Encapsulation of Secure Encrypted Data in a Deployable, Secure Communication System Allowing Benign, Secure Commercial Transport
a communication system and secure technology, applied in the field of computer and communication networks, can solve the problems of high installation and maintenance costs of secure data transport systems and the risk of being compromised
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
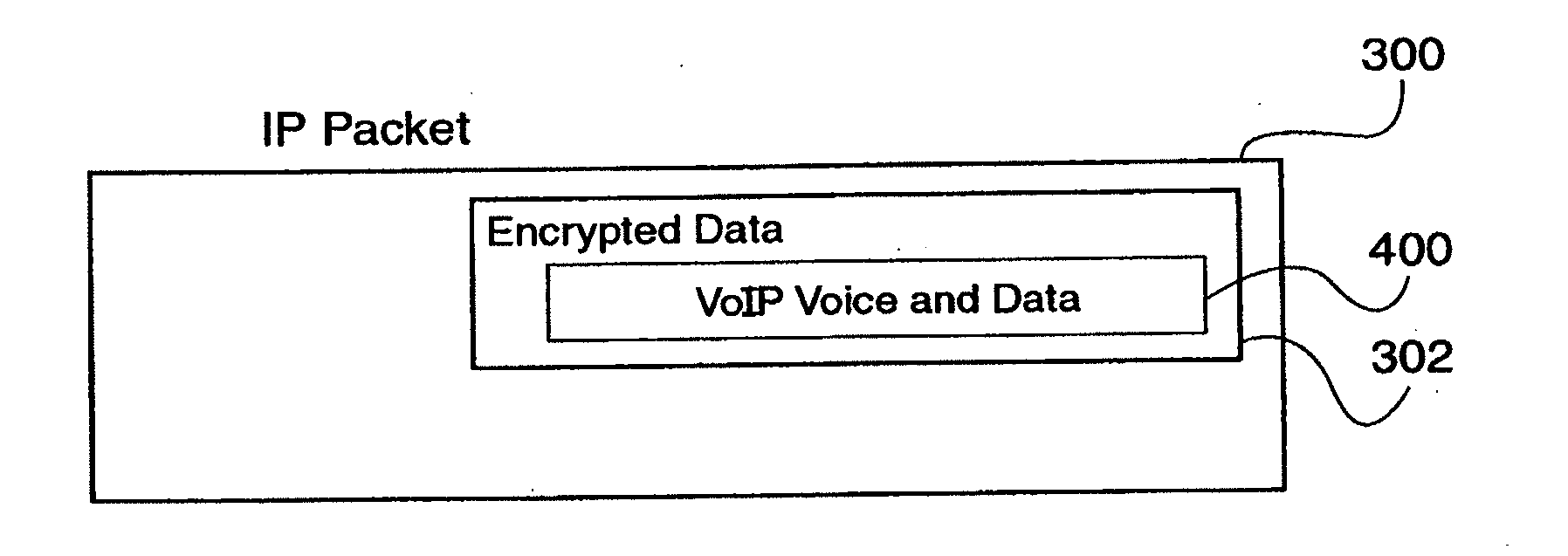
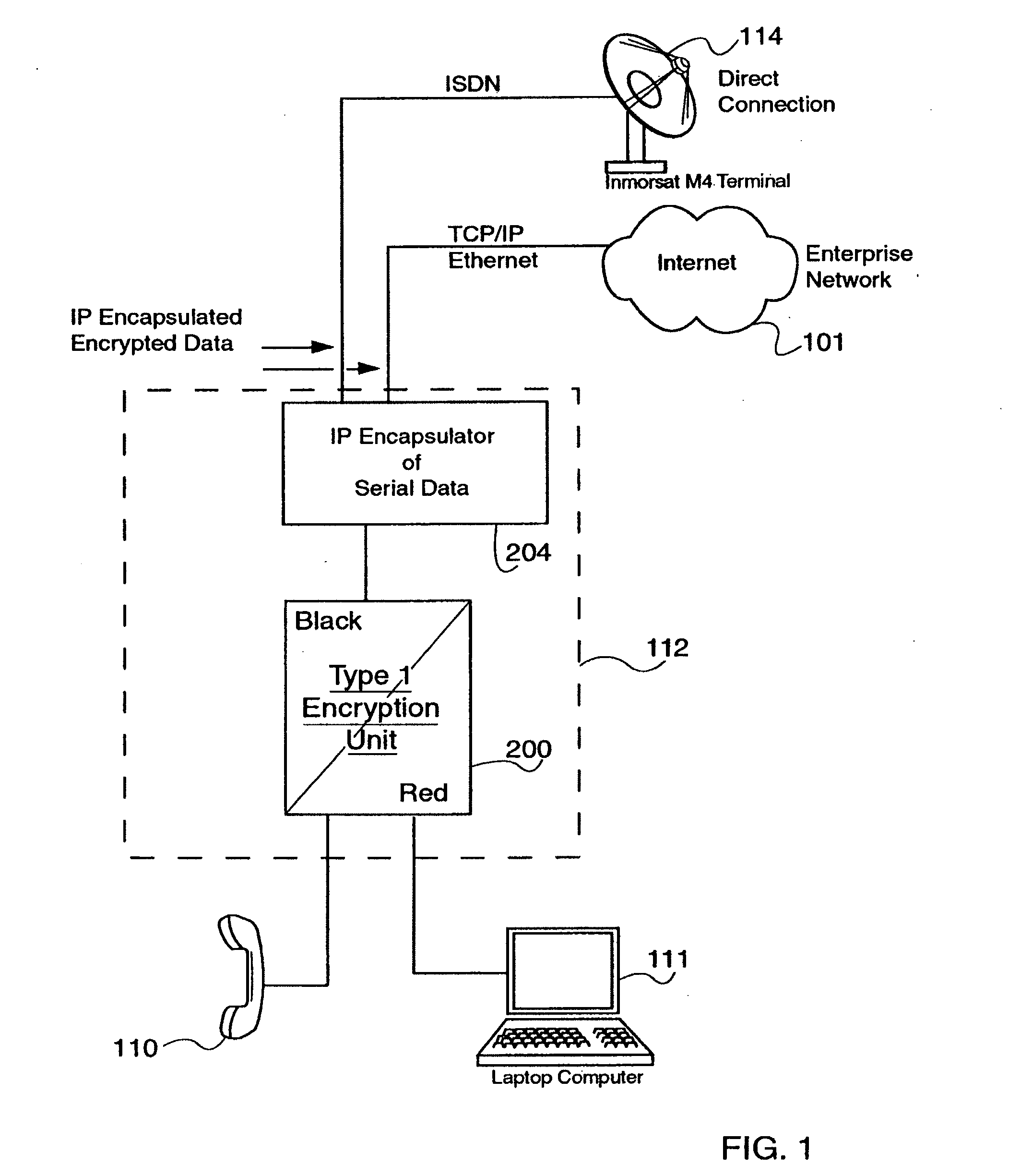
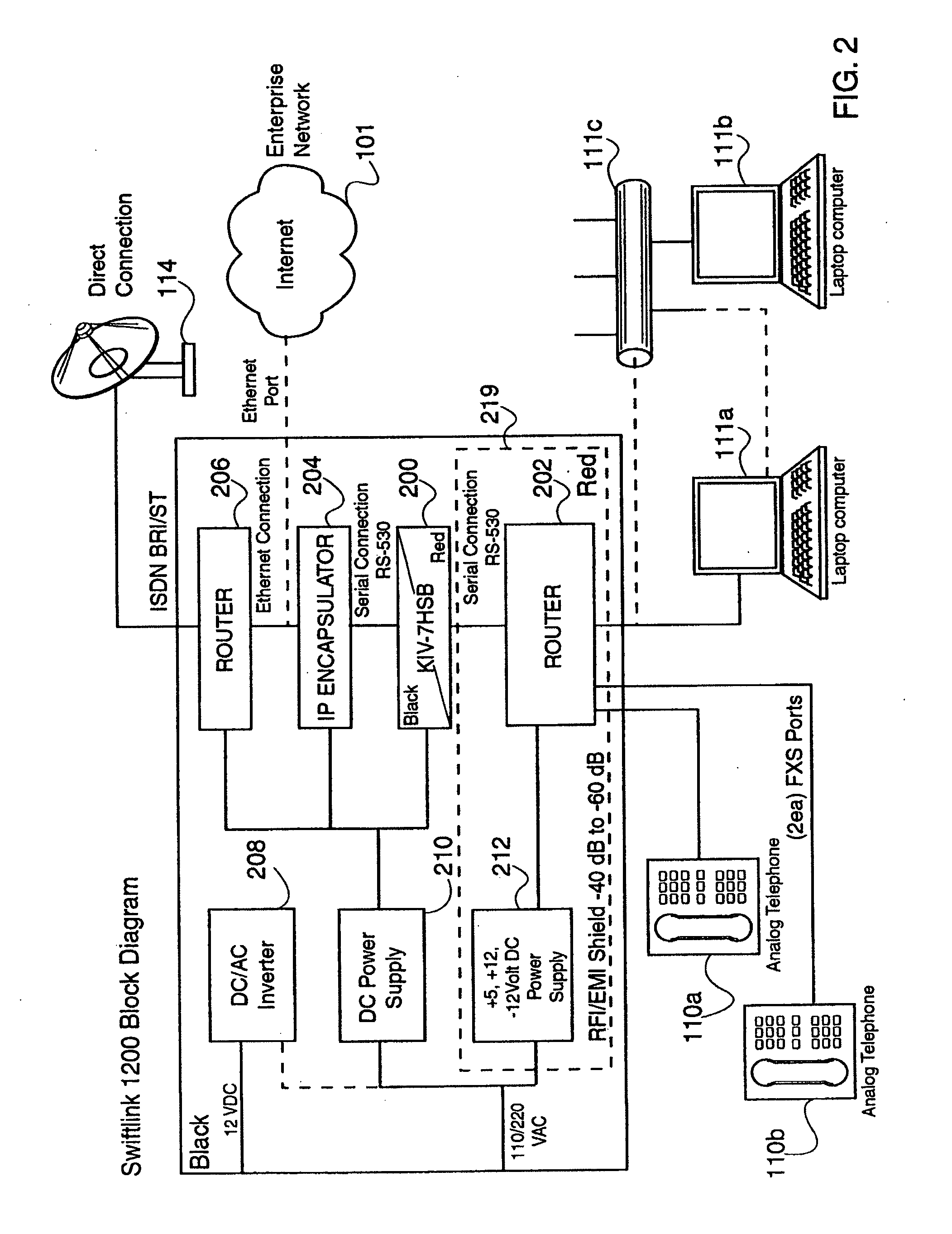
[0020]Sensitive, Type 1 KIV-encrypted data is encapsulated into IP packets in a remotely deployed, secure communication system. The IP packets are addressed to an IP device that removes the encapsulated, encrypted data and passes it to a similar Type 1 KIV device for decryption. However, the IP encapsulated, encrypted data is passed over the public Internet, taking advantage of the wide availability and flexibility of the Internet.
[0021]In this way, encrypted data need not be maintained within a totally secure network transmission system, because it doesn't look like government encrypted data (i.e., it doesn't look like a KIV signal). Rather, the encrypted data, being encapsulated in IP packets, looks just like any other commercial IP transmission from just about any other IP device. Thus, sensitive, encrypted data is made to appear as if it were any other commercial network data.
[0022]The present invention is embodied in a system that provides secure Voice-Over-IP (VOIP), video and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com