Patents
Literature
42 results about "Cloaking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Cloaking is a search engine optimization (SEO) technique in which the content presented to the search engine spider is different from that presented to the user's browser. This is done by delivering content based on the IP addresses or the User-Agent HTTP header of the user requesting the page. When a user is identified as a search engine spider, a server-side script delivers a different version of the web page, one that contains content not present on the visible page, or that is present but not searchable. The purpose of cloaking is sometimes to deceive search engines so they display the page when it would not otherwise be displayed (black hat SEO). However, it can also be a functional (though antiquated) technique for informing search engines of content they would not otherwise be able to locate because it is embedded in non-textual containers such as video or certain Adobe Flash components. Since 2006, better methods of accessibility, including progressive enhancement, have been available, so cloaking is no longer necessary for regular SEO.
Video cloaking and content augmentation
InactiveUS20040012613A1Good lookingIncrease contentImage enhancementRecord information storageAnimationCloaking
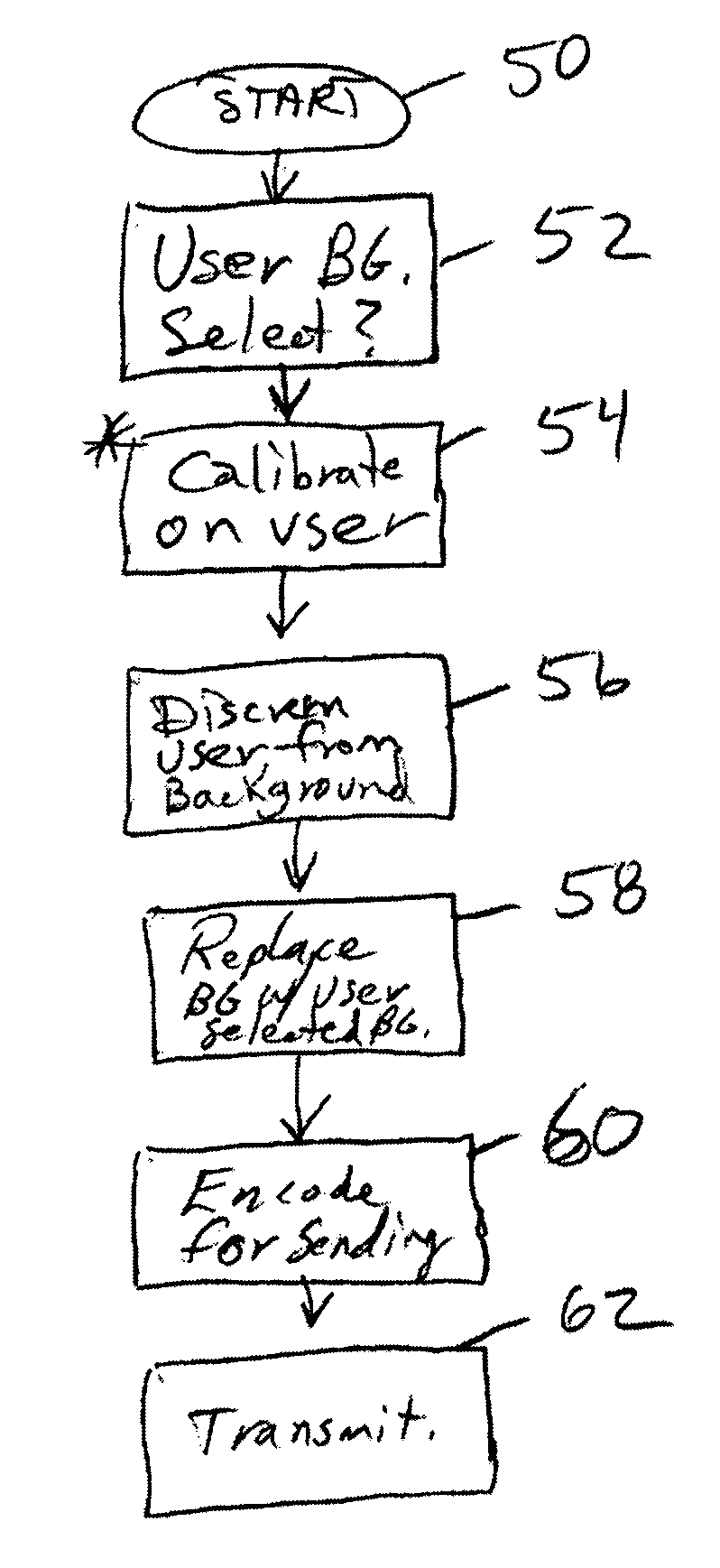
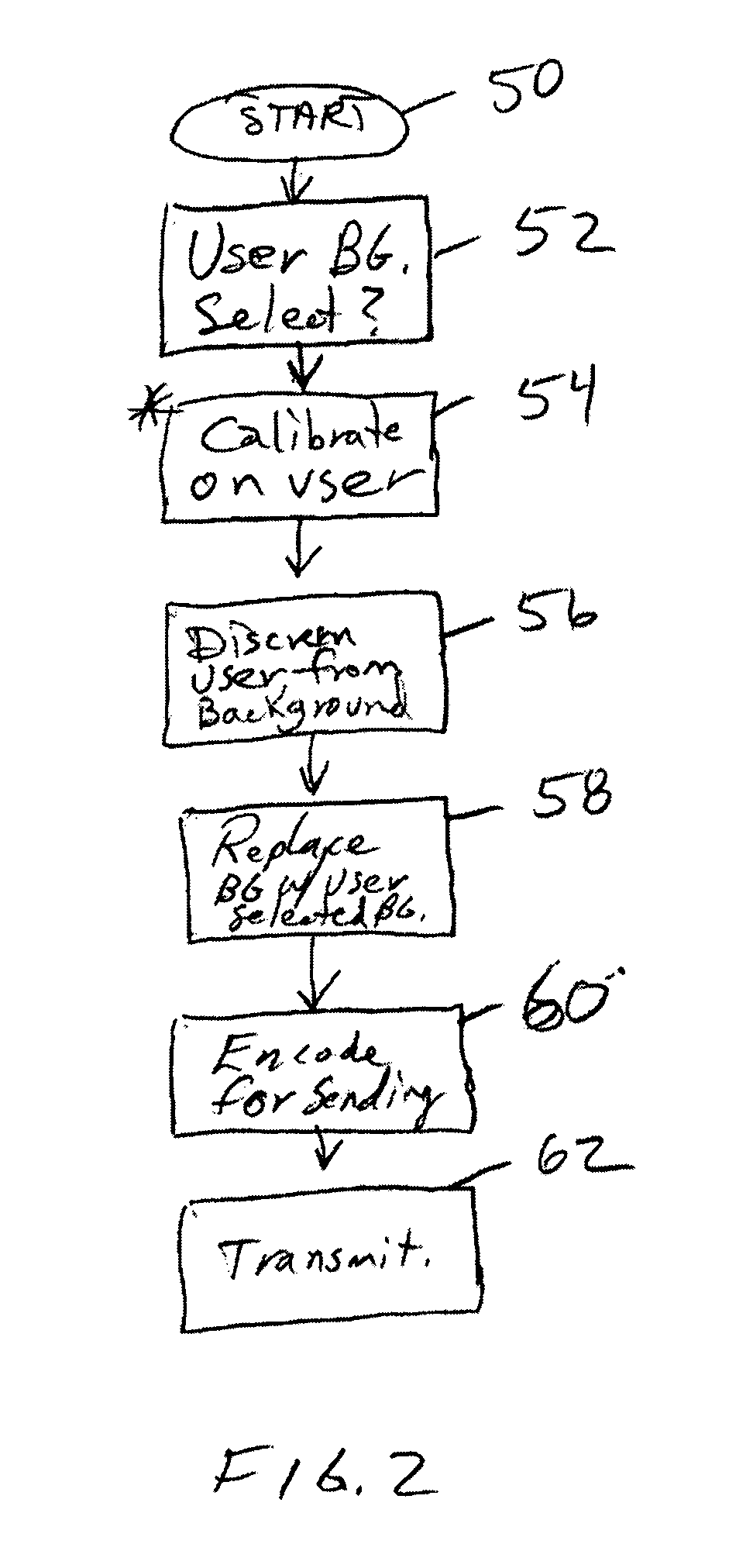
A video cloaking system for actively detecting unwanted background details in response to user selections, and replacing all or portion of the background with user selected content, such as static scenes, animations, or video. The user can represent themselves as they see fit, while hiding the normal background and adding entertainment value. A web enabled content system is also described that is configured to overlay web obtained content for preprogrammed video or audio content when it synchronizes with it. The user can humorous or meaningful content added to the content they view of listen to. Numerous additional system and methods are described.
Owner:RAST RODGER H
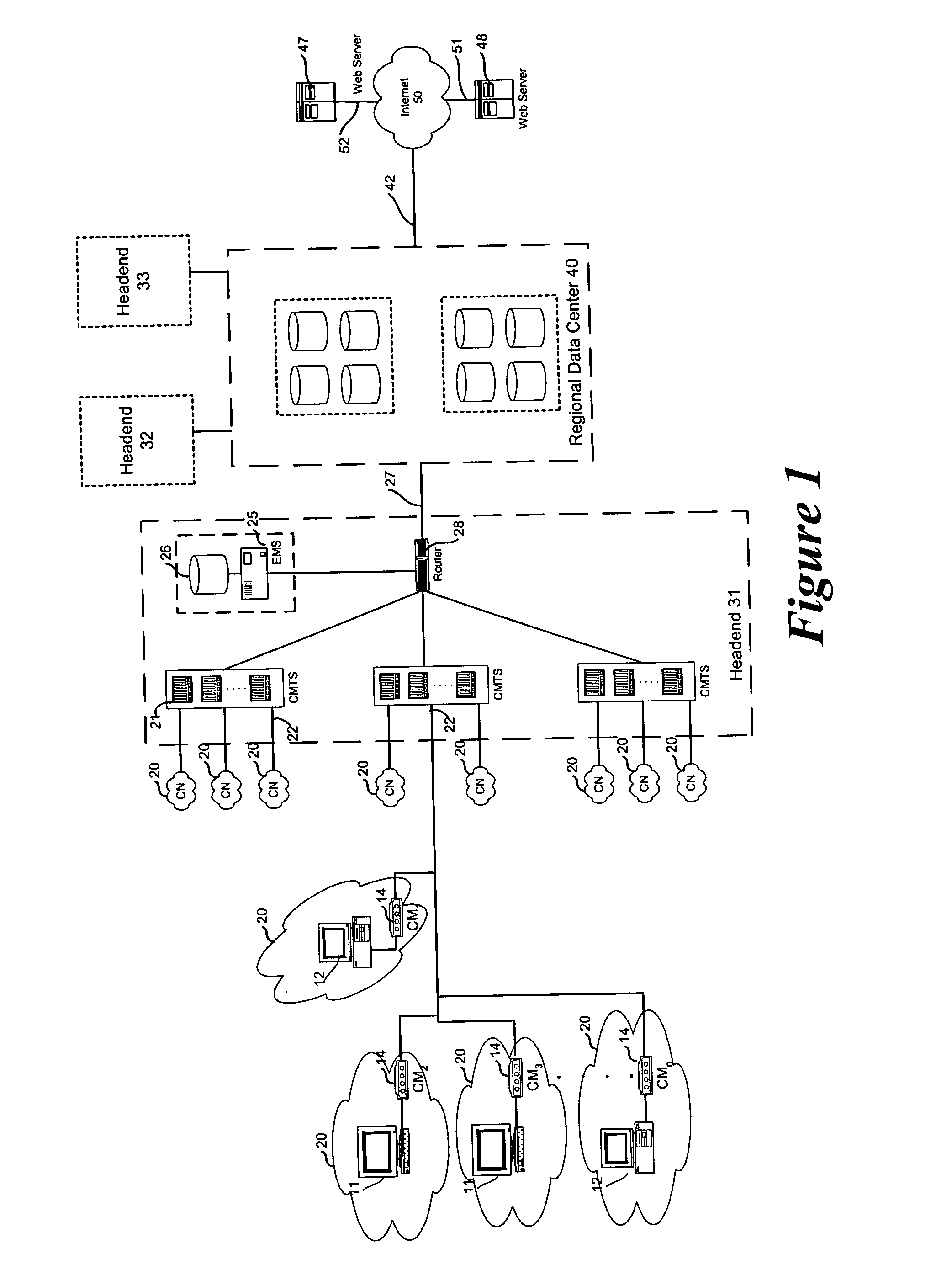
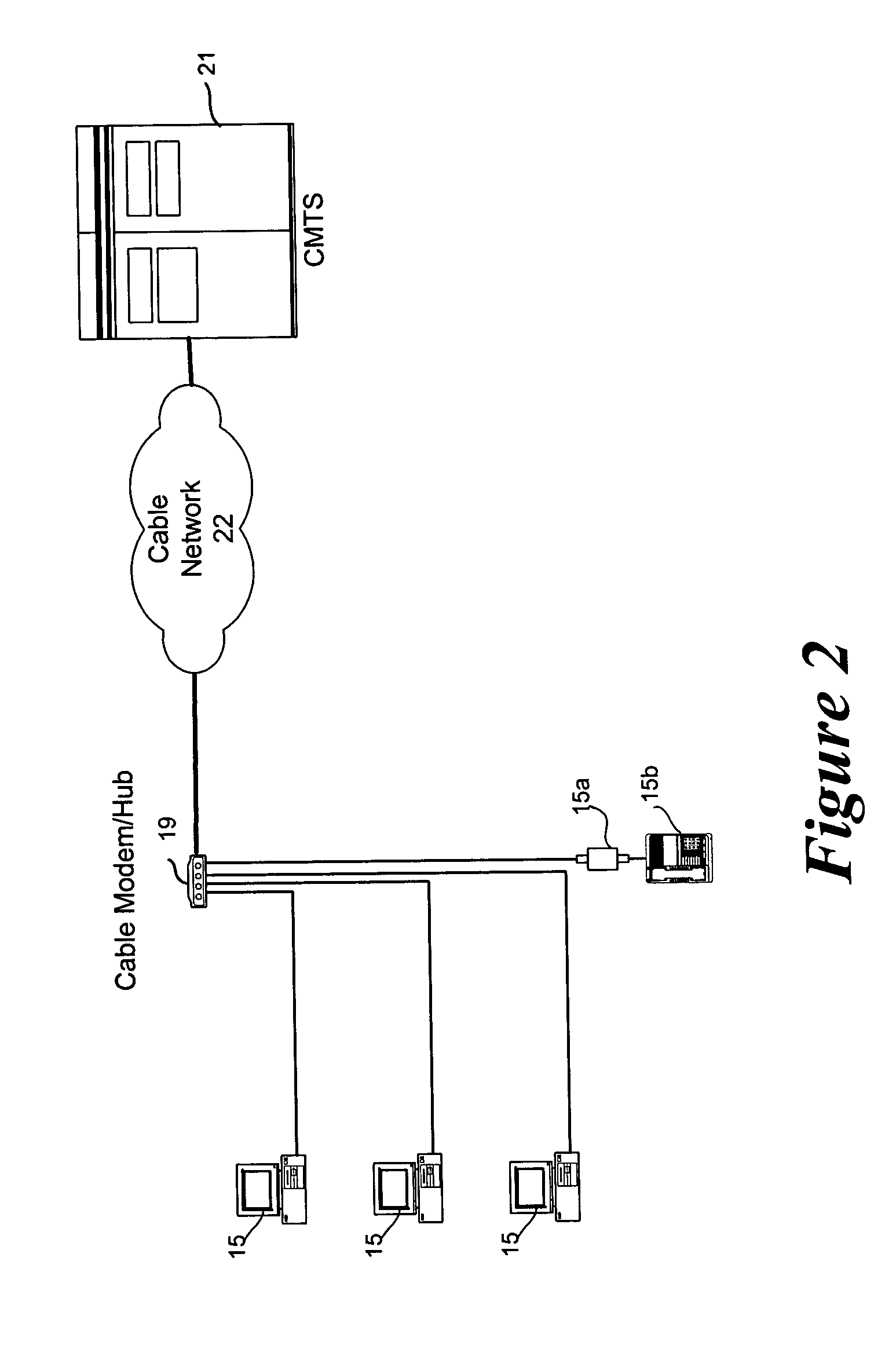
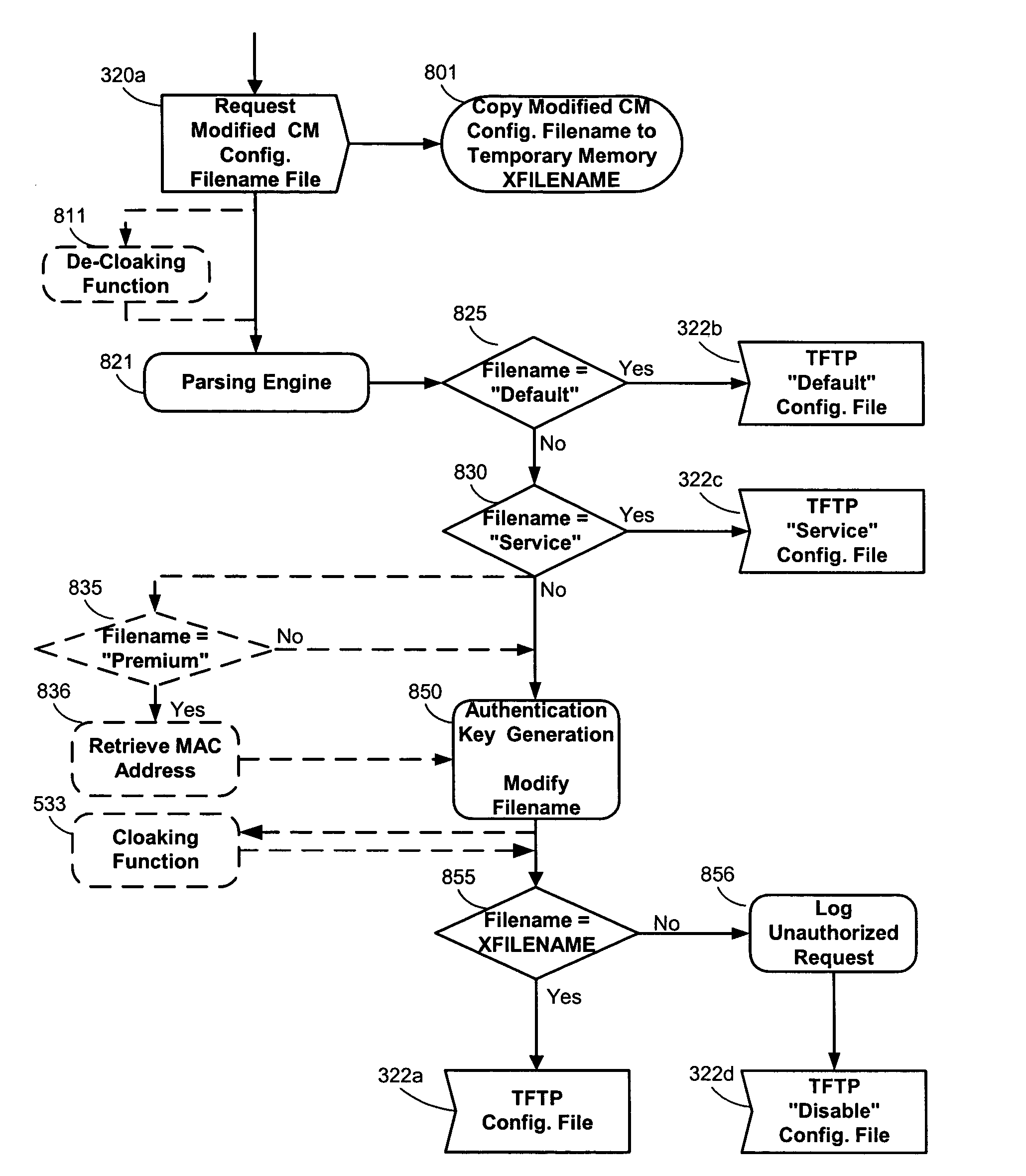
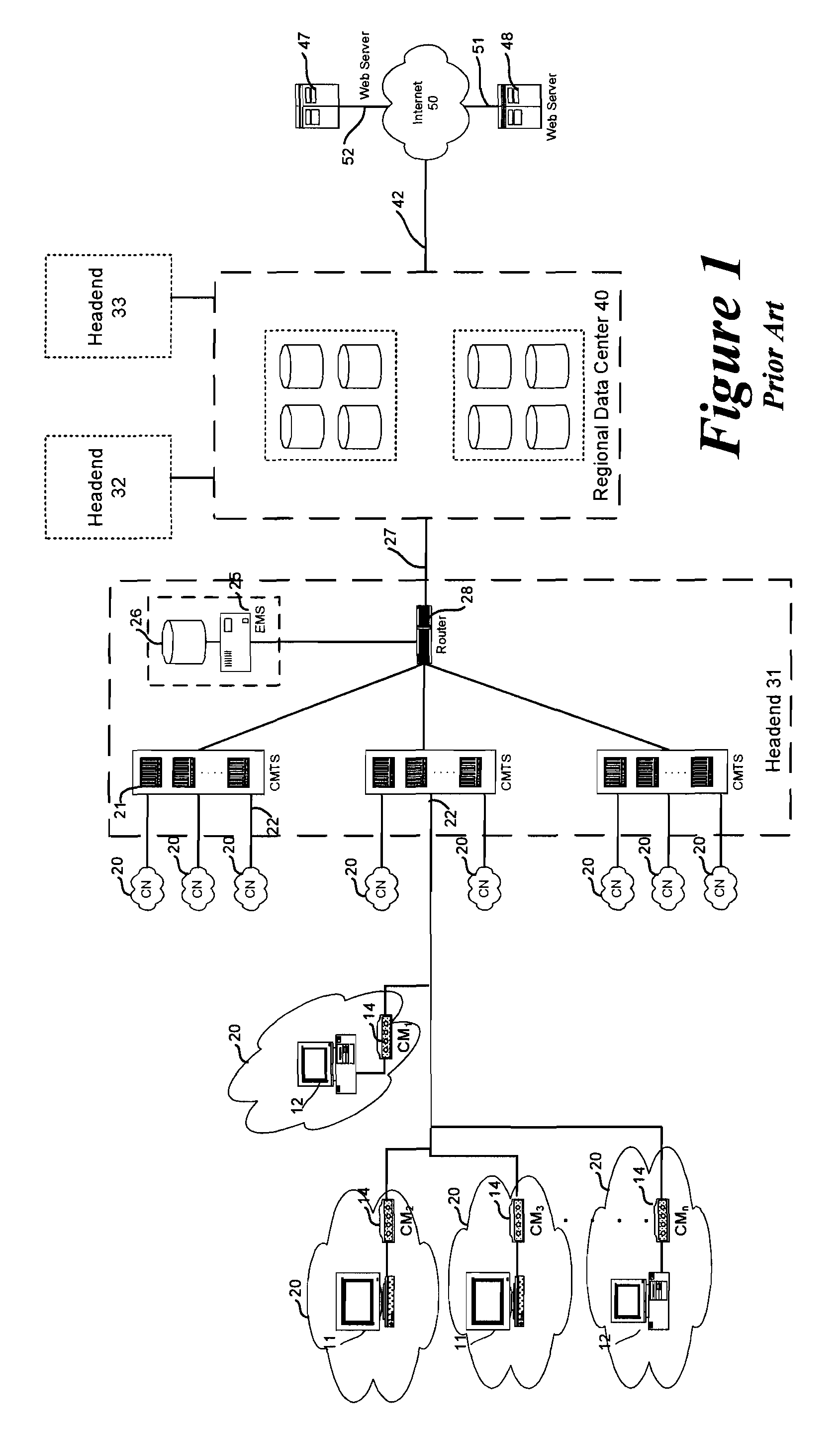
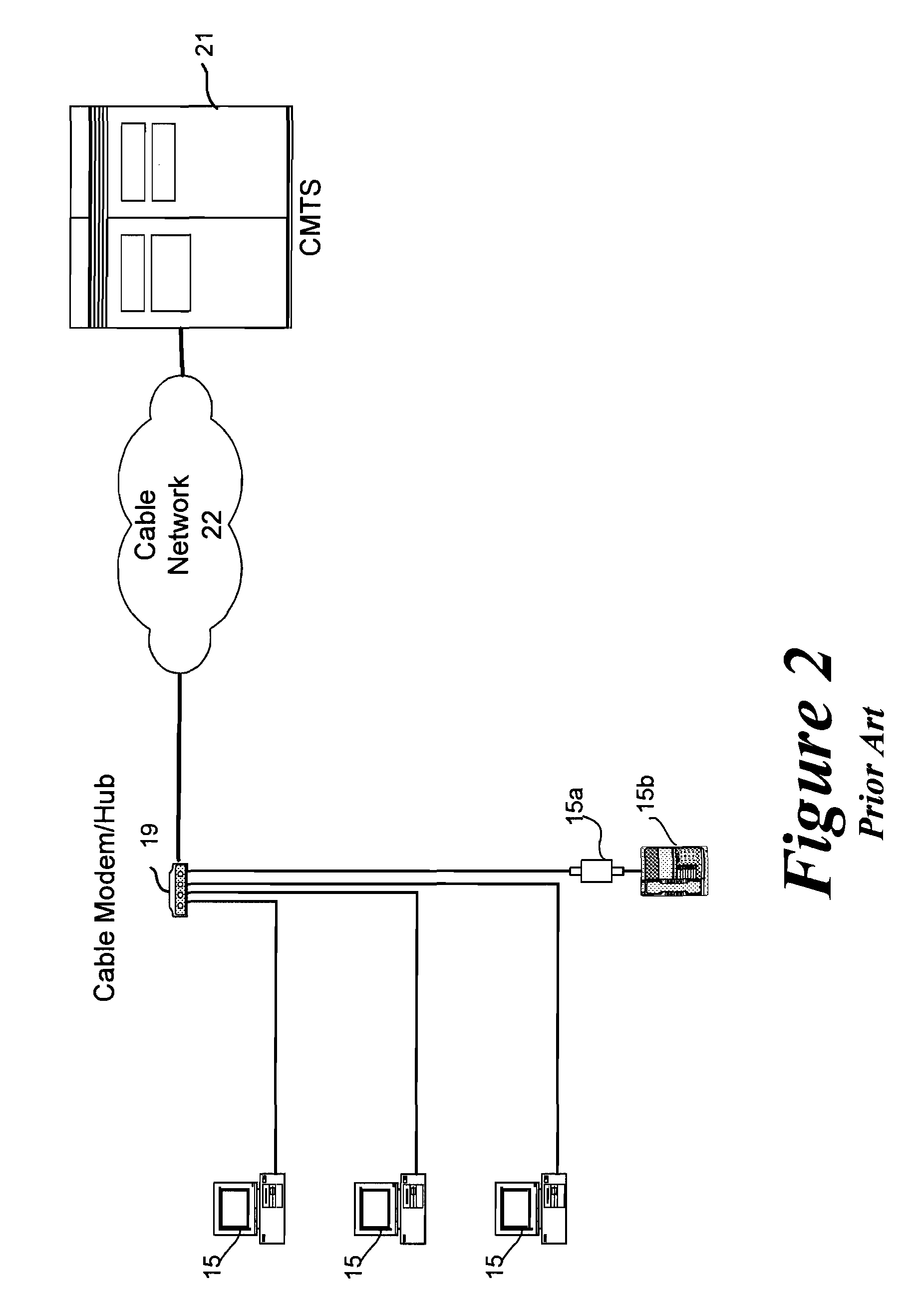
Method to block unauthorized access to TFTP server configuration files
ActiveUS20050005154A1Reduce and eliminate unauthorized accessDigital data processing detailsUser identity/authority verificationModem deviceIp address
The present invention teaches methods and systems for blocking unauthorized access to cable modem configuration files stored on trivial file transfer protocol (TFTP) servers. Filenames are modified by the DHCP to incorporate an authentication key (and optional cloaking) prior to transmission to the cable modem. When the TFTP server receives a modified filename, it also generates an authentication key. The authentication keys must match in order for the cable modem to receive the configuration file requested. At a minimum, authentication keys depend upon the un-modified filename, the cable modem IP address and a “coordination pass phrase” known to the TFTP server and DHCP server, but not known to the cable modem. Variations include optional cloaking, various actions performed for non-matching authentication keys, selection of authentication key generating algorithm and inclusion of cable modem MAC address in the authentication key for all cable modems or for premium service customer cable modems.
Owner:TIME WARNER CABLE ENTERPRISES LLC
Method to block unauthorized access to TFTP server configuration files
ActiveUS7293282B2Digital data processing detailsUser identity/authority verificationModem deviceIp address
The present invention teaches methods and systems for blocking unauthorized access to cable modem configuration files stored on trivial file transfer protocol (TFTP) servers. Filenames are modified by the DHCP to incorporate an authentication key (and optional cloaking) prior to transmission to the cable modem. When the TFTP server receives a modified filename, it also generates an authentication key. The authentication keys must match in order for the cable modem to receive the configuration file requested. At a minimum, authentication keys depend upon the un-modified filename, the cable modem IP address and a “coordination pass phrase” known to the TFTP server and DHCP server, but not known to the cable modem. Variations include optional cloaking, various actions performed for non-matching authentication keys, selection of authentication key generating algorithm and inclusion of cable modem MAC address in the authentication key for all cable modems or for premium service customer cable modems.
Owner:TIME WARNER CABLE ENTERPRISES LLC
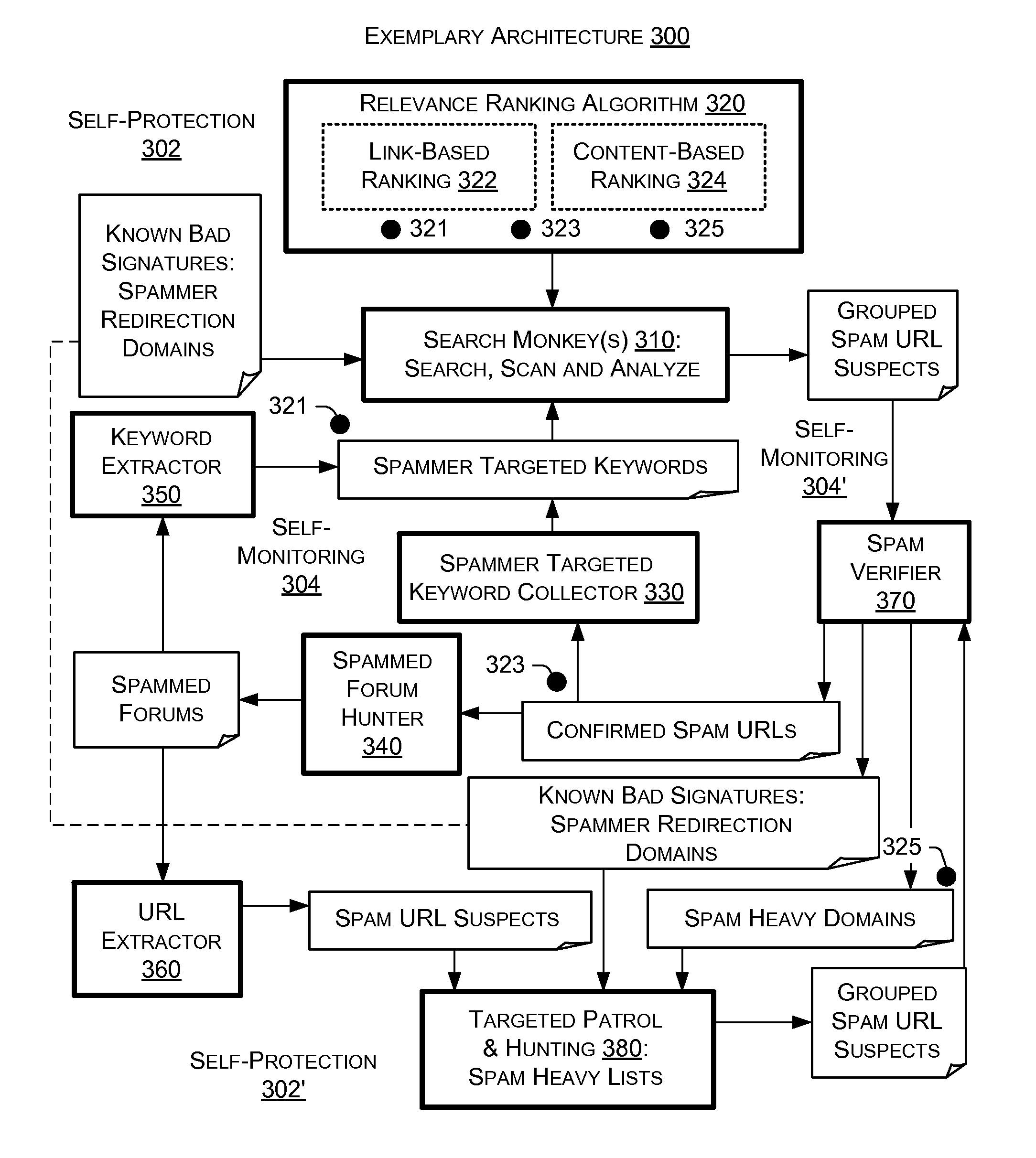
Search spam analysis and detection
ActiveUS20110087648A1Digital data processing detailsPlatform integrity maintainanceUniform resource locatorCloaking
Defeating click-through cloaking includes retrieving a search results page to set a browser variable, inserting a link to a page into the search results page and clicking through to the page using the inserted link. Investigating cloaking includes providing script associated with a suspected spam URL, modifying the script to de-obfuscate the script and executing the modified script to reveal cloaking logic associated with the script.
Owner:MICROSOFT TECH LICENSING LLC
Rare earth Fe basis suction wave material and method for making the same
InactiveCN101203127AImprove absorbing performanceWide shielding bandMagnetic/electric field screeningRare earthOxidation resistant
The invention discloses a nano-crystal tombar thite ferrous absorbing material with good absorbing property and a preparation method thereof. The material is characterized in that the lanthanon with the weight percentage of 2% and 70%, the iron with the weight percentage of 5% and 98% and the little amount of doping element are smelted into tombar thite-ferrous alloy; the tombar thite-ferrous alloy is reacted with hydrogen by hydrogen decrepitation method under the temperature range from 0 to 700 DEG C, is broken into fine powder or be ball grinded into fine powder, and then is reacted with hydrogen to generate composite material of rare earths hydride (RHx) and Alpha-Fe under the temperature range from 100 DEG C to 1000 DEG C; finally, the composite material is oxidized, nitridized or oxidized and nitridized under low temperature to produce the composite material mainly being rare earth oxide or nitride / Alpha-Fe composite material. The material of the invention has the advantages of high absorbing capability, wide shield wave band, good anti-corrosion property, anti-oxidation property and low price, and can be used in the fields of electro-magnetic shielding in building, information and communication technical secrecy and military cloaking technique, and so on.
Owner:SICHUAN UNIV
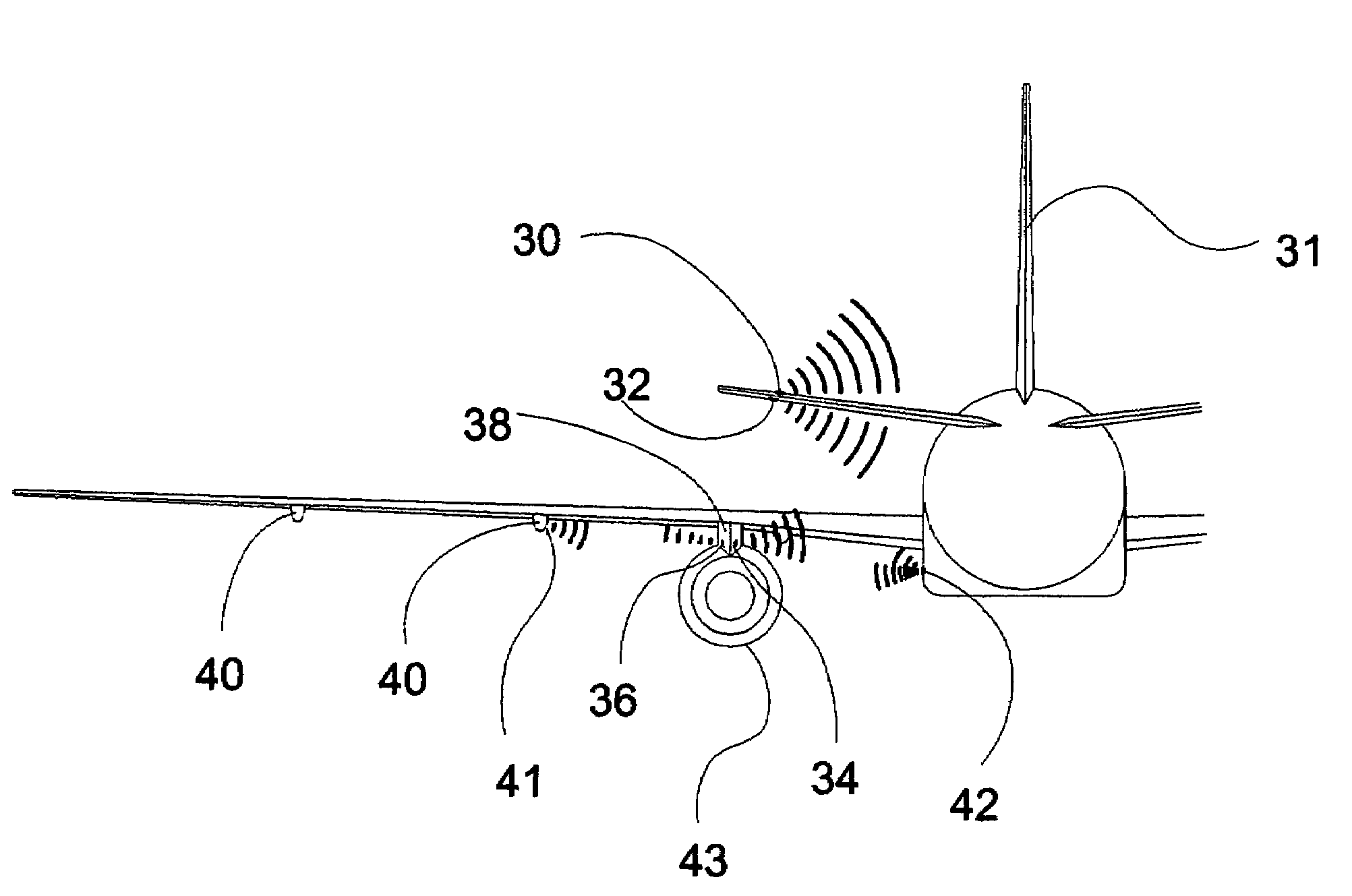
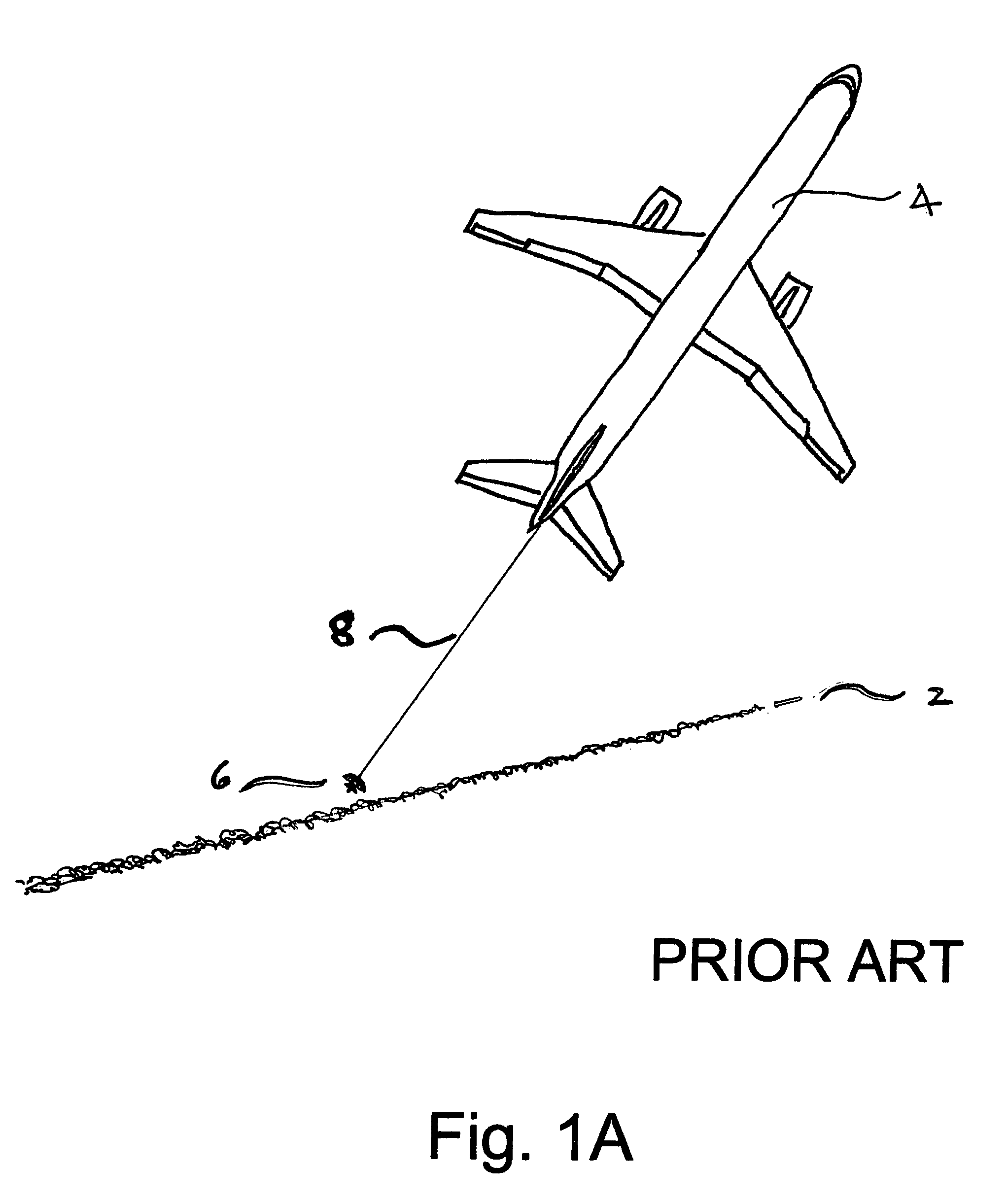
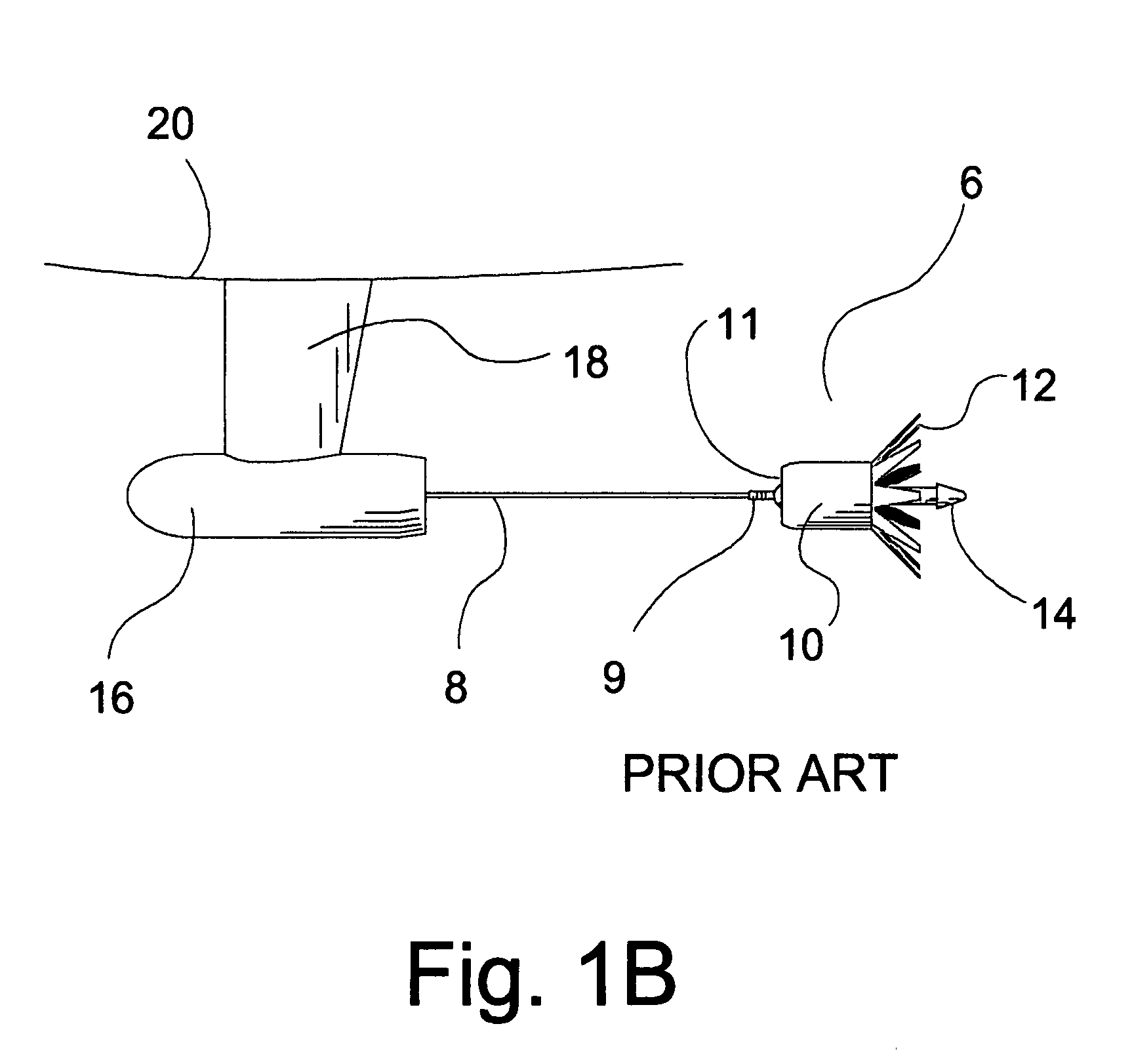
Aircraft defense system against manpads with IR/UV seekers
InactiveUS7523692B1Increase heightMinimize aerodynamic dragDefence devicesWave based measurement systemsGuidance systemSpectral bands
An inexpensive, efficient and lightweight integrated small decoy system towed behind an aircraft to power an intense IR emitter for drawing in a missile with an IR sensitive guidance system away from vulnerable parts of a defended aircraft is combined with a system for simultaneously cloaking the aircraft with spectral bands of atmospherically scattered UV solar radiation reflected, and radiated from UV radiant sources mounted on the aircraft to defend against advanced MANPADS missiles with guidance systems sensitive to UV shadows cast by an aircraft in a background sky radiance of atmospherically scattered solar UV. Both the reflected and direct cloaking UV emittance may be spatially and / or temporally modulated to confuse an incoming missile. The UV aspect of this invention may also be combined with other C-MANPADS missiles, such as DIRCM, to provide additional defensive capability.
Owner:BURNS ALAN ALEXANDER
Frequency selective surface in combined guidance system of active and passive radar
ActiveCN104064839AImprove survivabilityStrong penetrating powerRadiating element housingsWaveguide type devicesGuidance systemPassive radar
The invention discloses a frequency selective surface in a combined guidance system of an active / passive radar, and belongs to the technical field of frequency selective surfaces. The frequency selective surface solves the technical problems in the prior art that a mixed-type FSS passive radar is small in working bandwidth, the active / passive radar is narrow in dual-band pass interval, and the radars cannot be used for the combined guidance system. The frequency selective surface provided by the invention comprises a plurality of metal paster units and a plurality of electric-control lumped elements, wherein the plurality of metal paster units are arranged periodically, any two adjacent metal paster units are connected through one electric-control lumped element, and the interior of each metal paster unit is provided with an opening. When the electric-control lumped elements are connected, the frequency selective surface has the high-pass filtering characteristic, can achieve the switching function of the passive radar which works at wide frequency band. When the electric-control lumped elements are disconnected, the frequency selective surface has the characteristic of wide-interval double-band pass. The frequency selective surface can be used for the cloaking of an antenna of an active / passive combined guidance weapon, and improves the viability and capacity of defense penetration of the active / passive combined guidance weapon.
Owner:CHANGCHUN INST OF OPTICS FINE MECHANICS & PHYSICS CHINESE ACAD OF SCI
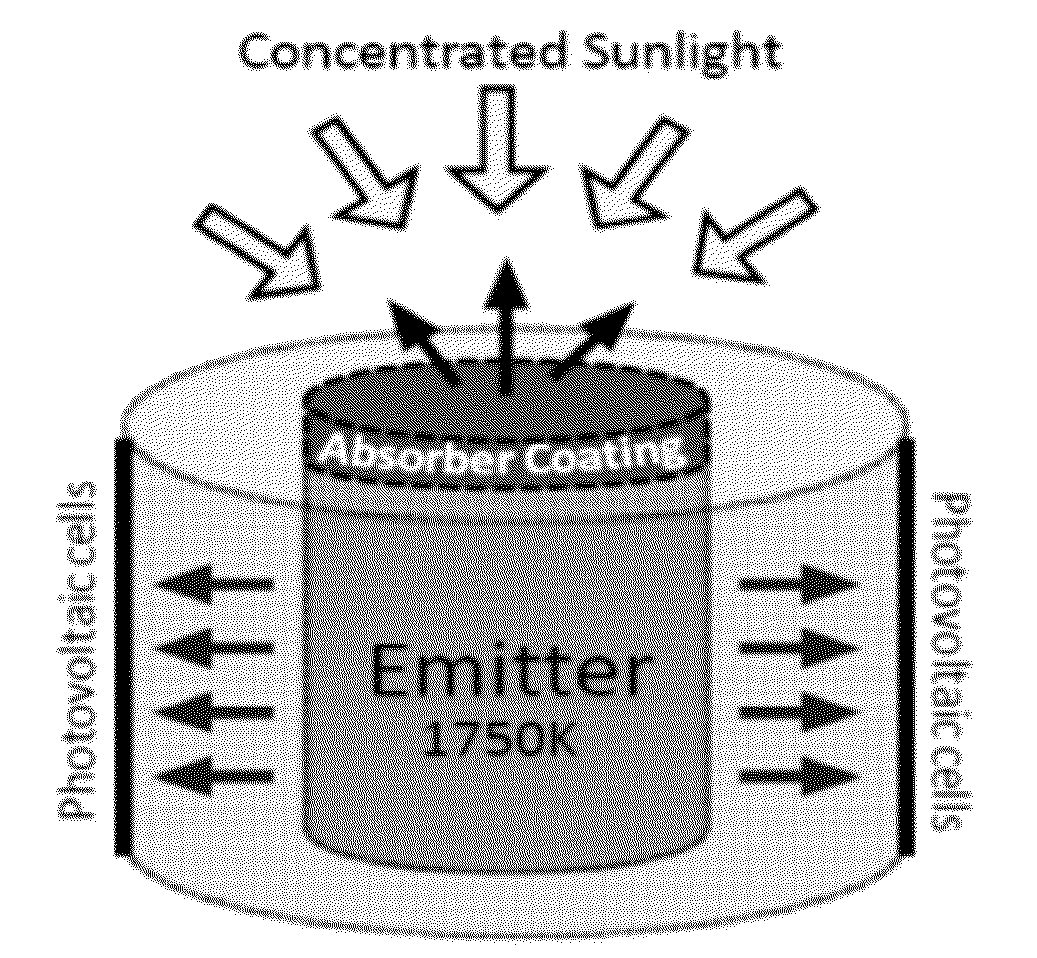
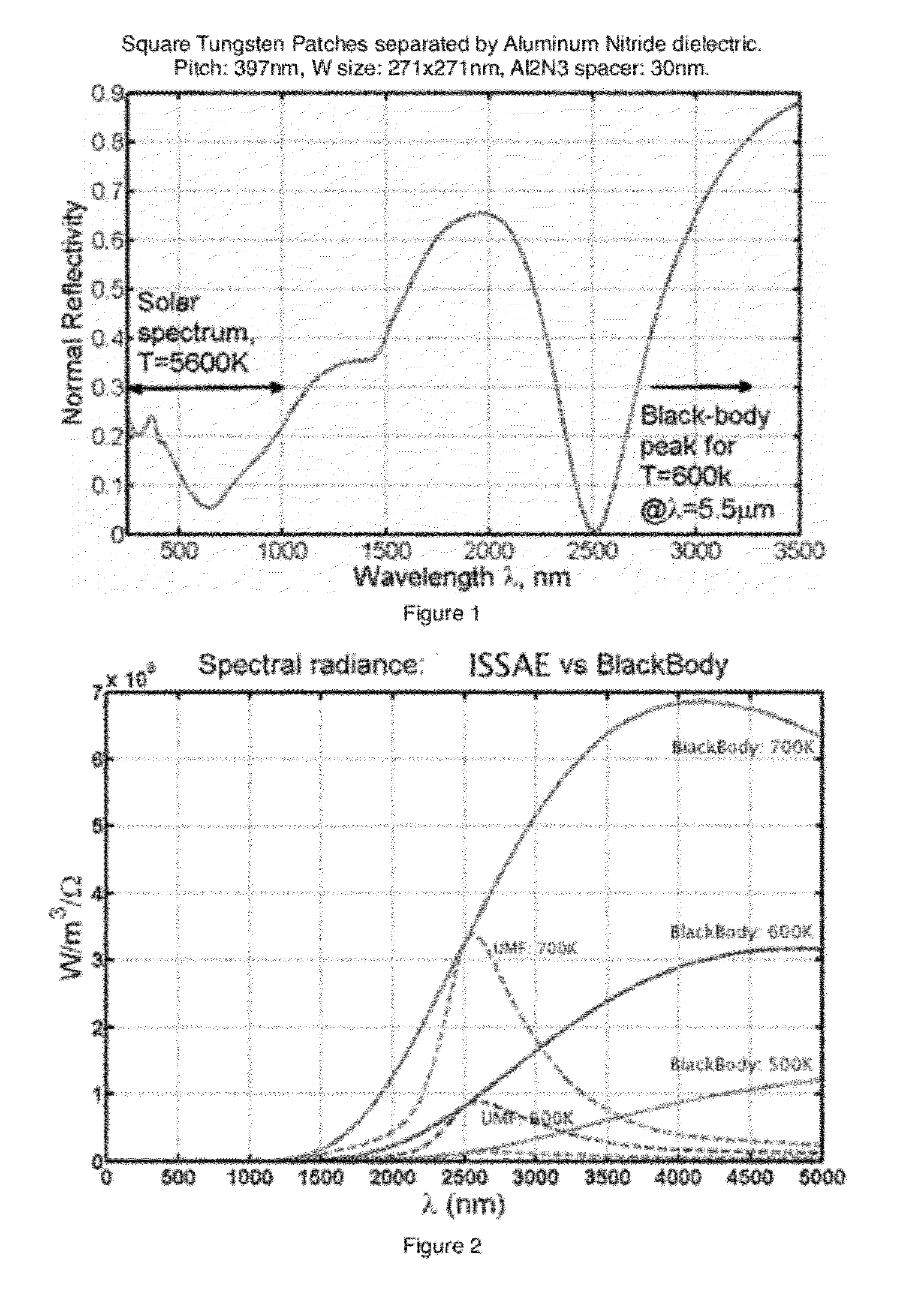
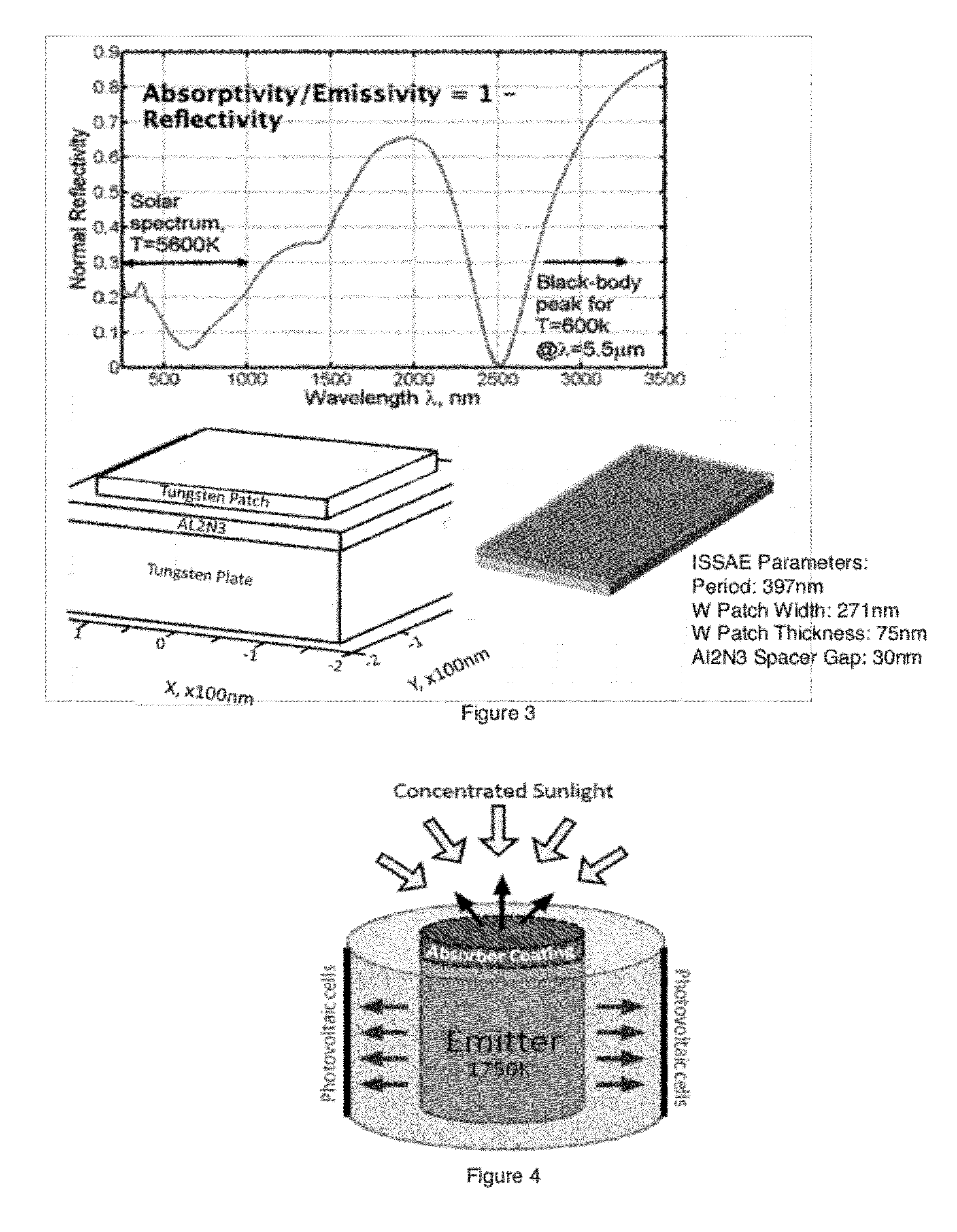
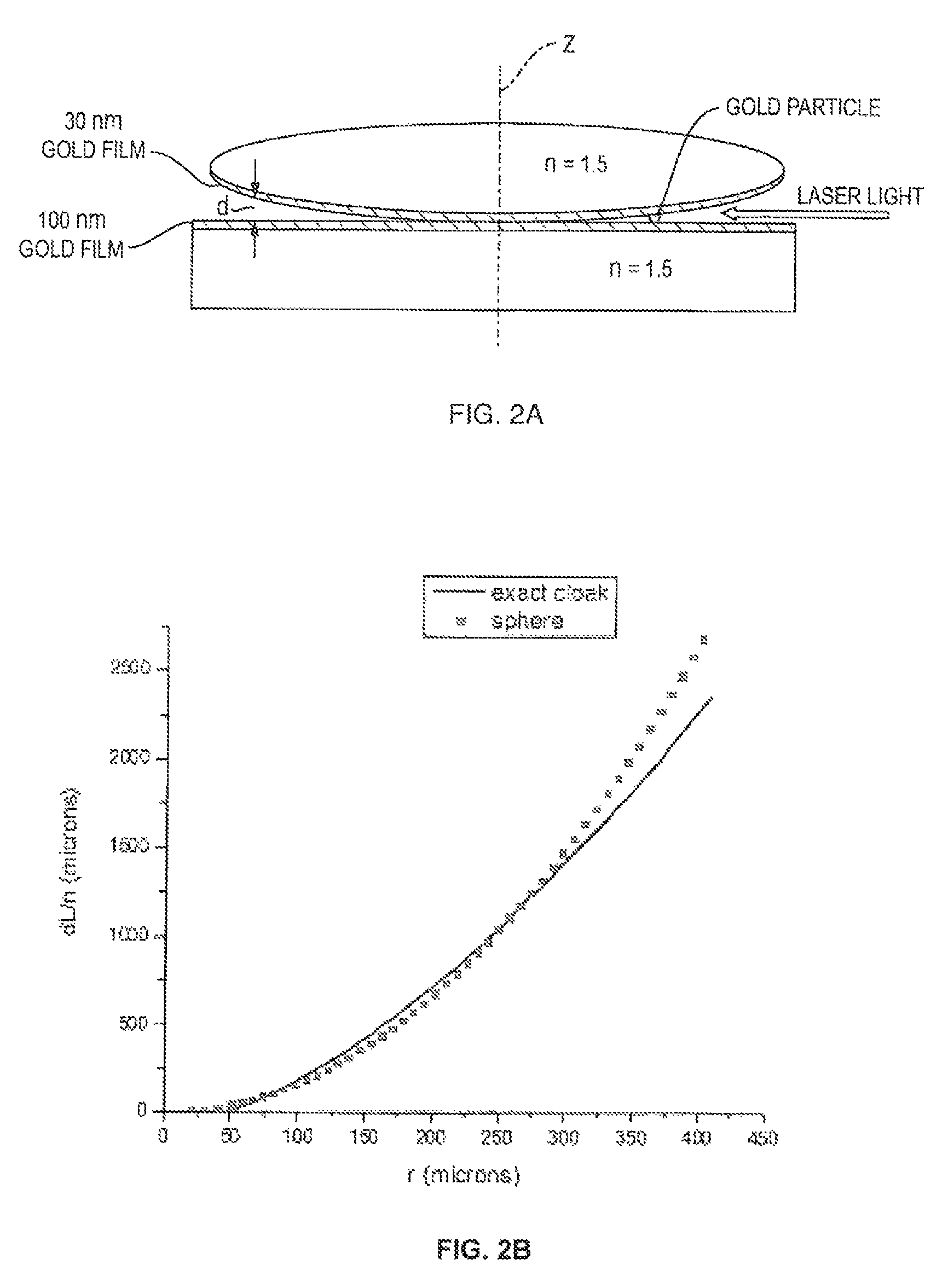
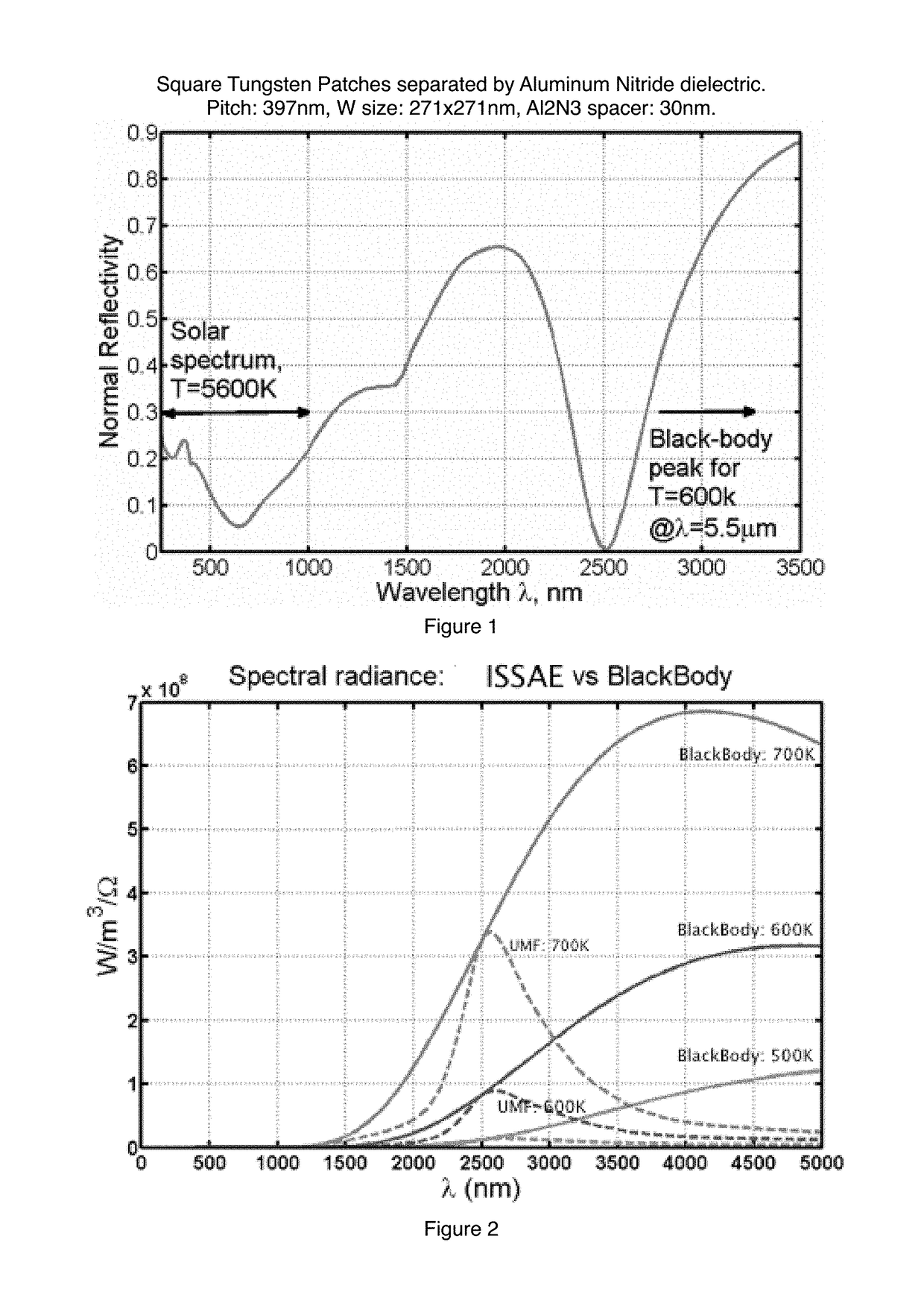
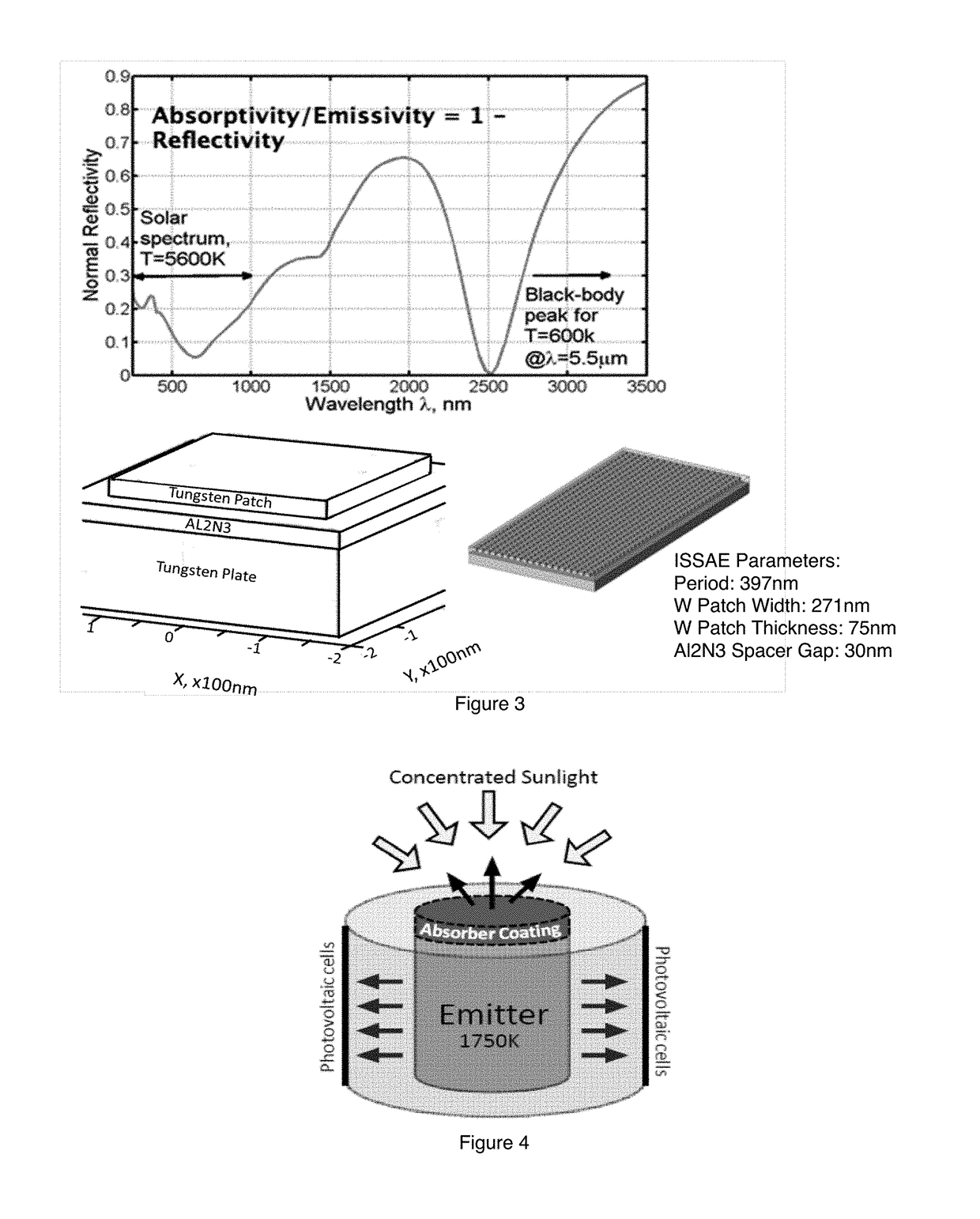
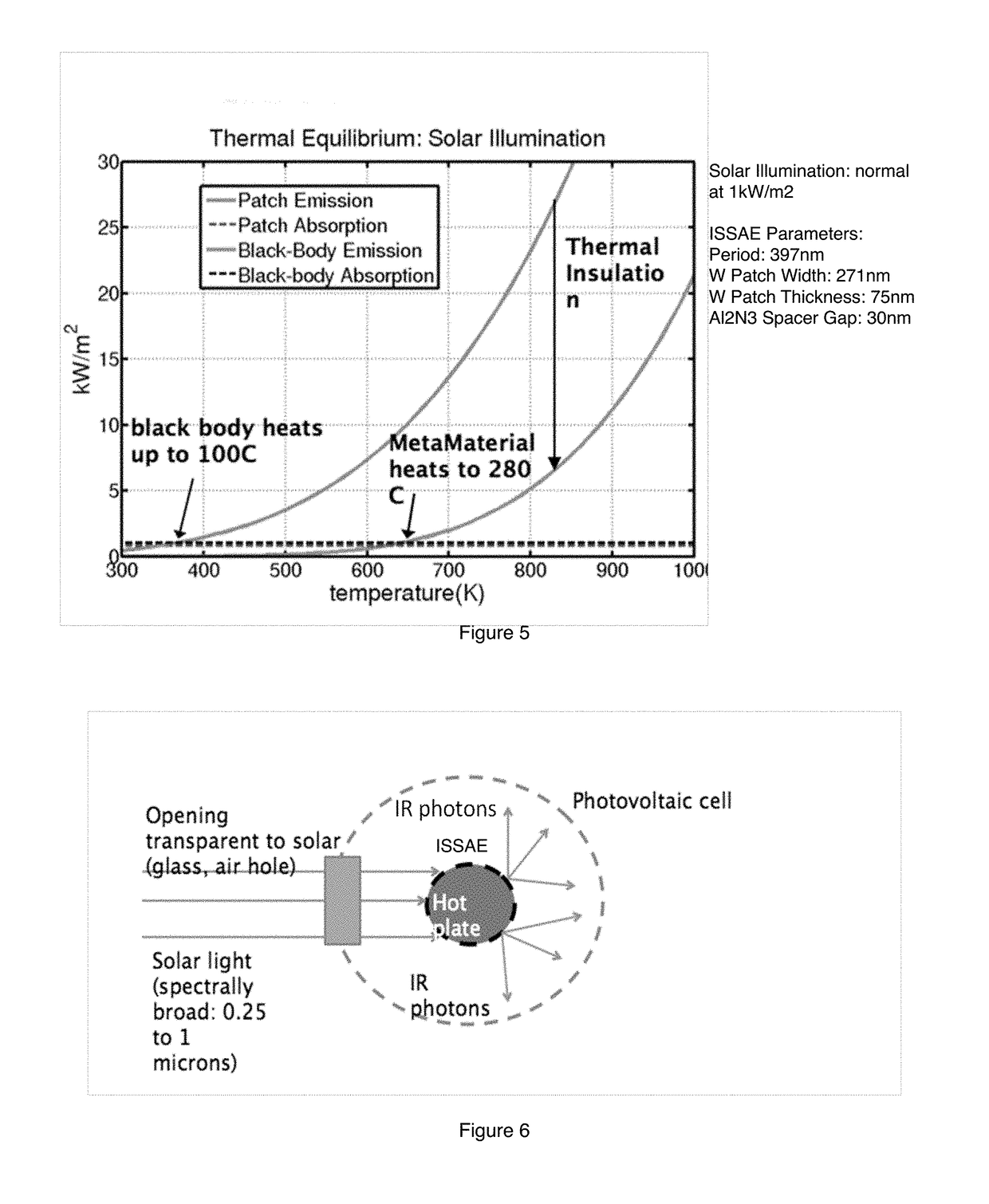
Thin-film integrated spectrally-selective plasmonic absorber/ emitter for solar thermophotovoltaic applications
ActiveUS20120312360A1Improve efficiencySolar heating energyPV power plantsThermophotovoltaicInfrared emitter
Thin-film integrated spectrally-selective plasmonic absorber / emitter (ISSAE) that is simultaneously (i) an efficient sunlight absorber; (ii) an efficient heat insulator that enables modest sunlight concentration to produce a high temperature by reducing infrared emission by a hot surface; (iii) a spectrally-selective infrared emitter that supplies infrared photons of the right energy to a targeted photovoltaic cell, thereby matching its bandgap. Additionally, said ISSAE is sufficiently thin to enable its use as a wrapping / cloaking material for use with hot storage pipes containing heat exchange fluid. Said ISSAE is incorporated into a number of solar-conversion apparatus, taking advantage of the unique properties of said ISSAE.
Owner:IP EQUITY MANAGEMENT LLC
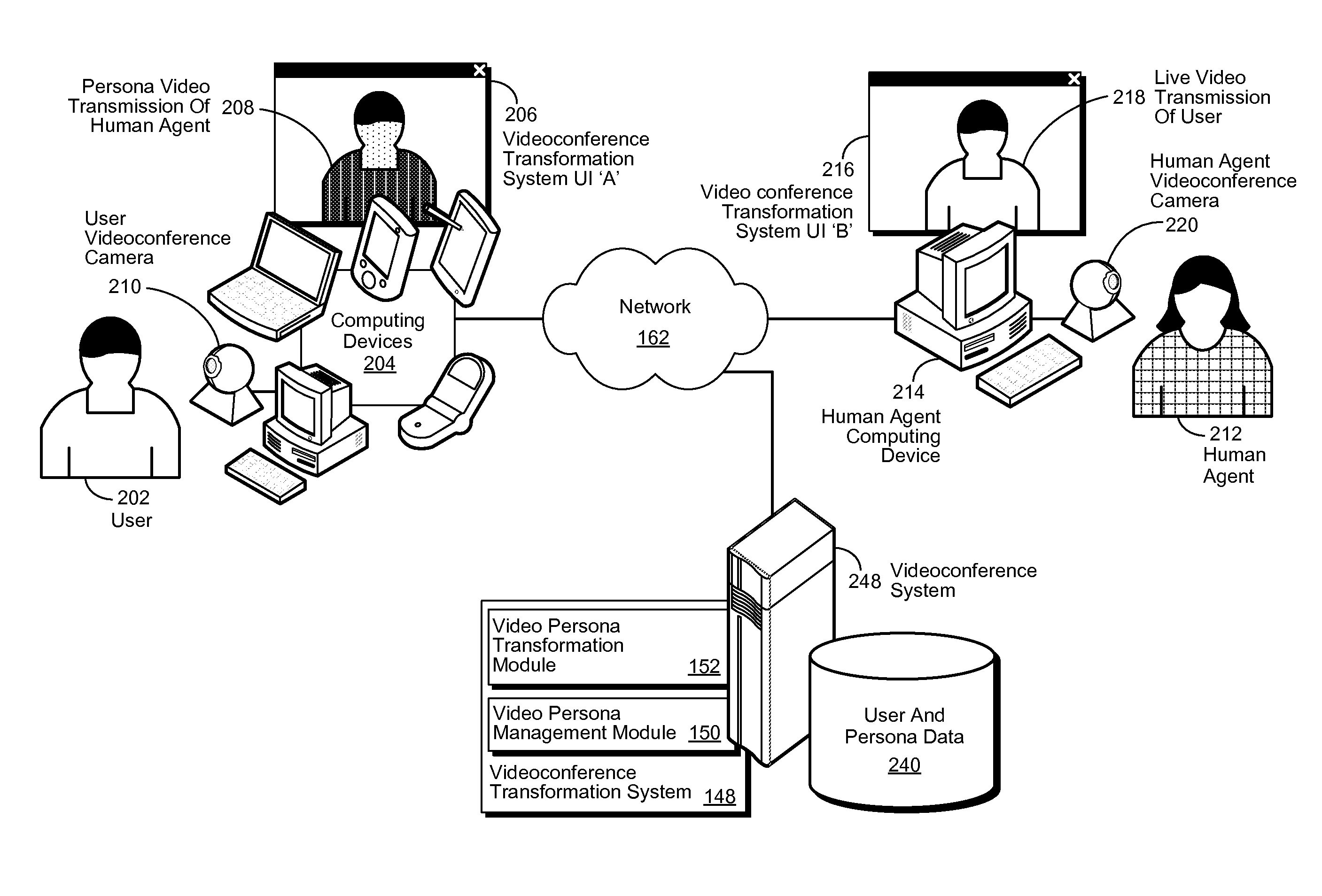
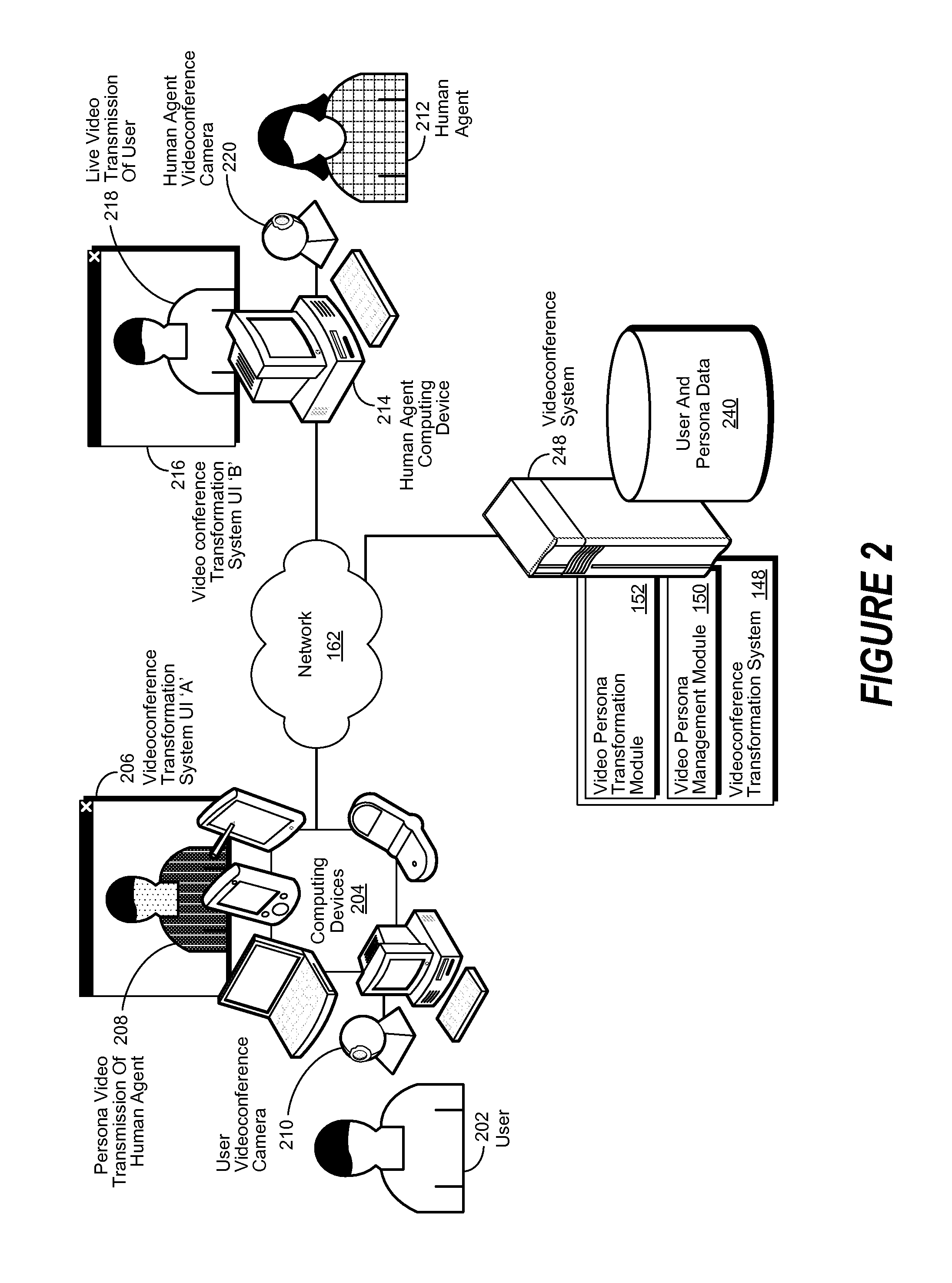
Systems and methods for videophone identity cloaking
ActiveUS8413218B1Television conference systemsDigital data processing detailsVideo transmissionHuman agent
A system, method, and computer-usable medium are disclosed for masking the identity of a human agent by transforming a live video transmission into a persona video transmission. A request is received from a user for a videoconference with a human agent. A persona is selected and associated with a human agent. The videoconference is then conducted, using data associated with the persona to transform the live video transmission of the human agent into a persona video transmission, which is correlated to the live video transmission.
Owner:USAA
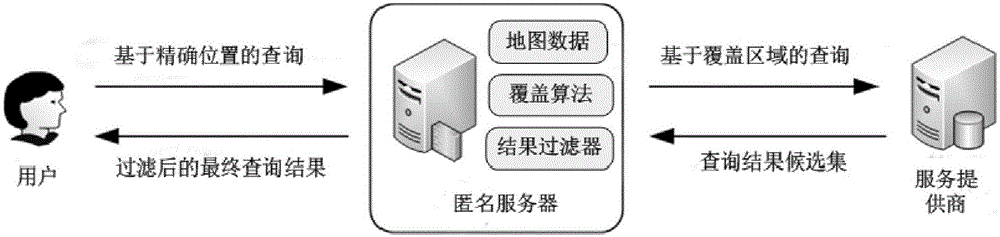
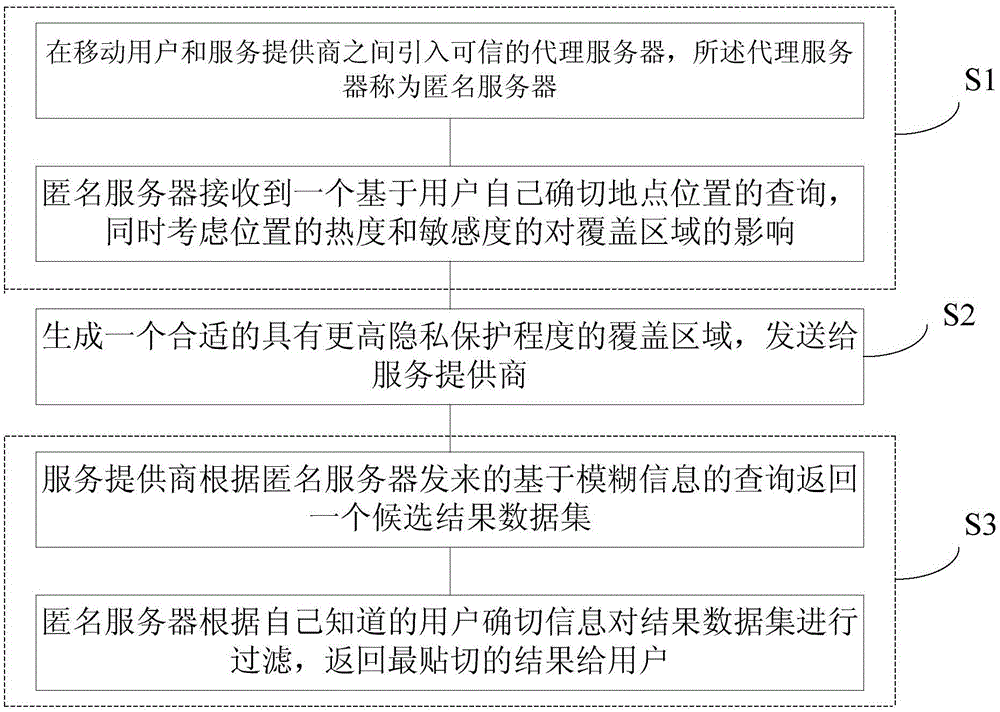
Location privacy protection method based on location sensitivity and hot degree in road network
ActiveCN105120431AImprove performanceLocation information based serviceSecurity arrangementData setService provision
The invention discloses a location privacy protection method based on location sensitivity and hot degree in a road network. The location privacy protection method comprises the steps that: S1, a credible proxy server is introduced between a mobile user and a service provider, wherein the proxy server is called an anonymous server; S2, the anonymous server receives a query based on a user's own exact location, takes the influence of hot degree and sensitivity of the location on a cloaking region into account, generates an appropriate cloaking region with higher privacy protection degree, and sends the cloaking region to the service provider; S3, and the service provider returns a candidate result data set according to the query based on fuzzy information sent by the anonymous server, and the anonymous server filters the result data set according to known exact information of the user and returns a most appropriate result to the user. The location privacy protection method considers the correlativity between hot degree and sensitivity of the location comprehensively, and prevents an attacker from conjecturing a sensitive location where the user has dwelled in the region according to dwell time of the user in the cloaking region.
Owner:SUN YAT SEN UNIV
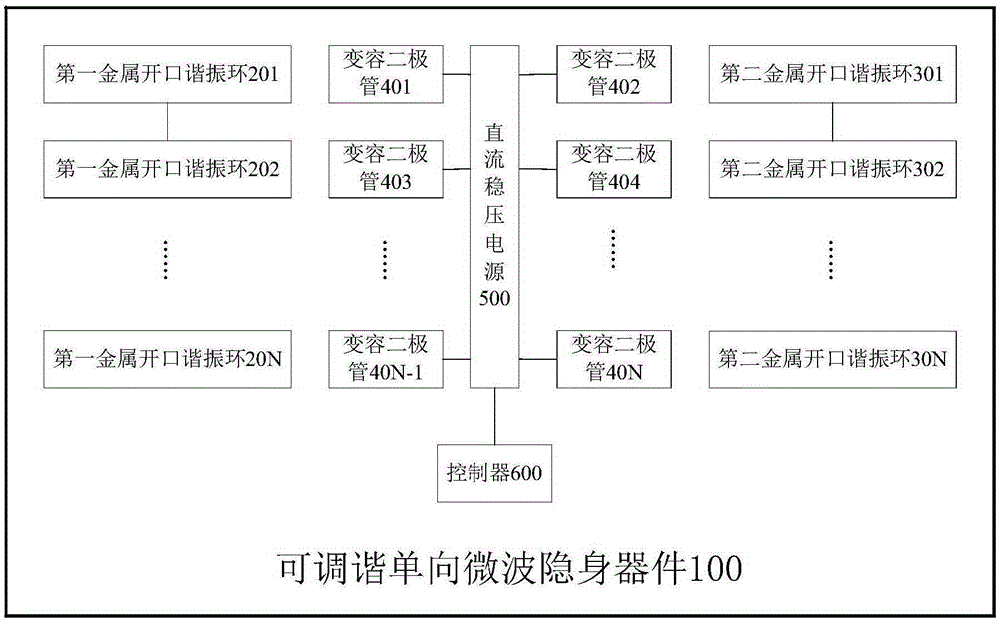
Tunable unidirectional microwave cloaking device
ActiveCN105244627AStealth implementationEasy to controlAntennasMicrowaveElectromagnetic wave transmission
The invention discloses a tunable unidirectional microwave cloaking device. The tunable unidirectional microwave cloaking device includes a first metal opening resonance ring array, a second metal opening resonance ring array, a plurality of variable capacitance diodes which correspondingly are arranged at the opening of each first metal opening resonance ring in the first metal opening resonance ring array and at the opening of each second metal opening resonance ring in the second metal opening resonance ring array, a direct-current voltage-stabilized power supply, and a controller, wherein the controller is used for controlling the output voltage of the direct-current voltage-stabilized power supply to regulate end voltage at two ends of each variable capacitance diode so as to change the capacitance values of the variable capacitance diodes, so that a frequency characteristic curve can be shifted. According to the cloaking device provided by the embodiment of the invention, control on electromagnetic wave transmission paths and phases can be realized through the resonance effects of the metal resonance rings, and obstacles in a cloaking region can be cloaked, and the frequency characteristic curve of the device can be shifted, so that the cloaking of electromagnetic wave waves in different frequency bands can be realized. The tunable unidirectional microwave cloaking device has the advantages of simple structure and easiness in control.
Owner:TSINGHUA UNIV
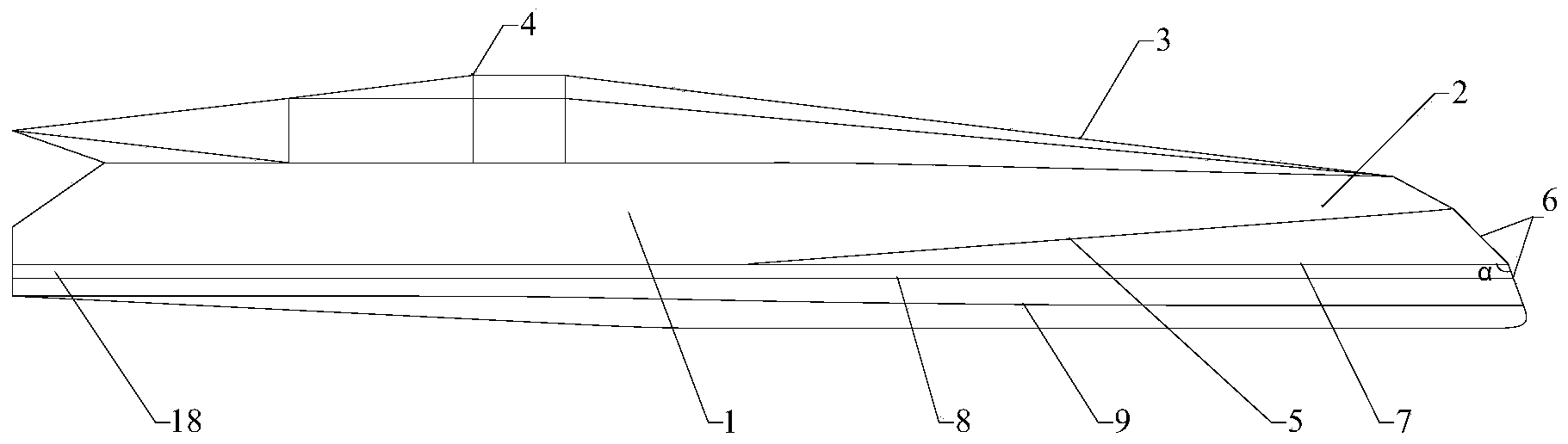
Wave absorbing type wave piercing yacht
InactiveCN103770903AImprove lateral stabilityIncrease the areaWatercraft hull designHull stemsEngineeringCloaking
The invention discloses a wave absorbing type wave piercing yacht. The wave absorbing type wave piercing yacht comprises a main yacht body, and two rigid sheet bodies which are respectively and symmetrically connected onto two sides of the tail of the main yacht body in bridging mode, wherein a channel is formed between the main yacht body and each vertical rigid sheet body on each side of the main yacht body, and the two channels are symmetrically formed on the left side and the right side of the main yacht body, and used to increase stability and absorb waves. The wave absorbing type wave piercing yacht is based on an original single wave piercing type yacht, and deficiencies of the original single wave piercing type yacht are improved by adding the sheet bodies on two sides of the main yacht body, and furthermore the wave absorbing type wave piercing yacht has the advantages of being high in navigational speed, adaptive to multiple sea states, small in wave rise, suitable for inland rivers, lakes and coastal regions, and applicable to yachts, seaborne high speed interception boats and the like, and having certain cloaking and wave piercing properties.
Owner:SHANGHAI JIAO TONG UNIV
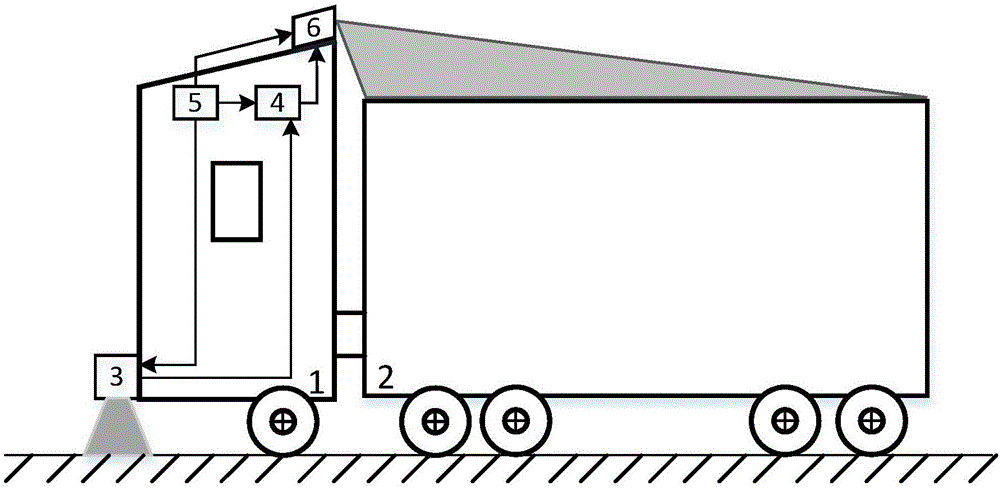
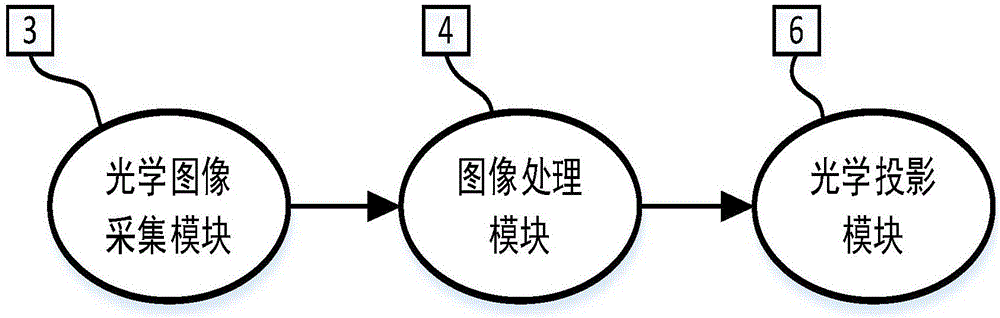
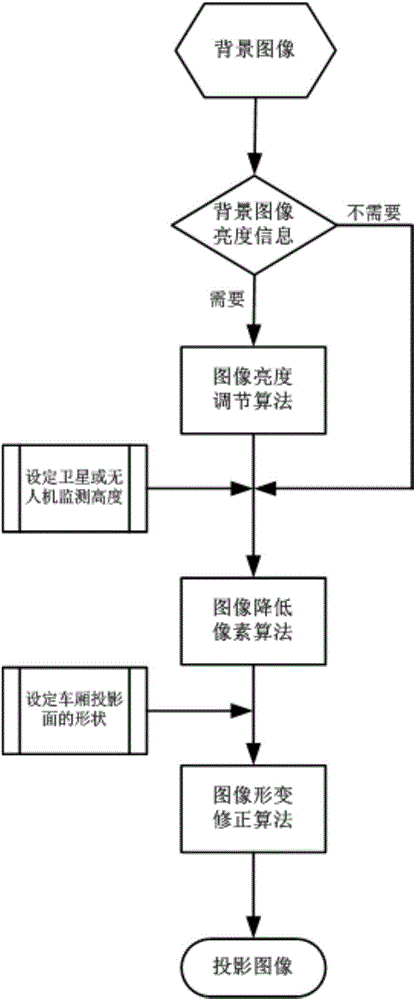
Real-time-optical-projection-based vehicle camouflage apparatus and method
InactiveCN106534816ASimple compositionLow costProjectorsPicture reproducers using projection devicesImaging processingUncrewed vehicle
The invention relates to an optical cloaking device and method, especially to a real-time-optical-projection-based vehicle camouflage apparatus and method. The invention aims at providing a real-time-optical-projection-based vehicle camouflage apparatus and method, thereby realizing special vehicle camouflage under satellite monitoring or unmanned aerial vehicle aerial shooting and thus realizing effective cloaking. The vehicle camouflage apparatus comprises an optical image acquisition module (3), an image processing module (4), an optical projection module (6) and a power supply (5). In addition, the vehicle camouflage method includes the following steps that: step a, the optical image acquisition module (3) collects pavement and ambient environment background images in a vehicle driving direction and transmits the images to the image processing module (4); step b, the image processing module processes the background images and then transmits the processed images to the optical projection module (6); and step c, the optical projection module projects the processed images on the top of a carriage (2).
Owner:BEIJING INST OF SPACE LAUNCH TECH +2
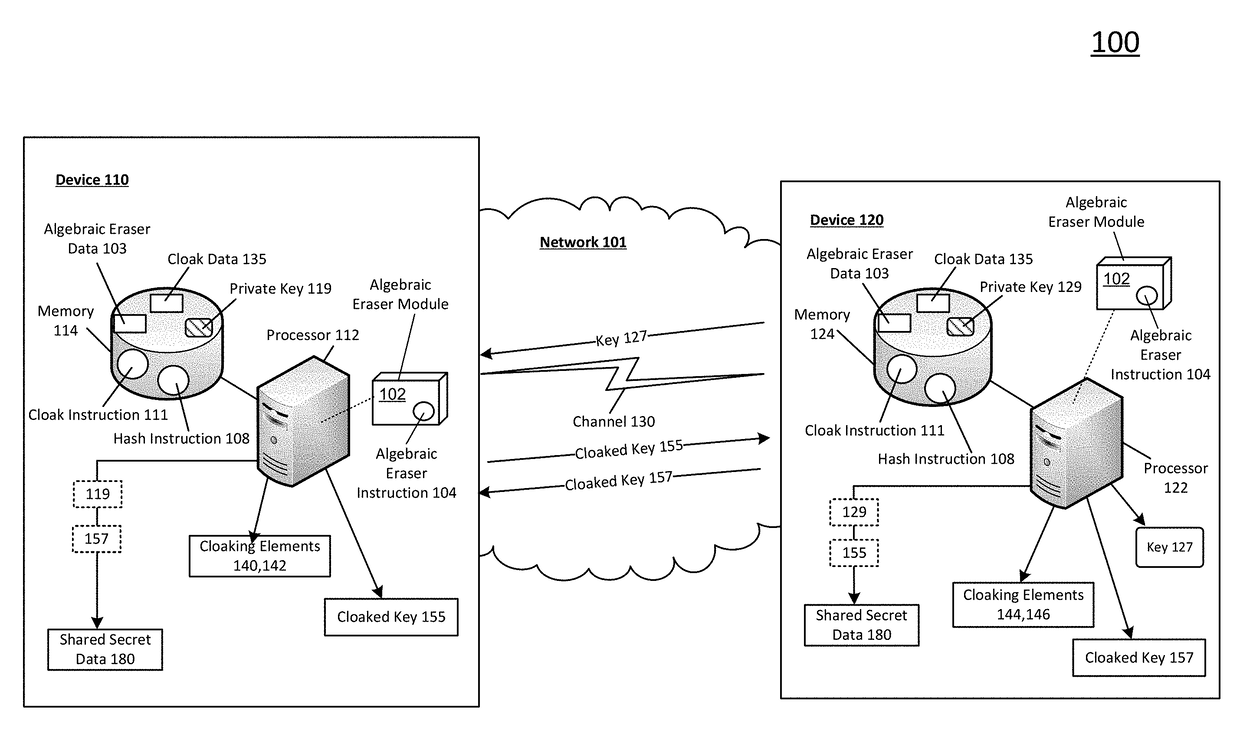
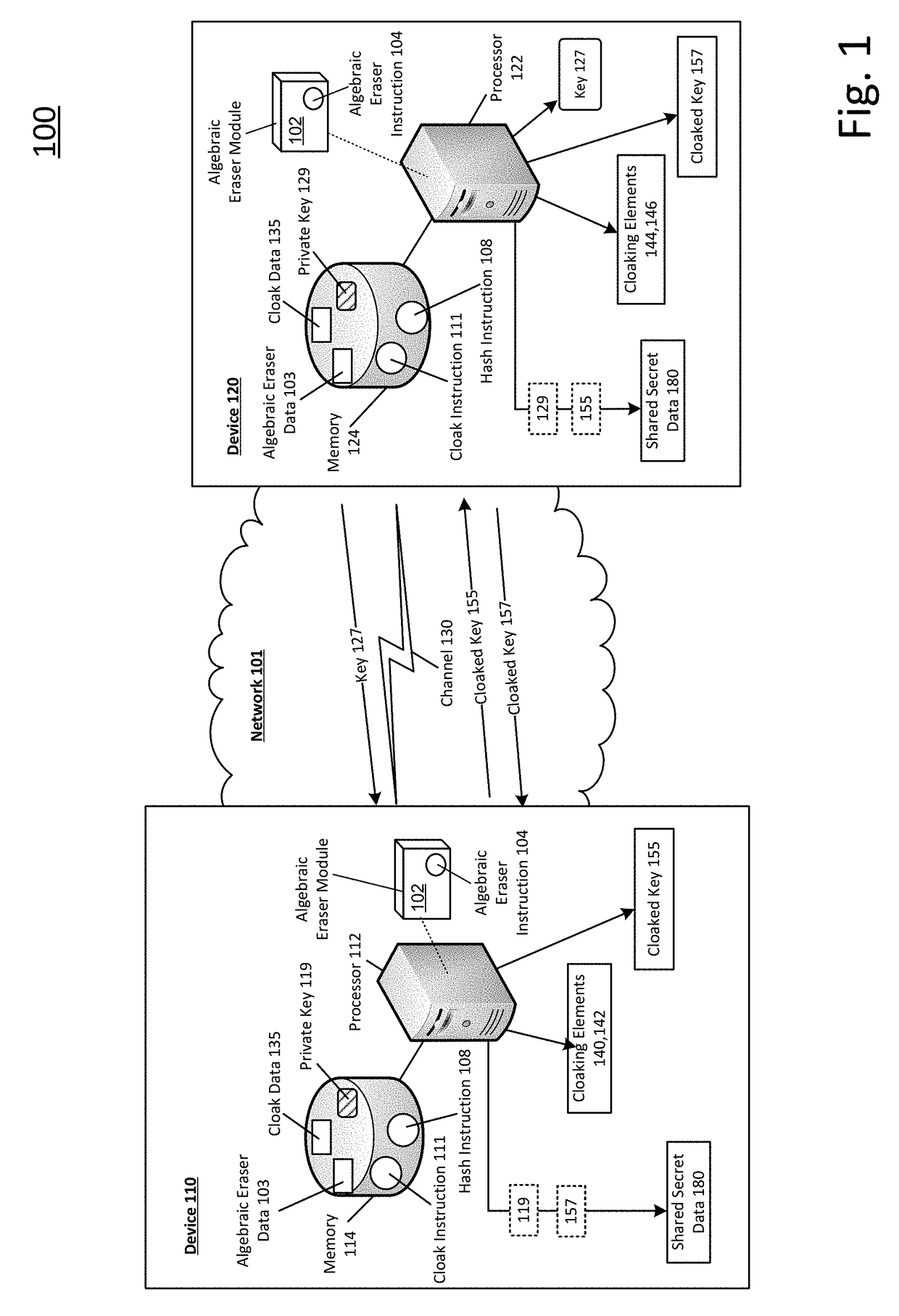
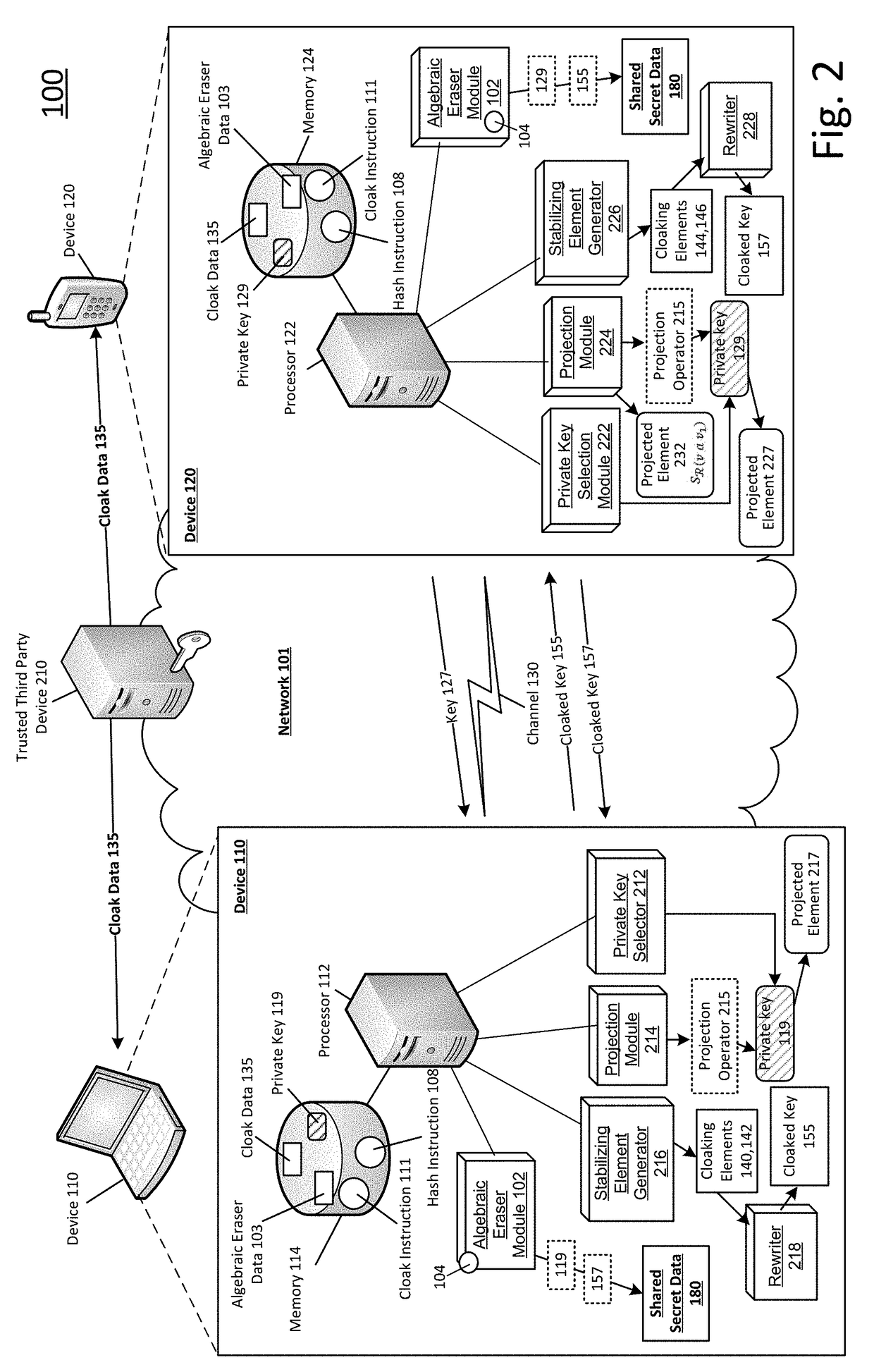
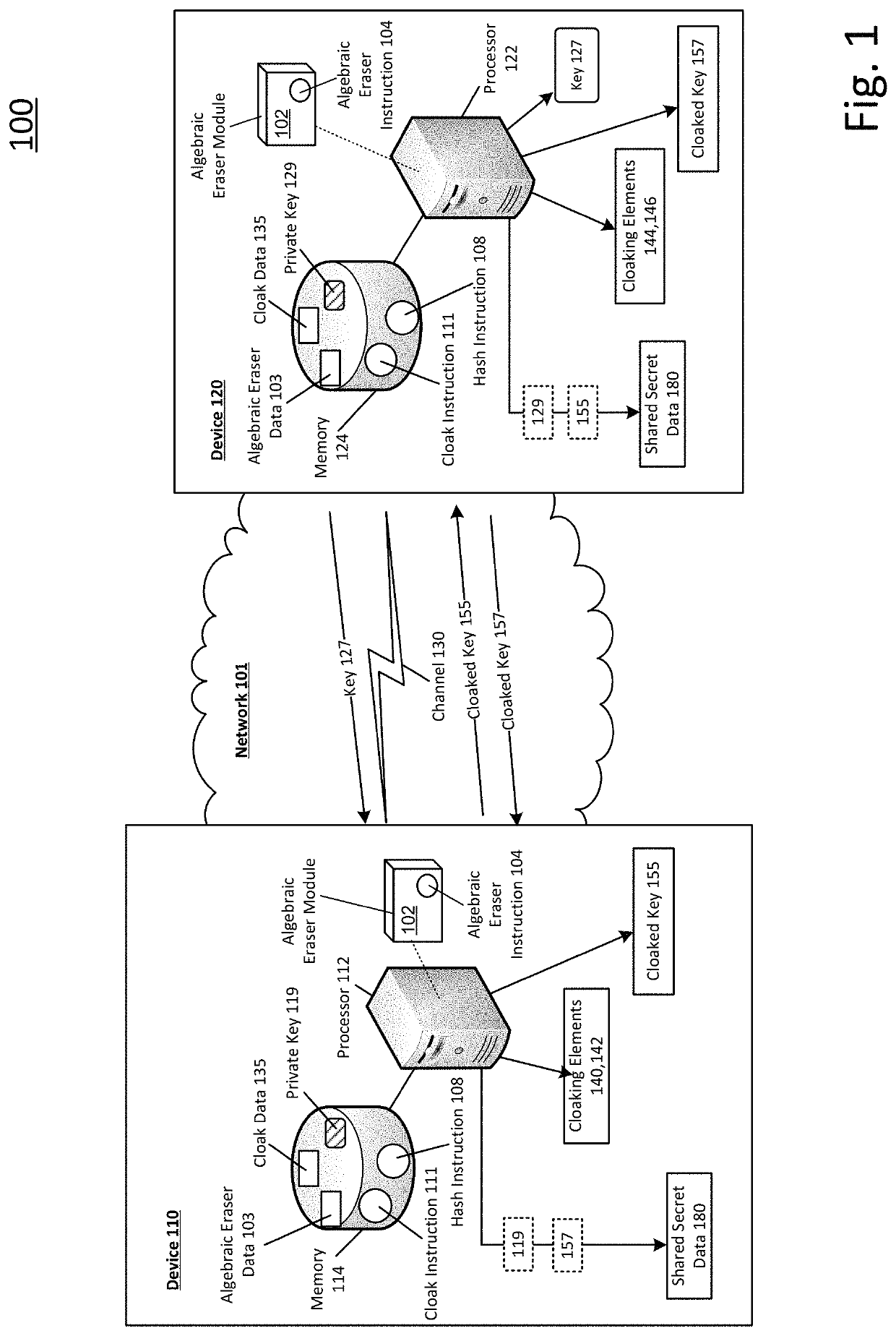
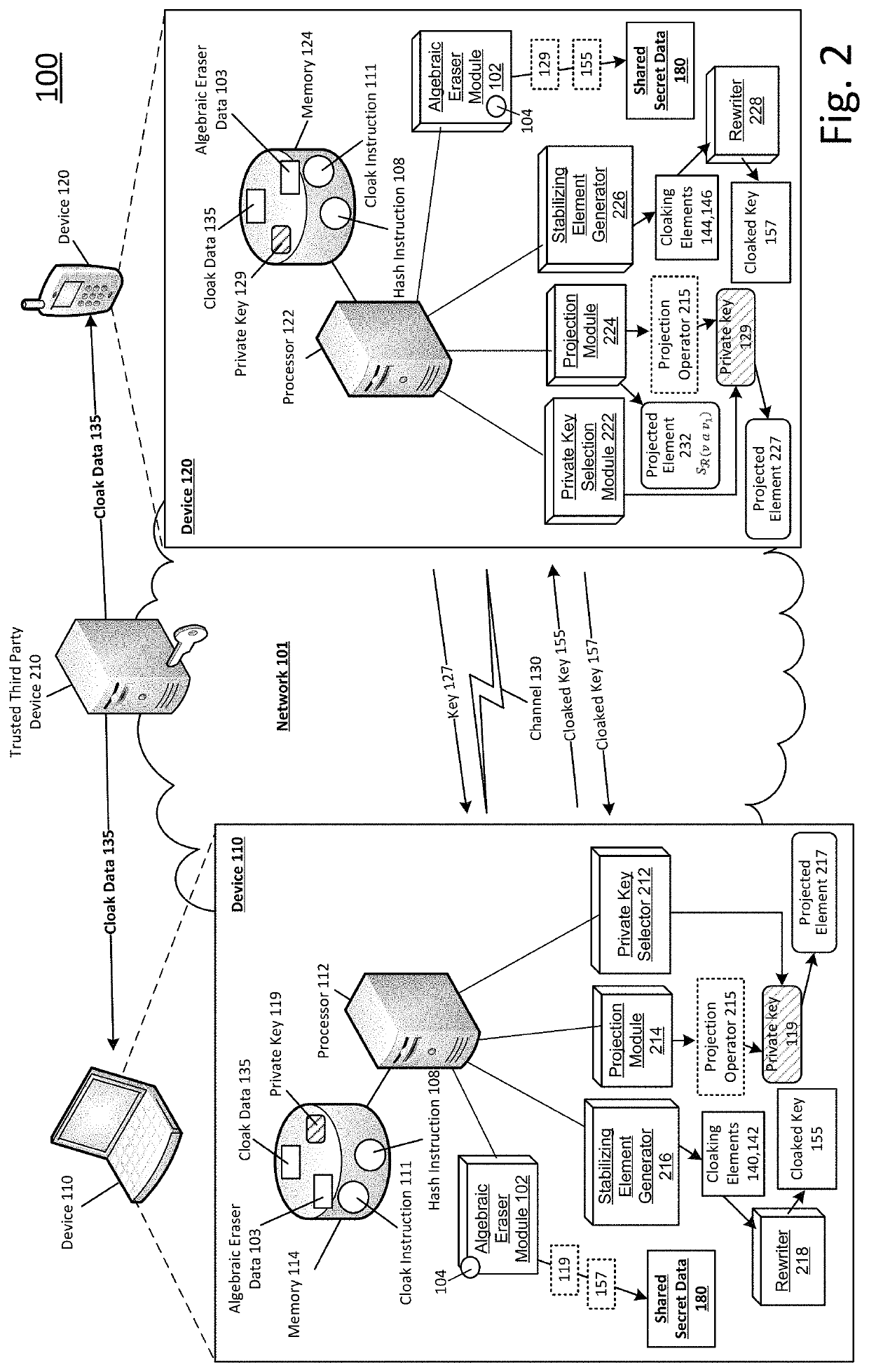
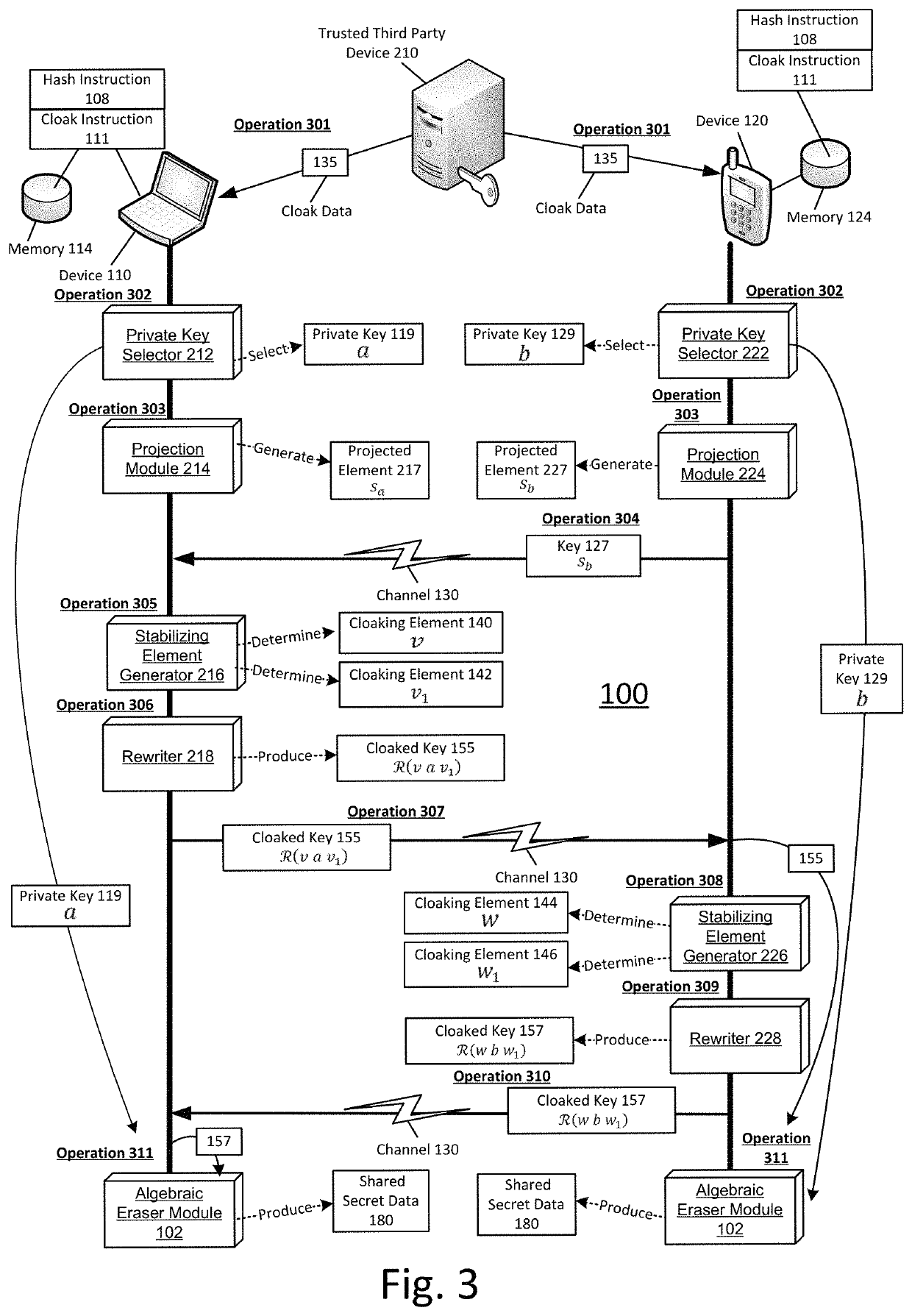
Shared secret communication system with use of cloaking elements
ActiveUS20180013554A1Efficiently indicatedEfficient productionKey distribution for secure communicationMultiple keys/algorithms usageCommunications systemCloaking
Systems and methods to produce cloaked keys and shared secret data are described. A first device may select a private key, for the first device, based on a first set of rewritten conjugates. The first device may receive a public key from a second device. The public key may be based on a private key of the second device. The private key of the second device may be based on a second set of rewritten conjugates. The first device may determine first and second cloaking elements based on the public key and the private key of the first device. The first device may produce a cloaked key based on the first and second cloaking elements, and the private key of the first device. The first device may produce shared secret data based on the private key of the first device and a second cloaked key from the second device.
Owner:SECURERF CORP
Dynamic cloaking device and dynamic cloaking method
InactiveCN103997606AReal-time acquisition of spatial position relationshipAchieve the invisible effectImage enhancementTelevision system detailsDistance sensorsCloaking
The invention discloses a dynamic cloaking device which comprises a display screen. The display screen is used for covering an object to be cloaked and provided with at least one display unit in an array mode. The back of the display unit is provided with a camera used for imaging of the background of the back of the display unit. A processor and a distance sensor are arranged in the display screen, wherein the distance sensor is used for measuring the distance from the human eyes to the geometric center of the display screen and the distance from the background to the geometric center of the display screen. The processor is respectively and electrically connected with the display unit, the camera and the distance sensor. A human eye catcher is arranged in the camera. The invention further discloses a dynamic cloaking method. According to the dynamic cloaking method, a display image of the display screen can be adjusted in real time according to the dynamic position of an observer, the technical effect of dynamic cloaking can be achieved, and the cloaking effect is better.
Owner:CHONGQING TECH & BUSINESS UNIV
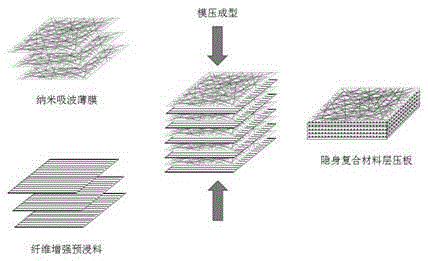
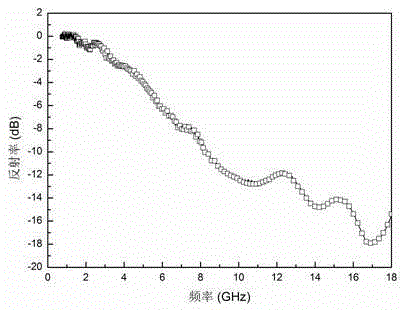
Method for functionally modifying composite material laminated board by radar absorbing nano-membrane
InactiveCN105383130AFunction increaseImprove mechanical propertiesSynthetic resin layered productsLaminationFiberRadar
The invention discloses a method for functionally modifying a composite material laminated board by a radar absorbing nano-membrane. The method comprises the following steps: preparing a uniform and steady resin solution by using nano particles and polyarylether resin; (2) preparing a radar absorbing nano-membrane by using the prepared resin solution through a film preparation process; (3) sufficiently dipping continuous filament or fabric and resin matrix to prepare a composite material prepreg; (4) covering the radar absorbing nano-membrane among the layers of the composite material prepreg, and preparing structure / function integrated cloaking composite material laminated board according to the composite material forming process. The method disclosed by the invention has the beneficial effects that the wave-absorbing functional layer is integrated into the preparation process of the composite material laminated board, and the integral wave-absorbing function and mechanical property of the composite materials can be greatly improved with low cost synchronously. The product has dual excellent functions of loading and cloaking and wide application prospect in the field of aerospace engineering.
Owner:SHENYANG AEROSPACE UNIVERSITY
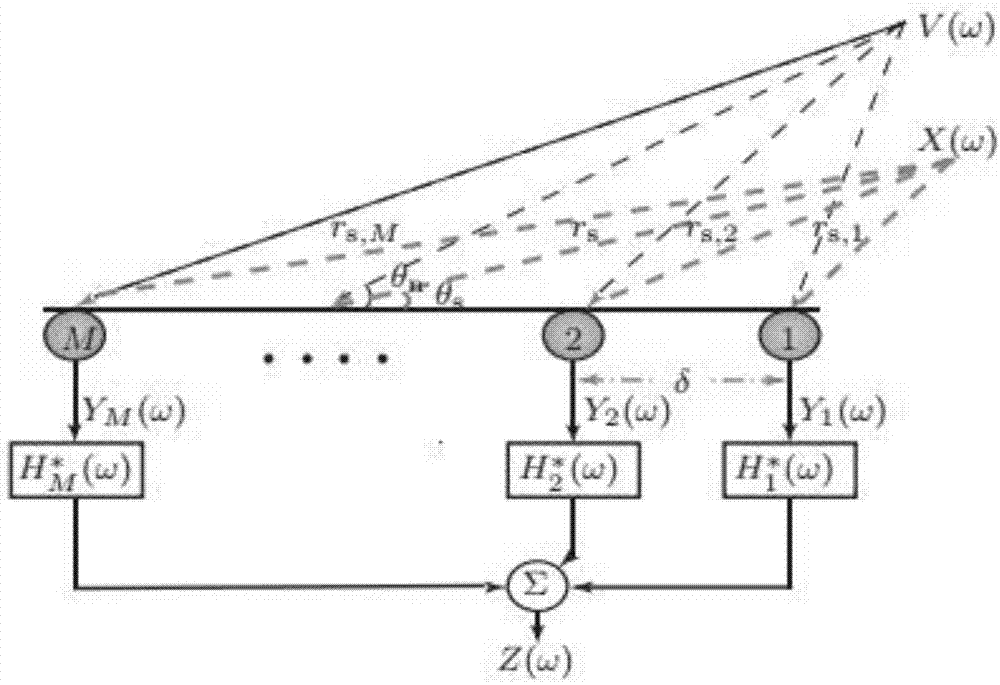
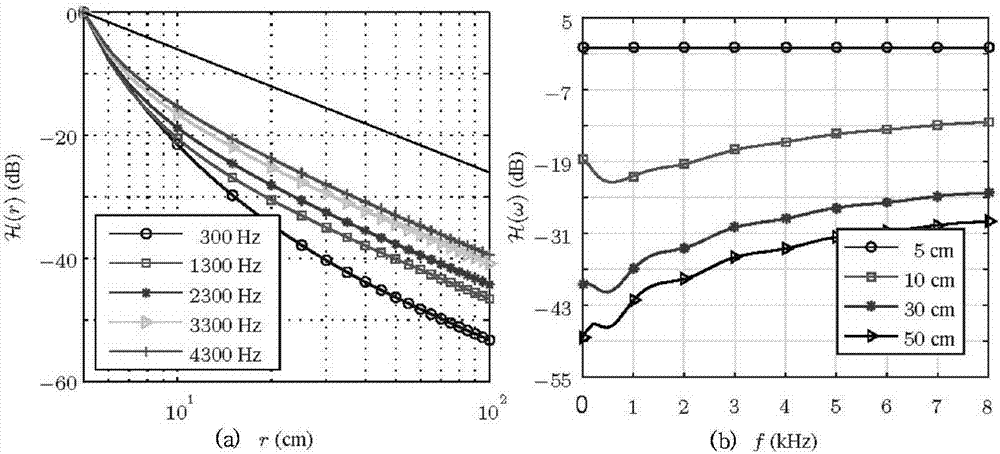
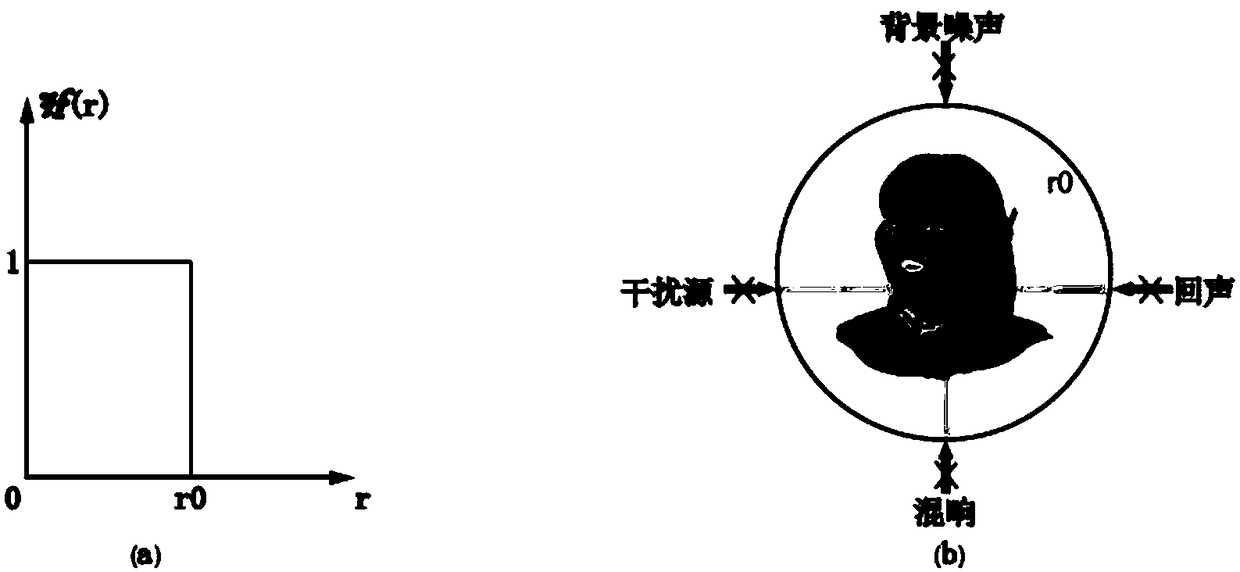
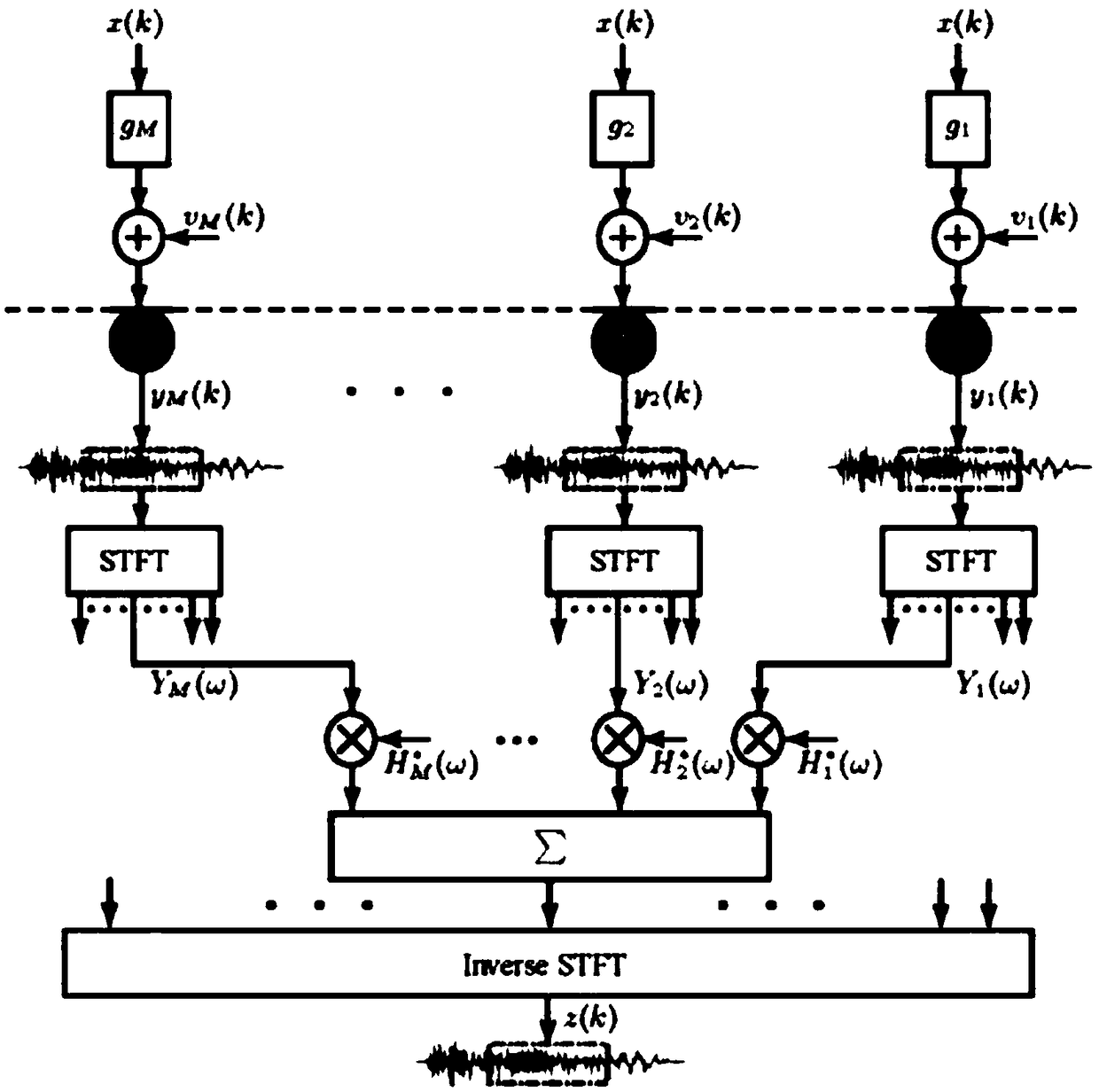
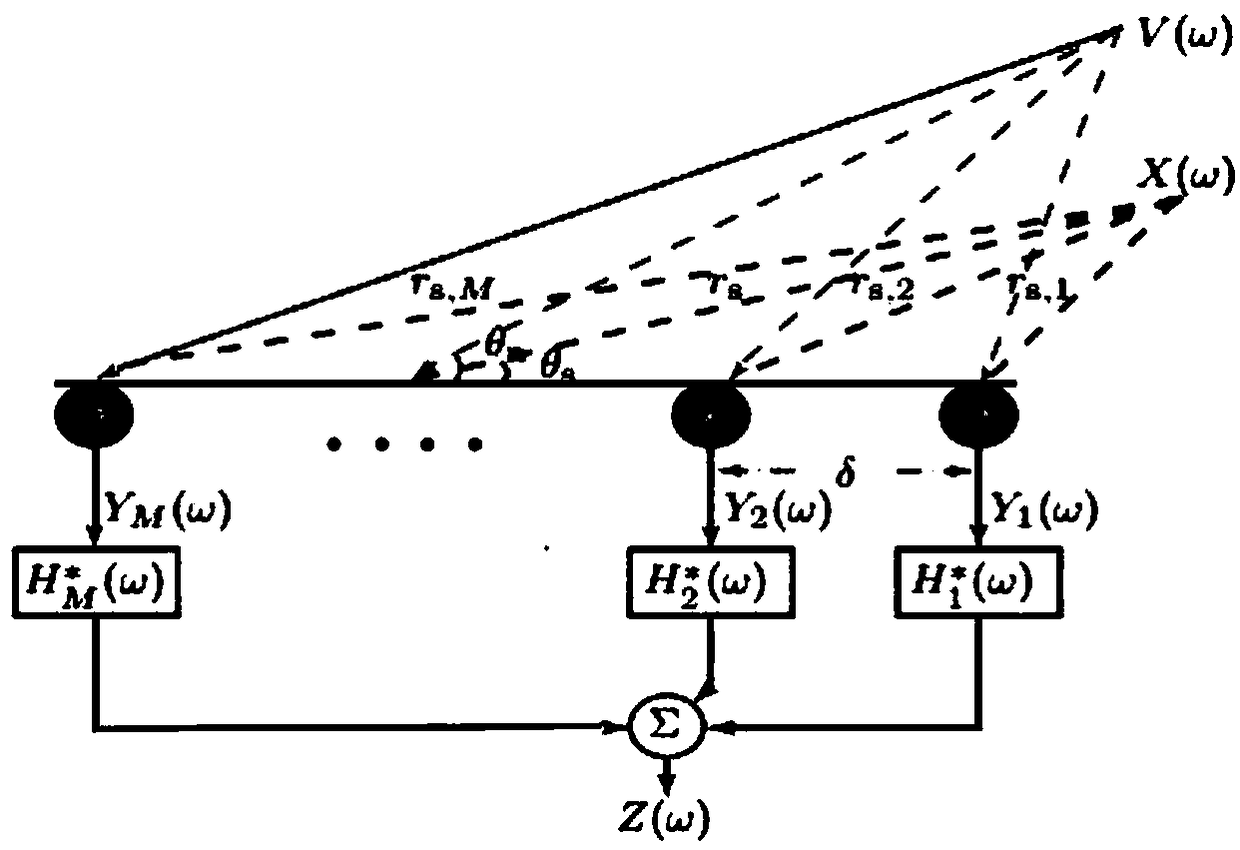
Acoustic cloaking method based on MVDR
The invention discloses a method for concealing sound based on MVDR. The method first uses short-time Fourier transform to decompose the time-domain signal received by the sensor array into frequency-domain sub-band signals, and constructs a sub-band signal based on MVDR on each sub-band. The hidden sound filter, so that the acoustic signal from the sound source within the hidden sound distance passes through the hidden sound filter without attenuation, and finally the estimated signal is obtained through inverse STFT. The invention has better sound hiding effect.
Owner:临境声学科技江苏有限公司
Single wave-piercing yacht
InactiveCN103786829ATaking into account the rapidityReduced detectabilityDefensive equipmentOffensive equipmentSeakeepingPolygonal line
A single wave-piercing yacht in the technical field of ships on water comprises a main yacht body, a mixed internally-inclining prow, a square stern and a full-closed upper-layer building. The mixed internally-inclining prow comprises a first column, a full-closed prow deck and a prow freeboard, wherein the first column is of a broken line structure, and the portion located above a waterline and the portion located under the waterline are provided with different sweepback angles. The rapidity and seakeeping of the single wave-piercing yacht are reasonably considered by using the mixed internally-inclining prow, and the yacht can easily pierce waves. By adopting the mixed internally-inclining prow and the full-closed, smooth and wave-piercing upper-layer building, the detectability is reduced, the yacht has good cloaking capacity, and meanwhile the probability that the yacht running in the waves at high speed encounters wave impact can be reduced. The controllability of a thin and long ship form is improved by adopting spray water propulsion. The single wave-piercing yacht can serve as a houseboat, a seaborne high-speed interceptor yacht and the like.
Owner:SHANGHAI JIAO TONG UNIV
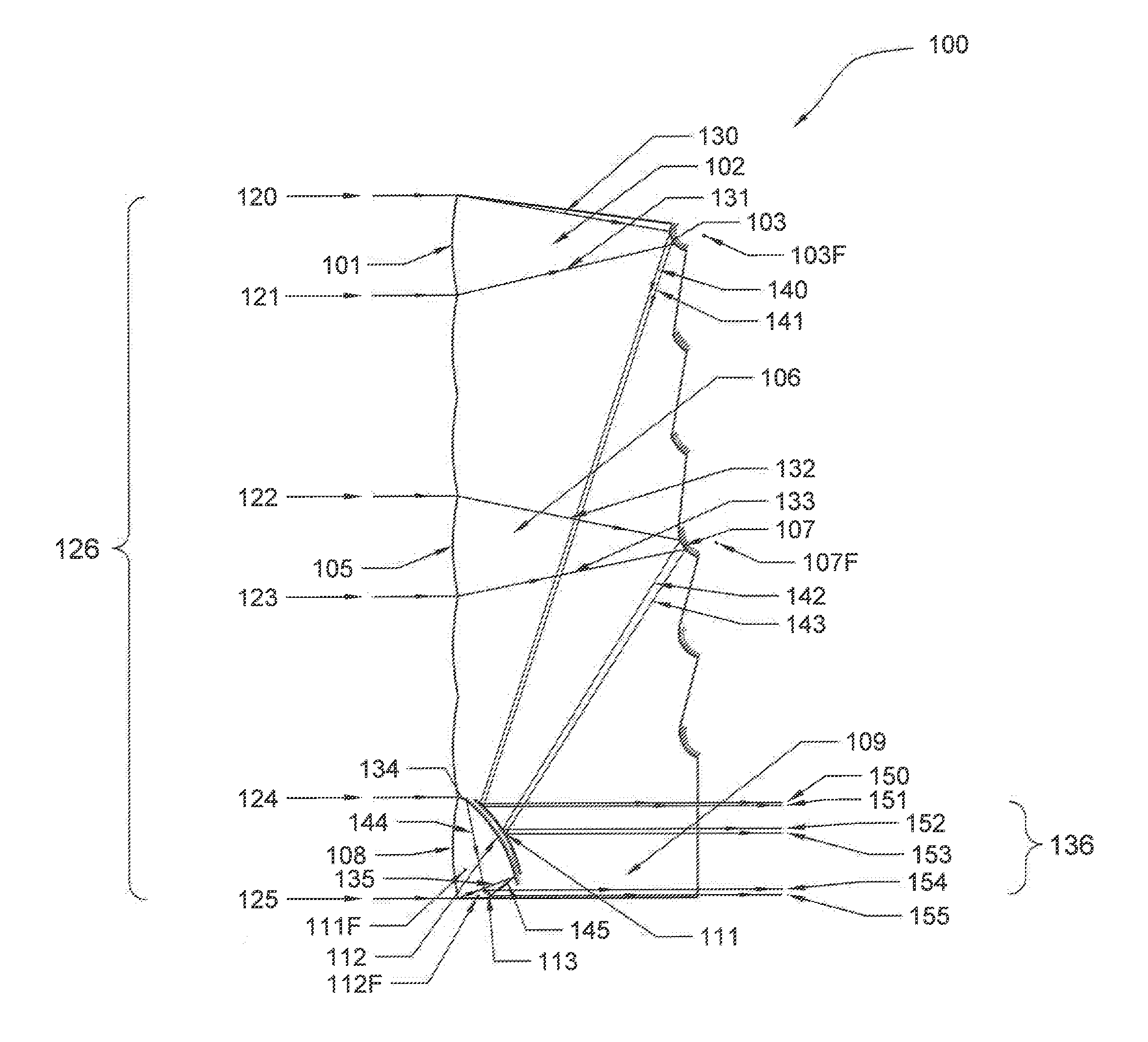
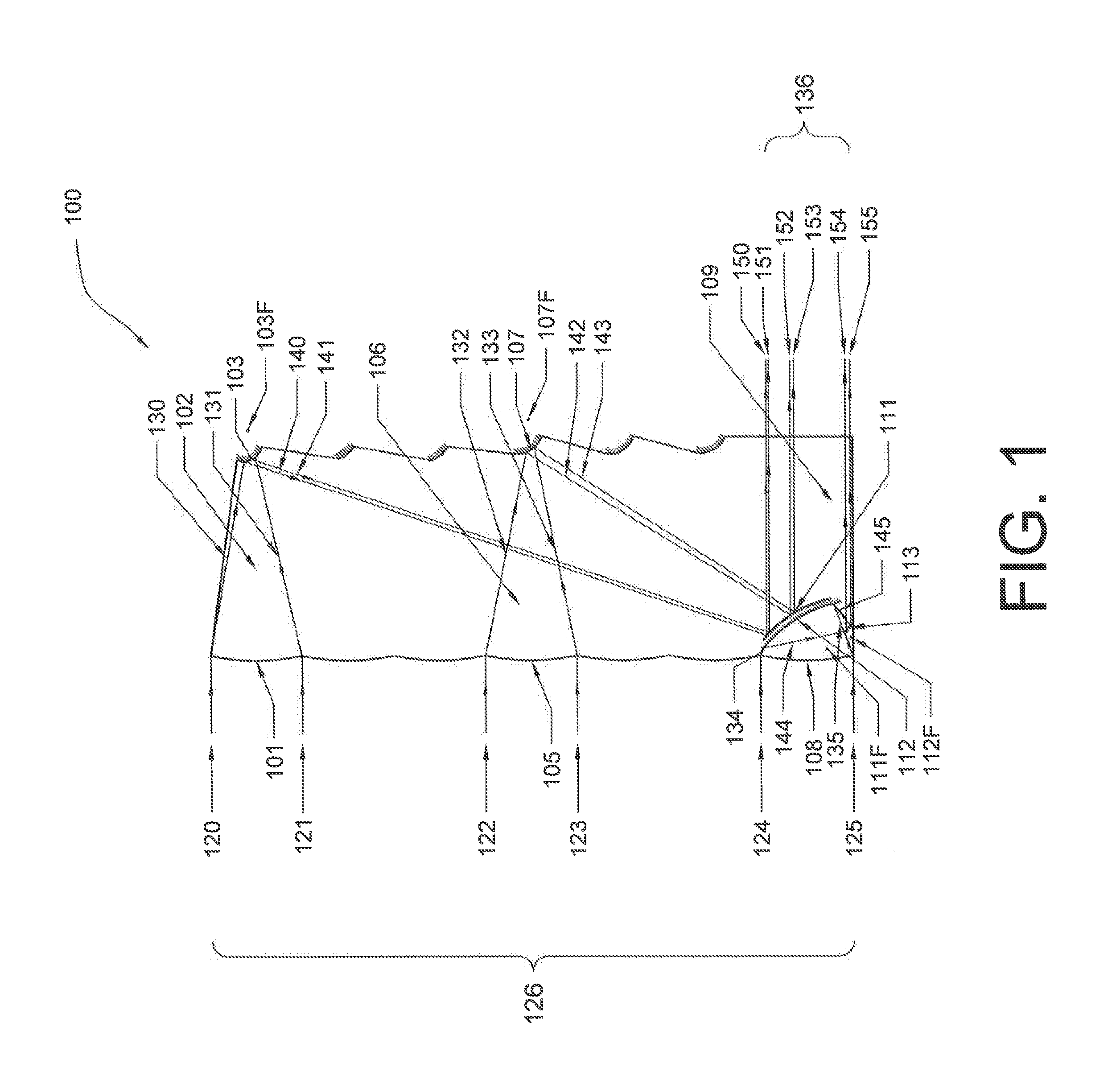
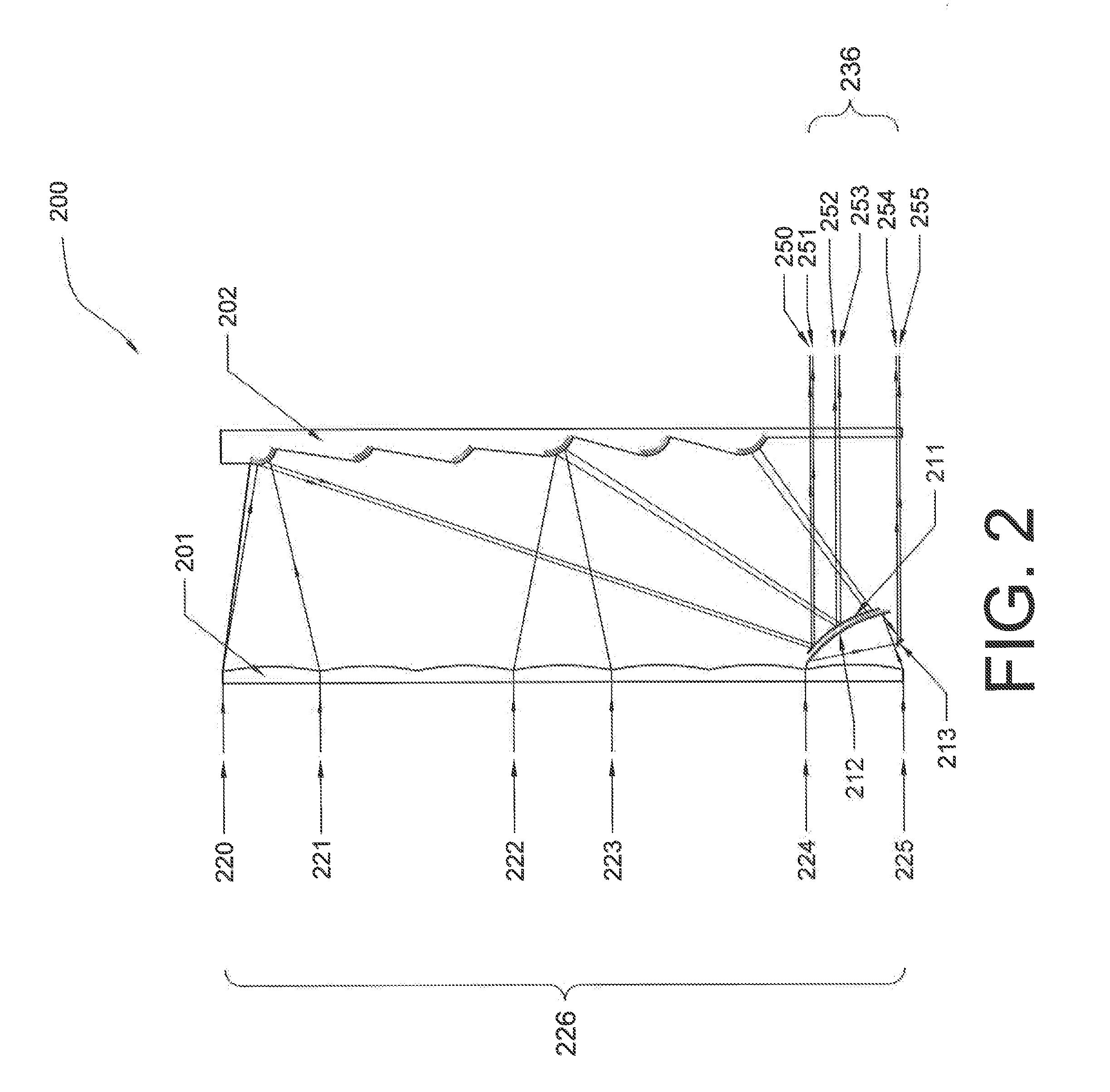
Hybrid optical devices, and applications using same including optical cloaking system
InactiveUS20150234100A1Reduce the depth dimensionReduced longitudinal dimensionMirrorsMountingsCloakingOptics
A hybrid optical device for compressing light, including a first part which receives incident light shining on the device, wherein the first part is formed into sections along at least one direction thereof, wherein the sections receive respective portions of the light received by the first part, and individually compress and redirect the received portions of light, a second part which includes plural reflective surfaces which receive the compressed light from the sections of the first portion and further compress and redirect the portions of light, and a third part which receives the further compressed portions of light from the sections of the second part, and redirects same such that the light is output from the device.
Owner:LU WEIMIN
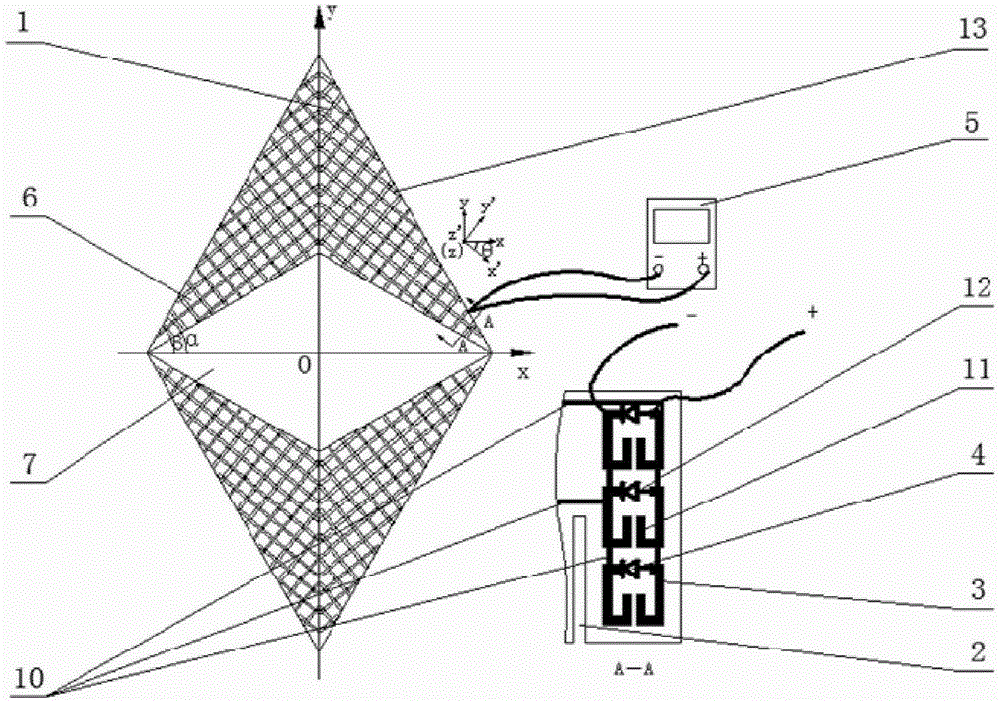
Apparatus and method for invisbility cloaking
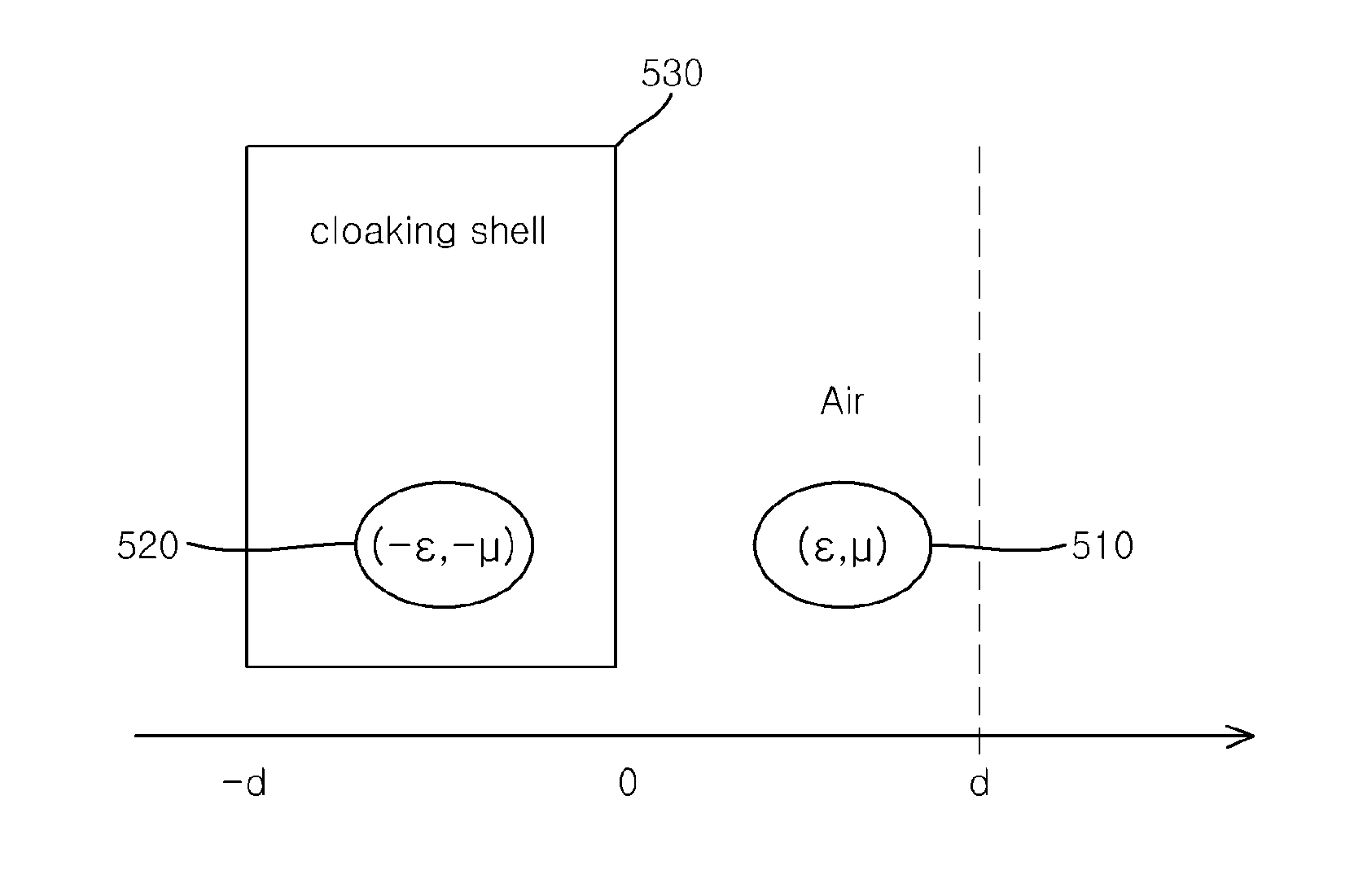
InactiveUS20160298935A1Improving the cloaking of a target objectWave based measurement systemsRadiating element housingsRefractive indexEngineering
A cloaking apparatus and method are disclosed herein. The cloaking apparatus for cloaking a target object using meta-material includes a compensation unit, and a cloaking cell. The compensation unit is disposed in a second space surrounding part of a first space including the target object, and is composed of a first meta-material having a predetermined negative refractive index. The cloaking shell is configured to surround part of the compensation unit, and is composed of a second meta-material. The negative refractive index may be a negative refractive index that is adapted to cloak the target object by compensating for the positive refractive index of the first space.
Owner:UNIV OF SEOUL IND COOP FOUND
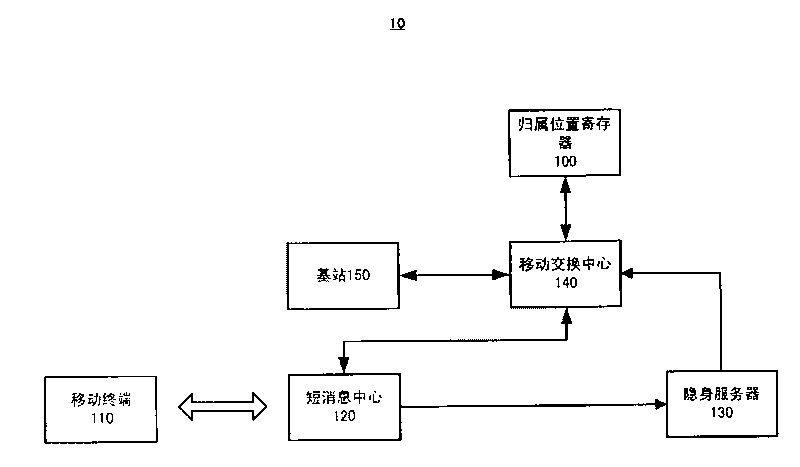
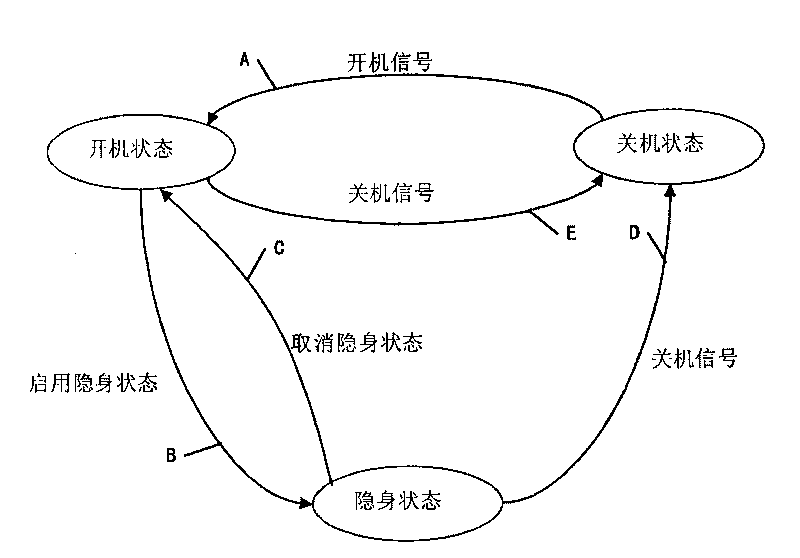
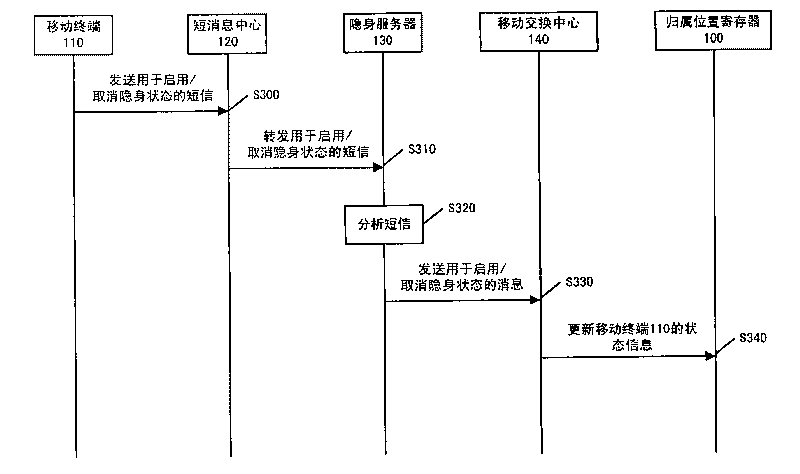
Method and device for realizing cloaking of mobile terminal
The invention relates to a method and a device for realizing the cloaking of a mobile terminal, wherein the method executed by a mobile switching center comprises the following steps of: receiving information from the other device and for requesting to provide passive service for the mobile terminal; acquiring the state information of the mobile terminal, which is stored at a network side; judging whether the mobile terminal is in a cloaking state or not on the basis of the acquired state information; and when a judgment result is positive, stopping providing the passive service for the mobile terminal. The method and the device for realizing the cloaking of the mobile terminal enable users not to receive the passive service under the condition of using active service.
Owner:爱思开电讯投资(中国)有限公司
Shared secret communication system with use of cloaking elements
ActiveUS10505722B2Key distribution for secure communicationMultiple keys/algorithms usageCommunications systemCloaking
Owner:SECURERF CORP
Cloaking method based on difference beam forming
InactiveCN108337605AGood voice hiding effectSignal processingTransducer circuitsSensor arrayTime domain
The invention discloses a cloaking method based on difference beam forming. According to the method, by means of short time Fourier transform, a time-domain signal received by a sensor array is decomposed into frequency-domain sub-band signals, cloaking filters based on N-order difference beam forming are constructed on various sub-bands, therefore, a sound signal from a sound source within the cloaking distance passes through the cloaking filters in an unattenuated mode, and finally an estimated signal is obtained through inverted STFT. The cloaking method has the good cloaking effect.
Owner:临境声学科技江苏有限公司
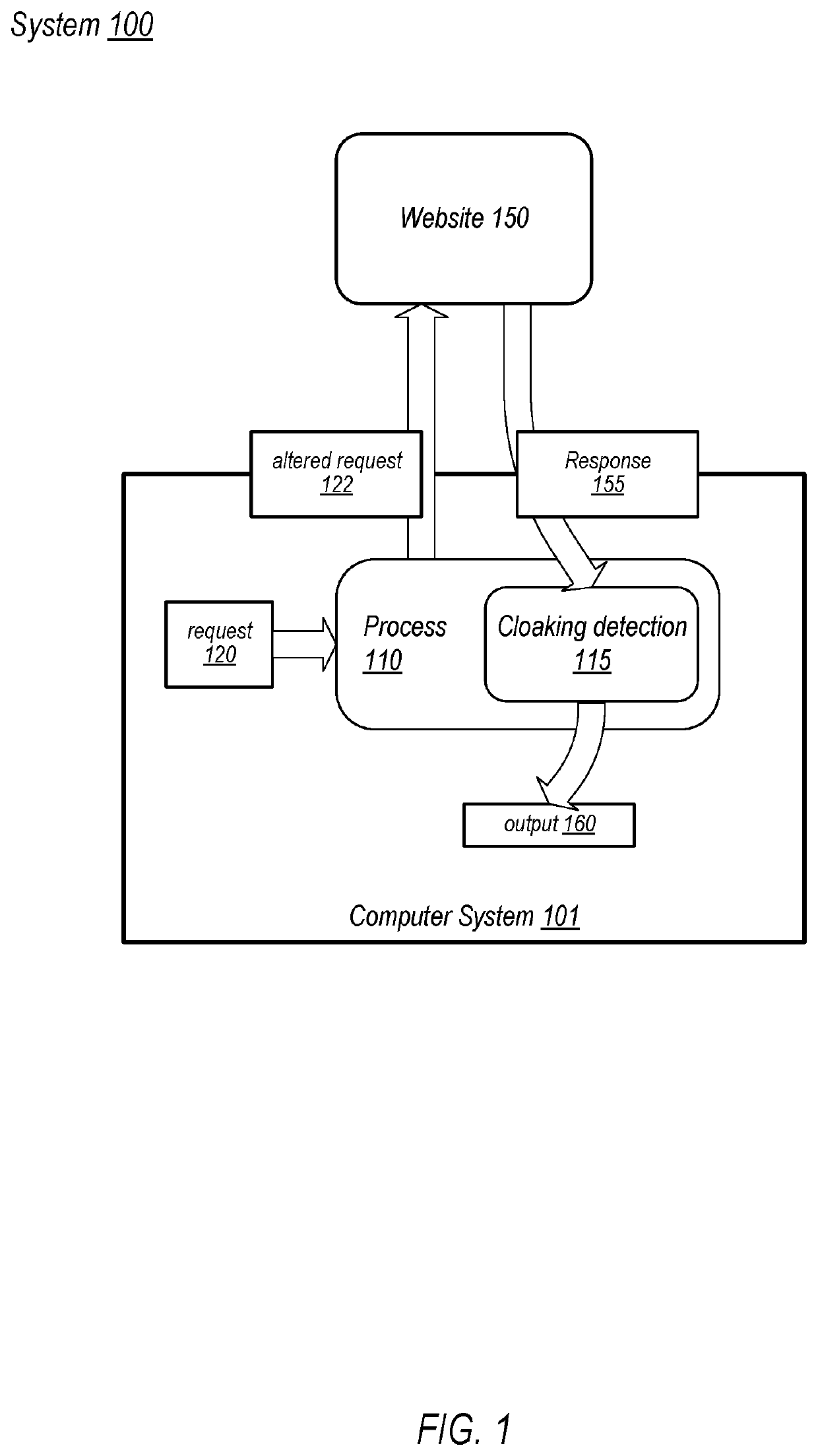
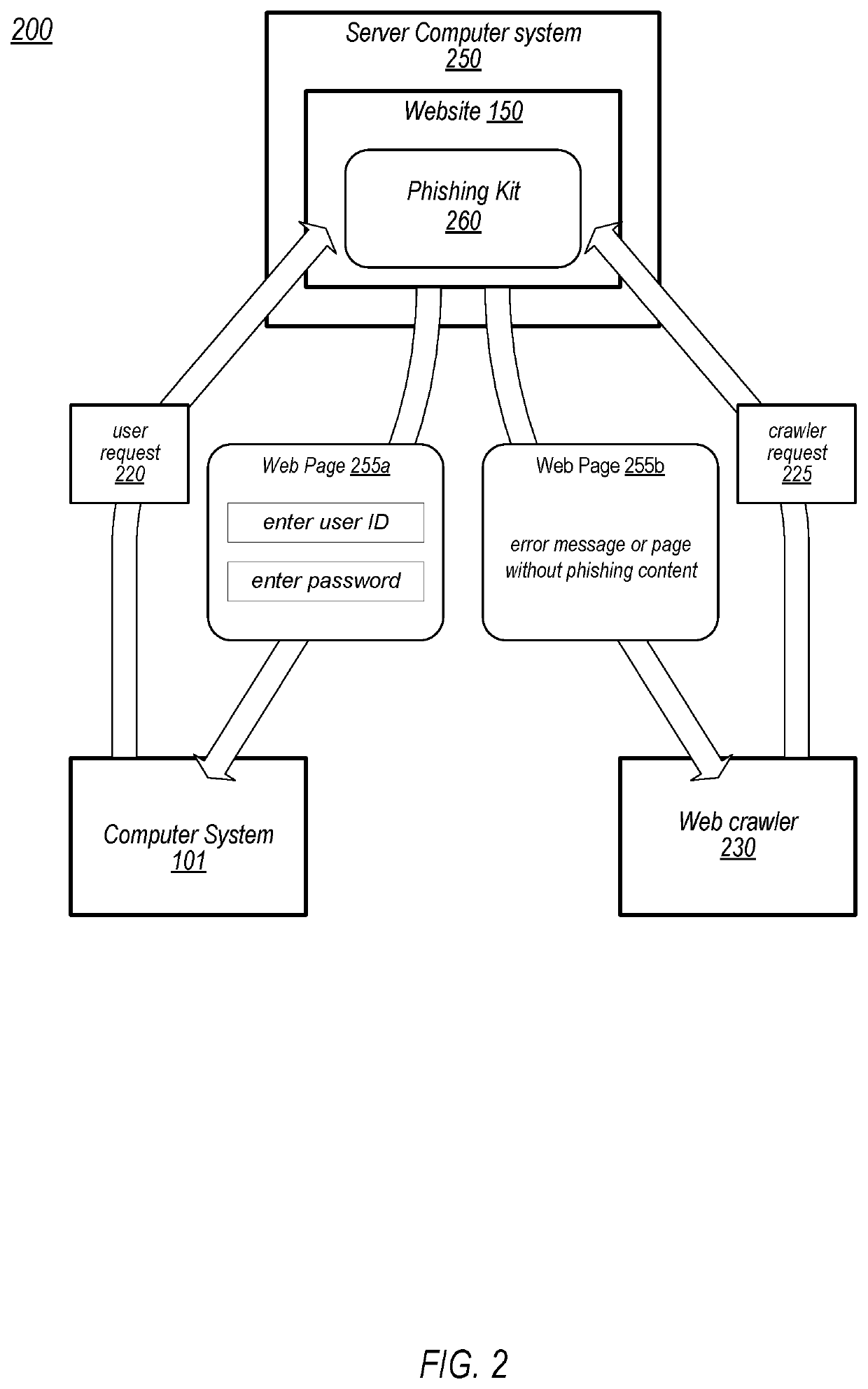
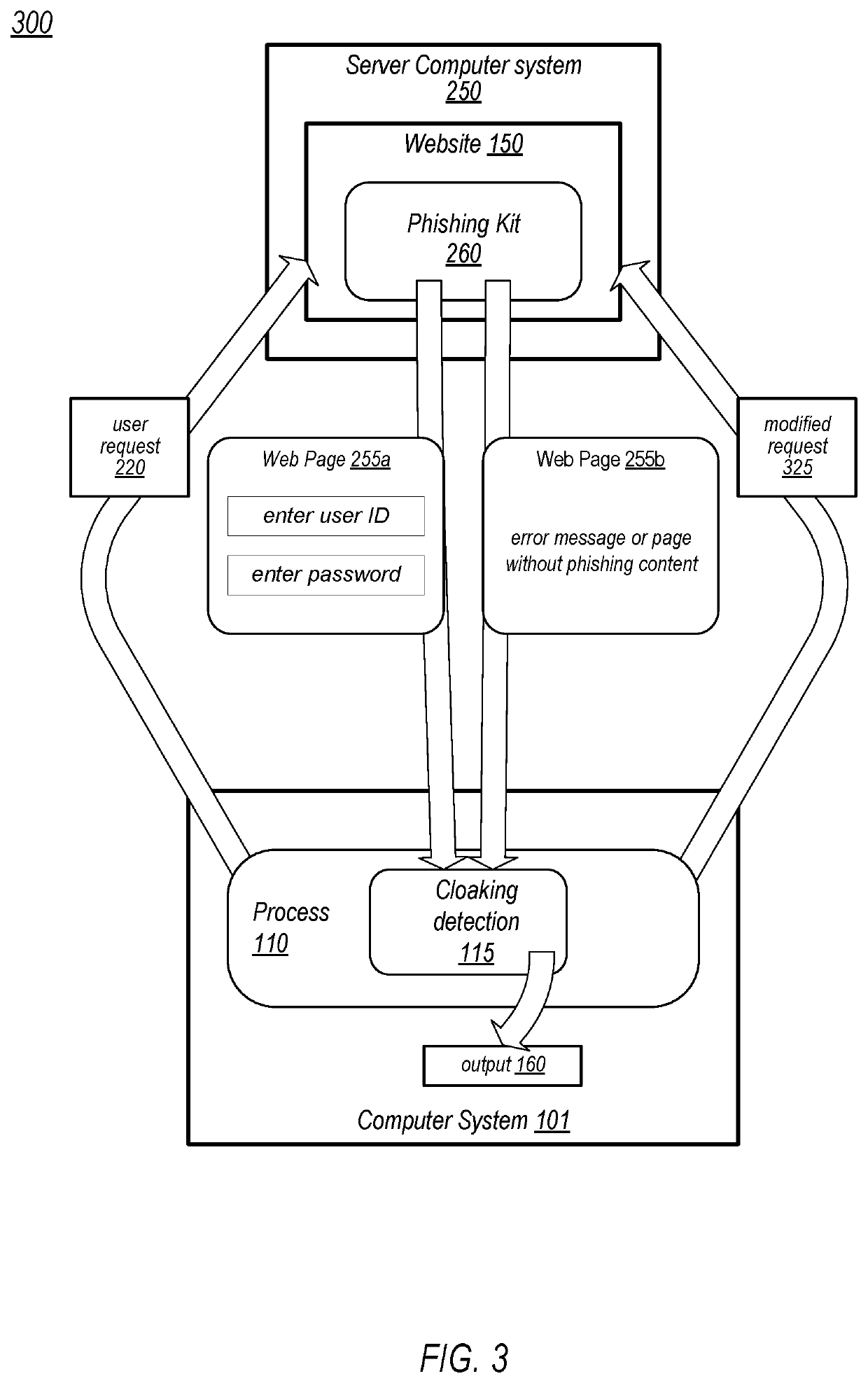
Neutralizing Evasion Techniques of Malicious Websites
Techniques are disclosed relating to methods that include a process, executing on a computer system, receiving a request to access a website, and altering the request to include one or more characteristics of anti-malware scanners. The method further includes the process sending the altered request to the website, and receiving a response to the altered request. The method also includes the process detecting whether the received response utilizes one of a known set of anti-malware cloaking techniques, and providing, based on the detecting, an output indicative of an outcome of the altered request.
Owner:PAYPAL INC
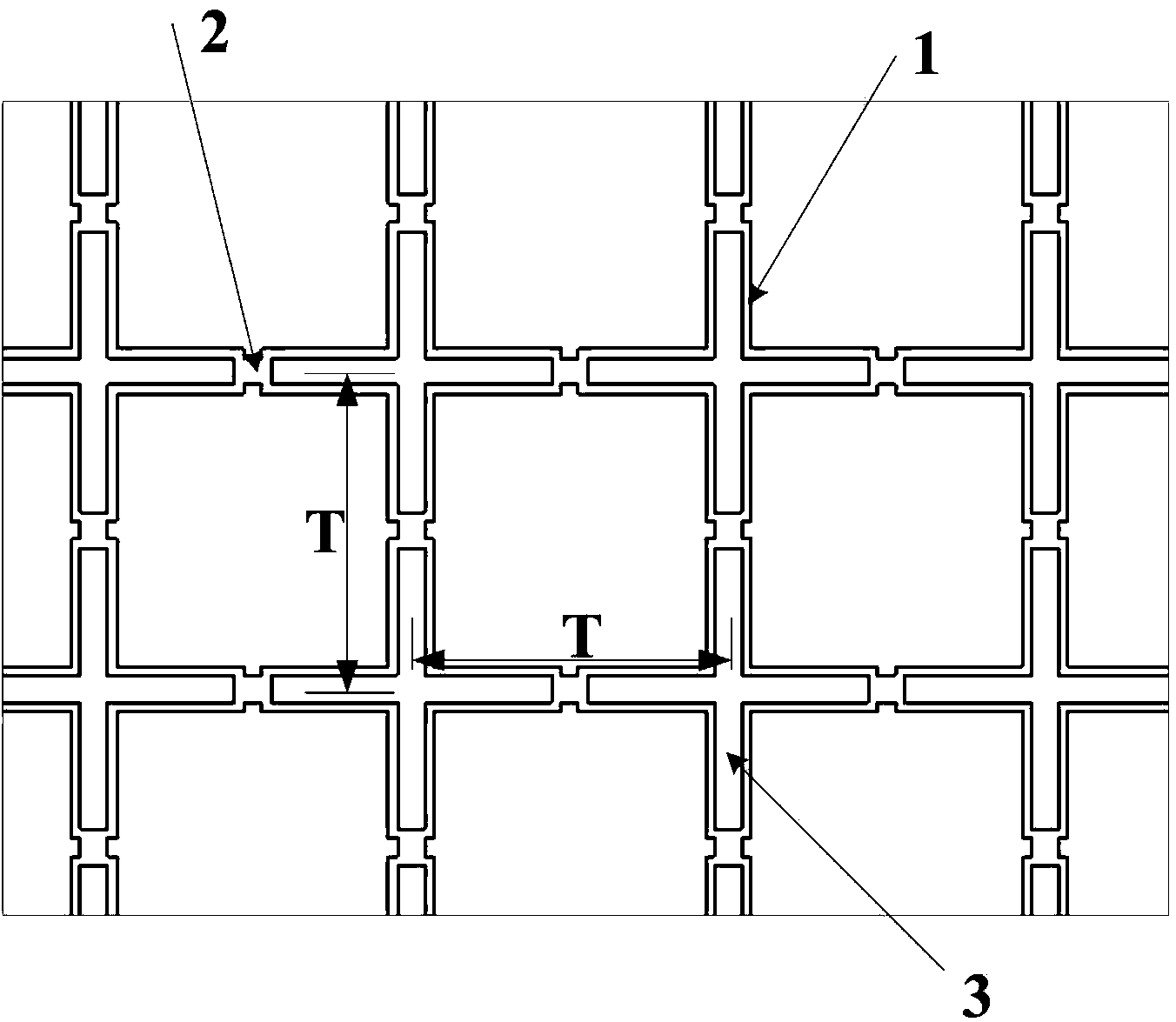
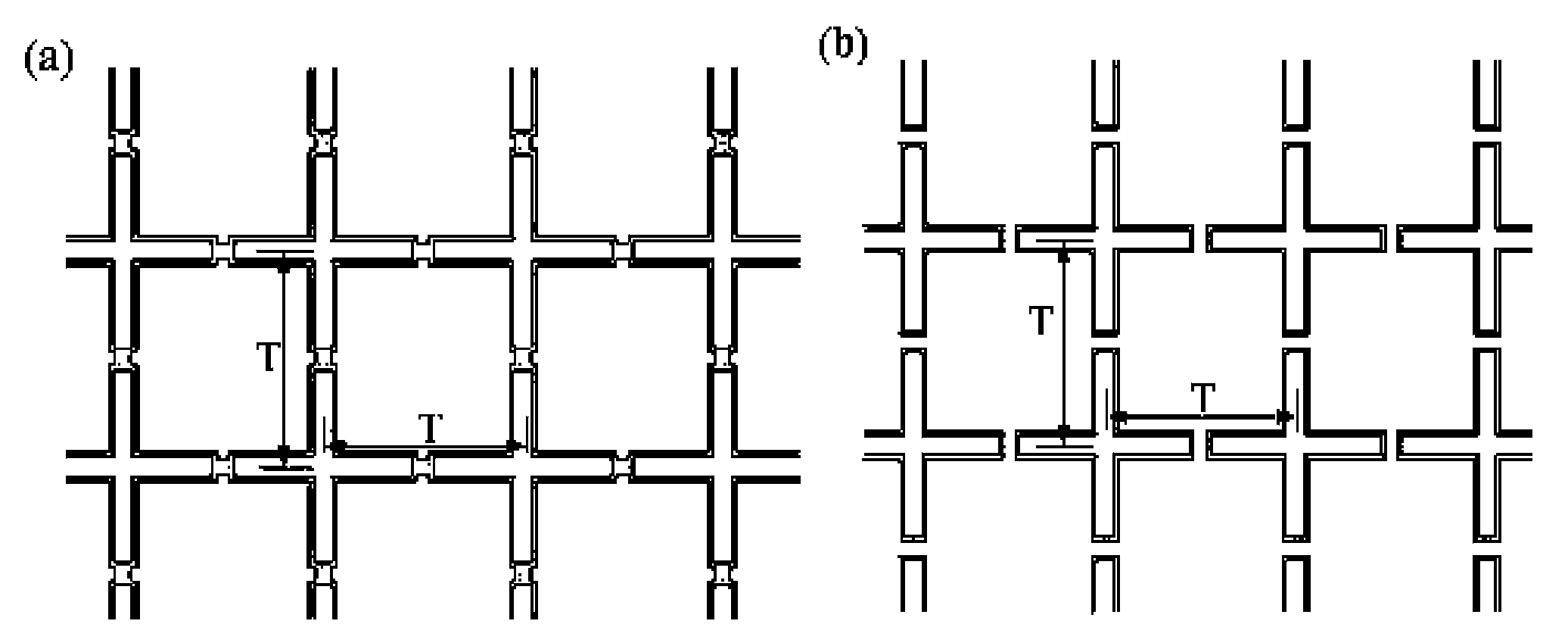
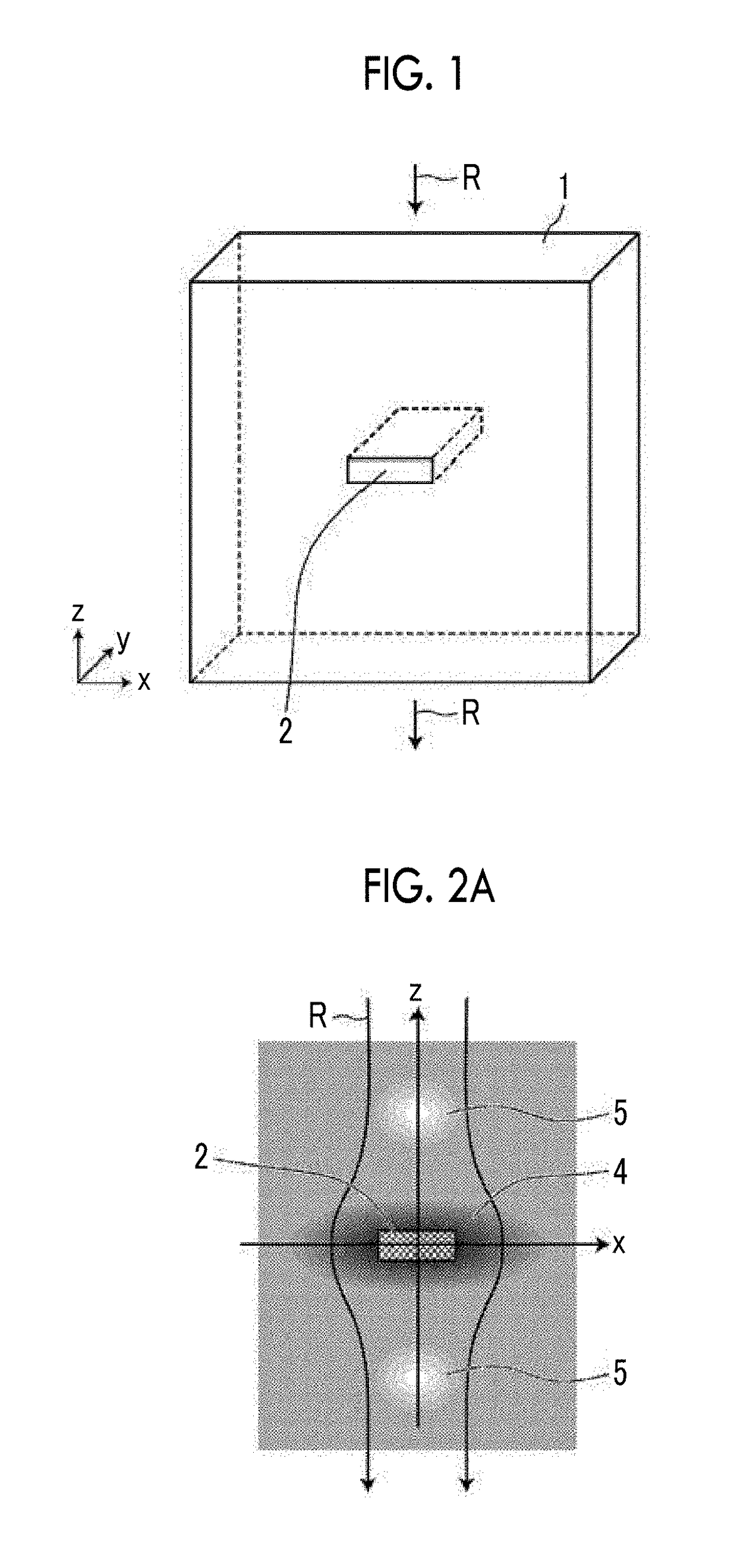
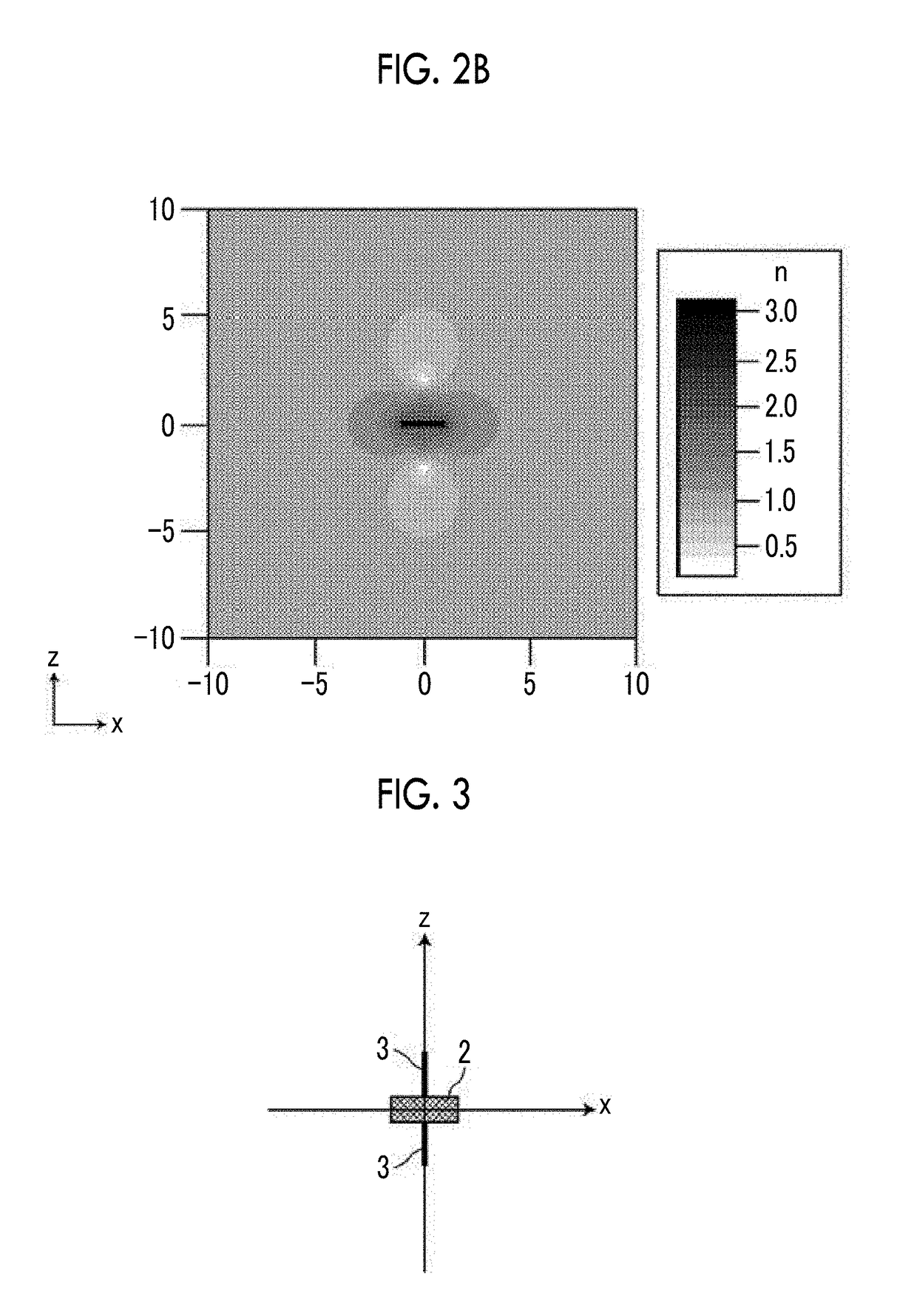
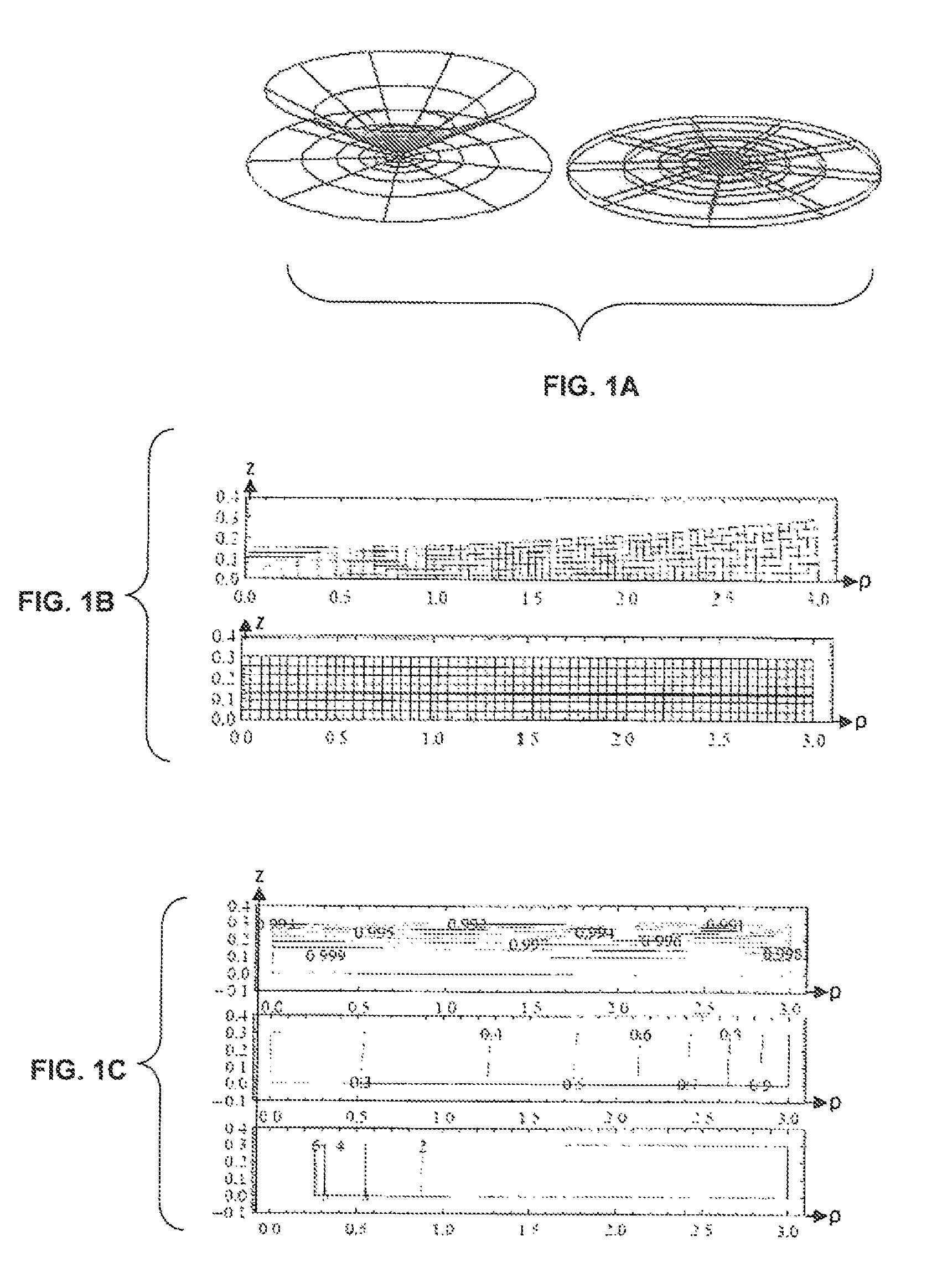
Electromagnetic cloaking structure and method for manufacturing the same
ActiveUS20170176580A1Wave based measurement systemsCamouflage devicesOptical axisComputational physics
In an electromagnetic cloaking structure, a refractive index distribution has a high refractive index region which is provided around a shielding space and has a maximum value in a plane surrounding the shielding space and in which a refractive index decreases gradually from the centroid of the shielding space along a radial line passing through the plane so as to be close to an average refractive index and a low refractive index region which has a minimum value at two points having the shielding space and the high refractive index region interposed therebetween on a virtual optical axis passing through the shielding space and in which the refractive index increases gradually from the two points in a direction opposite to the high refractive index region on the virtual optical axes, on which the two points are placed, so as to be close to the average refractive index.
Owner:FUJIFILM CORP
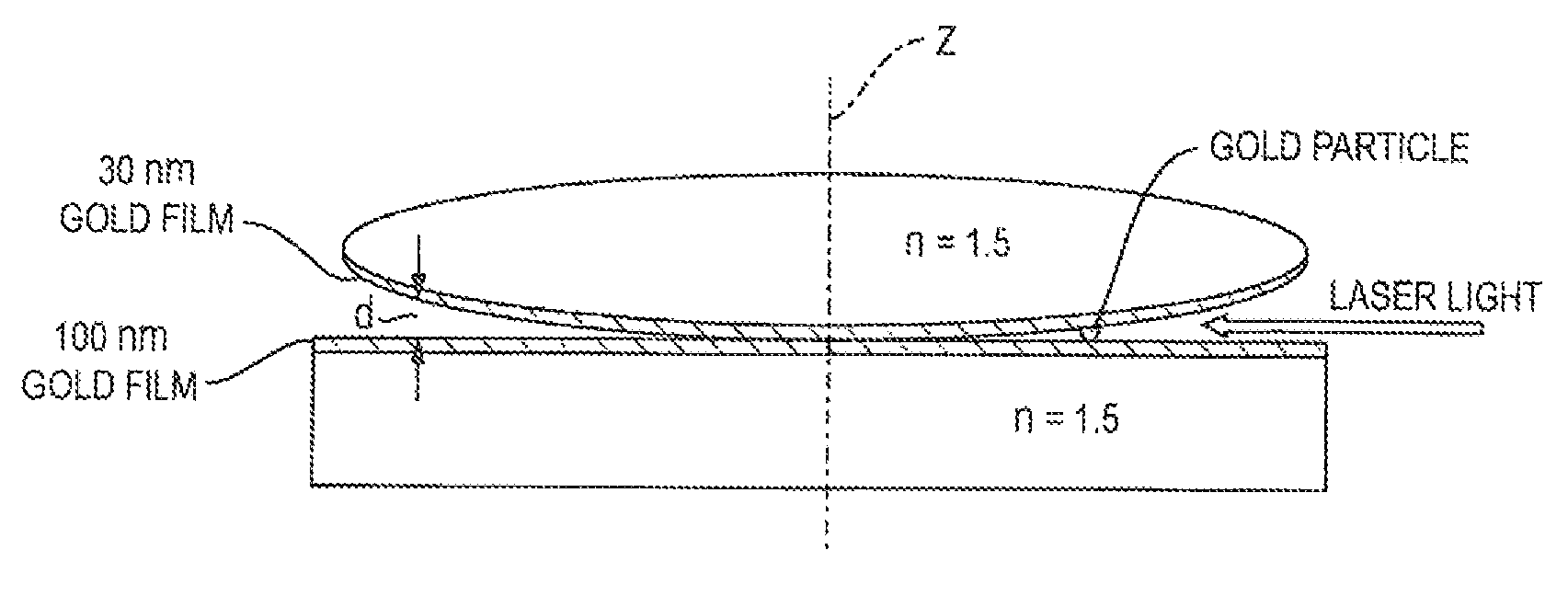
Anisotropic metamaterials emulated by tapered waveguides: application to electromagnetic cloaking
InactiveUS8509578B2Coupling light guidesOptical waveguide light guideElectromagnetic shieldingBroadband
A method for carrying out electromagnetic cloaking using metamaterial devices requiring anisotropic dielectric permittivity and magnetic permeability may be emulated by specially designed tapered waveguides. This approach leads to low-loss, broadband performance in the visible frequency range, which is difficult to achieve by other means. We apply this technique to electromagnetic cloaking. A broadband, two-dimensional, electromagnetic cloaking is demonstrated in the visible frequency range on a scale ˜100 times the wavelength. Surprisingly, the classic geometry of Newton rings is suited for an experimental demonstration of this effect.
Owner:VERCO MATERIALS +1
Thin-film integrated spectrally-selective plasmonic absorber/ emitter for solar thermophotovoltaic applications
Owner:IP EQUITY MANAGEMENT LLC
Rare earth Fe basis suction wave material and method for making the same
InactiveCN100518480CImprove absorbing performanceWide shielding bandMagnetic/electric field screeningRare earthOxidation resistant
The invention discloses a nano-crystal tombar thite ferrous absorbing material with good absorbing property and a preparation method thereof. The material is characterized in that the lanthanon with the weight percentage of 2% and 70%, the iron with the weight percentage of 5% and 98% and the little amount of doping element are smelted into tombar thite-ferrous alloy; the tombar thite-ferrous alloy is reacted with hydrogen by hydrogen decrepitation method under the temperature range from 0 to 700 DEG C, is broken into fine powder or be ball grinded into fine powder, and then is reacted with hydrogen to generate composite material of rare earths hydride (RHx) and Alpha-Fe under the temperature range from 100 DEG C to 1000 DEG C; finally, the composite material is oxidized, nitridized or oxidized and nitridized under low temperature to produce the composite material mainly being rare earth oxide or nitride / Alpha-Fe composite material. The material of the invention has the advantages of high absorbing capability, wide shield wave band, good anti-corrosion property, anti-oxidation property and low price, and can be used in the fields of electro-magnetic shielding in building, information and communication technical secrecy and military cloaking technique, and so on.
Owner:SICHUAN UNIV
Cloaking and watermark of non-coded information
ActiveUS20190124345A1Computer security arrangementsImage data processing detailsComputer graphics (images)File system
A computer system for the creation of subliminal image or watermarks where the apparent video is an “obvious” image and a subliminal or “clandestine” image or watermark is hidden within the data structure. The concept is envisioned for the cloaking of images, sound, video or like digitized non-coded information. The cloaked files may be intended for storage, transmission, or clandestine placement in a public file system. The watermark may be used for the subliminal marking of a source of a file, its creation, or for tagging copyrighted information.
Owner:THE QUANTUM GROUP +1
Cloaked electromagnetic field sensor
InactiveUS20140203819A1Signature reductionMinimize impactResistance/reactance/impedenceAntenna detailsElectromagnetic fieldGuide tube
A cloaked field sensor apparatus and system using a cloaking barrier sheath to substantially enclose the surface of a transmitter conduit exposed to an electromagnetic field being measured to reduce the field sensor's interference with the electromagnetic field being measured. Multiple cloaked field sensor apparatuses may be aligned in an array and use identical or different cloaking barrier sheaths.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com