communicates a request for purchase of goods and services to a merchant, the goods and / or services being selected from these listed together with their price quotes on the merchant's computer or website connected to a network, such as the Internet. The merchant then communicates a request for a token and an update key to the clearing server, the token being previously purchased by the consumer and residing on a clearing server device. The update key is used as an authorization to modify the value of the token, i.e., to decrement and to increment. The merchant forwards the purchased merchandise to the consumer. When consumer discontinues making purchases at the selected merchant, the merchant returns the updated token to the clearing server. A new key is necessary to make the next purchase. This is the case even where the requesting merchant is the same as that from whom the last purchase was made. When the token is requested, if the token was used after its initial purchase, the present value of the token is made certain by receipt on the clearing server of informational downloads from the merchants.
Owner:UZO CHIJIOKE CHUKWUEMEKA
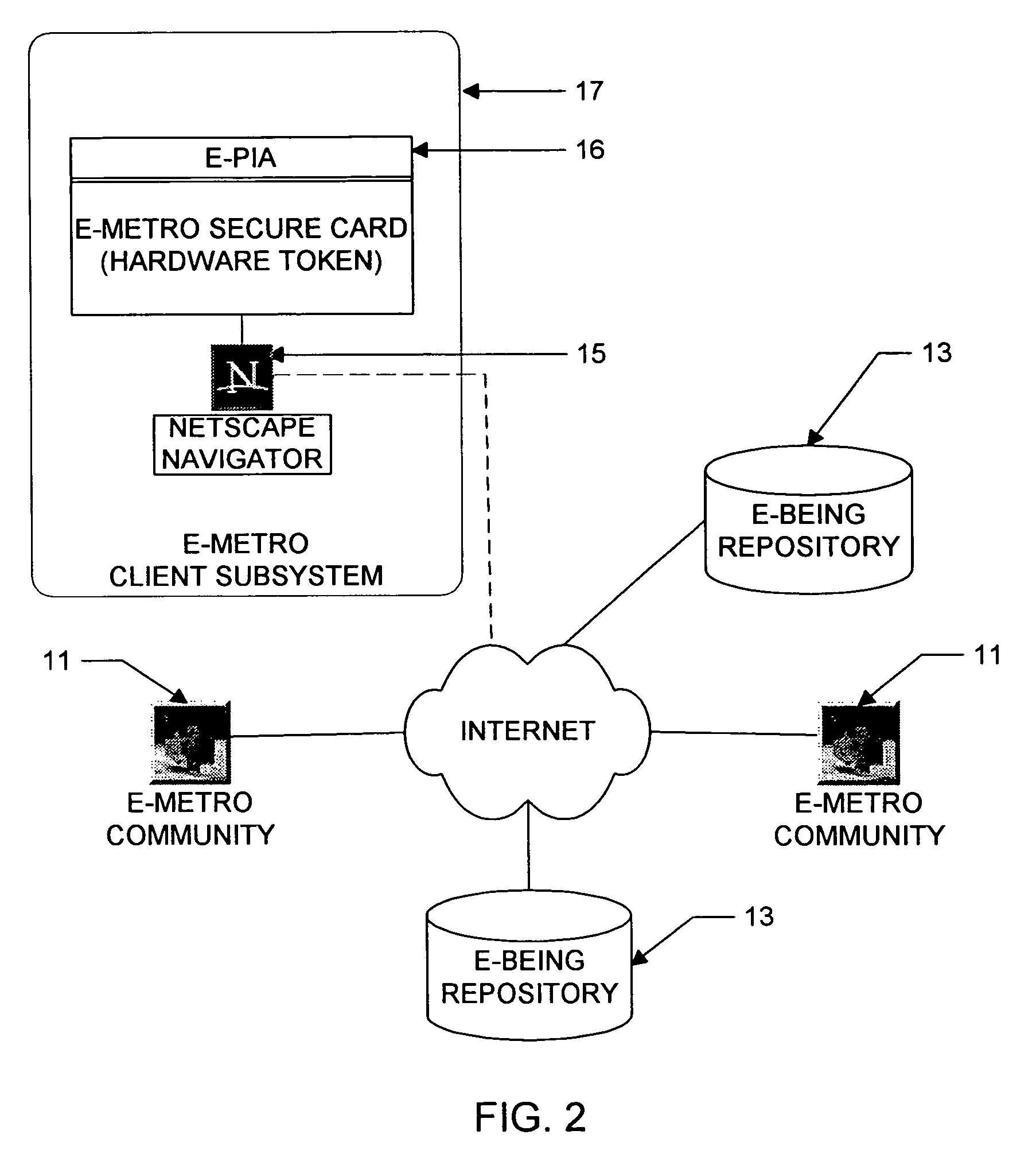
Personal information security and exchange tool
InactiveUS7289971B1Facilitates formation and useEasy to useFinanceComputer security arrangementsCommand and controlElectricity market
Utilization of the E-Metro Community and Personal Information Agents assure an effective and comprehensive agent-rule based command and control of informational assets in a networked computer environment. The concerns of informational privacy and informational self-determination are addressed squarely by the invention affording persons and entities a trusted means to author, secure, search, process, and exchange personal and / or confidential information in a networked computer environment. The formation of trusted electronic communities wherein members command and control their digital persona, exchanging or brokering for value the trusted utility of their informational assets is made possible by the invention. The present invention provides for the trusted utilization of personal data in electronic markets, providing both communities and individuals aggregate and individual rule-based control of the processing of their personal data.
Owner:CYVA RES HLDG
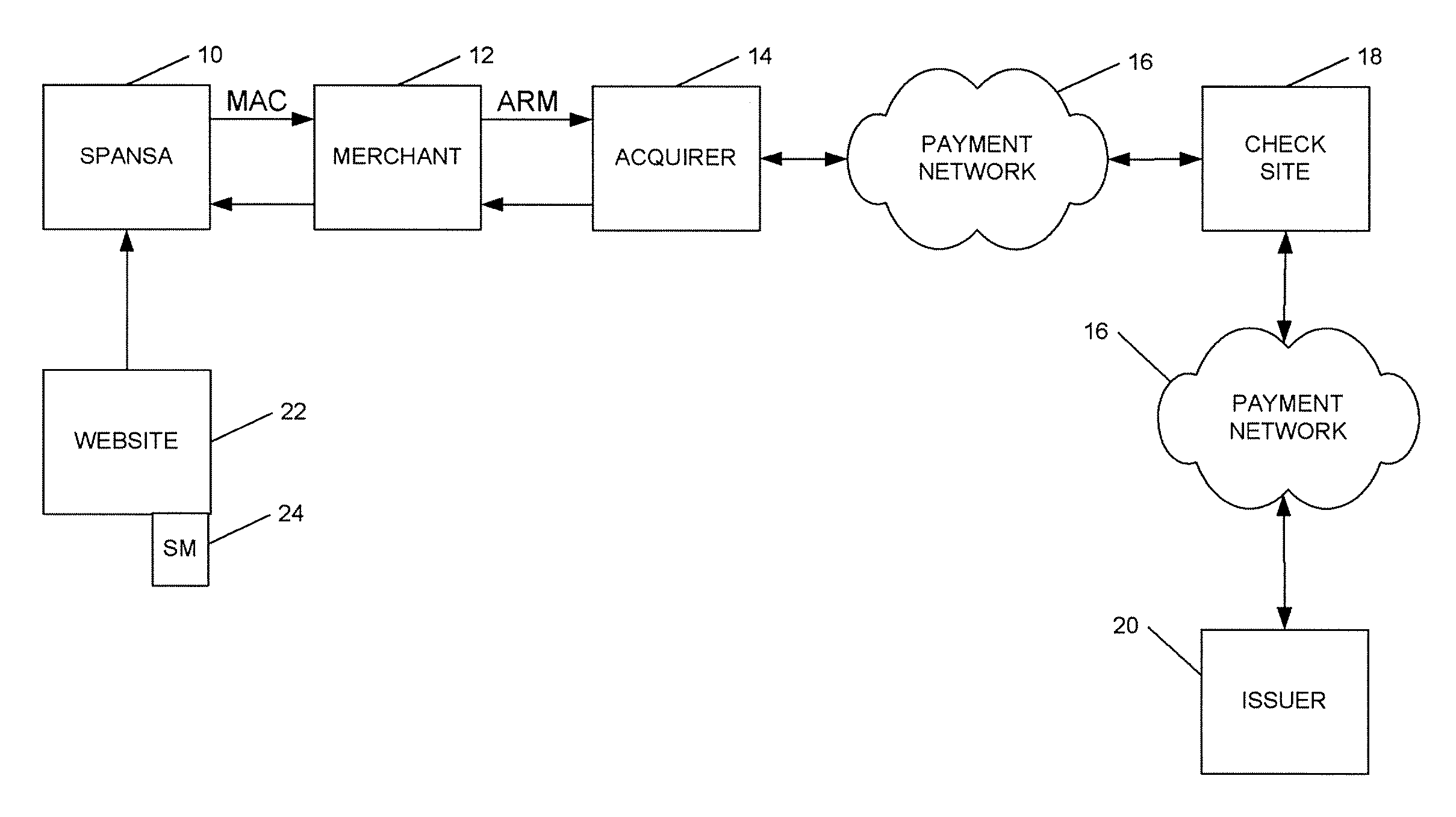
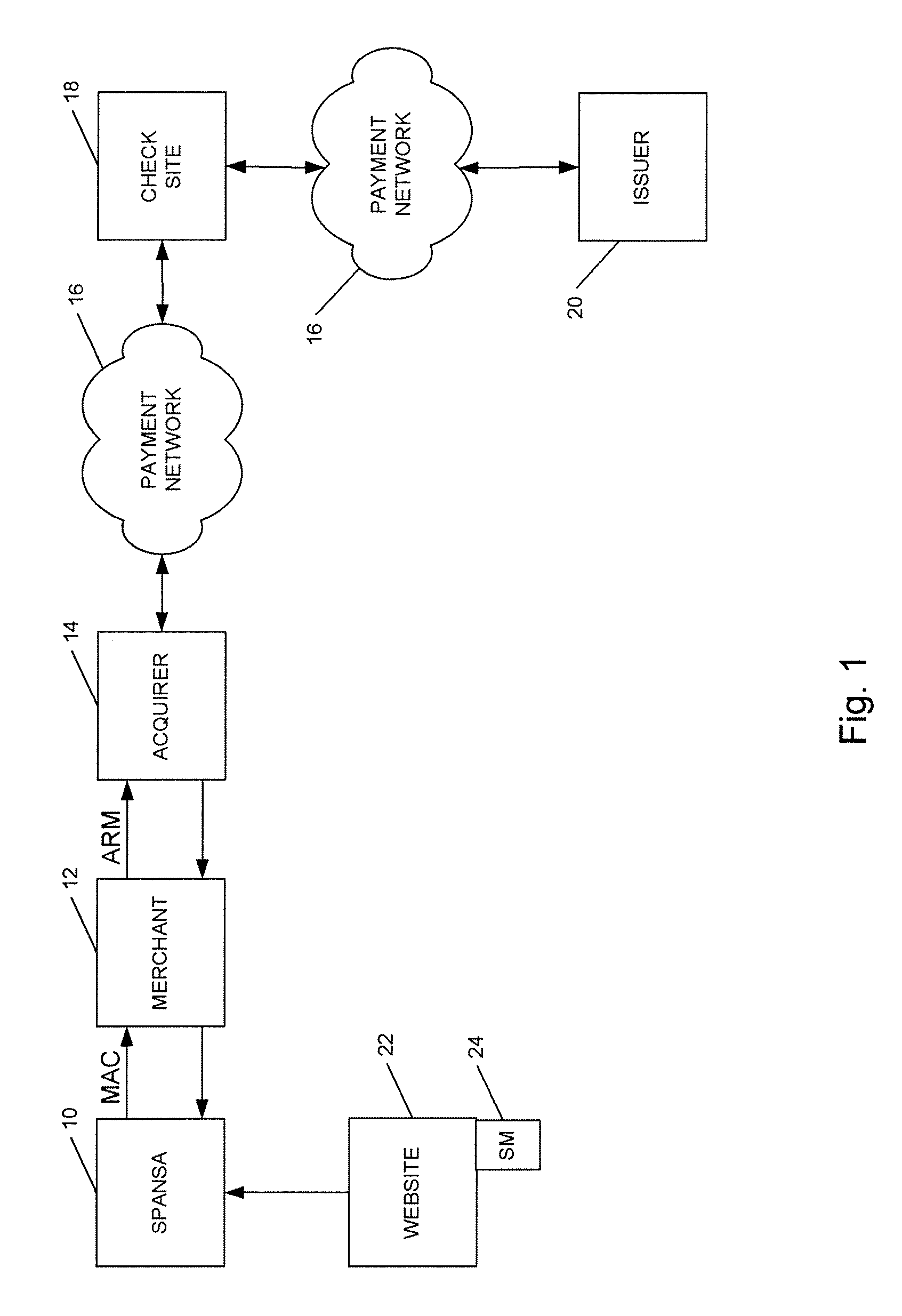
Method and system for conducting secure payments over a computer network without a pseudo or proxy account number
A method is provided for conducting an electronic transaction with a payment account number having a certain amount of available funds, using a payment network and a “check site”. The method comprises the following steps: (a) generating a secret key associated with the payment account number; (b) using the secret key to generate a message authentication code (“MAC”) specific to the transaction; (c) generating an authorization request message including the message authentication code; (d) forwarding the authorization request message over the payment network to the check site for verifying the authenticity of the MAC; (e) verifying the message authentication code by the check site using the secret key; (f) responding to the authorization request message over the payment network based on the available funds and the transaction amount.
Owner:MASTERCARD INT INC
Contextual transaction token methods and systems
ActiveUS20150112870A1Electronic credentialsProtocol authorisationMachine learningTransaction processing system
Embodiments of the present invention are directed to methods, systems, apparatuses, and computer-readable mediums for generating and providing a transaction token that may provide contextual information associated with the token. Accordingly, the transaction token may provide any entities within a transaction processing system immediate information about the context in which the token was generated, how the token may be used, and any other information that may be pertinent to processing the token.
Owner:VISA INT SERVICE ASSOC
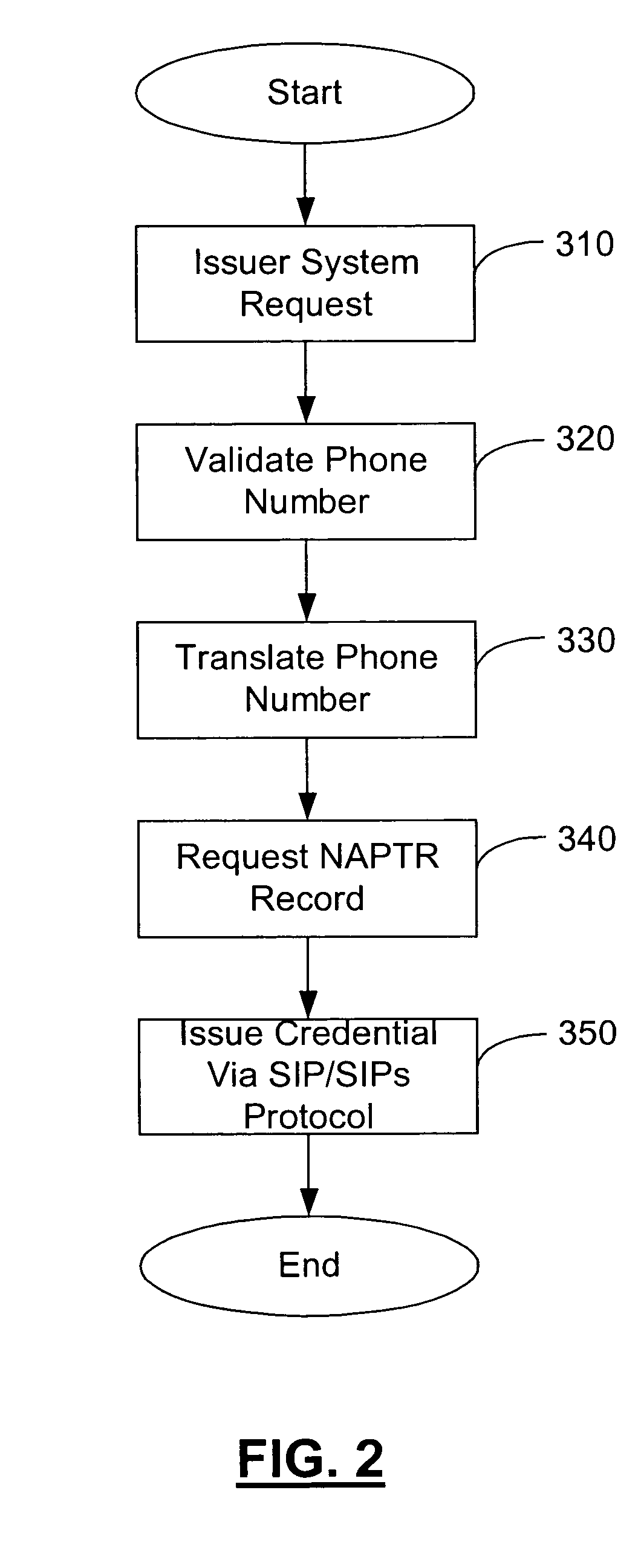
Method and apparatus for managing credentials through a wireless network
ActiveUS8700729B2Convenient and efficient and secure distributionNear-field in RFIDData switching by path configurationCredit cardSystems design
A novel system and methodology for conducting financial and other transactions using a wireless device. Credentials may be selectively issued by issuers such as credit card companies, banks, and merchants to consumers permitting the specific consumer to conduct a transaction according to the authorization given as reflected by the credential or set of credentials. The preferred mechanism for controlling and distributing credentials according to the present invention is through one or more publicly accessible networks such as the Internet wherein the system design and operating characteristics are in conformance with the standards and other specific requirements of the chosen network or set of networks. Credentials are ultimately supplied to a handheld device such as a mobile telephone via a wireless network. The user holding the credential may then use the handheld device to conduct the authorized transaction or set of transactions via, for example, a short range wireless link with a point-of-sale terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
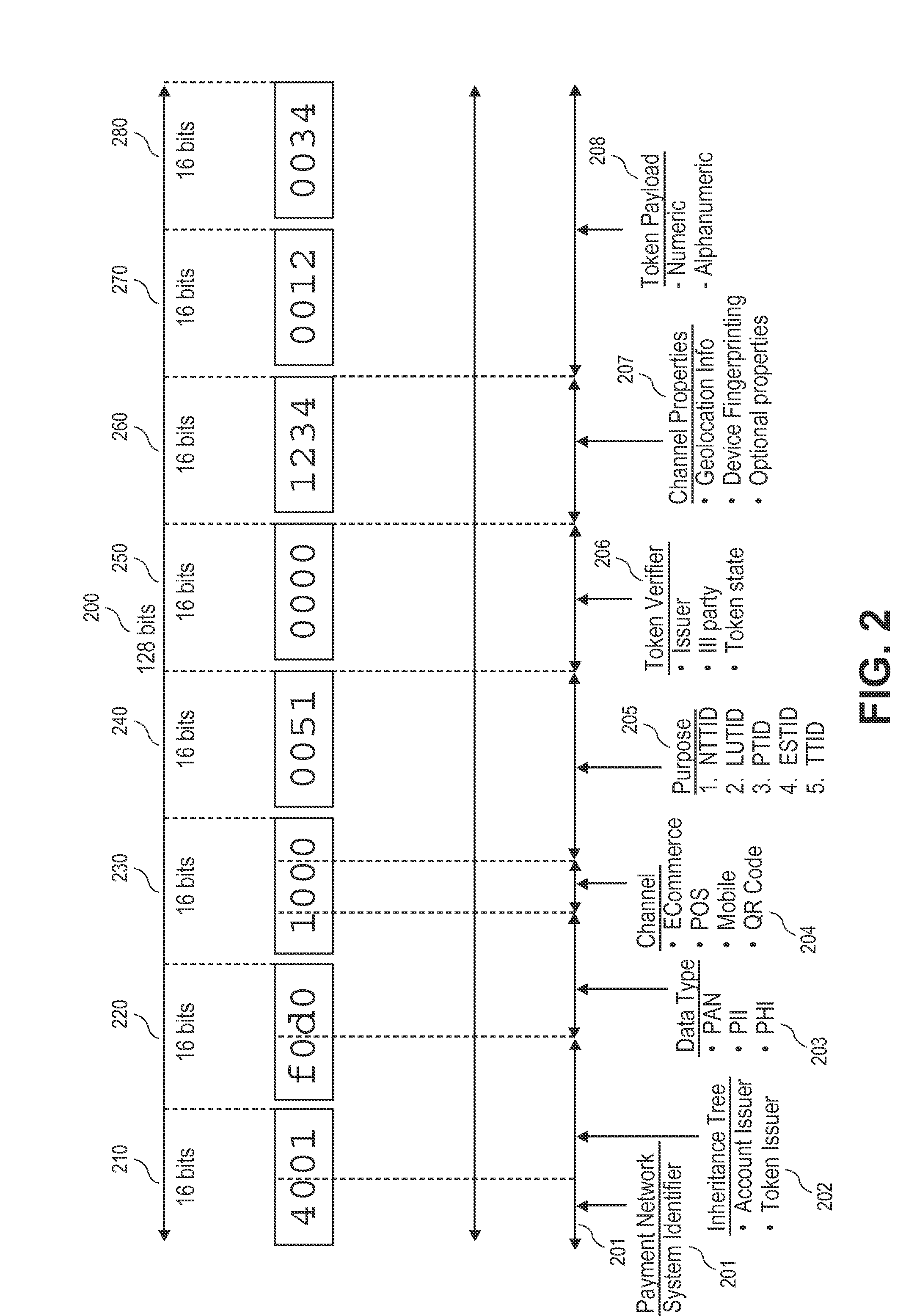
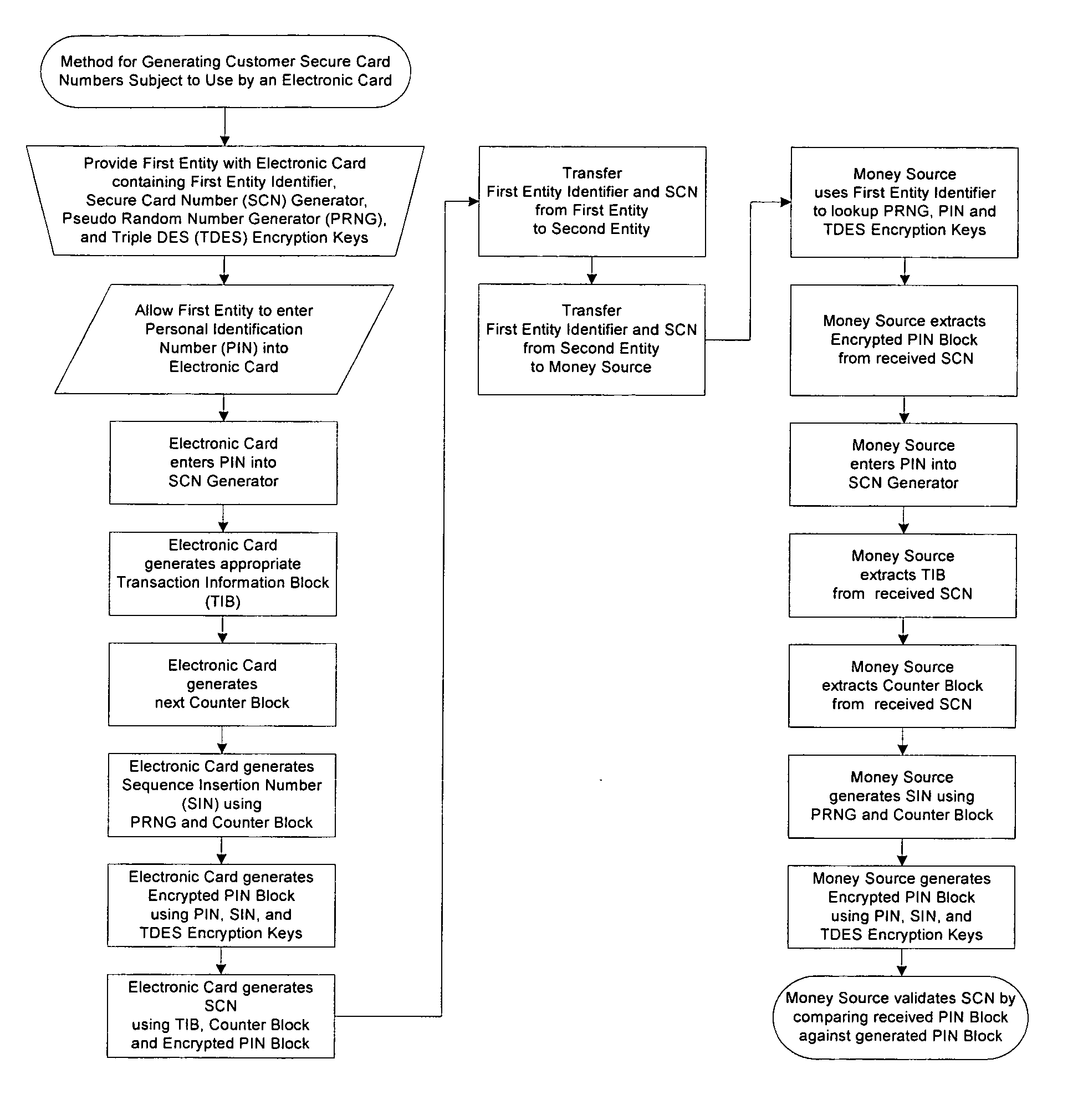
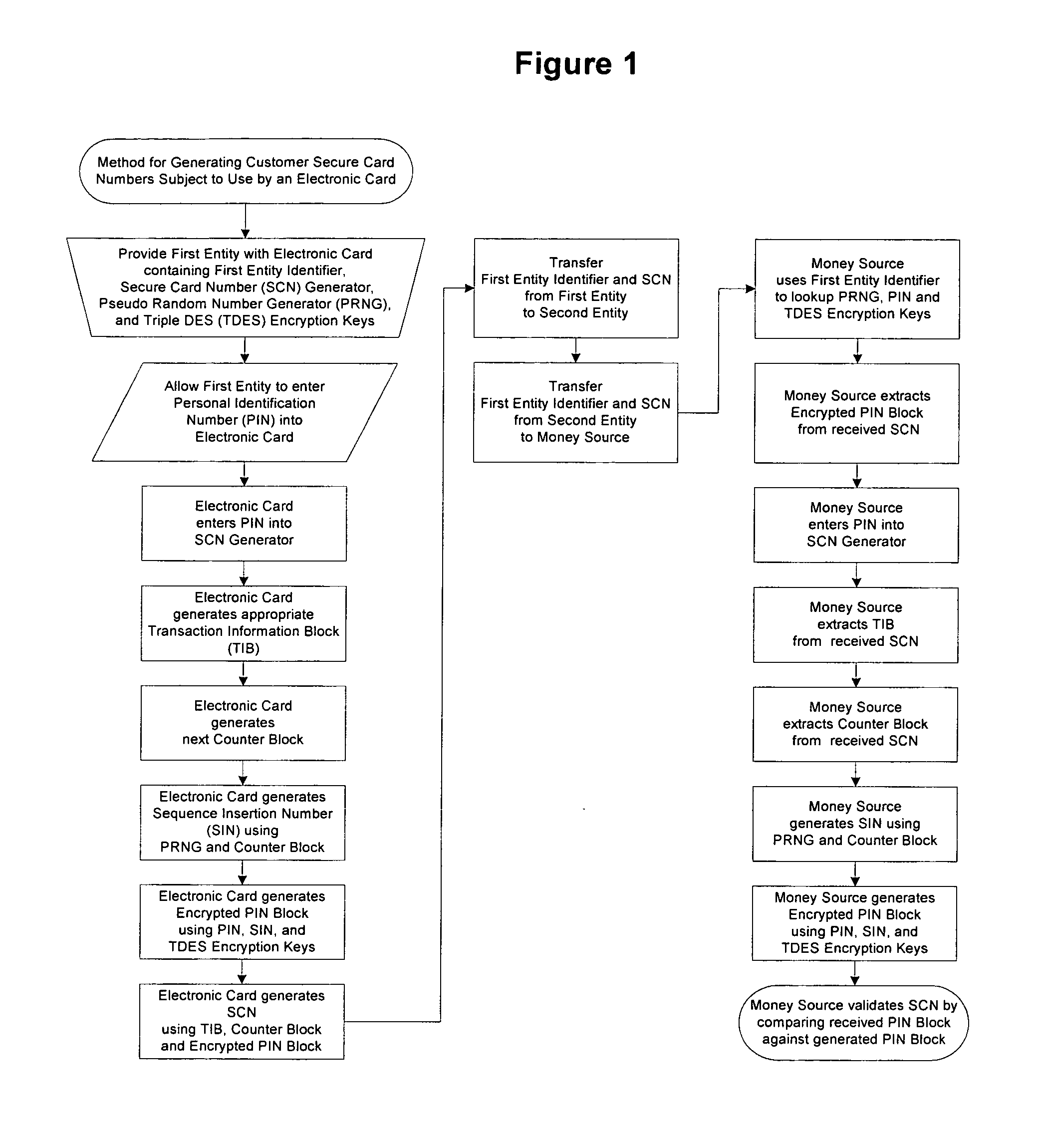
Method for generating customer secure card numbers
A method for providing secure transactions generates a Secure Card Number (“SCN”) for a first entity that is transferred with a first entity identifier to a second entity and then to a money source that verifies that the transaction is valid by use of the first entity identifier and the SCN. The SCN includes a 0Transaction Information Block (“TIB”), a Counter Block, and an encrypted Personal Identification Number (“PIN”) Block. The SCN is transferred to the money source in an account number or a non-account data field. The money source can use the TIB to determine whether the SCN should be used once or multiple times or to identify one of several physical devices, all of which are issued to the first entity, used to generate the SCN. The money source validates the SCN by duplicating the encryption process used to create an encrypted PIN Block and comparing the result to the encrypted PIN Block received with the transaction. A Triple Data Encryption Standard algorithm encrypts a PIN Block generated from a PIN, a Sequence Insertion Number (“SIN”) and a known starting value. The SIN can be a combination of three seed values and a random value generated by a Pseudo Random Number Generator (“PRNG”) initialized with the seed values. A Counter value is associated with the Counter Block and the seed values.
Owner:PRIVASYS
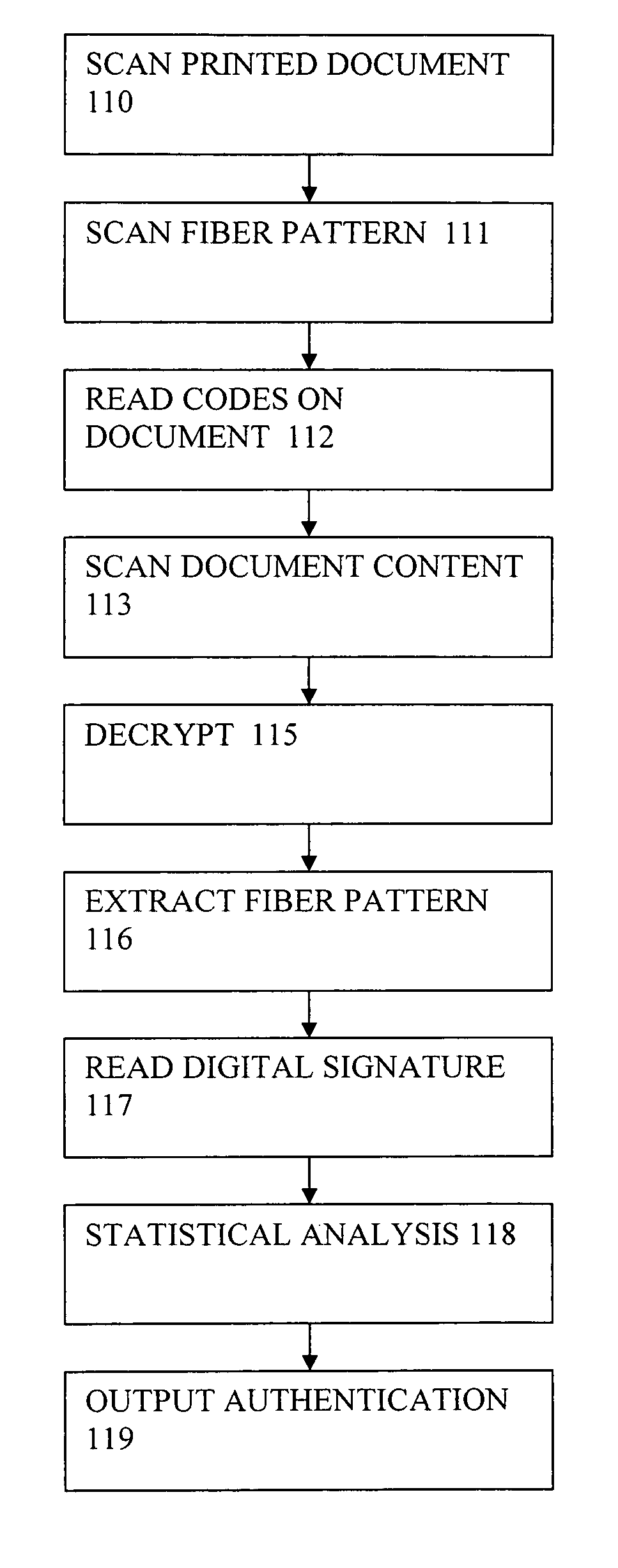
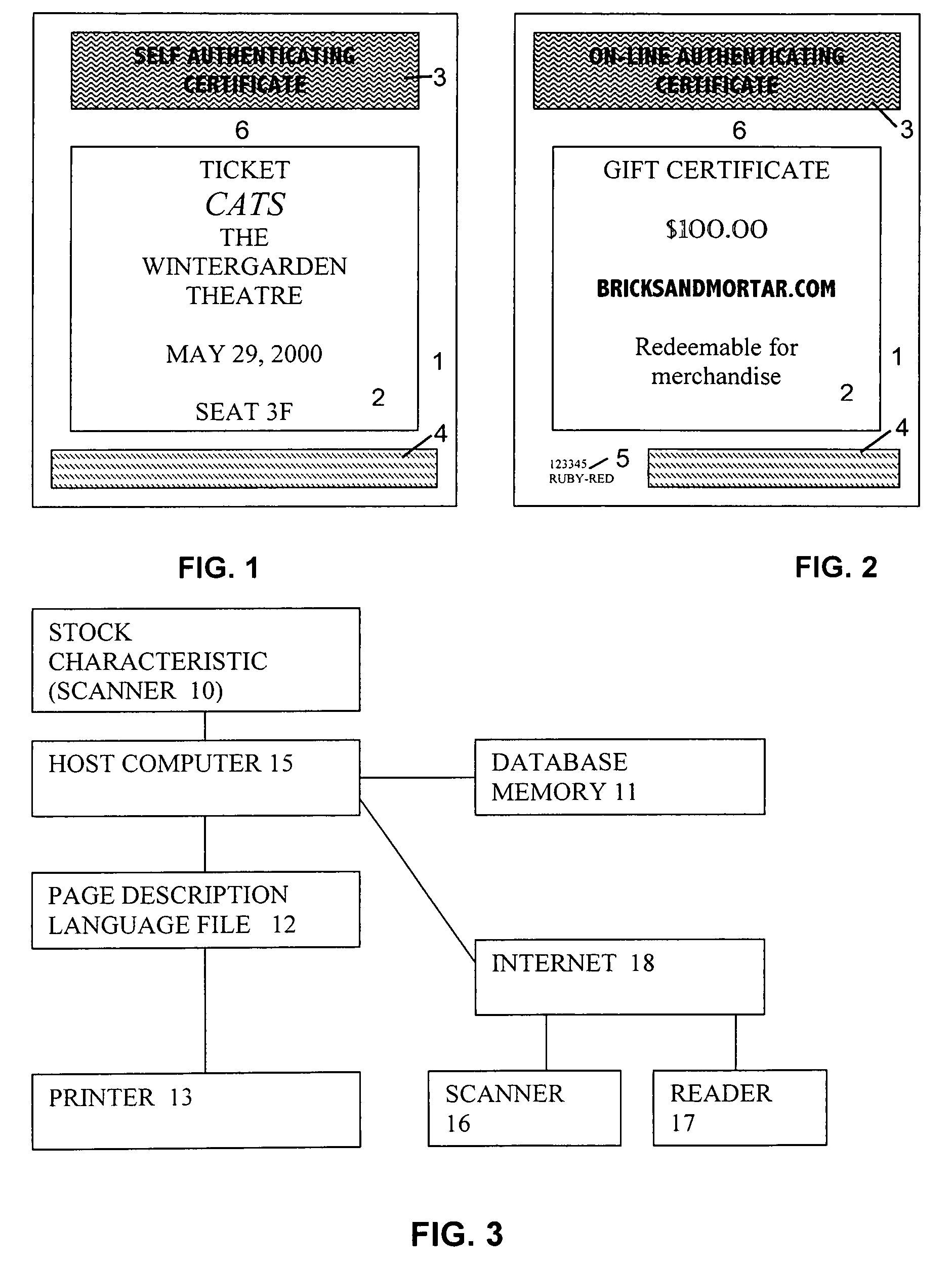
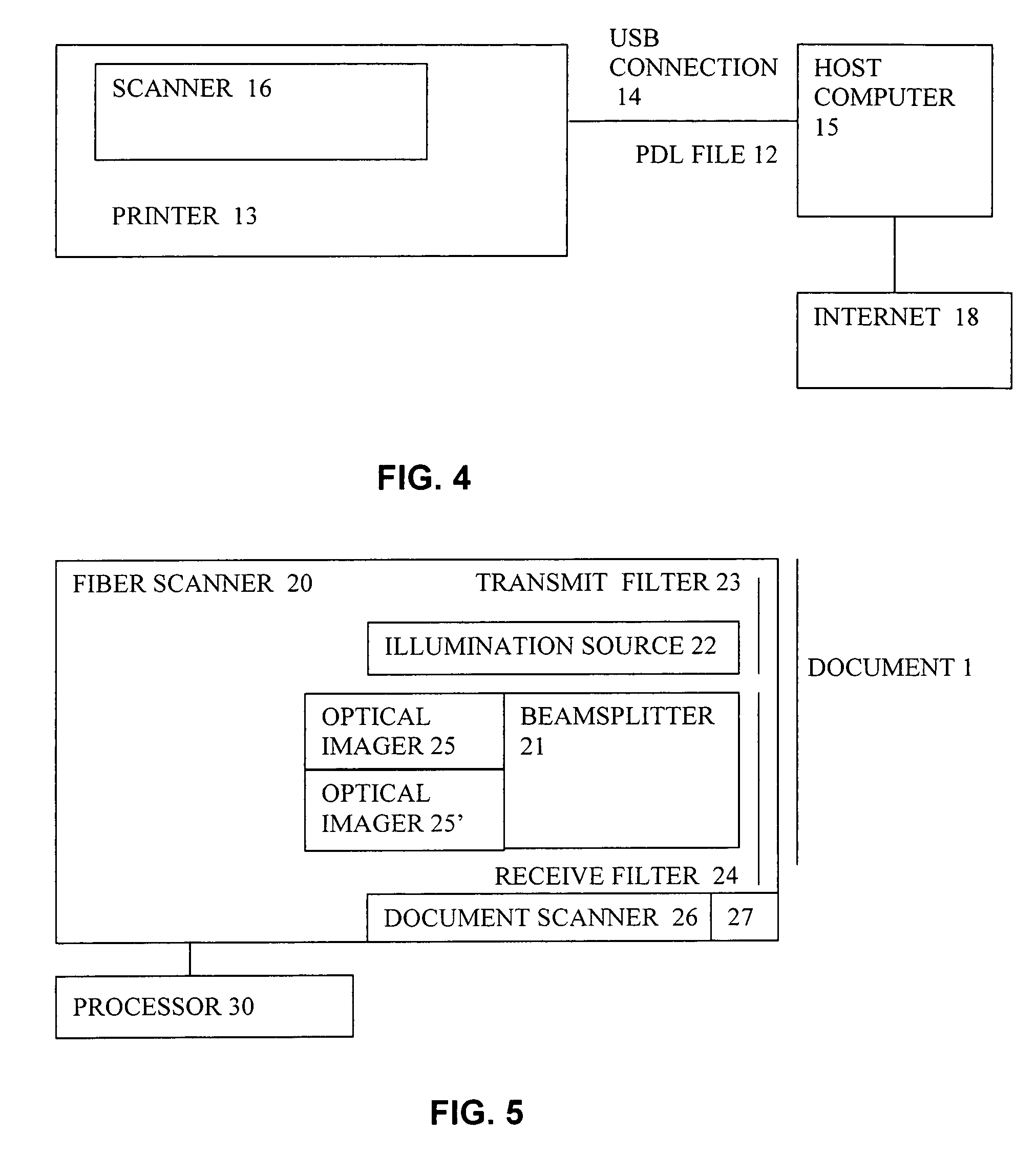
System and method for production and authentication of original documents
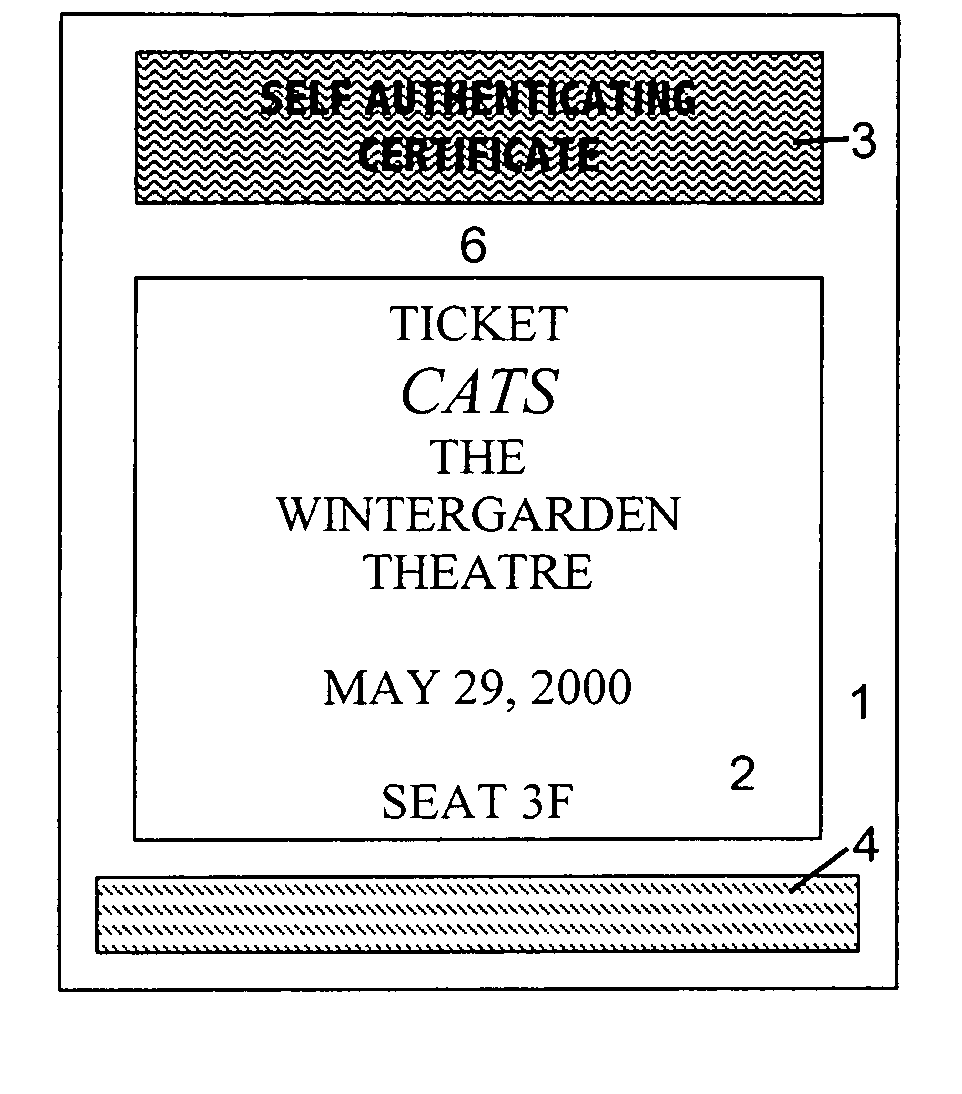
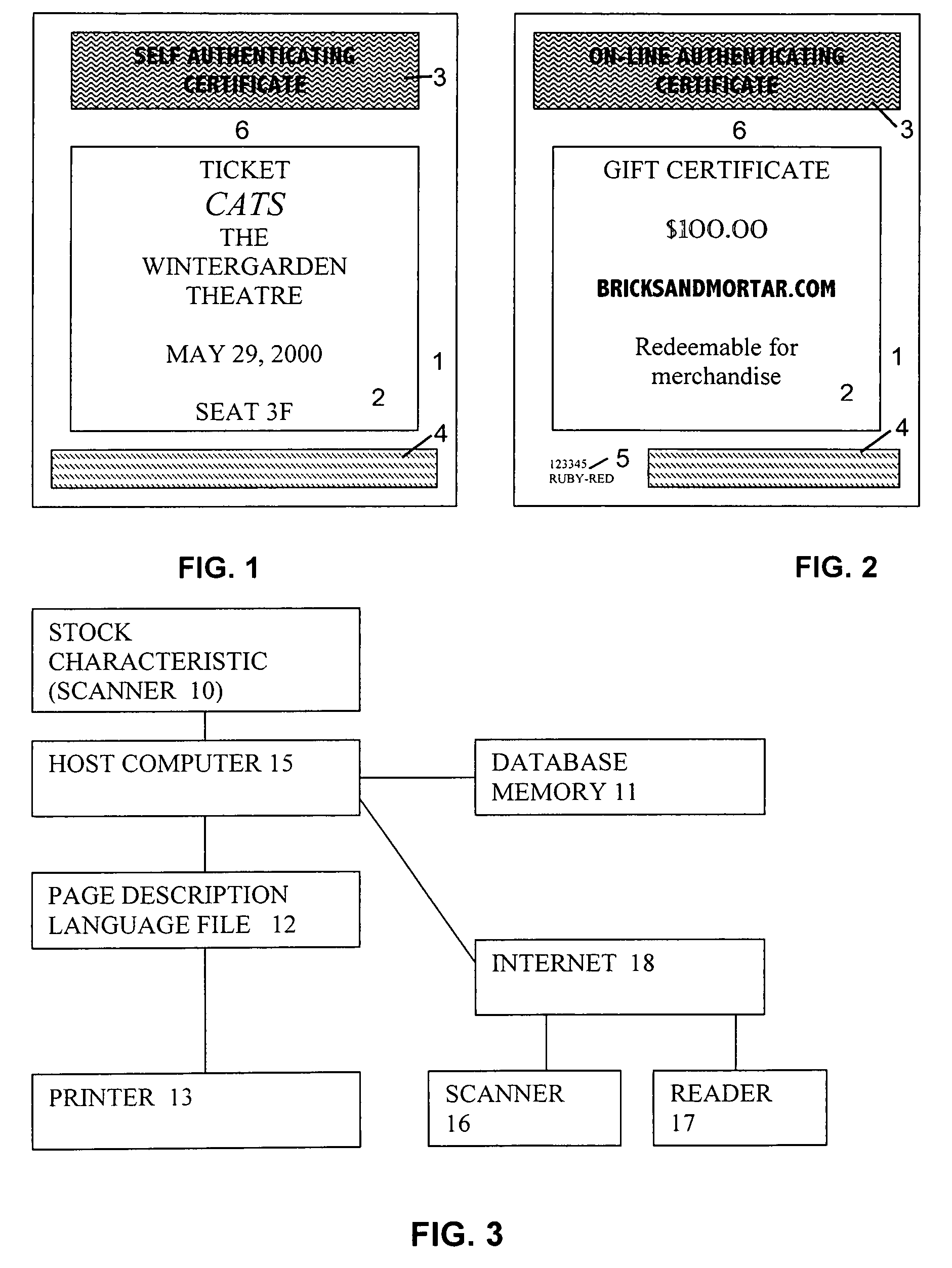
InactiveUS7080041B2Improve shielding effectImprove accuracyOther printing matterUser identity/authority verificationDocument IdentifierLogical security
A system and method for authenticating documents and content thereof. A counterfeit resistant document recording medium is provided, having thereon a predefined unique document identifier and at least one security feature. The recording medium is thereafter imprinted with document content, which typically varies between documents. The document content is stored in a database, indexed by an associated document identifier. The document may then be authenticated by checking the security feature and comparing the stored document content with a perceived document content. The system provides a number of opportunities for commercial exploitation, including sales of identified recording media, recording of information in a database, on-line authentication transactions, differential accounting for document validations and counterfeit identifications, imprinting devices, authentication devices, and the like. The system prevents counterfeiting of valuable documents through casual means by providing both physical and logical security.
Owner:ESECUREDOCS
Method and apparatus for making secure electronic payments
In accordance with the present invention, consumers and merchants use computing devices connected to a network, such as the Internet, through wired and wireless means, wherein the consumer connects to a clearing server device to purchase or retrieve previously purchased token, the consumer then connects to the merchant's computer or website to attain price quotes of goods and services, selects the goods and / or services to be purchased, and then communicates a request for purchase to the merchant. The merchant then communicates a request for an update key to the clearing server. The update key is used as an authorization to modify the value of the token. To debit the customer the decrement key is requested and to credit the customer an increment key is asked for. An overwrite key is another type of update key. Together with the overwrite key a replacement token is provided to the merchant who in turn forwards the new token to the customer. As an aspect of the invention, if the token was not previously used, the clearing server simply issues the update key. If, however, it is determined that the token was used, the amount paid by the consumer to a previous merchant is determined the token adjusted and the overwrite key together with the new token is returned to the merchant. The merchant then forwards the purchased merchandise, the update key, and possibly a new token to the consumer.
Owner:AMPACASH CORP
System and method for production and authentication of original documents
InactiveUS20050038756A1Improve shielding effectImprove accuracyOther printing matterUser identity/authority verificationDocument IdentifierPaper document
A system and method for authenticating documents and content thereof. A counterfeit resistant document recording medium is provided, having thereon a predefined unique document identifier and at least one security feature. The recording medium is thereafter imprinted with document content, which typically varies between documents. The document content is stored in a database, indexed by an associated document identifier. The document may then be authenticated by checking the security feature and comparing the stored document content with a perceived document content. The system provides a number of opportunities for commercial exploitation, including sales of identified recording media, recording of information in a database, on-line authentication transactions, differential accounting for document validations and counterfeit identifications, imprinting devices, authentication devices, and the like. The system prevents counterfeiting of valuable documents through casual means by providing both physical and logical security.
Owner:ESECUREDOCS
Methods for purchasing of goods and services
InactiveUS20050027543A1Reducing credit card fraudRisk minimizationPayment circuitsElectronic credentialsThird partyPurchasing
A method for conducting a purchasing agreement for goods and services between a consumer and a merchant through a trusted a third party and using a wireless network includes generating, by the consumer, a first view of the agreement and transmitting the first view of the agreement to the third party, generating, independently by the merchant, a second view of the agreement and transmitting the second view of the agreement to the third party, and receiving, by the third party the consumer view of the agreement and the merchant view of the agreement, verifying identities of the merchant and the consumer and that the details of the independently generated views of the agreements are consistent and taking action to execute the purchasing agreement if the conditions are satisfied. The third party includes a Secure Transaction Server.
Owner:PCMS HOLDINGS INC
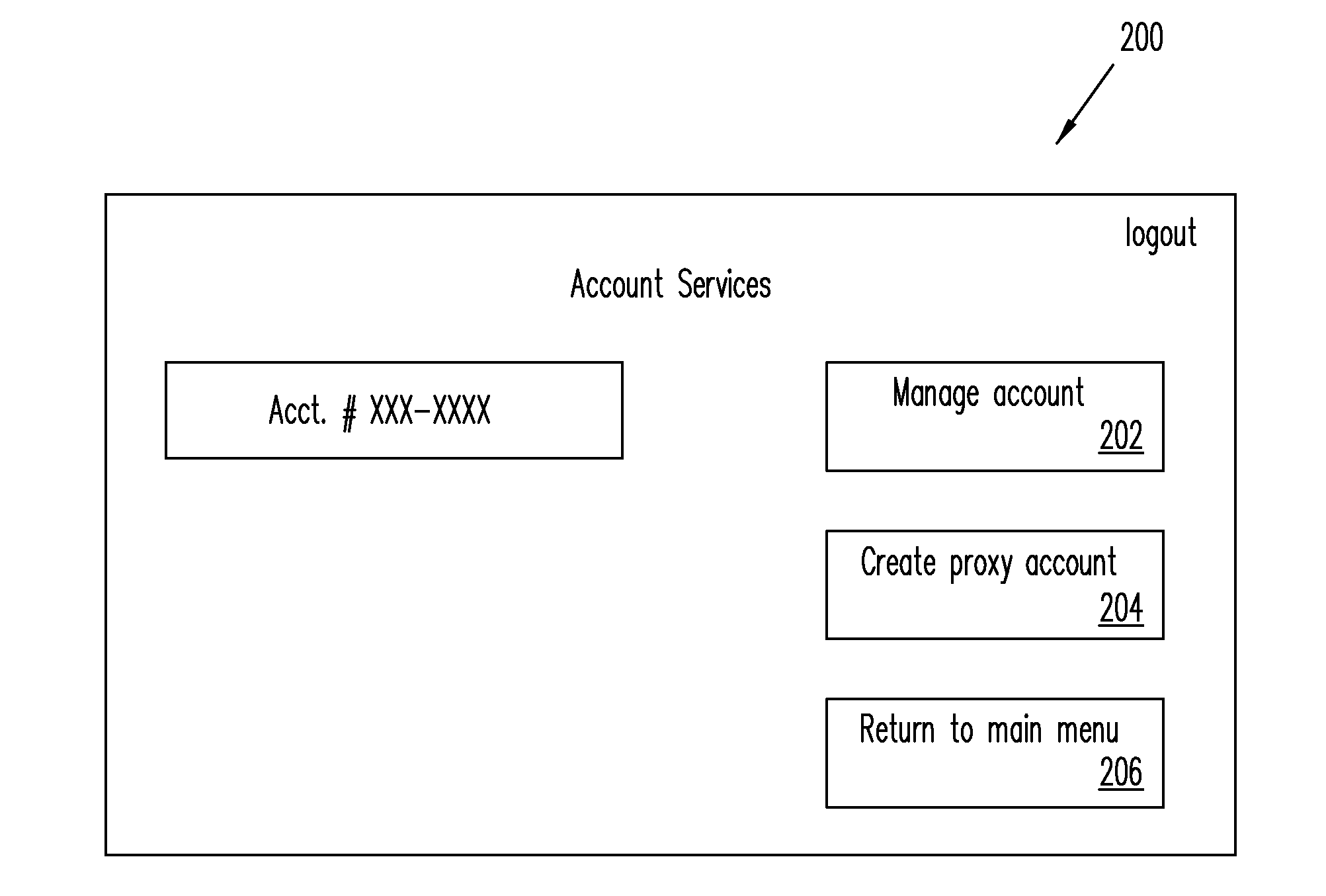
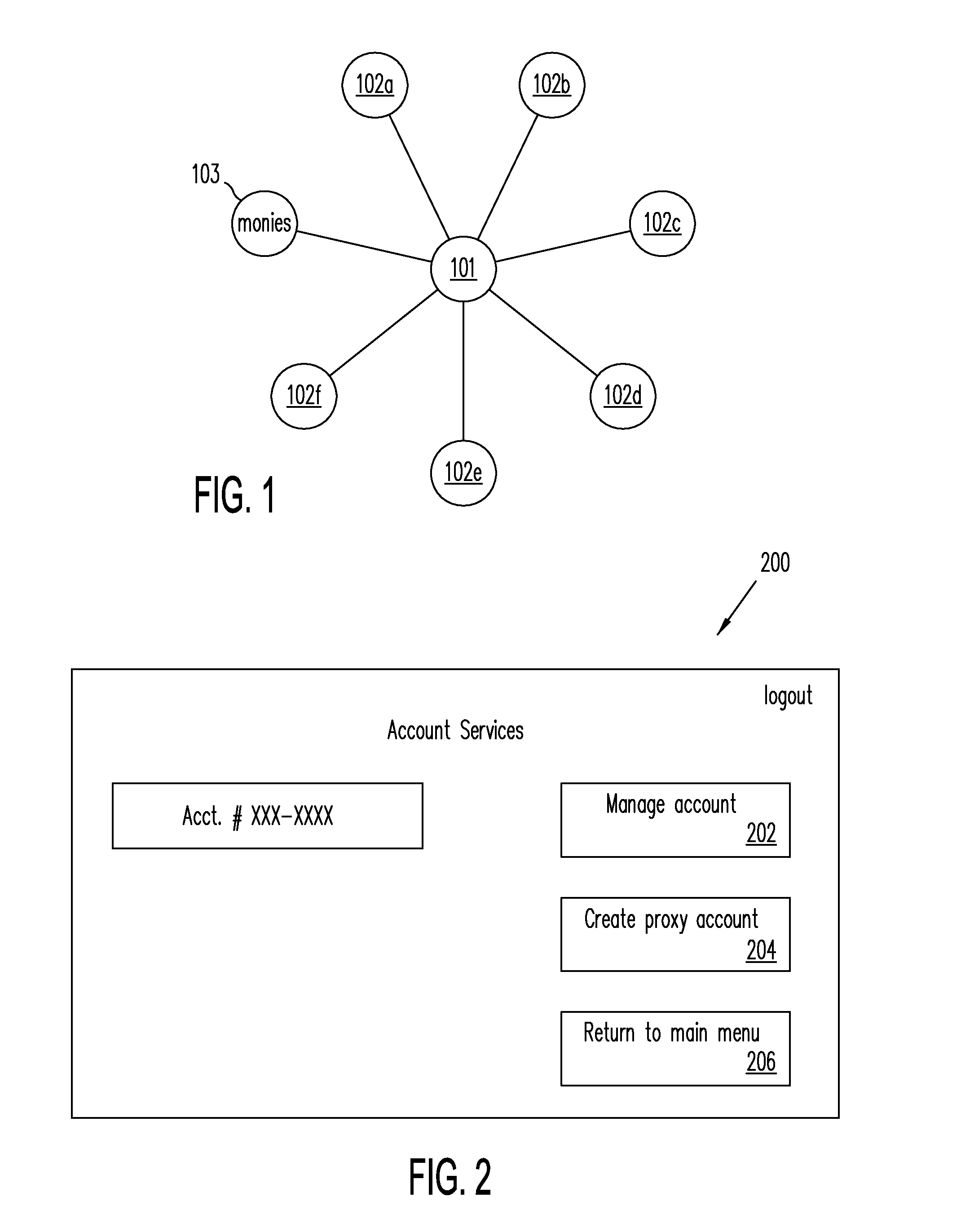
Systems, Methods, and Computer Program Products for Using Proxy Accounts
An electronic device including an input / output interface operable to receive an input from a user and communicate an output to the user, a transceiver operable to electronically communicate with a computer network, a computer processor operable to execute instructions, and a memory storage operable to store the instructions, the memory storage further comprising a program module that is operable to: receive credentials for a proxy payment account, where the proxy payment account is linked to a primary payment account and not linked directly to a method of payment underlying the primary payment account, and make payment at a Point of Sale (POS) using the received credentials.
Owner:PAYPAL INC
Selective data encryption using style sheet processing for decryption by a client proxy
InactiveUS6978367B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureDocument preparation
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Method and system for conducting secure payments over a computer network
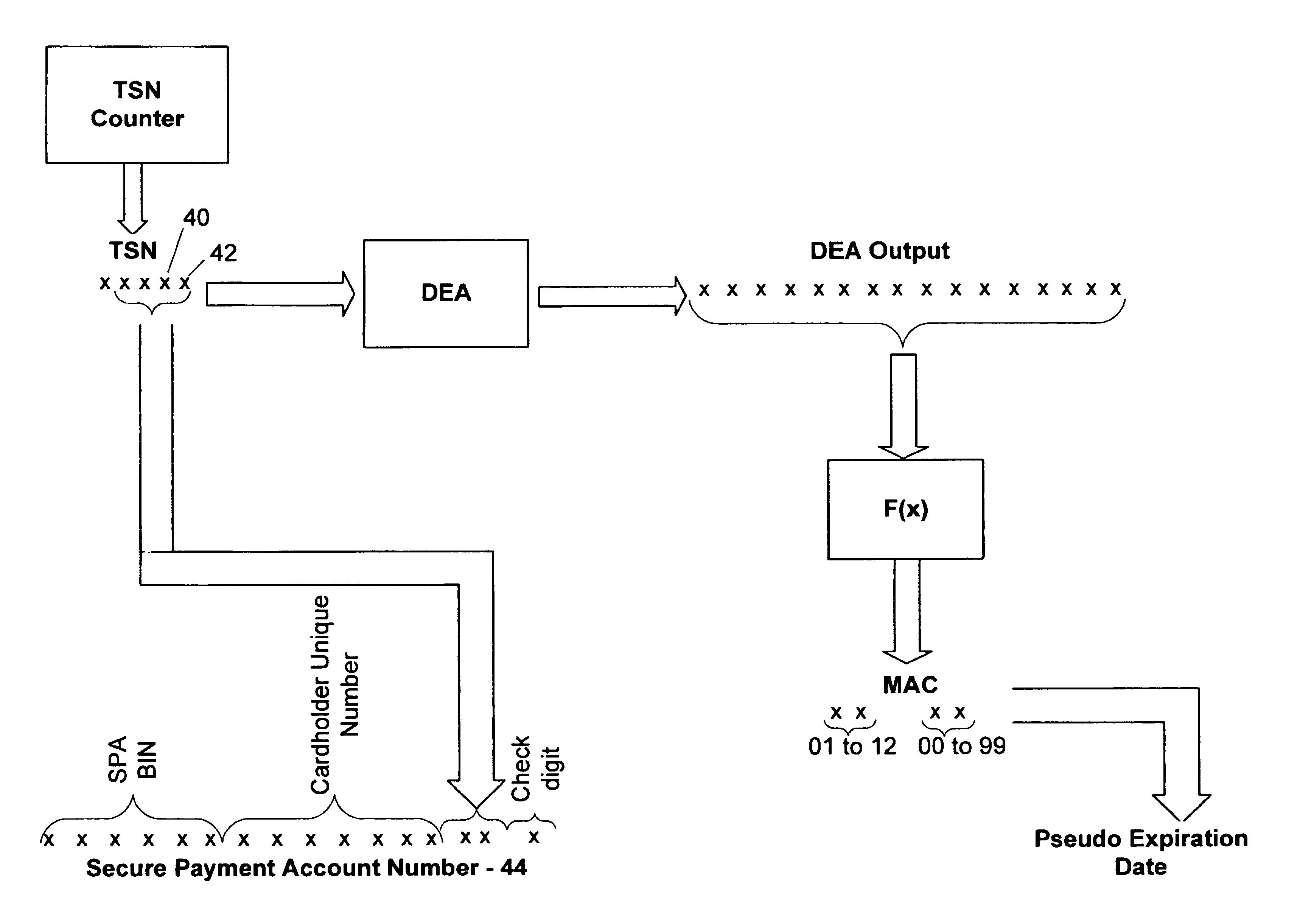
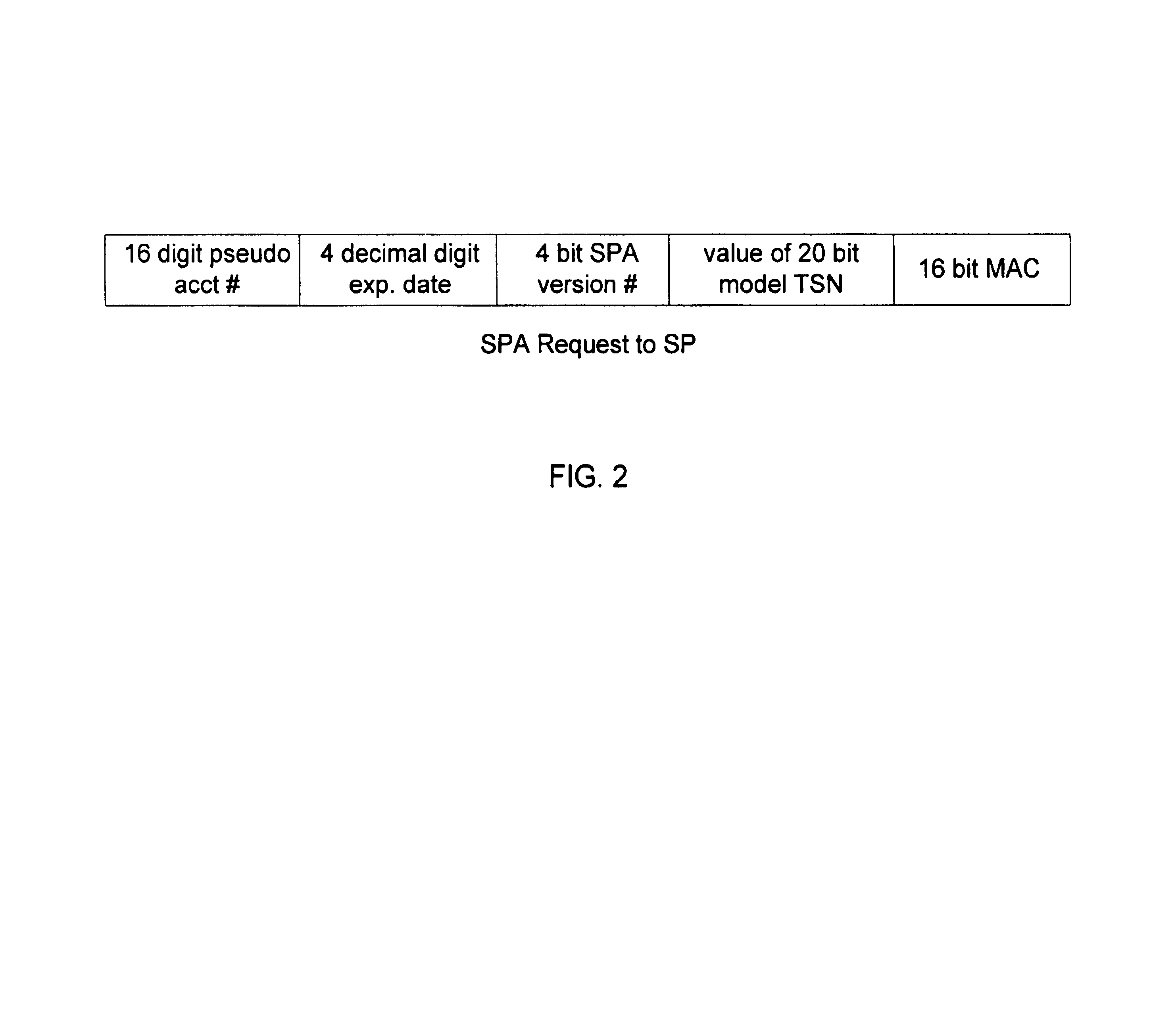
A secure method of conducting an electronic transaction over a public communications network is provided which utilizes a pseudo-expiration date in the expiration date field of an authorization request. One of the preferred methods comprises:generating a per-card key associated with an account number;generating a message authentication code using the per-card key;converting the message authentication code into a pseudo expiration date;generating an authorization request for the transaction, the request having an expiration date field containing the pseudo expiration date; andverifying the message authentication code based on the pseudo expiration date.Another embodiment of the invention includes a method of conducting an electronic transaction over a public communications network, with a payment account number having an associated pseudo account number, comprising:(a) providing the pseudo account number with a control field indicating one of a plurality of key-generation processes to be used to generate an authentication key;(b) generating an authentication key associated with the pseudo account number using one of the plurality of key-generation processes indicated in the control field of the pseudo account number;(c) using the authentication key to generate a message authentication code specific to the transaction;(d) generating an authorization request message including the message authentication code and the pseudo account number; and(e) verifying the message authentication code using the indicated key-generation process and the authentication key.
Owner:MASTERCARD INT INC
Methods and apparatus for conducting electronic transactions
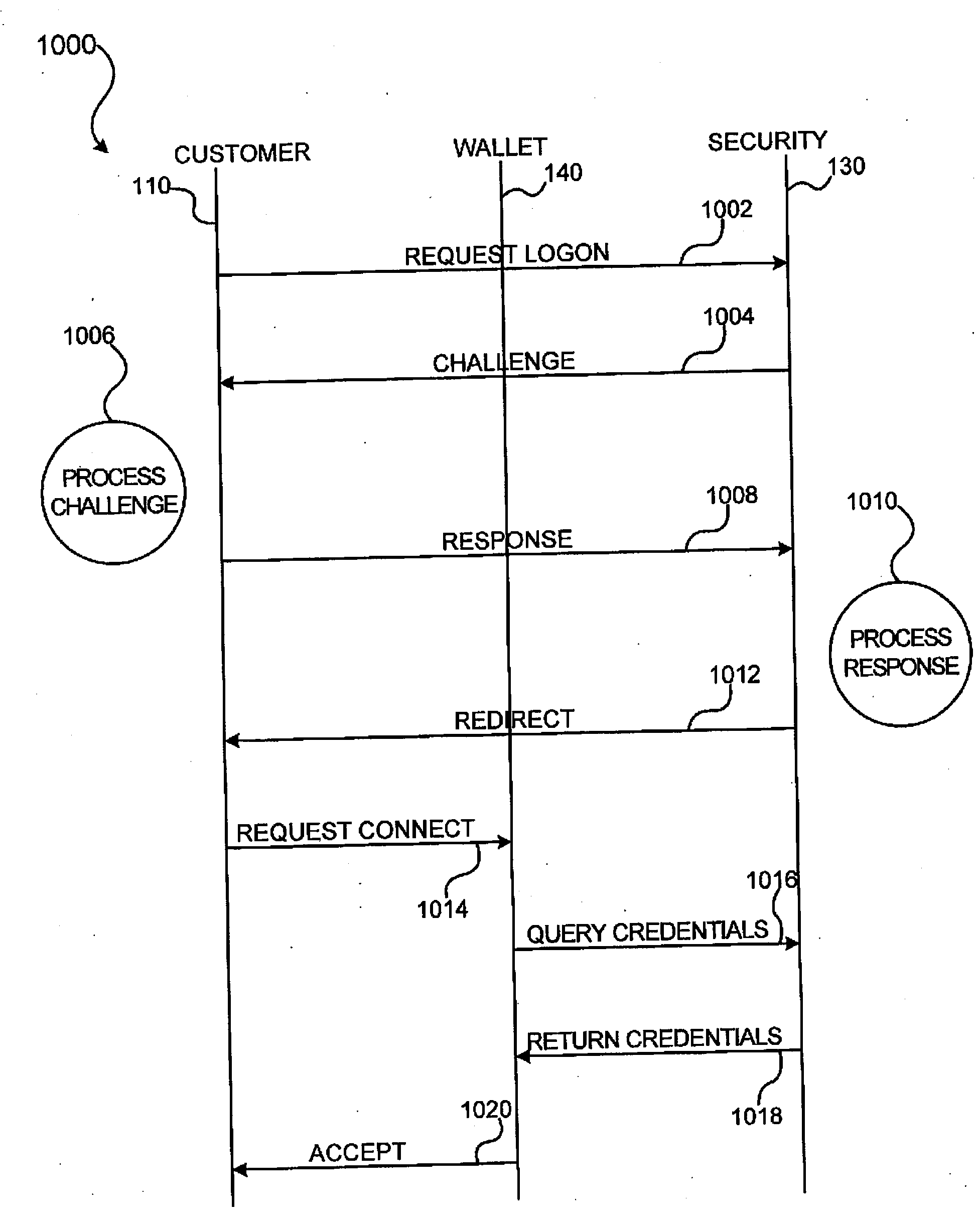
InactiveUS20090076966A1Enhanced reliability and confidenceReduce security risksComplete banking machinesAcutation objectsAuthorization certificateChallenge response
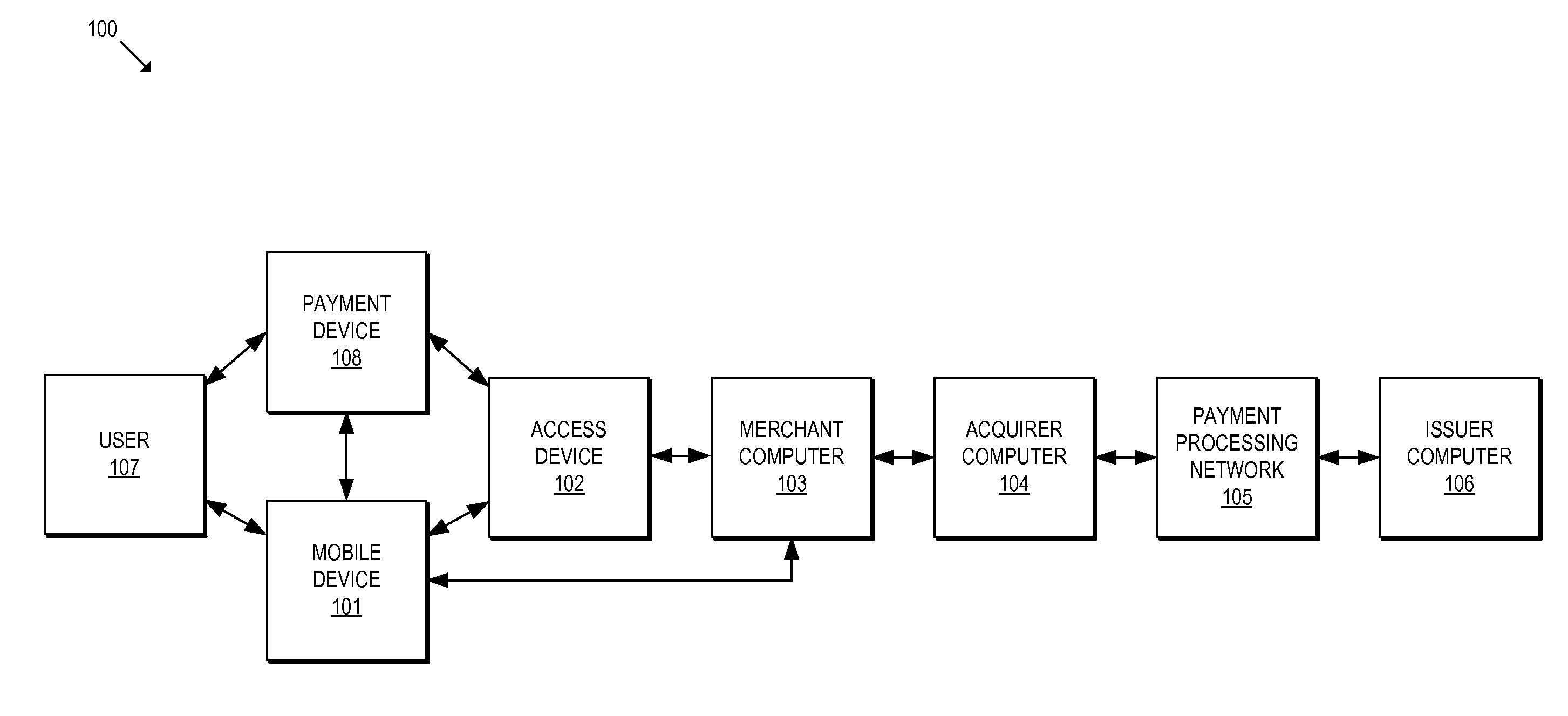
A system and method for facilitating electronic transactions using an intelligent instrument is disclosed. An authorization server enables users to obtain authorization credentials through the use of the intelligent instrument by issuing a challenge to an intelligent token of the intelligent instrument. The intelligent token generates a challenge response and transmits the challenge response to the authorization server, which assembles credentials including a key for the electronic transaction upon validating the response. The authorization server sends the assembled credentials to the intelligent instrument and the intelligent instrument transmits the assembled credentials to the authorization server during a subsequent transaction. The authorization server validates the assembled credentials and provides authorization for the transaction in response to the validating the assembled credentials.
Owner:LIBERTY PEAK VENTURES LLC
Digital downloading jukebox system with user-tailored music management, communications, and other tools
InactiveUS20060062094A1Improve convenienceDecreasing intimidationTelevision system detailsDigital data processing detailsCredit cardComputer network
A digital downloading jukebox system including a mechanism for delivering custom services to a recognized user, including services for creating playlists, communicating with others, accessing other features, etc. is provided. In some exemplary embodiments, after a user is recognized, the jukebox system allows users to access a special front-end via the Internet or on an actual jukebox. Then, the user may, for example, create playlists, share songs with friends, send messages to friends, and access other value-added content. Other exemplary embodiments allow users to become certified, charging them for services without requiring constant inputting of coinage or credit card information. Such a system preferably learns about networks of friends, and enables managers to send similar messages to regular customers and / or others known to the system.
Owner:TOUCHTUNES MUSIC CORP
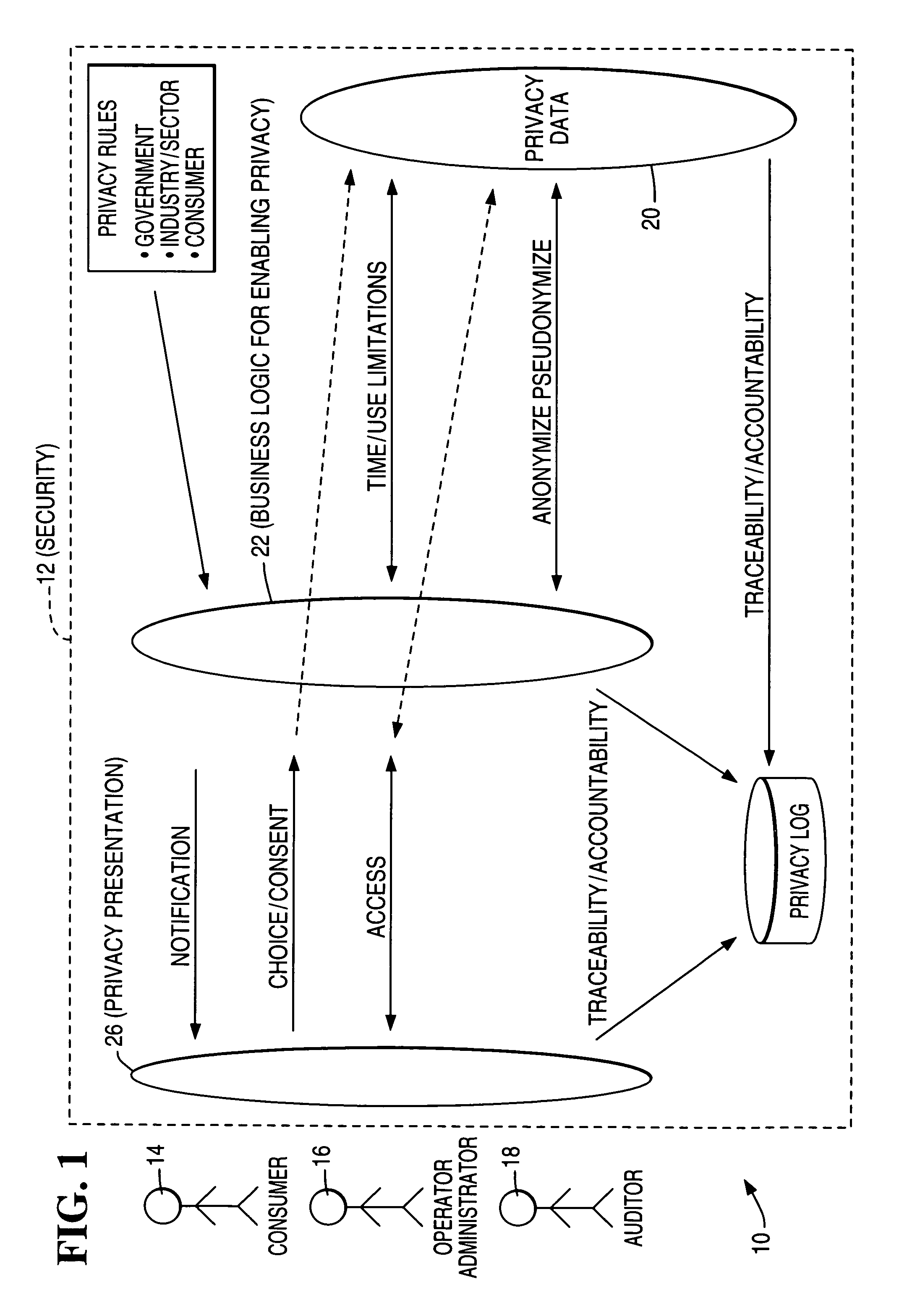
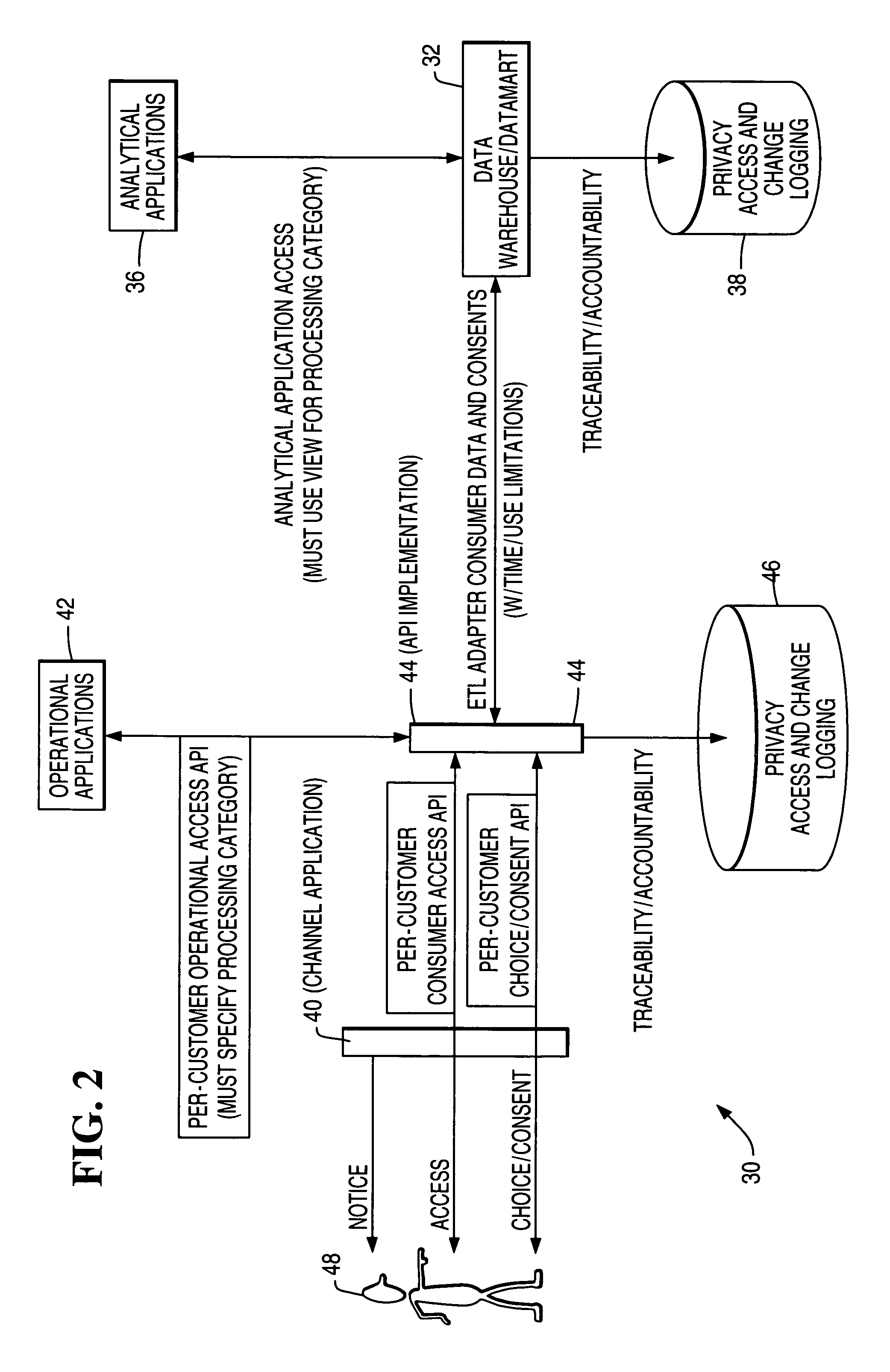
Architecture and method for operational privacy in business services
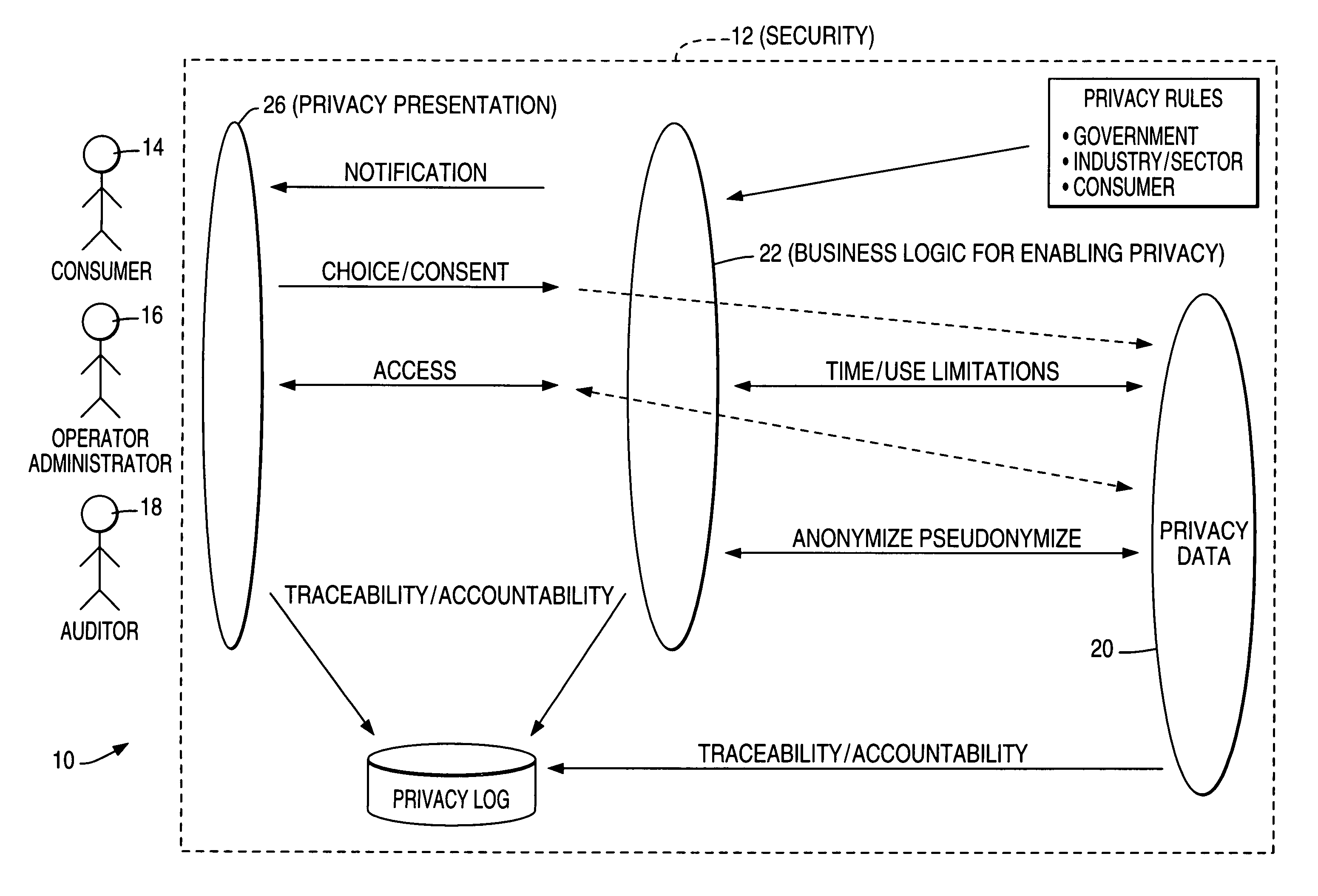
Consent-based application programming interfaces (APIs) are used to provide privacy access controls to operational systems for business services accomplished particularly in an electronic and / or networked environment. An API implementation device or host provides a link between a channel application, configured to provide an interface with a customer, and privacy data as used by operational applications and obtained from databases such as data warehouses. The privacy APIs provide per-customer choice / consent to obtaining and / or retrieval of privacy information / data and per-customer access thereto. In one form, the privacy APIs are used in business initiated self service applications wherein an activity or event triggers business to customer initiation.
Owner:TERADATA US
Online card present transaction
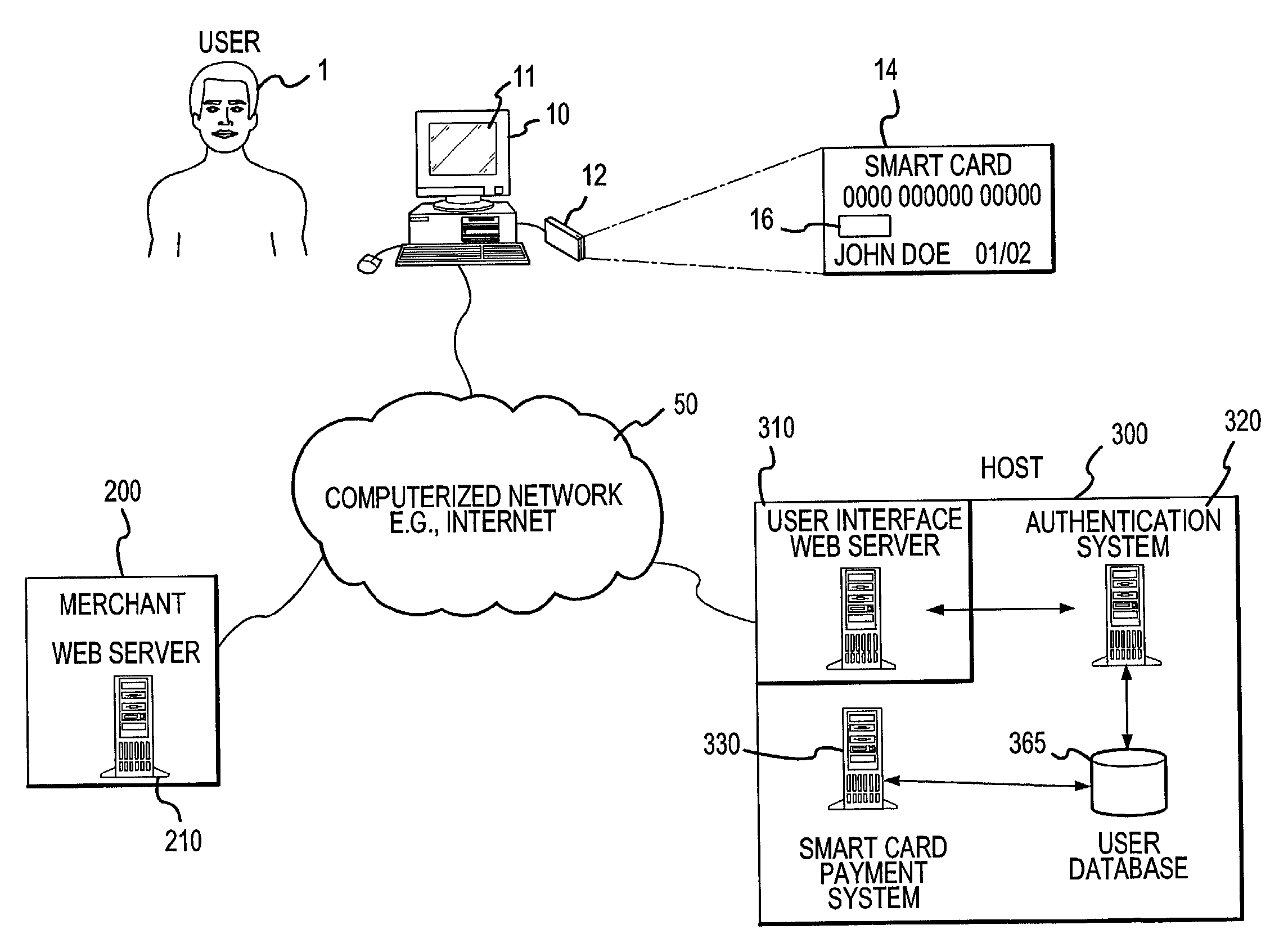
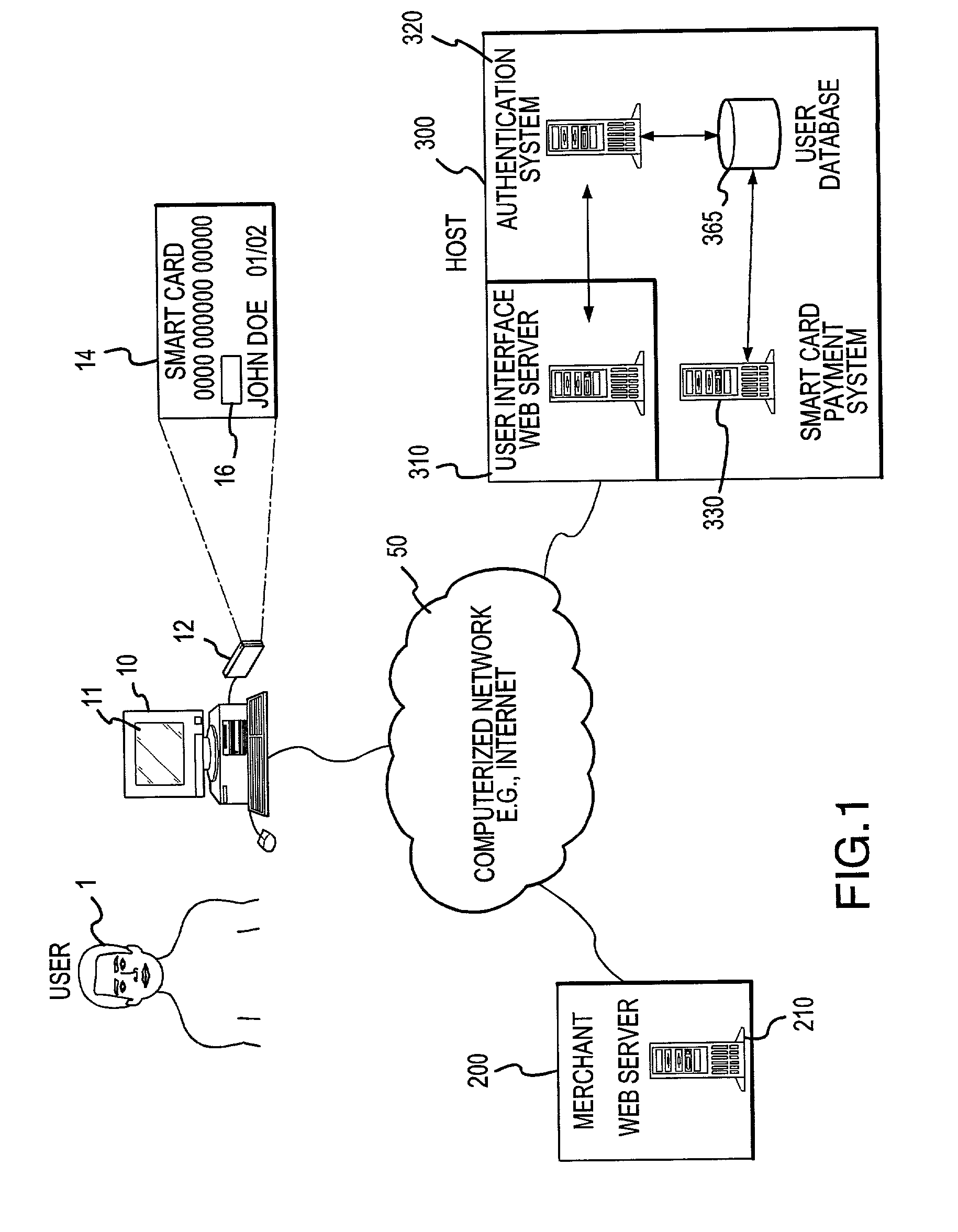
InactiveUS7292999B2Easy to optimizeRemove the burdenSecret communicationBuying/selling/leasing transactionsThe InternetPublic network
An online card-present transaction system facilitates card-present type transactions with a merchant over a public network. A host system is configured to accept authentication data from a user via an authentication device. The host system, after authenticating a user is configured to retrieve the user's account information from a user database system and translate a user account number into a temporary transaction number. The temporary transaction number is then transmitted directly from the host system to the merchant, thereby eliminating the need for the user to send to the merchant over the internet, the user's transaction account number.
Owner:LIBERTY PEAK VENTURES LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com