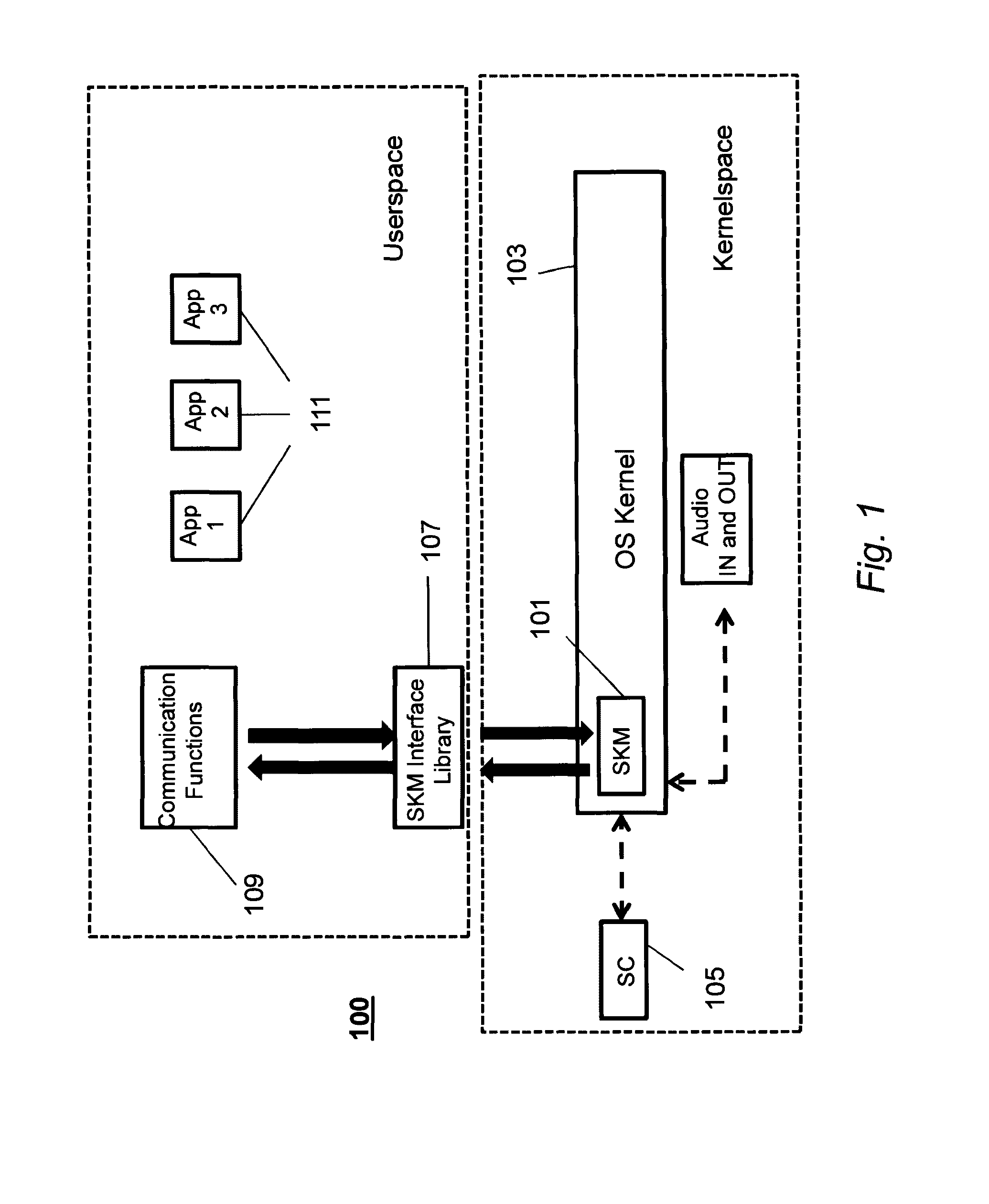
Patents
Literature
103 results about "Secure voice" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
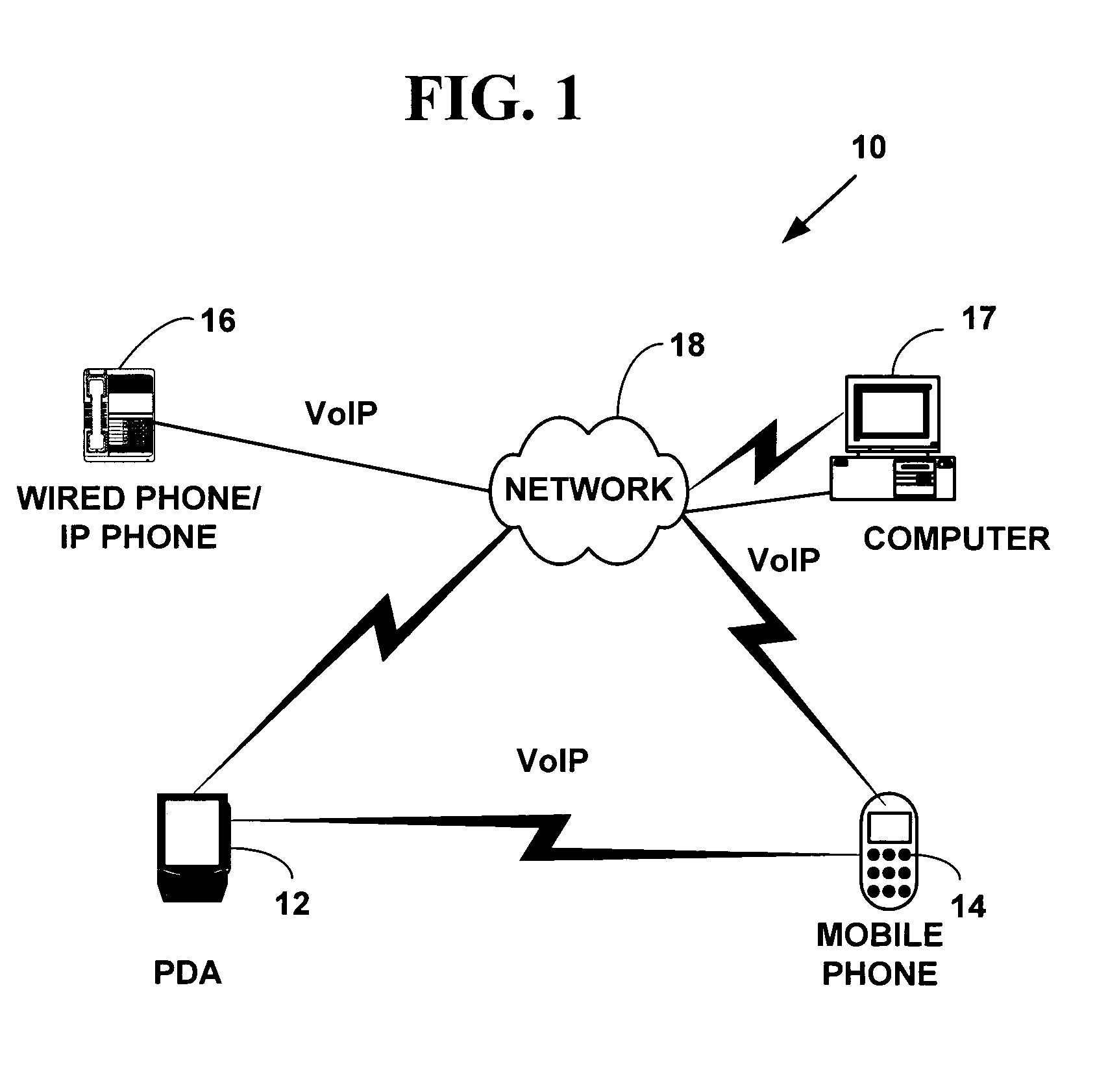
Secure voice (alternatively secure speech or ciphony) is a term in cryptography for the encryption of voice communication over a range of communication types such as radio, telephone or IP.
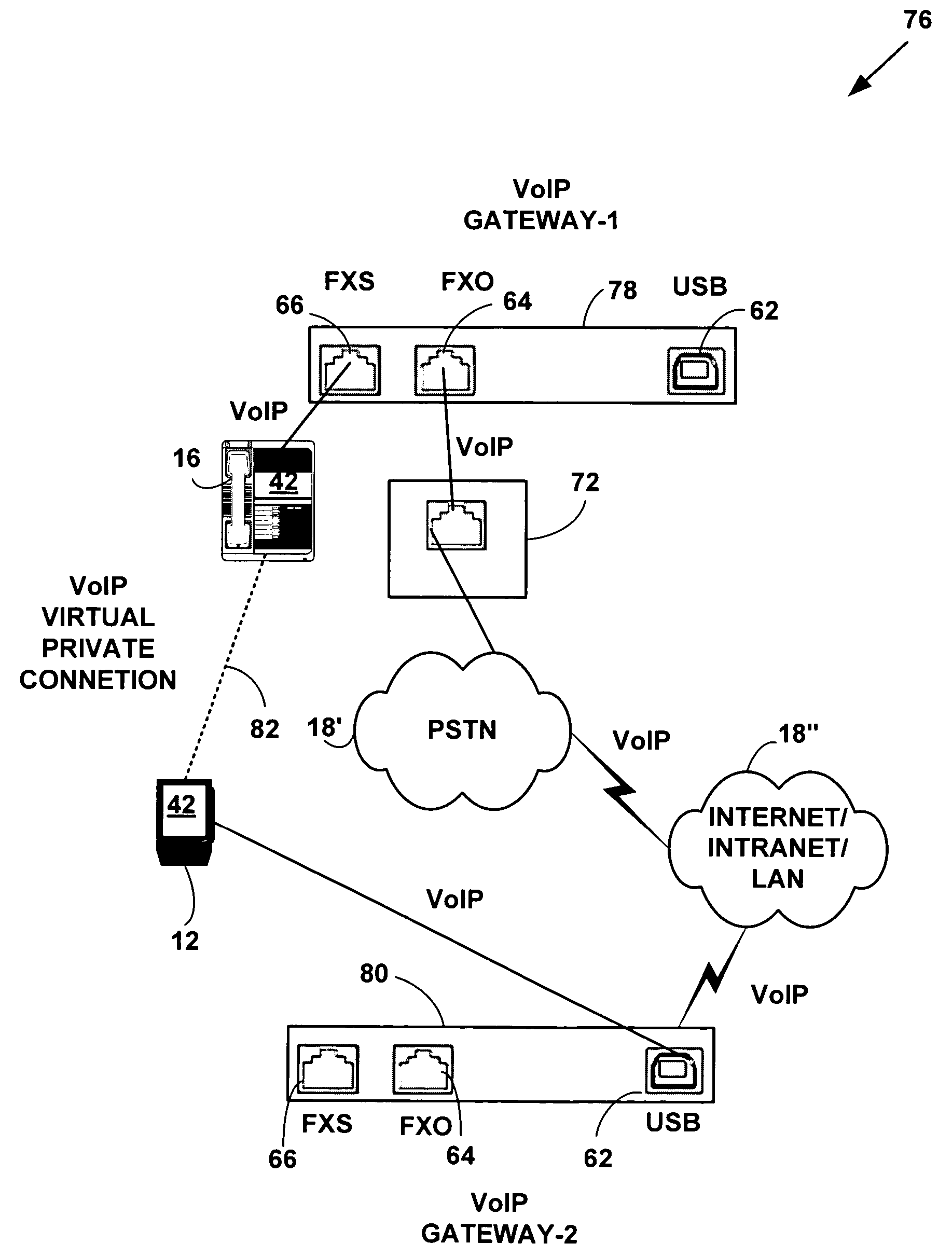
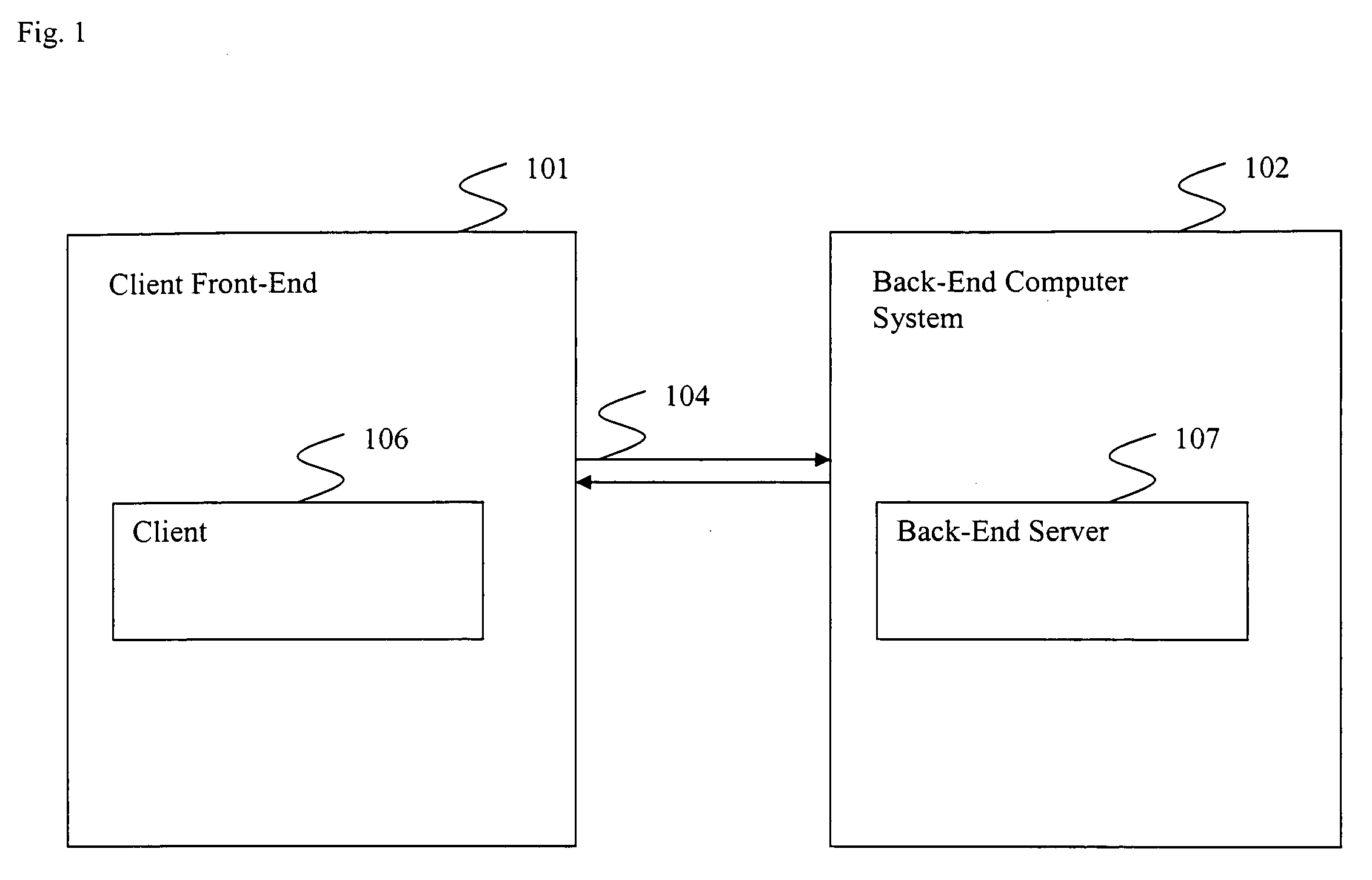
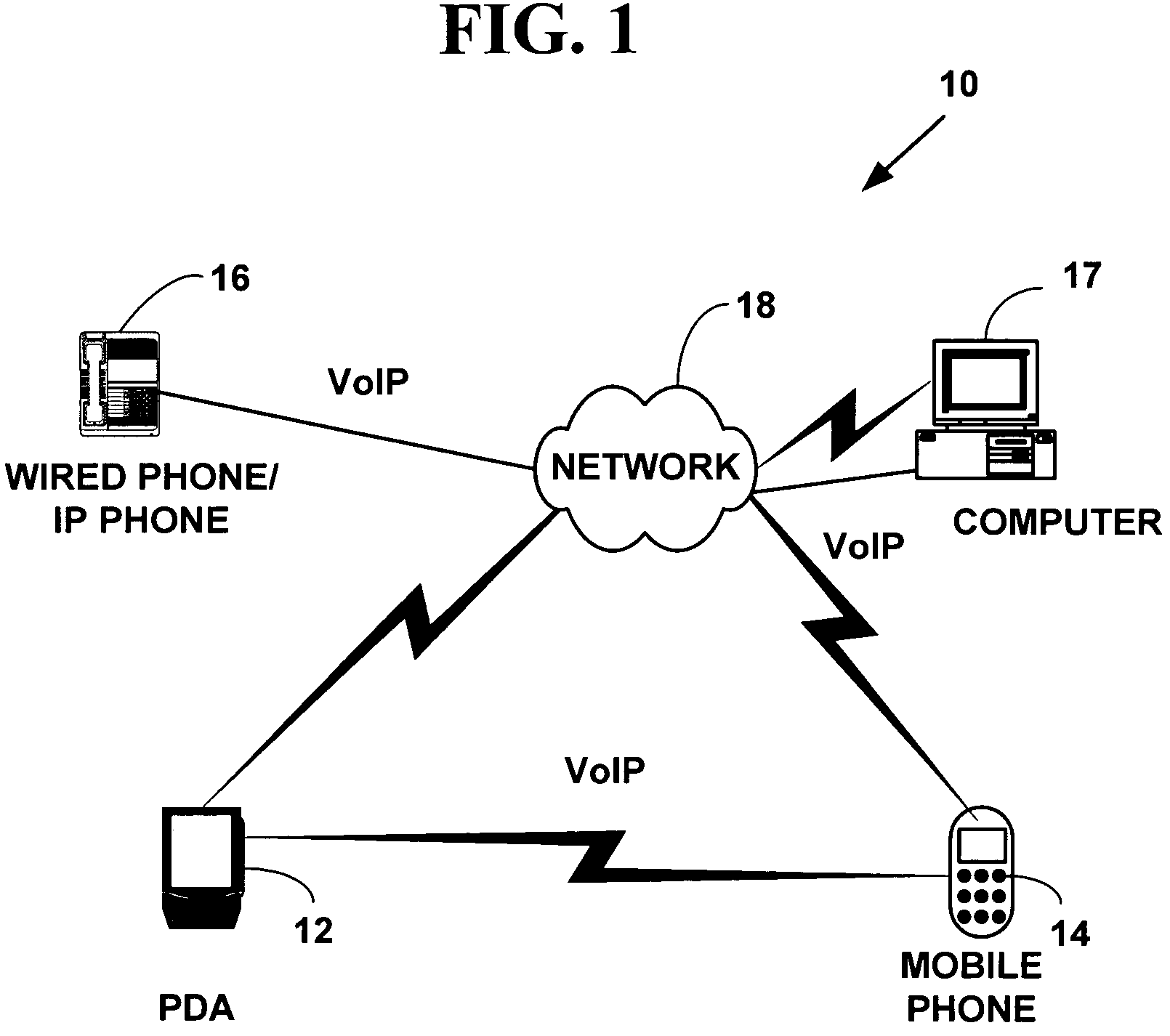
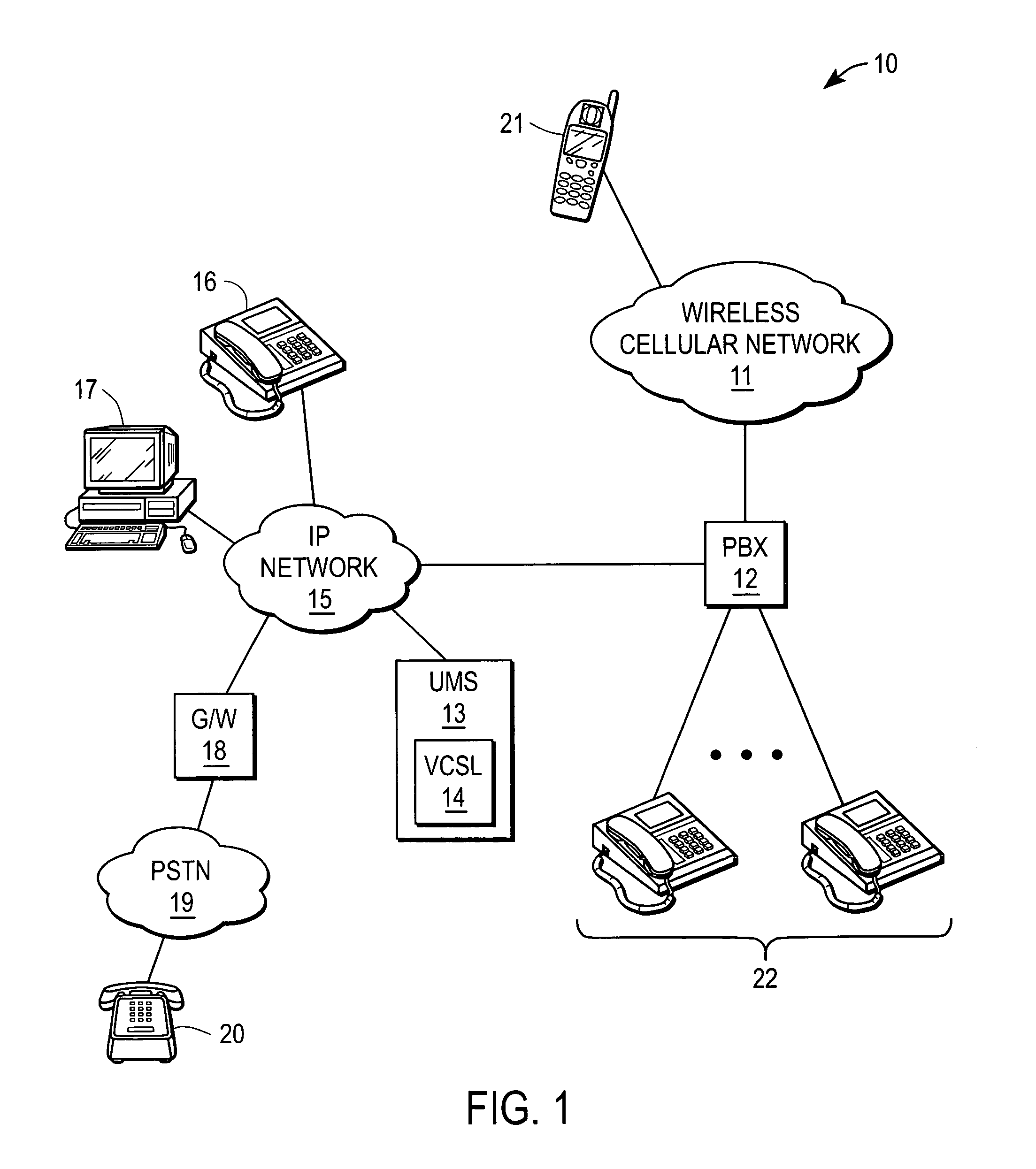
Method and system for providing private virtual secure Voice over Internet Protocol communications
InactiveUS20060187900A1Maintain privacyInterconnection arrangementsFrequency-division multiplex detailsVoice communicationPrivate network
A method and system for secure Voice over Internet Protocol (IP) (VoIP) communications. The method and system provide secure VoIP voice calls, video, Instant Messaging (IM), Short Message Services (SMS), or Peer-to-Peer (P2P) communications while maintaining privacy over the Internet and other communications networks such as the pubic switched telephone network (PSTN) to and from any network device through a virtual private network infrastructure interconnecting private VoIP network devices. The method and system allow a network device to function as an IP private branch exchange (PBX) or a private VoIP gateway and provide and control VoIP voice communications without using other public or private VoIP gateways or VoIP servers or devices on a communications network such as the PSTN or the Internet.
Owner:LESAVICH HIGH TECH LAW GRP SC
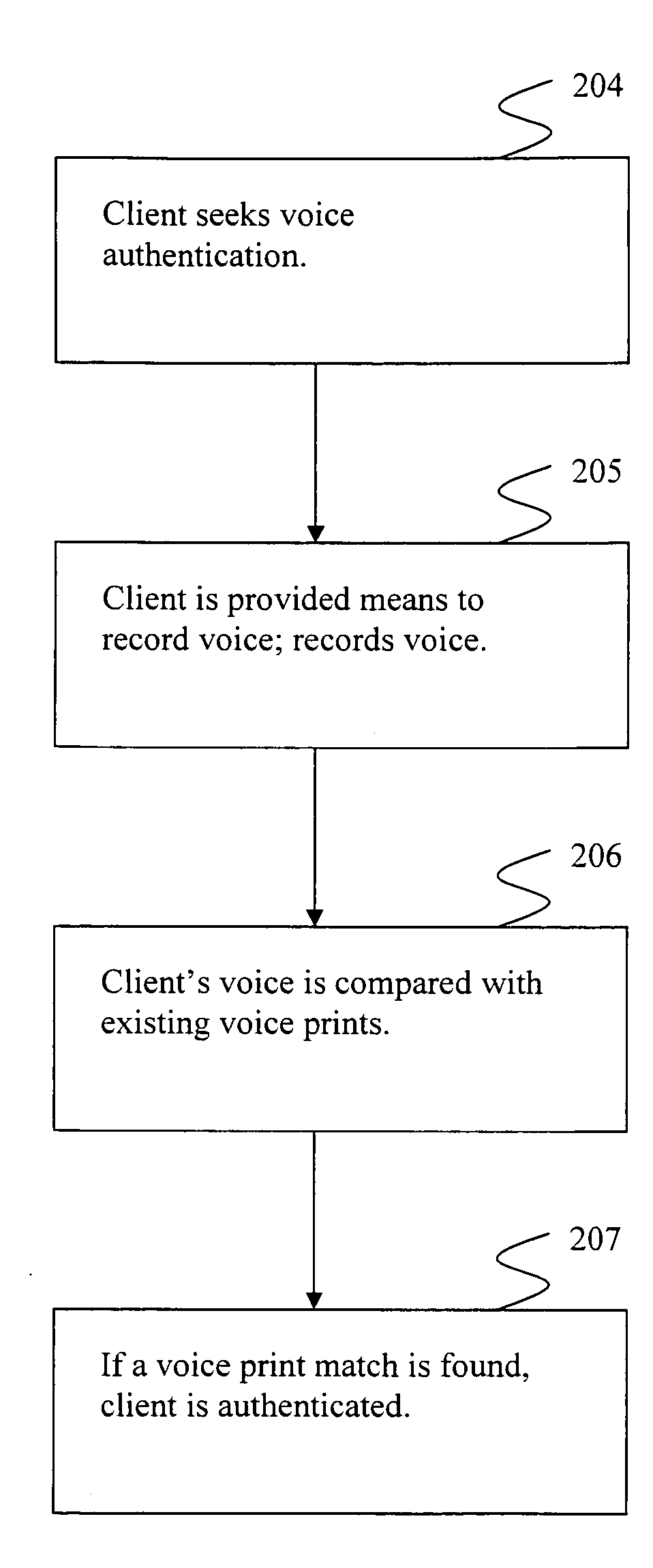
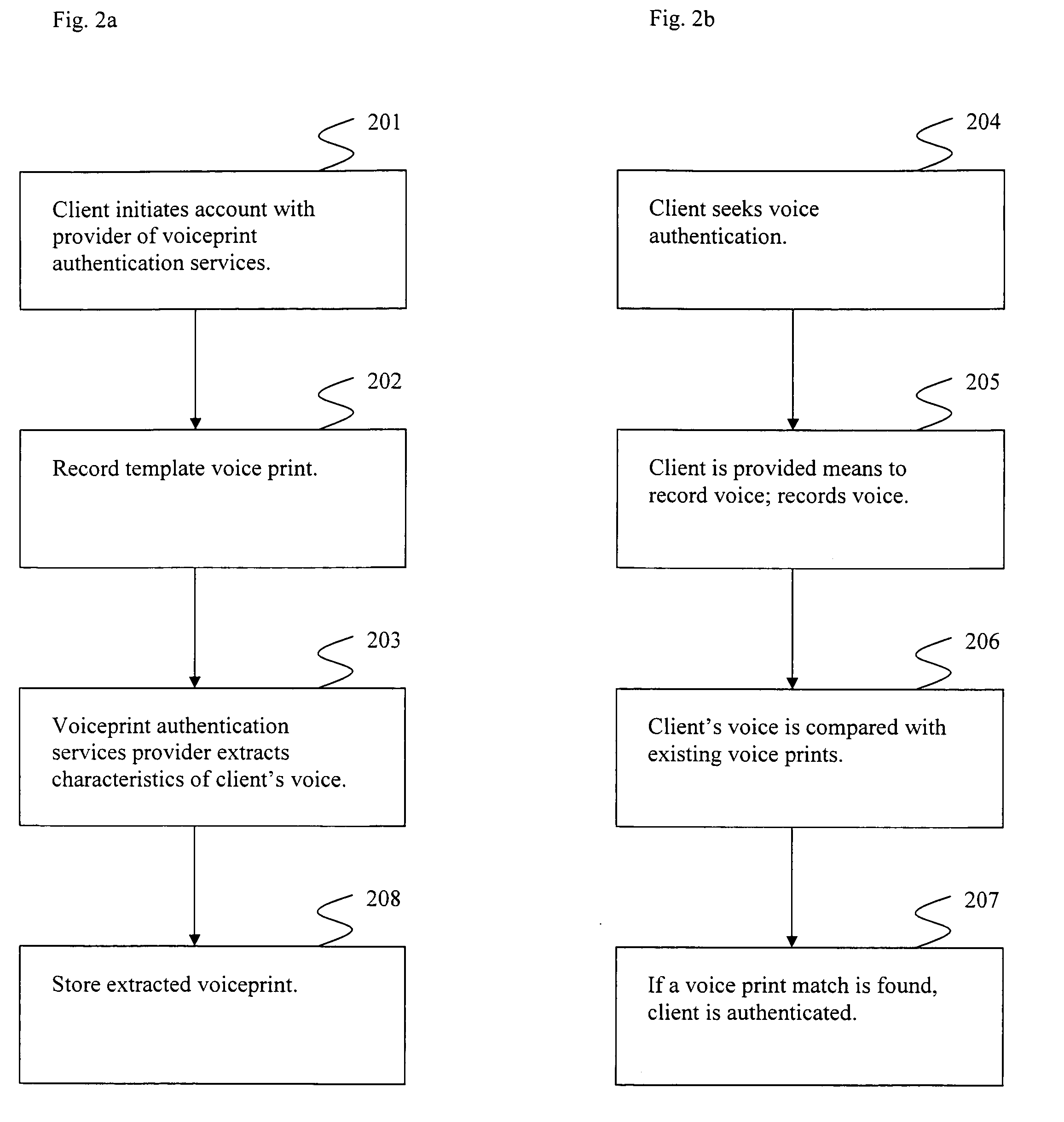
Voice print identification portal
InactiveUS20080256613A1Digital data processing detailsMultiple digital computer combinationsSecure voiceSpeech identification
Systems and methods providing for secure voice print authentication over a network are disclosed herein. During an enrollment stage, a client's voice is recorded and characteristics of the recording are used to create and store a voice print. When an enrolled client seeks access to secure information over a network, a sample voice recording is created. The sample voice recording is compared to at least one voice print. If a match is found, the client is authenticated and granted access to secure information.Systems and methods providing for a dual use voice analysis system are disclosed herein. Speech recognition is achieved by comparing characteristics of words spoken by a speaker to one or more templates of human language words. Speaker identification is achieved by comparing characteristics of a speaker's speech to one or more templates, or voice prints. The system is adapted to increase or decrease matching constraints depending on whether speaker identification or speaker recognition is desired.
Owner:VOICEIT TECH
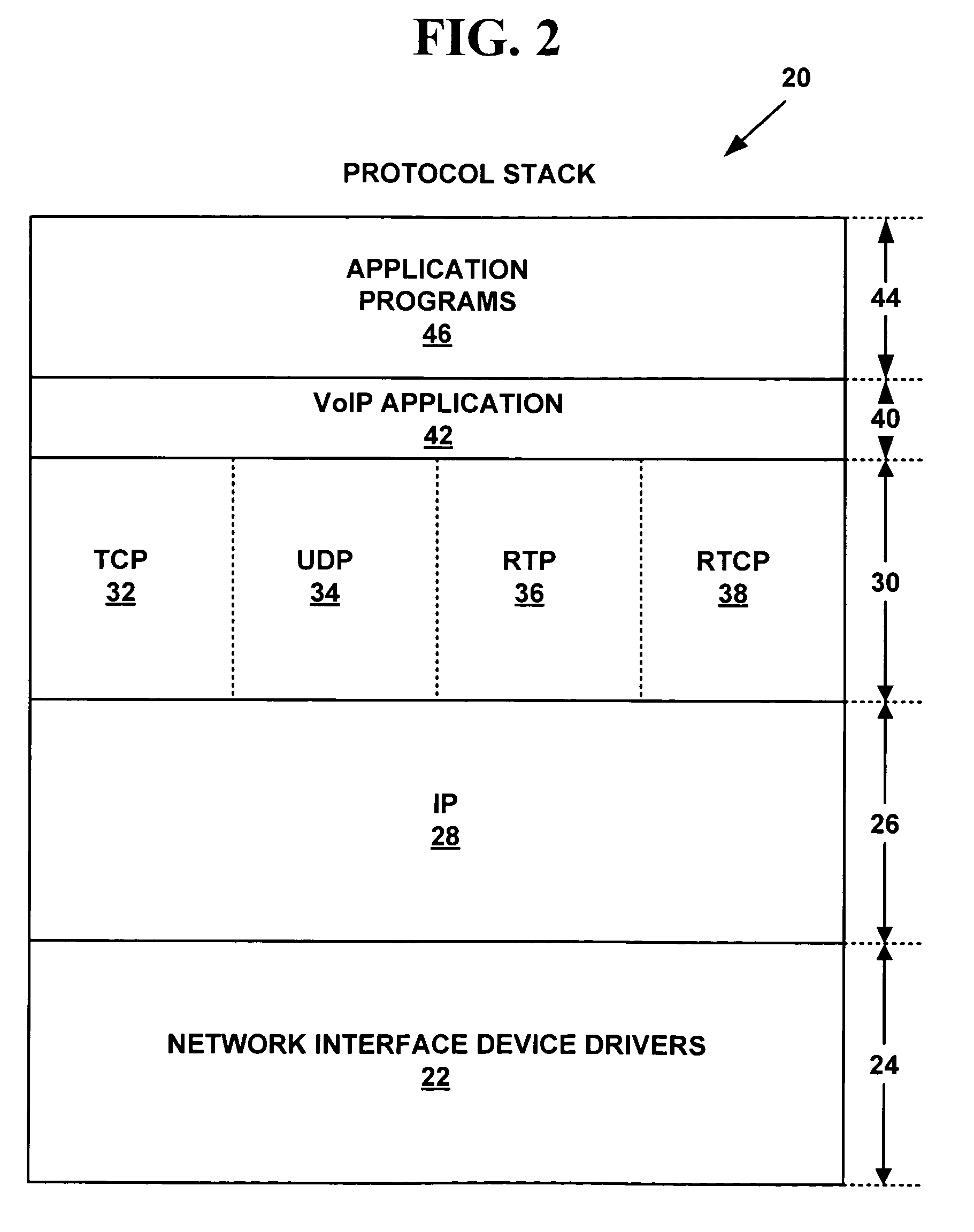
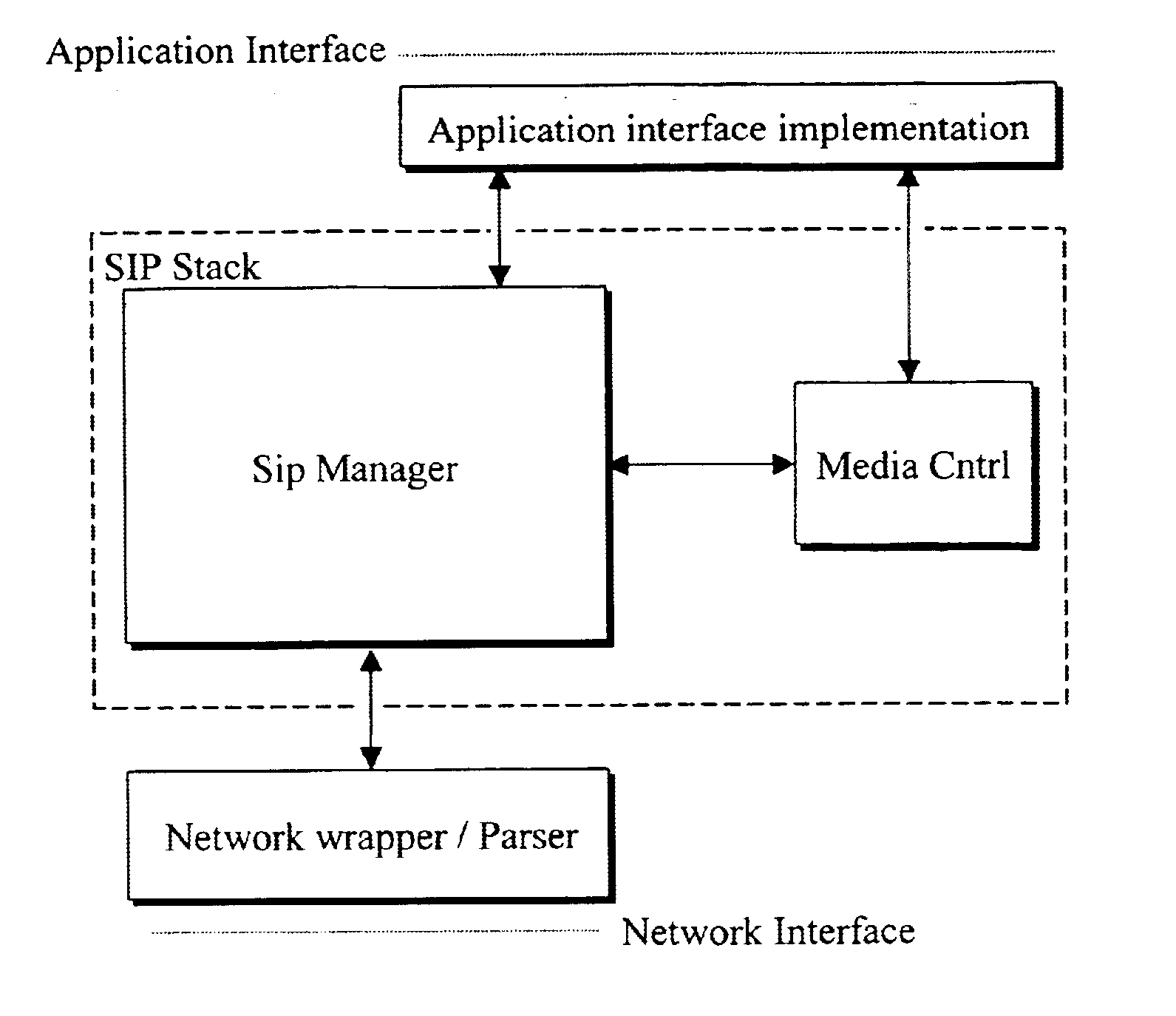
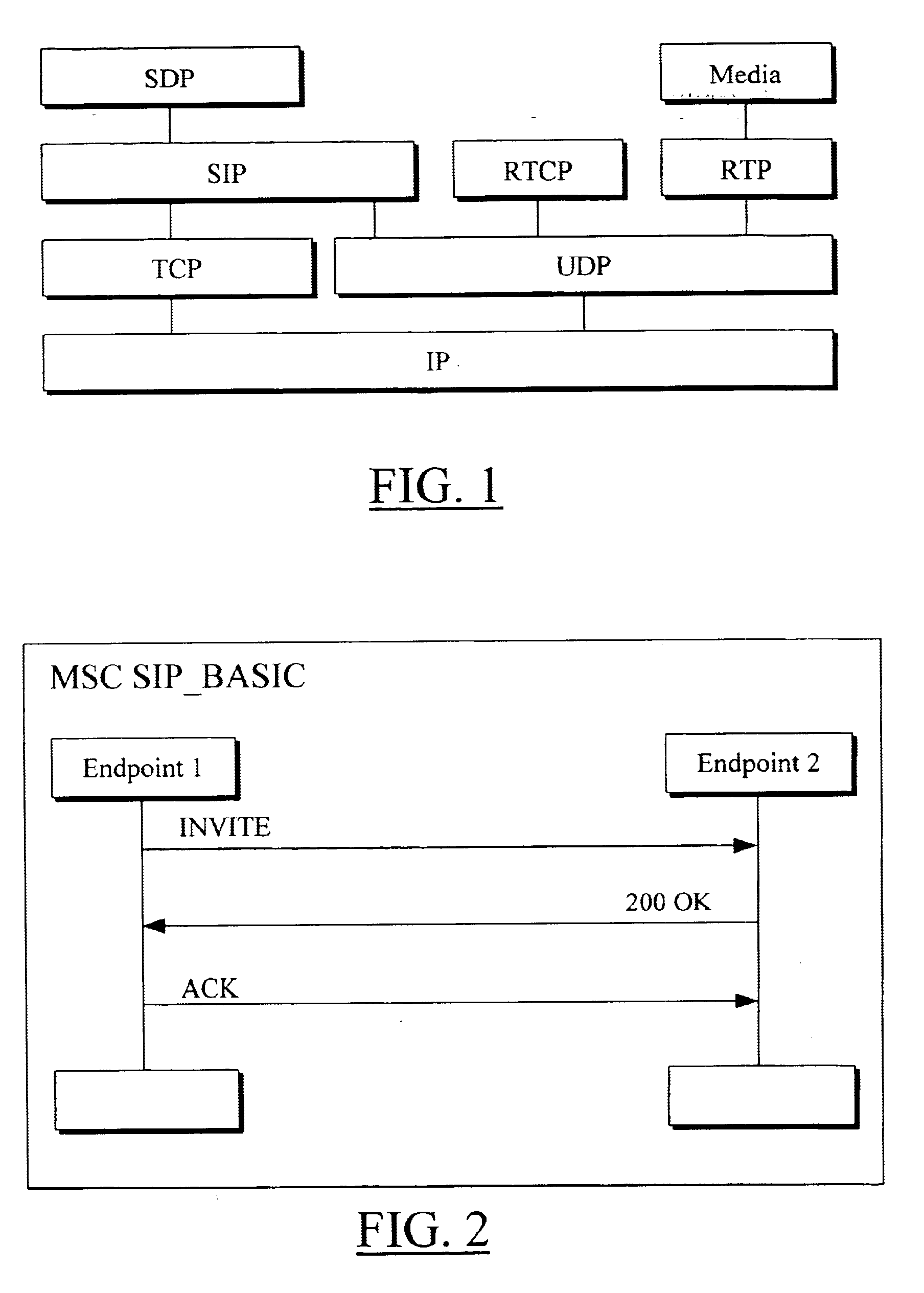
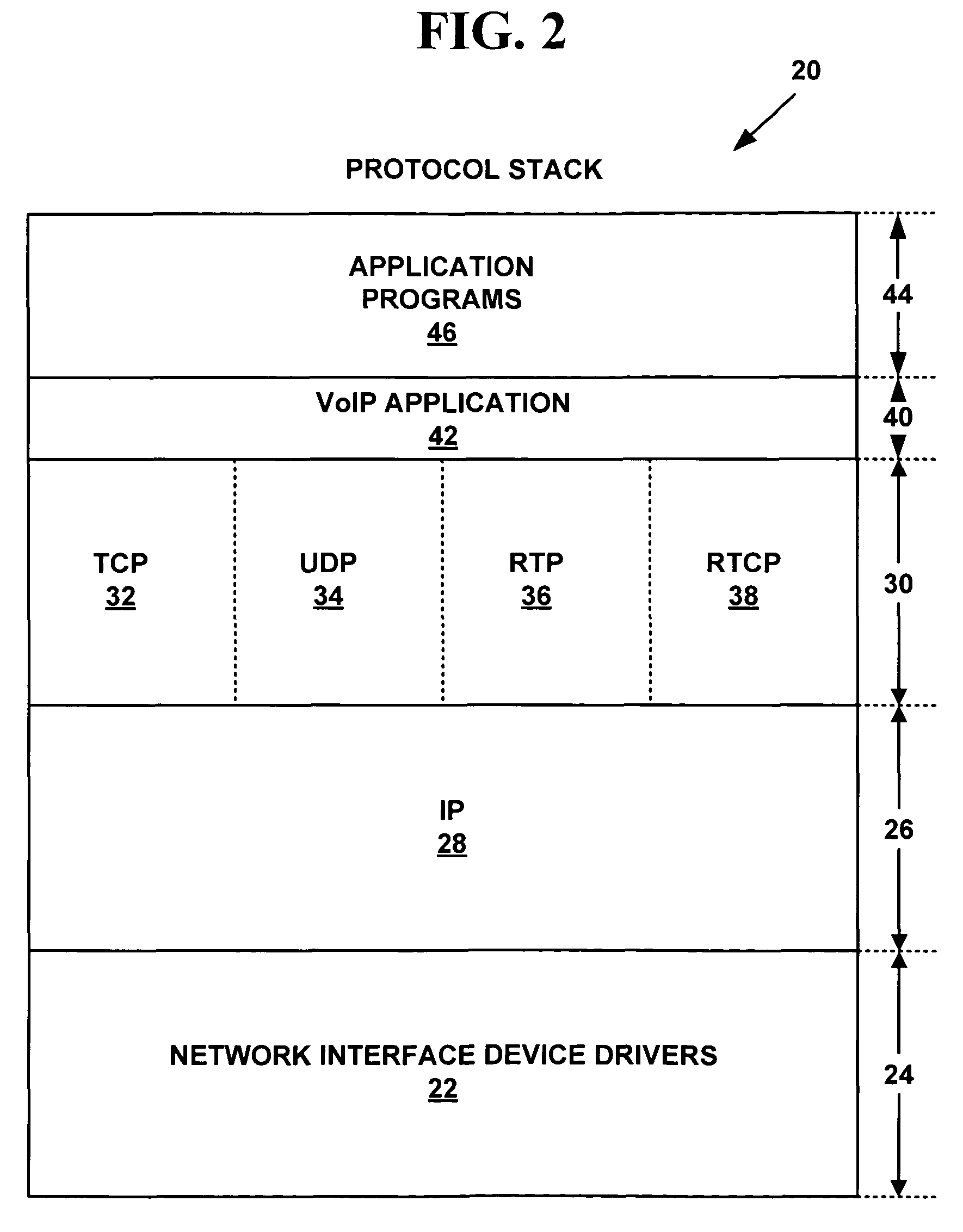
VoIP terminal security module, SIP stack with security manager, system and security methods
InactiveUS6865681B2Interconnection arrangementsUser identity/authority verificationModularitySecure voice
A secure voice over internet protocol (VoIP) terminal includes a modular security manager for use in conjunction with a protocol stack thereof, wherein the security manager includes a plurality of interfaces to the stack. In an SIP embodiment, these may include a security stack interface (SSA) between an SIP manager of an SIP stack and the security manager, a security terminal interface (SST) between a telephony application and the security manager, a security media interface (SSM) between the security manager and a media controller, and a security manager application interface (SMA) between the security manager and a security application (PGP) outside the stack.
Owner:NOKIA TECHNOLOGLES OY
Securing Voice over IP traffic
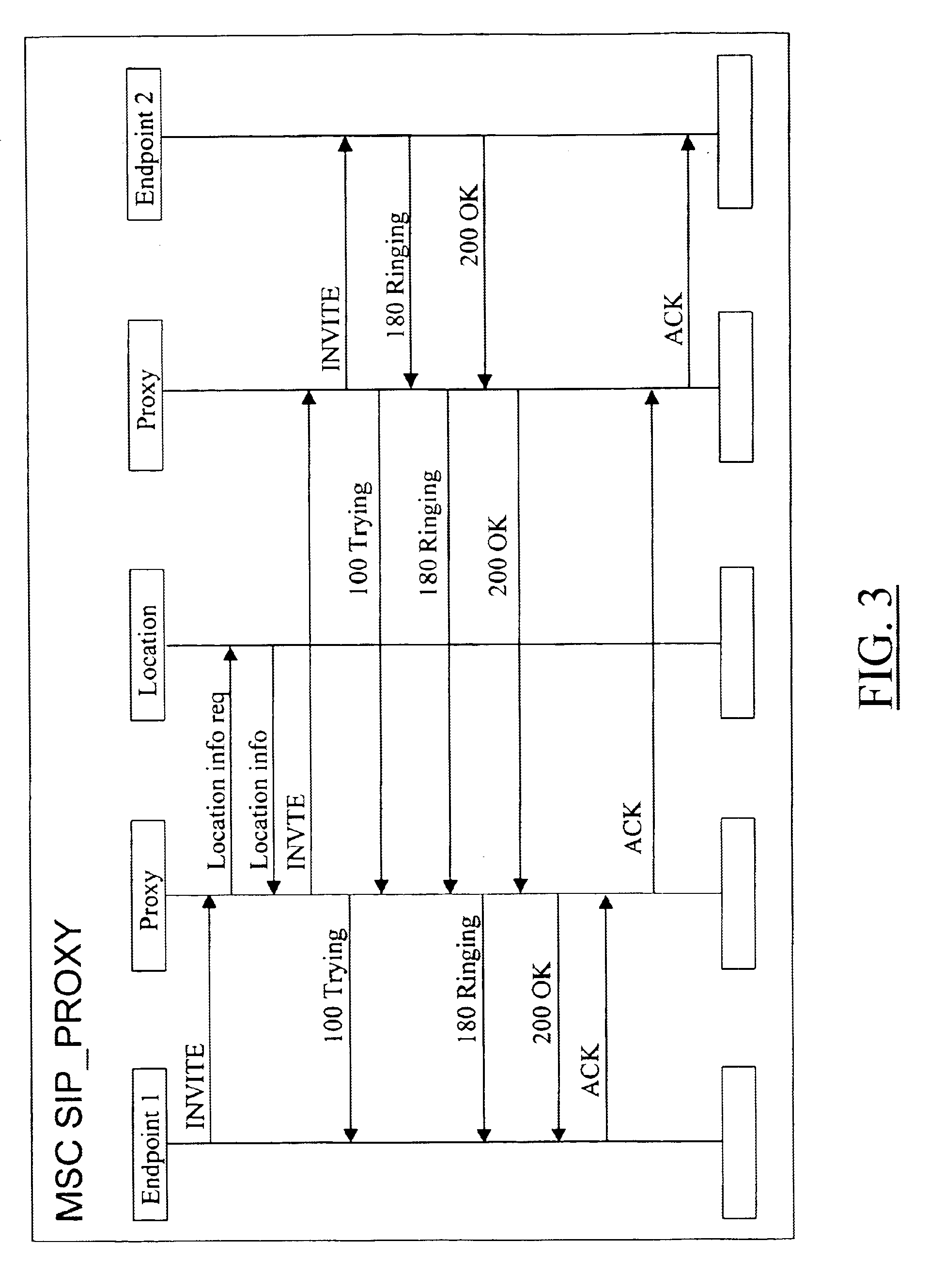
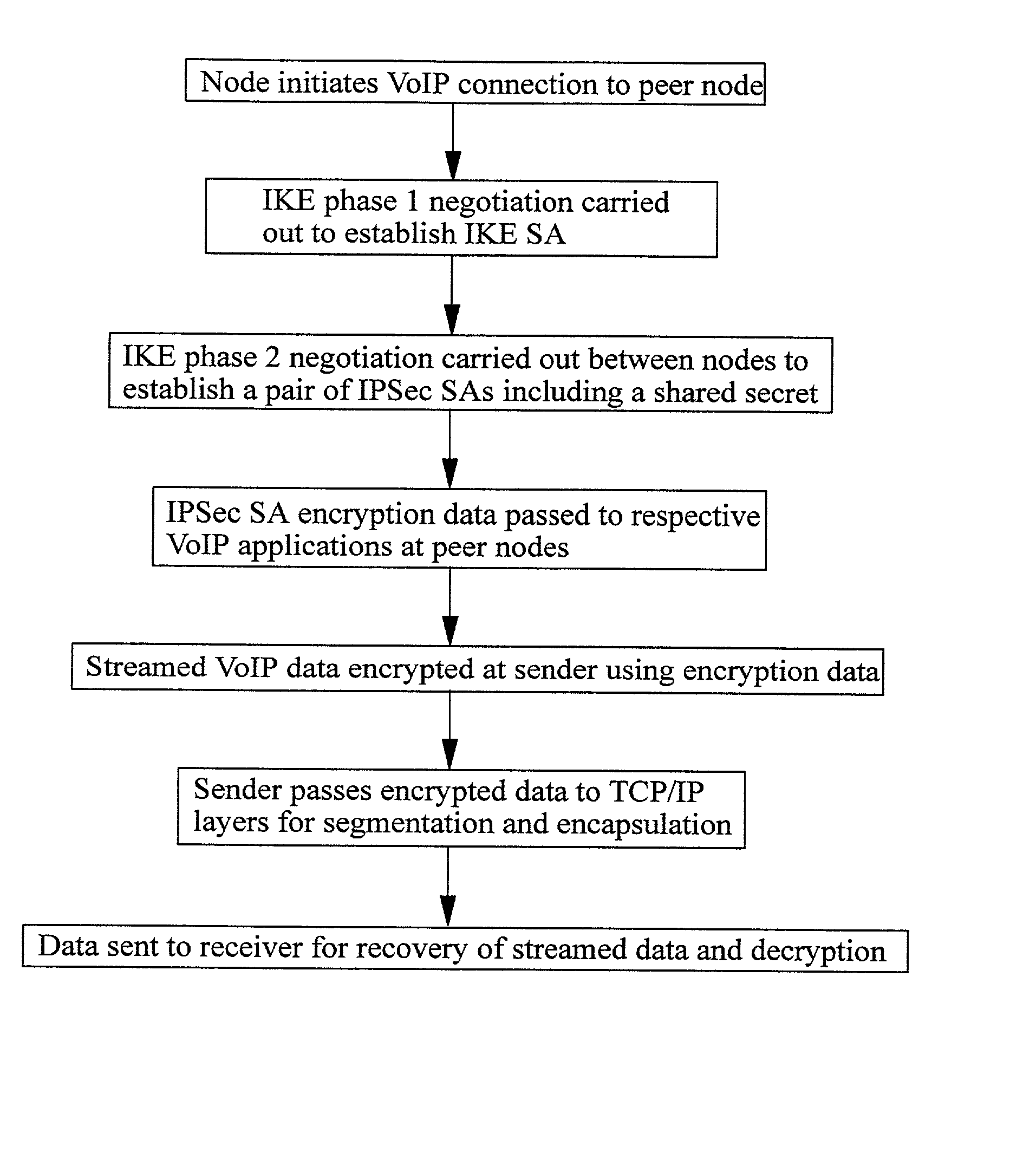
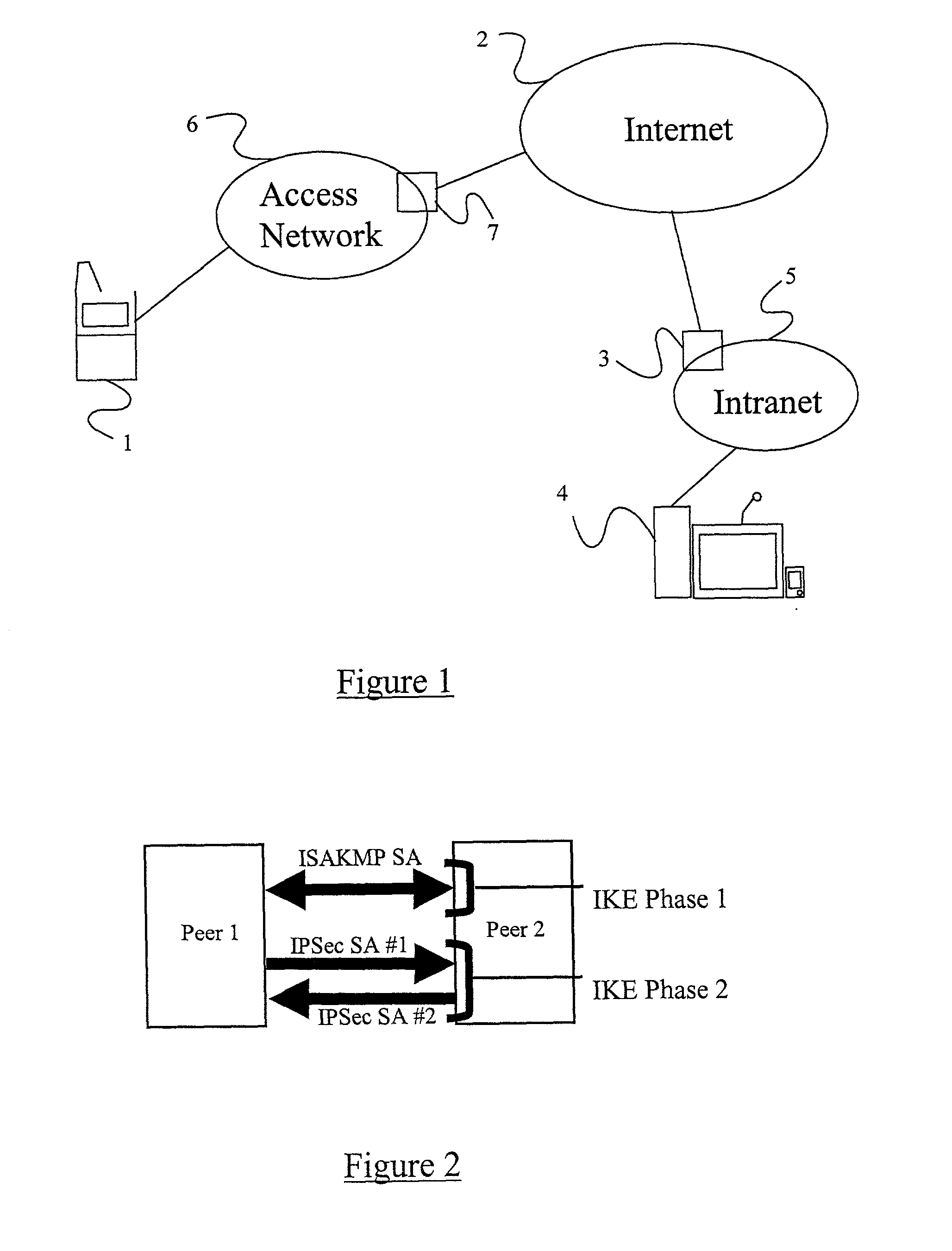
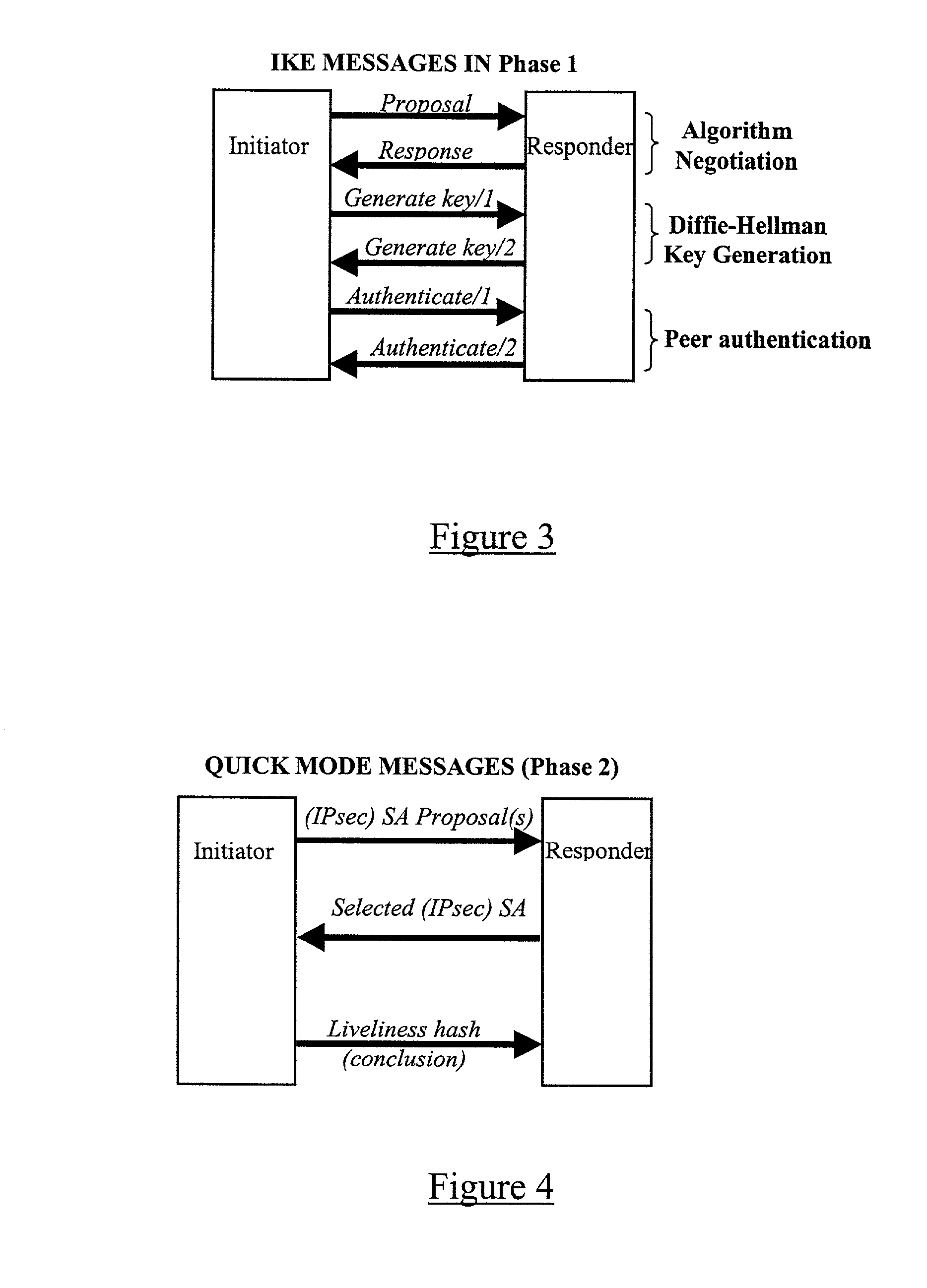
A method of sending streamed data over an IP network from a first node 1 to a second node 4, the method comprising using Internet Key Exchange (IKE) to establish an IKE security association (SA) between the first and second nodes 1,4. A shared secret is established between the first and second nodes using the IKE SA, and the streamed data encrypted at the first node 1 with a cipher using the shared secret or a key derived using the shared secret. IP datagrams are constructed containing in their payload, segments of the encrypted streamed data, the datagrams not including an IPSec header or headers. The IP datagrams are then sent from the first node 1 to the second node 4.
Owner:TELEFON AB LM ERICSSON (PUBL)
PCS pocket phone/microcell communication over-air protocol
InactiveUS6532365B1Extend battery lifeSpatial transmit diversityError detection/prevention using signal quality detectorMobile Telephone ServiceSecure voice
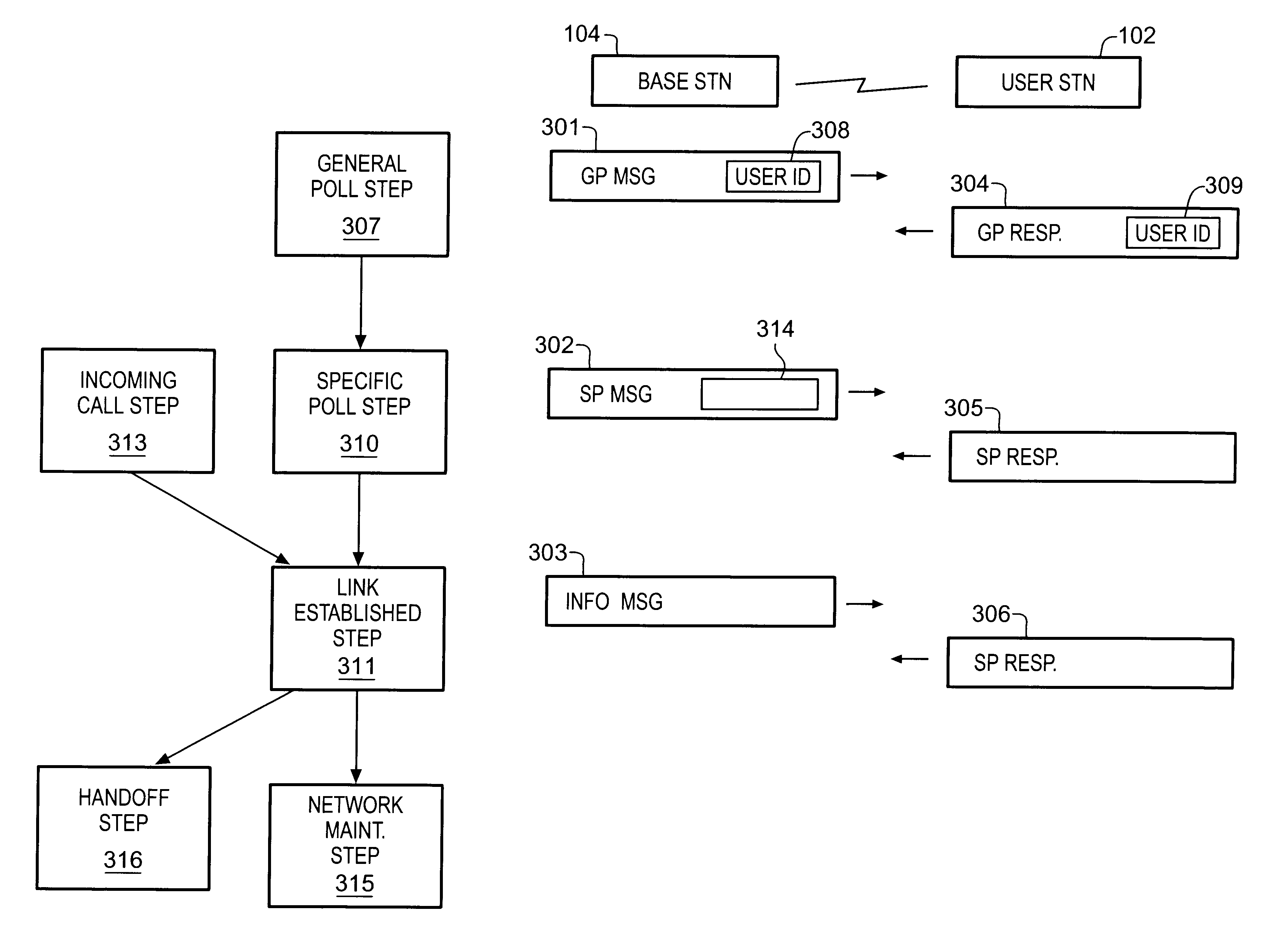
A simple and flexible over-air protocol for use with a mobile telephone system, having hand-held telephones in a microcell or other type of cellular communication system. A method in which user stations communicate with one or more base stations to place and receive telephone calls, in which the user stations are provided a secure voice or data link and have the ability to handoff calls between base stations while such calls are in progress. Each base station has a set of "air channels" to which it transmits in sequence. The air channels supported by each base station are called that base station'a "polling loop". A user station receives general polling information on an unoccupied air channel, transmits responsive information to the base station, and awaits acknowledgment from the base station. Each base station may therefore simultaneously maintain communication with as many user stations as there are air channels in its polling loop. The ability of a user station to communicate on any unoccupied air channel makes the protocol air-channel agile, while the stability of user station and base station clocks may define air channels, gaps, and minor frames.
Owner:INTEL CORP
Method and system for providing private virtual secure Voice over Internet Protocol communications
InactiveUS7852831B2Interconnection arrangementsFrequency-division multiplex detailsVoice communicationPrivate network
A method and system for secure Voice over Internet Protocol (IP) (VoIP) communications. The method and system provide secure VoIP voice calls, video, Instant Messaging (IM), Short Message Services (SMS), or Peer-to-Peer (P2P) communications while maintaining privacy over the Internet and other communications networks such as the pubic switched telephone network (PSTN) to and from any network device through a virtual private network infrastructure interconnecting private VoIP network devices. The method and system allow a network device to function as an IP private branch exchange (PBX) or a private VoIP gateway and provide and control VoIP voice communications without using other public or private VoIP gateways or VoIP servers or devices on a communications network such as the PSTN or the Internet.
Owner:LESAVICH HIGH TECH LAW GRP SC
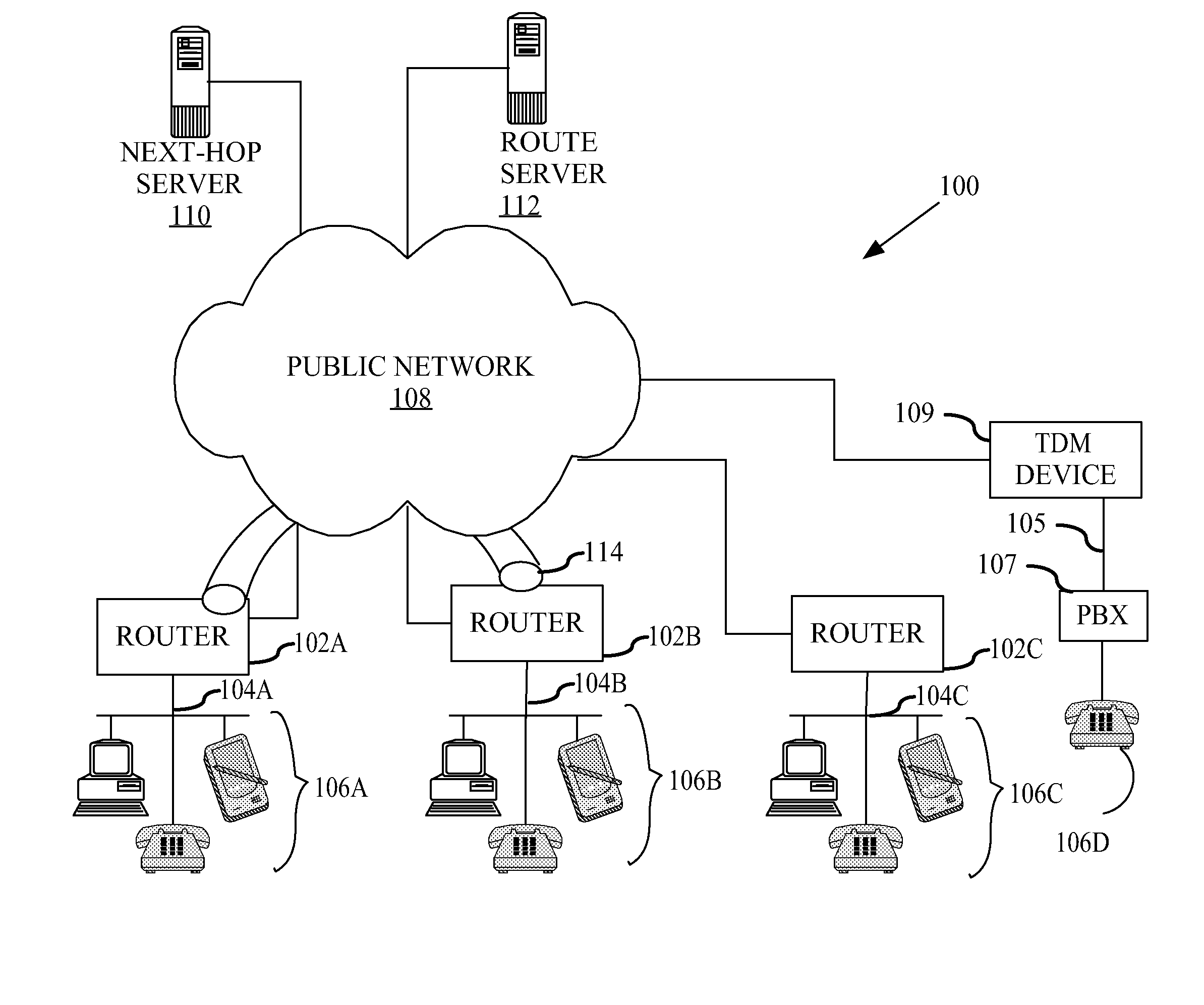
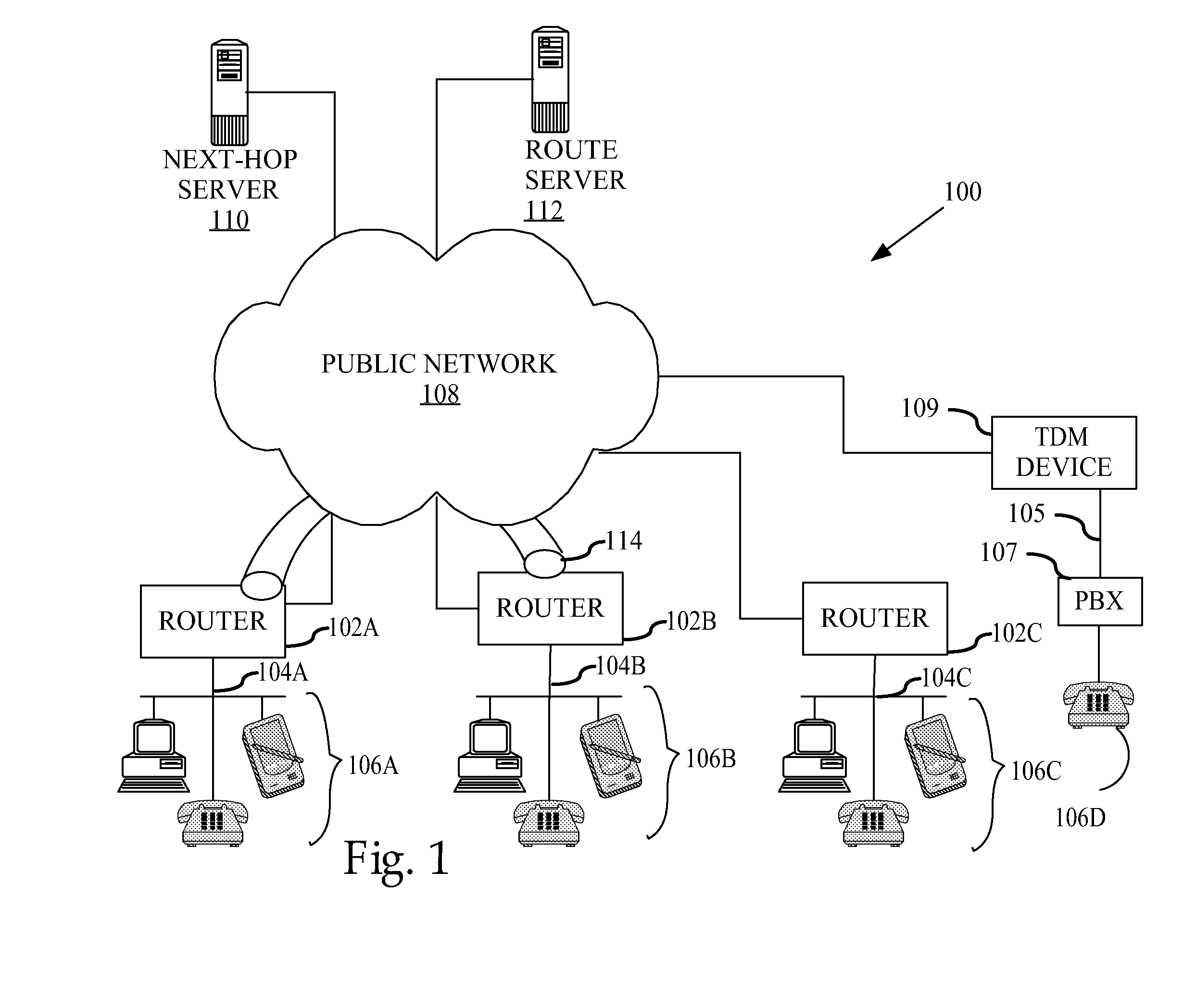
Method and apparatus for dynamically securing voice and other delay-sensitive network traffic
InactiveUS20080229095A1Computer security arrangementsMultiple digital computer combinationsTraffic capacityPrivate network
A method comprises receiving a request for secure network traffic from a device having a private network address at a source node, obtaining the private network address of a requested destination device at a destination node from a route server based on signaling information associated with the request, obtaining the public network address of the destination node associated with the private network address, creating in response to the request a virtual circuit between the source node and the destination node based on the public network address of the destination node, and encrypting network traffic for transporting at least from the source node to the destination node through the virtual circuit. The process is dynamic in that the virtual circuit is created in response to the request. Hence, the process operates as if a fully meshed network exists but requires less provisioning and maintenance than a fully meshed network architecture. Furthermore, the process is readily scalable as if a hub and spoke network exists but is more suitable for delay-sensitive traffic, such as voice and video, than a hub and spoke network architecture.
Owner:CISCO TECH INC
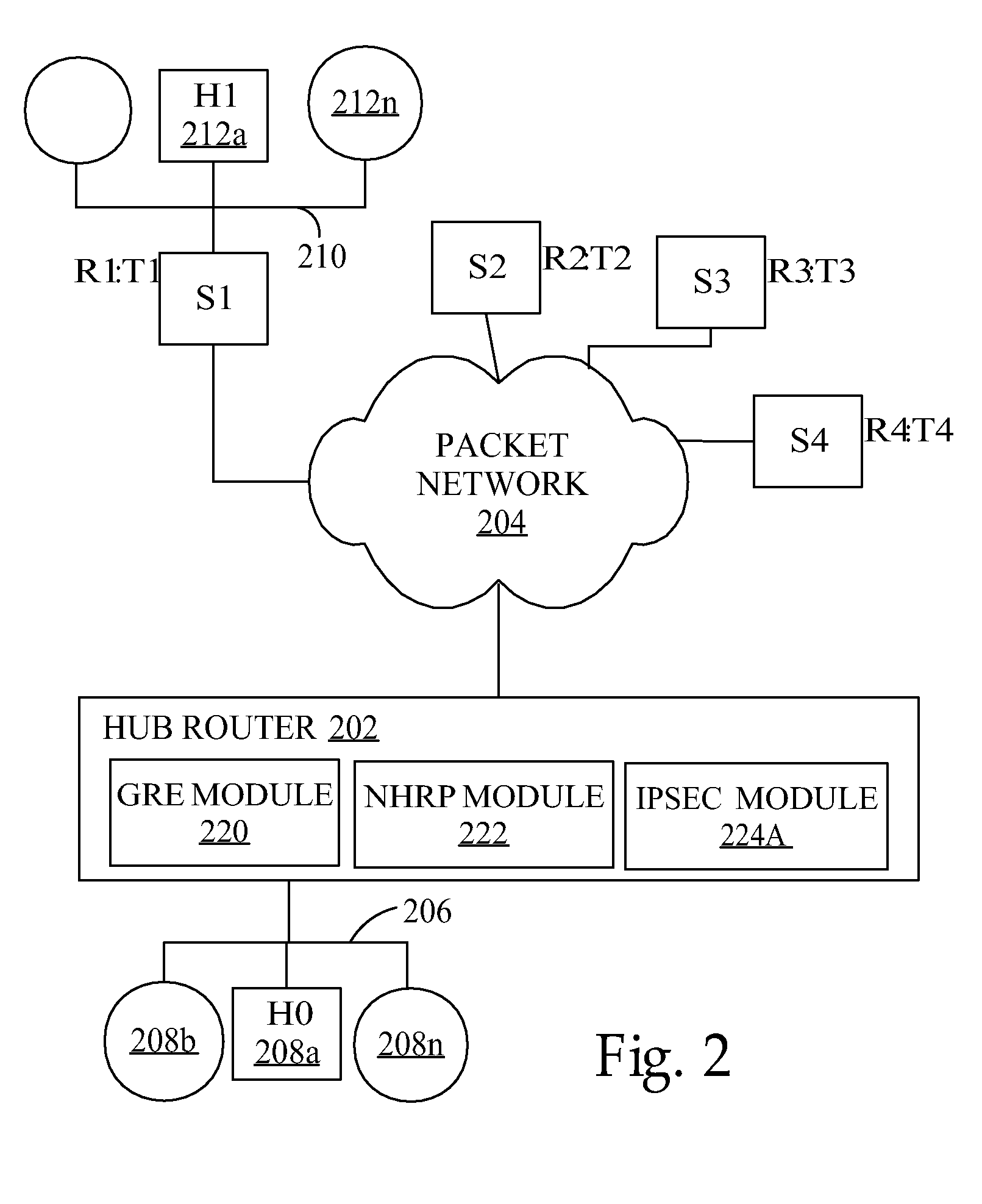
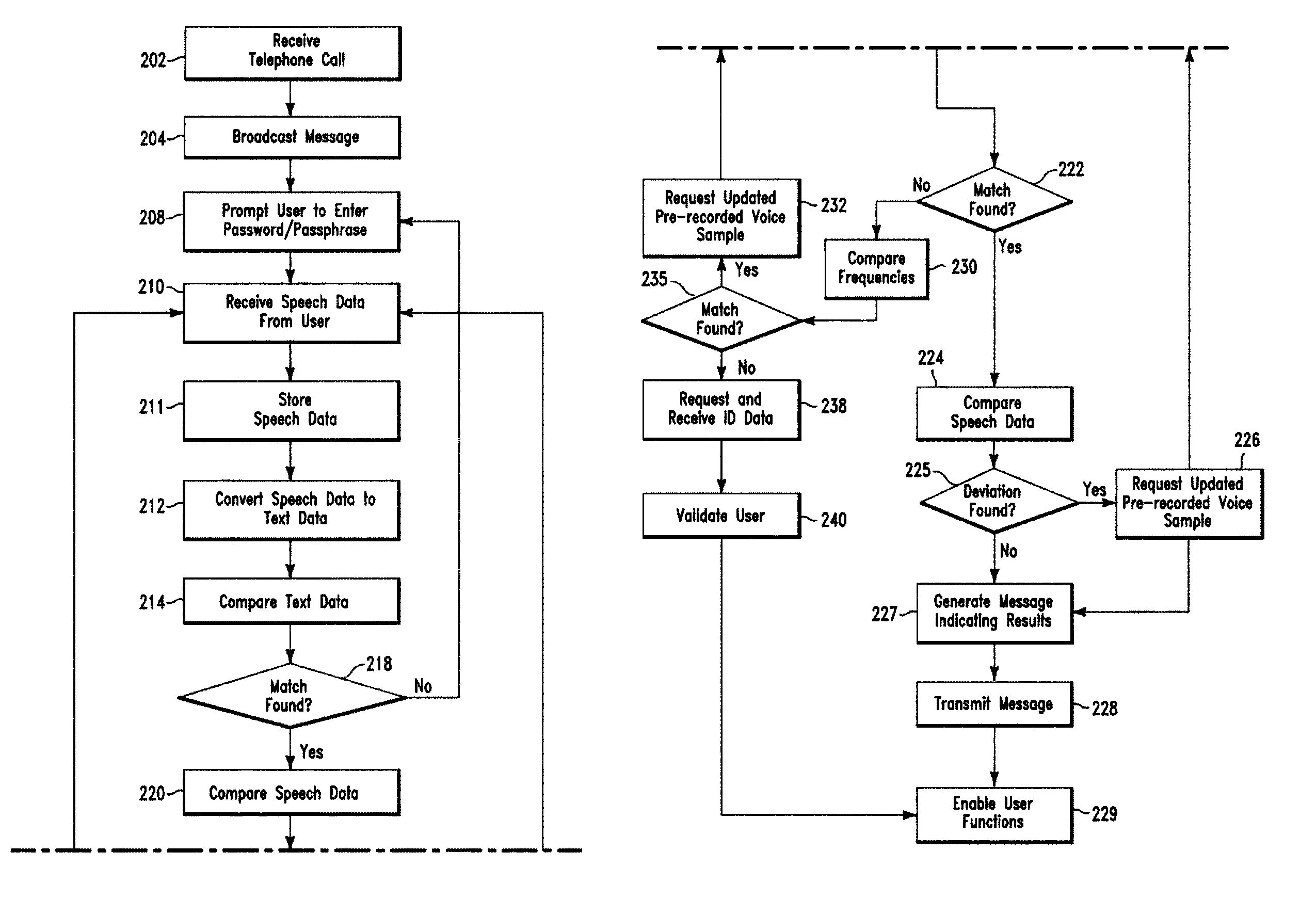
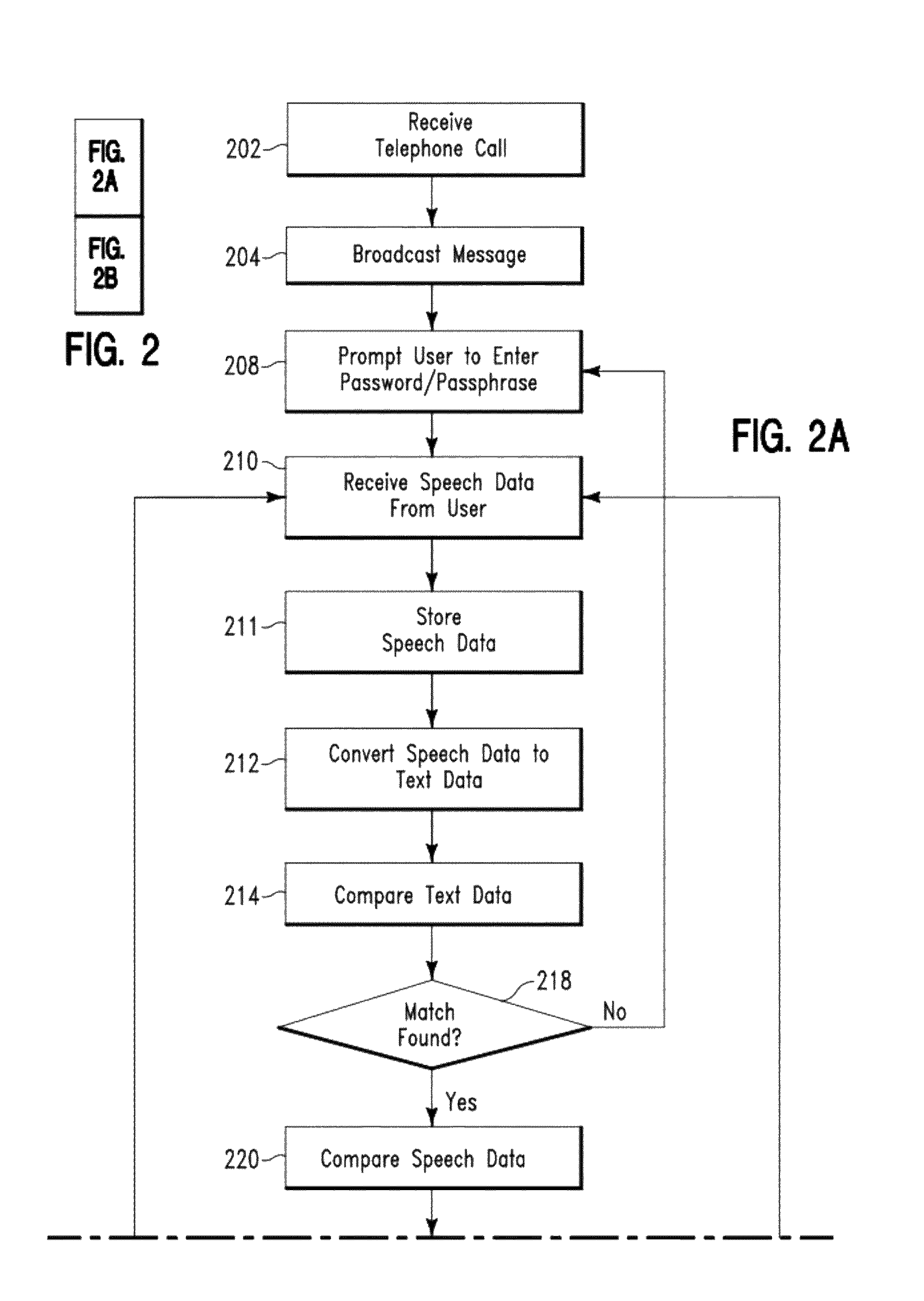
Secure voice transaction method and system
ActiveUS8194827B2Communication securityUnauthorised/fraudulent call preventionDigital data processing detailsPassphraseFrequency spectrum
A security method and system. The method includes receiving by a computing system, a telephone call from a user. The computing system comprises an existing password / passphrase and a pre-recorded voice sample associated with the user. The computing system prompts the user to enter a password / passphrase using speech. The computing system receives speech data comprising a first password / passphrase from the user. The computing system converts the speech data to text data. The computing system first compares the text data to the first password / passphrase and determines a match. The computing system compares the speech data to the pre-recorded voice sample to determine a result indicating whether a frequency spectrum associated with the speech data matches a frequency spectrum associated with the pre-recorded voice sample. The computing system transmits the result to the user.
Owner:MICROSOFT TECH LICENSING LLC
Secure voice biometric enrollment and voice alert delivery system
InactiveUS20110260832A1Electric signal transmission systemsDigital data processing detailsSuccessful completionVoice communication
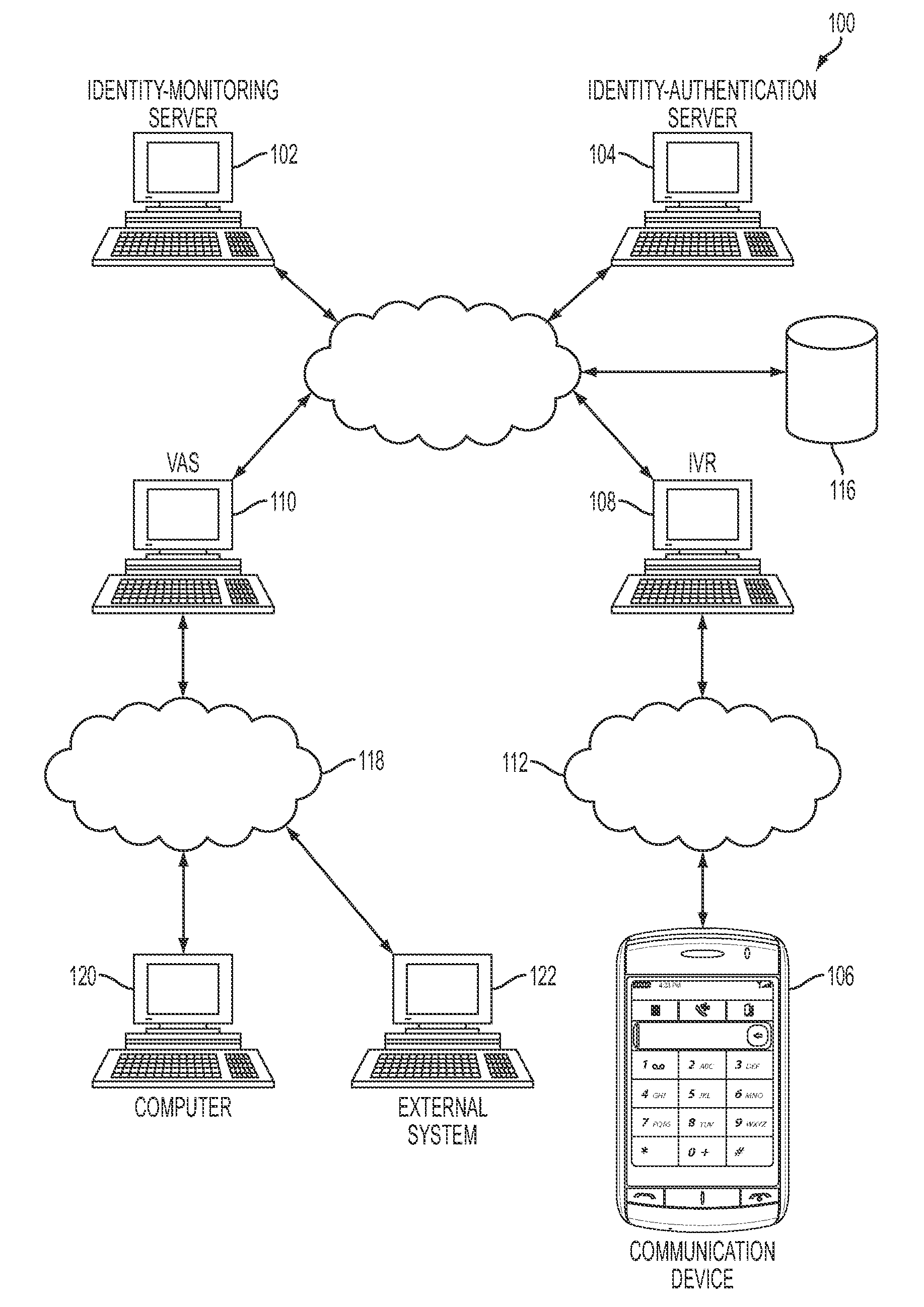
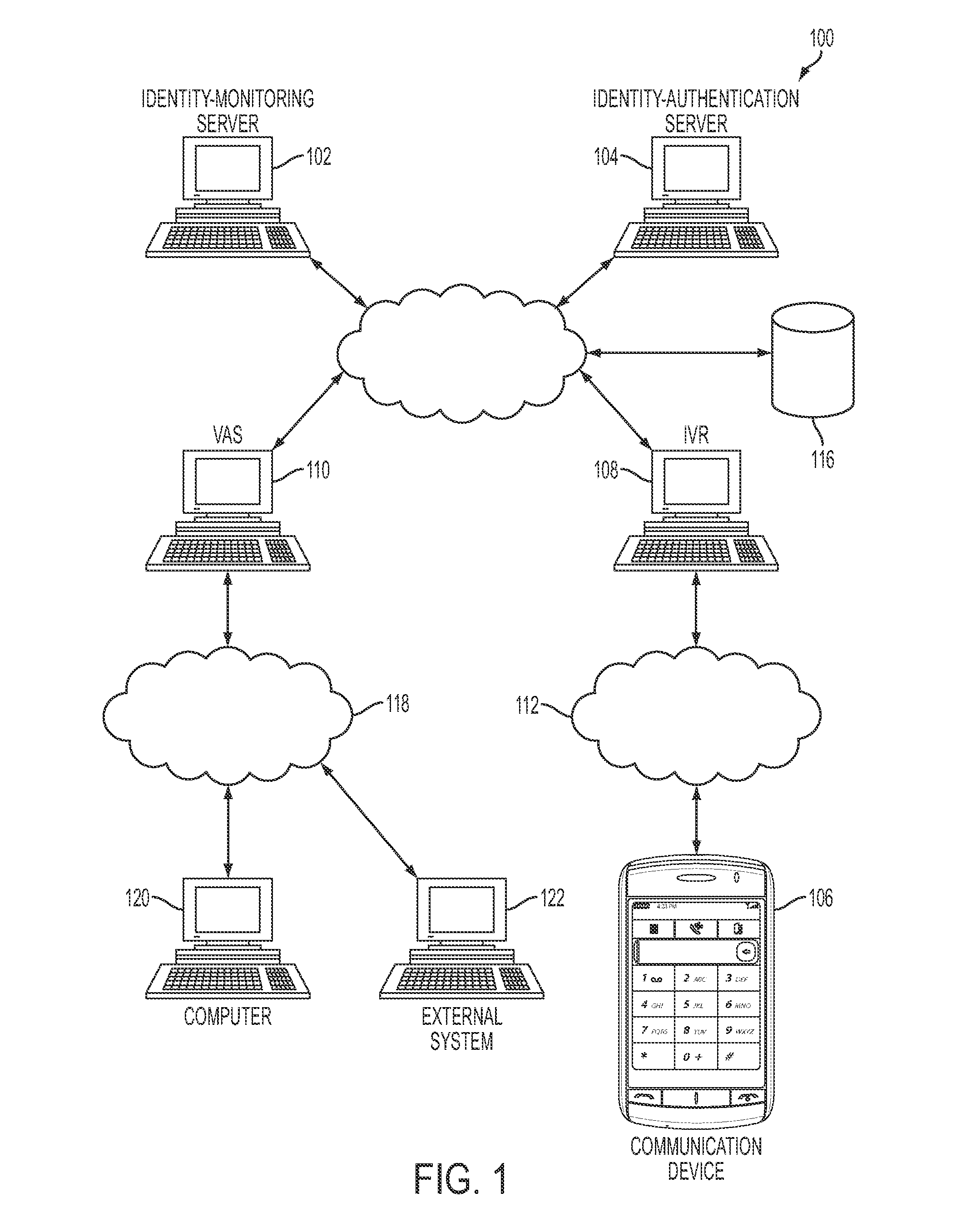
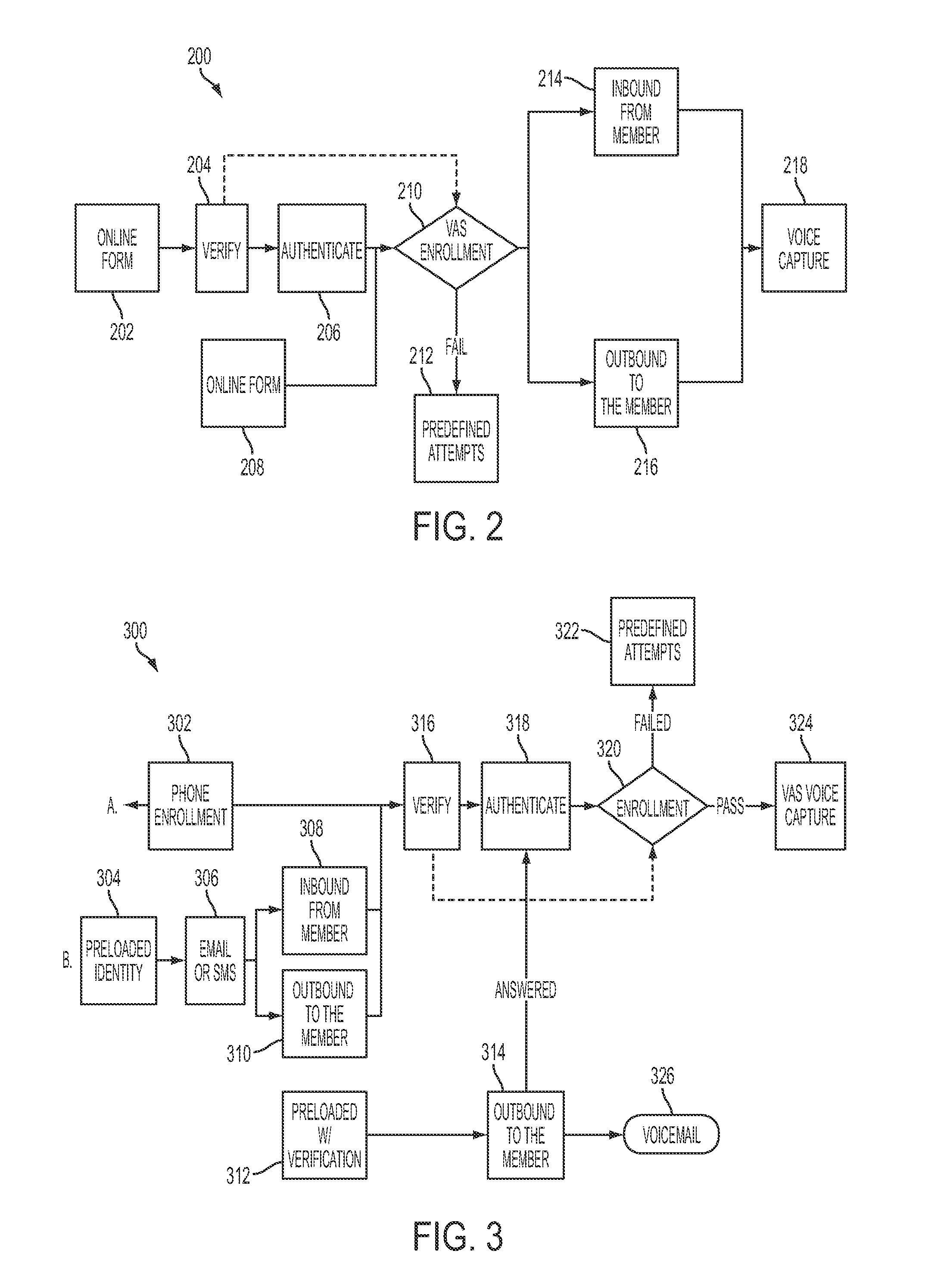
In one embodiment, a method includes enrolling a potential enrollee for an identity-monitoring service. The enrolling includes acquiring personally-identifying information (PII) and capturing a voiceprint. Following successful completion of the enrolling, the potential enrollee is an enrollee. The method further includes, responsive to an identified suspicious event related to the PII, creating an identity alert, establishing voice communication with an individual purporting to be the enrollee, and performing voice-biometric verification of the individual. The voice-biometric verification includes comparing one or more spoken utterances with the voiceprint. Following successful completion of the voice-biometric verification, the individual is a verified enrollee. In addition, the method includes authorizing delivery of the identity alert to the verified enrollee.
Owner:CSIDENTITY CORP
Secure speech
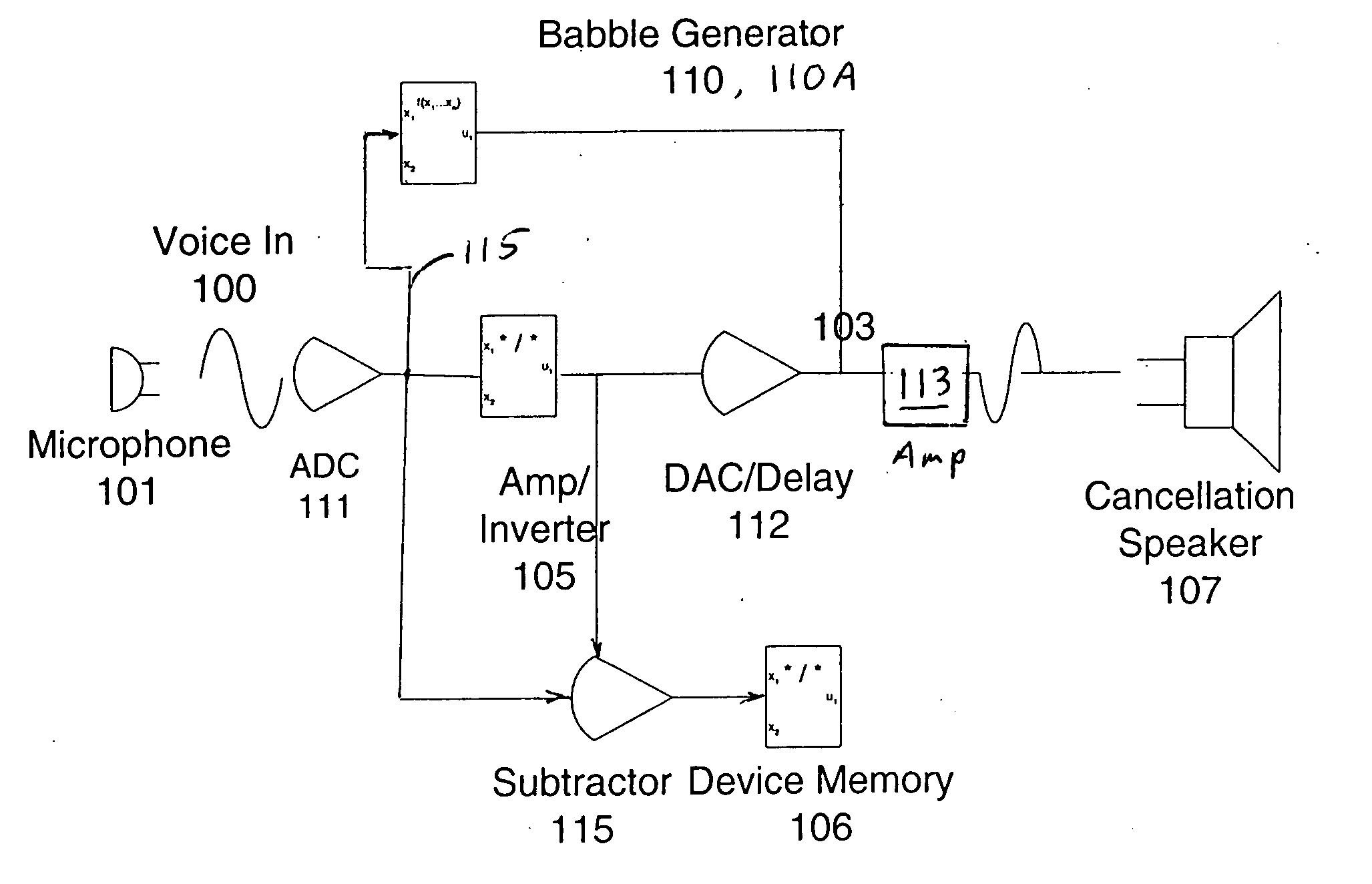
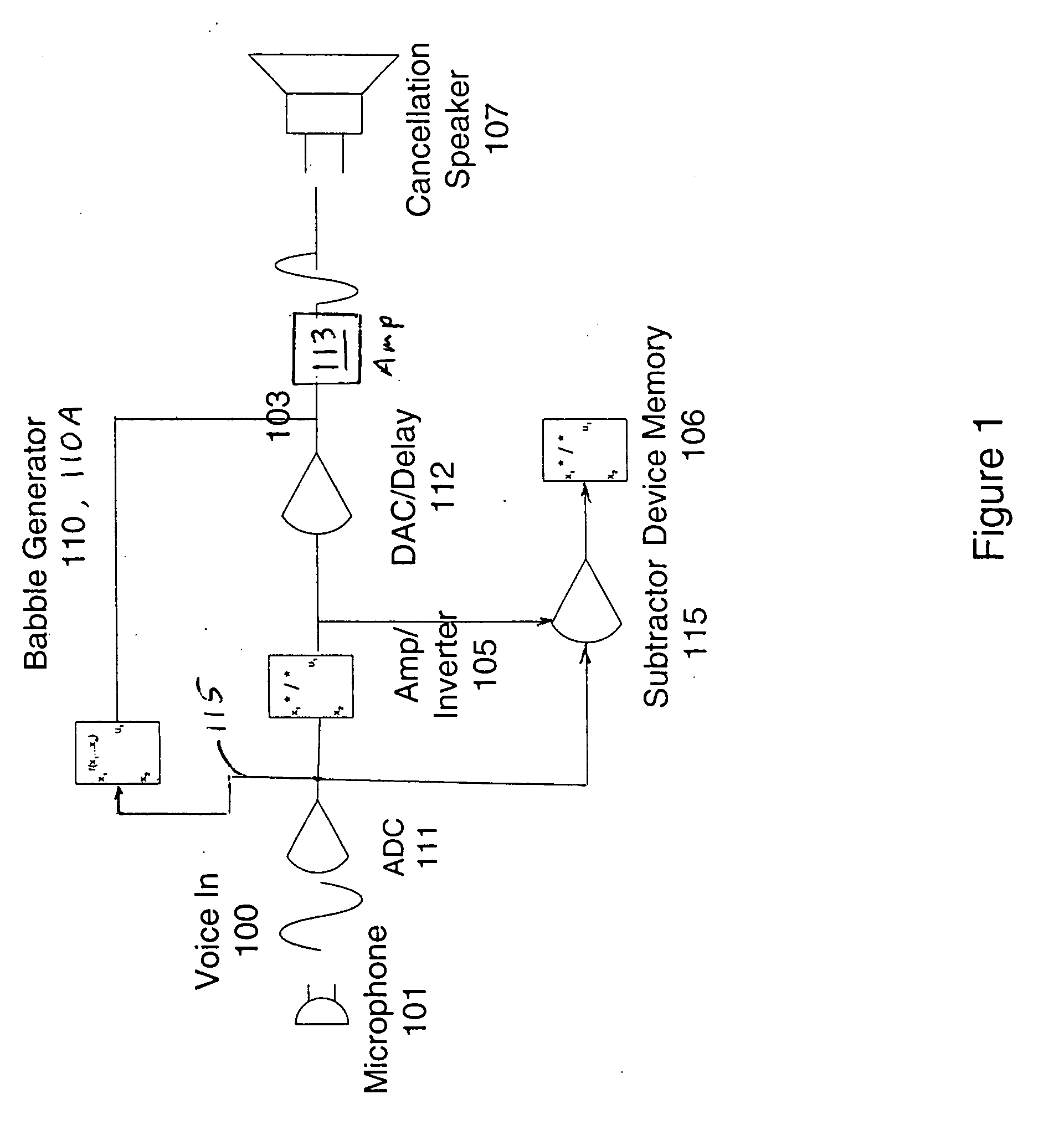
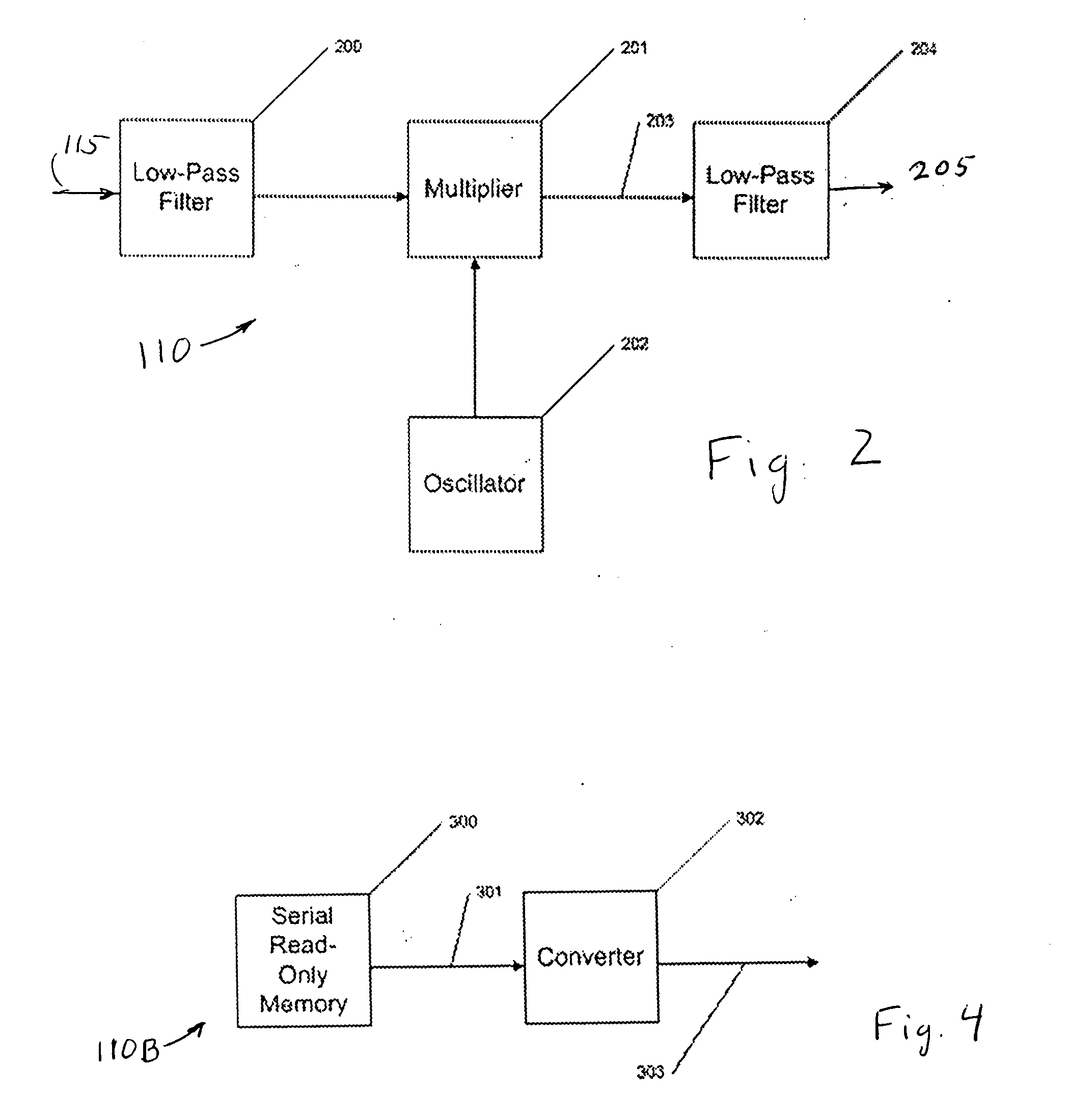
InactiveUS20050065778A1Privacy can be assuredEavesdropping prevention circuitsSpeech analysisSignal generatorSpeech sound
A method, apparatus and computer product for masking speech. The system includes a signal acquiring apparatus for generating an electrical signal representative of the speech; a processing apparatus for using the electrical signal to provide an audio signal which cancels the speech; and a signal generator, also referred to as a babble generator, for providing a speech masking signal to mask any speech not canceled. The masking signal is generated by processing the speech in one of several ways so that its content is not intelligible.
Owner:IBM CORP
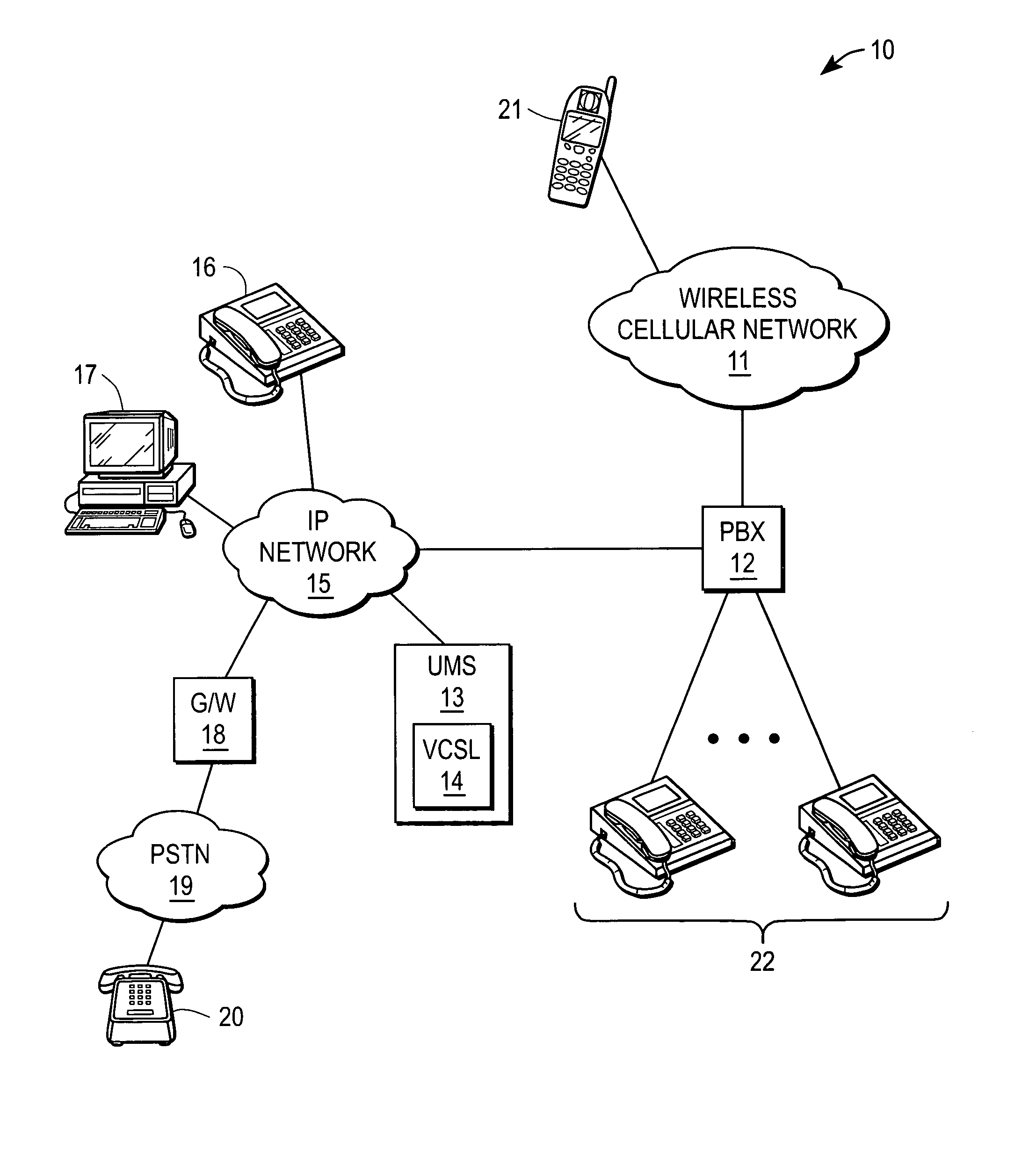
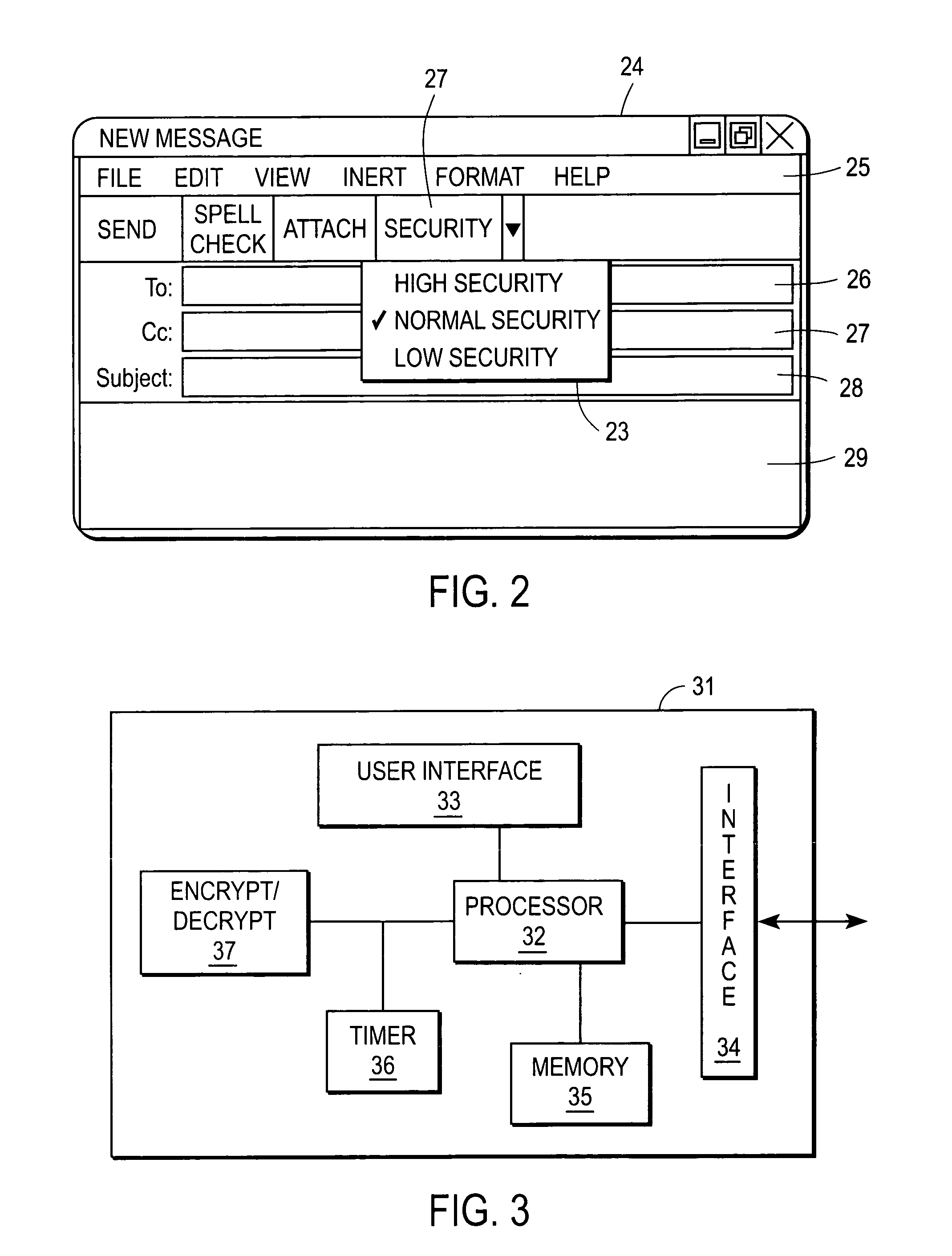
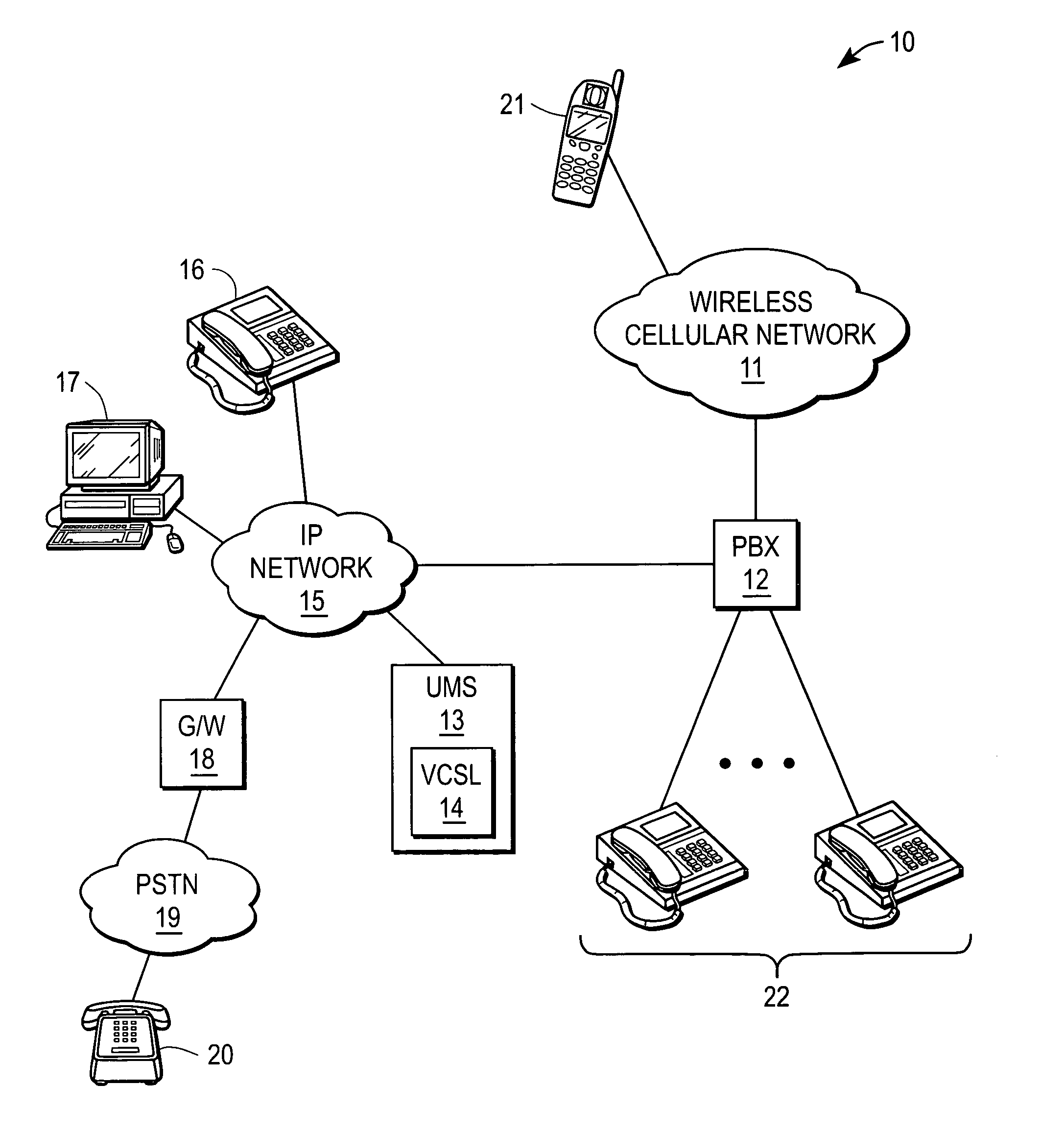
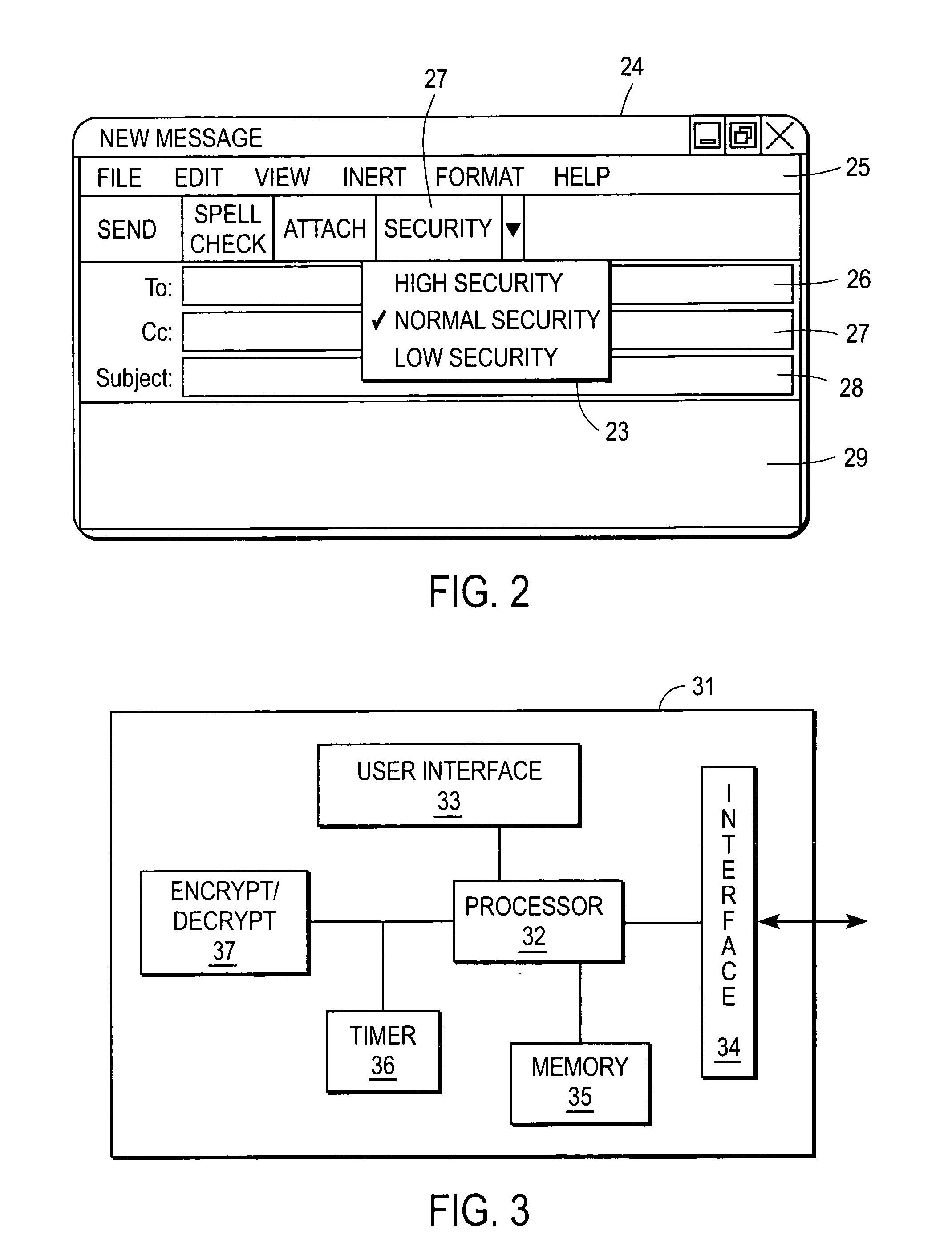
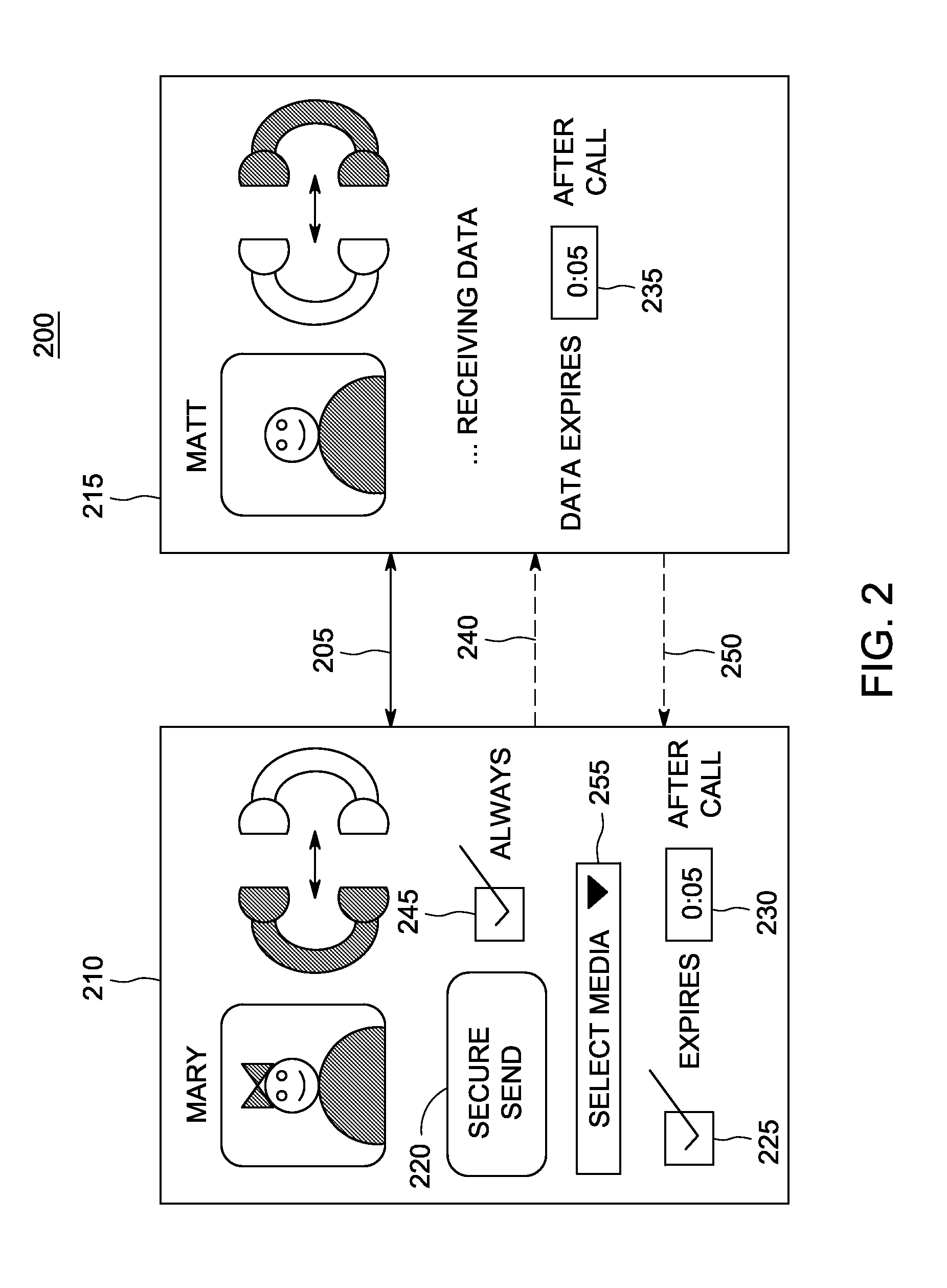
Secure voice communication channel for confidential messaging
A unified messaging system includes a unit to store a message operable to store a message sent to a user, the message having a selectable security attribute set to a one of a plurality of levels. A module associated with the unit operates to secure a voice channel used by the user to listen to the message when the selectable security level is set to a high level indicating encryption. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
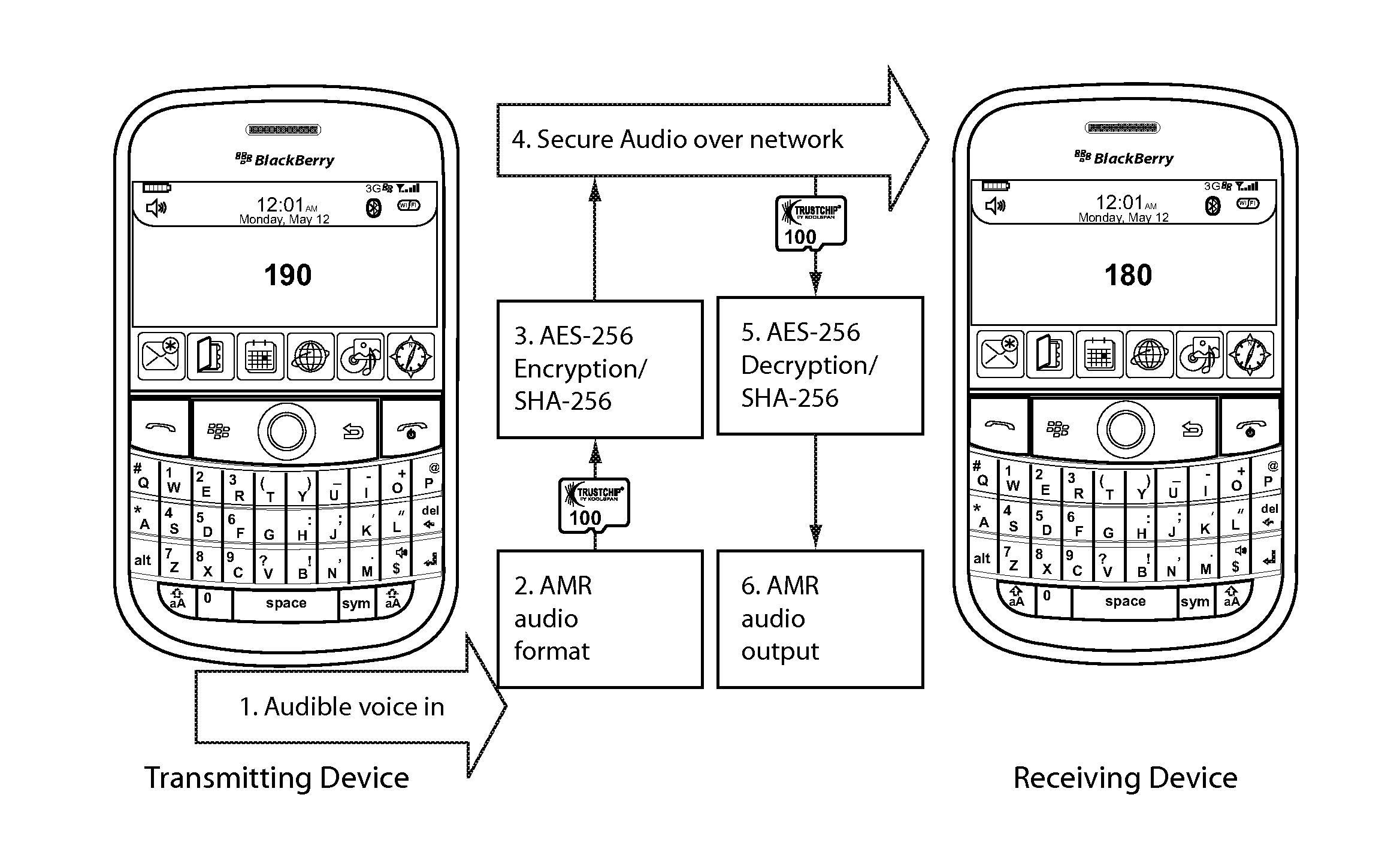
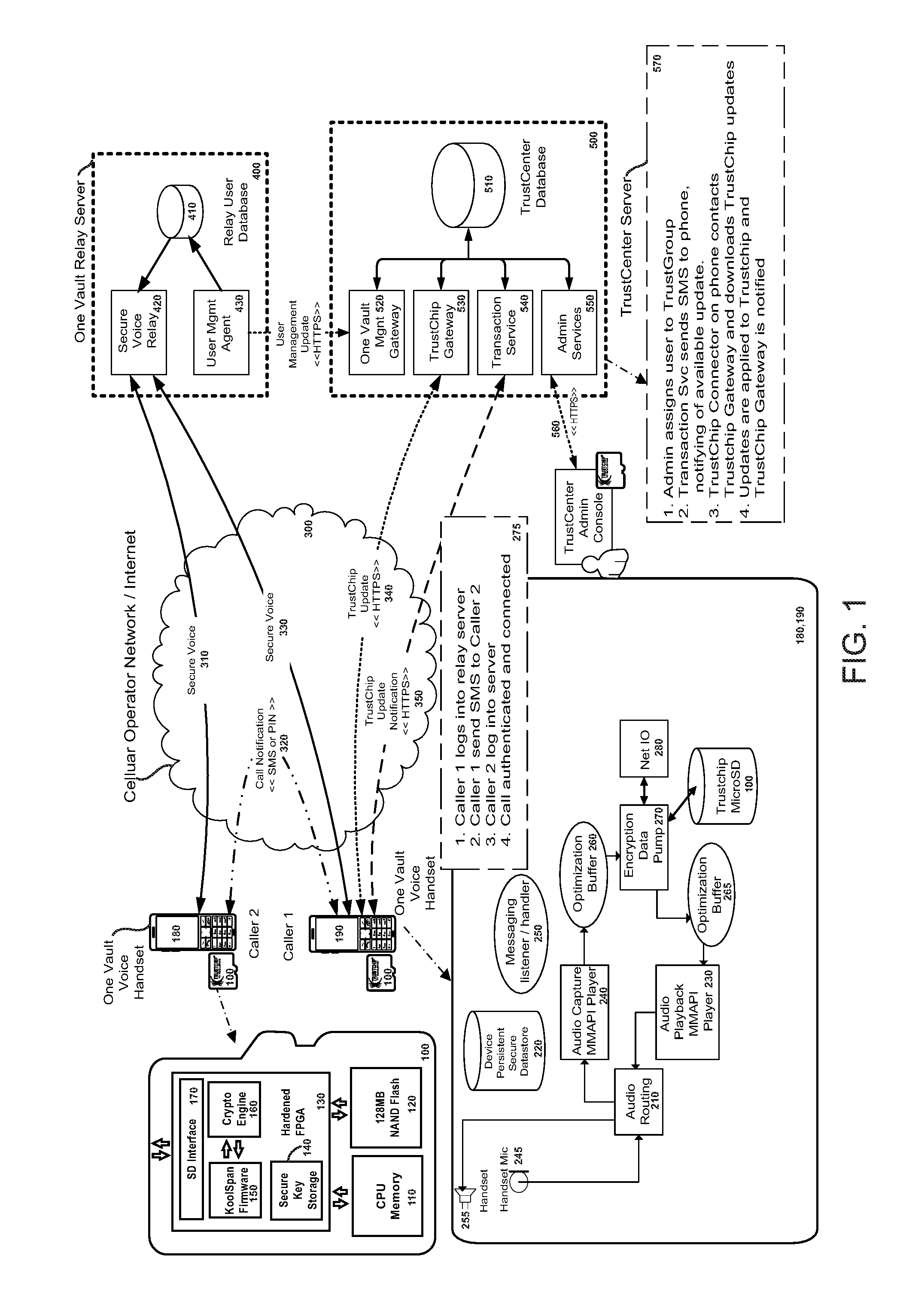
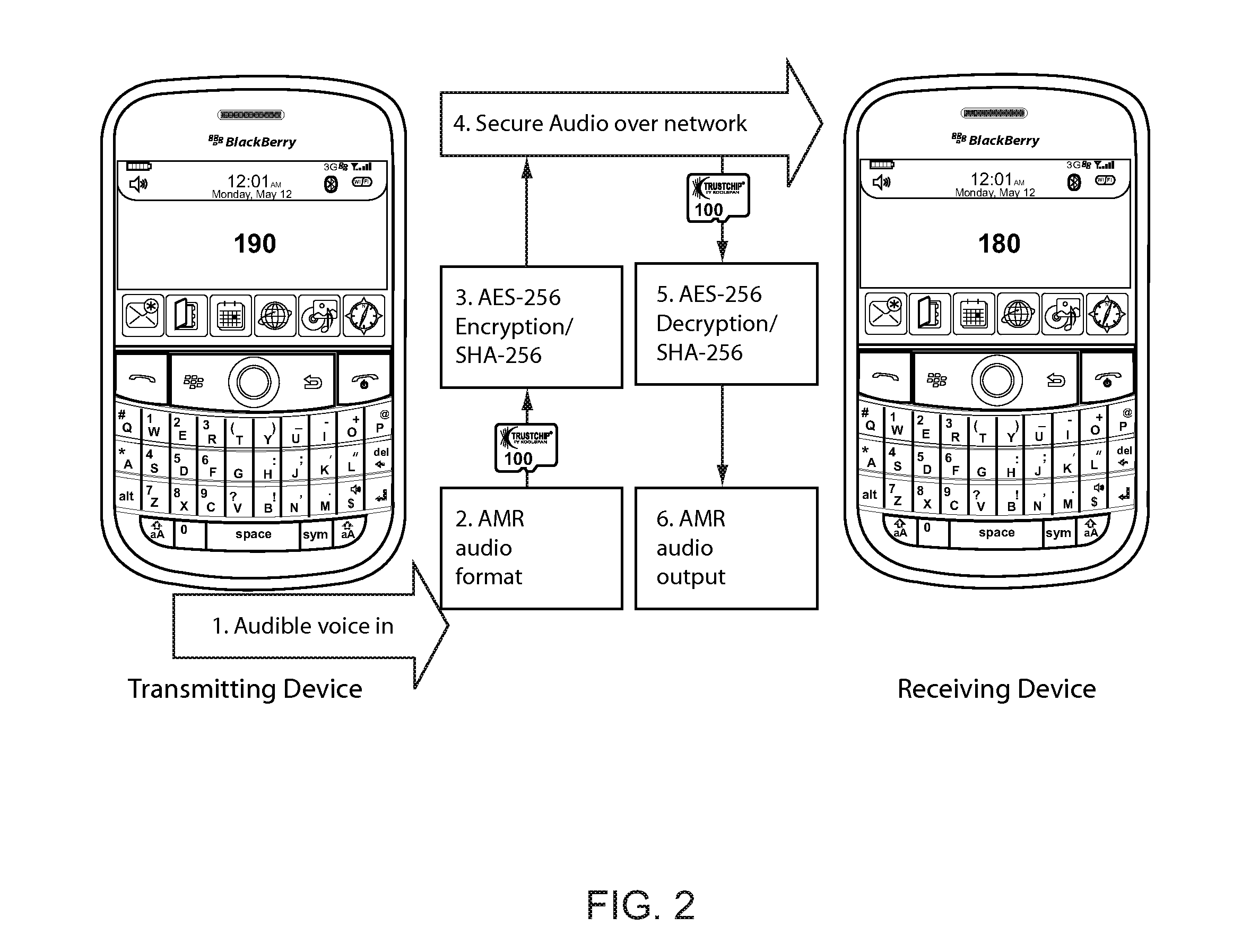
One vault voice encryption
ActiveUS20110222688A1Low call latencyLow performance resultSecret communicationSecurity arrangementComputer hardwareVoice communication
The present invention provides a secure voice solution for the BlackBerry 9000 (BlackBerry Bold™) Rather than make encrypted voice calls through traditional GSM cellular phone calls, the present invention instead receives voice data from the user using the device microphone and built-in media player software in the device. This data is then encrypted and then sent as an IP packet. The device then receives, as IP packets, encrypted voice communication from the other party in the encrypted call, which in turn are decrypted in the device and then played back on a second media player running on the device. The present invention takes advantage of the device's ability to run two media players simultaneously to in effect, simulate a cellular telephone call. As a result, an encrypted call can be made with PDA-type devices such as the Blackberry@ and also such calls can be made using different data paths (cellular, WiFi, Bluetooth, or the like) as the calls are made by sending and receiving data over the Internet, not as traditional cellular data signals.
Owner:KOOLSPAN
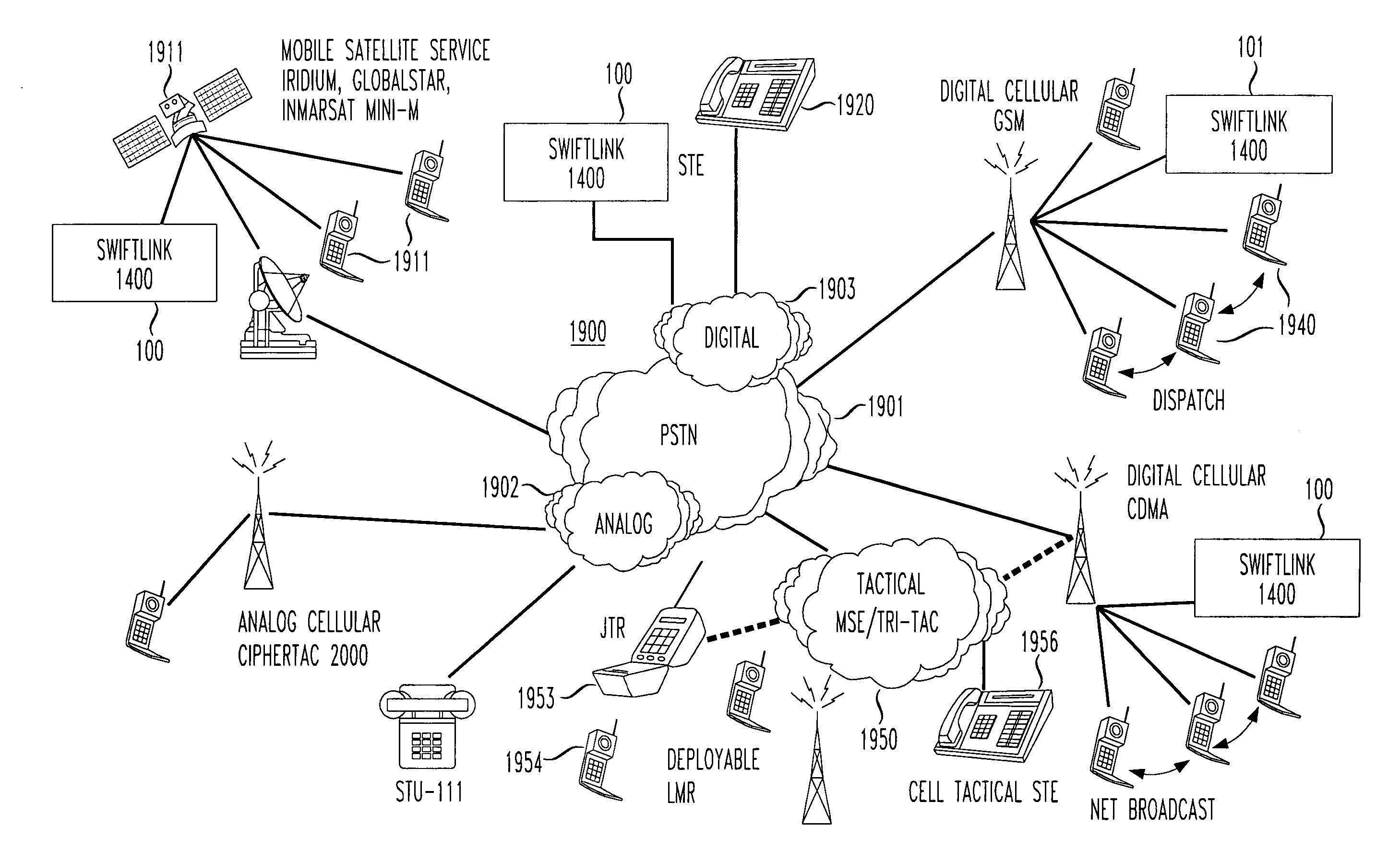
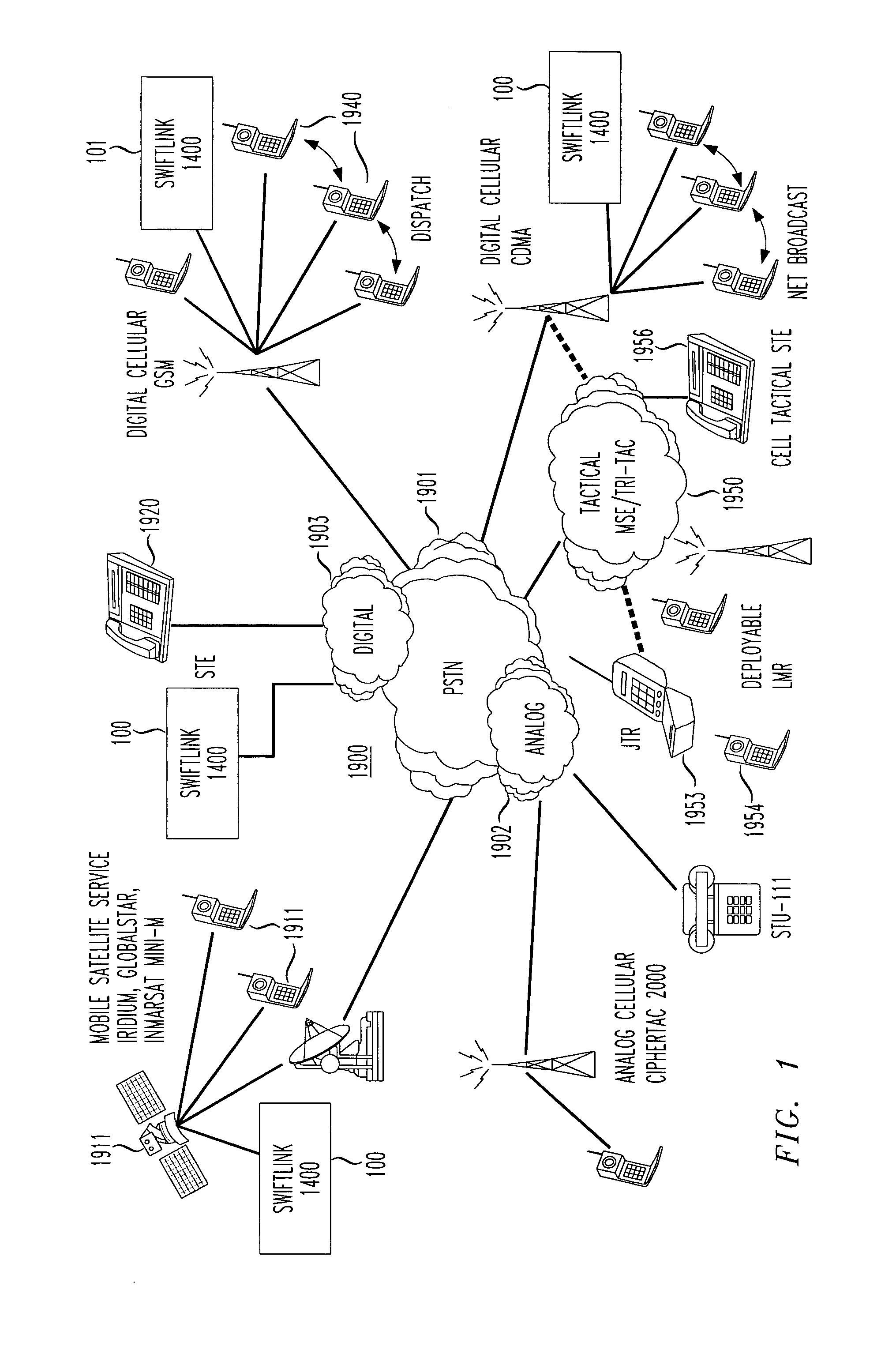
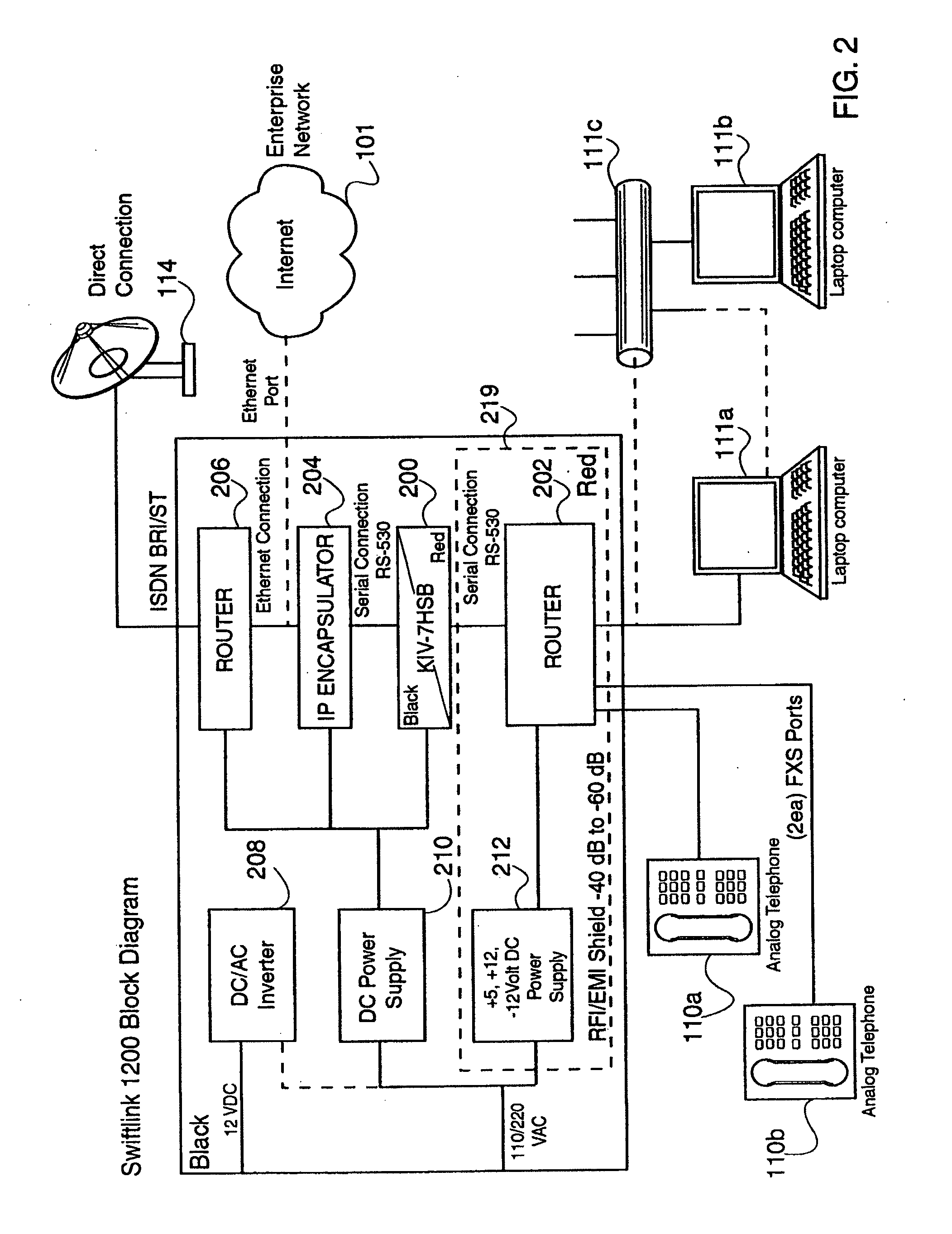
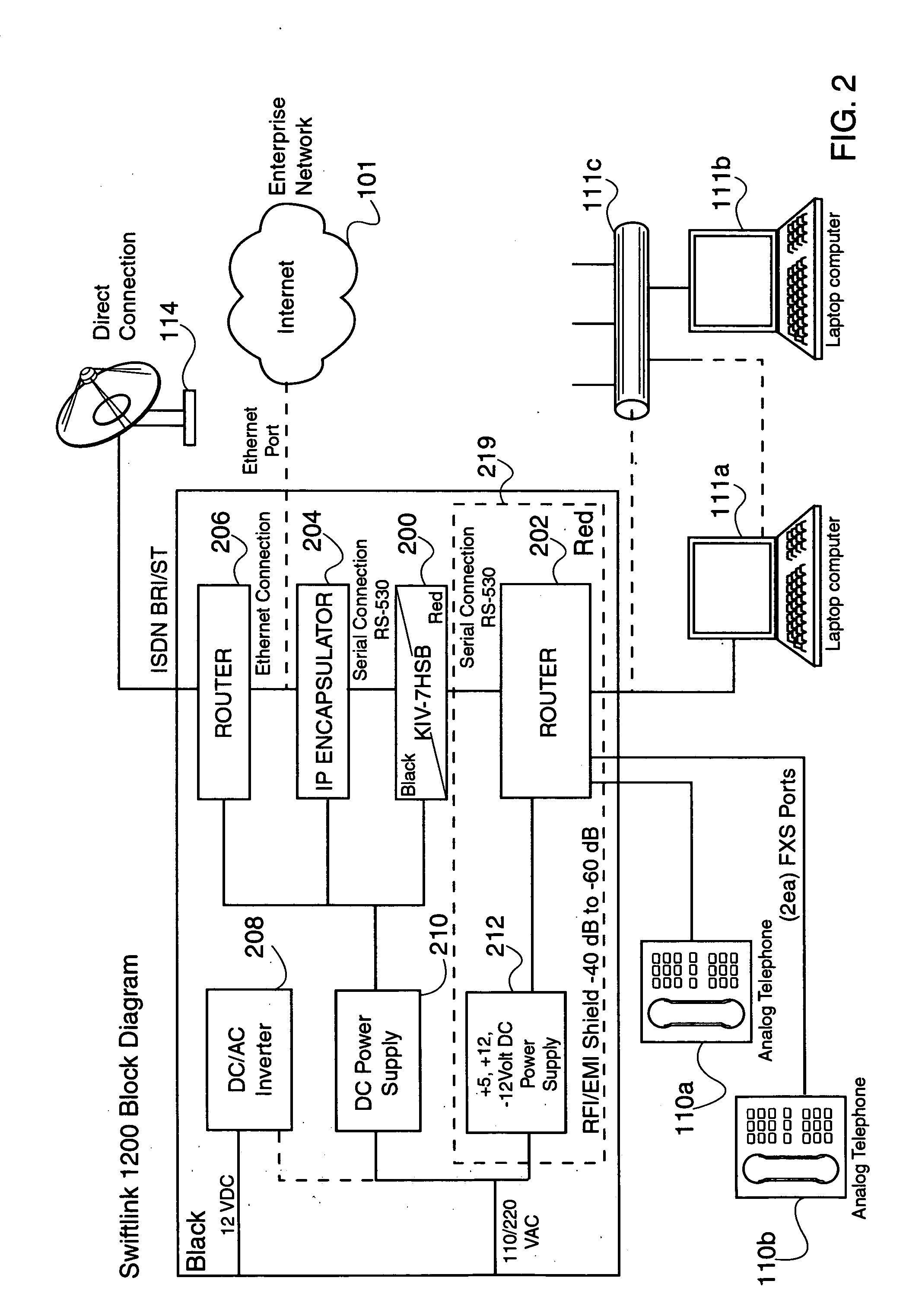
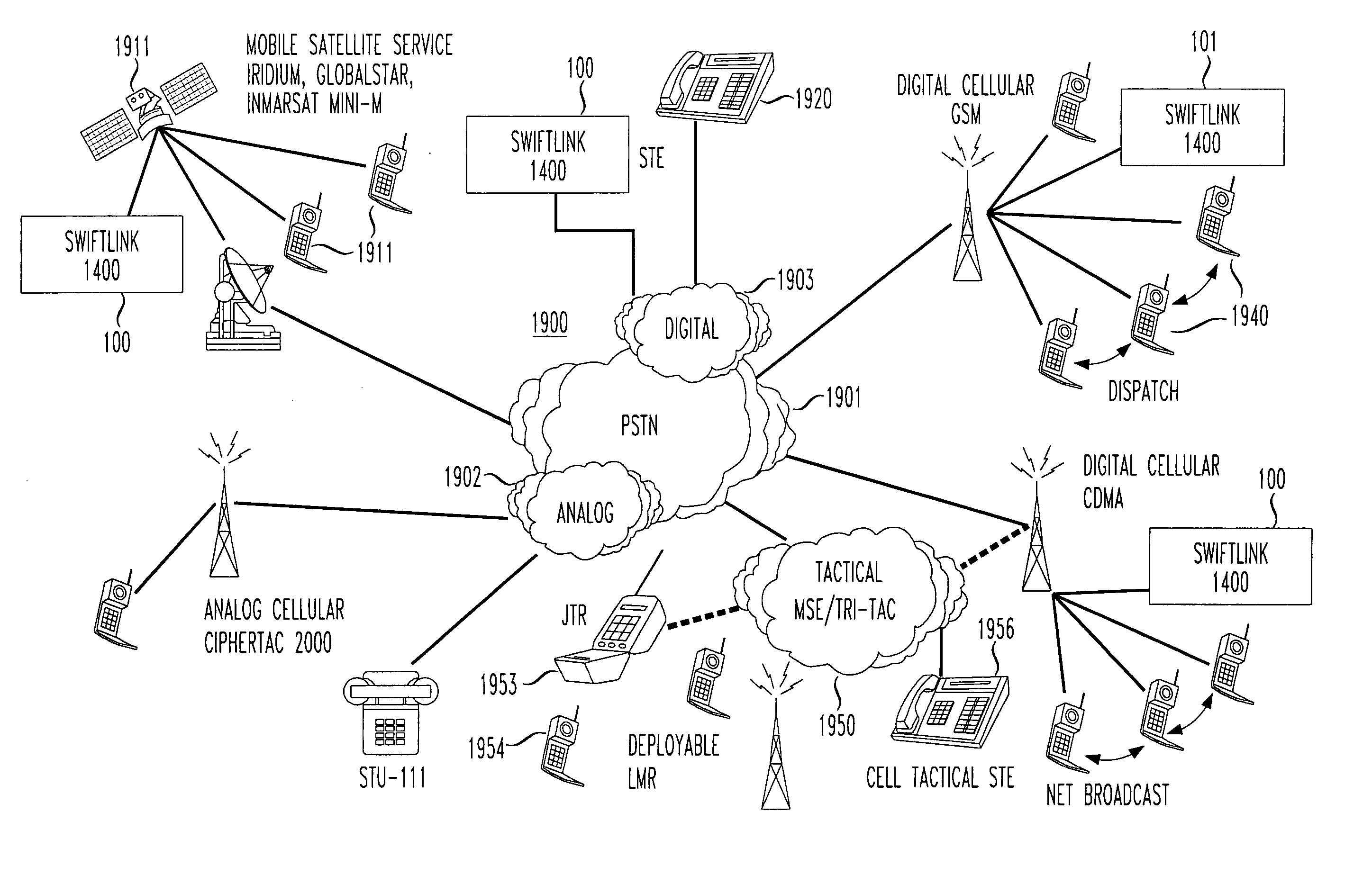
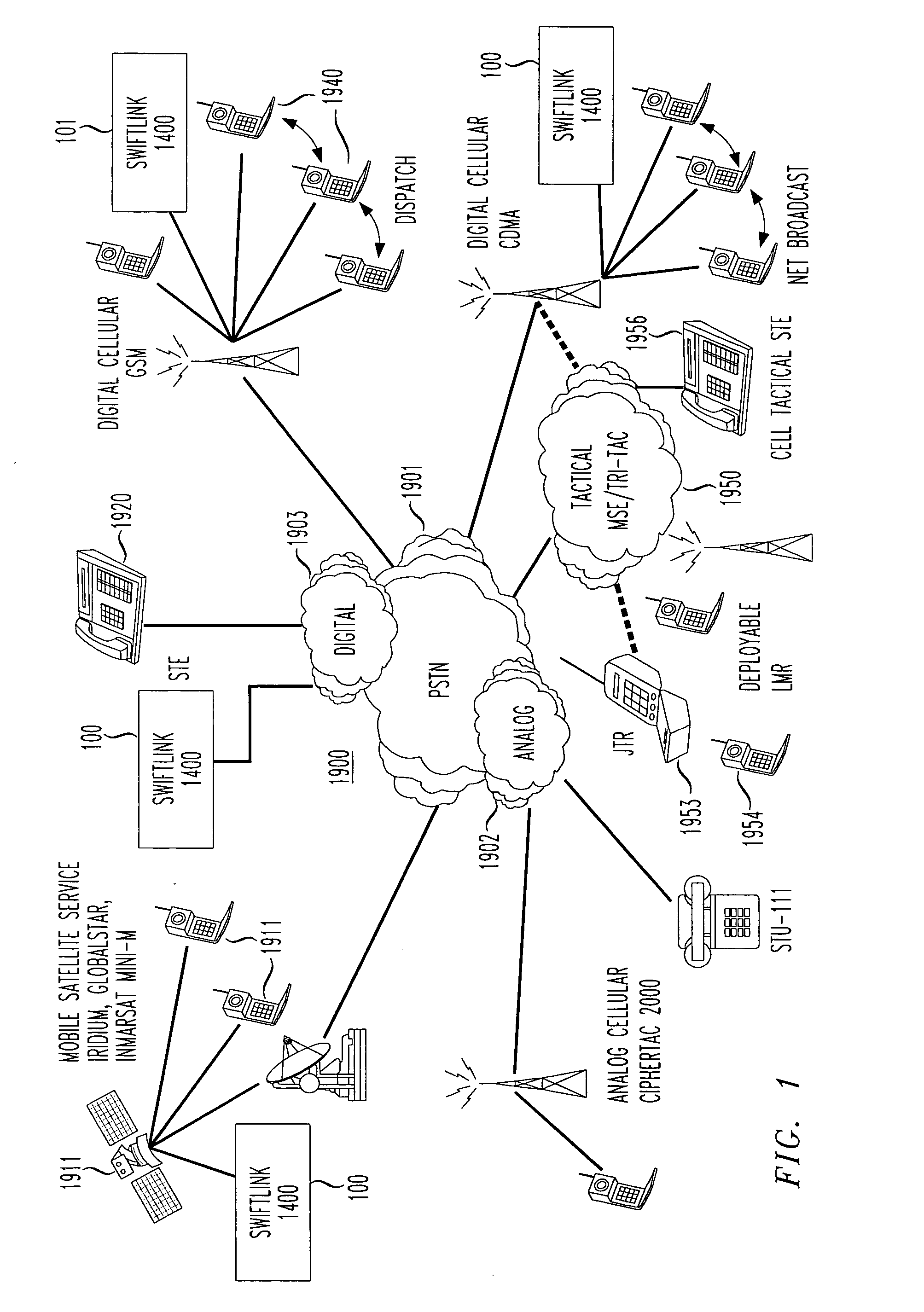
Standard telephone equipment (STE) based deployable secure cellular communication system
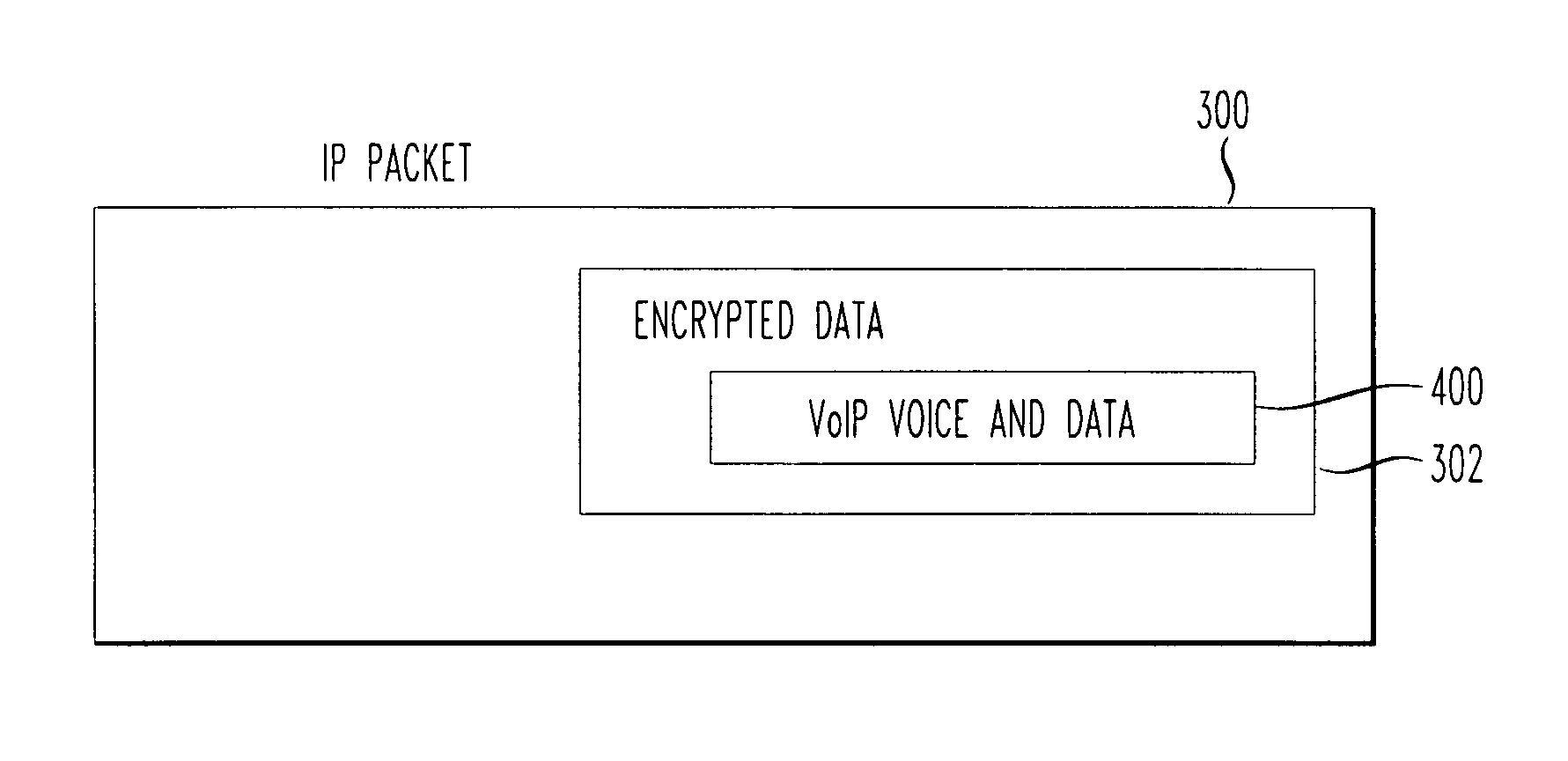
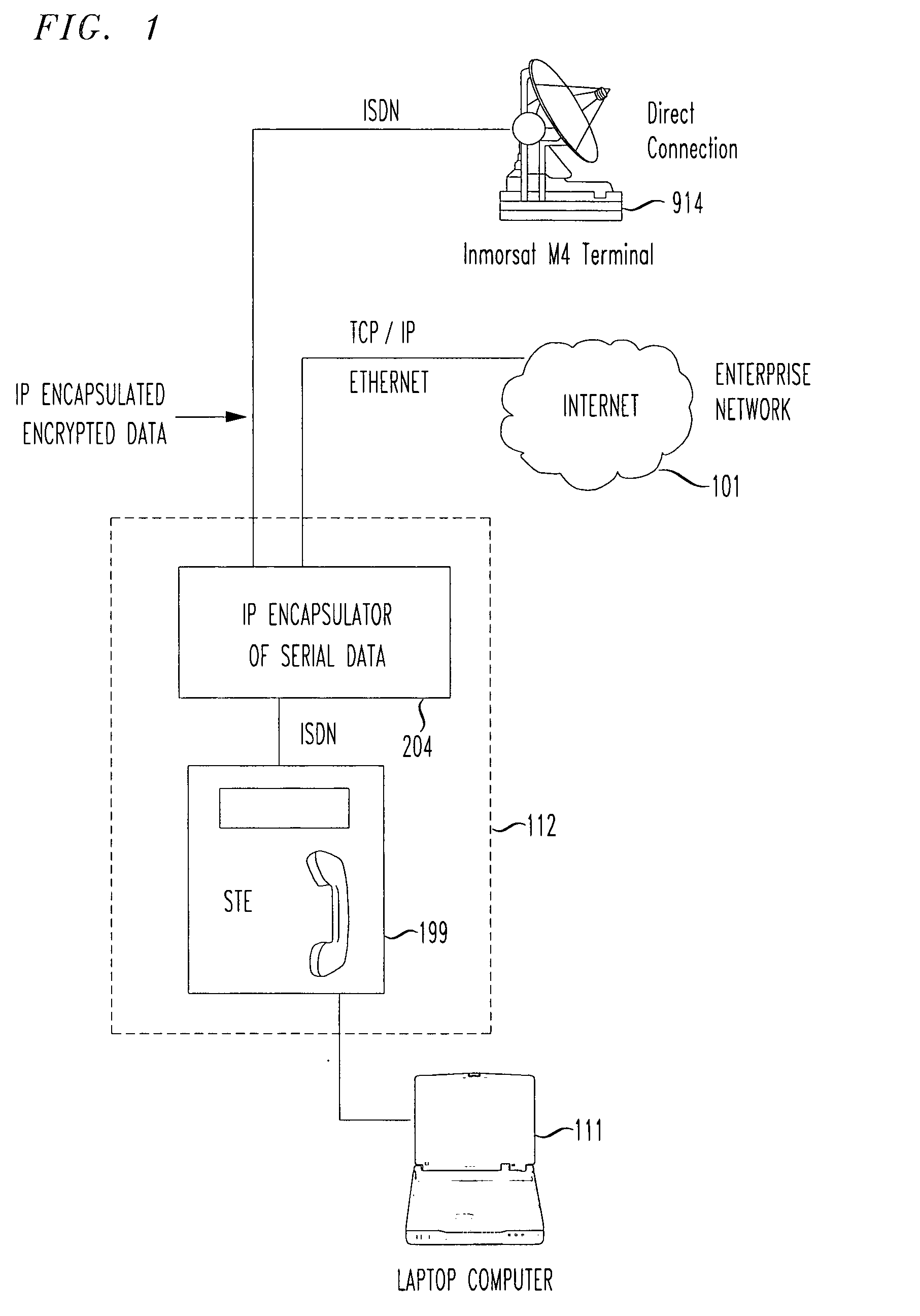
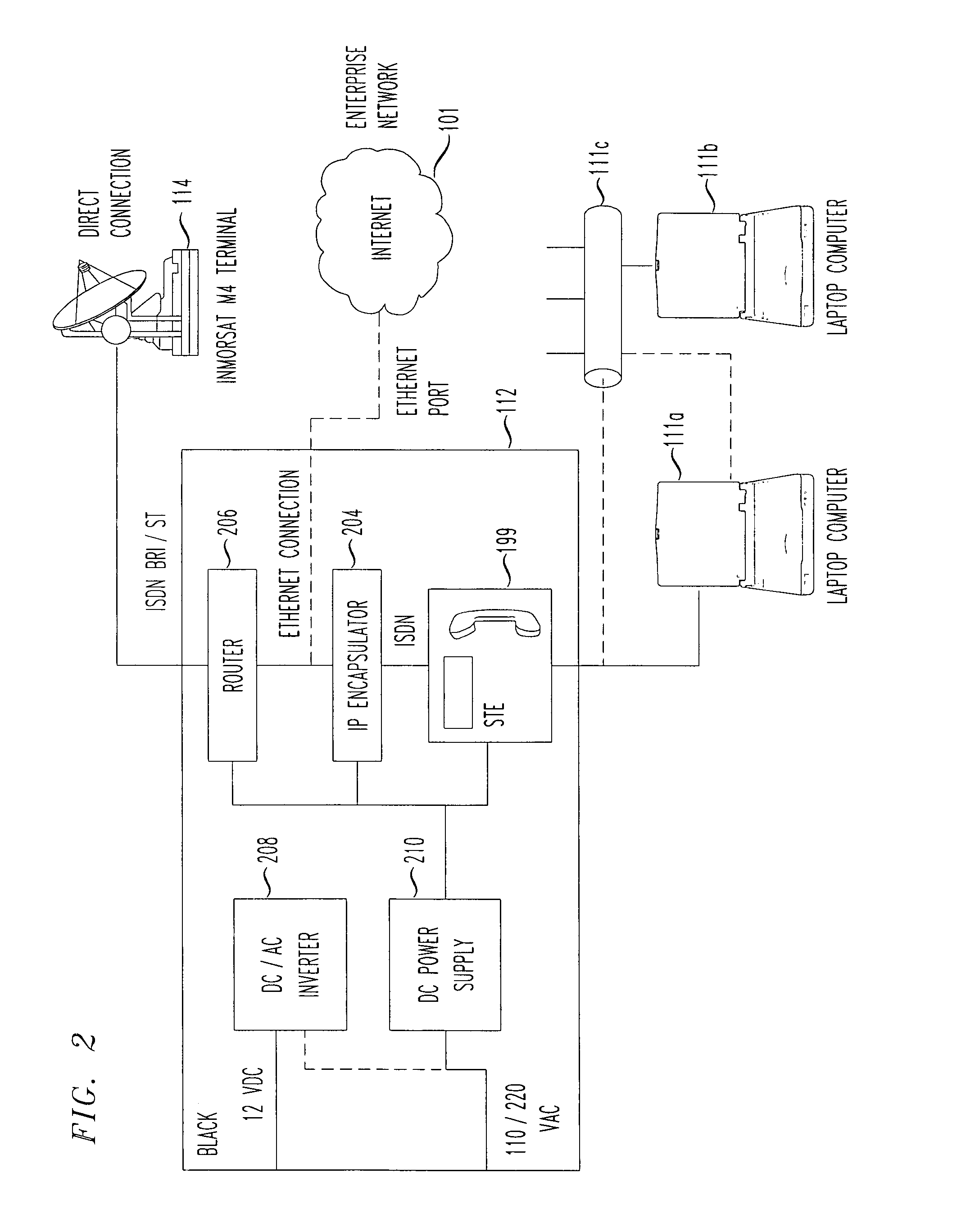
A deployable secure cellular communication system comprises an encryption device, an Internet Protocol (IP) encapsulator to encapsulate an output of the encryption device within IP packets, and a network interface to allow transport of the IP packets to a public IP network. The encryption device may be an STE device, the output of which is encapsulated into IP packets addressed to a matching IP encapsulator / decapsulator device over a public IP network, that then passes to a similar STE or other encryption device for decryption. Secure Voice-Over-IP (VoIP), video and data network functionality in a single, small size deployable case, to a remote user. Most importantly, bulk encrypted (i.e., secure) data is communicated over a public IP network.
Owner:TELECOMM SYST INC
Secure voice communication channel for confidential messaging
A unified messaging system includes a unit to store a message operable to store a message sent to a user, the message having a selectable security attribute set to a one of a plurality of levels. A module associated with the unit operates to secure a voice channel used by the user to listen to the message when the selectable security level is set to a high level indicating encryption. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
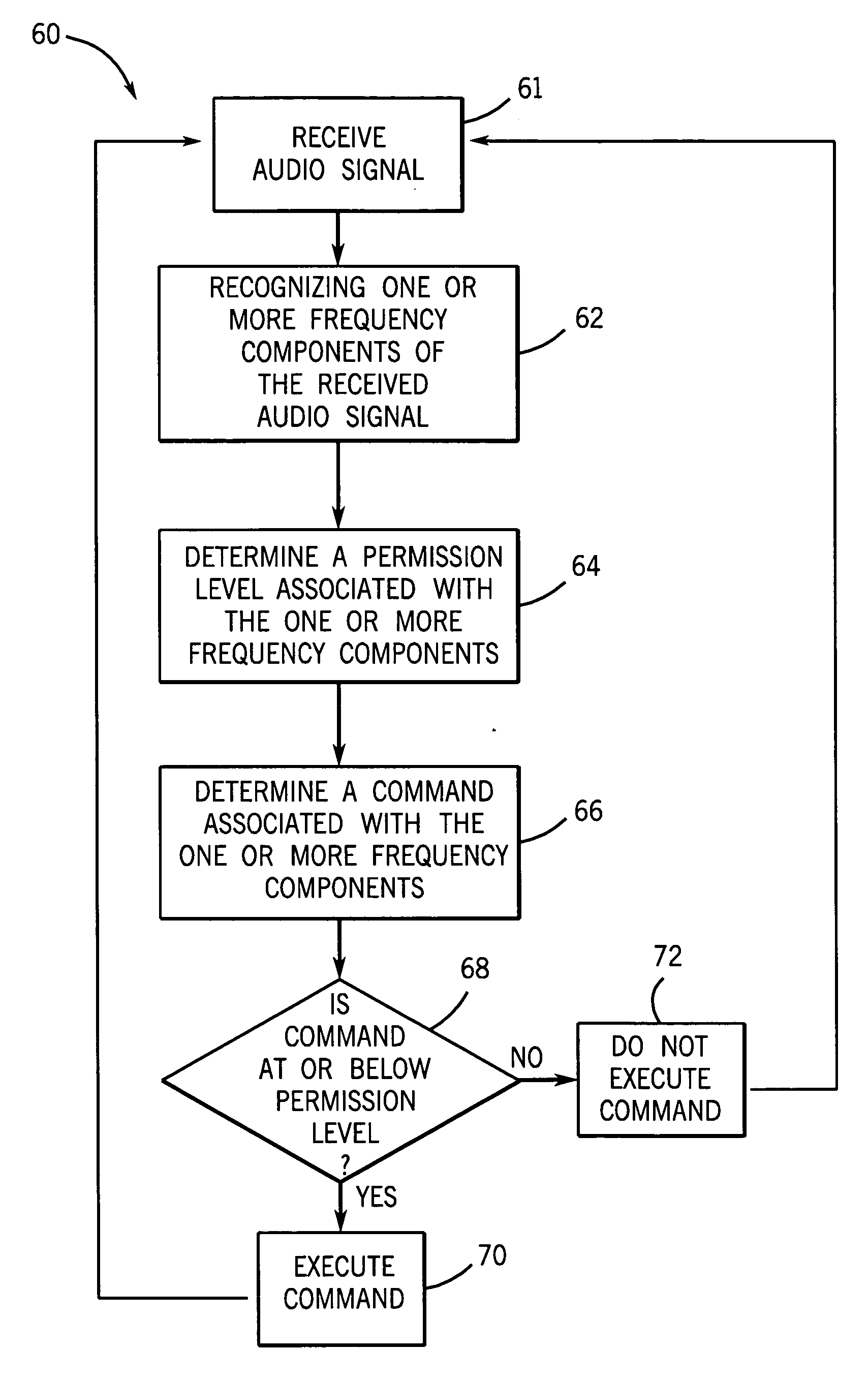
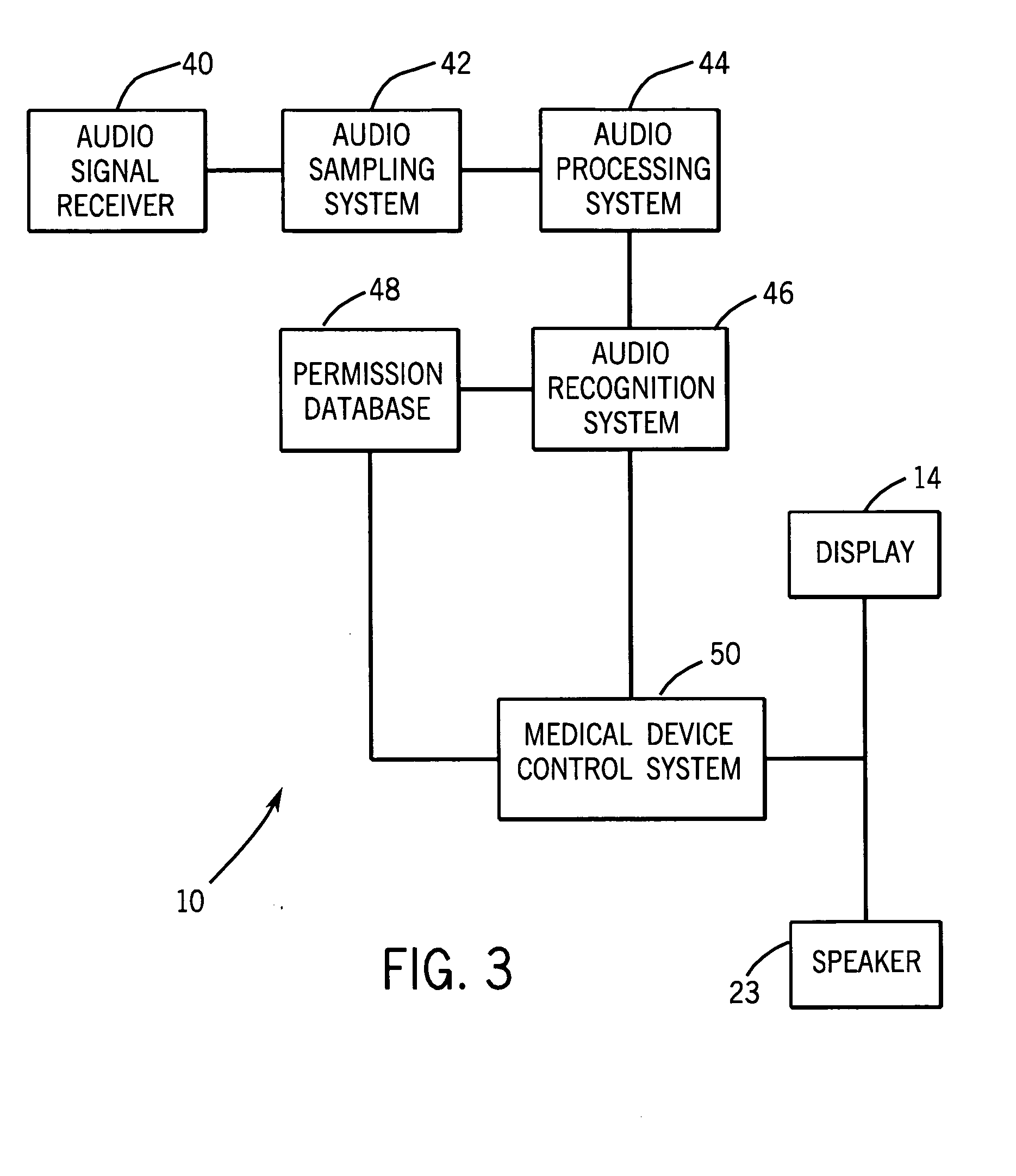
System and method for secure voice identification in a medical device
InactiveUS20080082339A1Local control/monitoringDiagnostic recording/measuringComputer hardwareSecure voice
There is provided a system and method for secure voice identification in a medical device. More specifically, in one embodiment, there is provided a method comprising receiving an audio signal, identifying one or more frequency components of the received audio signal, determining a permission level associated with the one or more frequency components, determining a medical device command associated with the one or more frequency components, wherein the medical device command has a permission level, and executing the medical device command if the permission level of the medical device command is at or below the permission level associated with the one or more frequency components.
Owner:TYCO HEALTHCARE GRP LP
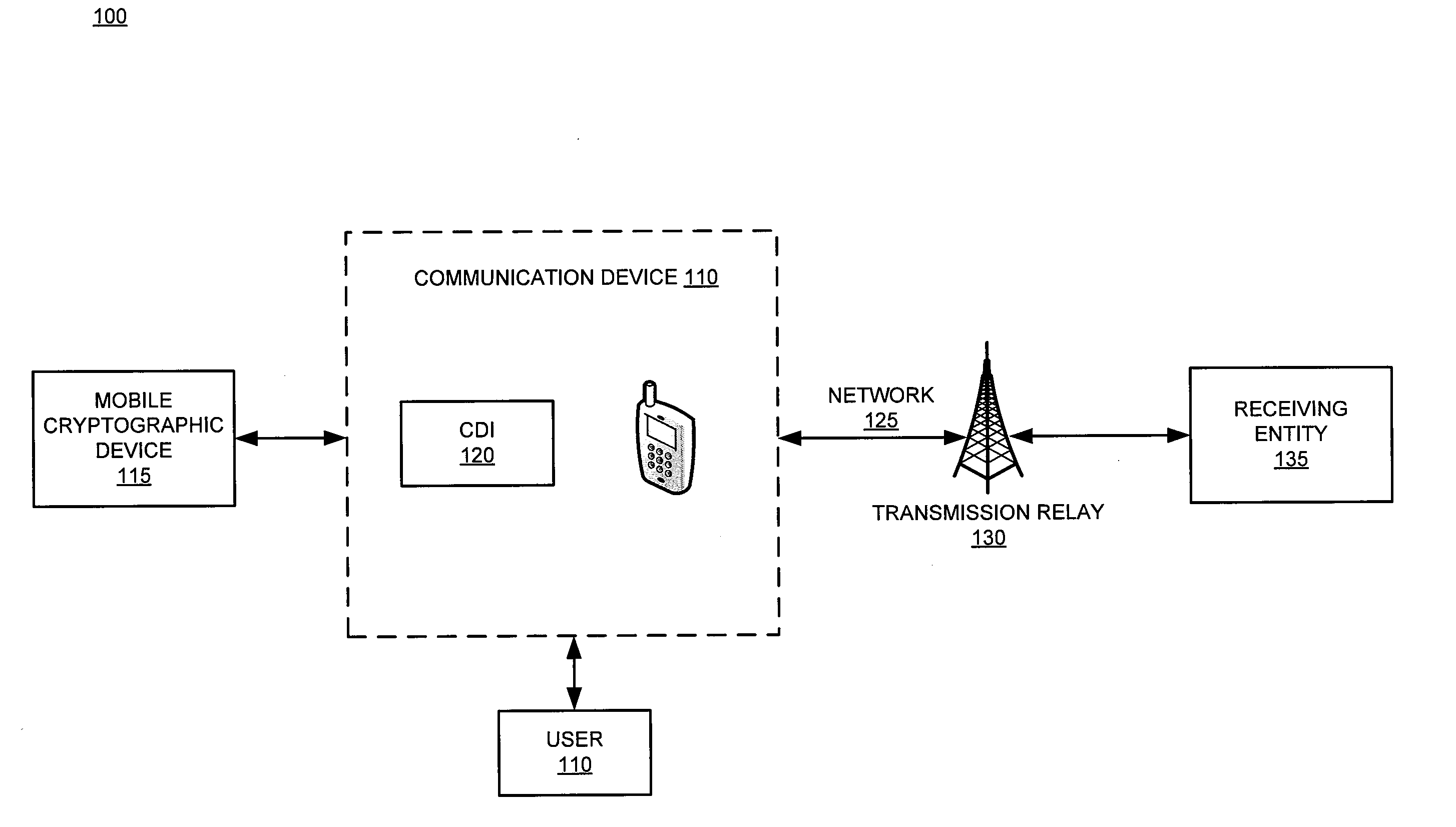
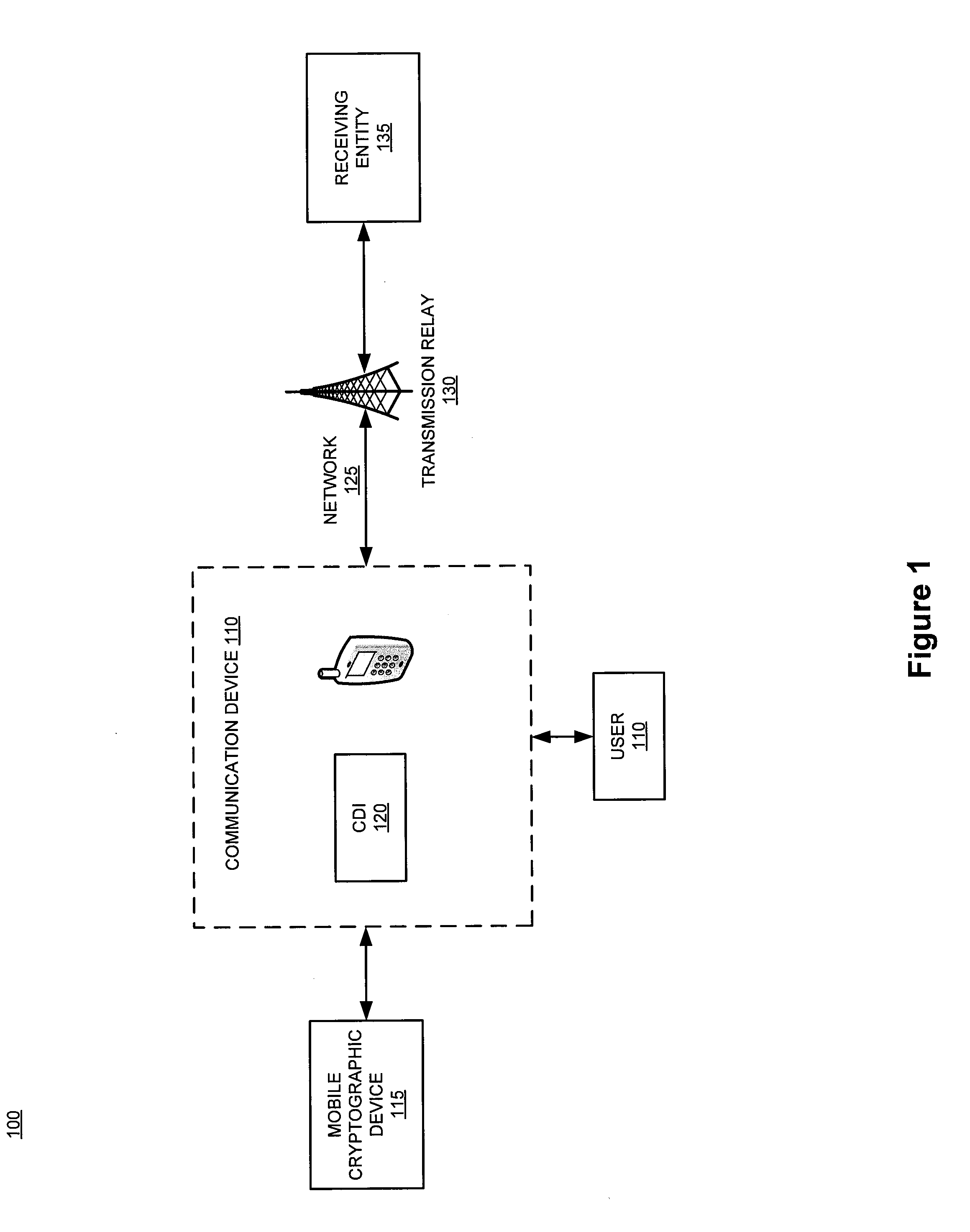
Device and system for facilitating communication and networking within a secure mobile environment
ActiveUS20120269346A1Facilitates secure communicationSecret communicationTransmissionSecure communicationSecure transmission
The present invention relates generally to facilitating secure voice and data communication by way of a commercially available communication device (i.e., smartphone / smartdevice). Specifically, the device and system for pairing a specialized cryptographic device with a non-specialized communication device, wherein the two devices engage in bidirectional communication to facilitate encryption of voice and data for secure transmission over a network. While providing the sensitive cryptographic features for secure communications, the cryptographic device further implements and enforces security policies for the communication device by way if an intermediary native application executed at the communication device. The encryption device is suitably designed to be carried discreetly and may be used in conjunction with a commercially available communication device.
Owner:APRIVA
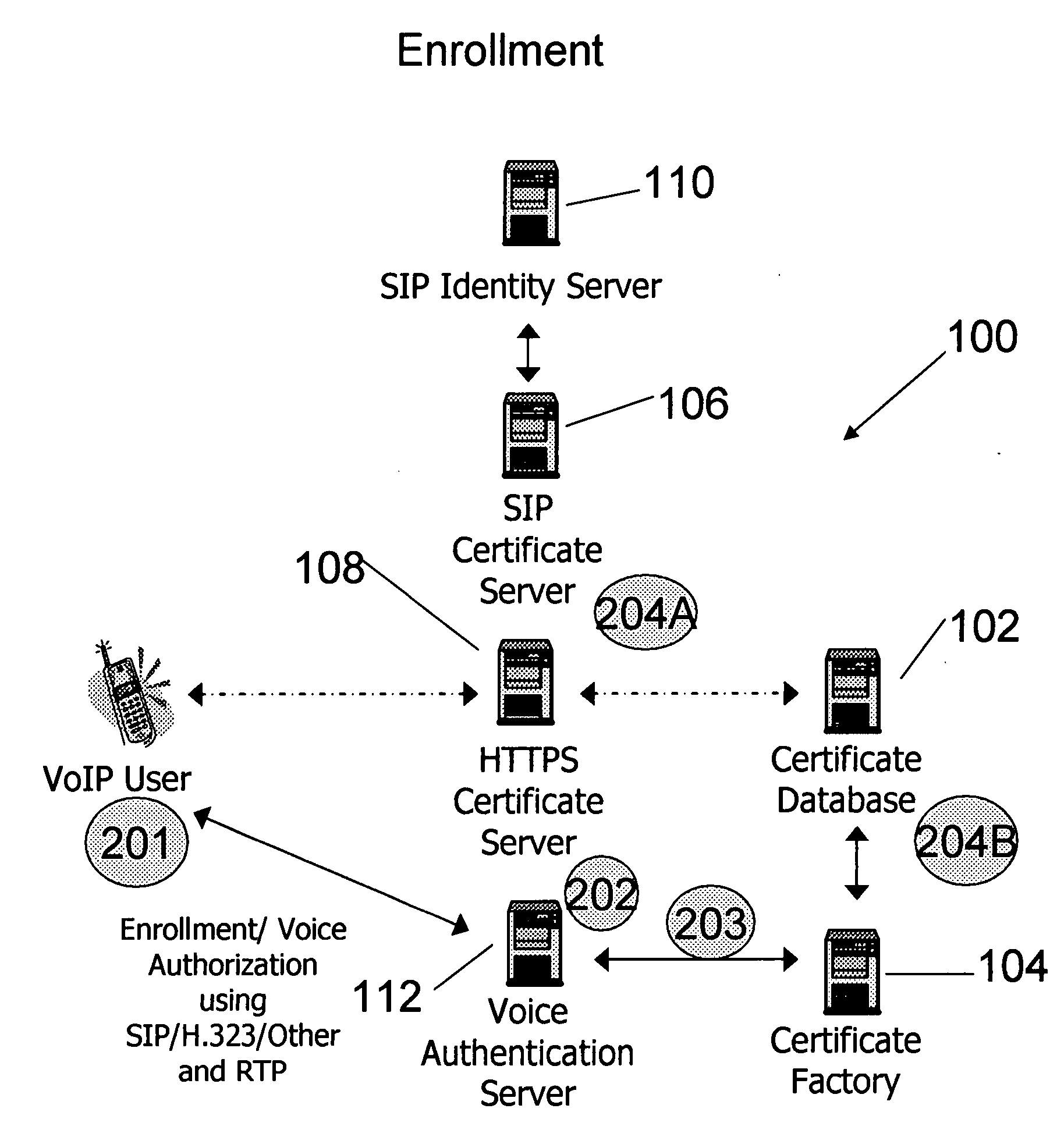
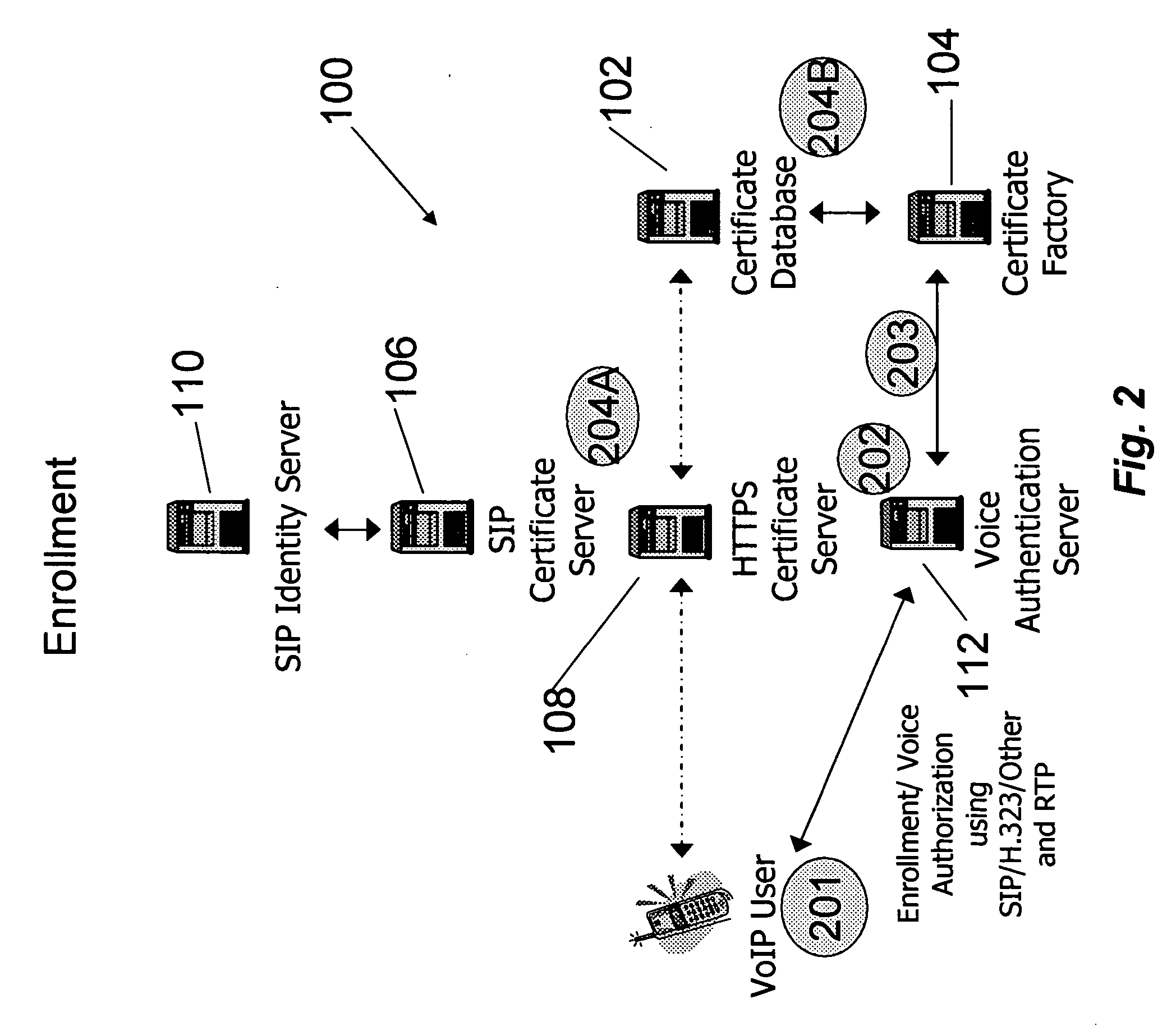
System and method for securely storing and accessing credentials and certificates for secure VoIP endpoints
InactiveUS20070150726A1Low costNone of methods is secureSecuring communicationSession Initiation ProtocolSecure voice
A system and method for enabling secure Voice over IP (VoIP) communication includes receiving a request for the generation of a certificate to be used in conjunction with a VoIP communication, generating a certificate in response to the request, the certificate being generated based, at least in part, on a voice sample of a user that made the request, and thereafter making the certificate available for use to enable secure VoIP communication. The system and method preferably leverages the session initiation protocol (SIP).
Owner:PULVER COM
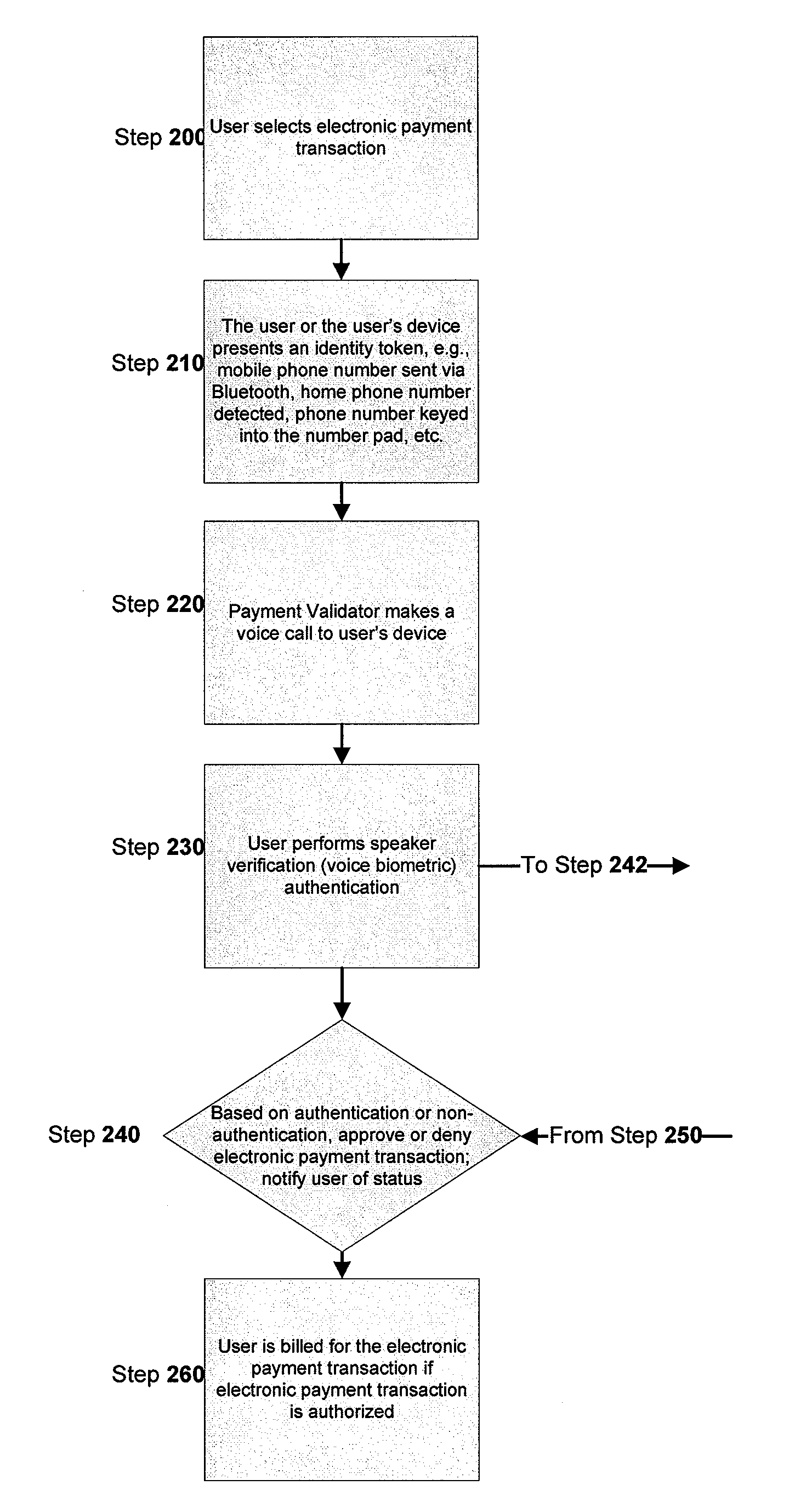
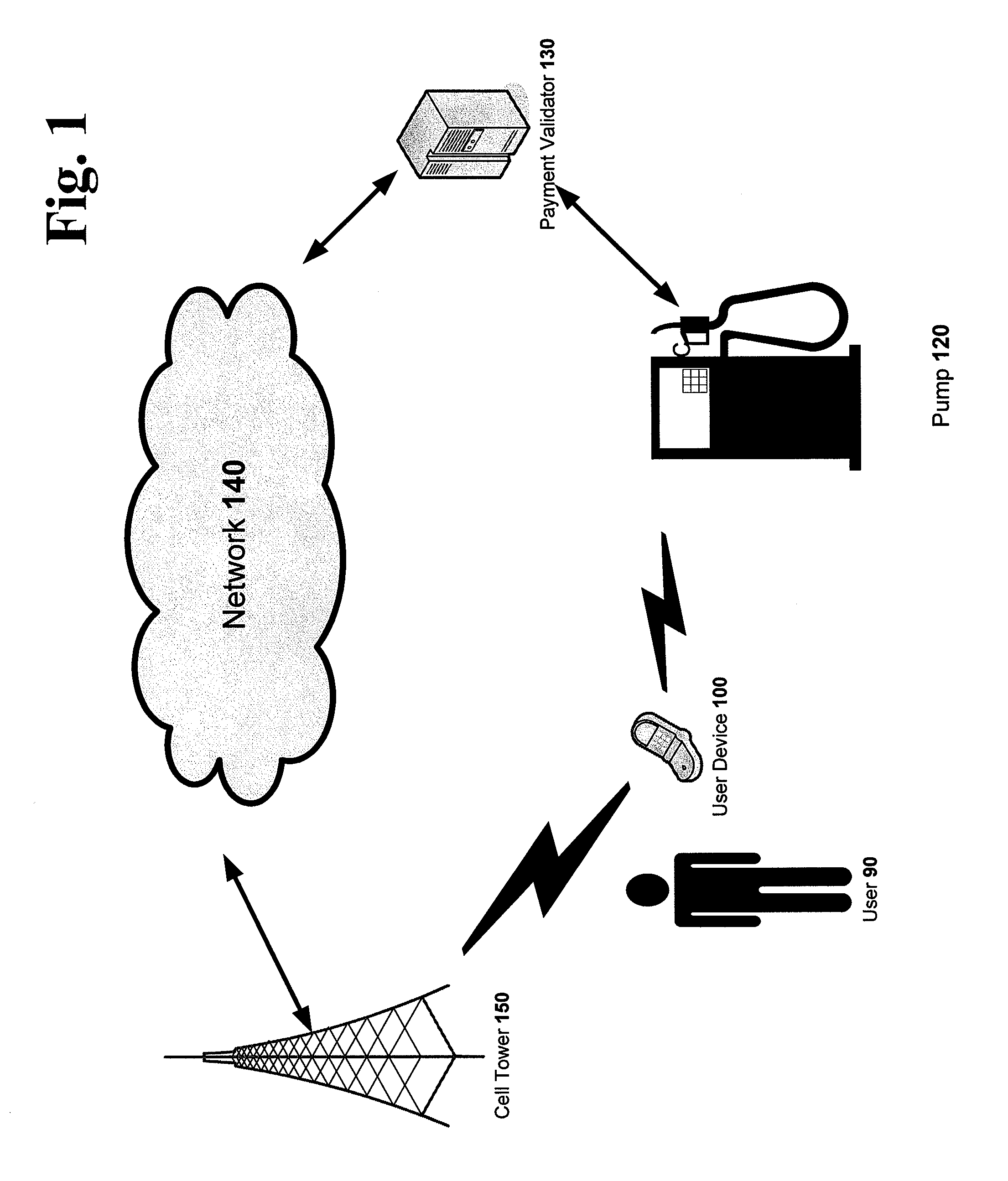
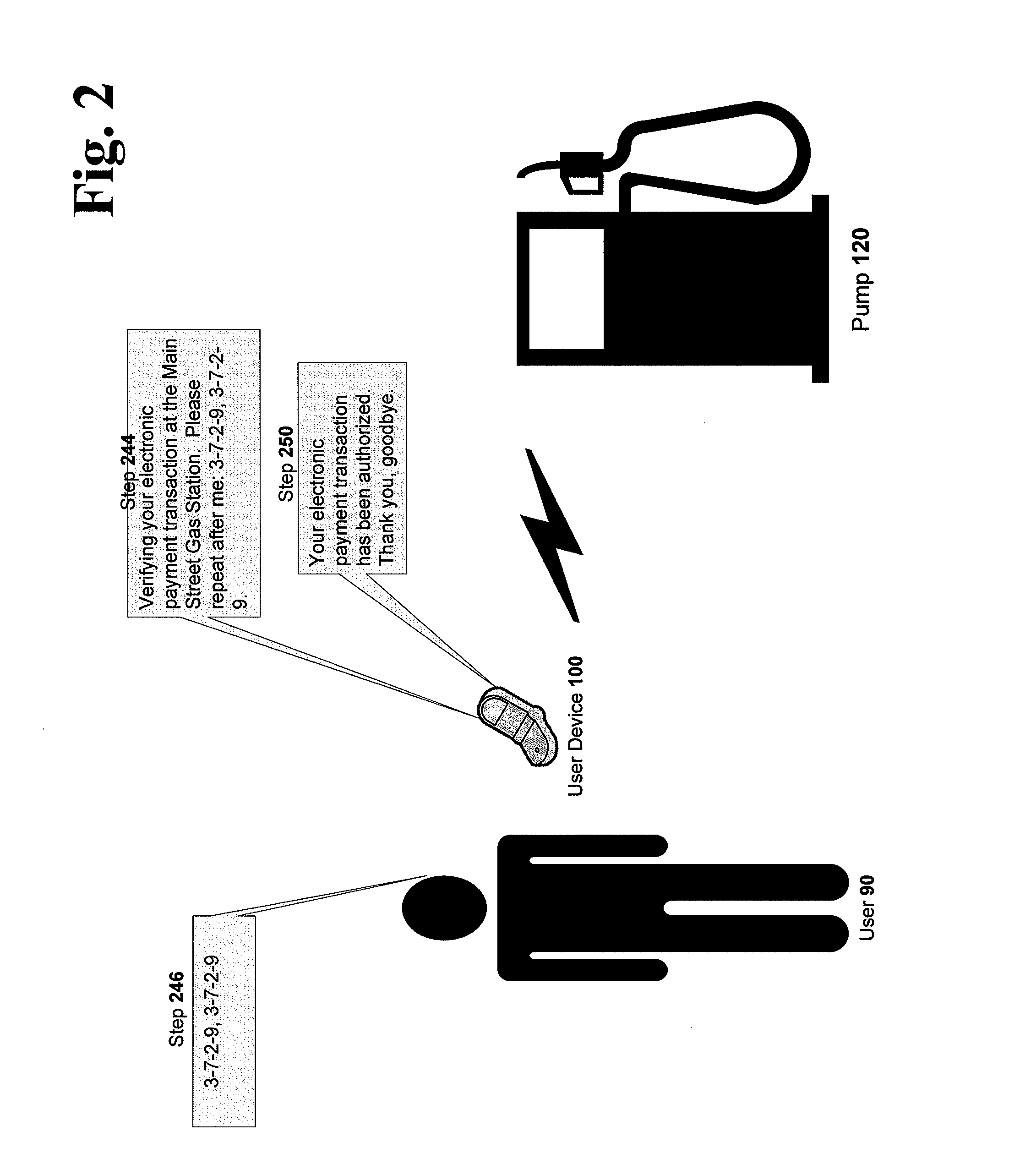
Methods and Systems For Secure Voice-Authenticated Electronic Payment
This application discloses systems, methods, and processes for providing a secure, voice-authenticated form of electronic payment from a device. The described exemplary system provides an infrastructure for receiving an electronic payment request, verifying the request using voice authentication, and allowing or denying the request based on the authentication or non-authentication of the user.
Owner:VERIZON PATENT & LICENSING INC
Reach-back communications terminal with selectable networking options
InactiveUS20050210234A1Public key for secure communicationSecret communicationSecure communicationTelecommunications network
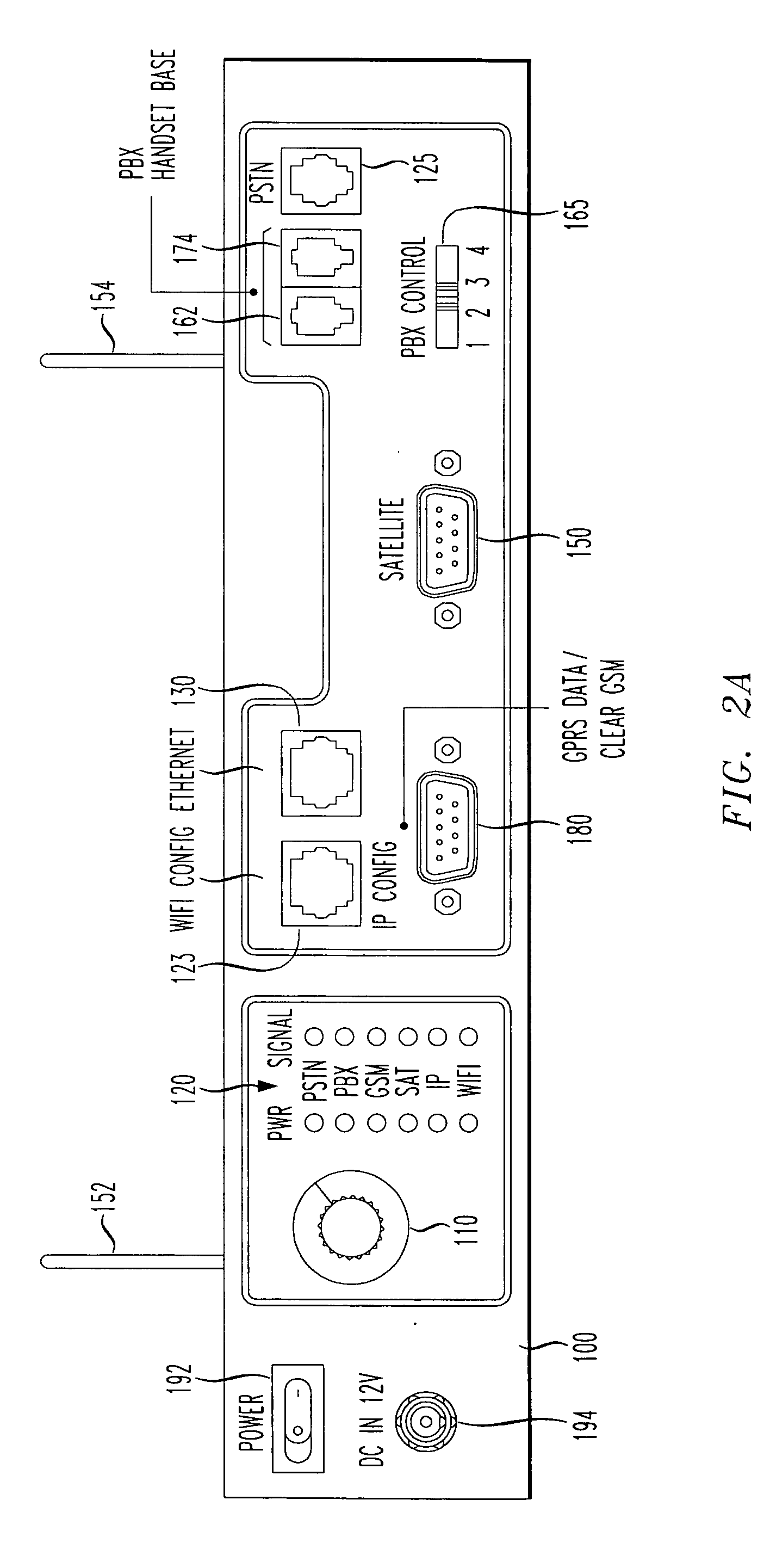
A reach back secure communications terminal that offers immediate and secure voice, data and video connectivity to multiple telecommunications networks, high availability and reliable connectivity, total access to vital resources, and secure extension to the home office. Integrated components simplify access to varied networks allowing deployed users to select and connect quickly to a network that best supports their present mission. Commercial or optional NSA Type 1 encryption may be implemented. Networking options include any of PSTN, PBX, GSM (or CDMA or other cell telephone standard), SAT, IP and WiFi. During secure call setup, the reach-back communications terminal exchanges public keys with a remote terminal using FNBDT signaling. Traffic encryption is performed using the NIST approved Advanced Encryption System (AES) standard (Rijndael) and a 128-bit random key (2{circumflex over ( )}128 possible keys).
Owner:TELECOMM SYST INC
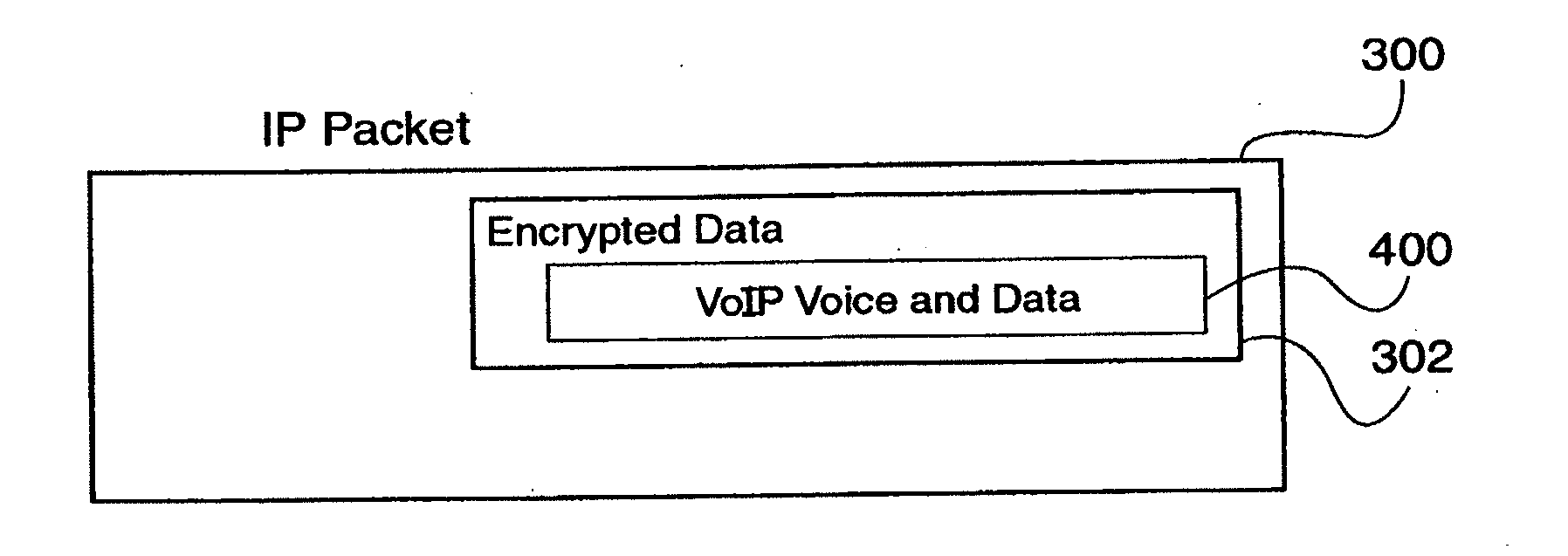
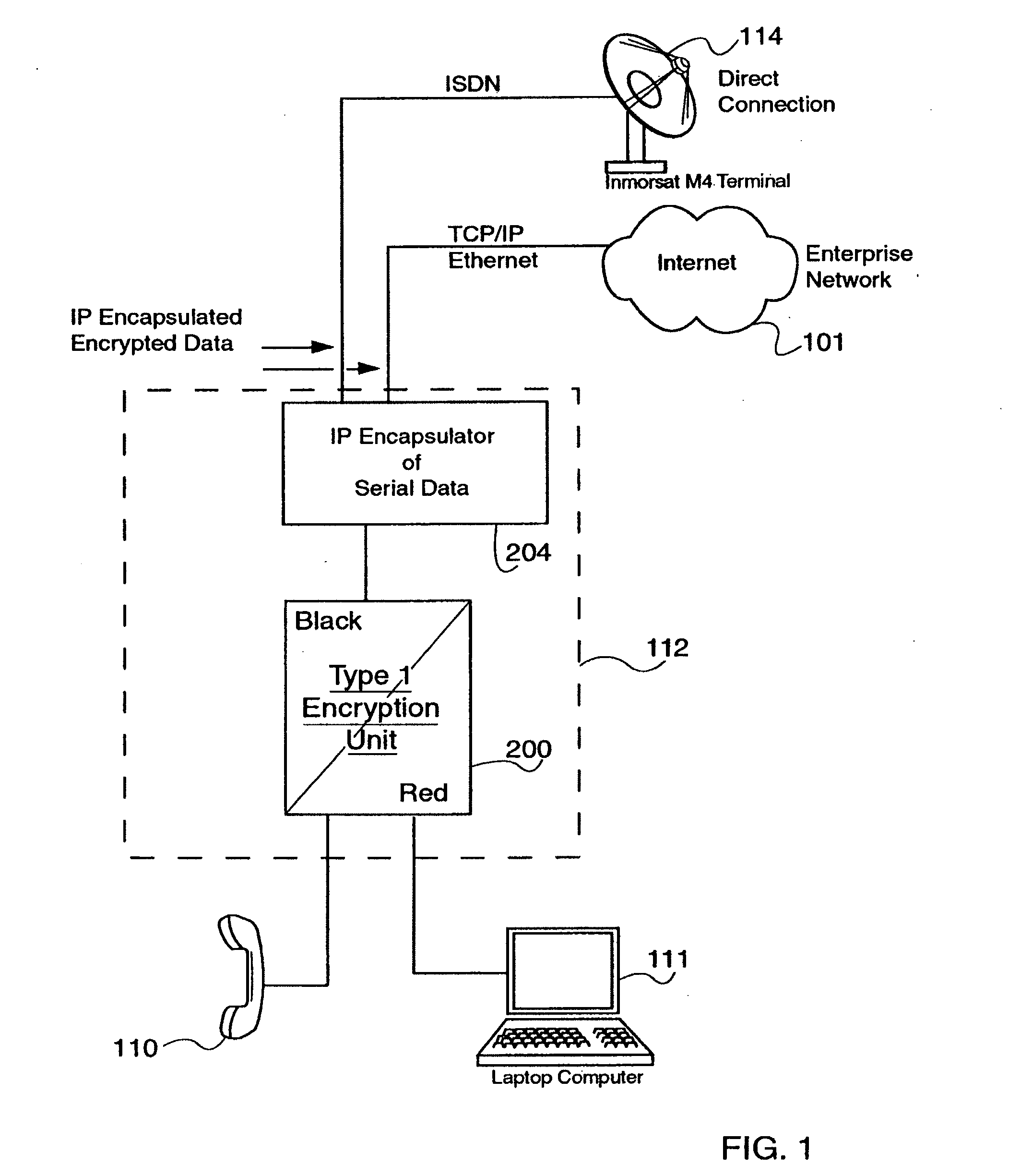
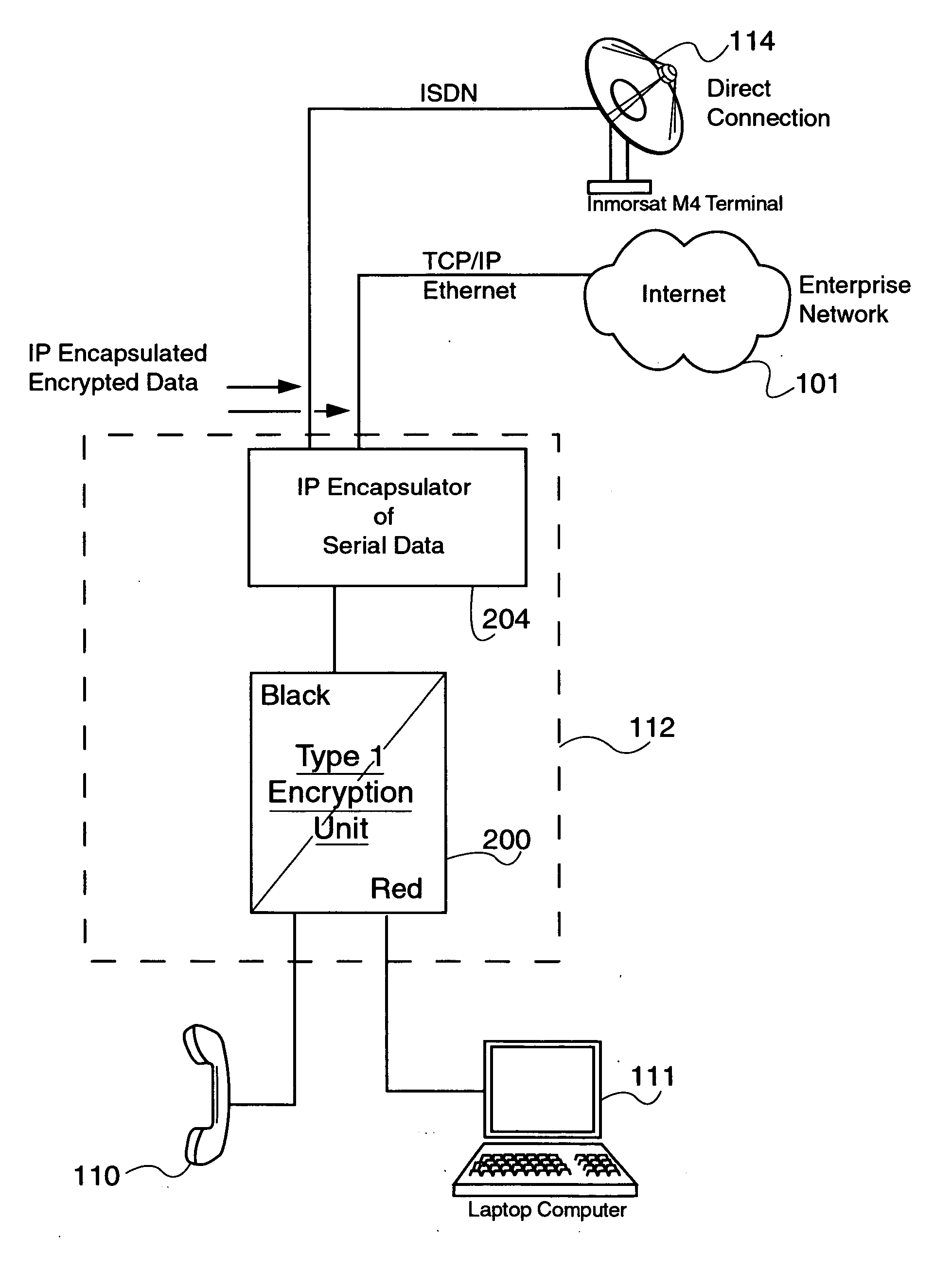
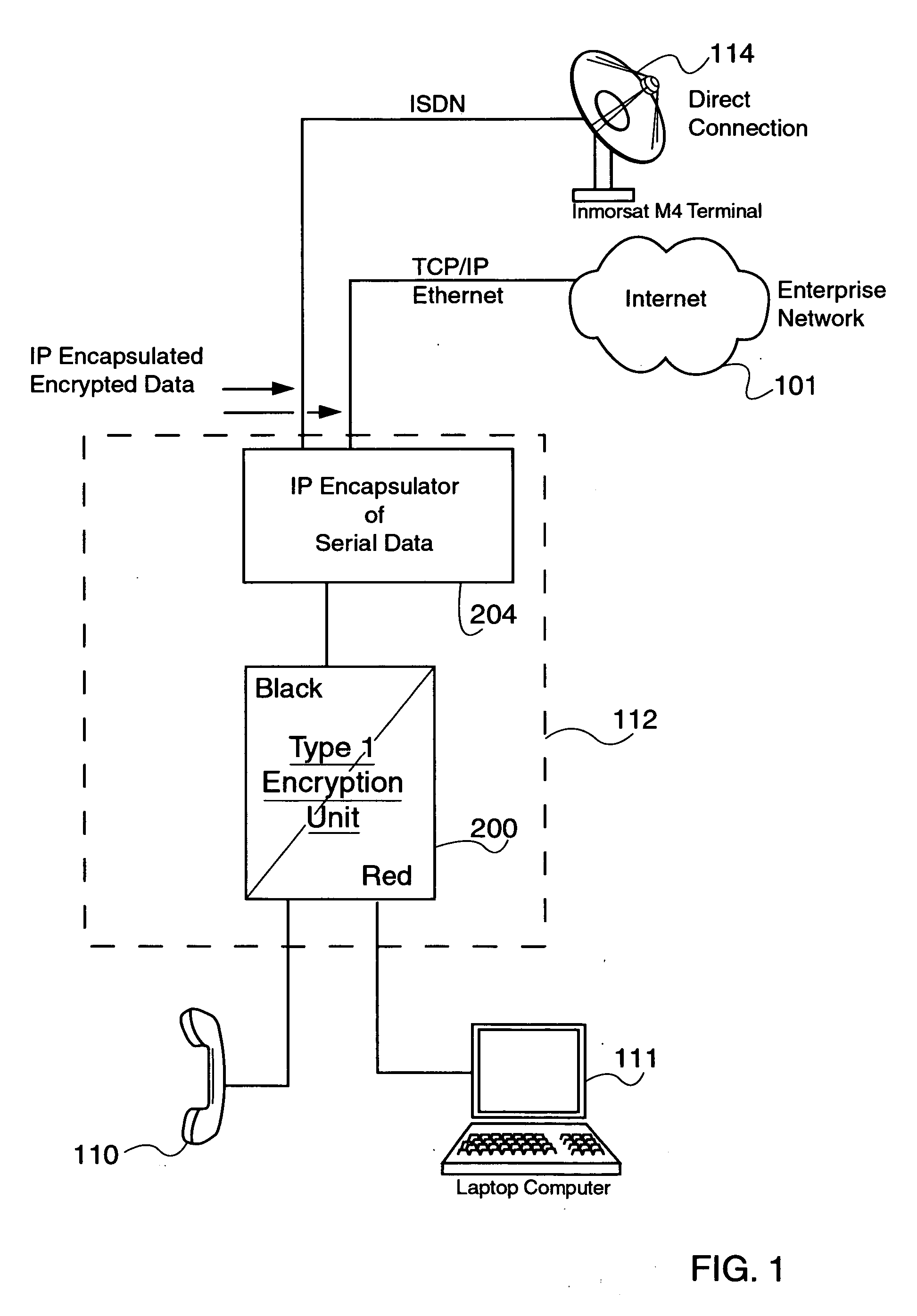
Encapsulation of Secure Encrypted Data in a Deployable, Secure Communication System Allowing Benign, Secure Commercial Transport
Sensitive, Type 1 KIV-encrypted data is encapsulated into IP packets in a remotely deployed, secure communication system. The IP packets are addressed to a matching IP encapsulator / decapsulator device over the public Internet or other IP protocol network, that then passes it to a similar Type 1 KIV device for decryption. Thus, sensitive, encrypted data is made to appear as if it were any other commercial network data, cloaking it in the vast and busy world of the Internet. The present invention is embodied in a system that provides secure Voice-Over-IP (VOIP), video and data network functionality in a single, small size deployable case, to a remote user. Most importantly, the embodiment allows for the routing of bulk encrypted (i.e., secure) data over a public network, e.g., the Internet.
Owner:TELECOMM SYST INC
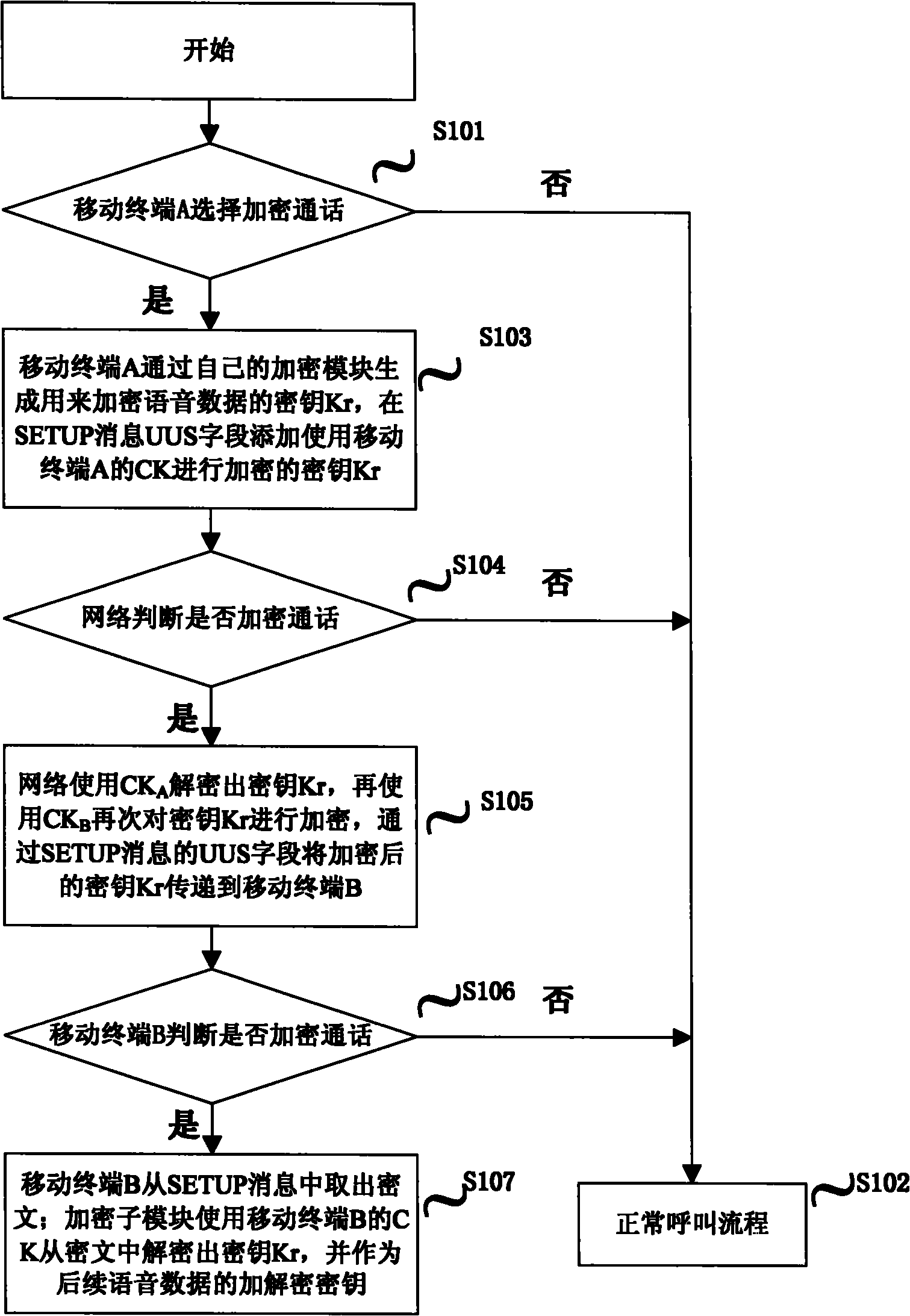
Mobile communication system and voice call encryption method thereof
InactiveCN101917711AVoice communication securityTransmissionSecurity arrangementComputer hardwareVoice communication
The invention discloses a mobile communication system and a voice call encryption method in the mobile communication system, and belongs to the technical field of mobile communication. In the mobile communication system, a calling terminal generates a voice key for voice encryption / decryption, and the voice key is encrypted by using a shared key factor of the calling terminal and then transmitted to a network side; the network side decrypts the encrypted voice key according to the shared key factor of the calling terminal, encrypts the voice key by using a shared key factor of a called terminal and transmits the encrypted voice key to the called terminal; and the called terminal decrypts the encrypted voice key by using the shared key factor of the called terminal, and acquires the voice key. The calling terminal and the called terminal perform encrypted voice call by using the voice key. The voice key used by voice communication can be encrypted and transmitted, and the calling and called terminals perform more secure voice call by using the shared voice key.
Owner:ZTE CORP
Secure voice and data method and system
InactiveUS20160337857A1Unauthorised/fraudulent call preventionAutomatic exchangesSecure voiceSpeech sound
The present invention provides a method and system for securing mobile communications with a smartphone In a preferred embodiment of the present invention a secure method for controlling the microphones of the smartphone is provided. This method avoids that the phone can be exploited as a spy-phone, recording sounds and voices while in standby. In an embodiment the smartphone is hardened since the operating system is closed and no apps can be added or upgraded once the firmware is deployed. In an embodiment of the invention GPS data are secured in order to prevent unauthorized access to them. GPS data, similarly to audio ones, can be encrypted in kernel space restricting their access only to cryptographically trusted apps.
Owner:TELSY ELETTRONICA E TELECOMM SPA
Encapsulation of secure encrypted data in a deployable, secure communication system allowing benign, secure commercial transport
Sensitive, Type 1 KIV-encrypted data is encapsulated into IP packets in a remotely deployed, secure communication system. The IP packets are addressed to a matching IP encapsulator / decapsulator device over the public Internet or other IP protocol network, that then passes it to a similar Type 1 KIV device for decryption. Thus, sensitive, encrypted data is made to appear as if it were any other commercial network data, cloaking it in the vast and busy world of the Internet. The present invention is embodied in a system that provides secure Voice-Over-IP (VOIP), video and data network functionality in a single, small size deployable case, to a remote user. Most importantly, the embodiment allows for the routing of bulk encrypted (i.e., secure) data over a public network, e.g., the Internet.
Owner:TELECOMM SYST INC
Method and Apparatus for wireless spread spectrum communication with preamble processing period
InactiveUS6947469B2Reduce Inter-Cell InterferenceExtend battery lifePower managementTransmission control/equalisingMobile Telephone ServiceHand held
A simple and flexible over-air protocol for use with a mobile telephone system, having hand-held telephones in a microcell or other type of cellular communication system. A method in which user stations communicate with one or more base stations to place and receive telephone calls, in which the user stations are provided a secure voice or data link and have the ability to handoff calls between base stations while such calls are in progress. Each base station has a set of “air channels” to which it transmits in sequence. The air channels supported by each base station are called that base station's “polling loop”. A user station receives general polling information on an unoccupied air channel, transmits responsive information to the base station, and awaits acknowledgment from the base station. Each base station may therefore simultaneously maintain communication with as many user stations as there are air channels in its polling loop. The ability of a user station to communicate on any unoccupied air channel makes the protocol air-channel agile, while the stability of user station and base station clocks may define air channels, gaps, and minor frames.
Owner:INTEL CORP
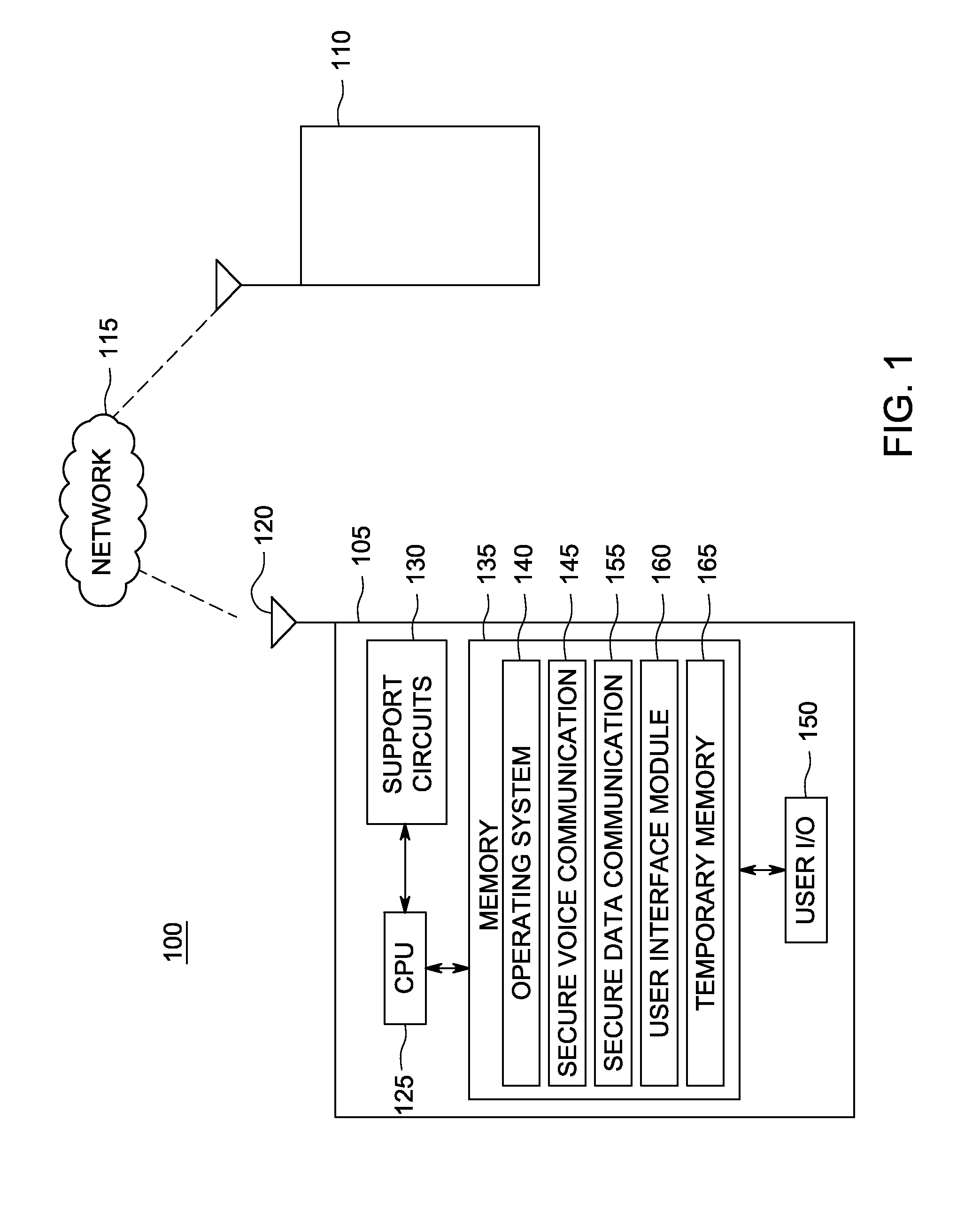
Mobile modular communication system
ActiveUS20100165571A1Digital data processing detailsPrinted circuit board receptaclesTelecommunications linkCommunications system
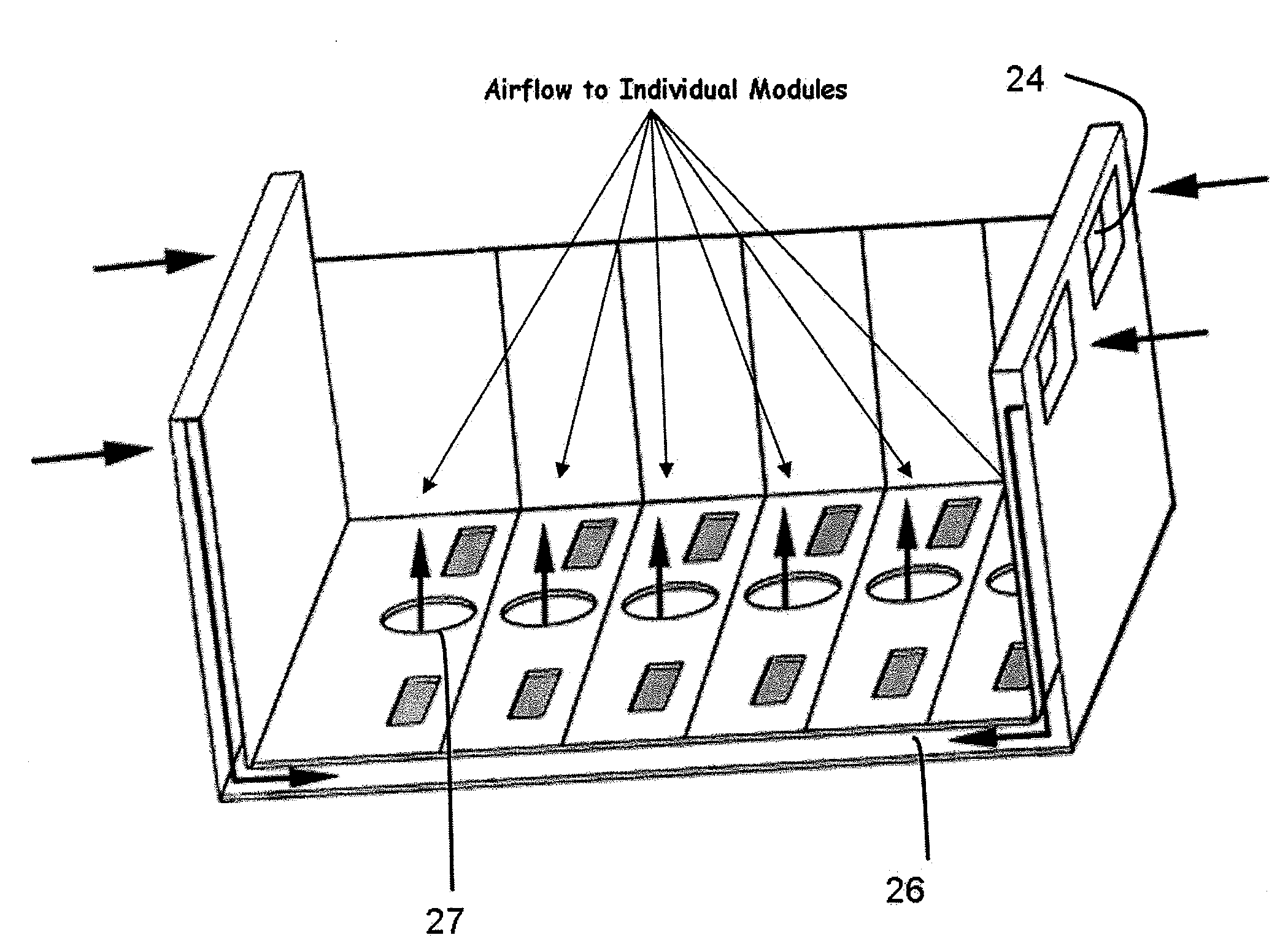
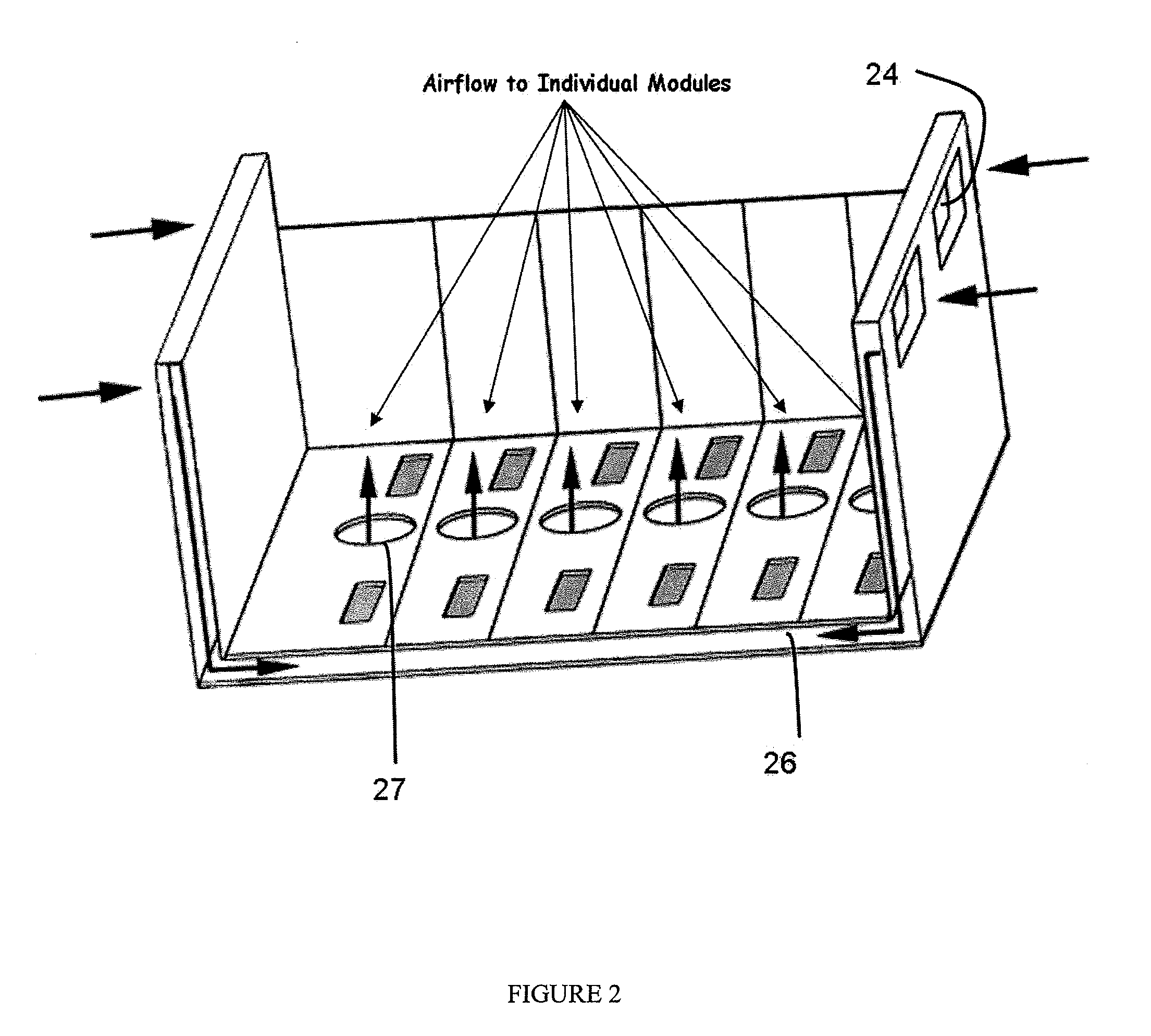
A mobile, modular communications device, featuring a multiple-slot base chassis designed to support a plurality of individual user-configurable and interchangeable personality modules, capable of providing the ability to accept secure / classified user communications, including voice, data and video, the means to encrypt or secure such user communications through either internal or external encryption capabilities, the means to optimize the secure voice, data and video communications for transmission across a remote reachback communications link and the ability to provide multiple network / uplink reachback transmission alternatives, such as local area networks, satellites, cellular, ISDN or other forms of fixed or wireless communications. The invention is intended to provide a standardized, structured and modular approach to the provisioning of different technologies within the overall system and to be capable of being deployed as a man-carry or rack-embedded unit.
Owner:CUBIC CORPORATION
Secure transmission of media during a communication session
ActiveUS20140280982A1Multiple digital computer combinationsWireless network protocolsComputer hardwareSecure transmission
Methods for secure transmission of data during a communication session are provided herein. In some embodiments, the method includes establishing a secure voice communication session between a first electronic device and second electronic device in a communications network, and sending secure data over the established voice communication session using information associated with the established voice communication session.
Owner:VONAGE BUSINESS
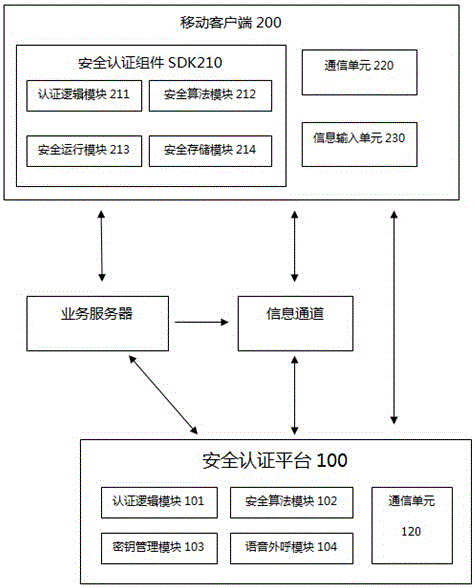
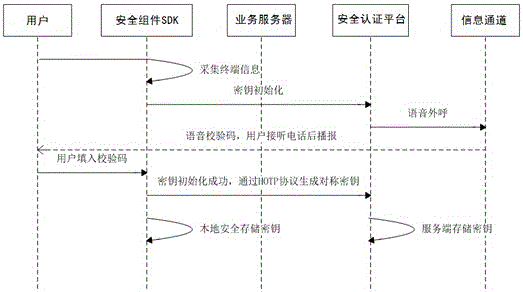
System and method for performing transaction security authentication in mobile device
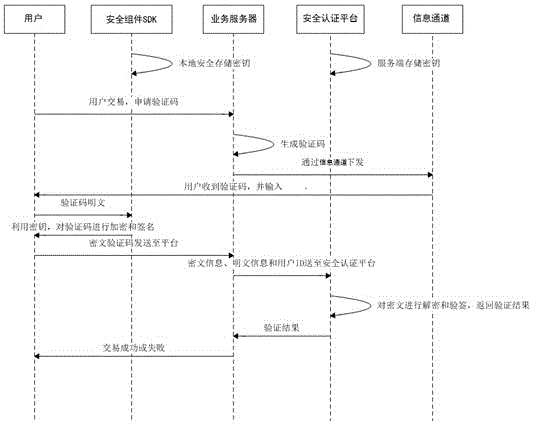
ActiveCN106027501AImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationPaymentCommunication unit
The invention relates to a system and a method for performing transaction security authentication in a mobile device. The system provided by the invention is characterized by comprising a mobile client having a communication unit, an information input unit and a security component SDK; a security authentication platform having a communication unit, a voice call-out module for performing secure voice communication with an information channel, an authentication logic module 1 for completing authentication logic of the mobile client, a security algorithm module 1 for achieving an encryption algorithm, and a secret key management module for securely storing and managing one or more secret keys of the plurality of mobile clients; the security component SDK comprises an authentication logic module 1, a security algorithm module 2, a secure operation module for preventing the SDK from being decompiled or dynamically debugged, and a secure storage module for ensuring that the secret keys are securely stored at the mobile client. The system and method have the advantages that the secret key can be generated by voice calling, the secret key can also be securely stored and applied to related encryption and security authentication operations, and thus the security of virtual payment is improved.
Owner:BEIJING TRUSFORT TECH CO LTD
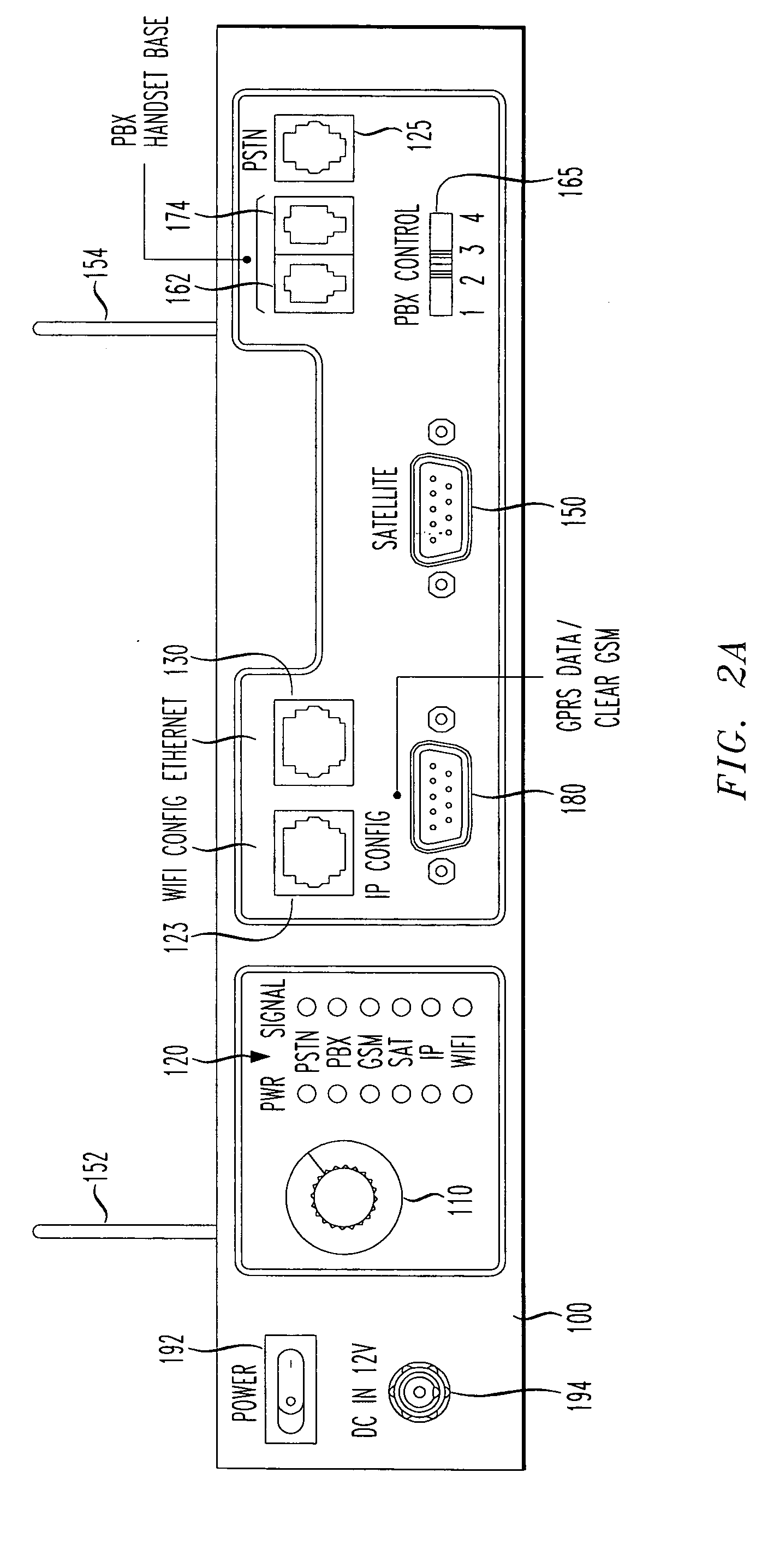
Encryption STE communications through private branch exchange (PBX)
InactiveUS20050210235A1Digital data processing detailsUser identity/authority verificationSecure communicationSecure voice
A reach back secure communications terminal includes a digital PBX adapter that offers immediate and secure voice, data and video connectivity over any of various commercially available PBX systems. In addition to use with a PBX system, integrated components simplify access to varied networks allowing deployed users to select and connect quickly to a network that best supports their present mission. Commercial or optional NSA Type 1 encryption may be implemented. Networking options include any of PSTN, PBX, GSM (or CDMA or other cell telephone standard), SAT, IP and WiFi. The digital PBX adapter includes an audio mixer that converts a 4-wire input from a handset jack of a PBX handset base, into a 2-wire output destined for an encryption unit (FNBDT). The user determines a necessary gain of the audio mixer for the particular PBX system by trial and error using a multi-position switch.
Owner:TELECOMM SYST INC
Hospital instant communication system and instant communication method
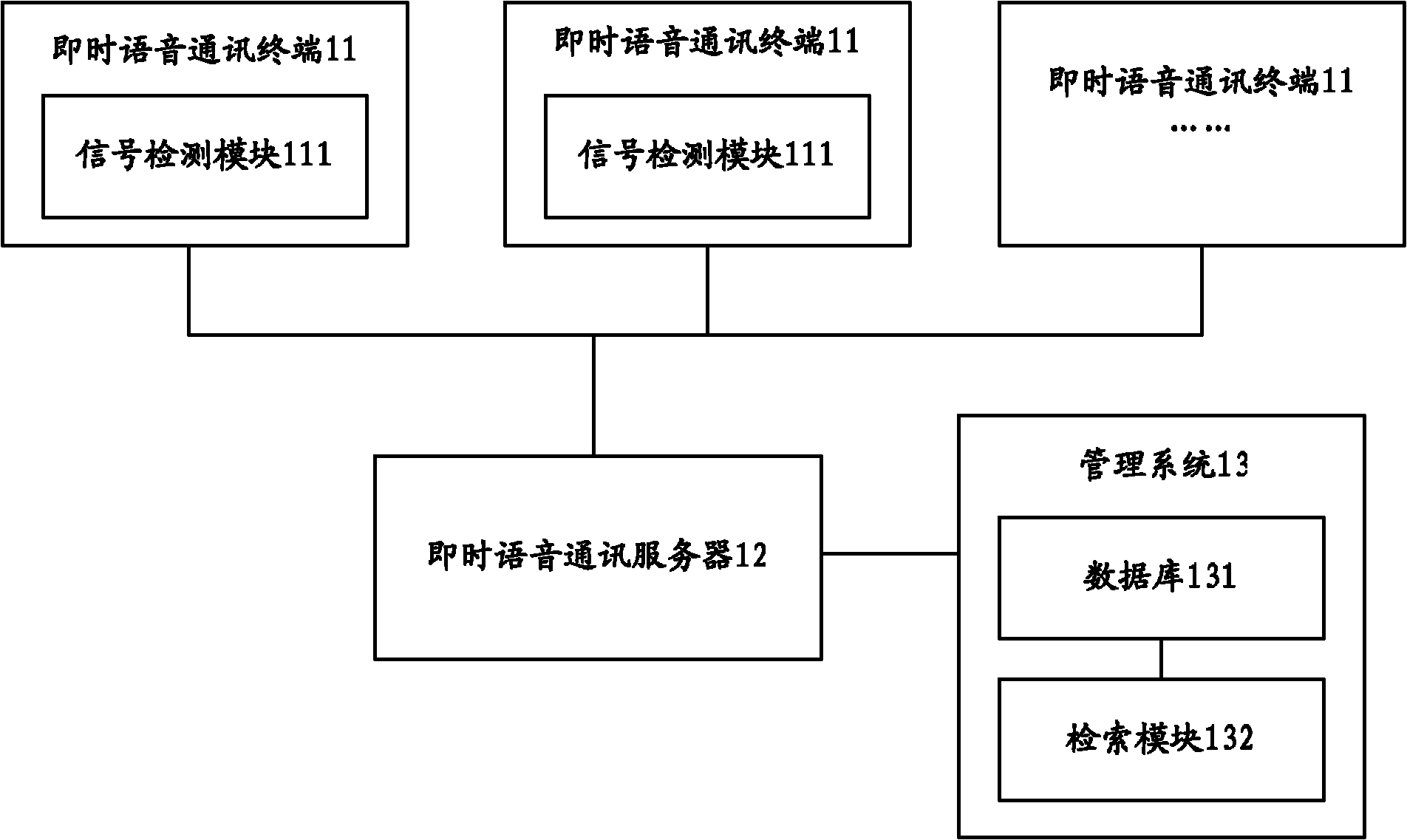
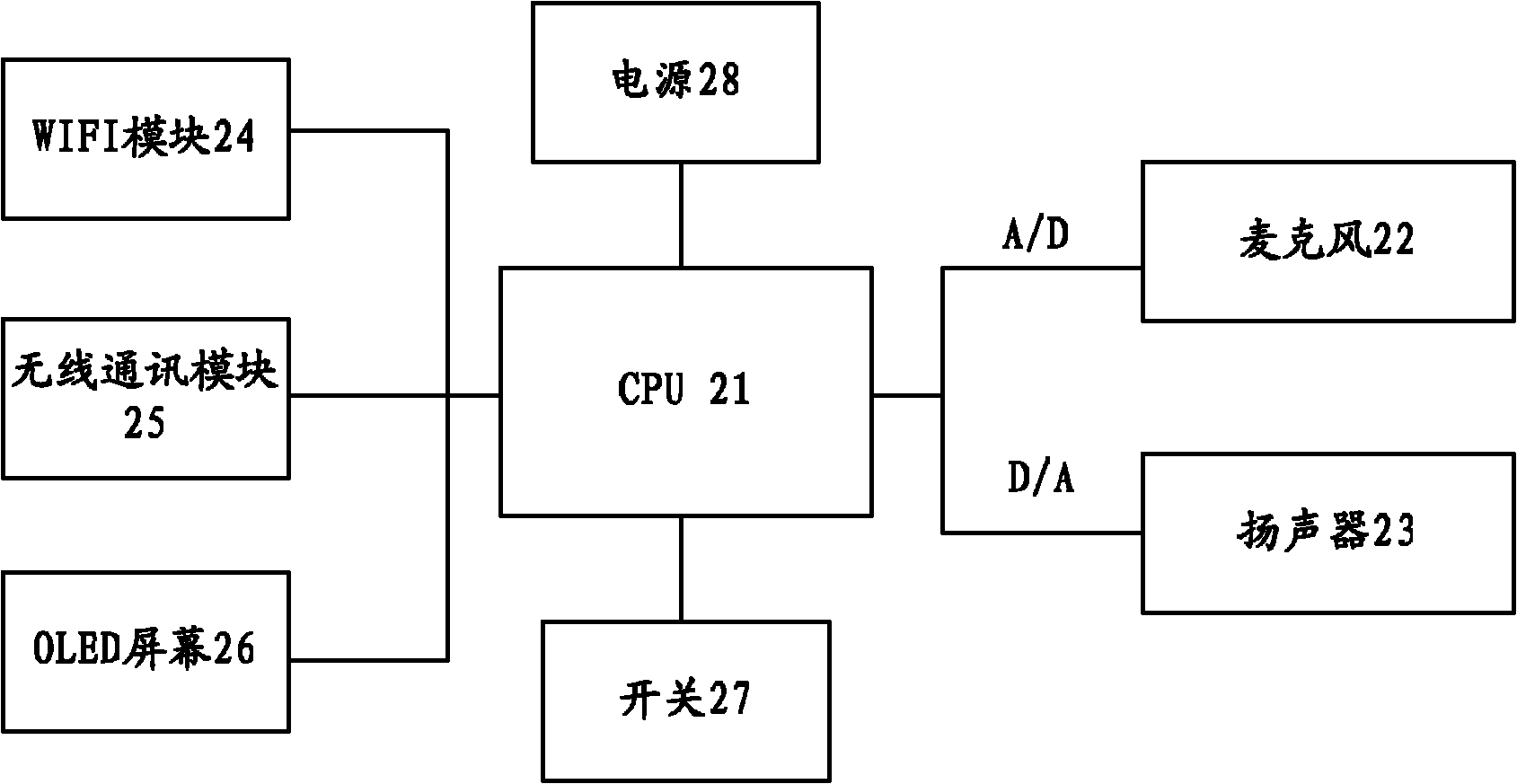
InactiveCN102131156AImprove work efficiencyWork lessAssess restrictionMessaging/mailboxes/announcementsVoice communicationSecure voice
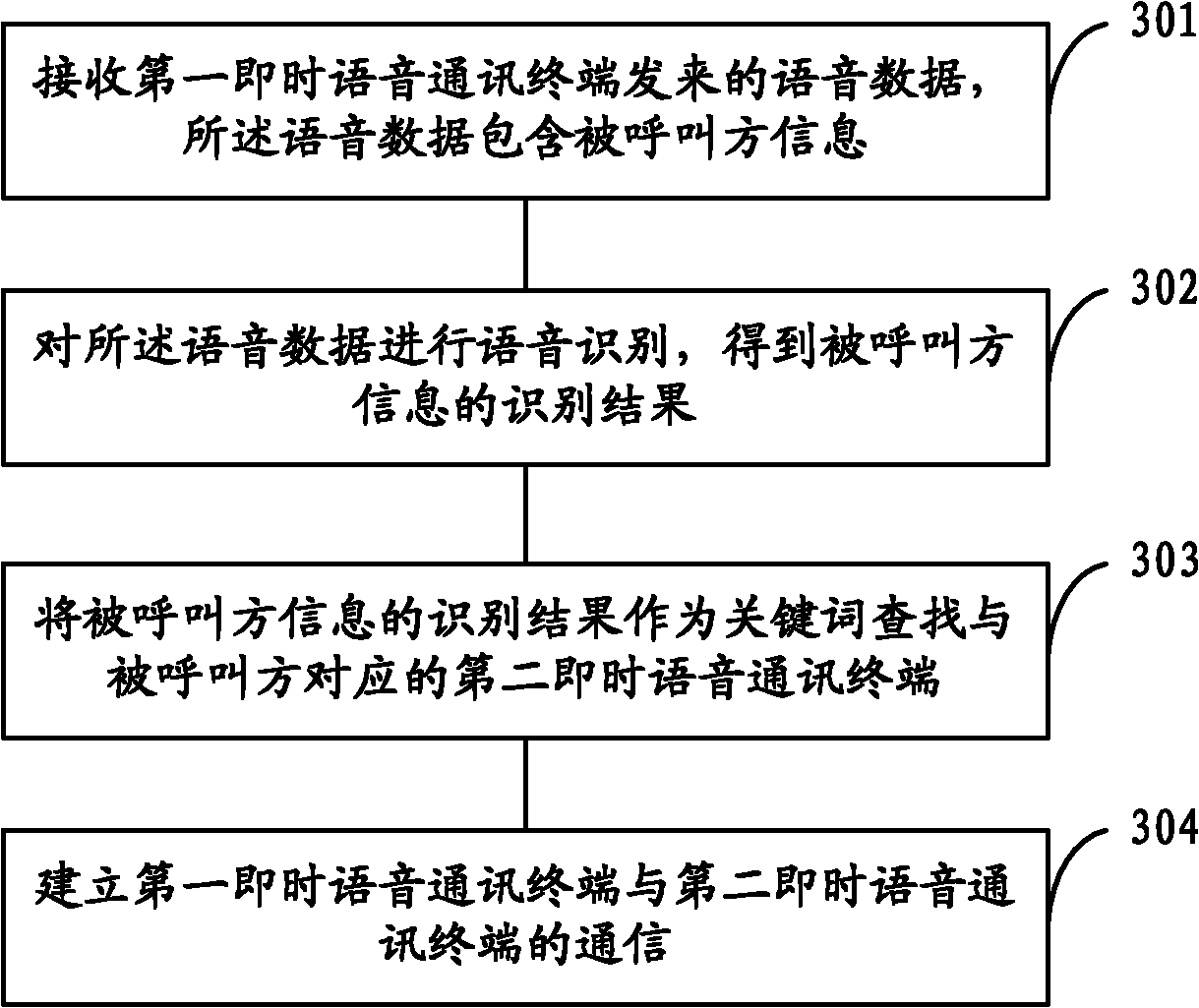
The invention provides a hospital instant communication system and an instant communication method so as to solve the instant communication problem among the hospital staff. The system comprises a first instant voice communication terminal, a second instant voice communication terminal, an instant voice communication server and a management system, wherein the first instant voice communication terminal sends voice data comprising the called party information to an instant voice communication server; the instant voice communication server is used for receiving voice data, performing voice recognition to obtain the recognition result of the called party information, and sending the recognition result to a management system; the instant voice communication server is also used for establishing communication between the first instant voice communication terminal and the second instant voice communication terminal when the management system searches the second instant voice communication terminal; and the management system is used for searching for the second instant voice communication terminal corresponding to the called party by taking the recognition result of the called party information as a keyword, and sending the search result to the instant voice communication server. Through the invention, timely, reliable and secure voice communication can be provided among the hospital staff.
Owner:上海华美络信息技术有限公司
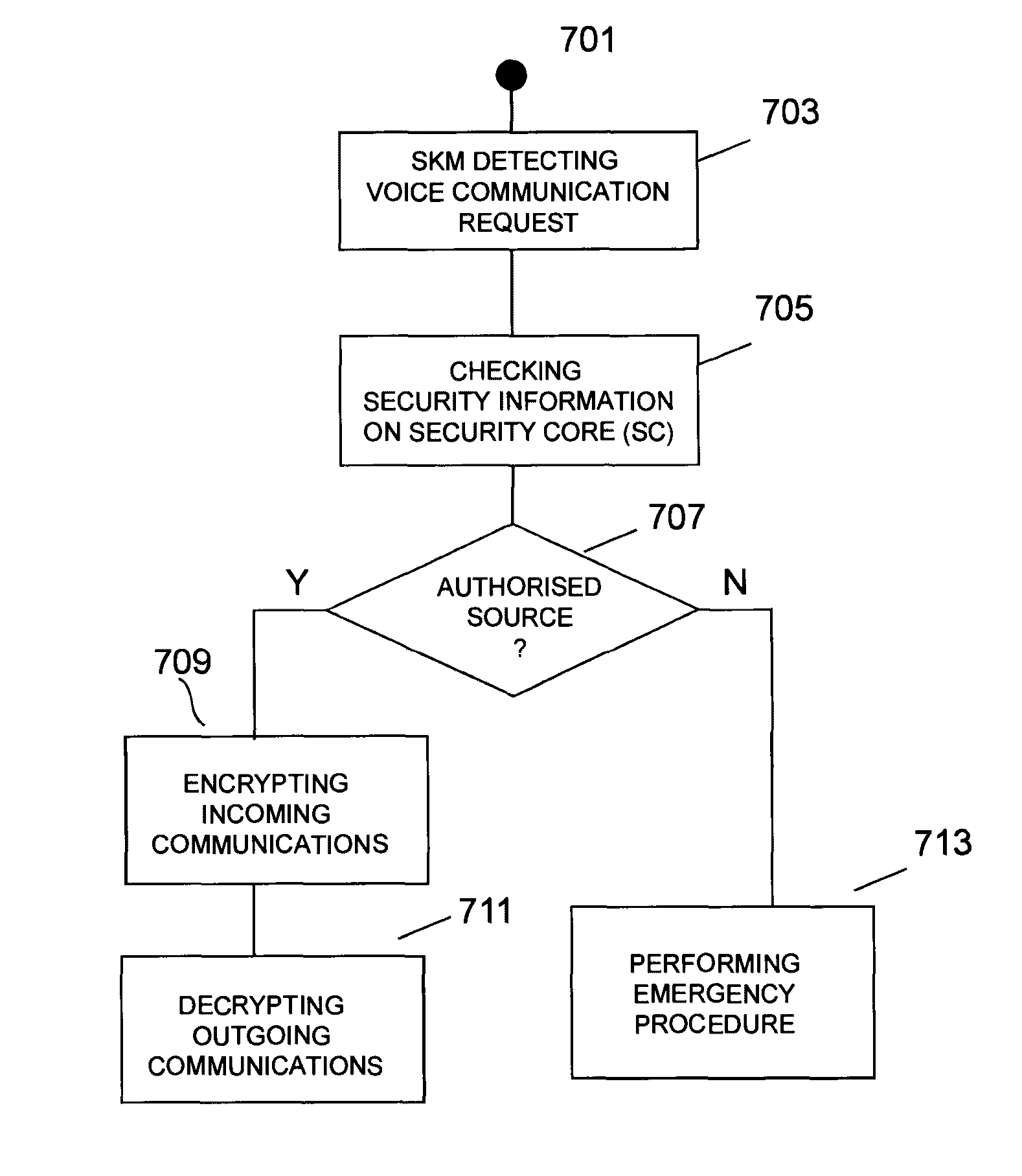
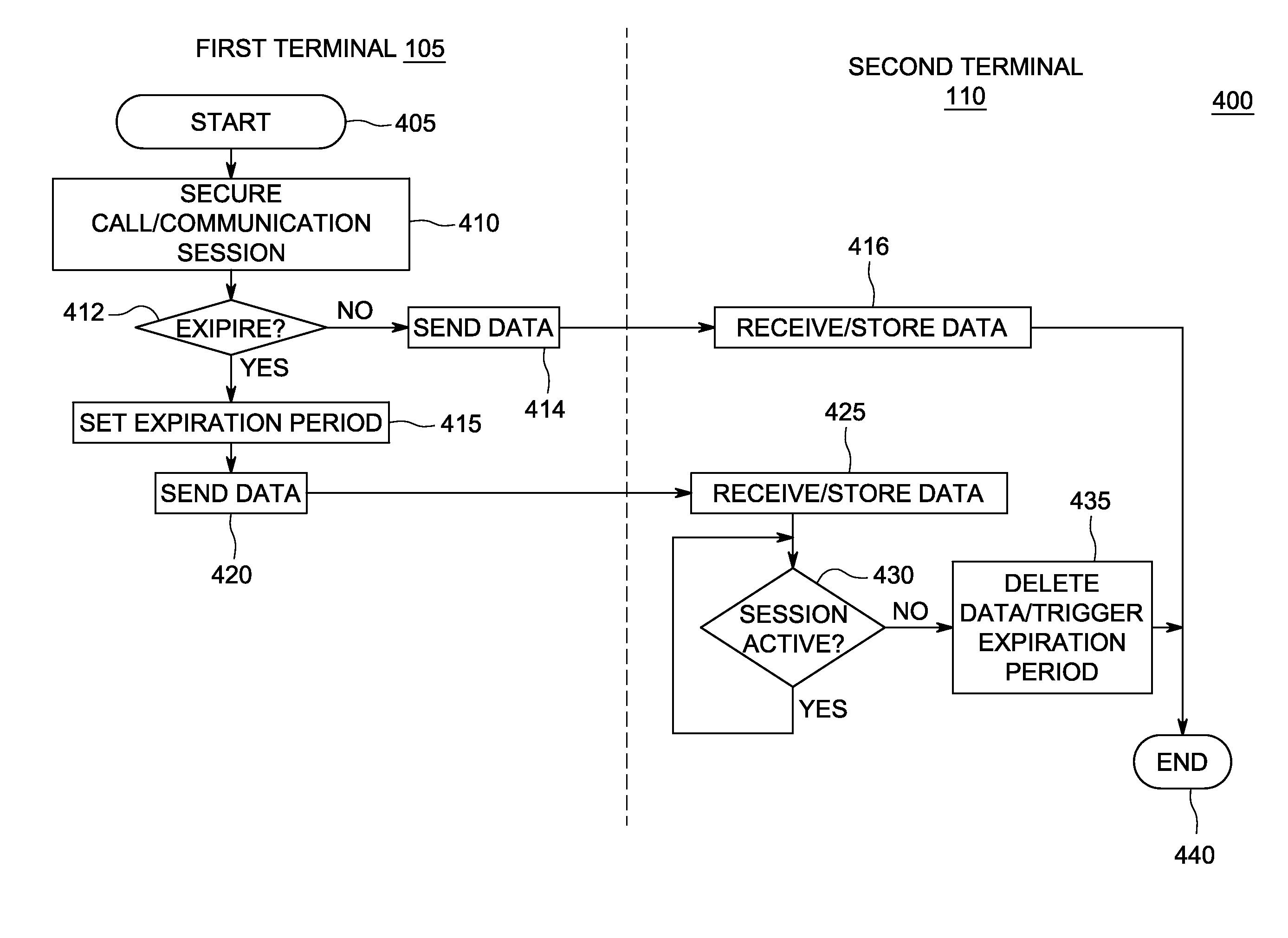
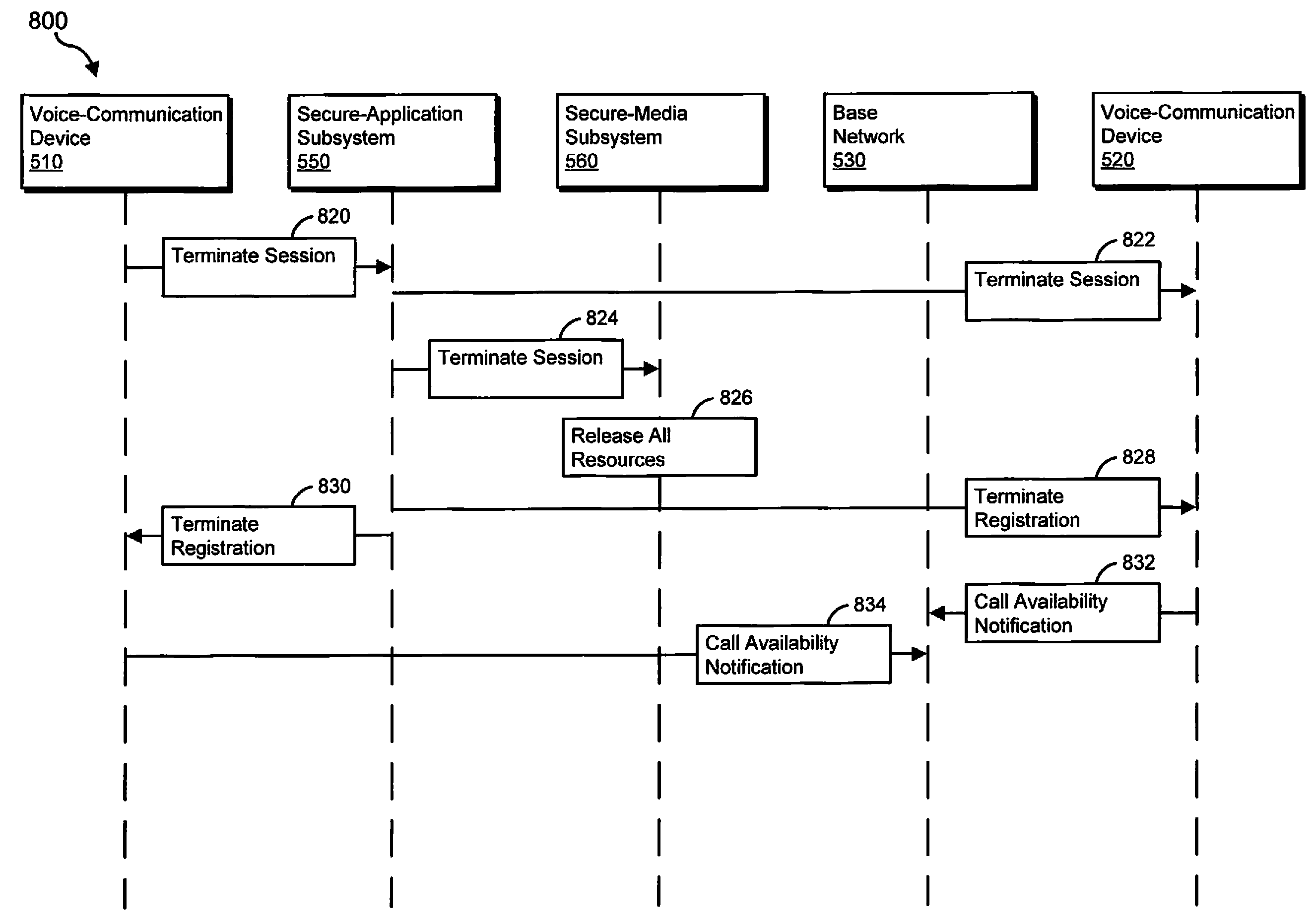
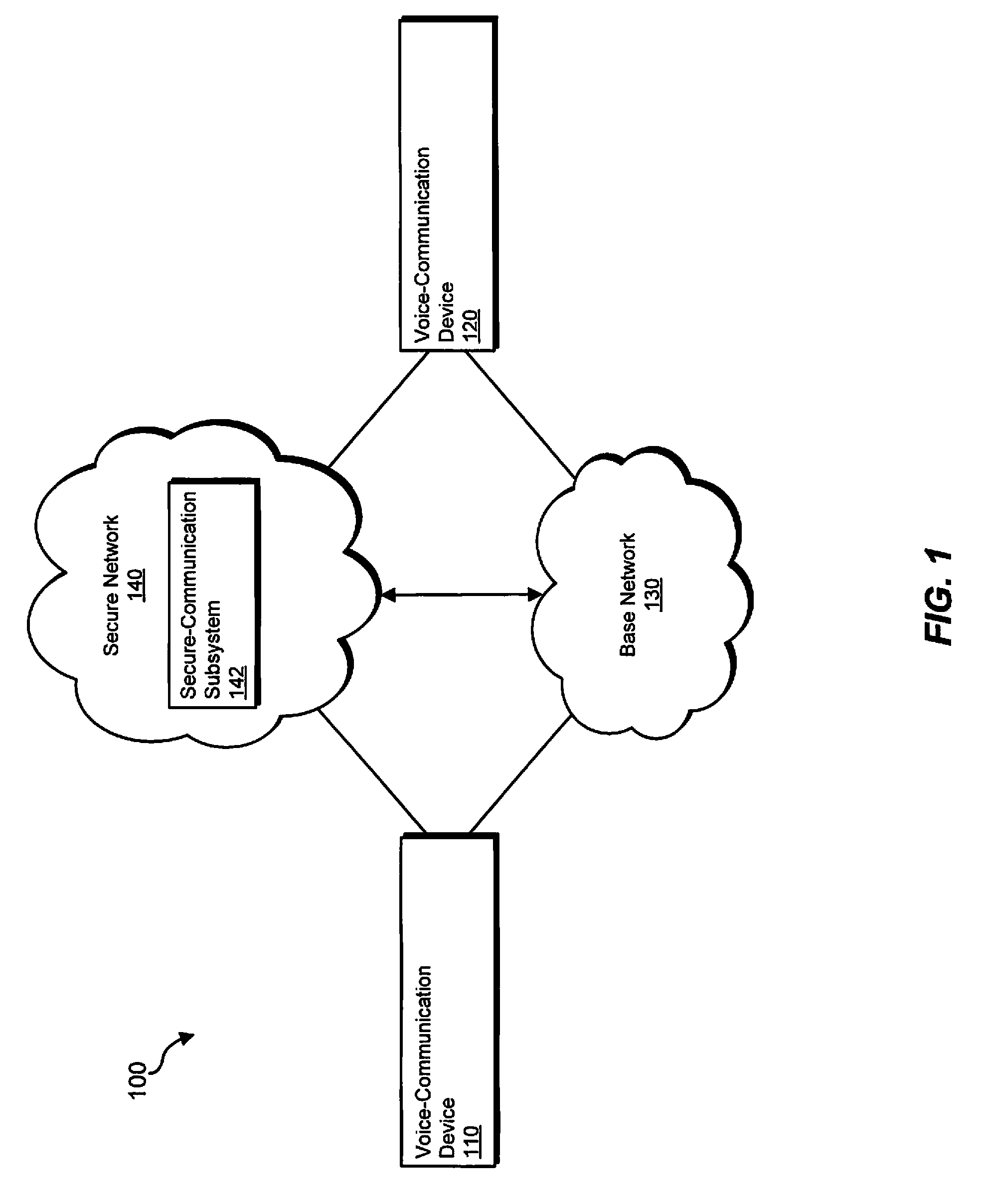
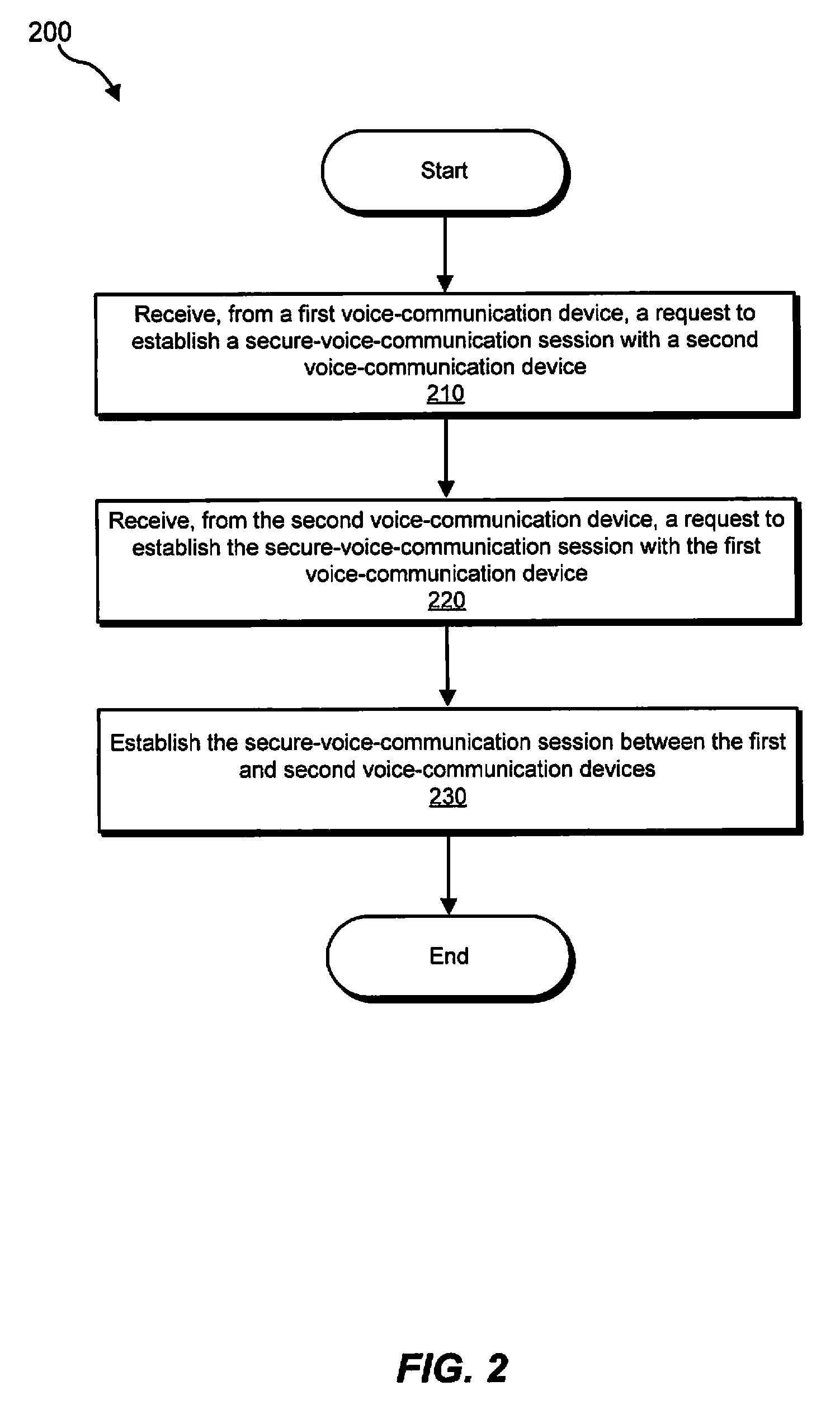
Methods, systems, and apparatus for handling secure-voice-communication sessions
ActiveUS20100167692A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsVoice communicationSecure voice
An exemplary computing system may receive a first request from a first voice-communication device to establish a secure-voice-communication session with a second voice-communication device. The computing system may also receive a second request from the second voice-communication device to establish the secure-voice-communication session with the first voice-communication device. The computing system may establish the secure-voice-communication session between the first and second voice-communication devices. Corresponding methods, apparatus, and computer-readable media are also disclosed.
Owner:VERIZON PATENT & LICENSING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com