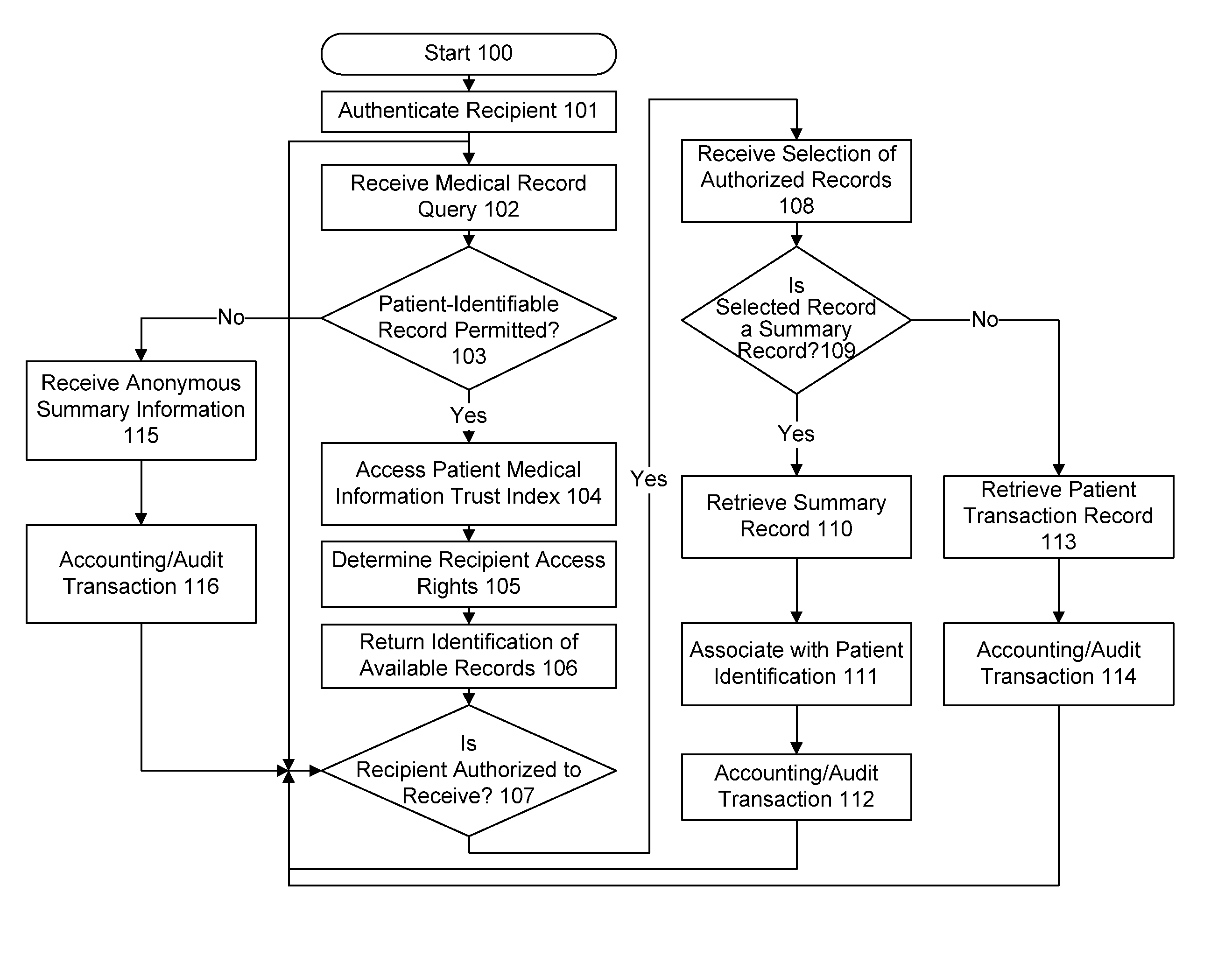
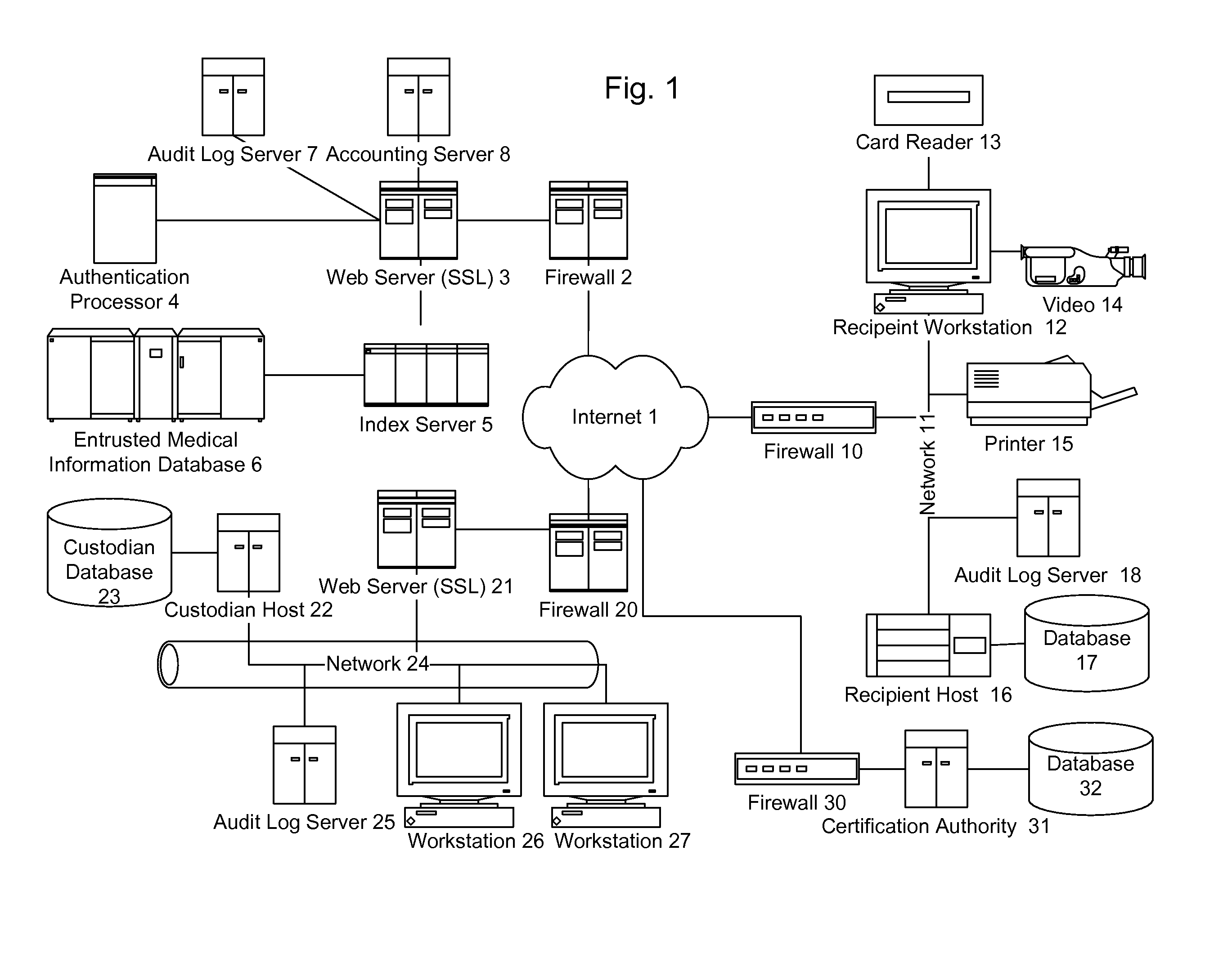
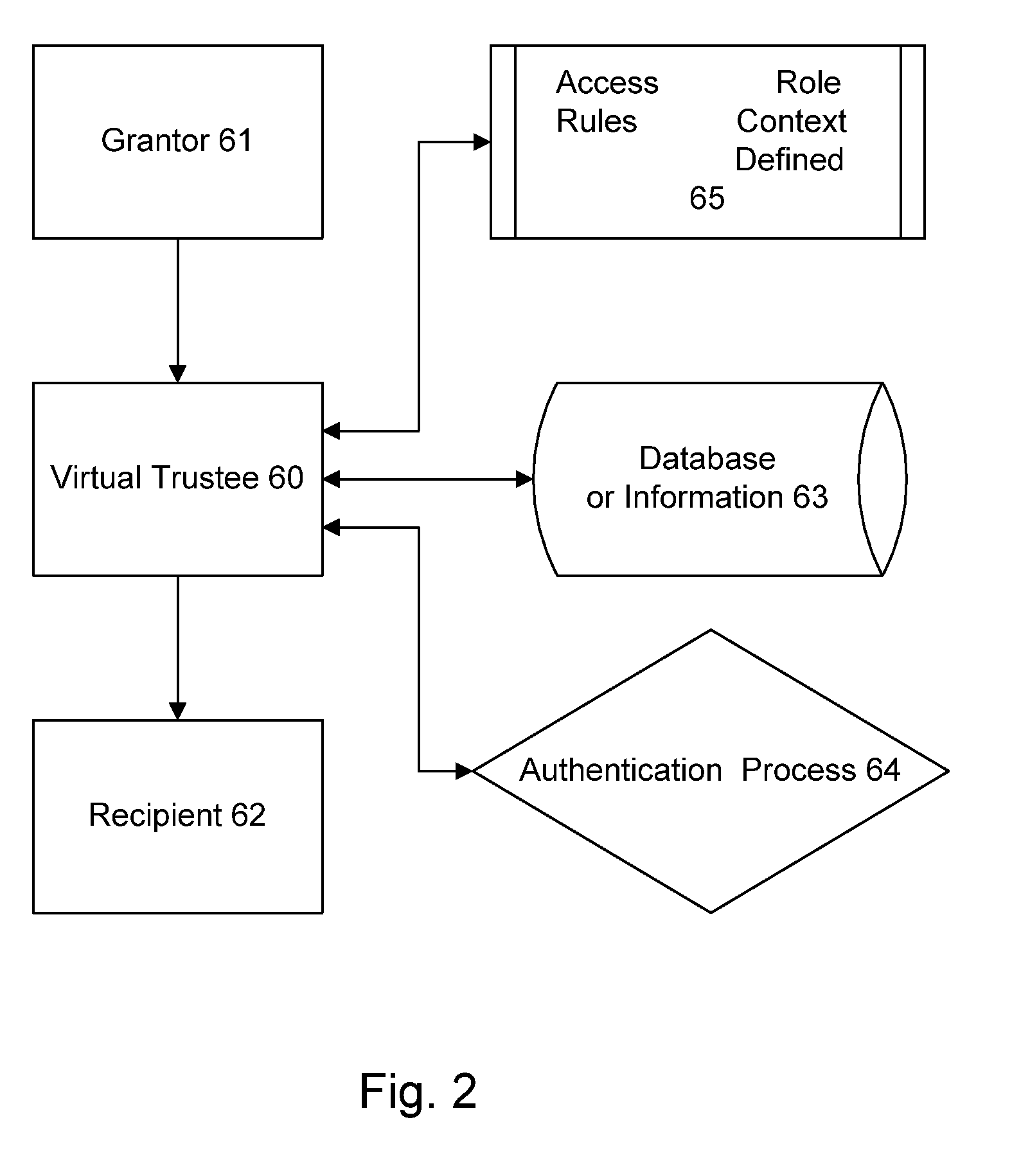
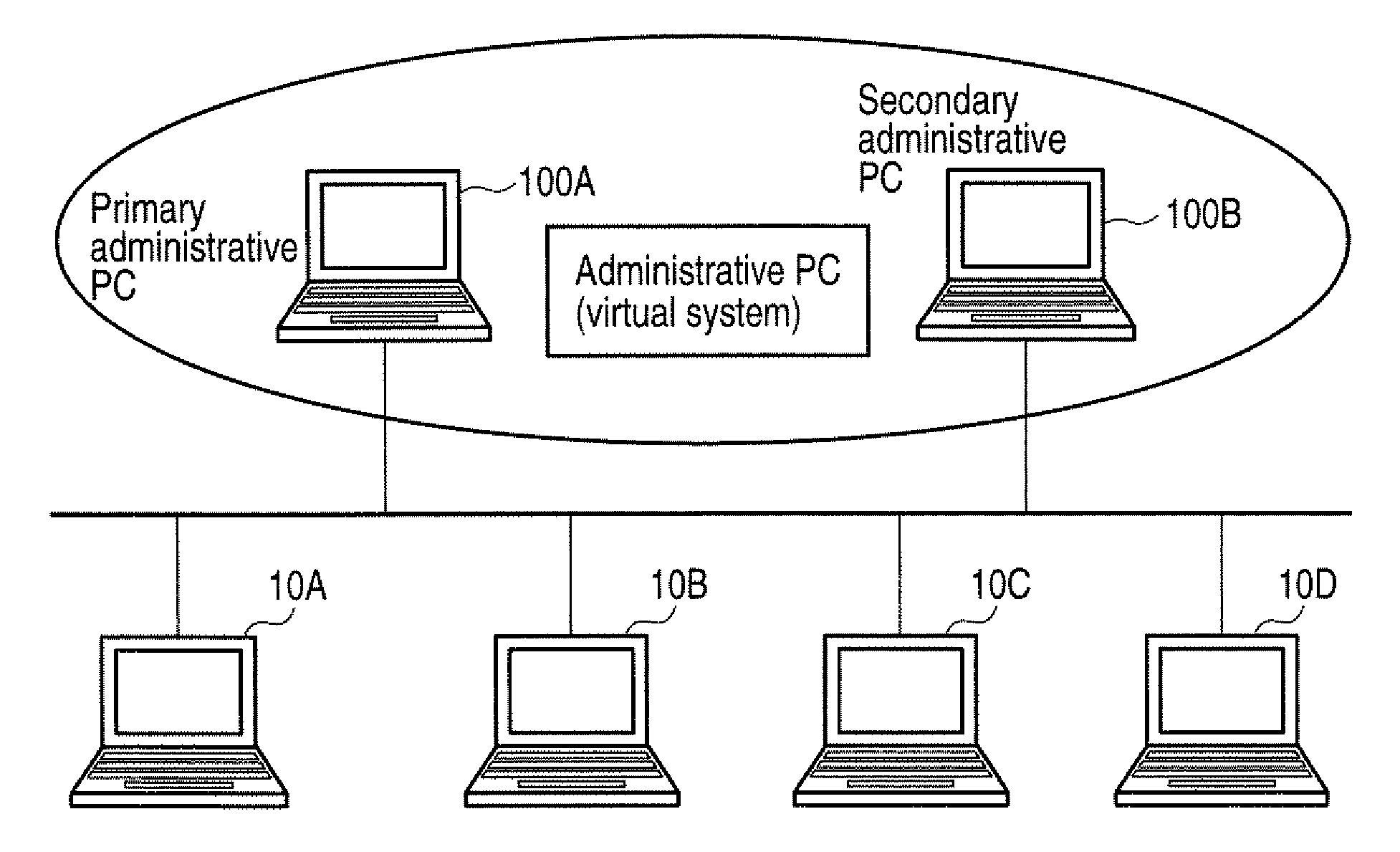
Patents
Literature
2636 results about "Security information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
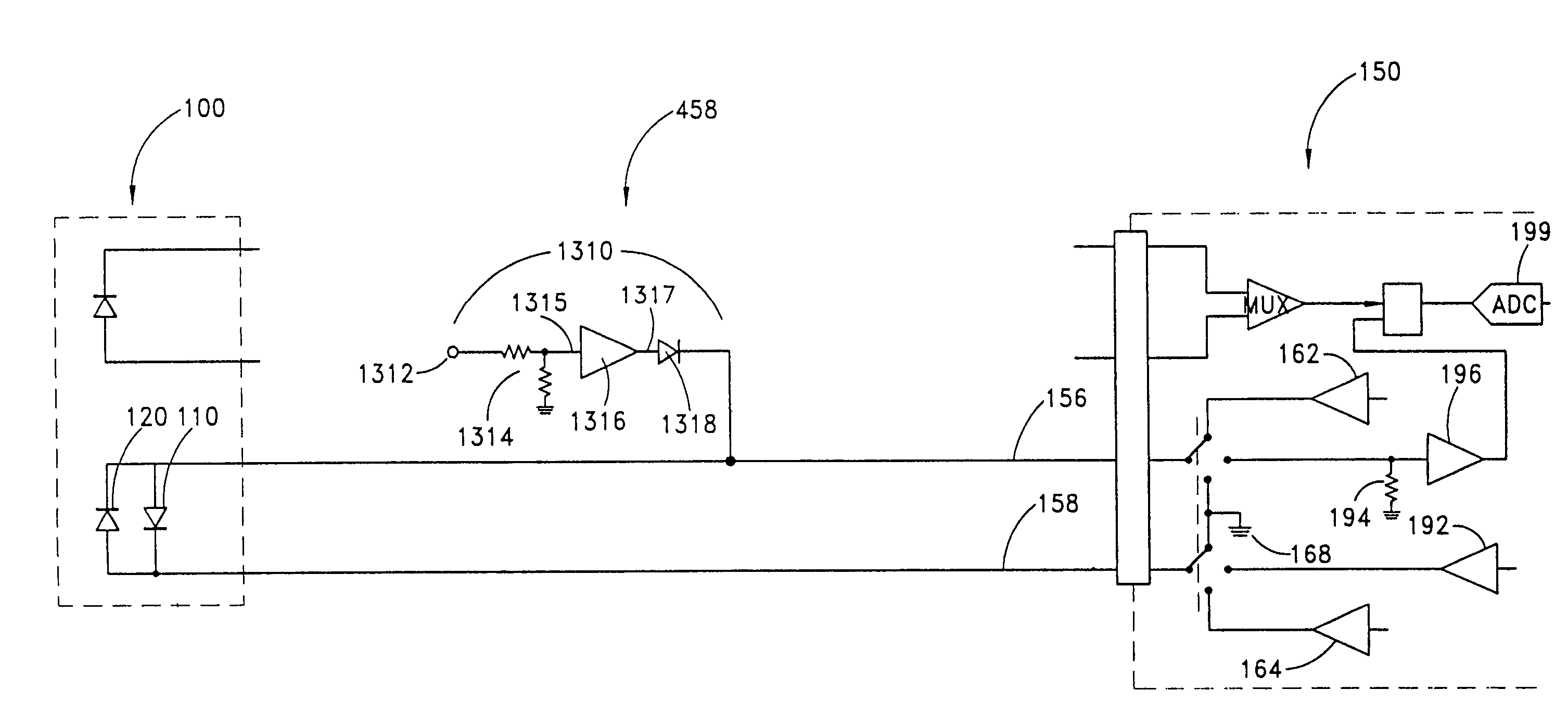
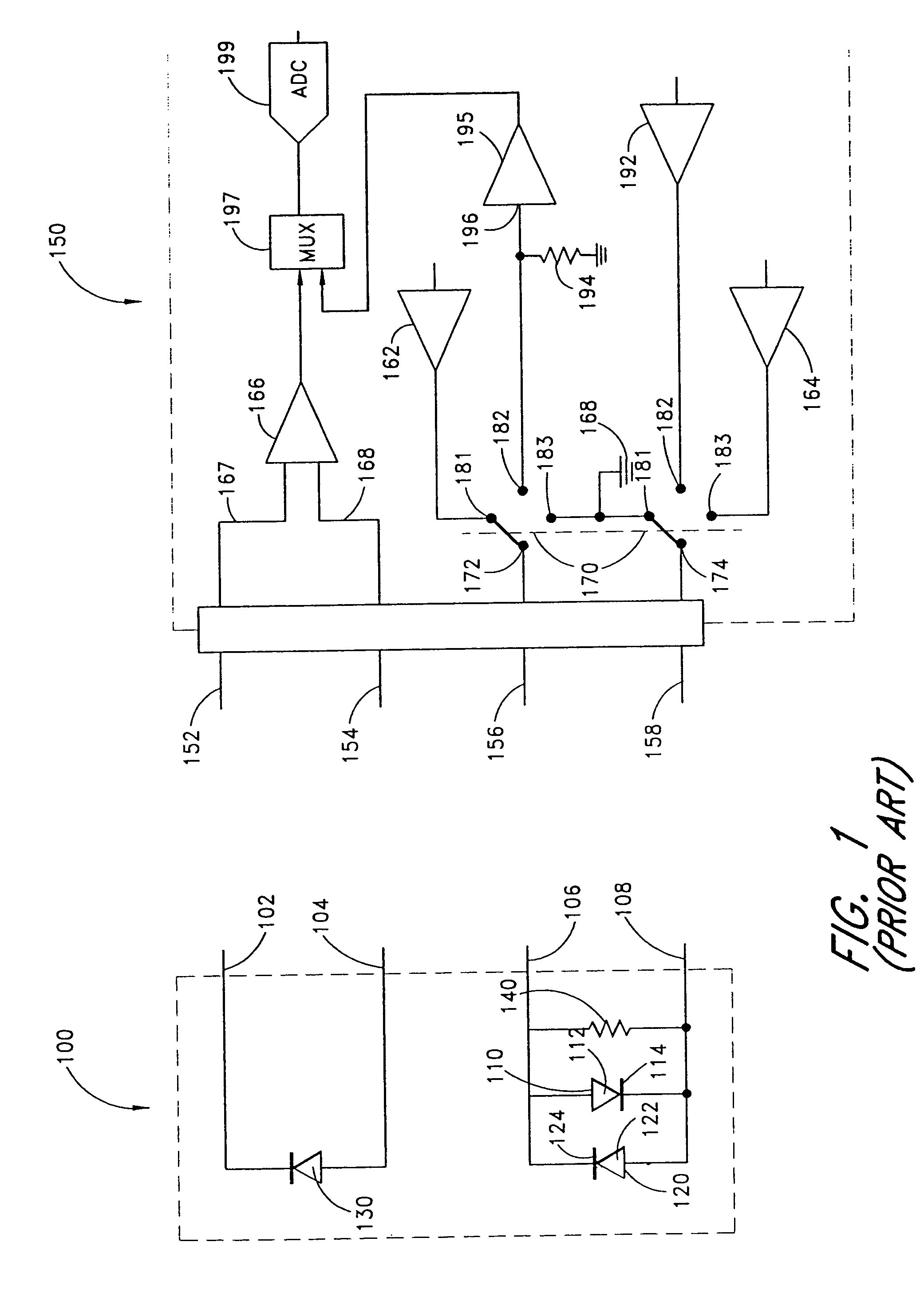
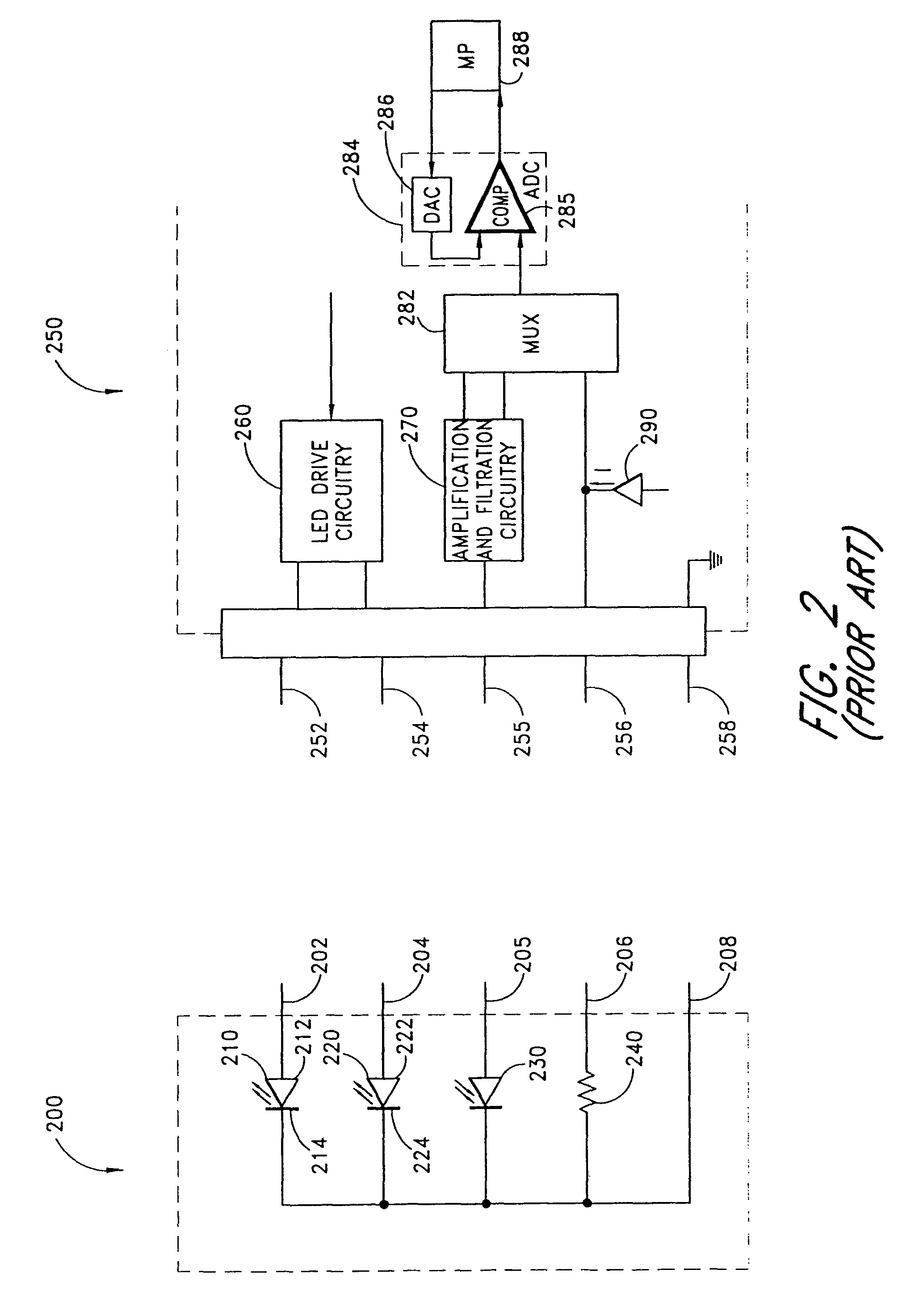
Pulse oximetry sensor adaptor
InactiveUS6993371B2Avoid complex processCost of very criticalDiagnostic recording/measuringSensorsAudio power amplifierPulse oximetry
An adapter allows the interconnection of a sensor originating from one manufacturer to be coupled with conventionally incompatible monitors originating from other manufacturers to form a properly functioning pulse oximetry system. The adapter matches a sensor driver in a monitor to the current requirements and light source configuration of a sensor. The adapter also matches a sensor's light detector signal level to the dynamic range requirements of a monitor preamplifier. Further, the adapter provides compatible sensor calibration, sensor type and security information to a monitor. The adapter may have a self-contained power source or it may derive power from the monitor, allowing both passive and active adapter components. The adapter is particular suited as an adapter cable, replacing a conventional patient cable or sensor cable as the interconnection between a sensor to a monitor in a pulse oximetry system.
Owner:JPMORGAN CHASE BANK NA
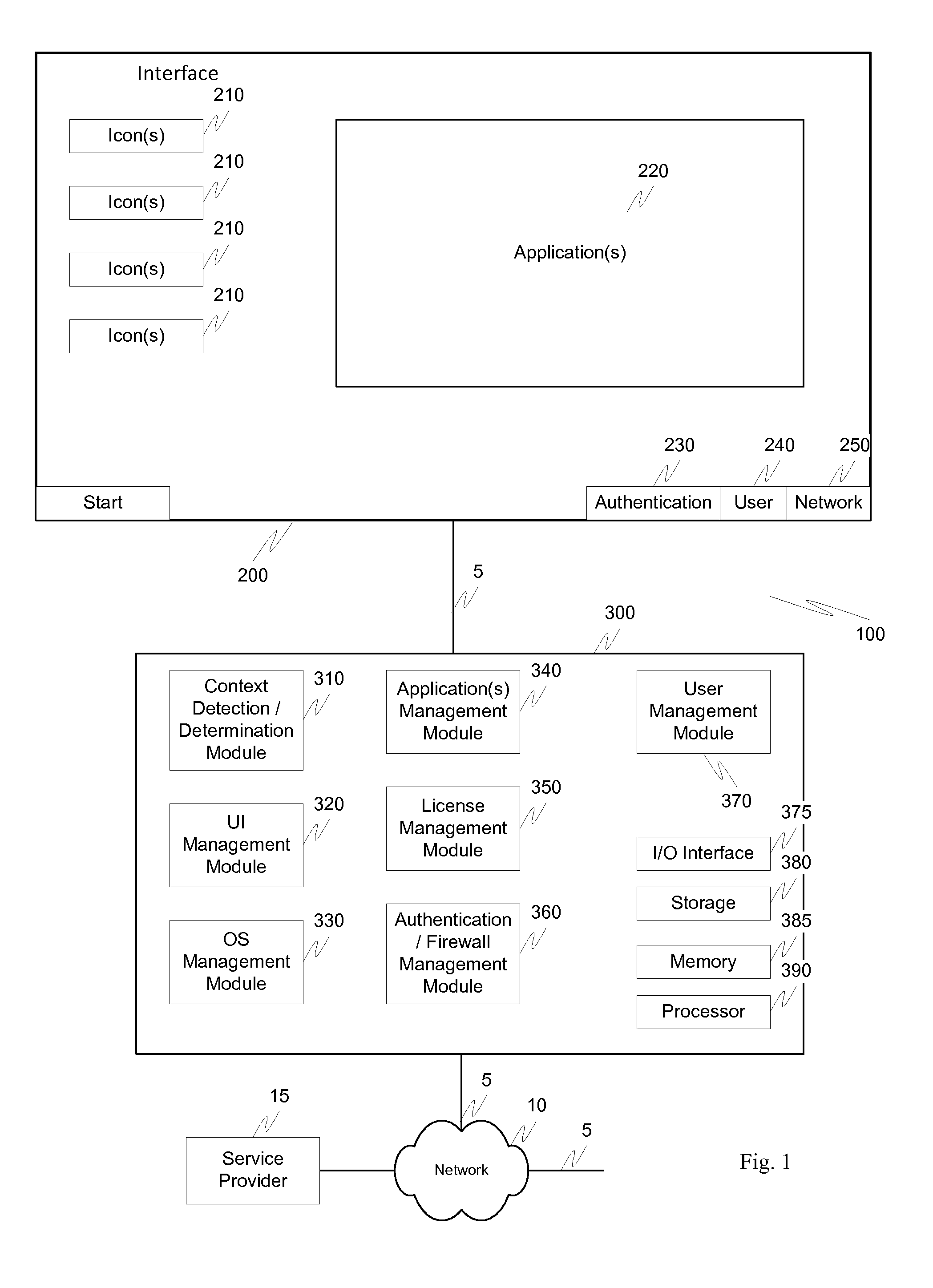
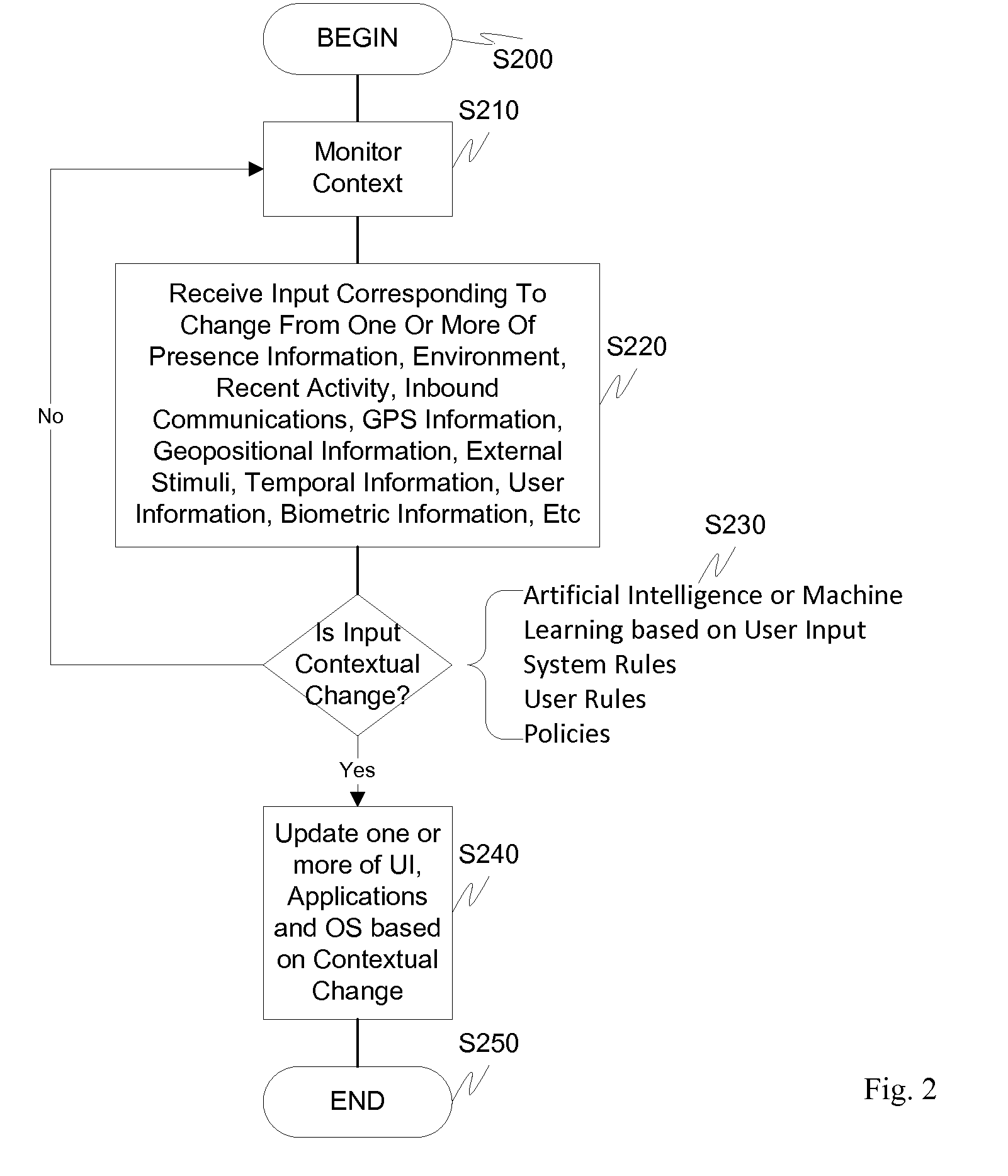
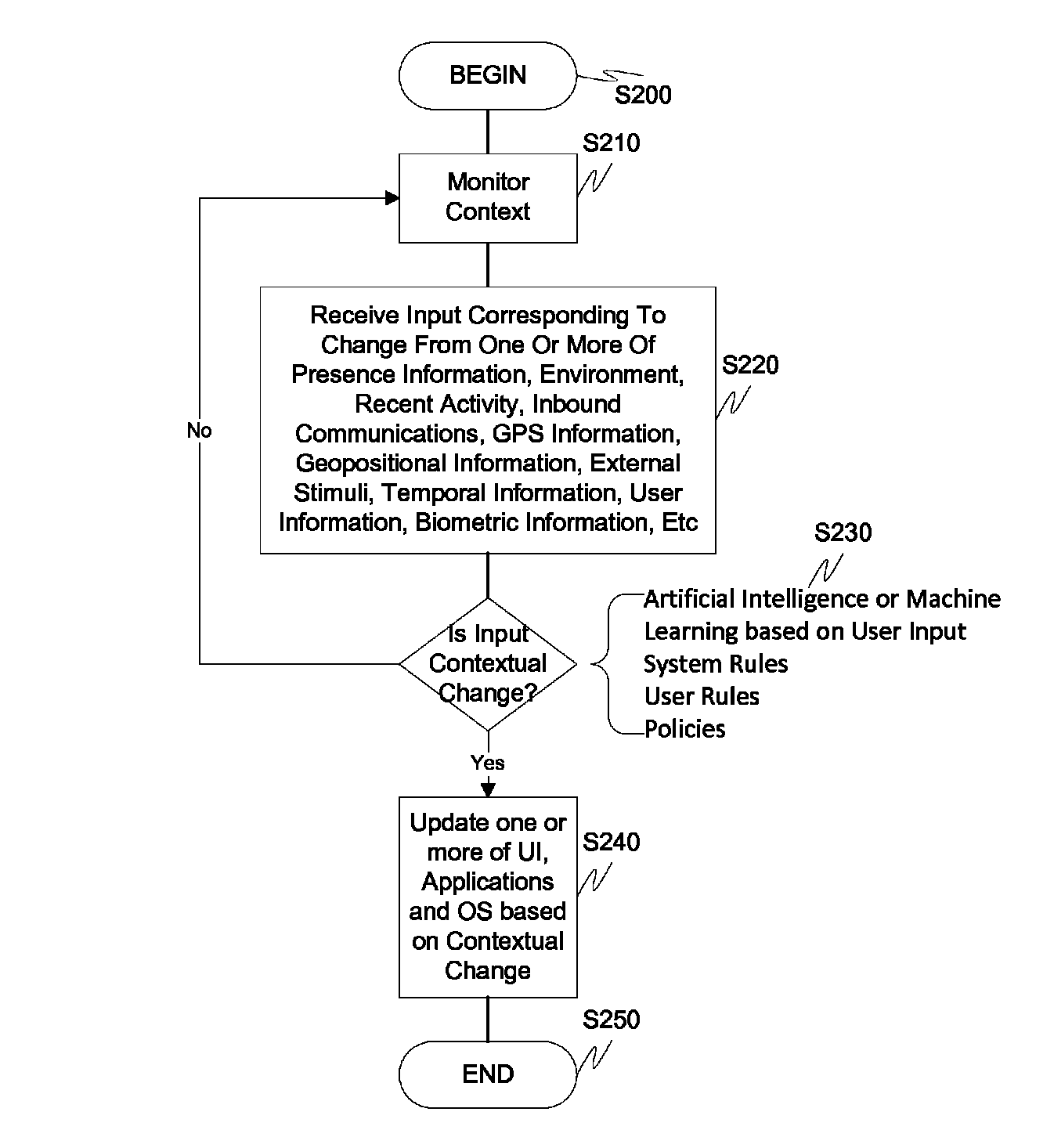
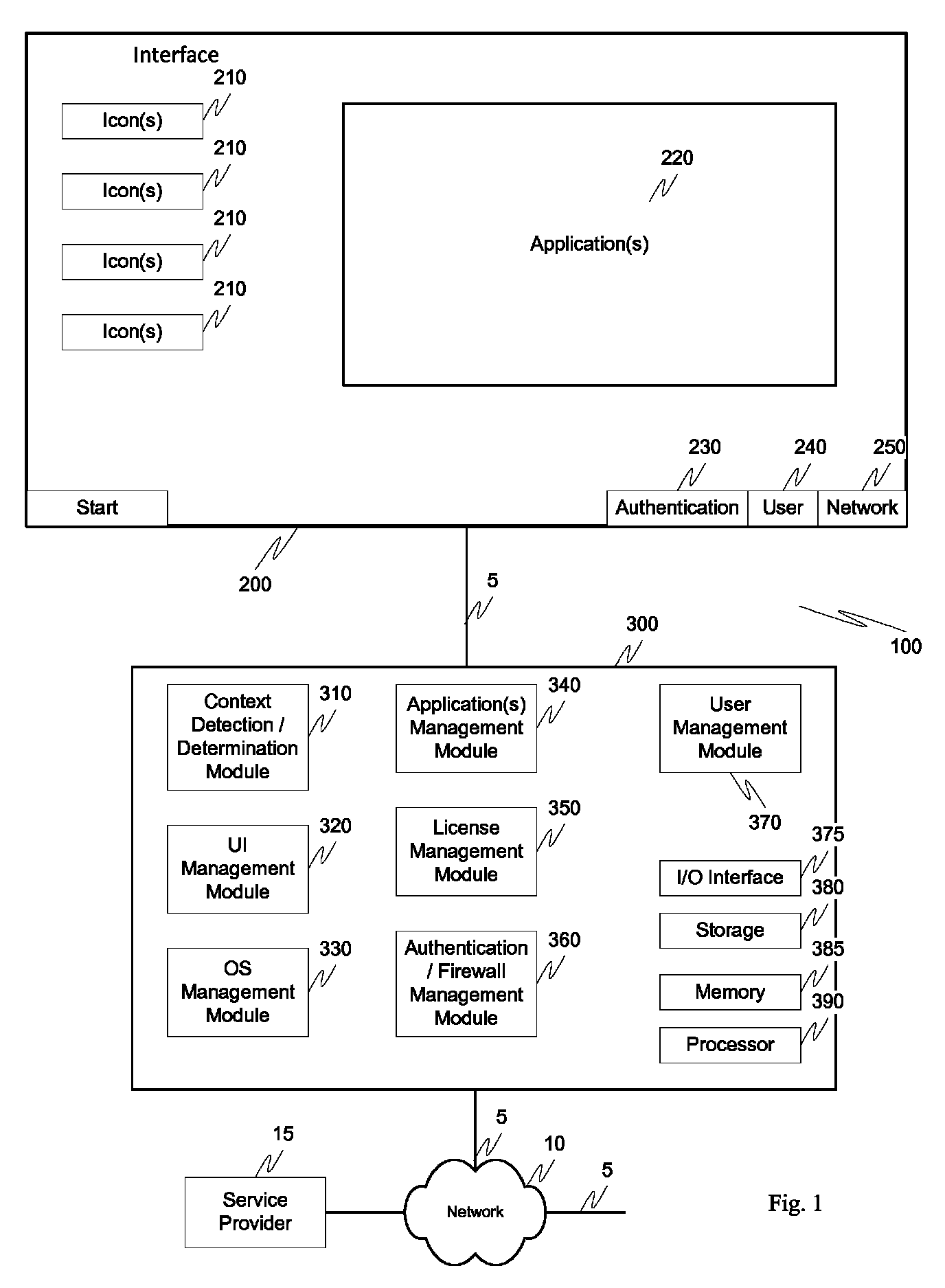
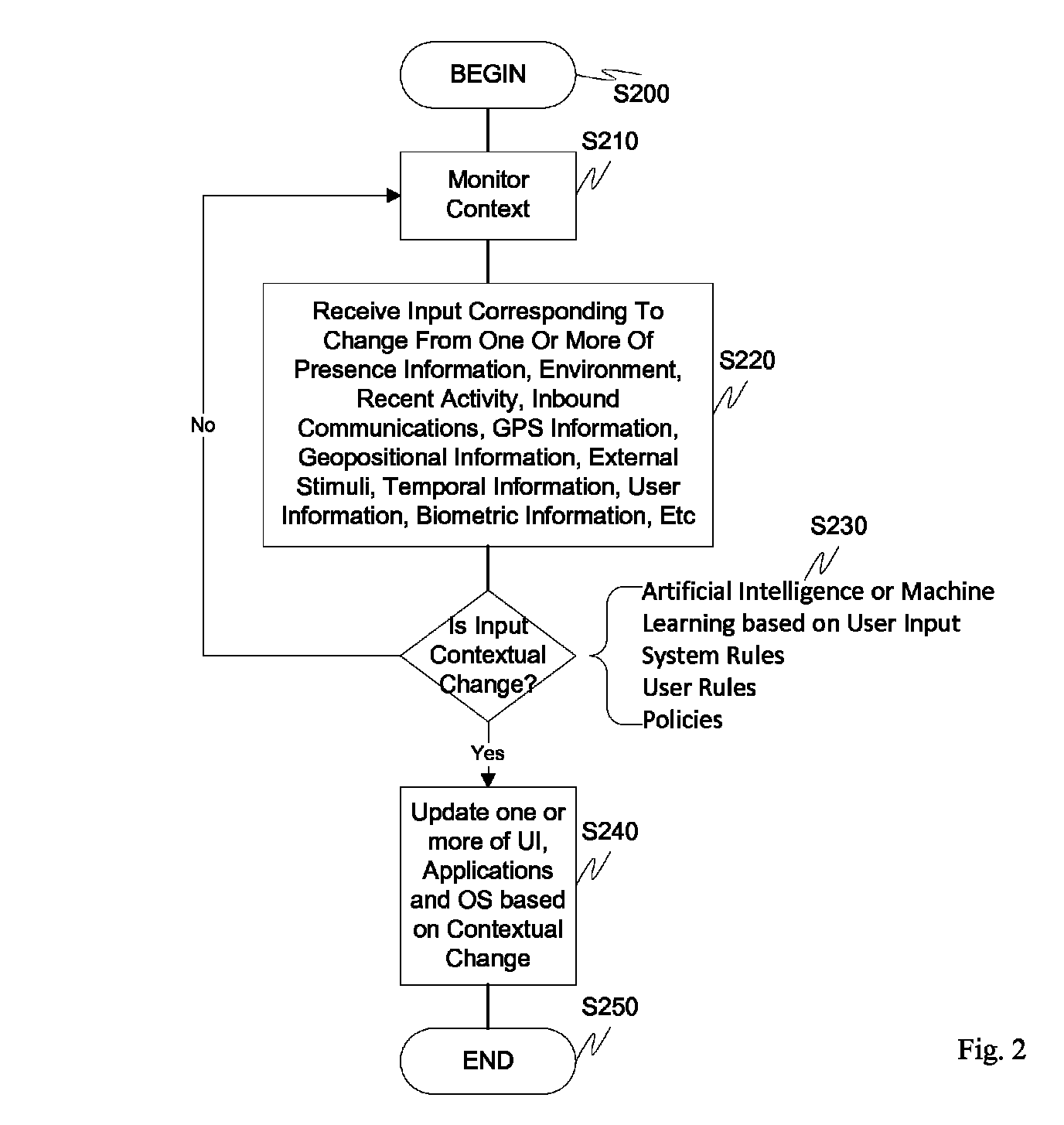
Screen icon manipulation by context and frequency of use
ActiveUS20110072492A1More user confidenceDigital data processing detailsMultiple digital computer combinationsTemporal informationOutbound communication
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
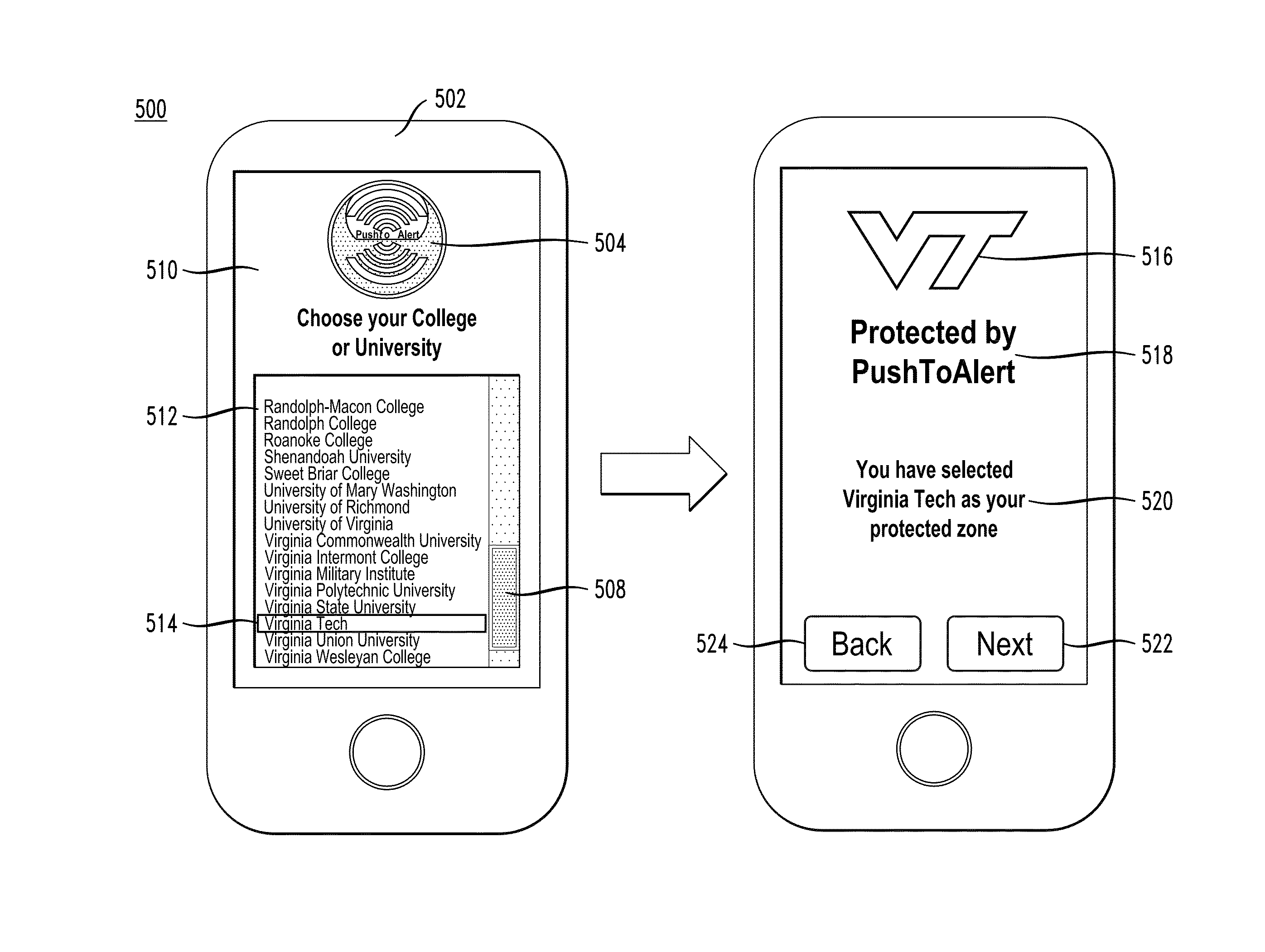
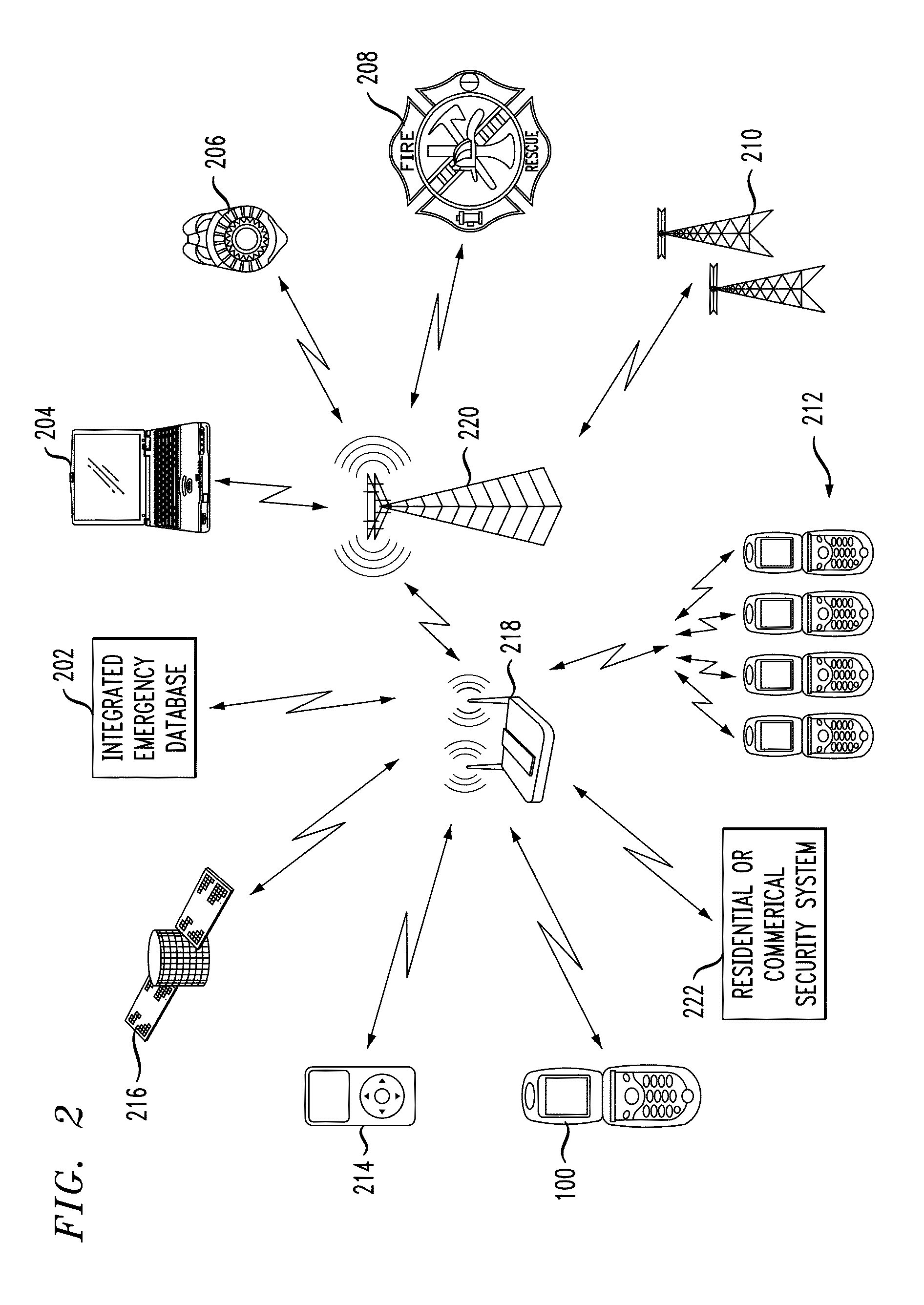
Personal safety mobile notification system
ActiveUS20130183924A1Well formedBiocideHydroxy compound active ingredientsGlobal Positioning SystemMobile device
In described embodiments, a system establishes a perimeter around an area, and mobile devices within the established perimeter communicate with a server that provides and collects personal and asset safety information. The provided information might enable users associated with the mobile devices to plan actions or take routes based on a given criteria, such as a safest route, through display on the mobile device. The collected information from the mobile device might be location, emergency event, environmental factors, sensor information and the like, which might then be communicated to users and / or administrators of the system. Location information, such as through global positioning system (GPS), might provide tracking of mobile devices and users or assets associated with each mobile device. GPS functionality associates latitude, longitude and elevation (X-Y-Z coordinate axis) data with the collected and provided information.
Owner:LIQUID RARITY EXCHANGE LLC
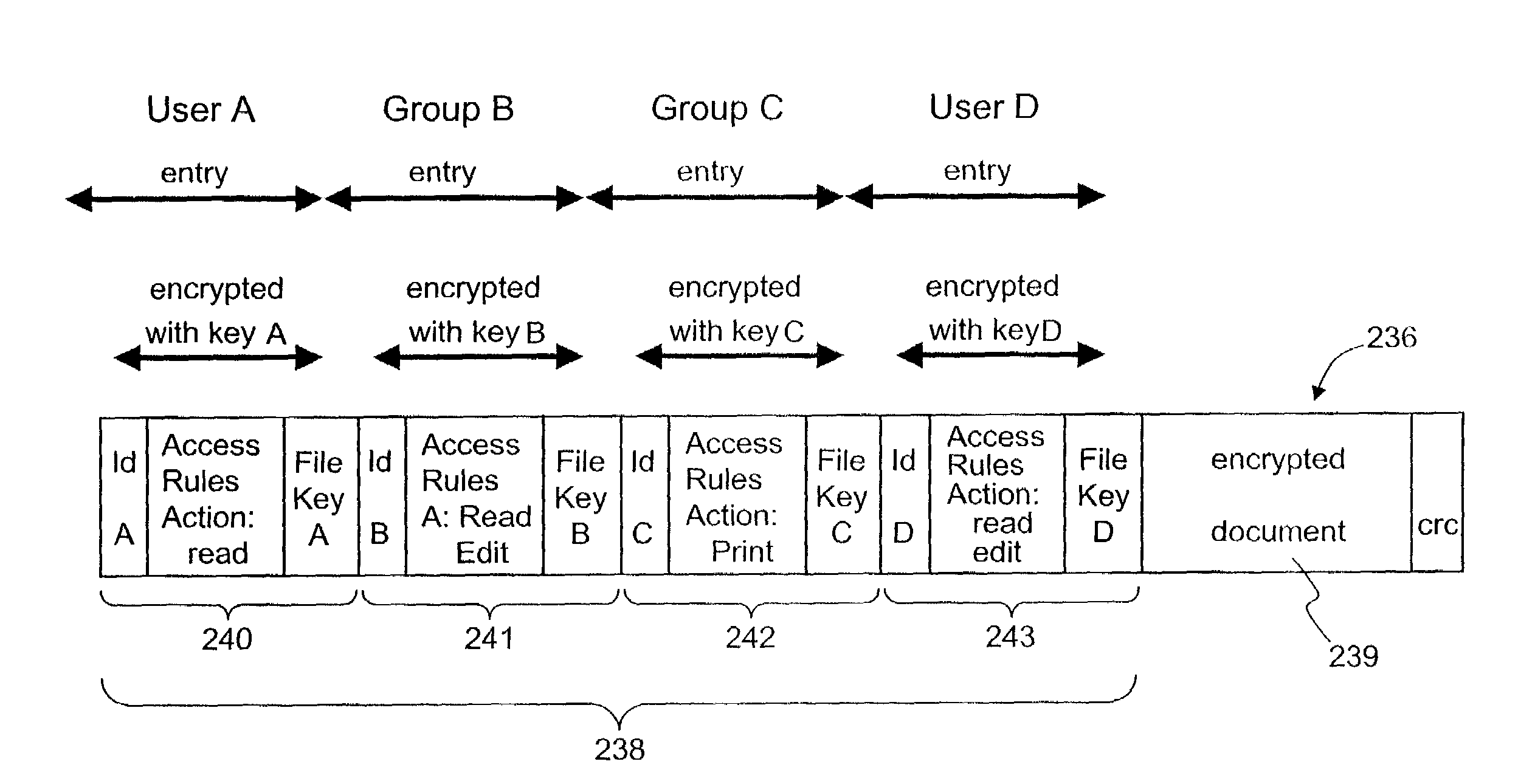
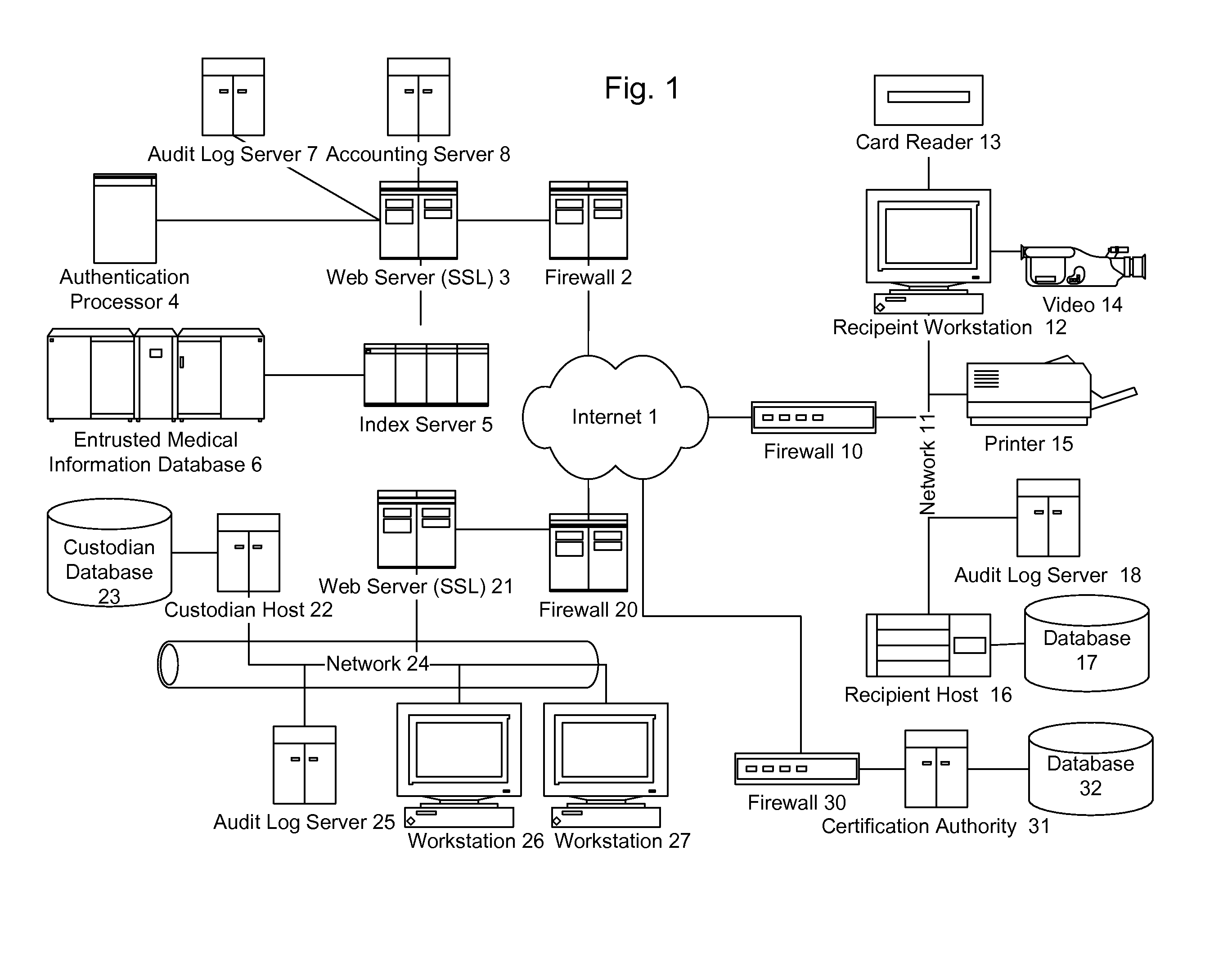
Secured data format for access control
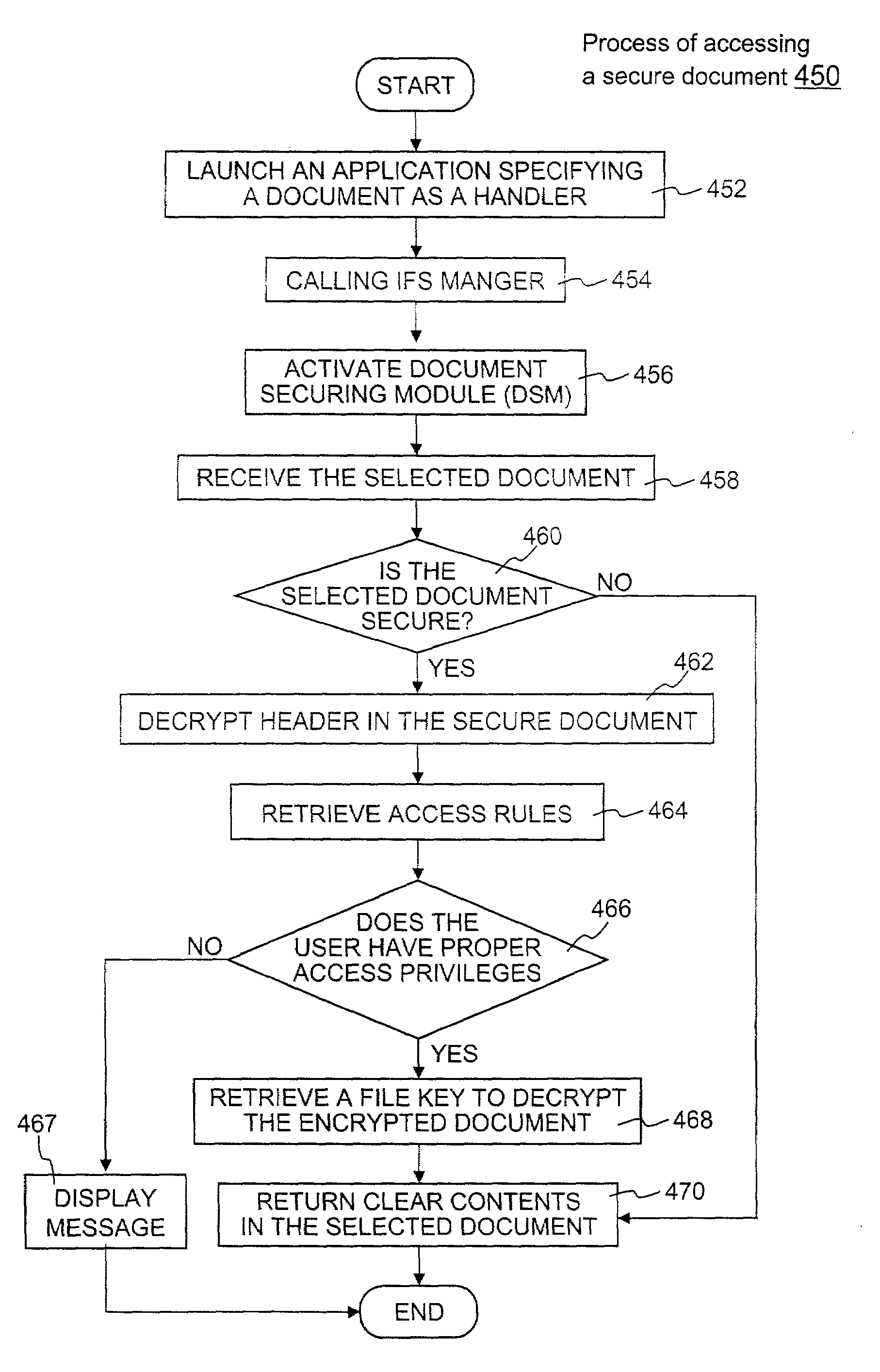
ActiveUS7380120B1Facilitate access control managementGood synchronizationDigital data processing detailsUser identity/authority verificationMedia access controlDocumentation
In a system for providing access control management to electronic data, techniques to secure the electronic data and keep the electronic data secured at all times are disclosed. According to one embodiment, a secured file or secured document includes two parts: an attachment, referred to as a header, and an encrypted document or data portion. The header includes security information that points to or includes the access rules and a file key. The access rules facilitate restrictive access to the secured document and essentially determine who / when / how / where the secured document can be accessed. The file key is used to encrypt / decrypt the encrypted data portion. Only those who have the proper access privileges are permitted to retrieve the file key to encrypt / decrypt the encrypted data portion.
Owner:INTELLECTUAL VENTURES I LLC
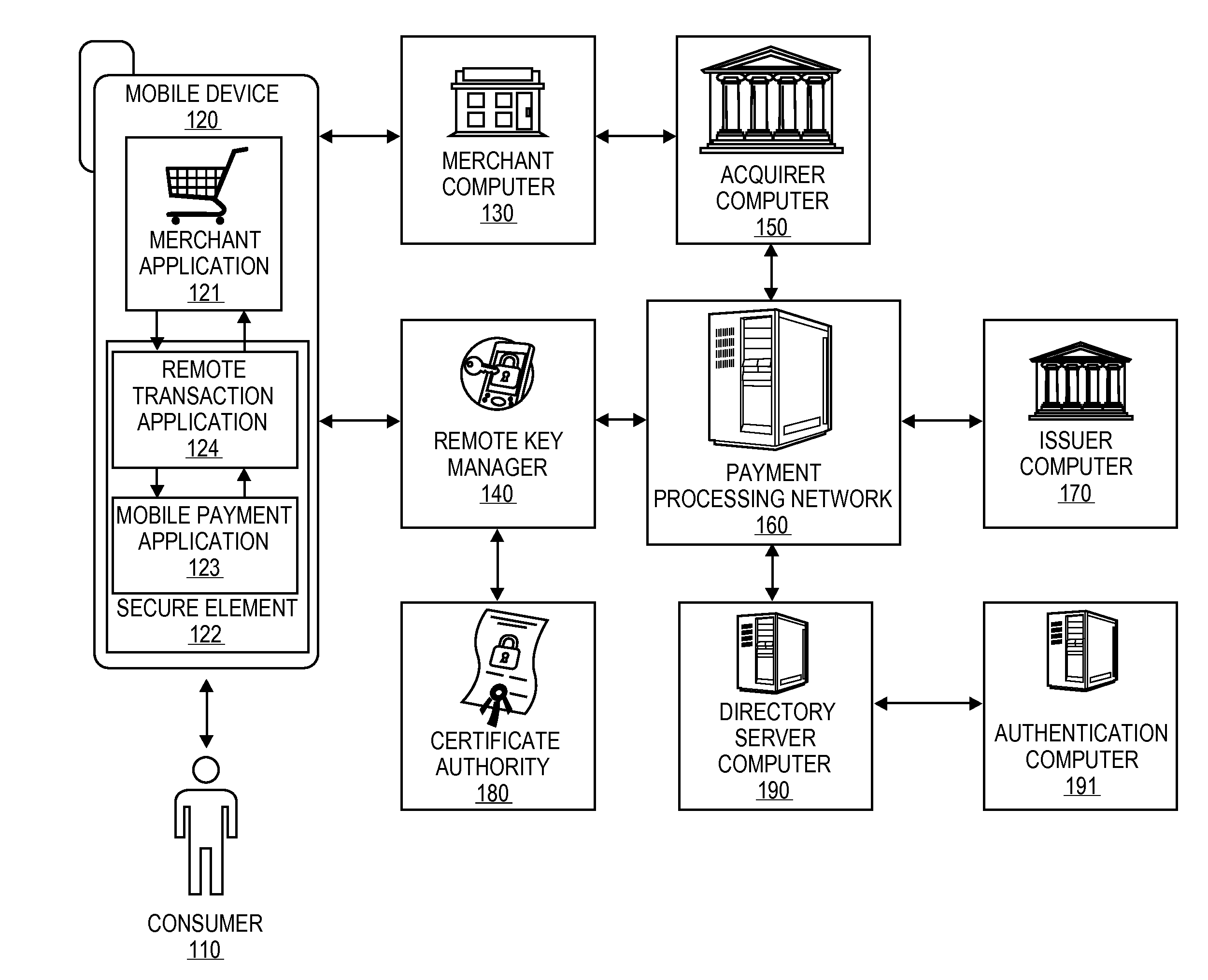
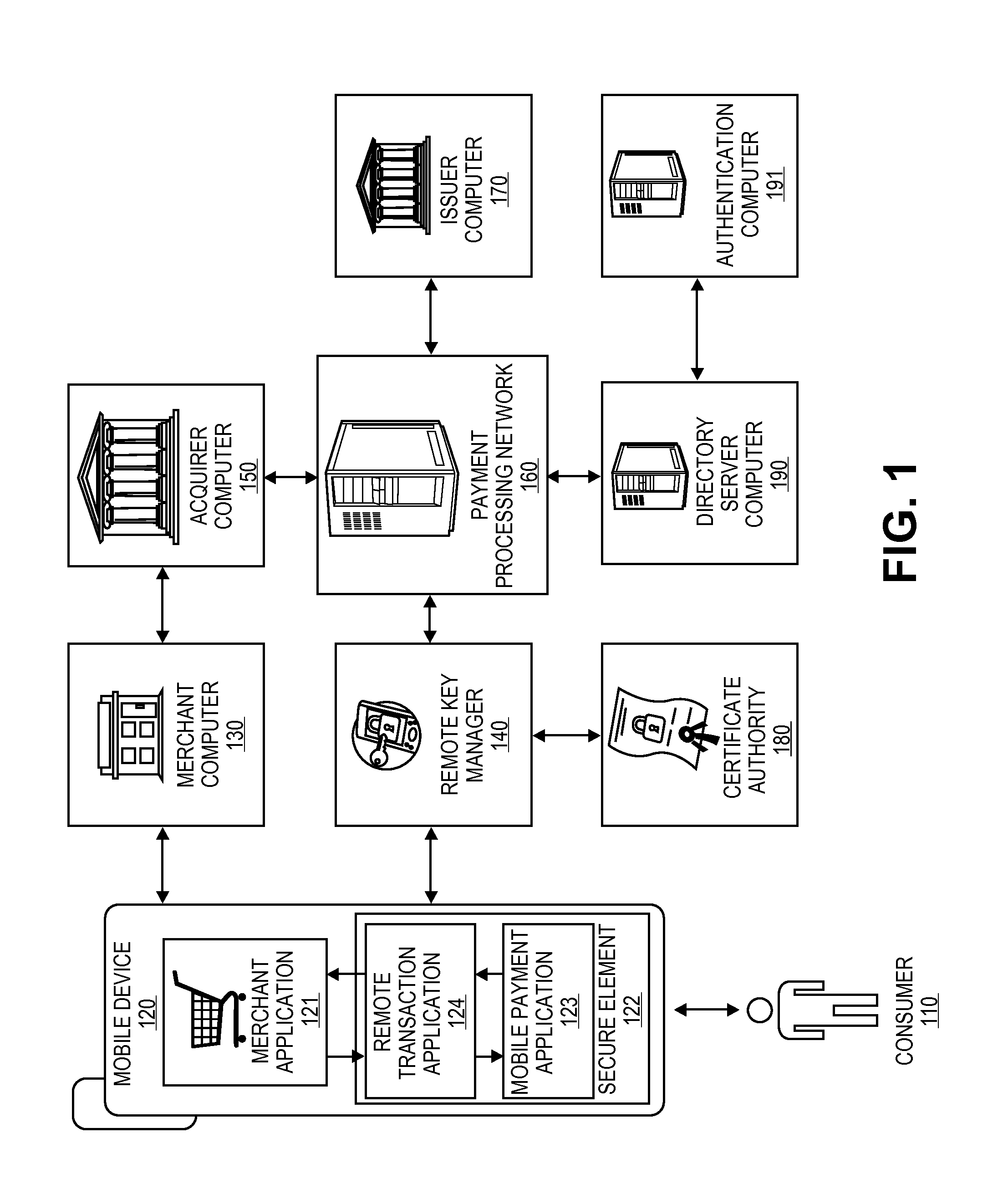
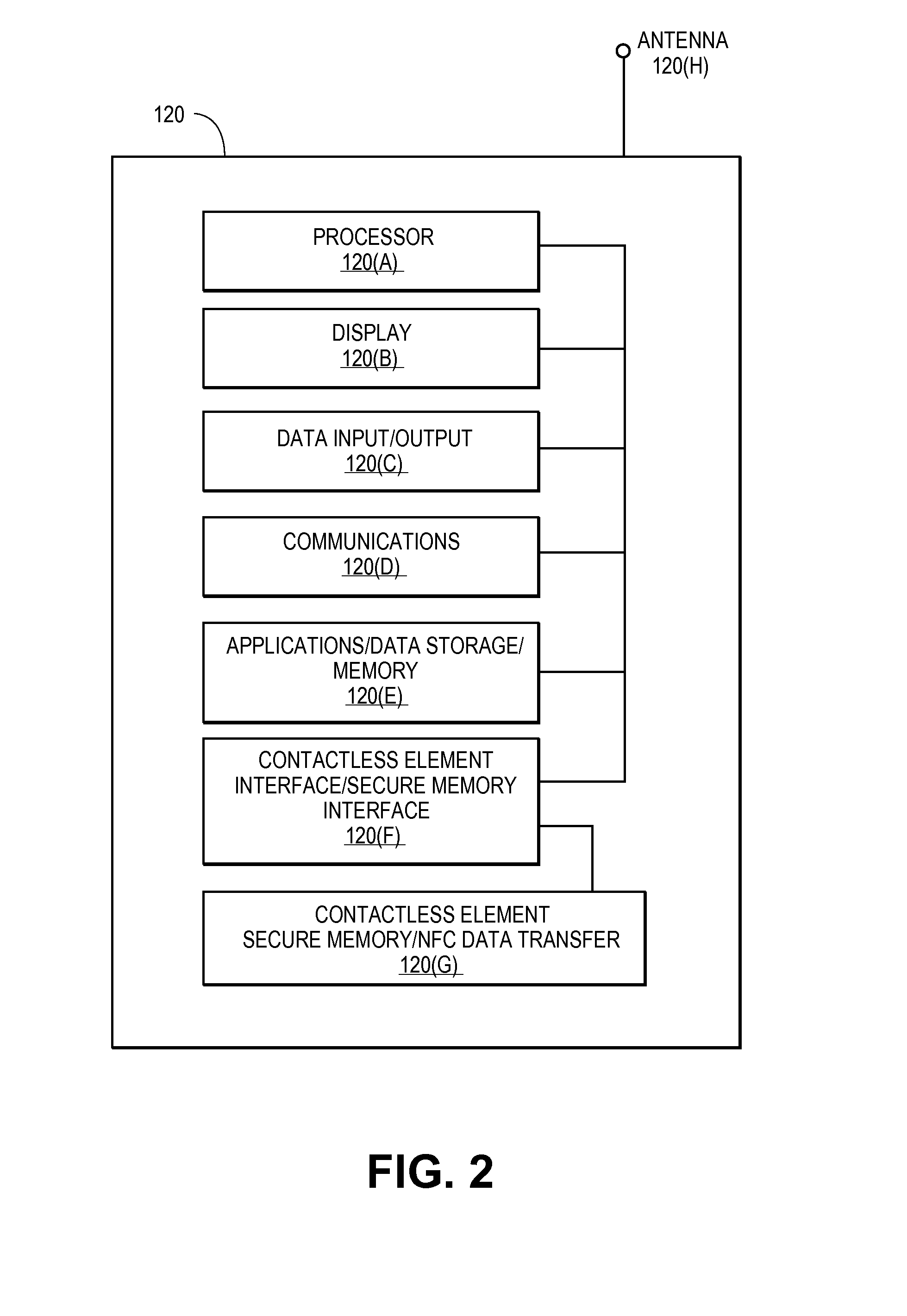
Secure Remote Payment Transaction Processing Including Consumer Authentication
ActiveUS20150088756A1Improve security levelProtocol authorisationPayment transactionEncryption decryption
Embodiments of the invention are directed to methods, apparatuses, computer-readable media, and systems for securely processing remote transactions. One embodiment is directed to a method of processing a remote transaction initiated by a communication device. The method comprising a server computer receiving a payment request including encrypted payment information that is encrypted using a first key. The encrypted payment information including security information. The method further comprises decrypting the encrypted payment information using a second key, obtaining an authentication response value for the remote transaction from an authentication computer associated with an issuer, updating the decrypted payment information to include the authentication response value, re-encrypting the decrypted payment information using a third key, and sending a payment response including the re-encrypted payment information to a transaction processor. The transaction processor decrypting the re-encrypted payment information using a fourth key and initiating a payment transaction using the decrypted payment information.
Owner:VISA INT SERVICE ASSOC
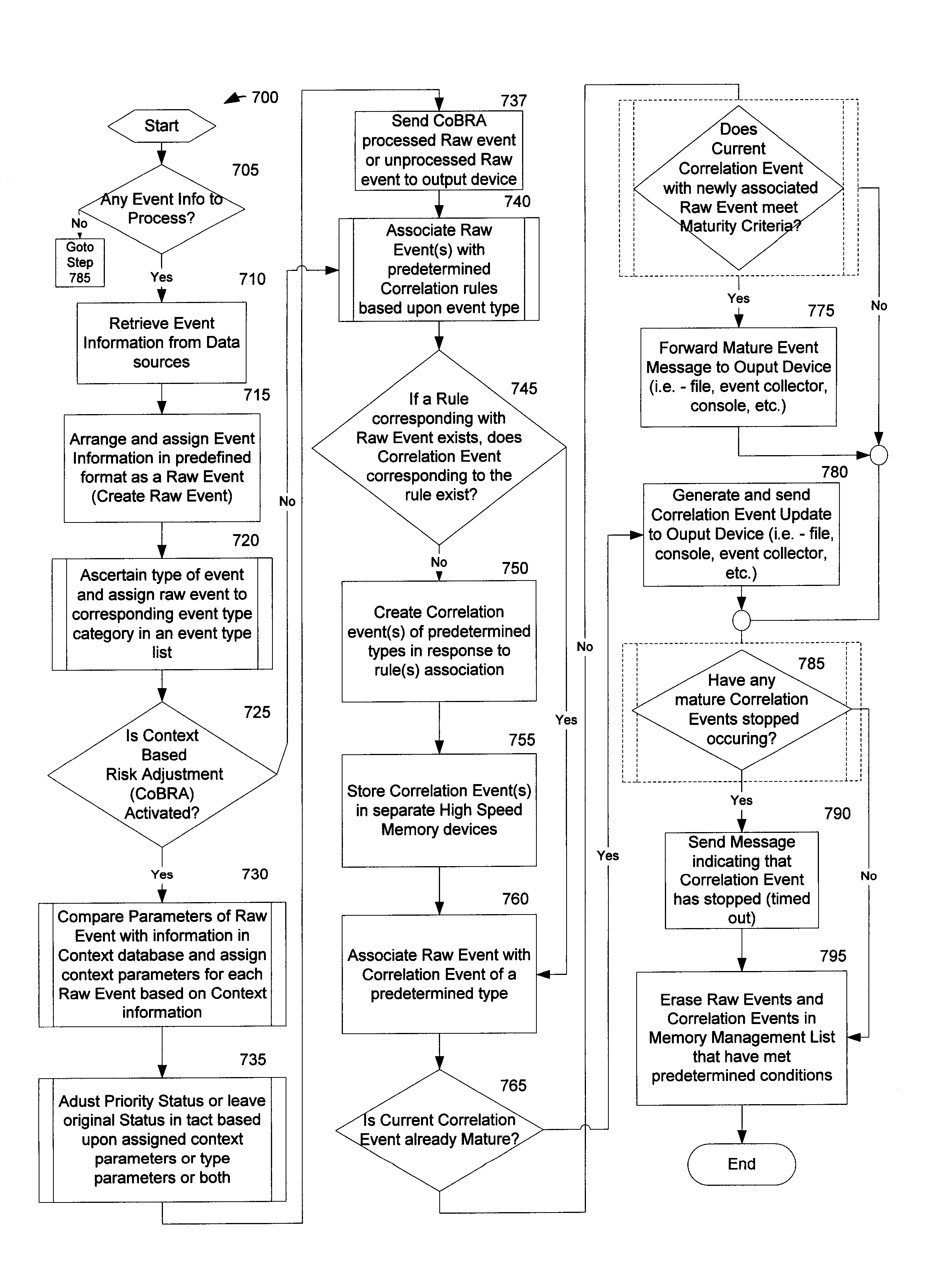
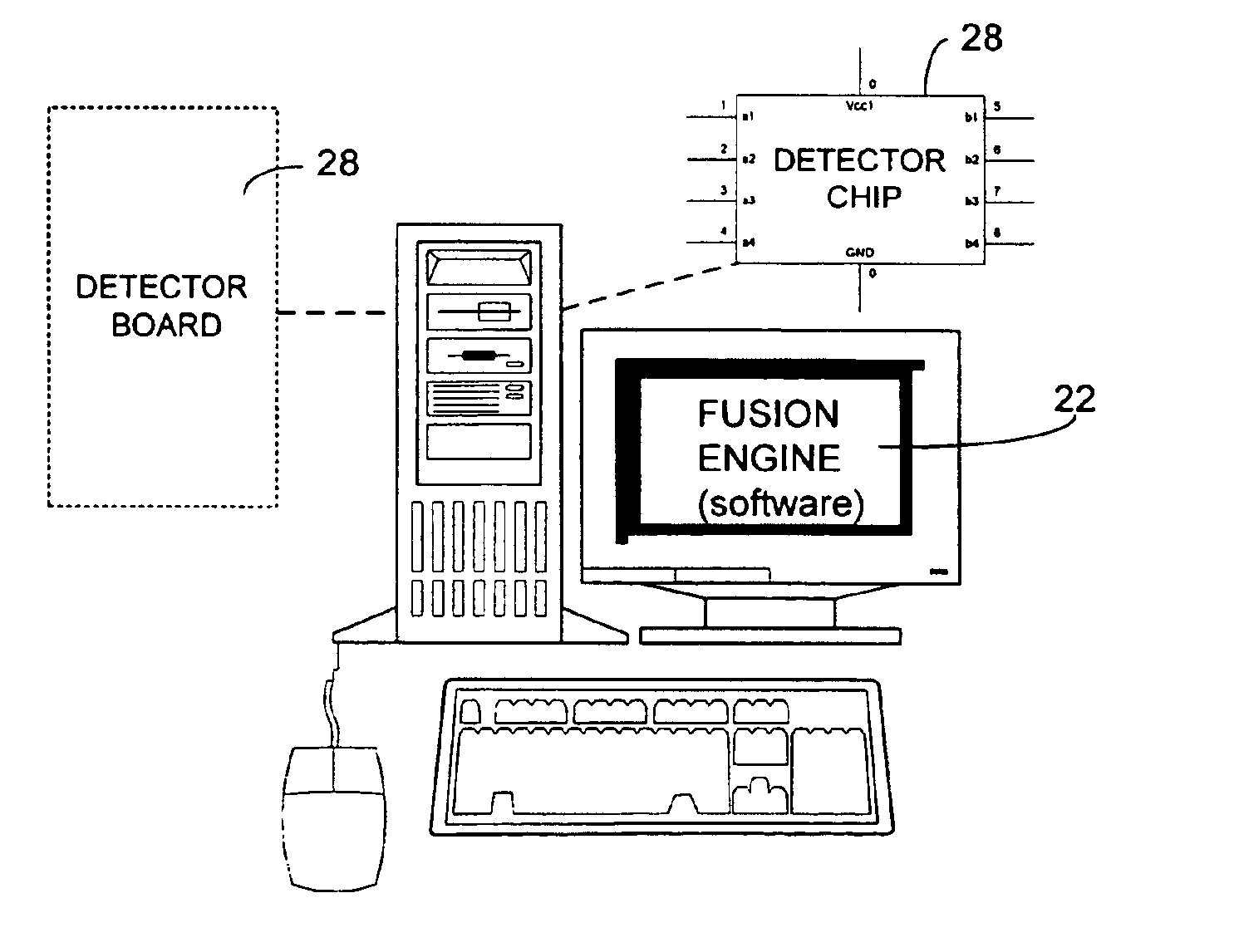
Method and System for Managing Computer Security Information
InactiveUS20020078381A1Efficient managementReduce processing speedMemory loss protectionDigital data processing detailsTraffic capacitySafety management systems
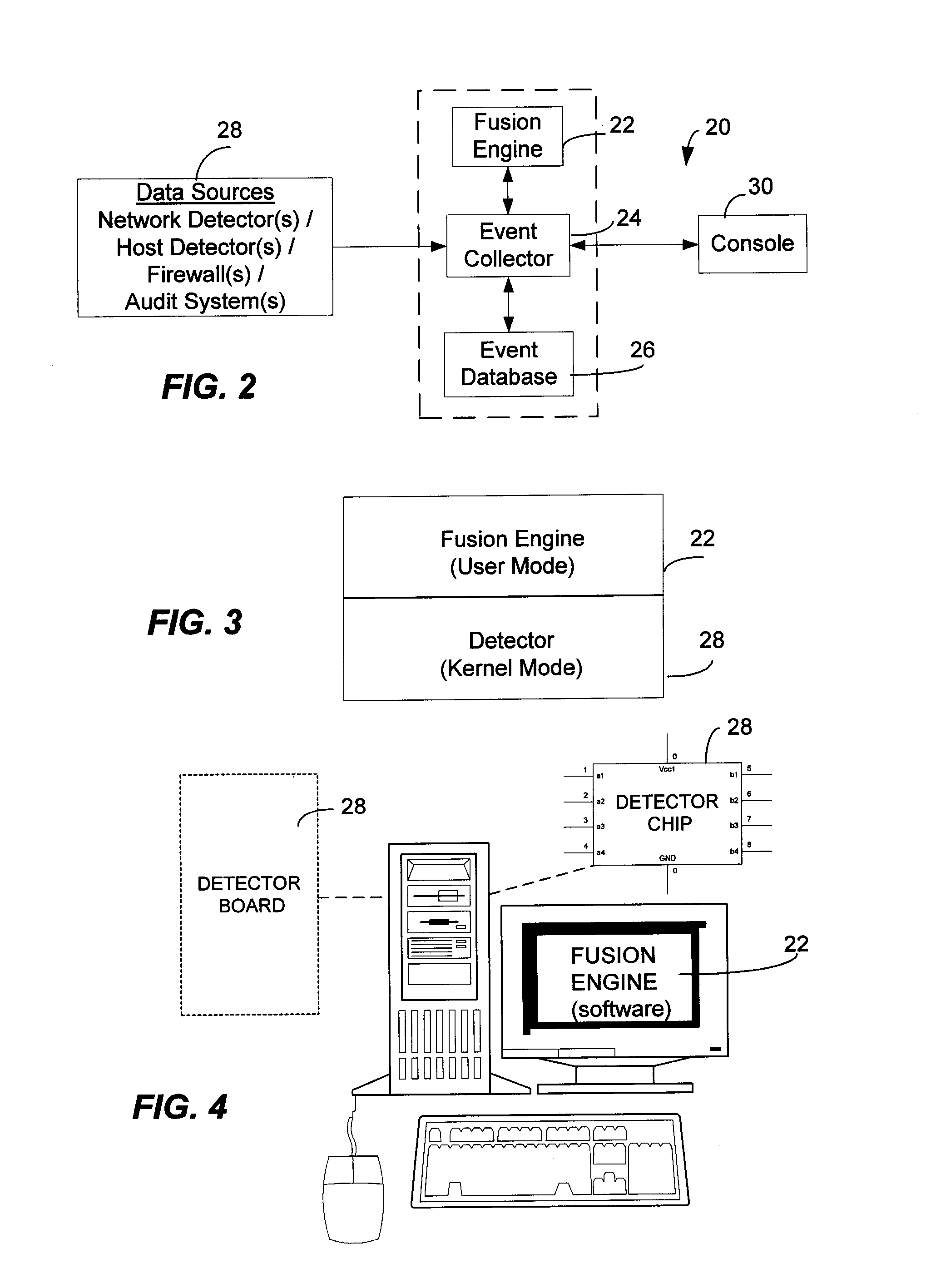
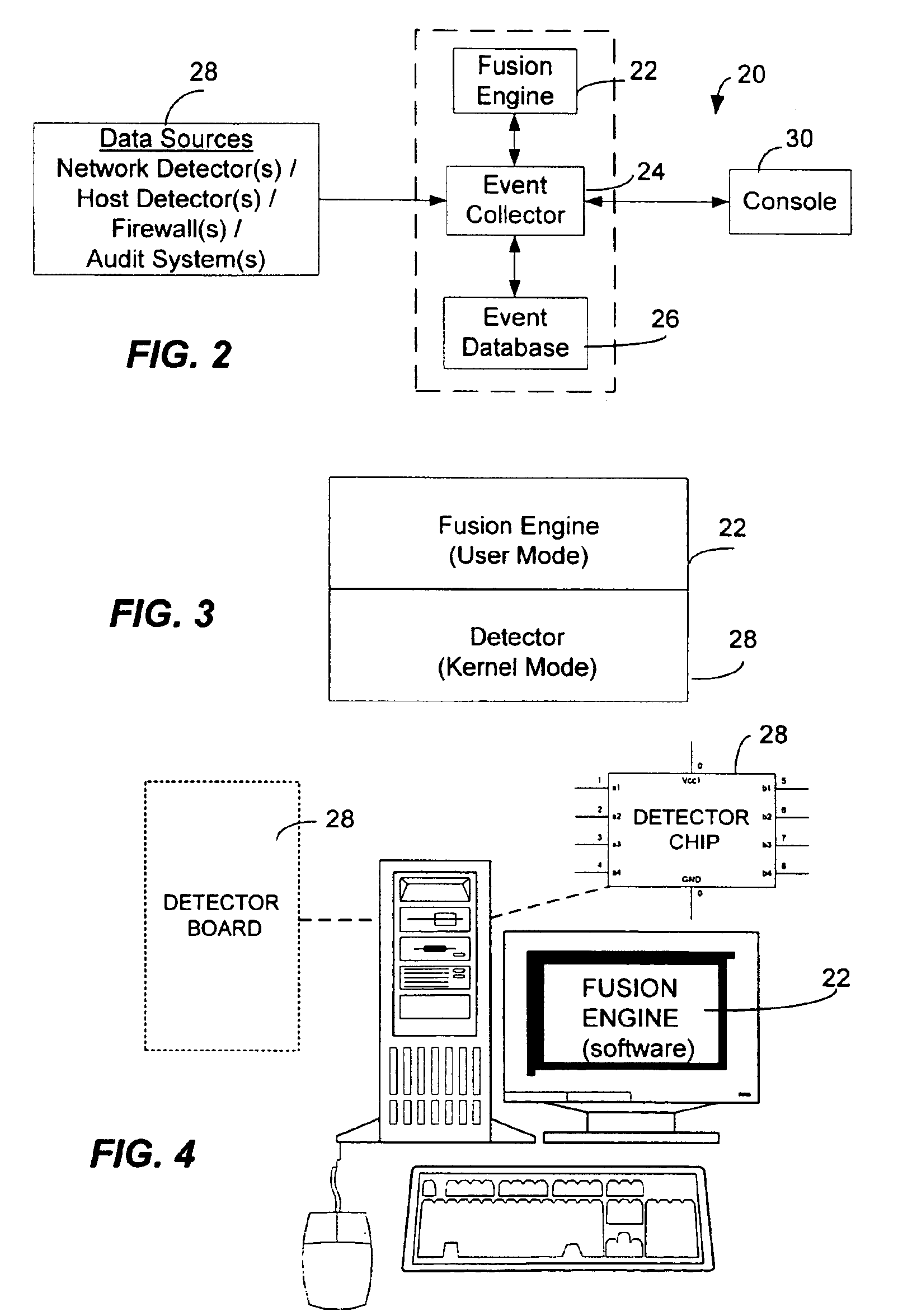
<heading lvl="0">Abstract of Disclosure< / heading> A security management system includes a fusion engine which "fuses" or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:IBM CORP
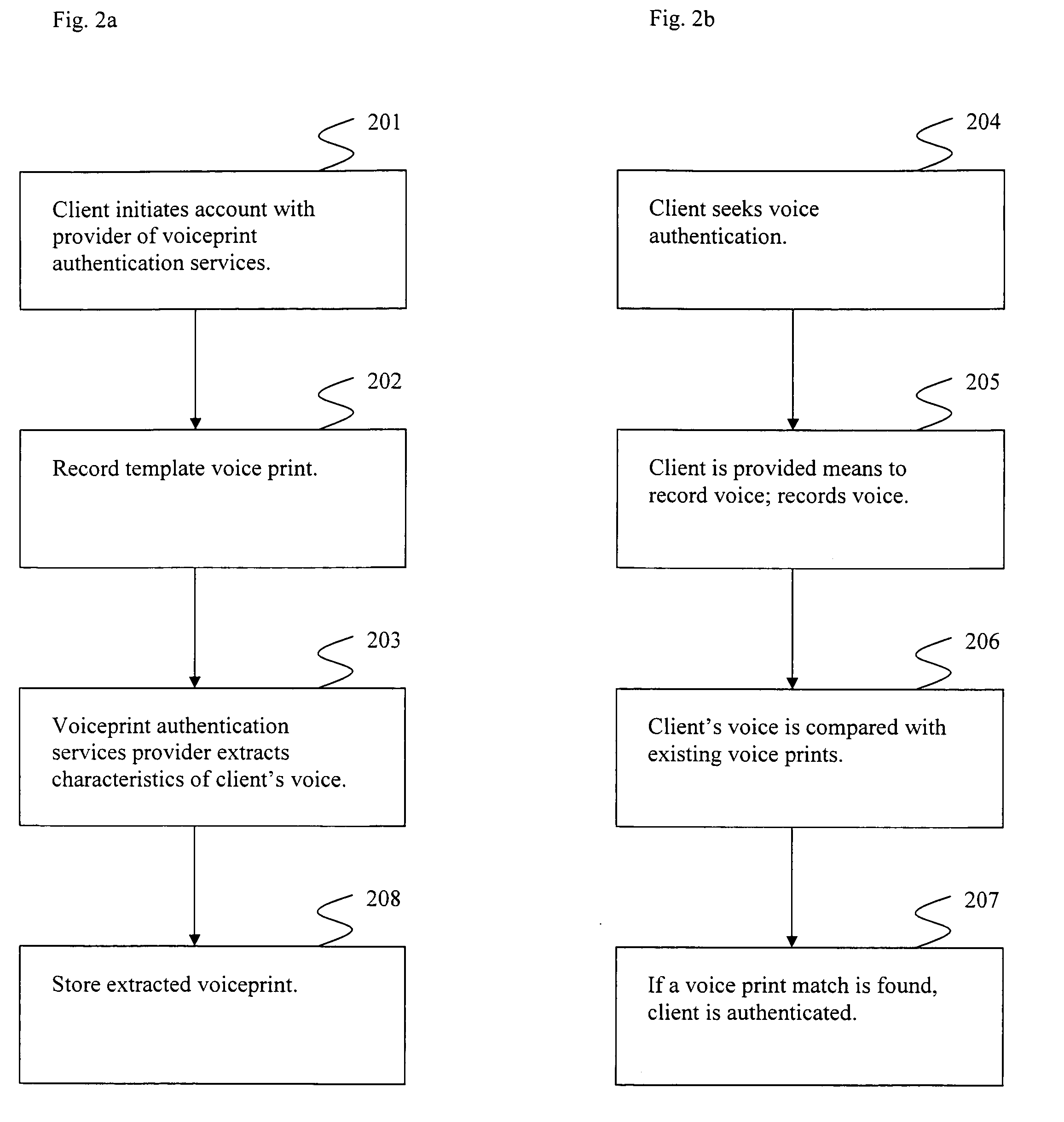
Voice print identification portal
InactiveUS20080256613A1Digital data processing detailsMultiple digital computer combinationsSecure voiceSpeech identification
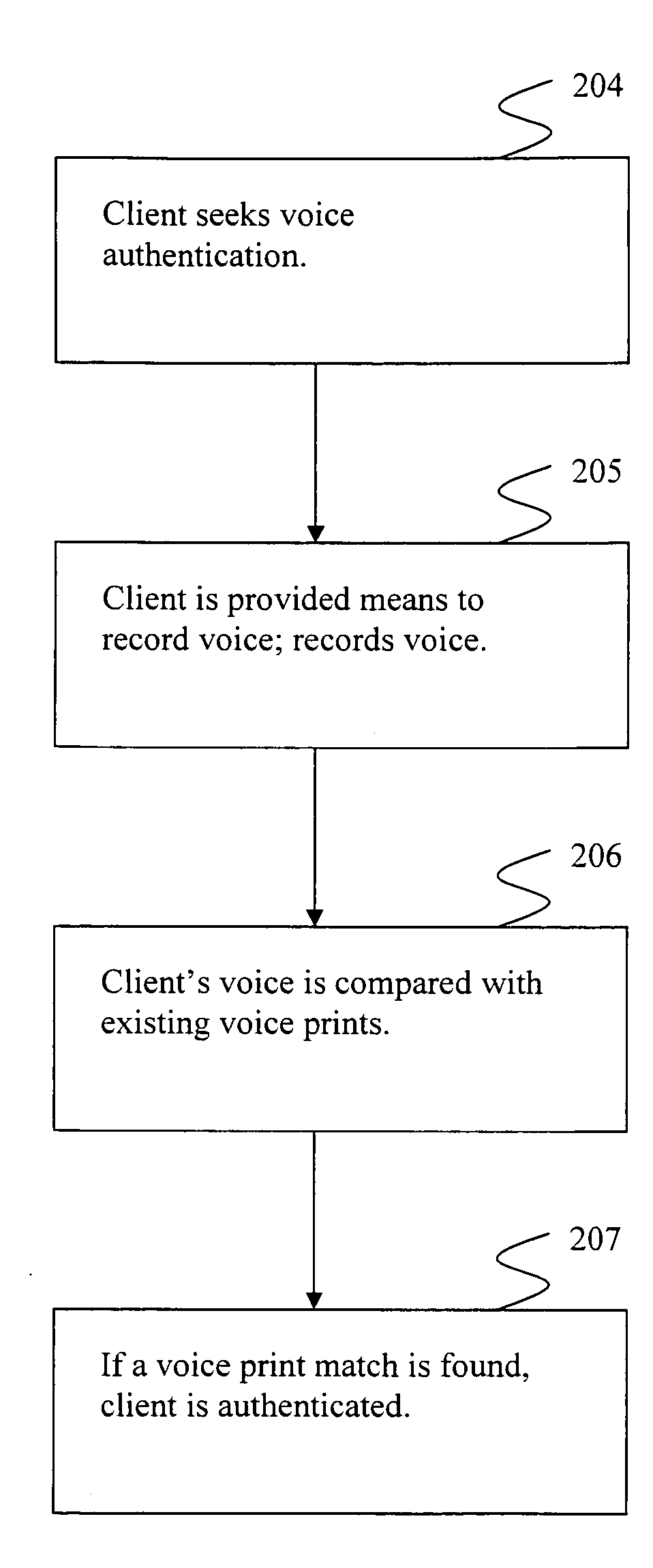
Systems and methods providing for secure voice print authentication over a network are disclosed herein. During an enrollment stage, a client's voice is recorded and characteristics of the recording are used to create and store a voice print. When an enrolled client seeks access to secure information over a network, a sample voice recording is created. The sample voice recording is compared to at least one voice print. If a match is found, the client is authenticated and granted access to secure information.Systems and methods providing for a dual use voice analysis system are disclosed herein. Speech recognition is achieved by comparing characteristics of words spoken by a speaker to one or more templates of human language words. Speaker identification is achieved by comparing characteristics of a speaker's speech to one or more templates, or voice prints. The system is adapted to increase or decrease matching constraints depending on whether speaker identification or speaker recognition is desired.
Owner:VOICEIT TECH
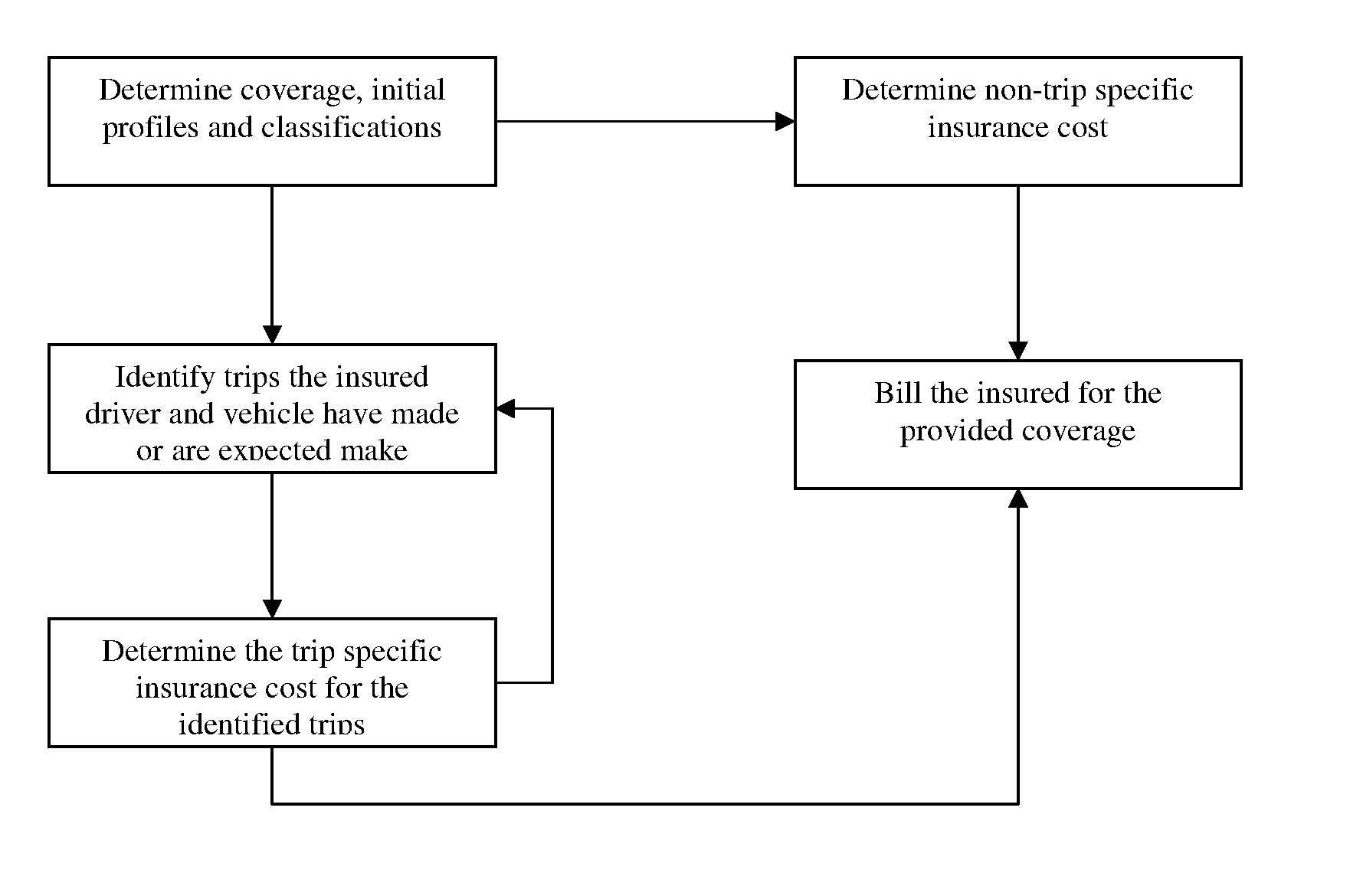
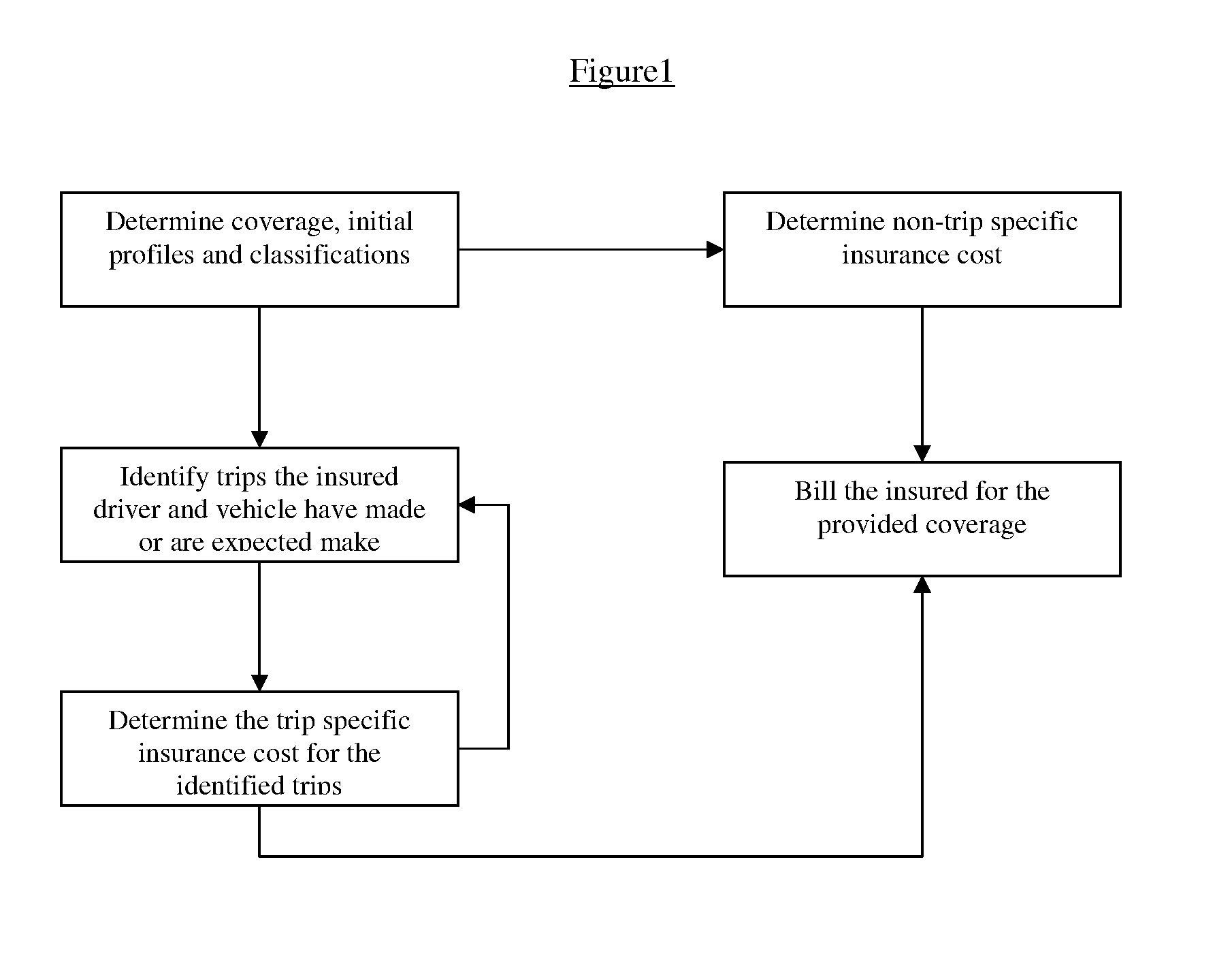
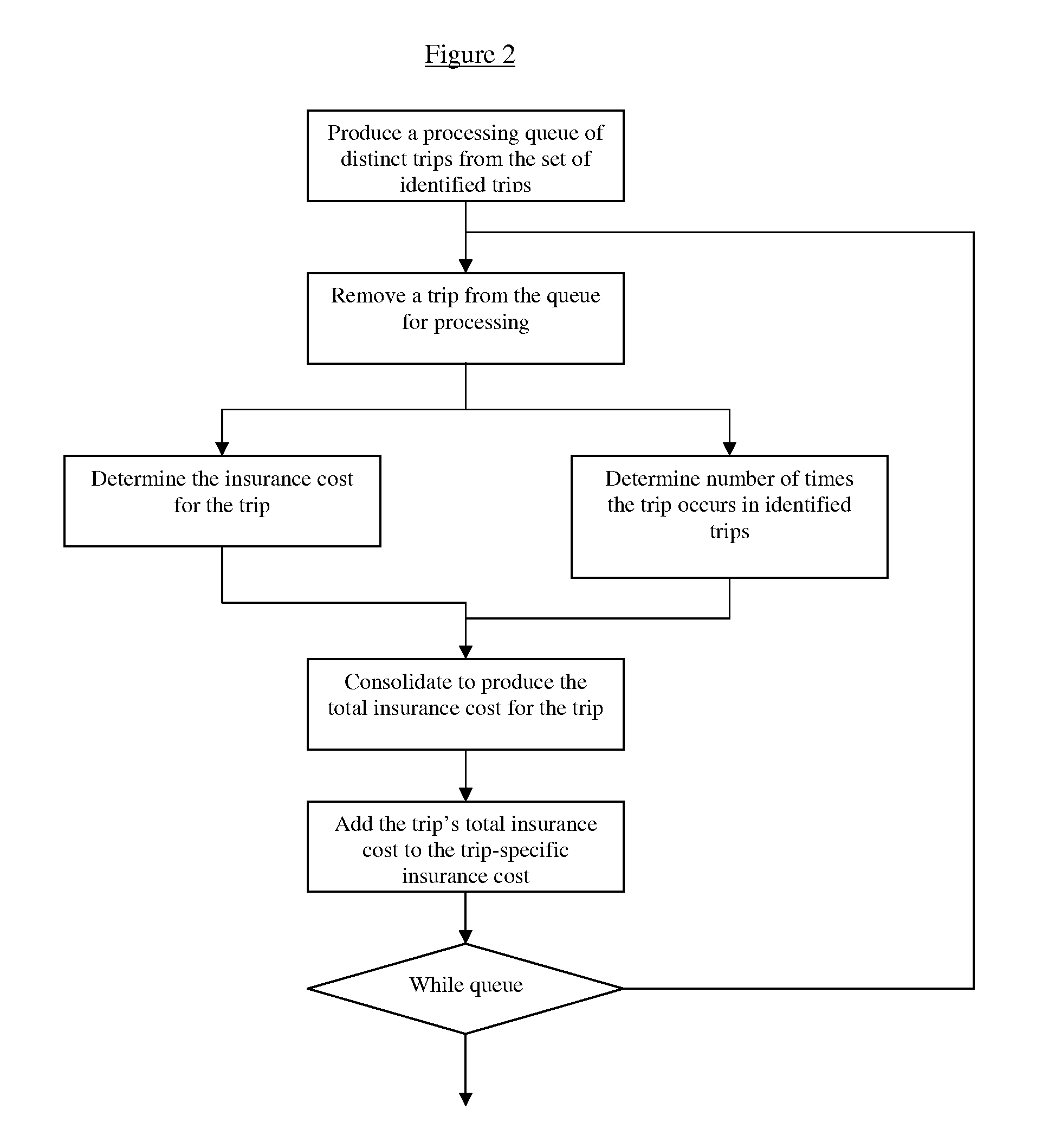
Route based method for determining cost of automobile insurance
A method and system of determining cost of automobile insurance based on safety characteristics of road segments comprising routes expected to be followed on trips insured vehicle and driver have made or are expected to make over the time period the insurance contract is in force. The method comprises steps of identifying the trips, selecting routes expected to be followed on the said trips, determining the probability of each selected route being followed on a trip, evaluating the safety characteristics of roads comprising the routes, consolidating the route safety information with the assigned route probabilities and other risk classifications to produce cost of insurance for the identified trips. The results are further consolidated with the cost of insurance due to risk exposures other than those of the identified trips to produce a final insurance cost.
Owner:SUROVY MARTIN
Screen icon manipulation by context and frequency of Use
ActiveUS8972878B2More user confidenceDigital data authenticationSubstation equipmentTemporal informationOutbound communication
Dynamic device management is provided based on a change in context. The management can be for one or more of icons, application, operating system(s), preferences, display characteristics, and the like. Detection and / or monitoring of one or more of presence information, environmental information, user information, recent activity information, inbound / outbound communication information, external stimuli information, geopositional information, temporal information, calendar information, user information, biometric information, and security information can be used as inputs to determining a change in this context.
Owner:AVAYA INC
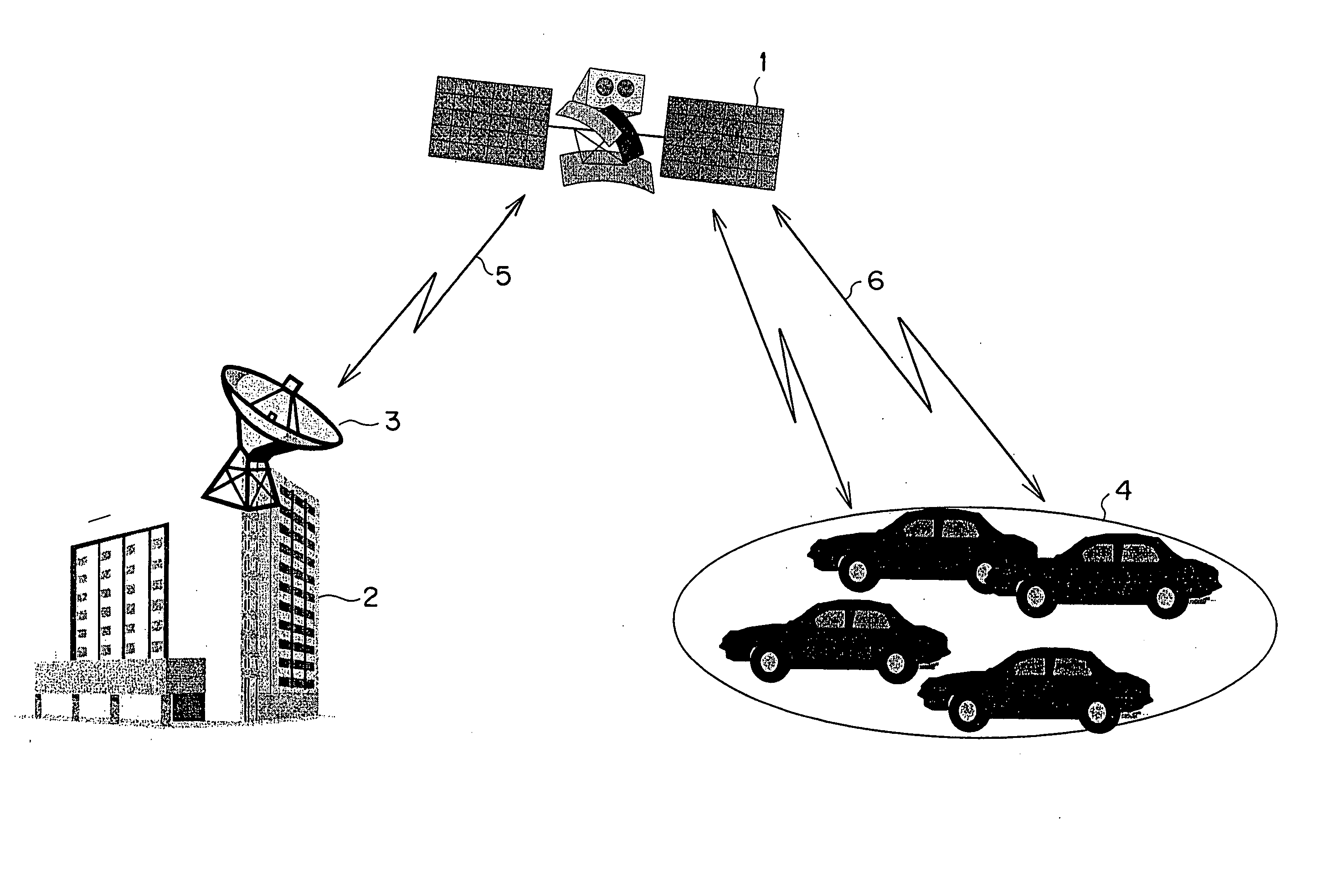
Vehicle managing method
InactiveUS20060136291A1Vehicle testingRegistering/indicating working of vehiclesComputer scienceSecurity information
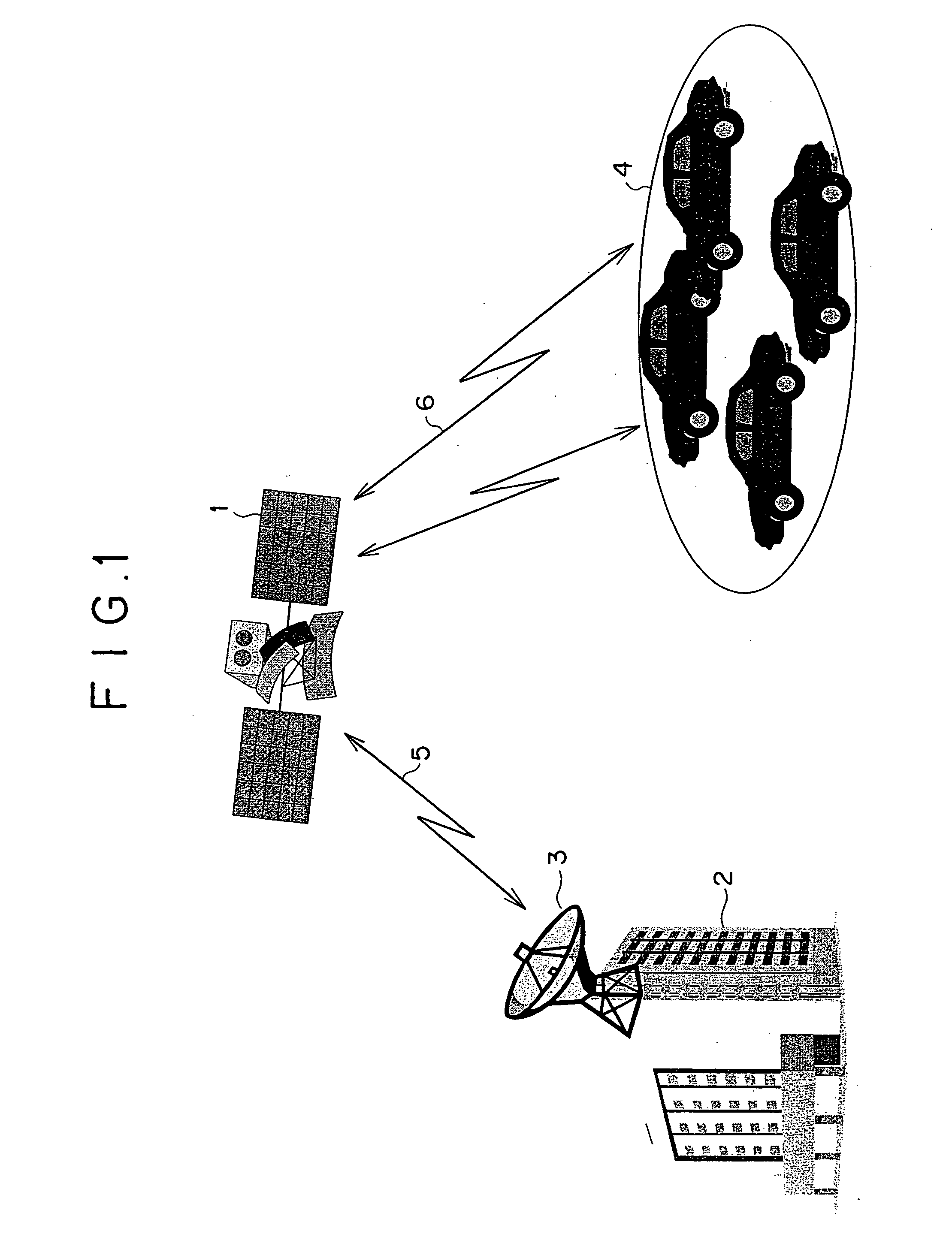
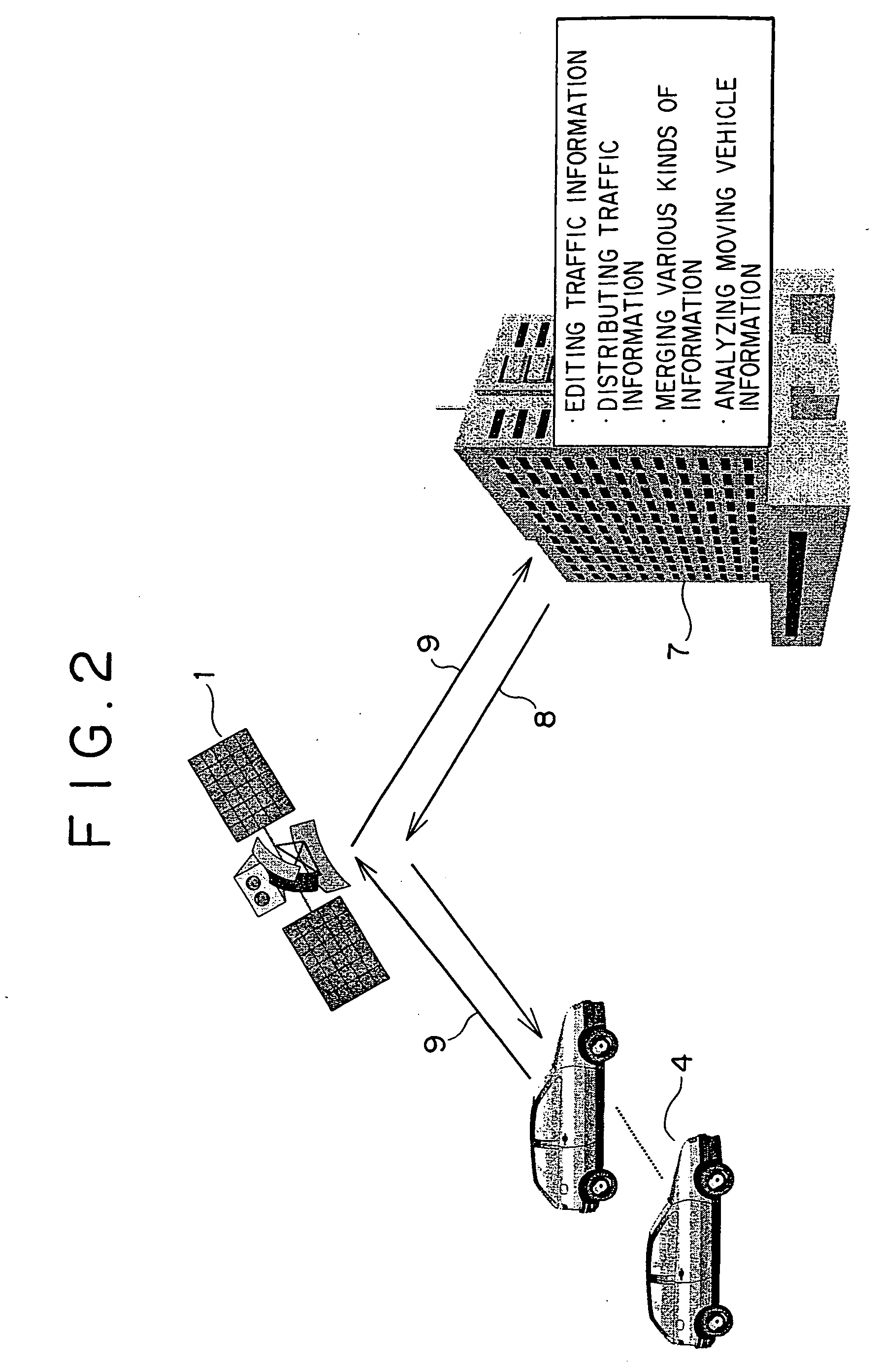
A vehicle overall interactive managing method is disclosed. Uplink information transmitted by way of an artificial satellite to a center includes emergency information and periodic information. Downlink information transmitted from the center via the artificial satellite to each vehicle includes audio and image. There is provided at a ground station a movable body overall information management system that is provided with databases storing various types of data and an analysis system. Mandatory automobile inspection information, user information, traffic and road information, safety information, and other types of information are distributed to each of information requiring organizations through this system.
Owner:HITACHI LTD
Profiling cyber threats detected in a target environment and automatically generating one or more rule bases for an expert system usable to profile cyber threats detected in a target environment
InactiveUS20150163242A1Efficiently presentedEasy to identifyMemory loss protectionError detection/correctionSecurity information and event managementSecurity information
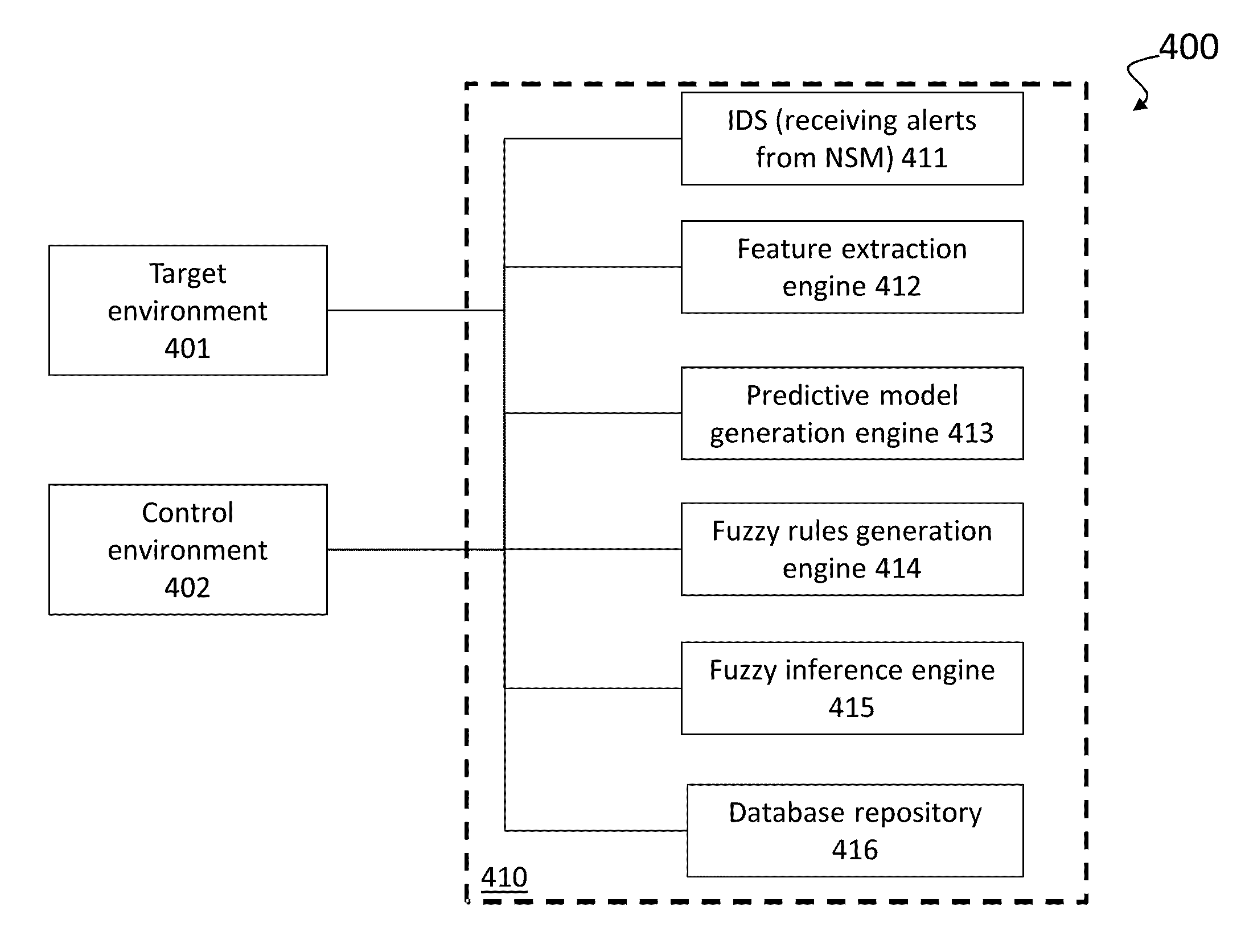
A computer implemented method of profiling cyber threats detected in a target environment, comprising: receiving, from a Security Information and Event Manager (SIEM) monitoring the target environment, alerts triggered by a detected potential cyber threat, and, for each alert: retrieving captured packet data related to the alert; extracting data pertaining to a set of attributes from captured packet data triggering the alert; applying fuzzy logic to data pertaining to one or more of the attributes to determine values for one or more output variables indicative of a level of an aspect of risk attributable to the cyber threat.
Owner:CYBERLYTIC
Method and apparatus for securing electronic data
ActiveUS7681034B1Facilitate access control managementGood synchronizationDigital data processing detailsUnauthorized memory use protectionPathPingEngineering
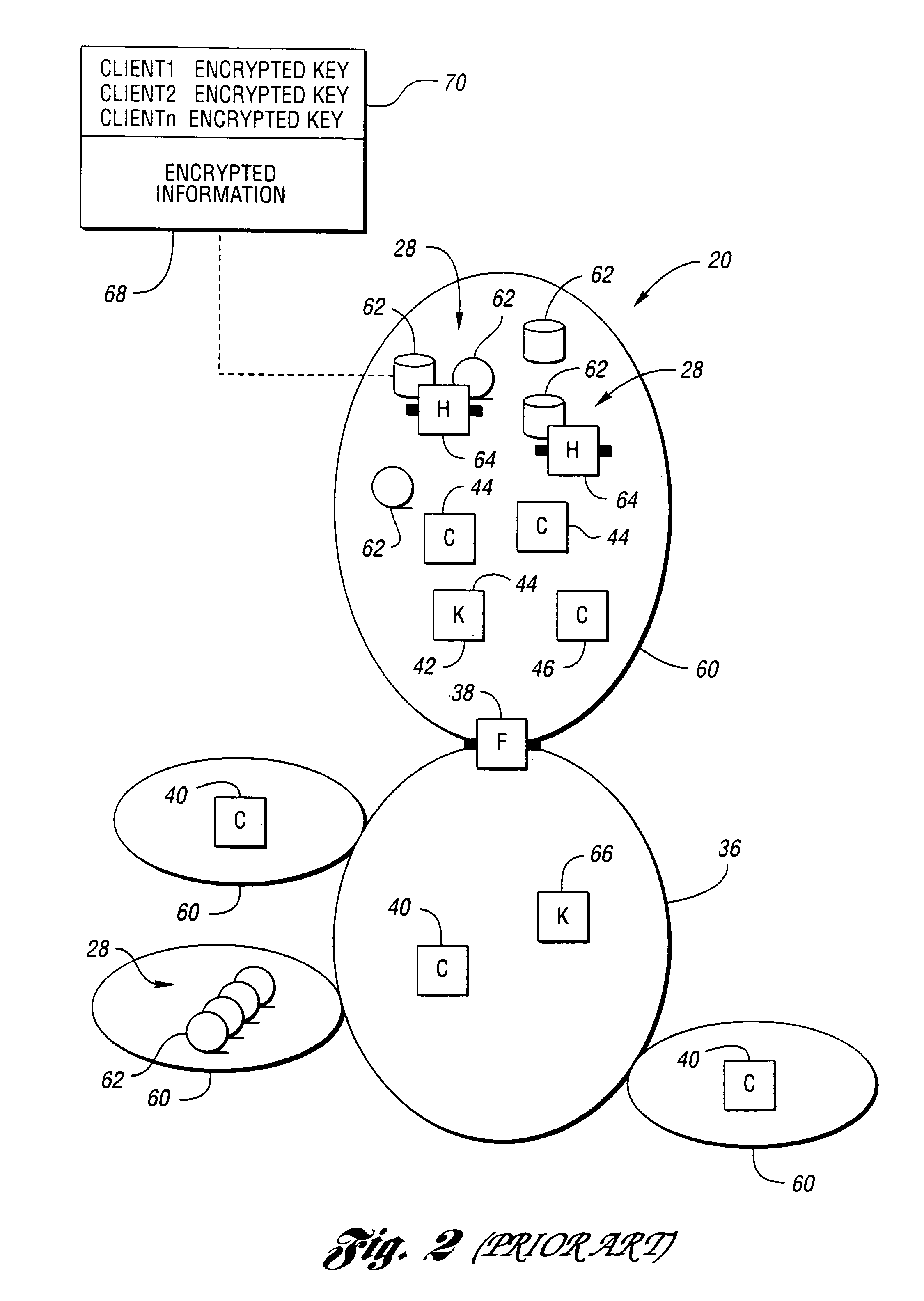
Techniques for securing electronic data and keeping the electronic data secured at all times are disclosed. According to one embodiment, a client module in a client machine is configured to provide access control to secured documents that may be located in a local store, another computer machine or somewhere over a data network. The client module includes a document-securing module configured to operate in a path through which a document being accessed is caused to pass so that the document can be examined or detected for the security nature. If the document is secured, the document-securing module obtains a user or group key to decrypt security information in the secured document for access rules therein. If a user accessing the document is determined to have the access privilege to the secured document, a file key is retrieved from the security information and a cipher module is activated to decrypt the encrypted data portion with the file key. Likewise, if a document is to be secured, the cipher module encrypts clear data from the document to create the encrypted data portion. The document-securing module integrates proper or desired security information with the encrypted data portion to produce the secured document.
Owner:INTELLECTUAL VENTURES I LLC
Systems and methods for secure wireless transactions
InactiveUS20100082490A1Ensure safetyImprove securityDigital data processing detailsComputer security arrangementsCommunications systemSecurity information
There is provided systems and methods for to conducting wireless transactions using portable electronic devices. Specifically, for example, a method of conducting a wireless transaction is provided that includes initiating a wireless transaction using a short range wireless communication system of a portable electronic device. The method also includes obtaining security information via at least one secondary system of the portable electronic device and utilizing the security information obtained via the at least one secondary system to authenticate the portable electronic device for the wireless transaction.
Owner:APPLE INC
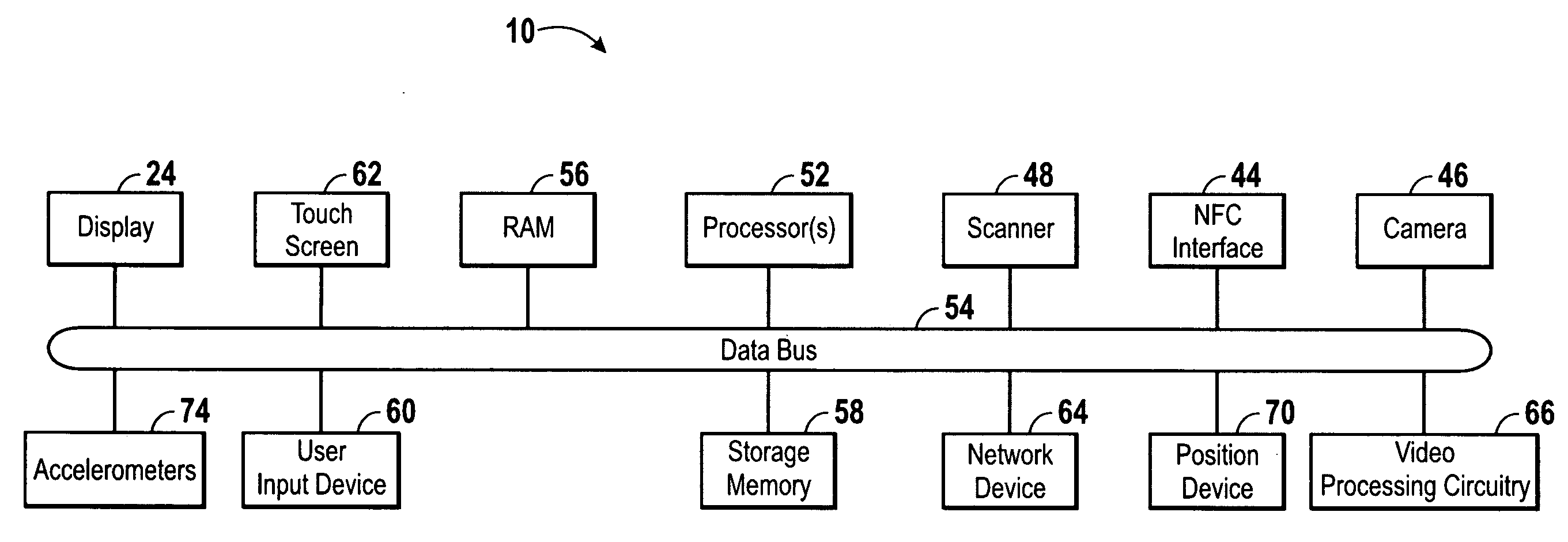
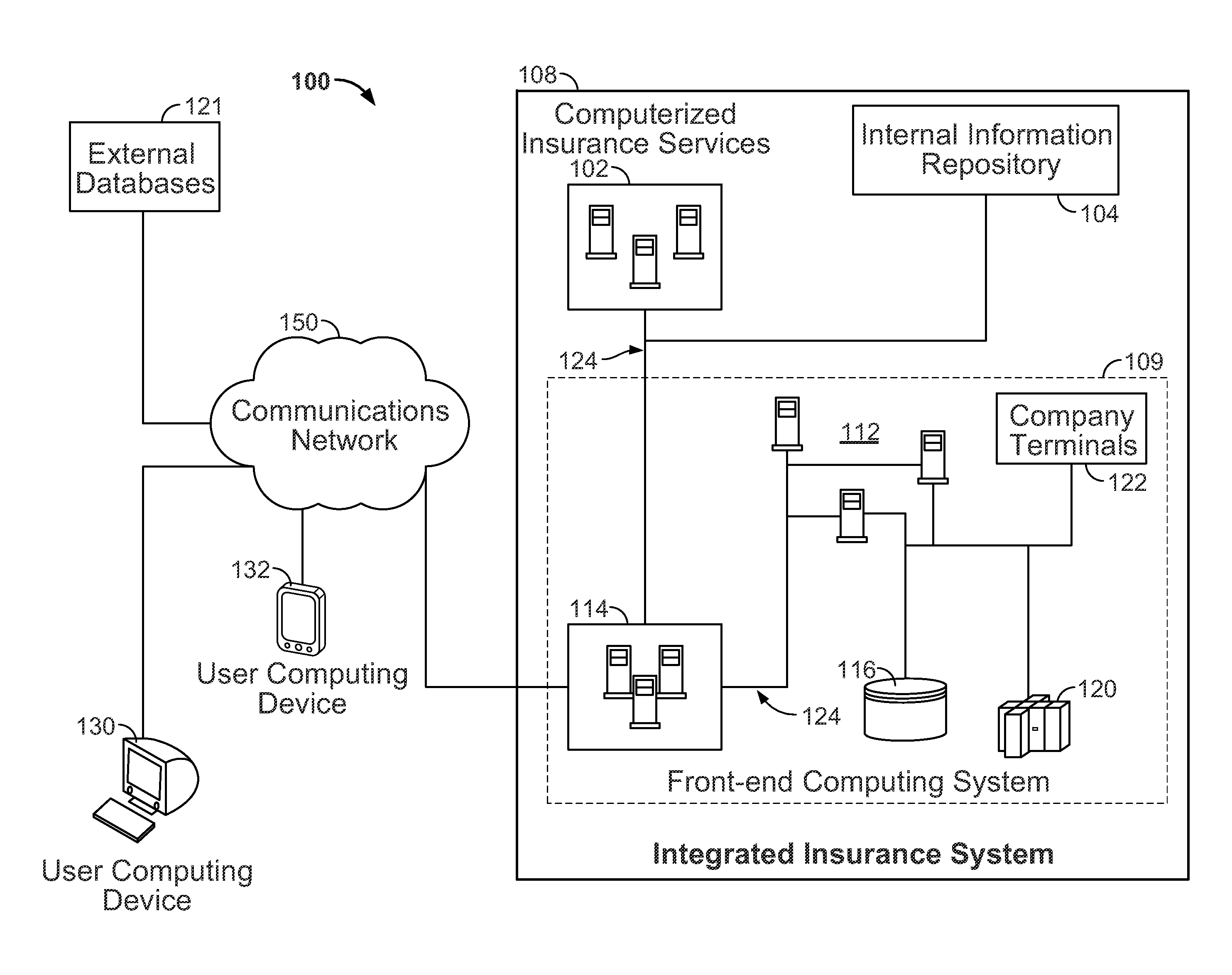
System and method for secure self registration with an insurance portal
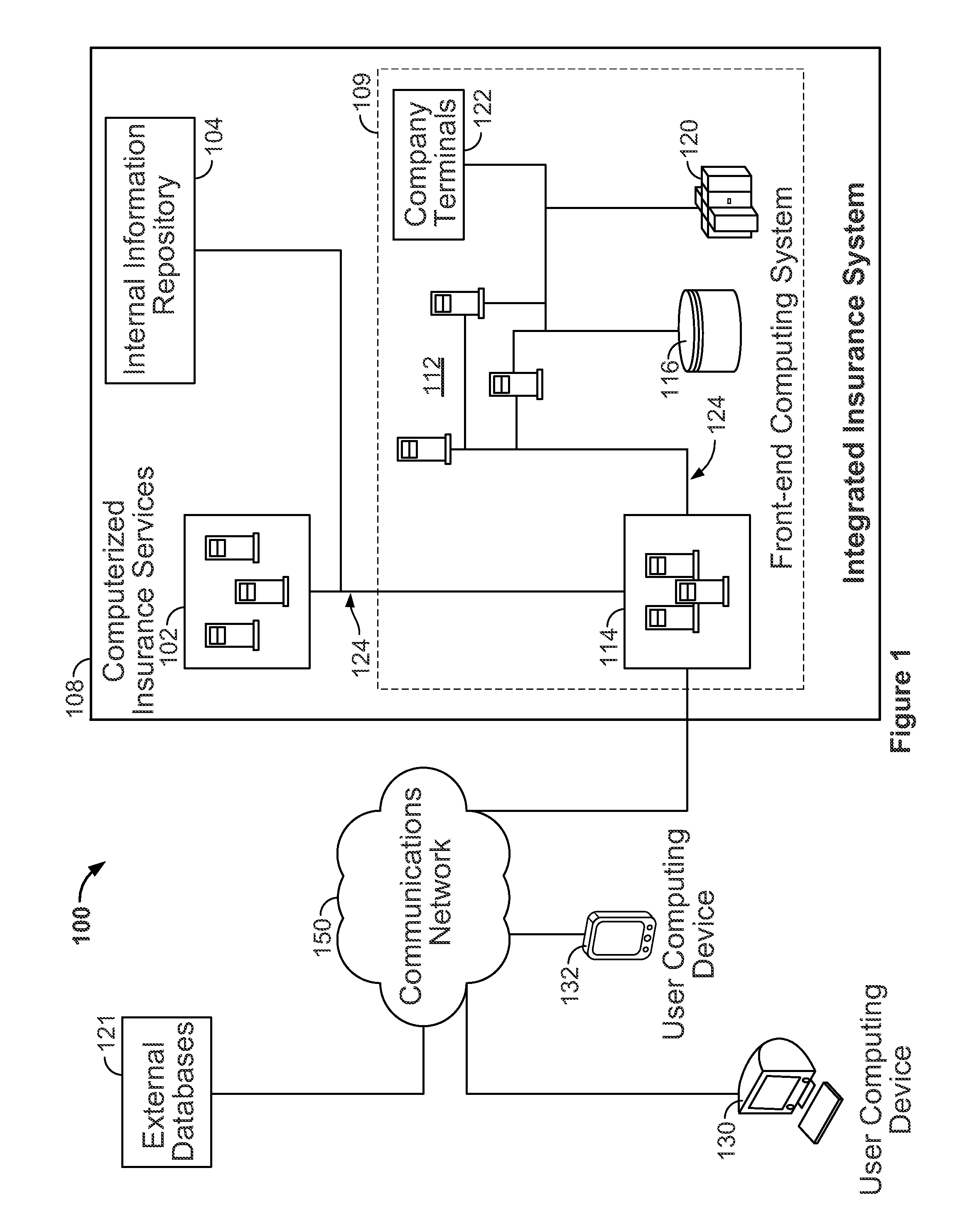
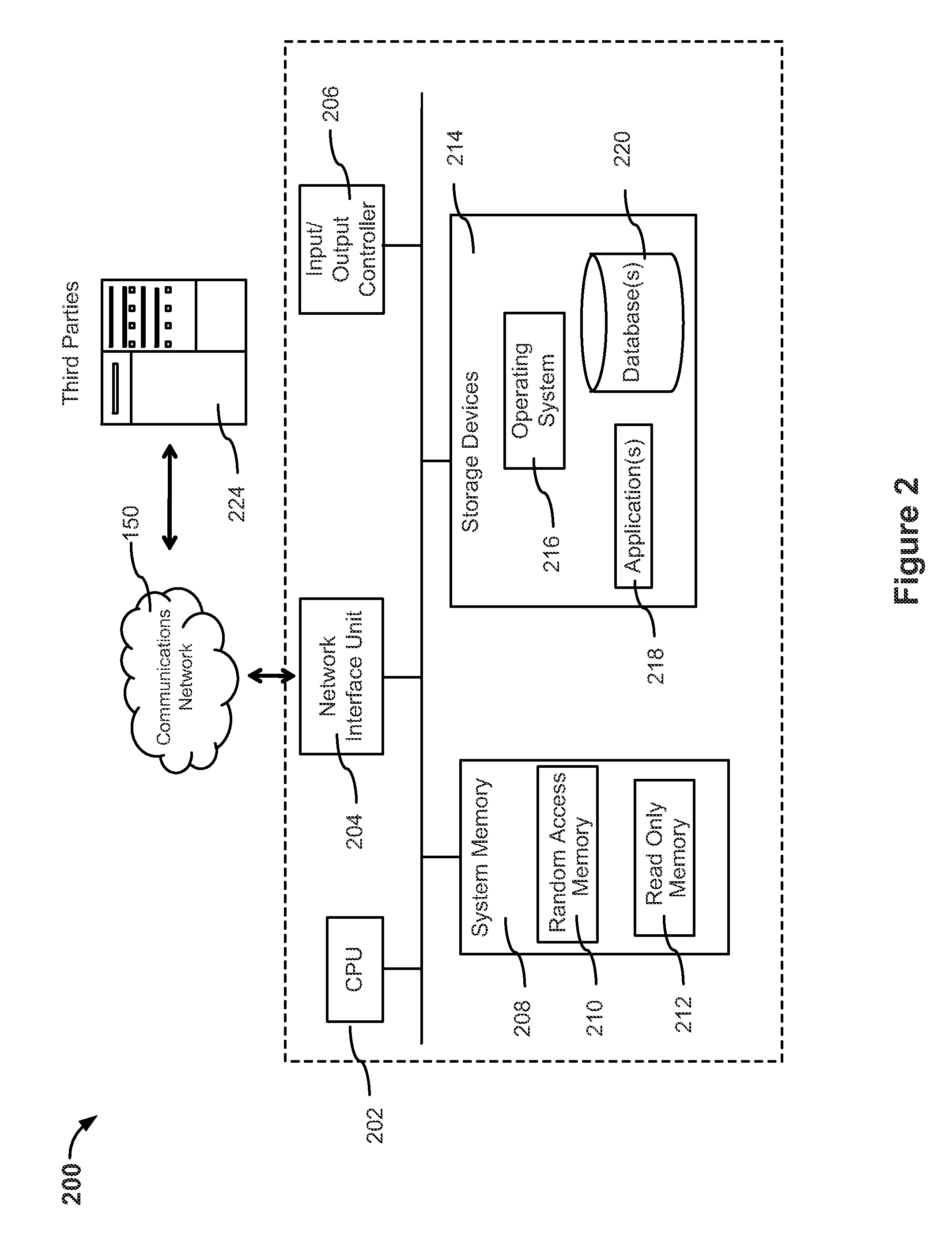
InactiveUS8682698B2Secure and accurate self-registrationSimpler and flexible interfaceFinanceElectronic accessInternet privacy
Systems and methods are disclosed herein for processing a first-time registration request for electronic access to a plurality of computerized insurance services. A network interface is configured to communicate with the plurality of computerized insurance services by interfacing with a plurality of disparate information platforms and communicating with a user computing device. A memory stores a portal module, a profile module, and a security module, each in the form of computer executable instructions, which, when executed by a processor, cause the system to receive a user identity, a first-time registration request of the user identity, and one or more secure information items associated with the user identity from the user computing device, determine a verification score for the user identity based on the one or more secure information items, and selectively register the user identity with a plurality of the computerized insurance services based on the verification score.
Owner:HARTFORD FIRE INSURANCE
Personal safety mobile notification system
In described embodiments, a system establishes a perimeter around an area, and mobile devices within the established perimeter communicate with a server that provides and collects personal and asset safety information. The provided information might enable users associated with the mobile devices to plan actions or take routes based on a given criteria, such as a safest route, through display on the mobile device. The collected information from the mobile device might be location, emergency event, environmental factors, sensor information and the like, which might then be communicated to users and / or administrators of the system. Location information, such as through global positioning system (GPS), might provide tracking of mobile devices and users or assets associated with each mobile device. GPS functionality associates latitude, longitude and elevation (X-Y-Z coordinate axis) data with the collected and provided information.
Owner:LIQUID RARITY EXCHANGE LLC
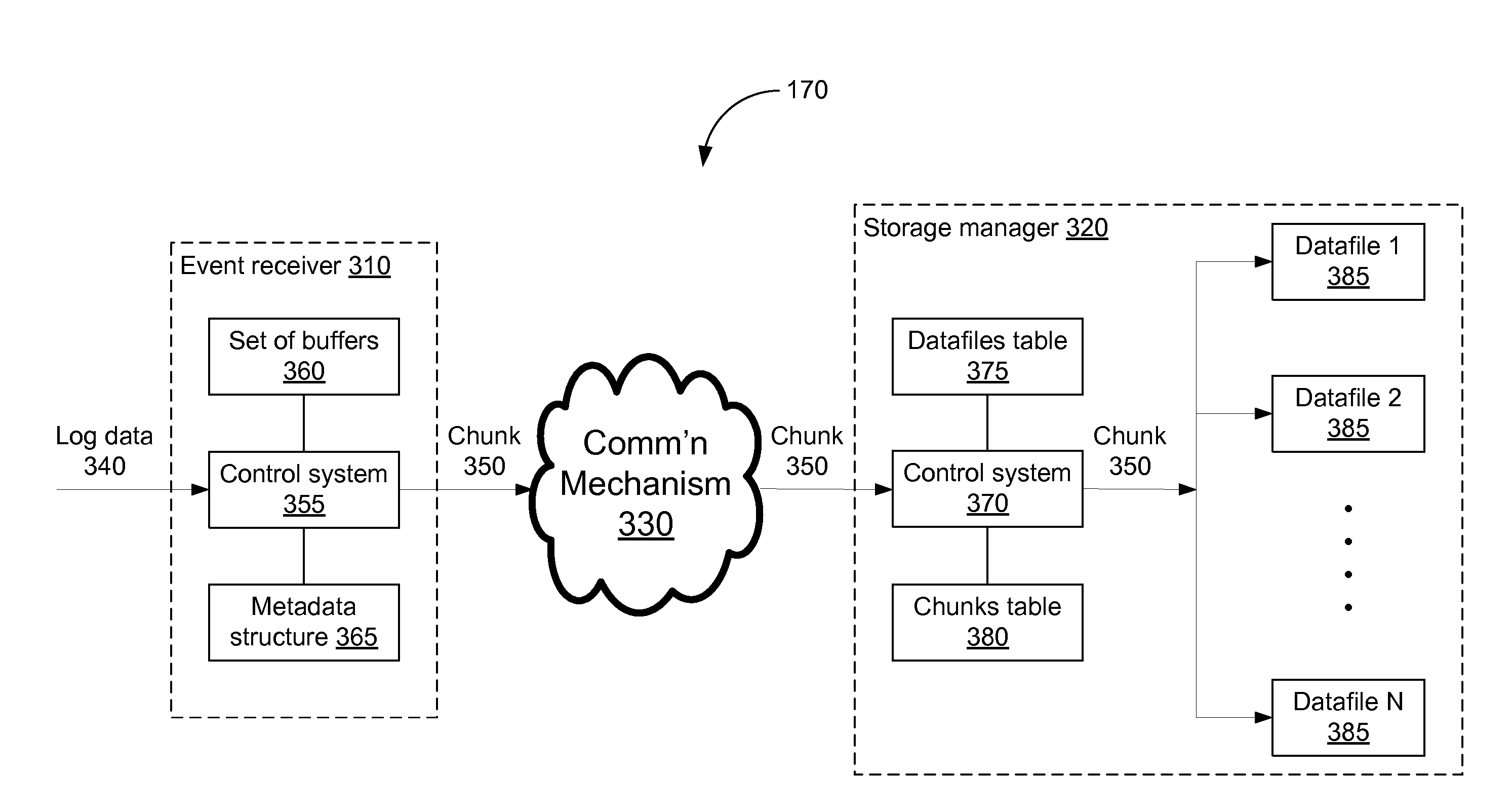
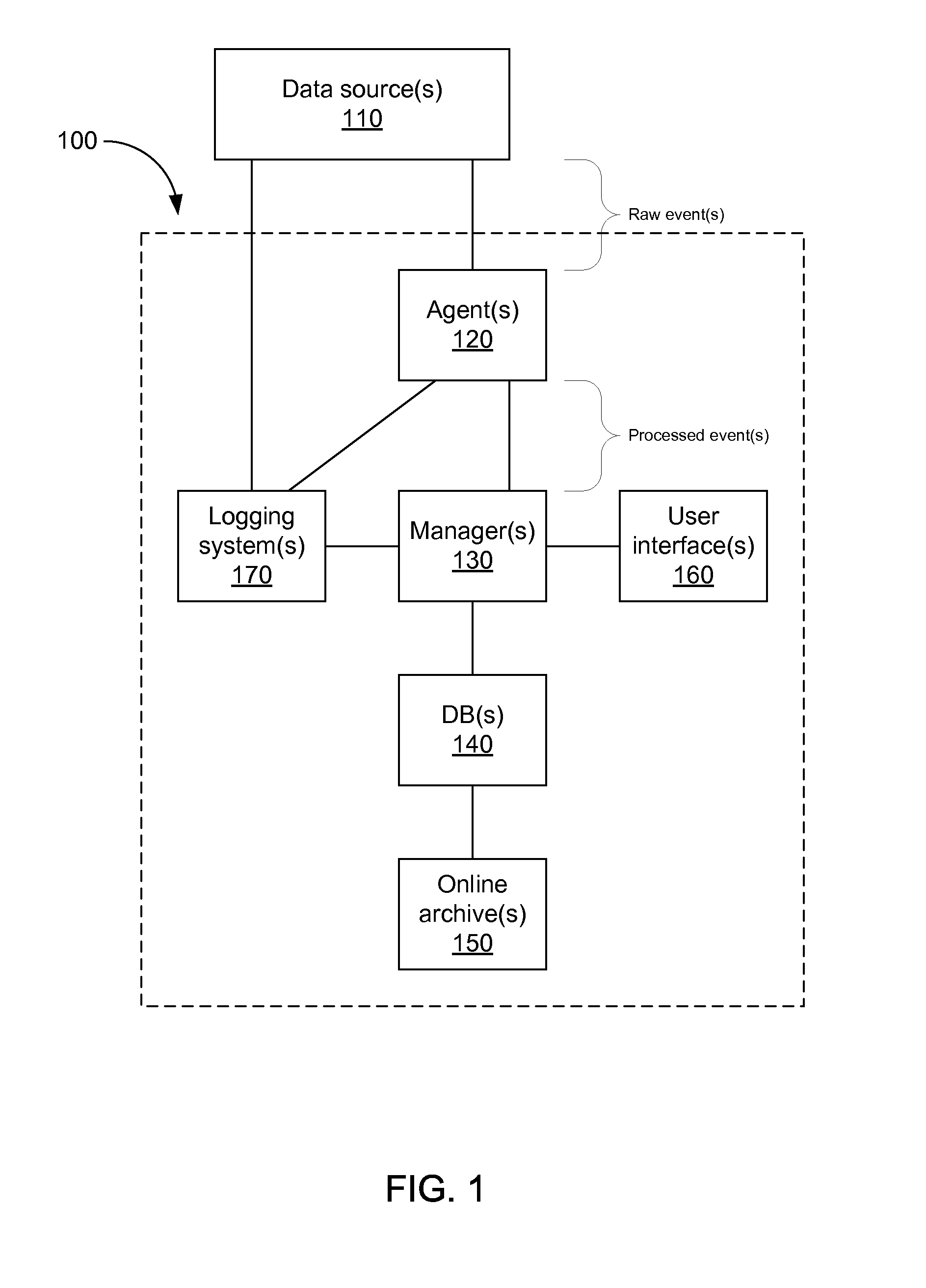
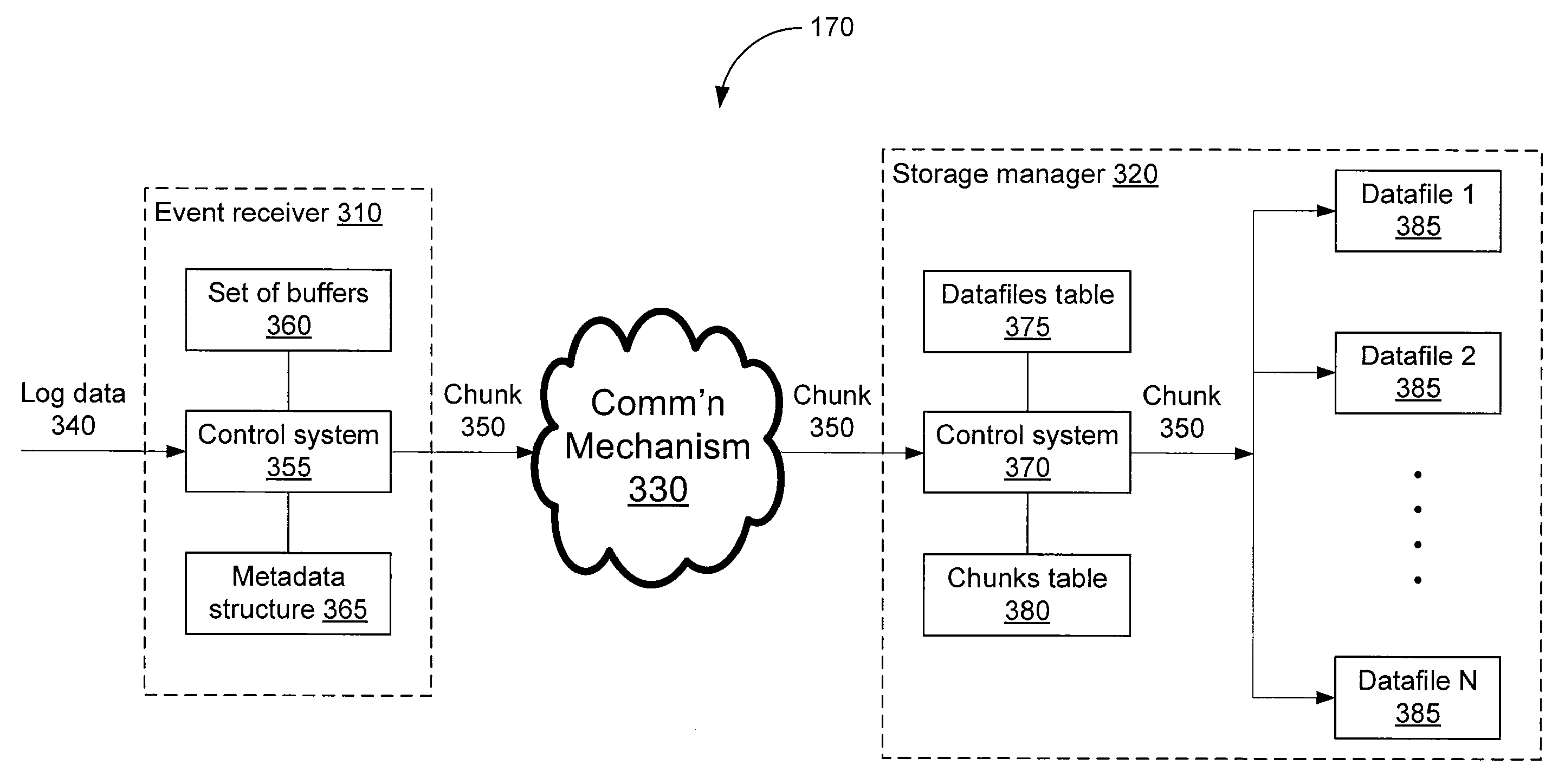
Storing log data efficiently while supporting querying
A logging system includes an event receiver and a storage manager. The receiver receives log data, processes it, and outputs a column-based data “chunk.” The manager receives and stores chunks. The receiver includes buffers that store events and a metadata structure that stores metadata about the contents of the buffers. Each buffer is associated with a particular event field and includes values from that field from one or more events. The metadata includes, for each “field of interest,” a minimum value and a maximum value that reflect the range of values of that field over all of the events in the buffers. A chunk is generated for each buffer and includes the metadata structure and a compressed version of the buffer contents. The metadata structure acts as a search index when querying event data. The logging system can be used in conjunction with a security information / event management (SIEM) system.
Owner:MICRO FOCUS LLC
Information record infrastructure, system and method
InactiveUS20100241595A1Low costIncrease the number ofDigital data processing detailsTelemedicineSecurity ruleInformation infrastructure
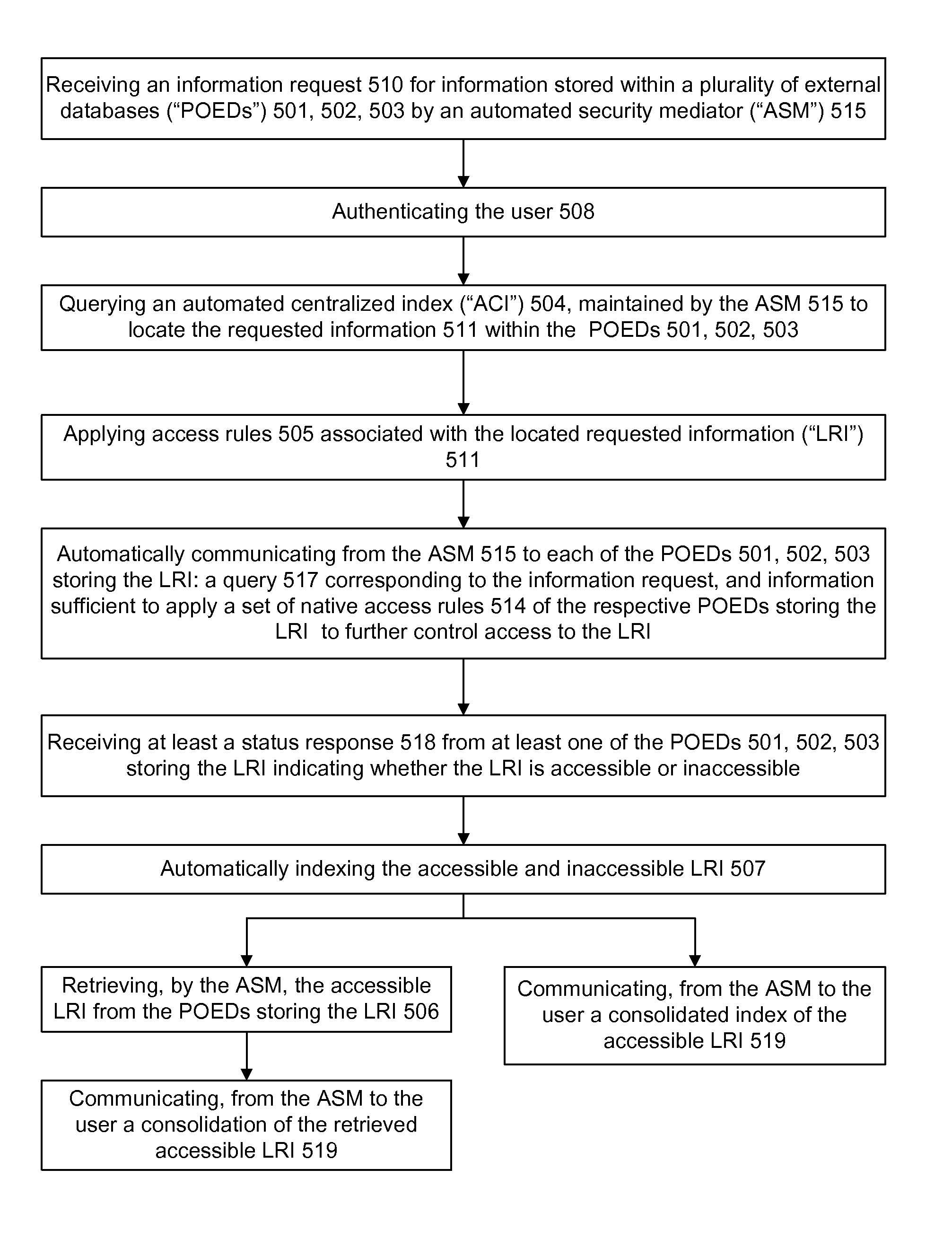
A security mediator, comprising an input configured to receive a user information request; an automated index, stored in a memory, configured to store information for determining which of a plurality of remote databases stores information responsive to the request; an automated security rule base, stored in a memory, containing rules applicable to information responsive to the request stored in the plurality of remote databases; a communication port configured to communicate to a plurality of remote databases which store information responsive to the request: security information, a query corresponding to the request and associated rules applicable to the information responsive to the request at the respective remote database; and at least one processor being configured to apply at least one security rule responsive to the query of the automated security rule base, and index information derived from a plurality of the remote databases, in a manner which permits application of the rules and which restricts insecure use of the index.
Owner:RPX CORP
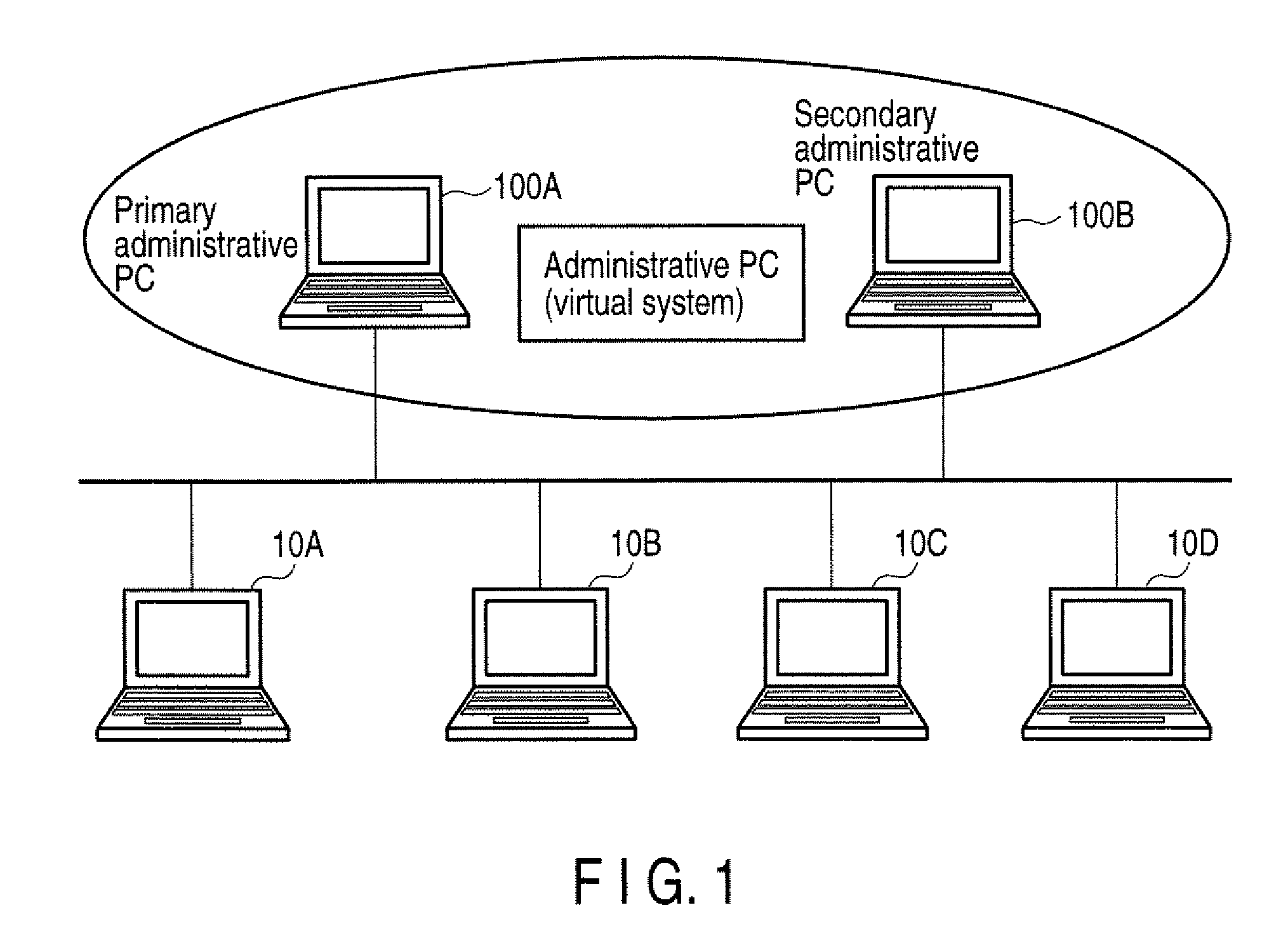
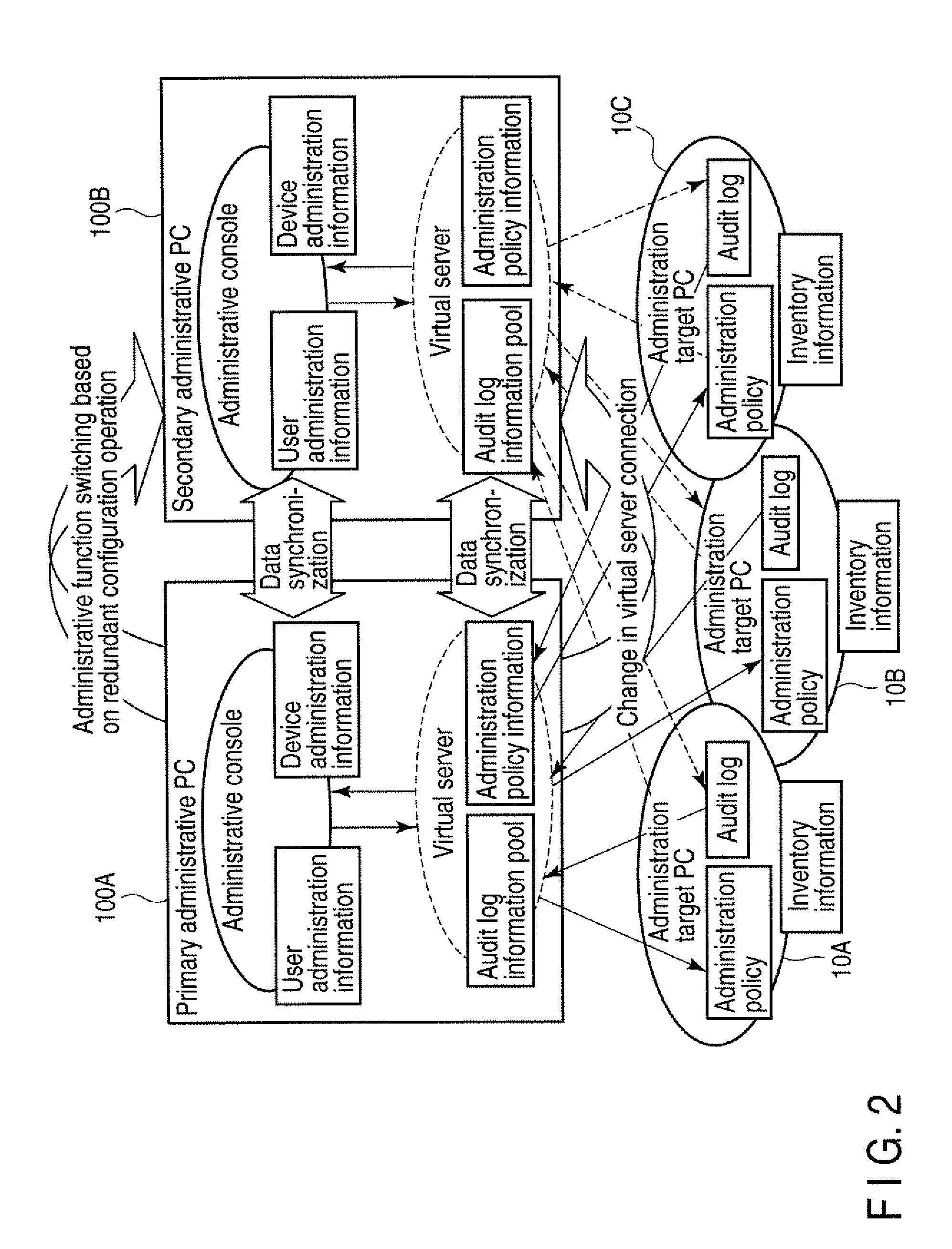
Information Processing System and Control Method for Information Processing System
InactiveUS20100064044A1Digital computer detailsPlatform integrity maintainanceInformation processingNetwork connection
According to one embodiment, an information processing system includes a managed information processing apparatus connected with a network, and a plurality of first information processing apparatuses including a first monitor module which controls each software resource to simultaneously run on one hardware resource, the software resources including a first software resource including a first program has a function of administrating security information required to control an operation of the managed information processing apparatus, wherein one first information processing apparatus selected from the plurality of first information processing apparatuses executes the first program, and the security information of the one selected first information processing apparatus is synchronized with that of a newly selected first information processing apparatus when changing the first information processing apparatus which executes the first program from the selected first information processing apparatus to the newly selected first information processing apparatus,
Owner:KK TOSHIBA
Management of multiple connections to a security token access device
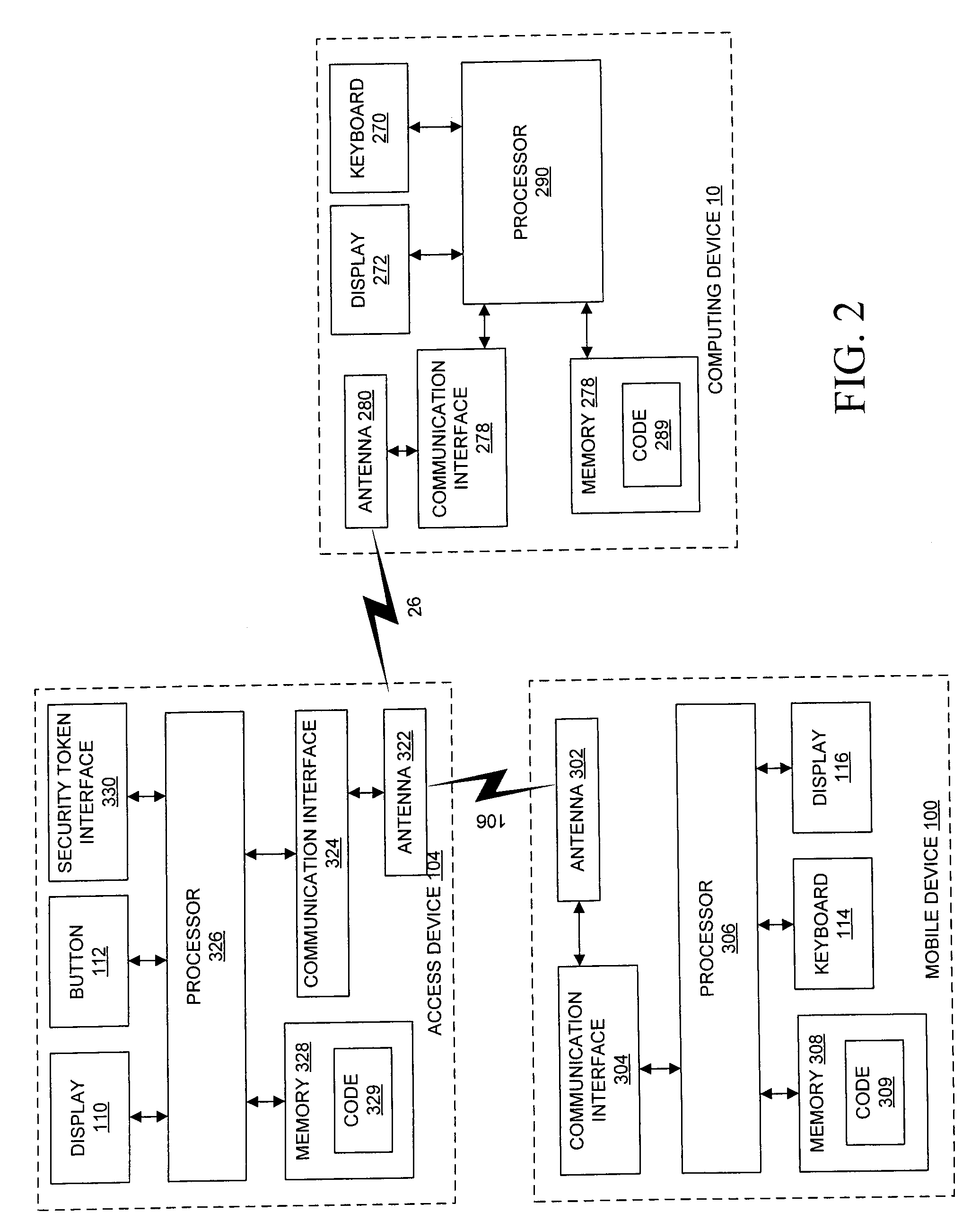
ActiveUS20080016537A1Digital data processing detailsUnauthorized memory use protectionUser devicePairing
A security token access device, a user device such as a computing device or communications device, and a method for managing multiple connections between multiple user devices and the access device. The access device maintains connection information, including security information, for each user device securely paired with the access device. Each time a new user device is paired with the access device, the access device transmits a notification to the user devices already paired to the user device. A user may provide instructions to the access device to terminate a pairing with one of the user devices by overwriting at least a portion of the connection information associated with the designated user device. A user device may further request a listing of all user devices currently paired with the access device.
Owner:MALIKIE INNOVATIONS LTD
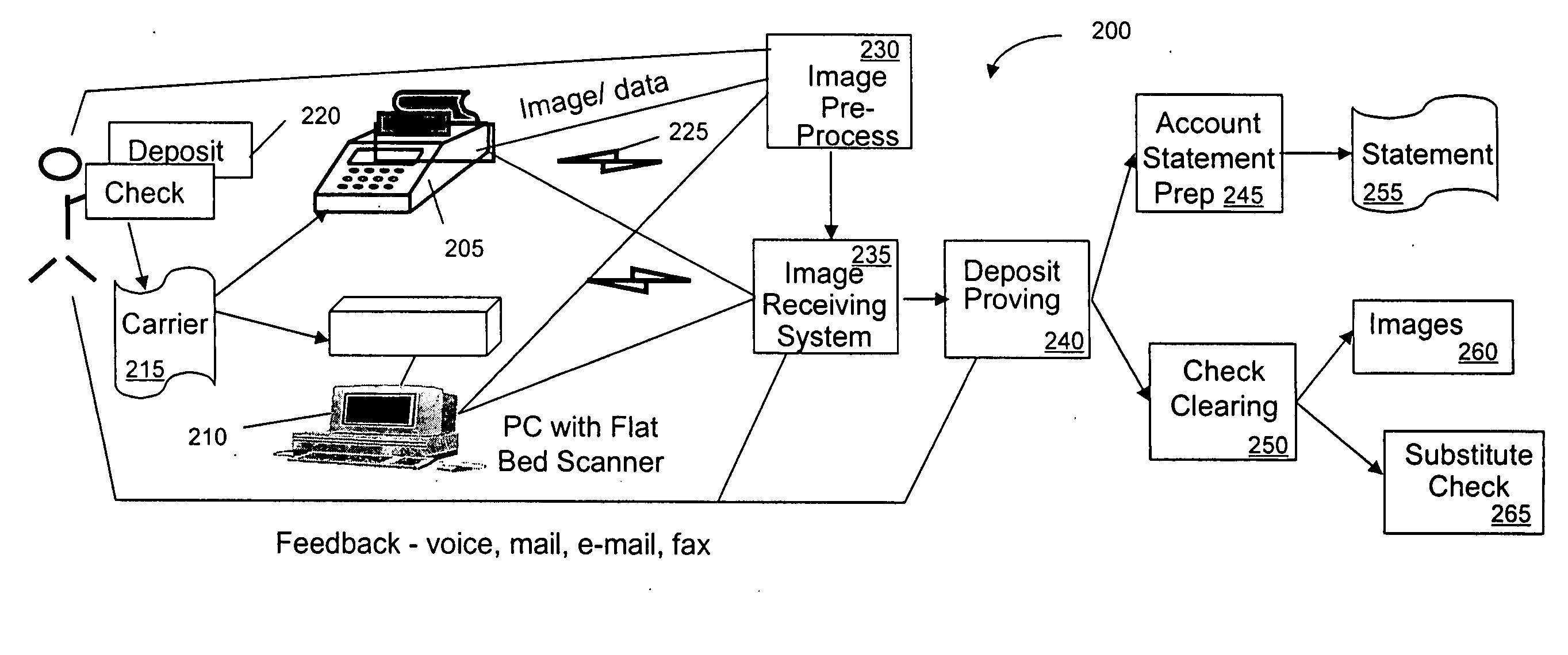
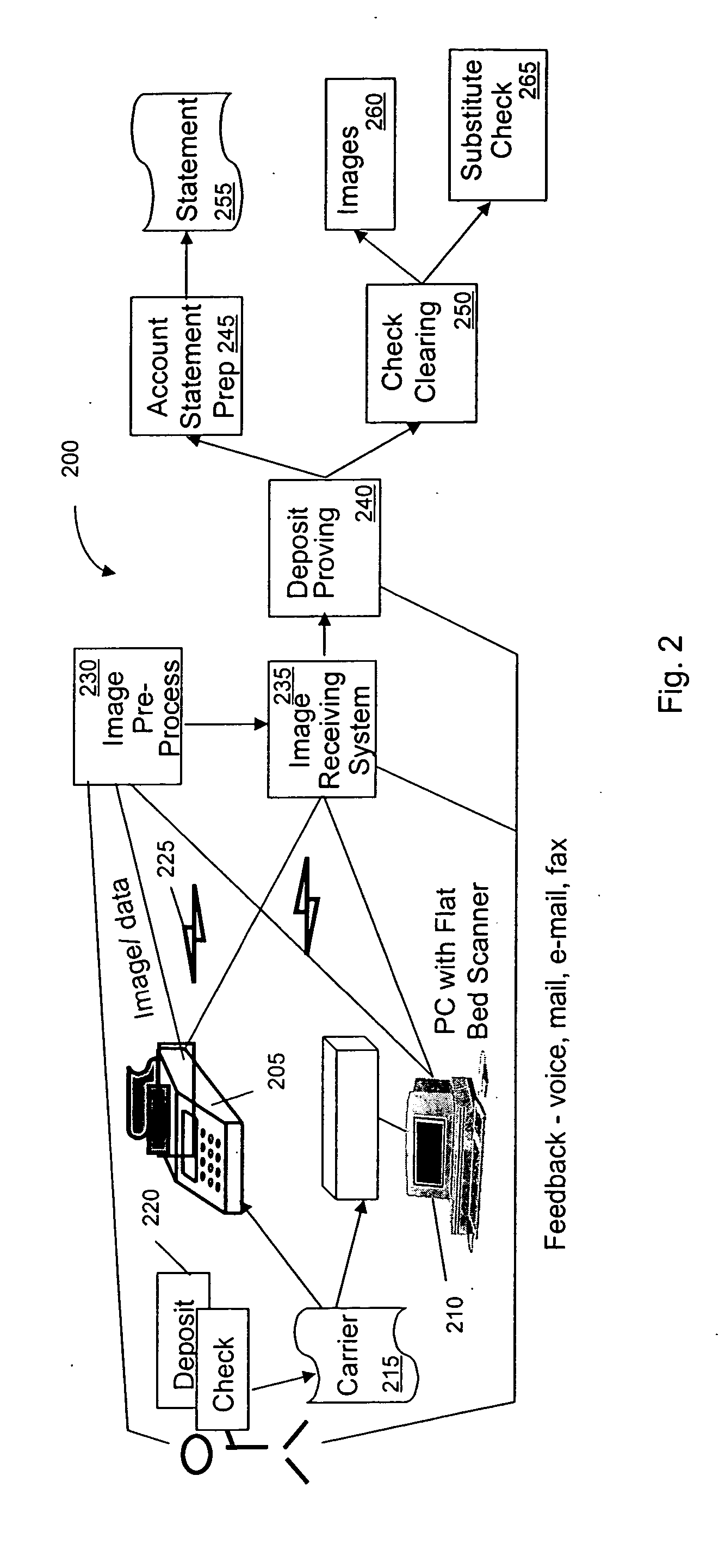
Ubiquitous imaging device based check image capture
A method or corresponding apparatus for remote transmission of a negotiable instrument. In an example embodiment, the process provides a carrier that secures a negotiable instrument. Next, the process creates a unique identifier, associated with the carrier, and generates an electronic image of the negotiable instrument. After generating the electronic image, the process transmits the electronic image of the negotiable instrument and the unique identifier to a remote location. The negotiable instrument may be transmitted via a fax, a scanner, a device designed to transmit electronic data, other image device compatible with ITU-T recommendations T.30 or T.4, or combination thereof. The process may also verify the negotiable instrument has a valid endorsement, verify image quality of the electronic image to ensure compliance with financial industry standards, or validate any received security information.
Owner:LIGHTHOUSE CONSULTING GROUP
Storing log data efficiently while supporting querying to assist in computer network security
ActiveUS20080162592A1Data processing applicationsError detection/correctionSystem of recordEvent management
A logging system includes an event receiver and a storage manager. The receiver receives log data, processes it, and outputs a data “chunk.” The manager receives data chunks and stores them so that they can be queried. The receiver includes buffers that store events and a metadata structure that stores metadata about the contents of the buffers. The metadata includes a unique identifier associated with the receiver, the number of events in the buffers, and, for each “field of interest,” a minimum value and a maximum value that reflect the range of values of that field over all of the events in the buffers. A chunk includes the metadata structure and a compressed version of the contents of the buffers. The metadata structure acts as a search index when querying event data. The logging system can be used in conjunction with a security information / event management (SIEM) system.
Owner:MICRO FOCUS LLC
Wireless device emergency services connection and panic button, with crime and safety information system
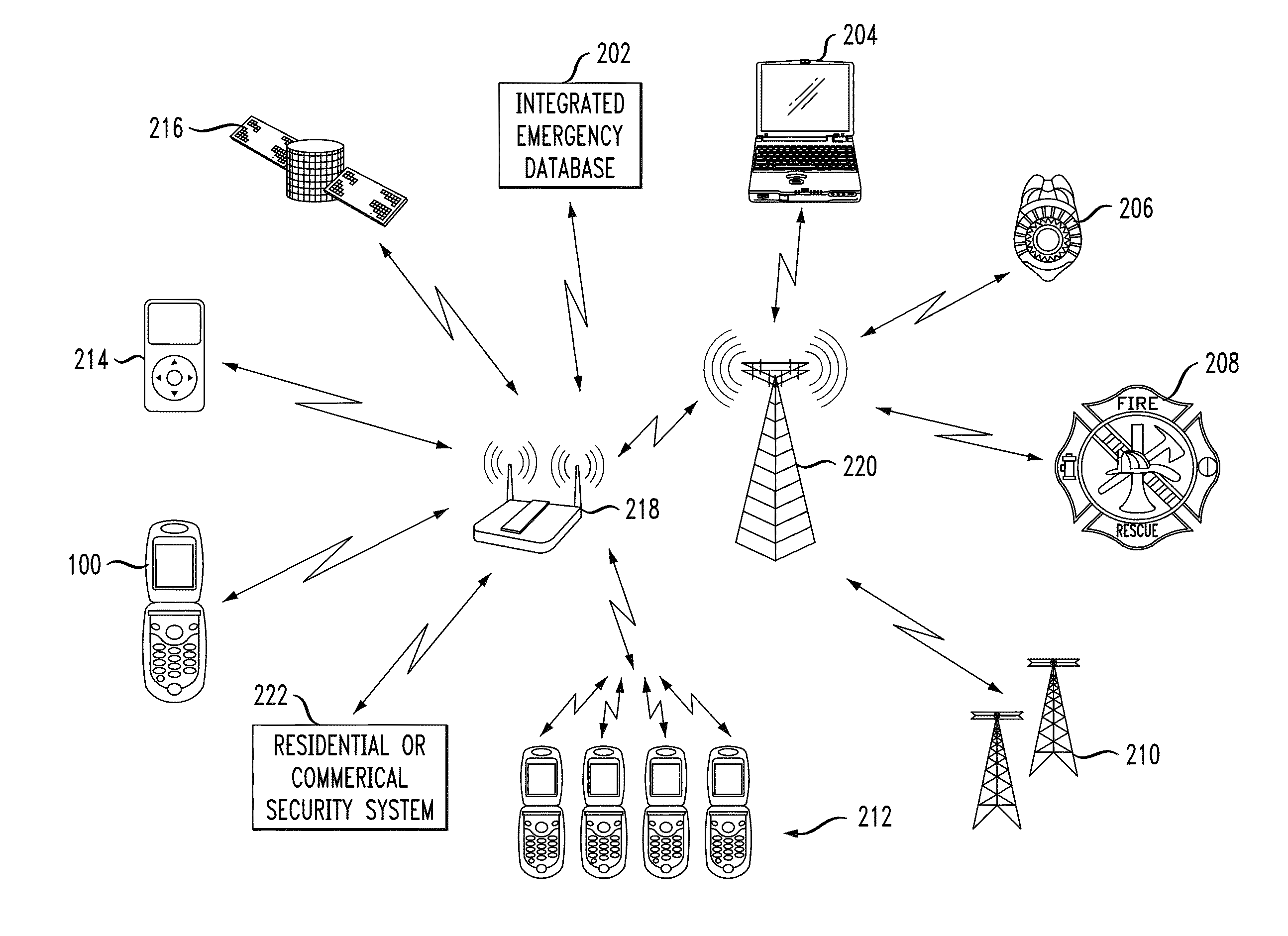
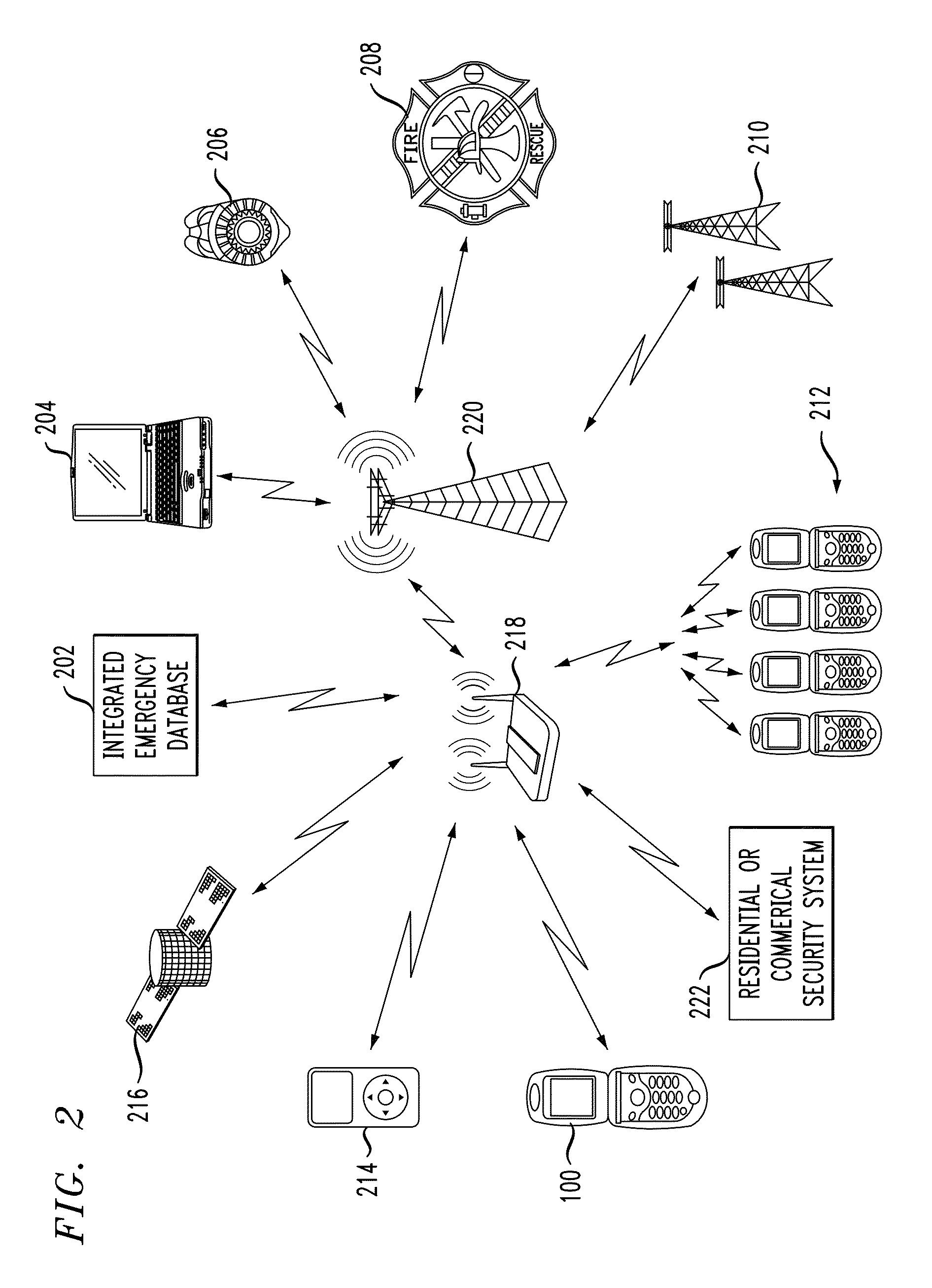
ActiveUS20110111728A1Emergency connection handlingConnection managementComputer terminalSecurity information
A system and method for providing a conduit to send information to emergency services from a wireless device. Systems and methods for registering an alarm button on a wireless device and sending to public and / or private emergency services providers information related to the wireless device including its location, information about a wireless device end user and / or subscriber associated with the wireless device, and information recorded by one or more wireless devices during and subsequent to the time the alarm button is activated.
Owner:CELLULAR MOBILE ROUTING CO LLC +1
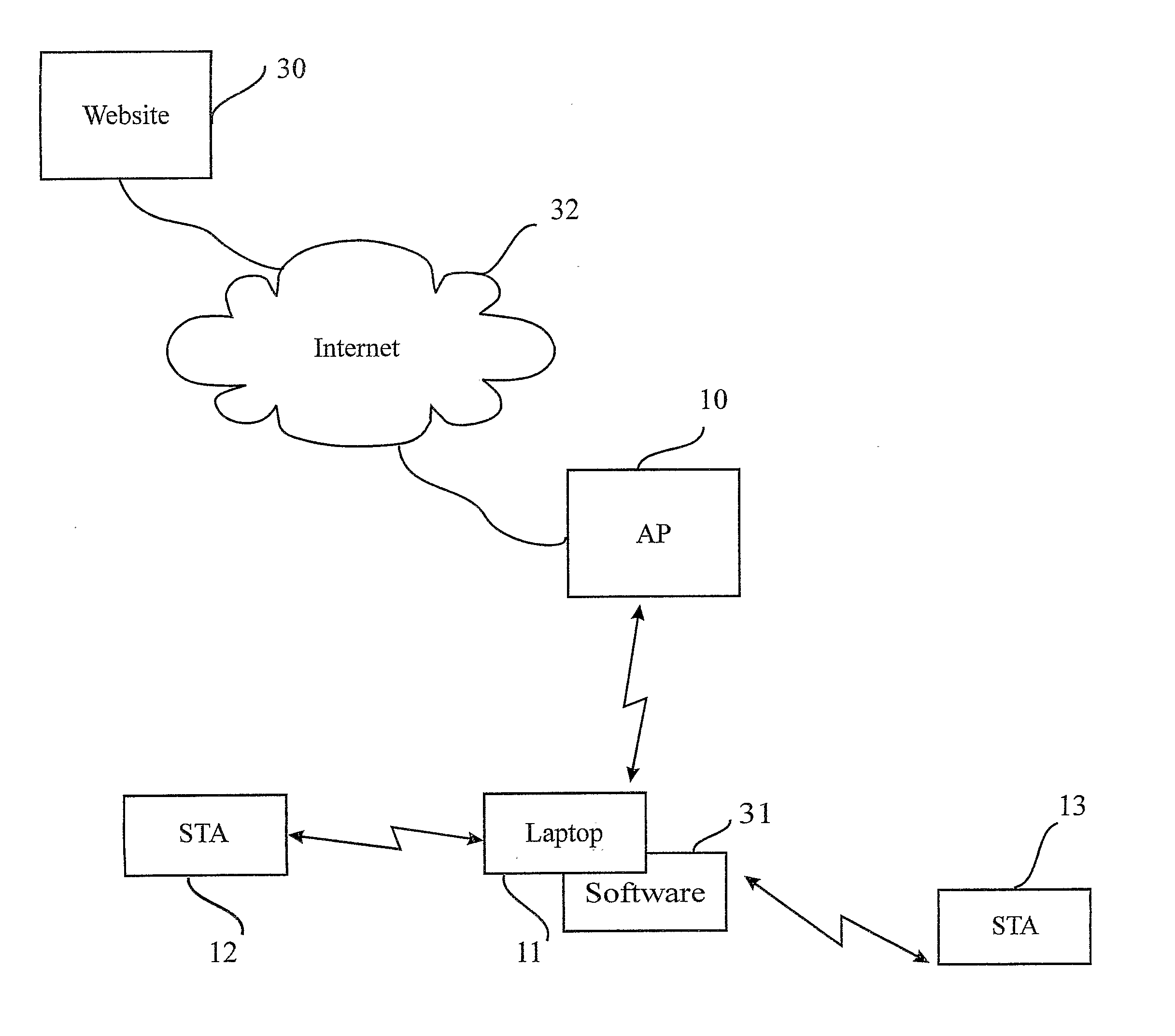
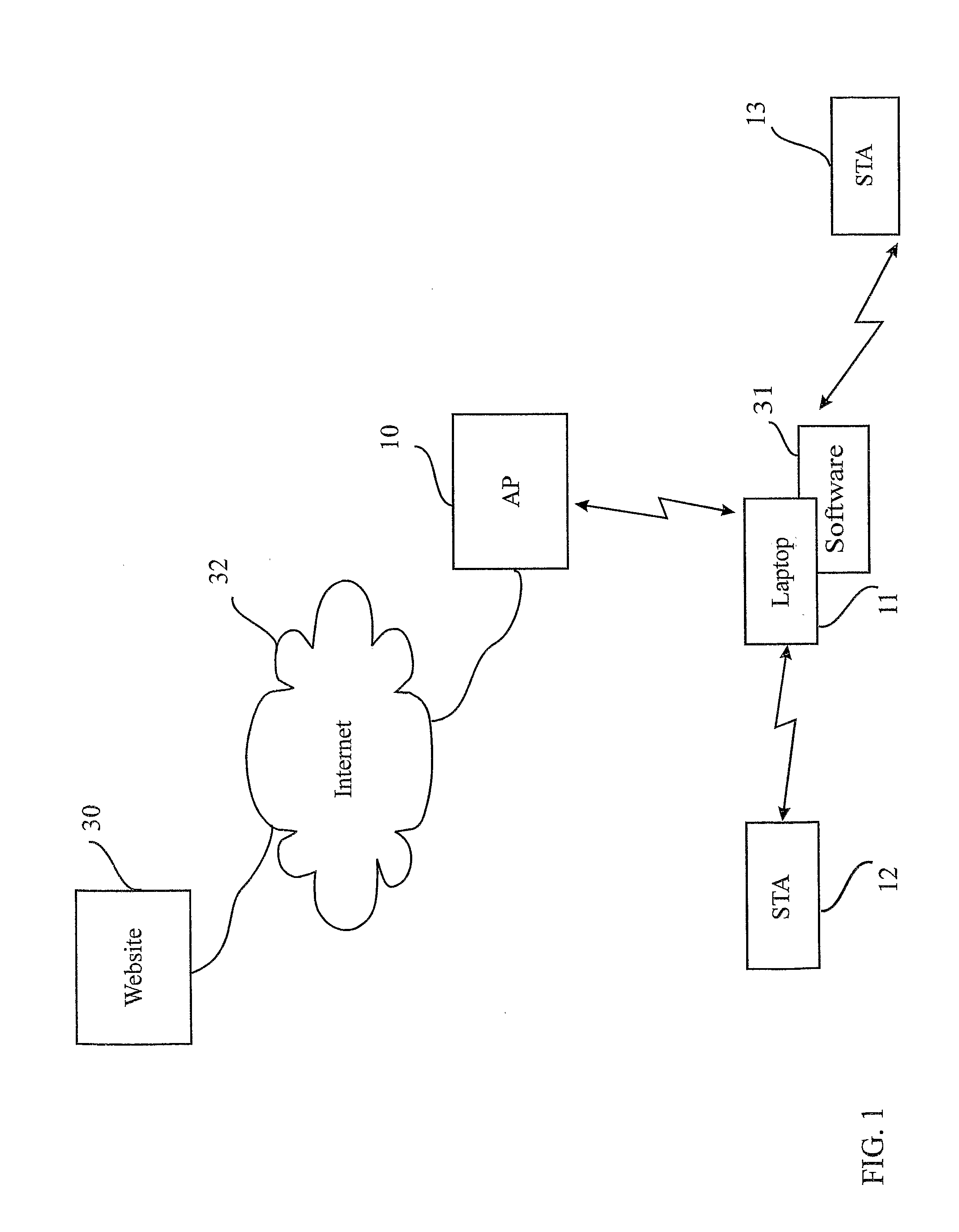
Wireless internet system and method
ActiveUS20100296441A1Light burdenFirmly connectedNetwork topologiesConnection managementSecurity parameterSecurity information
A method for providing a wireless Internet connection to WiFi-enabled devices (STAs) comprising: wirelessly connecting a first STA to the Internet through a first AP with a first SSID; remaining connected to the first Access Point (AP), the first STA creates a software-based wireless AP with a second SSID for wirelessly connecting other STAs to the Internet through the first STA. A software module running on the first STA allows a second STA a wide access to the Internet only if the second STA has a copy of the software module running installed and active therein. A method for configuring STAs to connect to a wireless network, comprising: a customer first connects a STA by wire to its network; a software on the STA copies to the STA the security information gained through the wired connection, thus setting the security parameters for the STA.
Owner:BARKAN WIRELESS ACCESS TECH
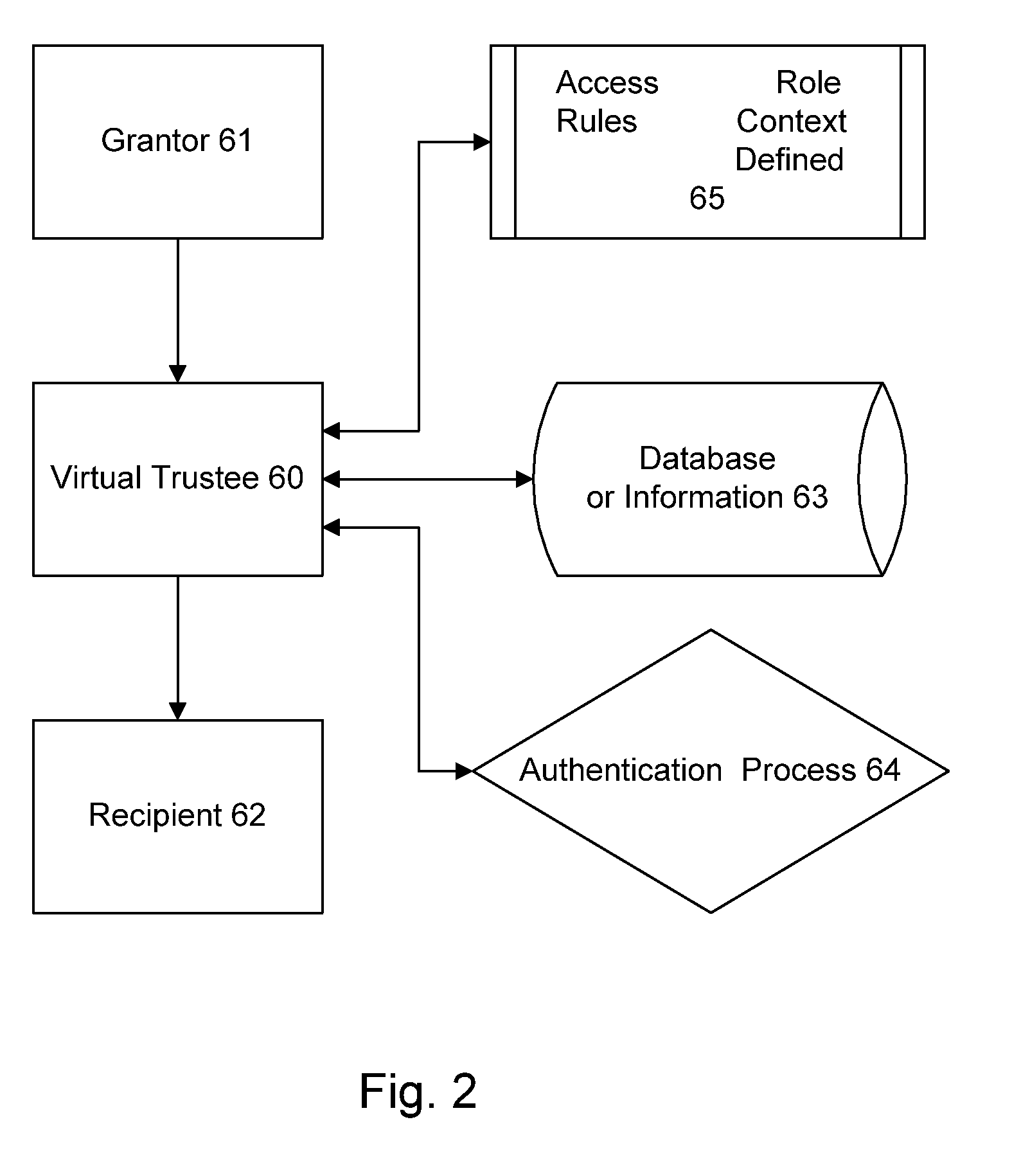
Method and system for secure information handling
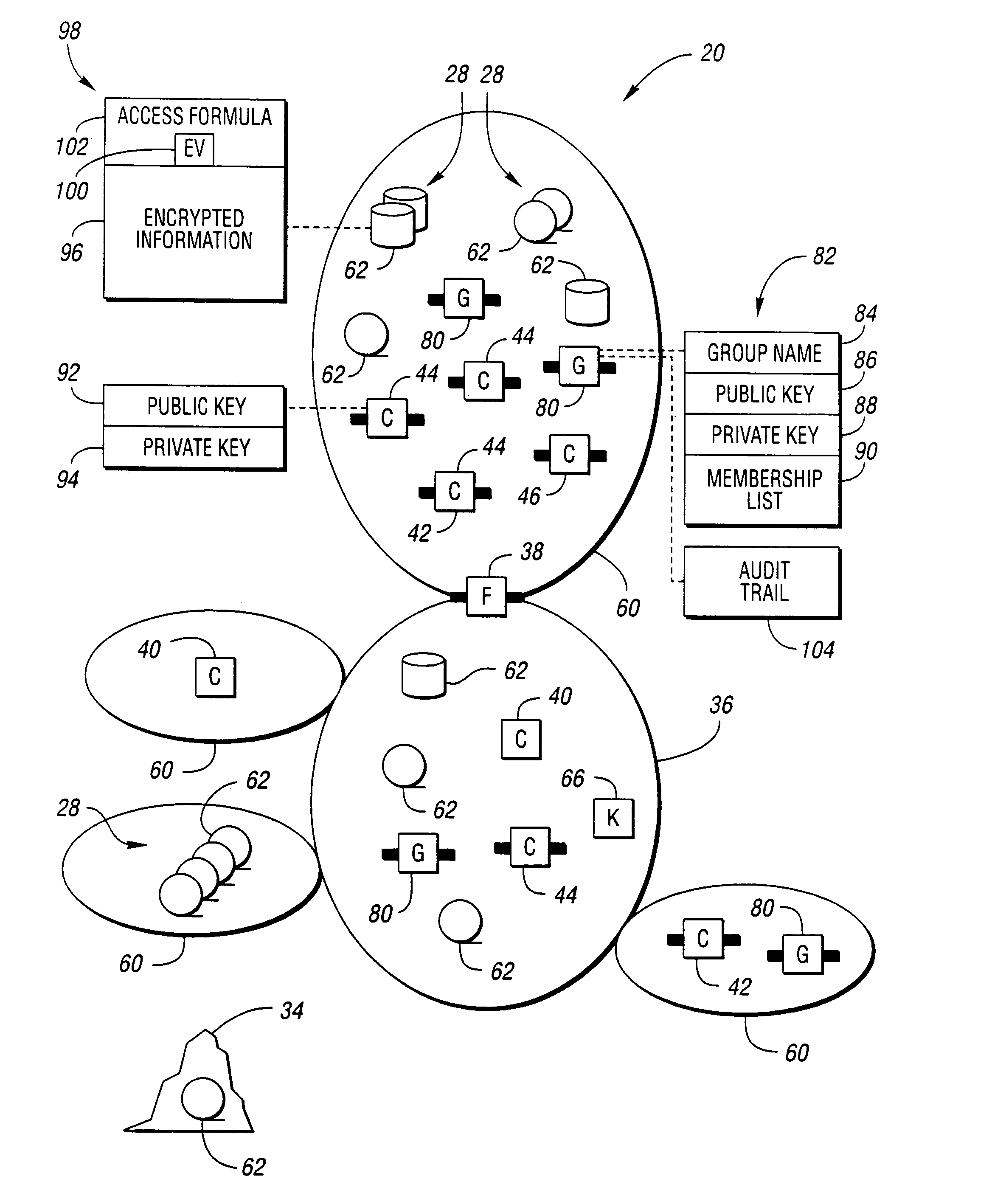
InactiveUS6957330B1Safe handlingSafe storageKey distribution for secure communicationUser identity/authority verificationClient-sideSecurity information
Information that must remain secure is often stored on untrusted storage devices. To increase security, this information is encrypted by an encryption value prior to storing on the untrusted storage device. The encryption value itself is then encrypted. The encryption value is decrypted by correctly solving an access formula describing a function of groups. Each group includes a list of at least one consumer client. A requesting consumer client is granted access to the information if the requesting consumer client is a member of at least one group which correctly solves the access formula.
Owner:ORACLE INT CORP
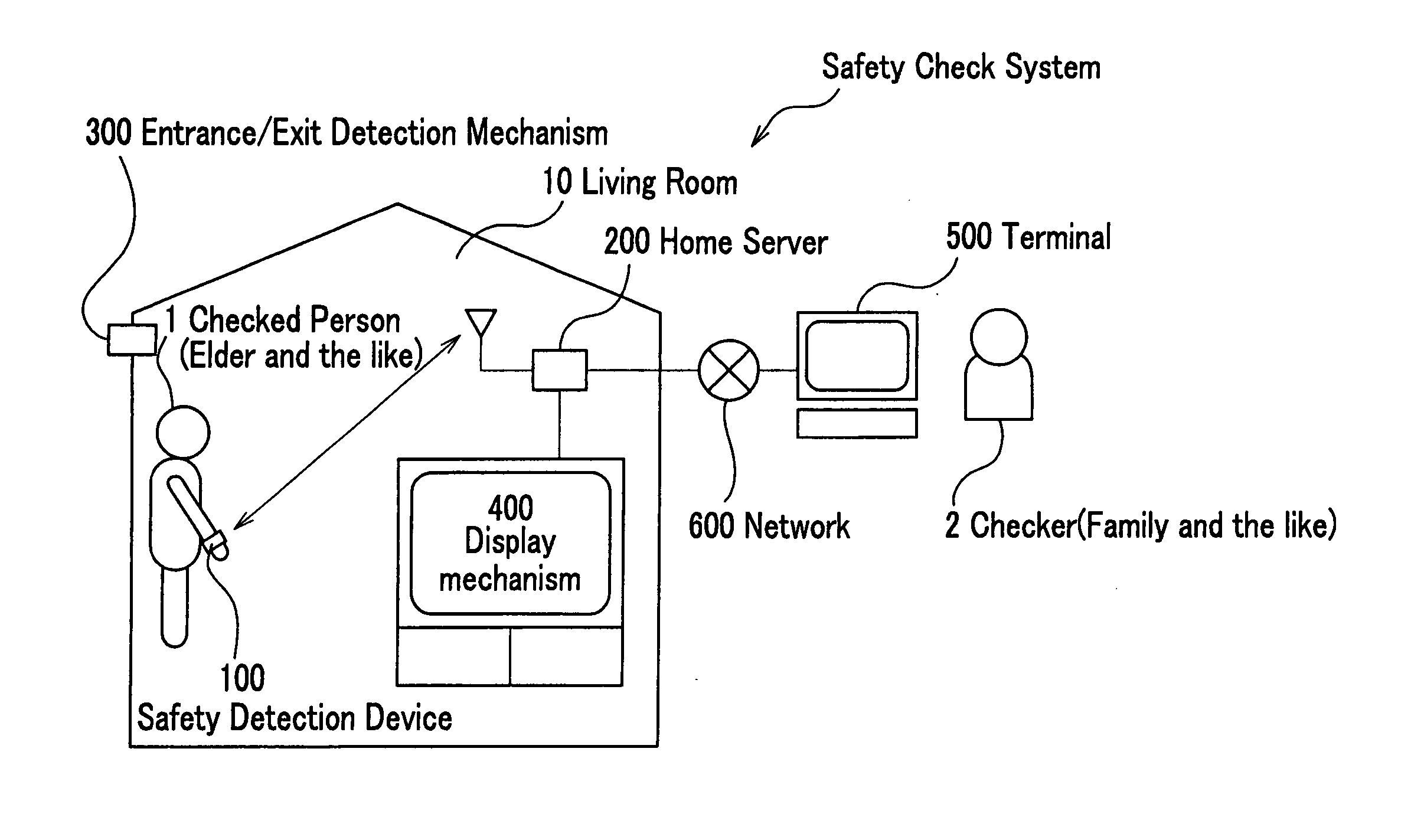
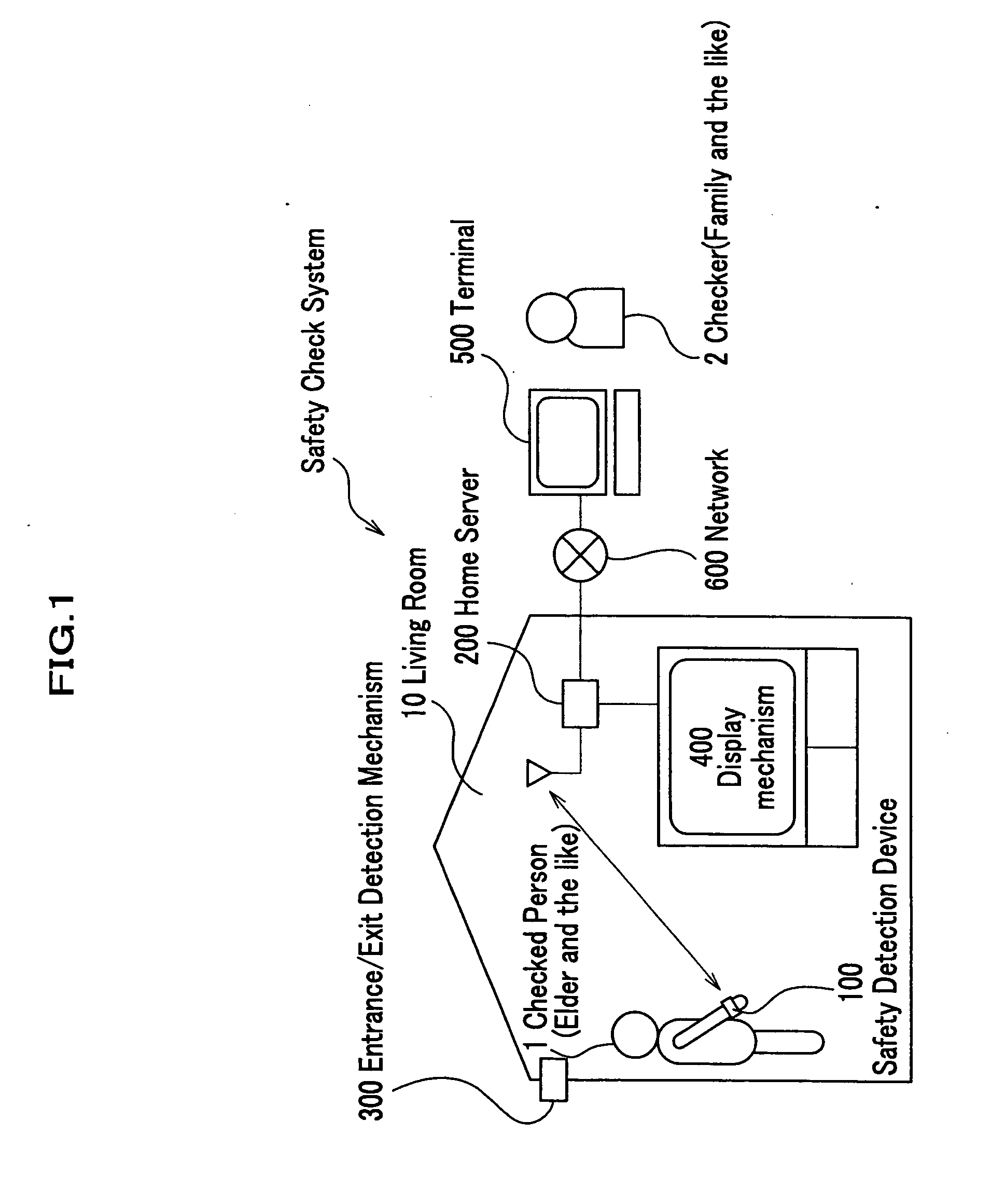
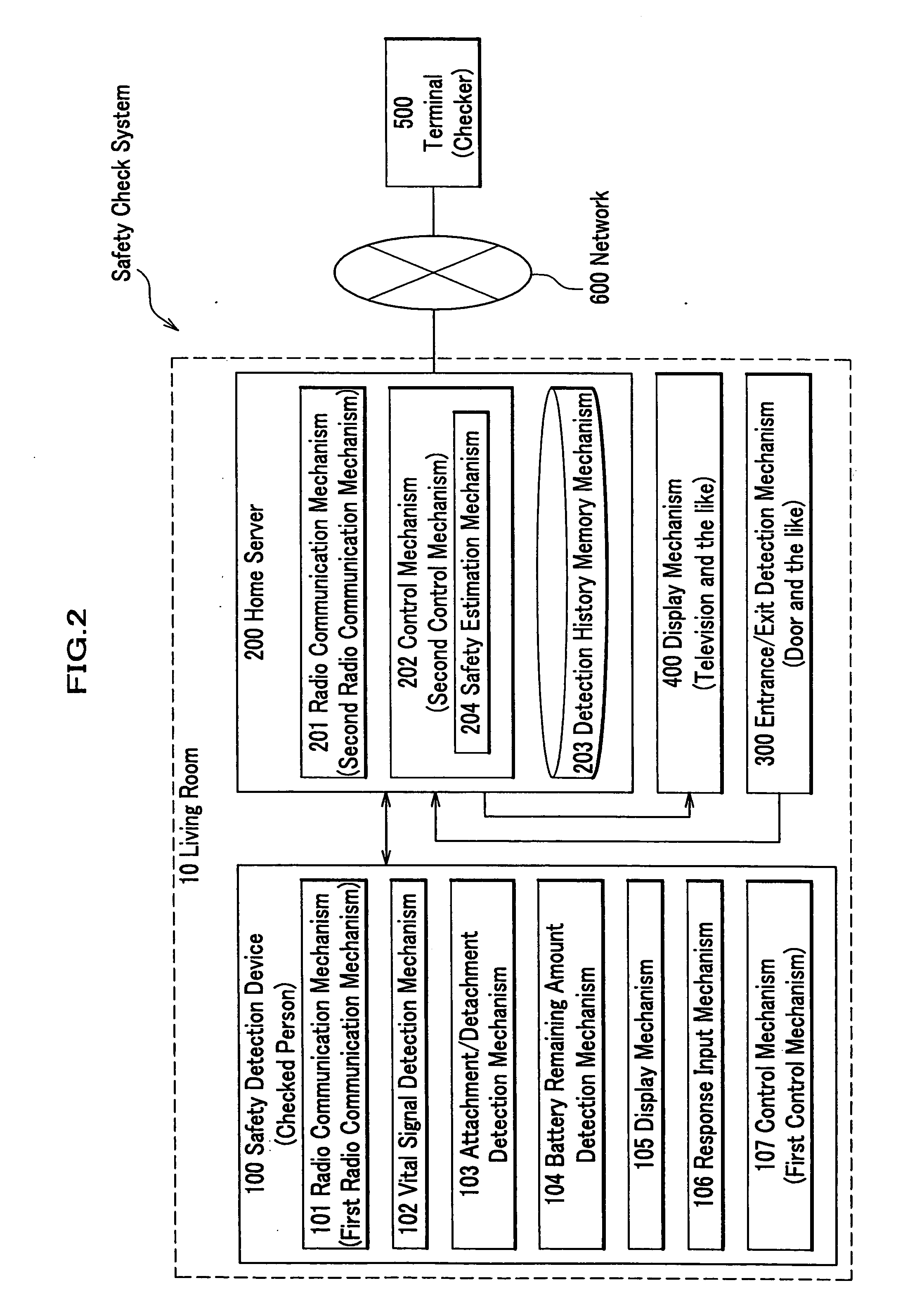
Safety check system, method, and program, and memory medium for memorizing program therefor
A safety check system of the invention is equipped with a safety detection device attached to a body of a checked person, a server for accumulating various pieces of information, and a terminal of a checker for executing a safety check of the checked person, wherein the detection device is equipped with a first radio communication mechanism for making a radio communication with the server, a vital signal detection mechanism for detecting a vital signal of the checked person, and a first control mechanism for creating safety information of the checked person; and the server is equipped with a second radio communication mechanism for making a radio communication with the detection device, a detection history memory mechanism for memorizing a detection history of the checked person, and a second control mechanism for sending the detection history of the checked person in the detection history memory mechanism to the terminal.
Owner:HITACHI LTD
Information record infrastructure, system and method
InactiveUS8380630B2Low costIncrease the number ofDigital data processing detailsTelemedicineSecurity ruleInformation infrastructure
A security mediator, comprising an input configured to receive a user information request; an automated index, stored in a memory, configured to store information for determining which of a plurality of remote databases stores information responsive to the request; an automated security rule base, stored in a memory, containing rules applicable to information responsive to the request stored in the plurality of remote databases; a communication port configured to communicate to a plurality of remote databases which store information responsive to the request: security information, a query corresponding to the request and associated rules applicable to the information responsive to the request at the respective remote database; and at least one processor being configured to apply at least one security rule responsive to the query of the automated security rule base, and index information derived from a plurality of the remote databases, in a manner which permits application of the rules and which restricts insecure use of the index.
Owner:RPX CORP
Method and system for managing computer security information
InactiveUS7089428B2Efficient managementMemory loss protectionDigital data processing detailsInternet trafficSafety management systems
A security management system includes a fusion engine which “fuses” or assembles information from multiple data sources and analyzes this information in order to detect relationships between raw events that may indicate malicious behavior and to provide an organized presentation of information to consoles without slowing down the processing performed by the data sources. The multiple data sources can comprise sensors or detectors that monitor network traffic or individual computers or both. The sensors can comprise devices that may be used in intrusion detection systems (IDS). The data sources can also comprise firewalls, audit systems, and other like security or IDS devices that monitor data traffic in real-time. The present invention can identify relationships between one or more real-time, raw computer events as they are received in real-time. The fusion engine can also assess and rank the risk of real-time raw events as well as mature correlation events.
Owner:INT BUSINESS MASCH CORP
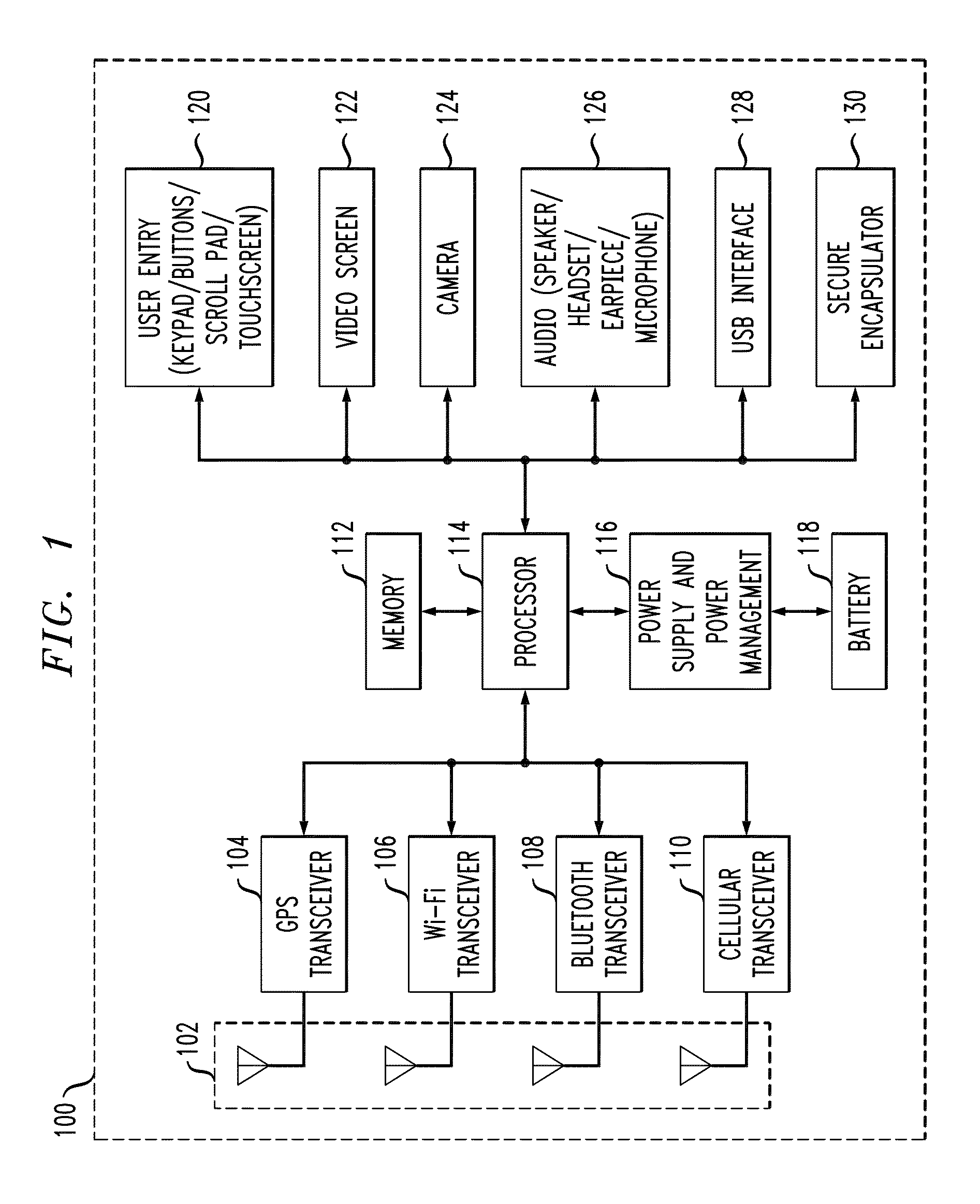
Method and system for improving client server transmission over fading channel with wireless location and authentication technology via electromagnetic radiation
InactiveUS7647024B2Facilitate communicationImprove efficiencyUnauthorised/fraudulent call preventionEavesdropping prevention circuitsAuthentication serverElectromagnetic radiation
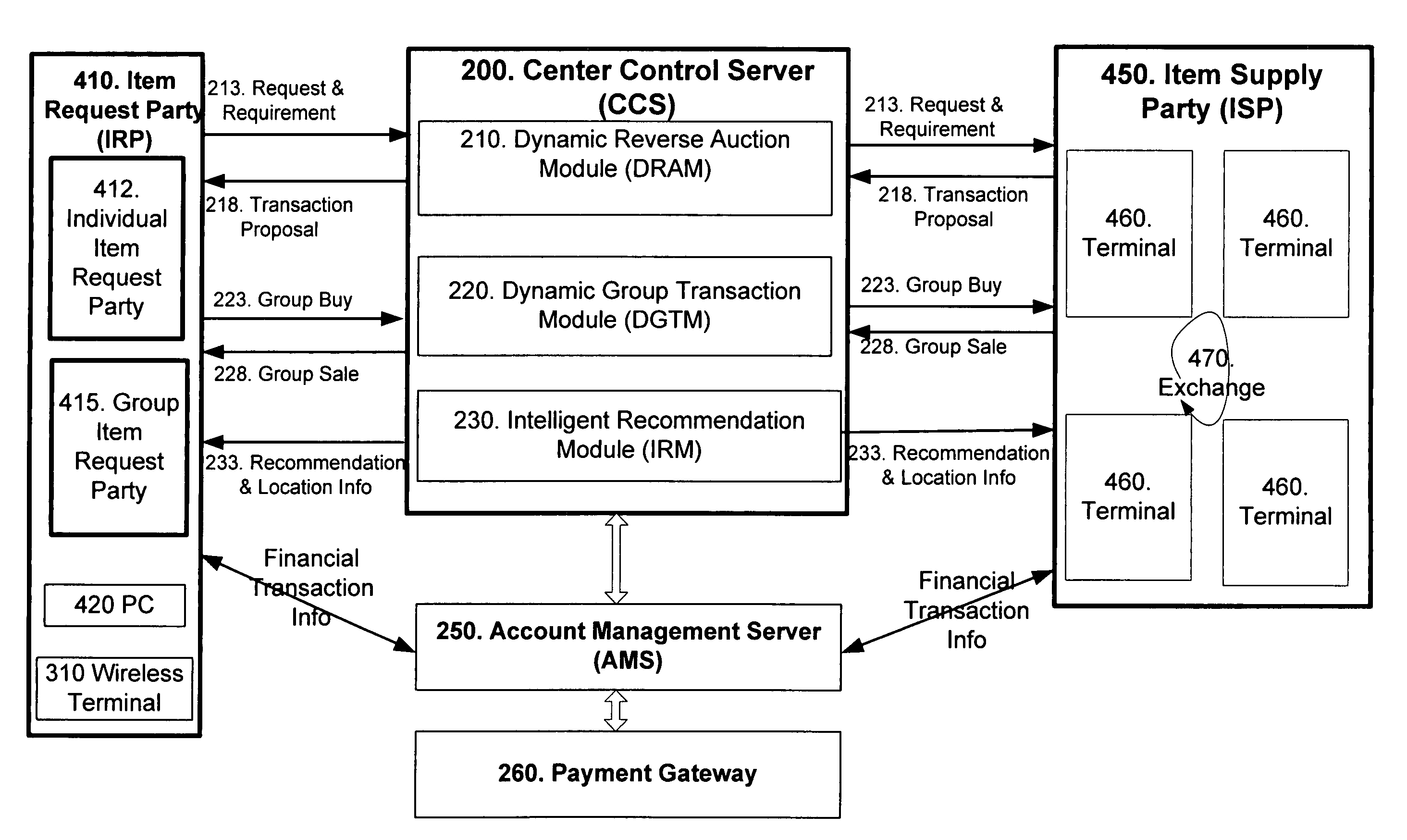
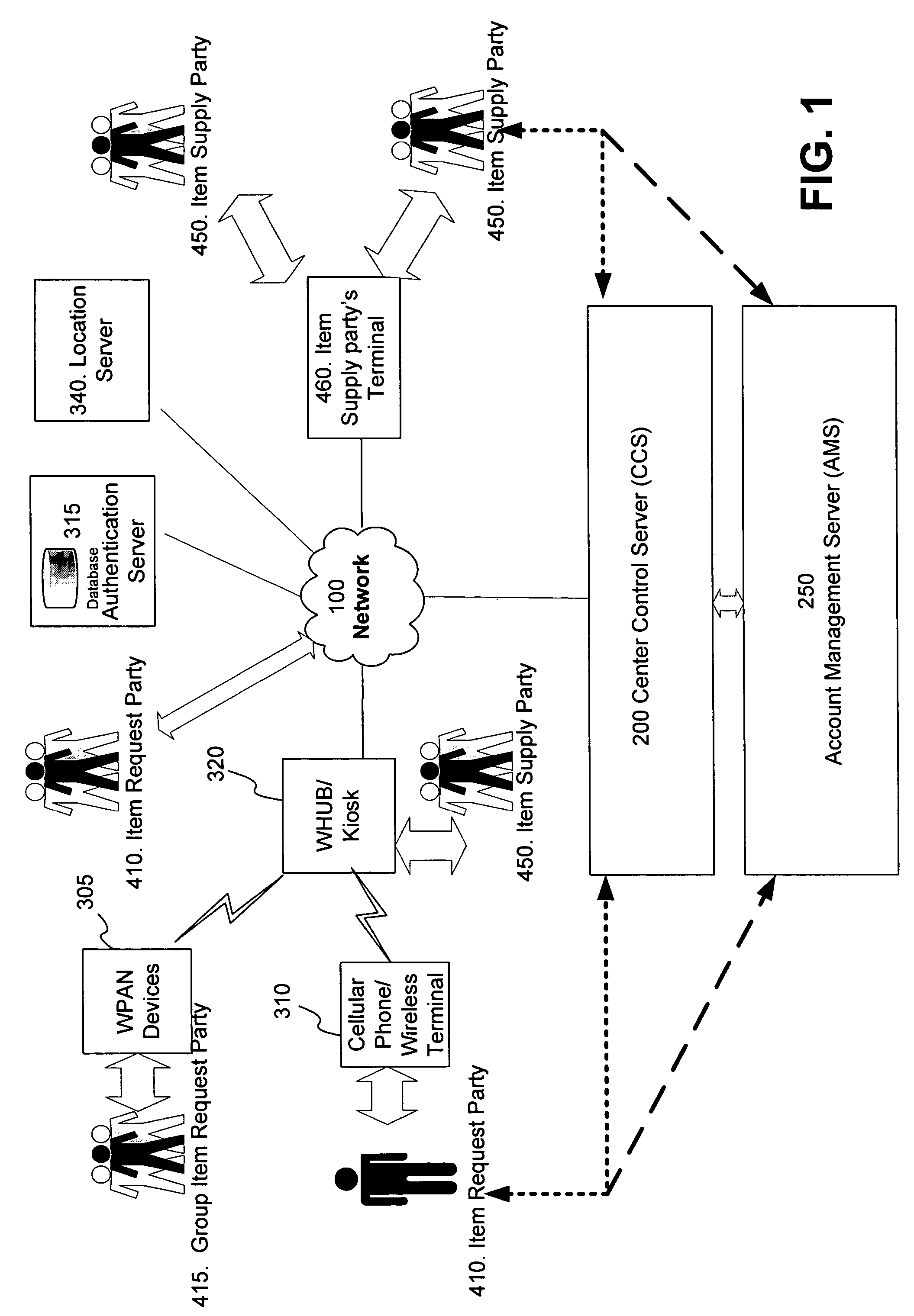
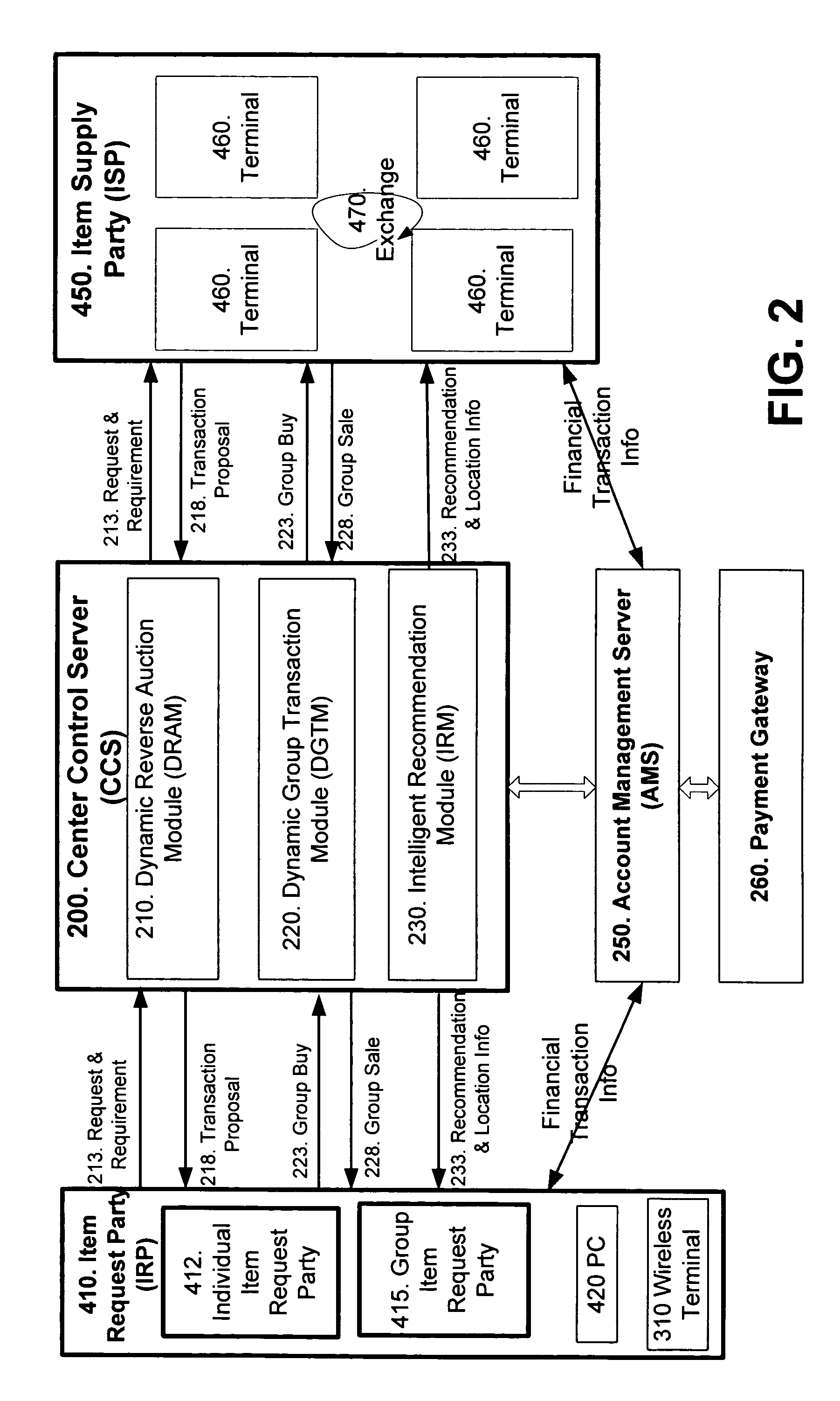
Wireless personal area network (Zigbee, Bluetooth, UWB) and wireless identification technologies (Near Field Communication (NFC), Radio Frequency Identification (RFID)) are implemented in particular client server functions and communications. Connected with an Authentication Server, a wireless HUB authenticates user identification and provides the user with access to secure data communication with a wireless terminal such as a cellular phone or a PDA. A Location Server provides user locations via methods such as RSSI, TDOA, and GPS and sends location information to a Center Control Server and the Authentication Server. With location information, the Center Control Server initiates and optimizes secure information processes and coordinates the functions of servers and user terminals.
Owner:INNOVATION SCI LLC
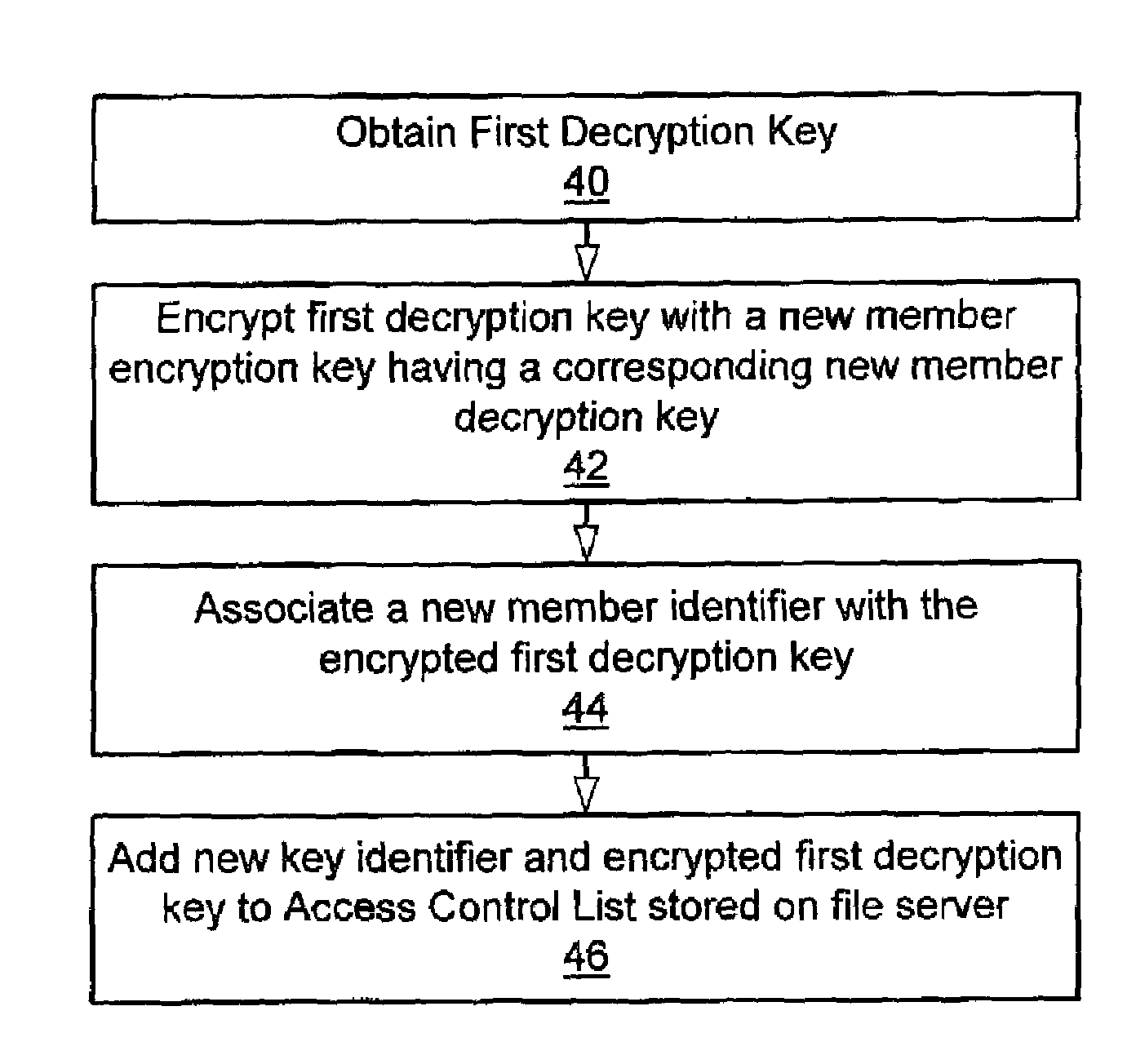
Method and apparatus for using non-secure file servers for secure information storage
InactiveUS7178021B1Safe storageEasy accessKey distribution for secure communicationPublic key for secure communicationClient-sideData storing
A method and apparatus for utilizing a non-secure file server for storing and sharing data securely only among clients and groups authorized to read and modify the data. A first client that desires to store data on the file server encrypts the data with a first encryption key having an associated first decryption key. The client encrypts the first decryption key with a second encryption key having an associated second decryption key known to the first client. Additionally, the first decryption key is encrypted with respective encryption keys of other clients or groups intended to have access to the data stored on the file server and the clients and groups retain their respective decryption keys. All of the encrypted first decryption keys are stored within an access control list in association with the encrypted data on the non-secure file server. In response to an indication that the data should be transmitted to one of the clients, the file server returns to the client the encrypted data along with at least the applicable encrypted first decryption key for the respective client. The client is able to decrypt the first decryption key and decrypt the data using the unencrypted first decryption key. The data may then be modified and securely stored on the file server as described above. The first decryption key may also be encrypted with a second encryption key having a second decryption key known to members of a group or a group server. The first encryption key encrypted with the group second encryption key is stored in the access control list so that group members can obtain access to the encrypted data stored on the file server.
Owner:ORACLE INT CORP
Mobile key using read/write RFID tag
ActiveUS20050242921A1Lessening and even eliminating needEasy to updateElectric signal transmission systemsMultiple keys/algorithms usageBiometric dataAuthorization
A mobile key includes an RFID tag associated with a memory. The memory holds a secure access code. An authorization status for a person or item associated with the mobile key is determined by interrogating the mobile key using an RFID interrogation field. Security information, such as a secure identifier or access code, physical measurement data, or biometric data may be provided by the mobile key. The key may also comprise a wireless communication device, such as a cellular telephone. Security information, such as an access code, may be provided to the key using the wireless communication device or other communications network.
Owner:INTERMEC IP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com