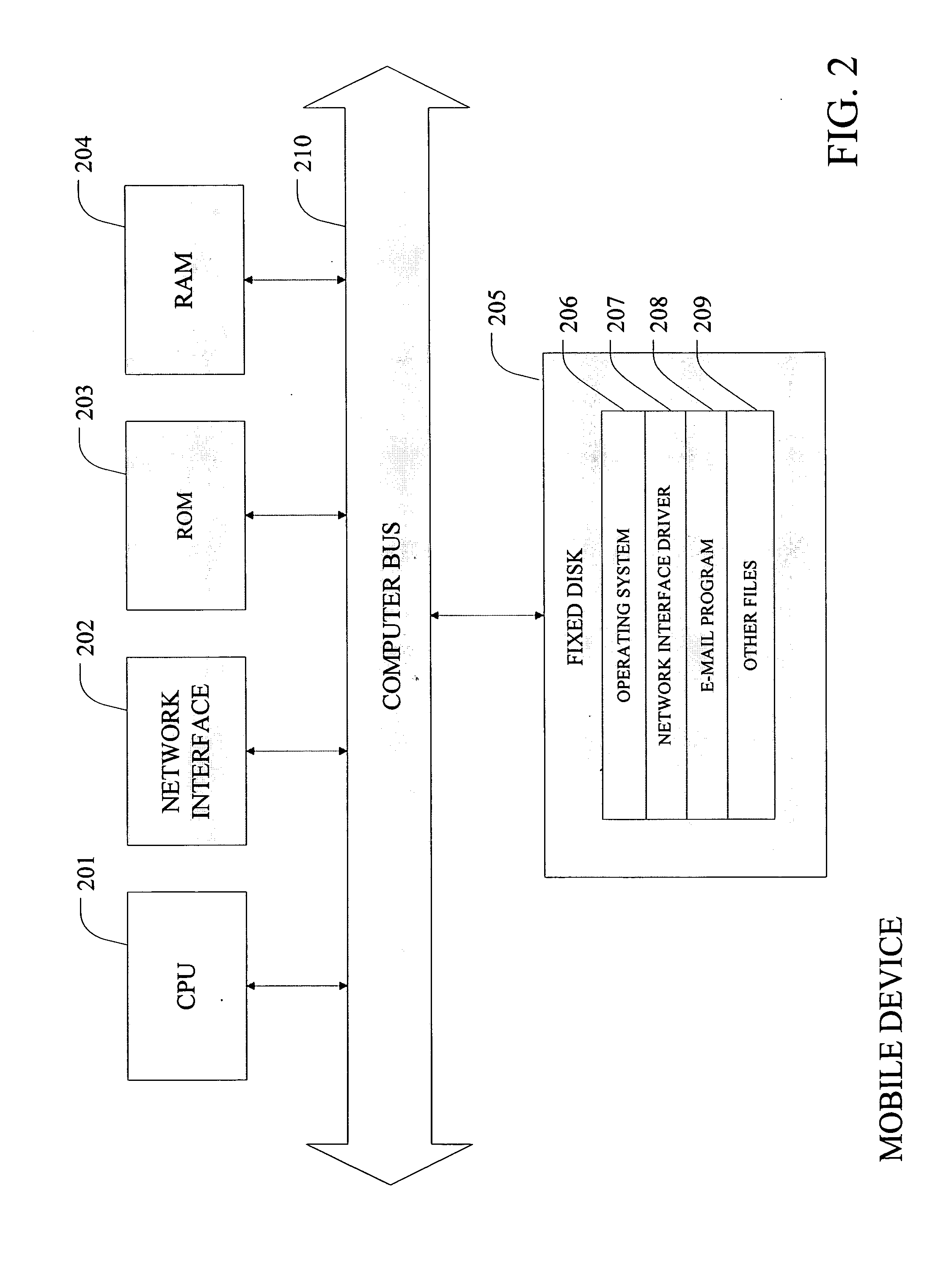
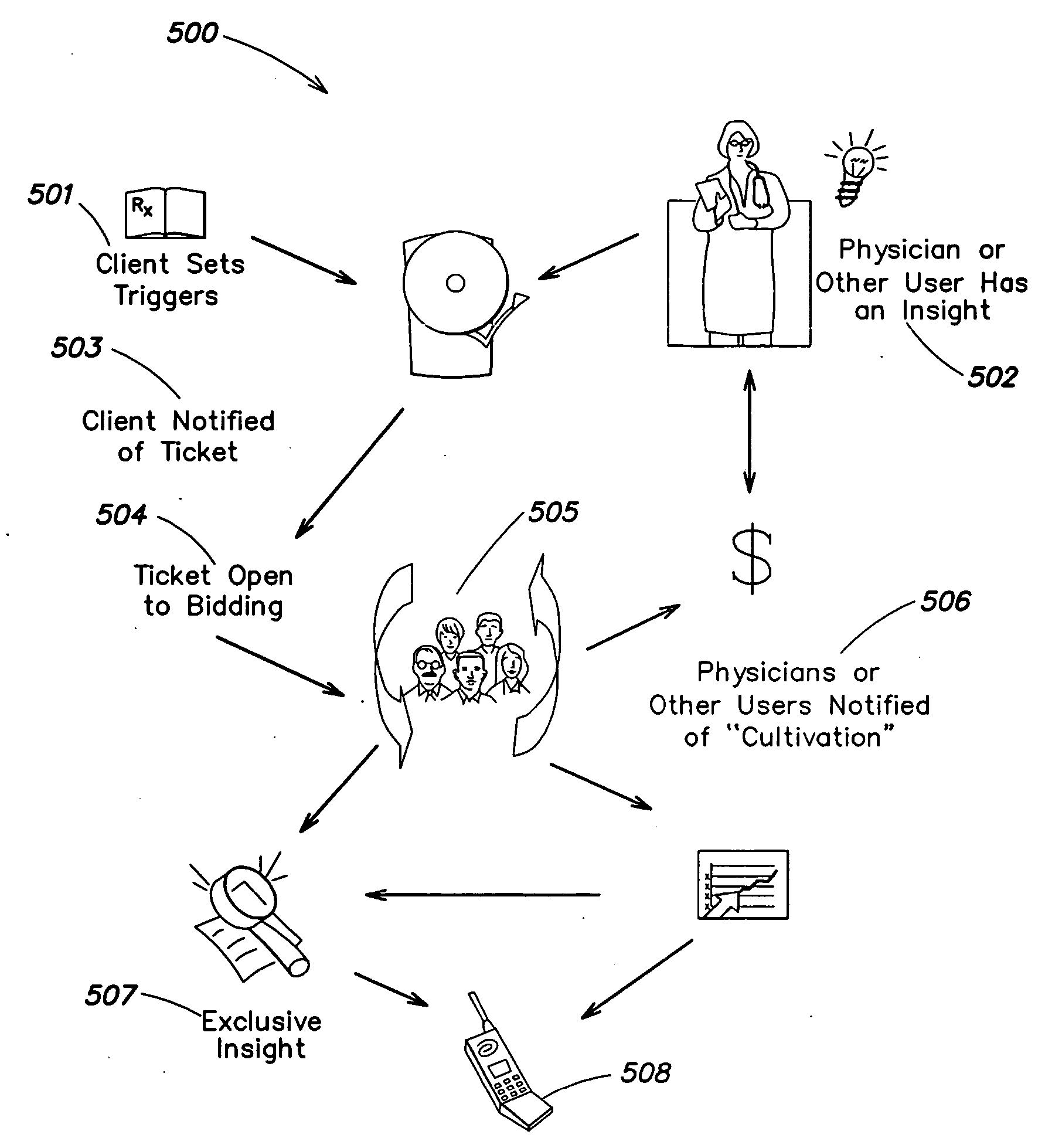
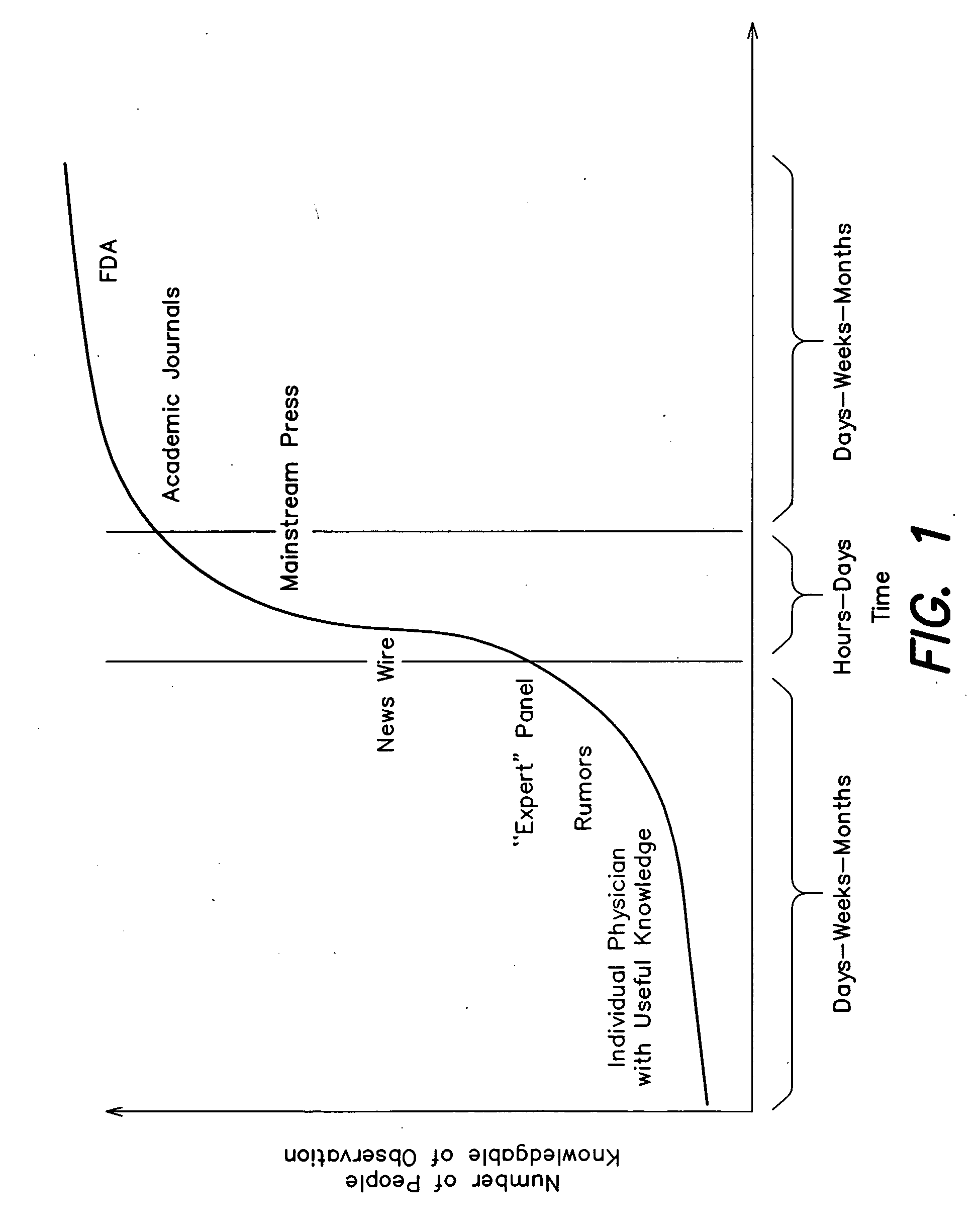
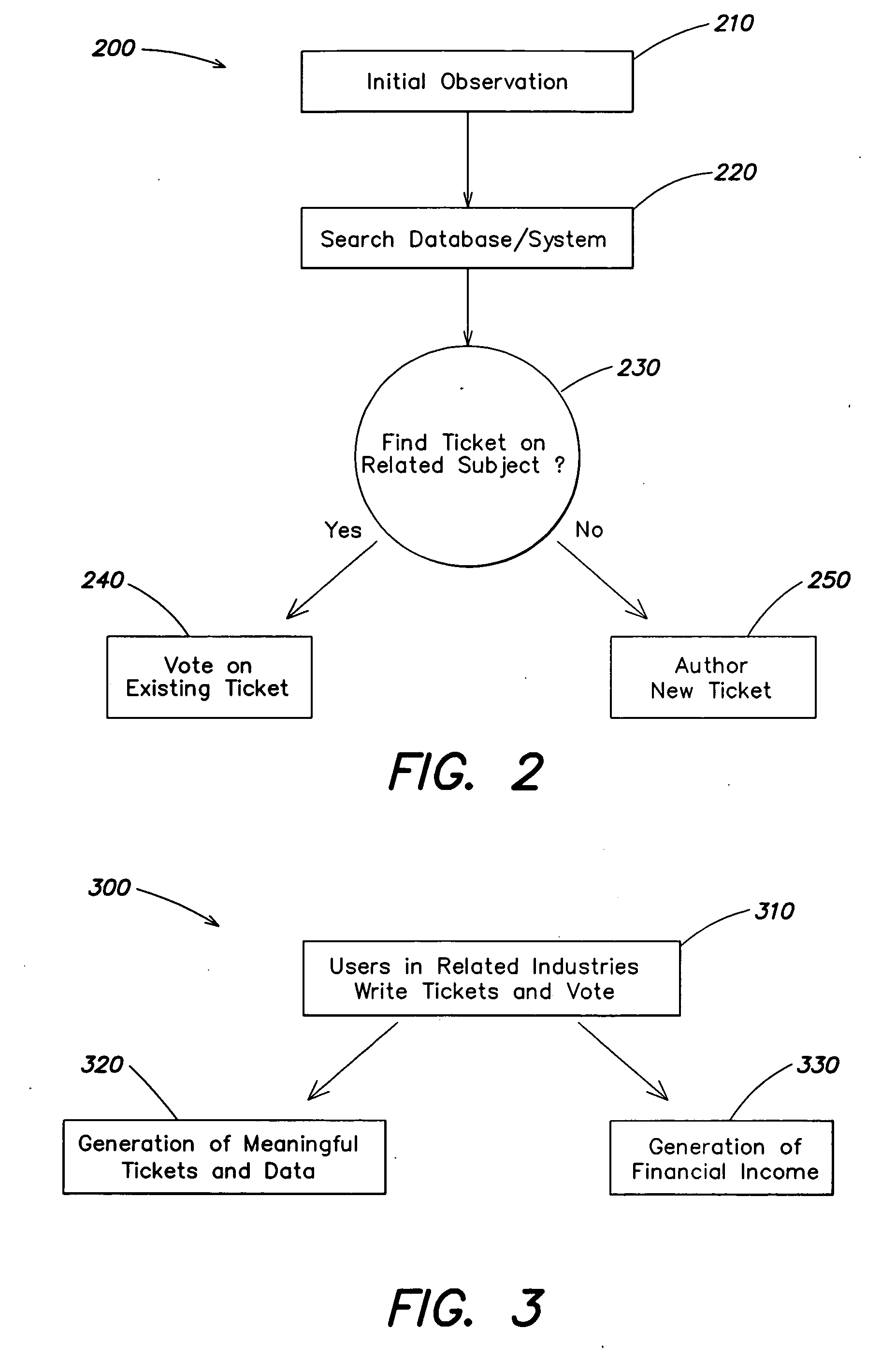
Patents
Literature
158 results about "Information agents" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and Method for Distributed Denial of Service Identification and Prevention
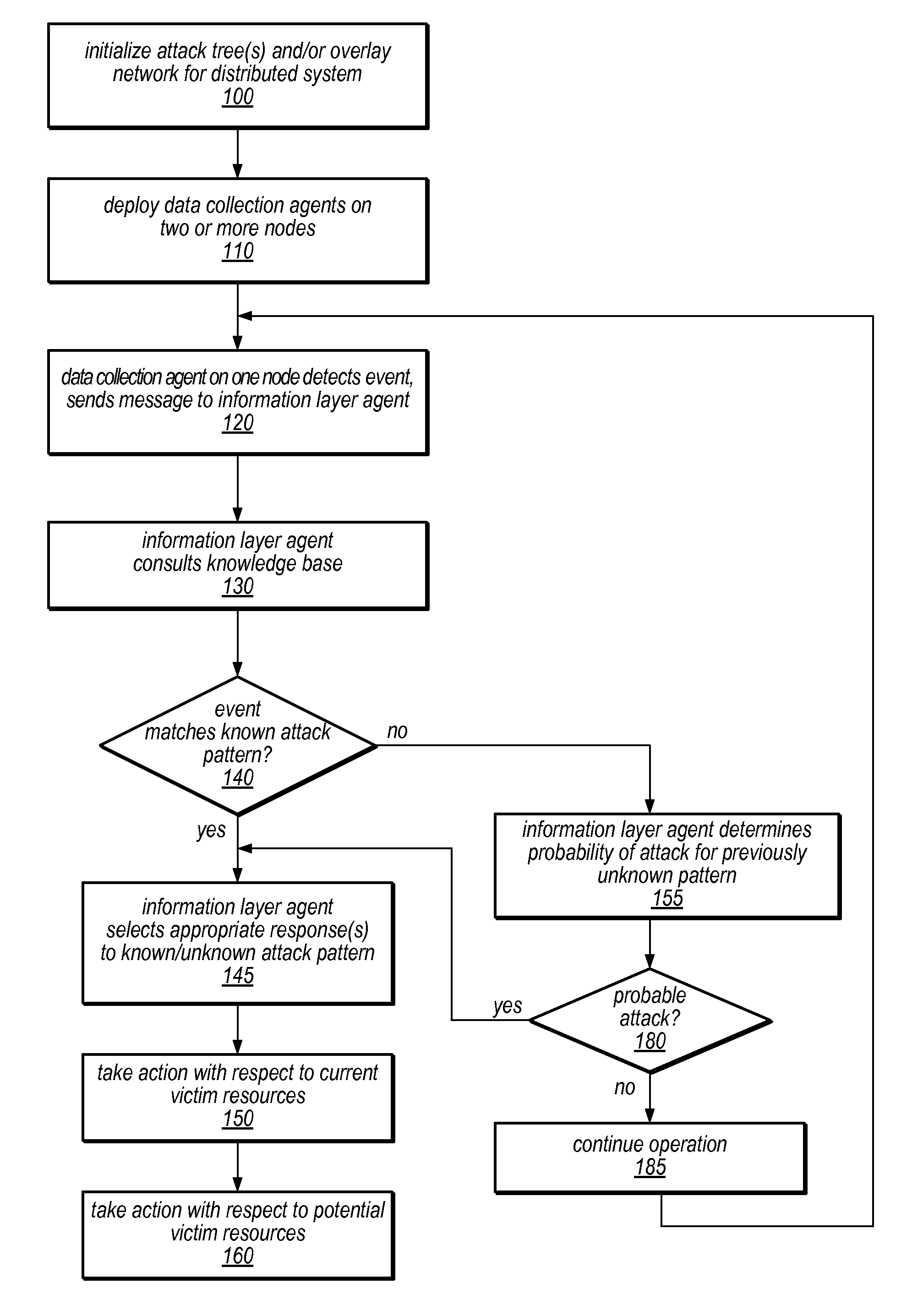
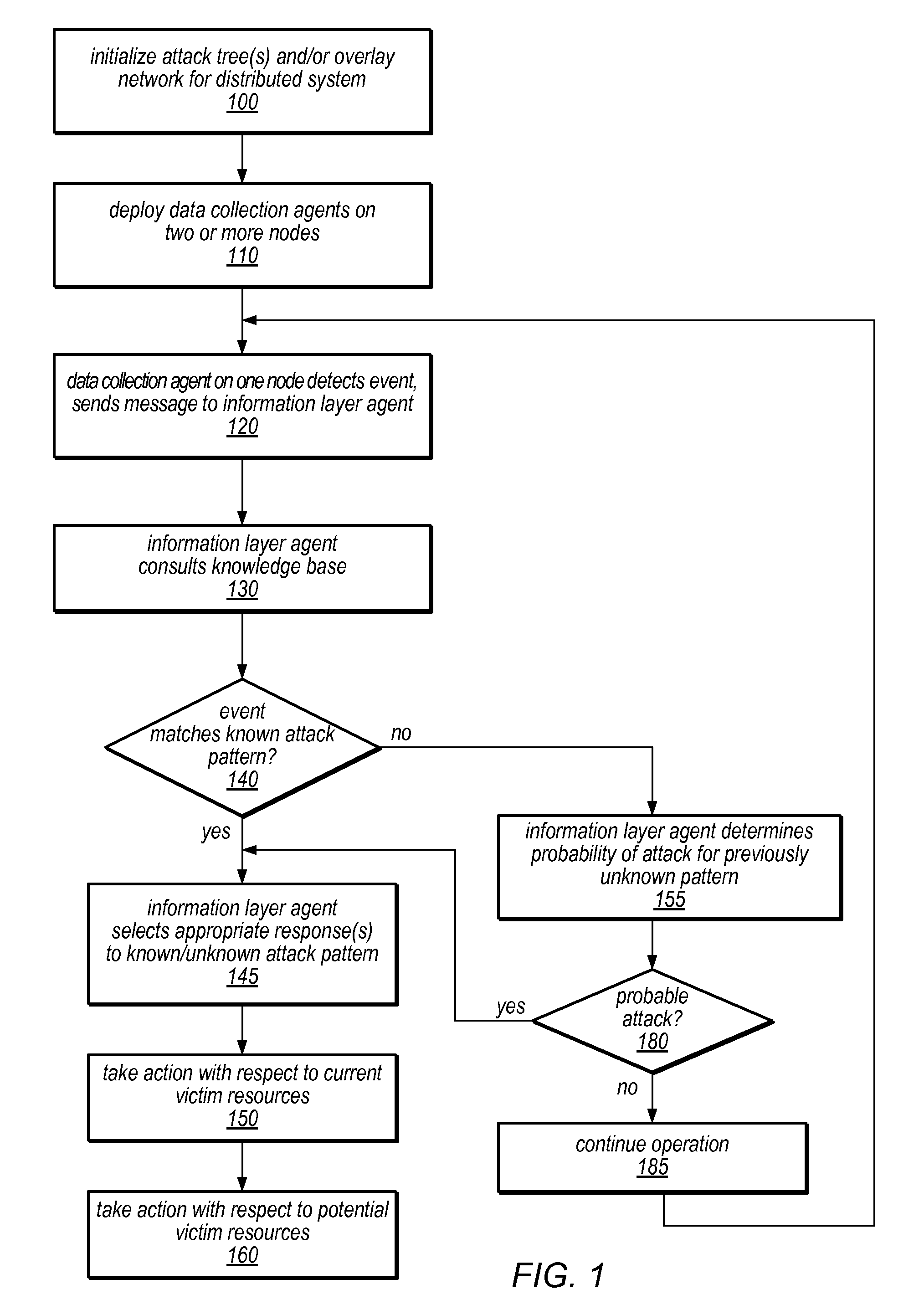
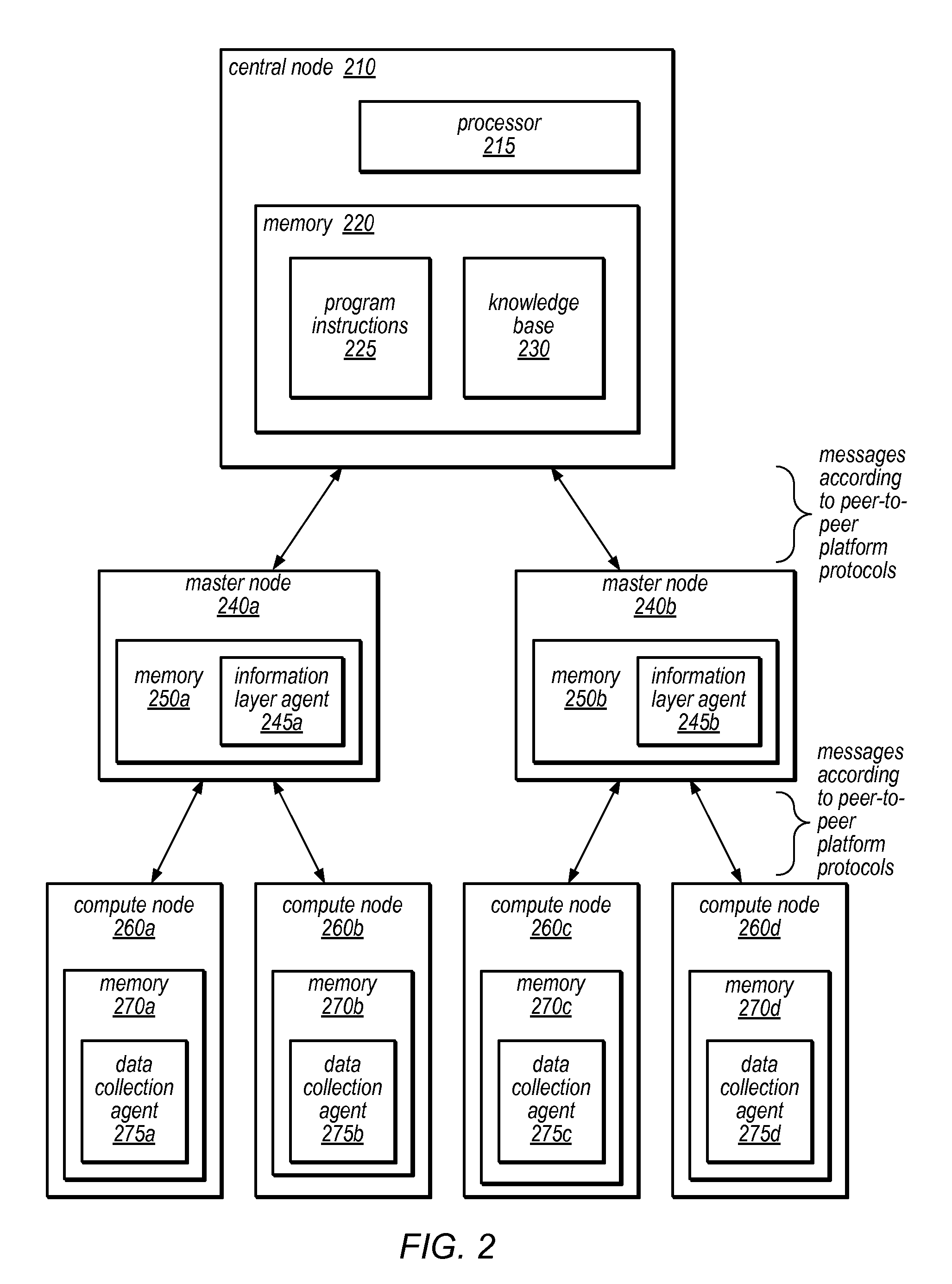
Systems and methods for discovery and classification of denial of service attacks in a distributed computing system may employ local agents on nodes thereof to detect resource-related events. An information later agent may determine if events indicate attacks, perform clustering analysis to determine if they represent known or unknown attack patterns, classify the attacks, and initiate appropriate responses to prevent and / or mitigate the attack, including sending warnings and / or modifying resource pool(s). The information layer agent may consult a knowledge base comprising information associated with known attack patterns, including state-action mappings. An attack tree model and an overlay network (over which detection and / or response messages may be sent) may be constructed for the distributed system. They may be dynamically modified in response to changes in system configuration, state, and / or workload. Reinforcement learning may be applied to the tuning of attack detection and classification techniques and to the identification of appropriate responses.
Owner:ORACLE INT CORP
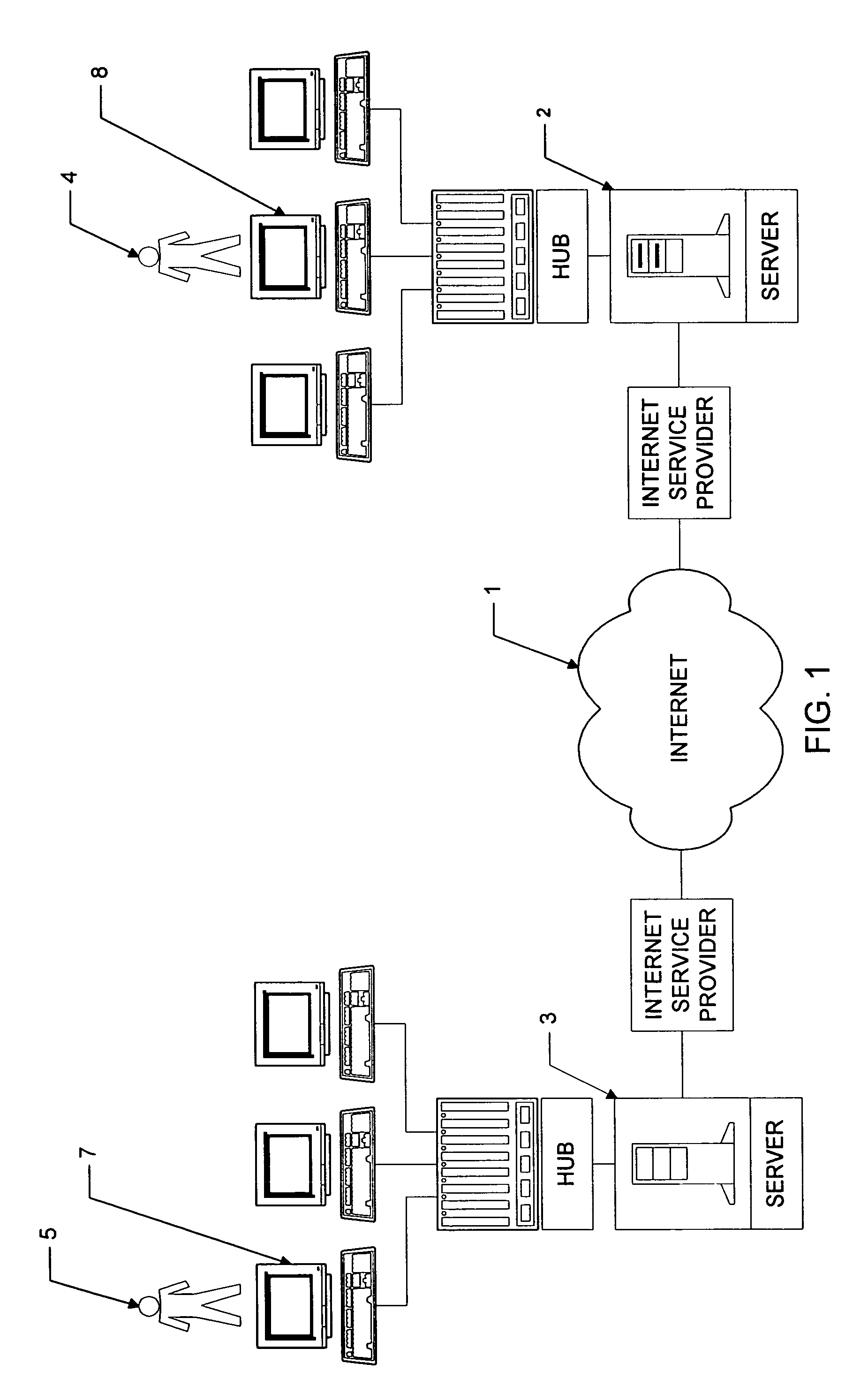
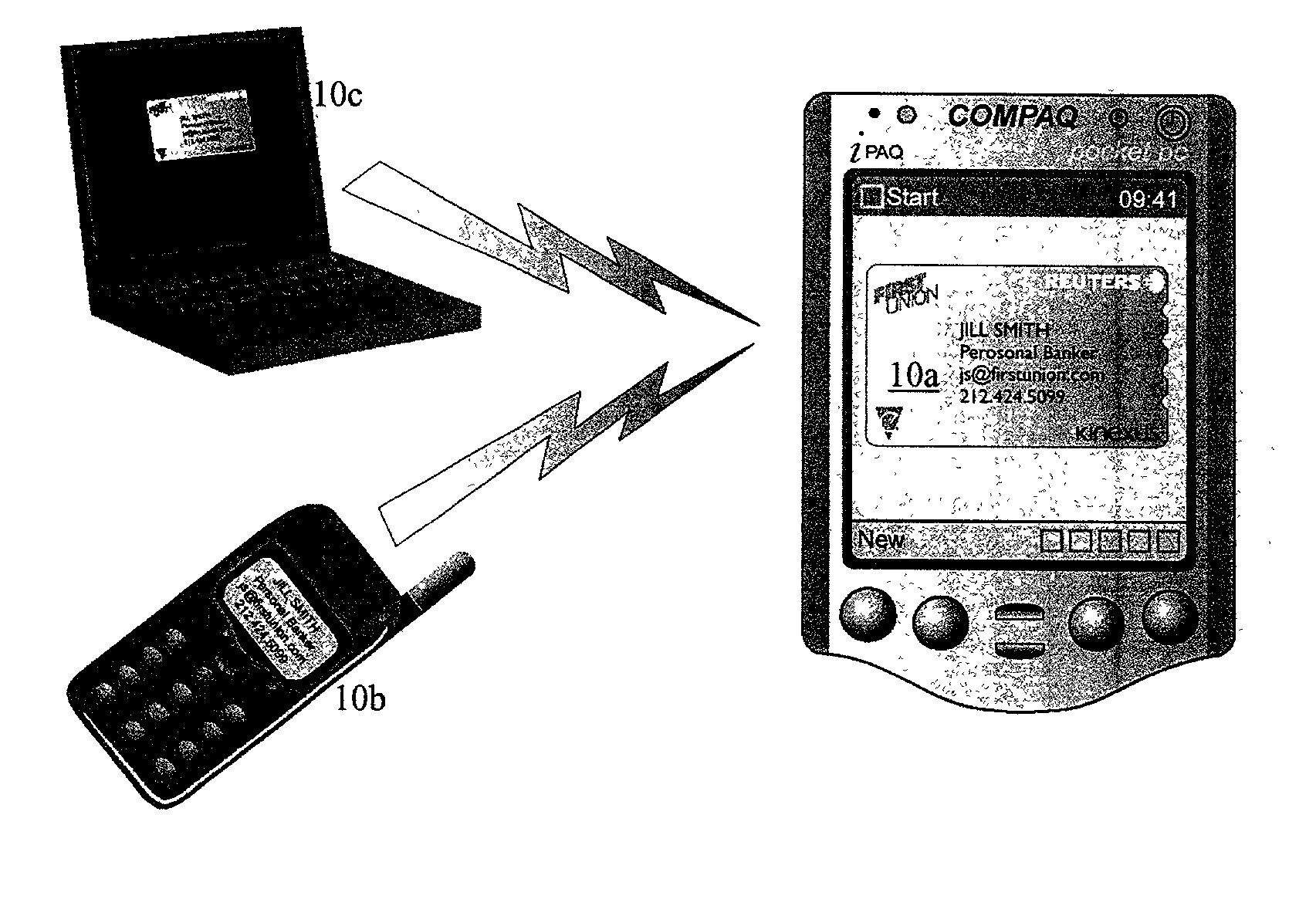
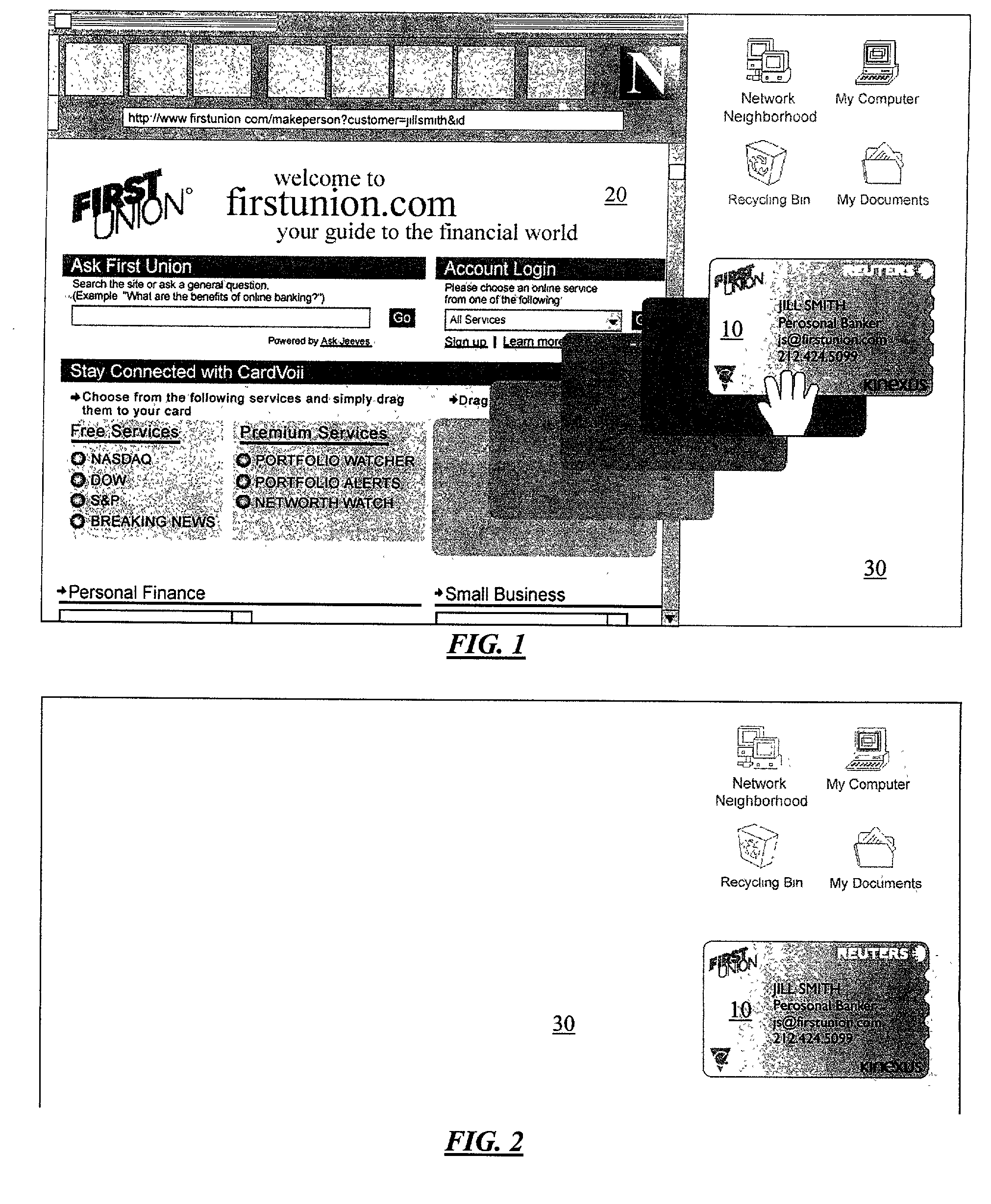
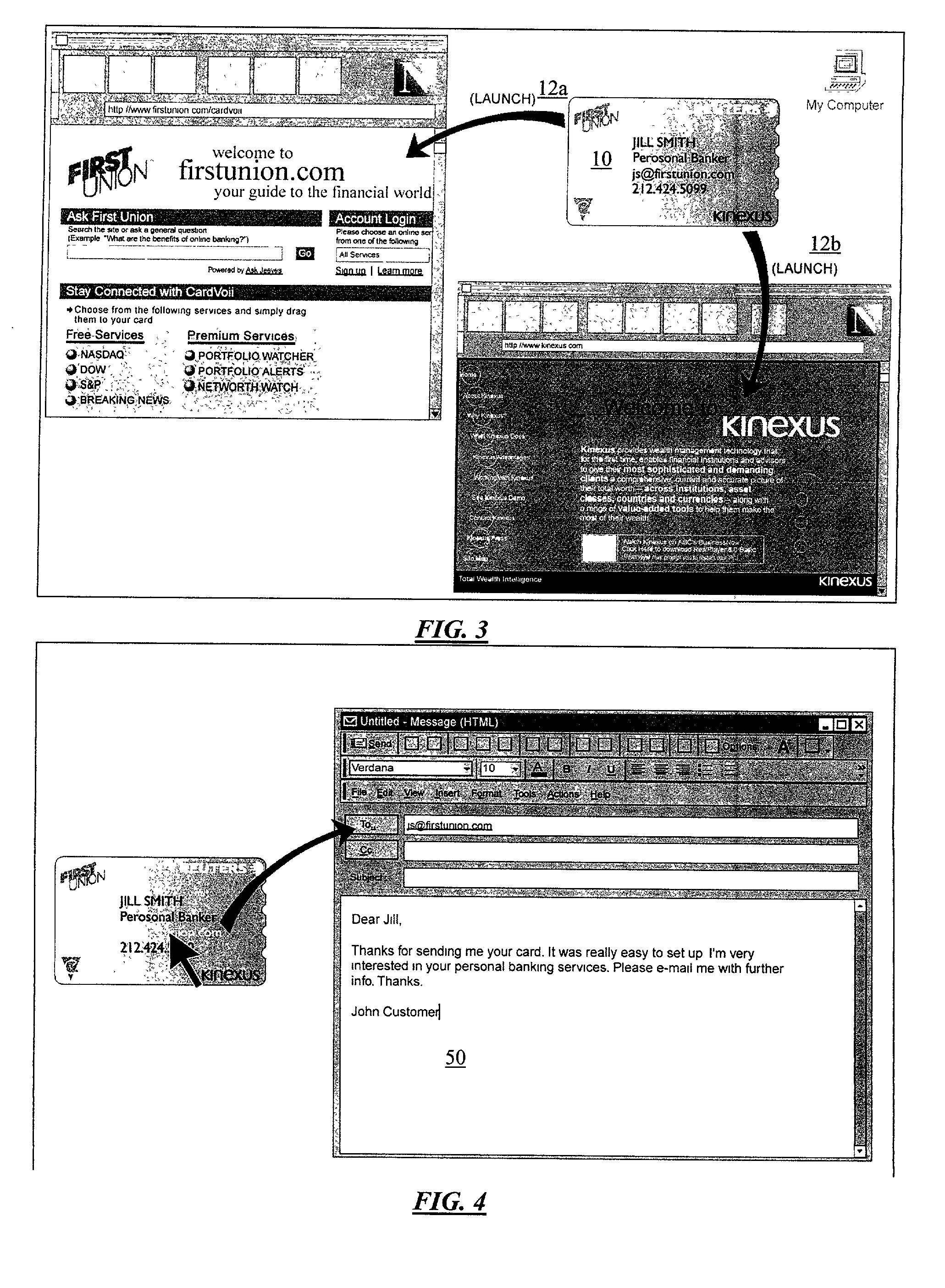
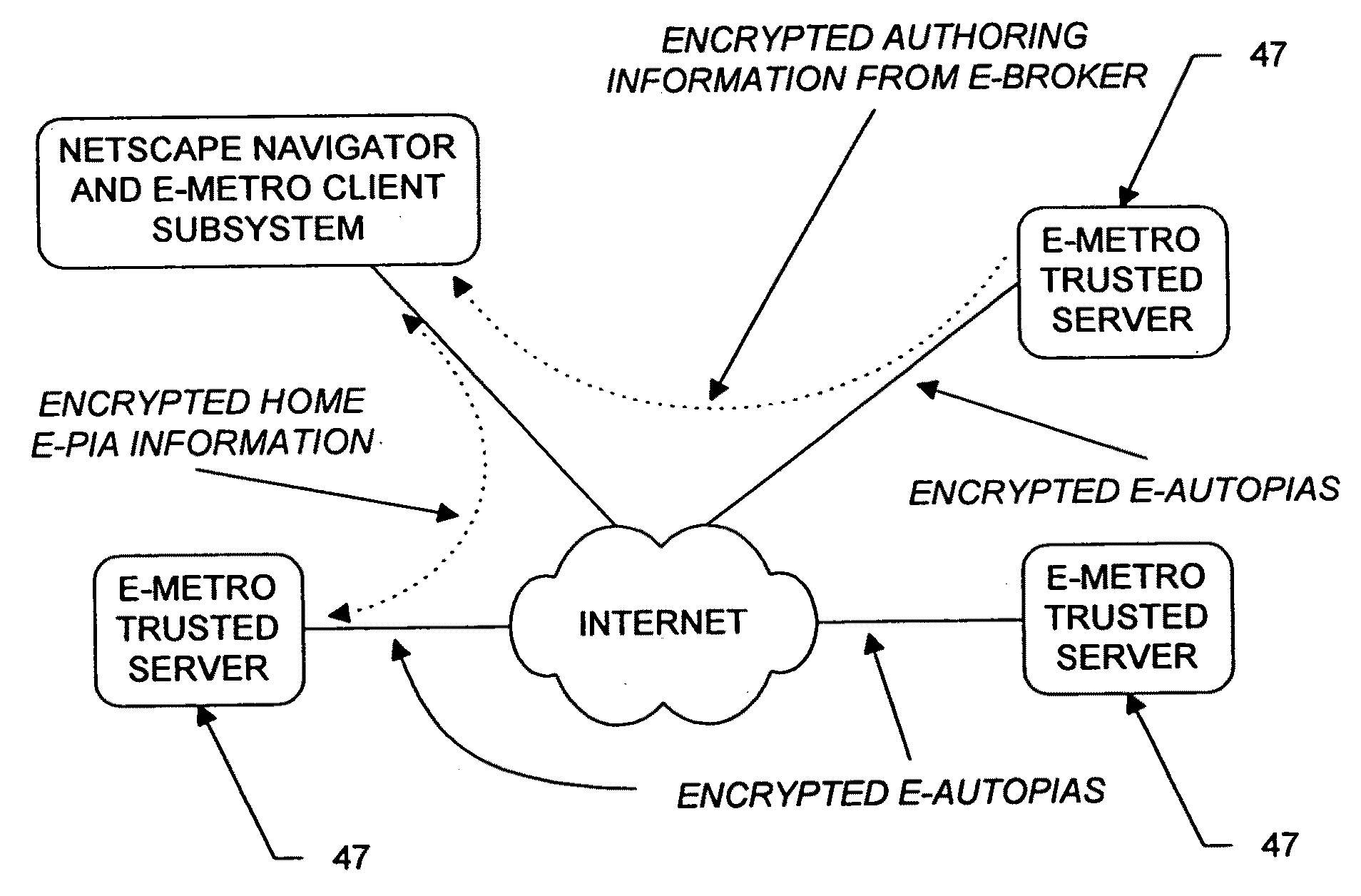
Personal information security and exchange tool
InactiveUS7289971B1Facilitates formation and useEasy to useFinanceComputer security arrangementsCommand and controlElectricity market
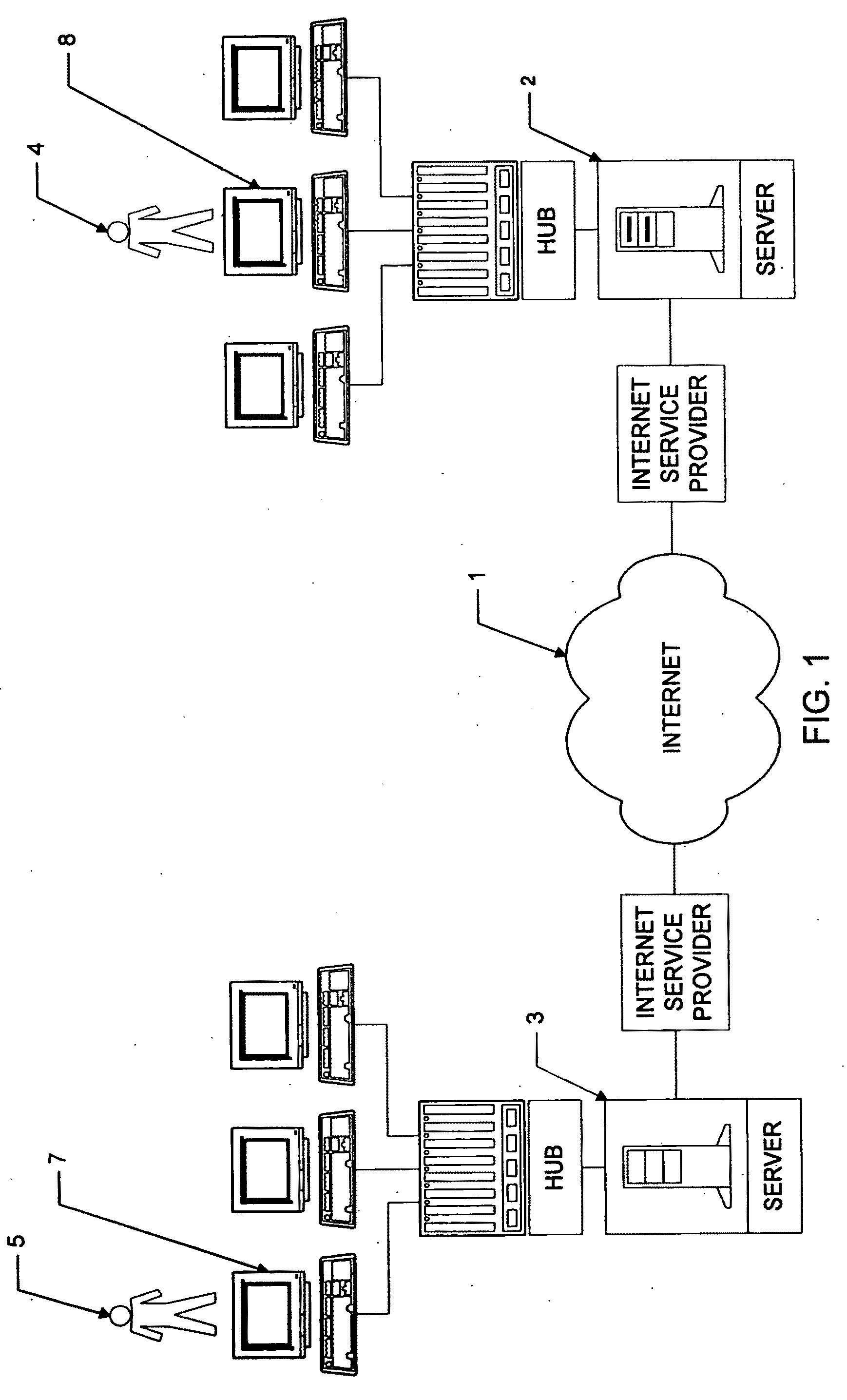
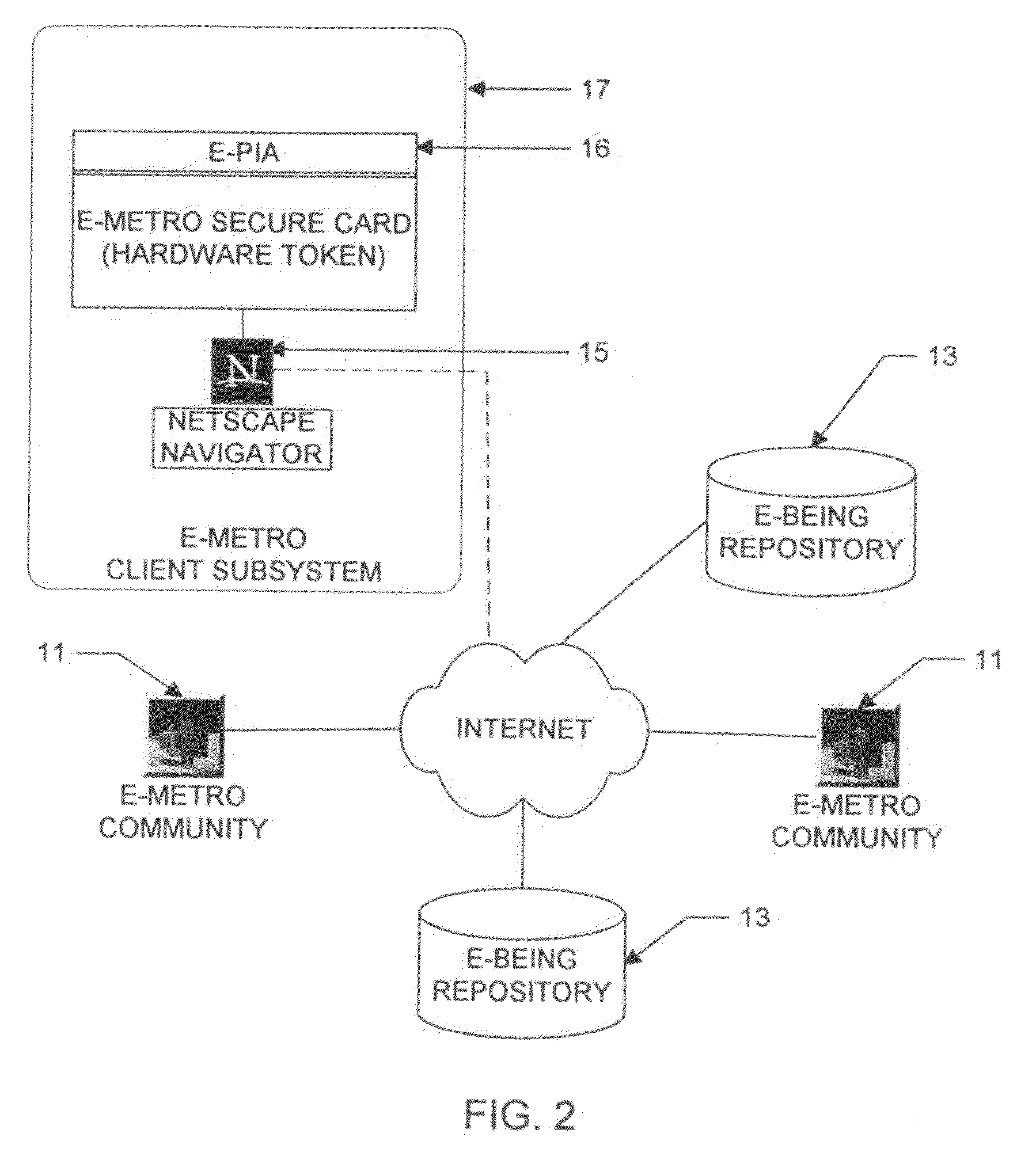
Utilization of the E-Metro Community and Personal Information Agents assure an effective and comprehensive agent-rule based command and control of informational assets in a networked computer environment. The concerns of informational privacy and informational self-determination are addressed squarely by the invention affording persons and entities a trusted means to author, secure, search, process, and exchange personal and / or confidential information in a networked computer environment. The formation of trusted electronic communities wherein members command and control their digital persona, exchanging or brokering for value the trusted utility of their informational assets is made possible by the invention. The present invention provides for the trusted utilization of personal data in electronic markets, providing both communities and individuals aggregate and individual rule-based control of the processing of their personal data.
Owner:CYVA RES HLDG
Wrapper induction by hierarchical data analysis
InactiveUS6606625B1Easy to useAccurate extractionData processing applicationsWeb data indexingInductive algorithmDocumentation
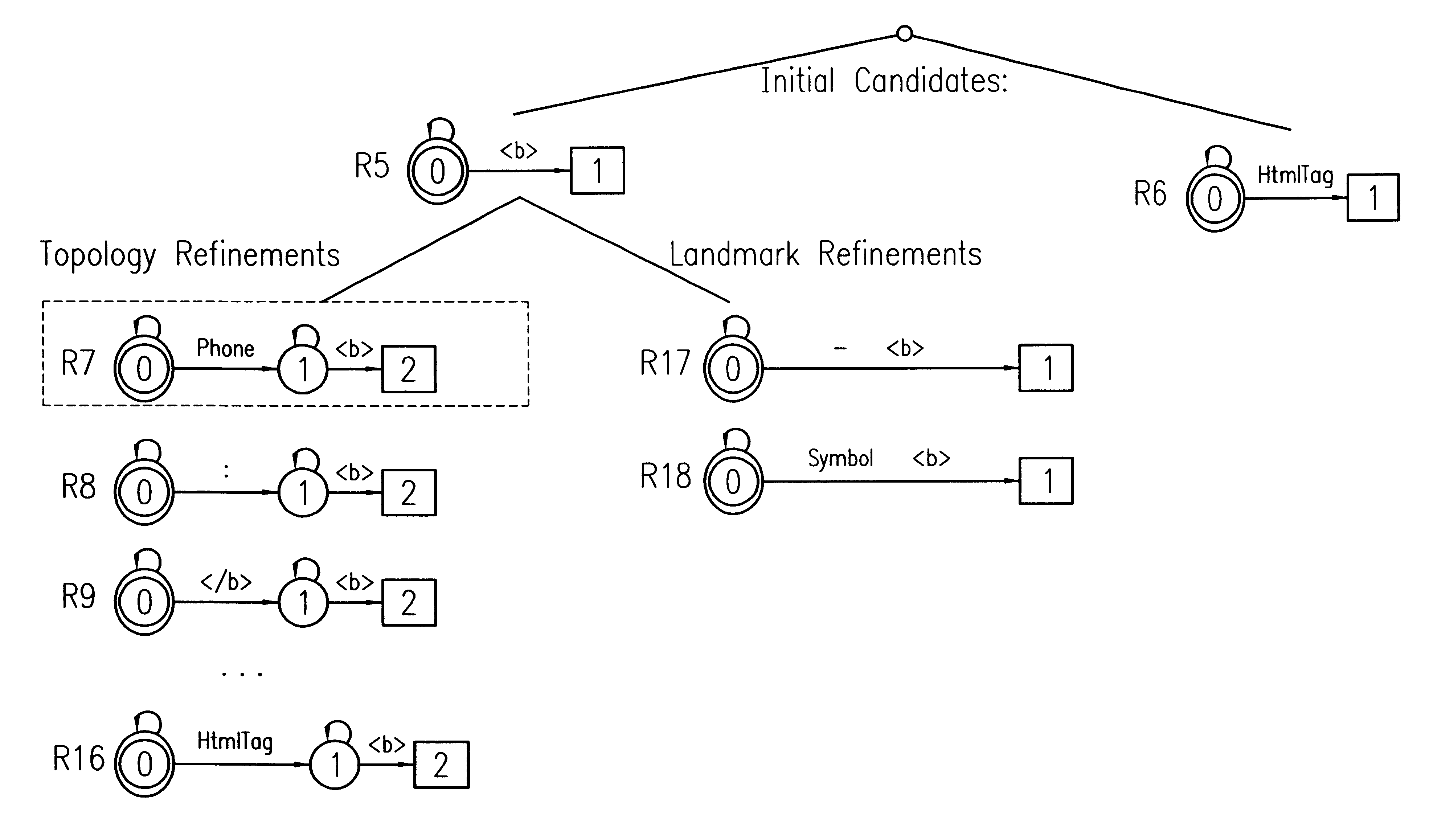
An inductive algorithm, denominated STALKER, generating high accuracy extraction rules based on user-labeled training examples. With the tremendous amount of information that becomes available on the Web on a daily basis, the ability to quickly develop information agents has become a crucial problem. A vital component of any Web-based information agent is a set of wrappers that can extract the relevant data from semistructured information sources. The novel approach to wrapped induction provided herein is based on the idea of hierarchical information extraction, which turns the hard problem of extracting data from an arbitrarily complex document into a series of easier extraction tasks. Labeling the training data represents the major bottleneck in using wrapper induction techniques, and experimental results show that STALKER performs significantly better than other approaches; on one hand, STALKER requires up to two orders of magnitude fewer examples than other algorithms, while on the other hand it can handle information sources that could not be wrapped by prior techniques. STALKER uses an embedded catalog formalism to parse the information source and render a predictable structure from which information may be extracted or by which such information extraction may be facilitated and made easier.
Owner:UNIV OF SOUTHERN CALIFORNIA +1
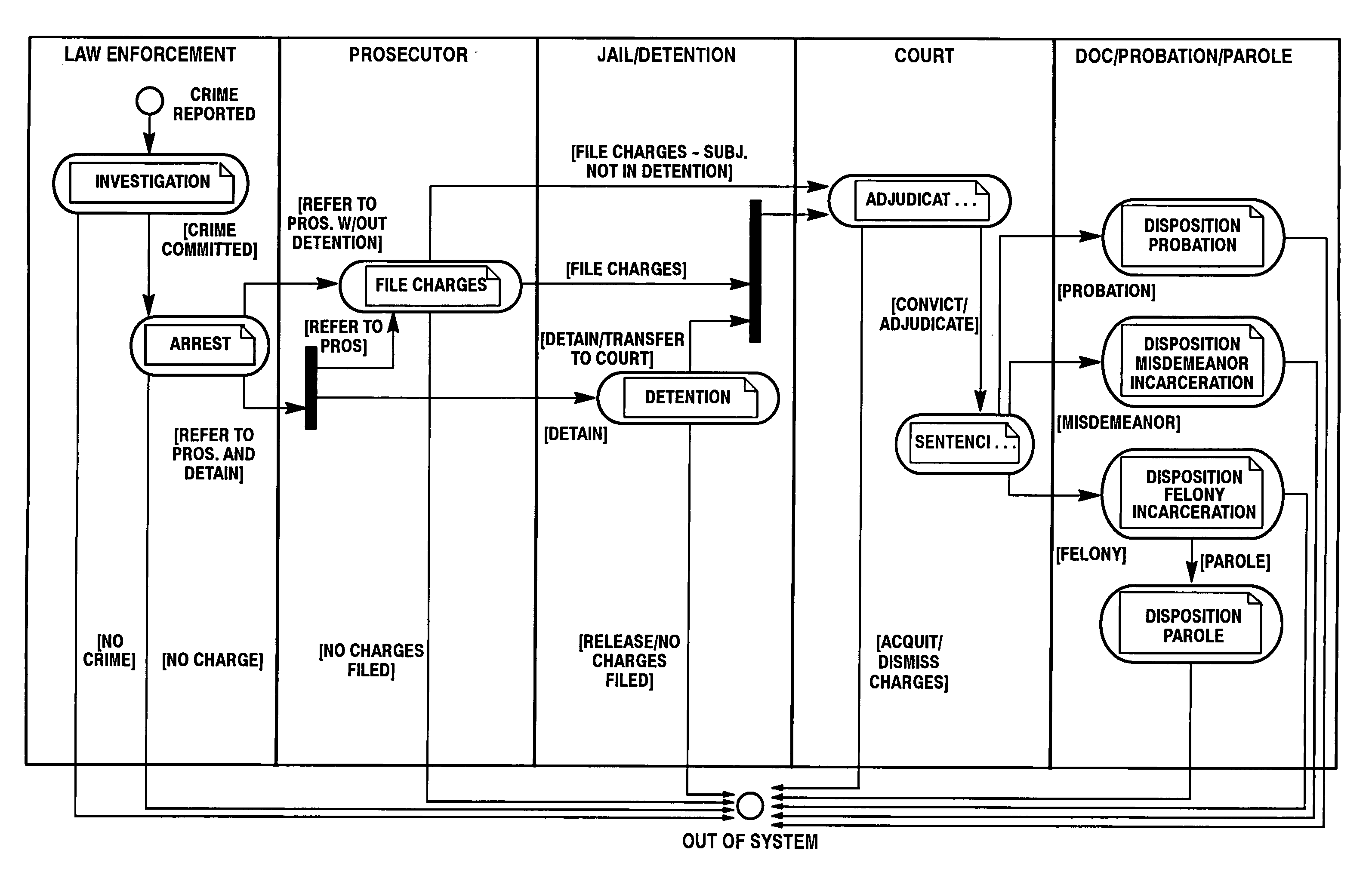
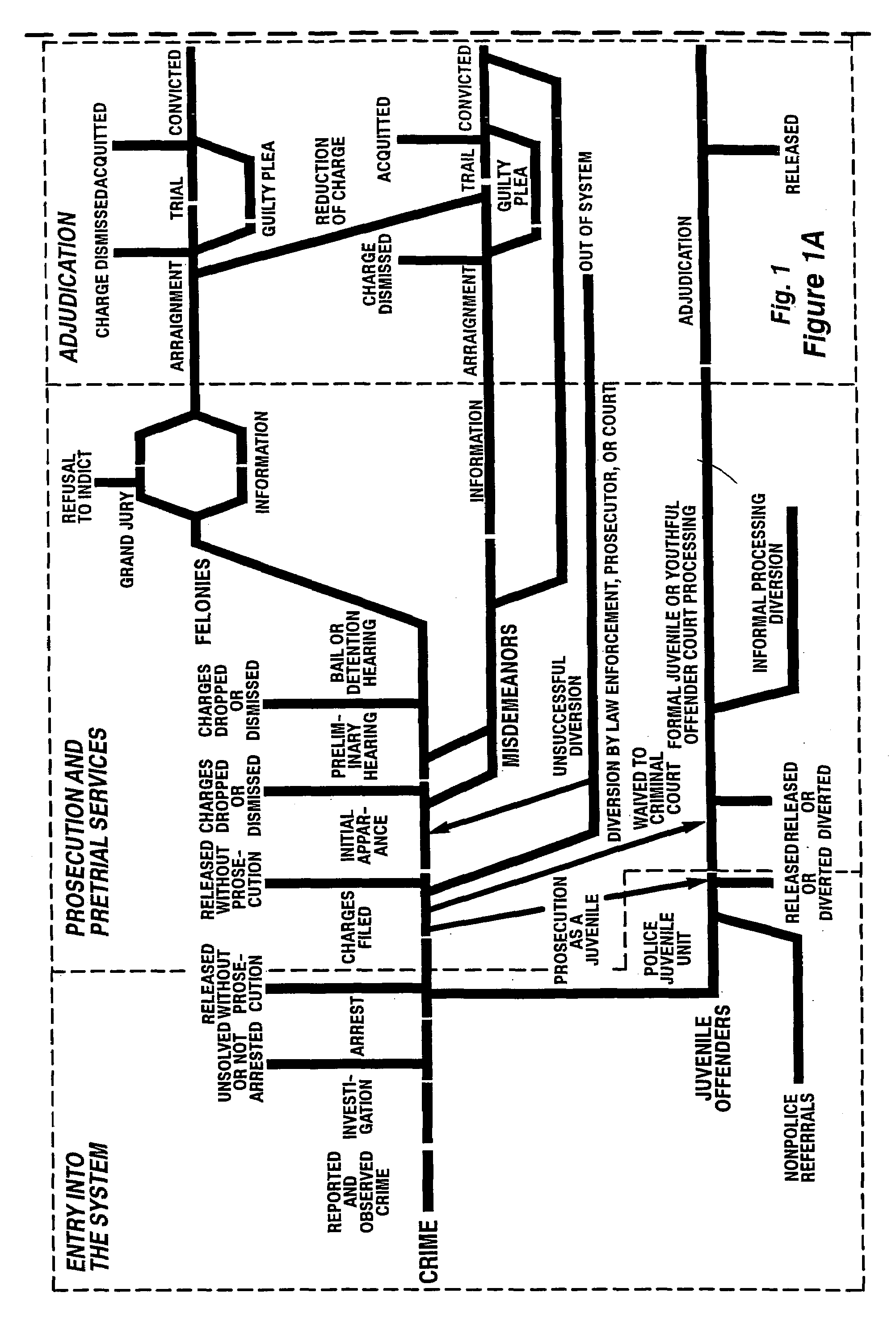
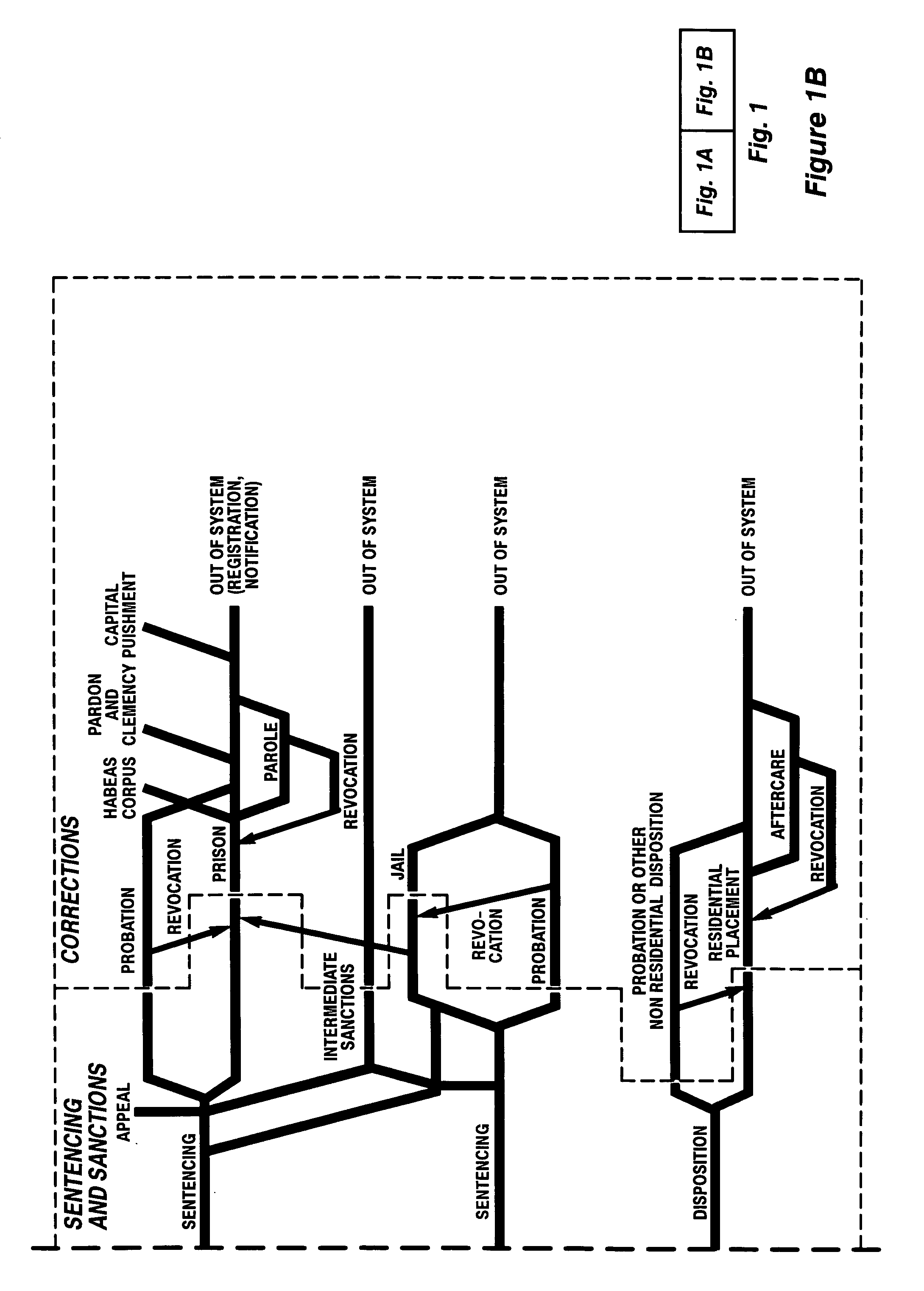
Platform independent model-based framework for exchanging information in the justice system
InactiveUS20050216555A1Guaranteed message deliveryData processing applicationsMultiple digital computer combinationsCost effectivenessSoftware agent
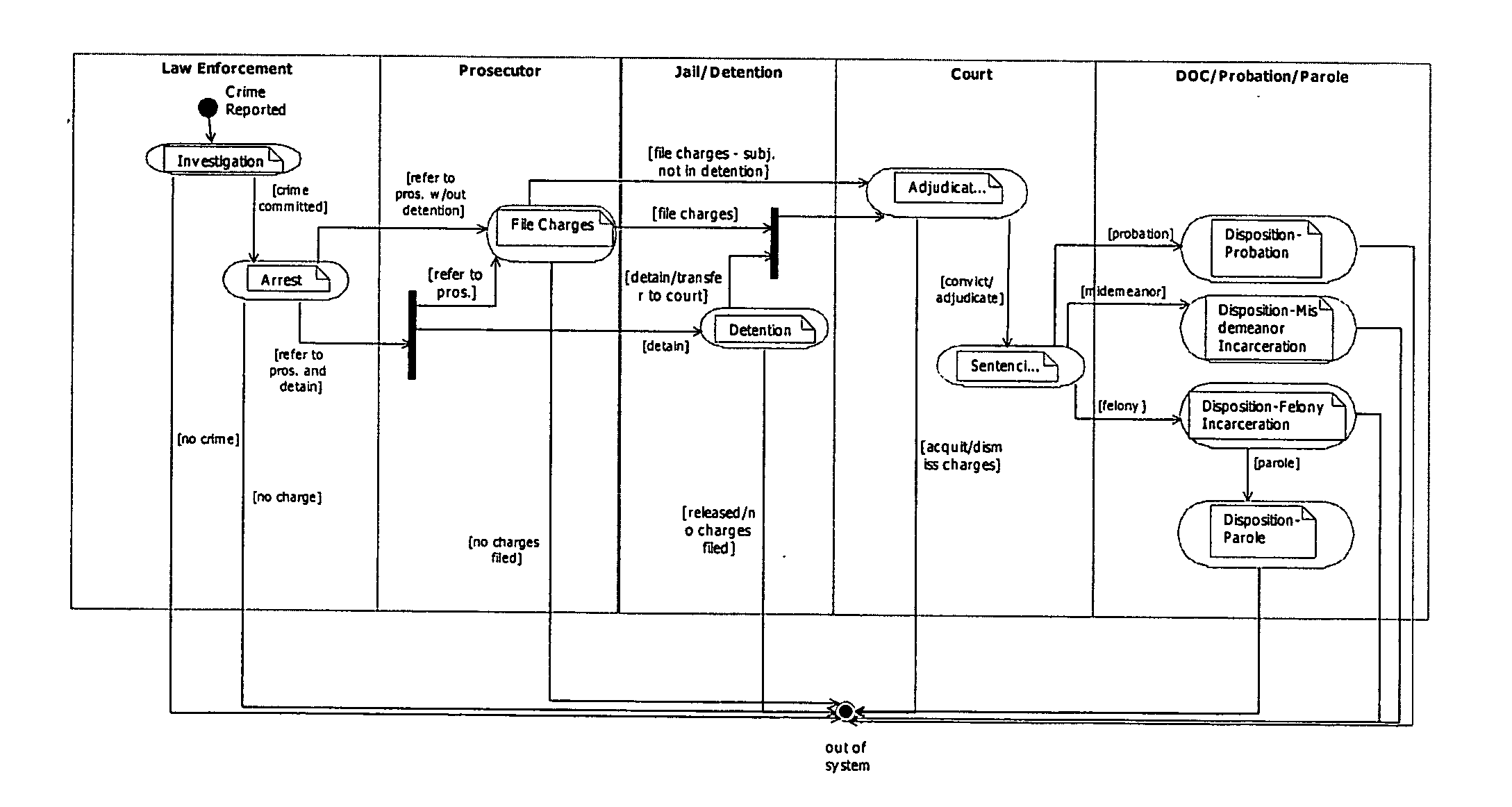
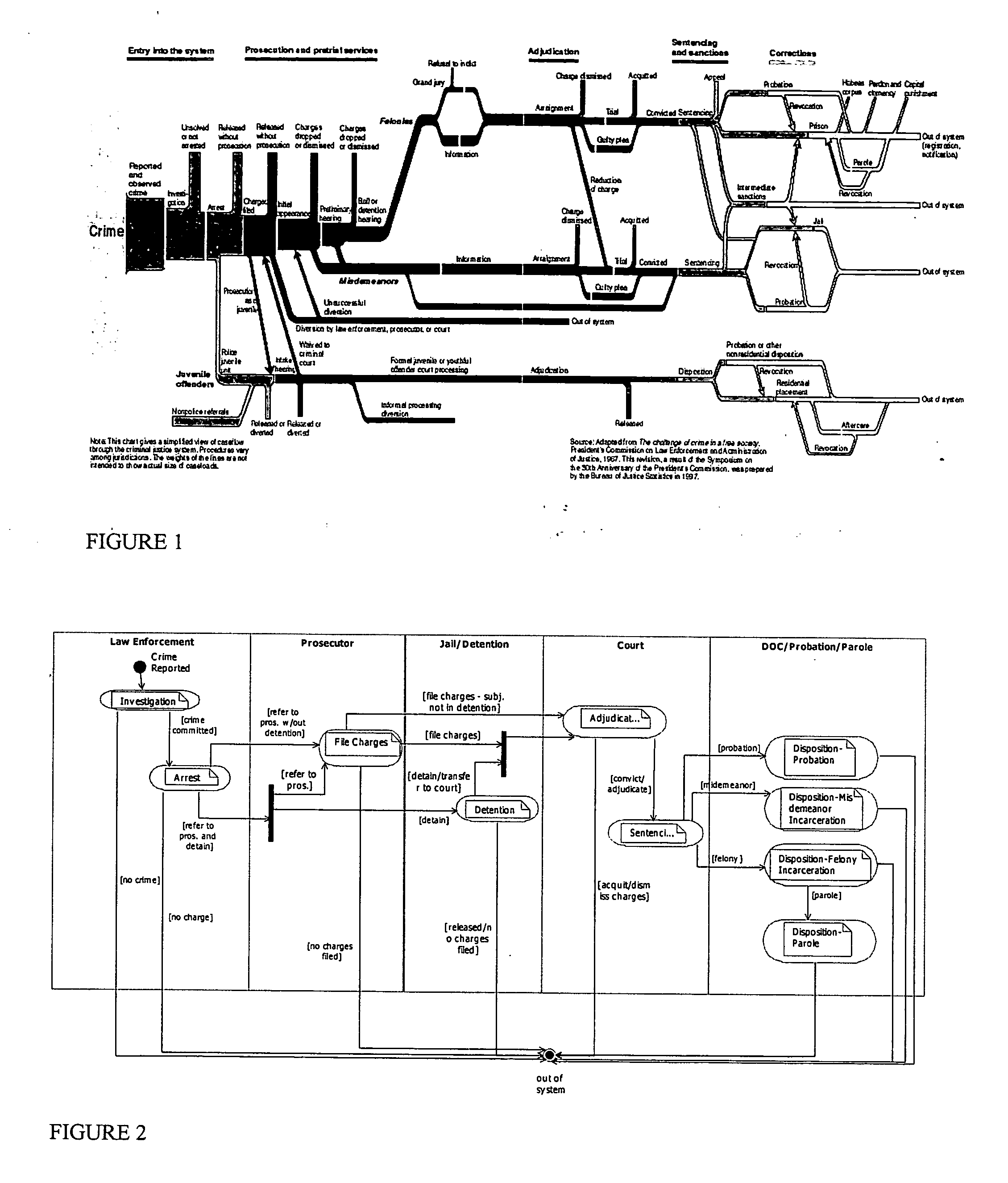
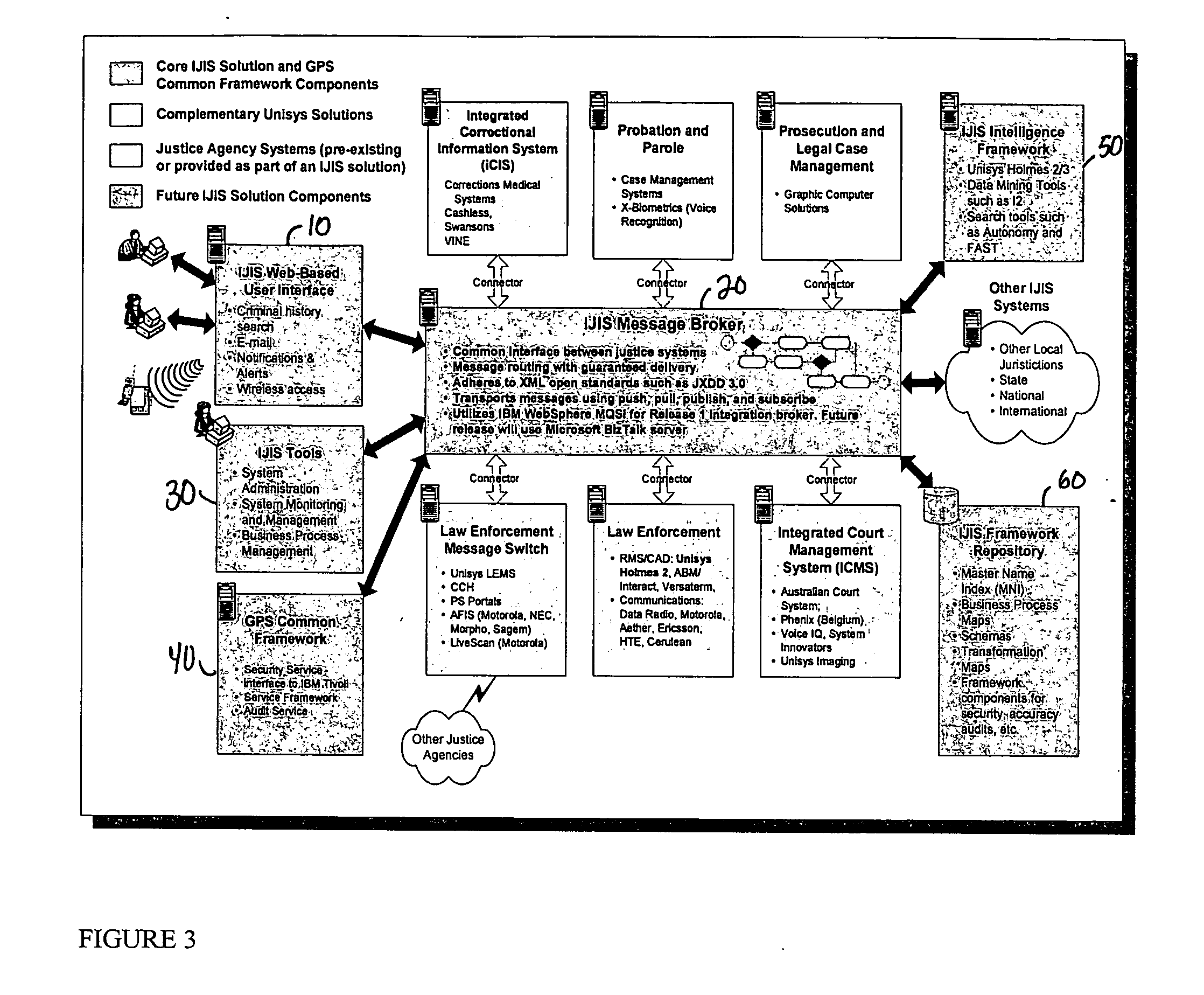
A platform independent model for exchanging information among numerous entities in a justice system with diverse system components is implemented in a hub and spoke arrangement. Each spoke includes a software agent that communicates with a system component of an entity of the justice system, translates from a common communication format to a communication format of the system component, and manages the timing of the flow of information to / from the system component. The hub includes an information broker that communicates with each agent in the common communication format, determines what information is needed by which entity, and routes the needed information to / from respective agents for the entities that need the information. The platform independent model includes a plurality of traceable and linked UML models that define the information broker from a business use case model through to a platform independent solution model for implementation on a given solution platform. Since these UML models are readily modifiable and traceable for changes to the justice system, they facilitate implementation of the system in a cost-effective manner from one customer to the next without requiring system redesign.
Owner:UNISYS CORP
Platform independent model-based framework for exchanging information in the justice system
InactiveUS7181493B2Data processing applicationsDigital data processing detailsSoftware agentInformation agents
A platform independent model for exchanging information among numerous entities in a justice system with diverse system components is implemented in a hub and spoke arrangement. Each spoke includes a software agent that communicates with a system component of an entity of the justice system, translates from a common communication format to a communication format of the system component, and manages the timing of the flow of information to / from the system component. The hub includes an information broker that communicates with each agent in the common communication format, determines what information is needed by which entity, and routes the needed information to / from respective agents for the entities that need the information. The platform independent model includes a plurality of traceable and linked UML models that define the information broker from a business use case model through to a platform independent solution model for implementation on a given solution platform. Since these UML models are readily modifiable and traceable for changes to the justice system, they facilitate implementation of the system in a cost-effective manner from one customer to the next without requiring system redesign.
Owner:UNISYS CORP
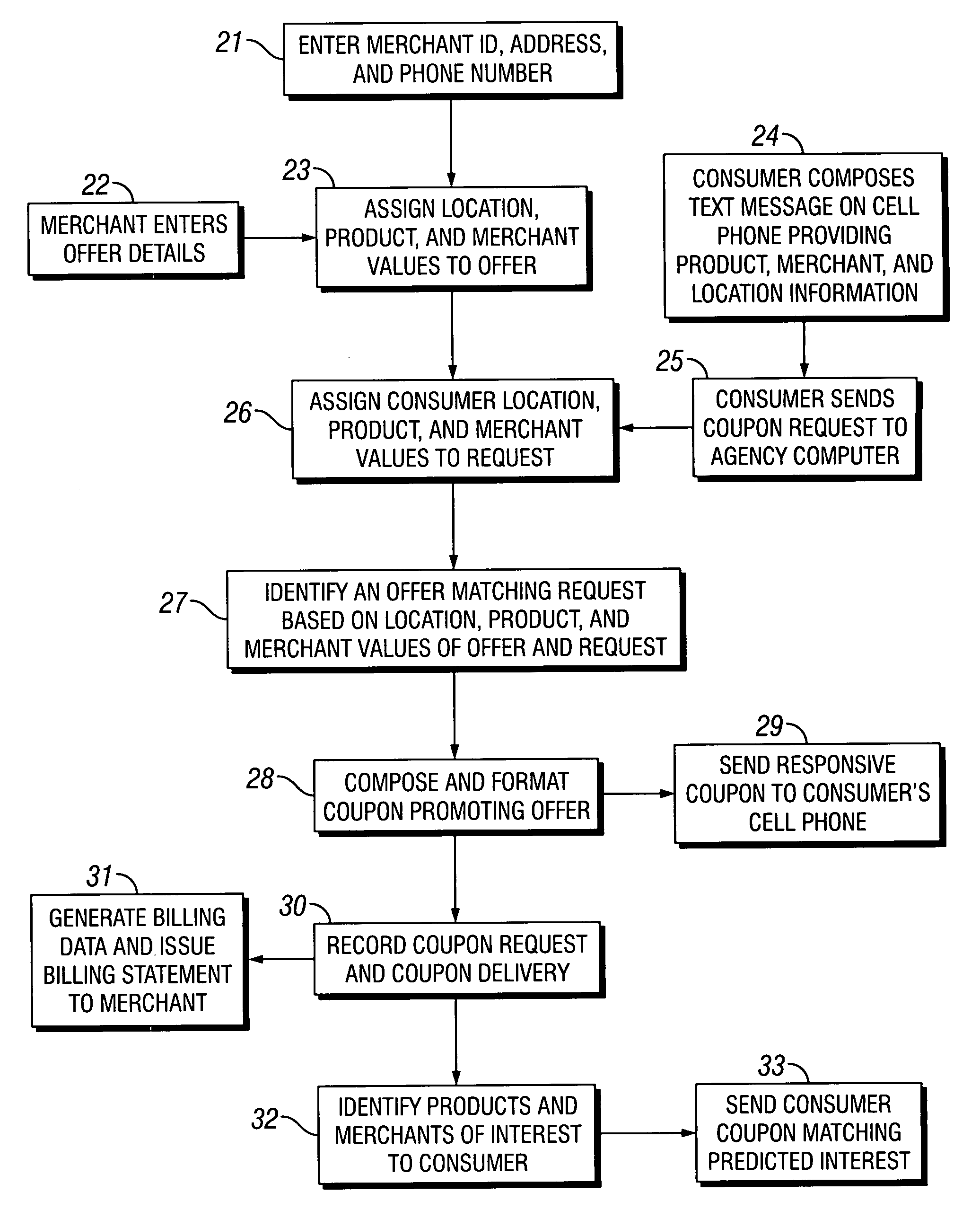
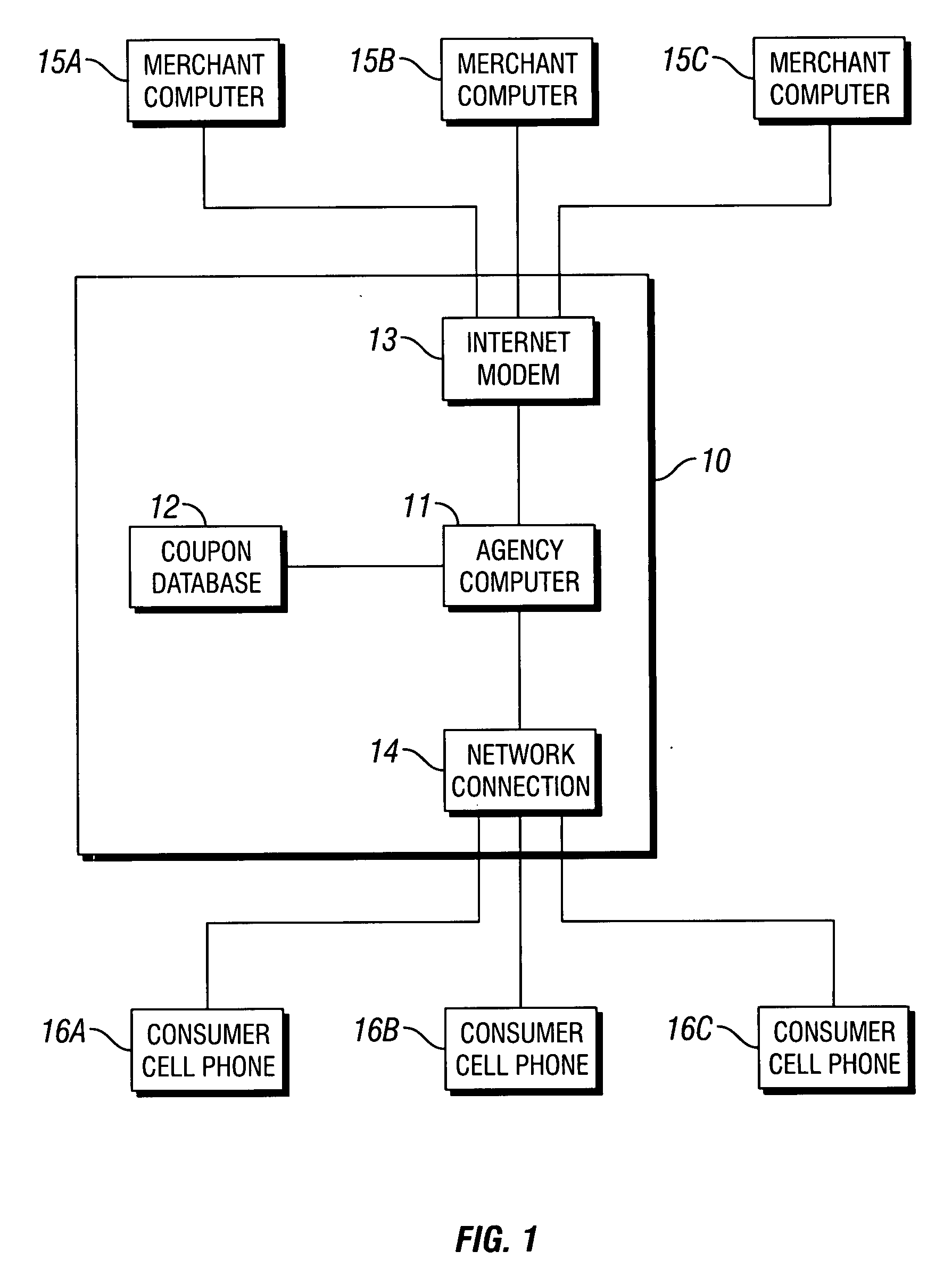
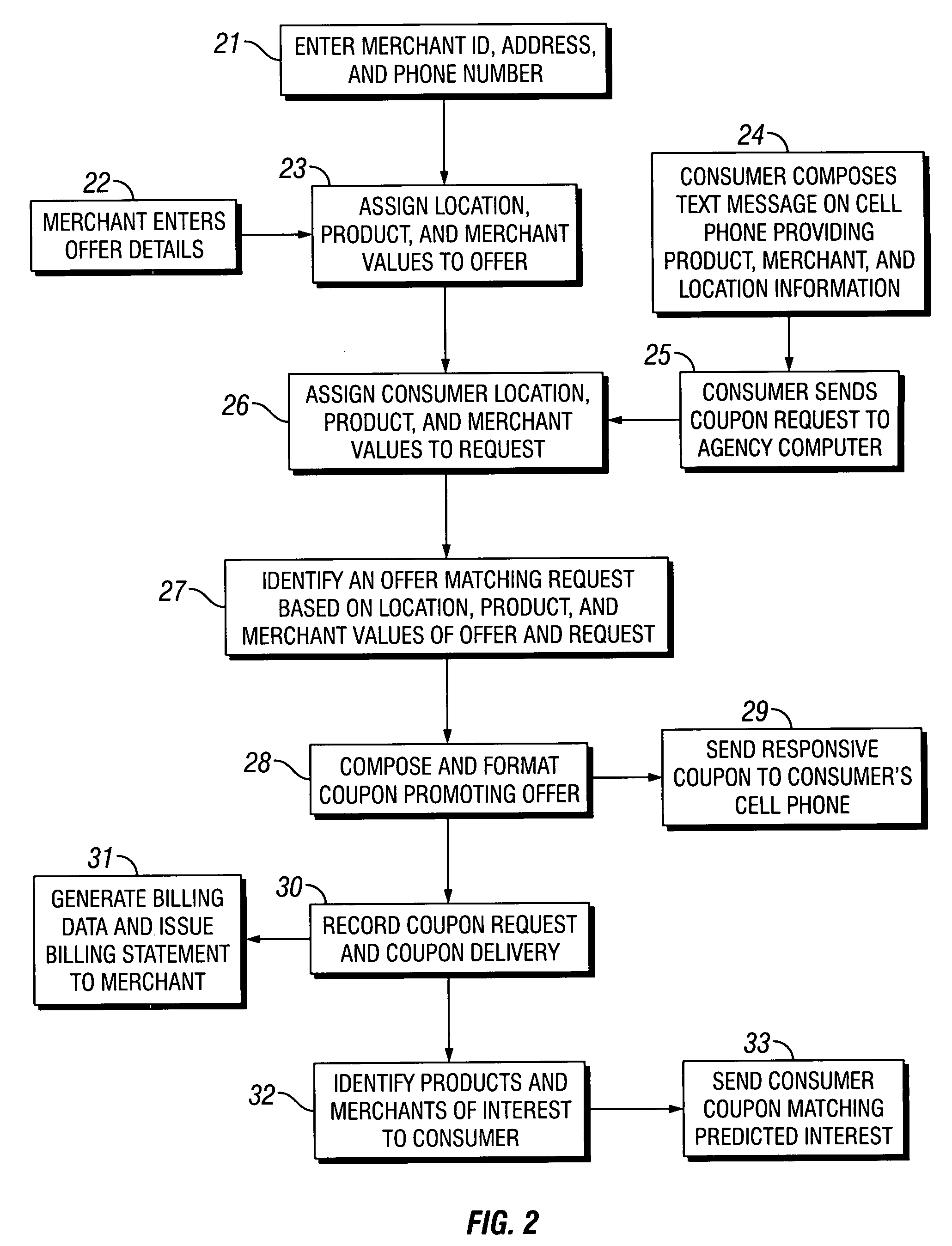
Coupons and systems for generating coupons on demand
InactiveUS20080027810A1High redemption ratePromote effectiveMarketingSystem identificationInformation agents
Coupons which are displayed as a text message on a mobile telecommunication device and include a code uniquely identifying the coupon are provided for. Systems for generating coupons on demand are also provided for. The system comprises an agency computer having access to a coupon database. The coupon database comprises information on offers and a location value assigned to each offer. The agency computer is connectable to a mobile communications network or other network for transmitting electronic mail. It receives requests for coupons from consumers that are transmitted via the network. Preferably, the requests originate from cells phones or other mobile telecommunication devices and are transmitted to the agency computer via a mobile communications network. The request is a text message that includes information identifying the consumer's location. The agency computer system identifies a coupon in the coupon database that is responsive to the coupon request based on the consumer's location and the offer location value. It then sends the identified coupon to the consumer via the network.
Owner:WHAMMOBILE
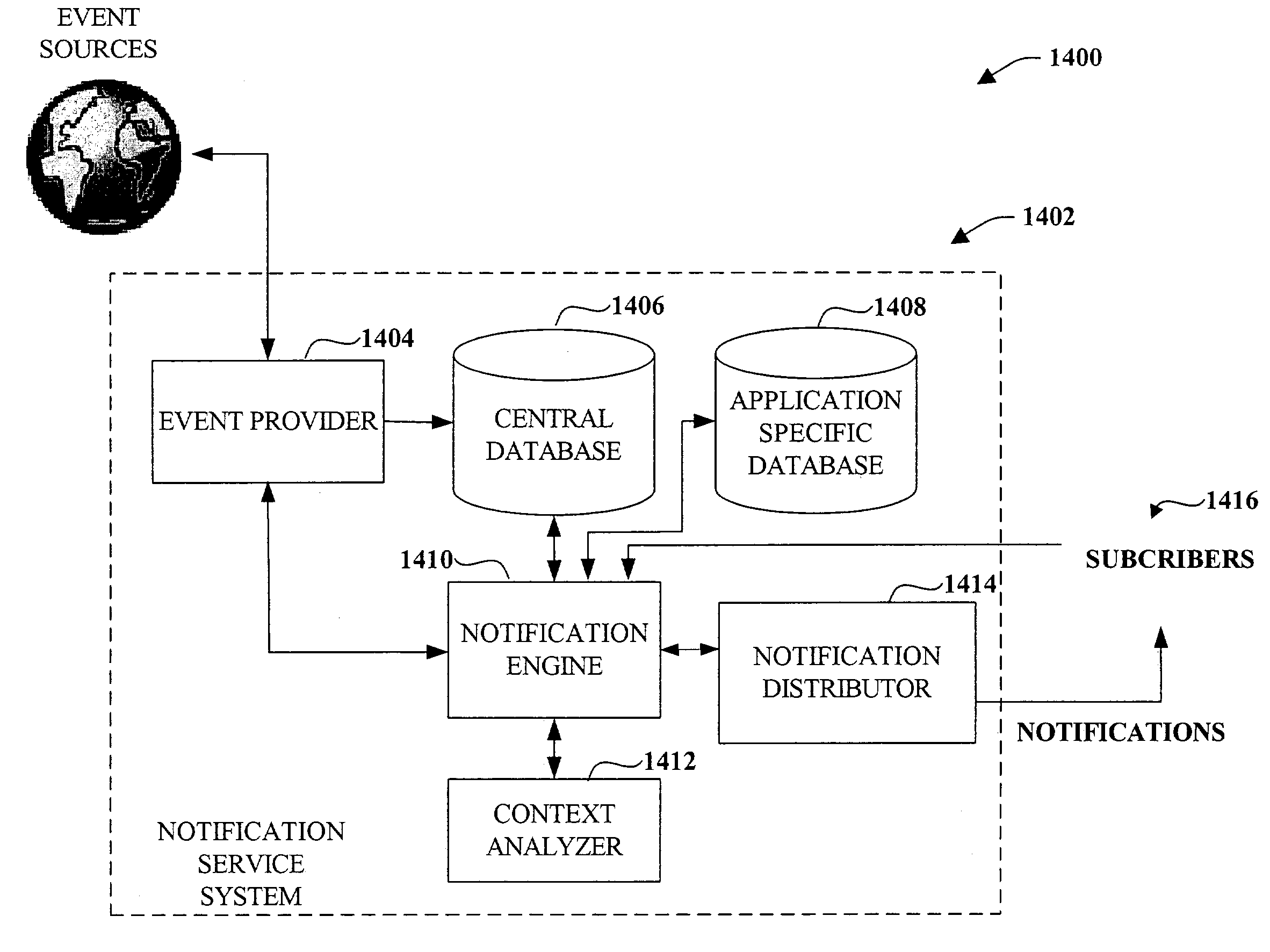
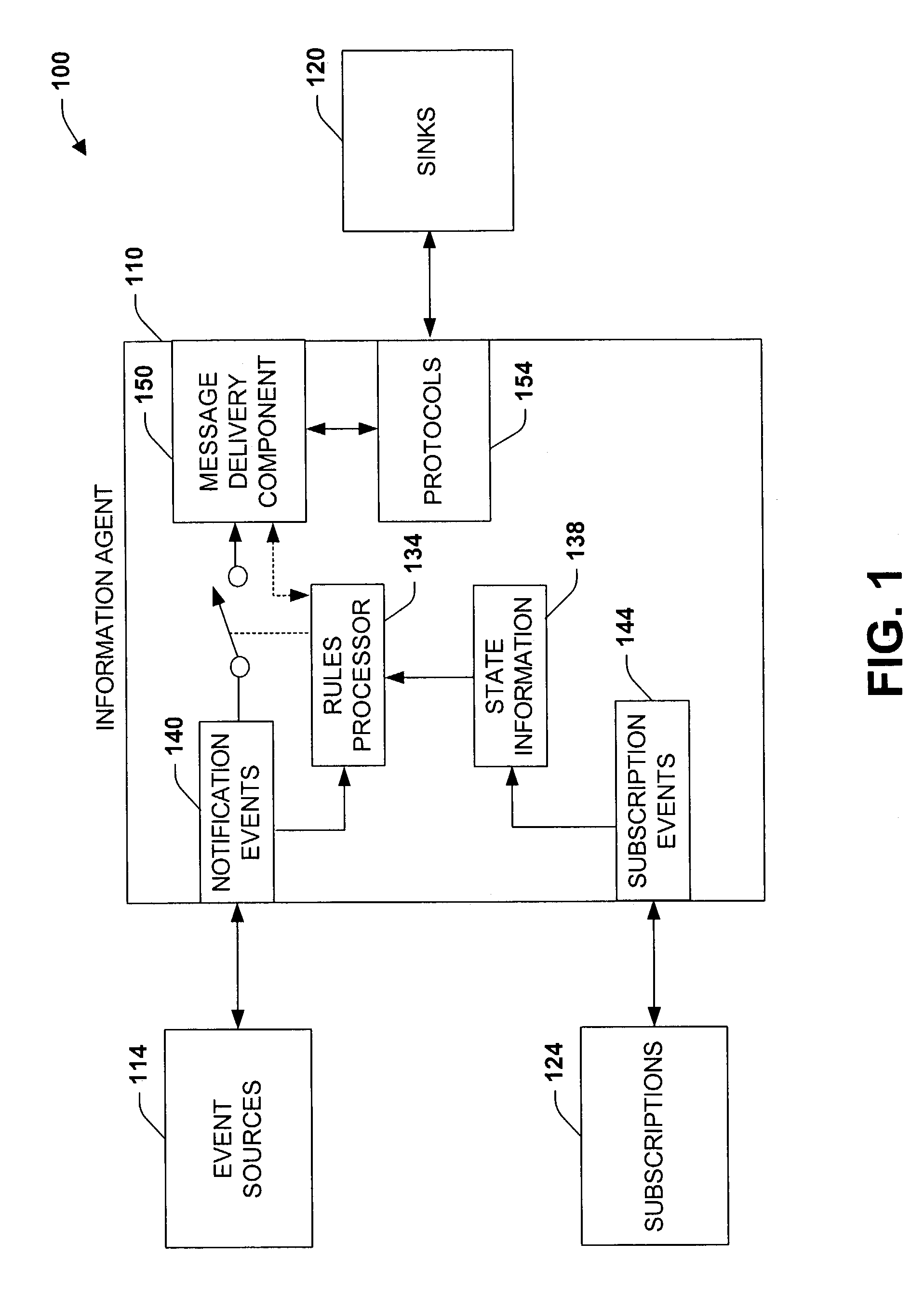
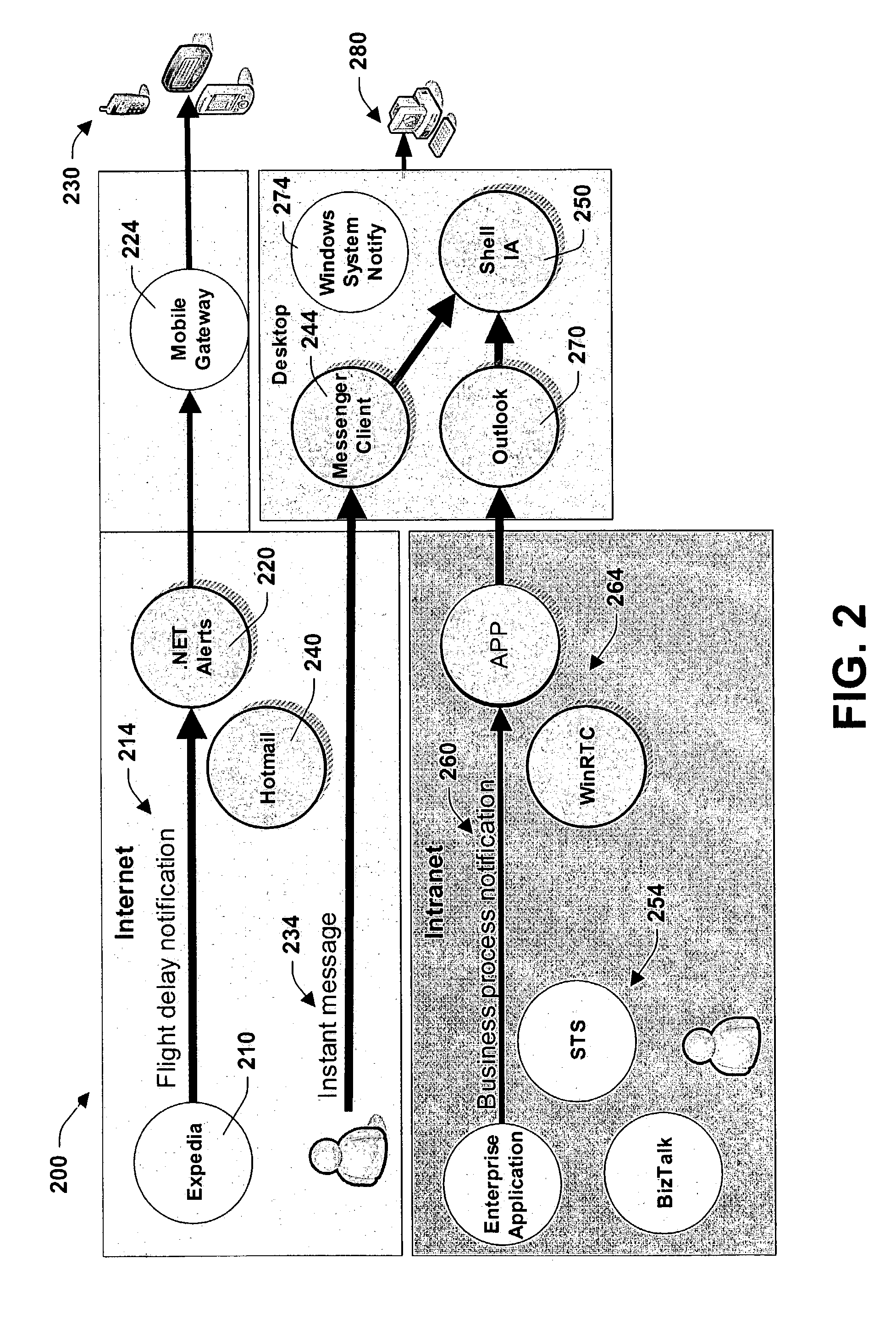
Expression and flexibility framework for providing notification(s)
InactiveUS7209916B1Reduce unnecessary distractionsFacilitate efficient deliveryData processing applicationsDigital data processing detailsData centerApplication software
The present invention relates to a system and methodology to facilitate timely delivery of notifications and performance of automated actions for users in the framework of an ad-hoc rules processing environment. An information agent operates as a distributed application to perform automated actions for users in accordance with user preferences and context. Various rules can be executed to delay, inhibit, and / or enable an action such as sending notifications according to the preferences and current user states as determined from the context. The rules can include data centric matching logic, set-oriented execution rules, rule ordering / interaction hierarchies, and ad-hoc Boolean combinations, for example.
Owner:MICROSOFT TECH LICENSING LLC
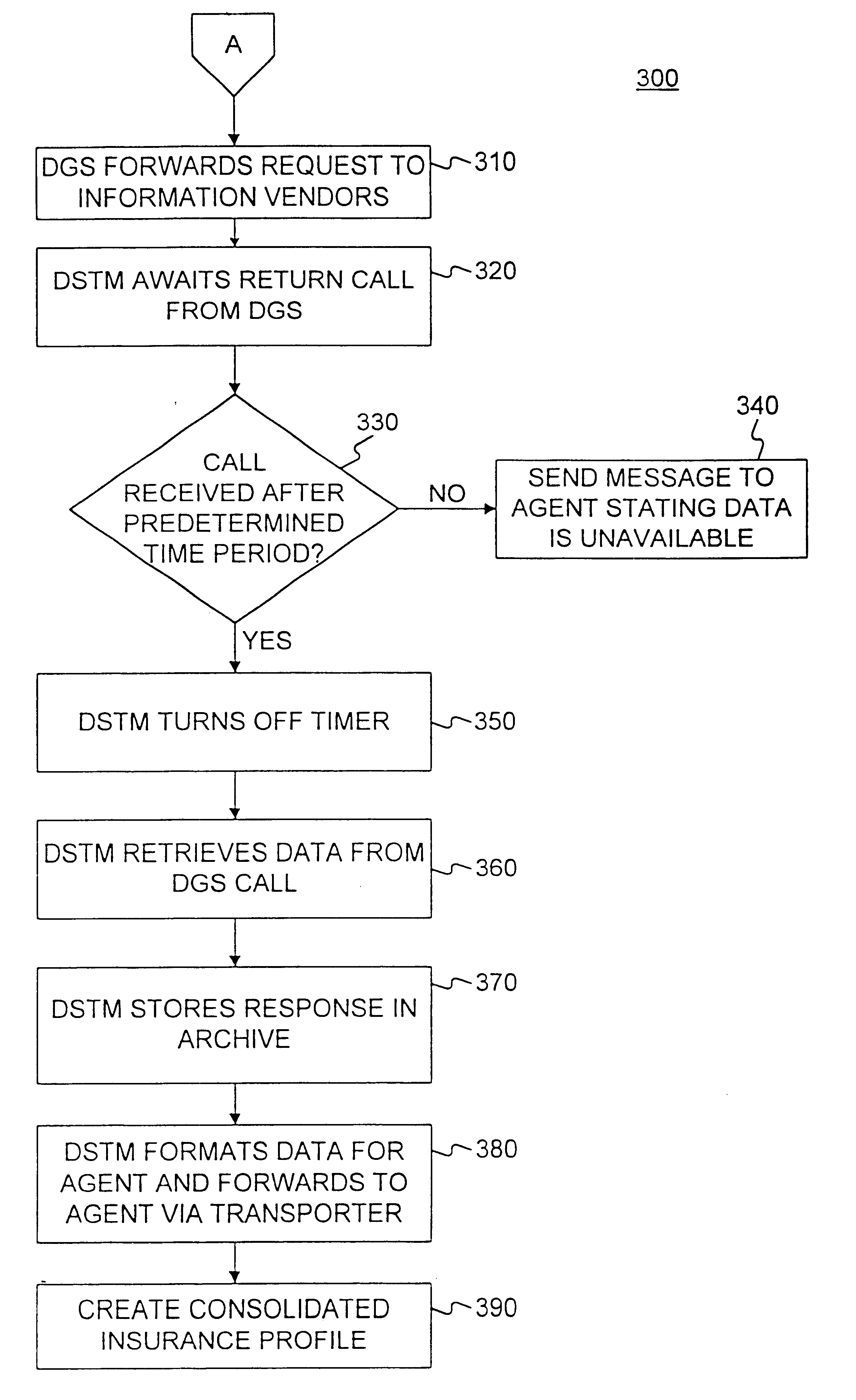
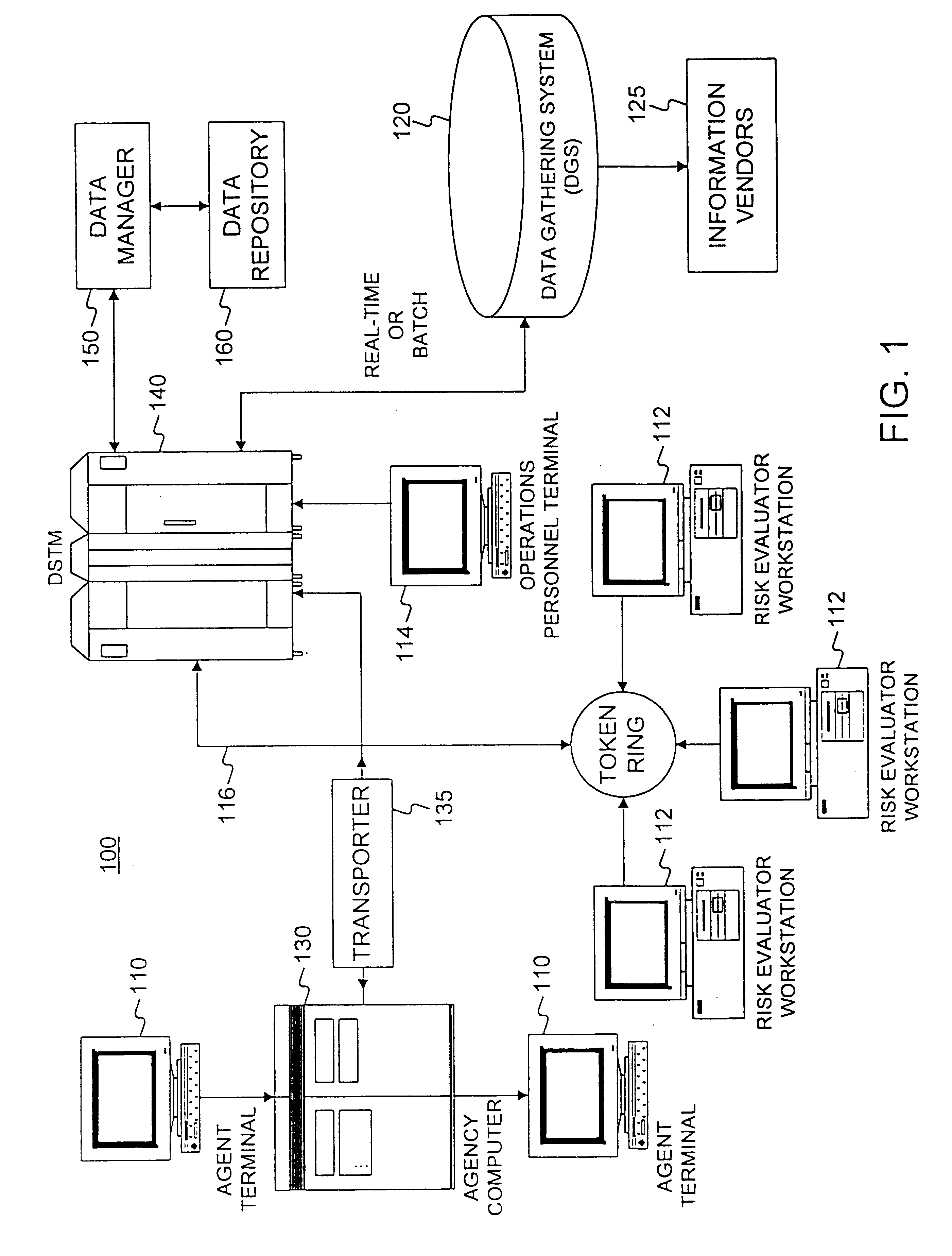
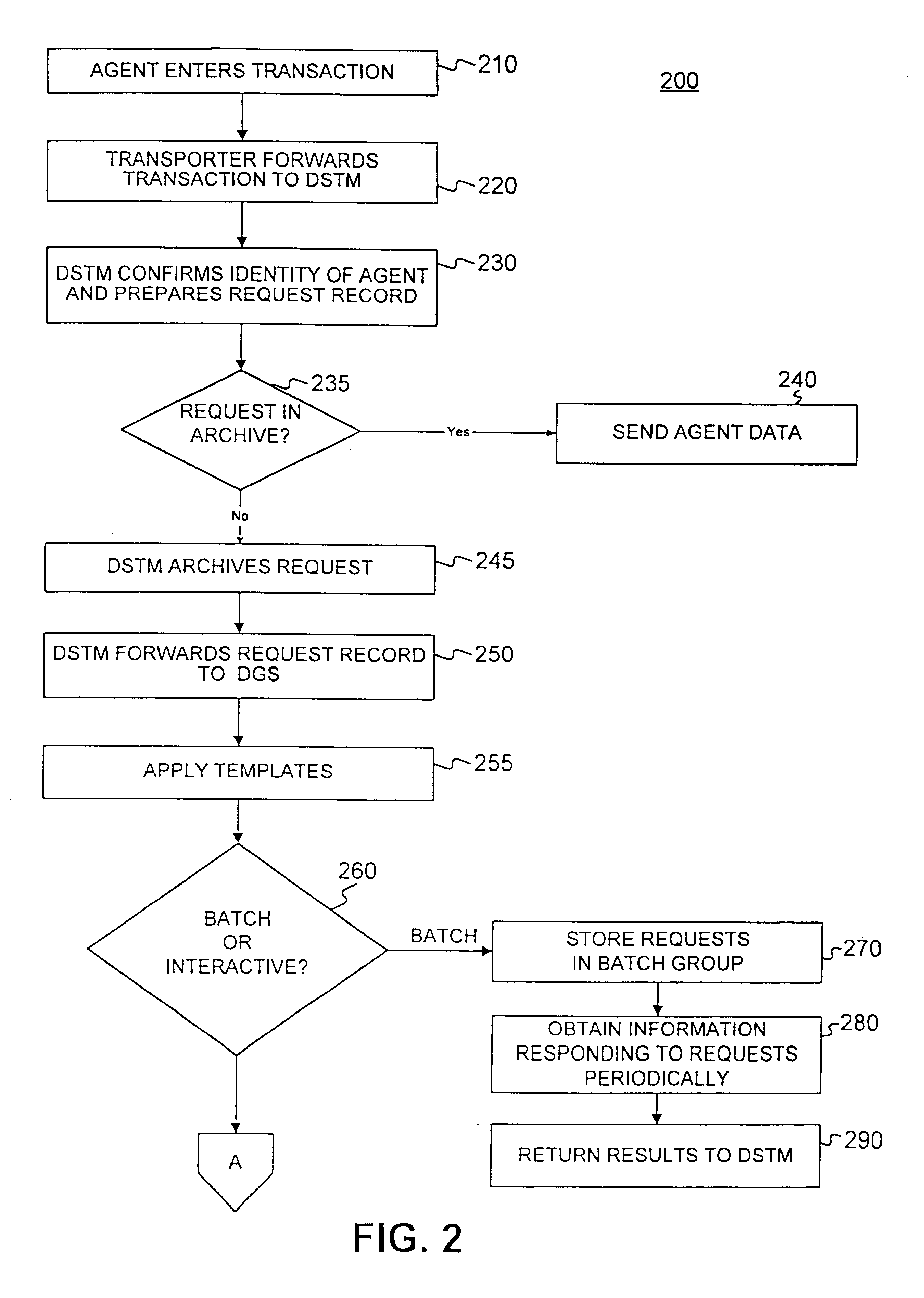
Method and apparatus for obtaining data from vendors in real time
InactiveUS6584467B1FinanceMultiple digital computer combinationsComputer networkApplication software
A system and method of controlling a computer network to obtain information needed to render risk evaluative decisions from vendors in real time. The information may be obtained for agents preparing insurance applications or for an automated application processing system. Agents or automated application processing systems require access to an external vendor to obtain information about a customer, such as car accident or credit records. The request for data must be formatted to be read by the vendor system, which sends the responding data in real time. This responding data is forwarded to the requesting party for further processing of the application.
Owner:ALLSTATE INSURANCE
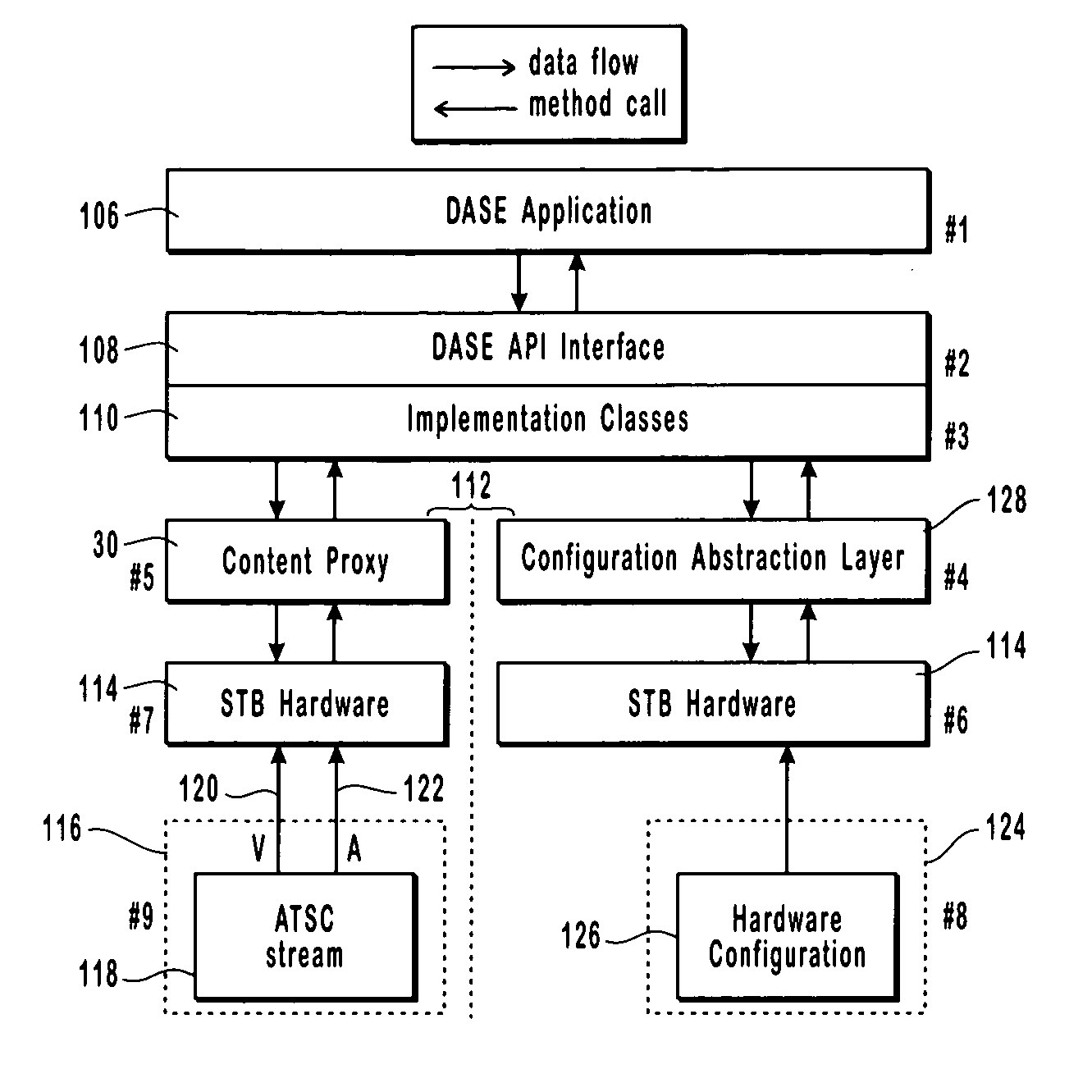
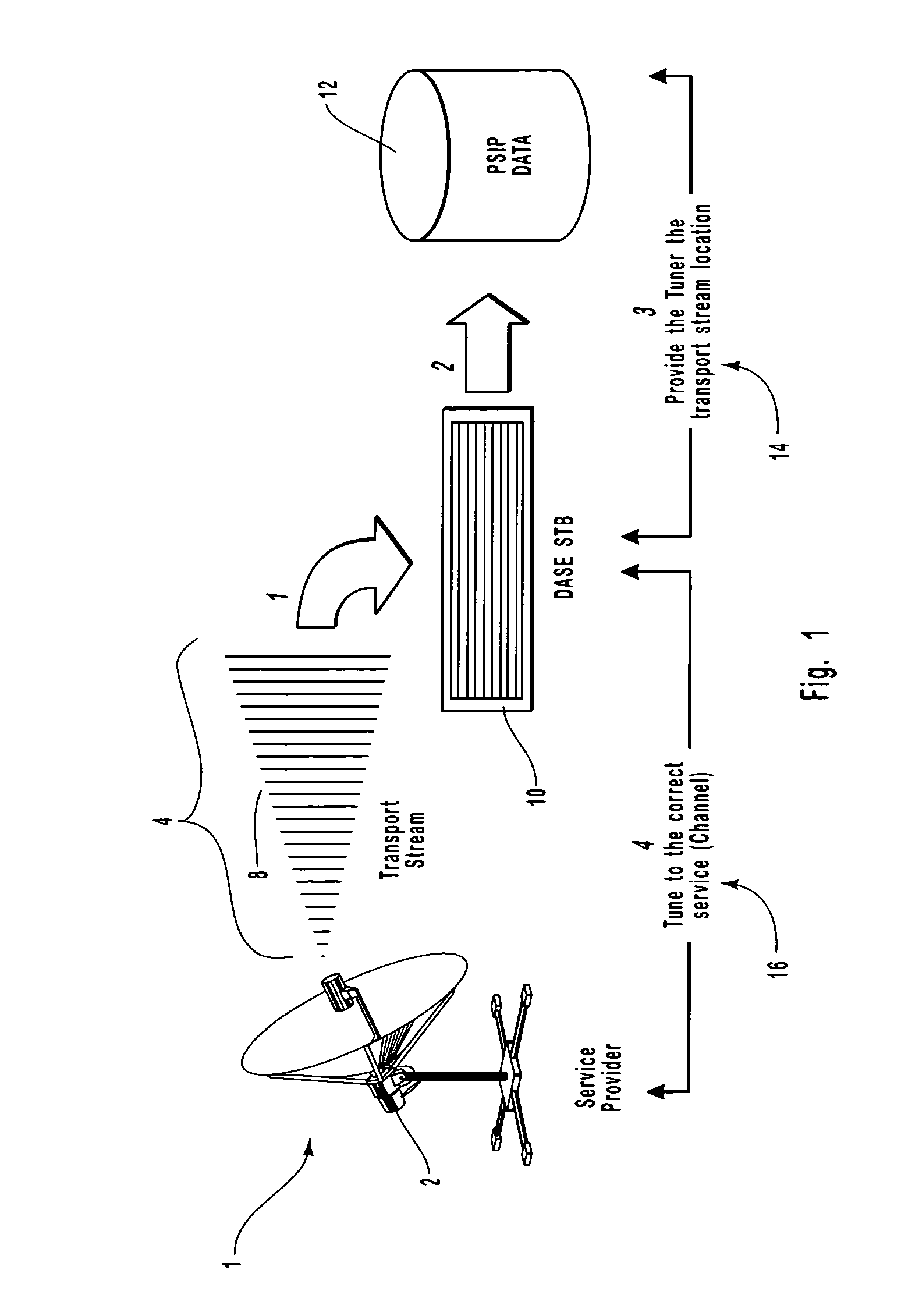
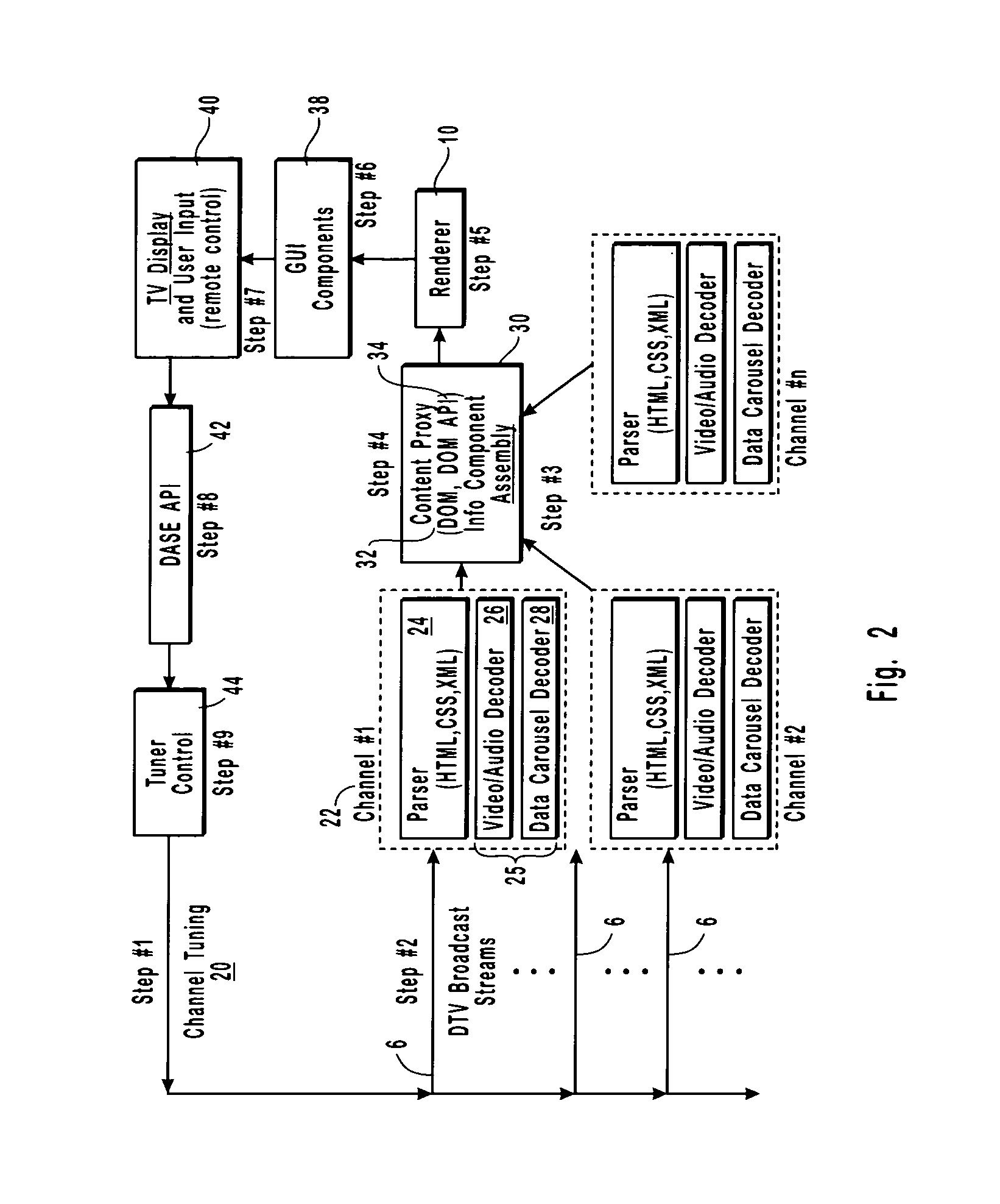
Content proxy method and apparatus for digital television environment
ActiveUS7028331B2Eliminate needAnalogue secracy/subscription systemsMultiprogramming arrangementsExtensible markupApplication software
The present invention describes and claims a new system and technique or method for decoupling the interpretation of broadcast content information from the display of this information. The information may exist in any of the available types, such as audio, video, or data. In addition, the information may be received in any form, such as streaming or non-streaming, combinations of the two, or even parts thereof. The decoupling and encapsulating of the broadcast content information is accomplished using a content proxy. All content information in the content proxy is accessed via an Application Program Interface. The content proxy employs a hierarchical Document Object Model (DOM) that contains Program and System Information Protocol (“PSIP”) data, that has been converted to an eXtendible Markup Language format using a conversion algorithm, broadcast content data, as well as content data or information about all of the hardware, software, and appliances connected within the networked environment. The proxy concept is applicable to the design and implementation of a Digital TV broadcast rendering device within a Digital TV Application Software Environment framework.
Owner:SHARP KK
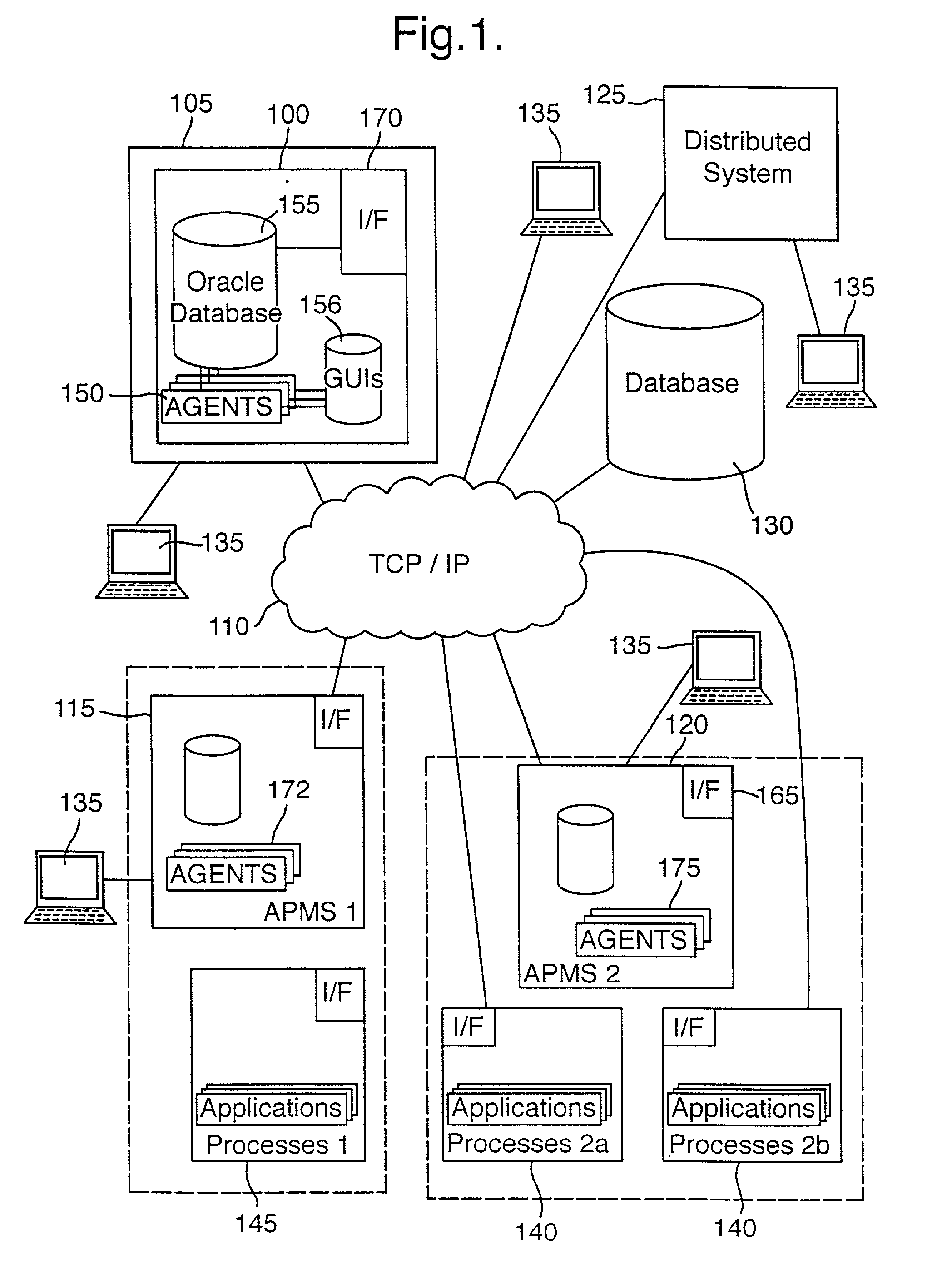
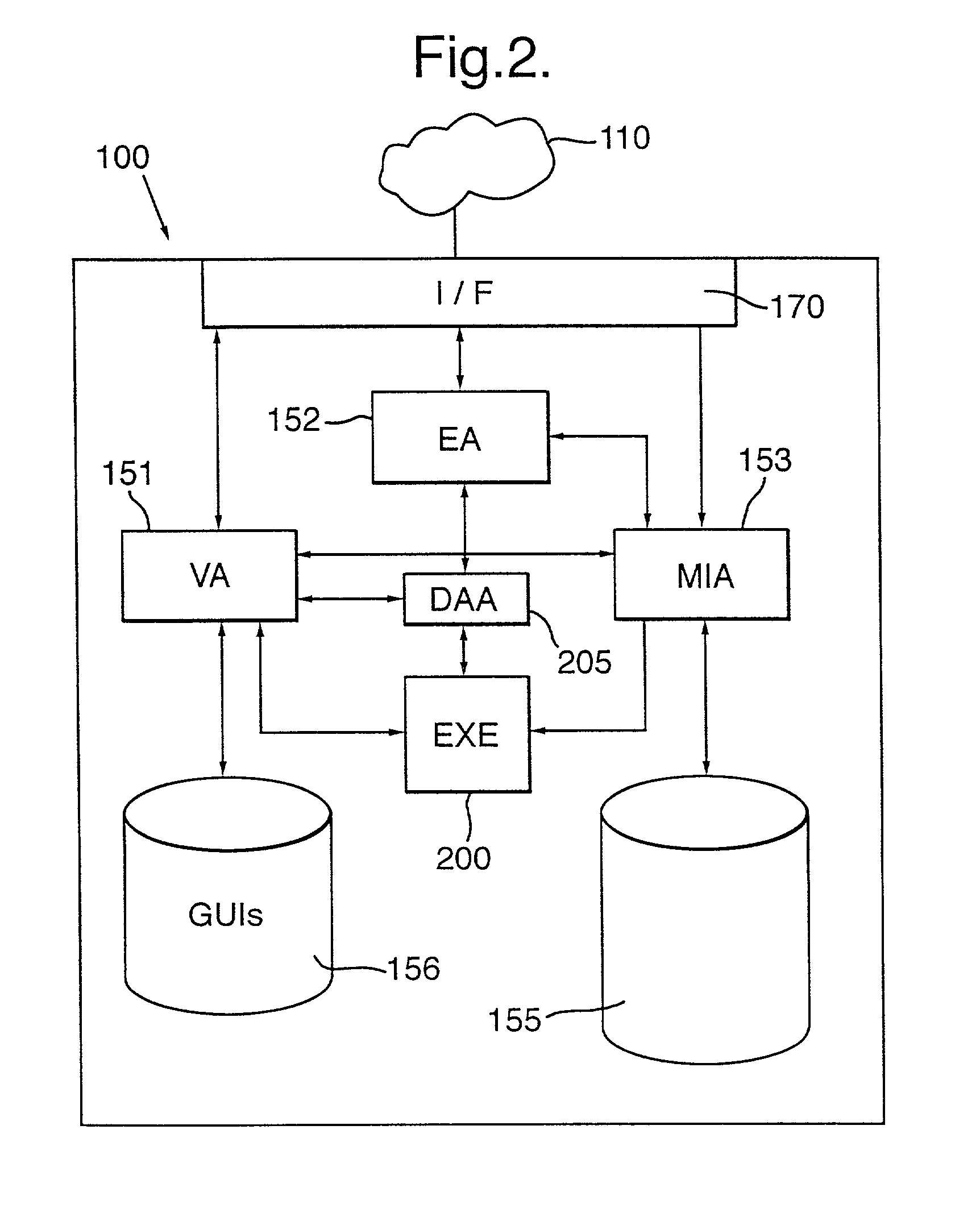
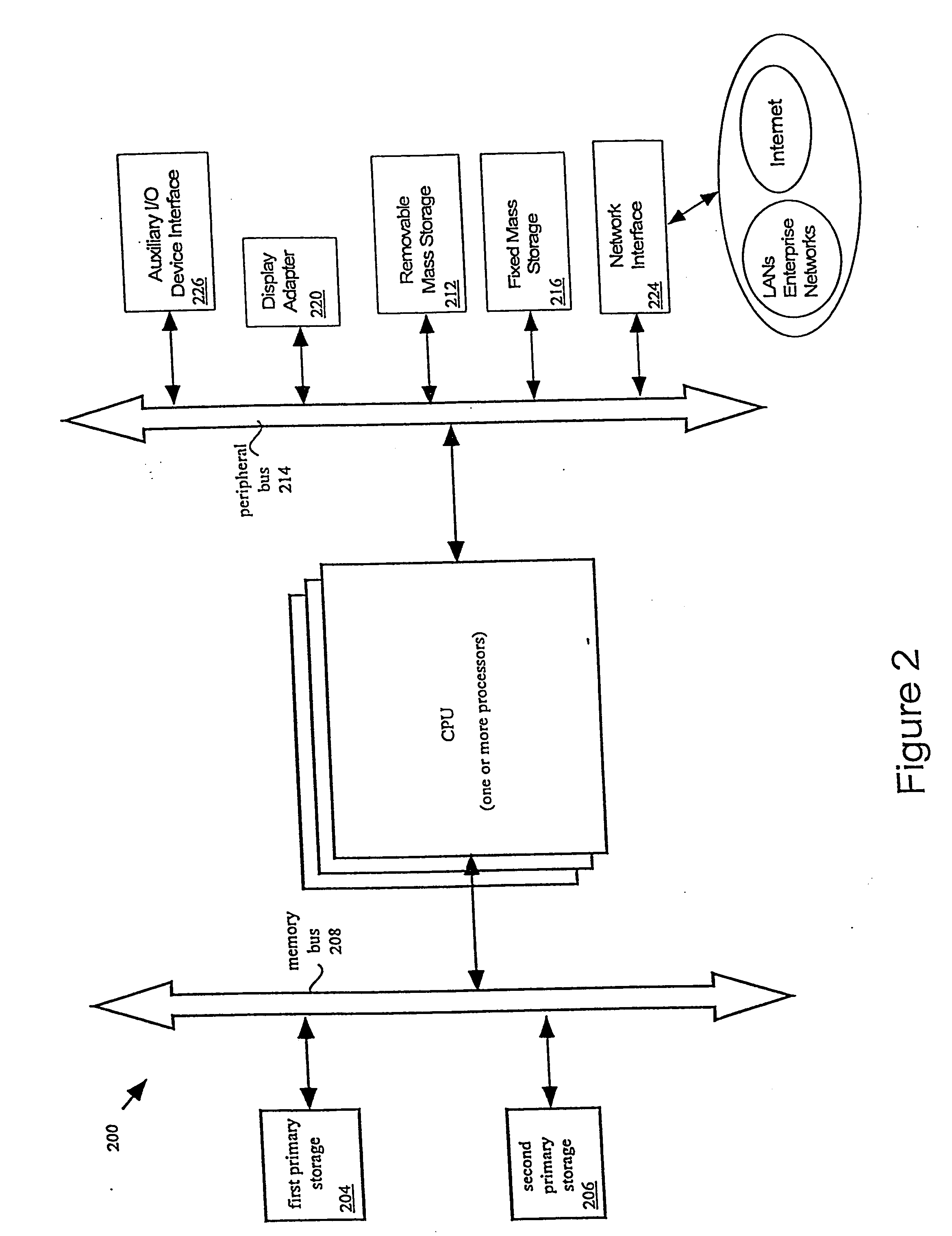
Distributed software system visualization
InactiveUS7155715B1Easy to adaptData processing applicationsDigital data processing detailsGraphicsGraphical user interface
A data management system stores and visualizes data generated during process management. The data management system provides different data management services and definitions of these are stored in a database. Management of data in this database is carried out by a collection of software agents, one of which, the management information agent, can access, update and download data in or from the database. Stored separately are graphical user interfaces which are downloaded to a user in accordance with the relevant service definition stored in the database when the user requests a particular data access service.
Owner:BRITISH TELECOMM PLC
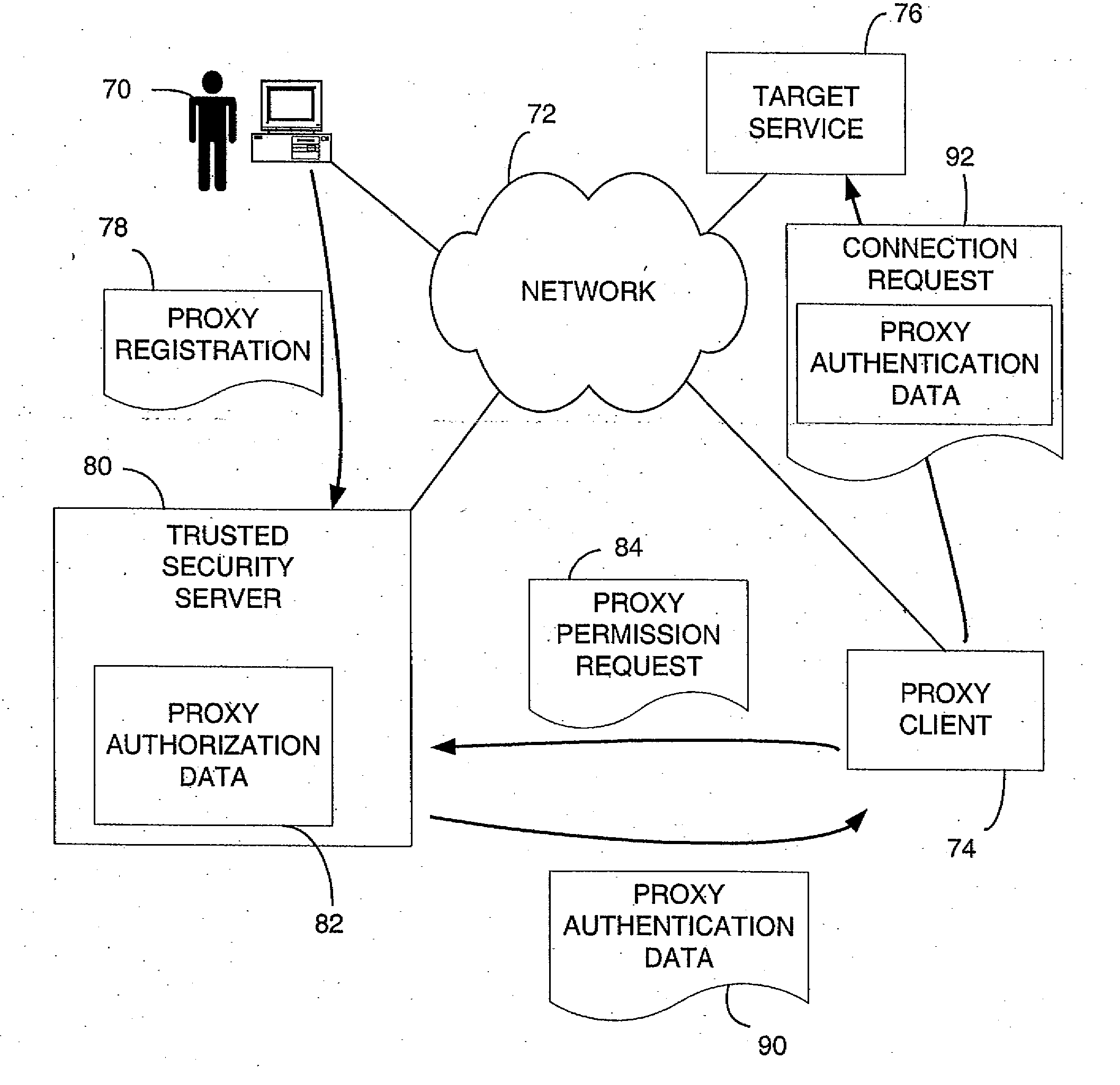
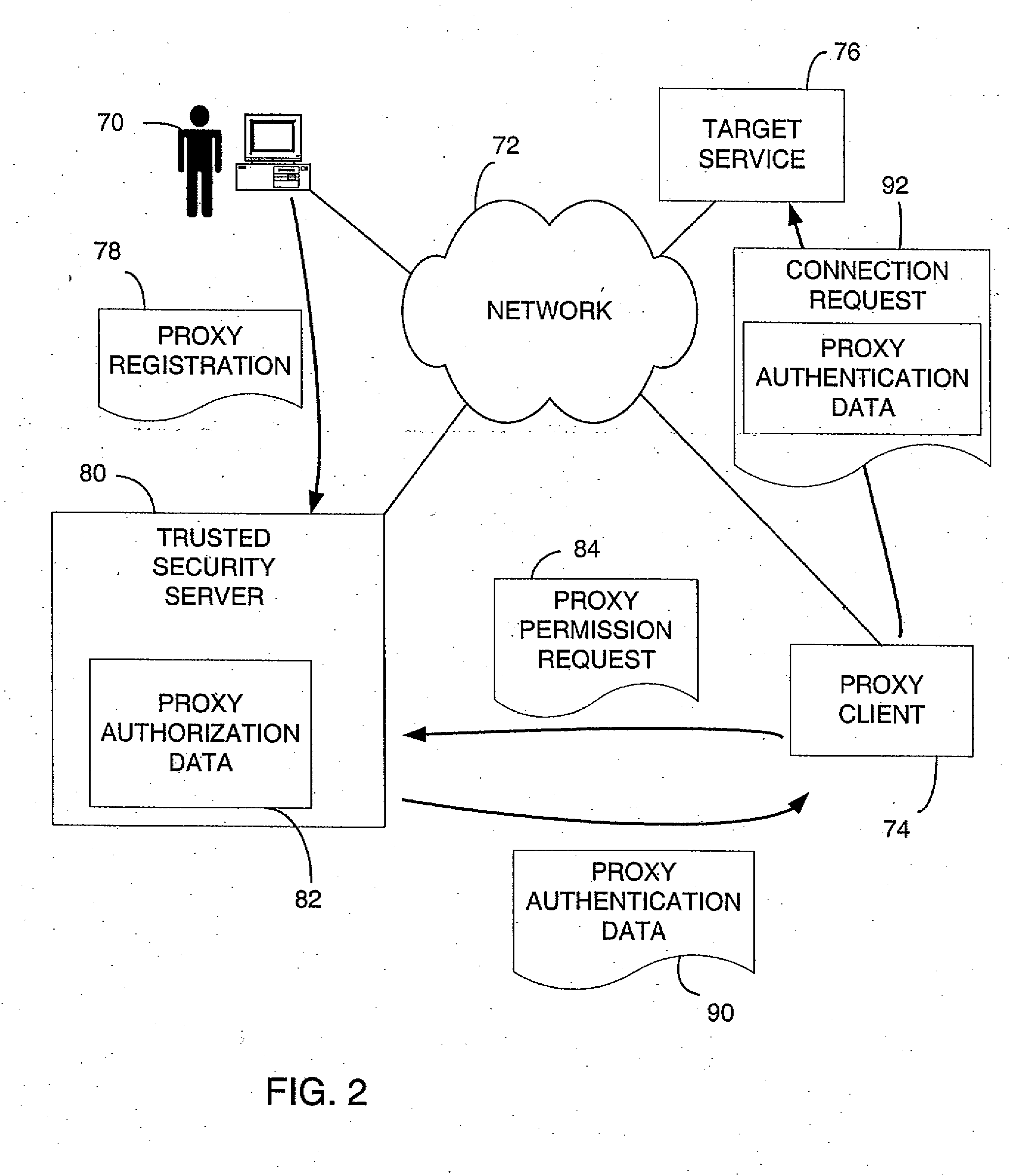
System and Method of Proxy Authentication in a Secured Network
InactiveUS20060225132A1Data processing applicationsDigital data processing detailsClient-sideNetwork service
A method of controlling access to network services enables an authorized proxy client to access a service on behalf of a user. To permit the client to function as a proxy, the user registers proxy authorization information with a trusted security server. The proxy authorization information identifies the proxy client and specifies the extent of proxy authority granted to the proxy client. When the proxy client wants to access a target service on behalf of the user, it sends a proxy request to the trusted security server. The trusted security server checks the proxy authorization information of the user to verify whether the request is within the proxy authority granted to the proxy client. If so, the trusted security server returns to the proxy client a data structure containing information recognizable by the target service to authenticate the proxy client for accessing the target service on behalf of the user.
Owner:MICROSOFT TECH LICENSING LLC
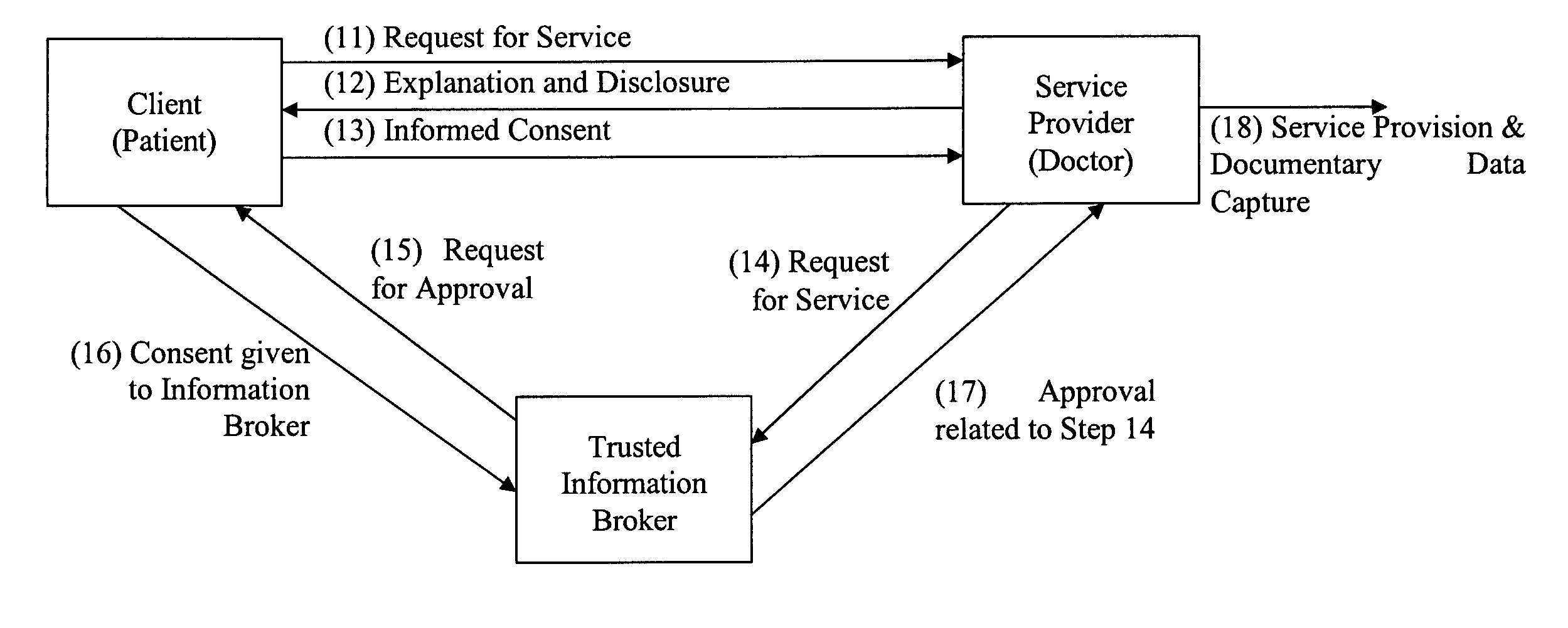
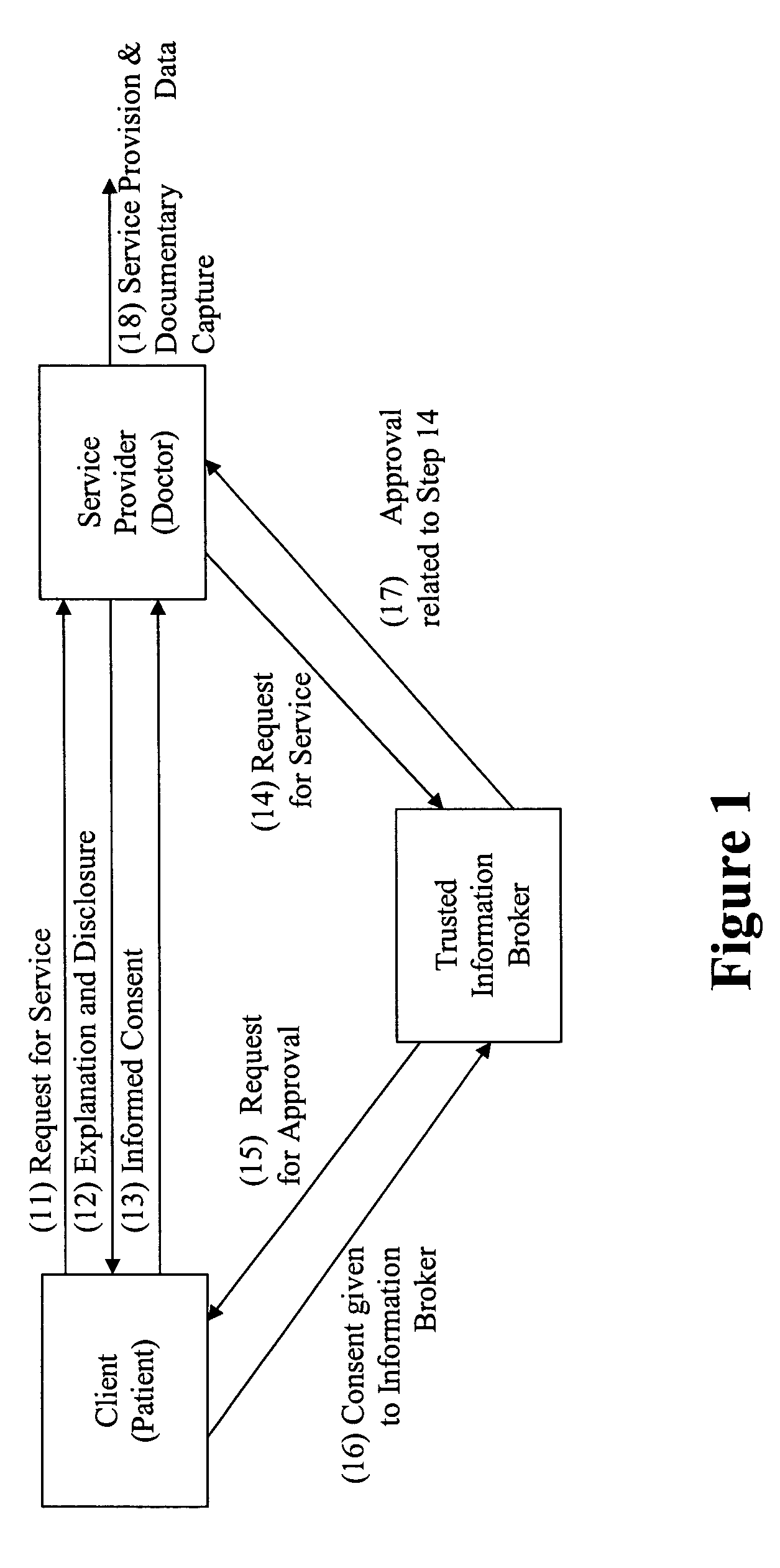
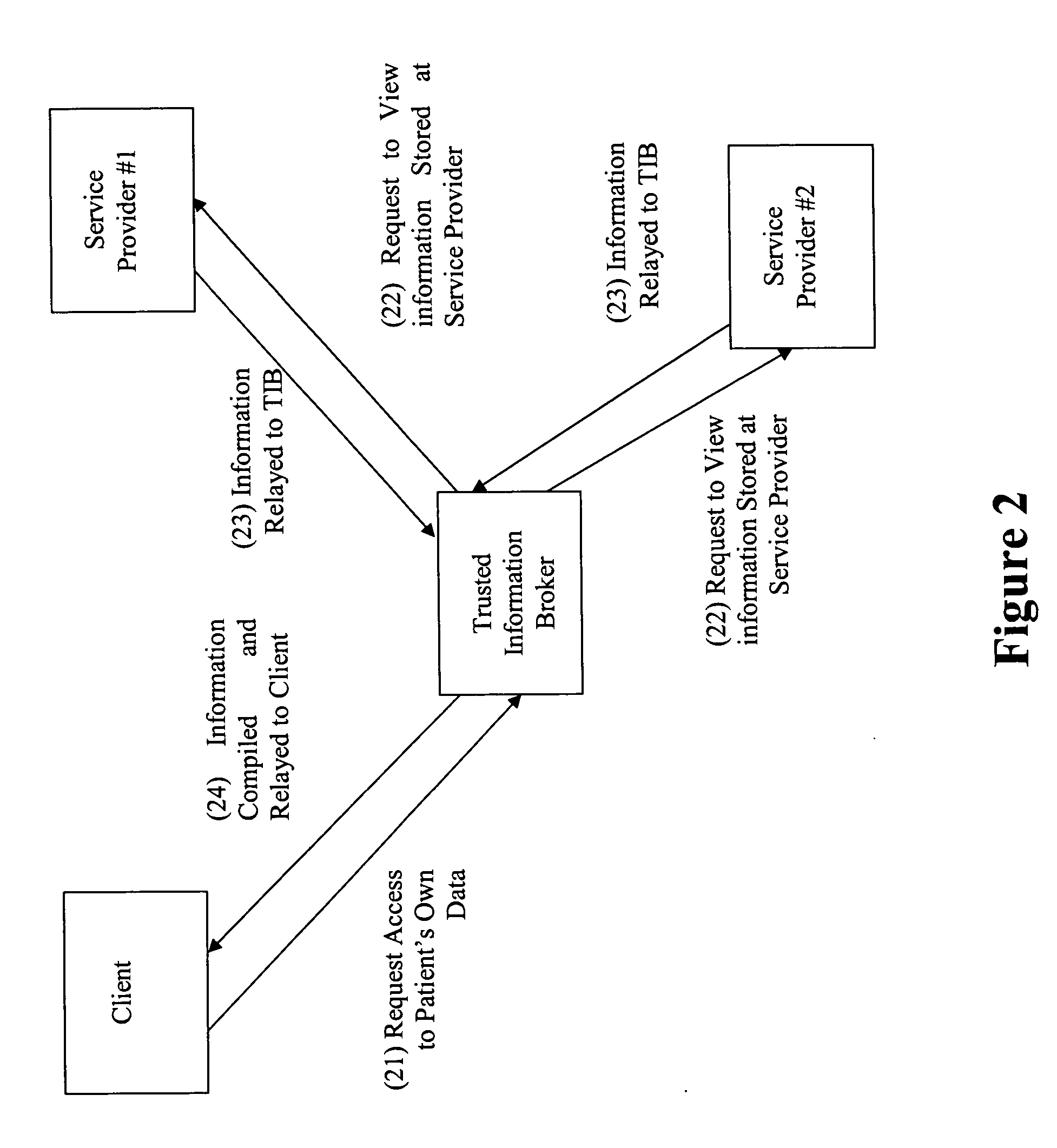
Privacy compliant consent and data access management system and methods
ActiveUS20060026042A1Easy to solveMany choicesFinanceMultiple keys/algorithms usageInternet privacyData access
An information management system for restricting access to personal data in compliance with law or regulation includes a database having restricted records stored therein, at least one of the records including an identification of a client or group of clients about whom said record concerns. A computer system under the control of a trusted information broker is configured to receive via a communication medium a request initiated by a requester for access to at least one of the restricted records in the database, the request including an identification of the requester. The computer system is further configured to transmit a request for consent to the client and receive an indication from the client that the client consents or does not consent to access to the restricted record by the requestor. The computer system grants or denies access to the restricted records based upon the indication from the client.
Owner:PRIVIT
Method and apparatus for a portable information agent
InactiveUS20020129092A1Improve user interactionDiscounts/incentivesCathode-ray tube indicatorsInteractive graphicsApplication software
A method and system for providing enhanced intelligent agents that are moveable by a user from a browser application to a desktop. In specific embodiments, agents provide advanced interactive graphics and communications back to a server.
Owner:ENVOII +1
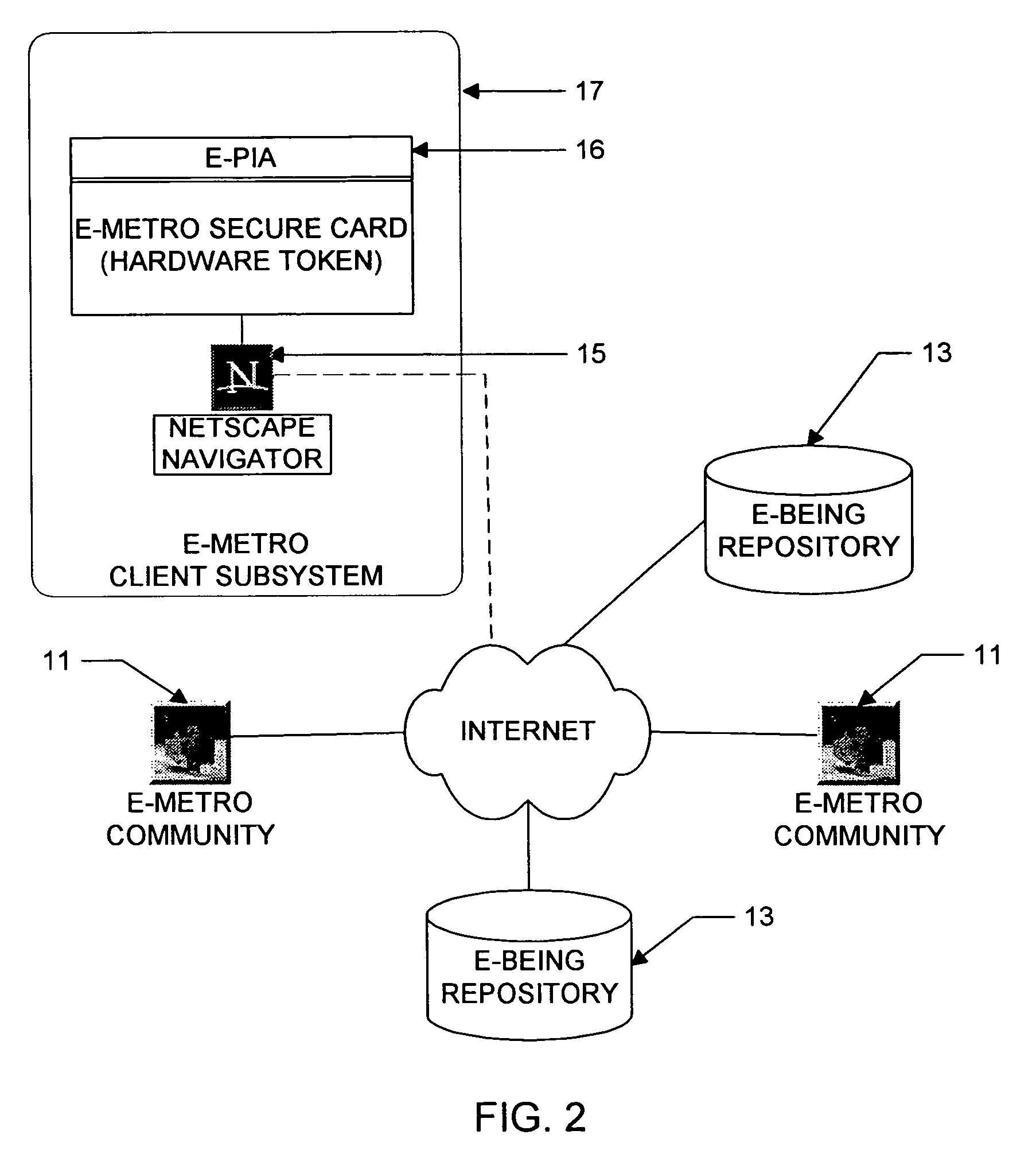
E-Bazaar featuring personal information security
InactiveUS20090119222A1Facilitates formation and useEasy to useUser identity/authority verificationOffice automationCommand and controlData treatment
Utilization of the E-Metro Community and Personal Information Agents assure an effective and comprehensive agent-rule based command and control of informational assets in a networked computer environment. The concerns of informational privacy and informational self-determination are addressed squarely by the invention affording persons and entities a trusted means to author, secure, search, process, and exchange personal and / or confidential information in a networked computer environment. The formation of trusted electronic communities wherein members command and control their digital persona, exchanging or brokering for value the trusted utility of their informational assets is made possible by the invention. The present invention provides for the trusted utilization of personal data in electronic markets, providing both communities and individuals aggregate and individual rule-based control of the processing of their personal data.
Owner:CYVA RES HLDG
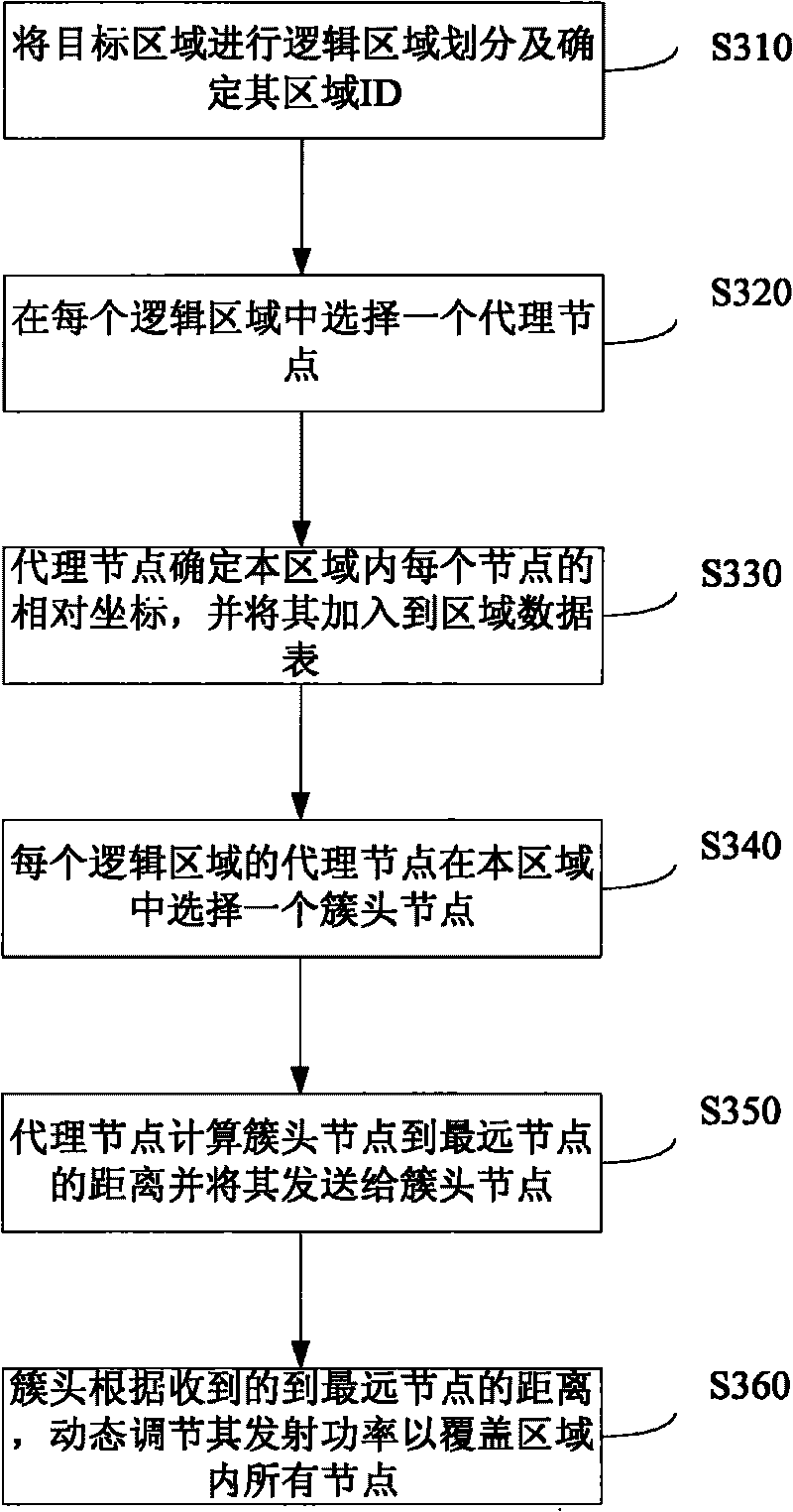
Clustering method and device, routing method and device of cluster head and base station
InactiveCN101729331AExtend task periodImprove management efficiencyData switching by path configurationHigh level techniquesLow loadReal-time computing
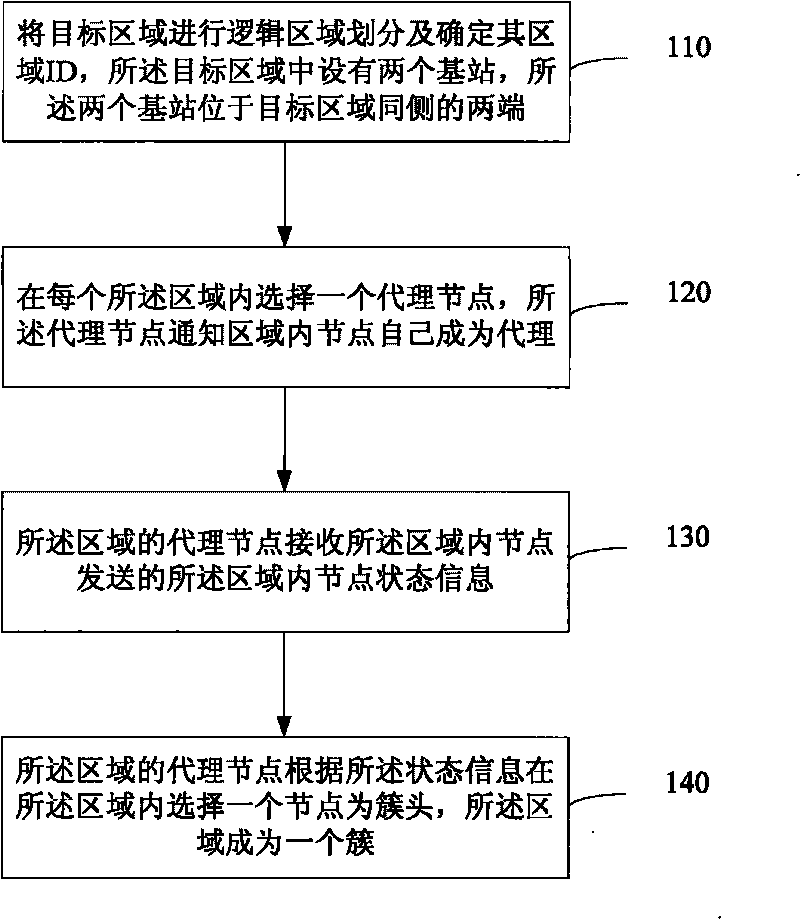
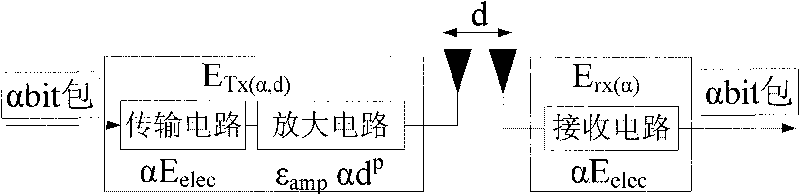
The embodiment of the invention discloses clustering method and device, routing method and device of a cluster head and a base station, belonging to the technical field of wireless sensor networks. The clustering method comprises the steps of: carrying out logic region division on a target region and determining a region ID of the target region; selecting one agent node in each region, wherein a node in an agent node notification region is used as an agent; sending node state information by the node in an agent node receiving region; and selecting one node in the region by the agent node according to the information as the cluster head, wherein the region becomes one cluster. The routing method comprises the steps of: selecting one base station in which a link has lower load when transmitting data from two base stations; determining the gradient of the cluster head according to the region ID in the cluster to transmit the data to the selected base station along the diminishing direction of gradient; selecting N cluster heads with gradient less than that of a source cluster head as a next hop cluster head to transmit the data along the direction of the selected base station by the source cluster head; and selecting N cluster heads with gradient less than that of a middle hop cluster head as a next ho cluster head to transmit the data along the direction of the selected base by the middle hop cluster head.
Owner:HUAWEI TECH CO LTD +1
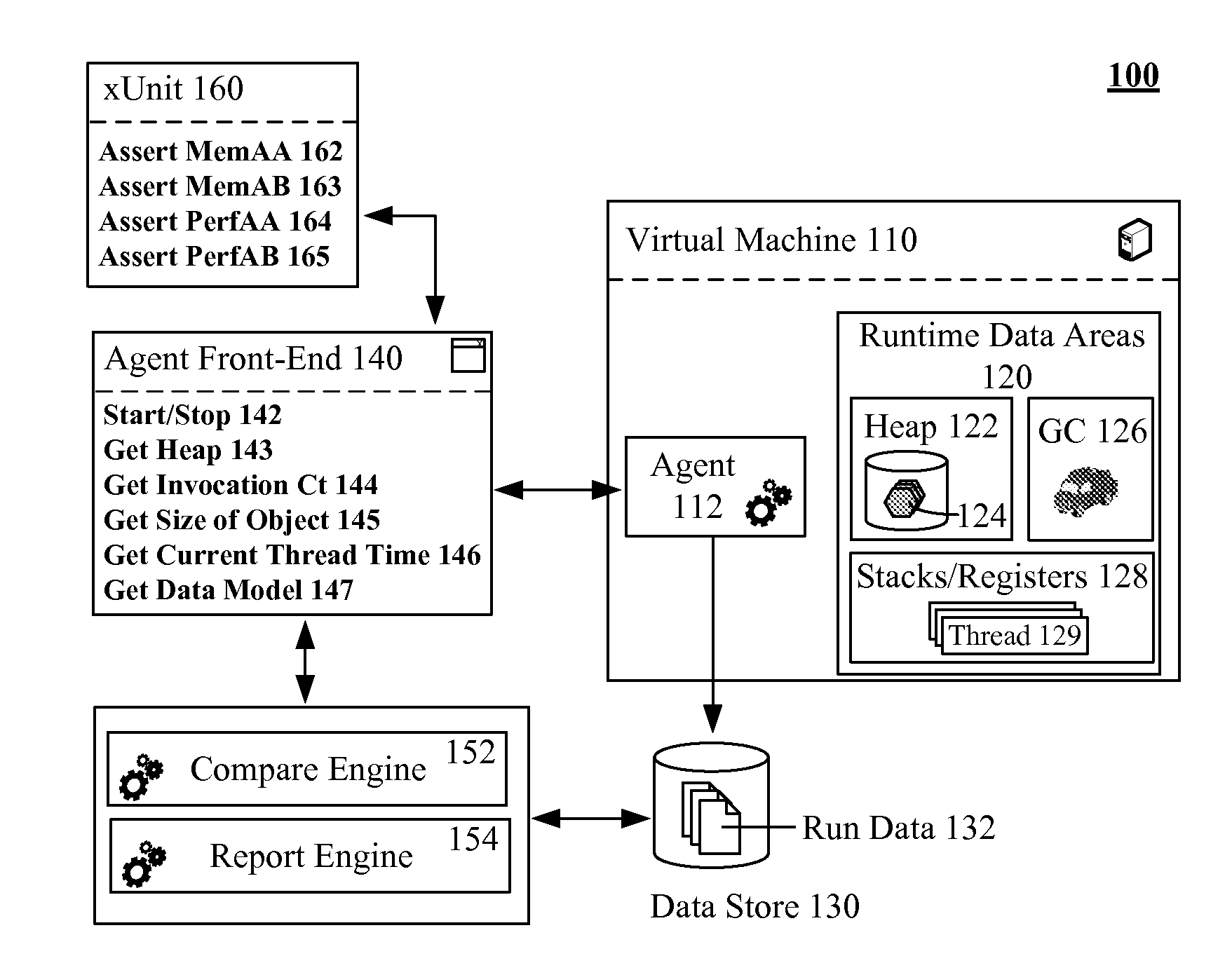
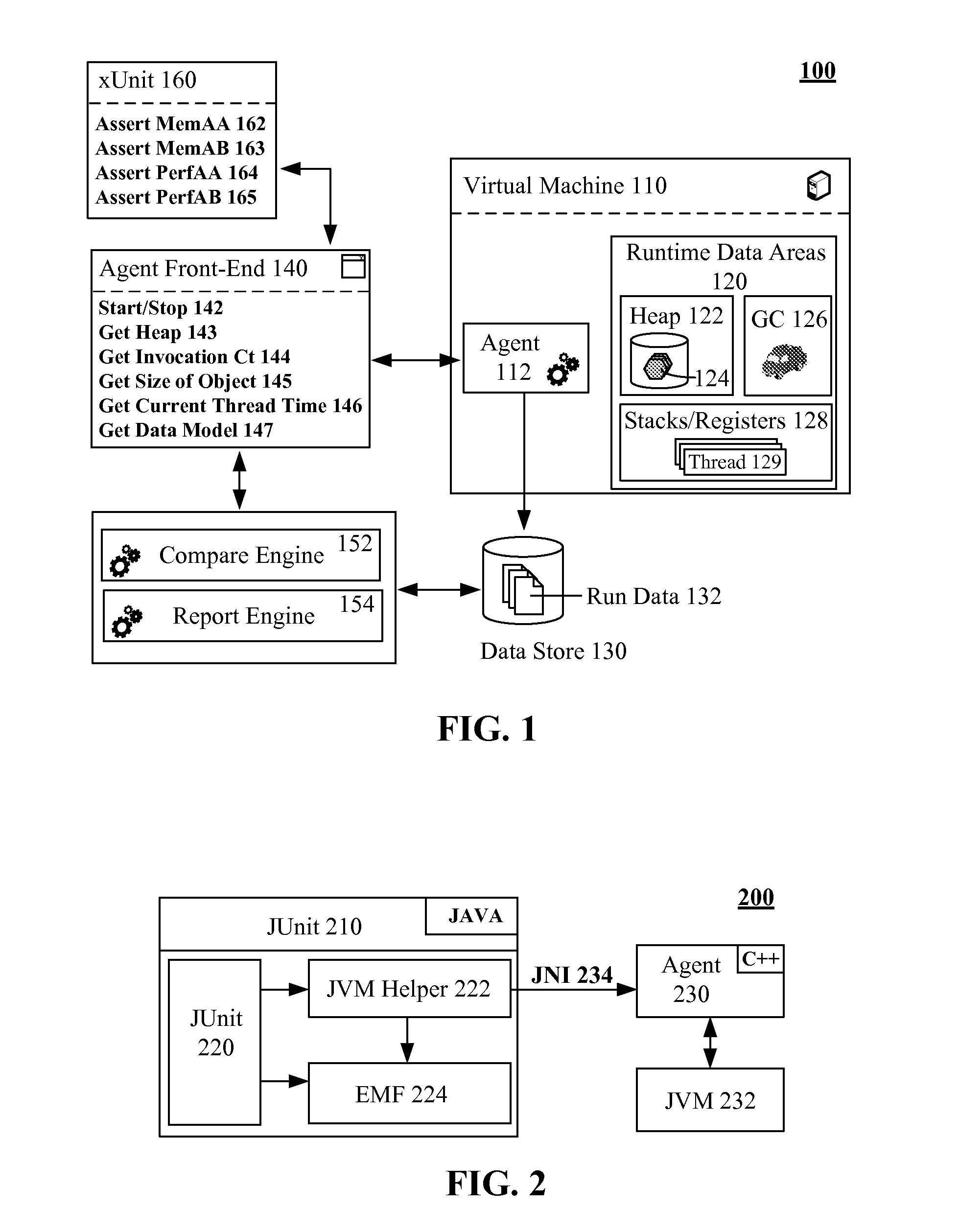
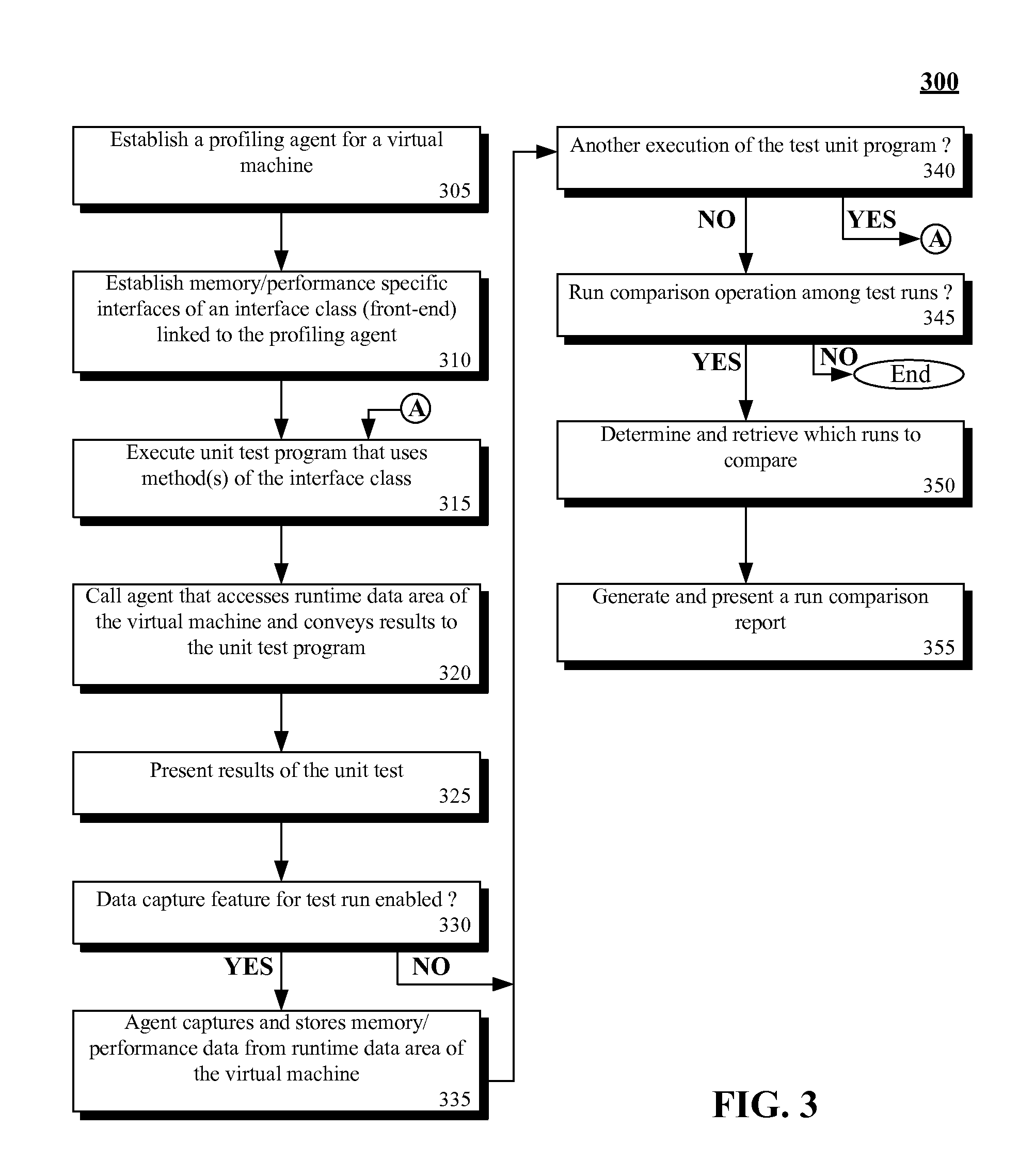
Adding a profiling agent to a virtual machine to permit performance and memory consumption analysis within unit tests
InactiveUS20090172664A1Promptly compareError detection/correctionSoftware simulation/interpretation/emulationParallel computingTerm memory
The present invention discloses a solution for adding a profiling agent to a virtual machine (VM), which permits unit test programs to access information relating to memory and performance from runtime data areas of the VM. Operations permitted by the agent can include starting / stopping VM monitor, getting objects from the heap, retrieving an invocation count, determining a size of an instantiated object, getting a current thread time, and the like. Memory and performance information gathered during a test can be stored for later analysis under a test version identifier. A comparison engine can create reports that use the stored performance and memory data, which can help developers compare memory / performance deltas among different unit versions. In one embodiment, the VM can be a JAVA VIRTUAL MACHINE (JVM) and the unit test programs can be JUNIT programs.
Owner:IBM CORP
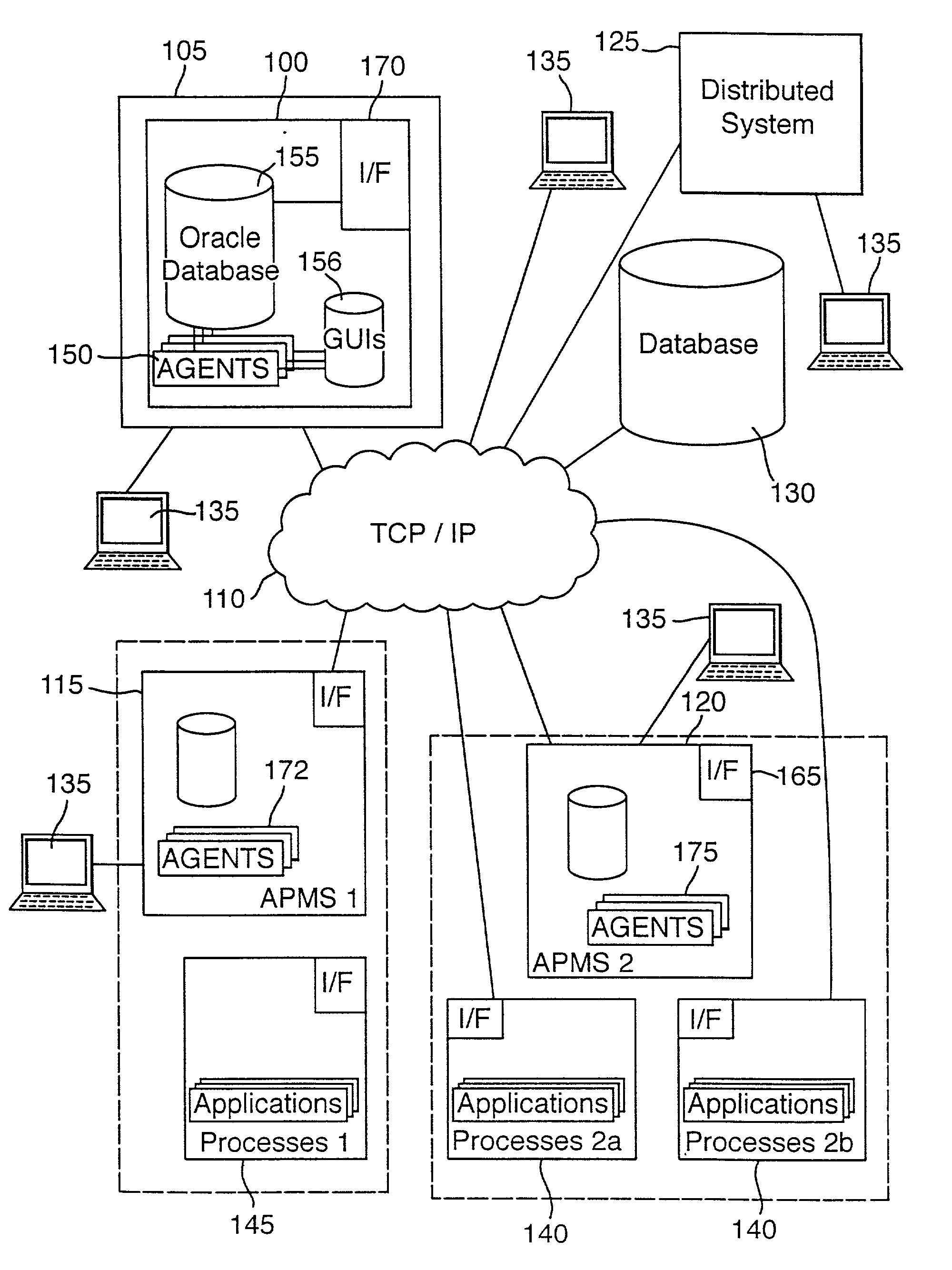
Enterprise computer system
Owner:SOFTWARE AG USA
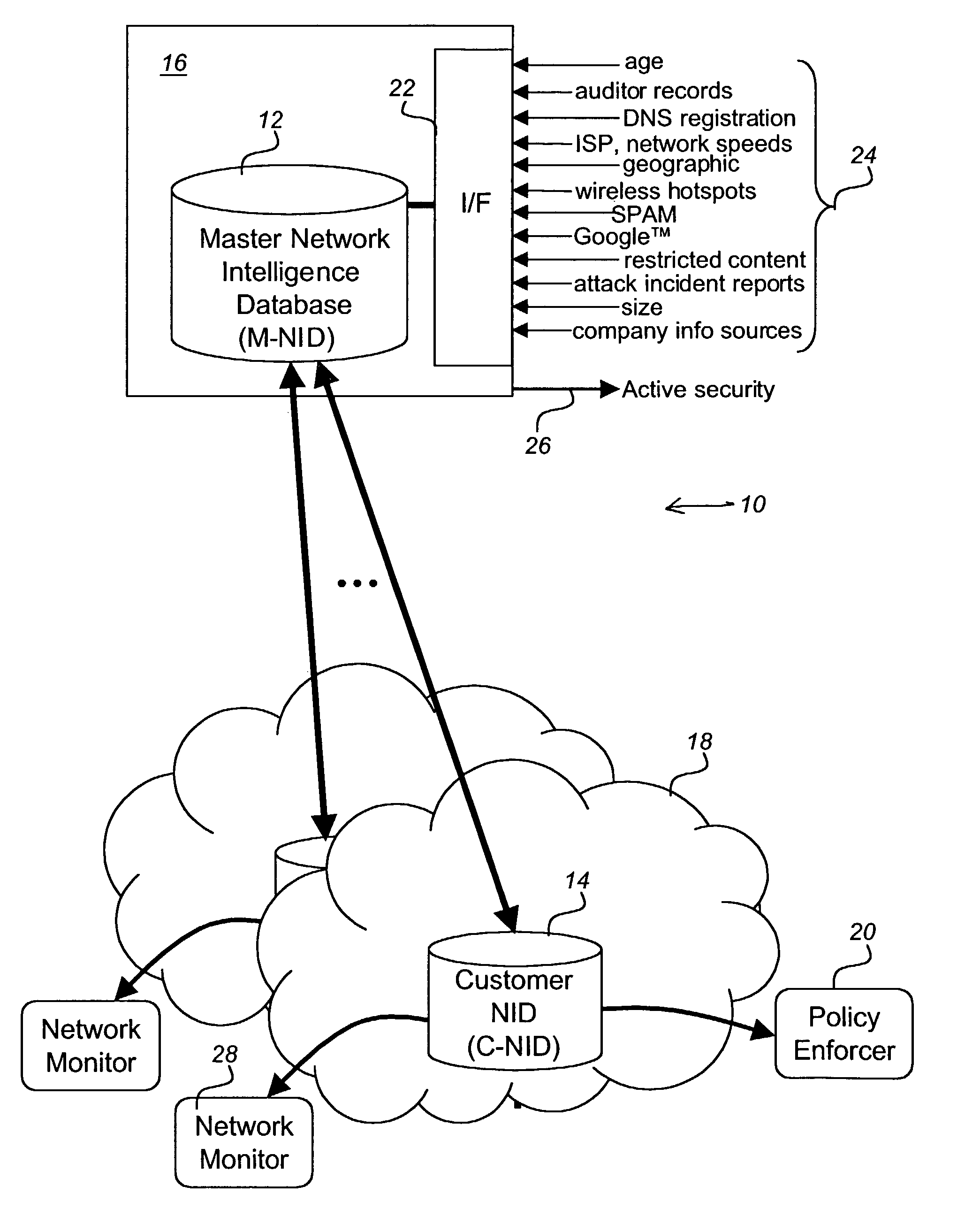
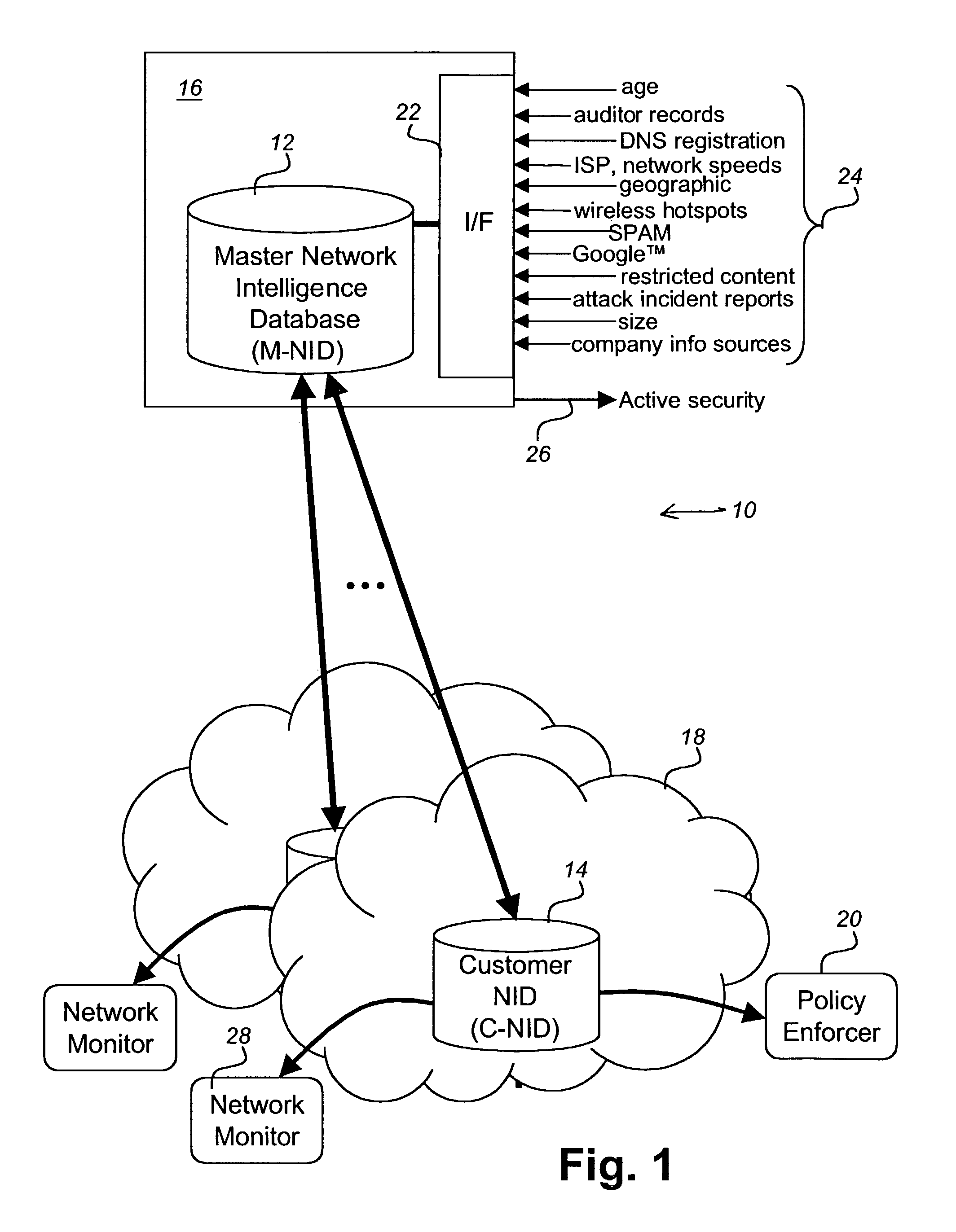
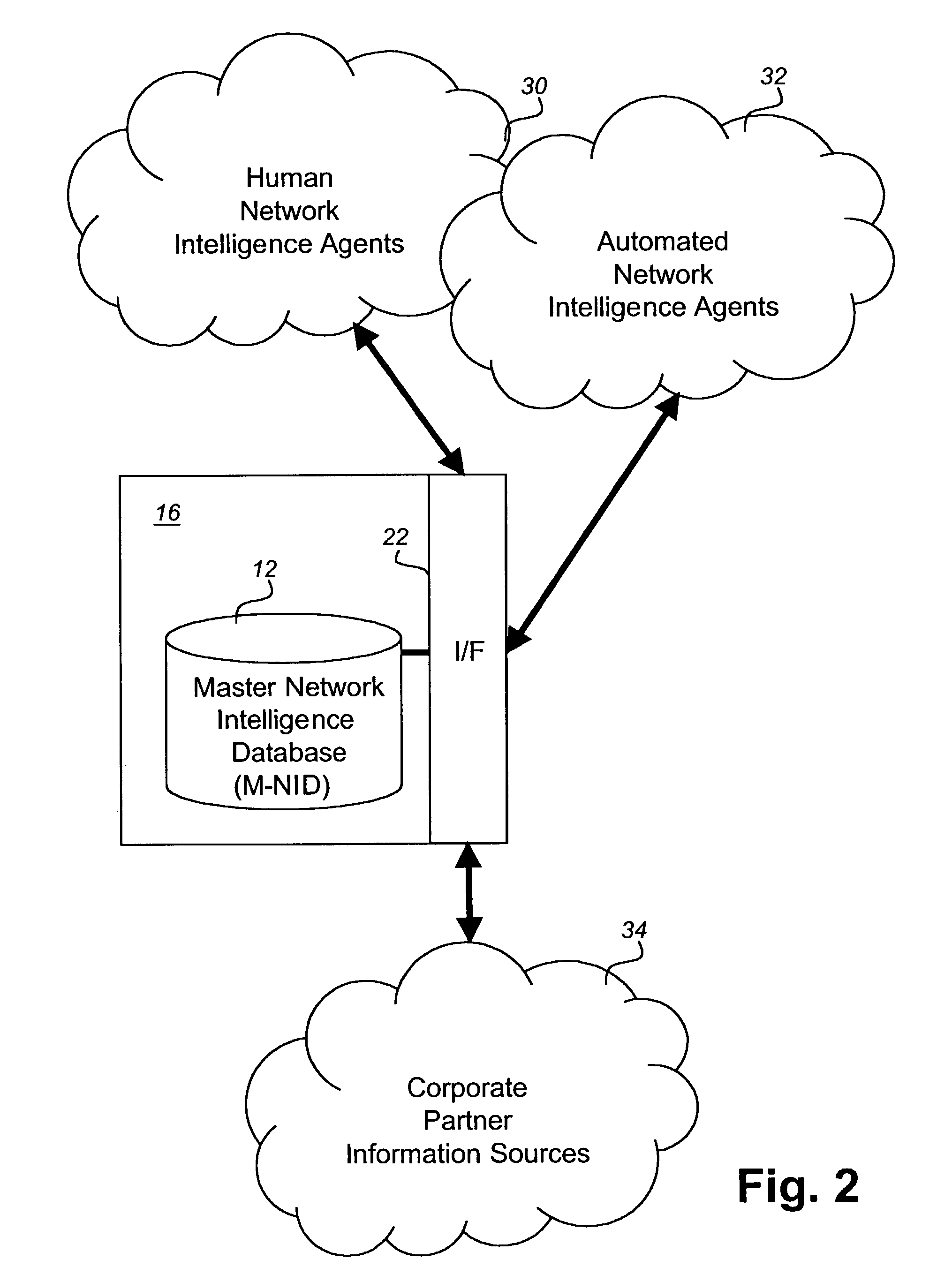
Network intelligence system
ActiveUS8024795B2Memory loss protectionDigital data processing detailsProxy serverSecurity information
A network security system takes an active approach to network security. This is accomplished by providing intelligence about other networks. A master network intelligence database is established that uses a plurality of network information agents for gathering information about networks and providing the information to the master network intelligence database. A customer network security system is then able to secure the customer network in dependence upon information received from the master network intelligence. Security information includes at least one of hostility level on the Internet, collected from numerous sites; security event history; spam levels; hosted services; public wireless; organization type; organization associations; peer ISPs; bandwidth connection to the Internet; active security measures; number of users on the network; age of the network; inappropriate content served; industry; geographic placement; open proxy servers; and contact information.
Owner:IBM CORP
Method and system for printing electronic mail
InactiveUS20060082807A1Digital computer detailsDigital output to print unitsElectronic documentEmail address
Printing an electronic document by dynamically creating a destination identifier and transmitting the electronic document with the destination identifier to a destination e-mail address. A server dynamically stores the electronic document with the associated destination identifier and waits to receive the identification-account information from an input device. An agent verifies the inputted identification-account information with the destination identifier stored on the server. The electronic document(s) associated with the destination identifier is then sent to the printer for printing upon verification.
Owner:CANON DEV AMERICAS
Method and apparatus for conducting an information brokering service
InactiveUS20070061219A1Accurately reflectEasy to measureMarket predictionsFinanceSubject matterComputer science
A system and method is provided that provides an early indication of consensus of opinion among a number of users regarding an event or observation indicated by a user. Such an opinion may be interesting to an information consumer, who may be interested in determining the outcome of the consensus relating to the event or observation, or may otherwise desire to perform surveillance or survey of a particular issue or subject. Such recognition of early events or observations may be useful in different areas, such as healthcare, finance, etc., where initial observations, if provided early, allow resulting decisions to be made much earlier. The opinion may, for instance, be used as an early indicator of problem with a product, company, etc. that would permit an information consumer to perform an action at a much earlier point than if he / she relied on traditional sources of information. Thus, such opinion information may be invaluable as a tool for monitoring events.
Owner:SERMO
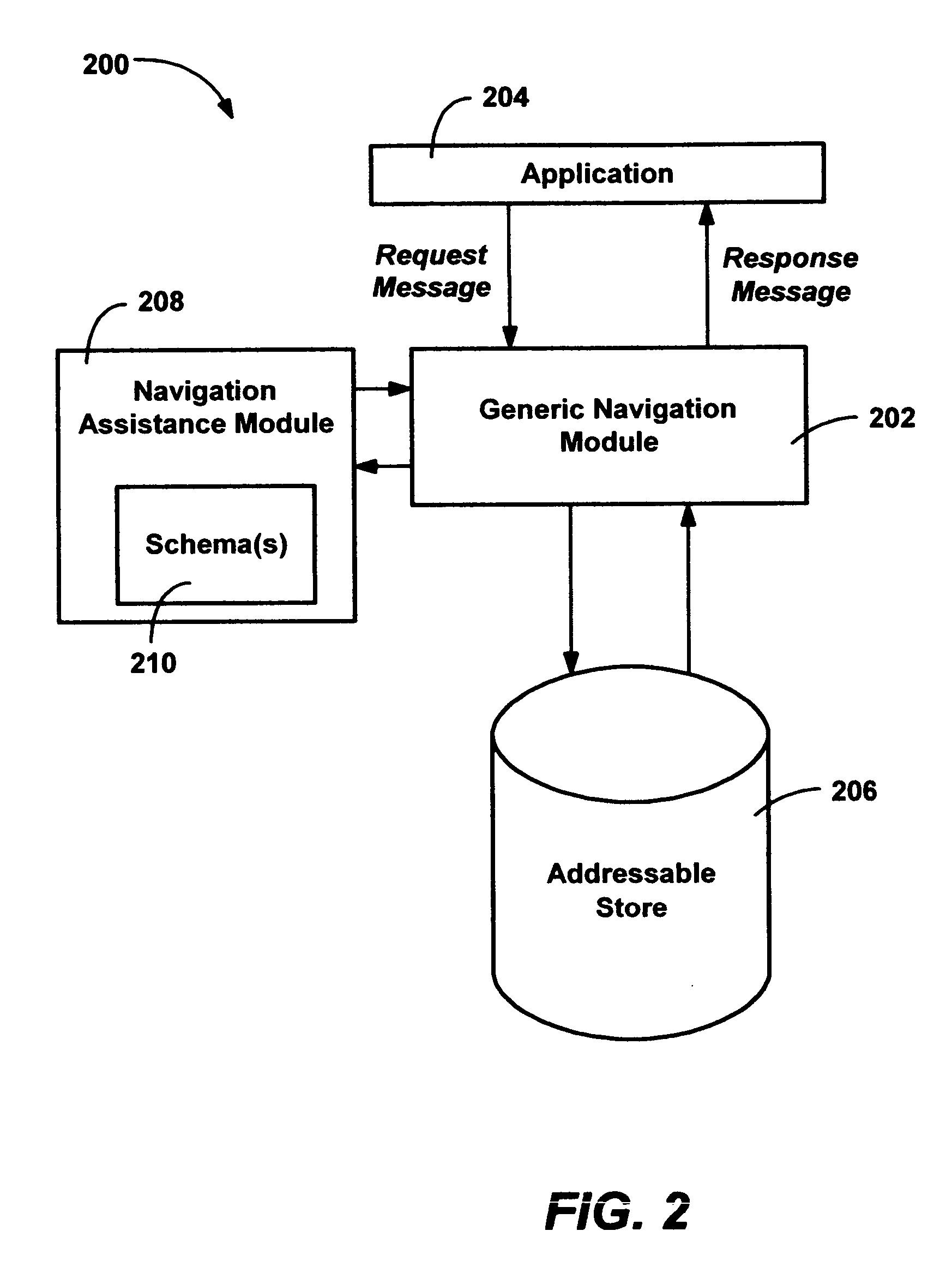
Schemas for a notification platform and related information services
InactiveUS20050278344A1Special service provision for substationDigital data processing detailsInformation processingInformation type
Owner:MICROSOFT TECH LICENSING LLC
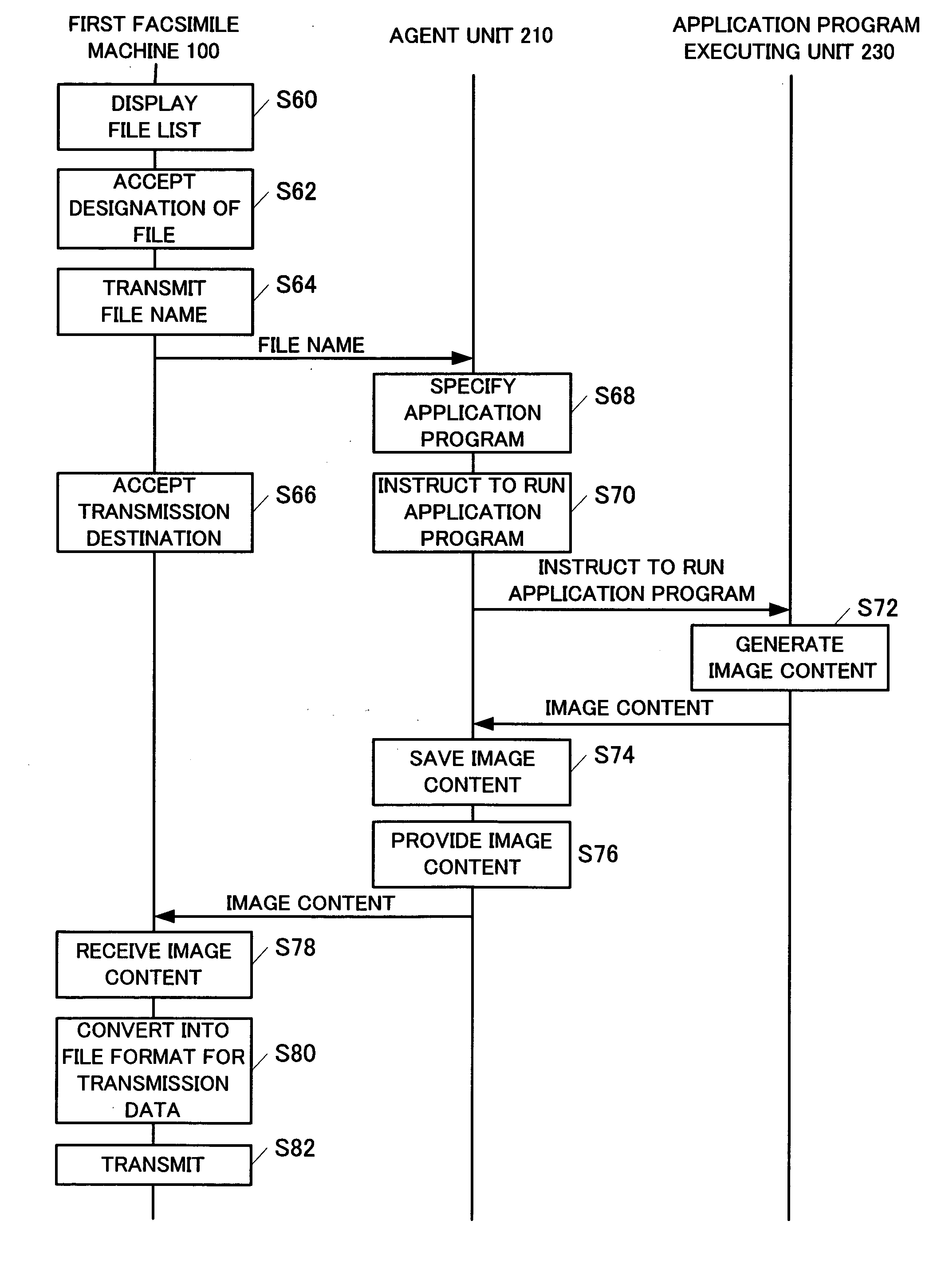
Facsimile machine and data conversion device
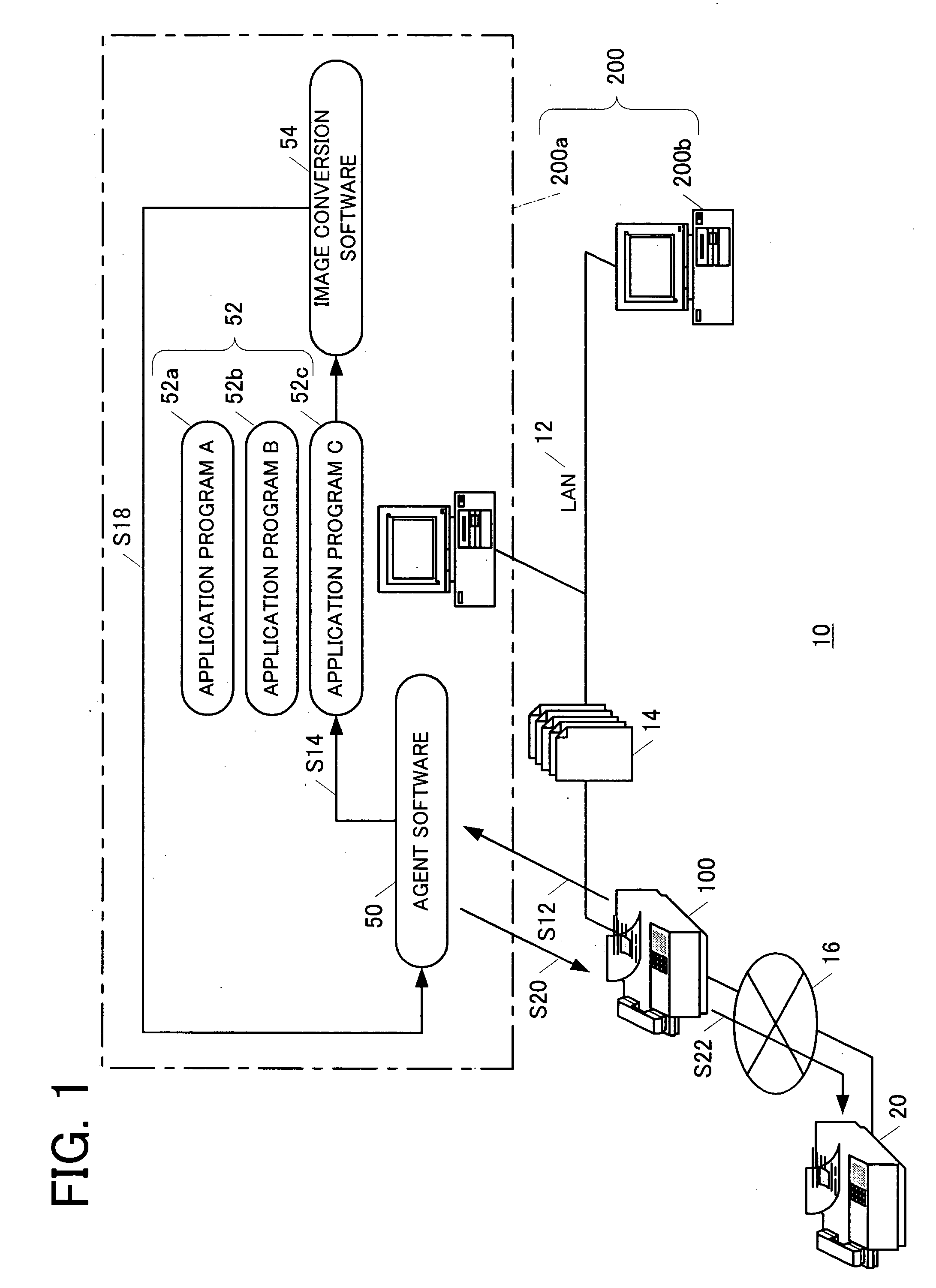
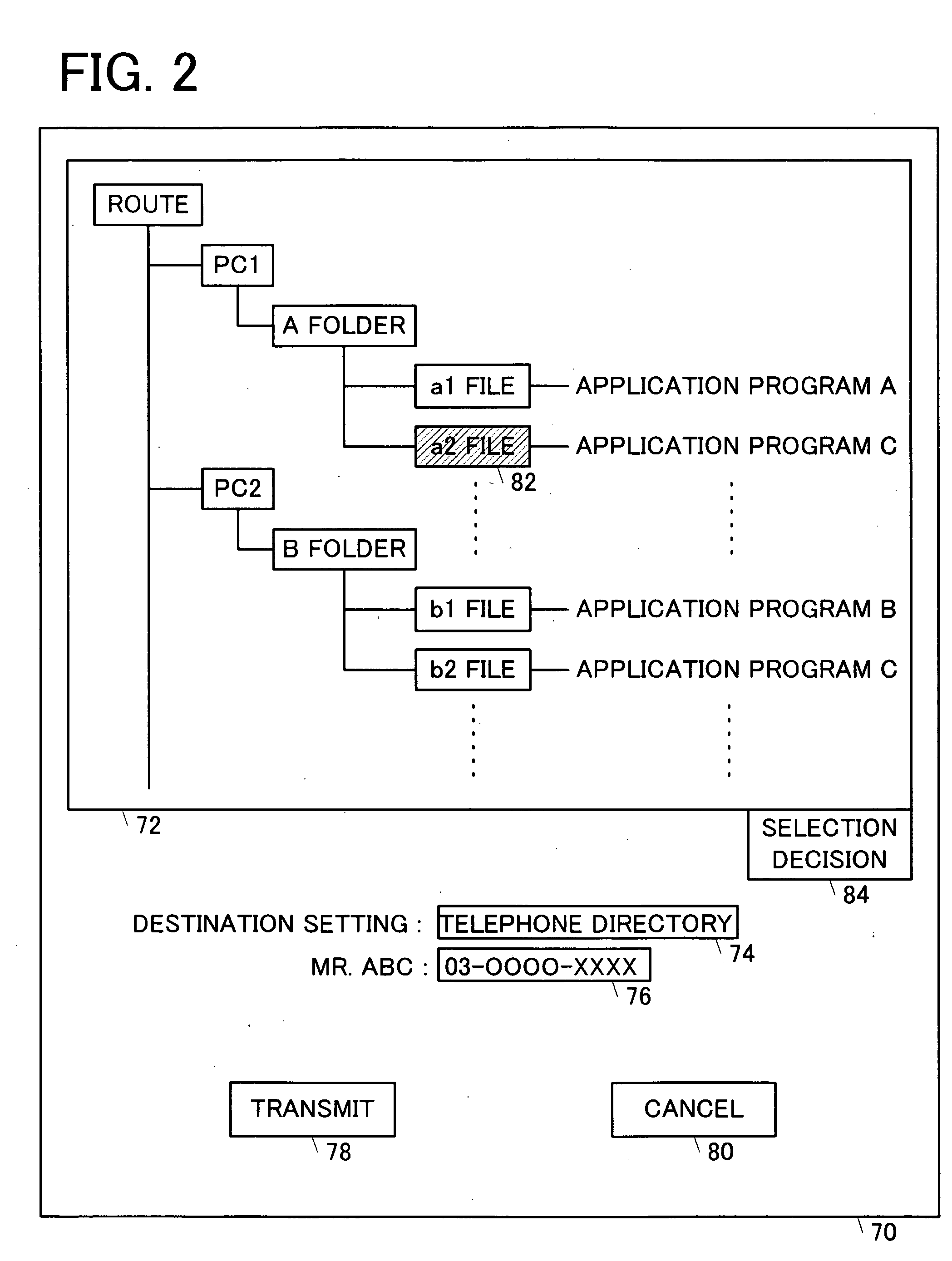
InactiveUS20050088686A1Improve toleranceImprove failureDigital computer detailsPictoral communicationFacsimile transmissionInformation agents
A facsimile machine provides file specifying information of a transmission file to an agent software. The agent software runs an appropriate application program in accordance with the file specifying information. By using this function, a prescribed file on a data conversion device is converted directly into an image content via a network from the facsimile machine. Accordingly, a facsimile transmission of the image content to a prescribed destination can be carried out just by an operation from the facsimile machine. As a result, an efficiency of a facsimile transmission process is improved.
Owner:MURATA MASCH LTD
Enterprise computer system
A scalable enterprise computer system having the capability to provide transaction security as well as providing subscription filtering is described. As a method of transacting an event in the enterprise computer system a connection with an information broker by the publishe established after which it is determined if the event registered with the information broker. Next, a subscription corresponding to the registered event by a subscriber is accepted by the information broker, after which a platform neutral event is created that is then populated with event content which is then published to and received by the information broker.
Owner:SOFTWARE AG USA
Architecture for a system of portable information agents
InactiveUS7472157B2Enhance and track user interactionDiscounts/incentivesFinanceInteractive graphicsApplication software
A method and system for providing enhanced intelligent agents that are moveable by a user from a browser application to a desktop. In specific embodiments, agents provide advanced interactive graphics and communications back to a server.
Owner:ENVOII +1
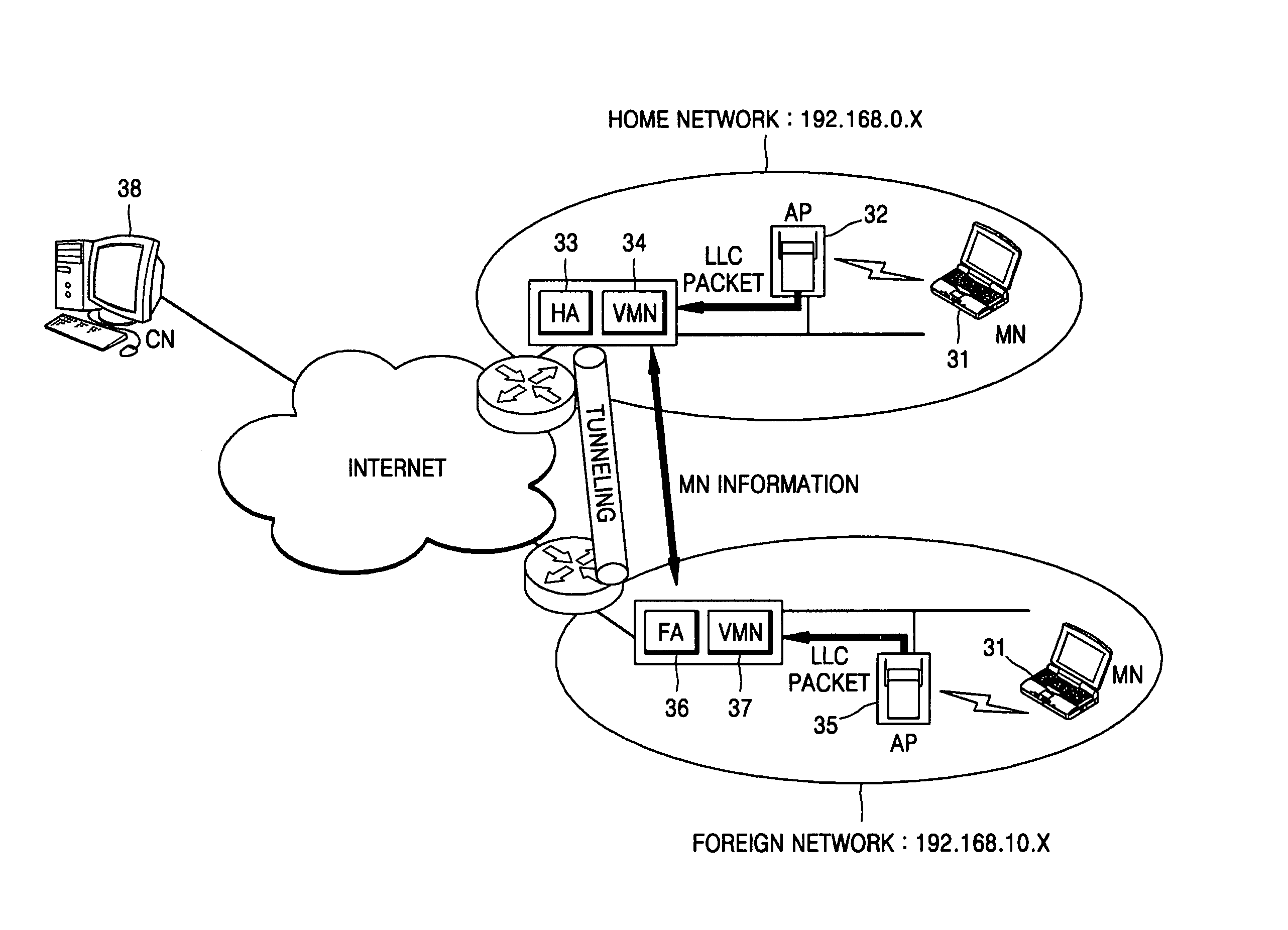
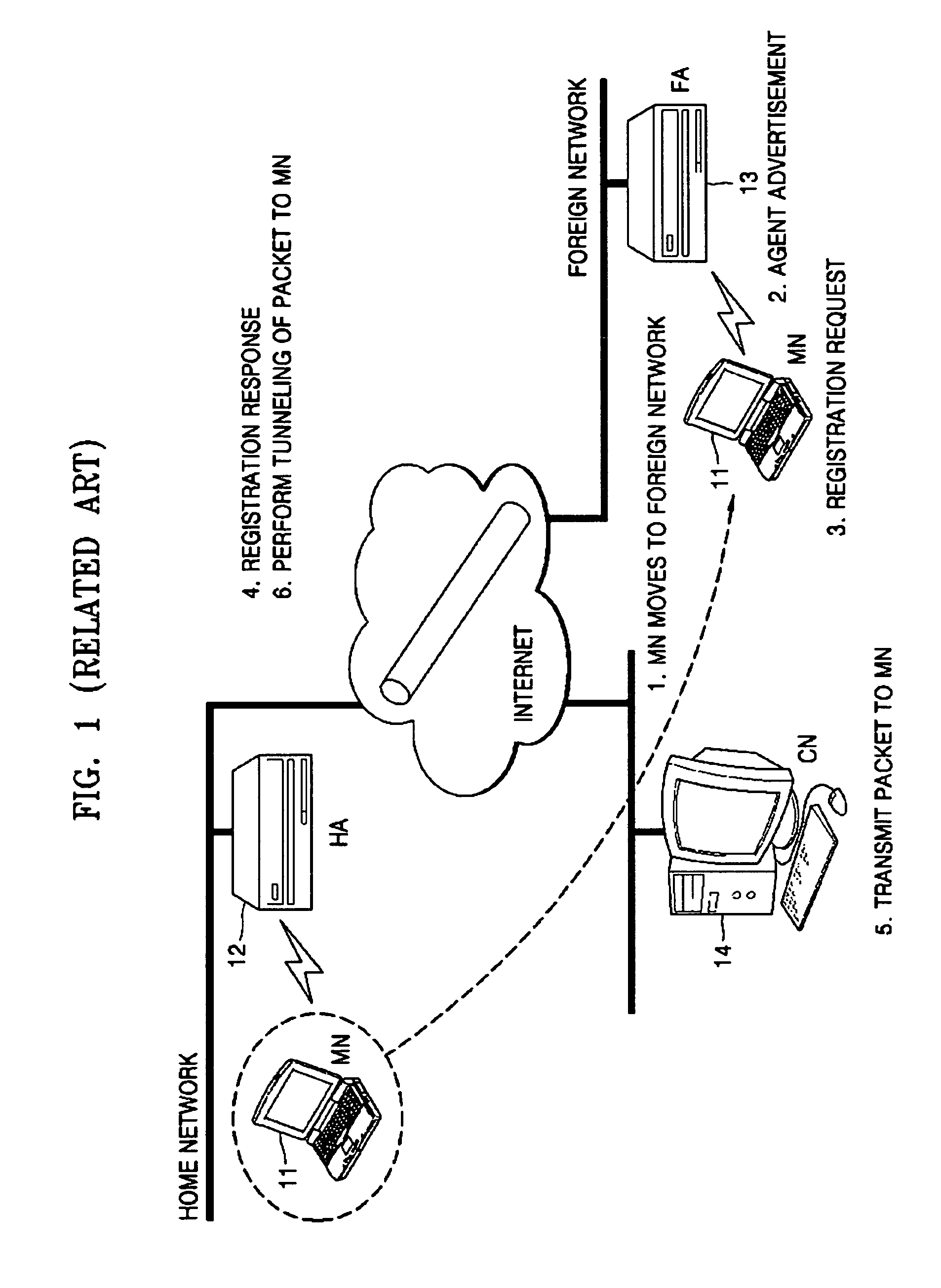
Method and apparatus for registering mobile node in a wireless local area network (LAN) environment
An apparatus and method for supporting mobility of a mobile terminal in a wireless local area network (LAN) environment deploying mobile IP are provided. The method for registering a mobile node using a virtual mobile node comprises: detecting whether or not a mobile node traveling among a plurality of networks is connected; and registering information on the mobile node whose connection is detected, with an agent relaying communication between the mobile node and a correspondent agent. By doing so, even when a mobile IP module is not installed, the mobile node can perform wireless communication seamlessly between networks in a wireless LAN environment deploying mobile IP.
Owner:SAMSUNG ELECTRONICS CO LTD
Schemas for a notification platform and related information services
InactiveUS20050278366A1Special service provision for substationDigital data processing detailsInformation processingUser device
Described is a schema-based notification platform that provides regularized notification handling including user control and normalization of the operation of policies across different information types and contexts. Information-service schemas and services are combined to build a content-sensitive and context-sensitive information service to communicate information to recipient devices of users that subscribe to those services. An information agent service collects the information, and based on various criteria, determines if, when, and how to send and render the information, and to which subscribing client device or devices. The set of schemas include a notification schema that represents the subscription of a service to an information source and details about that information, and a device schema that represents information about user devices. The information agent service accesses criteria including user preferences and user contextual information, including presence information, location information, and schedule information along with people and groups data and extended-context data. Preferences about subscriptions and information handling policies may be stored and used at notification sources or in more central preference encodings. Access to multiple preferences is maintained, and a user interface is provided that allows users to inspect and control multiple subscriptions in one conceptual place.
Owner:MICROSOFT TECH LICENSING LLC
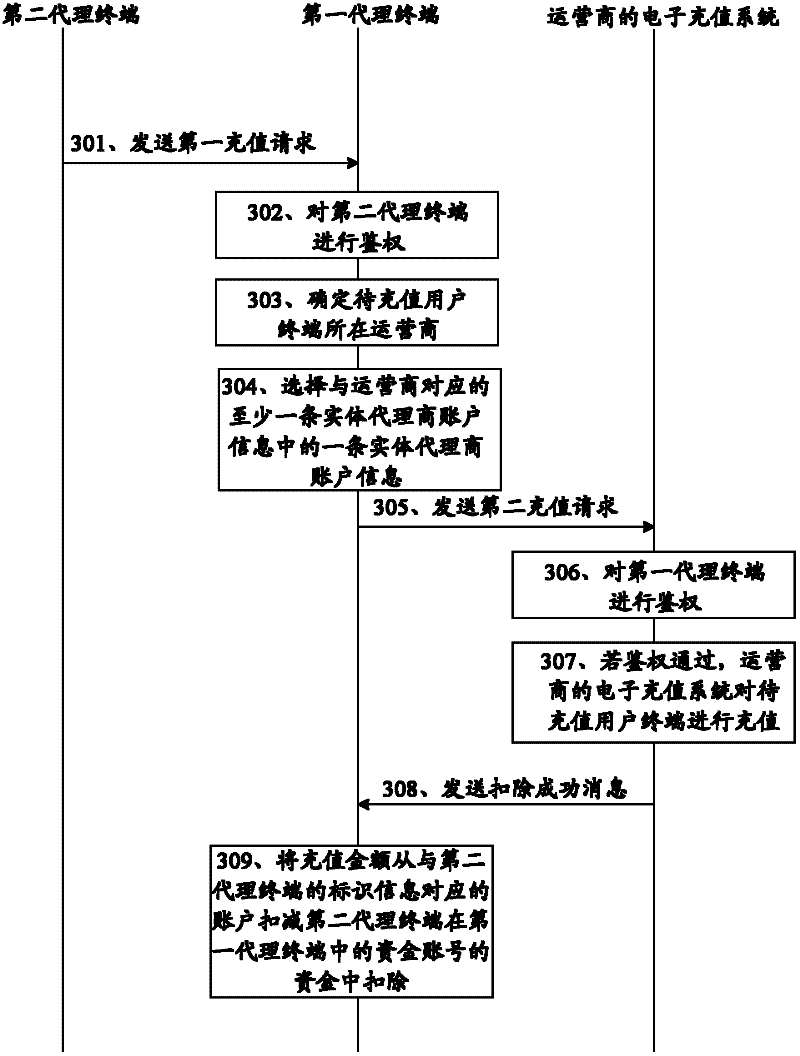
Electronic recharging method and agent terminal
InactiveCN102263867AExpand recharge abilityAccounting/billing servicesTransmissionComputer networkInformation agents
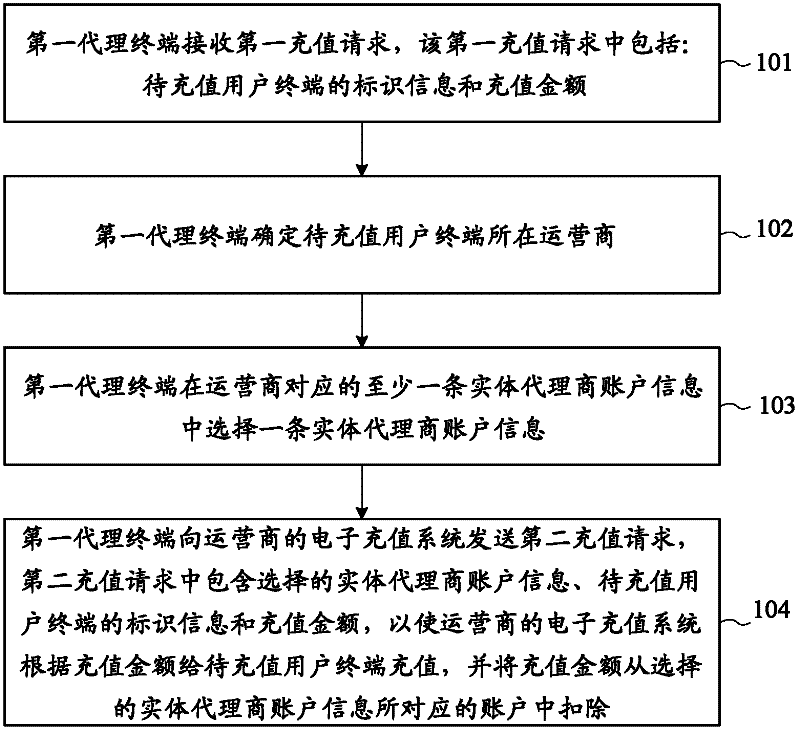
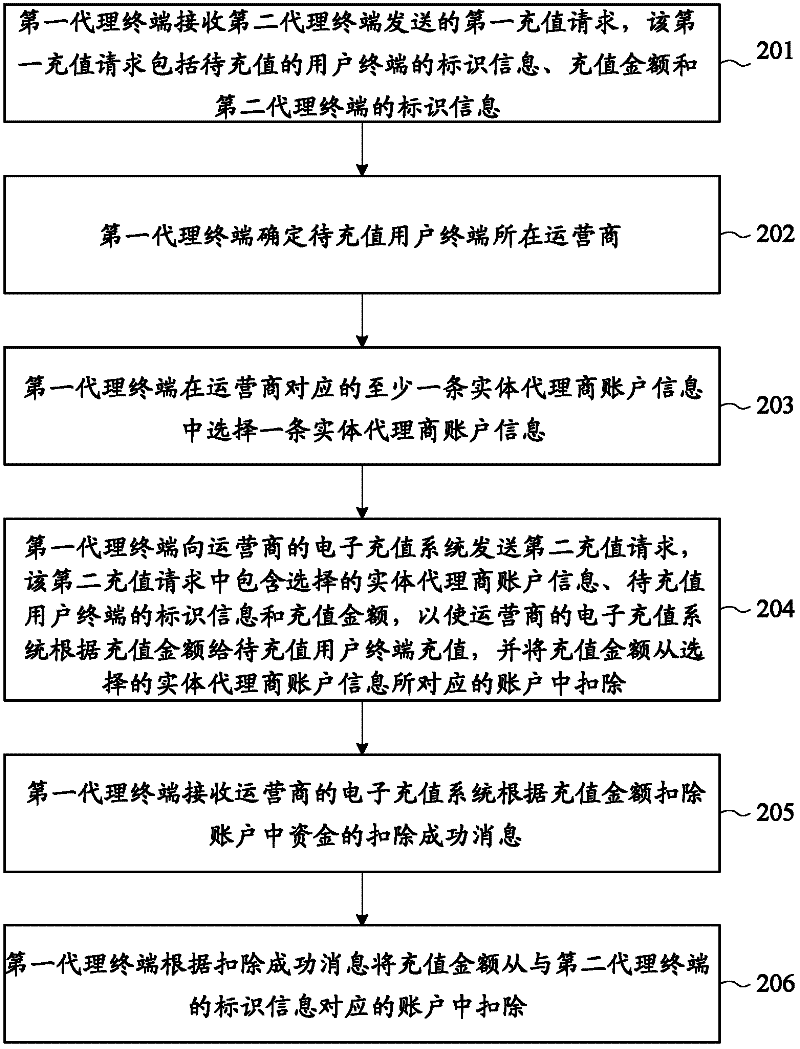
An embodiment of the present invention provides an electronic recharge method and an agent terminal. The electronic recharge method includes: the first agent terminal receives a first recharge request, and the first recharge request includes the identification information and the recharge amount of the user terminal to be recharged; the first agent terminal Determine the operator of the user terminal to be recharged; the first agent terminal selects one piece of entity agent account information from at least one piece of entity agent account information corresponding to the operator; the first agent terminal sends a second recharge request to the operator's electronic recharge system , the second recharge request includes the selected entity agent account information, the identification information of the user terminal to be recharged, and the recharge amount, so that the operator's electronic recharge system recharges the user terminal to be recharged according to the recharge amount, and the recharge The amount will be deducted from the account corresponding to the selected entity agent account information. The above method expands the recharging capability of the agency terminal in the prior art.
Owner:HUAWEI SOFTWARE TECH
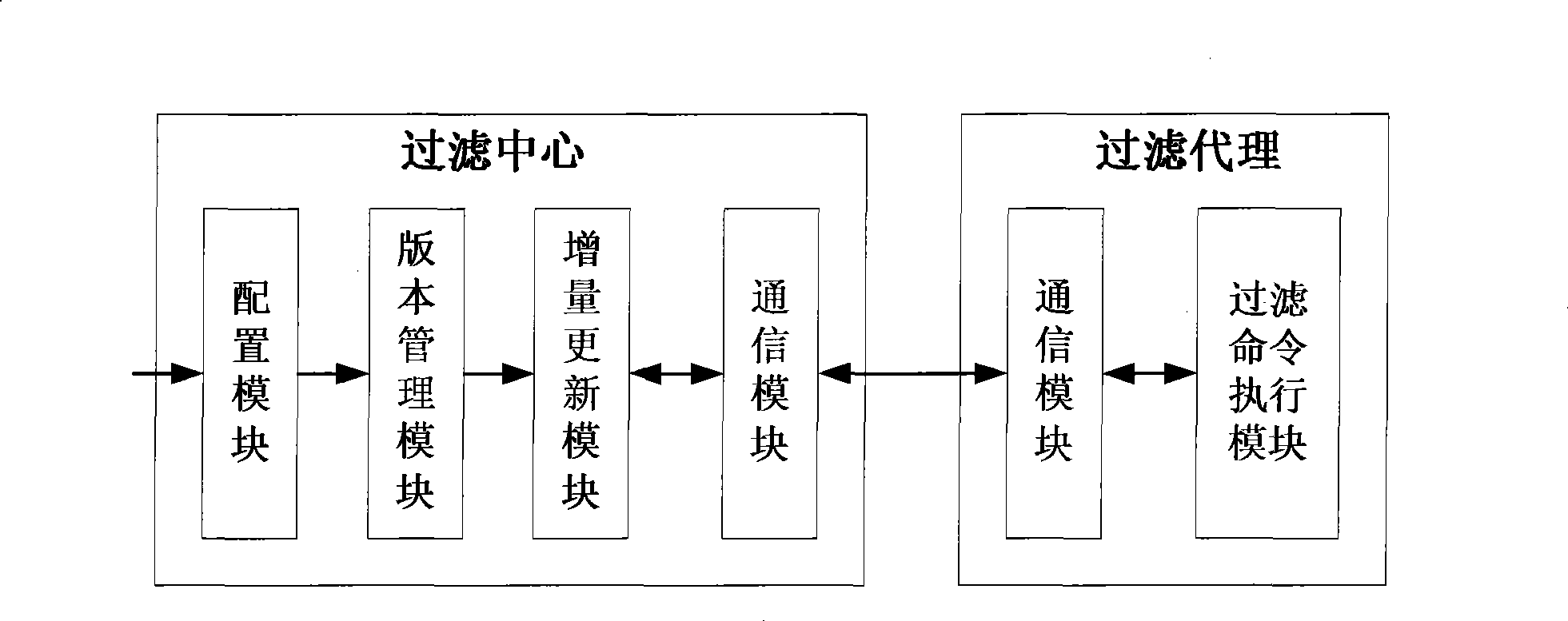
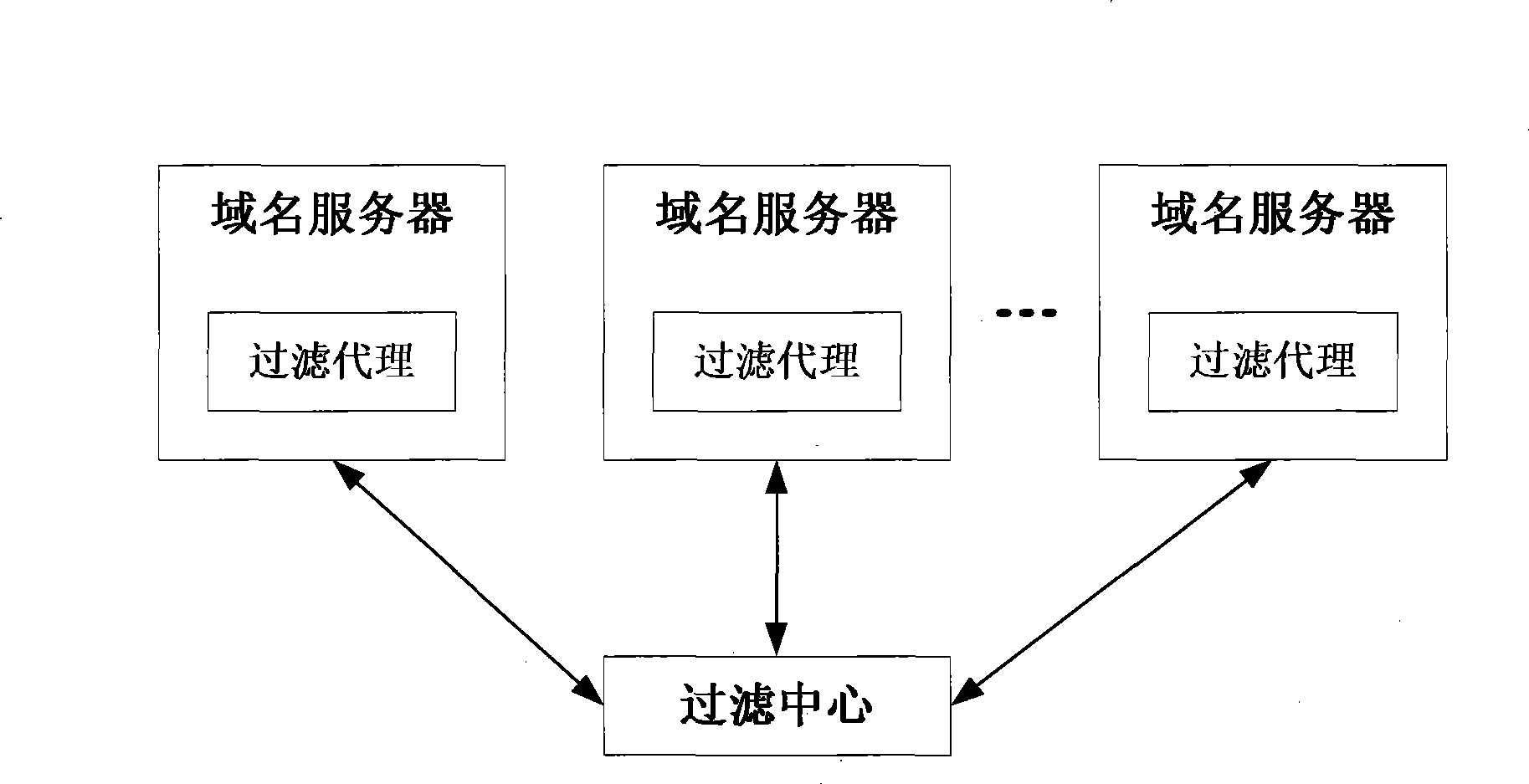
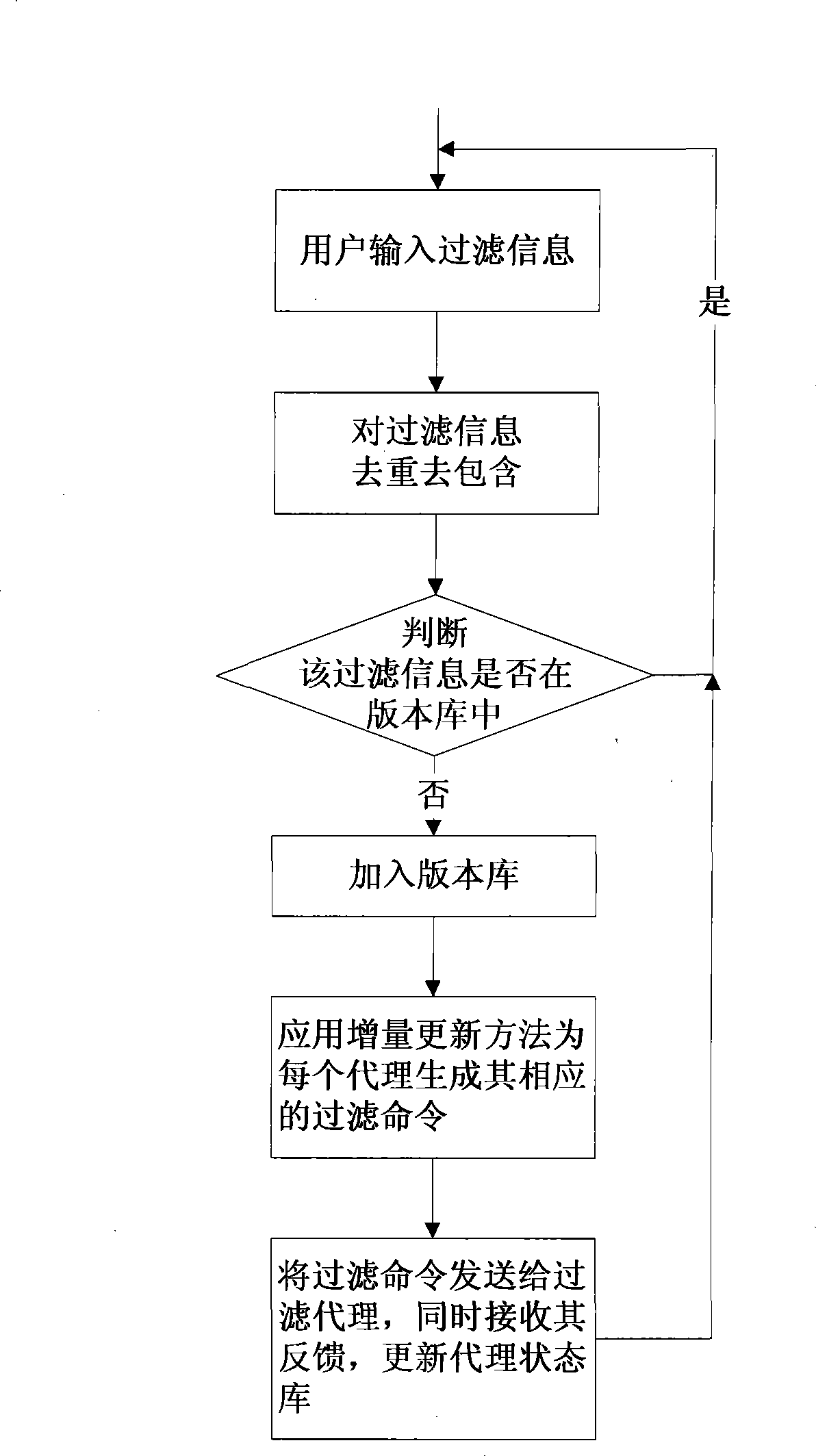
Domain name filtering system and method
The invention provides a filtering system for domain name, comprising a domain name server for achieving the domain name filter installed with a filtering proxy sub system and a filtering centre sub system for generating the filtering directive. The sub system filter center filter based on information entered by the user in light of filter sub system status information agent for the filtering agent sub system command to generate the corresponding filter; domain filtering proxy server sub system analysis and implementation of the filter orders received, according to modify the content filter command of the domain name server configuration file, the domain name server configuration file under the name of the content filter to filter the domain name. The present invention does not require the operation of the existing domain name server to do any changes, which are easy to implement, easy to maintain the advantages of the existing domain name and server stability and performance have no effect.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
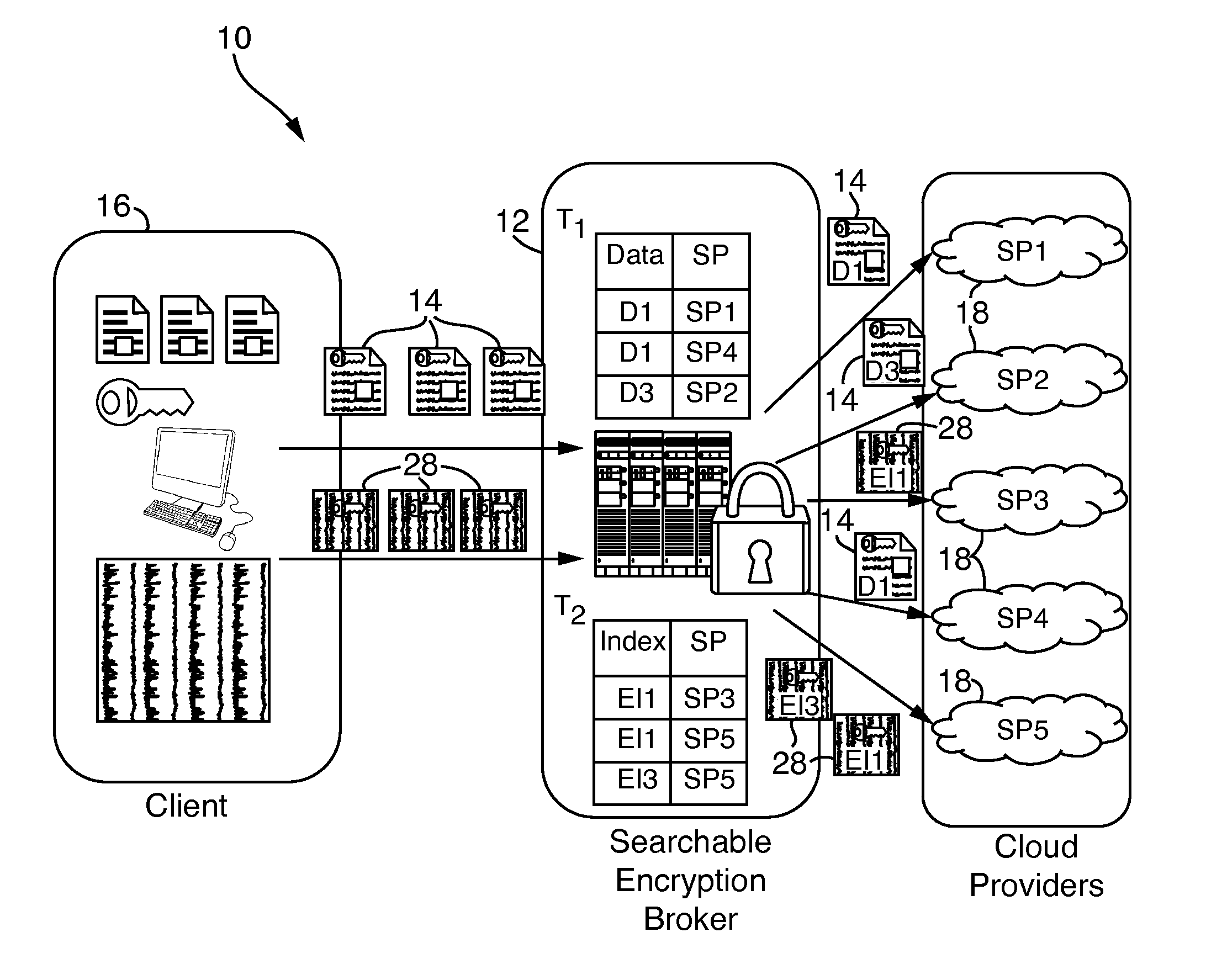
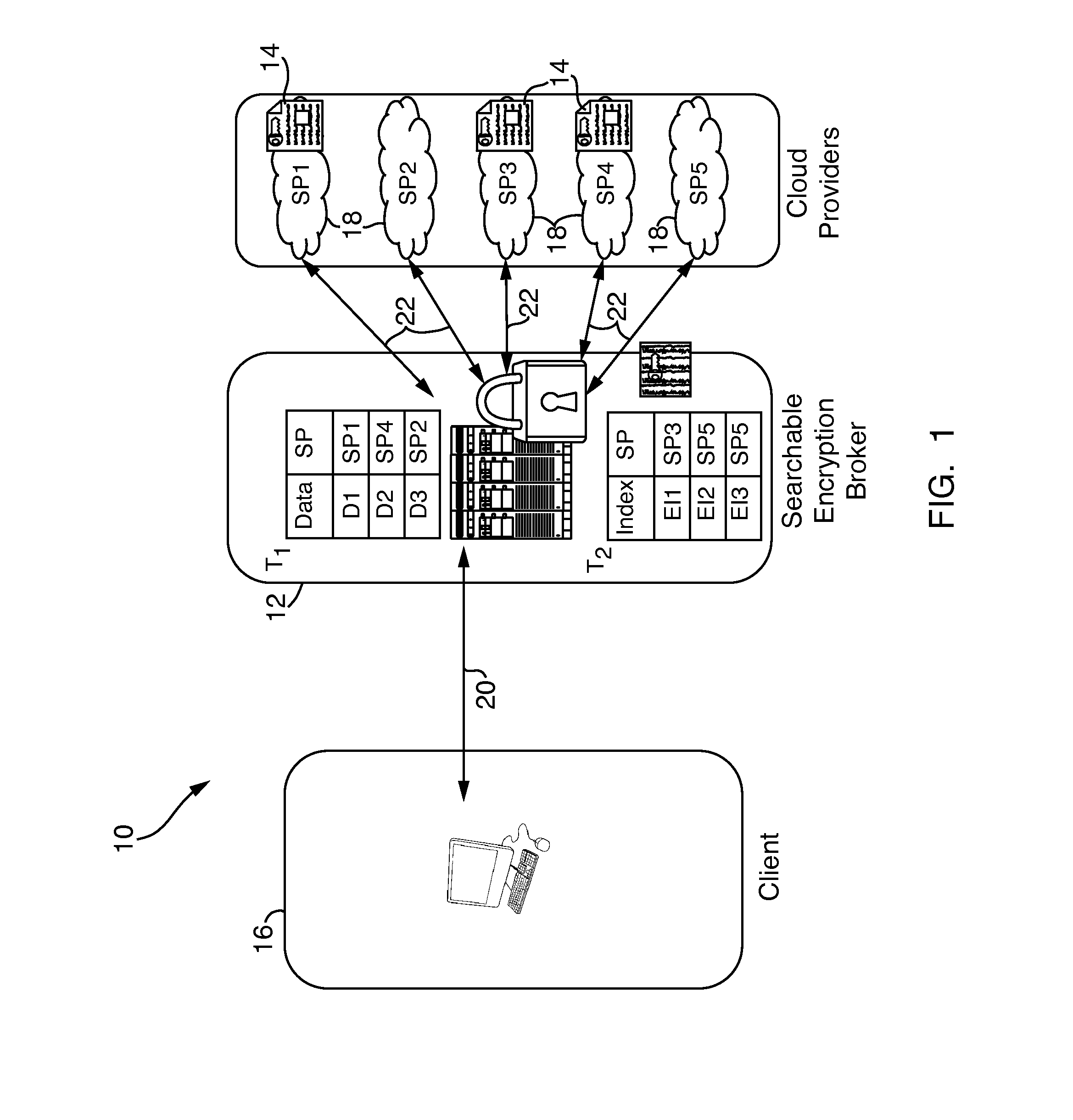
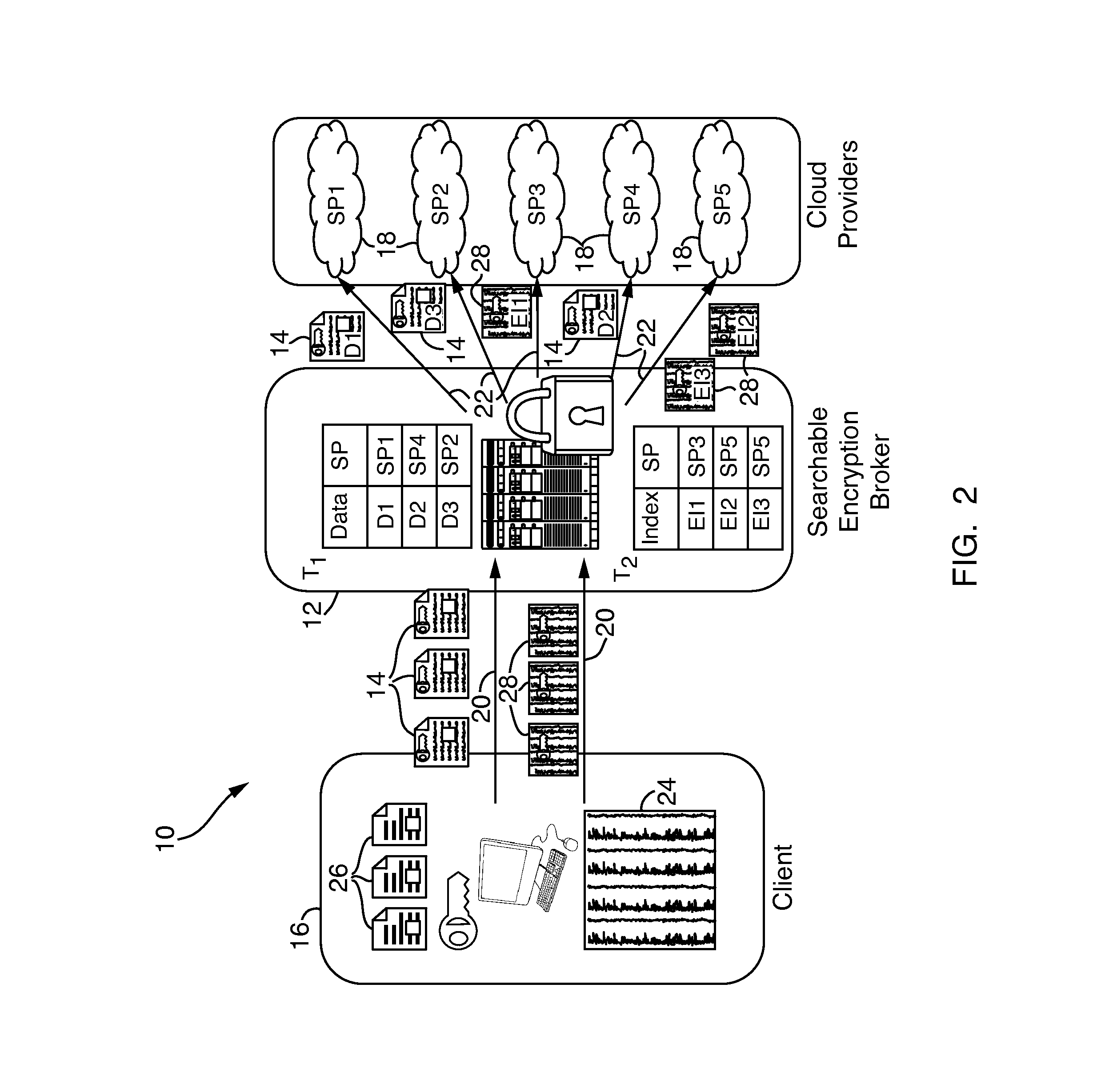
Systems and methods for enabling searchable encryption
ActiveUS20140359282A1Provides redundancyDigital data protectionTransmissionInternet privacyProxy server
A system and method for enabling searchable encryption of encrypted documents stored by a client on one or more storage providers includes a broker server in communication with the client and the one or more storage providers. The broker server is adapted to transfer the encrypted documents between the client and the one or more storage providers and to maintain information indicating where the encrypted documents are transferred. The broker server further stores information for at least one encrypted index for the encrypted documents and a test function for a searchable encryption mechanism used to encrypt the at least one encrypted index.
Owner:ALCATEL LUCENT SAS
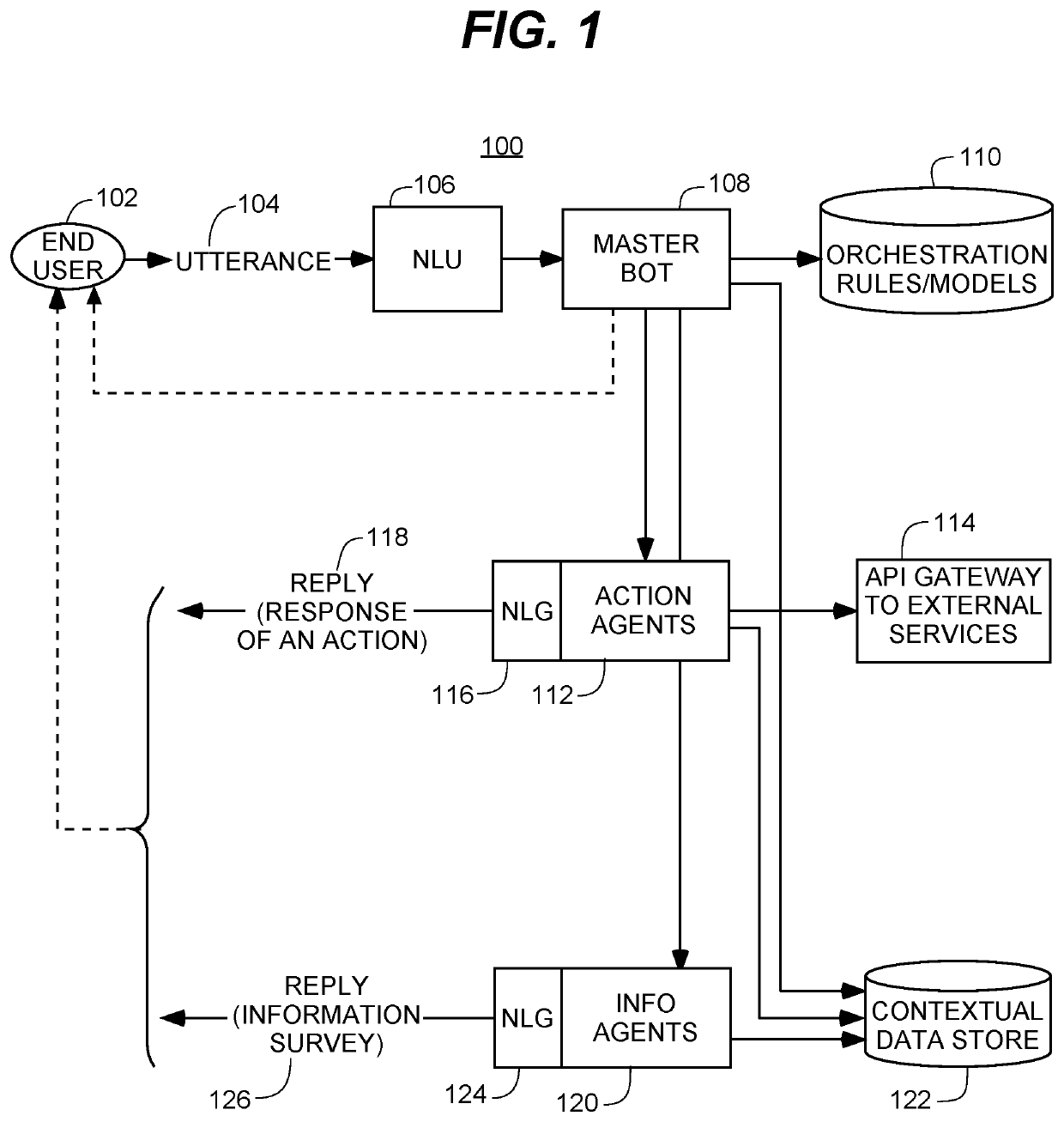
Methods and systems for deploying and managing scalable multi-service virtual assistant platform
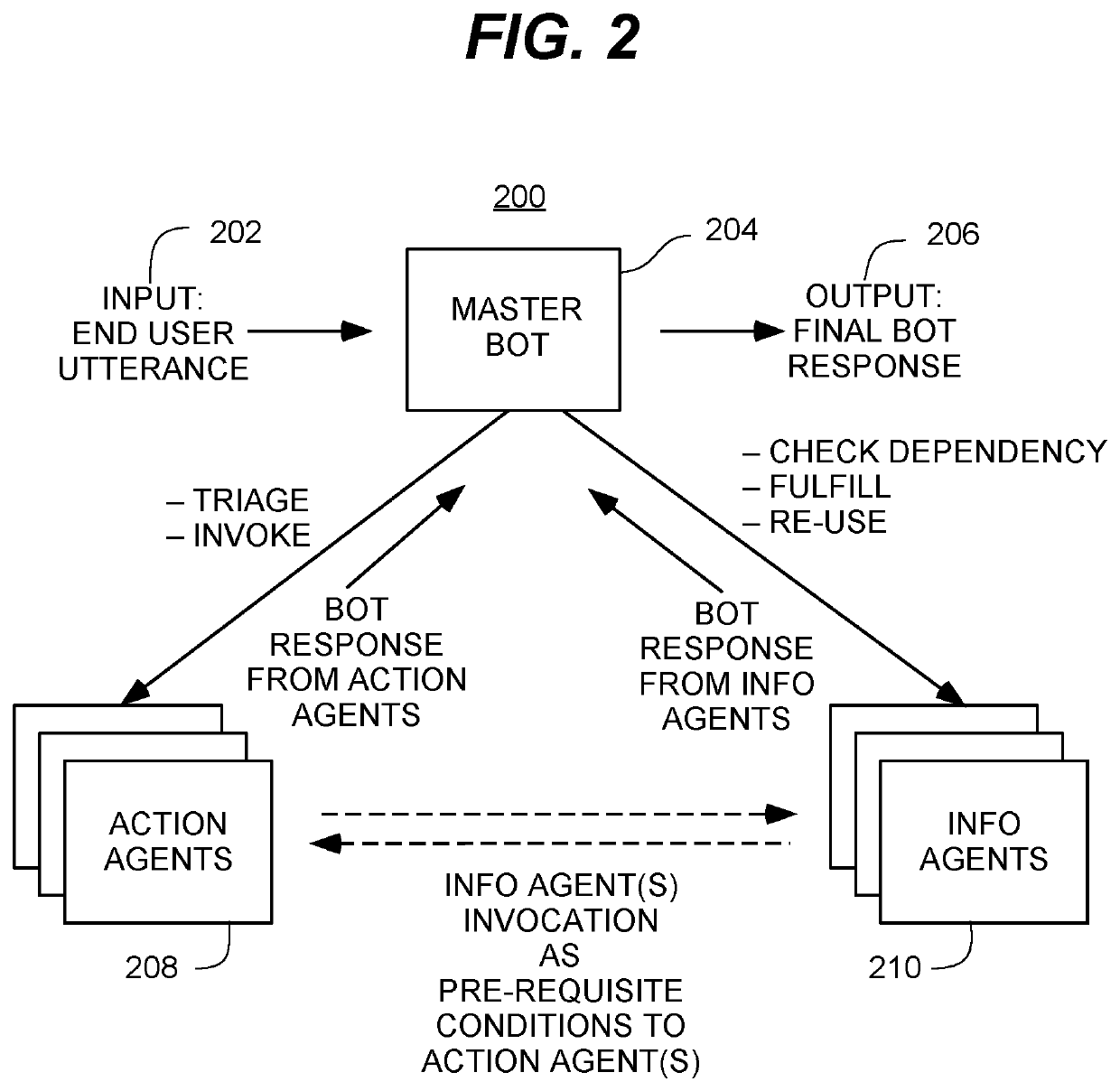
The present invention is a scalable multi-service virtual assistant platform that can construct a fluid and dynamic dialogue by assembling responses to end user utterances from two kinds of agents, information agents and action agents. The information agents and action agents are managed by a masterbot or arbiter. The virtual assistant can gain new skills by getting instructions about a new service expressed in a form of pre-requisites and action combinations; the virtual assistant platform automatically handles dialogue generation, arbitration and optimization to survey prerequisites from the end user, and eventually to take action. The present invention allows a large number of services to implemented using a small number of building blocks. These building blocks can be used to assemble a much larger number of services. In turn, each service can be delivered through a large variety of conversations with end users, enabling a fluid and dynamic dialogue to be seamlessly implemented.
Owner:LINC GLOBAL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com